Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
787results about "Data stream serial/continuous modification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Rechargeable battery pack and operating system
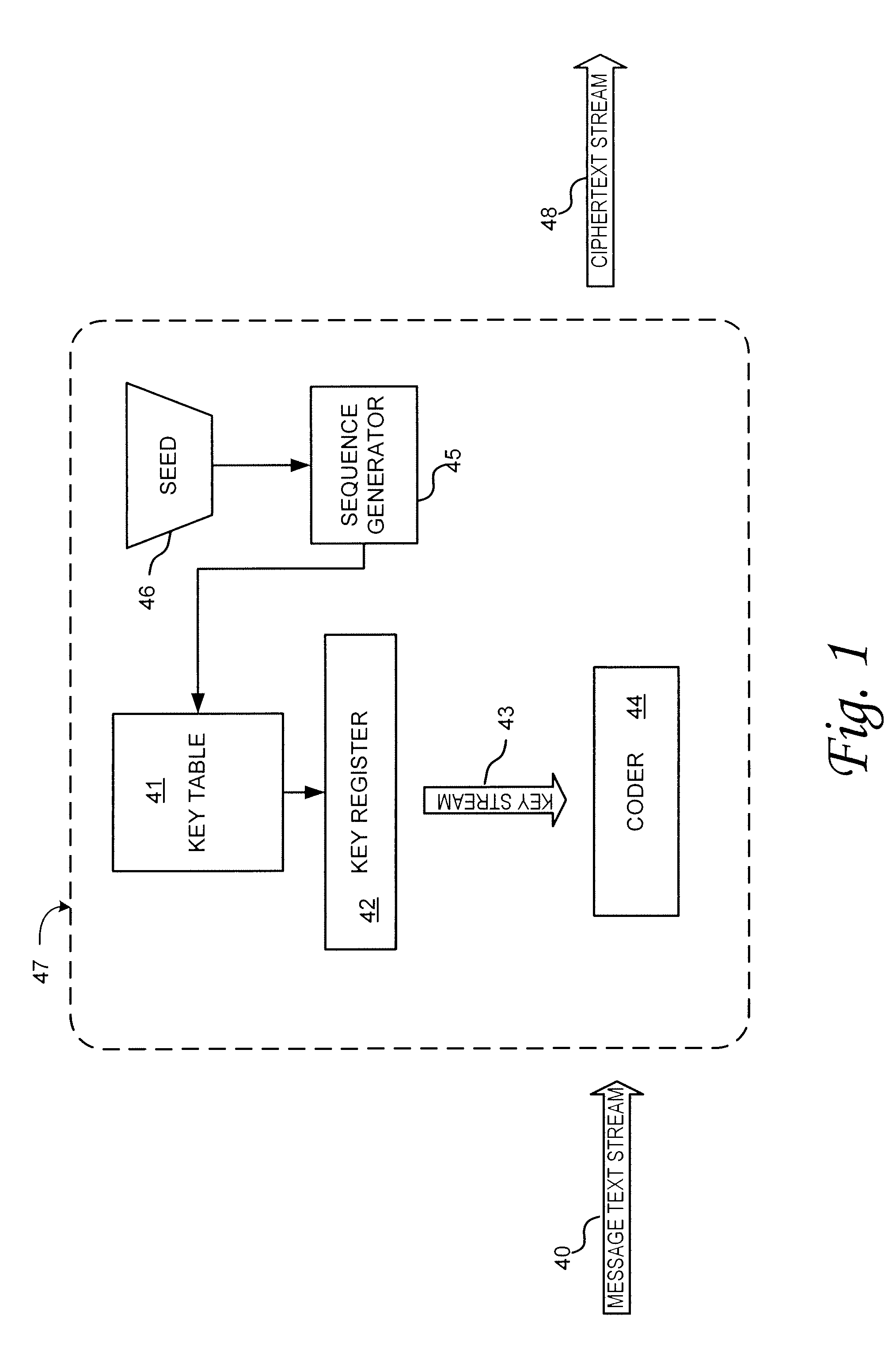
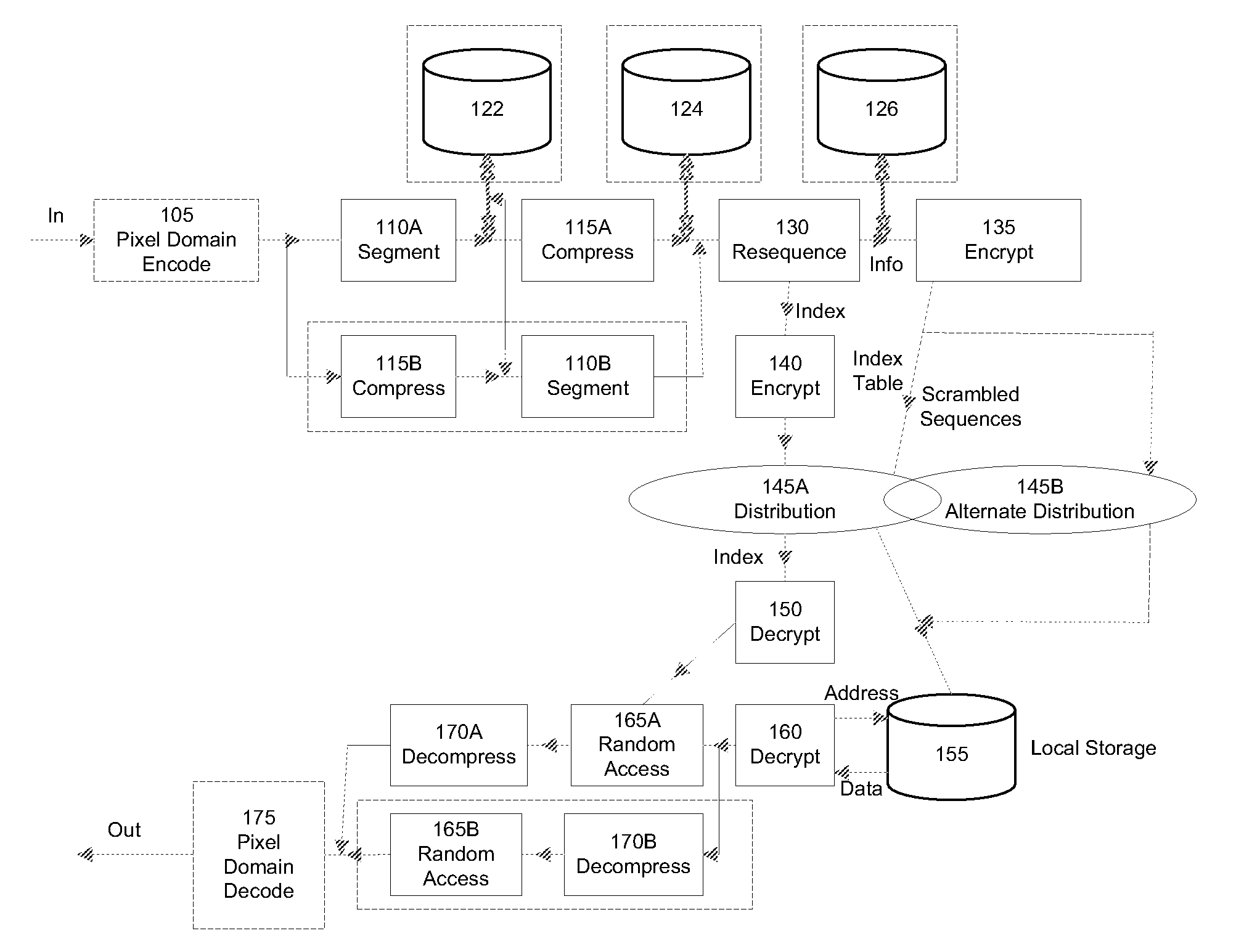
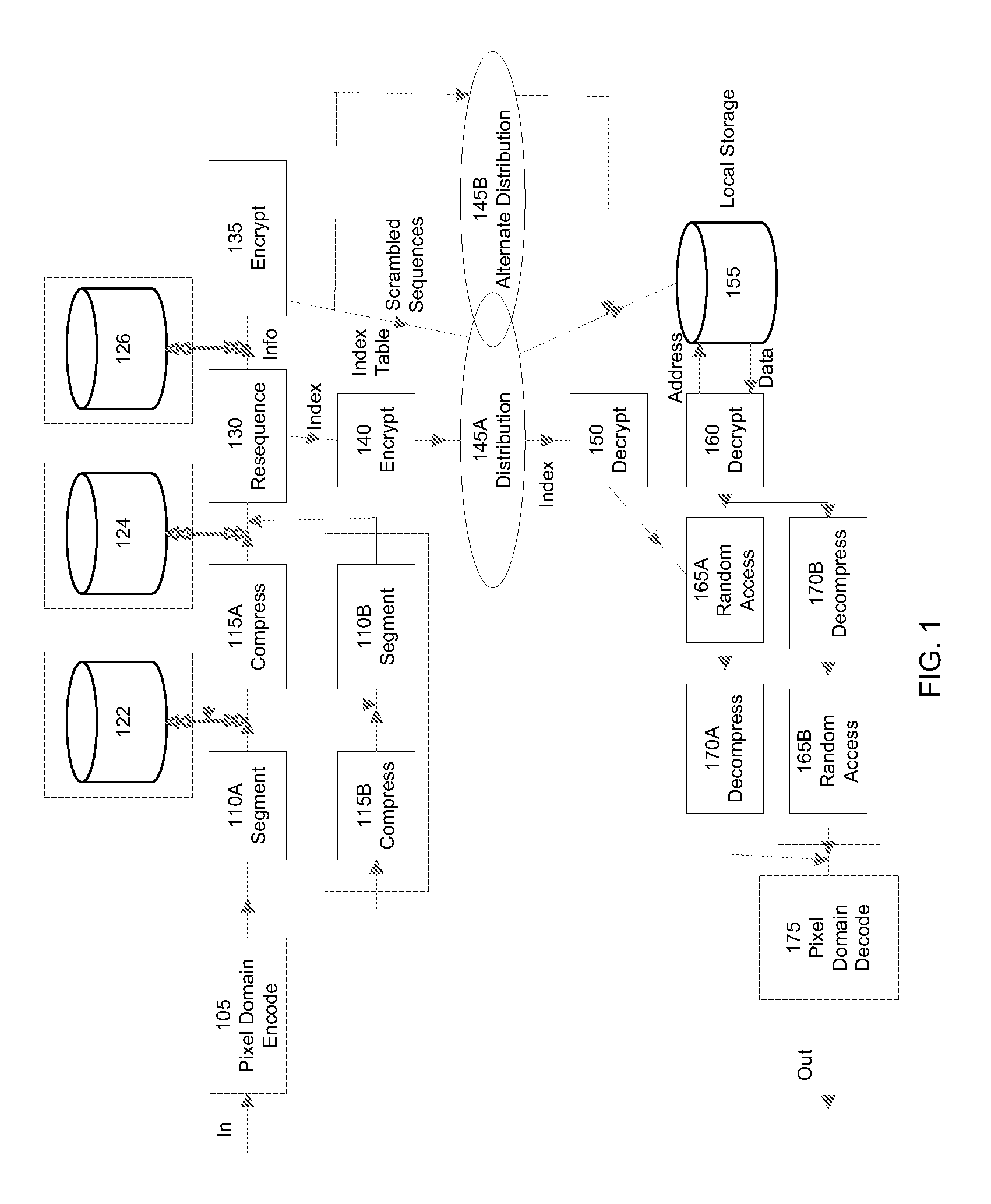
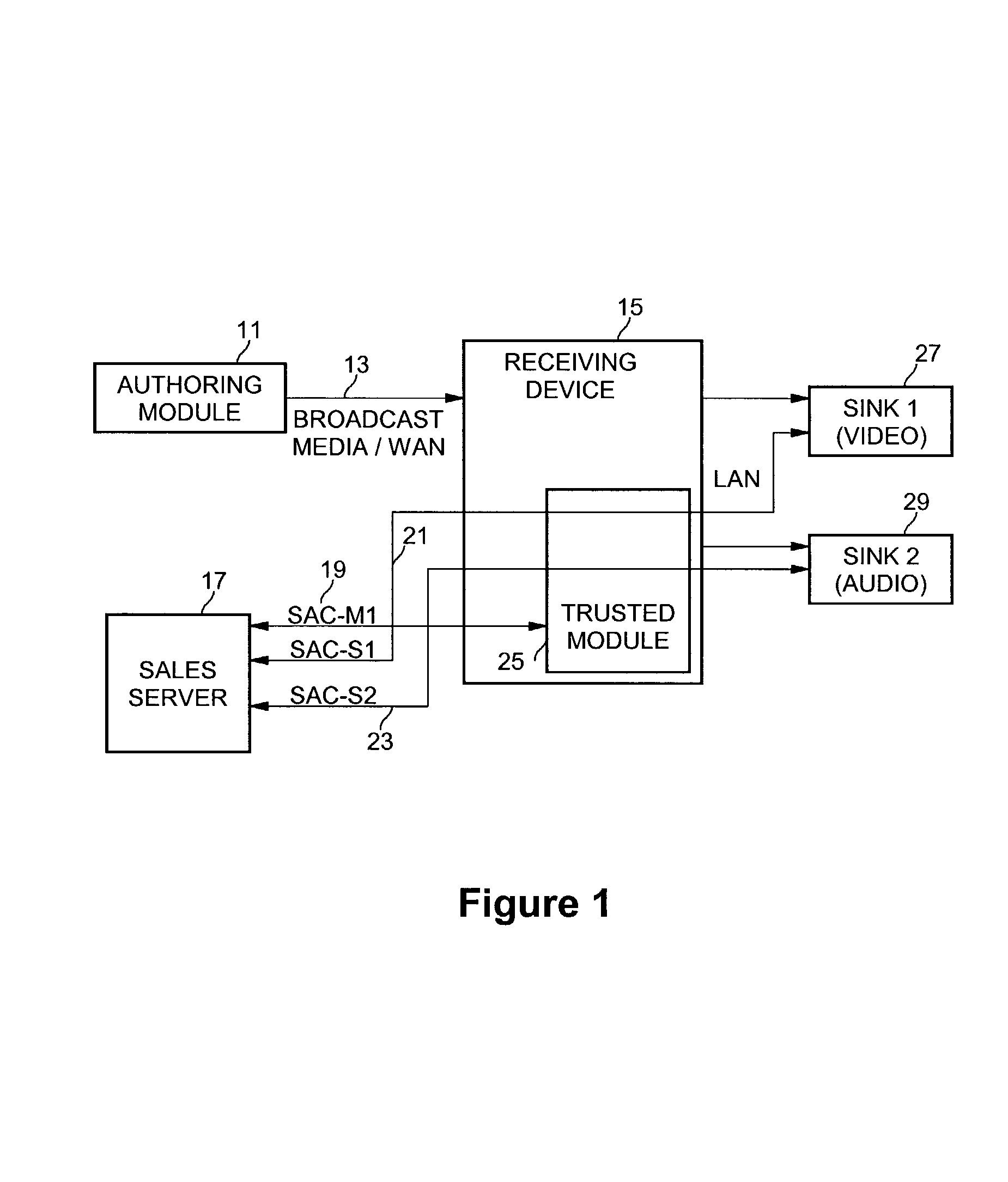
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
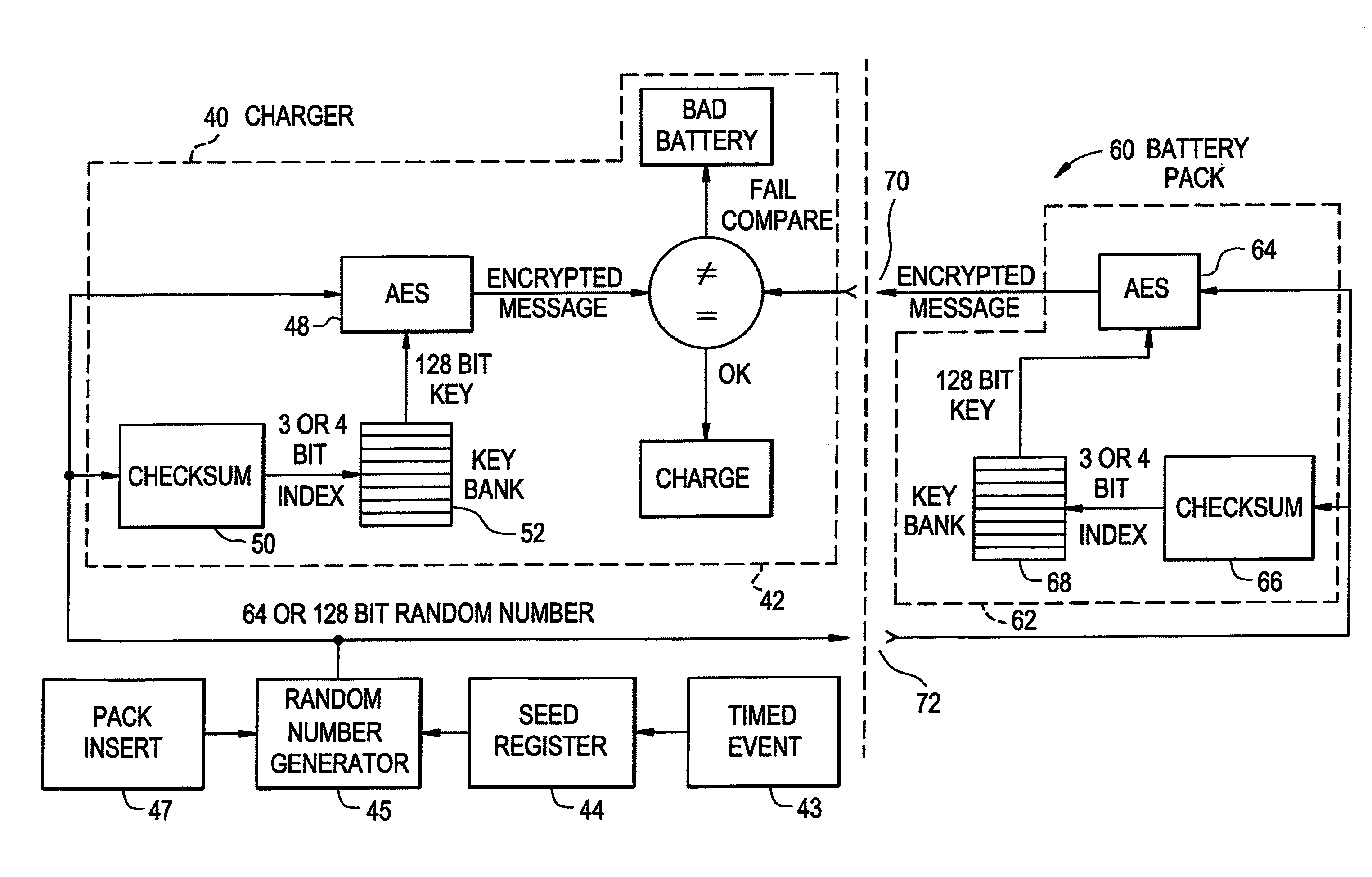
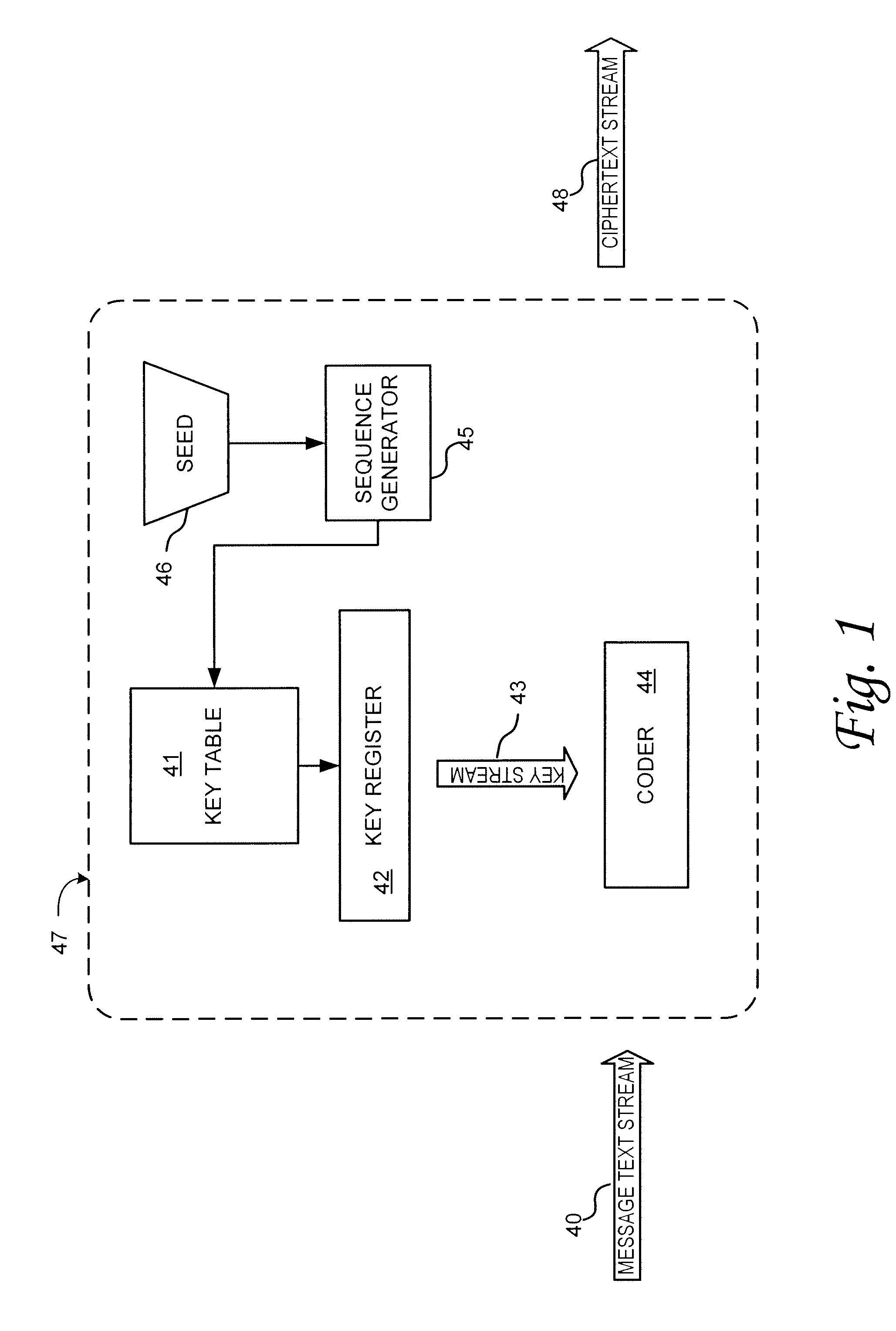
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
Chaotic cipher system and method for secure communication
ActiveUS20100211787A1Key distribution for secure communicationData stream serial/continuous modificationSecure communicationArray data structure
The present invention provides a method for a data encryption device to perform network communications, the method comprising obtaining an indexed array of encryption keys, wherein the indexed array of encryption keys is shared with a data decryption device; obtaining a message to be encrypted; using a first random or pseudorandom number to determine an index; obtaining a first key from the array of encryption keys, wherein the first key corresponds to the index; selecting a second key from the plurality of encryption keys; encrypting the message using the first key and a second random or pseudorandom number; encrypting the index using the second key and a third random or pseudorandom number; transmitting the encrypted message and the encrypted index to the data decryption device.
Owner:MERCURY MISSION SYST LLC
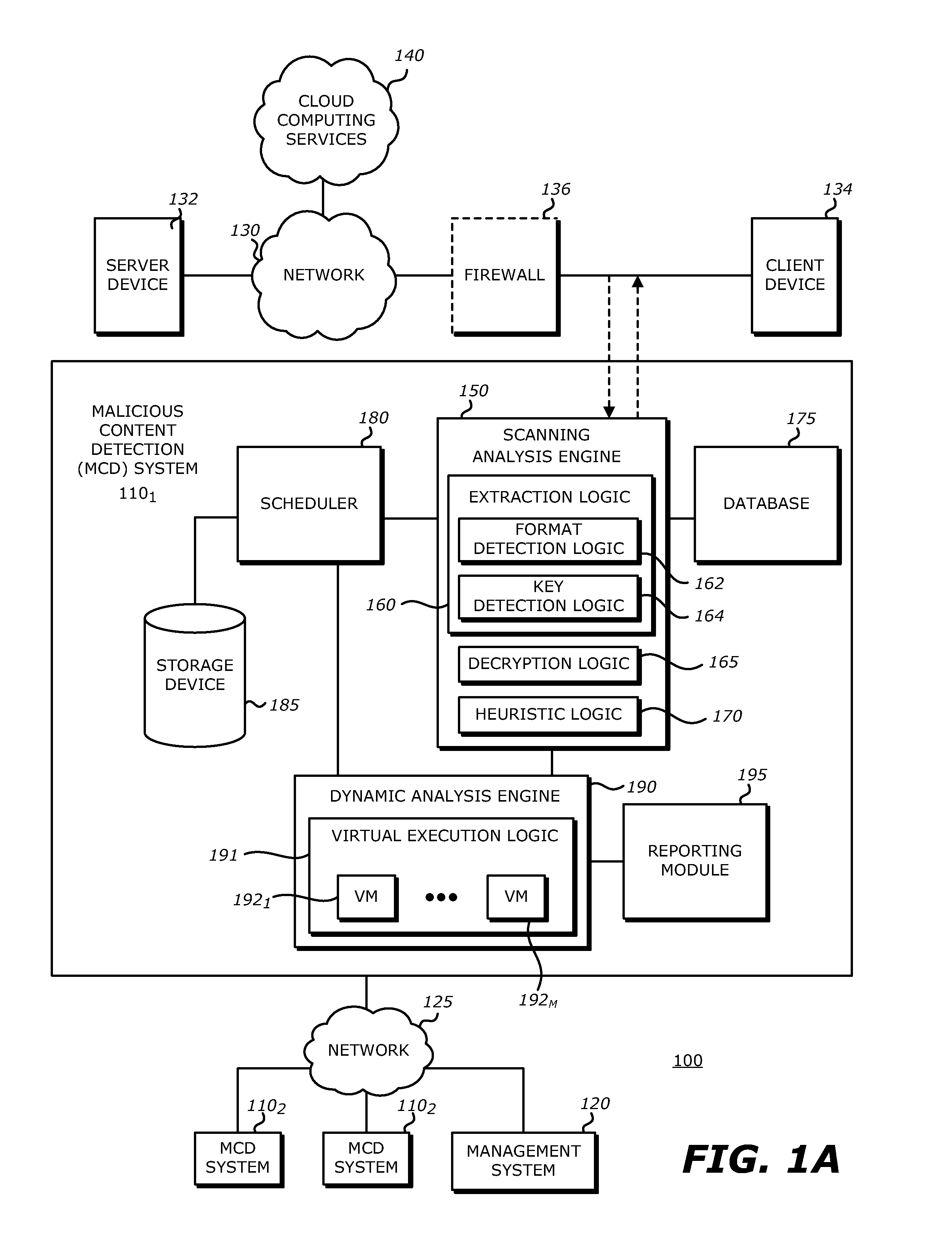
System, apparatus and method for conducting on-the-fly decryption of encrypted objects for malware detection
ActiveUS9189627B1Key distribution for secure communicationData stream serial/continuous modificationMalwareSoftware
According to one embodiment, a computerized method comprises receiving an encrypted object and conducting a first static scanning operation on the encrypted object to decrypt the encrypted object in real-time. Thereafter, a second static scanning operation is conducted on the decrypted object to determine whether the decrypted object is suspected of including malware. Based on the results of the second static scanning operation, the decrypted object may be classified to identify a suspected presence of malware.
Owner:FIREEYE SECURITY HLDG US LLC +1
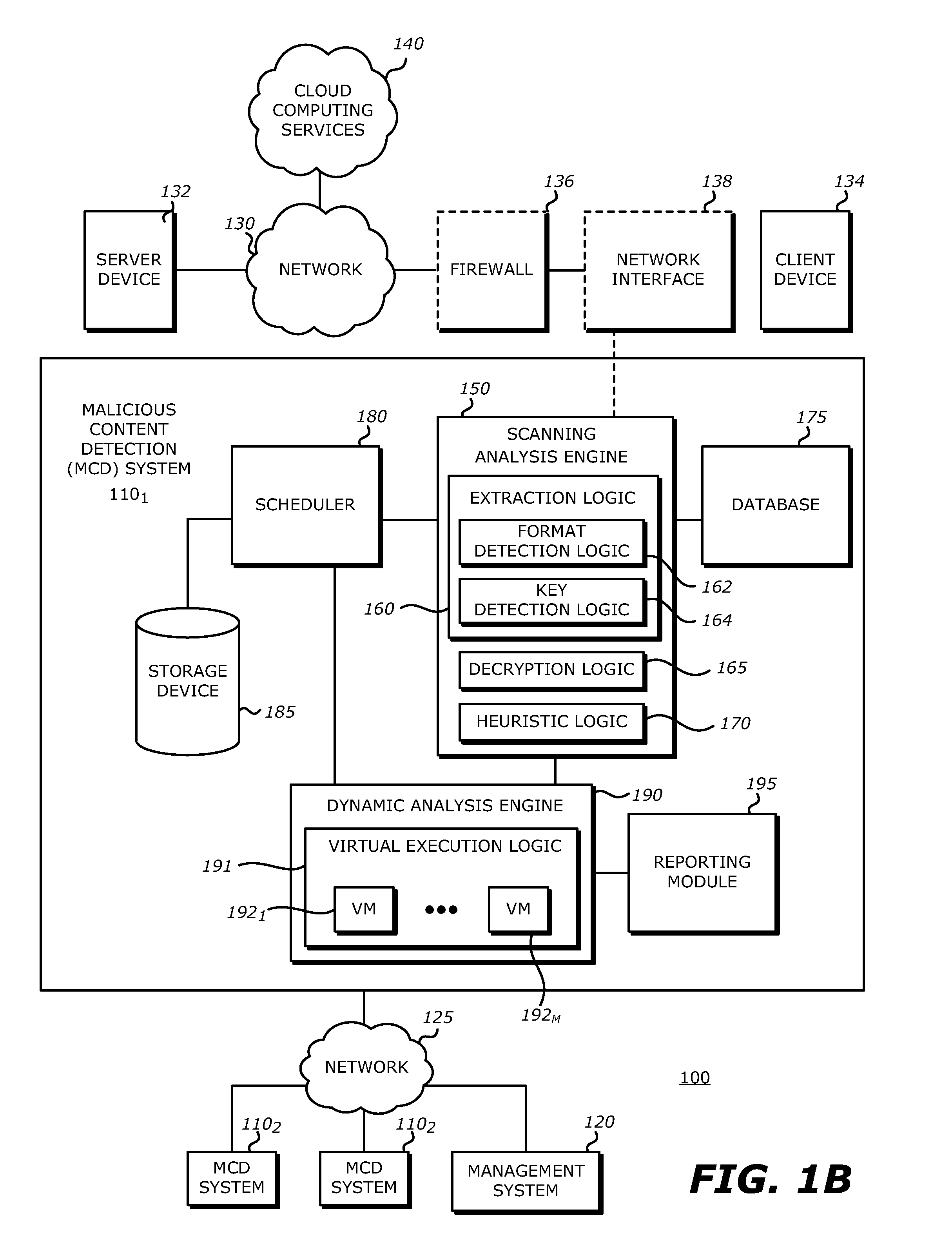
Interactive video collaboration framework
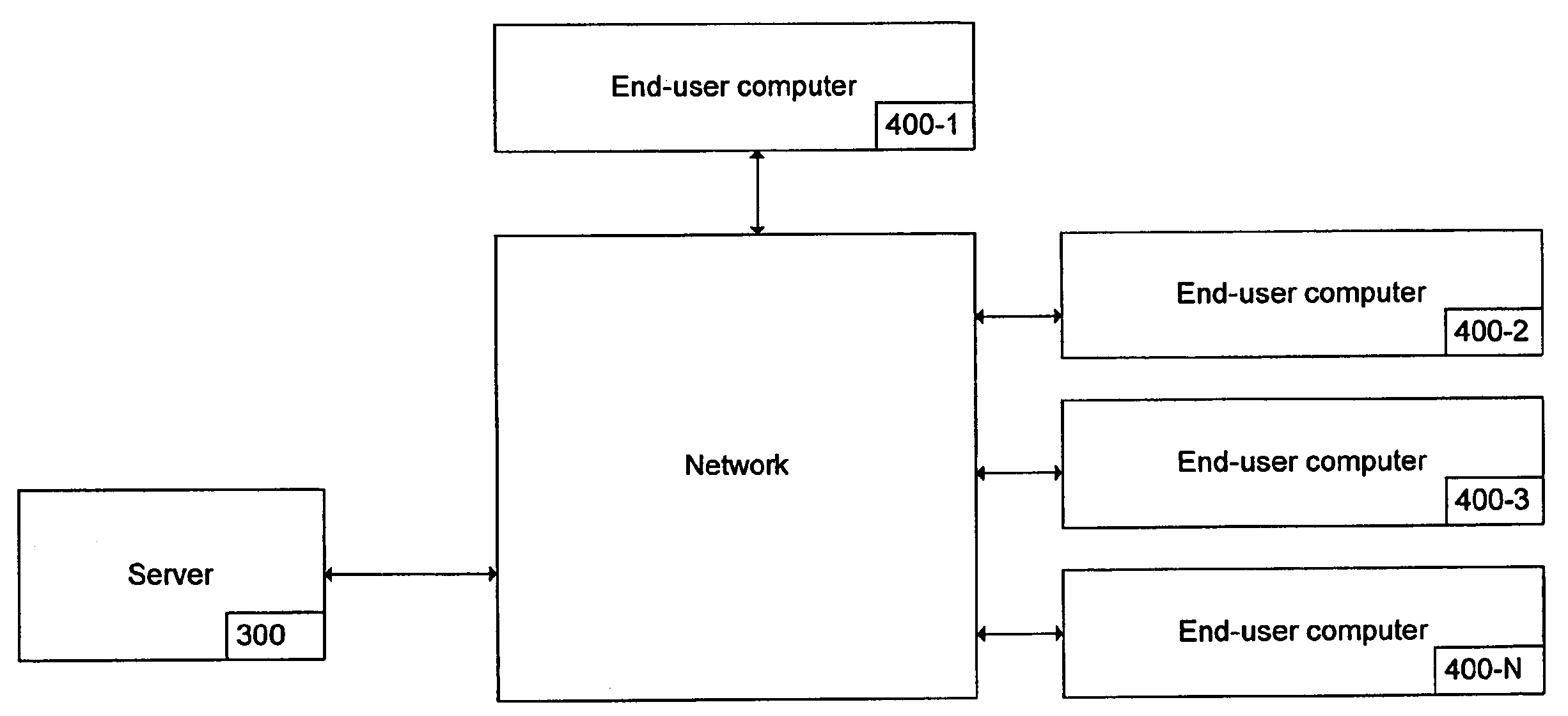
ActiveUS20060087987A1Special service provision for substationMultiplex system selection arrangementsData streamInteractive video
A system for providing interactive collaboration between a plurality of users. The system includes a profile respository for storing a priority level for each of said plurality of users and providing addresses for accessing each of said plurality of users. A media content server indexes audio and video data within the system. A data server stores the audio and video data at locations identified by indexing data located at the media content server. An acquisition processor provides audio and video data streams to requesting ones of the plurality of users. Audio and video data streams are located based on indexing data within the media content server and accessed according to a priority level for each requesting user. A communication processor controls bidirectional communication between requesting users according to the priority level for each requesting user.
Owner:VECTORMAX CORP
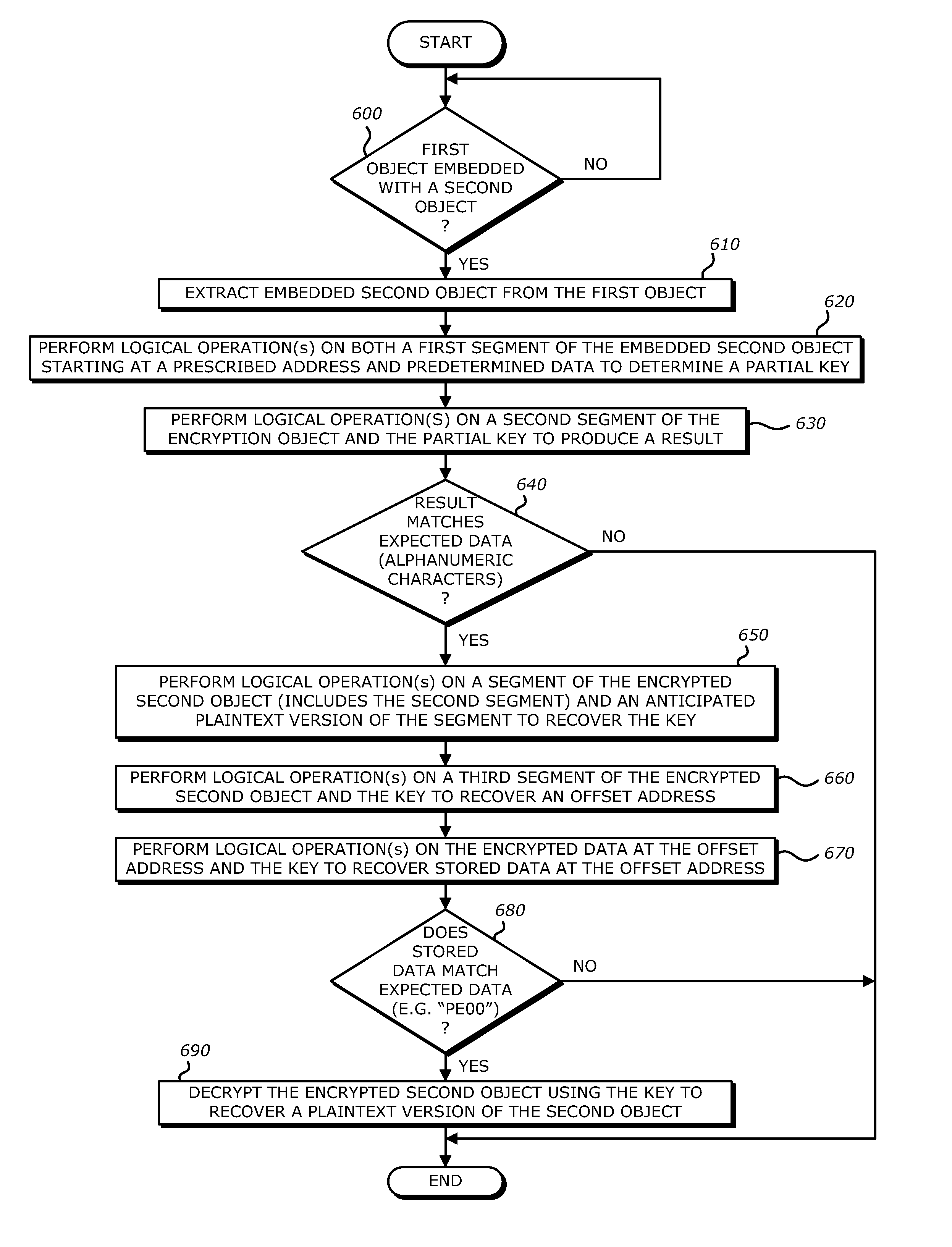
System, apparatus and method for conducting on-the-fly decryption of encrypted objects for malware detection
ActiveUS9560059B1Key distribution for secure communicationData stream serial/continuous modificationComputer hardwareLogical operations
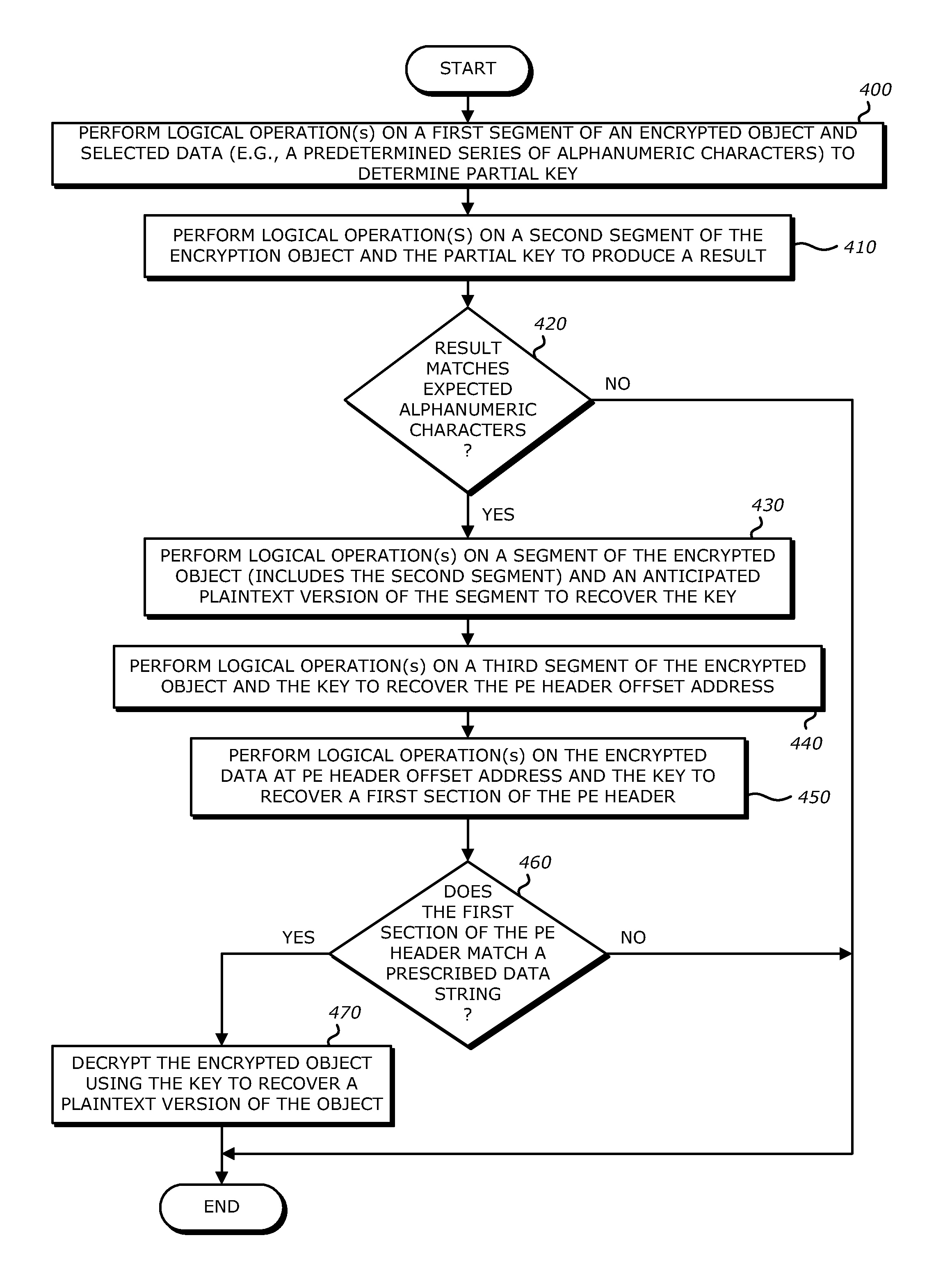
A decryption scheme for recover of a decrypted object without a cryptographic key is described. First, logical operation(s) are conducted on data associated with a first data string expected at a first location within an object having the predetermined format and data within the encrypted object at the first location to recover data associated with a portion of a cryptographic key from the encrypted object. Thereafter, logical operation(s) are conducted on that data and a first portion of the encrypted object at a second location to produce a result. Responsive to the result including data associated with the plaintext version of the second data string, logical operation(s) are conducted on a second portion of the encrypted object and the data associated with the plaintext version of the second data string to recover data associated with the cryptographic key. Thereafter, the encrypted object may be decrypted using the cryptographic key.
Owner:FIREEYE SECURITY HLDG US LLC +1
Agile network protocol for secure communications with assured system availability
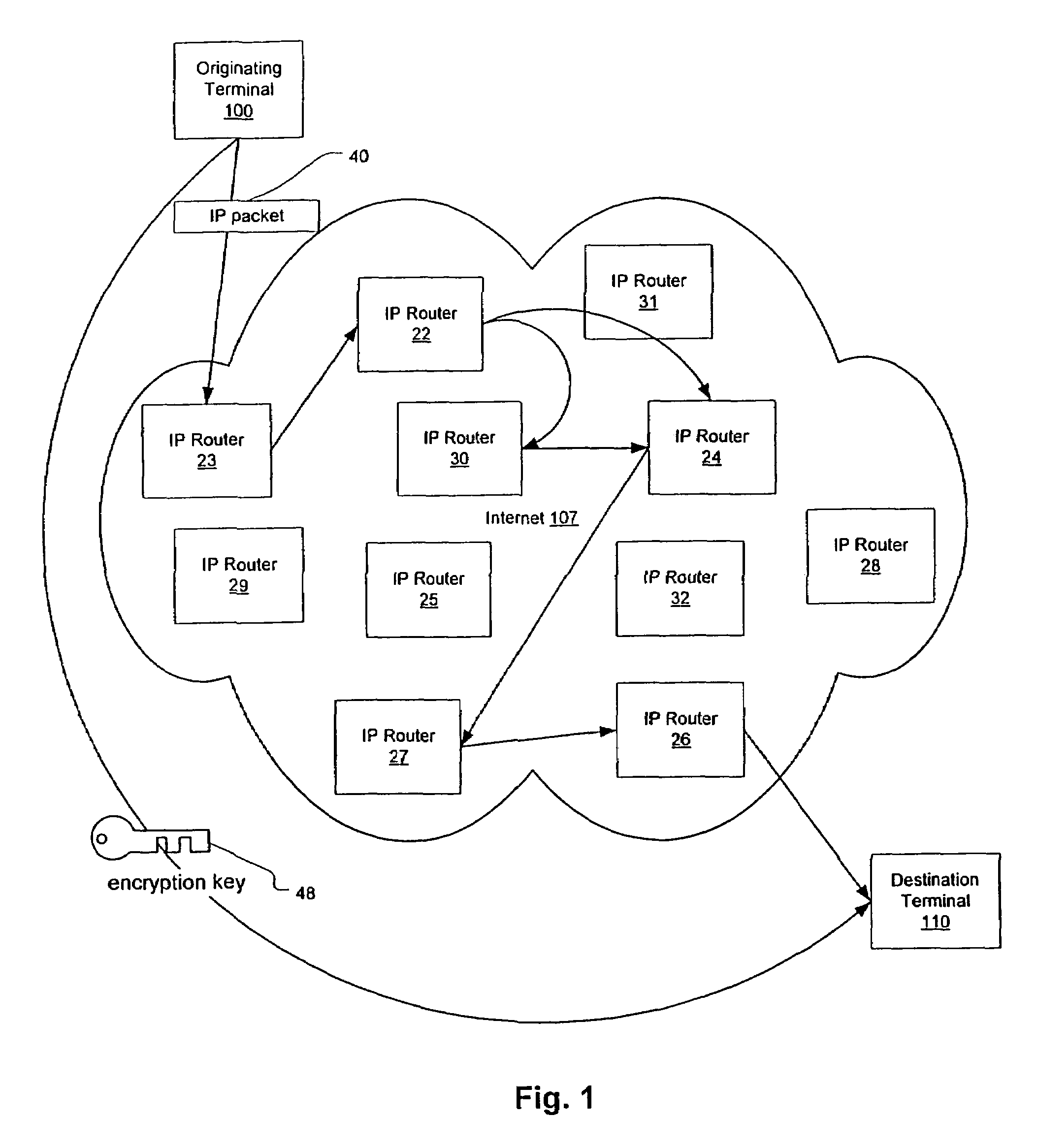
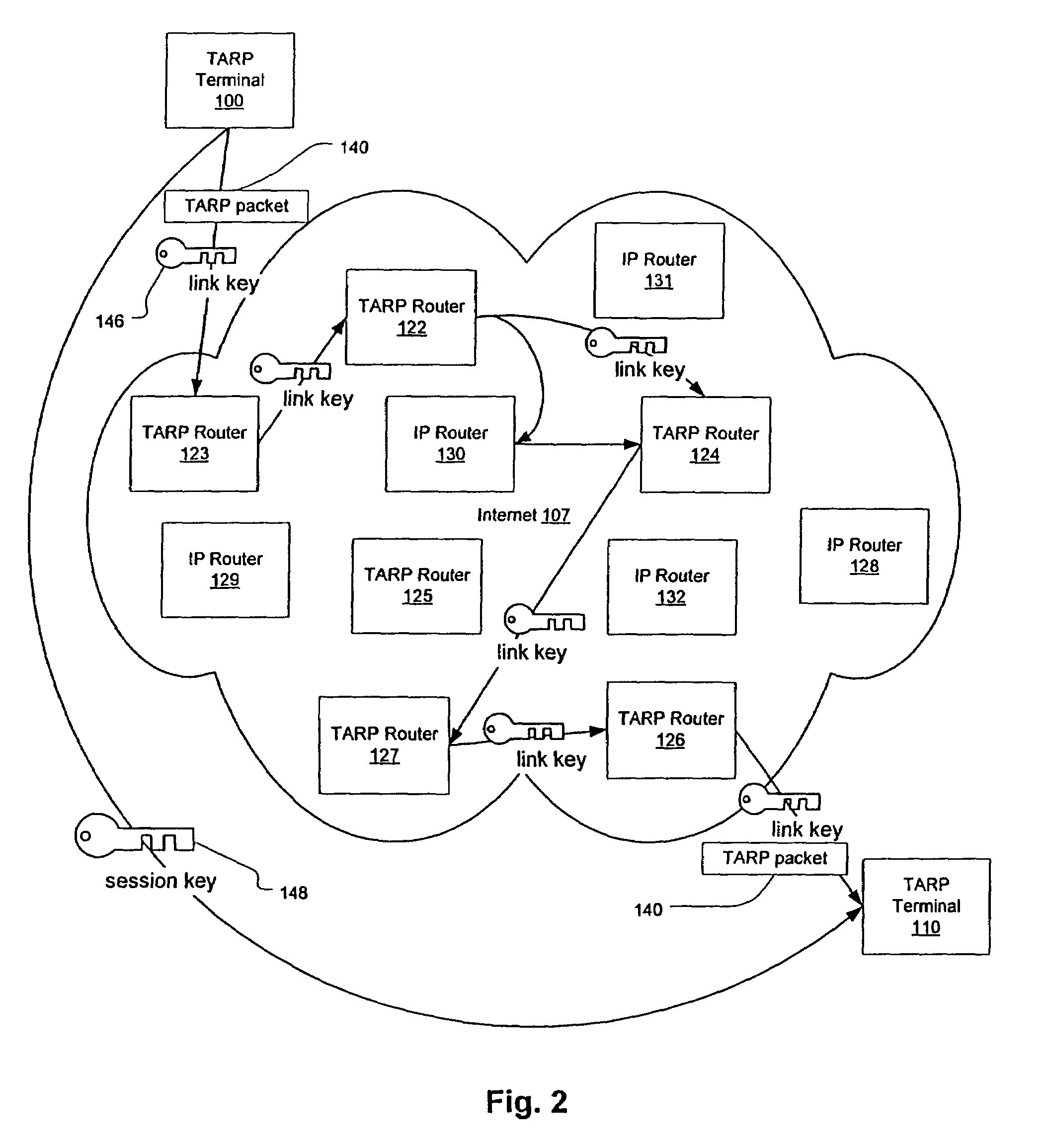
InactiveUS7010604B1Reduce network loadSmall sizeKey distribution for secure communicationData stream serial/continuous modificationDiscriminatorComputer hardware
A plurality of computer nodes communicates using seemingly random IP source and destination addresses and (optionally) a seemingly random discriminator field. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are rejected. In addition to “hopping” of IP addresses and discriminator fields, hardware addresses such as Media Access Control addresses can be hopped. The hopped addresses are generated by random number generators having non-repeating sequence lengths that are easily determined a-priori, which can quickly jump ahead in sequence by an arbitrary number of random steps and which have the property that future random numbers are difficult to guess without knowing the random number generator's parameters. Synchronization techniques can be used to re-establish synchronization between sending and receiving-nodes. These techniques include a self-synchronization technique in which a sync field is transmitted as part of each packet, and a “checkpoint” scheme by which transmitting and receiving nodes can advance to a known point in their hopping schemes. A fast-packet reject technique based on the use of presence vectors is also described. A distributed transmission path embodiment incorporates randomly selected physical transmission paths.
Owner:VIRNETX
Selectively encrypting different portions of data sent over a network
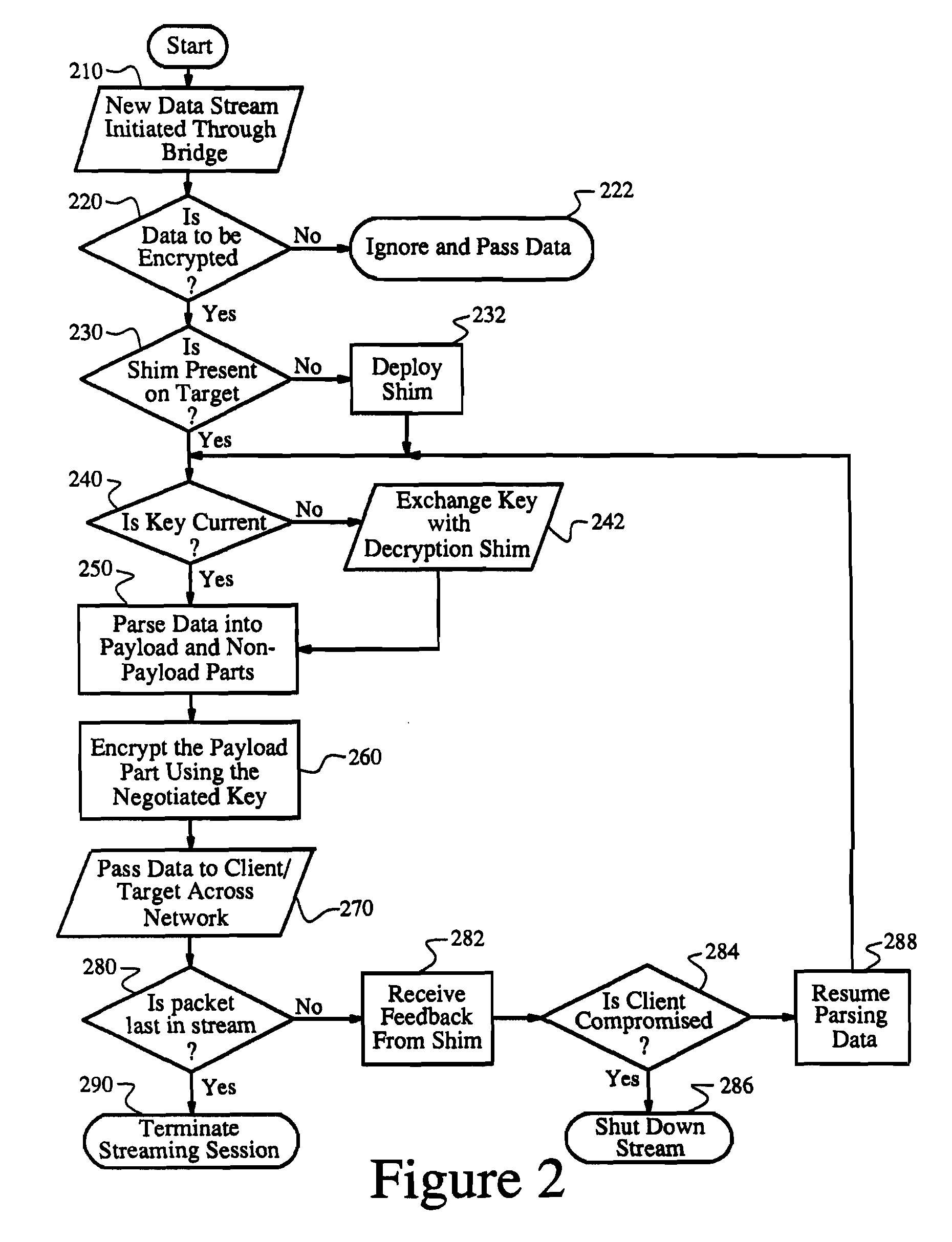
InactiveUS7376831B2Data stream serial/continuous modificationTelevision systemsNetwork packetClient-side
An apparatus, system, and method are directed towards parsing and selectively encrypting different portions of data in real-time, decrypting the encrypted data in real-time, and passing the data to a media player on a client computer or other network capable device. Data in a network packet may be parsed into payload and non-payload portions. The payload portion of the packet data may then be examined to determine whether a predefined type of the data is recognized. For example, in one embodiment, the predefined data type may be media content. If the payload portion is recognized as a predefined data type, then it may be selectively encrypted. The selectively encrypted payload portion and non-payload portion of the packet may then be combined, such that the non-payload portion may be employed by firewalls, proxies, and / or NATs to route the packet towards the client computer or other network capable device.
Owner:GOOGLE LLC
Method, system and medium for analog encryption in a flash memory
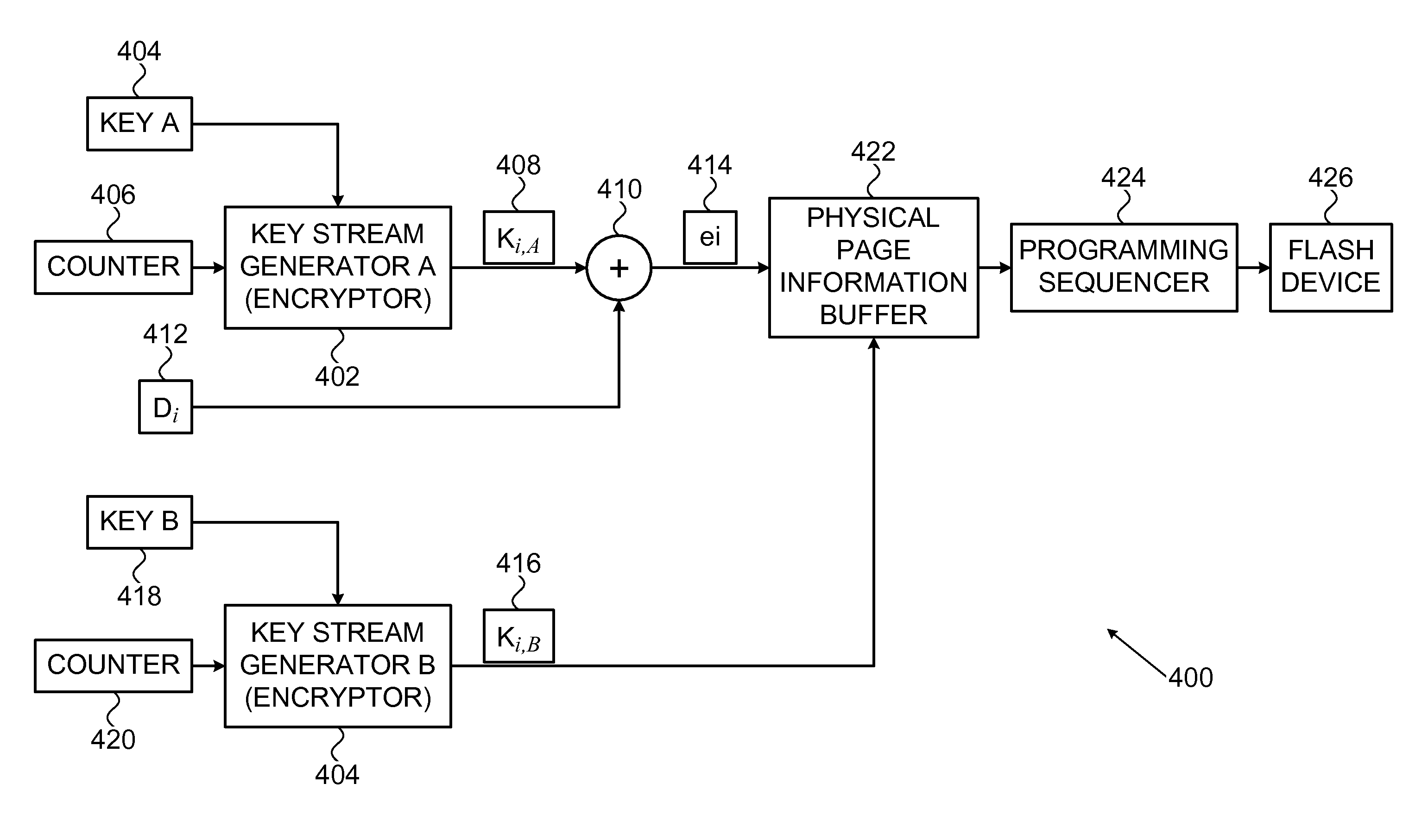
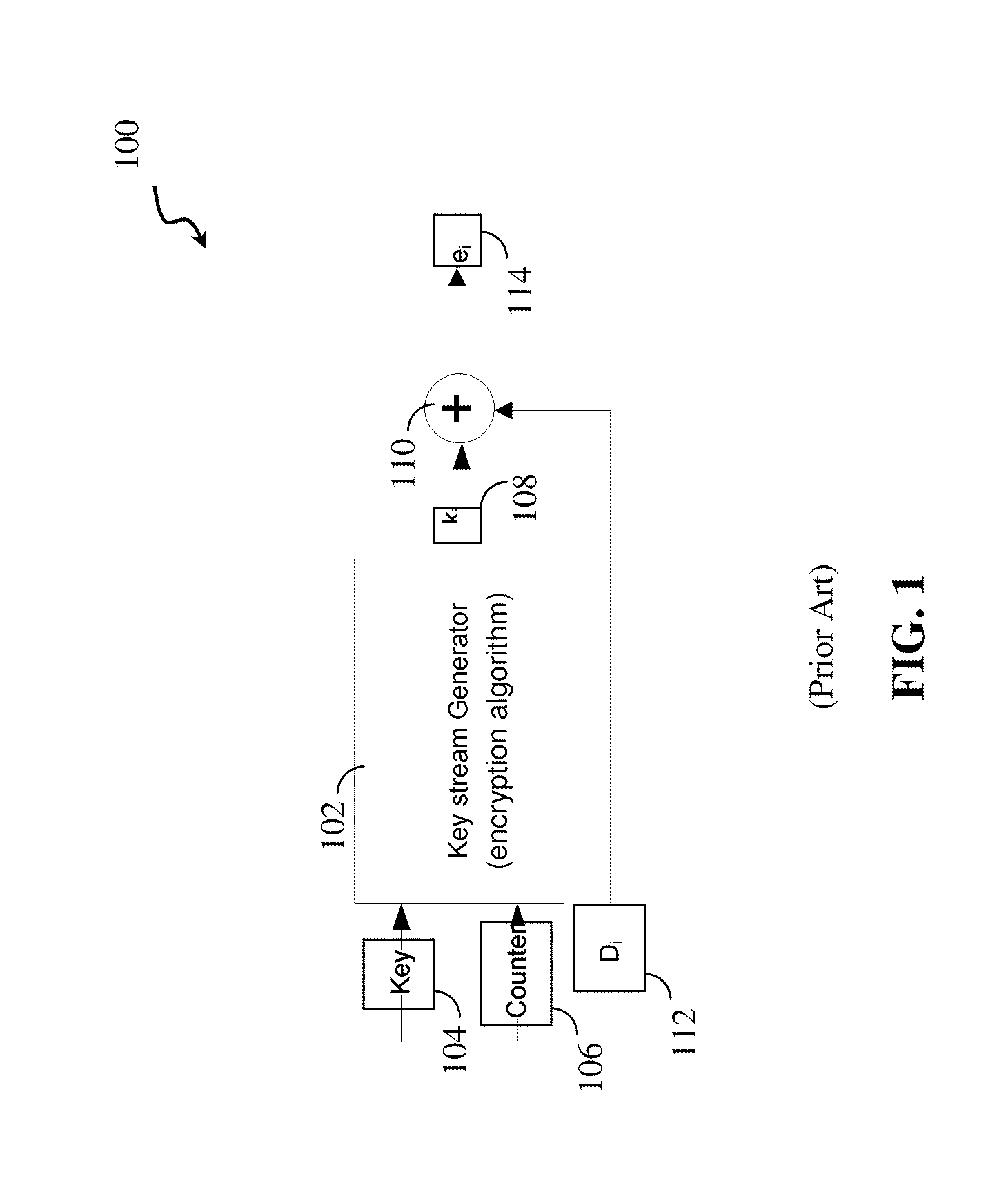
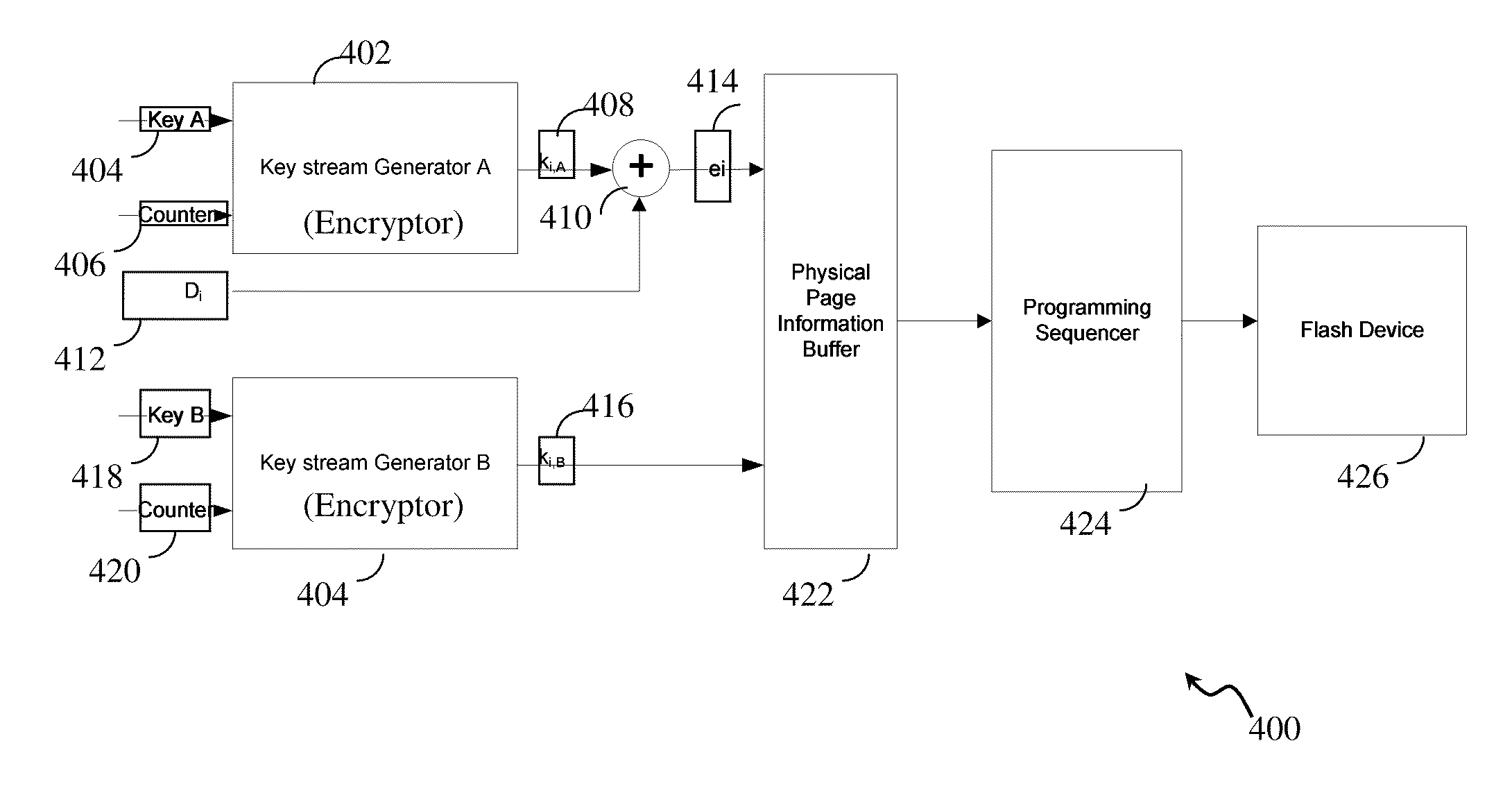
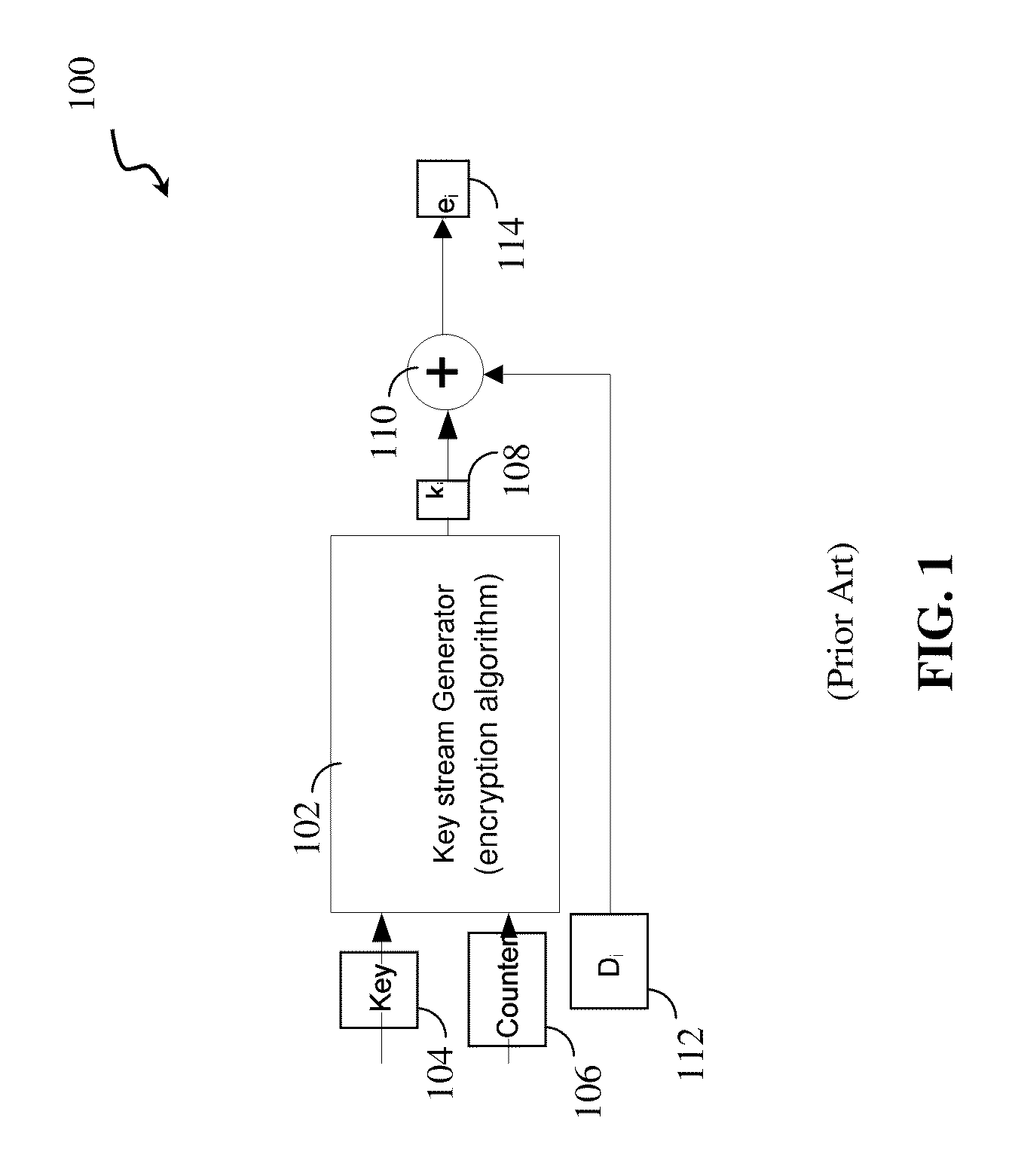
ActiveUS20110246792A1Multiple keys/algorithms usageData stream serial/continuous modificationData streamCipher
A system and method for analog encryption and decryption. A threshold level encryption key stream is generated and a programming level for each bit of a cipher data stream, with each bit having a one or zero state, is determined, where a threshold for distinguishing between the one or zero state for each bit varies based on a corresponding entry in the threshold level encryption key steam. Each bit of the cipher data stream in a cell of a memory is programmed based on the programming level.
Owner:AVAGO TECH INT SALES PTE LTD
Secure information distribution system utilizing information segment scrambling
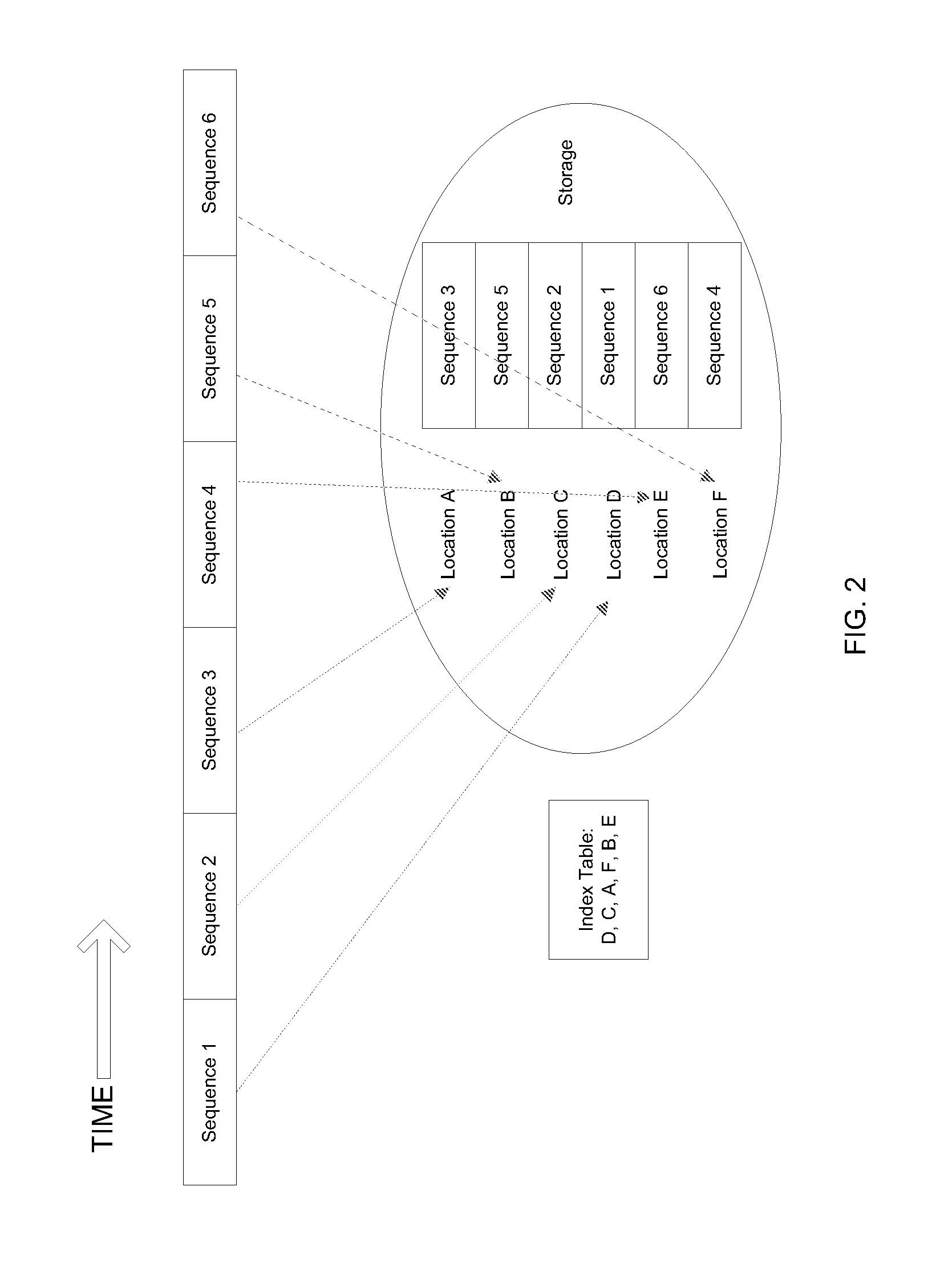
InactiveUS7457415B2Data stream serial/continuous modificationMultiple keys/algorithms usageDistribution systemComputer security
Owner:AKIKAZE TECH
Method and system for microprocessor data security
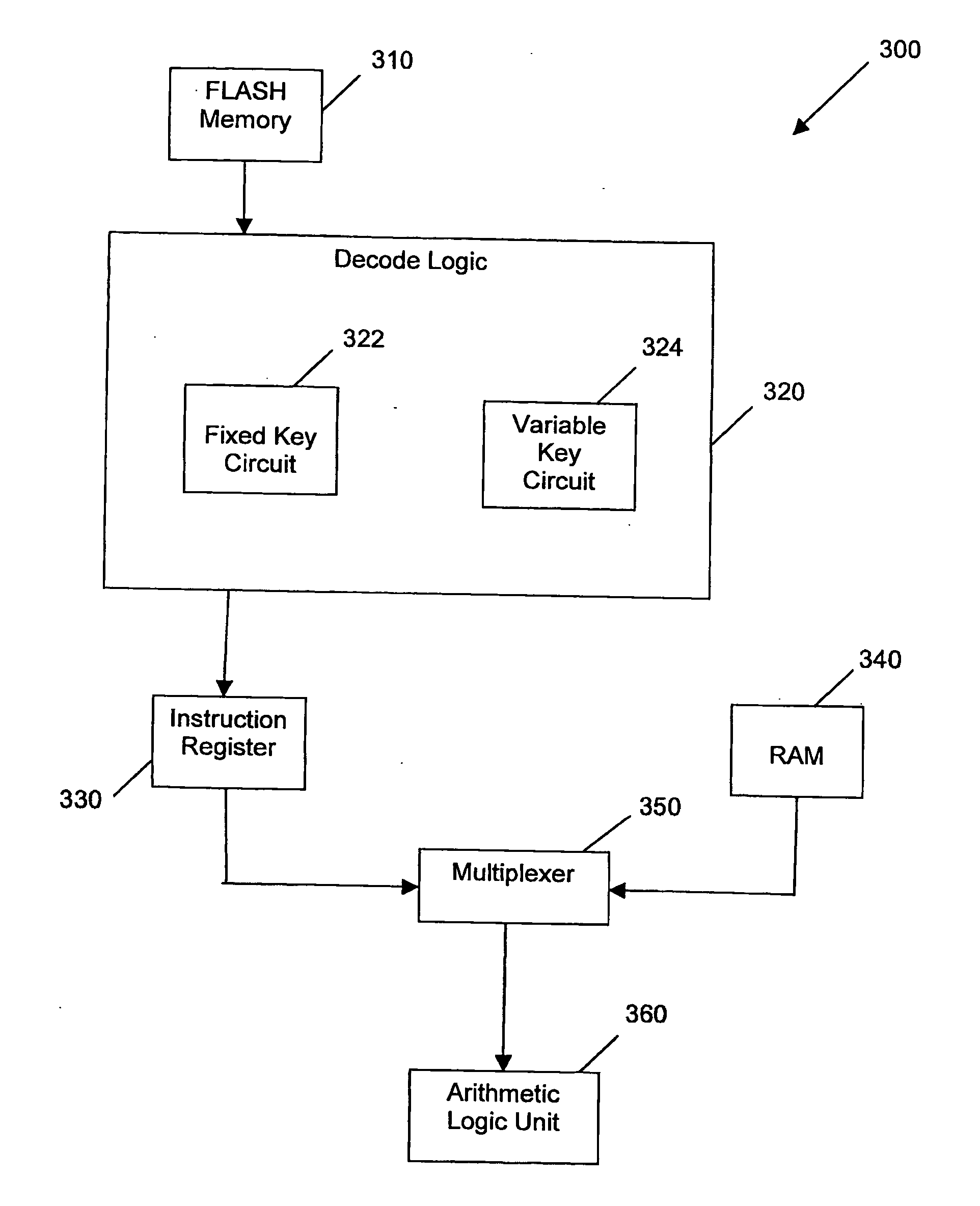
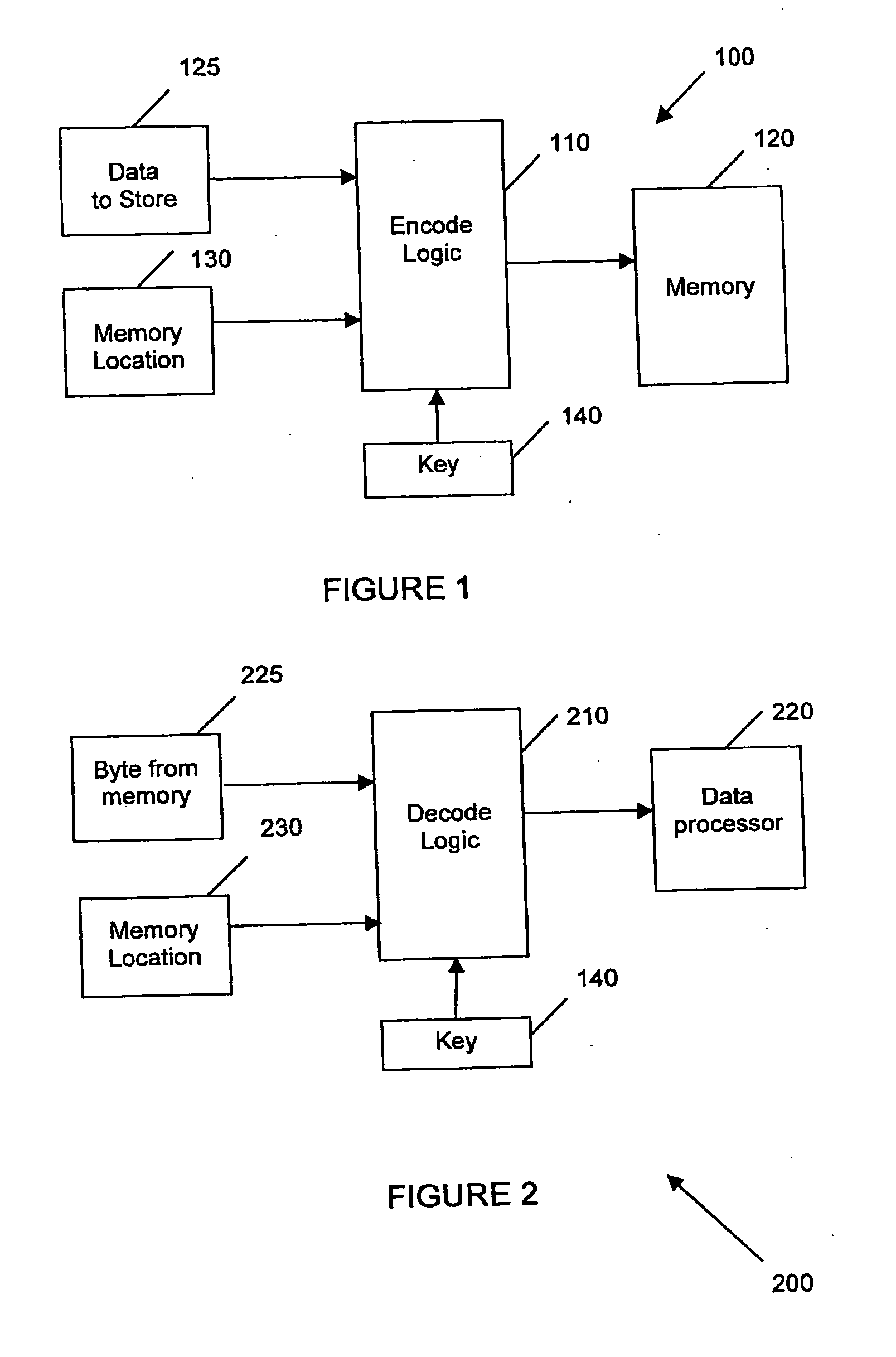
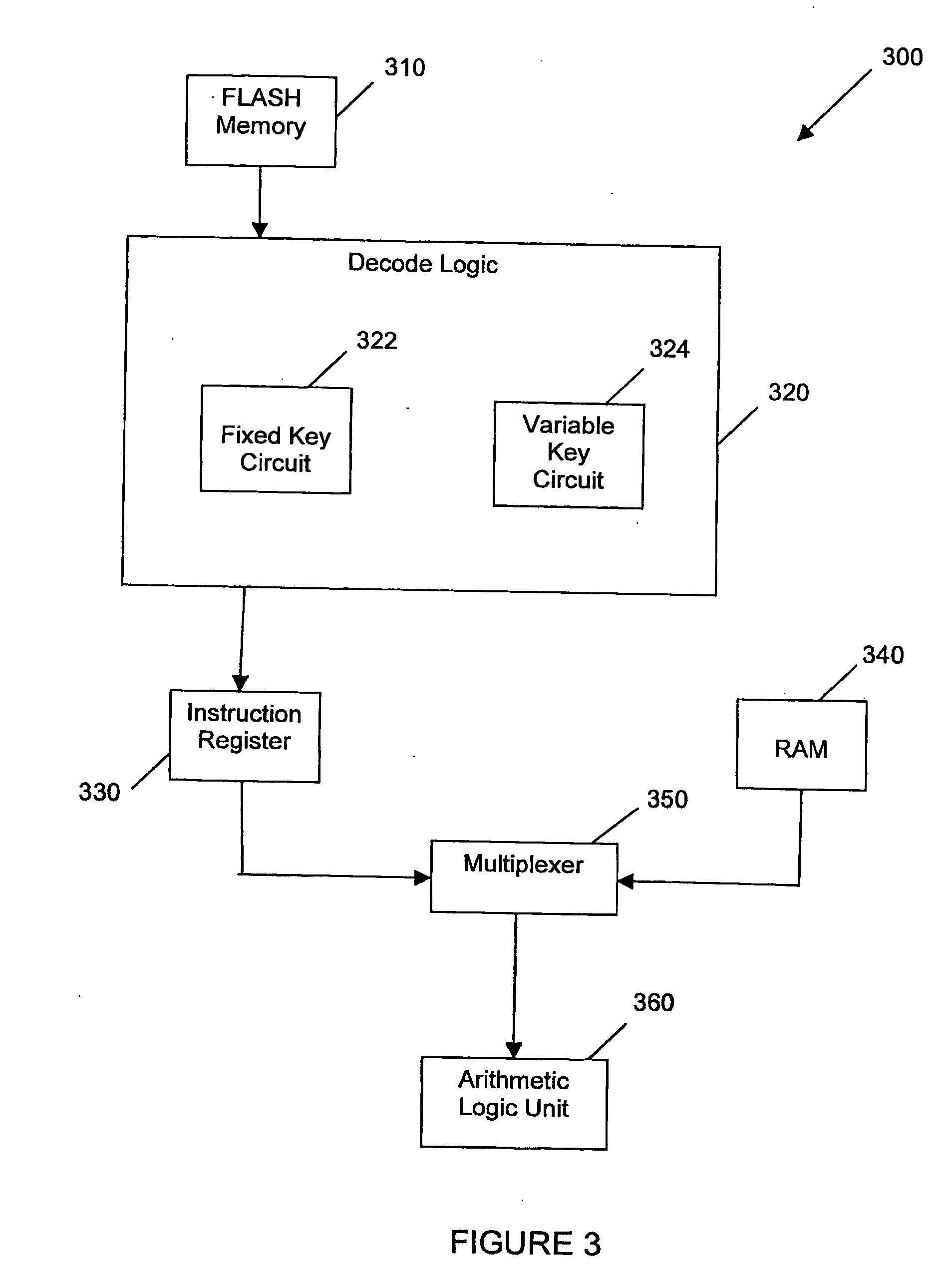
InactiveUS20070172053A1Improve securityAvoid loopholesData stream serial/continuous modificationUser identity/authority verificationByteEncryption
Embodiments of the invention relate generally to methods and systems for microprocessor data security, involving data encryption and decryption of stored data in, or in communication with, a computer microprocessor. Such encryption and decryption can be performed on a per-byte basis. Such encryption and decryption involves performing a logic operation on the byte using a decryption key or encryption key to generate a respective decrypted byte or encrypted byte. The key can be fixed or variable or a combination of both. The key is encoded in a dedicated hard-wired key circuit within the microprocessor and accessible to encryption and decryption circuitry within the microprocessor.
Owner:UNIVERSAL DATA PROTECTION CORP
Method, system and medium for analog encryption in a flash memory
ActiveUS20110302428A1Multiple keys/algorithms usageData stream serial/continuous modificationComputer scienceEncryption
A system and method for analog encryption and decryption, in which the encryption and encoding processes are interrelated, such that by failing to decrypt the retrieved data, decryption fails.
Owner:AVAGO TECH INT SALES PTE LTD
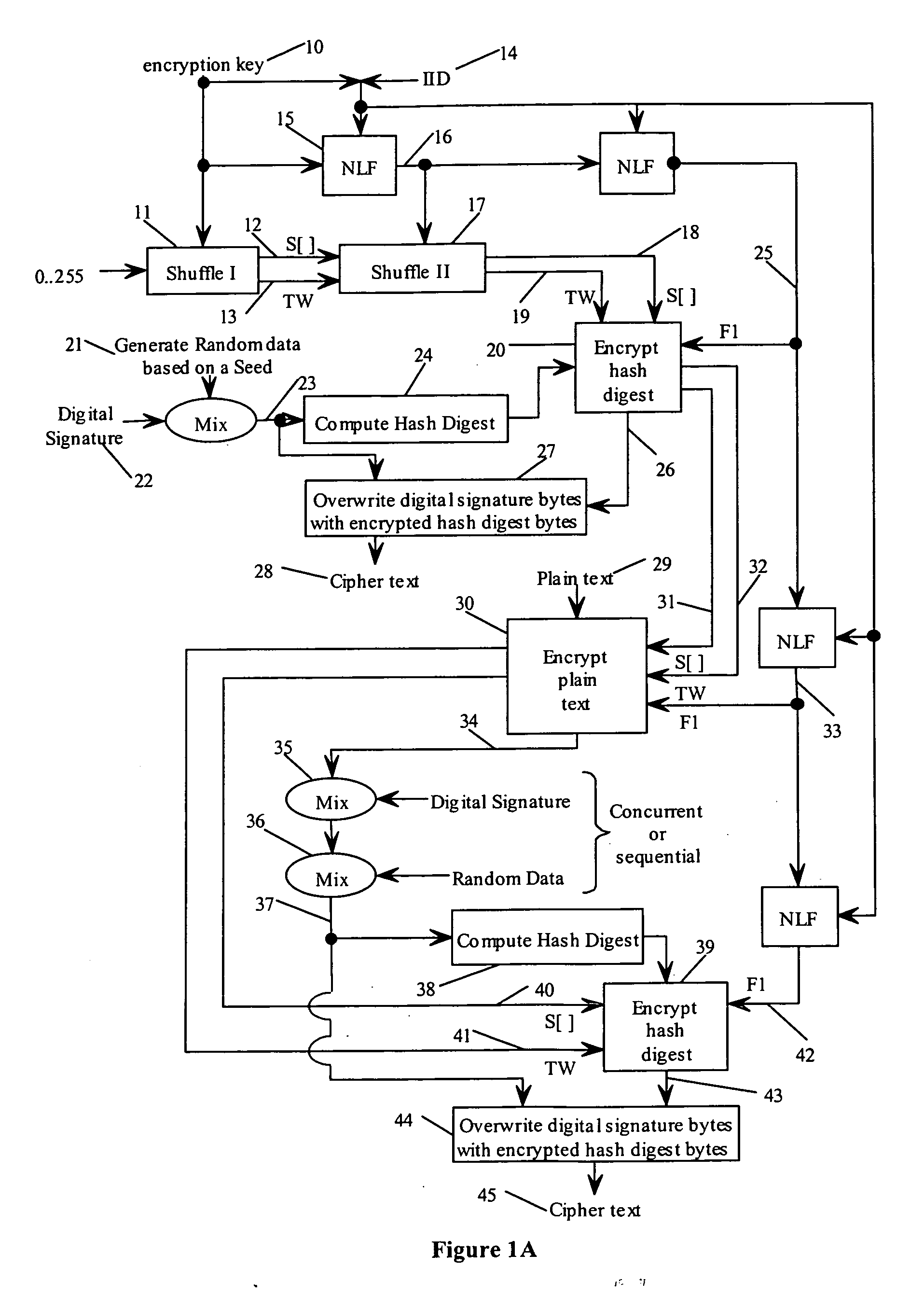
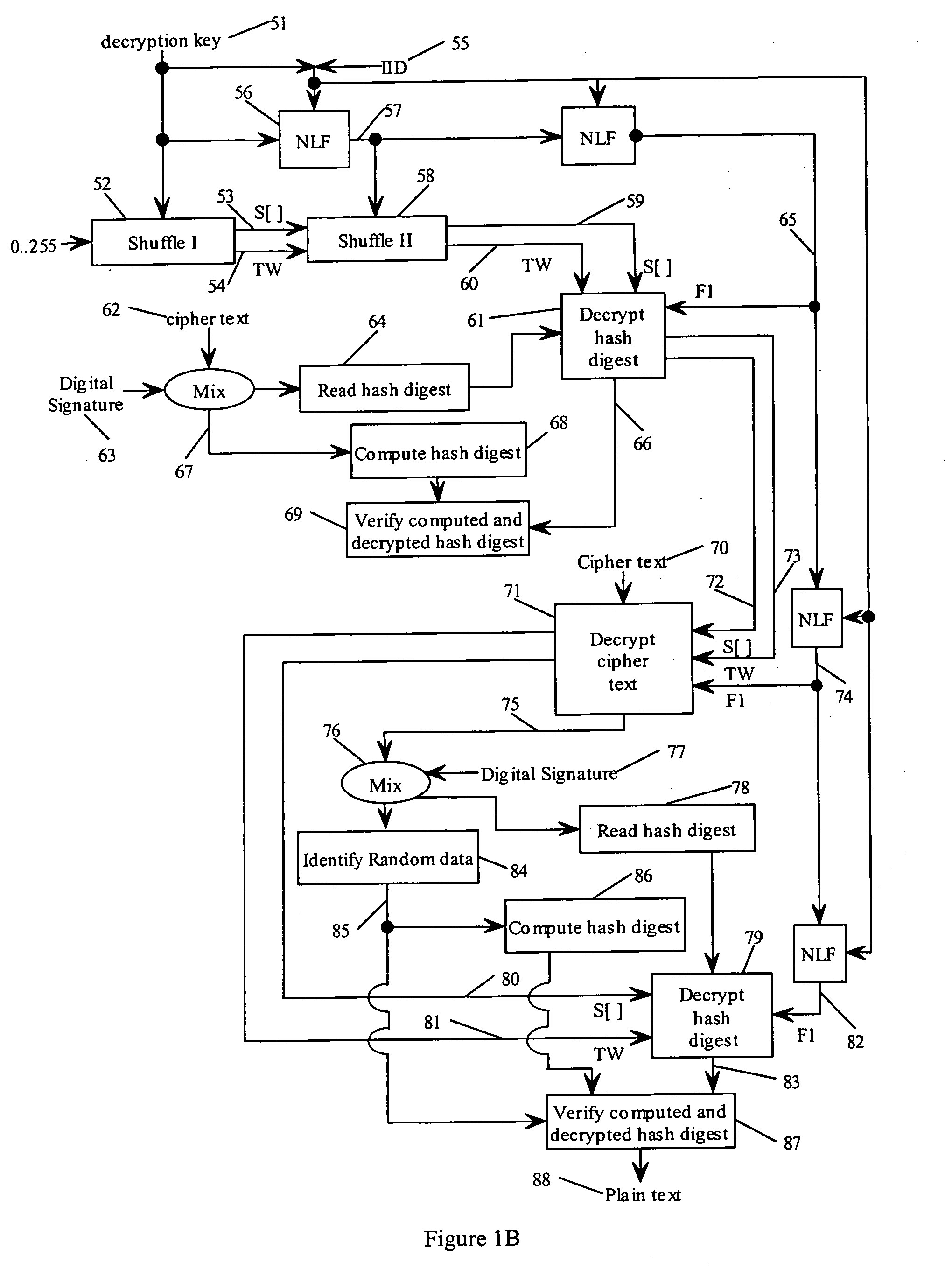
State-varying hybrid stream cipher
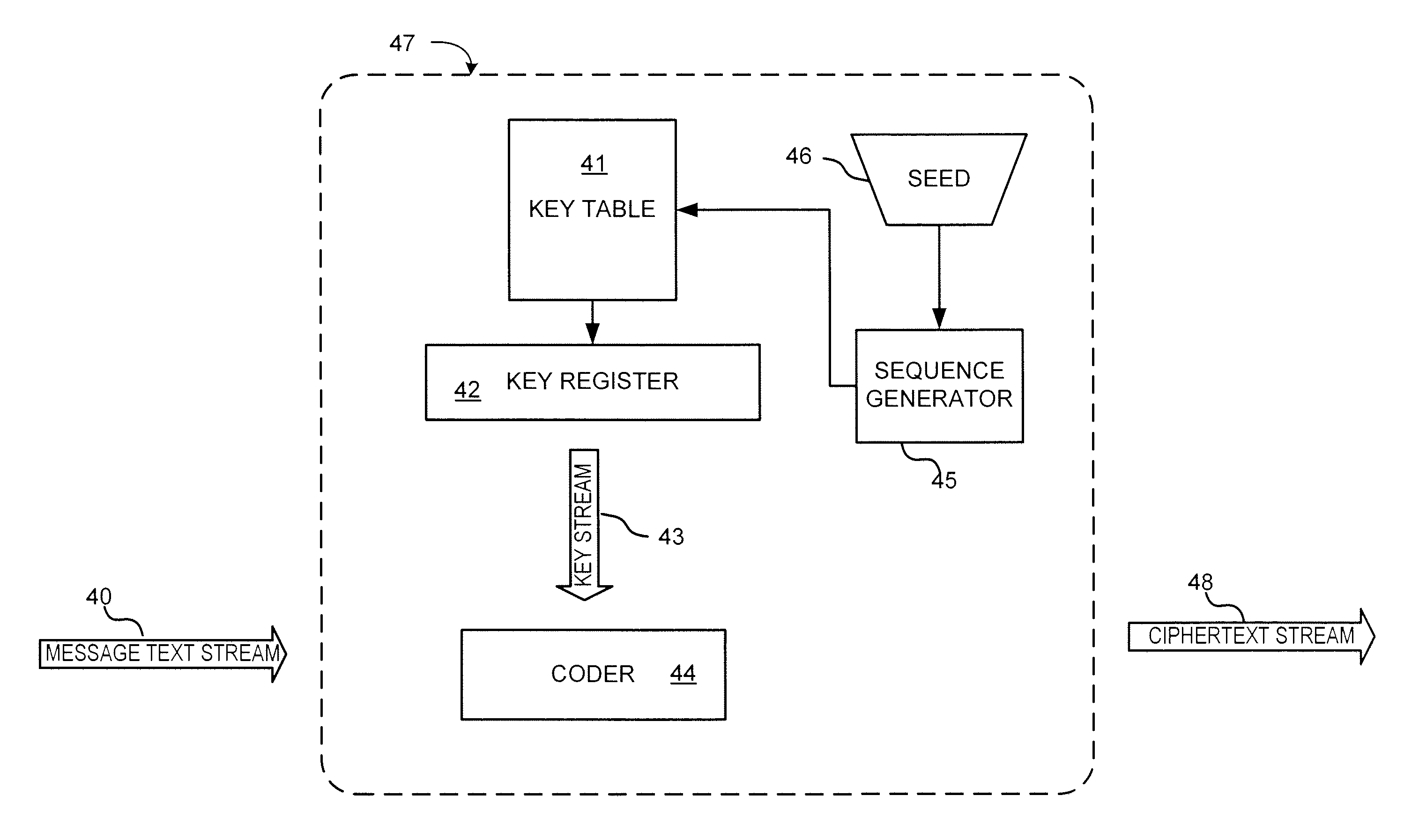
InactiveUS7103181B2Data stream serial/continuous modificationSecret communicationAlgorithmCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
Method for combining transfer functions with predetermined key creation
InactiveUS7664263B2Data stream serial/continuous modificationDigital data processing detailsComputer hardwareGranularity
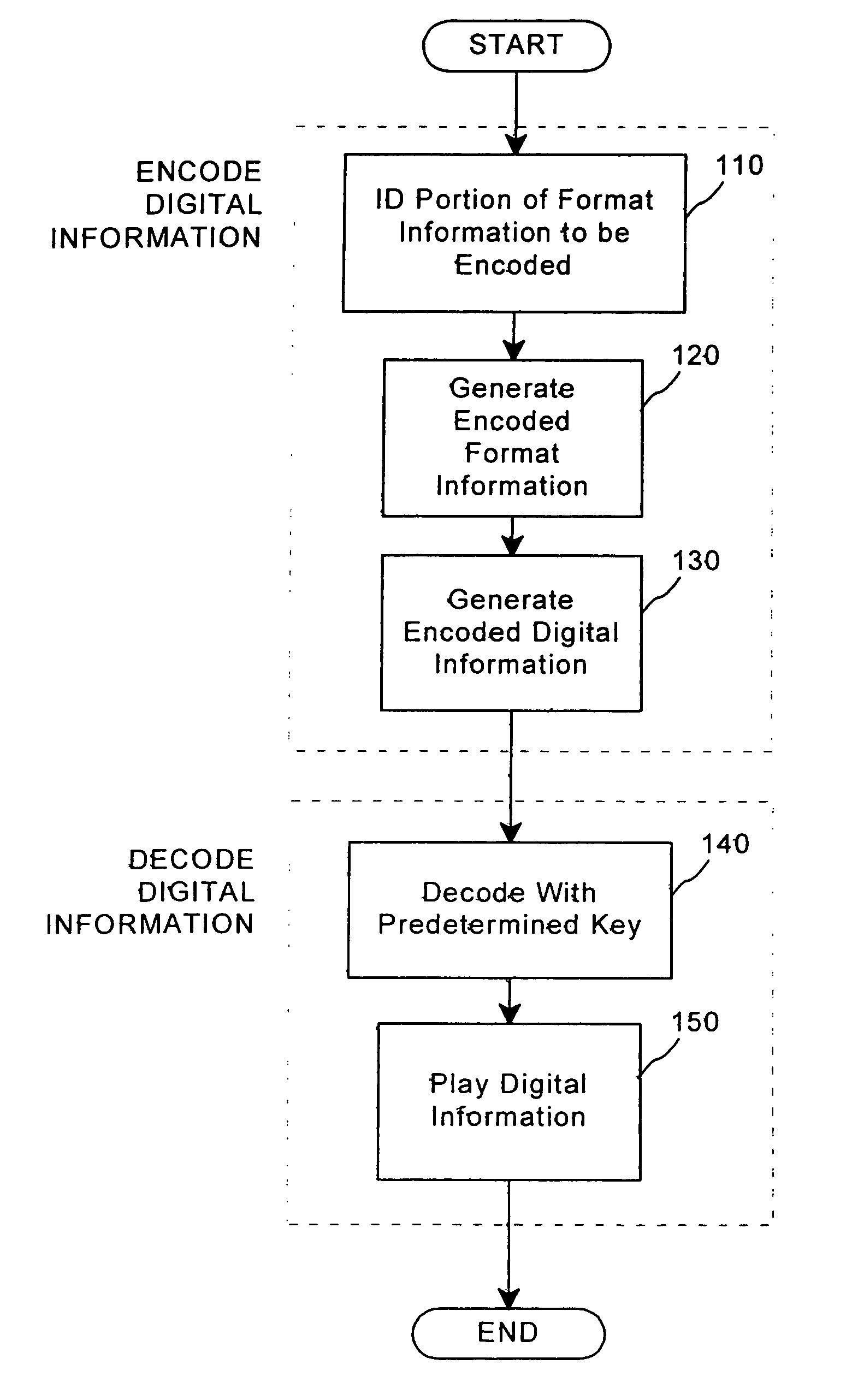
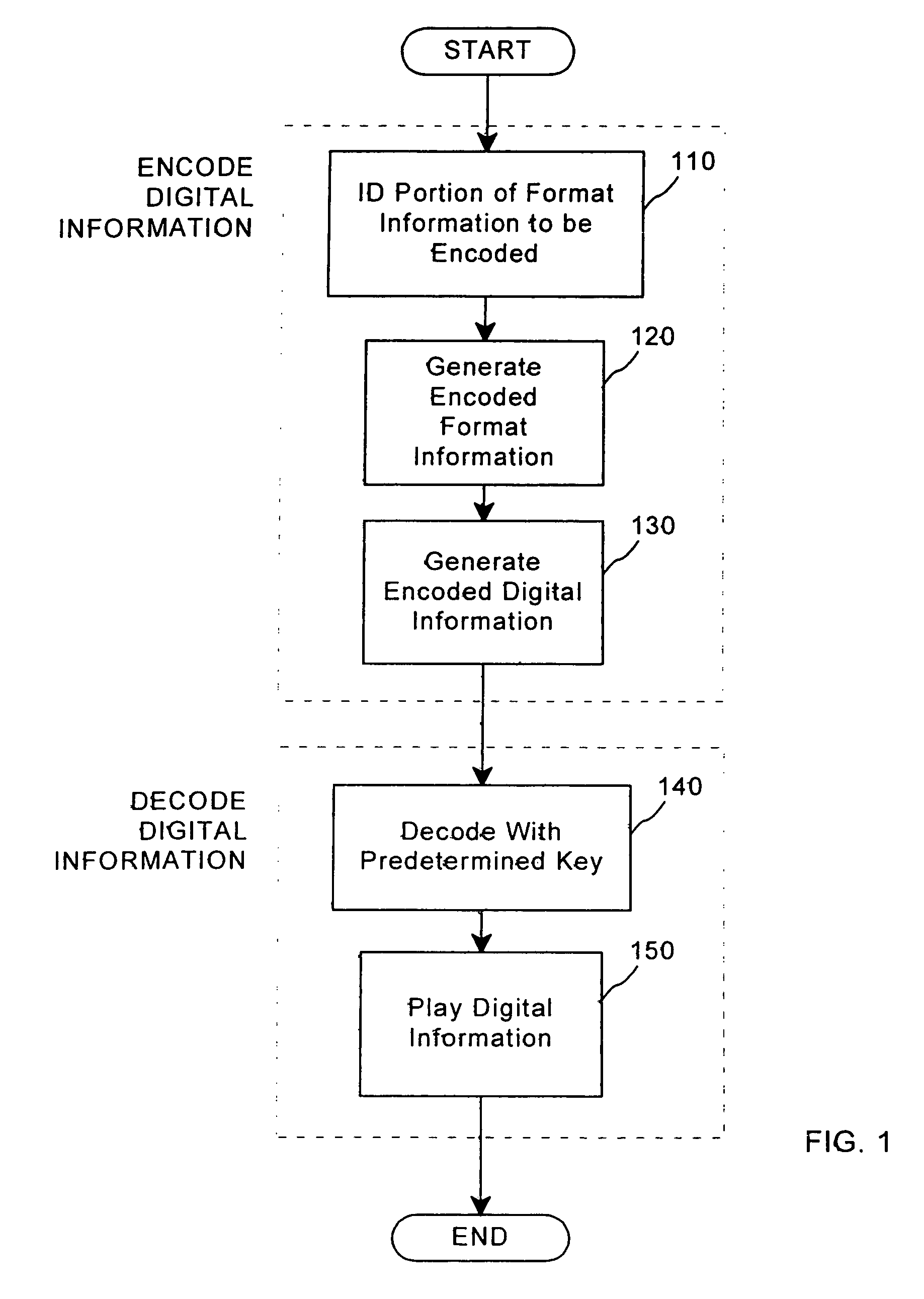
A method for combining transfer functions with predetermined key creation. In one embodiment, digital information, including a digital sample and format information, is protected by identifying and encoding a portion of the format information. Encoded digital information, including the digital sample and the encoded format information, is generated to protect the original digital information. In another embodiment, a digital signal, including digital samples in a file format having an inherent granularity, is protected by creating a predetermined key. The predetermined key is comprised of a transfer function-based mask set to manipulate data at the inherent granularity of the file format of the underlying digitized samples.
Owner:WISTARIA TRADING INC
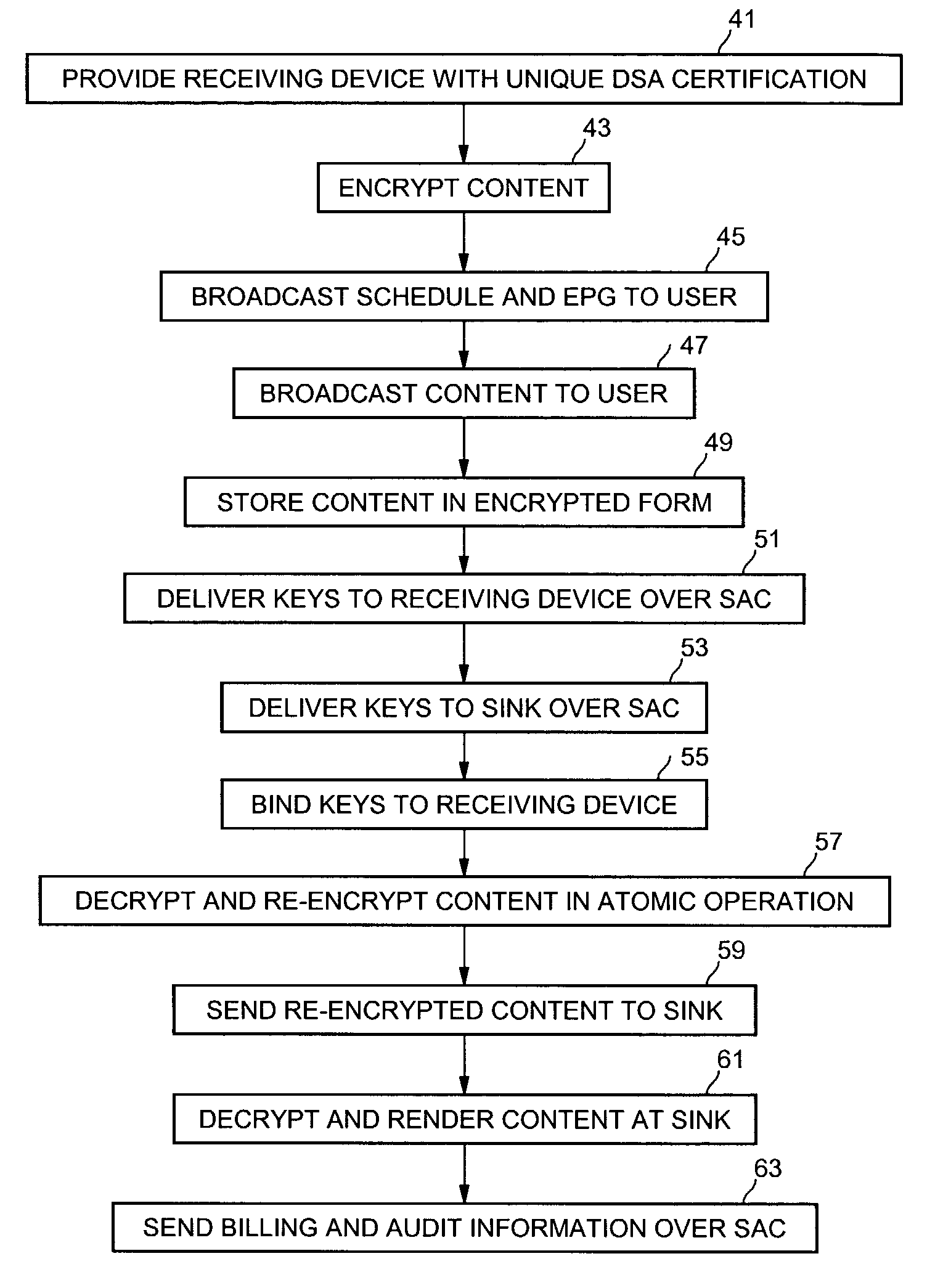
Secure Distribution of Content
InactiveUS20140310527A1Avoid attackKey distribution for secure communicationData stream serial/continuous modificationCryptosystemComputer science
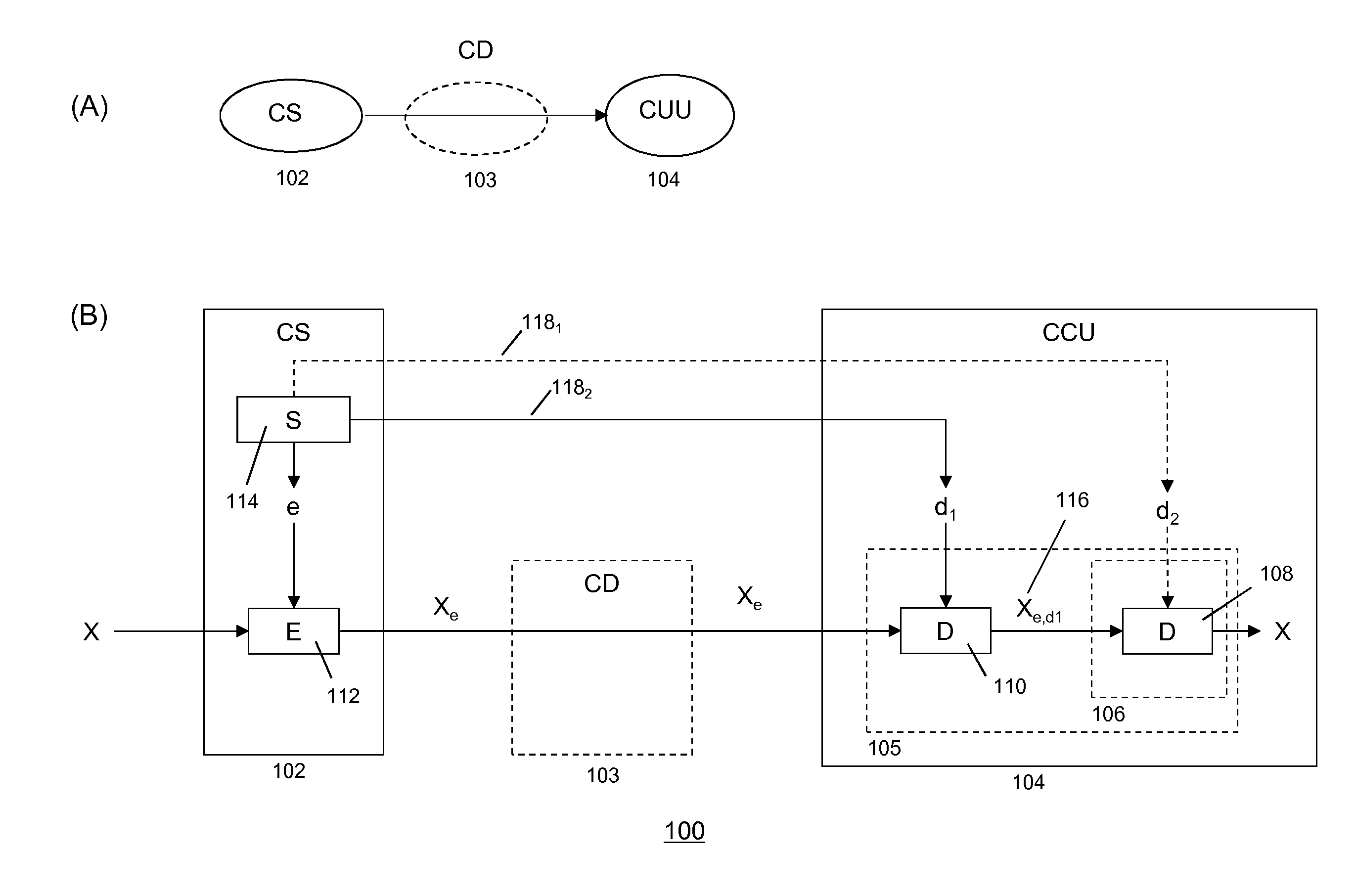
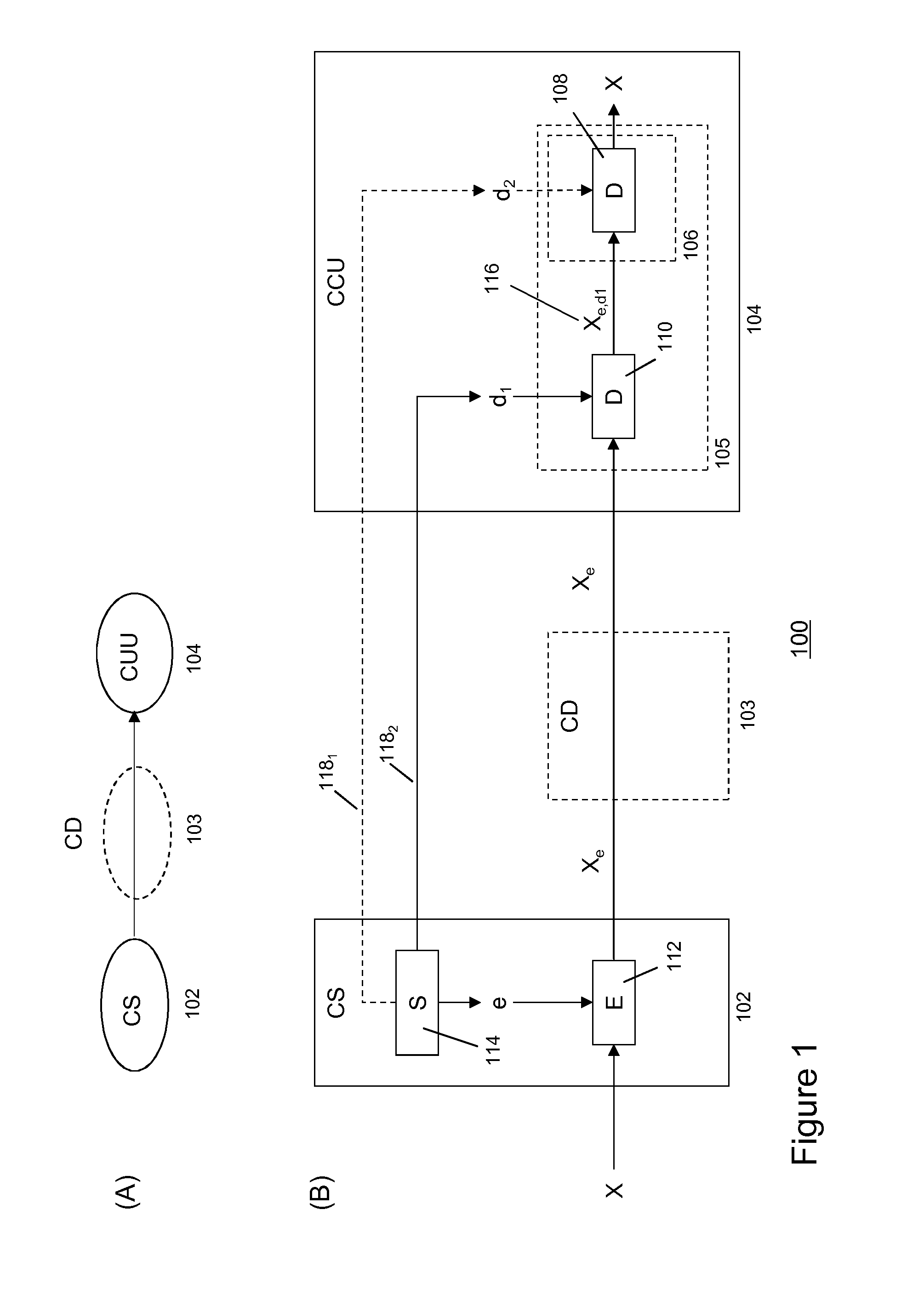
Methods and systems are described for enabling secure delivery of a content item from a content source to a content receiving device associated with a decryption module configured for use with a split-key cryptosystem comprising encryption and decryption algorithms E and D, a cipher algorithm for generating encryption and decryption keys e,d on the basis of secret information S and a split-key algorithm for splitting e and / or d into i different split-encryption keys e1, e2, . . . , ei and / or k different split-decryption keys d1, d2, . . . , dk respectively, such that Ddk(Ddk-1( . . . (Dd2(Dd1(Eei(Eei-1( . . . (Ee2(Ee1(X)) . . . ))=Ddk(Ddk-1( . . . (Dd2(Dd1(Xe1, e2, . . . , ei))=X wherein i,k≧1 and i+k>2, wherein the method comprises: provisioning said decryption module with first split-key information comprising at least a first split-key; generating second split-key information comprising at least a second split-key on the basis of said first split-key information, said decryption key d and, optionally, said secret information S; and, provisioning said decryption module with said at least second split-key 1 information for decrypting an encrypted content item Xe on the basis of said first and second split-key information and decryption algorithm D in said decryption module.
Owner:KONINK KPN NV +1
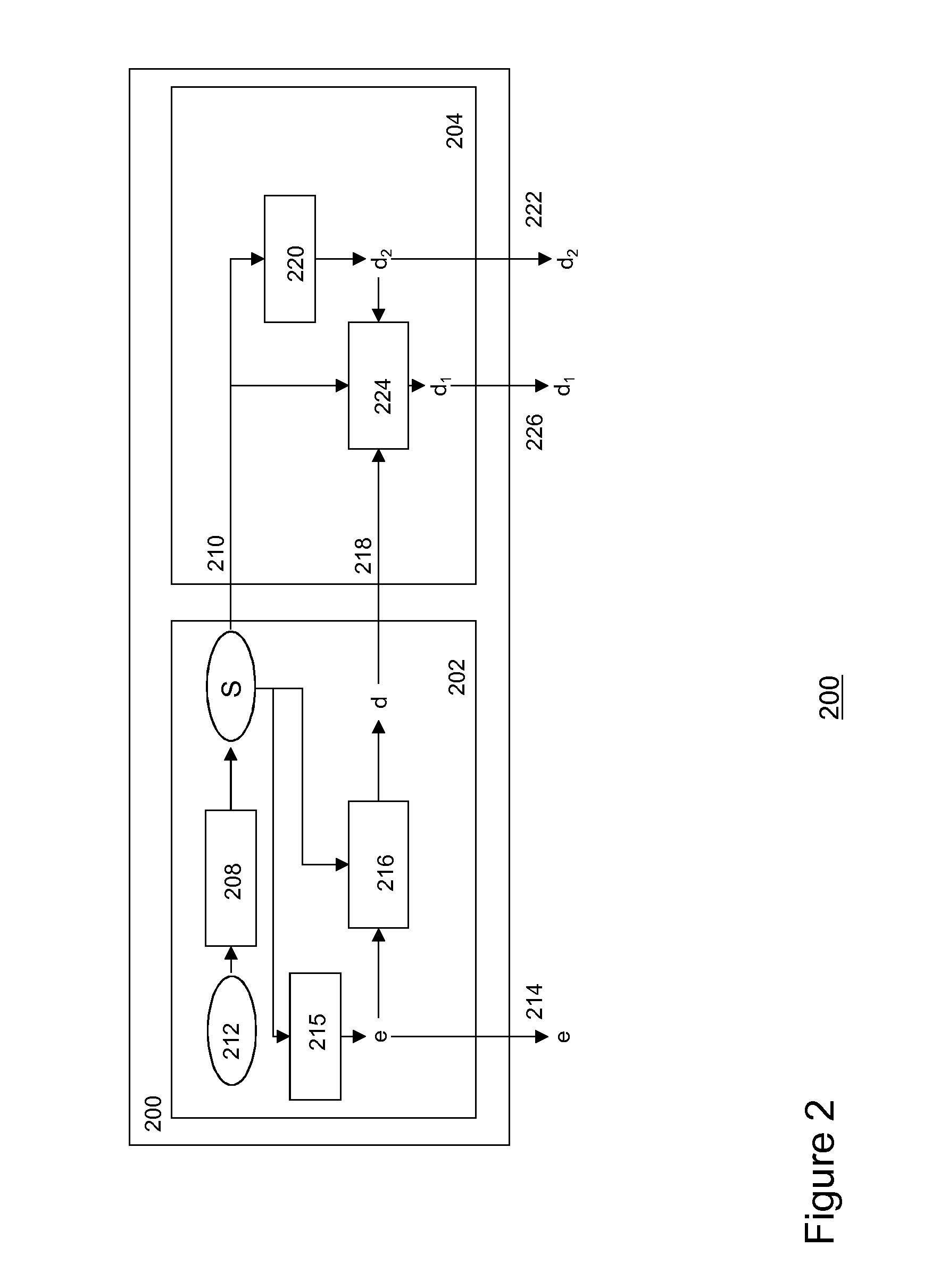
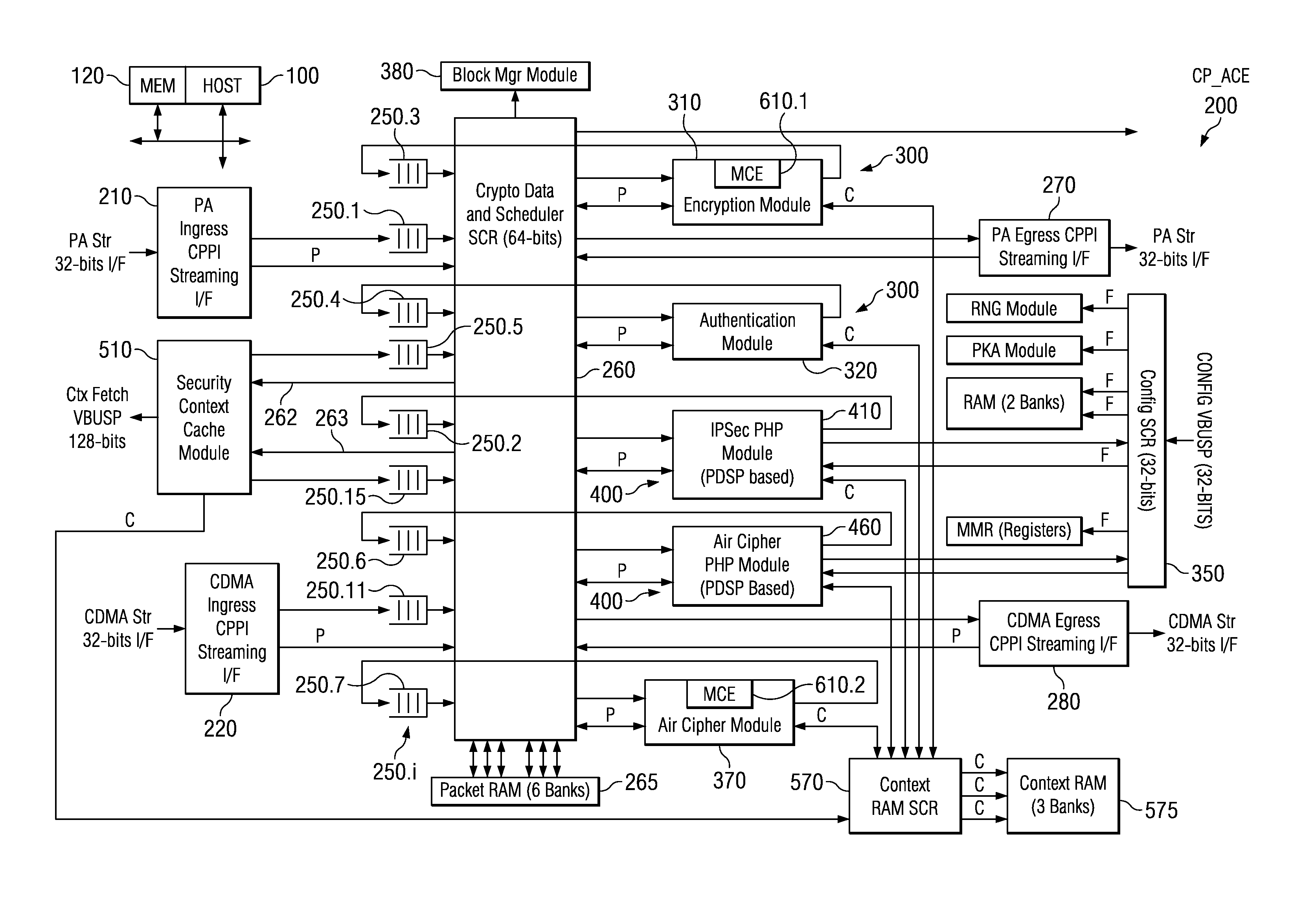
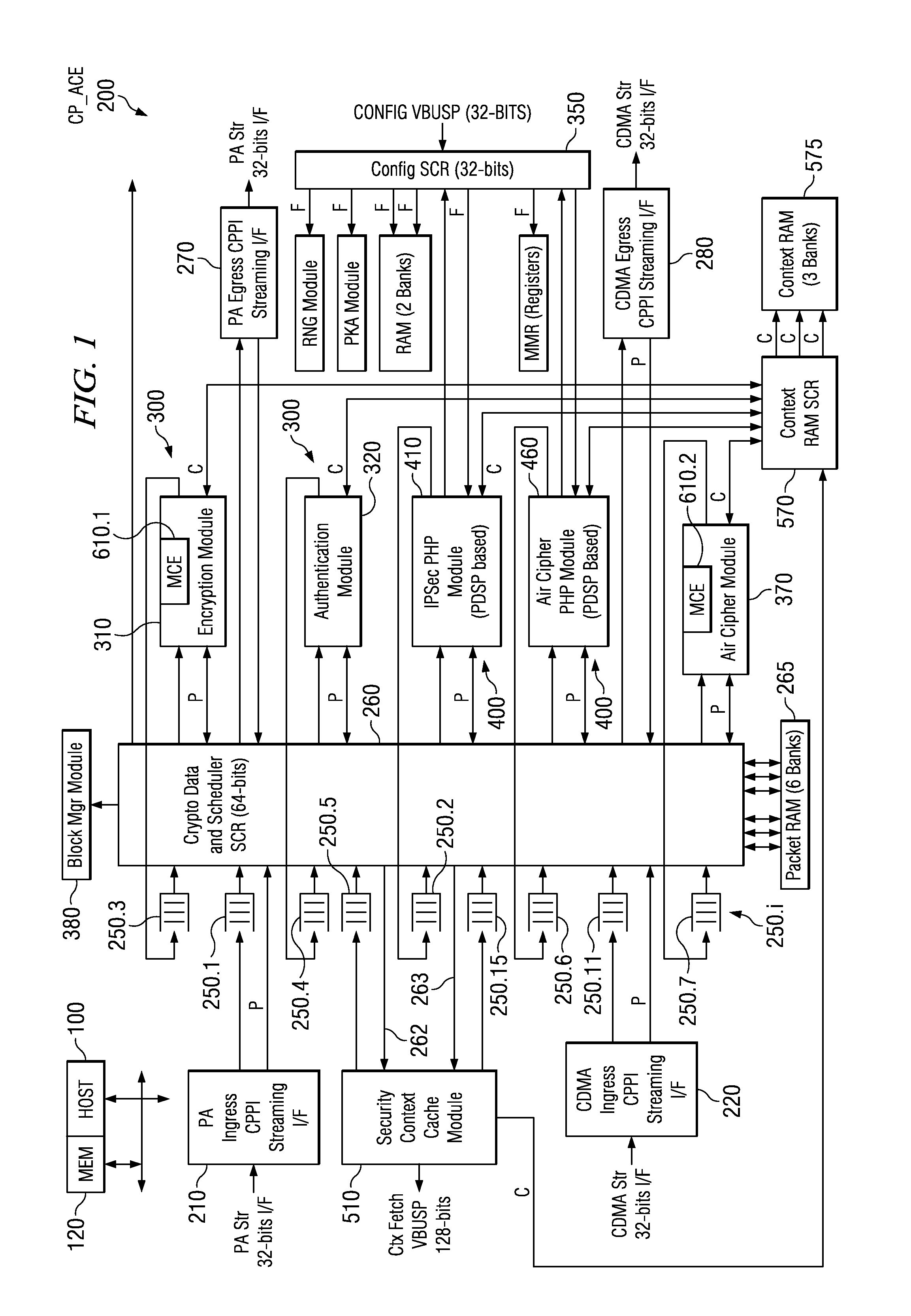
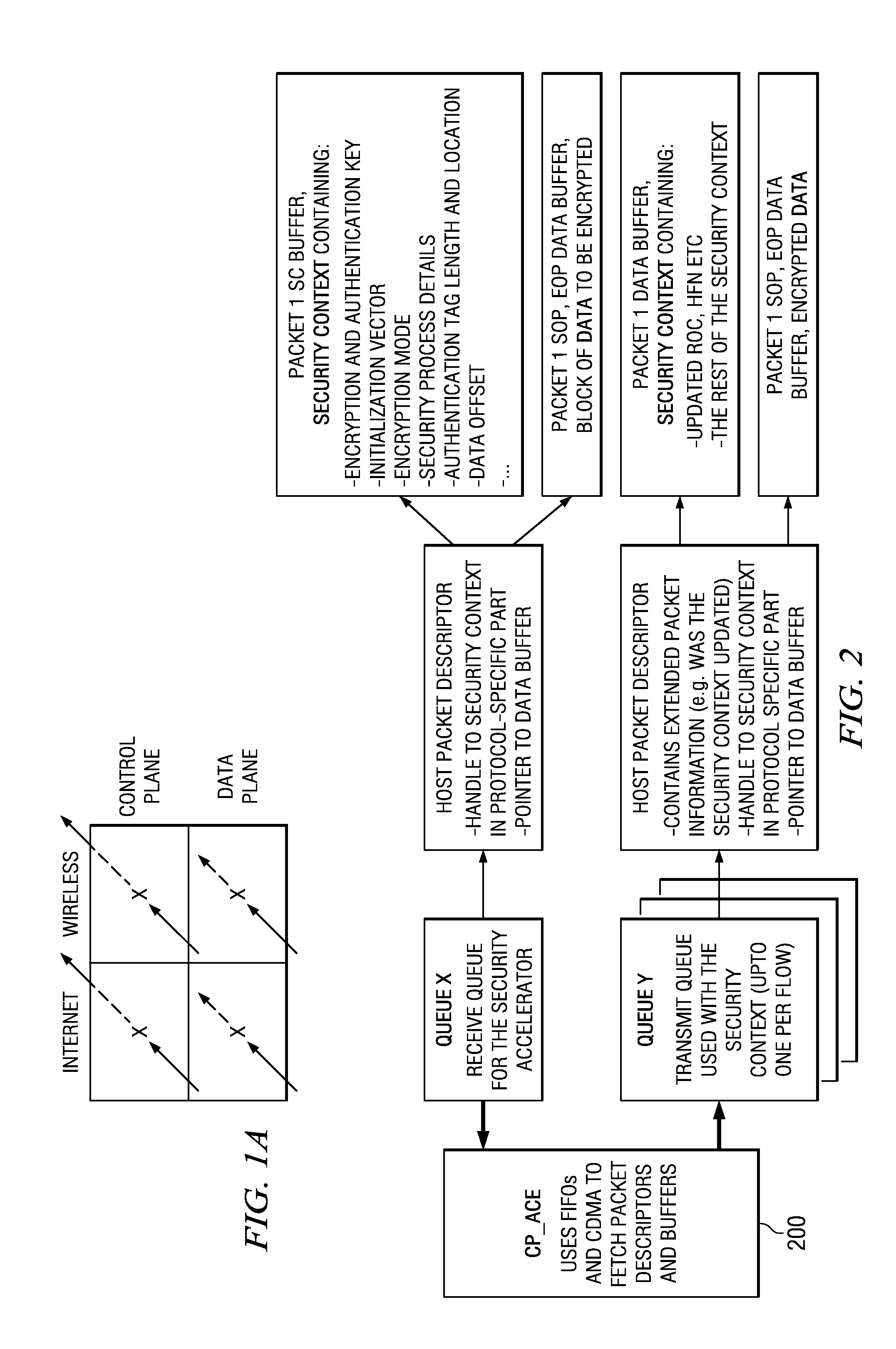
Security Processing Engines, Circuits and Systems and Adaptive Processes and Other Processes
ActiveUS20120011351A1Data stream serial/continuous modificationUser identity/authority verificationSafe handlingMaster processor
An electronic circuit (200) includes one or more programmable control-plane engines (410, 460) operable to process packet header information and form at least one command, one or more programmable data-plane engines (310, 320, 370) selectively operable for at least one of a plurality of cryptographic processes selectable in response to the at least one command, and a programmable host processor (100) coupled to such a data-plane engine (310) and such a control-plane engine (410). Other processors, circuits, devices and systems and processes for their operation and manufacture are disclosed.
Owner:TEXAS INSTR INC
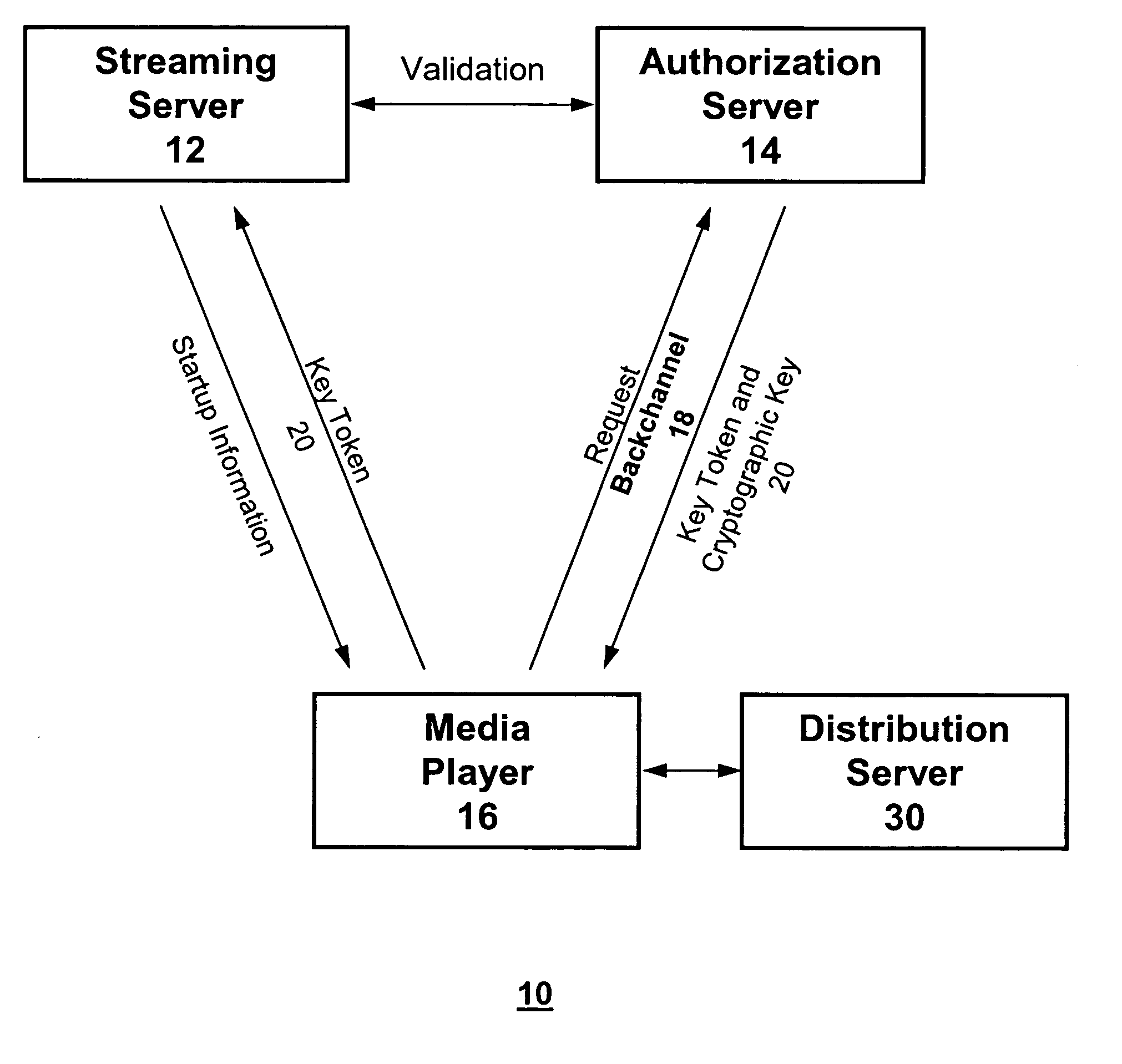
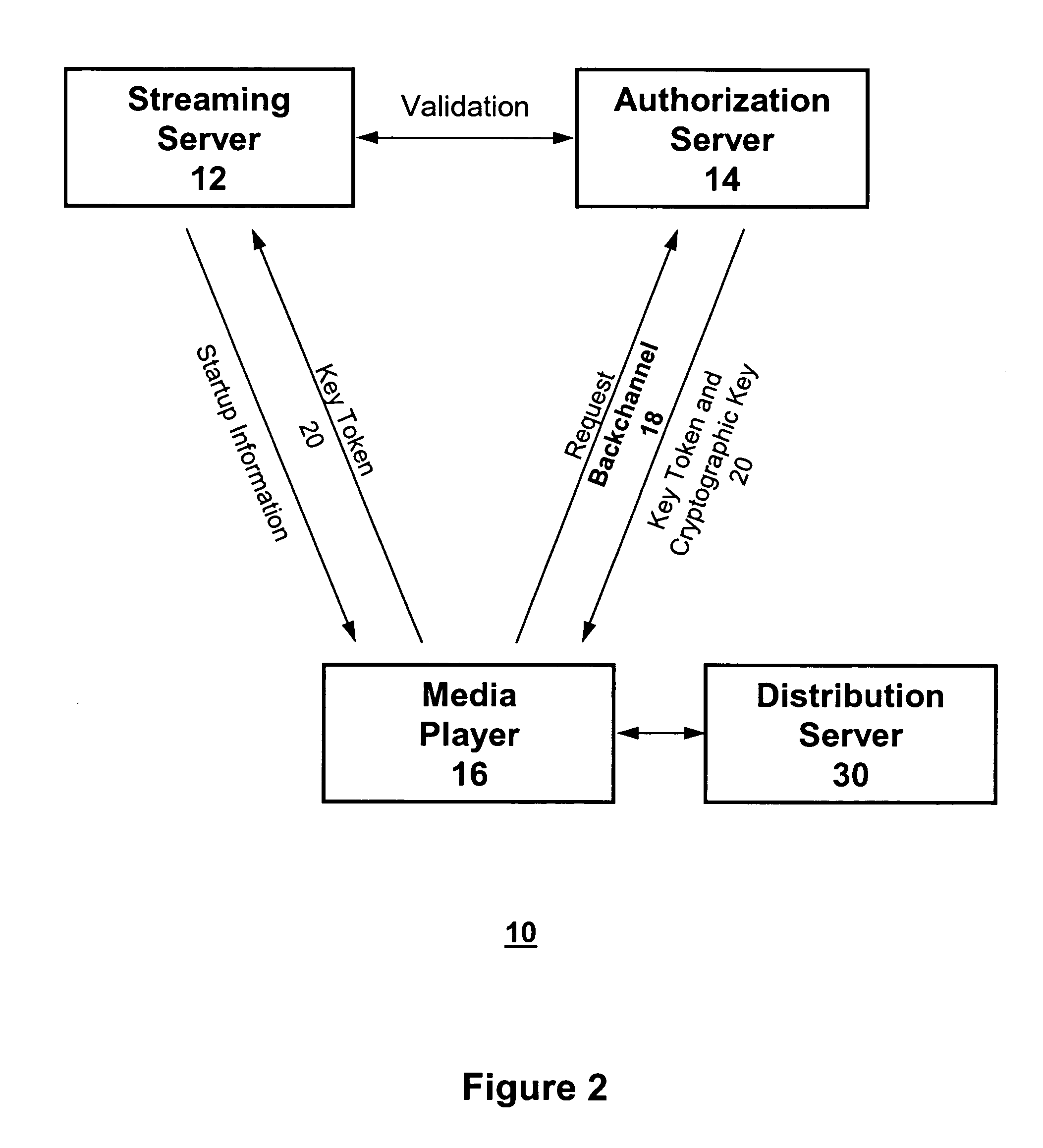
Method and system for authorizing multimedia multicasting
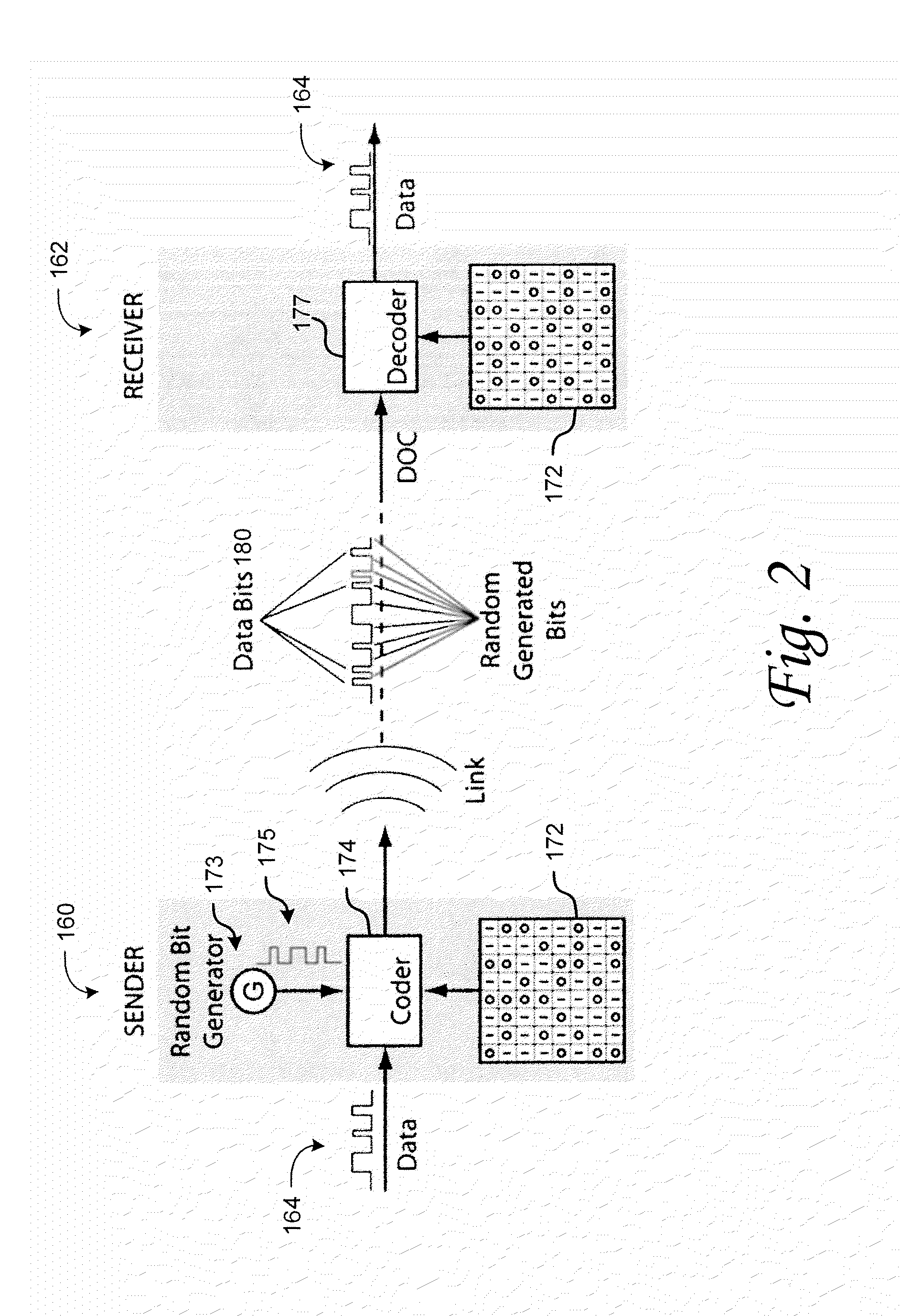
ActiveUS20060085862A1Improve securityMinimize bandwidthRandom number generatorsTelevision conference systemsData streamAuthorization
A multicasting authorization system comprises a streaming server, an authorization server, a user system and a distribution server. The distribution server provides a multicast data stream over multicast channels. A user system requests and receives an authorization code from an authorization server to receive the multicast data stream, and provides the authorization code to a streaming server. A streaming server, coupled to both an authorization server and a user system sends start up information for accessing the multicast data stream to the user system upon validation of the authorization code. The multicast datastream is encrypted and the user system maintains a connection with the authorization server which provides a cryptographic key for use in decrypting the encrypted multicast datastream.
Owner:VECTORMAX CORP
Chaotic cipher system and method for secure communication
ActiveUS20120250863A1Key distribution for secure communicationData stream serial/continuous modificationSecure communicationArray data structure
The present invention provides a method for a data encryption device to perform network communications, the method comprising obtaining an indexed array of encryption keys, wherein the indexed array of encryption keys is shared with a data decryption device; obtaining a message to be encrypted; using a first random or pseudorandom number to determine an index; obtaining a first key from the array of encryption keys, wherein the first key corresponds to the index; selecting a second key from the plurality of encryption keys; encrypting the message using the first key and a second random or pseudorandom number; encrypting the index using the second key and a third random or pseudorandom number; transmitting the encrypted message and the encrypted index to the data decryption device.
Owner:MERCURY MISSION SYST LLC
Secured redundant memory subsystem
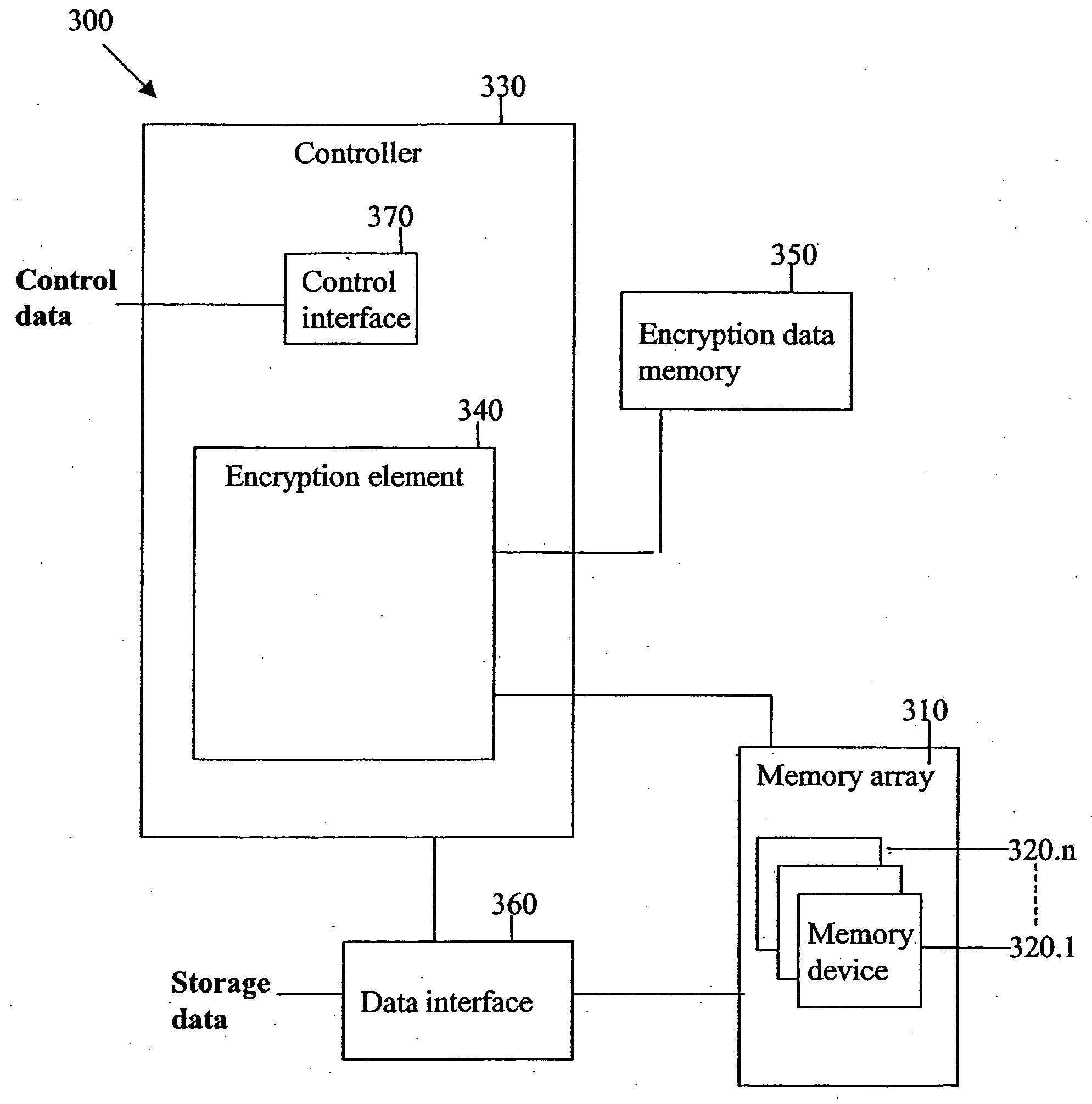
InactiveUS20060053308A1Easy accessData stream serial/continuous modificationUser identity/authority verificationSolid-state storageRAID
A storage device consists of multiple solid state memory devices and a memory controller. The memory devices are configured as a redundant array, such as a RAID memory array. The memory controller performs data encryption to provide secured access to the array. The encryption may be performed with an encryption data sequence which is stored on a separate memory element.
Owner:RAIDY 2 GO
Method and apparatus for encrypting data transmitted over a serial link
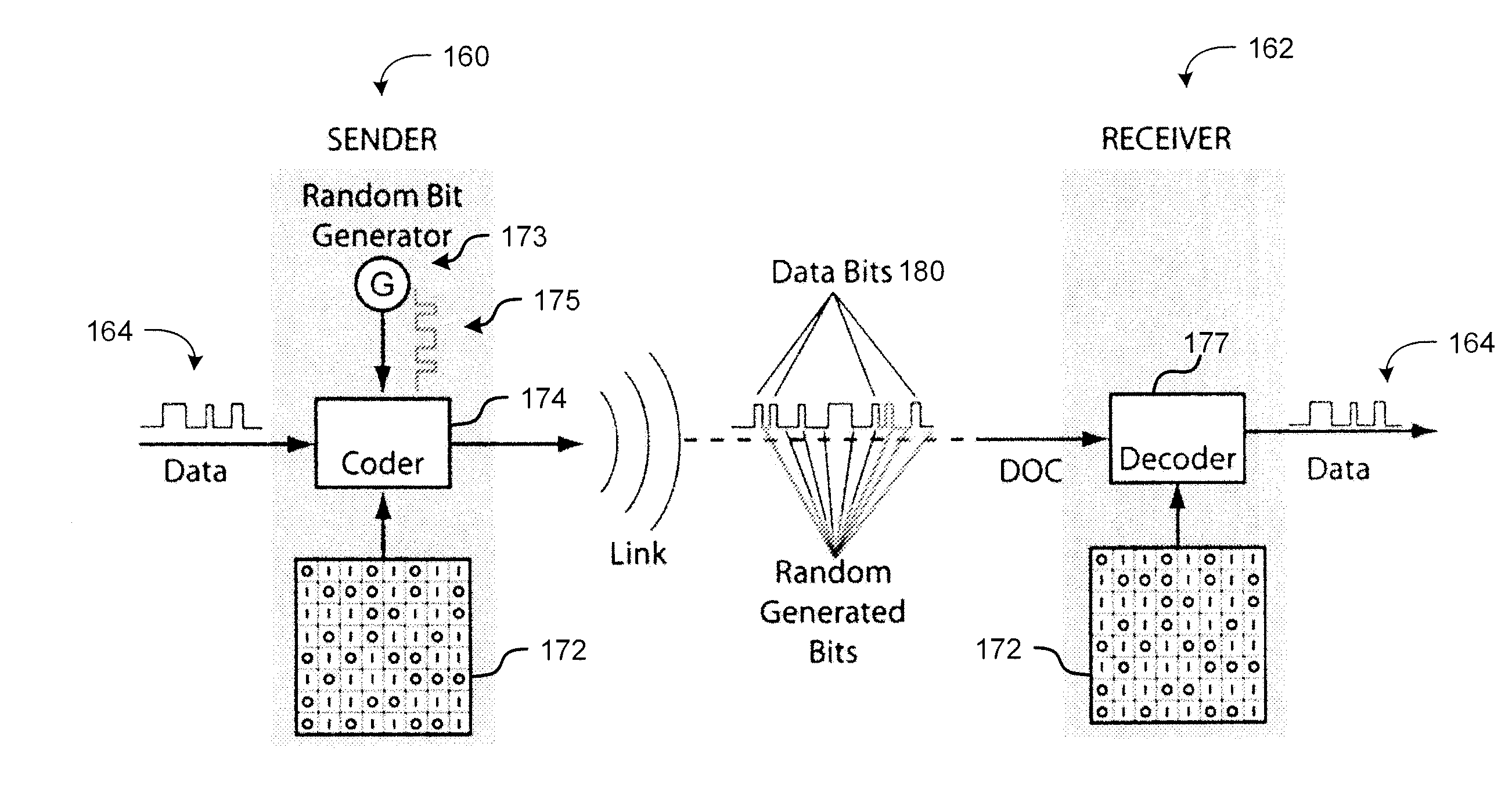
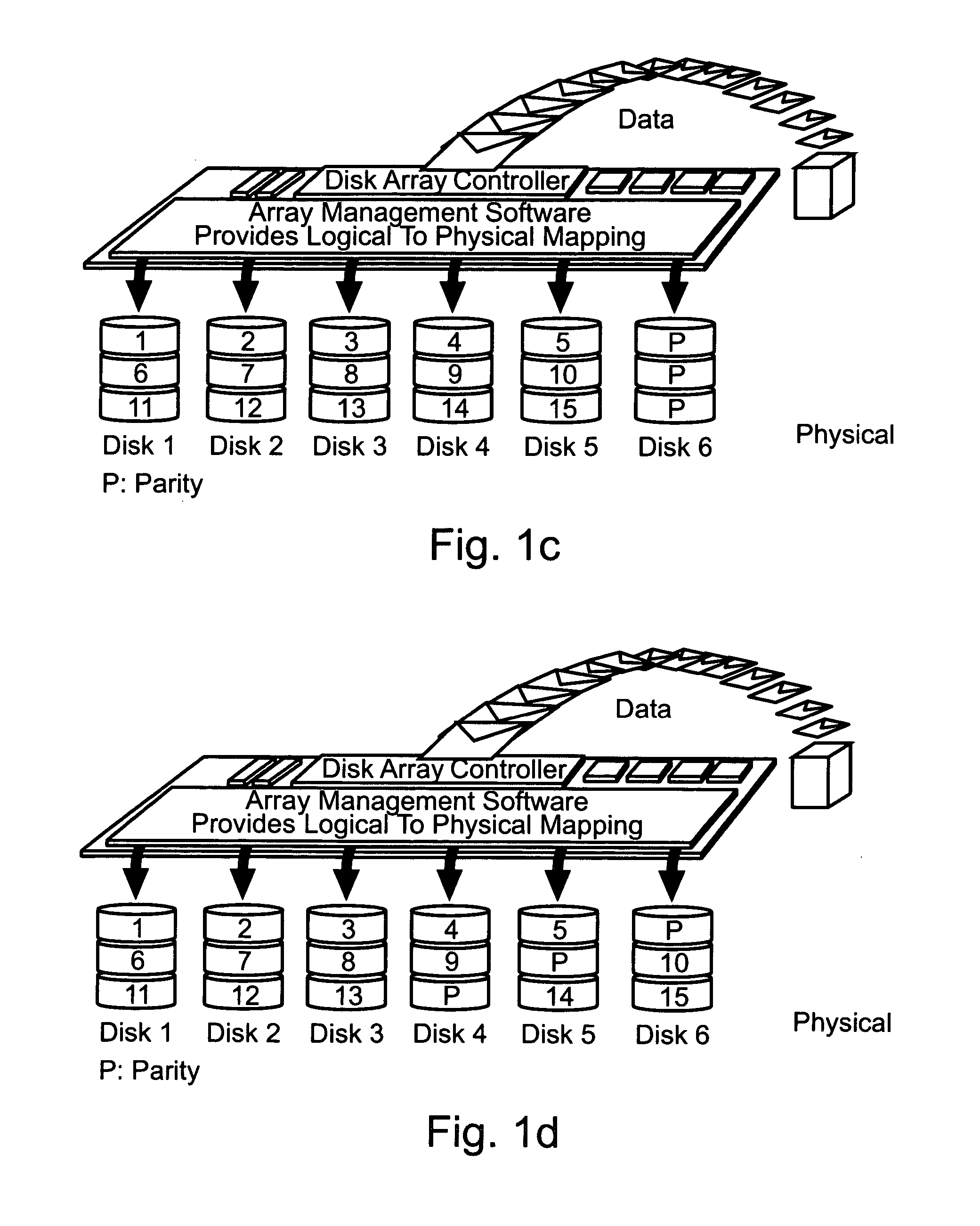
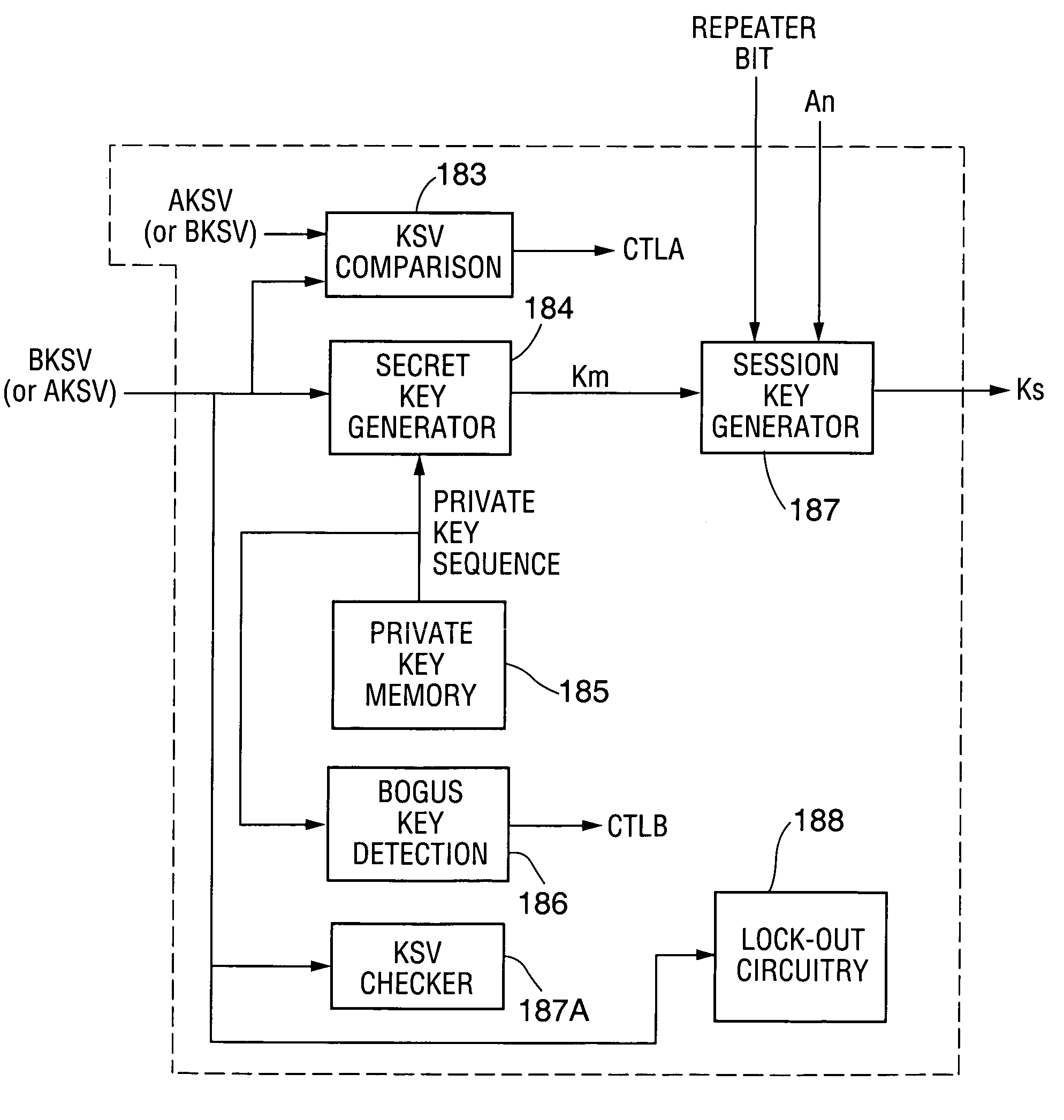
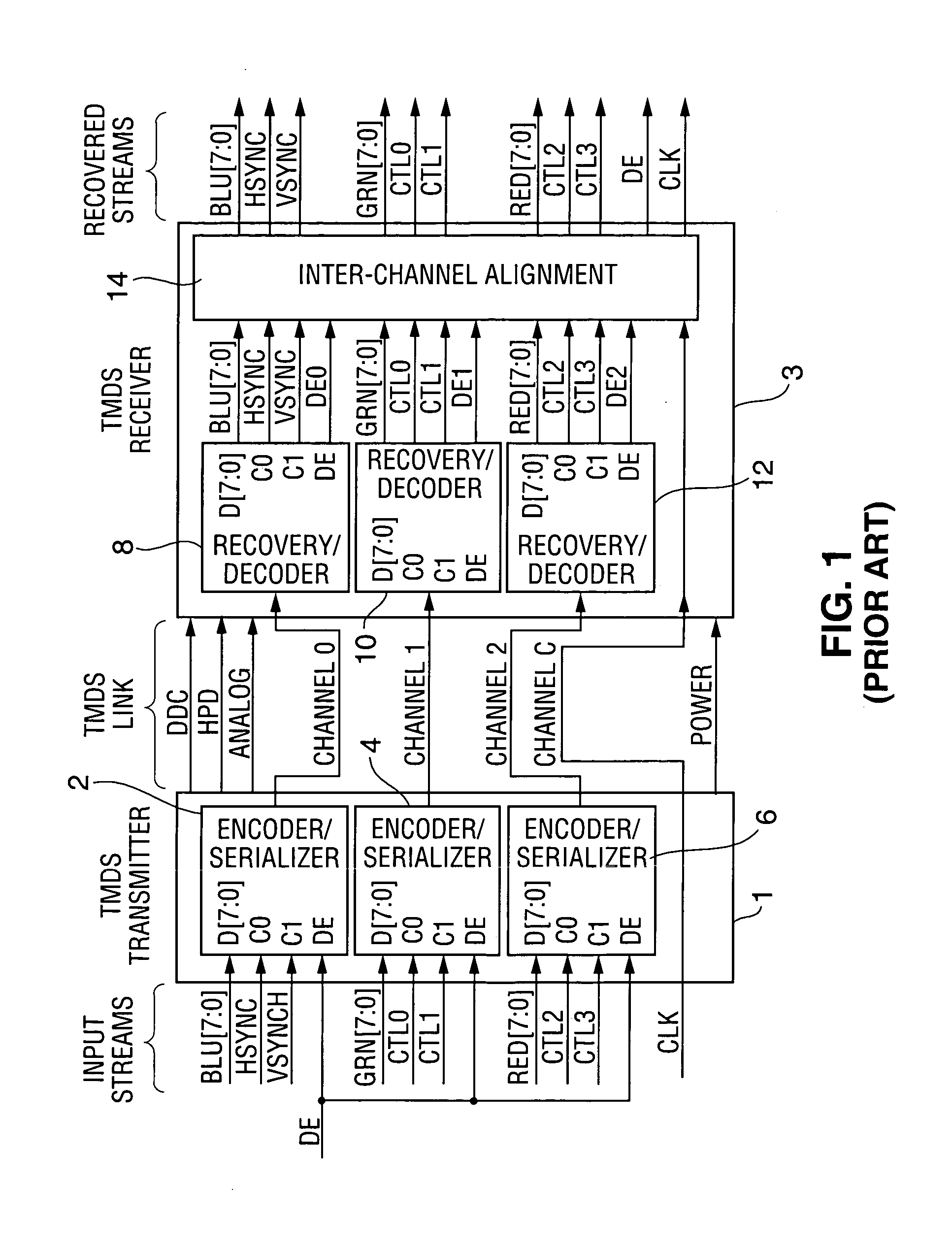
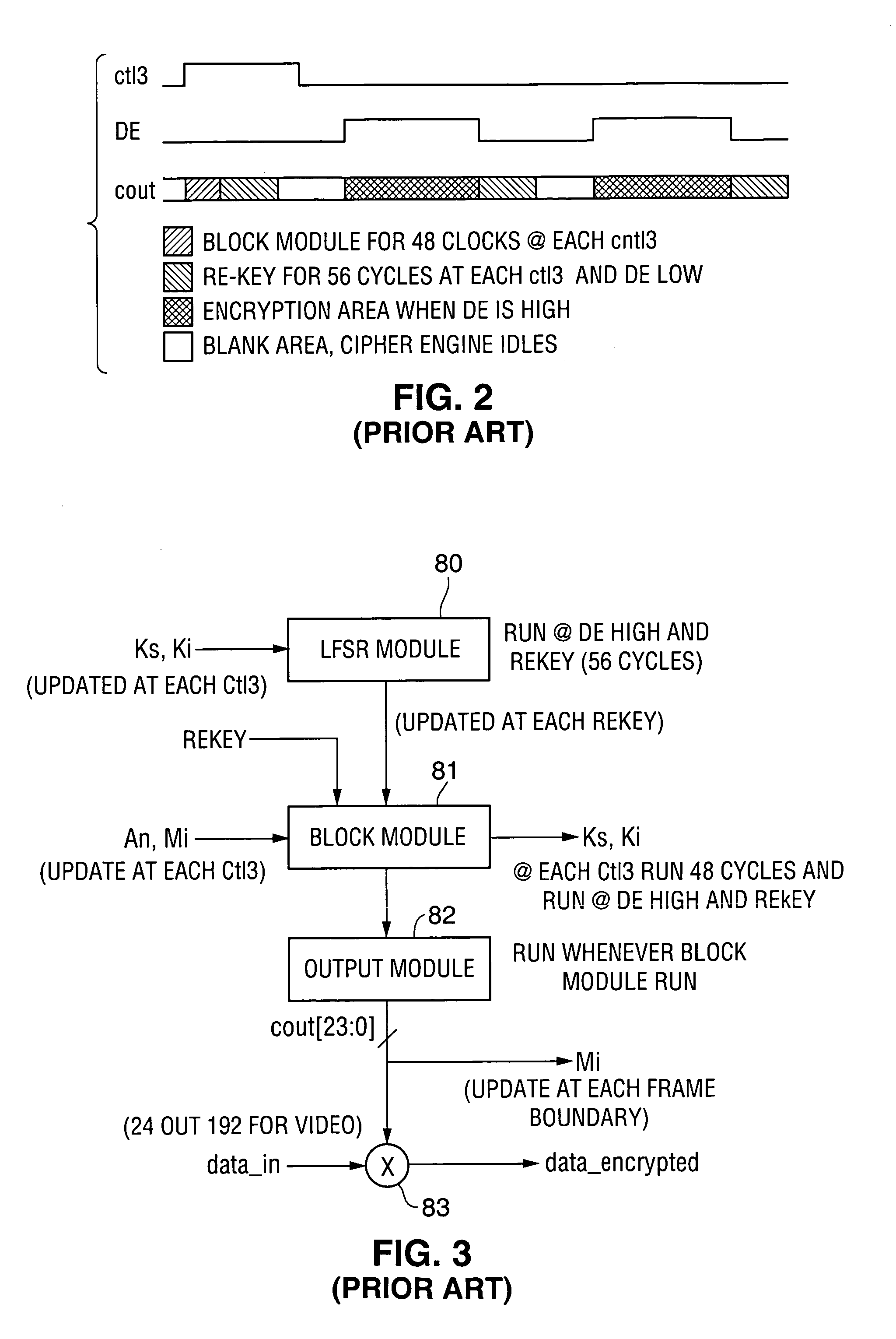
ActiveUS7131004B1Improve performanceSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer hardwareCommunications system
A communication system including a transmitter, a receiver, and a serial link (for example, a TMDS-like link) in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such systems, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for authenticating a receiver prior to transmission of encrypted data to the receiver over a serial link. Each transmitter, receiver, and cipher engine is configured to implement a content protection protocol in a manner that implements at least one and preferably more than one of a class of attack prevention features disclosed herein. In preferred embodiments the invention is employed to encrypt data in accordance with the High-bandwidth Digital Content Protection (“HDCP”) protocol, or a modified version of the HDCP protocol.
Owner:LATTICE SEMICON CORP
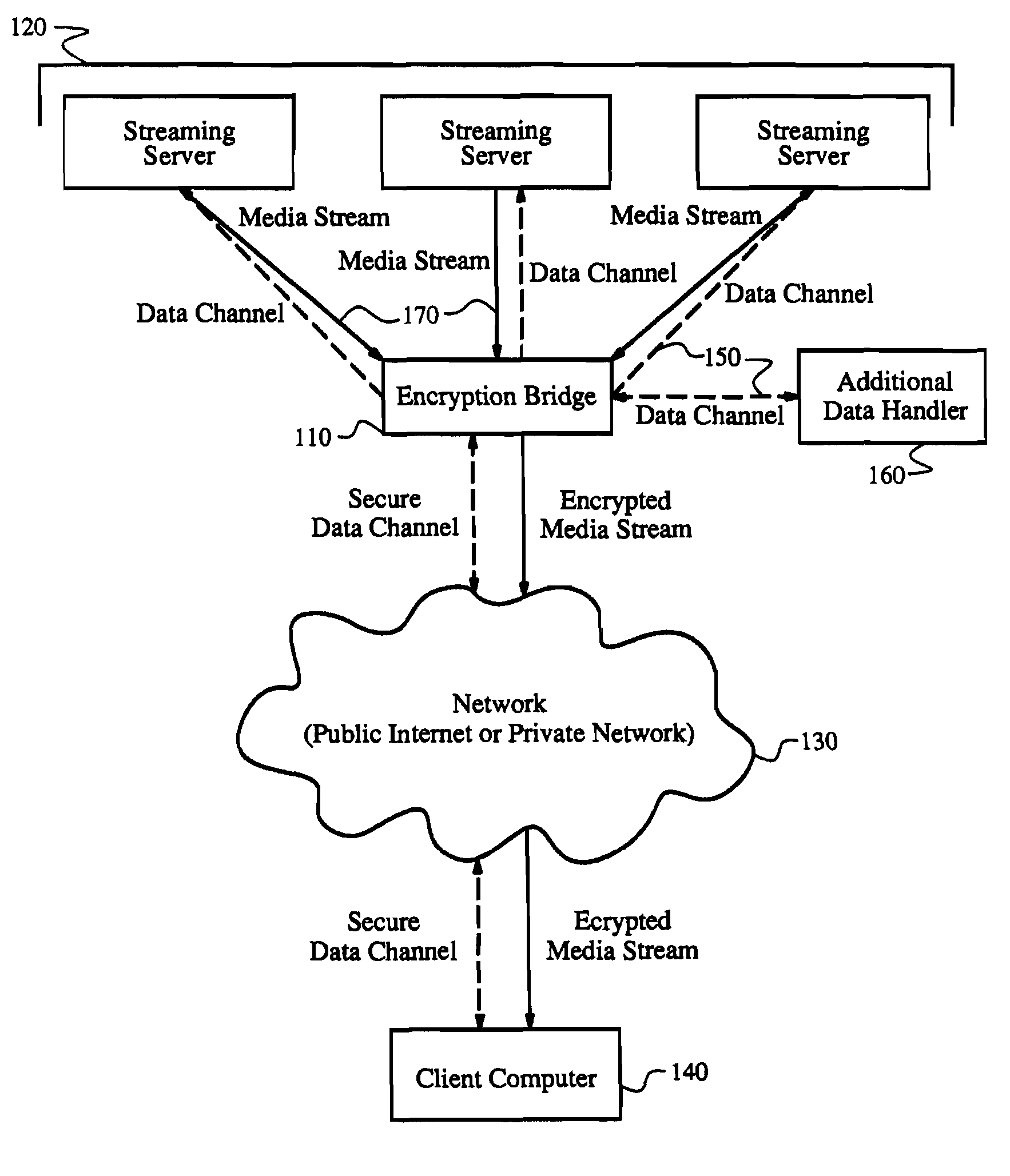
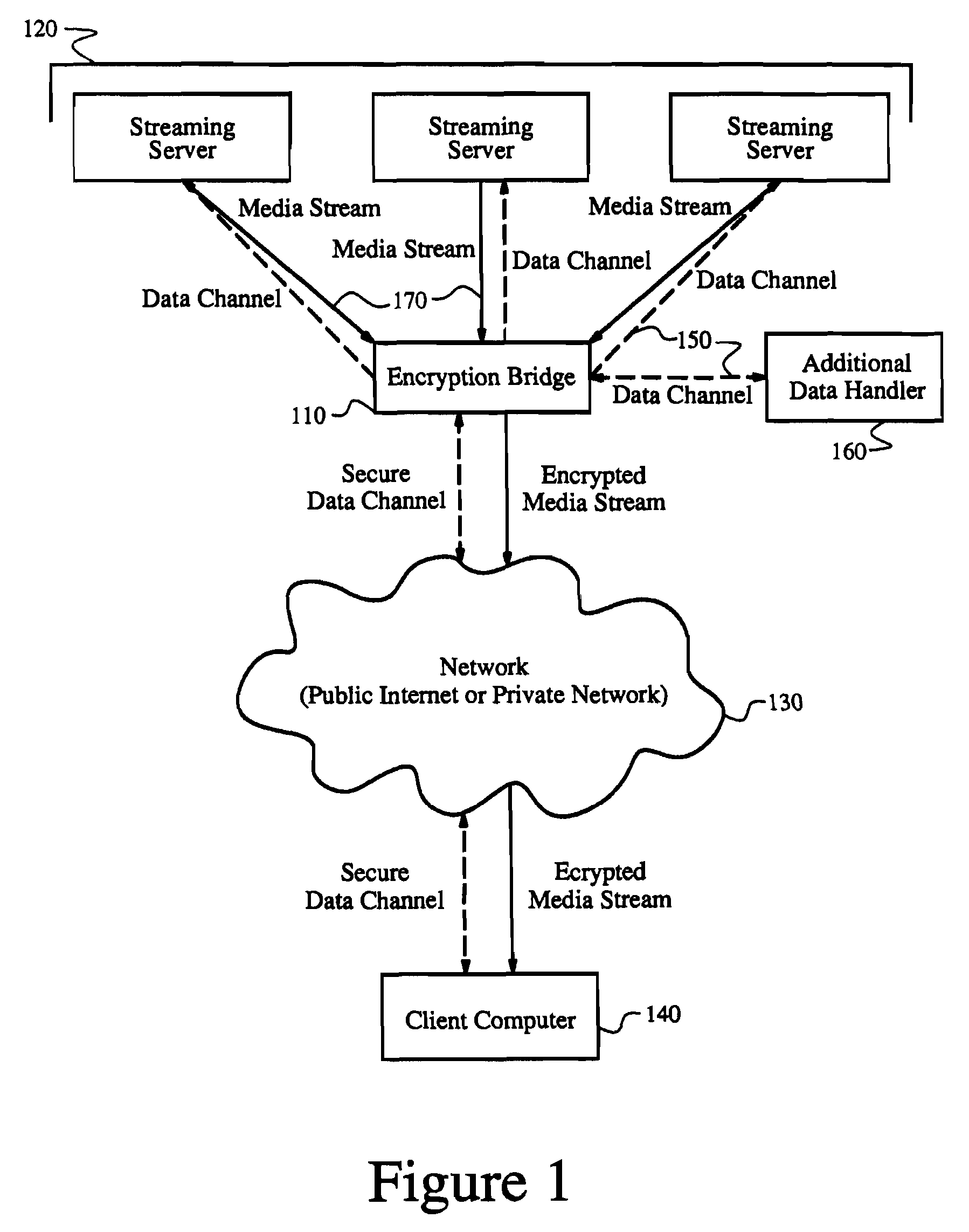
Systems and methods for transcoding and place shifting media content
ActiveUS20110055864A1Enhanced transcodingImprove abilitiesMultiple keys/algorithms usageData stream serial/continuous modificationDigital videoVideo player
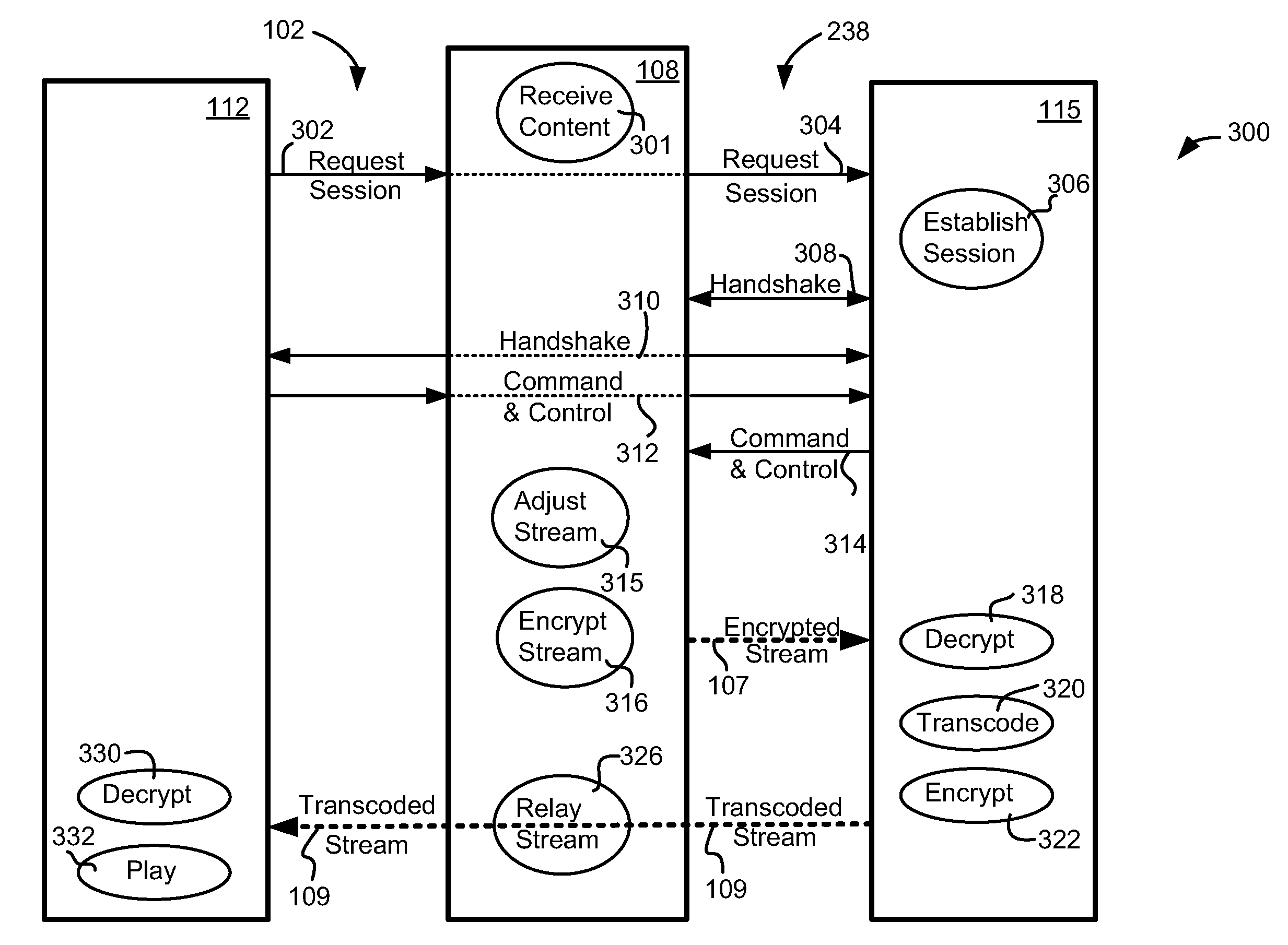
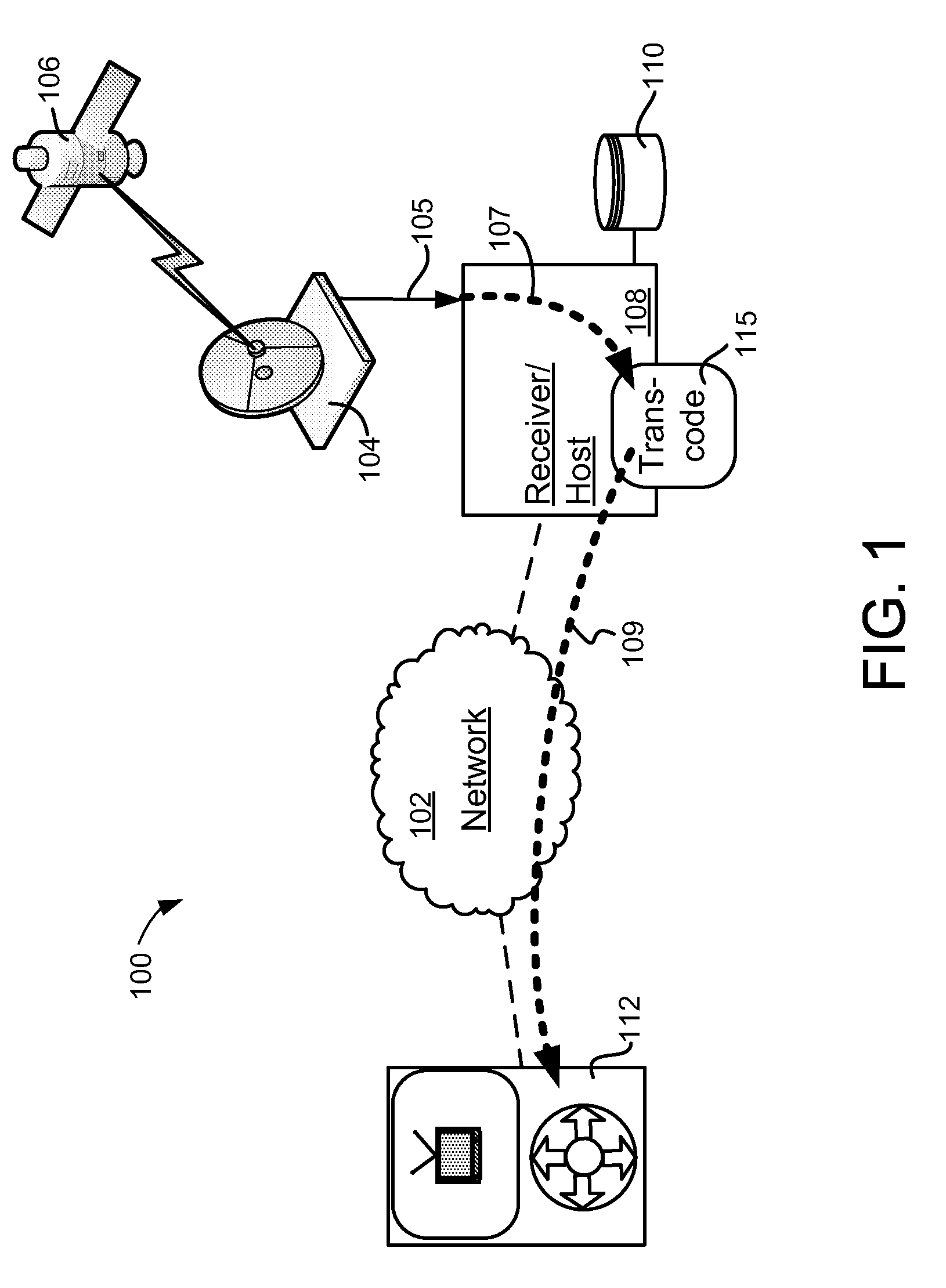
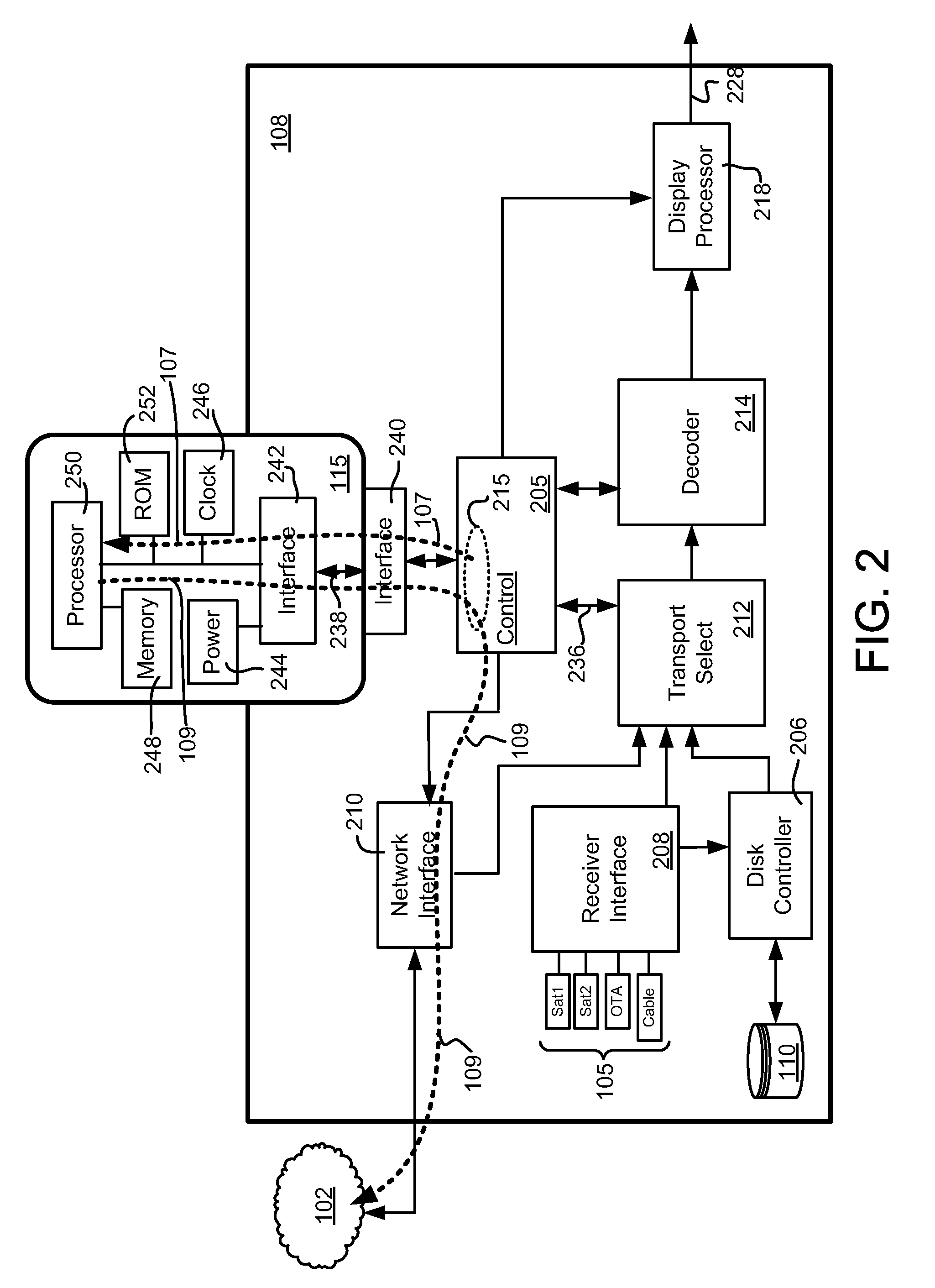
A set-top box (STB), digital video recorder (DVR), video player or other host device receives and interacts with a transcode module to provide enhanced transcoding capabilities that may be useful in placeshifting or other applications. The transcode module includes a host interface that couples to and communicates with the host device. The transcode module also includes a processor that receives an encrypted media stream from the host device via the bus interface, decrypts the encrypted media stream, transcodes the encrypted media stream to a different format, re-encrypts the transcoded stream, and provides the re-encrypted media stream to the host device via the host interface. The transcoded media content may be placeshifted to a remote player, stored at the host, or used for any other purpose.
Owner:SLING MEDIA LLC
State-varying hybrid stream cipher
InactiveUS20060291650A1Data stream serial/continuous modificationUser identity/authority verificationState variationCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:ANANTH VISWANATH
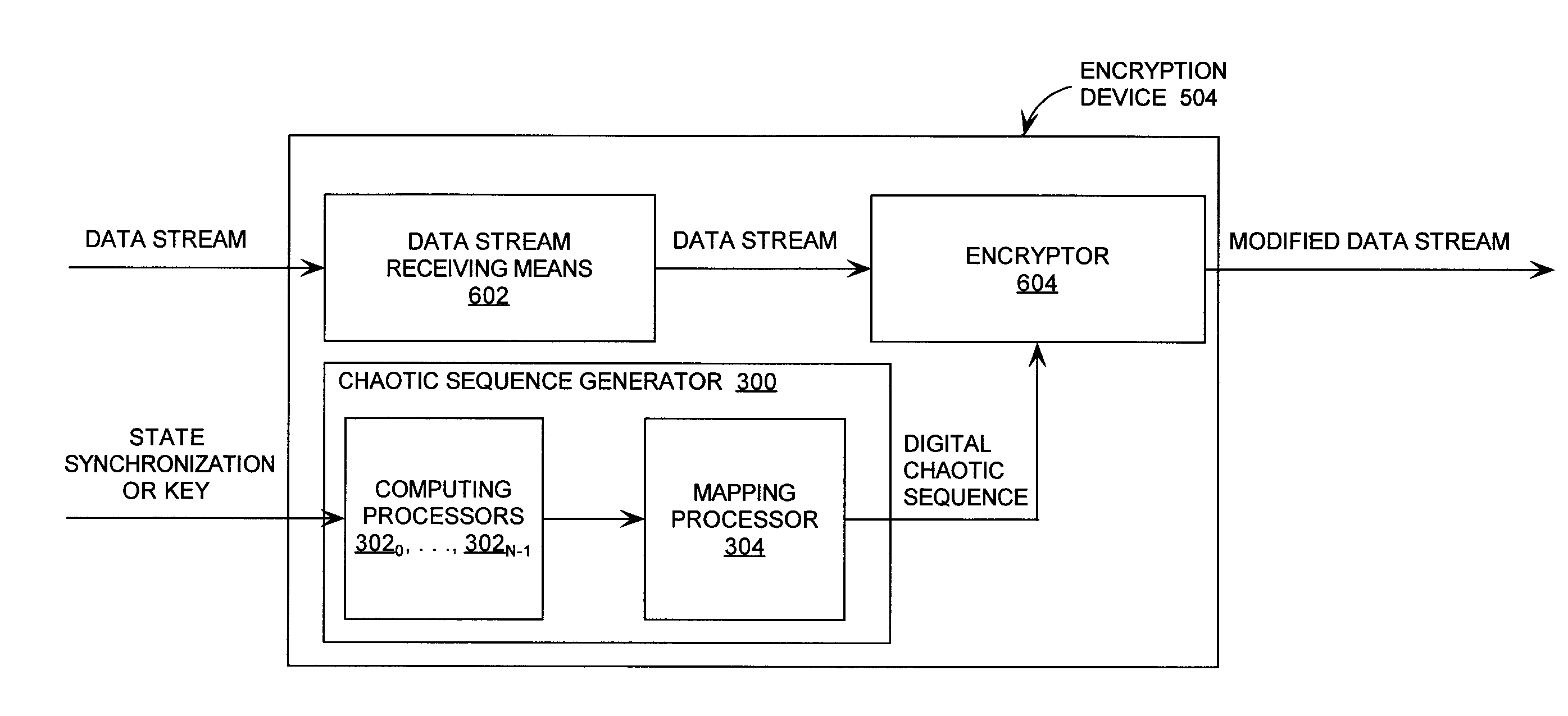
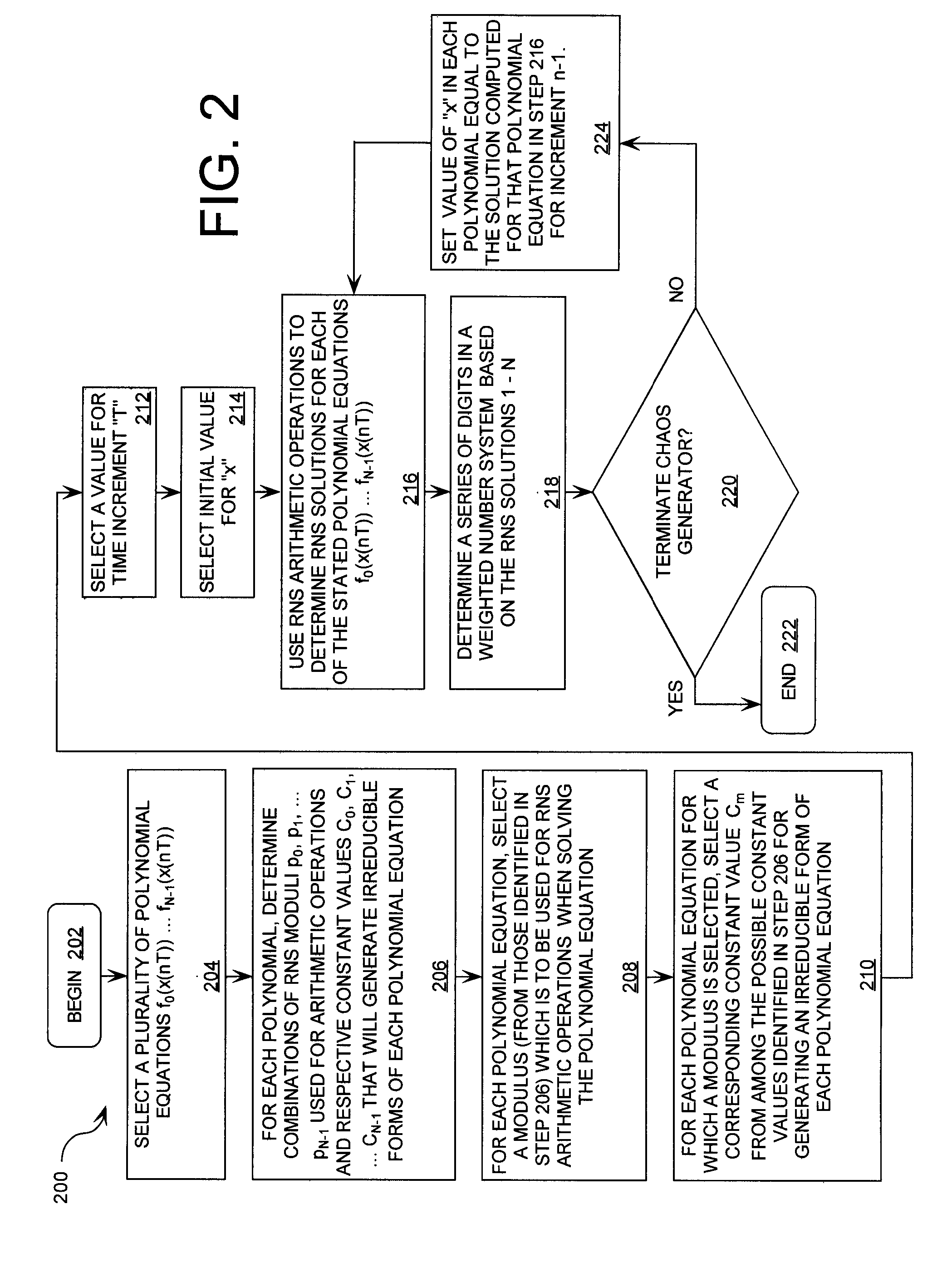
Cryptographic system incorporating a digitally generated chaotic numerical sequence
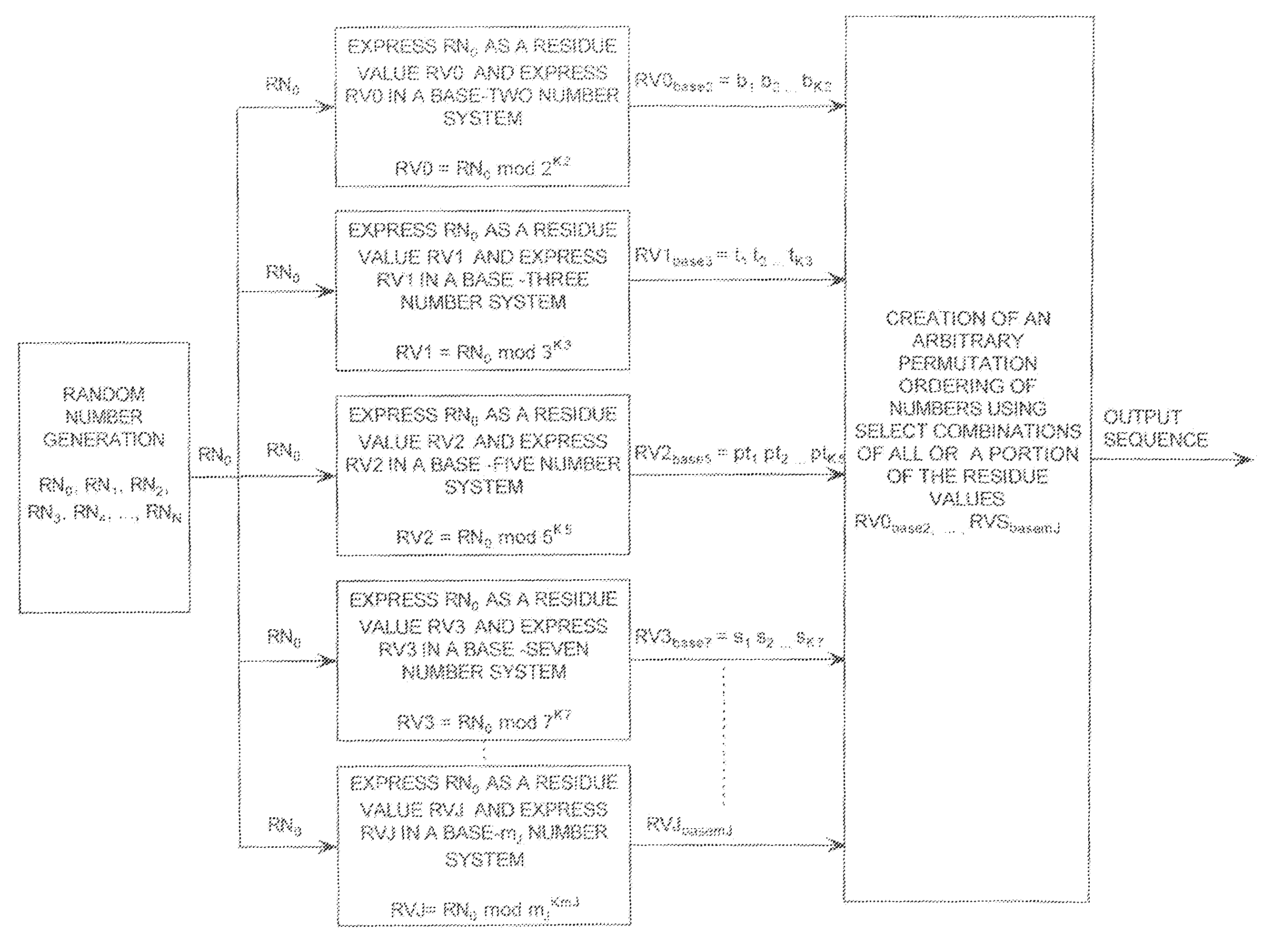
ActiveUS20090196420A1Data stream serial/continuous modificationSecret communicationNumbering systemData stream
A cryptographic system (CS) is provided. The CS (500) is comprised of a data stream receiving device (DSRD), a chaotic sequence generator (CSG) and an encryptor. The DSRD (602) is configured to receive an input data stream. The CSG (300) includes a computing means (3020, . . . , 302N-1) and a mapping means (304). The computing means is configured to use RNS arithmetic operations to respectively determine solutions for polynomial equations. The solutions are iteratively computed and expressed as RNS residue values. The mapping means is configured to determine a series of digits in the weighted number system based on the RNS residue values. The encryptor is coupled to the DSRD and CSG. The encryptor is configured to generate a modified data stream by incorporating or combining the series of digits with the input data stream.
Owner:HARRIS CORP
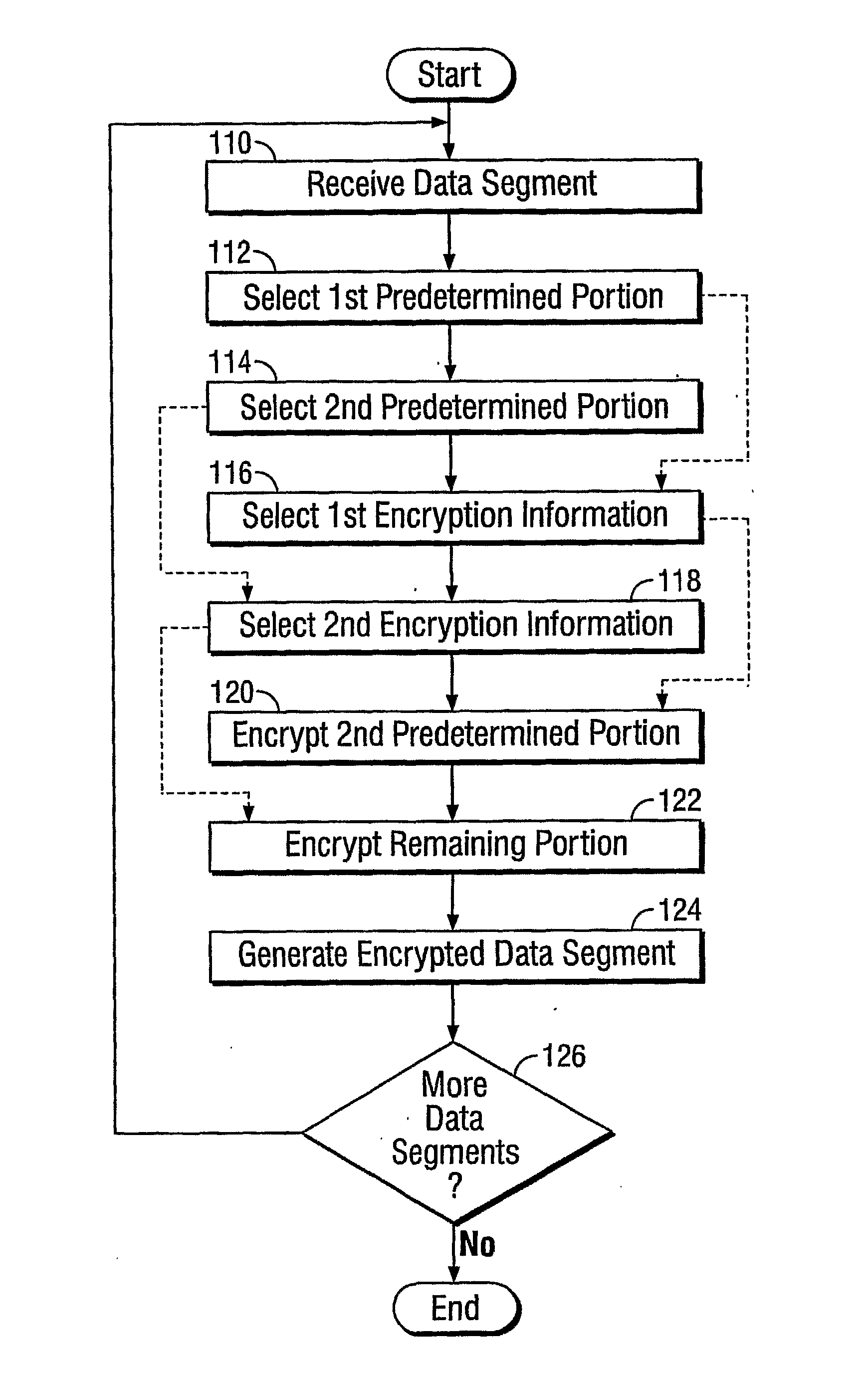
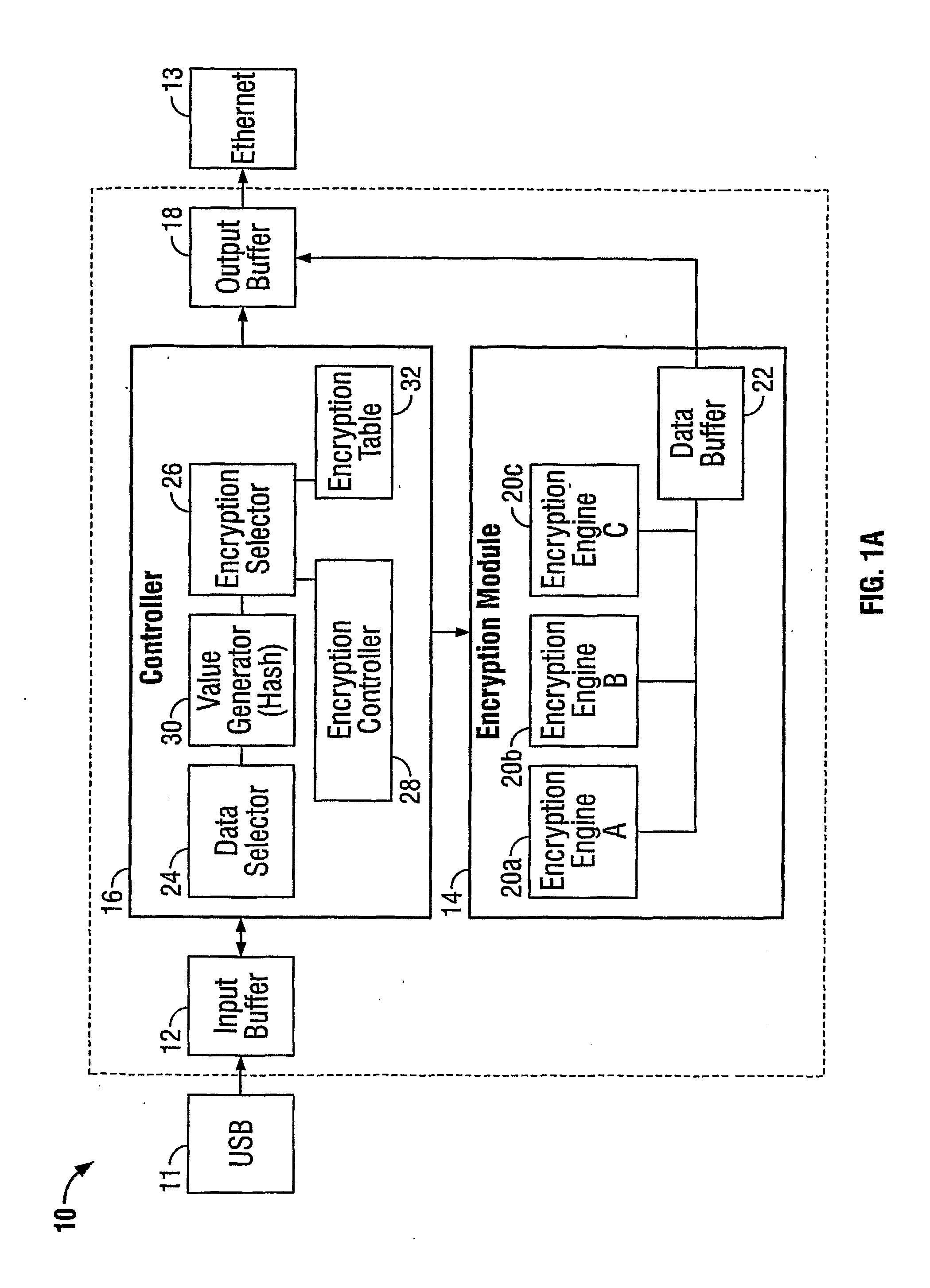
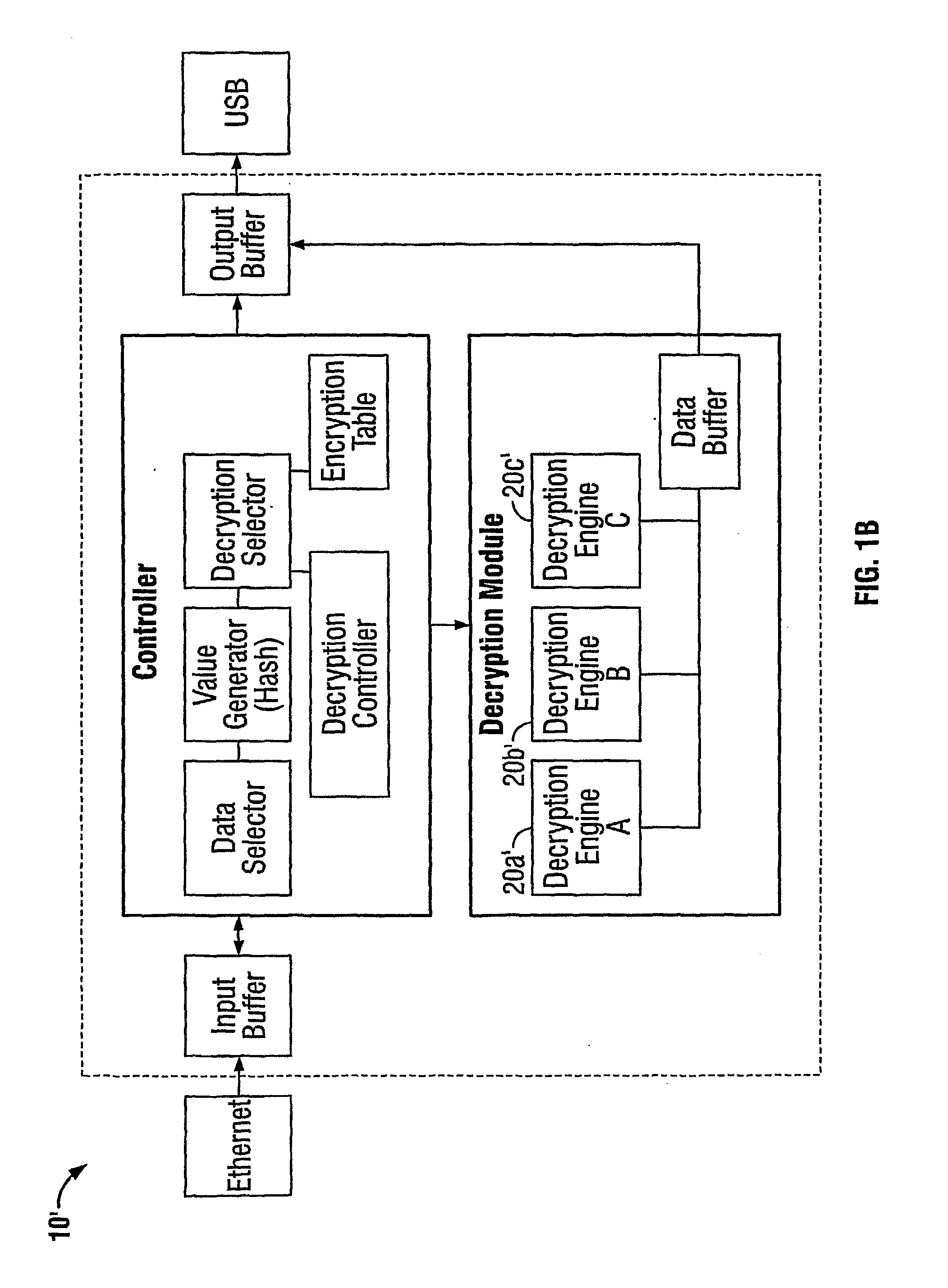
Method and apparatus for cryptographically processing data
InactiveUS20070154018A1Data stream serial/continuous modificationUser identity/authority verificationData segmentCipher
A method and apparatus cryptographically process data including a plurality of data segments. The cryptographic process includes (a) receiving a plurality of data segments, (b) selecting, for each data segment, a set of encryption information based on data contained in a predetermined portion of the data segment to be encrypted, and (c) encrypting each data segment using the set of encryption information selected for the data segment. At least one of an encryption algorithm, an encryption key, and an encryption parameter may be changed for each data segment based on the data contained in the predetermined portion. The predetermined portion may include a first predetermined portion for selecting a first set of encryption information, and a second predetermined portion for selecting a second set of encryption information, the encryption information including an encryption algorithm, an encryption key, and optionally an encryption parameter.
Owner:IVI HLDG
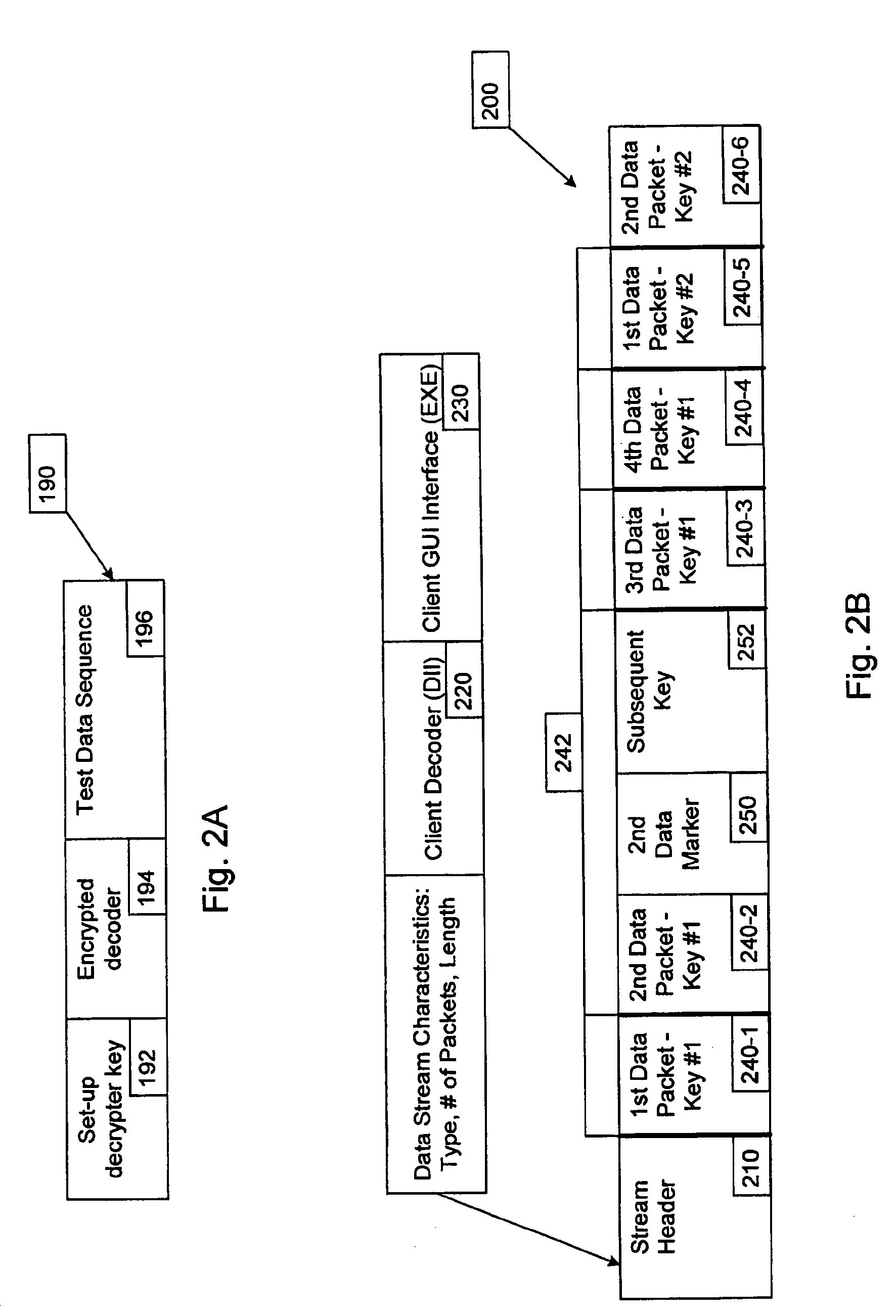
Method and apparatus for streaming data using rotating cryptographic keys
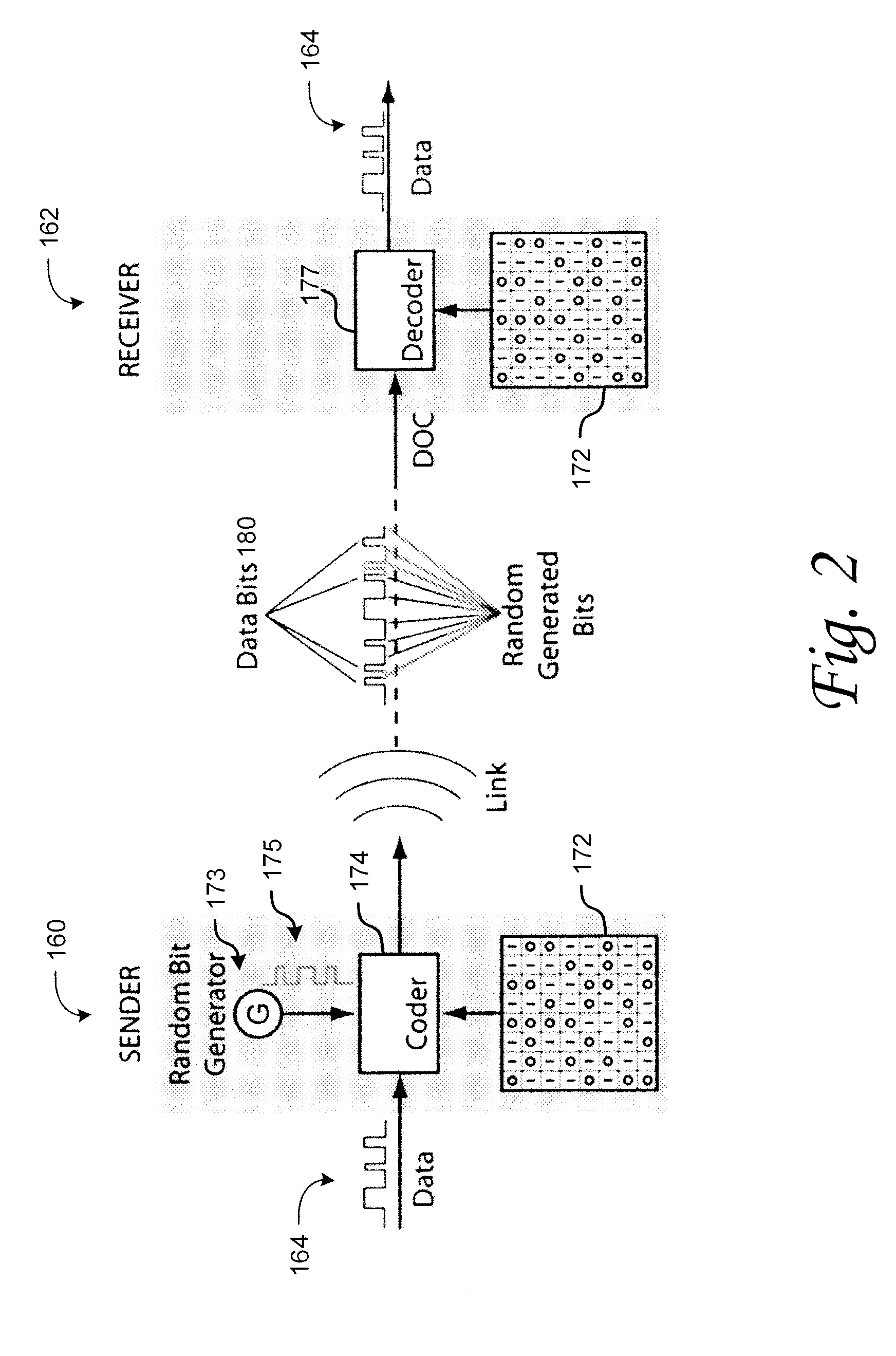
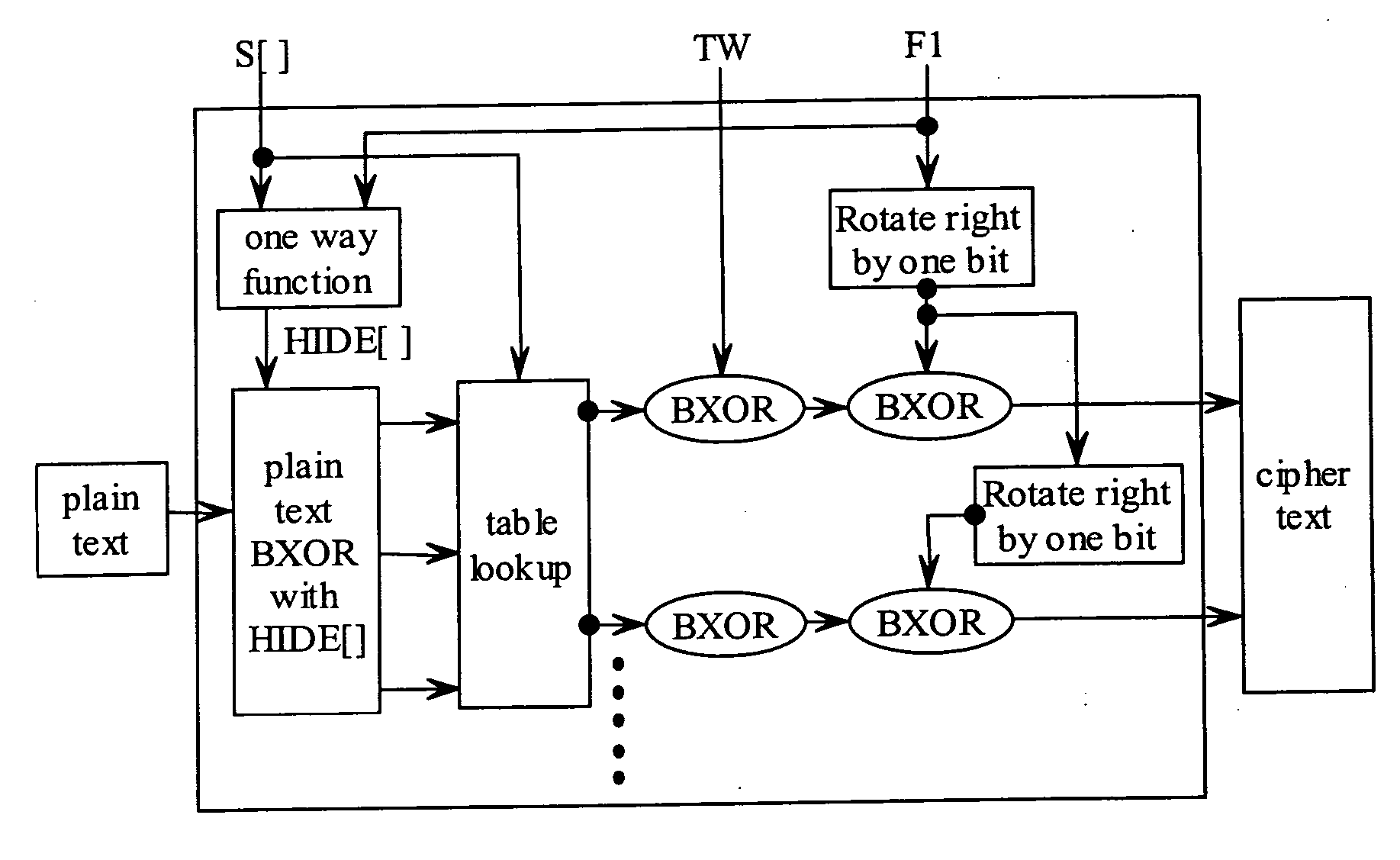
InactiveUS7050583B2Easy to copyData stream serial/continuous modificationComputer security arrangementsDigital dataStreaming data
A method of producing a stream of digital data. The method includes determining a plurality of portions within the stream of digital data, such that a portion of the stream of digital data is encrypted with an encryption key that is capable of being decrypted by a decryption key and the portion including therein another decryption key capable of decrypting a subsequent portion of the stream of digital data, and the subsequent portion of the stream of digital data is encrypted with another encryption key that is capable of being decrypted by the another decryption key. The method also includes transmitting the stream of digital data, including the portion and the subsequent portion.
Owner:ETREPPID TECH
Encryption method and apparatus with forward secrecy and random-access key updating method
InactiveUS7095850B1Generate efficientlyComputationally efficientData stream serial/continuous modificationSecret communicationOne-way functionRekeying
An encryption method and apparatus that provides forward secrecy, by updating the key using a one-way function after each encryption. By providing forward secrecy within a cipher, rather than through a key management system, forward secrecy may be added to cryptographic systems and protocols by using the cipher within an existing framework. A random-access key updating method can efficiently generate one or more future keys in any order. Embodiments are applicable to forward secret ciphers that are used to protect protocols with unreliable transport, to ciphers that are used in multicast or other group settings, and to protection of packets using the IPSec protocols.
Owner:CISCO TECH INC
Selective and persistent application level encrytion for video provided to a client
ActiveUS20070160208A1Television system detailsData stream serial/continuous modificationComputer hardwareClient-side
A system, apparatus, and method are directed towards allowing ingestion of encrypted content into such as a VOD server, or PVR, or the like by selectively encrypting portions of a content stream based on various selection rules. In one embodiment, the selection rules include leaving selected portions of the content stream unencrypted, including packets that include a PES header; or video packets that include various trick play data such as picture start, GOP start, sequence start, sequence end data; PIDs associated with a PAT, PMT, or the like; while other portions of the content stream may be encrypted, including video and / or audio PIDs, or other video and / or audio portions. In still another embodiment, Entitlement Control Messages (ECMs) may be inserted that employ an encryption / decryption key rotation scheme, such as odd and / or even scrambling control bit structures, which may also be rotated based on a variety of conditions.
Owner:GOOGLE LLC
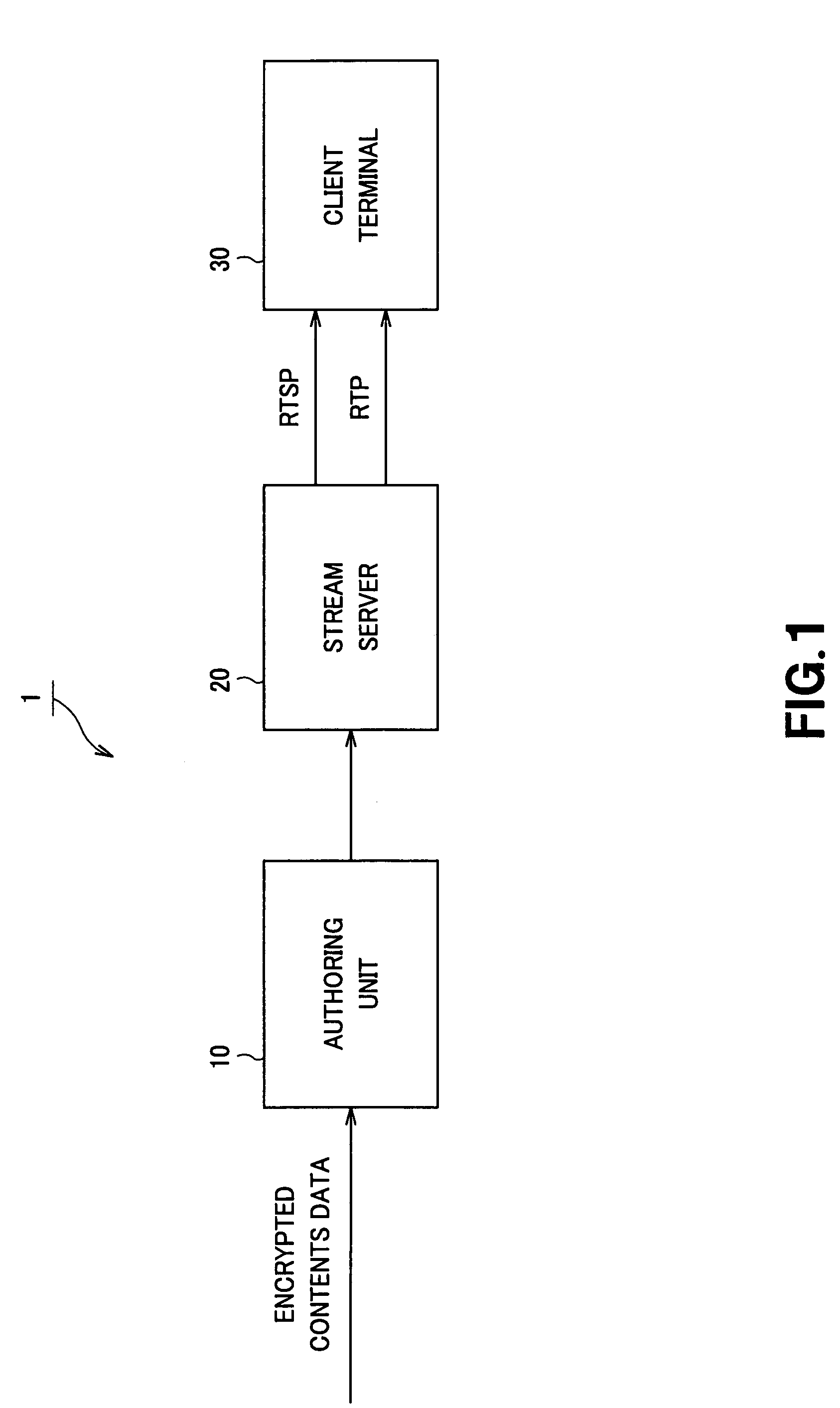
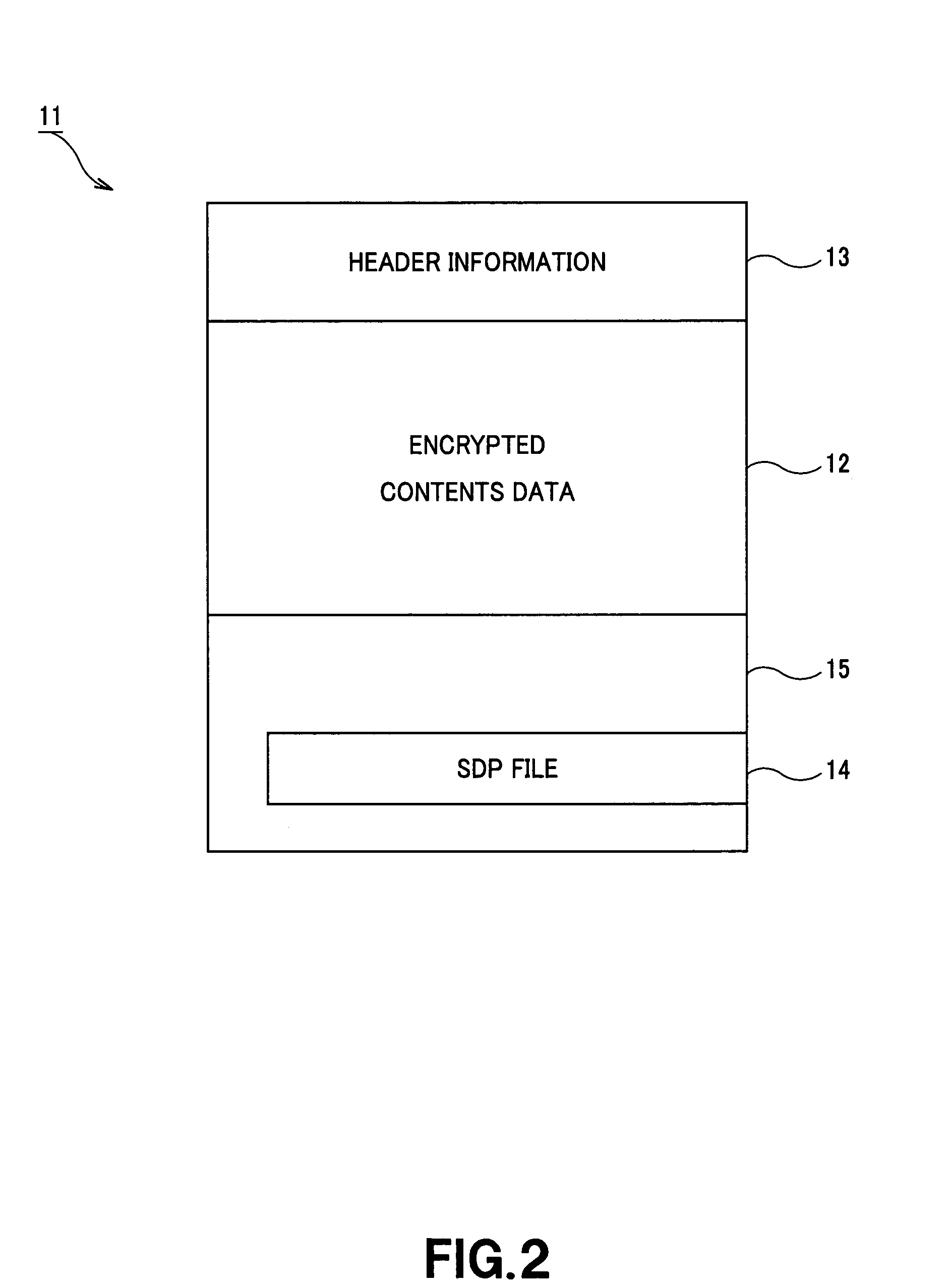
Streaming system for distributing encrypted data, and streaming method therefor
ActiveUS7337320B2Solve the real problemImprove securityKey distribution for secure communicationData stream serial/continuous modificationComputer networkSystem structure
The present invention is directed to a streaming system for encrypting encrypted data such as music and image, etc. to perform stream distribution thereof. Client terminals (30) used in this system structure leaves of the hierarchical tree structure, and hold a key set consisting of a route key, node keys and the own leaf key on a path of this tree structure, whereby SDP file is transmitted from a stream server (20). In the SDP file, there is stored encrypted information consisting of EKB including data encrypted by selection key that only specific client terminal holds and encrypted contents key data in which contents key has been encrypted. Only specific client terminal having selection key in key set (selected client terminal) decodes contents key from selection key to decode encrypted contents data caused to undergo stream distribution into contents data to perform real time reproduction thereof.
Owner:SONY CORP
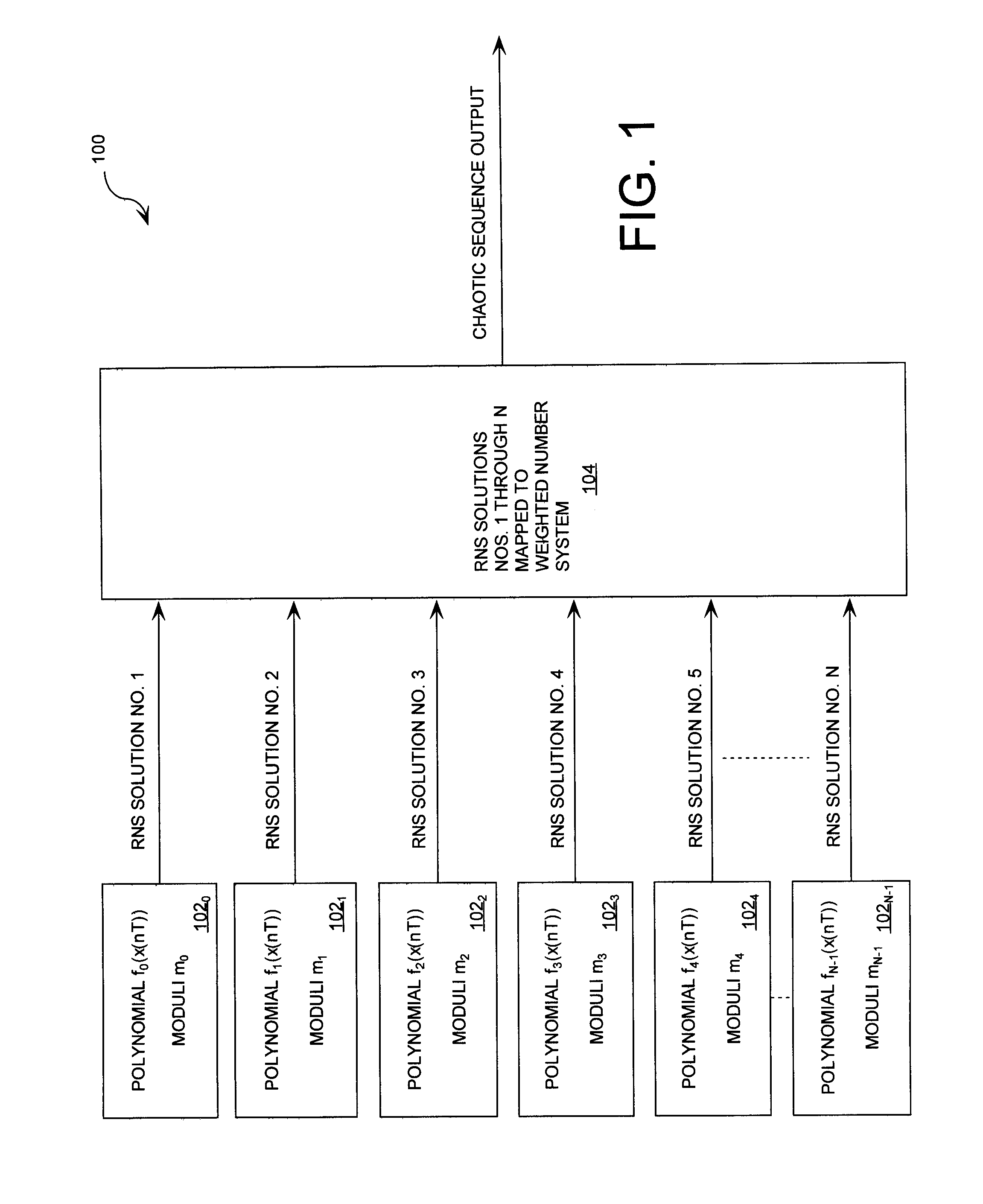
Cryptographic system configured for extending a repetition period of a random sequence
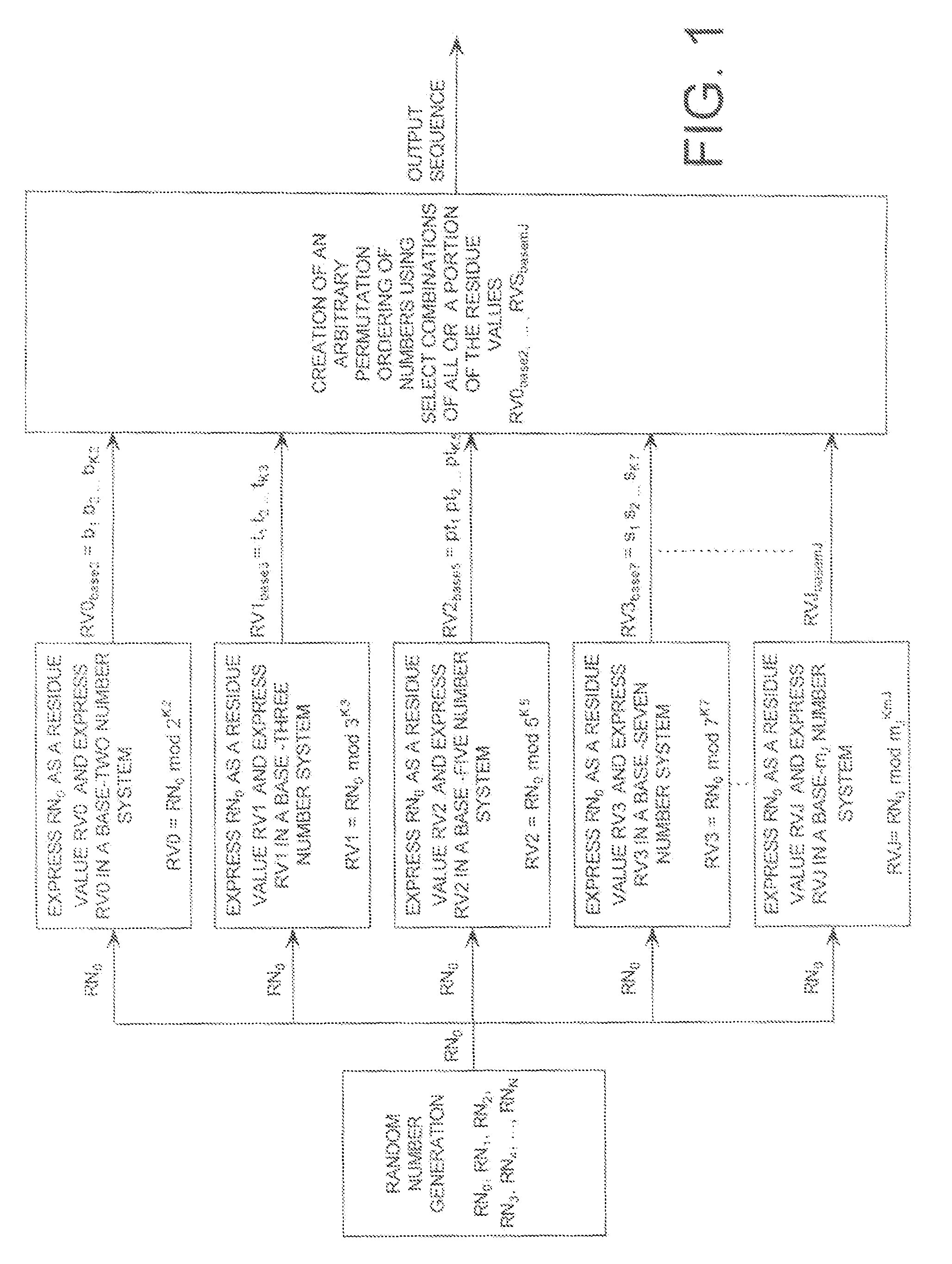
ActiveUS20090110197A1Data stream serial/continuous modificationDigital data processing detailsData streamNumbering system
A cryptographic system (CS) is provided. The CS (500) is comprised of a data stream receiving means (DSRM), a ring generator (RG) and an encryptor. The DSRM (602) provides a data stream (DS). The RG (400) includes a computing (404-408), converting (404-408) and permutation (410) means. The computing means is configured to perform RNS arithmetic operations to express a random number in a random number sequence as RNS residue values (RNSRV). The converting means is configured to convert each RNSRV to a relatively prime number system so that each RNSRV includes at least one digit. The permutation means is configured to generate an arbitrary permutation ordering of output sequence numbers (OSNs) using a select combination of digits associated with each RNSRV. The arbitrary permutation ordering is determined using a cyclic structure. The encryptor is configured to generate a modified data stream by combining the OSNs and DS.
Owner:HARRIS CORP
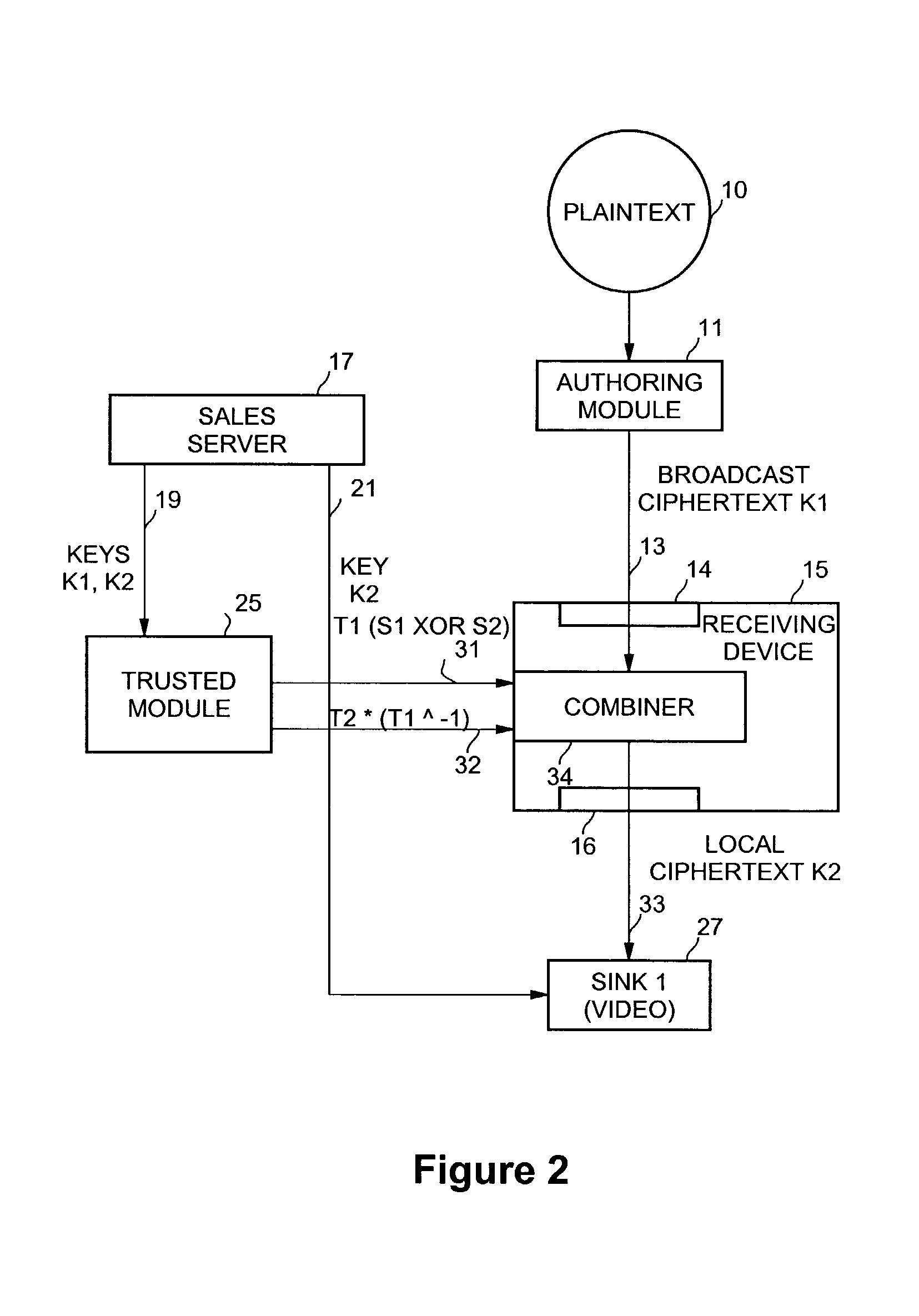
Method and apparatus for simultaneous decryption and re-encryption of publicly distributed content via stream ciphers
InactiveUS7184550B2Key distribution for secure communicationData stream serial/continuous modificationSecure communicationKey generation
Secure communication from one encryption domain to another using a trusted module. In one embodiment, the invention includes receiving encrypted streamed content encrypted with a first key, generating a substitution key stream based on the first key and a second key, generating a transposition key stream based on the first and second keys, and simultaneously decrypting and re-encrypting the encrypted streamed content using a combination of the substitution and transposition streams to produce re-encrypted streamed content encrypted with the second key.
Owner:INTEL CORP
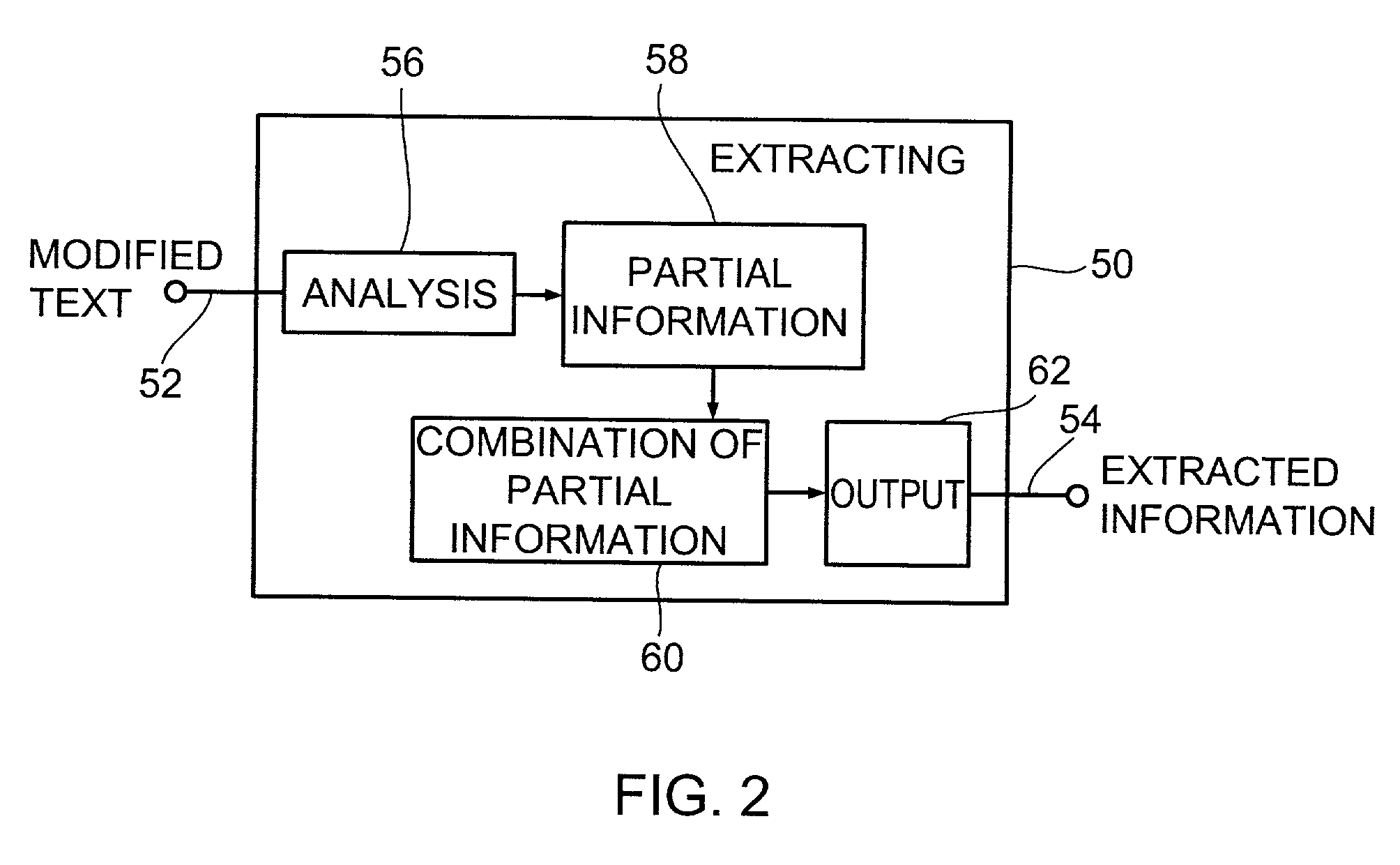
Device and method for hiding information and device and method for extracting information
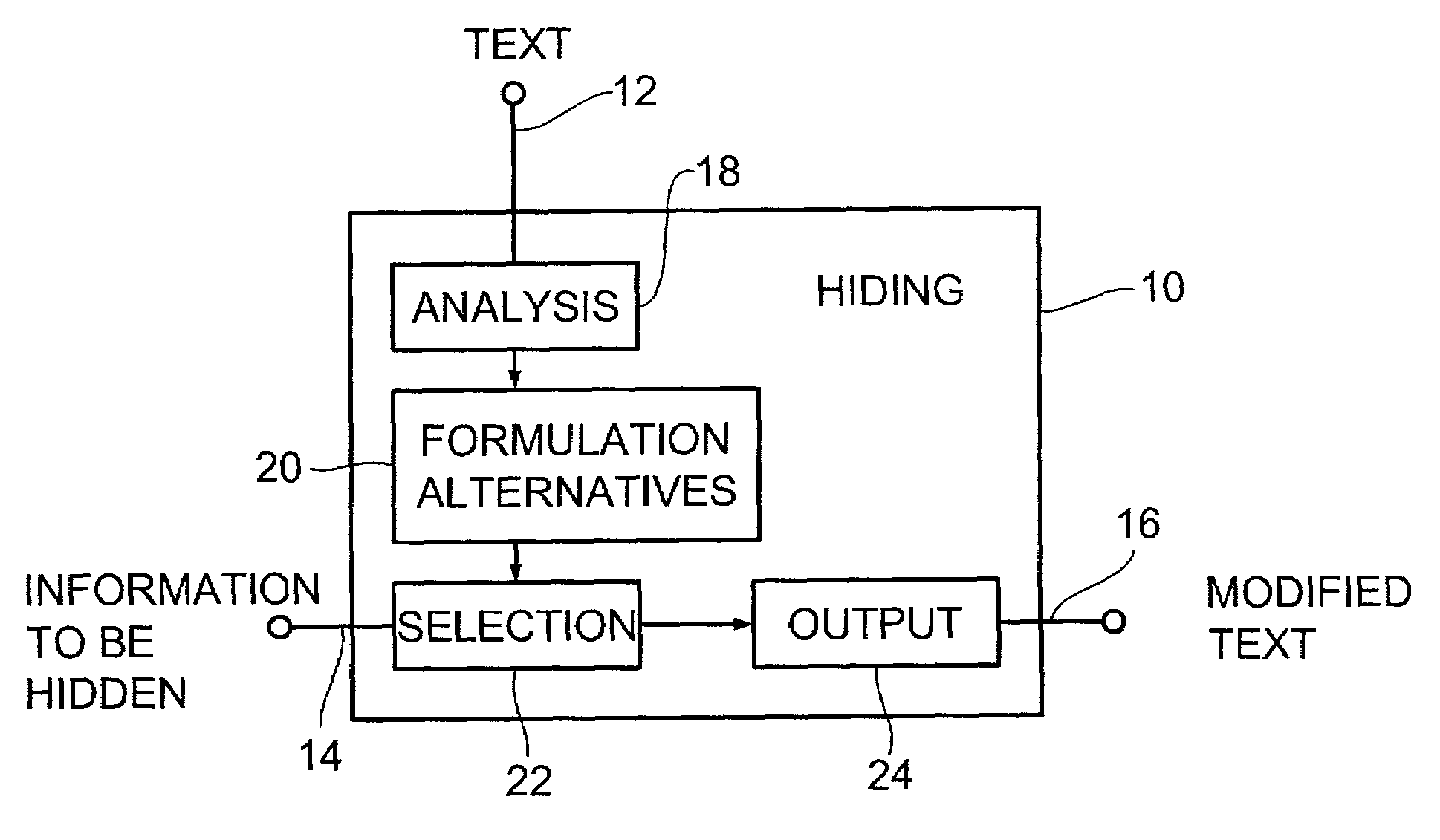
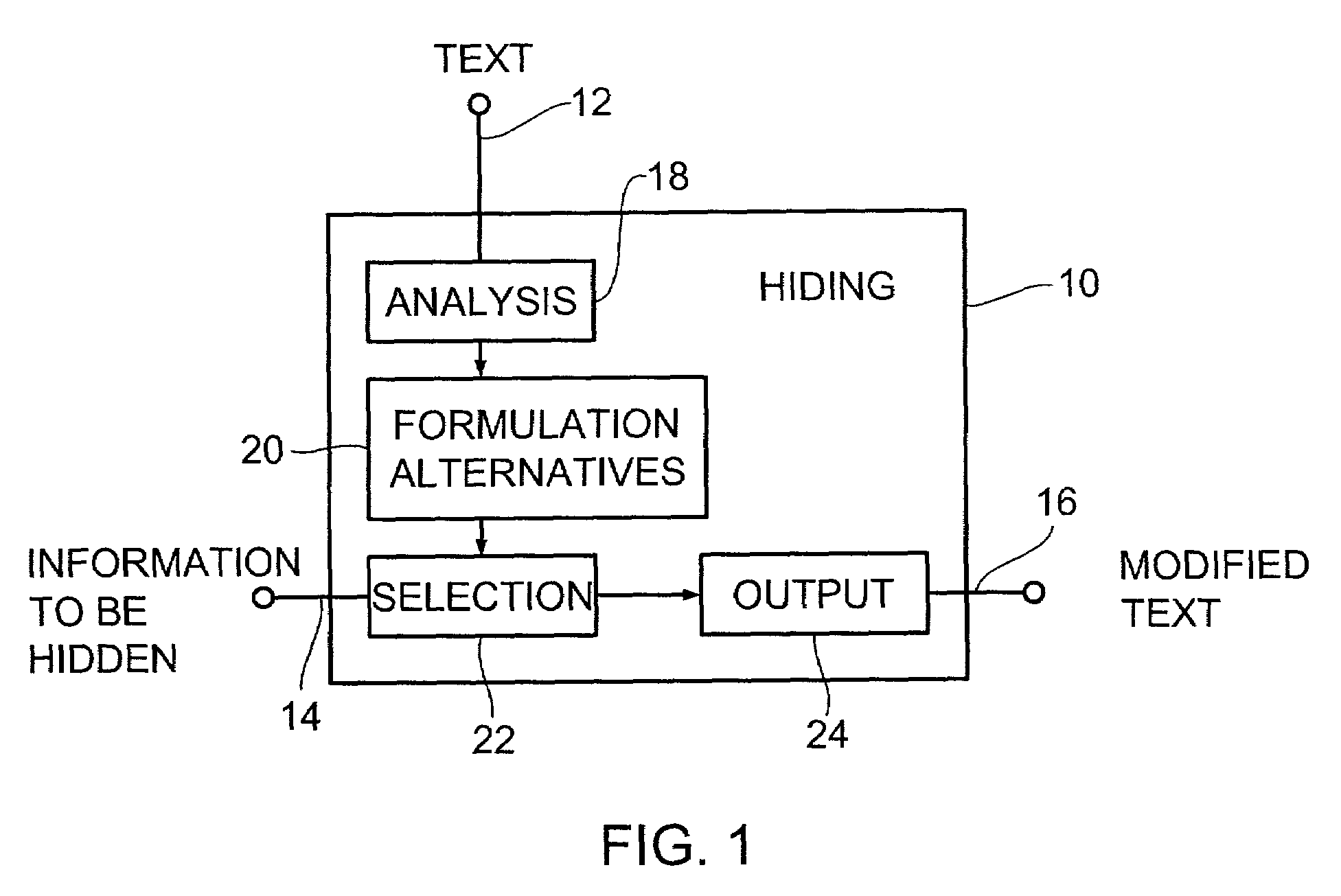
InactiveUS7167825B1Improve robustnessEasy to identifyData stream serial/continuous modificationSecret communicationParaphraseLanguage analysis
A device for hiding information in a text comprises a mechanicanism for providing the text, means for linguistically analyzing the text to produce text components, for determining a plurality of formulation alternatives for the text by varying the order of the text components and, optionally, in addition by using synonyms for text components, determining every formulation alternative is grammatically correct for the text and has essentially the same meaning as the text. Certain partial information is allocated to every sequence and / or to every synonym or to every paraphrase.
Owner:POTTER THOMAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com