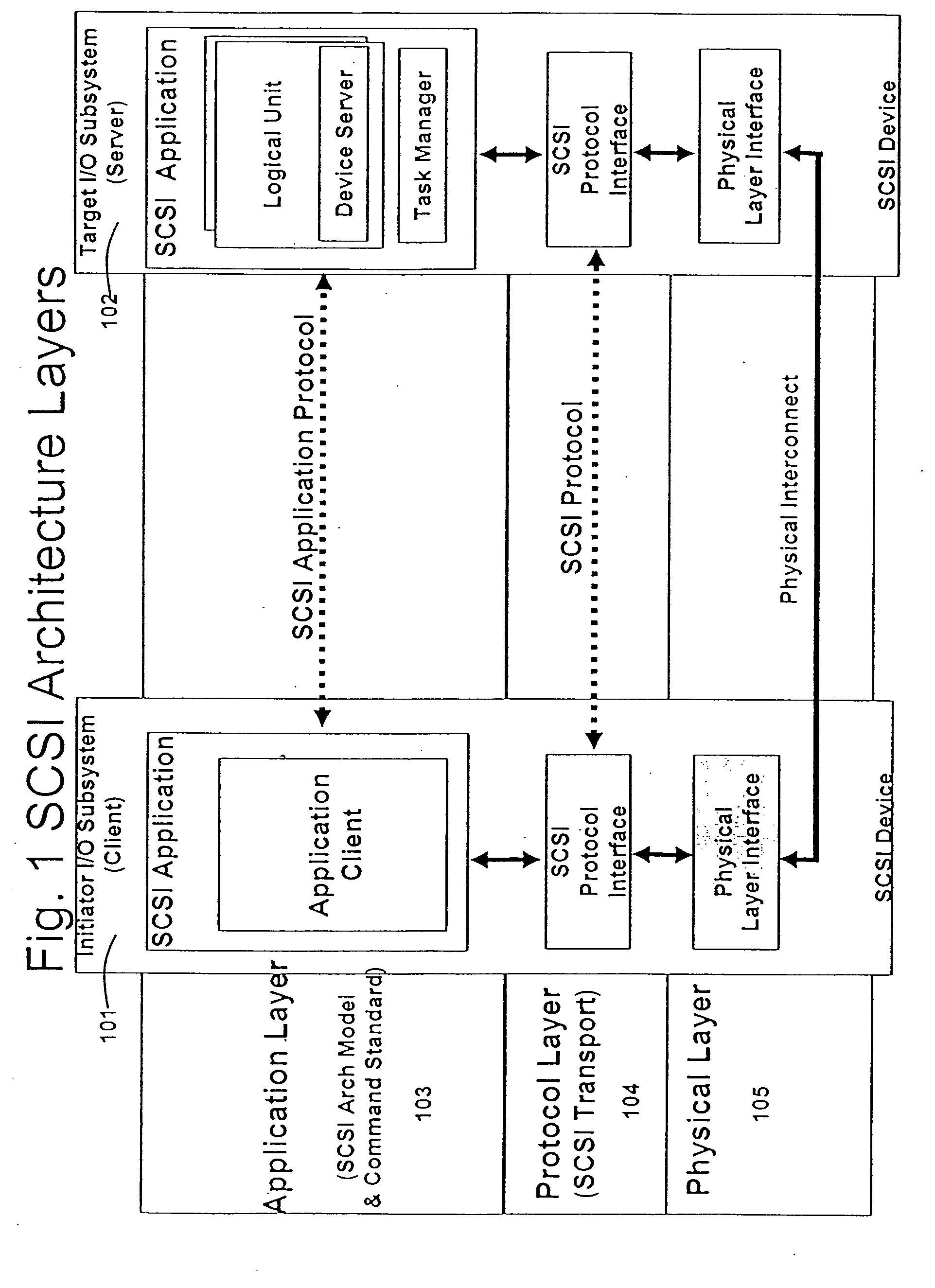
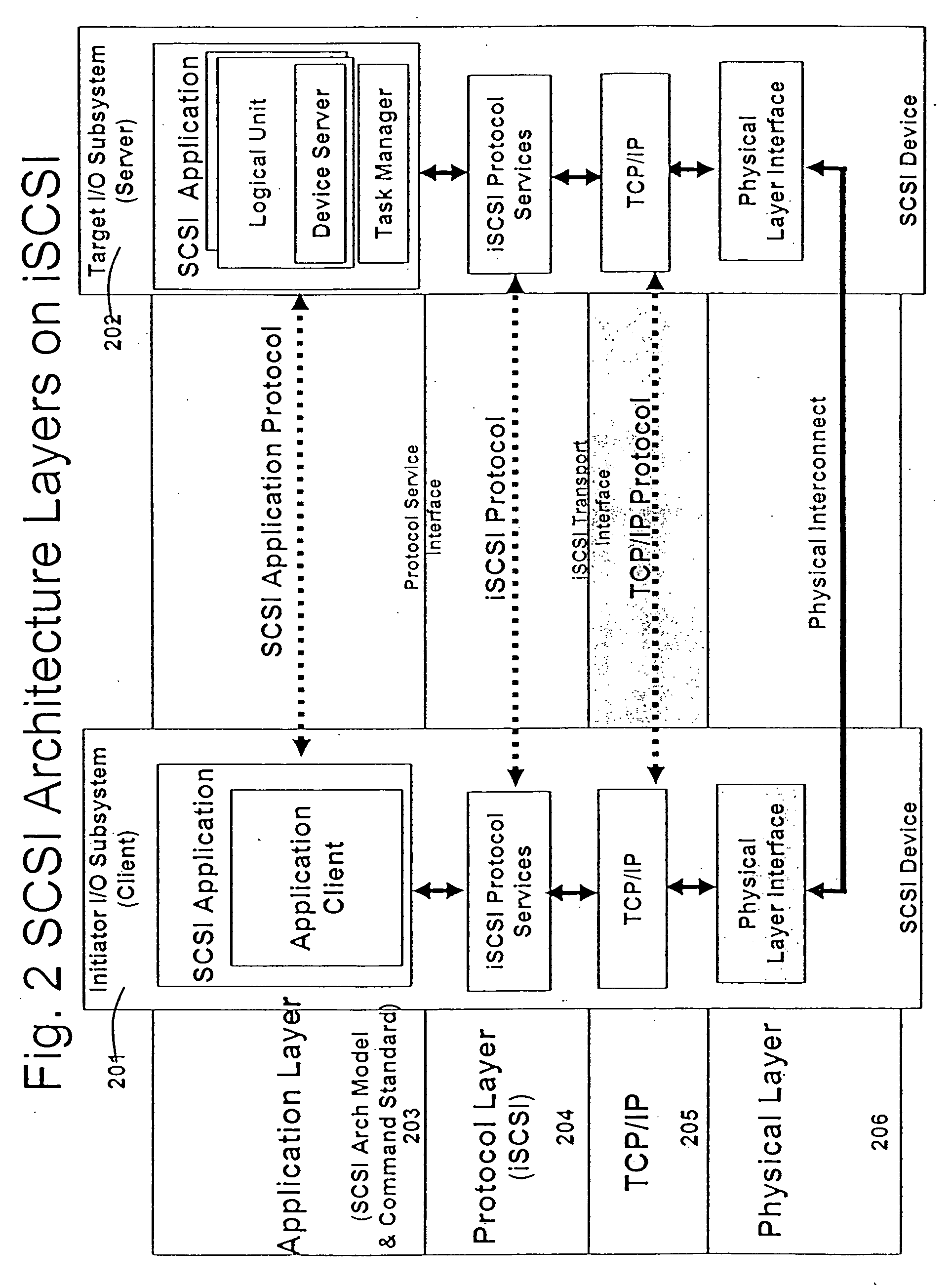
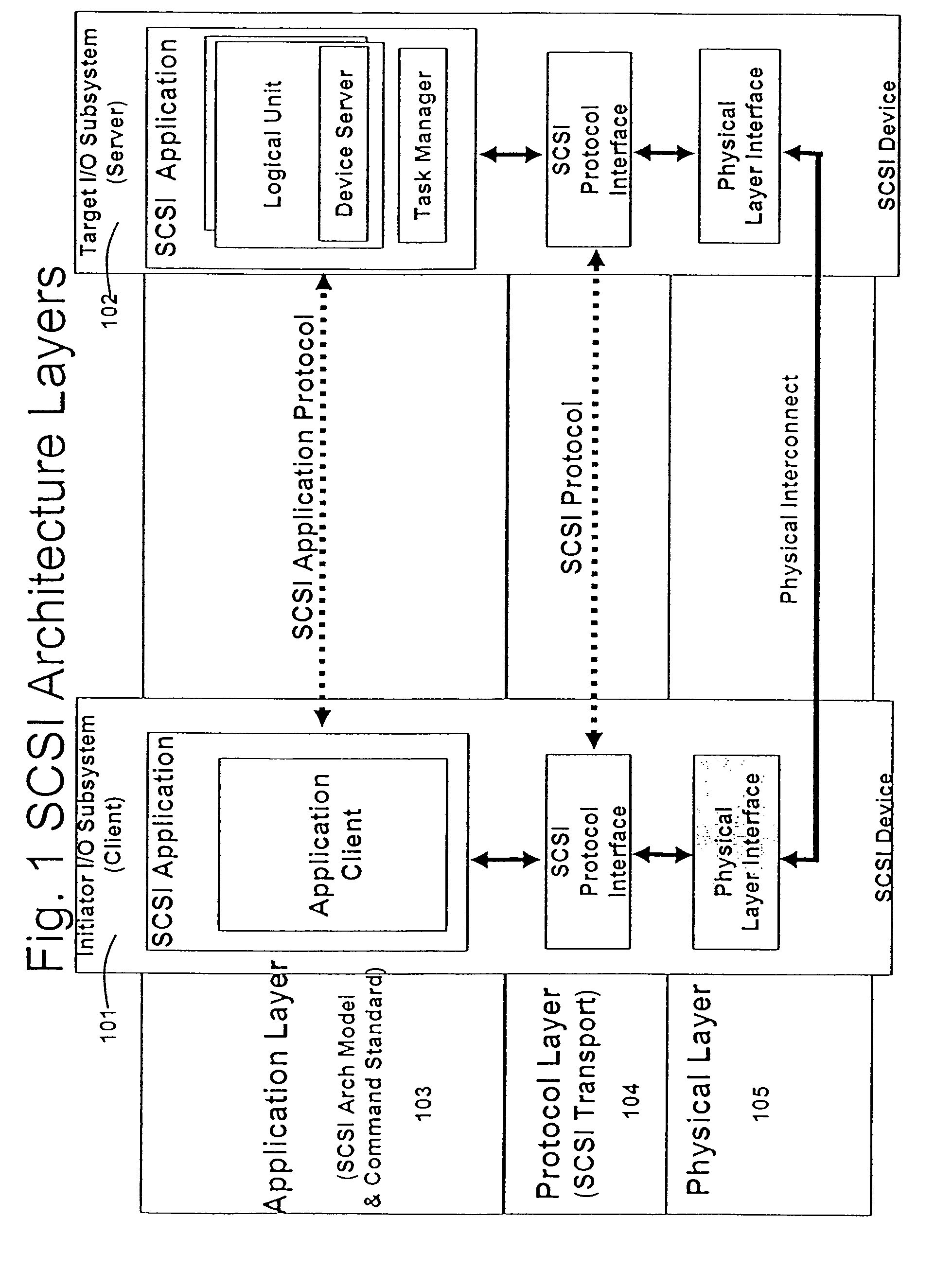
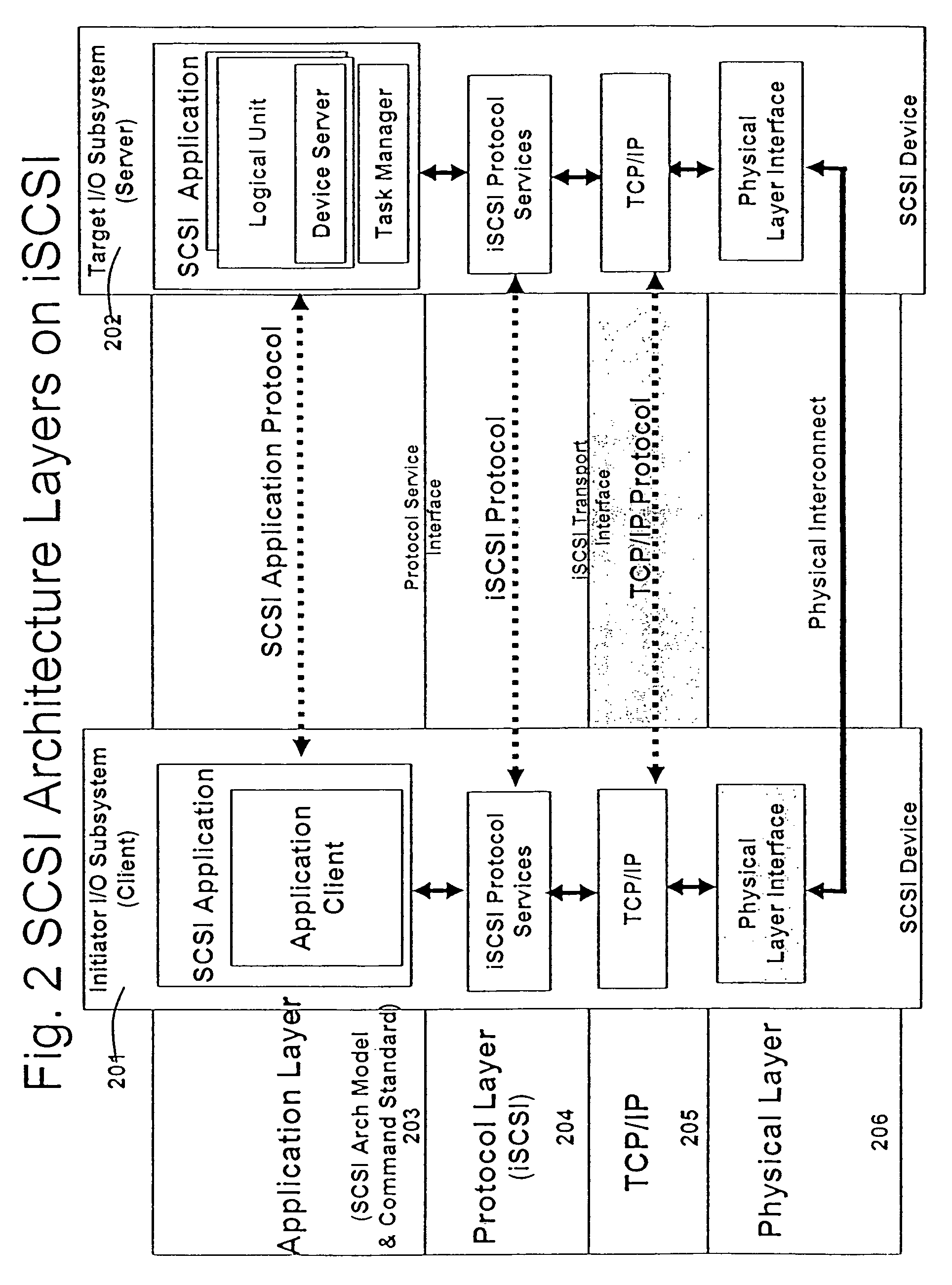
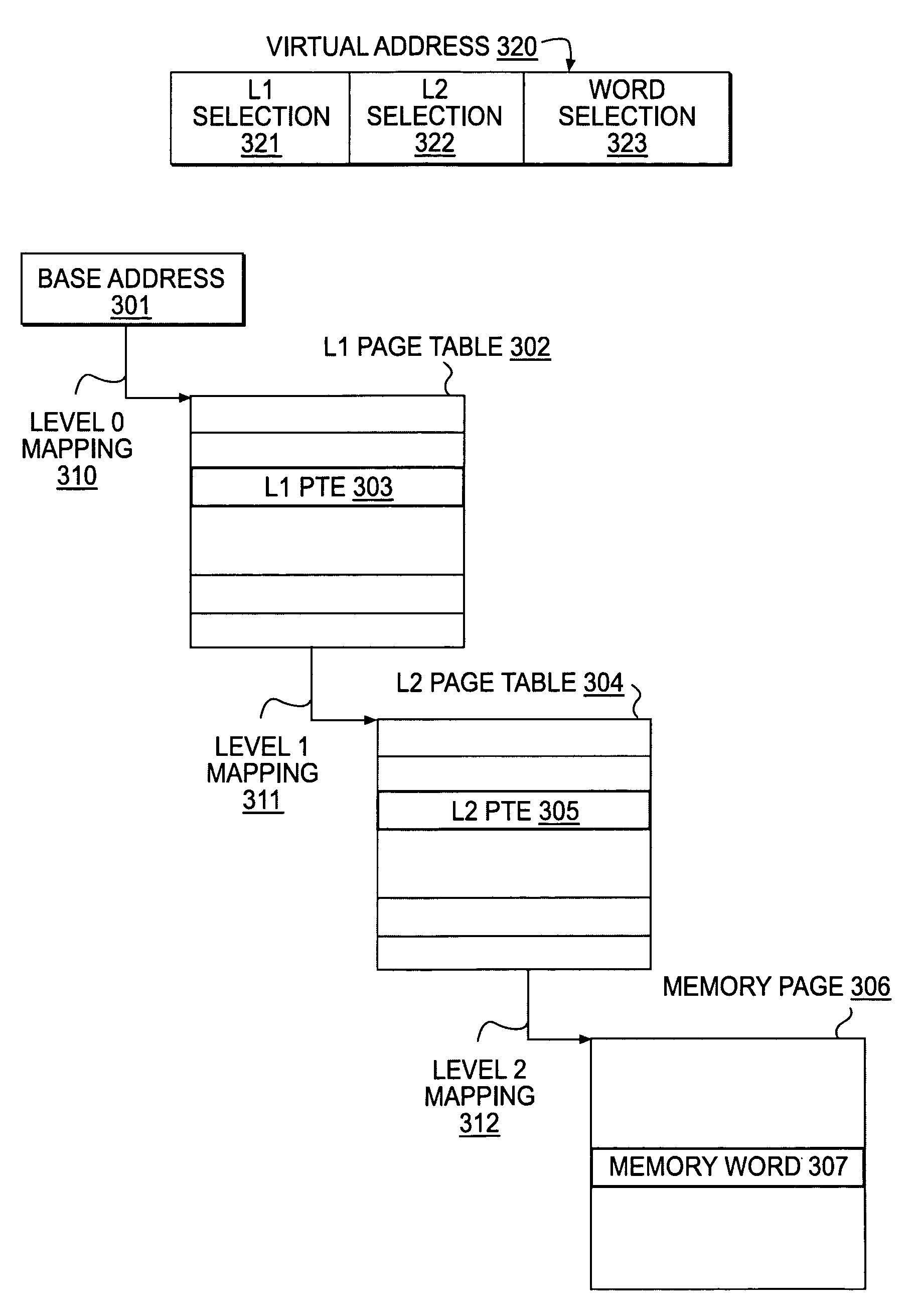
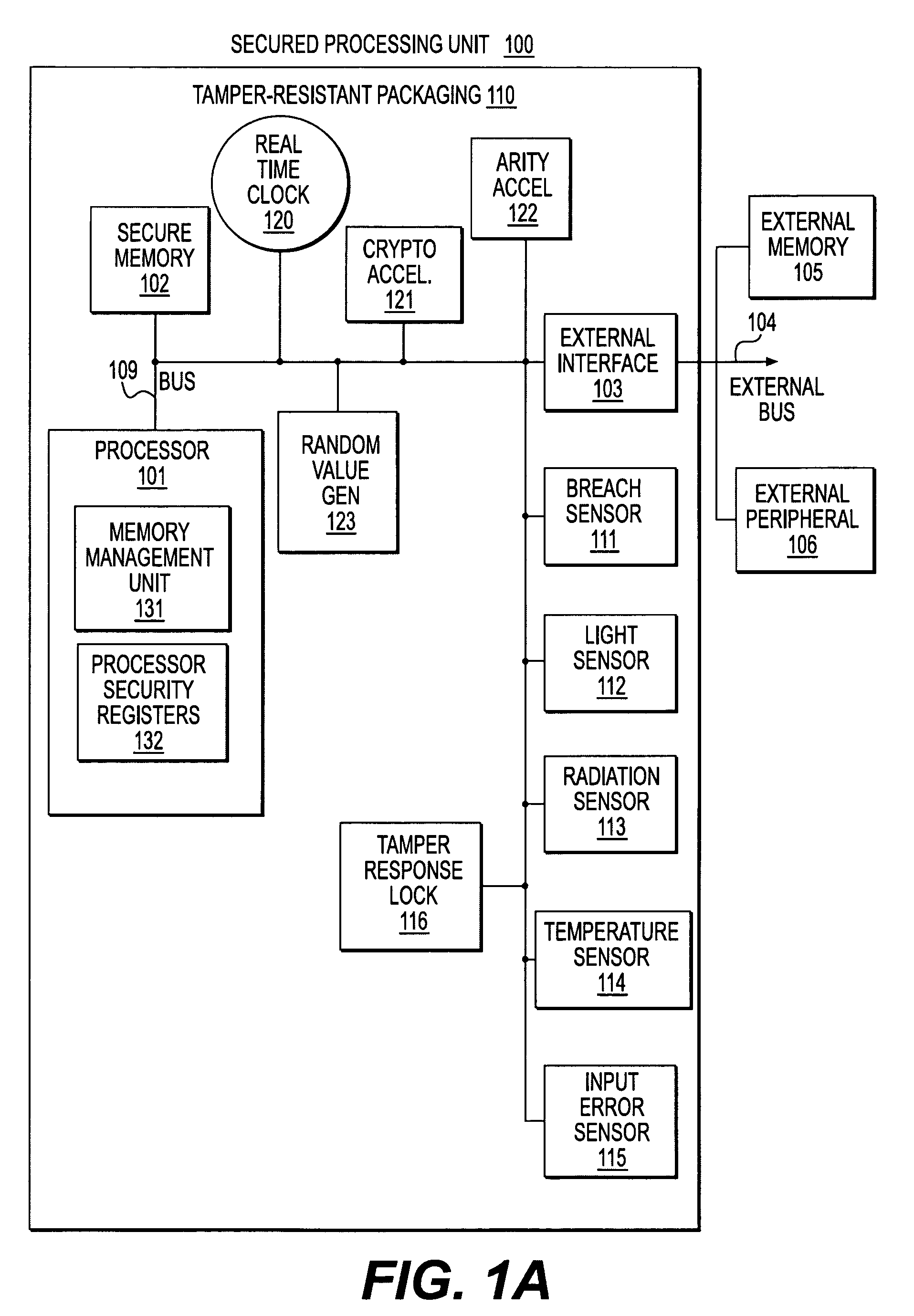
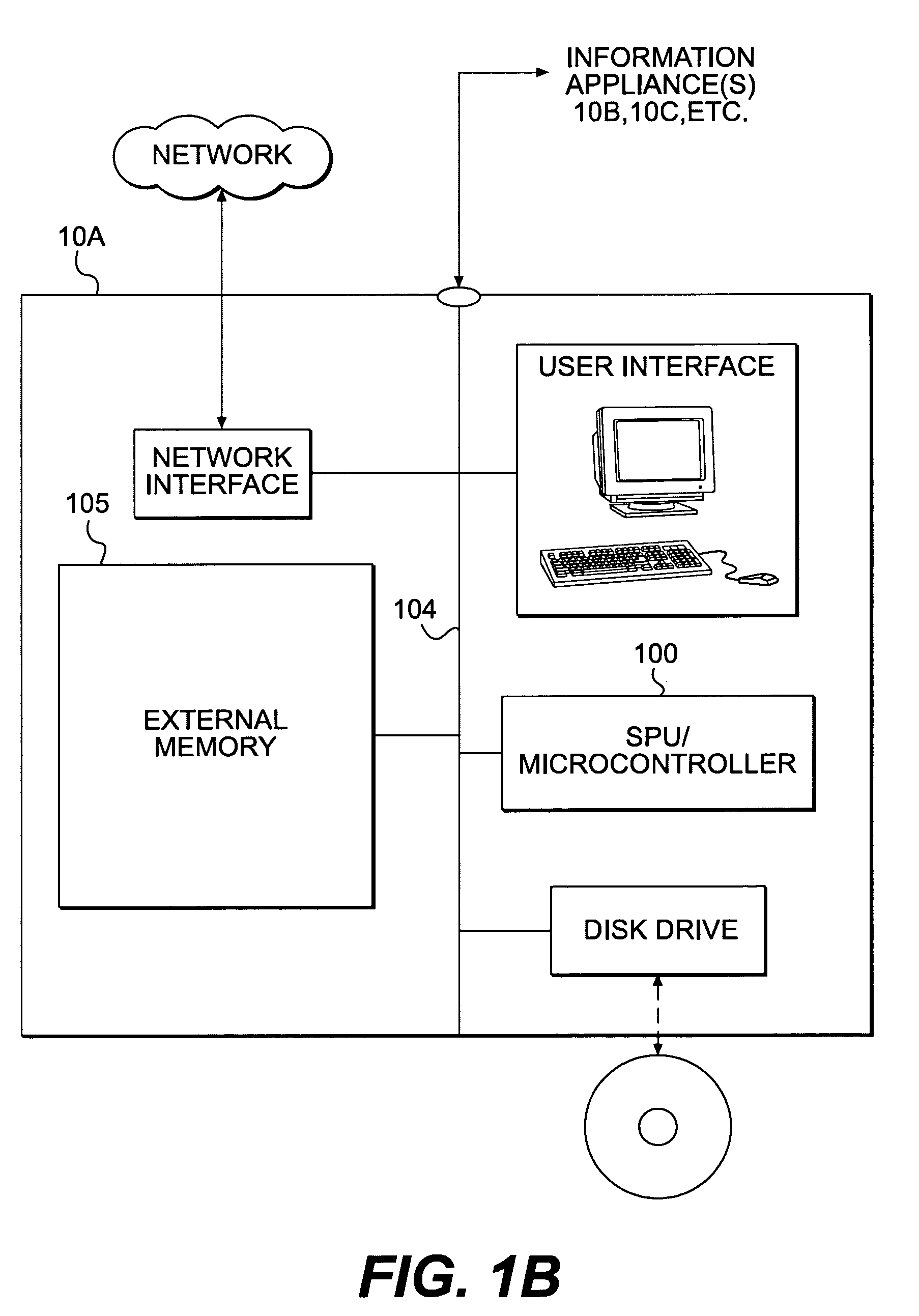
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1031 results about "Safe handling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safe patient handling means a process, based on scientific evidence on causes of injuries, that uses safe patient handling equipment rather than people to transfer, move, and reposition patients in all health care facilities to reduce workplace injuries. This process also reduces the risk of injury to patients.
Video-Based Privacy Supporting System
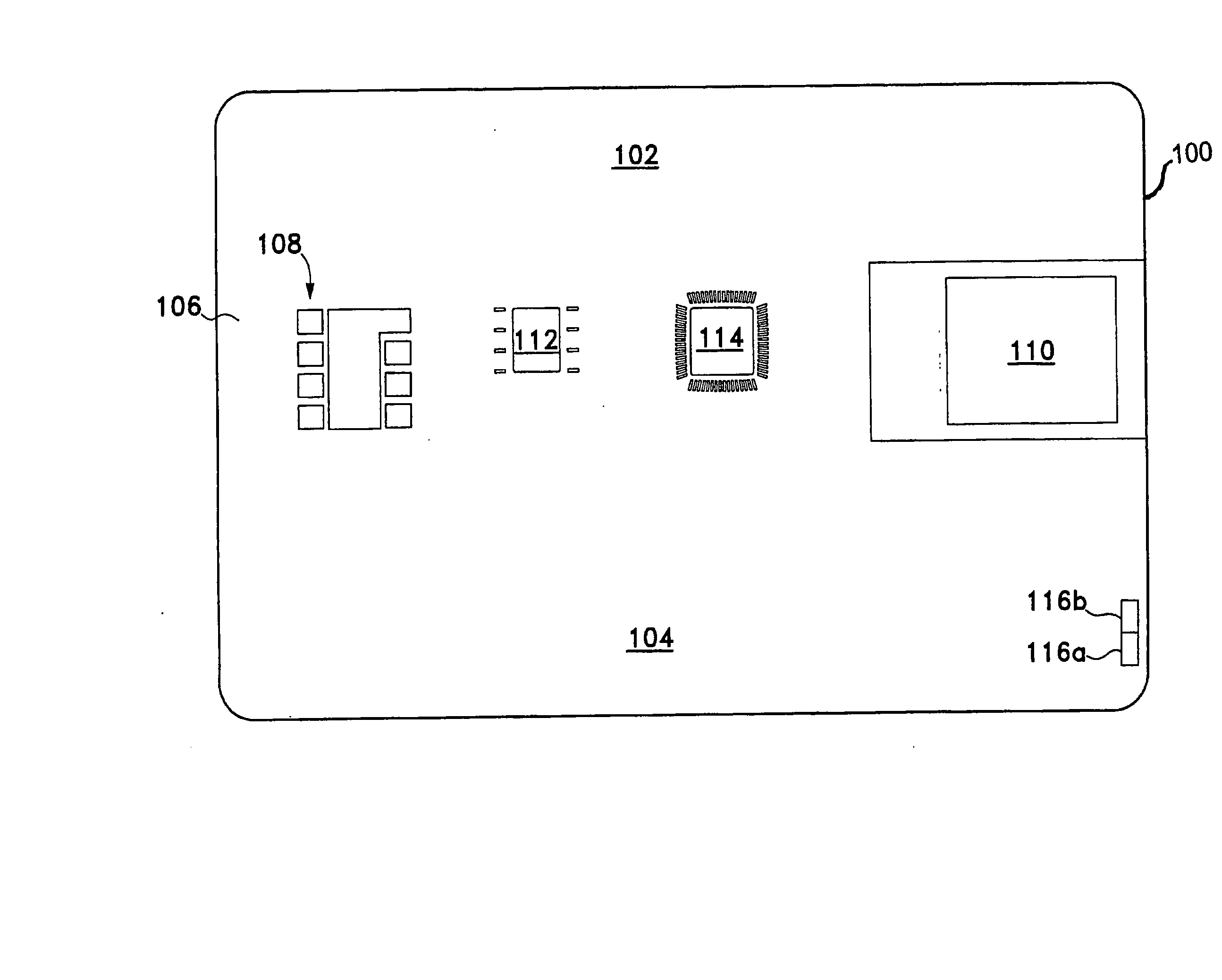
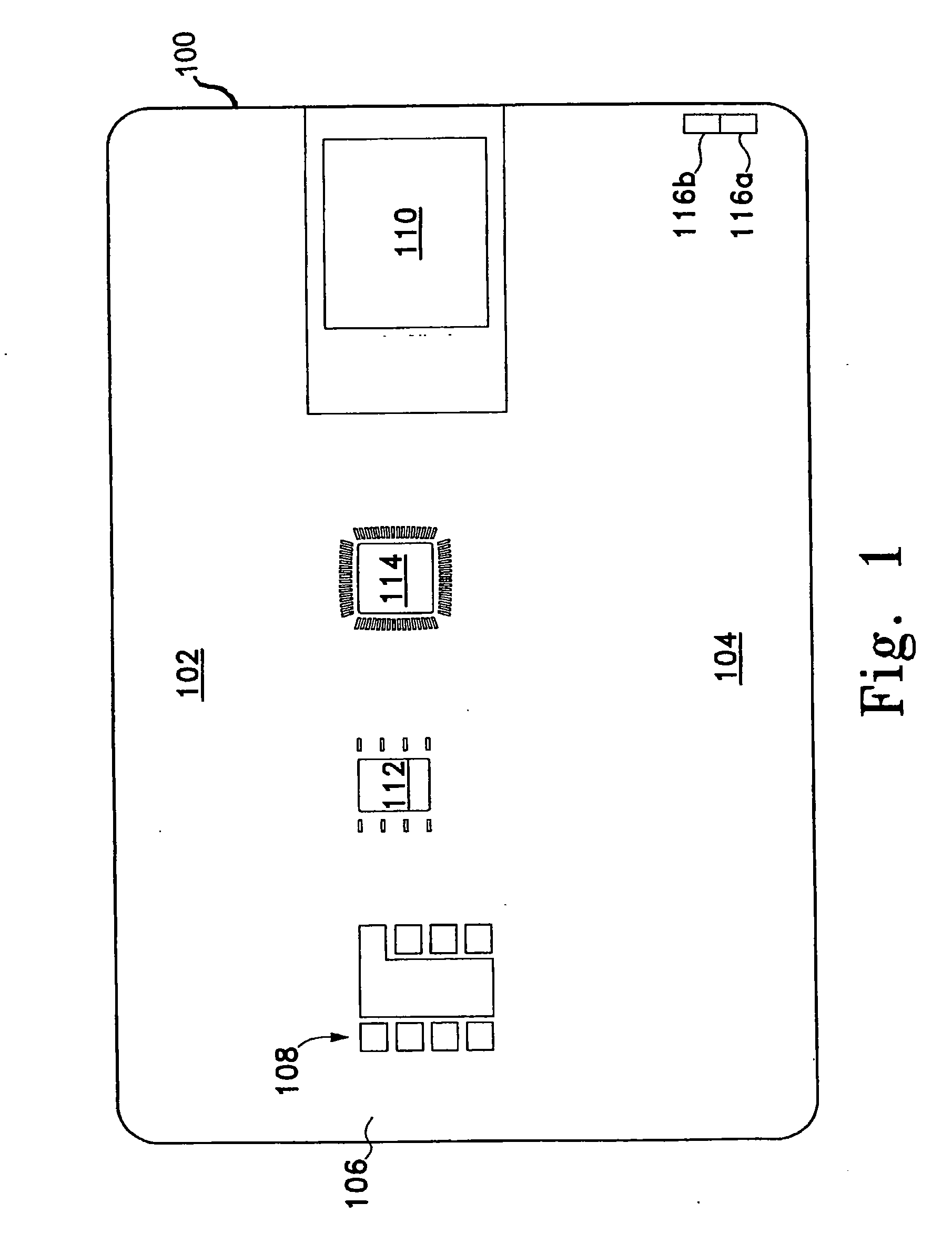
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
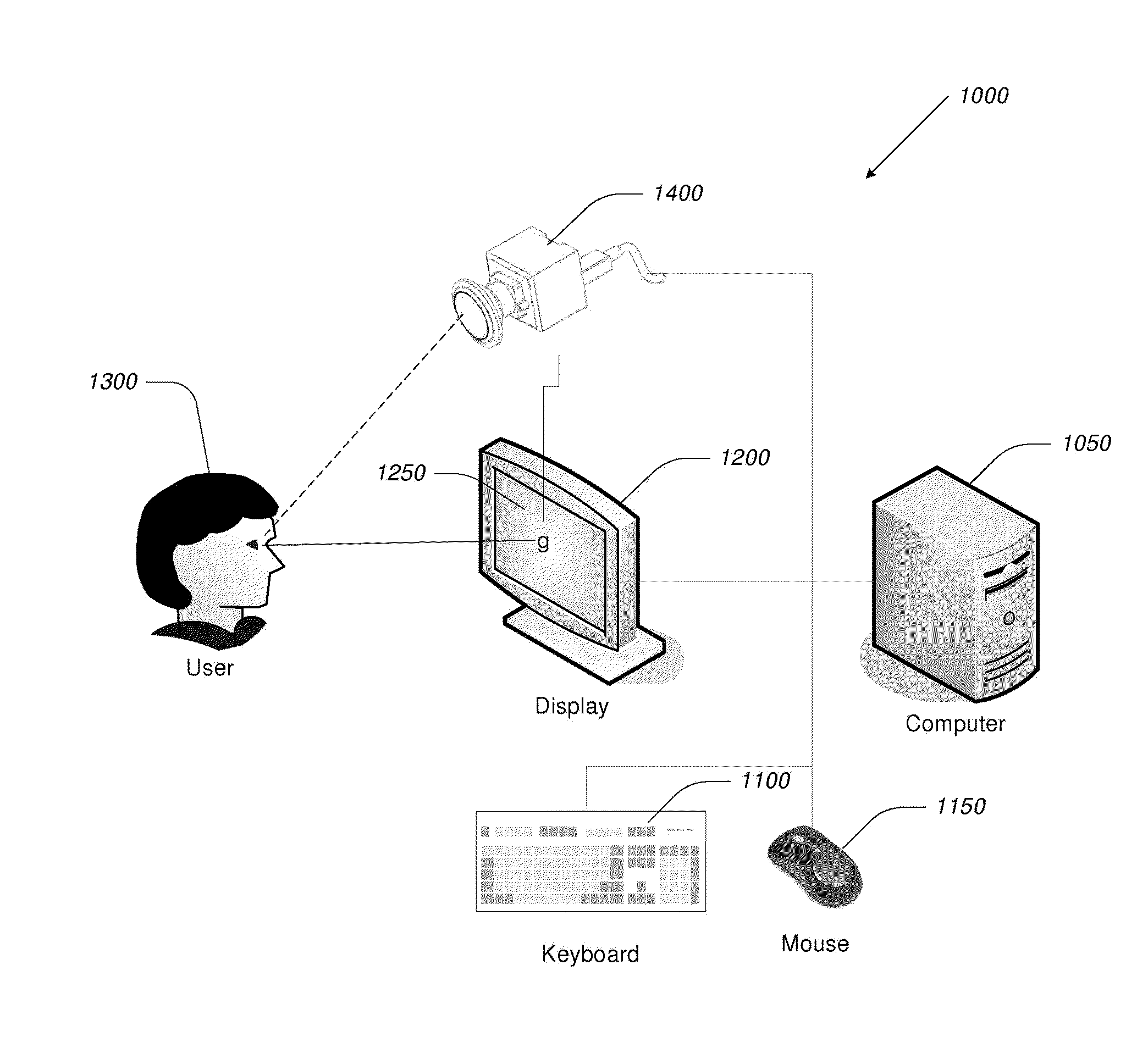
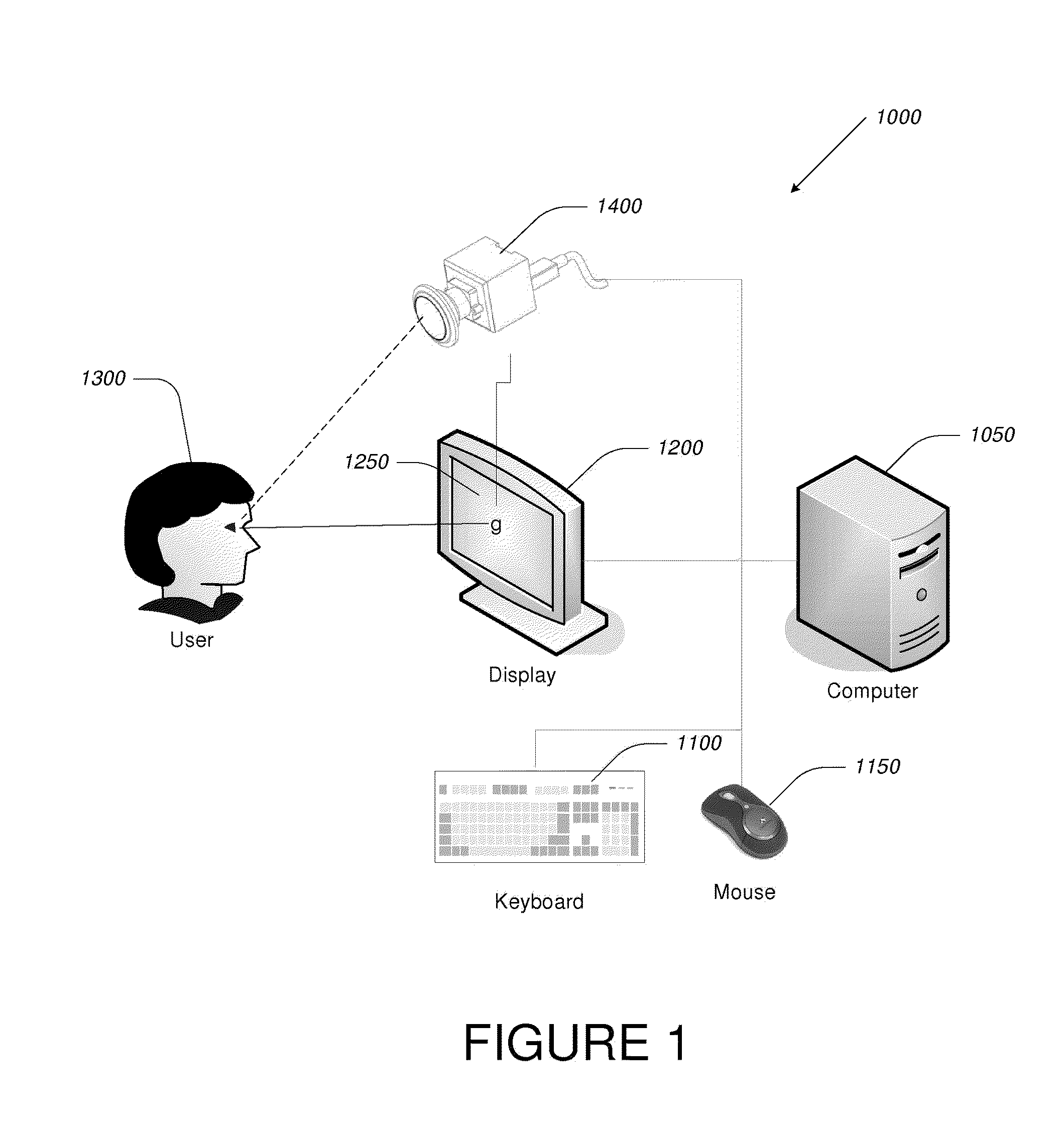
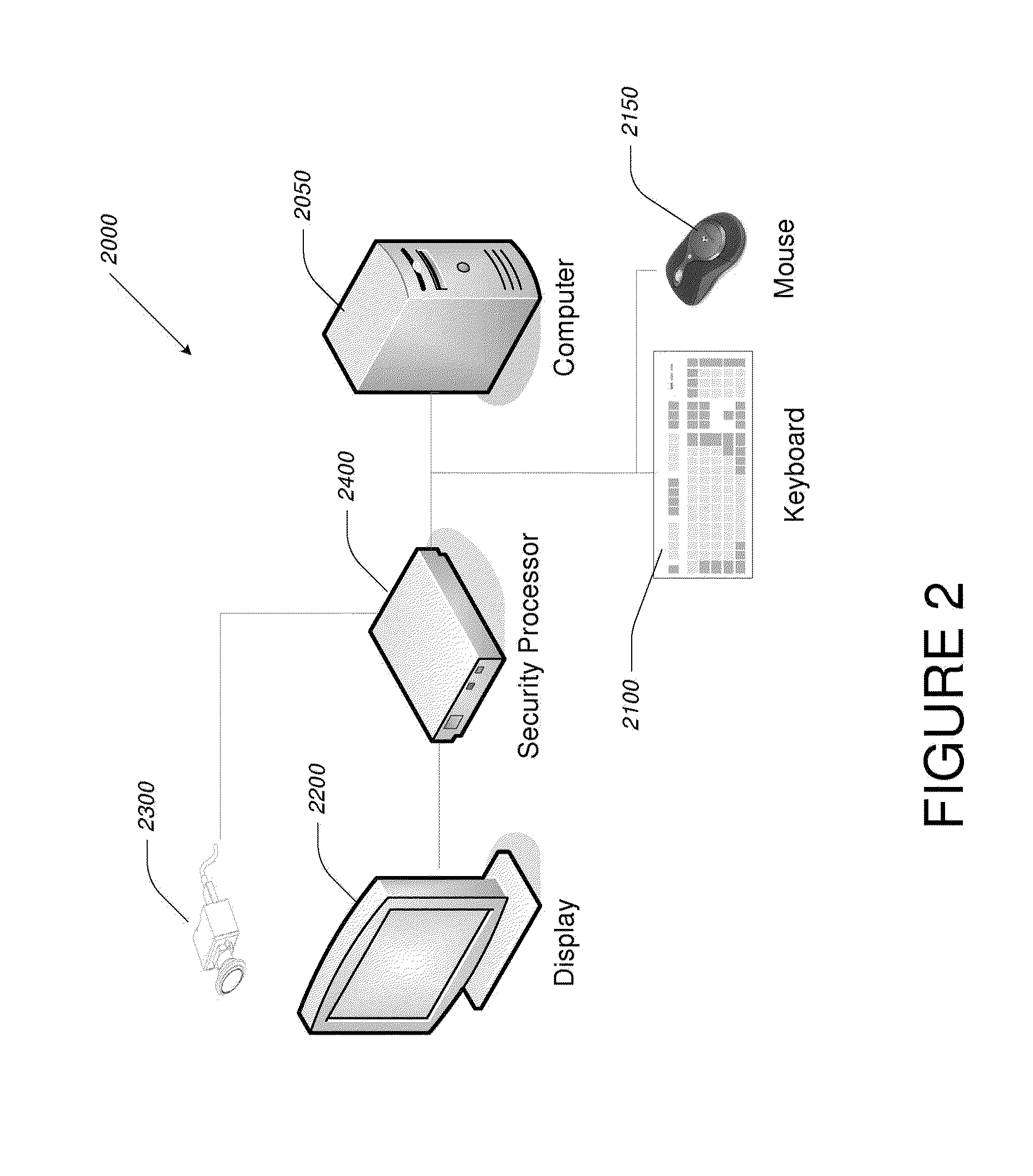
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
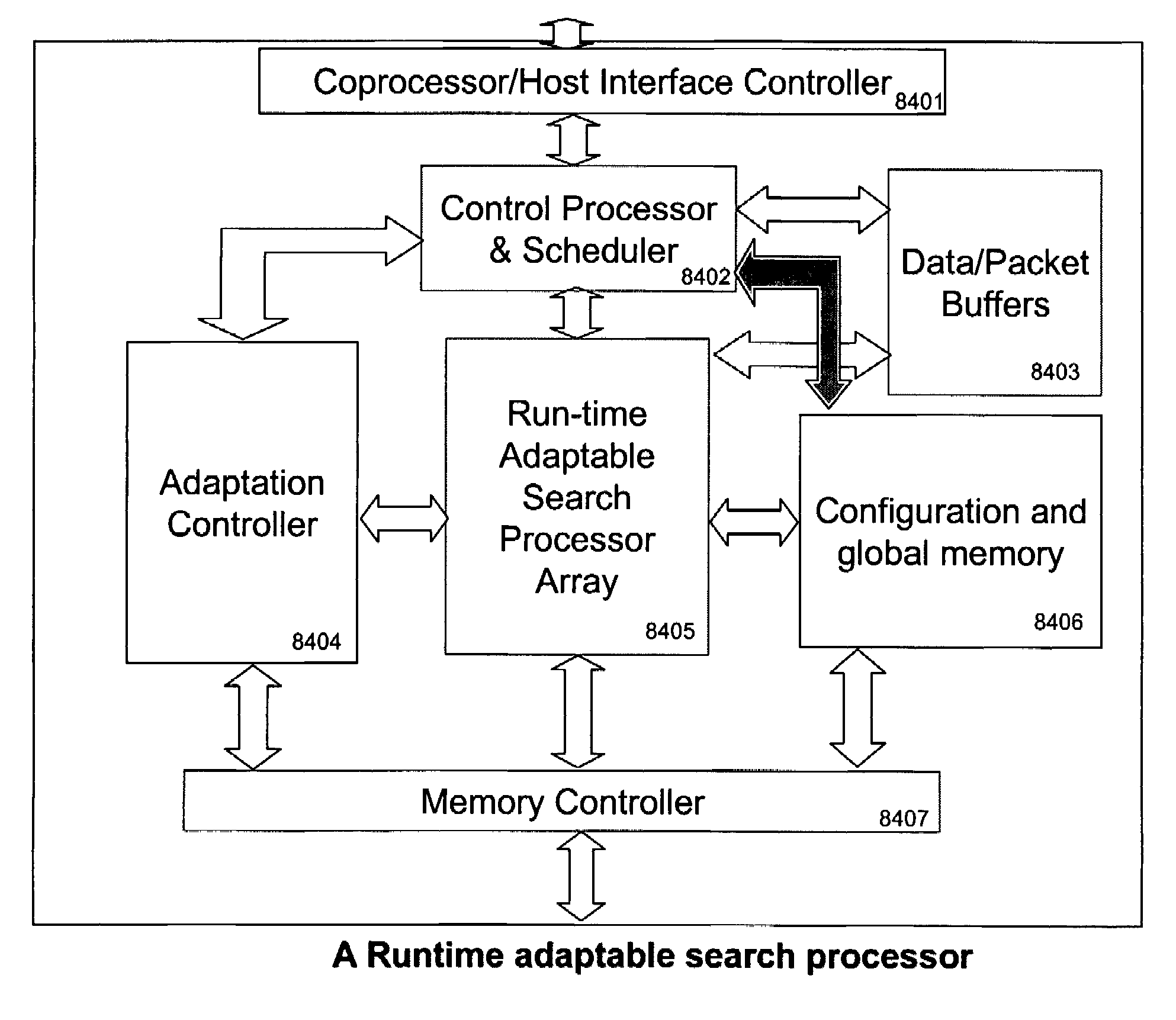
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Secure processing unit systems and methods
InactiveUS7124170B1Low costLow additional costMemory architecture accessing/allocationData processing applicationsMicrocontrollerUnit system
A hardware Secure Processing Unit (SPU) is described that can perform both security functions and other information appliance functions using the same set of hardware resources. Because the additional hardware required to support security functions is a relatively small fraction of the overall device hardware, this type of SPU can be competitive with ordinary non-secure CPUs or microcontrollers that perform the same functions. A set of minimal initialization and management hardware and software is added to, e.g., a standard CPU / microcontroller. The additional hardware and / or software creates an SPU environment and performs the functions needed to virtualize the SPU's hardware resources so that they can be shared between security functions and other functions performed by the same CPU.
Owner:INTERTRUST TECH CORP
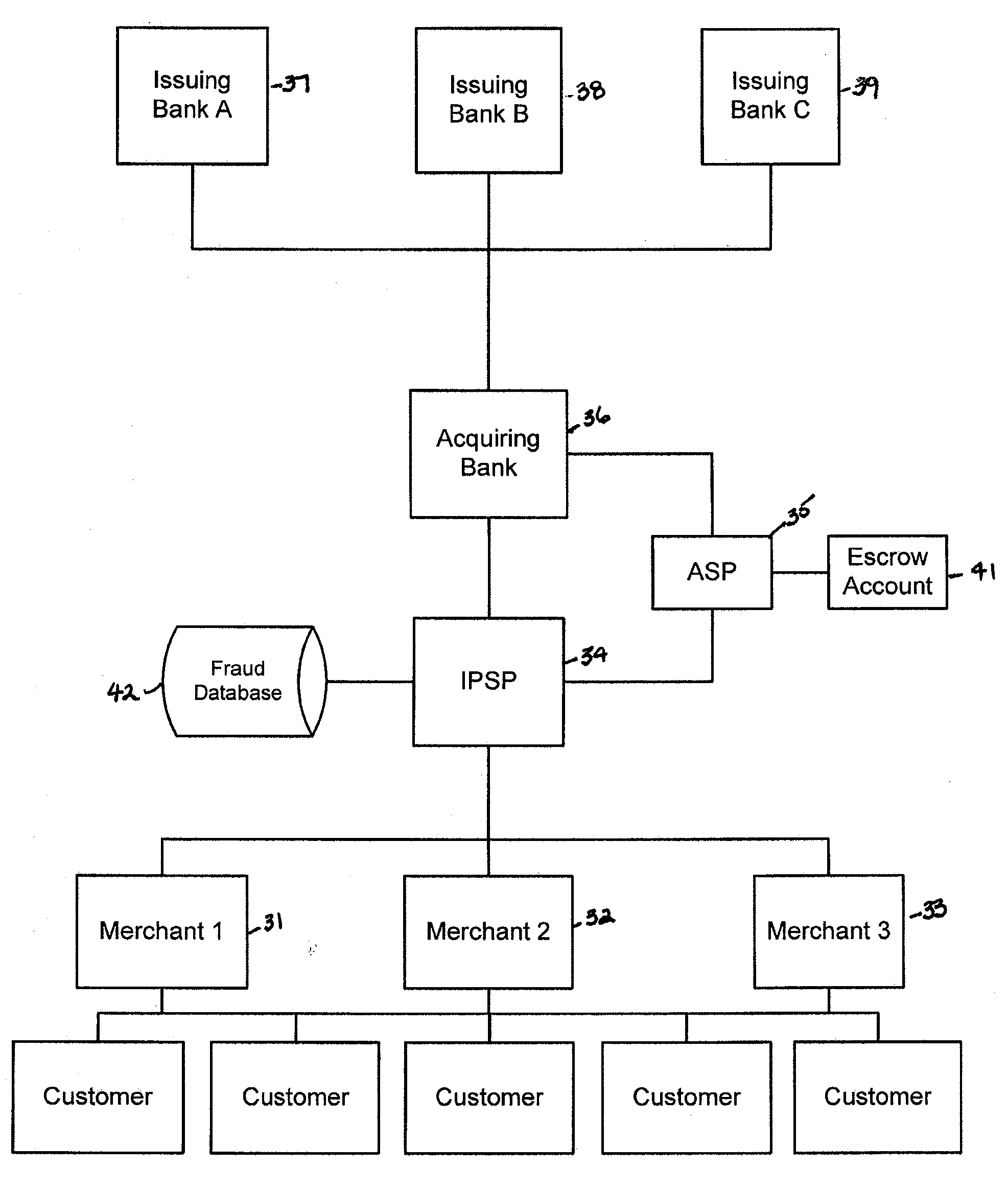
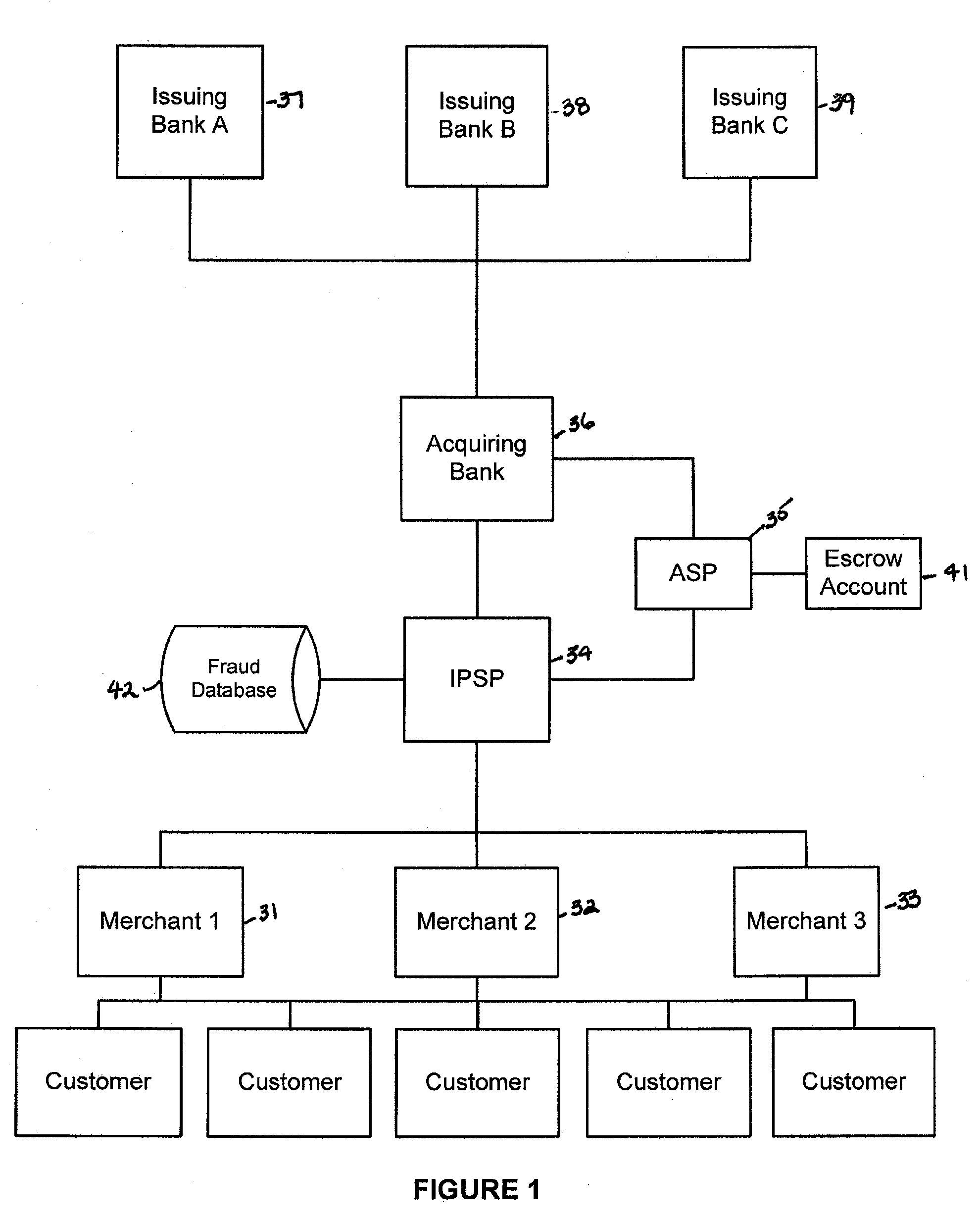
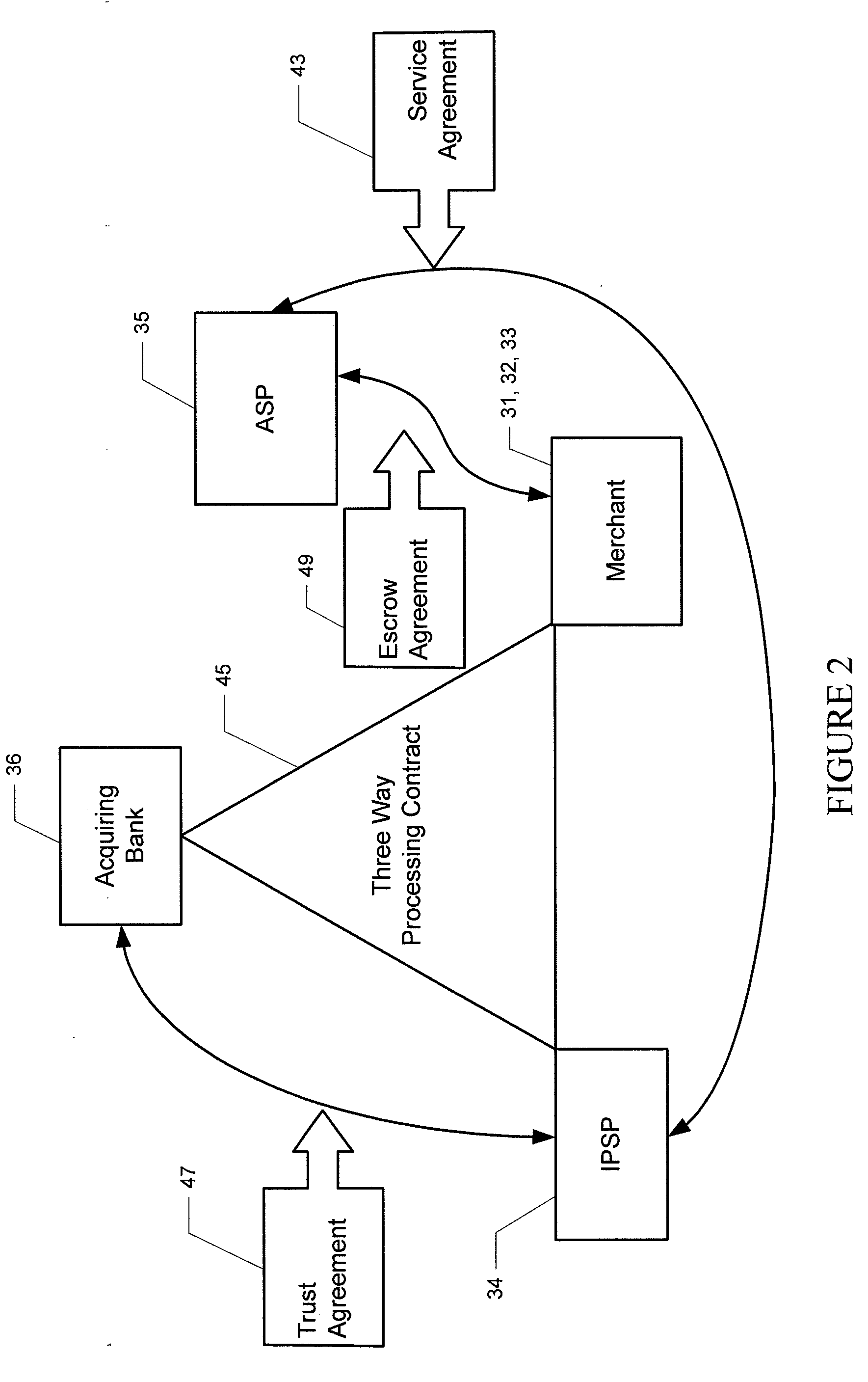
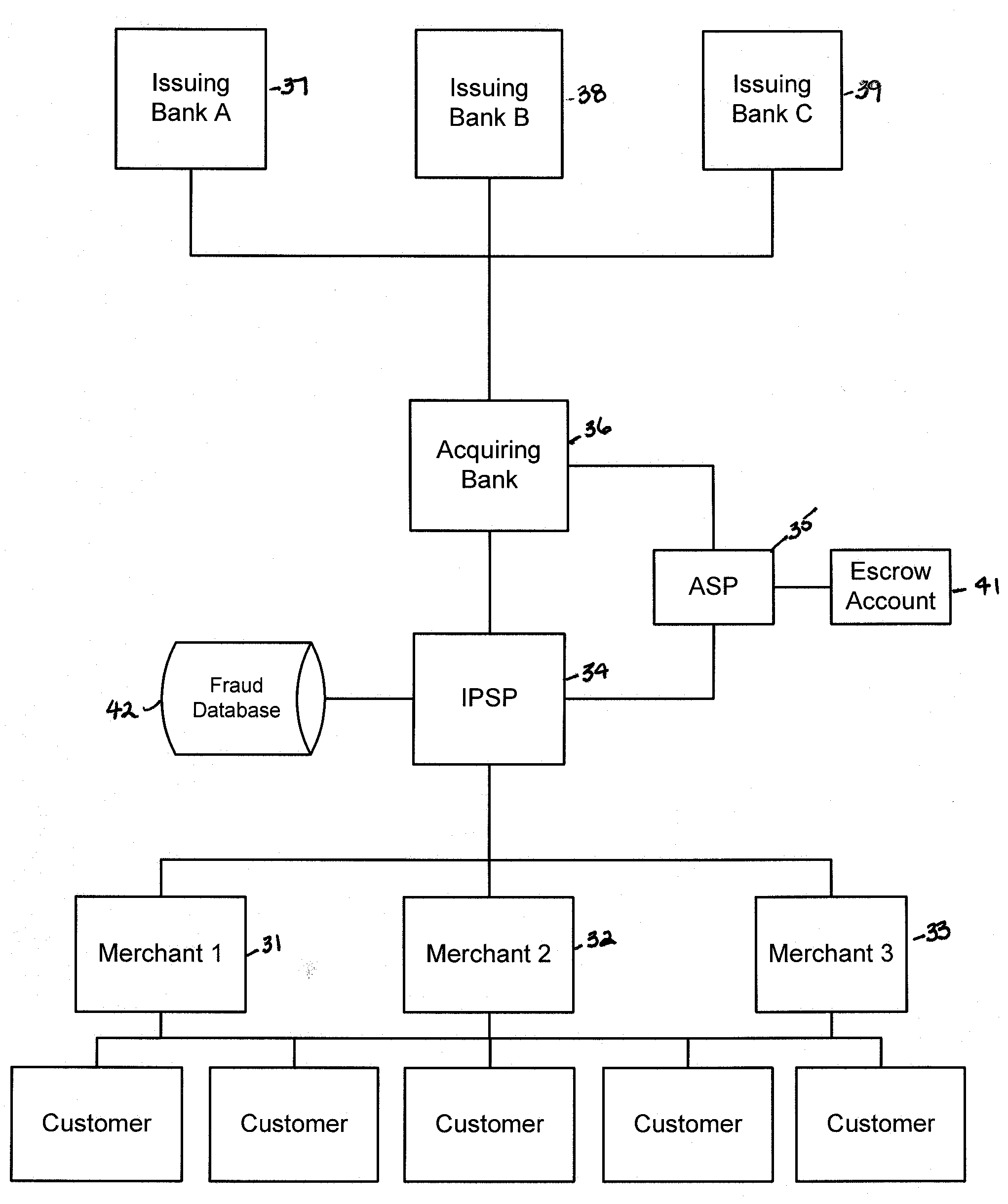
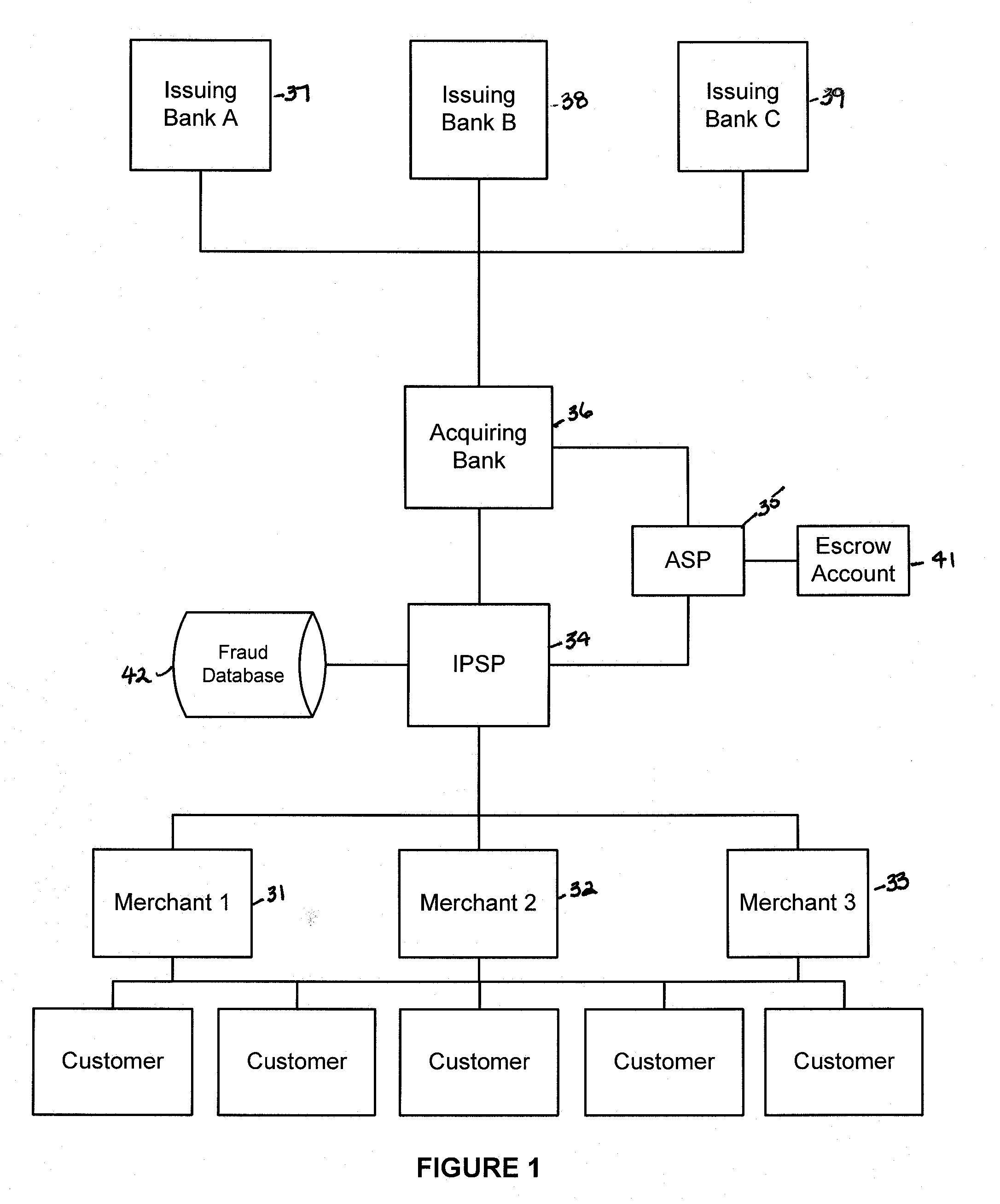
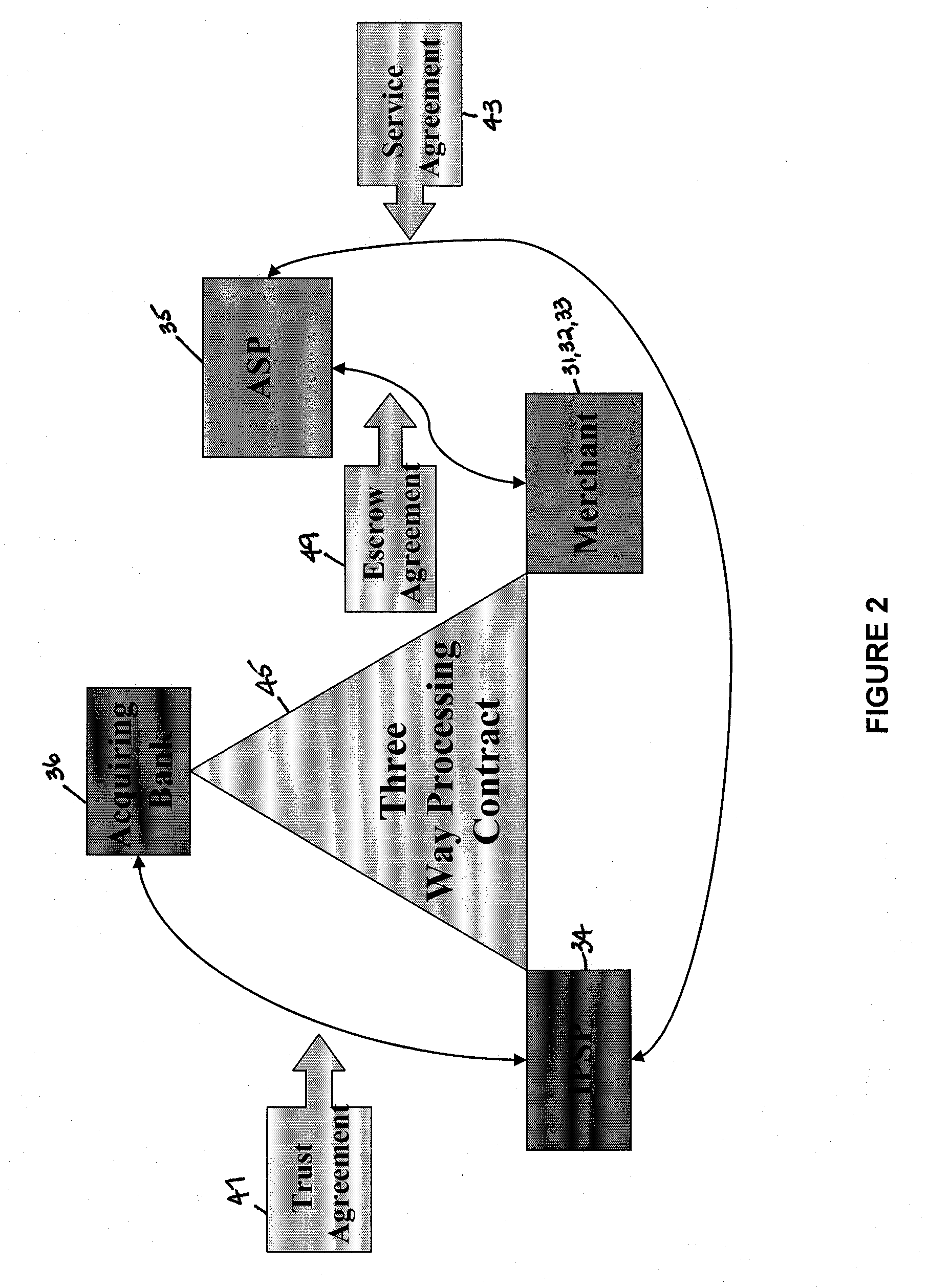
Financial transactions systems and methods
InactiveUS20100106611A1Reduce percentageFinanceApparatus for meter-controlled dispensingPayment transactionService provision
Various embodiments of the invention provide a more secure financial transaction system for e-commerce sectors that (1) more securely processes payment transactions, (2) helps to protect merchants and banks against fraudulent transactions, money laundering, and underage gambling, and (3) helps to limit other abuses in areas of e-commerce that are perceived to pose special risks, such as Internet gaming, travel, and consumer purchasing of electronic goods. To accomplish the above goals, various embodiments of the financial transaction system (1) establish operating and transaction processing protocols for merchants, Internet payment service providers, acquiring banks, and card schemes and (2) provide automated systems for monitoring and securely processing payment and financial transactions.
Owner:TRUST PAYMENTS LTD
Methods and devices for microfluidic point-of-care immunoassays
ActiveUS20090181411A1Endpoint detectionReduce incubation timeBioreactor/fermenter combinationsBiological substance pretreatmentsPoint of careSystems design
Microfluidic methods and devices for heterogeneous binding and agglutination assays are disclosed, with improvements relating to mixing and to reagent and sample manipulation in systems designed for safe handling of clinical test samples.
Owner:PERKINELMER HEALTH SCIENCES INC
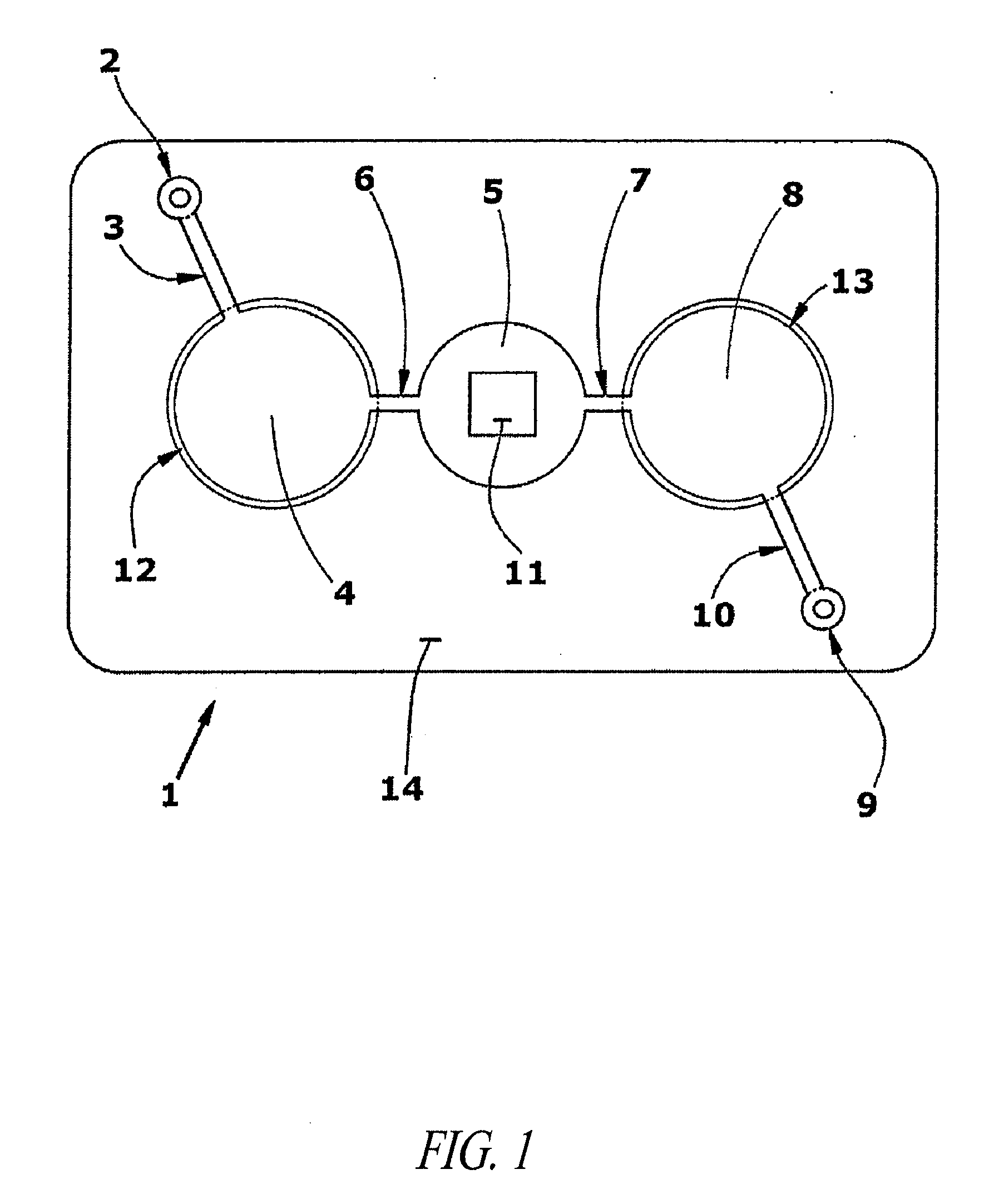
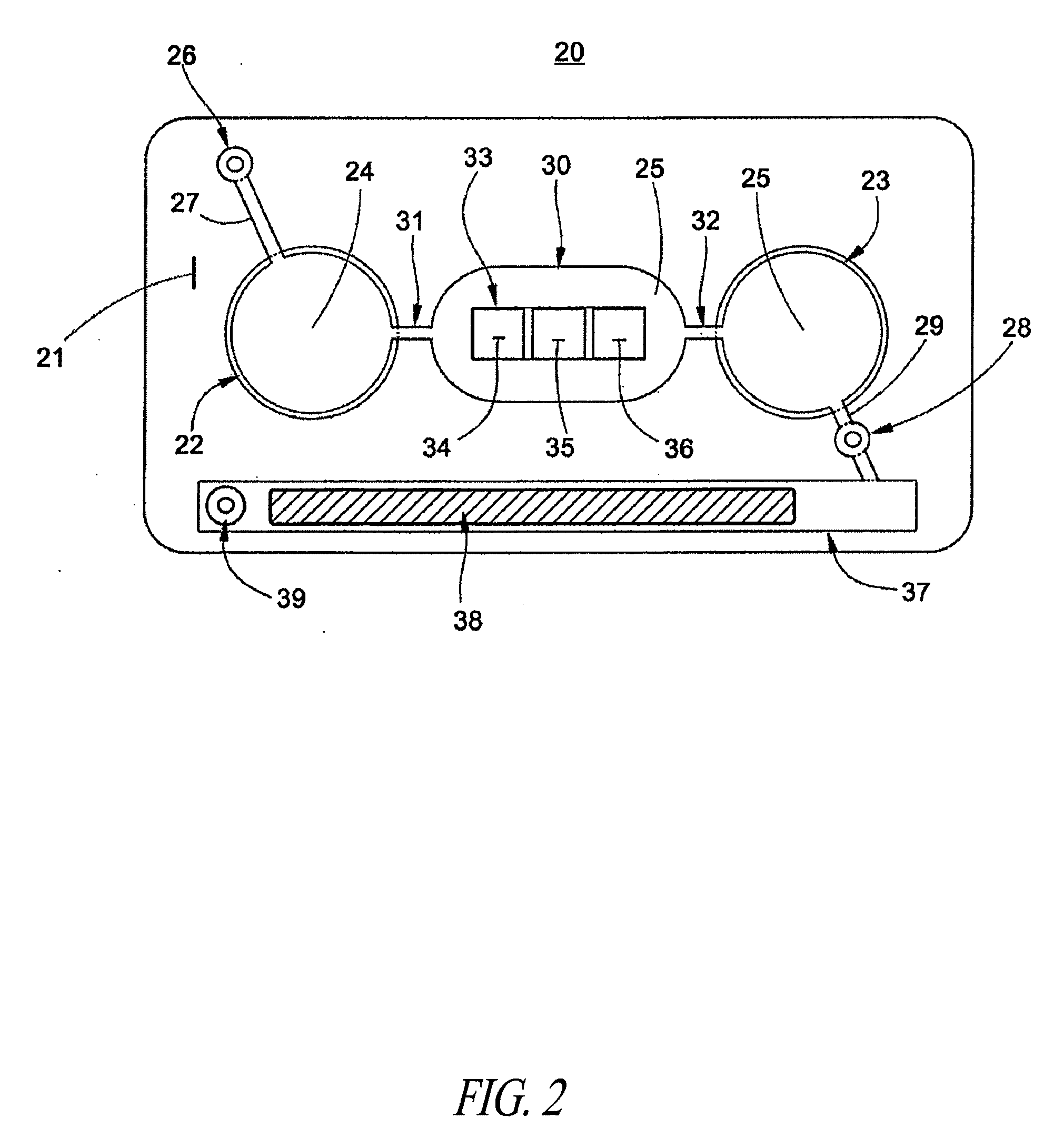
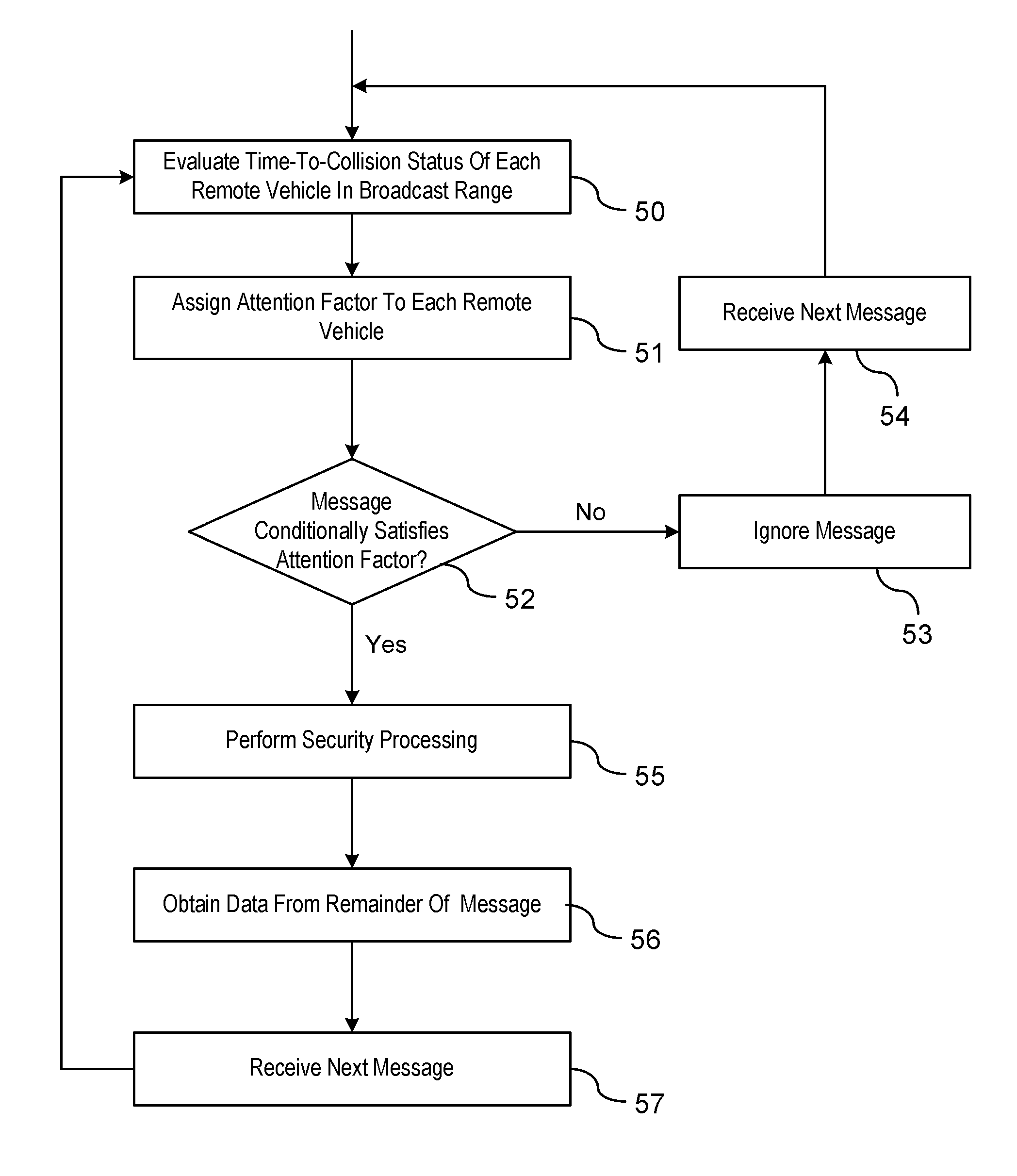
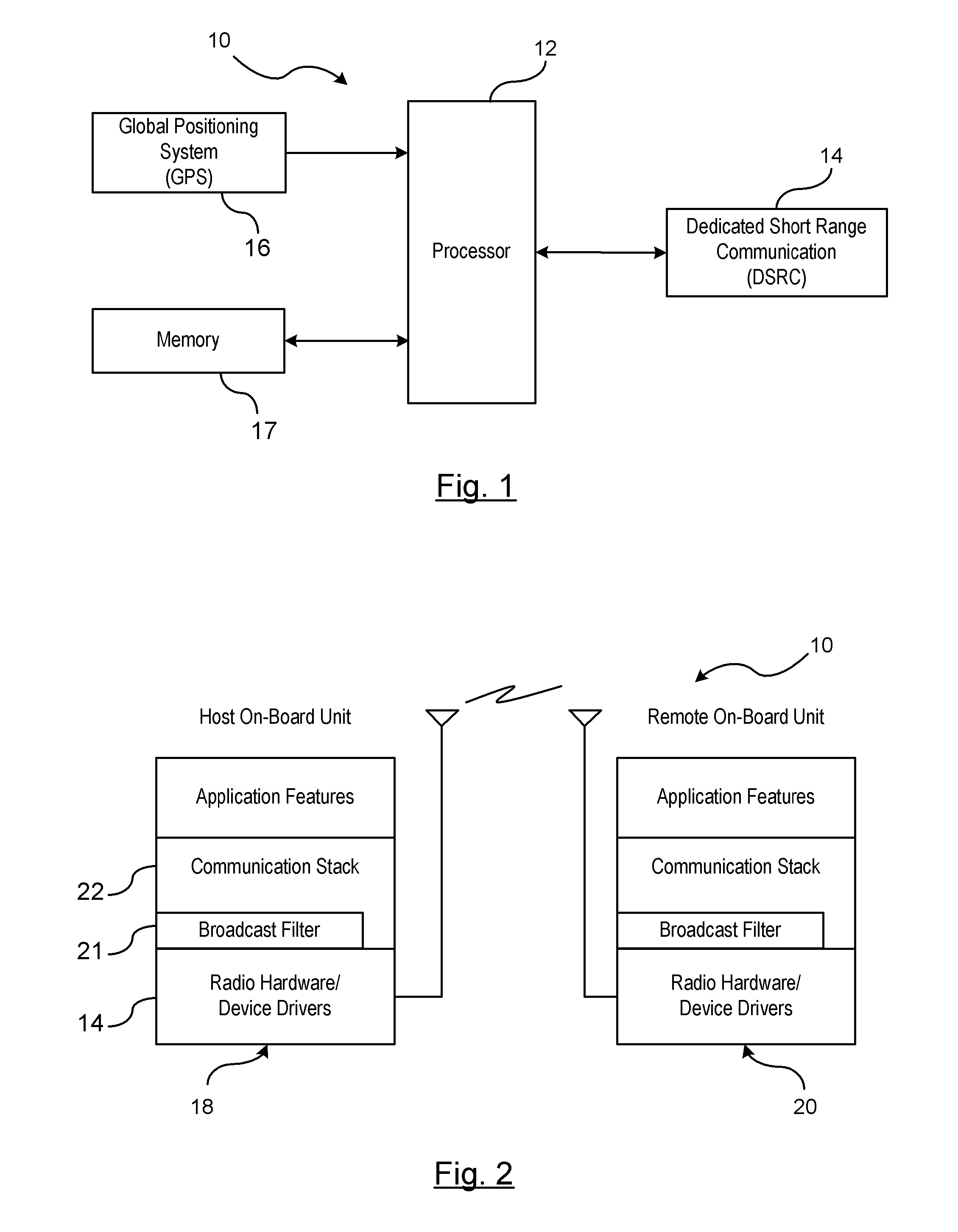
A lean v2x security processing strategy using kinematics information of vehicles
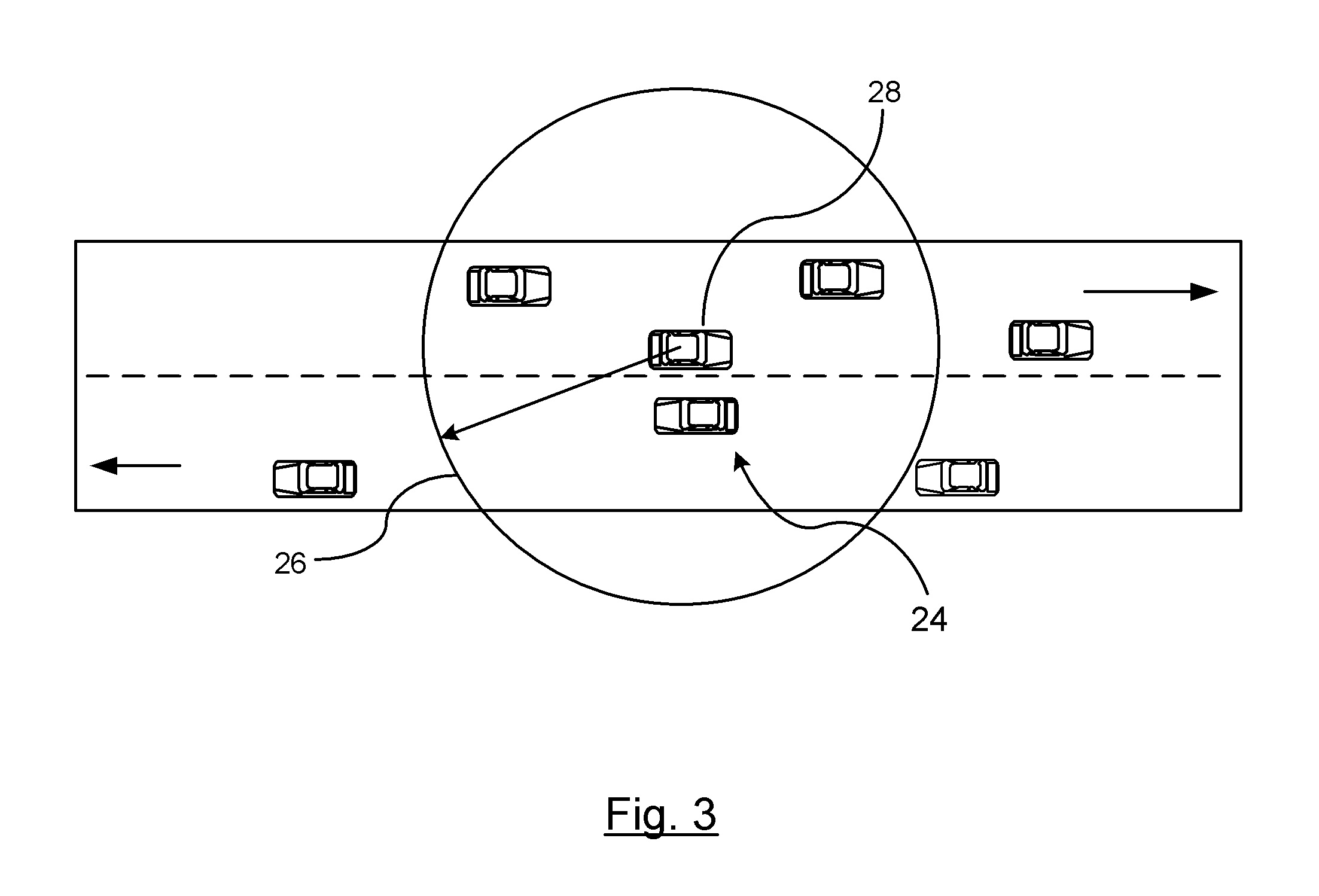
ActiveUS20110140968A1Reduce loadLess-expensive and low computationalDirection finders using radio wavesAnti-collision systemsKinematicsEngineering
A vehicle-to-vehicle communication filtering system is provided to selectively process broadcast messages between a host vehicle and a remote vehicle. A processing unit evaluates a time-to-collision status between the host vehicle and the remote vehicle sending the message. The time-to-collision status is a function of a relative distance and a relative velocity between the host vehicle and the remote vehicle which are determined from data provided within a first portion of the message received from the remote vehicle. An attentive factor is assigned to each of the remote vehicles based on the time-to-collision with respect to each remote vehicle. The attentive factor identifies a proportion of messages broadcast from the remote vehicle to be targeted for security processing. Security processing of the message is performed based on a second portion of the message unless the attentive factor indicates the message should be ignored.
Owner:GM GLOBAL TECH OPERATIONS LLC
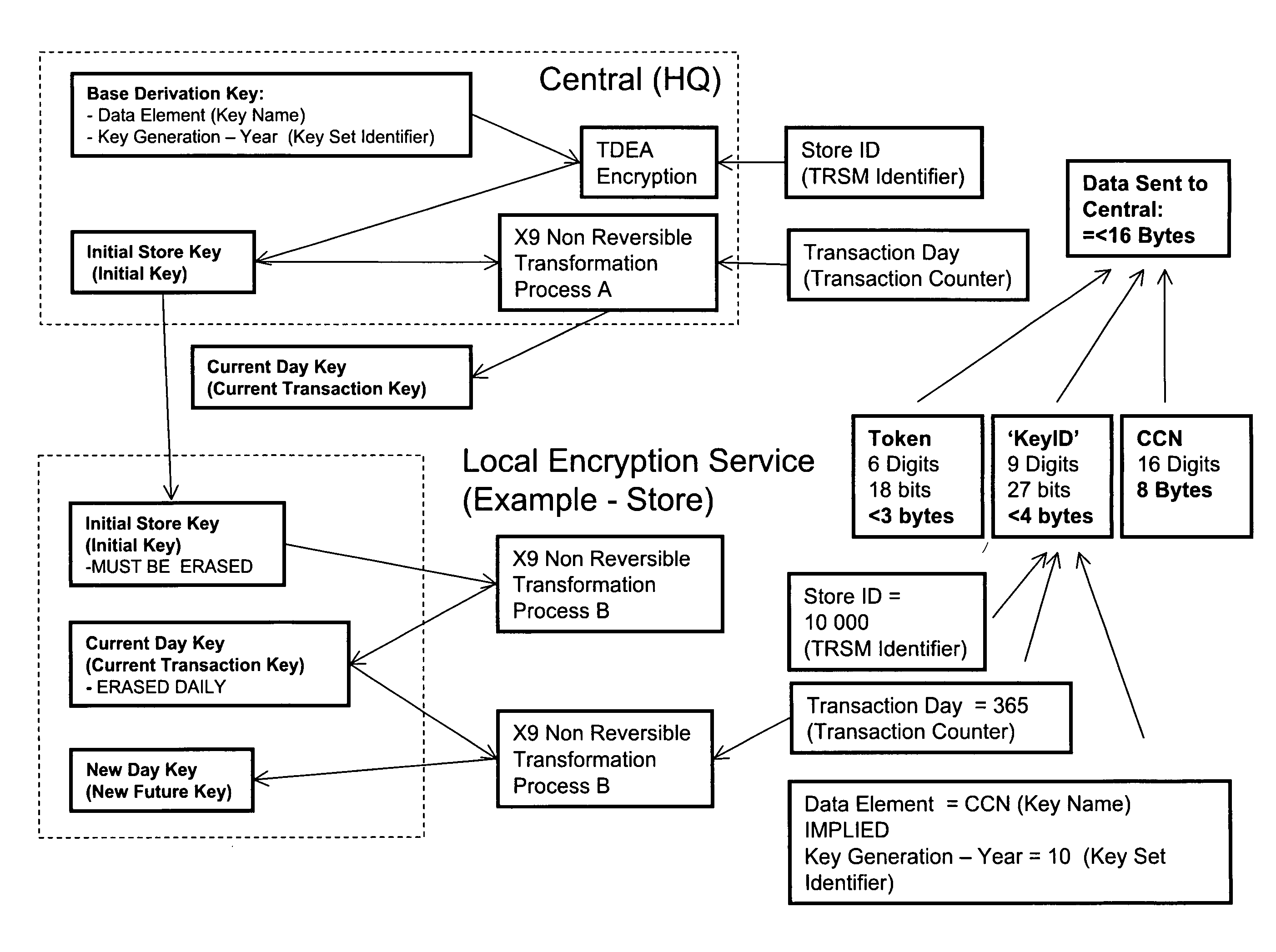
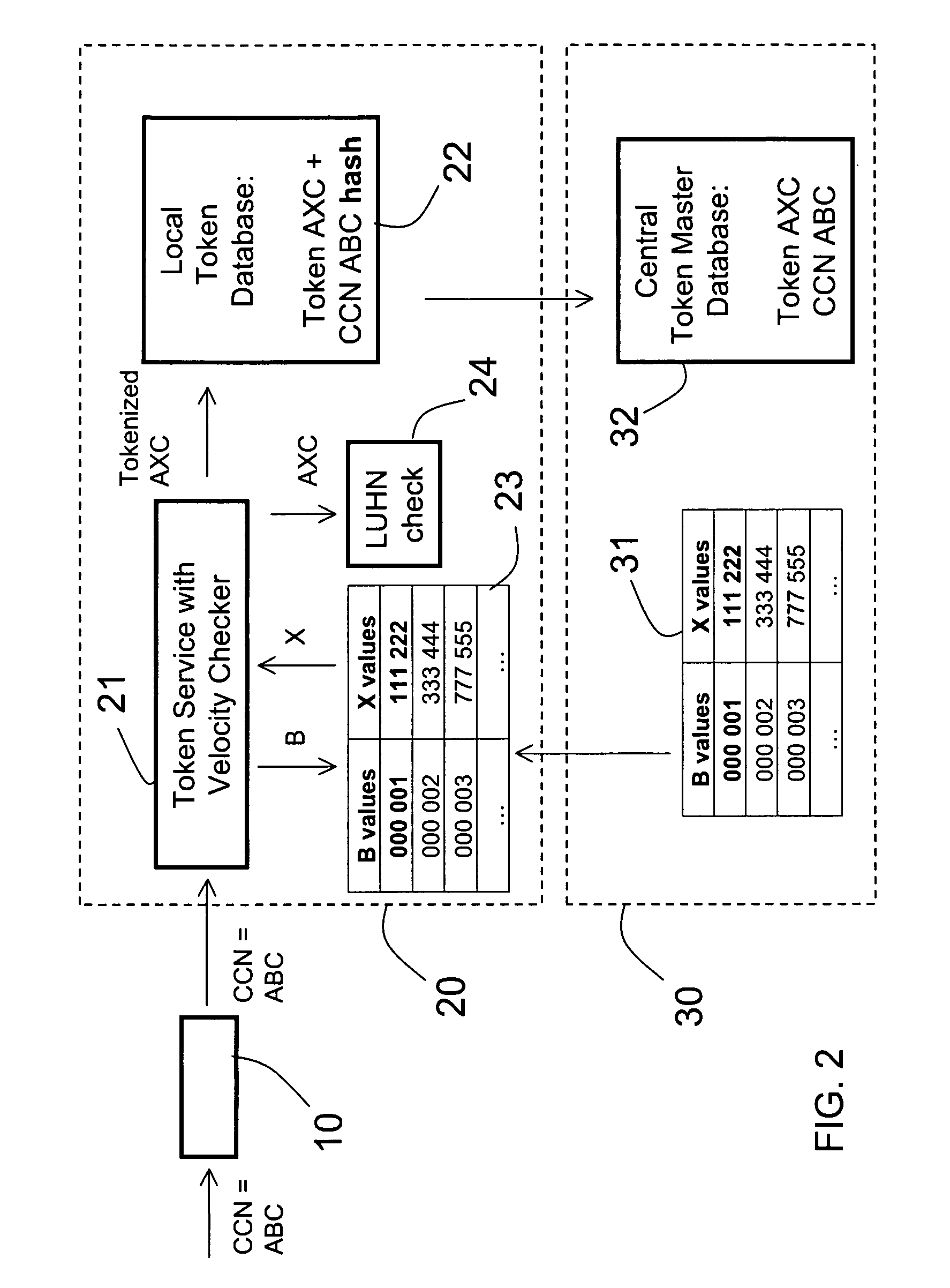
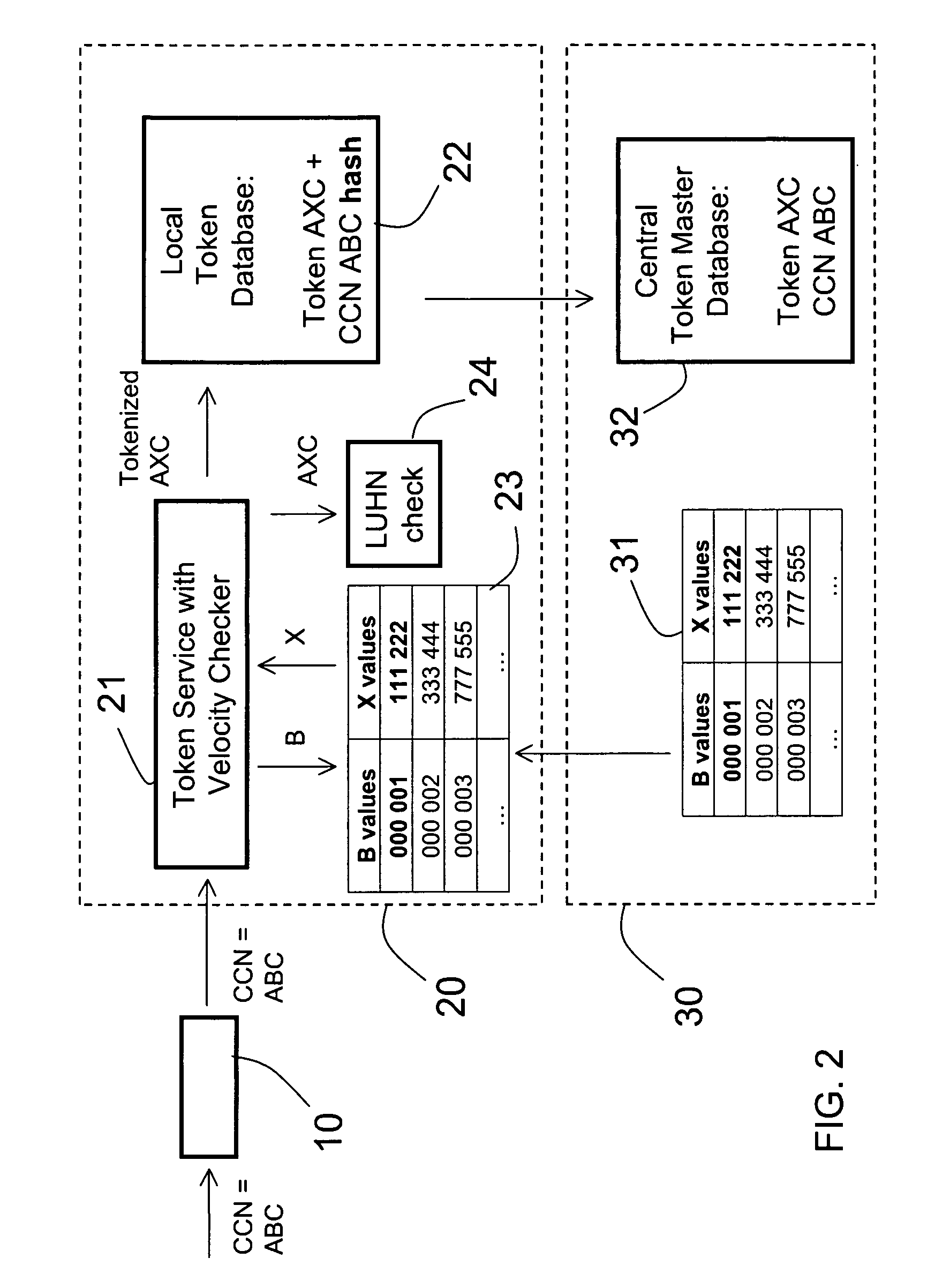
Method and apparatus for tokenization of sensitive sets of characters
ActiveUS8578176B2Reduce demandImprove forecastAcutation objectsUnauthorized memory use protectionComputer networkSafe handling
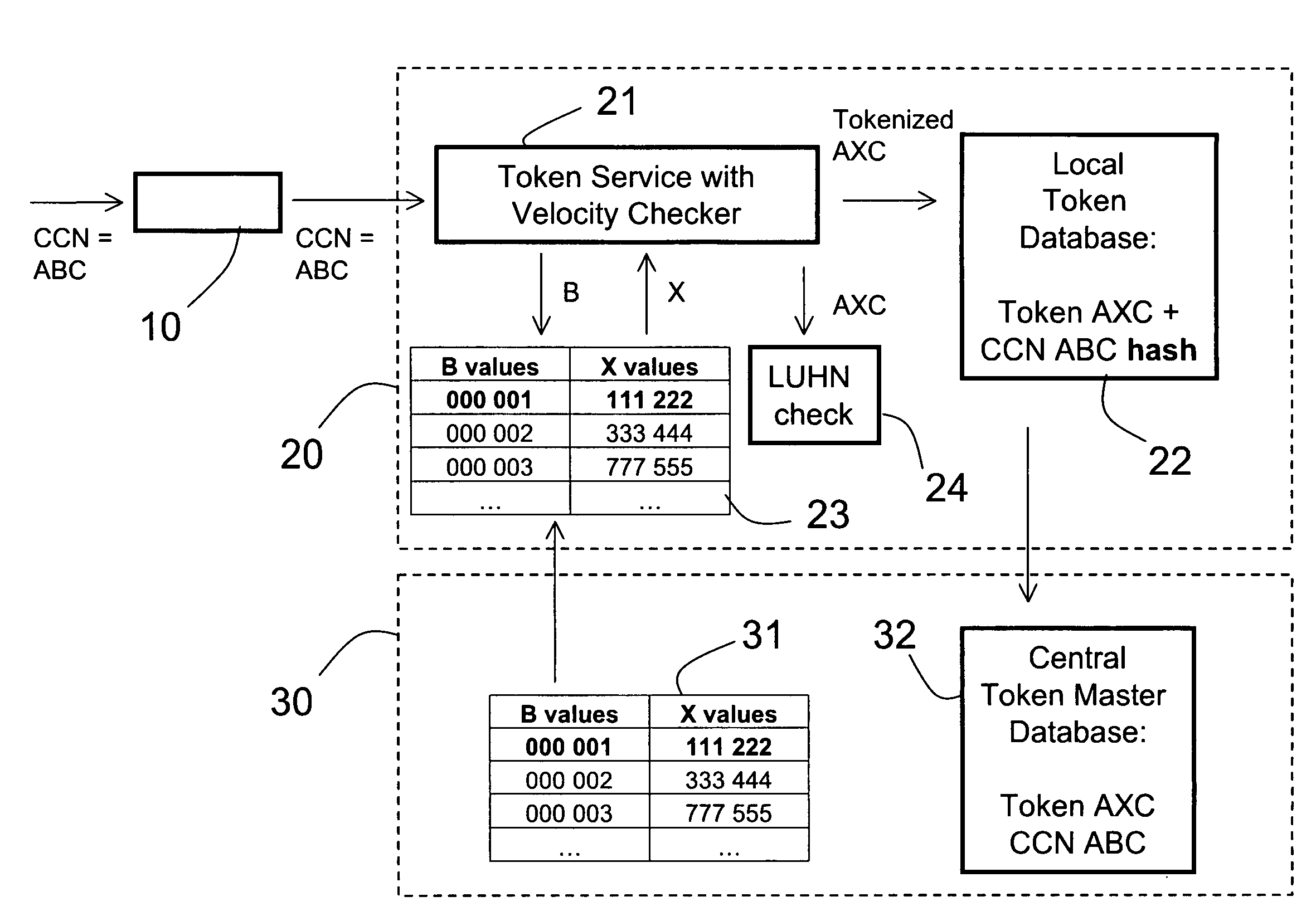
A method and system for secure handling of sensitive sets of characters in a distributed hierarchical system are disclosed, comprising at least one local server on a lower hierarchic level and at least one central server at a higher hierarchic level. The method comprises the steps: receiving a sensitive set of characters in said local server; replacing a part of said sensitive set of characters with a token to form a tokenized set of characters, said token belonging to a subset of possible tokens assigned to the local server by the central server; transferring at least one of said sensitive set of characters and said tokenized set of characters to the central server; and canceling said sensitive set of characters from said local server within a limited time from said transferring, while maintaining said tokenized set of characters in a local database connected to said local server.
Owner:PROTEGRITY CORP
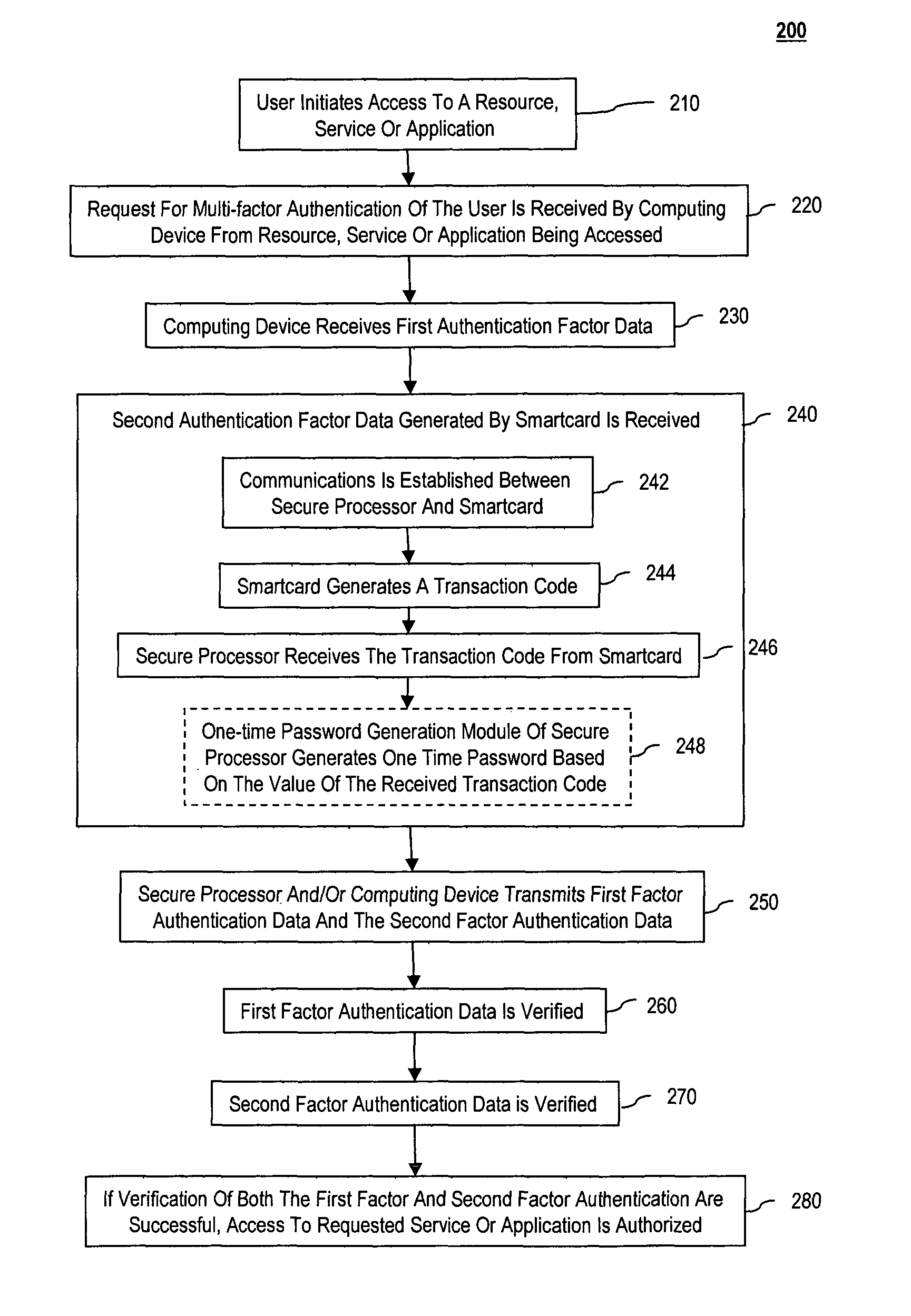
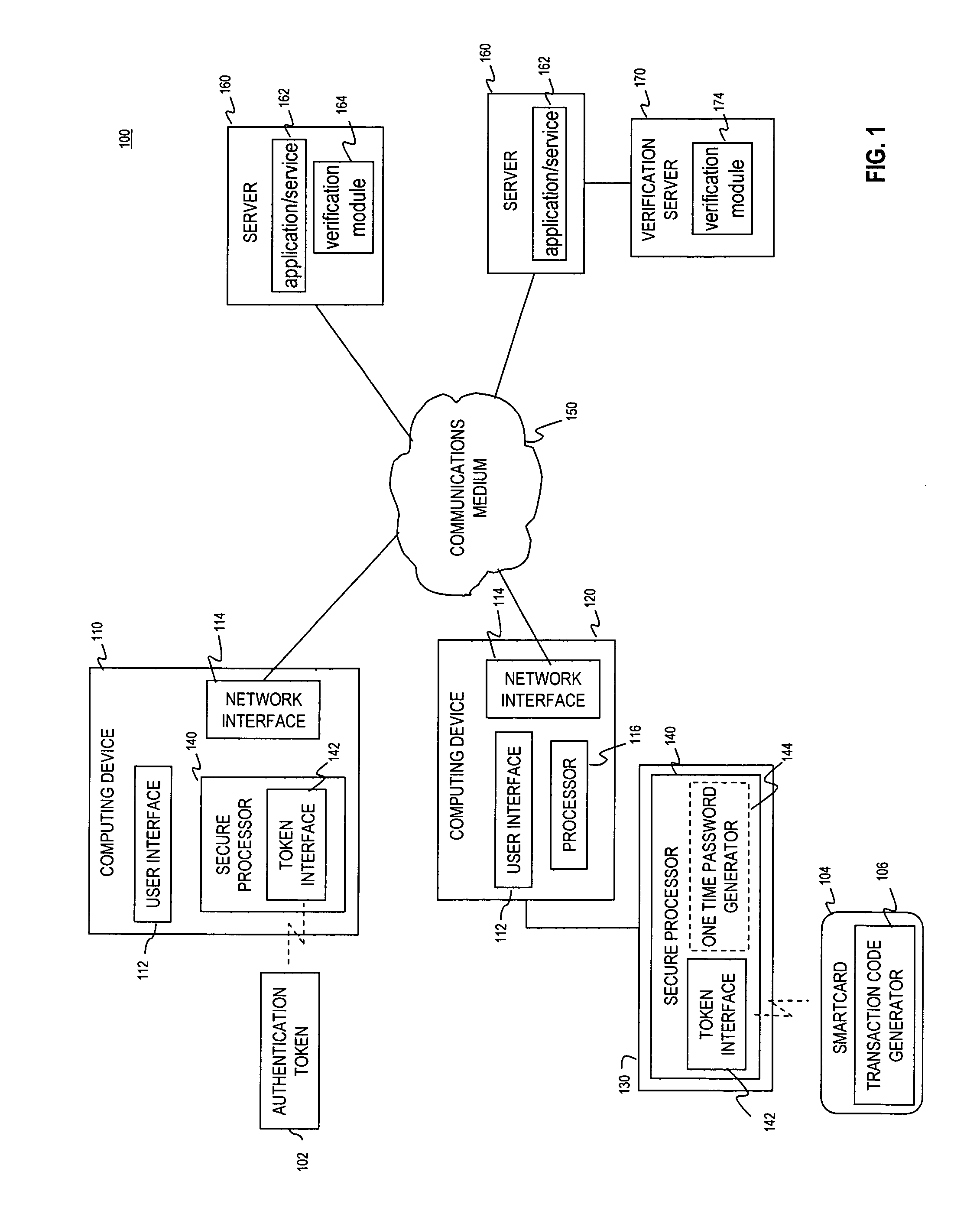
Multi-factor authentication using a smartcard
ActiveUS8245292B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
Systems and methods for determining regulations governing financial transactions conducted over a network
Various embodiments of the invention provide a more secure financial transaction system for e-commerce sectors that (1) more securely processes payment transactions, (2) helps to protect merchants and banks against fraudulent transactions, money laundering, and underage gambling, and (3) helps to limit other abuses in areas of e-commerce that are perceived to pose special risks, such as Internet gaming, travel, and consumer purchasing of electronic goods. To accomplish the above goals, various embodiments of the financial transaction system (1) establish operating and transaction processing protocols for merchants, Internet payment service providers, acquiring banks, and card schemes and (2) provide automated systems for monitoring and securely processing payment and financial transactions.
Owner:TILLY BAKER +1
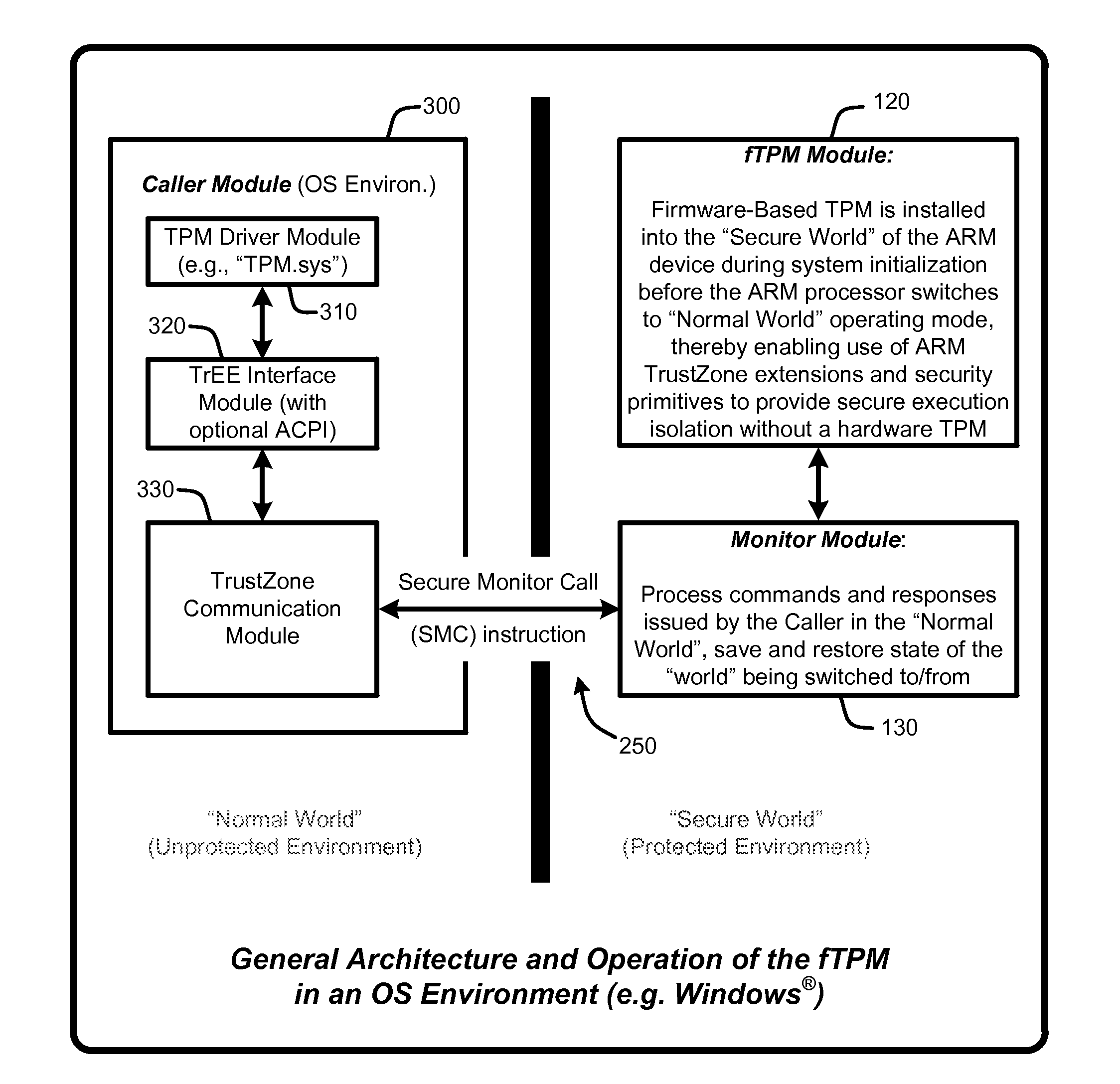
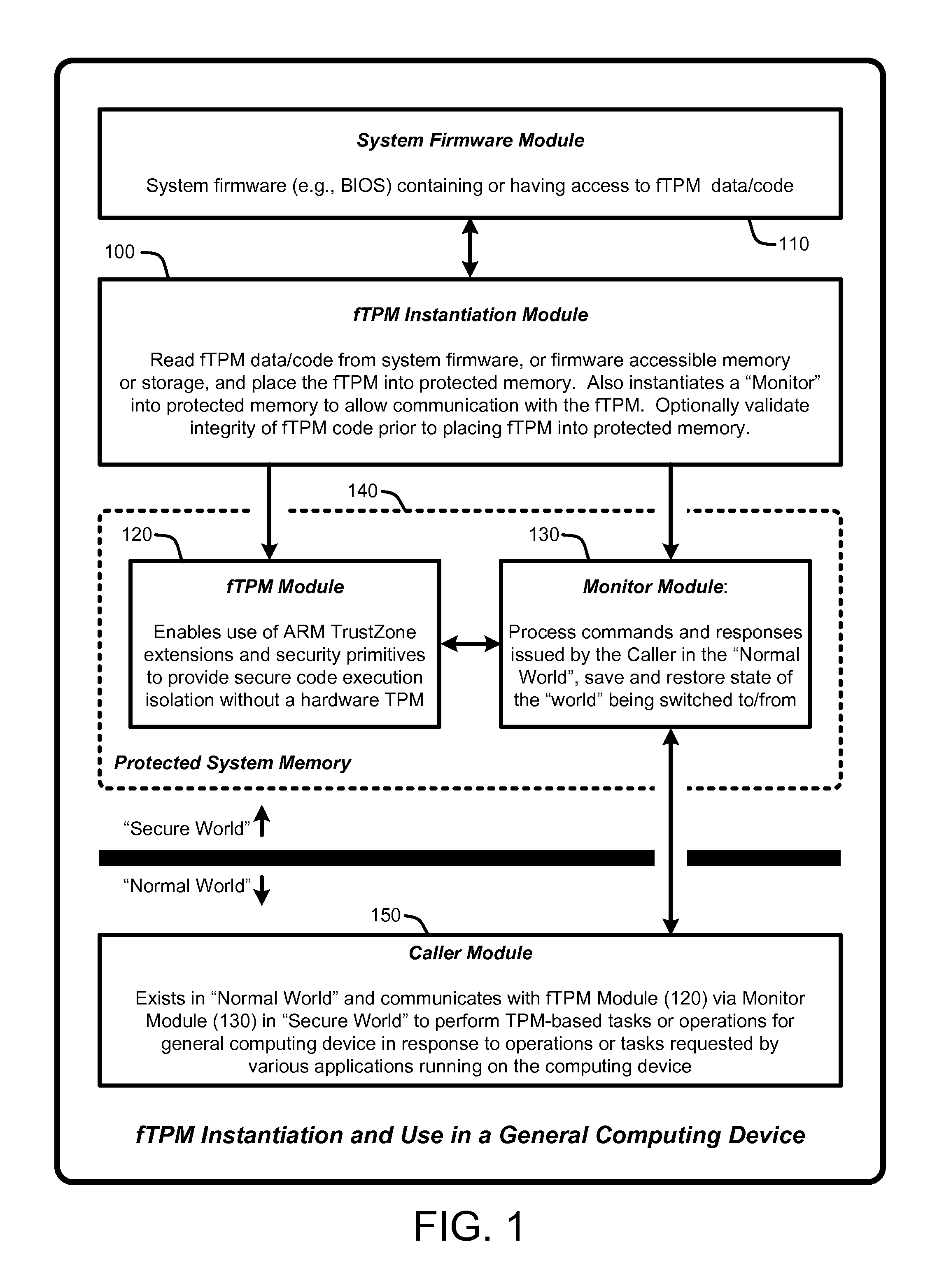
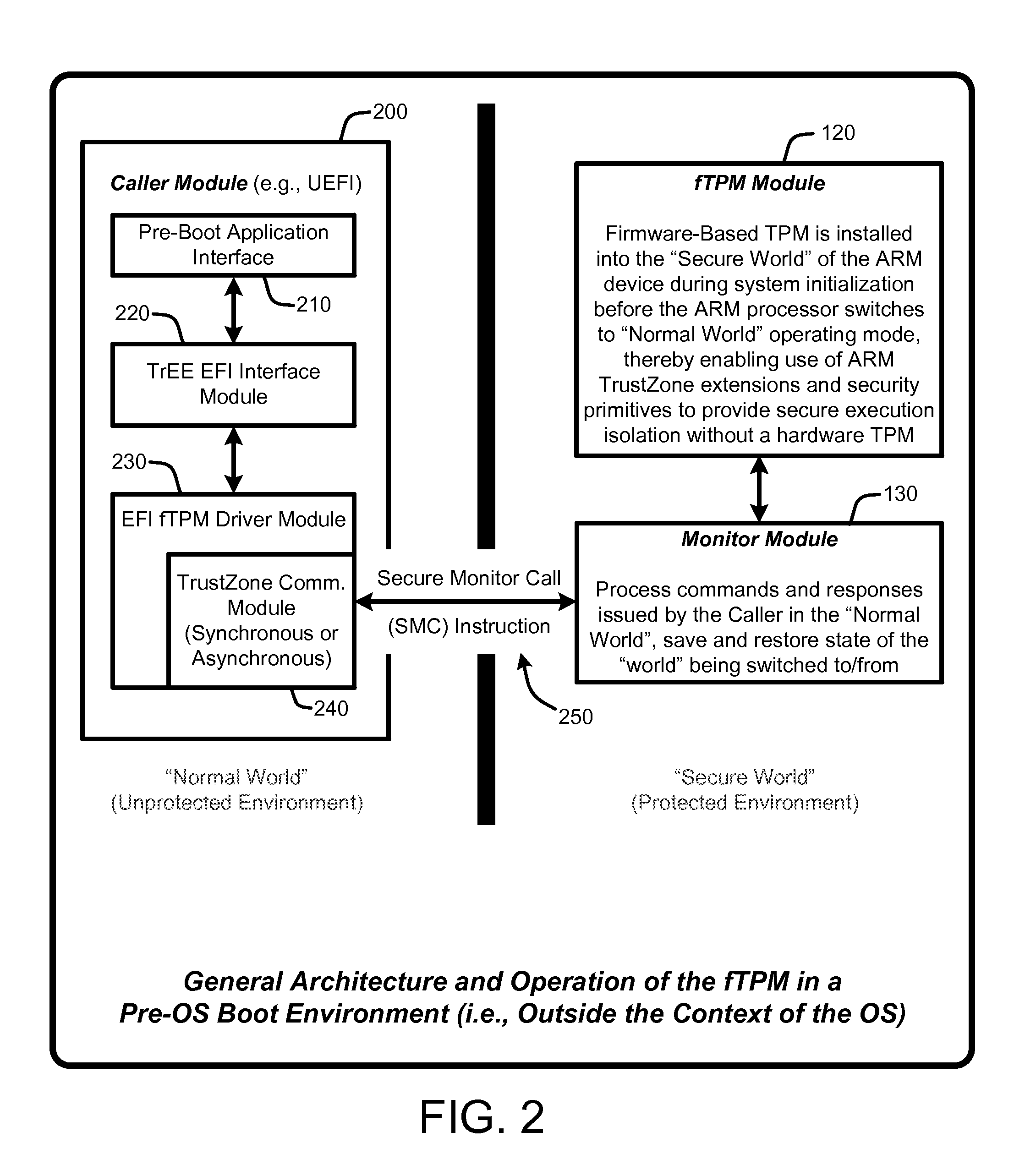
Firmware-based trusted platform module for arm processor architectures and trustzone security extensions
ActiveUS20130031374A1Increase costReduce system costDigital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleSafe handling
A “Firmware-Based TPM” or “fTPM” ensures that secure code execution is isolated to prevent a wide variety of potential security breaches. Unlike a conventional hardware based Trusted Platform Module (TPM), isolation is achieved without the use of dedicated security processor hardware or silicon. In general, the fTPM is first instantiated in a pre-OS boot environment by reading the fTPM from system firmware or firmware accessible memory or storage and placed into read-only protected memory of the device. Once instantiated, the fTPM enables execution isolation for ensuring secure code execution. More specifically, the fTPM is placed into protected read-only memory to enable the device to use hardware such as the ARM® architecture's TrustZone™ extensions and security primitives (or similar processor architectures), and thus the devices based on such architectures, to provide secure execution isolation within a “firmware-based TPM” without requiring hardware modifications to existing devices.
Owner:MICROSOFT TECH LICENSING LLC
Secure Biometric Verification of Identity
InactiveUS20080019578A1Reduce computational complexityReduce probabilityImage analysisCharacter and pattern recognitionComputer hardwareData matching
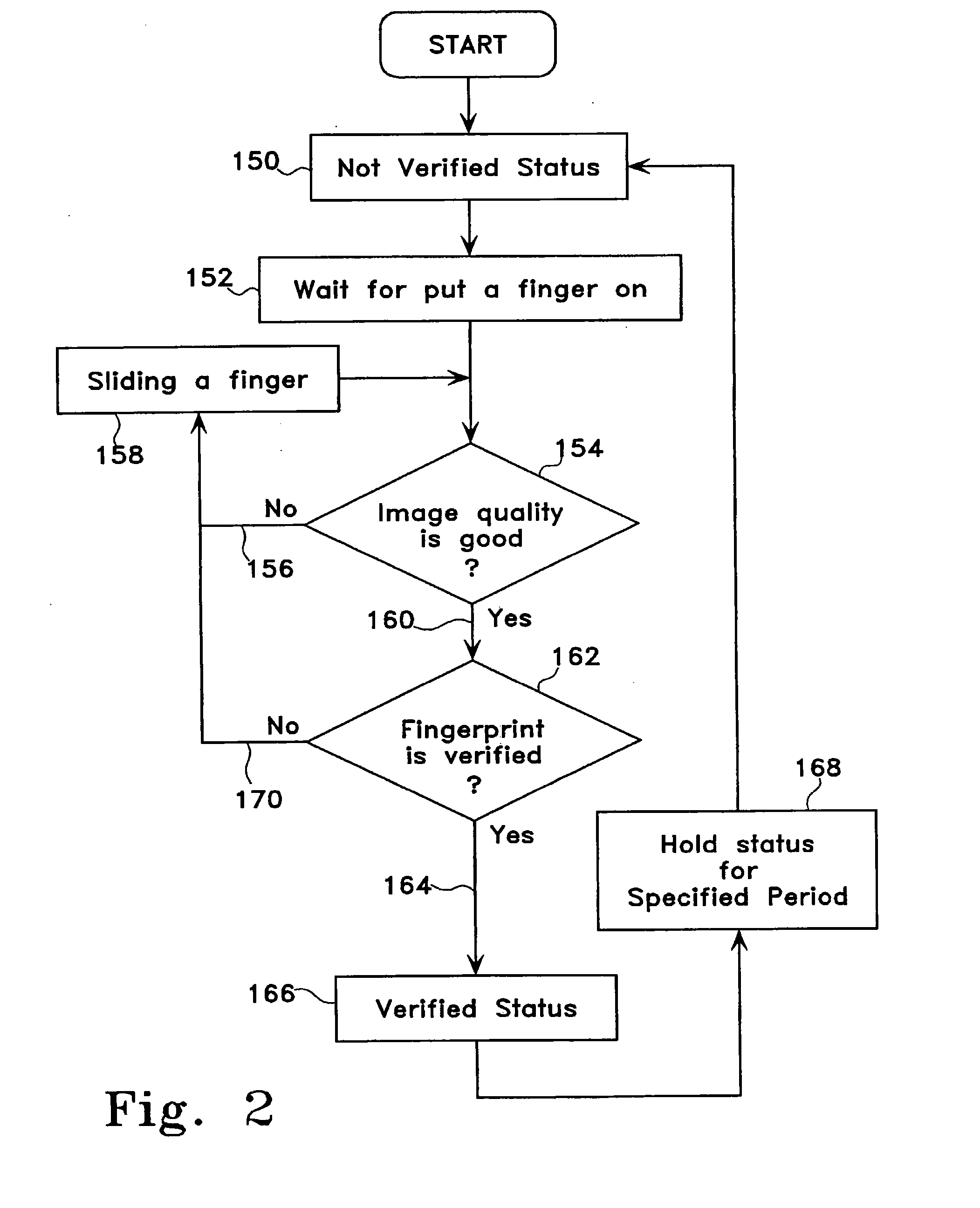
A high security identification card includes an on-board memory for stored biometric data and an on-board sensor for capturing live biometric data. An on-board processor on the card performs a matching operation to verify that the captured biometric data matches the locally stored biometric data. Only if there is a positive match is any data transmitted from the card for additional verification and / or further processing. Preferably, the card is ISO SmartCard compatible. In one embodiment, the ISO SmartCard functions as a firewall for protecting the security processor used for storing and processing the protected biometric data from malicious external attack via the ISO SmartCard interface. In another embodiment, the security processor is inserted between the ISO SmartCard Interface and an unmodified ISO SmartCard processor and blocks any external communications until the user's fingerprint has been matched with a previously registered fingerprint. Real-time feedback is provided while the user is manipulating his finger over the fingerprint sensor, thereby facilitating an optimal placement of the finger over the sensor. The card may be used to enable communication with a transactional network or to obtain physical access into a secure area.
Owner:IVI HLDG
System and method to secure boot uefi firmware and uefi-aware operating systems on a mobile internet device (MID)
InactiveUS20090327741A1Digital computer detailsComputer security arrangementsTTEthernetOperational system
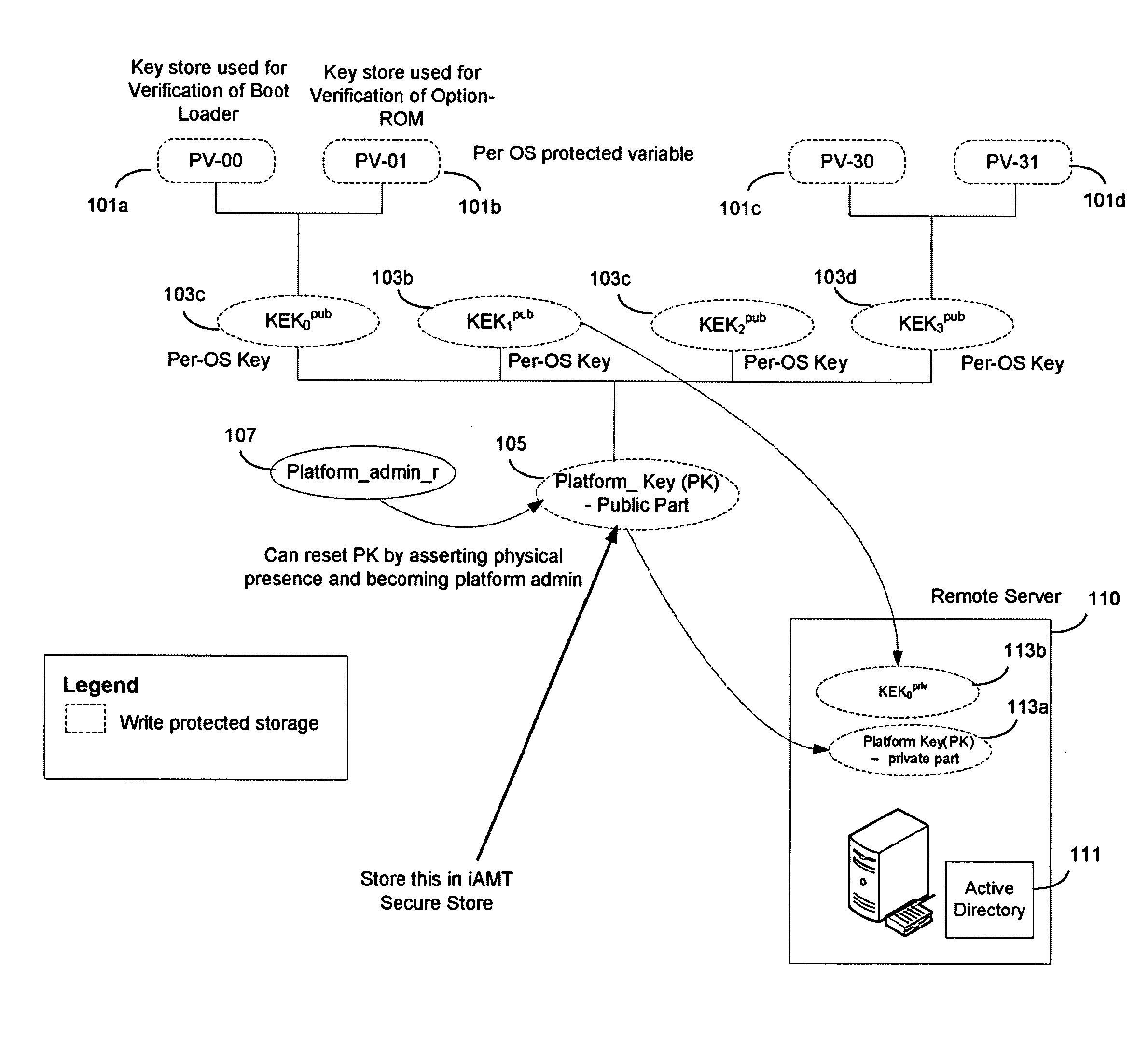
In some embodiments, the invention involves adding a capability for a platform owner or administrator to ensure that the firmware is only executed in an owner-authorized fashion, such as with signed components managed by a security processor. Embodiments may extend the Core Root of Trust for Measurement (CRTM), via use of a cryptographic unit coupled to the security processor in a mobile Internet device (MID) as a Root-of-Trust for Storage (RTS) Storage Root Key (SRK), into a unified extensible firmware interface (UEFI) Platform Initialization (PI) image authorization and boot manager. Other embodiments are described and claimed.
Owner:INTEL CORP
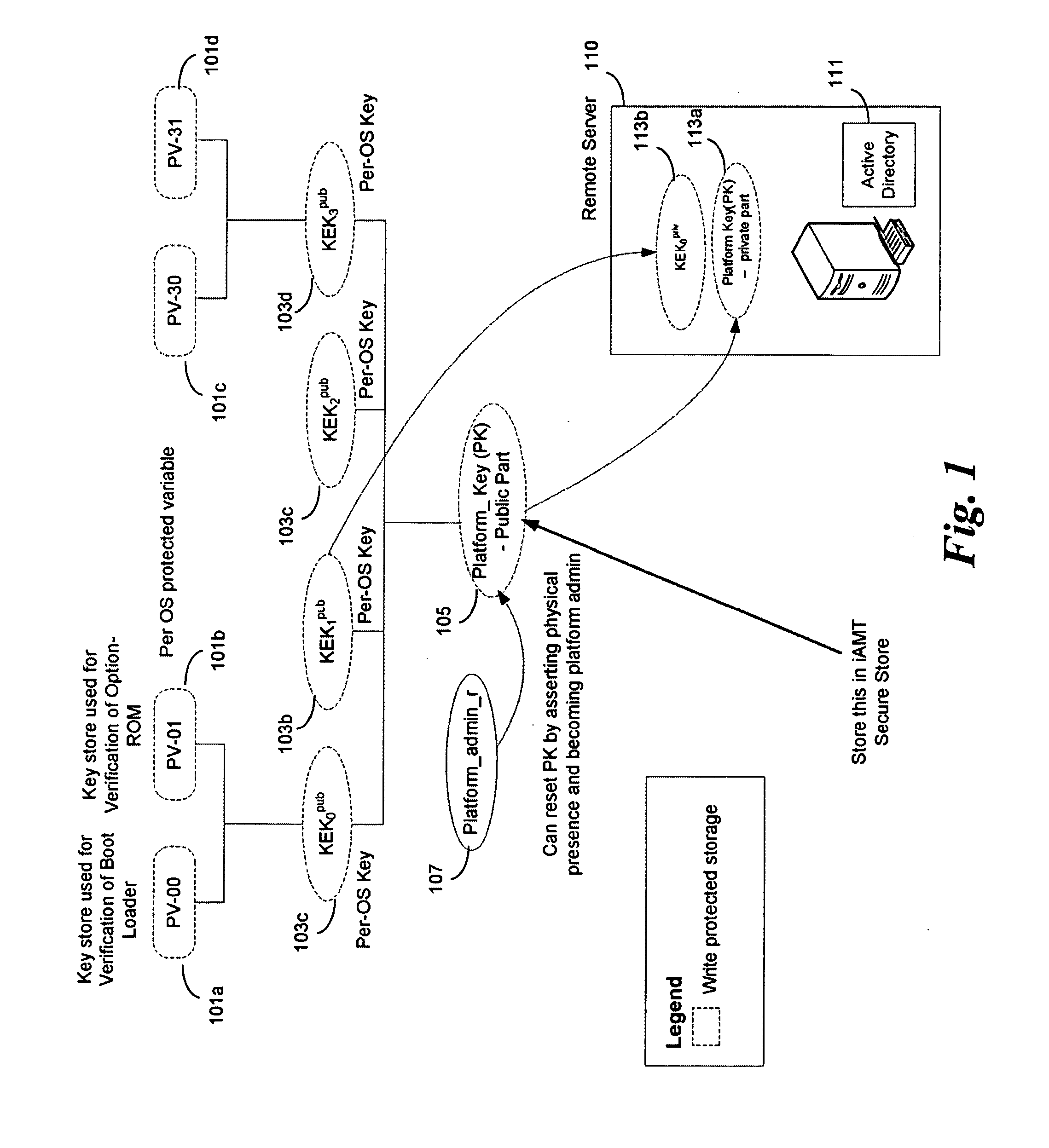
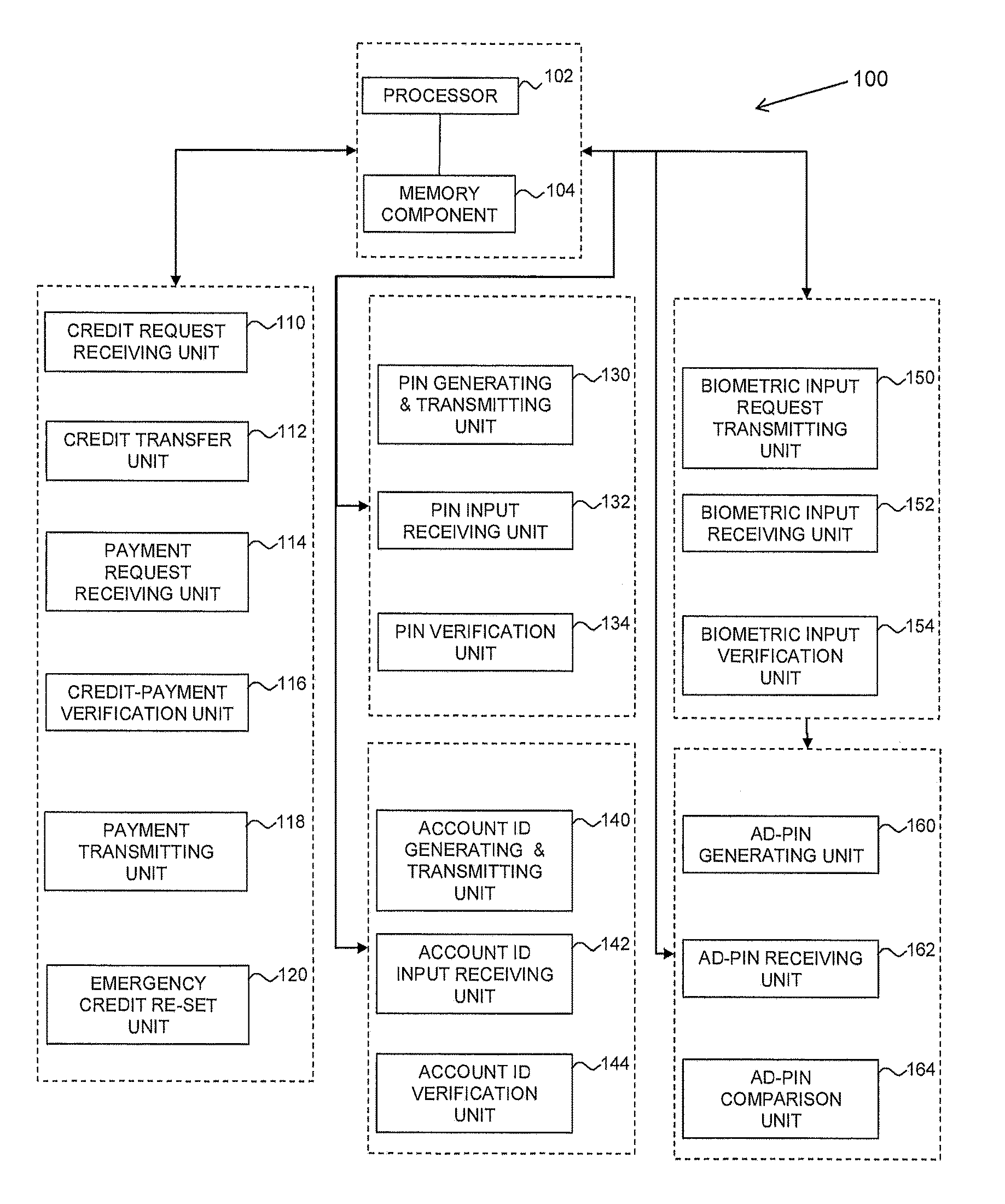
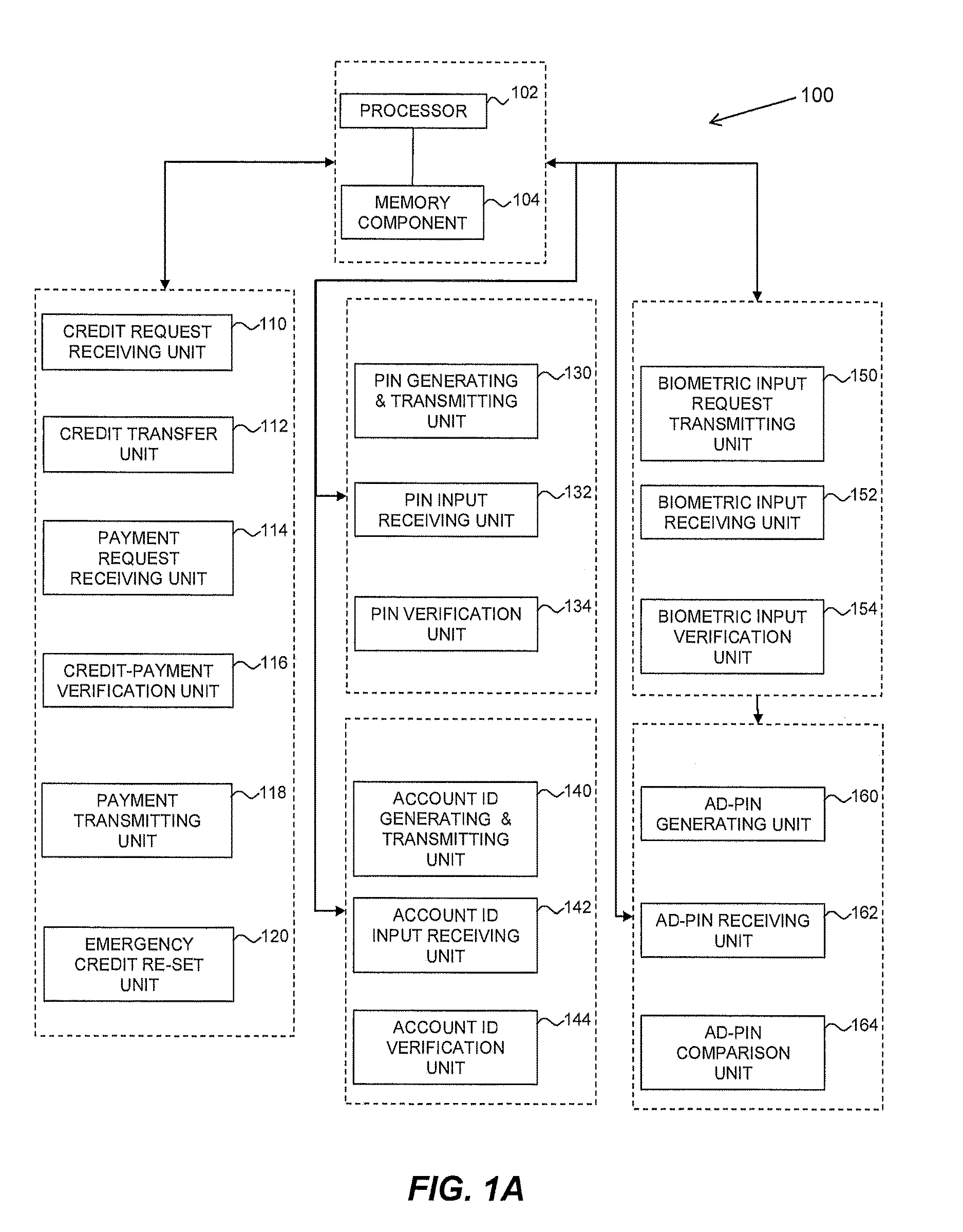
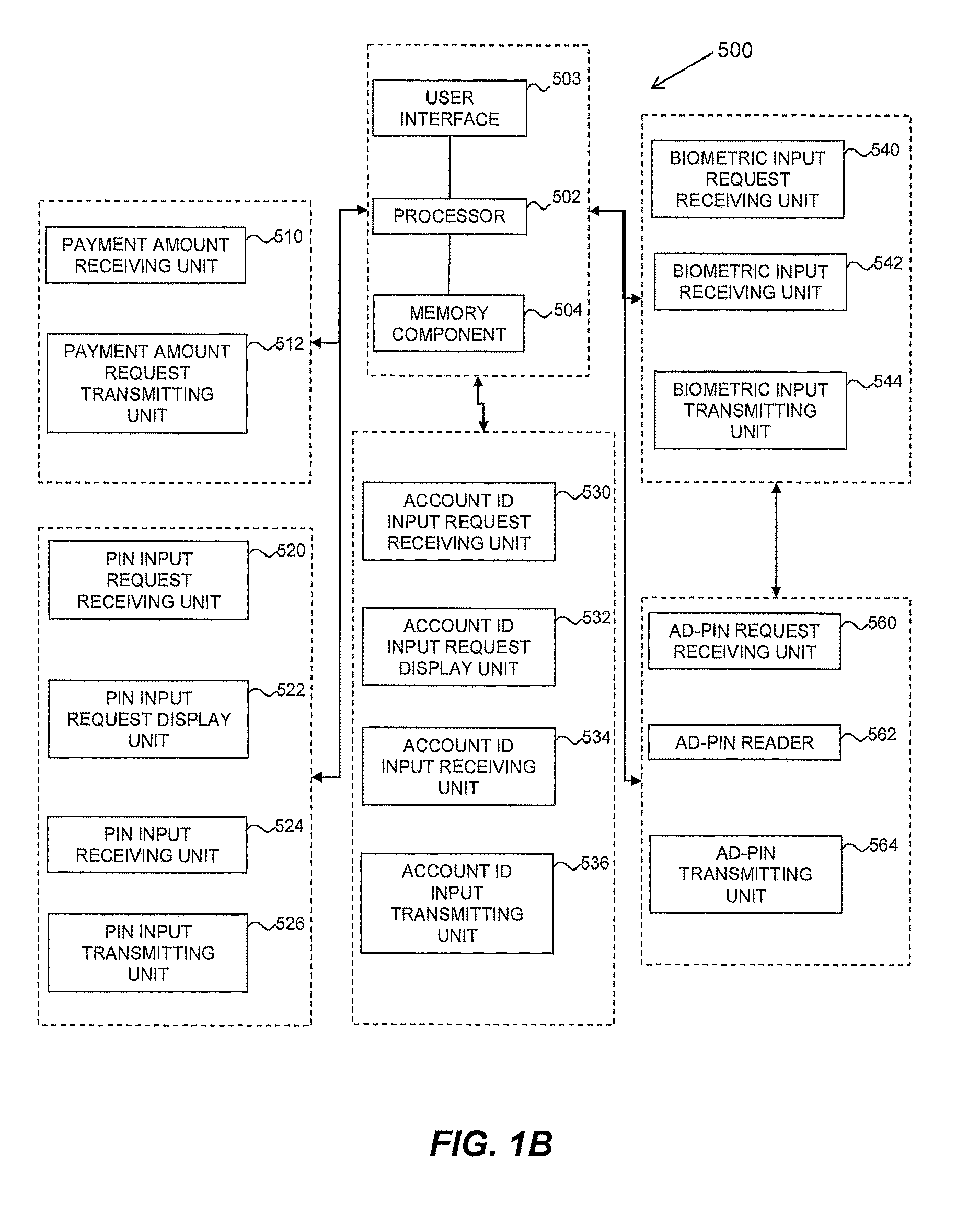
Method and system for secured processing of a credit card
Methods and systems for processing credit transactions system include or implement the steps generating a first automated dynamic PIN (AD-PIN) unique to a request for a credit amount with a first algorithm and comparing with a second AD-PIN independently generated by a customer device using a second identical algorithm. The AD-PIN is then identically changed by both the first and second algorithms before the next transaction. The generation and exchange of AD-PINs may be conditional upon or supplemented by biometric verification of the customer identity.
Owner:DIAMOND SUN LABS
Apparatus for providing a secure processing environment
InactiveUS20020129245A1User identity/authority verificationInternal/peripheral component protectionComputer hardwareSafe handling
An apparatus for providing a secure processing environment is disclosed. In one embodiment, the apparatus includes a read / write memory for storing encrypted information. It also includes a processor, a cipherer and an authenticator. The cipherer is in communication with the read / write memory for receiving encrypted information therefrom and is configured to decrypt the encrypted information into decrypted information to be returned to the memory for subsequent use by the processor. The authenticator authenticates the decrypted information prior to use by the processor and re-authenticates the information prior to re-encryption by the cipherer.
Owner:CASSAGNOL ROBERT D +4
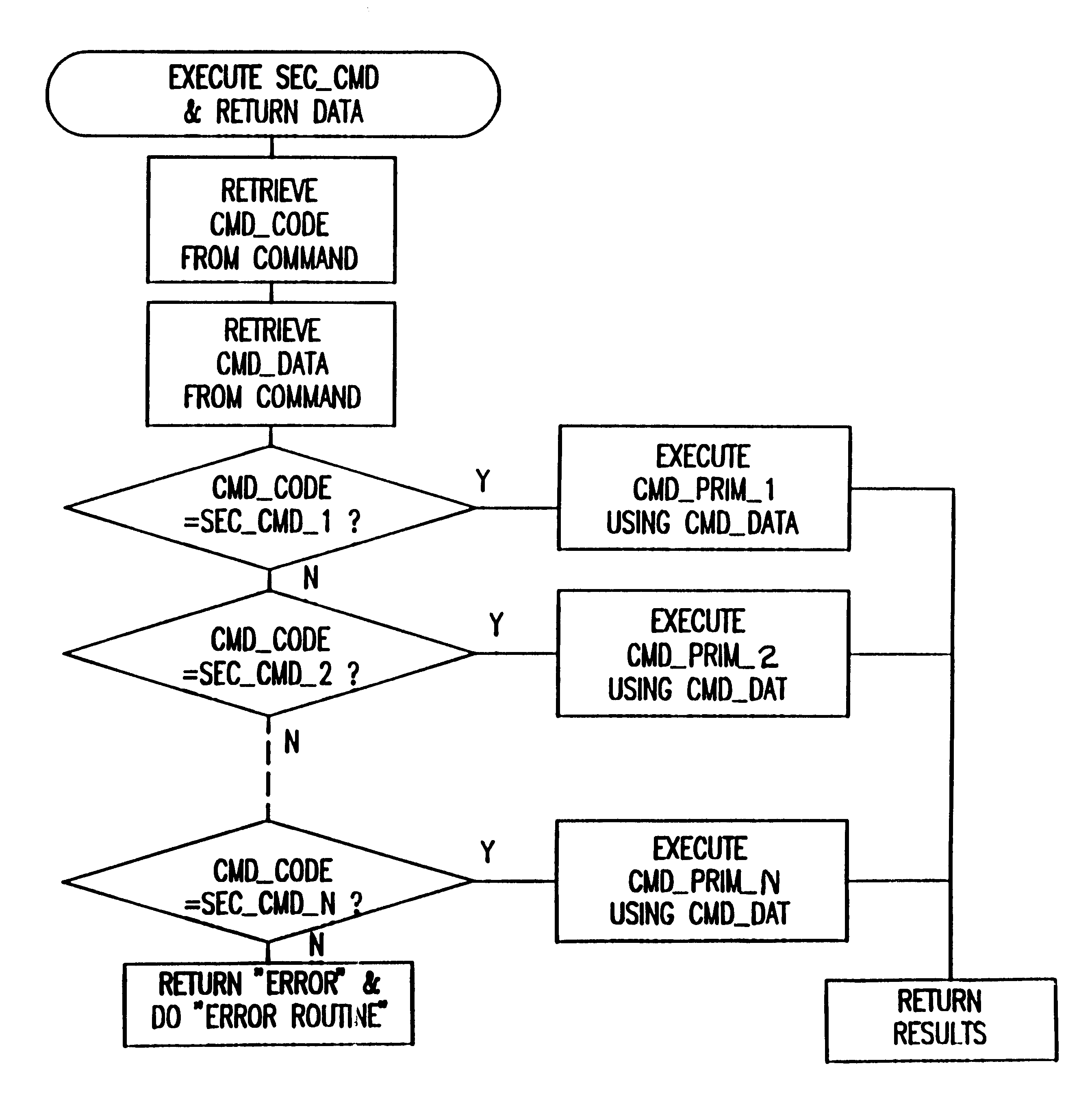
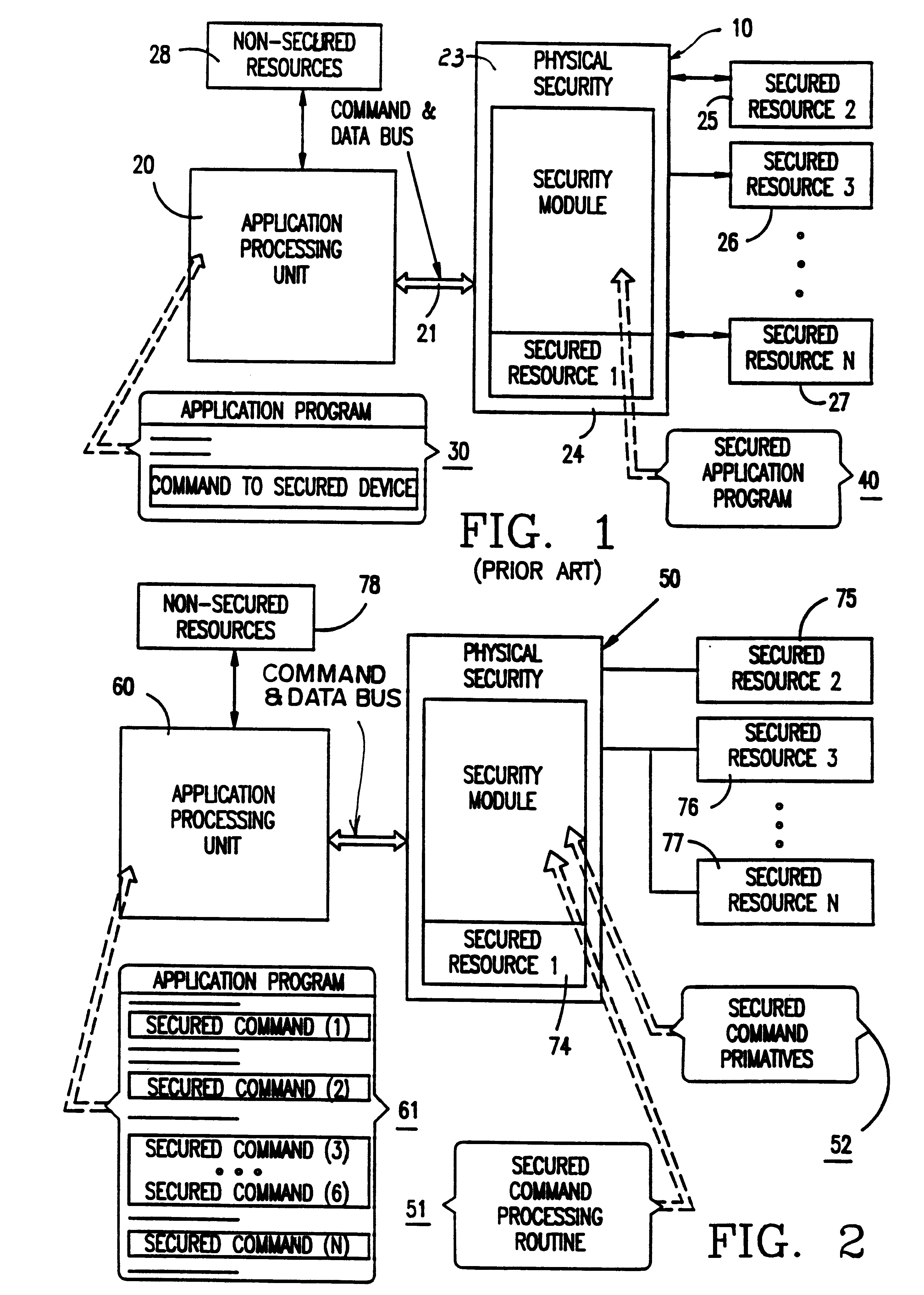
Method and apparatus for operating resources under control of a security module or other secure processor
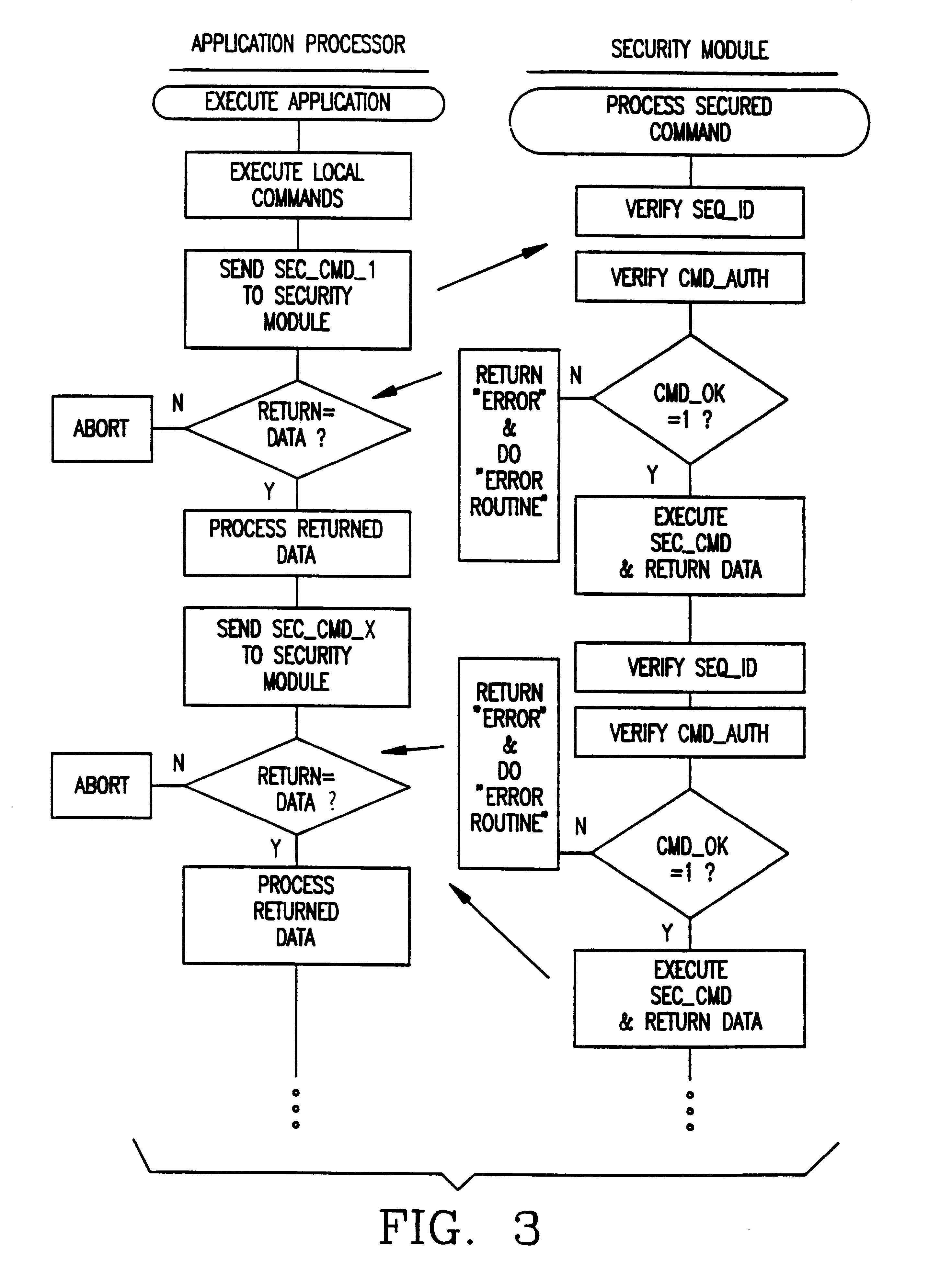
InactiveUS6226749B1Improve operational flexibilityDigital data processing detailsDigital data protectionComputer hardwareSequence ID
A method and apparatus for operating a set of resources under the control of a secure processor, e.g. security module, having a command authentication means and a command execution means, to achieve secure control of the resources. The secure processor stores a set of command primitives for functional control of the resources. A set of defined commands for invoking command primitives has either a secured command format including a command sequence ID, a command code, and a set of command data items or a non-secured command format including a command code and a set of command data items. The secure processor stores a command set up table including command type flags to designate each command as a secured command or a non-secured command. An application program running in an external device includes a plurality of the defined commands in either secured command format or the non-secured command format and these are sent one at a time to the secure processor for execution. The secure processor looks up each received command in the command set up table, and if the command is a non-secured command it immediately executes associated command primitives. If the command is a secured command, the secure processor tests both its authenticity and regularity and only executes the associated command primitives if the command passes both tests.
Owner:HEWLETT PACKARD DEV CO LP
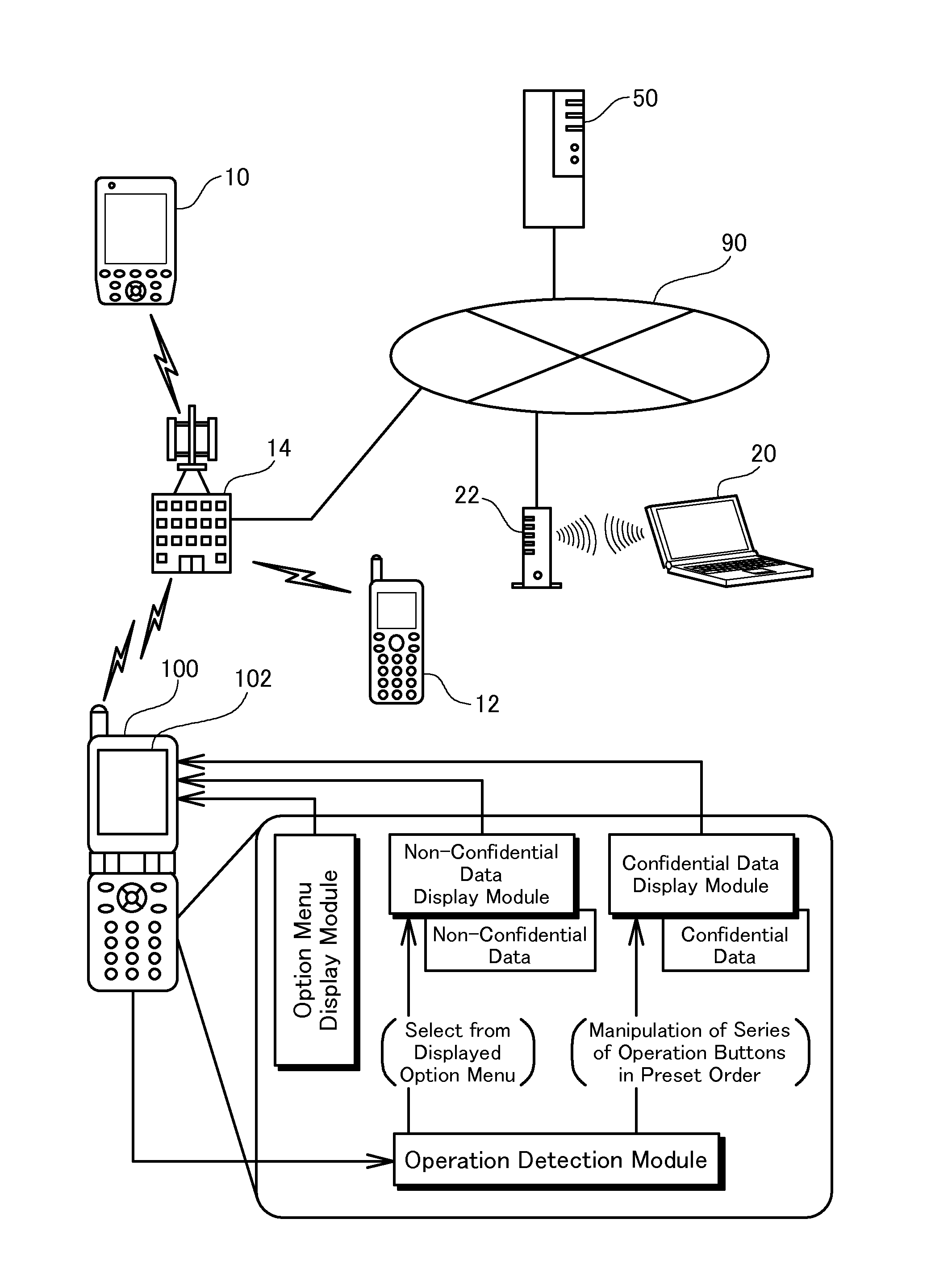
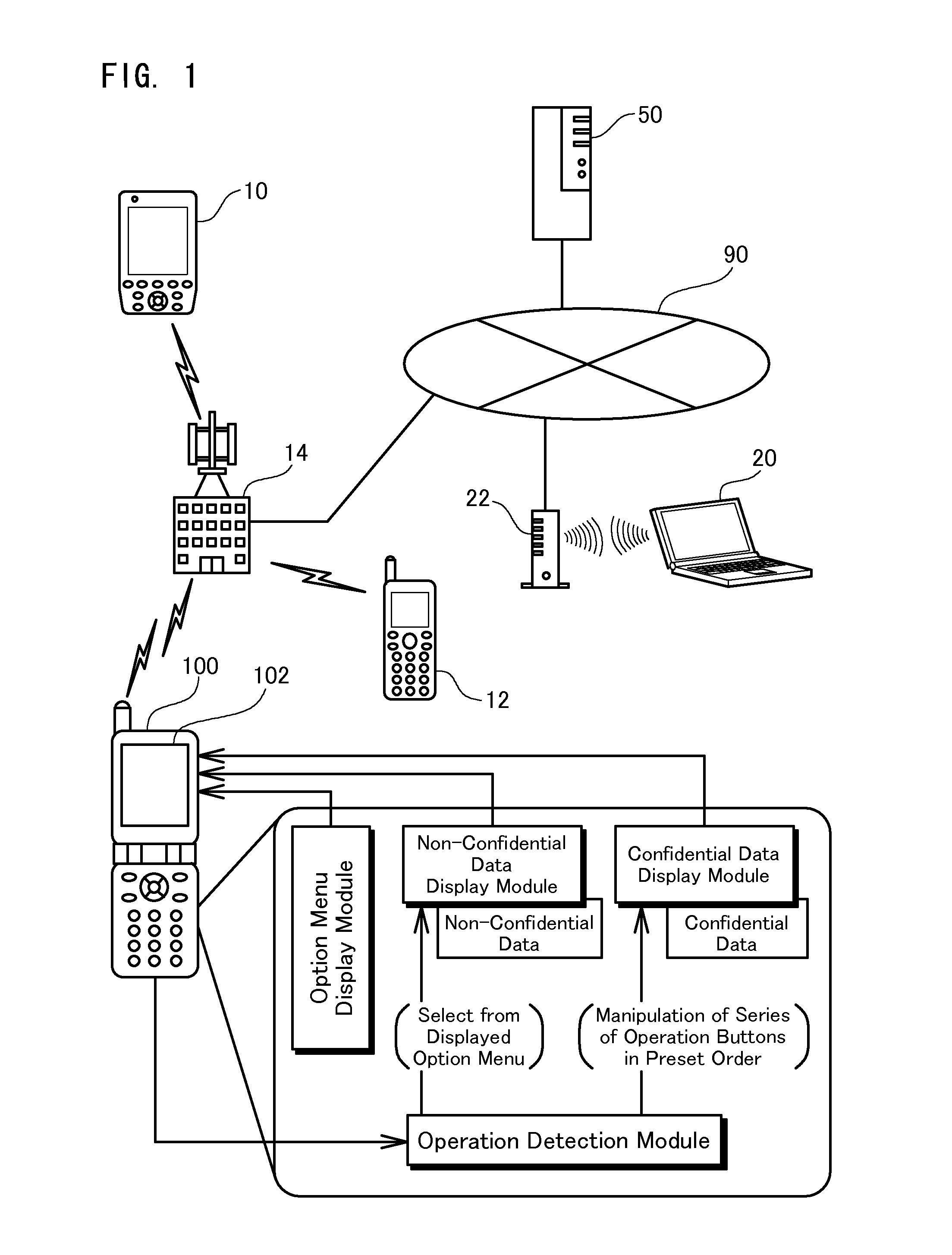
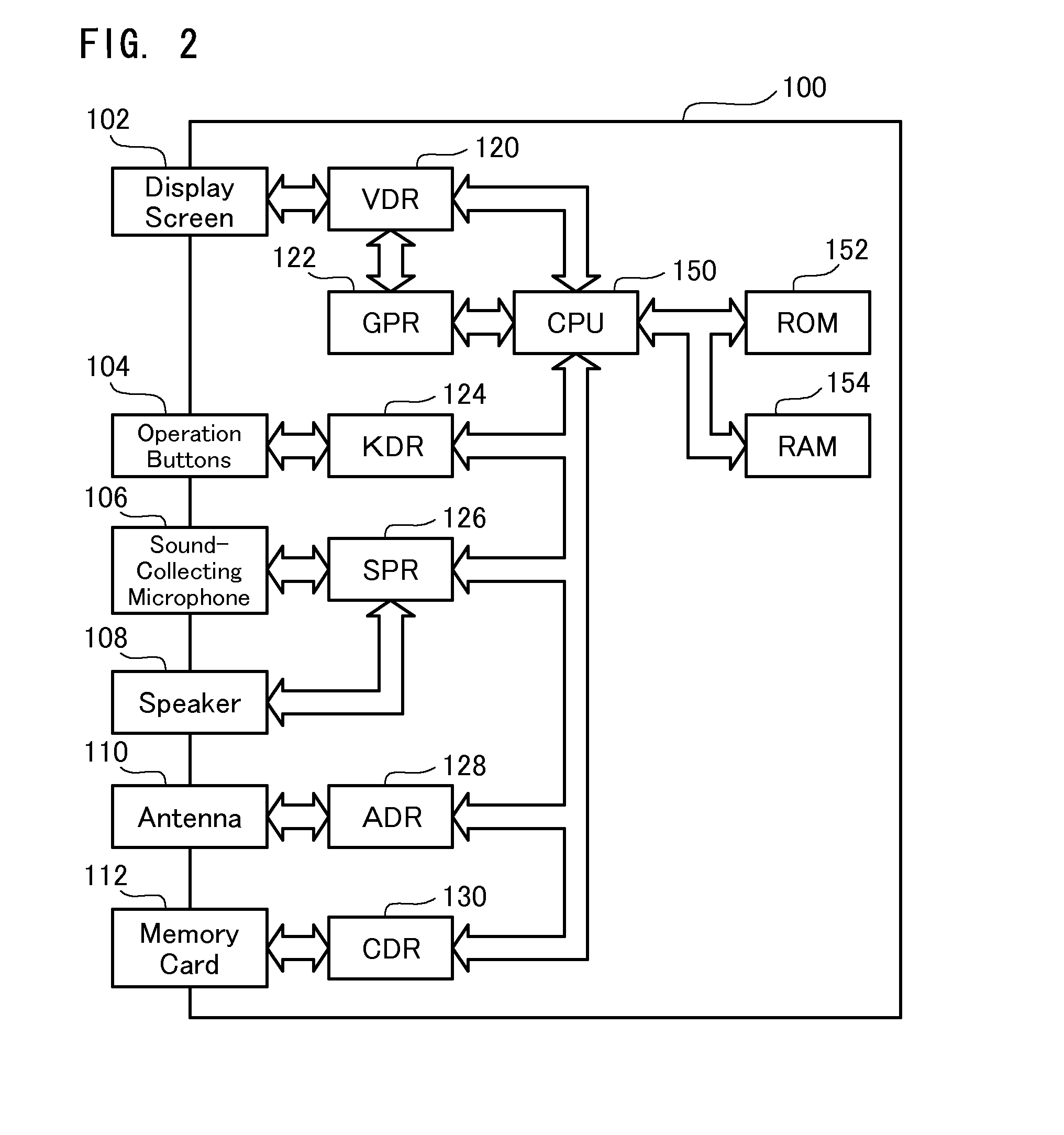
Information terminal device and character data display method
InactiveUS20070271608A1Safe and secure of confidential dataReduce the possibilityDigital data processing detailsUser identity/authority verificationData displayInternet privacy
The information terminal device of the invention has a first function of displaying non-confidential data in a selectable manner on its display screen and, in response to the user's selection of the non-confidential data, showing the details of the non-confidential data. The information terminal device also has a second function of displaying confidential data in a selectable manner and, in response to the user's selection of the confidential data, showing the details of the confidential data. The first function is given as one normally selectable menu option and is activated by the user's selection of the corresponding menu. The second function is, however, not given as a normally selectable menu option and is triggered only by the user's series of operations of an operation unit in a preset sequence. No operation-related display appears on the display screen of the information terminal device during the user's series of operations of the operation unit. The information terminal device of this configuration does not hint even the presence of confidential data to any third person and thus effectively prevents the third person from analyzing or decoding the data stored in the information terminal device and having illegal access to the confidential data. This arrangement of the invention desirably enables the safe handling of confidential data without the potential for leakage of the confidential data from the information terminal device.
Owner:SUNSOFT
Solar, catalytic, hydrogen generation apparatus and method
InactiveUS20060048808A1High thermodynamic availabilityLoss in efficiencySolar heating energySolar heat collector controllersThermal energyPorosity
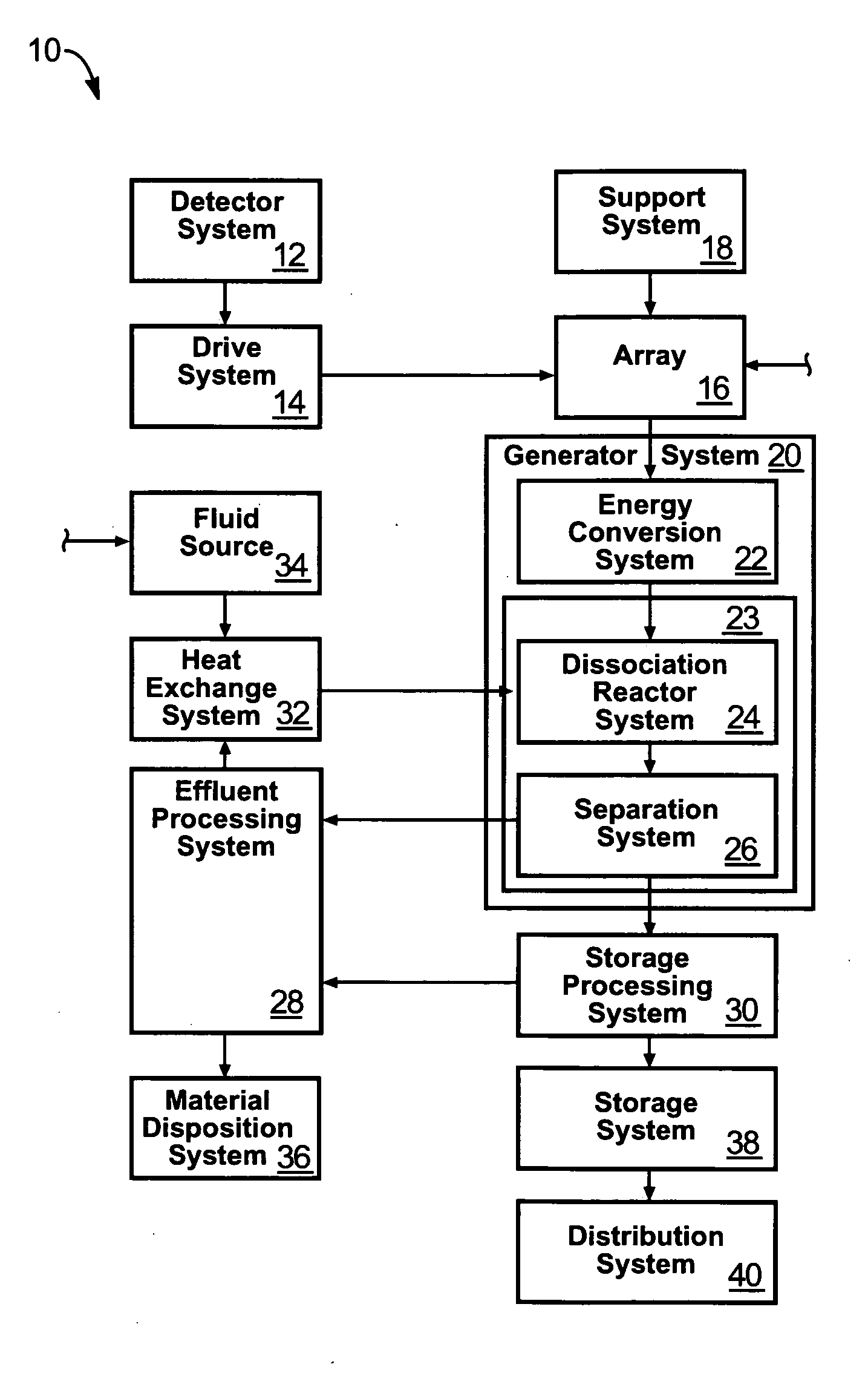
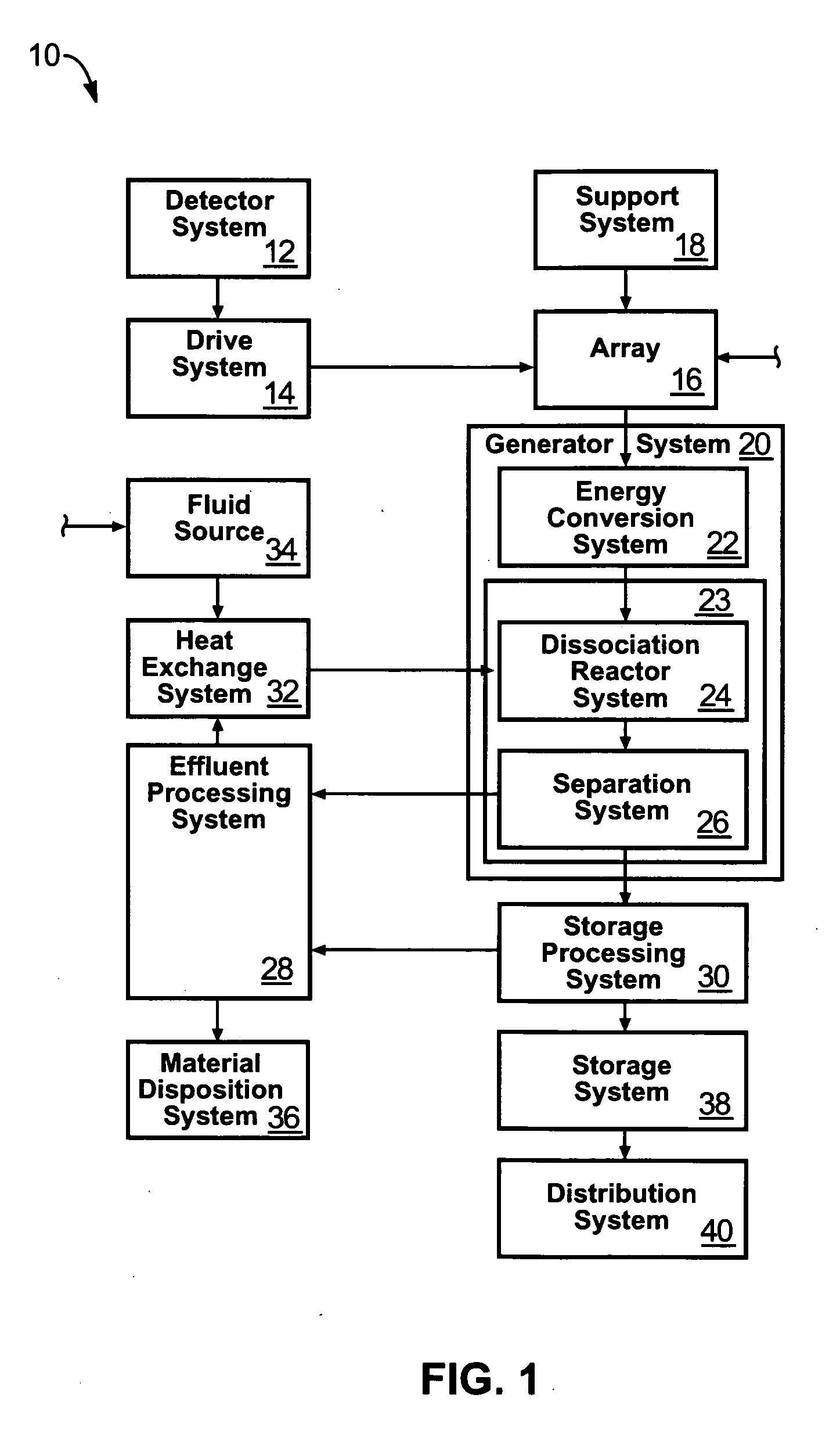
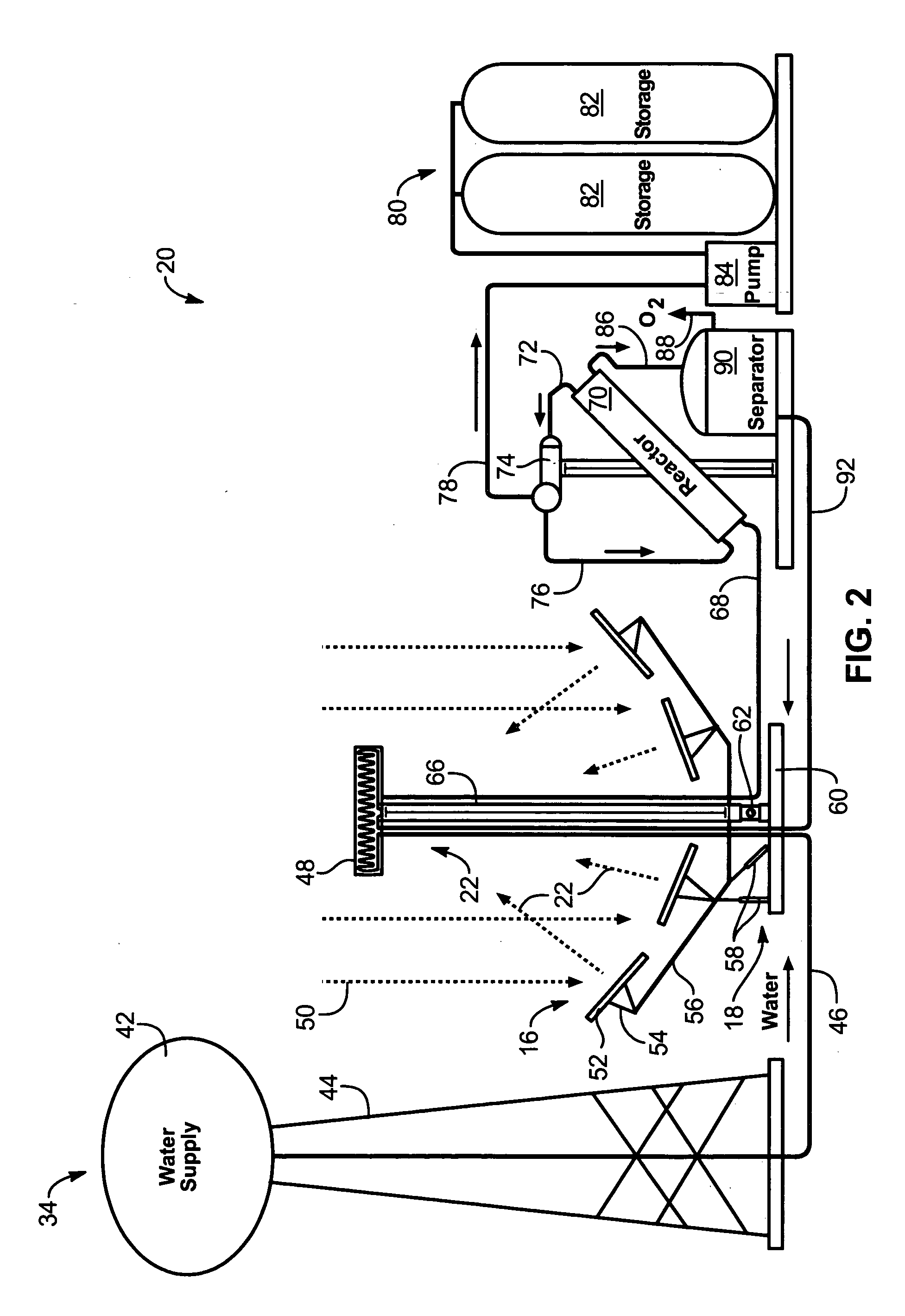
An apparatus for producing hydrogen may include a collector of radiation to concentrate solar radiation on a converter having an absorptivity to convert the solar radiation to thermal energy to drive a chemical process using a feedstock to dissociate into an output chemical and a byproduct. A separator separates the output and byproduct, after which a reactor reacts the output to form a storage chemical, reactive to produce energy but sufficiently stable for safe handling outside designation as an energetic material. The separator may have a porosity to substantially pass hydrogen and block oxygen and water. A sweep gas may sweep hydrogen away from the separation barrier to change equilibrium. Catalysts may reduce temperature of dissociation and a subsequent reaction to combine it in a more stable, storable form.
Owner:PURESCI
Techniques for efficient security processing
InactiveUS20030142818A1Efficient executionImprove efficiencyInternal/peripheral component protectionCommunication jammingCryptographic protocolSafe handling
A programmable security processor for efficient execution of security protocols, wherein the instruction set of the processor is enhanced to contain at least one instruction that is used to improve the efficiency of a public-key cryptographic algorithm, and at least one instruction that is used to improve the efficiency of a private-key cryptographic algorithm.
Owner:NEC CORP
Achieving high assurance connectivity on computing devices and defeating blended hacking attacks
ActiveUS7490350B1Improve integrityAttack is still possibleMultiple digital computer combinationsInternal/peripheral component protectionCommunications systemPrivate network
System and techniques for protecting wireless communication systems from blended electronic attacks that may combine wireless and computer attacks. One embodiment is an integrated hardware and software firewall / protection system that provides a protection scheme that may include an additional functional processing layer between the hardware firewall and a mobile terminal. This additional functional processing layer performs an extra layer of communications and security processing, including such features as management of Internet Connection Firewall (ICF) functions, key generation for firewall and virtual private network (VPN) functions, and packet inspection and filtering.
Owner:TECNICA
Methods for integrated fast pyrolysis processing of biomass
ActiveUS20110258914A1Improve collection efficiencyMinimizes water contentDirect heating destructive distillationBiofuelsPre treatmentSafe handling
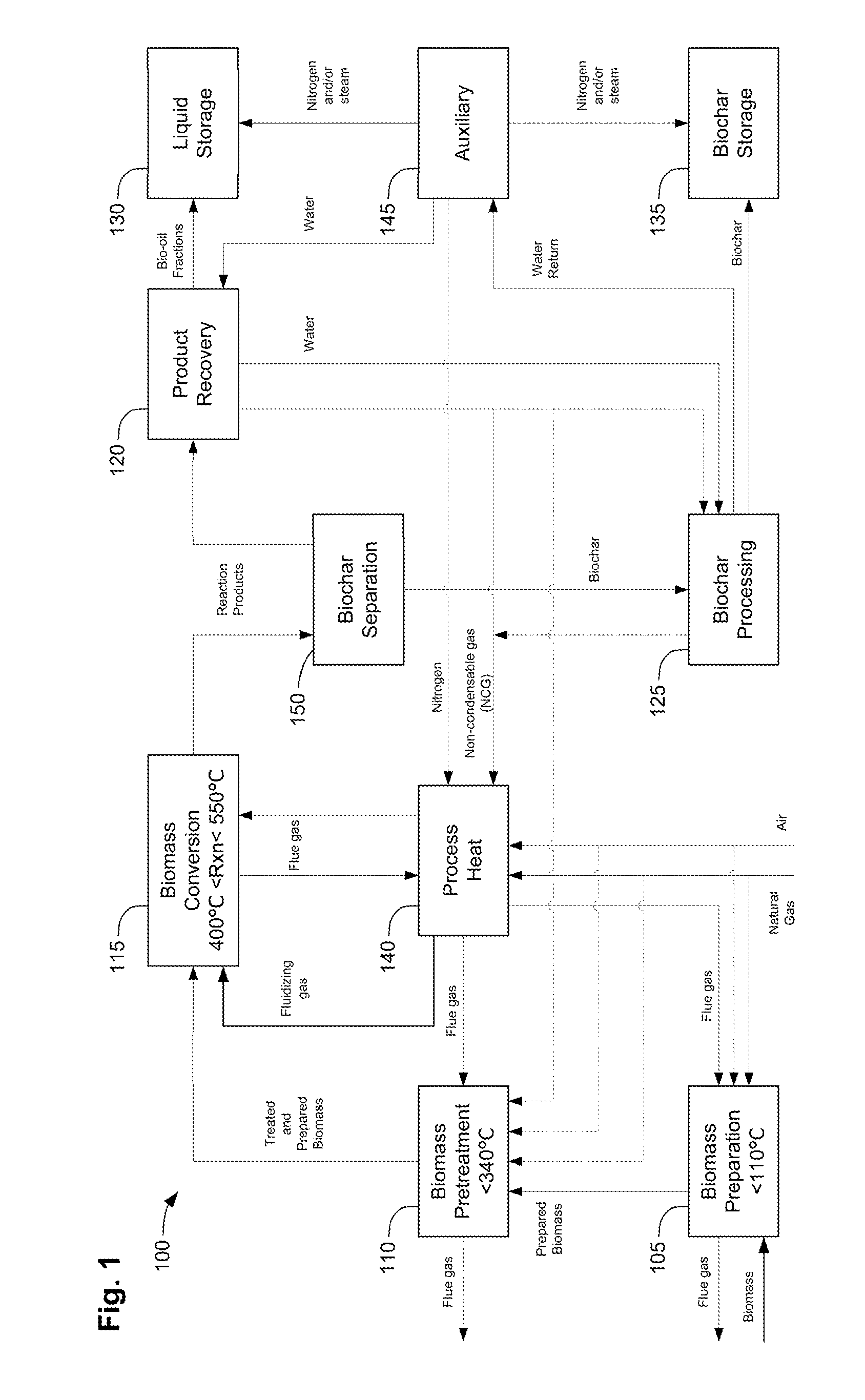
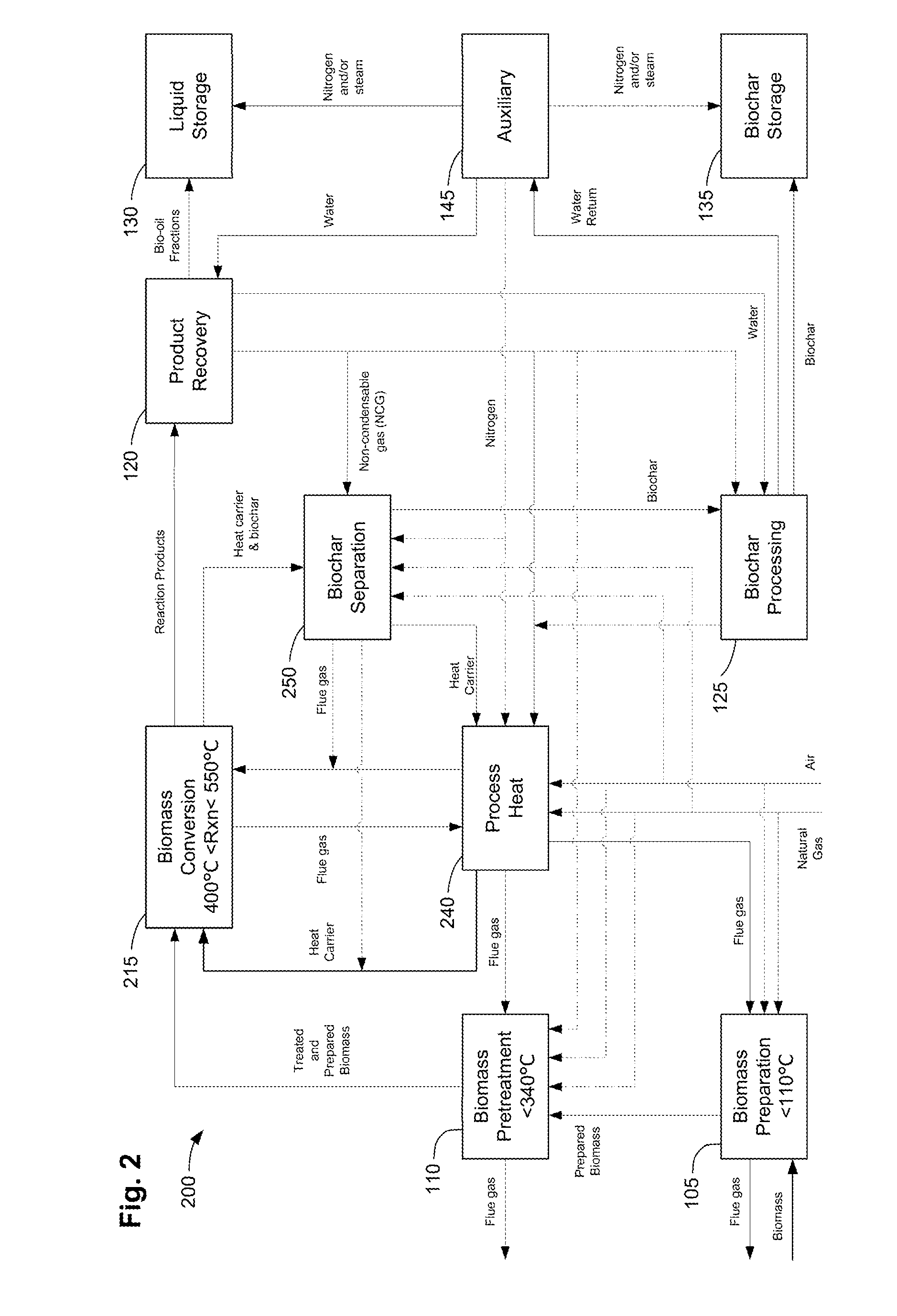
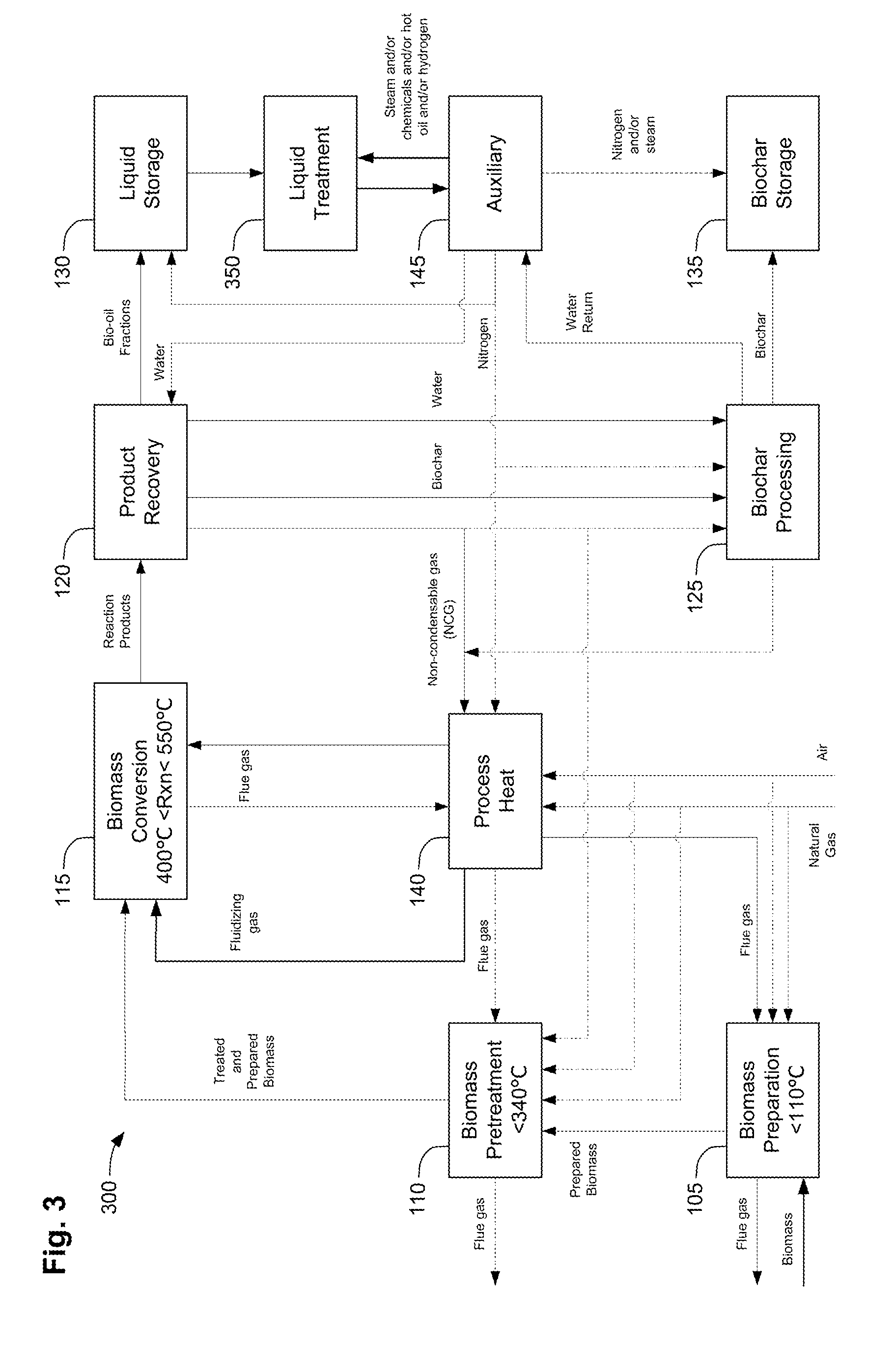
Methods, process, apparatus, equipment, and systems are disclosed for converting biomass into bio-oil fractions for chemicals, materials, feedstocks and fuels using a low-cost, integrated fast pyrolysis system. The system improves upon prior art by creating stable, bio-oil fractions which have unique properties that make them individually superior to conventional bio-oil. The invention enables water and low-molecular weight compounds to be separated into a final value-added fraction suitable for upgrading or extracting into value-added chemicals, fuels and water. Initial bio-oil fractions from the process are chemically distinct, have low-water content and acidity which reduces processing costs normally associated with conventional bio-oil post-production upgrading since fewer separation steps, milder processing conditions and lower auxiliary inputs are required. Biochar is stabilized so that it can be handled safely. The integrated fast pyrolysis process includes biomass storage, preparation, pretreatment, and conversion, product recovery and processing to create and store stable biochar and bio-oil fractions.
Owner:AVELLO BIOENERGY
Offload processing for secure data transfer
InactiveUS20030105977A1Safe handlingMultiple digital computer combinationsProgram controlPlaintextSafe handling
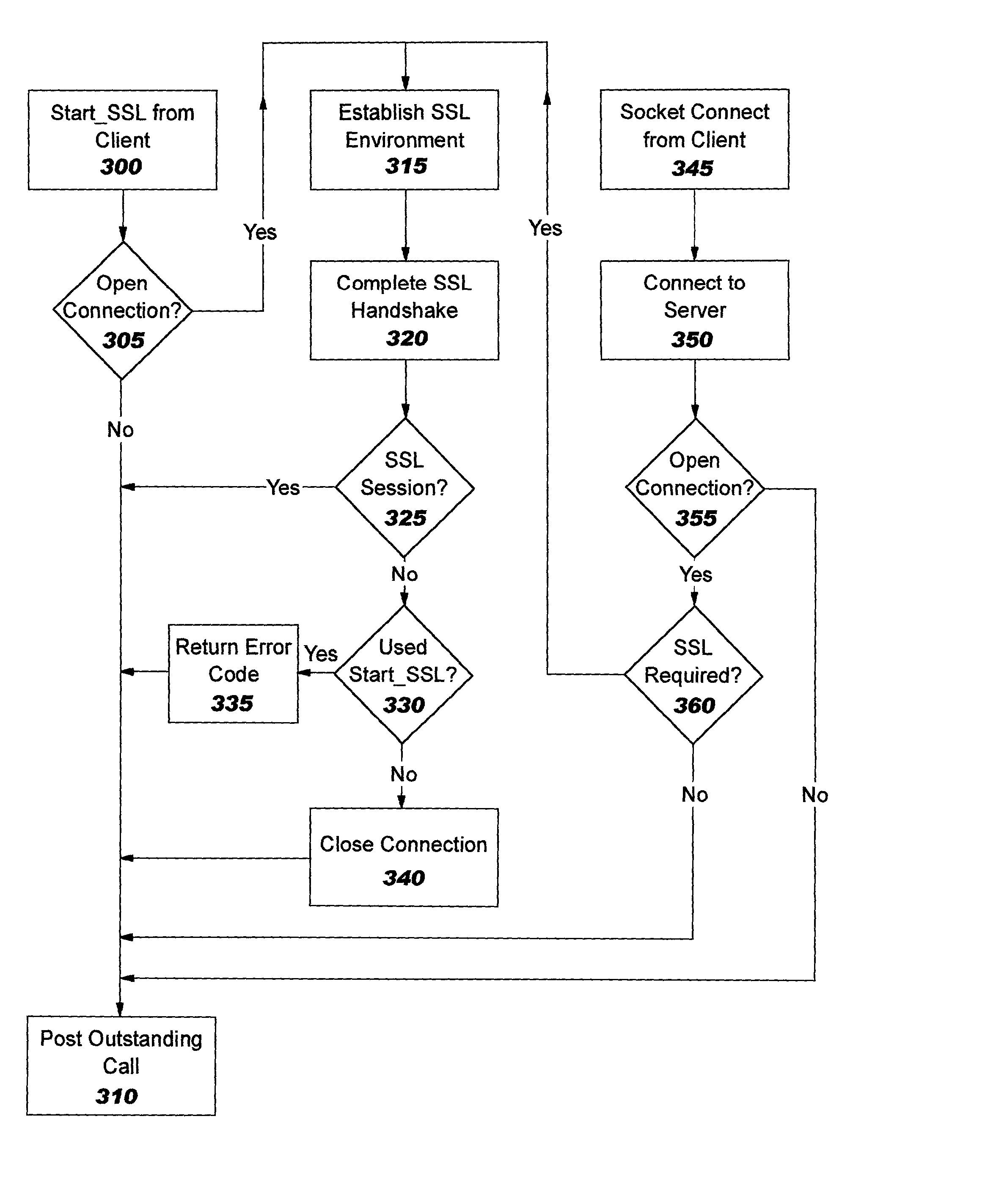
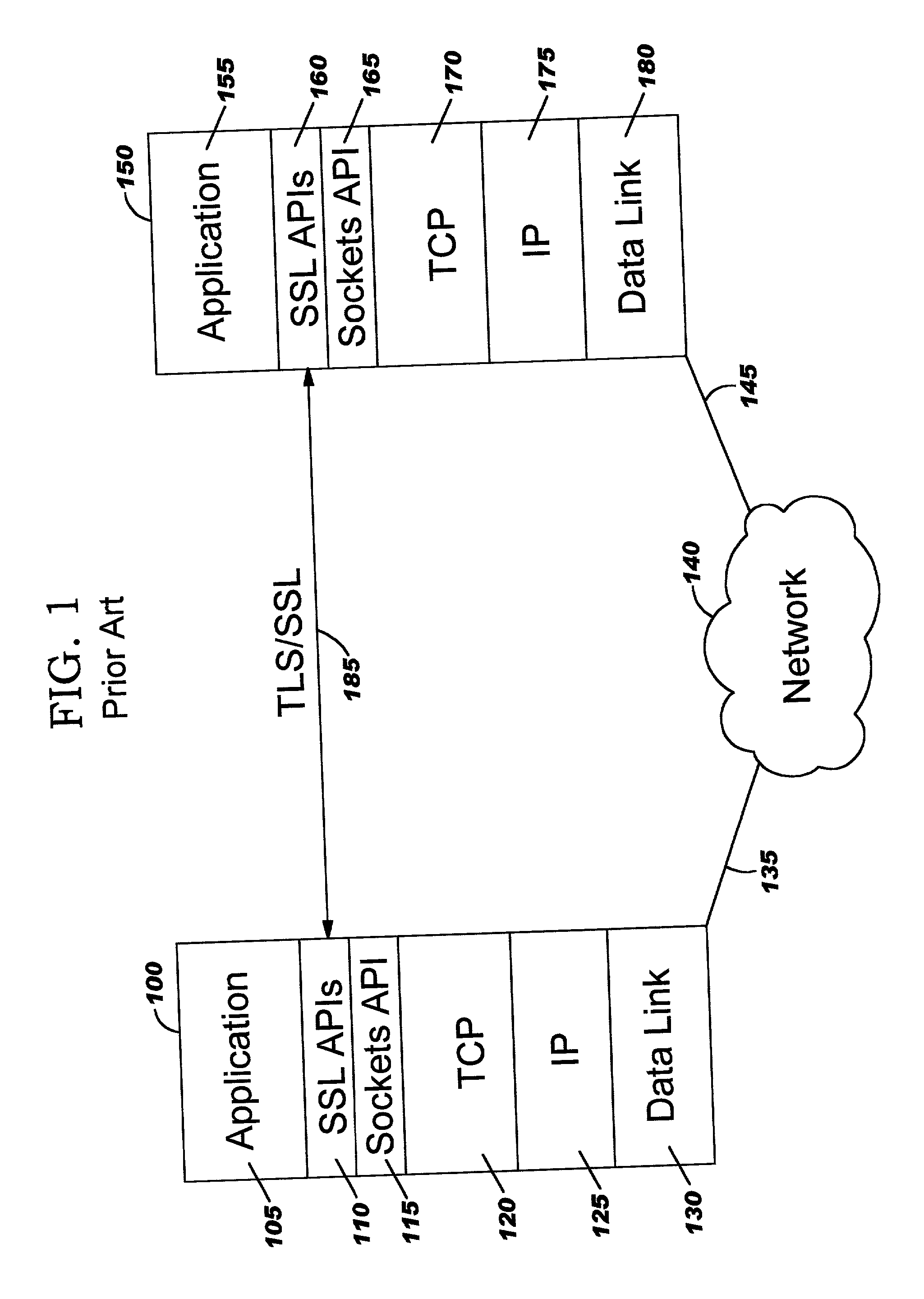
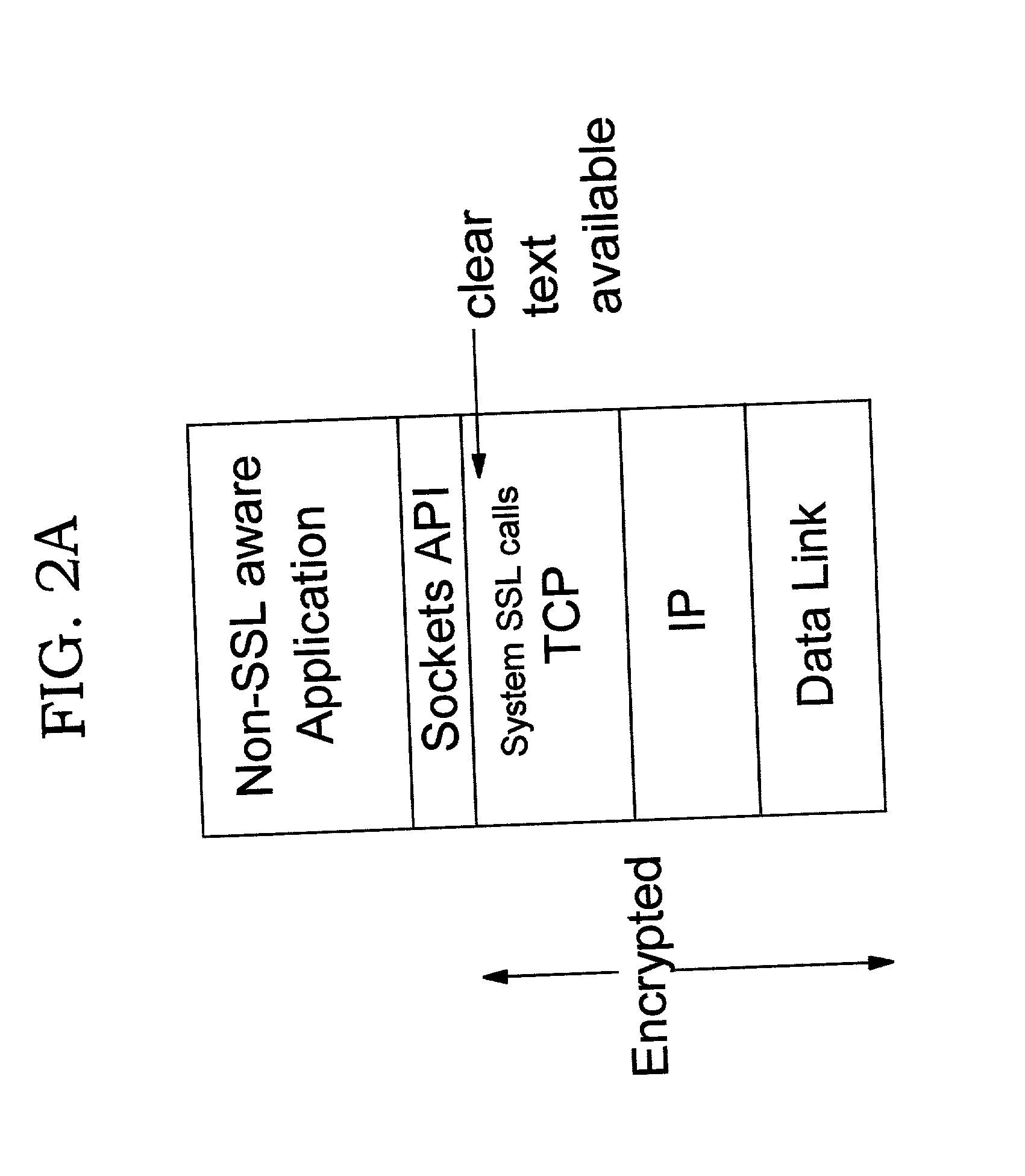
Improvements in security processing are disclosed which enable security processing to be transparent to the application. Security processing (such as Secure Sockets Layer, or "SSL", or Transport Layer Security, or "TLS") is performed in (or controlled by) the stack. A decision to enable security processing on a connection can be based on configuration data or security policy, and can also be controlled using explicit enablement directives. Directives may also be provided for allowing applications to communicate with the security processing in the stack for other purposes. Functions within the protocol stack that need access to clear text can now be supported without loss of security processing capability. No modifications to application code, or in some cases only minor modifications (such as inclusion of code to invoke directives), are required to provide this security processing. Improved offloading of security processing is also disclosed, which provides processing efficiencies over prior art offloading techniques.
Owner:IBM CORP
Method and apparatus for tokenization of sensitive sets of characters
ActiveUS20090249082A1Simple methodSafe handlingAcutation objectsUnauthorized memory use protectionComputer networkServer allocation
A method and system for secure handling of sensitive sets of characters in a distributed hierarchical system are disclosed, comprising at least one local server on a lower hierarchic level and at least one central server at a higher hierarchic level. The method comprises the steps: receiving a sensitive set of characters in said local server; replacing a part of said sensitive set of characters with a token to form a tokenized set of characters, said token belonging to a subset of possible tokens assigned to the local server by the central server; transferring at least one of said sensitive set of characters and said tokenized set of characters to the central server; and canceling said sensitive set of characters from said local server within a limited time from said transferring, while maintaining said tokenized set of characters in a local database connected to said local server.
Owner:PROTEGRITY CORP
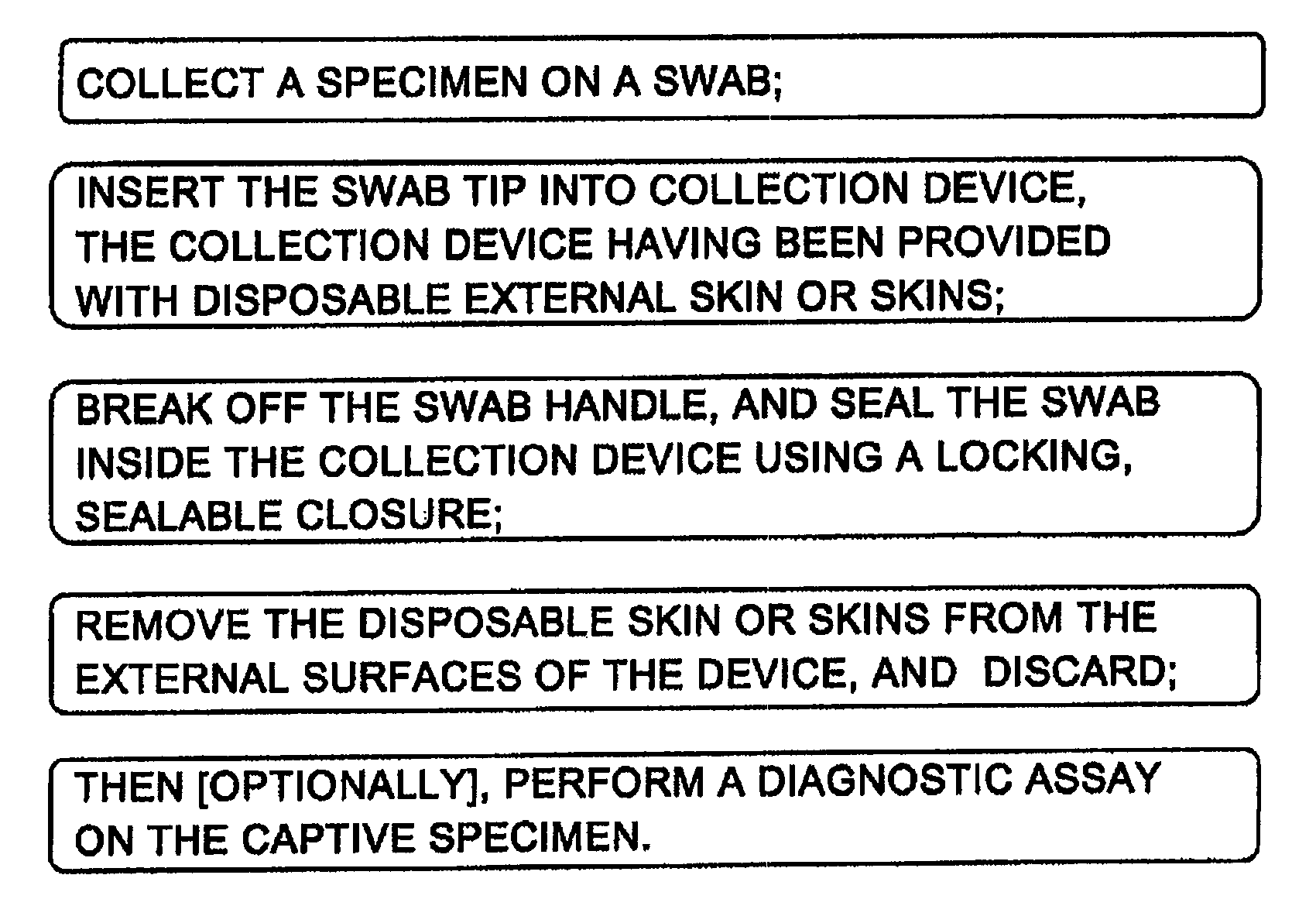
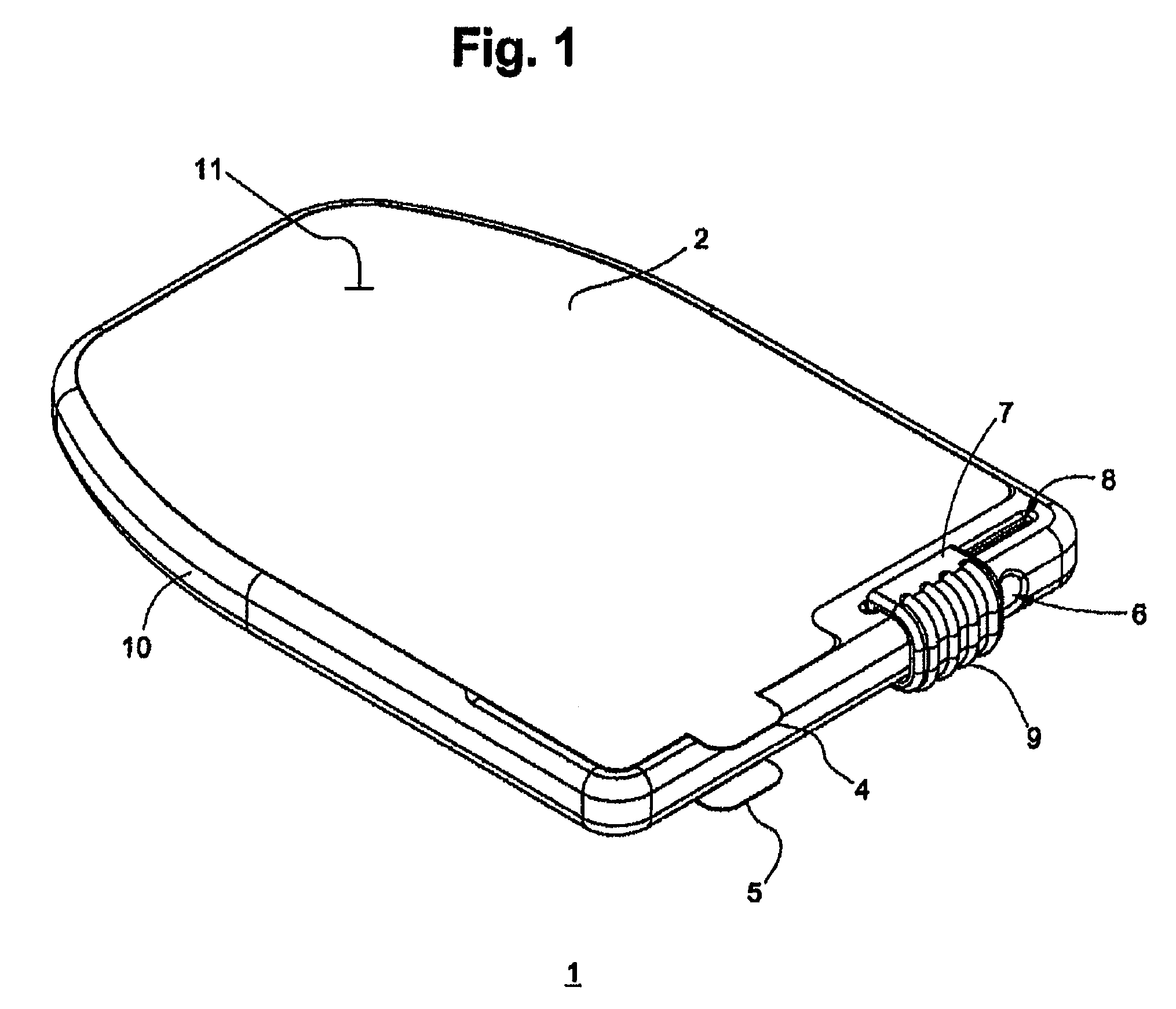
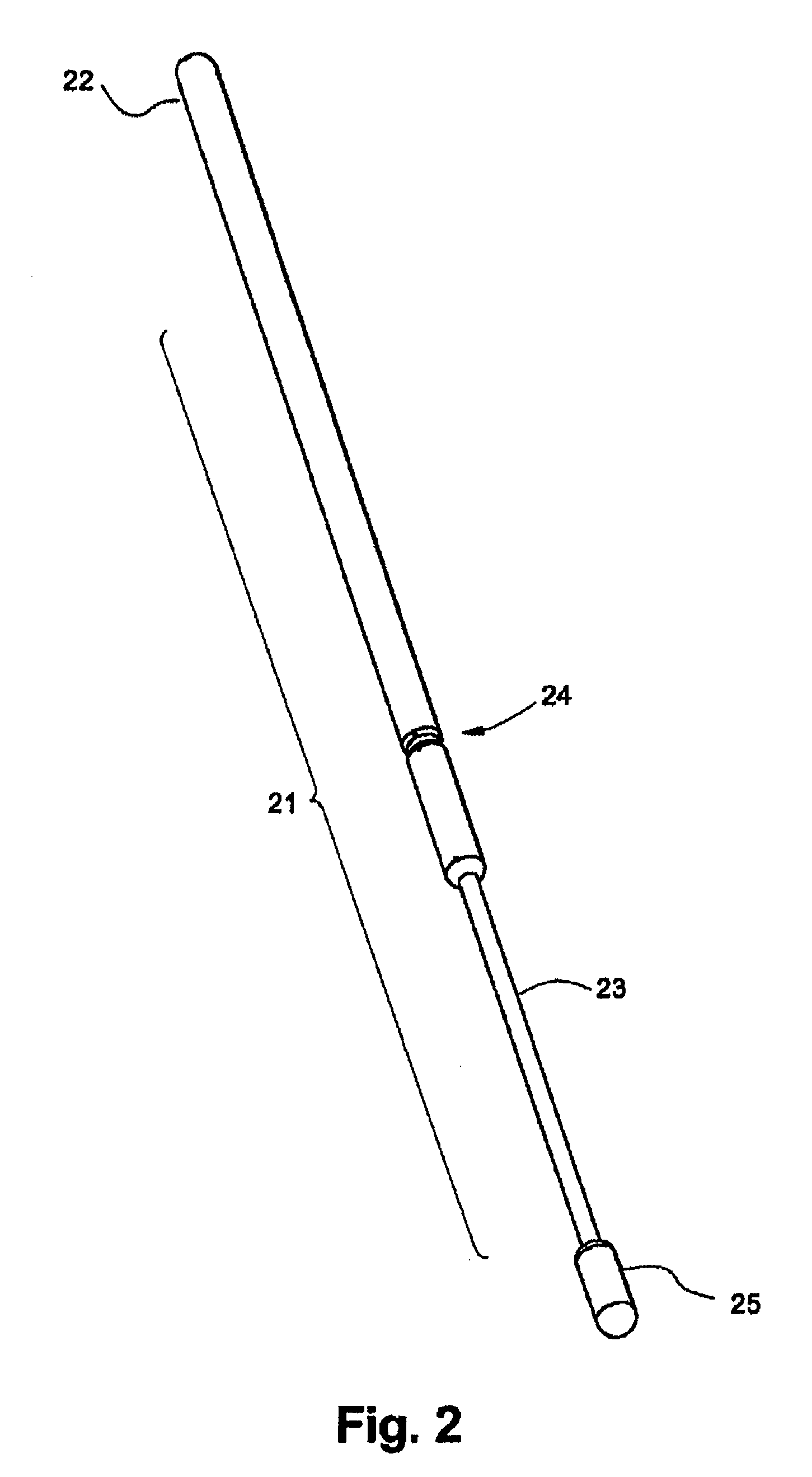
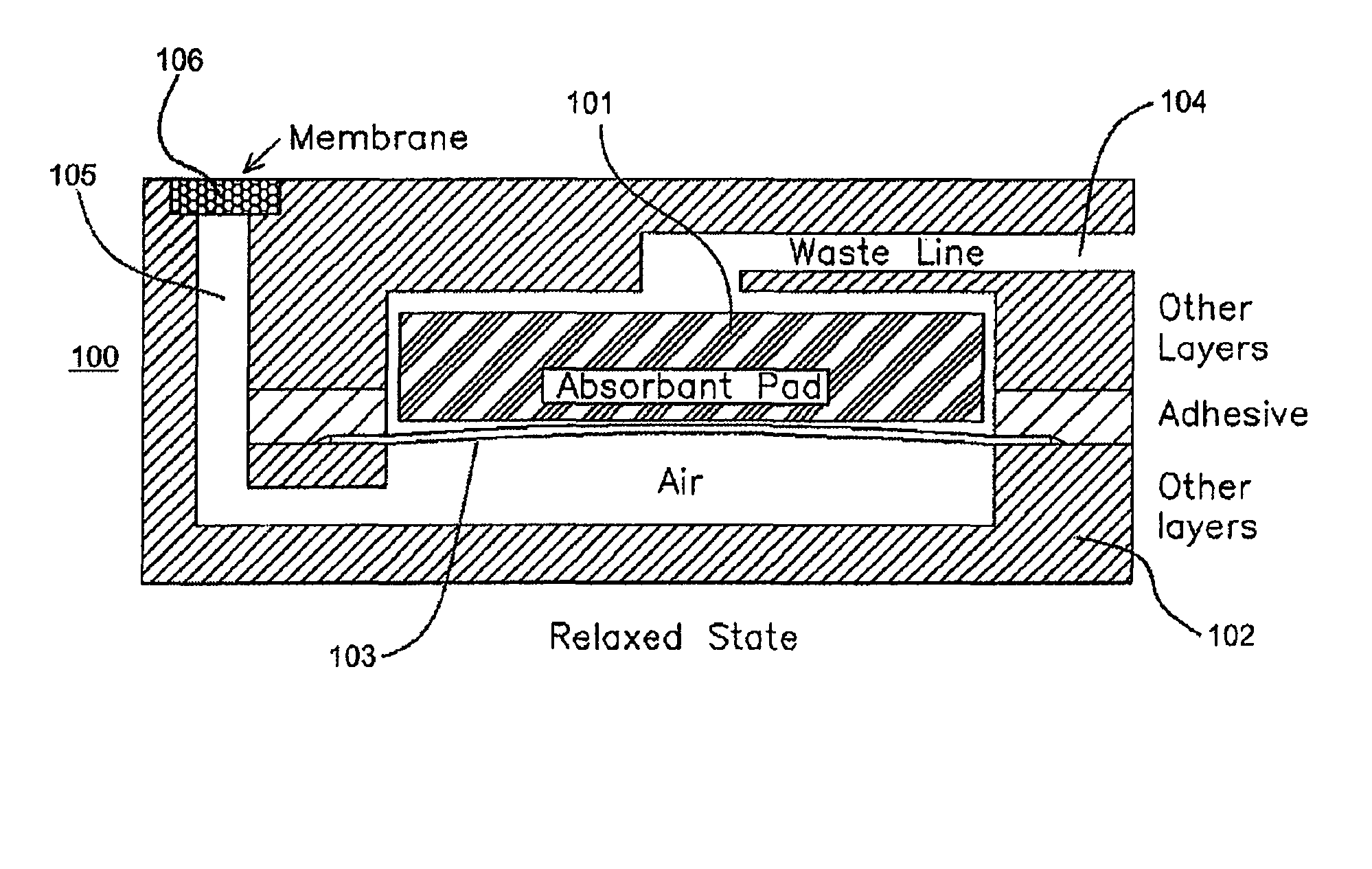
Sanitary swab collection system, microfluidic assay device, and methods for diagnostic assays
ActiveUS8216832B2Contamination riskBioreactor/fermenter combinationsBiological substance pretreatmentsAssayCollection system
Biohazard specimen collection containers are provided with an external disposable skin, that is stripped away and discarded after the biohazardous specimen is collected, thus reducing or eliminating objectionable or dangerous residues on the outside surfaces of the container. Further, we teach that the sample collection container with external disposable skin may also serve as an integrated microfluidic biosample processing and analytical device, thereby providing a single entry, disposable assay unit, kit and system for “world-to-result” clinical diagnostic testing. These integrated assay devices are provided with synergic, multiple safe-handling features for protecting healthcare workers who handle them. The modified collection containers and analytical devices find application, for example, in PCR detection of infectious organisms or pathogenic markers collected on a swab.
Owner:PERKINELMER HEALTH SCIENCES INC
Runtime adaptable security processor
InactiveUS20120117610A1Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer security arrangementsSpecial data processing applicationsInternal memoryApplication software
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
Sanitary swab collection system, microfluidic assay device, and methods for diagnostic assays
ActiveUS20100274155A1Contamination riskBioreactor/fermenter combinationsBiological substance pretreatmentsAssayCollection system
Biohazard specimen collection containers are provided with an external disposable skin, that is stripped away and discarded after the biohazardous specimen is collected, thus reducing or eliminating objectionable or dangerous residues on the outside surfaces of the container. Further, we teach that the sample collection container with external disposable skin may also serve as an integrated microfluidic biosample processing and analytical device, thereby providing a single entry, disposable assay unit, kit and system for “world-to-result” clinical diagnostic testing. These integrated assay devices are provided with synergic, multiple safe-handling features for protecting healthcare workers who handle them. The modified collection containers and analytical devices find application, for example, in PCR detection of infectious organisms or pathogenic markers collected on a swab.
Owner:PERKINELMER HEALTH SCIENCES INC
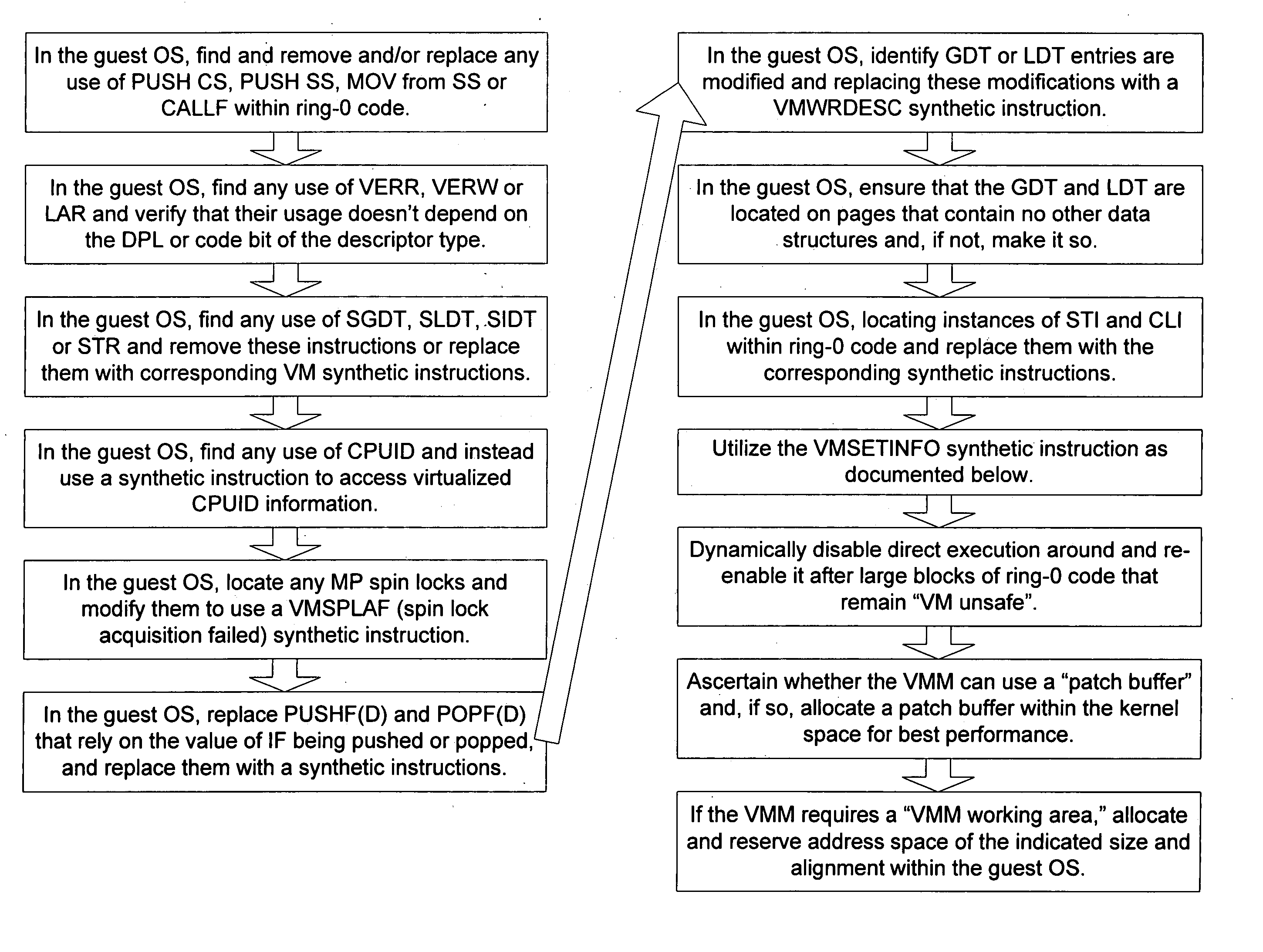
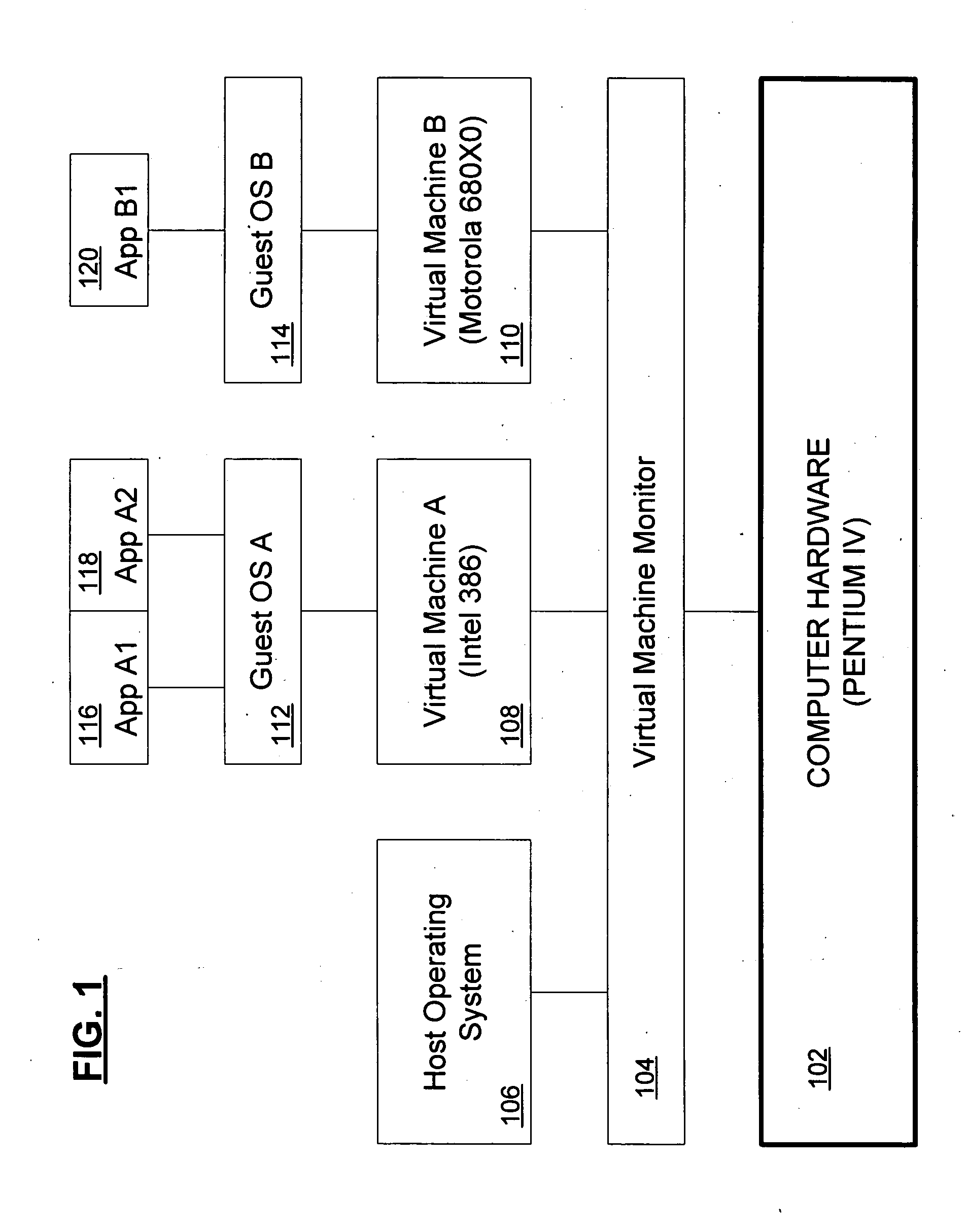
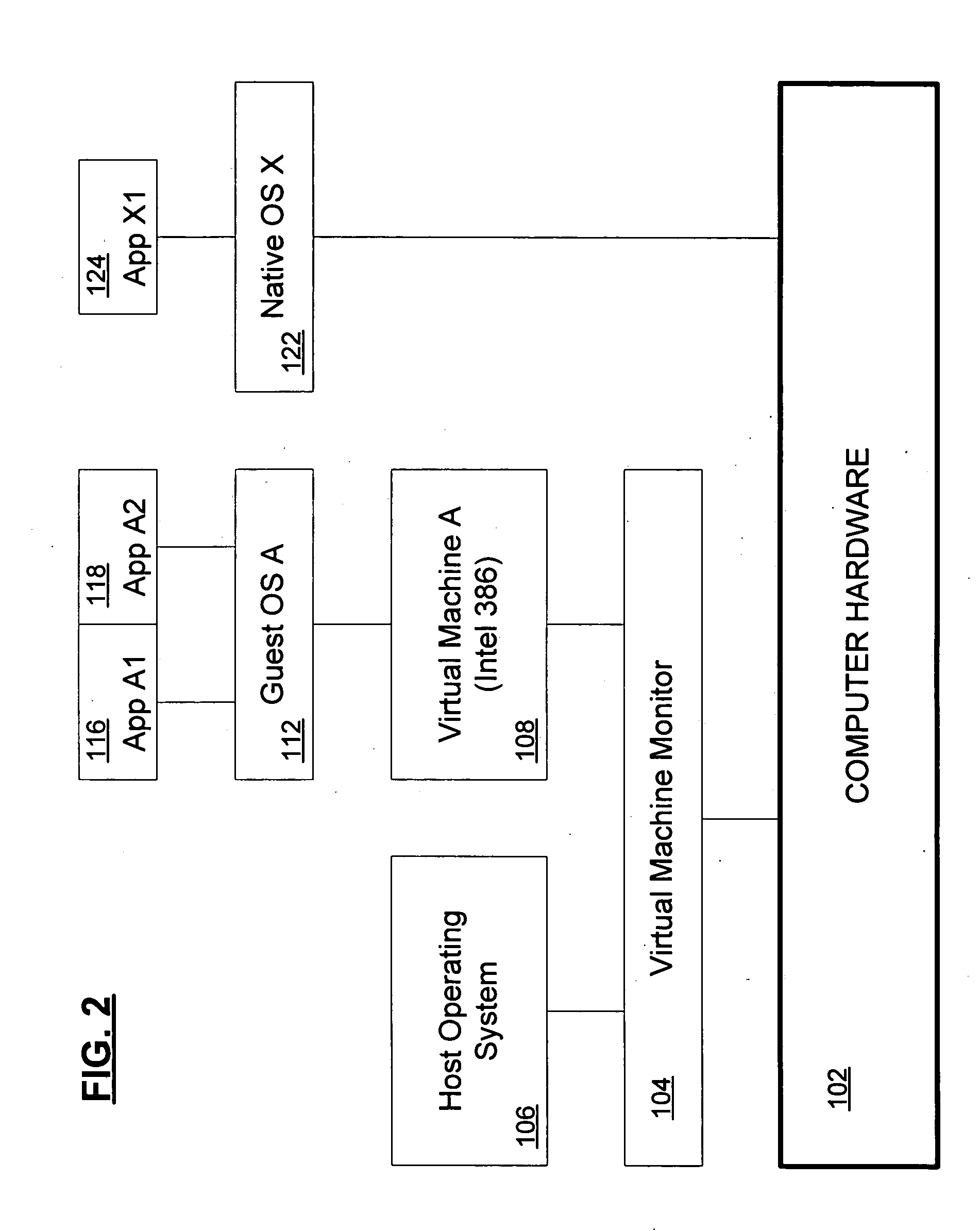
Systems and methods for using synthetic instructions in a virtual machine
ActiveUS20050081199A1Process safetyMuch-improved processor virtualizationDigital computer detailsMultiprogramming arrangementsSafe handlingVirtual machine
The present invention compensates for the shortcomings in x86 processor architectures by providing a set of “synthetic instructions” that cause a trap and thereby provide an opportunity for the virtual machine (VM) to process the instructions safely. By using instructions that are “illegal” to the x86 architecture, but which are nonetheless understandable by a virtual machine, the method of using these synthetic instructions to perform well-defined actions in the virtual machine that are otherwise problematic when performed by traditional instructions to an x86 processor but provide much-improved processor virtualization for x86 processor systems.
Owner:MICROSOFT TECH LICENSING LLC
Methods and devices for microfluidic point-of-care immunoassays
ActiveUS8110392B2Reduce incubation timeMean flow velocityBioreactor/fermenter combinationsShaking/oscillating/vibrating mixersPoint of careSystems design
Microfluidic methods and devices for heterogeneous binding and agglutination assays are disclosed, with improvements relating to mixing and to reagent and sample manipulation in systems designed for safe handling of clinical test samples.
Owner:PERKINELMER HEALTH SCIENCES INC
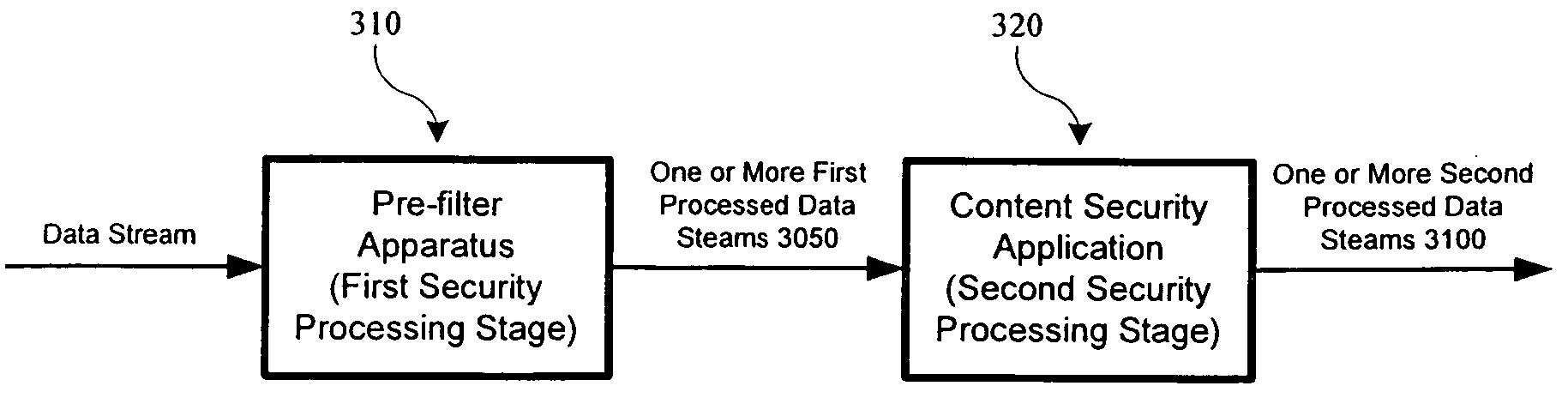
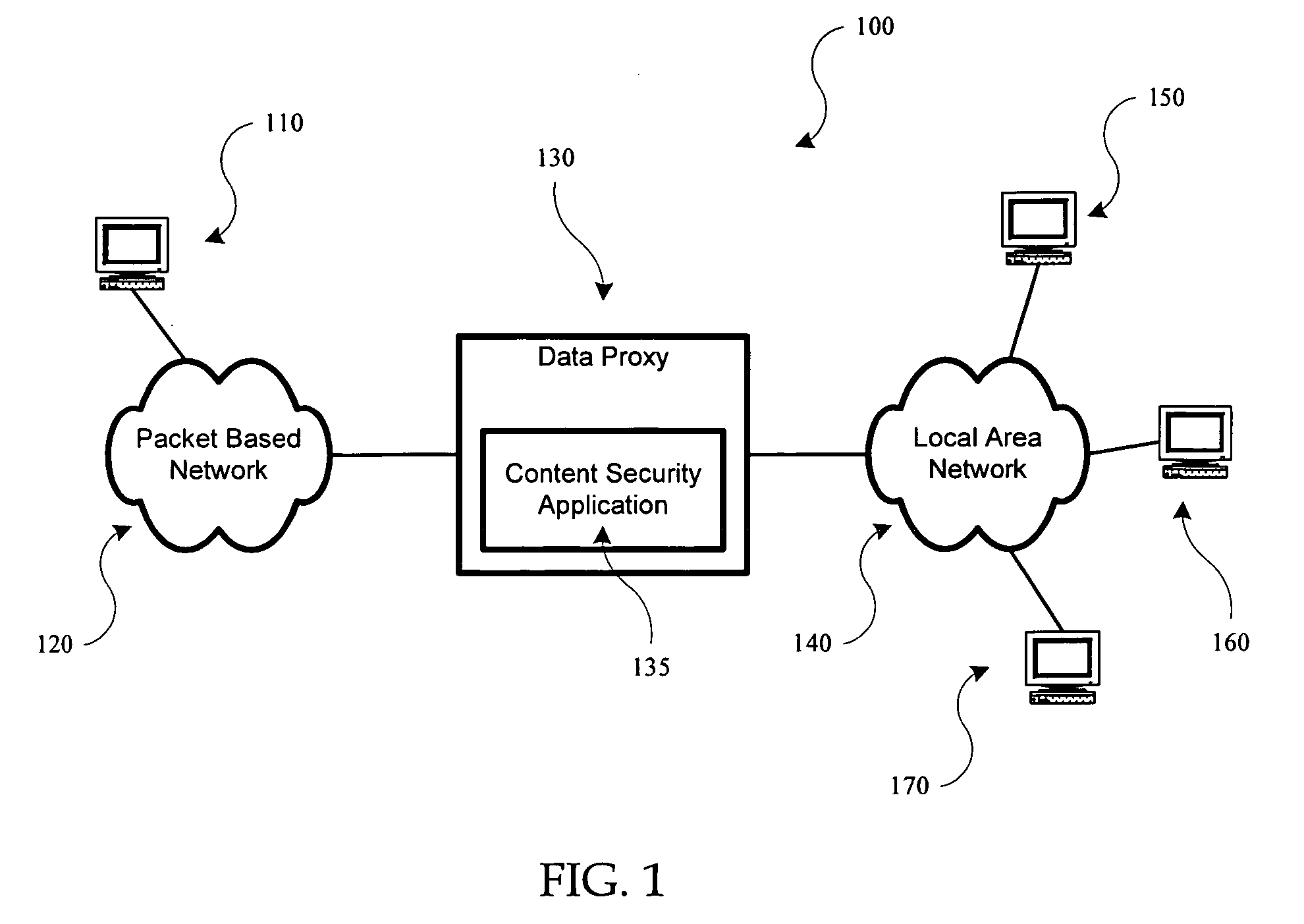
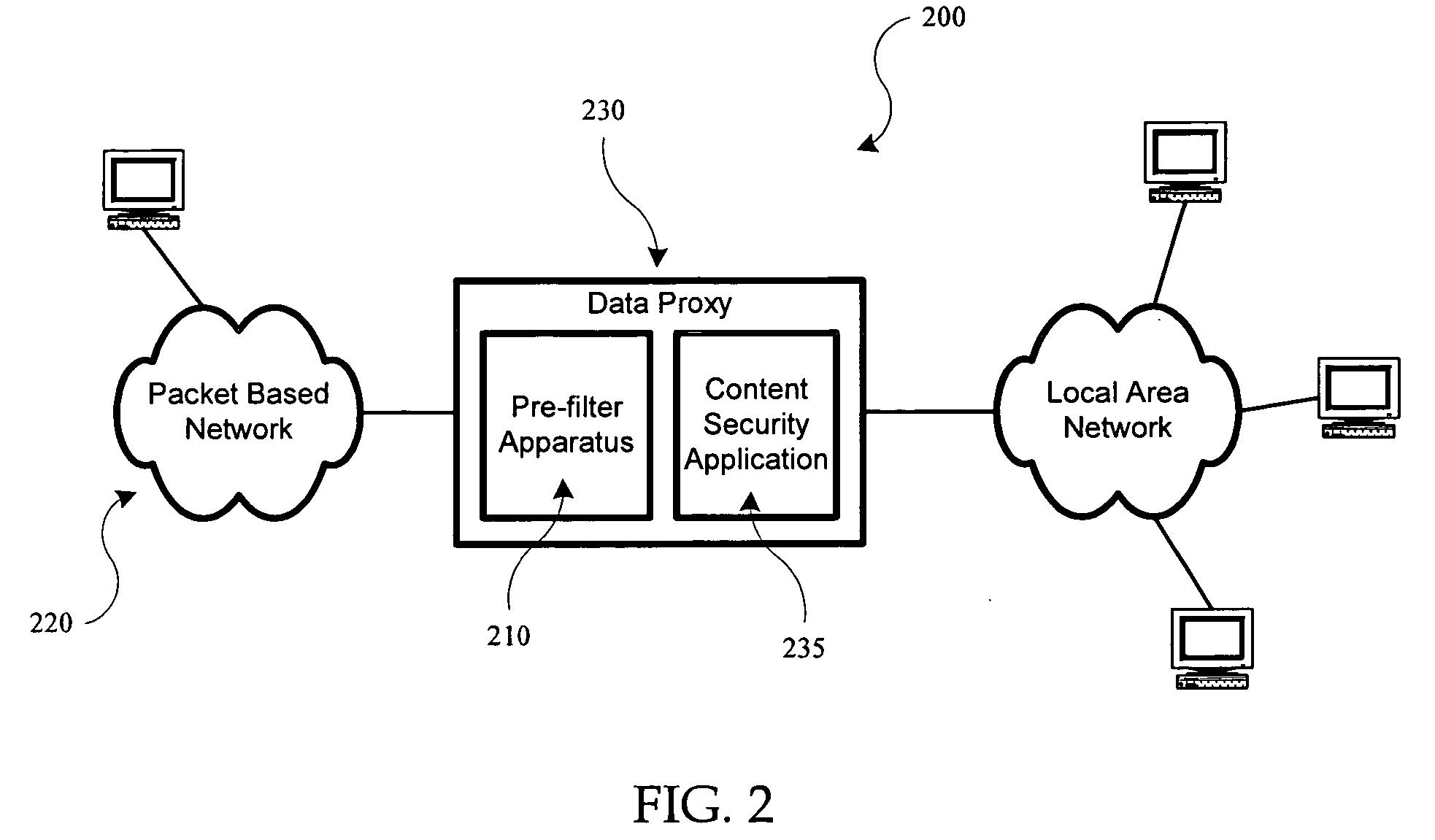
Apparatus and method for acceleration of security applications through pre-filtering
A first security processing stage performs a first multitude of tasks and a second security processing stage performs a second multitude of tasks. The first and second multitude of tasks may include common tasks. The first security processing stage is a prefilter to the second security processing stage. The input data received as a data stream is first processed by the first security processing stage, which in response, generates one or more first processed data streams. The first processed data streams may be further processed by the second security processing stage or may bypass the second security processing stage. The first security processing stage operates at a speed greater than the speed of the second security processing stage.
Owner:INTEL CORP +1
System for SSL re-encryption after load balance
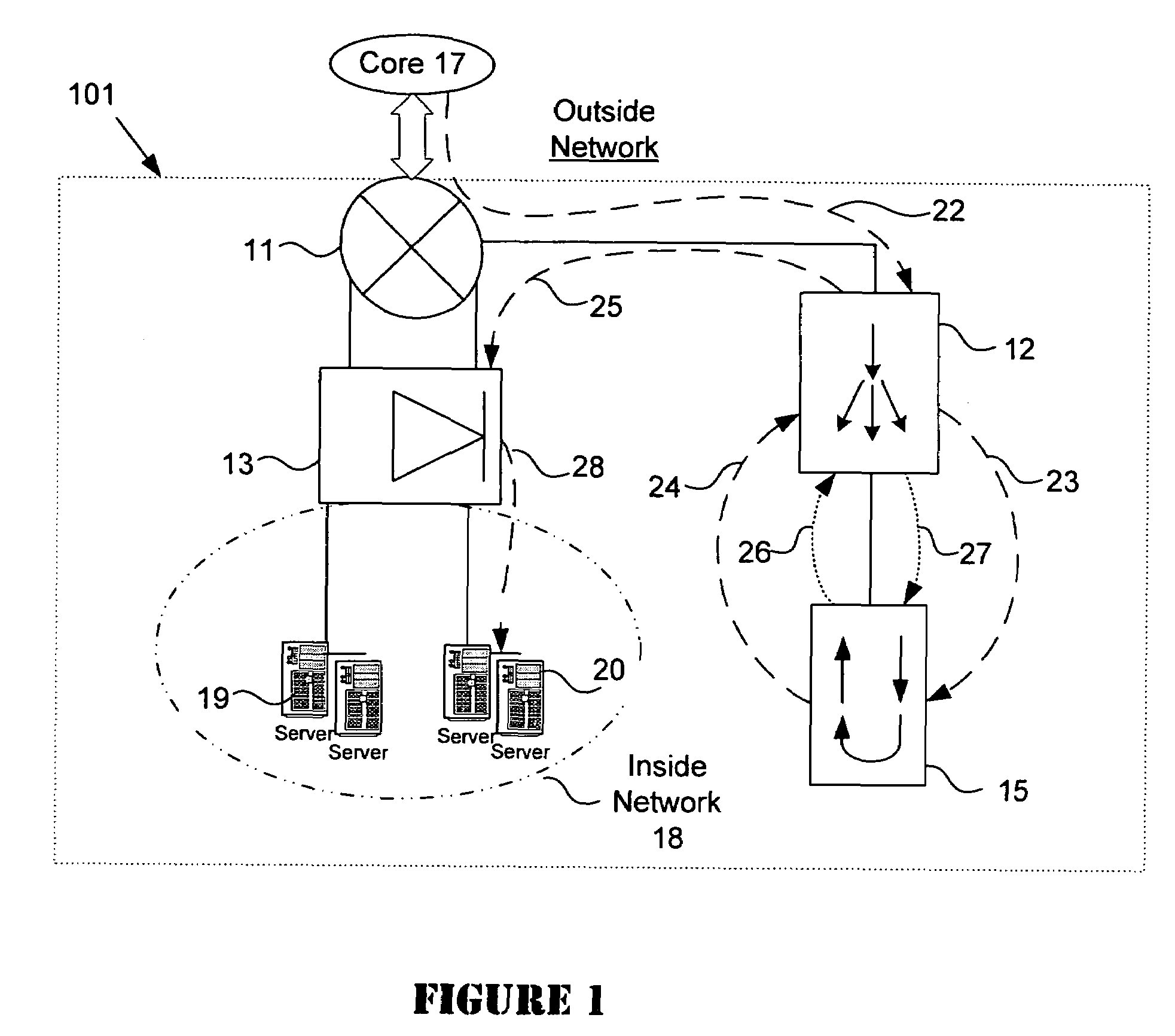
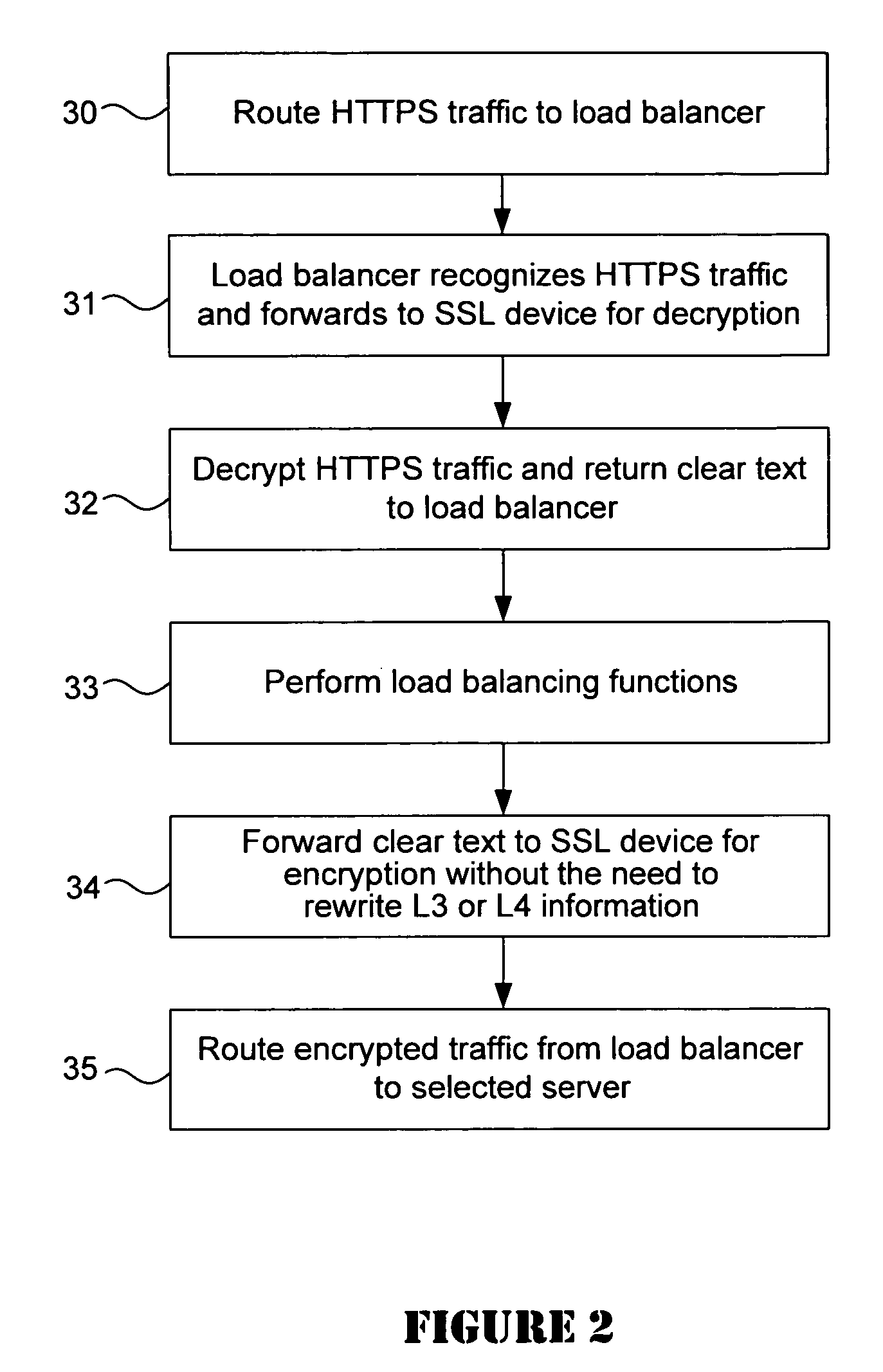
A data center provides secure handling of HTTPS traffic using backend SSL decryption and encryption in combination with a load balancer such as a content switch. The load balancer detects HTTPS traffic and redirects it to an SSL offloading device for decryption and return to the load balancer. The load balancer then uses the clear text traffic for load balancing purposes before it redirects the traffic back to the SSL offloading device for re-encryption. Thereafter, the re-encrypted traffic is sent to the destination servers in the data center. In one embodiment, the combination with the back-end SSL with an intrusion detection system improves security by performing intrusion detection on the decrypted HTTPS traffic.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com