Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3399results about "Acutation objects" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
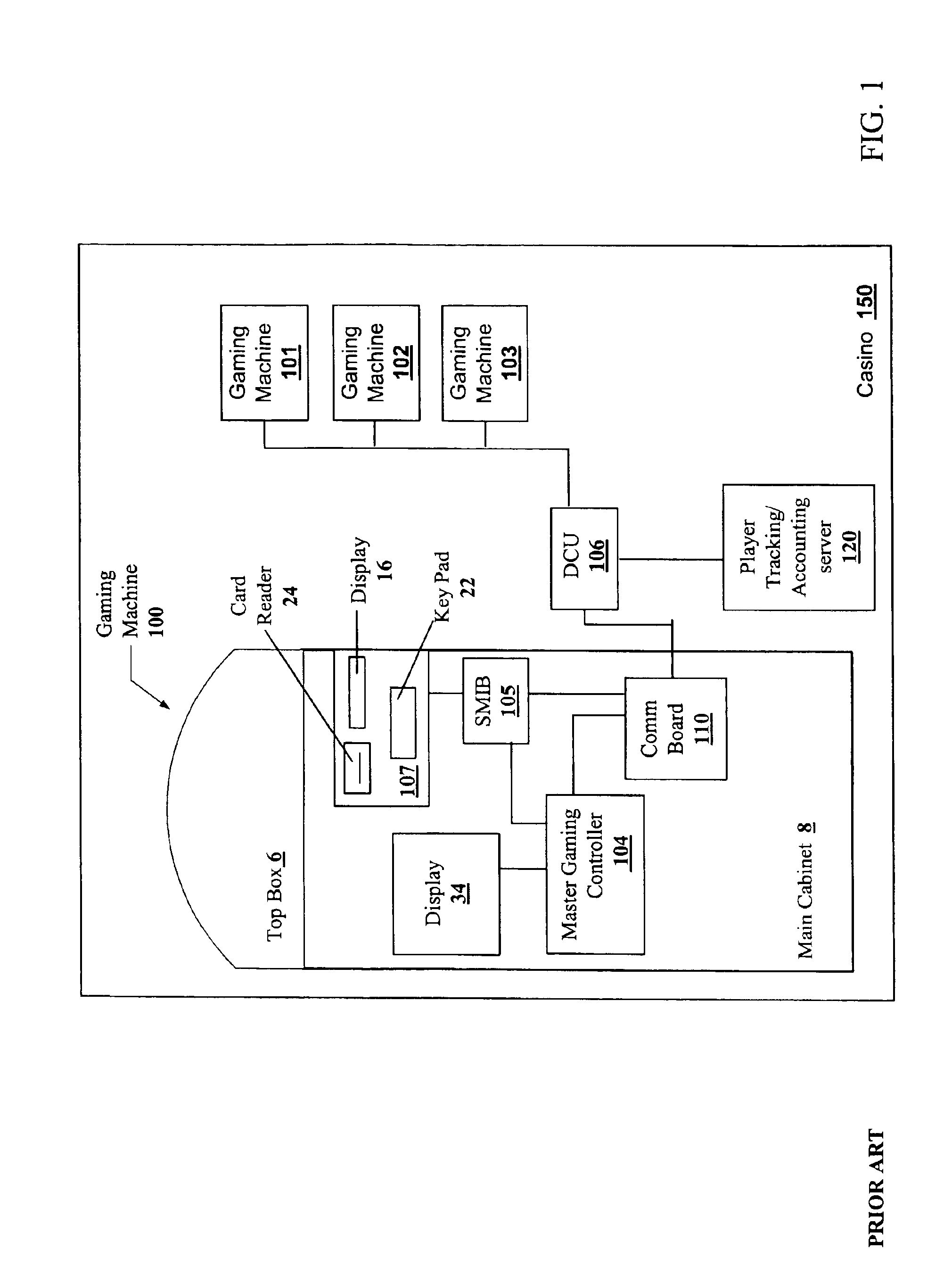
Distributed electronic entertainment method and apparatus
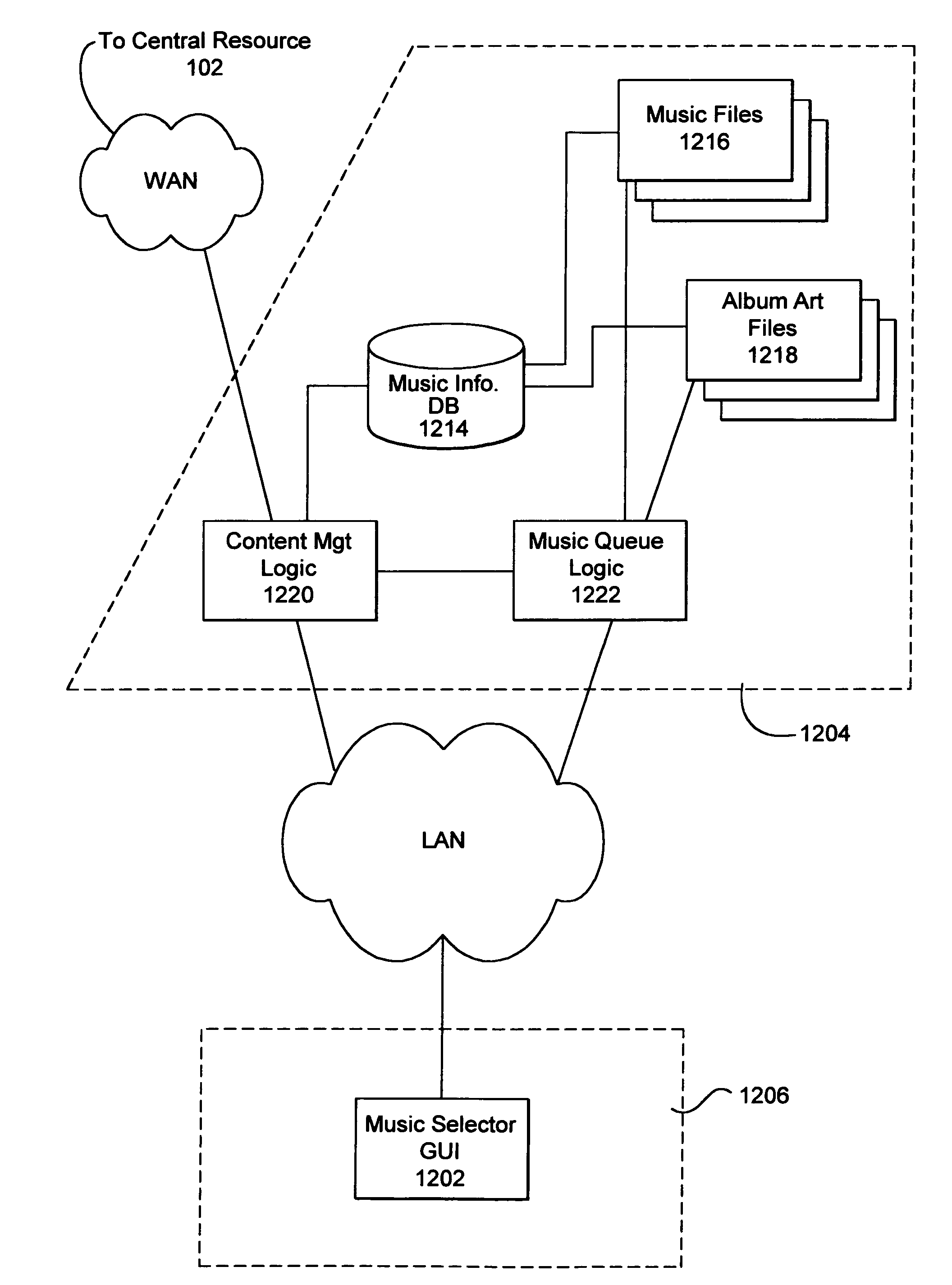
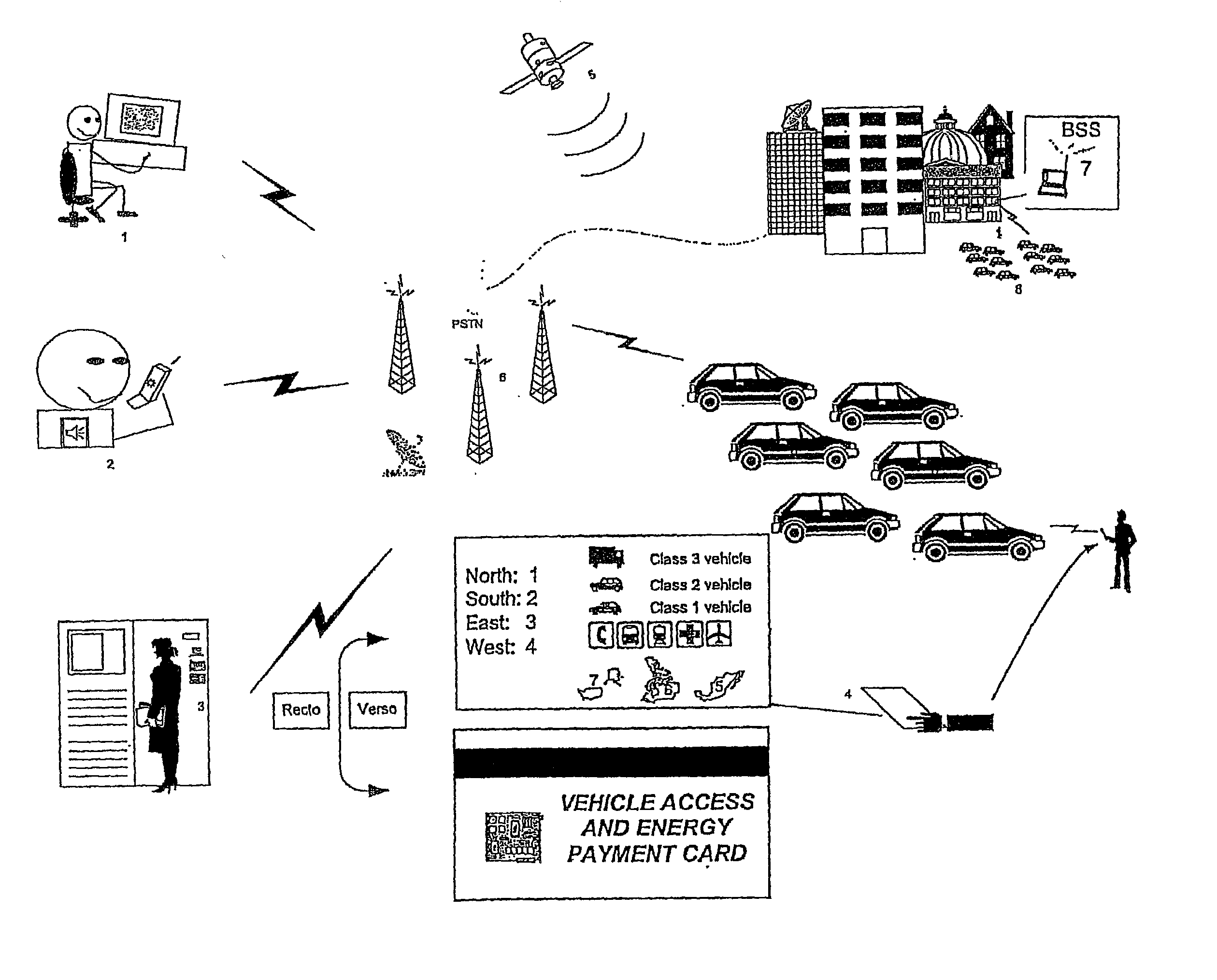
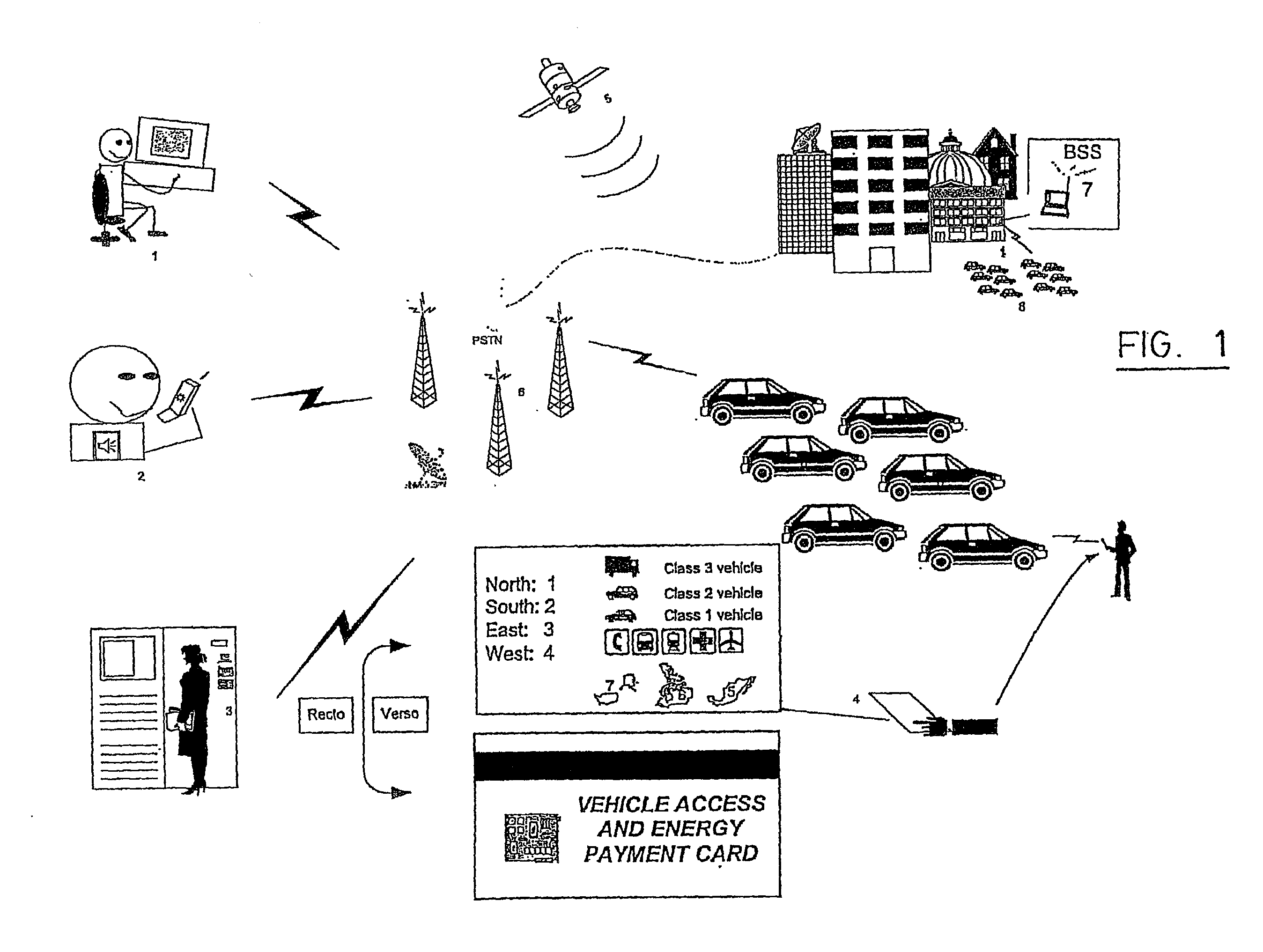
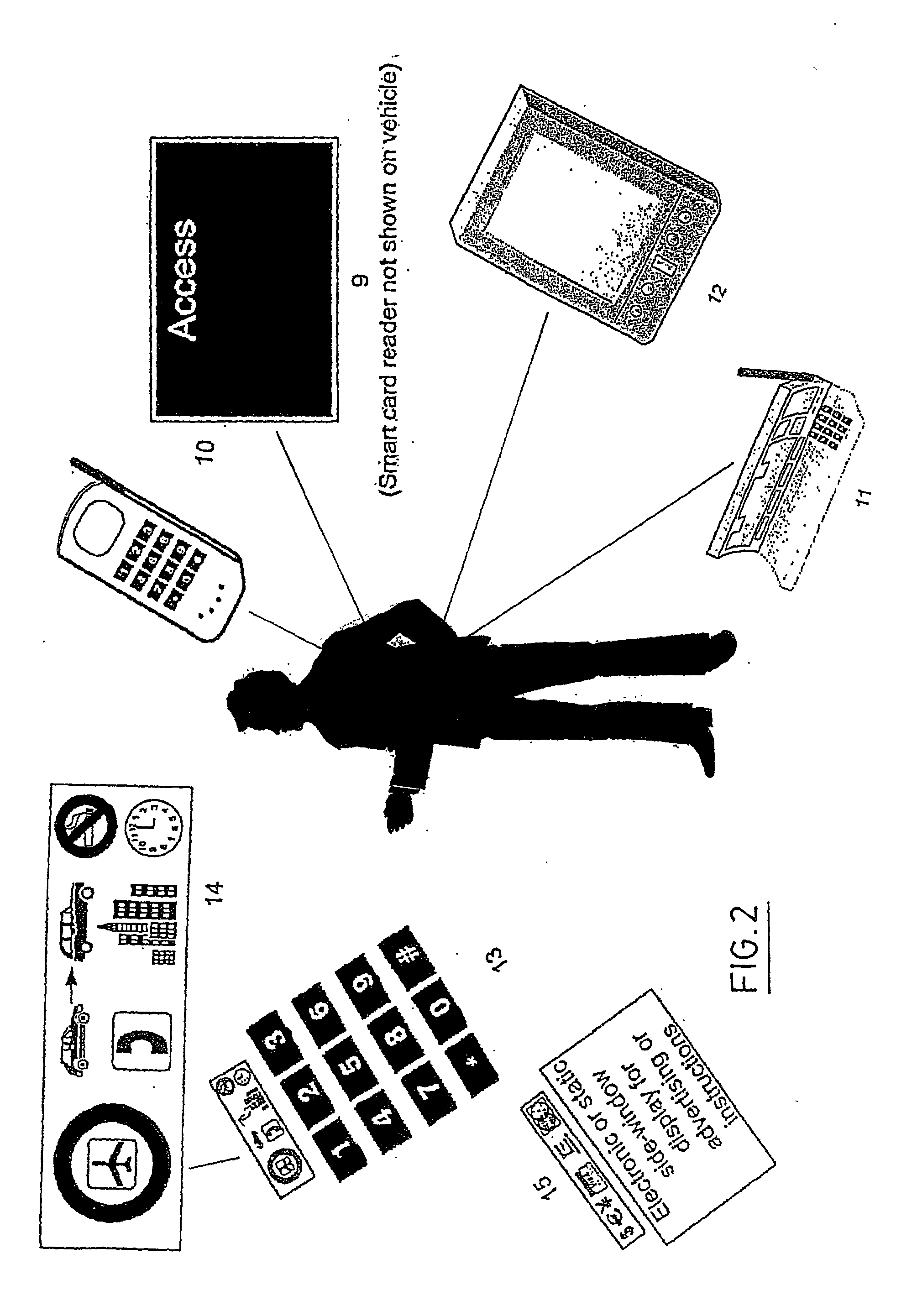
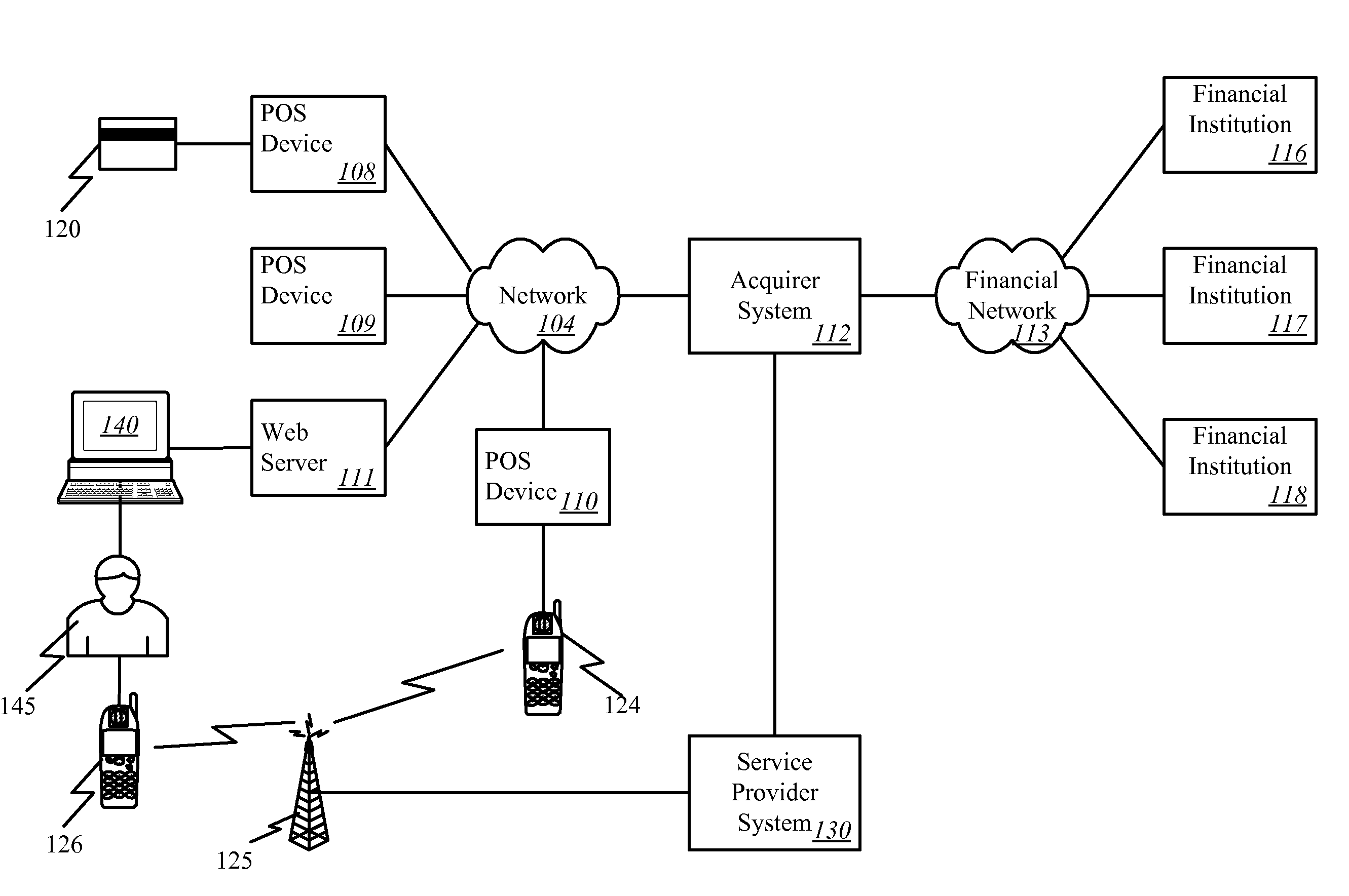
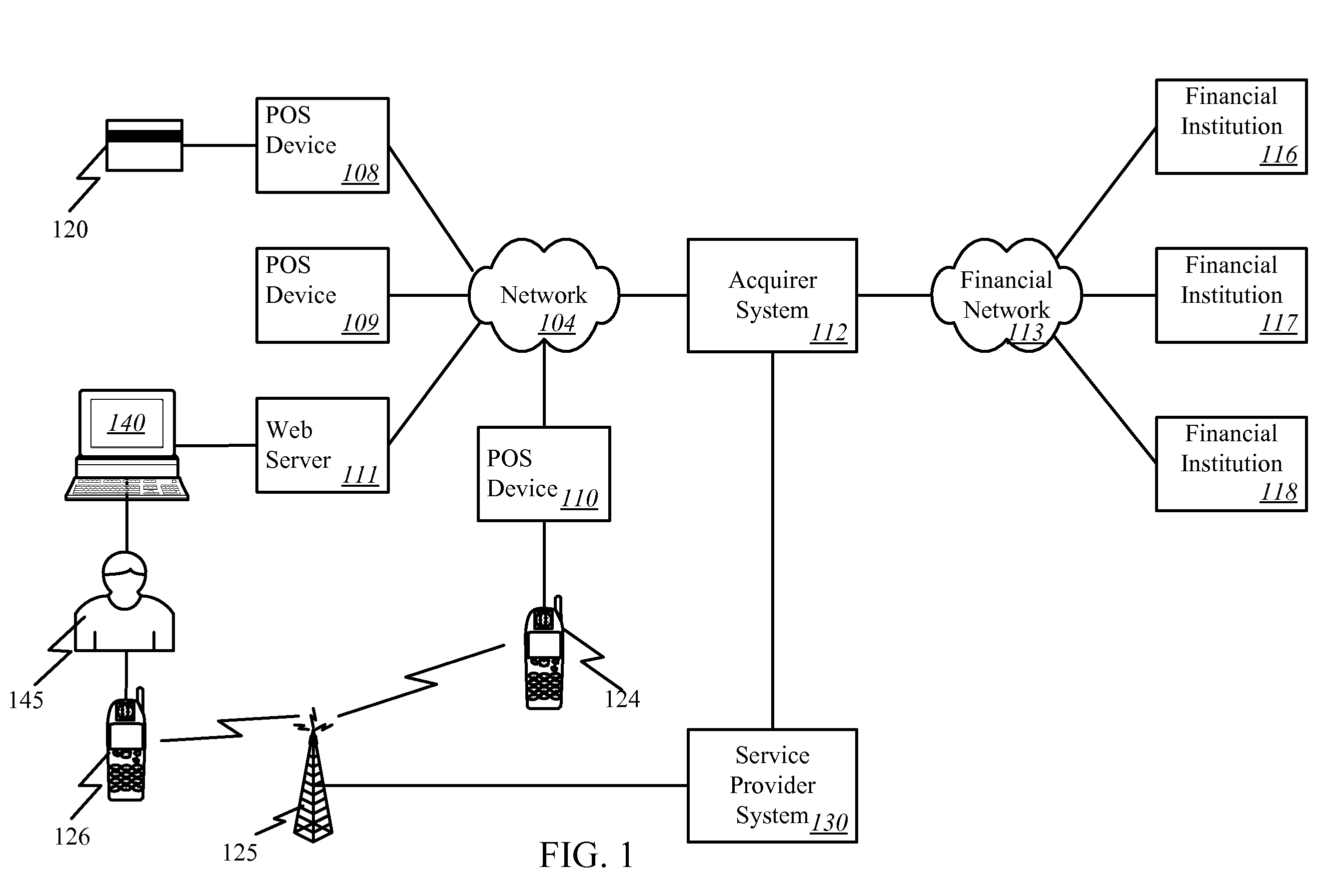
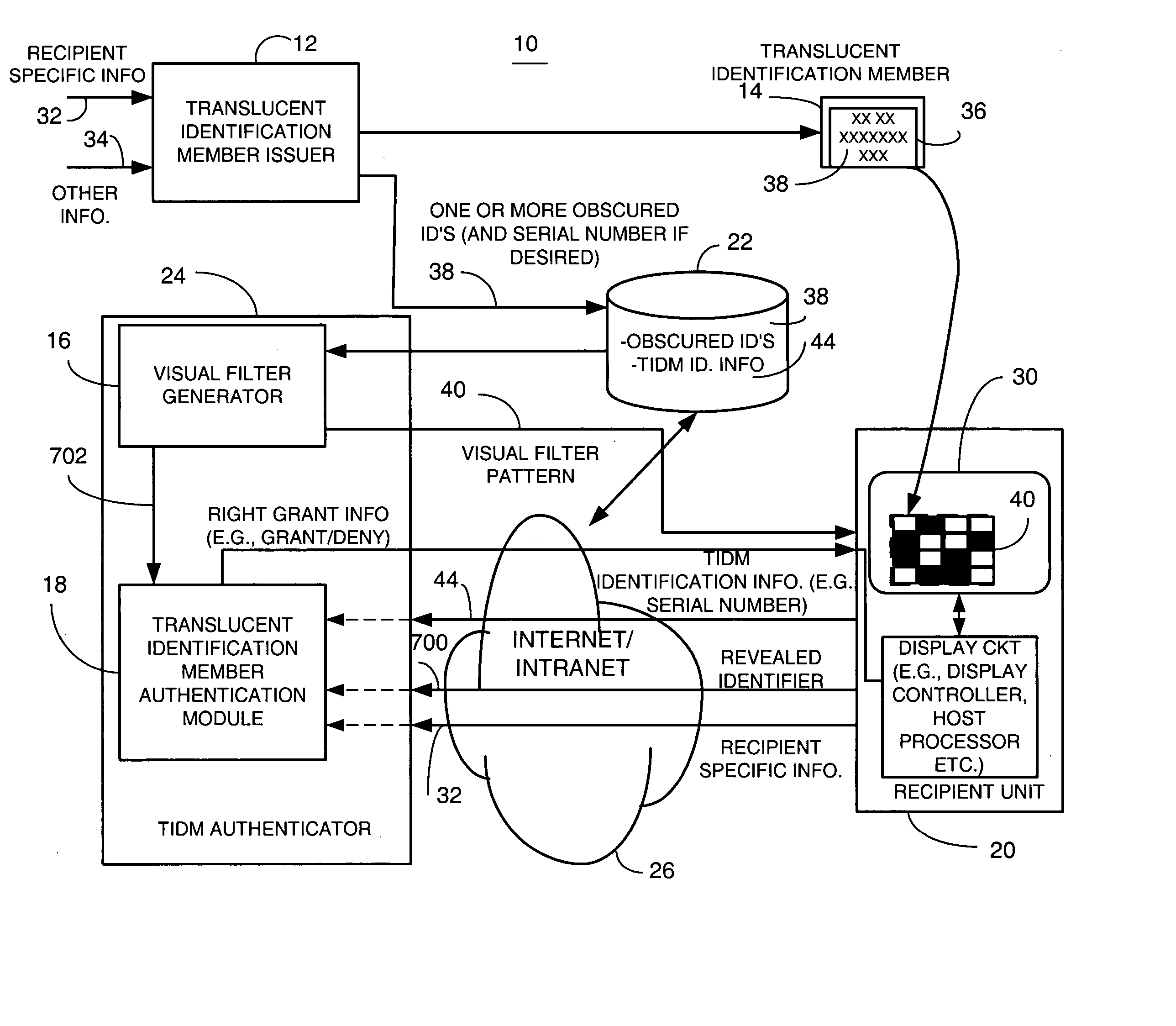
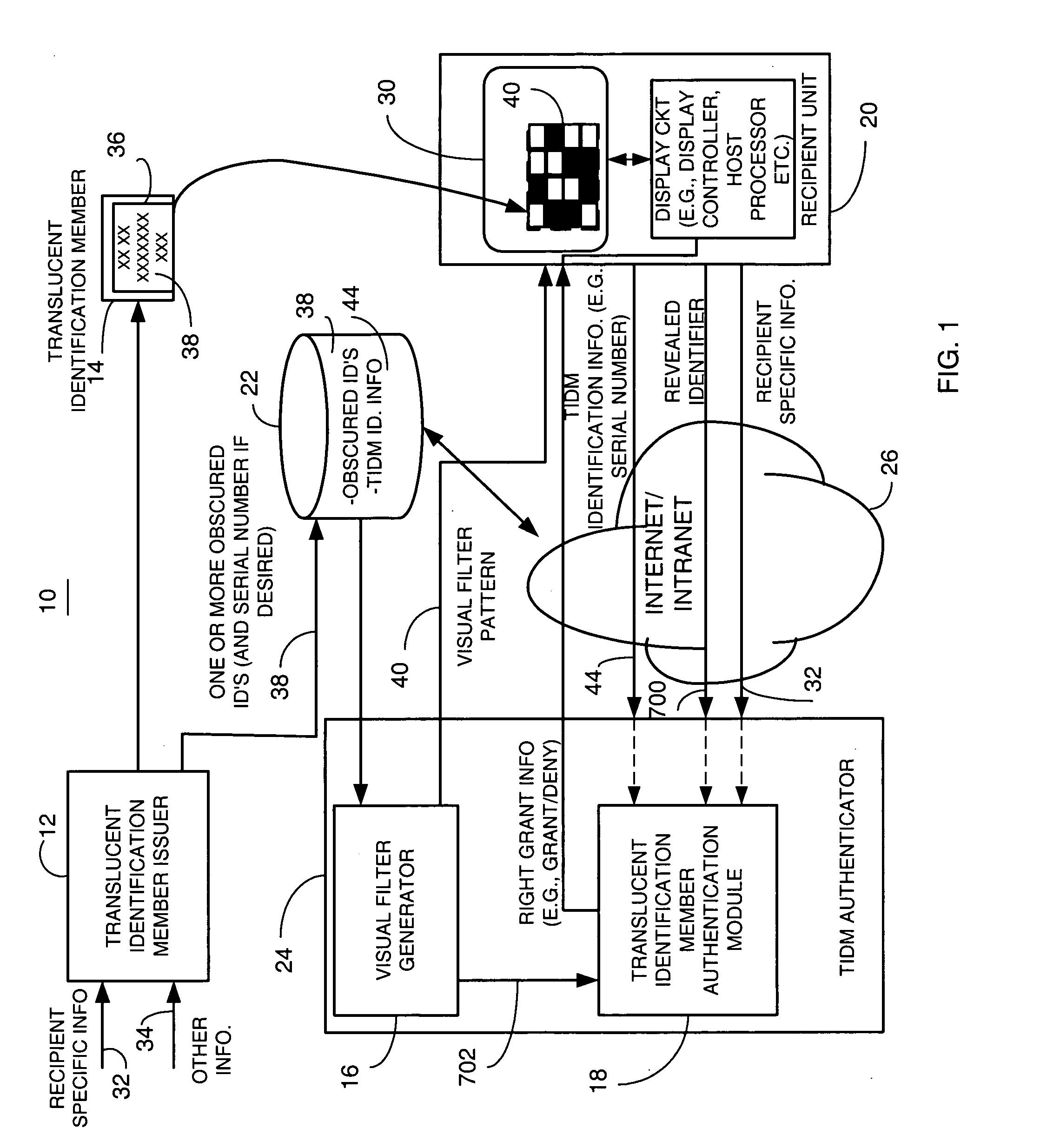
A distributed electronic entertainment method and apparatus are described. In one embodiment, a central management resource is coupled to multiple out-of-home venues through a wide area network (WAN). The central management resource stores content and performs management, monitoring and entertainment content delivery functions. At each venue at least one entertainment unit is coupled to the WAN. Multiple entertainment units in a venue are coupled to each other through a local area network (LAN). In one embodiment, an entertainment unit includes a user interface that comprises at least one graphical user interface (GUI). The entertainment unit further comprises a local memory device that stores entertainment content comprising music, a peripheral interface, and a user input device. A plurality of peripheral devices are coupled to the at least one entertainment unit via the peripheral interface, wherein a user, through the user input device and the user interface, performs at least one activity from a group comprising, playing music, playing electronic games, viewing television content, and browsing the Internet.
Owner:AMI ENTERTAINMENT NETWORK
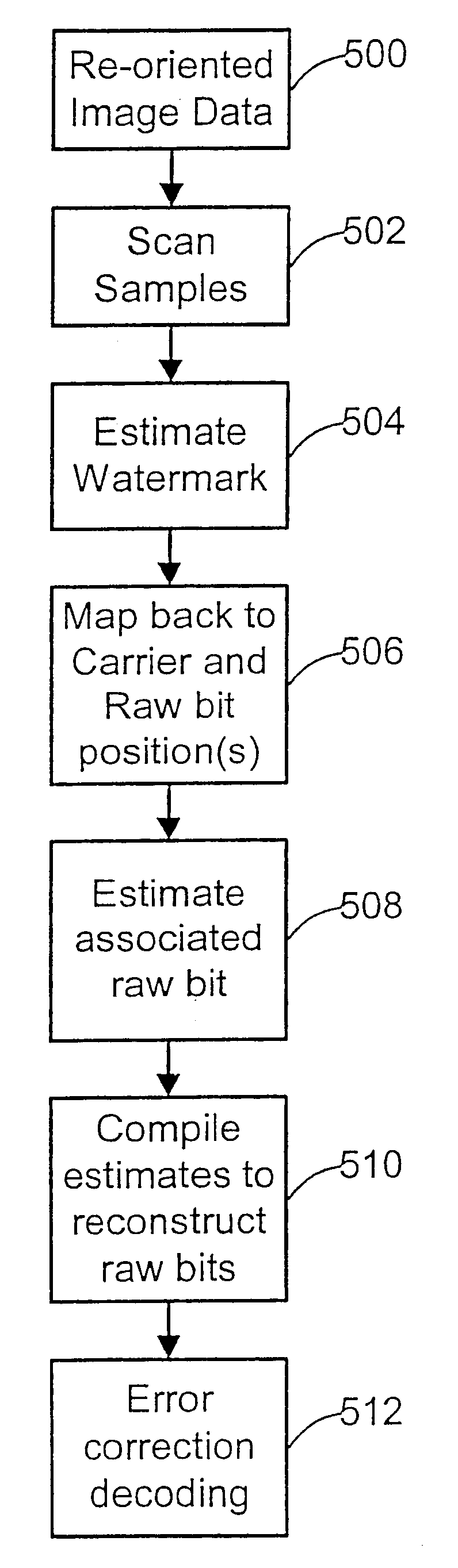
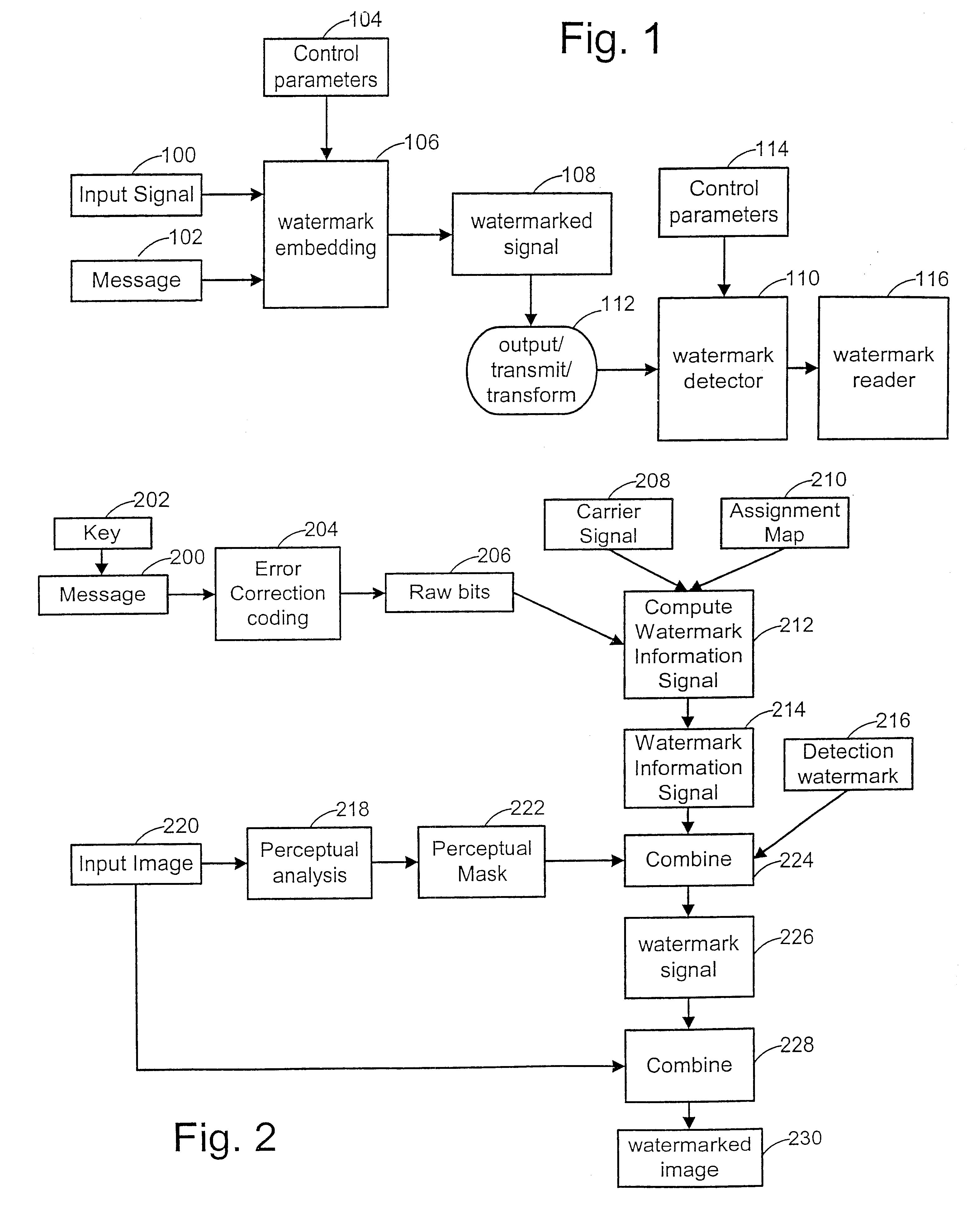
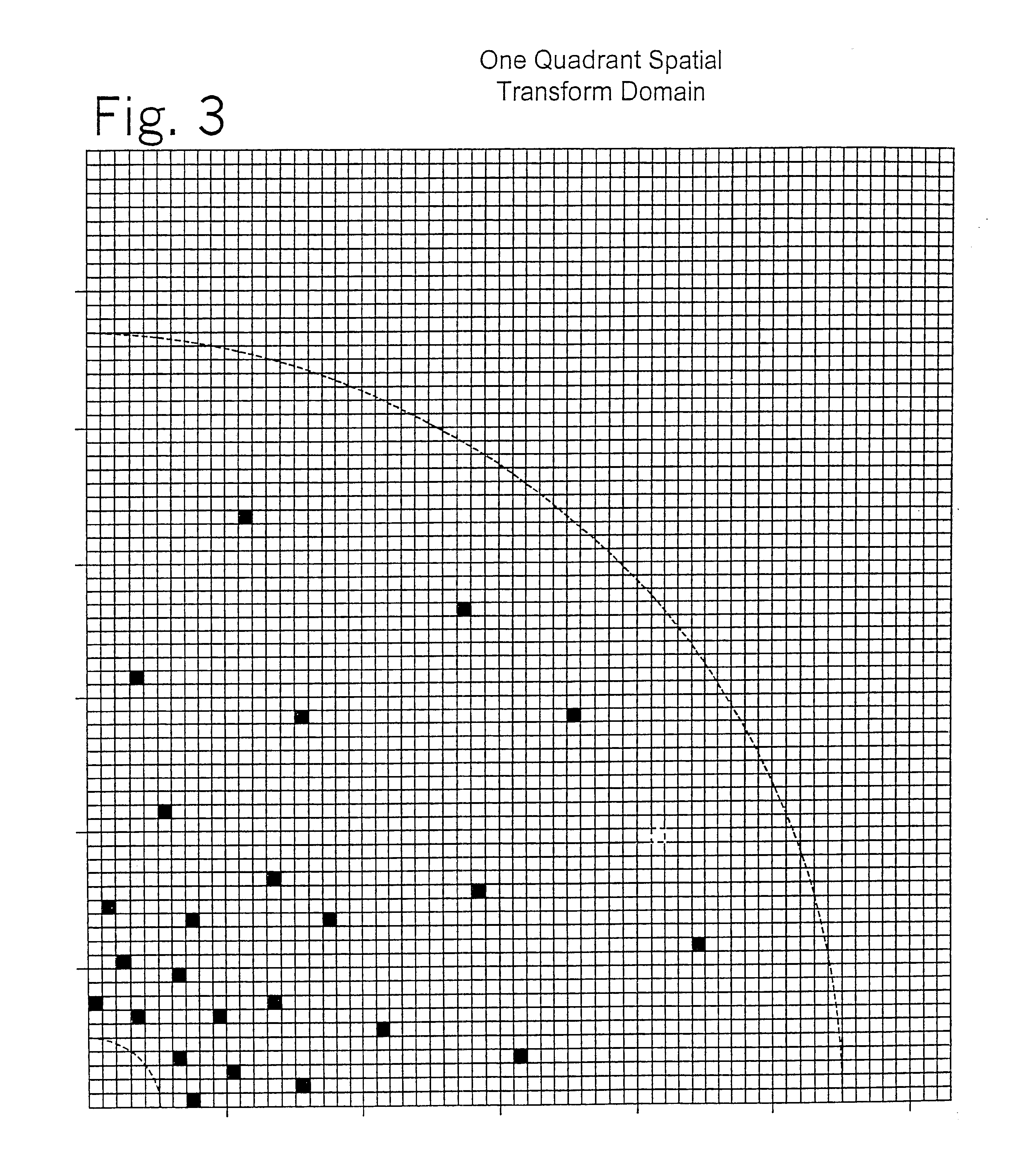
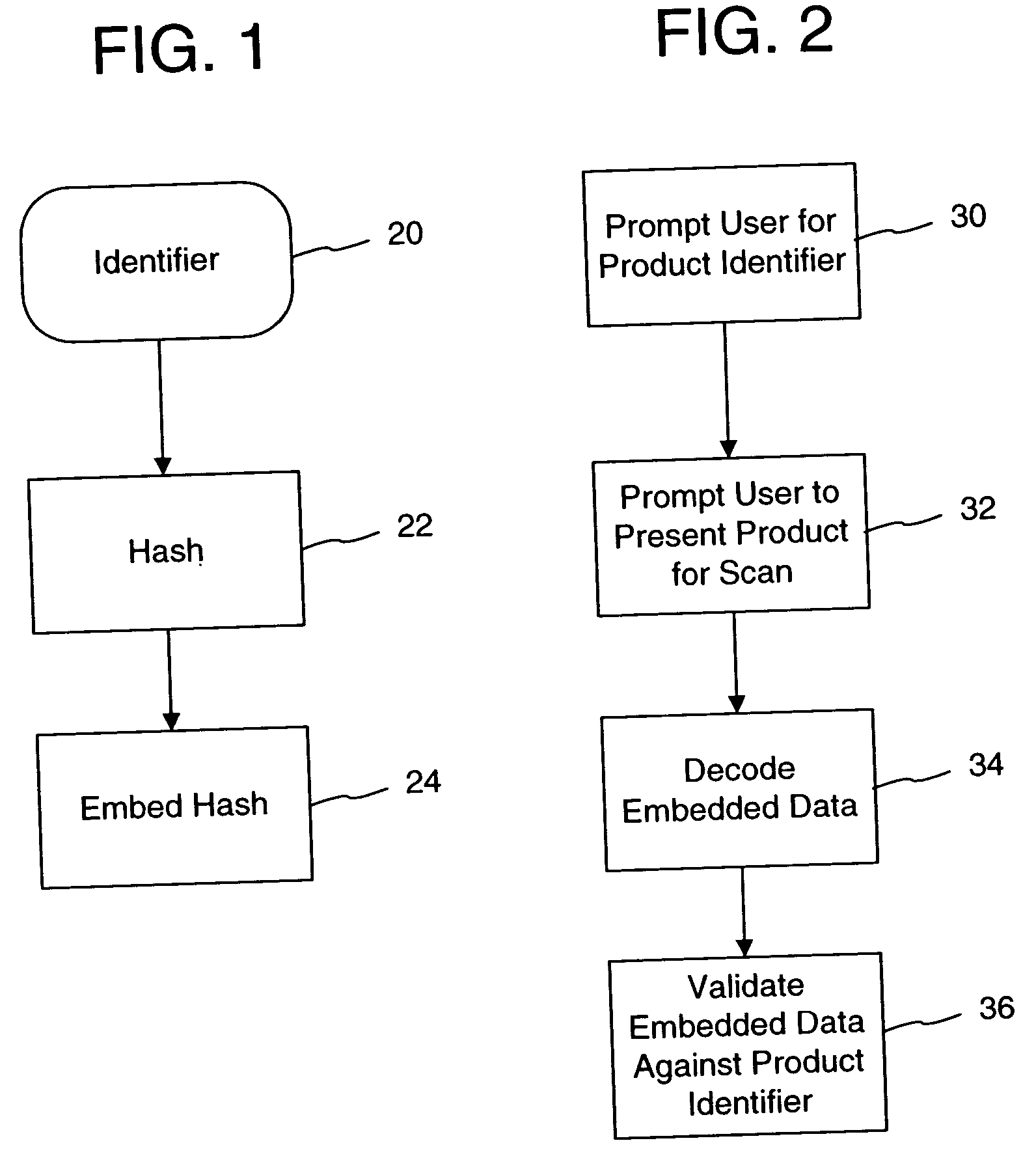
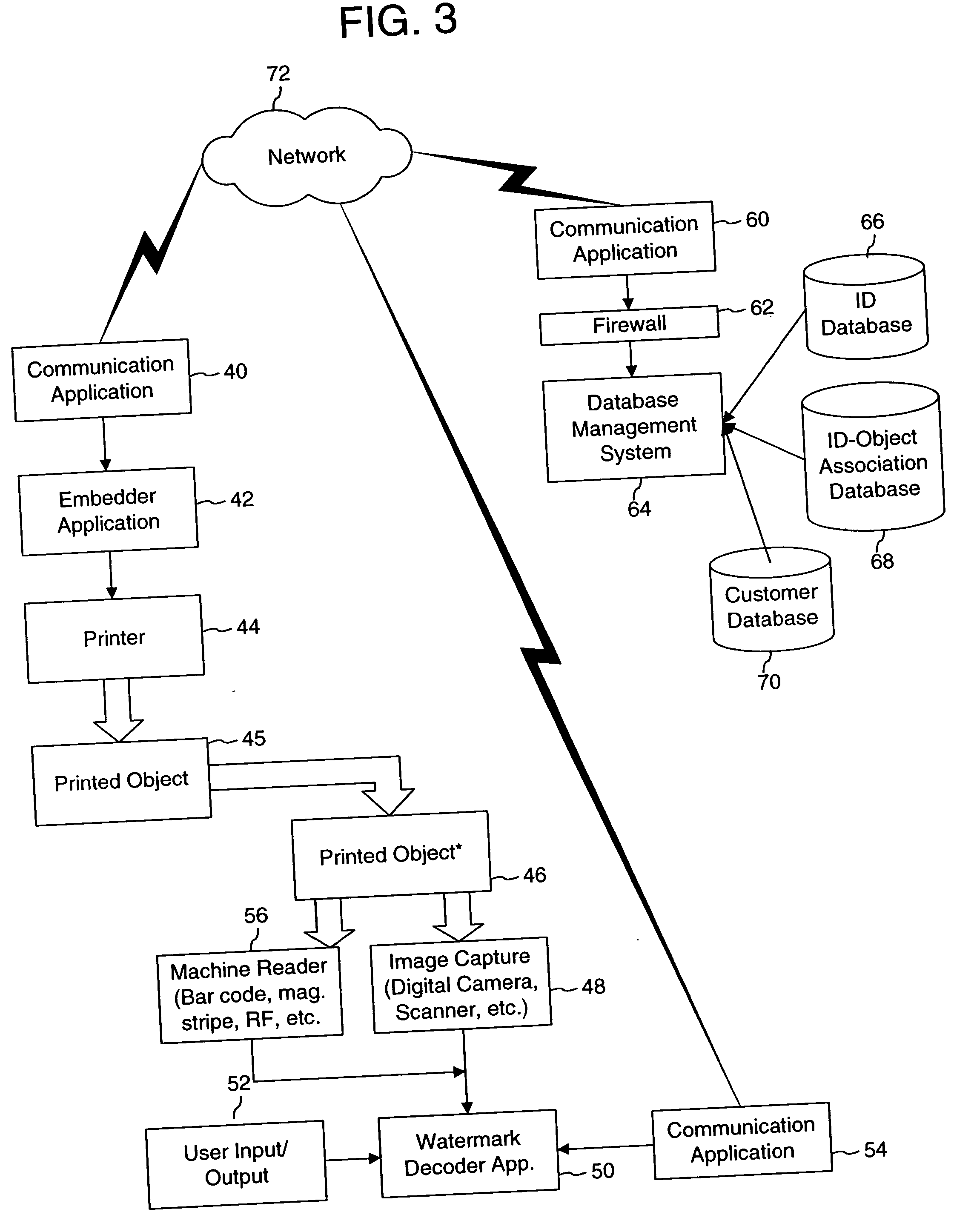
Watermark embedder and reader
InactiveUS6614914B1Mitigates effect of printingEasy to detectCoin-freed apparatusRecord information storageGraphicsComputer hardware
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Linking of computers based on optical sensing of digital data
InactiveUS6311214B1Reduce businessLow costCoin-freed apparatusRecord information storageDigital dataBusiness card
A printed object, such as an item of postal mail, a book, printed advertising, a business card, product packaging, etc., is steganographically encoded with plural-bit data. When such an object is presented to an optical sensor, the plural-bit data is decoded and used to establish a link to an internet address corresponding to that object.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Data transmission system and data transmitting method
Owner:SHARP KK
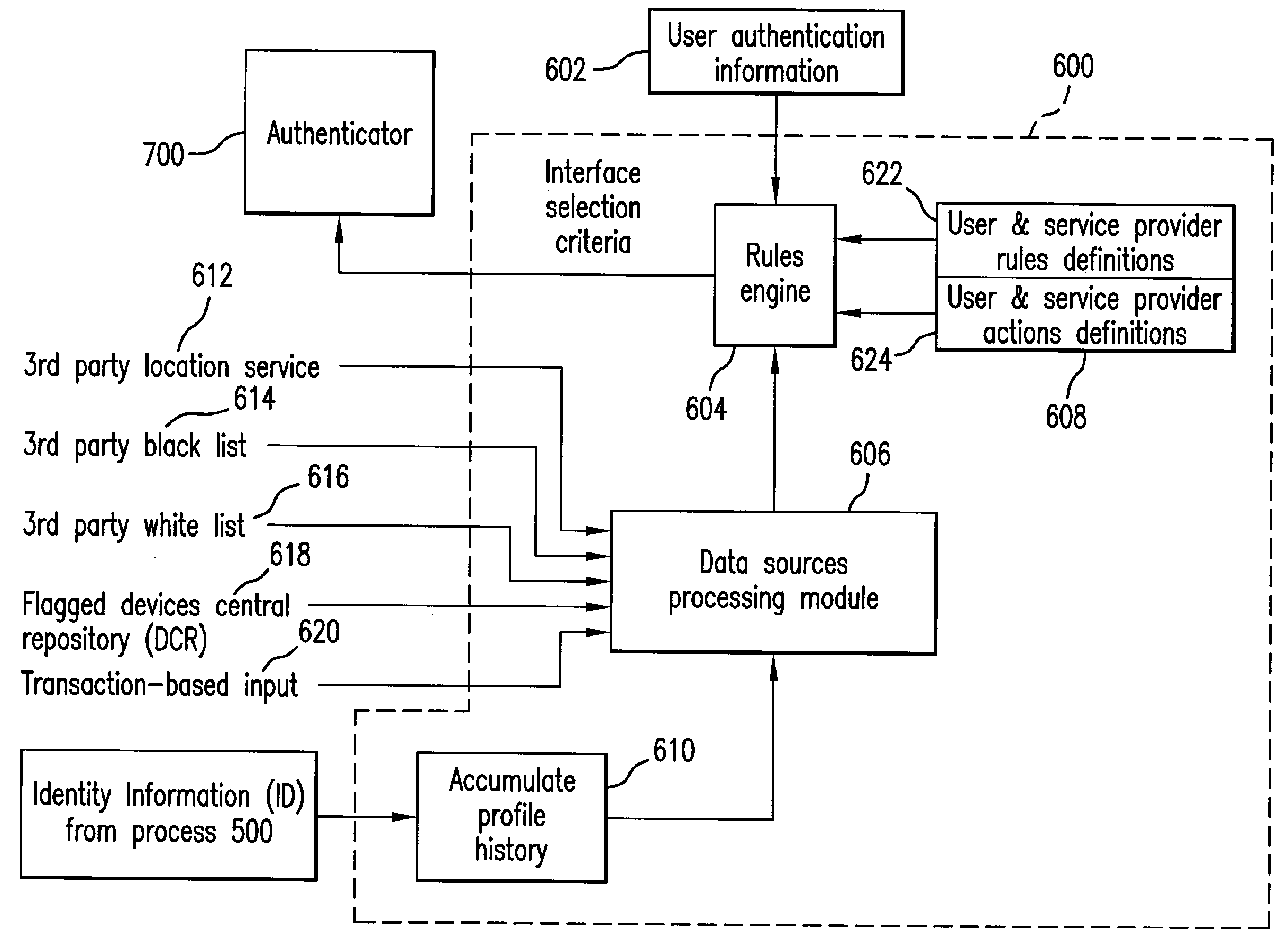
System and method for fraud monitoring, detection, and tiered user authentication
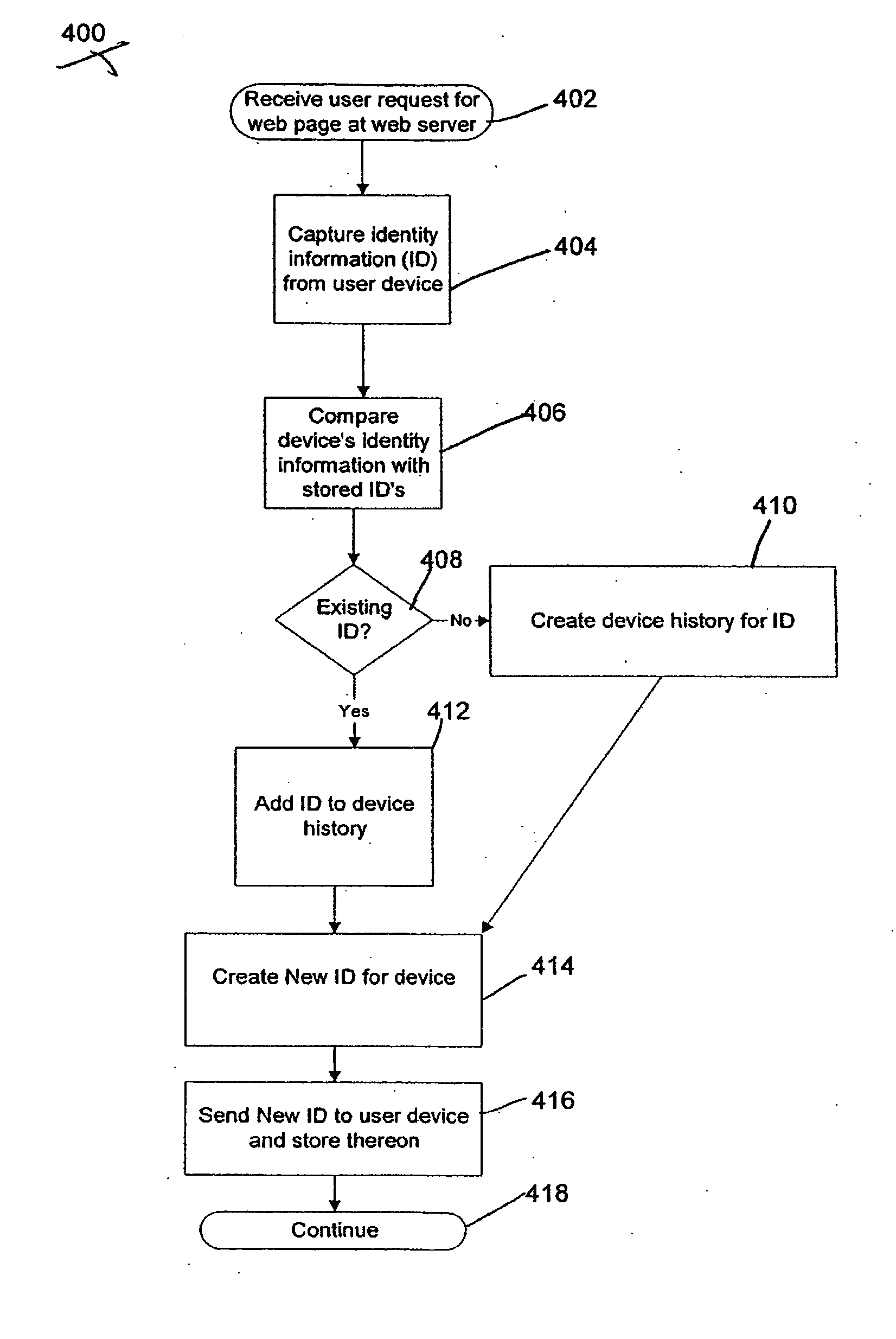
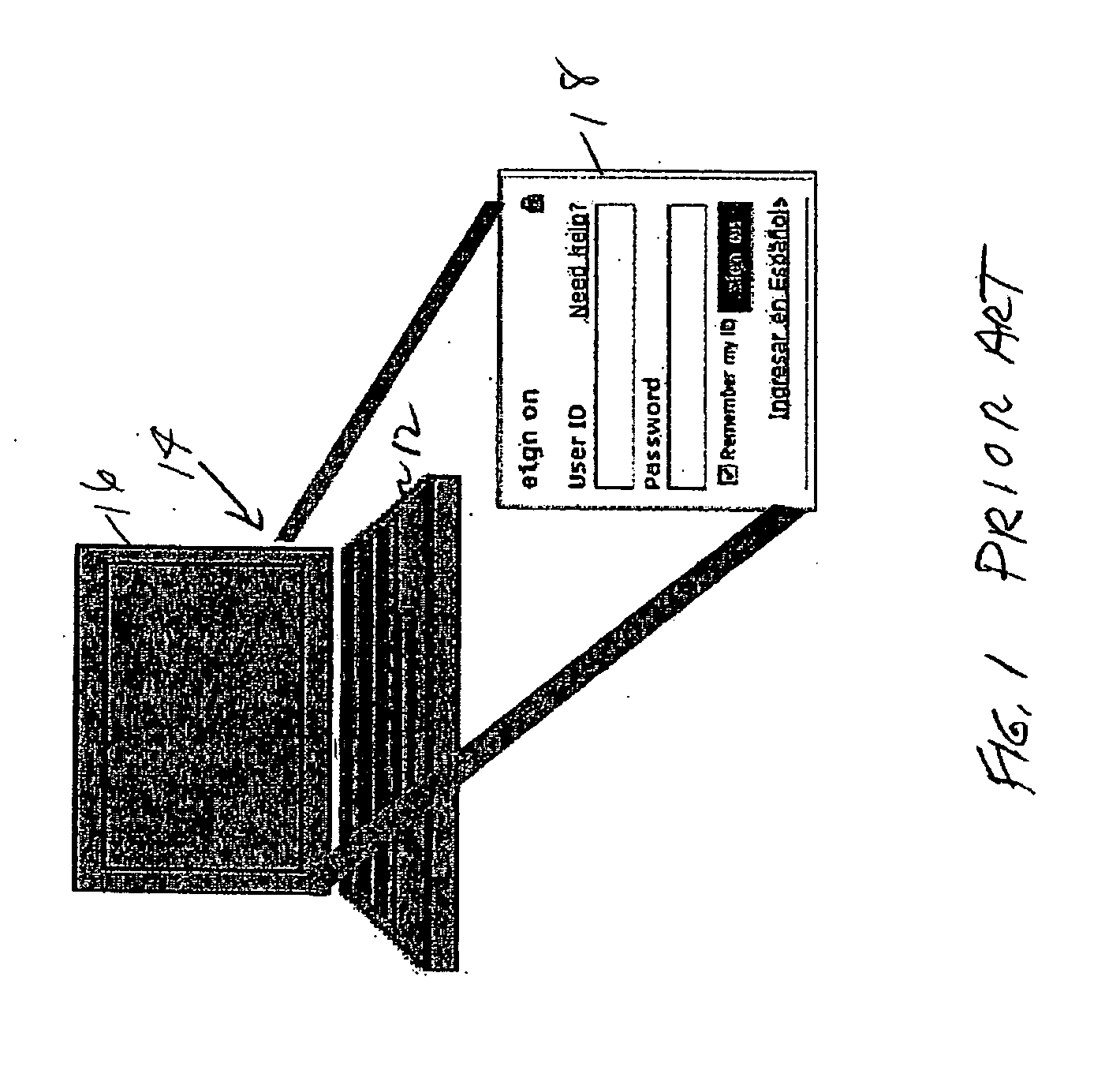
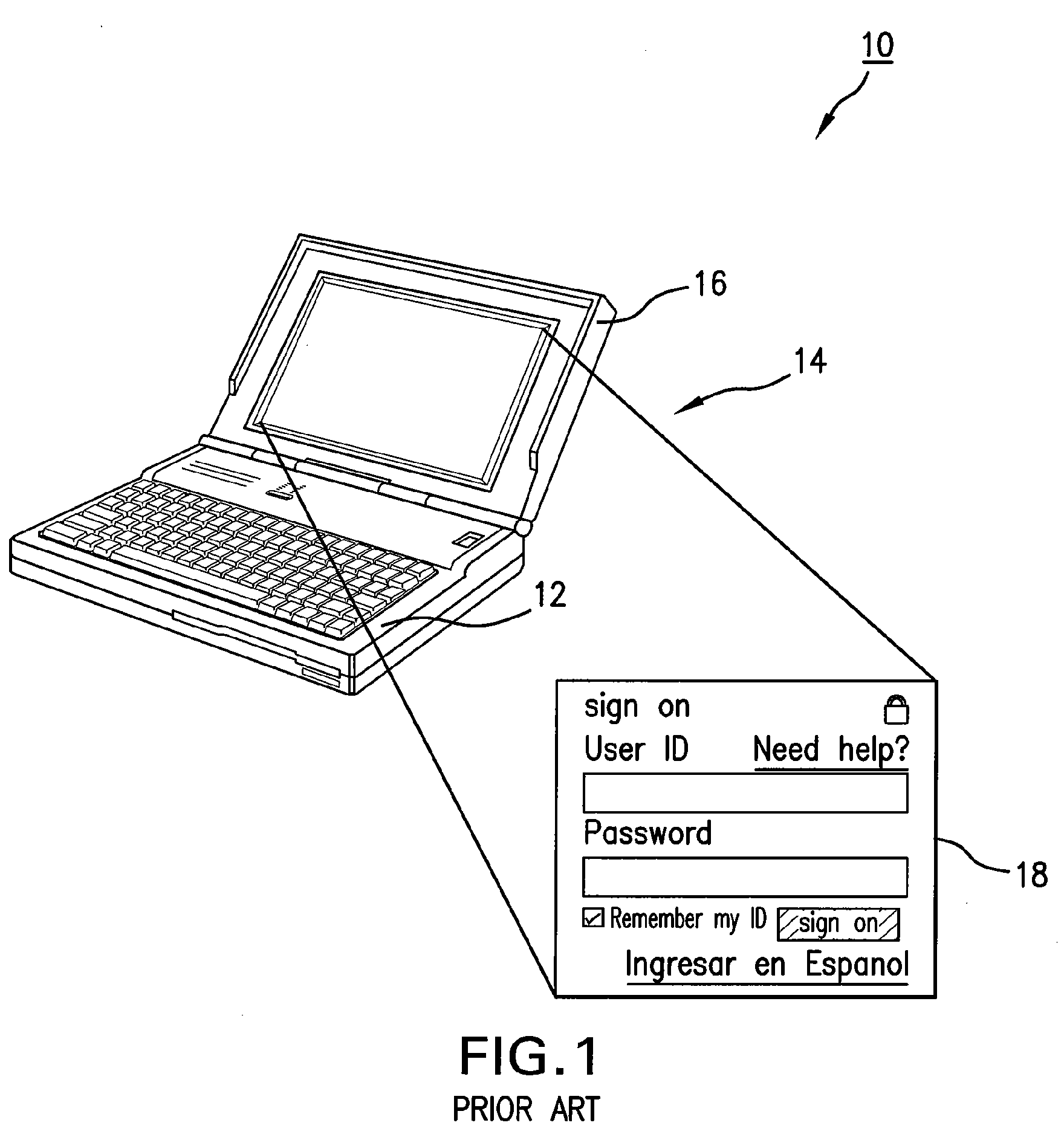
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
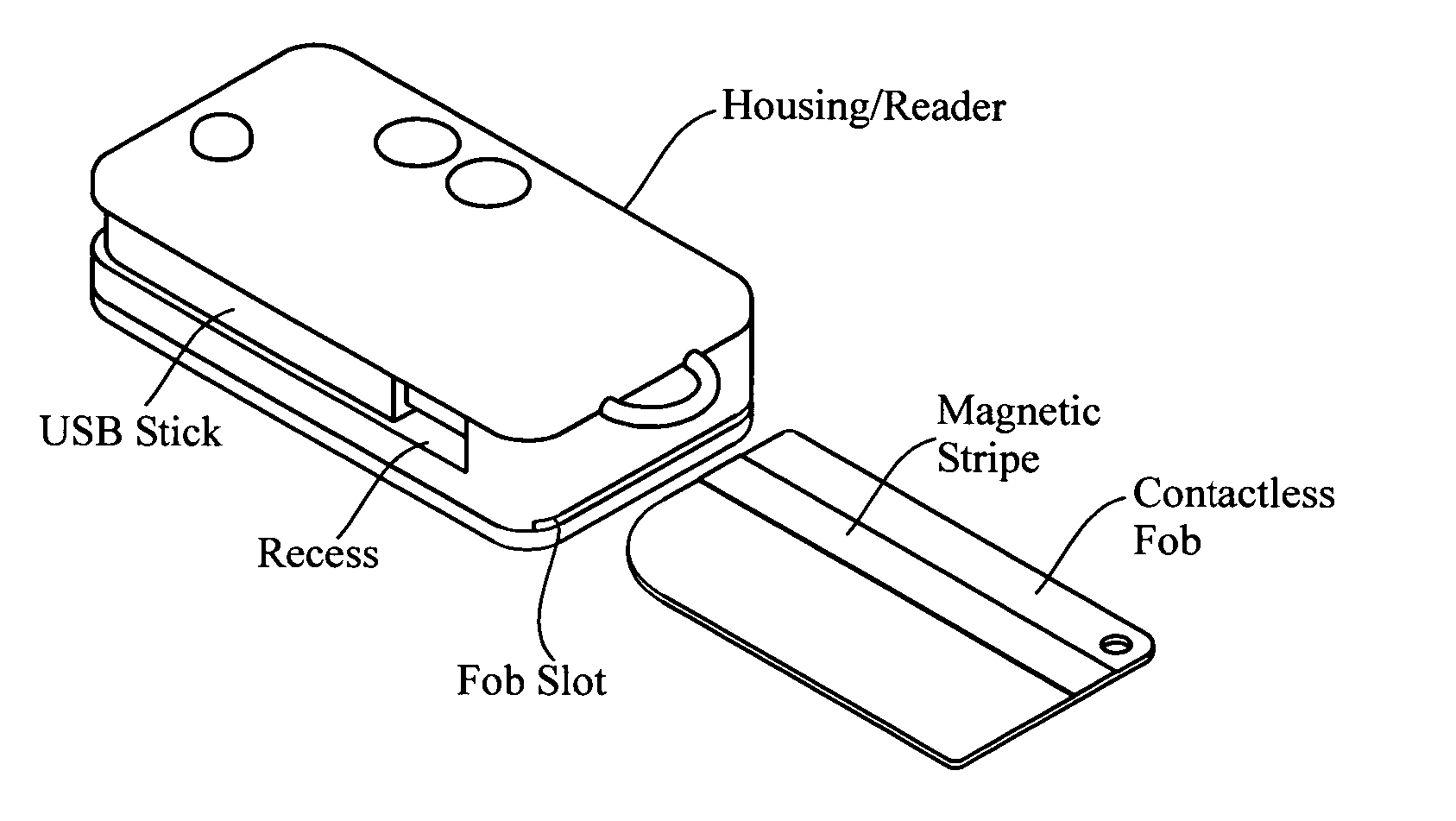
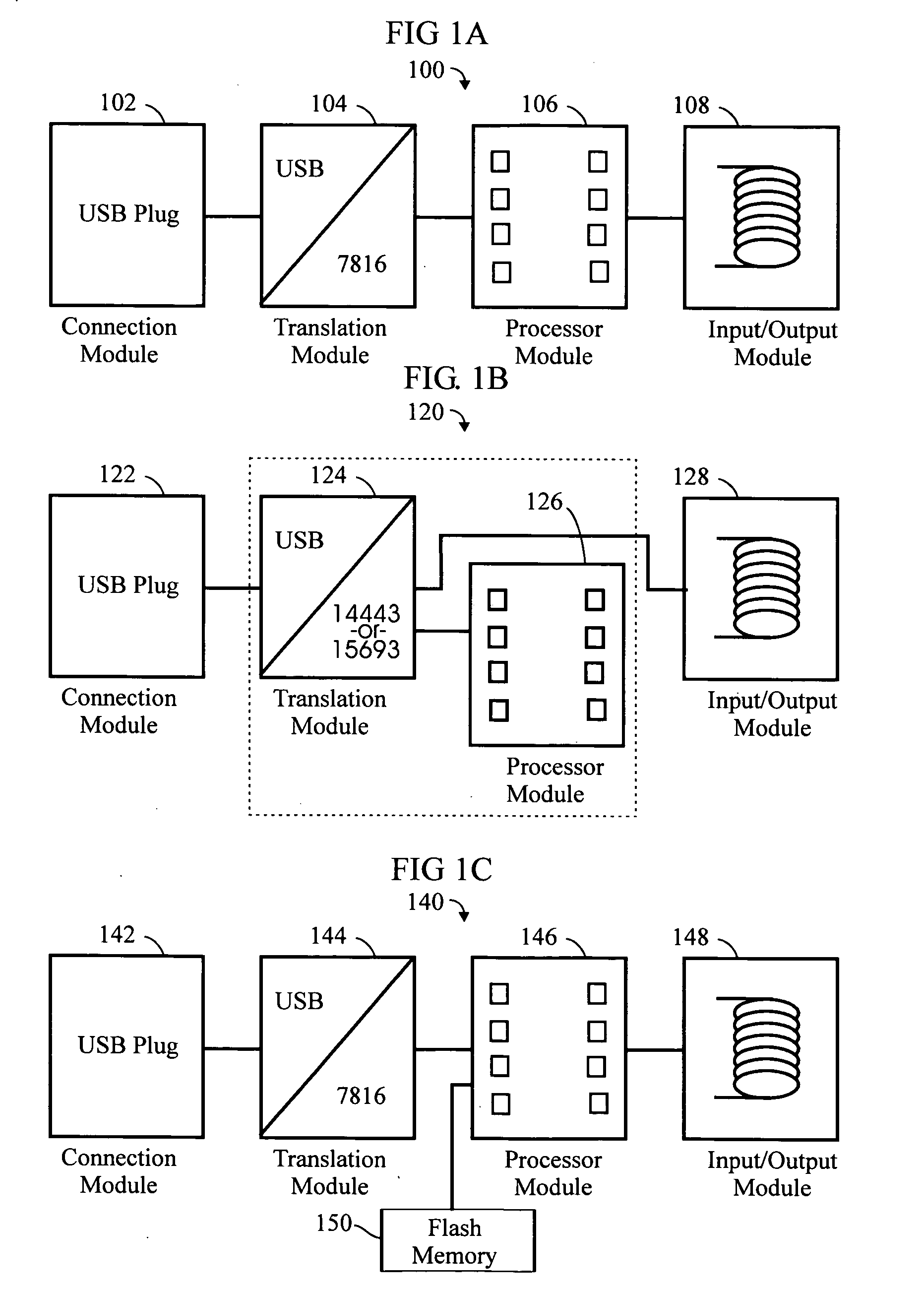
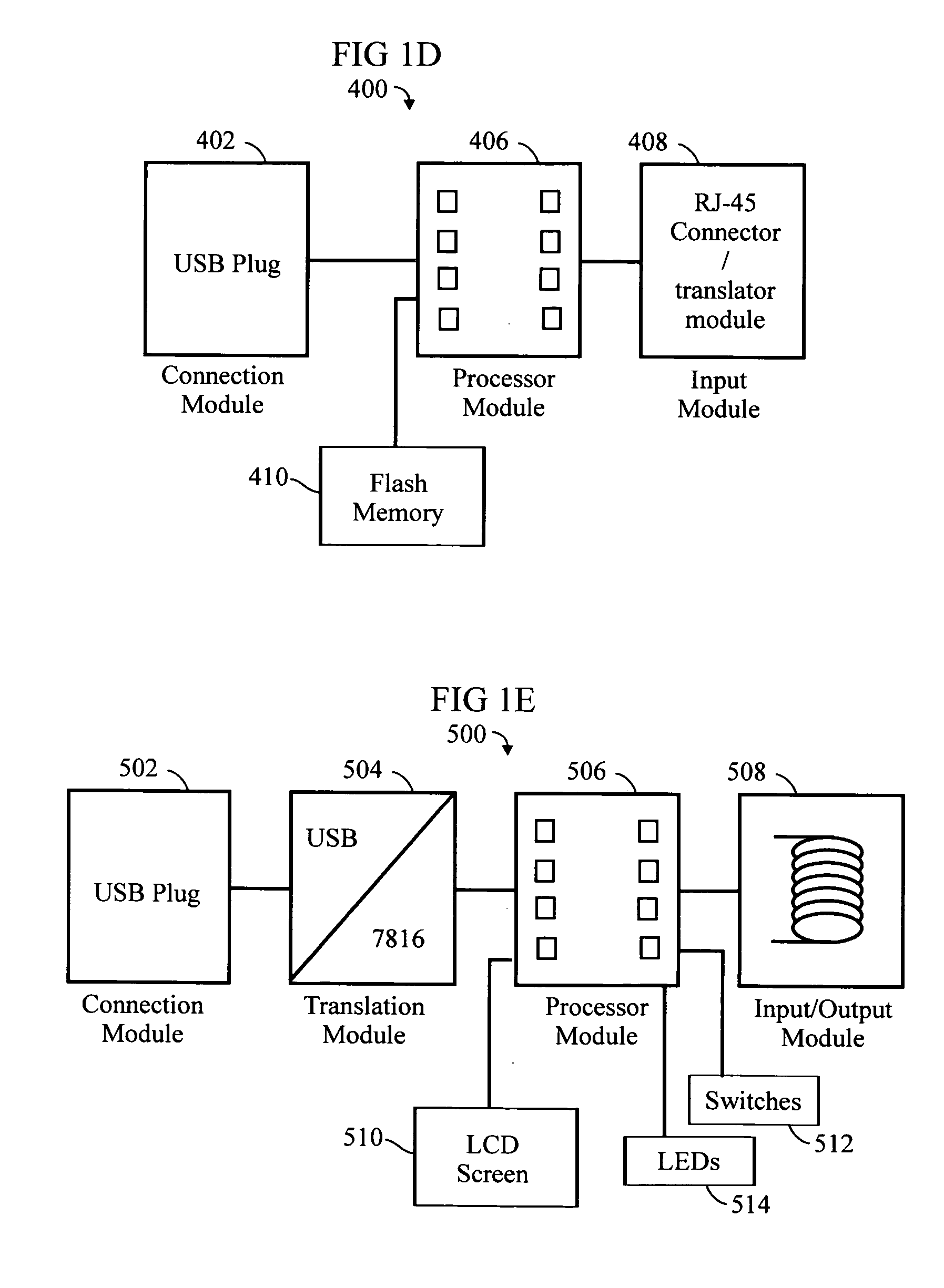
RFID token with multiple interface controller
InactiveUS20060208066A1Acutation objectsBroadcast information characterisationComputer moduleSmart card
An RFID token apparatus has a connection module for interfacing with an appliance capable of communicating and interacting with remote servers and networks, a translation module for moving signals between a USB interface and a smart card interface, a processor module which may be capable of operating as a dual-interface (DI) chip; and an input / output module having at least one RF antenna and a modulator. An RFID-contactless interface according to ISO 14443 & ISO 15693 and / or NFC. A wireless interface according to Zigbee, Bluetooth, WLAN 802.11, UWB, USB wireless and / or any similar interface. An RFID reader apparatus has a housing; a slot for a contact or contactless fob; and a USB stick alternately protruding from the housing and retracted within the housing.
Owner:DPD PATENT TRUST
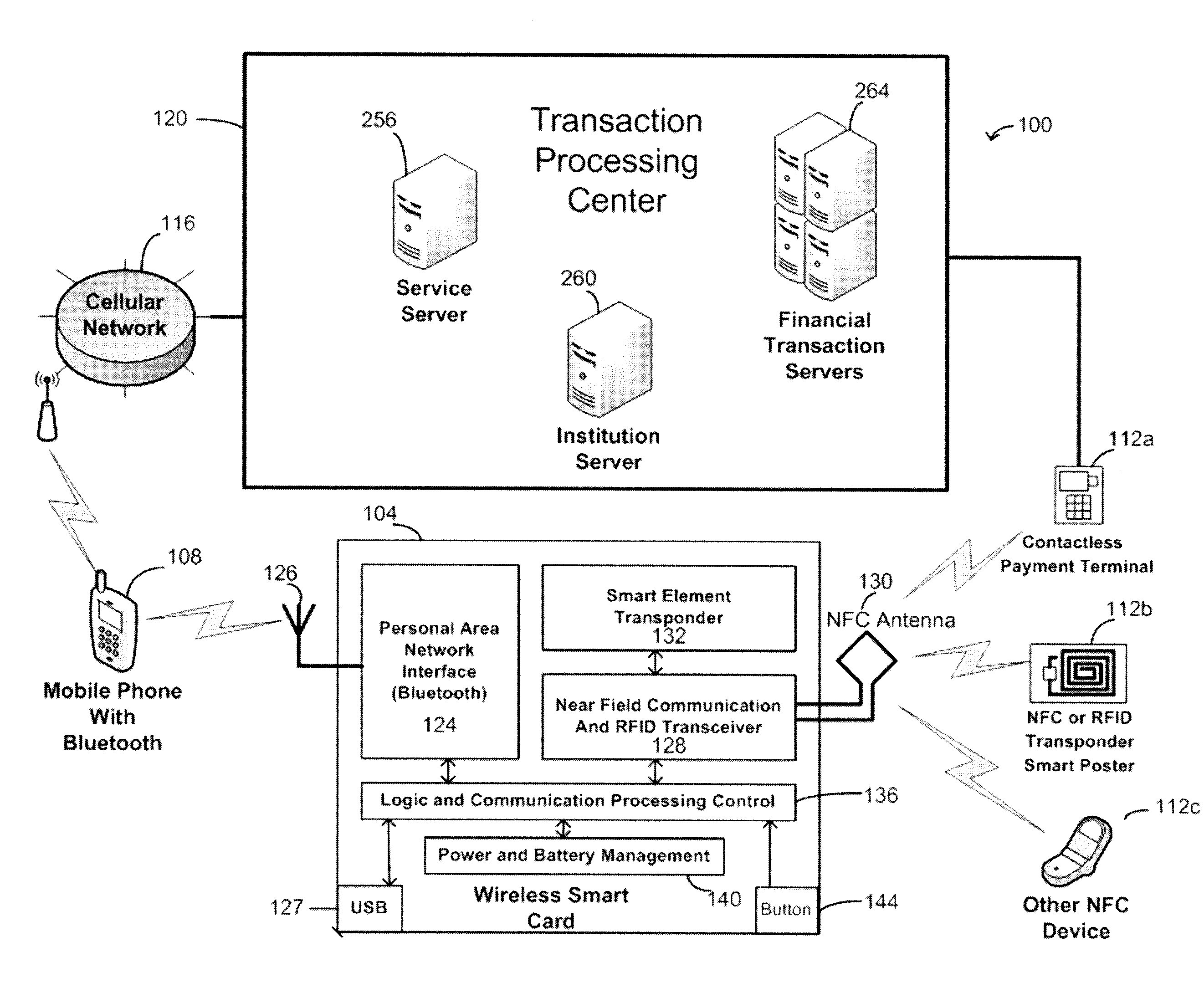
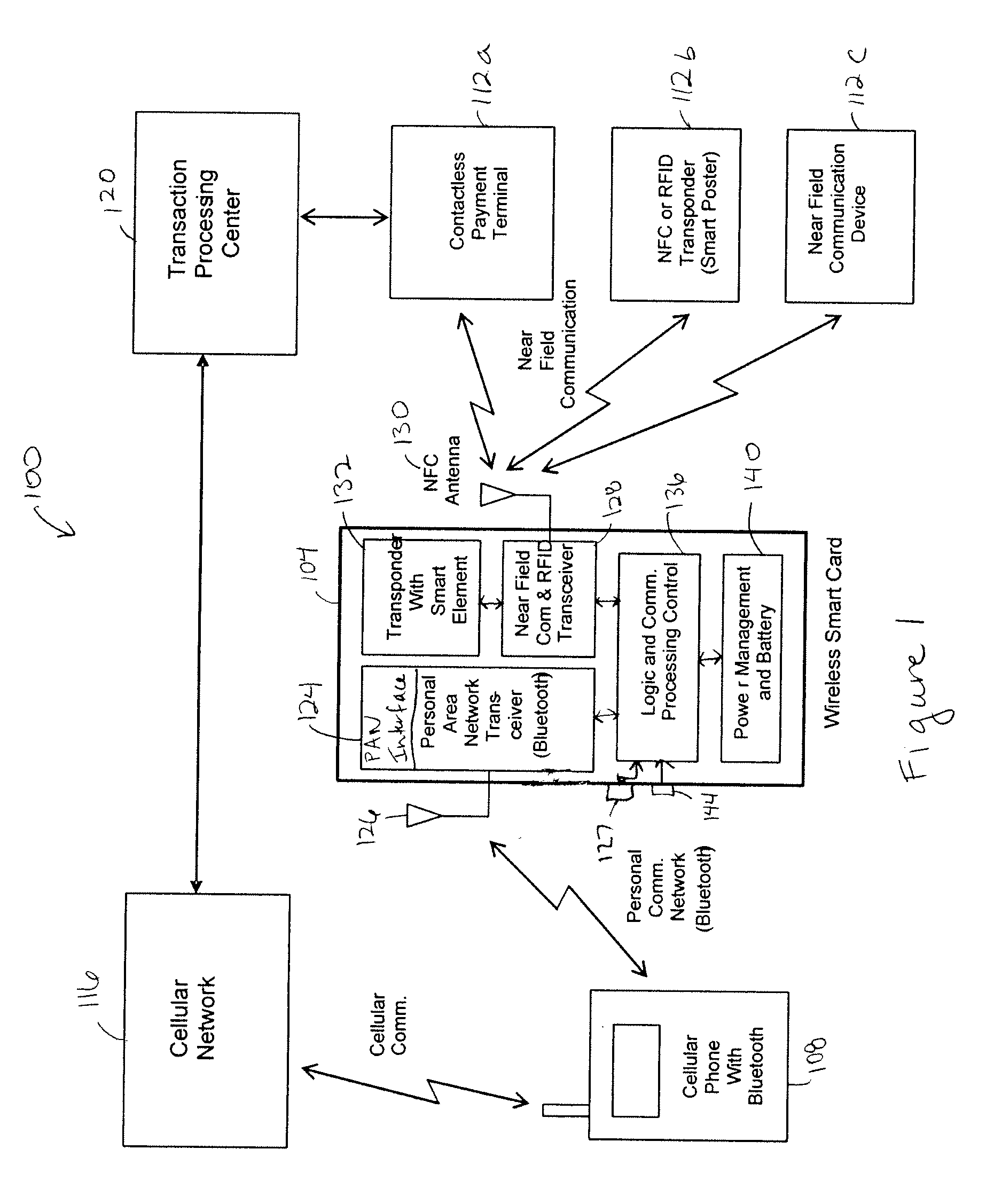
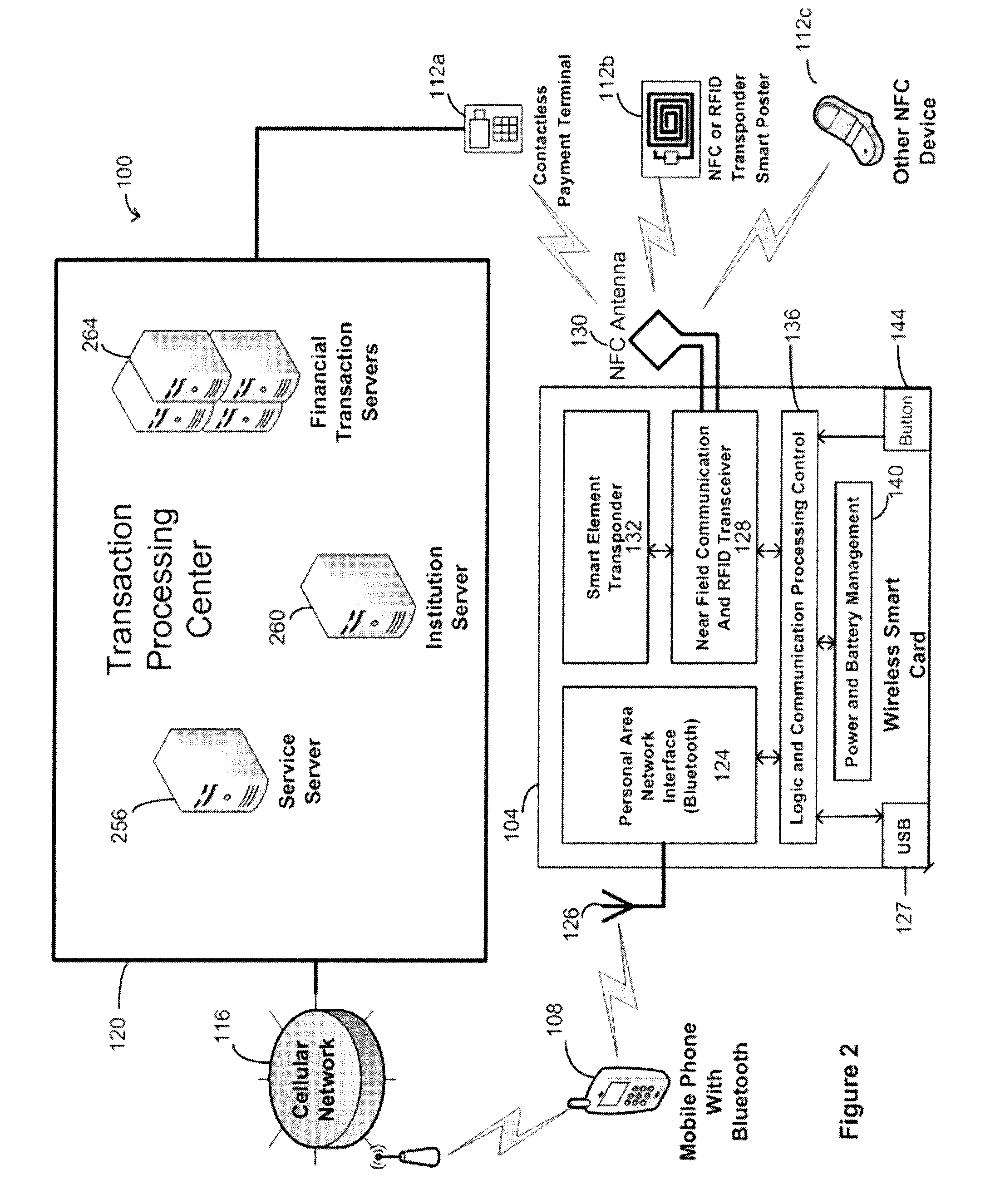
Wireless smart card and integrated personal area network, near field communication and contactless payment system
A wireless smart card having a personal area network transceiver, such as a Bluetooth transceiver, to couple the wireless smart card with a mobile communication device, and a near field communication (NFC) and radio-frequency identification (RFID) transceiver to couple the wireless smart card to a wireless transaction device, and a transponder with a secure element to allow secure communications between the mobile communication device with the wireless smart card and the wireless smart card and the wireless transaction device is described. The wireless smart card allows, for example, contactless payment through a Bluetooth-enabled mobile communication device without modification to the mobile communication device.
Owner:WIRELESS DYNAMICS
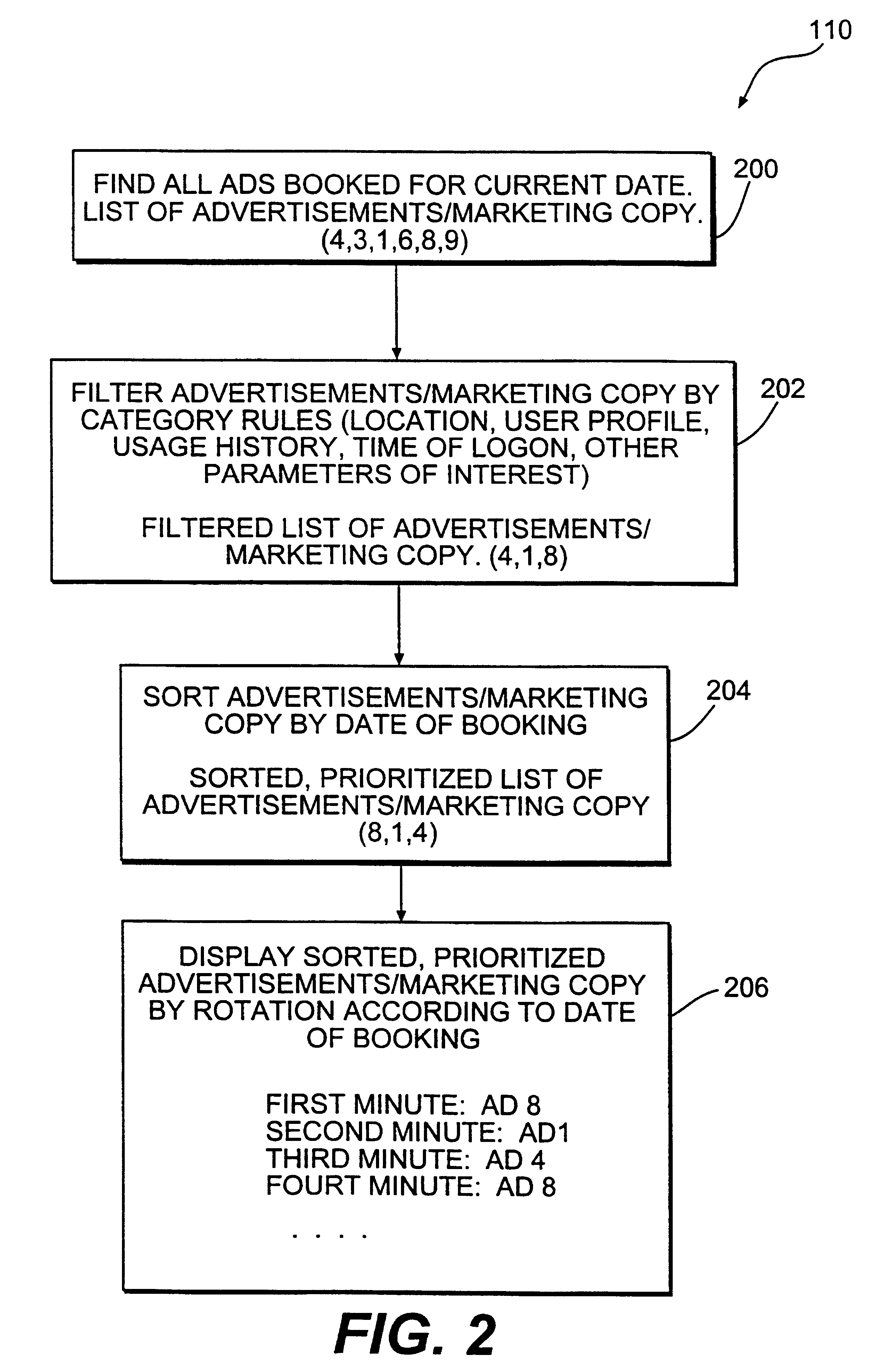
Method and system for providing personalized online services and advertisements in public spaces
InactiveUS6847969B1Without time-consuming searchingComplete banking machinesAcutation objectsPersonalizationPersonal details
A method and system for providing, personalized and integrated online services for communications and commercial transactions both in private and public venues. The invention provides personalized information that is conveniently accessible through a network of public access stations (or terminals) which are enabled by a personal system access card (e.g., smart card). The invention also provides advertisers the opportunity to directly engage action; and potential user-consumers with selected advertising or marketing content based on each user's profile and usage history.
Owner:STREETABPACE
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Server for reconfiguring control of a subset of devices on one or more kiosks
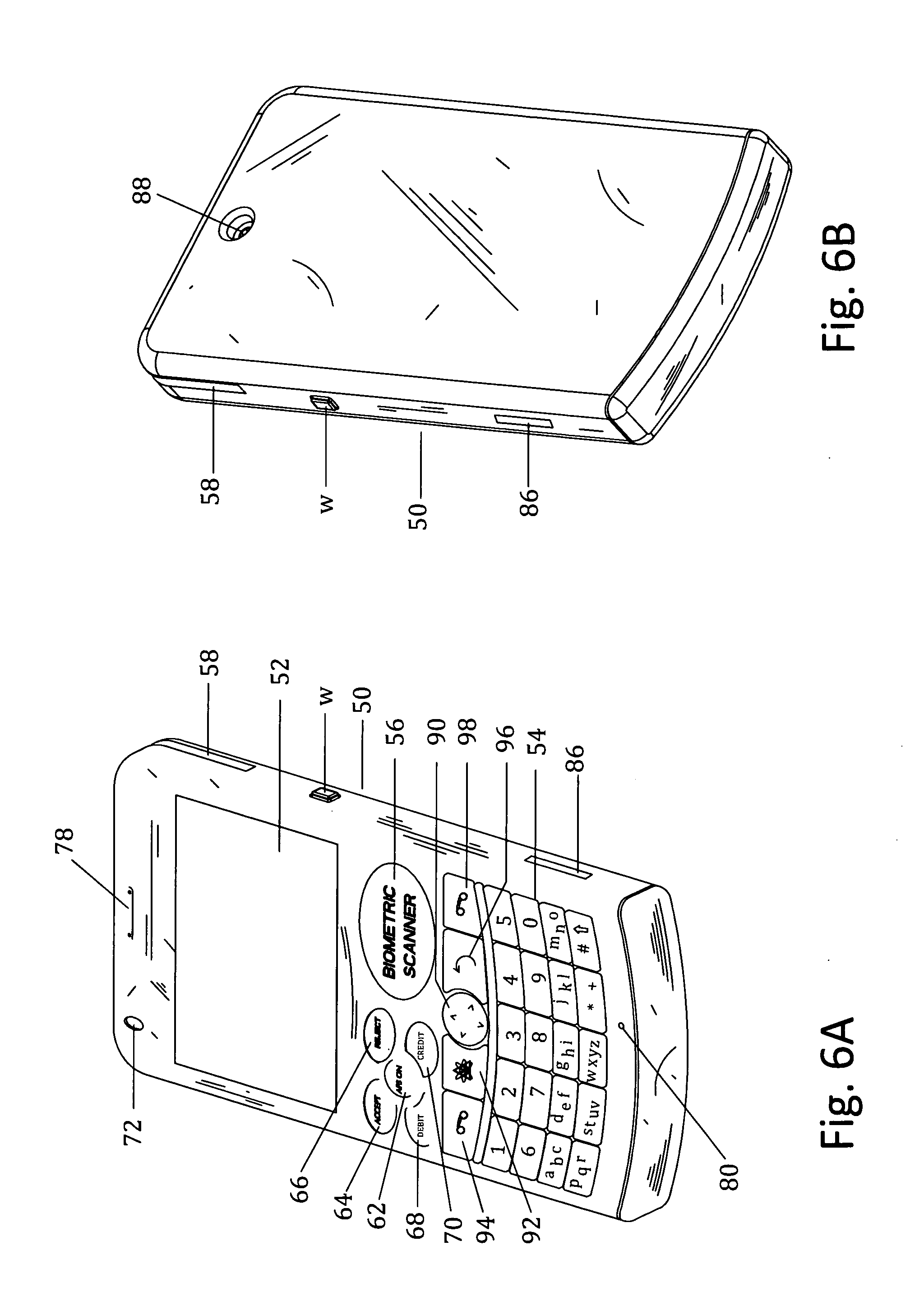
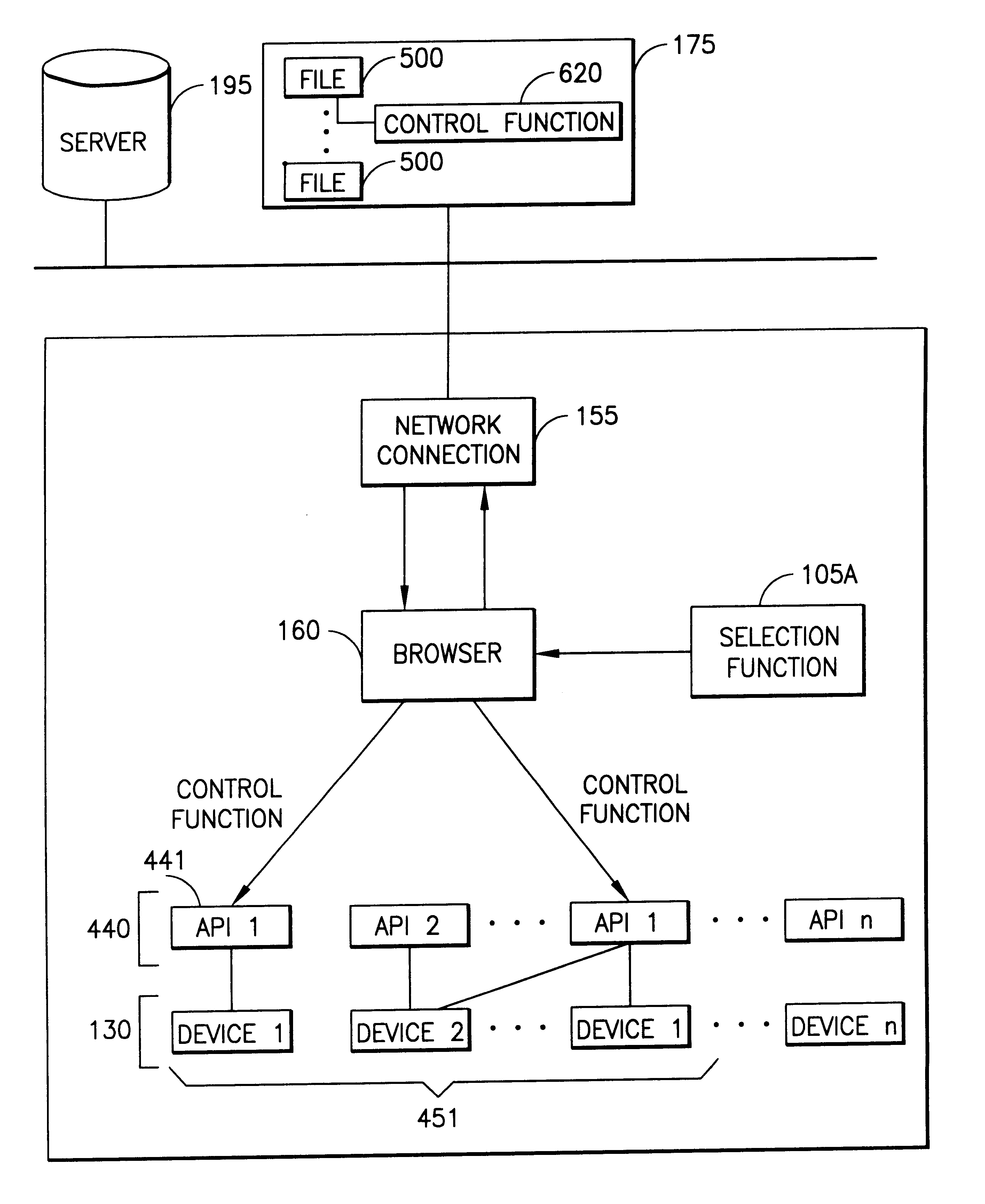
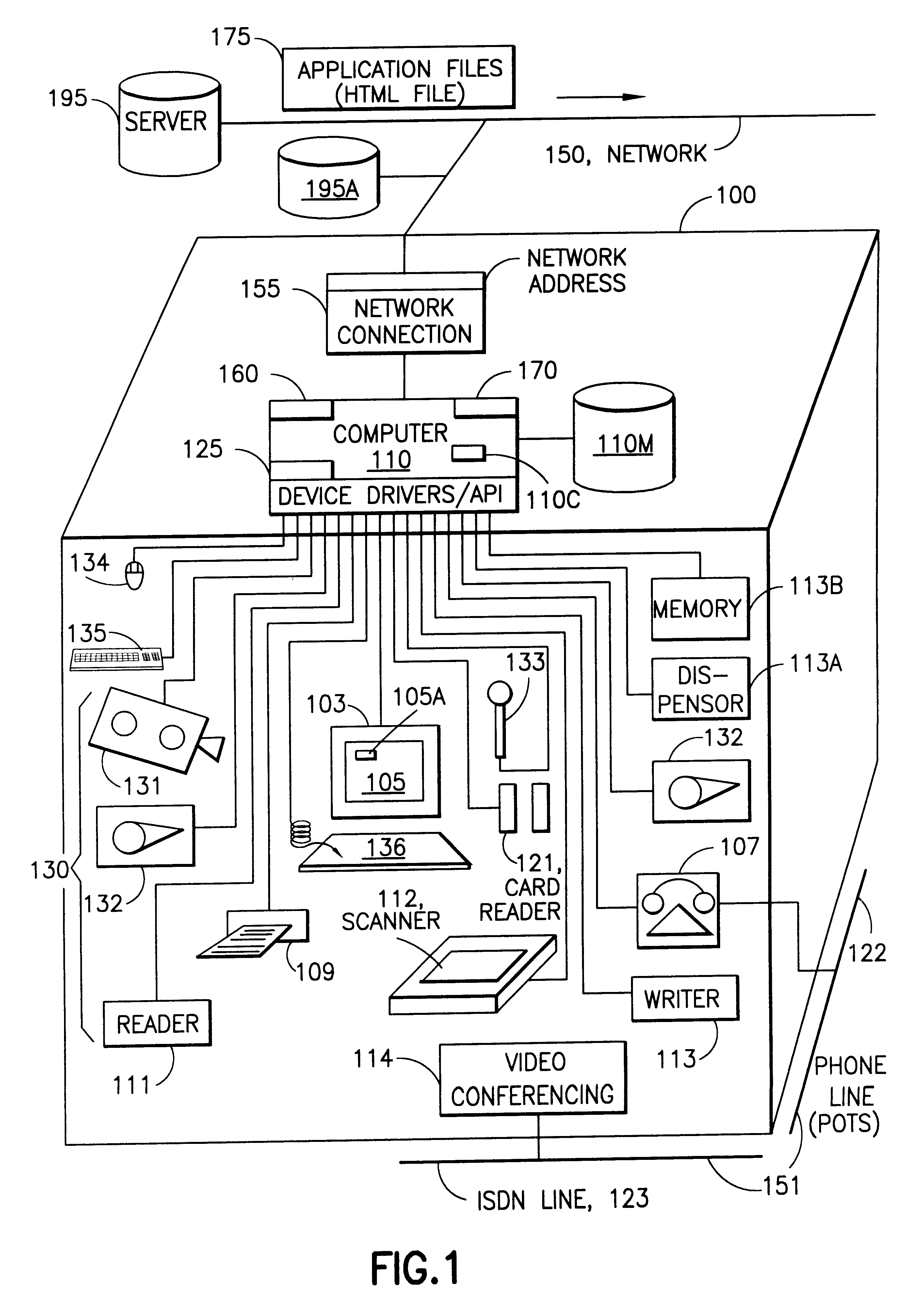
InactiveUS6195694B1Faster and reliable accessLow costAcutation objectsData switching by path configurationM-governmentComputer terminal
A server system that is connected to one or more networks, e.g., the Internet, corporate or government intranets, extranets, etc. The server has one or more application files or configuration sets that the server serves to from one or more kiosks on the network. The configuration sets are application specific. (An application is a use for which the kiosks are configured or reconfigured.) One or more of the files in the configuration sets include one or more embedded (control) programs that are used to control the local APIs of one or more of the devices on the kiosk. In this way, the devices are controlled to configure the kiosk to perform the application.
Owner:IBM CORP
Method, system and computer readable medium for web site account and e-commerce management from a central location
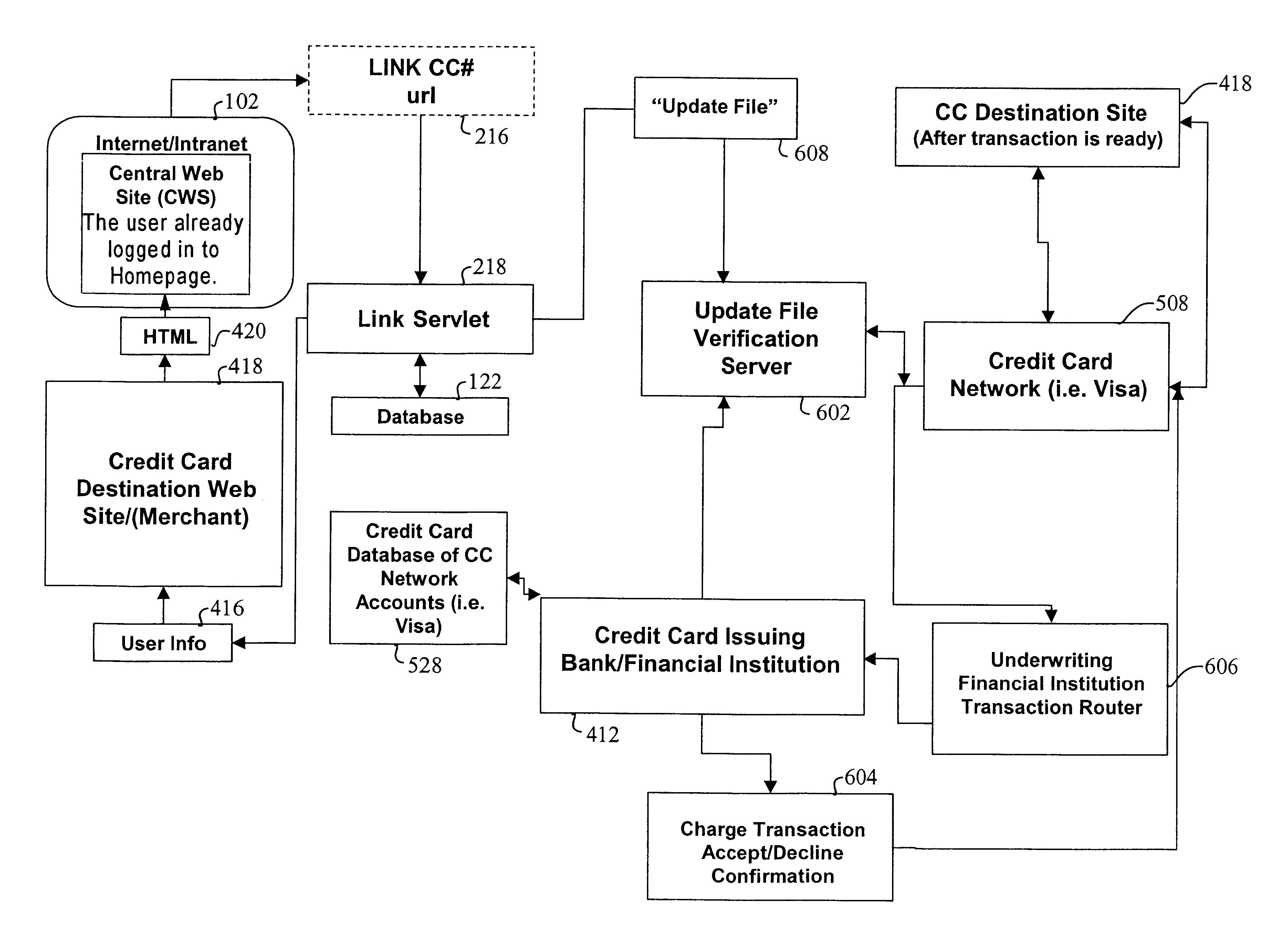
InactiveUS6879965B2Minimizing activation timeMinimizing financial exposureComplete banking machinesAcutation objectsWeb siteData field
A method, system and computer readable medium for, from a central Web site, performing at least one of registering a user at a destination Web site, logging in a user at a destination Web site and managing an online financial transaction at a destination Web site, including parsing a form Web page of the destination Web site to extract form data fields therefrom; mapping form data fields of a central Web site form to corresponding extracted form data fields of the form Web page of the destination Web site; and using the mapped form data fields to perform at least one of registering a user at the destination Web site, logging in a user at the destination Web site and managing an online financial transaction of a user at the destination Web site. In another aspect, there is provided a method, system and computer readable medium for managing an online or offline financial transaction of a user, from a central Web site, including generating financial transaction account information for a user based on existing credit or debit card information; gathering from the user one or more limits that are applied to a financial transaction performed based on the financial transaction account information; receiving from a source information indicating that an online or offline financial transaction using the financial transaction account information is in progress; applying the one or more limits gathered from the user to approve or disapprove the online or offline or online financial transaction that is in progress; and transmitting an approval or disapproval signal to the source based on a result of the applying step.
Owner:SLINGSHOT TECH LLC
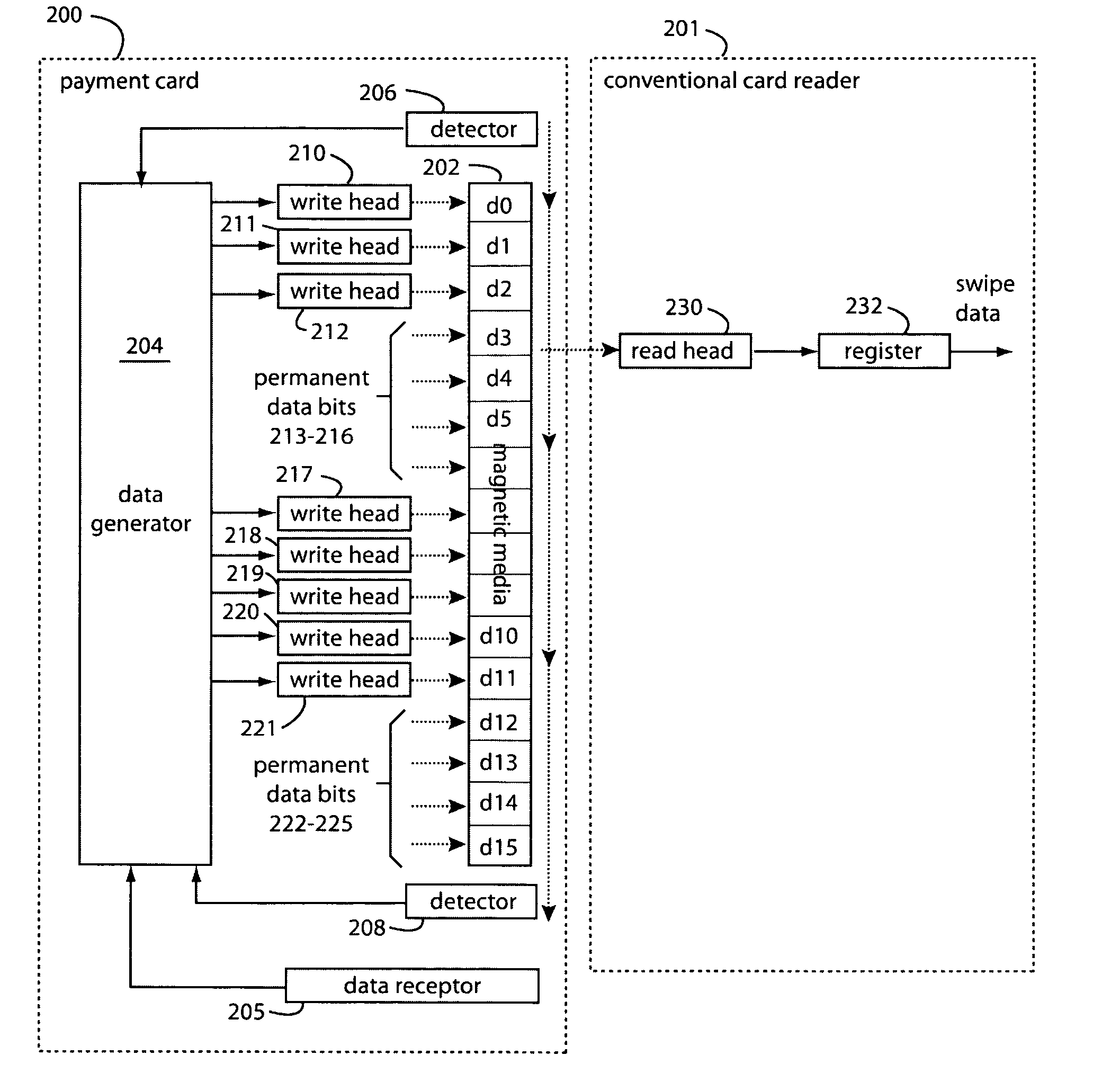
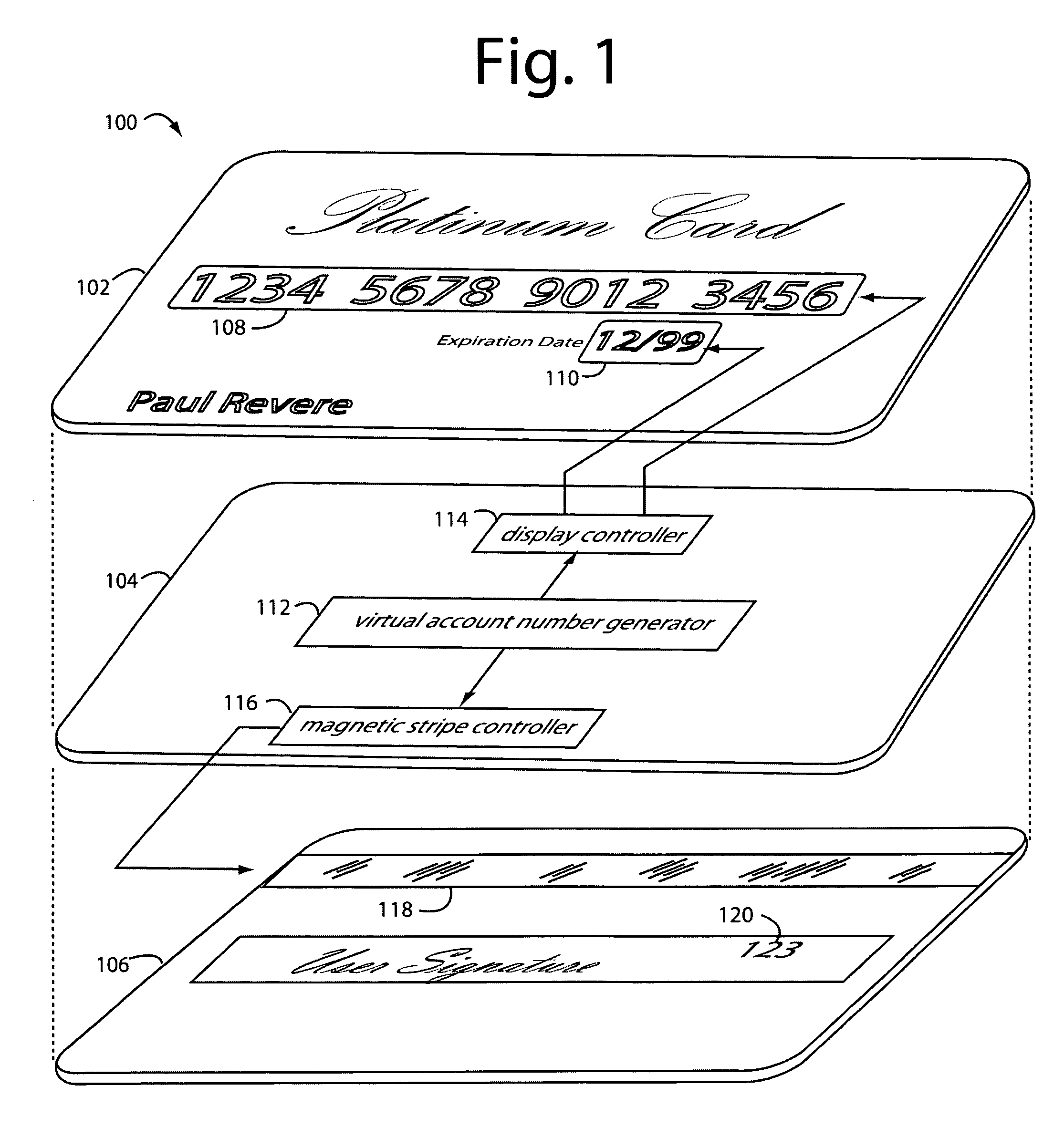
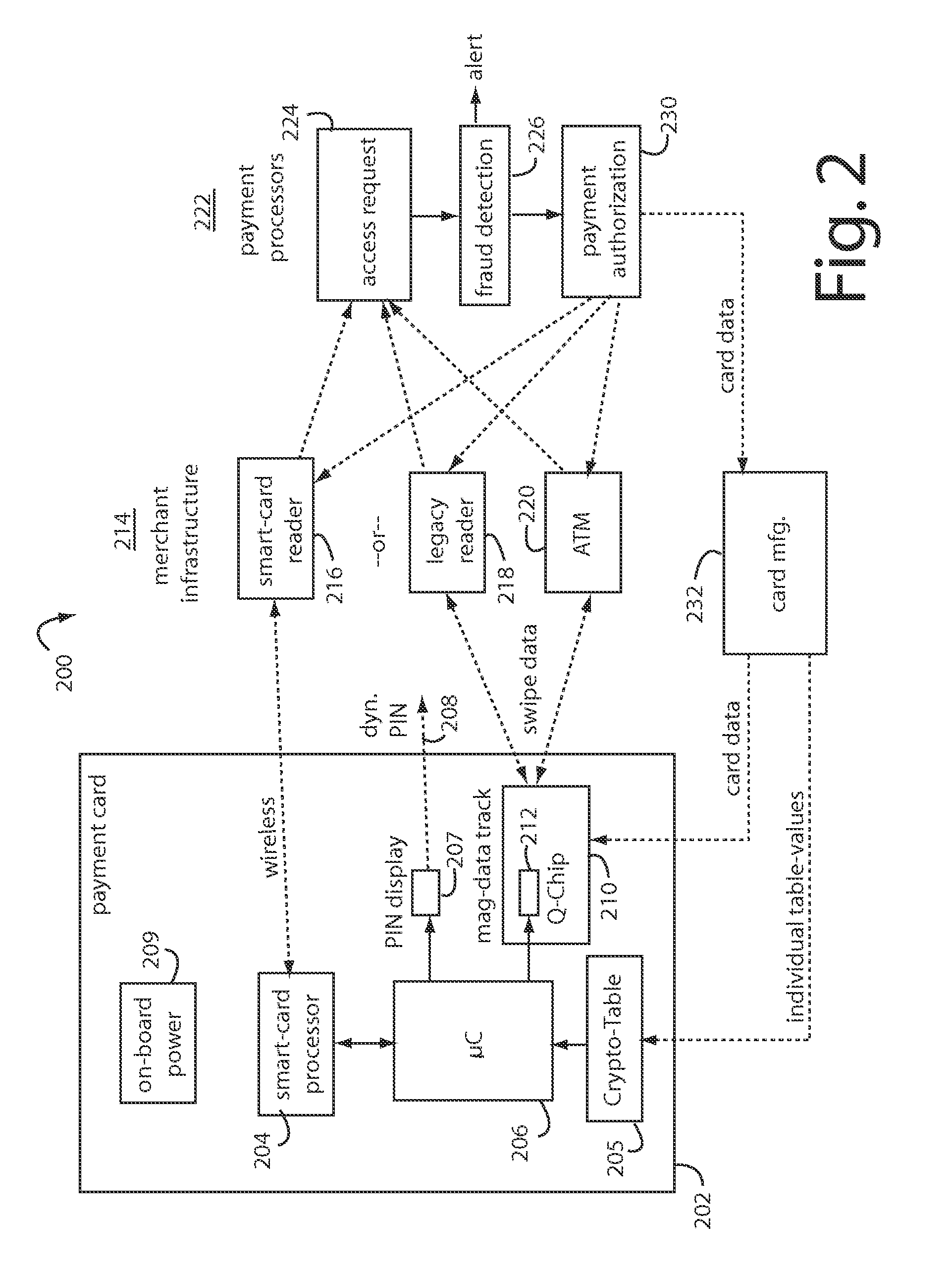
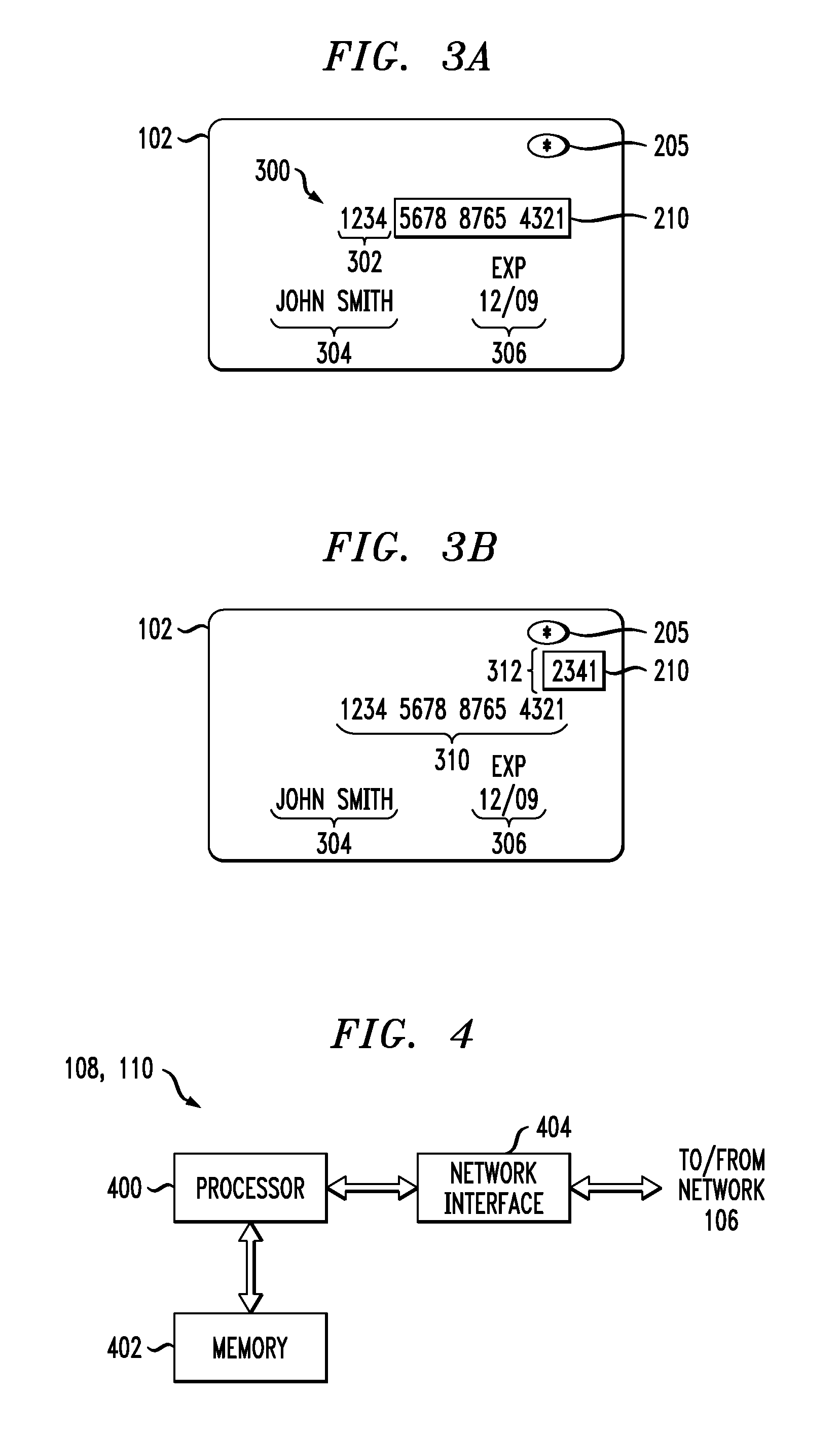
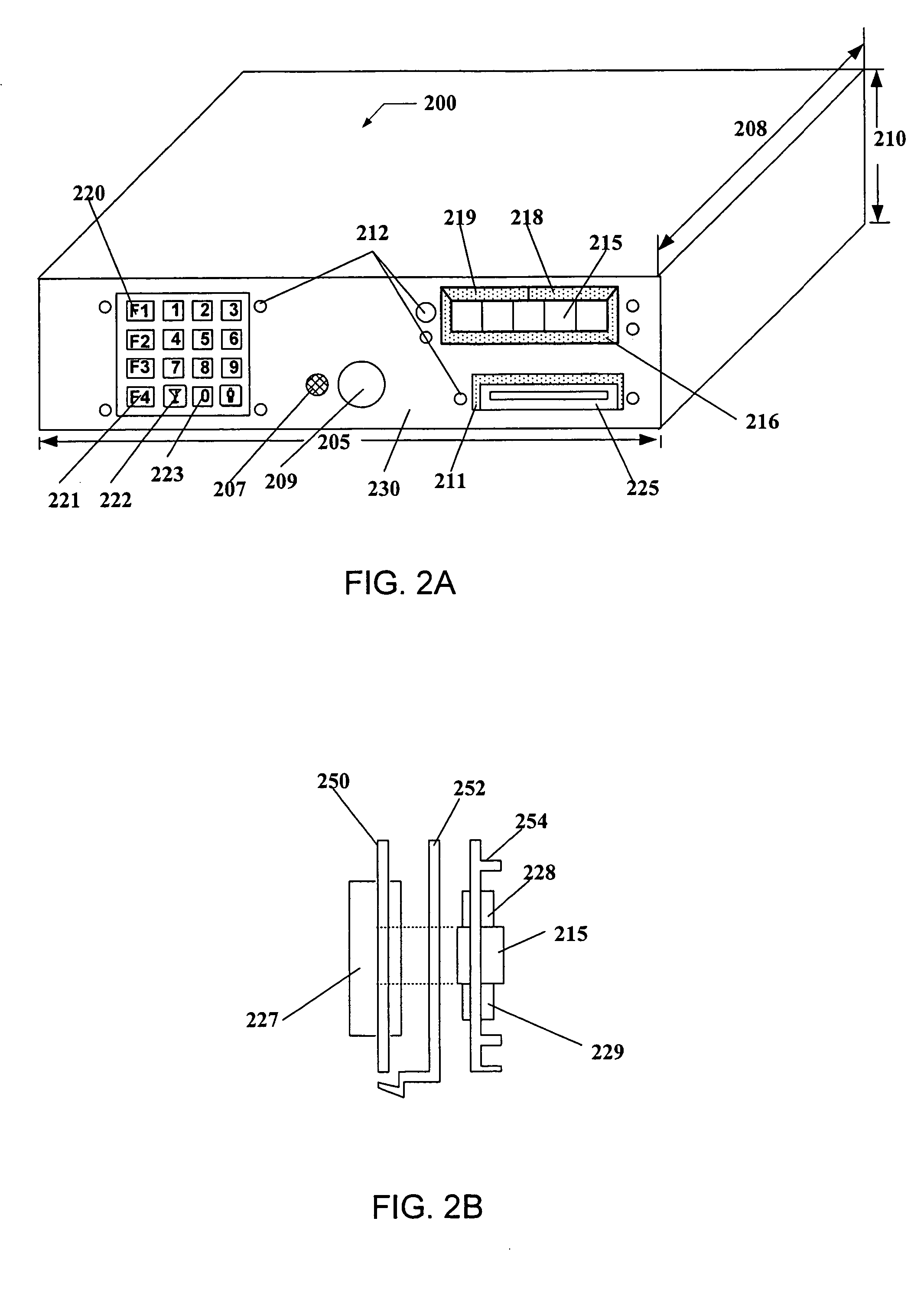
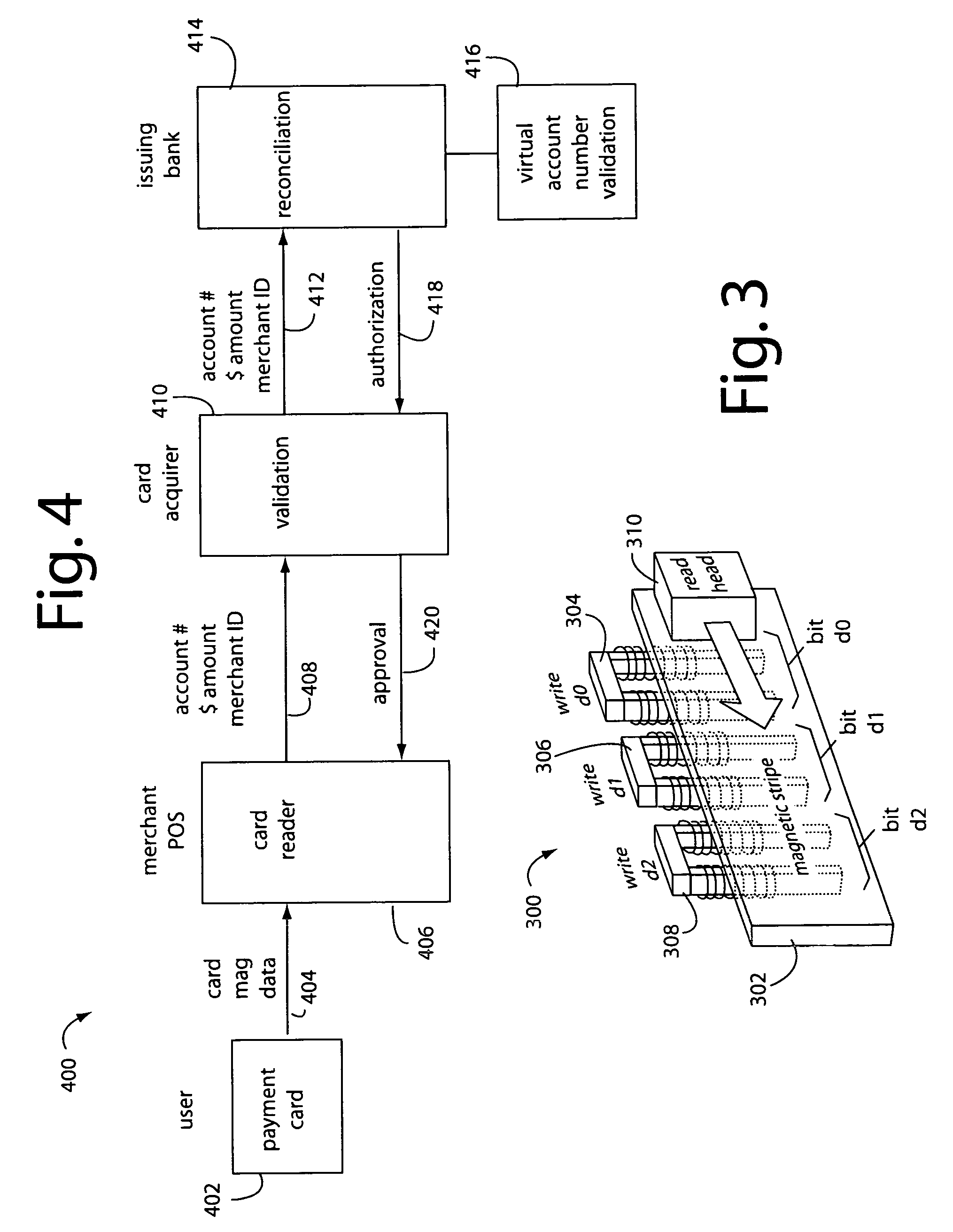
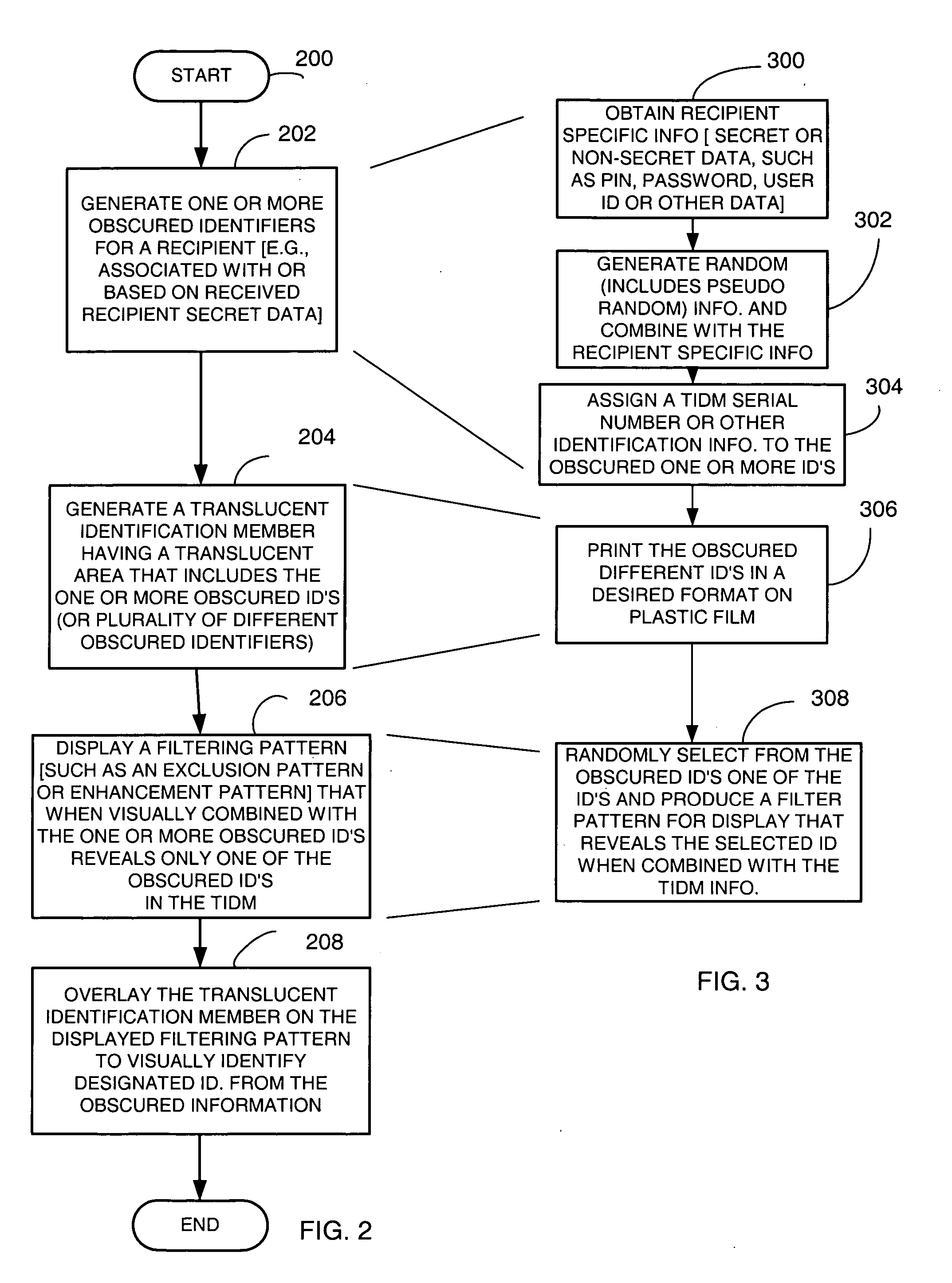
Payment card with internally generated virtual account numbers for its magnetic stripe encoder and user display
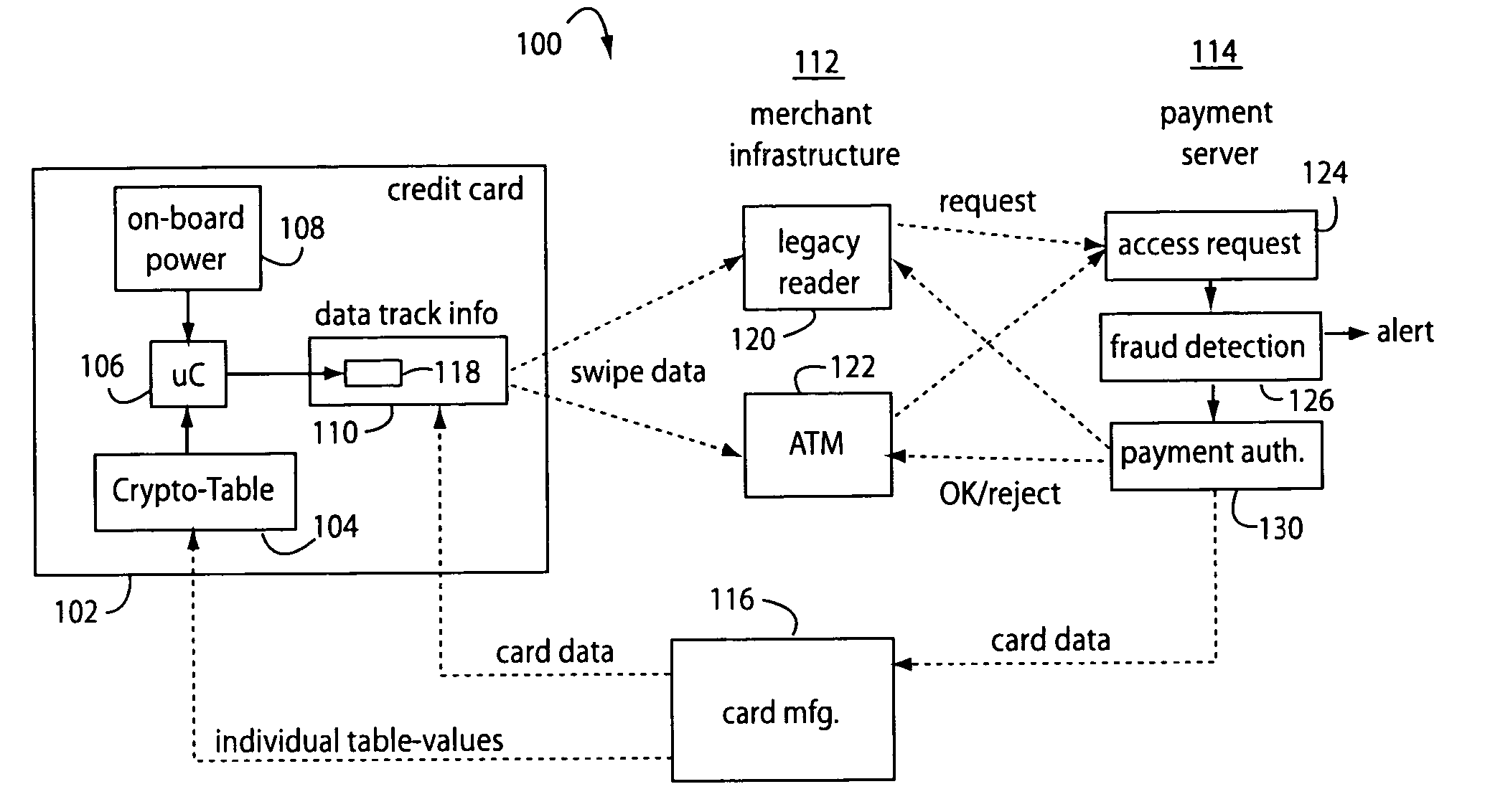
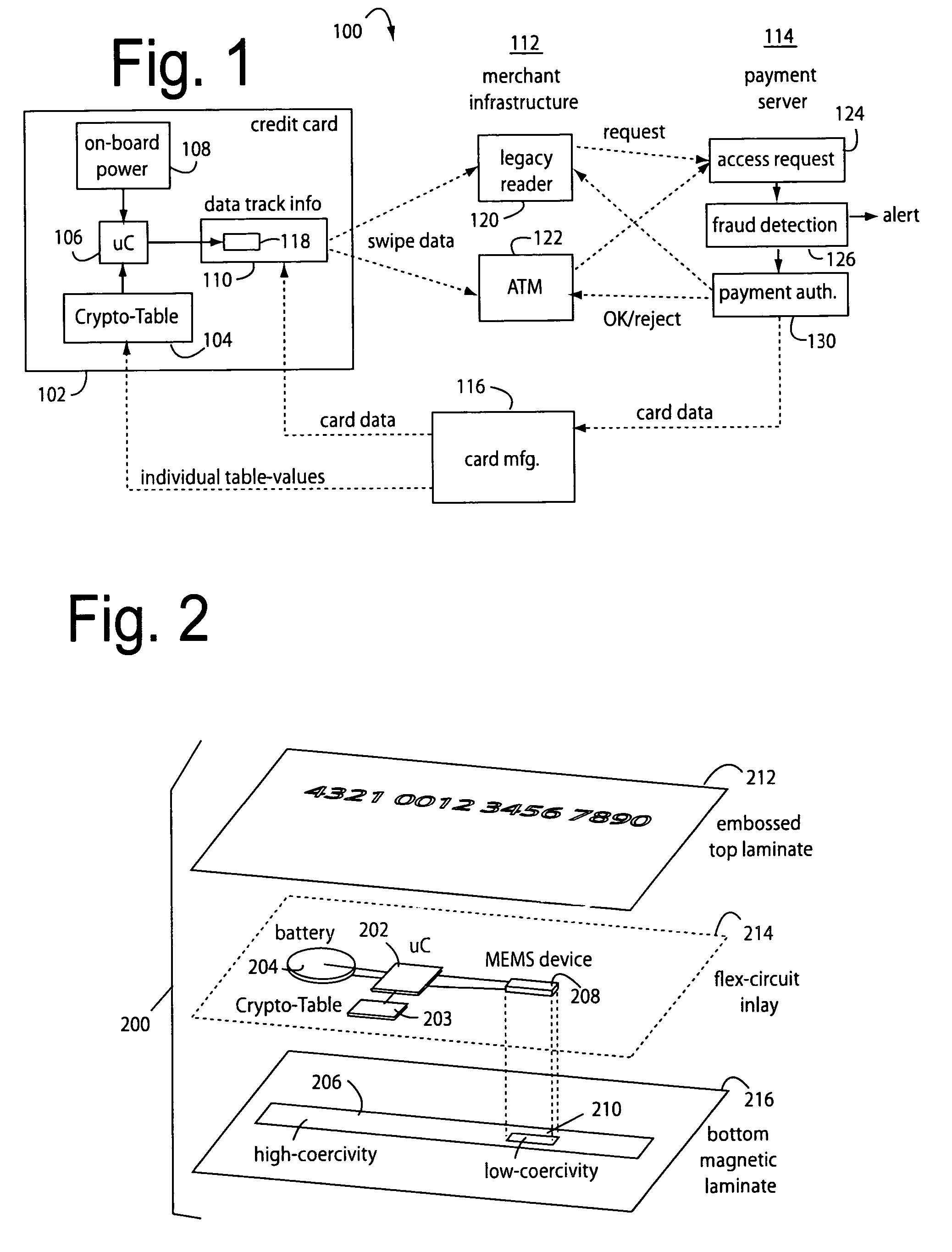
A payment card comprises an internal virtual account number generator and a user display for online transactions. Offline transactions with merchant card readers are enabled by a magnetic array positioned behind the card's magnetic stripe on the back. The internal virtual account number generator is able to program the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, it is discarded and put on an exclusion list.
Owner:FITBIT INC
Payment card financial transaction authenticator
InactiveUS20080201264A1Sufficient dataAcutation objectsFinanceCryptographic nonceFinancial transaction
A payment card financial transaction authenticates for providing overall financial network security computes a number of results from a cryptographic key that match values that were selectively used to personalize individual payment cards with their individual user identification and account access codes. An account access code is later presented daring a financial transaction involving at least one of those individual payment cards. A dynamic portion is included in a merchant's magnetic reading of the payment card. Then authenication can proceed by matching it with values computed from the cryptographic key.
Owner:FITBIT INC
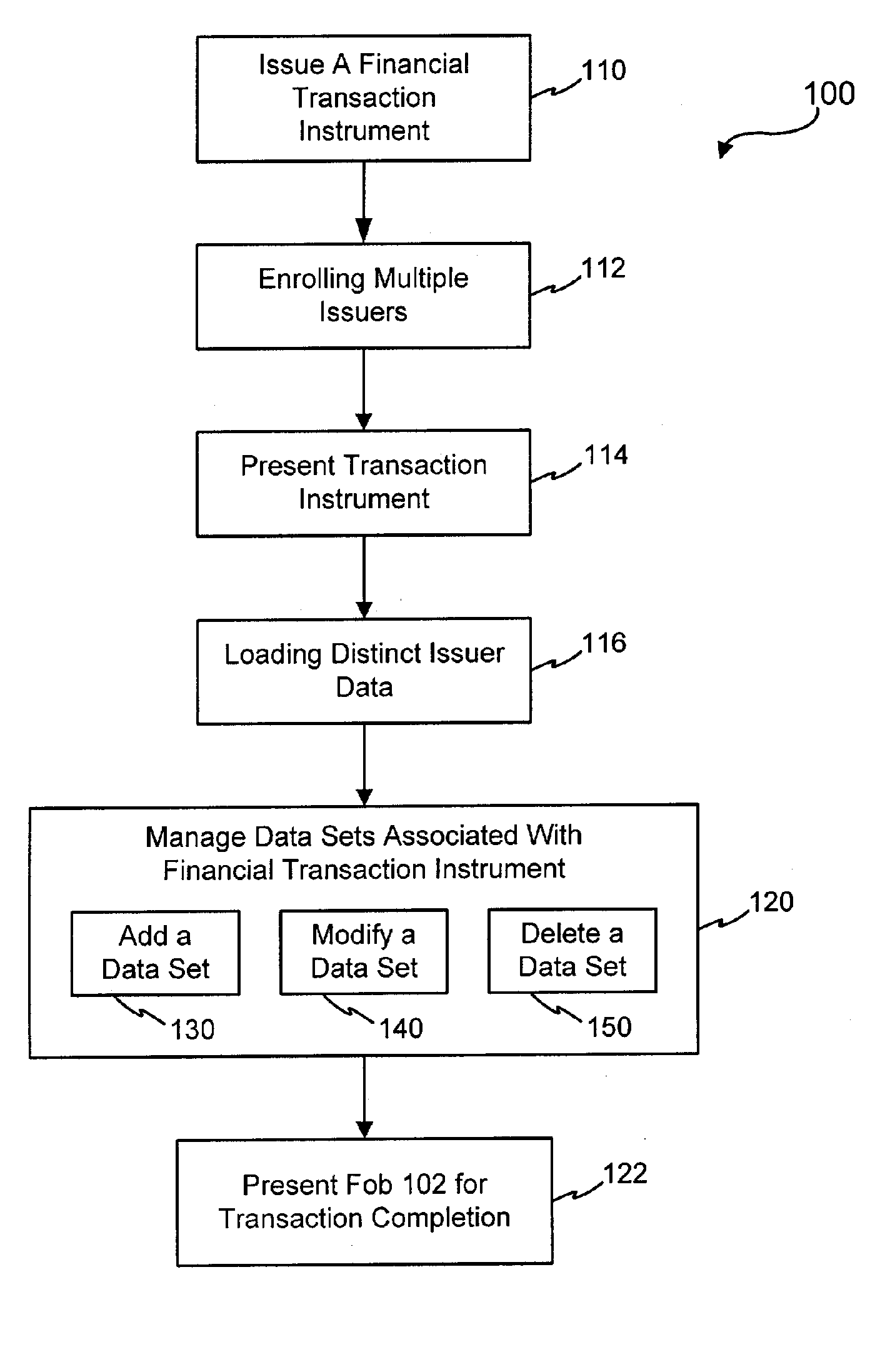
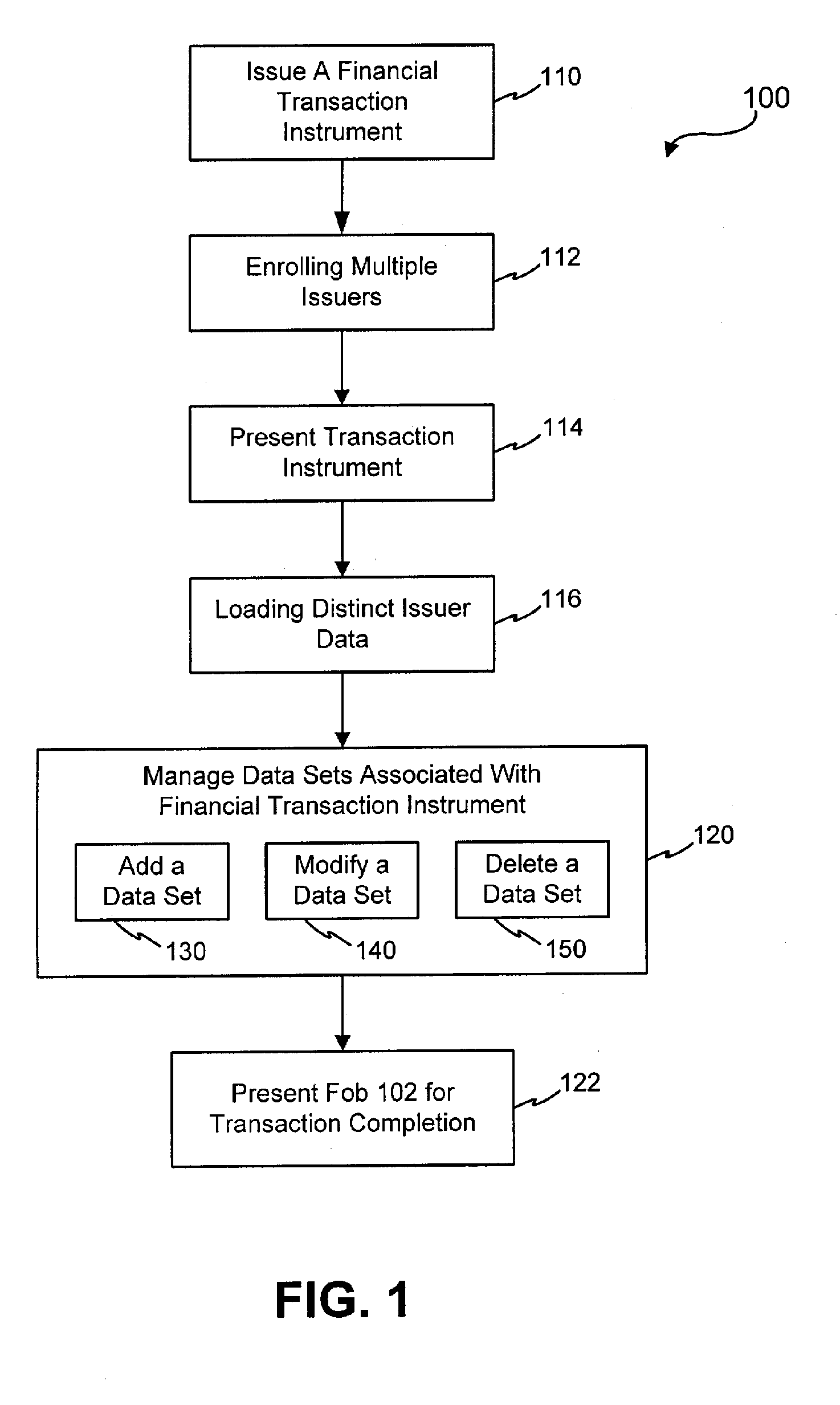
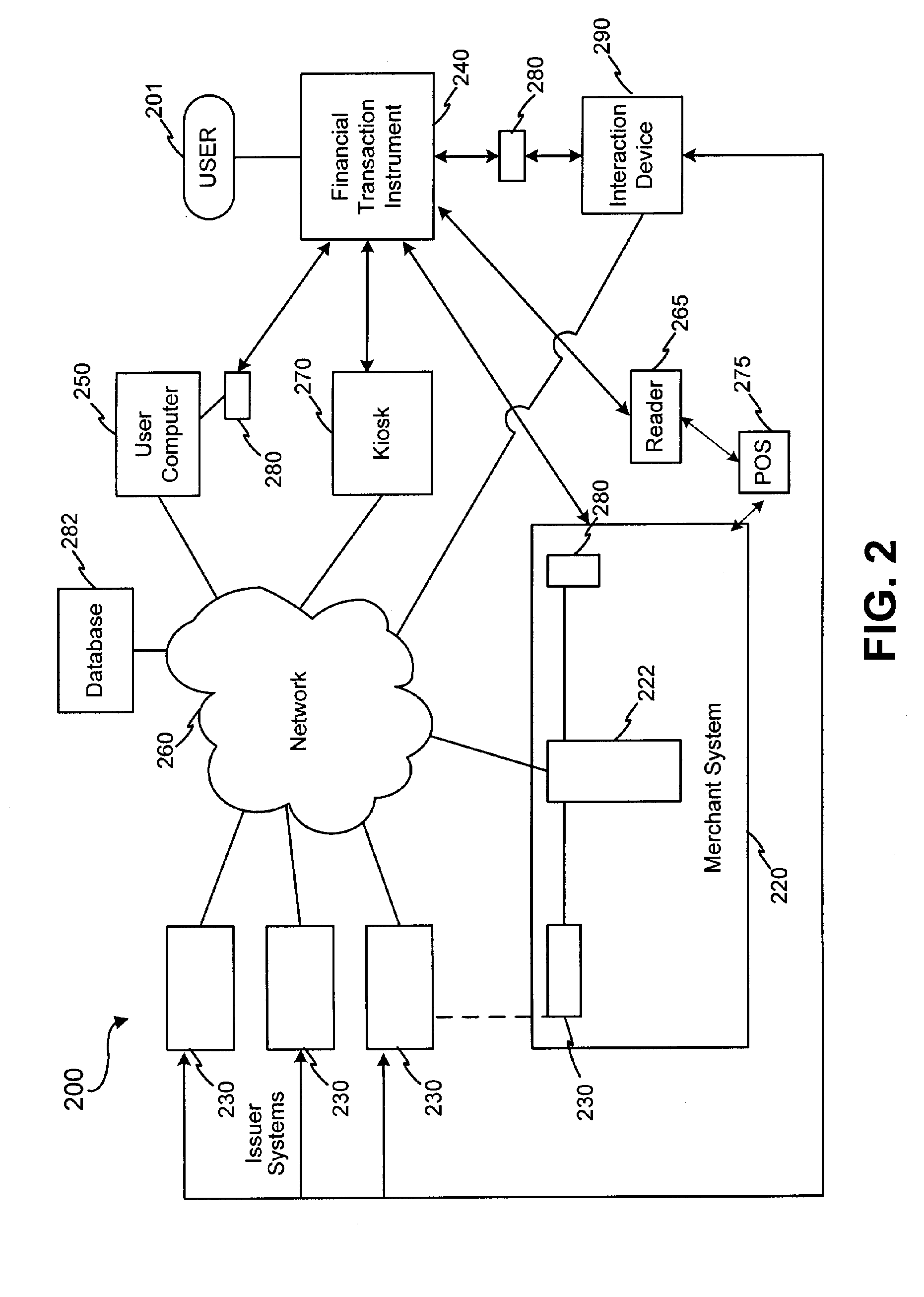
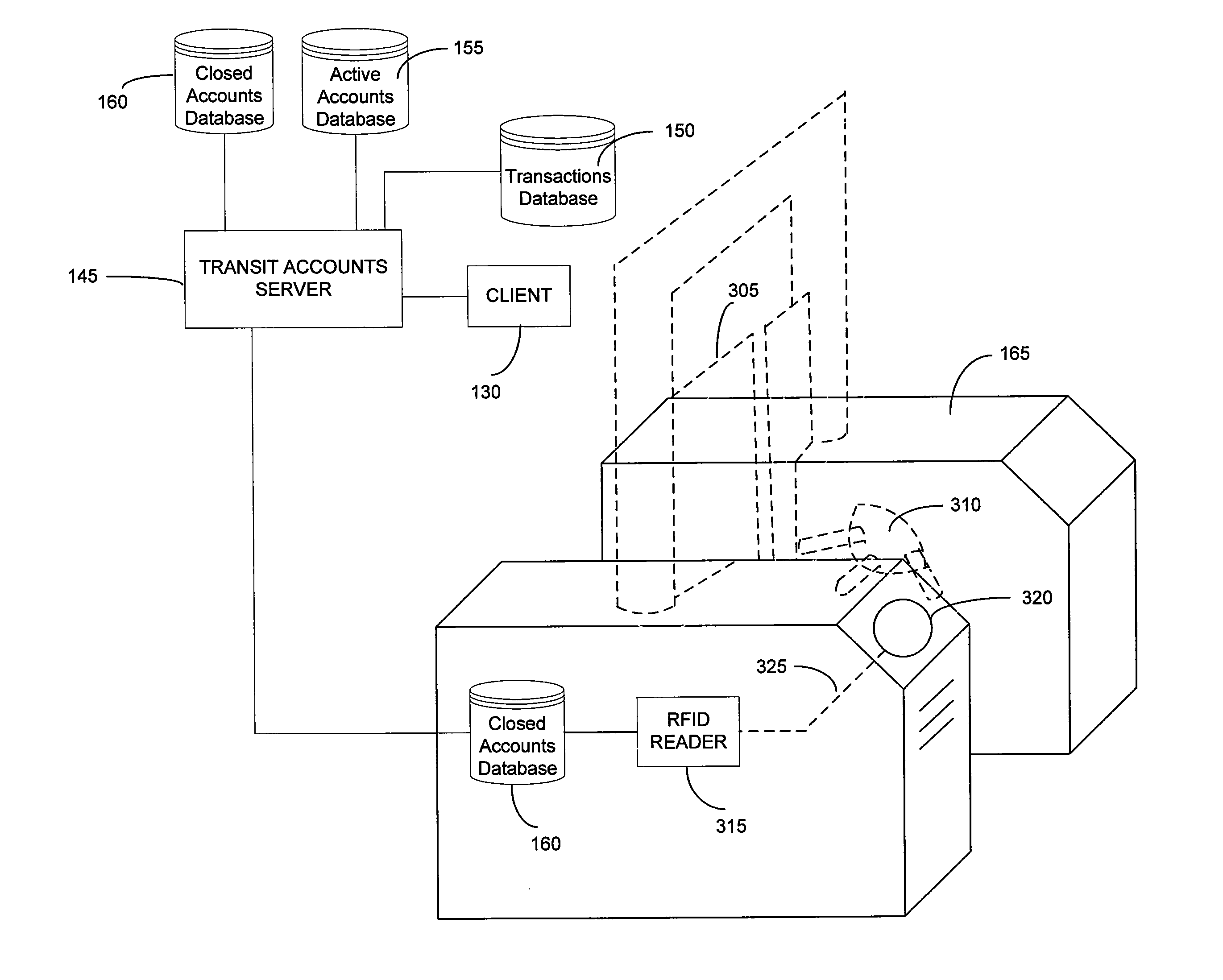
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
InactiveUS20050171898A1Easy to manageEliminate needAcutation objectsFinanceData setFinancial transaction
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
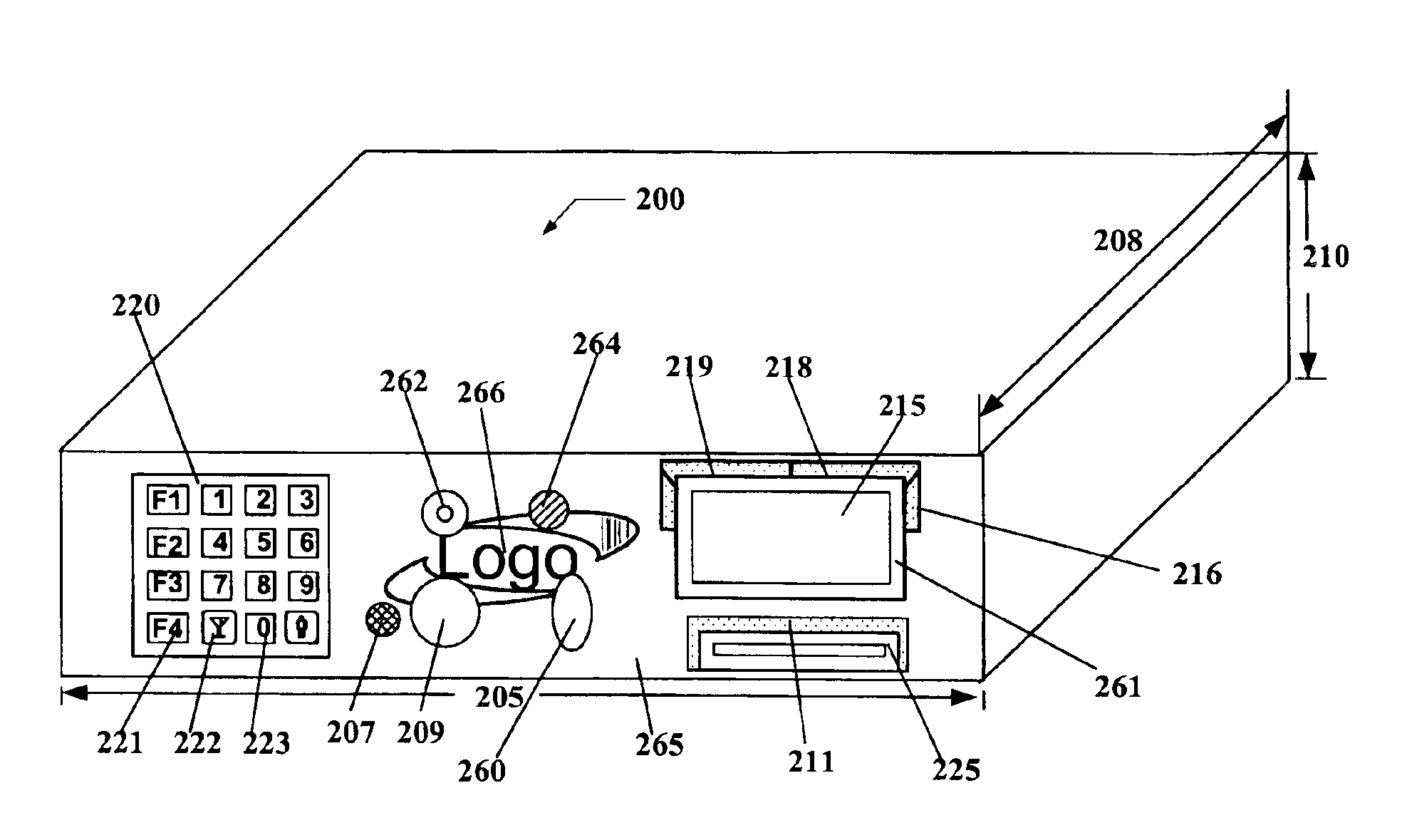
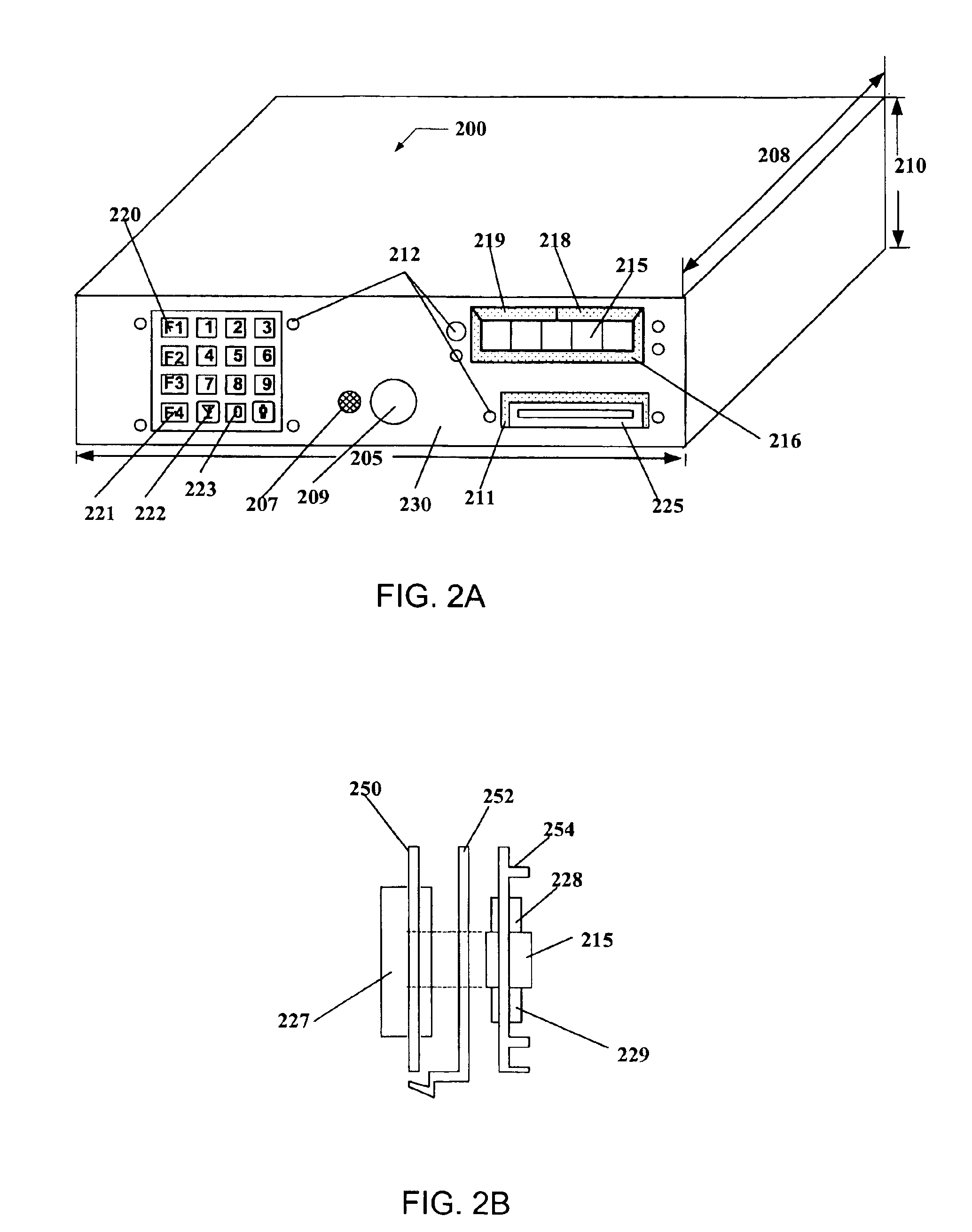
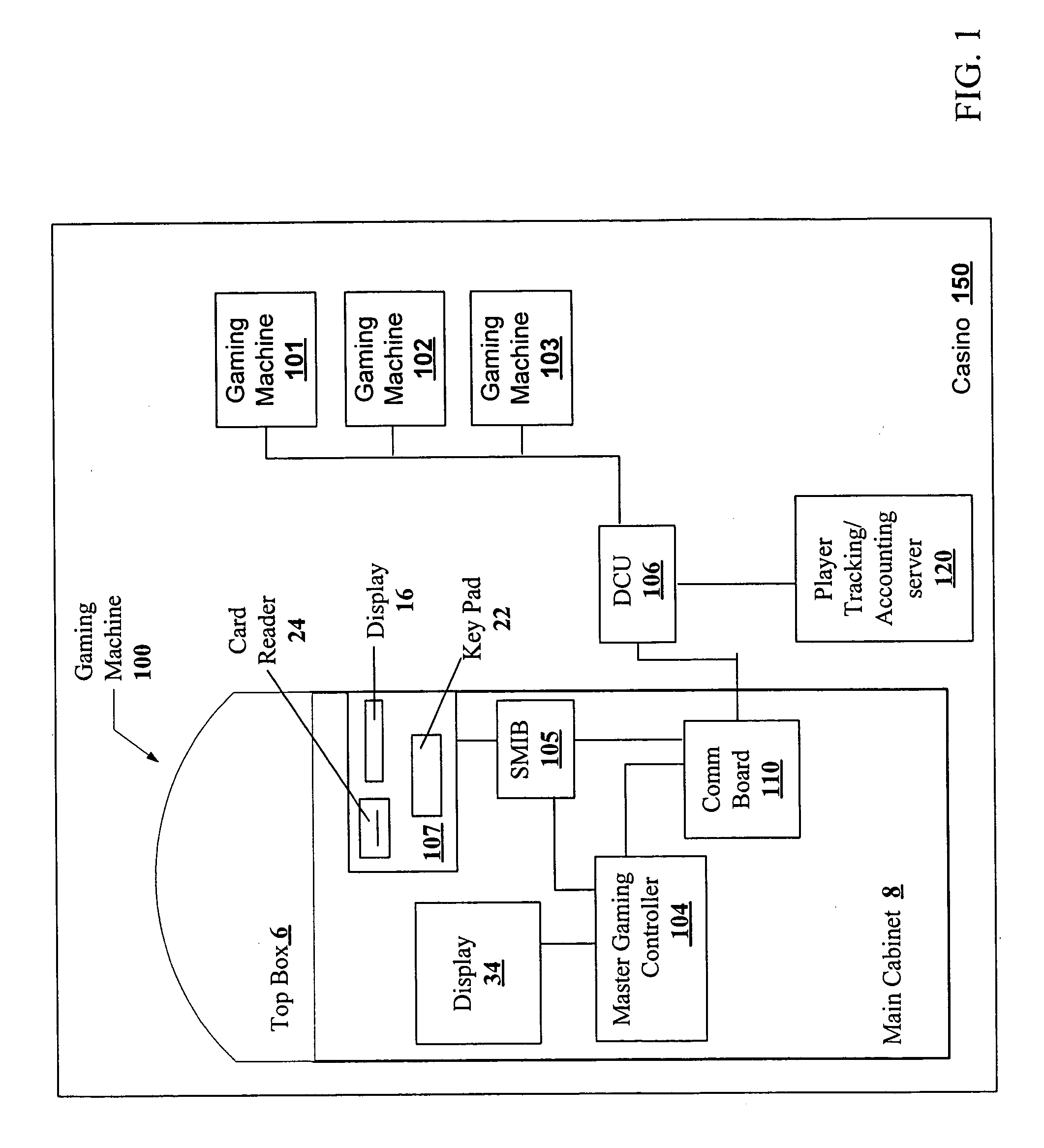
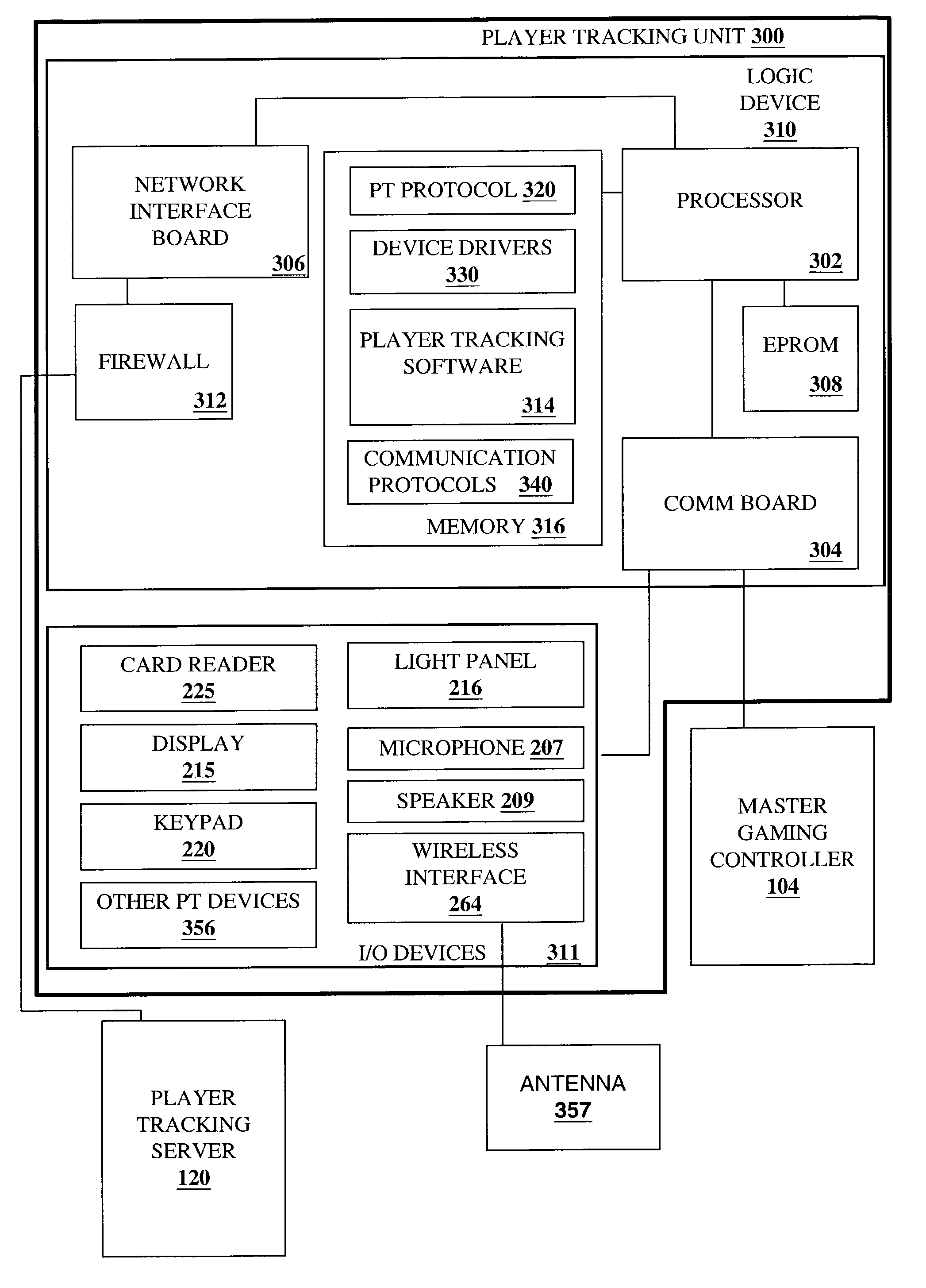
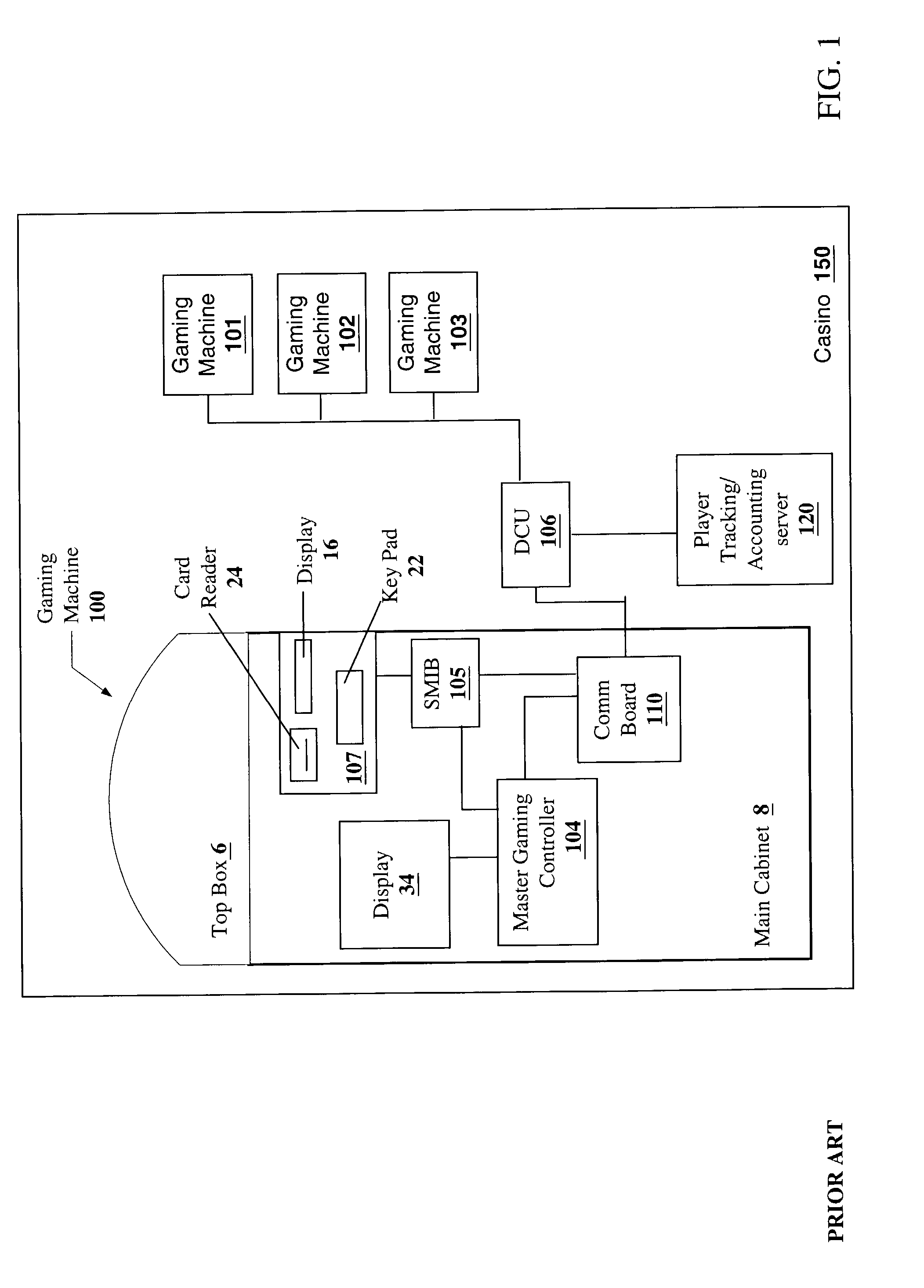
Player tracking communication mechanisms in a gaming machine
InactiveUS6908387B2Acutation objectsApparatus for meter-controlled dispensingDisplay deviceLoudspeaker
A disclosed a player tracking unit provides a display, one or more illumination devices adjacent to the display and a logic device designed to control illumination of the illumination devices in a manner that visually conveys gaming information to an individual viewing the devices. A speaker may be also provided on the player tracking unit to aurally convey gaming information such as voice messages designed to inform or instruct the player in some manner. The player tracking unit may include a wireless interface device designed or configured to allow player tracking information to be automatically downloaded from a portable wireless device carried by the player or player status information to be communicated to a casino service representative carrying a portable wireless device.
Owner:IGT
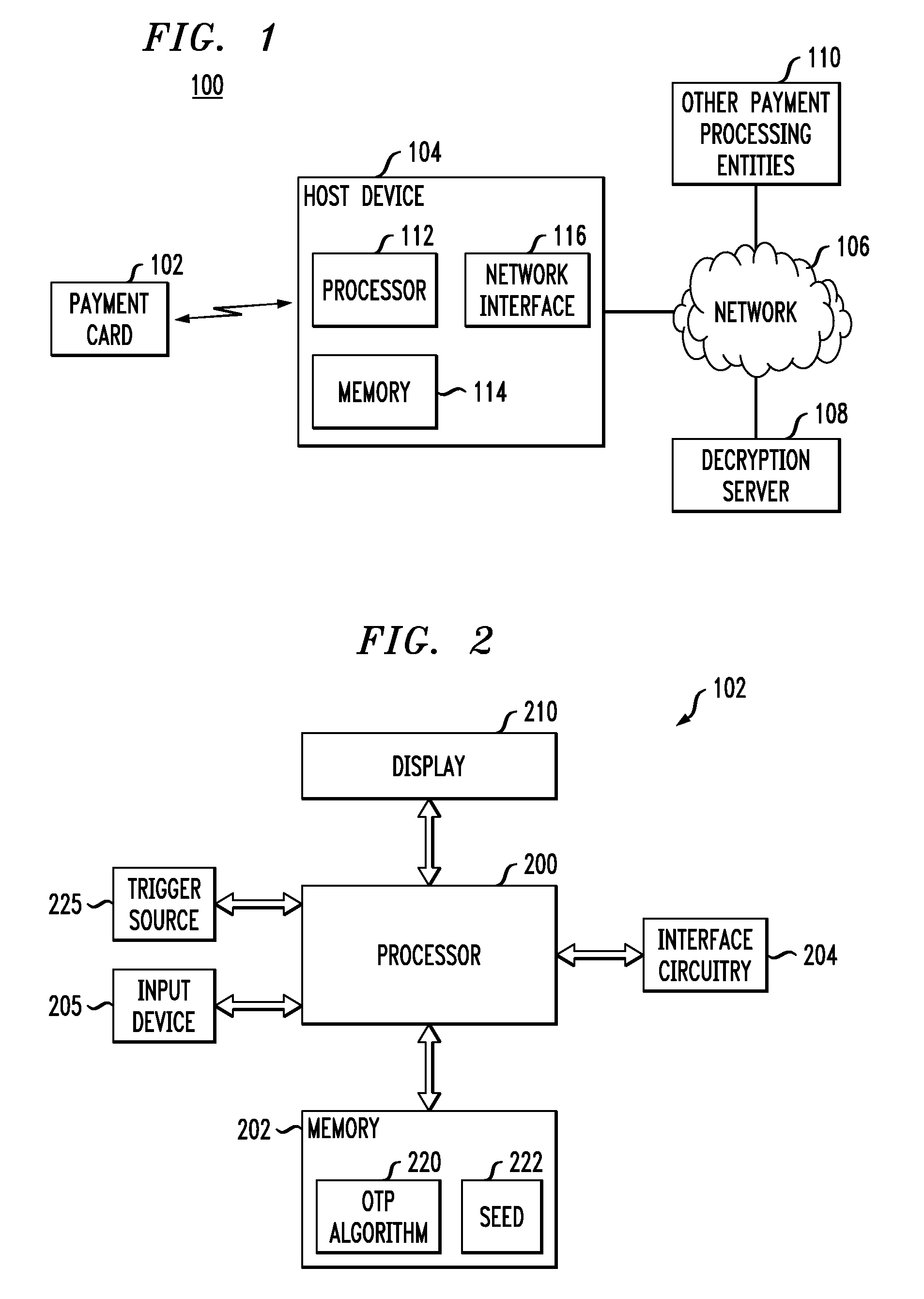
Payment Card with Dynamic Account Number
ActiveUS20090048971A1Avoid processing delaysOvercomes drawbackAcutation objectsFinanceDisplay devicePayment order
A payment card comprises a processor, a trigger source coupled to the processor, and a display for outputting at least a portion of a dynamic account number under control of the processor responsive to the trigger source. The dynamic account number is determined based at least in part on a seed stored in the payment card and an output of the trigger source. In an illustrative embodiment, the dynamic account number is generated utilizing a time-based or event-based one-time password algorithm. For example, in a time-based embodiment, the trigger source may comprise a time of day clock, with the dynamic account number being determined based at least in part on the seed and a current value of the time of day clock. In an event-based embodiment, the trigger source may comprise an event counter, with the dynamic account number being determined based at least in part on the seed and a current value of the event counter.
Owner:EMC IP HLDG CO LLC
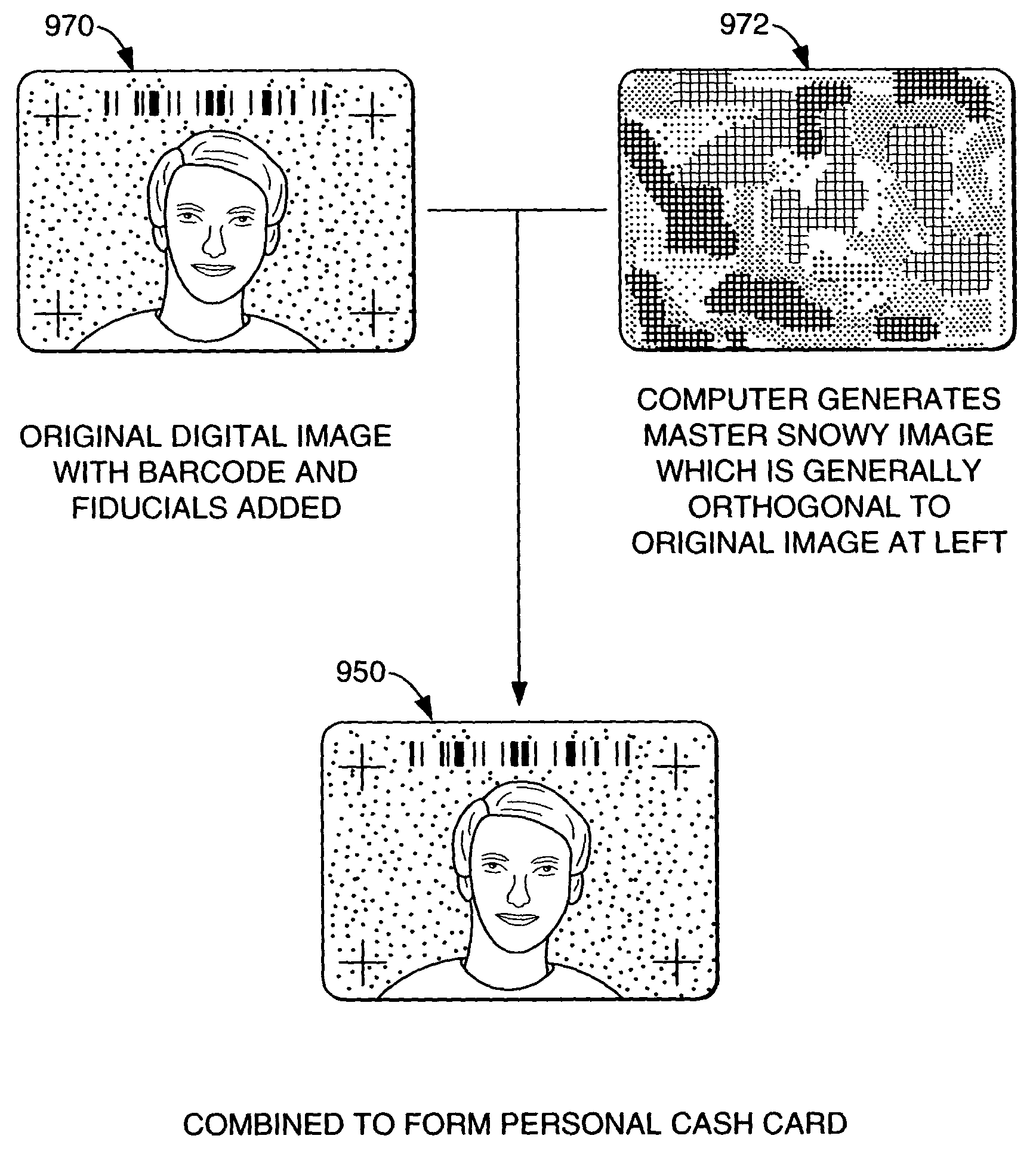
Digital authentication with digital and analog documents
InactiveUS20040153649A1More dataCompact formDigitally marking record carriersDigital data processing detailsAuthentication information
The disclosure describes systems for creating and authenticating printed objects using authentication information. Techniques for incorporating authentication information into digital representations of objects and using the authentication information to authenticate the objects are also provided.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
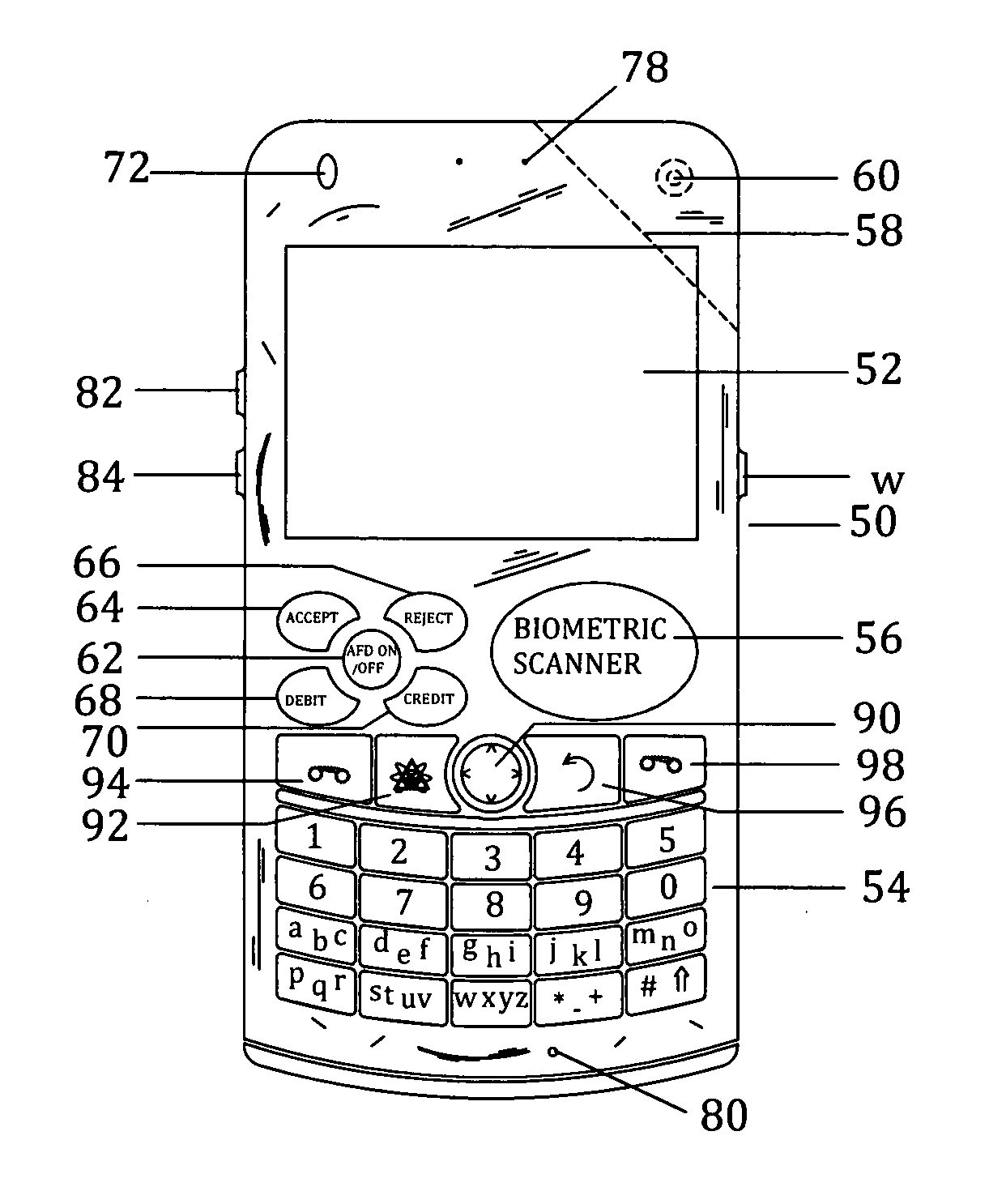
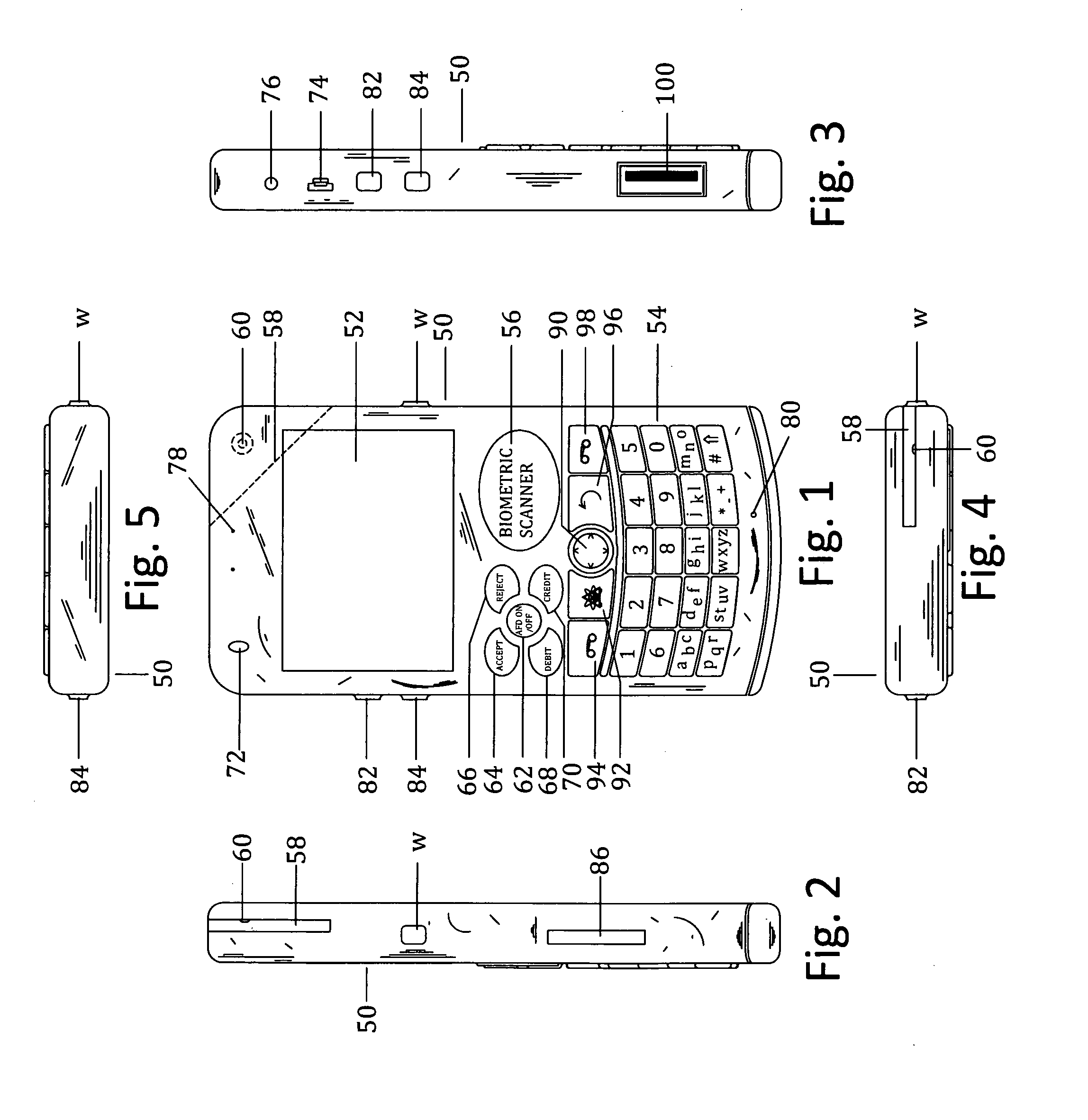
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
System and method for automating a vehicle rental process
InactiveUS20020186144A1Eliminate needLower the thresholdElectric signal transmission systemsTicket-issuing apparatusCommunication unitOn board
The present invention concerns an automated vehicle rental system for a fleet of rental vehicles, where the vehicles are geographically distributed and normally locked when not rented. At least one of the vehicles, when not in use, is parked in an unguarded location. The system has a vehicle communications unit for enabling communication to and from the vehicle, user-carried electronic devices, or other readers, and for interfacing with the user. An on-board unit (OBU) is located on each of the vehicles for interfacing with the vehicle communications unit, and with a door unlocking mechanism. The system further has a central reservations, management and location system (CRMLS) in communication through a communications network with each OBU, the CRMLS performing all reservations and management functions, and being linked to a database containing a location and availability of each of thr vehicles and a rate for rental, the CRMLS also being provided with an allocation manager system for geographically allocating vehicles. In order to access the vehicle, the system also includes a key being borne by the user. The system minimizes the human intervention in the rental process, and is more user-friendly.
Owner:ZOOP MOBILITY NETWORK
System and method for mass transit merchant payment
InactiveUS20060278704A1Eliminate needRelieving userAcutation objectsTicket-issuing apparatusTransit systemFinancial transaction
Methods, systems and computer program products are provided for enabling payment of transit system fees using a financial transaction instrument. Entry is permitted onto a transit system by recognition of information included in an identification number stored on a financial transaction instrument. The identification number stored on the financial transaction instrument is associated with a transit system fee registered for each use of the transit system. A plurality of transit system fees associated with the same identification number from use of the financial transaction instrument is aggregated, and payment for the aggregated transit system fees is requested from a transaction account associated with the financial transaction instrument.
Owner:LIBERTY PEAK VENTURES LLC
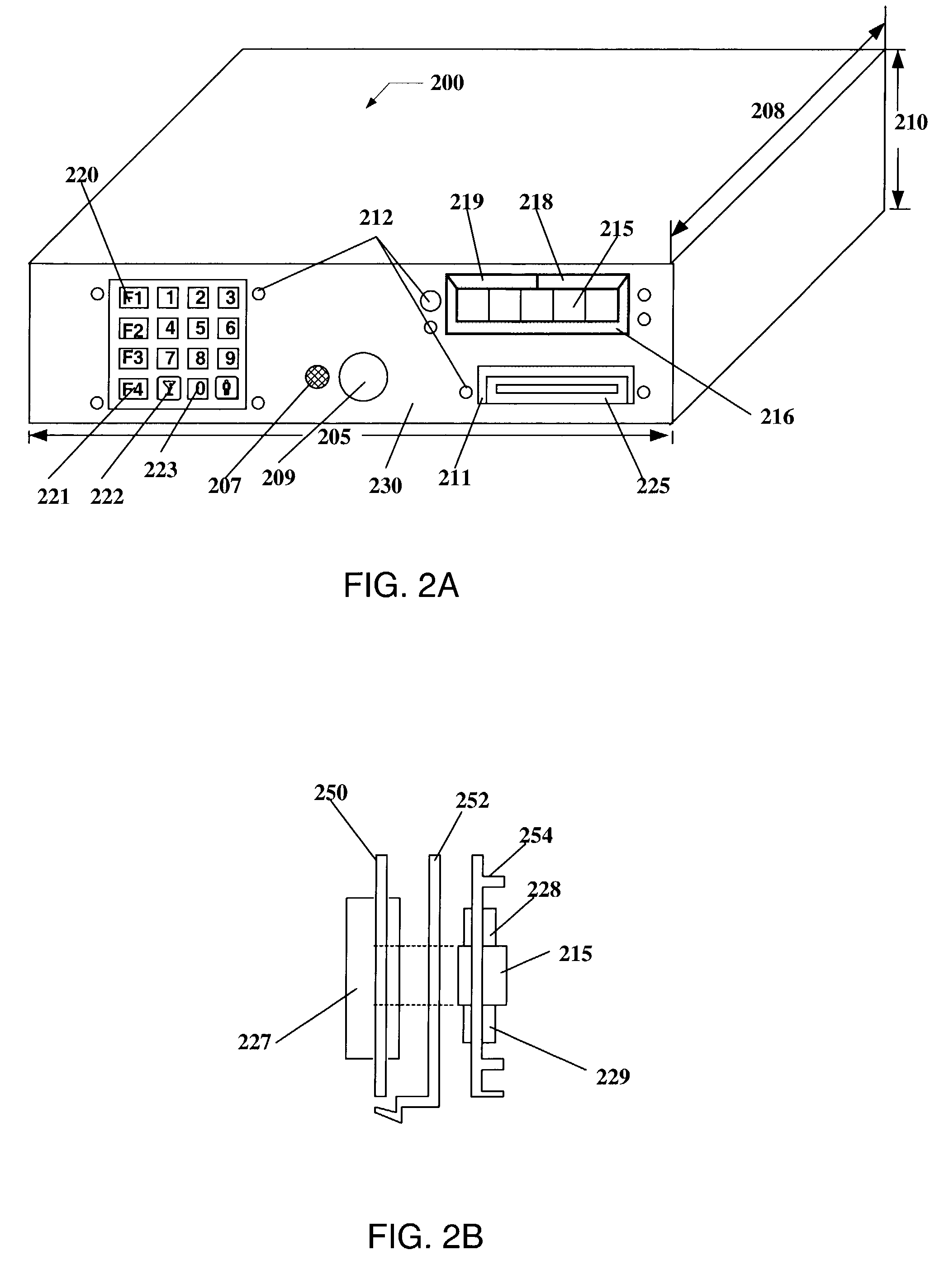
Player tracking communication mechanisms in a gaming machine
InactiveUS20050239546A1Acutation objectsApparatus for meter-controlled dispensingWeb browserDisplay device
A disclosed player tracking unit provides a display and a player tracking controller designed or configured to provide a web-browser on the display. The player tracking unit may include one or more input devices that can receive selections associated with the web-browser. Furthermore, the player tracking unit can include a multimedia board for processing digitally formatted program files for output on the display.
Owner:IGT
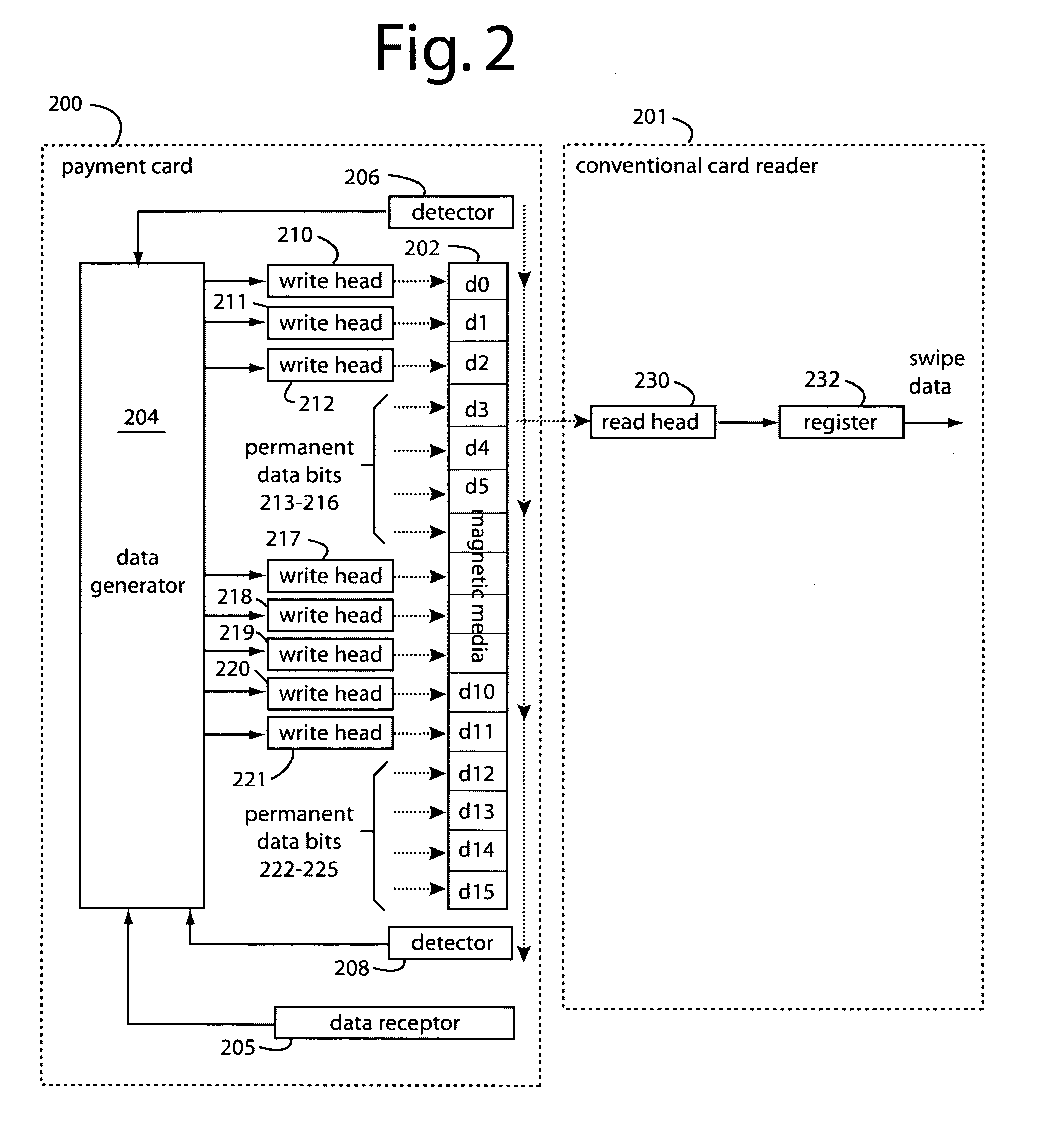
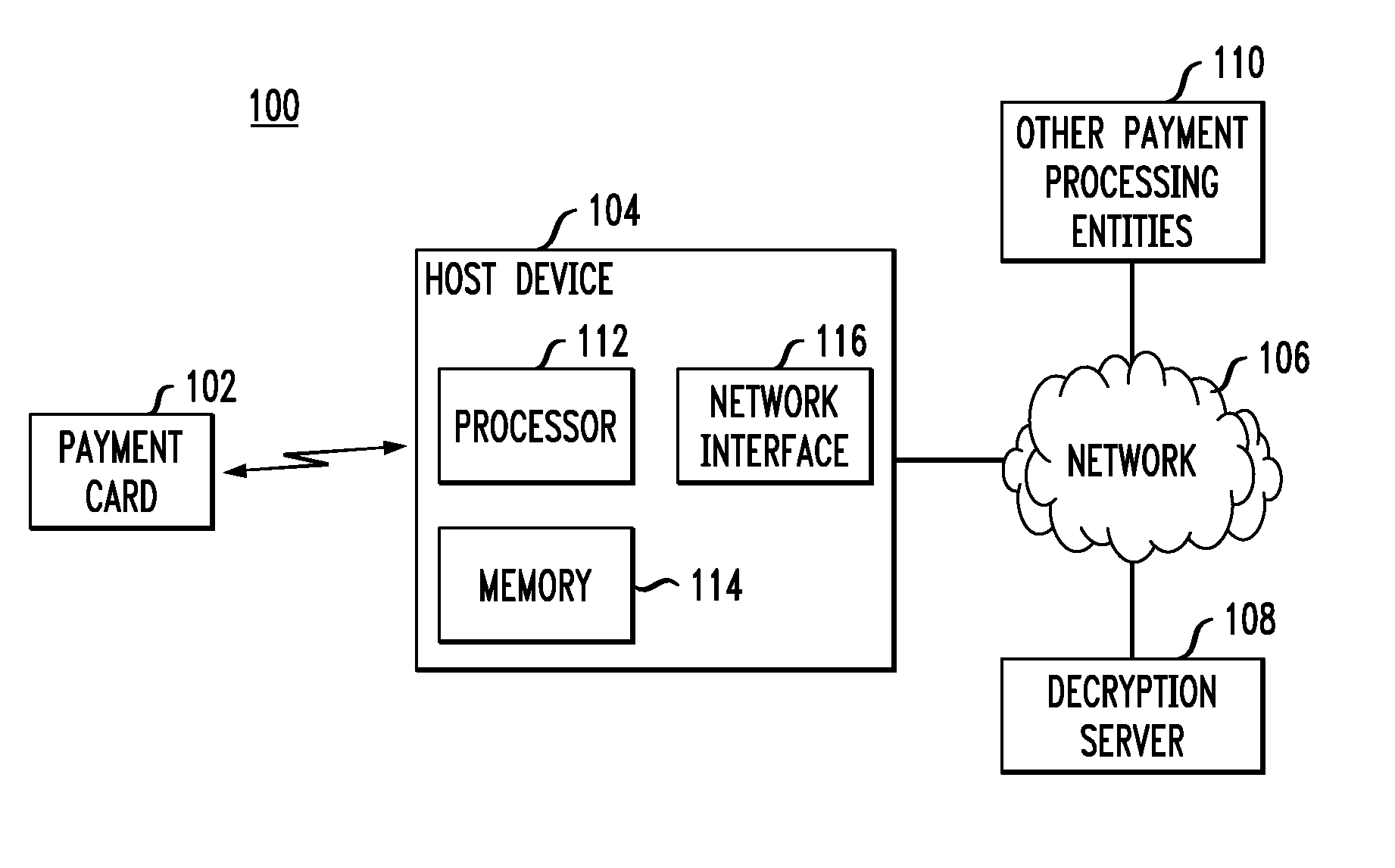
Automated payment card fraud detection and location
A payment card fraud detection business model comprises an internal virtual account number generator and a user display for Card-Not-Present transactions. Card-Present transactions with merchant card readers are enabled by a magnetic array internally associated with the card's magnetic stripe. The internal virtual account number generator is able to reprogram some of the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, such is discarded and put on an exclusion list or reserved for a specific merchant until the expiration date. A server for the issuing bank logs the merchant locations associated with each use or attempted use, and provides real-time detection of fraudulent attempts to use a virtual account number on the exclusion list. Law enforcement efforts can then be directed in a timely and useful way not only where the fraud occurs but also at its origination.
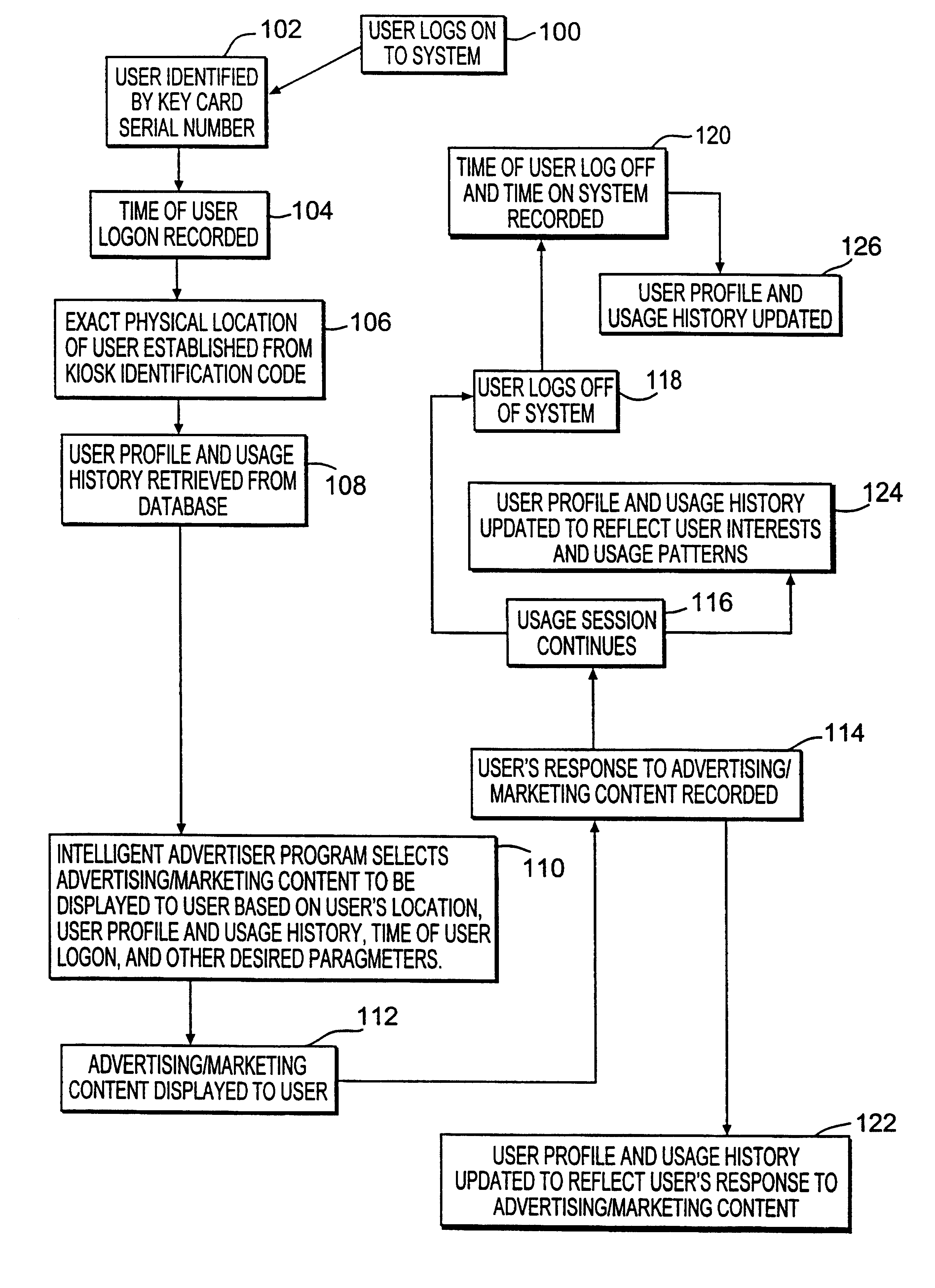
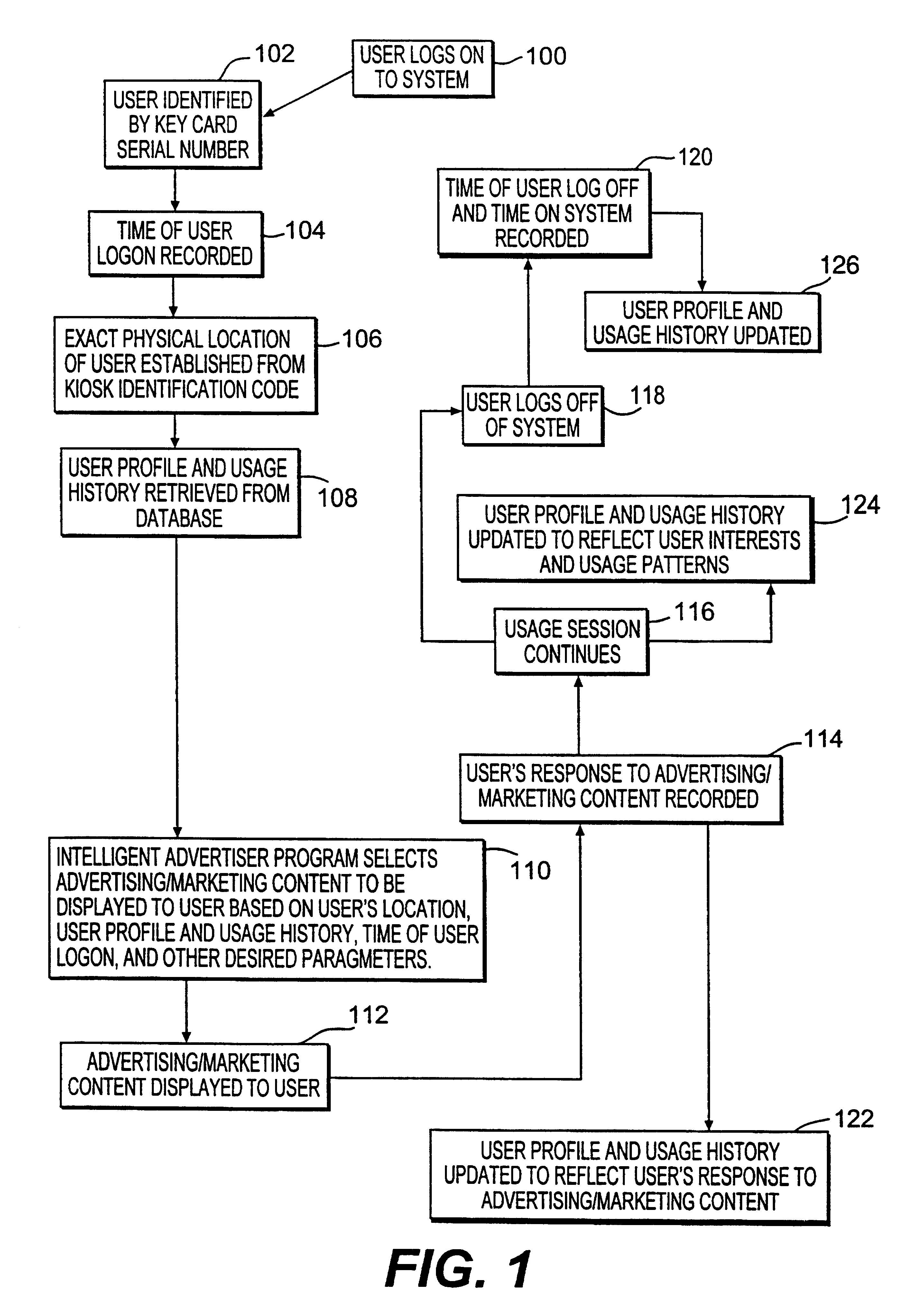
Owner:FITBIT INC
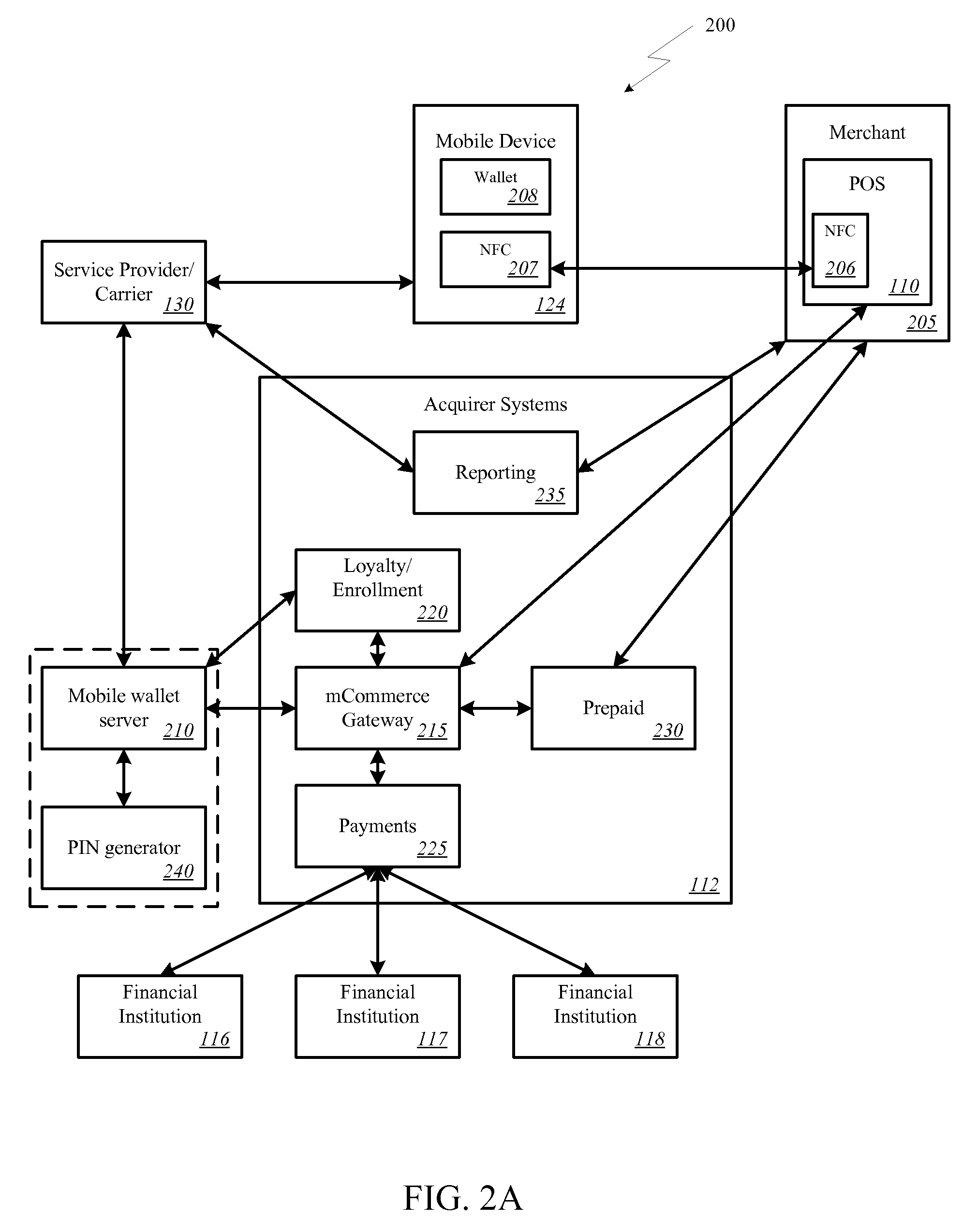
Onetime Passwords For Mobile Wallets
ActiveUS20090104888A1Near-field transmissionUnauthorised/fraudulent call preventionNetworked systemOne-time password
A mobile wallet and network system using onetime passwords for authentication is disclosed according to one embodiment of the invention. A onetime password may be generated at a mobile wallet server and transmitted to the mobile device. The onetime password may then be used to authenticate the user of the mobile wallet when completing a transaction. Authentication may require entry of the onetime password and confirmation that the onetime password entered matches the onetime password sent by the mobile wallet server. In other embodiments of the invention, a mobile wallet and a mobile wallet server are in sync and each generate the same onetime password at the same time. These onetime passwords may then be used to authenticate the user of the mobile wallet.
Owner:FIRST DATA
Player tracking communication mechanisms in a gaming machine
InactiveUS7112138B2Streamline relocation processAcutation objectsApparatus for meter-controlled dispensingDisplay deviceAudio frequency
A disclosed a player tracking unit provides a multimedia interface with a display and an interface to one or more sound projection devices and a multimedia board for processing digitally formatted program files for output on the multimedia interface. The player tracking unit may provide menus of audio and video programs, such as a menu for a musical jukebox or a menu for a video-on-demand service. Using a “TV-like” interface, a user may be able to select a program to output on the multimedia interface and control playback features of the program.
Owner:IGT
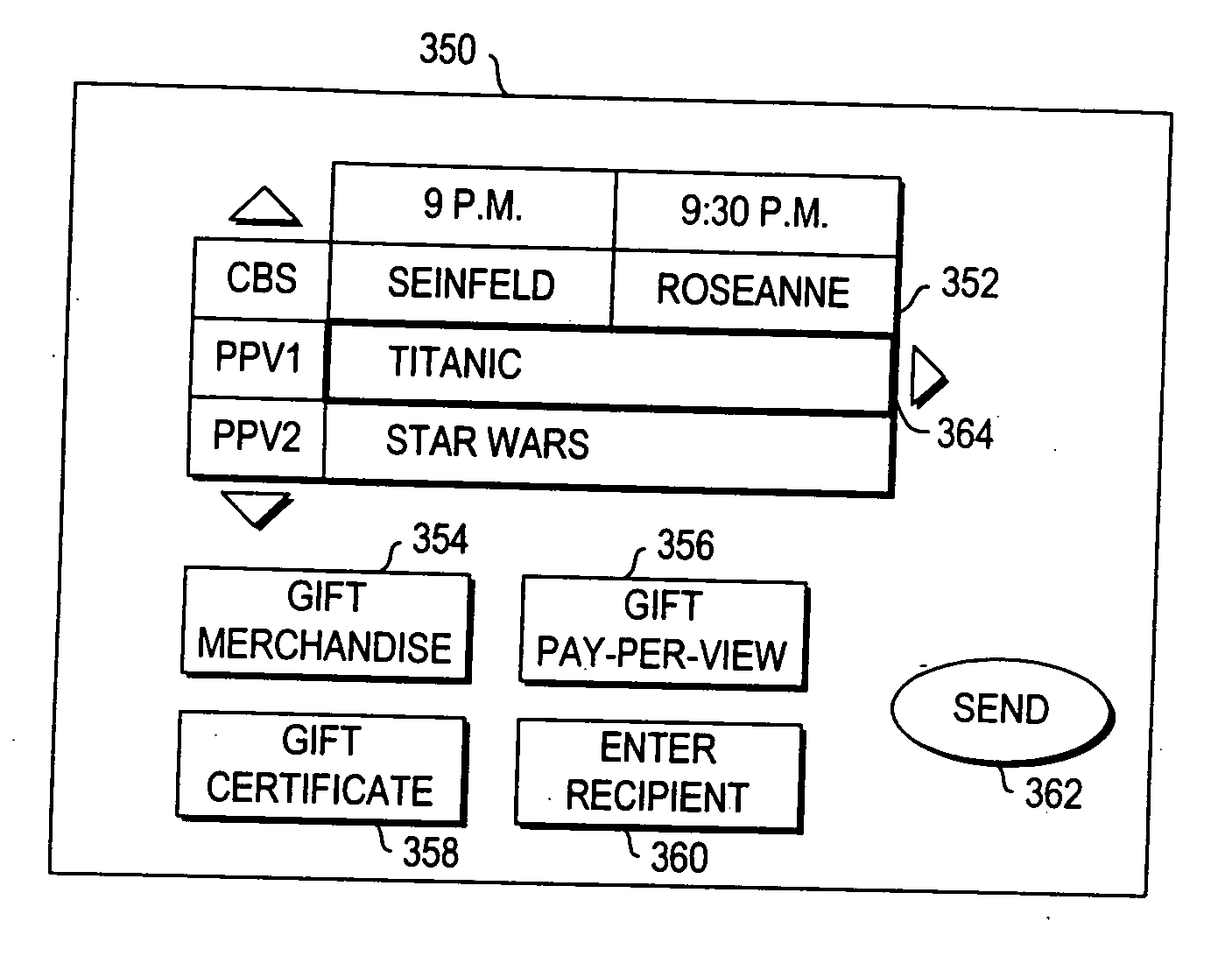
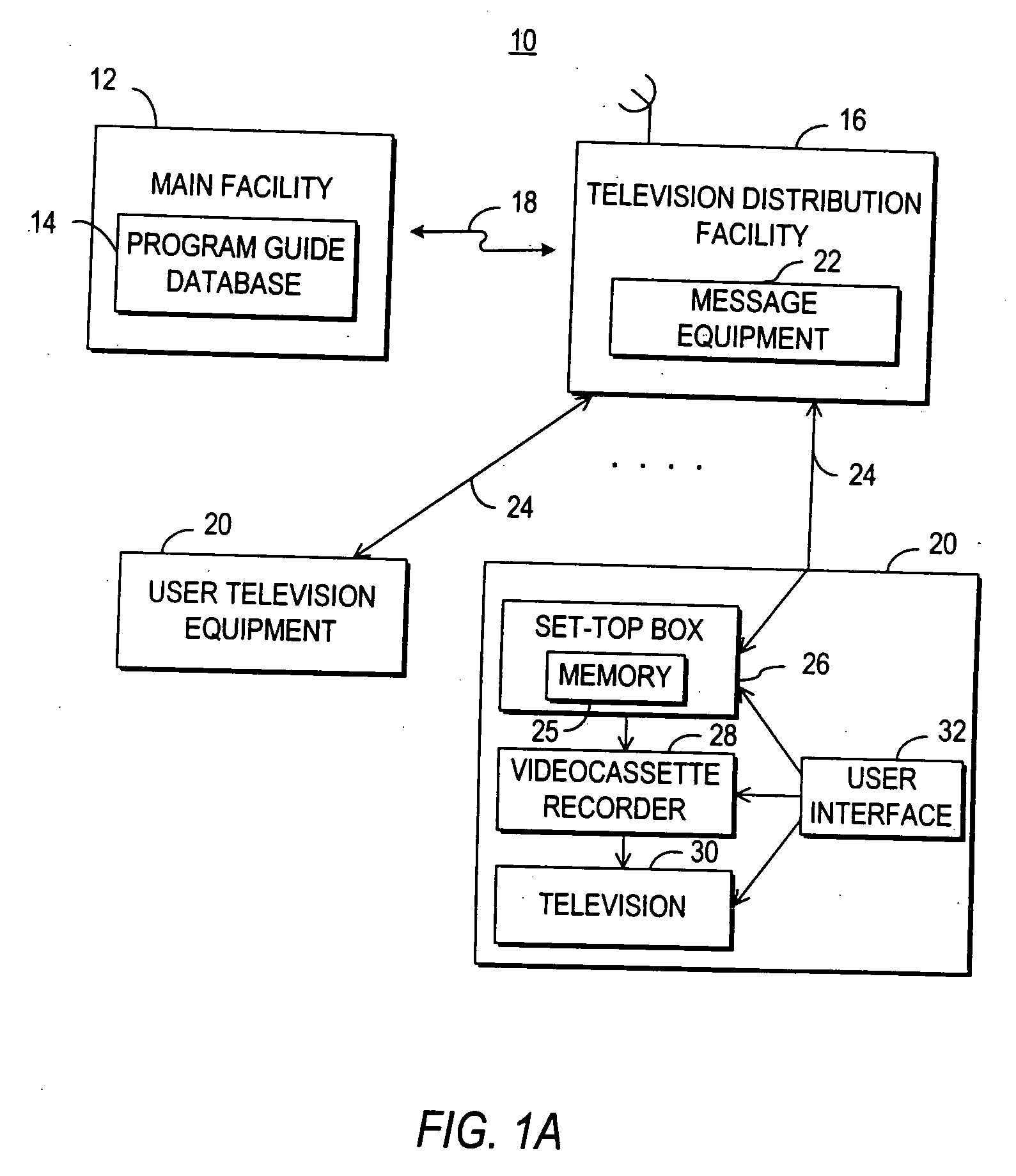
Systems and methods for providing a program as a gift using an interactive application
InactiveUS20060190966A1Eliminate needTelevision system detailsAcutation objectsNetwork connectionInteractive television
A television message system is provided that allows users at user television equipment devices that are connected to a television distribution facility to transmit messages to each other relating to a television program or other suitable subject. The television message system permits users to participate in evaluations, contests, promotions, and surveys related to a television program while watching that television program. The television message system also permits users to compose and send a message to a television program entity. Users can send messages through the television message system to users at personal computers who are connected to the user's television distribution facility through a communications network. The television message system also allows a user to purchase a gift related to television programming for a recipient. The gift may be an electronic gift certificate for pay-per-view programming. The television message system may be based on an interactive television program guide or a set-top box application implemented on a set-top box.
Owner:UNITED VIDEO PROPERTIES
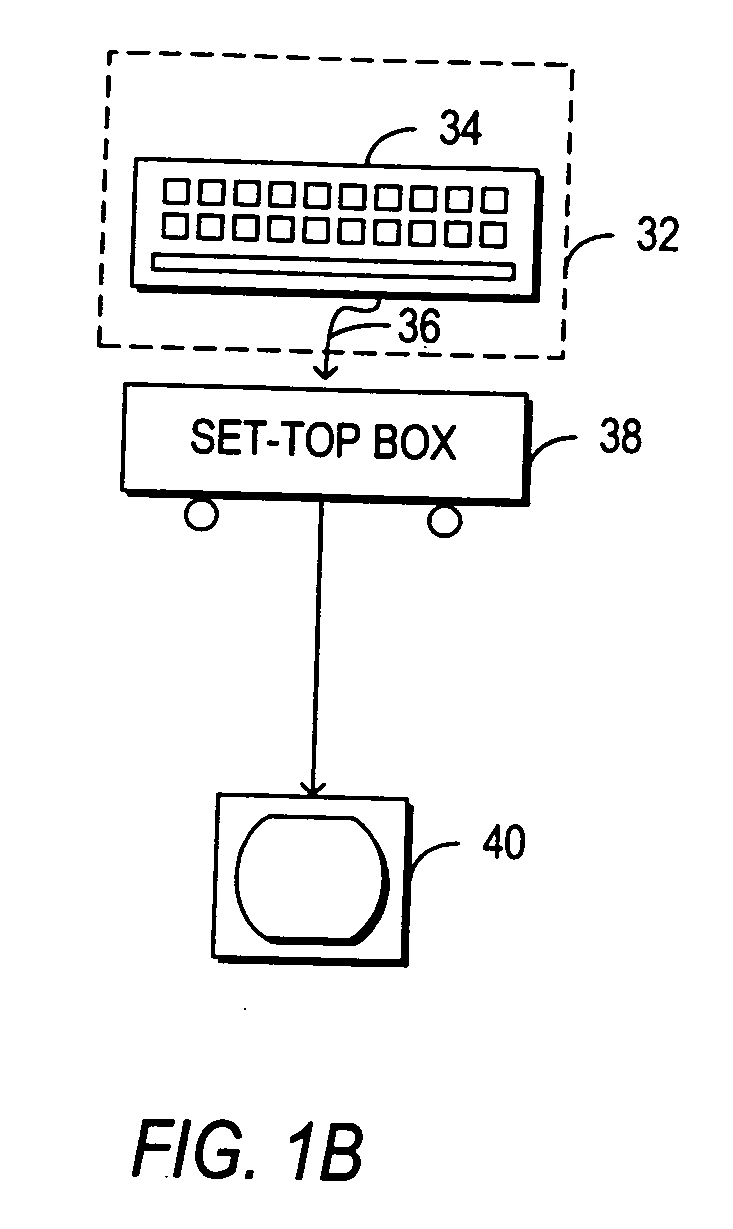
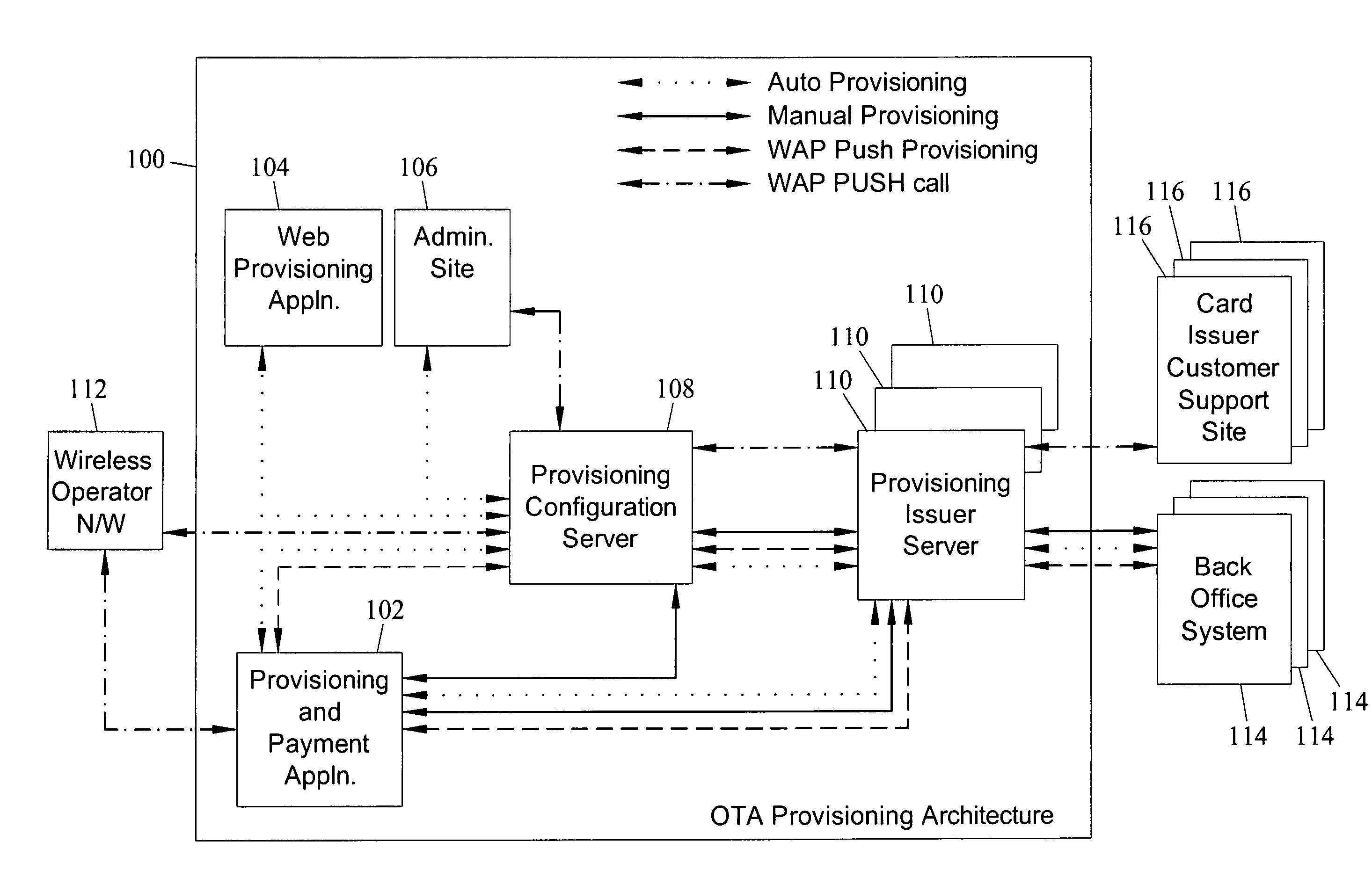
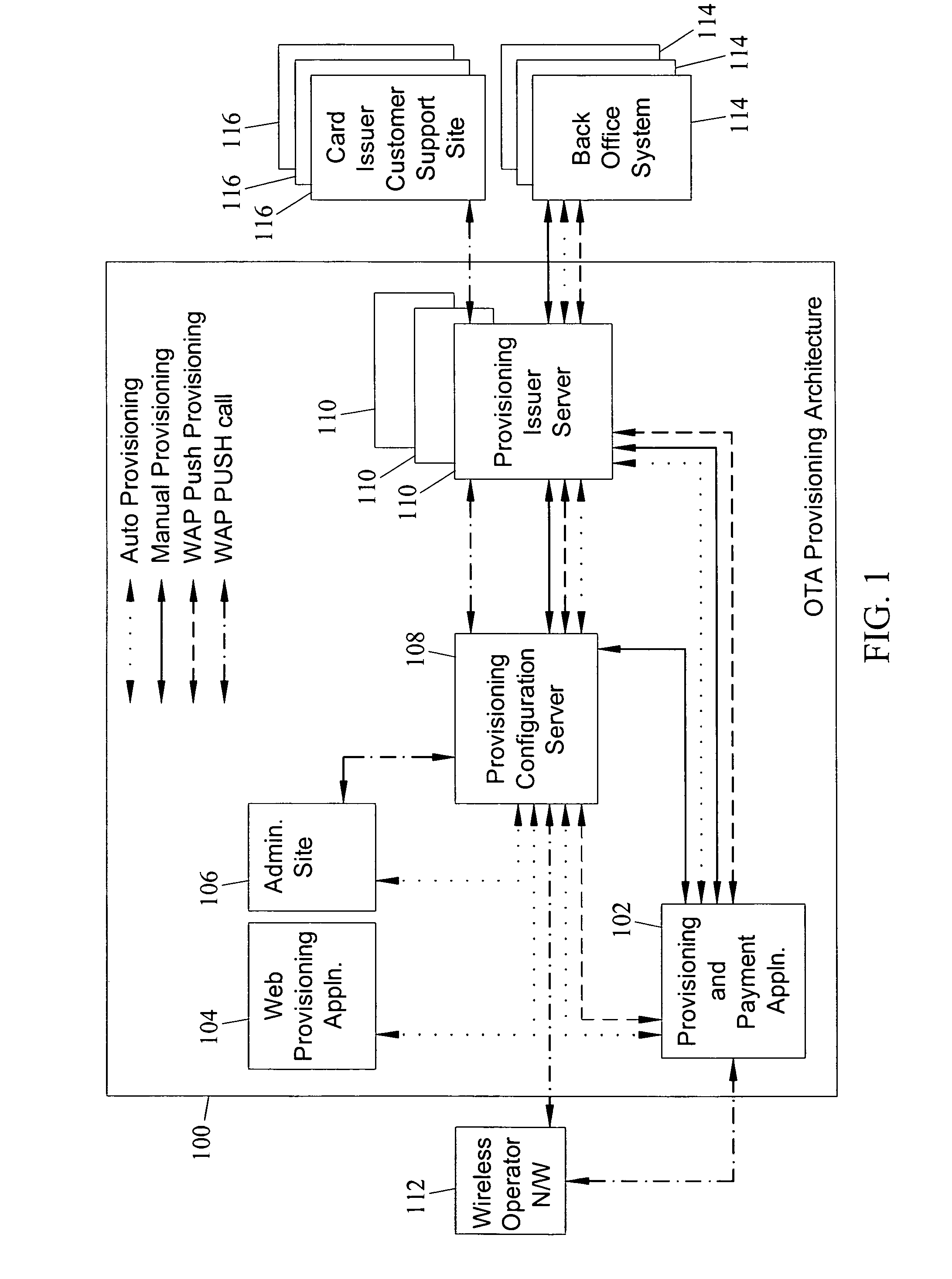
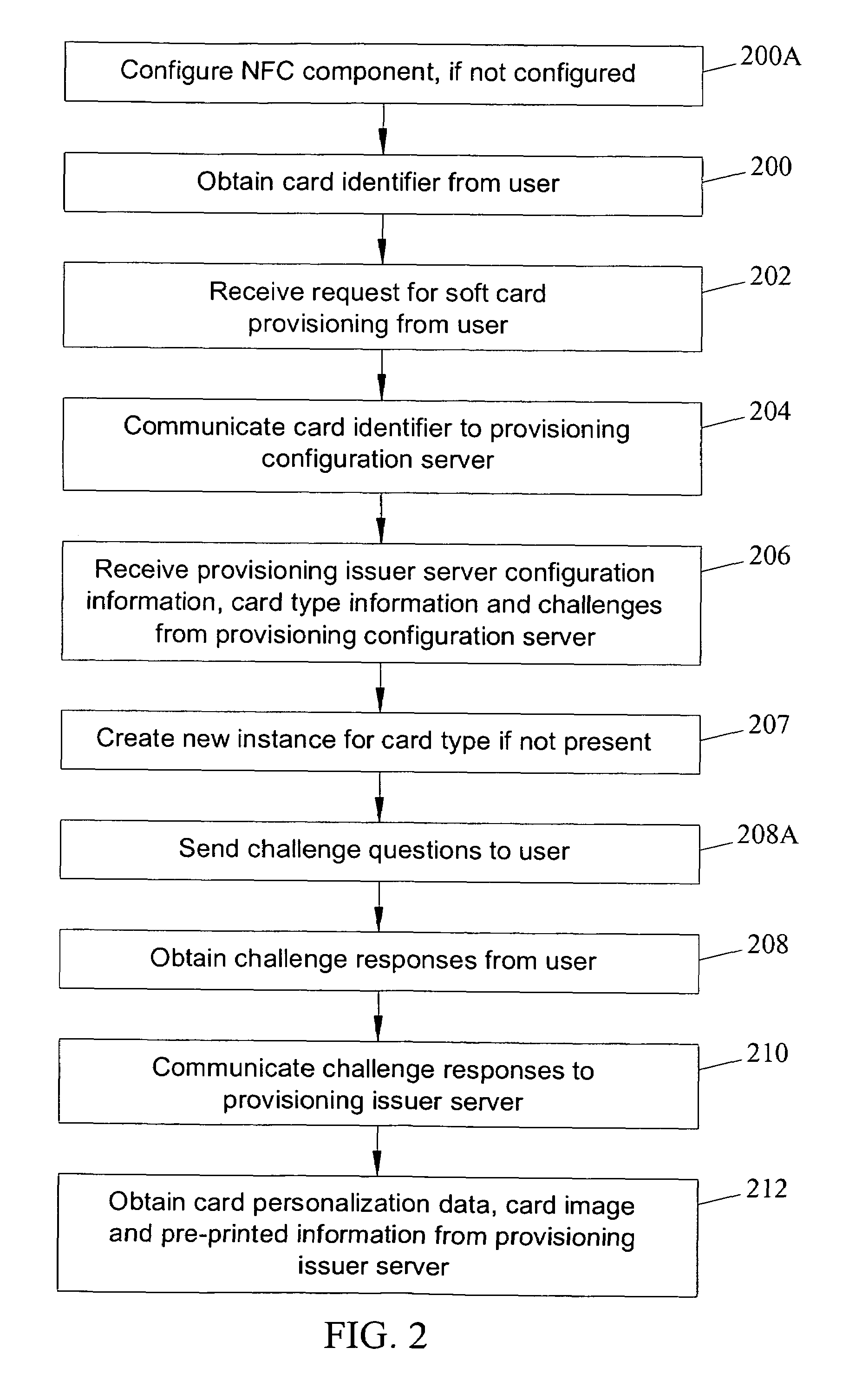
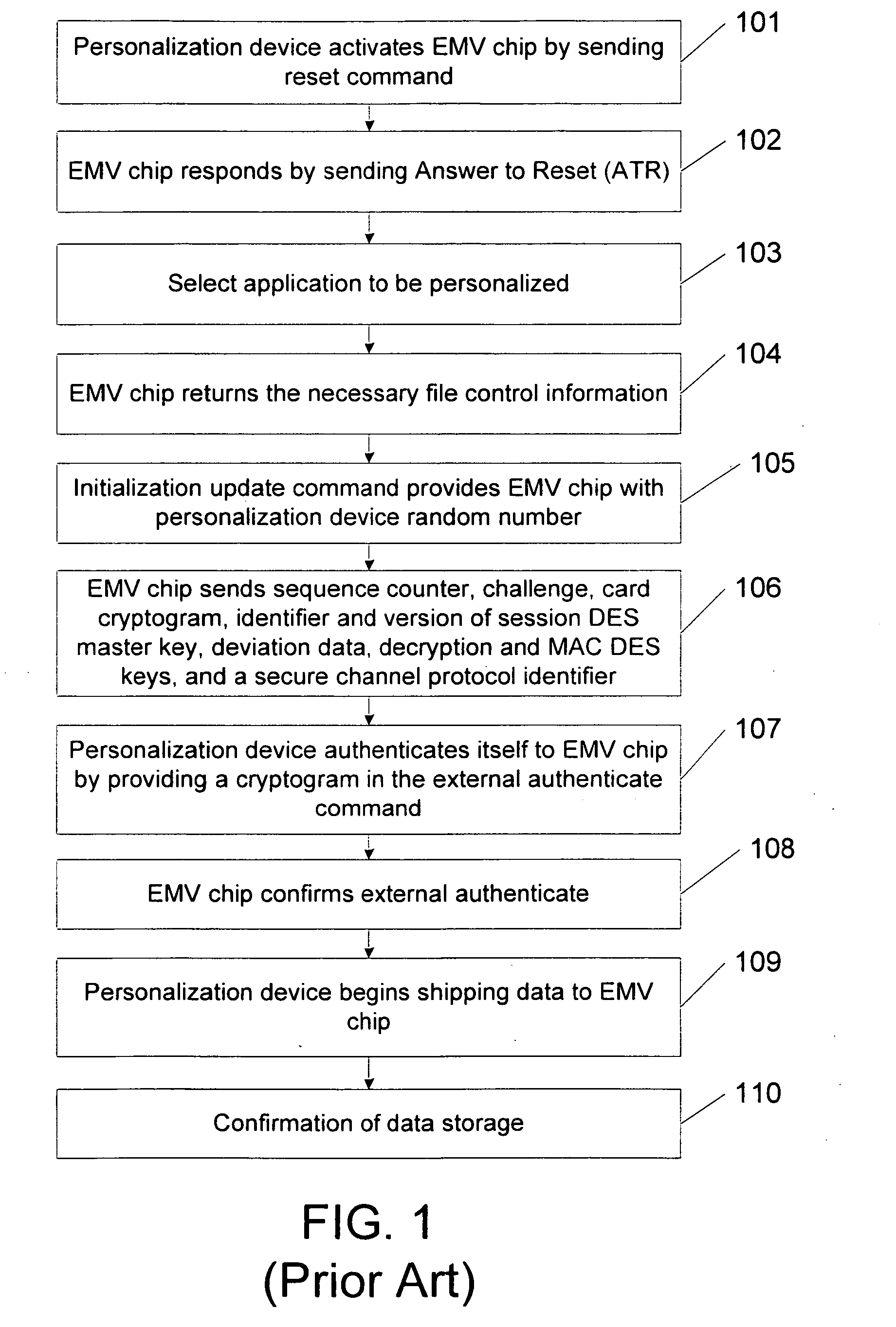
Methods, systems and computer program products for over the air (OTA) provisioning of soft cards on devices with wireless communications capabilities
ActiveUS7469151B2Shorten the timeEliminate needAcutation objectsSpecial service for subscribersComputer hardwarePersonalization
Methods, systems, and computer program products for over the air provisioning of soft cards on devices with wireless communications capabilities are disclosed. According to one method, a soft card provisioning application is instantiated on a device with wireless communications capabilities. A card number for a soft card desired to be provisioned on the device is obtained from a user of the device. The card number is communicated to a provisioning configuration server over an air interface. Card-issuer-specific challenges corresponding to the card number and a provisioning issuer server network address are obtained from the provisioning configuration server. The challenges are presented to the user, and the user's responses to the challenges are received. A connection is made to the provisioning issuer server corresponding to the network address. The challenge responses are communicated to the provisioning issuer server. Soft card personalization data for activating the soft card is received from the provisioning issuer server. The soft card is provisioned for use on the device based on the personalization data.
Owner:MASTERCARD INT INC
Method and apparatus for providing authentication using policy-controlled authentication articles and techniques
A method and apparatus provides first or second factor authentication by providing selectability of a plurality of second factor authentication policies associated with a second factor authentication article. The first or second factor authentication article includes authentication information, such as a plurality of data elements in different cells or locations on the authentication article, which can be located by using corresponding location information. The method and apparatus provides second factor authentication based on the first or second factor authentication article by enforcing at least one of the plurality of selected authentication policies.
Owner:ENTRUST
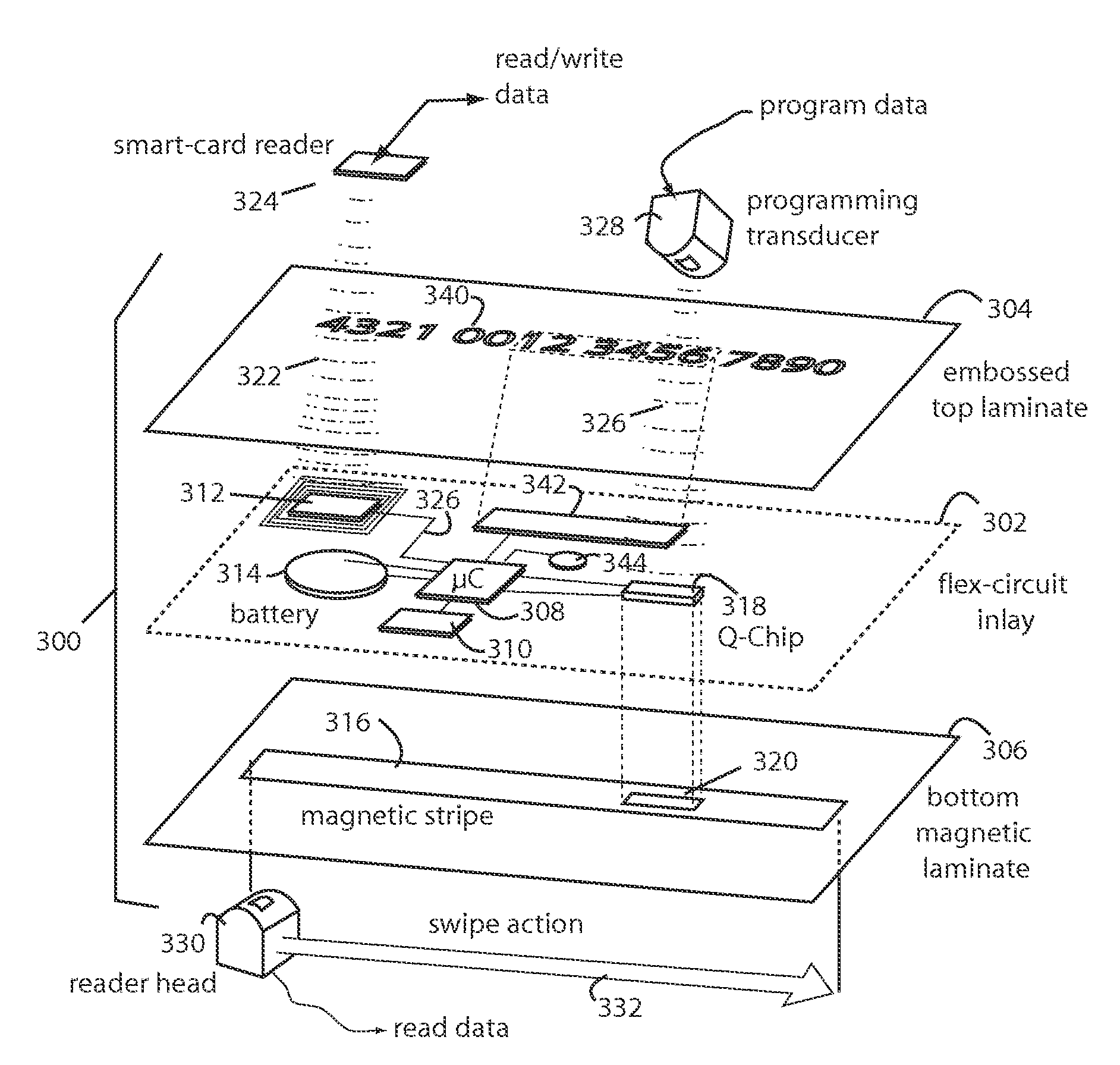
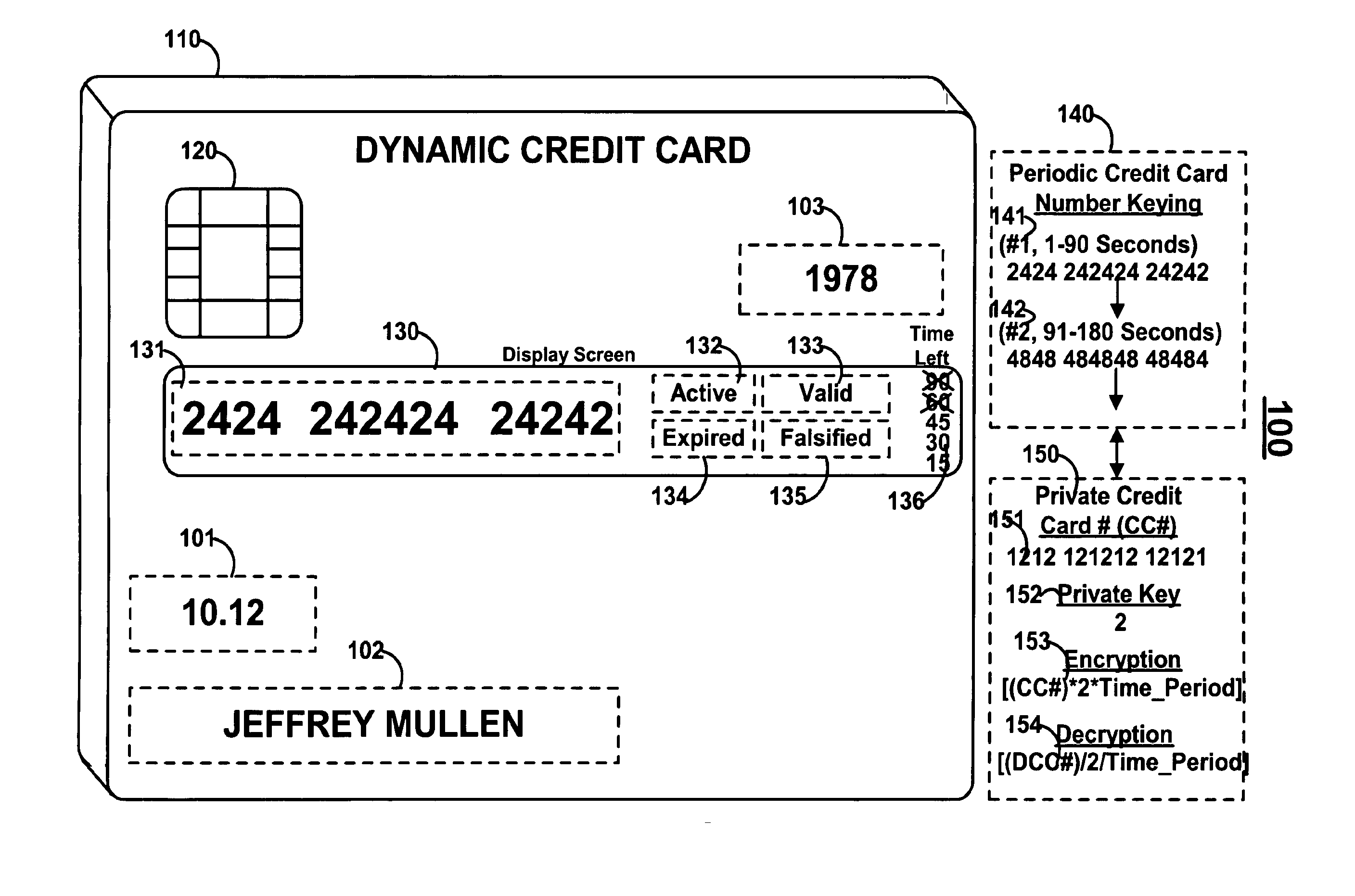
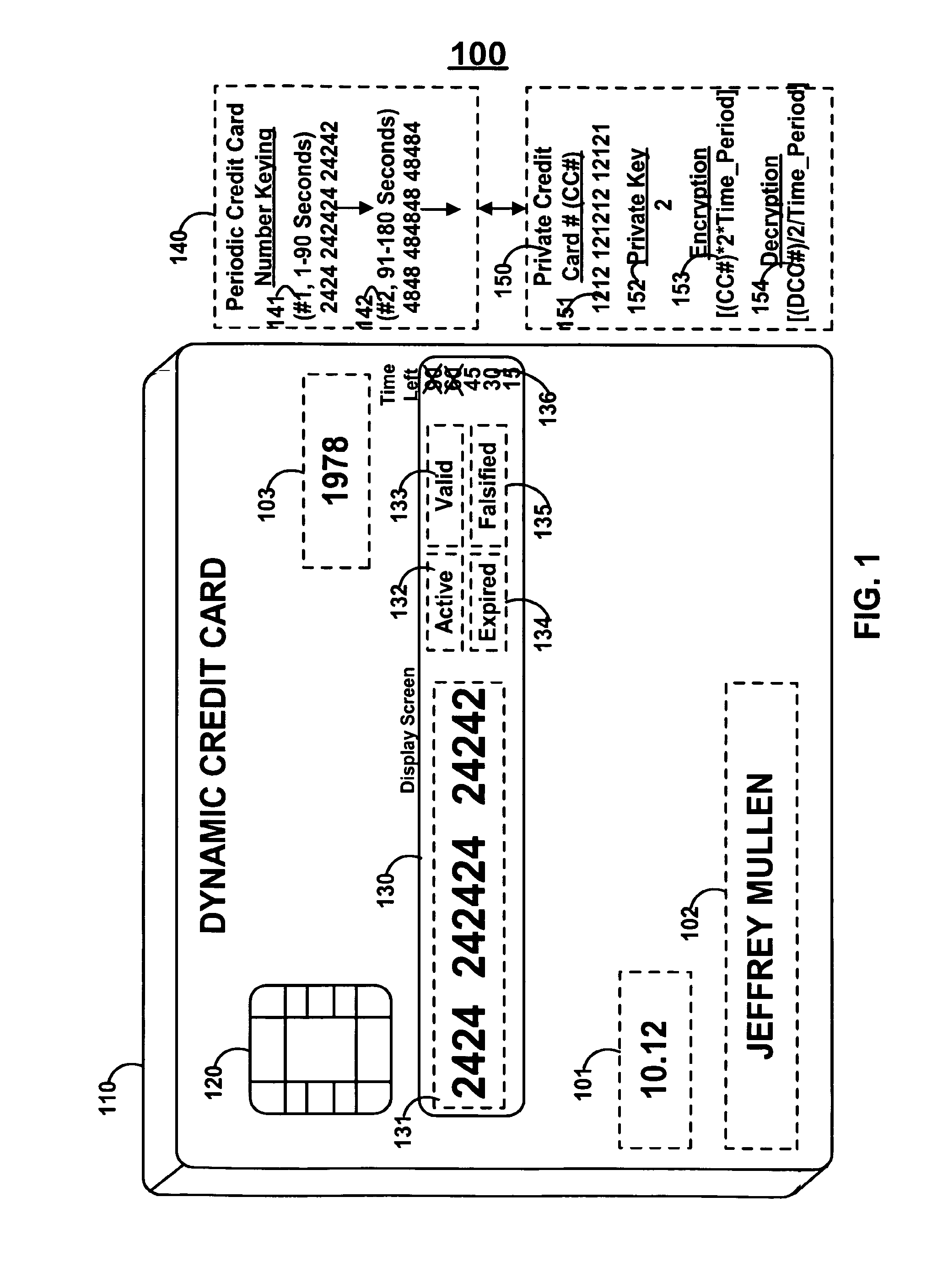
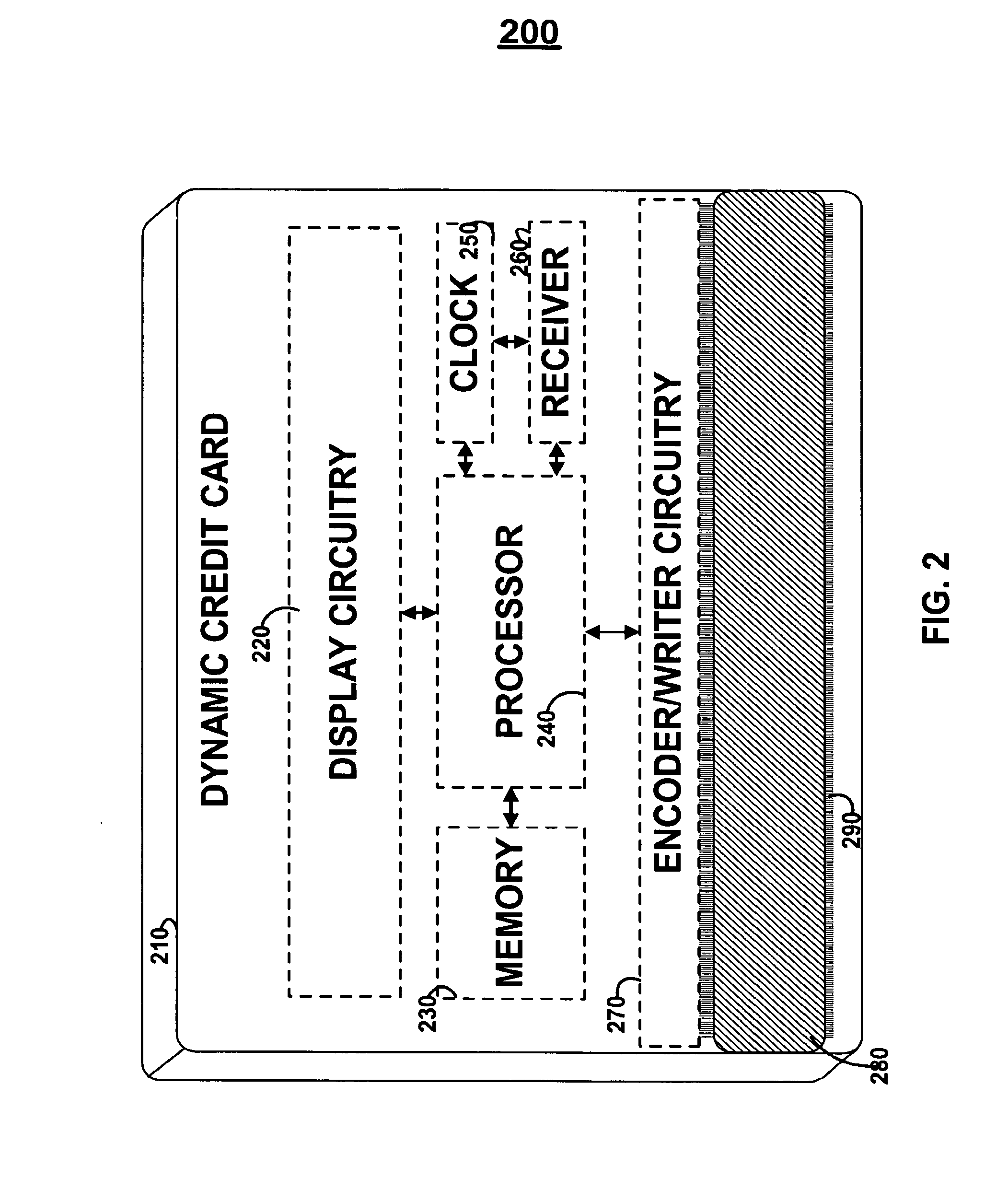
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
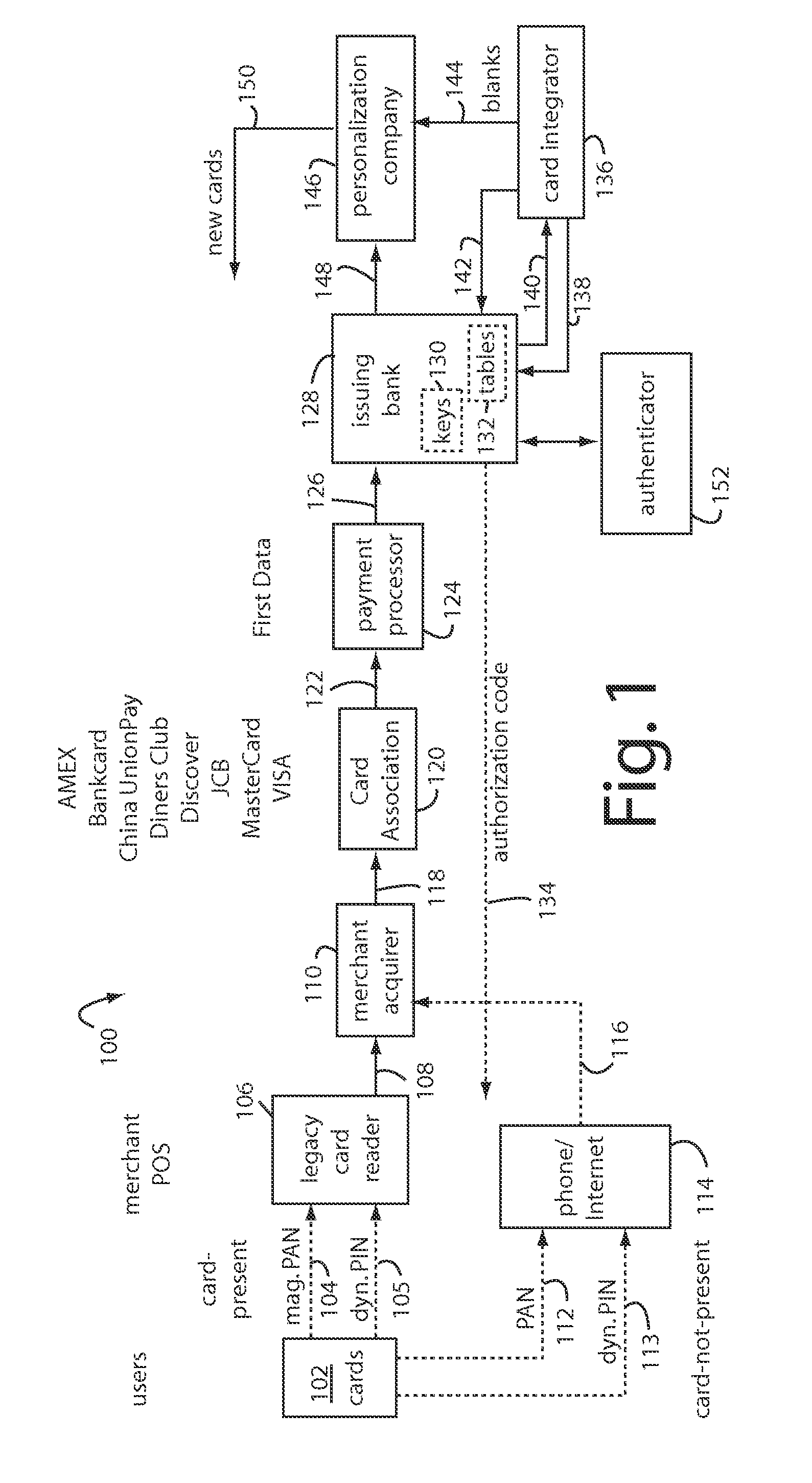
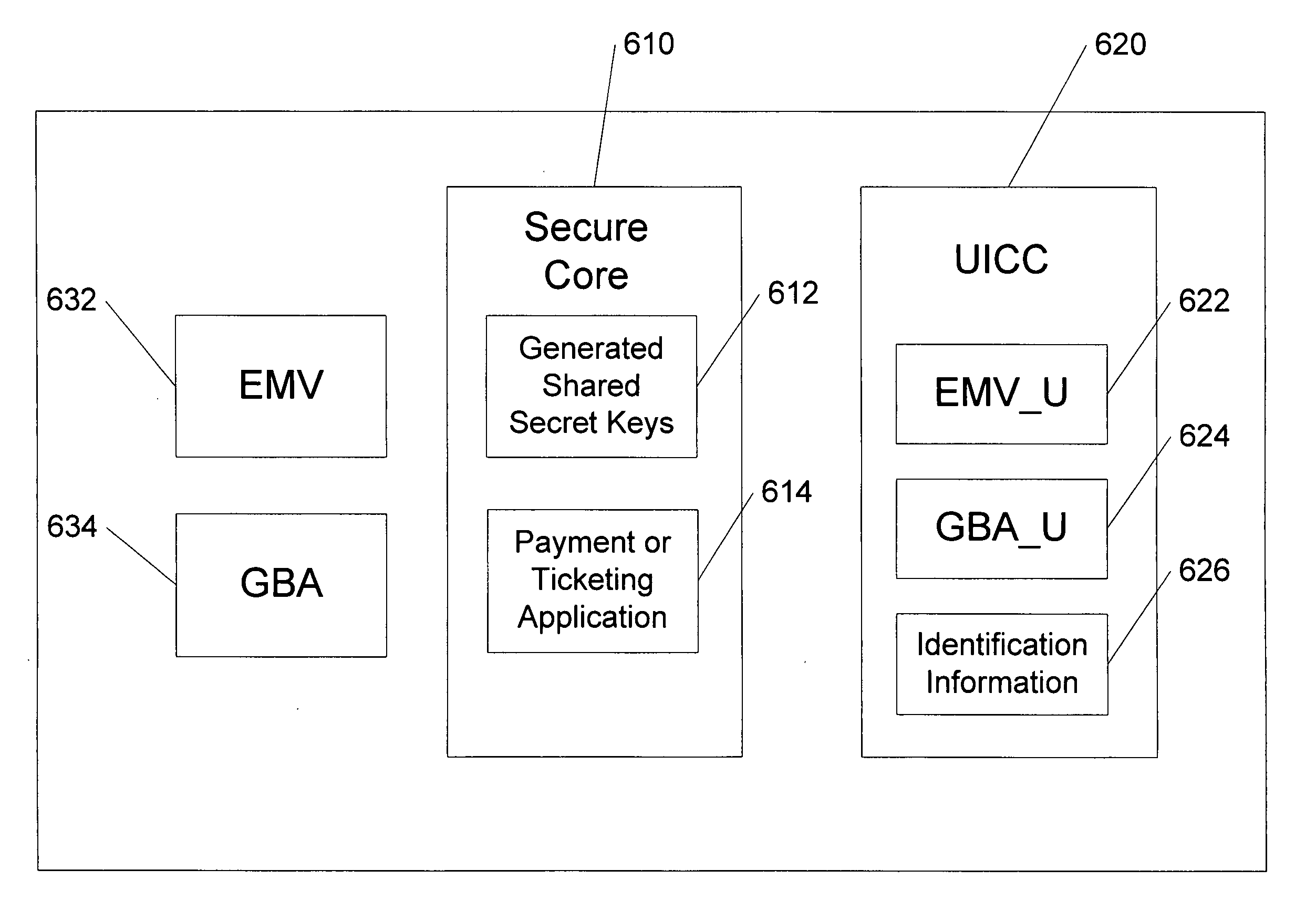
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
Popular searches
Analogue secracy/subscription systems Color television details Carrier indicating arrangements Two-way working systems Video games Recording on magnetic disks Input/output processes for data processing Character and pattern recognition Plural information simultaneous broadcast Recording signal processing
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com