Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3939 results about "Biometric trait" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
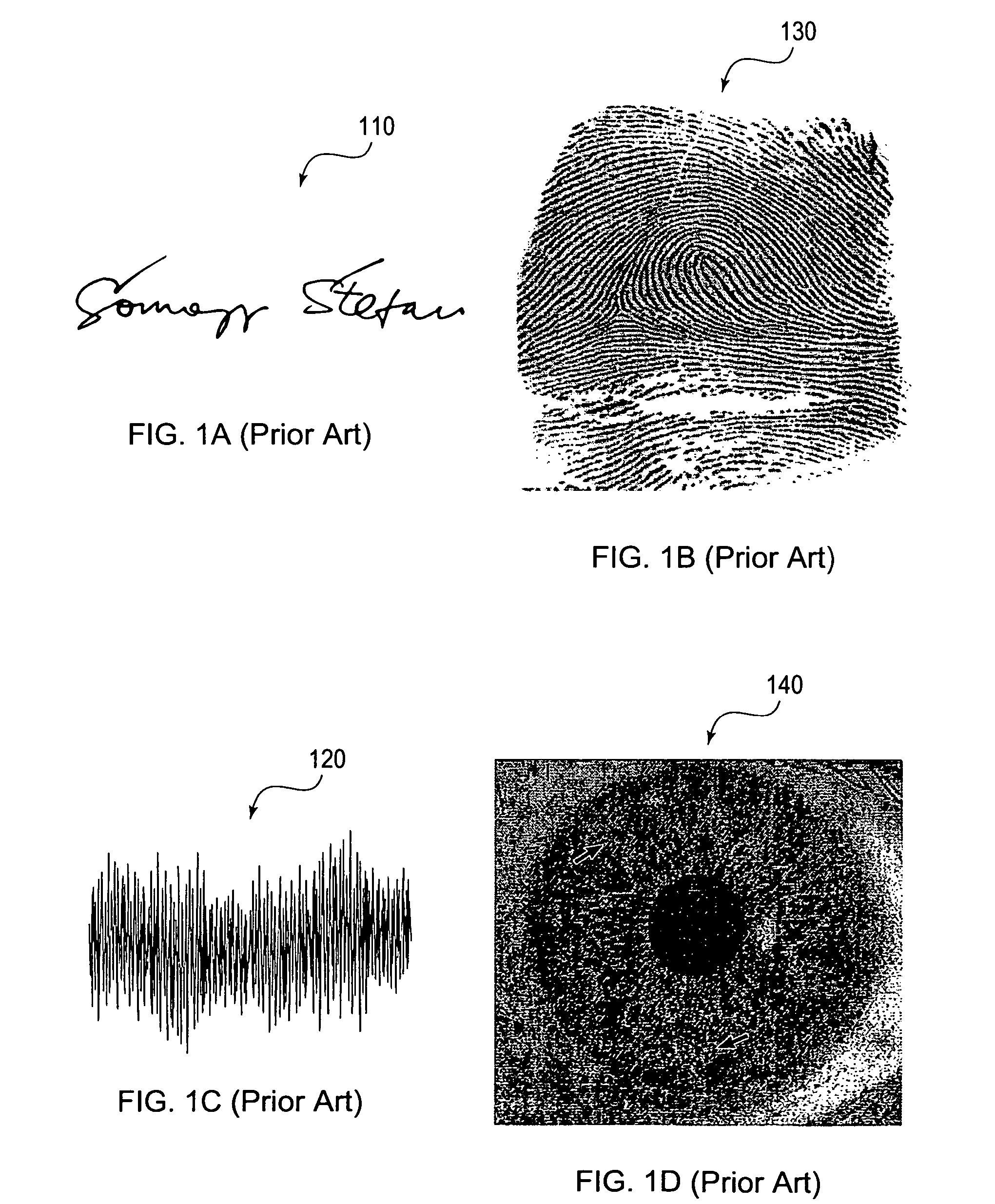
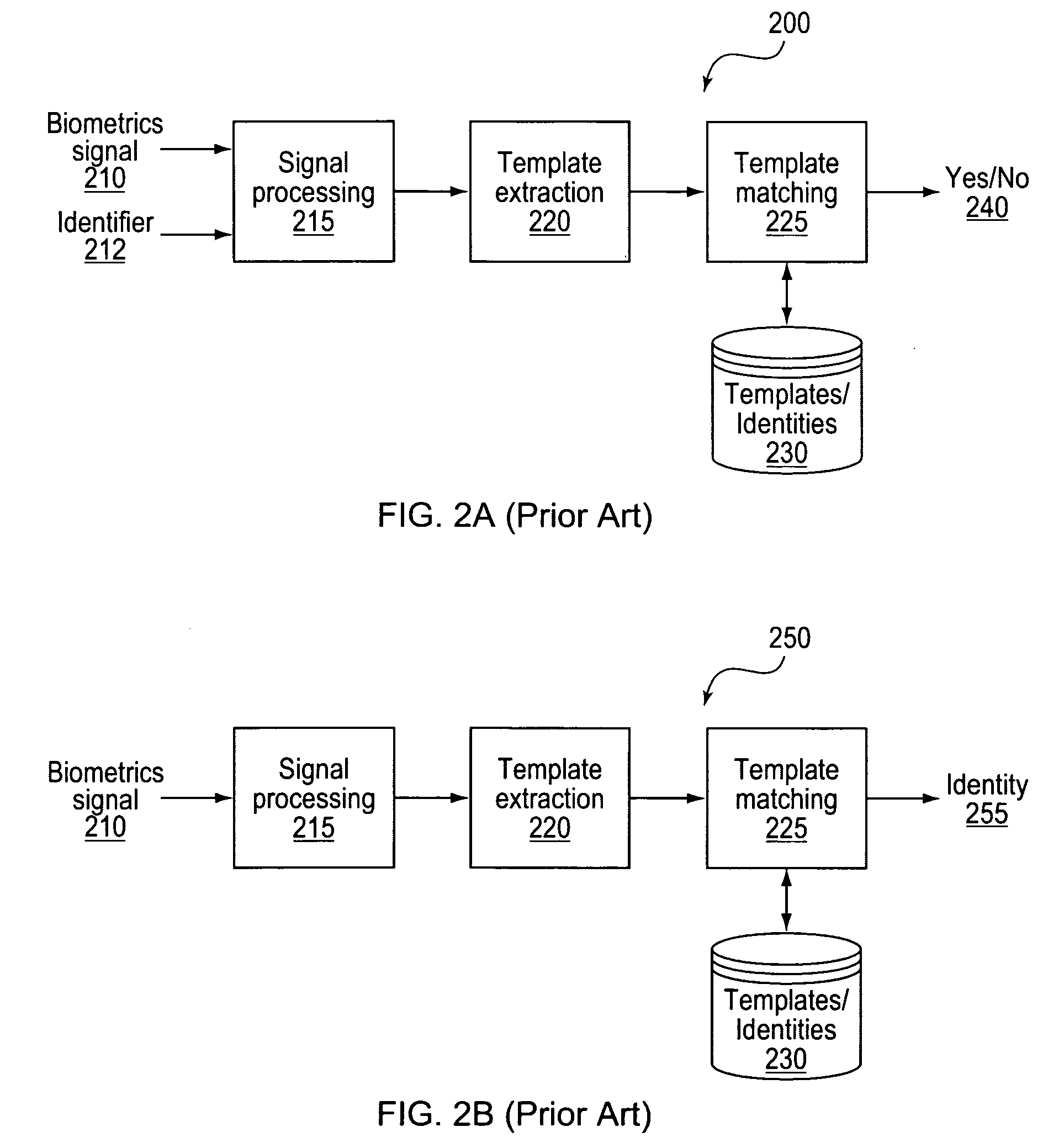
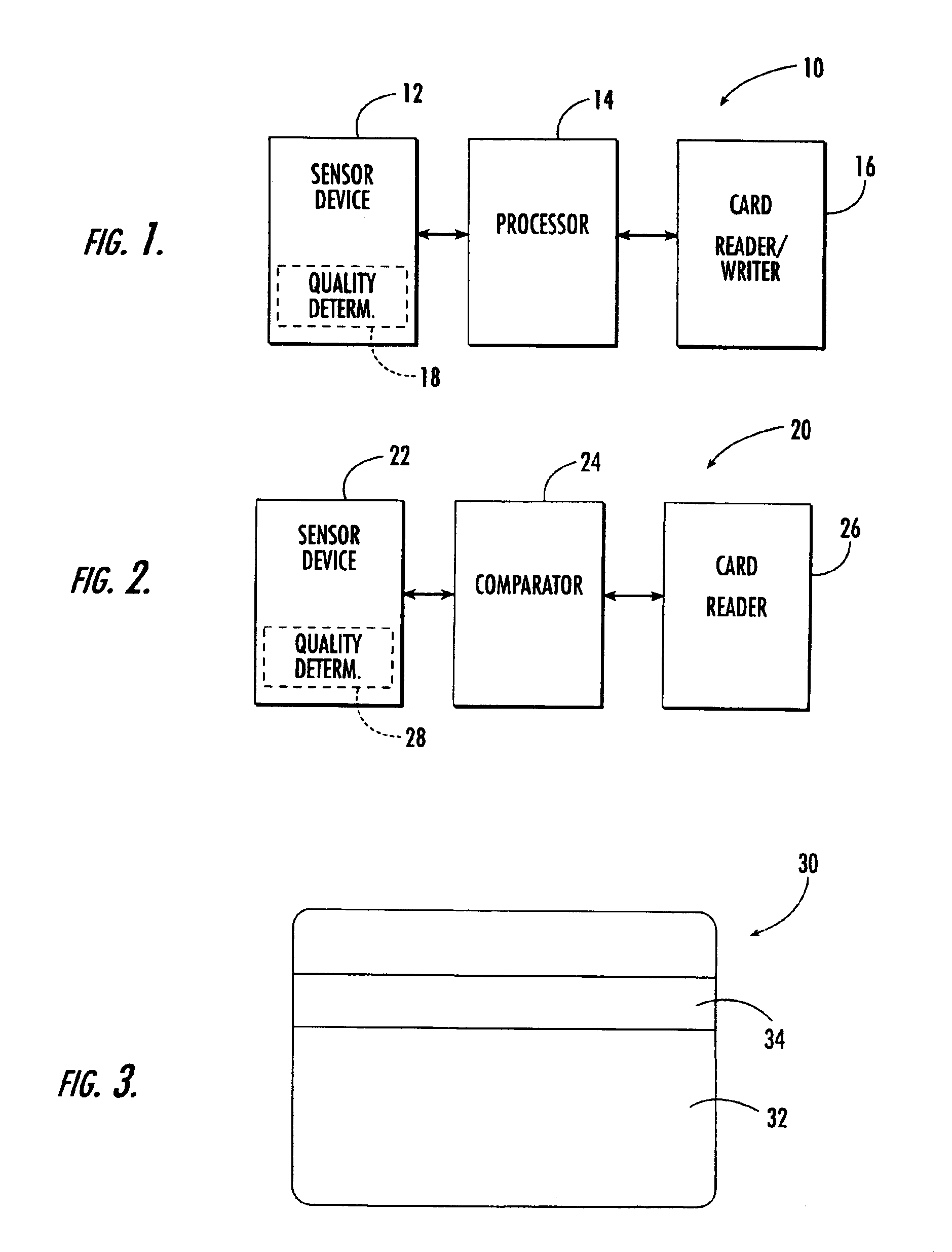
Srivas Chennu. Biometric recognition (also known as biometrics) refers to the automated recognition of individuals based on their biological and behavioral traits (ISO/IEC JTC1 SC37). Examples of biometric traits include fingerprint, face, iris, palmprint, retina, hand geometry, voice, signature and gait.
Method and system for biometric recognition based on electric and/or magnetic characteristics
InactiveUS6898299B1Electric signal transmission systemsDigital data processing detailsElectricityBiological body
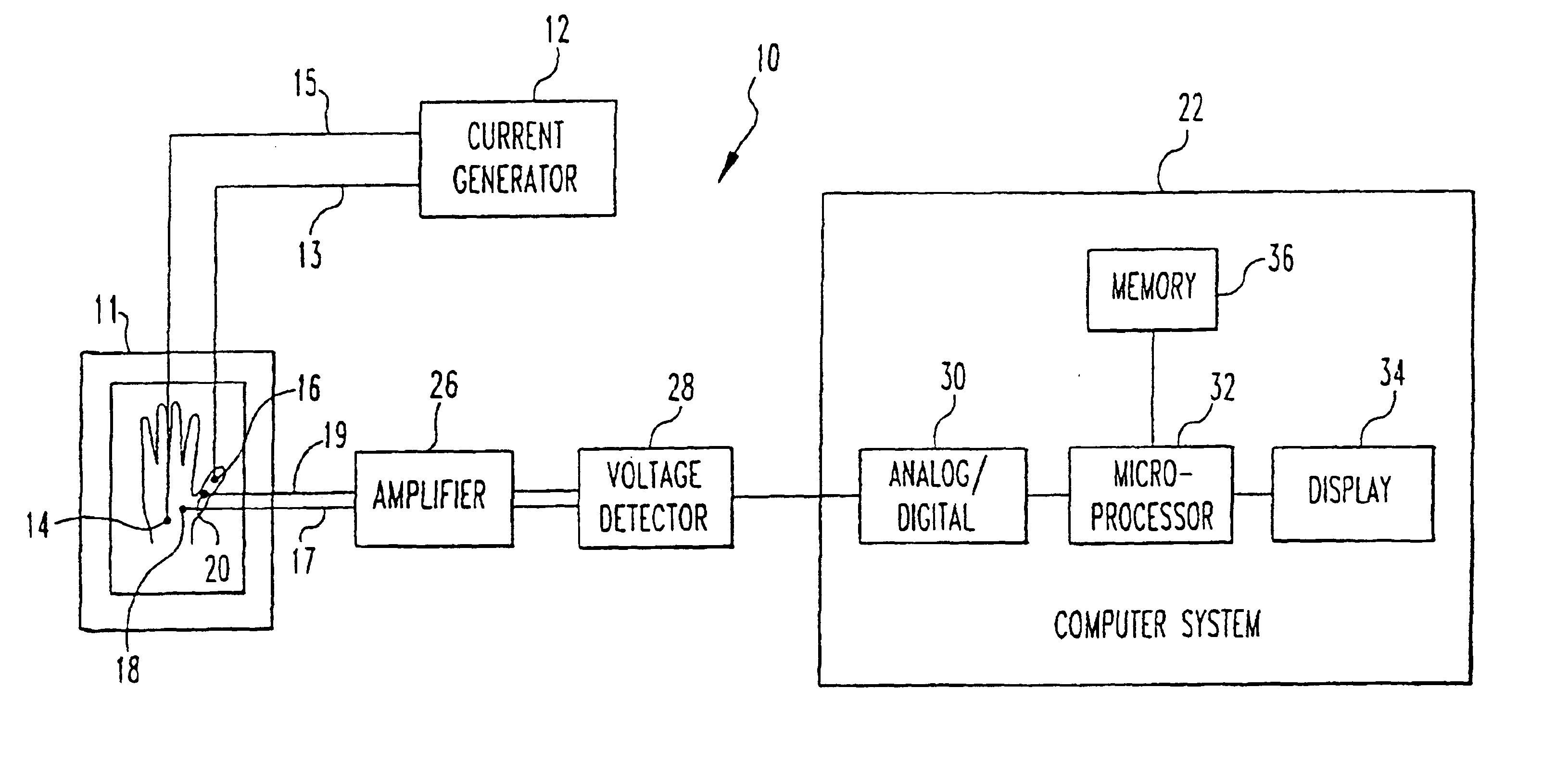
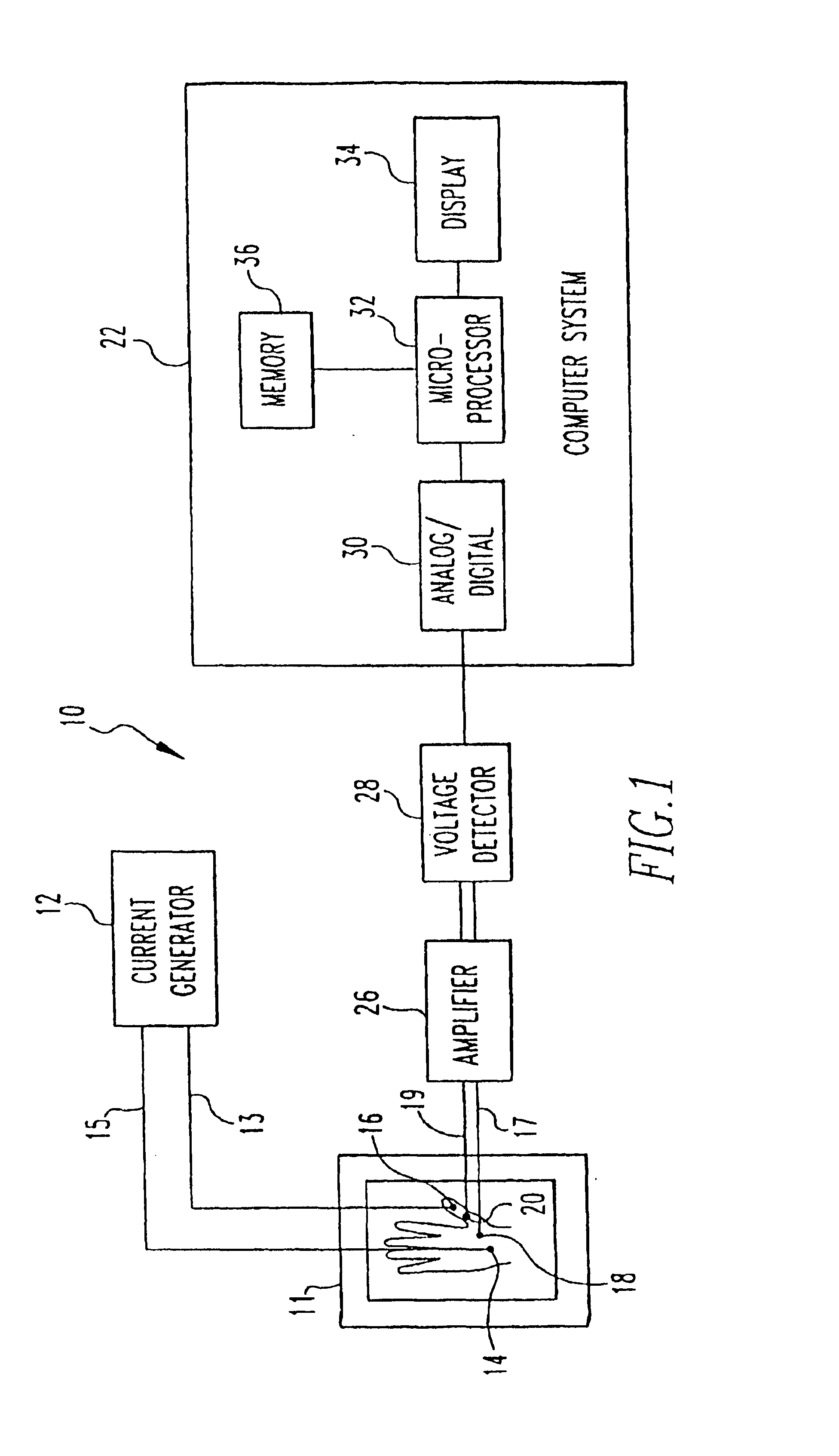
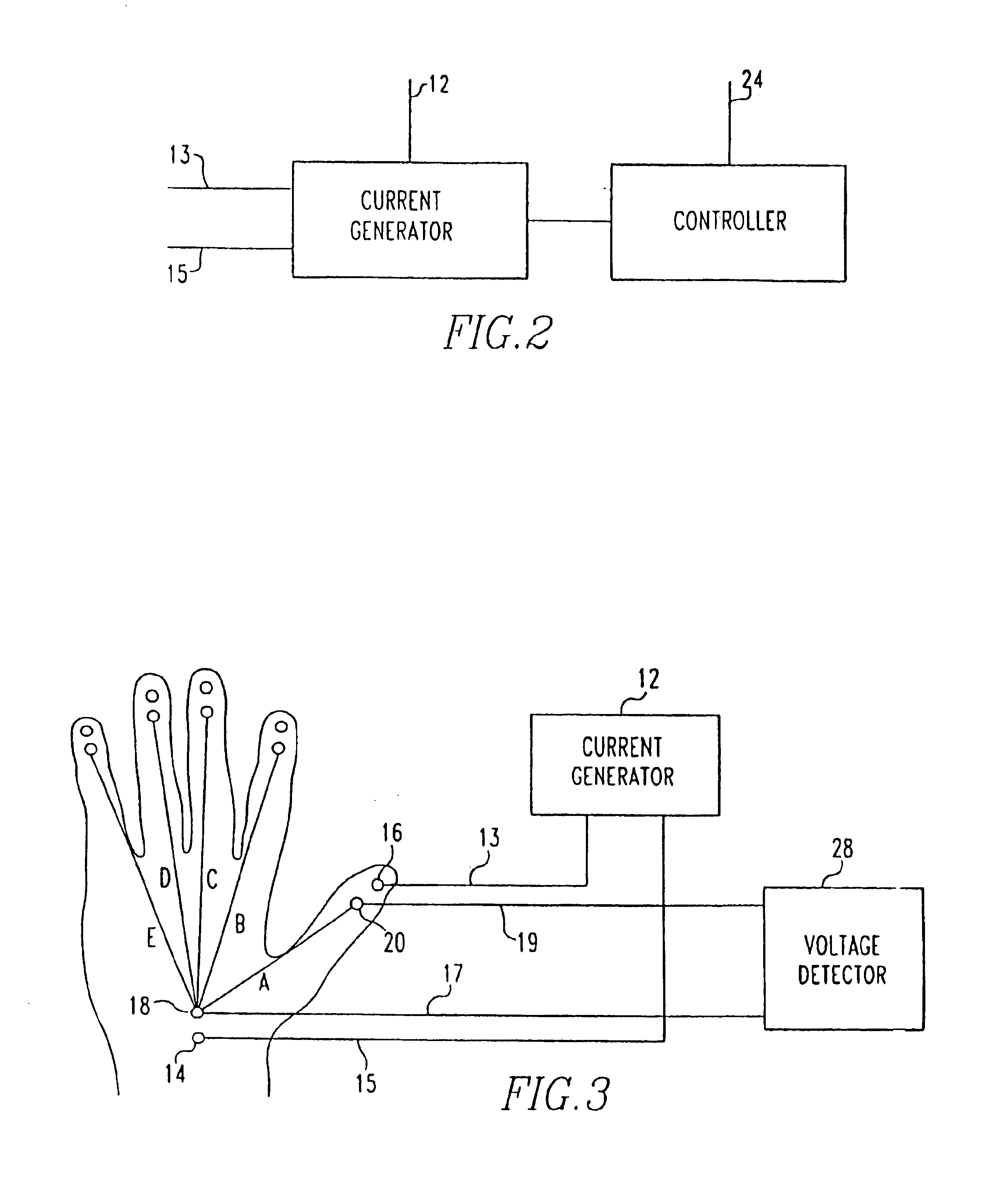
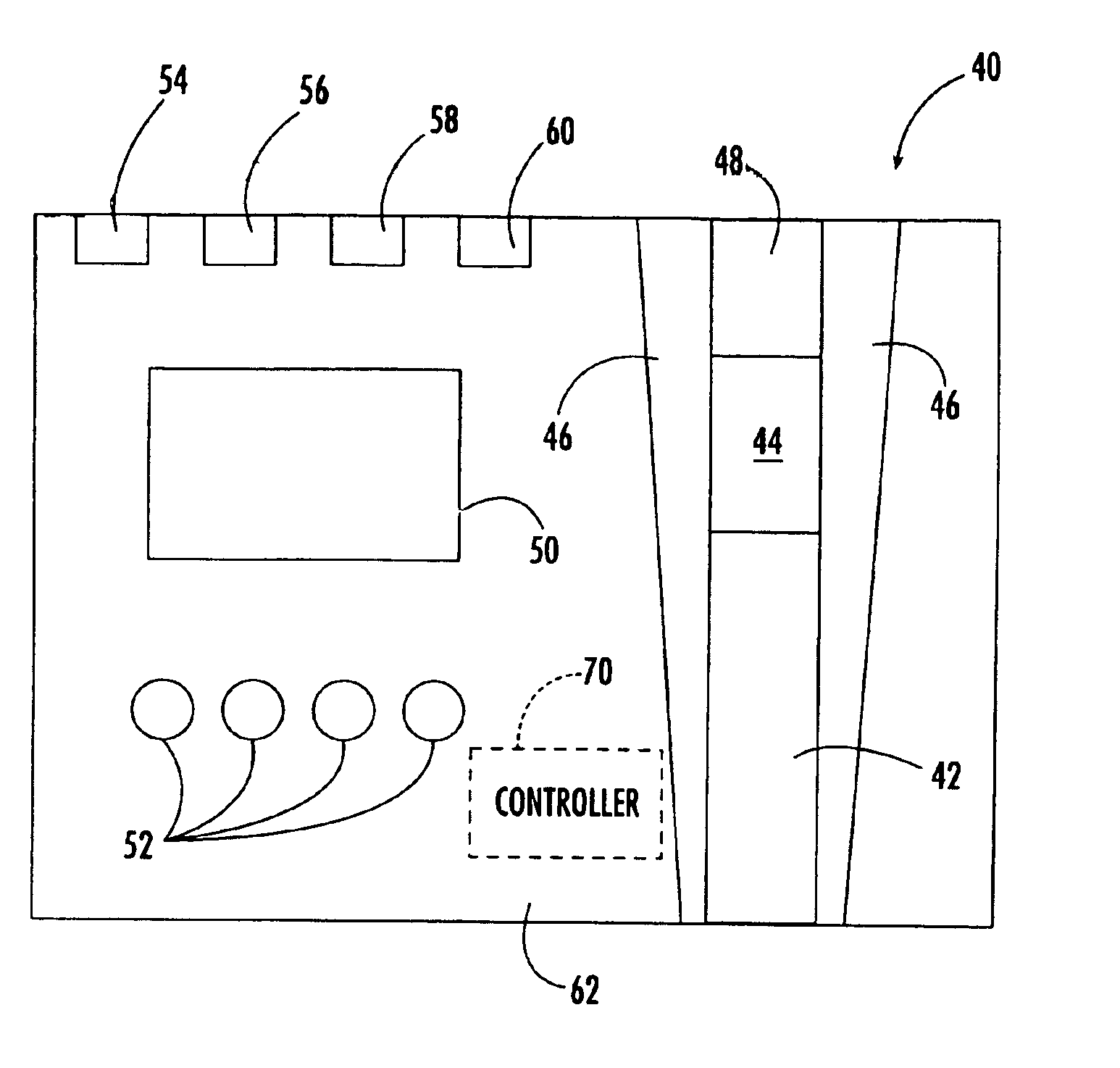
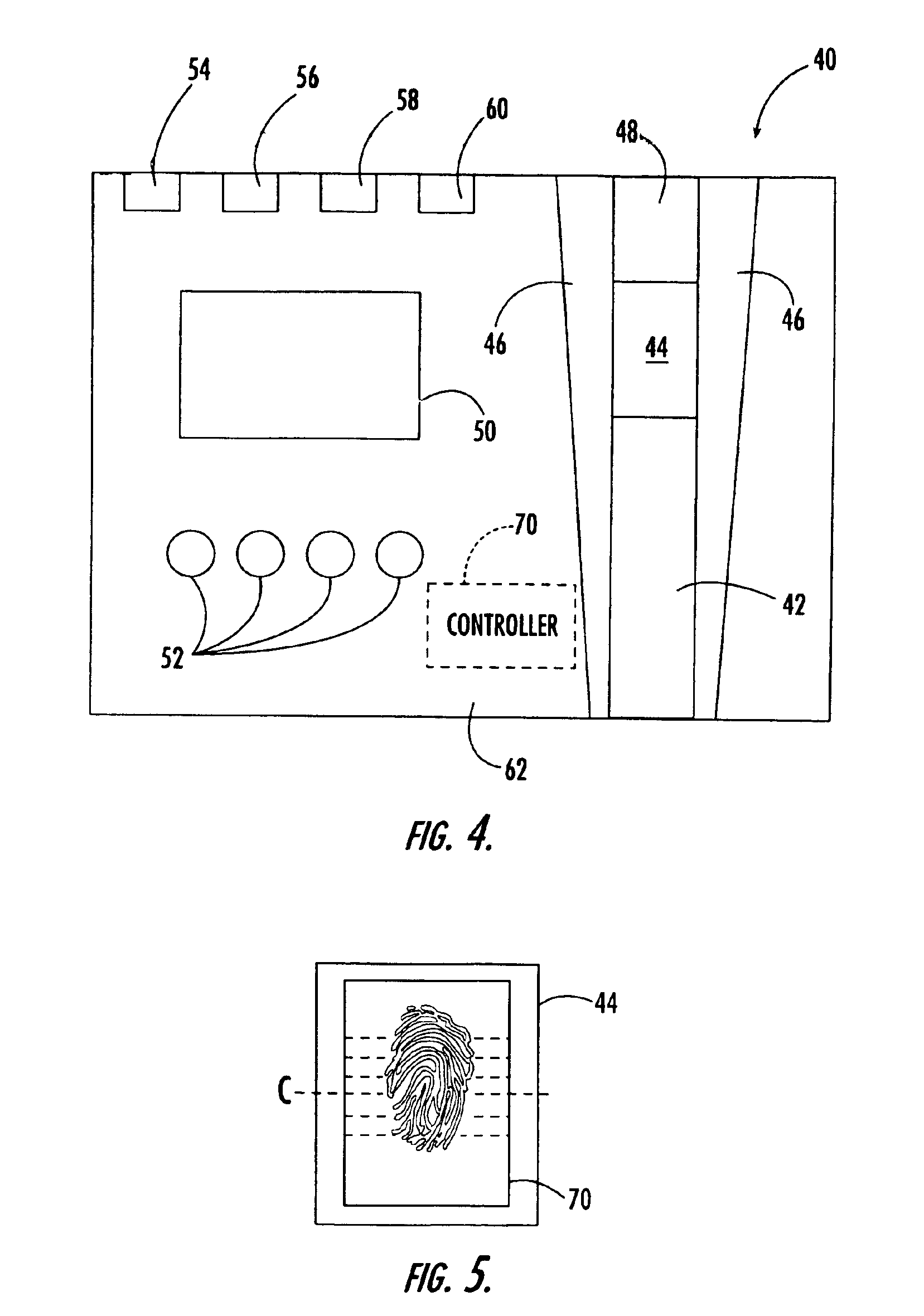
A method and apparatus for authenticating an individual living organism by recognizing a unique internal electric and / or magnetic and / or acoustic characteristic, which comprises a biometric signature, involve presenting a body part to a sensing device that senses the signature. The sensed presented biometric signature is compared to a known biometric signature to authenticate the individual. This authentication can then be used to authorize any of a wide variety of actions by the individual, such as accessing equipment or an area, or to perform actions, such as conducting financial transactions. A card having sensors is used to sense the biometric signature which is read by a card reader and sent to a local or remote reader for biometric signature comparison.
Owner:GR INTELLECTUAL RESERVE LLC
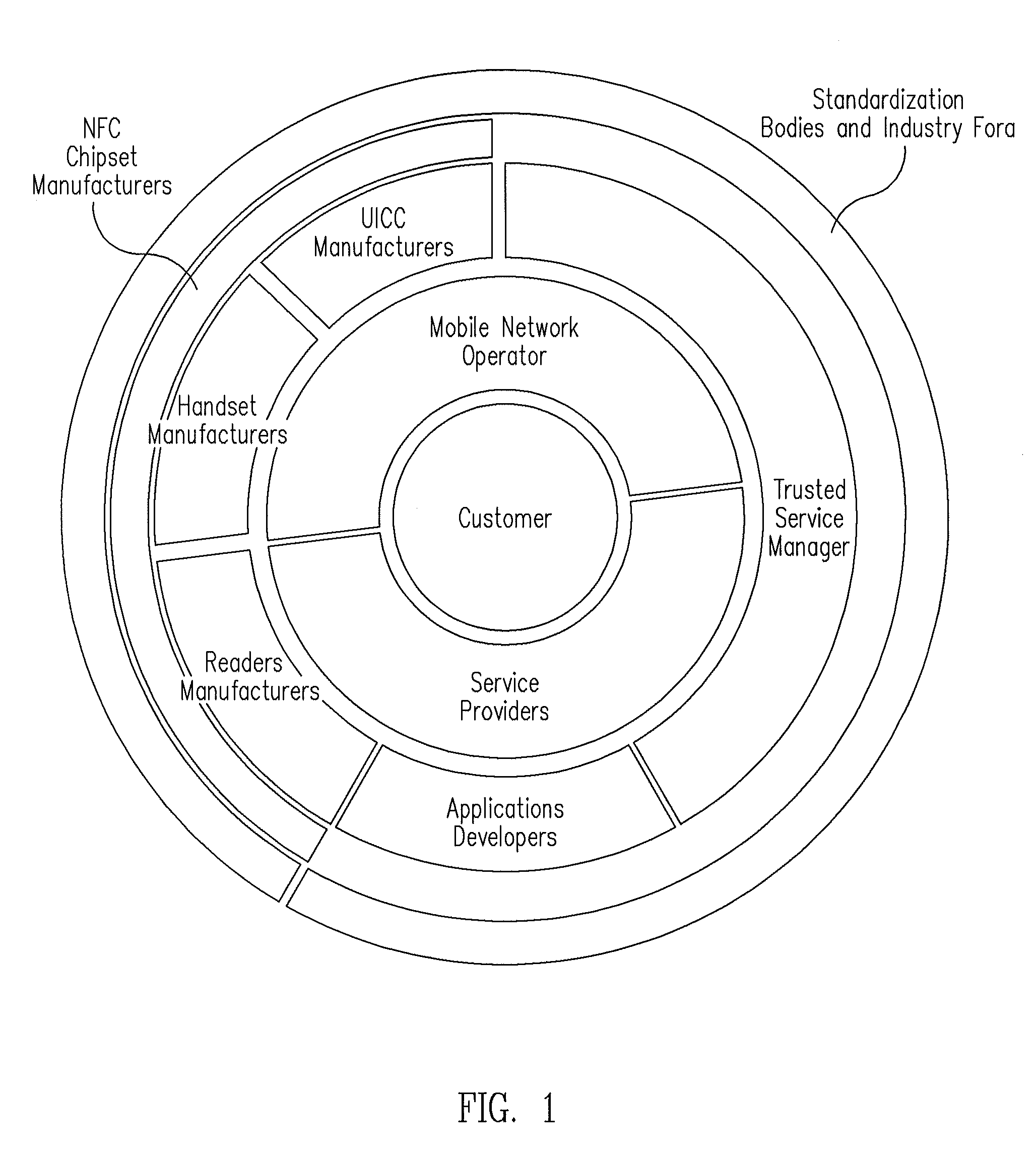
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
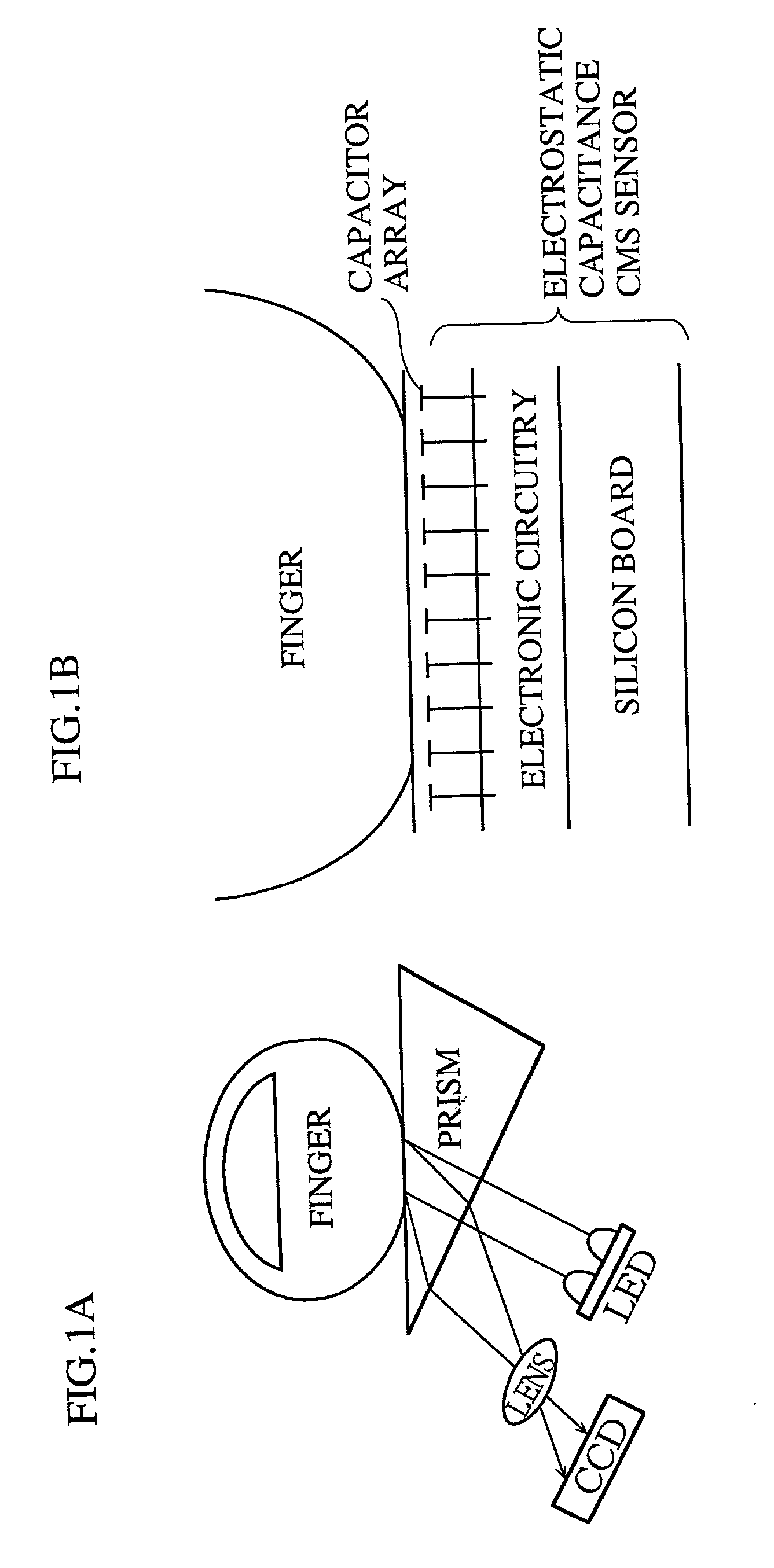
Apparatus for identity verification, a system for identity verification, a card for identity verification and a method for identity verification, based on identification by biometrics
InactiveUS20010026632A1Improve reliabilityLow costImage analysisUser identity/authority verificationCommunication interfaceImaging processing
An identity verification system is used to identify persons with high accuracy, while avoiding direct contact with the device to prevent any negative psychological reaction from a user. The system includes: a camera unit and an image processing unit for obtaining object images of body parts (such as fingerprints and irides) by scanning, without physical contact; an image display unit for displaying layered images of the body part as scanned and a guide showing the body part in an optimal position; a control unit for extracting biometric characteristic data from object images and sending the data to a verification server after encrypting by an encryption unit; and a communications interface unit.
Owner:PANASONIC CORP
Random biometric authentication utilizing unique biometric signatures
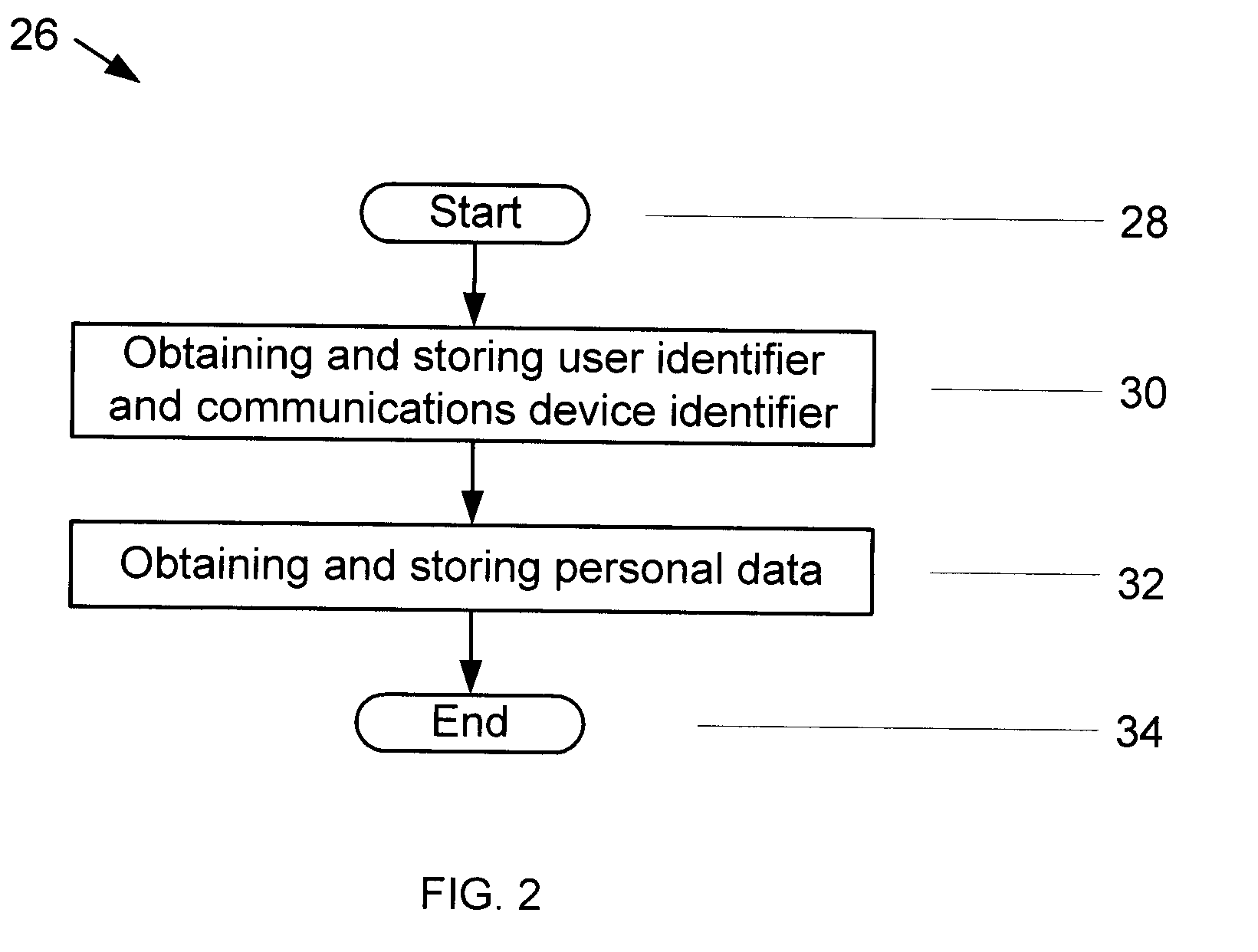
InactiveUS20030163710A1Accurate authenticationSecure user accessDigital data processing detailsUser identity/authority verificationUser inputLayer thickness
A user can be challenged to provide at least one randomly selected biometric attribute. The randomly selected biometric attribute input by the user is automatically compared to a plurality of biometric attributes of the user contained in a user profile. The user can then be authenticated if the randomly selected biometric attribute input by the user matches at least one of the plurality of biometric attributes of the user contained in the user profile. Biometric attributes analyzed according to the methods and systems of the present invention, include, but are not limited to, for example, fingerprints, iris, retina, and / or tissue characteristics, such as skin morphology, skin layer thickness, collage density and orientation, tissue hydration, optical patent length differences, etc.
Owner:IP VENUE LLC
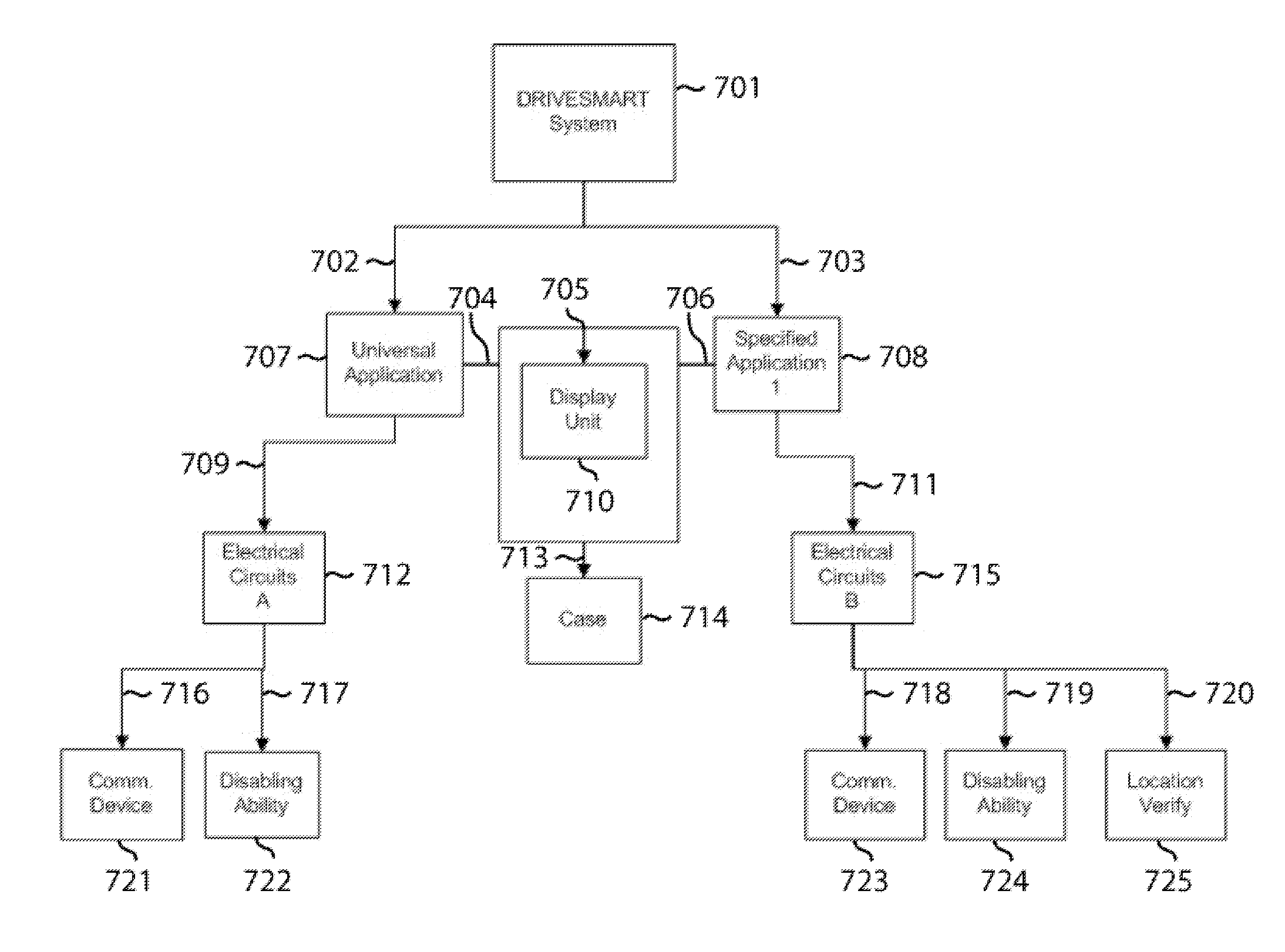
System and method for driver reaction impairment vehicle exclusion via systematic measurement for assurance of reaction time
InactiveUS20110304465A1Prevents DUI without social stigmaAlarmsDriver input parametersDriver/operatorMotor skill
A system and method for measuring impairment in an operator and stopping an impaired operator from operating a vehicle. The method empirically measures an operator's cognitive and motor skills requisite for safely operating a motorized vehicle and verifies the person's identity. The invention includes three interlocking major subsystems. The first subsystem provides generalized impairment measurement unit. The second subsystem interfaces with the impairment measurement unit and a vehicle ignition system and ensures the vehicle does not start if the operator is impaired. The third system determines whether the person blowing into a drug and alcohol analyzer connected to the first system is that person by detecting a various biometric. If the operator is not impaired and their identity is verified the vehicle ignition is enabled. If the operator is indeed impaired beyond a level requisite to safely operate the vehicle the ignition is disabled.
Owner:BOULT TERRANCE E +1
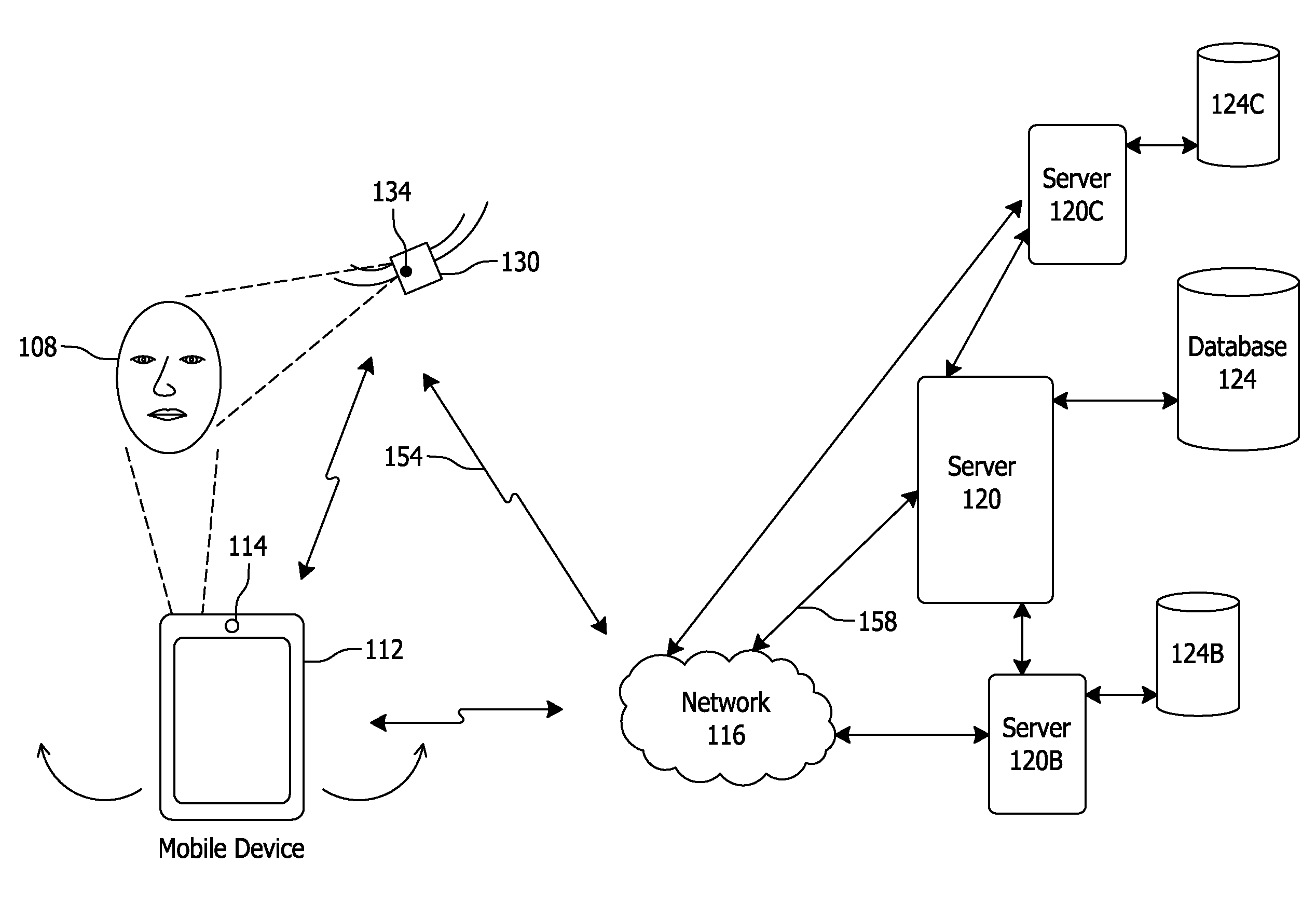
Facial Recognition Authentication System Including Path Parameters
ActiveUS20160063235A1Improve securityAuthorization may be expandedDigital data processing detailsMultiple digital computer combinationsInternet privacyAuthentication system
Systems and methods for enrolling and authenticating a user in an authentication system via a user's camera of camera equipped mobile device include capturing and storing enrollment biometric information from at least one first image of the user taken via the camera of the mobile device, capturing authentication biometric information from at least one second image of the user, capturing, during imaging of the at least one second image, path parameters via at least one movement detecting sensor indicating an authentication movement of the mobile device, comparing the authentication biometric information to the stored enrollment biometric information, and comparing the authentication movement of the mobile device to an expected movement of the mobile device to determine whether the authentication movement sufficiently corresponds to the expected movement.
Owner:FACETEC INC
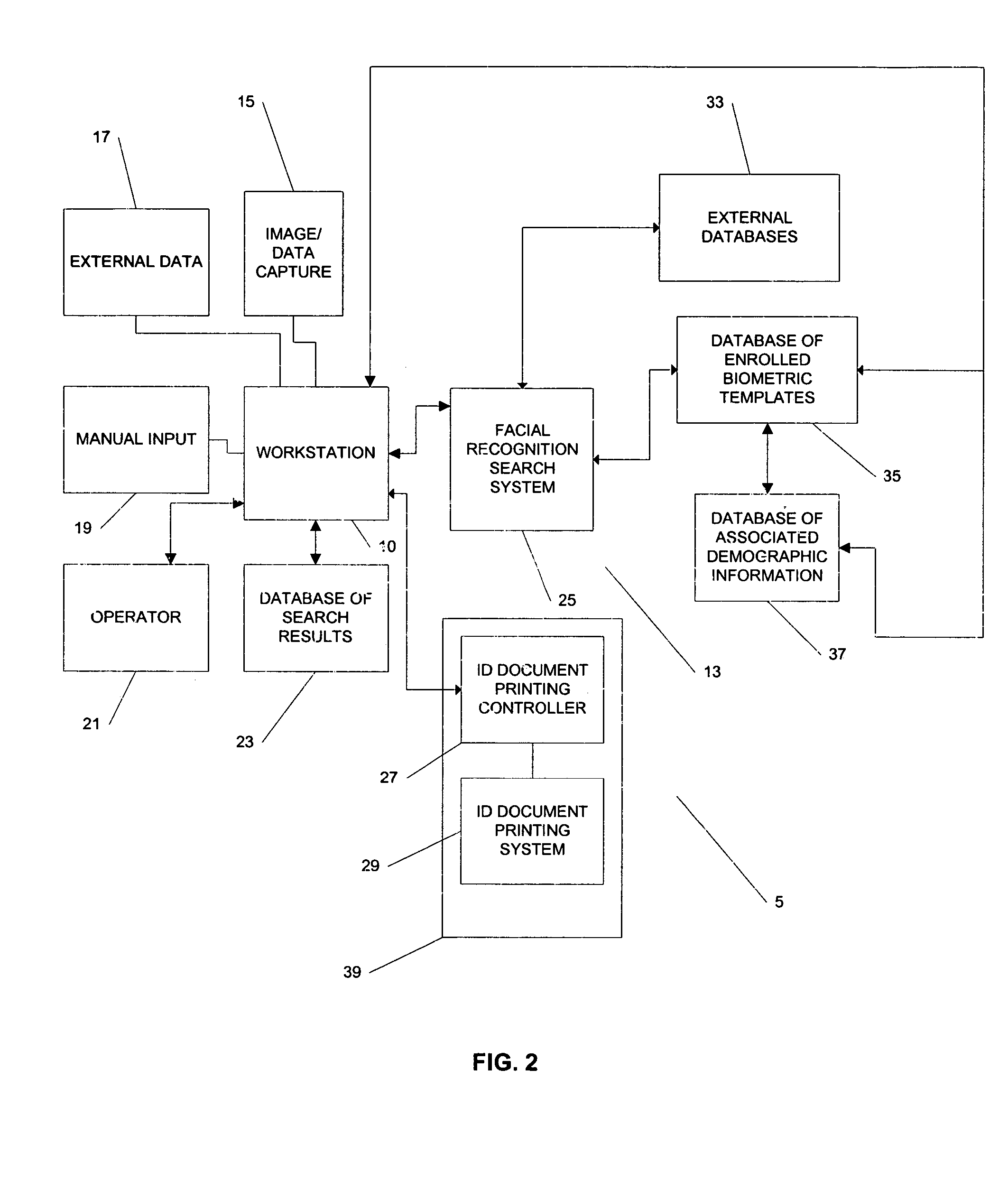
Systems and methods for managing and detecting fraud in image databases used with identification documents
ActiveUS7804982B2Prevent fraudReduce theftCharacter and pattern recognitionIndividual entry/exit registersDocument preparationWorkstation
We provide a system for issuing identification documents to a plurality of individuals, comprising a first database, a first server, and a workstation. The first database stores a plurality of digitized images, each digitized image comprising a biometric image of an individual seeking an identification document. The first server is in operable communication with the first database and is programmed to send, at a predetermined time, one or more digitized images from the first database to a biometric recognition system, the biometric recognition system in operable communication with a second database, the second database containing biometric templates associated with individuals whose images have been previously captured, and to receive from the biometric recognition system, for each digitized image sent, an indicator, based on the biometric searching of the second database, as to whether the second database contains any images of individuals who may at least partially resemble the digitized image that was sent. The a workstation is in operable communication with the first server and is configured to permit a user to review the indicator and to make a determination as to whether the individual is authorized to be issued an identification document or to keep an identification document in the individual's possession.
Owner:L 1 SECURE CREDENTIALING
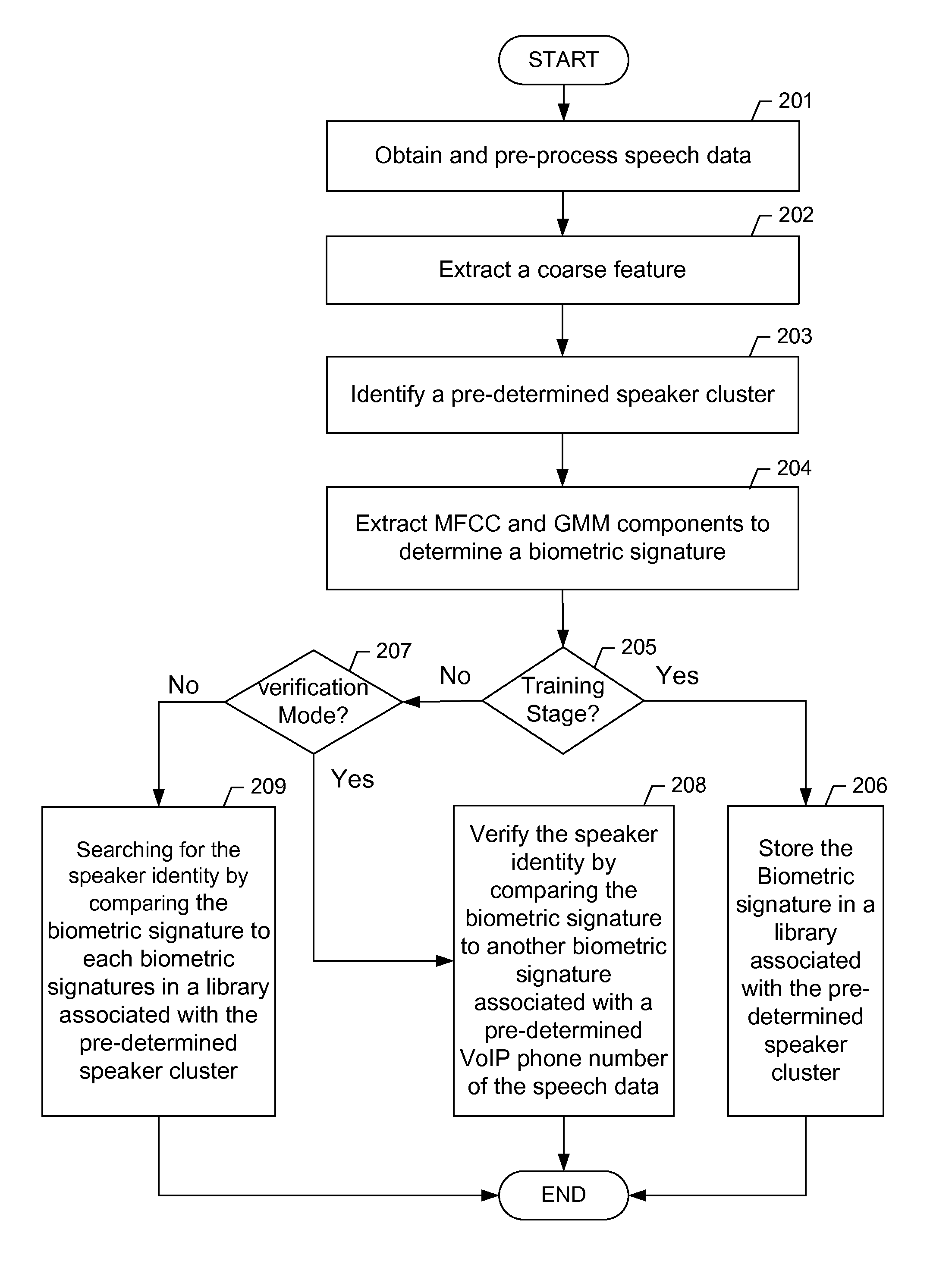
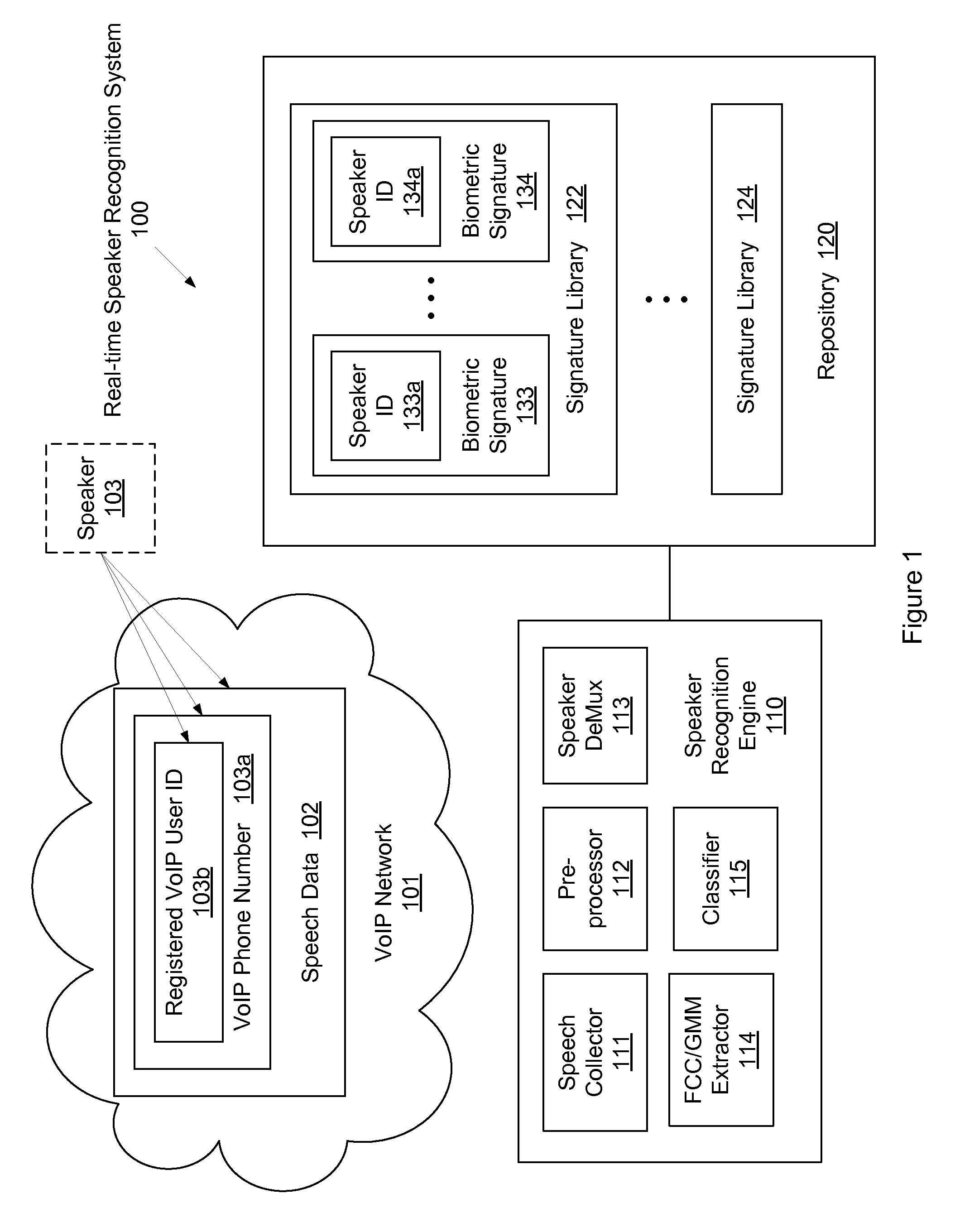
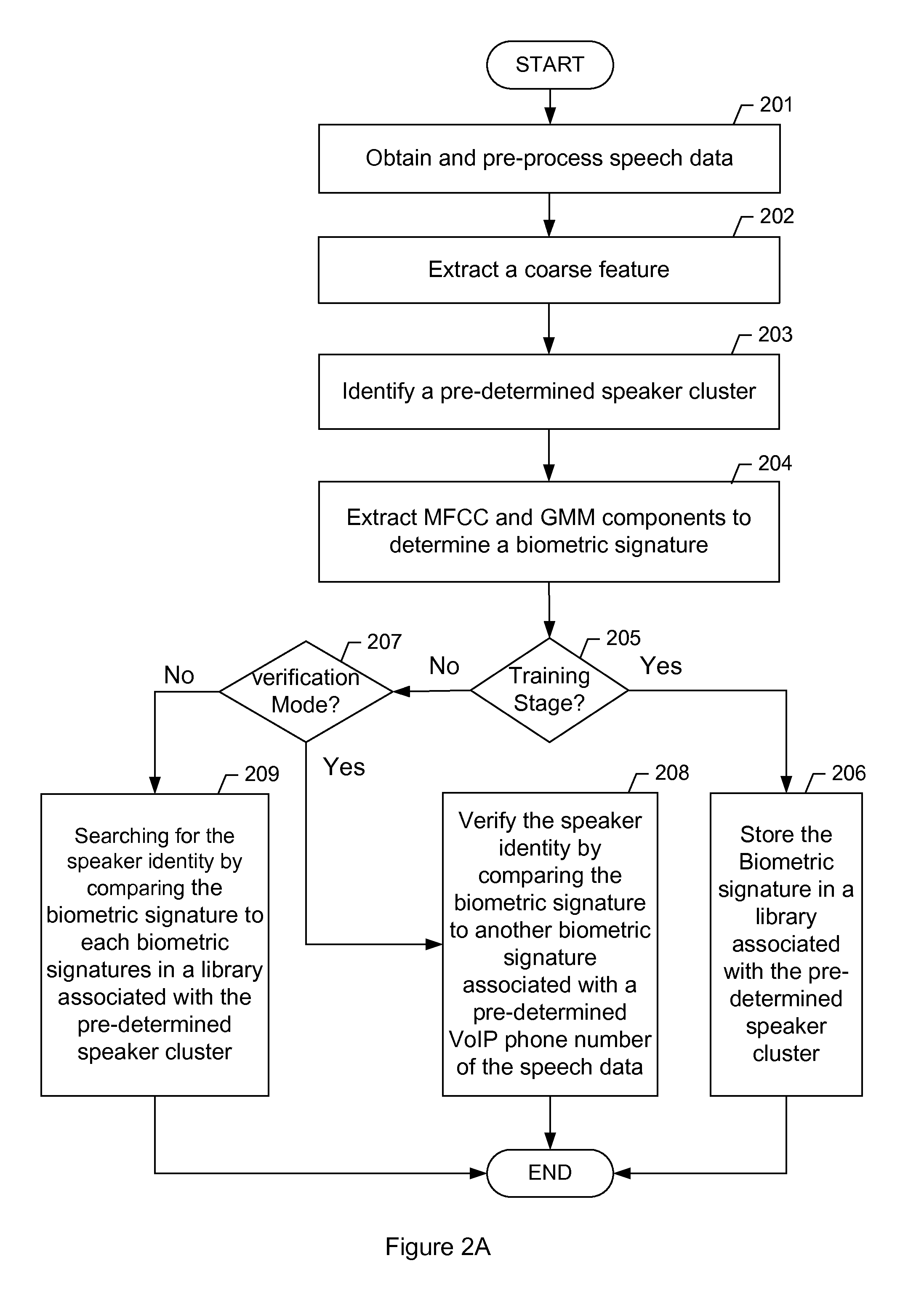
Hierarchical real-time speaker recognition for biometric VoIP verification and targeting
A method for real-time speaker recognition including obtaining speech data of a speaker, extracting, using a processor of a computer, a coarse feature of the speaker from the speech data, identifying the speaker as belonging to a pre-determined speaker cluster based on the coarse feature of the speaker, extracting, using the processor of the computer, a plurality of Mel-Frequency Cepstral Coefficients (MFCC) and a plurality of Gaussian Mixture Model (GMM) components from the speech data, determining a biometric signature of the speaker based on the plurality of MFCC and the plurality of GMM components, and determining in real time, using the processor of the computer, an identity of the speaker by comparing the biometric signature of the speaker to one of a plurality of biometric signature libraries associated with the pre-determined speaker cluster.
Owner:THE BOEING CO
System and method for enabling continuous or instantaneous identity recognition based on physiological biometric signals
ActiveUS20140188770A1Medical data miningPerson identificationPattern recognitionIdentity recognition
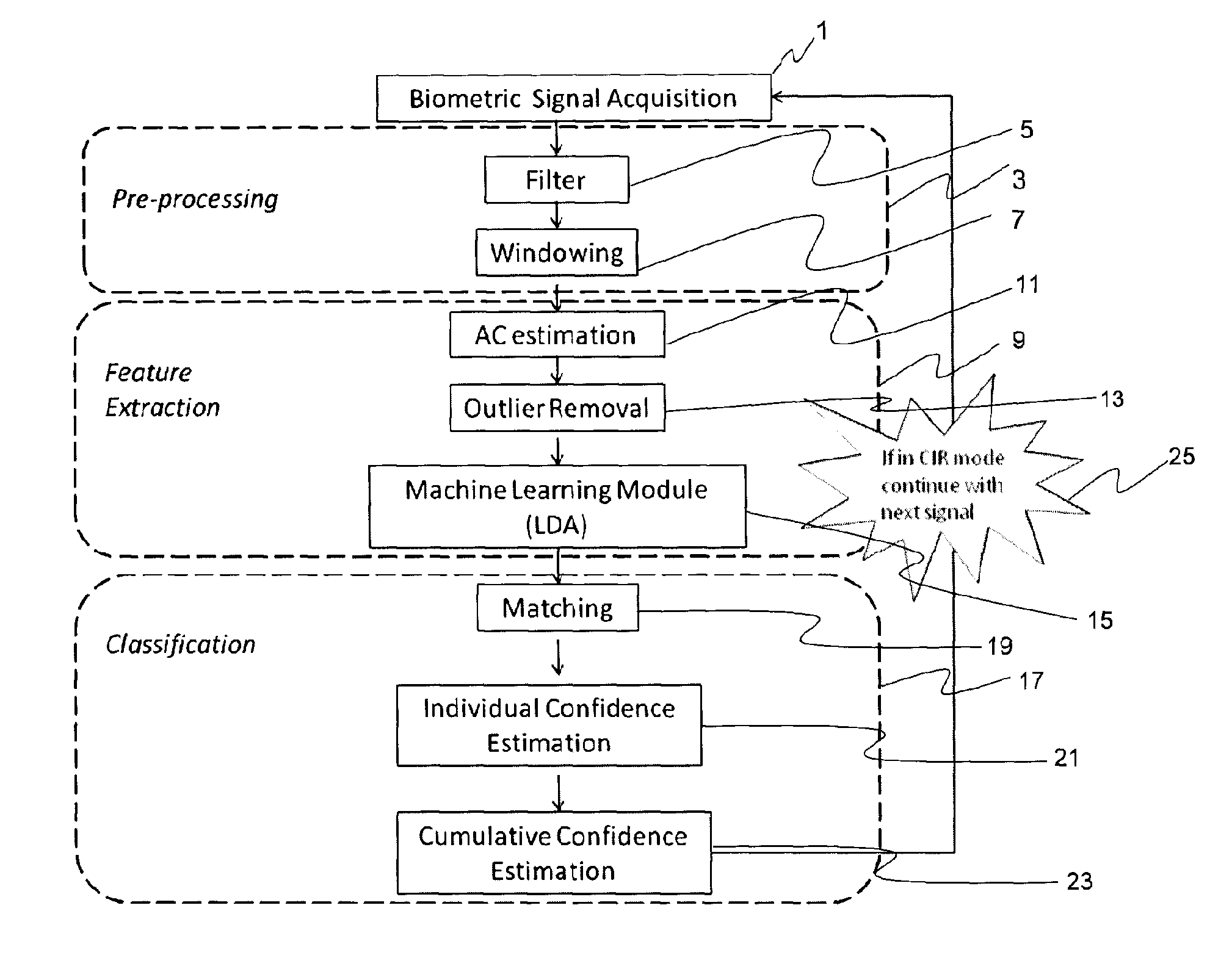
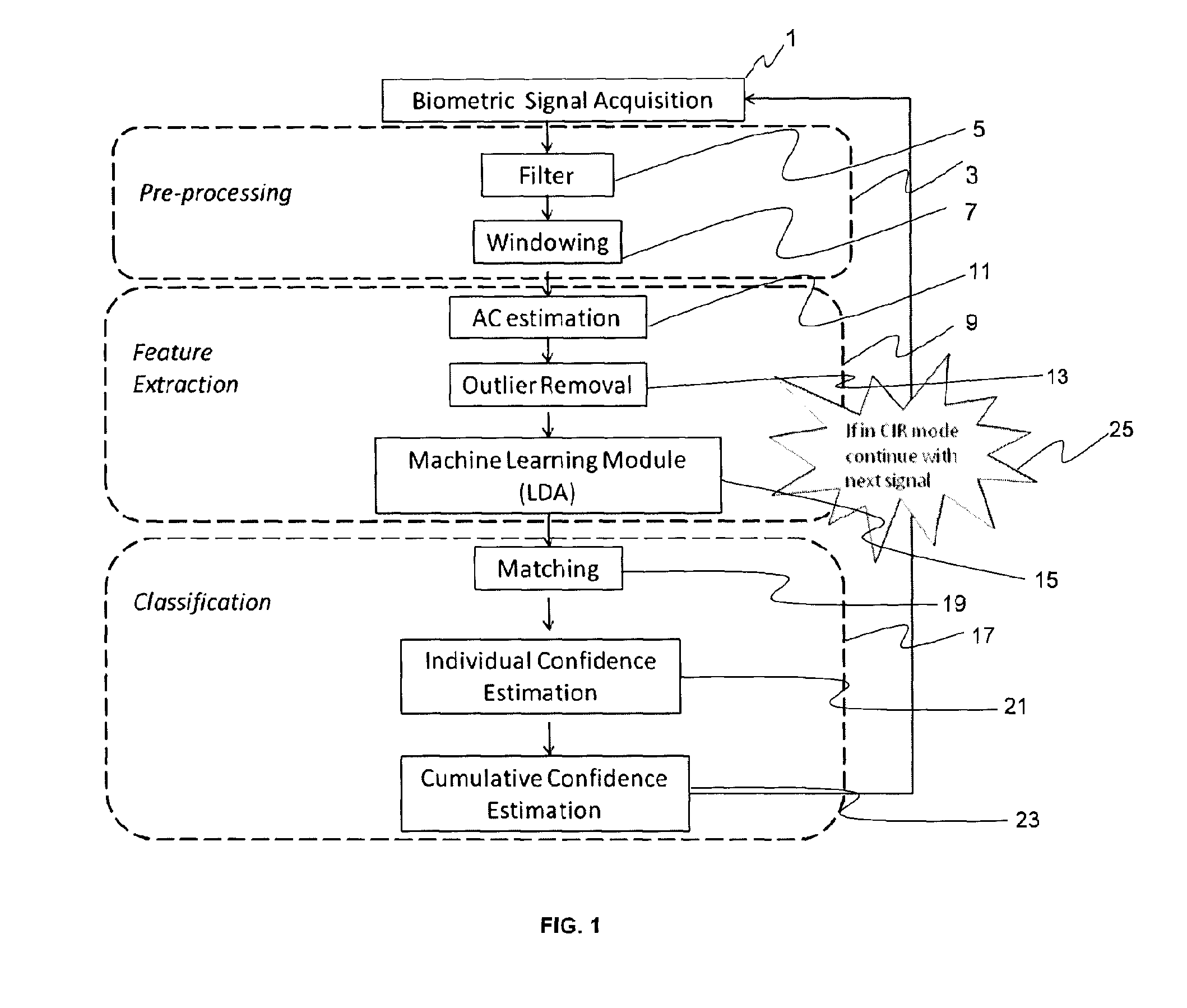
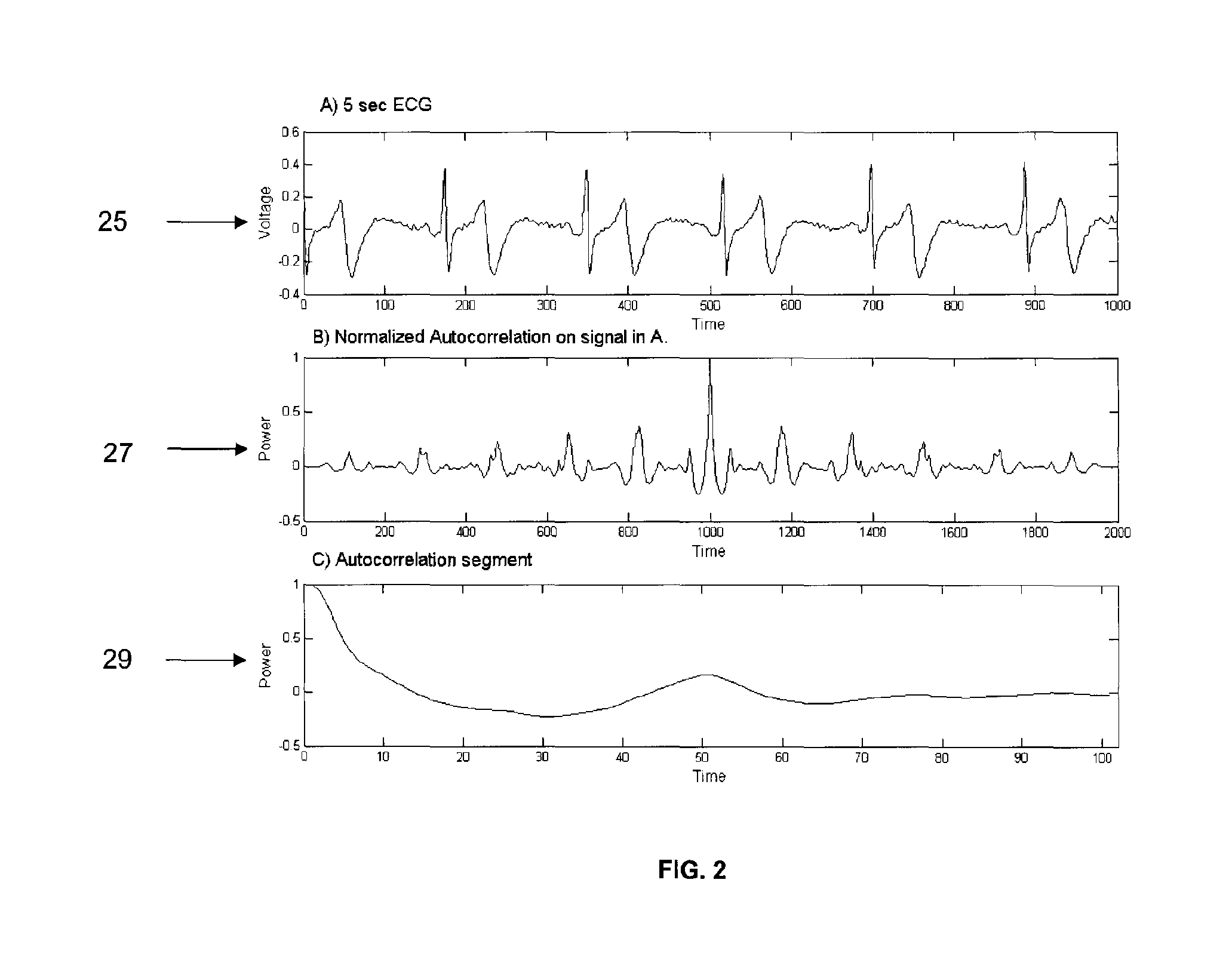
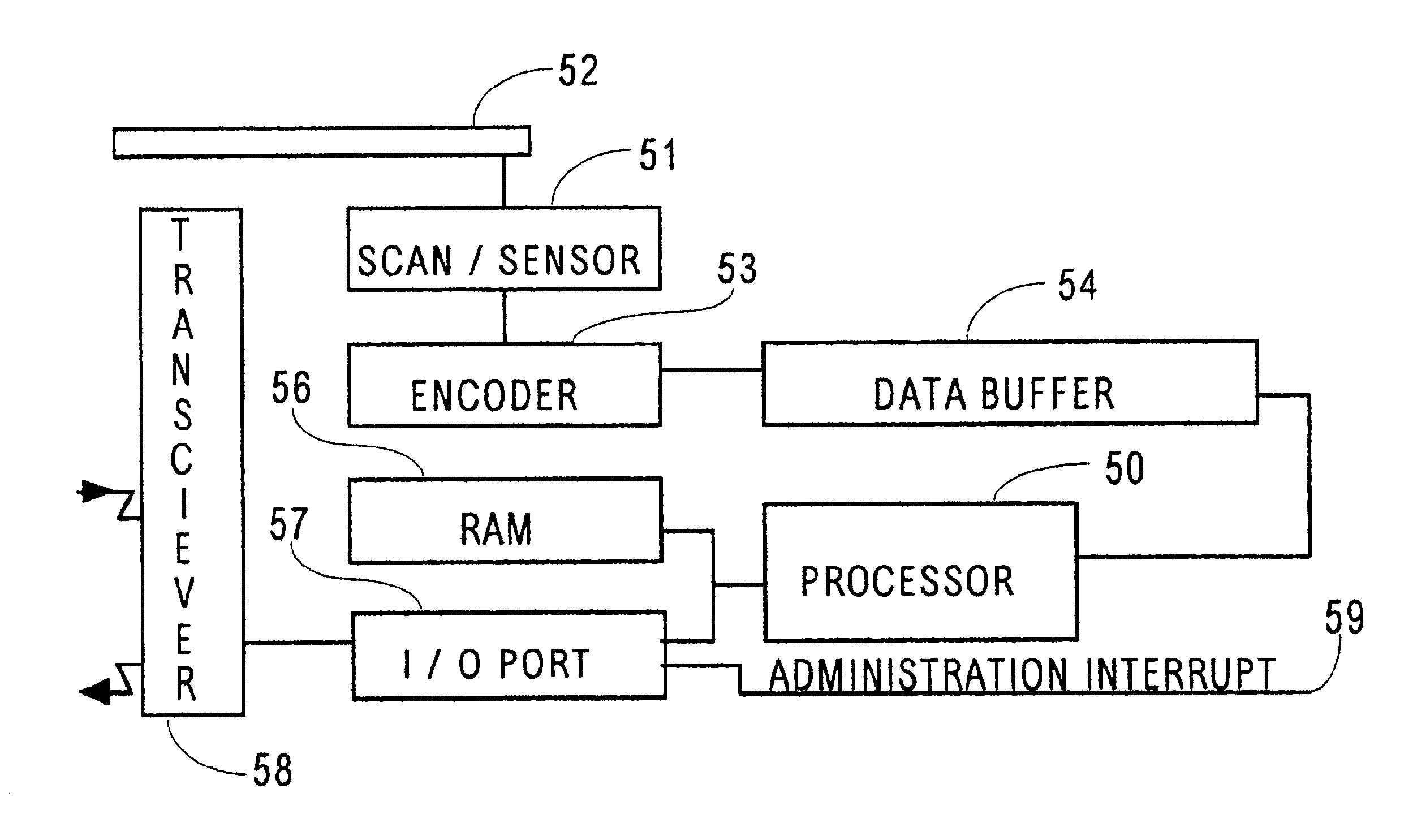
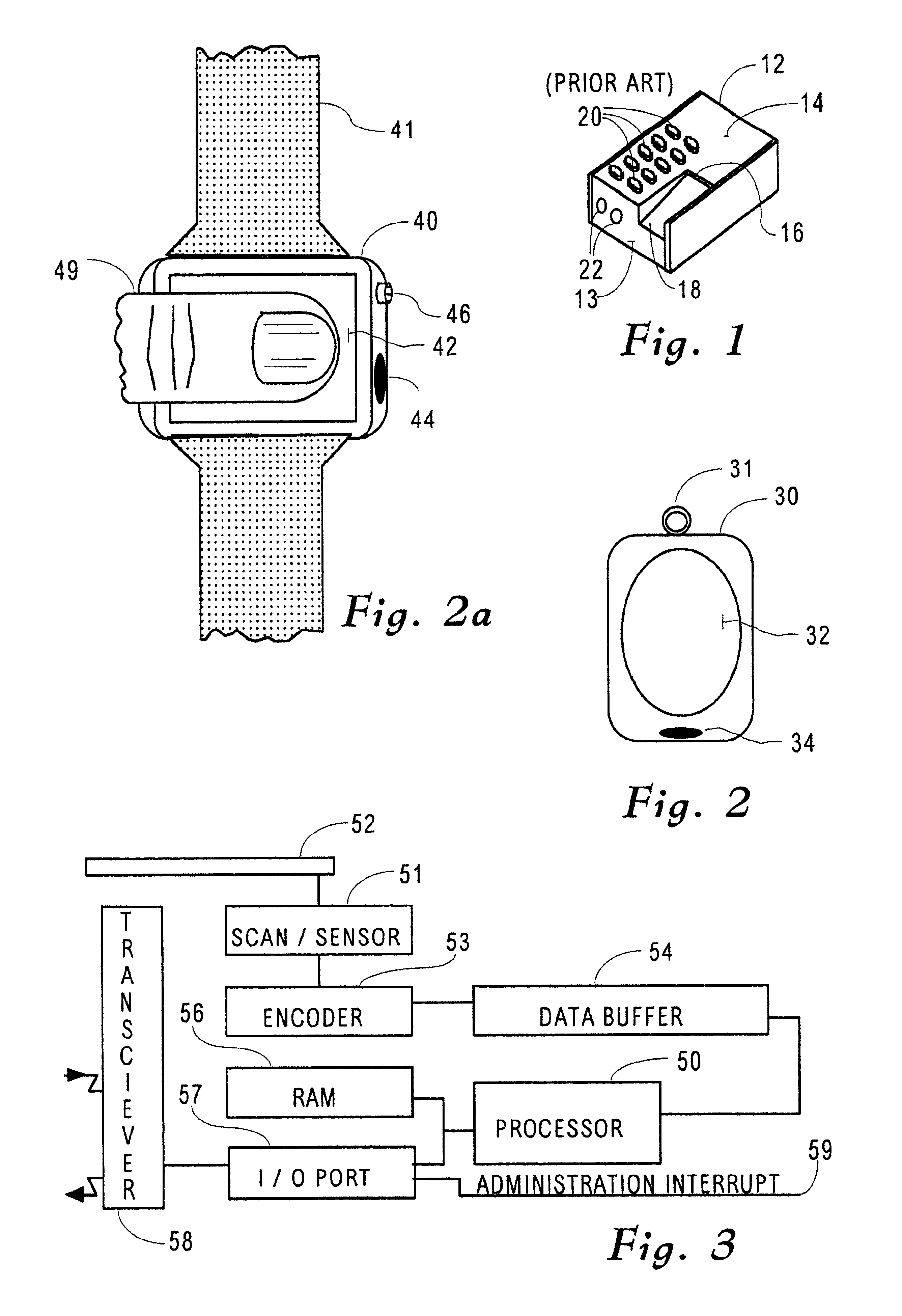
The present invention is a biometric security system and method operable to authenticate one or more individuals using physiological signals. The method and system may comprise one of the following modes: instantaneous identity recognition (MR); or continuous identity recognition (CIR). The present invention may include a methodology and framework for biometric recognition using physiological signals and may utilize a machine learning utility. The machine learning utility may be presented and adapted to the needs of different application environments which constitute different application frameworks. The present invention may further incorporate a method and system for continuous authentication using physiological signals and a means of estimating relevant parameters.
Owner:NYMI
Methods and systems for authenticating users
ActiveUS20110035788A1Reduce transaction riskReduce riskDigital data processing detailsUser identity/authority verificationWorkstationOne-time password
A method of authenticating users to reduce transaction risks includes indicating a desire to conduct a transaction, inputting information in a workstation, and determining whether the inputted information is known. Moreover, the method includes determining a state of a communications device when the inputted information is known, and transmitting a biometric authentication request from a server to an authentication system when the state of the communications device is enrolled. Additionally, the method includes obtaining biometric authentication data in accordance with a biometric authentication data capture request with the communications device, biometrically authenticating the user, generating a one-time pass-phrase and storing the one-time pass-phrase on the authentication system when the user is authenticated, comparing the transmitted one-time pass-phrase against the stored one-time pass-phrase, and conducting the transaction when the transmitted and stored one-time pass-phrases match.
Owner:DAON TECH
Security access method and apparatus
InactiveUS6877097B2Electric signal transmission systemsDigital data processing detailsComputer hardwareWireless transmission
Owner:ACTIVIDENTITY
Identity verification system
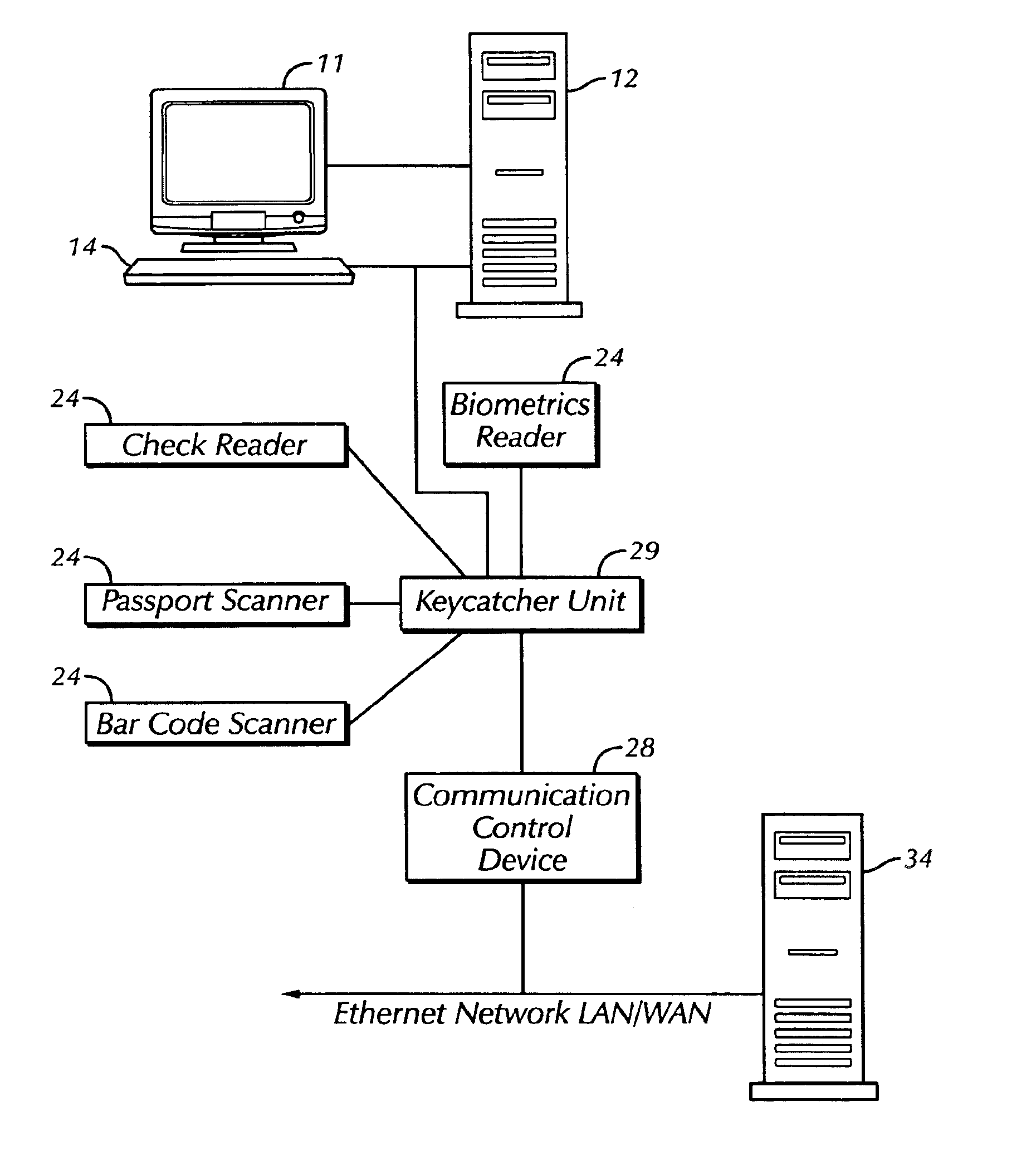
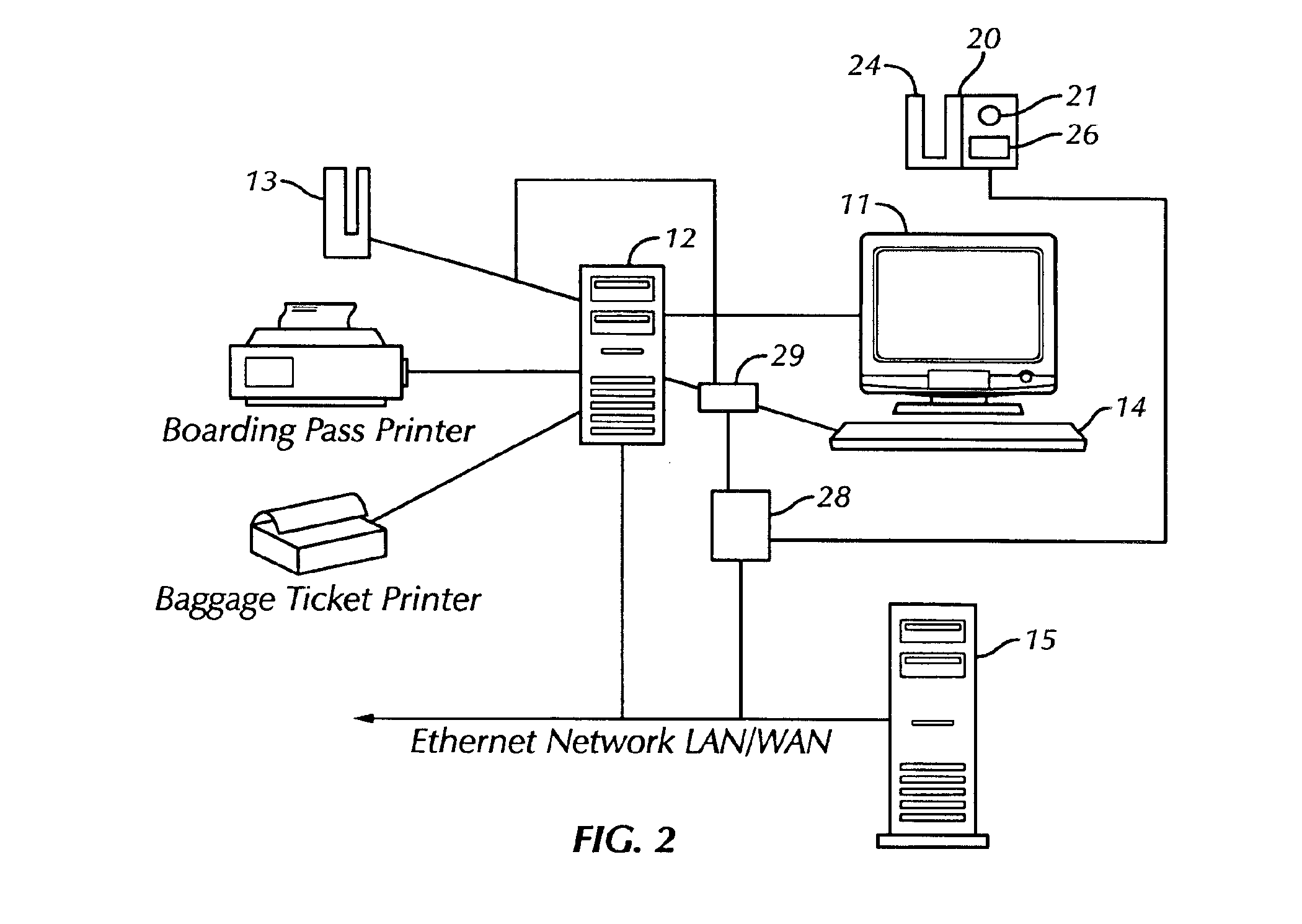
The present invention is a security system that utilizes an identity verification system having a biometrics component, such as but not limited to a face, fingerprint, or iris recognition system. The system connects a biometric data entry device such as a standard analogue or digital camera to a communication control device which captures, compresses and digitizes the biometric data as well as converts data from data input devices and sends the compressed and digitized biometric data along with the data from a data input device to a central processing unit for processing by a biometric recognition system and comparison to stored biometric data.
Owner:BIOCOM
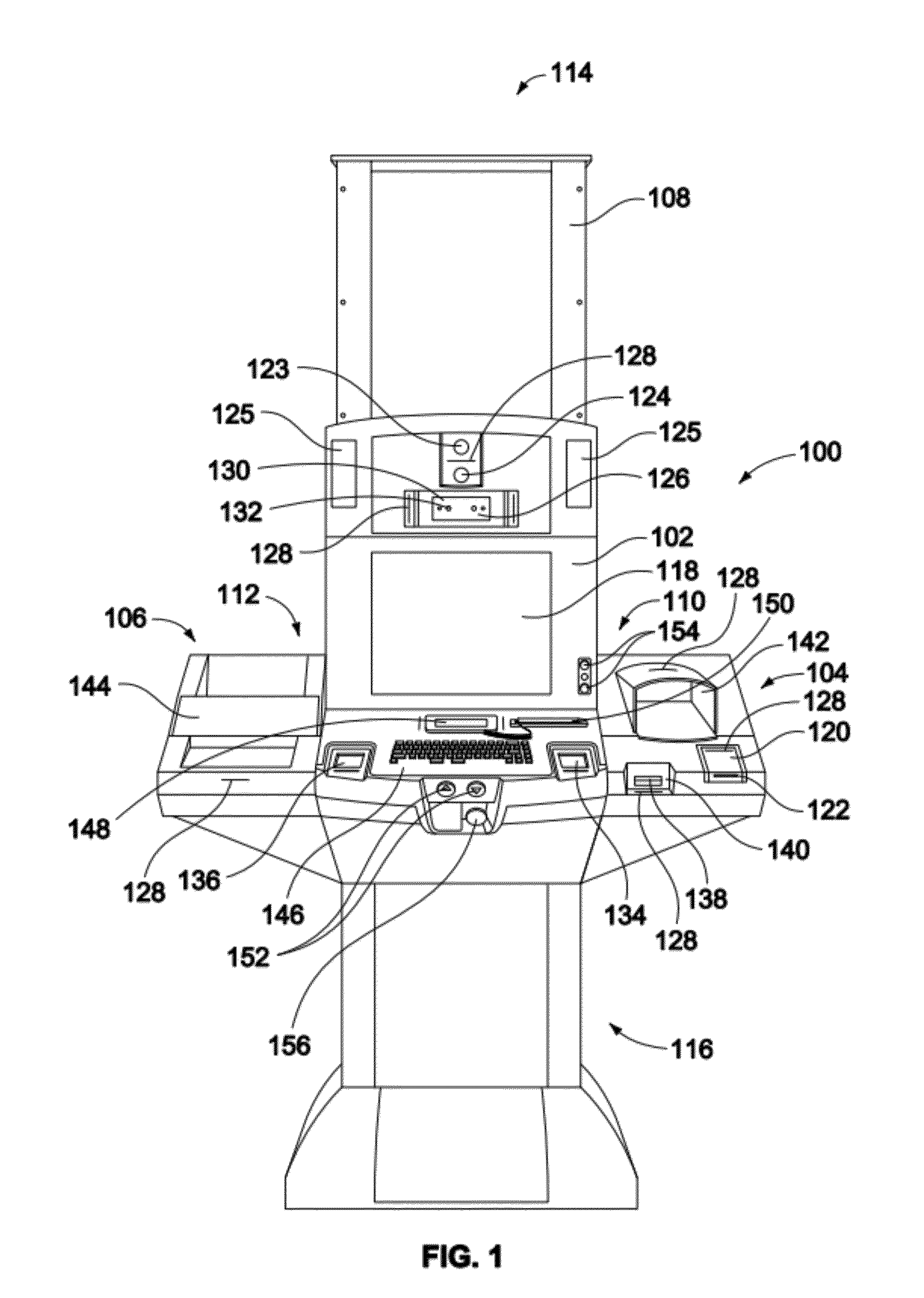
Multi-biometric enrollment kiosk including biometric enrollment and verification, face recognition and fingerprint matching systems
ActiveUS20120293642A1Easy to transportEasy to installDigital data processing detailsAnalogue secracy/subscription systemsComputer scienceEmbedded system
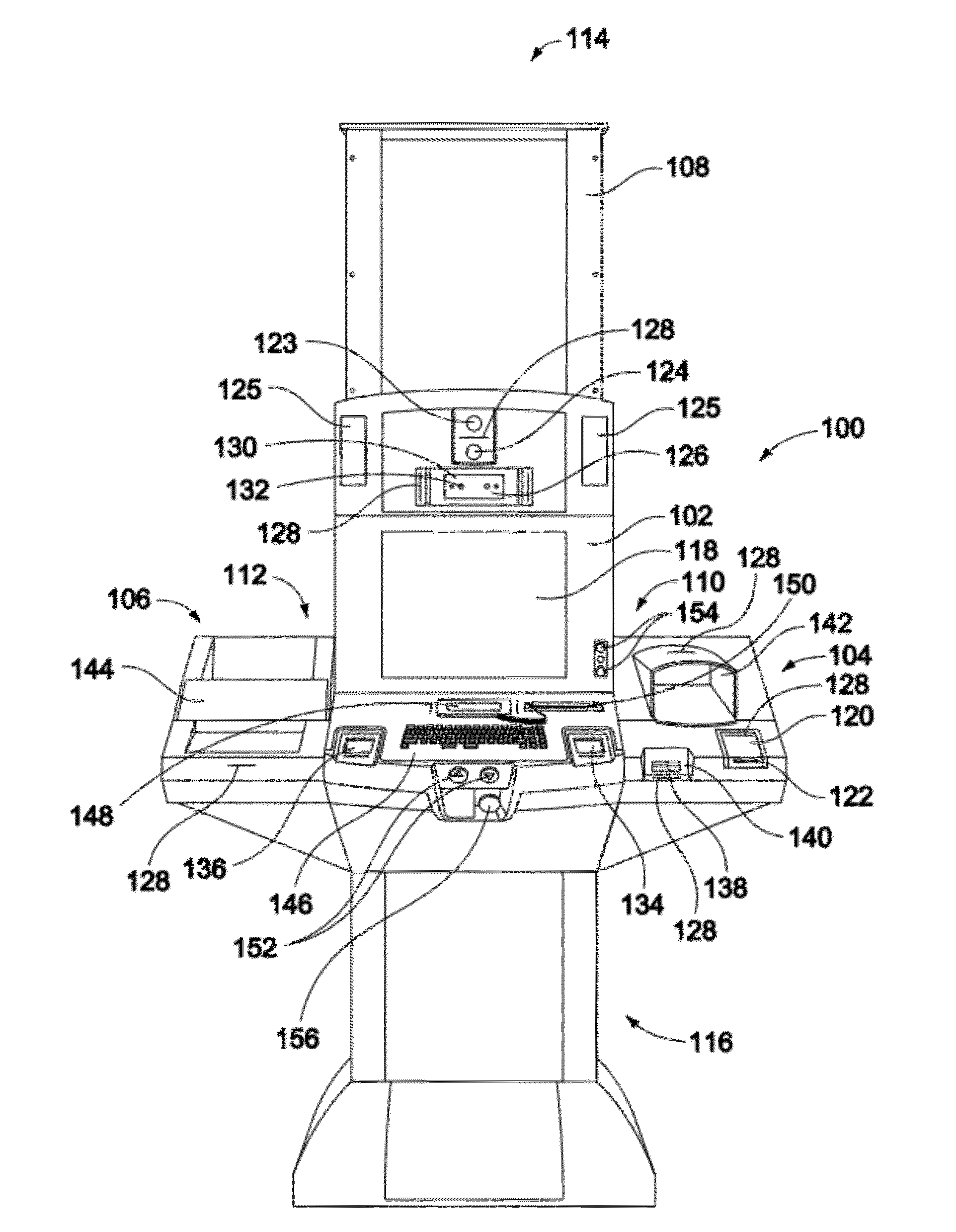
A biometric and identity enrollment kiosk for collecting personal data includes a slidable main module and at least one modifiable section removably coupled to the main module. The main module includes a processor and one or more biometric sensing devices coupled to the processor. The one or more biometric sensing devices include a right fingerprint sensor coupled to the processor and a left fingerprint sensor coupled to the processor. The right fingerprint sensor is positioned proximate a right end of the main module and the left fingerprint sensor is positioned proximate a left end of the main module. The right fingerprint sensor is positioned a predetermined distance apart from the left fingerprint sensor. The at least one modifiable section includes at least one first input device coupled to the processor.
Owner:NEXTGENID
Security marking and security mark
InactiveUS20050156318A1Semiconductor/solid-state device detailsNanoinformaticsPlatinumProduct Identifier
The application discloses a security mark consisting of a plurality of layers, of which the cover layers are highly conductive films and the layers of the card core are films of varying transparency. One layer carries information, which can be read directly, if desired, above a security print, while the transparent conductive layer has an additional security markings, such as biometric or product identifiers marking which can be read conductively only with the aid of a special reader. All the layers consist of polymers, papers or mixtures which can be fused together to form a laminate which is fused together. The conductive layers form conductive traces which may be formed with single-walled or multi walled nano tubes or they can be formed from multiple layers or dispersions containing, carbon nano tubes, carbon nano tubes / antimony tin oxide, carbon nano tubes / platinum, or carbon nano tubes / silver, carbon, silver or carbon nano tubes / silver-cloride. An alternative layer can be formed from a separate conductive layer or suitable dispersion and the encoding accomplished by overlaying a nonconductive trace.
Owner:DOUGLAS JOEL S
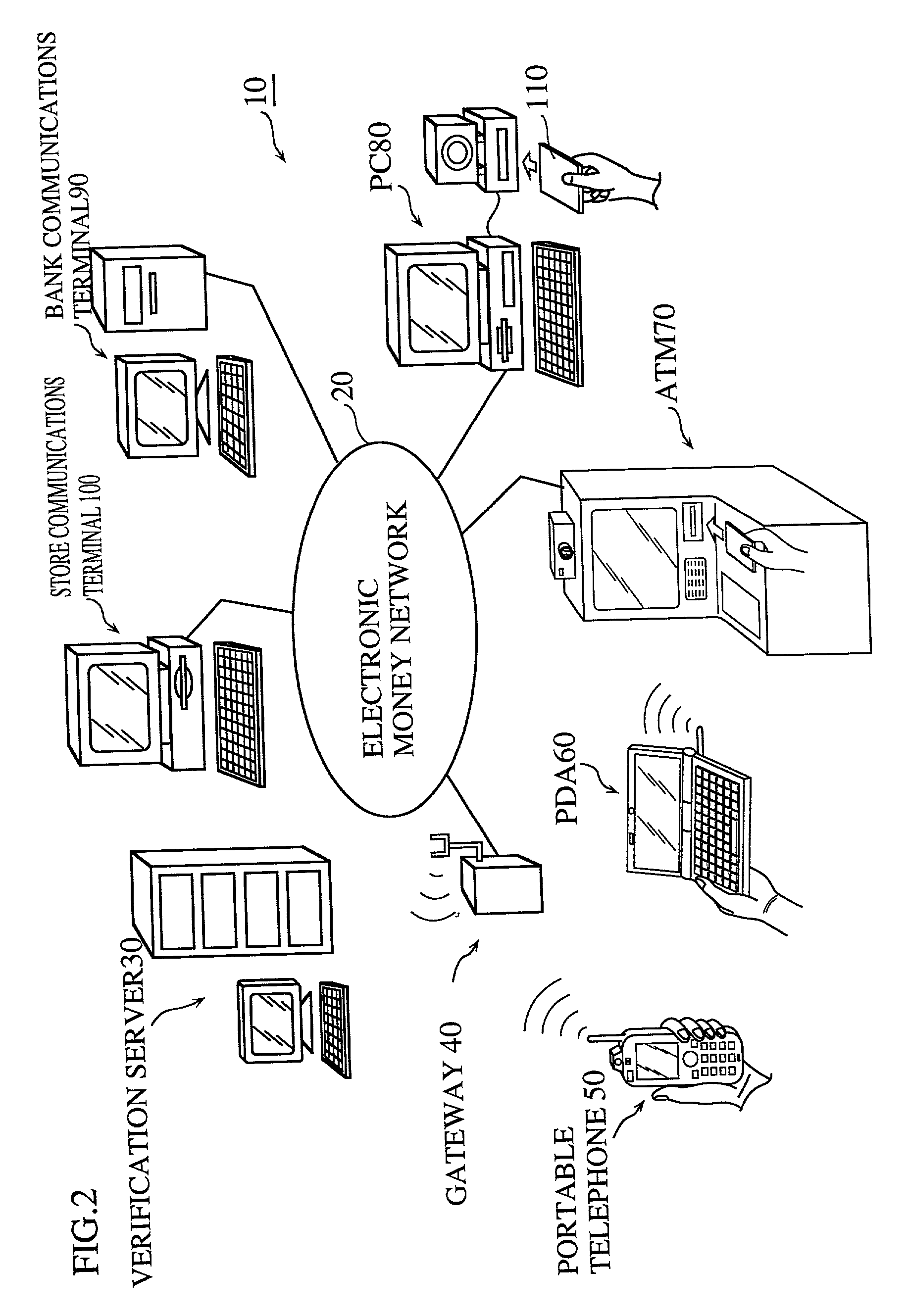
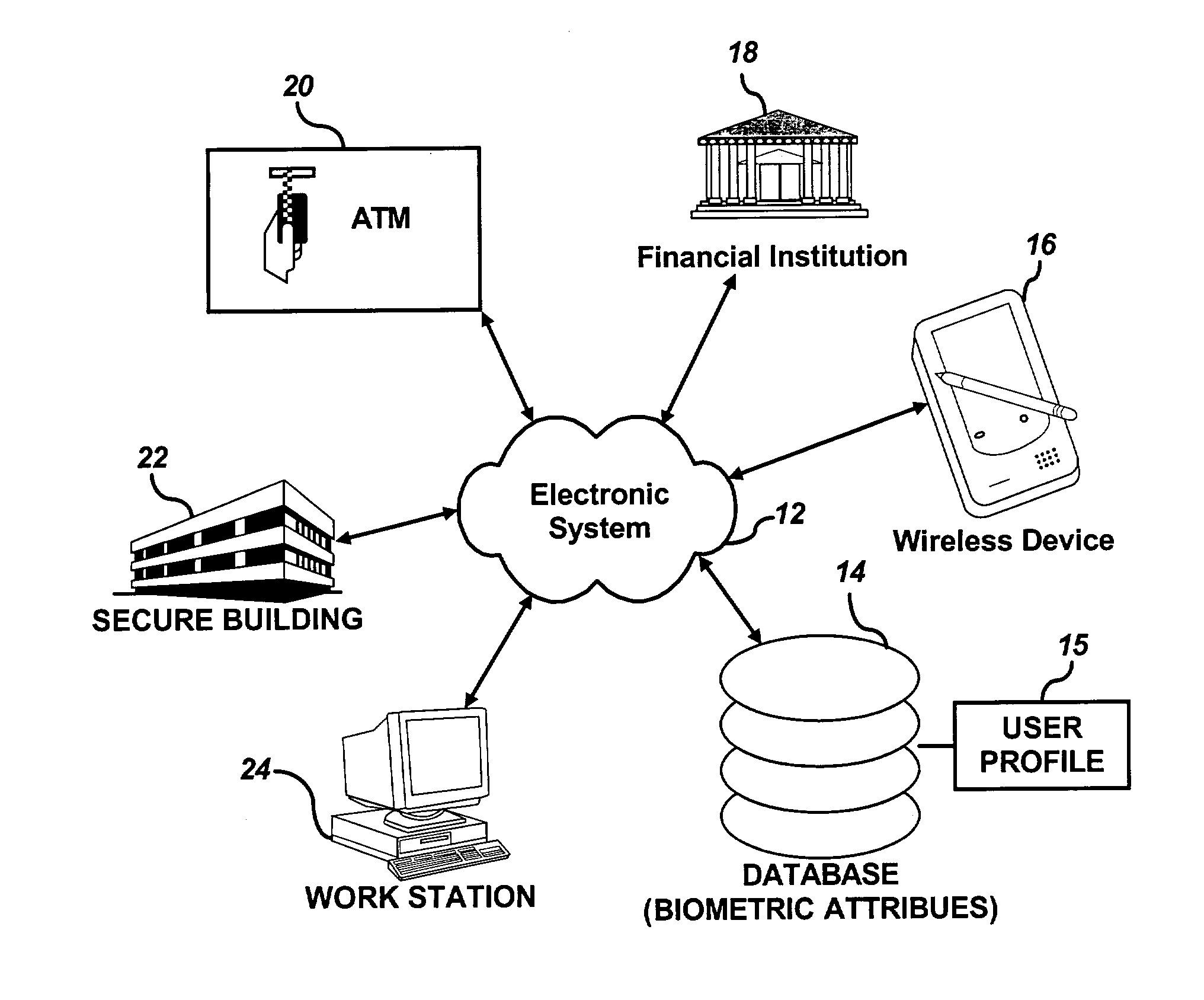
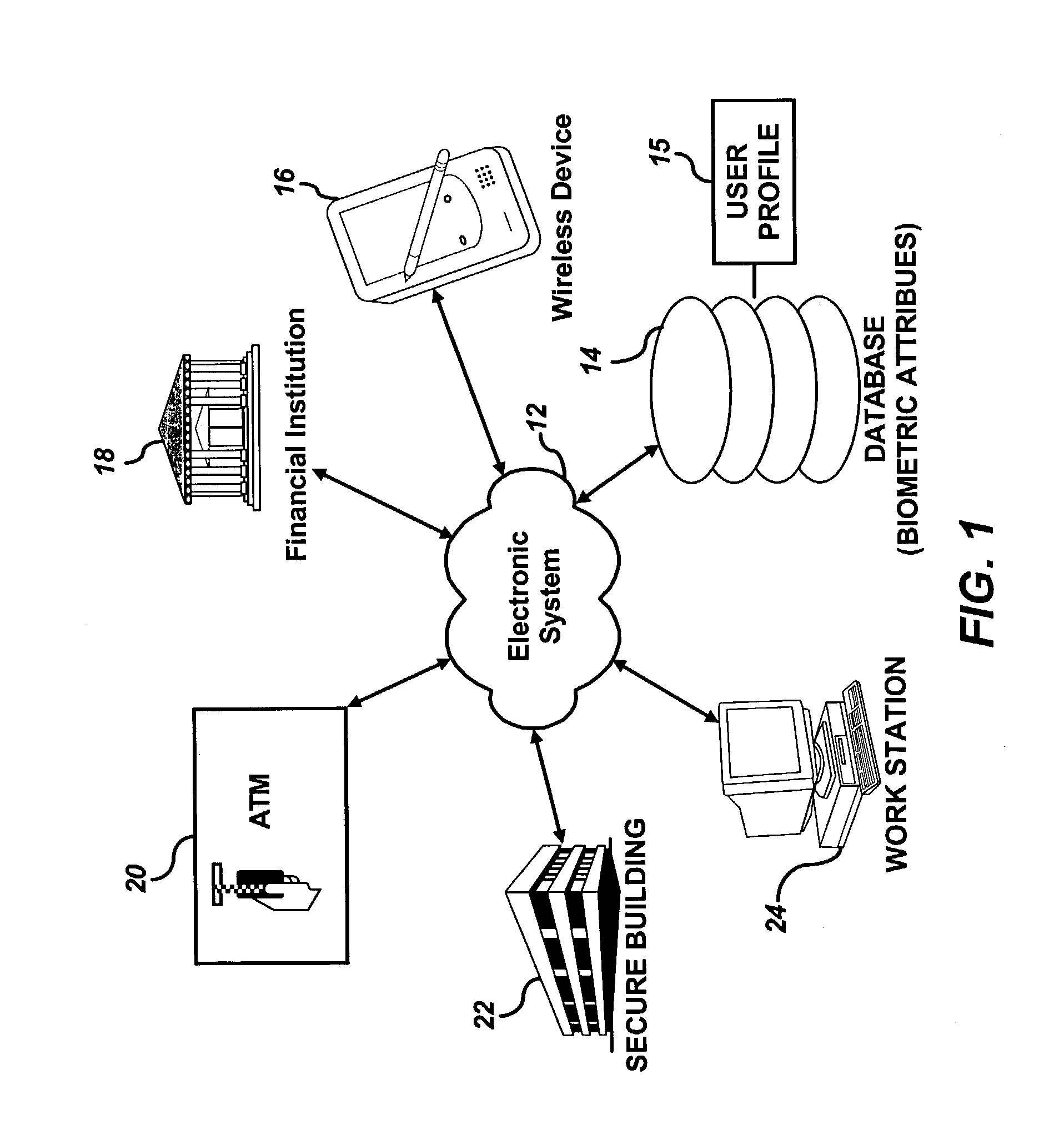
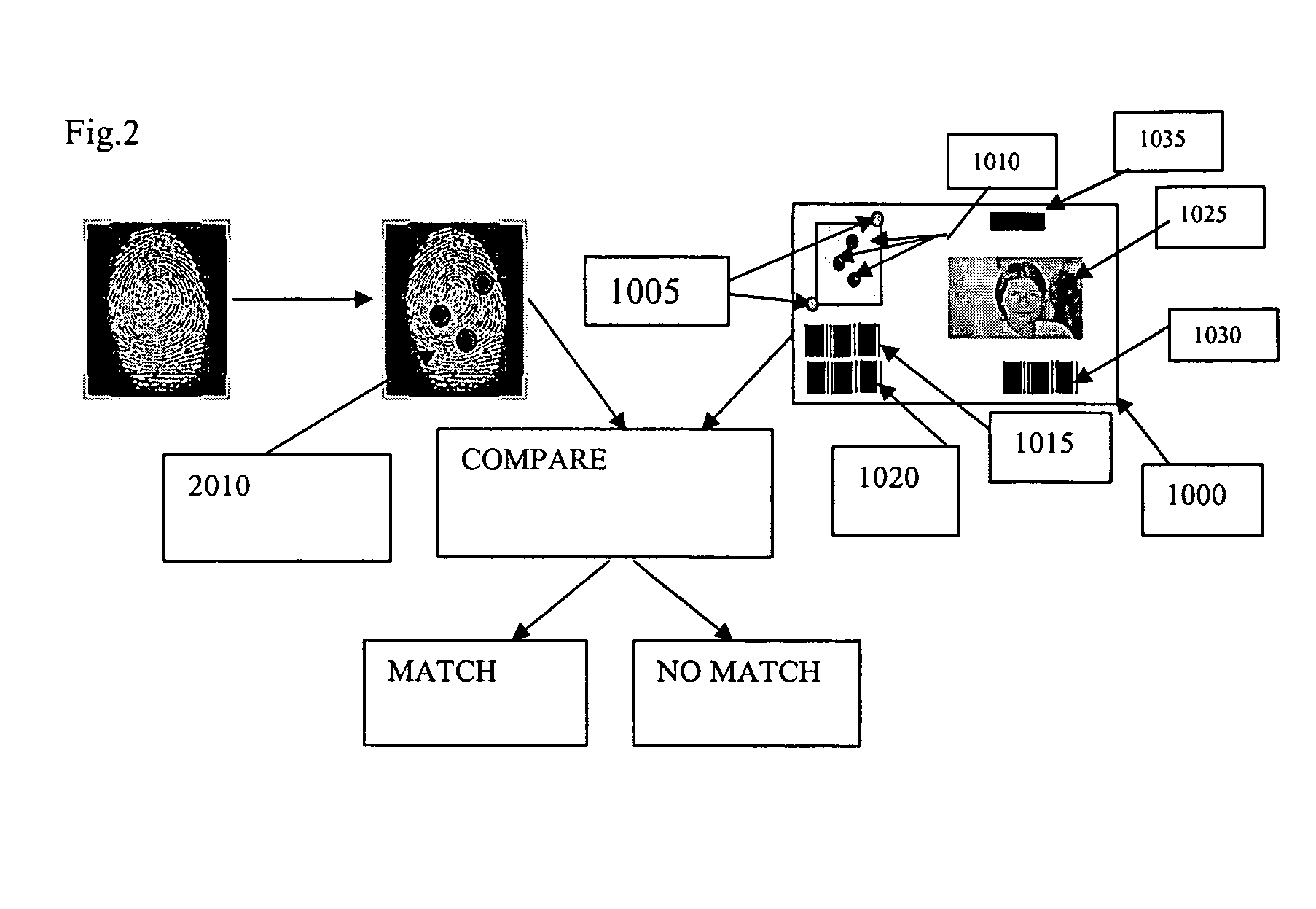
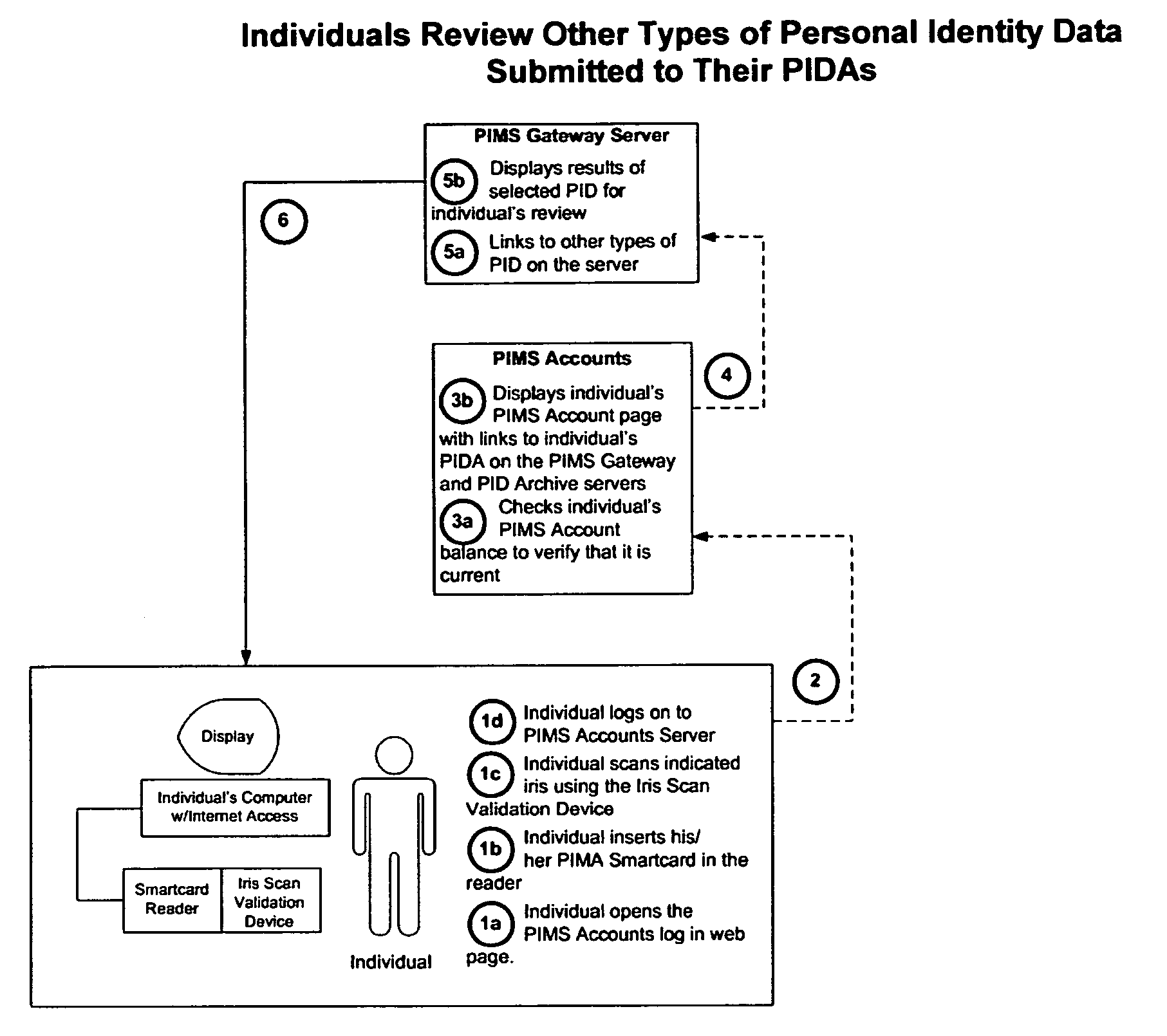
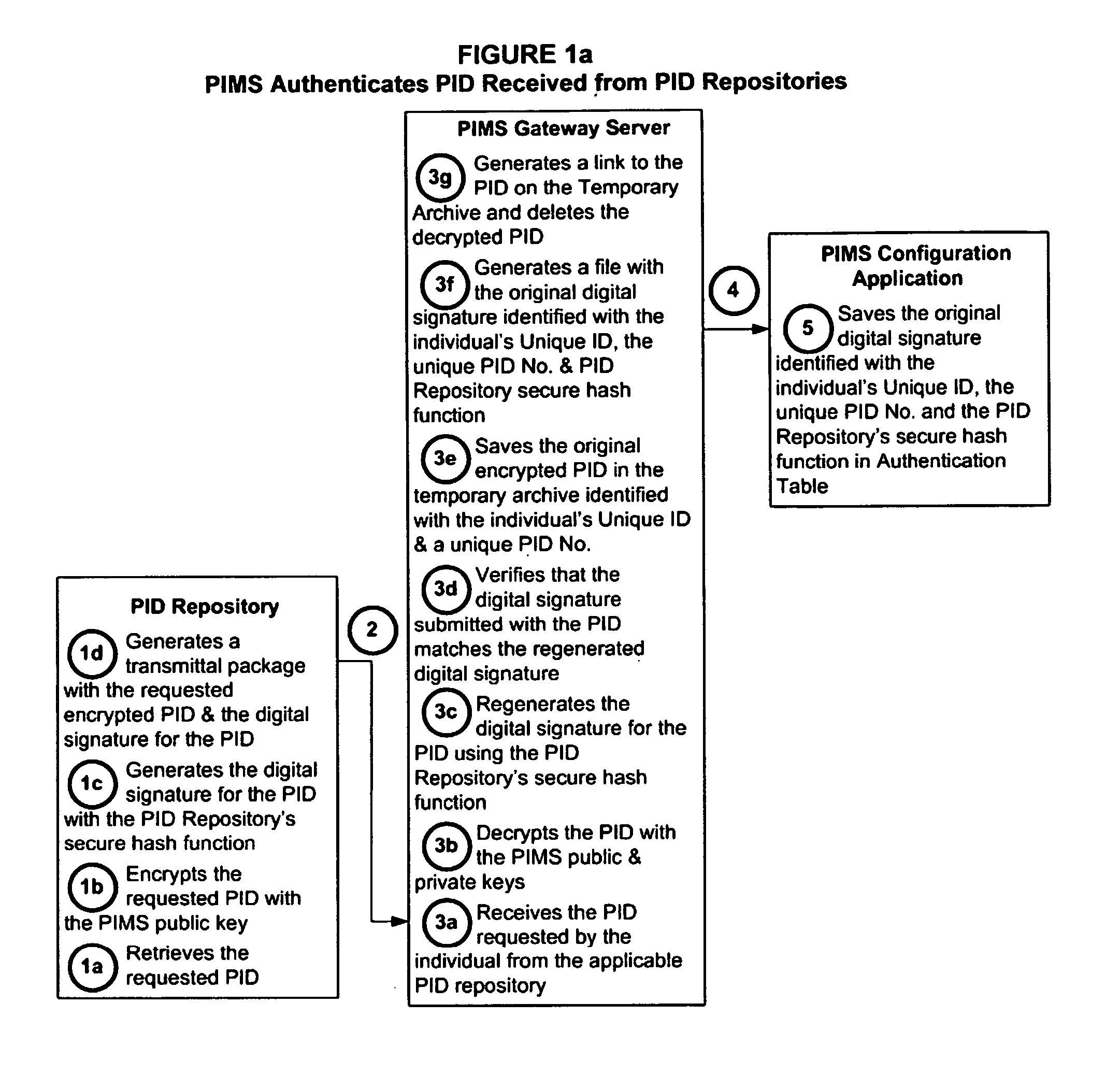
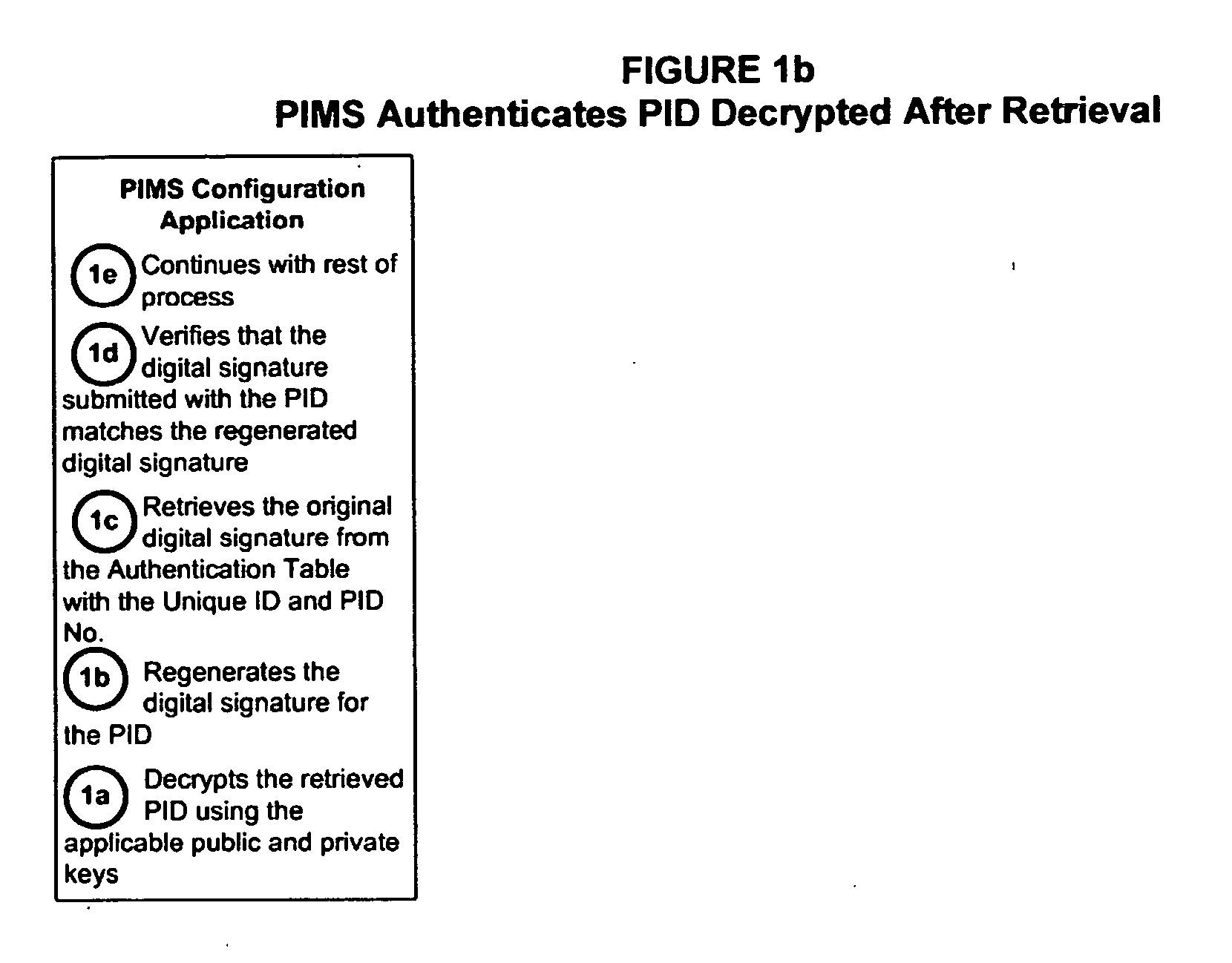
Personal identity data management
InactiveUS20060034494A1Public key for secure communicationUser identity/authority verificationSocial Security numberSmart card
Systems, methods and apparatus for personal identity data management permit individuals to manage their criminal background, credit history, employment, demographic and educational information, for example, to establish their credentials and to help protect their good names. All access to this personal identity data, including the biometrics that uniquely establish the individuals' identity, is under the personal control of the individuals, with access limited to others only with their specific authorization. The subject systems, methods and apparatus include at least two separate archives that store encrypted data about individuals that can be accessed only via the individuals' biometrics specific to the archives and unique Identification Numbers. The Identification Numbers are encrypted when they are associated with the individuals' demographic data, which includes their names, Social Security Numbers and the Unique Identifiers assigned by the system to each of the individuals. Public / private key encryption is used to encrypt the Personal Identity Data maintained in the archives and the Identification Numbers maintained in a Personal Identity Management Service configuration application server that links the rest of the system to the archives. To permit the private keys to be securely retained for use in regenerating a. Smartcard in case of loss or damage, separate segments of the private key are stored on different servers each of which requires submittal of a different biometric, which must match the biometric associated with the private key segment.
Owner:NAT BACKGROUND DATA
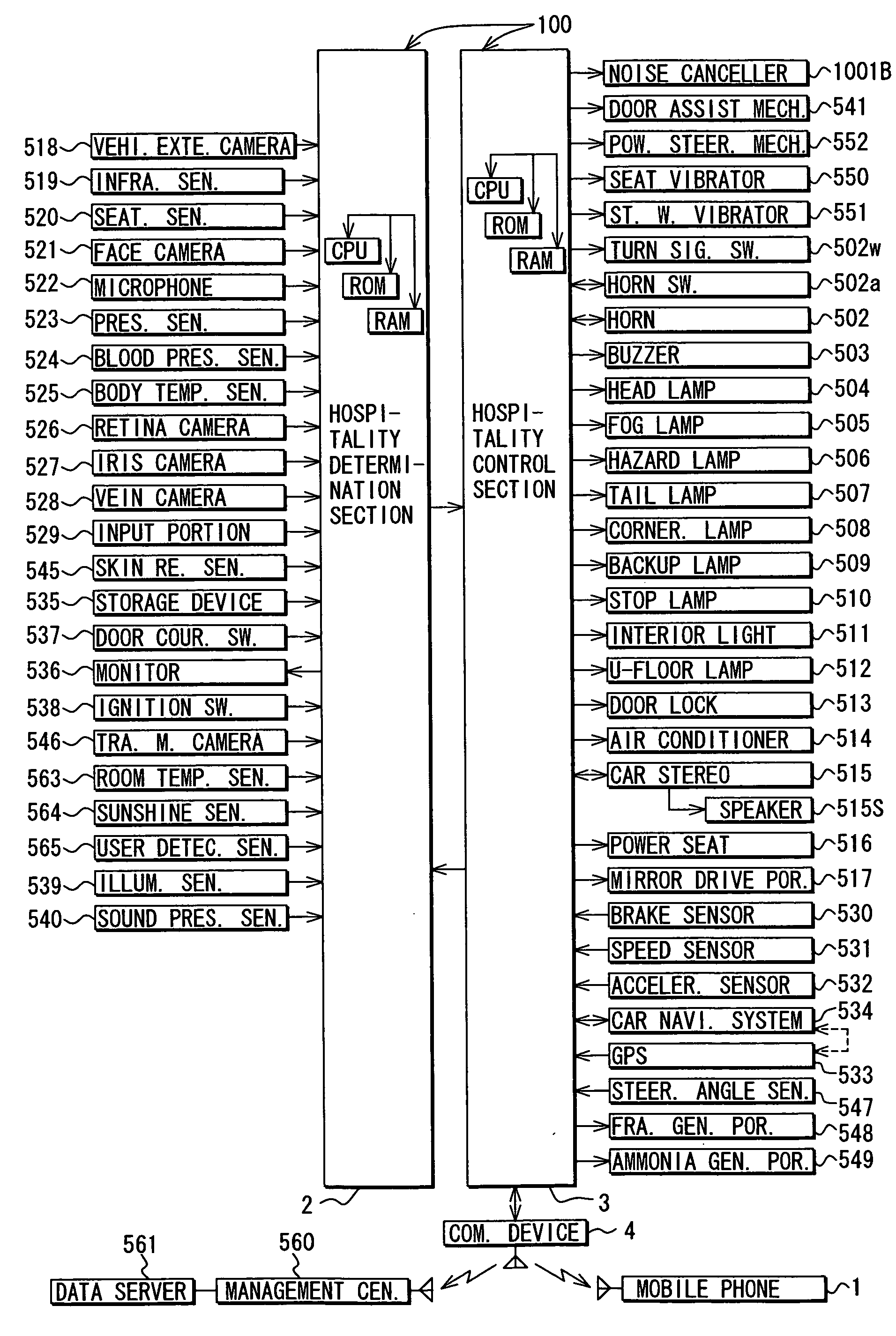
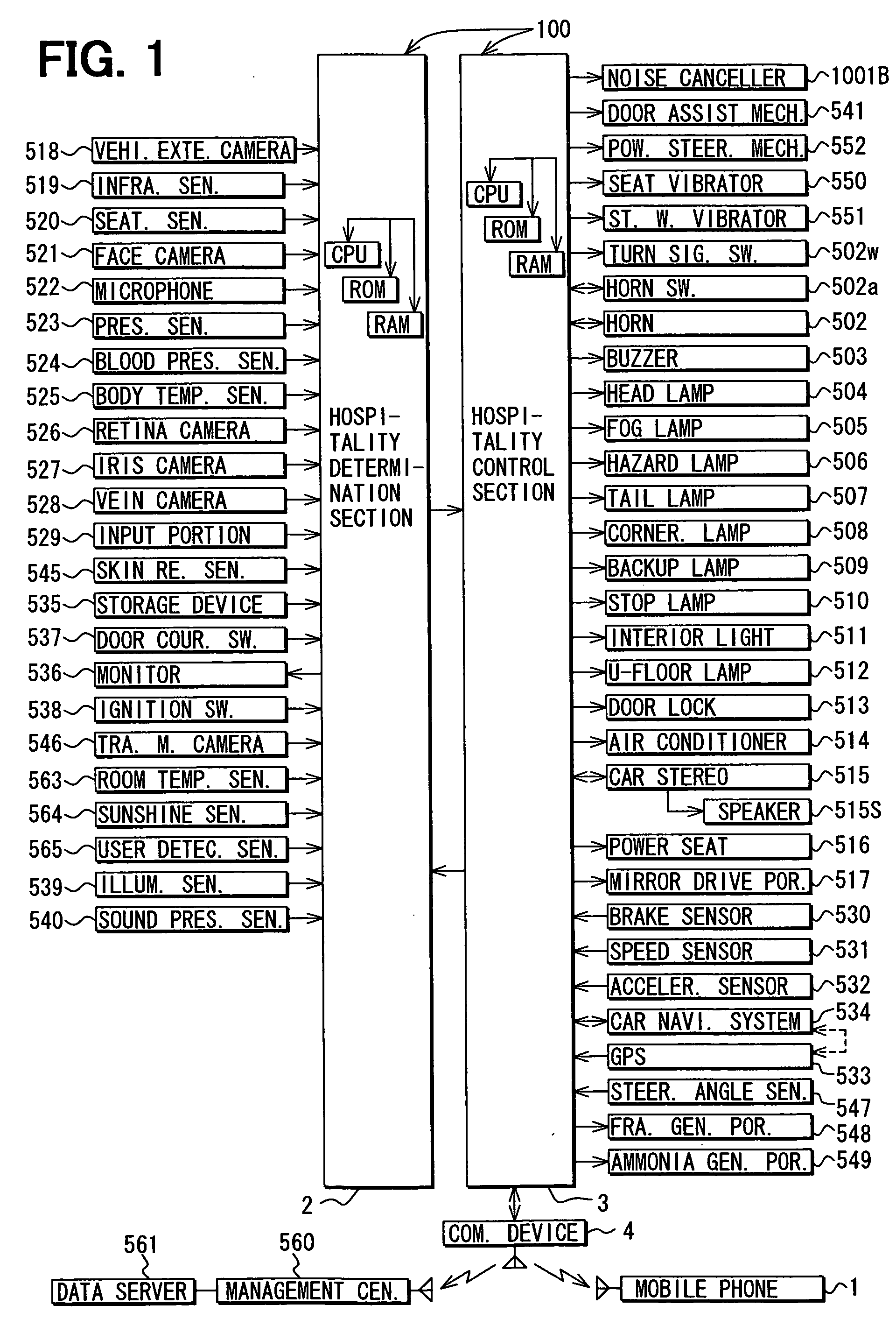
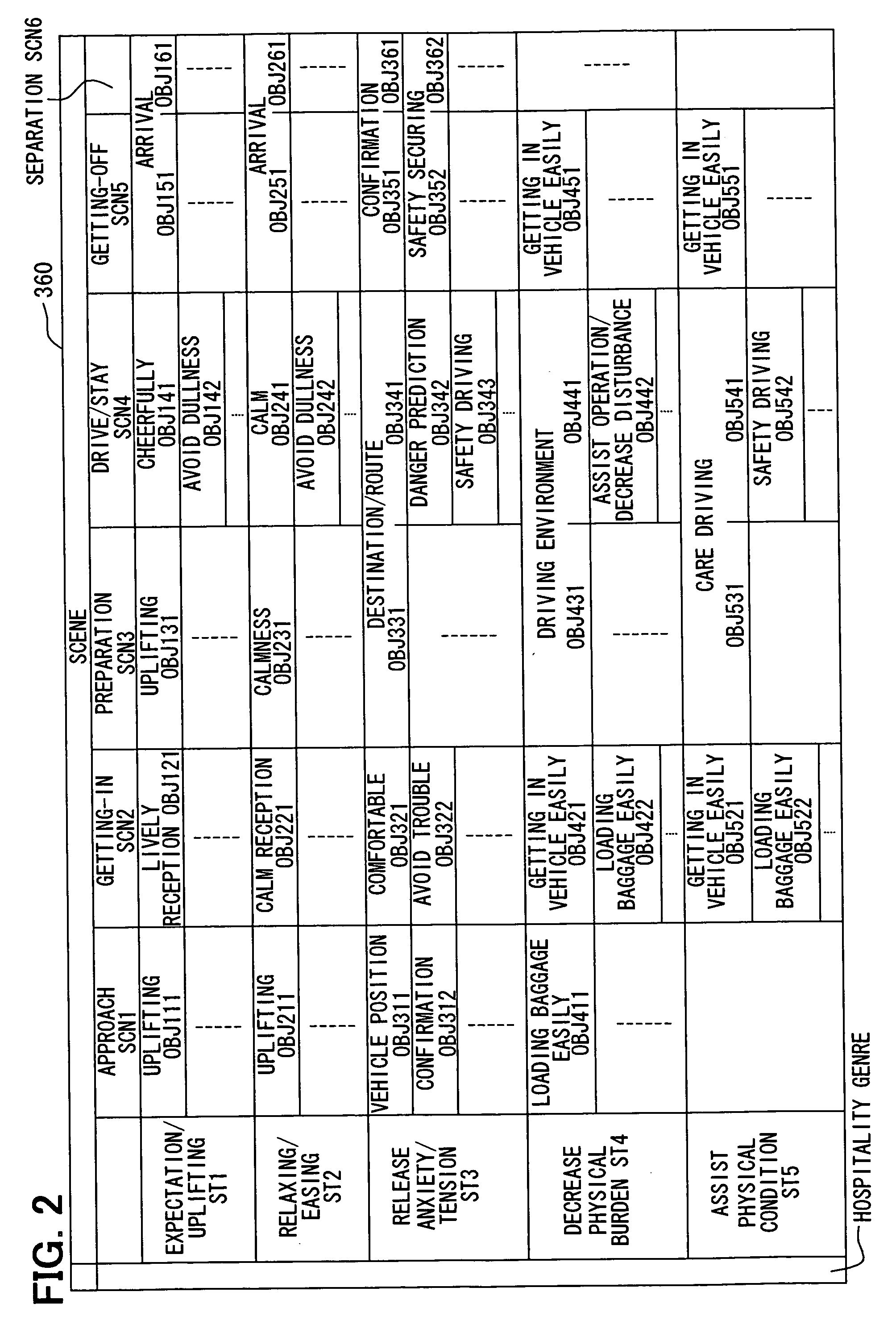
Vehicular user hospitality system
ActiveUS20060235753A1Accurate and fine serviceImprove satisfactionLighting circuitsAnti-theft devicesEmbedded systemIn vehicle
Owner:DENSO CORP
Fingerprint biometric machine representations based on triangles
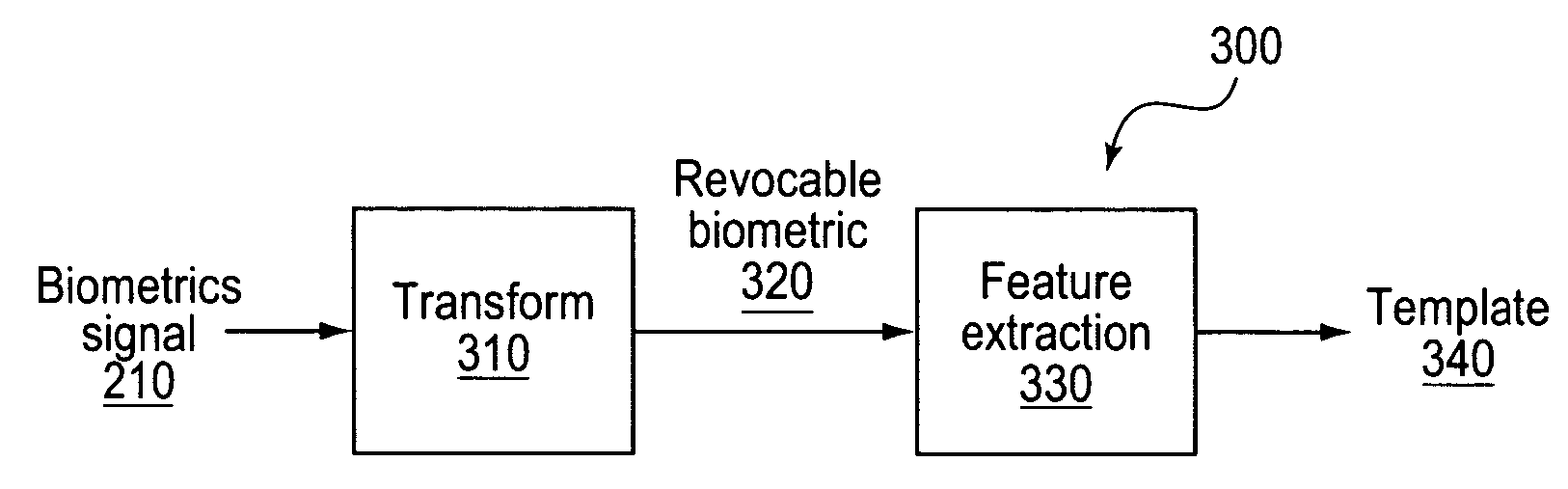
There is provided an apparatus, method, and program storage device for representing biometrics. The apparatus includes a biometric feature extractor and a transformer. The biometric feature extractor is for extracting features corresponding to a biometric depicted in an image, and for defining one or more sets of one or more geometric shapes by one or more of the features. Each of the one or more geometric shapes has one or more geometric features that is invariant with respect to a first set of transforms applied to at least a portion of the image. The transformer is for applying the first set of transforms to the at least a portion of the image to obtain one or more feature representations that include one or more of the one or more geometric features, and for applying a second set of transforms to the one or more feature representations to obtain one or more transformed feature representations.
Owner:IBM CORP
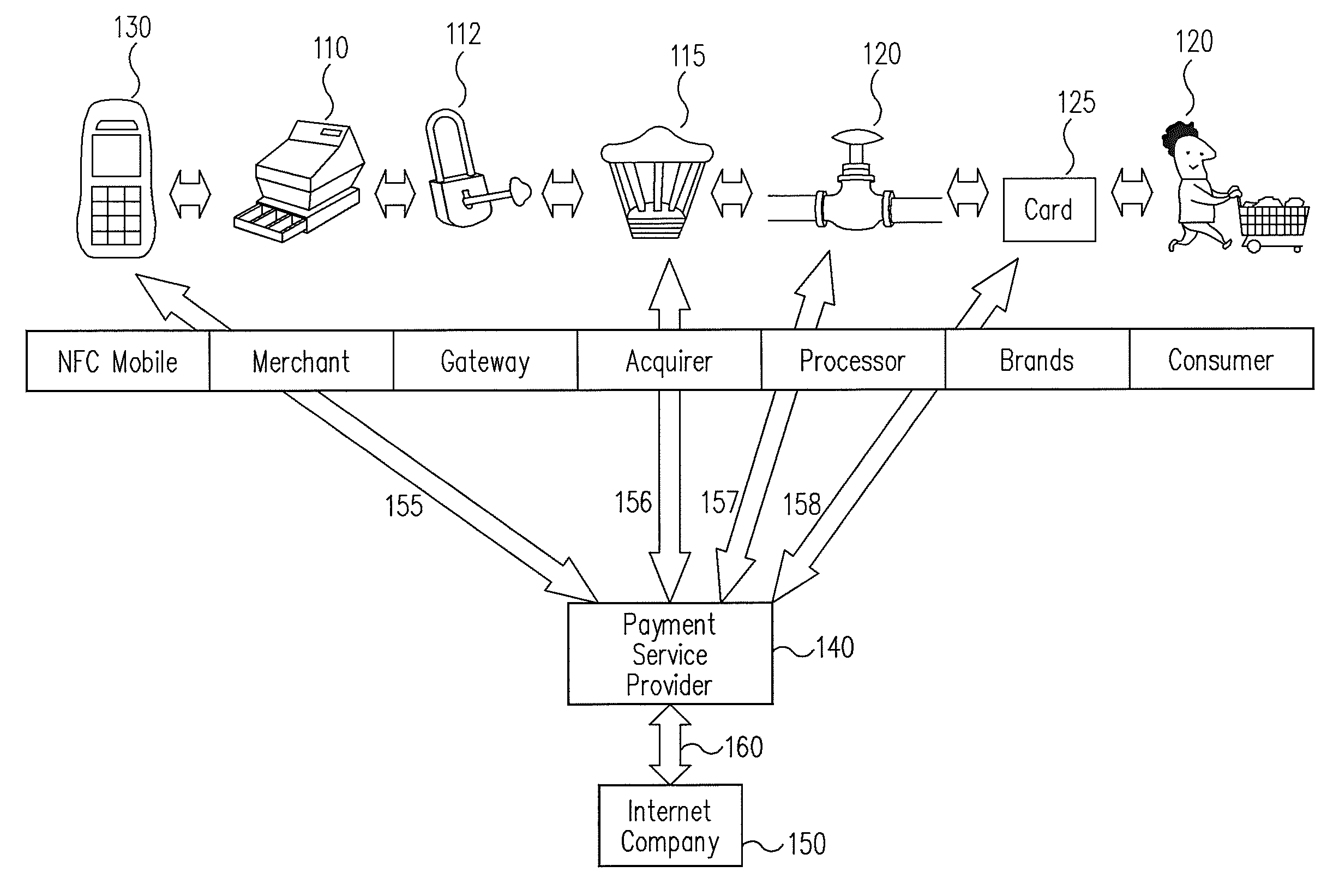
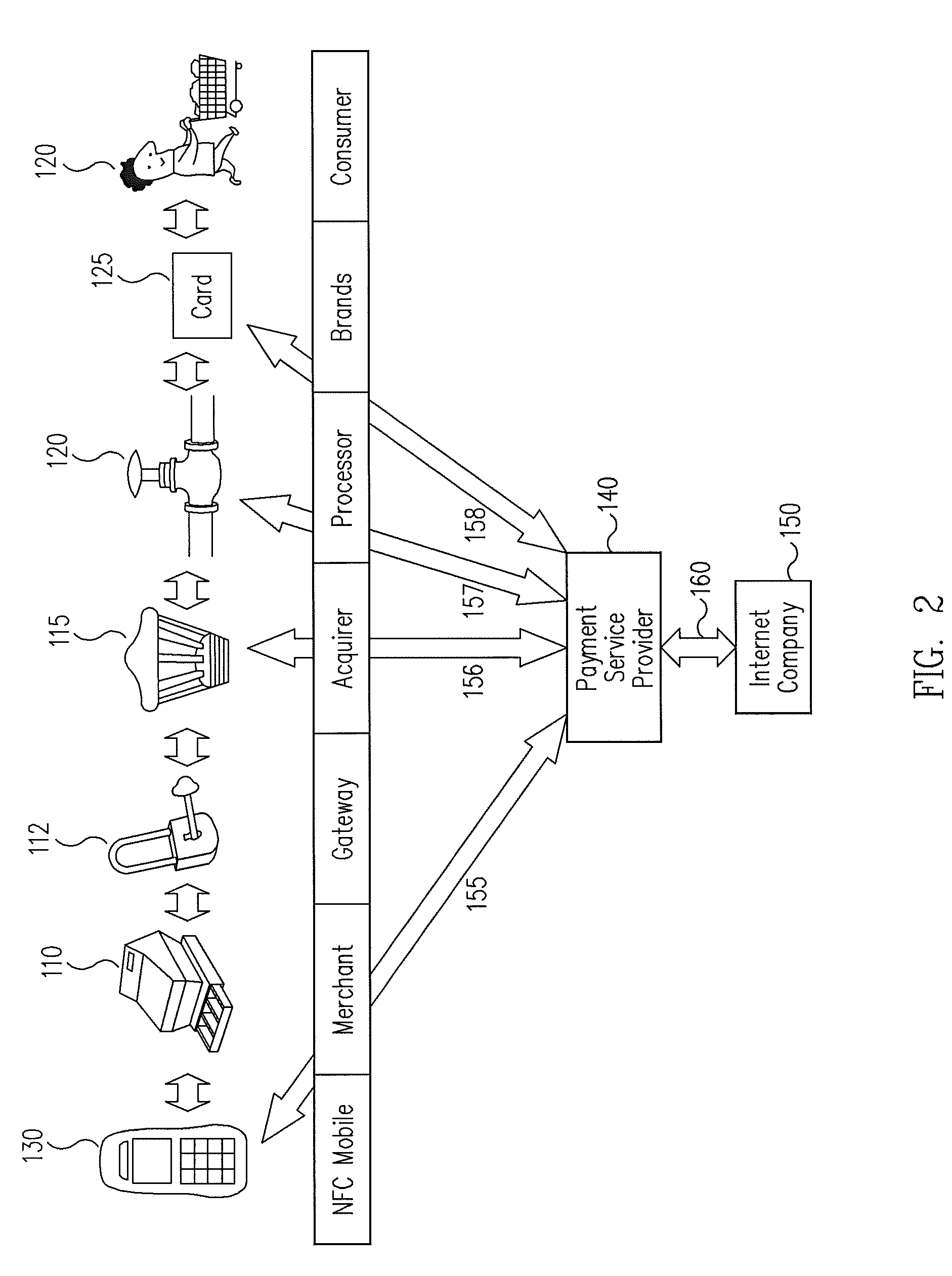
Systems and methods for non-traditional payment using biometric data
InactiveUS20070052517A1Convenient transactionFacilitate payment transactionElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareBiometric data
Facilitating transactions using non-traditional devices and biometric data to activate a transaction device is disclosed. A transaction request is formed at a non-traditional device, and communicated to a reader, wherein the non-traditional device may be configured with an RFID device. The RFID device is not operable until a biometric voice analysis has been executed to verify that the carrier of the RFID equipped non-traditional device is the true owner of account information stored thereon. The non-traditional device provides a conduit between a user and a verification system to perform biometric voice analysis of the user. When the verification system has determined that the user is the true owner of one or more accounts stored at the verification system, a purchase transaction is facilitated between the verification system. Transactions may further be carried out through a non-RF device such as a cellular telephone in direct communication with an acquirer / issuer or payment processor
Owner:LIBERTY PEAK VENTURES LLC
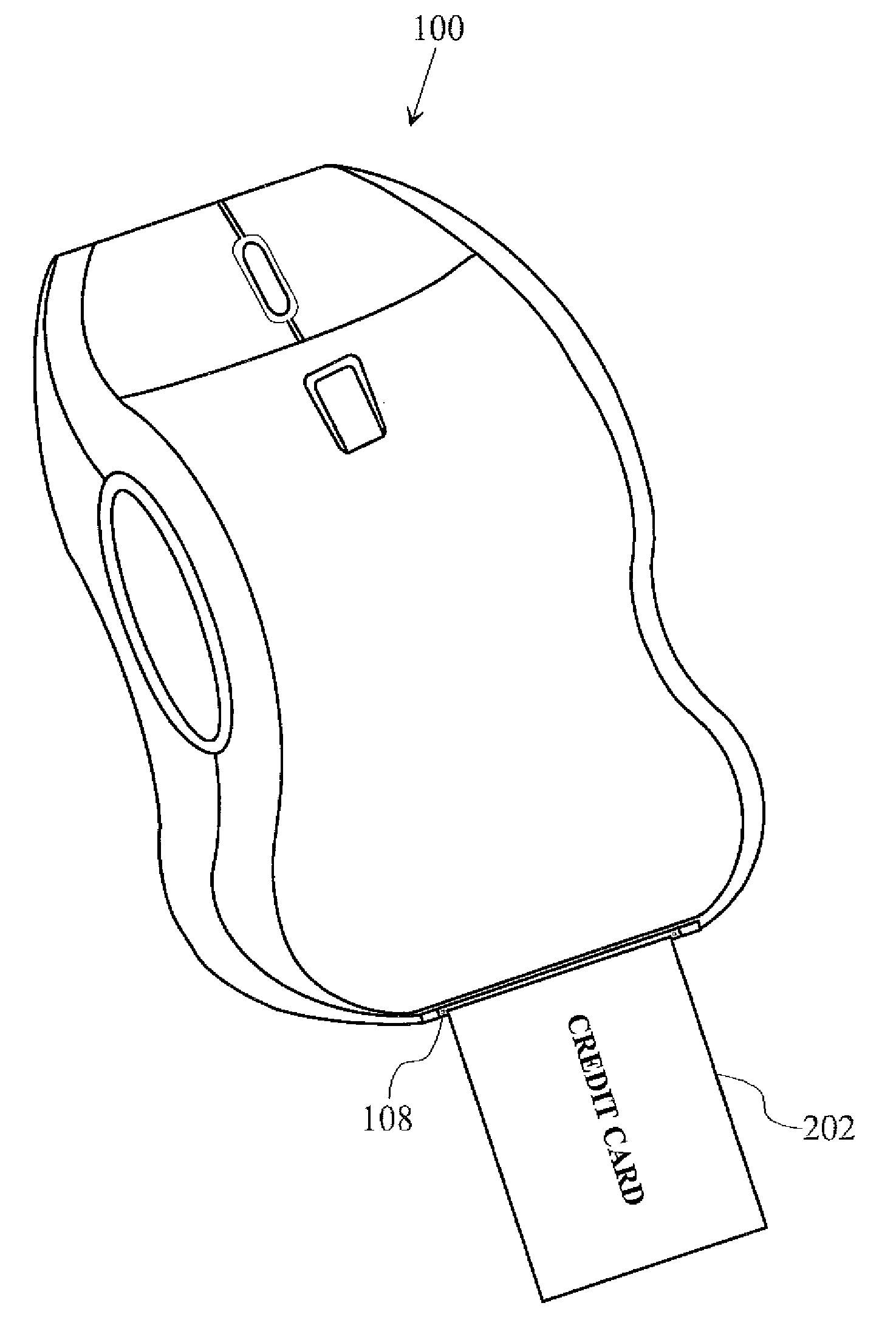
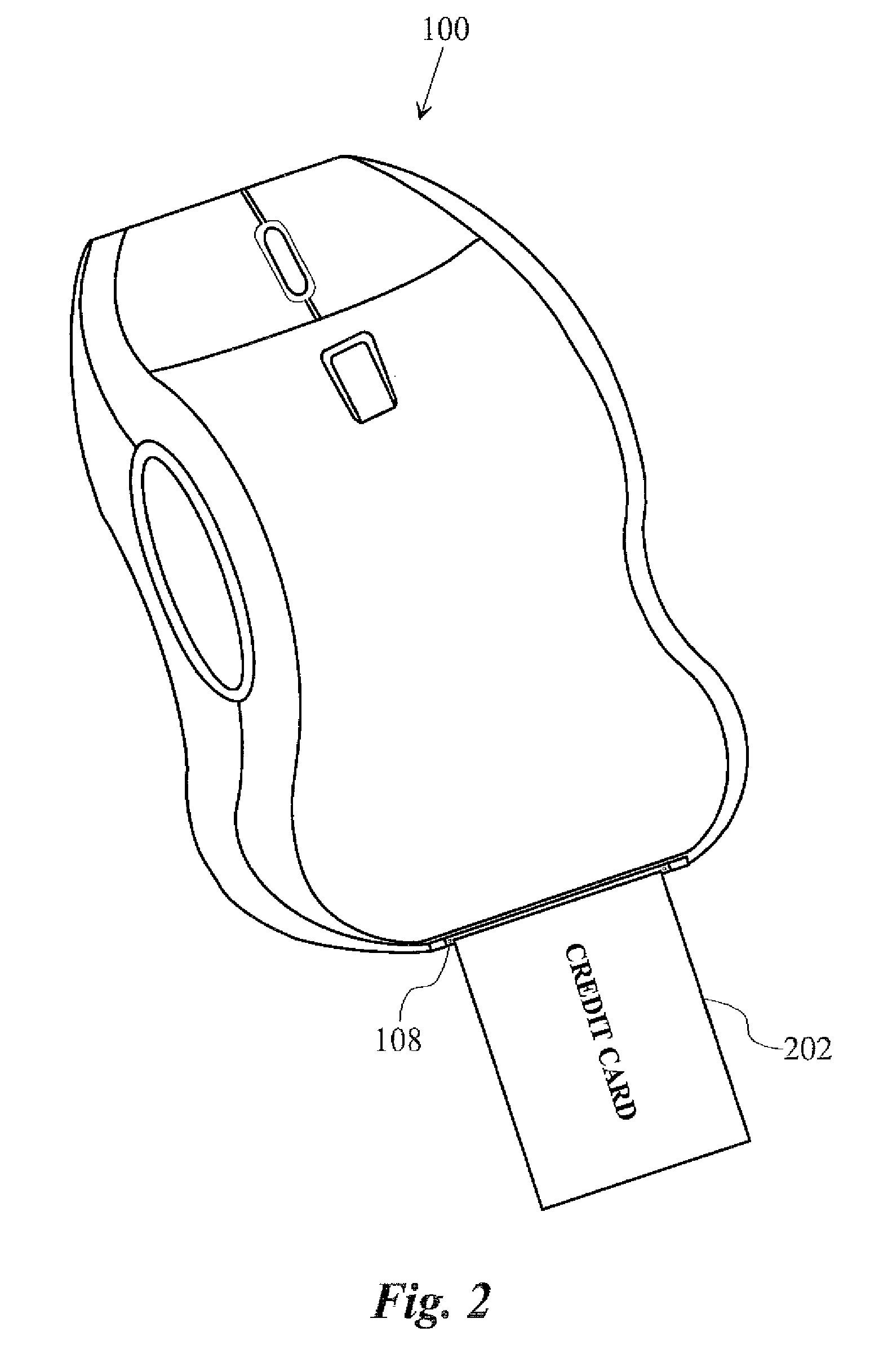
Wireless Biometric Computer Mouse with Integrated Credit Card Reader
InactiveUS20090289110A1Great efficiencyGood safetyAcutation objectsCathode-ray tube indicatorsGraphical user interfaceSoftware
Accordingly, in an embodiment of the invention, a computer mouse is provided and includes a digital medium for storing executable software and user data, a wireless transceiver, a credit card reader, and a biometric scanner. A user operating the mouse connected to a computing appliance may validate stored credit card information as belonging to the user by performing a biometric match of biometrics of the user taken by the biometric scanner against biometrics and profile data stored in a network-based data server, and whereupon a successful match of biometrics invokes a graphics user interface stored on the digital medium to display on a display device accessible to the computing appliance, the interface containing the credit card information belonging to the authenticated user for the one or more cards authenticated.
Owner:OI HLDG 1 LLC
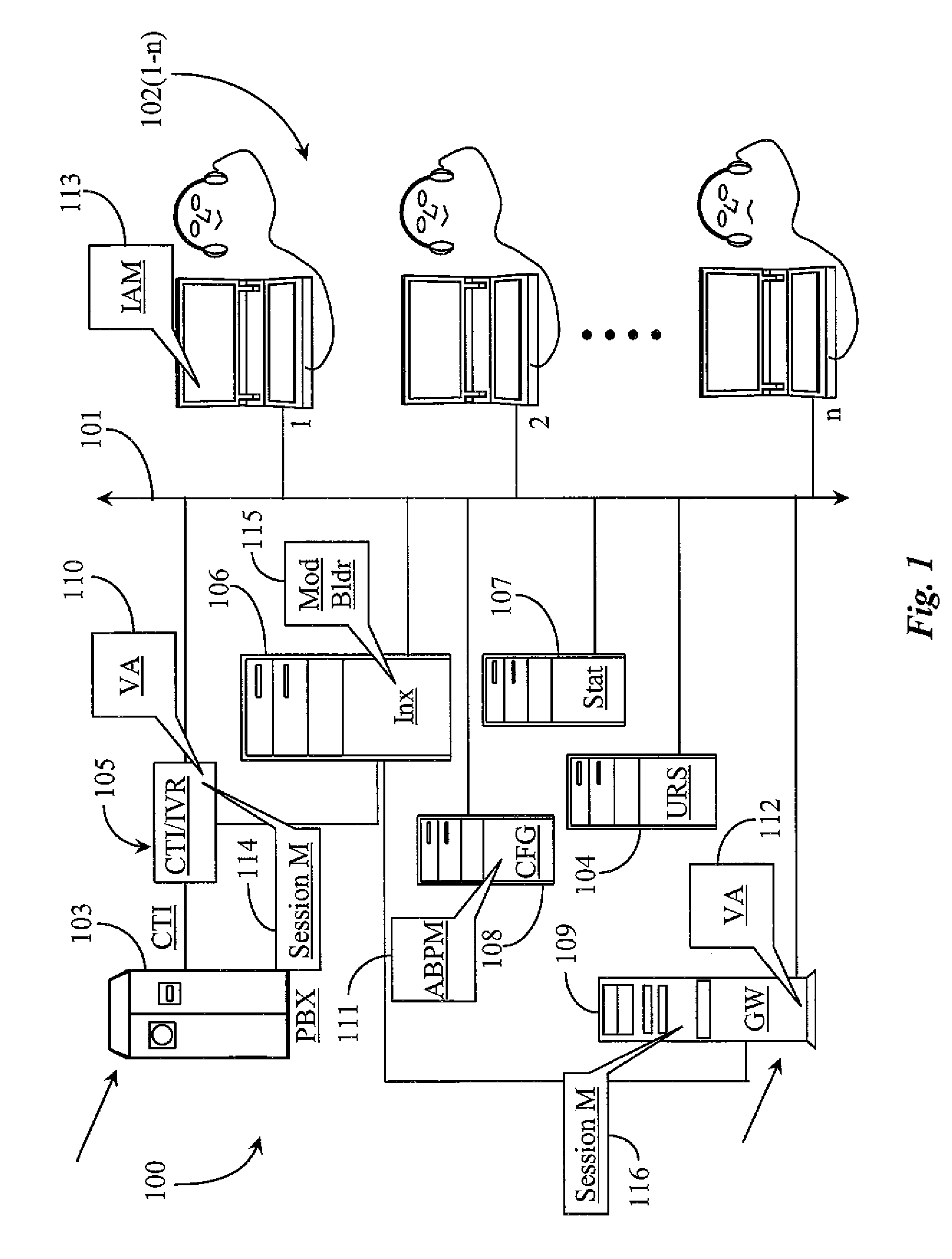
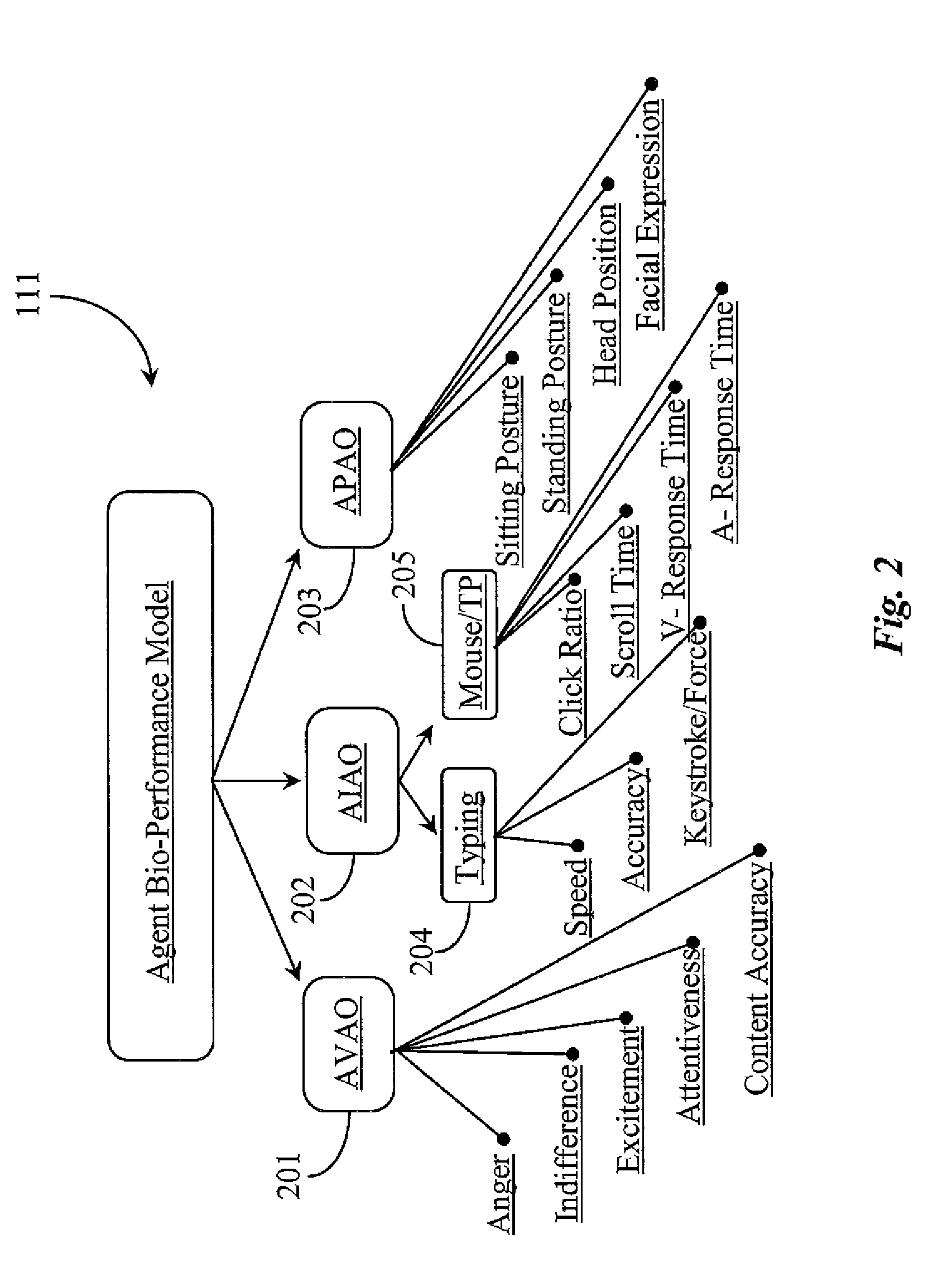
System for Routing Interactions Using Bio-Performance Attributes of Persons as Dynamic Input
ActiveUS20100158238A1Improve contact center efficiencyPreserve customer loyaltySpeech analysisCharacter and pattern recognitionSkill setsSpeech sound
A system for routing an interaction has a queue for staging the interaction, a router running a routing strategy for routing the interaction, and a number of object models maintained for a number of agents, the object models defining one or more agent skills, the values of the object models dynamically affected by real-time bio-metrics of the agents obtained through ongoing monitoring of voice and input actions of the agents. The routing strategy routes the interaction based on comparison of the dynamically-affected skill values of the agents, as evidenced in the object models.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
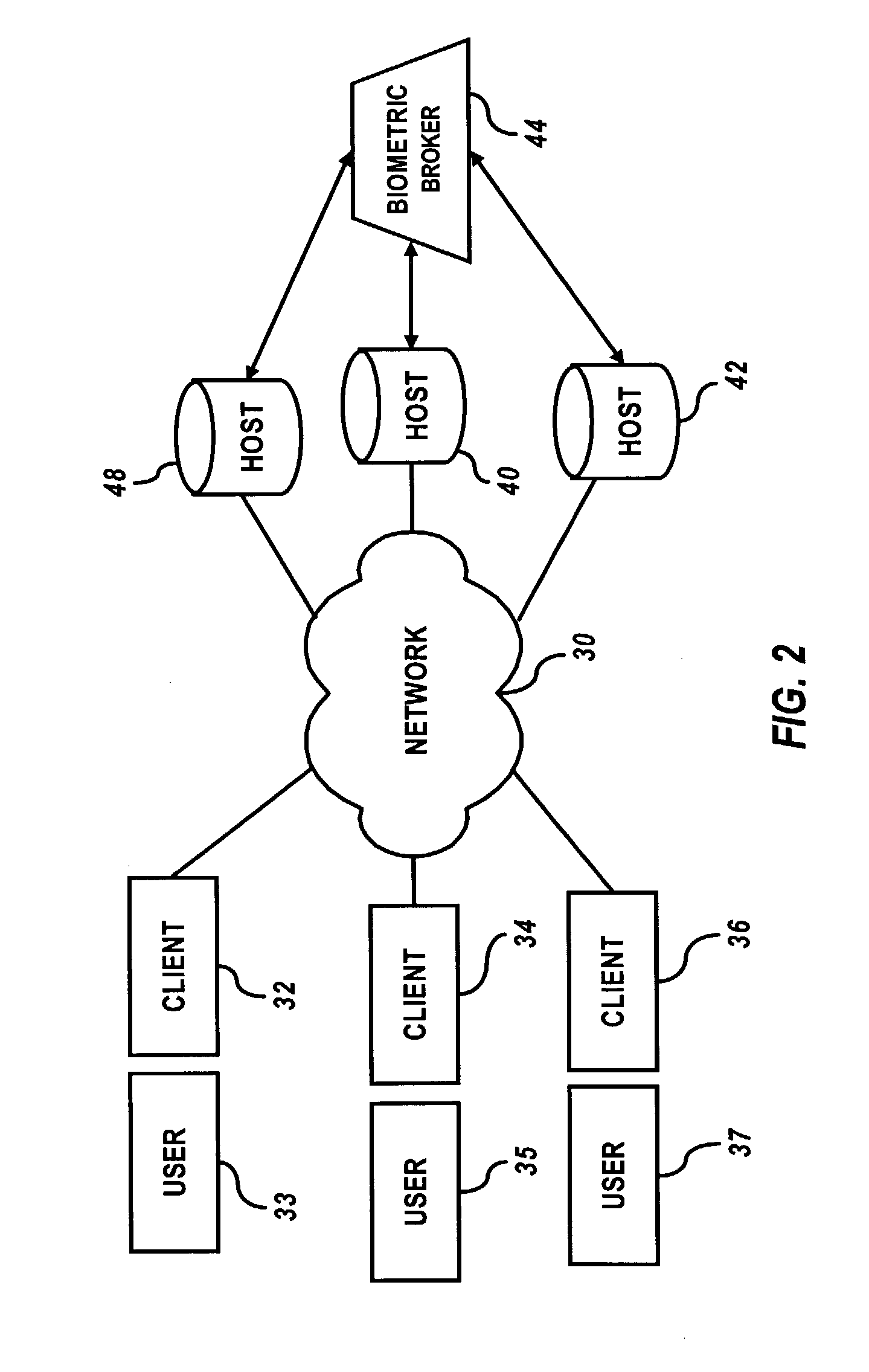
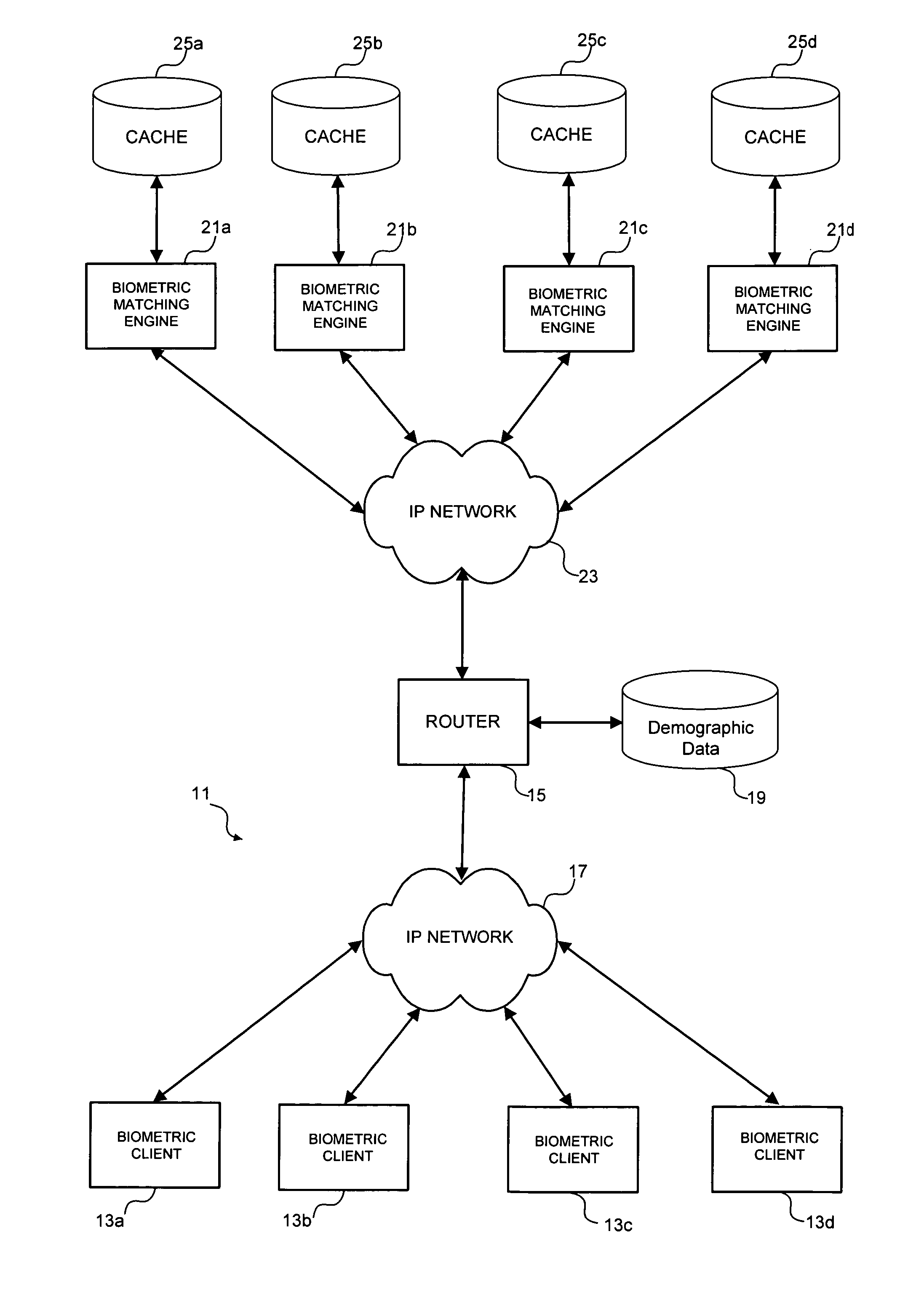
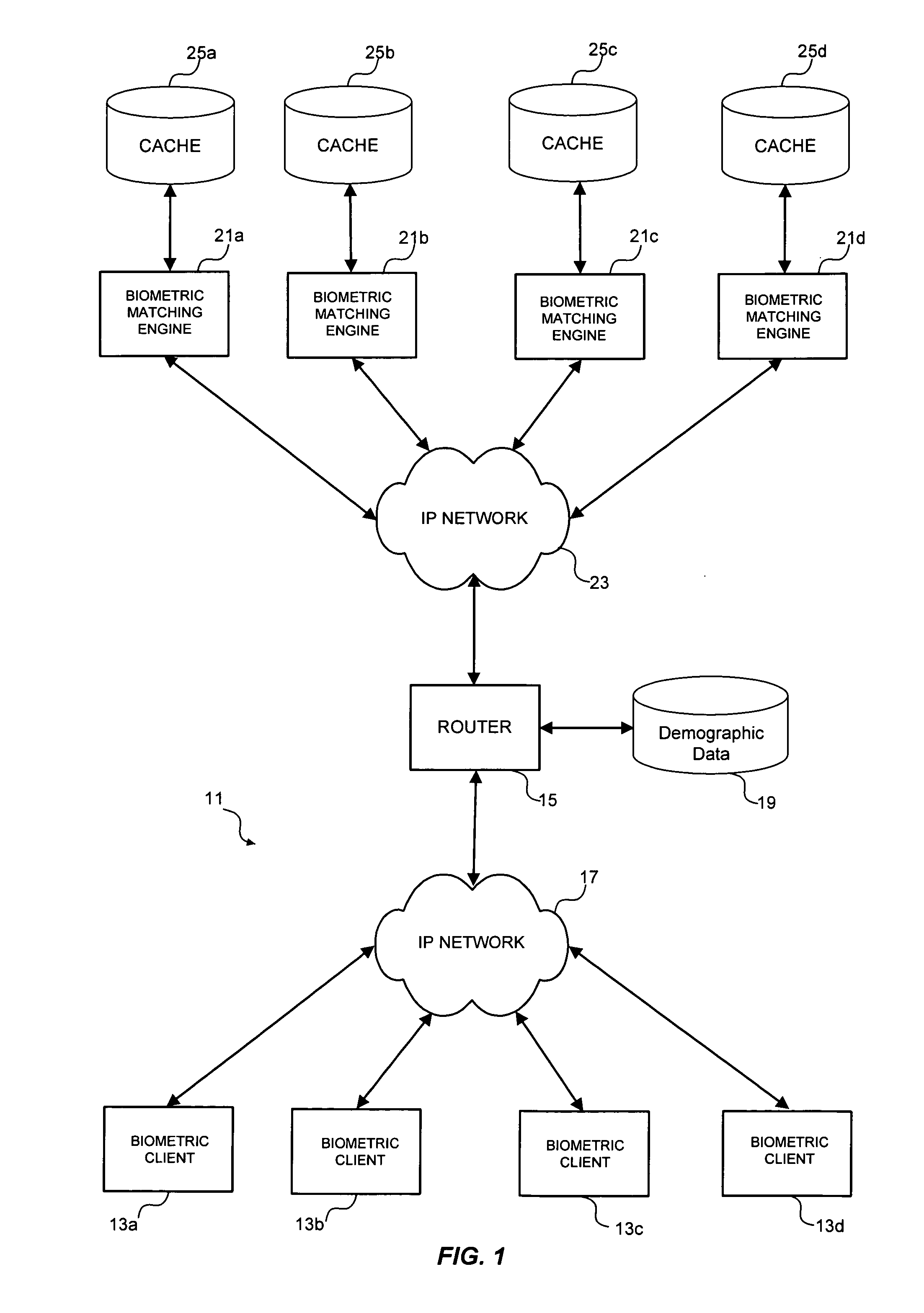
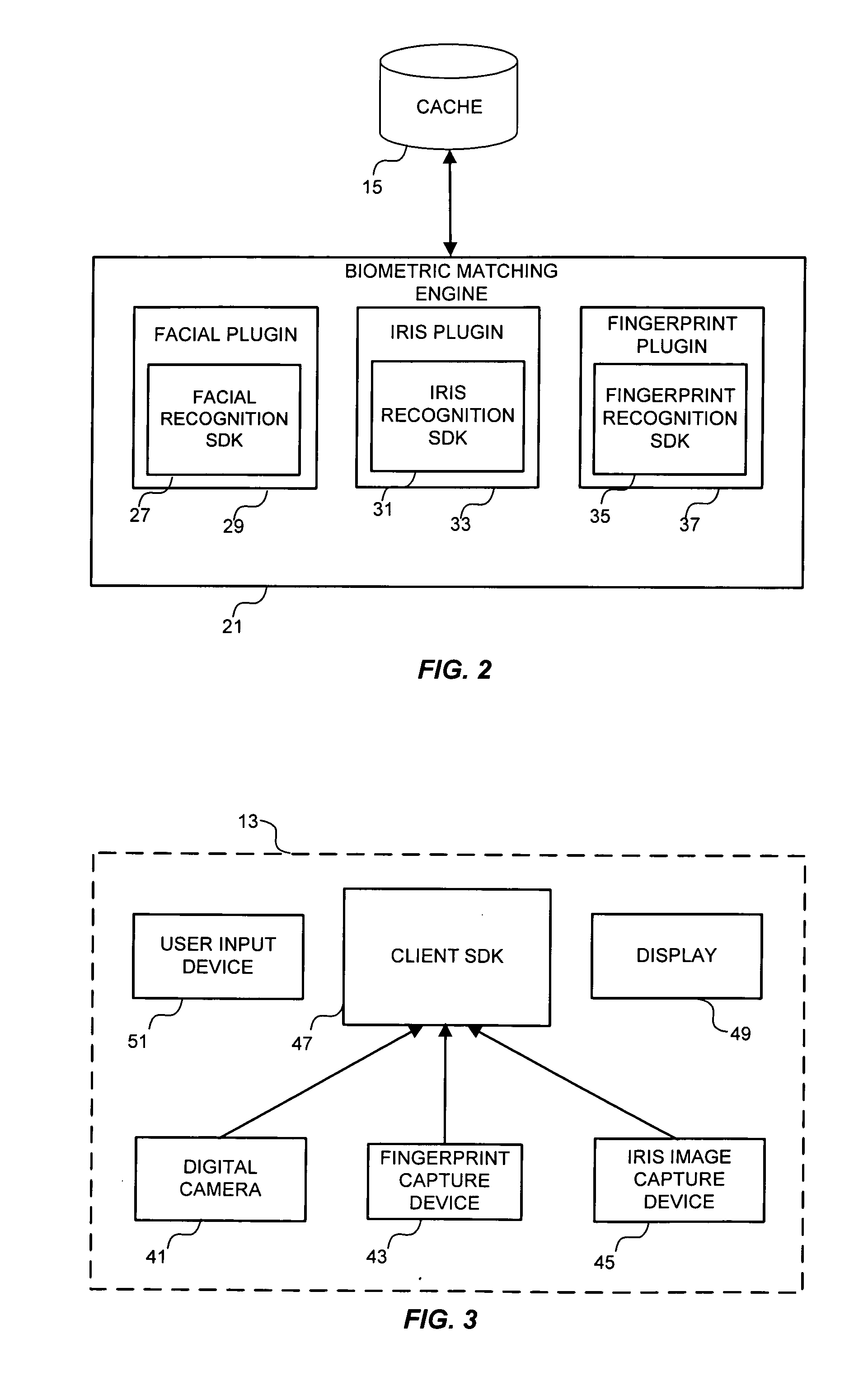
Multimodal biometric platform
ActiveUS20060104485A1Electric signal transmission systemsImage analysisBiometric dataAuthentication system
A multimodal biometric identification or authentication system includes a plurality of biometric clients. Each of the biometric clients may include devices for capturing biometric images of a plurality of types. The system includes a router in communication with the biometric clients. The router receives biometric images from, and returns biometric scores or results to, the biometric clients. The system includes a plurality of biometric matching engines in communication with the router. Each biometric matching engine includes multiple biometric processors. Each biometric processor is adapted to process biometric data of a particular type. The biometric matching engines transmit and receive biometric data to and from the router.
Owner:IMAGEWARE SYST
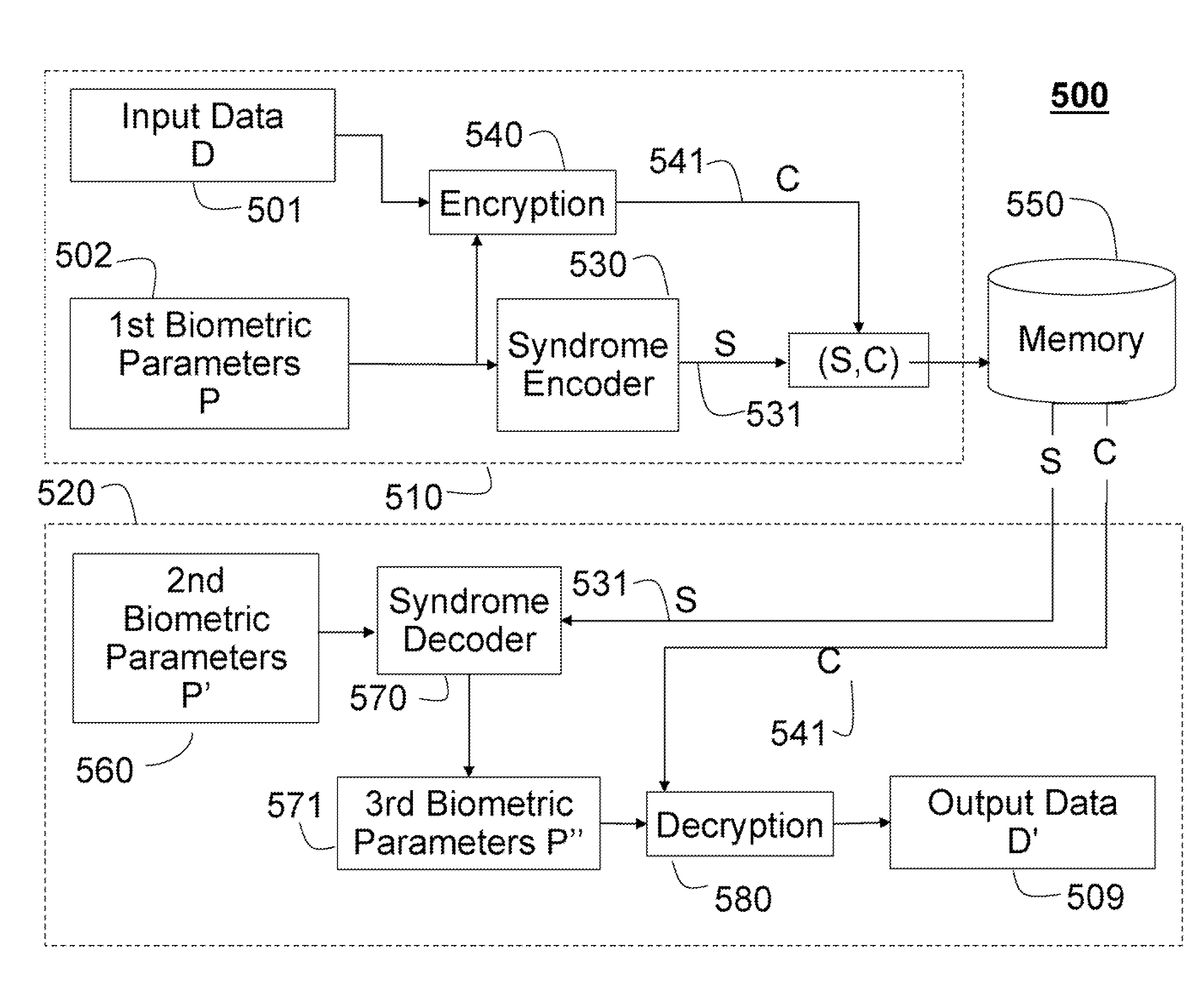
Biometric Based User Authentication and Data Encryption
InactiveUS20070174633A1Efficient modelingEfficient use ofUser identity/authority verificationSpeech analysisBiometric dataUser authentication
Biometric parameters acquired from human forces, voices, fingerprints, and irises are used for user authentication and access control. Because the biometric parameters are continuous and vary from one reading to the next, syndrome codes are applied to determine biometric syndrome vectors. The biometric syndrome vectors can be stored securely while tolerating an inherent variability of biometric data. The stored biometric syndrome vector is decoded during user authentication using biometric parameters acquired at that time. The syndrome codes can also be used to encrypt and decrypt data.
Owner:MITSUBISHI ELECTRIC RES LAB INC
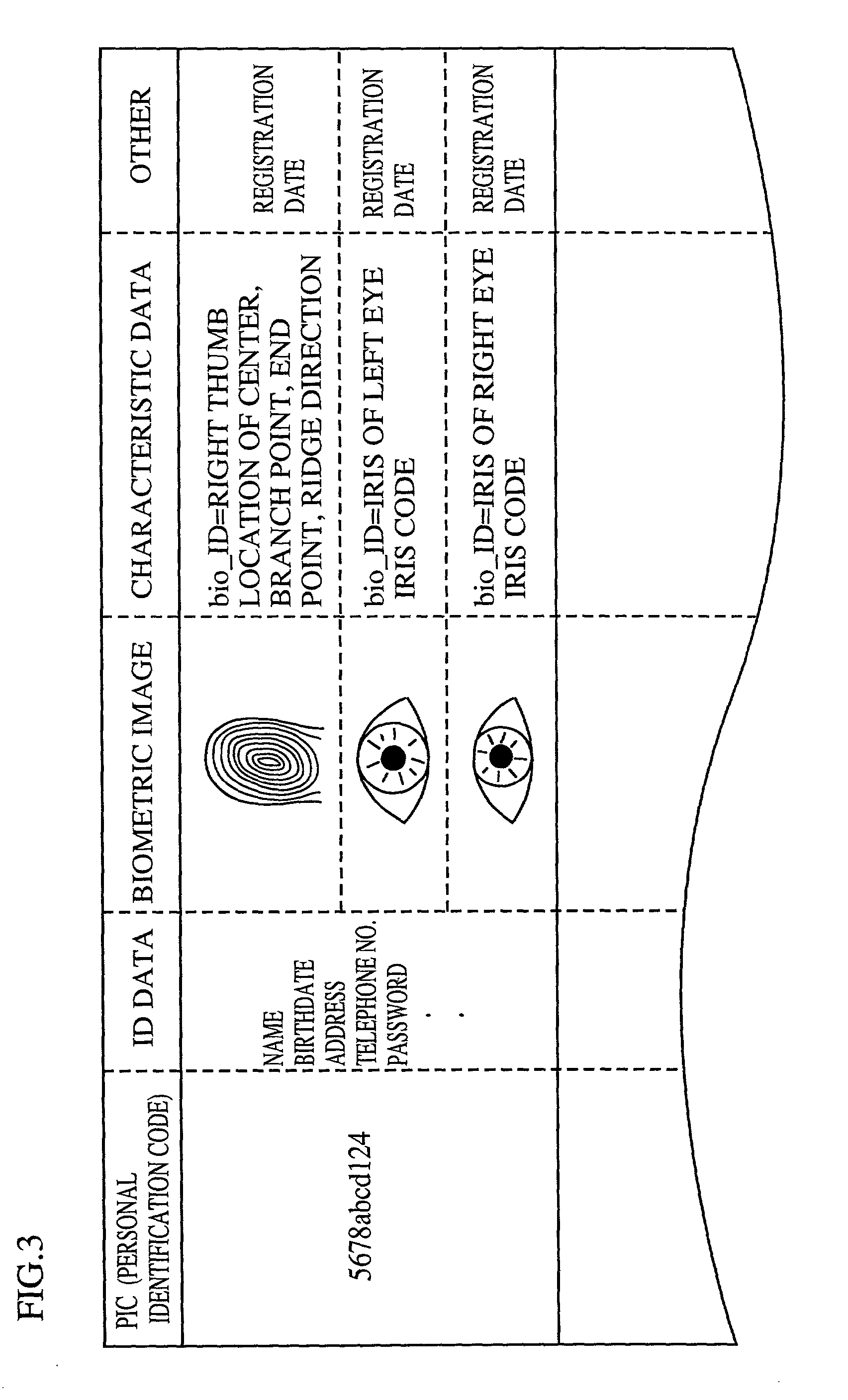
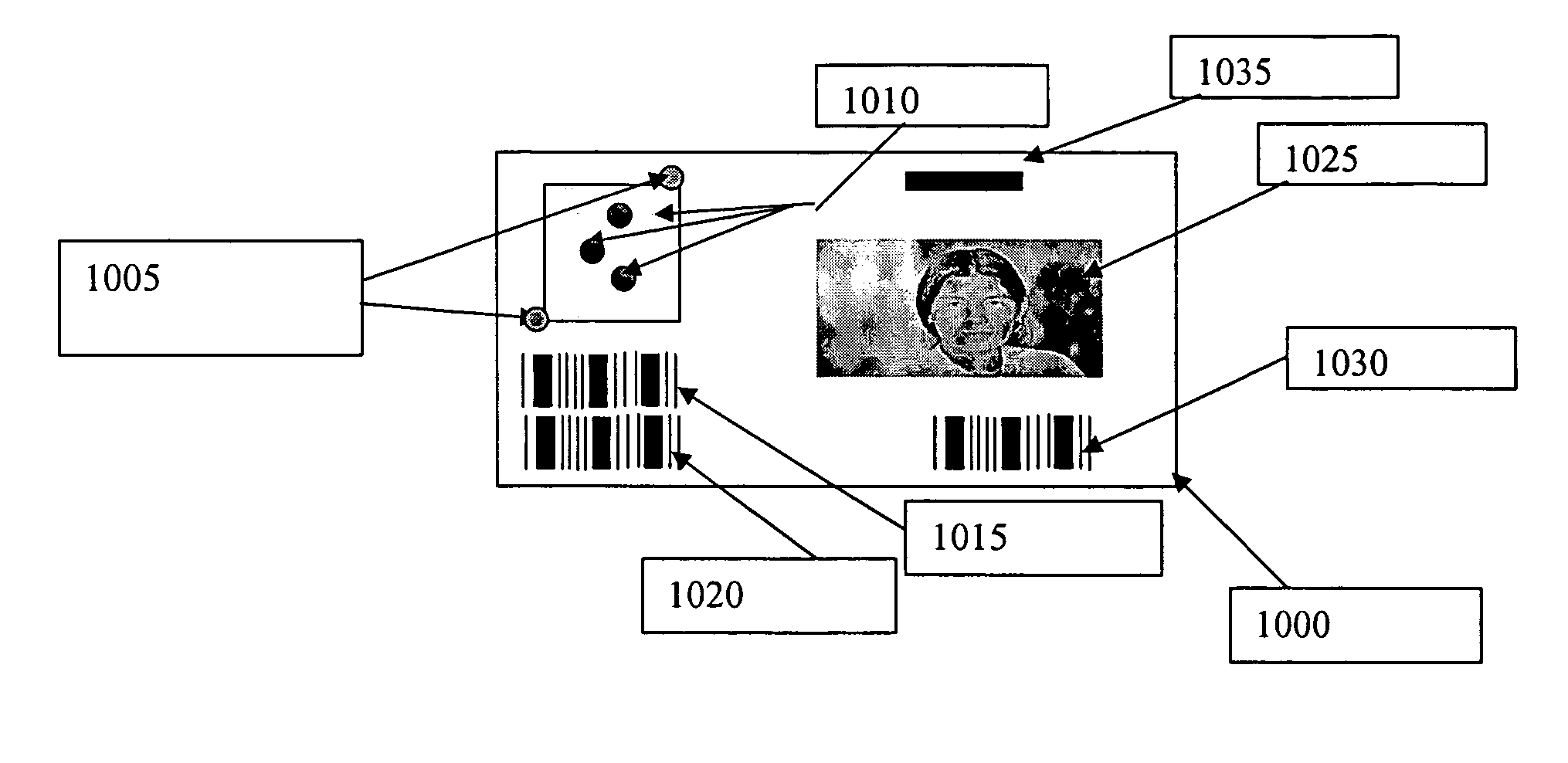
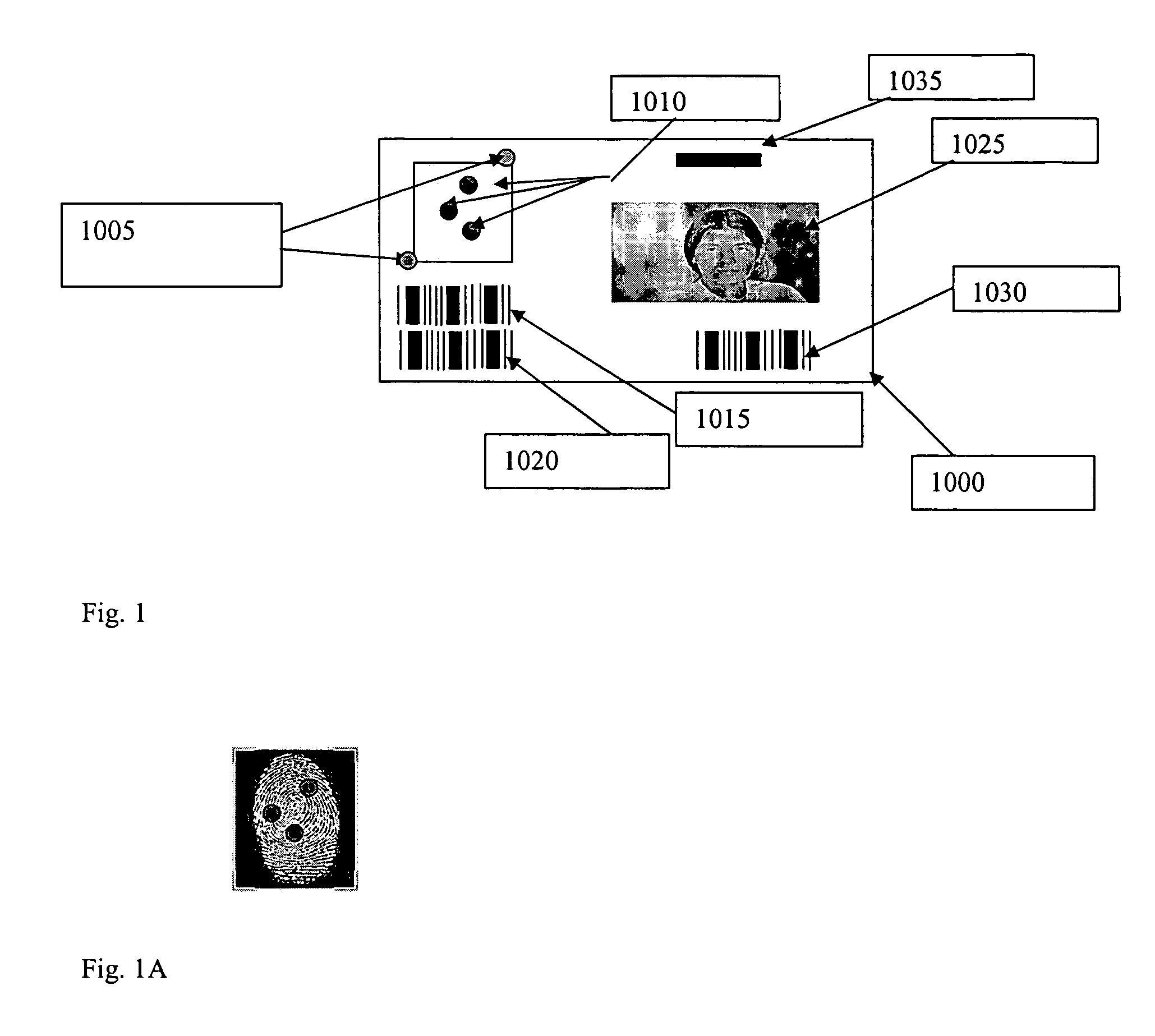
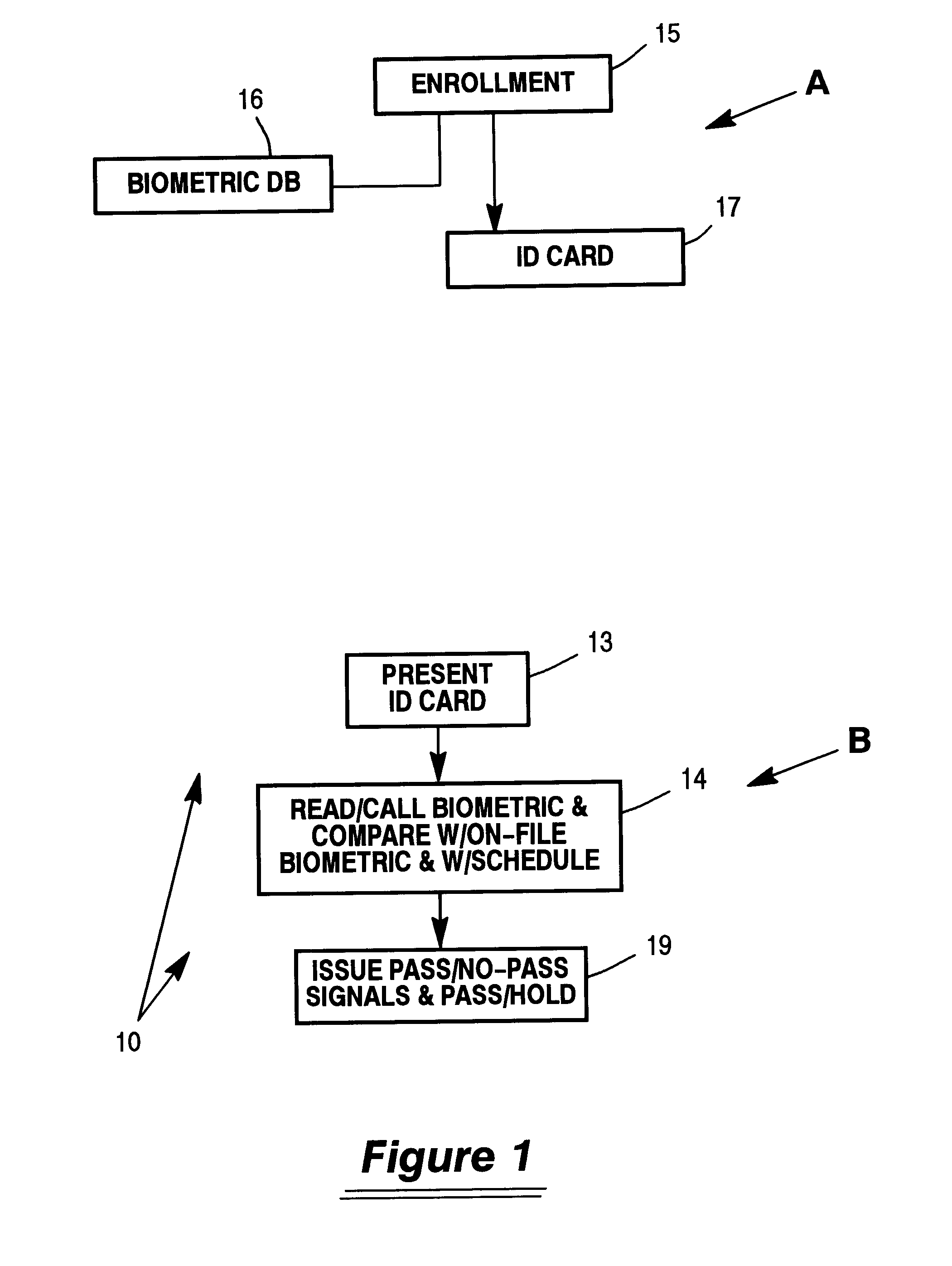
Biometric identification system using biometric images and personal identification number stored on a magnetic stripe and associated methods
InactiveUS6959874B2Digital data authenticationBiometric pattern recognitionPersonal identification numberBiometric data
The system and method store biometric information and a personal identification number (PIN) on a token having a magnetic storage medium. A biometric image is captured, biometric data is produced and a PIN is provided by an authorized user. The biometric data and PIN are stored on the magnetic storage medium of the token for subsequent use in verifying an authorized user of the token.
Owner:III HLDG 1
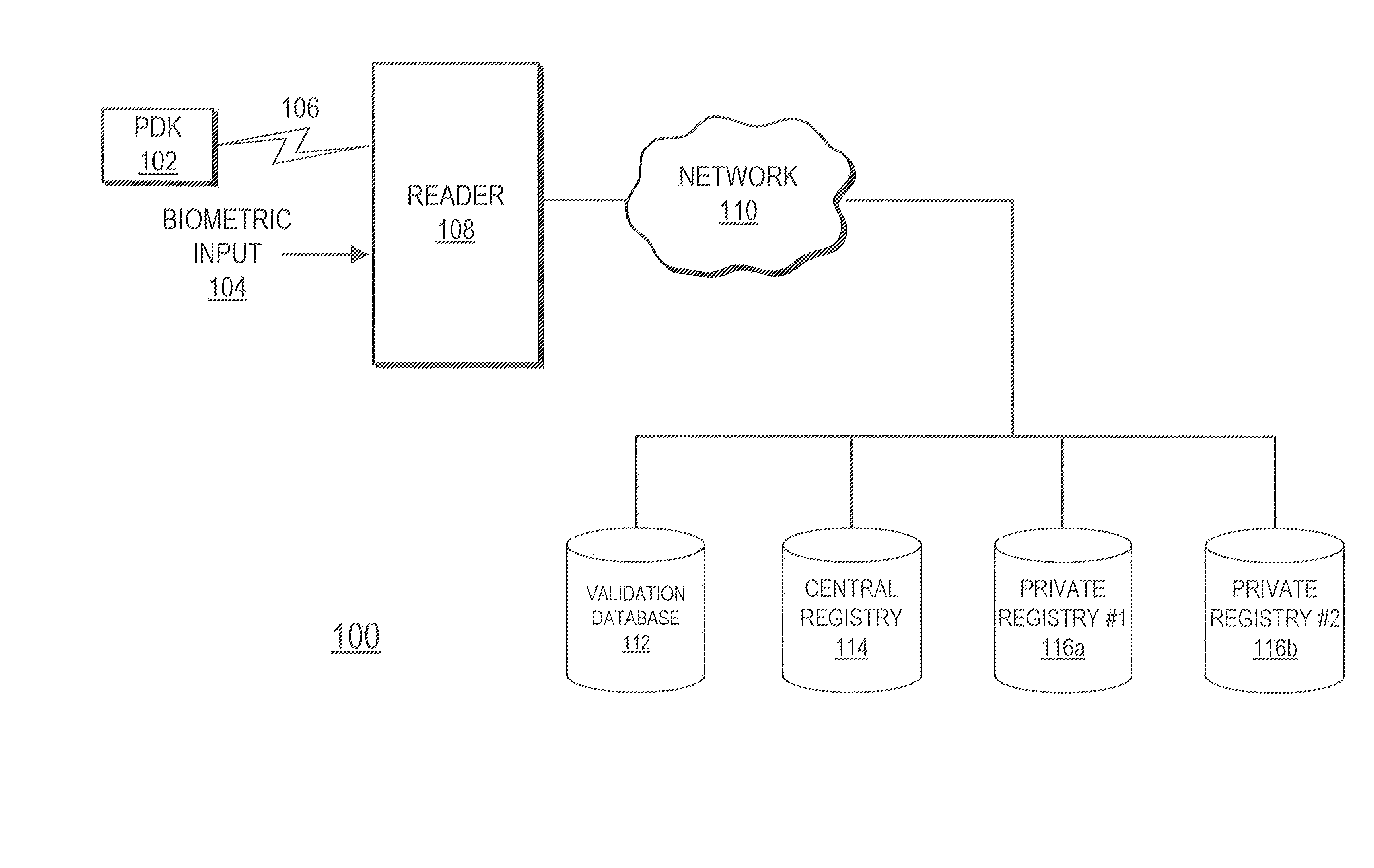
Single step transaction authentication using proximity and biometric input
ActiveUS20070245158A1Efficient and secure and highly reliable authenticationAcutation objectsUser identity/authority verificationWireless transmissionTransaction processing
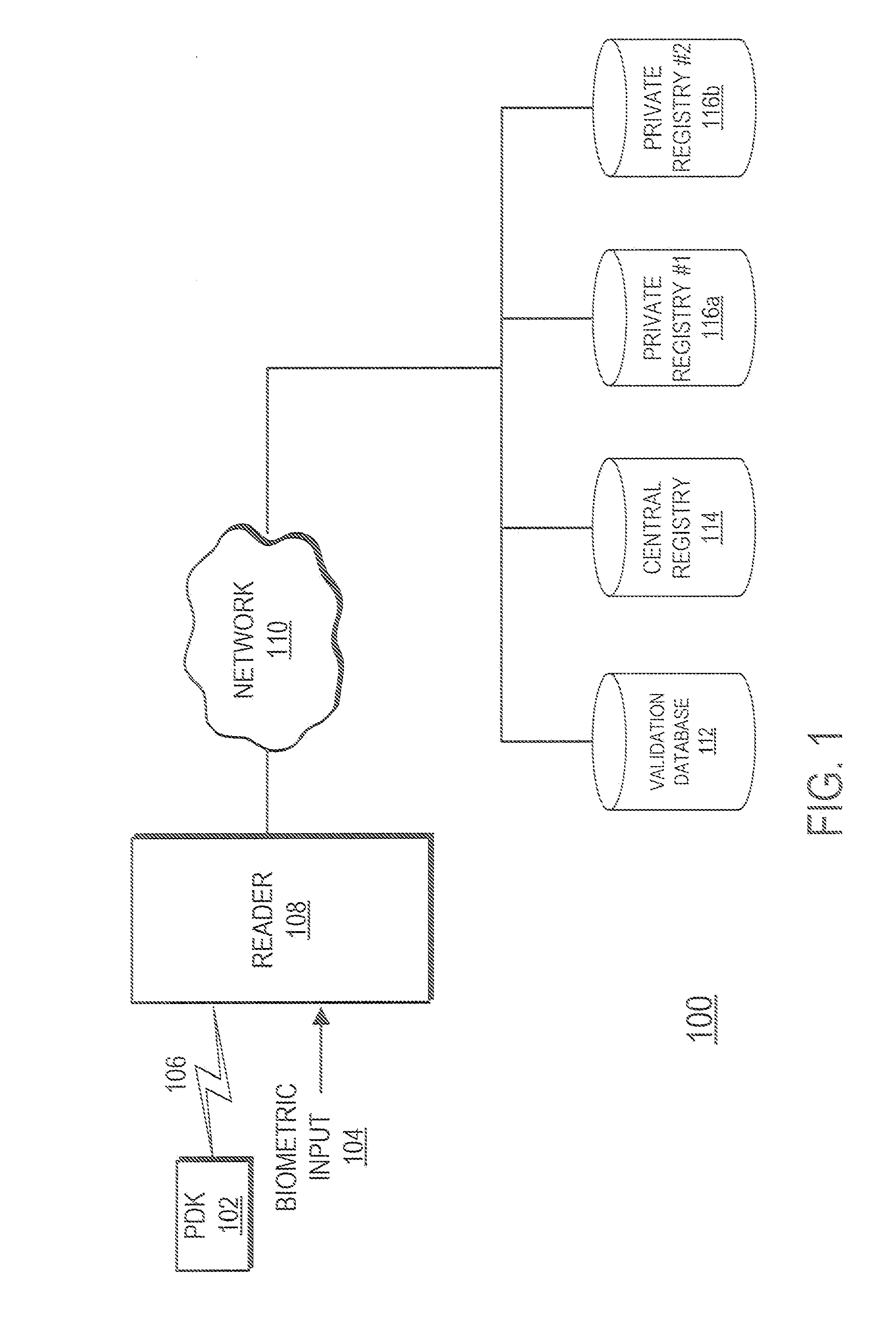
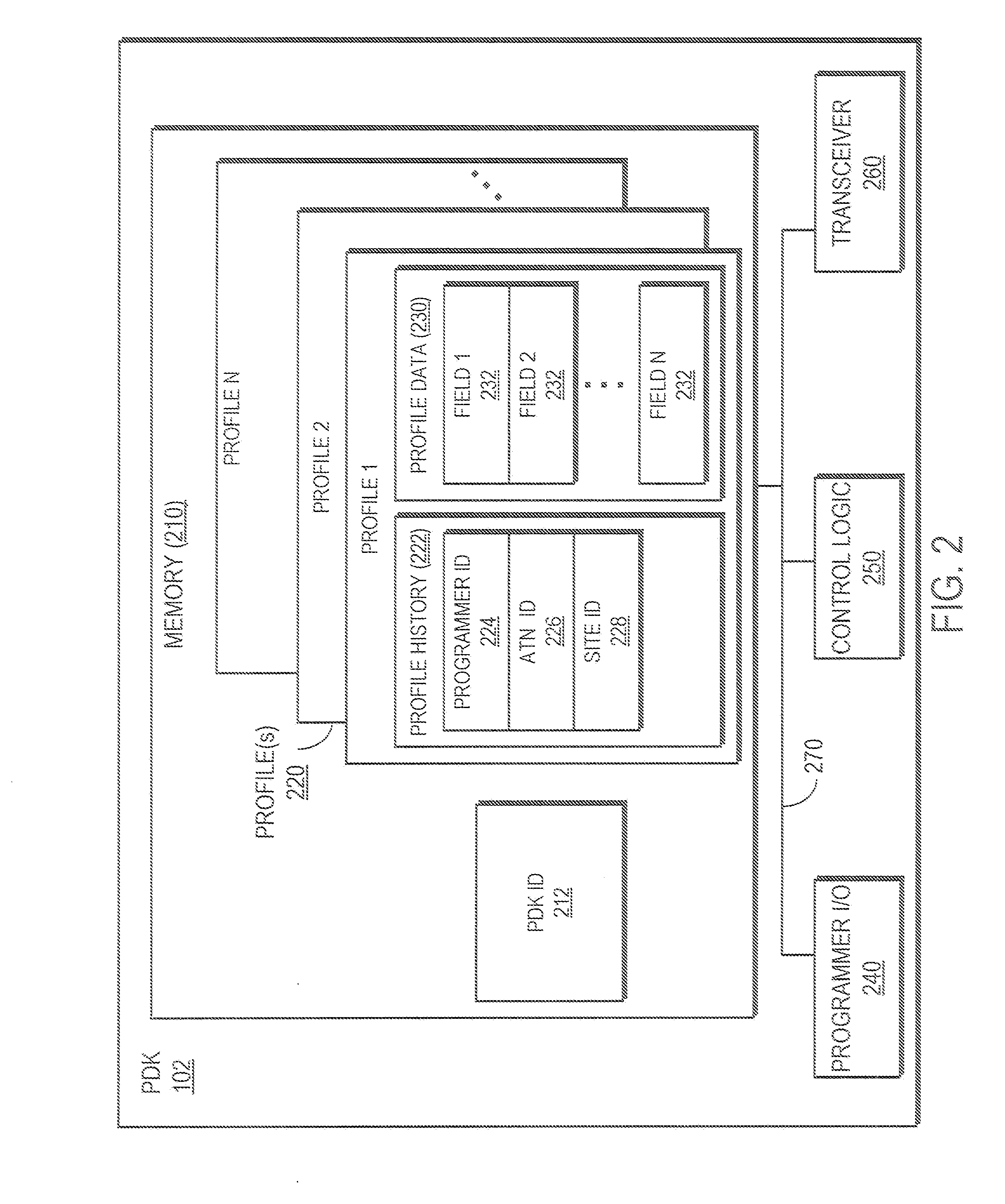
A system and method provide efficient, secure and highly reliable authentication for transaction processing and / or access control applications in which only biometric input is required from the user. A Personal Digital Key stores a biometric profile that comprises a representation of physical or behavioral characteristics that are uniquely associated with an individual that owns and carries the PDK. The PDK wirelessly transmits the biometric profile over a secure wireless transaction to a Reader for use in a biometric authentication process. The Reader compares the received biometric profile to a biometric input acquired at the point of transaction in order to determine if the transaction should be authorized.
Owner:PROXENSE
Apparatus and method for authenticating user according to biometric information
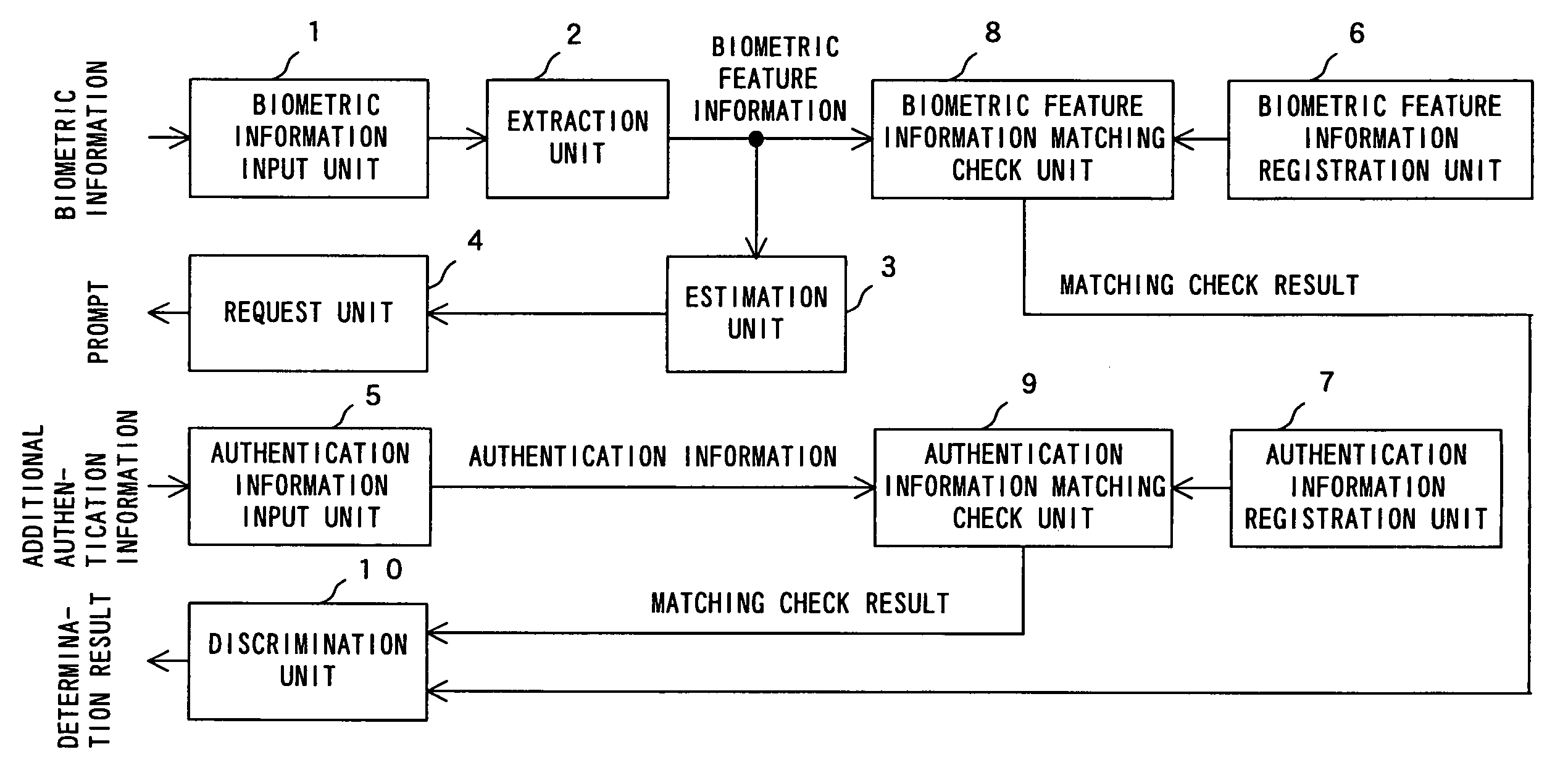
InactiveUS7007298B1Digital data processing detailsUser identity/authority verificationComputer scienceSpeech sound
An apparatus and a method authenticates a user according to biometric information such as a fingerprint, voice, etc. A biometric information input unit inputs biometric information. An extraction unit extracts biometric information extracts biometric feature information from the input biometric information. An estimation unit estimates the matching precision of the extracted biometric feature information. A request unit requests an input of additional authentication information. An authentication information input unit inputs authentication information. A biometric feature information registration unit preliminarily stores registered biometric feature information. An authentication information registration unit preliminarily stores additional registered authentication information. A biometric feature information matching check unit has a matching check between the extracted biometric feature information and the registered biometric feature information. An authentication information matching check unit has a matching check between the input authentication information and the registered authentication information. A determination unit computes the matching precision by combining the matching check result about the biometric feature information with the matching check result about the additional authentication information, and determines based on the computation result whether or not the user is authenticated.
Owner:FUJITSU LTD
System for biometric security using a FOB
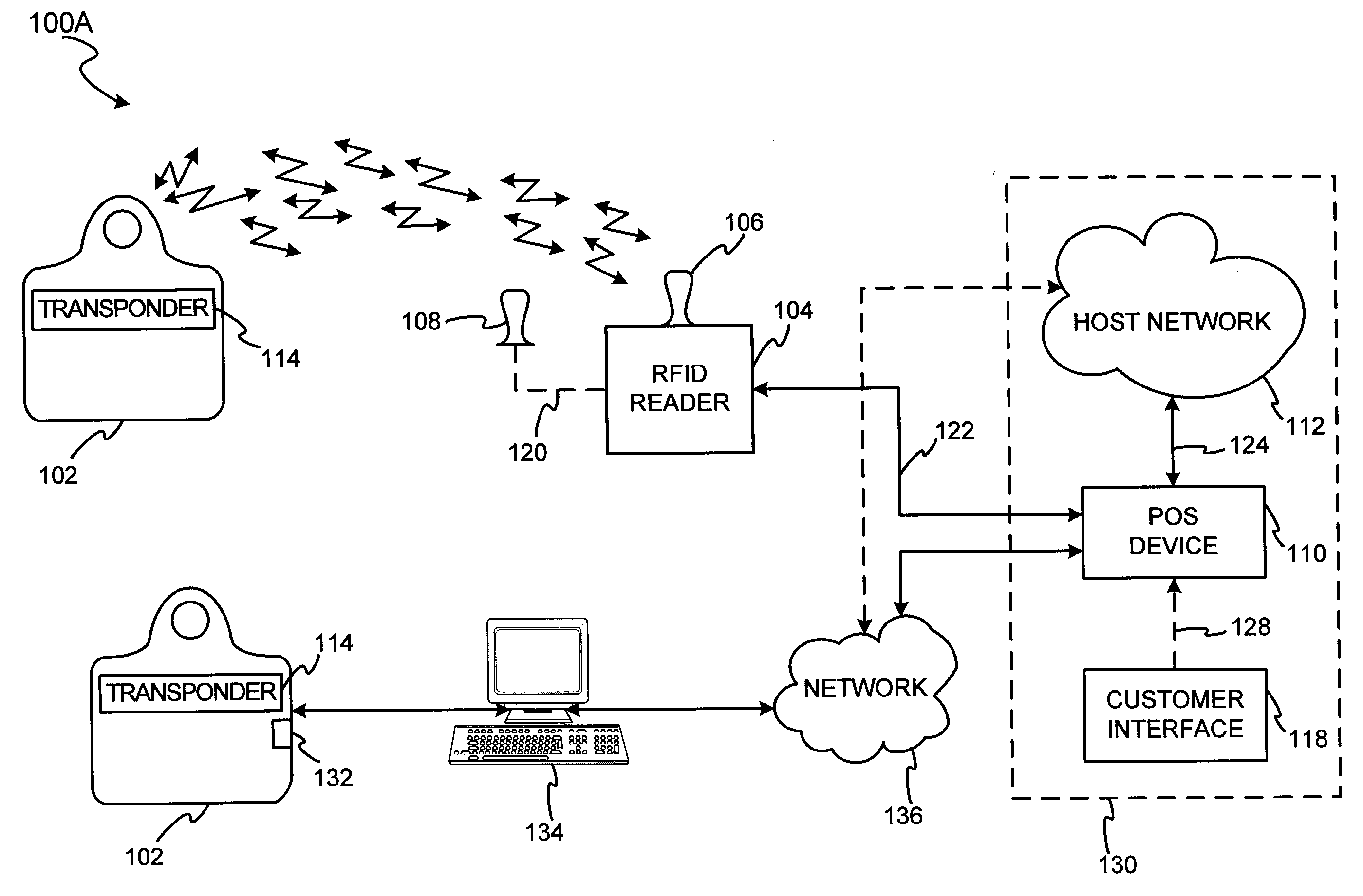
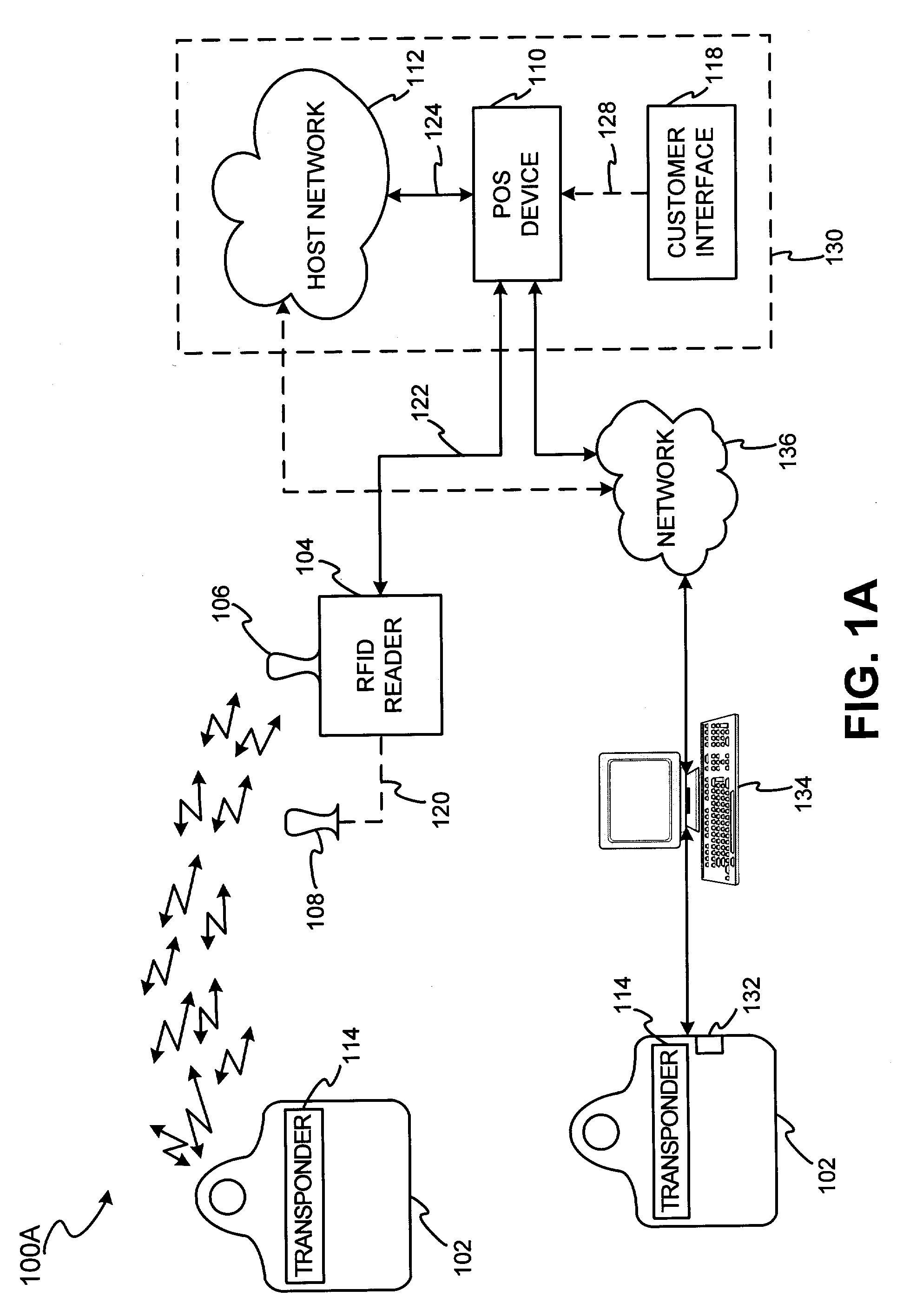
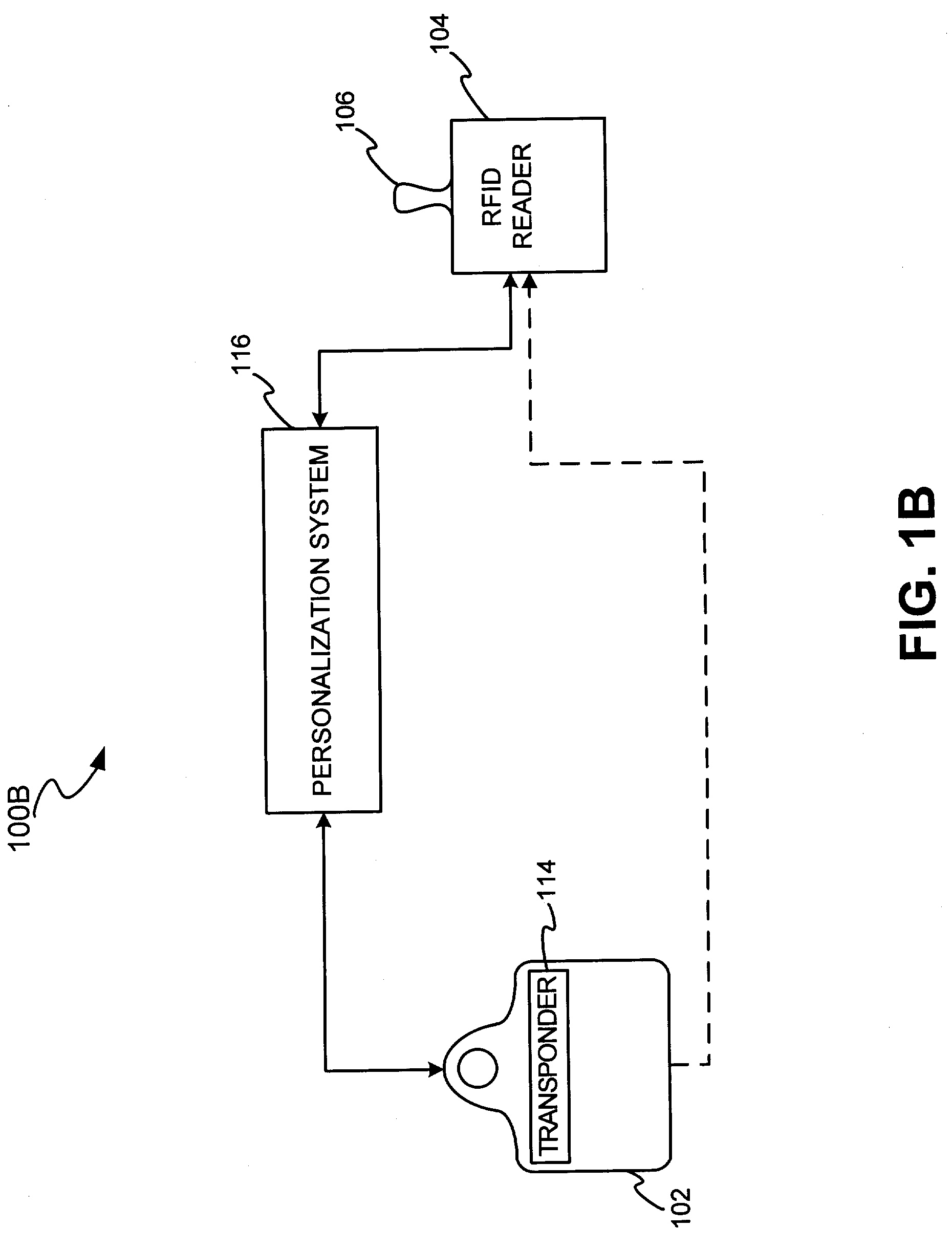
InactiveUS7303120B2Easy to completeLimited accessDigital data processing detailsComputer security arrangementsSecurity systemBiometric trait
The present invention discloses a system and methods for biometric security using biometrics in a transponder-reader system. The biometric security system also includes a biometric sensor that detects biometric samples and a device for verifying biometric samples. In one embodiment, the biometric security system includes a transponder configured with a biometric sensor. In another embodiment, the system includes a reader configured with a biometric sensor. The device for verifying samples compares the biometric samples with information stored on databases.
Owner:LIBERTY PEAK VENTURES LLC
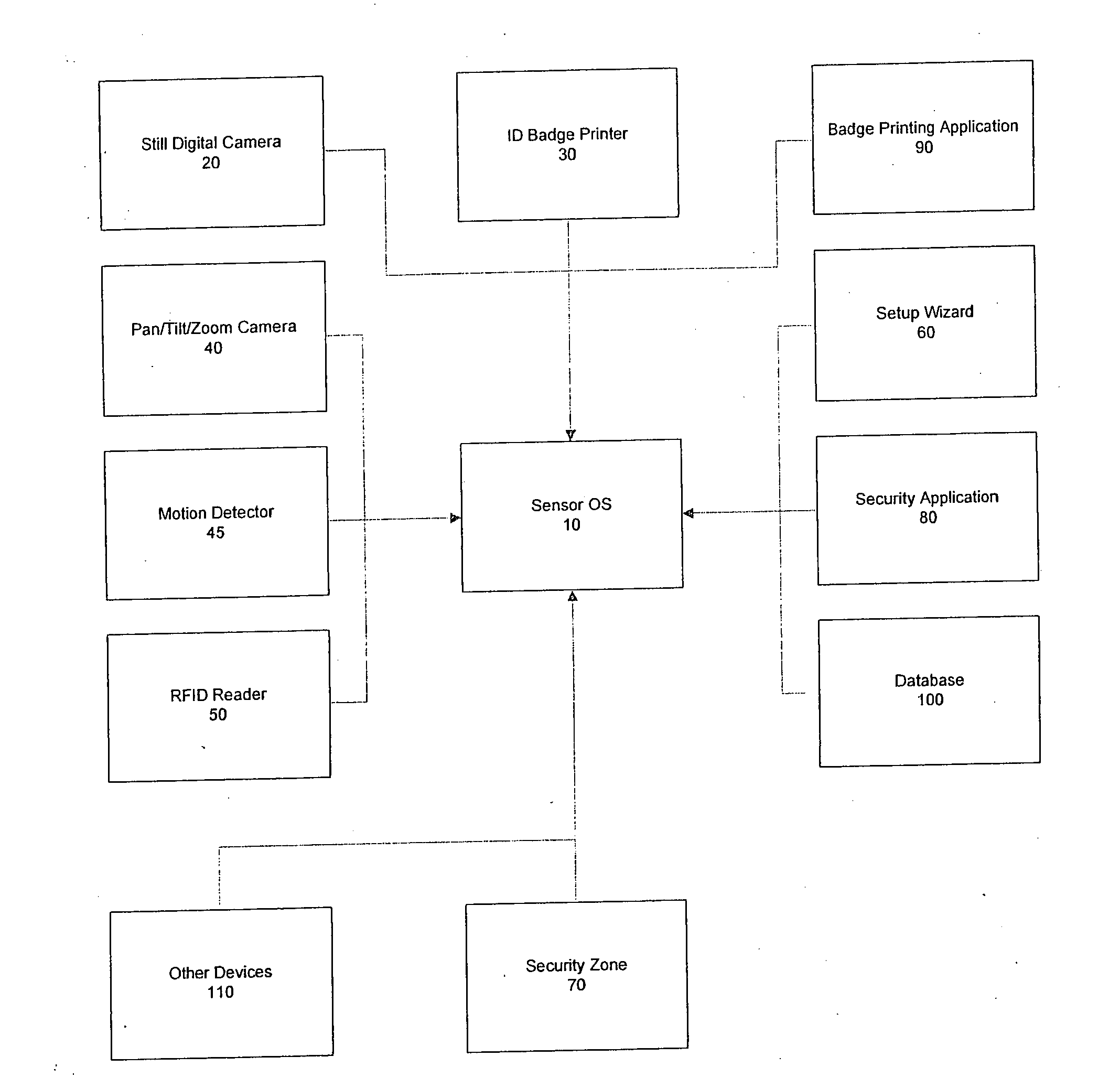
Access control system with RFID and biometric facial recognition
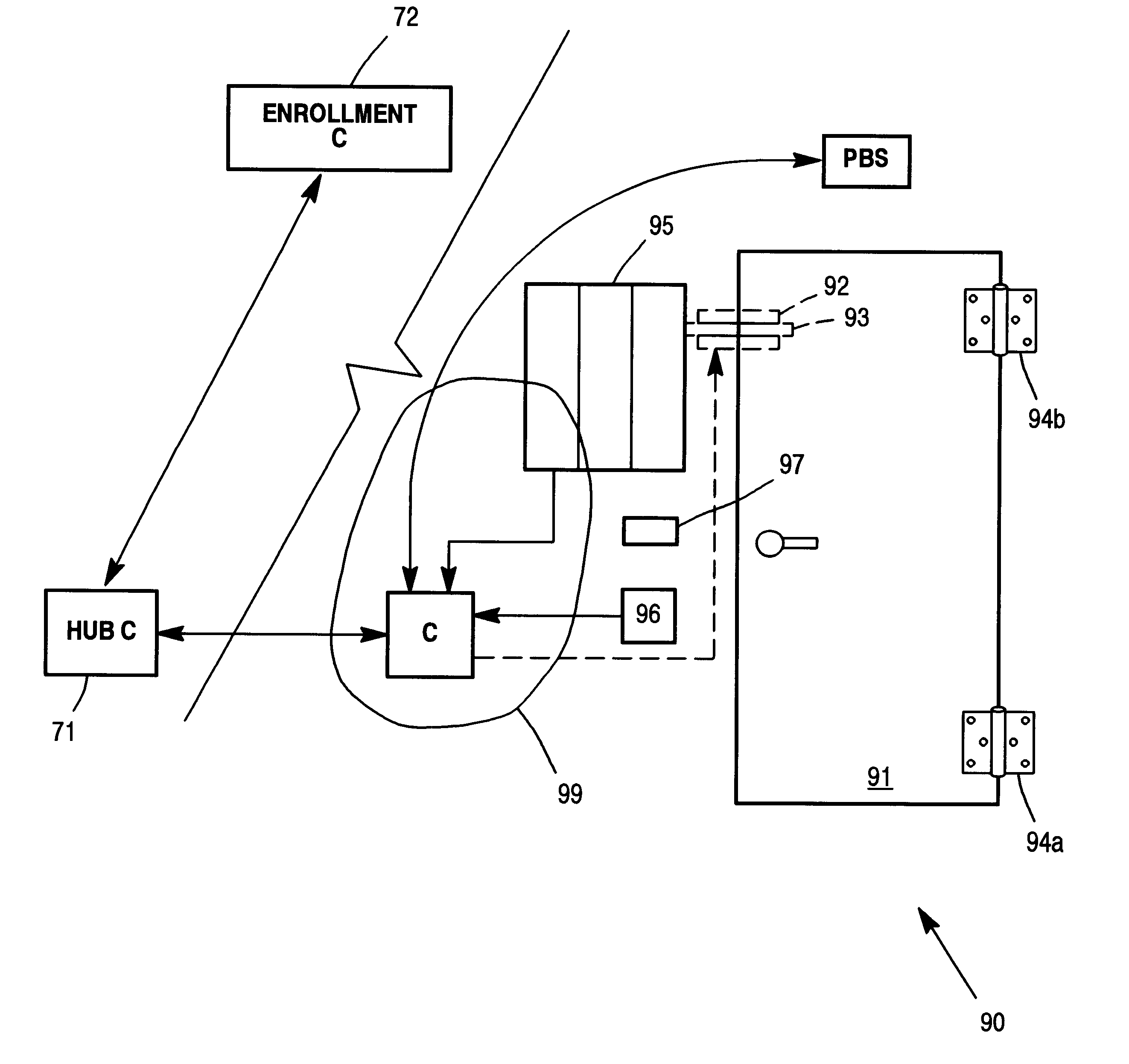
InactiveUS20070252001A1Accurate identificationIndividual entry/exit registersVerifying markings correctnessDigital dataRadio frequency signal
A biometric identification system which uses a UHF radio frequency identification (RFID) tag storing a first set of specified biometric information on an identity card; which bears a facial picture of the card carrier. An identification system comprising an antenna using radio frequency signals and a reader is used to read the first set of specified biometric information from the tag when the identify card is within sensing range of the identification system. A camera captures and digitalizes the facial features of the card carrier when the card carrier approaches a designated area and transmits this digital data to a computer which compares the first set of specified biometric information obtained by the reader from the identity card and the second set of digital facial information obtained from the camera to the stored biometric information to determine if the two sets of biometric information are a match.
Owner:KAIL KEVIN J +2
High security identification system for entry to multiple zones
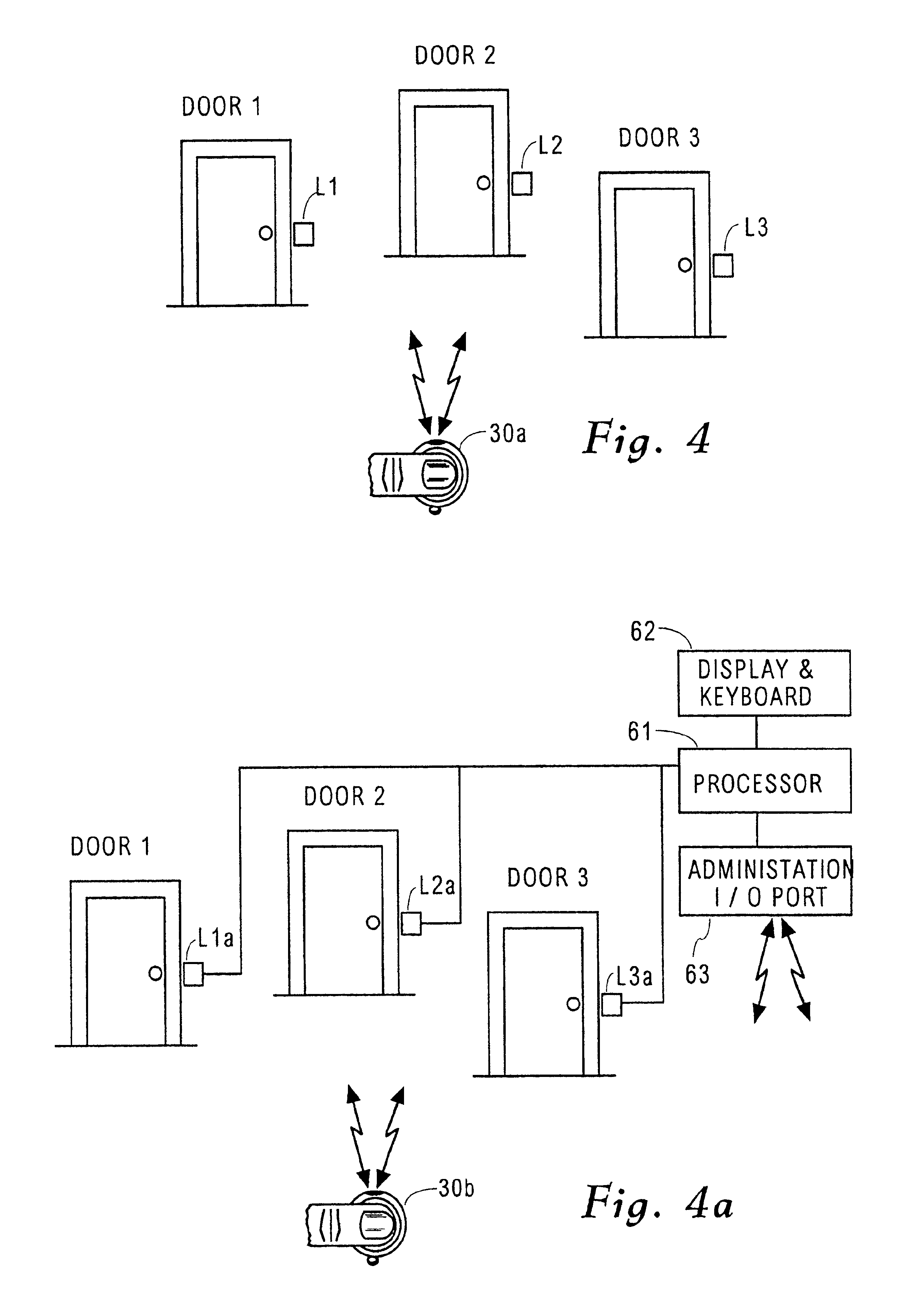
InactiveUS6867683B2Less-expensive and flexibleReduce usageProgramme controlElectric signal transmission systemsData fileBiometrics
Control over access by individuals to a group of high security facilities and zones within such facilities is accomplished with use of biometric readers at each access door as well as a quick ID reading device that is not required to contain biometric information. Enrollment at a secure facility where biometrics are maintained for each individual establishes a multipart data file for each individual, each part of which may be accessed by different actors in the system. The individuals allowed security to various facilities can only be in a single facility at a given time and also control their own schedule.
Owner:UNISYS CORP
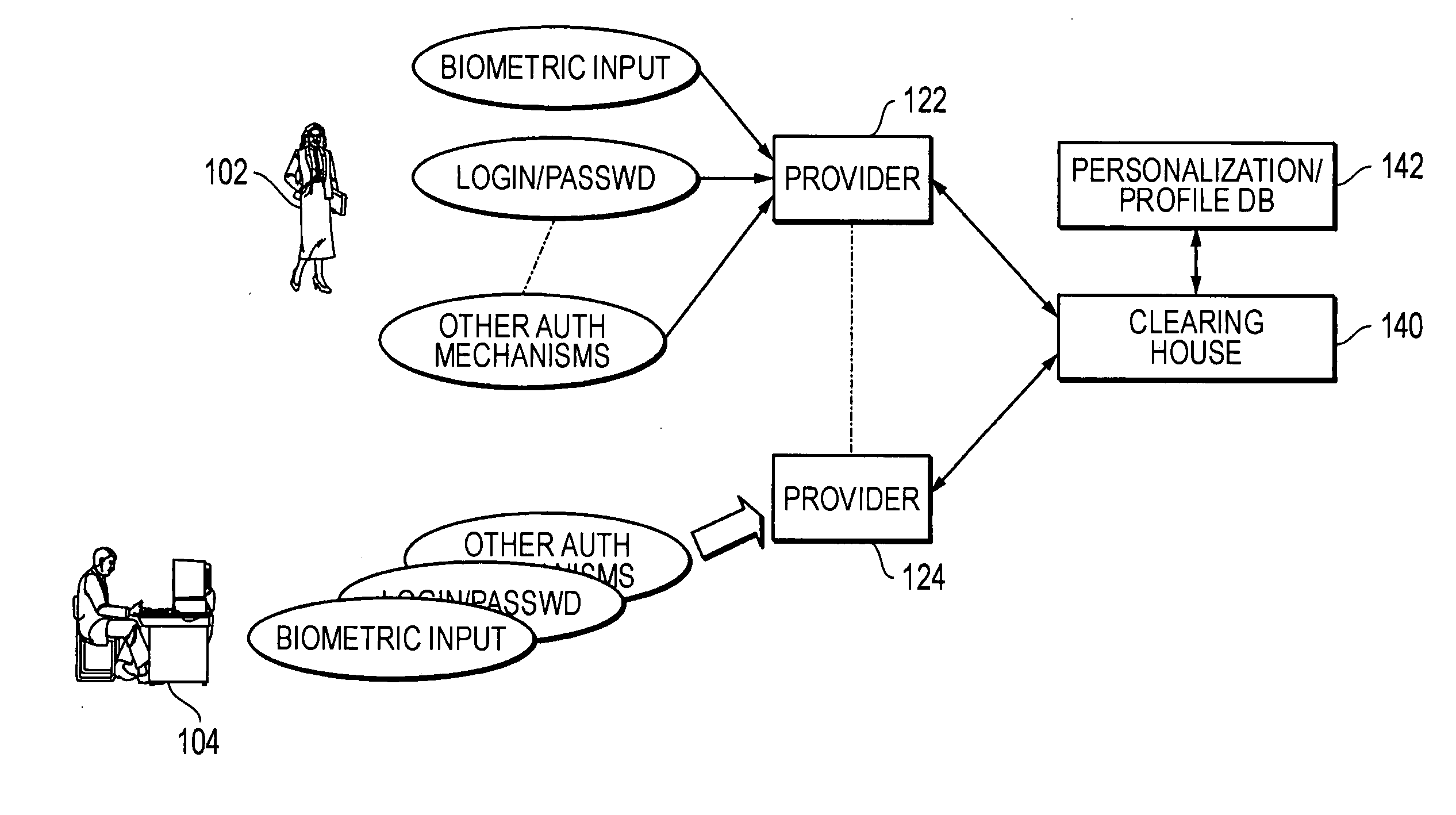
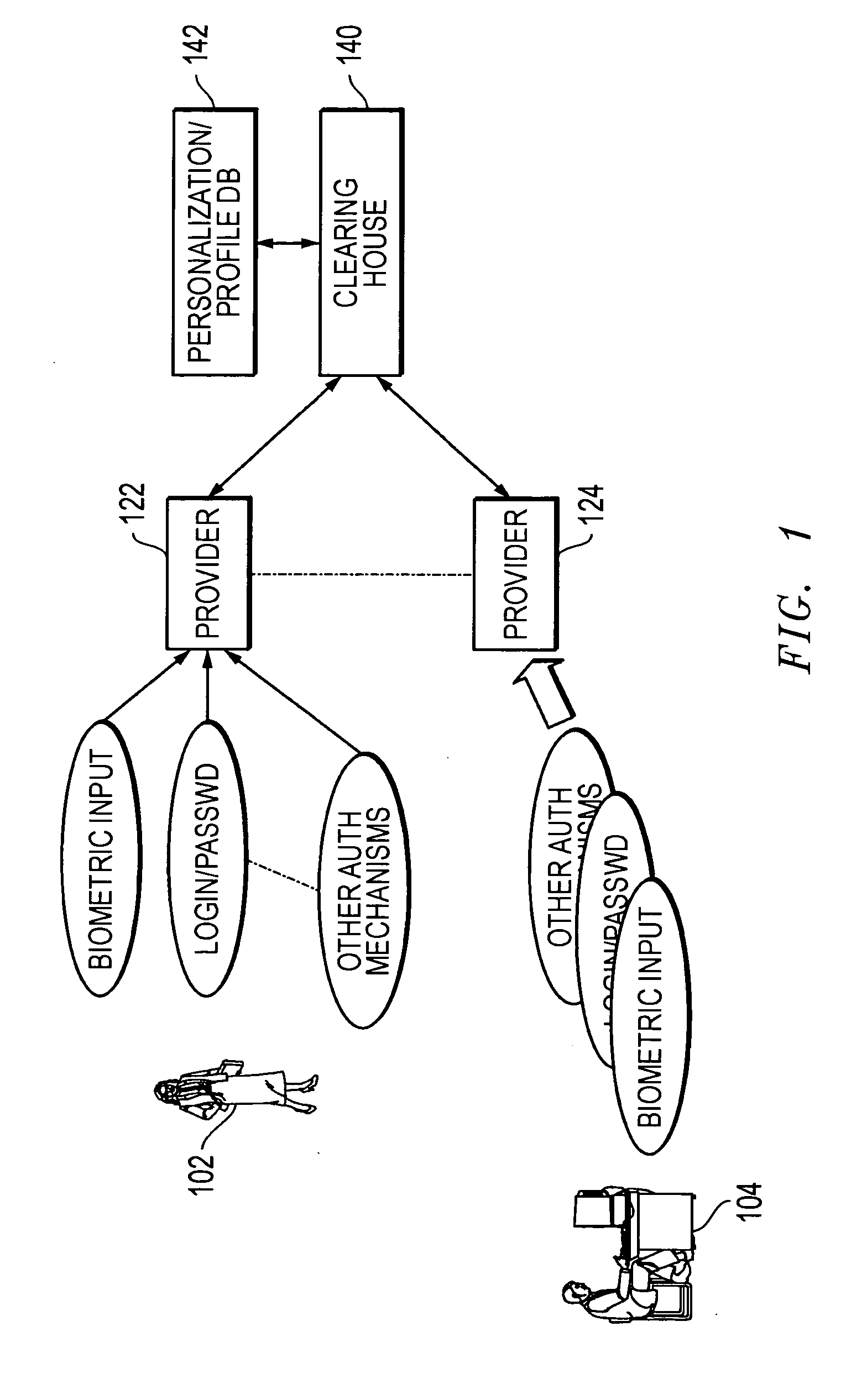
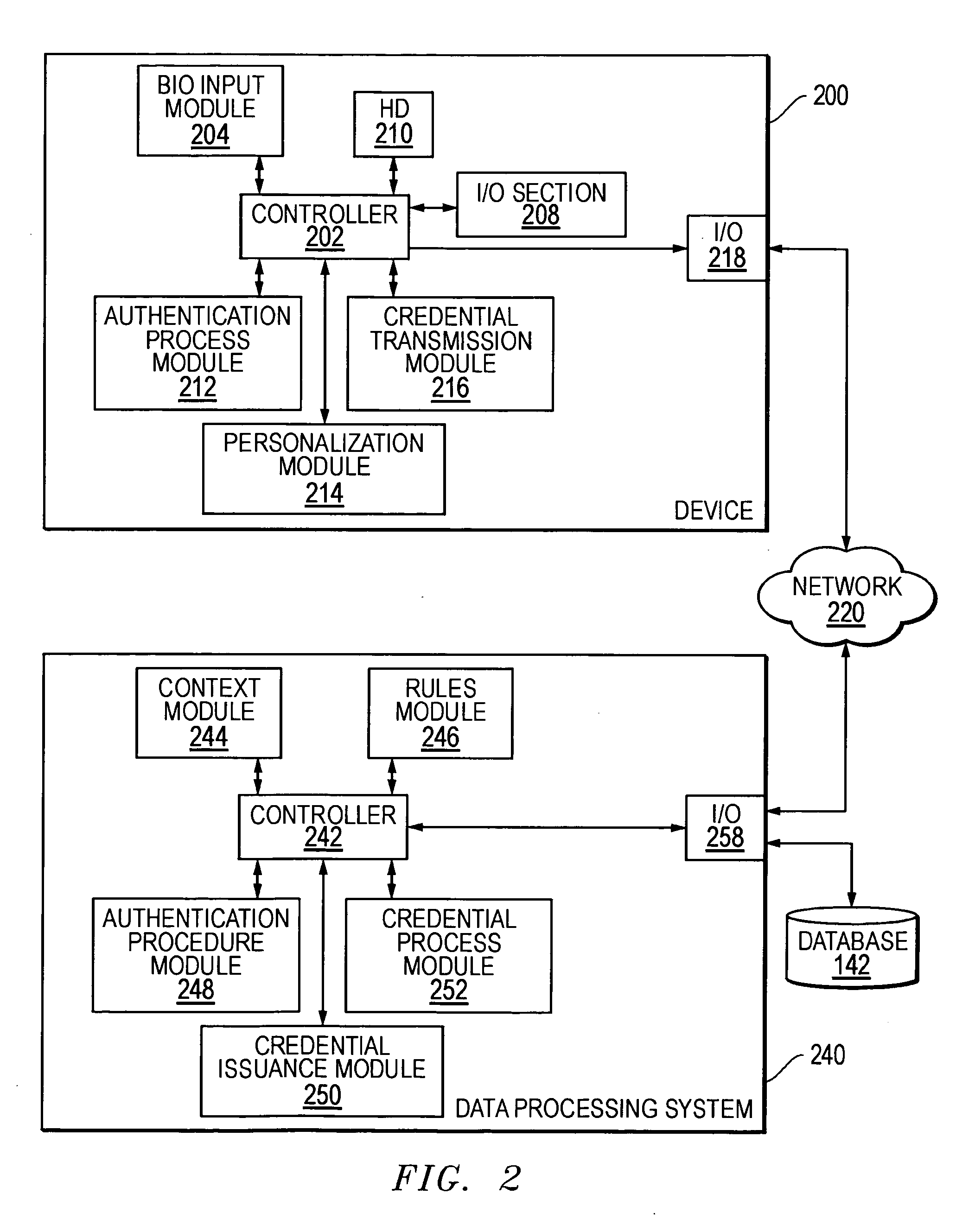
Methods and systems for using data processing systems in order to authenticate parties
InactiveUS20070079136A1Digital data processing detailsUser identity/authority verificationData processing systemBiometric data
Methods and systems perform authentication based at least in part of the context of the transaction. In one embodiment, the context can be determined and trigger different rules with regard to access to the information or ability to immediately execute the transaction. In another embodiment, a method can include registering a device as a trusted device. The device can include a biometric input module. Biometric data can be used to authenticate a user, and the user may be requested to resubmit biometric data during the same session. In a further embodiment, a hacker may obtain unauthorized access to a victim's account information. The hacker may not be authenticated because he would not have access to a currently valid credential.
Owner:SBC KNOWLEDGE VENTURES LP
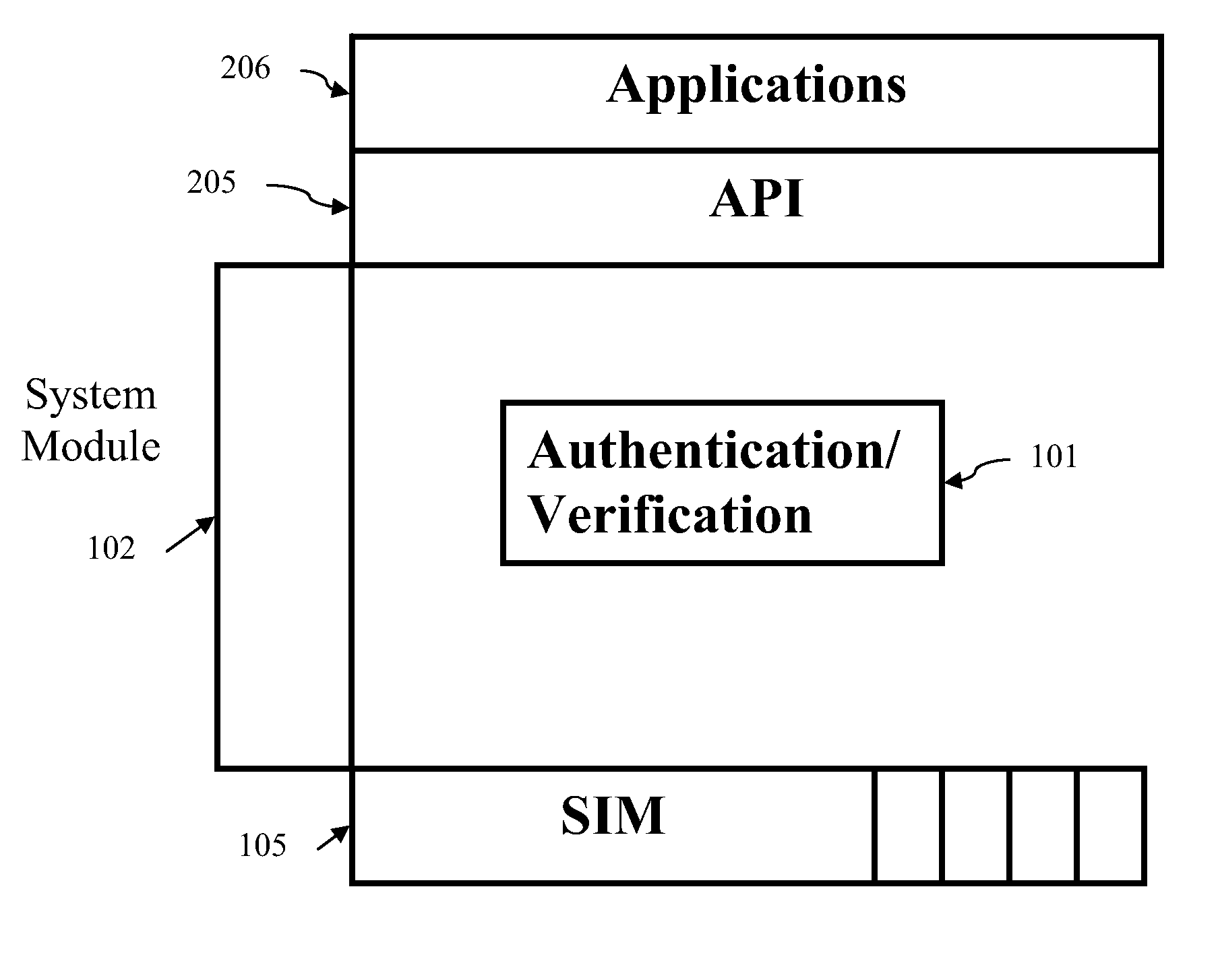
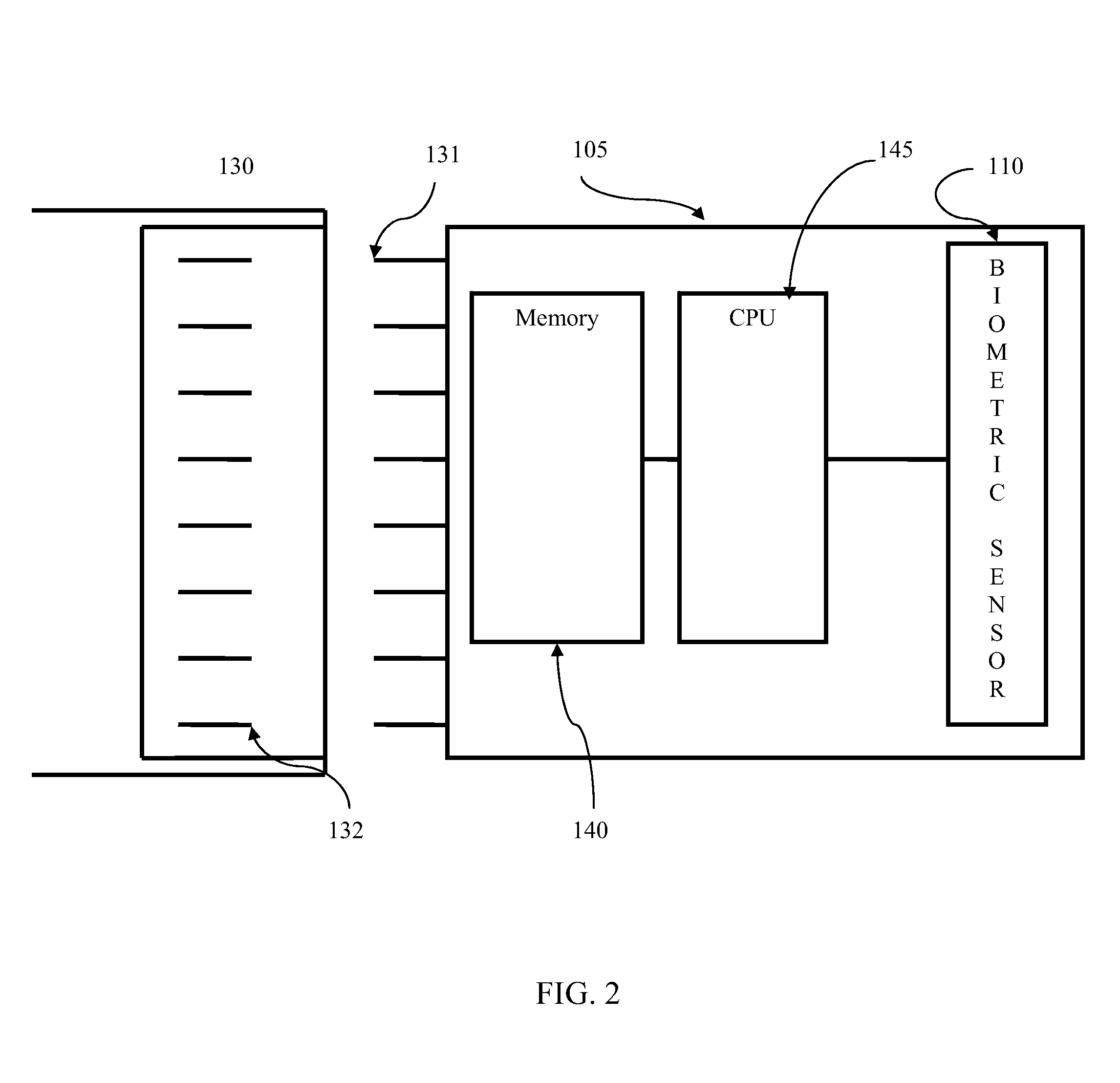
Biometric smart card for mobile devices
InactiveUS20090191846A1Acutation objectsUnauthorised/fraudulent call preventionSmart cardMobile device
A method and apparatus for controlling access to the data stored on a smart card for use in mobile devices. A user initializes the smart card memory by saving an authentication credential in memory. Subsequently, when various applications executed on the mobile device seek to retrieve the data stored in the smart card memory, the user must submit to an authentication process before access to the data stored in the smart card memory is granted. Embodiments utilize biometric traits and biometric templates stored in memory as authentication credentials. Biometric sensors are provided with the smart card so that a candidate biometric trait can be generated and compared with a biometric template stored in memory. If the biometric trait matches the stored biometric template, then access to the data stored in the smart card is granted.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com