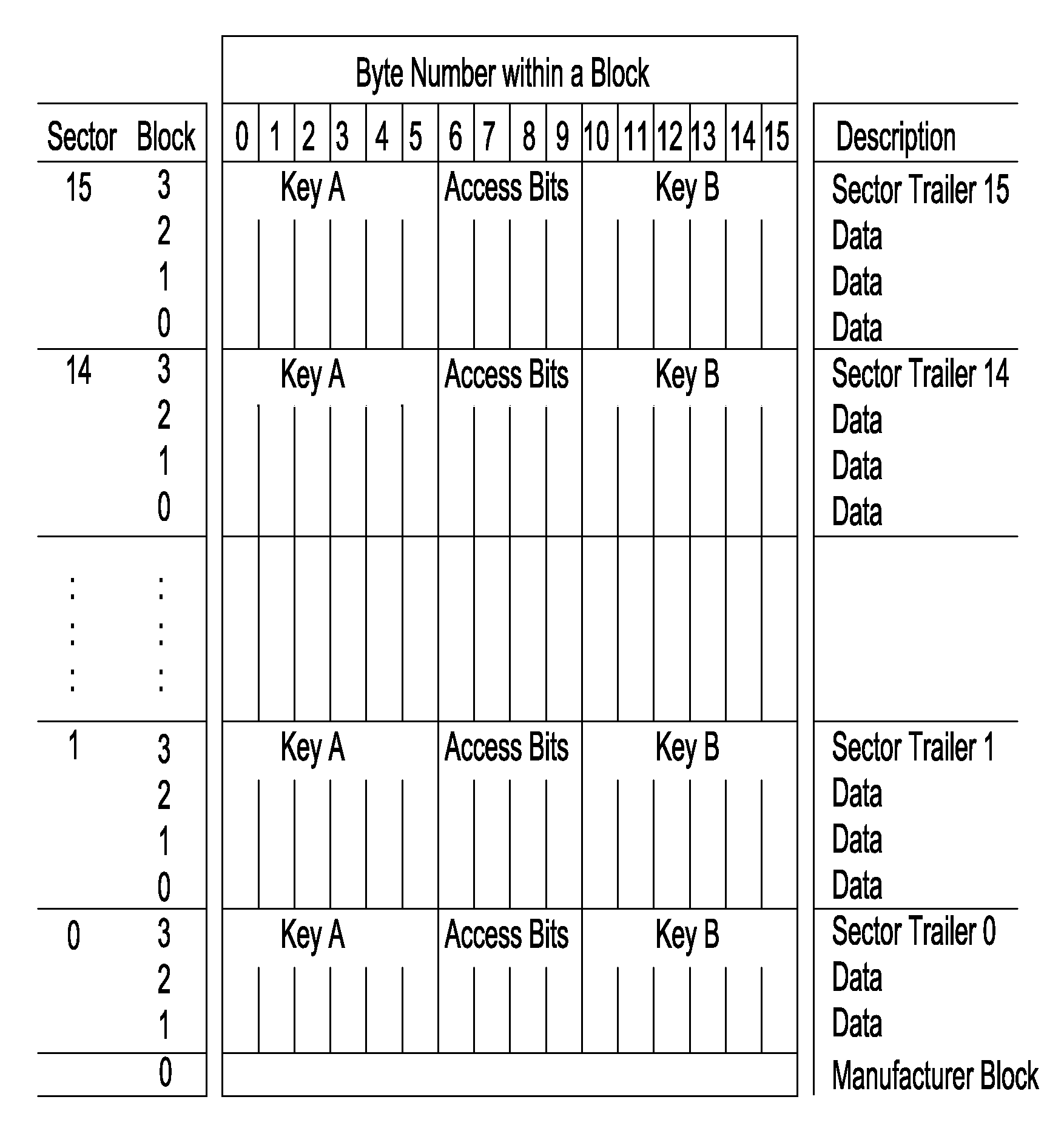
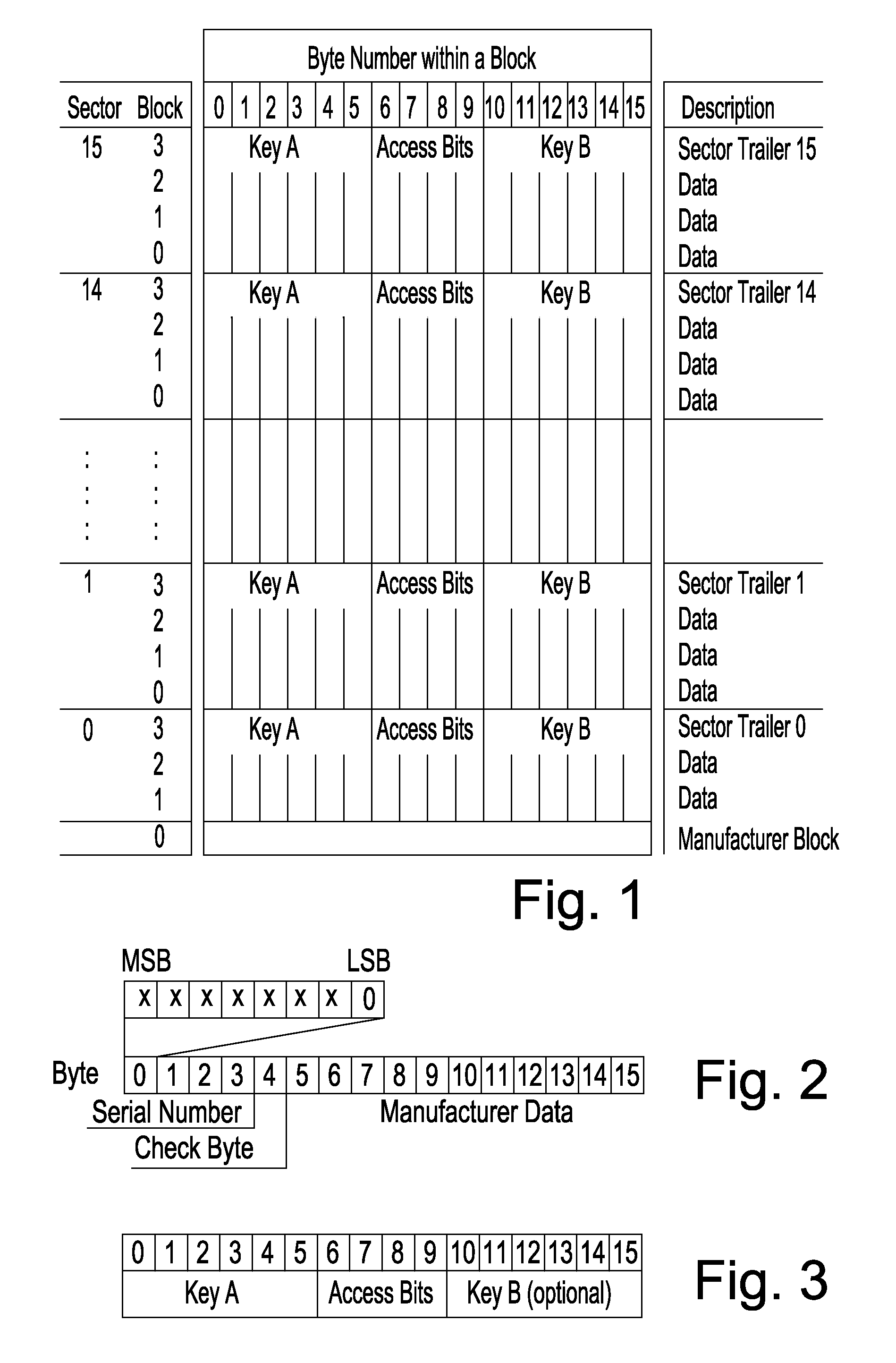
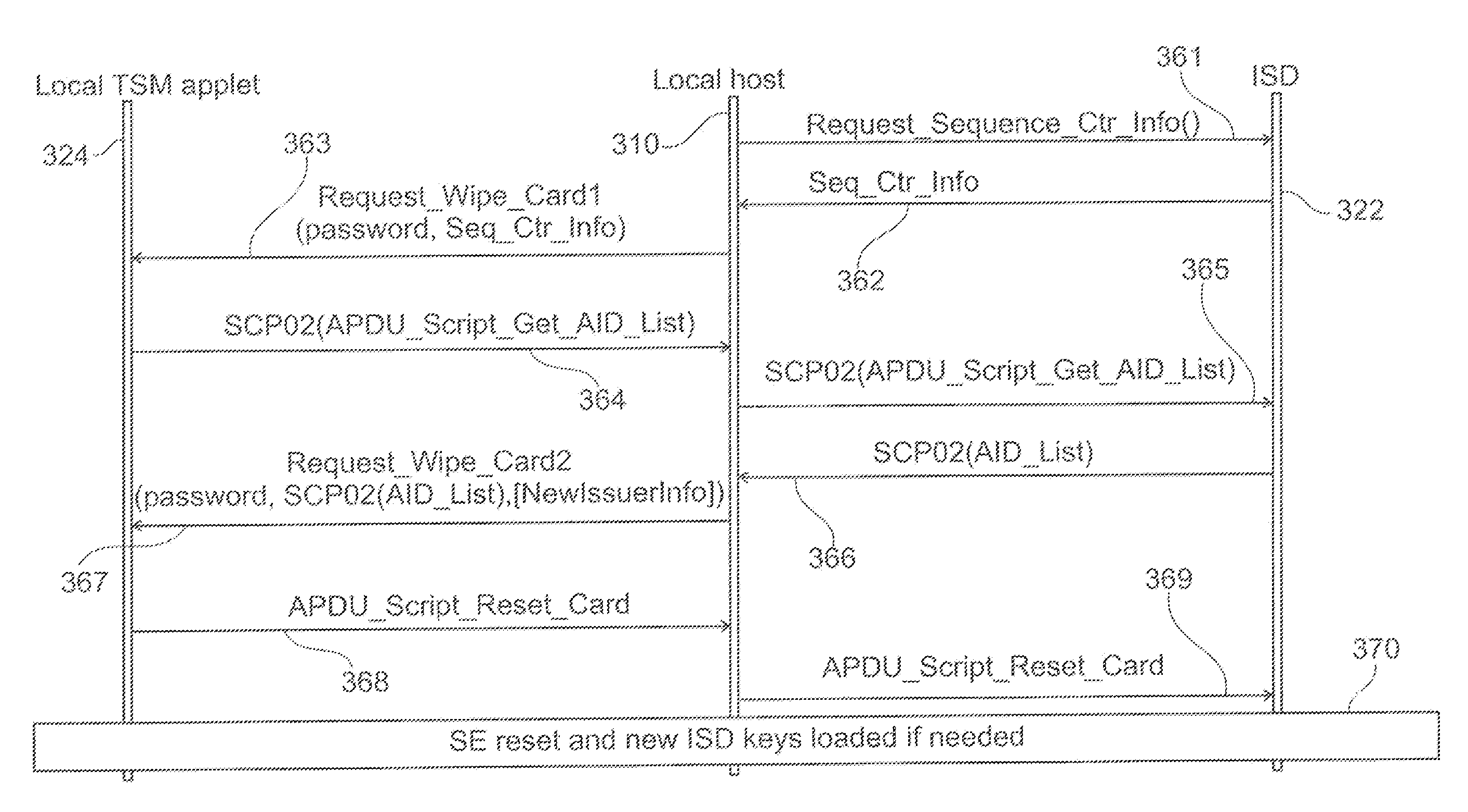
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
86 results about "Trusted service manager" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
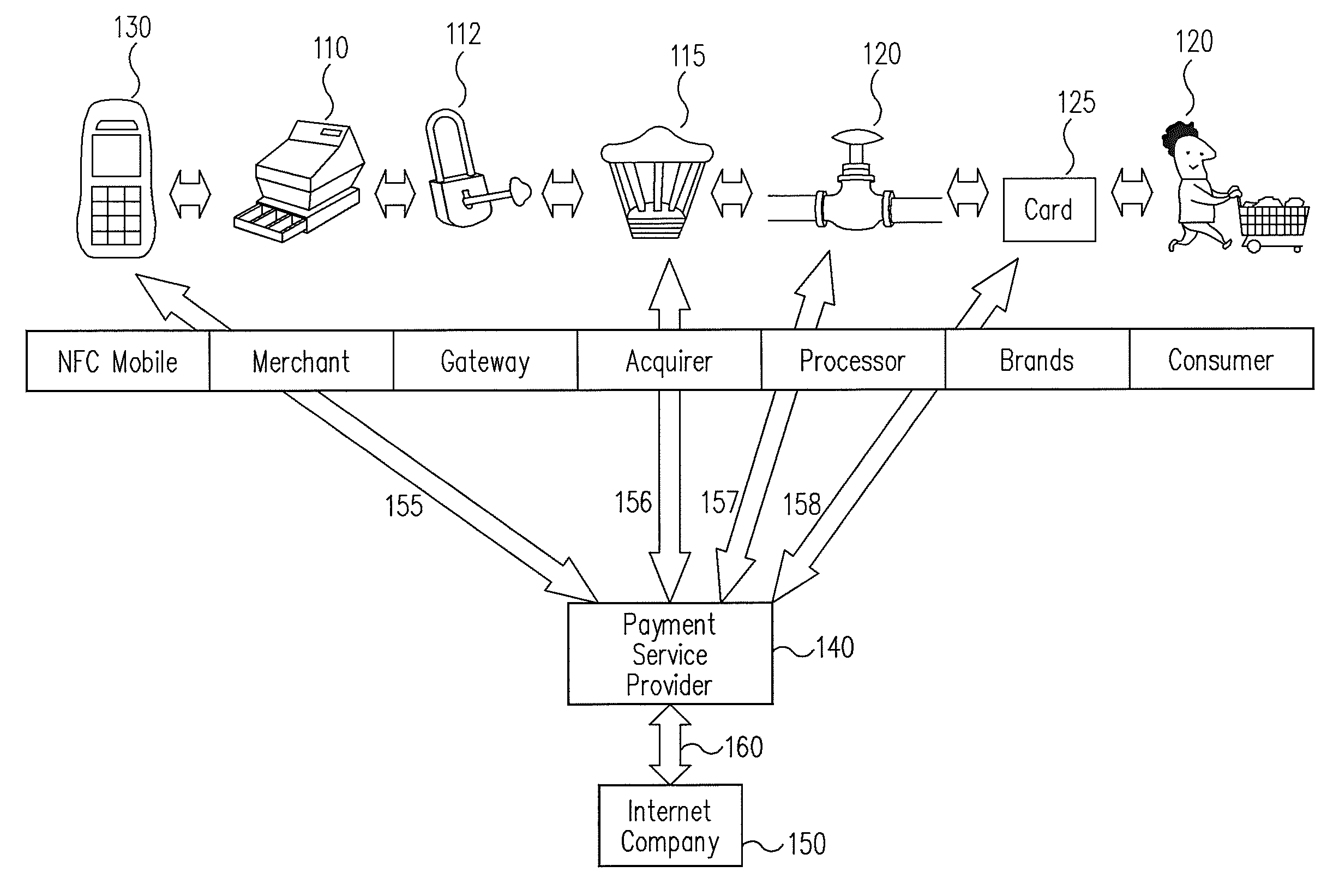
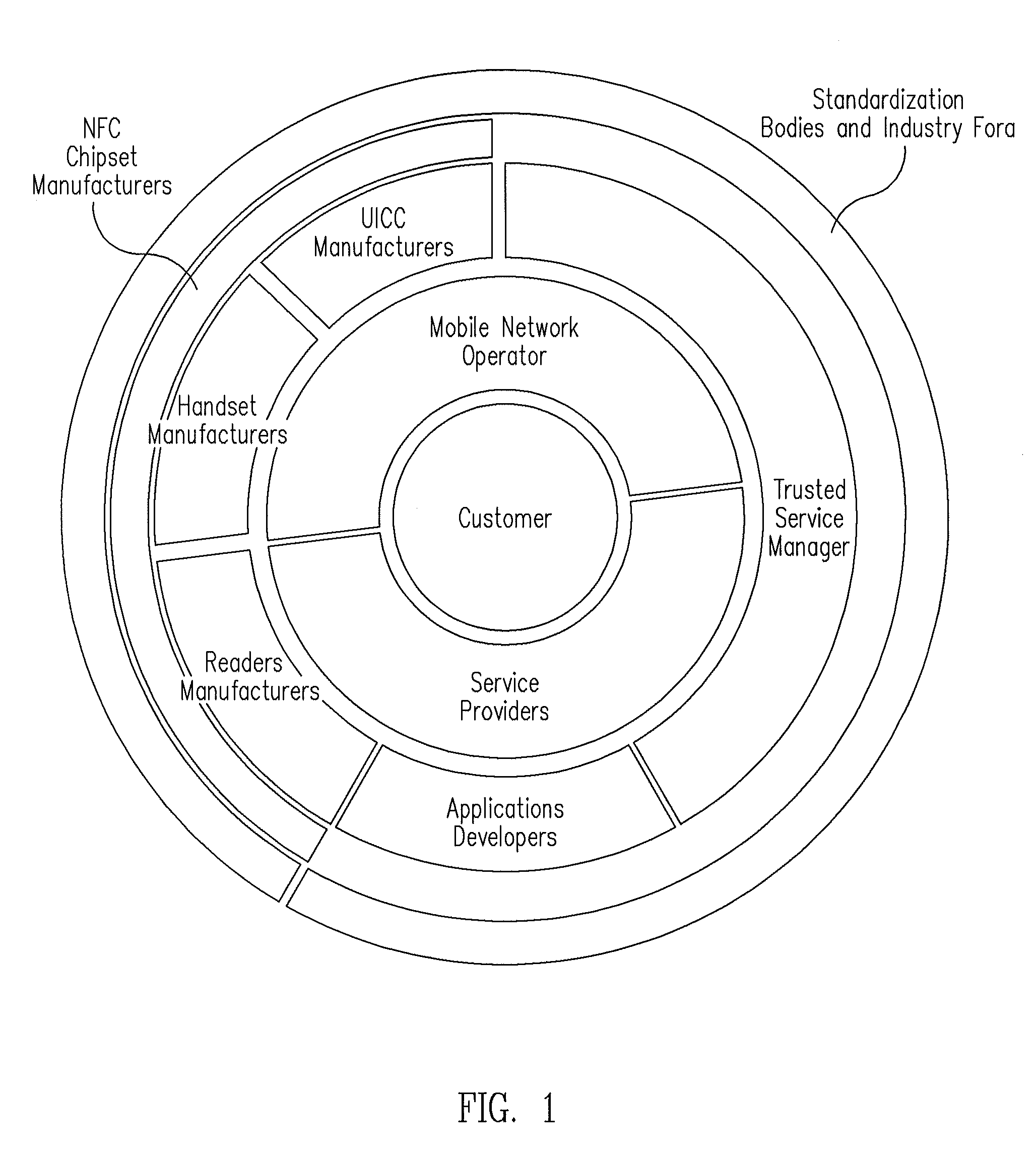
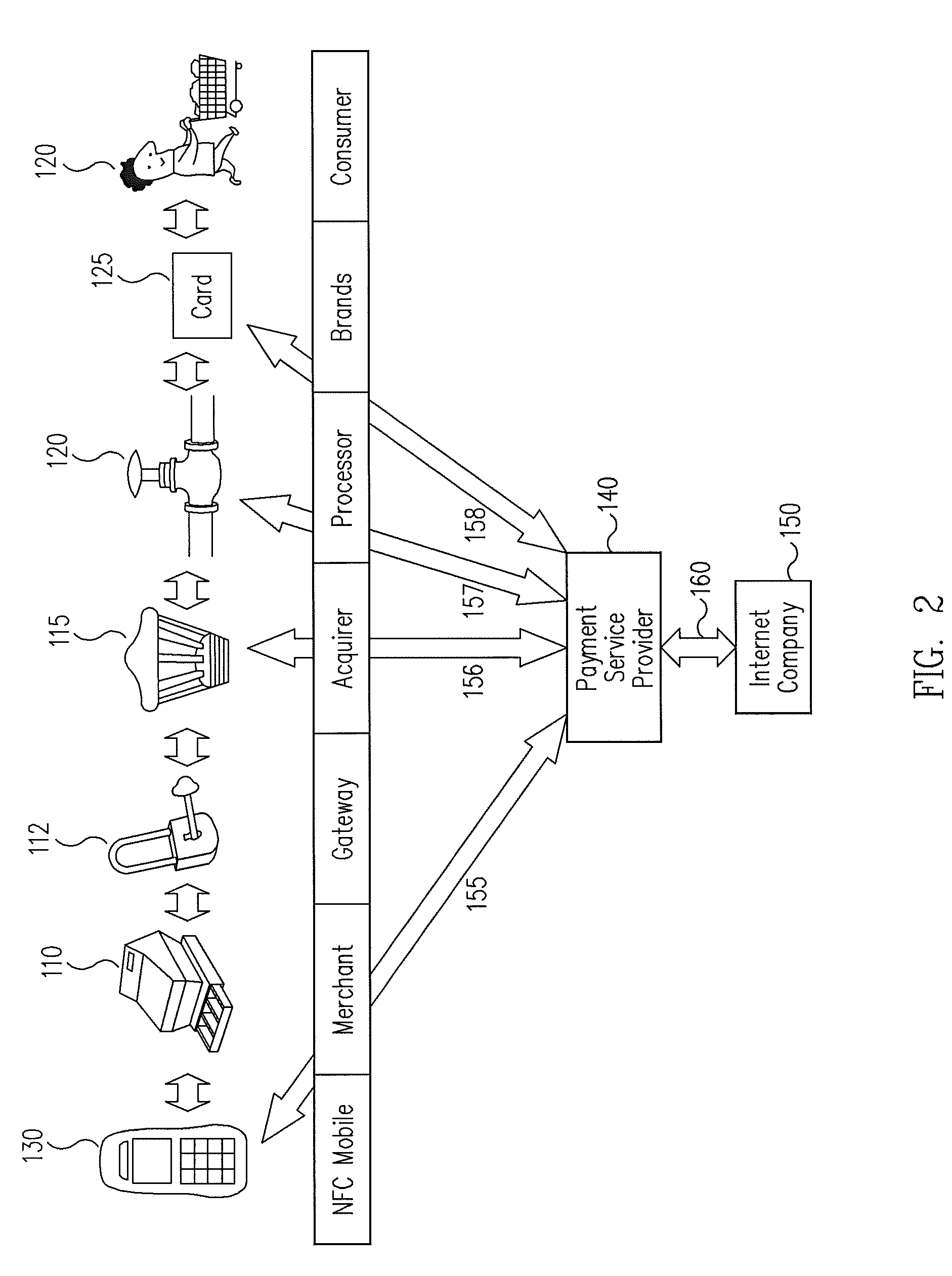
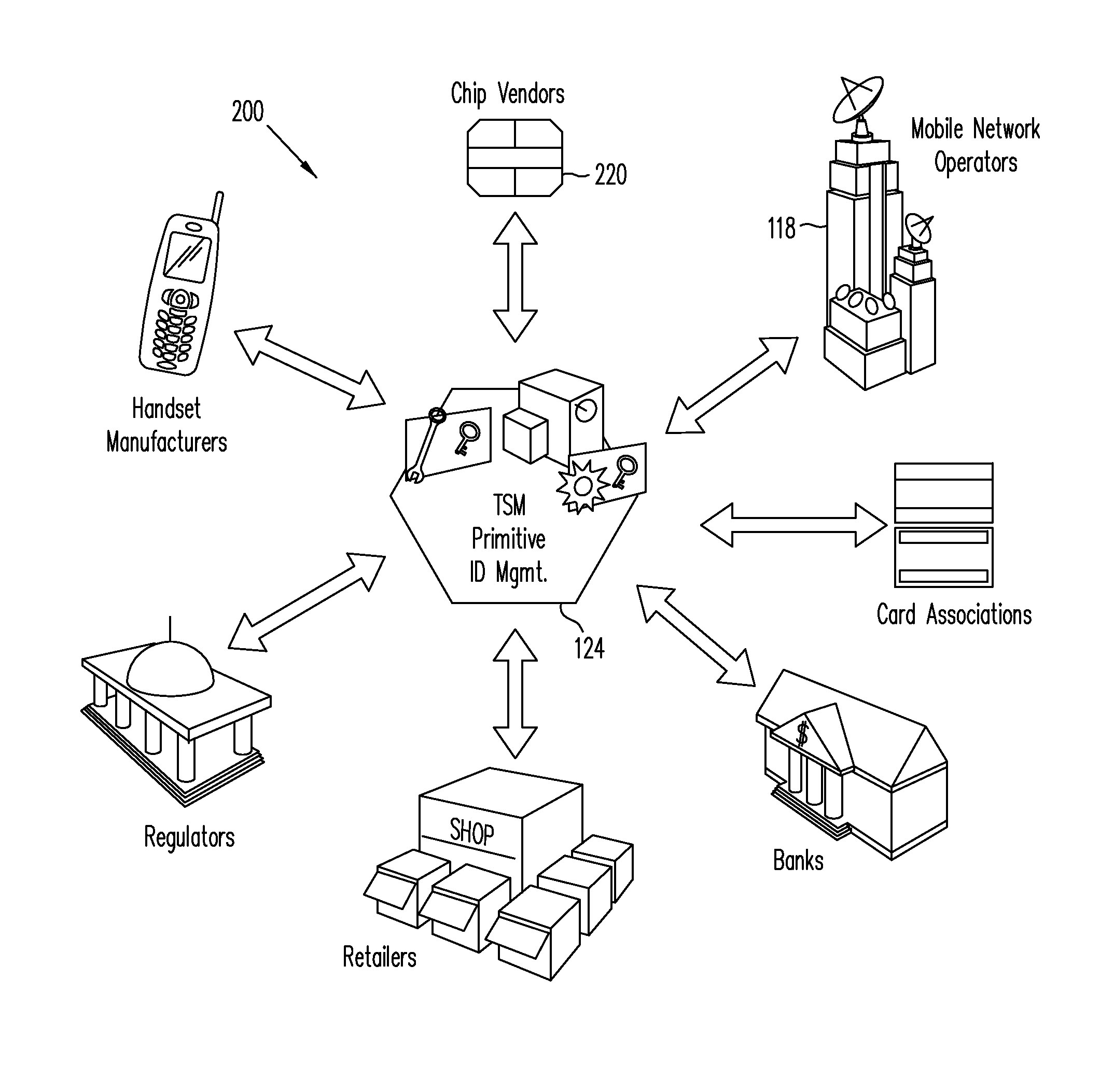
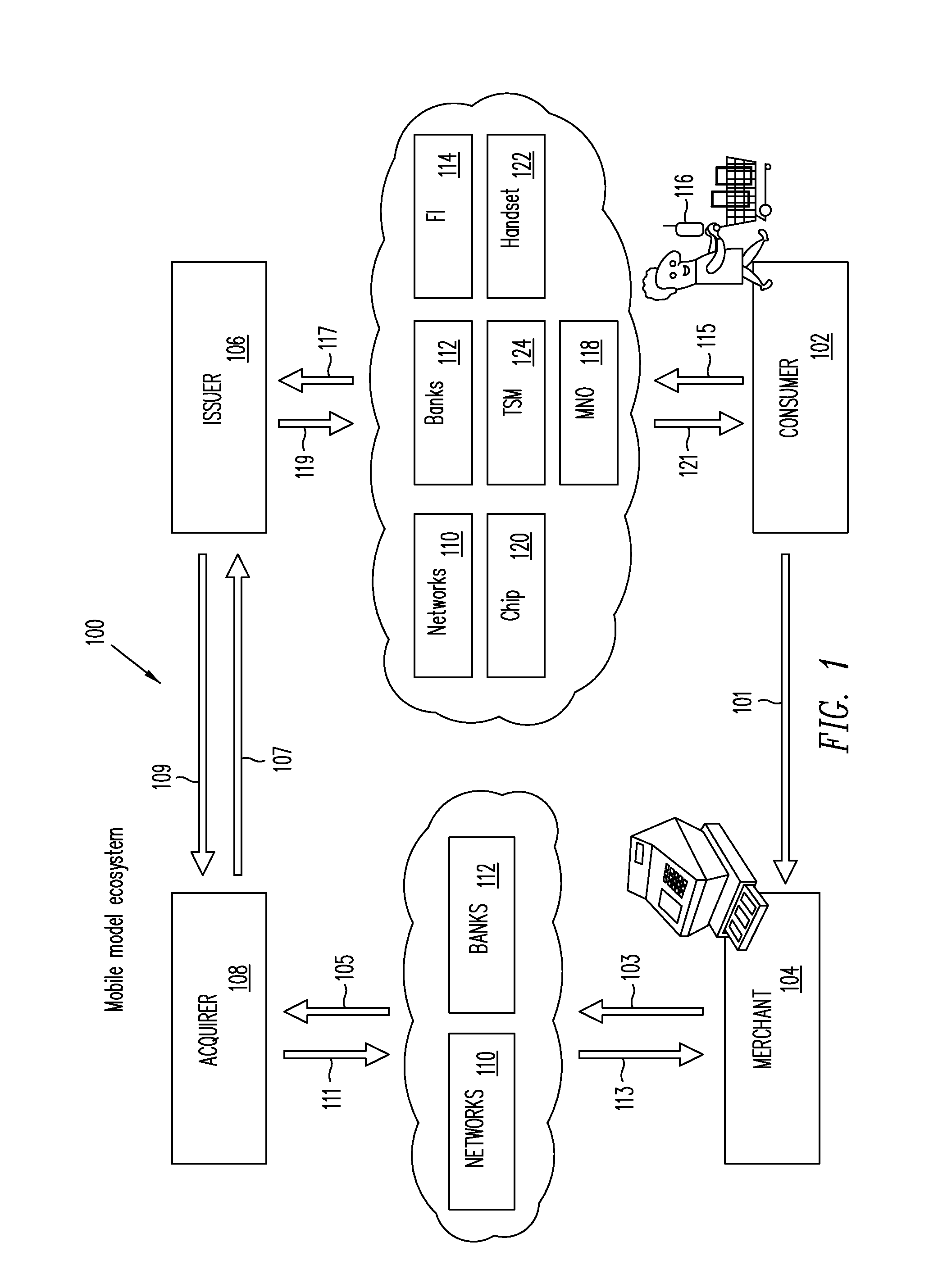
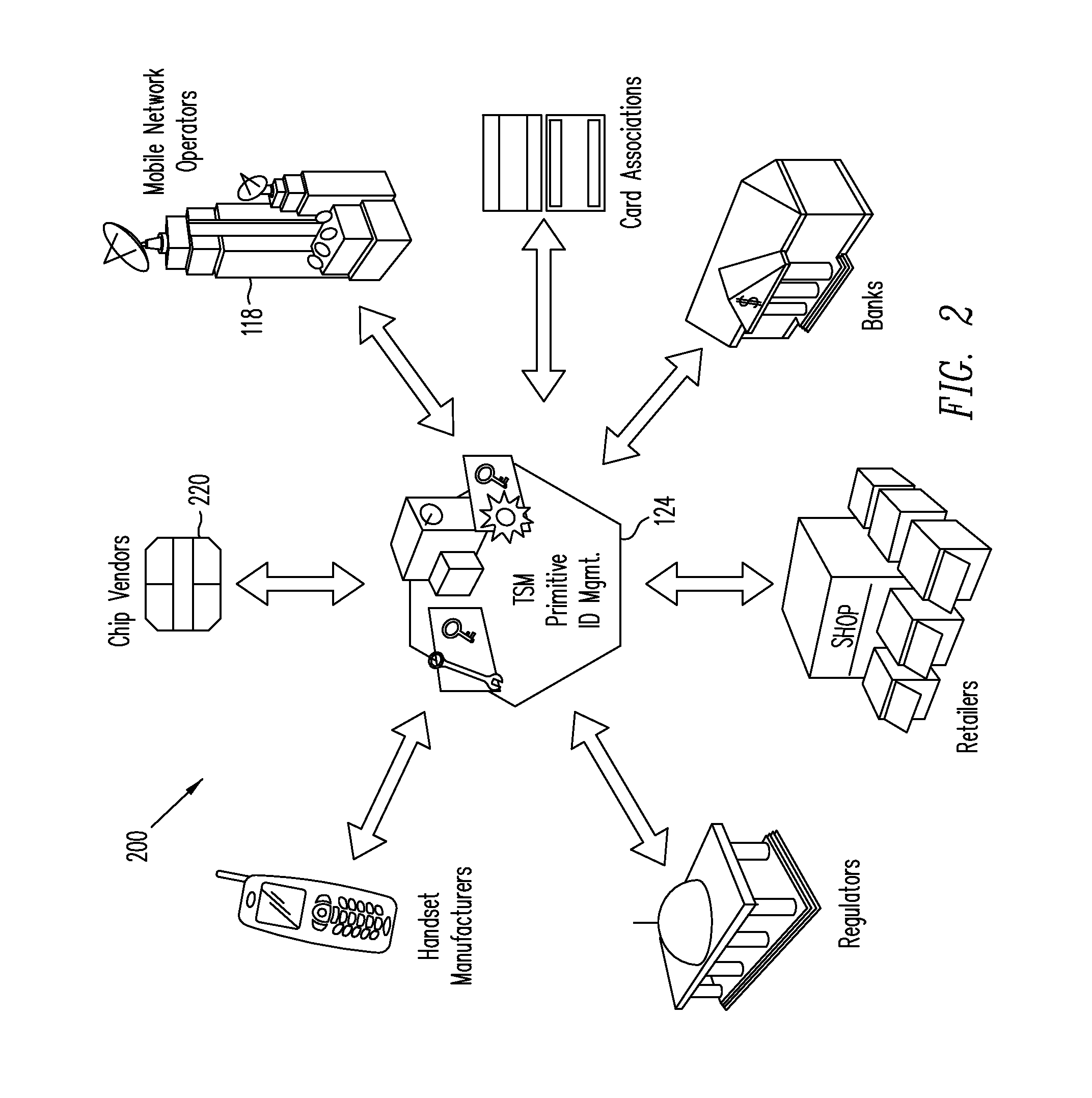
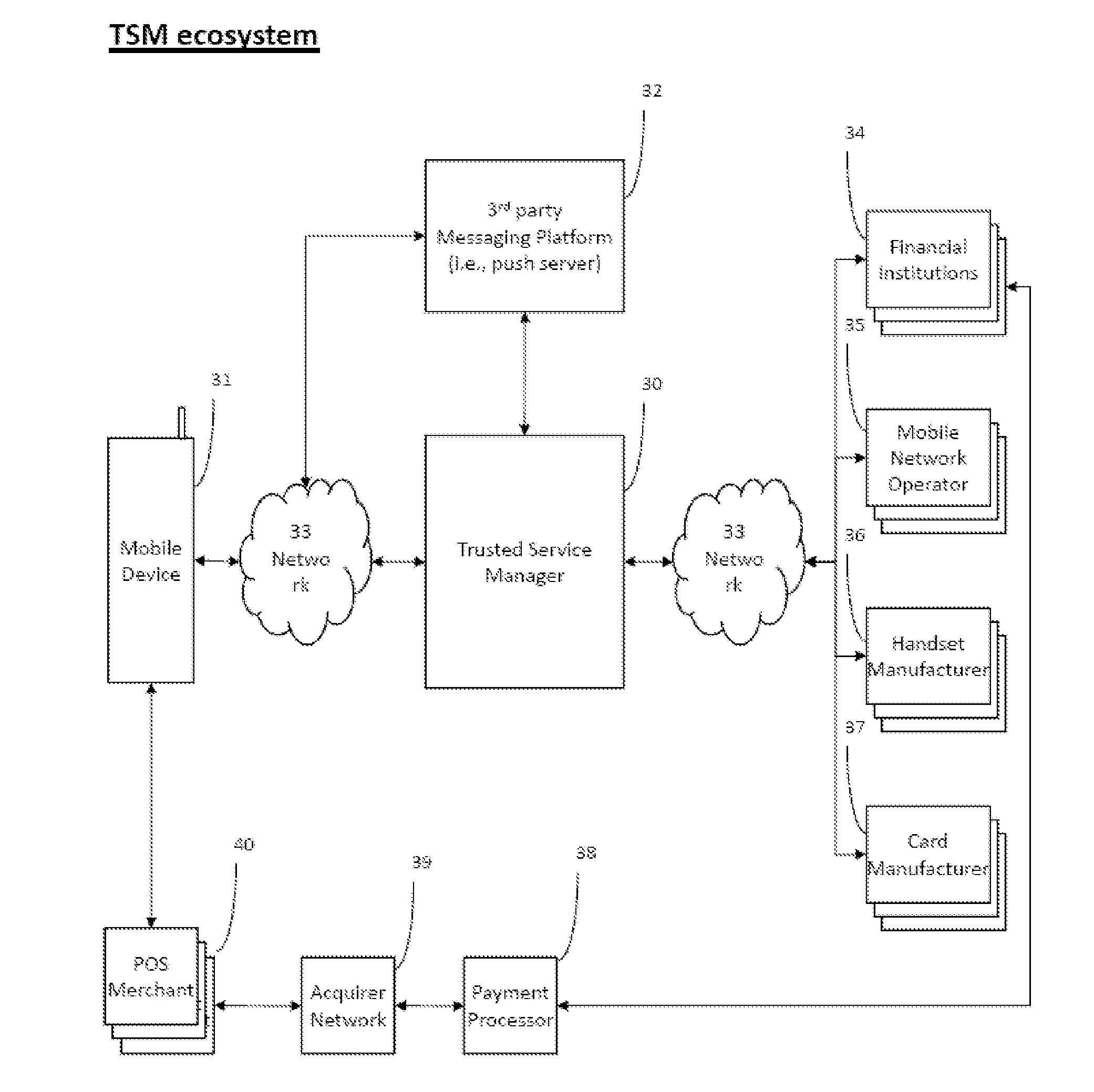
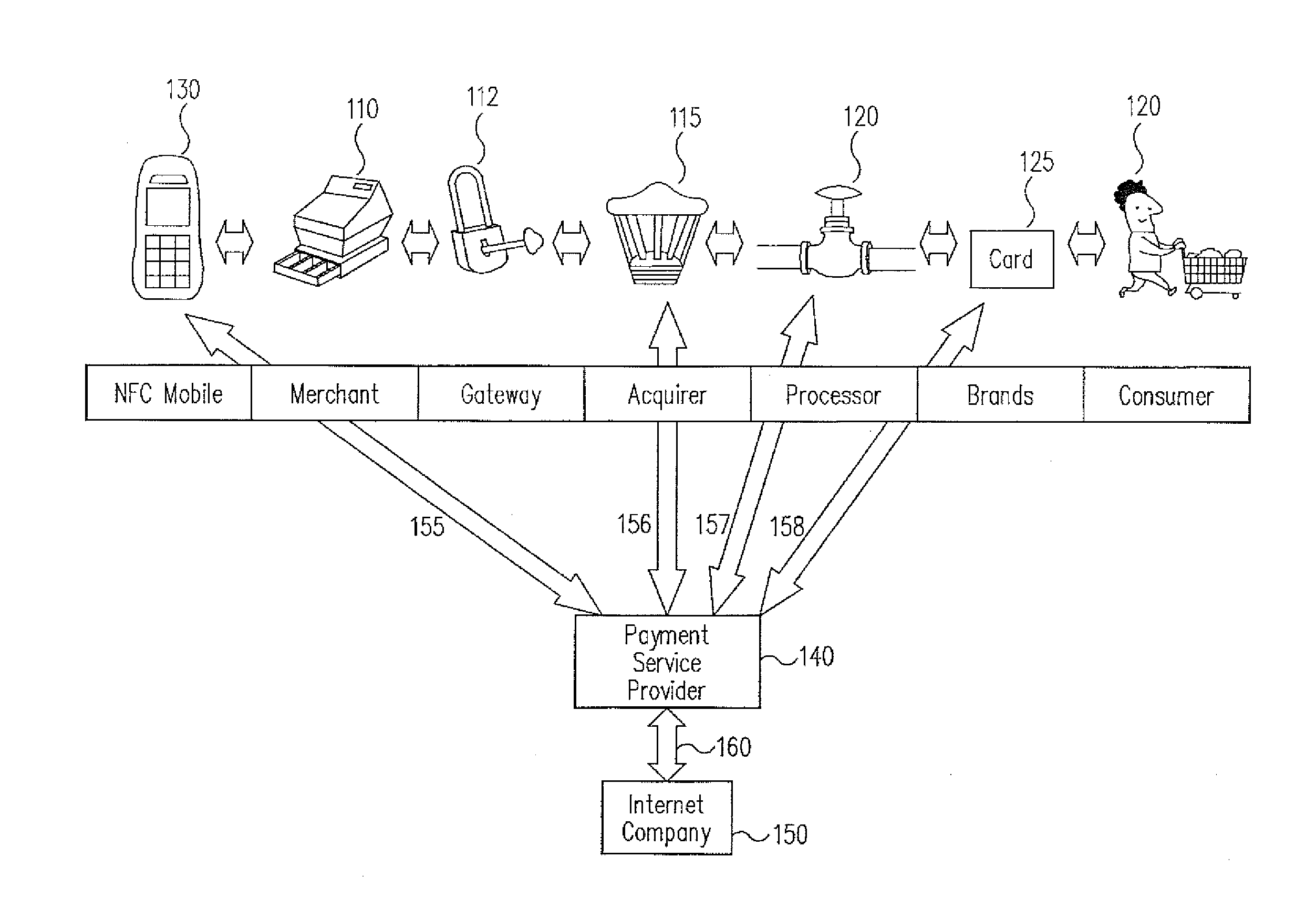
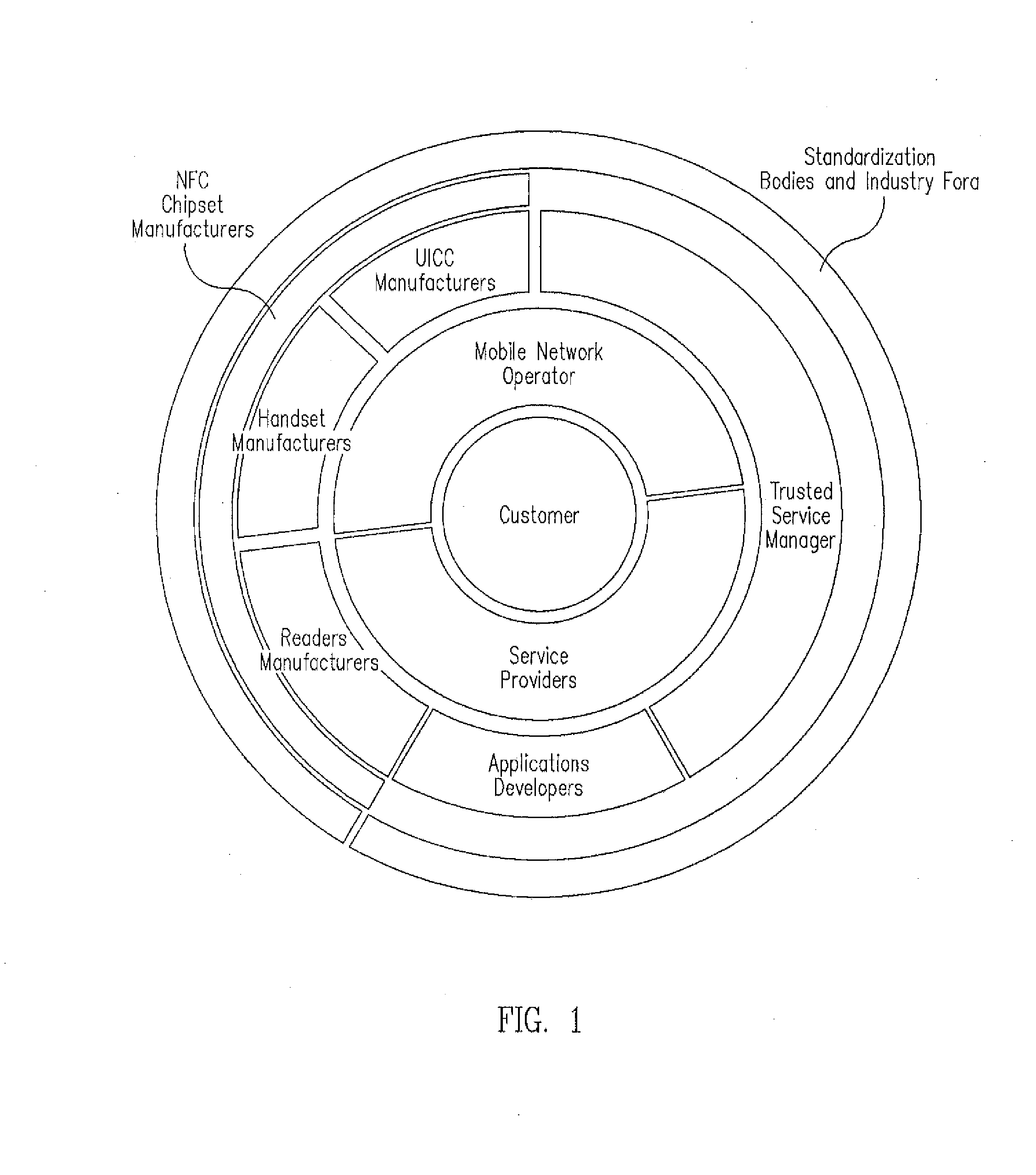
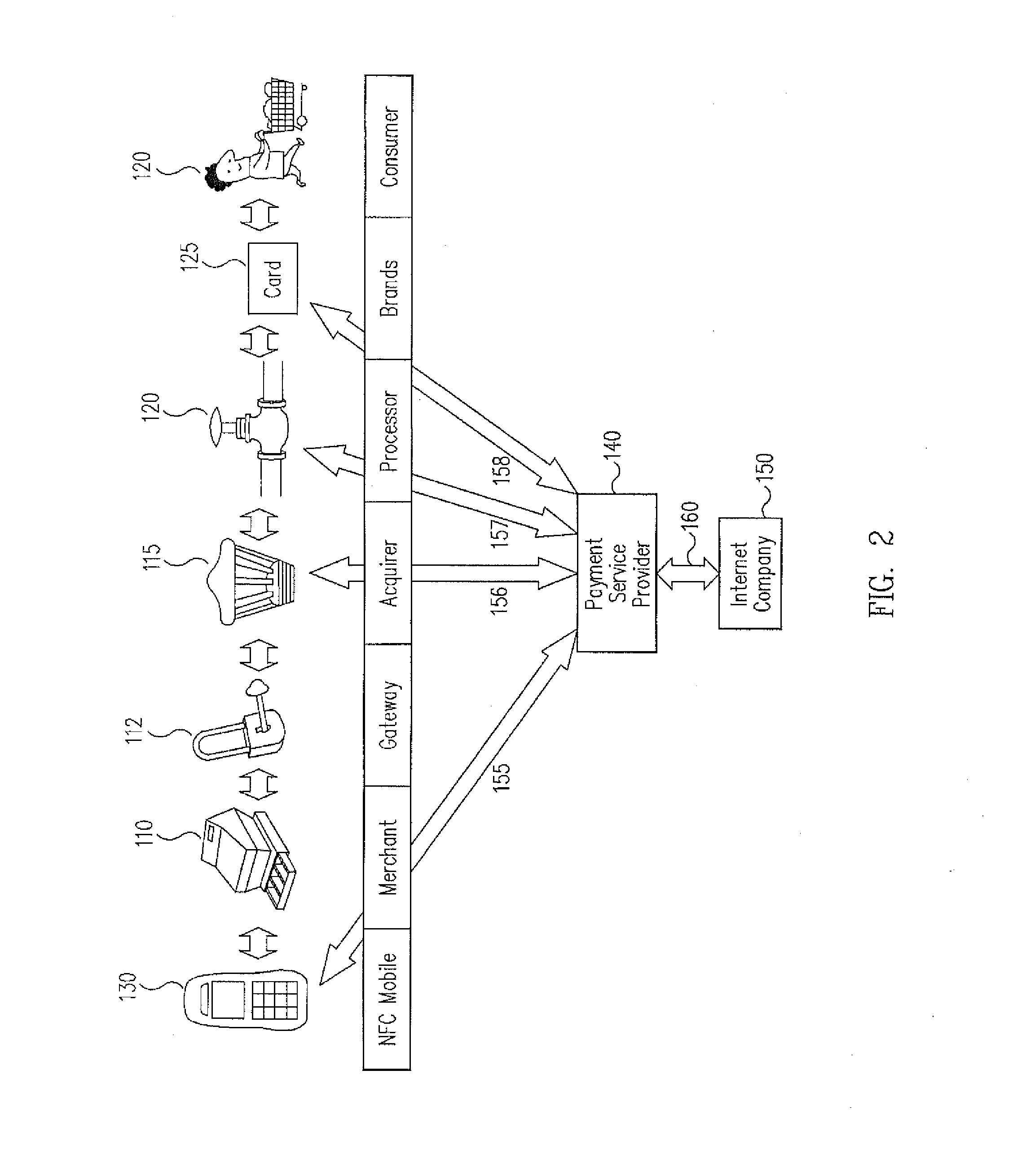
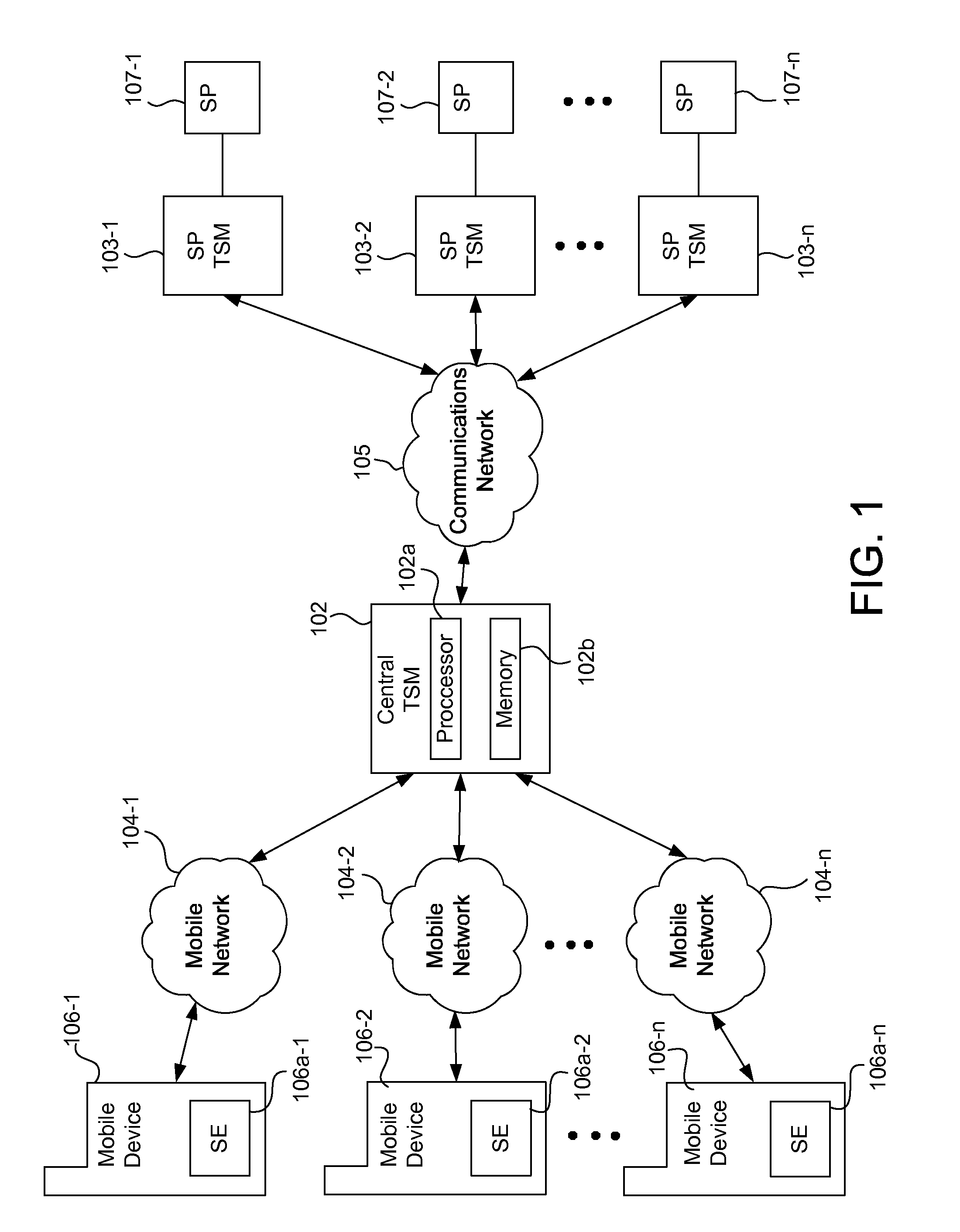
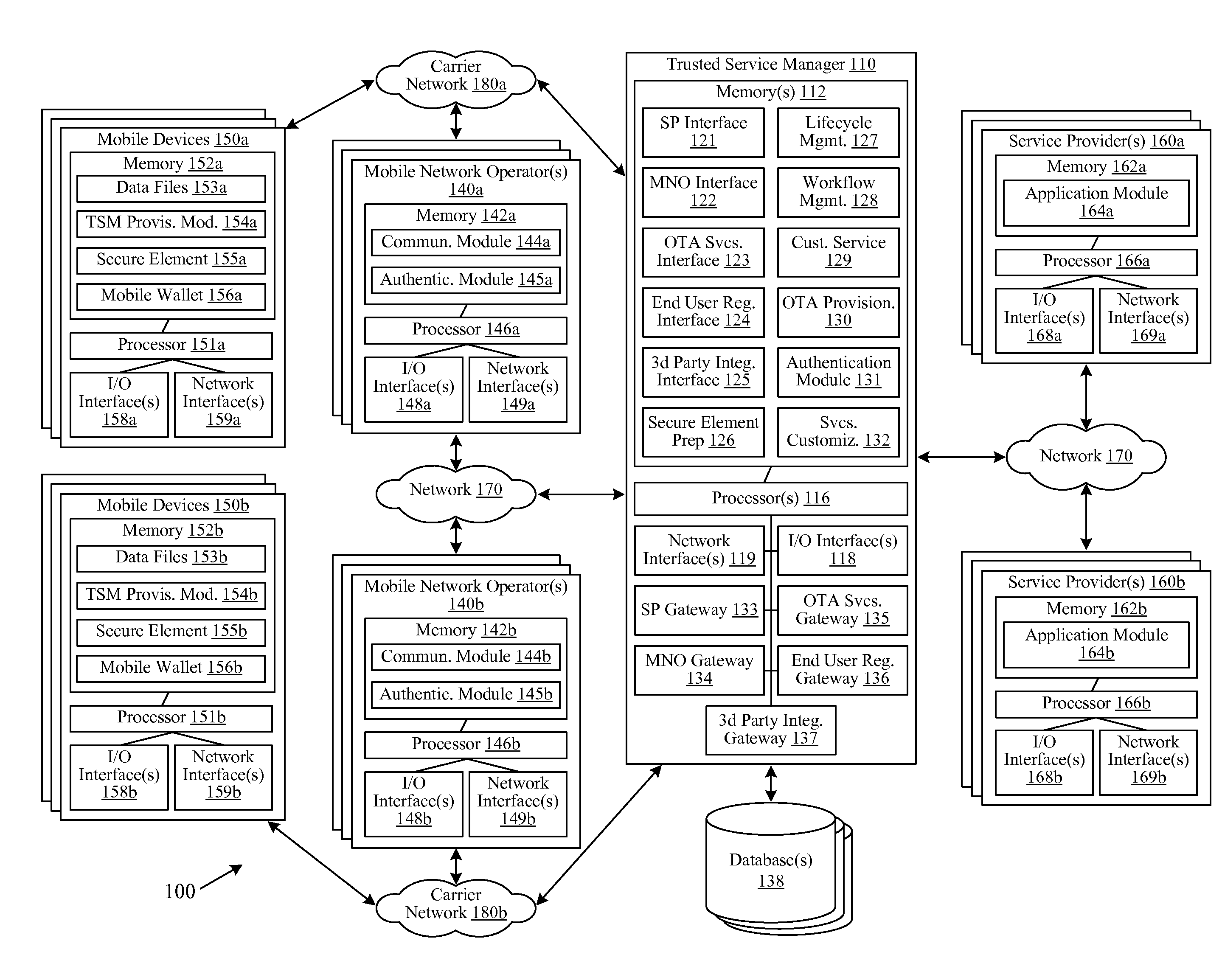
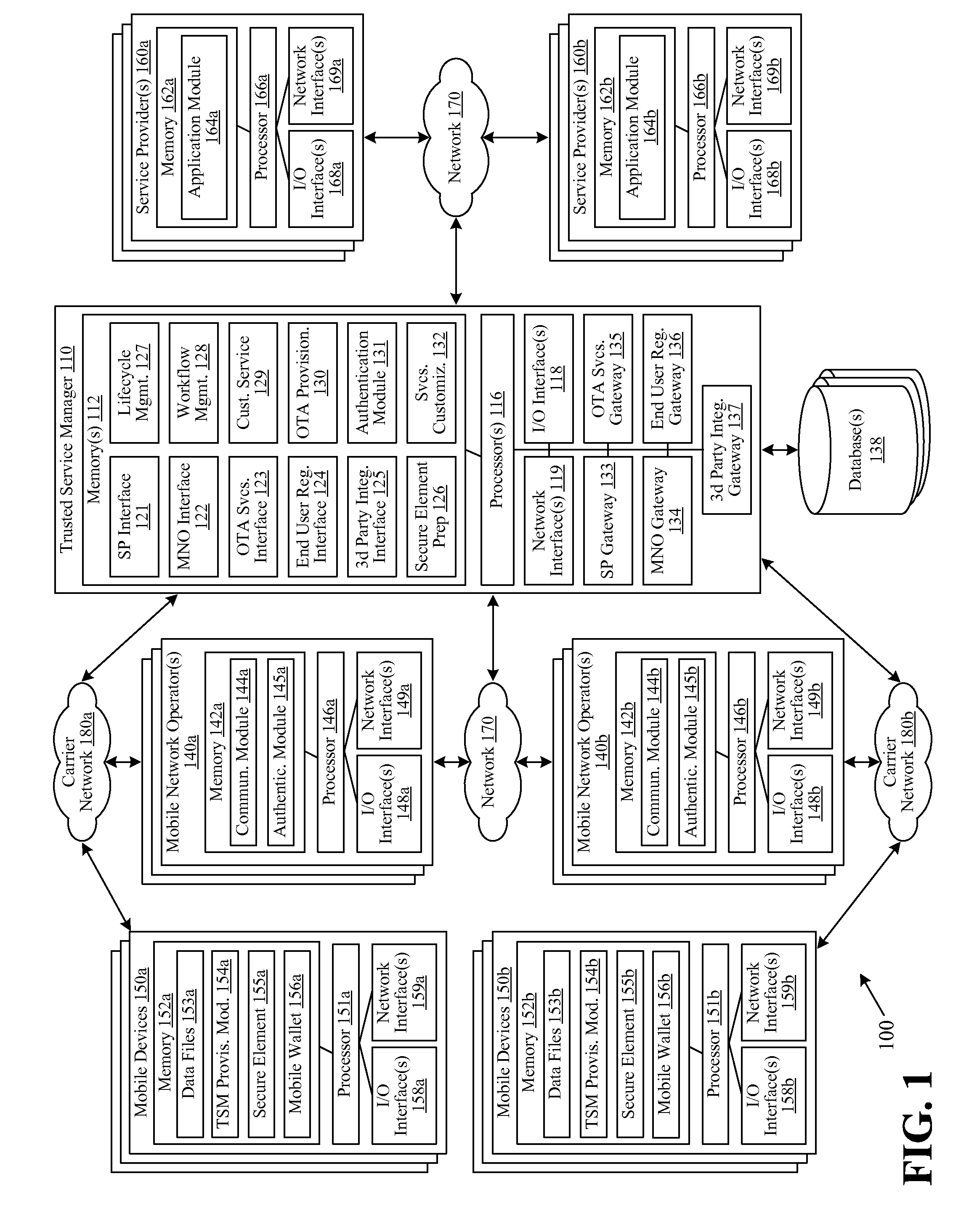
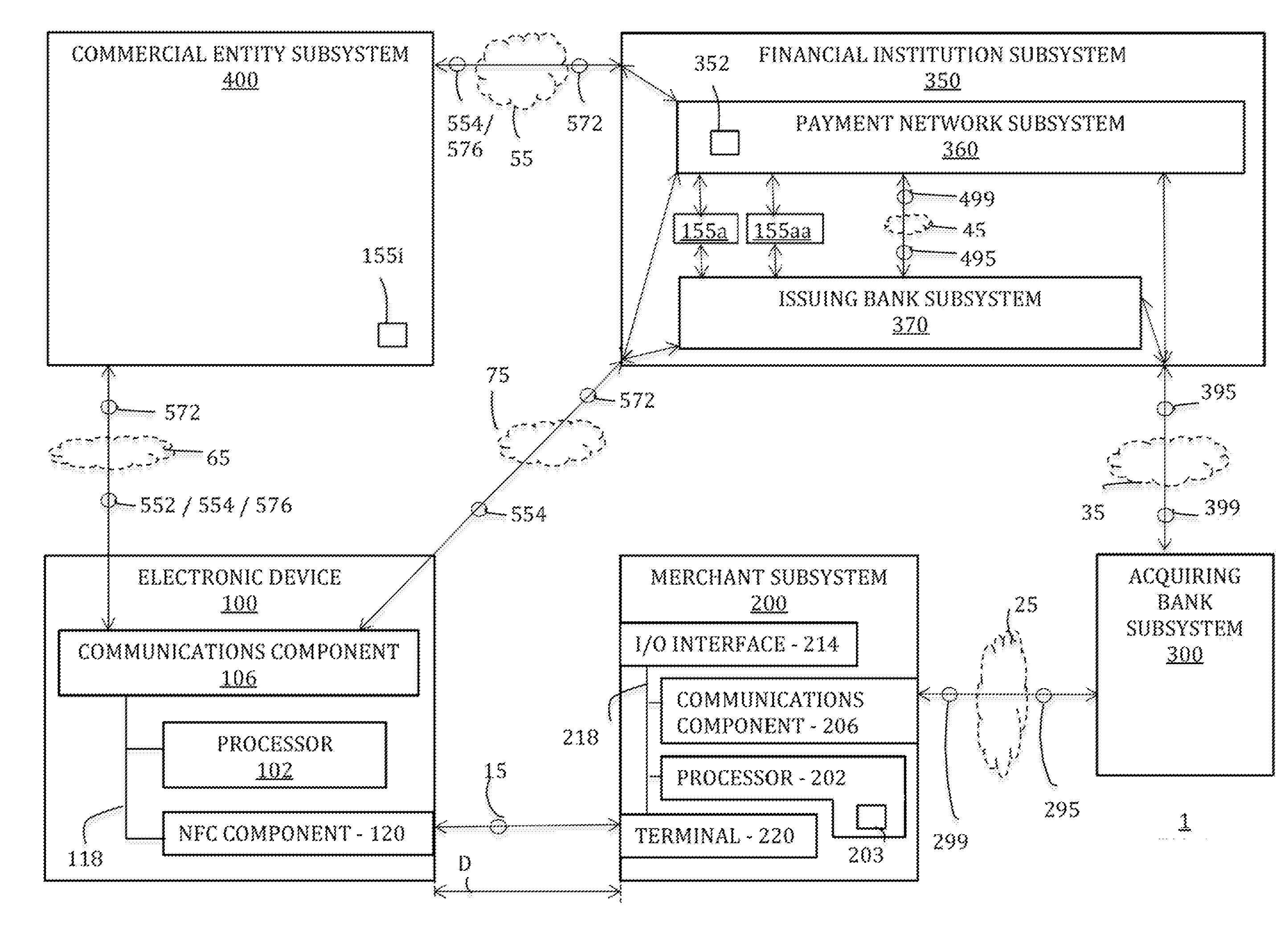
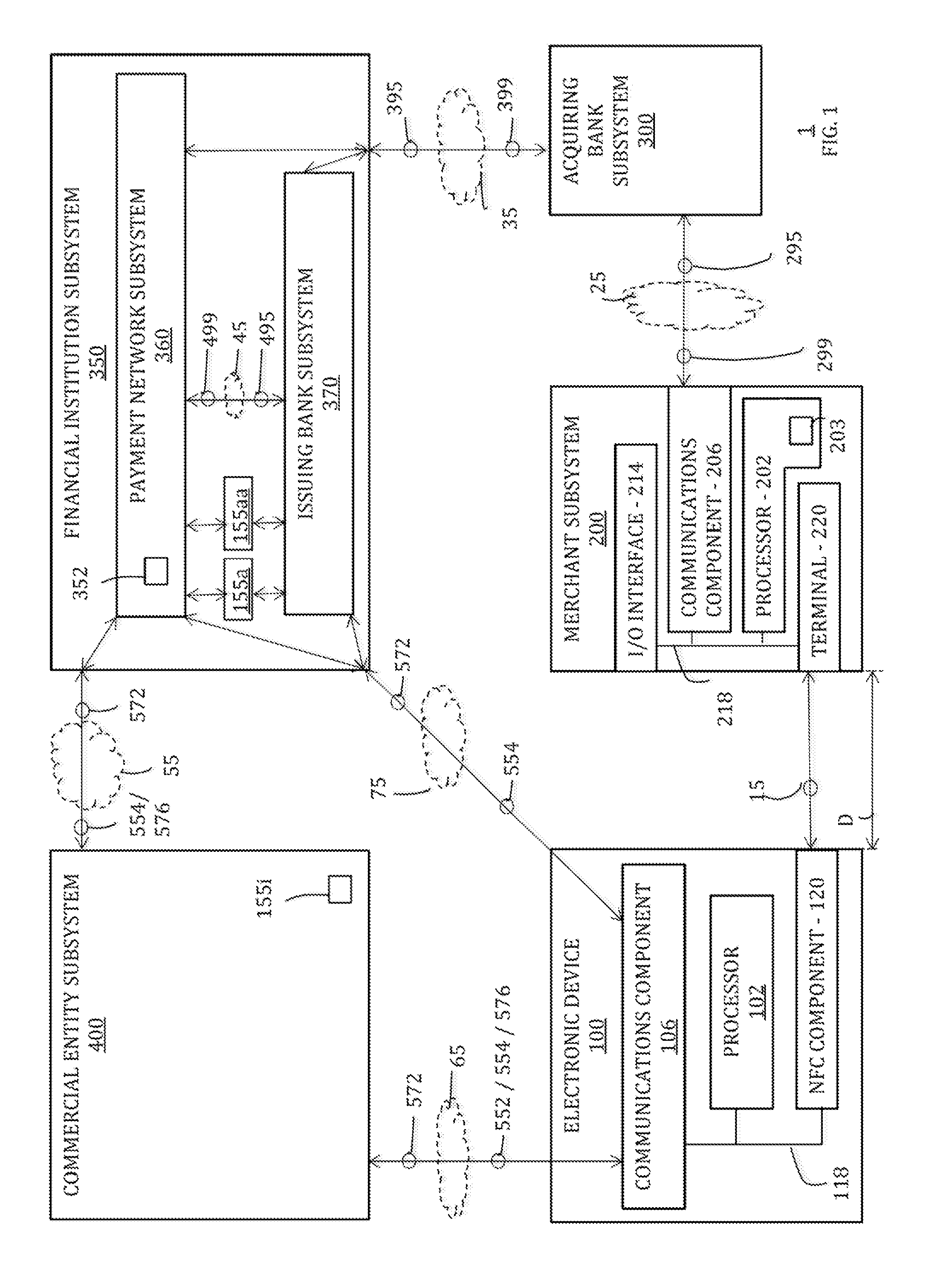
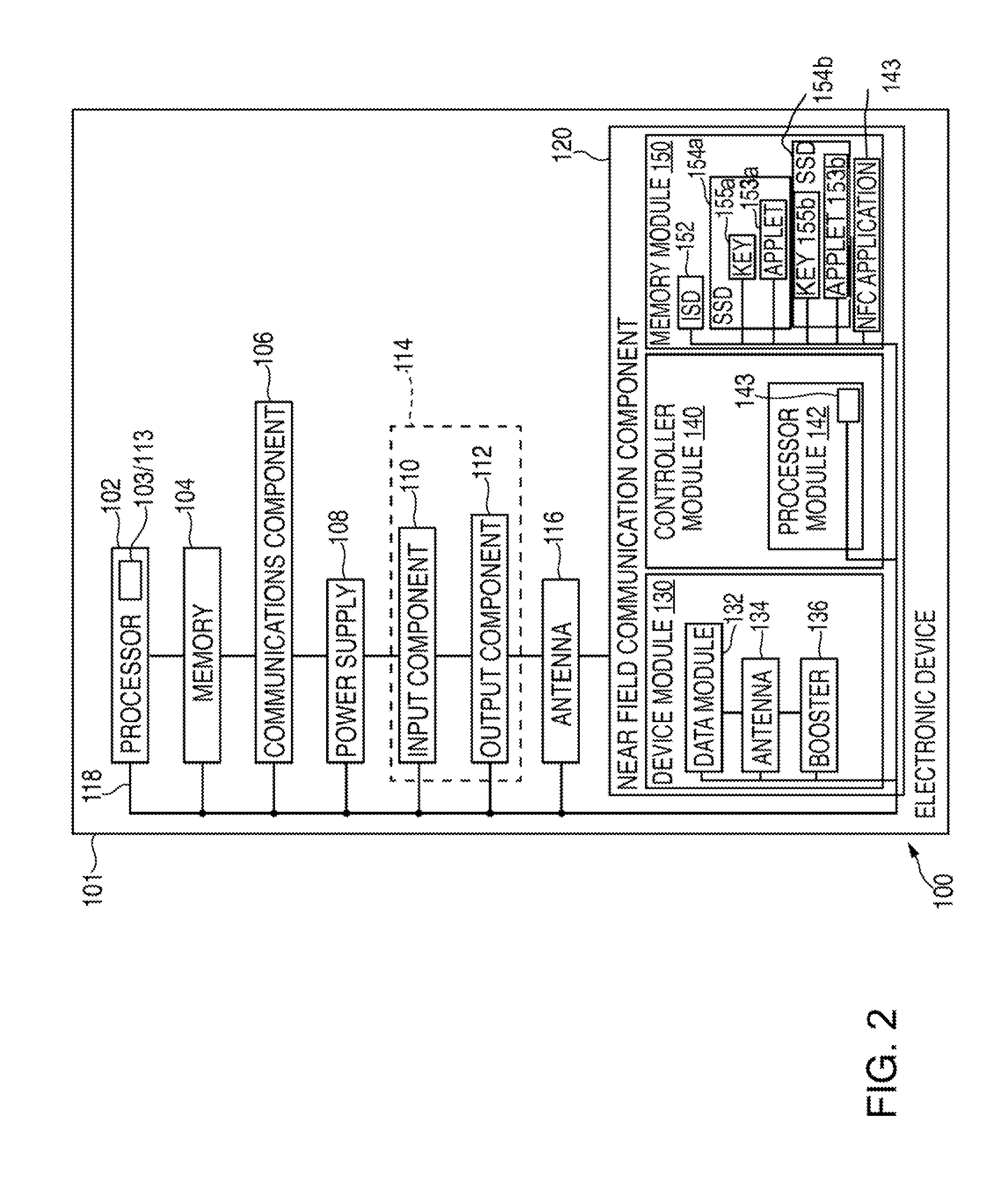
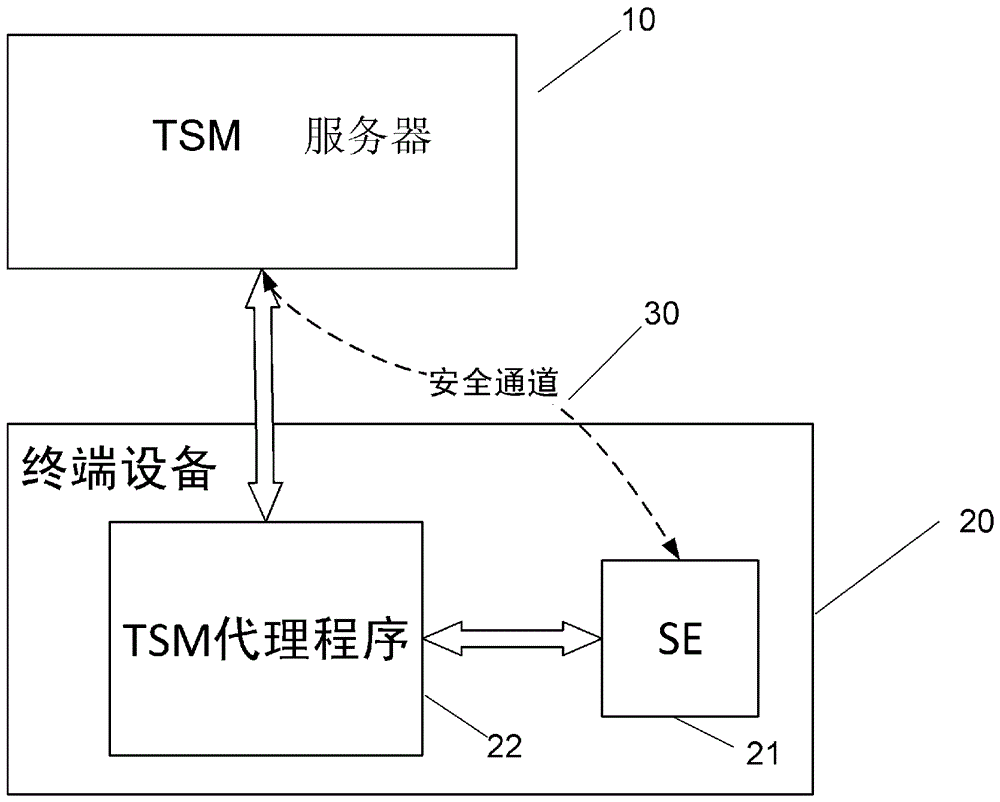
A trusted service manager (TSM) is a role in a near field communication ecosystem. It acts as a neutral broker that sets up business agreements and technical connections with mobile network operators, phone manufacturers or other entities controlling the secure element on mobile phones. The trusted service manager enables service providers to distribute and manage their contactless applications remotely by allowing access to the secure element in NFC-enabled handsets.
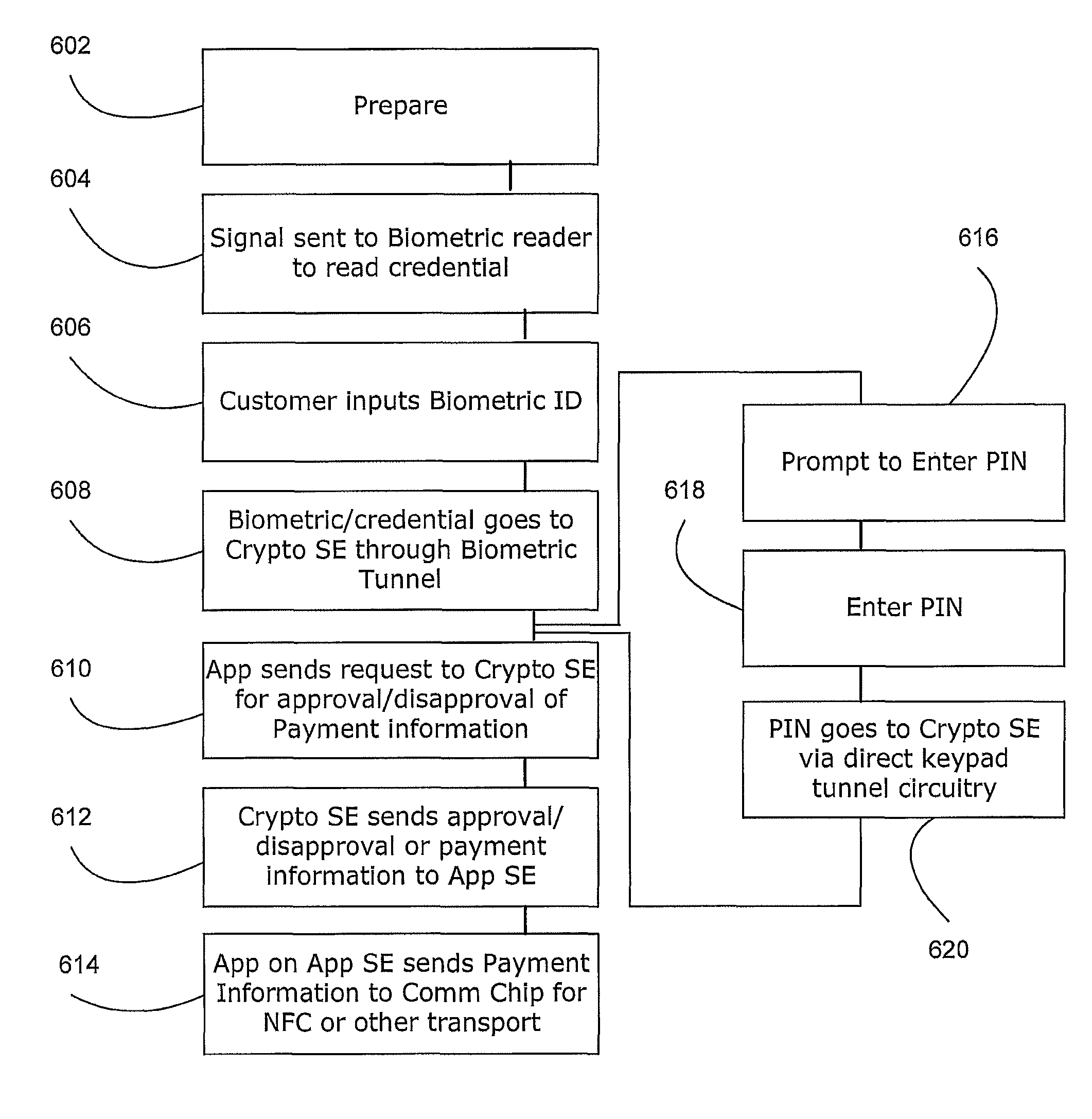
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
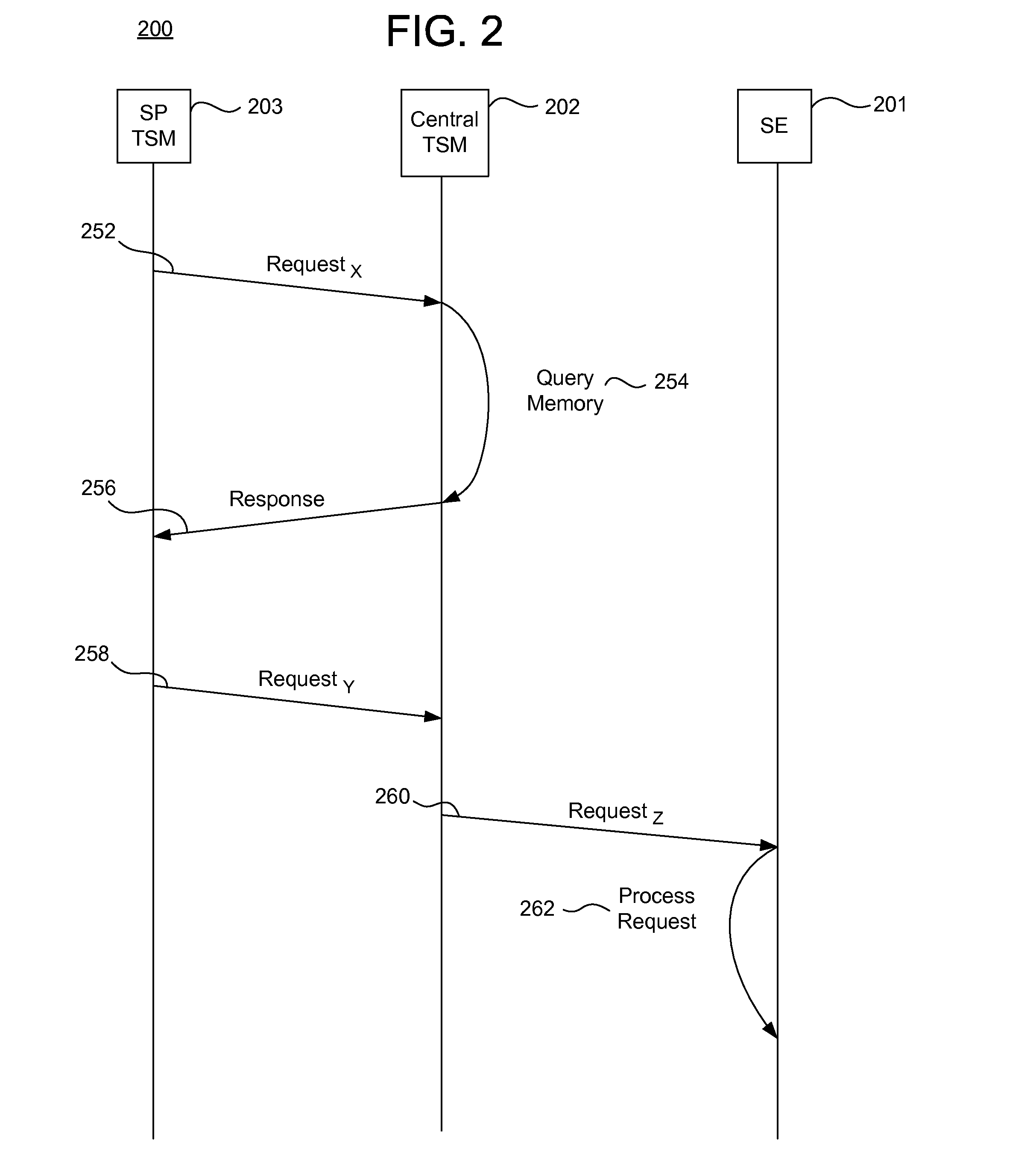
Systems, methods, and computer program products for interfacing multiple service provider trusted service managers and secure elements
ActiveUS20130111599A1Easily and securely communicateKey distribution for secure communicationDigital data processing detailsComputer networkTerm memory
System, methods, and computer program products are provided for interfacing between one of a plurality of service provider (SP) trusted service managers (TSM) and one of a plurality of secure elements (SE). A first request including a mobile subscription identifier (MSI) is received from an SP TSM over a communications network. At least one memory is queried for SE data including an SE identifier corresponding to the MSI. The SE data is transmitted to the SP TSM over the communications network. A second request based on the SE data is received from the SP TSM over the communications network. A third request, based on the second request, is transmitted, over a mobile network, to an SE corresponding to the SE data. The mobile network is selected from multiple mobile networks, and is determined based on the SE data queried from the memory.
Owner:GOOGLE LLC
Trusted service manager (TSM) architectures and methods
ActiveUS20090307142A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPaymentFinancial transaction
A client device comprises a first secure element and a second secure element. The first secure element comprises a first computer-readable medium having a payment application comprising instructions for causing the client device to initiate a financial transaction. The second secure element comprises a second computer-readable medium having a security key, a payment instrument, stored authentication data and instructions for generating a secure payment information message responsive to the payment application. The secure payment information message comprises the payment instrument and is encrypted in accordance with the security key.
Owner:PAYPAL INC
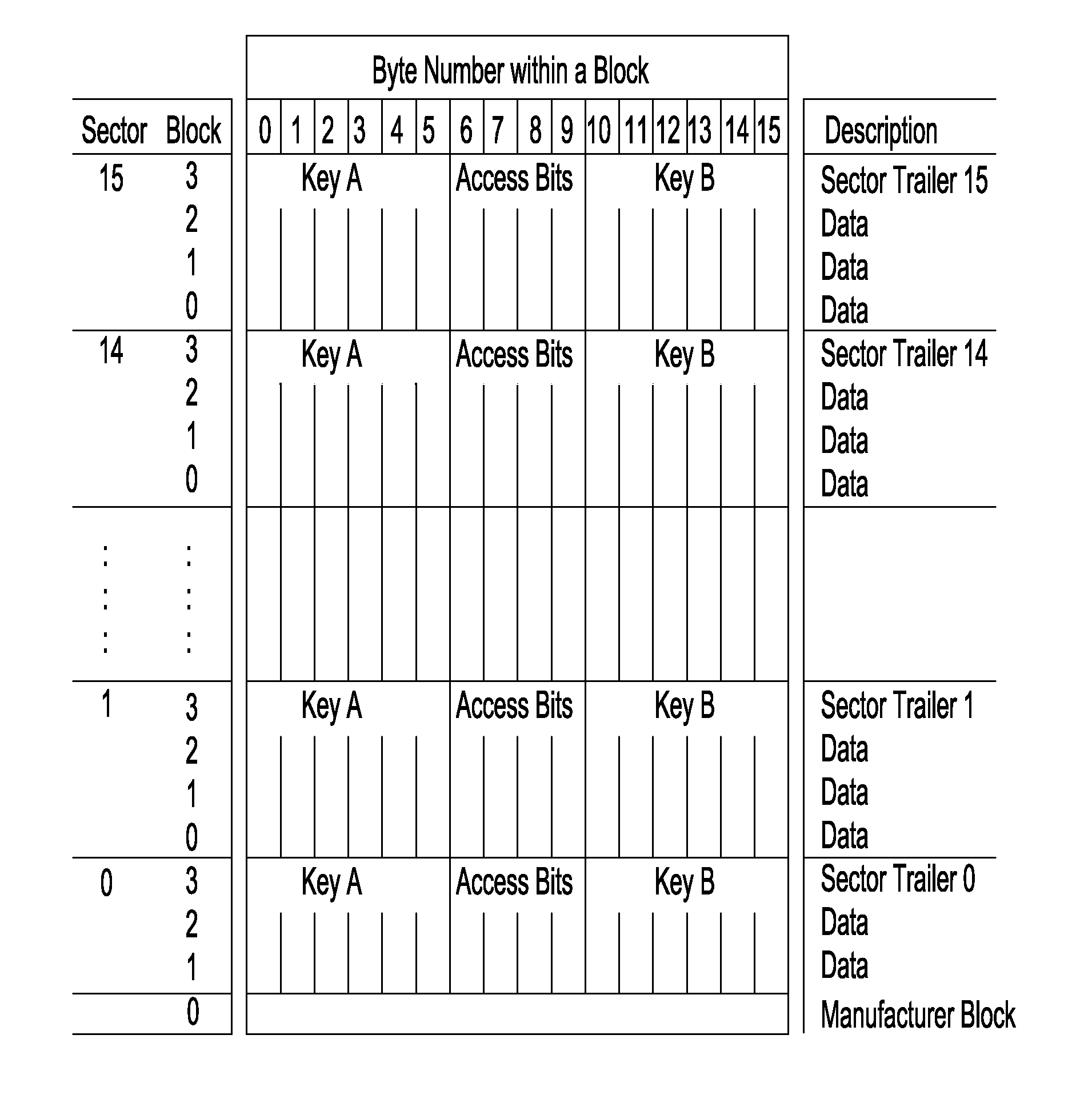
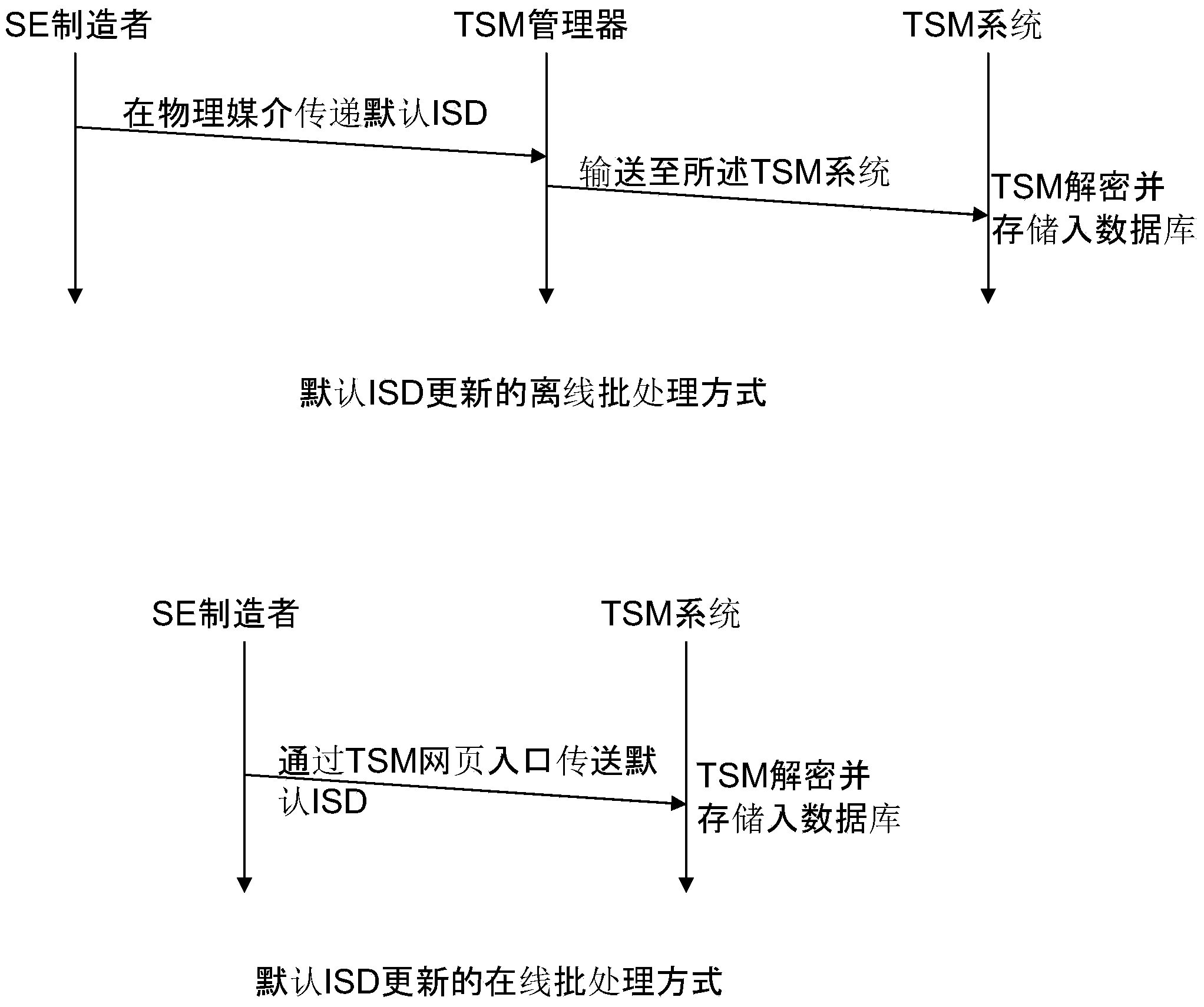
Method, system and trusted service manager for securely transmitting an application to a mobile phone
ActiveUS20100291896A1Avoid disadvantagesReliable cooperationAcutation objectsUnauthorised/fraudulent call preventionService provisionUnique identifier
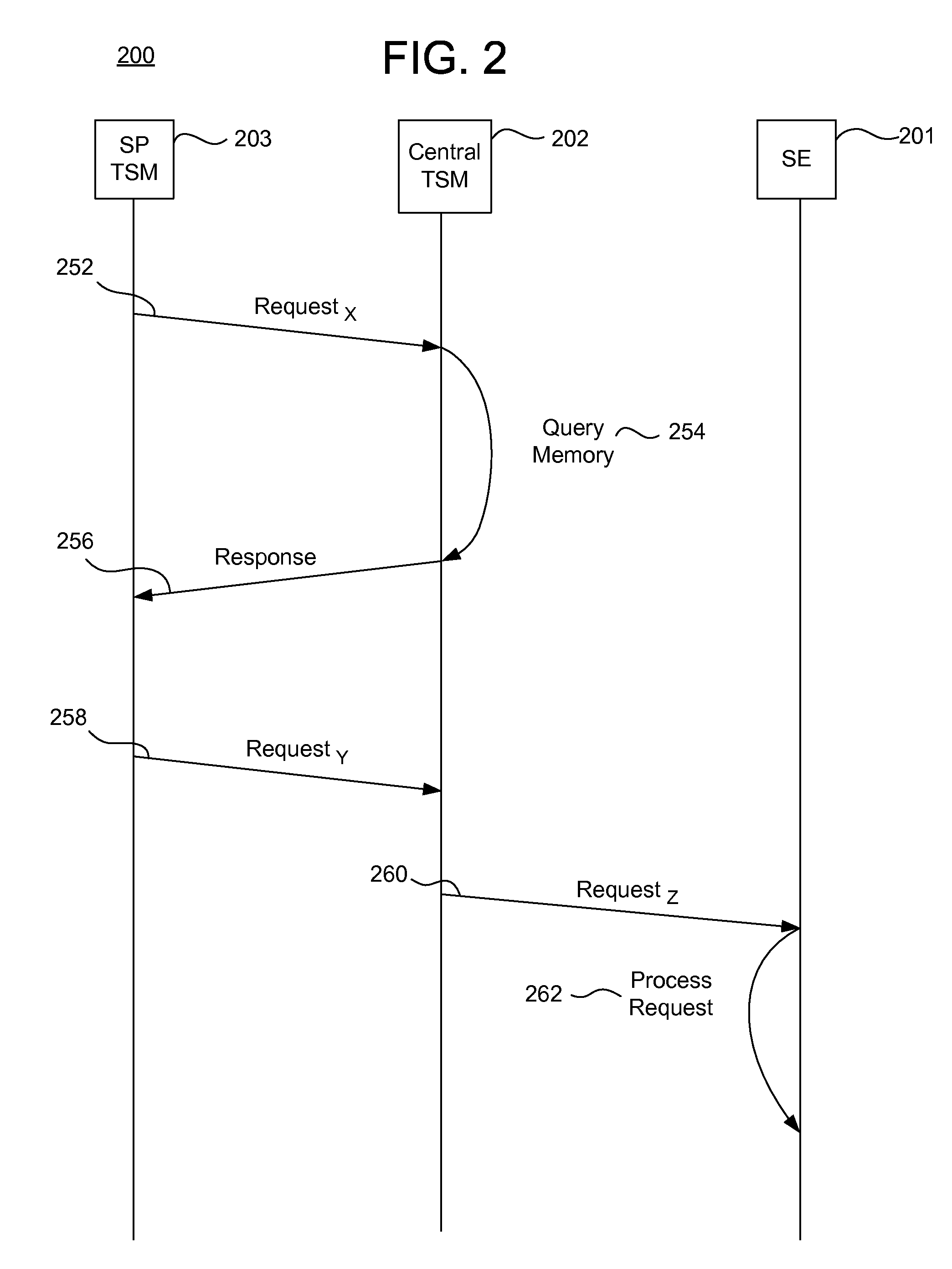
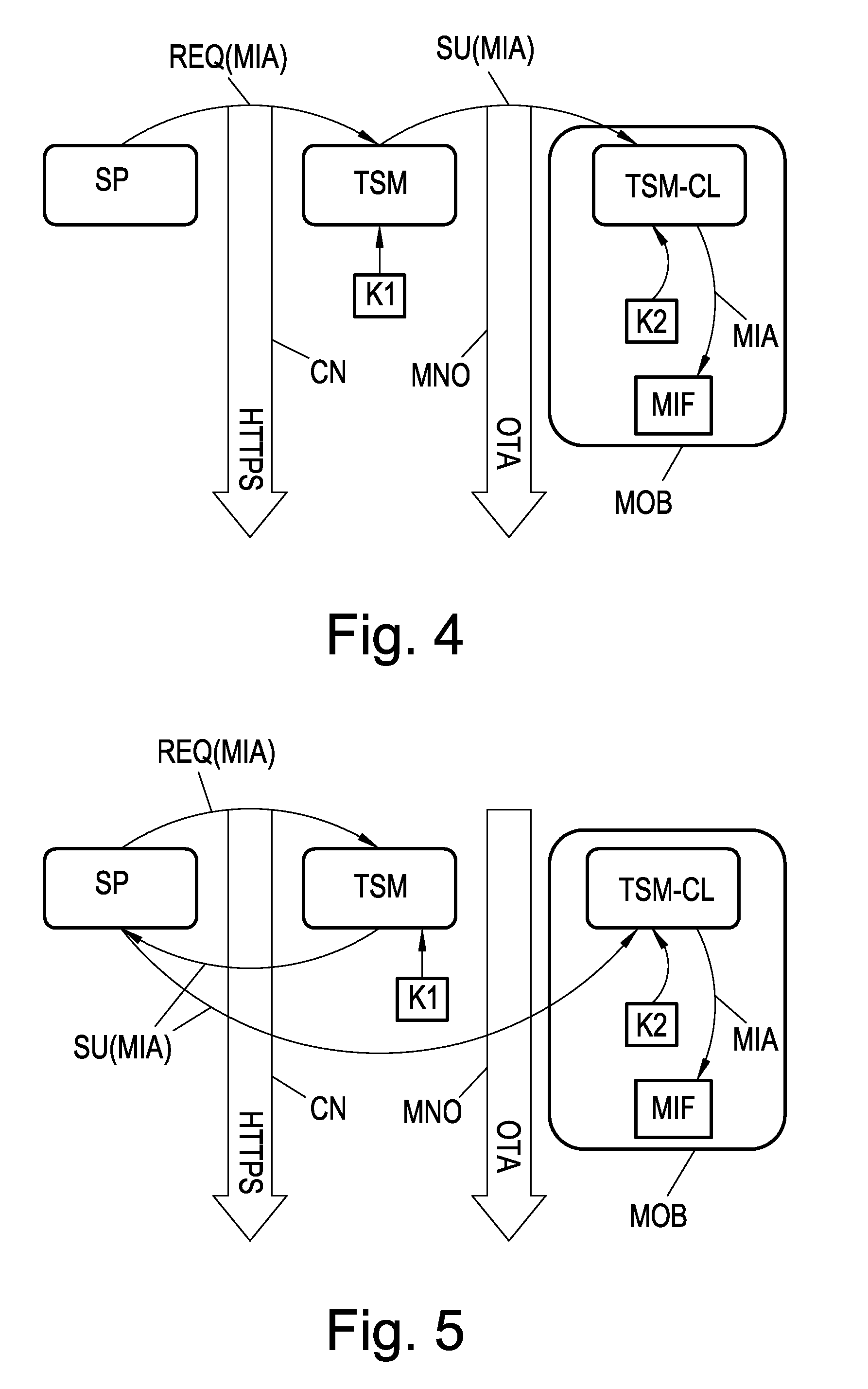
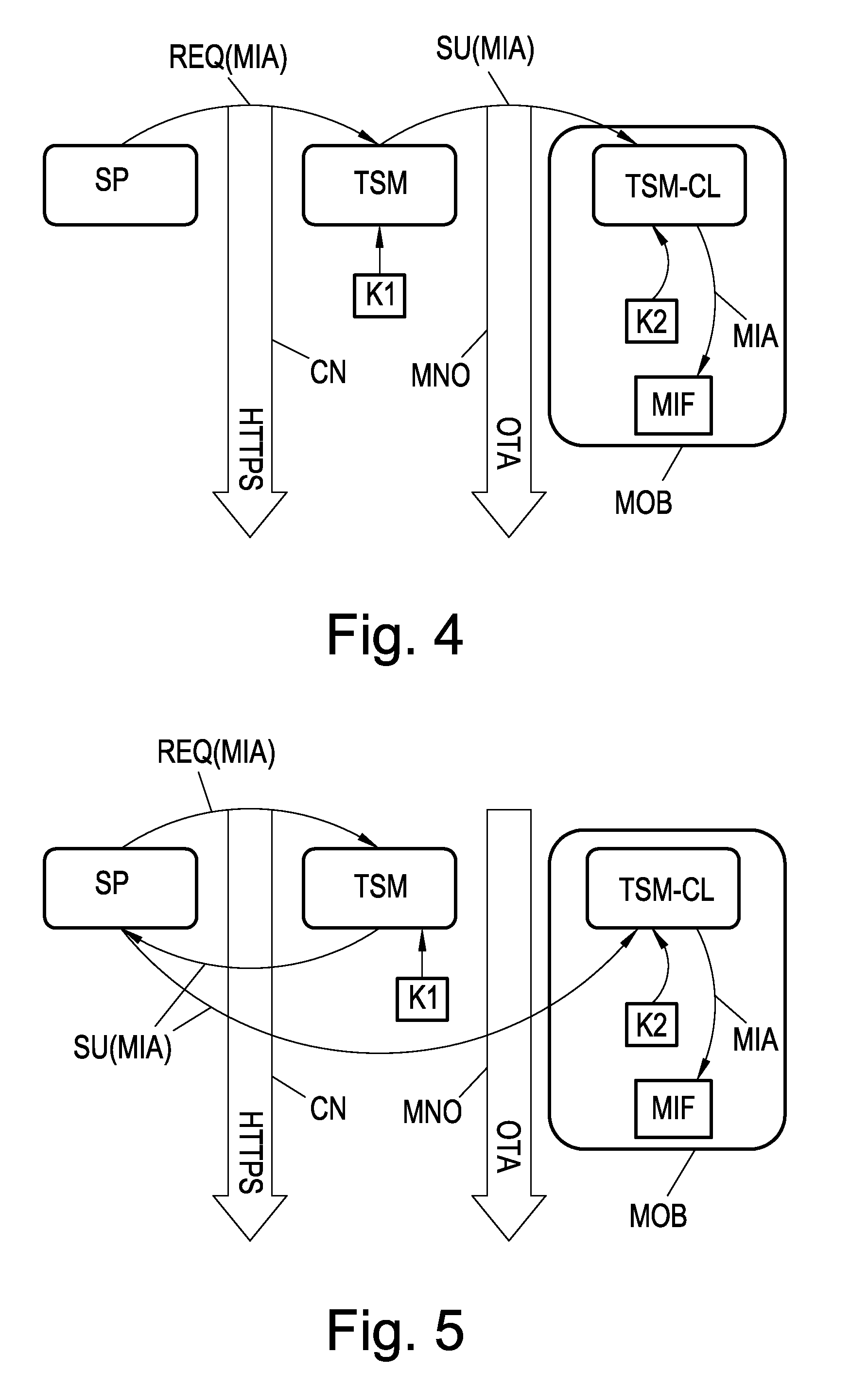
A Trusted Service Manager (TSM) receives via a first communication channel from a Service Provider (SP) a request (REQ(MIA)) that contains an application (MIA) together with a unique identifier of a mobile phone (MOB), particularly its telephone number. The mobile phone (MOB) is equipped with a memory device (MIF) that comprises multiple memory sectors being protected by sector keys. Preferably the memory device (MIF) is a MIFARE device. The TSM extracts the application (MIA) and the unique identifier from the received request, assigns destination sector(s) and associated sector key(s) of the memory device (MIF), compiles the application (MIA), the sector key(s) and the sector number(s) of the destination sector(s) into a setup-message (SU(MIA)), encrypts the setup-message and transmits it to either the mobile phone via a second communication channel or the Service Provider via the first communication channel (CN). If the setup-message (SU(MIA)) is transmitted to the Service Provider, the Service Provider sends it over the second communication channel to the mobile phone.
Owner:NXP BV
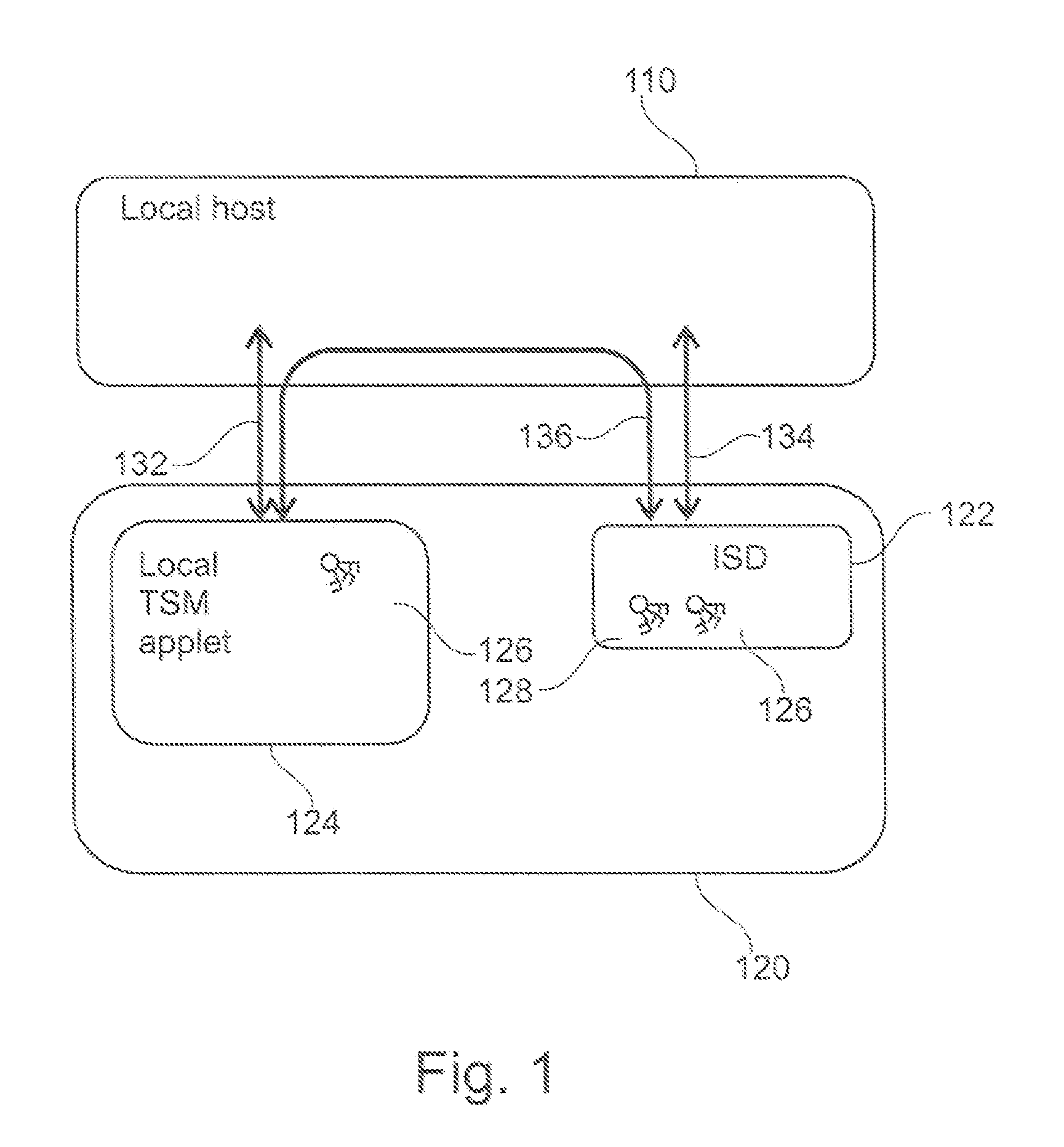
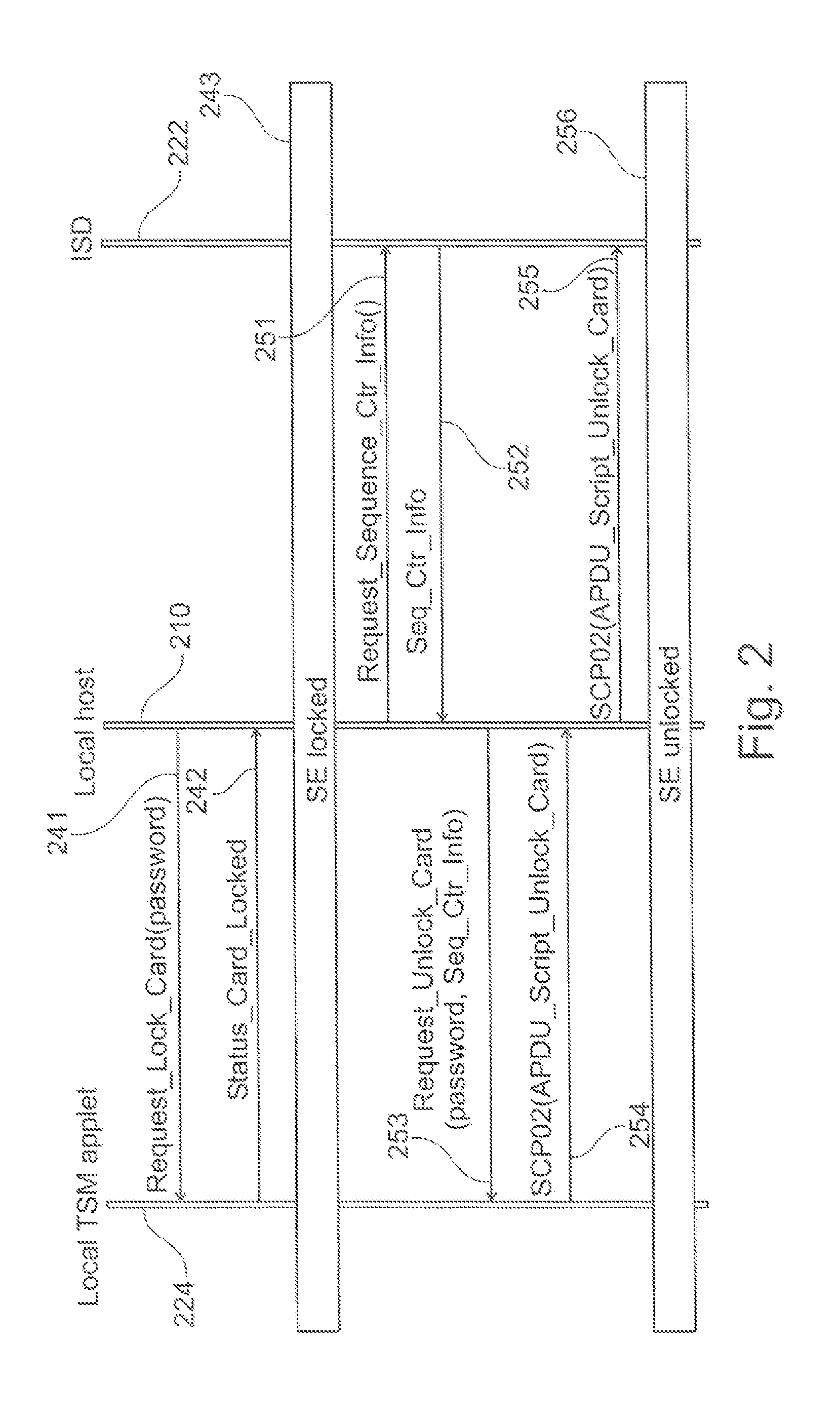
Local trusted service manager
ActiveUS20140047235A1Possible to provideDigital data authenticationProgram controlProgram unitTrusted service manager
Owner:NXP BV
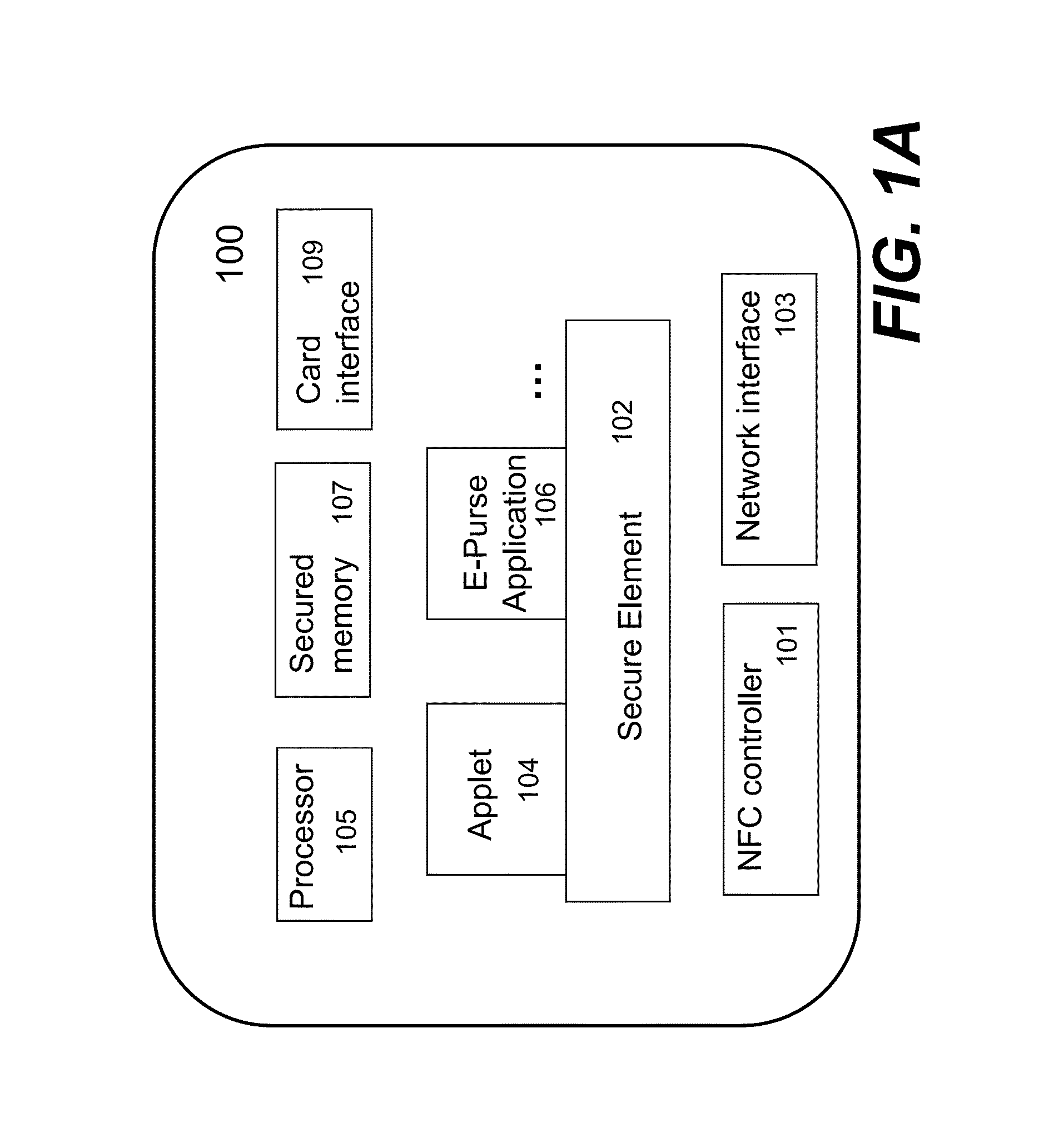
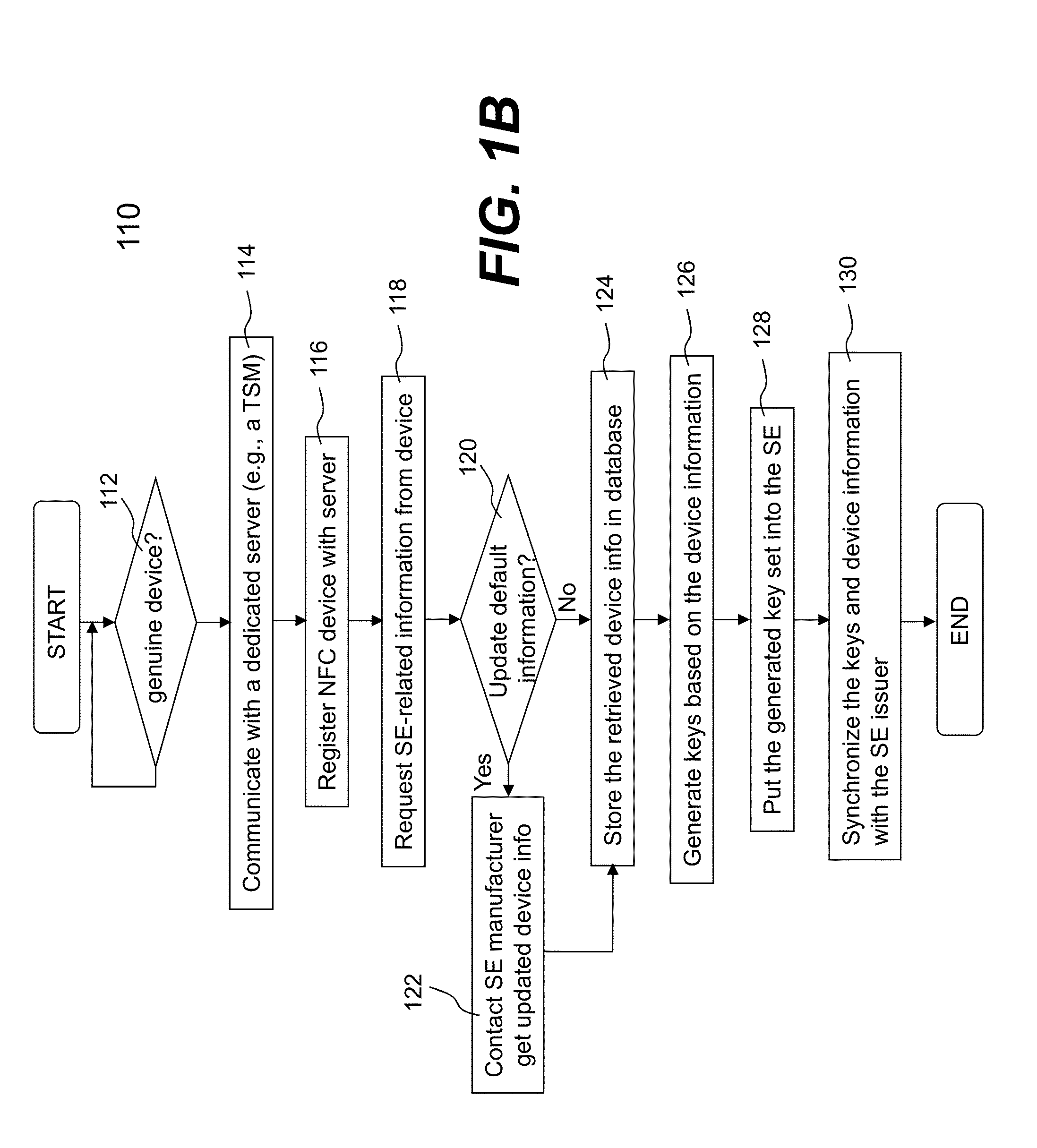
System and method for provisioning over the air of confidential information on mobile communicative devices with non-uicc secure elements
ActiveUS20120172089A1Service provisioningInternal/peripheral component protectionComputer hardwareMobile device
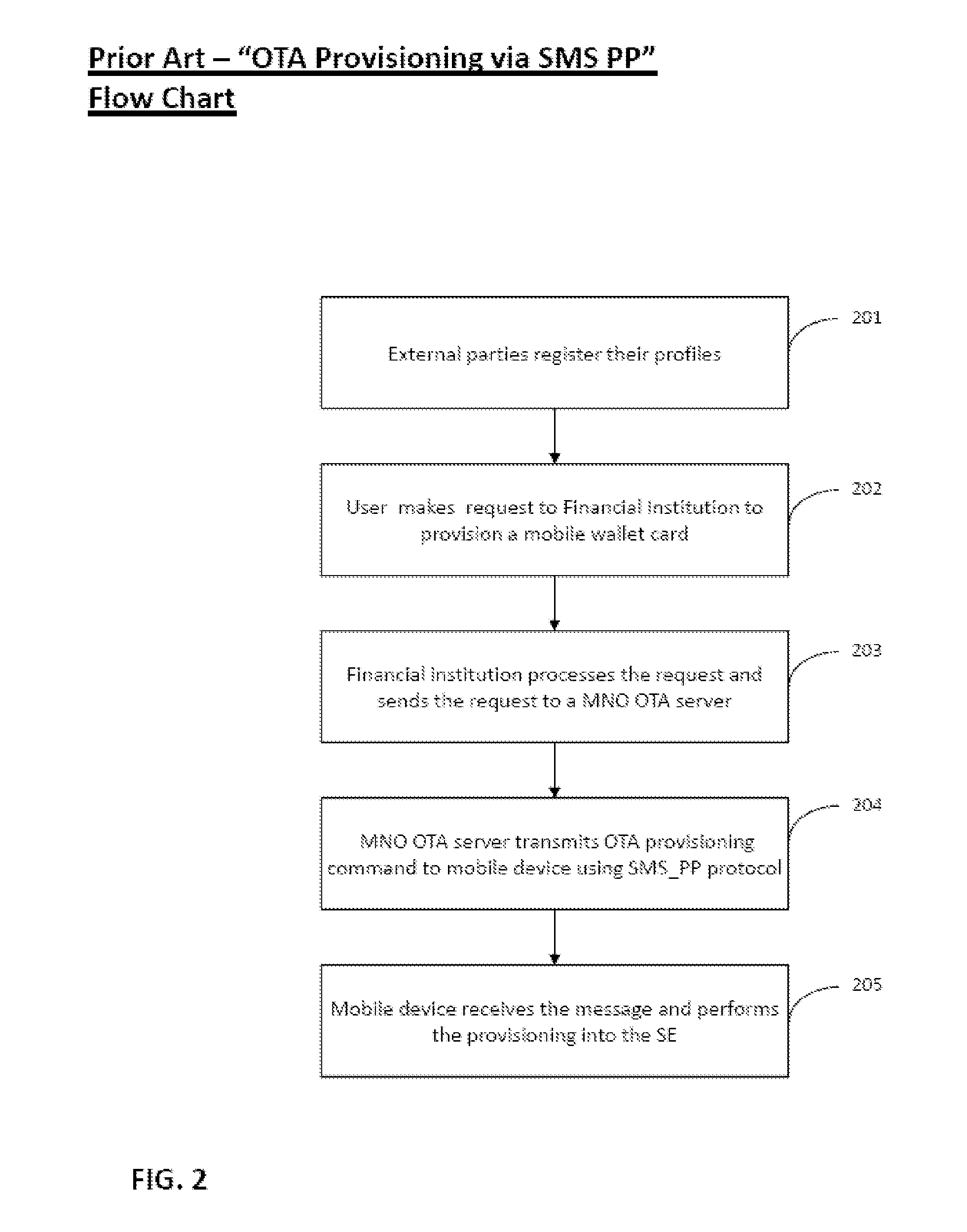
A method for over-the-air (OTA) provisioning a non-Universal Integrated Circuit Card (UICC) type secure element (SE) of a mobile device, including receiving a request to initialize an OTA proxy of a mobile device; initializing the OTA proxy; receiving provisioning data through the OTA proxy; and provisioning the received data into the SE, in which the SE is a non-UICC type SE. A mobile device to provision secure data OTA in a non-UICC type SE including an OTA proxy to connect to a Trusted Service Manager (TSM) system, and to receive provisioning data from the TSM system; a near-field-communication (NFC) enabled chip to conduct a contactless transaction; and a SE to store information provisioned through OTA proxy, in which the SE is a non-UICC type SE.
Owner:MOZIDO CORFIRE - KOREA
Biometric authentication of mobile financial transactions by trusted service managers
InactiveUS20140025520A1Convenient transactionAcutation objectsHand manipulated computer devicesFinancial transactionTrusted service manager
In one embodiment, a method comprises storing a biometric trait of a user in a data communication device of the user, comparing a biometric trait input into the device with the biometric trait stored in the device, generating a certificate authenticating the user within the device if the biometric trait input into the device matches the biometric trait stored in the device, and facilitating a financial transaction of the user using the certificate.
Owner:PAYPAL INC
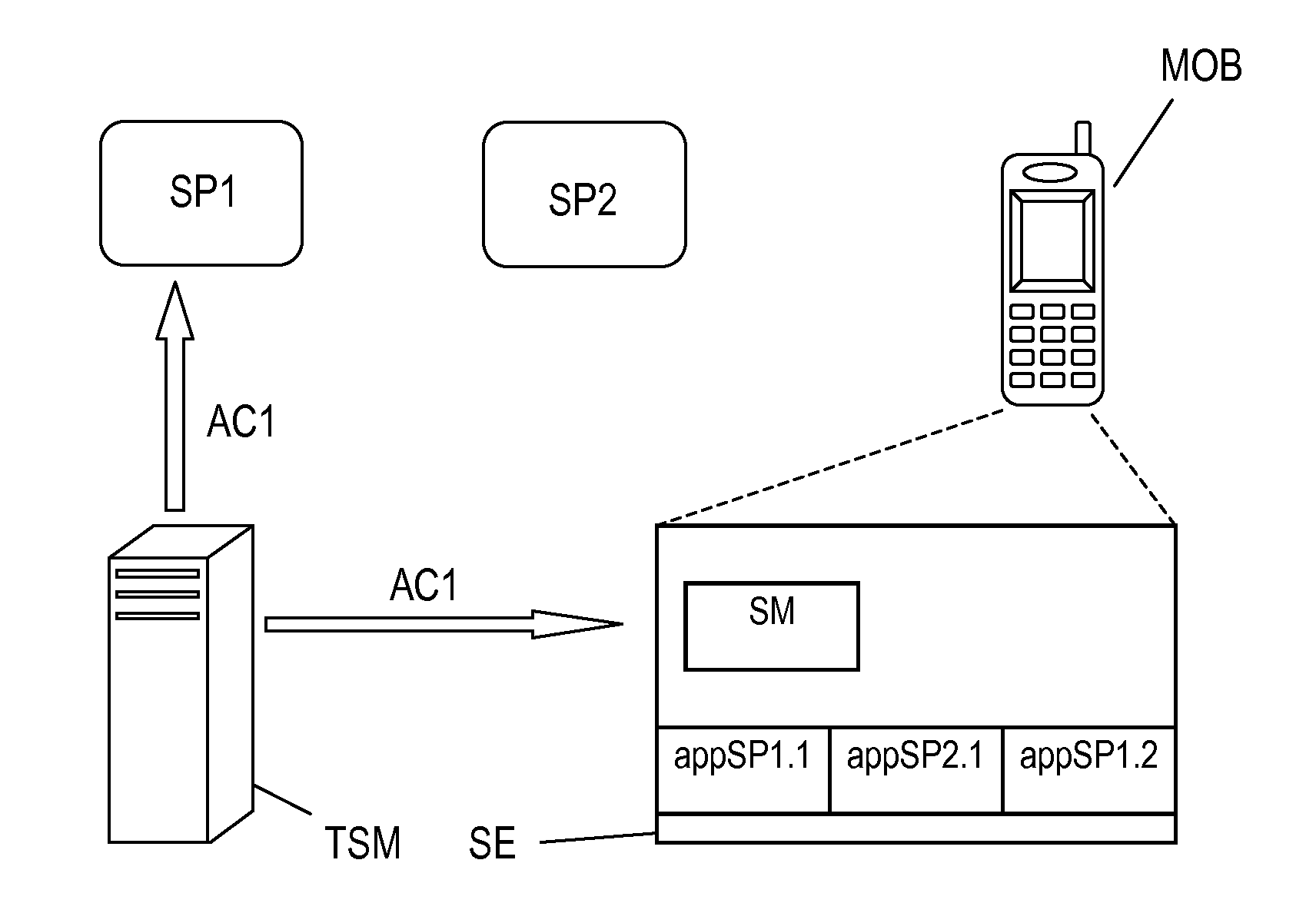
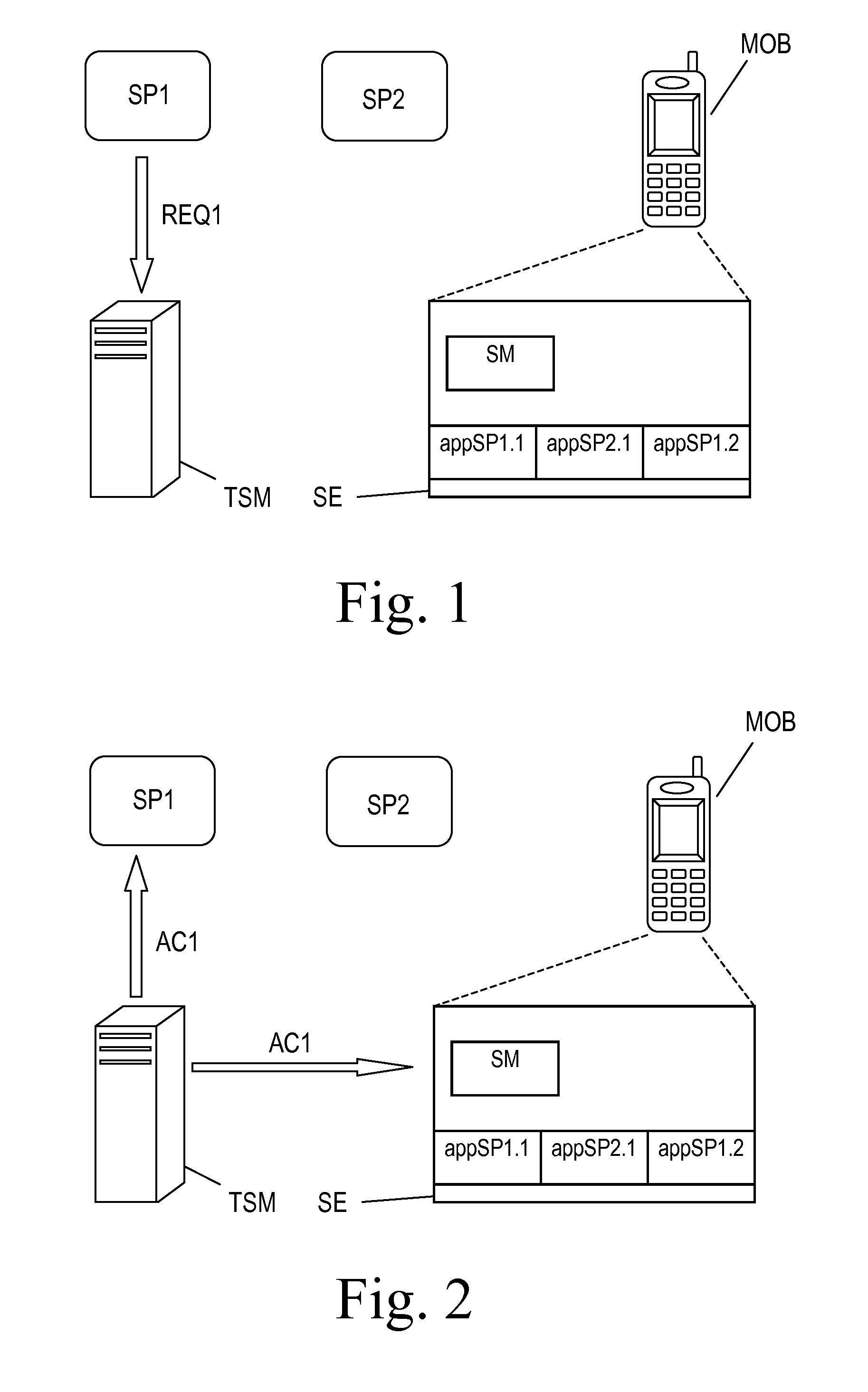
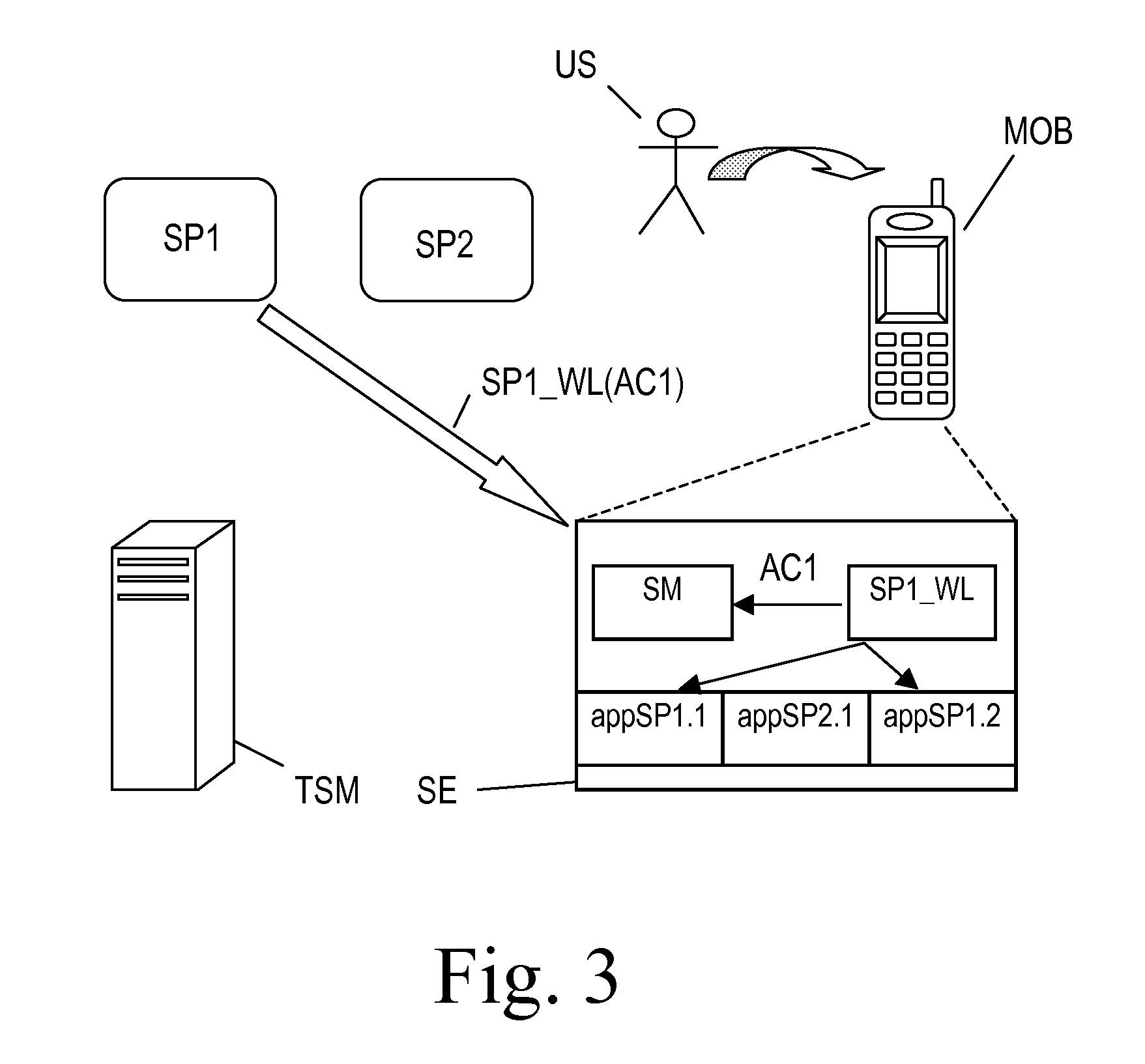
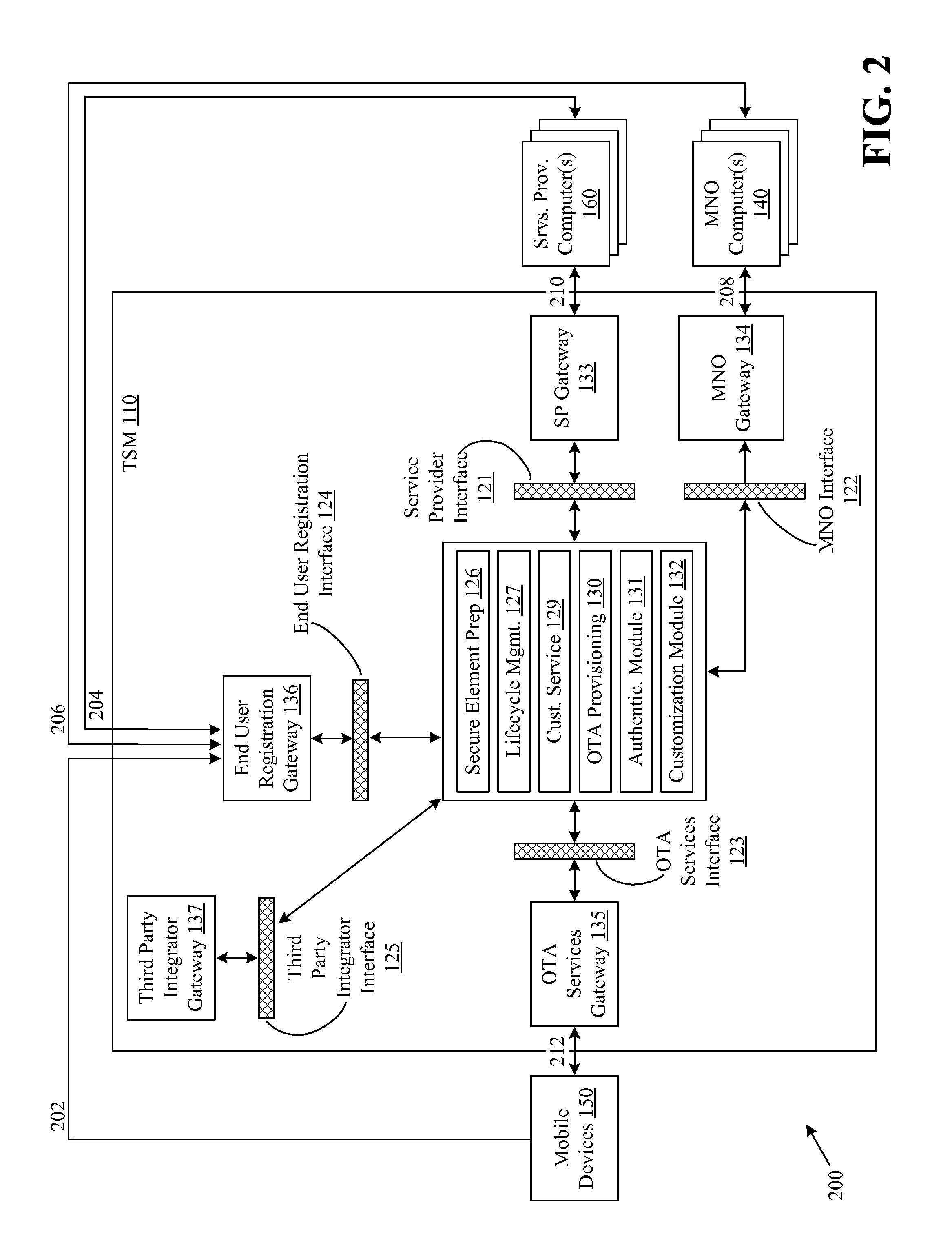
Method, system, trusted service manager, service provider and memory element for managing access rights for trusted applications
ActiveUS20100205432A1Digital data protectionPayment architectureService provisionPayment service provider
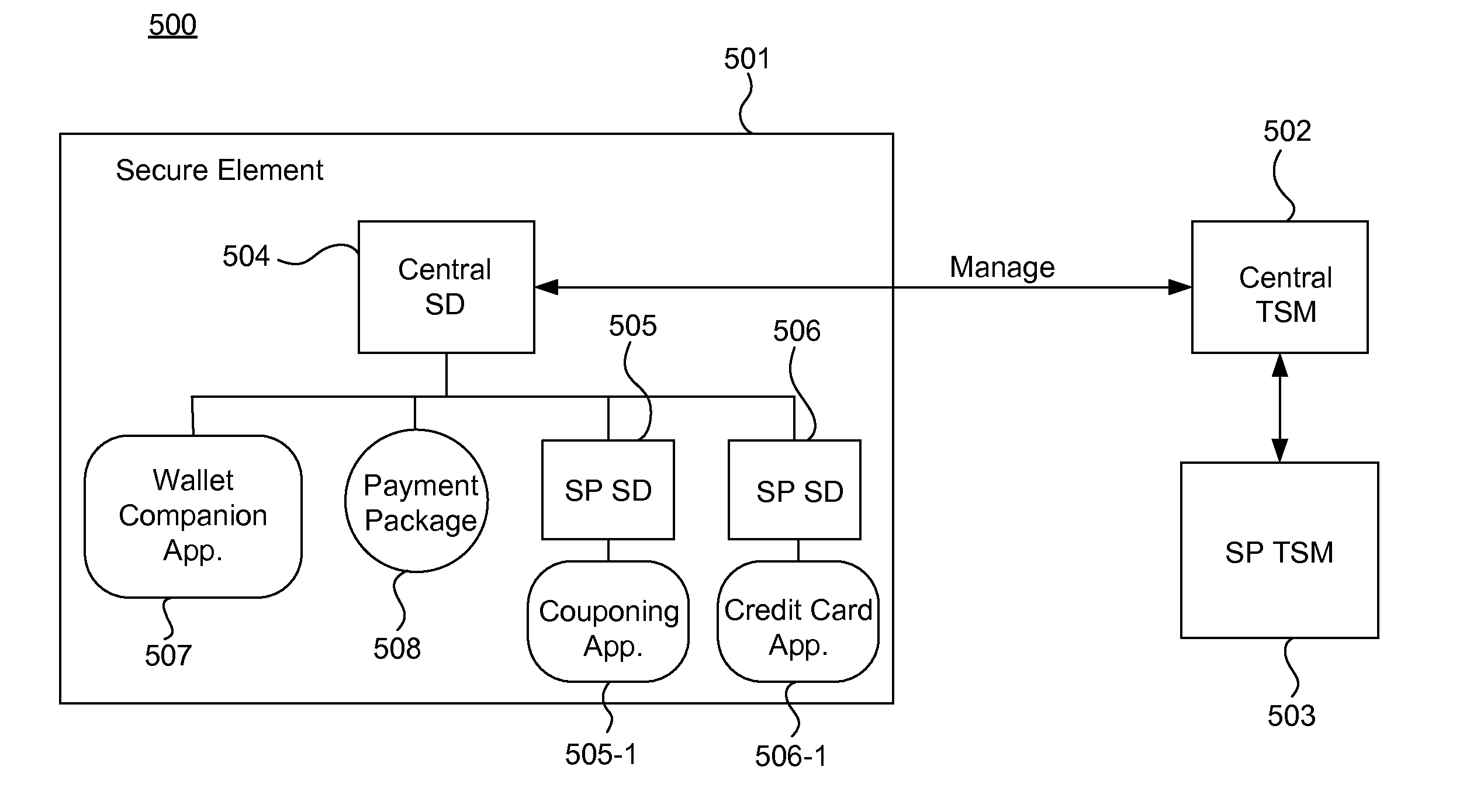
A method for granting trusted applications (SP1_WL) of a Service Provider (SP1, SP2) access to applications (appSP1.1, appSP1.2; appSP2.1) of that Service Provider (SP1, SP2) that have been stored in a secure element (SE) comprises: the Service Provider (SP1, SP2) transmits a request (REQ1) for granting access to its applications to a Trusted Service Manager (TSM); the Trusted Service Manager (TSM) generates an access right code (AC1) and transmits it to both the Service Provider (SP1, SP2) and a service manager (SM) in the secure element (SE); the Service Provider (SP1, SP2) generates the trusted application (SP1_WL), provides it with the access right code (AC1) and sends it to the secure element (SE); the trusted application (SP1_WL) connects to the service manager (SM) with the access right code (AC1) whereupon the service manager (SM) grants the wallet (SP1_WL) access to the applications (appSP1.1, appSP1.2; appSP2.1).
Owner:NXP BV
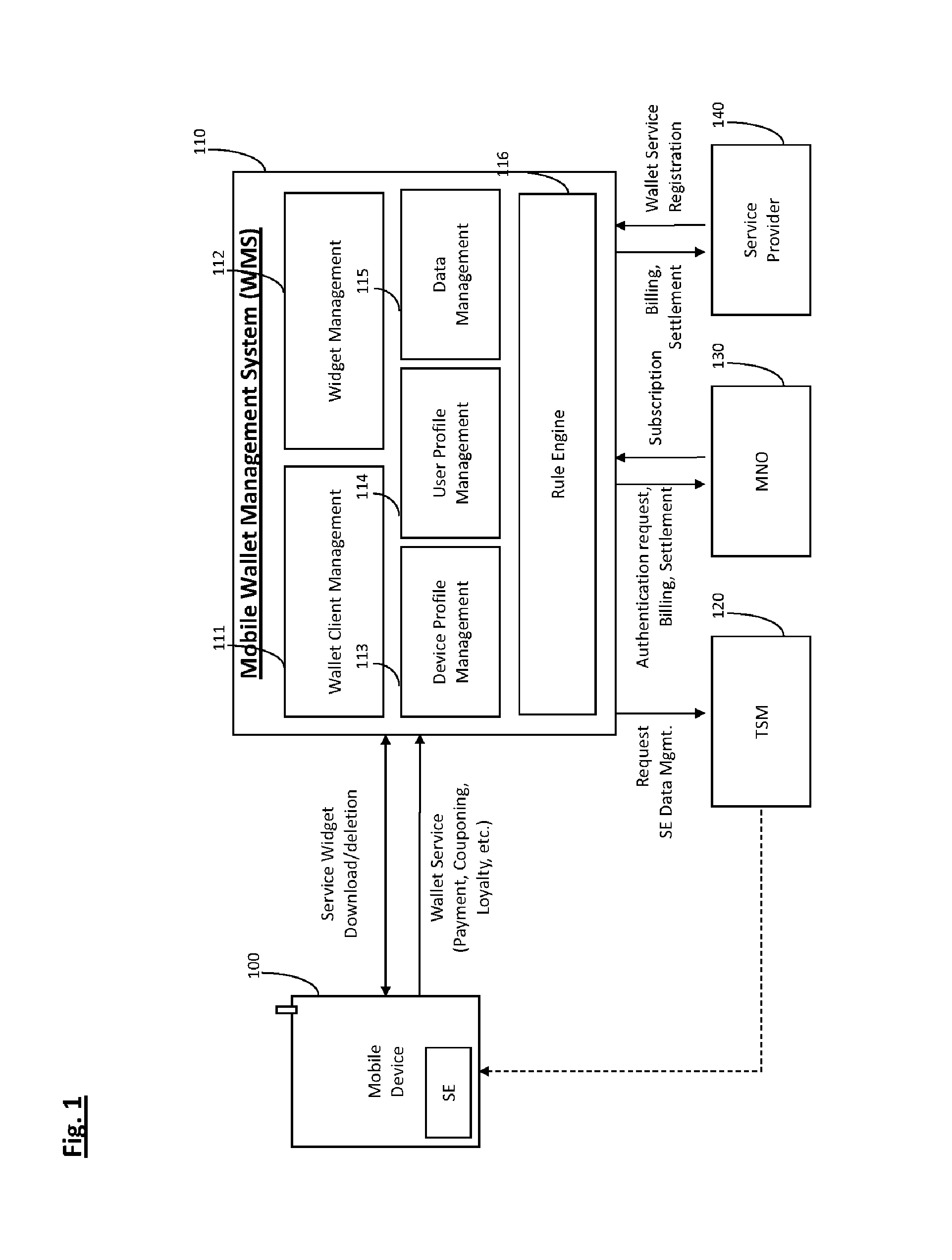
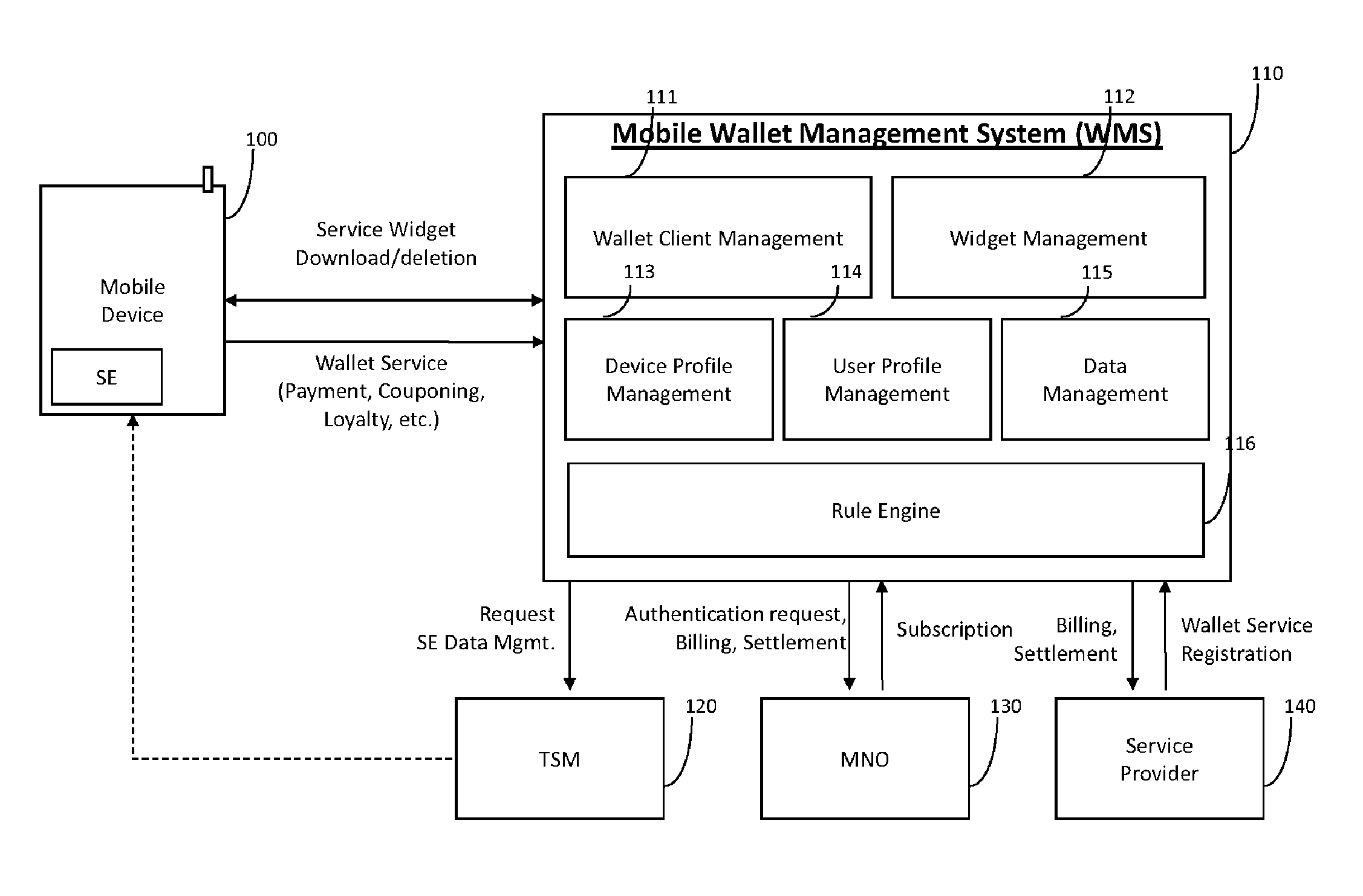
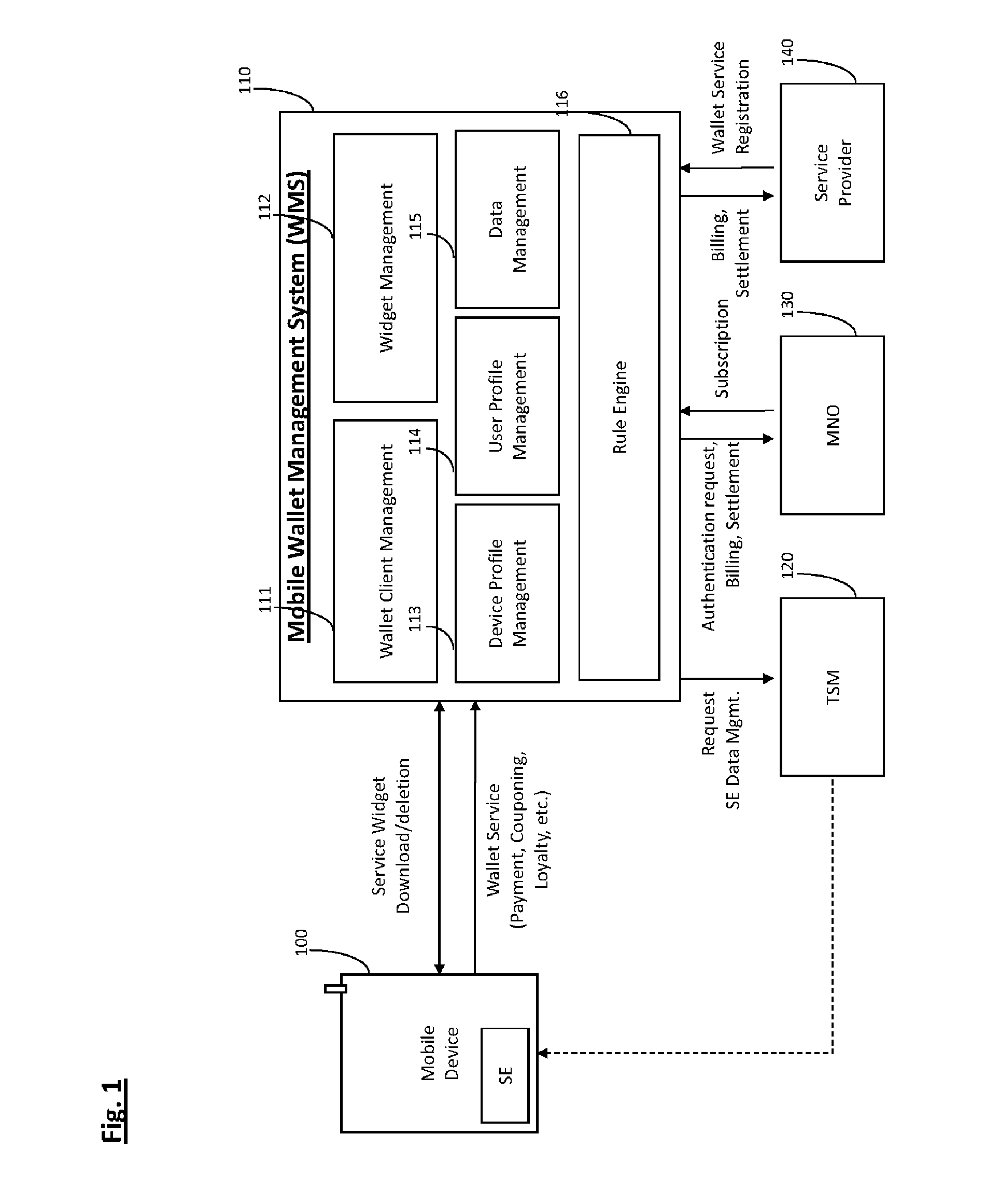
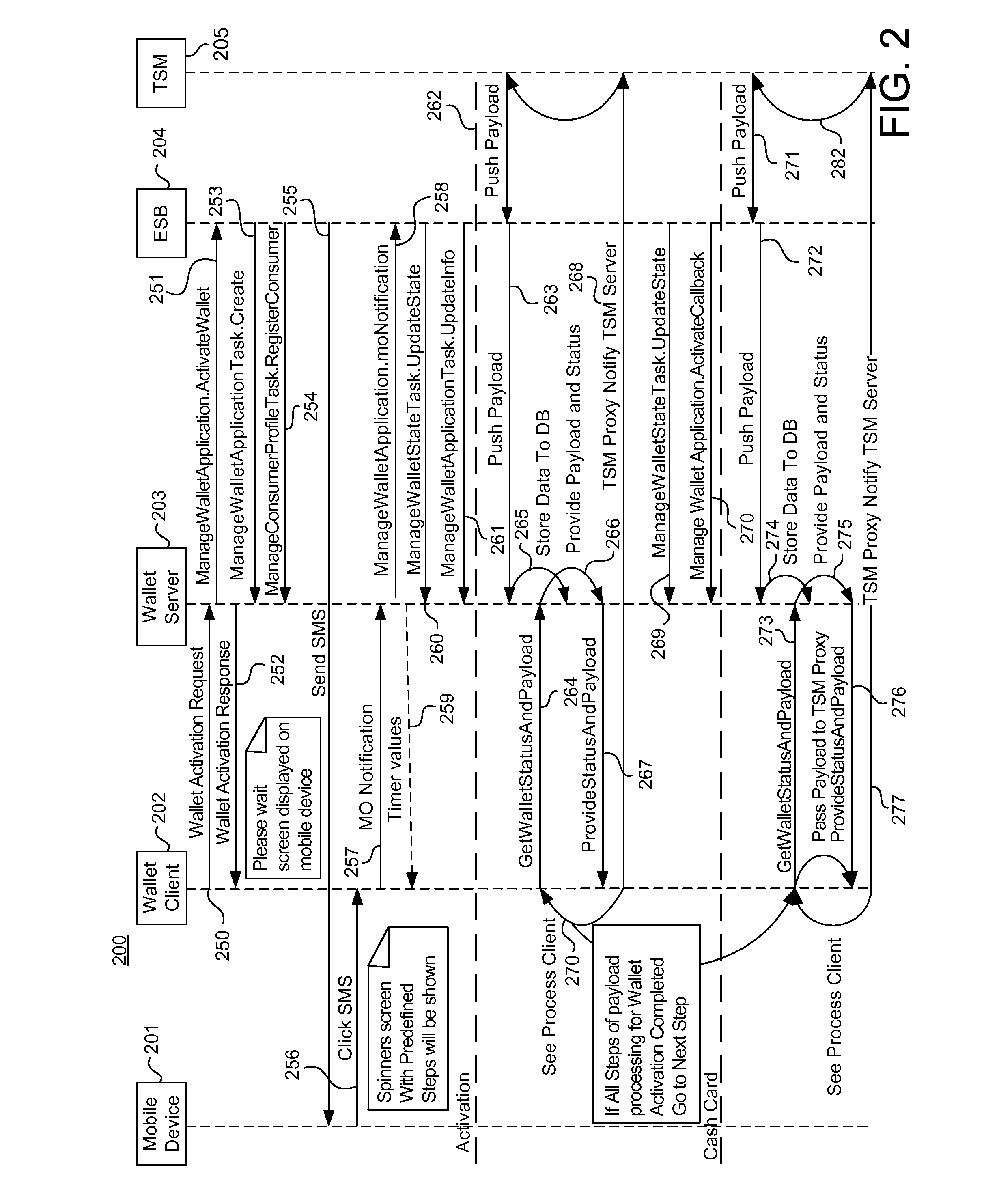
System and method for managing mobile wallet and its related credentials
A method for provisioning a contactless card applet in a mobile device with a mobile wallet application, including activating the mobile wallet application, connecting to a Trusted Service Manager (TSM) system, synchronizing the mobile wallet application with the TSM system, displaying a contactless card applet based on attributes of the mobile device, receiving a selection of a contactless card applet, retrieving a widget and a wallet management applet (WMA) corresponding to the contactless card applet, and provisioning the selected contactless card applet, the widget, and the WMA. A wallet management system (WMS) in a non-transitory storage medium to store and manage mobile wallet account information including a wallet client management component, a widget management component, a device profile management component, and a rule engine.
Owner:FINTIV INC +1
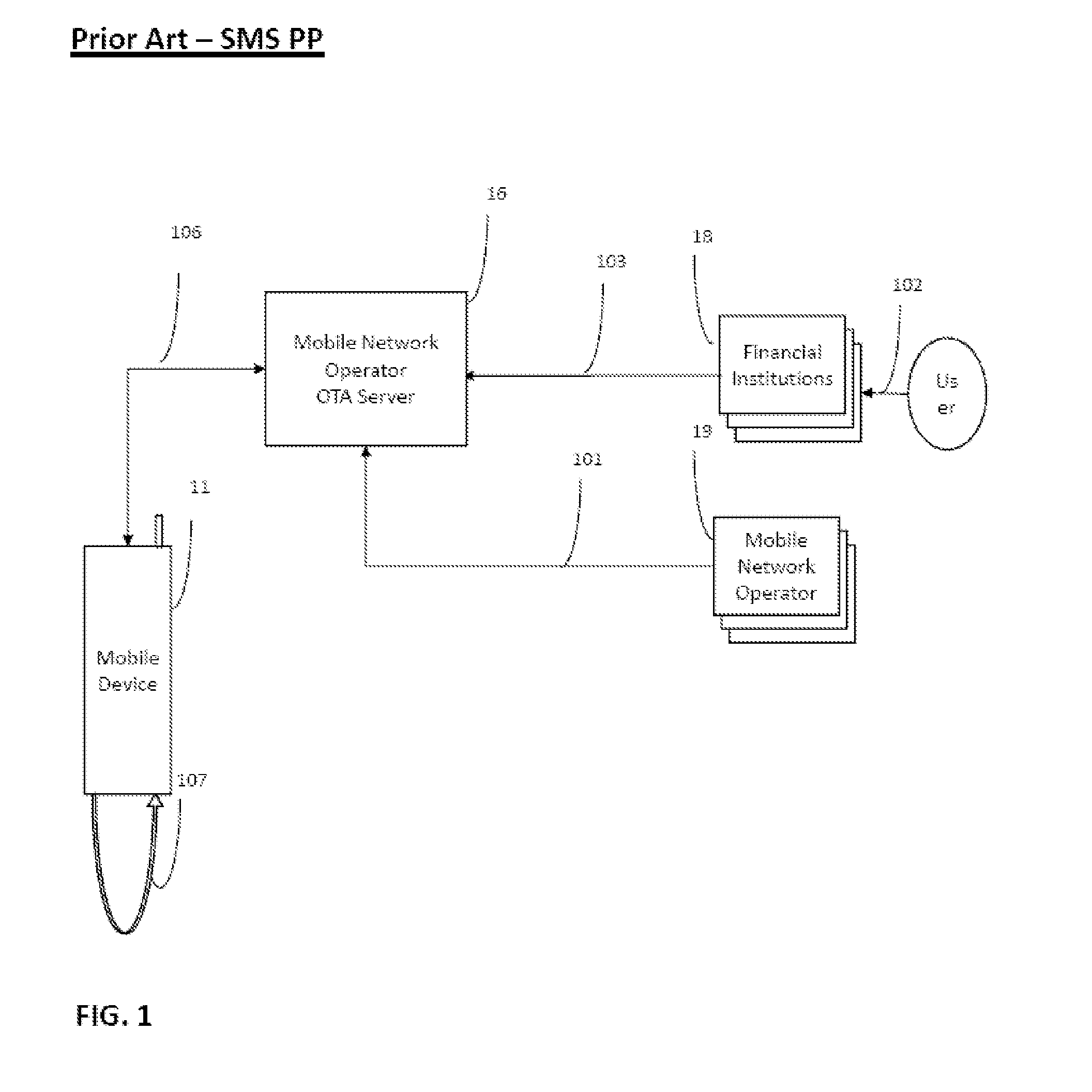
Sim locking
Where a smartcard is embedded or inaccessible within a cellular telecommunications device (i.e. an eUICC), locking the smartcard (or the subscription associated with the smartcard) to a particular MNO while allowing the MNO to be altered legitimately presents a challenge. A method is described using policy control tables stored in a trusted service manager registry and / or the smartcard's data store. By maintaining the policy control table, any MNO subscription may be downloaded / activated on the smartcard but the device will be prevented from accessing the desired MNO because that access would violate the lock rules.
Owner:VODAFONE IP LICENSING
Trusted Service Management Process
InactiveUS20130139230A1Minimal effortEfficient managementKey distribution for secure communicationDigital data processing detailsPersonalizationFinancial transaction
Techniques for providing trusted management services (TSM) are described. According to one aspect of the techniques, a secure element (SE) is personalized via the TSM. A process is provided to personalize an SE with multiple parties involved and orchestrated by a party or a business running the TSM, hence as a trusted service manager (TSM). The TSM brings the parties together to recognize the SE being personalized so that subsequent transactions can be authorized and carried out with a device embedded with the SE. In operation, each of the parties may load a piece of data into the SE, including registration information, various services or application data, and various keys so that subsequent transactions can be carried out with or via an authorized party and in a secured and acknowledgeable manner.
Owner:RFCYBER CORP
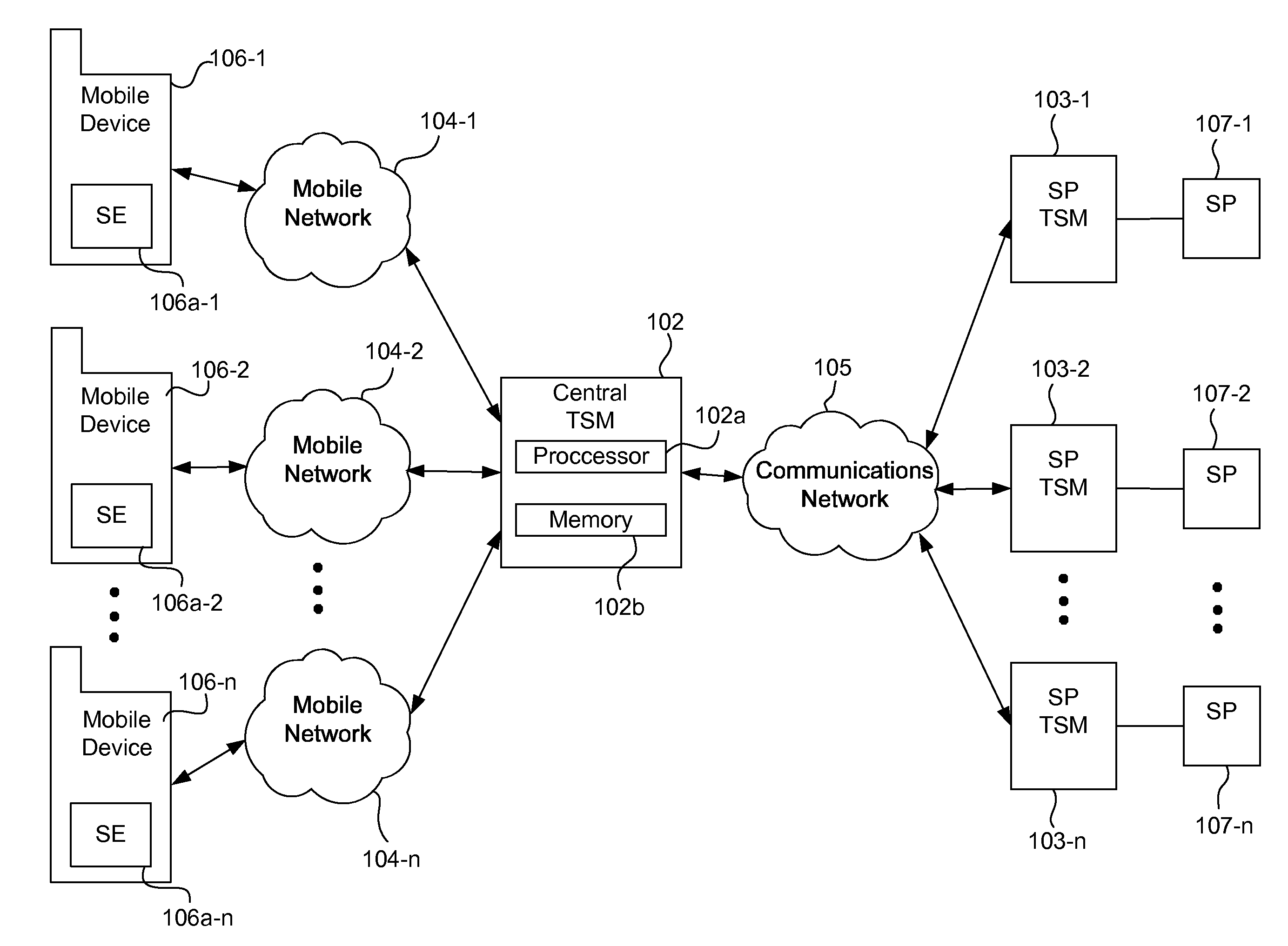
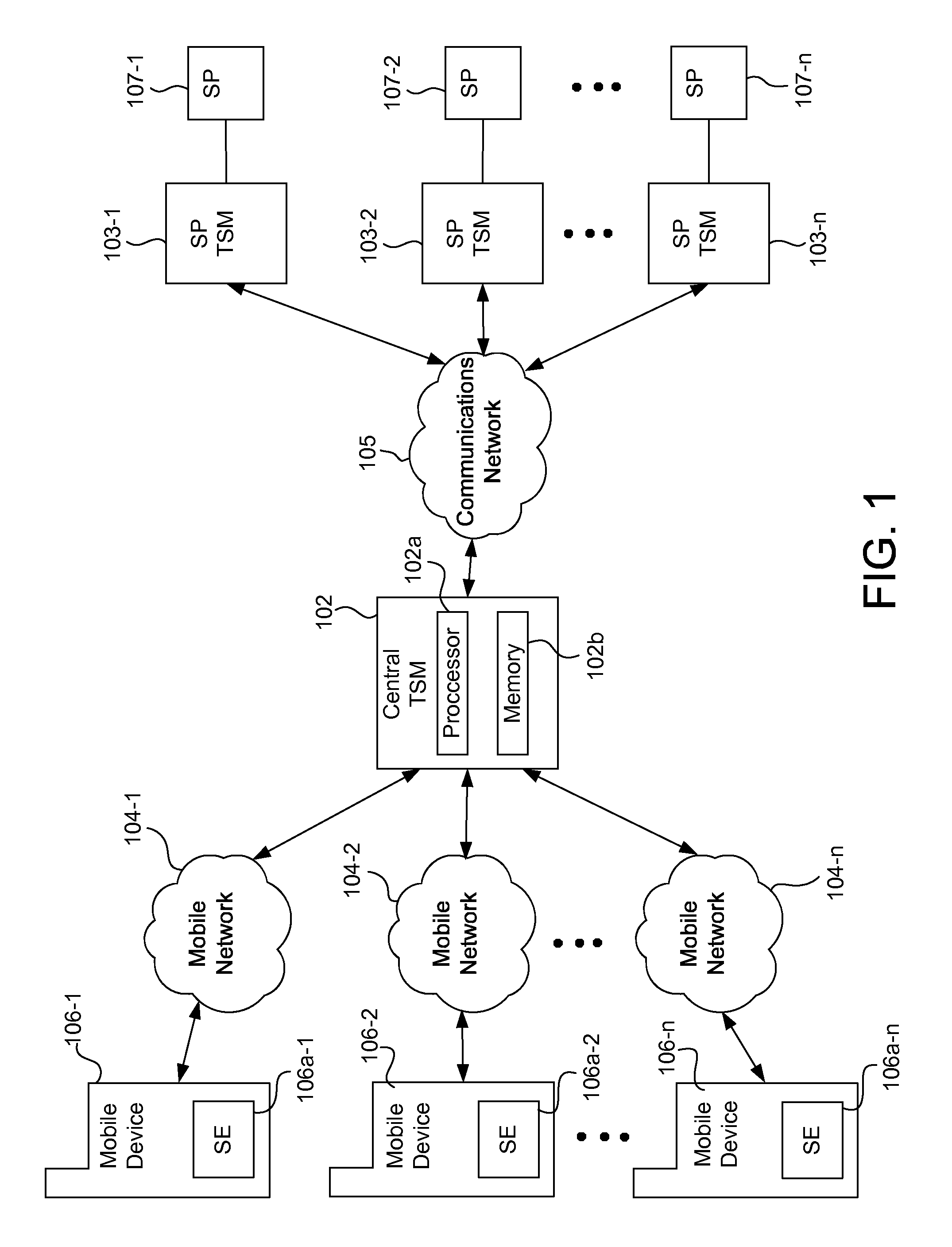
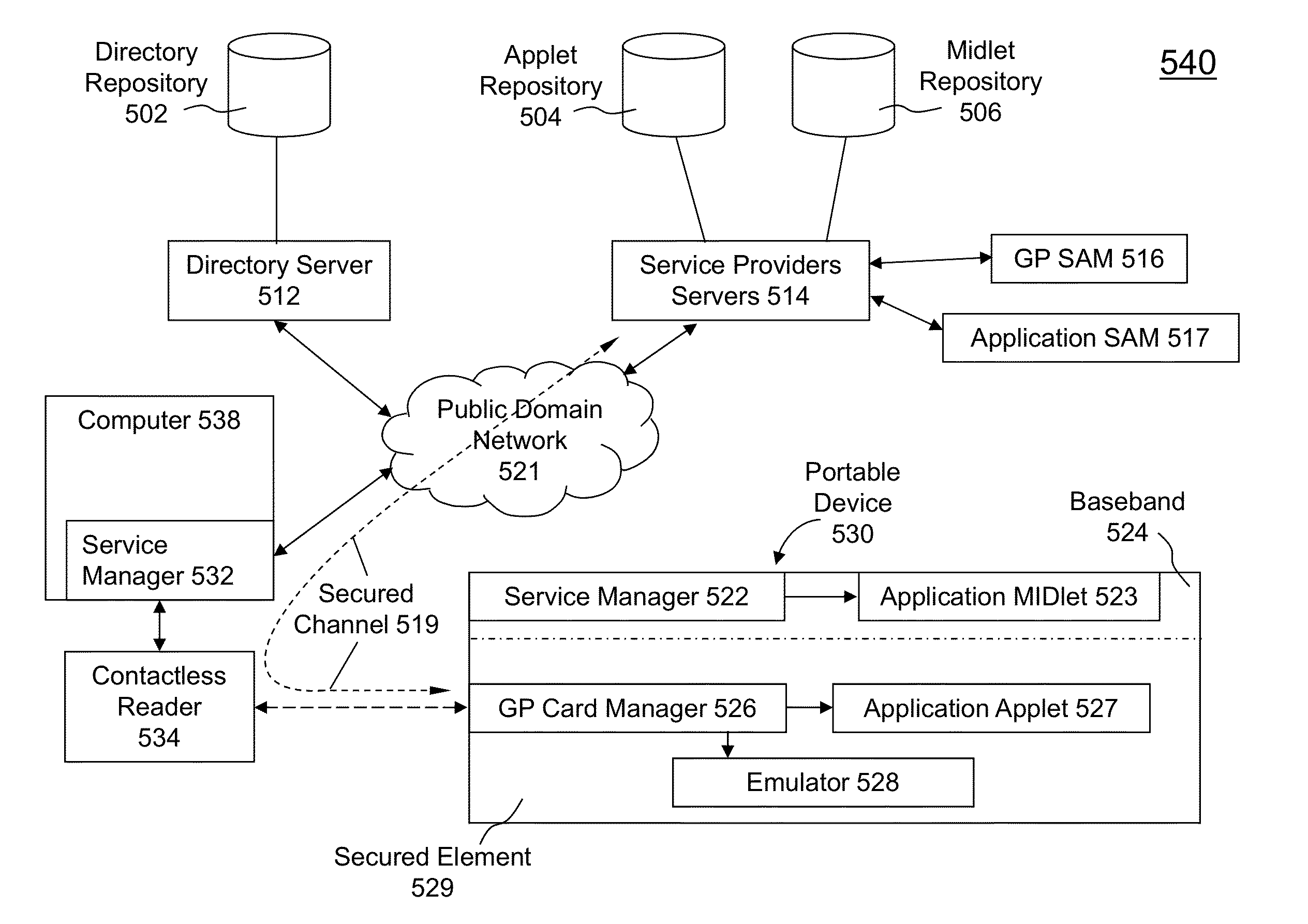
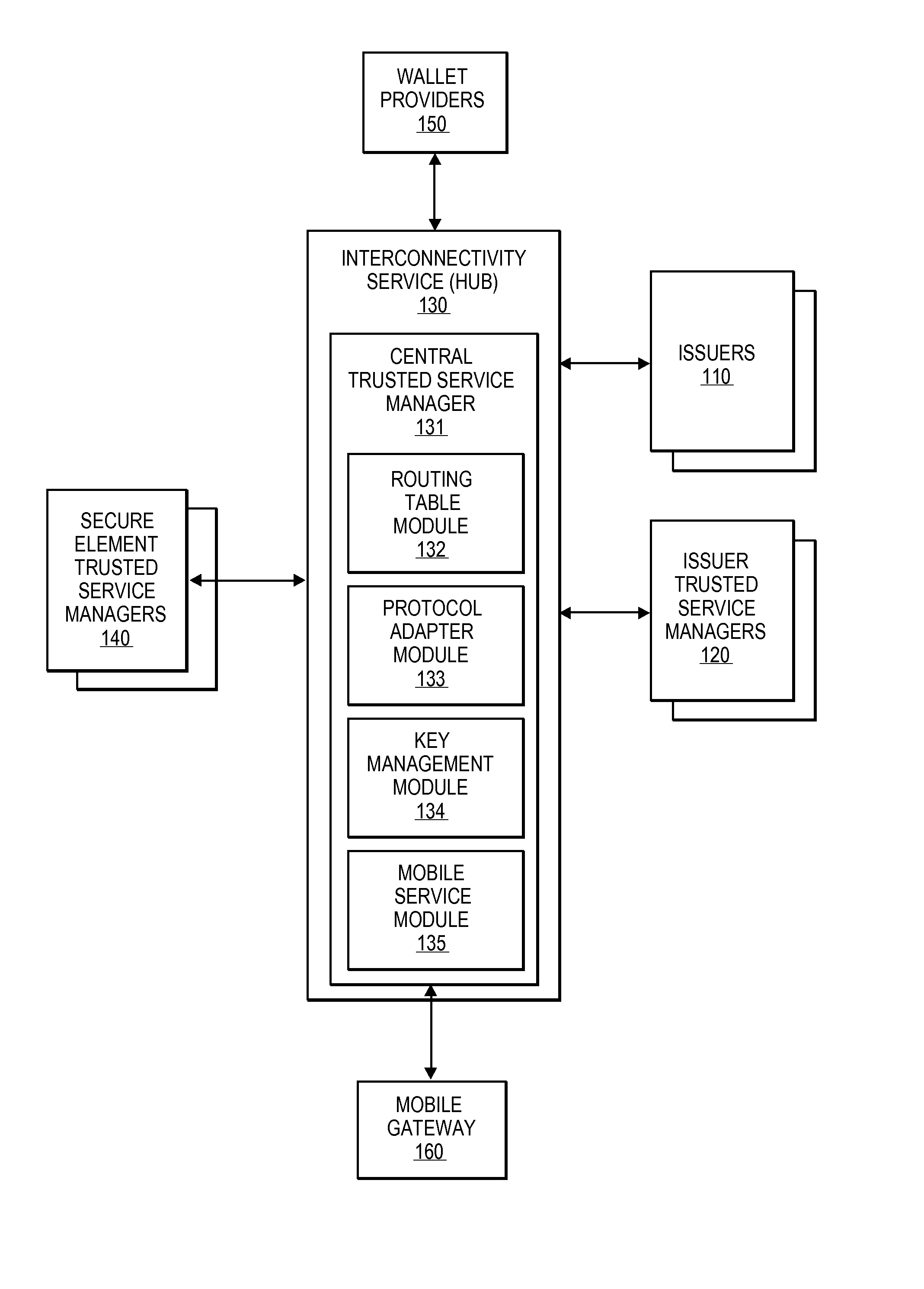
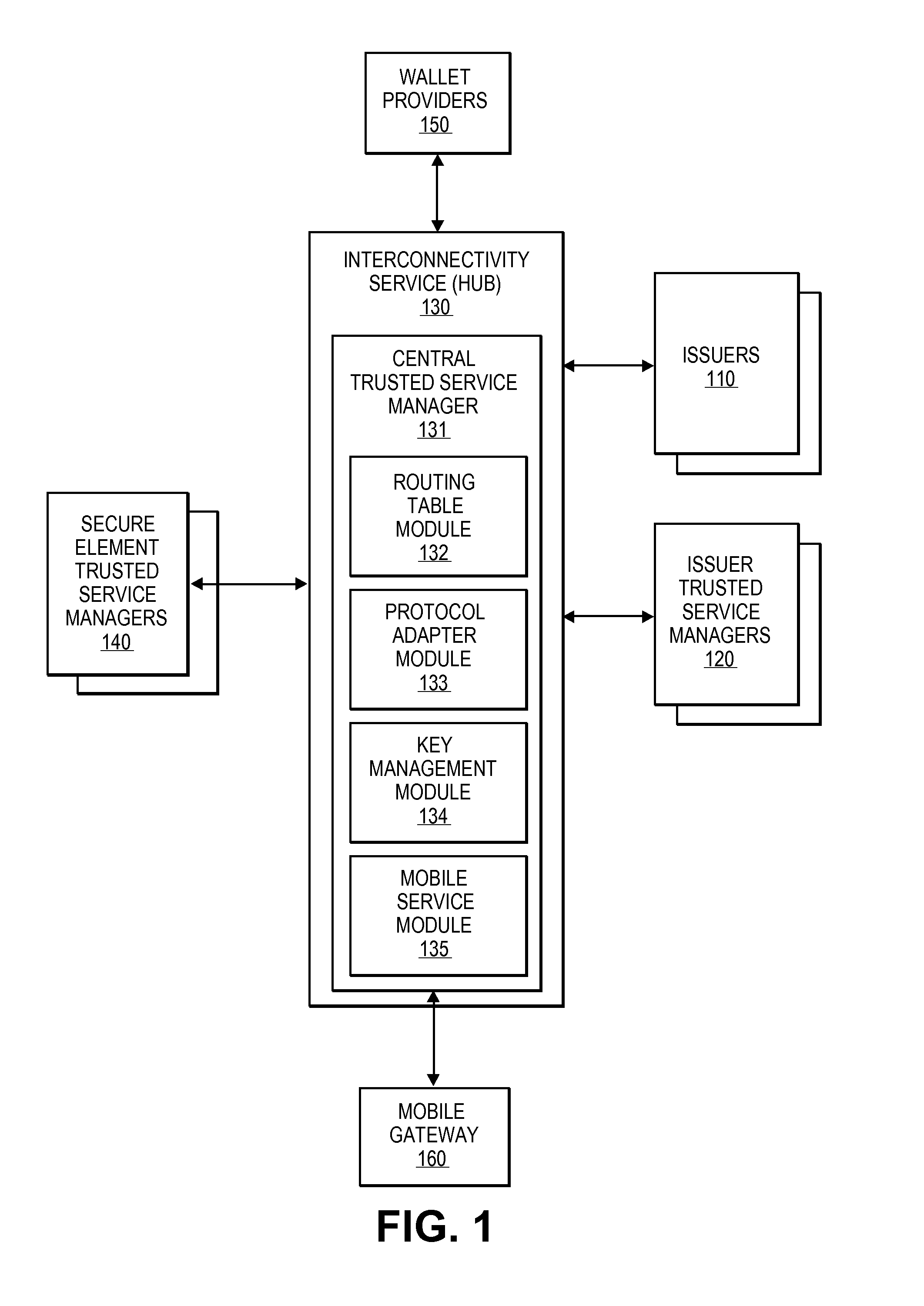
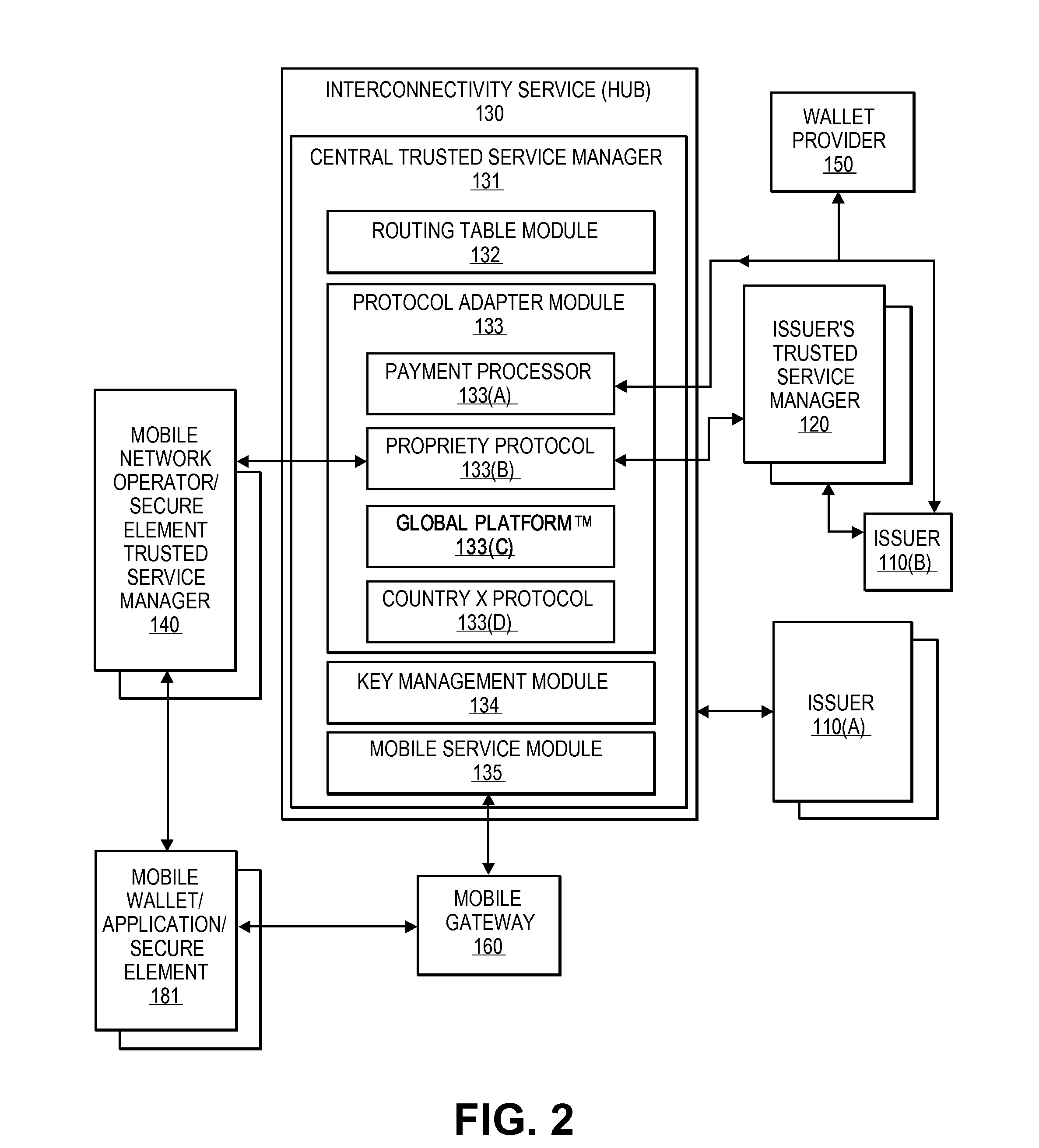
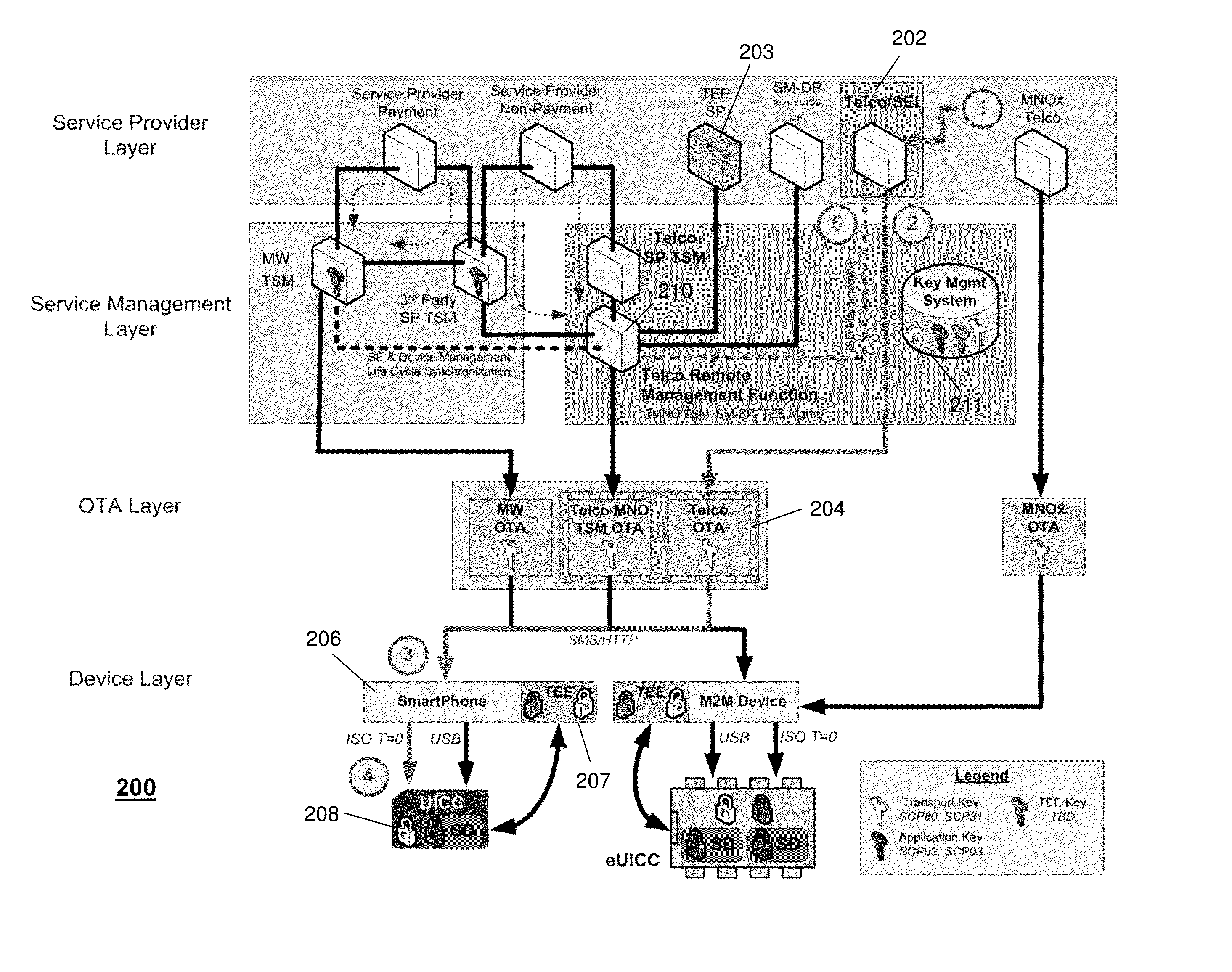
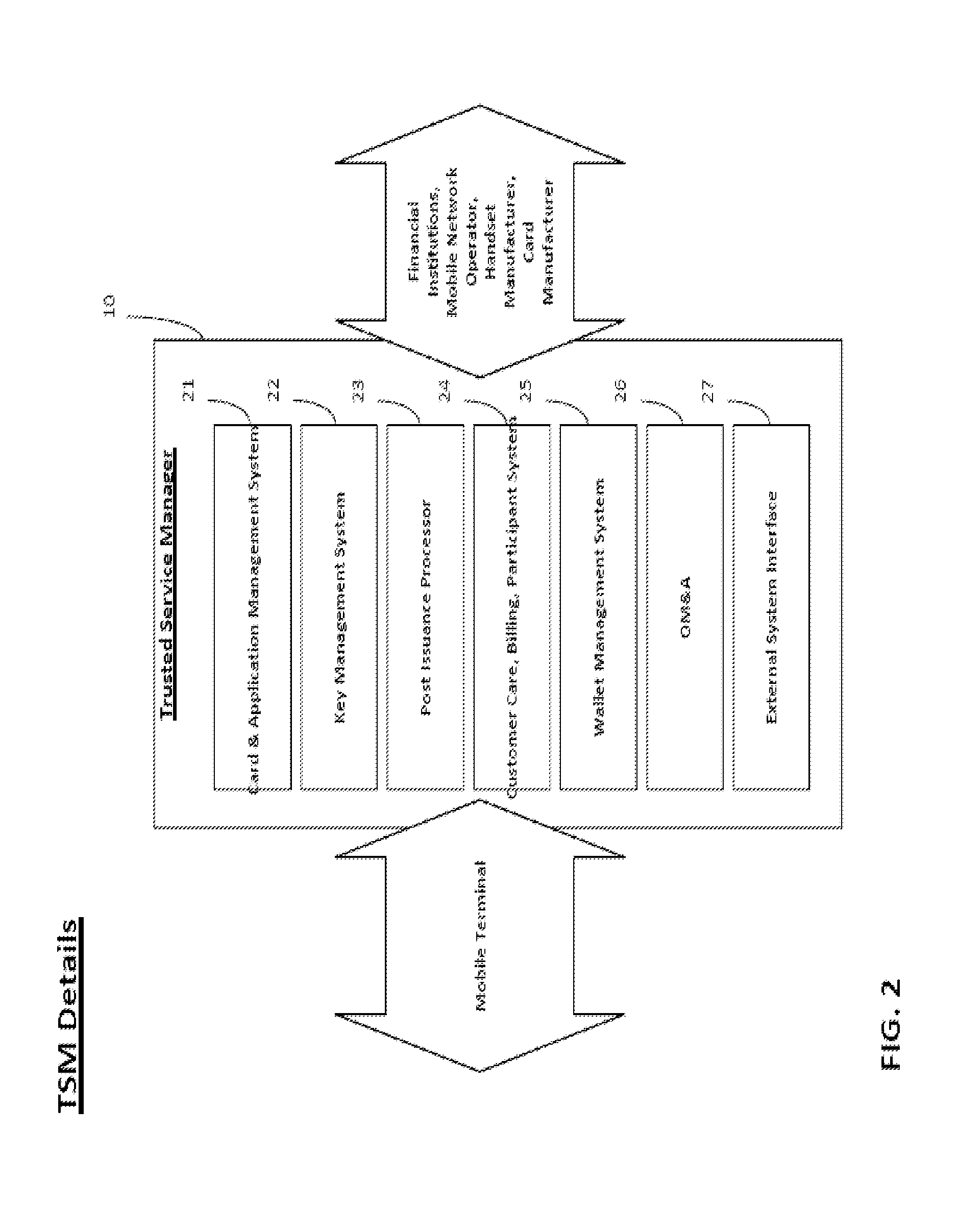
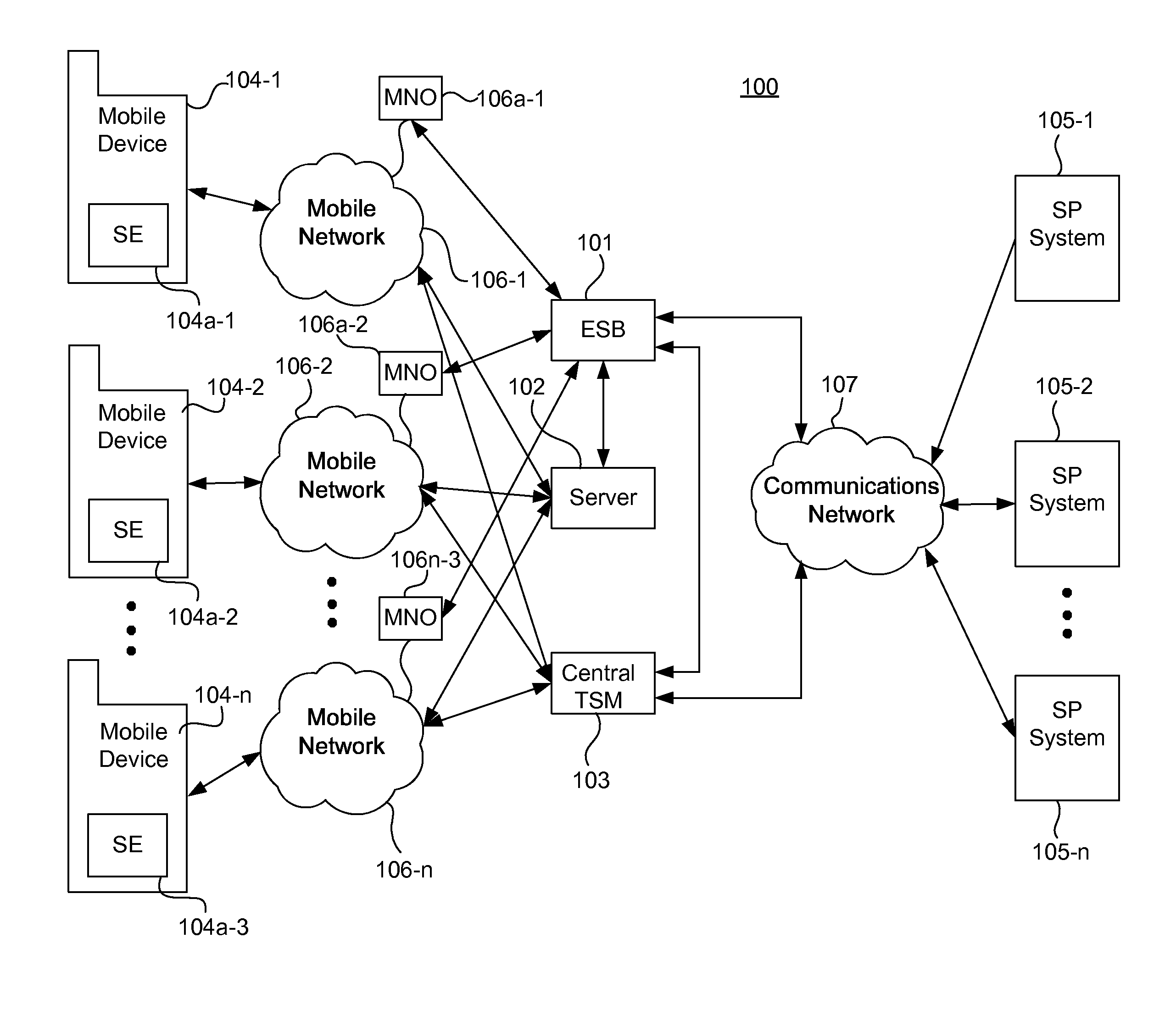
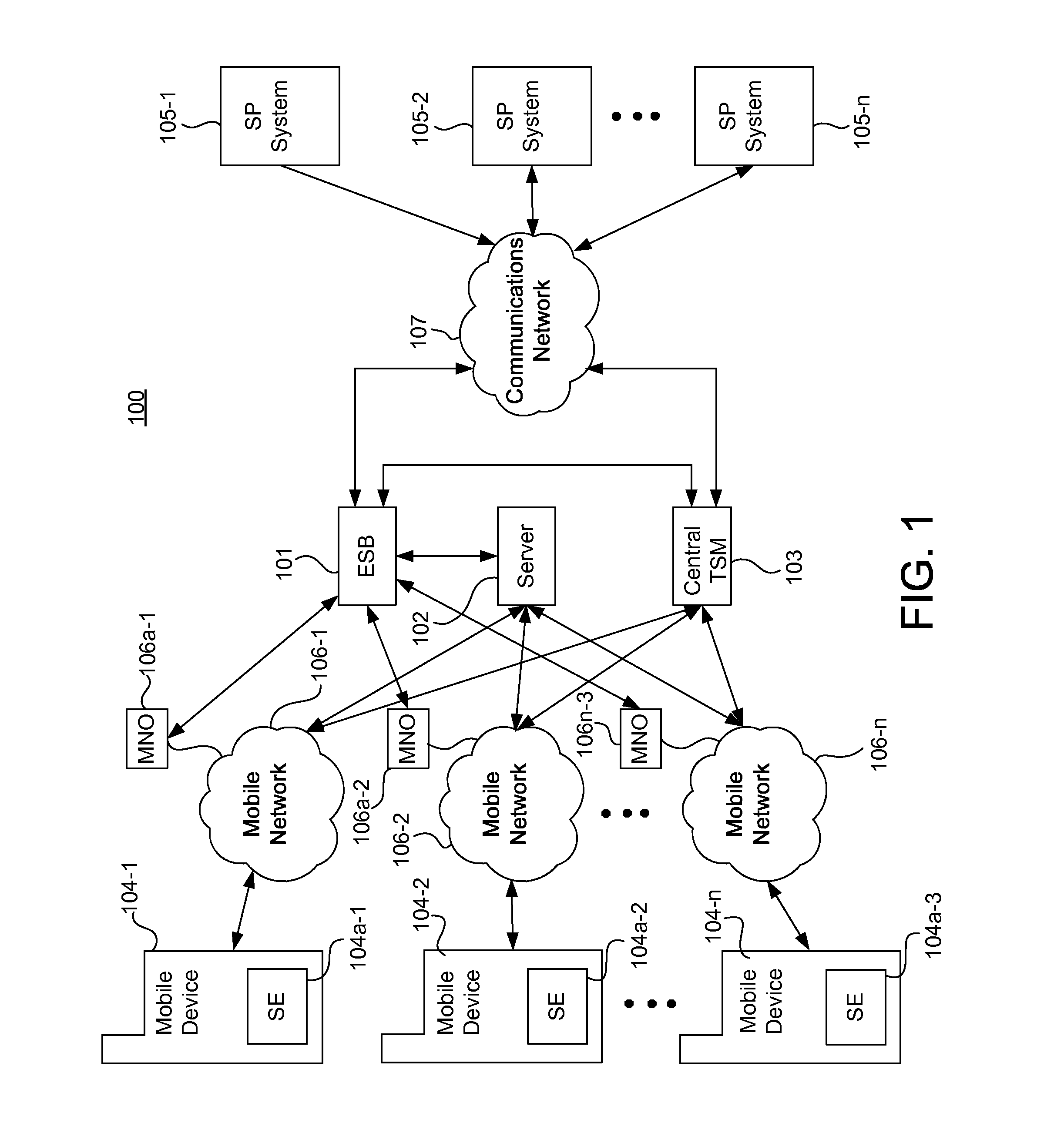
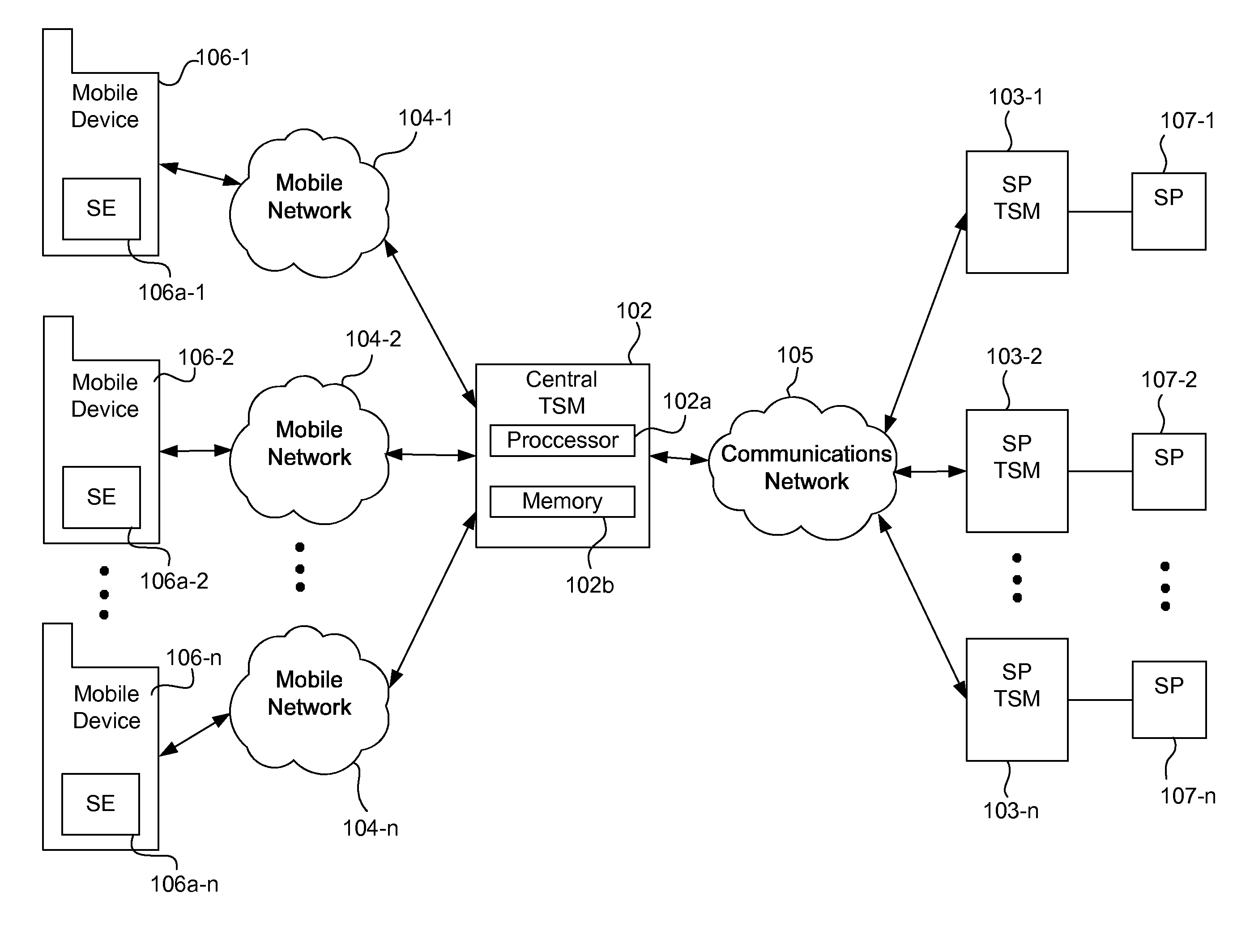
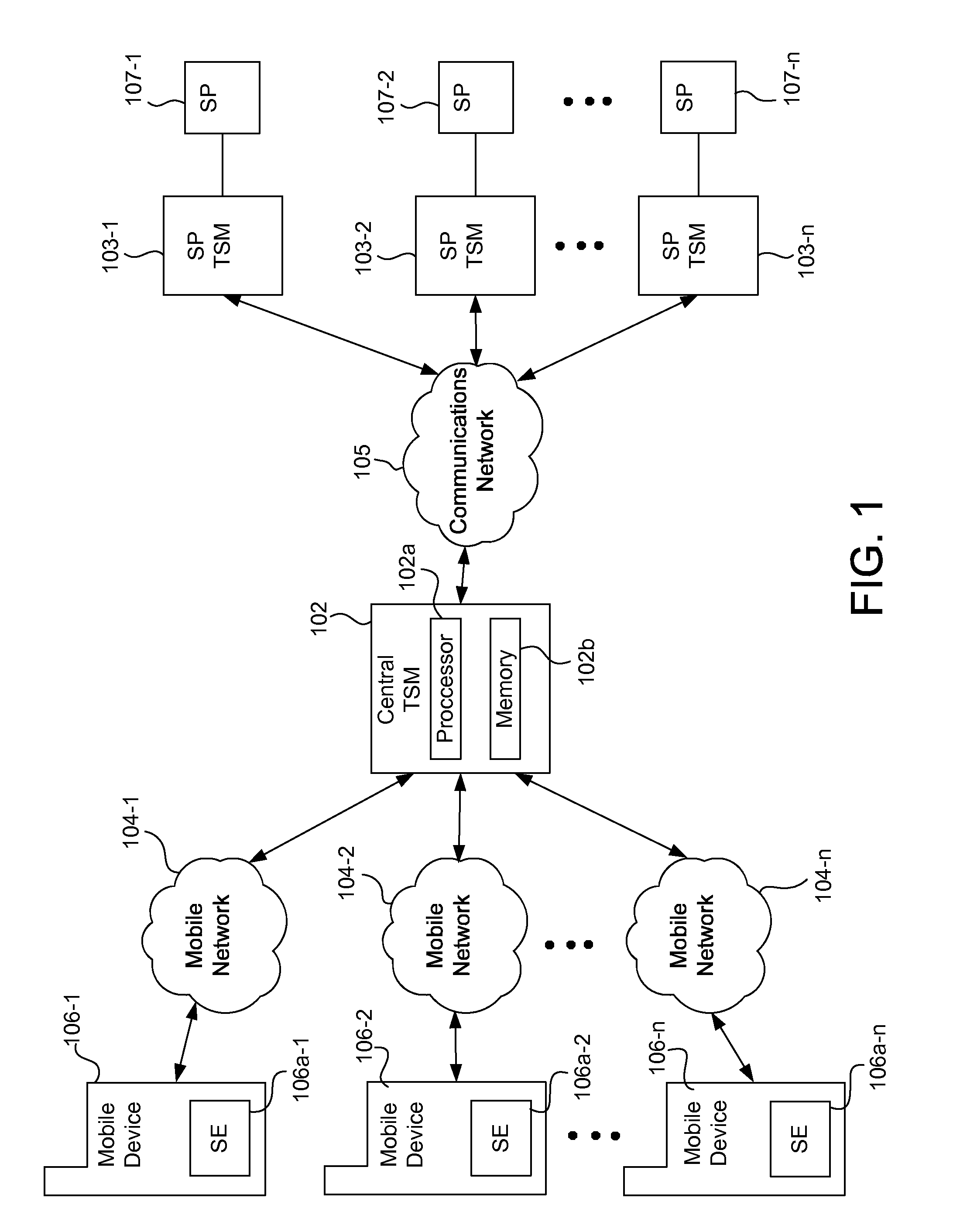
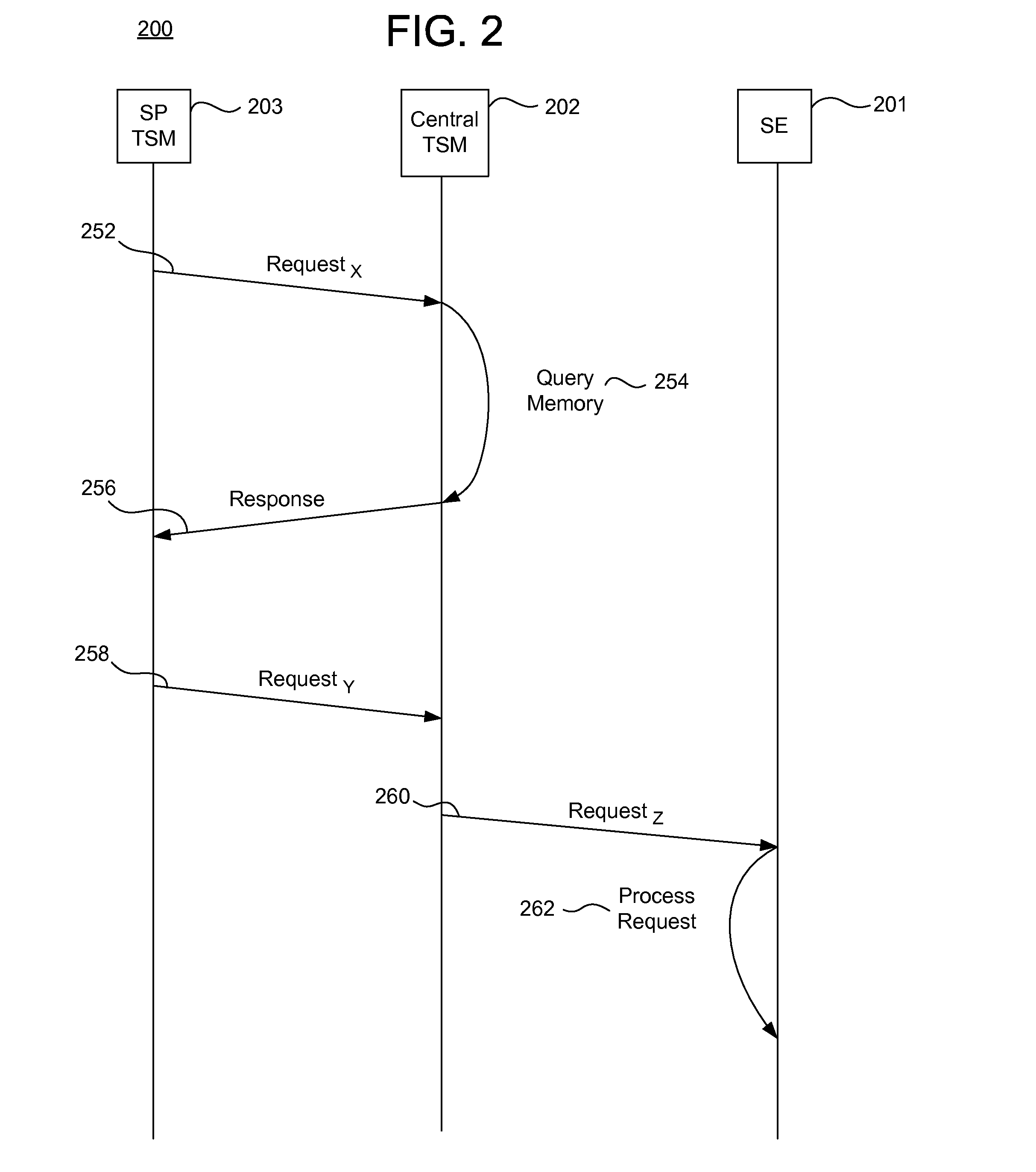
Integrated mobile trusted service manager
Embodiments of the invention are directed to a centralized trusted service manager system in the form of a trusted service manager interconnectivity service hub, which facilitates and provides communications between entities involved in mobile contactless provisioning and payment systems. One embodiment of the present invention is directed to a method for processing a wallet request from a wallet provider associated with mobile communication device including a secure element through an interconnectivity hub. The method comprises receiving a wallet request in first protocol, determining an issuer associated with the account identifier, and obtaining application data. The method further comprises determining a trusted service manager associated with the secure element from among a plurality of trusted service manager computers using a routing table. Additionally, the method includes determining a second protocol and obtaining a secure element key for completing a request from a secure element trusted service manager using the second protocol.
Owner:VISA INT SERVICE ASSOC
Systems, methods, and computer program products for managing secure elements
ActiveUS20130111546A1Easily and securely communicateKey distribution for secure communicationUser identity/authority verificationProcessing InstructionInternet privacy
Systems, methods, and computer program products are provided for performing content management operations. At least one memory stores data, and a central security domain manages instructions on behalf of one or more service provider security domains. The instructions are received, over a network, from a trusted service manager. The instructions are processed in at least one of the one or more determined service provider security domains, using the data stored in the at least one memory. The data includes one or more generic applications, each of which can be instantiated for one or more service providers.
Owner:GOOGLE LLC
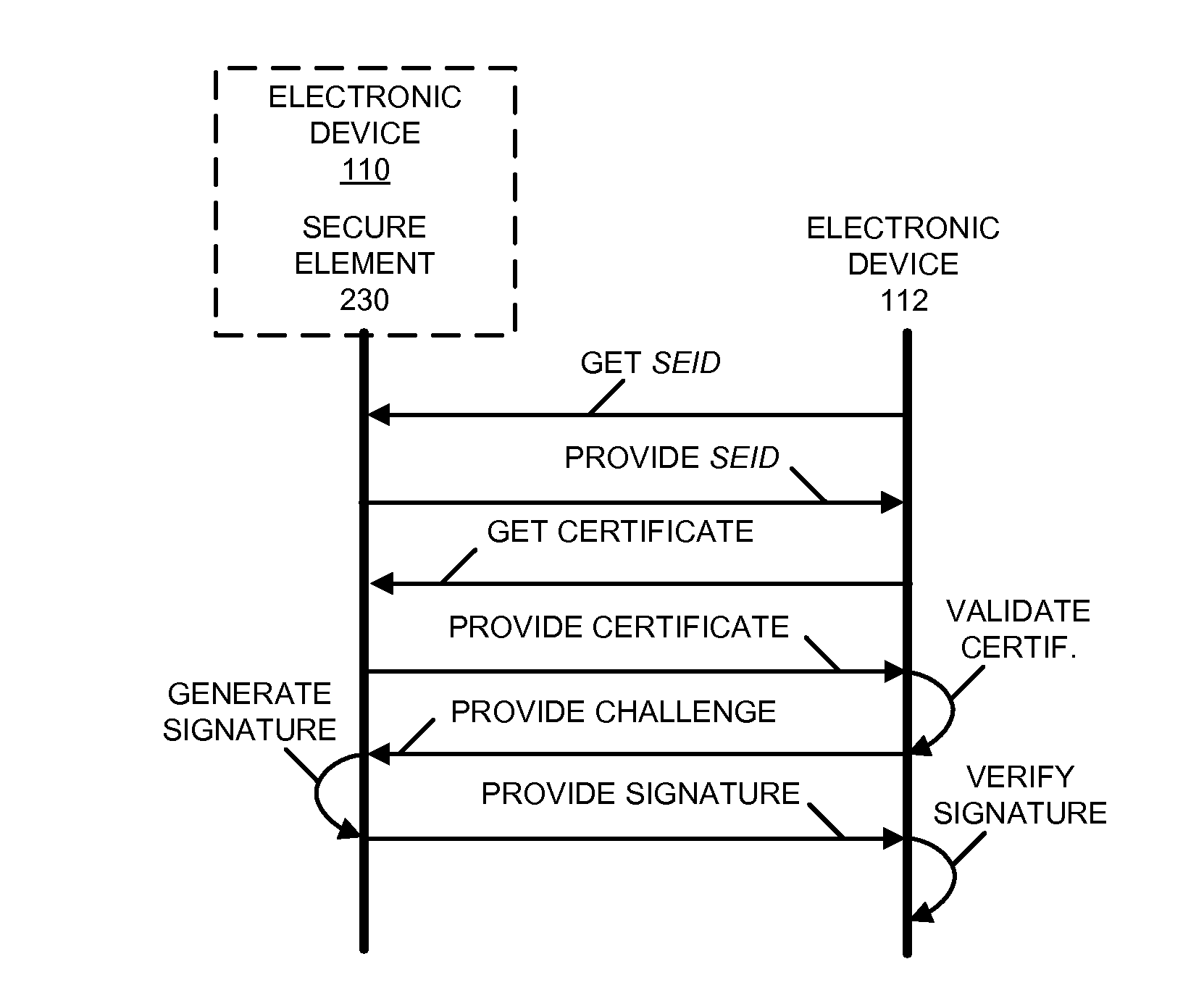
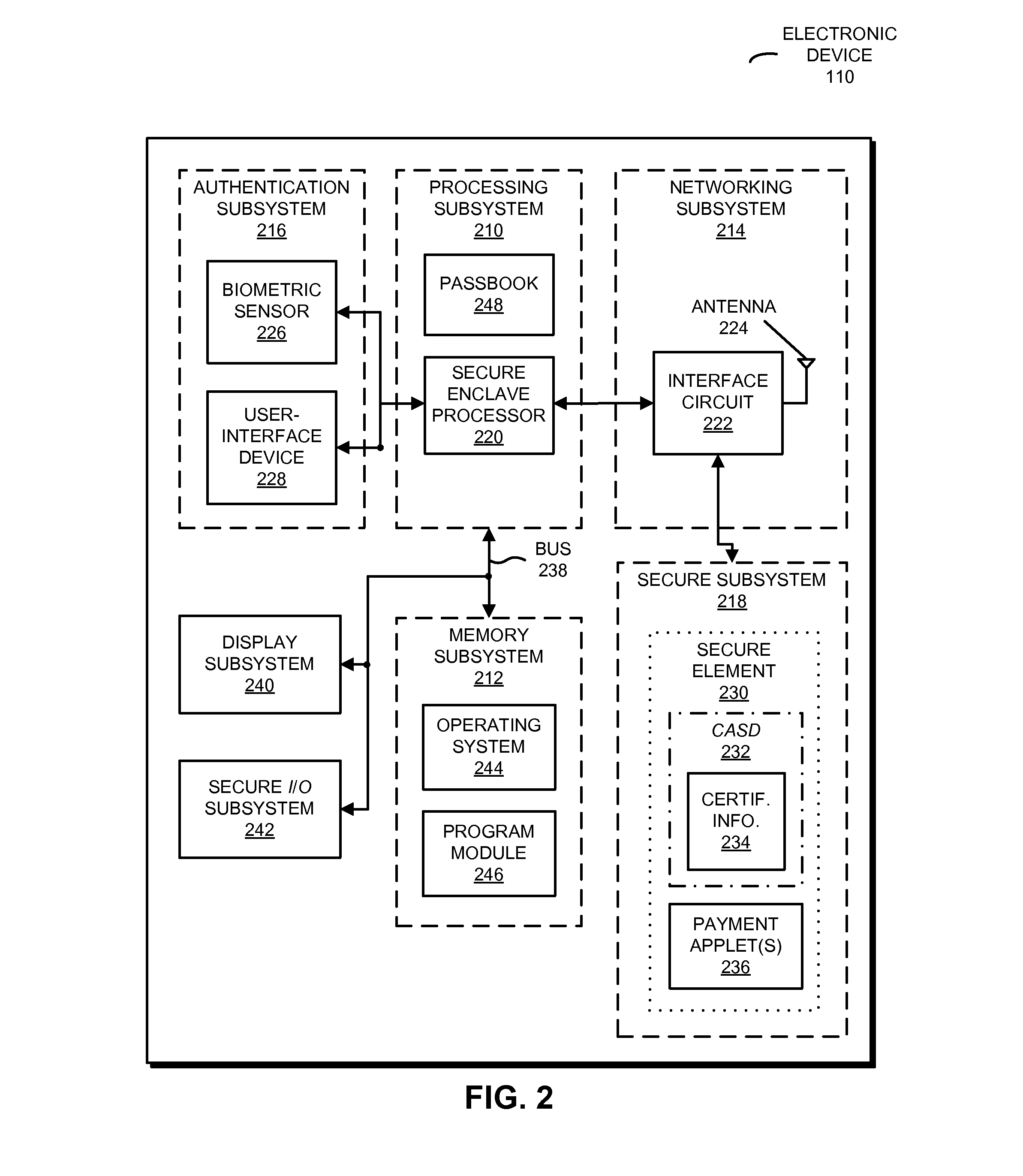
Spoofing protection for secure-element identifiers
ActiveUS20160286391A1User identity/authority verificationElectronic credentialsDigital signatureCellular telephone
The disclosed embodiments related to a first electronic device (such as a cellular telephone) that includes a secure element. In response to a challenge and a request for a secure-element identifier associated with the secure element, which are received from a second electronic device (such as a trusted services manager that loads content onto the secure element), the secure element provides to the second electronic device: the secure-element identifier, a certificate associated with a provider of the secure element, and a digital signature. The digital signature may include a signed version of the challenge and the secure-element identifier, which are encrypted using an encryption key associated with a provider of the secure element. In this way, the second electronic device may certify the secure element.
Owner:APPLE INC
System and method for managing mobile wallet and its related credentials
ActiveUS8843125B2Service provisioningUnauthorised/fraudulent call preventionClient-sideApplication software
A method for provisioning a contactless card applet in a mobile device with a mobile wallet application, including activating the mobile wallet application, connecting to a Trusted Service Manager (TSM) system, synchronizing the mobile wallet application with the TSM system, displaying a contactless card applet based on attributes of the mobile device, receiving a selection of a contactless card applet, retrieving a widget and a wallet management applet (WMA) corresponding to the contactless card applet, and provisioning the selected contactless card applet, the widget, and the WMA. A wallet management system (WMS) in a non-transitory storage medium to store and manage mobile wallet account information including a wallet client management component, a widget management component, a device profile management component, and a rule engine.
Owner:FINTIV INC +1
Methods for provisioning universal integrated circuit cards
ActiveUS20140140509A1Internal/peripheral component protectionSecret communicationComputer hardwareTrusted service manager
A system is described that can perform a method for receiving a request to modify a universal integrated circuit card, generating a package comprising configuration data for modifying the universal integrated circuit card, instructing an over-the-air system to transmit the package encrypting the package with a transport key to generate an encrypted package, and transmitting the encrypted package to a communication device communicatively coupled to the universal integrated circuit card to provision the universal integrated circuit card. The system can also perform a method of providing a mobile network operator trusted service manager system information relating to the configuration data to enable the mobile network operator trusted service manager system to manage content and memory allocation of the universal integrated circuit card.
Owner:AT&T MOBILITY II LLC +1
Method, system and trusted service manager for securely transmitting an application to a mobile phone
ActiveUS8391837B2Reliable cooperationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsService provisionUnique identifier
A Trusted Service Manager (TSM) receives via a first communication channel from a Service Provider (SP) a request (REQ(MIA)) that contains an application (MIA) together with a unique identifier of a mobile phone (MOB), particularly its telephone number. The mobile phone (MOB) is equipped with a memory device (MIF) that comprises multiple memory sectors being protected by sector keys. Preferably the memory device (MIF) is a MIFARE device. The TSM extracts the application (MIA) and the unique identifier from the received request, assigns destination sector(s) and associated sector key(s) of the memory device (MIF), compiles the application (MIA), the sector key(s) and the sector number(s) of the destination sector(s) into a setup-message (SU(MIA)), encrypts the setup-message and transmits it to either the mobile phone via a second communication channel or the Service Provider via the first communication channel (CN). If the setup-message (SU(MIA)) is transmitted to the Service Provider, the Service Provider sends it over the second communication channel to the mobile phone.
Owner:NXP BV
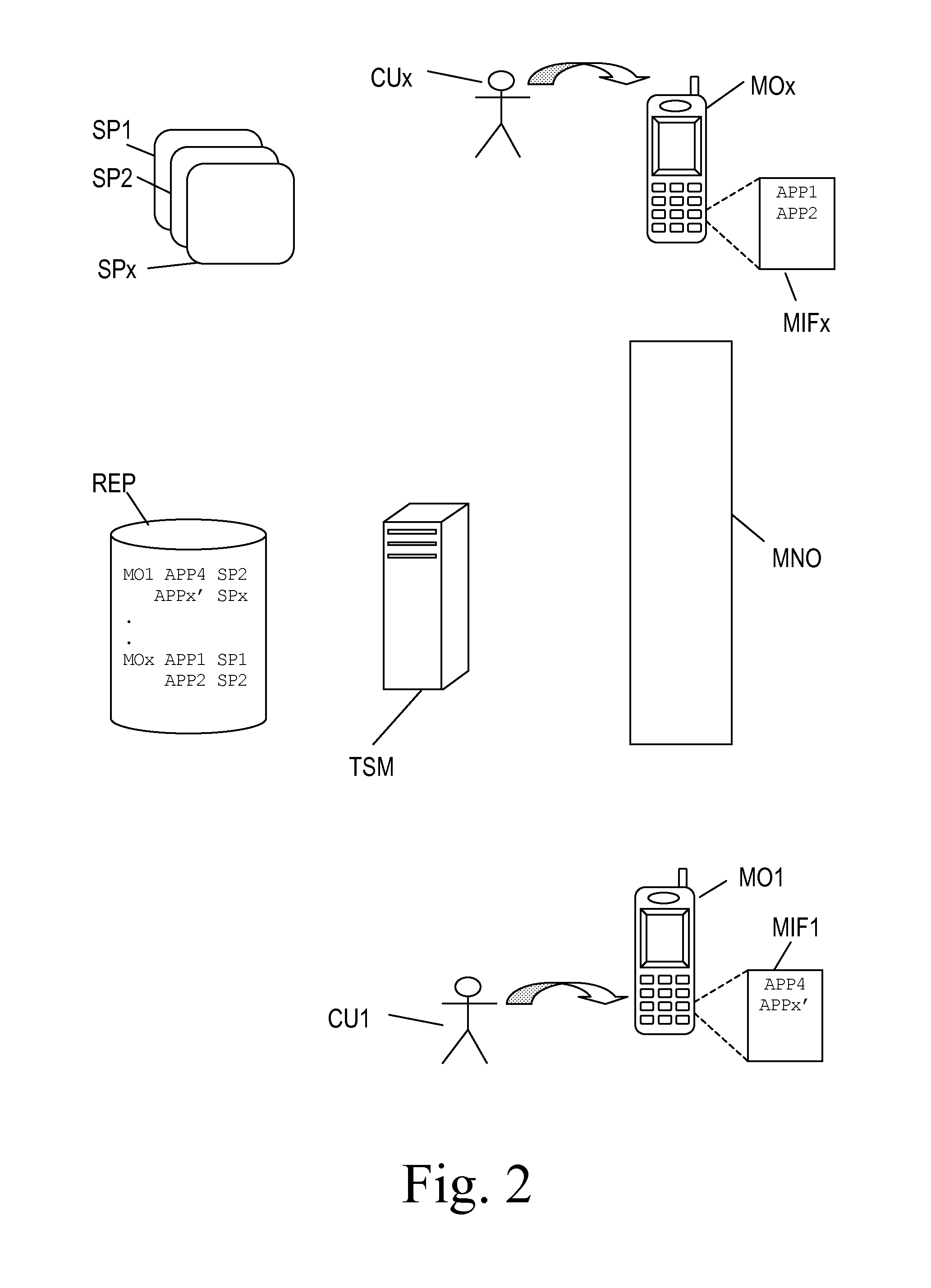
Sharing or reselling NFC applications among mobile communication devices
InactiveUS20100323681A1Service provisioningAutomatic exchangesService provisionTrusted service manager
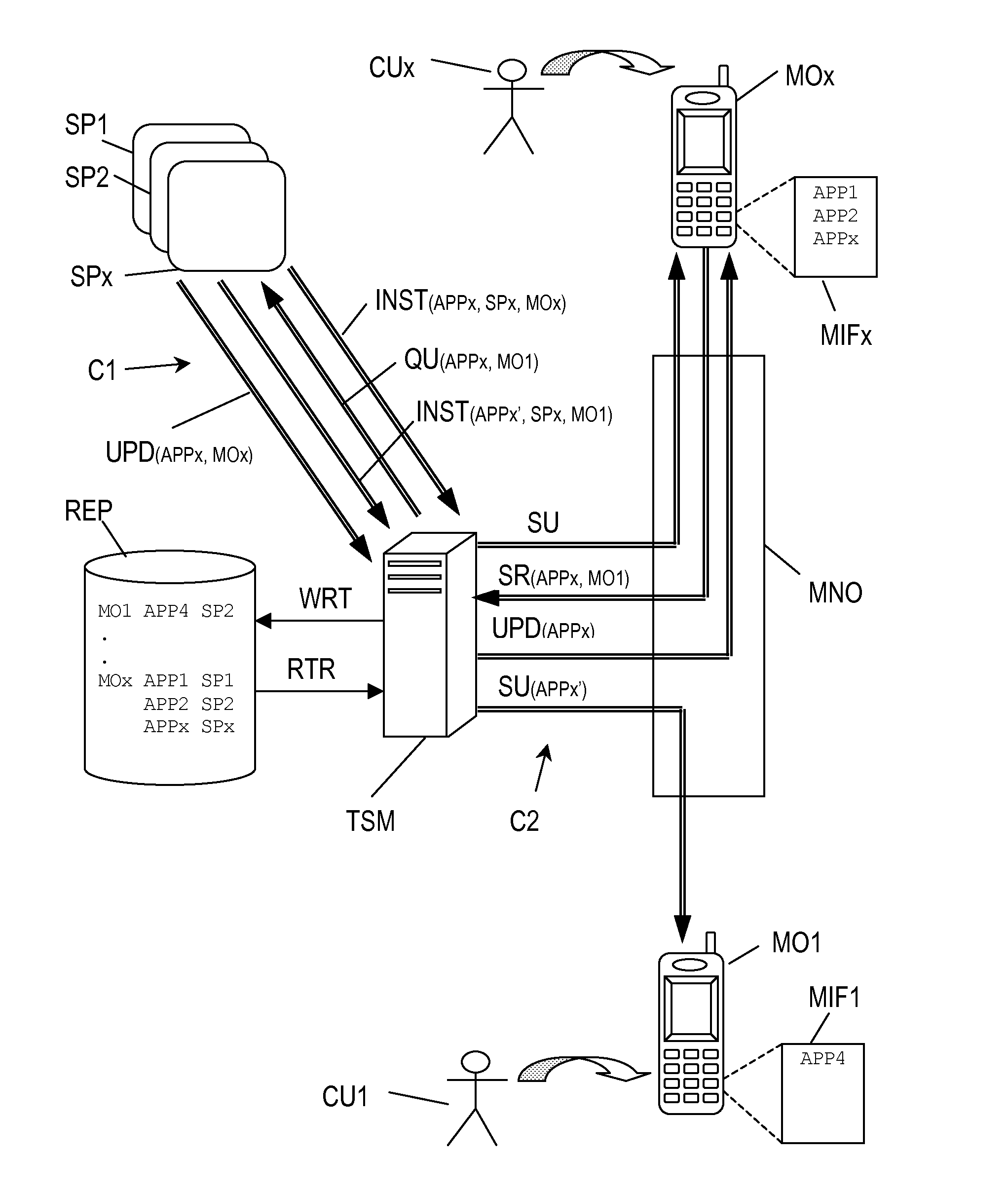
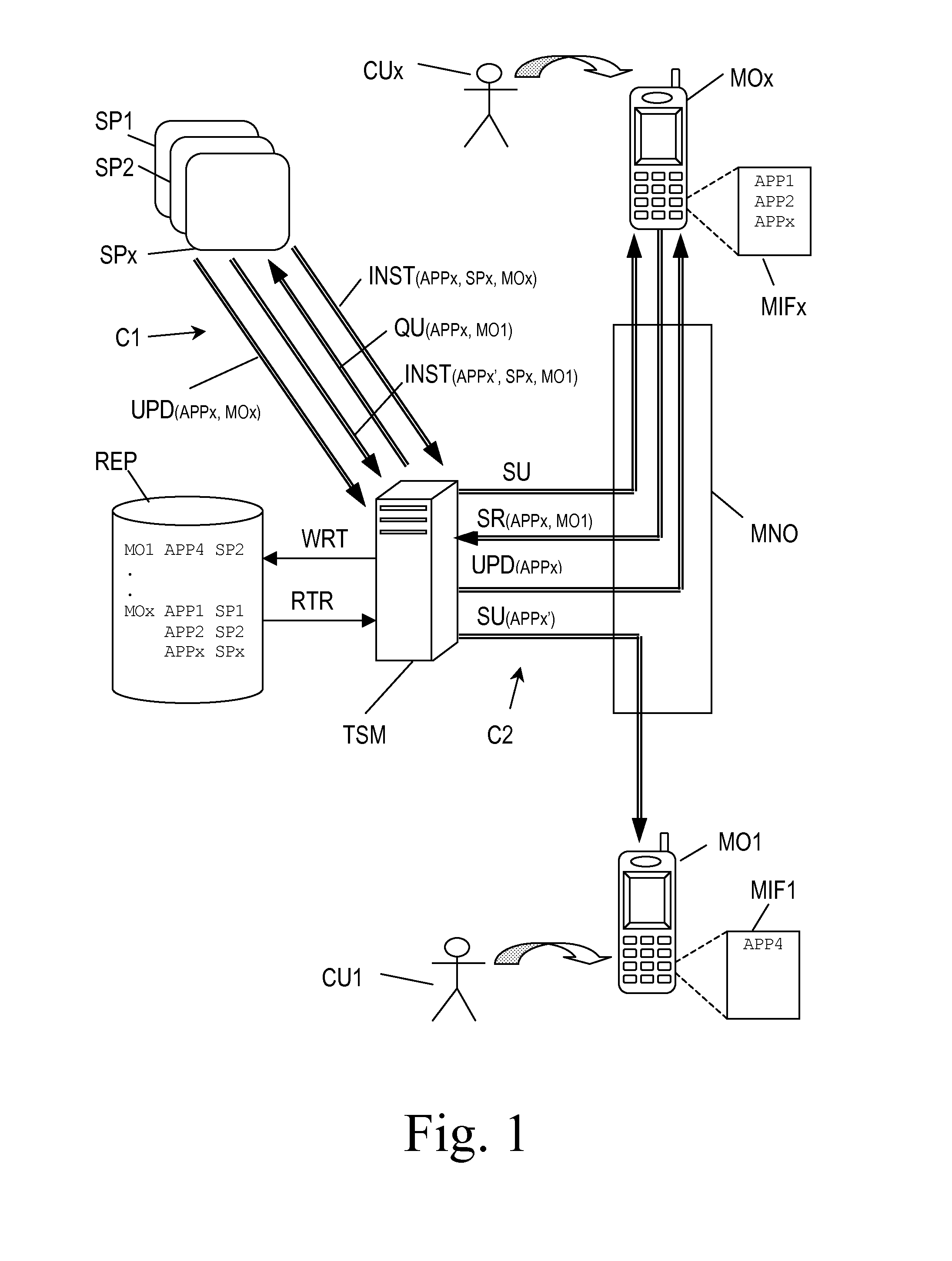
A method for sharing applications (APPI, APP2, APPx; APP4) being stored in a source mobile communication device (MOx; MOI) with a destination mobile communication device (MO1; MOx) comprises: transmitting a sharing request (SR) from the source mobile communication device (MOx; MO1) to a Trusted Service Manager (TSM) with information about the application and the destination mobile communication device (MO1; MOx); at the Trusted Service Manager (TSM), retrieving the Service Provider (SP1, SP2, SPx) that has provided said application and sending a query (QU) to it; at the Service Provider (SP1, SP2, SPx), sending an installation request (INST) to the Trusted Service Manager (TSM) with an adapted version (APPx′) of the application and update instructions (UPD) for the source mobile communication device (MOx; MO1); at the Trusted Service Manager (TSM), getting the adapted application (APPx′) installed in the destination mobile communication device (MO1; MOx) and updating the source mobile communication device (MOx; MO1).
Owner:GEMPLU
Trusted service manager (TSM) architectures and methods
ActiveUS8108318B2Unauthorised/fraudulent call preventionDigital data processing detailsTrusted service managerComputer security
A client device comprises a first secure element and a second secure element. The first secure element comprises a first computer-readable medium having a payment application comprising instructions for causing the client device to initiate a financial transaction. The second secure element comprises a second computer-readable medium having a security key, a payment instrument, stored authentication data and instructions for generating a secure payment information message responsive to the payment application. The secure payment information message comprises the payment instrument and is encrypted in accordance with the security key.
Owner:PAYPAL INC
Systems and Methods for Identifying Devices by a Trusted Service Manager
Embodiments of the invention provide systems and methods for identifying devices by a trusted service manager. According to one example embodiment of the invention, a method for identifying communications is provided. The method can include receiving, by a service provider from a device, a message comprising card production life cycle (CPLC) information associated with a secure element incorporated into the device; and evaluating, by the service provider, the received CPLC information in order to identify the secure element.
Owner:FIRST DATA
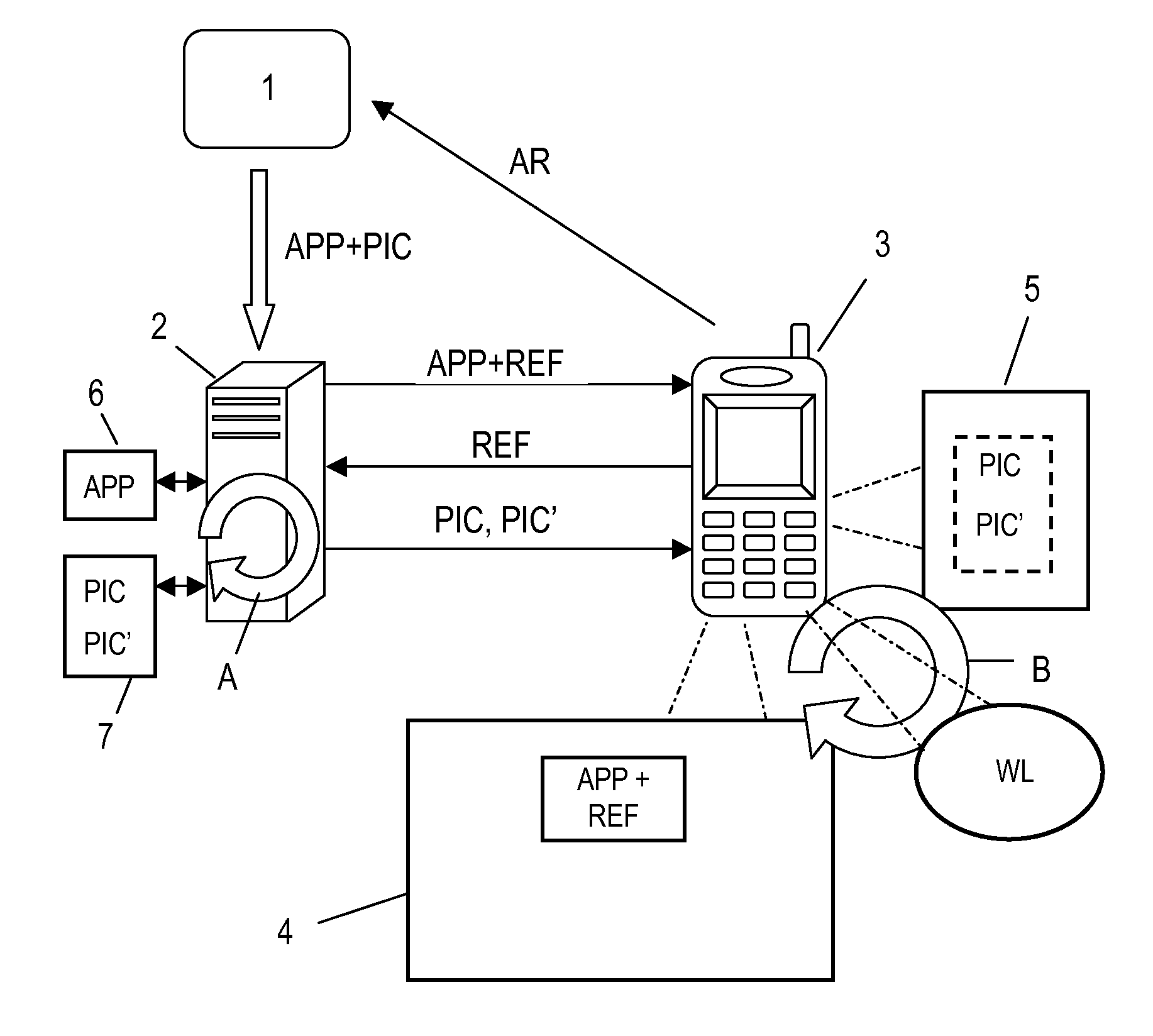
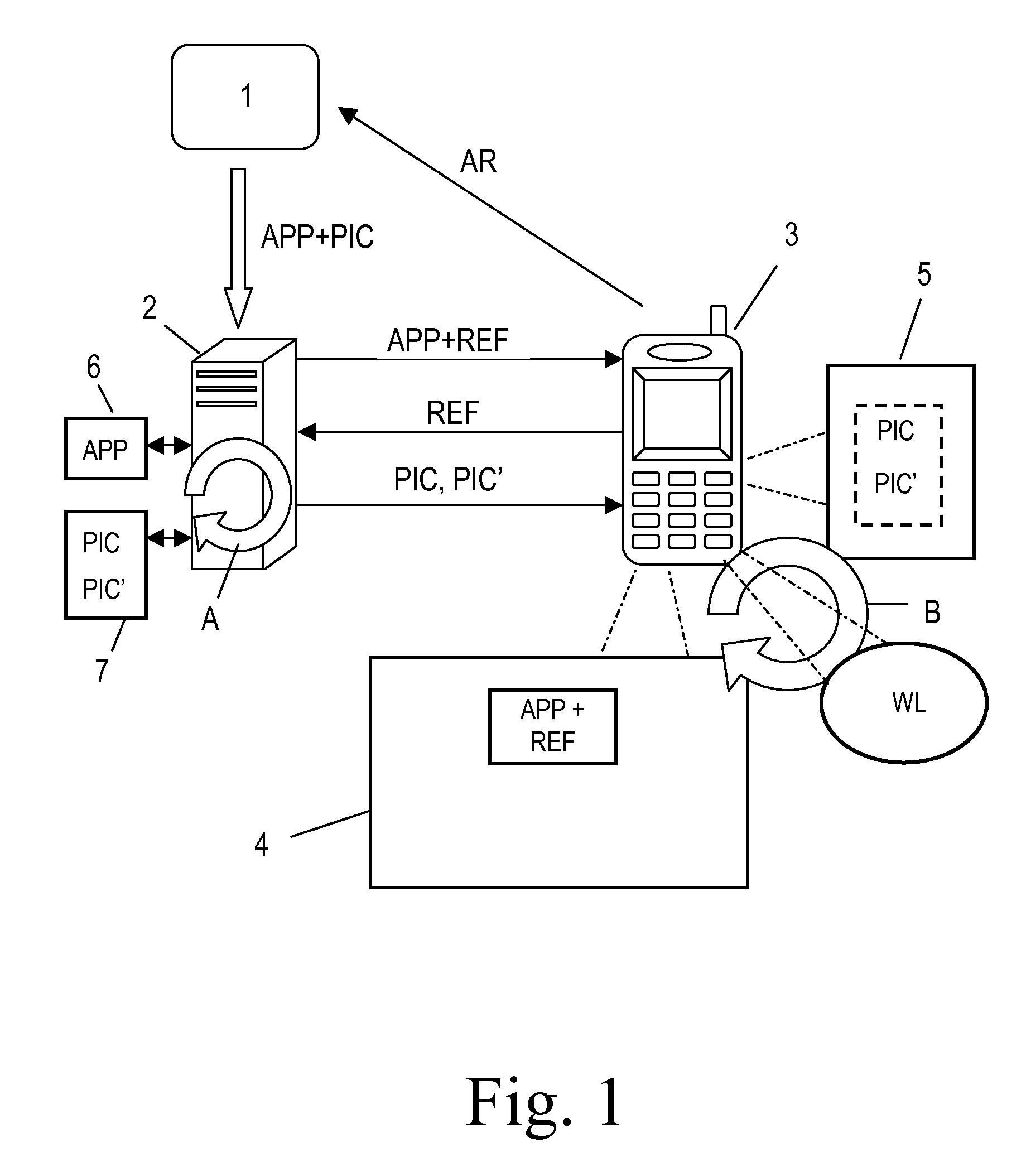
Method for installing and managing NFC applications with pictures
A method for installing a NFC application (APP) that includes a picture (PIC) in a mobile communication device (3) comprises: at a Service Provider (1) transmitting the NFC application (APP) together with the picture (PIC) to a Trusted Service Manager (2); at the Trusted Service Manager (2), separating the picture (PIC) from the NFC application (APP) and storing it and transmitting the NFC application (APP) together with a reference (REF) to a storage location of the picture (PIC) to the mobile communication device (3); at the mobile communication device (3), installing the NFC application (APP) together with the reference (REF) and retrieving the picture (PIC) by sending the reference (REF) to the Trusted Service Manager (2) requesting download of the picture (PIC); at the Trusted Service Manager (2), fetching the picture (PIC) from the storage location indicated by the reference (REF) and downloading it to the mobile communication device (3).
Owner:GEMPLU
Apparatus and Method for Managing Security Domains for a Universal Integrated Circuit Card
ActiveUS20170295158A1Service provisioningInternal/peripheral component protectionStructure of Management InformationSecurity domain
A device that incorporates the subject disclosure may perform, for example, generating a security domain root structure for a universal integrated circuit card of an end user device, where the security domain root structure includes a hierarchy of a link provider operator security domain above a mobile network operator trusted security domain, where the link provider operator security domain enables transport management by a link provider operator, and where the mobile network operator trusted security domain enables card content management and subscription eligibility verification by a mobile network operator trusted service manager. Other embodiments are disclosed.
Owner:AT&T INTPROP I LP
Method and system for providing controllable trusted service manager
ActiveCN103530775AControl personalization/configurationEasy to deployPayment architectureTransmissionEmbedded securitySecurity domain
Techniques for realizing or providing controllable trusted service management are disclosed. The techniques are related to empowering a service provider with application provisioning and applet and secure element (SE) management capabilities. A service management module, herein referred to as Controllable TSM or CTSM, is provided to a service provider to provision certain applications distributed through the service provider. A system or platform contemplated in this invention allows a service provider to operate under a supplementary security domain (SSD) installed by an SE issuer or an updated SSD key set exclusively known to the service provider. Such a platform is designed to support embedded SE (eSE) and can be extended to support UICC-based SE. With the CTSM, a service provider can use the SSD to personalize applets installed on each SE securely and independently.
Owner:深圳市可秉资产管理合伙企业(有限合伙)
System and method for managing ota provisioning applications through use of profiles and data preparation
ActiveUS20120174189A1Service provisioningDigital data processing detailsOriginal dataComputer terminal
A method using a non-transitory processor for providing an application product including receiving an application profile, a key profile, a secure element (SE) profile, and a mobile terminal profile; establishing a link between the received profiles, in which the link is established for assembling the application product; and applying a limitation to the application product, in which the applied limitation determines whether the application product is accessible to a user. A method using a non-transitory processor for data preparation in a Trusted Service Manager (TSM) including receiving data from a service provider, in which the received data is in a Data Grouping Identifier (DGI) format or a raw data format; and processing the data using at least one of a logical data preparation and a physical data preparation.
Owner:MOZIDO CORFIRE - KOREA
Systems, methods, and computer program products for managing wallet activation
Systems, methods, and computer program products are provided for managing activation in a mobile wallet. A wallet activation request is received from a wallet client. The wallet activation request is transmitted to a central trusted service manager (TSM). One or more push messages including activation data are received from the TSM, and the push messages are transmitted to the wallet client, in response to a second request from the wallet client while the wallet client is in an active state.
Owner:GOOGLE LLC
Systems, methods, and computer program products for managing secure elements
ActiveUS8875228B2Key distribution for secure communicationUser identity/authority verificationProcessing InstructionSecurity domain
Systems, methods, and computer program products are provided for performing content management operations. At least one memory stores data, and a central security domain manages instructions on behalf of one or more service provider security domains. The instructions are received, over a network, from a trusted service manager. The instructions are processed in at least one of the one or more determined service provider security domains, using the data stored in the at least one memory. The data includes one or more generic applications, each of which can be instantiated for one or more service providers.
Owner:GOOGLE LLC
Deletion of credentials from an electronic device
ActiveUS20150178723A1Digital data processing detailsMultiple digital computer combinationsSecurity domainTrusted service manager
Systems, methods, and computer-readable media for managing credentials are provided. In one example embodiment, an electronic device may include a secure element with a security domain element stored on the secure element. The electronic device may also include a processor component that may be configured to, inter alia, permanently terminate the functionality of the security domain element, after the functionality has been permanently terminated, communicatively couple the electronic device to a trusted service manager, and transmit data to the communicatively coupled trusted service manager that may be usable by the trusted service manager to determine that the functionality has been permanently terminated. Additional embodiments are also provided.
Owner:APPLE INC
Method and system for providing controllable trusted service manager
InactiveUS20140031024A1Easy to deployEase of deploymentKey distribution for secure communicationAutomatic exchangesPersonalizationService provision
Techniques for realizing or providing controllable trusted service management are disclosed. The techniques are related to empowering a service provider with application provisioning and applet and secure element (SE) management capabilities. A service management module, herein referred to as Controllable TSM or CTSM, is provided to a service provider to provision certain applications distributed through the service provider. A system or platform contemplated in this invention allows a service provider to operate under a supplementary security domain (SSD) installed by an SE issuer or an updated SSD key set exclusively known to the service provider. Such a platform is designed to support embedded SE (eSE) and can be extended to support UICC-based SE. With the CTSM, a service provider can use the SSD to personalize applets installed on each SE securely and independently.
Owner:RFCYBER CORP
Method for carrying out security management on security element and communication system
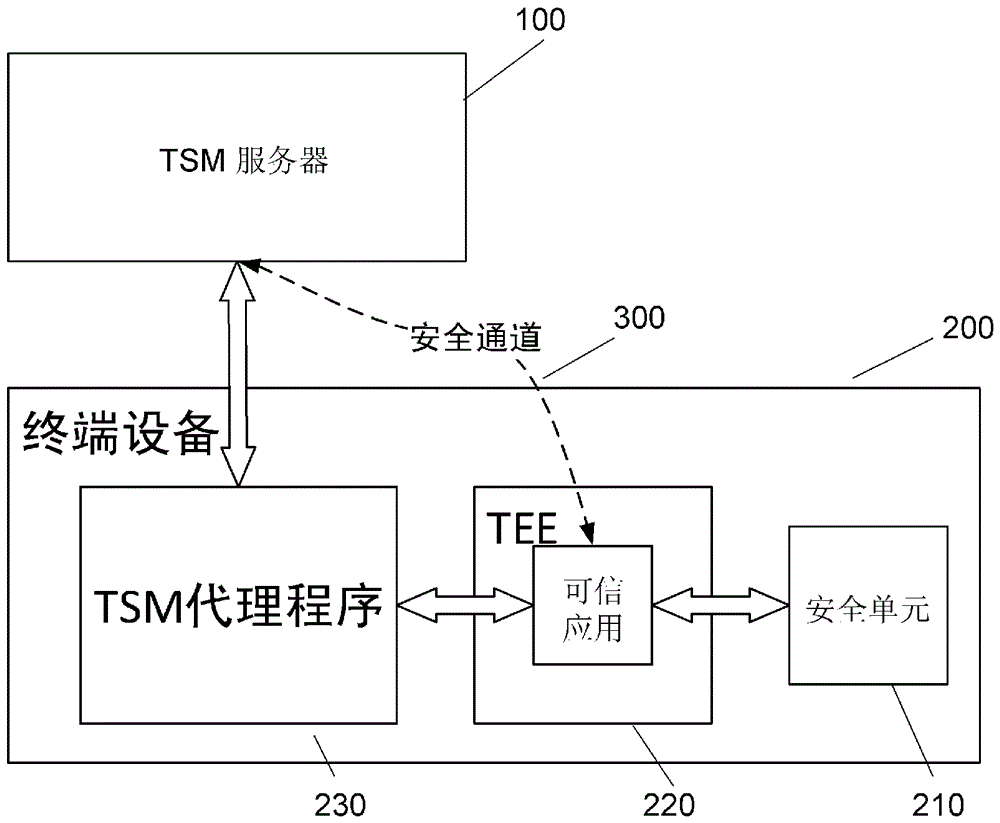
InactiveCN106102054AEnsure safetyIncrease success rateSecurity arrangementCommunications systemTerminal equipment
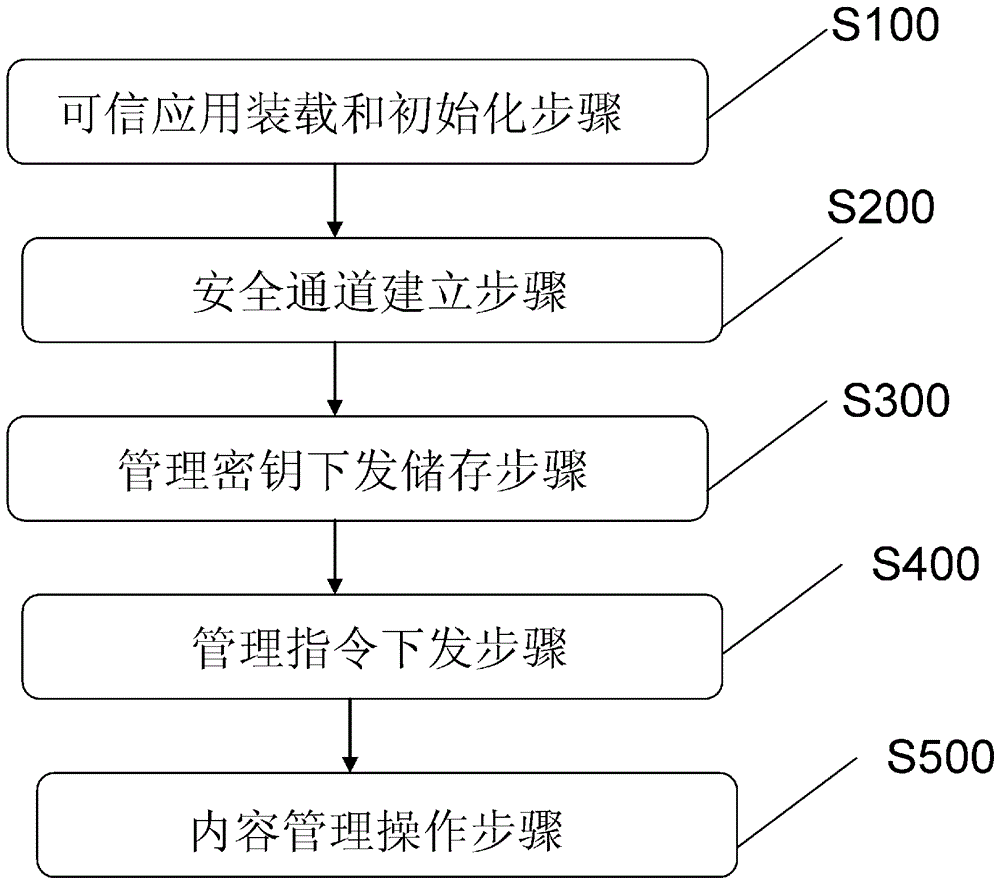
The invention relates to a method for carrying out security management on a security element and a communication system realized by employing the method. The method comprises the steps of loading a trusted application in a terminal device; establishing a security channel between the trusted application and a trusted service manager server; issuing a management key to the trusted application by the trusted service manager server through the security channel, and storing the management key by the trusted application; issuing a management instruction to the trusted application by the trusted service manager server through the security channel, and storing the management instruction by the trusted application; and carrying out content management on the security element by the trusted application based on the management key and the management instruction. According to the method and the system, on the basis of ensuring the data security, the networking times is reduced, and the performance efficiency of a take is improved.
Owner:SHENZHEN XUEQIU SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com