Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
341 results about "Universal Integrated Circuit Card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
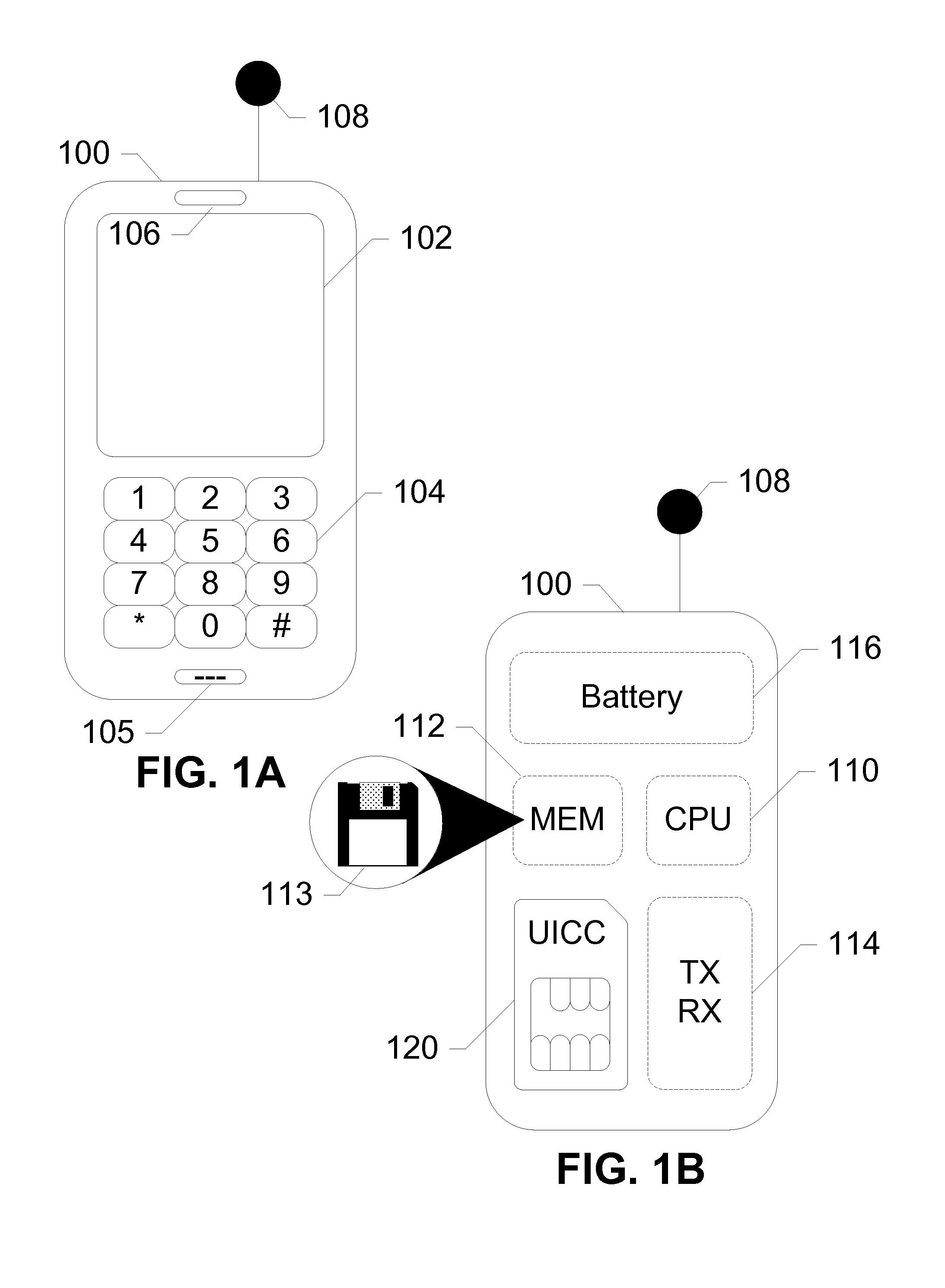
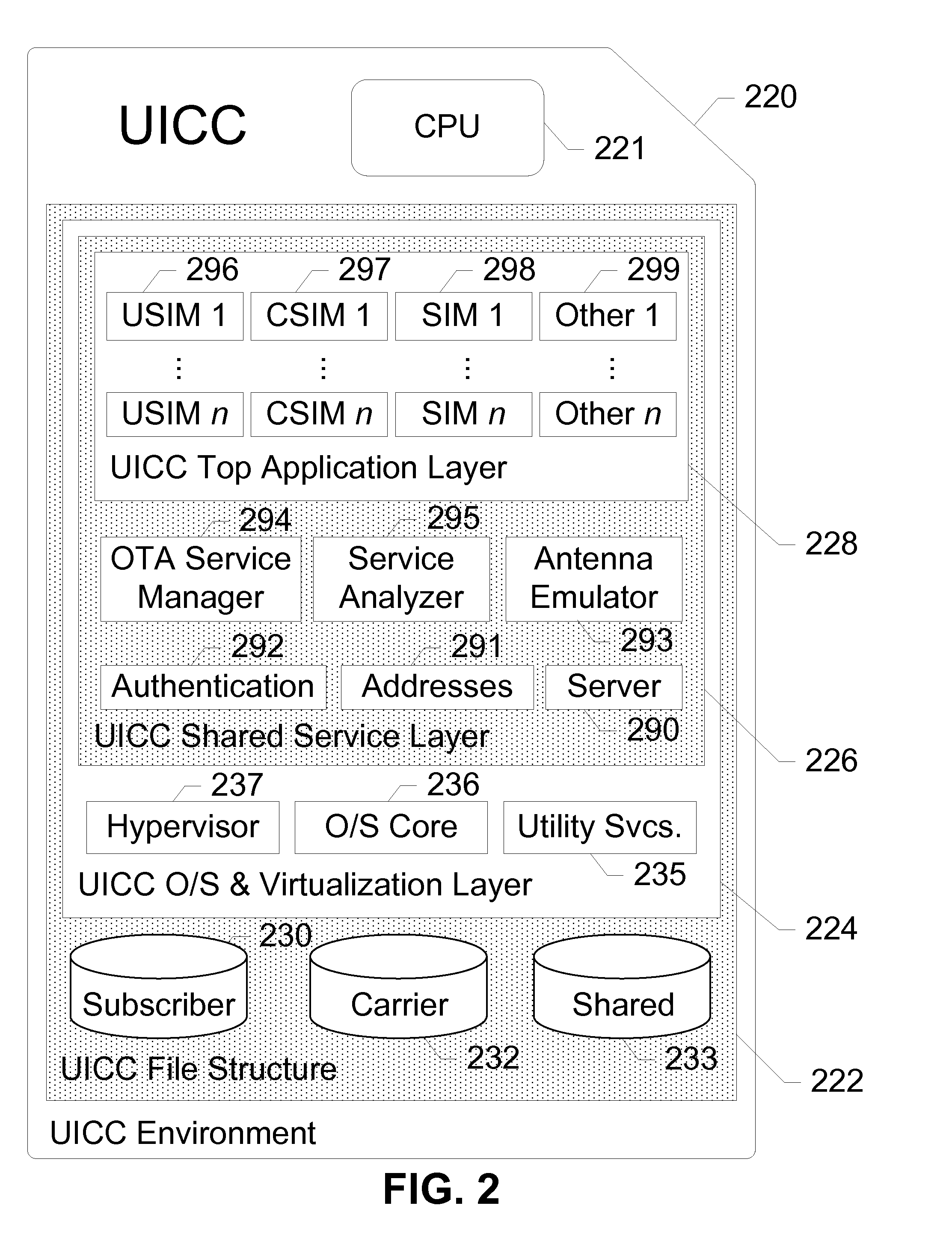
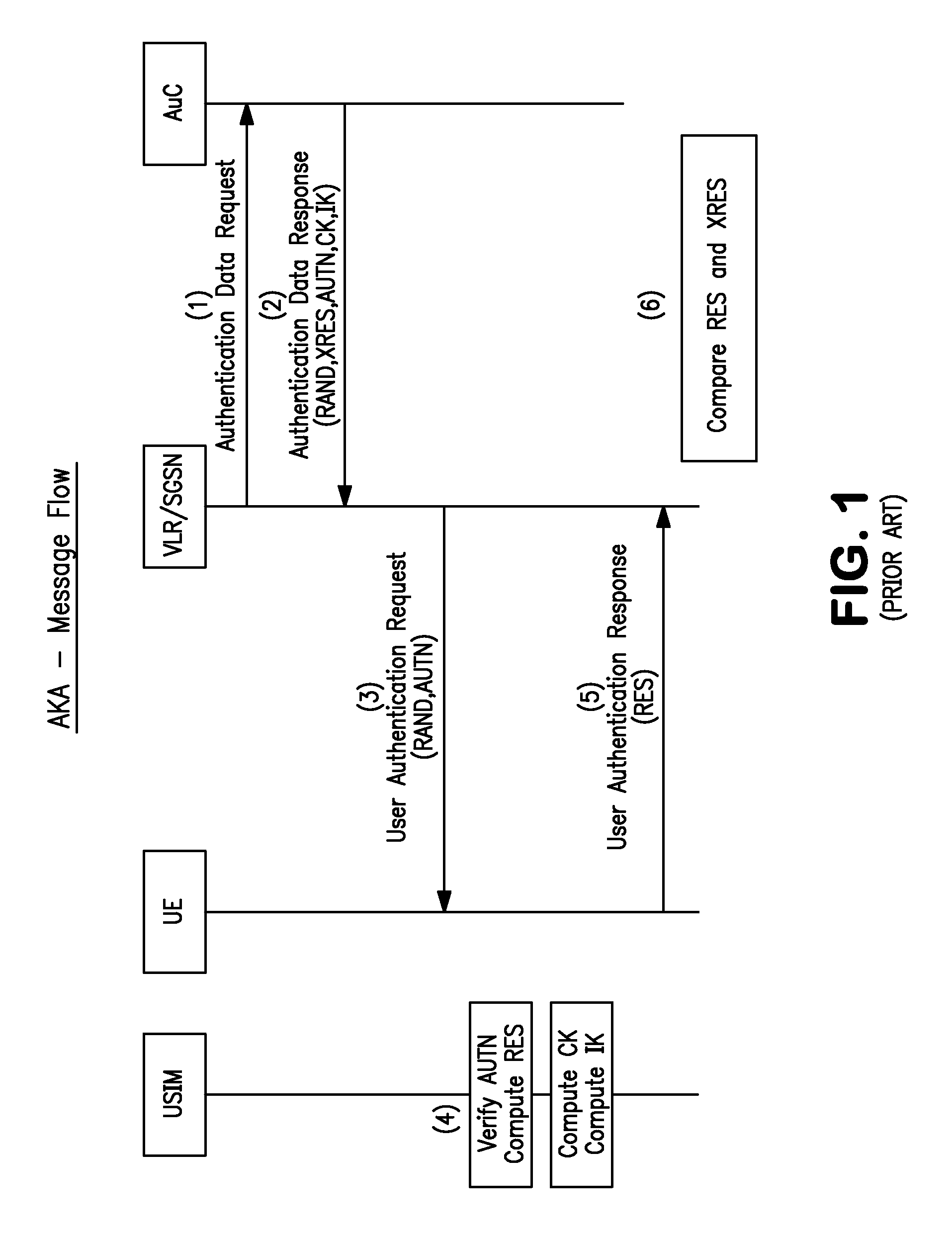
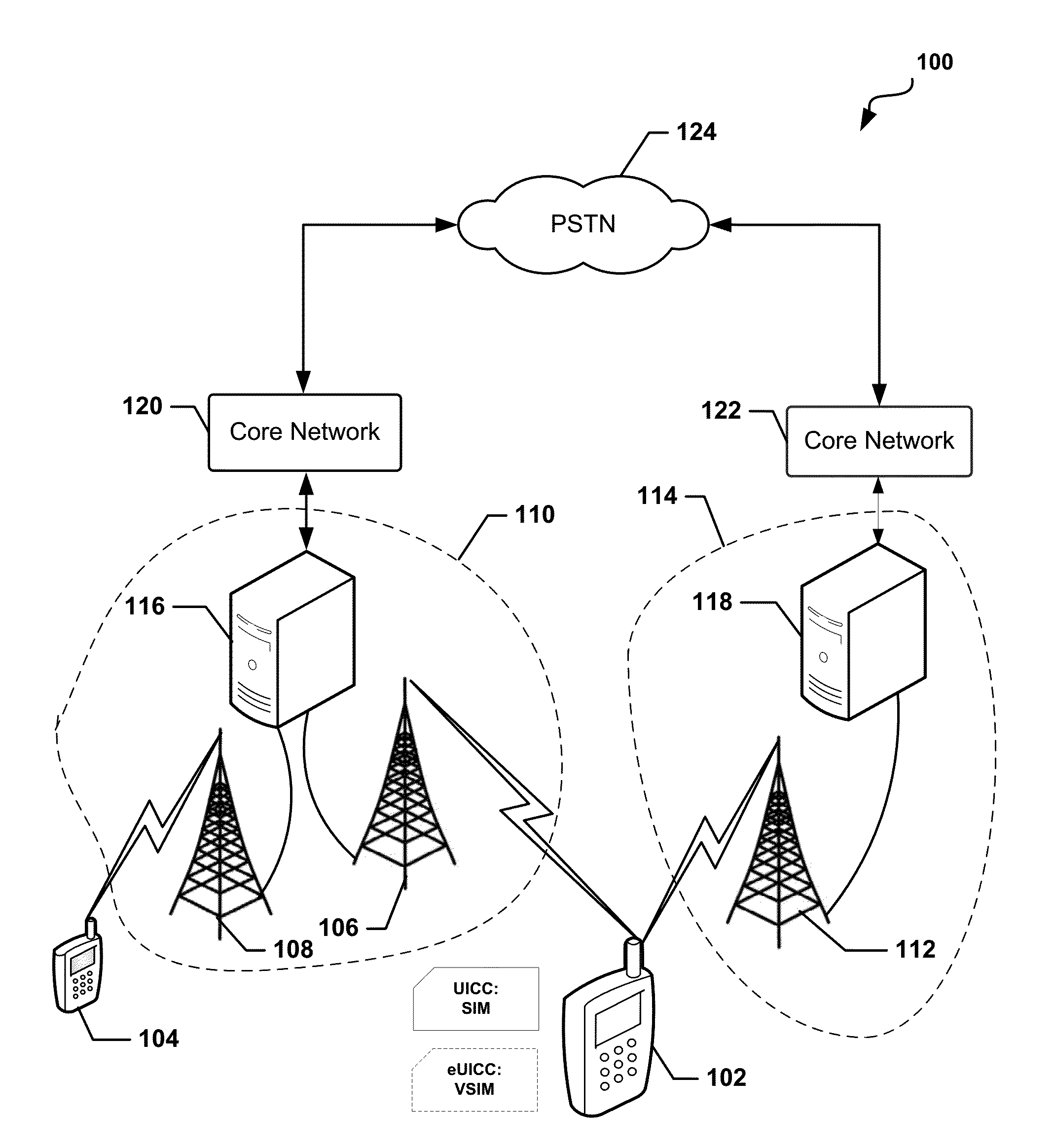
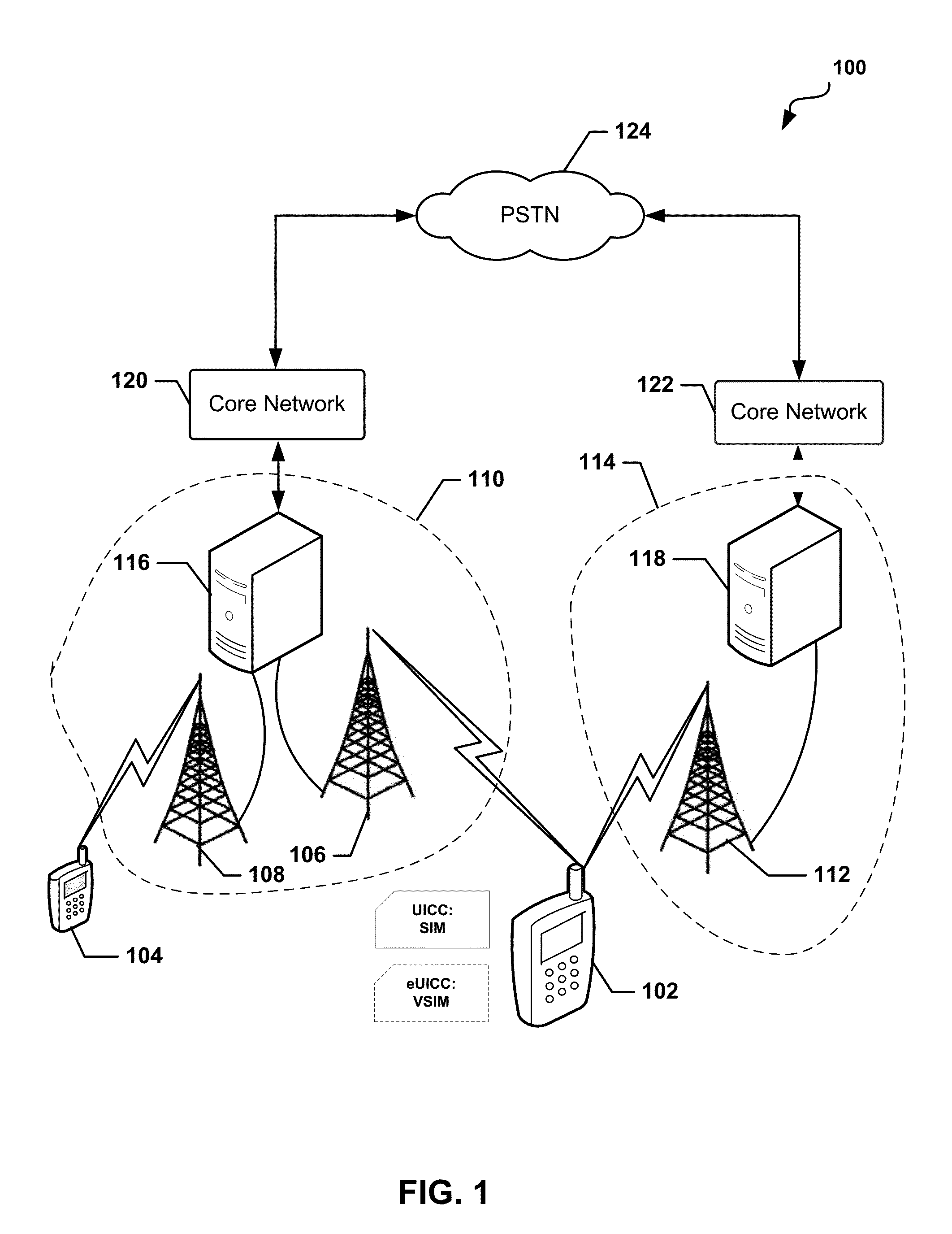
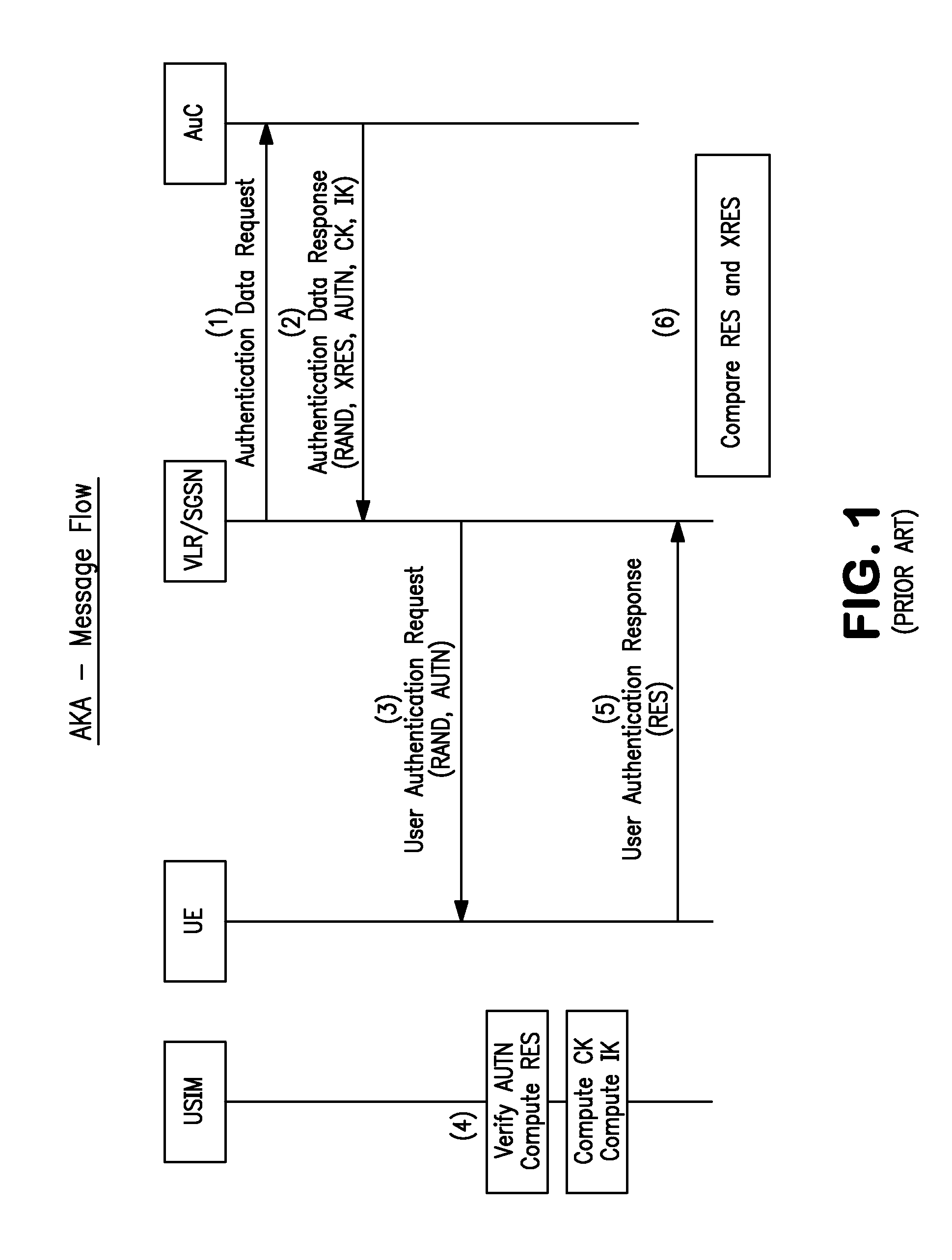
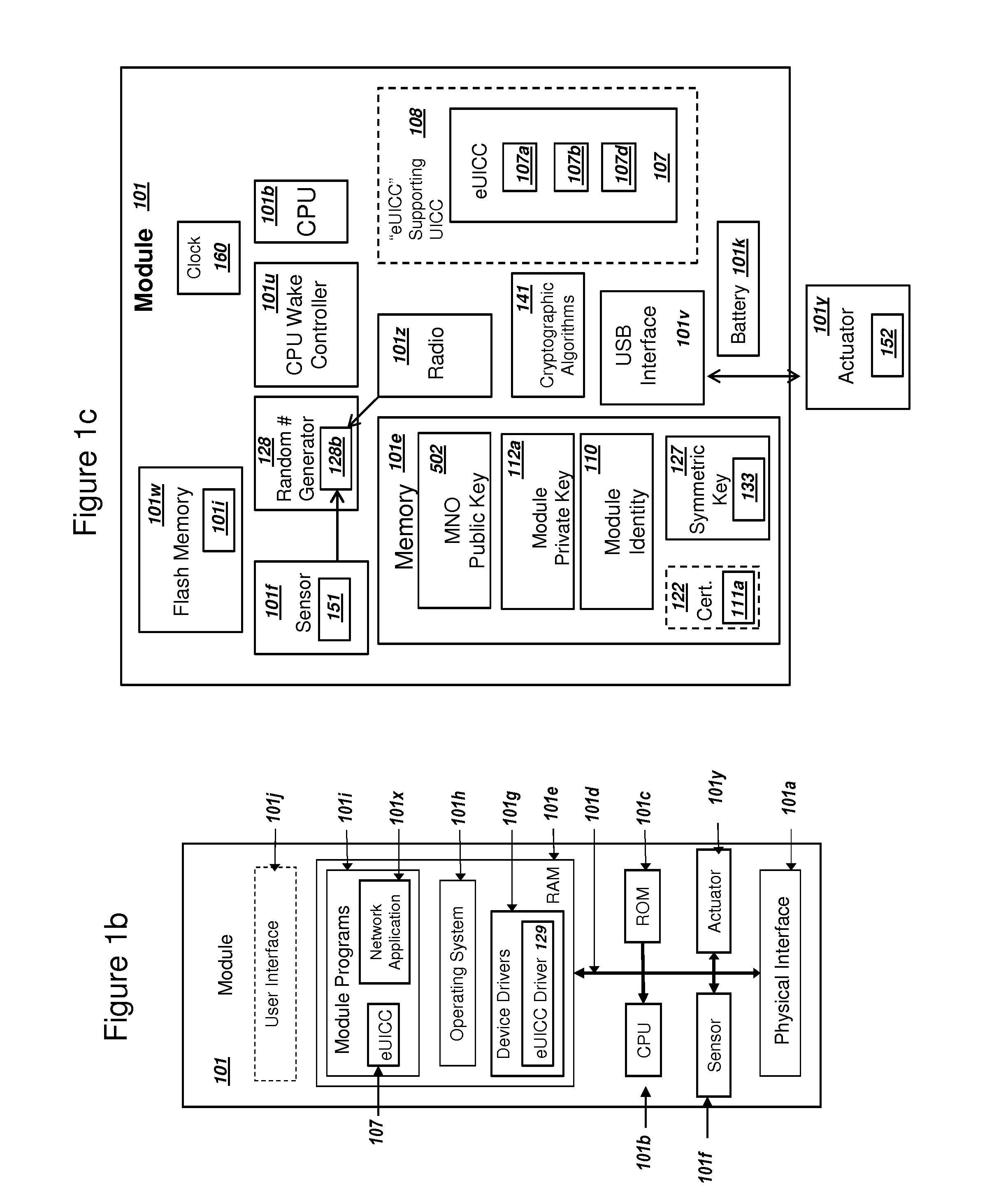
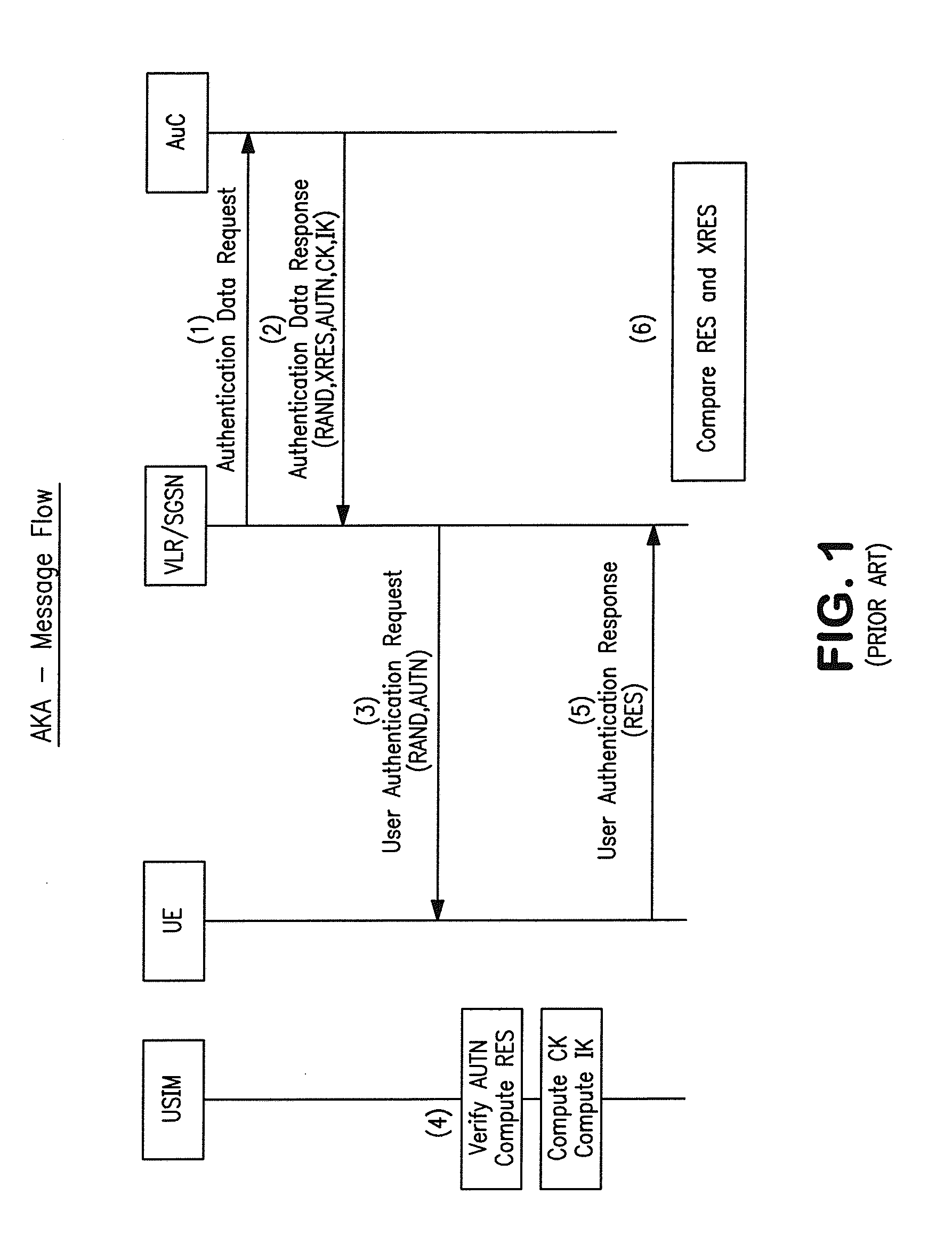
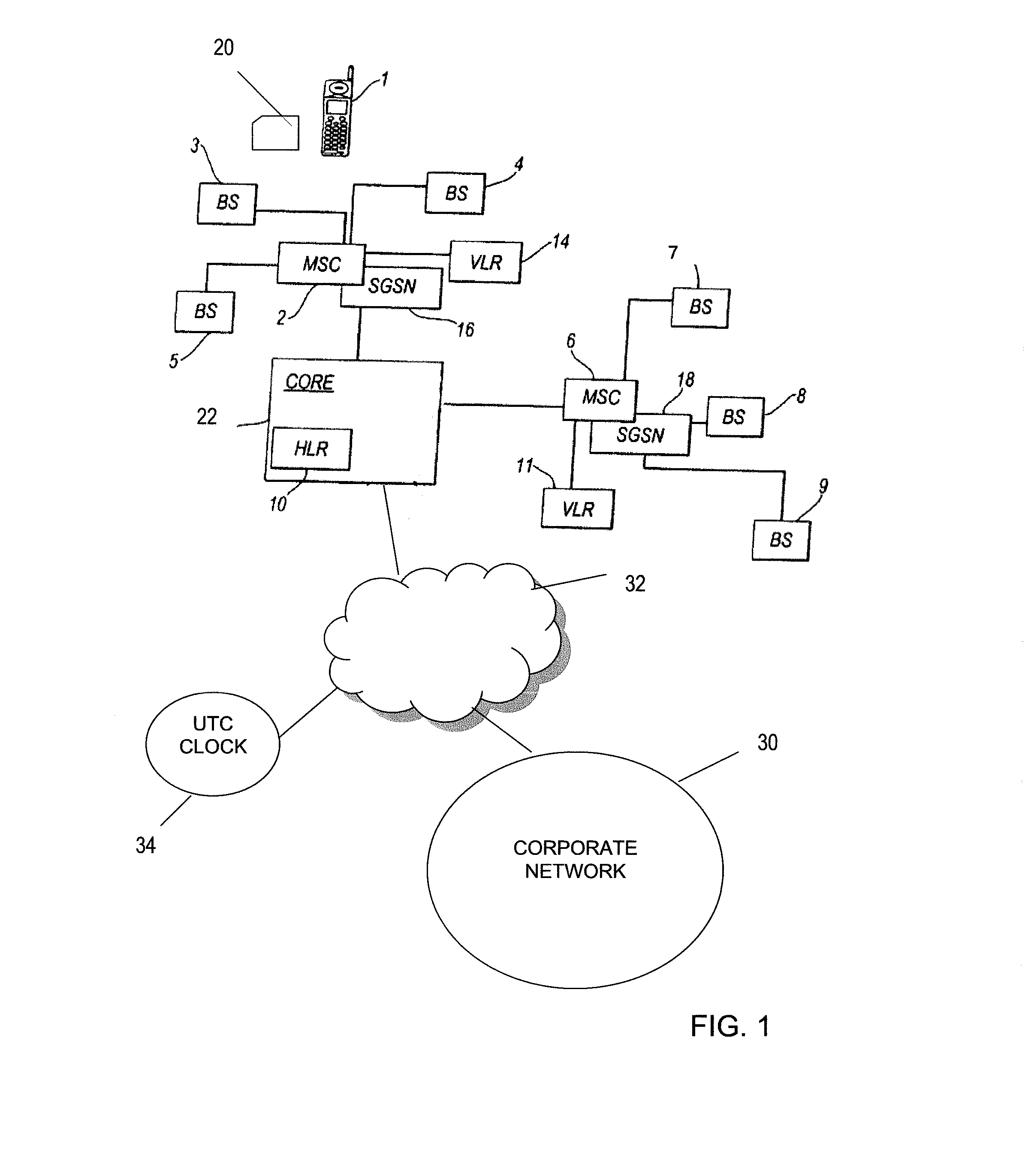
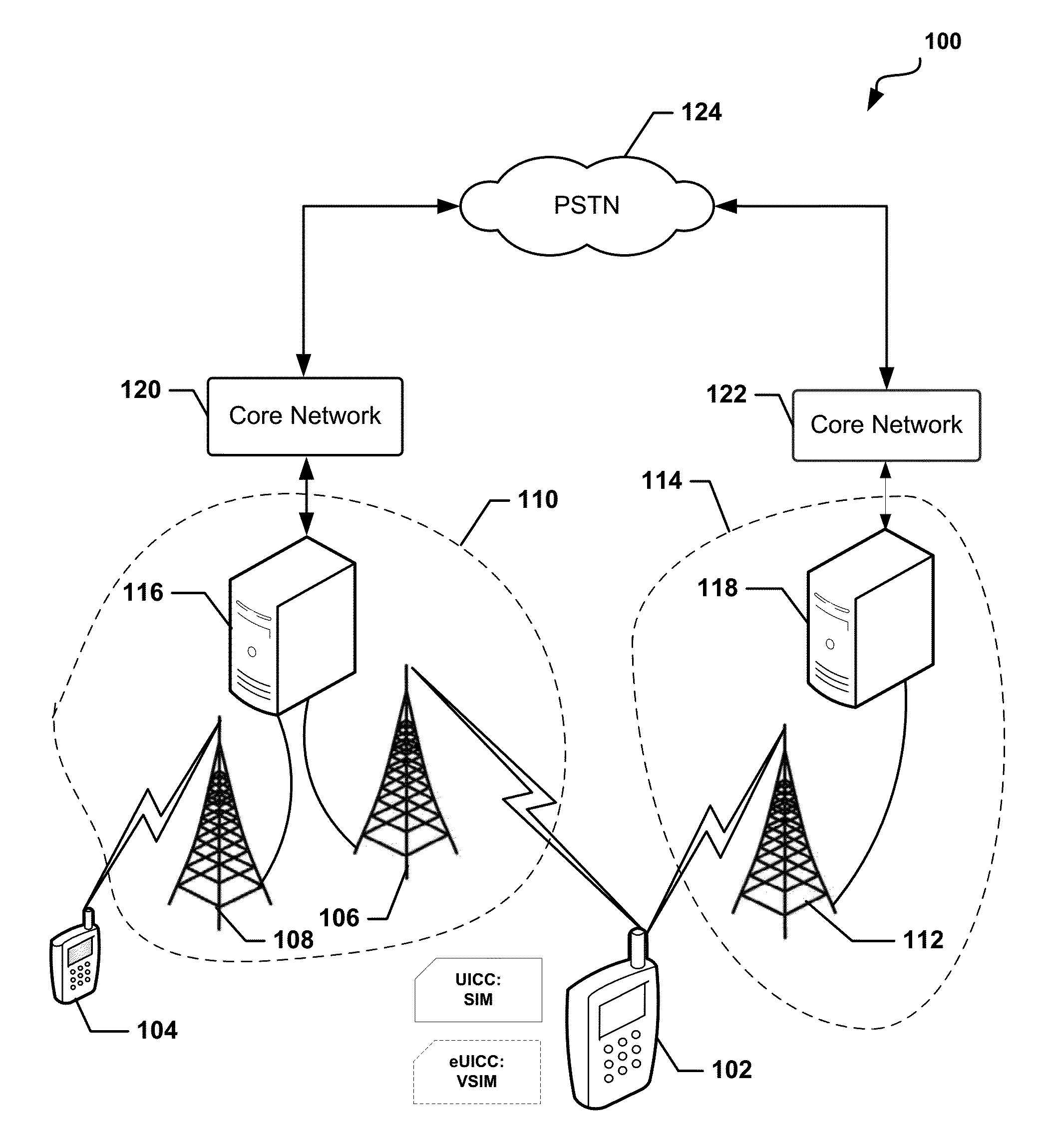
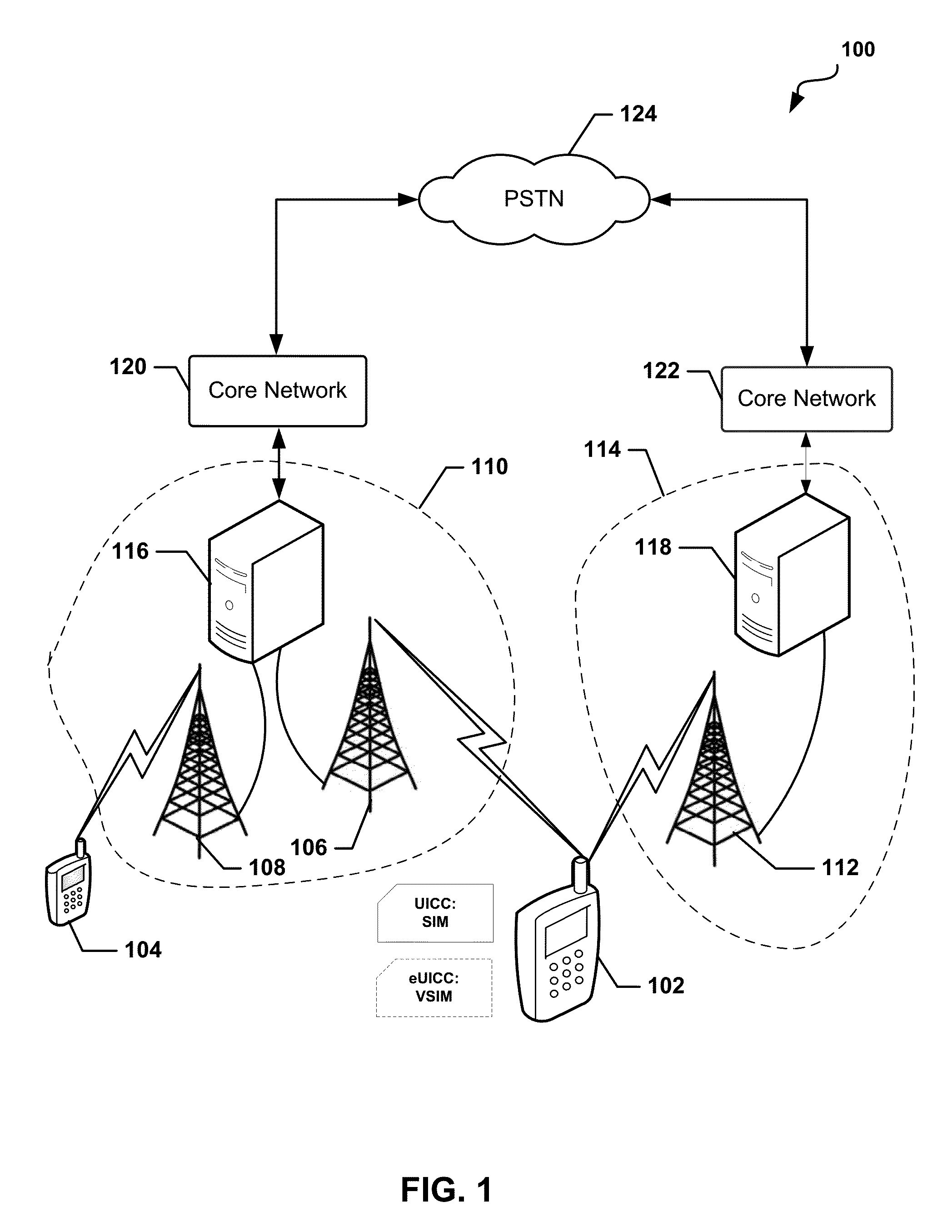
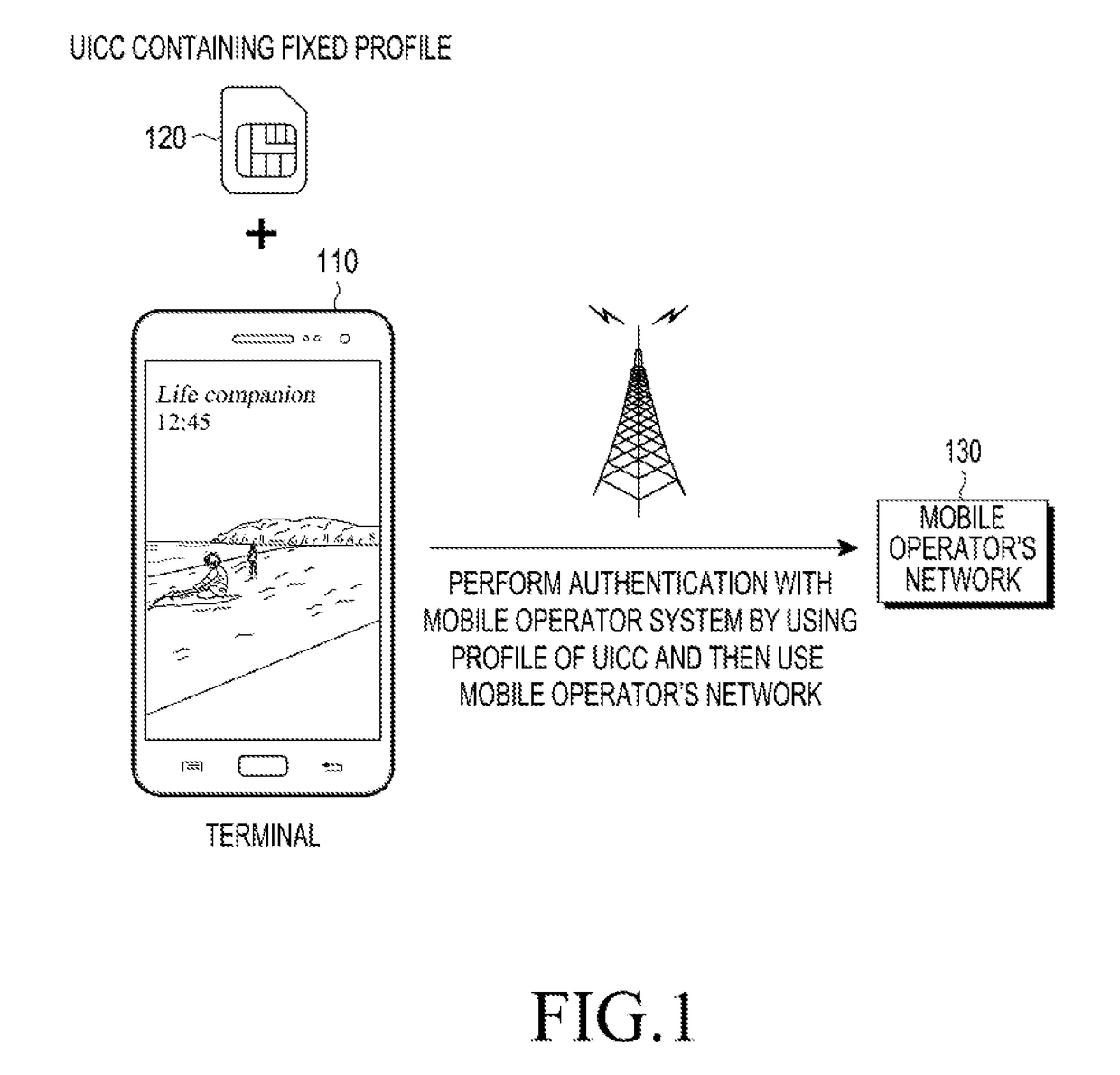
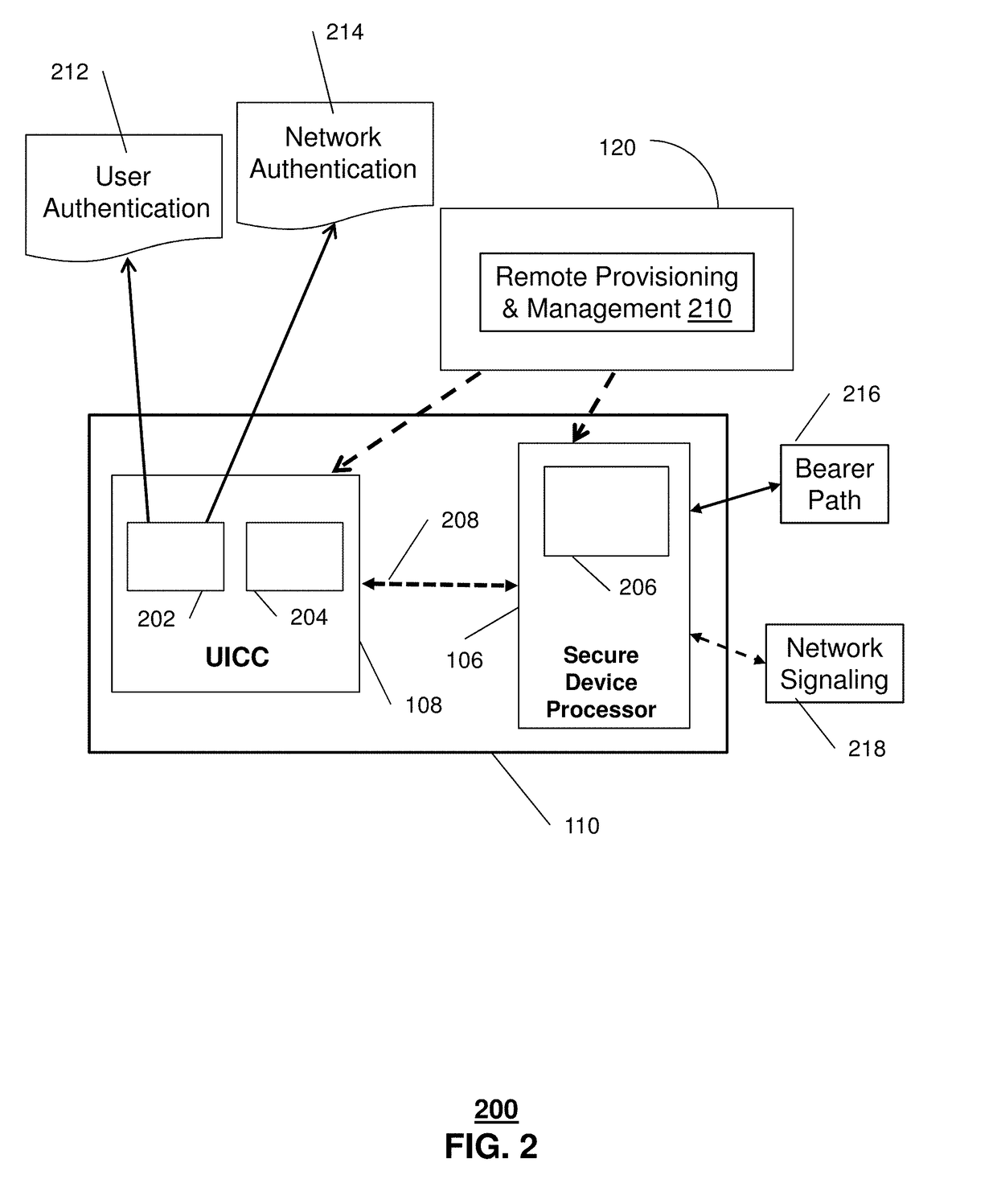
The universal integrated circuit card (UICC) is the smart card used in mobile terminals in GSM and UMTS networks. The UICC ensures the integrity and security of all kinds of personal data, and it typically holds a few hundred kilobytes.
Methods and apparatus for large scale distribution of electronic access clients
ActiveUS20130227646A1Large distributionDigital data processing detailsMultiple digital computer combinationsElectronic accessSecurity software
Methods and apparatus for large scale distribution of electronic access control clients. In one aspect, a tiered security software protocol is disclosed. In one exemplary embodiment, a server electronic Universal Integrated Circuit Card (eUICC) and client eUICC software comprise a so-called “stack” of software layers. Each software layer is responsible for a set of hierarchical functions which are negotiated with its corresponding peer software layer. The tiered security software protocol is configured for large scale distribution of electronic Subscriber Identity Modules (eSIMs)
Owner:APPLE INC
UICC Carrier Switching Via Over-The-Air Technology
ActiveUS20130023235A1Eliminate needService provisioningUnauthorised/fraudulent call preventionVirtual userCarrier signal
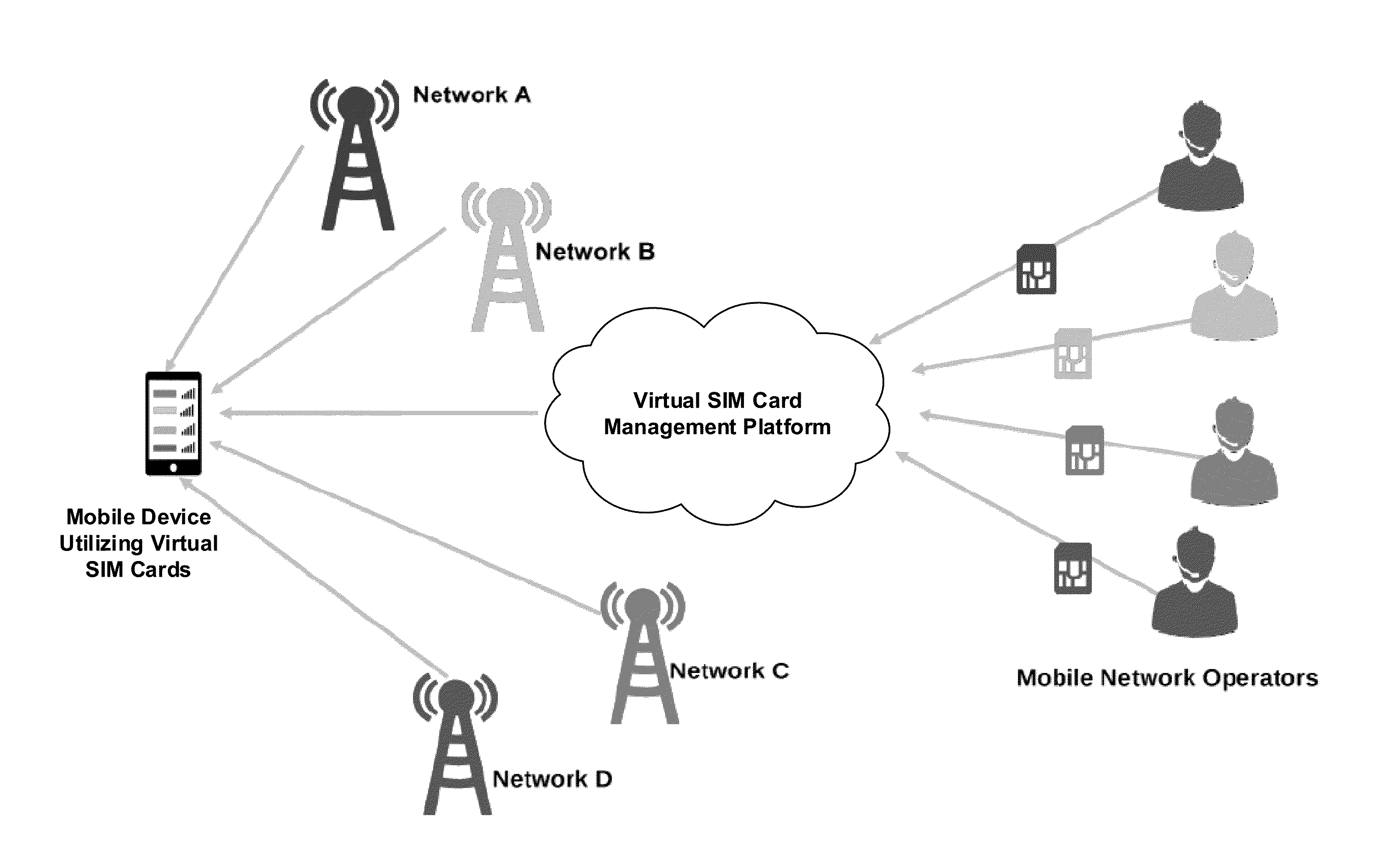
Devices, systems, and methods are disclosed which relate to provisioning a universal integrated circuit card (UICC) with multiple services. The UICC enables a wireless communication device to communicate through multiple carriers by using a unique virtual subscriber identity module (SIM) to register with each carrier. The unique virtual SIM is one of a plurality of virtual SIMs stored on and managed by the UICC. A carrier network includes a server for provisioning a new virtual SIM on a UICC over-the-air (OTA) when a new customer requests a service such as voice, data, or other type of service. These UICCs may also include logic to automatically select the best carrier for a voice call depending on the user settings.
Owner:AT&T INTPROP I L P
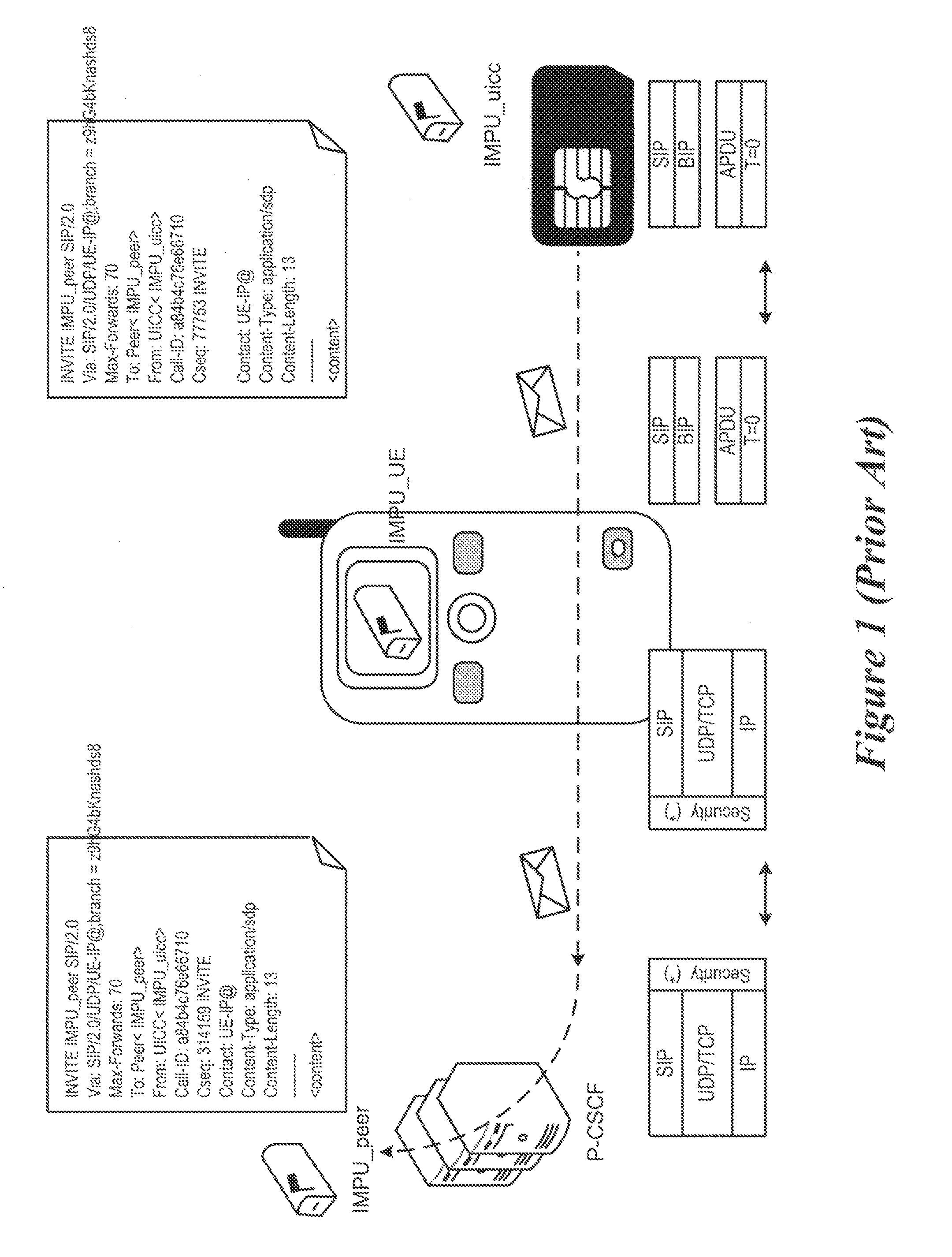
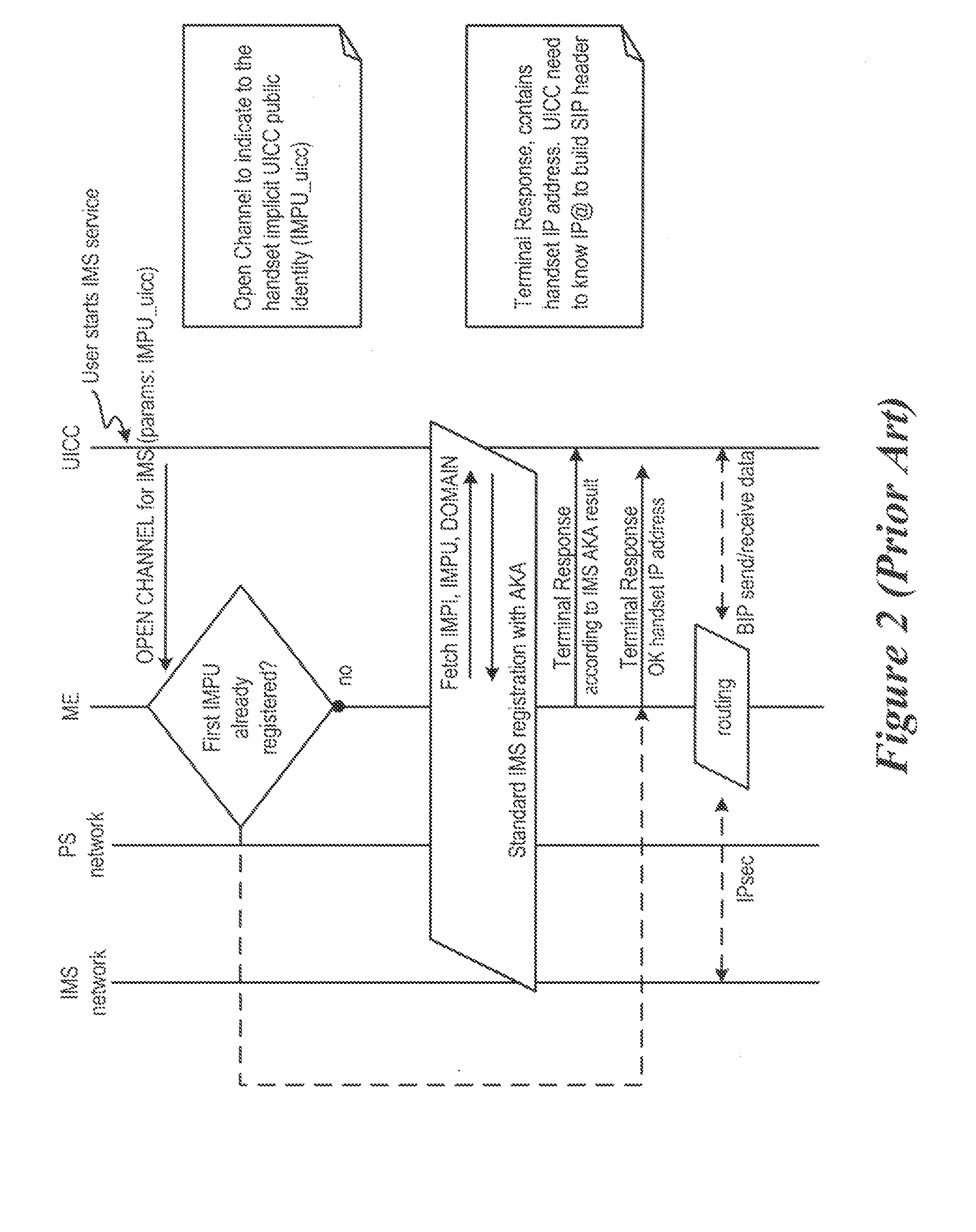
Method and system for end-to-end communication between a universal integrated circuit card and a remote entity over an IP-based wireless wide area network and the internet
InactiveUS20050259673A1Data switching by path configurationWireless network protocolsBrick and mortarWide area network
End-to-end communication between a UICC and a remote node on a network without requiring implementation of special purpose protocols at the remote node. The UICC operates to transmit a command using a first protocol from the UICC to the terminal to request the terminal to open a data channel to the network. The wireless terminal operates to, in response to the request to open a data channel, attempt to open a channel to the network. Upon indication that a data channel has successfully been opened: the UICC operates to transmit datagrams of a second protocol to the wireless terminal using the first protocol. The wireless terminal operates to receive the datagrams from the UICC and to transmit the datagrams received from the UICC to the network using the second protocol. The wireless terminal operates to receive datagrams of the second protocol from the remote entity and to transmit the datagrams from the remote entity to the UICC using the first protocol.
Owner:AXALTO SA
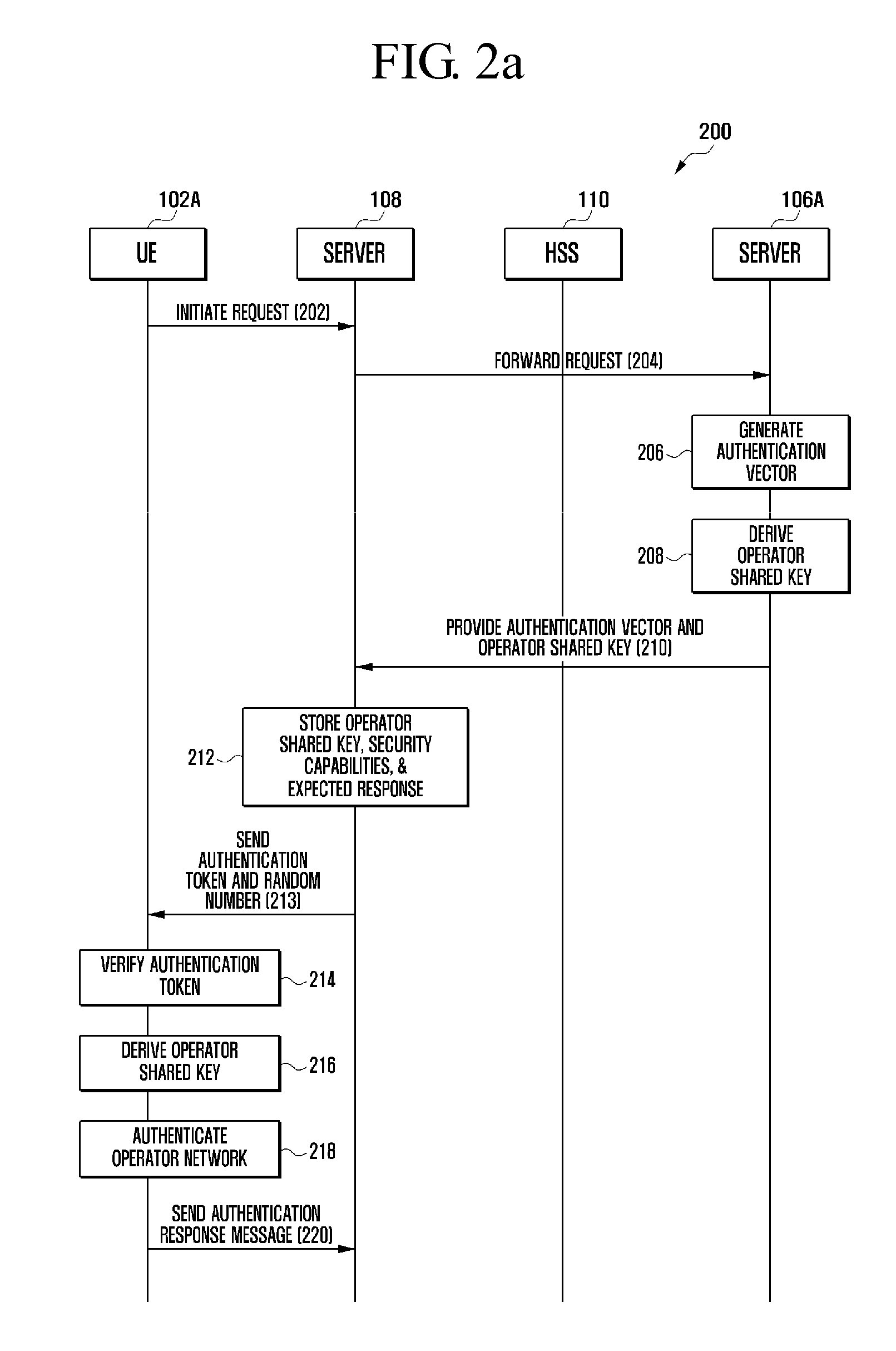
Method and system for secured remote provisioning of a universal integrated circuit card of a user equipment
ActiveUS20130012168A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwarePublic land mobile network
The present invention provides a method and system for secured remote provisioning of a universal integrated circuit card of a user equipment. A system includes a user equipment for initiating a request for remote provisioning of an universal integrated circuit card (UICC) in the user equipment, where the request for remote provisioning includes a machine identifier (MID) associated with the user equipment and a public land mobile network (PLMN) identifier (ID) associated with an network operator. The system also includes at least one shared key management server for dynamically generating security keys and an operator shared key using the security keys, the MID. Moreover, the system includes an operator network for generating a subscription key using the operator shared key and an international mobile subscriber identity (IMSI), and provisioning the IMSI in a secured manner to the UICC of the user equipment using the security keys.
Owner:SAMSUNG ELECTRONICS CO LTD
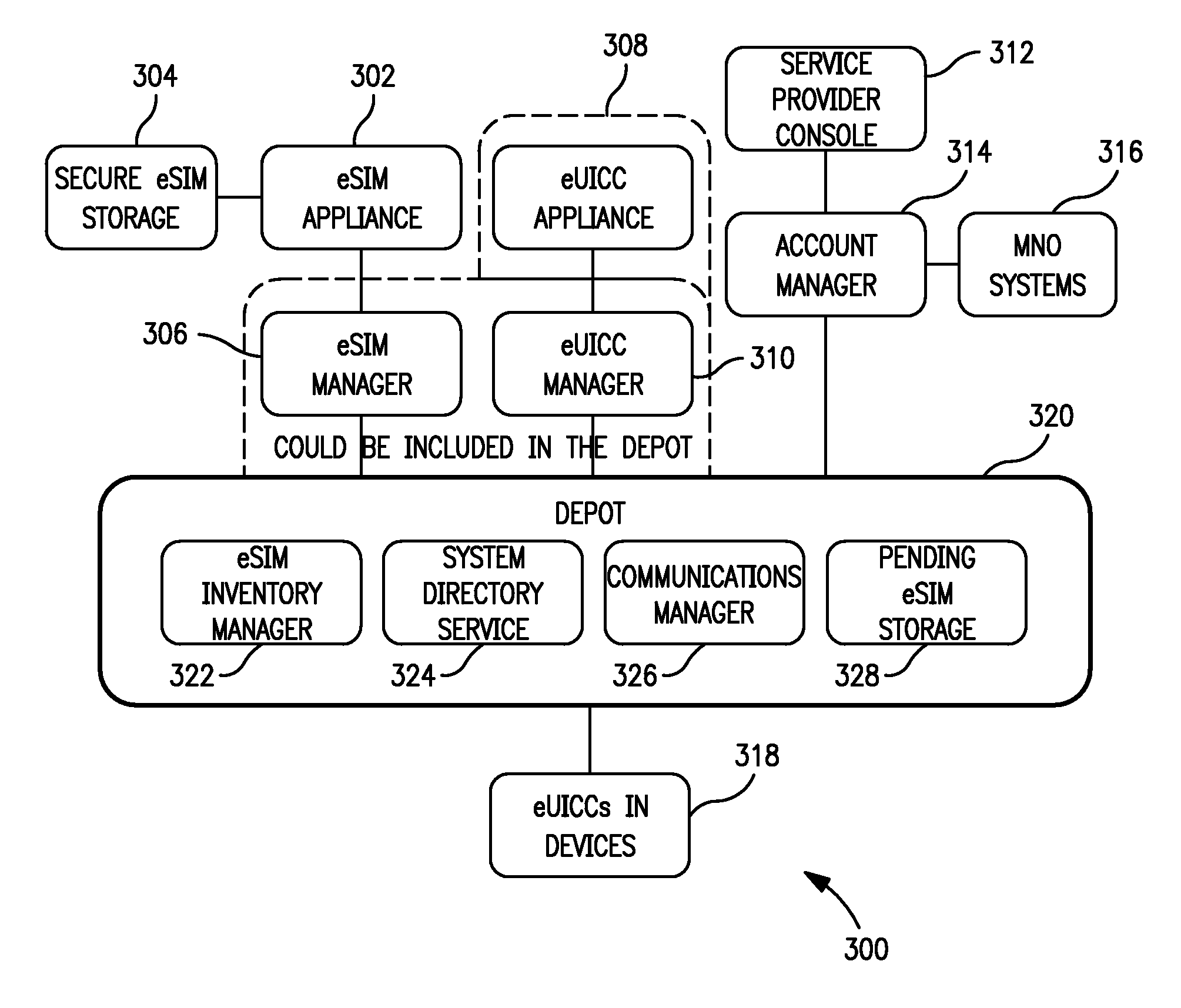
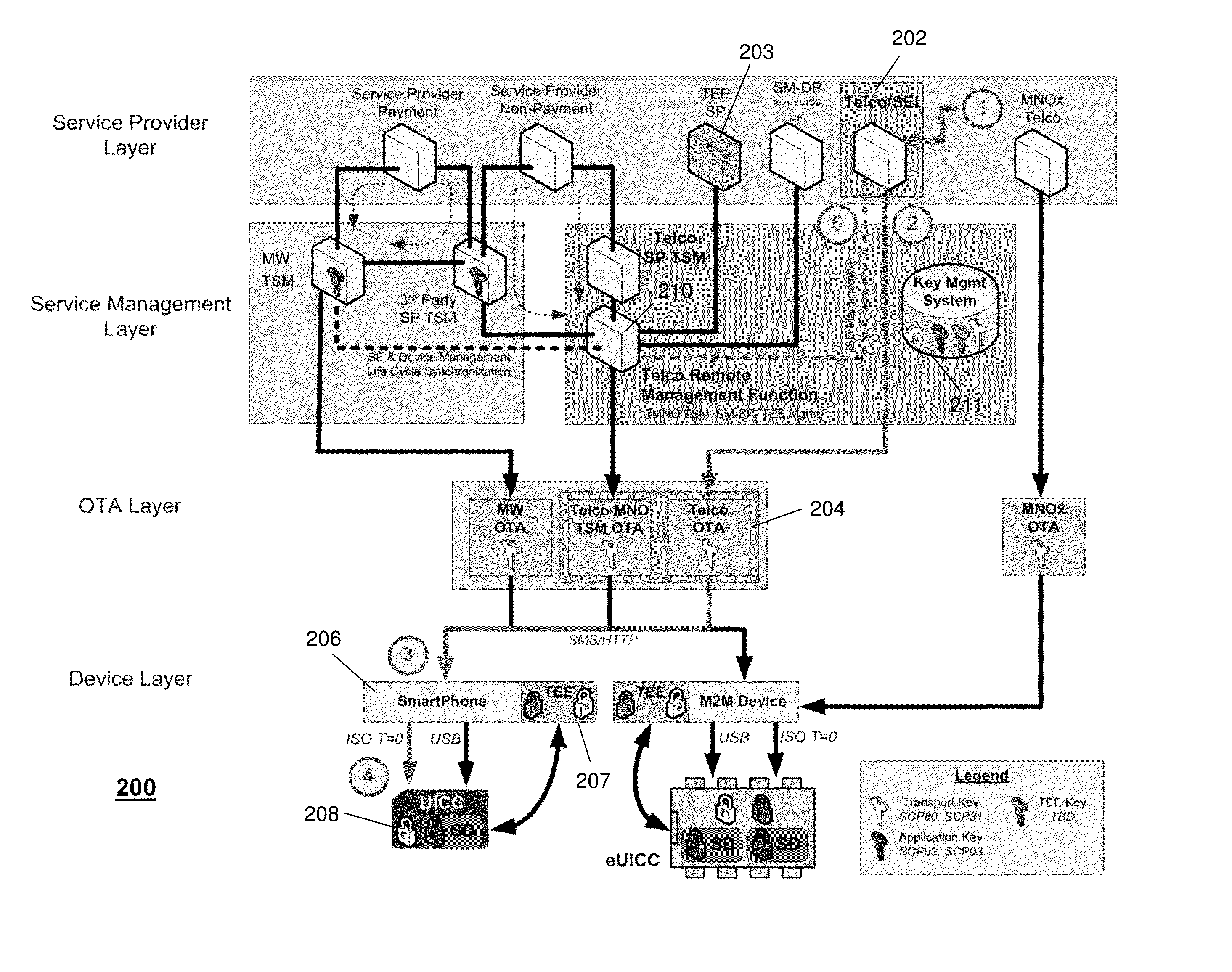
Electronic access client distribution apparatus and methods
ActiveUS20120331292A1Effective distributionEfficiently distributedDigital data processing detailsUser identity/authority verificationElectronic accessService provision
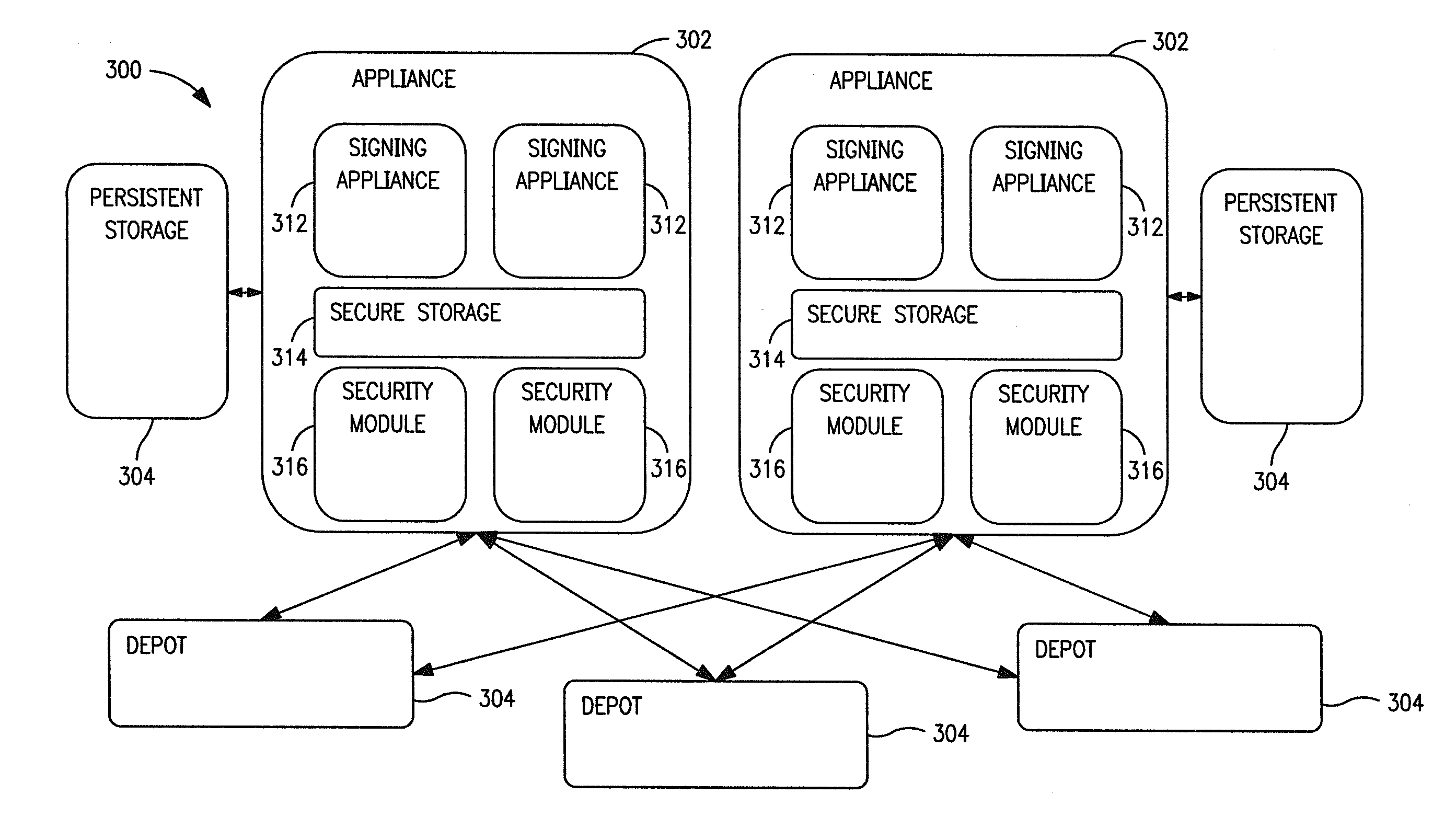
Apparatus and methods for distributing access control clients. In one exemplary embodiment, a network infrastructure is disclosed that enables delivery of electronic subscriber identity modules (eSIMs) to secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs), etc.) The network architecture includes one or more of: (i) eSIM appliances, (ii) secure eSIM storages, (iii) eSIM managers, (iv) eUICC appliances, (v) eUICC managers, (vi) service provider consoles, (vii) account managers, (viii) Mobile Network Operator (MNO) systems, (ix) eUICCs that are local to one or more devices, and (x) depots. Moreover, each depot may include: (xi) eSIM inventory managers, (xii) system directory services, (xiii) communications managers, and / or (xiv) pending eSIM storages. Functions of the disclosed infrastructure can be flexibly partitioned and / or adapted such that individual parties can host portions of the infrastructure. Exemplary embodiments of the present invention can provide redundancy, thus ensuring maximal uptime for the overall network (or the portion thereof).
Owner:APPLE INC
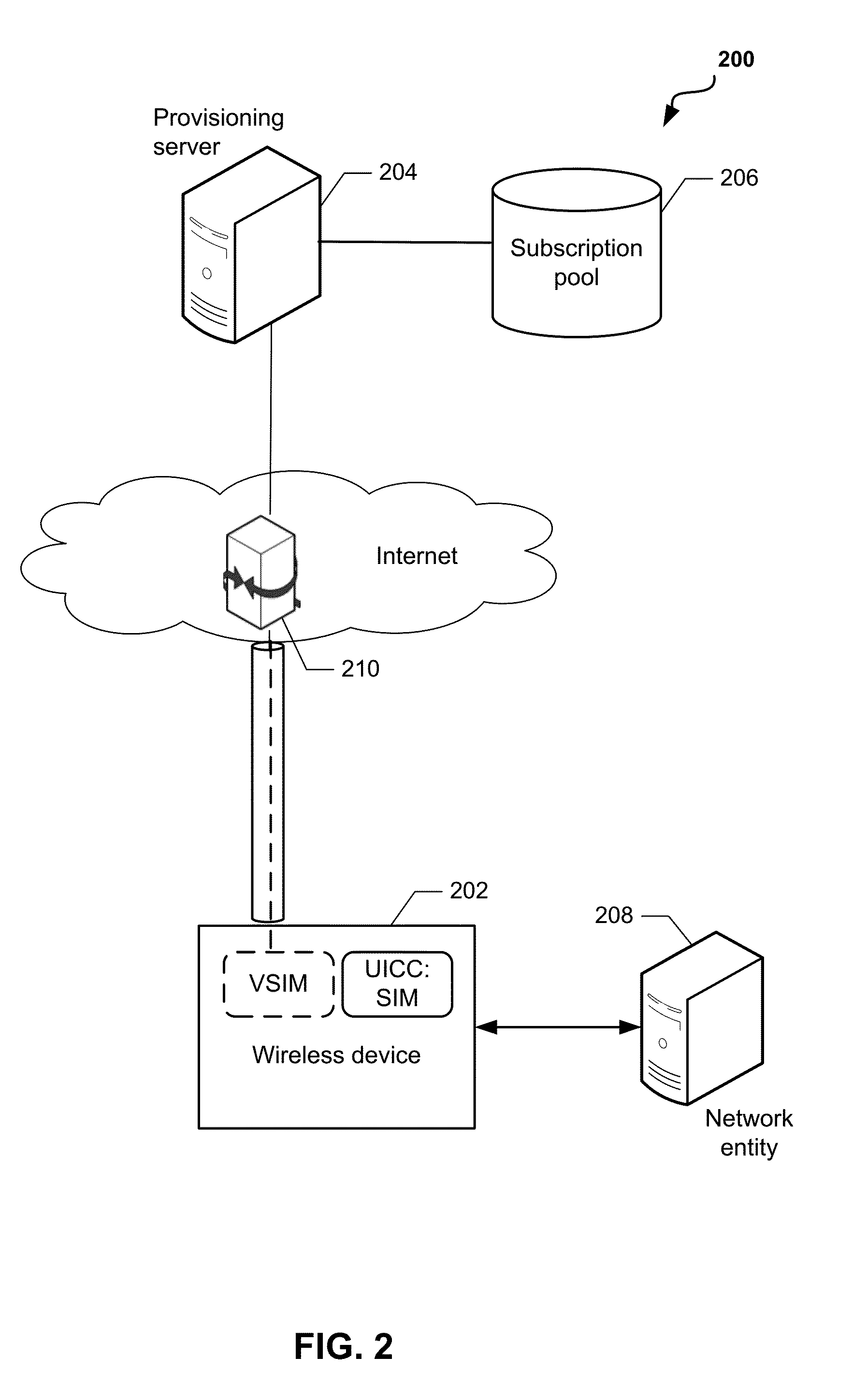
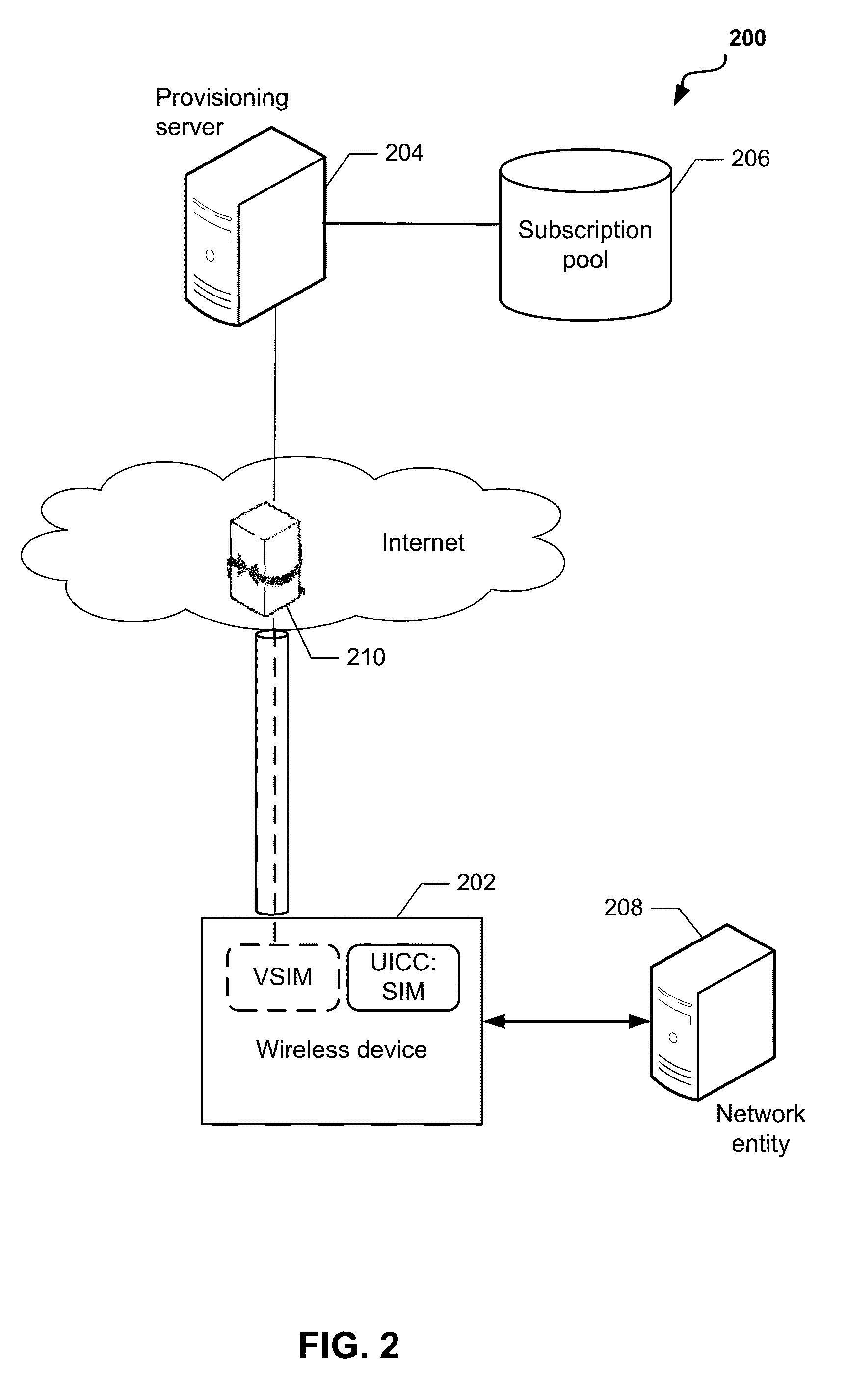
System and Methods for Dynamic SIM Provisioning on a Dual-SIM Wireless Communication Device
ActiveUS20150304506A1Accounting/billing servicesSecurity arrangementComputer hardwareCredential management
Methods and devices for dynamic VSIM provisioning on a multi-SIM wireless device having a first SIM as a Universal Integrated Circuit Card (UICC) and a virtual SIM (VSIM). A provisioning server may receive updated information from the wireless device, and based at least partially on the received information, determine whether the SIM profile on the VSIM of the wireless device should be changed. To change the SIM profile, the provisioning server may determine whether remote credential management procedures are enabled. If so, the provisioning server may select a new SIM profile from a plurality of SIM profiles, and provision the new SIM profile in the VSIM using remote credential management procedures. If remote credential management procedures are unavailable, the provisioning server may select a remote SIM from a plurality of remote SIMs associated with the provisioning server, and run the remote SIM to execute authentication processes for the wireless device.
Owner:QUALCOMM INC
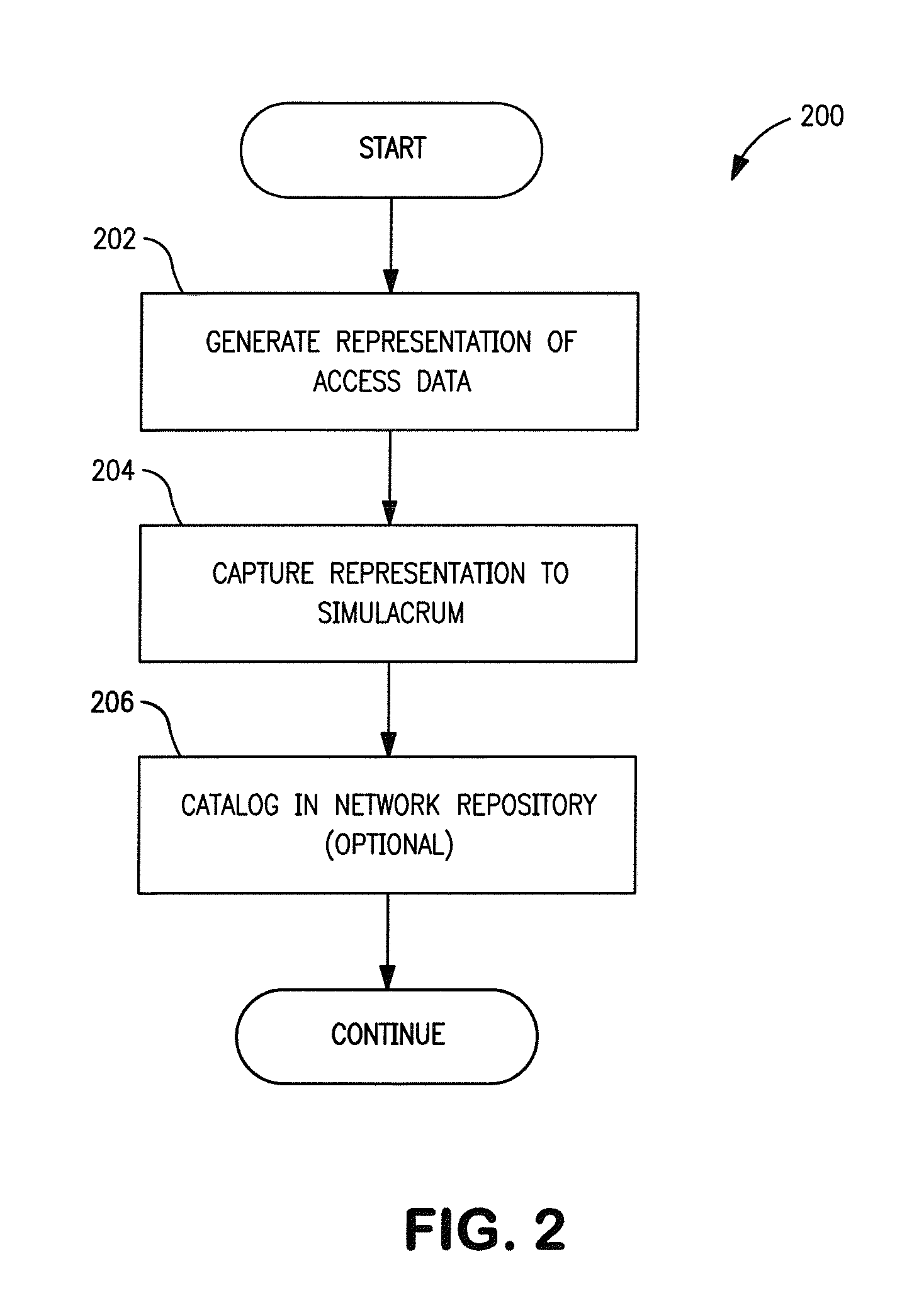
Simulacrum of physical security device and methods
ActiveUS20120117635A1Service provisioningDigital data processing detailsSoftware emulationPhysical security
A simulacrum security device and methods. In one embodiment, a simulacrum or likeness of a physical security device is provided for use in conjunction with a software emulation of the security device. In one implementation, a “faux SIM card” is provided that does not contain Subscriber Identification Module (SIM) information itself, but instead enables a user to download Electronic SIM (eSIM) information (e.g., from a network or eSIM server) which is loaded into a software emulation of a Universal Integrated Circuit Card (UICC) device. The faux card is printed with an activation code, scan pattern, or other activation or access information. The subscriber purchases the faux card, and enters the activation code into a device; the entered activation code enables the device to log onto a network, and download the appropriate eSIM data. Delivery of eSIM information as enabled by the faux card addresses deficiencies in existing SIM distribution schemes, provides users with an enhanced perception of security, and further addresses various legal requirements.
Owner:APPLE INC
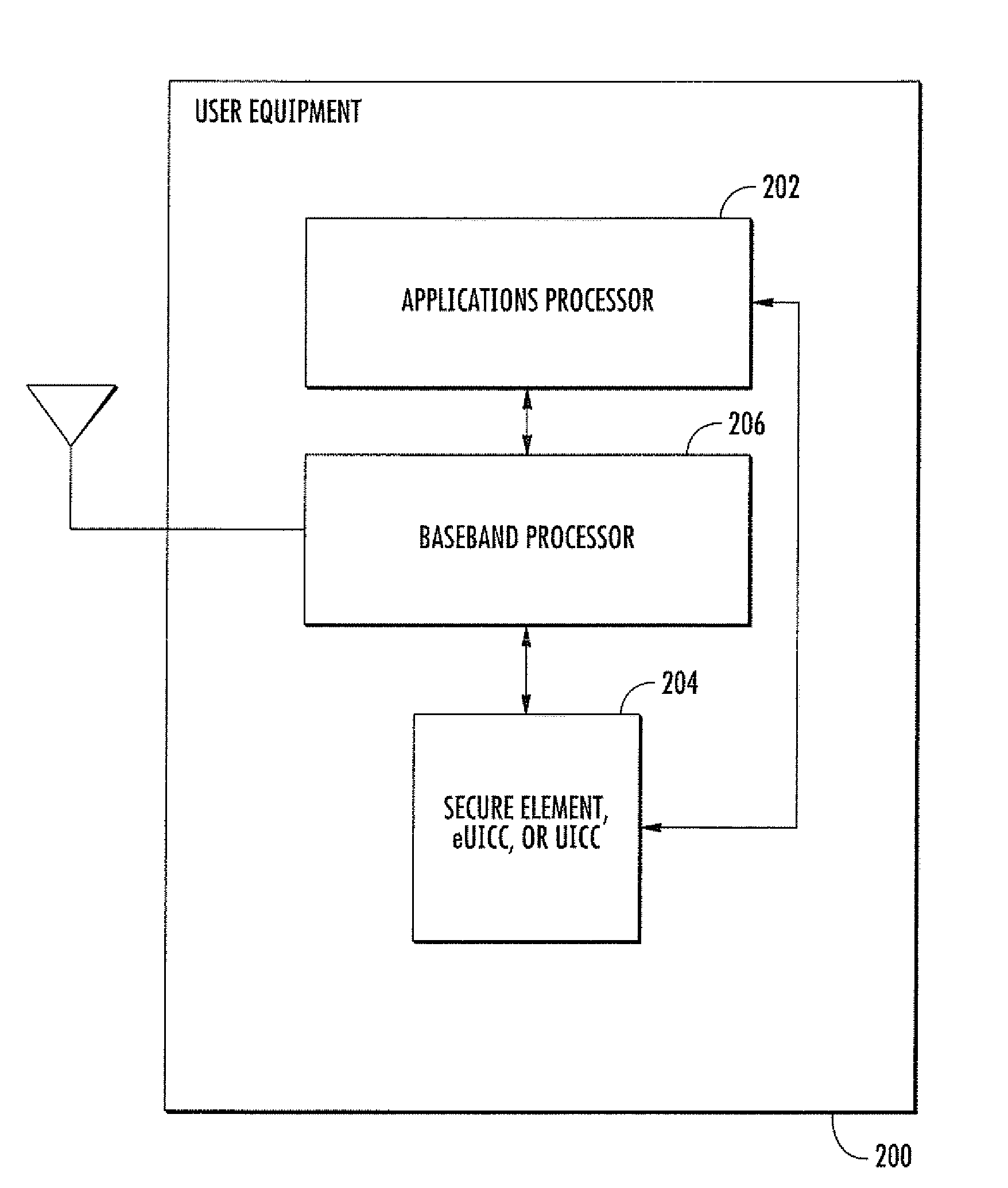
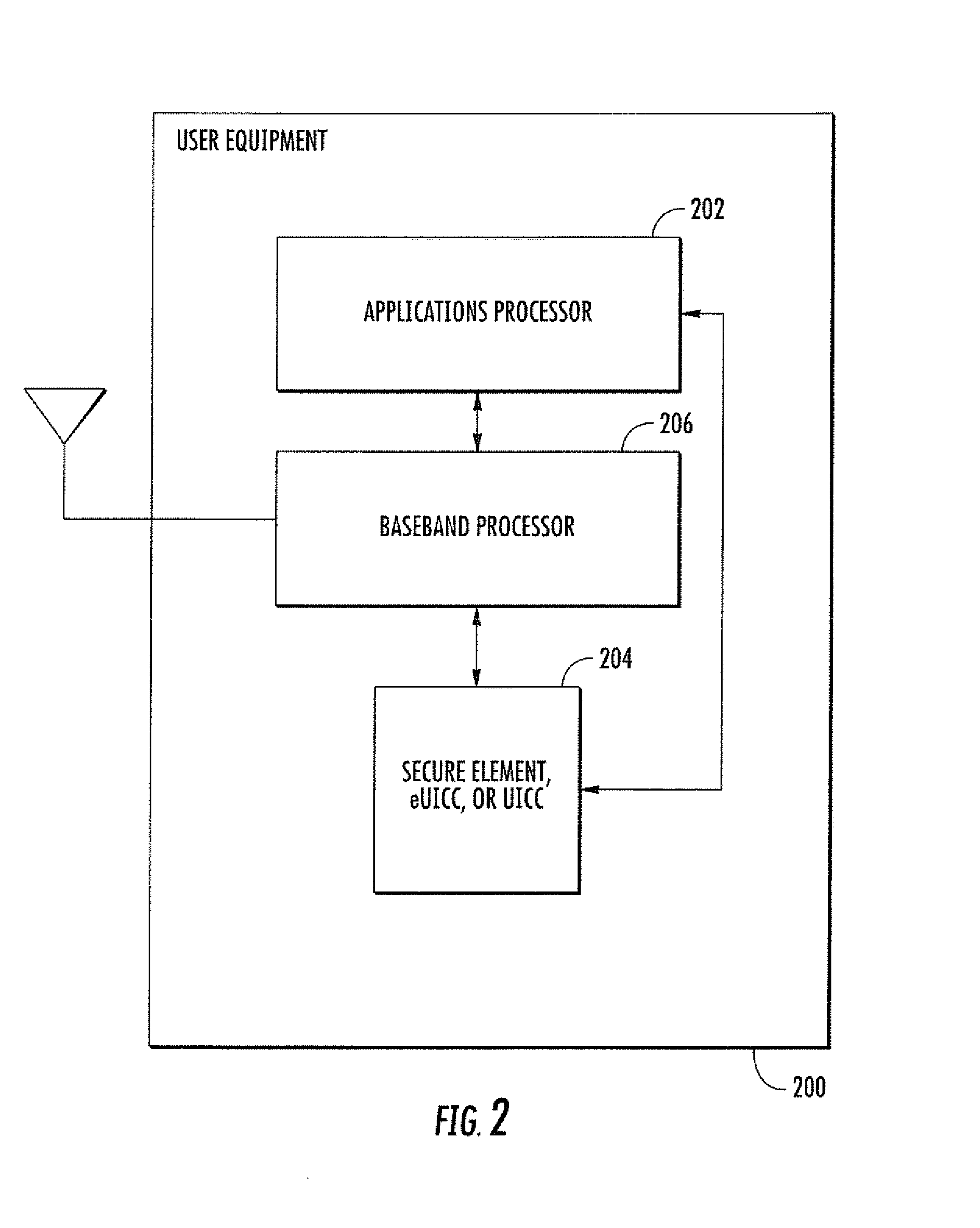
Methods and apparatus for managing data within a secure element
ActiveUS20140073375A1Satisfies needService provisioningSubstation equipmentComputer moduleApplication software
Apparatus and methods for managing and sharing data across multiple access control clients in devices. In one embodiment, the access control clients comprise electronic Subscriber Identity Modules (eSIMs) disposed on a embedded Universal Integrated Circuit Card (eUICC). Each eSIM contains its own data. An Advanced Subscriber Identity Toolkit application maintained within the eUICC facilitates managing and sharing multiple eSIMs' data for various purposes such as sharing phonebook contacts or facilitating automatic switch-over between the multiple eSIMs (such as based on user context).
Owner:APPLE INC
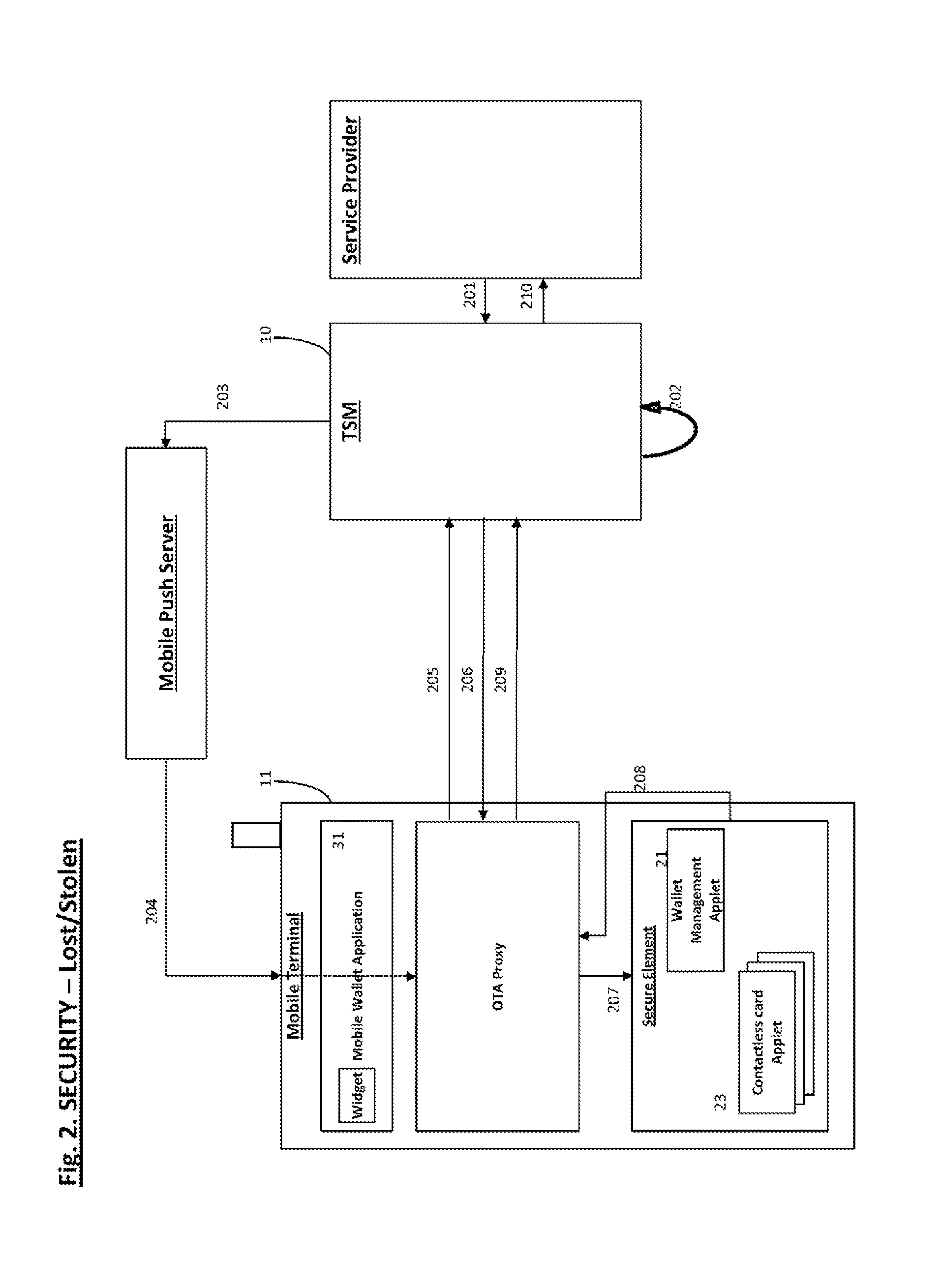
System and method for provisioning over the air of confidential information on mobile communicative devices with non-uicc secure elements
ActiveUS20120172089A1Service provisioningInternal/peripheral component protectionComputer hardwareMobile device
A method for over-the-air (OTA) provisioning a non-Universal Integrated Circuit Card (UICC) type secure element (SE) of a mobile device, including receiving a request to initialize an OTA proxy of a mobile device; initializing the OTA proxy; receiving provisioning data through the OTA proxy; and provisioning the received data into the SE, in which the SE is a non-UICC type SE. A mobile device to provision secure data OTA in a non-UICC type SE including an OTA proxy to connect to a Trusted Service Manager (TSM) system, and to receive provisioning data from the TSM system; a near-field-communication (NFC) enabled chip to conduct a contactless transaction; and a SE to store information provisioned through OTA proxy, in which the SE is a non-UICC type SE.
Owner:MOZIDO CORFIRE - KOREA
Methods and apparatus for providing management capabilities for access control clients
InactiveUS20130122864A1Satisfies needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSoftware updateClient-side
Methods and apparatus for managing access control clients (e.g., electronic Subscriber Identity Modules (eSIMs)). In one embodiment, secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs)) and management entities of secure elements are associated with credentials. Post-deployment managerial operations can be executed, by transmitting the requested operation with the appropriate credentials. For example, a device can receive secure software updates to electronic Subscriber Identity Modules (eSIMs), with properly credentialed network entities.
Owner:APPLE INC
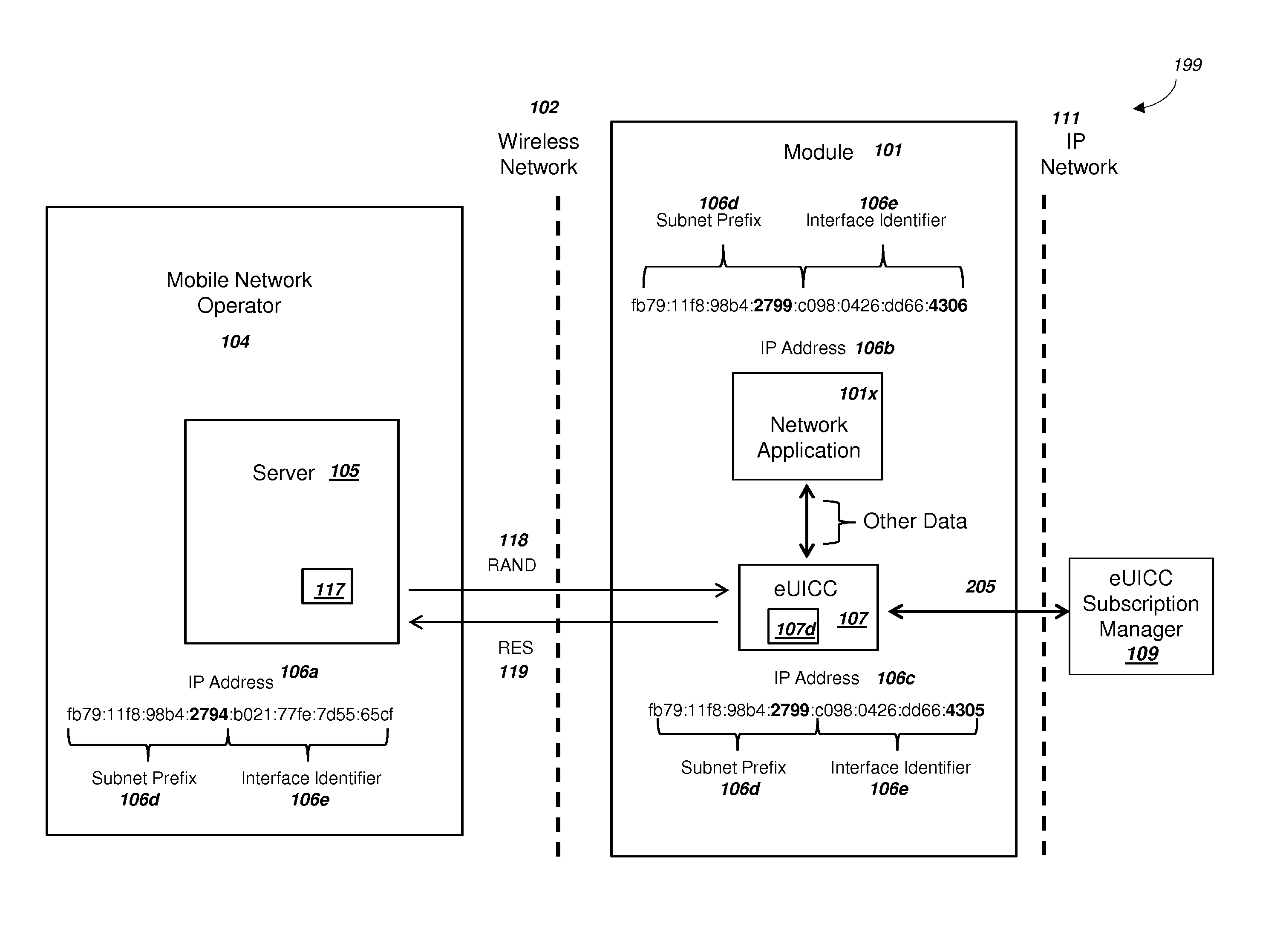
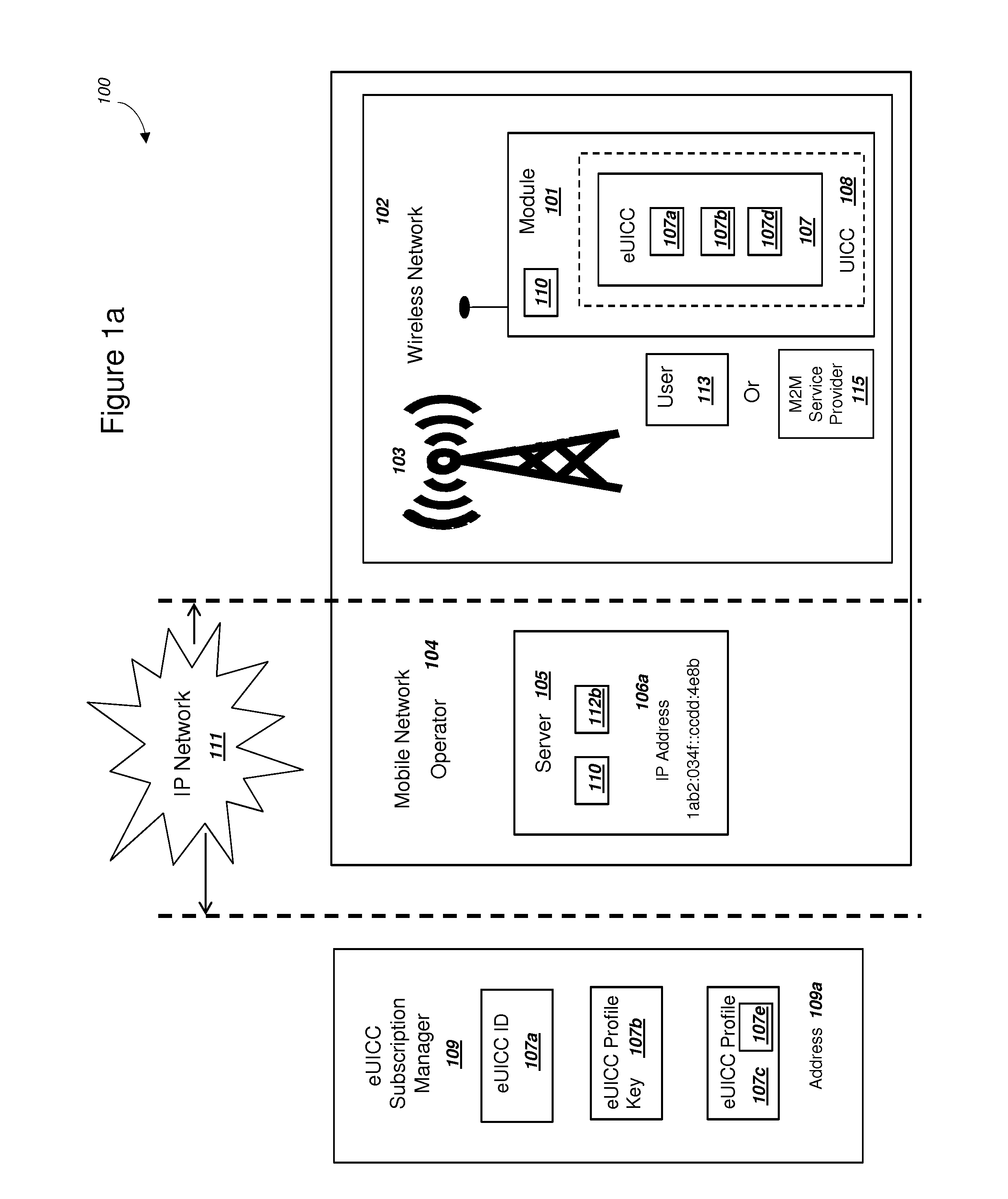
Embedded Universal Integrated Circuit Card Supporting Two-Factor Authentication
ActiveUS20150163056A1Increase flexibilityLow costKey distribution for secure communicationSecurity arrangementPlaintextComputer hardware
A module with an embedded universal integrated circuit card (eUICC) can include a profile for the eUICC. The profile can include a first and second shared secret key K for authenticating with a wireless network. The first shared secret key K can be encrypted with a first key, and the second shared secret key K can be encrypted with a second key. The module can (i) receive the first key, (ii) decrypt the first shared secret key K with the first key, and (iii) subsequently authenticate with the wireless network using the plaintext first shared secret key K. The wireless network can authenticate the user of the module using a second factor. The module can then (i) receive the second key, (ii) decrypt the second shared secret key K, and (iii) authenticate with the wireless network using the second shared secret key K. The module can comprise a mobile phone.
Owner:NIX JOHN A +1
System and method for secure containment of sensitive financial information stored in a mobile communication terminal
InactiveUS20120171992A1Service provisioningUnauthorised/fraudulent call preventionComputer terminalApplication software
A method for securing information over-the-air (OTA) in a non-Universal Integrated Circuit Card (UICC) type secure element (SE) of a mobile terminal including receiving a request to initialize an OTA proxy of a mobile terminal, initializing the OTA proxy, receiving a request to secure information, and securing, using the OTA proxy, the requested information in the non-UICC type SE. A method for reconstructing a mobile wallet application including receiving a request to reconstruct the mobile wallet application for a user; transmitting stored mobile wallet application information associated with the user to the mobile terminal; receiving mobile terminal information and SE information; and transmitting a stored application associated with the mobile wallet application information to the mobile terminal. A mobile terminal to secure information OTA in a non-UICC type SE including an OTA proxy to receive a securing command from a TSM, and a non-UICC SE.
Owner:MOZIDO CORFIRE - KOREA
Apparatus and methods for distributing and storing electronic access clients
ActiveUS20120260086A1Efficiently distributedEffective controlPublic key for secure communicationUser identity/authority verificationElectronic accessBottle neck
Apparatus and methods for efficiently distributing and storing access control clients within a network. In one embodiment, the access clients include electronic Subscriber Identity Modules (eSIMs), and an eSIM distribution network infrastructure is described which enforces eSIM uniqueness and conservation, distributes network traffic to prevent “bottle necking” congestion, and provides reasonable disaster recovery capabilities. In one variant, eSIMs are securely stored at electronic Universal Integrated Circuit Card (eUICC) appliances which ensure eSIM uniqueness and conservation. Access to the eUICC appliances is made via multiple eSIM depots, which ensure that network load is distributed. Persistent storage is additionally described, for among other activities, archiving and backup.
Owner:APPLE INC
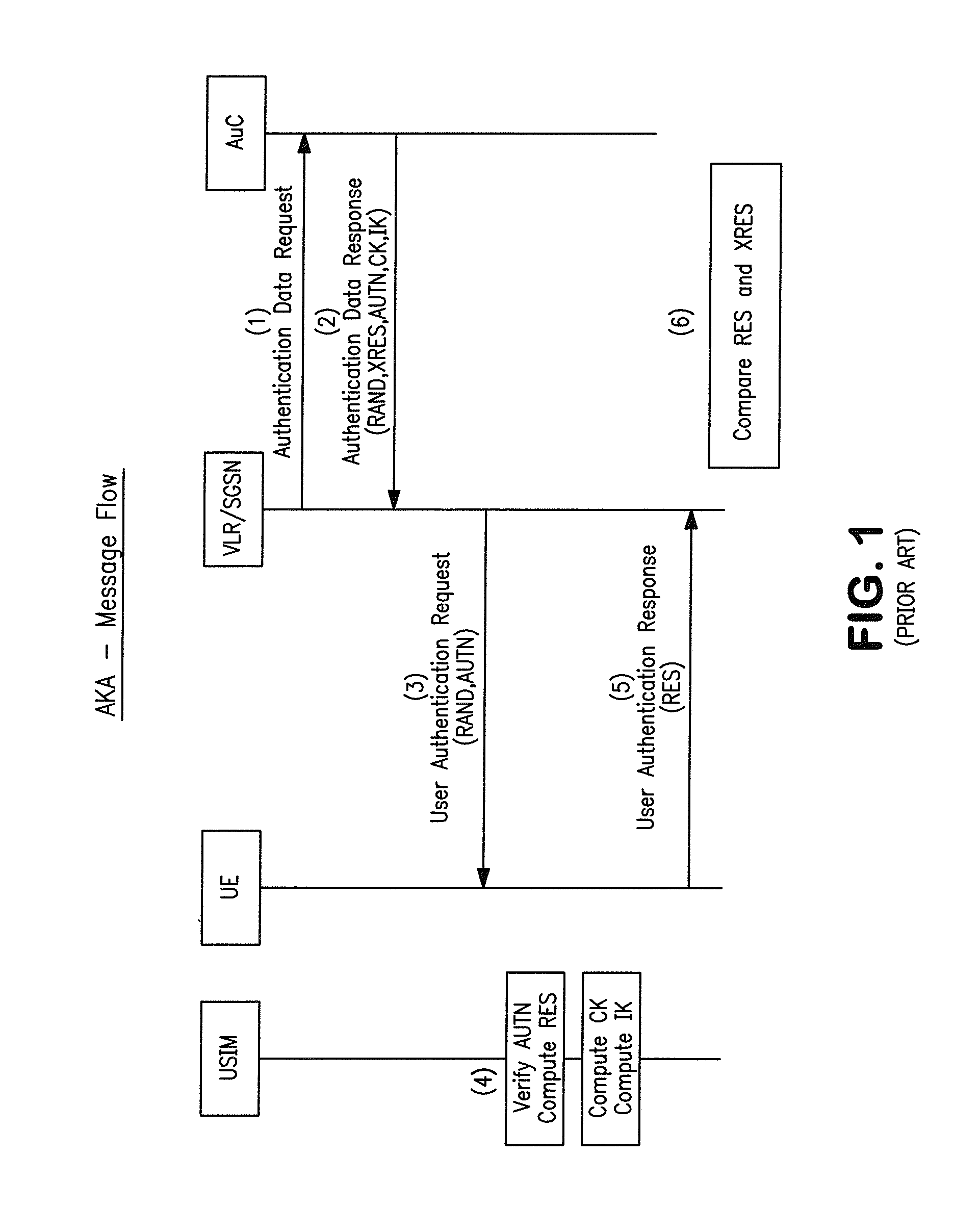
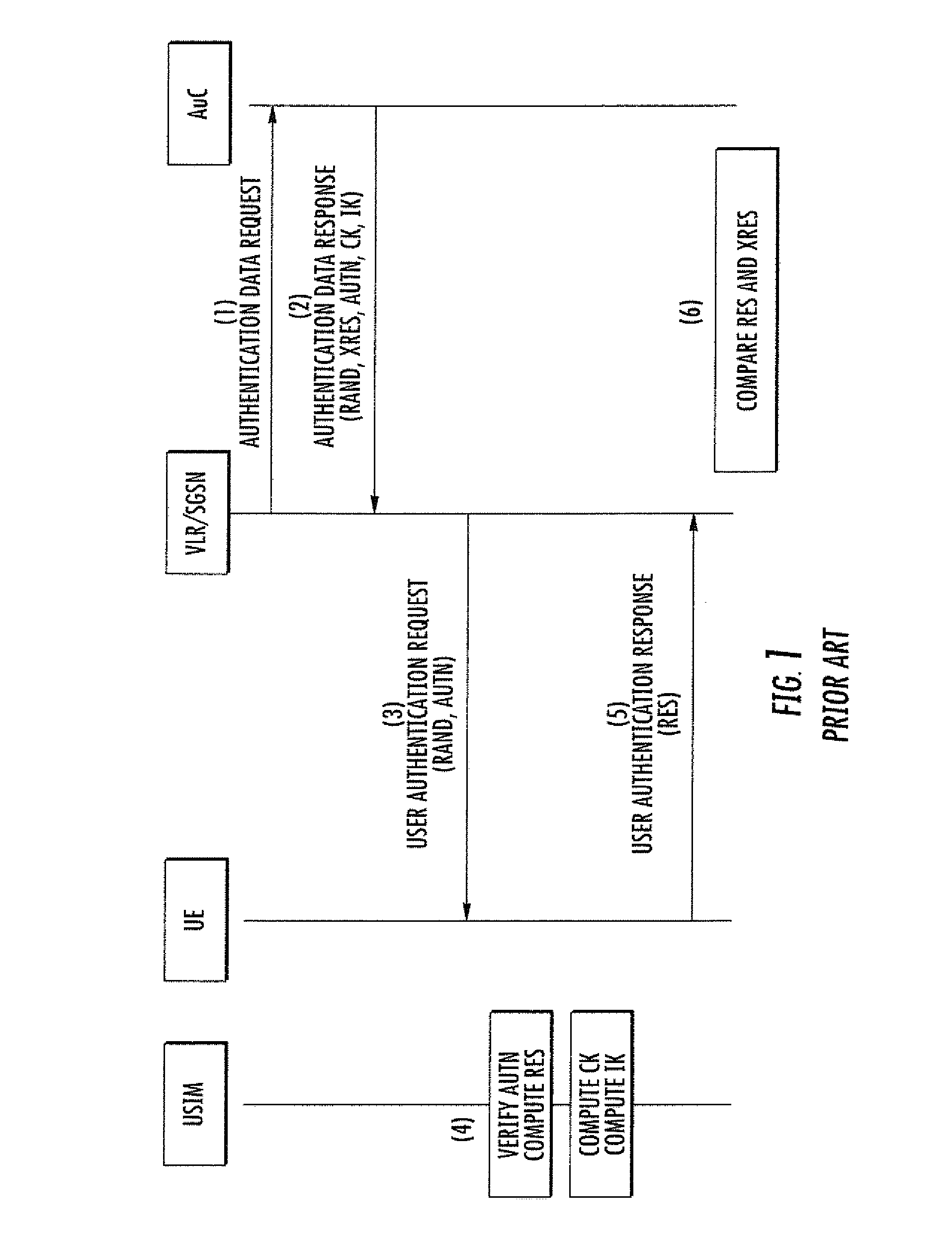
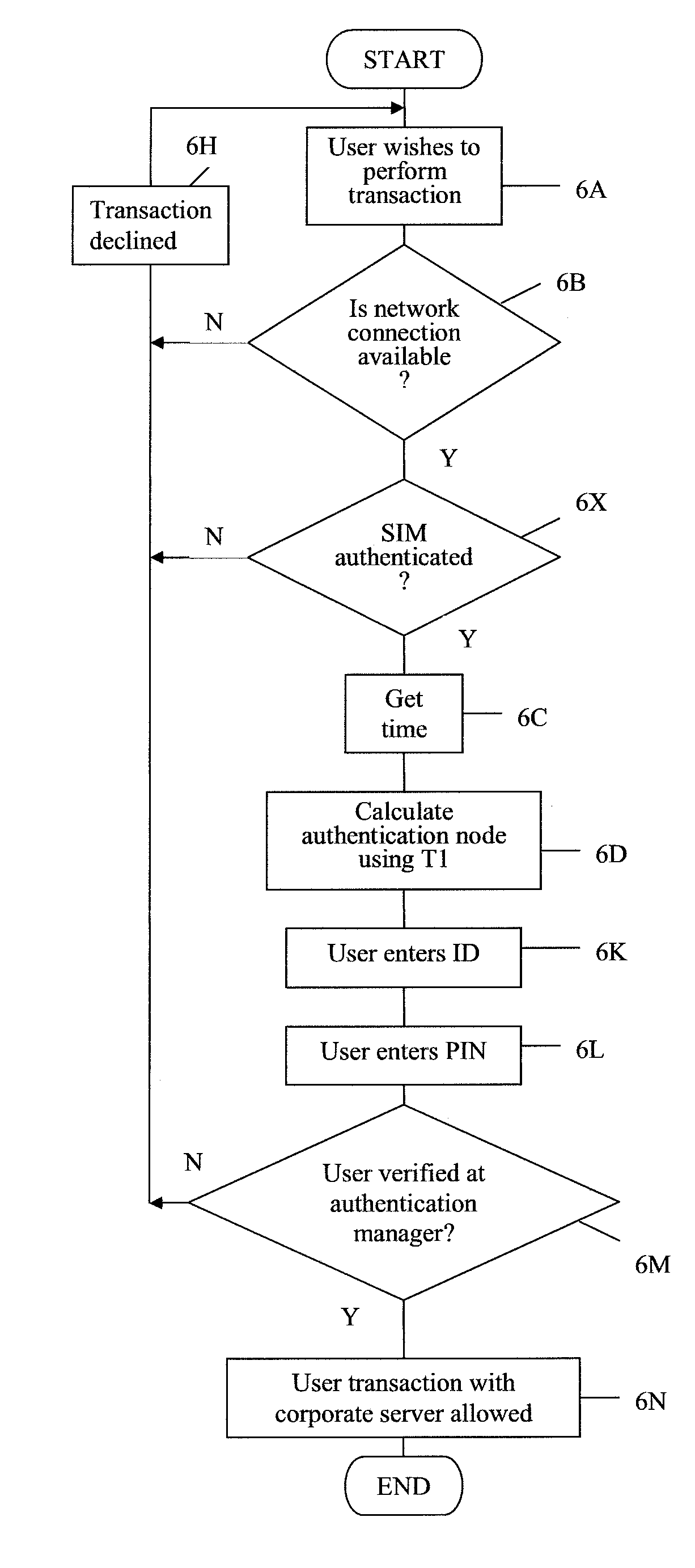
Authentication
InactiveUS20120047563A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwarePassword
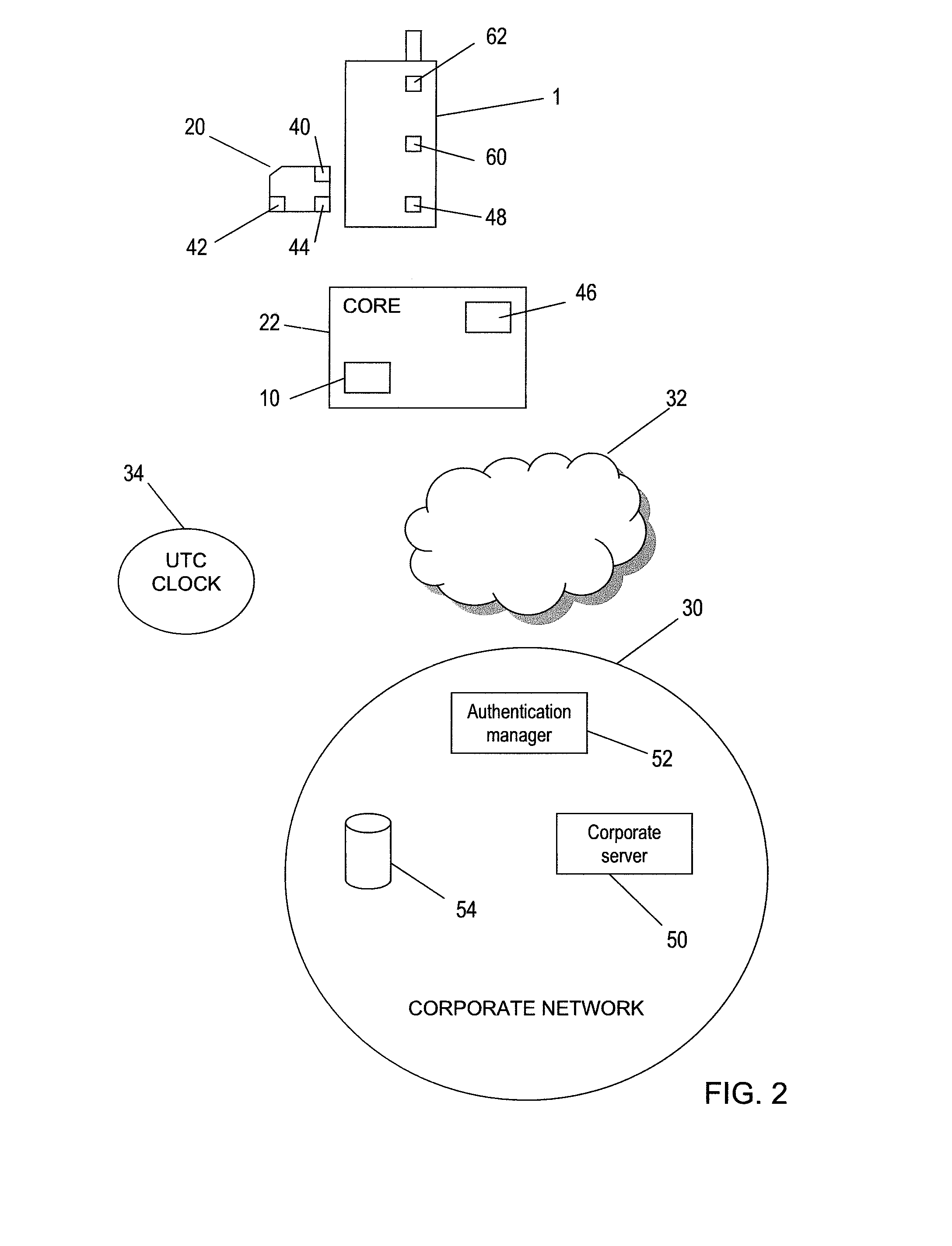
An arrangement for authenticating a transaction between a user's mobile device and an entity such as a corporate server is disclosed. The user's universal integrated circuit card (UICC) is adapted to generate a time-dependent authentication code which is dependent on a time value and which is usable to authenticate the transaction only during a predetermined period. A time verification processor verifies a time value to ensure that the time-dependent authentication code was generated based on the correct time value. The time value is based on the UTC time obtained from UTC clock. The verified time is used to generate a “one-time” password (authentication code) by the authentication code calculator of the UICC. This is used to authenticate a transaction with the corporate network.
Owner:VODAFONE IP LICENSING
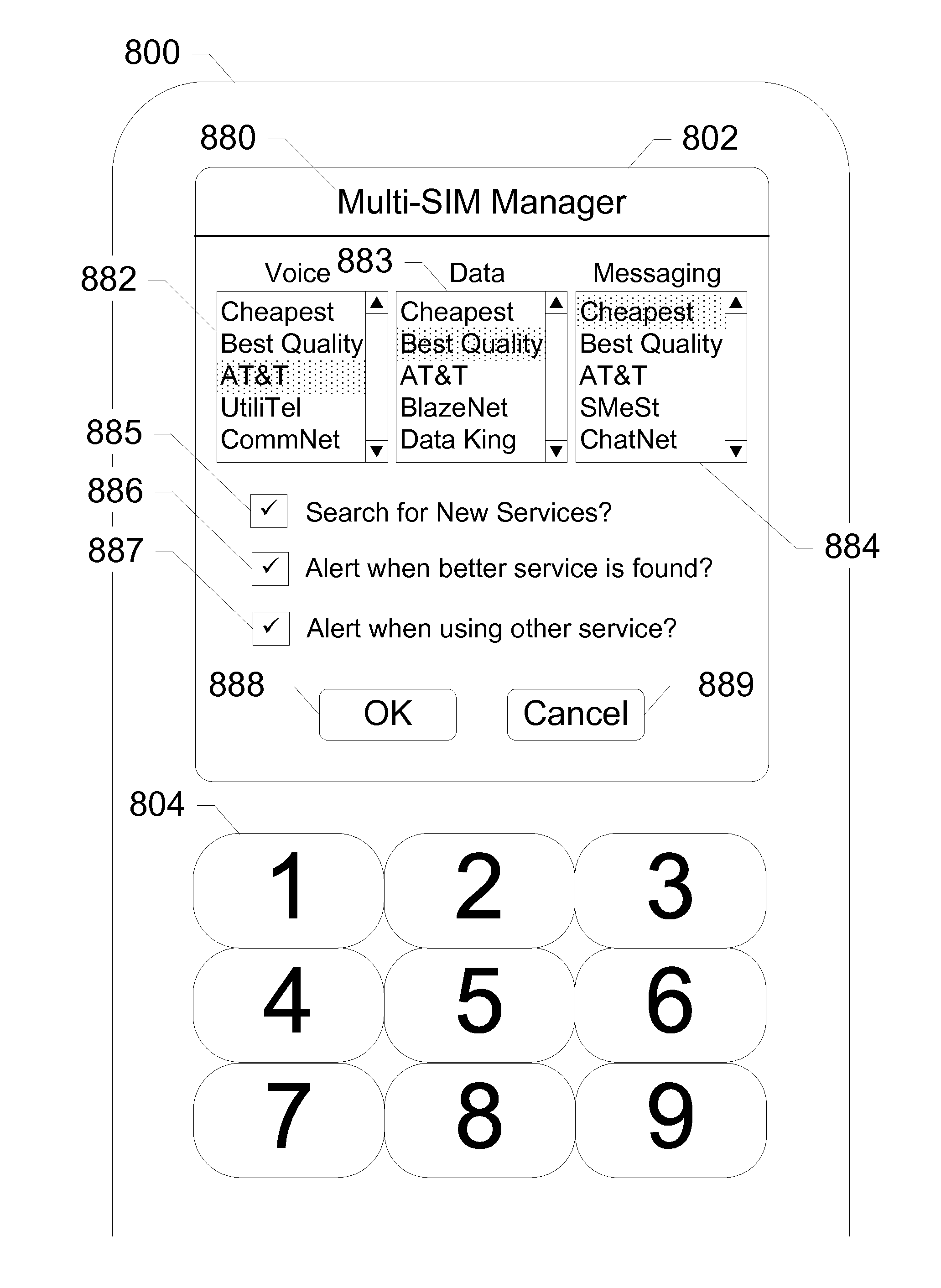
Apparatus and methods for selecting services of mobile network operators
ActiveUS20130340059A1Service provisioningUser identity/authority verificationComputer scienceMobile network operator
A system that incorporates teachings of the subject disclosure may include, for example, a method for detecting, by a first device including a least one processor and a first Universal Integrated Circuit Card (UICC), a second device having a second UICC, detecting, by the first device, that the second UICC is unprovisioned, selecting, by the first device, one of a plurality of selectable options, where the selection identifies a first network operator selected from a plurality of network operators, receiving, by the first device, first credential information of the first network operator, and transmitting, by the first device, to the second device the first credential information for enabling the second device to facilitate establishment of communication services with network equipment of the first network operator according to the first credential information. Other embodiments are disclosed.
Owner:AT&T MOBILITY II LLC
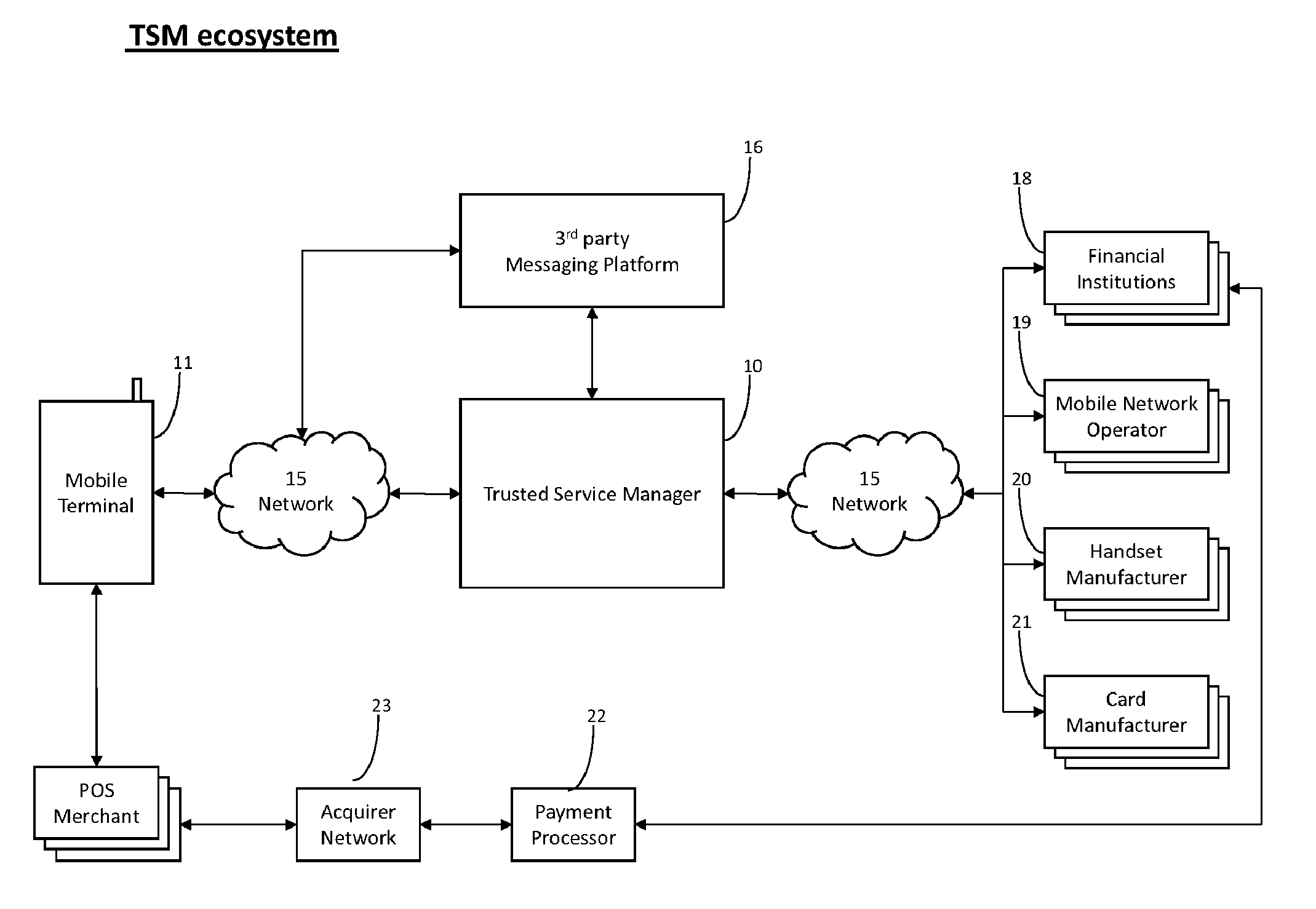
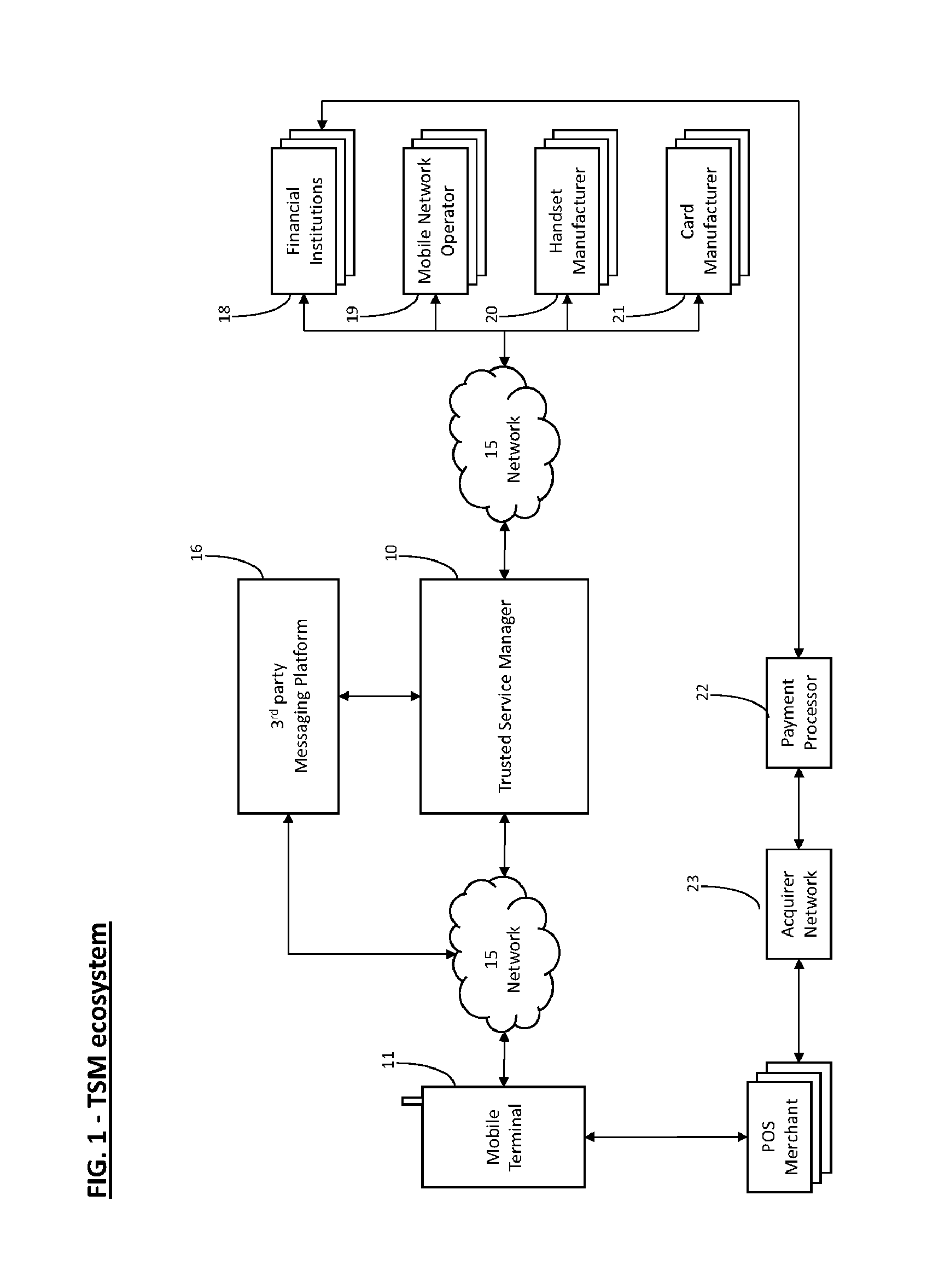
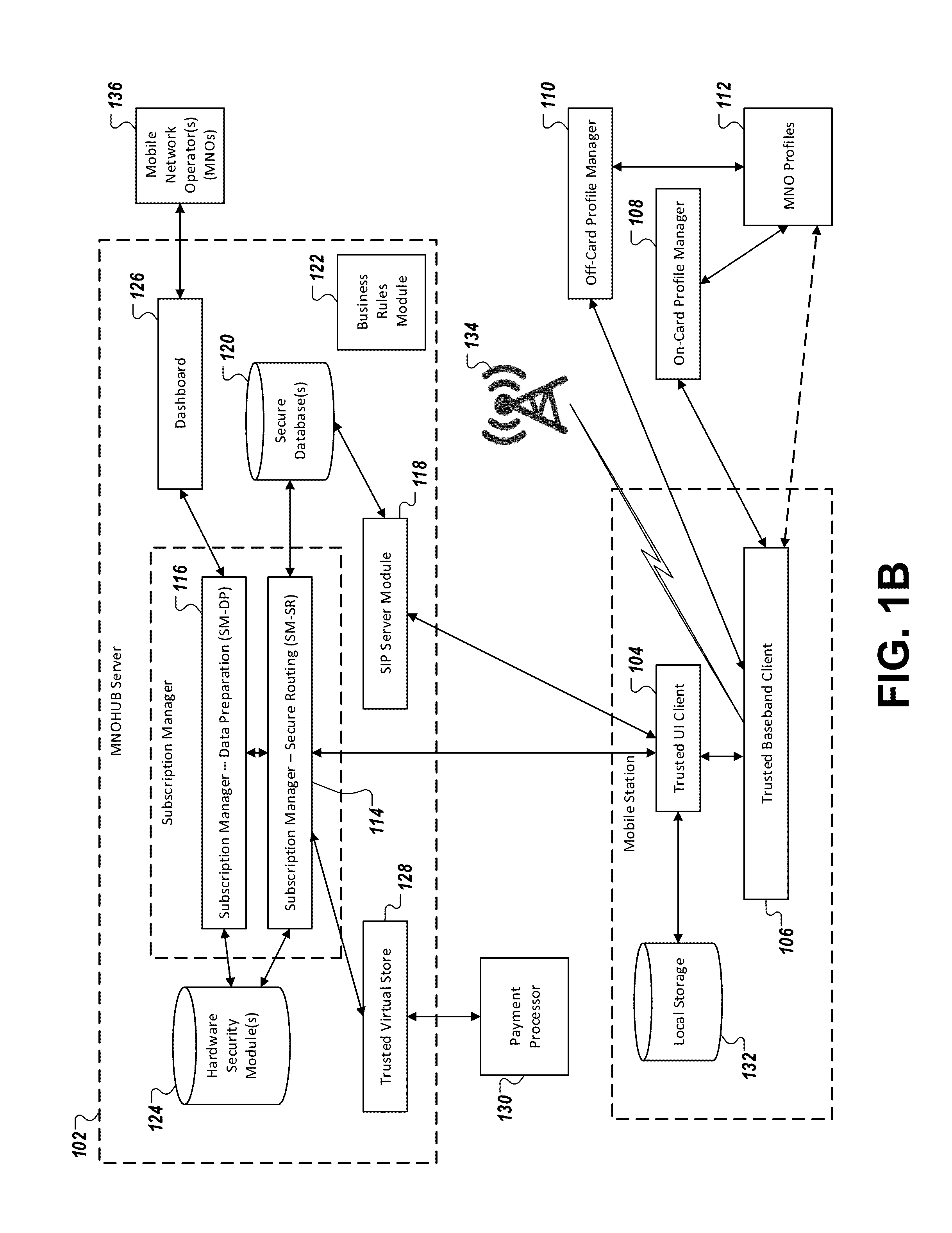
Apparatuses, methods and systems for interfacing with a trusted subscription management platform
ActiveUS20160007190A1Improve communication experienceService provisioningAccounting/billing servicesSession Initiation ProtocolVirtualization
Apparatuses, methods, and systems are provided for implementing a trusted subscription management platform. The platform allows the remote creation, distribution and management of virtual subscriber identity module cards stored in a plurality of concurrent embedded Universal Integrated Circuit Cards (eUICCs). The eUICCs may be virtualized through a secure software module integrated within a mobile station or in a distant server. These eUICCs may be deployed in both hardware and software instances within the mobile station (or the distant server). In some embodiments, use of the trusted subscription management platform provides a Session Initiation Protocol (SIP) server module that facilitates the transmission of voice and data over Internet protocol services integrated within a phone application of the mobile station.
Owner:GIGSKY
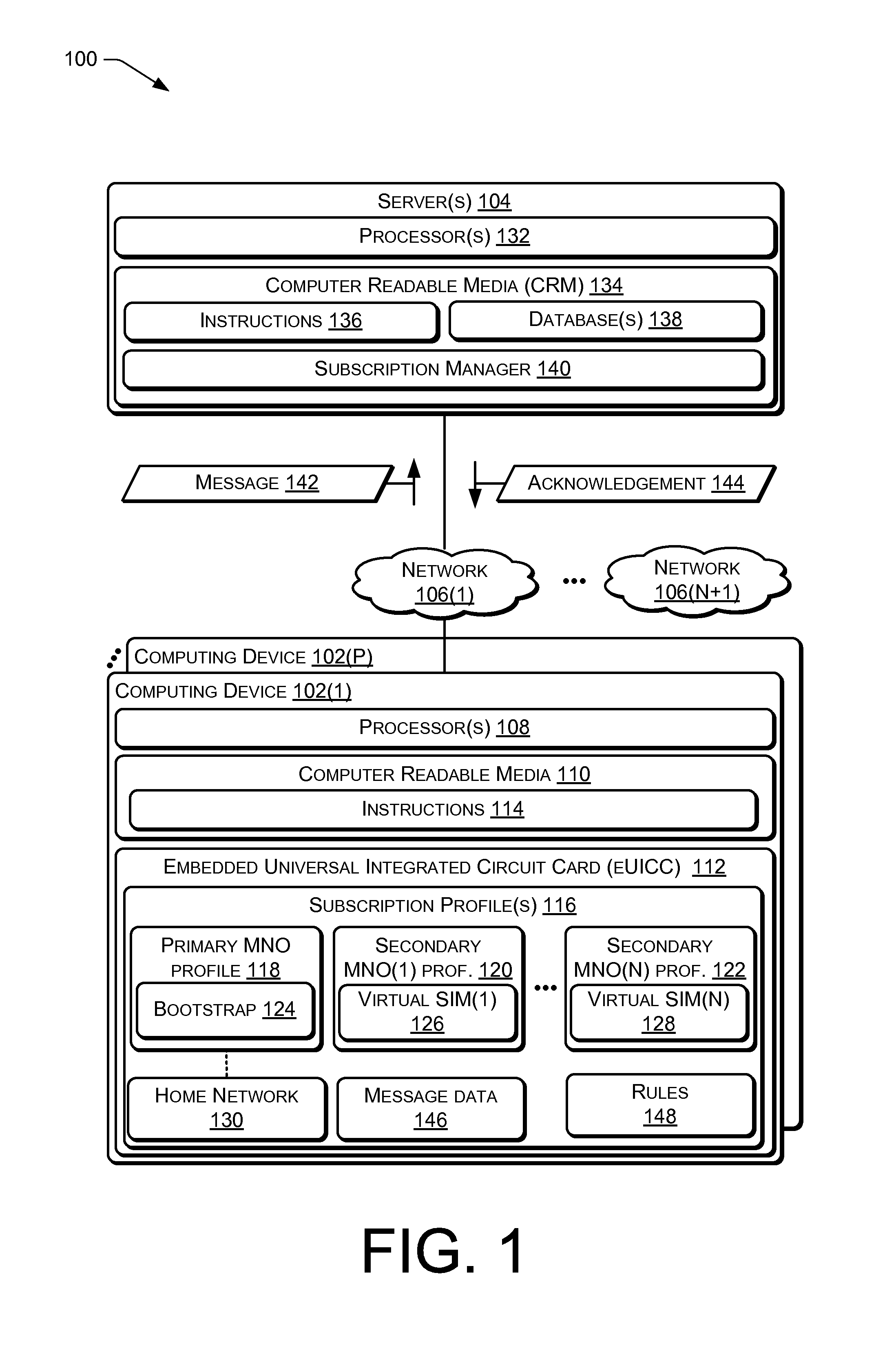
Polling by Universal Integrated Circuit Card for Remote Subscription
ActiveUS20150271662A1Error prevention/detection by using return channelWireless commuication servicesGeographic siteGeolocation
In some implementations, a universal integrated circuit card (UICC) of a computing device activates a primary mobile network operator (MNO) subscription profile associated with a primary MNO based on: (i) whether the computing device is connected to a network, (ii) whether the primary MNO subscription profile is active, and (iii) a number of unacknowledged messages to a message that is periodically sent from the computer to a server associated with the primary MNO. The primary MNO may provide network services to a first geographic area and a secondary MNO may provide network services to a second geographic area. After the computing device moves to the second geographic location from the first geographic location, the eUICC received a secondary MNO profile associated with the secondary MNO, activates the secondary MNO profile, and deactivates the primary MNO profile.
Owner:T MOBILE USA
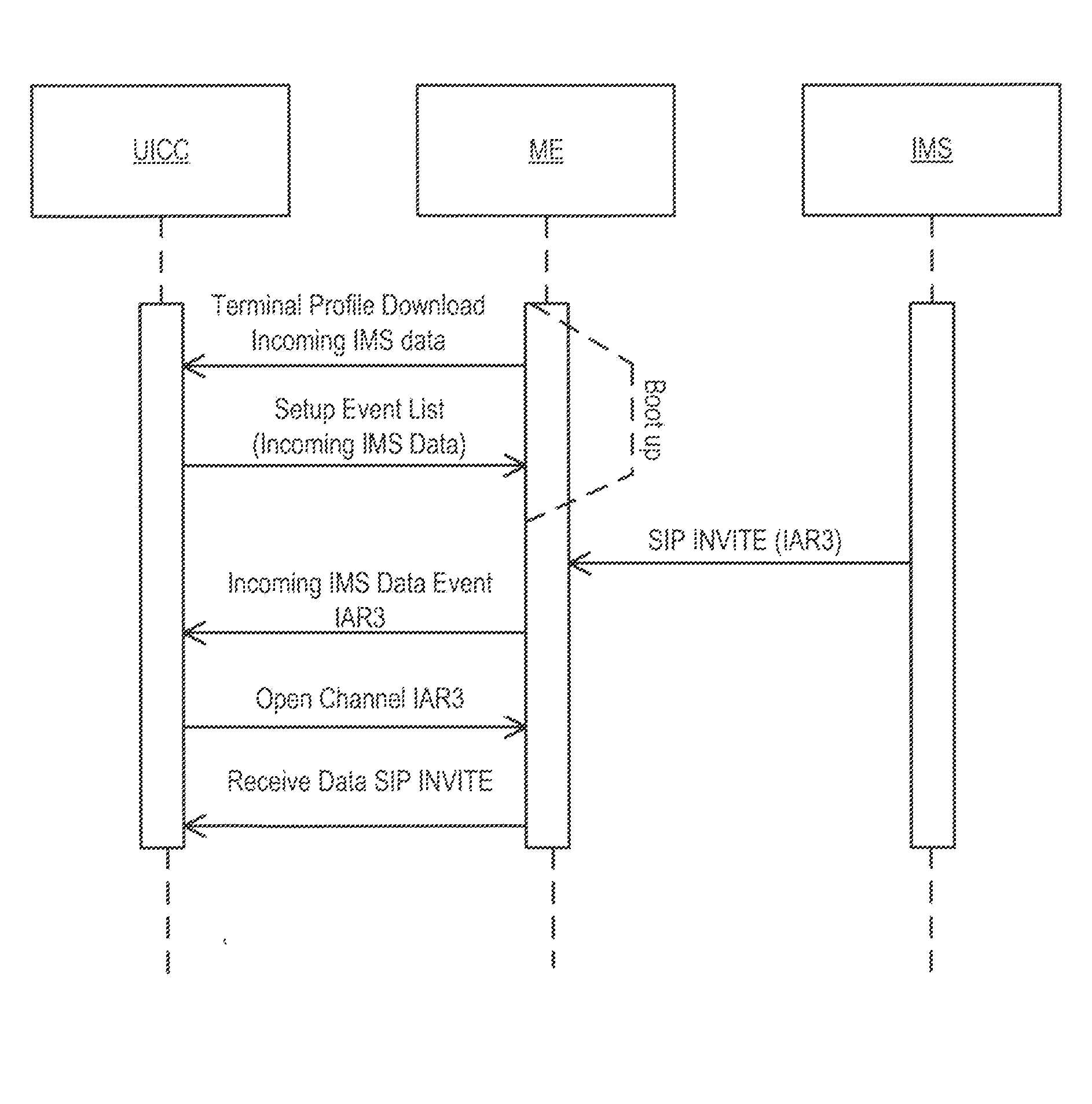
Card Application Toolkit Support for IP Multimedia Subsystem
ActiveUS20130203465A1Reduce unwanted SIP signalingSave resourcesService provisioningWireless network protocolsSession Initiation ProtocolProtocol for Carrying Authentication for Network Access
To consolidate session initiation protocol (SIP) messages a user equipment (UE) is made aware of all Internet Protocol (IP) multimedia subsystem (IMS) applications installed in its memory and on a universal integrated circuit card (UICC) and supported communication services. By obtaining this information before the initial IMS Registration, the UE can save resources by registering all local applications and communication services in single IMS registration.
Owner:BLACKBERRY LTD
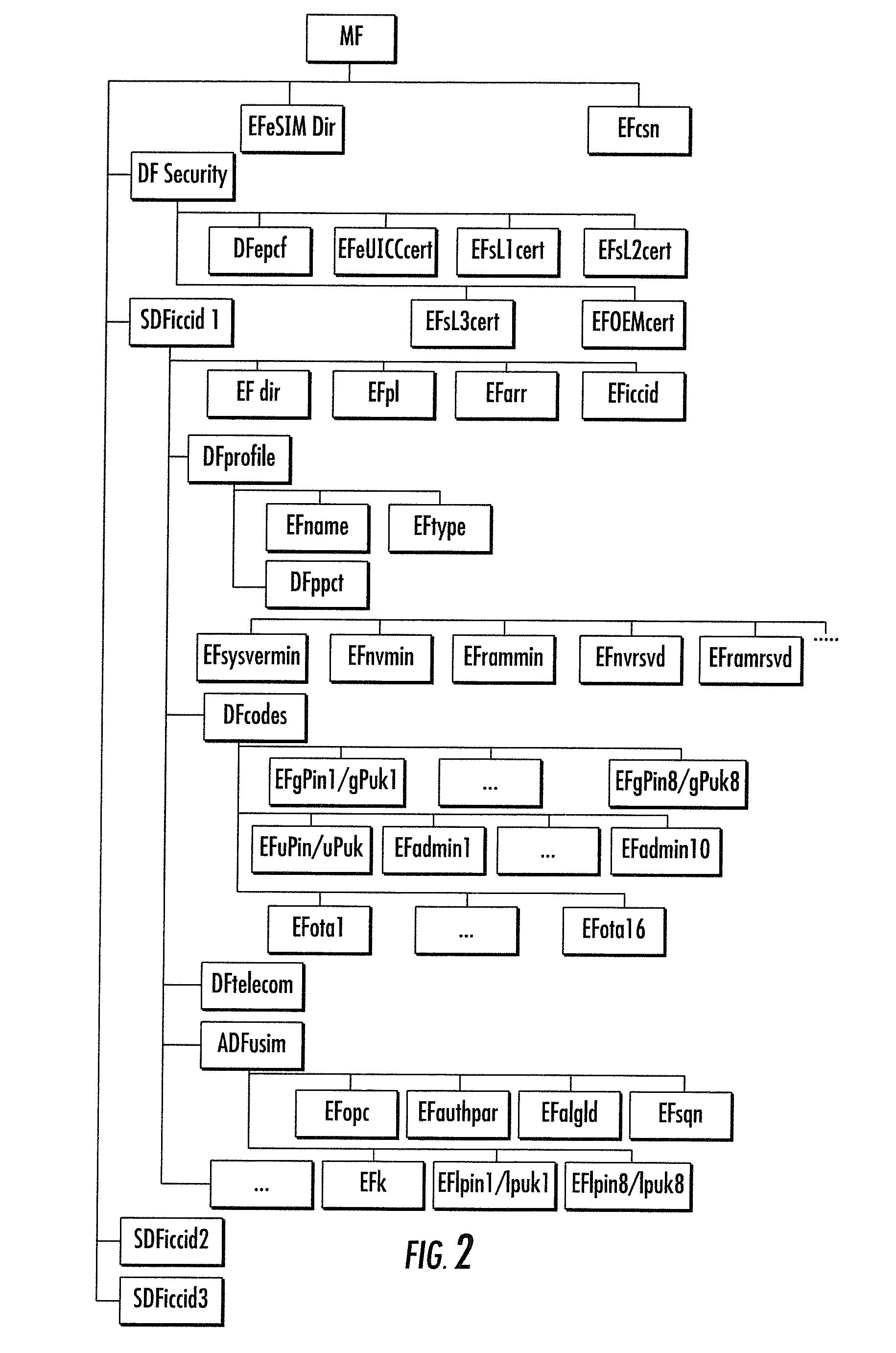
Methods for provisioning universal integrated circuit cards
ActiveUS20140140509A1Internal/peripheral component protectionSecret communicationComputer hardwareTrusted service manager
A system is described that can perform a method for receiving a request to modify a universal integrated circuit card, generating a package comprising configuration data for modifying the universal integrated circuit card, instructing an over-the-air system to transmit the package encrypting the package with a transport key to generate an encrypted package, and transmitting the encrypted package to a communication device communicatively coupled to the universal integrated circuit card to provision the universal integrated circuit card. The system can also perform a method of providing a mobile network operator trusted service manager system information relating to the configuration data to enable the mobile network operator trusted service manager system to manage content and memory allocation of the universal integrated circuit card.
Owner:AT&T MOBILITY II LLC +1
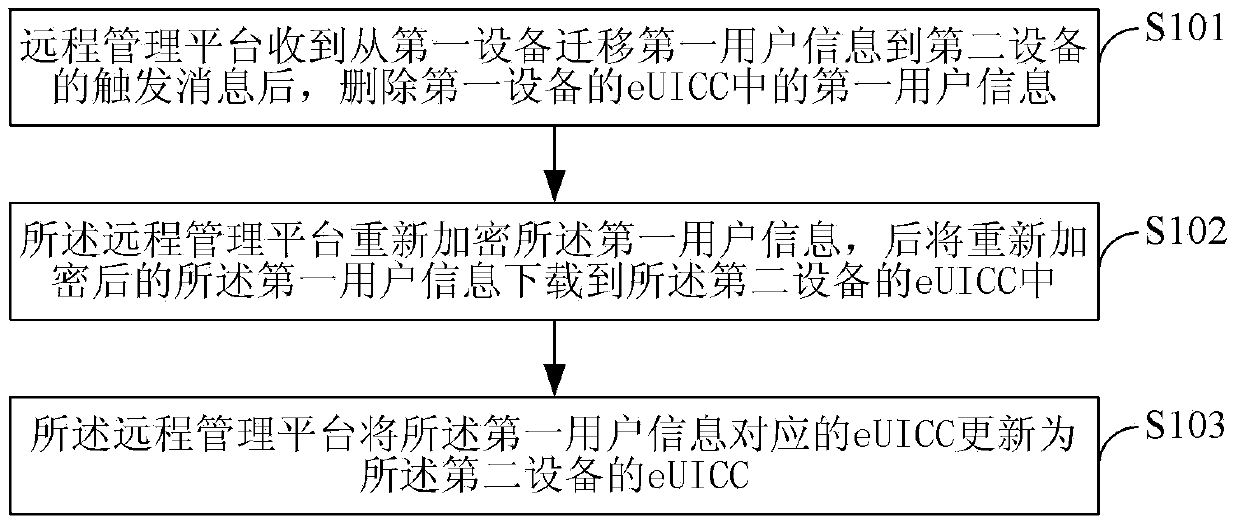
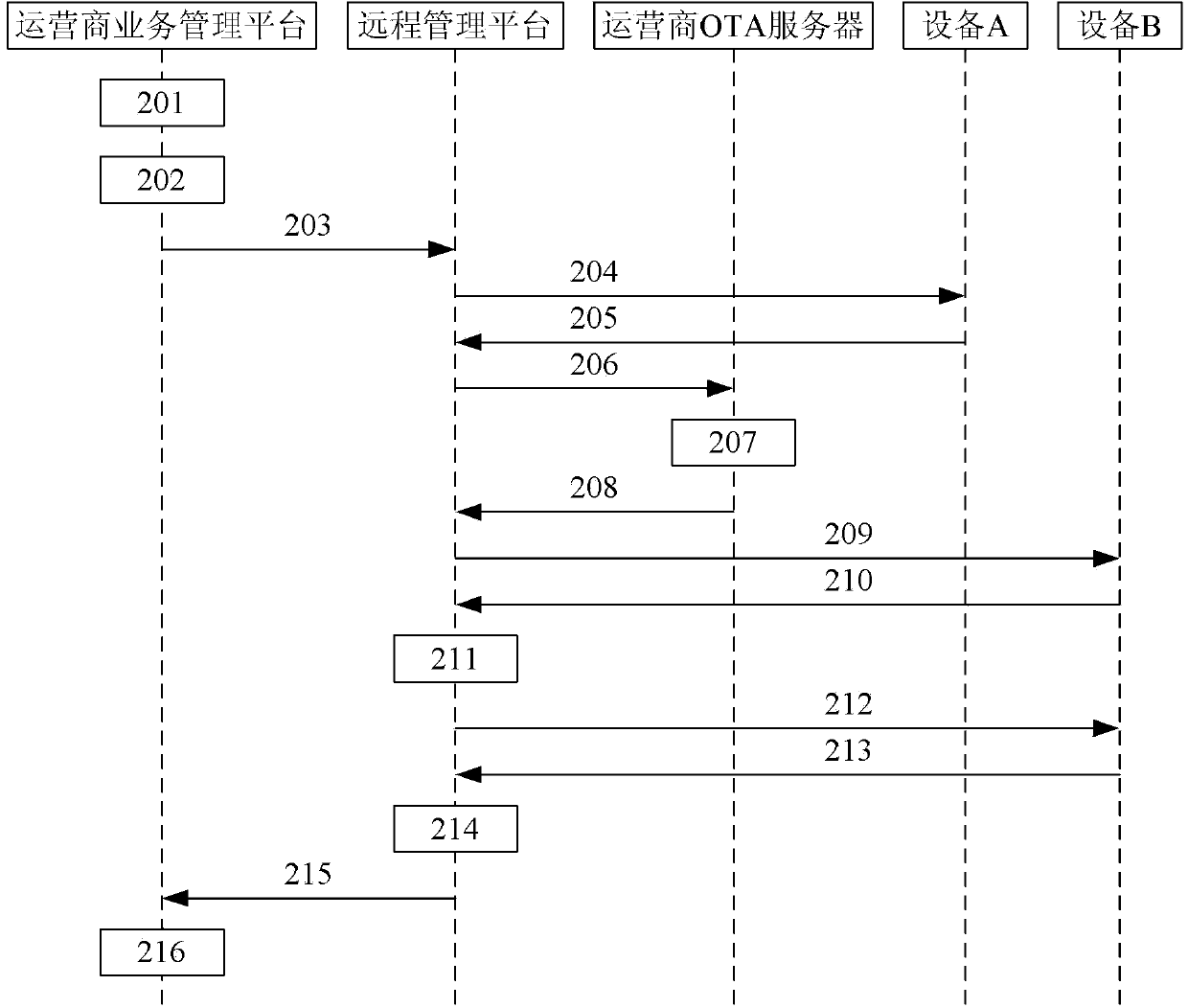
Method and system for migrating user information among internet of things equipment
The invention provides a method and a system for migrating user information among internet of things equipment. The method comprises the steps of deleting first user information in an embedded universal integrated circuit card eUICC of first equipment after a remote management platform receives trigger information of migrating the first user information from the first equipment to second equipment; after the first user information is successfully deleted, encrypting the first user information again by the remote management platform, and downloading the first user information which is re-encrypted to an eUICC of the second equipment; updating the eUICC corresponding to the first user information into the eUICC of the second equipment by the remote management platform. According to the system and the method, the interoperability of the user information in the eUICCs of different internet of things equipment is realized.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
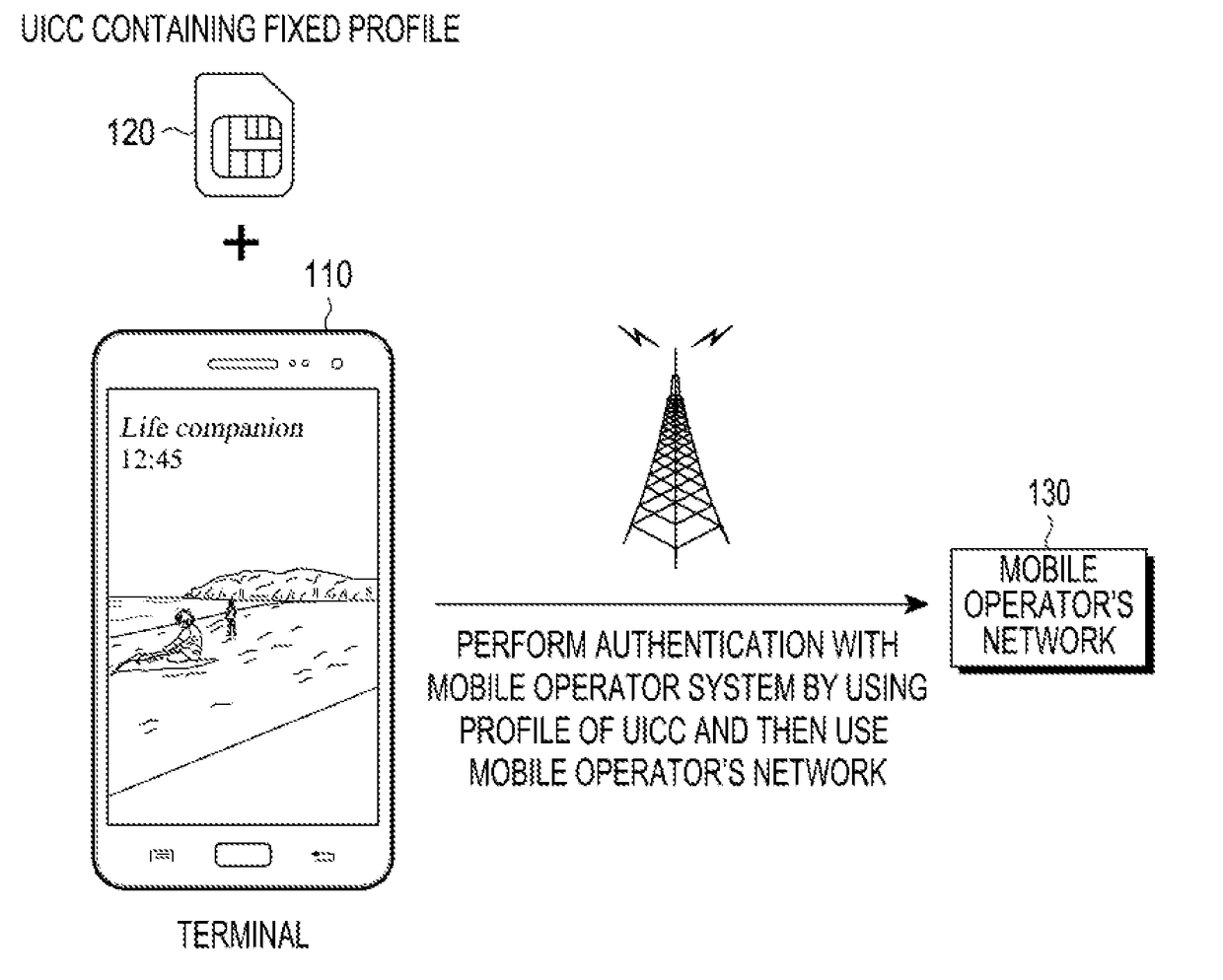
Device and operation method thereof
InactiveUS20160330608A1Security arrangementMachine-to-machine/machine-type communication serviceComputer hardwareCommunication unit
A device is disclosed. The device includes a communication unit configured to transmit a subscription request to a primary subscriber device and receive a provisioning profile in response to the subscription request and a universal integrated circuit card (UICC) configured to be provisioned based on the received provisioning profile.
Owner:SAMSUNG ELECTRONICS CO LTD
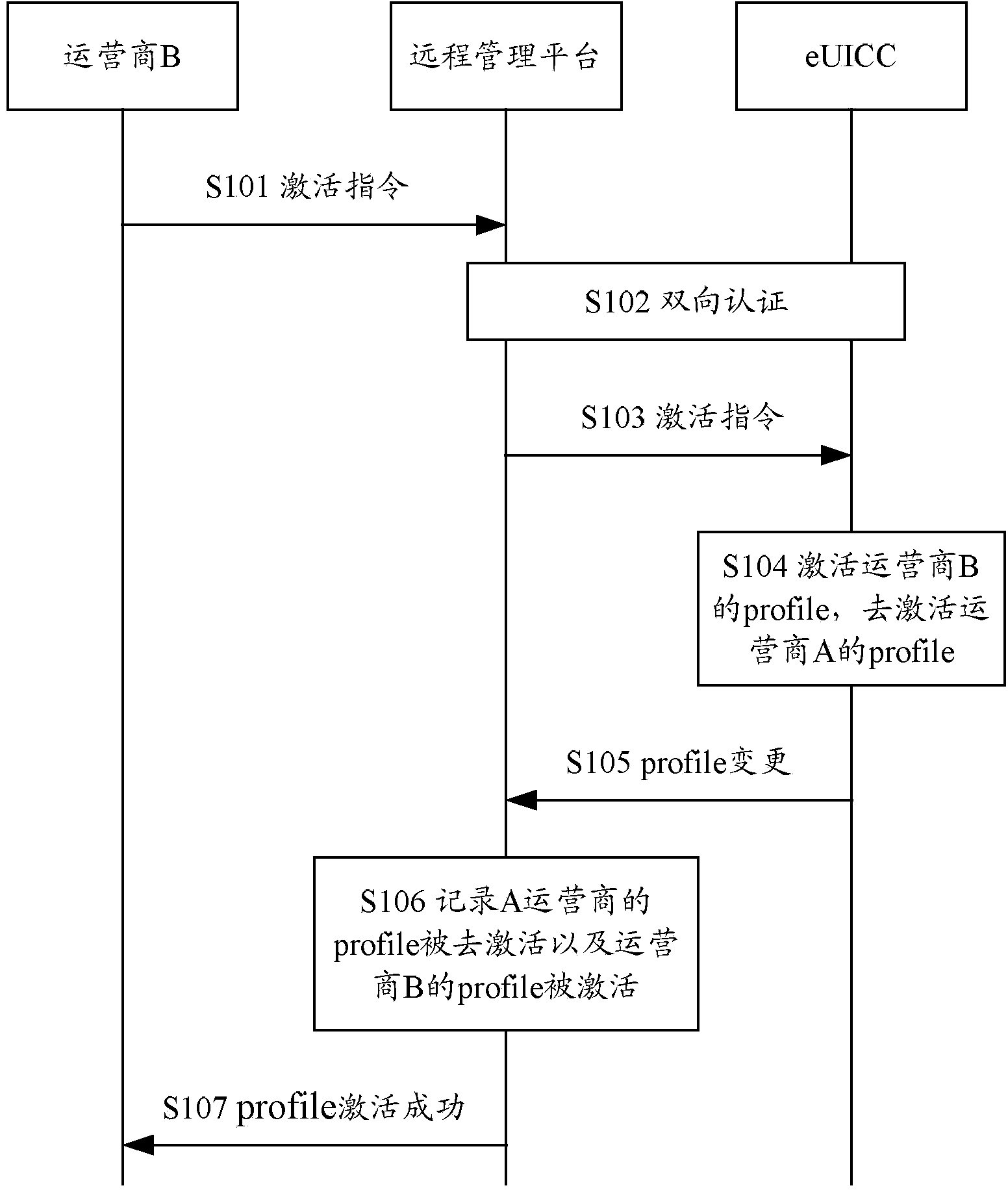
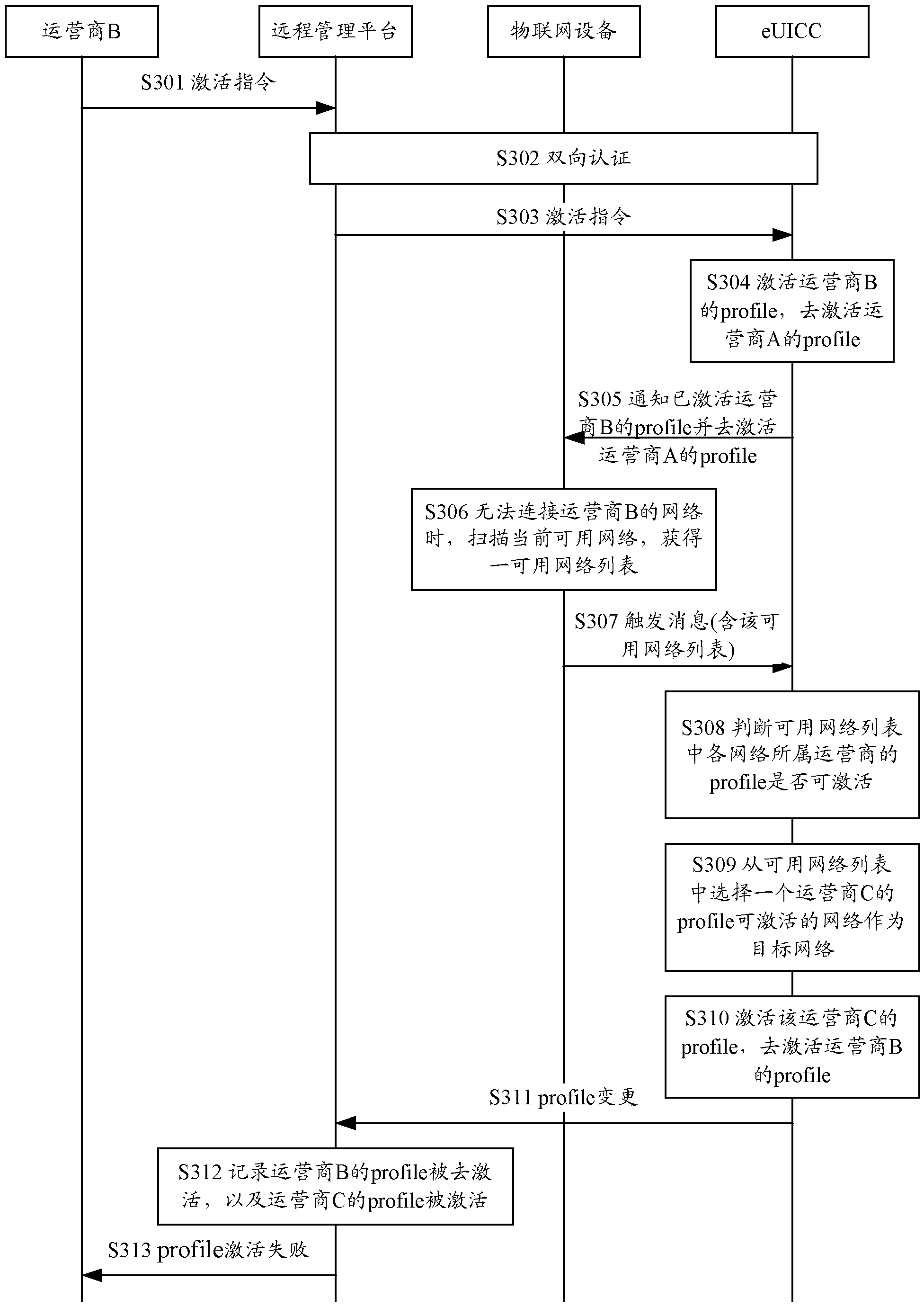
Profile activation system, eUICC and profile activation method of eUICC
InactiveCN103533634AAvoid Cyber RisksTransmissionWireless communicationActivation methodThe Internet
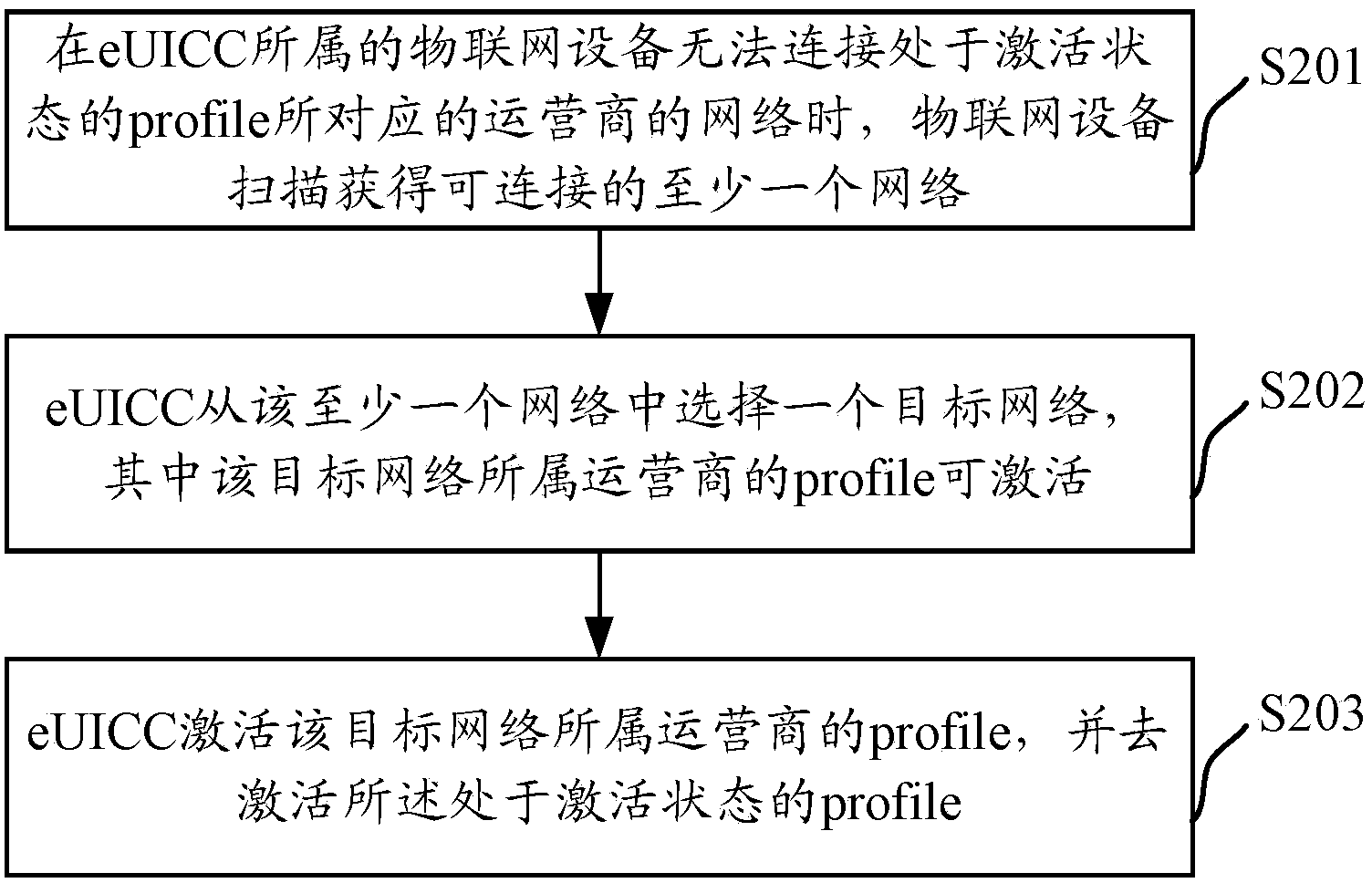
The invention discloses a profile activation system, an eUICC (Embedded Universal Integrated Circuit Card) and a profile activation method of the eUICC, which overcome the defect that Internet of Things equipment cannot access a corresponding network and cannot be connected with other networks possibly even the eUICC activates a profile successfully. The method comprises the steps that at least one connectable network is scanned and obtained when the Internet of Things equipment cannot be connected with the network of an operator corresponding to the profile in an activation state; the eUICC selects a target network from the at least one network, wherein a profile of the operator to which the target network belongs is activatable; and the eUICC activates the profile of the operator to which the target network belongs and activates the profile in the activation state. According to the system, the eUICC and the method, a risk that the Internet of Things equipment cannot be connected to the networks of any other operators possibly when the Internet of Things equipment cannot be connected with the network of the operator with the activated profile is avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
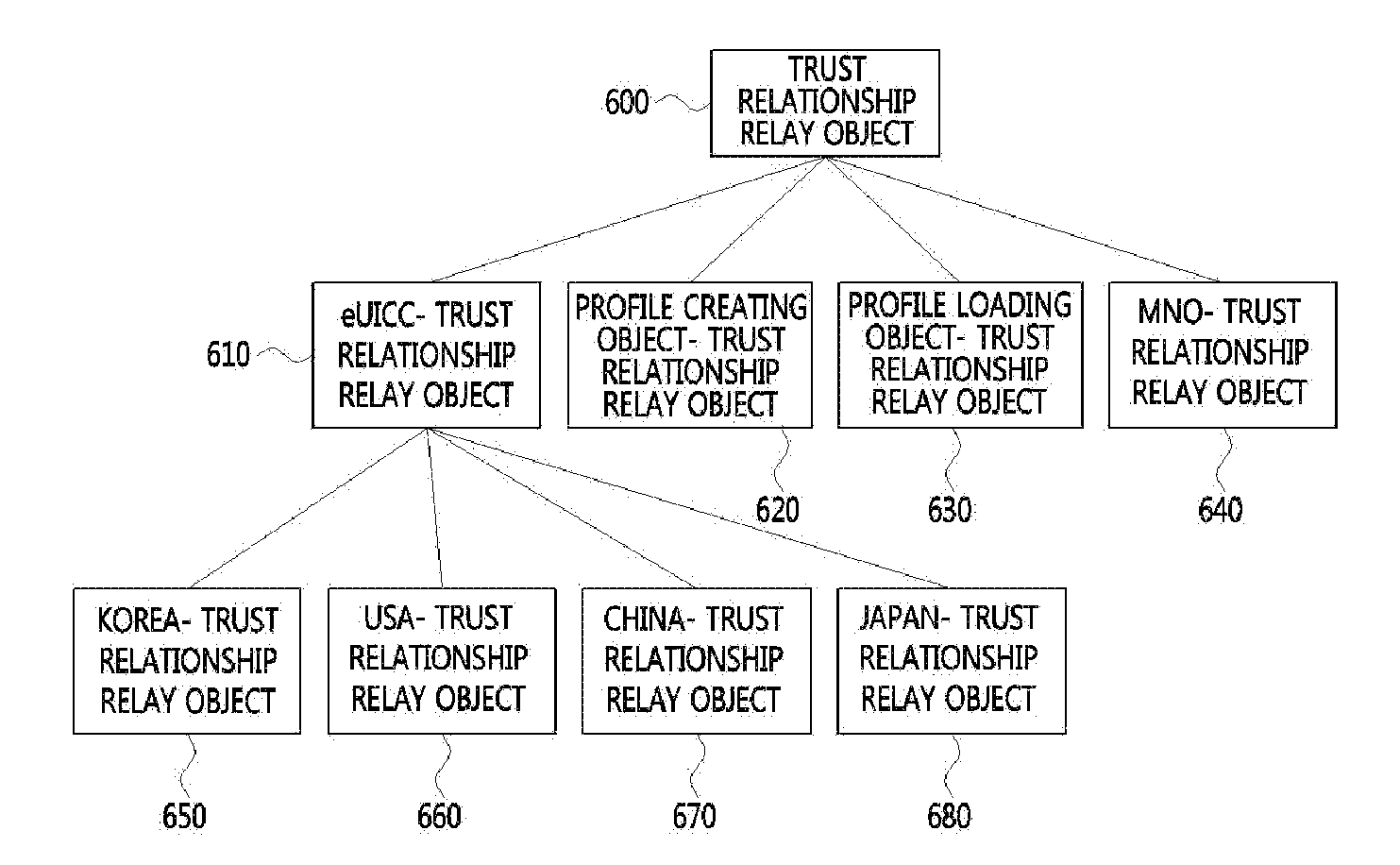
Method and apparatus of constructing secure infra-structure for using embedded universal integrated circuit card
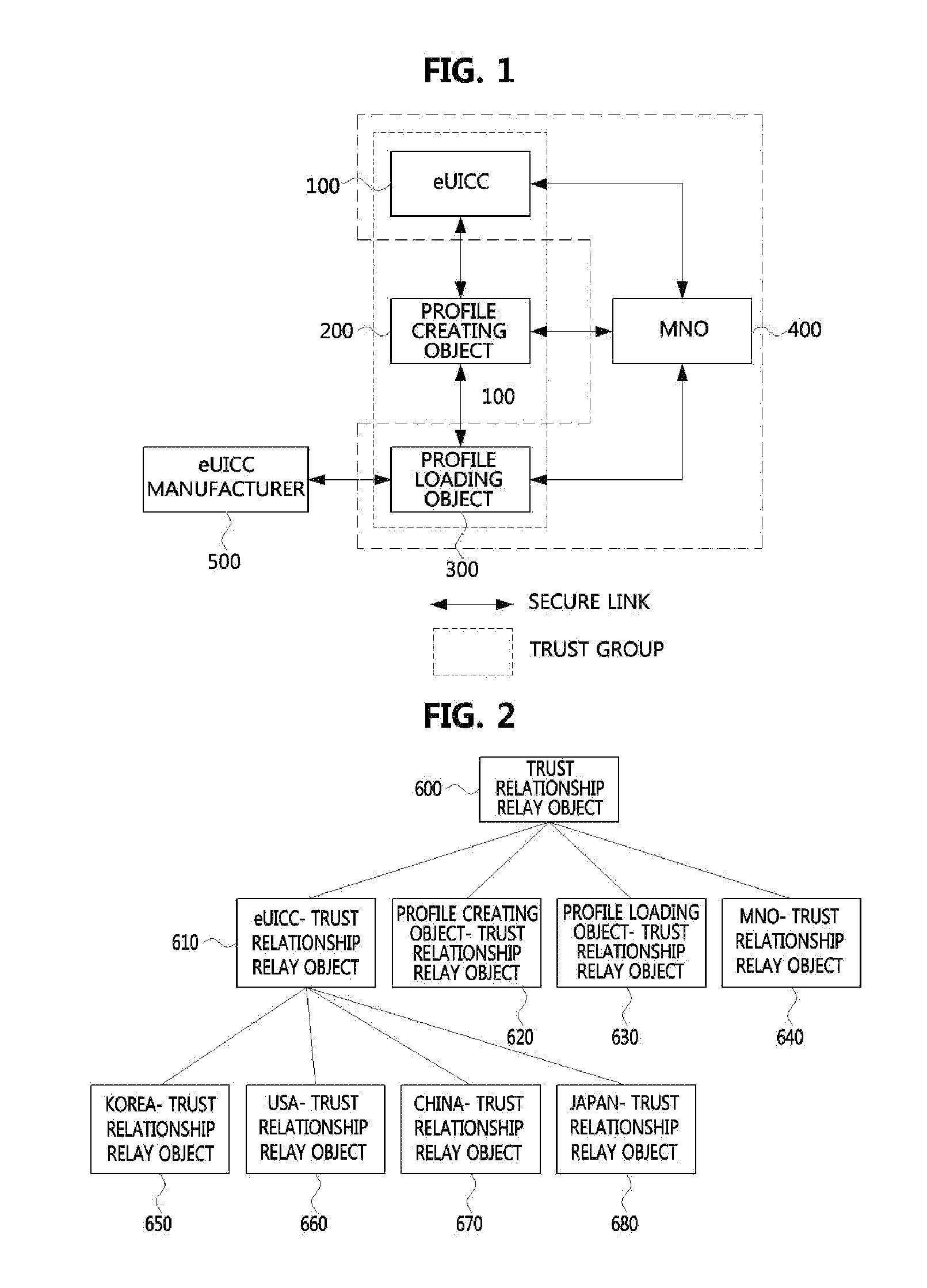
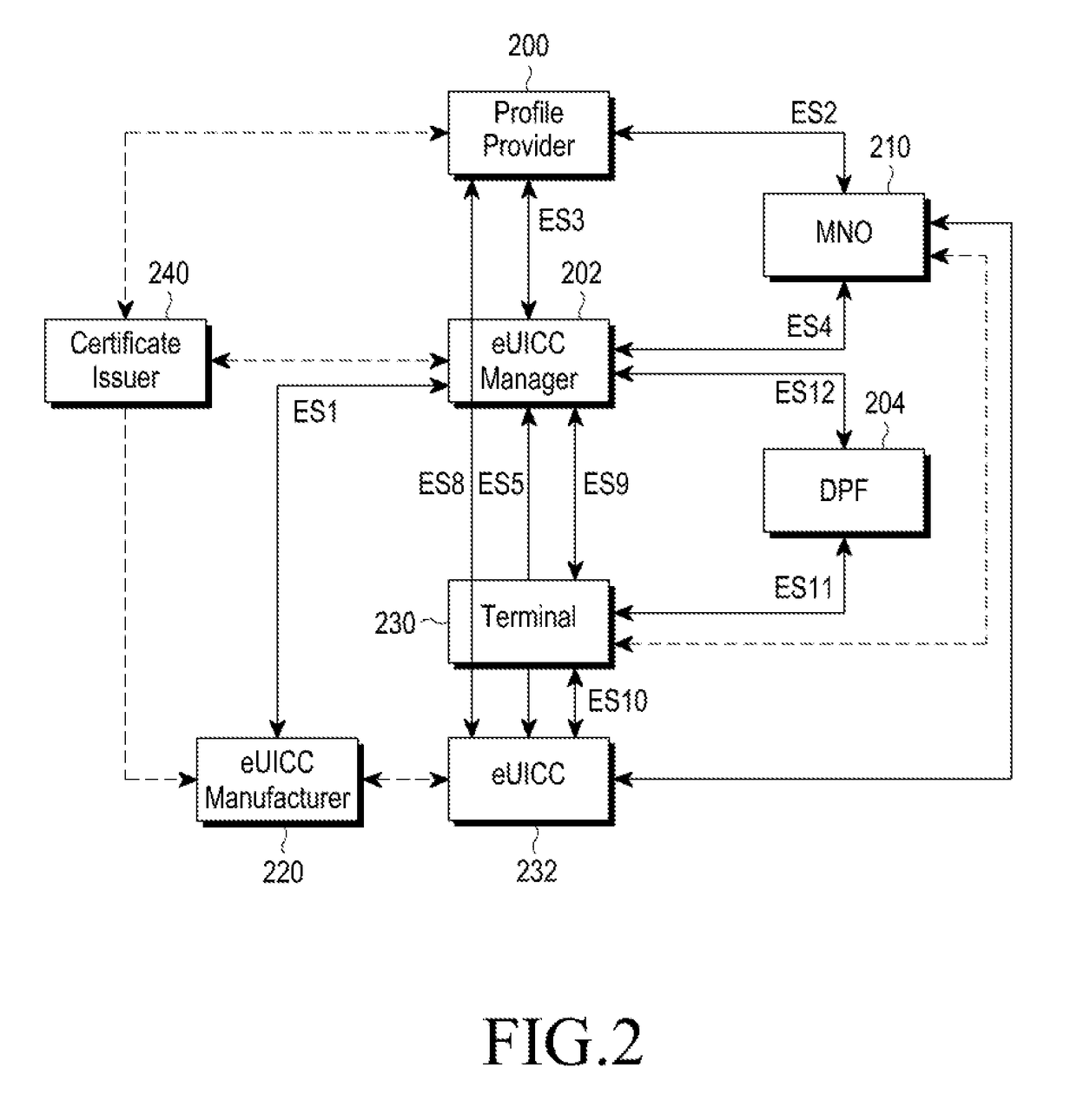
ActiveUS20130340040A1Improve the level ofFlexible authentication structureDigital data processing detailsMultiple digital computer combinationsInternet privacyTrust relationship
Provided are a method and device for building a security-based environment that uses an eUICC. A method of building a trust relationship in an eUICC environment includes transmitting, by a trust requesting object, a trust relationship requesting message including identification information and signature information of the trust requesting object to a trust verifying object, delivering, by the trust verifying object, the trust relationship requesting message to a trust relationship relay object and receiving trust information of the trust requesting object corresponding to the trust relationship requesting message from the trust relationship relay object, and verifying, by the trust verifying object, the signature information of the trust requesting object using the trust information of the trust requesting object.
Owner:SAMSUNG ELECTRONICS CO LTD
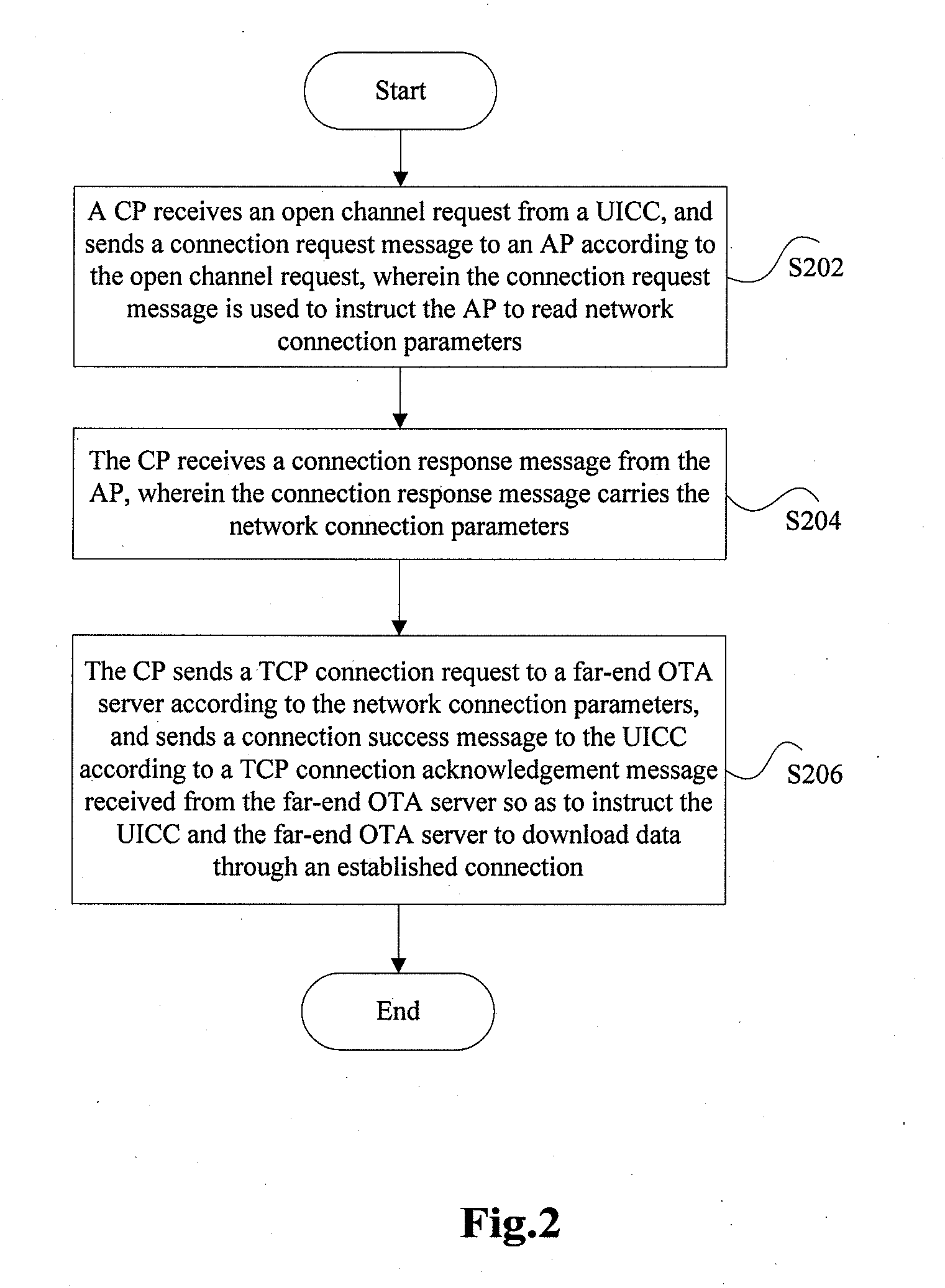
Data download method and terminal
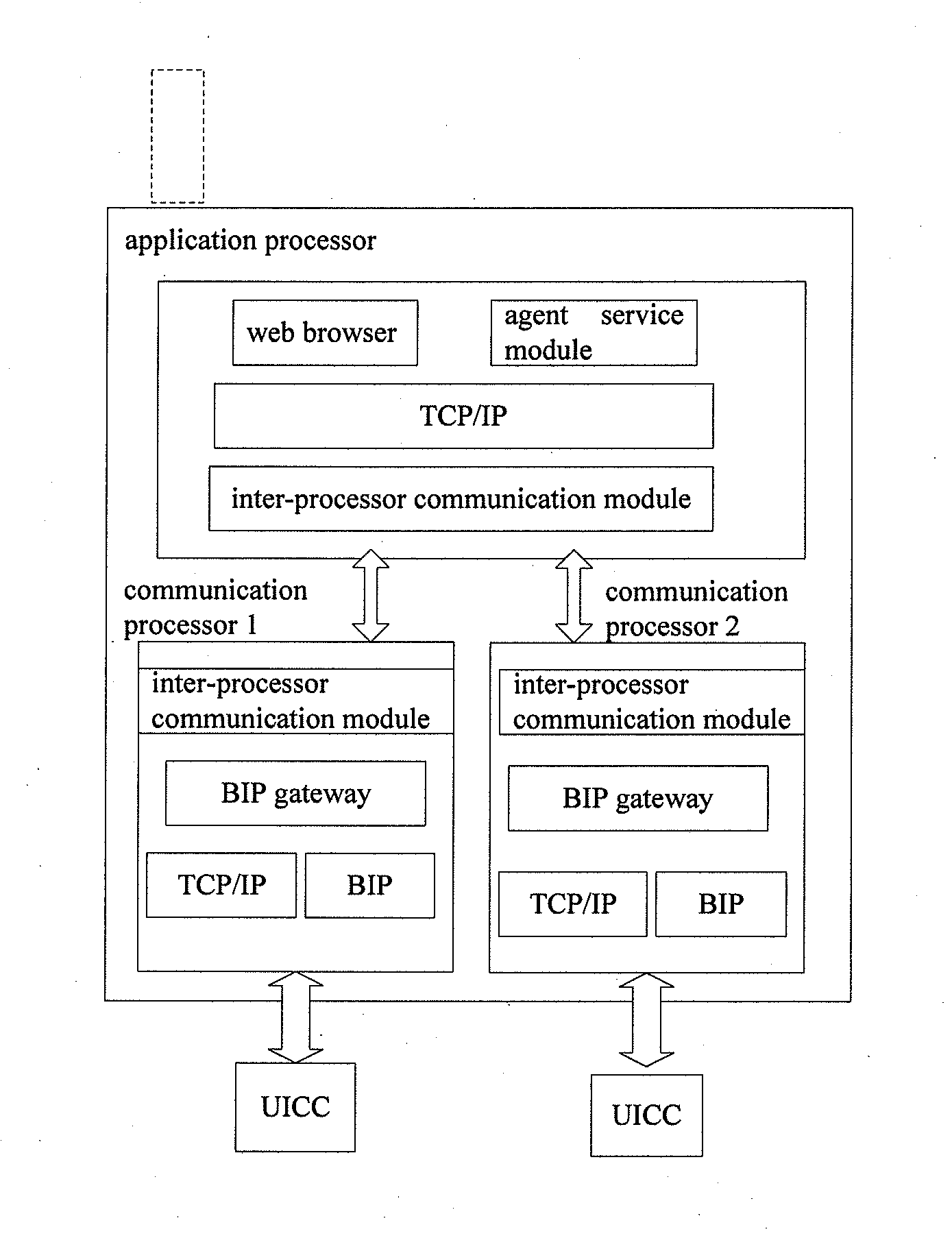
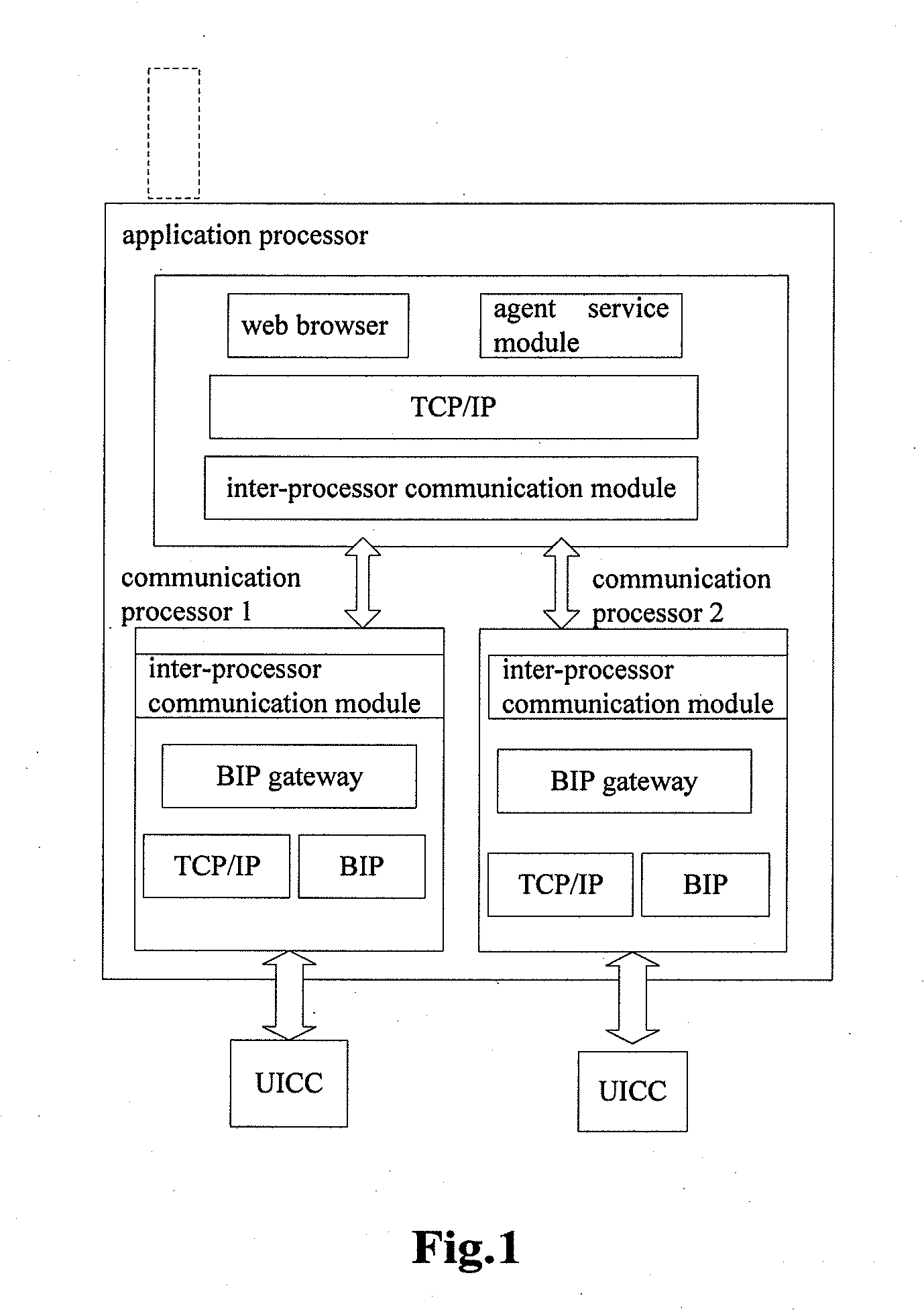
InactiveUS20120142332A1Solve the real problemService provisioningAutomatic exchangesComputer terminalProtocol for Carrying Authentication for Network Access
The present invention provides a data downloading method and a terminal, wherein the data downloading method includes: a communication processor receiving an open channel request from a universal integrated circuit card, and sending a connection request message to an application processor according to the open channel request; the communication processor sending a connection success message to the universal integrated circuit card, so as to instruct the universal integrated circuit card to download data The present invention not only enables a process of downloading an application over the air to the UICC by using the BIP (bearer independent protocol) protocol to be completed in a single processor, but also supports the process to be completed in multiple processors.
Owner:ZTE CORP
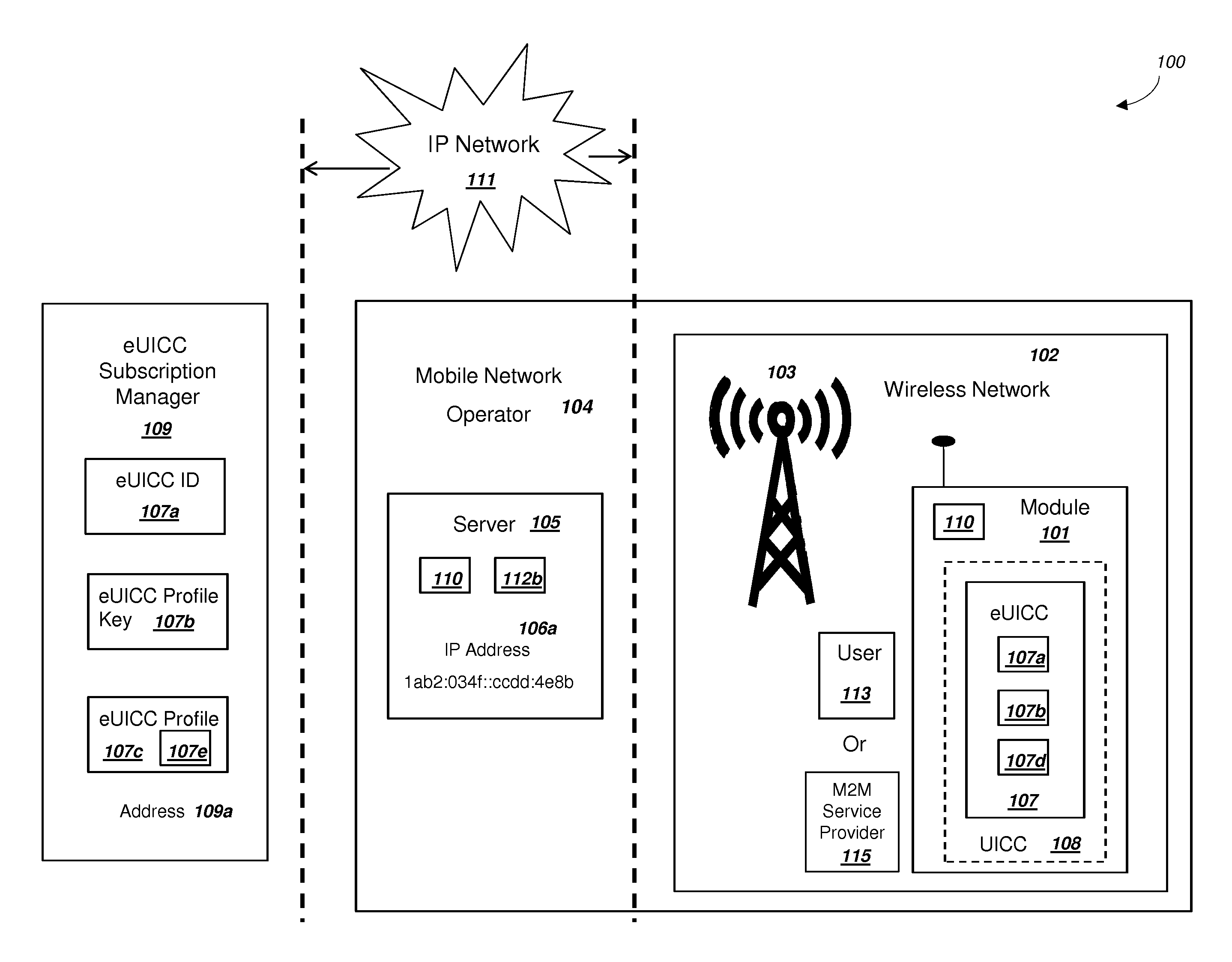
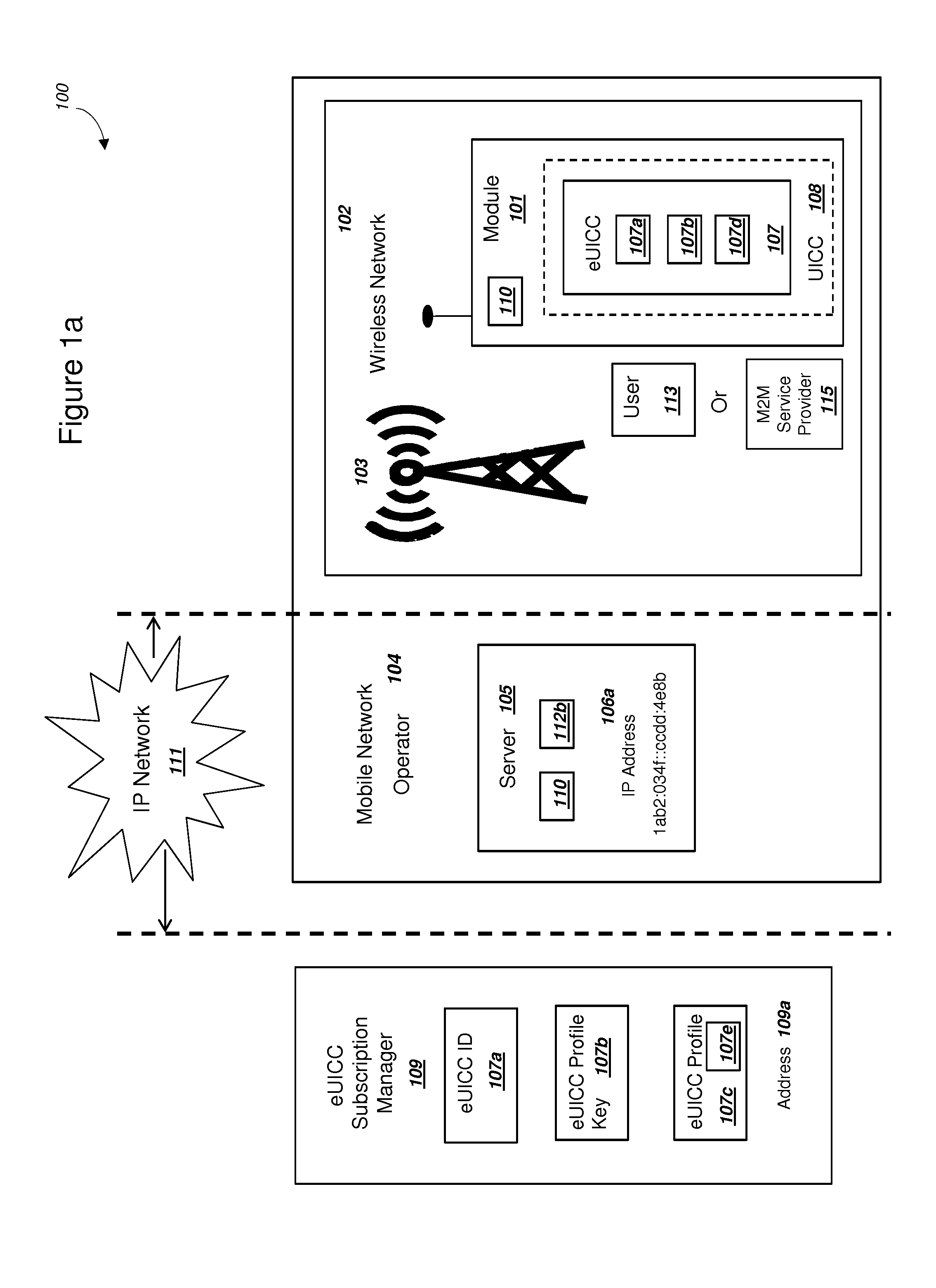
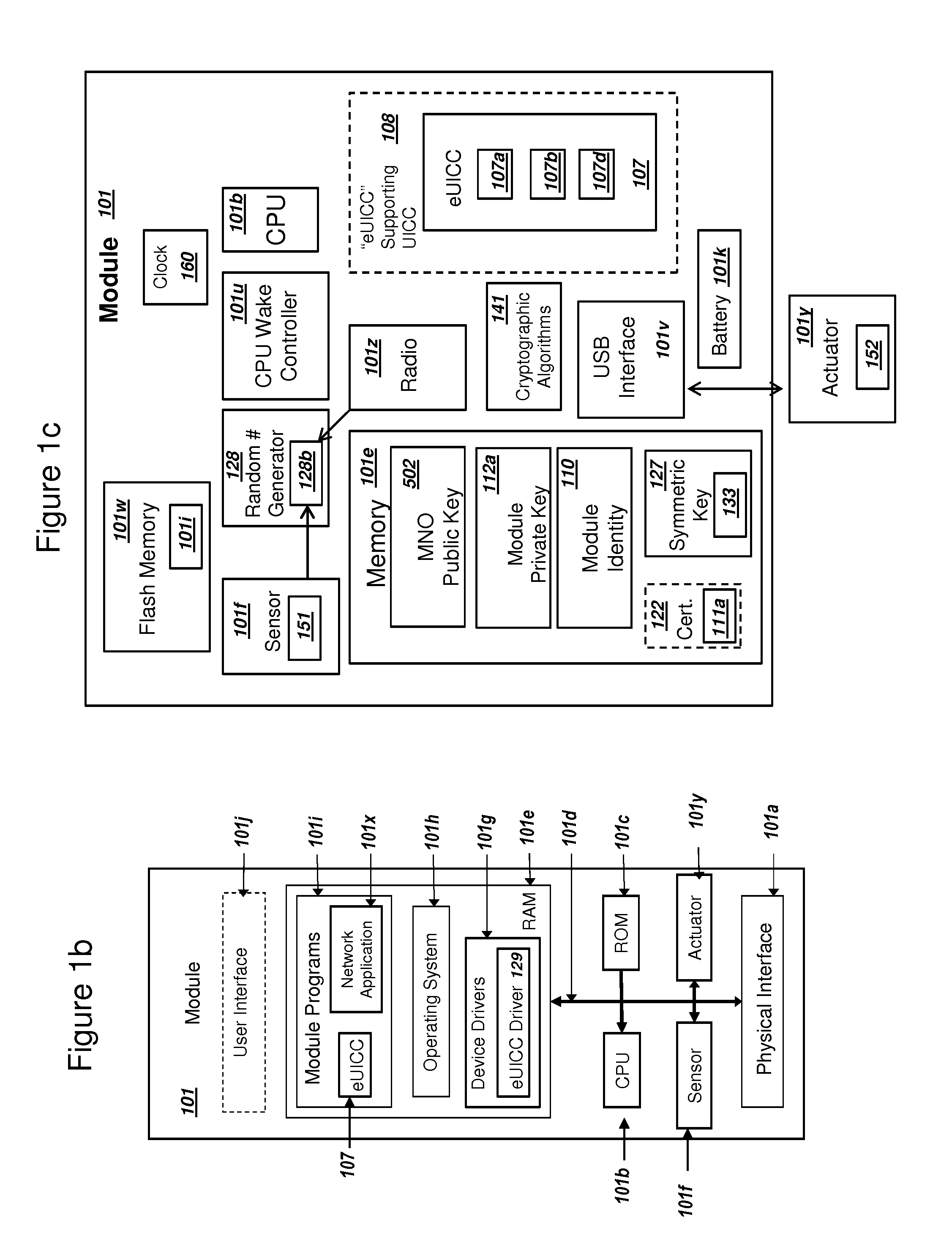
Network Supporting Two-Factor Authentication for Modules with Embedded Universal Integrated Circuit Cards
ActiveUS20150180847A1Improve the usefulnessIncrease valueUser identity/authority verificationSecurity arrangementKey authenticationEmbedded system
A network with a set of servers can support authentication from a module, where the module includes an embedded universal integrated circuit card (eUICC). The network can send a first network module identity, a first key K, and an encrypted second key K for an eUICC profile to an eUICC subscription manager. The second key K can be encrypted with a symmetric key. The module can receive and activate the eUICC profile, and the network can authenticate the module using the first network module identity and the first key K. The network can (i) authenticate the user of the module using a second factor, and then (ii) send the symmetric key to the module. The module can decrypt the encrypted second key K using the symmetric key. The network can authenticate the module using the second key K. The module can comprise a mobile phone.
Owner:NIX JOHN A +1
System and methods for dynamic SIM provisioning on a dual-SIM wireless communication device
ActiveUS9451098B2Accounting/billing servicesSubstation equipmentComputer hardwareCredential management
Methods and devices for dynamic VSIM provisioning on a multi-SIM wireless device having a first SIM as a Universal Integrated Circuit Card (UICC) and a virtual SIM (VSIM). A provisioning server may receive updated information from the wireless device, and based at least partially on the received information, determine whether the SIM profile on the VSIM of the wireless device should be changed. To change the SIM profile, the provisioning server may determine whether remote credential management procedures are enabled. If so, the provisioning server may select a new SIM profile from a plurality of SIM profiles, and provision the new SIM profile in the VSIM using remote credential management procedures. If remote credential management procedures are unavailable, the provisioning server may select a remote SIM from a plurality of remote SIMs associated with the provisioning server, and run the remote SIM to execute authentication processes for the wireless device.
Owner:QUALCOMM INC
Technique for managing profile in communication system
ActiveUS20180123803A1Multiple keys/algorithms usagePublic key for secure communicationCommunications systemMobile communication systems
Disclosed are: a communication technique and a system therefor for fusing, with IoT technology, a 5G communication system for supporting a data transmission rate higher than that of a 4G system. Provided is a method for installing a profile of a terminal having an embed universal integrated circuit card (eUICC) in a mobile communication system, the method comprising: requesting for an eUICC authentication certificate to an eUICC and receiving the eUICC authentication certificate; and transferring a profile package to the eUICC so as to install a profile, wherein the received eUICC authentication certificate further comprises an eUICC manufacturer (EUM) authentication certificate.
Owner:SAMSUNG ELECTRONICS CO LTD
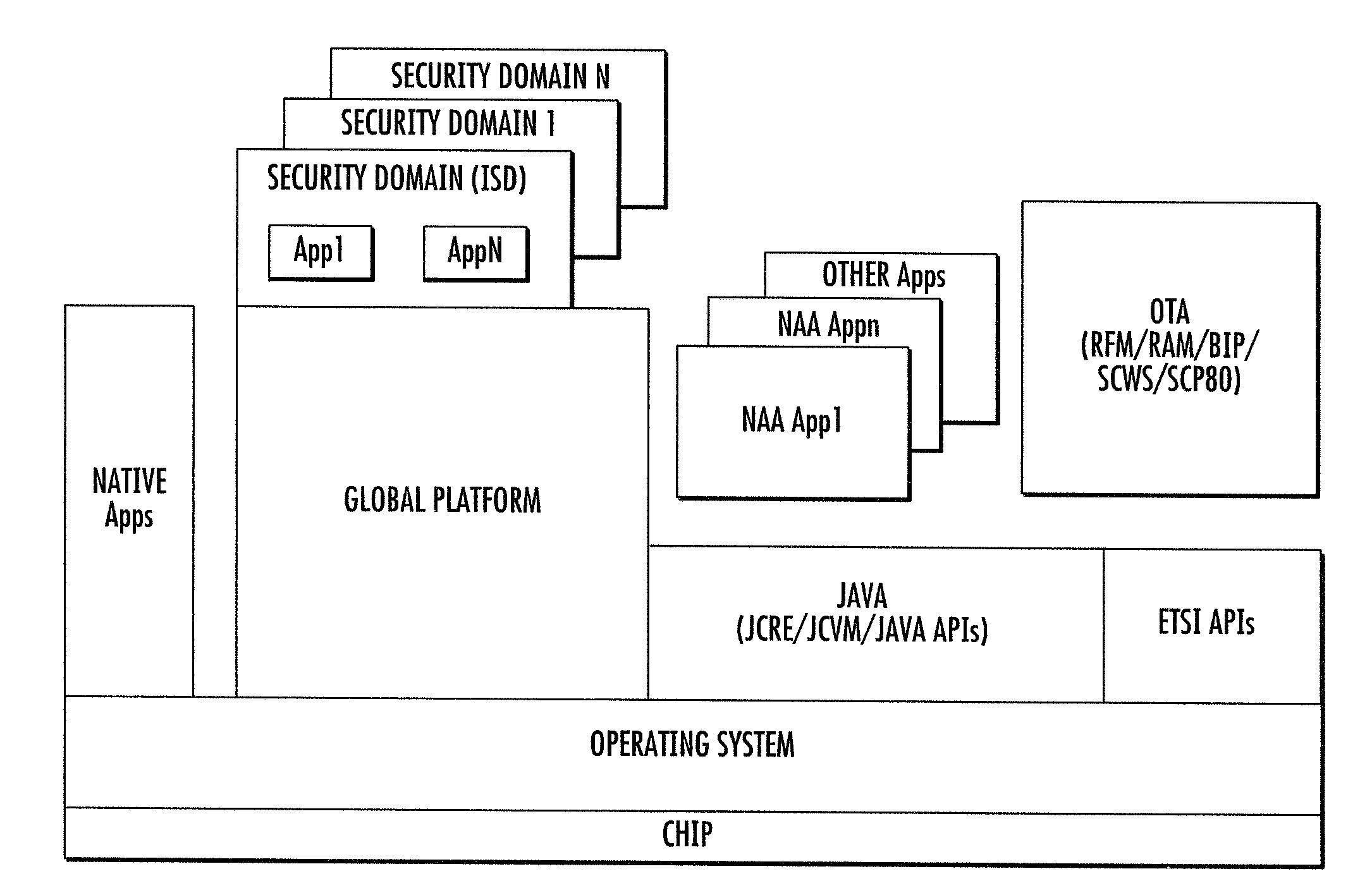
Apparatus and Method for Managing Security Domains for a Universal Integrated Circuit Card
ActiveUS20170295158A1Service provisioningInternal/peripheral component protectionStructure of Management InformationSecurity domain
A device that incorporates the subject disclosure may perform, for example, generating a security domain root structure for a universal integrated circuit card of an end user device, where the security domain root structure includes a hierarchy of a link provider operator security domain above a mobile network operator trusted security domain, where the link provider operator security domain enables transport management by a link provider operator, and where the mobile network operator trusted security domain enables card content management and subscription eligibility verification by a mobile network operator trusted service manager. Other embodiments are disclosed.
Owner:AT&T INTPROP I LP
Management method for embedded universal integrated circuit card, related equipment and system
ActiveCN104703199ARealize batch managementImprove management efficiencyConnection managementSubstation equipmentCommunications systemPublic land mobile network
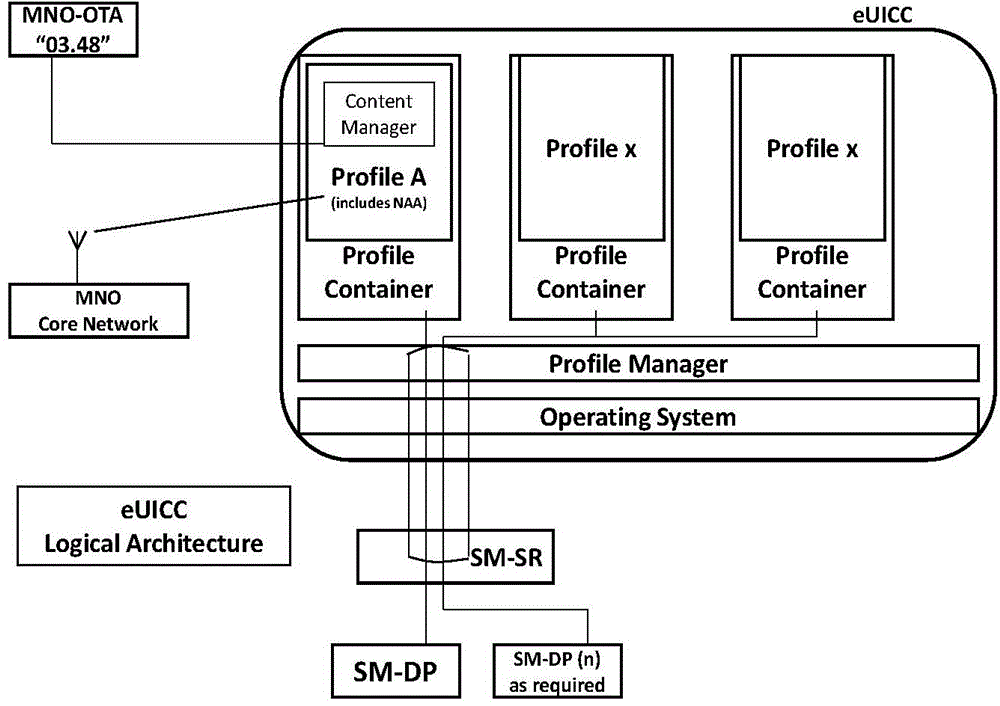
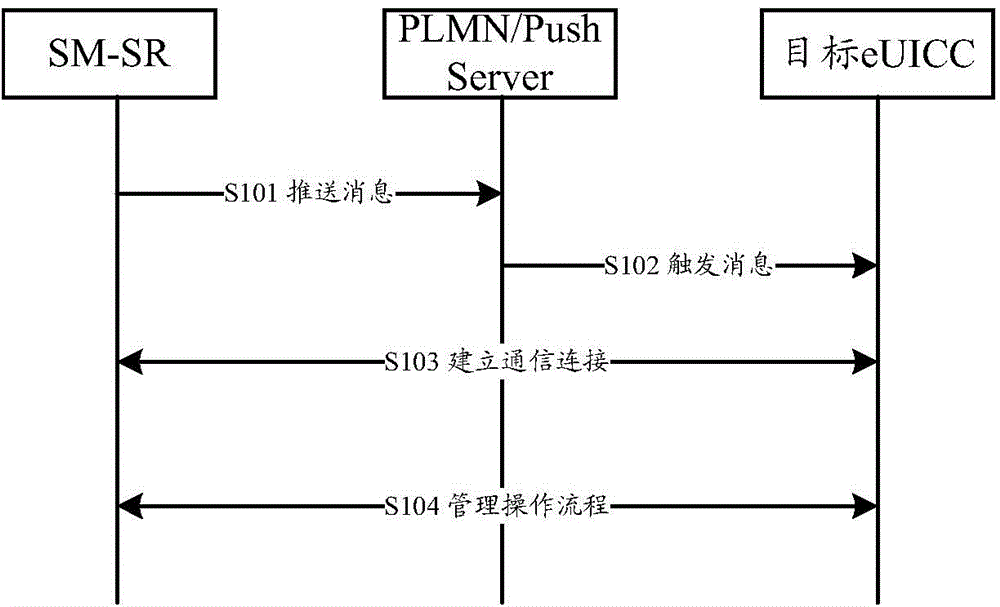
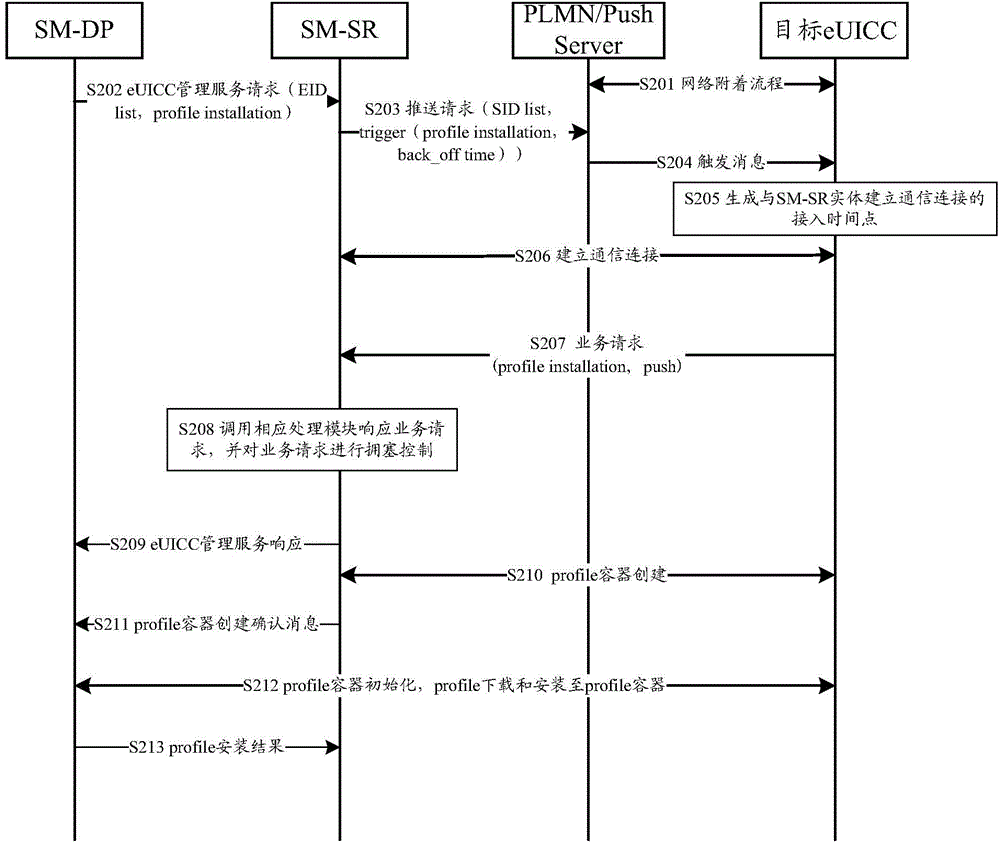
Disclosed is a management method for an embedded universal integrated circuit card (eUICC). The method comprises the following steps: sending, by a subscription manager-secure routing (SM-SR) entity, a push request comprising a trigger message and at least one user identifier to a public land mobile network (PLMN) / push server, so as to indicate that the PLMN / push server should push the trigger message to a target eUICC directed by the at least one user identifier, the trigger message being used to trigger the target eUICC to initiate communication with the SM-SR entity; establishing, by the SM-SR entity, a communication connection with the target eUICC; and executing, by the SM-SR entity, a management operation on the target eUICC by means of the communication connection. Also disclosed are a related device and a communication system. By means of the present invention, the batch management can be conducted on the eUICC, thereby improving the management efficiency.
Owner:HUAWEI DEVICE CO LTD
Mobile terminal with NFC function
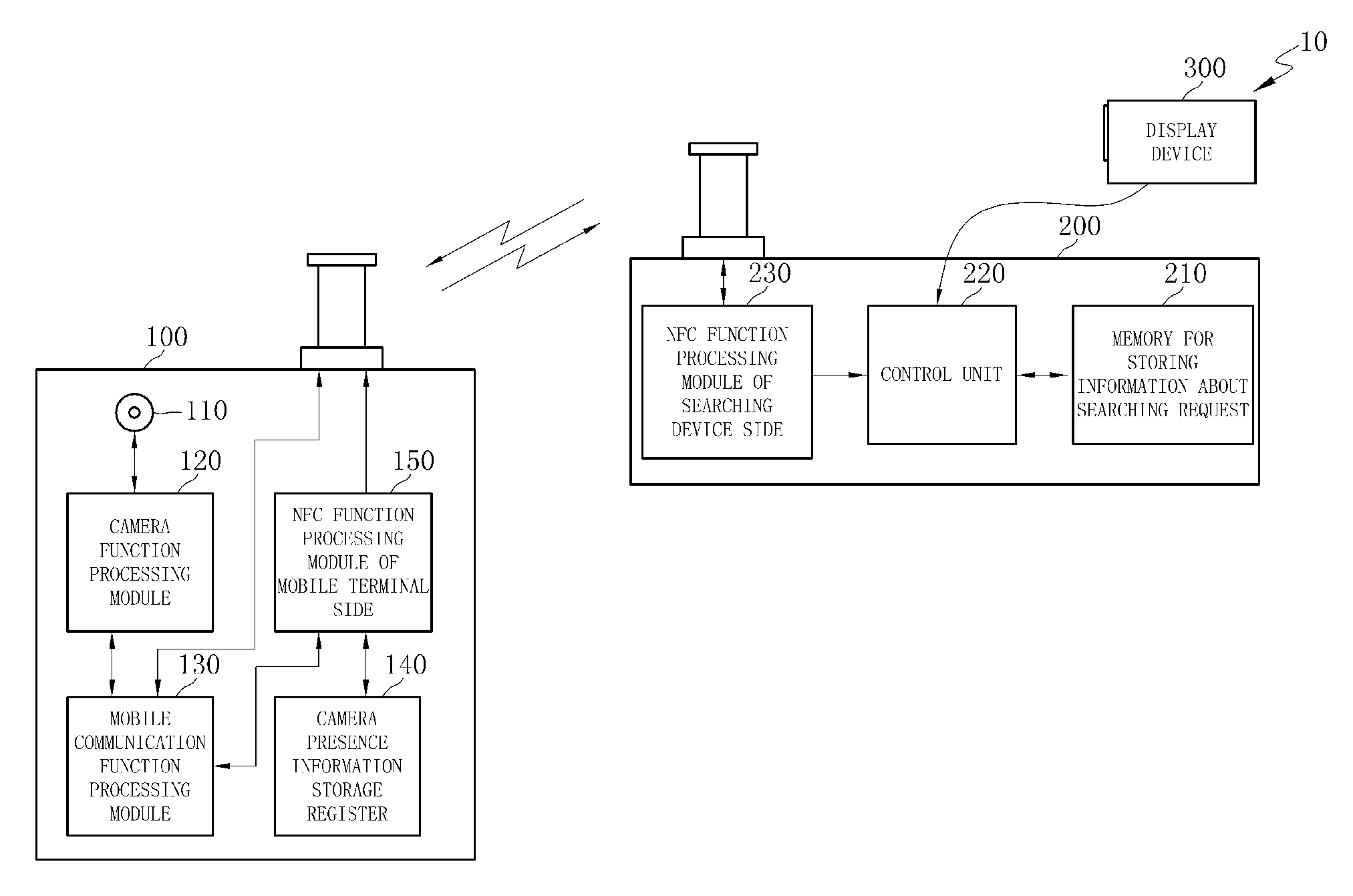
Disclosed herein is a mobile terminal with a Near Field Communication (NFC) function, the mobile terminal wirelessly connecting to a reader using NFC. An NFC controller wirelessly connects to the reader through an NFC antenna, and receives an Applet Identification (AID) signal and a function control signal used to control operational states of a plurality of functions provided to the mobile terminal from the reader. A base band unit receives the function control signal, and controls the operational states of functions selected from among the plurality of functions provided to and operated in the mobile terminal. A Universal Integrated Circuit Card (UICC) unit connects to the NFC controller, and records information about the subscriber of the mobile terminal. A Secure Element (SE) encodes and decodes the signal, which is transmitted and received between the mobile terminal and the reader, using a security algorithm.
Owner:AQ
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com