Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
682 results about "International mobile subscriber identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
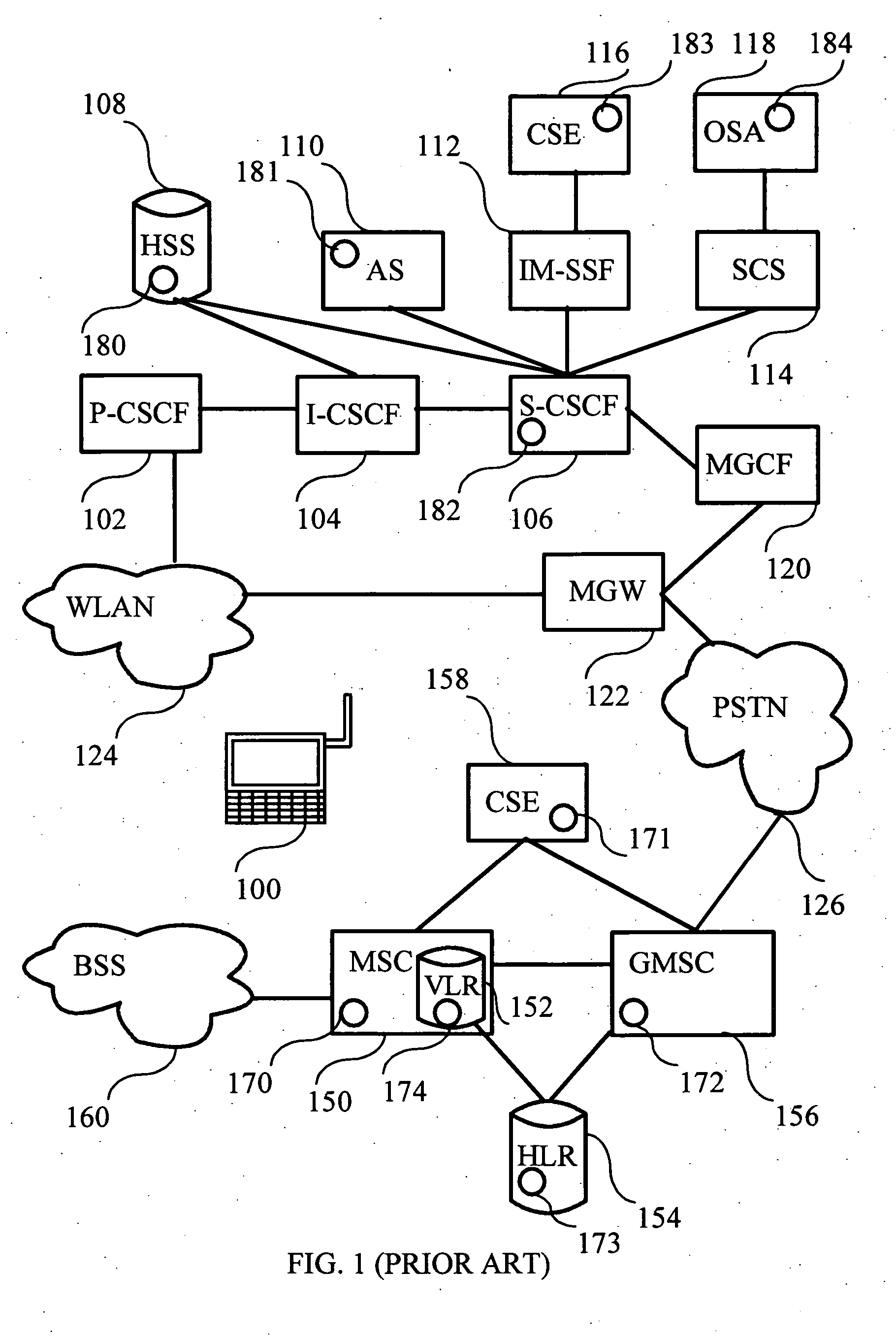
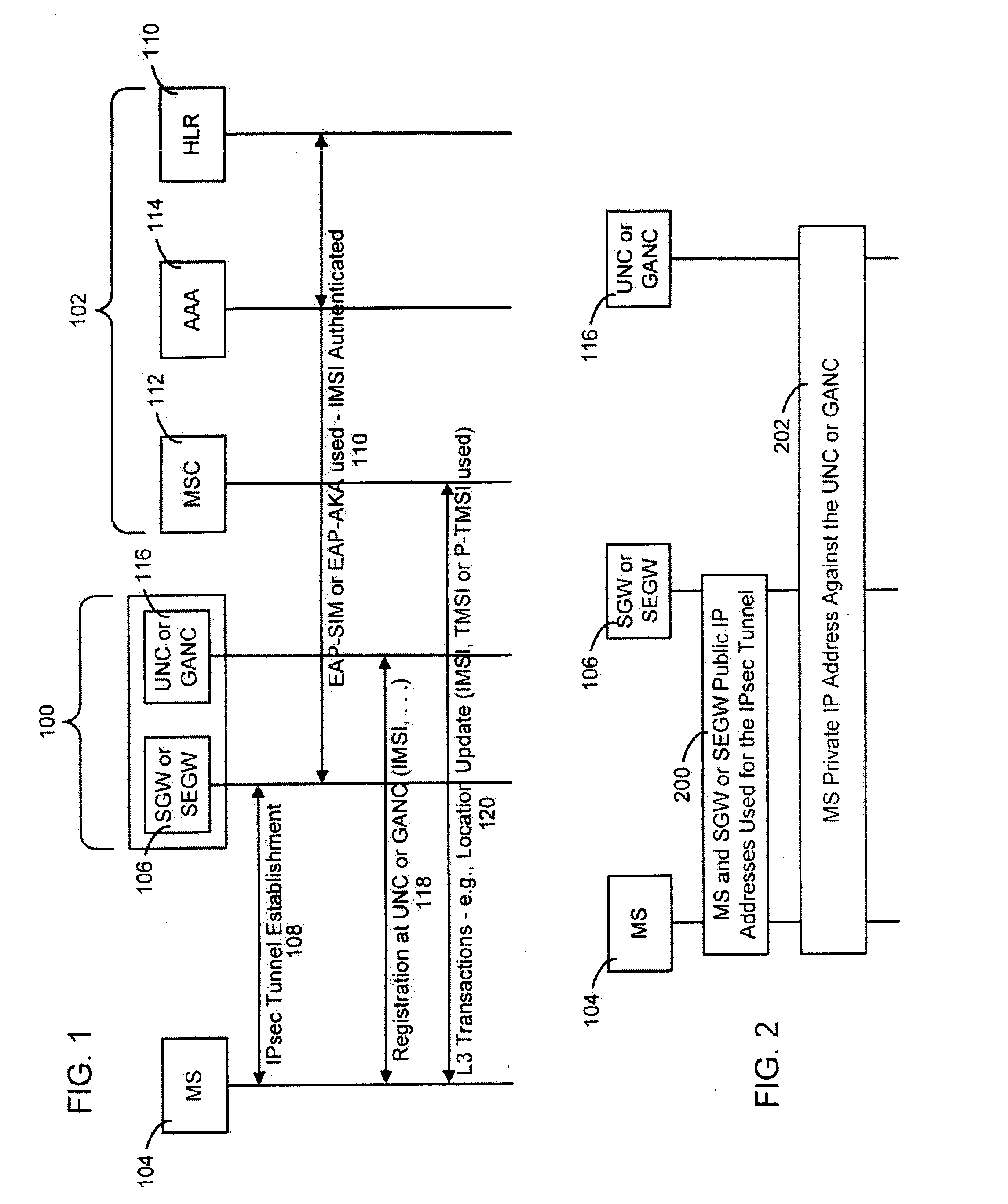
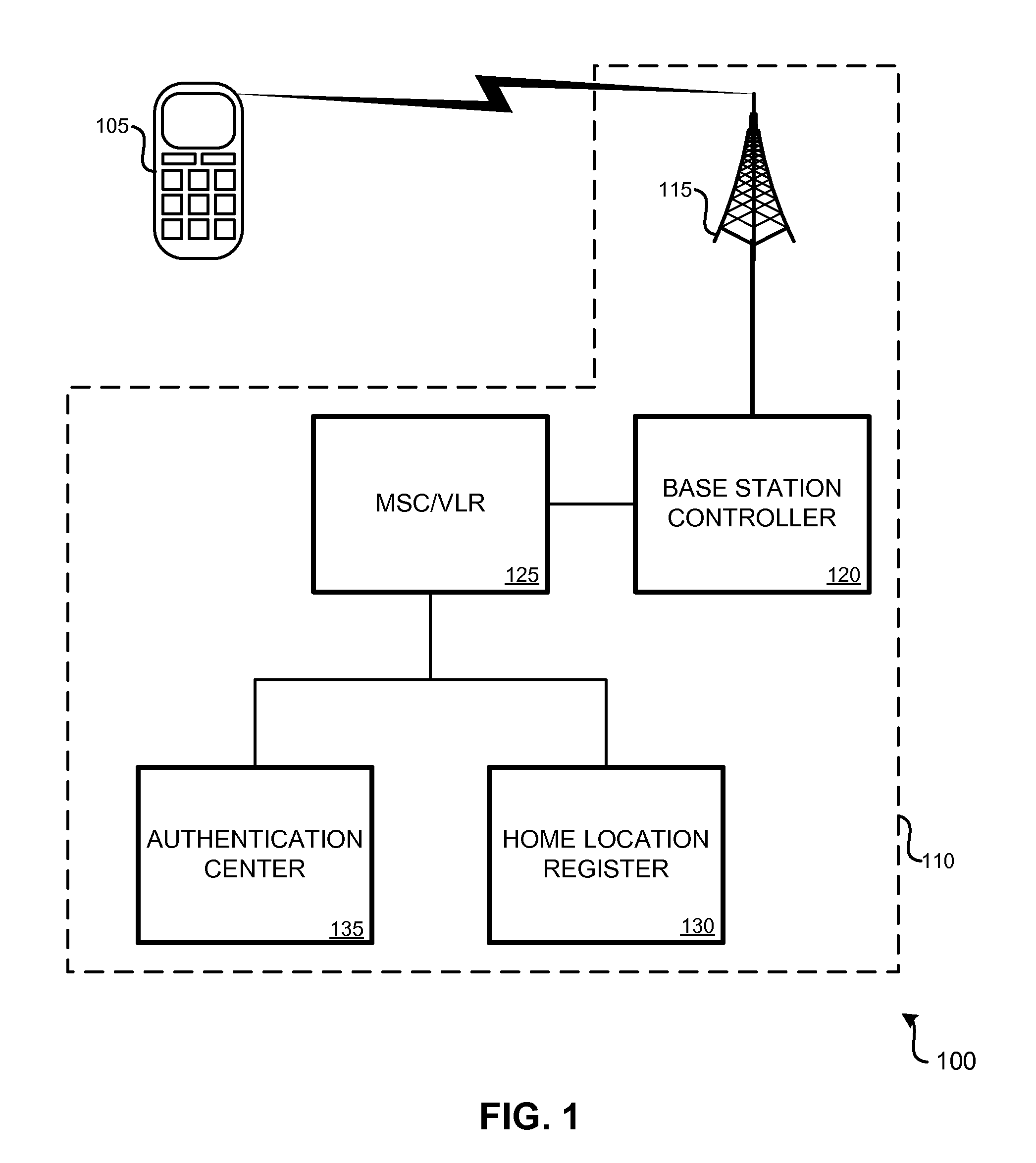
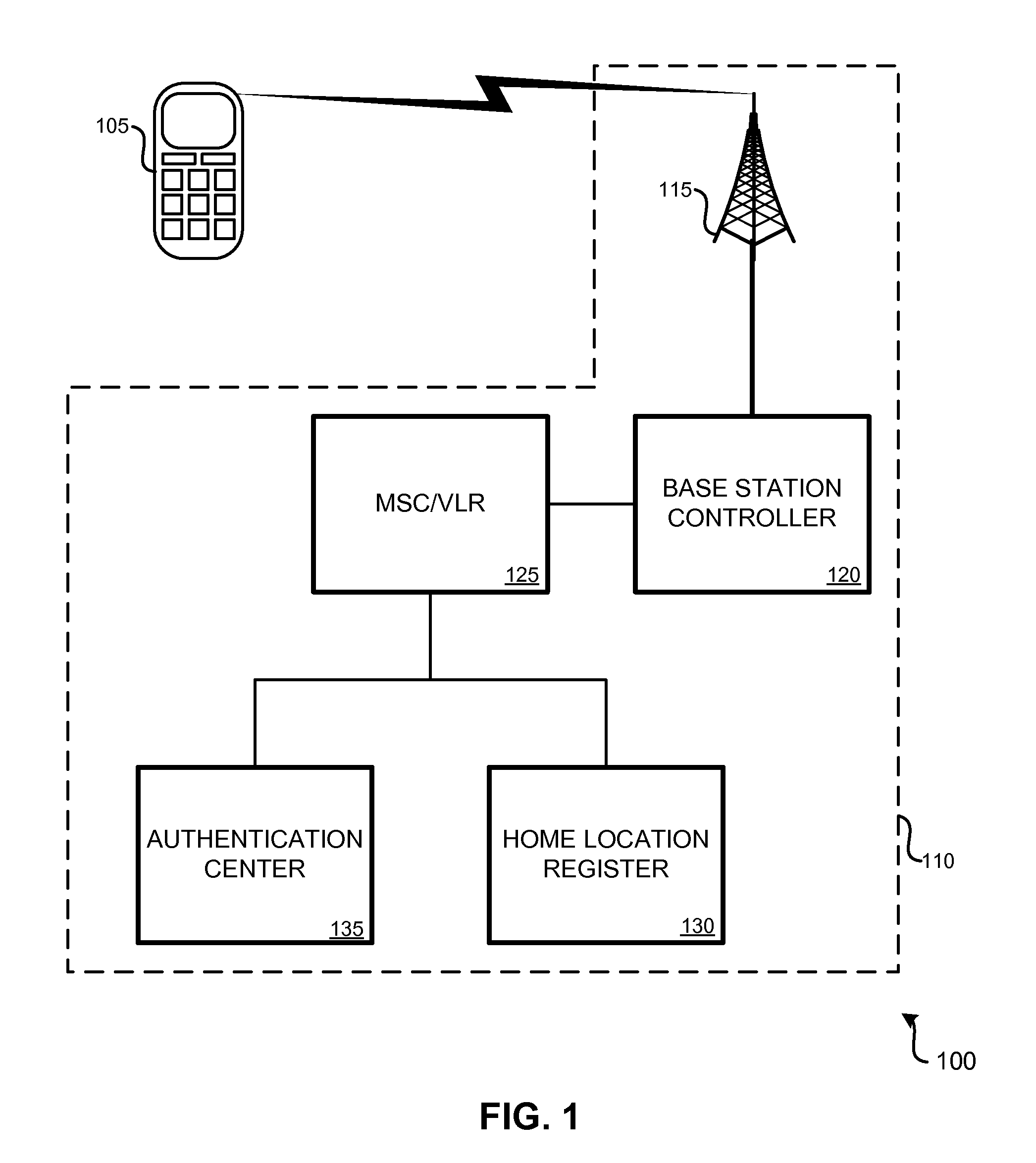
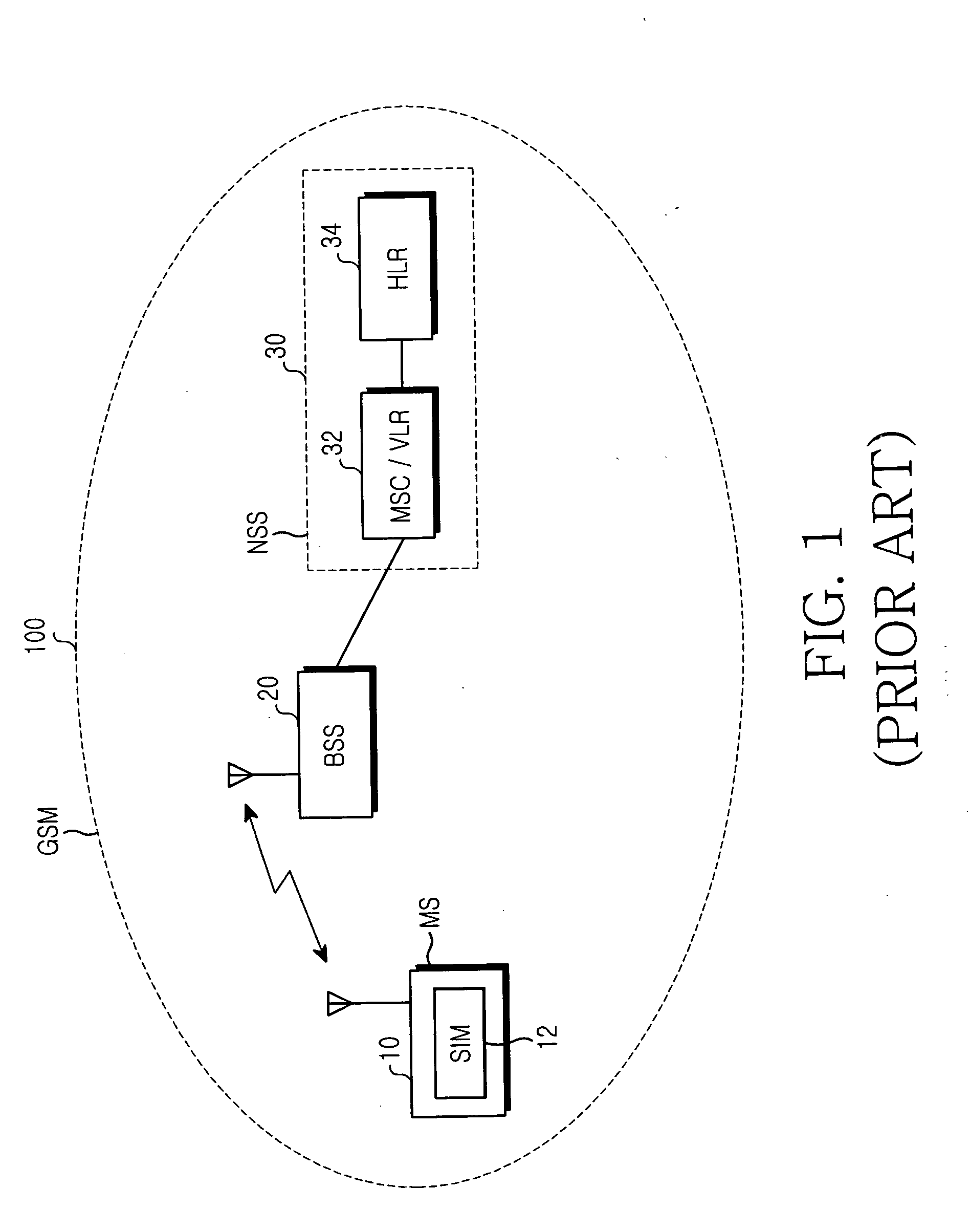
The international mobile subscriber identity or IMSI /ˈɪmziː/ is a number that uniquely identifies every user of a cellular network. It is stored as a 64-bit field and is sent by the mobile device to the network. It is also used for acquiring other details of the mobile in the home location register (HLR) or as locally copied in the visitor location register. To prevent eavesdroppers from identifying and tracking the subscriber on the radio interface, the IMSI is sent as rarely as possible and a randomly-generated TMSI is sent instead.
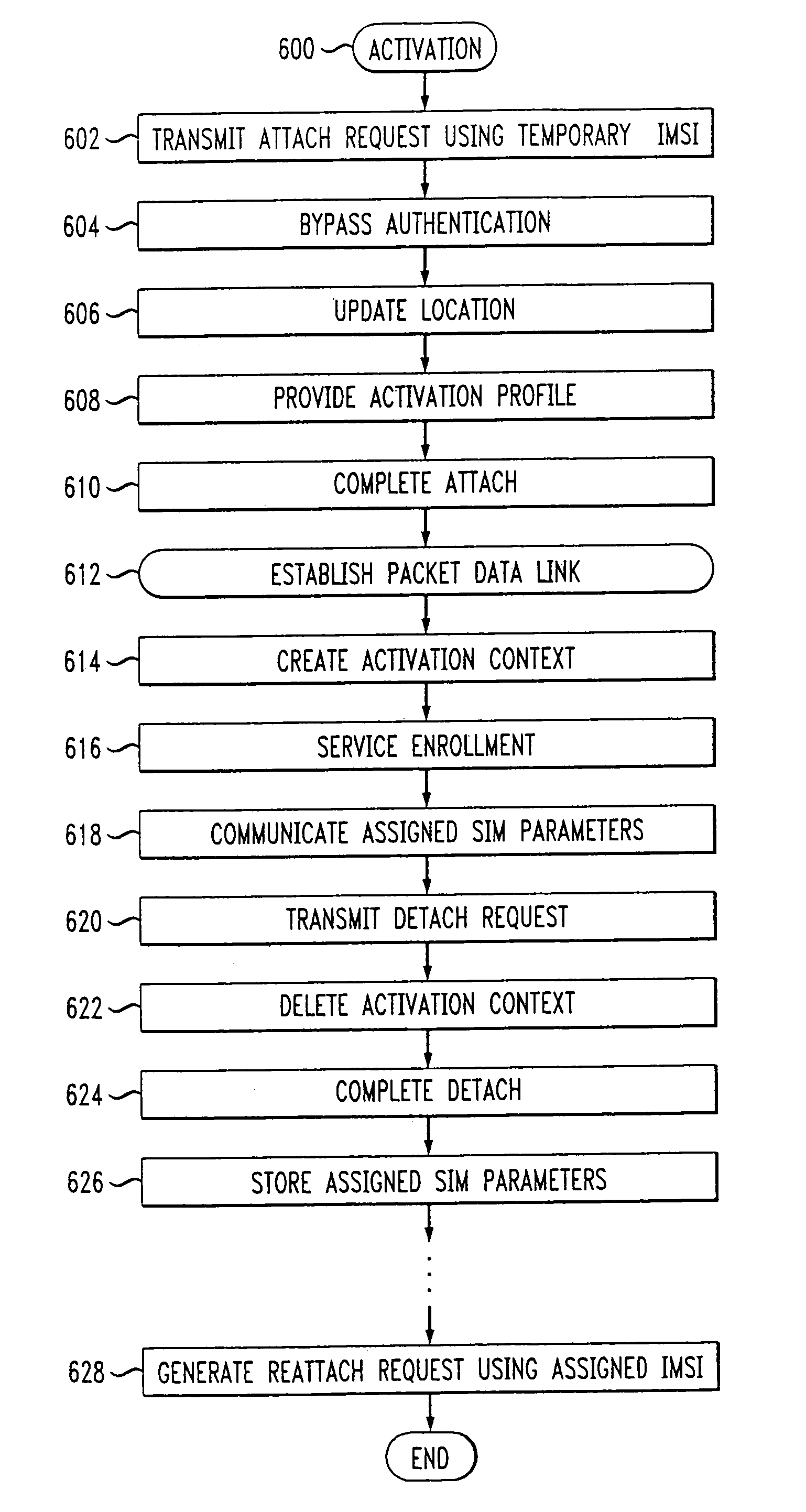
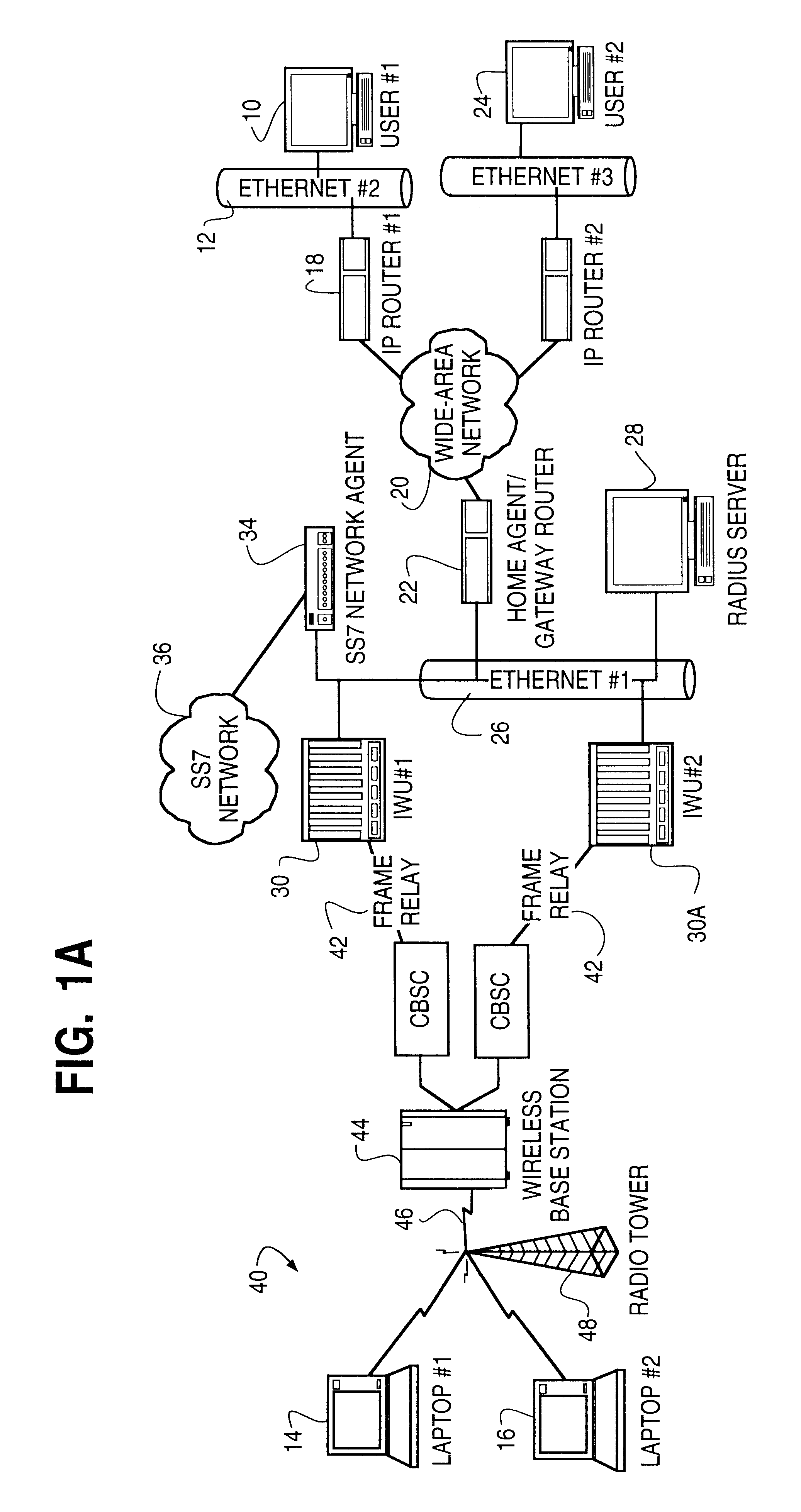
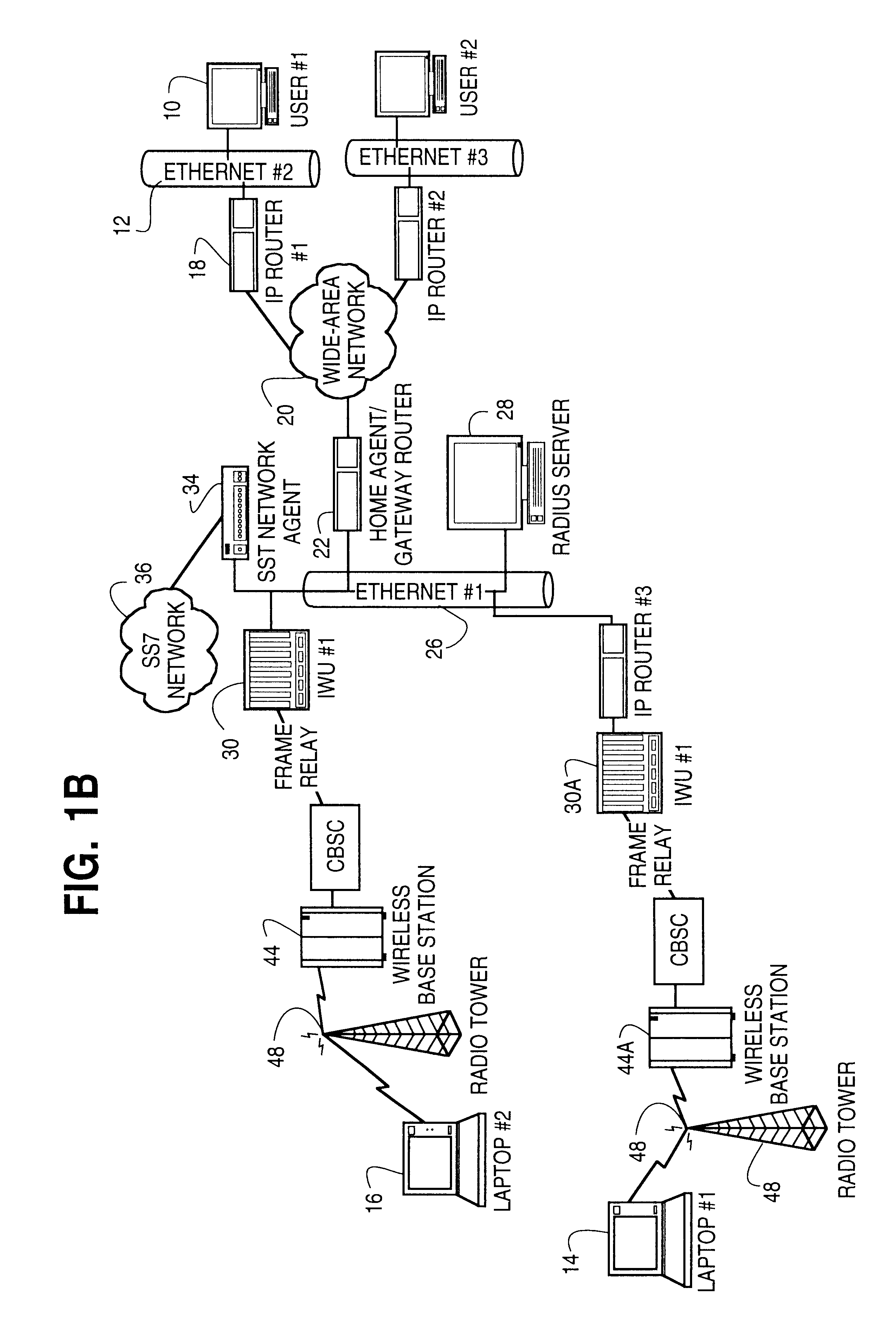
Activation and remote modification of wireless services in a packet network context
InactiveUS7266371B1The process is convenient and fastConvenient and quick mobile device activationRadio/inductive link selection arrangementsSubstation equipmentTerms of serviceThird generation
A third generation (3G) mobile communication system supports an over-the-air activation scheme utilizing a wireless packet data protocol. A subscriber identity module (SIM) is preloaded with temporary operating parameters such as a temporary international mobile subscriber identity (IMSI) that is used for initial access to a network. Once a packet data protocol communication link is established between the mobile device and a network support node, the user may remotely subscribe to a number of service terms using the mobile device. In addition, an activation procedure is carried out to assign permanent operating parameters, e.g., a permanent IMSI, to the SIM. After activation, the user can remotely modify existing terms or remotely enroll in additional service features via a wireless IP link between the mobile device and a network support node.
Owner:AT&T WIRELESS SERVICES
Radius-based mobile internet protocol (IP) address-to-mobile identification number mapping for wireless communication
InactiveUS6466571B1Data switching by path configurationWireless network protocolsIp addressCommunication device
A method of finding a mobile wireless communications device when an Internet Protocol (IP) packet from a remote user is sent to the device over an IP network. The mobile device does not have to register with the IP network in order to receive the IP. The method comprises the steps of receiving the IP packet at a home agent associated with a wireless communications network. The IP packet includes an IP address assigned to the device. If there is no current mobility binding record for the mobile device, instead of dropping the packet the home agent sends an access-request packet, containing the IP address, to an authentication server. The authentication server, e.g., a RADIUS server, maintains a table mapping the IP address for the device to an identification number uniquely associated with the device, such as the device's International Mobile Subscriber Identity number. The authentication server sends an access-accept packet to the home agent in the event that the device is authorized to receive the IP packet, in which case the access-accept packet includes the identification information. The home agent uses the identification number to locate, page and automatically connect the wireless device to the IP network via an InterWorking Unit (IWU) configured as a IP network access server.
Owner:UTSTARCOM INC
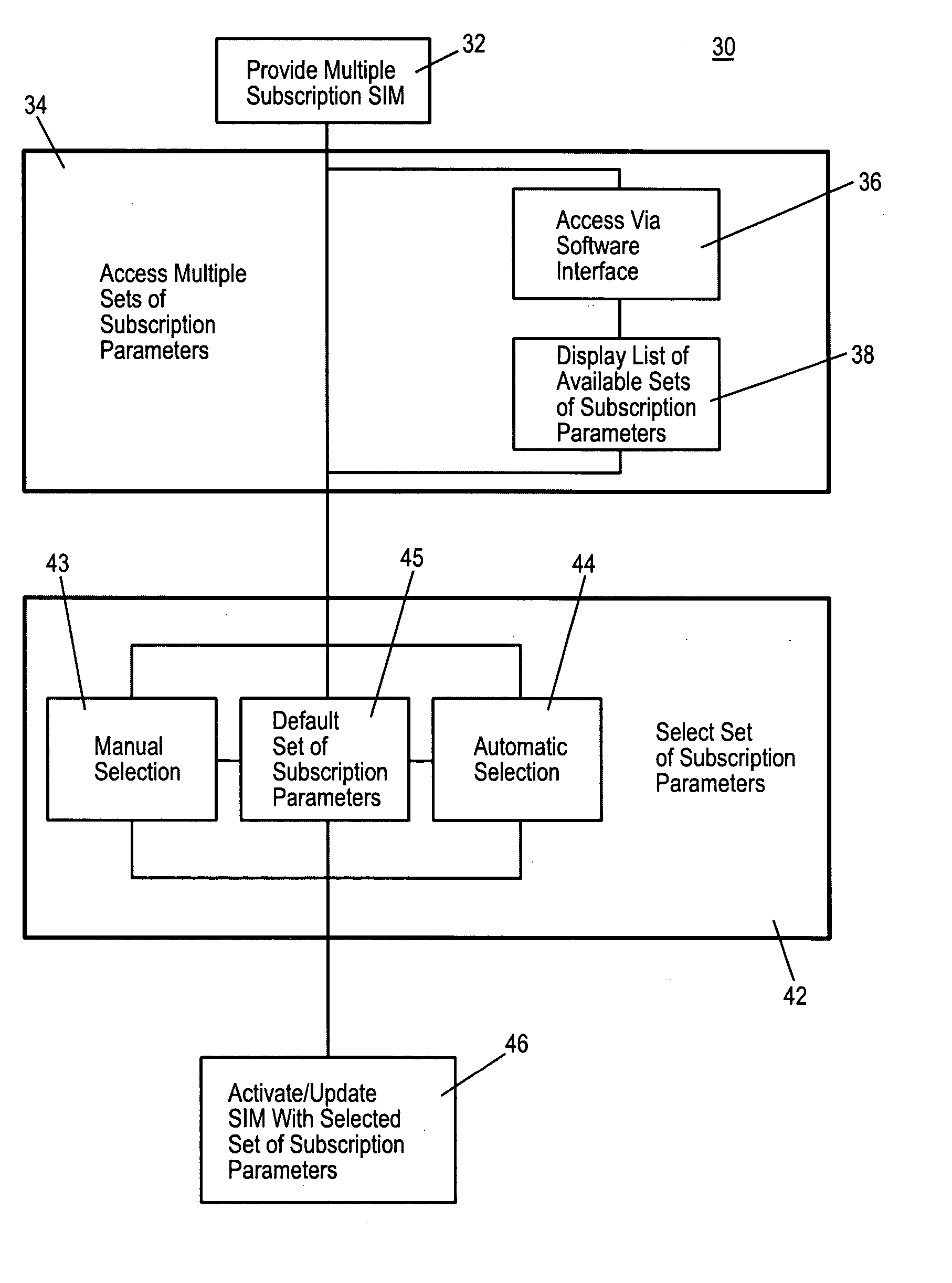
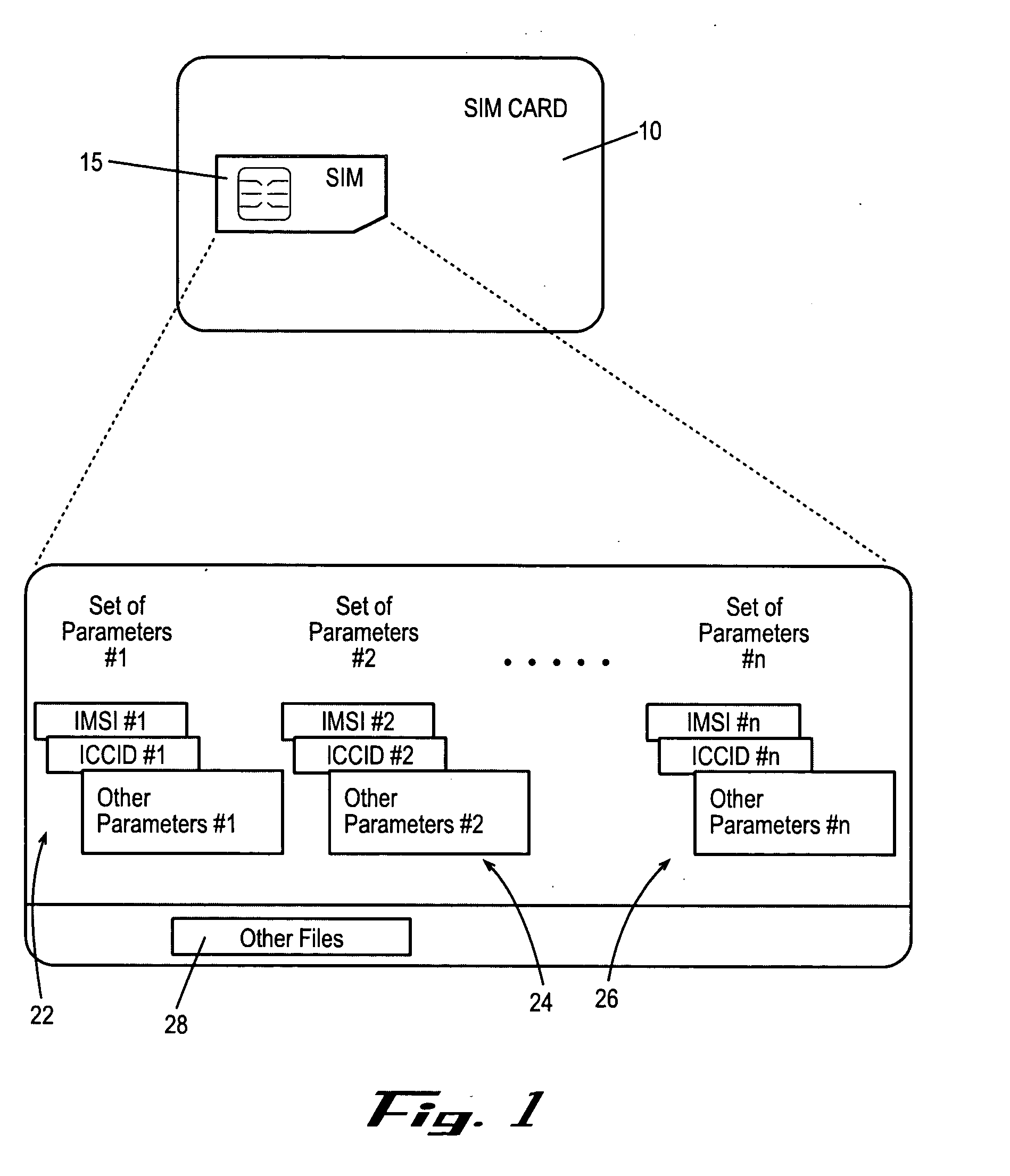
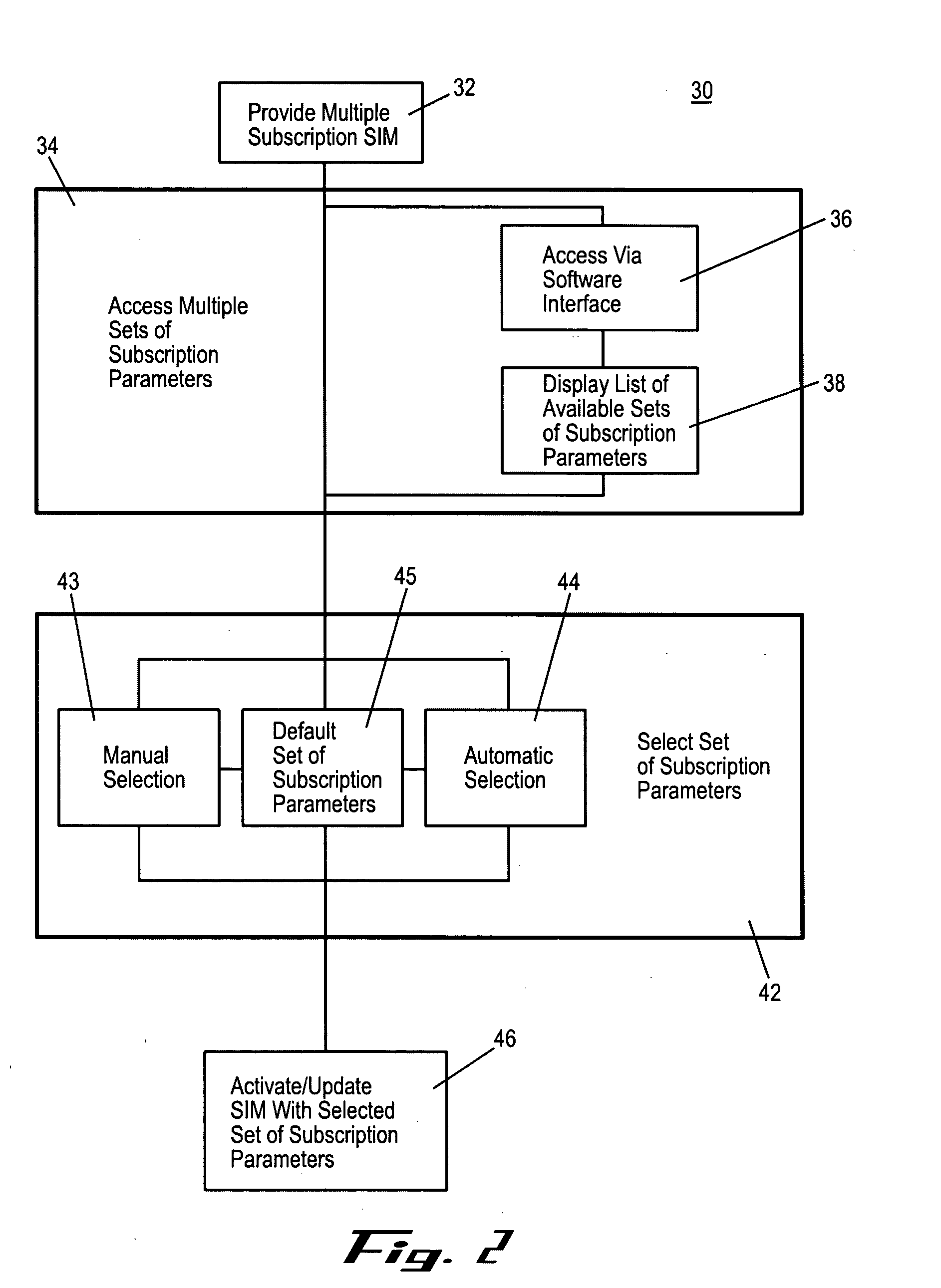
Multiple subscription subscriber identity module (SIM) card
ActiveUS20050164737A1Substation equipmentTransmissionSubscriber identity moduleInternational mobile subscriber identity
Embodiments of the invention include a multiple subscription subscriber identity module (SIM) card. The SIM card includes a plurality of sets of subscription parameters from which to select and activate a single set of parameters. The sets of subscription parameters each contain various information, e.g., information such as an Integrated Circuit Card Identifier (ICCID) and an International Mobile Subscriber Identity (IMSI), and are based on various criteria, e.g., different service regions of use for the electronic device on which the SIM card is installed. A set of subscription parameters is selected for a particular region of use either manually or automatically. The SIM card, which can include a software interface that provides a list of available sets of subscription parameters, is activated by updating the selected set of subscription parameters. Alternatively, a default set of subscription parameters is selected unless a different set of subscription parameters is selected manually from among the plurality of sets of subscription parameters. According to alternative embodiments of the invention, the selected set of subscription parameters can be deactivated and a different set of subscription parameters can be selected and updated to in the SIM card.
Owner:CINGULAR WIRELESS II LLC
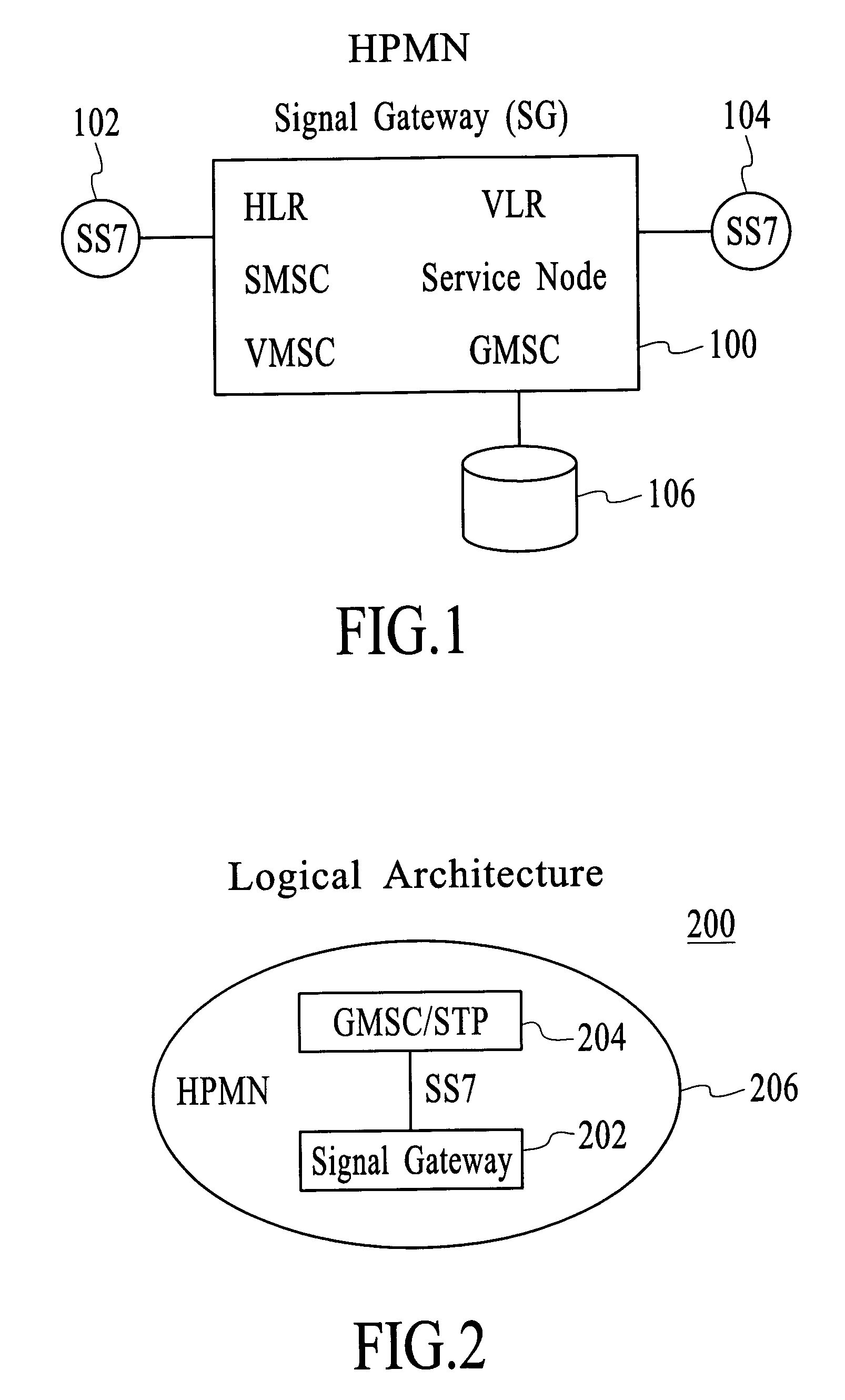
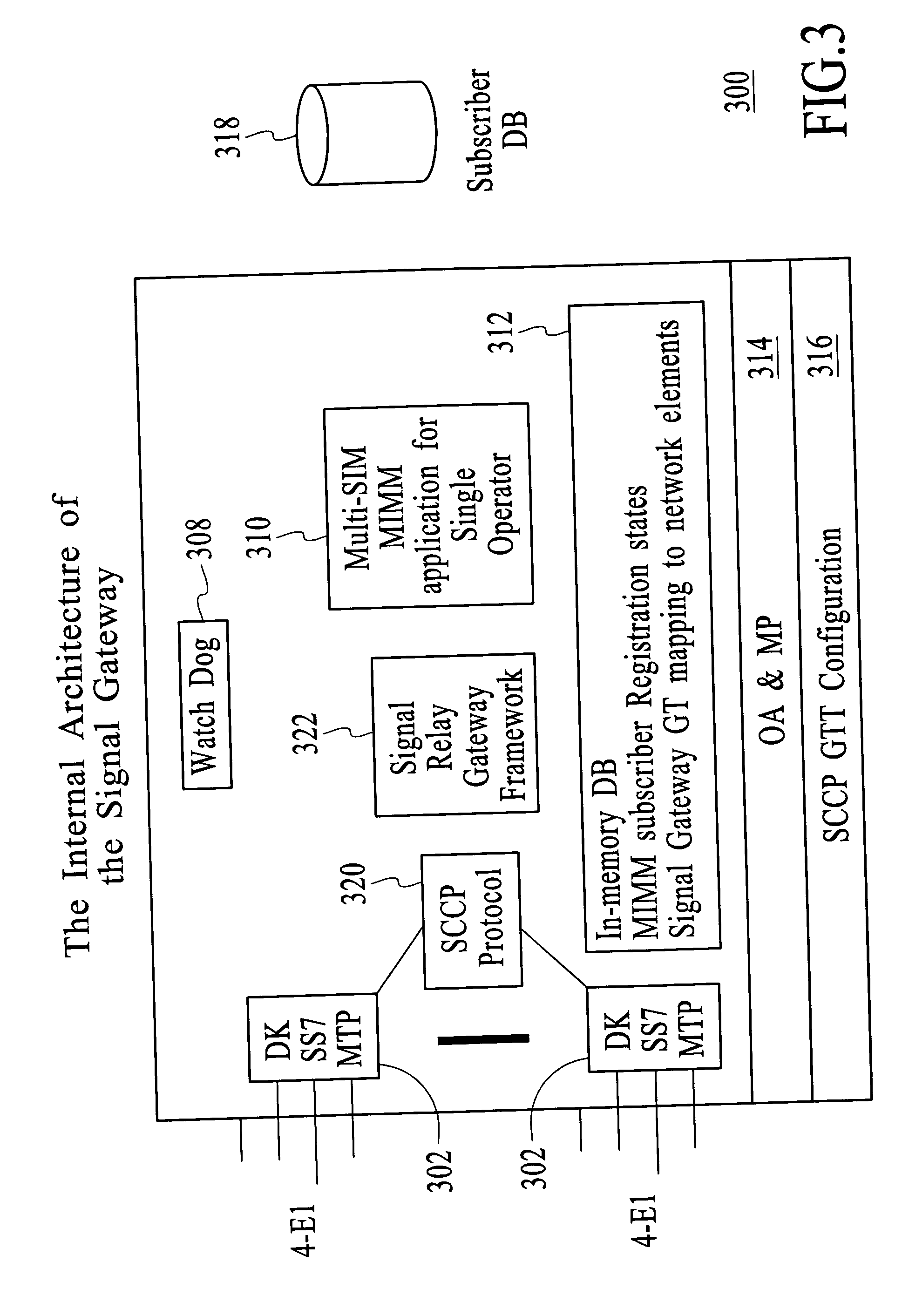
Multiple IMSI multiple/single MSISDN (MIMM/MISM) on multiple SIMs for a single operator
InactiveUS20050075106A1Interconnection arrangementsSpecial service for subscribersTelecommunicationsInternational mobile subscriber identity
A method and apparatus for a Multiple IMSI Multiple / Single MSISDN (MIMM / MISM) on Multiple SIMs service for a single mobile communications network operator. In one embodiment, a system includes a Signaling Gateway that includes a MIMM / MISM application. Embodiments include a designating a set of subscriber identity modules (SIMs) for a subscriber, wherein the set of SIMs is registered to the subscriber; and wherein the set of SIMs comprises multiple SIMs, each of which is useable in one or more mobile communication devices, and each of which comprises a different international mobile subscriber identity (IMSI). Embodiments further include configuring the set of SIMs and the network such that the subscriber presents a uniform appearance to entities communicating with the subscriber regardless of which SIM is used for the communication, wherein the subscriber can simultaneously carry on a voice call on one SIM and carry on a data session on another SIM.
Owner:ROAMWARE
Method and system for secured remote provisioning of a universal integrated circuit card of a user equipment
ActiveUS20130012168A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwarePublic land mobile network
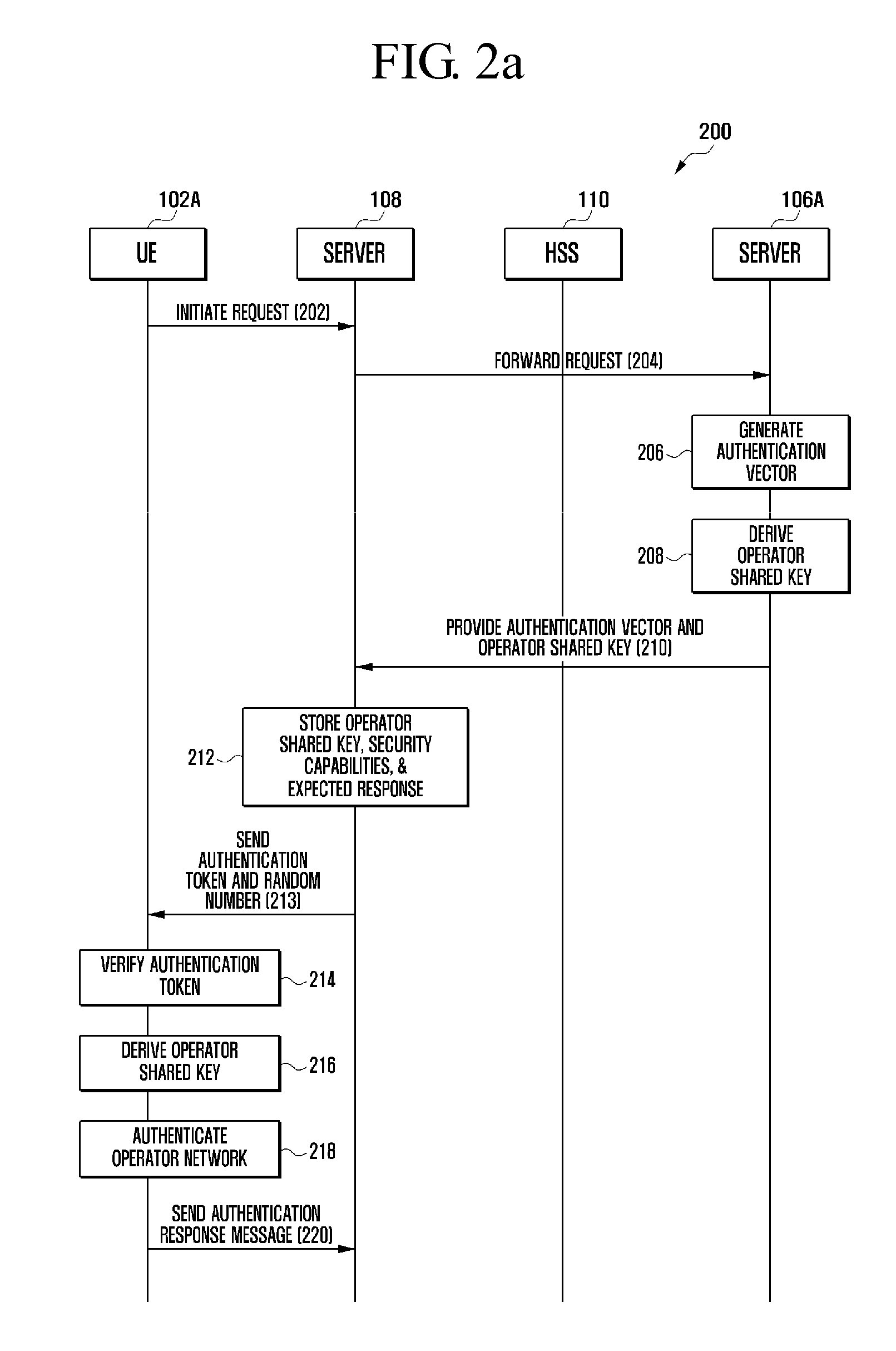
The present invention provides a method and system for secured remote provisioning of a universal integrated circuit card of a user equipment. A system includes a user equipment for initiating a request for remote provisioning of an universal integrated circuit card (UICC) in the user equipment, where the request for remote provisioning includes a machine identifier (MID) associated with the user equipment and a public land mobile network (PLMN) identifier (ID) associated with an network operator. The system also includes at least one shared key management server for dynamically generating security keys and an operator shared key using the security keys, the MID. Moreover, the system includes an operator network for generating a subscription key using the operator shared key and an international mobile subscriber identity (IMSI), and provisioning the IMSI in a secured manner to the UICC of the user equipment using the security keys.
Owner:SAMSUNG ELECTRONICS CO LTD
Wireless communication system and handover method therein
InactiveUS20100093358A1Avoiding a shortage of Primary Scrambling Codes (PCSs)Increase probabilityNetwork topologiesOrthogonal multiplexCommunications systemMacro base stations
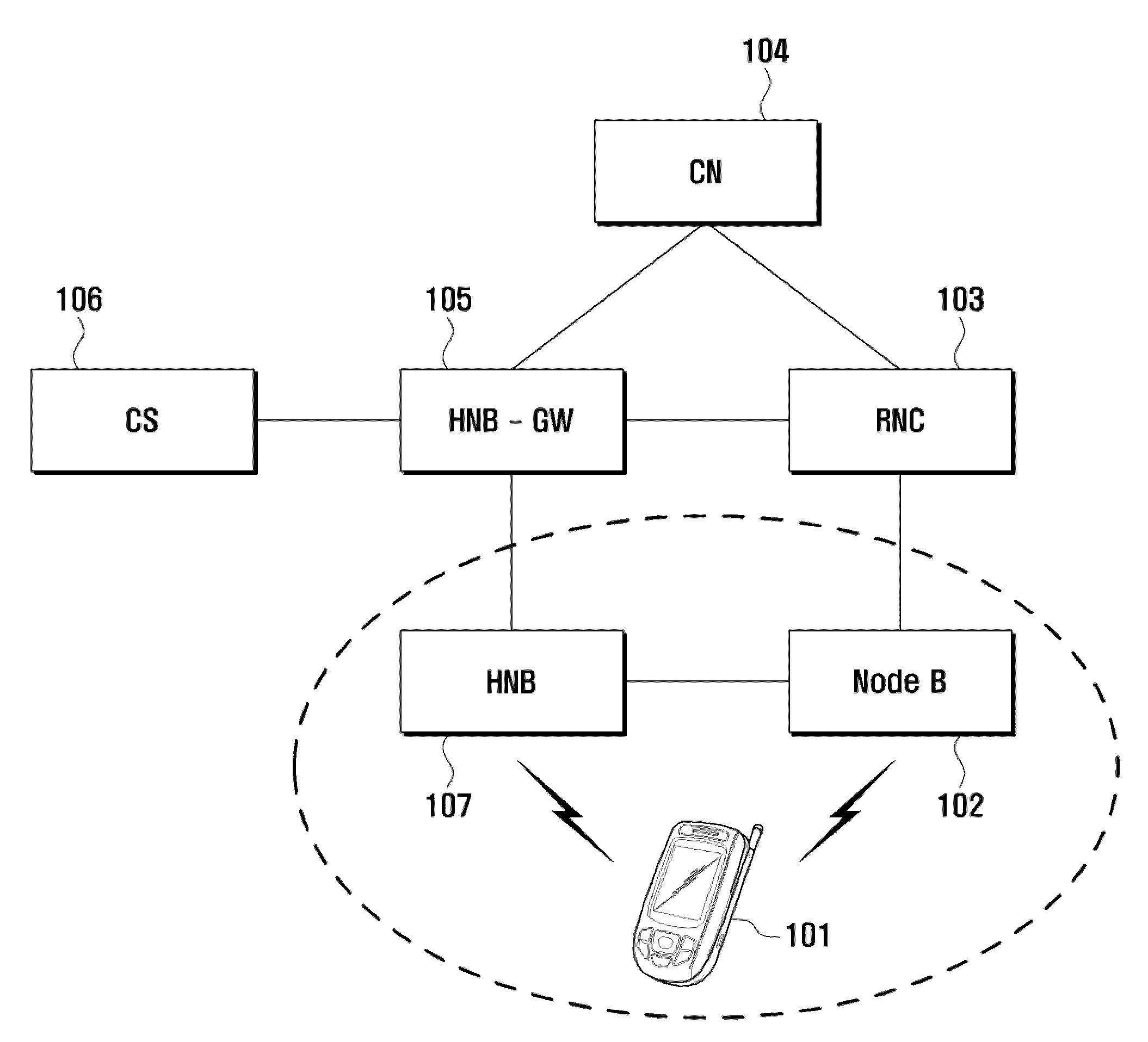
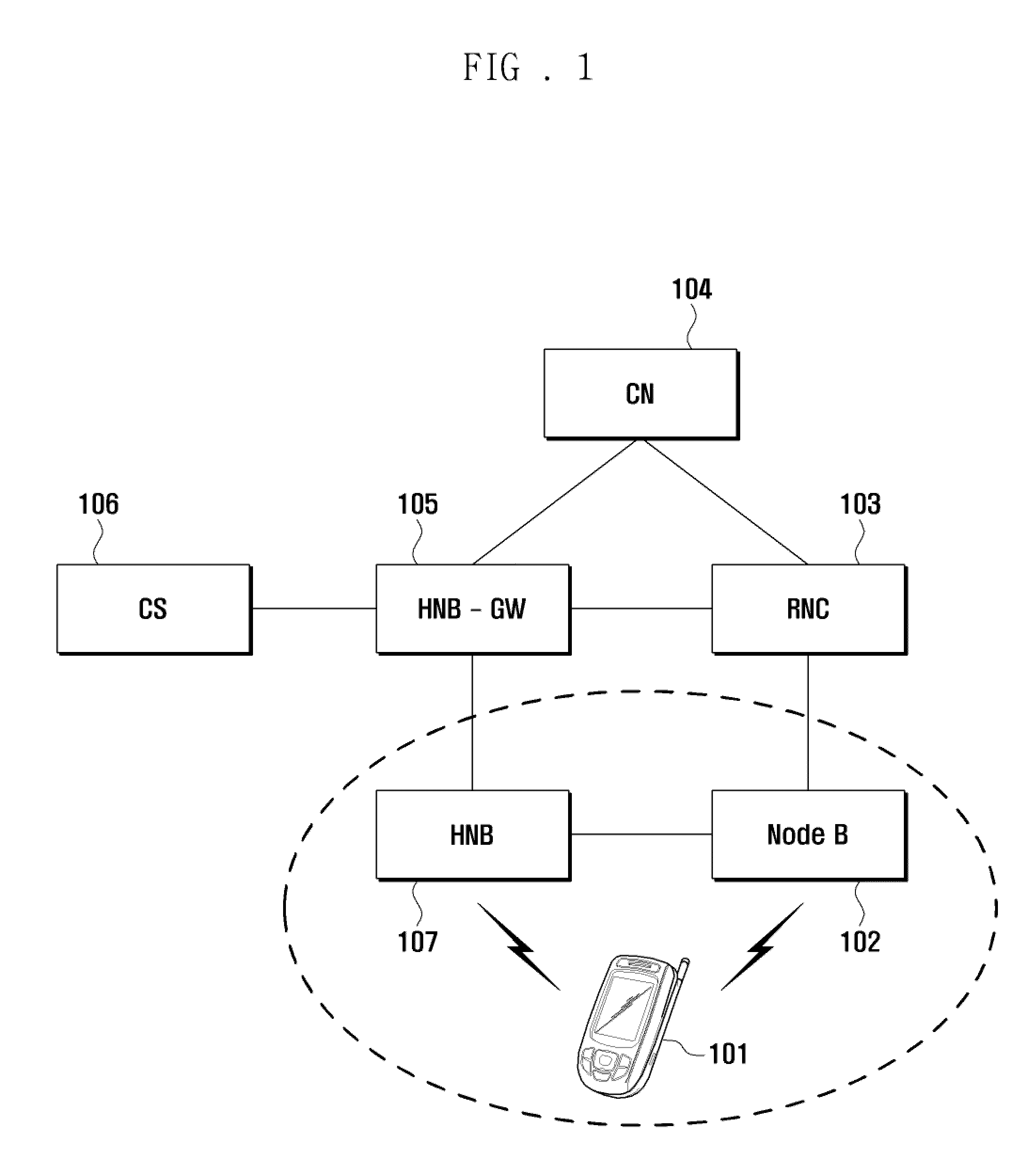
A wireless communication system and handover method for the wireless communication system are provided. A handover method for a wireless communication system including a plurality of femto cells and at least one macro cell within which the femto cells are disposed includes determining, at a Radio Network Controller (RNC), a handover of a terminal to a femto base station based on a measurement report of the terminal and preset handover parameters, sending a radio link setup request message to a femto base station gateway, the radio link setup request message including a uplink scrambling code and an International Mobile Subscriber Identity (IMSI) of the terminal and a Logical Cell Identifier (LCID) of femto base stations reusing frequency of a macro base station, searching, at the femto base station gateway, for femto base stations of which LCIDs match the LCID contained in the radio link setup request message, and performing, when only one LCID-matched femto base station is discovered, the handover of the terminal to the LCID-matched femto base station.
Owner:SAMSUNG ELECTRONICS CO LTD
Short-range wireless system and method for multimedia tags
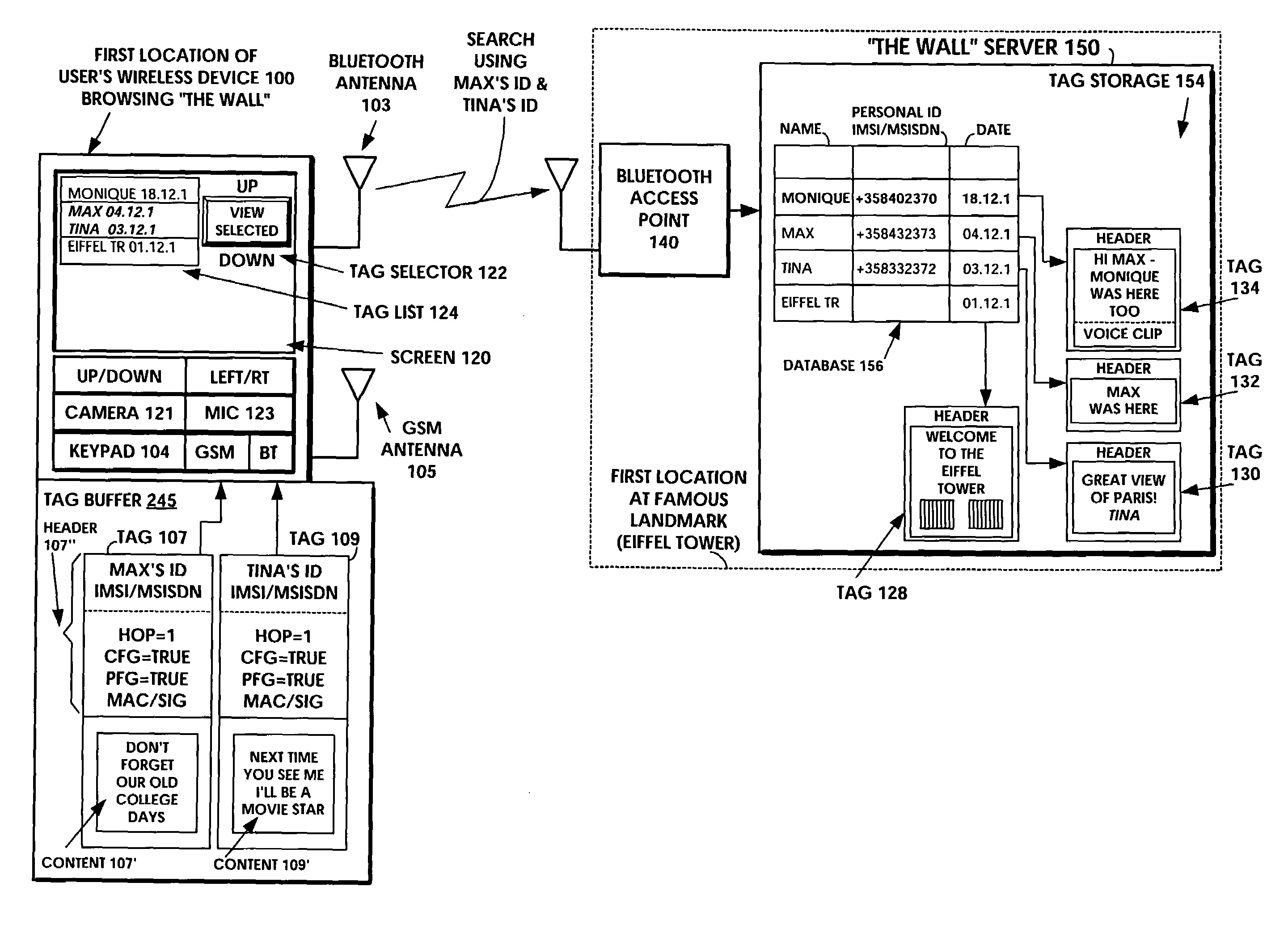
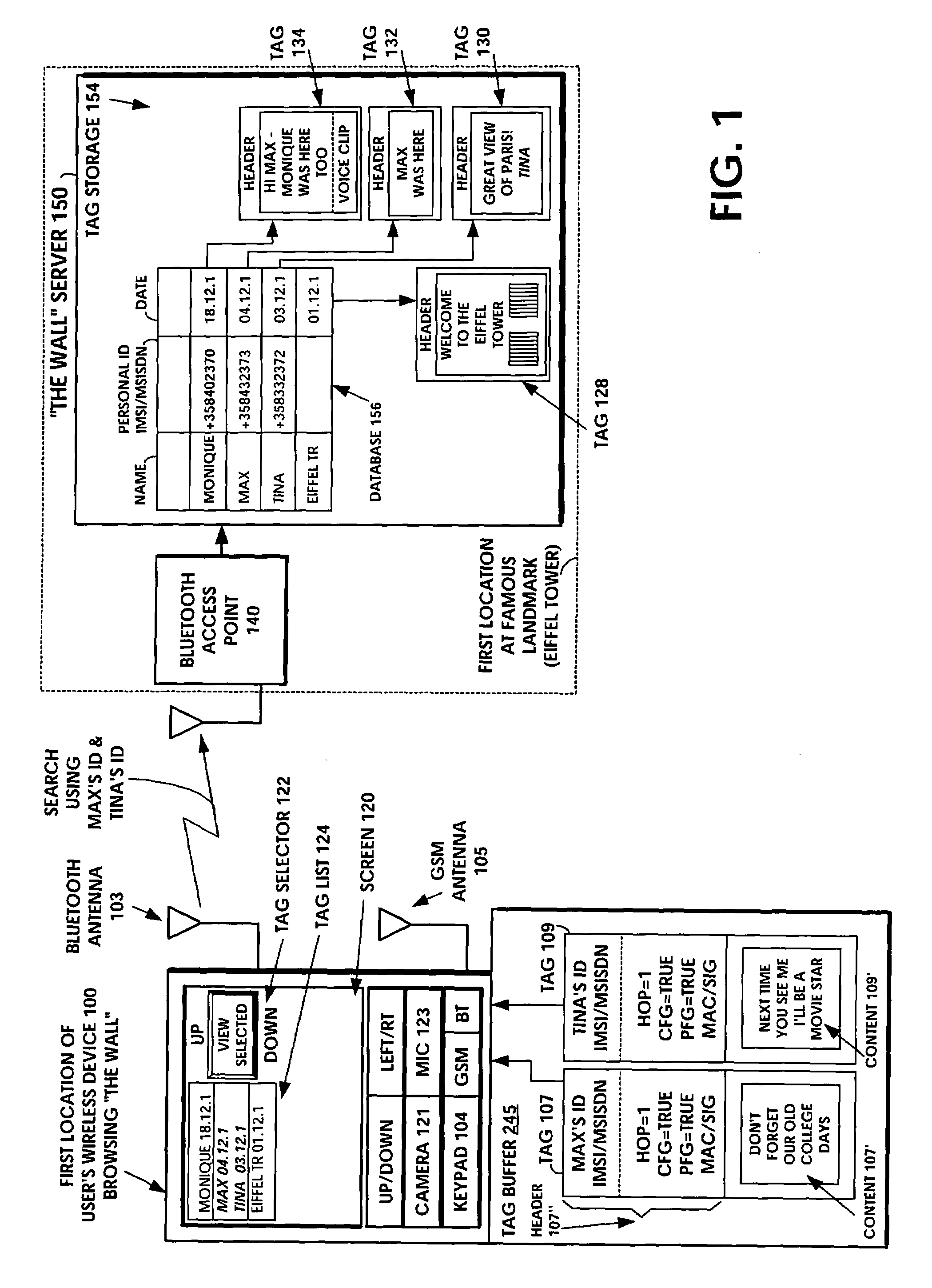
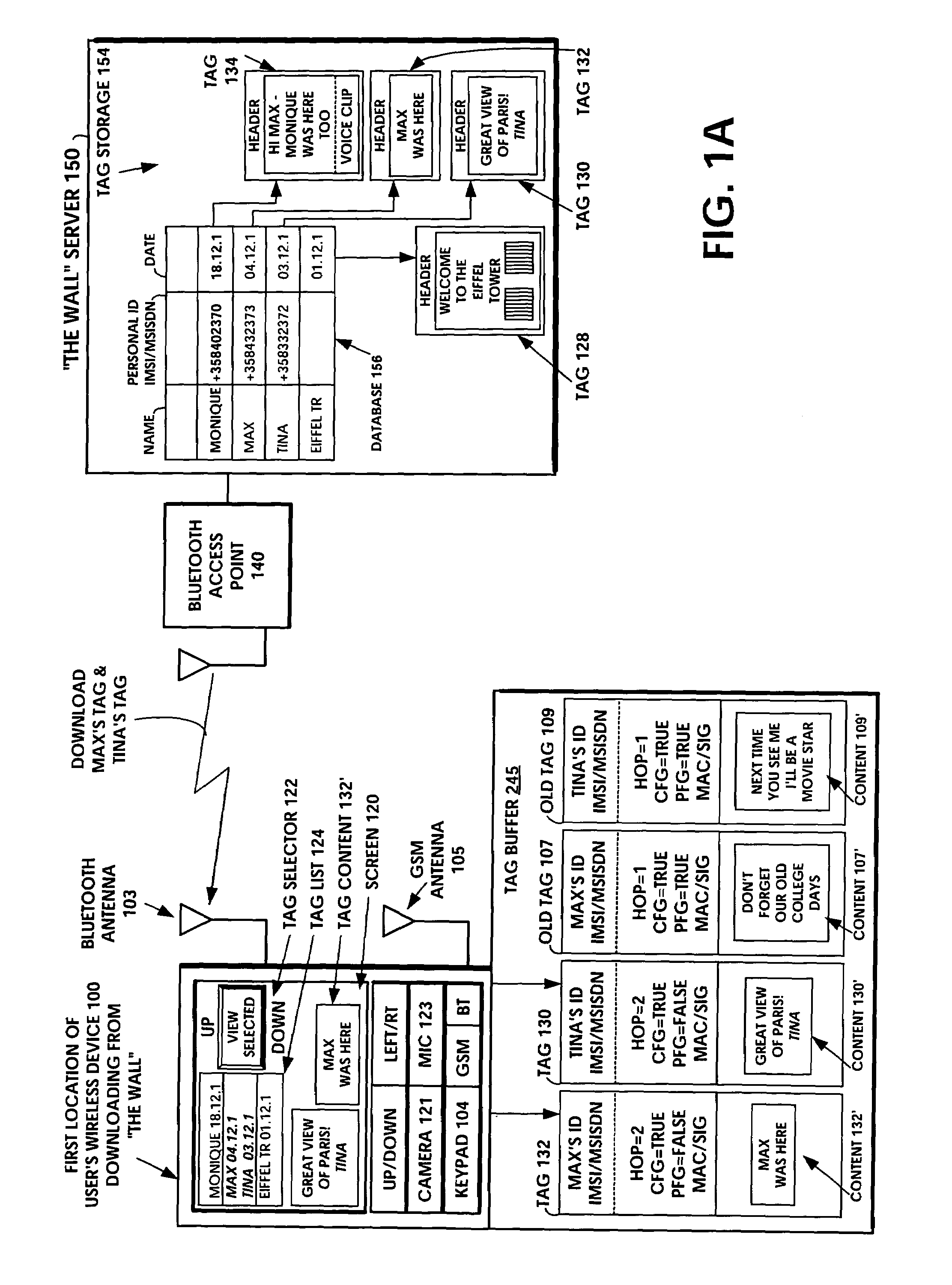
InactiveUS7340214B1Storage requirements is greatly reducedAvoid receivingError preventionFrequency-division multiplex detailsComputer hardwareHiperLAN
A short-range wireless system and method is disclosed to store and transfer a new type of multimedia data construct called a tag. A user can write text, create a voice clip and append it to the text, take a digital picture and append it to the text, to create a multimedia file as the content of a tag. The creation or modifying of the multimedia file can be done in the user's mobile wireless device or off line and then stored in the mobile device. The multimedia file is then incorporated into the tag or it can be referenced by a pointer in the tag. The multimedia file is artistic expression of the user and the tag uniquely associates the user's identity with the multimedia file by prohibiting alteration of the content after the user completes its creation. A content-originator flag (CFG) value in the tag is set to “false” during the period when the user is creating or modifying the tag's content. When the user completes editing the content of the tag, the content-originator flag (CFG) value is set to true, thereby freezing the content. The tag includes the user's ID, such as his / her international mobile subscriber identity (IMSI) or mobile station ISDN number (MSISDN). Subsequent viewers of the content can make a copy of the content and can then modify it, but they cannot authentically attribute the modified copy to the original user. The system can be implemented as a wireless personal area network (PAN) such as provided in the Bluetooth Standard or a wireless local area network (LAN) such as provided in the IEEE 802.11 Wireless LAN Standard and the HIPERLAN Standard.
Owner:NOKIA TECH OY
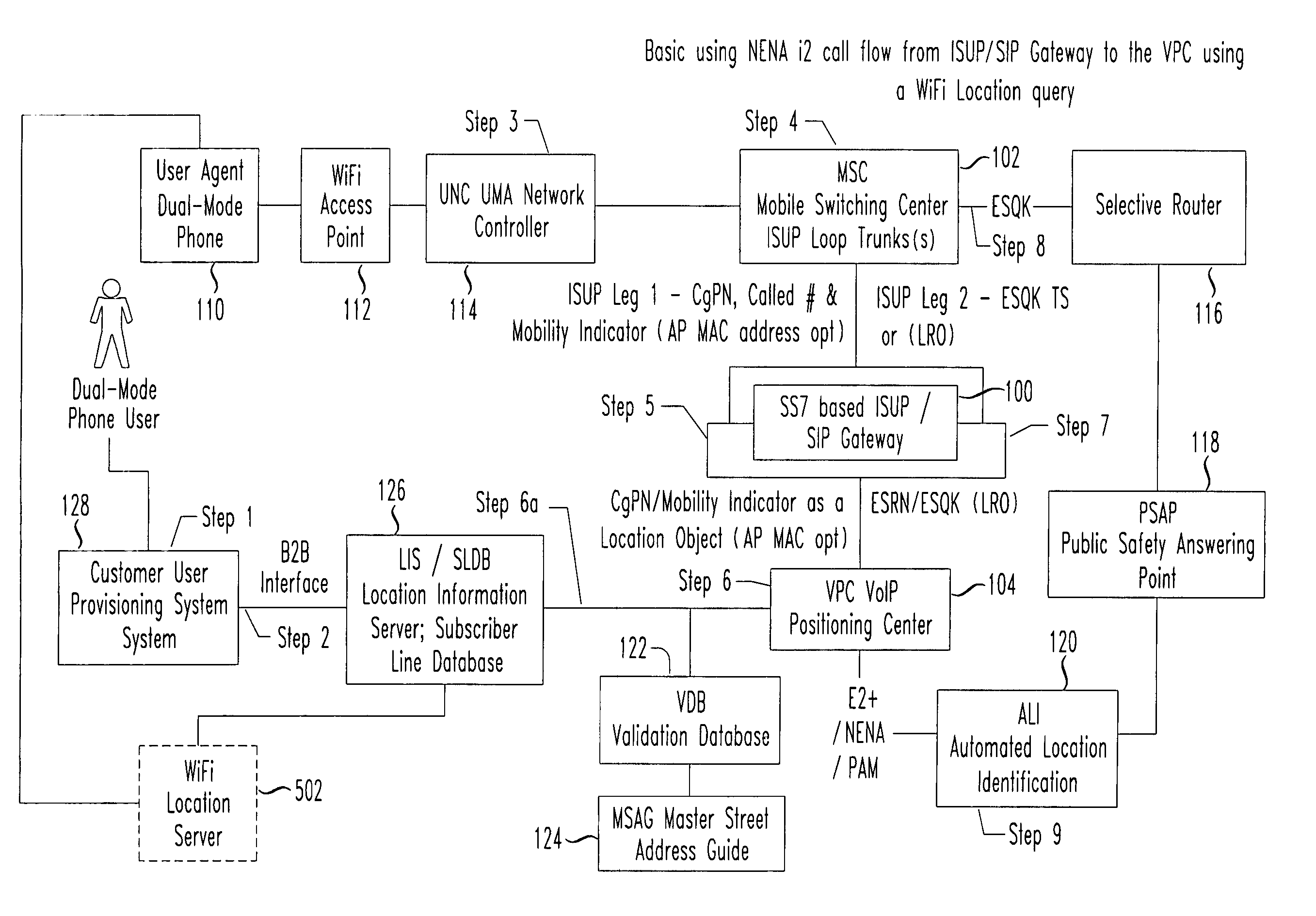
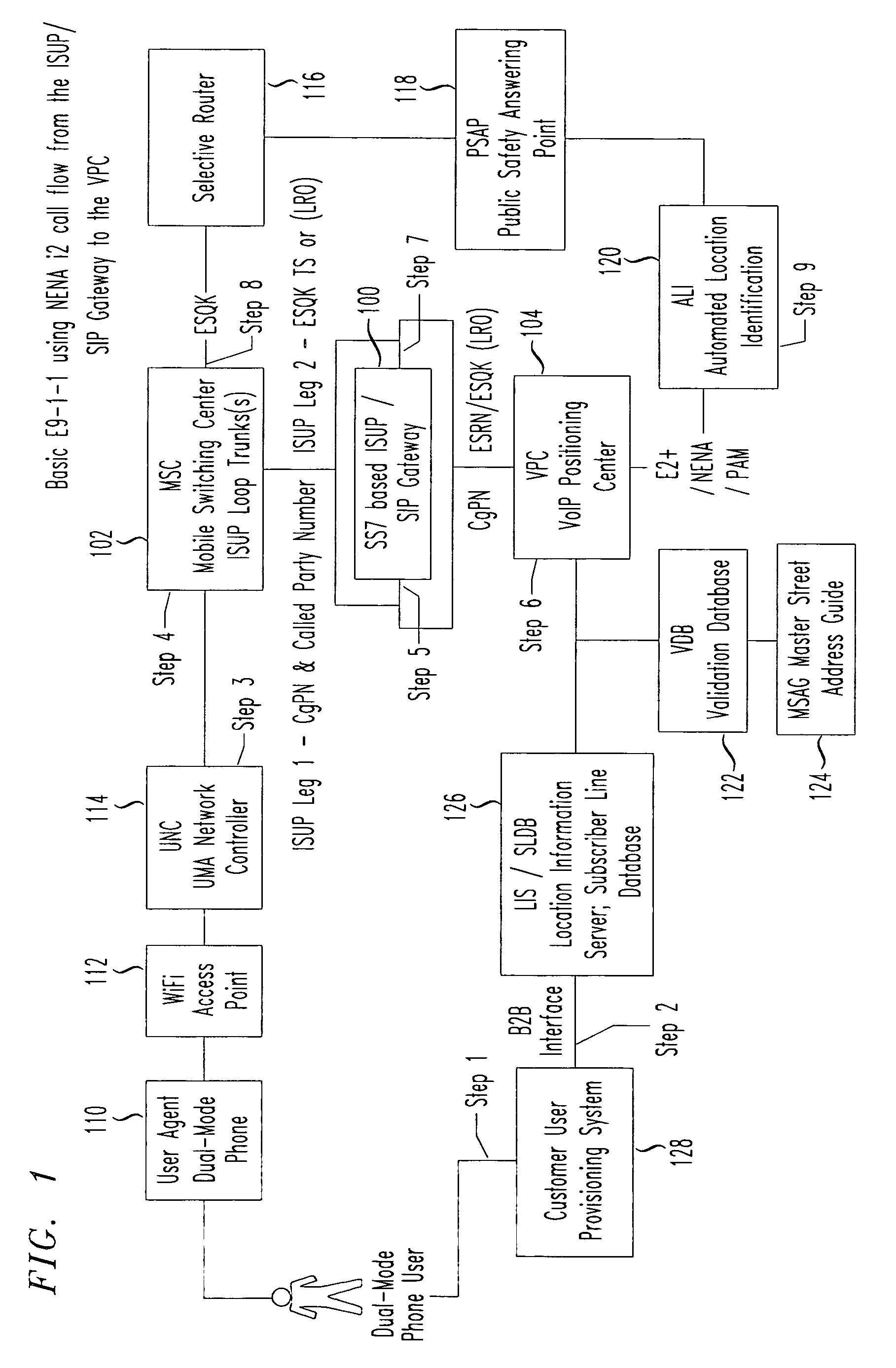
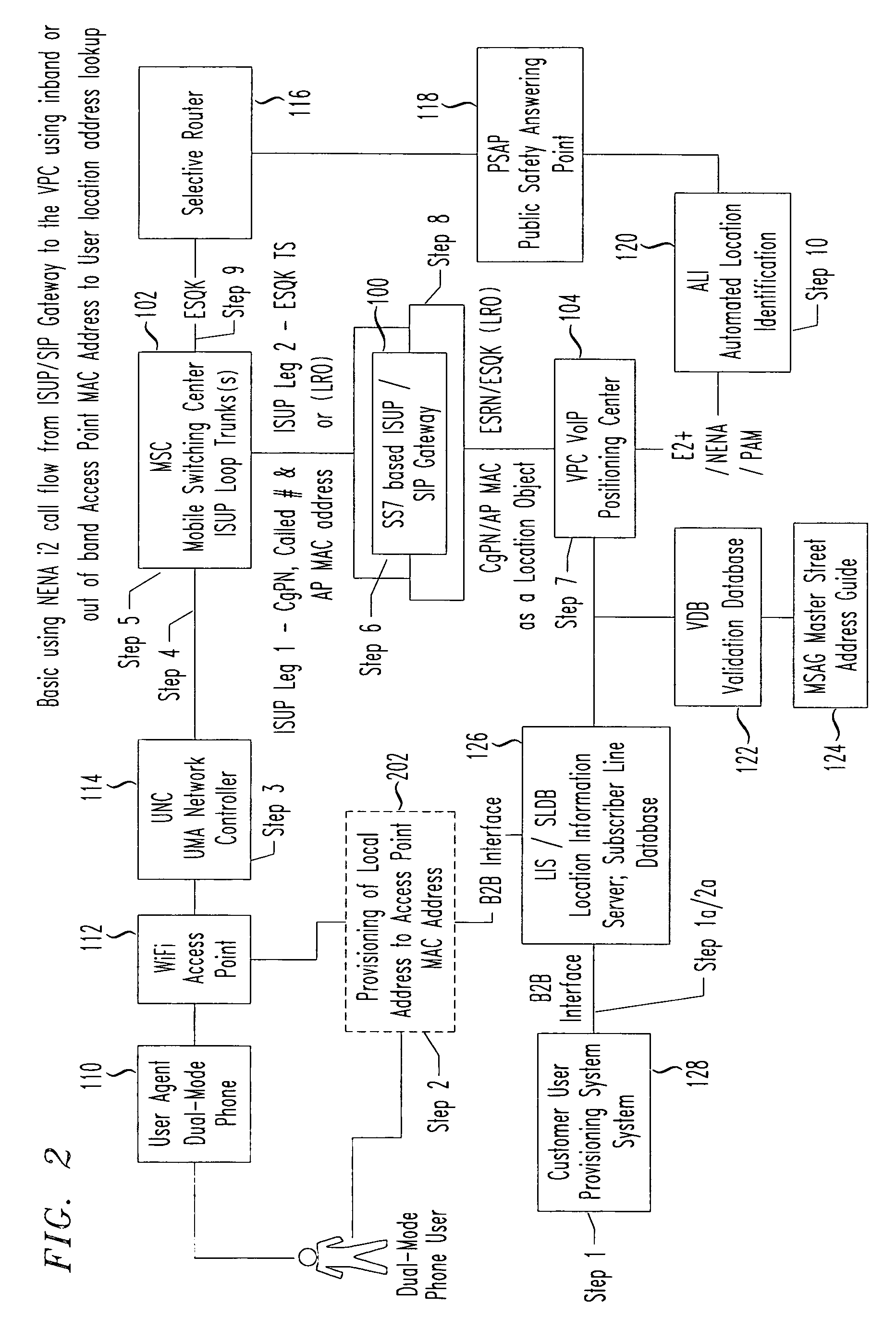
Integrated services user part (ISUP) /session initiation protocol (SIP) gateway for unlicensed mobile access (UMA) emergency services call flow
InactiveUS20070014282A1Emergency connection handlingPosition fixationSession Initiation ProtocolVoice over internet protocol voip
An ISUP / SIP gateway is implemented to encapsulate SS7 location requests from a switched telephone network into an Internet protocol SIP message including one or more location objects. The ISUP / SIP gateway is implemented between a mobile switching center (MSC) and a VoIP positioning center (VPC) to provide support of unlicensed mobile access (UMA) voice over Internet Protocol (VoIP) call routing, e.g., for E9-1-1, 4-1-1, 2-1-1, etc. The disclosed location objects that are encapsulated into a SIP message includes calling party number, called party number, CGI, International Mobile Subscriber Identity (IMSI), mobility indicator, and / or access point MAC address. At the SIP / ISUP gateway, SS7 integrated services user part (ISUP) location request messages are encapsulated within SIP. The SIP encapsulated location request message is then routed over the Internet to a destination VoIP positioning center (VPC).
Owner:TELECOMM SYST INC
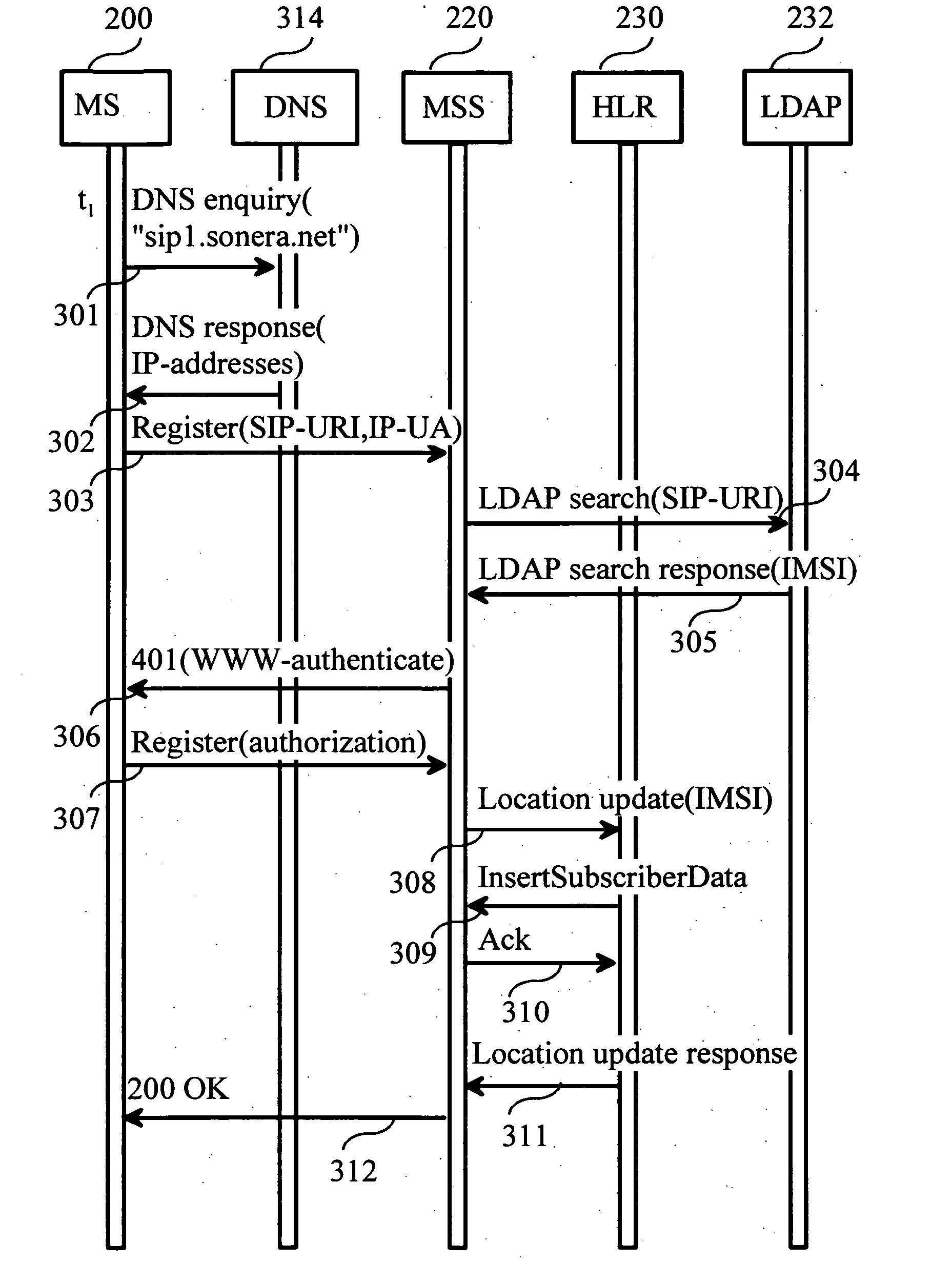
Method for the routing of communications to a voice over internet protocol terminal in a mobile communication system
ActiveUS20060142011A1Easy service deploymentEasy to operateSpecial service for subscribersConnection managementCommunications systemMobile communication systems
The invention relates to a method a method for routing calls and messages in a communication system. In the method a mobile station registers to a call control node using a logical name. The logical name is mapped in a directory to an international mobile subscriber identity. The call control node performs a location update to a home location register using the international mobile subscriber identity. The mobile station is reached using a called party number. As a terminating call or message is received to a core network, a roaming number is allocated for the mobile station, and the call or message is routed to the call control entity currently serving the mobile station. The call control node translates the called party number to the logical name using the directory.
Owner:NOKIA TECHNOLOGLES OY
Method For Securing a Near Field Communication Device of a Mobile Phone
InactiveUS20070123305A1Devices with card reading facilityNetwork topologiesData storingSubscriber identity module
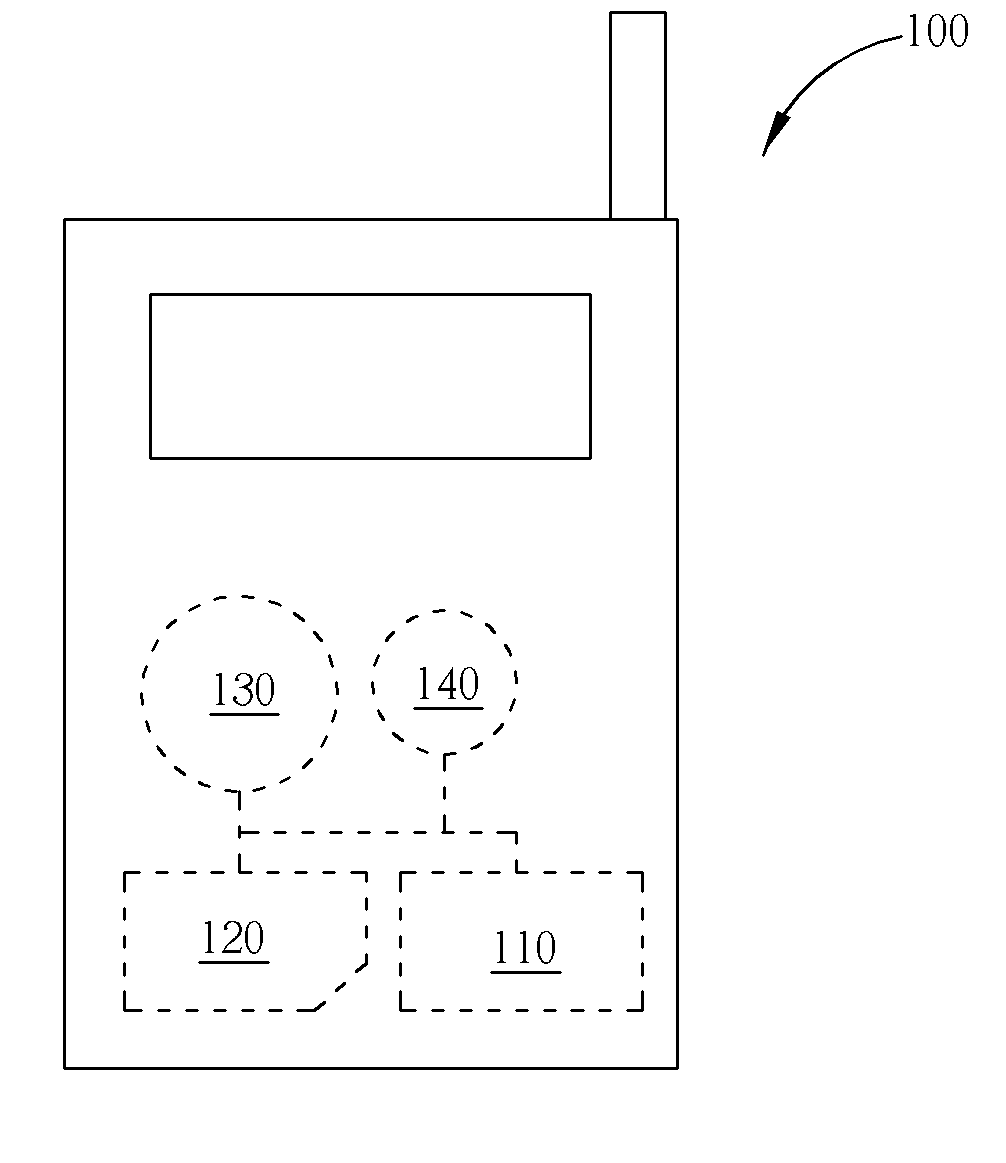
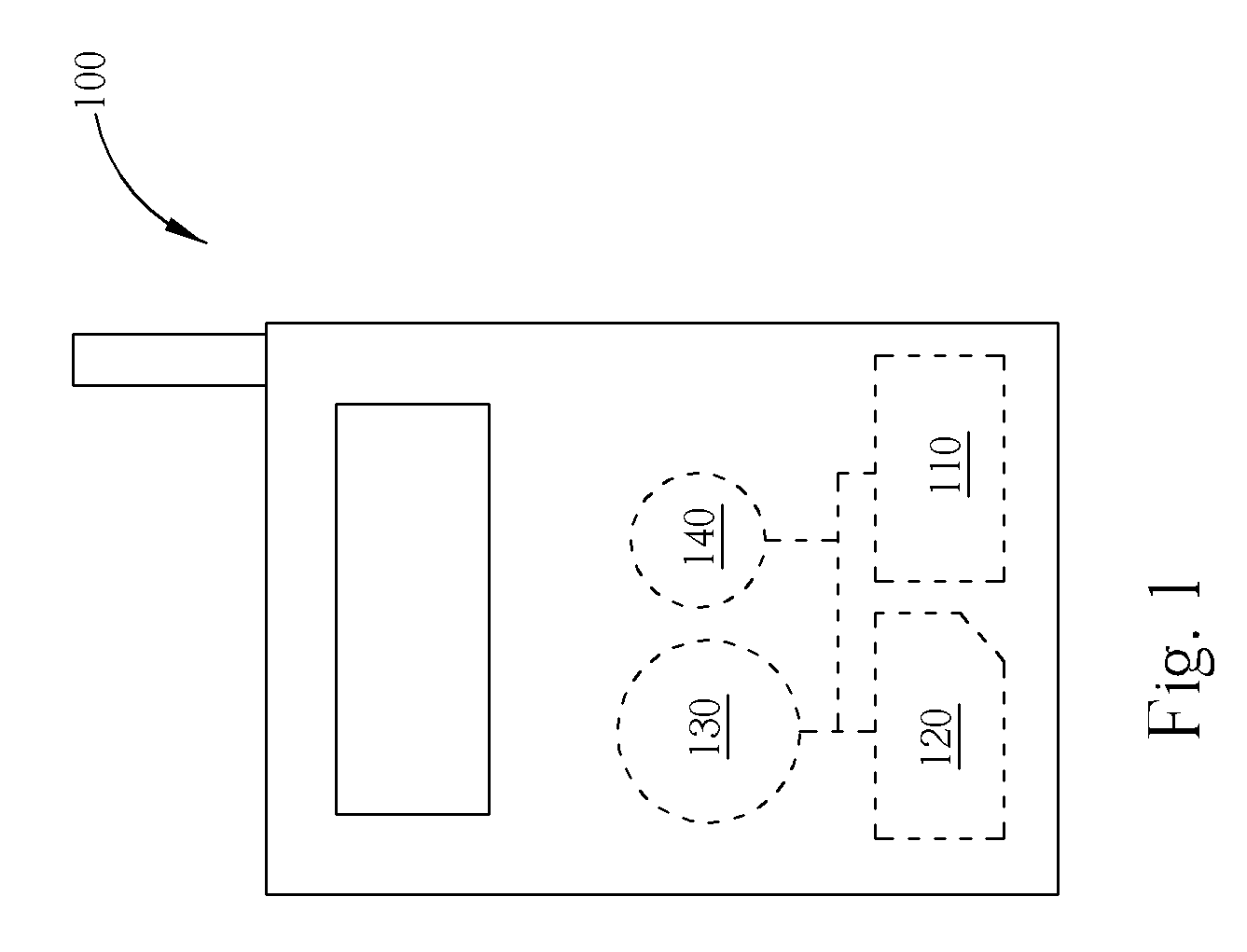
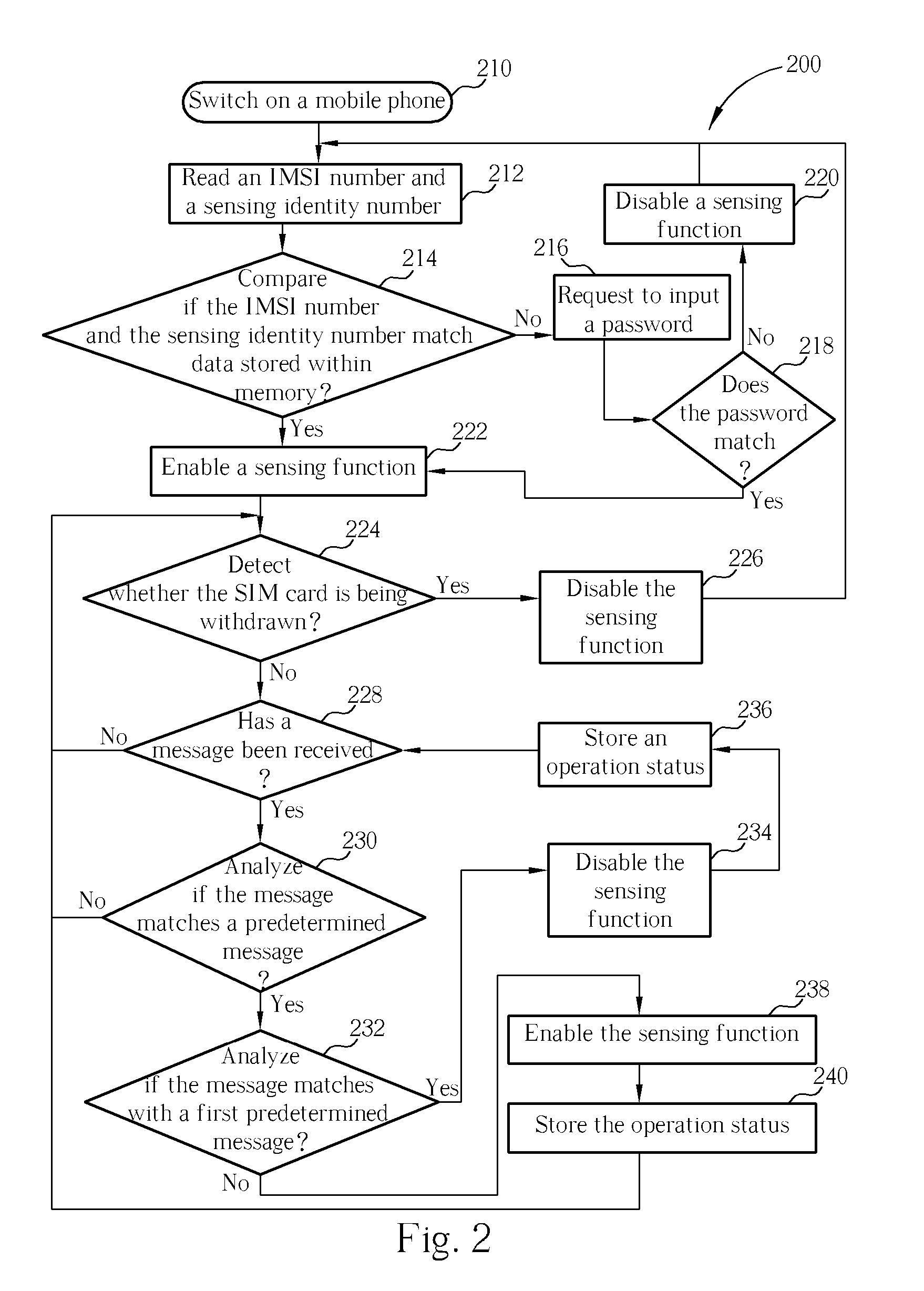
A security method includes reading an international mobile subscriber identity (IMSI) number of a subscriber identity module (SIM) card and an identity number of a near field communication (NFC) card of the mobile phone; detecting if the IMSI number matches first data stored in memory of the mobile phone, detecting if the identity number matches second data stored in the memory, and when the IMSI number and the identity number respectively match the first and the second set of data stored in the memory, the mobile phone enables the NFC card. The security method allows a consumer to feel more secure when the NFC card is used.
Owner:BENQ CORP
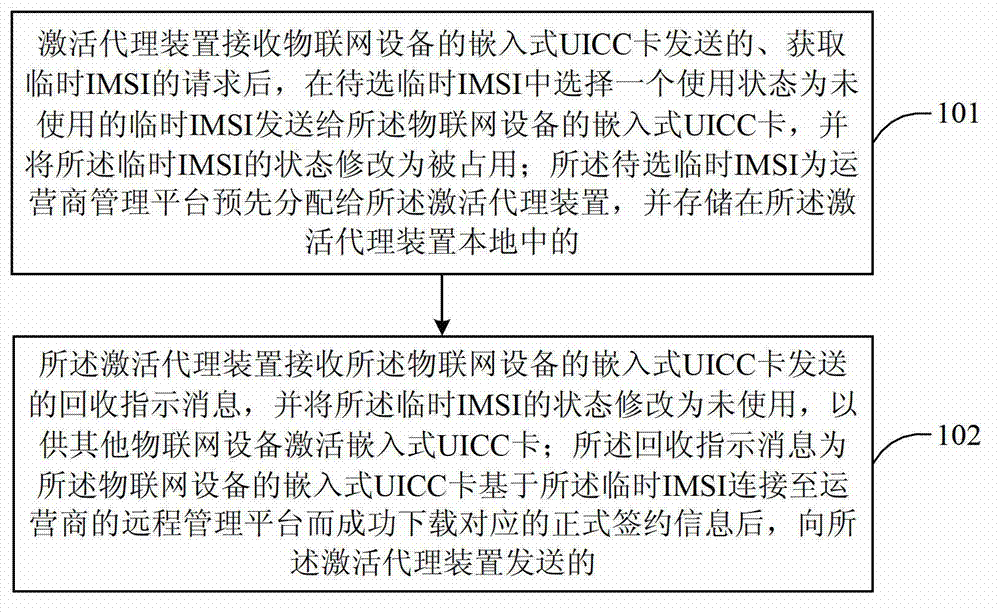
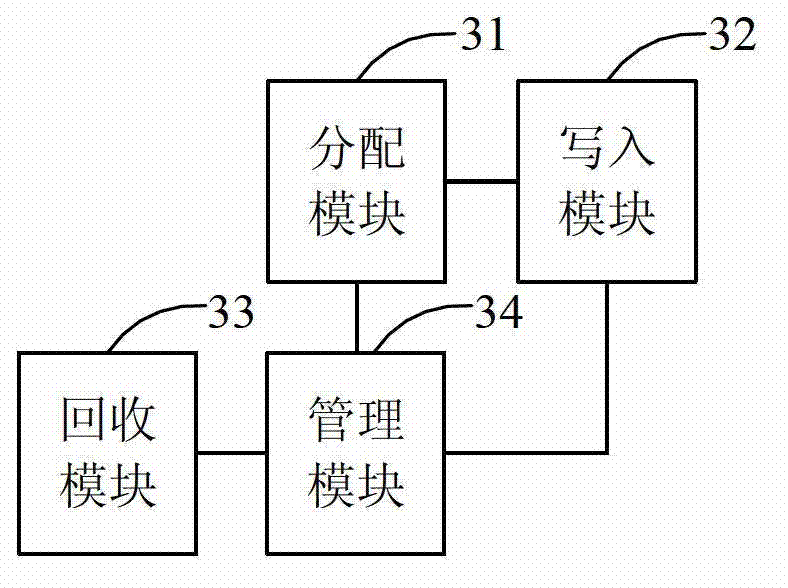
Embedded-type UICC activation processing method and embedded-type UICC activation processing device
ActiveCN103167465AIncrease profitSave resourcesNetwork data managementBiological activationOperating system
The invention provides an embedded-type UICC activation processing method and an embedded-type UICC activation processing device. The method comprises that an agency device is activated to receive a request which is sent by an embedded-type UICC and obtains a temporary international mobile subscriber identity (IMSI), then a using state is selected in to-be-selected temporary IMSIs as an unused IMSI and the using state is sent to an embedded-type UICC of an object networking, and the state of the temporary IMSI is modified to be an occupied state, the agency device is activated to receive recycling indicating information sent by the embedded-type UICC, after the embedded-type UICC of the object networking is connected to a remote management platform of an operator and succeeds in loading corresponding formal contraction information based on the temporary IMSI, and the recycling indicating information is sent to the activation agency device. The embedded-type UICC activation processing method and the embedded-type UICC activation processing device can improve utilization rate of the IMSI, and resources of a home location register (HLR) are saved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
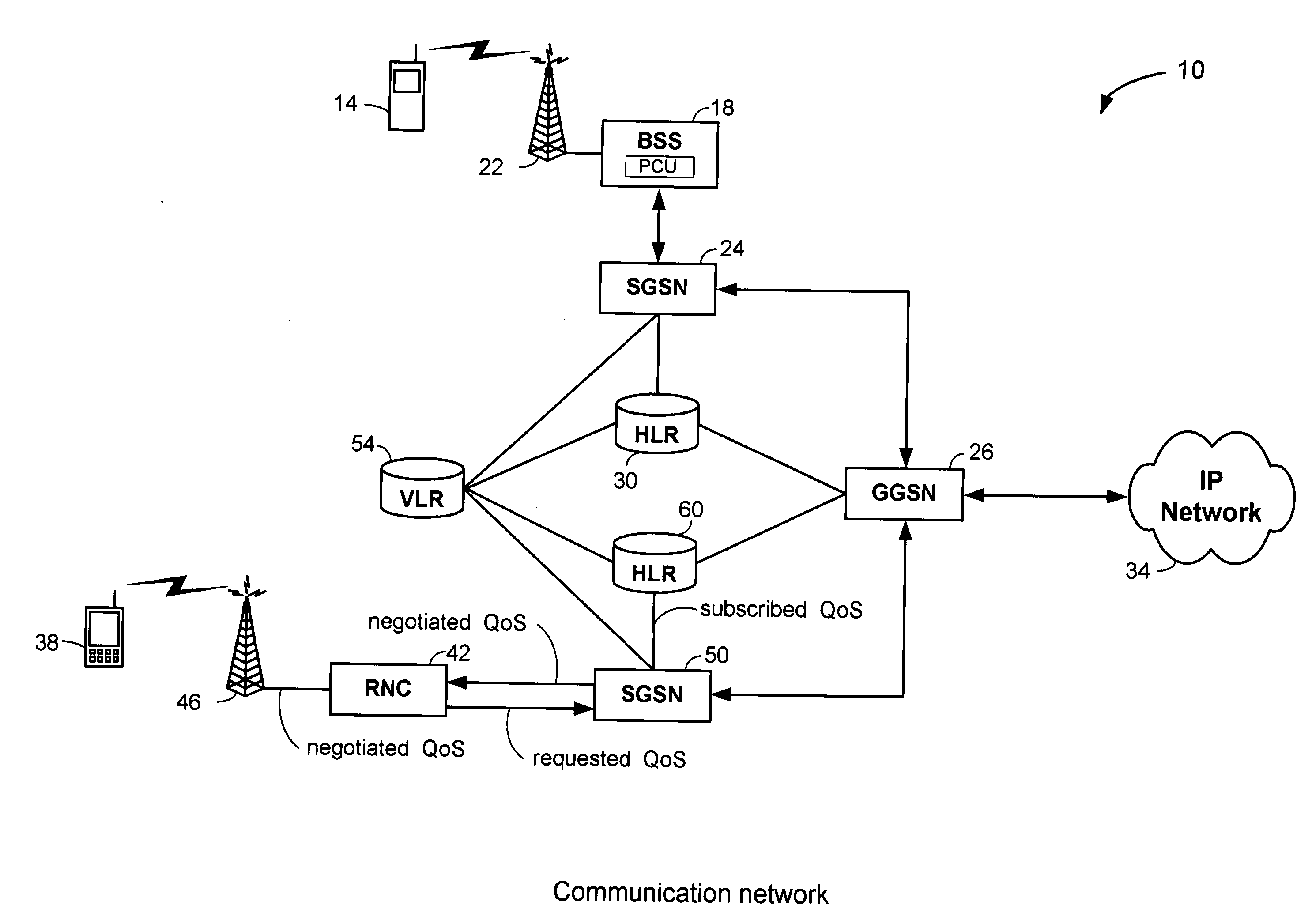
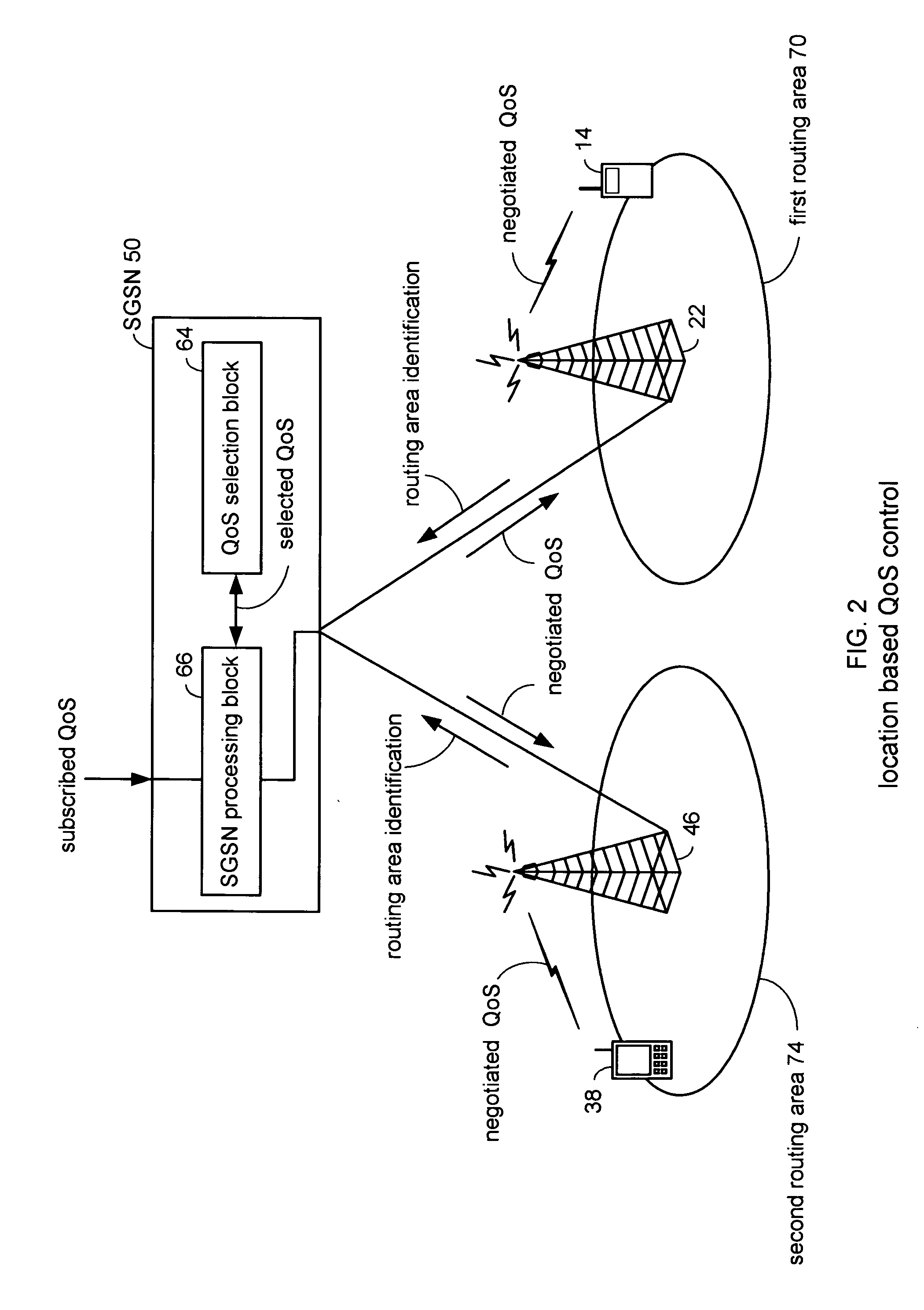
Location based quality of service (QoS) control
InactiveUS20070002868A1Network traffic/resource managementData switching by path configurationQuality of serviceMobile Web
A location based Quality of Service (QoS) is negotiated for each mobile terminal entering a mobile network. Each mobile terminal receives a routing area identification that identifies the mobile terminal's location. The routing area identification and International Mobile Subscriber Identity (IMSI) are transmitted to a QoS selection block within a QoS network element to map the mobile terminal to a QoS group and a corresponding QoS profile. The QoS selection block provides a selected QoS based on the QoS profile to the network element wherein the selected QoS rating is negotiated with the mobile terminal. The QoS negotiation includes using the selected QoS rating when the mobile terminal routing area maps to one of the corresponding QoS groups or using a subscribed QoS rating received from the roaming mobile terminal HLR when the mobile terminal routing area and IMSI do not map to one of the corresponding QoS groups.
Owner:KAPSCH CARRIERCOM FRANCE
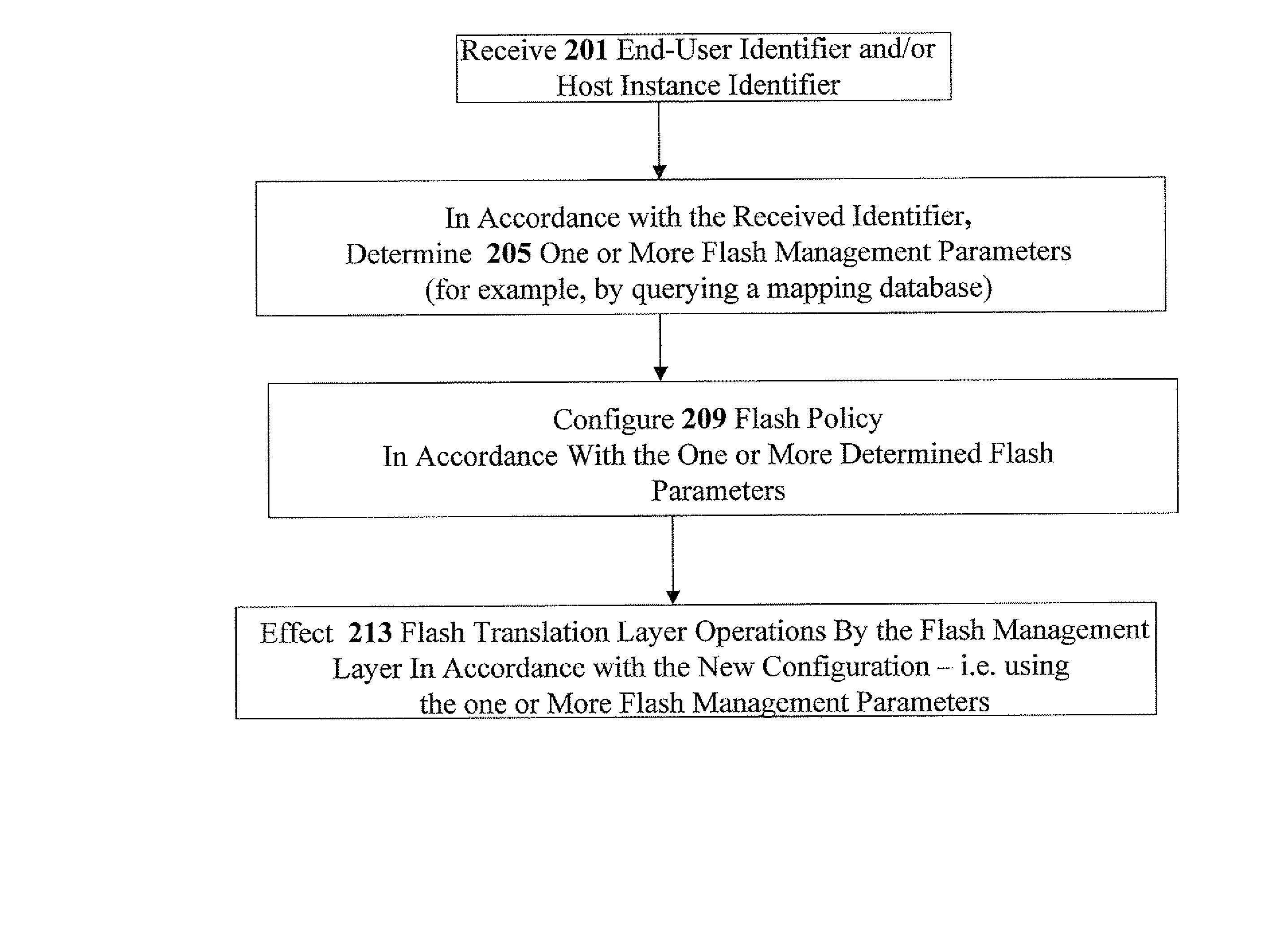
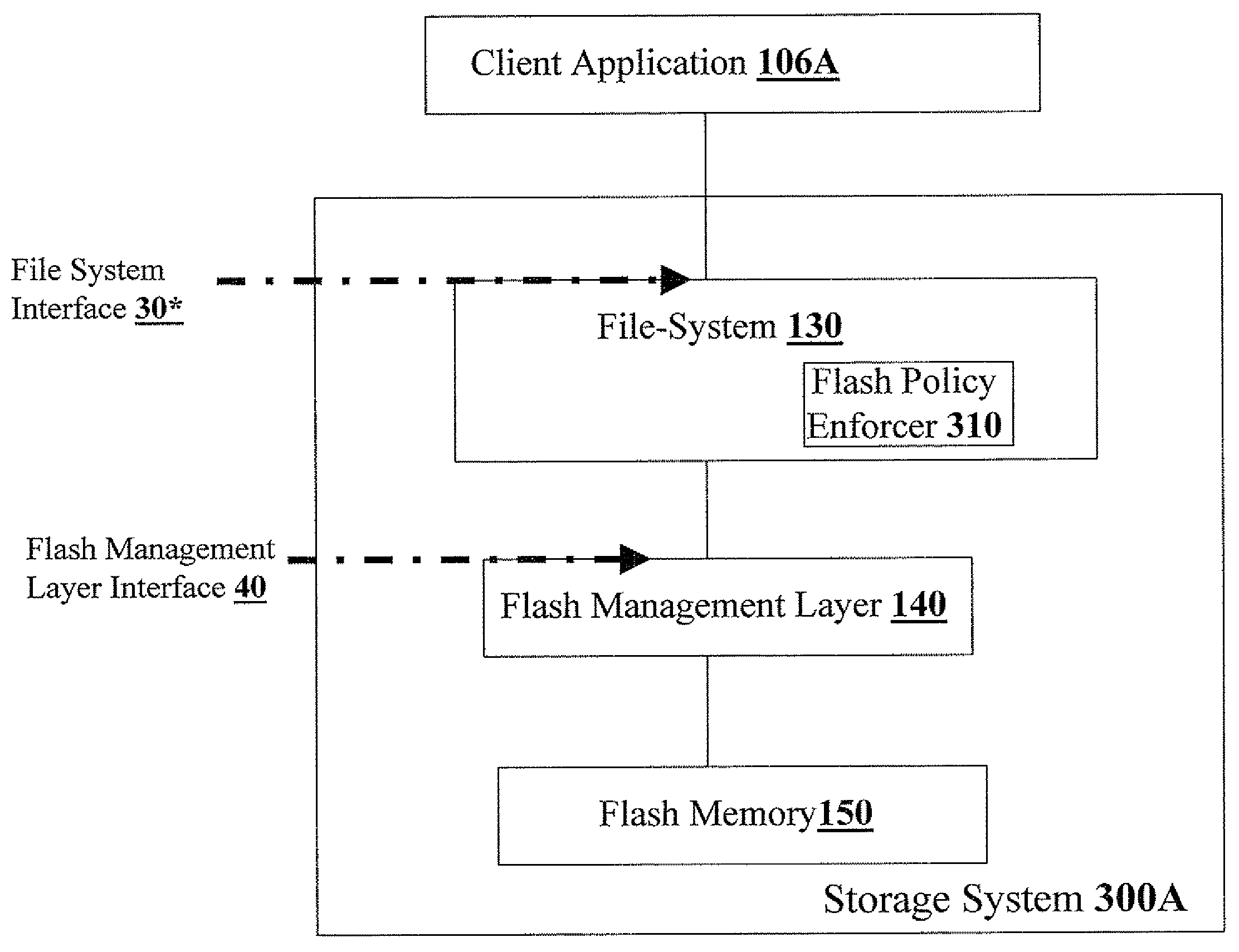
Identity-based flash management
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network
ActiveUS20060172732A1Minimizes O & M activityImprove standardizationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkGeneral Packet Radio Service
The present invention provides a method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network by receiving a message containing a mobile identity of a mobile station (MS) and dropping or rejecting the message whenever the received mobile identity does not match a stored mobile identity associated with the MS. The message is processed whenever the received mobile identity matches the stored mobile identity associated with the MS. The stored mobile identity is provided by a secure gateway. The mobile identity can be an International Mobile Subscriber Identity, Temporary Mobile Subscriber Identity, Packet Temporary Mobile Subscriber Identity, private Internet Protocol (IP) address or public IP address. The message can be a registration request, uplink message or a downlink message, such as a Mobility Management message, a General Packet Radio Service Mobility Management message, or a UMA or Unlicensed Radio Resources message.
Owner:TELEFON AB LM ERICSSON (PUBL)
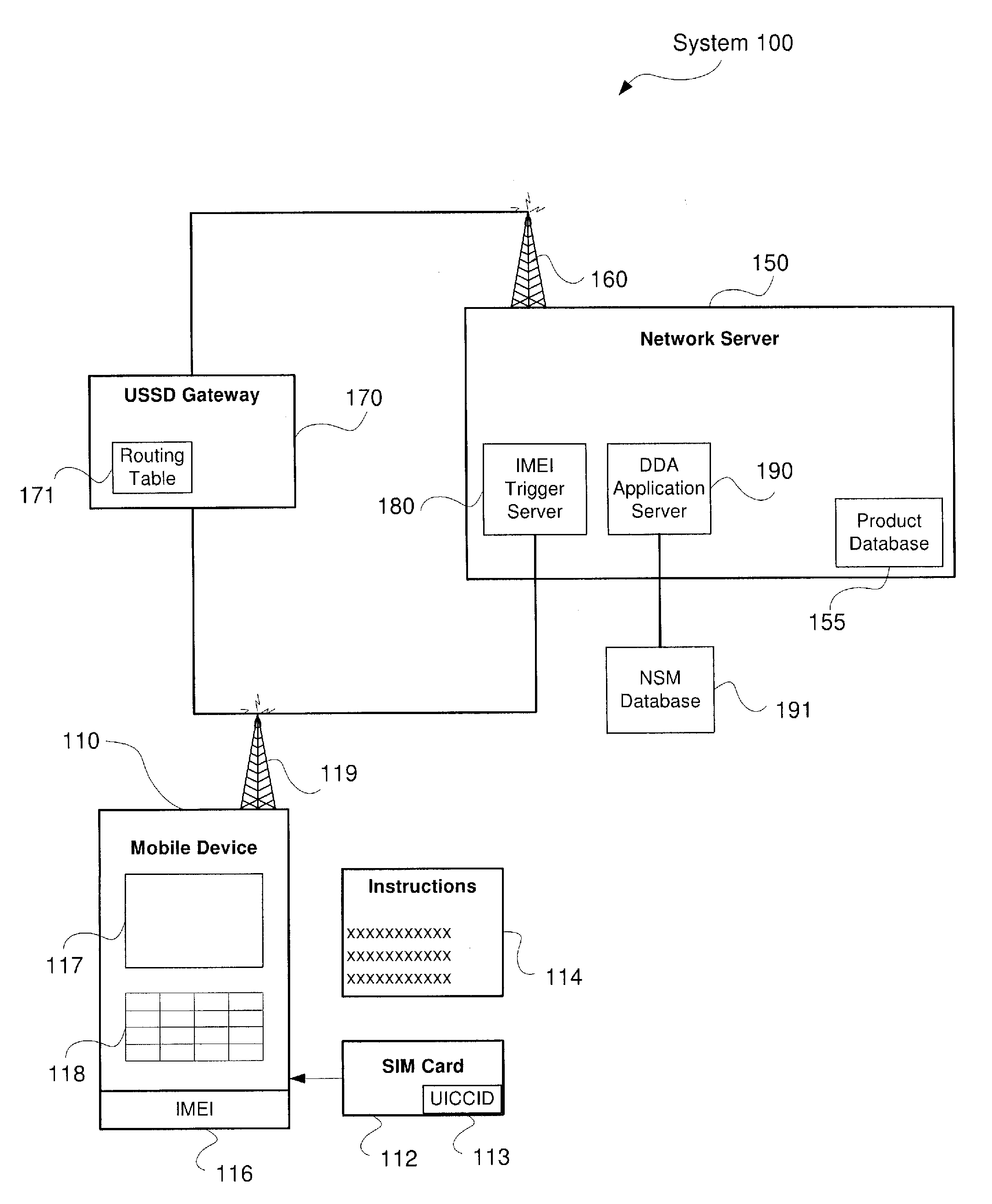
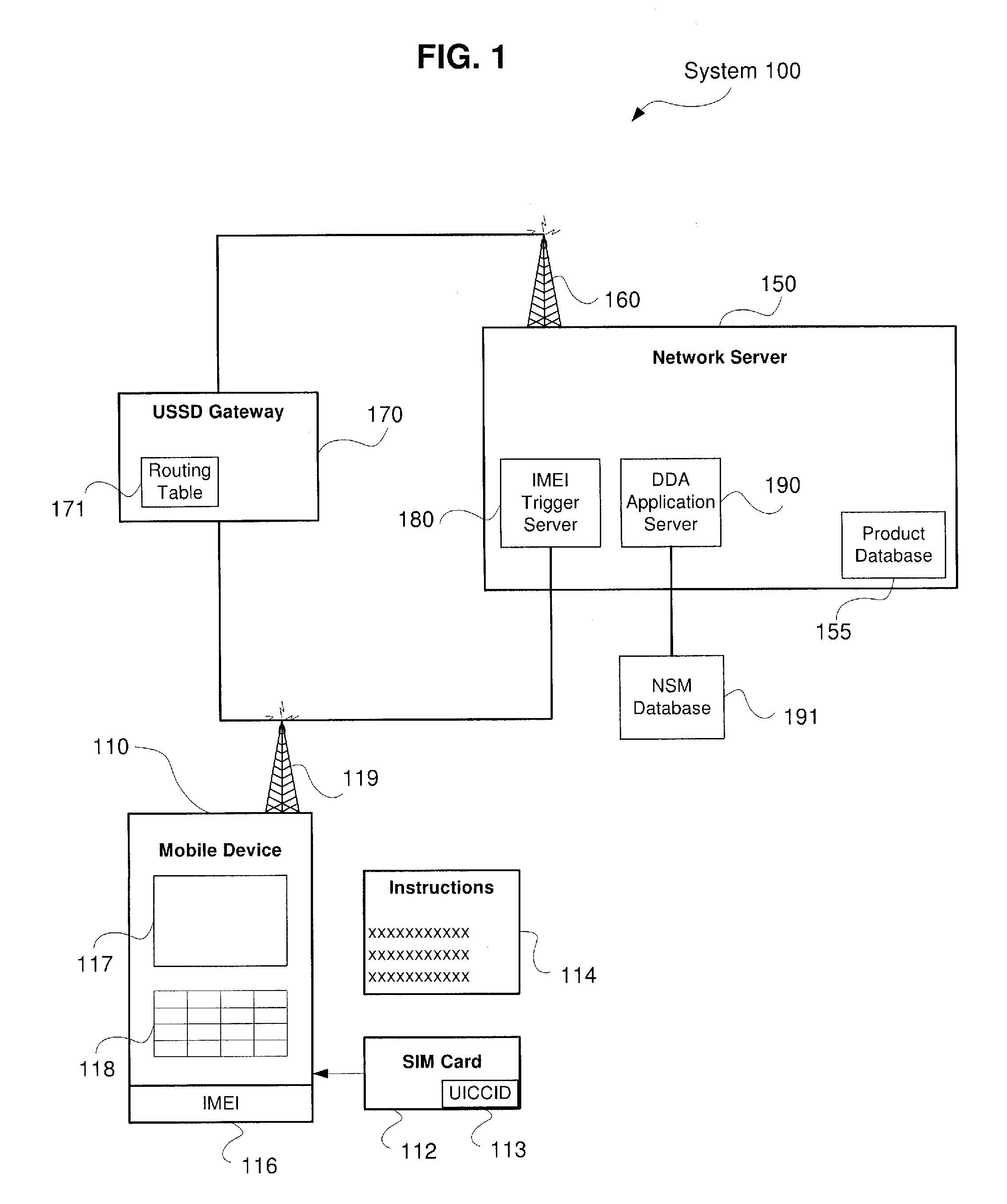
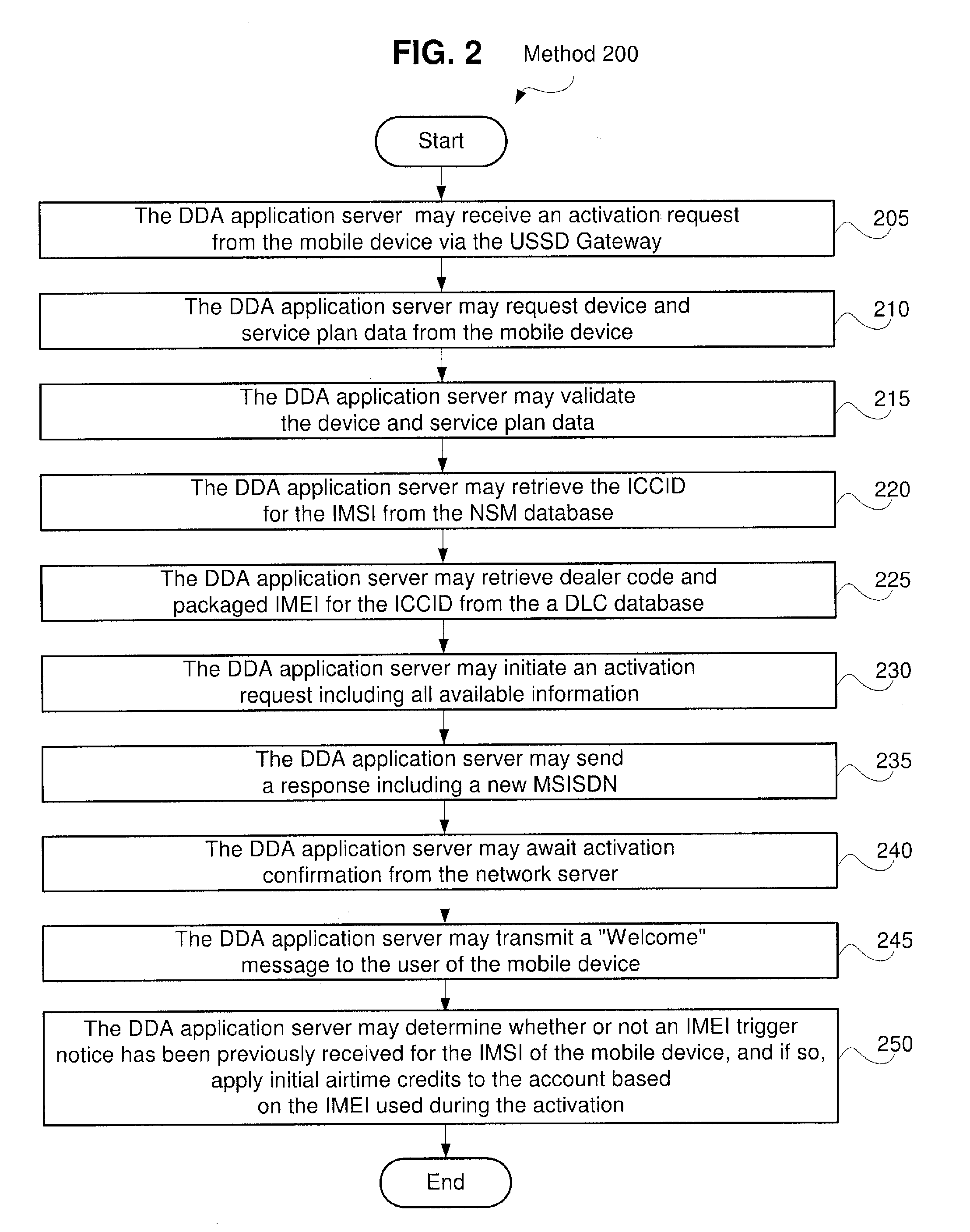
System and Method for Direct Device Activation
InactiveUS20110159843A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTransceiverBiological activation
Described herein are systems and methods for single-step direct activation of telecommunication services for a mobile device. One embodiment of the disclosure of this application is related to a system comprising a transceiver receiving product information from a mobile device and receiving service plan information from the mobile device, and a server verifying availability of service for the mobile device based on at least one of the product information and the service plan information, and activating telecommunication service with the mobile device. The received product information including an international mobile equipment identity (“IMEI”) number received from an IMEI trigger event and an international mobile subscriber identity (“IMSI”) number received from a pre-provisioned subscriber identity module (“SIM”) component. The server accesses a national SIM manager (“NSM”) database, wherein the NSM includes pre-populated pairing of IMSI numbers with corresponding integrated circuit card identification (“ICCID”) numbers, and the server further retrieves a corresponding ICCID number for the IMSI of the mobile device and including the corresponding ICCID number with the product information.
Owner:AT&T INTPROP I L P
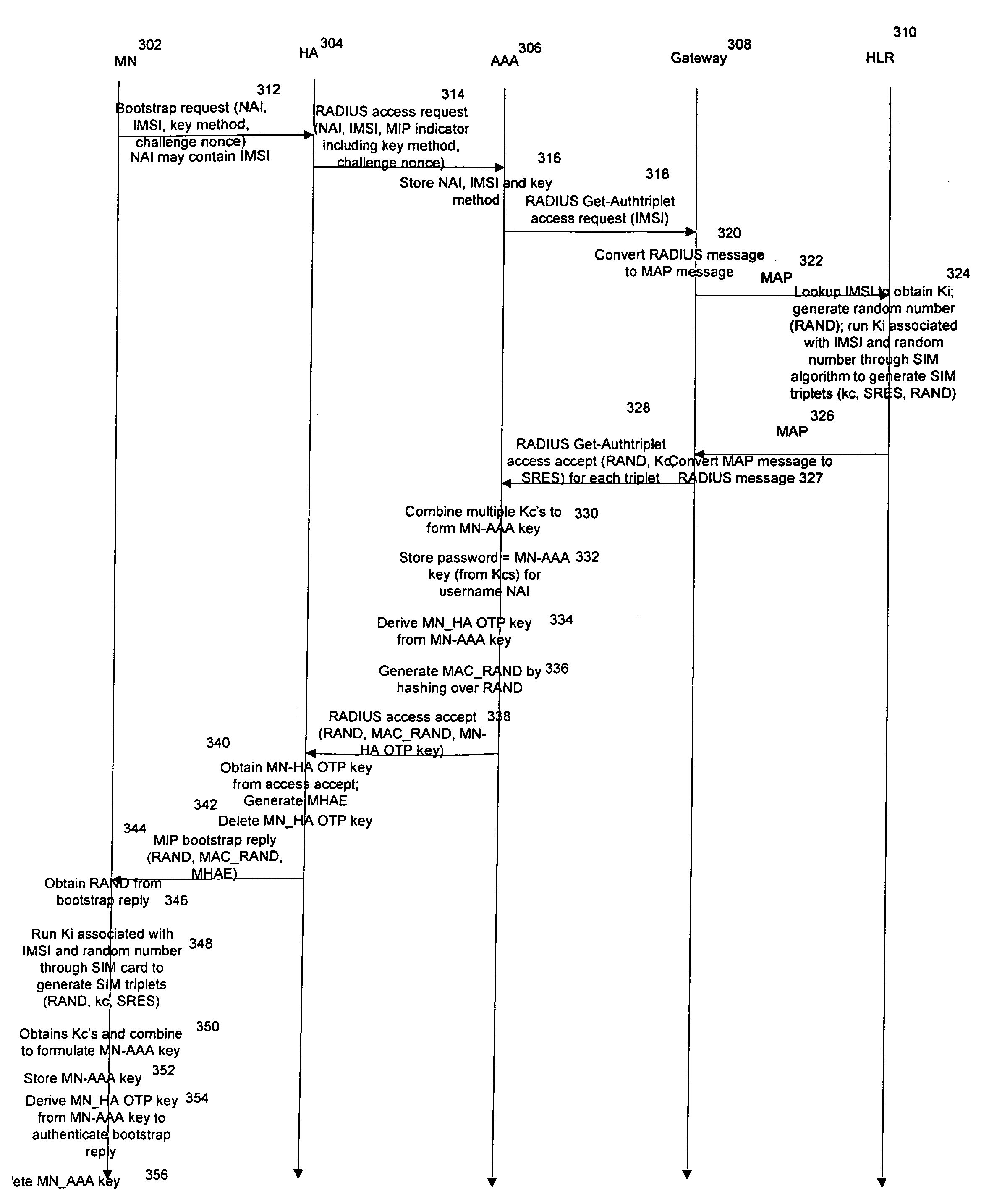
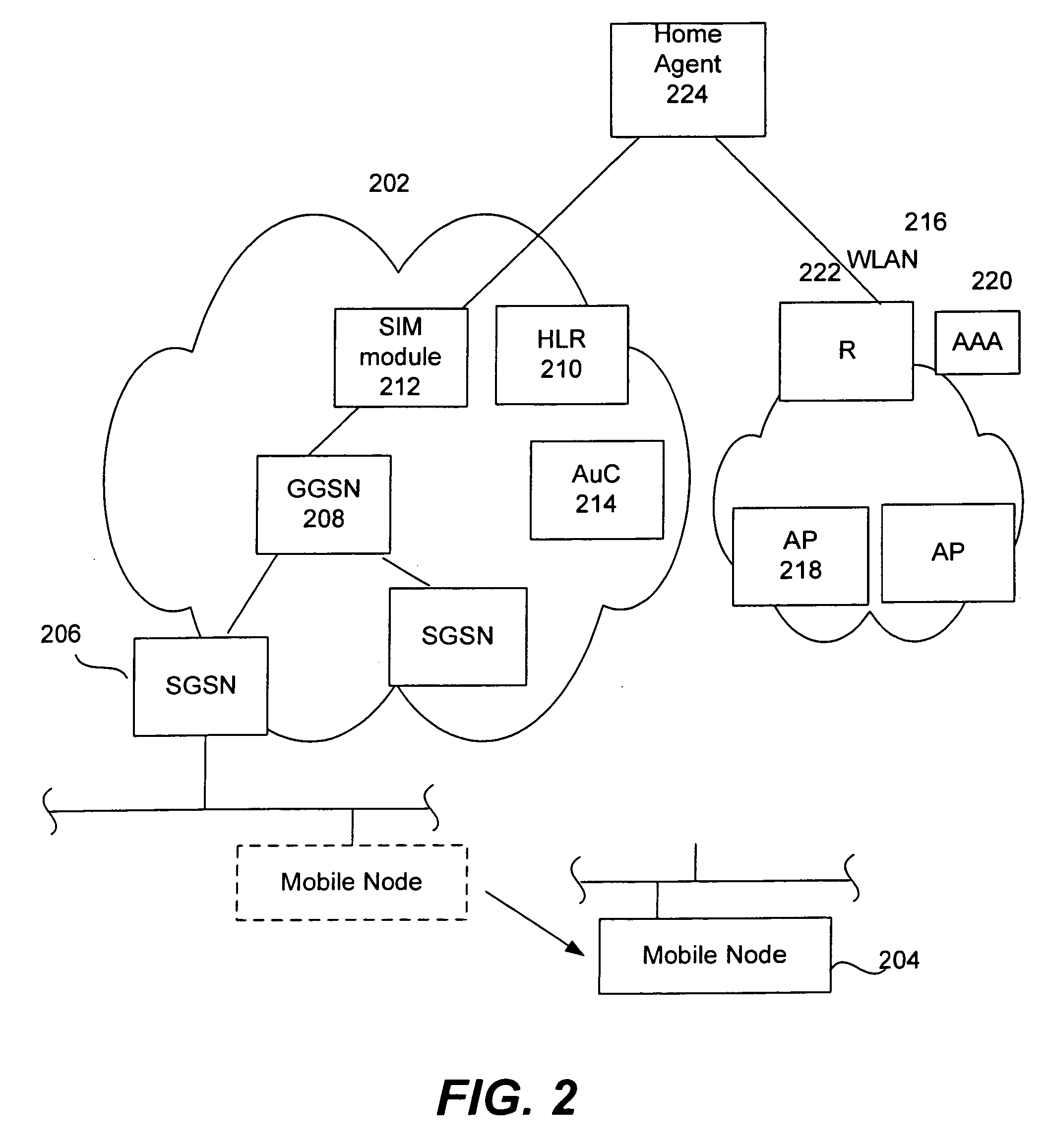
EAP/SIM authentication for Mobile IP to leverage GSM/SIM authentication infrastructure
InactiveUS20070091843A1Data switching by path configurationWireless network protocolsGSMInternational mobile subscriber identity
Methods and apparatus for dynamically generating a set of Mobile IP keys are disclosed. The set of Mobile IP keys is dynamically generated using an existing HLR / AuC authentication infrastructure. This is accomplished, in part, by obtaining an International Mobile Subscriber Identity (IMSI) that uniquely identifies a particular Mobile Node. Once a set of Mobile IP keys is generated from authentication information associated with the IMSI, the Mobile Node may register with its Home Agent using the set of Mobile IP keys.
Long term evolution-primary WIFI (lte-pw)
ActiveUS20180007587A1Latency can be tightly controlledUse minimizedTransmissionNetwork data managementVoice communicationNetwork address
A system and method of communication, comprising establishing a first connection between the user equipment and a first non-public packet switched network which assigns a first non-public packet switched network address to user equipment; establishing an open signaling channel which communicates between the user equipment and a remote server through a cellular telephone network according to a public switched telephone network address associated with an International mobile subscriber identity; communicating an identification of the first non-public network and the first non-public packet switched network address over the open signaling channel to the remote server; and establishing a real time voice communication from the remote server to the user equipment through the first connection based on a call routed through the remote server to the public switched telephone network address.
Owner:EVOLVE CELLULAR INC
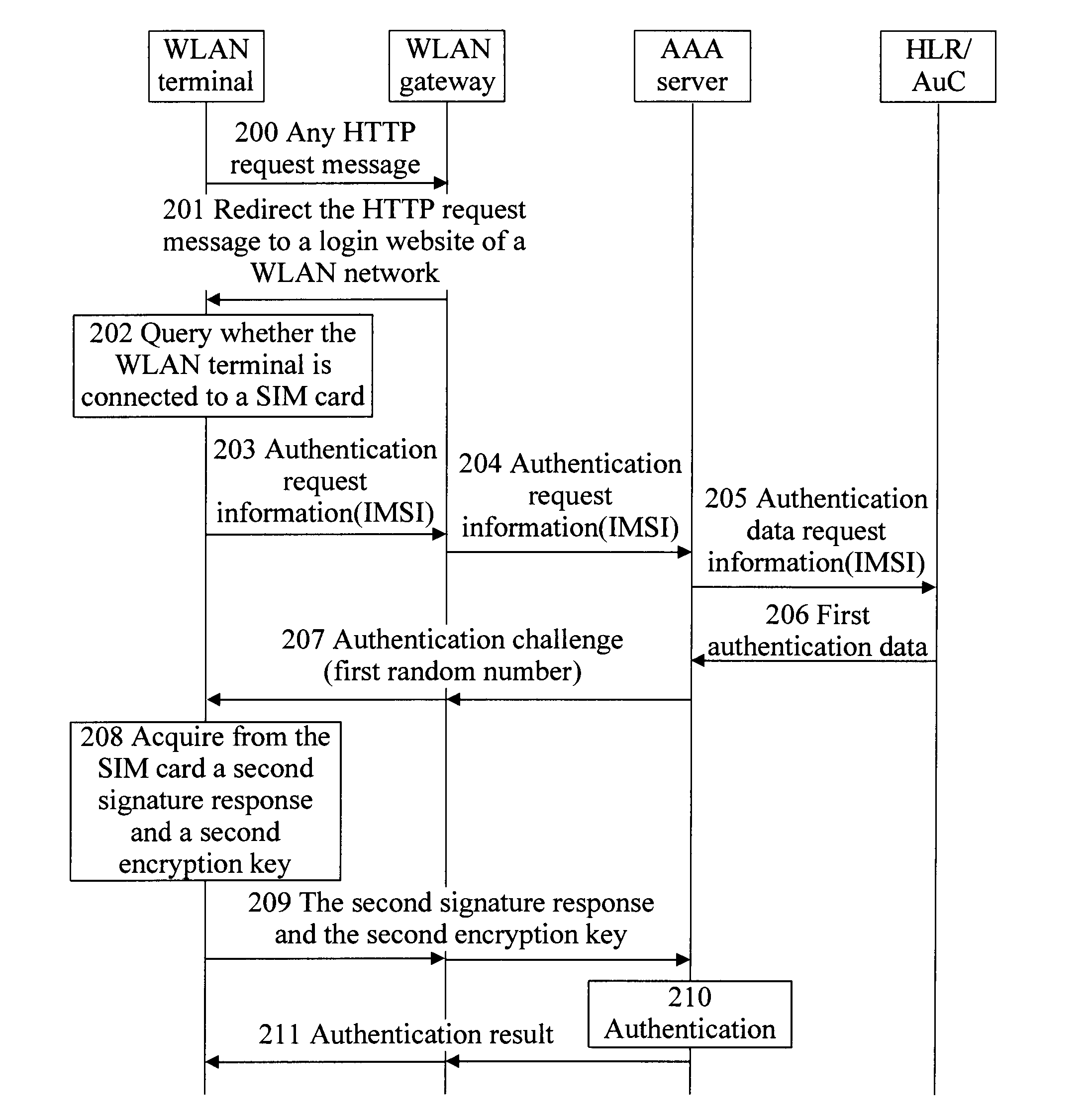
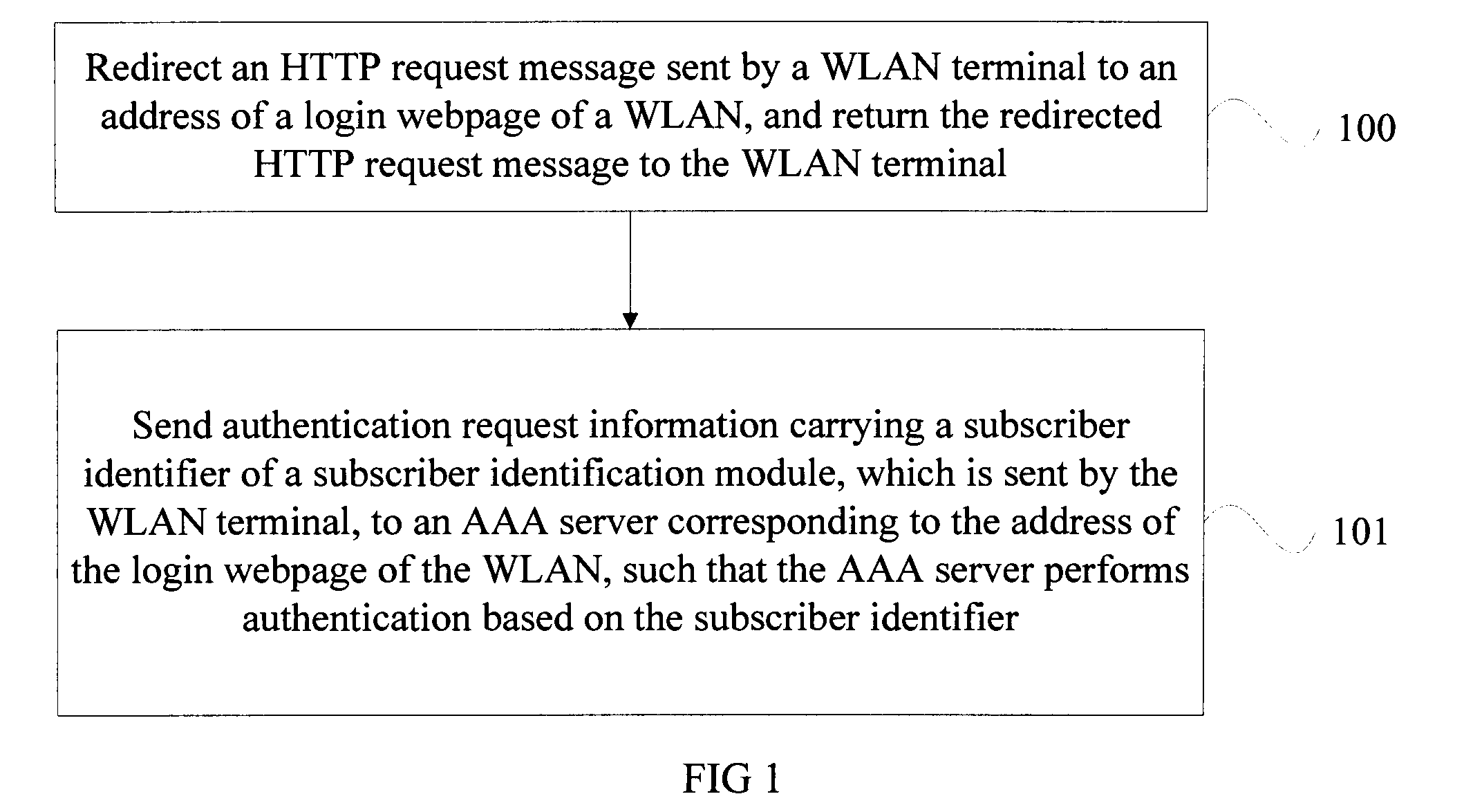
WLAN authentication method, WLAN authentication server, and terminal
ActiveUS20120144189A1Complex implementationOvercome disadvantagesDigital data processing detailsUser identity/authority verificationAuthentication serverComputer terminal
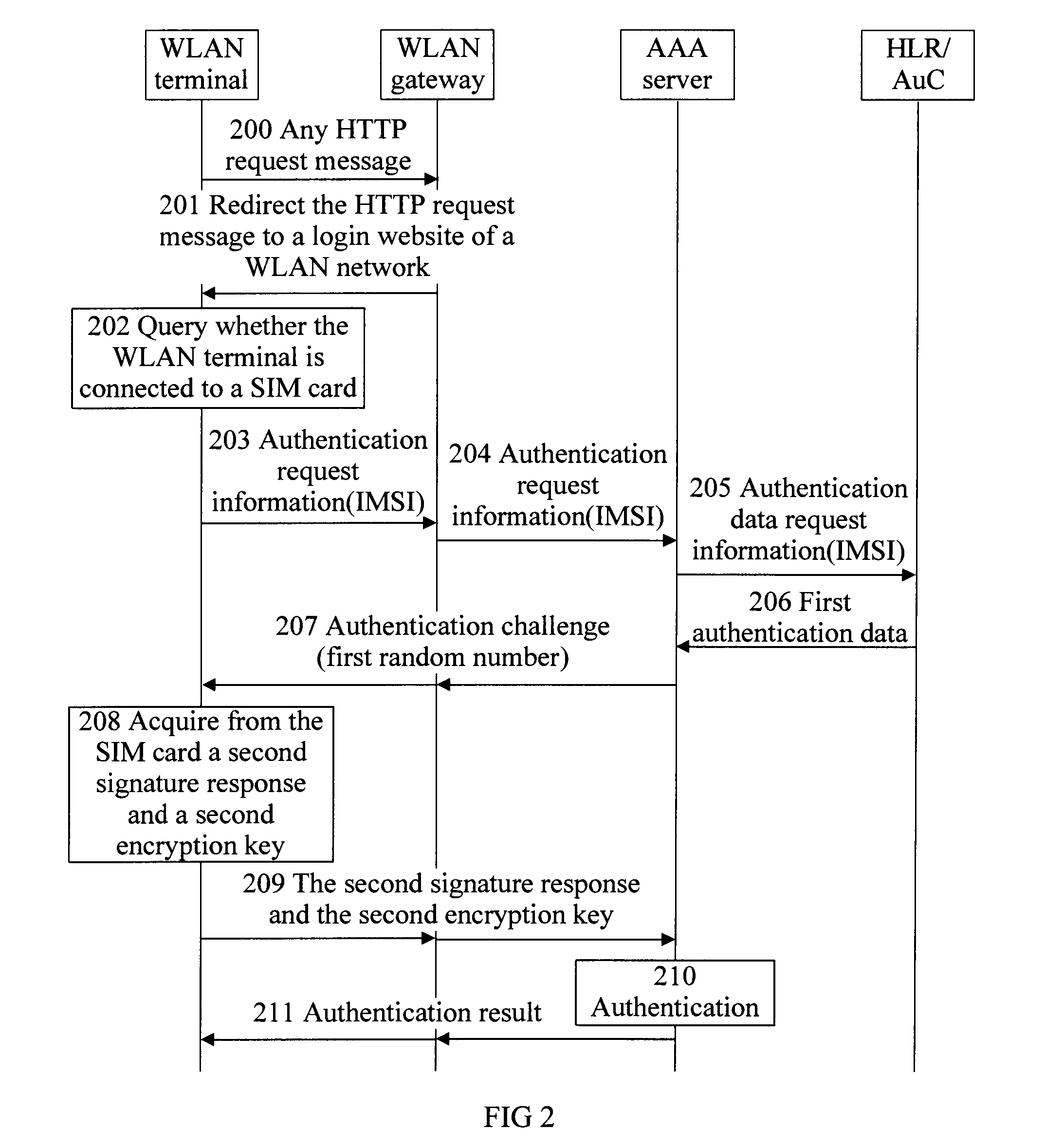
An authentication method, a server, and a terminal for a wireless local area network (WLAN) are provided. The method includes: redirecting a Hypertext Transfer Protocol (HTTP) request message sent by a WLAN terminal to an address of a login webpage of a WLAN network and returning the redirected HTTP request message to the WLAN terminal; sending authentication request information carrying an International Mobile Subscriber Identity (IMSI) identifier of a Subscriber Identity Module (SIM) card sent by the WLAN terminal to an Authentication / Authorization / Accounting (AAA) server corresponding to the address of the login webpage of the WLAN network, such that the AAA server performs authentication based on the IMSI identifier.
Owner:HUAWEI DEVICE CO LTD
Method and mobile communication device capable of resuming operating function of temporarily disabled SIM card
InactiveUS7840234B2Interconnection arrangementsUnauthorised/fraudulent call preventionPersonal identification numberMobile device
Owner:BENQ CORP
Extended wireless device activation
ActiveUS20120094634A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless mesh networkBiological activation
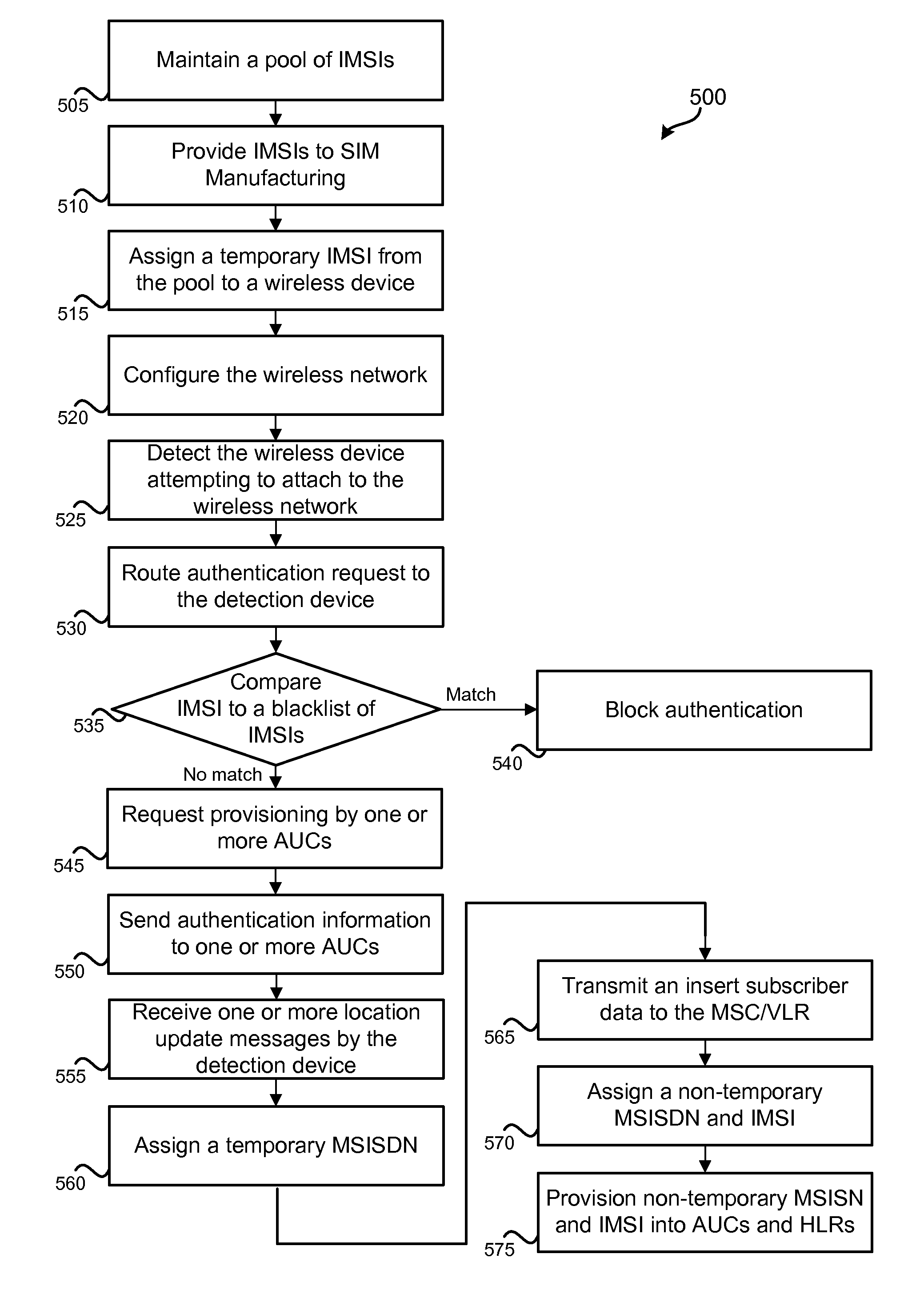
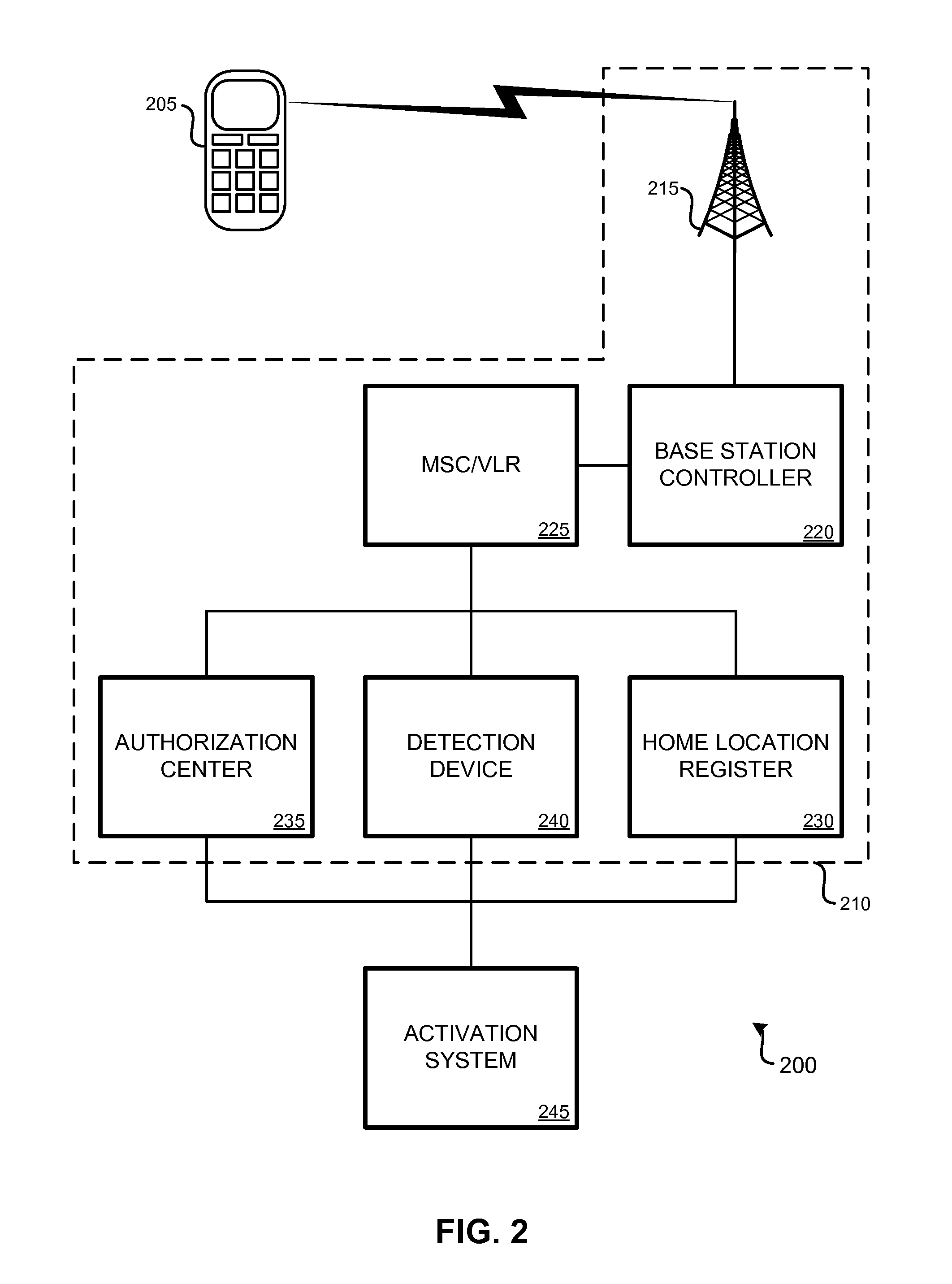
Various arrangements for activating a wireless device on a wireless network are presented. A request to attach to the wireless network may be received from the wireless device. The request may specify an international mobile subscriber identity (IMSI). An authentication message may be transmitted to a detection device of the wireless network. The IMSI may be compared to a set of stored blocked IMSIs. Each IMSI of the set of stored blocked IMSIs may be prohibited from being used to access the wireless network. It may be determined that the wireless device may that corresponds to the IMSI is permitted to be attached to the wireless network. In response to determining the wireless device is permitted to attach to the wireless network, authentication of the wireless device may occur.
Owner:PARTNER ONE ACQUISITIONS INC
Extended wireless device activation
ActiveUS8463258B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless mesh networkBiological activation
Various arrangements for activating a wireless device on a wireless network are presented. A request to attach to the wireless network may be received from the wireless device. The request may specify an international mobile subscriber identity (IMSI). An authentication message may be transmitted to a detection device of the wireless network. The IMSI may be compared to a set of stored blocked IMSIs. Each IMSI of the set of stored blocked IMSIs may be prohibited from being used to access the wireless network. It may be determined that the wireless device may that corresponds to the IMSI is permitted to be attached to the wireless network. In response to determining the wireless device is permitted to attach to the wireless network, authentication of the wireless device may occur.
Owner:PARTNER ONE ACQUISITIONS INC
Method for the routing of communications to a voice over internet protocol terminal in a mobile communication system
ActiveUS7400881B2Easy to operateEasy to serviceSpecial service for subscribersConnection managementCommunications systemProcessor register
The invention relates to a method a method for routing calls and messages in a communication system. In the method a mobile station registers to a call control node using a logical name. The logical name is mapped in a directory to an international mobile subscriber identity. The call control node performs a location update to a home location register using the international mobile subscriber identity. The mobile station is reached using a called party number. As a terminating call or message is received to a core network, a roaming number is allocated for the mobile station, and the call or message is routed to the call control entity currently serving the mobile station. The call control node translates the called party number to the logical name using the directory.
Owner:NOKIA TECH OY
Mobility solution selection for voice over eps
InactiveUS20100135246A1Well formedPromote coexistenceWireless commuication servicesNetwork connectionsSpeech soundHandover
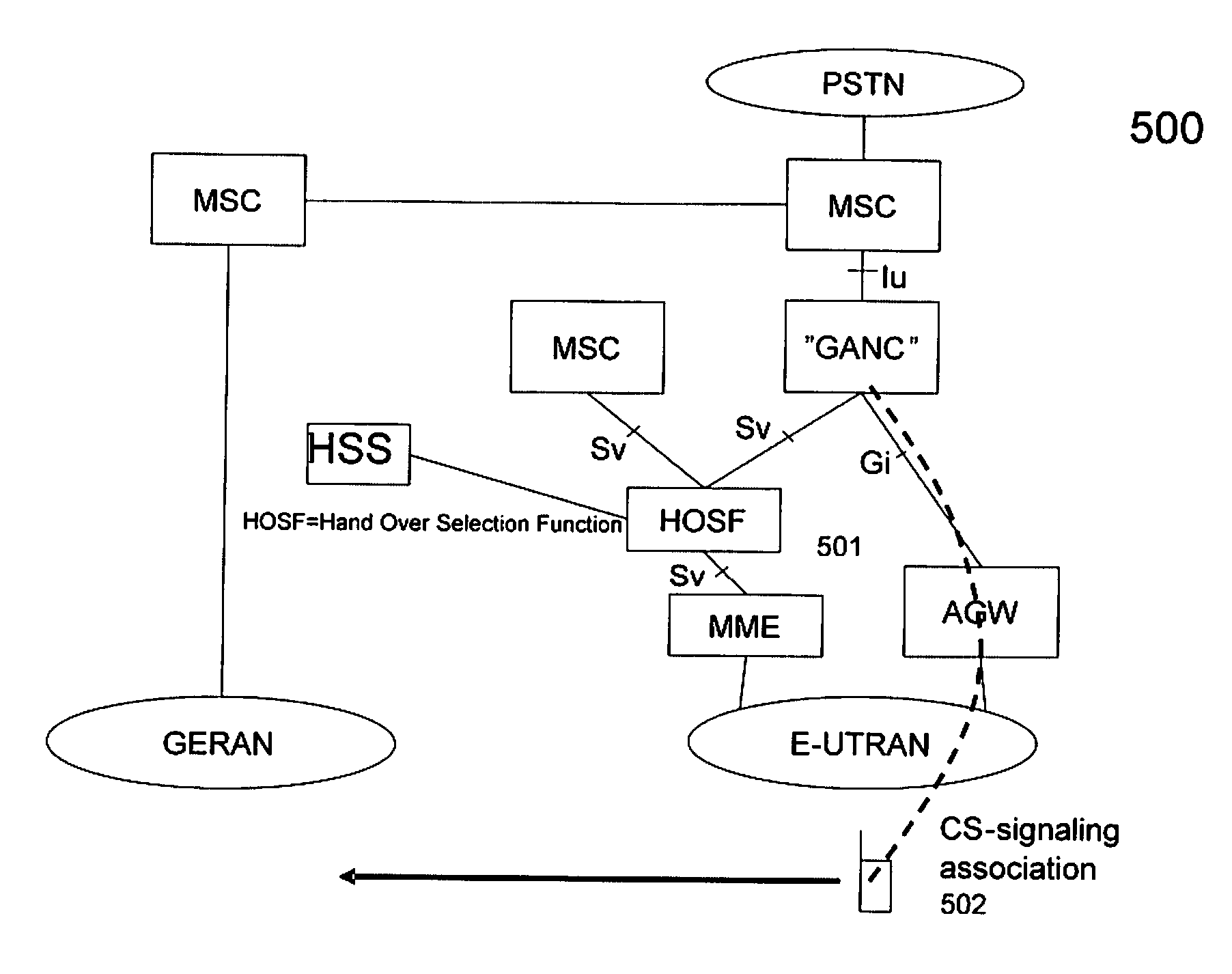
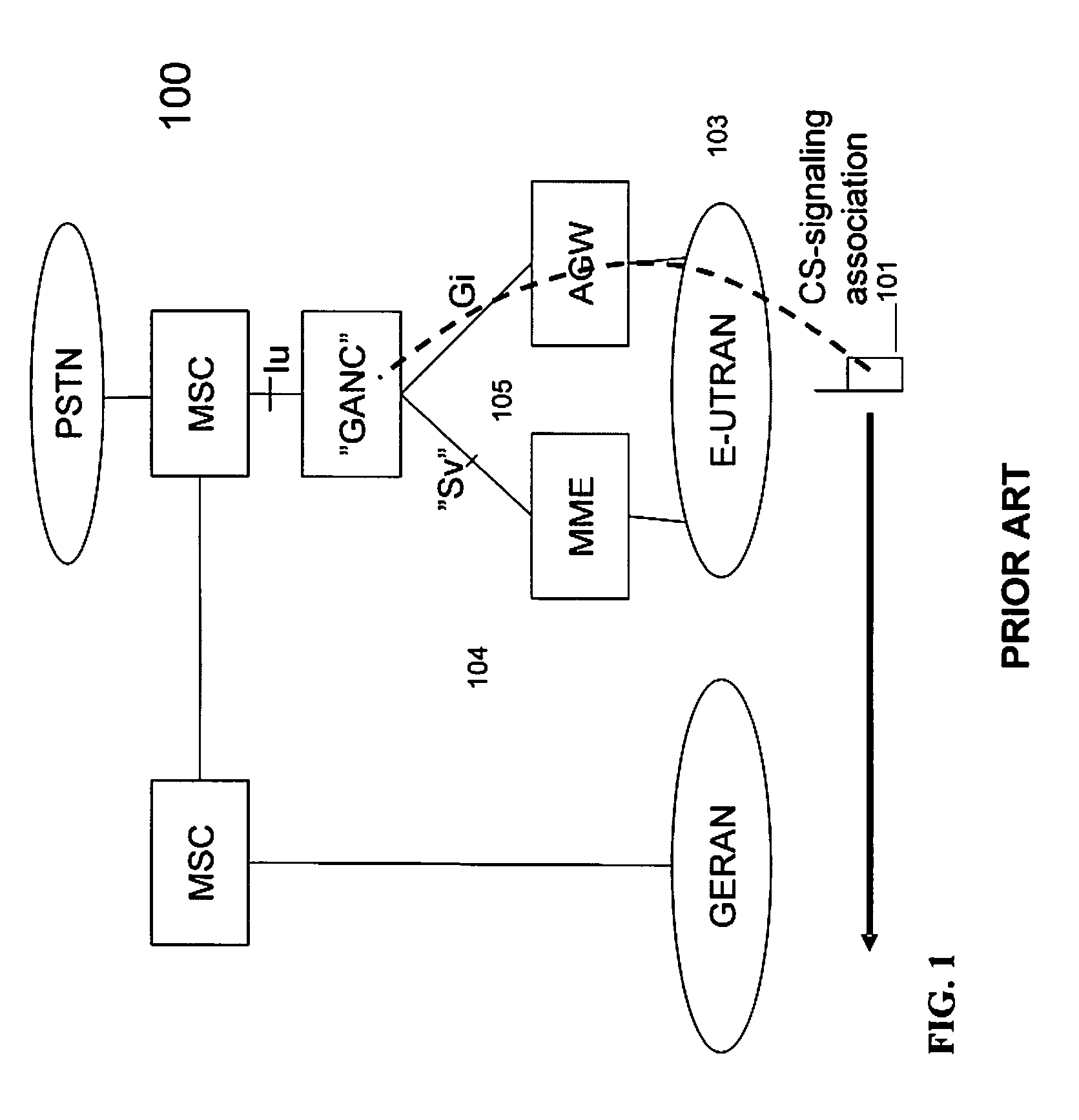
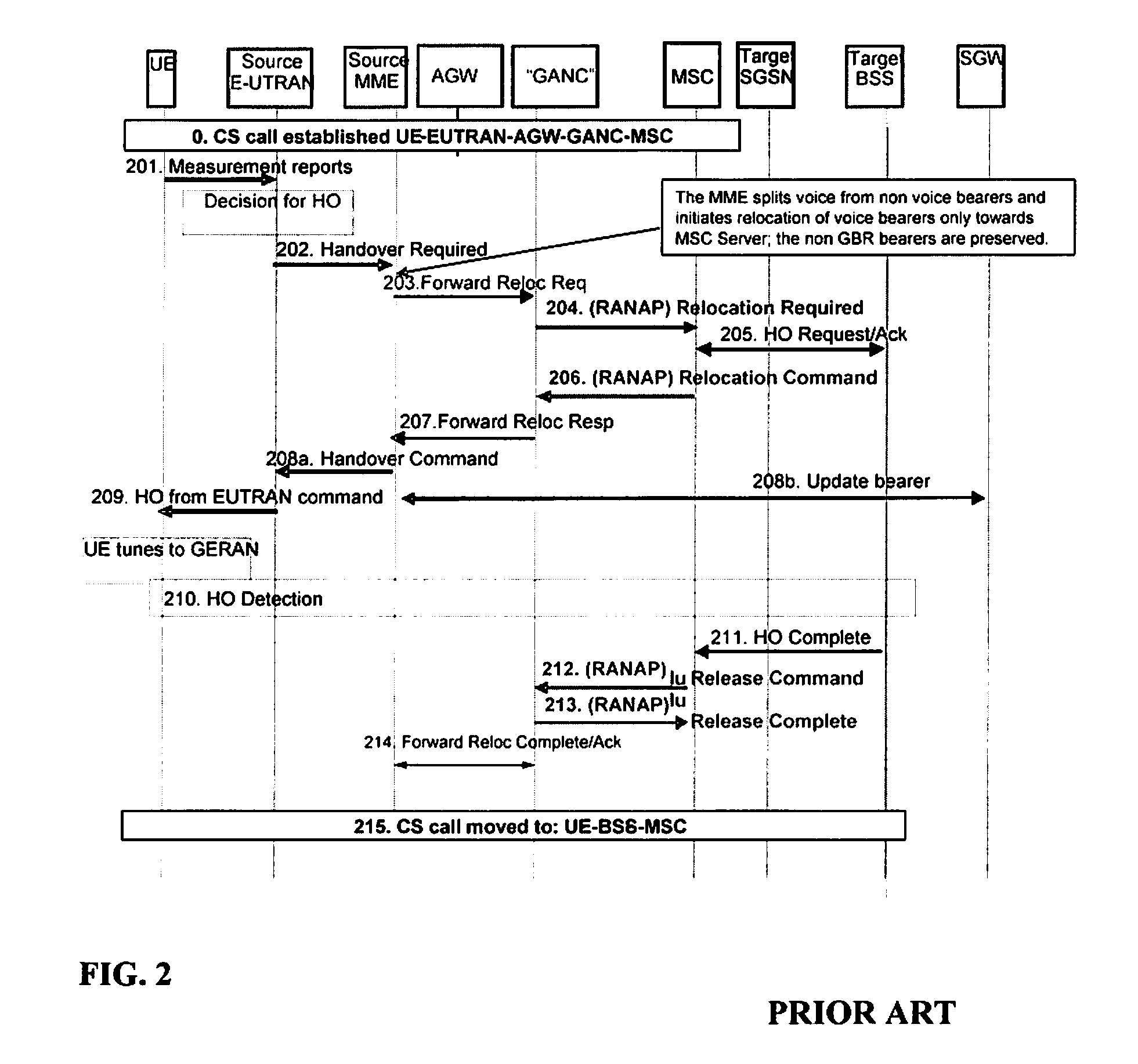
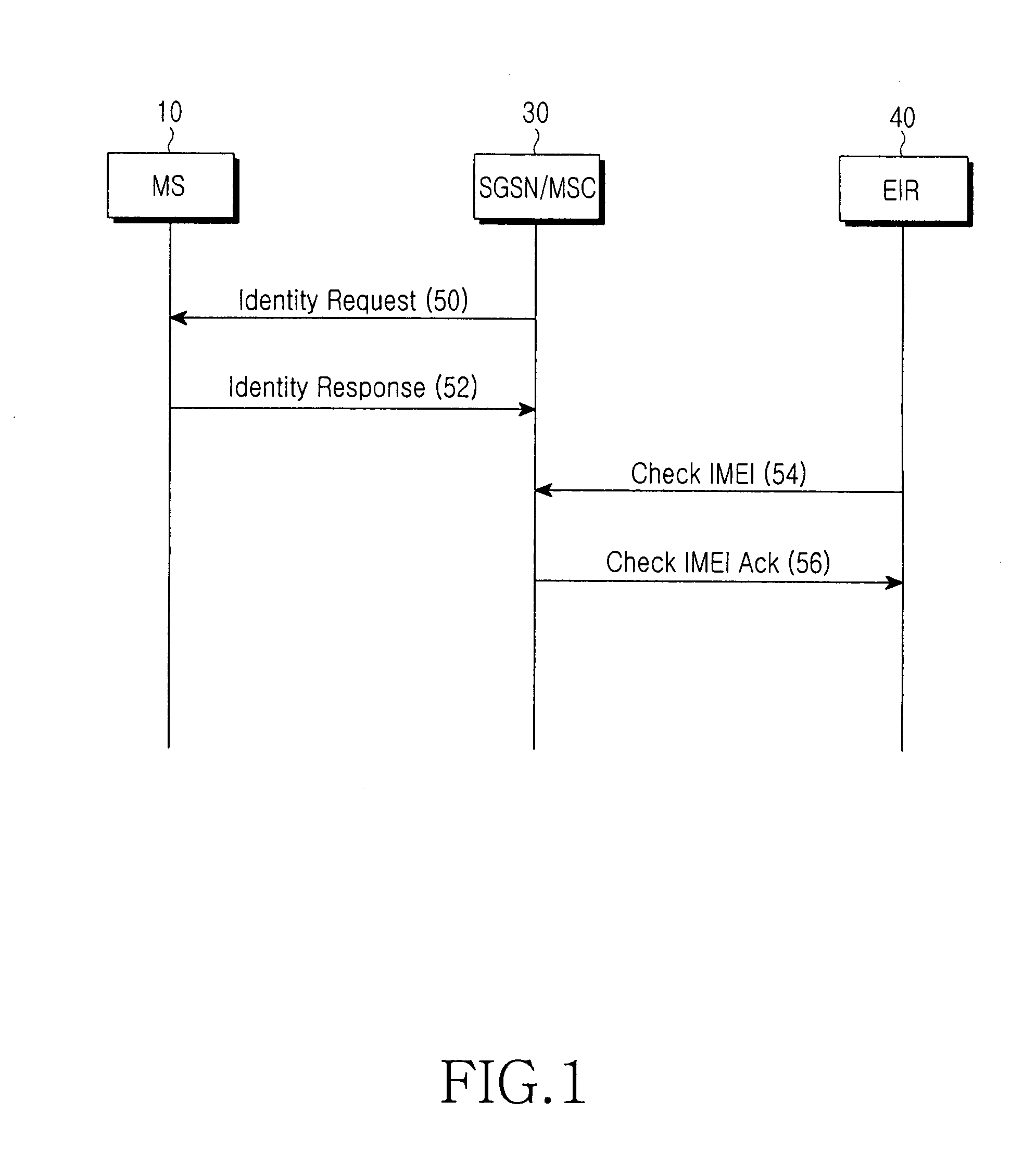
A method and apparatus for determining handover (HO) signaling in a communications network. The method of the present invention examines the International Mobile Subscriber Identity (IMSI) of a user equipment (UE) during HO and, based on the examination, determines whether Single Radio Voice Call Continuity (SRVCC) or circuit switched (CS) over Long Term Evolution (LTE) using a Generic Access Network Controller (GANC) should be used in the HO.
Owner:TELEFON AB LM ERICSSON (PUBL)
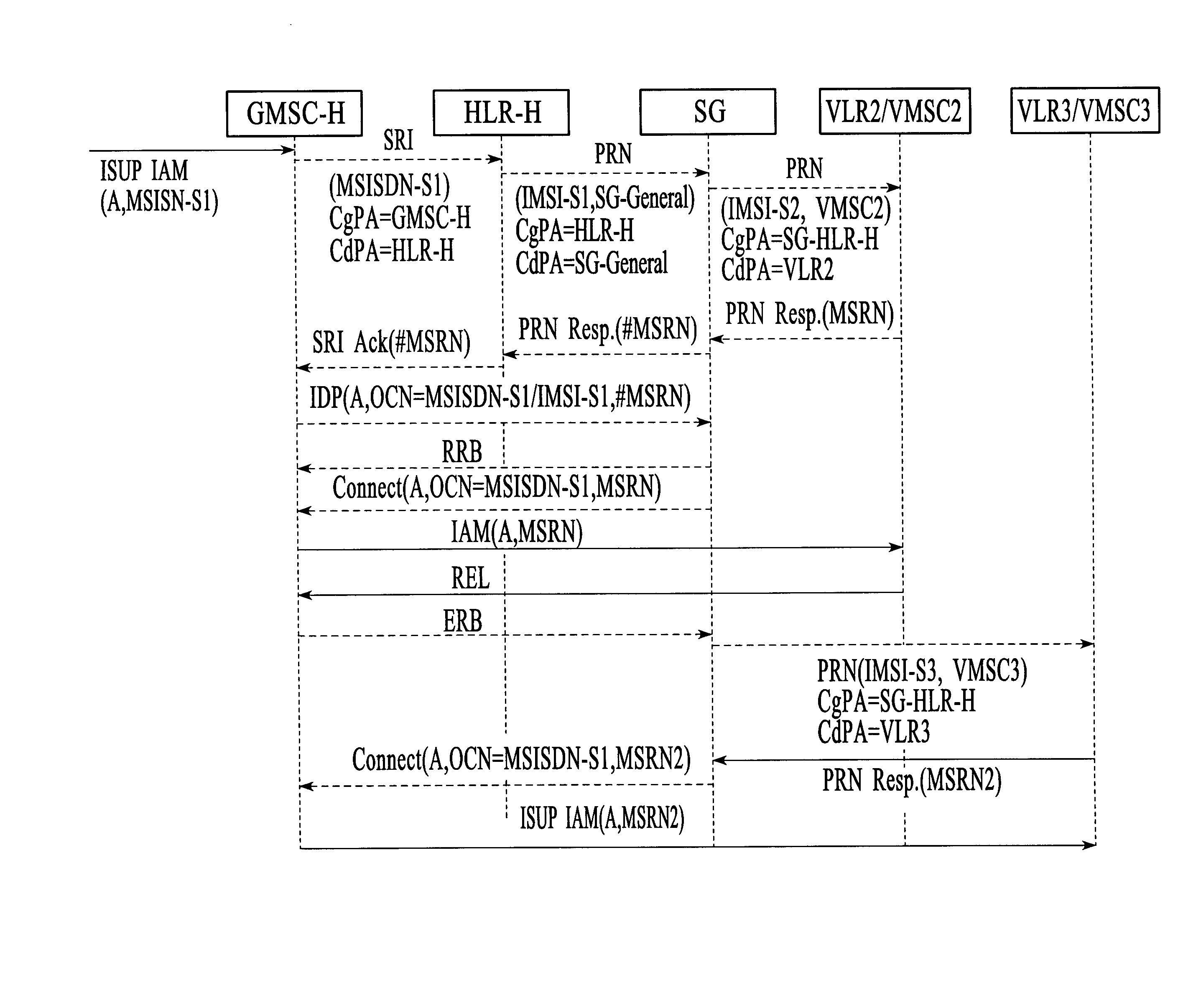
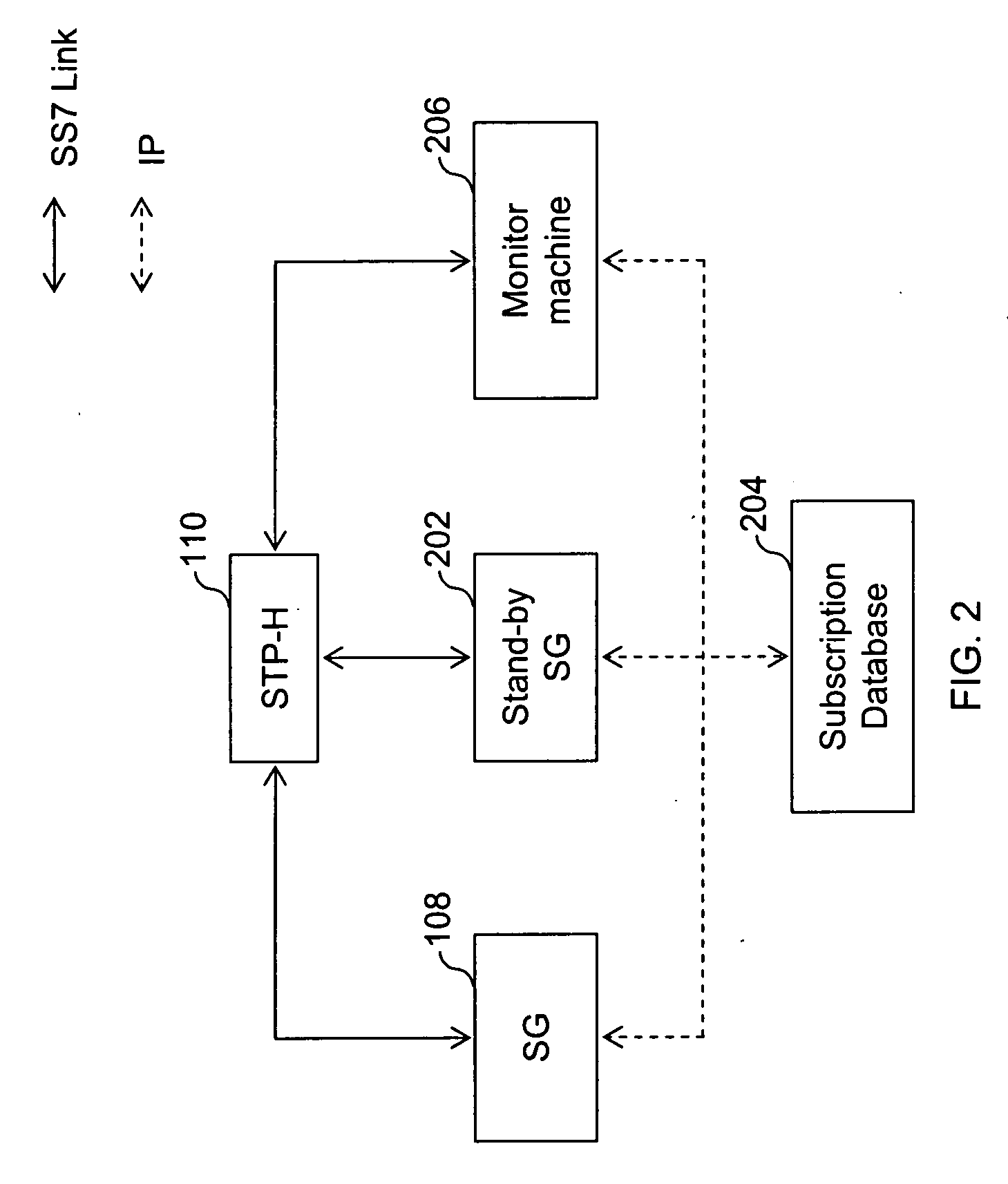
Method and system for providing mobile communication corresponding to multiple MSISDNs associated with a single IMSI
InactiveUS20070213075A1Radio/inductive link selection arrangementsWireless commuication servicesDirectory numberBiological activation
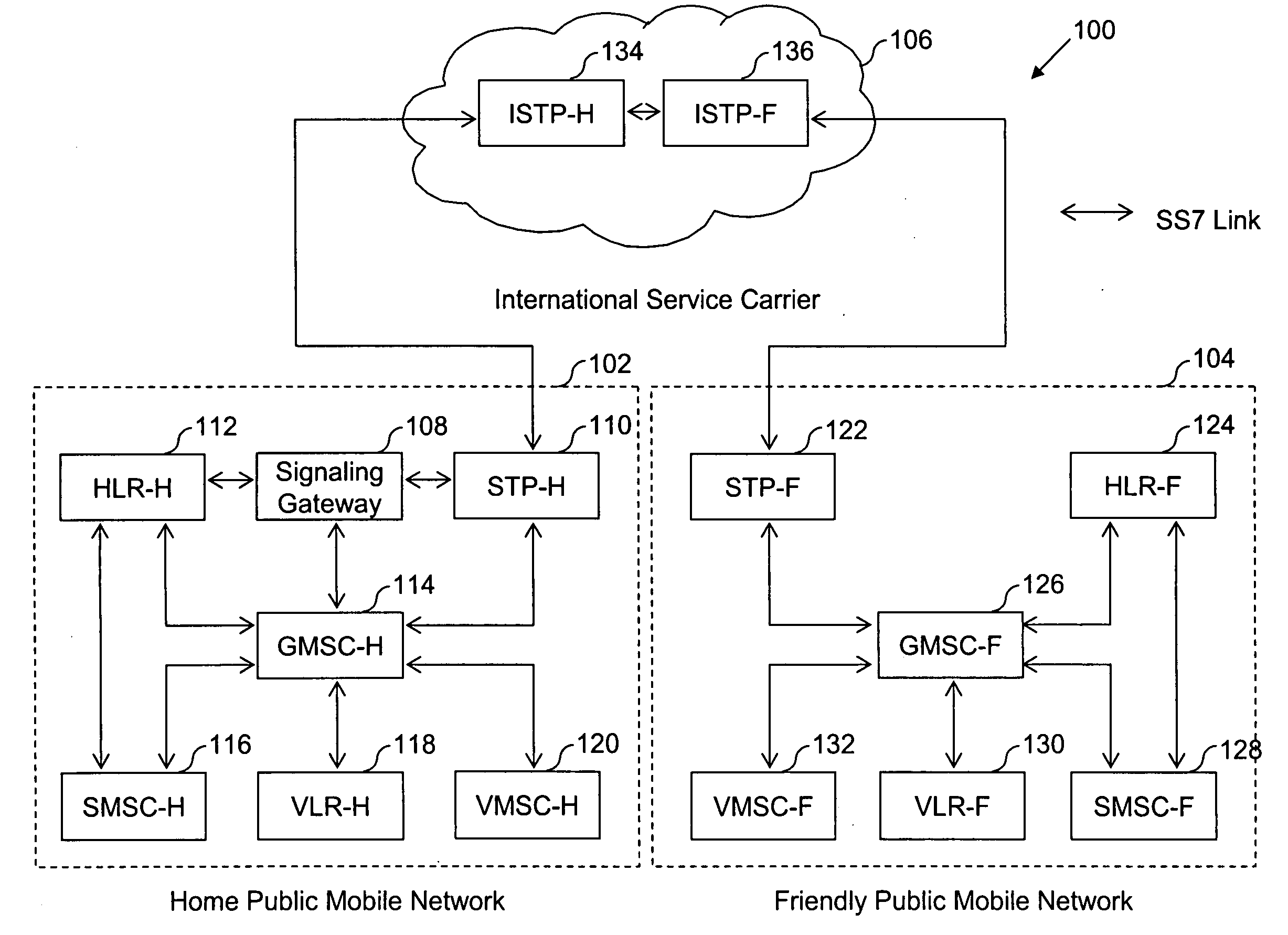
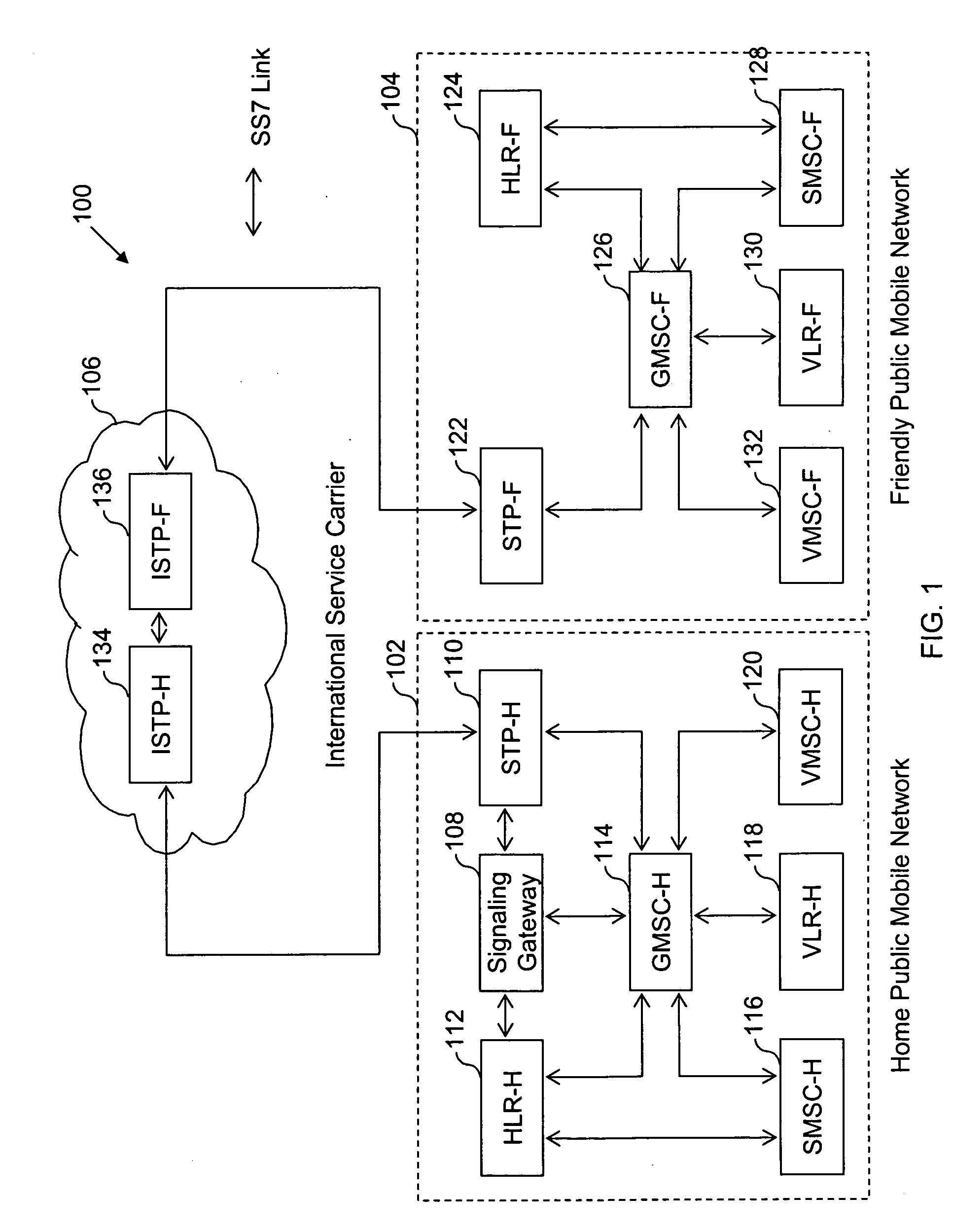
The present invention proposes a method for mobile communication. The method includes assigning one or more Mobile Station International Subscriber Directory Numbers (MSISDNs) to a subscriber of a Home Public Mobile Network (HPMN) upon receiving a subscription activation message from the subscriber at a Signaling Gateway (SG). The subscriber has an HPMN Subscriber Identity Module (SIM) with a corresponding HPMN International Mobile Subscriber Identity (IMSI) and an HPMN MSISDN. The method further includes creating an association of the MSISDNs with the HPMN MSISDN to facilitate signaling corresponding to the HPMN MSISDN and the MSISDNs associated with the subscriber.
Owner:ROAMWARE
Identity-based flash management
ActiveUS20090100215A1Memory architecture accessing/allocationMemory adressing/allocation/relocationContext dataIdentity provider
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Method and apparatus for using active and inactive mobile subscriber identification information in a device to provide services for a limited time period
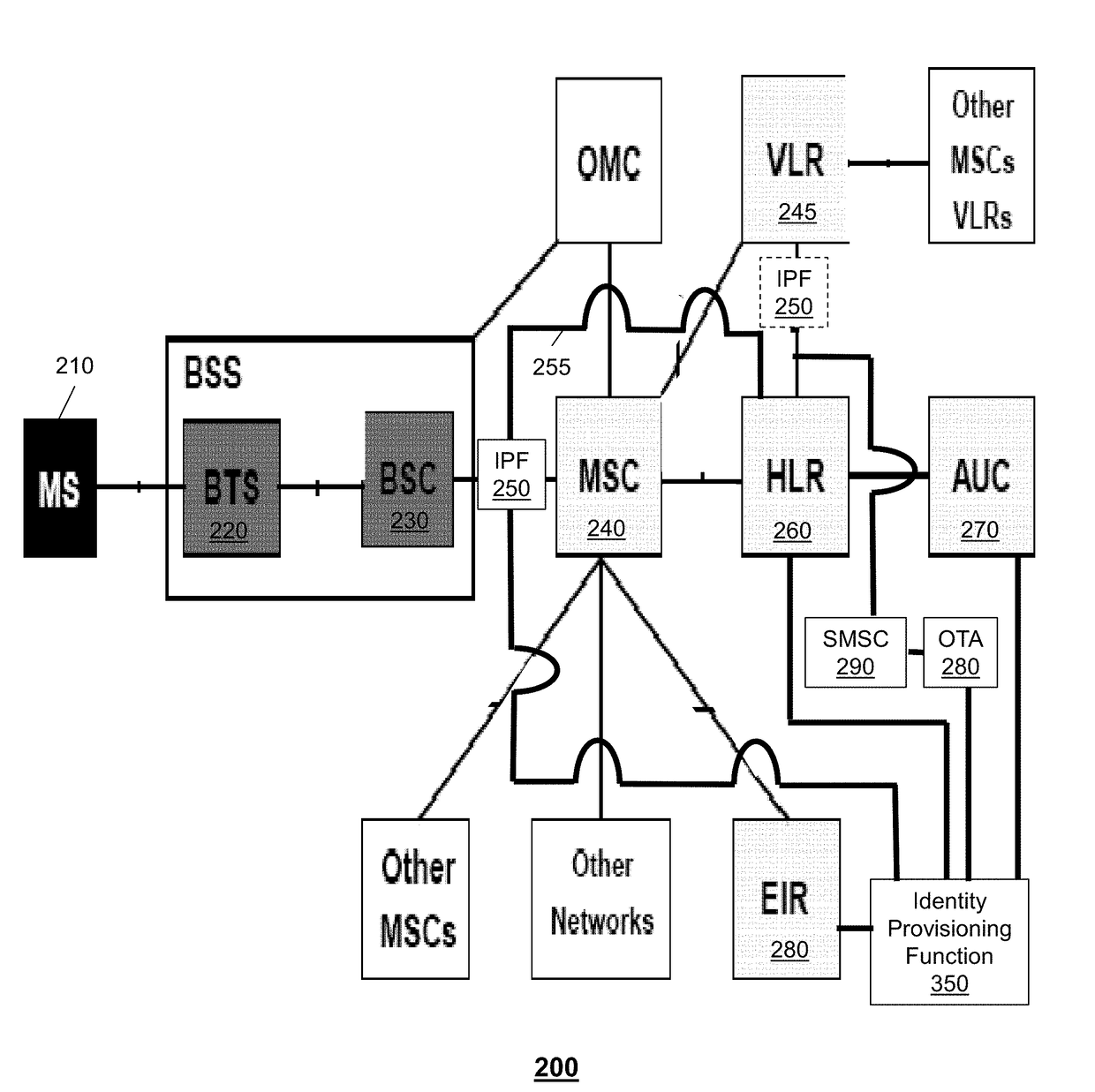
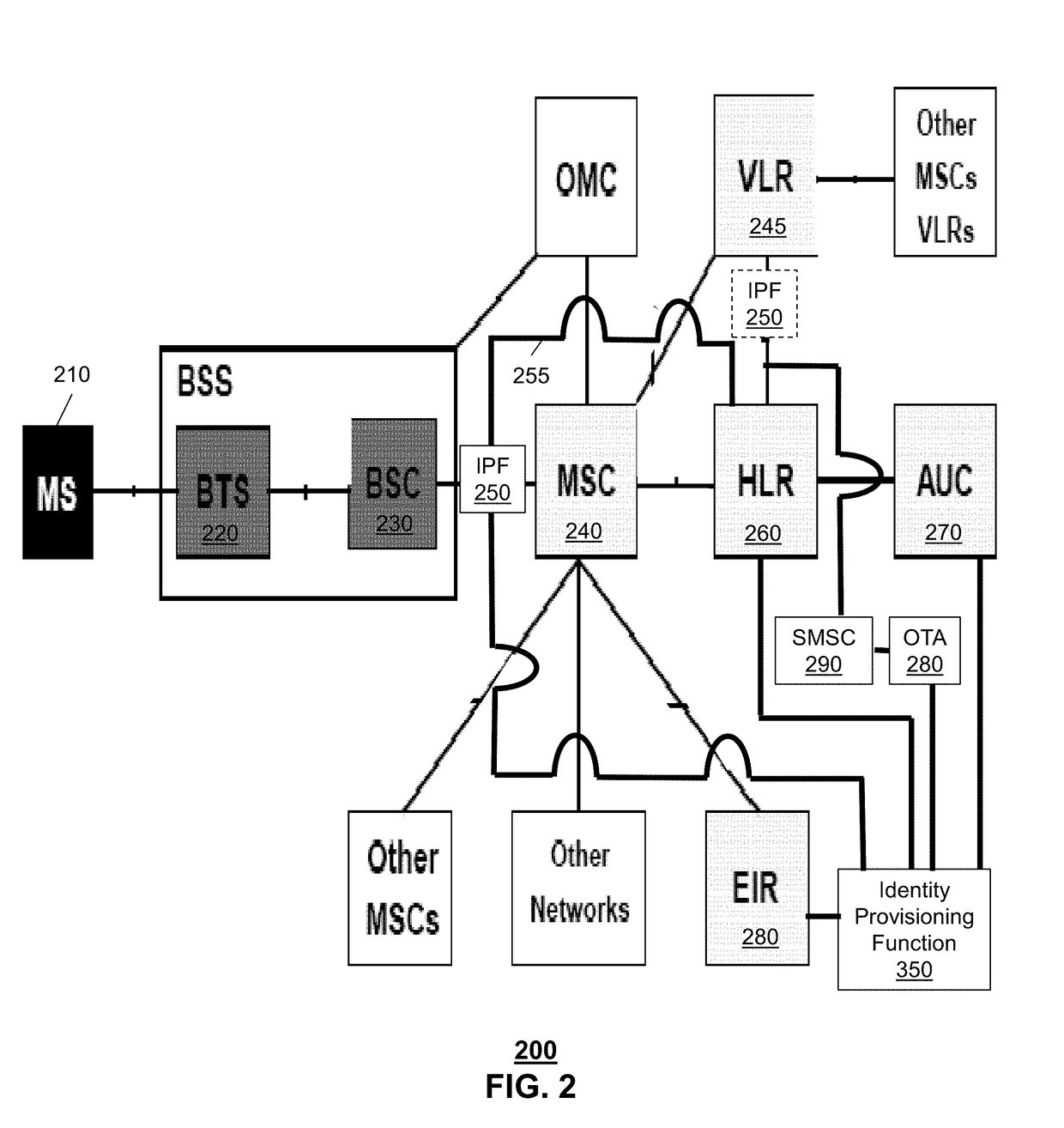
Aspects of the subject disclosure may include, for example, a system that receives a first notification indicating a first international mobile subscriber identity (IMSI) is being registered. A communication device sends a first registration request that includes the first IMSI to a registration function. Further, an identity proxy function intercepts the first registration request and sends the first notification to the device. In addition, the system receives from a billing server a request for services for the communication device. Further, the system provides a first Over-the-Air (OTA) message to the communication device that includes a second IMSI that is provisioned onto the communication device. Also, the system sends a first registration message to the registration function. The registration function includes a registry. The first registration message includes first instructions to indicate to the registration function to add the second IMSI to the registry. Other embodiments are disclosed.
Owner:AT&T INTPROP I L P +1
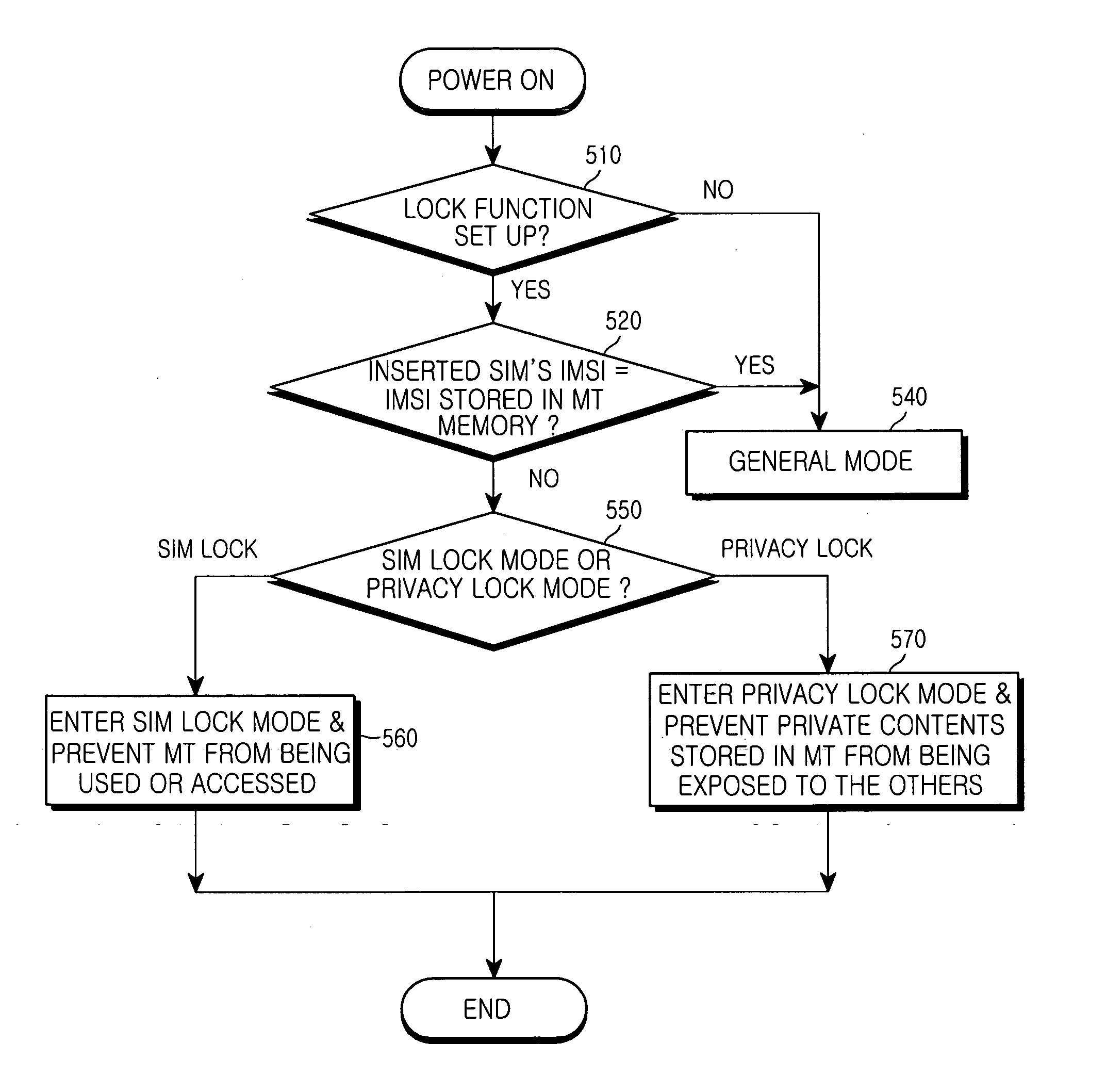
Mobile communication terminal for protecting private contents and method for controlling the same
InactiveUS20050075092A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsUser authenticationMobile communication systems
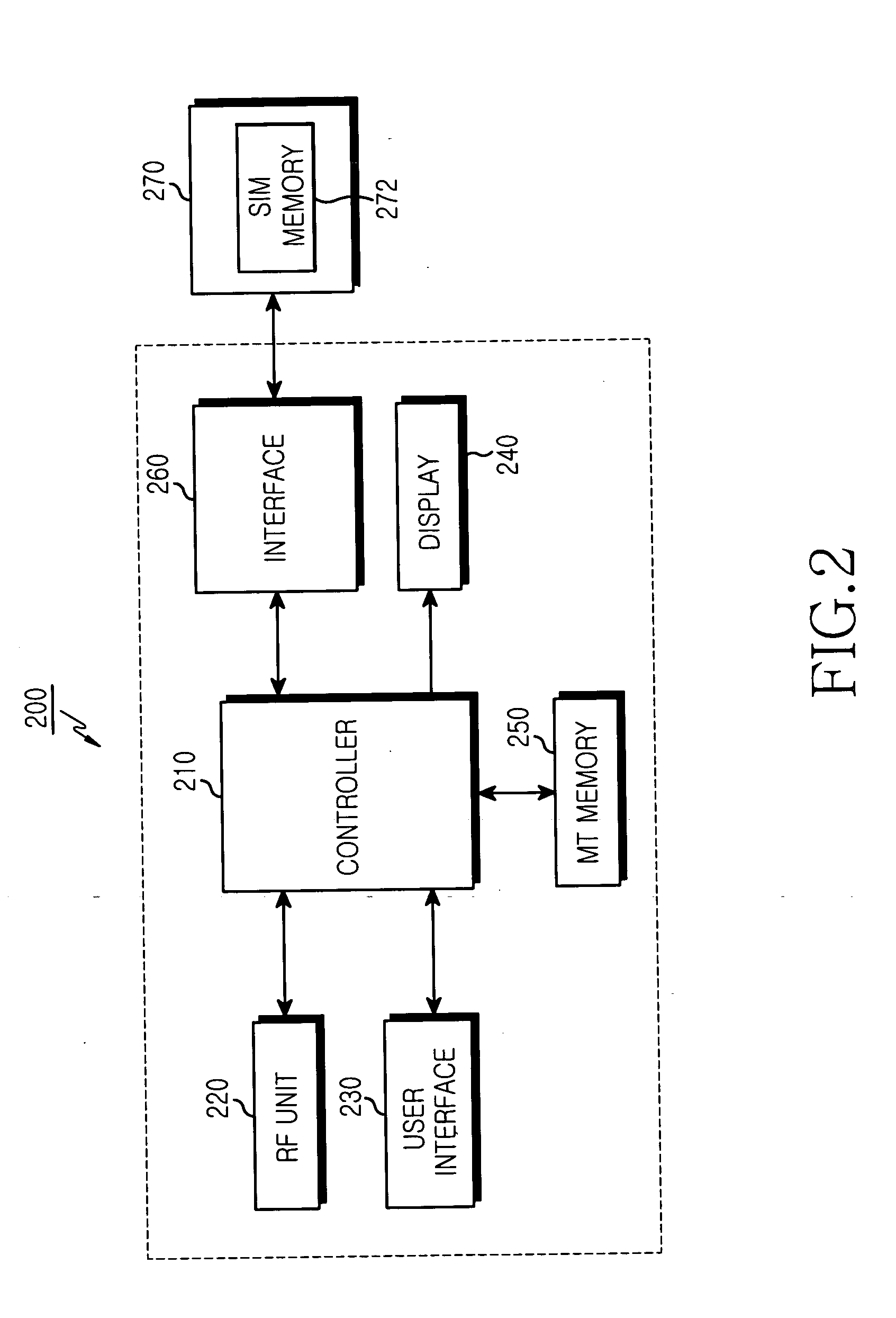
A mobile terminal for use in a Global System for Mobile communication (GSM) system. A mobile equipment (ME) for use in the GSM system includes a Subscriber Identity Module (SIM) card and a Mobile Terminal (MT). The SIM card stores International Mobile Subscriber Identity (IMSI) information used for subscriber authentication and private information. The MT stores the IMSI and private information of a user, and contains a controller, which reads IMSI information from the SIM card when the SIM card is inserted into the MT, and denies access to the stored private information when the read IMSI information of the inserted SIM card is different from the stored IMSI information.
Owner:SAMSUNG ELECTRONICS CO LTD
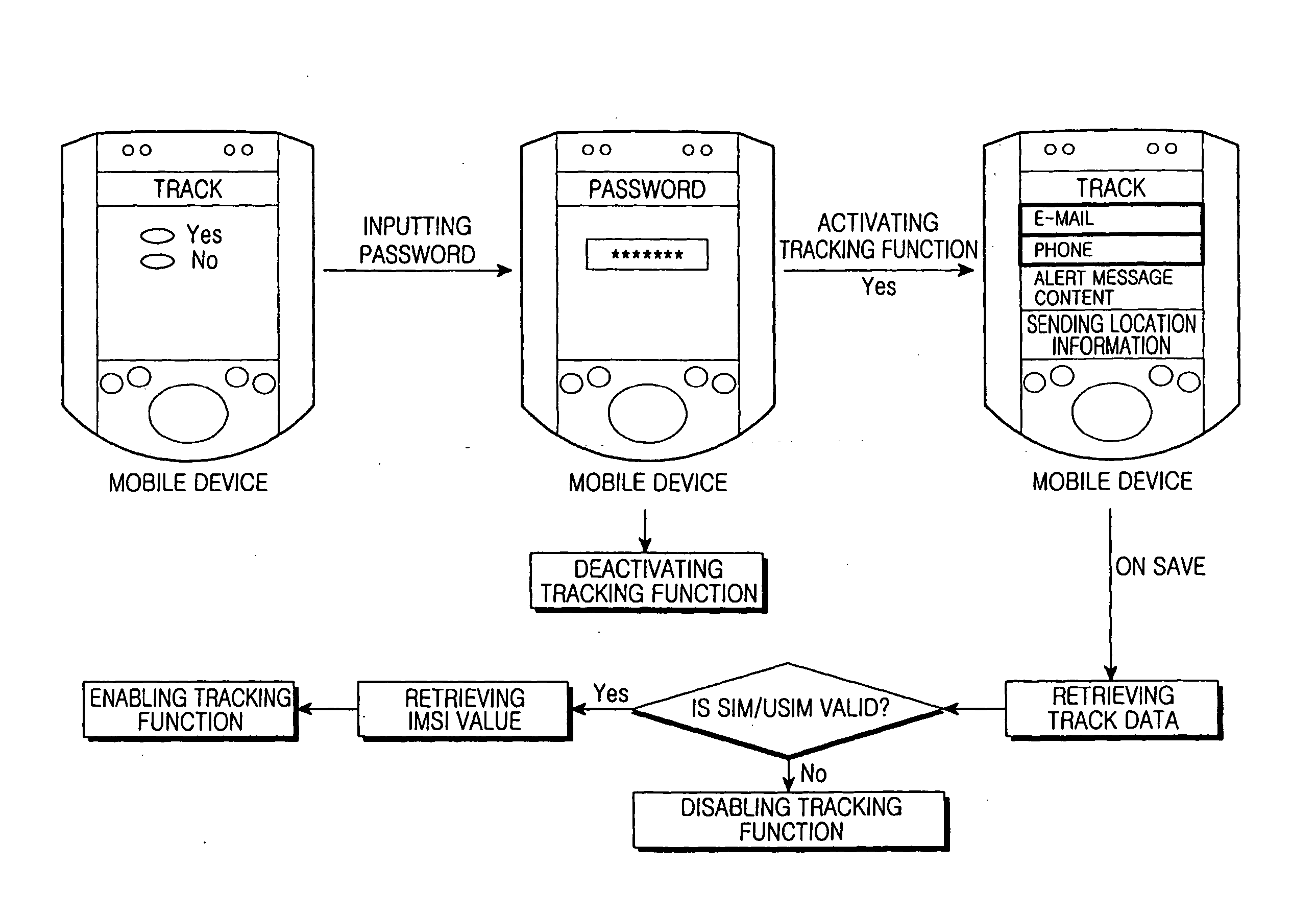
Method and system for tracking mobile communication device using MMS
ActiveUS20080076459A1Substation equipmentRadio/inductive link selection arrangementsEmail addressMobile device
A system and method for tracking a mobile electronic device, which is capable of accesses a wireless or wired network, using a Multimedia Messaging Service (MMS). The mobile device includes a storing function for storing one or more contact phone numbers or Email addresses. When the mobile communication device is lost or stolen and Subscriber Identity Module (SIM) card of the mobile terminal is changed, the mobile device verifies whether the SIM card is the same as that of the owner of the mobile device by comparing the International Mobile Subscriber Identity (IMSI) numbers of the two SIM cards. If the IMSI numbers are different, the mobile device activates a tracking feature. The tracking feature stealthily captures still images or motion pictures of the surrounding area and transfers those captured images / videos to a pre-stored contact phone numbers through a MMS or through a pre-stored Email address.
Owner:SAMSUNG ELECTRONICS CO LTD
Security protection method and security protection system for mobile terminal application
ActiveCN103188668AImprove securityImprove convenienceSecurity arrangementTerminal equipmentApplication security
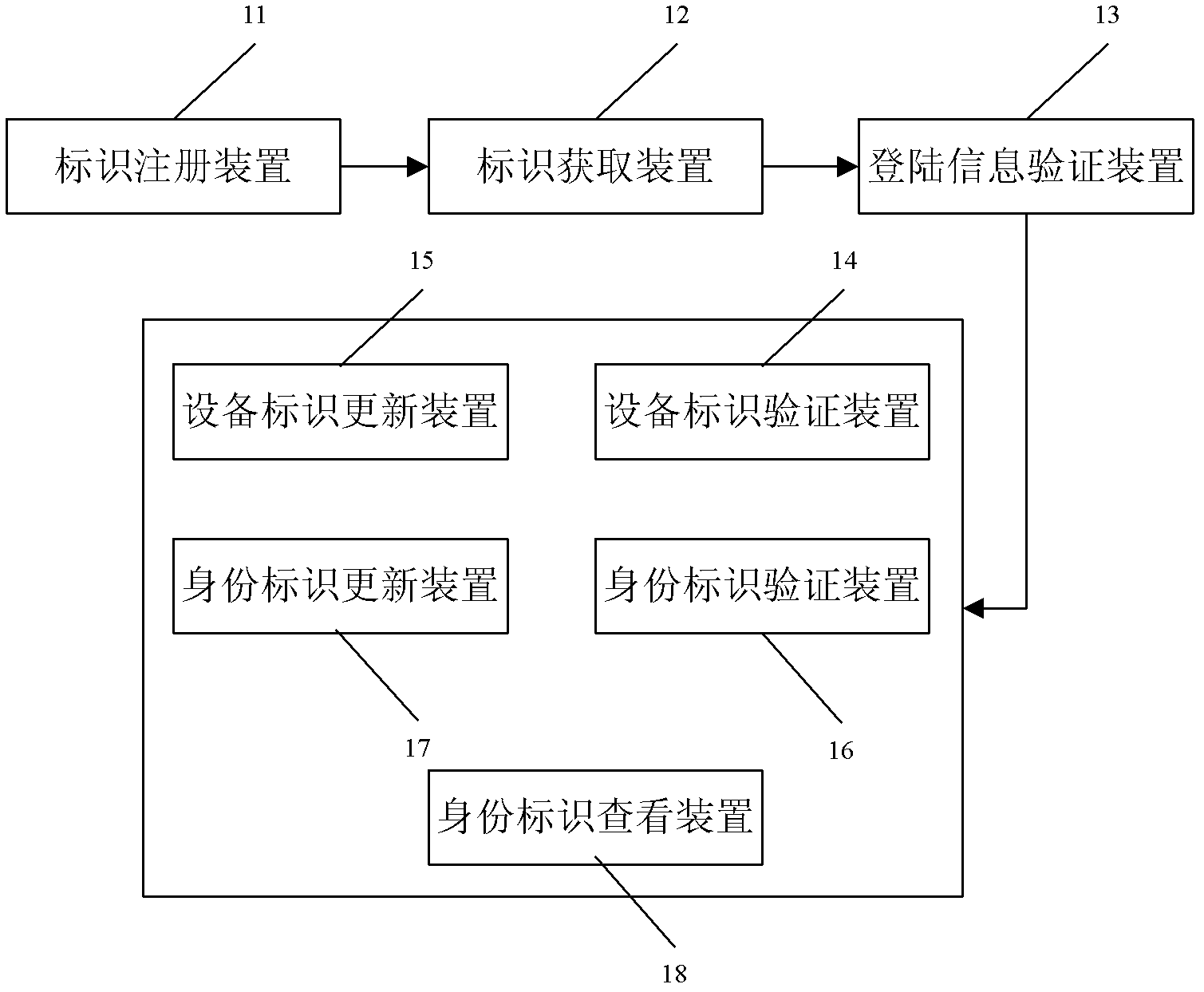
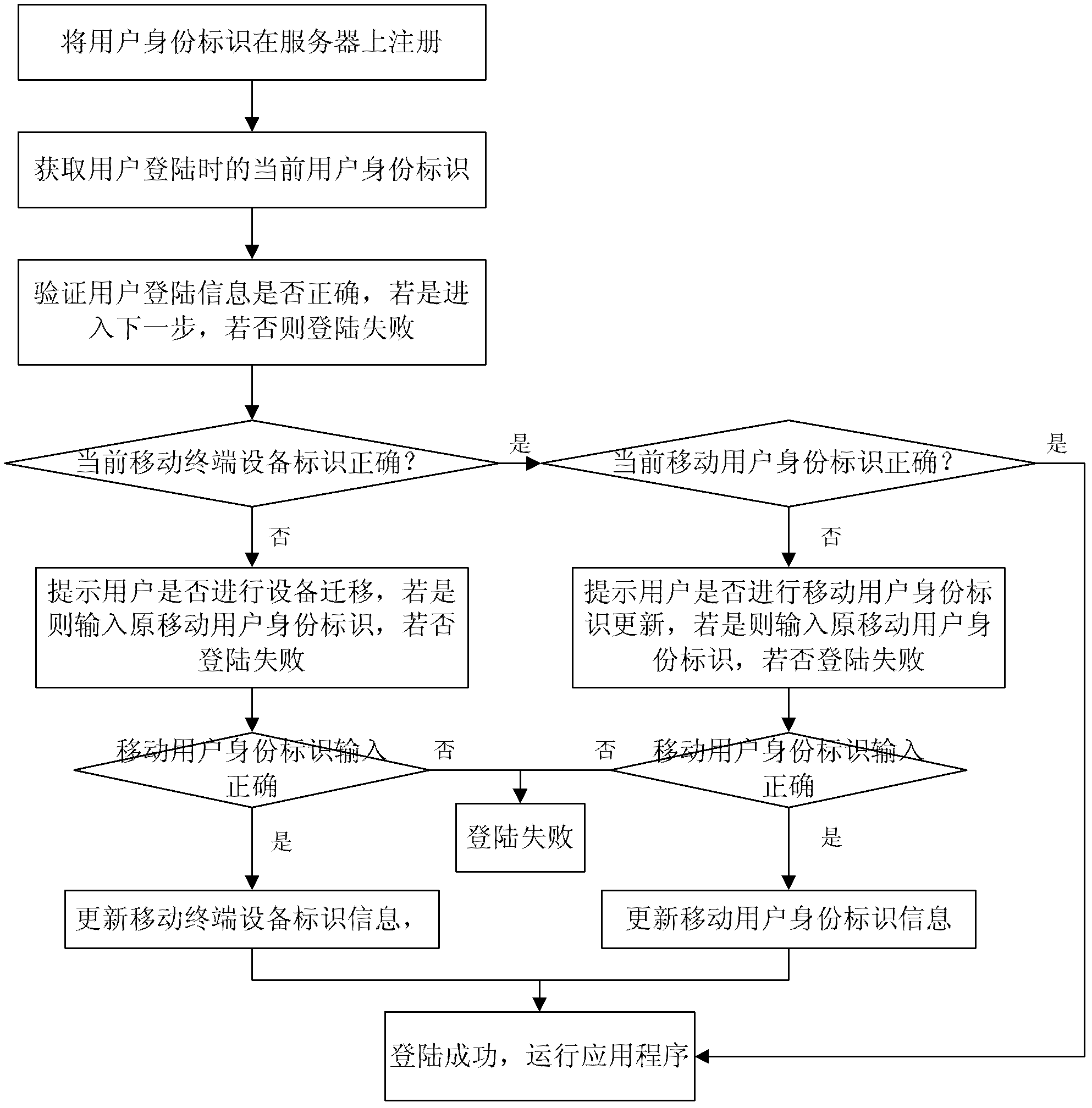
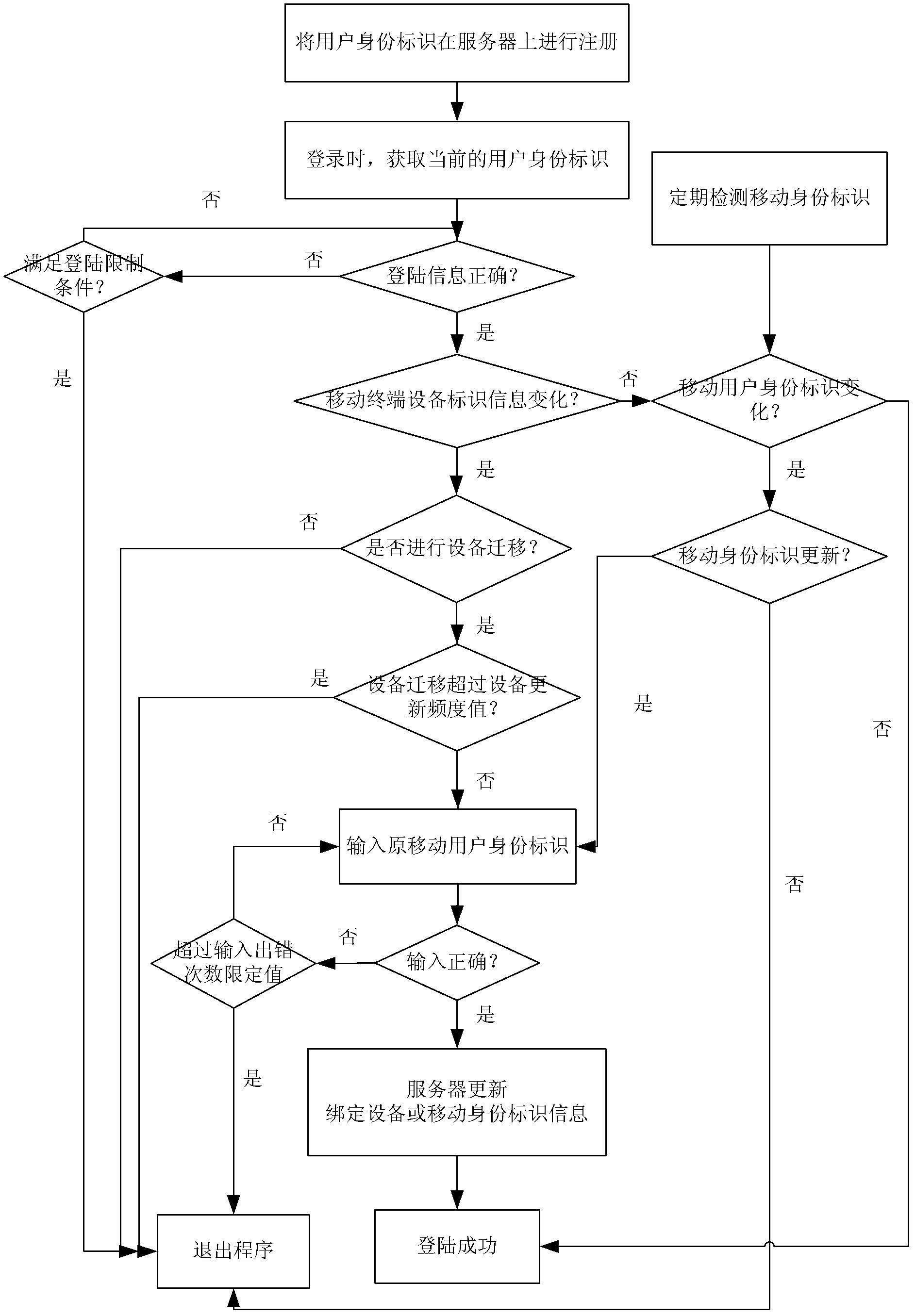
The invention discloses a security protection method and a security protection system for a mobile terminal application, and belongs to the field of terminal application security protection. The method comprises the steps that a mobile terminal equipment identity, a mobile subscriber identity and subscriber login information are sent to a server for registration during a registration course, and bound to form a subscriber identity; login information, the mobile terminal equipment identity and the mobile subscriber identity in the current subscriber identity are compared with the original subscriber identity in the server sequentially during a login course to determine information required to be updated; and updating is performed by authentication of the original mobile subscriber identity finally. According to the method and the system, a mobile terminal equipment information binding method is adopted, so that the security problems due to the fact that terminal equipment is updated, an SIM (Subscriber Identity Module) card number is replaced or the subscriber login information is stolen under the condition of single registration of a subscriber are solved, and the security and conveniences of the terminal application are improved.
Owner:方正国际软件(北京)有限公司
Automatic protecting method for computer system based on Bluetooth device authentication
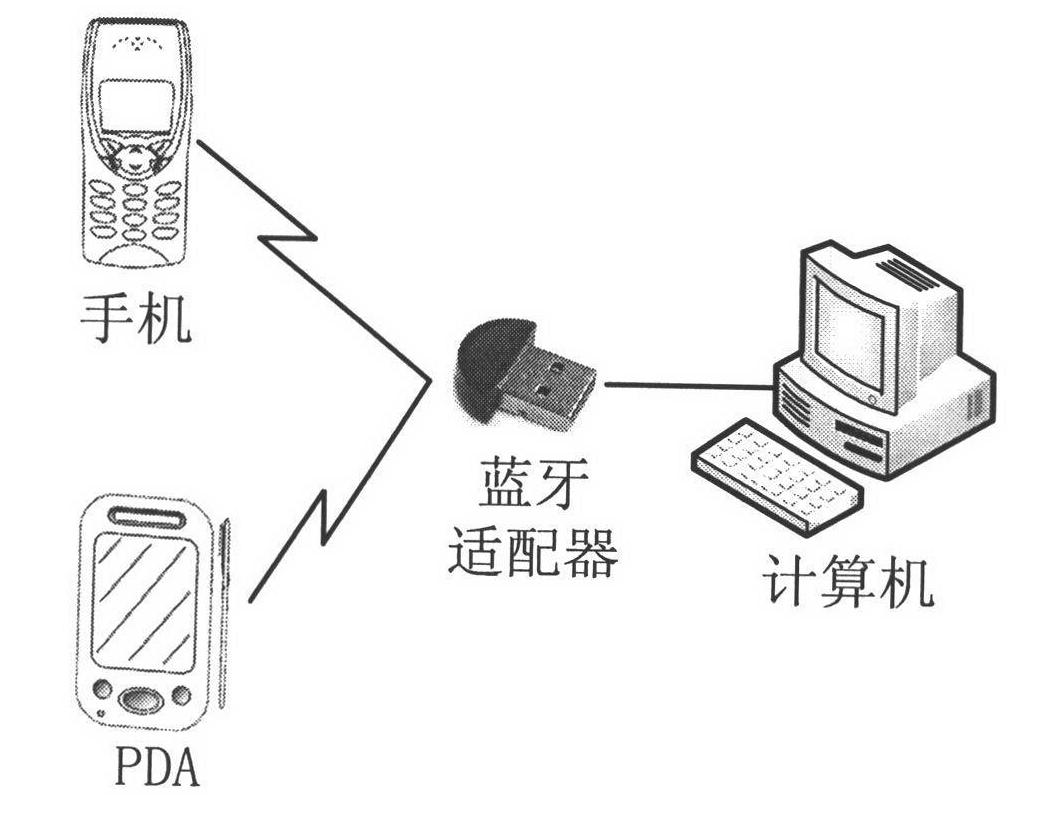
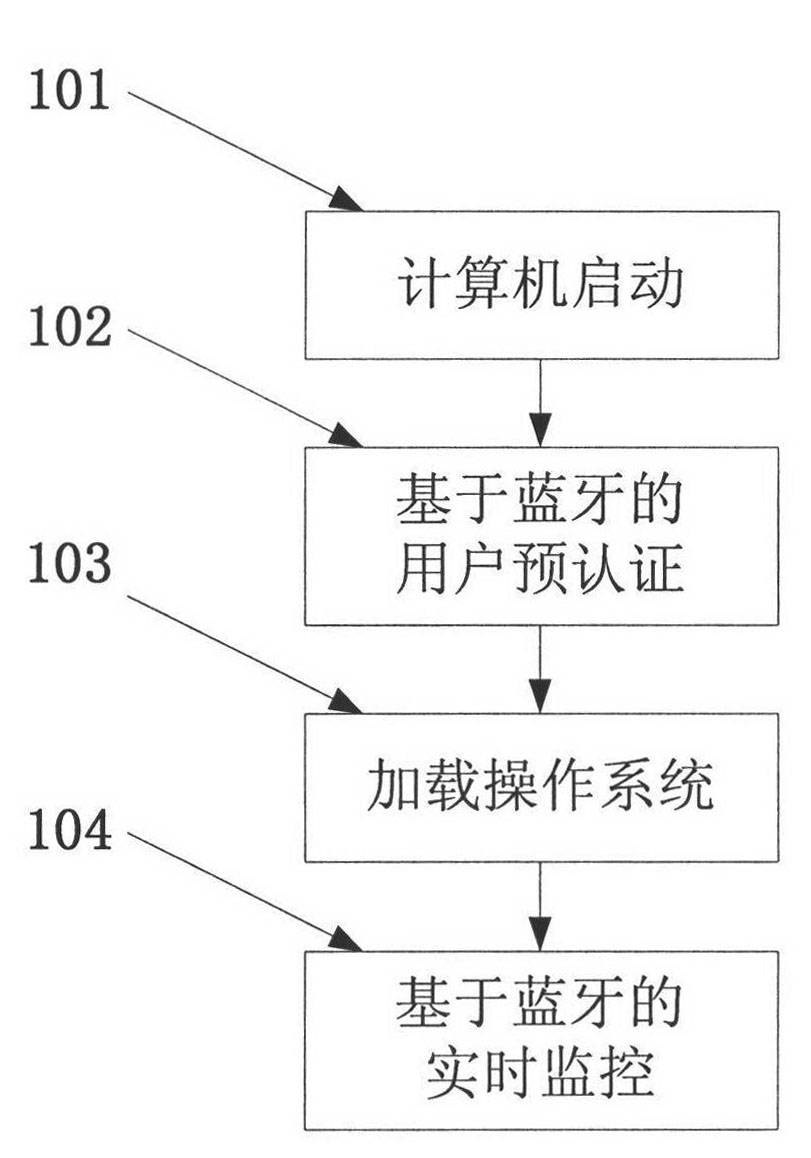
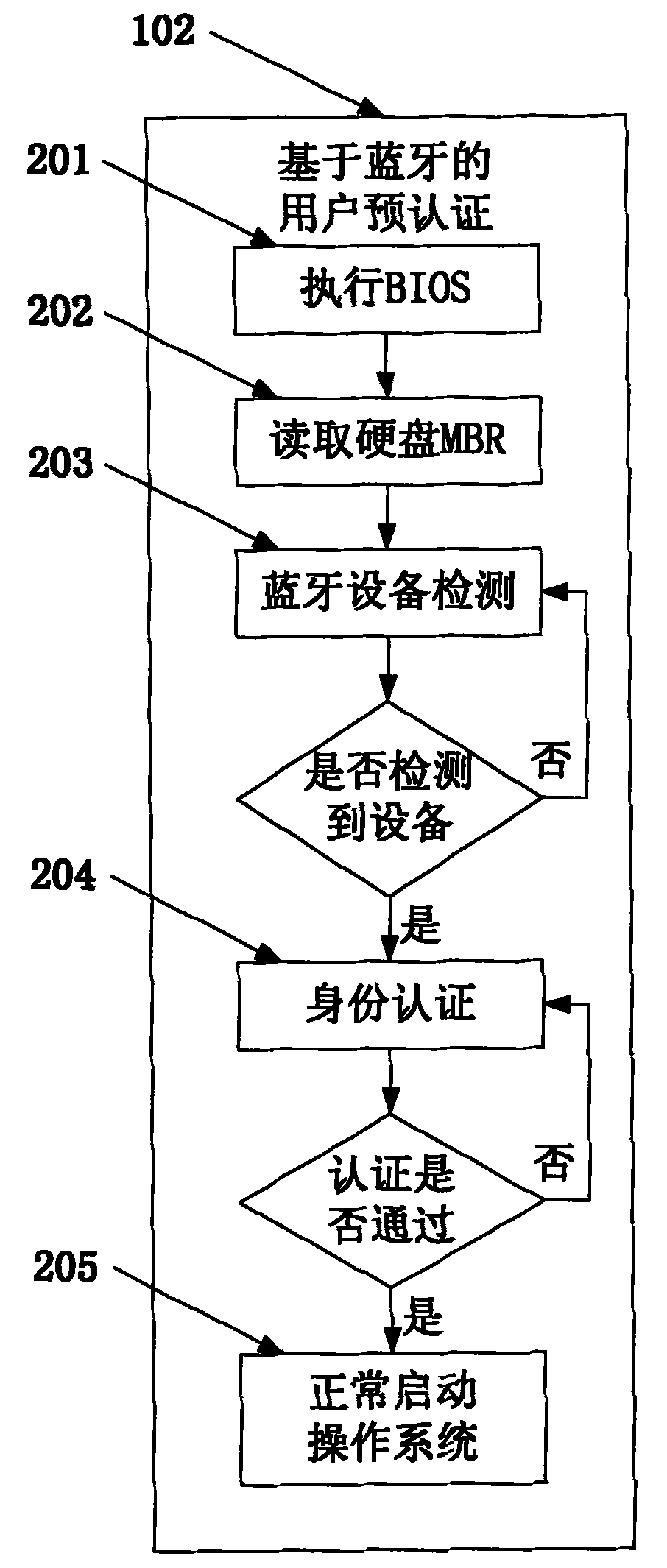
InactiveCN102184352AEasy to operateTransparent operationTransmission systemsInternal/peripheral component protectionProtocol for Carrying Authentication for Network AccessInternational mobile subscriber identity
The invention provides an automatic protecting method for a computer system based on Bluetooth device authentication. In the method, a control program is written in a disk MBR (Master Boot Record), and double authentication of hardware equipment and user identity is realized by combining a Bluetooth wireless transmitting protocol before an operating system is started and using a Bluetooth address, a PIN (Personal Identification Number) code and a mobile terminal IMSI (International Mobile Subscriber Identity) number. In an operation process of the operating system, automatic real-time monitoring is set, the system can be automatically locked and can not be operated once the Bluetooth device of a user deviates from the coverage area of a Bluetooth adapter; and the system can be automatically unlocked and recovered for operation once the Bluetooth device of the user returns to the coverage area.
Owner:SOUTHEAST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com