Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
89 results about "Instance Identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The unique identifier (UID) is an identifier that refers to only one instance—only one particular object in the universe. A part number is an identifier, but it is not a unique identifier—for that, a serial number is needed, to identify each instance of the part design.
Identity-based flash management
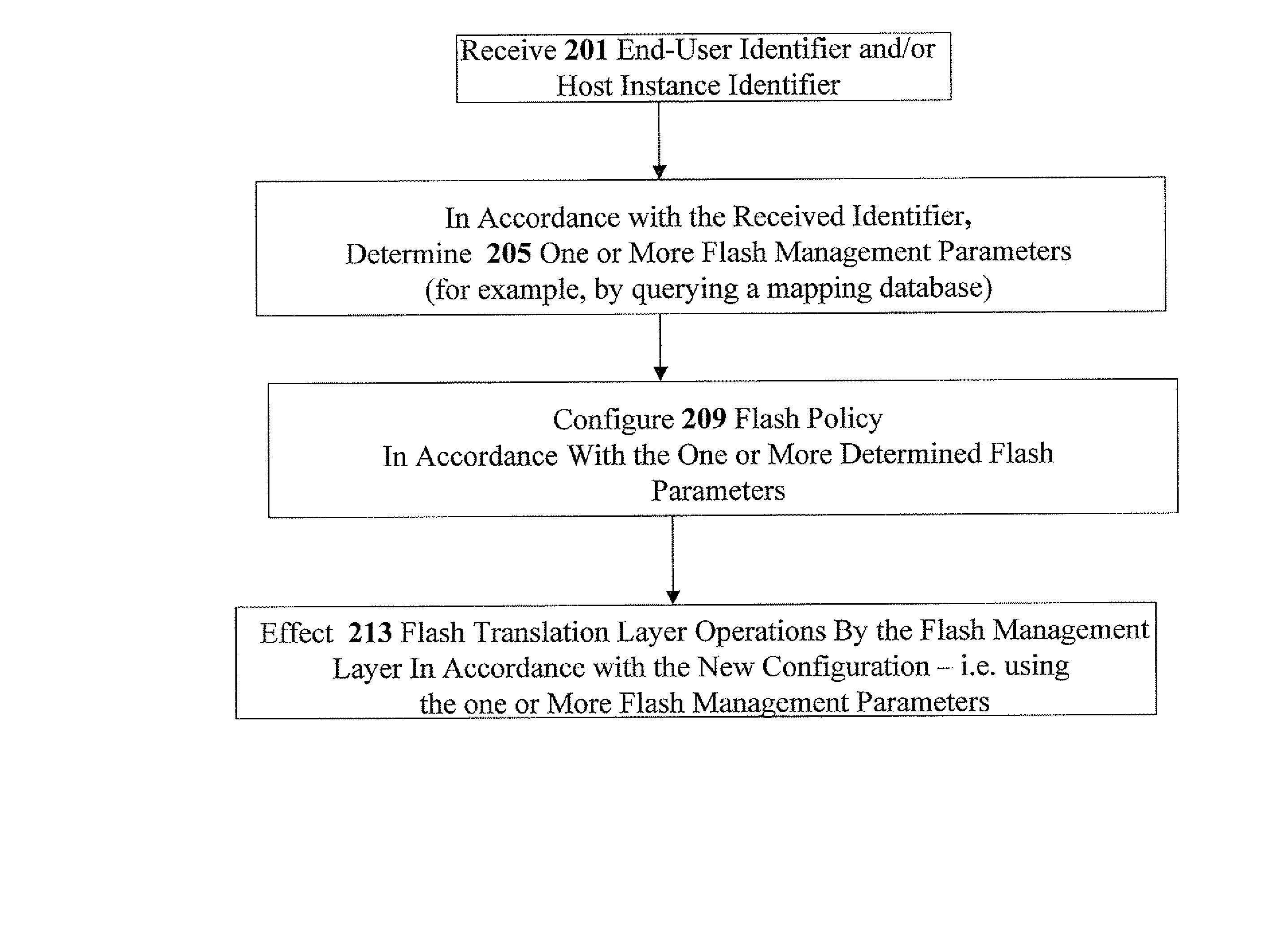
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Dynamic machine assisted informatics
InactiveUS20110125746A1Easy constructionDigital data processing detailsDatabase distribution/replicationData setSide information
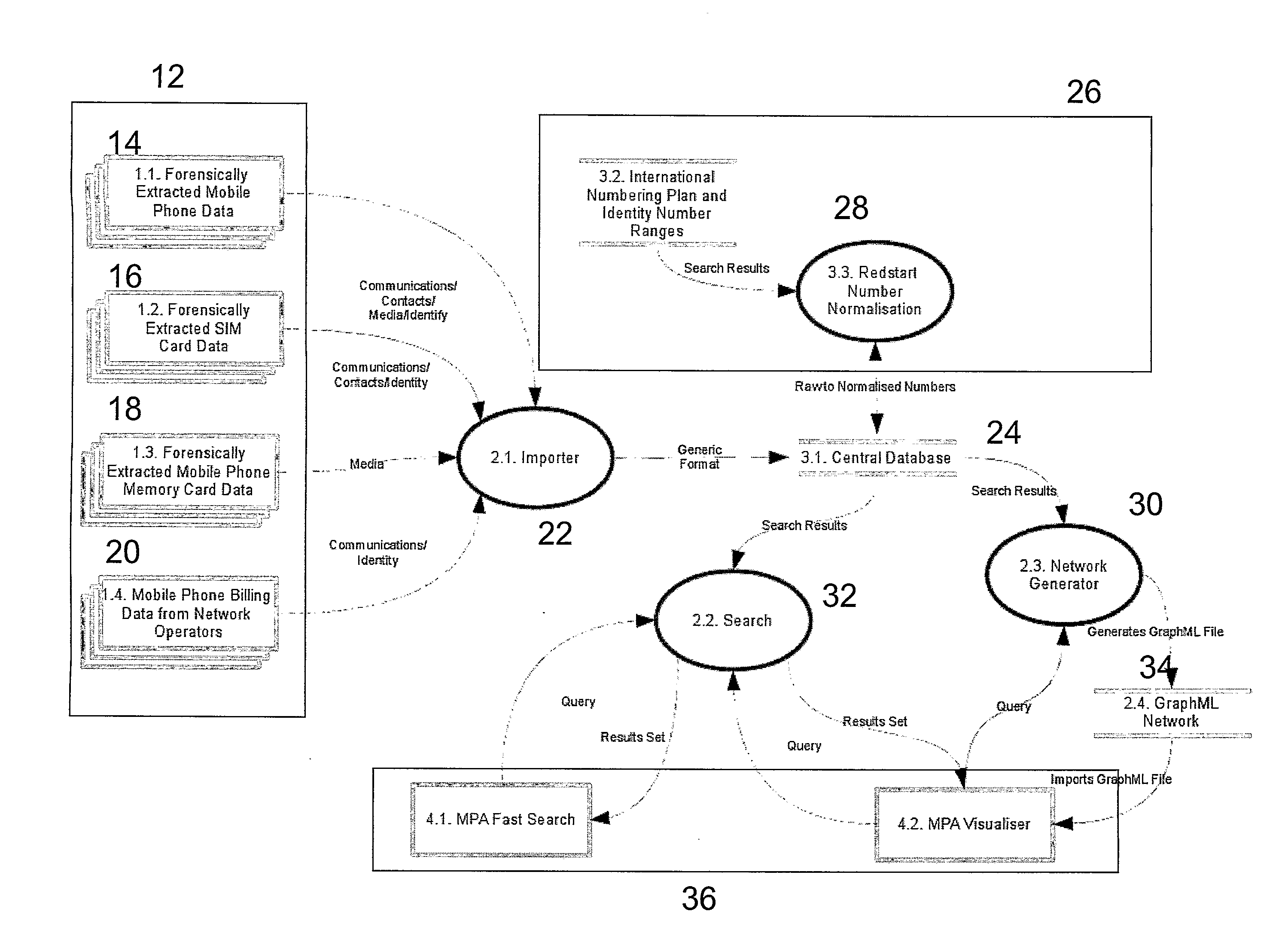
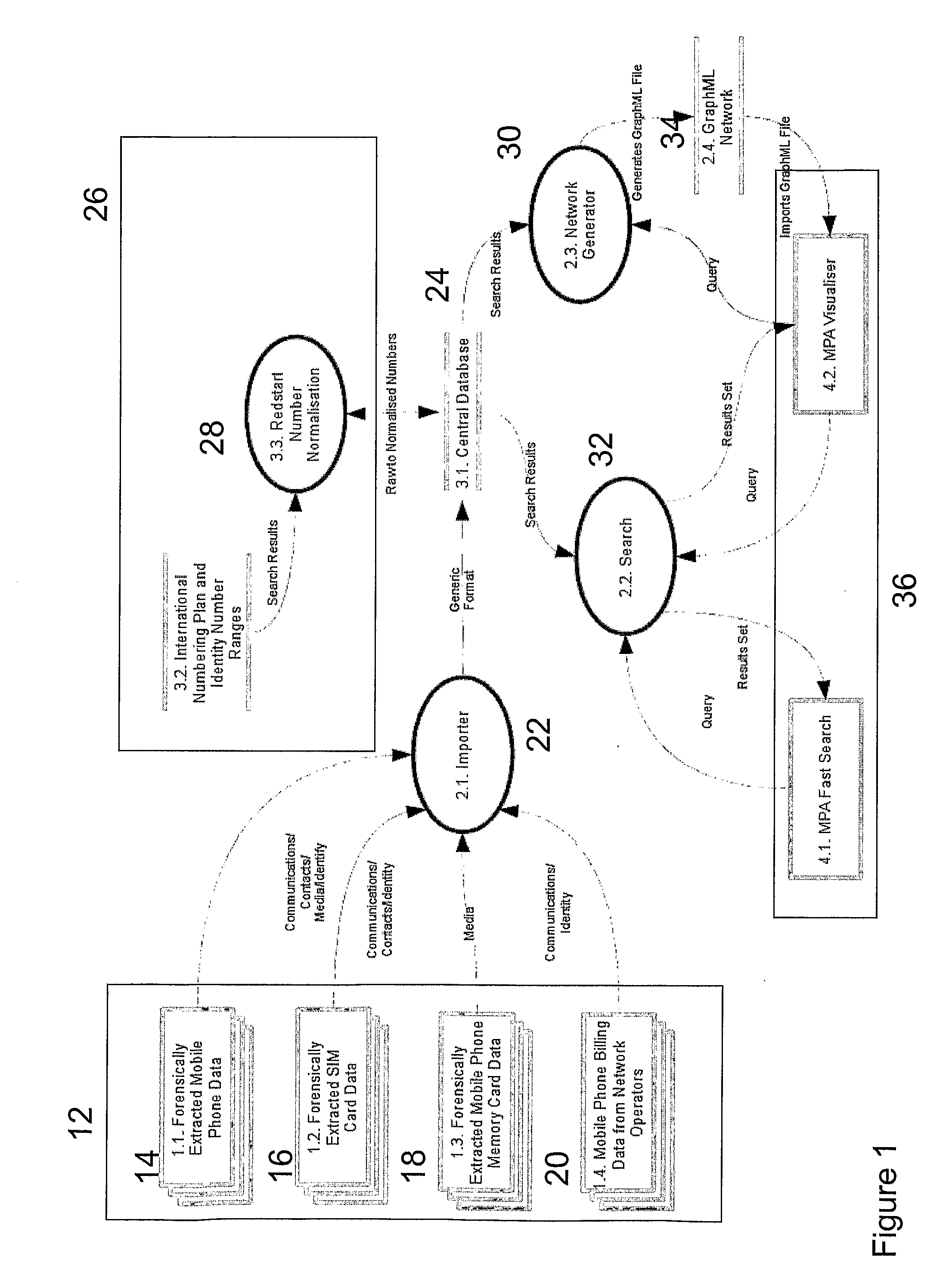
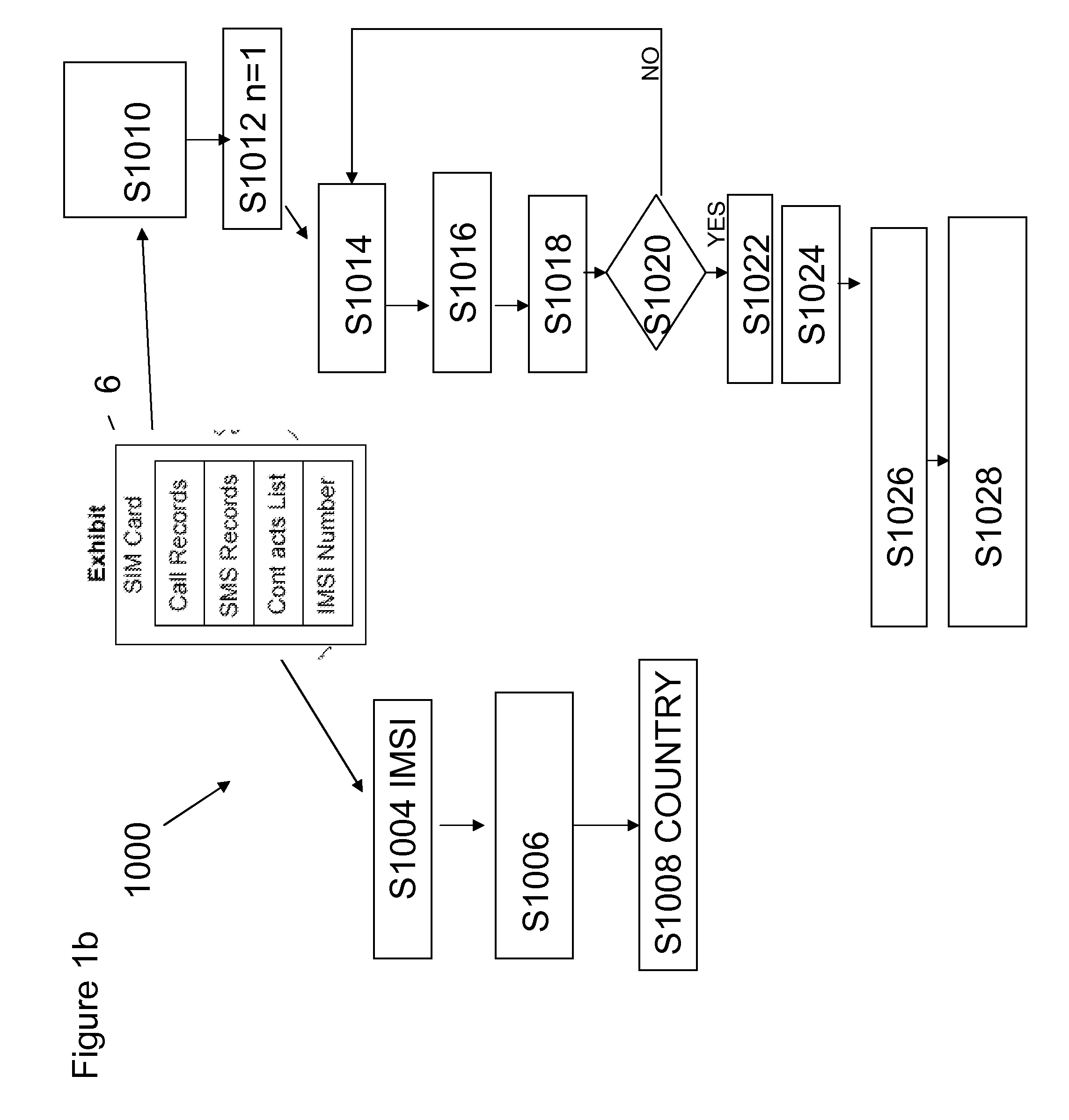
A method of identifying a network of actors within a data set, the method comprising: —importing data from one or more data sources; —normalising the data in one or more fields to create a consolidated data set; —identifying one or more networks based on identical or similar instances of one or more pieces of data in the consolidated data set; and —calculating a measure of influence of one or more of the actors in an identified network.
Owner:FORENSIC PATHWAYS
Datapath processing of service rules with qualifiers defined in terms of dynamic groups
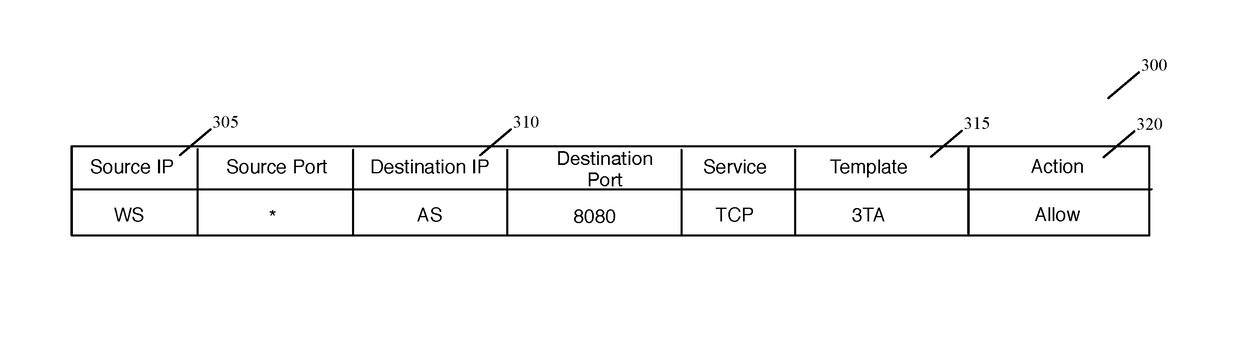
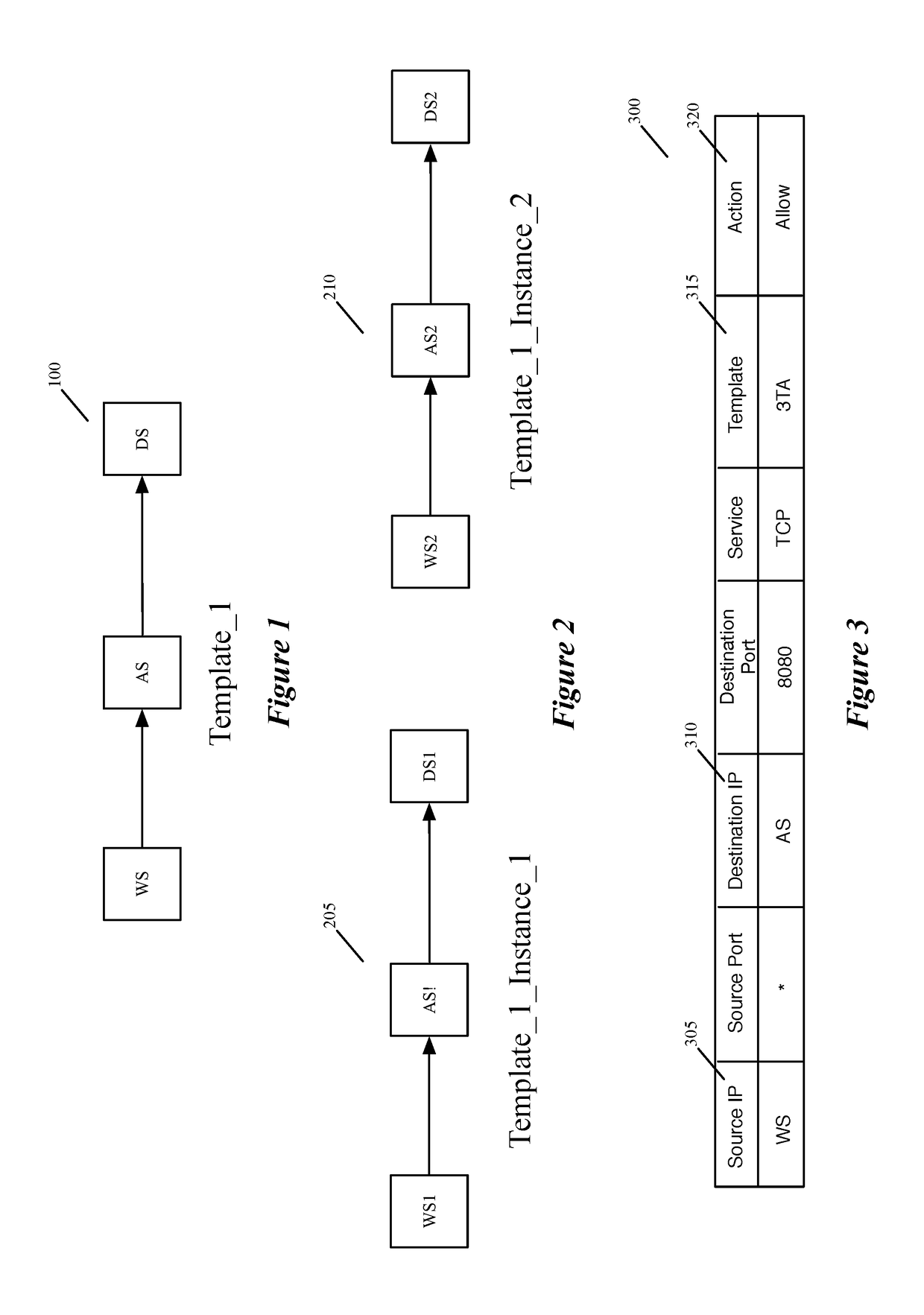
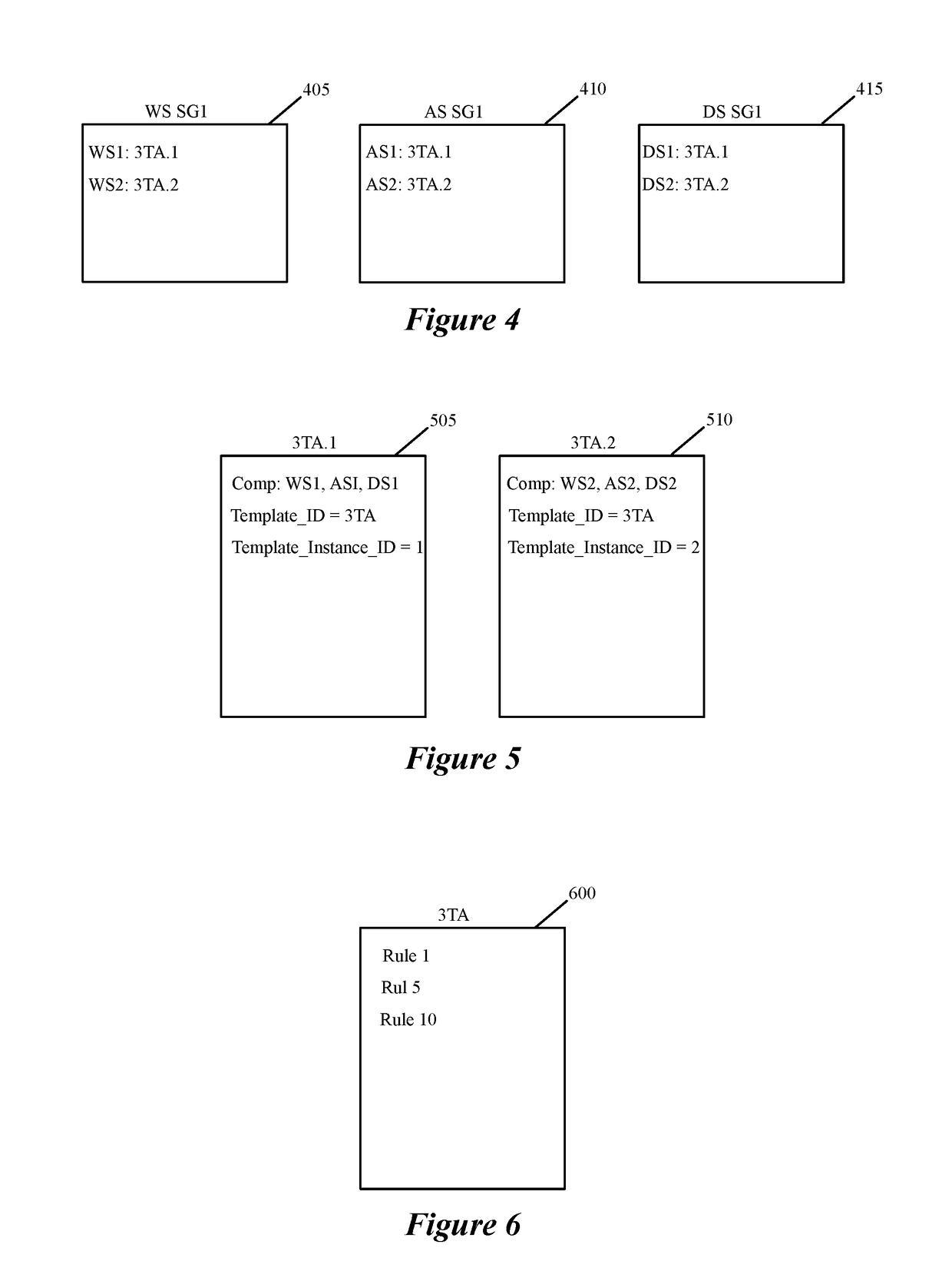
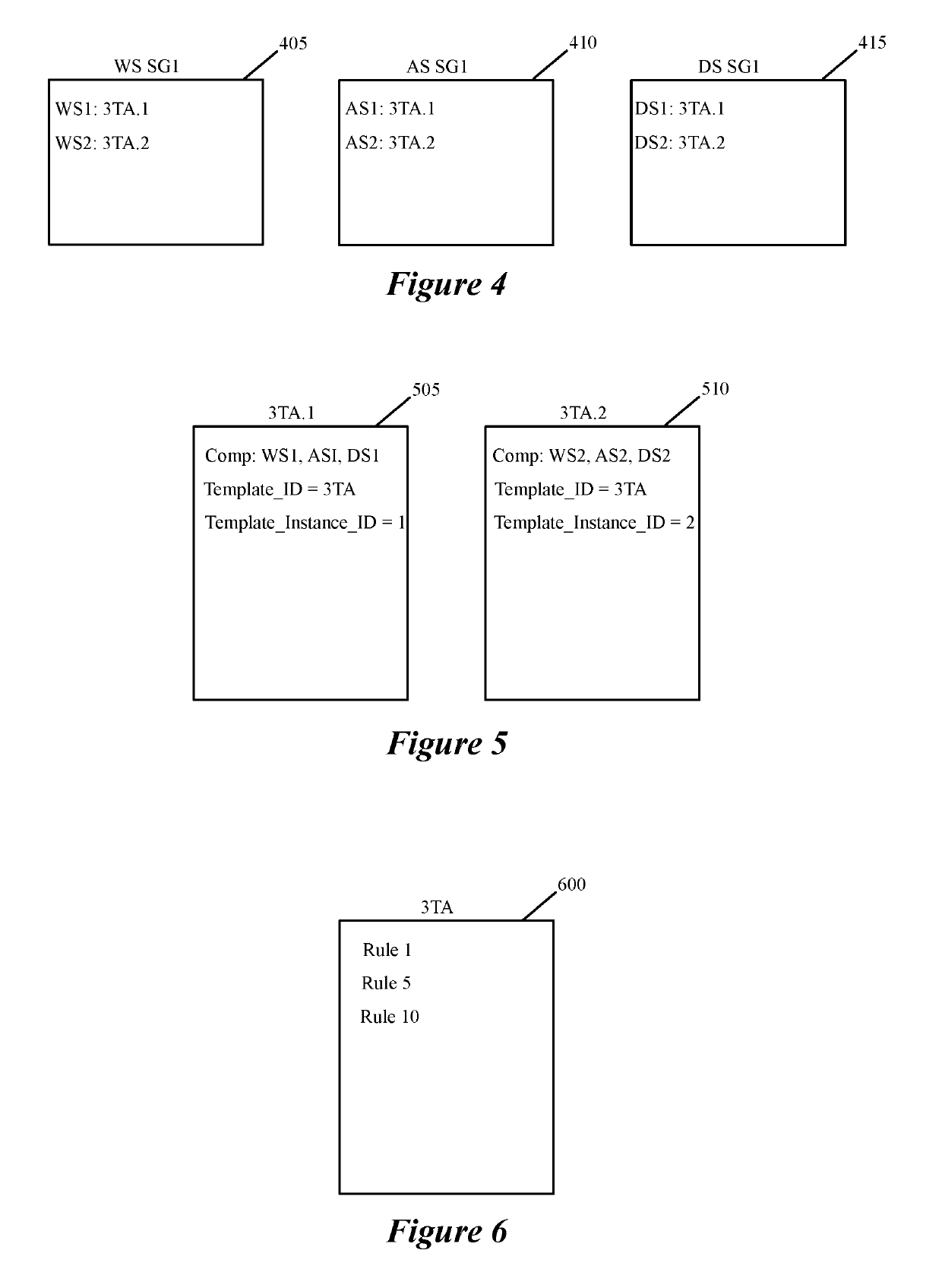
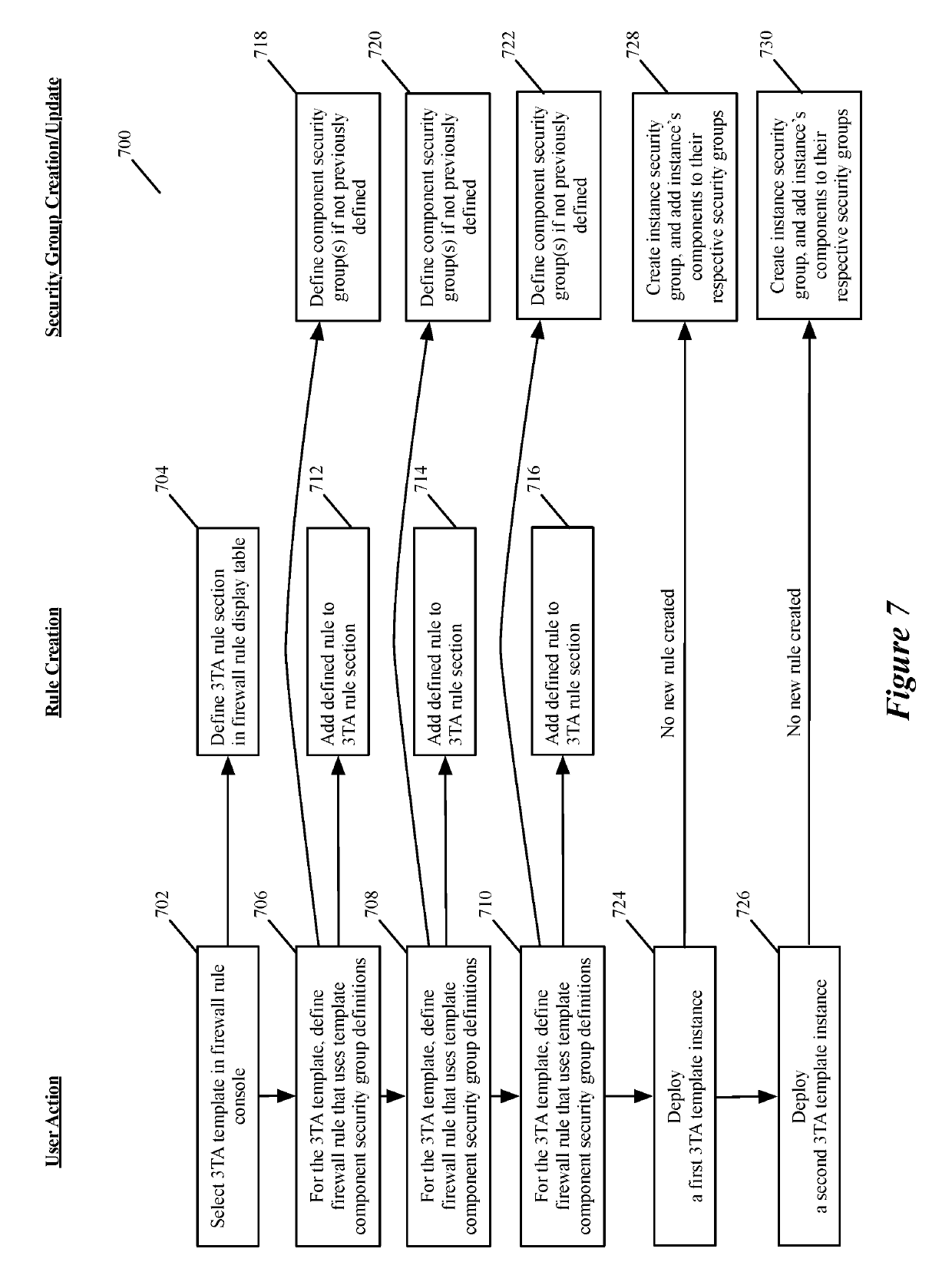
Some embodiments of the invention introduce cloud template awareness in the service policy framework. Some embodiments provide one or more service rule processing engines that natively support (1) template-specific dynamic groups and template-specific rules, and (2) dynamic security tag concepts. A service rule processing engine of some embodiments natively supports template-specific dynamic groups and rules as it can directly process service rules that are defined in terms of dynamic component groups, template identifiers, template instance identifiers, and / or template match criteria. Examples of such services can include any kind of middlebox services, such as firewalls, load balancers, network address translators, intrusion detection systems, intrusion prevention systems, etc.
Owner:NICIRA
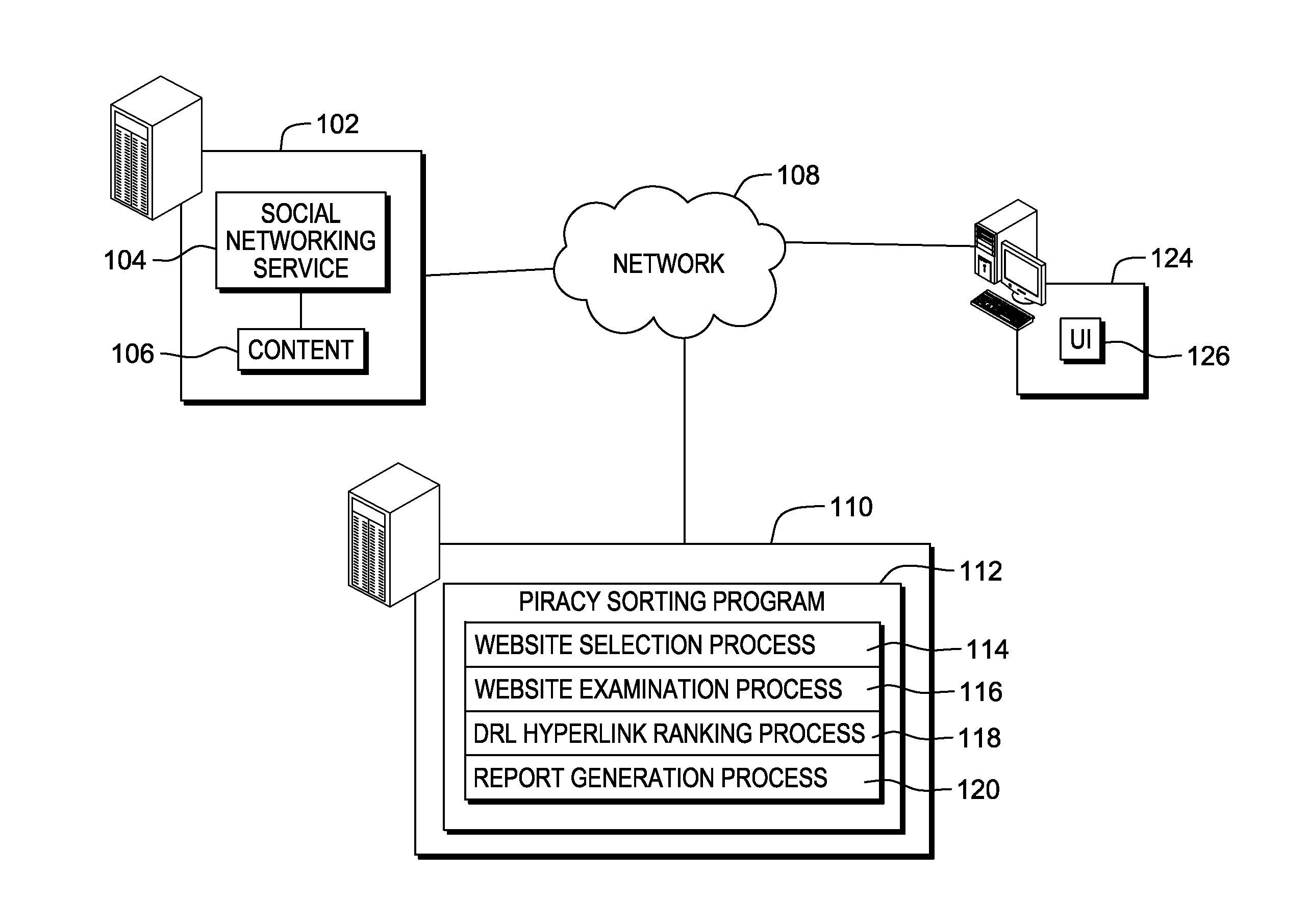
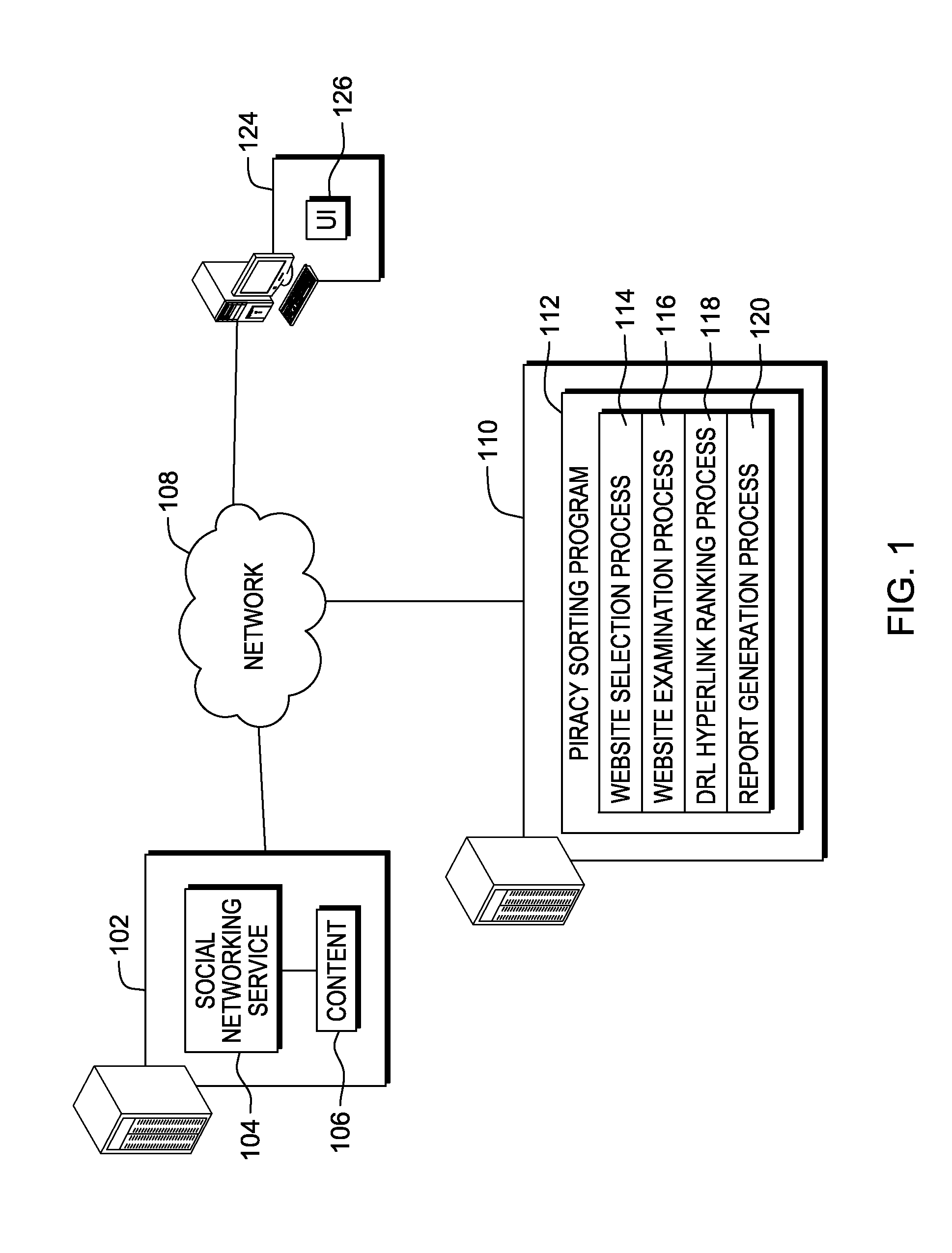
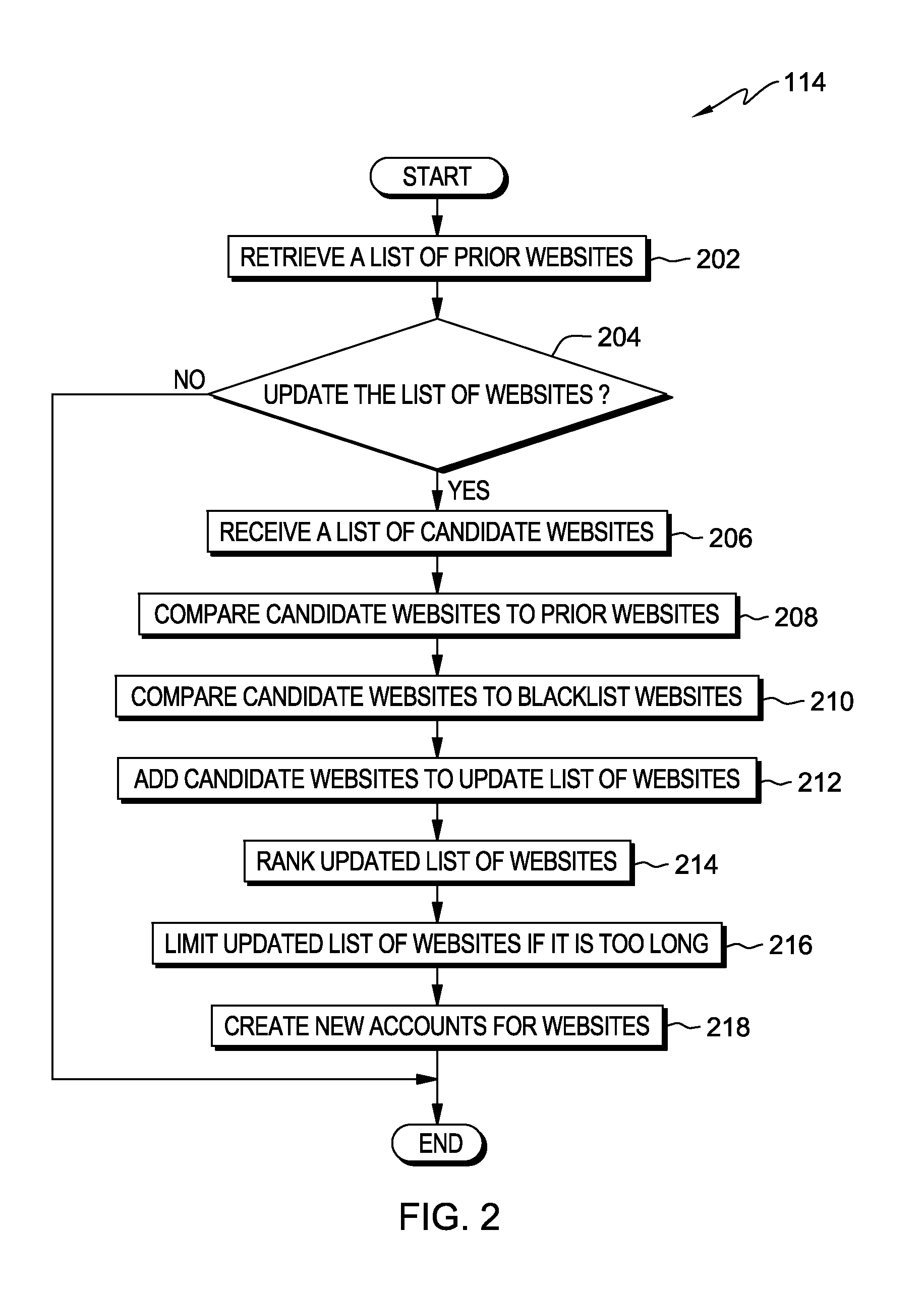
Identifying and ranking pirated media content
A computer identifies and ranks URL hyperlinks to possible pirated media content by searching a web page from a first website for one or more indicator keywords, wherein a strength of an indicator keyword is related to a likelihood of pirated media content. Responsive to locating a plurality of instances of the one or more indicator keywords, identifying a plurality of hyperlinks respectively associated with one or more of the plurality of instances. Weighting, the identified plurality of hyperlinks based on at least one of: a strength of associated indicator keywords, number of associated indicator keywords, number of times each hyperlink was identified, and date of posting. Ranking the plurality of hyperlinks according to weight indicating a relative likelihood that respective hyperlinks point to pirated media content in a ranked list.
Owner:GLOBALFOUNDRIES INC
Medical image processing method and device and storage medium
PendingCN110767291AHigh speedImprove loading speedProgram loading/initiatingMedical imagesComputer hardwareImaging processing
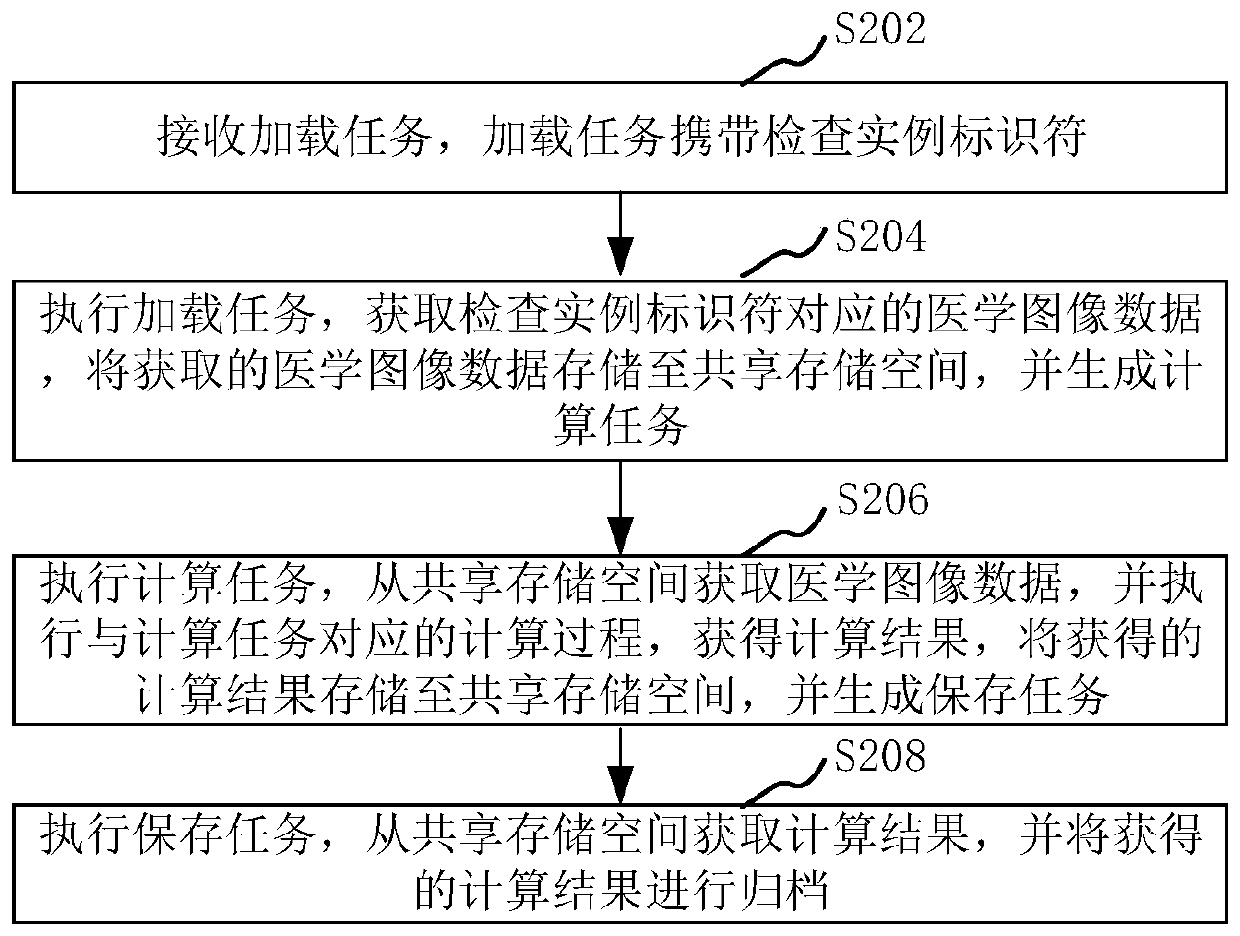
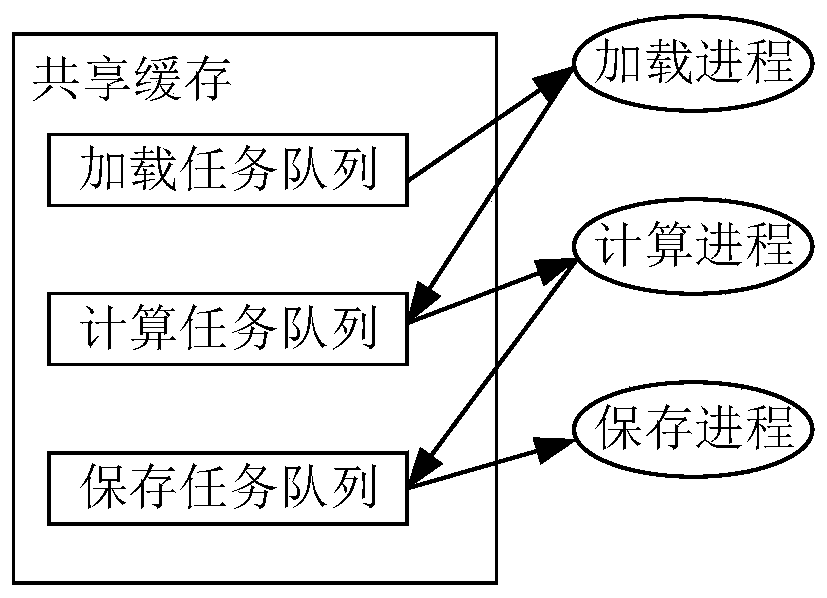
The invention relates to a medical image processing method and device and a storage medium. The method comprises steps of receiving a loading task, and carrying an examination instance identifier by the loading task; executing a loading task, obtaining medical image data corresponding to the examination instance identifier, storing the obtained medical image data in a shared storage space, and generating a calculation task; executing a calculation task, obtaining the medical image data from the shared storage space, executing a calculation process corresponding to the calculation task, obtaining the calculation result, storing the obtained calculation result in the shared storage space, and generating a storage task; executing the saving task, obtaining the calculation result from the shared storage space, and archiving the obtained calculation result. The method is advantaged in that processing efficiency can be improved.
Owner:WUHAN UNITED IMAGING HEALTHCARE CO LTD
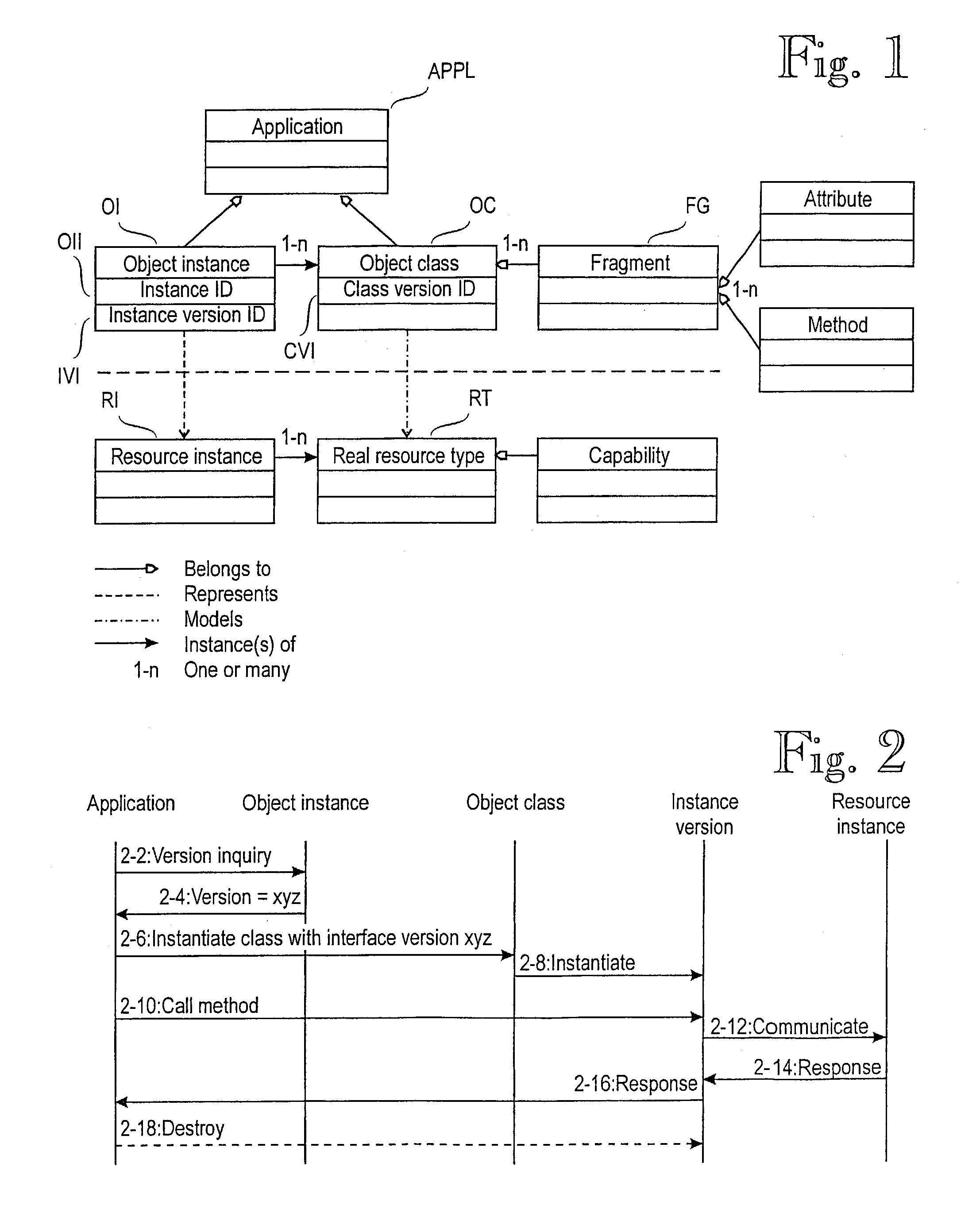
Managing composite objects in a network
InactiveUS7194727B2Reduce amountReduce in quantityDigital computer detailsData switching networksObject ClassComposite object
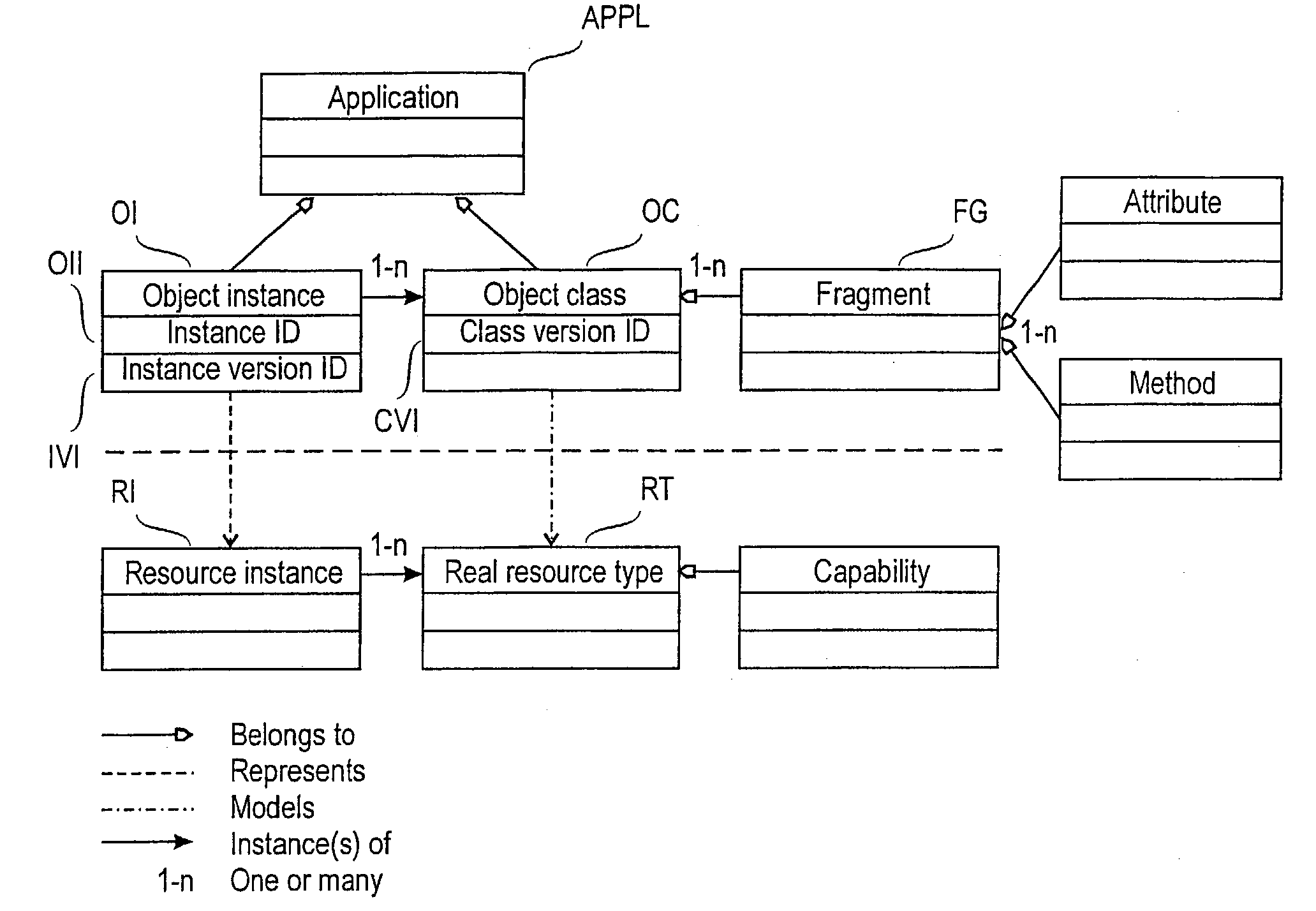
A software object model for modeling (resource instances and resource types in a network management system. The model comprises object instances and object classes. Each class comprises fragments of data and / or program code and is a generalization of one or more object instances. The model models each resource type by an object class and assigns to the class a class version identifier which indicates at least some capabilities of the resource instance / types and a collection of the fragments included in the class of the version in question. The model further models each resource instance by an object instance of the corresponding class, and assigns to the instance an object instance identifier and an instance version identifier which indicate the version of the class used for modeling the resource type in question.
Owner:NOKIA CORP
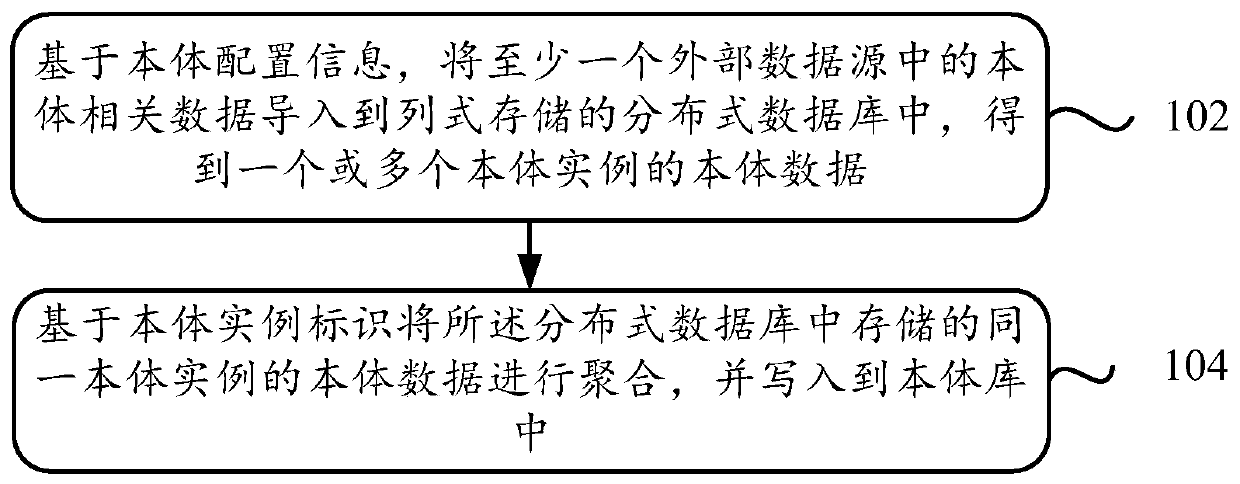
Data writing method and device of ontology library
ActiveCN110795476AAchieve conversionRelational databasesDatabase distribution/replicationExternal dataData source
The invention discloses a data writing method and device for an ontology library. The method comprises the following steps: importing ontology related data in at least one external data source into adistributed database stored in a column mode based on ontology configuration information, and obtaining ontology data of one or more ontology examples; wherein in the distributed database, ontology data of the same ontology instance from different external data sources is associated based on an ontology instance identifier; and aggregating the ontology data of the same ontology instance stored inthe distributed database based on the ontology instance identifier, and writing the ontology data into an ontology library.
Owner:北京百分点科技集团股份有限公司
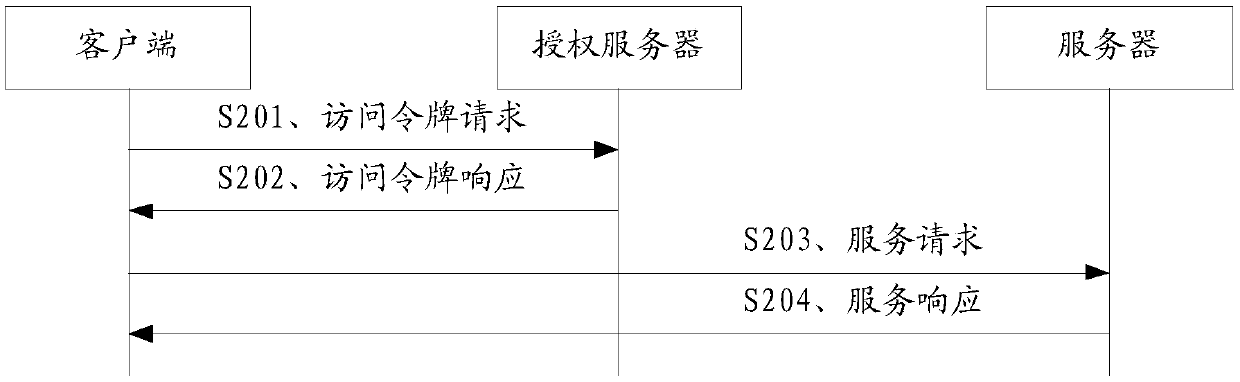
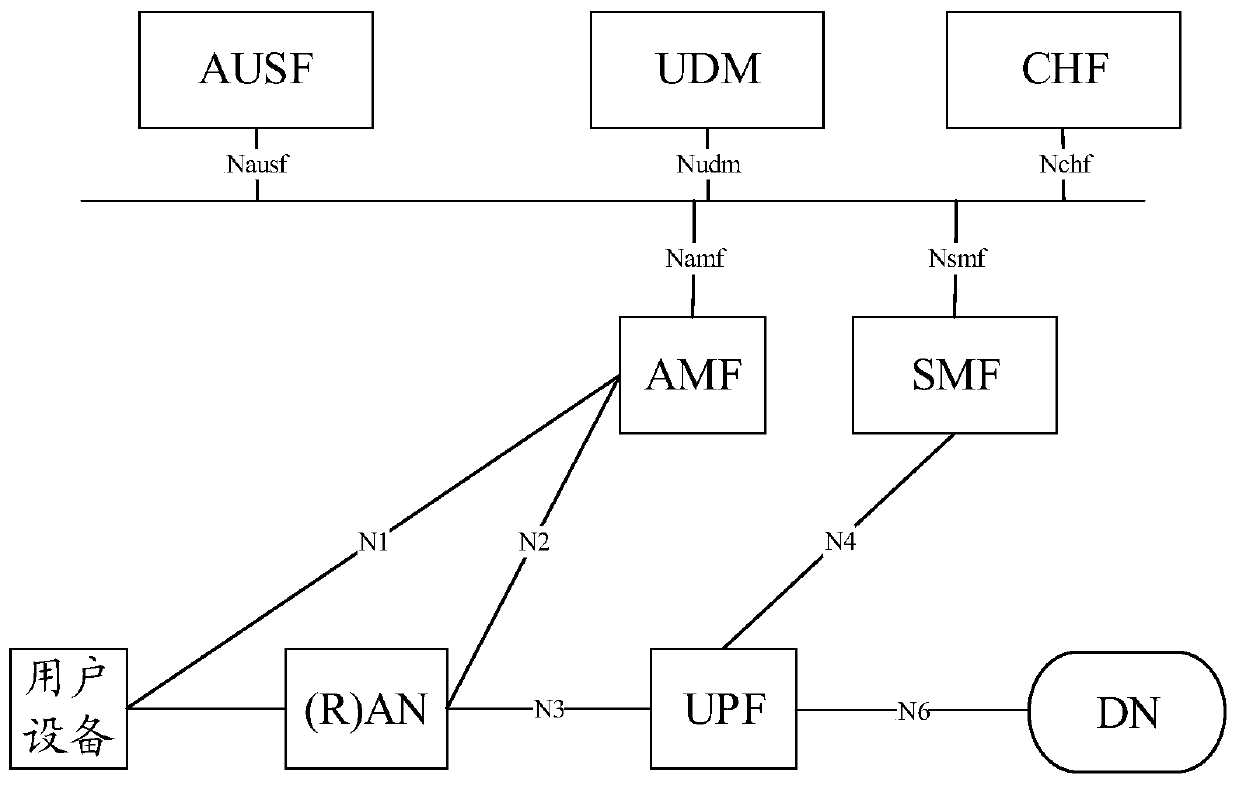
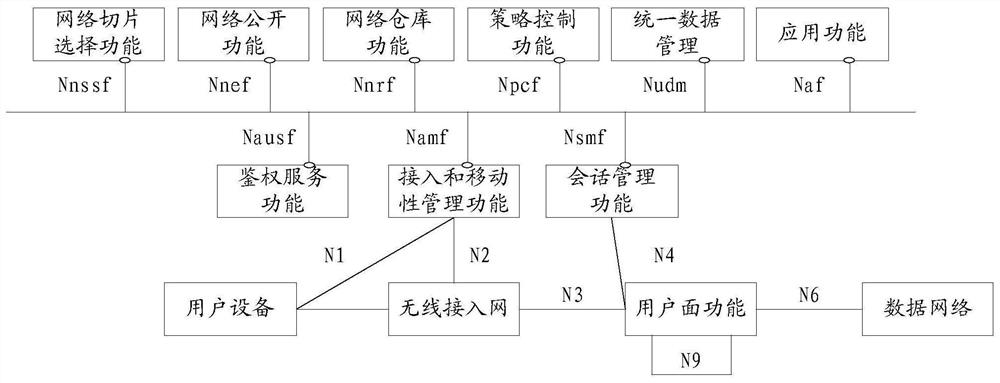
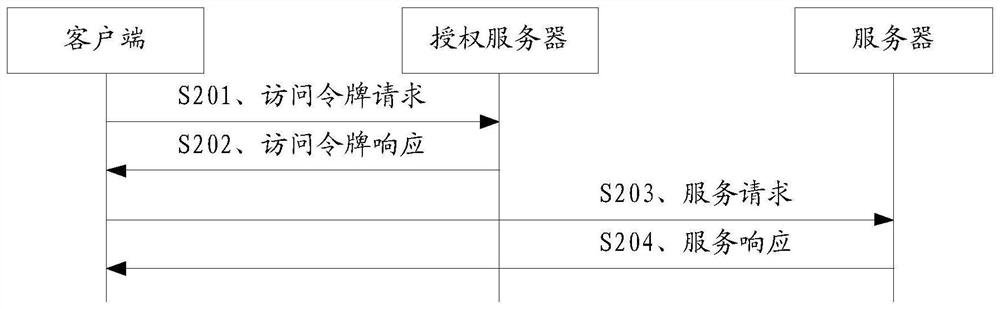
Service authorization method and communication device
ActiveCN111107047ATroubleshoot unauthorized servicesReduce security risksUser identity/authority verificationSecurity arrangementAccess tokenDistributed computing
The embodiment of the invention discloses a service authorization method and a communication device, and can solve the problem that a first server accesses a second server and does not obtain serviceauthorization in a scene that the second server is discovered by a client, so as to reduce the security risk of a servitization network. The method comprises the following steps that: a client replaces an access token for applying for a first server to access a second server and informs the first server; or, the first server applies for the access token by itself according to an instance identifier or resource identifier of the second server provided by the client.
Owner:HUAWEI TECH CO LTD
Method and system for managing cloud resources
ActiveUS20220156164A1Reduce chanceProgram controlRedundant hardware error correctionEngineeringCloud resources
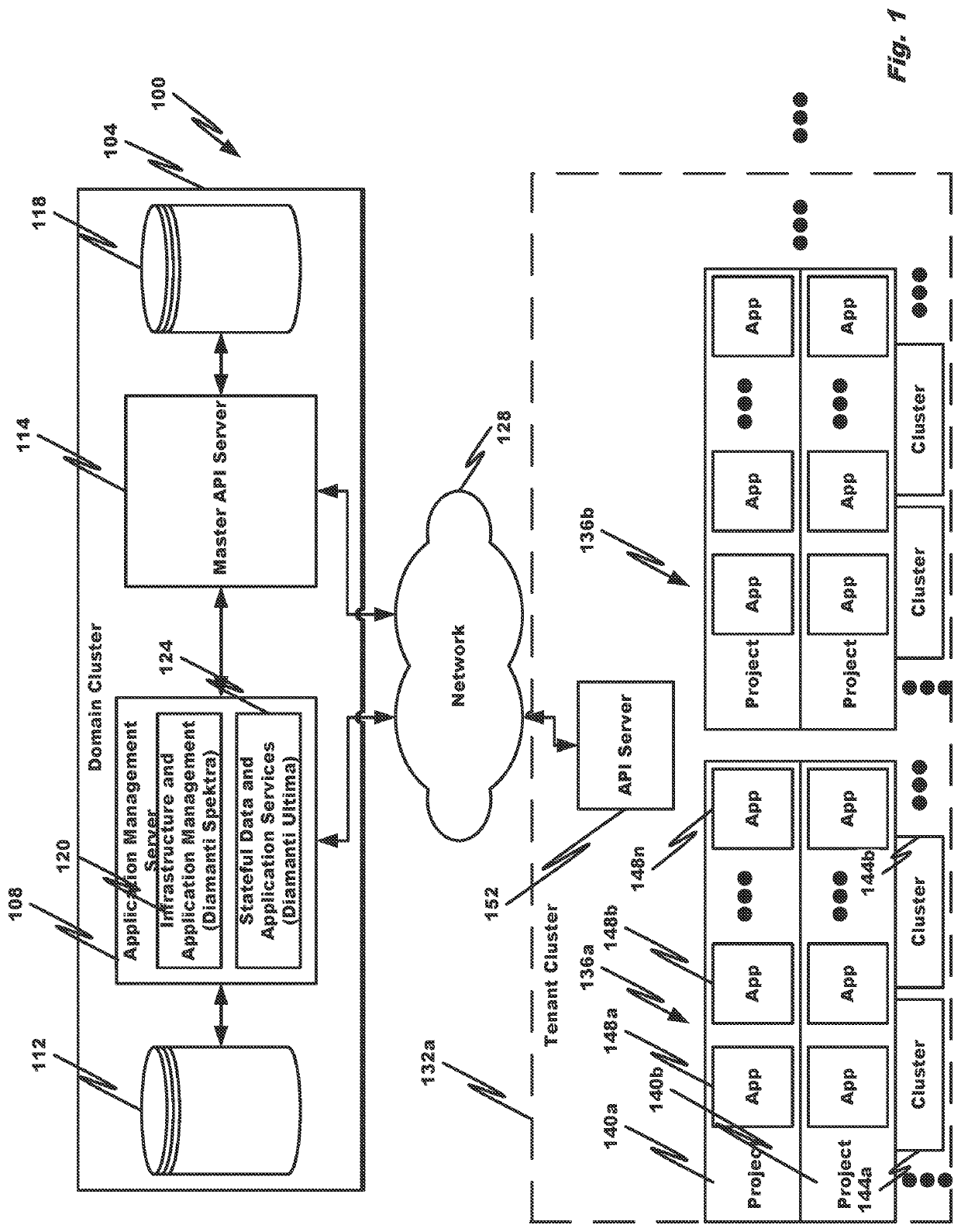
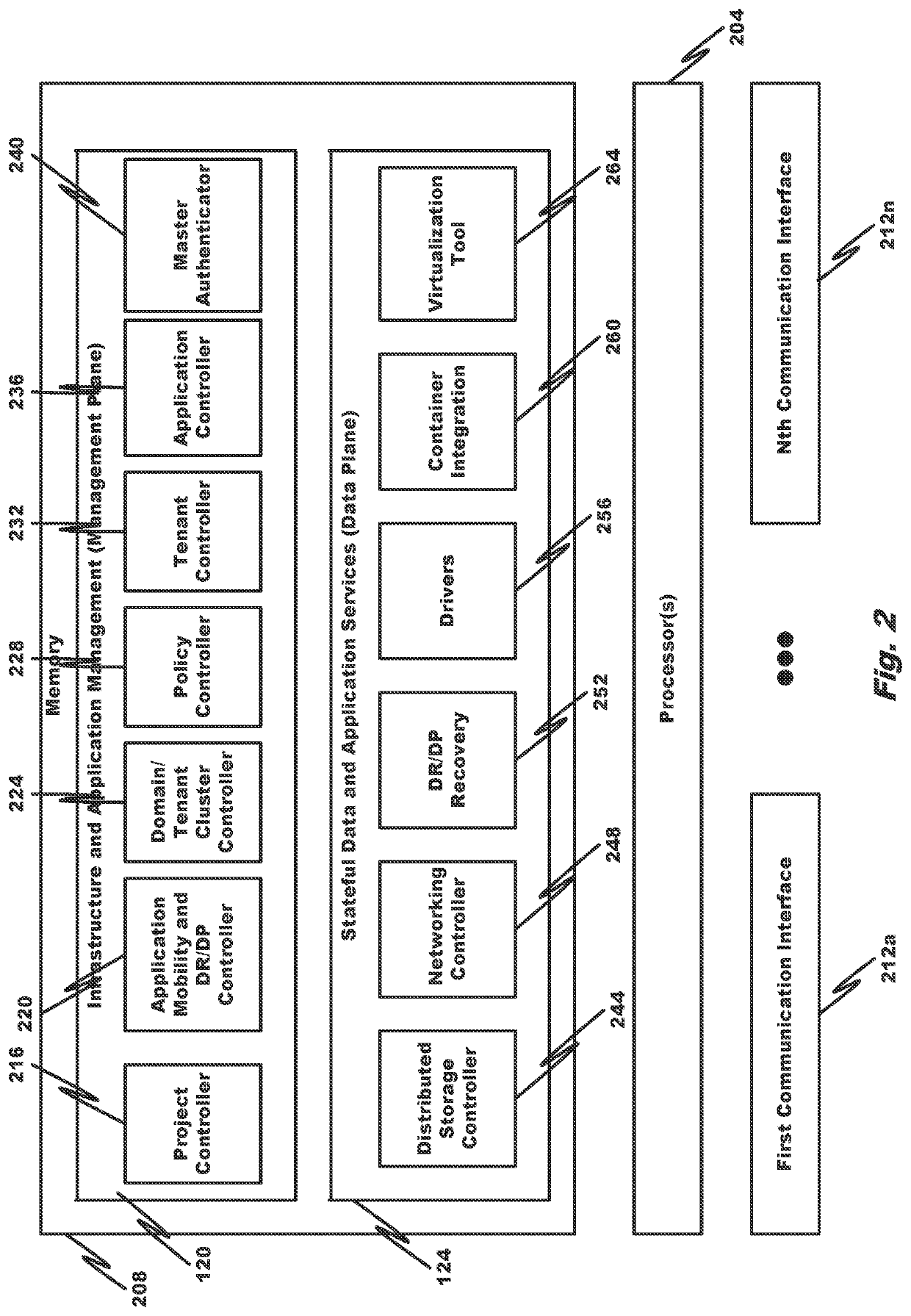
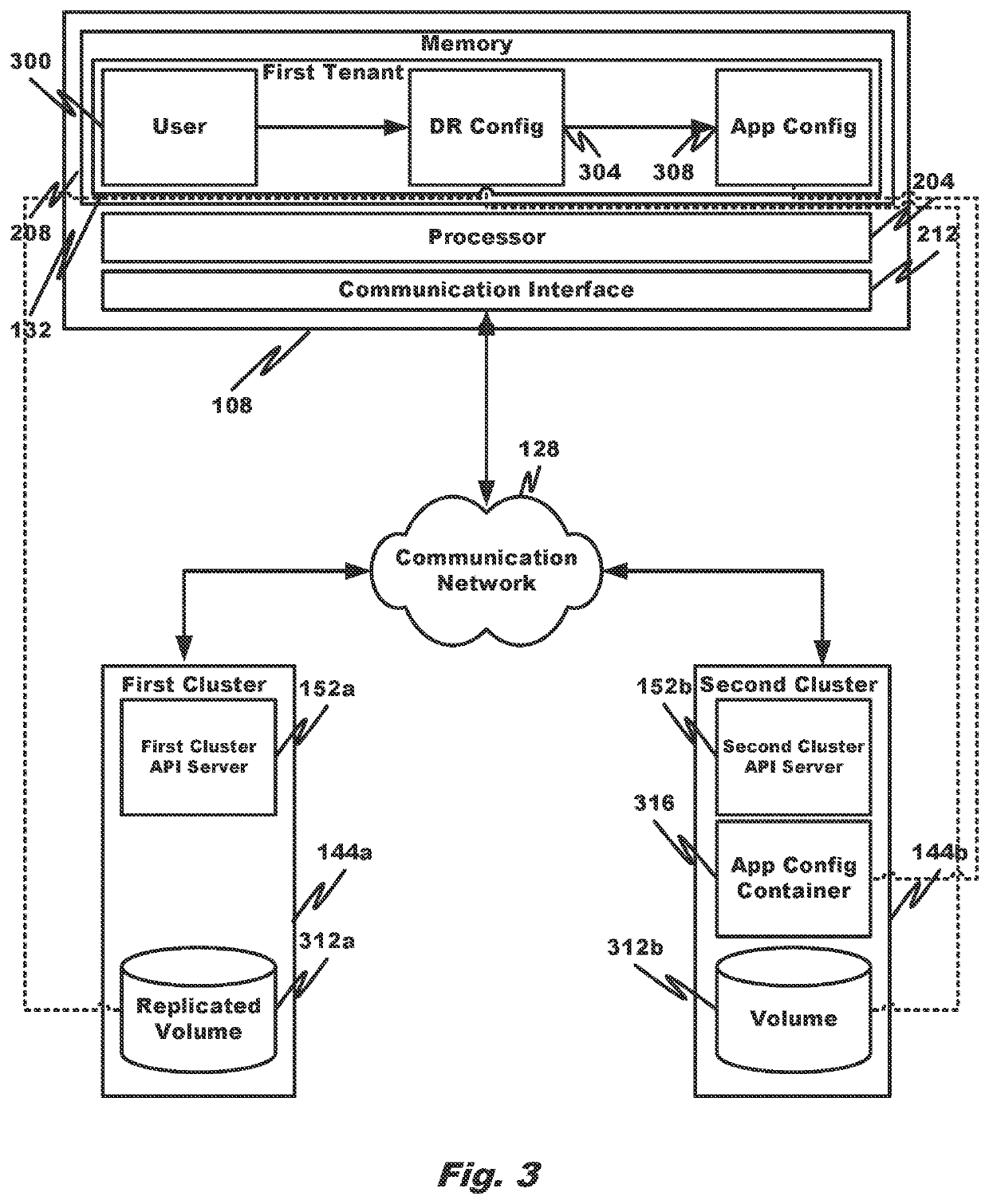
Embodiments of the disclosure provide systems and methods for enabling disaster recovery from a source cluster to a target cluster in a multi-cluster cloud-computing environment. A domain cluster configures a replicated data volume to be updated with data from a data volume of the source cluster, wherein the replicated data volume resides in the target cluster; determines that the target cluster is to replace the source cluster as an active cluster; rebuilds, in the target cluster, a new container instance to replace the container instance on the source cluster; configures the container instance to utilize the replicated data volume in the target cluster; and discontinues recognition of the data volume and container instance on the source cluster as being authoritative.
Owner:DIAMANTI INC
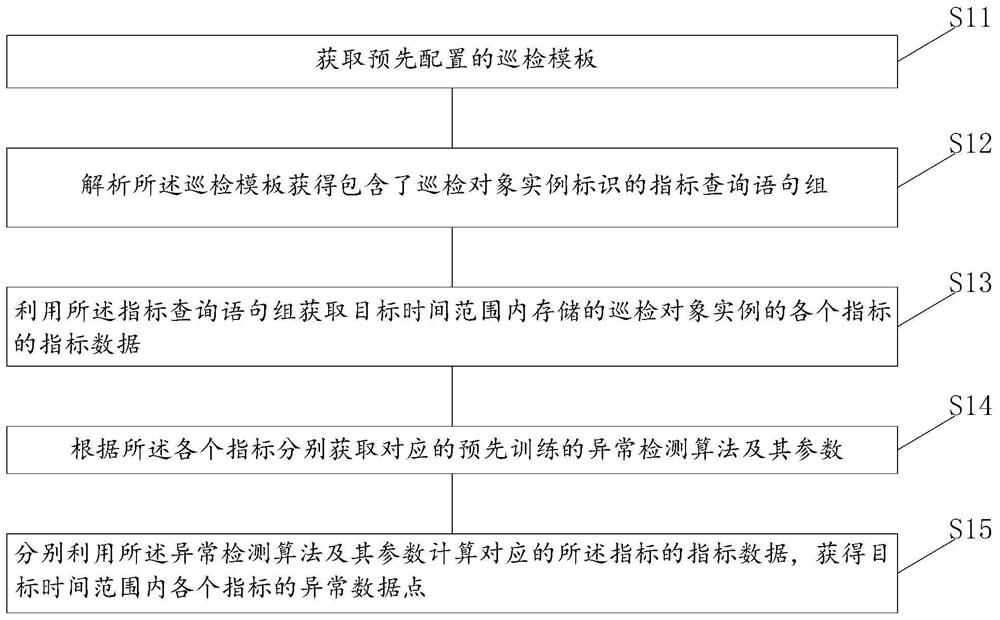
Index data-based inspection method, device and system
The embodiment of the invention discloses an index data-based inspection method, device and system, and the method comprises the steps: obtaining a pre-configured inspection template, and analyzing the inspection template to obtain an index query statement group comprising an inspection object instance identifier; utilizing the index query statement group to obtain index data of each index of an inspection object instance stored in a target time range; respectively obtaining a corresponding pre-trained anomaly detection algorithm and parameters thereof according to each index; and calculatingthe index data of the corresponding indexes by using the anomaly detection algorithm and the parameters of the anomaly detection algorithm to obtain abnormal data points of the indexes in a target time range. Compared with the prior art, the routing inspection template can meet routing inspection of multiple sets of applications or components of the same type, an independent script does not need to be written for each application or component, and the routing inspection template has good universality.
Owner:GUANGZHOU PINWEI SOFTWARE
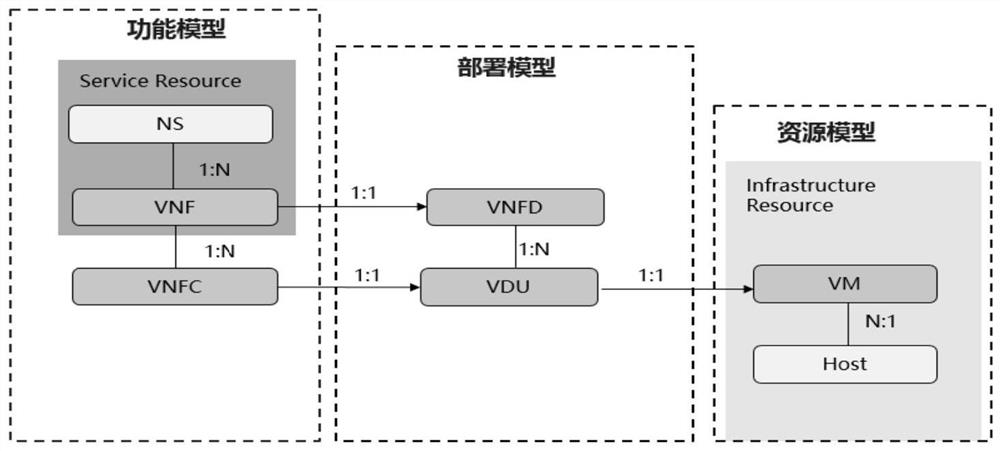
Containerized VNF deployment method and related equipment
PendingCN111949364AReduce deployment complexitySmooth evolutionTransmissionSoftware simulation/interpretation/emulationVirtualizationPackage management
The embodiment of the invention discloses a containerized VNF deployment method and related equipment. The containerized VNF deployment method comprises the steps of enabling a VNFM to receive a firstVNF instantiation request from an NFVO, wherein the first VNF instantiation request carries a first VNF instance identifier and a first virtual network function descriptor VNFD identifier; determining a container object packet identifier referenced by the VNFD represented by the first VNFD identifier; sending a container object package management request to the container management entity, and receiving a container object package management response from the container management entity, with the container object package management response being used for indicating that a container object instance in the container object package is successfully created; and creating a VNF instance represented by the first VNF instance identifier, and maintaining a mapping relationship between the first VNF instance identifier and the container object packet identifier. The embodiment of the scheme facilitates reduction of deployment complexity of the containerized VNF.
Owner:HUAWEI TECH CO LTD
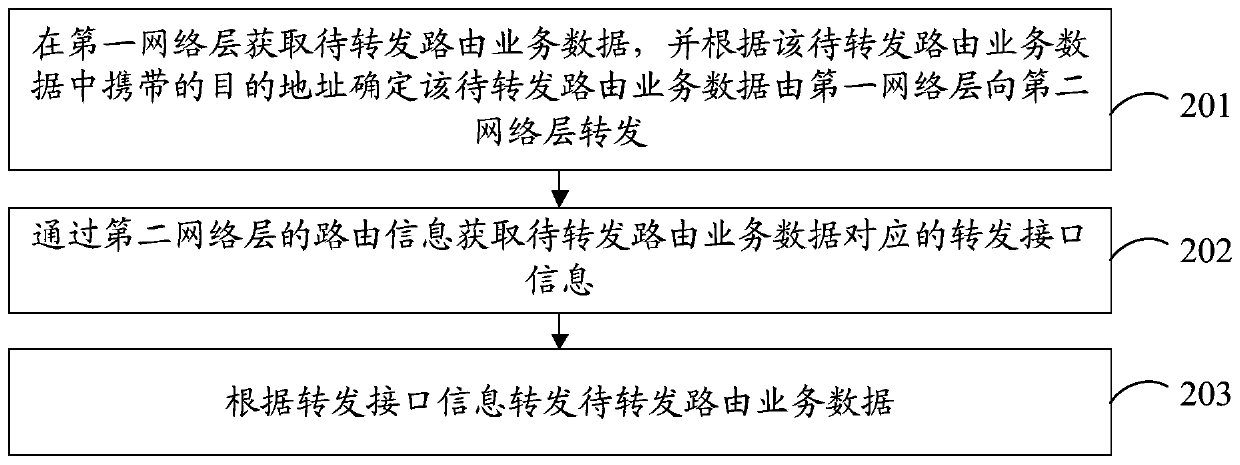
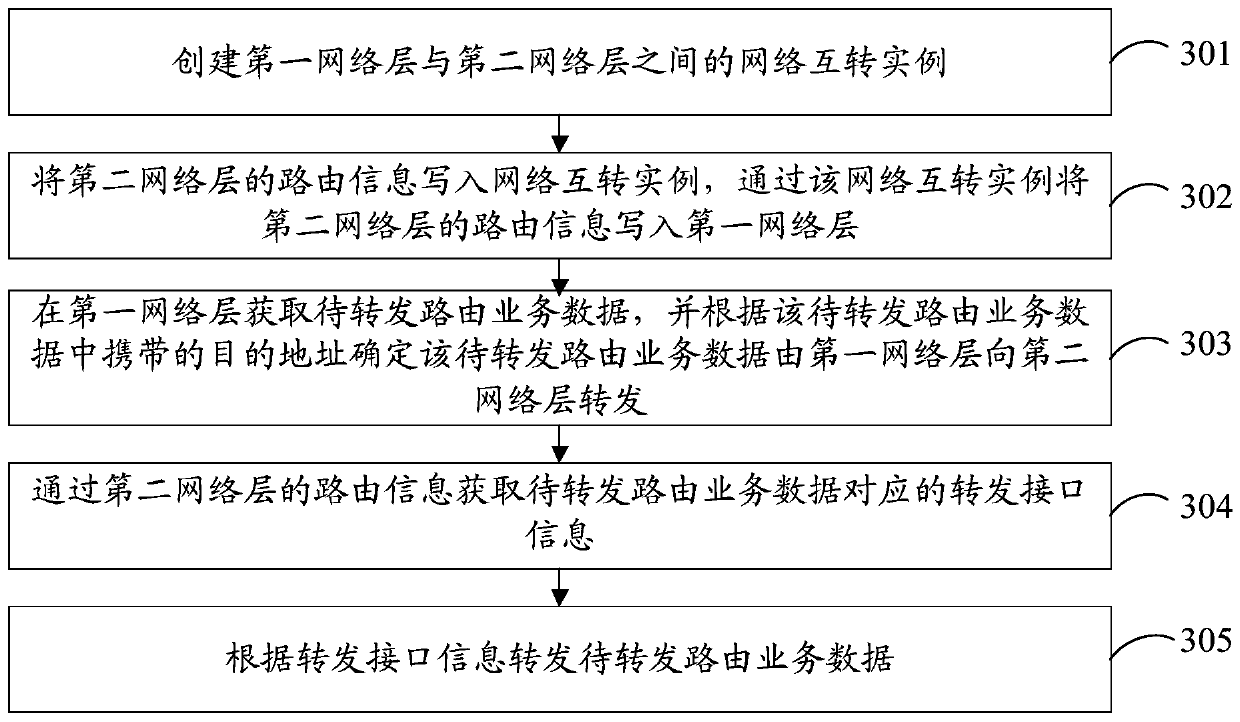
Data forwarding method and device, network equipment and computer readable storage medium
The invention provides a data forwarding method and device, network equipment and a computer readable storage medium, and relates to the technical field of virtual networks. The method is applied to an EVPN, and comprises the steps of obtaining to-be-forwarded routing service data in a first network layer, and determining that the to-be-forwarded routing service data is forwarded from the first network layer to the second network layer according to a destination address carried in the to-be-forwarded routing service data, wherein the first network layer and the second network layer are different types of network layers; acquiring forwarding interface information corresponding to the to-be-forwarded routing service data through the routing information of the second network layer, wherein the routing information of the second network layer is written according to a network interconversion instance, and the network interconversion instance comprises a first VPN instance identifier corresponding to the first network layer and a second VPN instance identifier corresponding to the second network layer; and forwarding the to-be-forwarded routing service data according to the forwarding interface information. According to the invention, mutual forwarding of routing service data between different types of network layers can be realized, and the reliability of communication is improved.
Owner:NEW H3C SECURITY TECH CO LTD
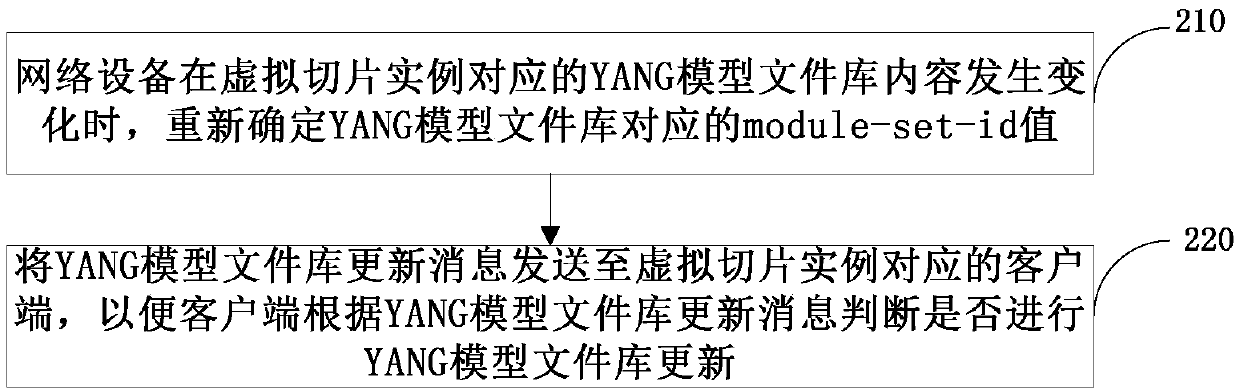
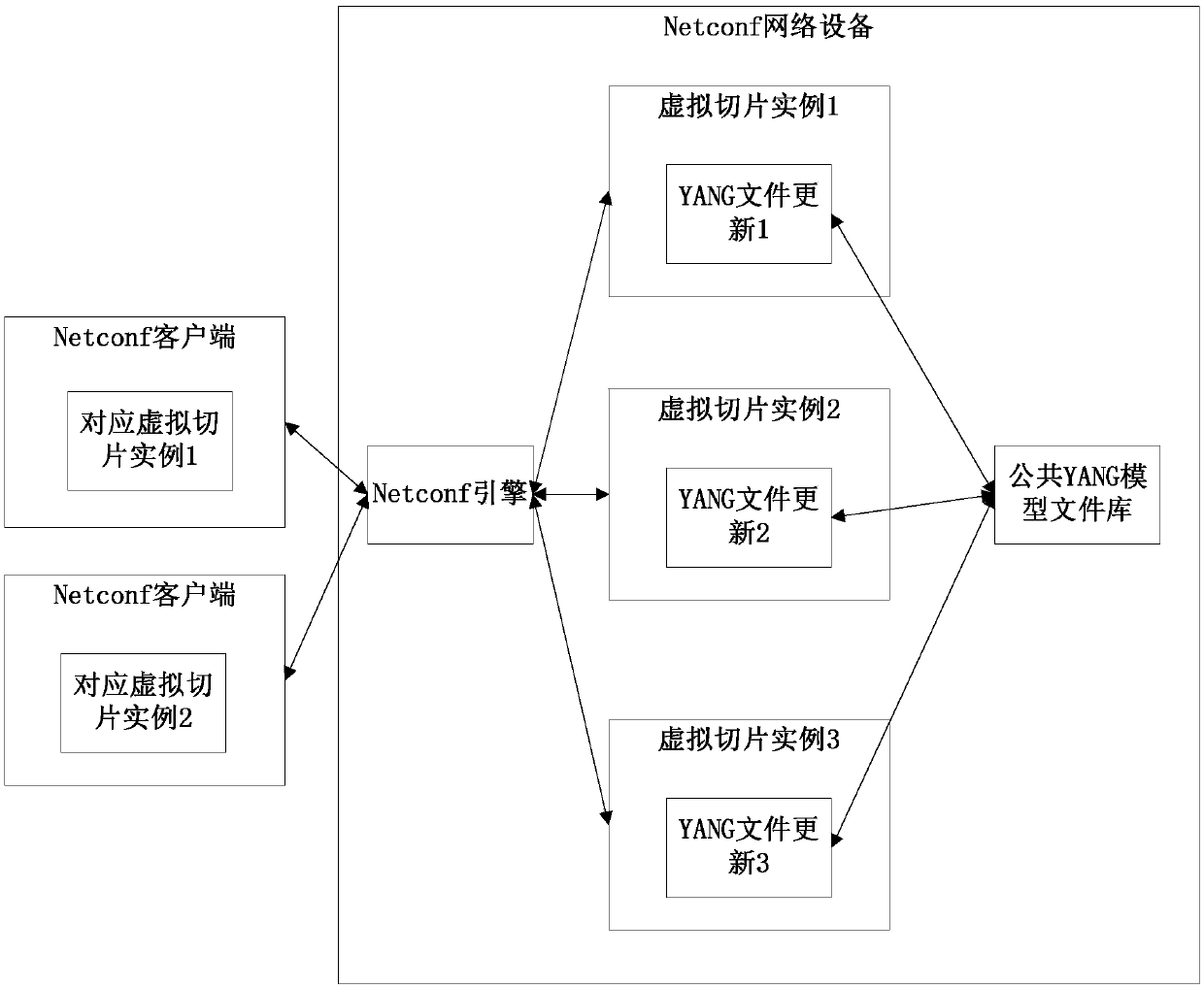
Method, device and system for updating YANG model file library
ActiveCN110768811AAvoid global updatesImprove operation and maintenance efficiencyEncryption apparatus with shift registers/memoriesData switching networksTheoretical computer scienceSlicing
The invention provides a method, device and system for updating a YANG model file library, and relates to the field of software defined networks. The method comprises the following steps: when the content of a YANG model file library corresponding to a virtual slice instance is changed, network equipment re-determines a model-set-id value corresponding to the YANG model file library; and a YANG model file library update message is sent to a client corresponding to the virtual slice instance, and the YANG model file library update message is sent to a client, so that the client judges whether to update the YANG model file library or not according to the YANG model file library update message, and the YANG model file library update message comprises a virtual slice instance identifier and amodel-set-id value. According to the method and the device, the client corresponding to each virtual slice instance can update the corresponding YANG model file library as required in time, unnecessary global update is avoided, and the operation and maintenance efficiency is improved.
Owner:CHINA TELECOM CORP LTD
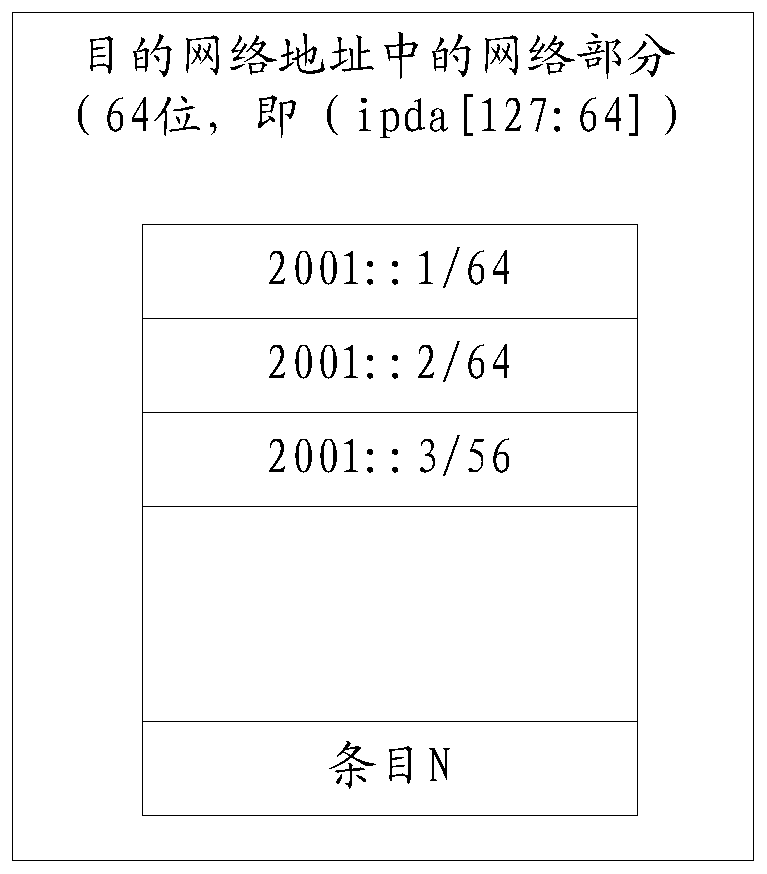
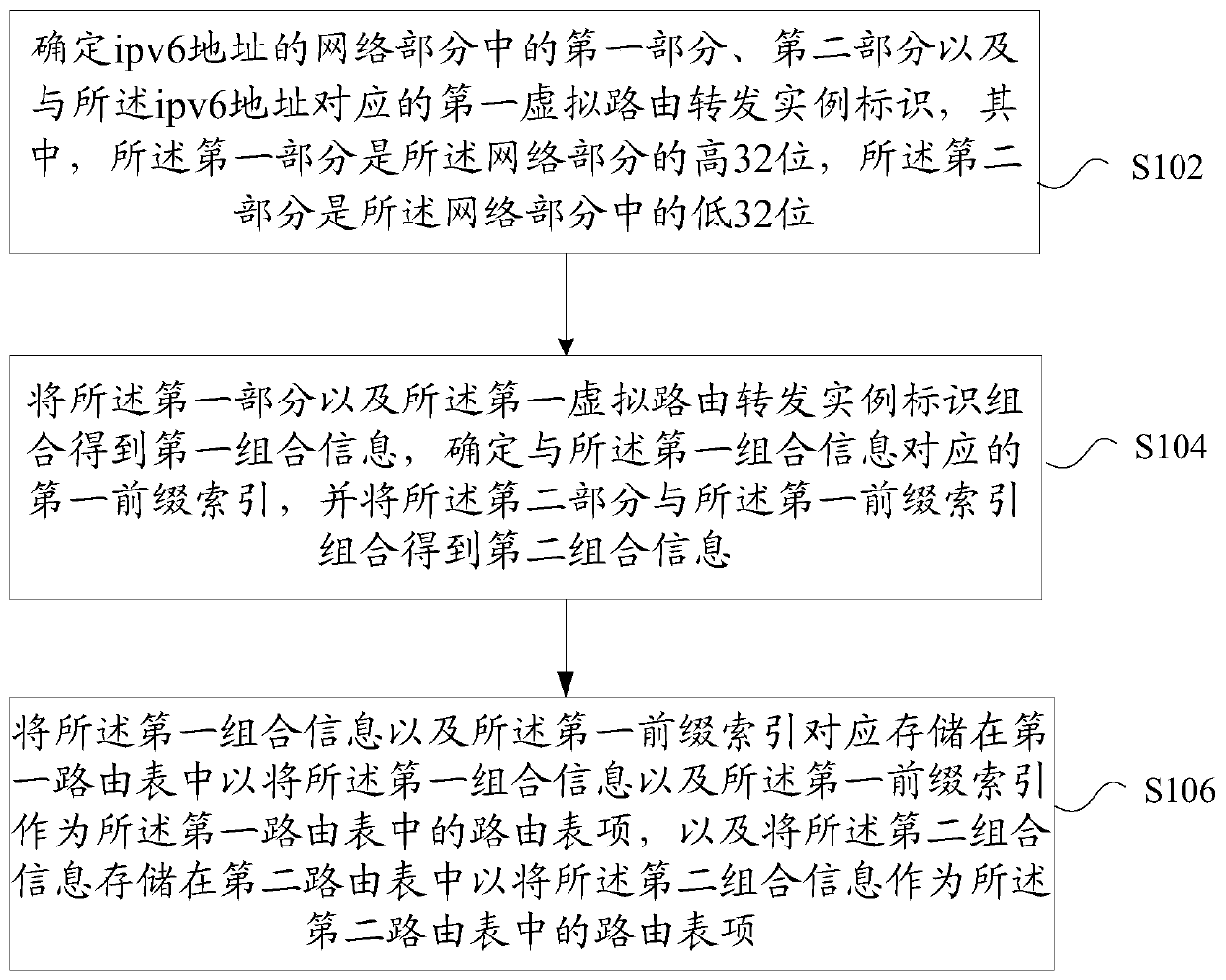
Routing table entry processing method and device
ActiveCN111131049AImprove table item specificationsSolve wasteData switching networksComputer networkRouting table
The invention provides a routing table entry processing method and device. The method comprises the steps of determining a first part and a second part in a network part of an ipv6 address and a firstvirtual routing forwarding instance identifier corresponding to the ipv6 address, wherein the first part is a high 32-bit of the network part, and the second part is a low 32-bit of the network part;combining the first part with the first virtual routing forwarding instance identifier to obtain first combined information, determining a first prefix index corresponding to the first combined information, and combining the second part with the first prefix index to obtain second combined information; and correspondingly storing the first combined information and the first prefix index in a first routing table so as to take the first combined information and the first prefix index as routing table entries in the first routing table, and storing the second combined information in a second routing table so as to take the second combined information as routing table entries in the second routing table. According to the invention, the problem of storage resource waste of ipv6 routing storagein related technologies is solved.
Owner:SUZHOU CENTEC COMM CO LTD
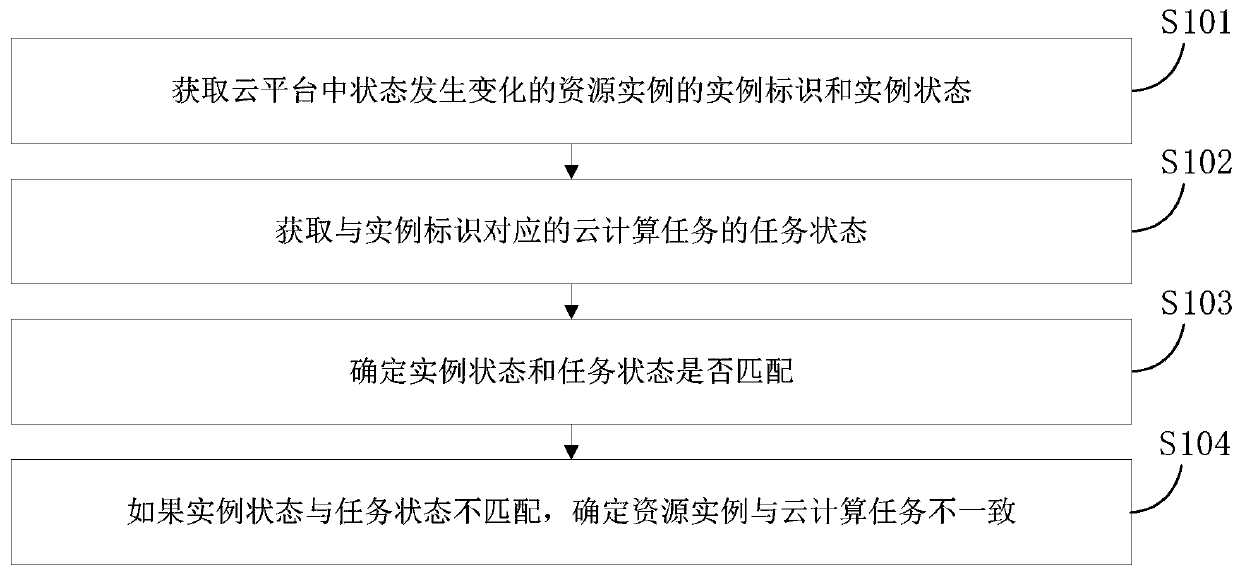
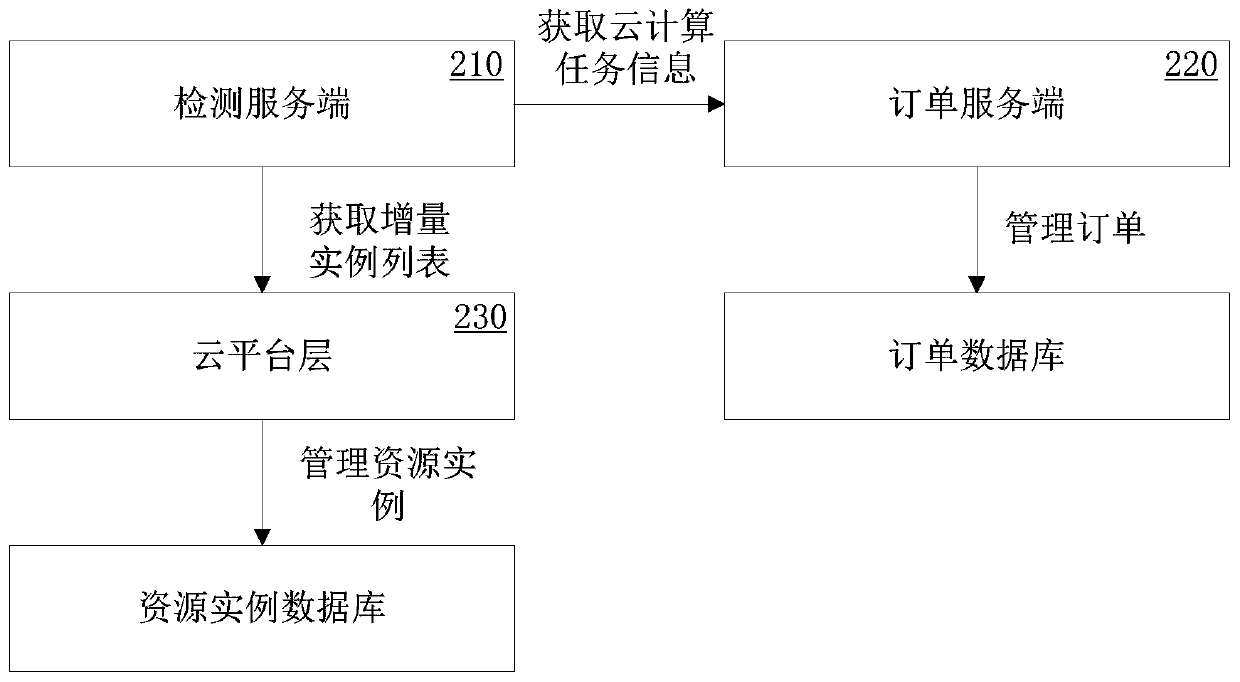
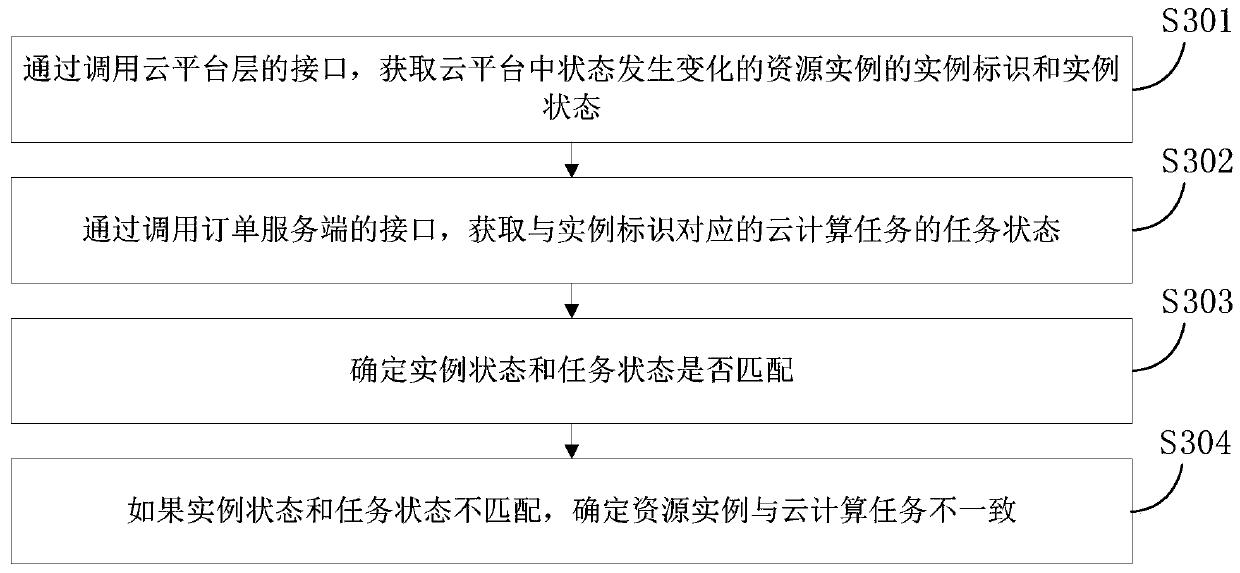
Data consistency detection method and device and electronic device
The embodiment of the invention provides a data consistency detection method and device and an electronic device. The method comprises the steps of obtaining an instance identifier and an instance state of a resource instance of which the state changes in a cloud platform; obtaining a task state of a cloud computing task corresponding to the instance identifier; determining whether the instance state is matched with the task state or not; and if the instance state is not matched with the task state, determining that the resource instance is inconsistent with the cloud computing task. Whether the resource instance is successfully created by the cloud platform or not can be obtained without an asynchronous interface, so that whether the resource instance is consistent with the cloud computing task or not can still be accurately detected even if an asynchronous message queue used for receiving and sending asynchronous messages in the cloud platform is abnormal.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
Identifier processing method, device and system for digital object in hydropower industry
ActiveCN112541834AMany categoriesBig amount of dataData processing applicationsSpecial data processing applicationsIdenticonData mining
The invention relates to a hydroelectric industry digital object identifier processing method, device and system. The method comprises the following steps: receiving an identifier generation request;when the identifier generation request contains the domain code, determining a newly added meta-class sequence number of the domain code, and allocating a meta-class identifier to the hydropower industry digital object according to the newly added meta-class sequence number; when the identifier generation request contains a meta-class identifier, determining a newly added class sequence number ofthe meta-class identifier, and allocating a class identifier according to the newly added class sequence number; when the identifier generation request contains a class identifier, determining a newlyadded instance sequence number of the class identifier, and allocating an instance identifier according to the newly added instance sequence number; and returning at least one of the meta-class identifier, the class identifier and the instance identifier to the user terminal. By adopting the method, the identification requirement of the hydropower industry field on the digital object can be met.
Owner:SOUTHERN POWER GRID PEAK LOAD & FREQUENCY REGULATION GENERATING CO LTD
System and method for network traffic processing based on federated services and user groups
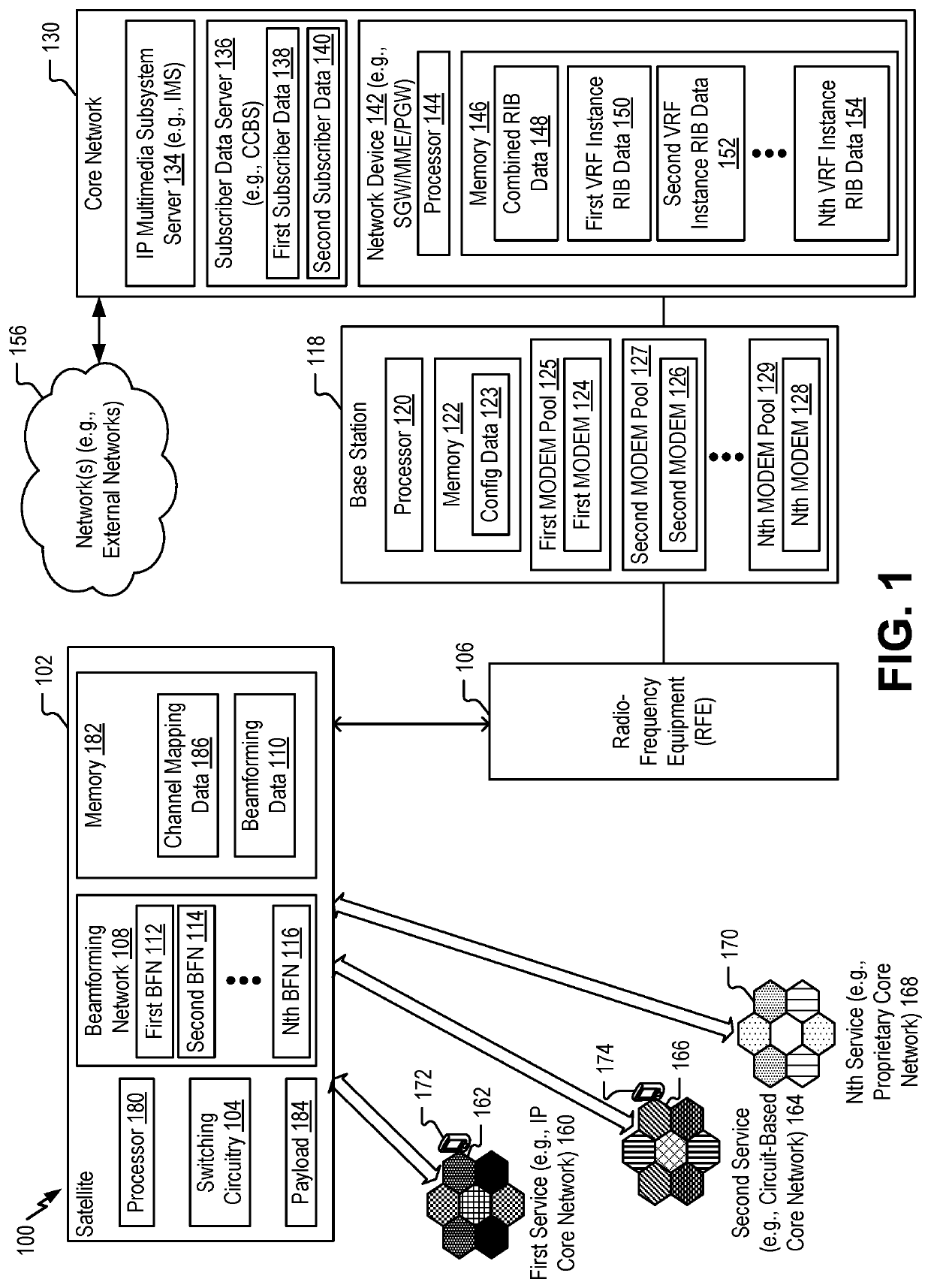
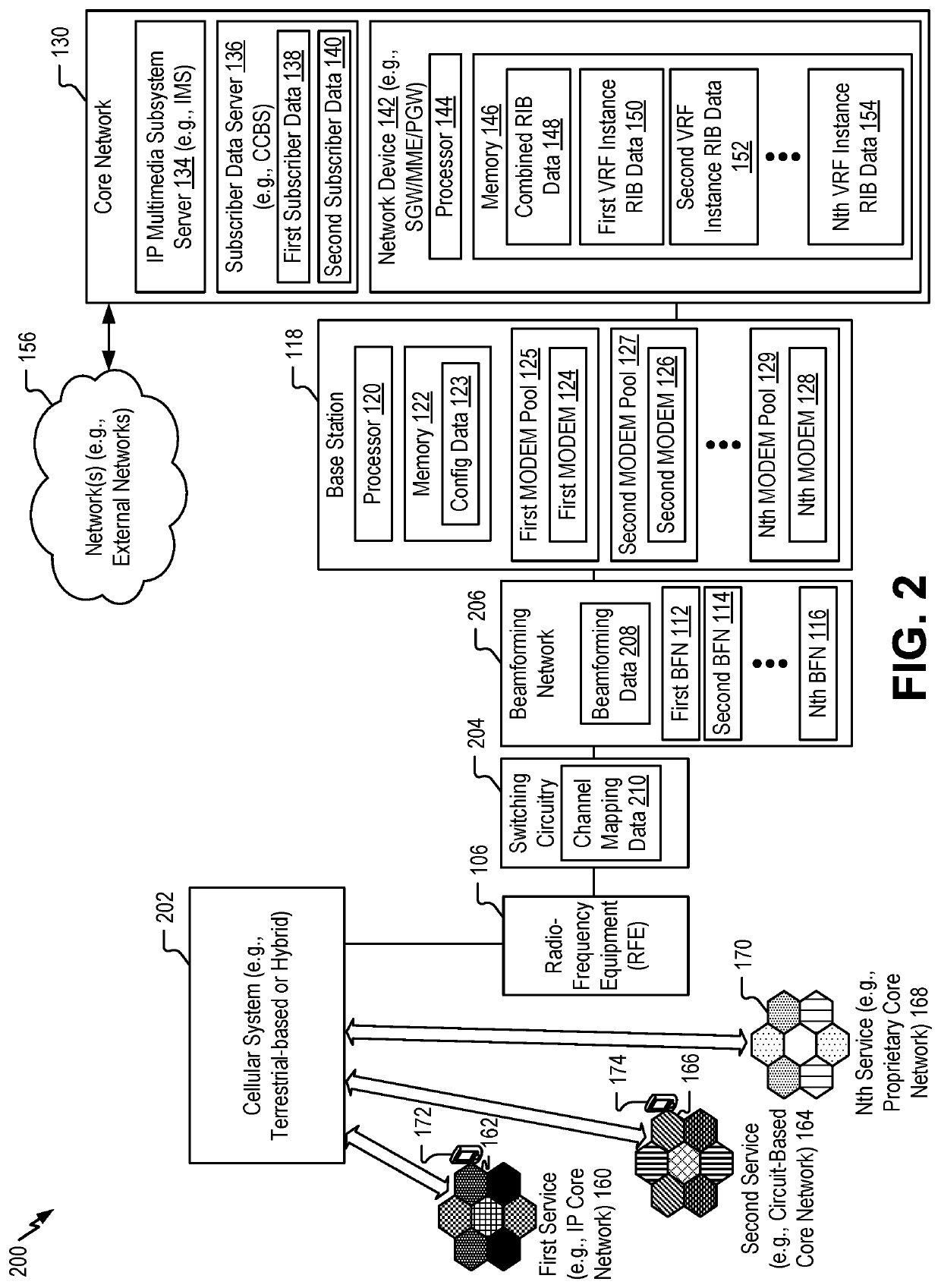
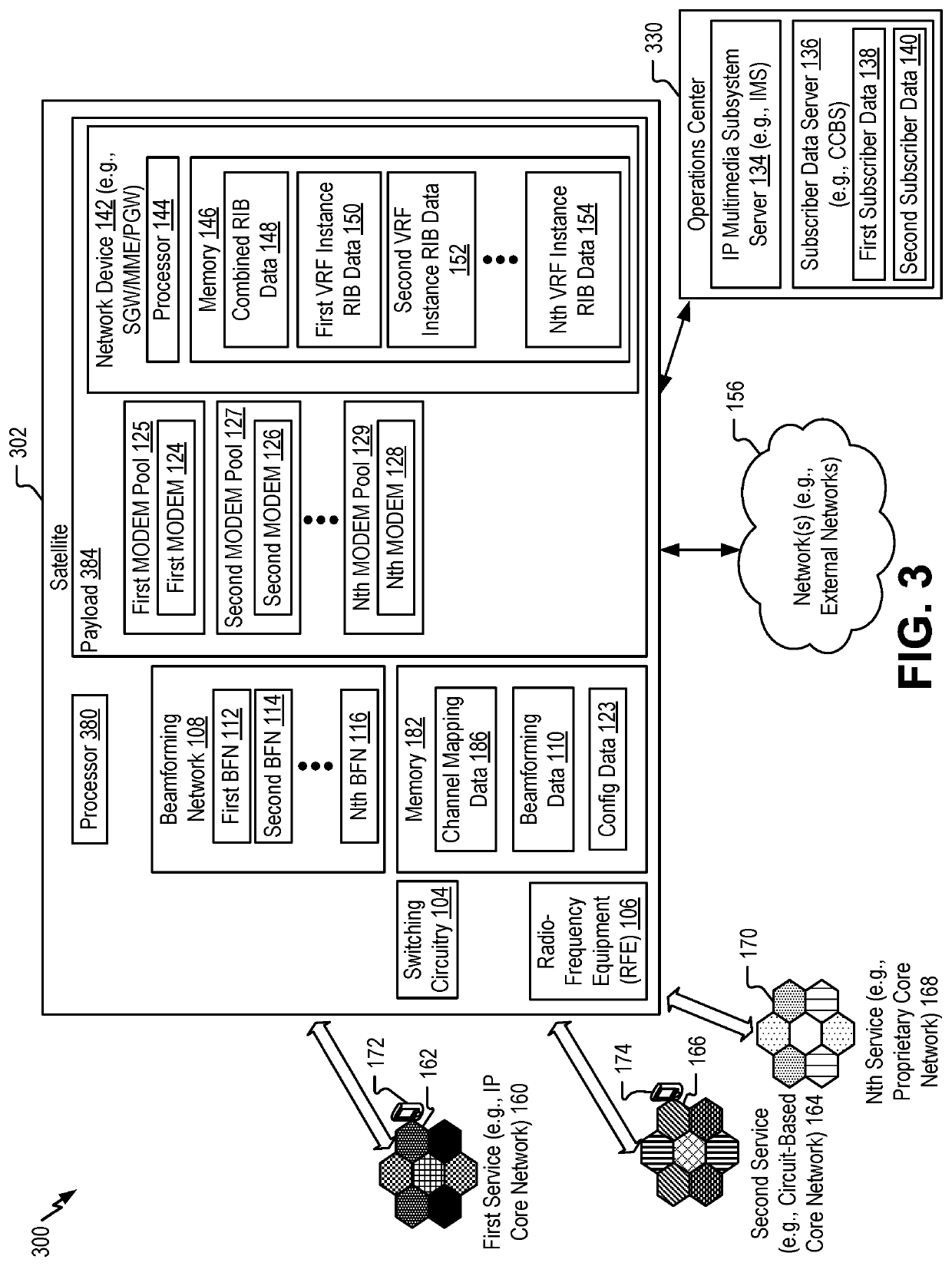
A system includes a first MODEM configured to generate a first data packet (including a first virtual routing and forwarding (VRF) instance identifier associated with a first service, a first user group, or both) based on a first radio-frequency (RF) signal and a second MODEM configured to generate a second data packet (including a second VRF instance identifier associated with a second service, a second user group, or both) based on a second RF signal. The system includes a network device configured to receive the first data packet, transmit a first packet (including a first header that includes a first indicator associated with a first VRF instance) to a first device via a network, receive the second data packet, and transmit a second packet (including a second header that includes a second indicator associated with a second VRF instance) to a second device via the network.
Owner:THE BOEING CO
Data processing method and device
PendingCN111221855AImprove extraction efficiencyReduce query time consumptionDatabase management systemsSpecial data processing applicationsAlgorithmEngineering
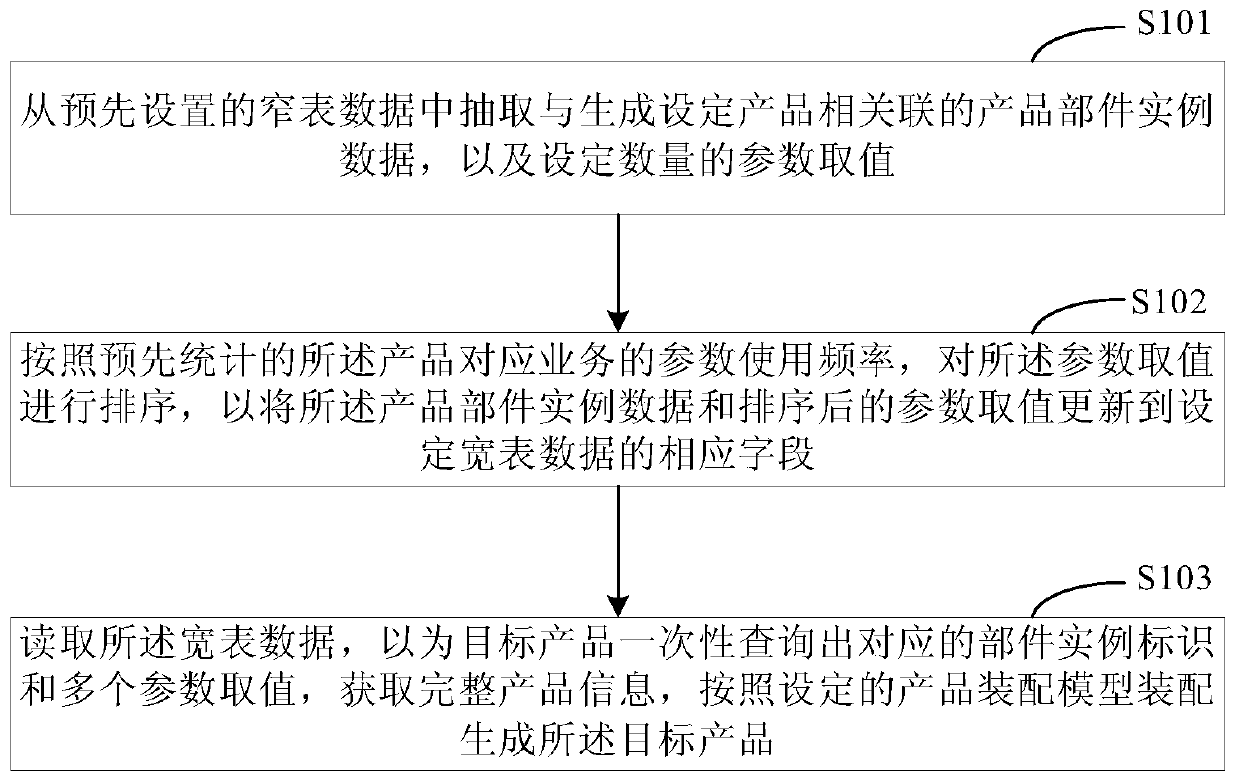
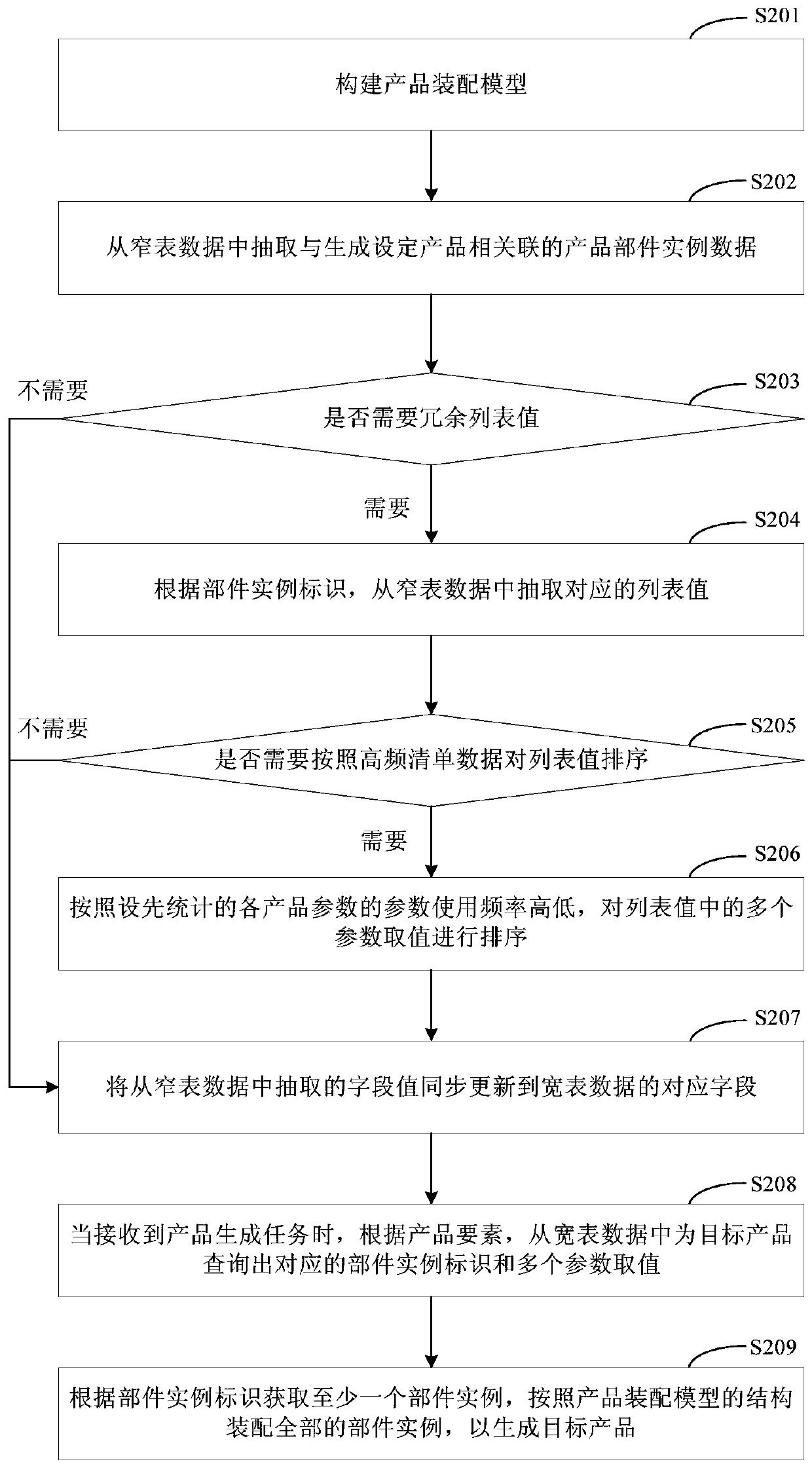
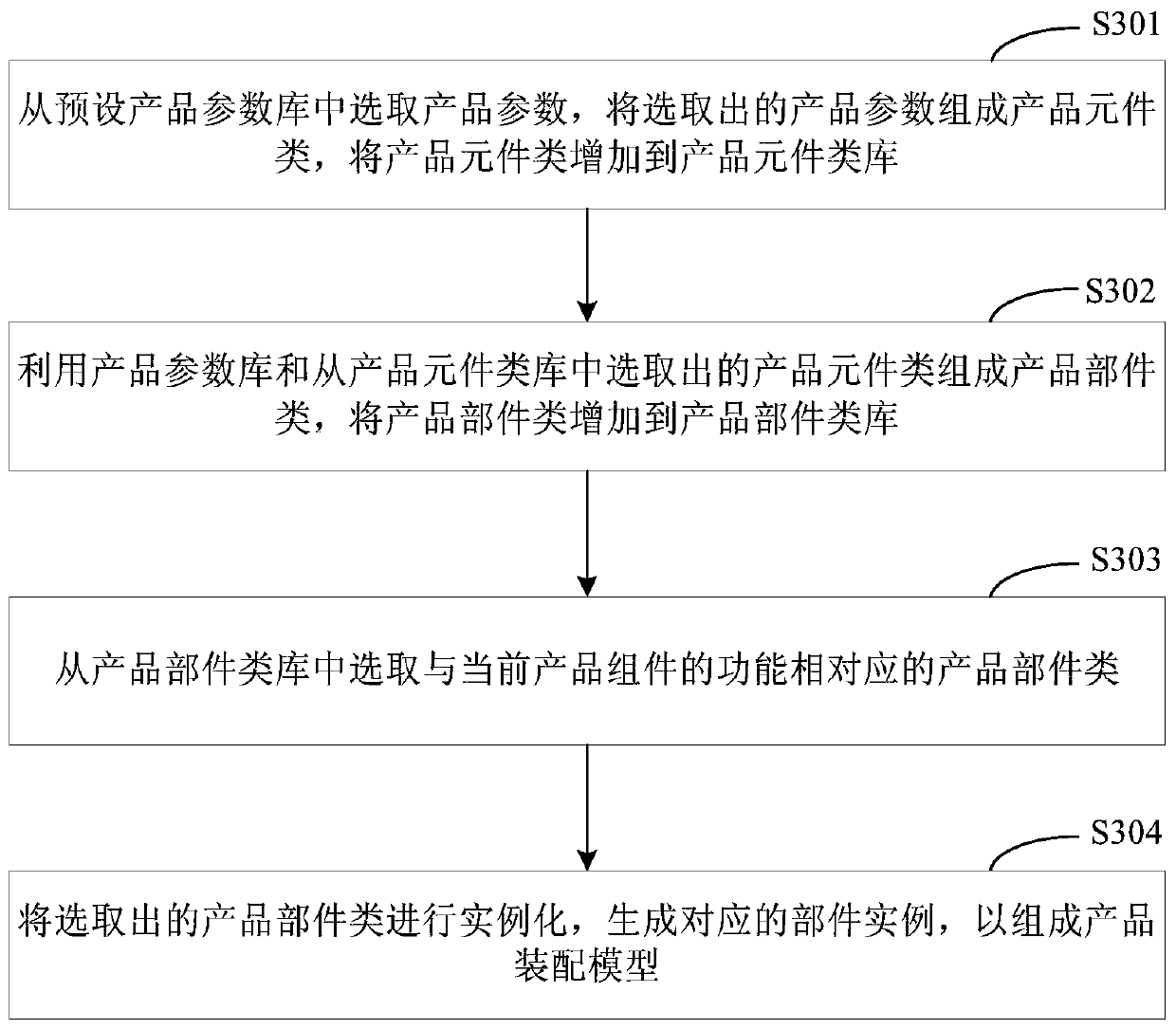
The invention discloses a data processing method and device, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: extracting product part instance data associated with generating a set product and parameter values of a set number from preset narrow table data; sorting the parameter values according to pre-counted parameter use frequencies of services corresponding to the products so as to update the product component instance data and the sorted parameter values to corresponding fields of the set wide table data; and reading thewide table data, querying a corresponding part instance identifier and a plurality of parameter values for the target product at one time, obtaining a part instance, and assembling according to a setproduct assembling model to generate the target product. According to the method, part of fields of the narrow table data are extracted and transferred to the wide table data, and then the wide tabledata is directly read to realize acquisition of the component instance so as to generate the target product, so that the query time is greatly shortened, and the influence on the system performance isreduced.
Owner:CHINA CONSTRUCTION BANK
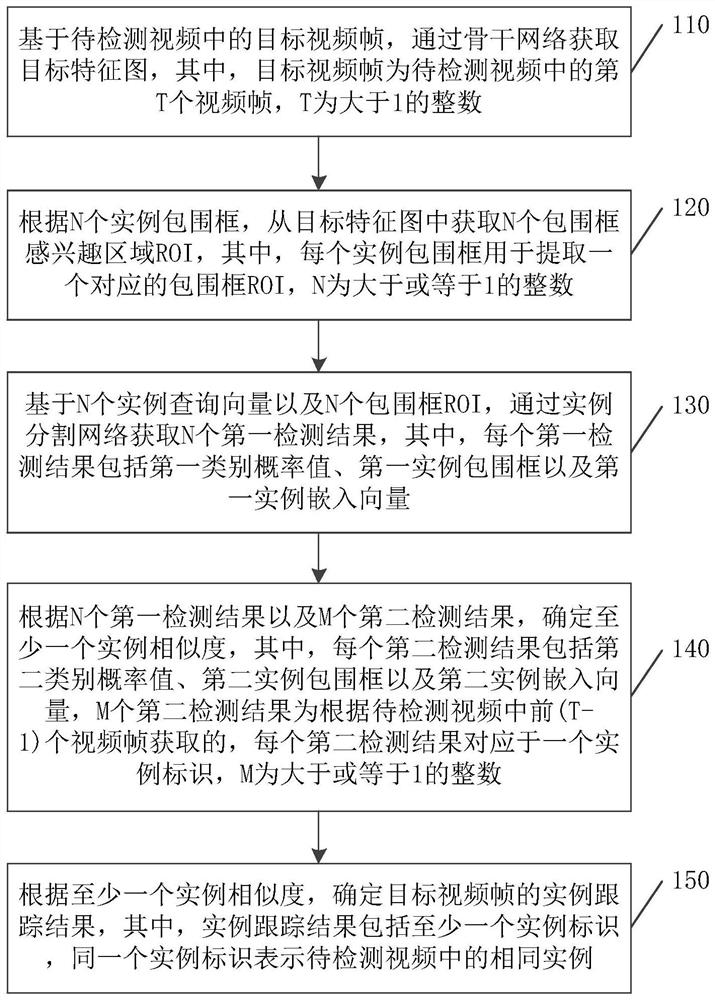
Video-based instance tracking method and device, equipment and storage medium
PendingCN113822134AImprove instance tracking efficiencyCharacter and pattern recognitionAlgorithmEngineering
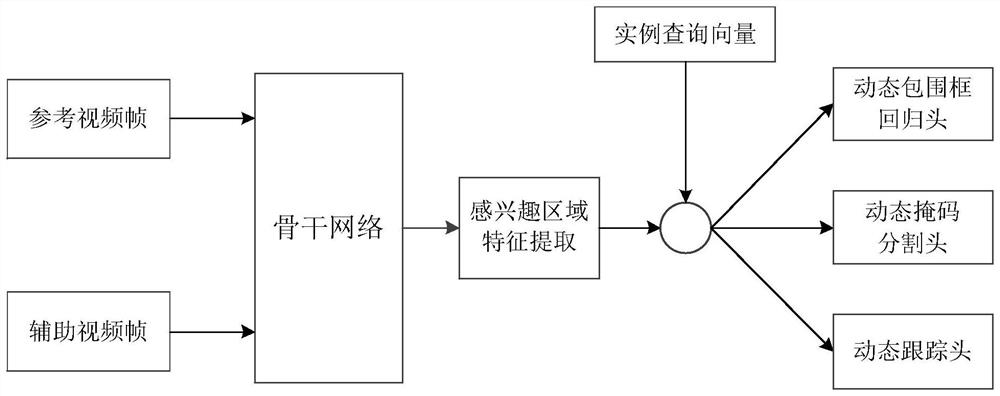
The invention discloses a video-based instance tracking method realized by adopting an artificial intelligence technology, and the method comprises the steps: obtaining a target feature map through a backbone network based on a target video frame in a to-be-detected video; according to the N instance bounding boxes, obtaining N bounding box regions of interest (ROI) from the target feature map; based on the N instance query vectors and the N bounding box ROIs, obtaining N first detection results through an instance segmentation network; determining at least one instance similarity according to the N first detection results and the M second detection results; and determining an instance tracking result of the target video frame according to the at least one instance similarity. The invention further provides a device, equipment and a storage medium. The end-to-end instance detection framework is constructed, instance detection independent of post-processing methods such as non-maximum suppression is realized, and the instance target is tracked based on the instance identifier, so that the instance tracking efficiency based on the video is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
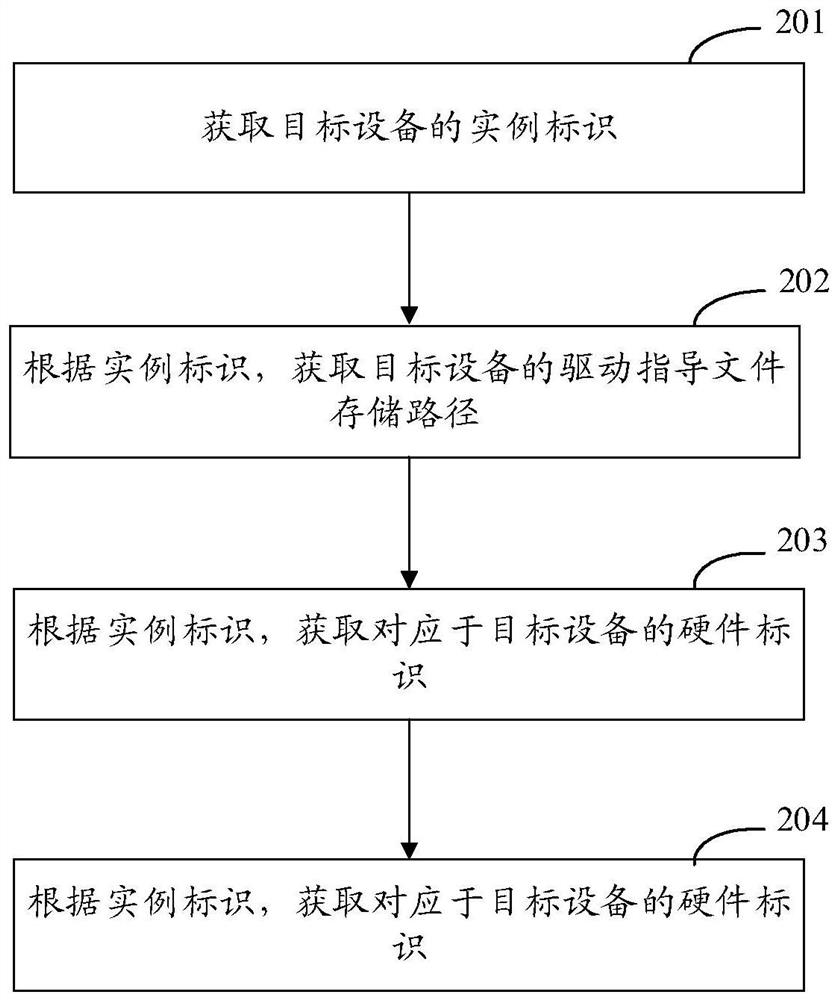
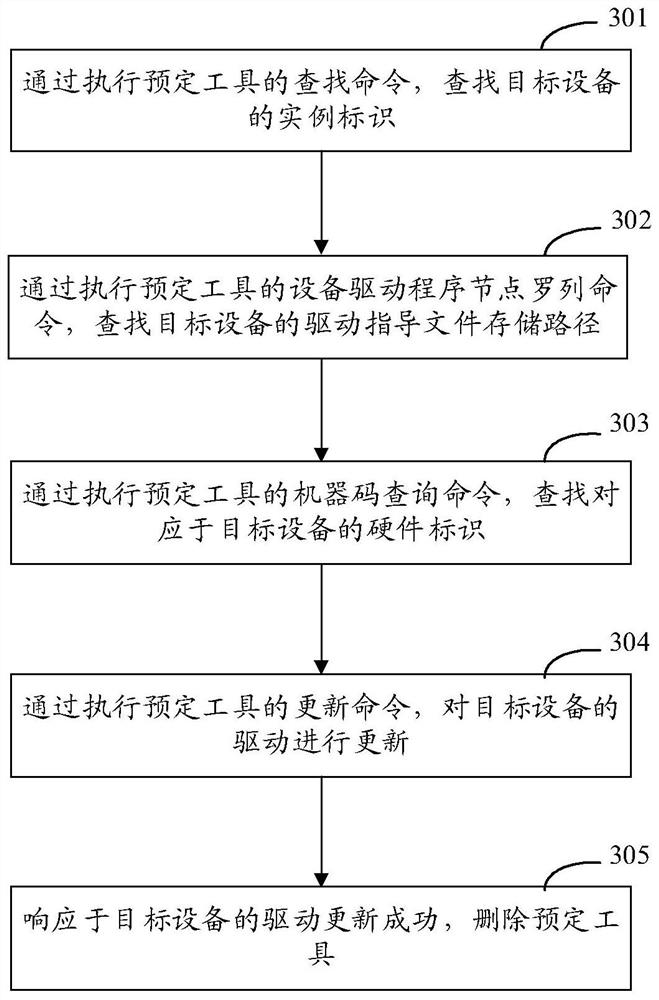
Equipment driving reloading method and device, equipment and storage medium
PendingCN112328328ASolve the problem that cannot be loadedEasy to understandVersion controlProgram loading/initiatingComputer hardwarePathPing
The embodiment of the invention discloses an equipment drive reloading method and device, equipment and a storage medium, and relates to the technical field of the Internet such as cloud computing andcloud service. The method comprises the steps of obtaining an instance identifier of a target device; according to the instance identifier, obtaining a drive guidance file storage path of the targetdevice; obtaining a hardware identifier corresponding to the target device according to the instance identifier; and updating the driver of the target device according to the driver guidance file storage path and the hardware identifier, thereby solving the problem that the driver cannot be loaded when the system of the target device is deployed, and reducing the manpower demand and deployment time of the system for deploying the target devices in batches.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
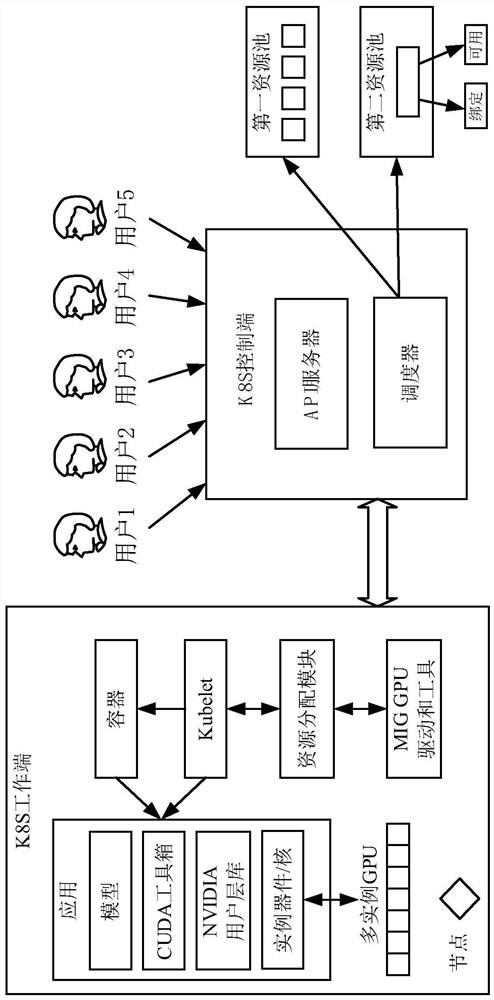
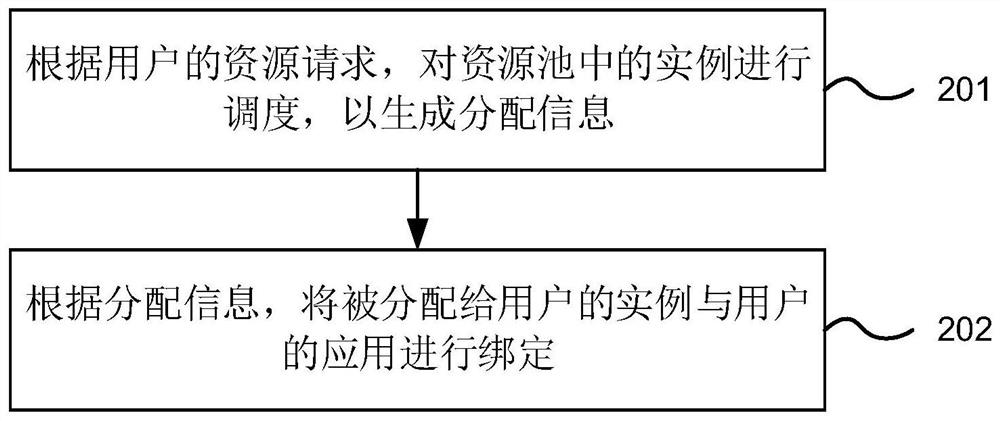
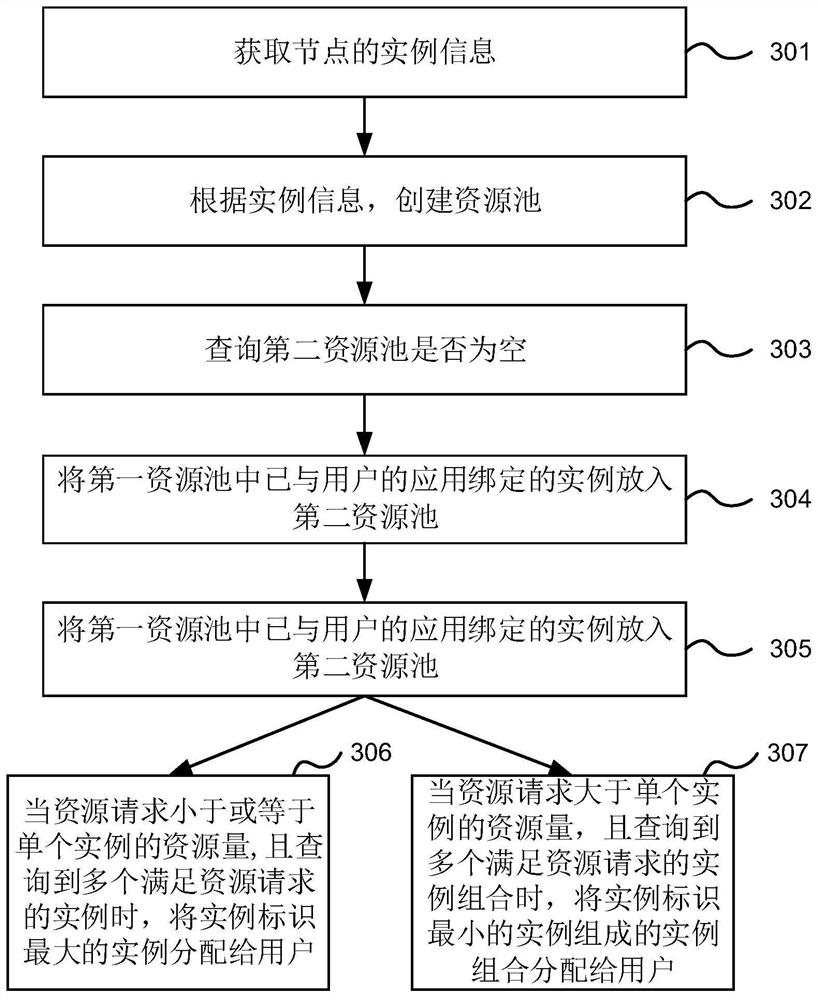
Resource configuration method and device, electronic equipment and computer readable storage medium
ActiveCN113419846AIncrease profitResponding to resource allocation needsResource allocationEnergy efficient computingResource poolResource allocation (computer)
The invention discloses a resource configuration method and device, electronic equipment and a computer readable storage medium. The method comprises: according to a resource request of a user, scheduling instances in a resource pool to generate allocation information, the resource request at least comprising a storage amount and a computing power amount requested by the user, and the allocation information at least comprising an instance identifier of an instance allocated to the user; and binding the instance allocated to the user with the application of the user according to the allocation information. According to the embodiment of the application, the instances in the resource pool can be scheduled according to the resource request of the user, so that the resource allocation information is generated, and the instances identified by the allocation information are bound with the application requested by the user, therefore, the resource allocation demand of the user can be more flexibly responded, and the utilization rate of actually used resources can be improved.
Owner:ALIBABA GRP HLDG LTD
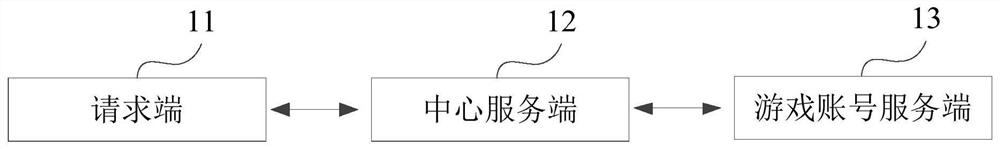
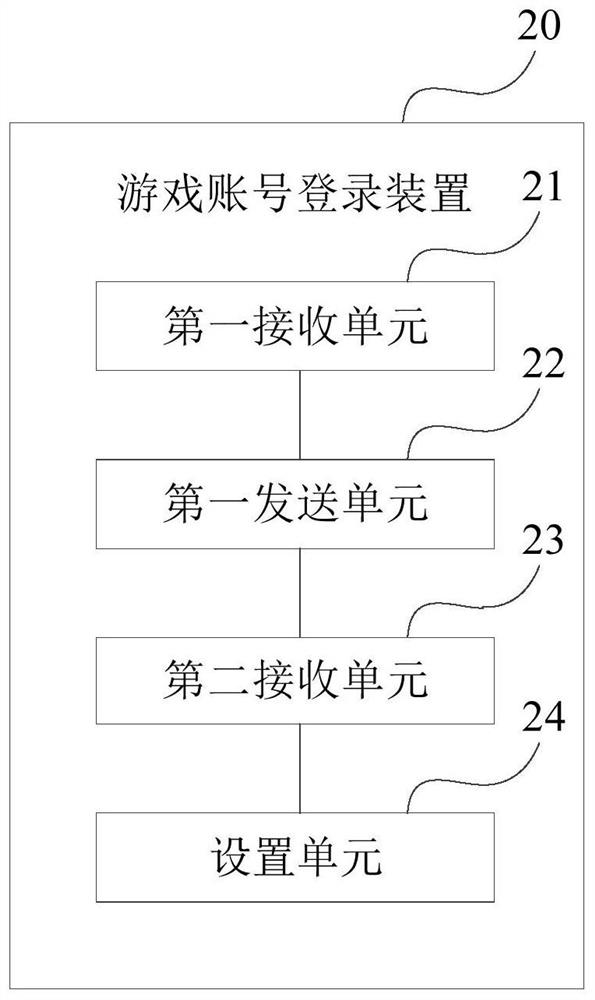
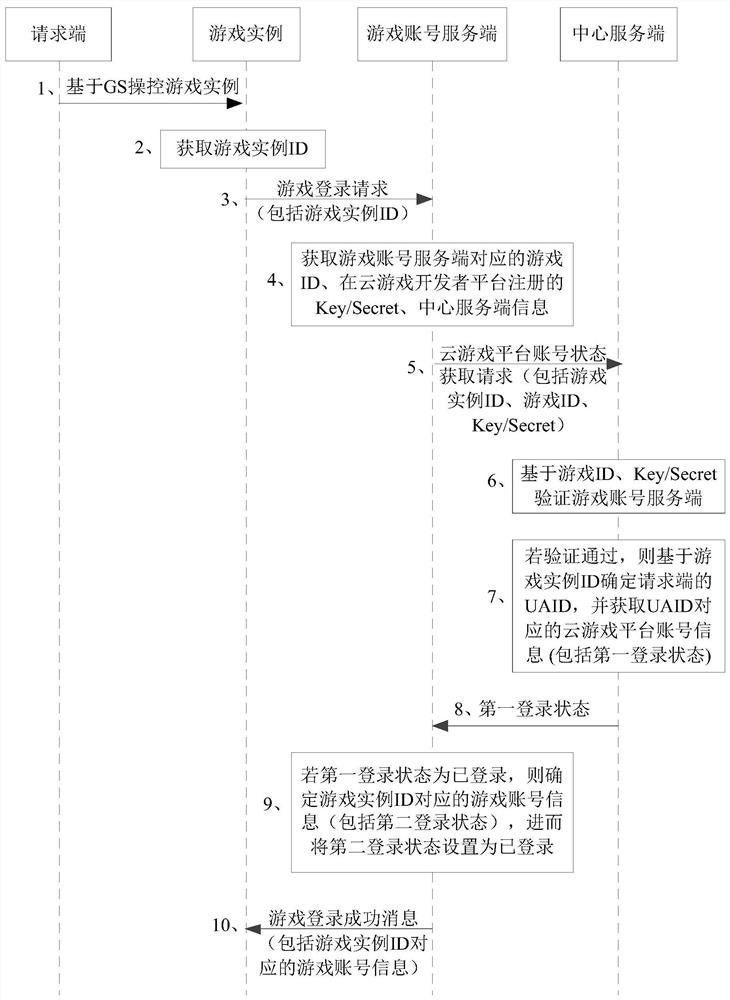
Game account login method and device, electronic equipment and storage medium
PendingCN113332710ASolve the problem of multiple tedious loginsSolve the problem of multiple cumbersome loginsVideo gamesEngineeringHuman–computer interaction
The embodiment of the invention discloses a game account login method and device, electronic equipment and a storage medium. In at least one embodiment of the application, a game account server receives a game login request to obtain a game instance identifier included in the game login request; further, a cloud game platform account number state obtaining request is sent to a central server side, and the request comprises the game instance identifier; and therefore, the game account server side receives the first login state of the cloud game platform account sent by the center server side, and sets the second login state of the game account corresponding to the game instance identifier as the logged-in state based on the first login state as the logged-in state. Therefore, when the user selects one game for playing, the game account server side can complete the login of the game account of the selected game on the basis of the account of the cloud game platform logged in by the user. Therefore, the user can directly use the cloud game as long as logging in the cloud game platform account once, and the problem that the user needs to log in the cloud game repeatedly and tediously when using the cloud game is solved.
Owner:XIAMEN YAJI SOFTWARE
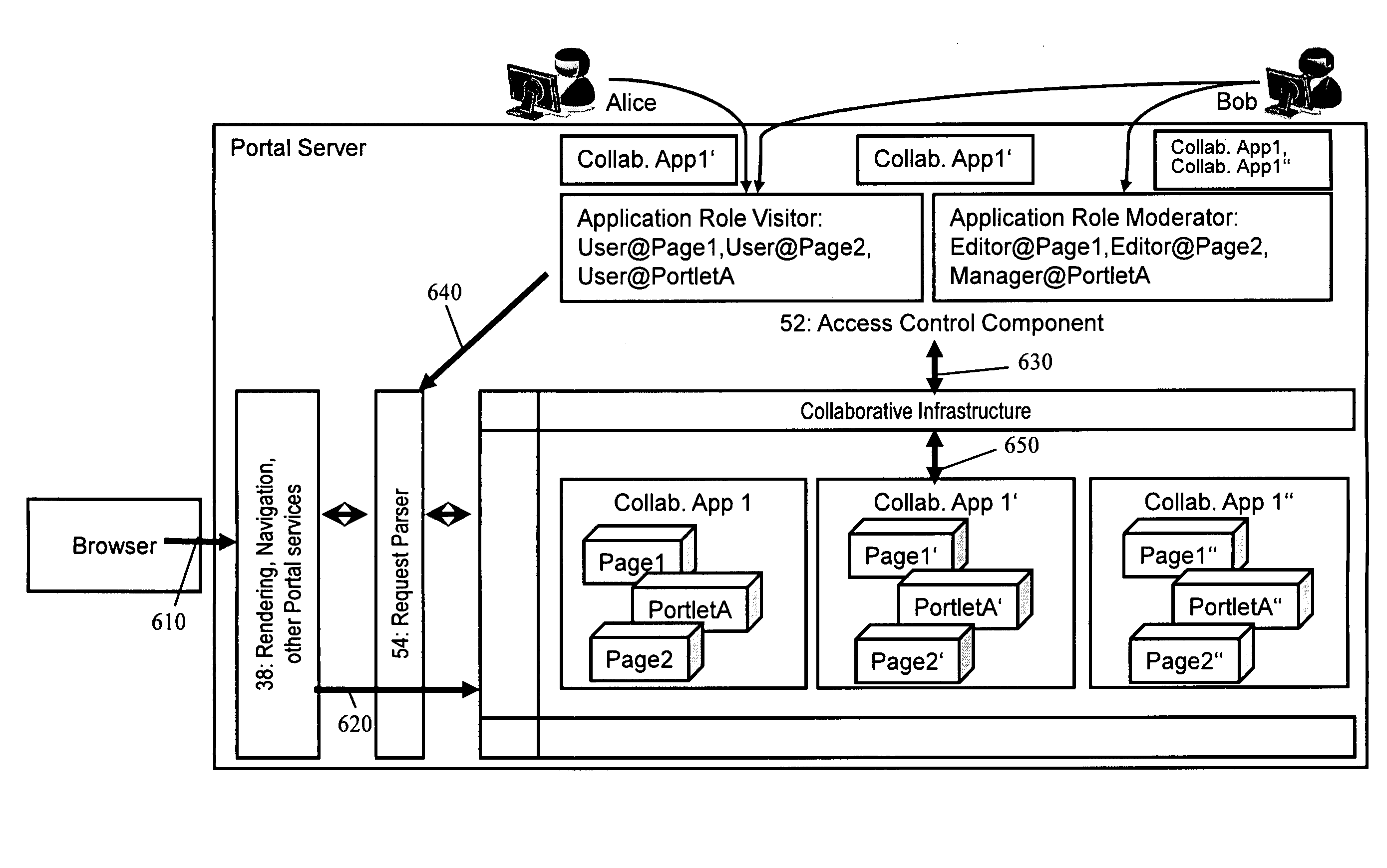
Access control on dynamically instantiated portal applications
InactiveUS8316420B2Improve abilitiesDigital data processing detailsComputer security arrangementsDatabaseResource use
The present invention relates to a method and system for controlling access rights to dynamically instantiated portal applications in a portal environment, wherein new instances of a portal application and respective access control information on resources used in the application are generated dynamically from an automated programmed mechanism, and wherein a user-application role mapping is demanded for the portal application by a respective runtime access control function implemented at the portal environment. The method includes: assigning an individual user-to-application role mapping to a respective individual one of the created instances of the portal application, wherein for each incoming user request to one of the created instances the runtime access control function checks a target application instance identifier, which identifies an individual application instance desired to be addressed by the incoming request; and granting access rights to incoming user requests according to the application roles as they are defined for the target application instance.
Owner:IBM CORP
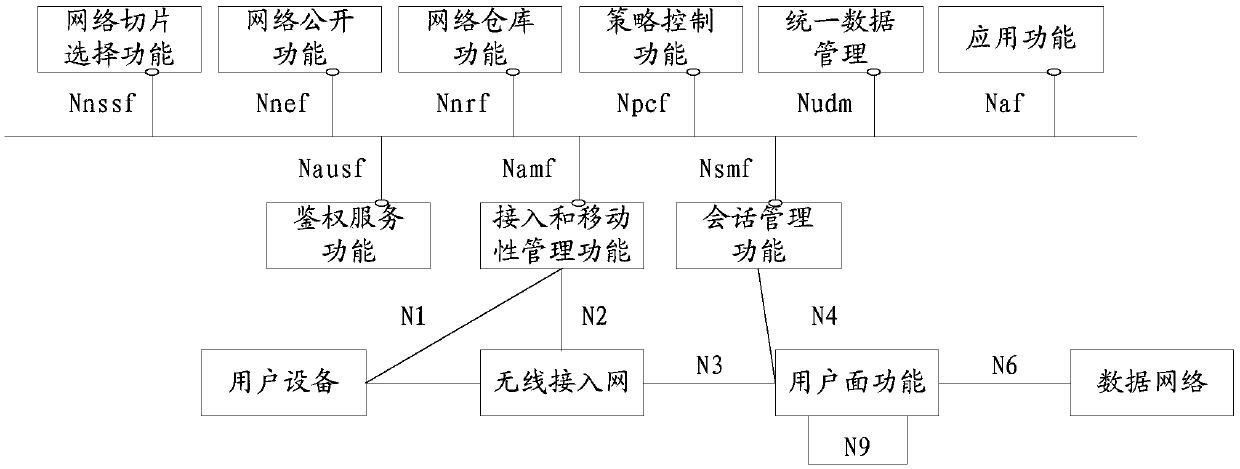
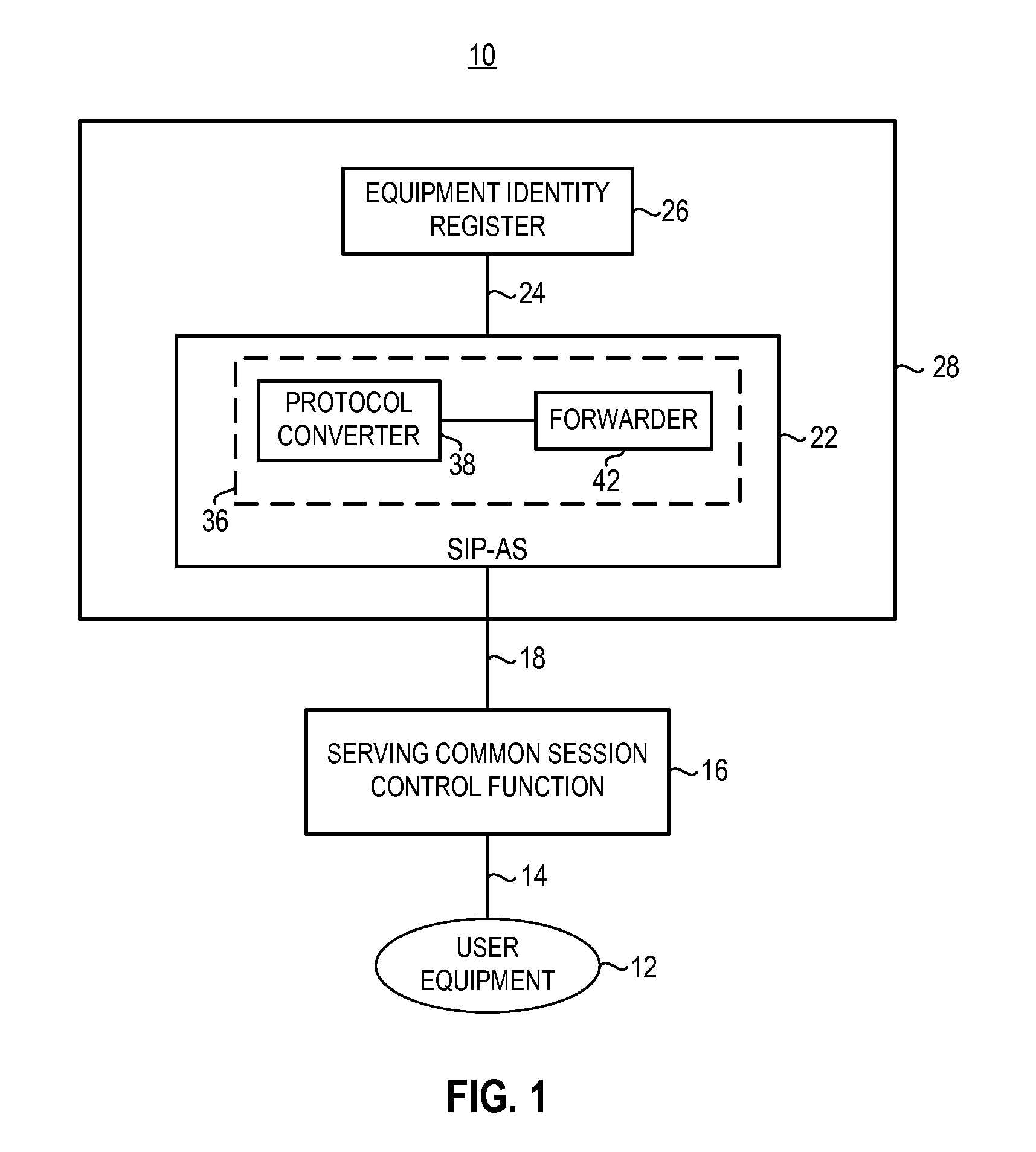
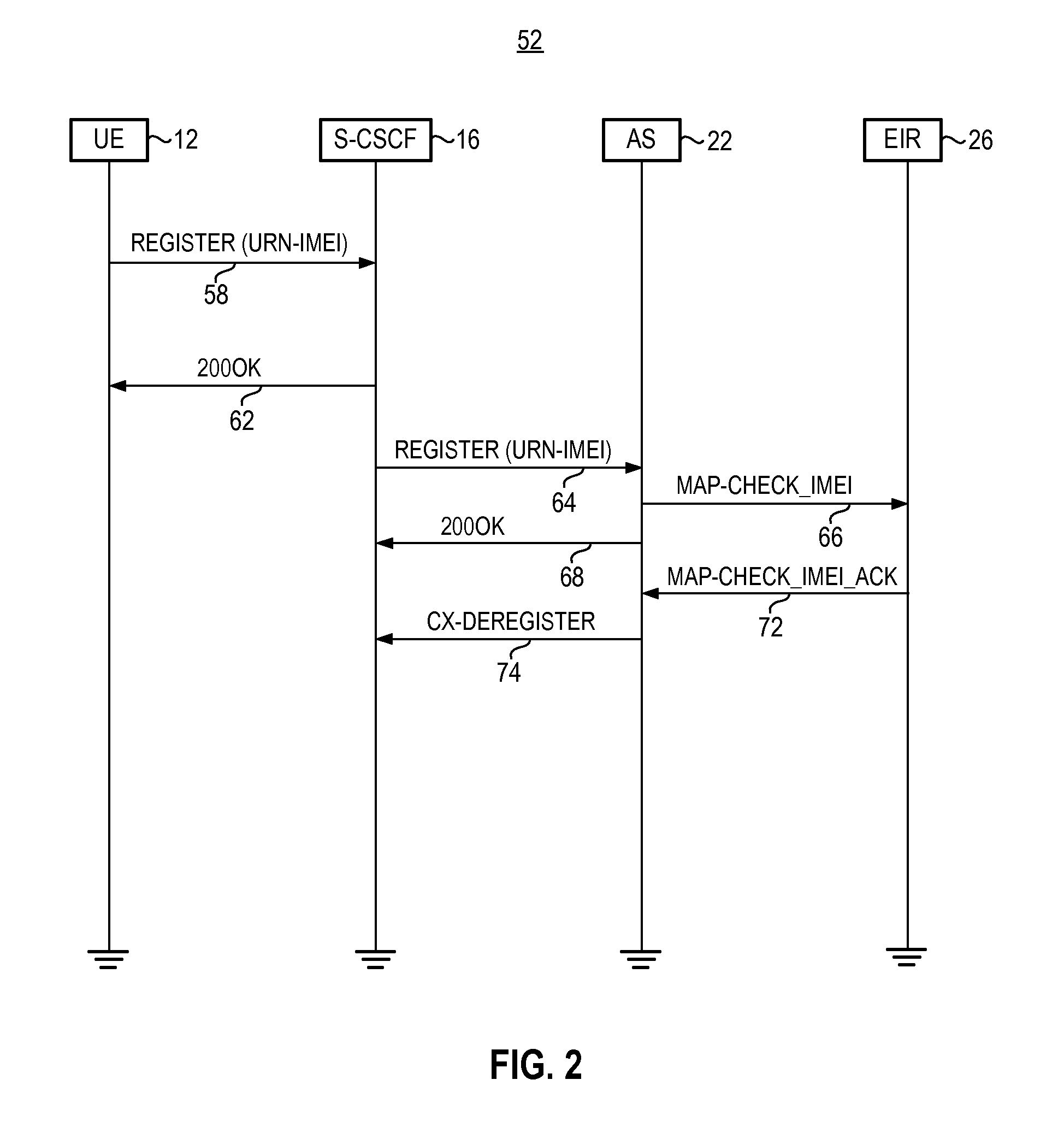
Apparatus, and associated method, for providing an instance identifier to a network database node of a mobile network
ActiveUS8412192B2Easy accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice registerApplication server
Apparatus, and an associated method, for an IMS (IP multimedia subsystem) mobile network to transfer an IMEI or IMEISV to an equipment ID register. A SIP, or other IP-based, message including the IMEI or IMEISV of a user equipment is converted by a protocol converter embodied at an application server into a MAP or DIAMETER message. A forwarder forwards on the MAP or DIAMETER message to EIR.
Owner:MALIKIE INNOVATIONS LTD
Method and system for improving alarm quality
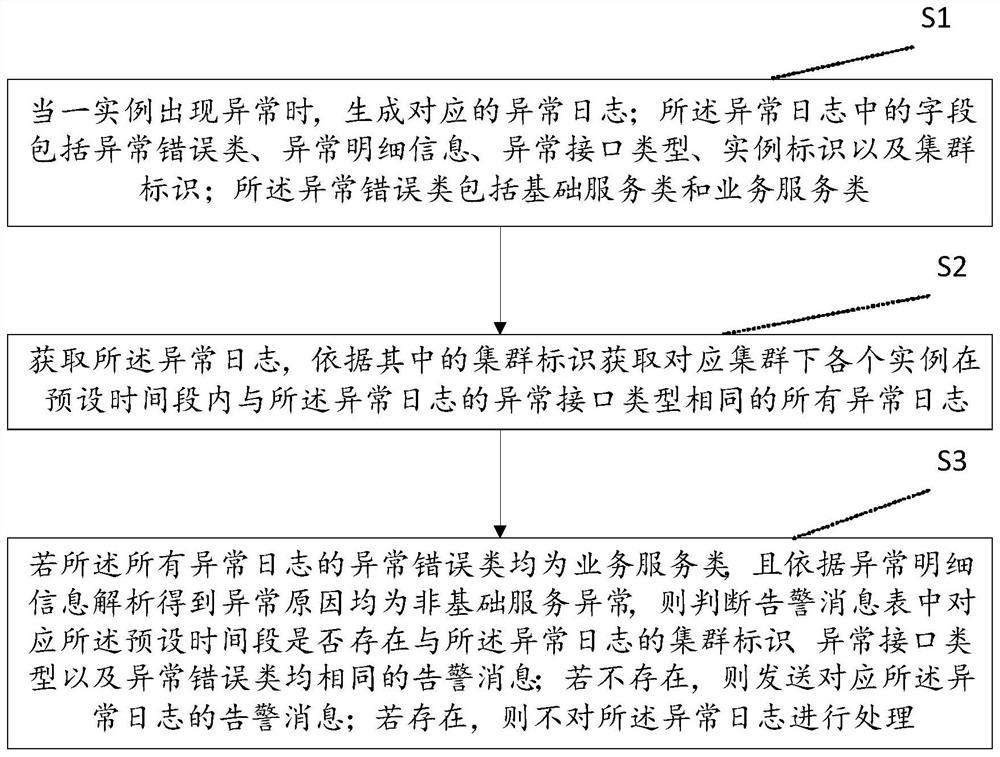
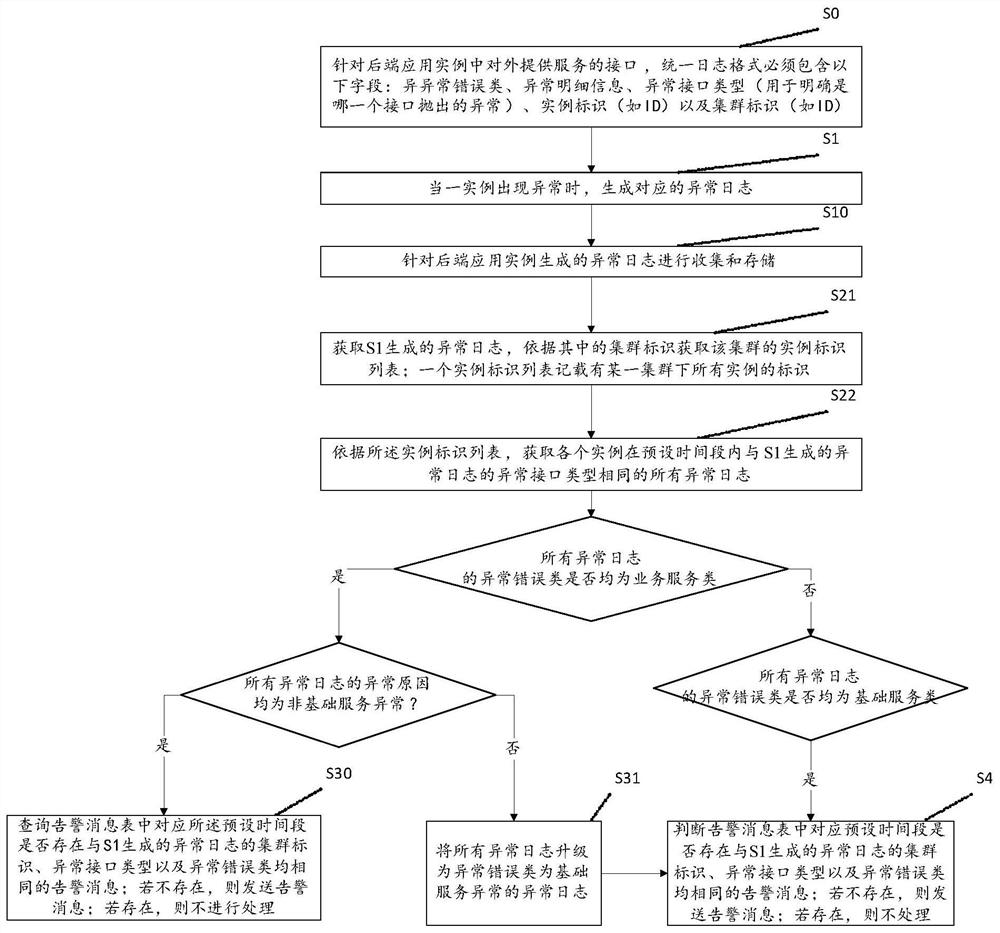
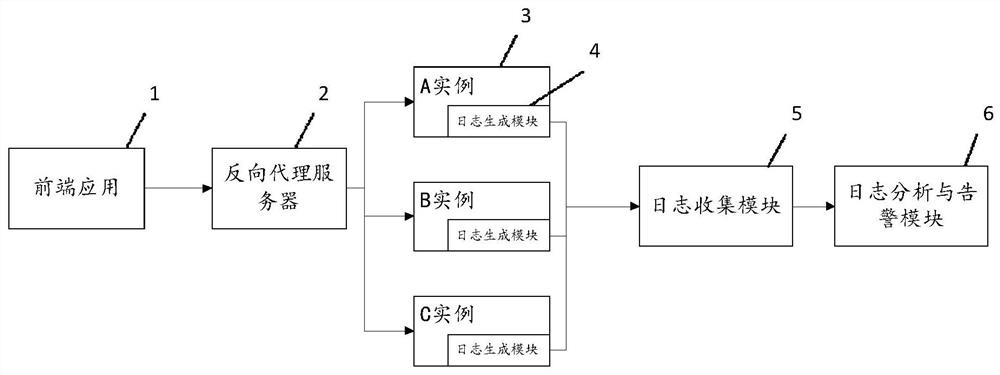
ActiveCN112104480AImprove targetingQuality improvementData switching networksAlarm messageBasic service
The invention discloses a method and system for improving alarm quality, and the method comprises the steps: S1, generating a corresponding abnormal log when an instance is abnormal, wherein the exception log comprises an exception error class, exception detail information, an exception interface type, an instance identifier and a cluster identifier; the abnormal error class comprises a basic service class and a business service class; S2, acquiring an abnormal log, and acquiring all abnormal logs of which each instance under the corresponding cluster has the same abnormal interface type as the abnormal log in a preset time period according to the cluster identifier; S3, if the abnormal error classes of all the abnormal logs are business service classes and the abnormal reasons are non-basic service abnormities, judging whether an alarm message which is the same as the cluster identifier, the abnormal interface type and the abnormal error classes exists in a corresponding preset time period in an alarm message table or not; if not, sending an alarm message; and if so, not processing. The number of alarm messages can be reduced, the alarm quality is improved, and the problem solvingefficiency is improved.
Owner:FUJIAN TIANQUAN EDUCATION TECH LTD
Creating and distributing template based service rules
Some embodiments of the invention introduce cloud template awareness in the service policy framework. Some embodiments provide one or more service rule processing engines that natively support (1) template-specific dynamic groups and template-specific rules, and (2) dynamic security tag concepts. A service rule processing engine of some embodiments natively supports template-specific dynamic groups and rules as it can directly process service rules that are defined in terms of dynamic component groups, template identifiers, template instance identifiers, and / or template match criteria. Examples of such services can include any kind of middlebox services, such as firewalls, load balancers, network address translators, intrusion detection systems, intrusion prevention systems, etc.
Owner:NICIRA
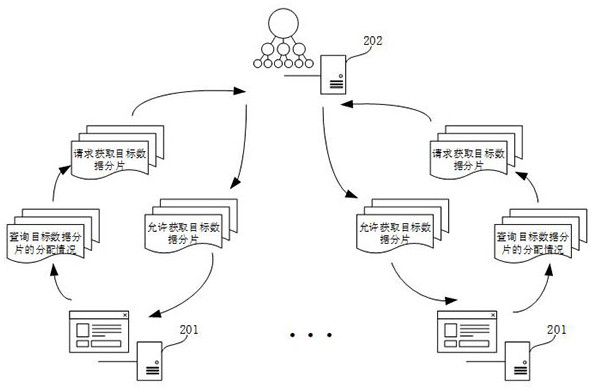
Data acquisition and distribution method and device, server and storage medium
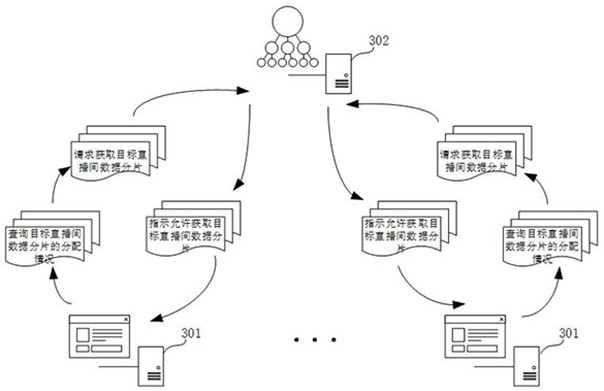
ActiveCN111930515AAvoid leakingRealize dynamic acquisitionResource allocationDistribution methodData acquisition
The invention relates to a data acquisition and distribution method and device, a server and a storage medium. The data acquisition method comprises the steps that a target instance node in a first server receives a target instance allocation record sent by a second server,wherein the target instance allocation record is used for recording instance identifiers corresponding to instance nodes for acquiring target data fragments; when the target instance allocation record meets an unallocated data judgment condition, a data allocation request is sent to a second server, wherein the data allocation request is used for requesting to obtain a target data fragment; a request result of the data allocation request fed back by the second server is received; and when the request result indicates that the target data fragment is allowed to be acquired, the target data fragment is acquired. By adopting the data acquisition and distribution method and device, the server and the storage medium provided by the invention, missing processing of the data can be avoided, and the reliability of data processing is improved.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
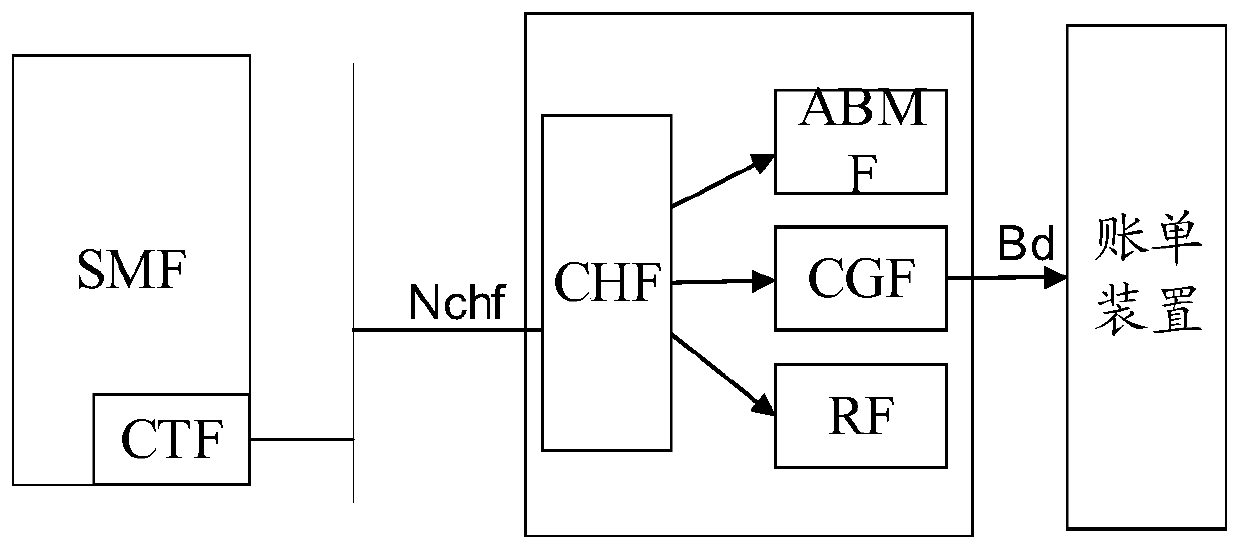
Charging method, device and system
ActiveCN111385754AMetering/charging/biilling arrangementsAccounting/billing servicesEngineeringUser charge
The embodiment of the invention discloses a charging method and a related product. The charging method comprises the following steps that according to an industry user identifier and a slice user identifier contained in a charging rule, a charging triggering CTF device determines that an industry user charging session exists between the CTF device and a charging function CHF device; when a charging triggering condition is satisfied, a charging request is sent to the CHF device through an industry user charging session existing between the CTF device and the CHF device according to the chargingrule, and the charging request carries the industry user identifier, the slice network instance identifier and charging data. By multiplexing existing industry user charging sessions, online sessionsof a CHF device and a CTF device can be reduced, and the resource utilization rate is increased.
Owner:HUAWEI TECH CO LTD
Service authorization method and communication device
The embodiment of the invention discloses a service authorization method and a communication device, which can solve the problem that a first server does not obtain service authorization when accessing a second server in a scene that the second server is found by a client, so as to reduce the security risk of a service network. The method comprises the following steps that: a client side applies for an access token of a first server to access a second server, and notifies the first server; or, the first server automatically applies for the access token according to the instance identifier or the resource identifier of the second server provided by the client.
Owner:HUAWEI TECH CO LTD
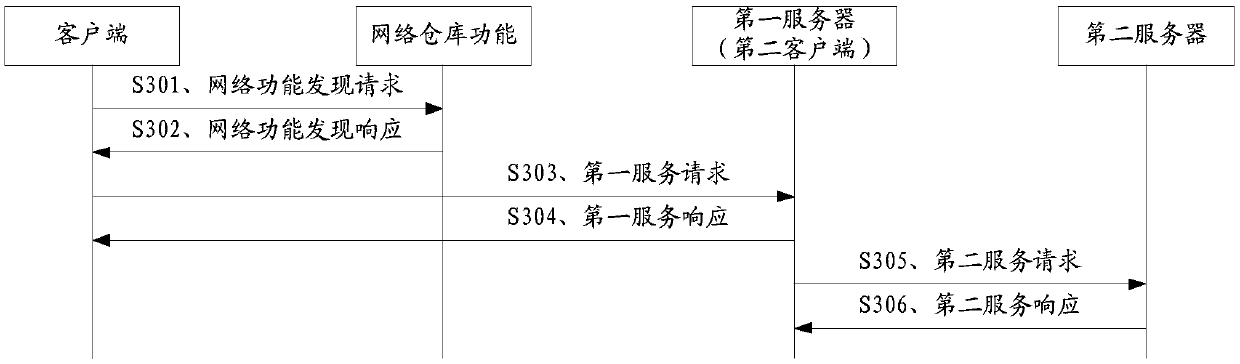
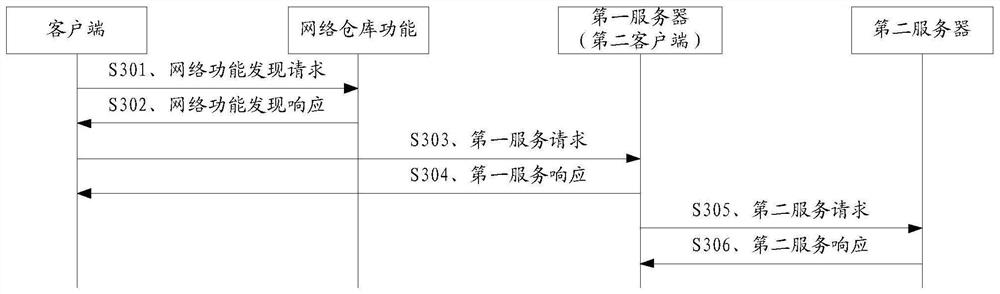
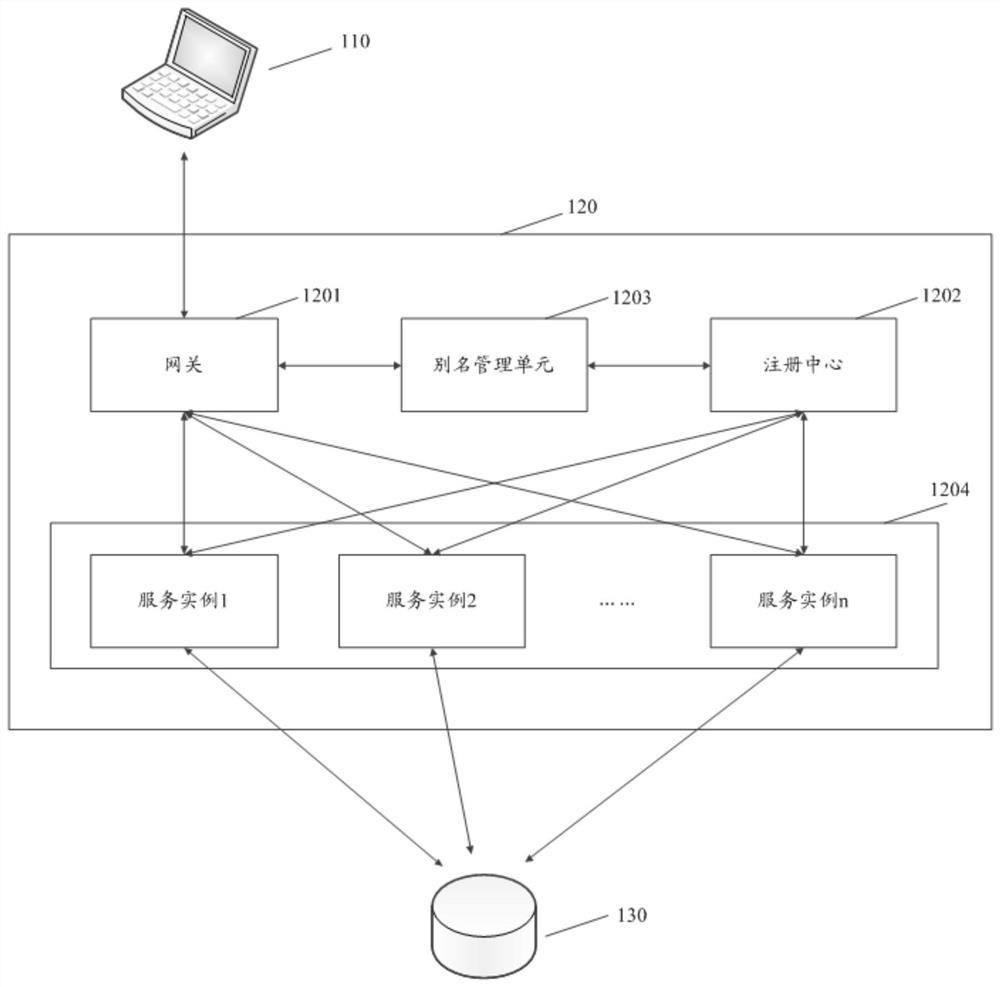
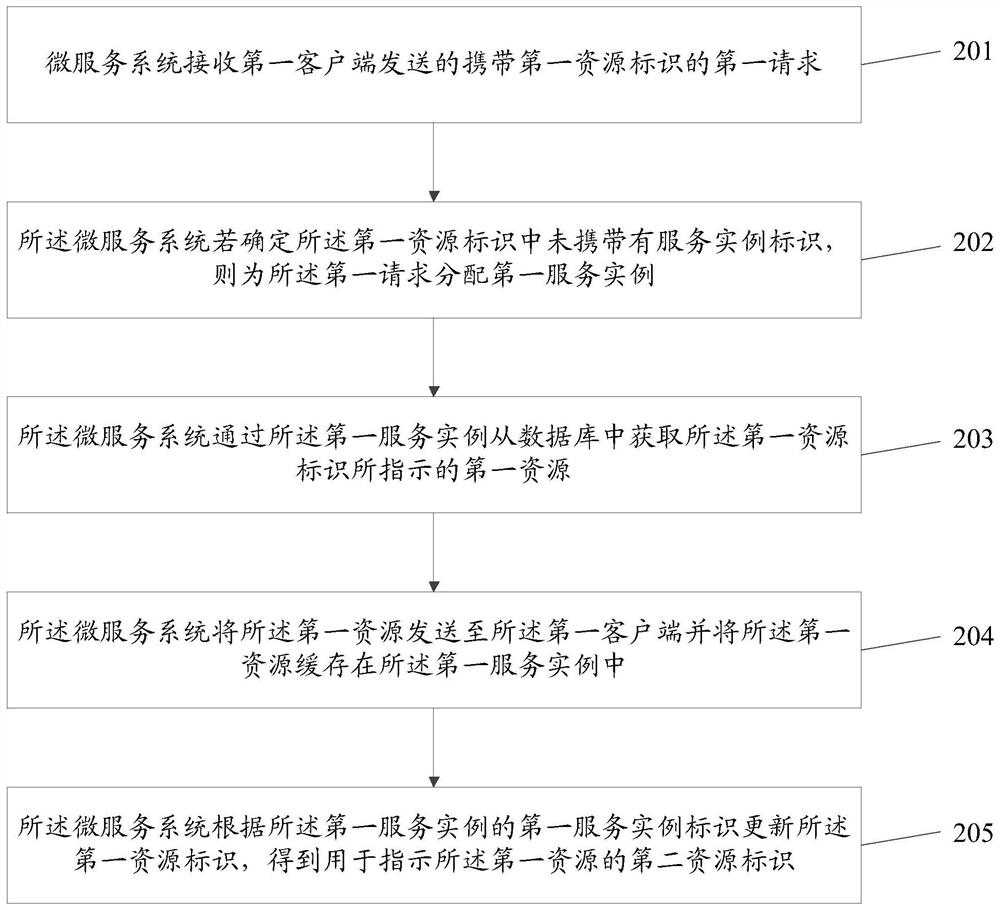
Request processing method and micro-service system
The invention relates to the field of Fintech, and discloses a request processing method and a micro-service system, the method comprises the steps: by the micro-service system, receiving a first request carrying a first resource identifier sent by a first client; if it is determined that the first resource identifier does not carry the service instance identifier, allocating a first service instance to the first request; obtaining a first resource indicated by the first resource identifier from a database through the first service instance; sending the first resource to the first client and caching the first resource in the first service instance; and updating the first resource identifier according to the first service instance identifier of the first service instance to obtain a secondresource identifier for indicating the first resource. According to the method, the micro-service system determines the service instance for the request of a certain resource, and the service instancecaches the resource after acquiring the resource from the database, so that the service instance can directly respond to the request when the subsequent request about the resource arrives at the micro-service system again.
Owner:WEBANK (CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com