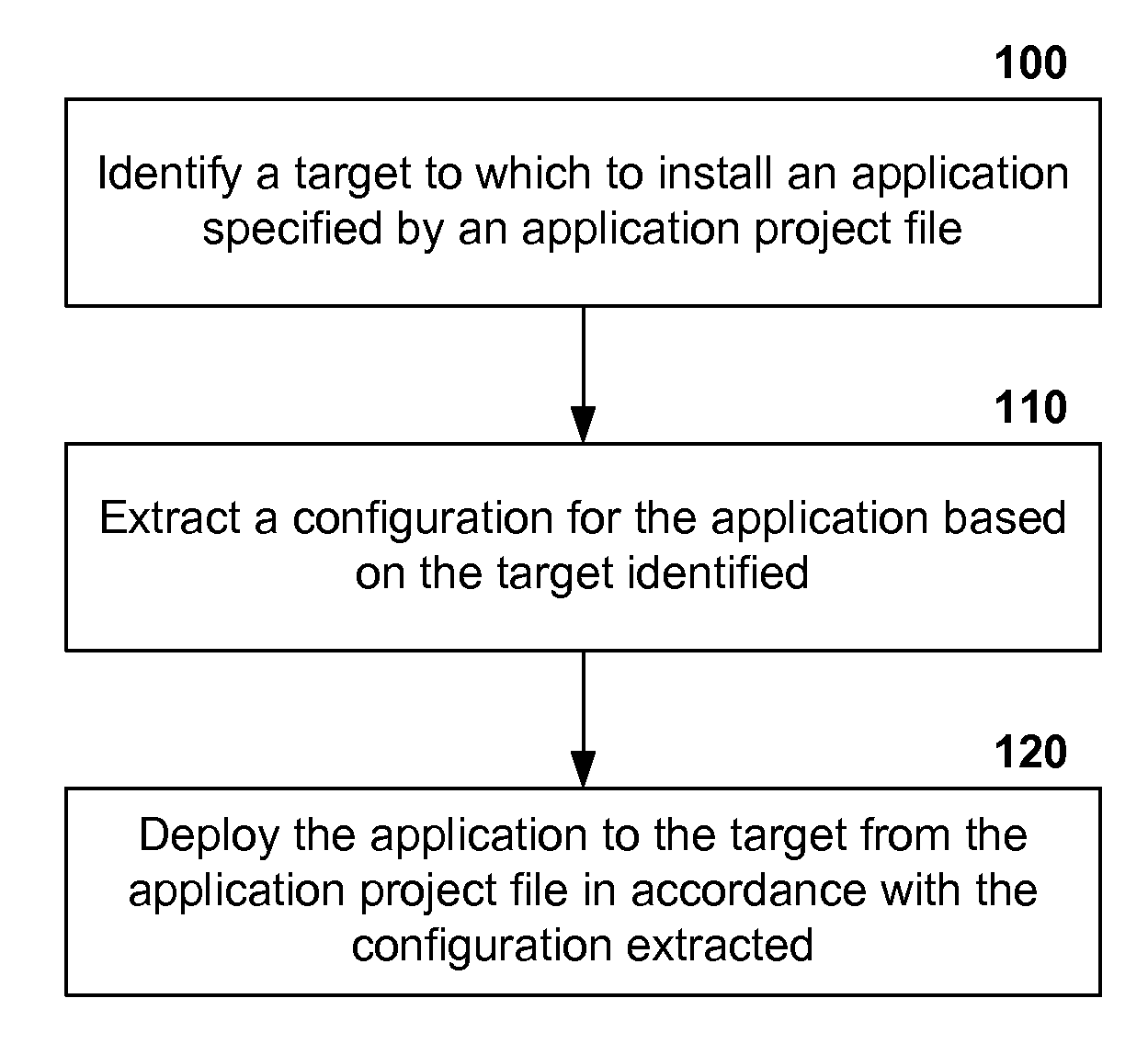
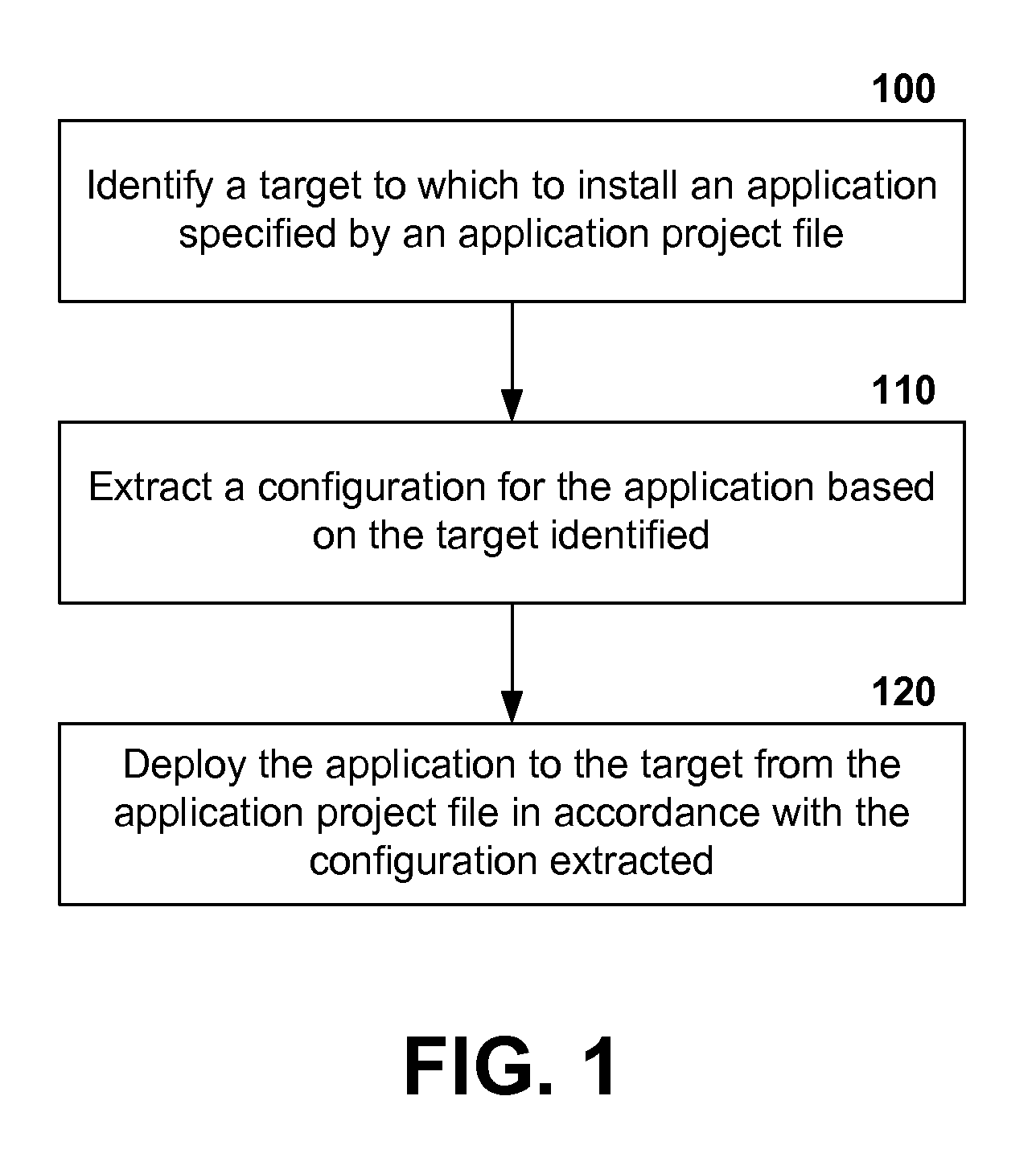
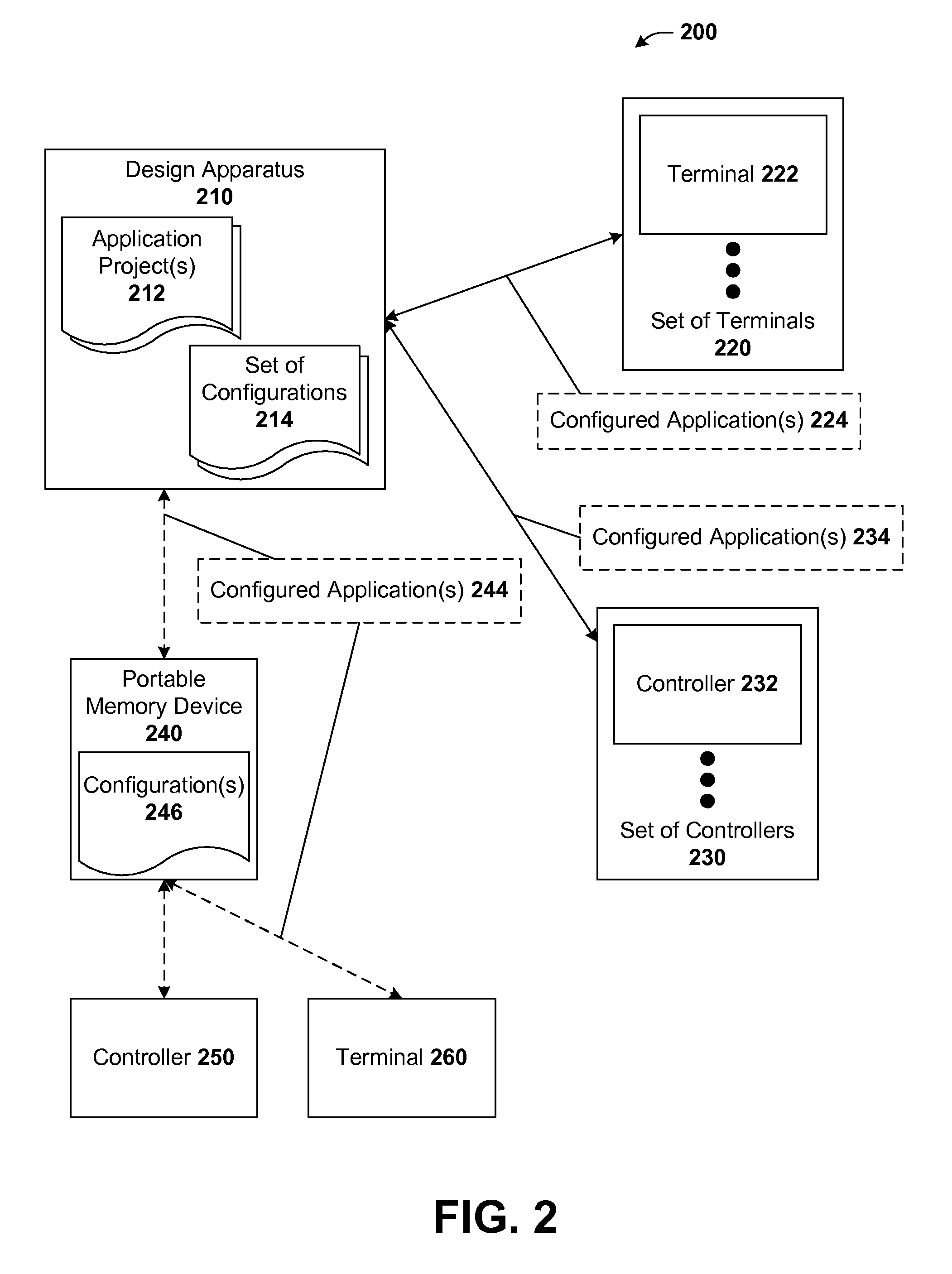
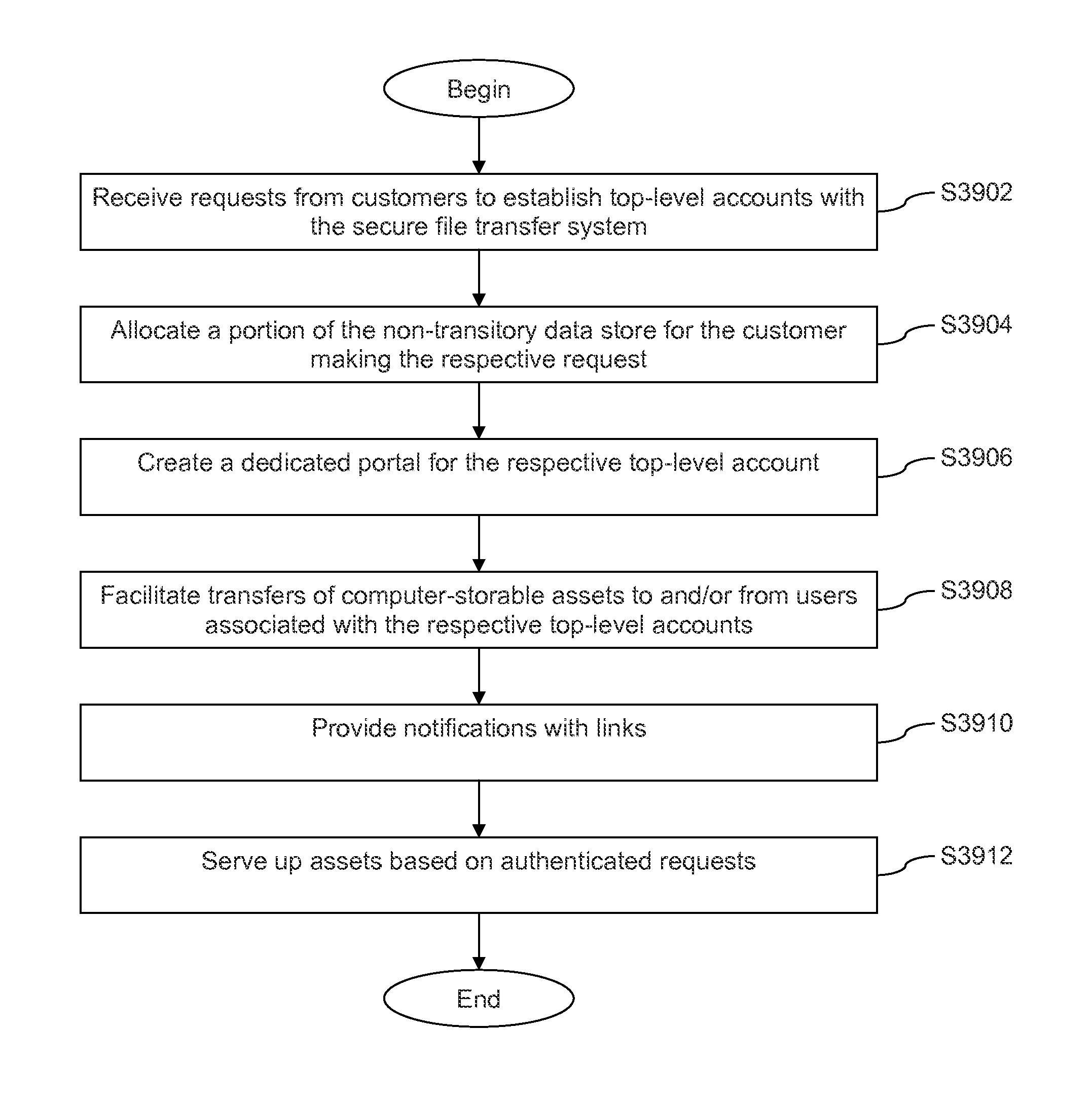
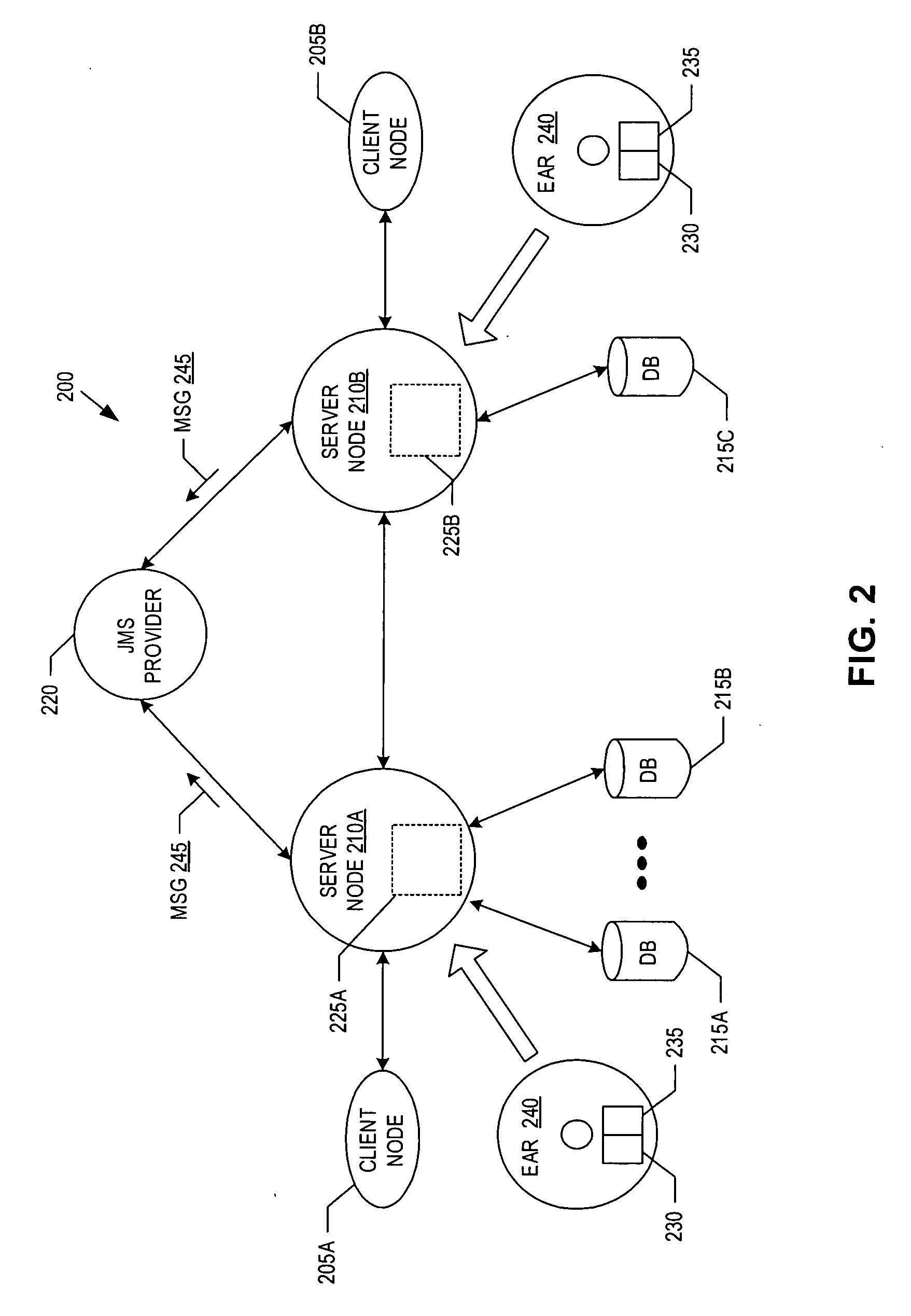
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
242 results about "Deployment time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
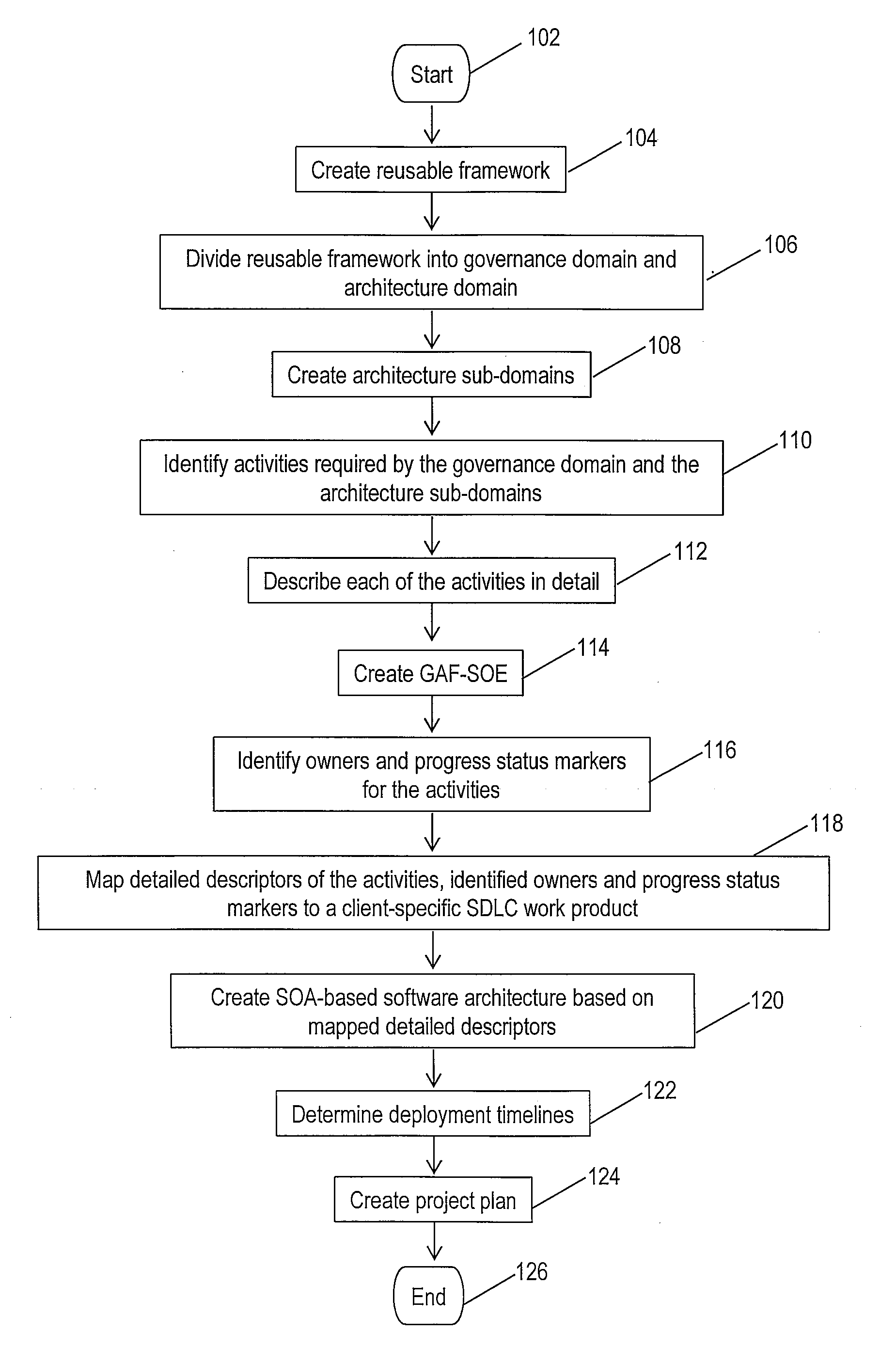
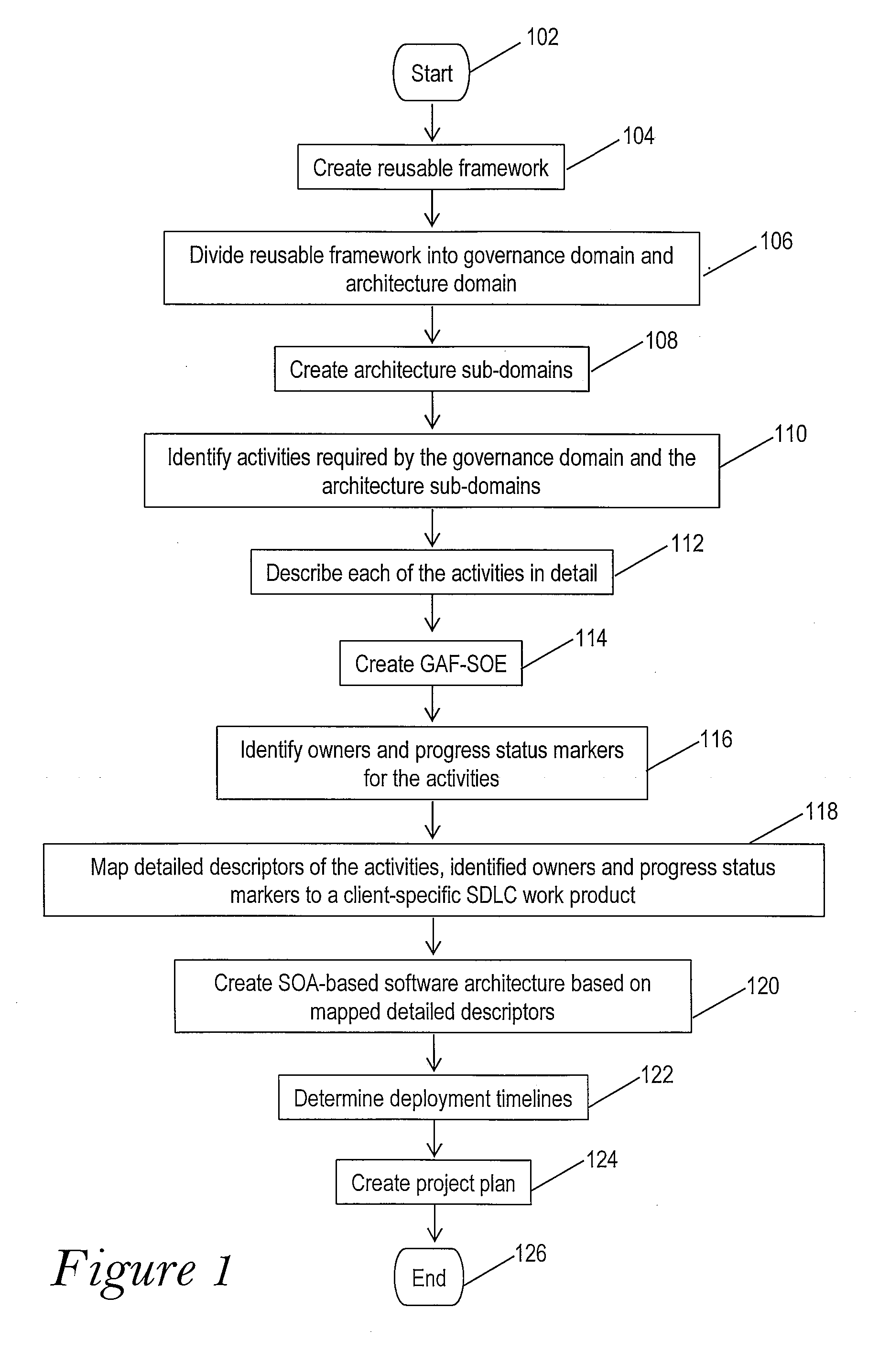
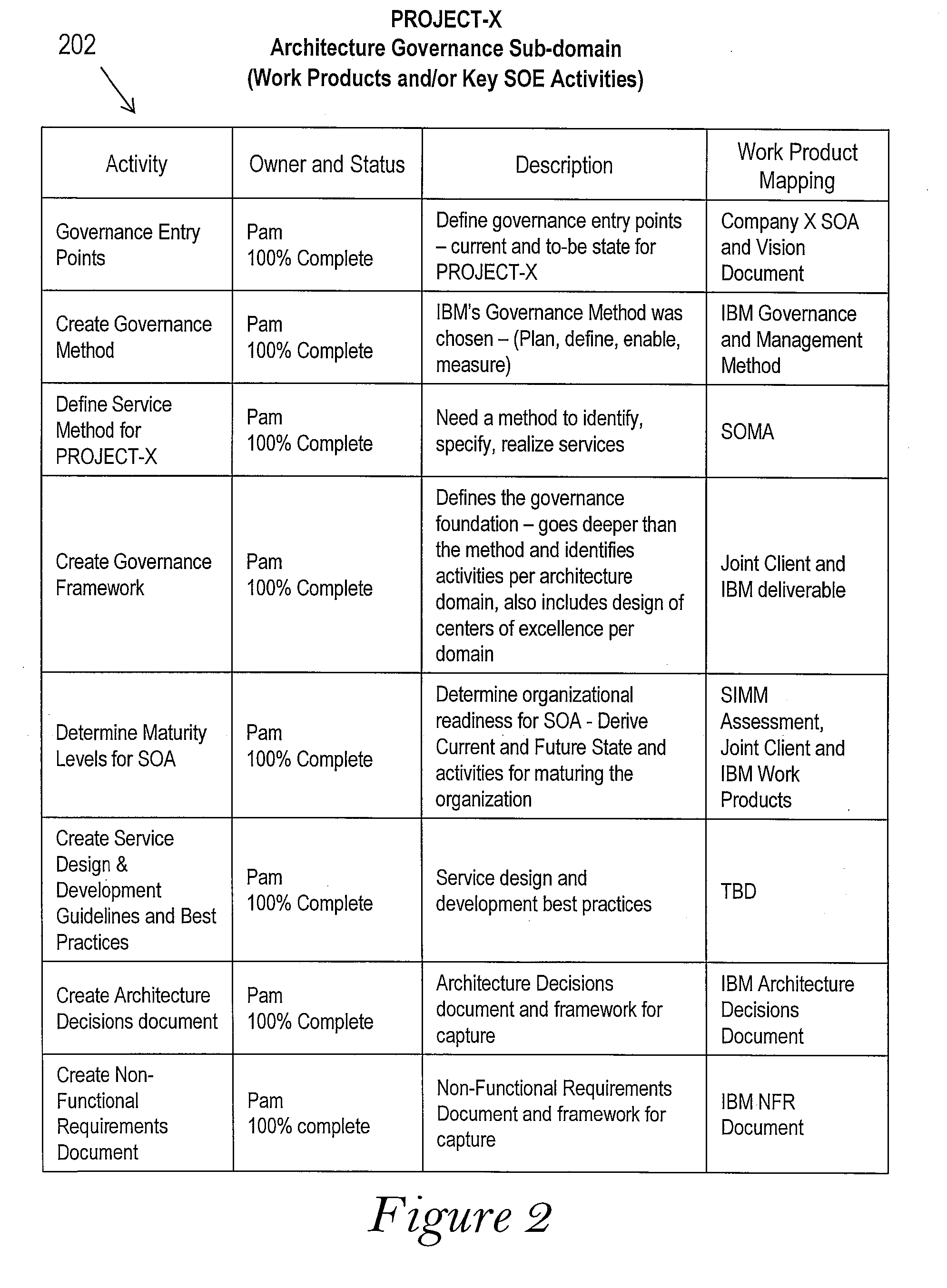
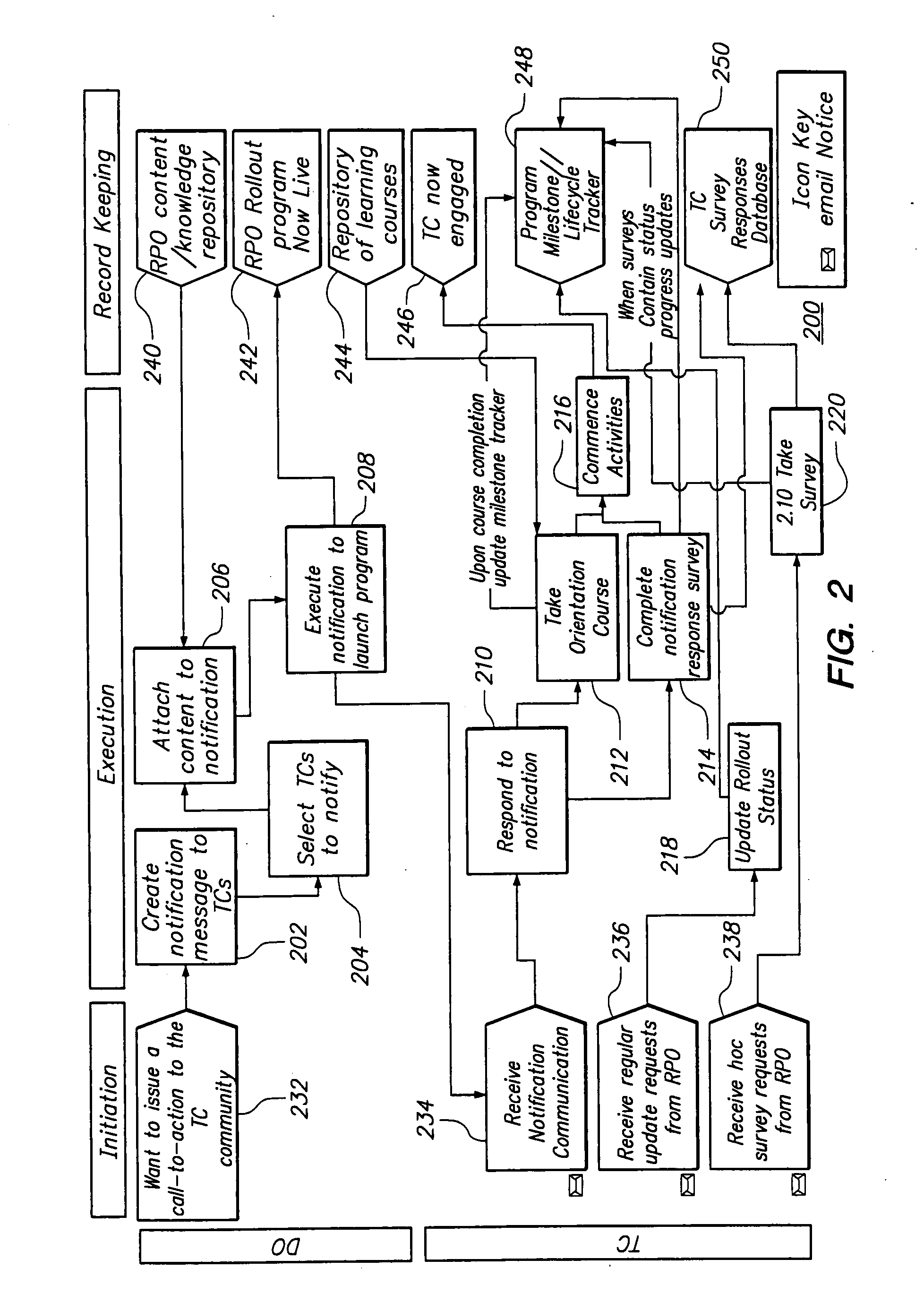
Governance Framework for Architecture Design in a Service Oriented Enterprise
InactiveUS20090064087A1Requirement analysisSpecific program execution arrangementsDeployment timeSoftware engineering
A reusable framework is utilized for creating a software architecture in a Service Oriented Architecture (SOA). After a general framework is created, that general framework is divided into a governance domain and an architecture domain. The architecture domain is further divided into architecture sub-domains within the architecture domain. Activities that are required for the governance domain and each of the architecture sub-domains and identified and described in detail, and owners and progress status markers for these activities are identified. The detailed descriptors of the activities, identified owners and progress status markers are then mapped onto a client-specific System Development Life Cycle (SDLC) work product to create an SOA-based software architecture. Deployment timelines for the governance domain and the architecture domain are determined, and a project plan for deploying the SOA-based software architecture is created.
Owner:IBM CORP
Method for rapid deployment of openstack cloud computing platform
InactiveCN104580519ARapid deploymentEmbody convenienceProgram loading/initiatingTransmissionDeployment timeCloud computing
The invention relates to a method for rapid deployment of an openstack cloud computing platform. A task of rapid deployment is completed by copying various system image files to network storage clusters through preset scripts according to custom identification rules. A made image template is duplicated according to made rules to generate other similar node images to complete a fast deployment process, an initial deployment management server can adopt various physical servers to carry out large-scale deployment tasks, and after construction of a cloud environment succeeds, a virtual machine can directly serve as a deployment management server to meet the requirement on flexible services so as to provide flexible services to subsequent cluster node deployment. The method is applicable to automatic deployment of various similar cloud platforms, deployment on each node server is not needed by adoption of the centralized deployment scheme, and accordingly deployment time is greatly shortened, simplicity and feasibility are achieved, and deployment efficiency and management flexibility are improved.
Owner:FUQING BRANCH OF FUJIAN NORMAL UNIV
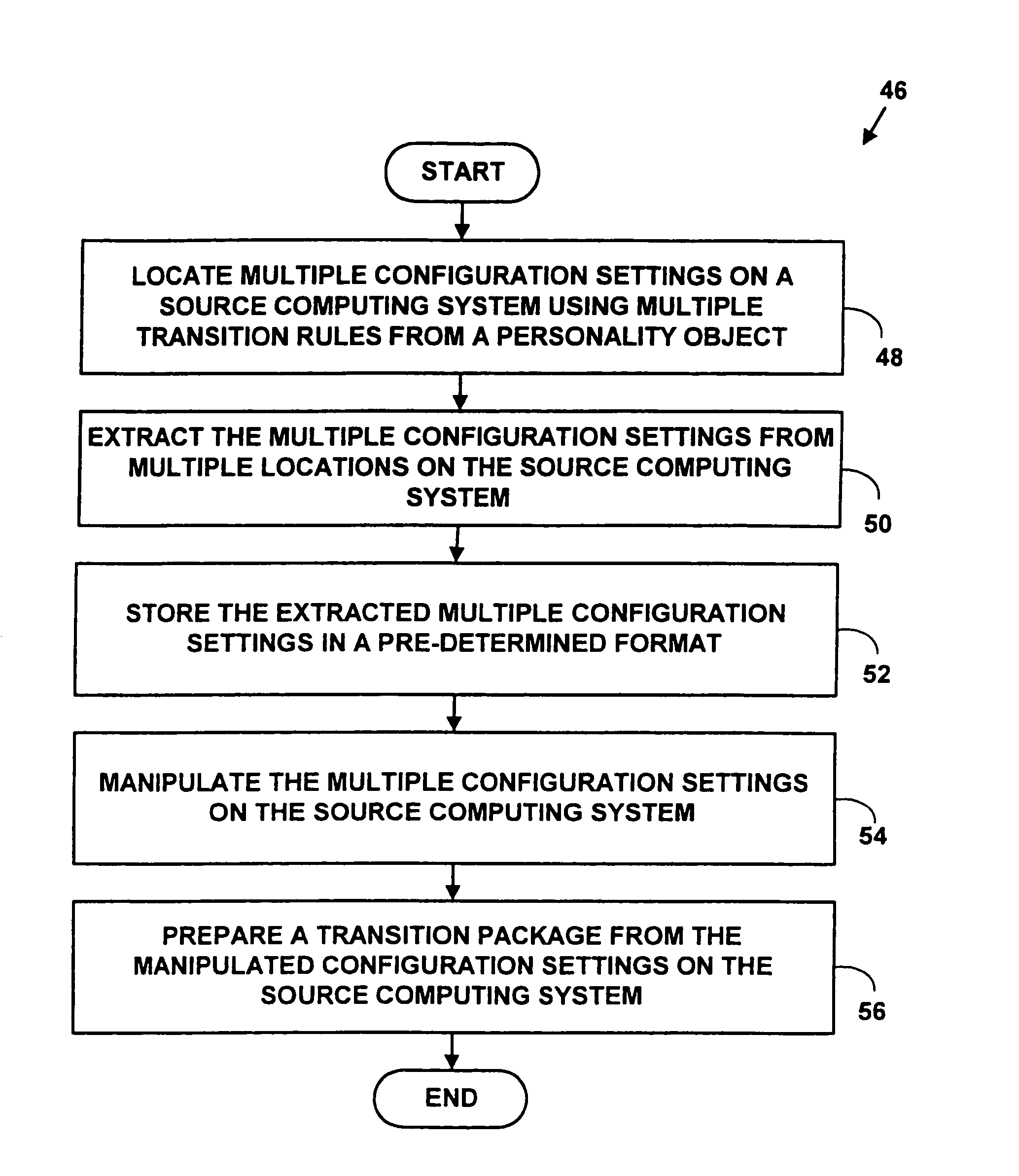
Method and system for automatically transitioning of configuration settings among computer systems
InactiveUS7346766B2Save resourcesShorten the timeDatabase updatingSoftware engineeringDeployment timeData file
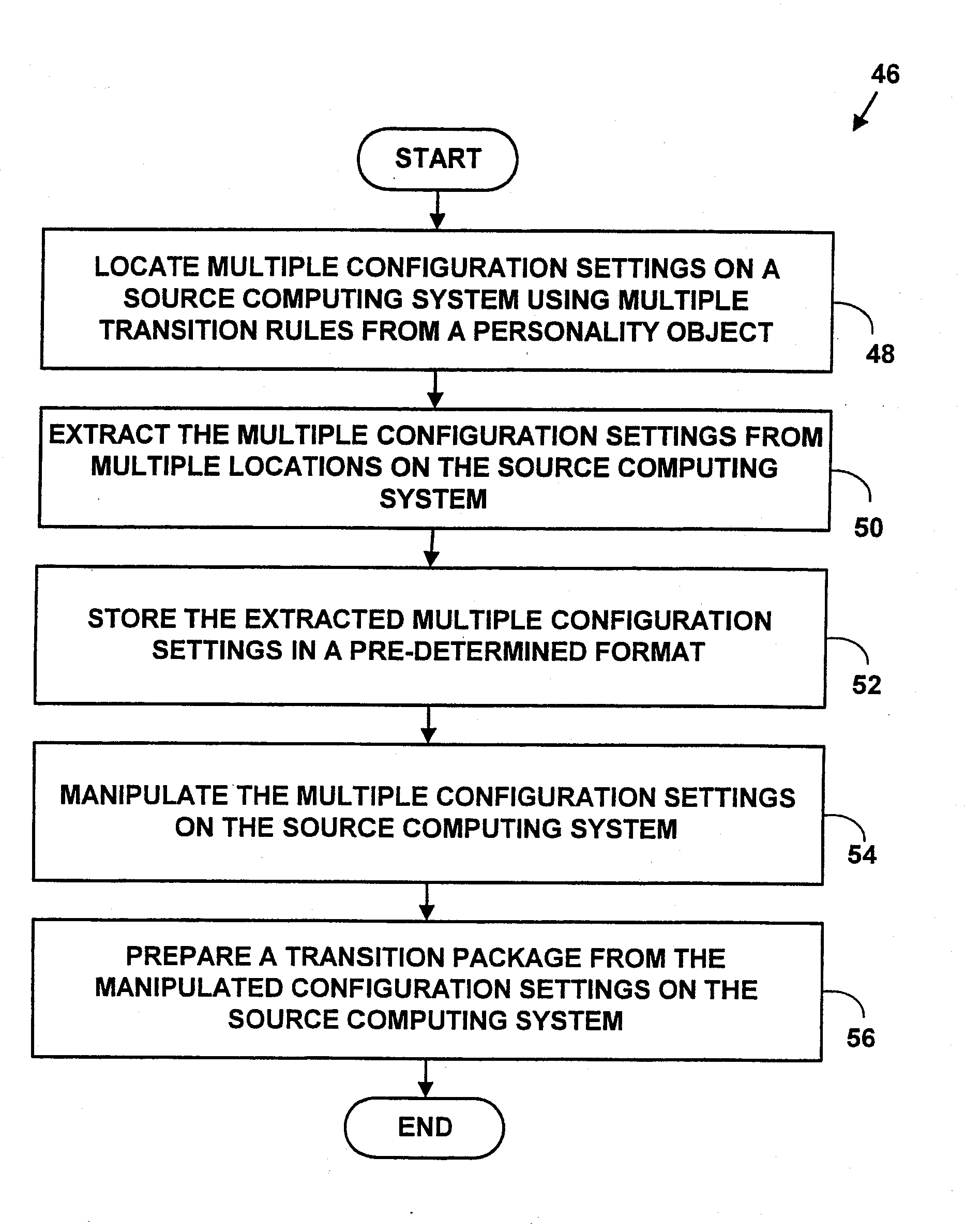
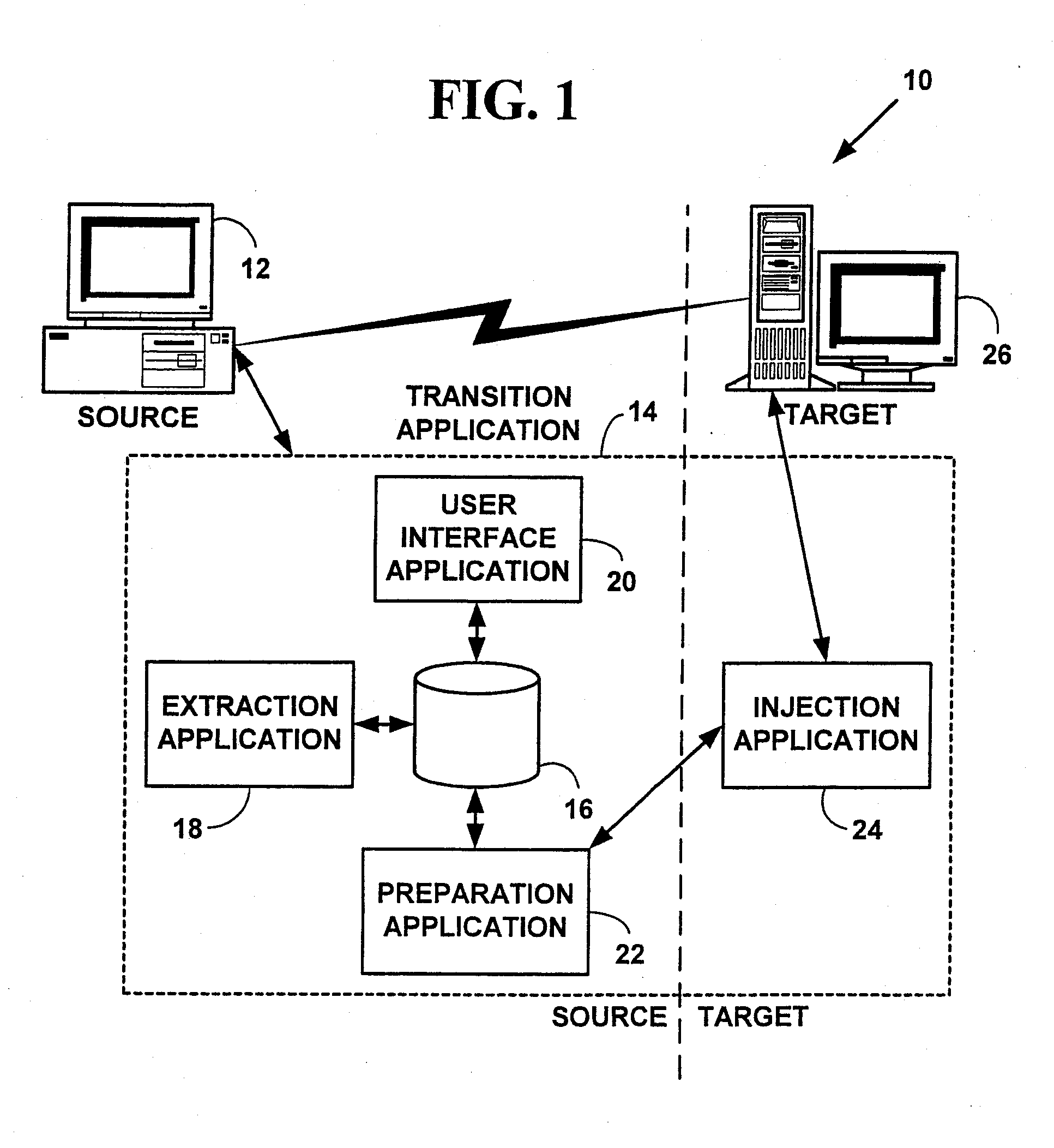
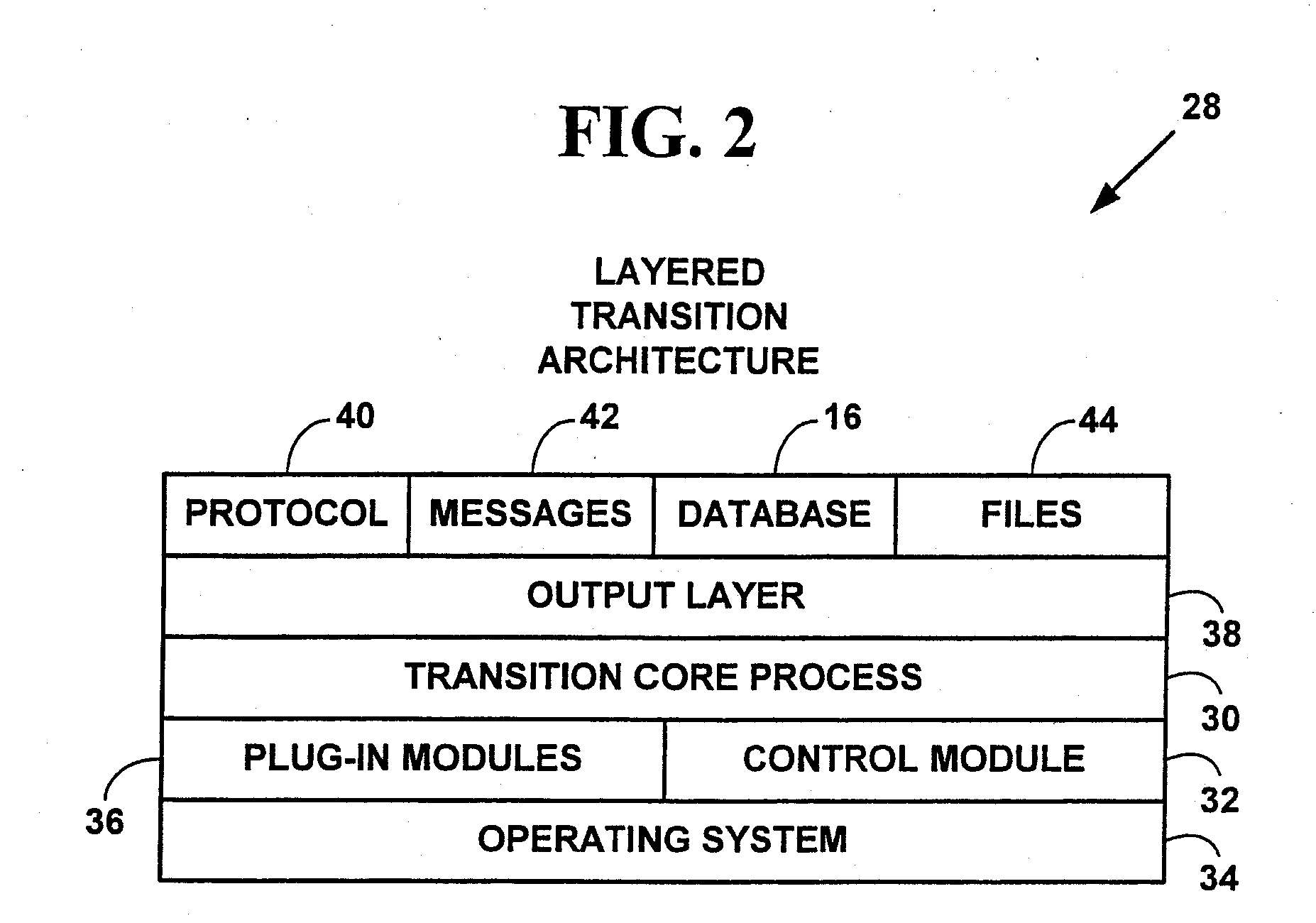
A method and system for automatically transitioning configuration settings among computer systems. Multiple configuration settings comprising a computer “personality” are located on a source computing system using multiple transition rules from a personality object. The computer personality includes customization choices, data files, electronic mail, system preferences, application customization choices, the network environment, browser information, etc. The configuration settings are extracted from multiple locations on the source computing system. The multiple extracted configuration settings are stored in a pre-determined transition format. The multiple extracted configuration settings are manipulated. A transition package is created from the multiple manipulated configuration settings. The transition package includes the multiple manipulated configuration settings. The transition package is sent to a target computing system. The transition package is infused on the target computing system to automatically transition configuration settings from the source computing system to the target computing system. The method and system may vastly reduce transition, configuration and deployment times for service providers, corporations, and end-users when a new computing system is deployed.
Owner:TRANXITION CORP
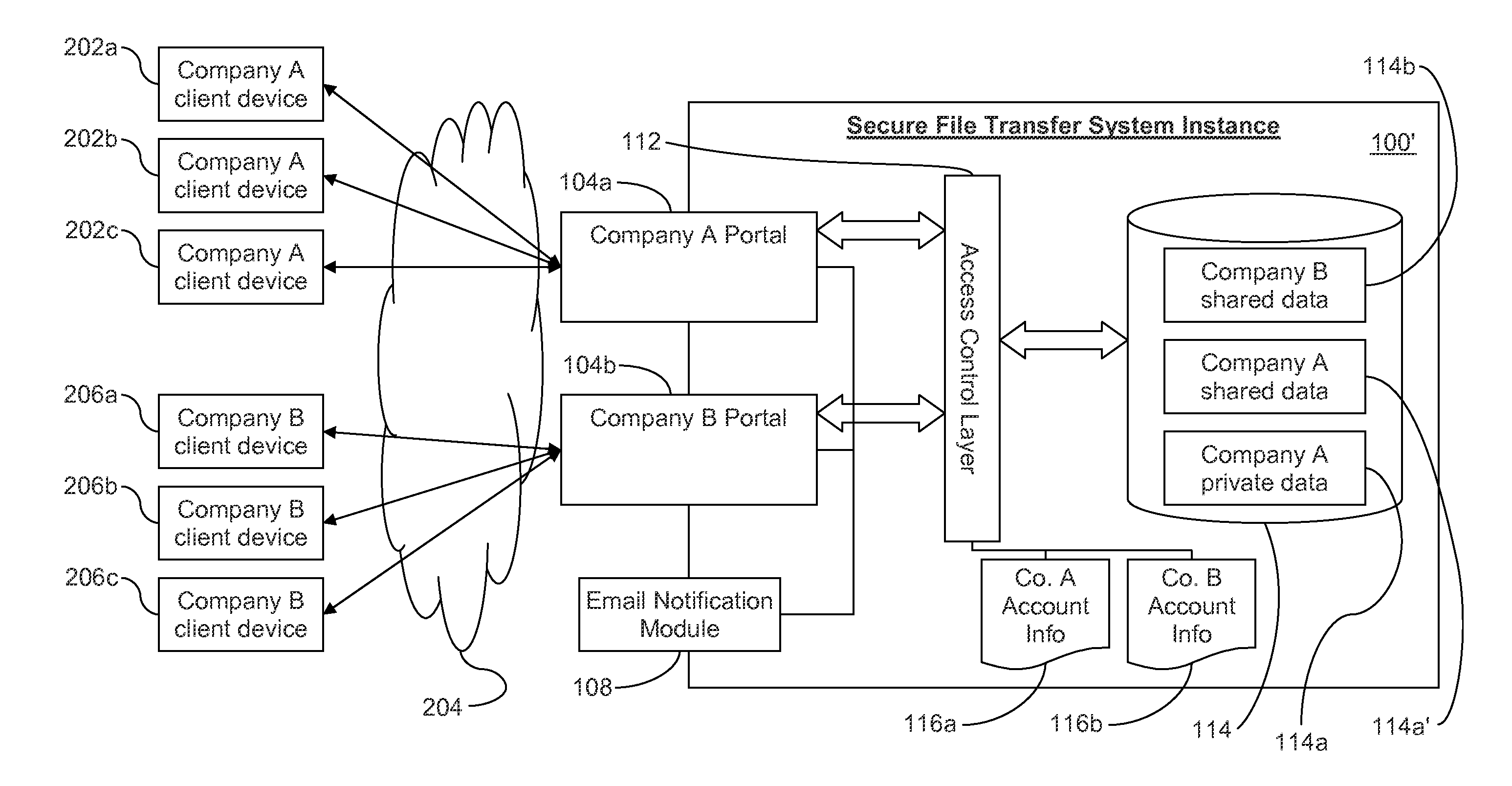
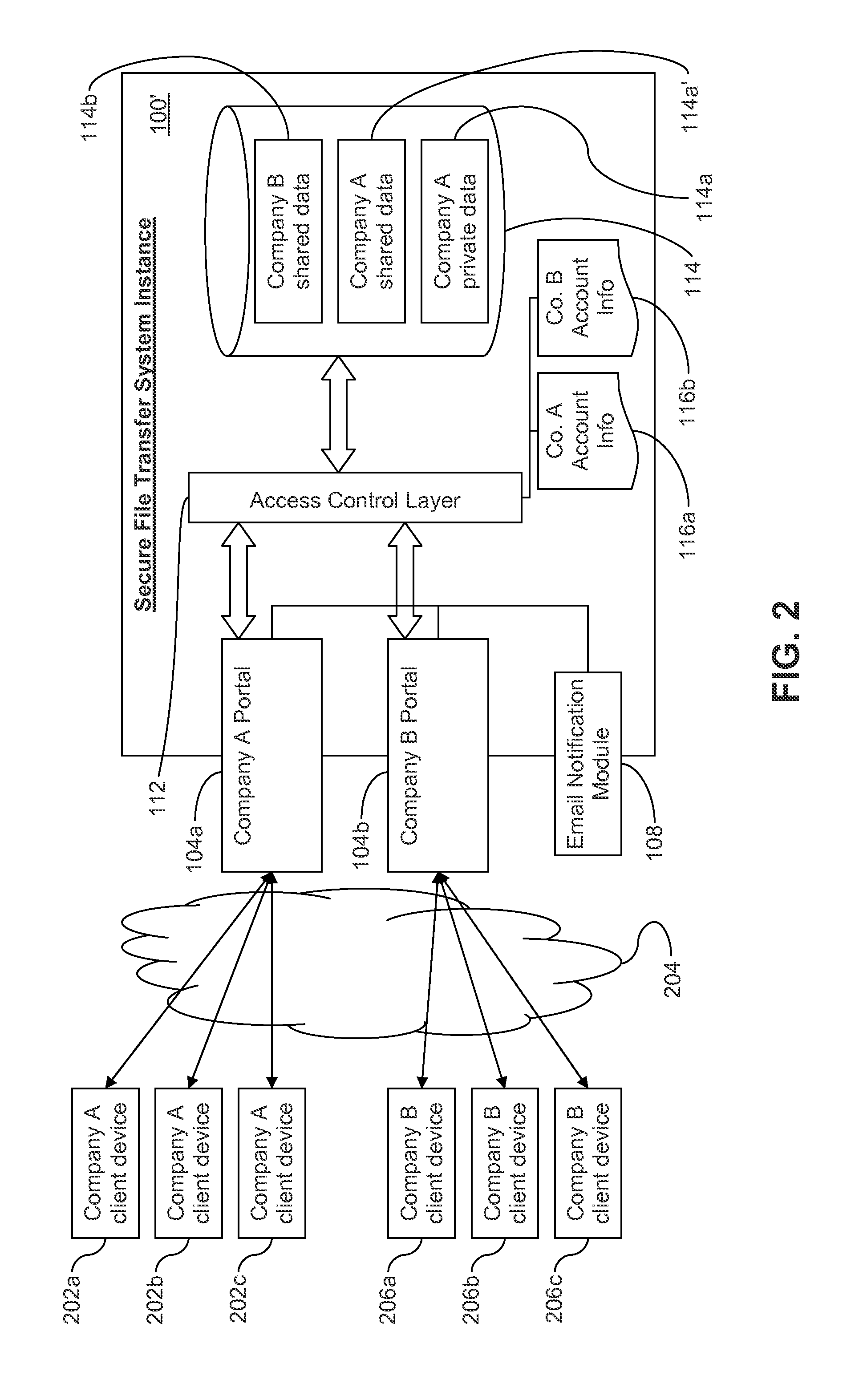
Secure file transfer systems and methods
ActiveUS20150242643A1Environmental impactNew efficiencyDigital data processing detailsAnalogue secracy/subscription systemsFile transmissionDeployment time
Certain example embodiments relate to file transfer systems and / or methods that enable a single provider to offer to different customers customizable file transfer solutions that are secure, scalable to handle enterprise-level amounts of data, and able to meet customer-specific needs even though such needs are not necessarily known in advance. Once initially set up, the file transfer solution of certain example embodiments delegates management of the customer-specific instances of the solution, optionally in a sub-delegatable manner and, thus, the single provider need not be consulted after specific initial instance deployment time (e.g., for security management and / or other routine maintenance issues).
Owner:AITHERAS +1
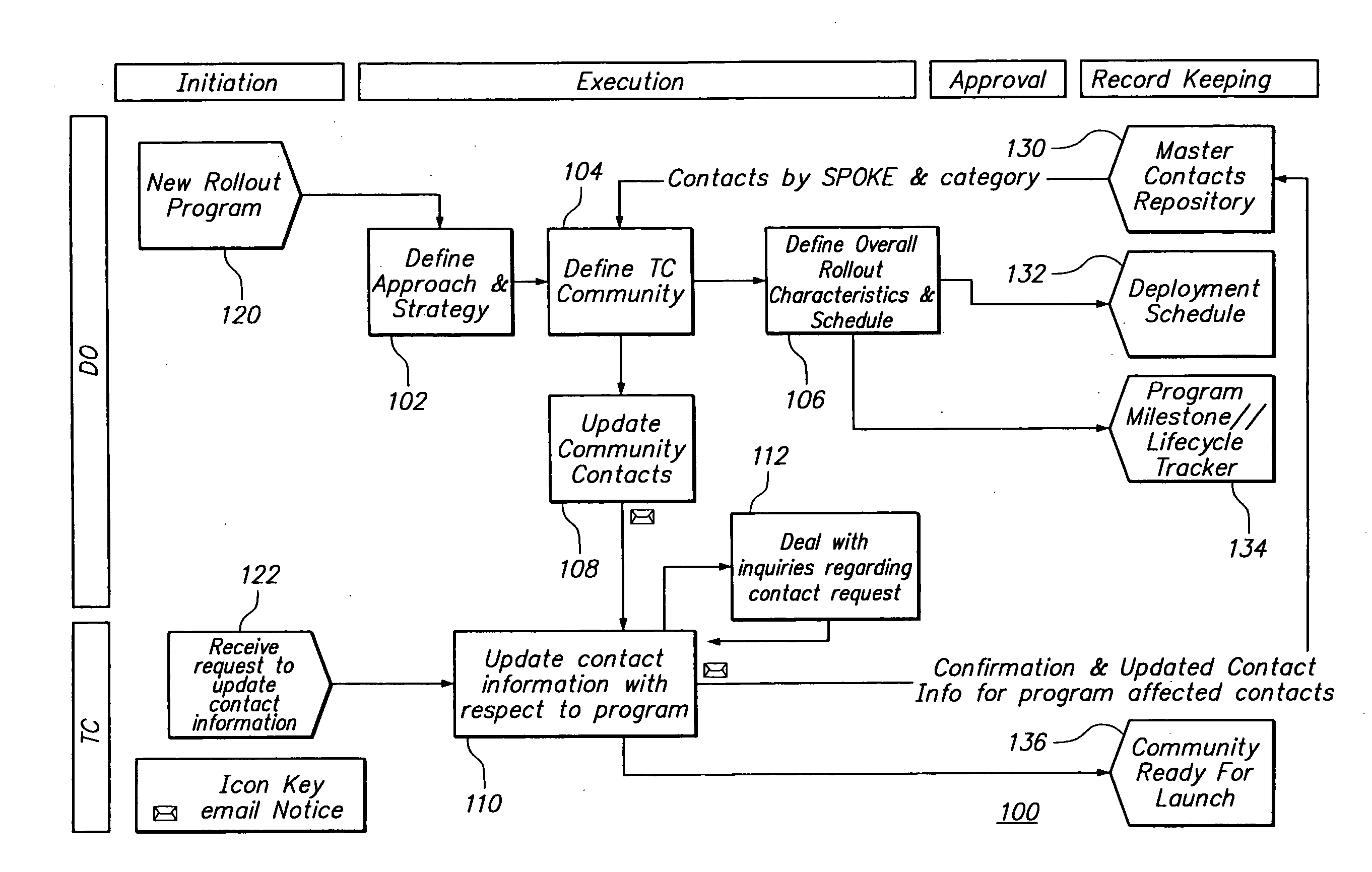
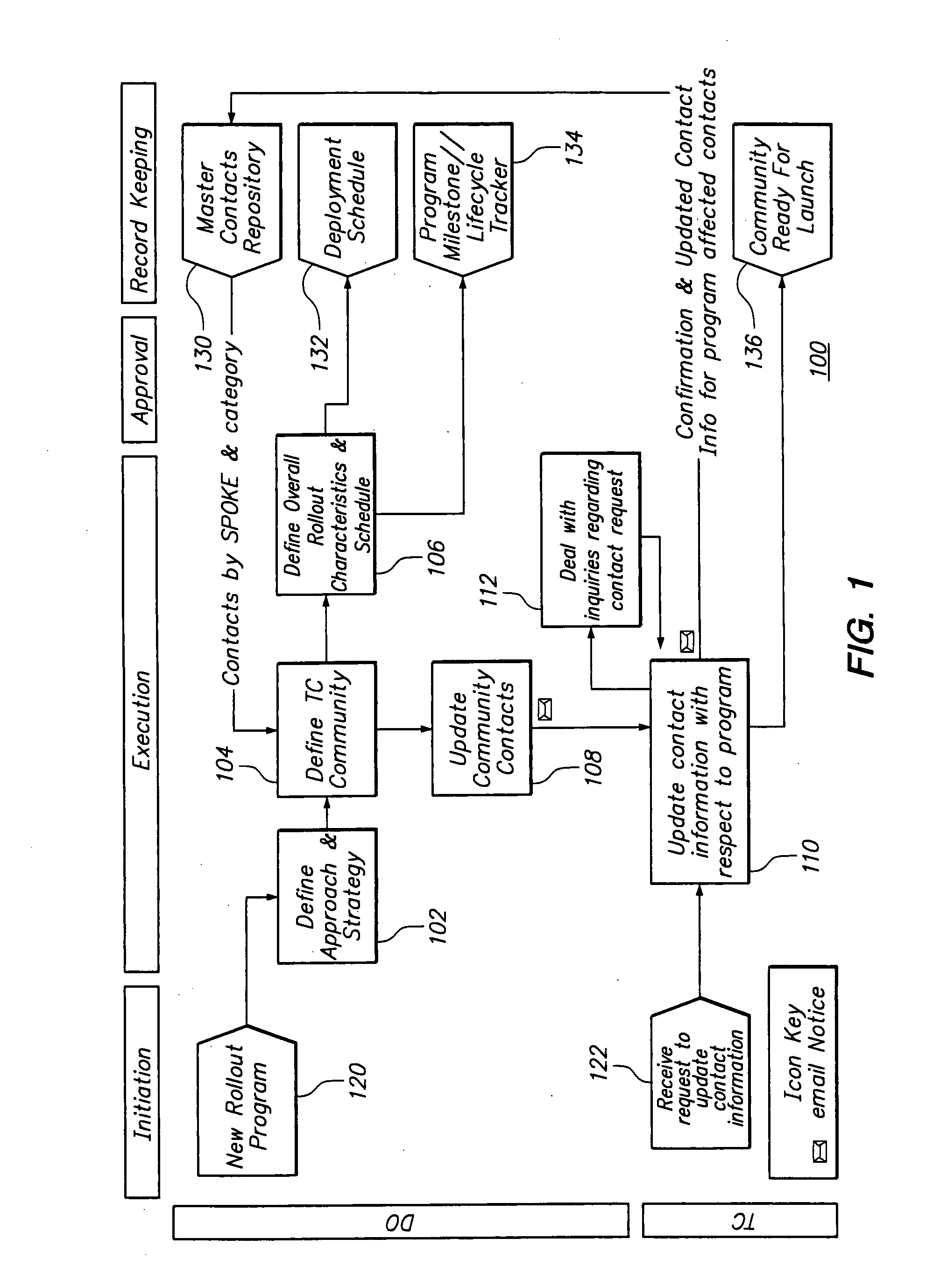
Systems, apparatus and methods for distributed deployment management
InactiveUS20070226679A1Efficient and configurable and effective managementResourcesSpecific program execution arrangementsProgram planningDeployment time
Systems, method, and apparatus for the definition and management of a deployment program are described. This may entail defining a deployment program having a deployment schedule, participation events, and a plurality of target constituents respectively having defined participation conditions in the deployment program that include at least one participation event in the deployment schedule. Segmentation of the plurality of target constituents is accommodated. In this fashion, sets of one or more target constituents are respectively members of different segments. Segmentation may be dynamic and actionable. Wave-based deployment and provision of a library of reusable deployment templates are also provided.
Owner:ROLLSTREAM
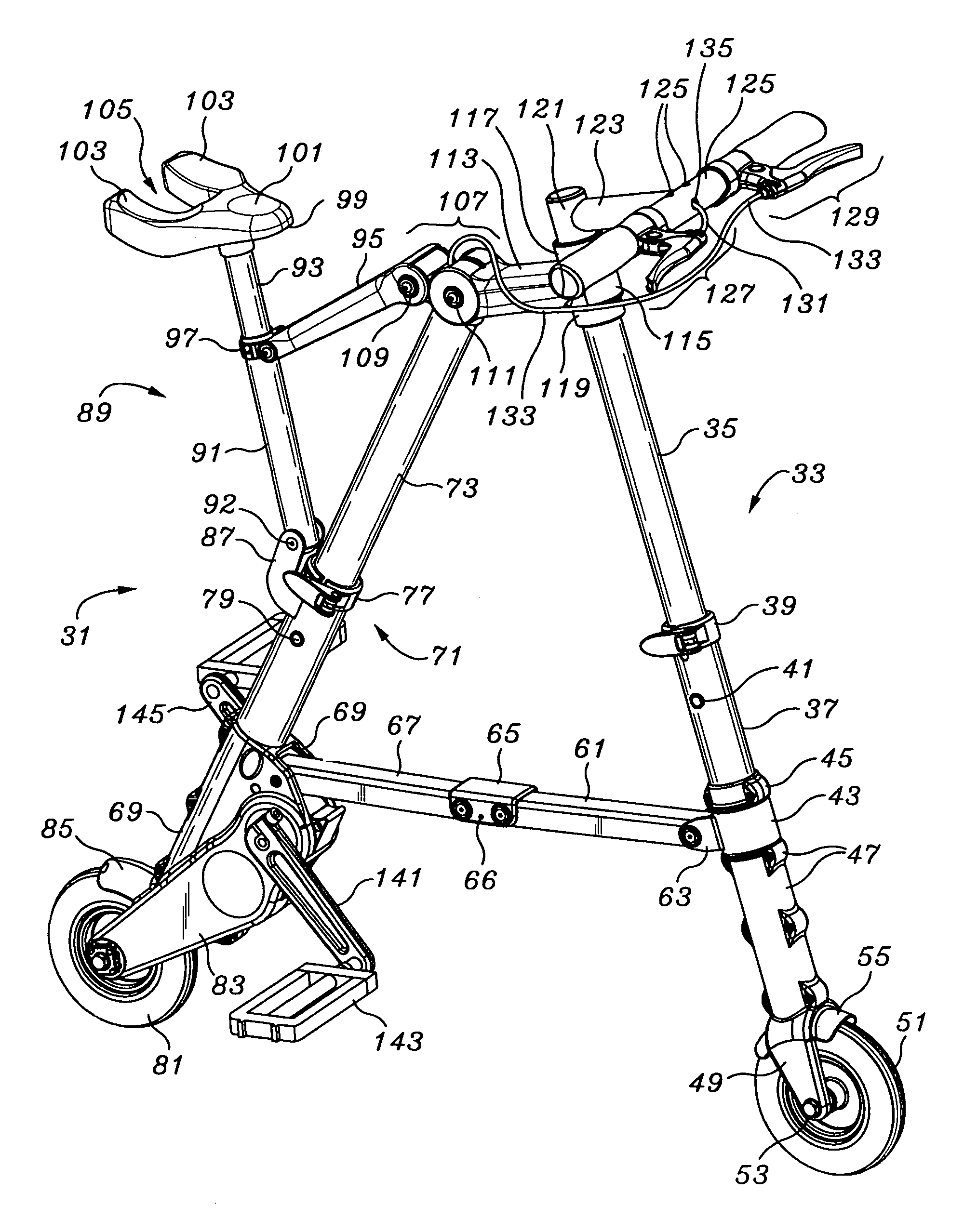
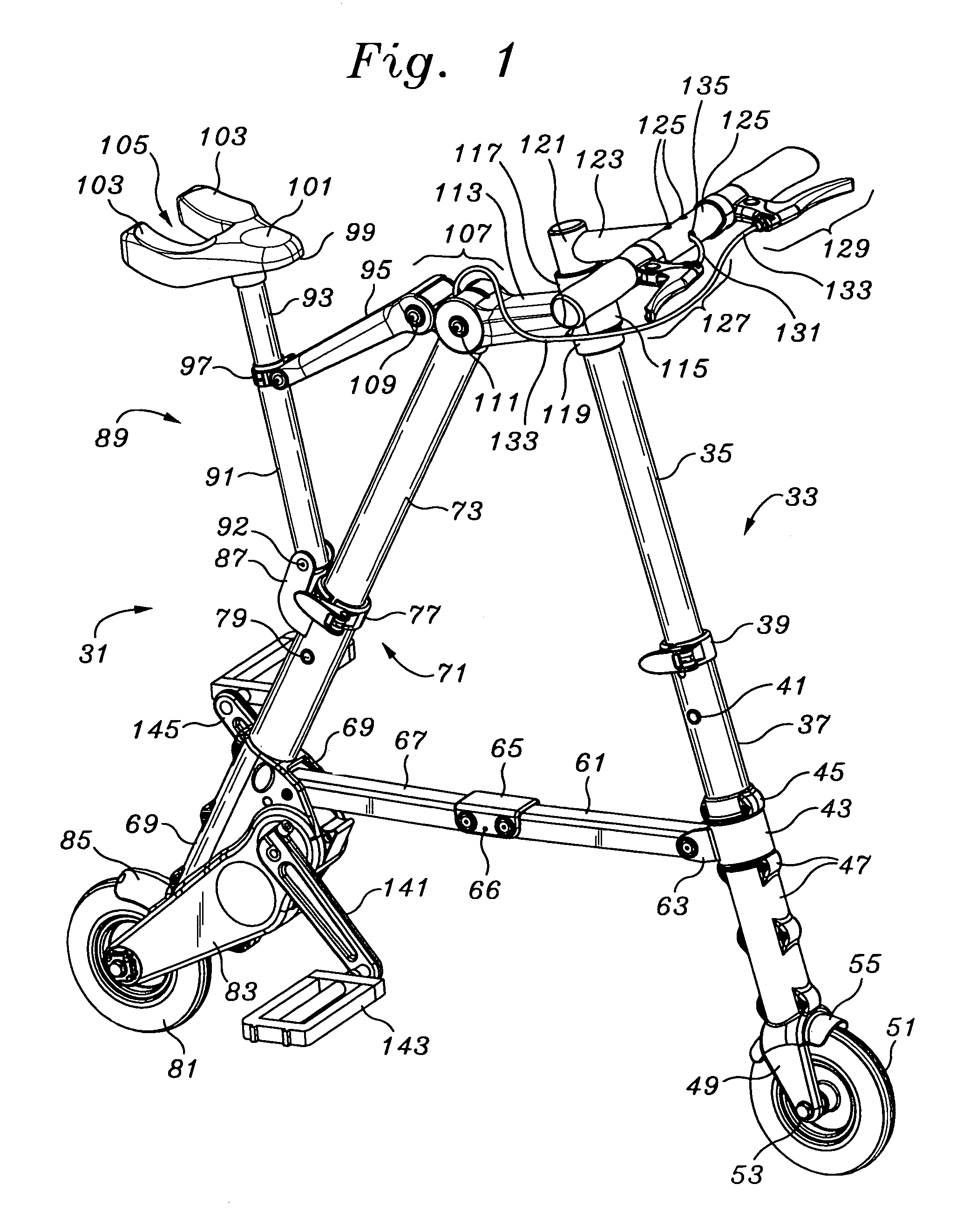
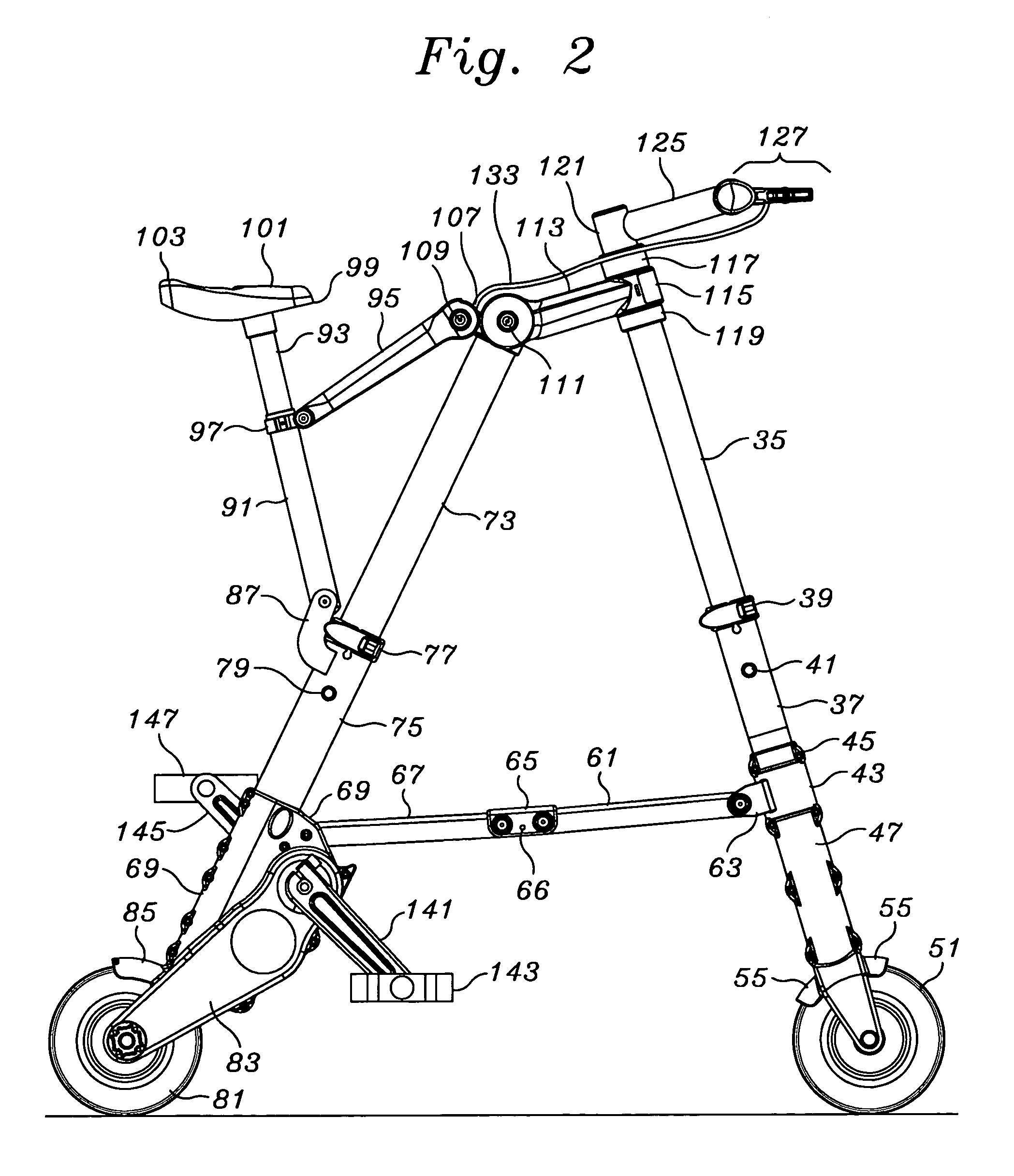
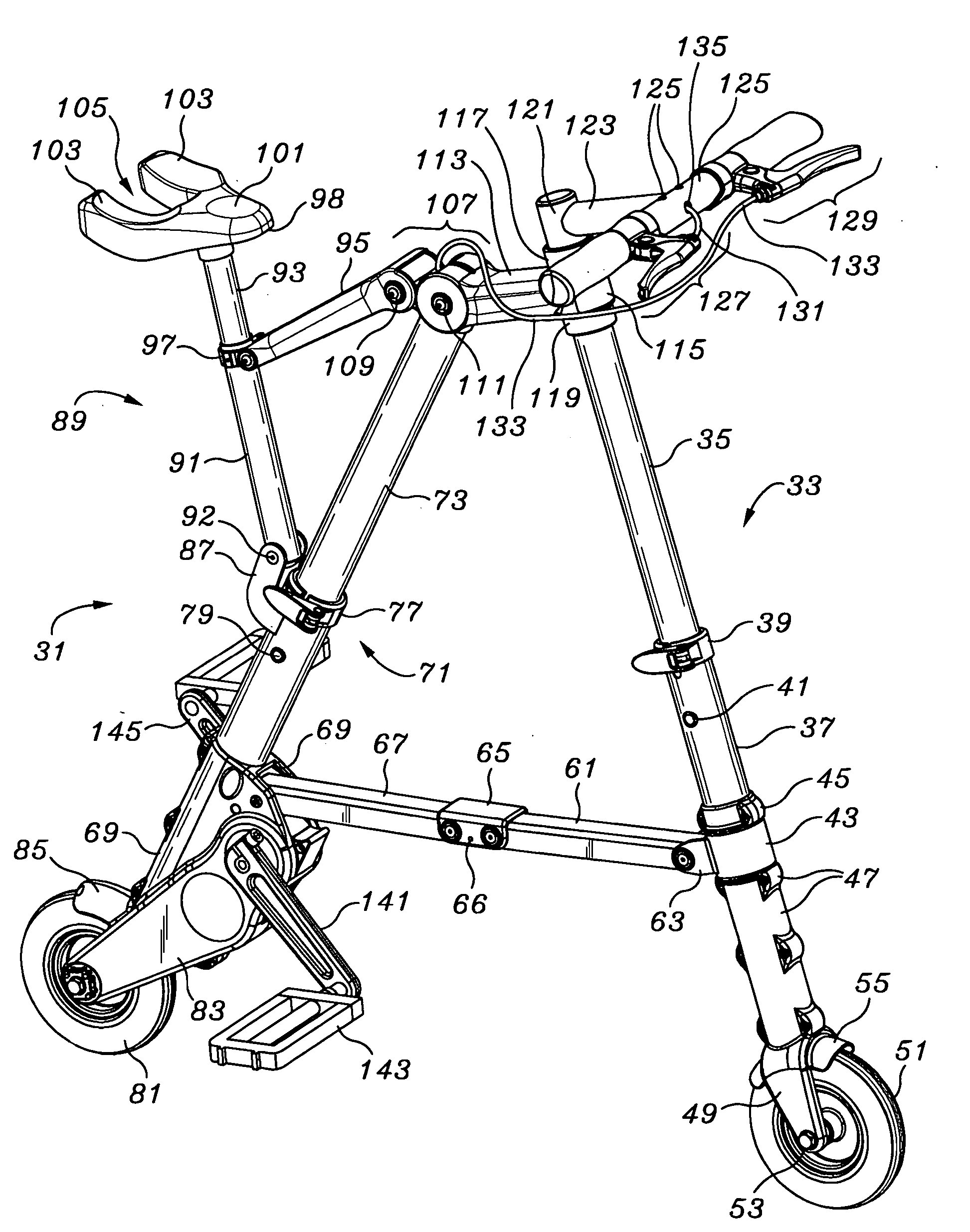
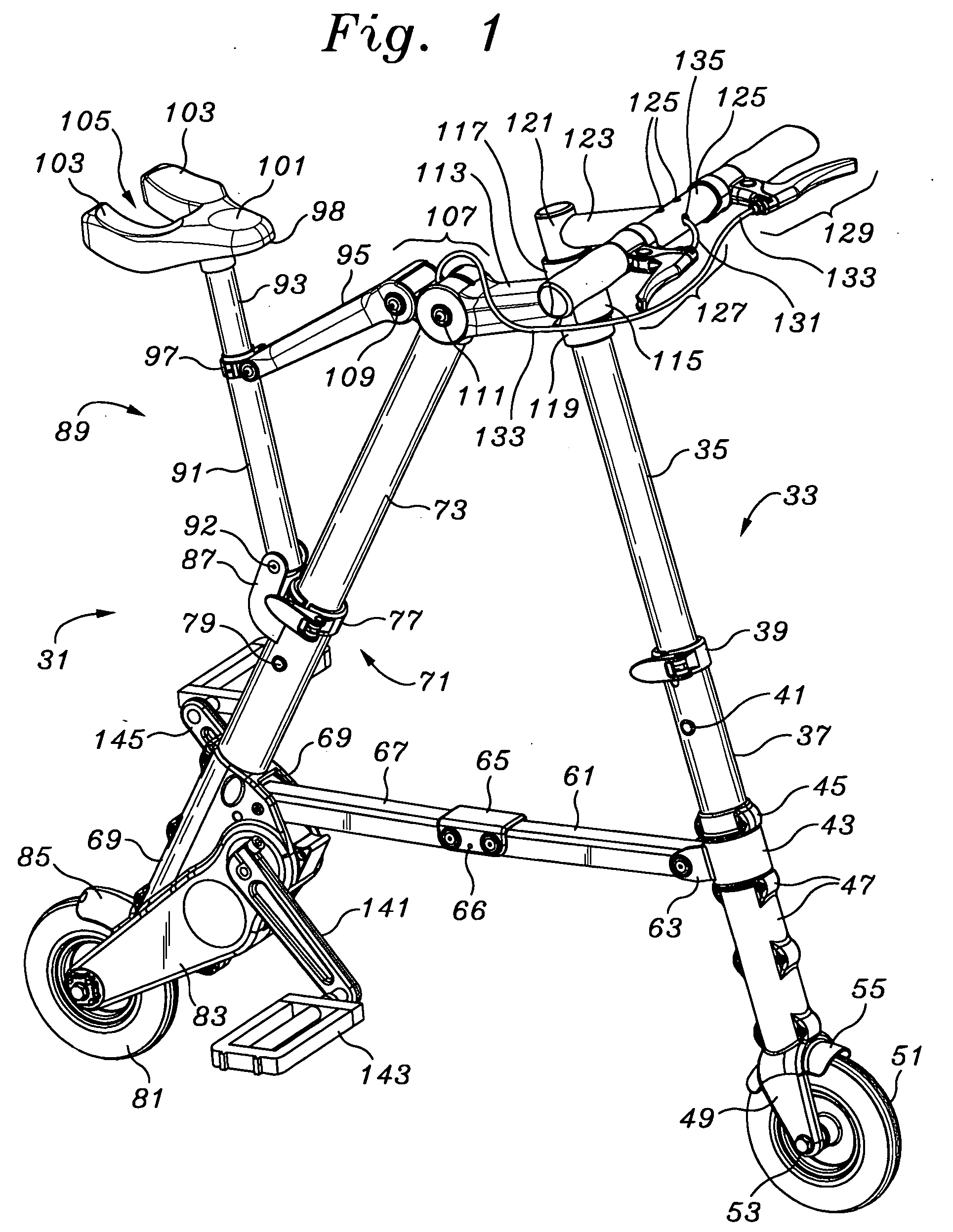
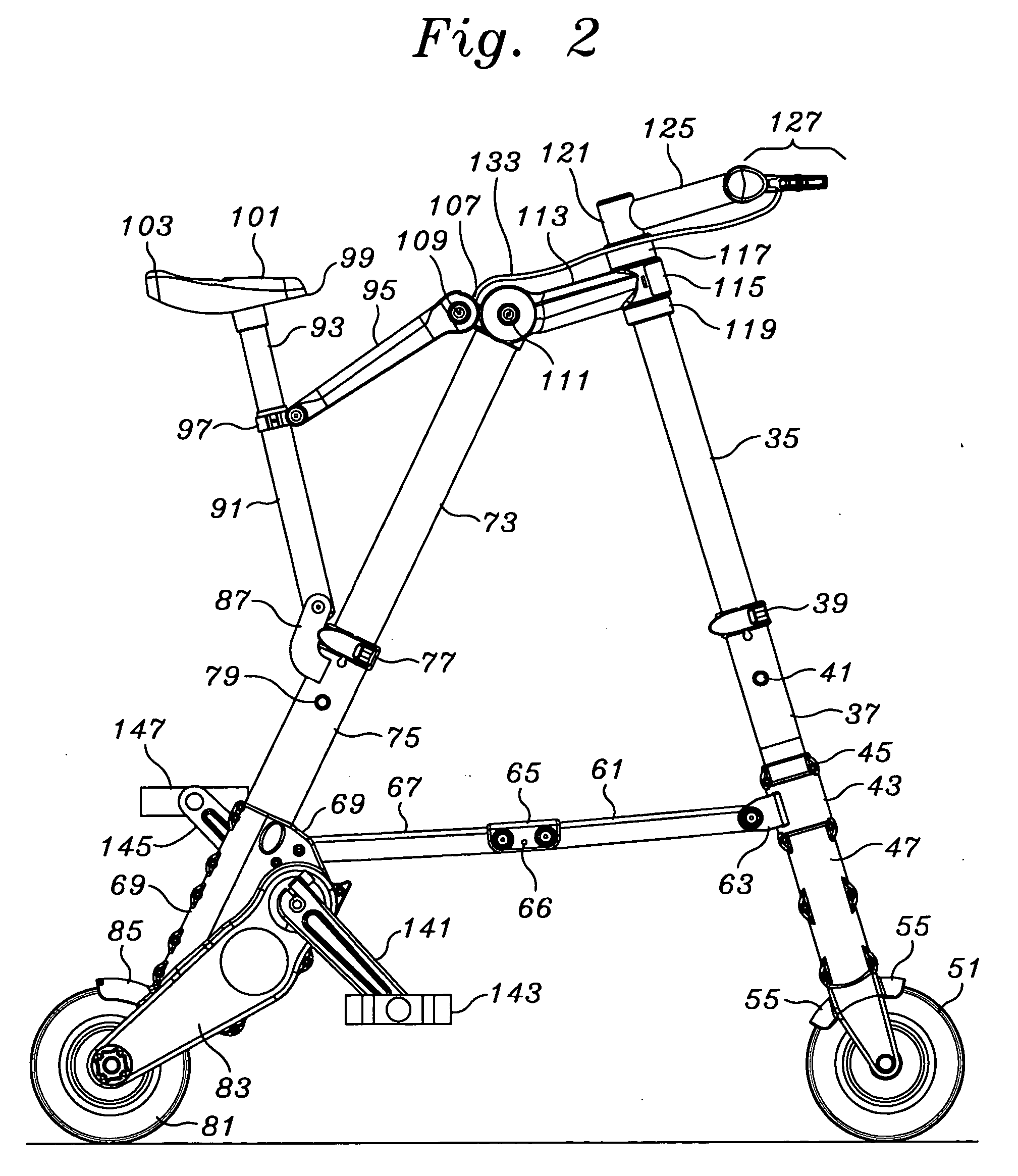
Portable folding bicycle
InactiveUS6986522B2Eliminate riskReadily be taken awayPassenger cyclesWheel based transmissionDeployment timeEngineering
Owner:SINCLAIR REFINING
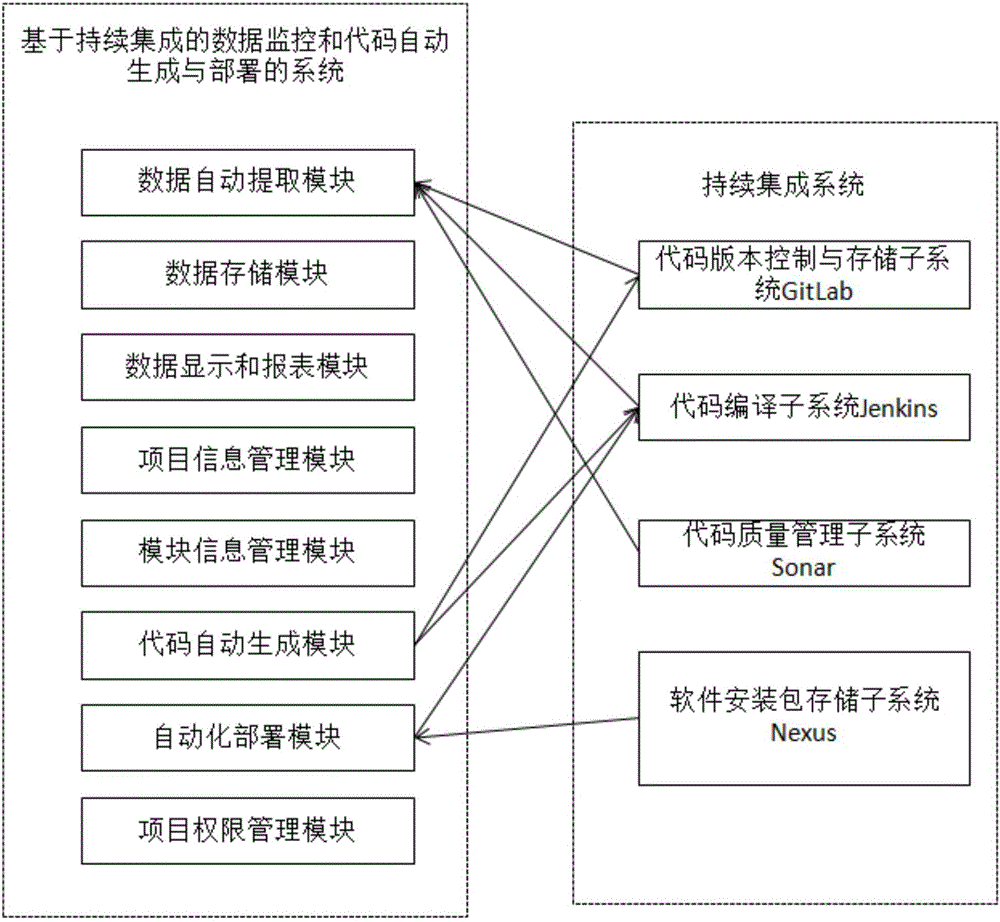
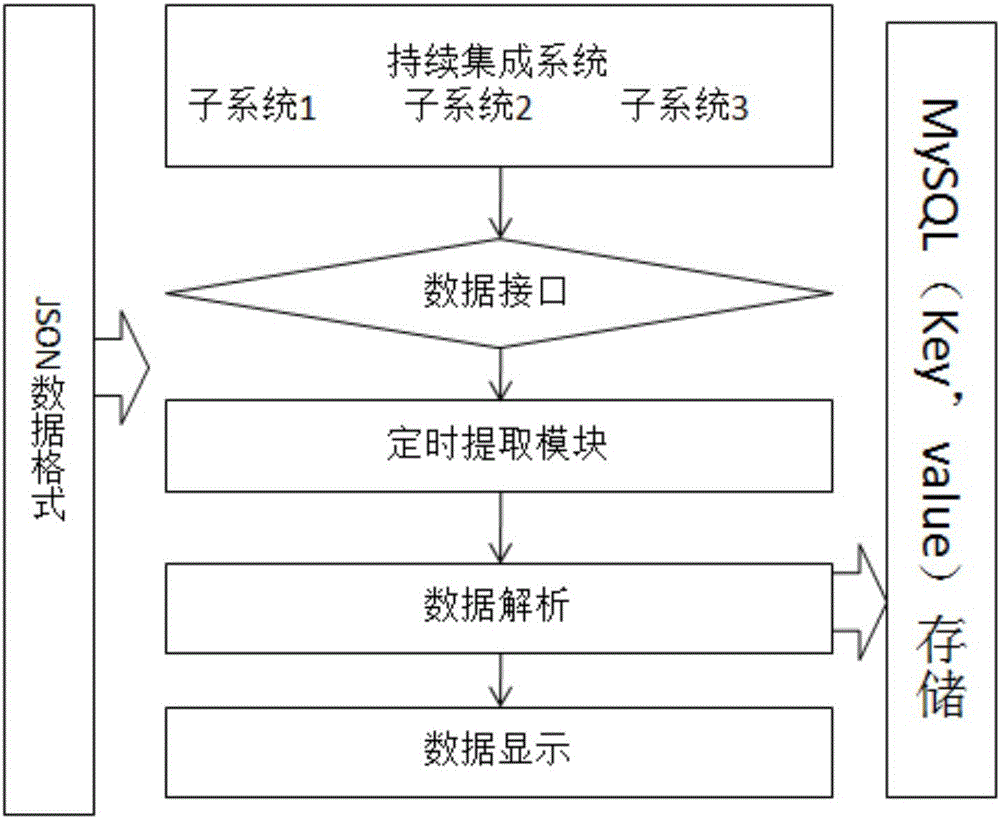
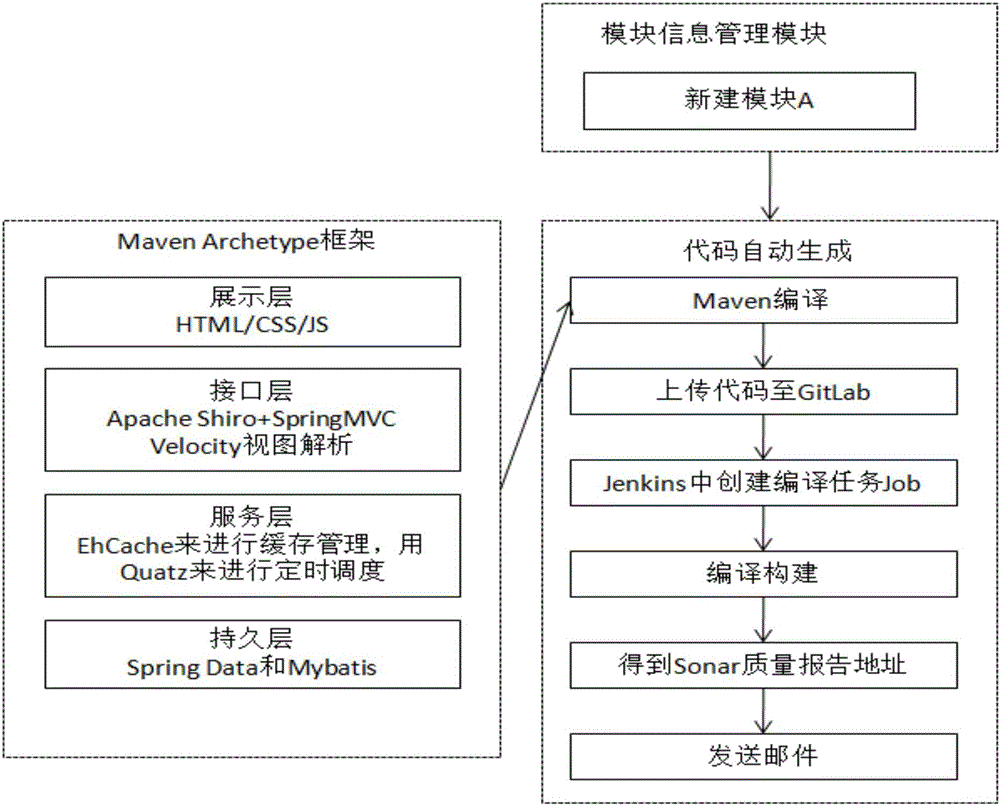
Data monitoring and code automatic generation and deployment system and method
ActiveCN106095408AReduce build timeEnsure consistencyVersion controlProgram loading/initiatingTest efficiencyContinuous integration
The invention discloses a data monitoring and code automatic generation and deployment system and method. Scattered index data of continuous integration subsystems can be automatically extracted and intensively displayed, so that the index data is effectively supervised and one-stop data monitoring is better realized. A framework code of a newly created module can be automatically generated, so that the framework establishment time of the newly created module is effectively shortened, the efficiency is improved, the consistency of framework codes of software products can be ensured, and the development and maintenance are easy. Furthermore, the automatic deployment method can be used for shortening the manual deployment time of a project and improving the development and test efficiency, and a Linux script template can assist a developer to process deployment of installation packages more easily as well as copy and execution of configuration files or dependent files.
Owner:浙江网新恒天软件有限公司
Contain cloud platform and server
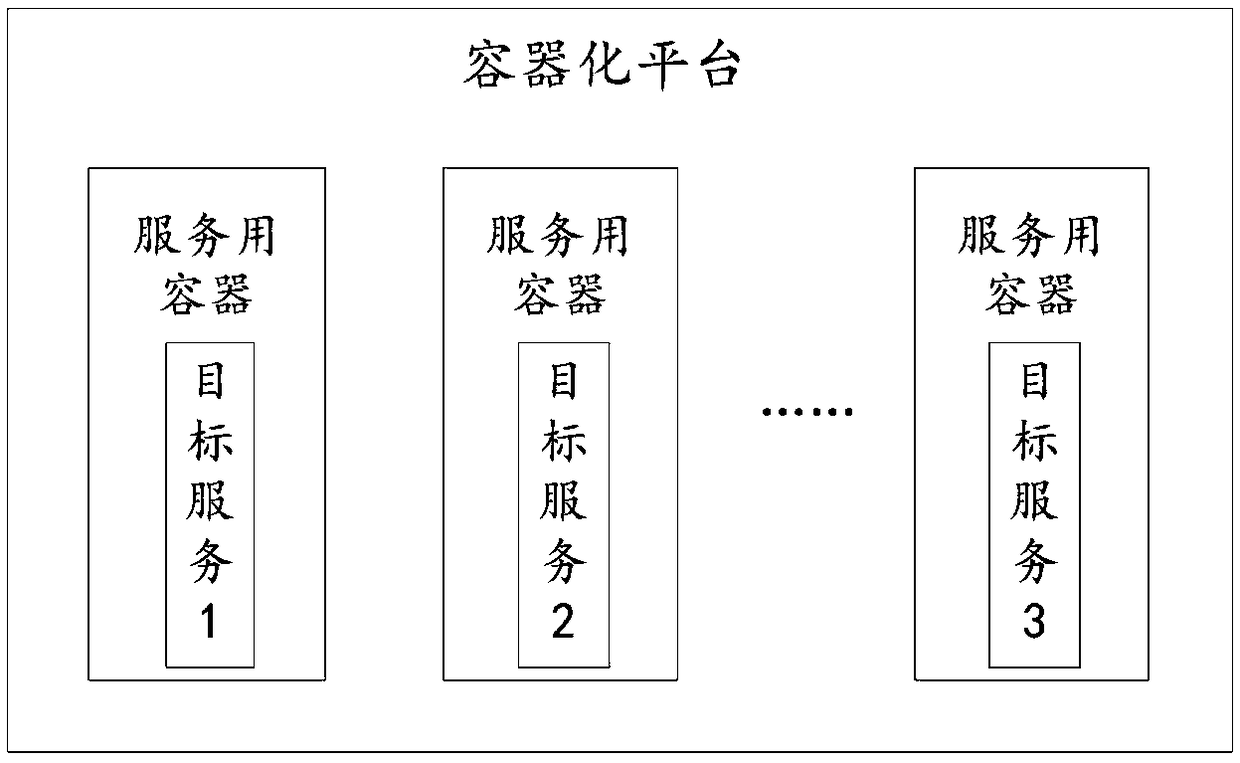
ActiveCN109062655AReduce maintenance difficultyReduce deployment timeTransmissionSoftware simulation/interpretation/emulationDeployment timeOperating system
The invention provides a container cloud platform and a server. The cloud platform is constructed by a distributed architecture based on the container technology. In the distributed architecture, at least one service container is included. The service container is used for running a target service, and the service container corresponds to the target service one by one. The containerized cloud platform provided by the invention has the function of container management, not only a simple container deployment scheme, but also the cloud platform can reduce the deployment time, reduce the maintenance difficulty and has the self-healing function. The cloud platform further provides container application management functions without maintaining complex yaml configuration files of kubernets. Platform services are separated by containers for easy maintenance, and each container can be limited by cpu, memory and io, which expands the flexibility of the platform.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for deploying, provisioning and storing initial filter criteria
InactiveUS20060140385A1Improve efficiencyEfficient storageInterconnection arrangementsSpecial service for subscribersDeployment timeDecomposition
The inventors provide herein methods for the decomposition of initial Filter Criteria (iFCs) into user-independent, global data and user specific data. In various embodiments of the present invention, the approach is based on Trigger point templates that represent families of trigger points, which are able to be instantiated to real trigger points by adding missing user specific data. Trigger point templates are specified at service deployment time and are instantiated to real trigger points and complemented with the other iFC components to form complete iFCs at the time of service subscription. It is demonstrated that the trigger point methods of the present invention facilitate the storing, provisioning and downloading of initial filter criteria and are beneficial in terms of at least storage and run-time efficiency.
Owner:ALCATEL-LUCENT USA INC
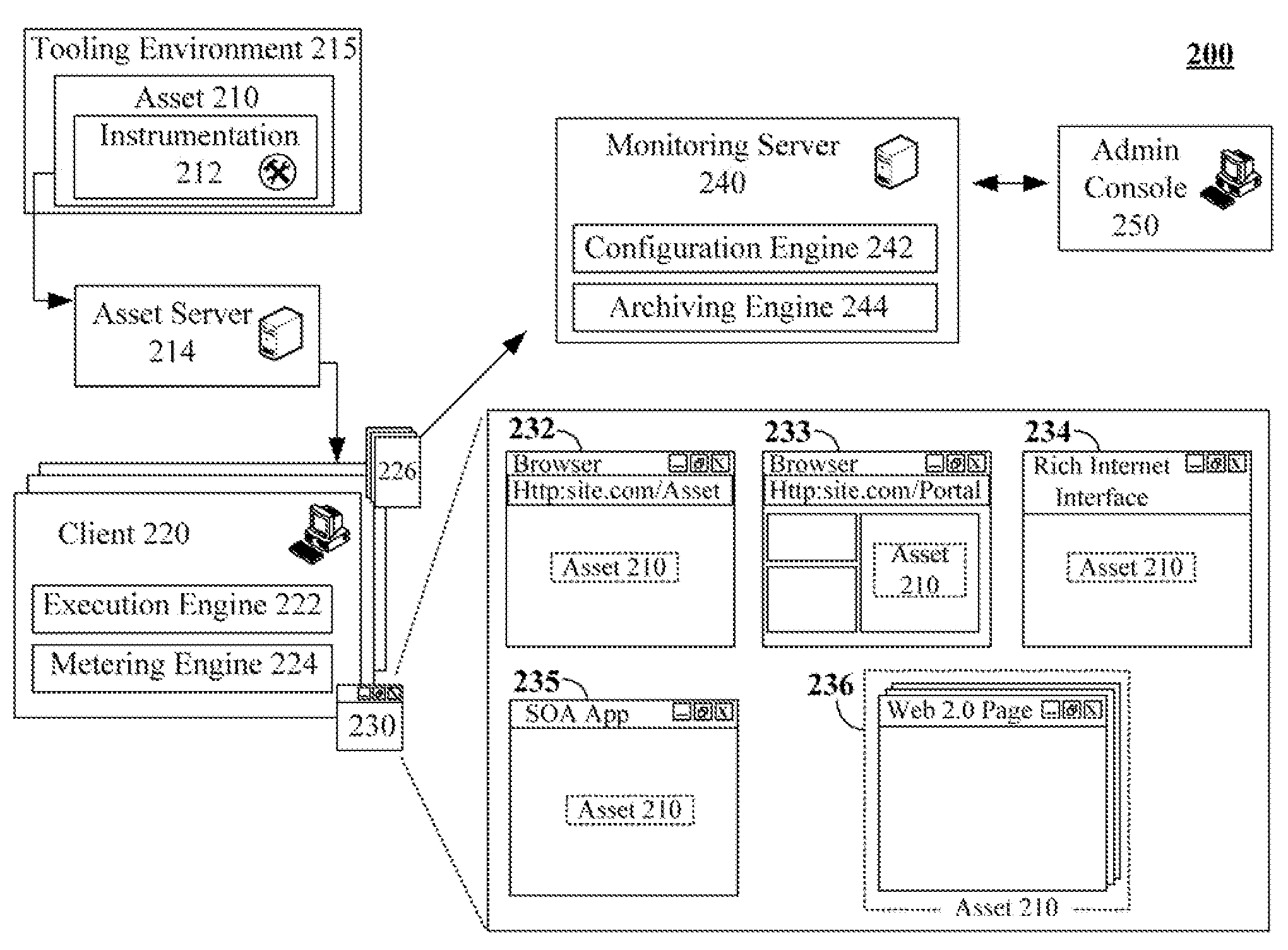
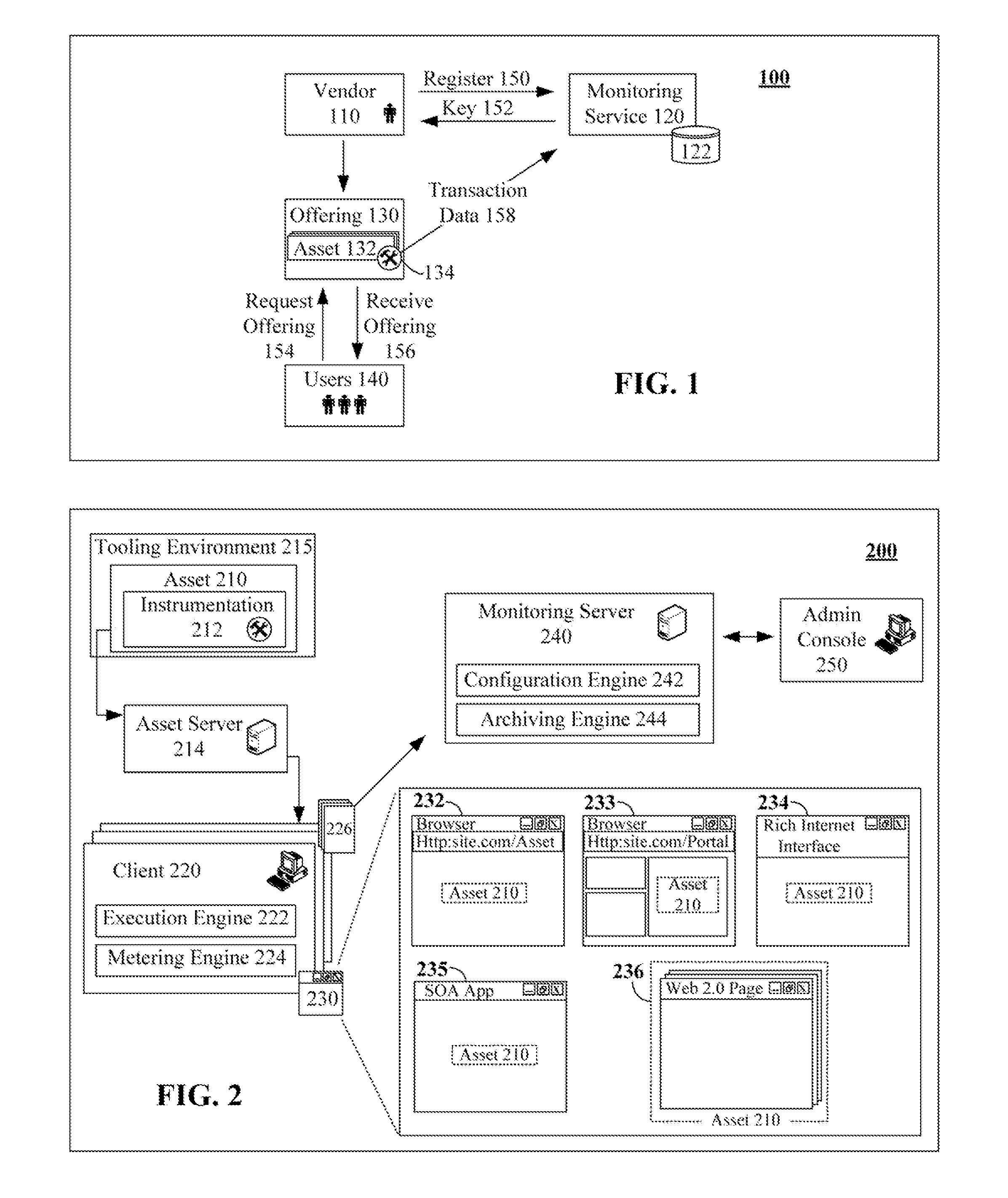
Non-intrusive asset monitoring framework for runtime configuration of deployable software assets
The present invention discloses a solution for metering, monitoring, and monetizing software assets. The solution can include a step of registering a software asset with a monitoring service. A unique identifying key for the software asset can be generated during registration. The software asset can then be instrumented for the monitoring service. The instrumentation can reference the software asset by the unique key. Specifics of the set of metrics that are to be monitored by the monitoring service for the software asset can be runtime, development time, and / or deployment time configurable. The instrumented software asset can convey transaction data to the monitoring server when used by clients. Analyzed results produced by the monitoring service pertaining to the software assets based upon the transaction data can be provided to authorize users of vendors associated with the software asset.
Owner:IBM CORP
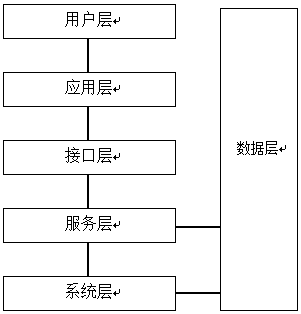
Hierarchical cloud management platform based on microservice architecture
InactiveCN107786379AReduce dependenceReduce deployment timeData switching networksDeployment timeInterface layer
The invention discloses a hierarchical cloud management platform based on a microservice architecture. The hierarchical cloud management platform comprises a user layer, an application layer, an interface layer, a service layer, a system layer and a data layer, wherein the user layer is an operation interface for realizing application management; the application layer is used for assembling a product according to order information submitted by a user; the interface layer is used for authorizing checking, scheduling and distributing to service instances; the service layer is used for acceptinga request forwarded from the interface layer and executing true service logic, each service can comprise multiple instances, and scheduling is carried out by virtue of the interface layer; the systemlayer is used for providing a supporting tool for the service layer and the interface layer; and the data layer is used for providing a data storage service for the service layer and the system layer.The hierarchical cloud management platform disclosed by the invention has the advantages that hierarchical conception is utilized, functions of each layer are clearly defined, and an open API interface is provided, so that the hierarchical structure lowers new function development difficulty, and new business deployment time is saved.
Owner:四川省龙逸凤集网络科技有限公司
Portable folding bicycle
InactiveUS20050263979A1Readily be taken awayReduced consciousnessPassenger cyclesWheel based transmissionDeployment timeEngineering
A folding bicycle presents a number of advantages over both conventional and other foldable bicycles. The folded size of 12×25×6 inches (305×635×153 millimeters) compares favorably to other folding bicycles, and its 11 lb (eleven pound, or 5 kilogram mass) weight is significantly superior to even the closest lightweight model at eighteen pounds, and about half of the average portable bike weight of twenty-two pounds. The folded volume of the bike at 1800 square inches is slightly over one cubic foot. The portable bicycle has a folding stowage time of about 10 seconds, and a deployment time of about 6 seconds. A folding pedal and handle bar design contributes significantly to a folded lateral profile.
Owner:SINCLAIR REFINING
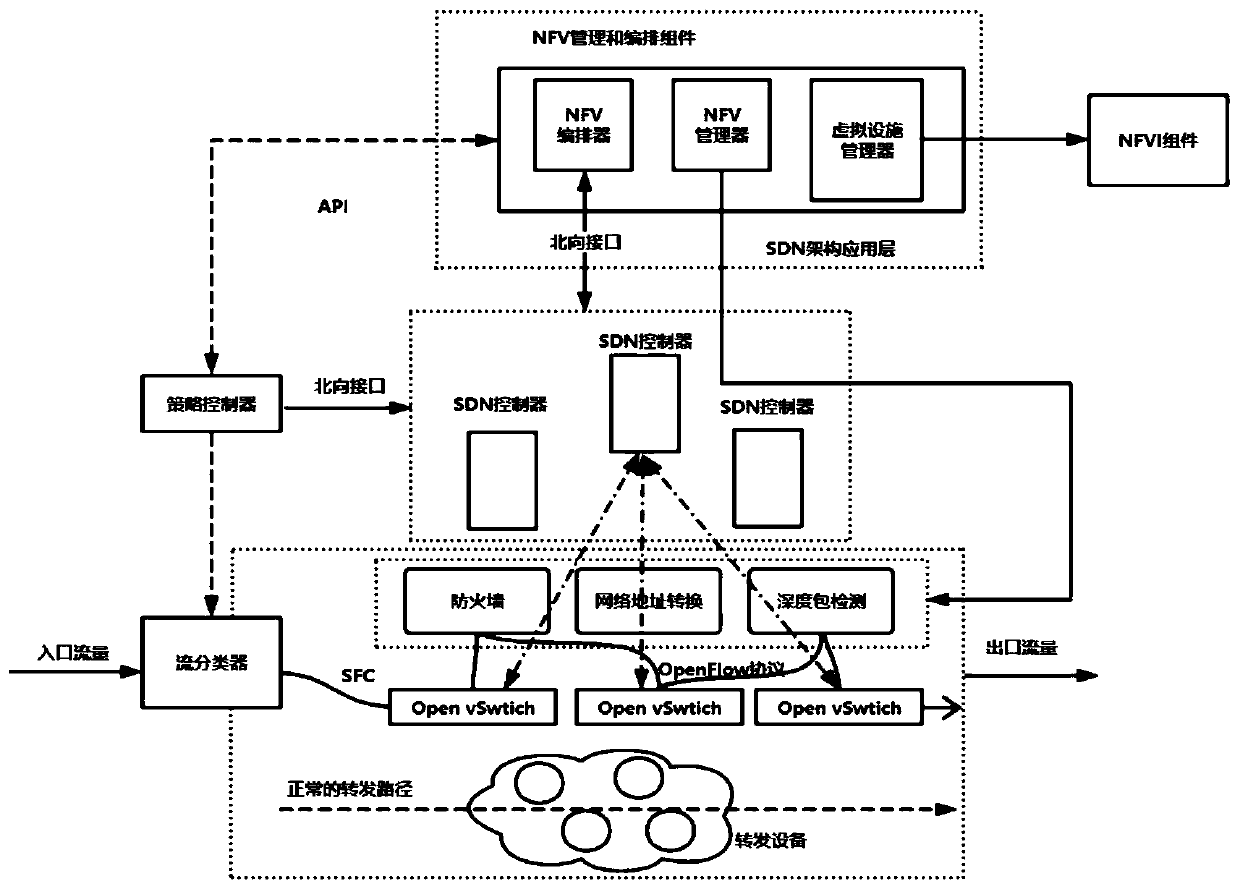
A service function chain deployment method based on SDN and NFV
ActiveCN109842528AImprove developmentEasy to updateData switching networksDeployment timeResource utilization
The invention discloses a service function chain deployment method based on SDN and NFV. A combination framework based on an SDN network and an NFV architecture and a modular deployment service function chain are established. Then, a service function chain deployment algorithm is carried out in the strategy controllers in the SDN network and the NFV architecture; after the user flow enters the network, the strategy controller performs strategy control; whether a network service function required by user traffic is matched with a VNF owned by a bottom layer or not is judged through a deploymentalgorithm of a service function chain; if not, the strategy control informs the management and arrangement component of the NFV of missing VNF information, and after obtaining the message, the management and arrangement component of the NFV deploys all the required VNFs into the corresponding virtual machines in a modular strategy through the NFV underlying facility resources to complete the whole deployment operation. The low time delay of the service function chain is ensured, the resource utilization rate of the service function chain is high, and the deployment time of the whole SFC is shortened.
Owner:XI AN JIAOTONG UNIV
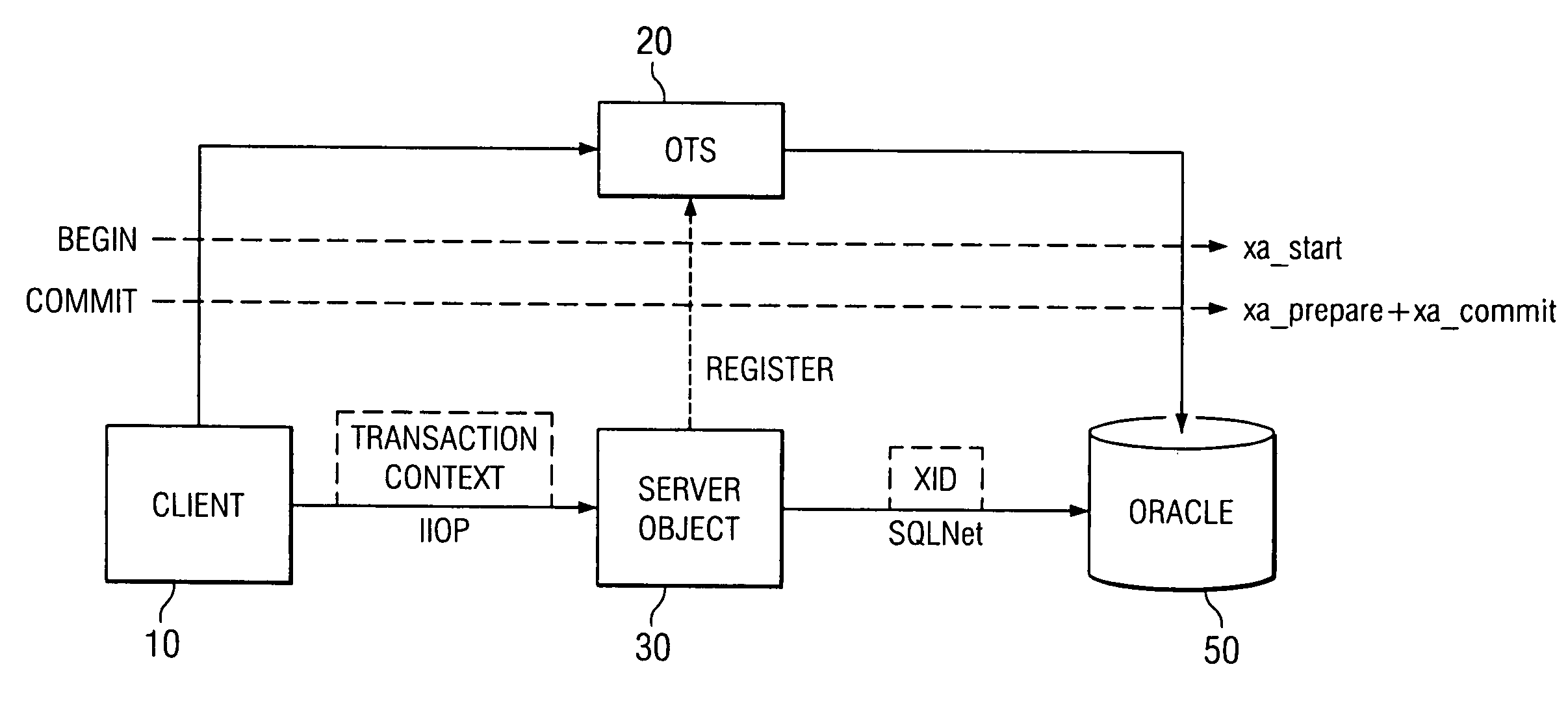
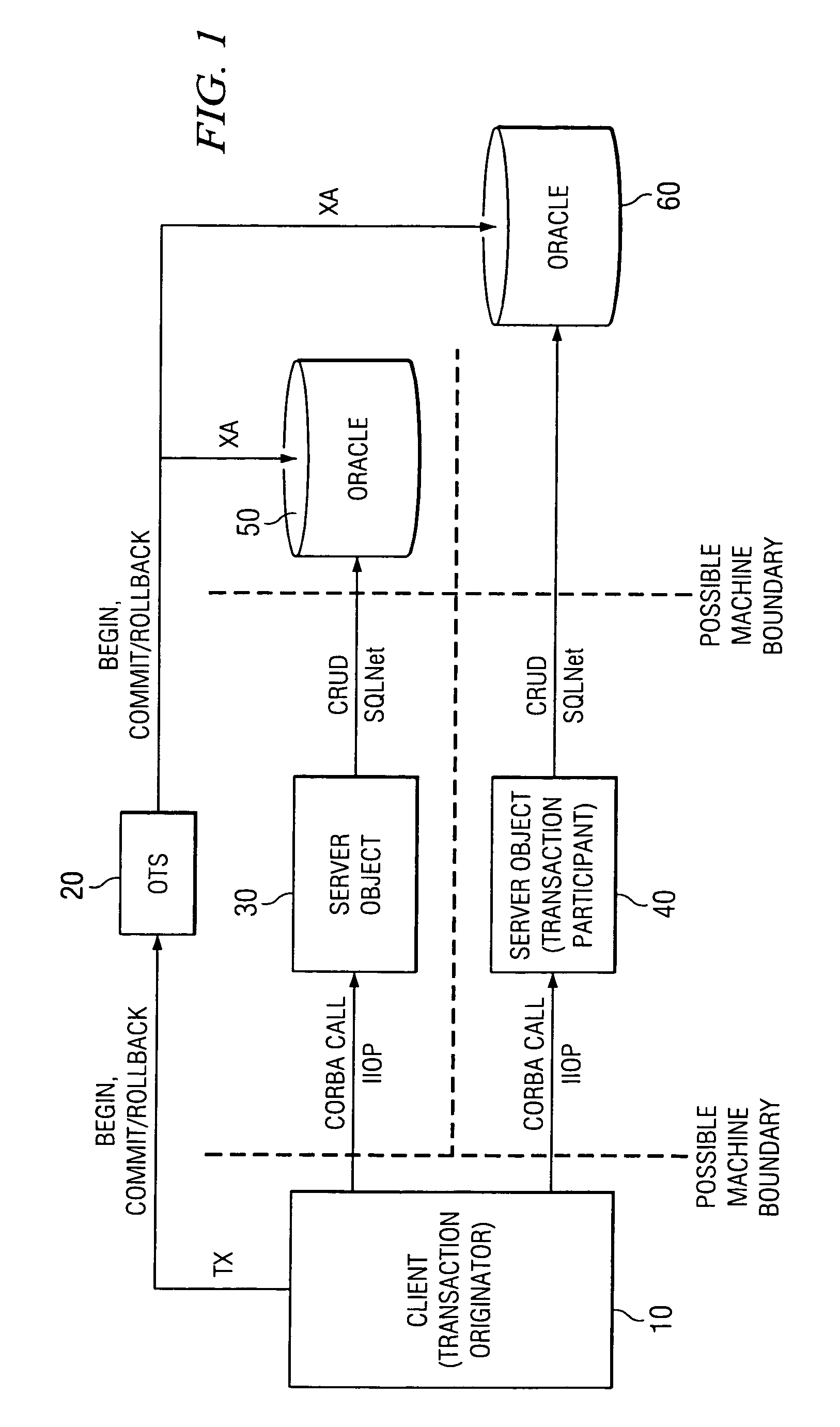
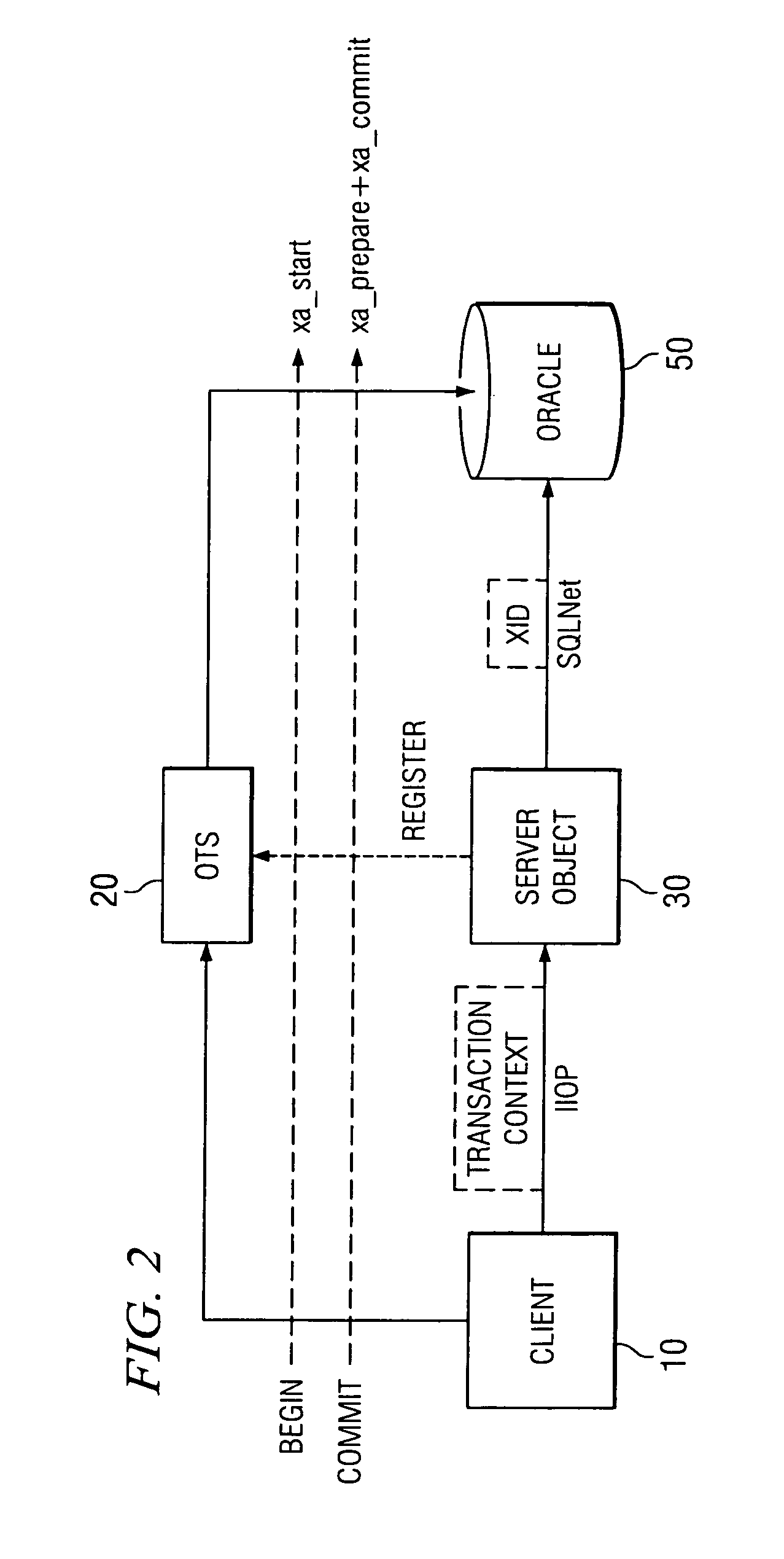
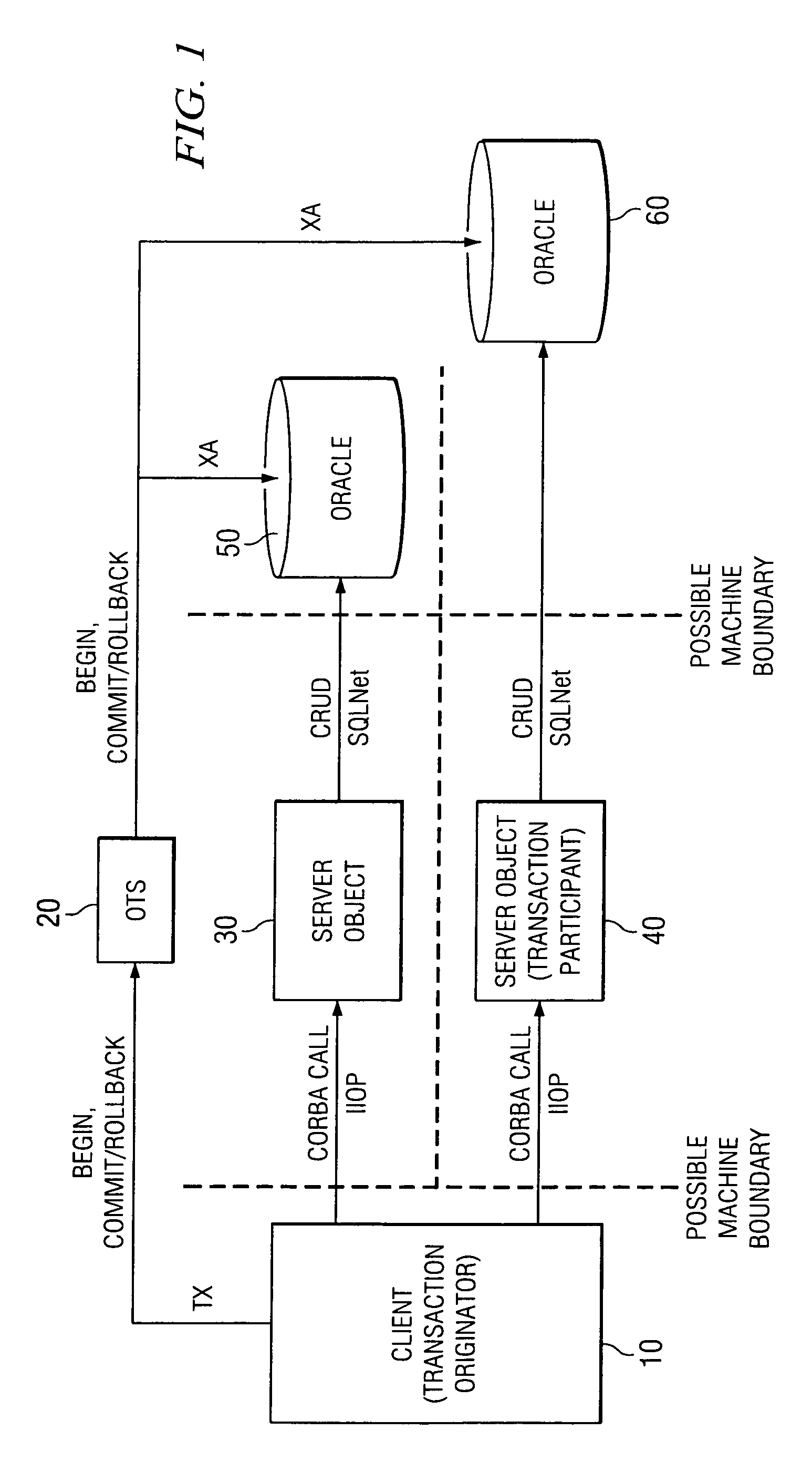
Method for middle-tier optimization in CORBA OTS
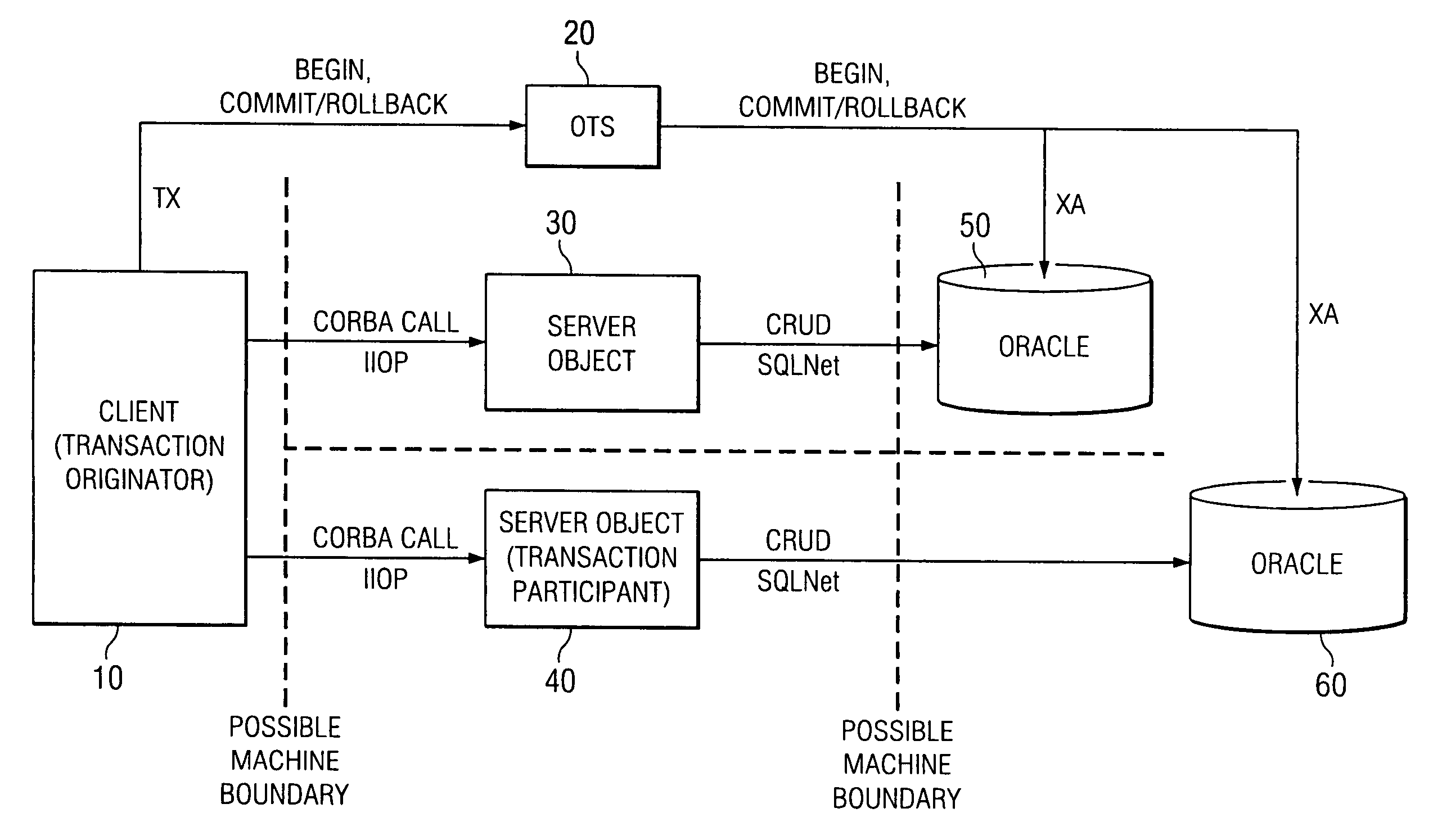
InactiveUS6973657B1Optimizing transactional behaviorInterprogram communicationTransmissionTransaction serviceDeployment time
To perform a distributed transaction in a CORBA environment, OTS (the CORBA Transaction Service) defines a process called “control object interpositioning”. It must be carried out on the server side to ensure transaction integrity. However, for middle-tier servers (servers that do not access a database directly) this process is not necessary. The control object can be simply passed through. However, the two propagation methods of OTS do not provide a good way to take advantage of this fact. The present invention defines a model by which the deployment nature of the server can be specified. Middle-tier or database-tier can be defined in a deployment descriptor file, which is read in deployment time by the server process. The present invention will optimize the middle-tier servers by bypassing the control object interpositioning process and handing the control object directly to the next tier, bringing noticeable performance gains for an n-tiered system.
Owner:T MOBILE INNOVATIONS LLC
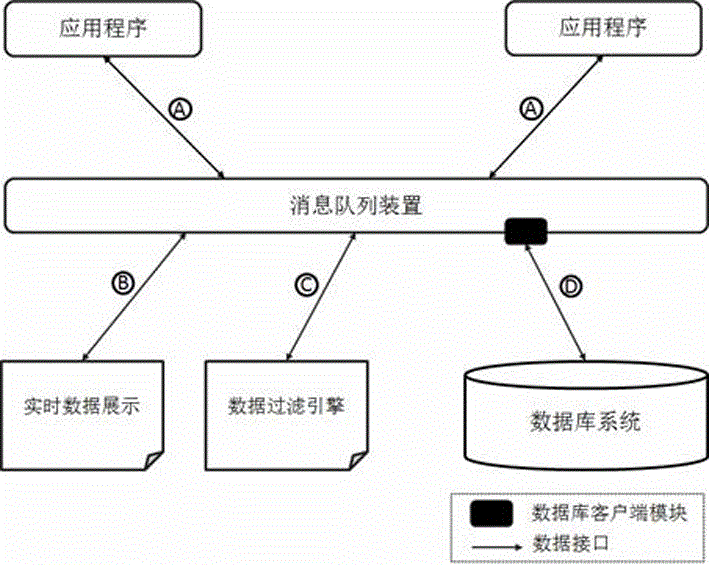
Real-time data processing and storage system
ActiveCN105956082AImprove compatibilityCan be deployed dynamicallyInterprogram communicationDatabase distribution/replicationTransmission protocolService development
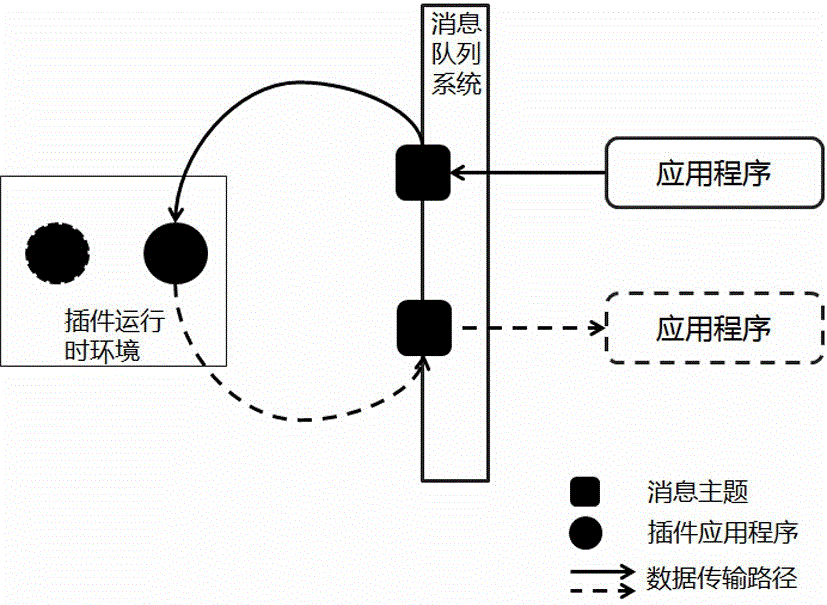
The invention discloses a real-time data processing system. Data filtering, processing and condition storage of data in a transmission process are realized in a Pub / Sub message queue topic mode based on a message queue data transmission channel constructed on a TCP or UDP transmission protocol. The system involved in the invention provides a flexible, dynamically deployable and pluggable real-time data processing framework, so that corresponding data processing systems can be quickly deployed and realized for different application environments and demands, services can be easily cloudized, scalability and expandability are achieved, the utilization efficiency of computing resources is improved, and the service development and deployment time is shortened.
Owner:深圳市致远优学教育科技有限公司
Apparatus and method for in-situ real-time observation of submarine sand waves
ActiveCN107631720ARealize in-situ real-time observationDocument the migration processOpen water surveyOcean bottomGrating
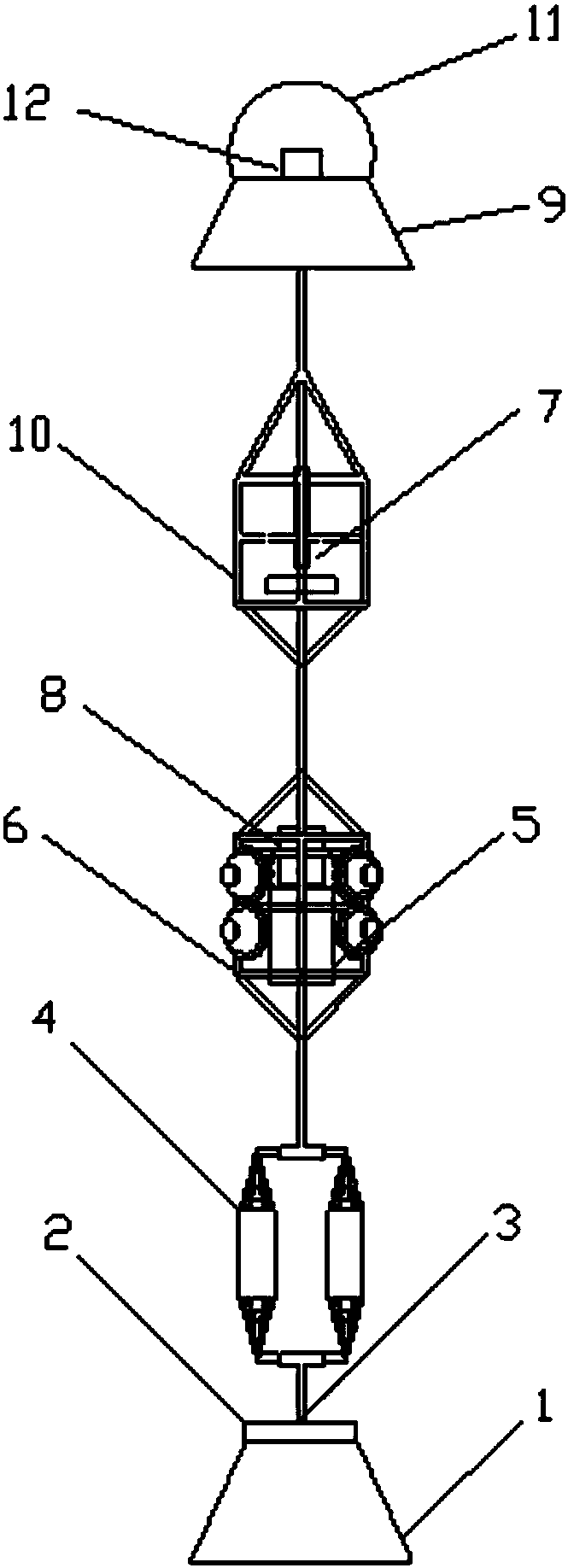
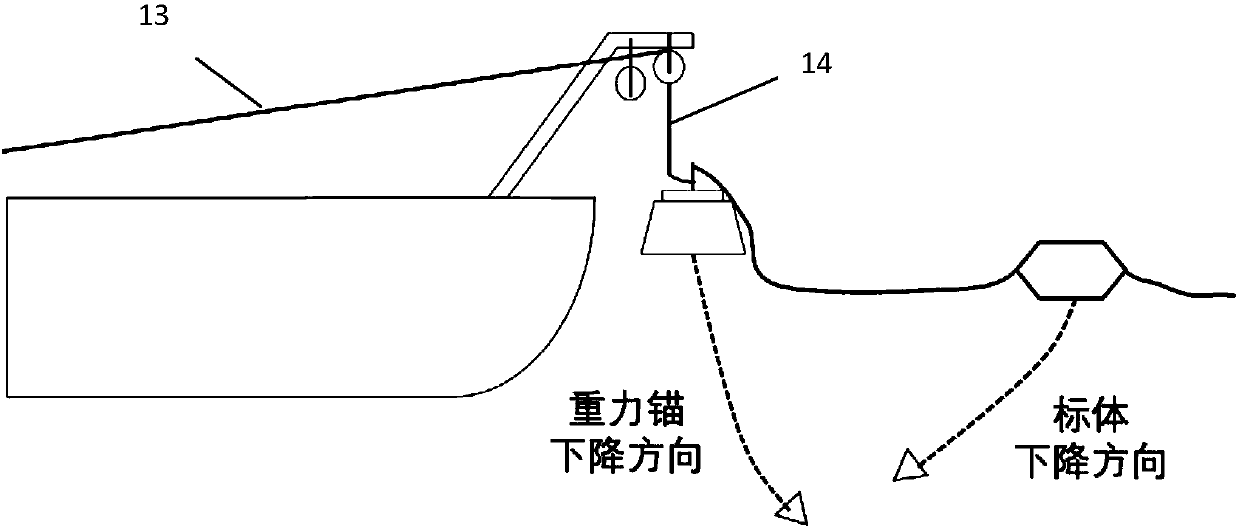
The invention relates to an apparatus and method for the in-situ real-time observation of submarine sand waves. The apparatus includes an observation system and auxiliary devices. The auxiliary devices comprise an auxiliary ship and a hoisting device; the observation system includes a gravity anchor, a fiber grating floating earth weight sensor, a Kevlar cable, an underwater acoustic releaser group, a lower floating ball bracket, a wave and tide gauge, an upper floating ball bracket, an MRU three-dimensional attitude sensor, a satellite communication machine, an imaging sonar, a solar cell anda main floating body. The principle of the apparatus and the method is characterized in that submarine pressure change caused by the migration of the submarine sand waves is observed, the time interval, elevation and wavelength data of two adjacent extreme submarine pressures are analyzed, and the migration rate of the submarine sand waves is calculated. The method includes the following steps: selection of an observation point and a deployment time, system deployment, recovery, and data processing. The apparatus and the method provide a new idea for the in-situ real-time observation of the submarine sand waves, have the characteristics of simple and easy device, long in-situ real-time measurement period and wide applicable water range, and can realize the in-situ real-time long-term observation of the migration of the submarine sand waves.
Owner:OCEAN UNIV OF CHINA
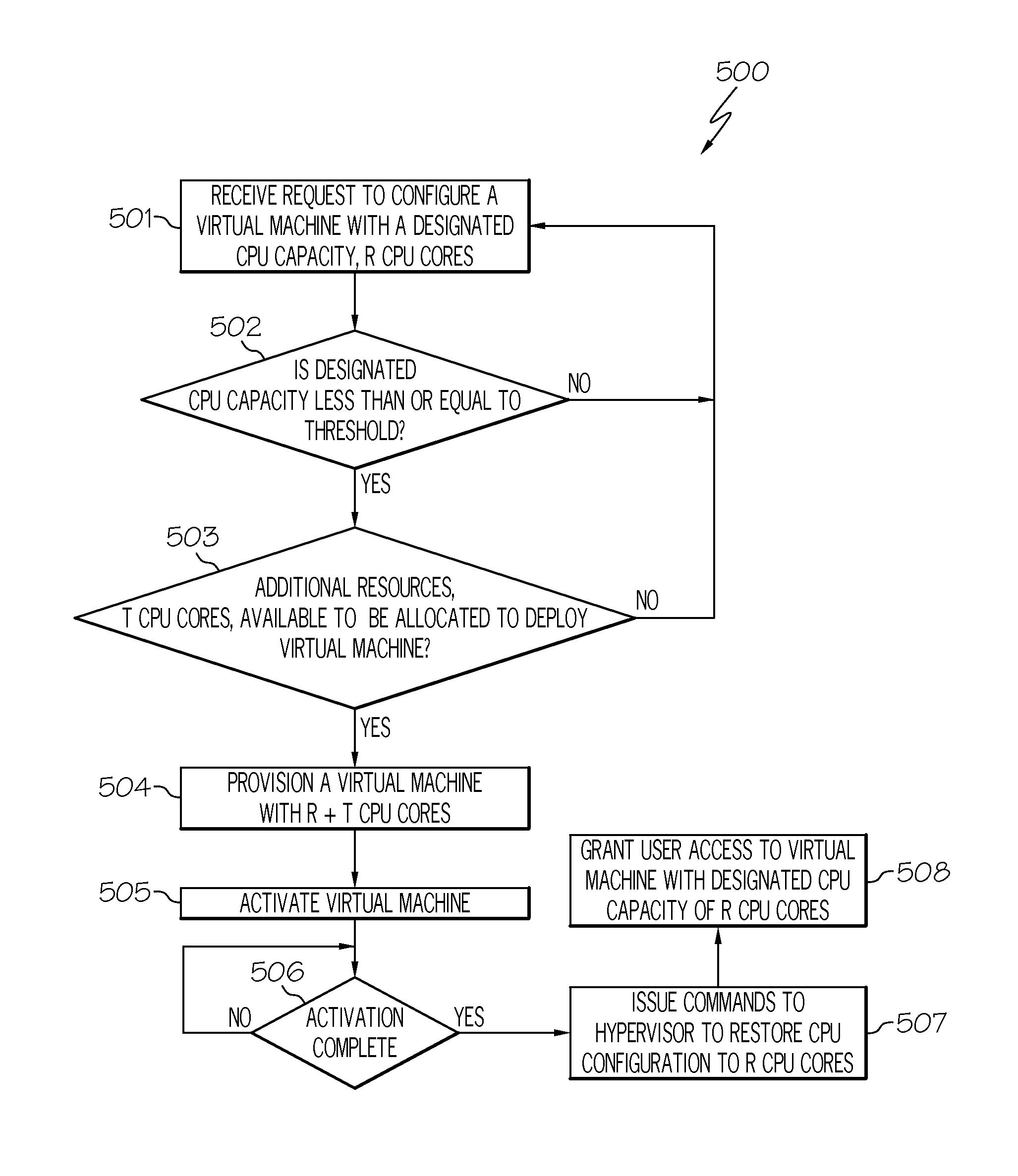
Optimizing virtual machine deployment time by temporarily allocating more processing resources during the initial deployment time of the virtual machine
ActiveUS20140059542A1Software simulation/interpretation/emulationMemory systemsOperational systemDeployment time
A method, system and computer program product for optimizing virtual machine deployment time. A cloud controller receives a request from a user to configure a virtual machine with a designated CPU capacity. If the designated CPU capacity is less than or equal to a threshold, then the cloud controller determines if there are additional cloud resources available to be allocated to deploy the virtual machine. If so, then the cloud controller allocates additional CPU capacity to the designated CPU capacity to be used to provision the virtual machine thereby enabling a multithreaded startup to initialize the operating system and middleware tiers so as to reduce the deployment time of the virtual machine. The additional resources would only be available during the initial deployment time of the virtual machine and removed before the user is granted access to the system when it comes online.
Owner:IBM CORP
Base station deployment method, network server and unmanned aerial vehicle
ActiveCN106454739AReduce deployment timeReduce the efficiency of deploymentRemote controlled aircraftLocation information based serviceDeployment timeGeolocation
The embodiment of the invention provides a base station deployment method, a network server and an unmanned aerial vehicle. The method comprises the steps of determining a target geographical range where a base station is to be deployed; determining a first base station and a second base station, and a candidate geographical location for deploying the base station between the first base station and the second base station according to signal coverage quality of each base station within the target geographical range; and determining a target geographical location where the base station to be deployed according to the signal coverage quality of the first base station and the second base station when the unmanned aerial vehicle carrying the base station reaches each candidate geographical location. According to the base station deployment method, the network server and the unmanned aerial vehicle provided by the embodiment of the invention, the signal coverage quality of the base station is automatically measured by using the characteristic that the unmanned aerial vehicle is rapid and flexible to deploy the base station, so that the deployment time of the base station is reduced, the automation degree of deployment of the base station is increased, and deployment efficiency of the base station is improved.
Owner:成都佰才邦技术有限公司
Multiple deployment of applications with multiple configurations in an industrial automation environment
ActiveUS9442476B2Program loading/initiatingProgramme control in sequence/logic controllersDeployment timeAutomation
Owner:ROCKWELL AUTOMATION TECH
Secure file transfer systems and methods
ActiveUS9135458B1Environmental impactNew efficiencyDigital data protectionTransmissionDeployment timeEnterprise level
Certain example embodiments relate to file transfer systems and / or methods that enable a single provider to offer to different customers customizable file transfer solutions that are secure, scalable to handle enterprise-level amounts of data, and able to meet customer-specific needs even though such needs are not necessarily known in advance. Once initially set up, the file transfer solution of certain example embodiments delegates management of the customer-specific instances of the solution, optionally in a sub-delegatable manner and, thus, the single provider need not be consulted after specific initial instance deployment time (e.g., for security management and / or other routine maintenance issues).
Owner:AITHERAS +1
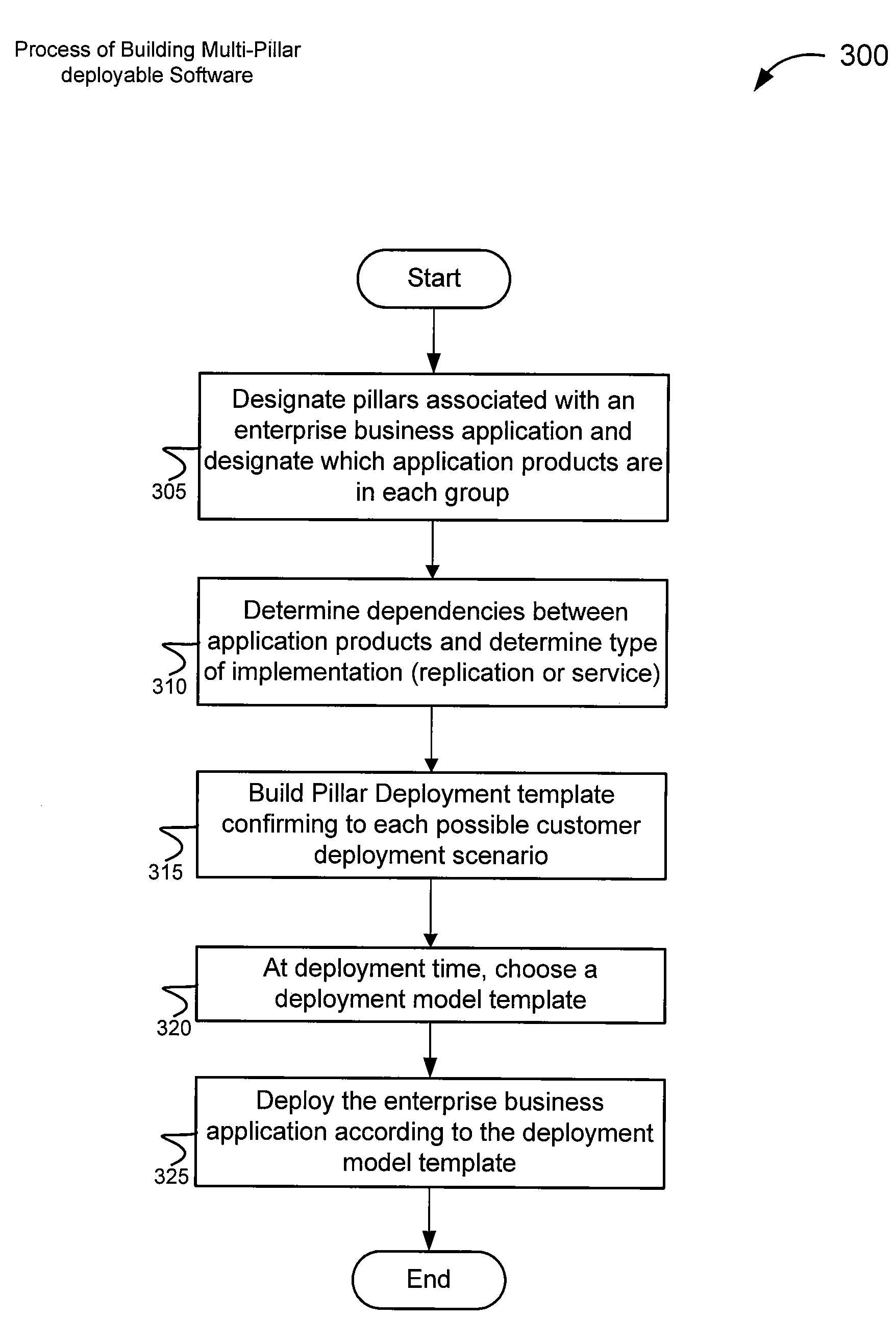
Methods and systems for supporting multiple deployment models of enterprise business applications
This disclosure describes, generally, methods and systems for supporting multiple deployment models for enterprise business applications. In one embodiment, the method may include designating pillars associated with an enterprise business application. Each pillar may include application units which comprise logical groupings for application units used in the enterprise business application. The method may further include determining which of the application units are dependent to more than one of the pillars. Furthermore, based on the determination of the dependent application units, the method may generate deployment code associated with the dependent application units which is configured to be deployment model independent. The method may then receive, at deployment time, a deployment model designation indicating a type of deployment model selected to be used for the enterprise business application. Then, the enterprise business application may be deployed according to the deployment model designation.
Owner:ORACLE INT CORP
Returning terminated virtual machines to a pool of available virtual machines to be reused thereby optimizing cloud resource usage and workload deployment time
ActiveUS20150261561A1Data switching networksSoftware simulation/interpretation/emulationDeployment timeNetwork addressing
A method, system and computer program product for optimizing cloud resources in utilizing a pool of virtual machines to service user workloads. A writeable partition is created to store middleware and user activity associated with a virtual machine obtained from a pool of available virtual machines to be deployed. In response to the obtained virtual machine being terminated, the contents of the created writeable partition are erased so that the data generated by the middleware and user activity will not be available for subsequent users. The virtual machine is later returned to the pool of available virtual machines after resetting its password and network address to a default state. In this manner, fewer cloud resources are used since resource intensive activities that were required in provisioning a new virtual machine can be eliminated since previously terminated virtual machines can be utilized in the pool of available virtual machines.
Owner:IBM CORP
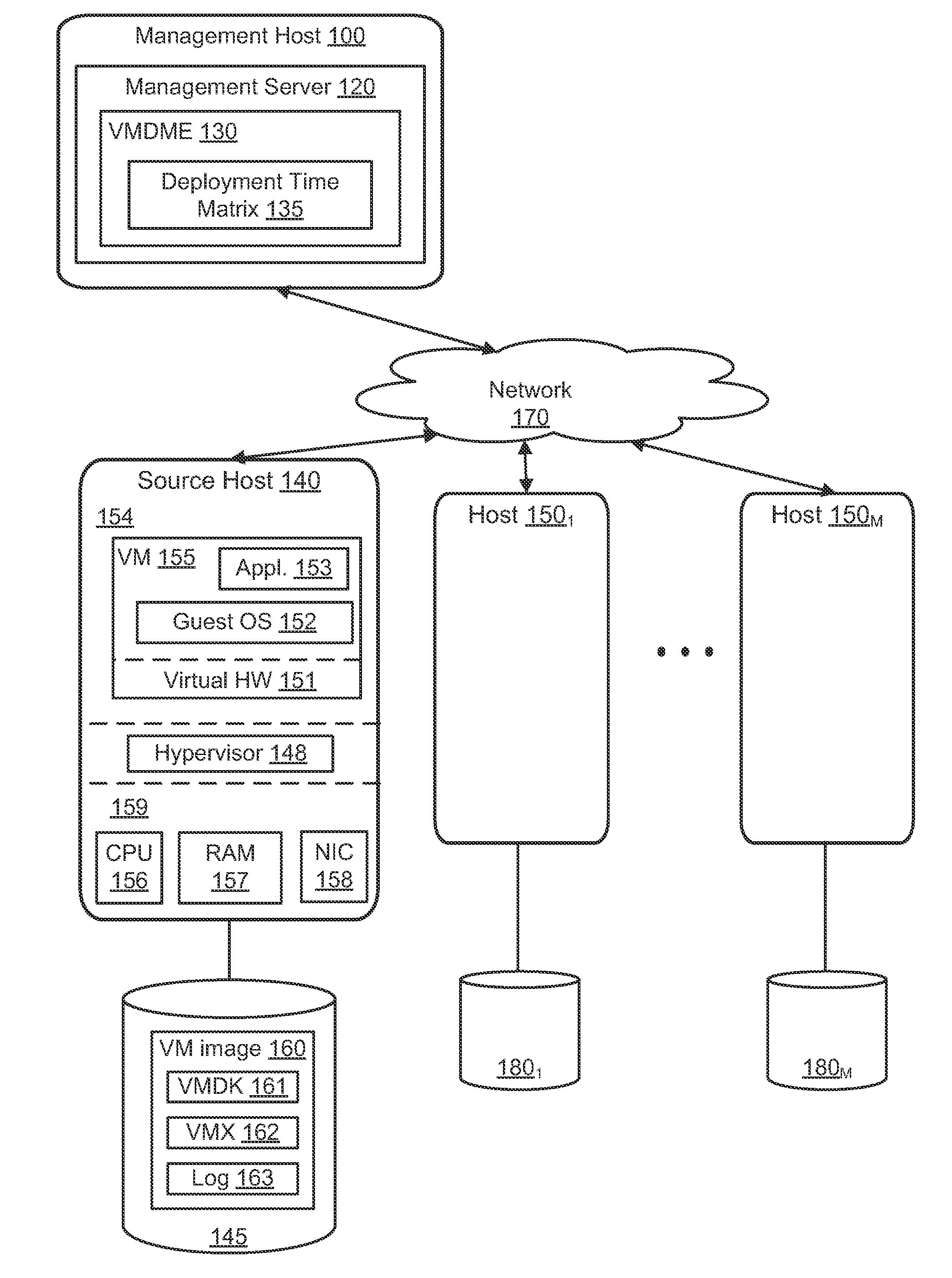
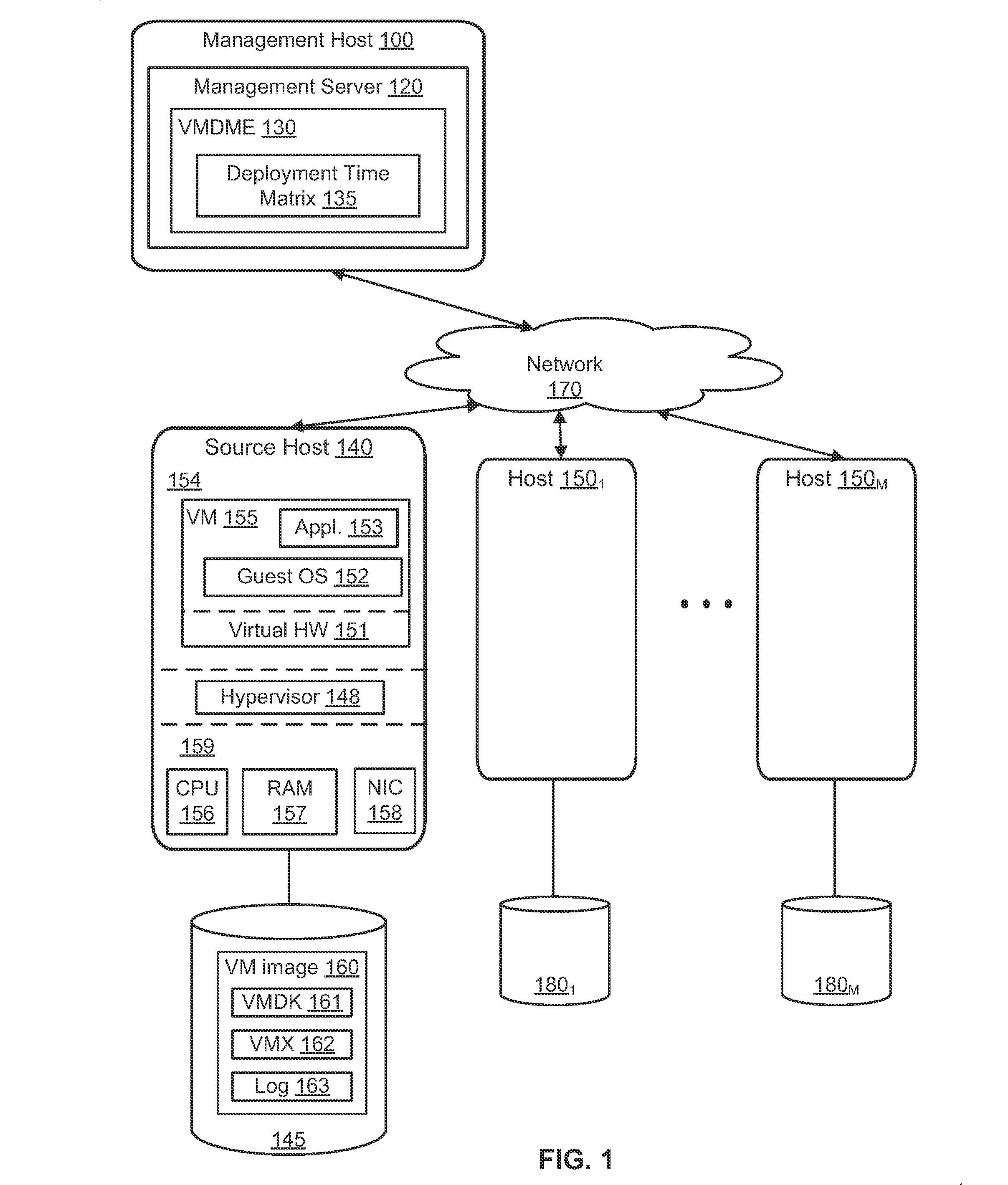
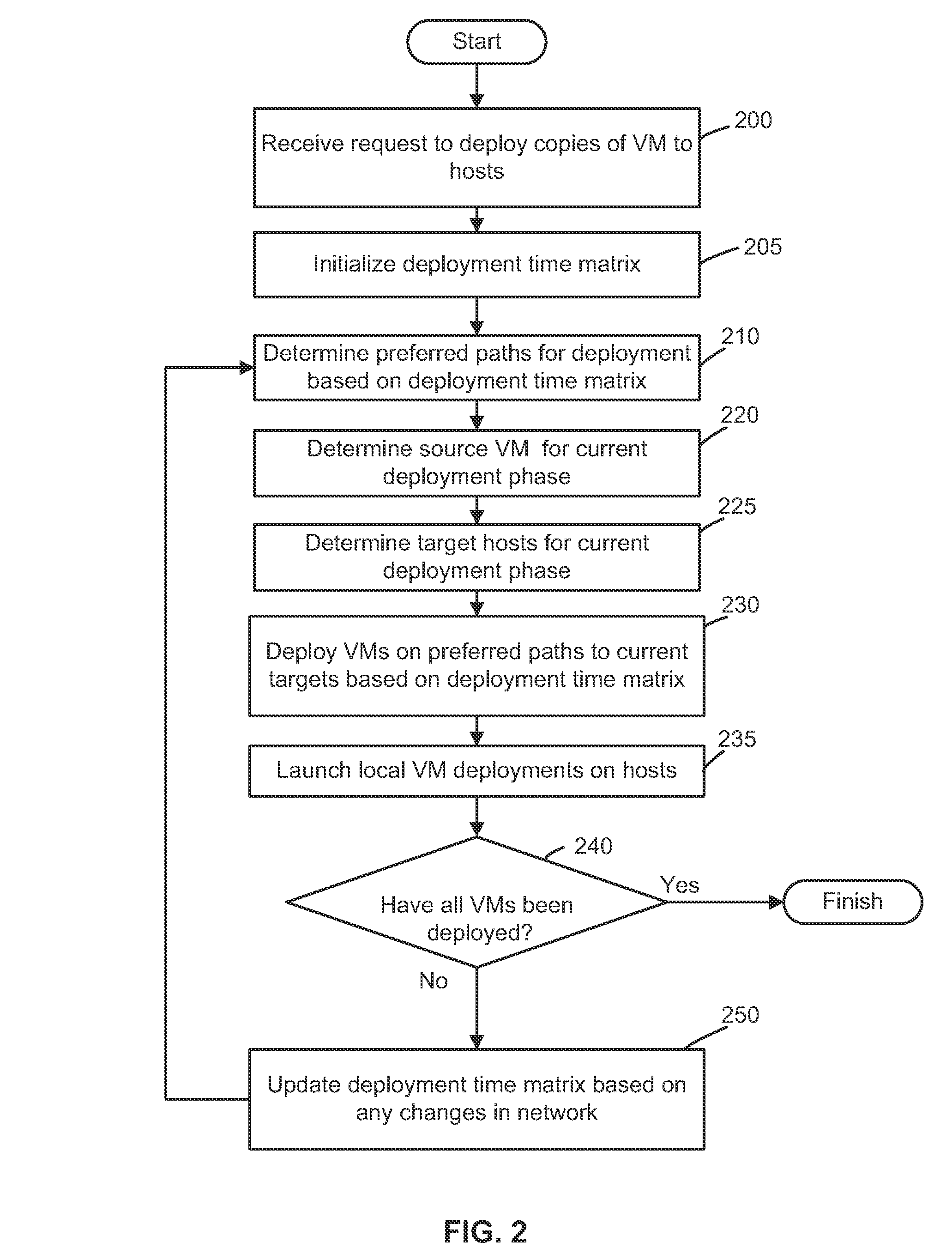
Virtual machine deployment and management engine
A virtual machine deployment and management engine deploys virtual machines to physical host computers based on a deployment time matrix. The deployment time matrix specifies approximate amounts of time used to clone or deploy a virtual machine from every host computer to every other host computer. The virtual machine deployment and management engine selects a deployment path based on the deployment times and executes the clone or deploy operations.
Owner:VMWARE INC
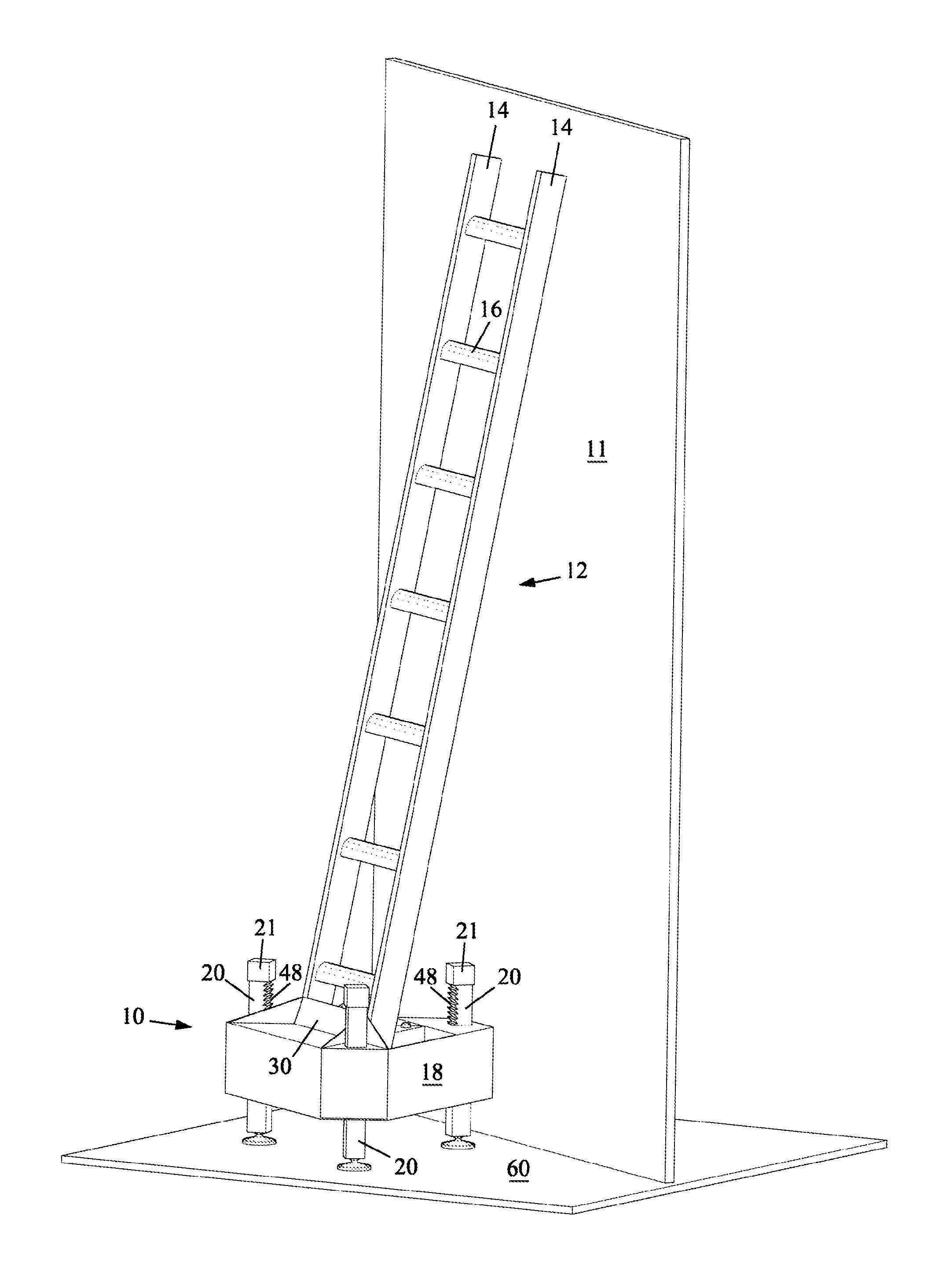
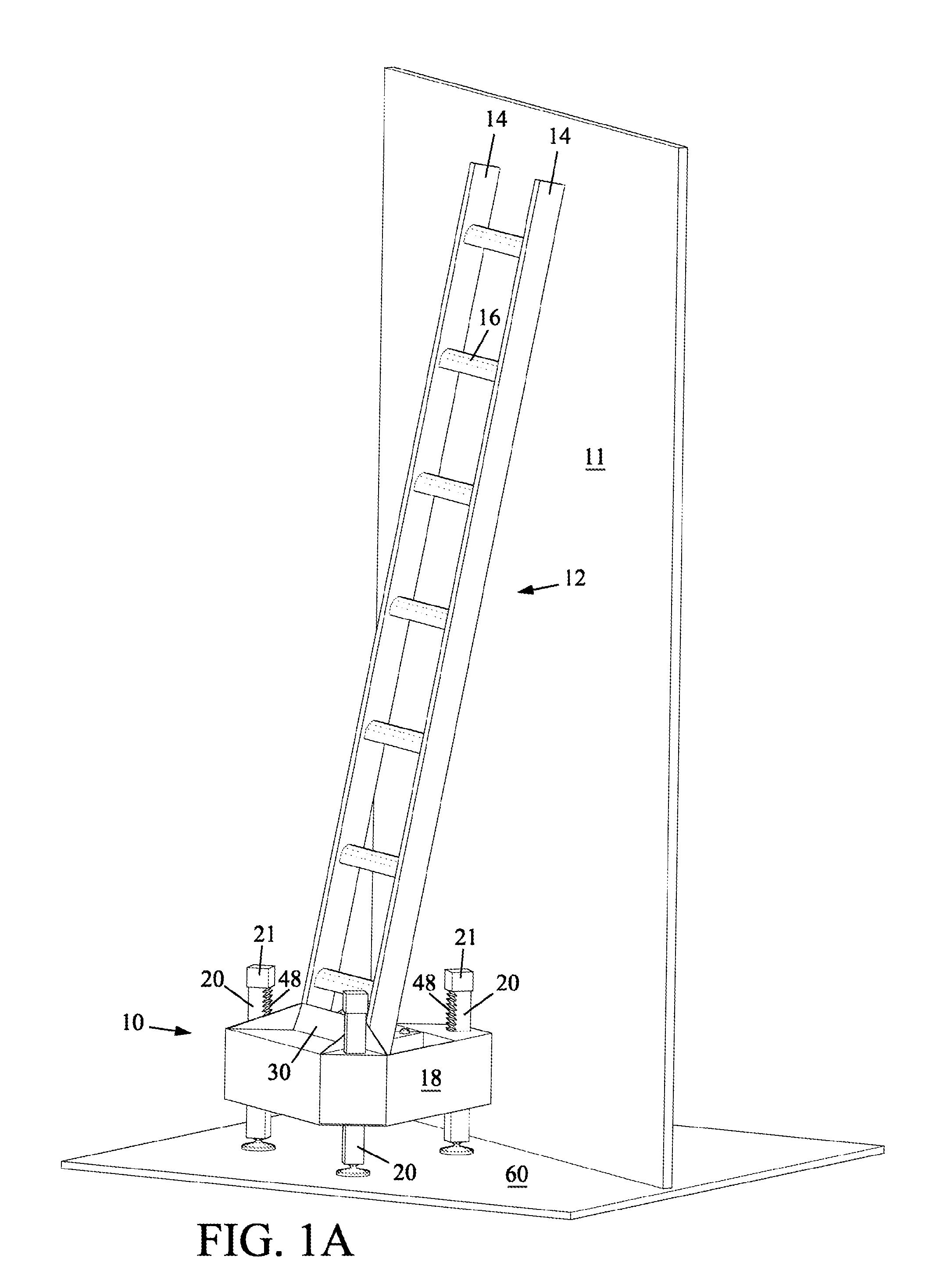
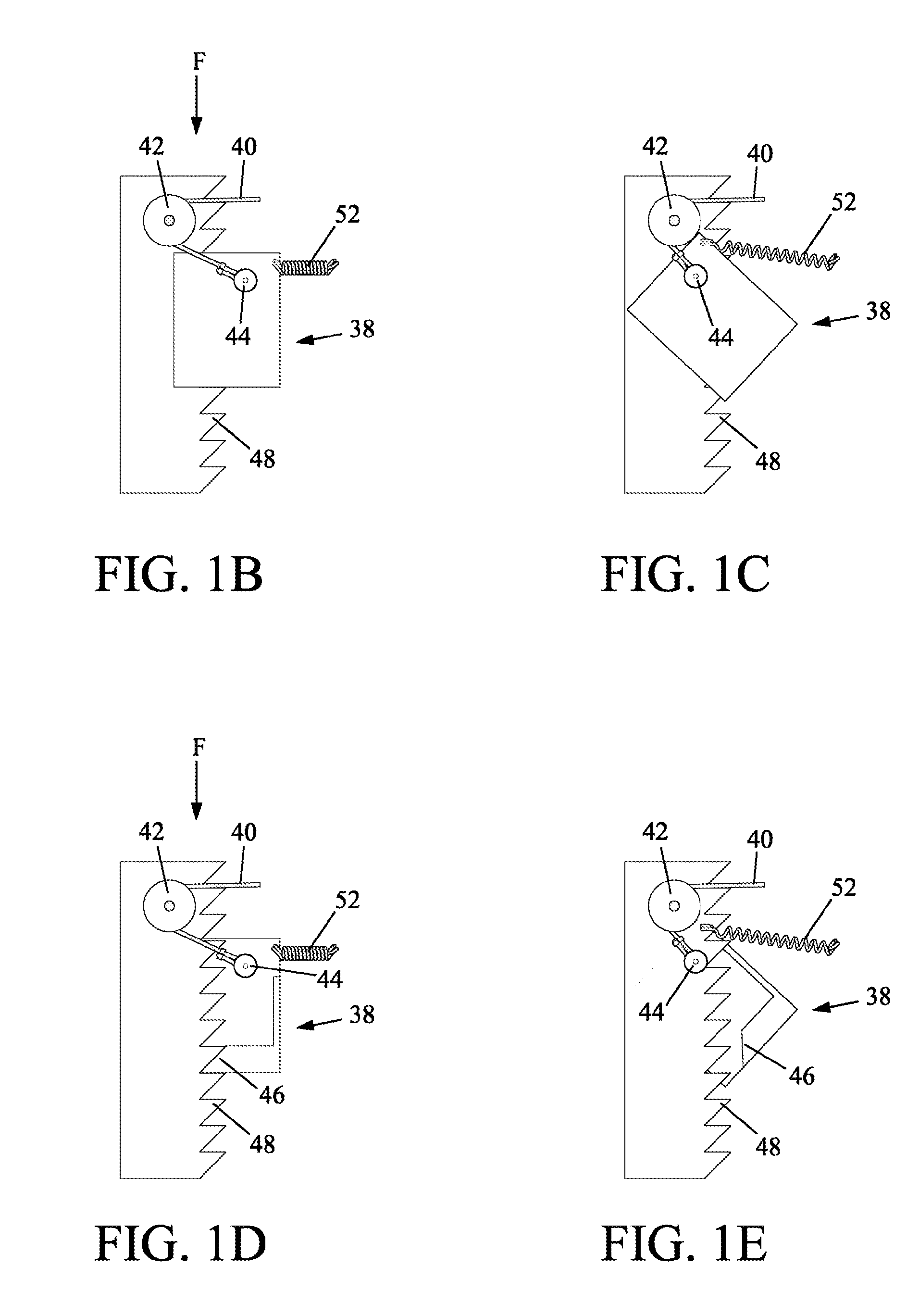
Ladder support device
A portable leveling device capable of supporting any types of ladders, scaffolds, and other objects requiring leveled support regardless of object size when a plurality of the devices is used. The device may be deployed by one hand automatically and instantly quick over a terrain of virtually any profile. The device is capable of projecting an extension ladder position eliminating human error and reducing deployment time when the ladder is actually positioned. The device is capable of indicating deployment faults before use and allows visual inspection of the parts at fault without disassembling. The device is lightweight, can be easily carried with one hand, and stored compactly.
Owner:MICHNIK ALISA +1
Method and system for automatically transitioning of configuration settings among computer systems
InactiveUS20080215867A1Delay transitionReduce configurationDatabase updatingSoftware engineeringDeployment timeData file
A method and system for automatically transiting configuration settings among computer systems. Multiple configuration settings comprising a computer “personality” are located on a source computing system using multiple transition rules from a personality object. The computer personality includes customization choices, data files, electronic mail, system preferences, application customization choices, the network environment, browser information, etc. The configuration settings are extracted from multiple locations on the source computing system. The multiple extracted configuration settings are stored in a pre-determined transition format. The multiple extracted configuration settings are manipulated. A transition package is created from the multiple manipulated configuration settings. The transition package includes the multiple manipulated configuration settings. The transition package is sent to a target computing system. The transition package is infused on the target computing system to automatically transition configuration settings from the source computing system to the target computing system. The method and system may vastly reduce transition, configuration and deployment times for service providers, corporations, and end-users when a new computing system is deployed.
Owner:TRANXITION CORP
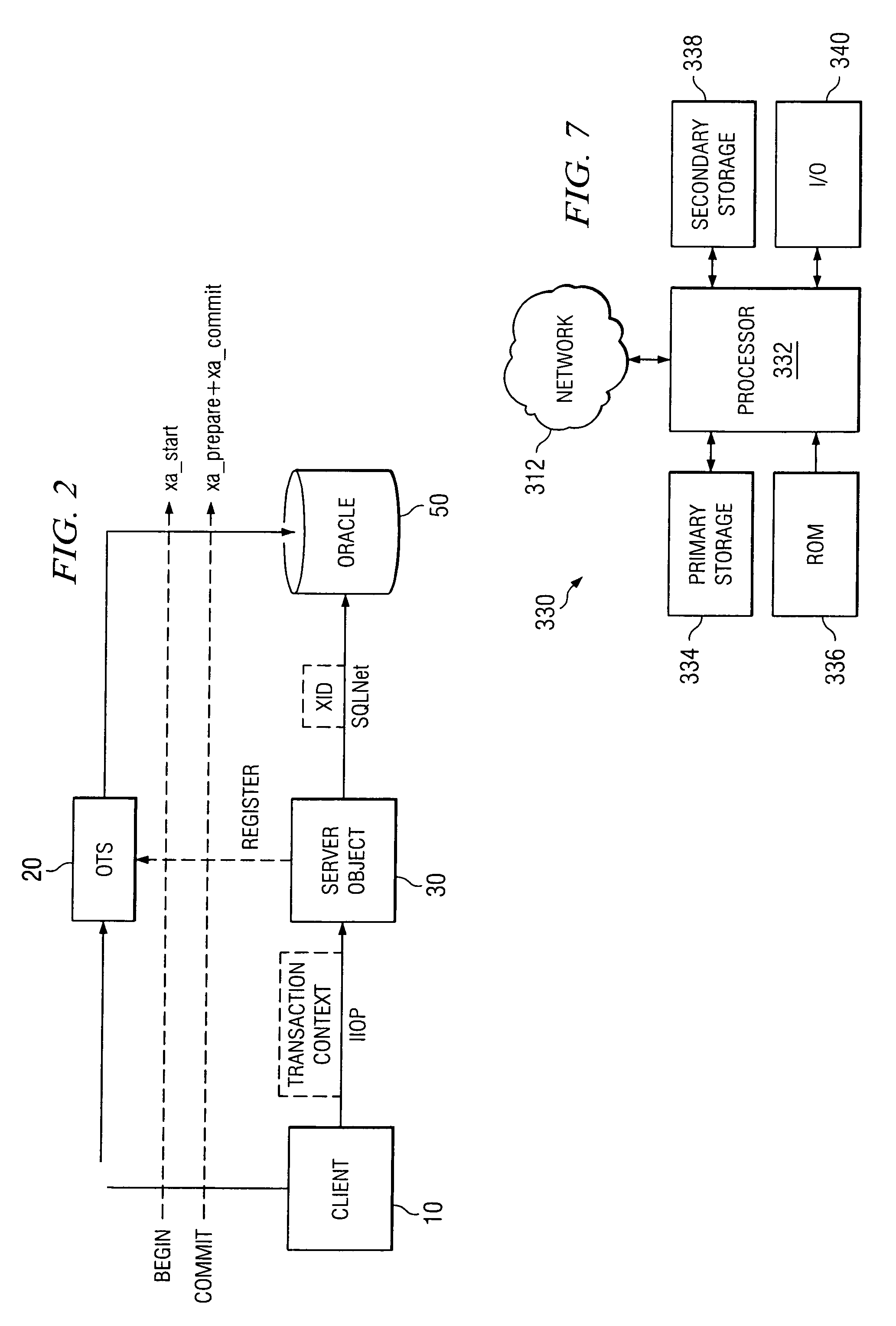
Method for deployment modification of transactional behavior in corba OTS
InactiveUS6944643B1Digital data information retrievalMultiple digital computer combinationsDeployment timeTransactional memory
The present invention extends the programming model of OTS by providing a unique model that offers both flexibility and ease of use. This model separates the transactional behavior of CORBA method from the IDL interface. The transactional behavior of the CORBA method is specified in a deployment descriptor file. Each method is associated with a transactional policy. The server reads the policies of the methods during deployment time and makes decisions of making the method transactional based on the policy. Changing the transactional policy of a method is as easy as modifying the deployment descriptor and redeploying the server. If either of the two usage models that OTS offers is used, making a method transactional means that the IDL interface has to change, causing all the software components in the system to re-compile. With the present invention, such a change can be accomplished without need for such recompilation.
Owner:SPRINT CORPORATION
System and method for bundling deployment descriptor files within an enterprise archive for fast reliable resource setup at deployment time
System and method to bundle deployment descriptors with enterprise archives (“EAR”). An application is bundled with at least one deployment descriptor file within an EAR. The deployment descriptor file defines properties to establish connectivity to network services. Syntax of the deployment descriptor files is verified with reference to rules definition files included within the application server. Connectivity to the network services is established based on the properties defined in the deployment descriptor files, if the syntax of the deployment descriptor files verifies as valid.
Owner:SAP AG
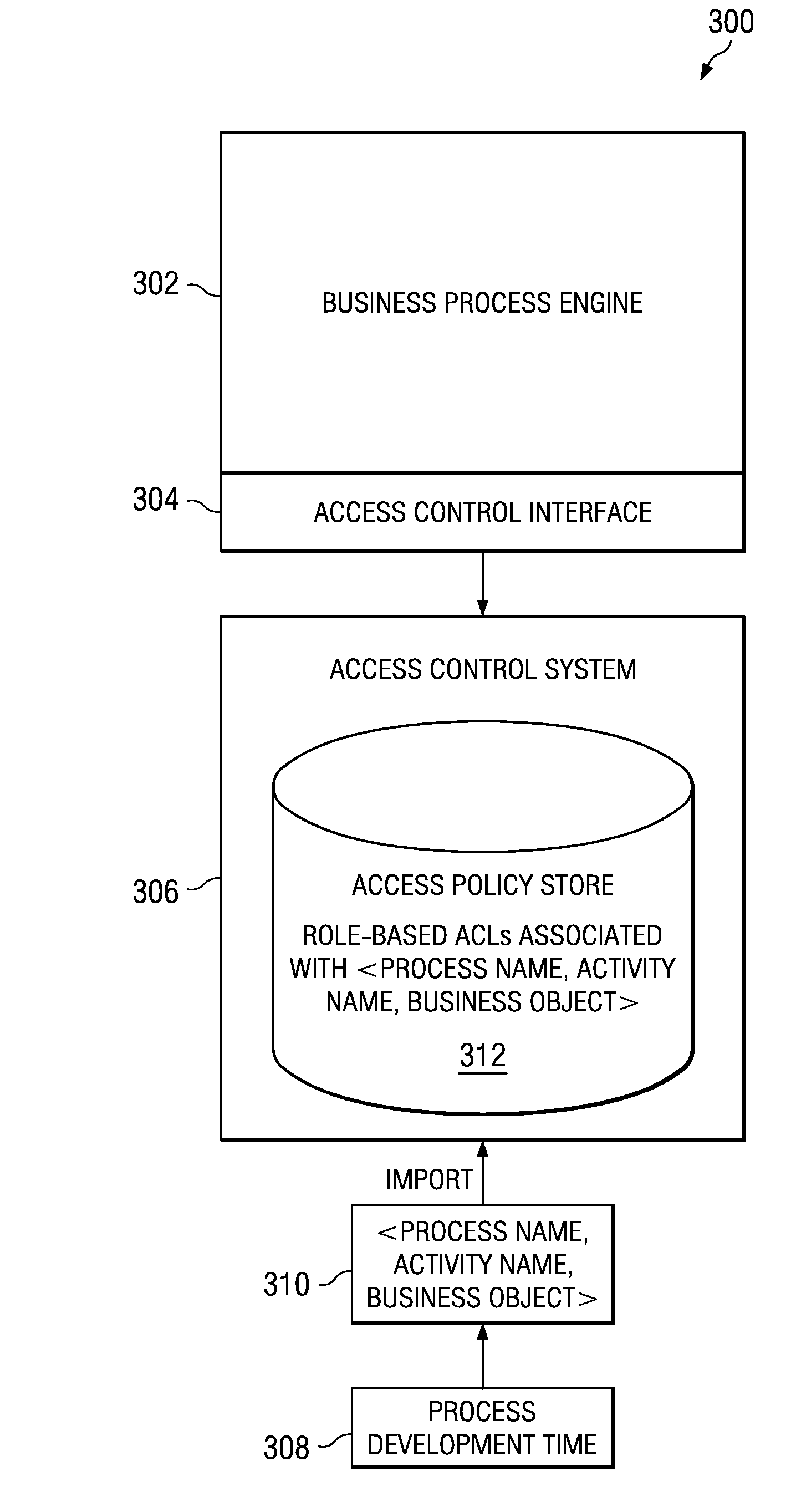
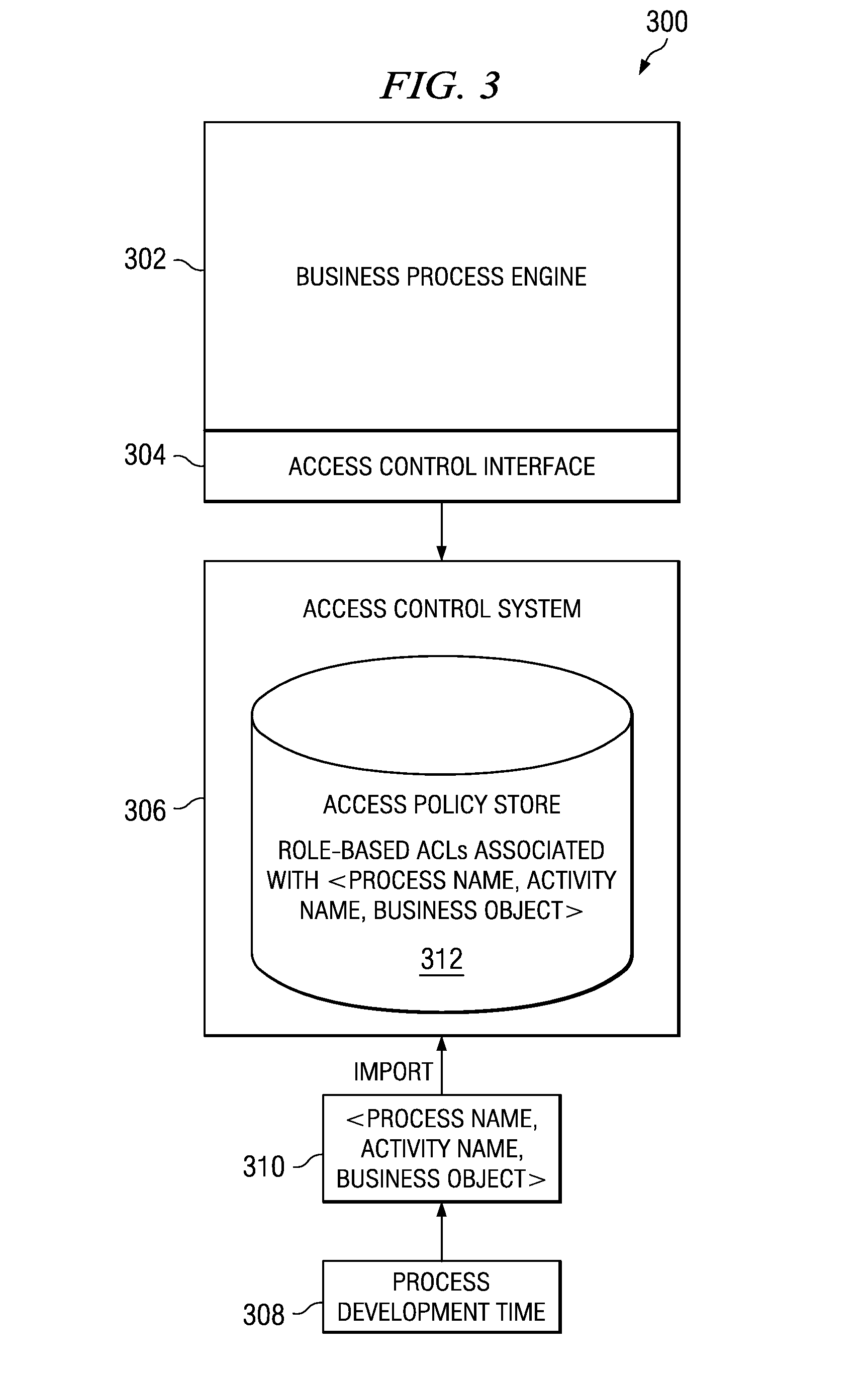
Policy-Based Access Control Approach to Staff Activities of a Business Process
InactiveUS20080263060A1Digital data information retrievalProgram controlData processing systemDeployment time
A computer implemented method, data processing system, and computer program product for dynamically binding business process activities to human entities at deployment time. Identification information about a staff activity in a business process is received from a process server at an access control system external to the process server. Responsive to initiation of the business process, the staff activity is resolved at the access control system at runtime by assigning the staff activity to a user based on an access policy of the access control system to form a staff activity assignment. The staff activity assignment is communicated from the access control system to the process server. The process allows the development of the business process to be entirely decoupled from staff activity resolution at runtime.
Owner:IBM CORP
Service management method and device for server cluster
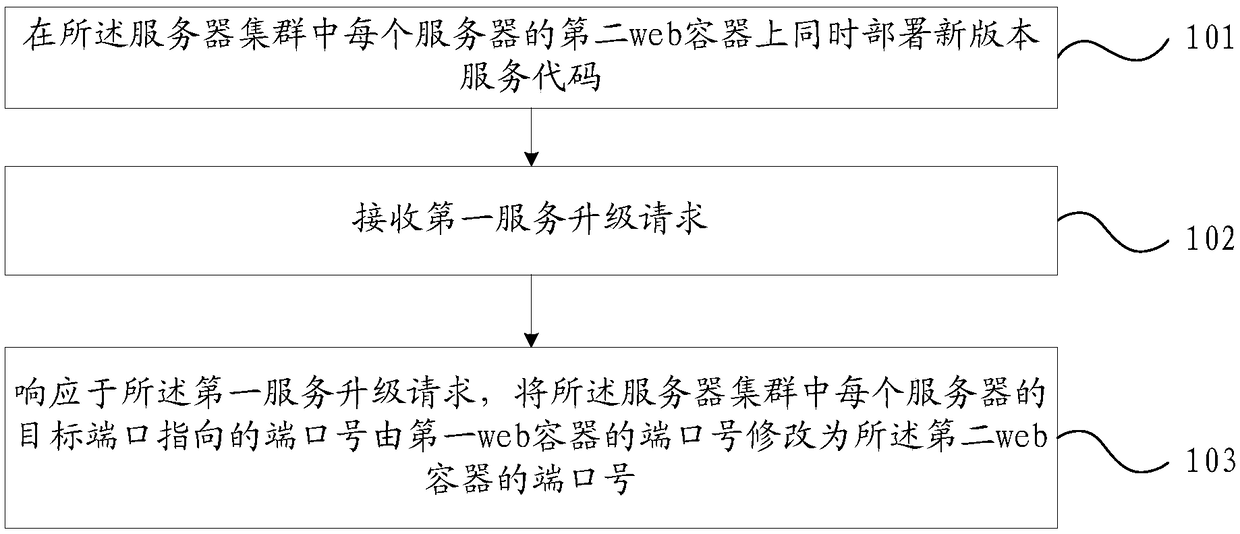
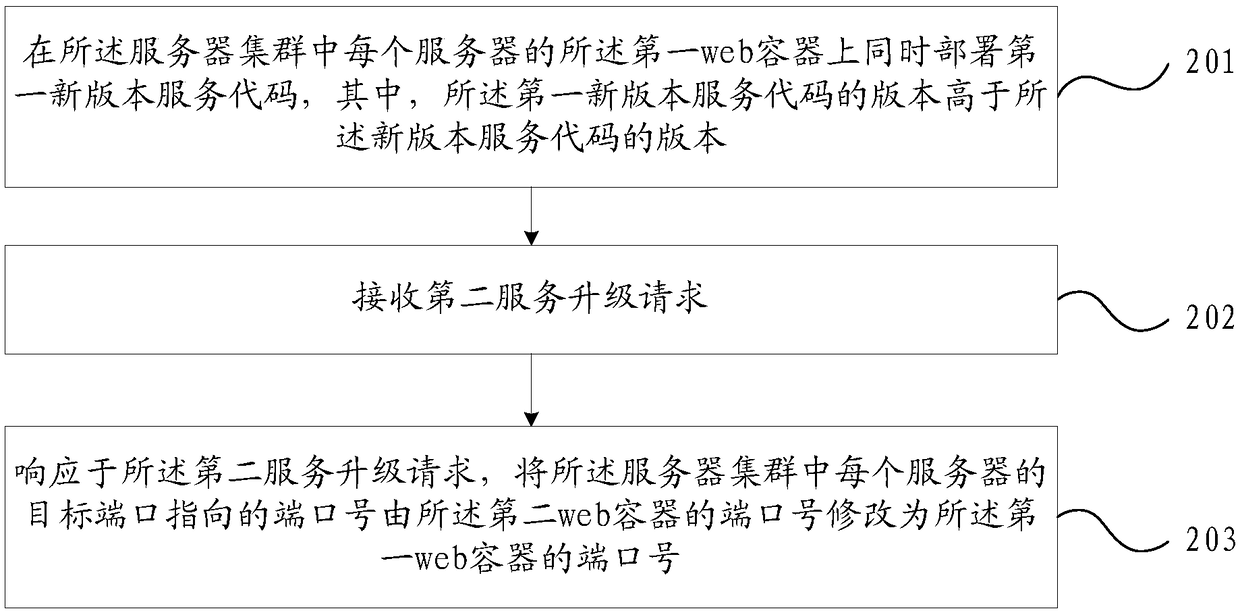
PendingCN109347652AReduce deployment timeReduce service escalation processing timeData switching networksSoftware deploymentDeployment timeWeb container
The invention provides a service management method and device for a server cluster. The method comprises the following steps: simultaneously deploying a new version of service code on a second web container of each server in the server cluster; receiving a first service upgrade request; modifying the port number pointed by a target port of each server in the server cluster into the port number ofthe second web container from the port number of a first web container in response to the first service upgrade request, wherein the target port is a port for pointing to the port number of the web container; and each server in the server cluster is preconfigured with a first web container and a second web container. According to the service management method and device for a server cluster in theinvention, two web containers are deployed on the server so that the new version of service code can be deployed to a plurality of second web containers in the cluster while the first web container is provided with a service, thereby reducing the code deployment time when the service of the server cluster is upgraded.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
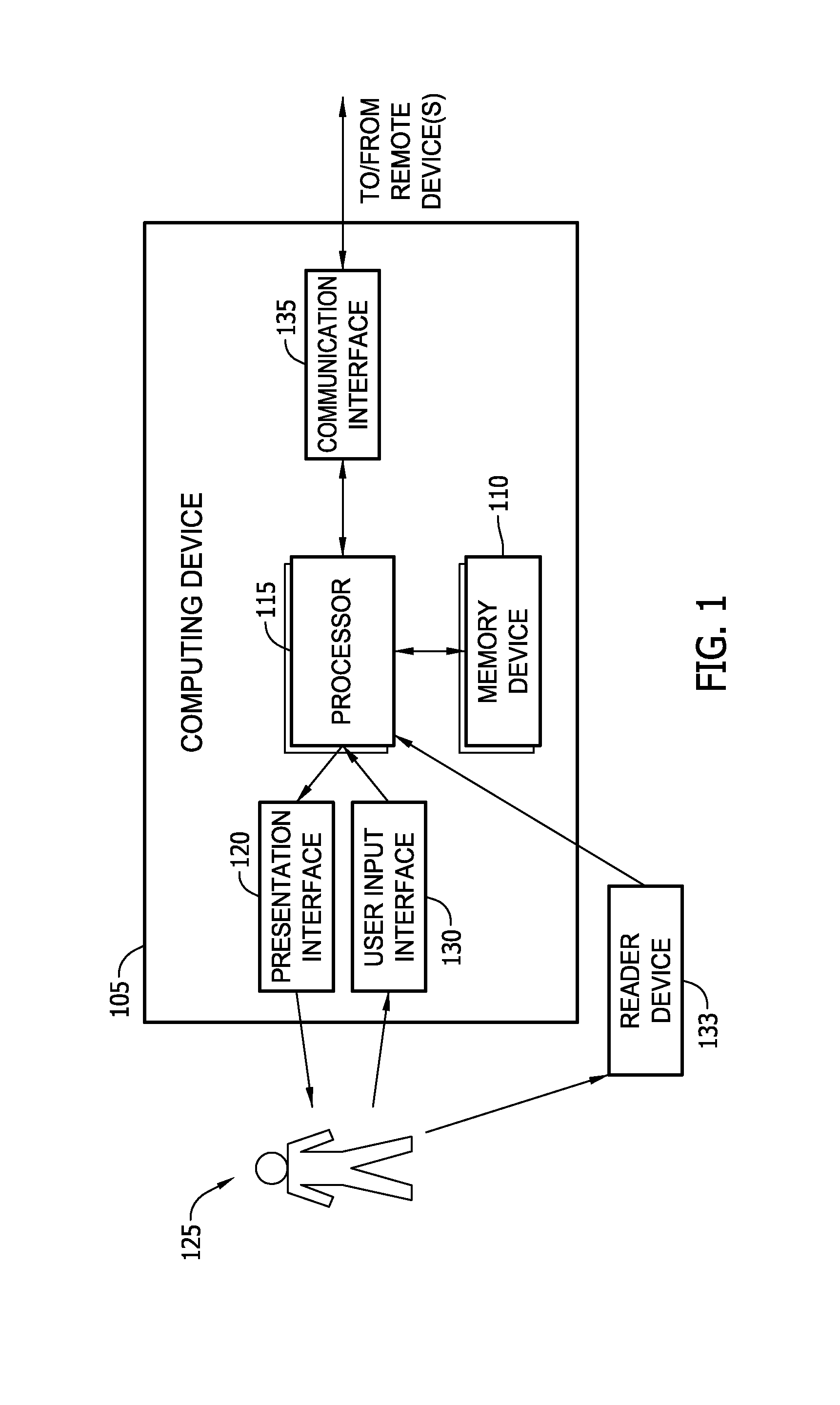
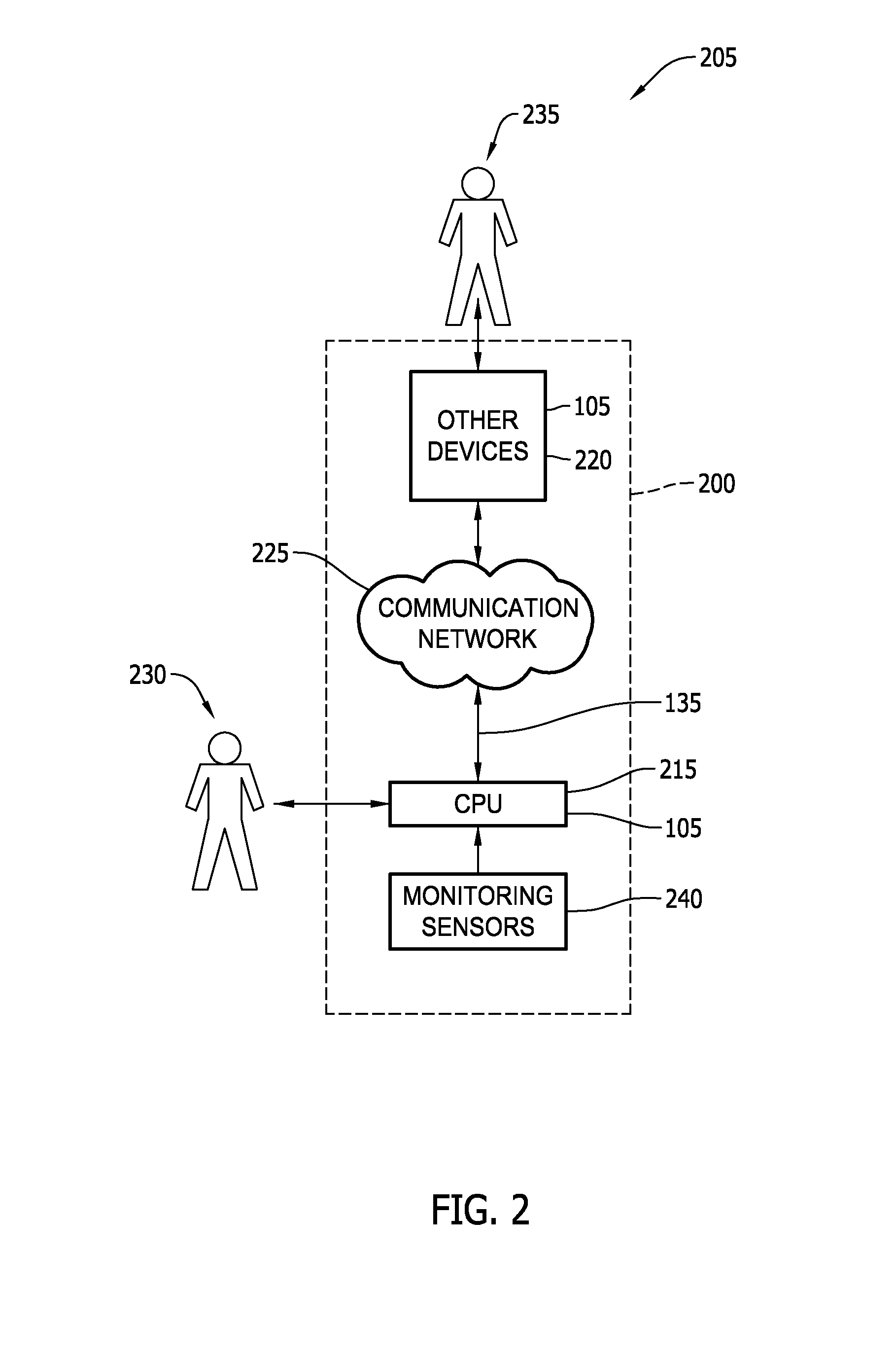
Method and system for use in facilitating patch change management of industrial control systems
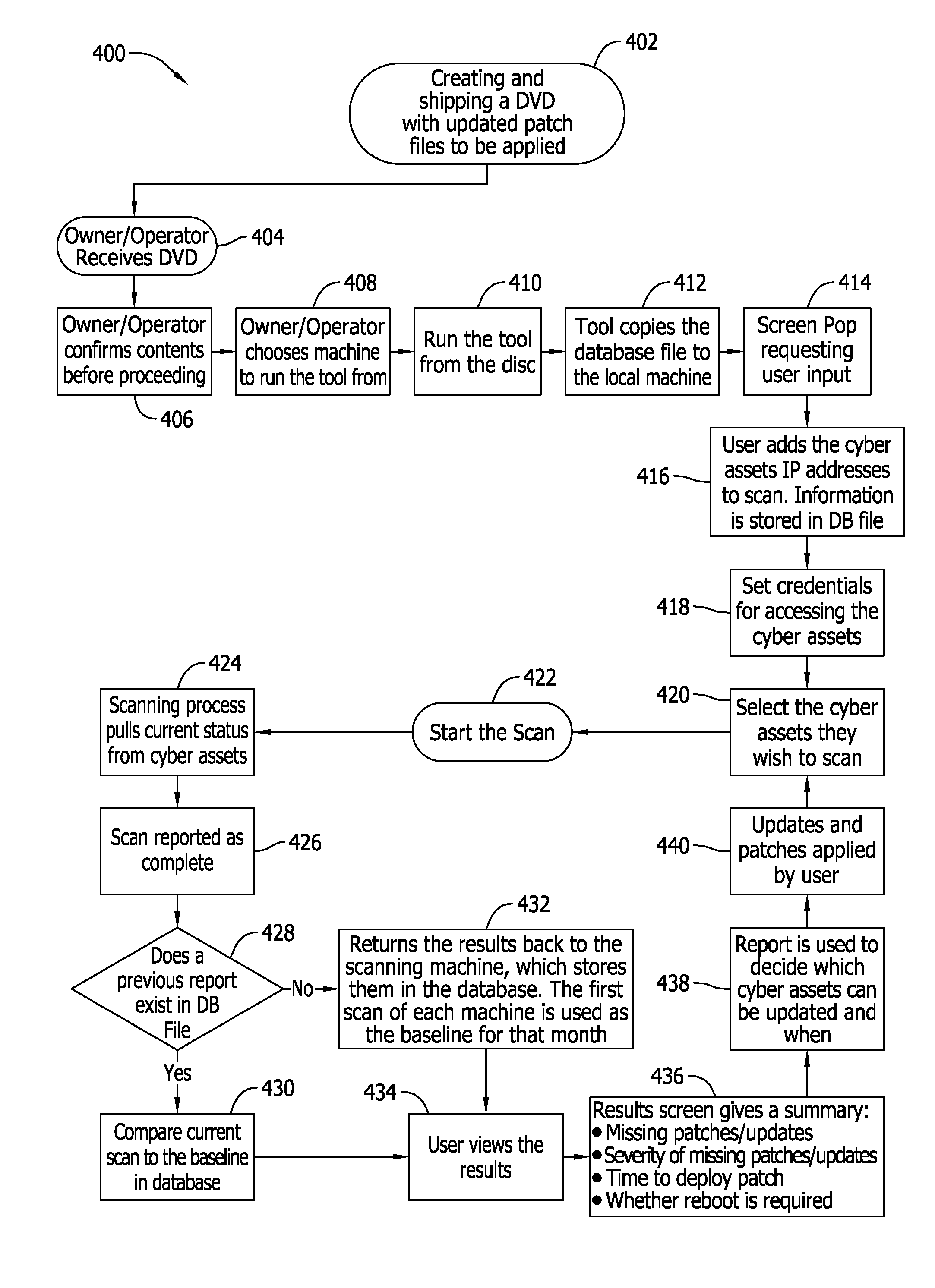
An offline patch change management system for an industrial facility includes at least one reader device configured to read patch update information stored on computer-readable storage media inserted therein. The industrial facility includes an industrial control system that includes at least cyber asset. The system also includes a memory device coupled to the reader device. The memory device is configured to store the patch update information. The system further includes a processor coupled to the memory device. The processor is programmed to scan the at least one cyber asset. The processor is also programmed to generate a scan report including a patch status for at least one patch not operatively resident on the at least one cyber asset. The scan report includes a deployment temporal period value for deployment of the patch.
Owner:BAKER HUGHES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com