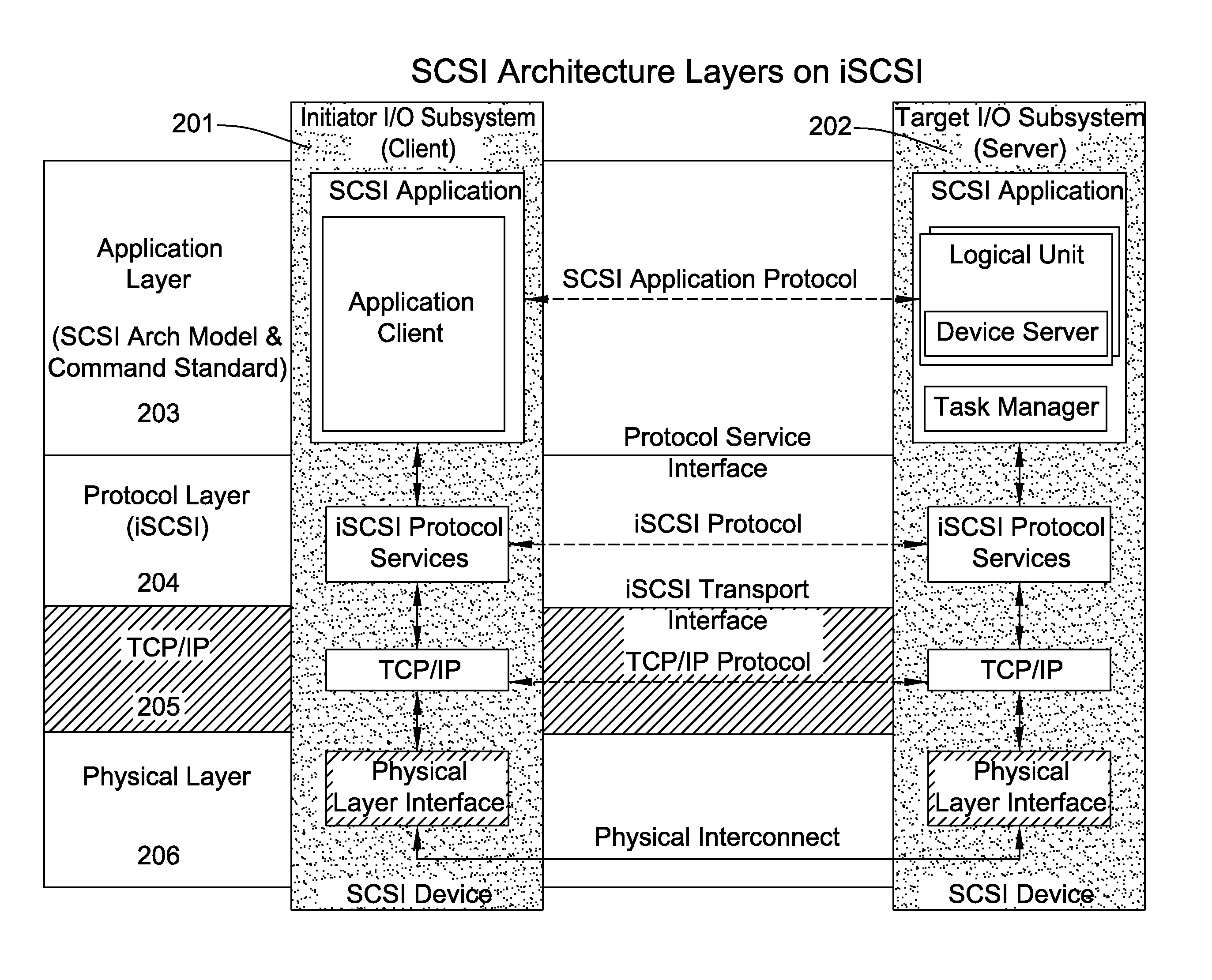
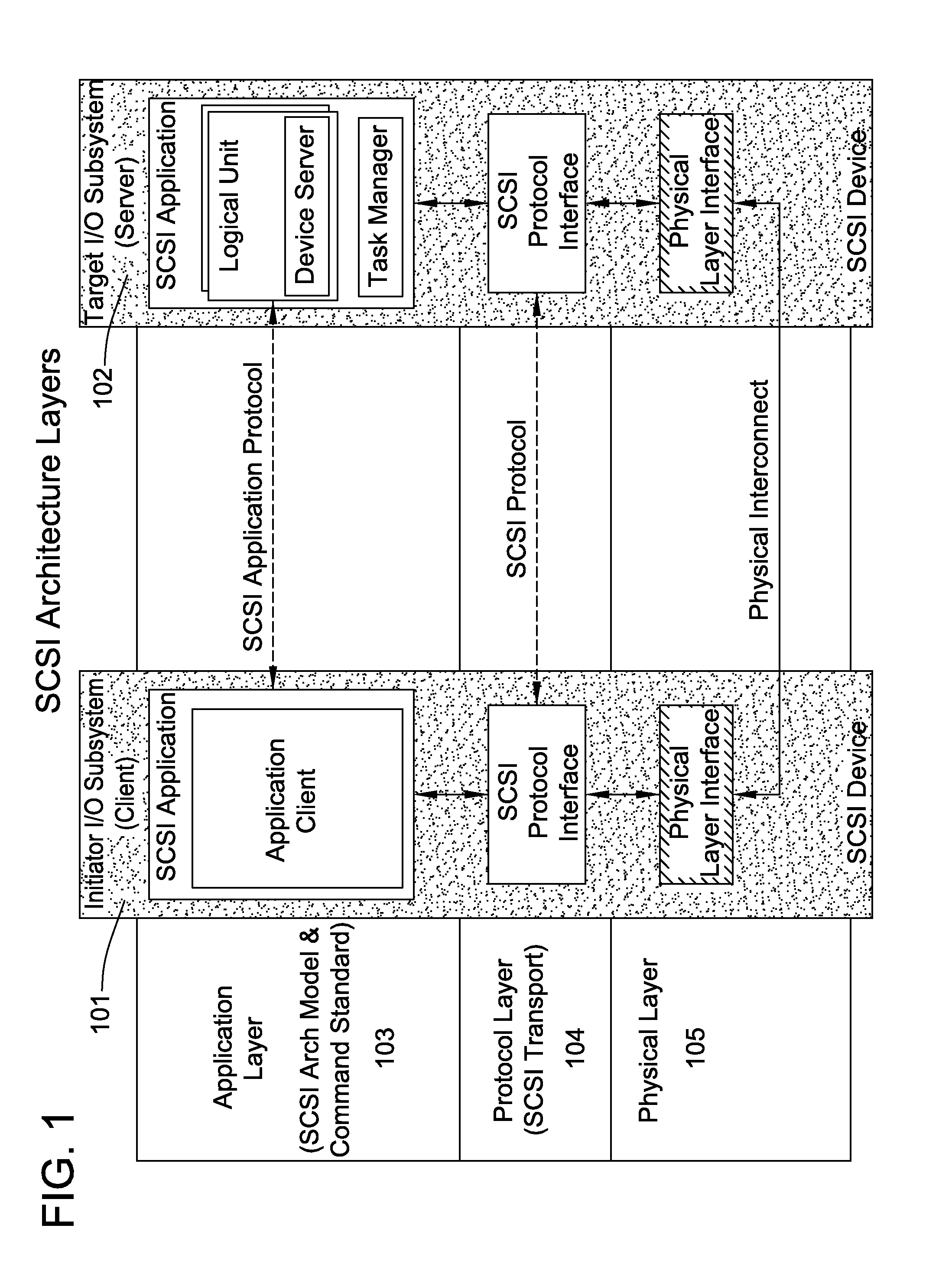
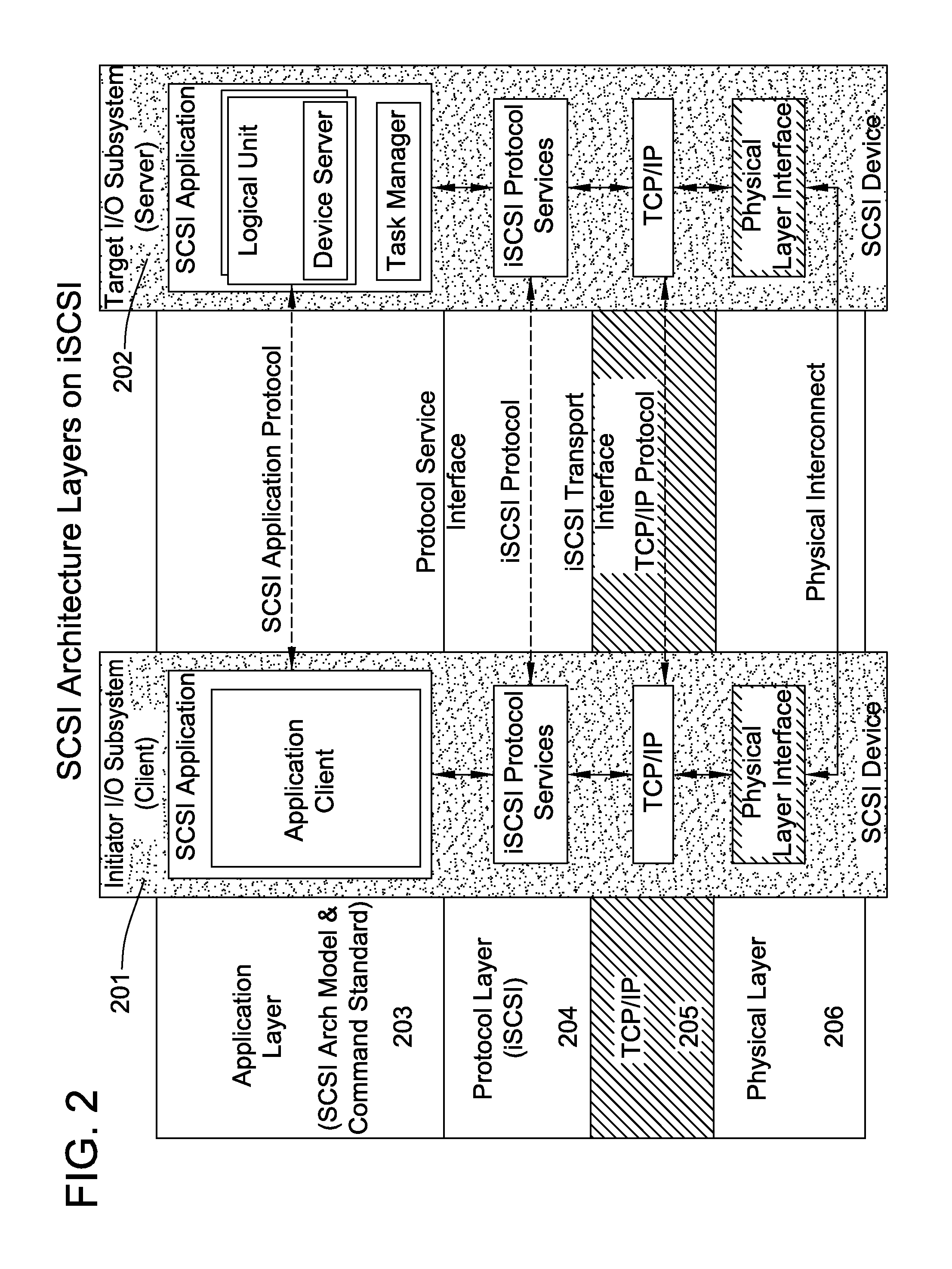
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1162 results about "Architecture of Integrated Information Systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The ARIS concept (Architecture of Integrated Information Systems) by August-Wilhelm Scheer aims to ensure that an enterprise information system can completely meet its requirements. This framework is based on a division of the model into description views and levels, which allows a description of the individual elements through specially designed methods, without having to include the entire model. The methodology serves as a systems development life cycle for mapping and optimizing business processes. These processes are mapped for each description view, starting with the business management question up to the implementation on data processing level.
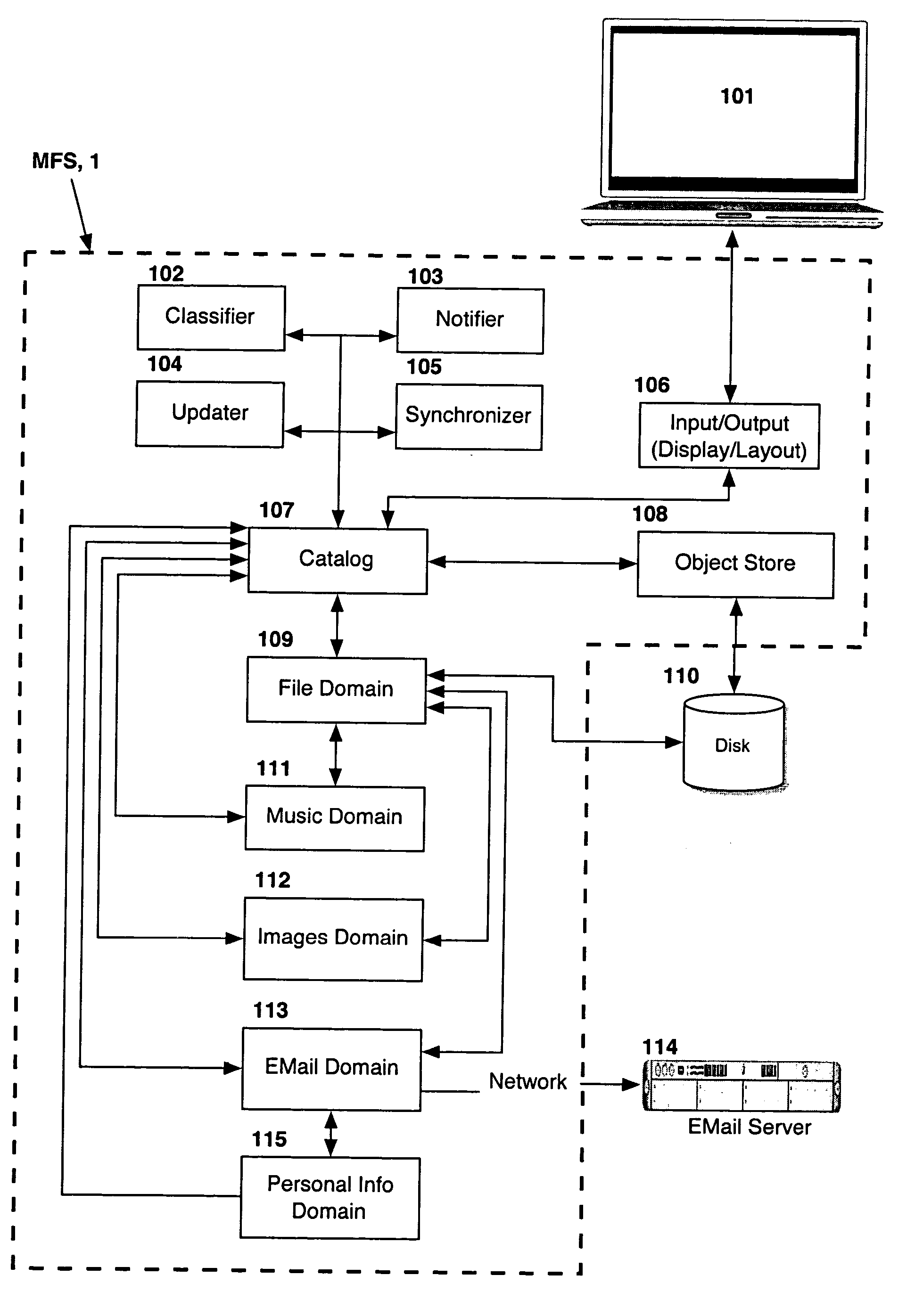
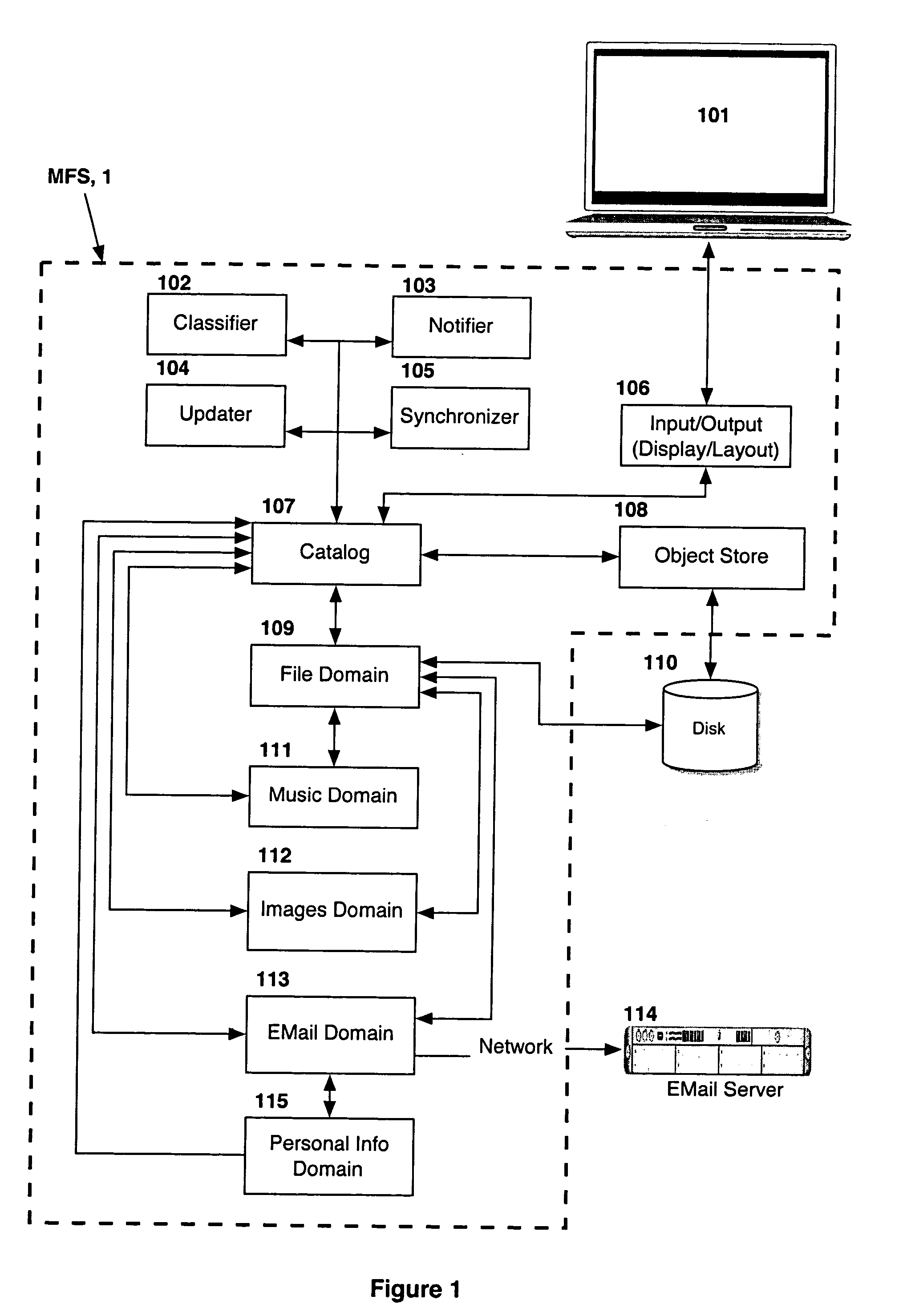
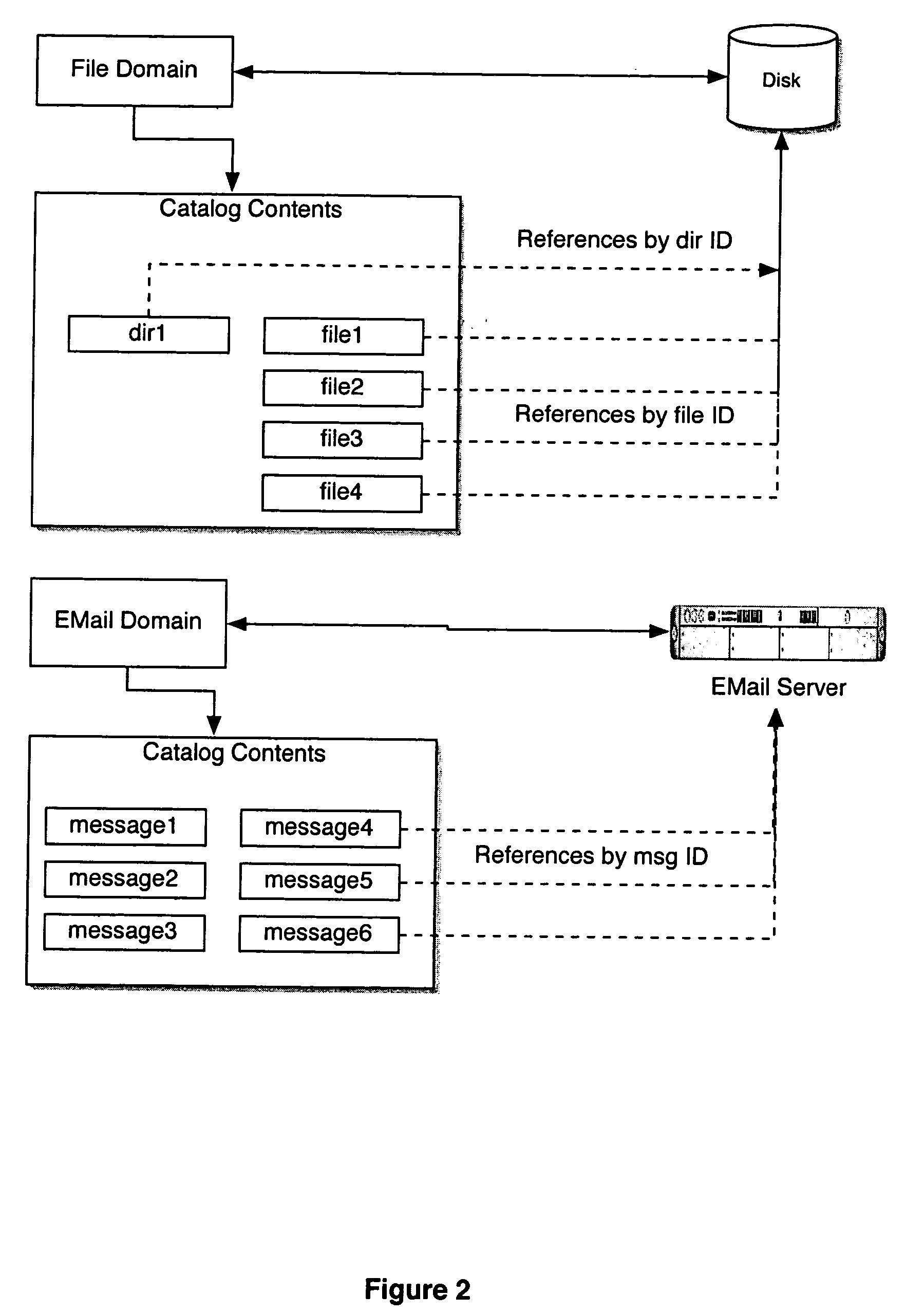
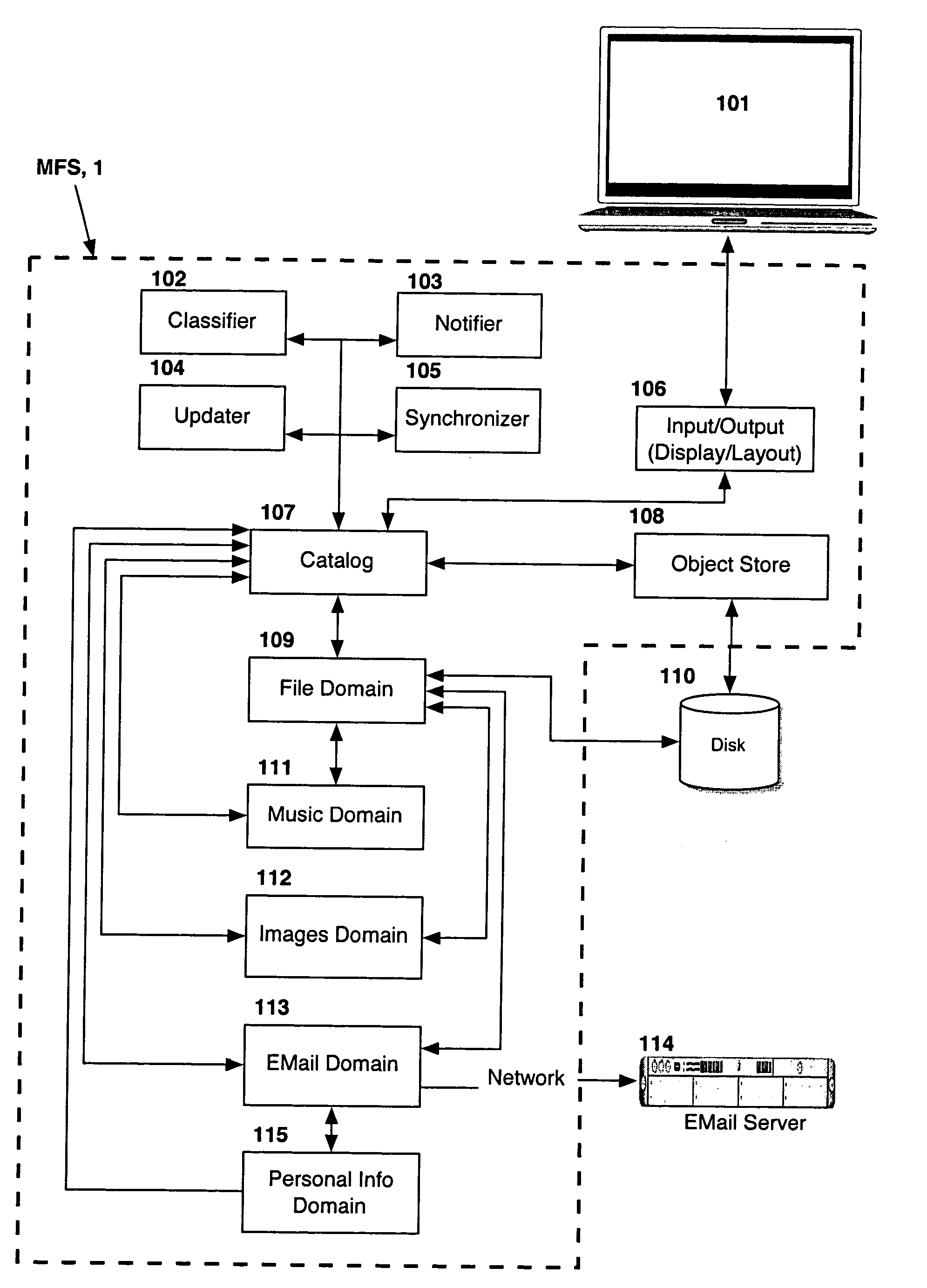
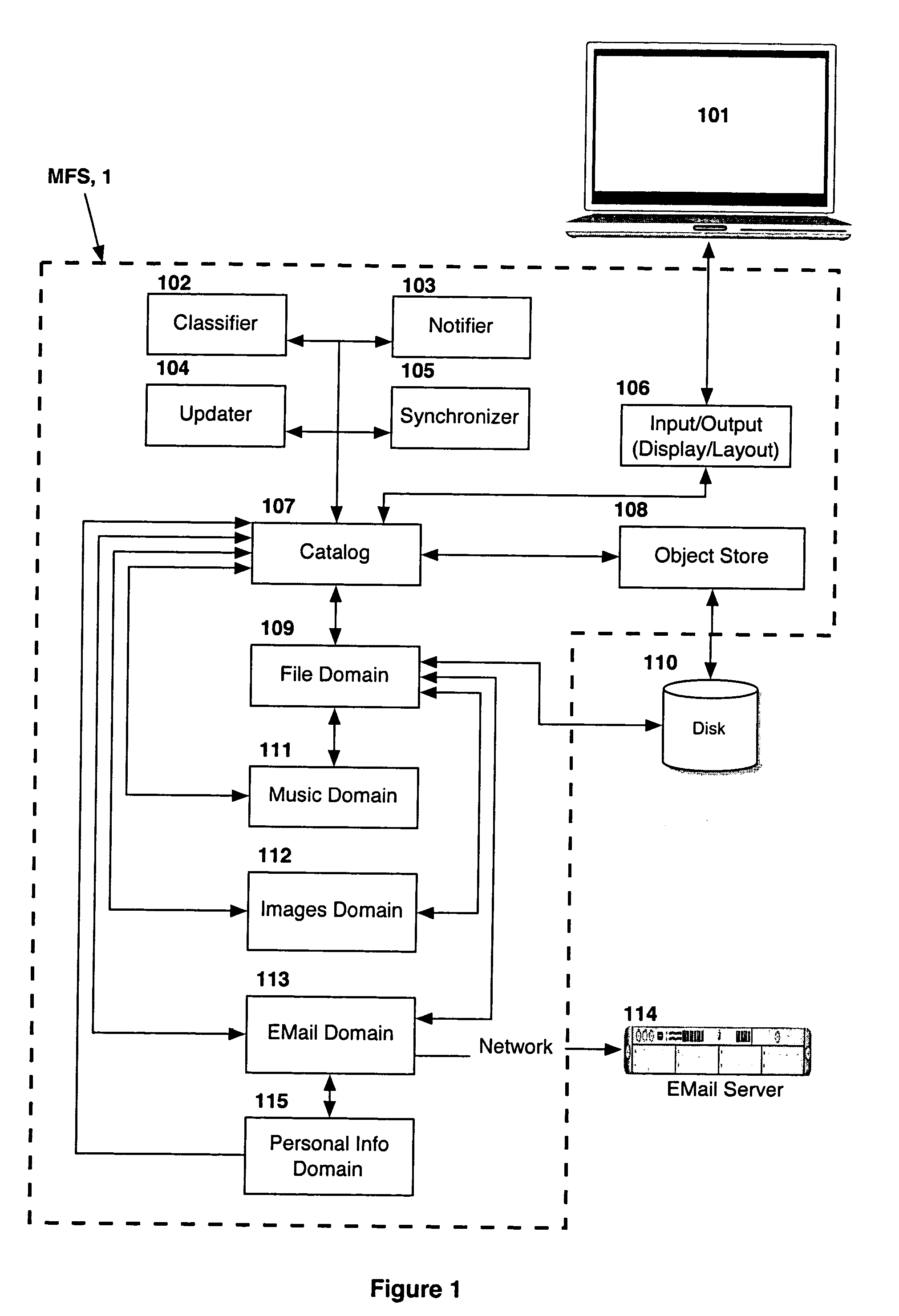
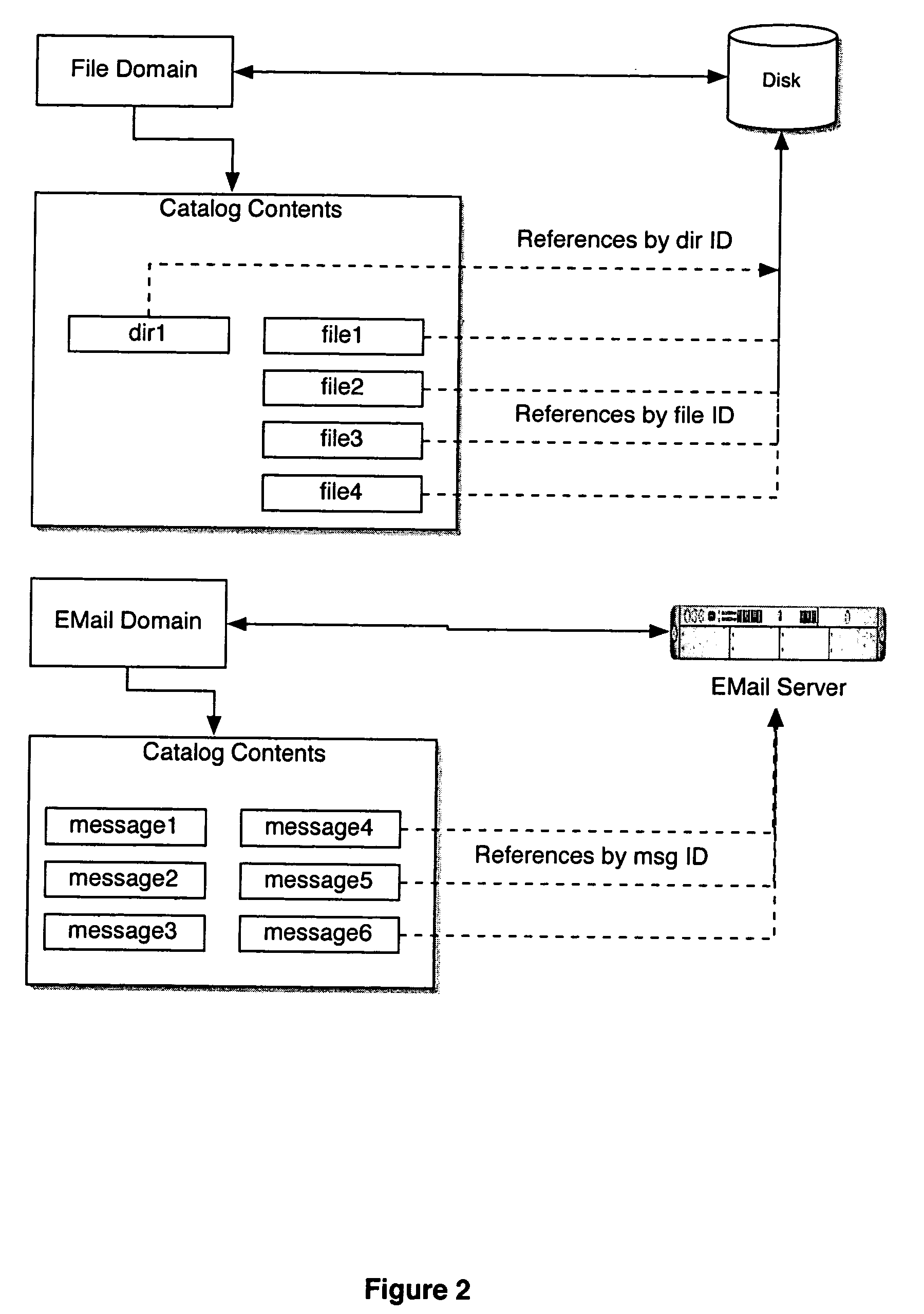
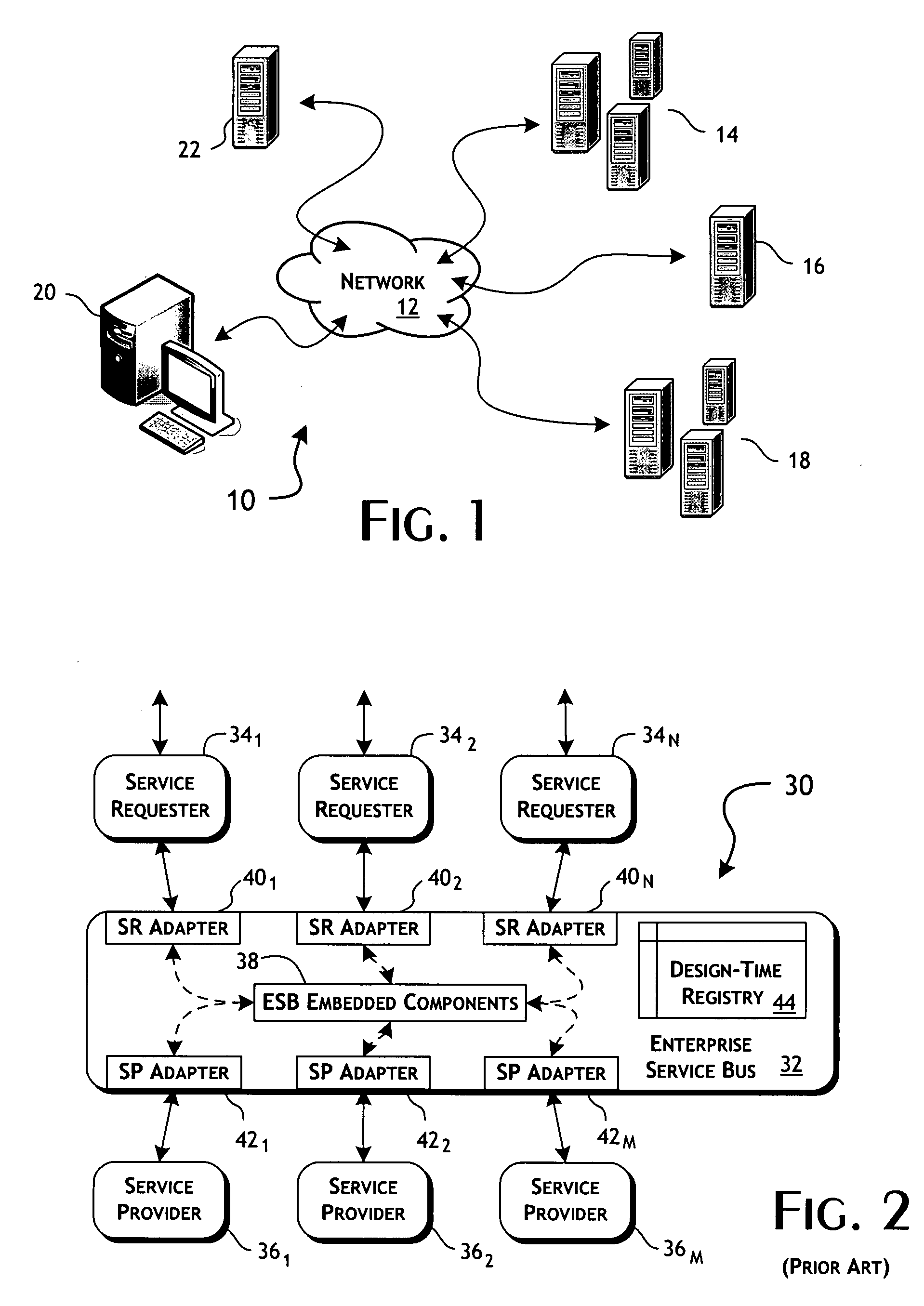
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS20040177319A1Efficient storageMultimedia data indexingFile access structuresComputer data processingData processing
A computer data processing system including a central processing unit configured with a novel integrated computer control software system for the management of data objects including dynamic and automatic organization, linking, finding, cross-referencing, viewing and retrieval of multiple objects regardless of nature or source. The inventive system provides underlying component architecture having an object-oriented database structure and a metadata database structure which is unique in storing only one instance of each object while linking the object to multiple collections and domains by unique metadata links for the grouping into and retrieval from any of the collections. The system employs configurable, extensible attribute / properties of data objects in metadata format, and a truly user-friendly configurable interface that facilitates faster, more unified, comprehensive, useful and meaningful information management. Additional features include a sticky path object hierarchy viewing system, key phrase linking, viewing by reference, and drag-and-drop relationship link creation.
Owner:EHIERARCHY LLC
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
Method and apparatus for building an intelligent automated assistant
A method and apparatus are provided for building an intelligent automated assistant. Embodiments of the present invention rely on the concept of “active ontologies” (e.g., execution environments constructed in an ontology-like manner) to build and run applications for use by intelligent automated assistants. In one specific embodiment, a method for building an automated assistant includes interfacing a service-oriented architecture that includes a plurality of remote services to an active ontology, where the active ontology includes at least one active processing element that models a domain. At least one of the remote services is then registered for use in the domain.
Owner:APPLE INC
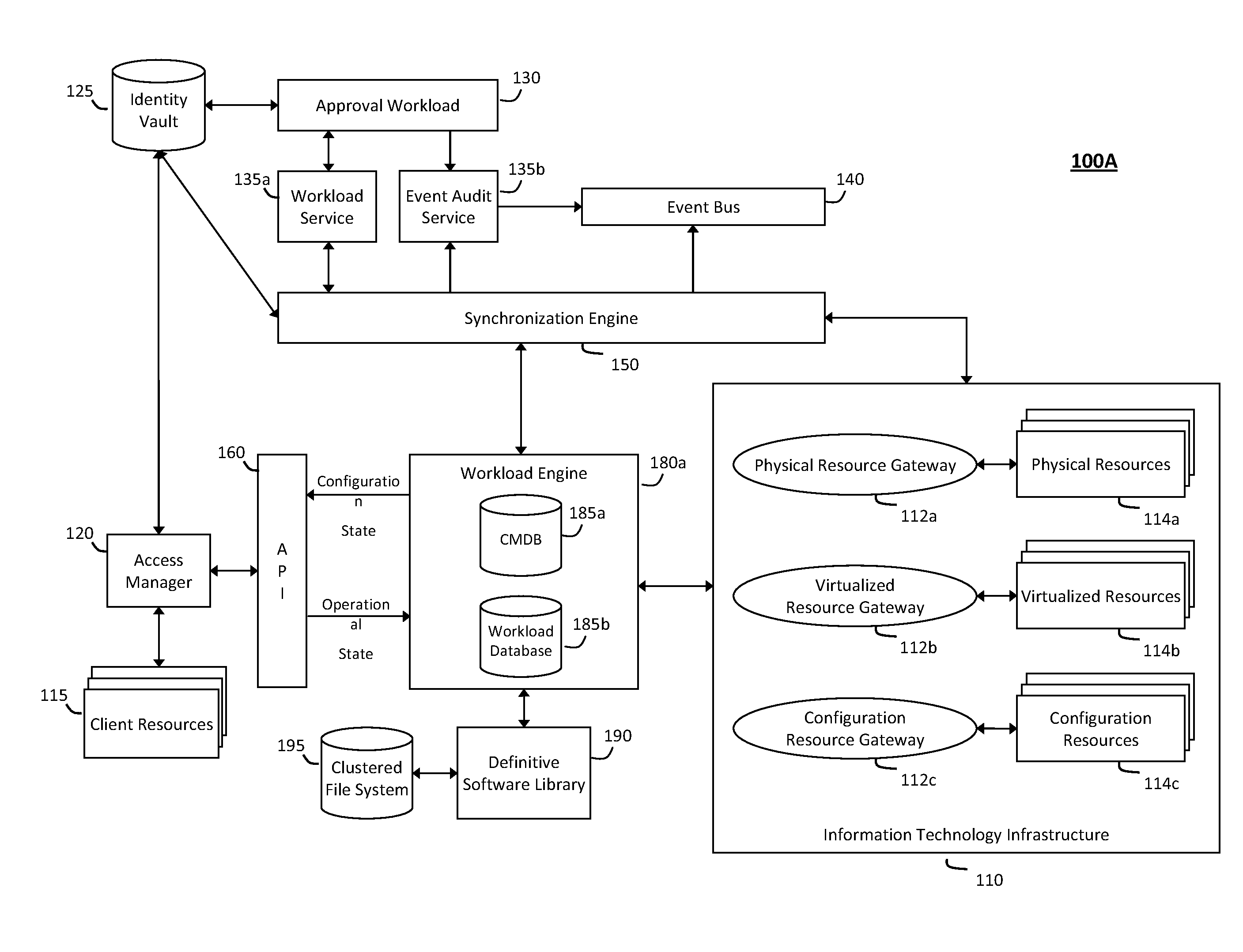
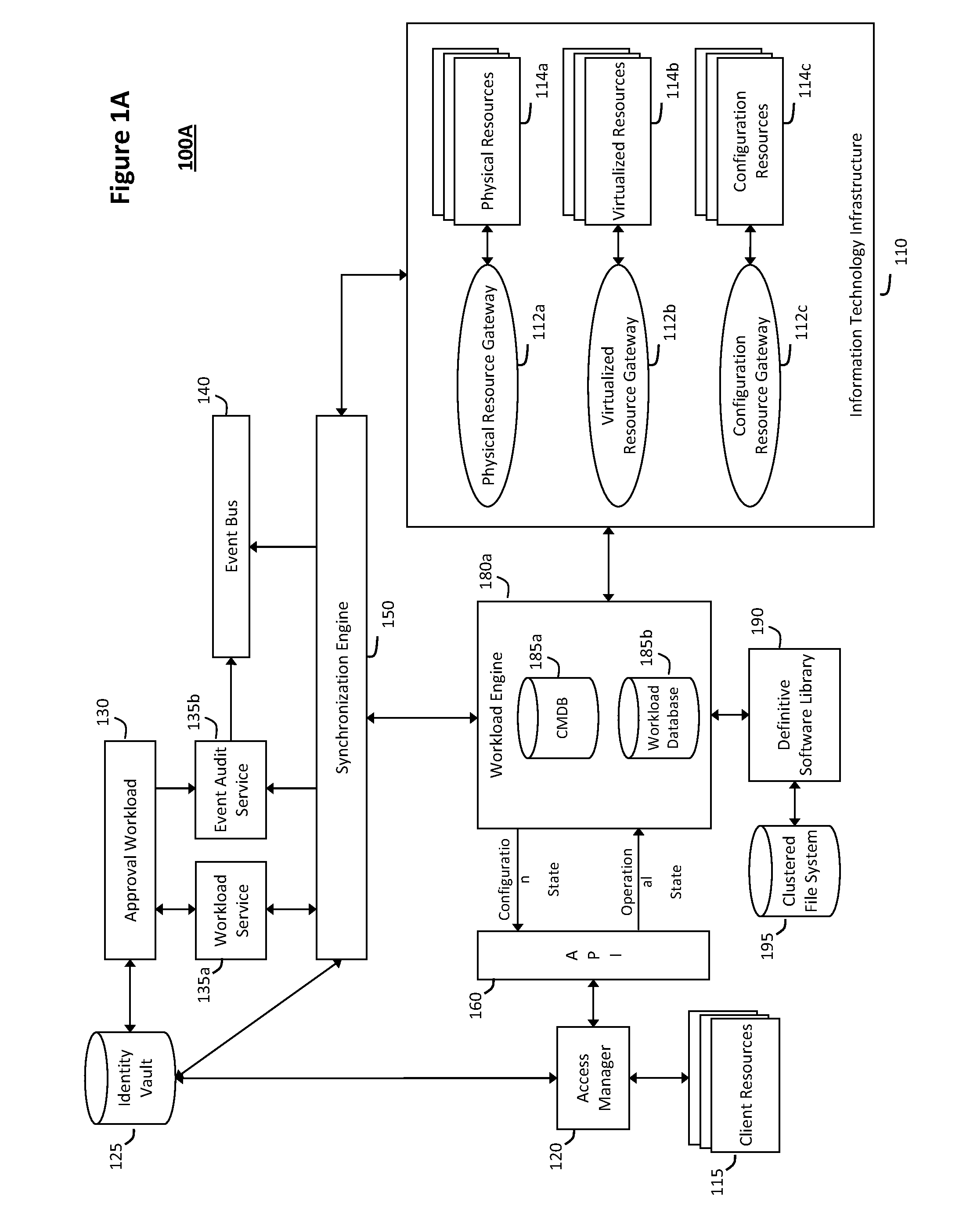
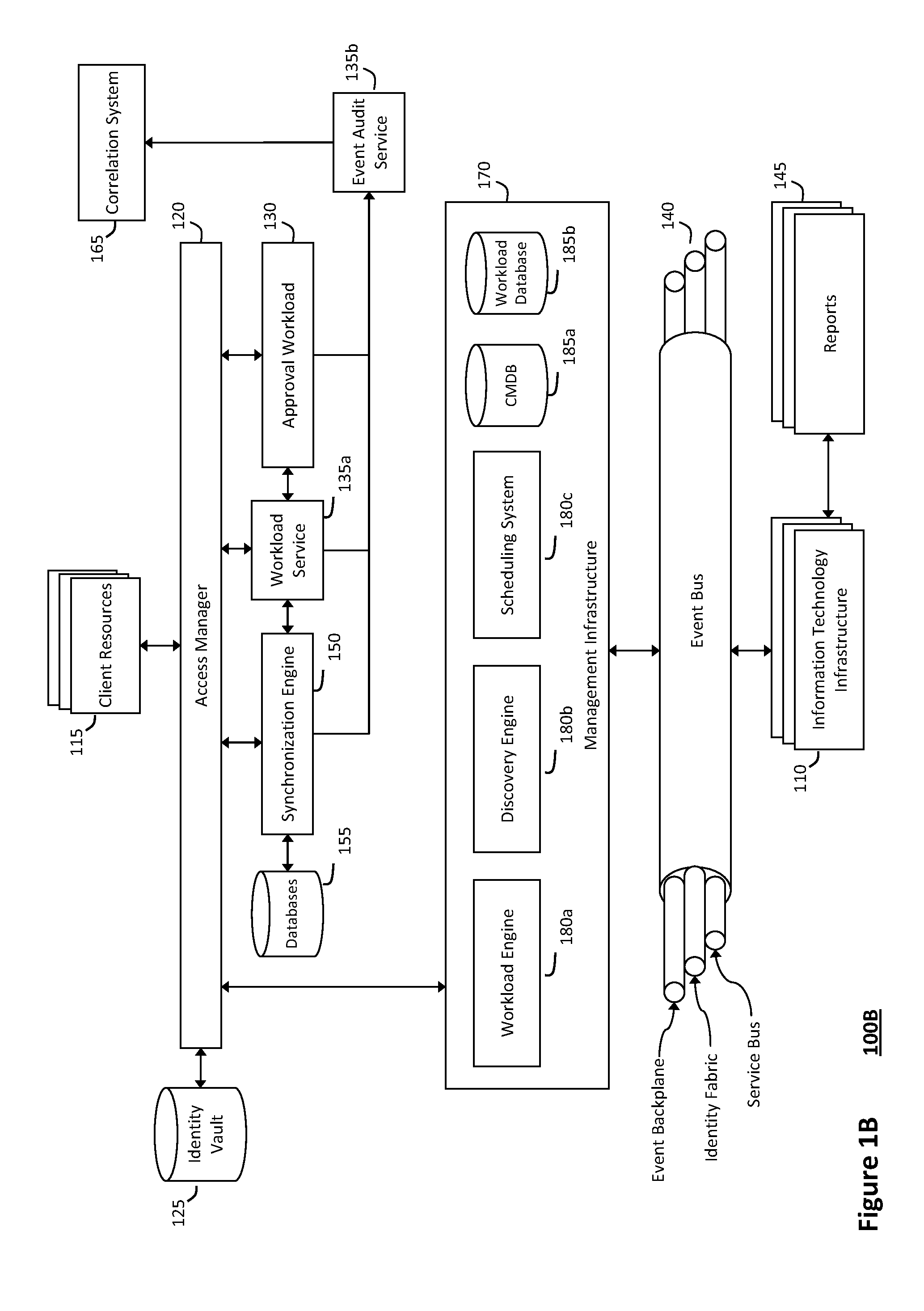
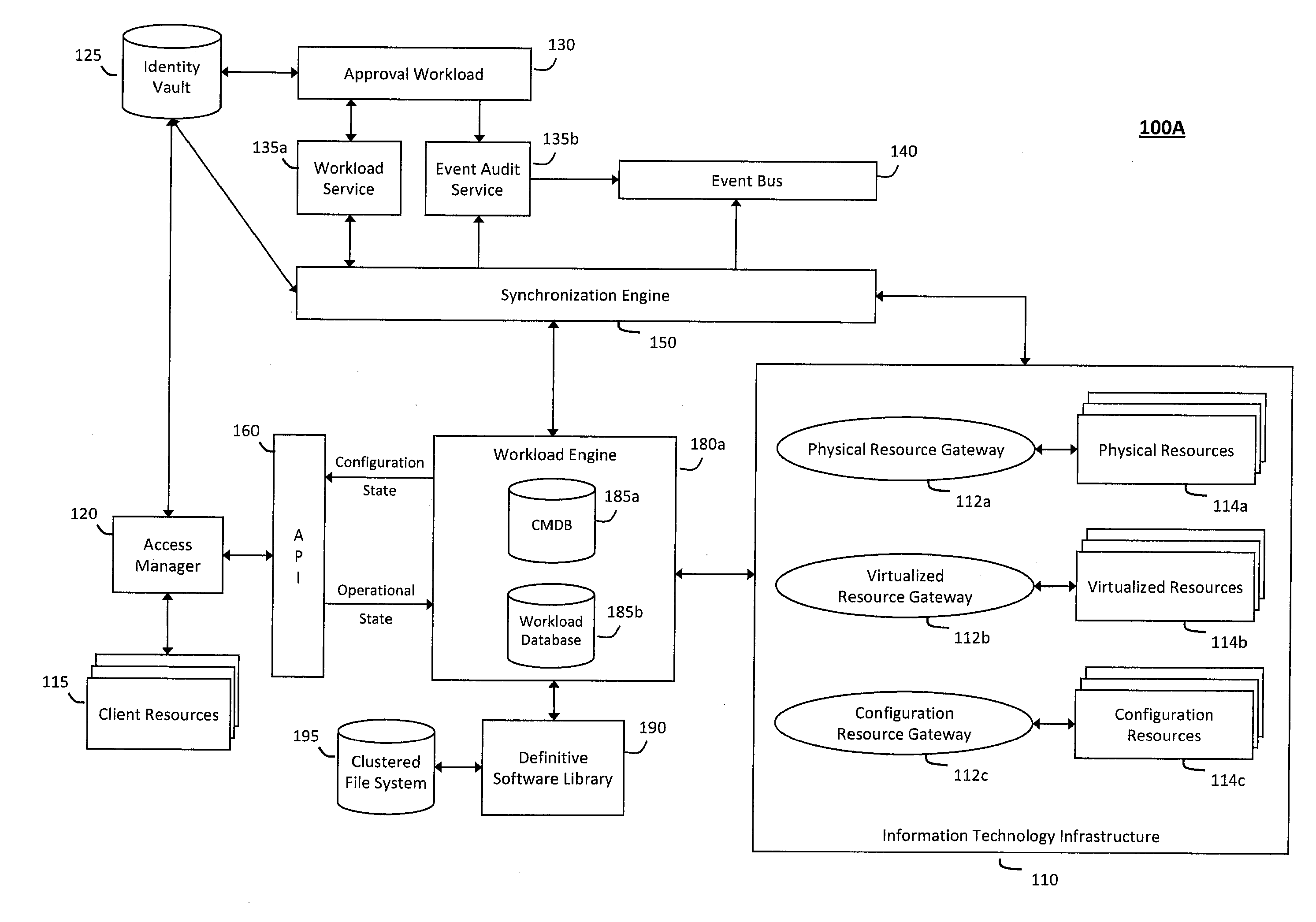
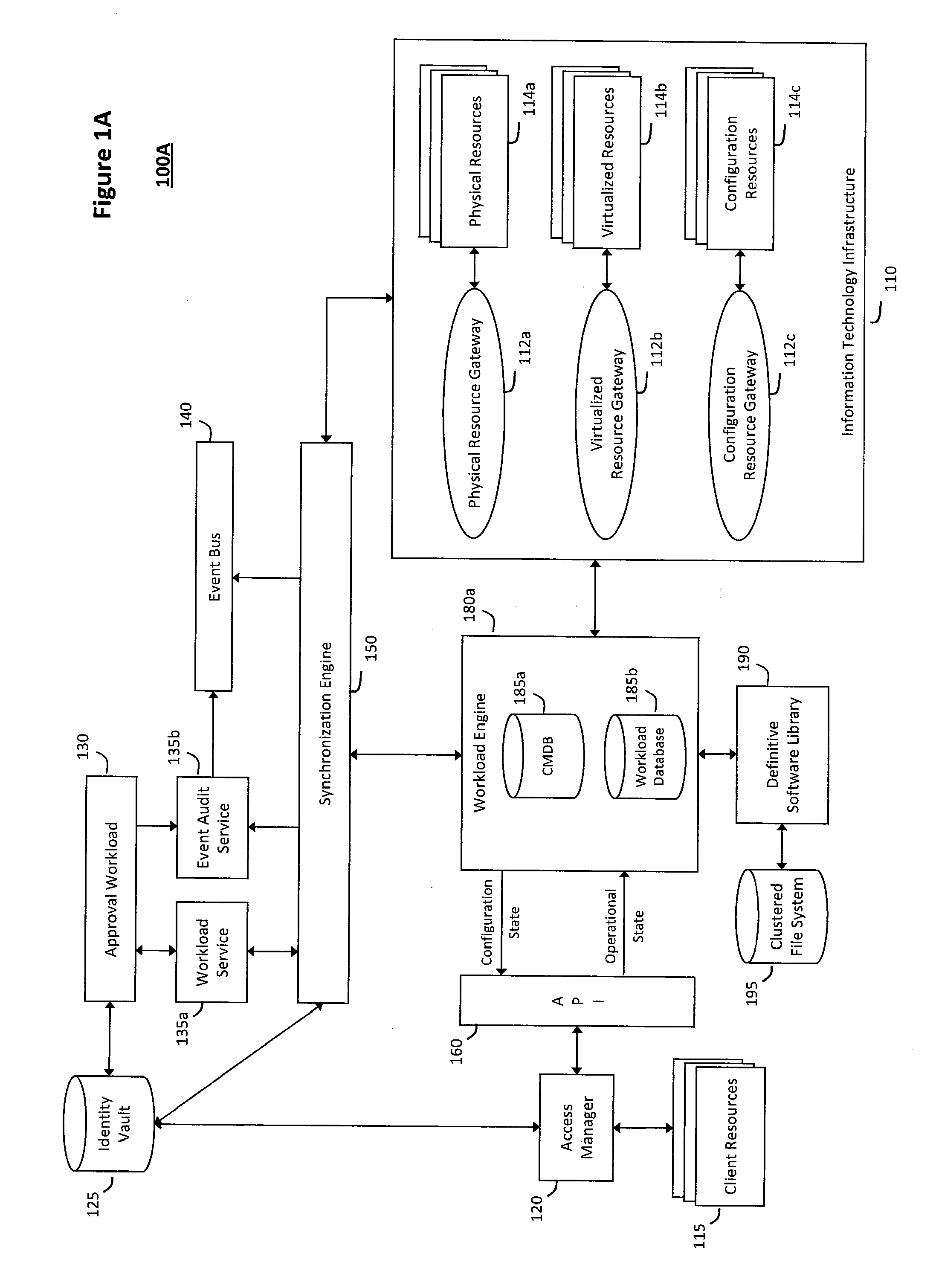
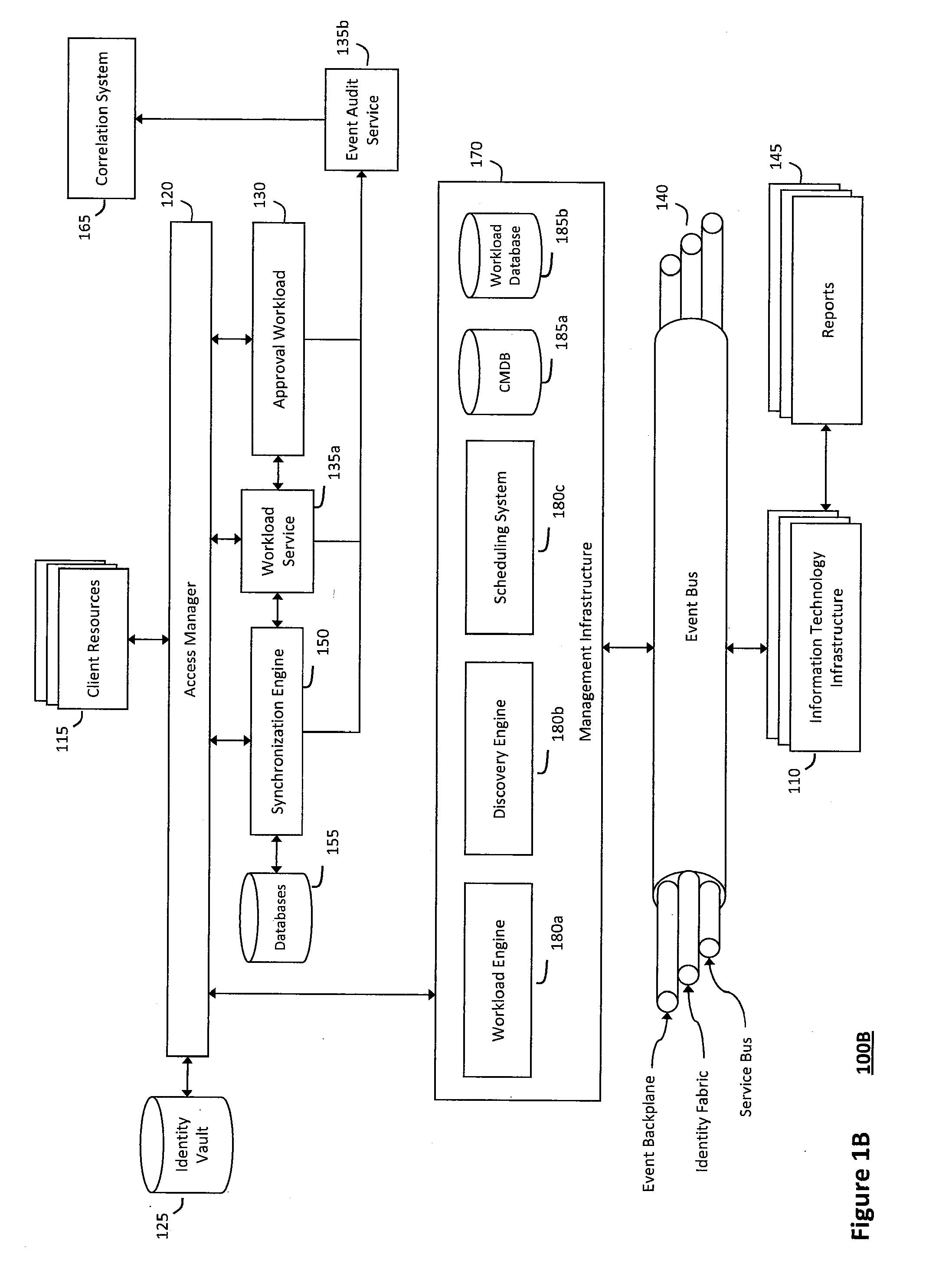
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
System and method for providing annotated service blueprints in an intelligent workload management system
InactiveUS20110126207A1Free computational resourceAgile and flexible managementMultiprogramming arrangementsDigital data authenticationService blueprintService-oriented architecture
The system and method described herein for providing annotated service blueprints in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for creating annotated service blueprints to provision and manage tessellated services distributed within an information technology infrastructure. For example, in response to a request to provision a service, a service blueprint describing one or more virtual machines may be created. The service blueprint may then be annotated to apply various parameters to the virtual machines, and the annotated service blueprint may then be instantiated to orchestrate the virtual machines with the one or more parameters and deploy the orchestrated virtual machines on information technology resources allocated to host the requested service, thereby provisioning the requested service.
Owner:MICRO FOCUS SOFTWARE INC
Triggering applications based on a captured text in a mixed media environment
ActiveUS20070050360A1Easy to optimizeFacilitate methodMultimedia data indexingSpecial data processing applicationsInformation retrievalApplication software
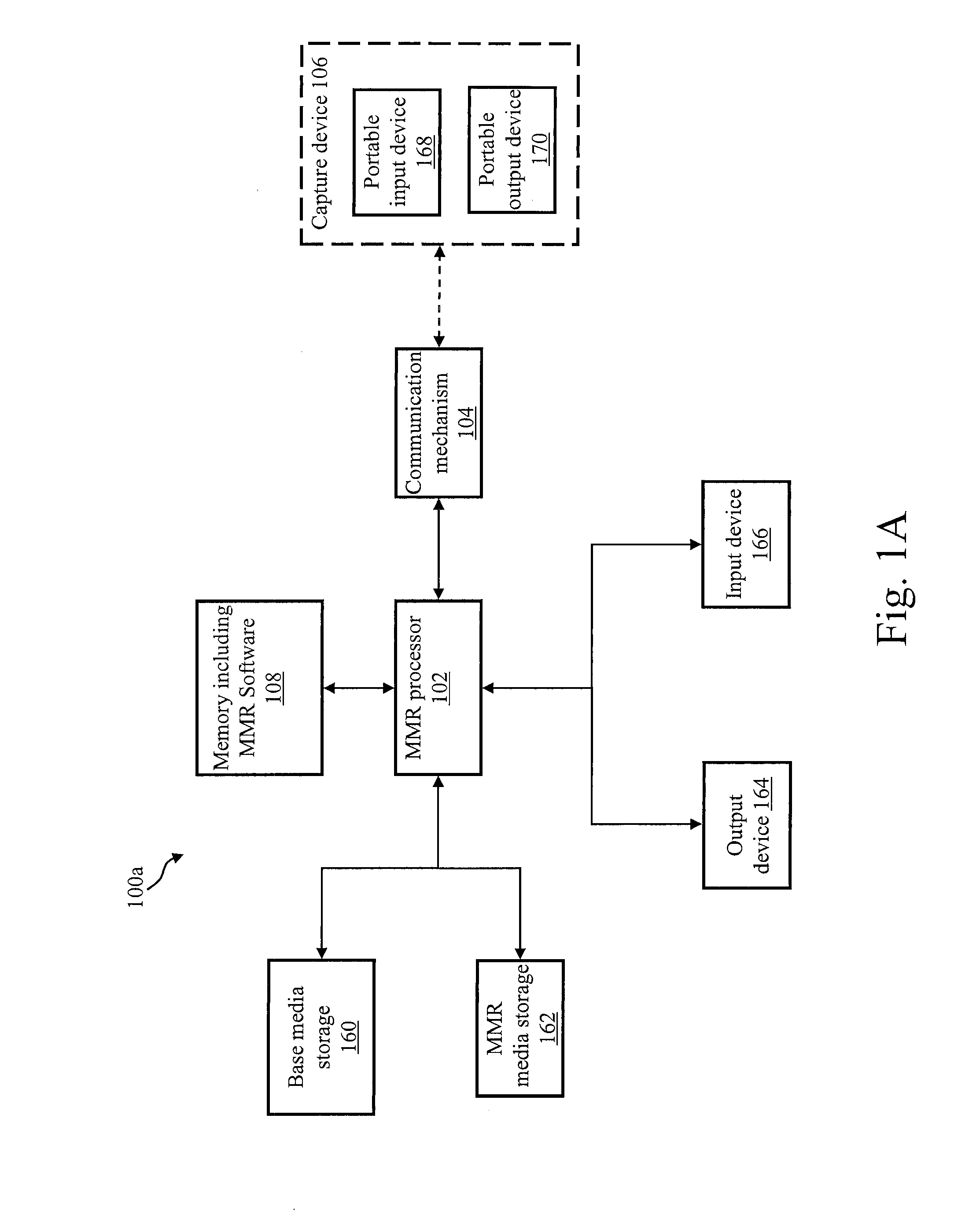
A Mixed Media Reality (MMR) system and associated techniques are disclosed. The MMR system provides mechanisms for forming a mixed media document that includes media of at least two types (e.g., printed paper as a first medium and digital content and / or web link as a second medium). In one particular embodiment, the MMR system includes an action processor and method, and MMR documents with an associated action. The MMR document structure is particularly advantageous because the ability to specify different actions for different MMR documents, combined with the ability to create any number of MMR documents for a particular location on any media, allows the MMR architecture to serve as a universal trigger or initiator for additional processing. In other words, addition processing or actions can be triggered or initiated based on MMR recognition. The action processor receives the output of the MMR recognition process which yields an MMR document including at least one action. The action processor executes that action which includes various commands to the MMR system or other systems coupled to the MMR system. The MMR system architecture is advantageous because an action can be executed by pointing the capture device at a block of text, and the action is performed. Example actions include retrieving the text in electronic form to the capture device, retrieving the specification for the action, inserting data to a MMR document, transferring data between documents, purchasing items, authoring actions or reviewing historical information about actions. The MMR system includes a variety of user applications (one or more actions) initiated by the MMR recognition of a text patch such as information retrieval for a travel guide book, stock listings or advertisements; information capture such as recording content from a conference, recording and storing multimedia associated with the document, capturing information for a calendar and on the fly authoring; purchasing media files for storage on any part of an MMR document.
Owner:RICOH KK
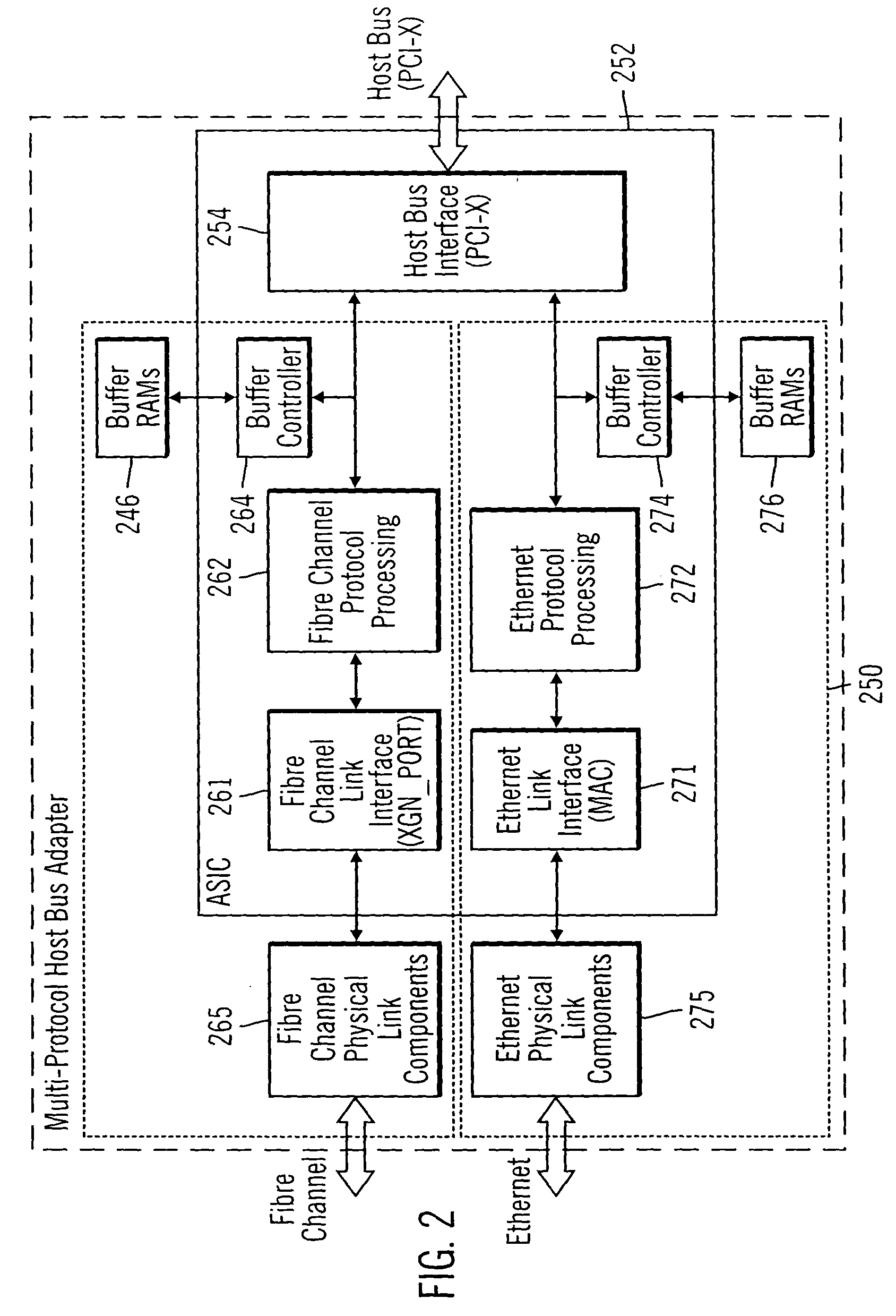
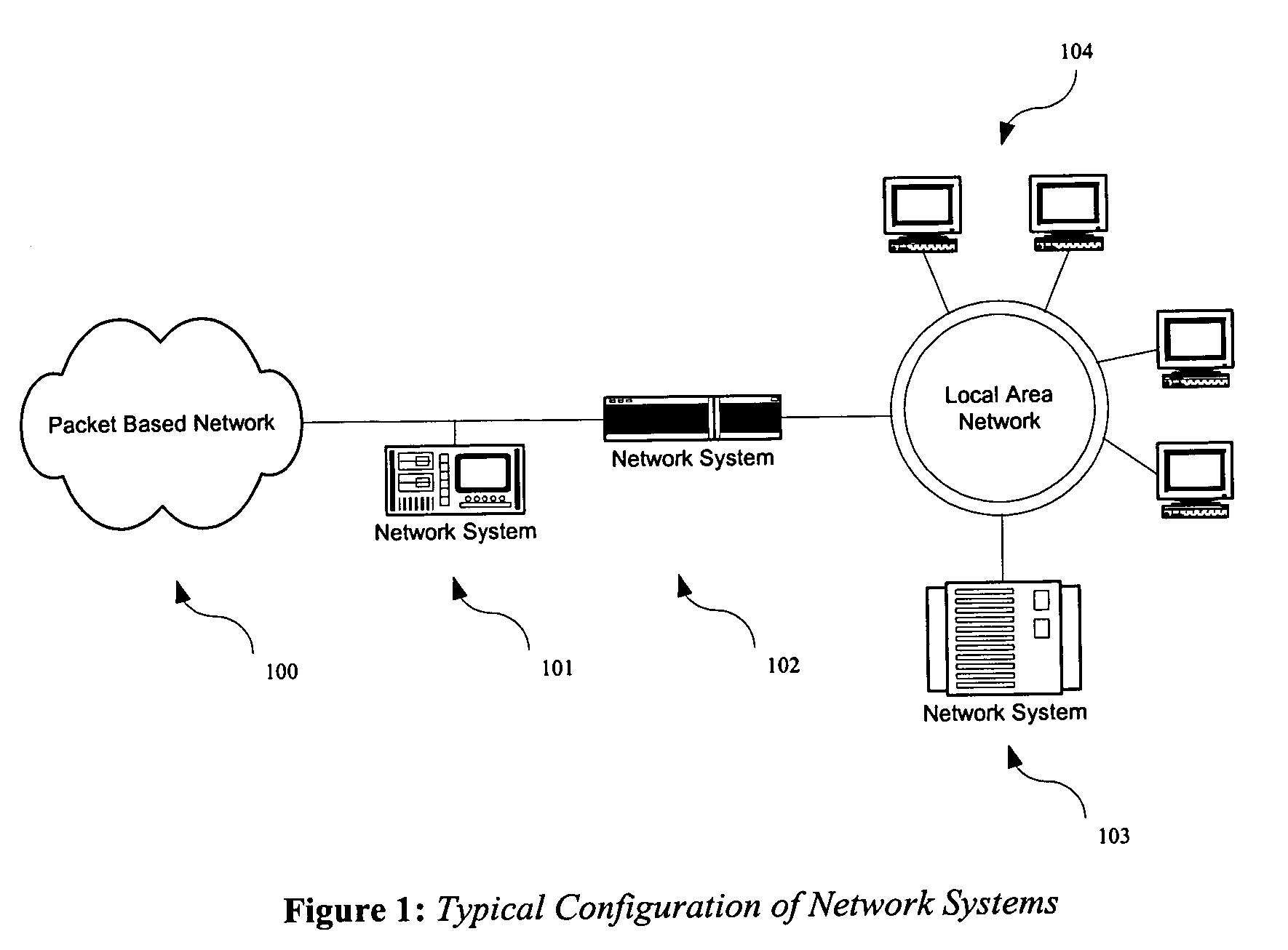
Integrated network interface supporting multiple data transfer protocols
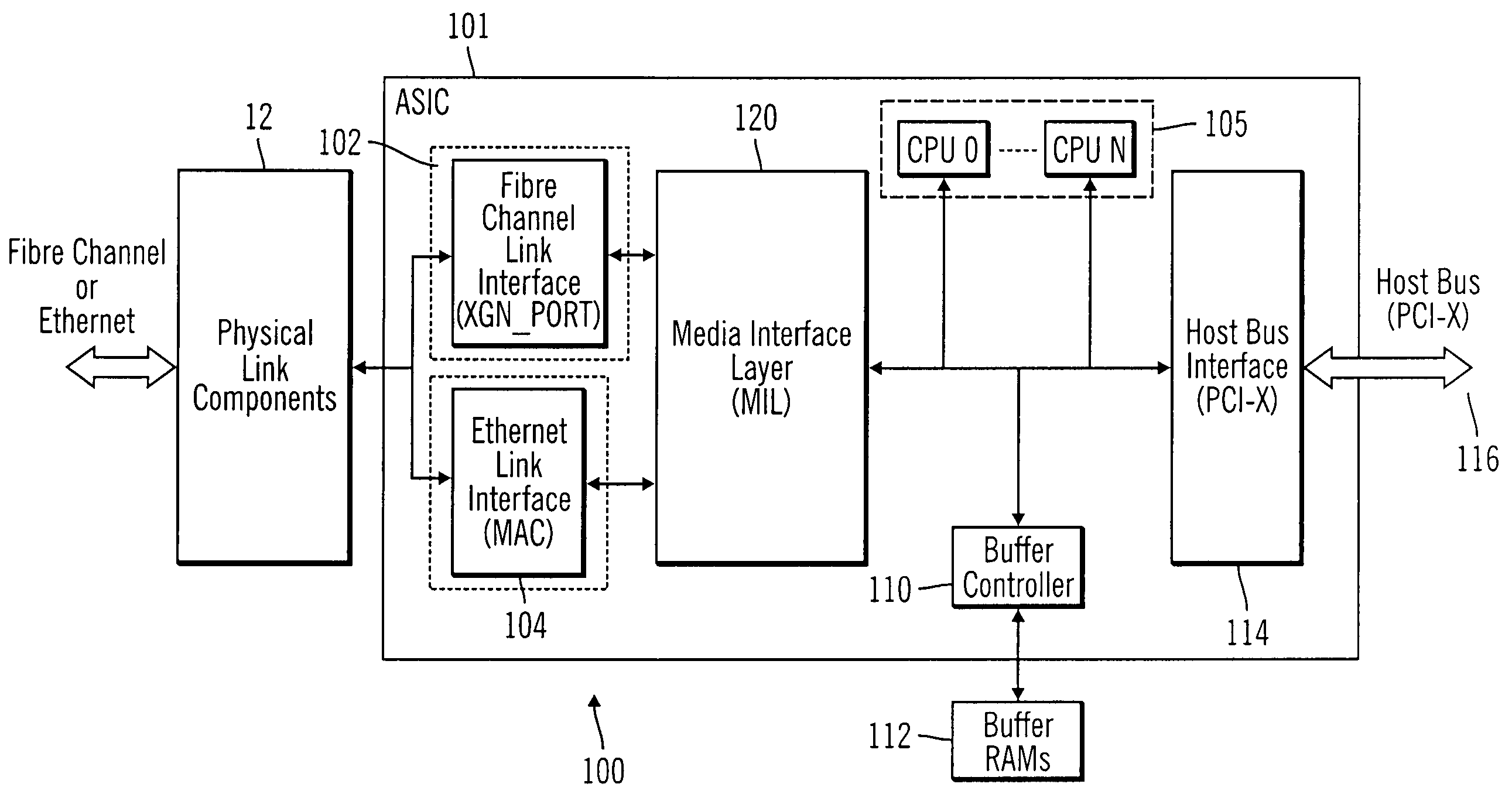
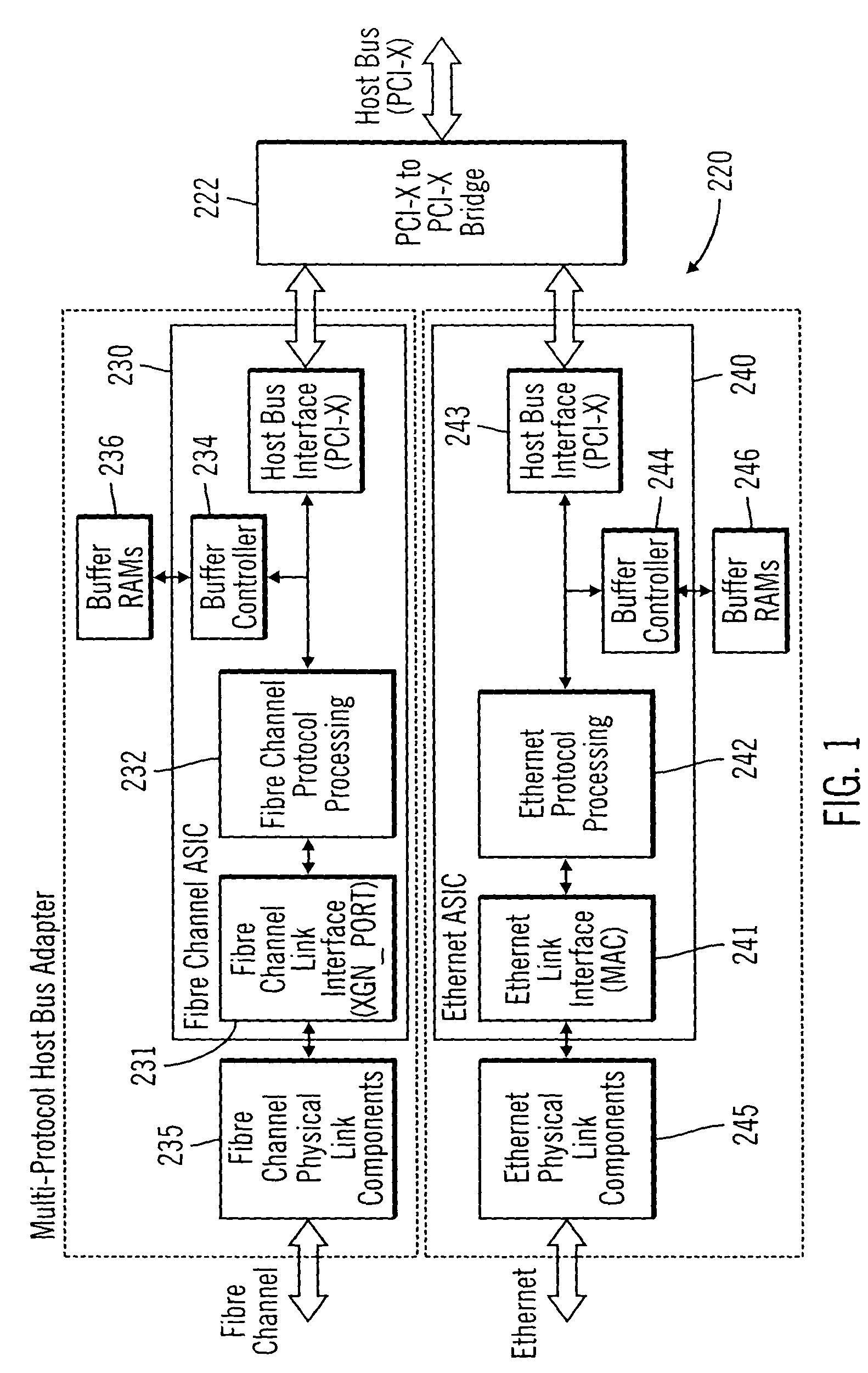
InactiveUS20050066045A1Overcome limitationsTime-division multiplexMultiple digital computer combinationsData streamNetwork interface device
An integrated network interface device that supports data exchange in two or more high-speed network data transfer protocols that are based on different standards of network data transfer architectures, wherein an incoming data stream formatted in accordance with a particular network data transfer standard is processed into data not subject to the network data transfer standard to be output for further processing by a host. In one aspect, a network interface device is provided with a set of shared or common protocol independent physical link components that are used to identify the operating protocol of the incoming data, and a set of dynamically or statically re-configurable, shared or common protocol independent data transfer processing components that support data exchange via the physical link components for all the supported protocols, which may include a protocol specific link interface for each supported protocol.
Owner:WAVECREST LAB LLC +1
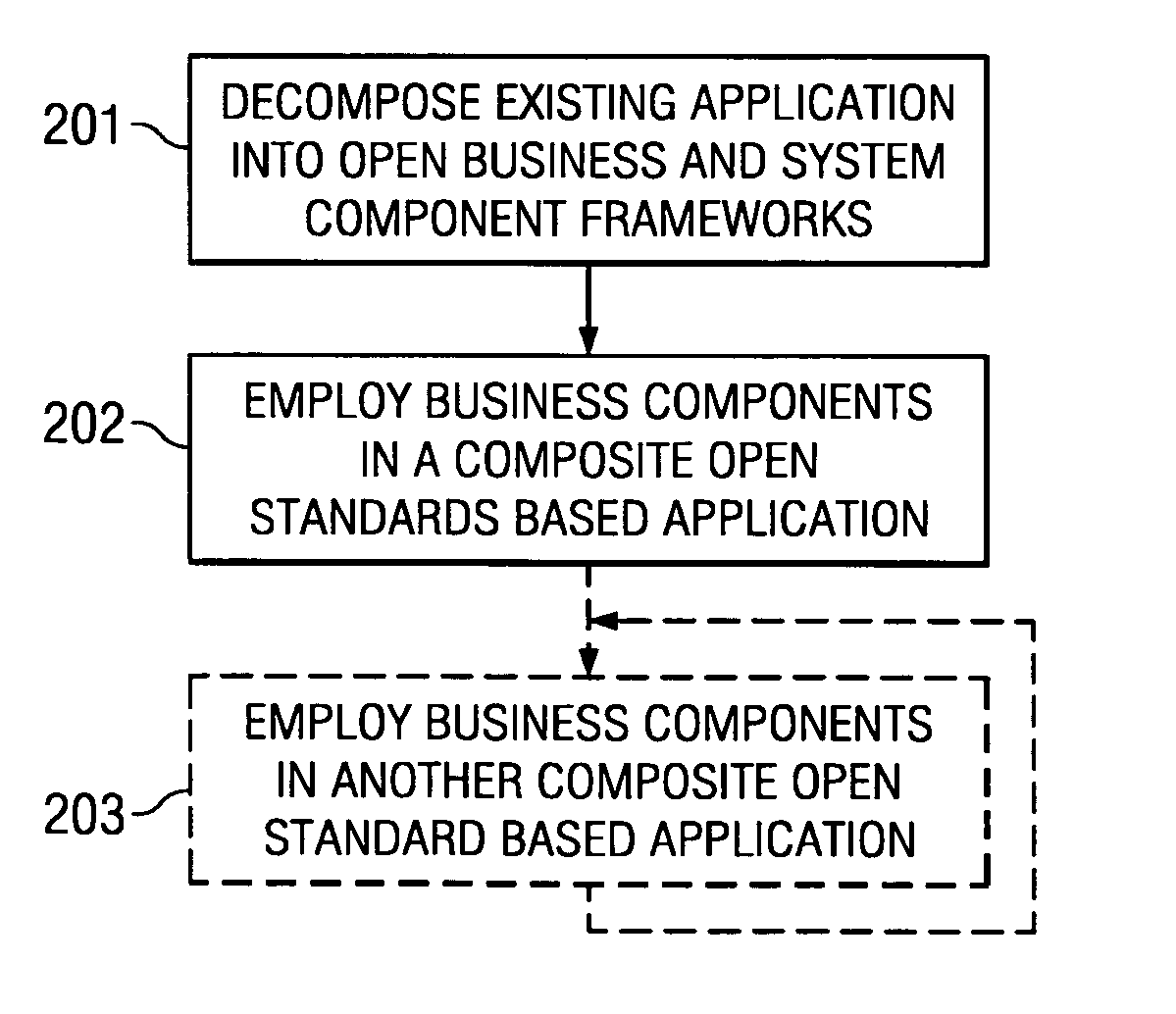
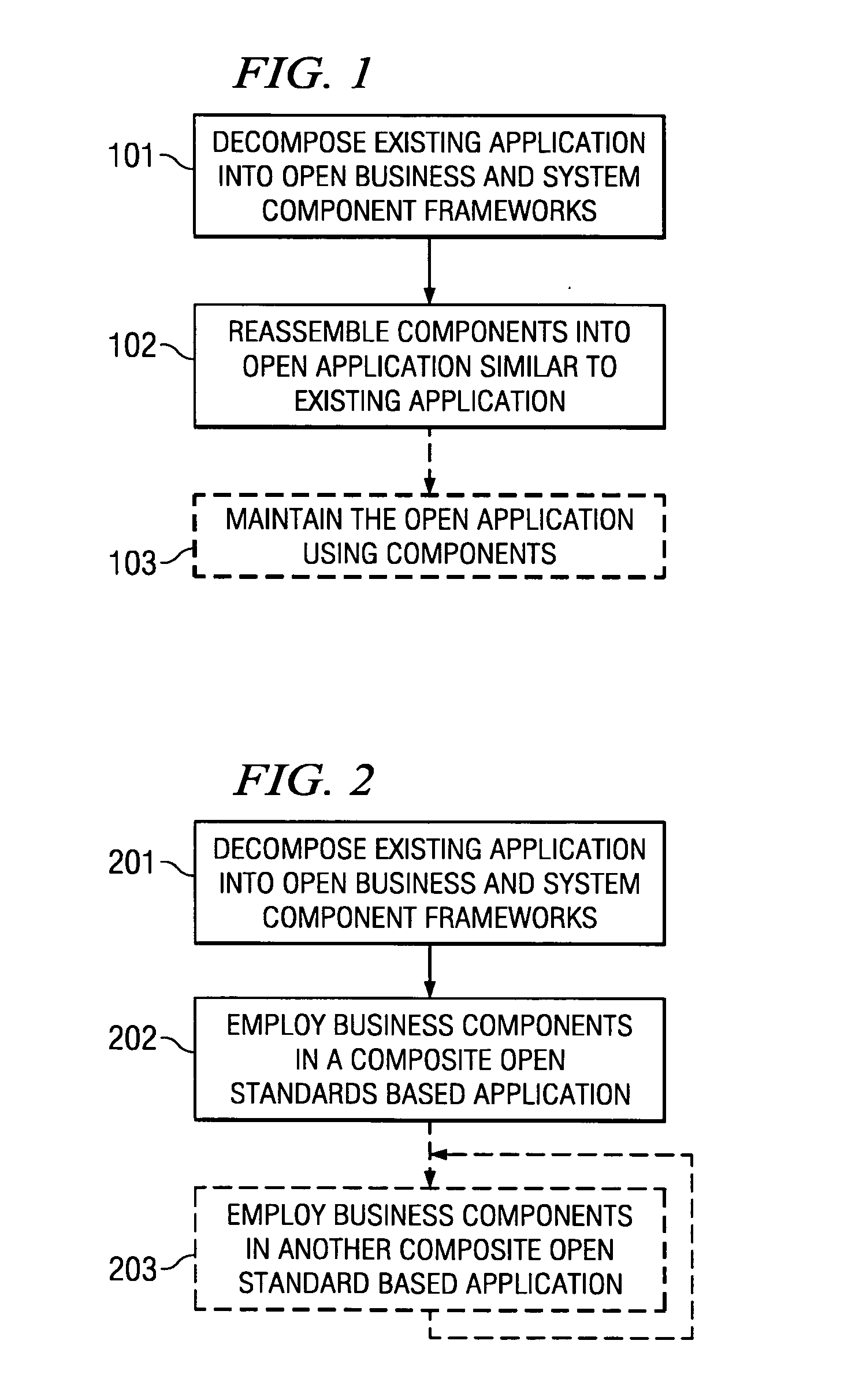
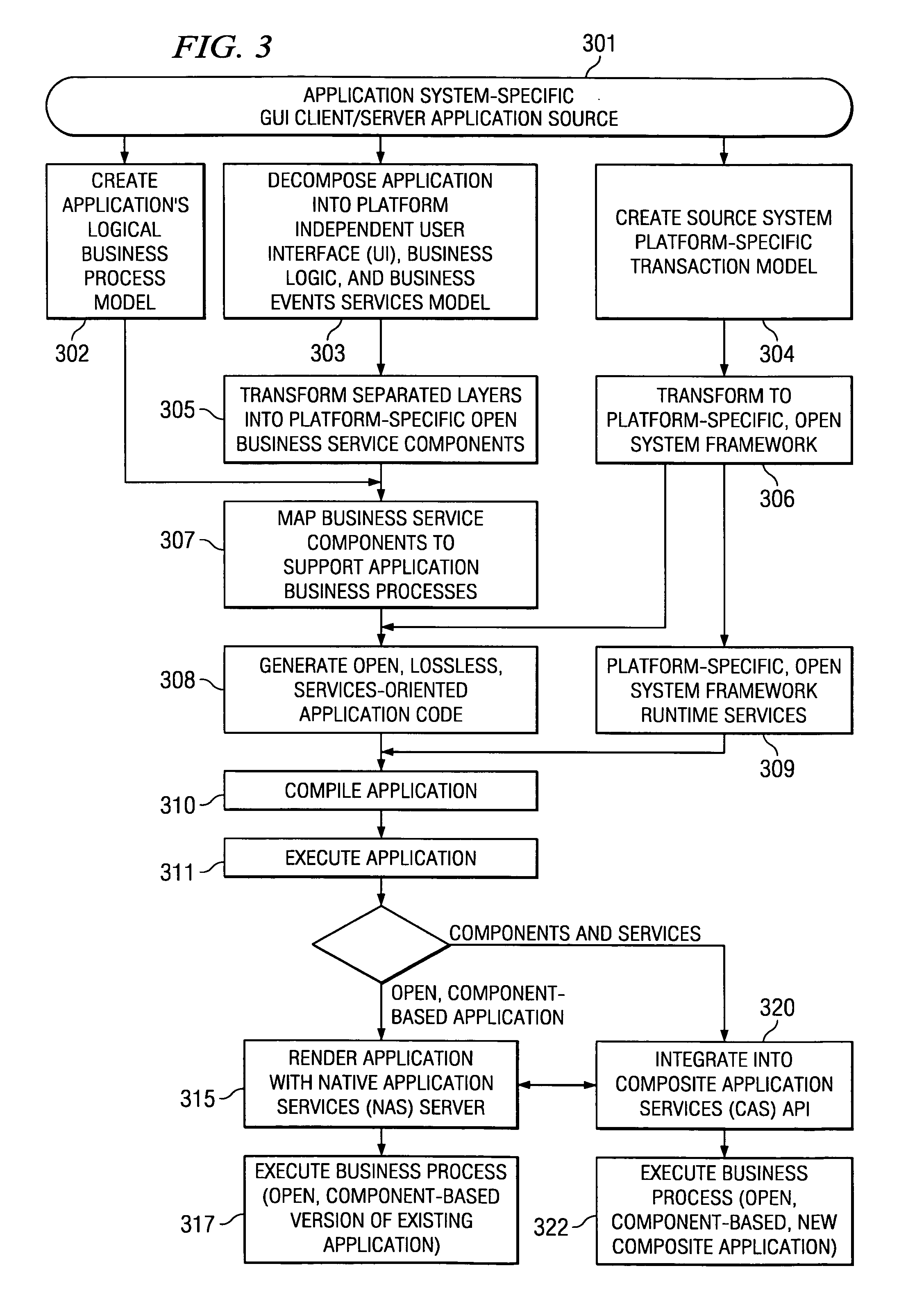
Systems and methods for modeling and generating reusable application component frameworks, and automated assembly of service-oriented applications from existing applications
InactiveUS20050144226A1Effective and meaningful supportLower barrierSoftware maintainance/managementMultiple digital computer combinationsService oriented applicationsBusiness process
Embodiments of systems and methods model and generate open reusable, business components for Service Oriented Architectures (SOAs) from existing client / server applications. Applications are decomposed into business component frameworks with separate user interface, business logic, and event management layers to enable service-oriented development of new enterprise applications. Such layers are re-assembled through an open standards-based, Native Application Services (NAS) to render similar or near identical transactional functionality within a new application on an open platform, without breaking former production code, and without requiring a change in an end-user's business processes and / or user experience. In addition, the same separated layers may form re-usable business components at any desired level of granularity for re-use in external composite applications through industry-standard interfaces, regardless of usage, context, or complexity in the former Client / Server application.
Owner:SAP AG
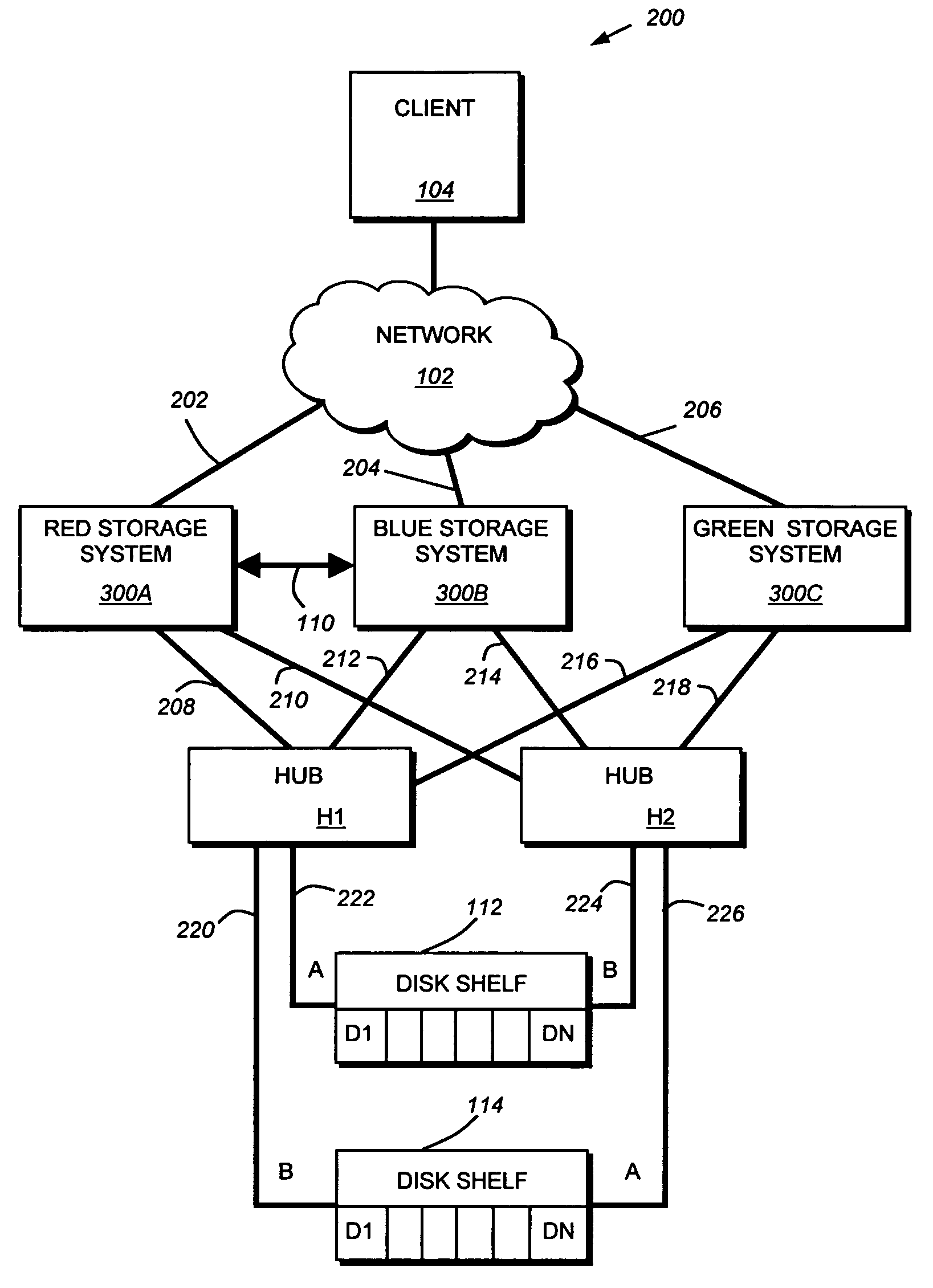
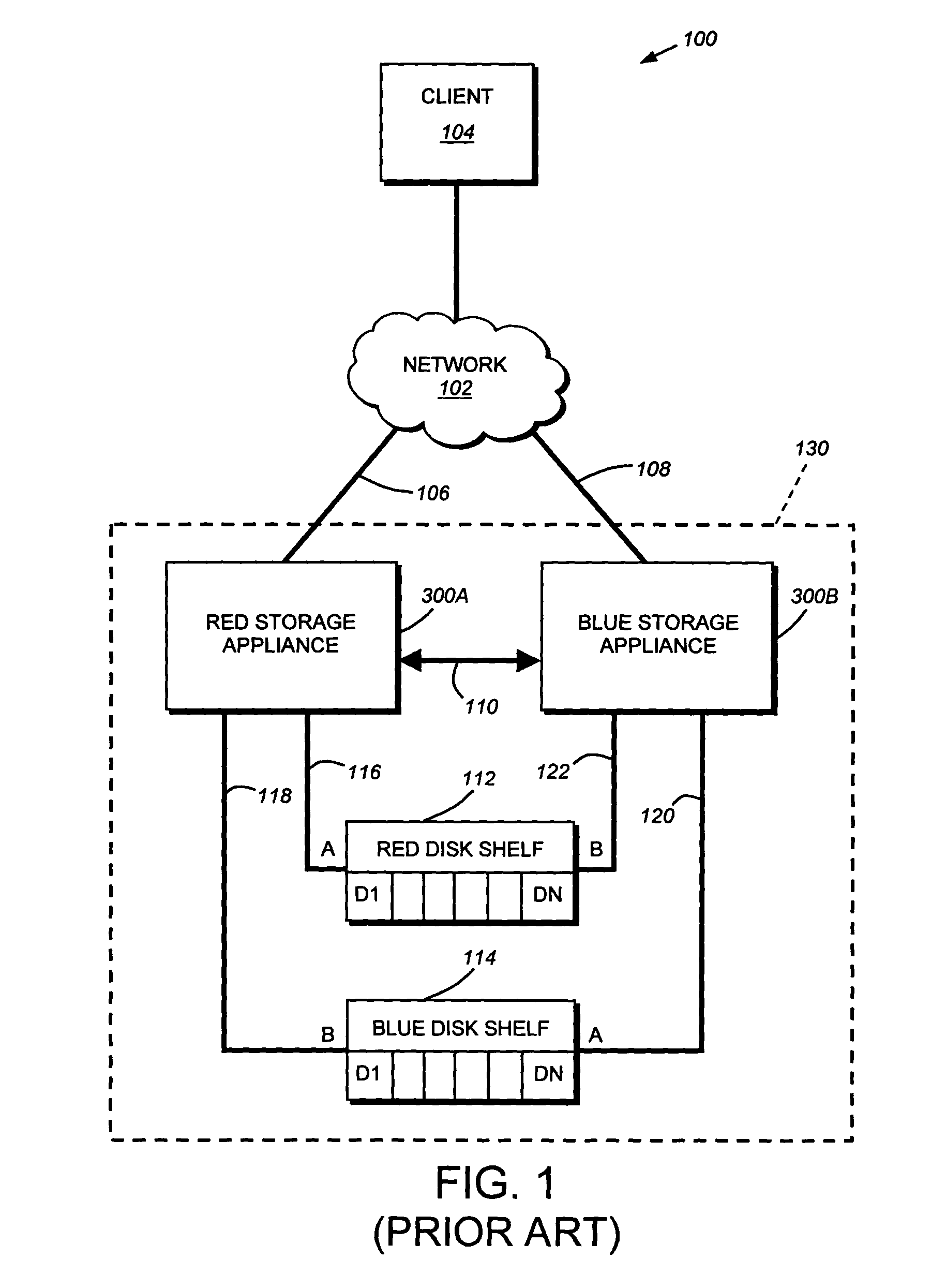
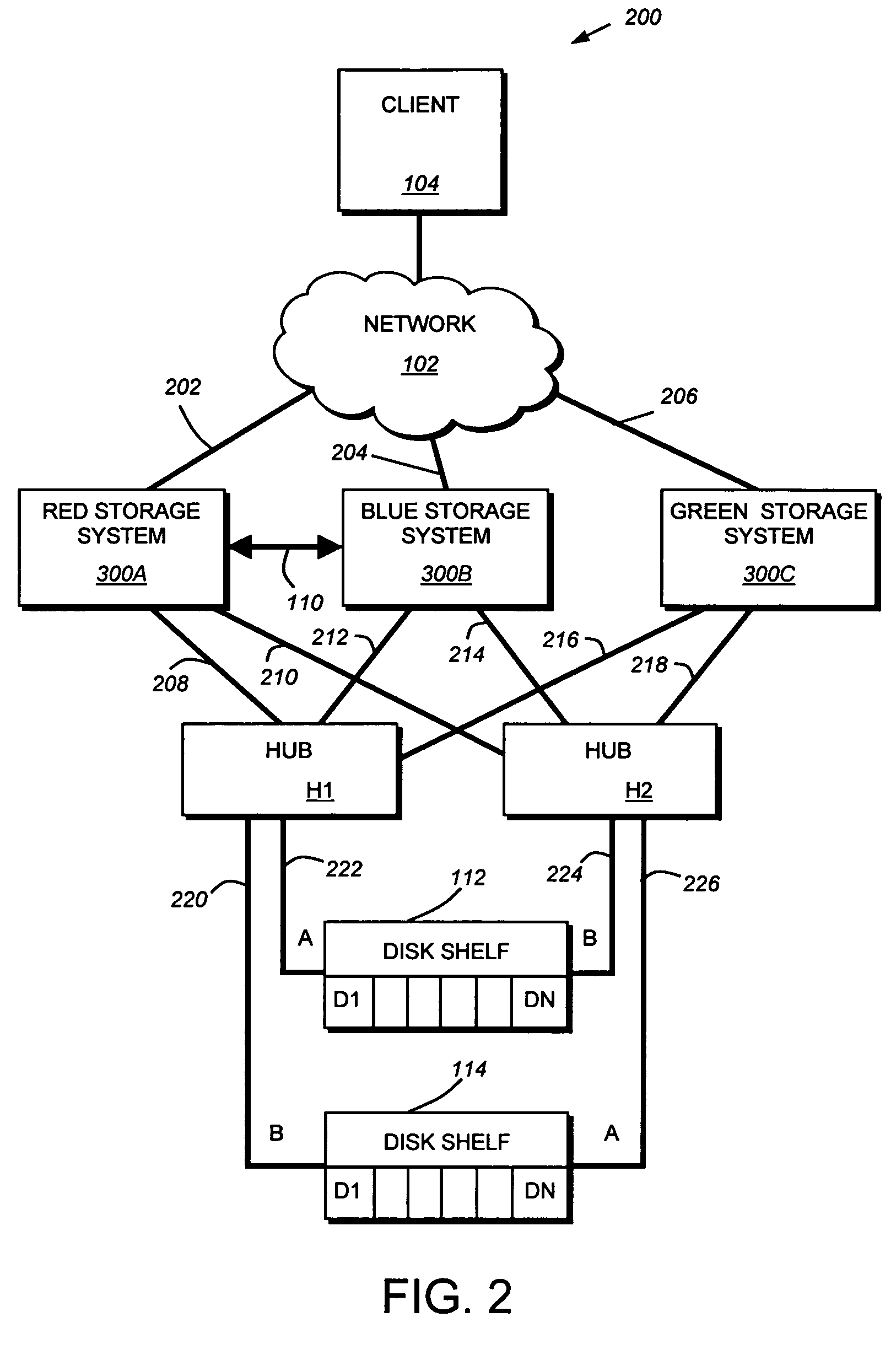
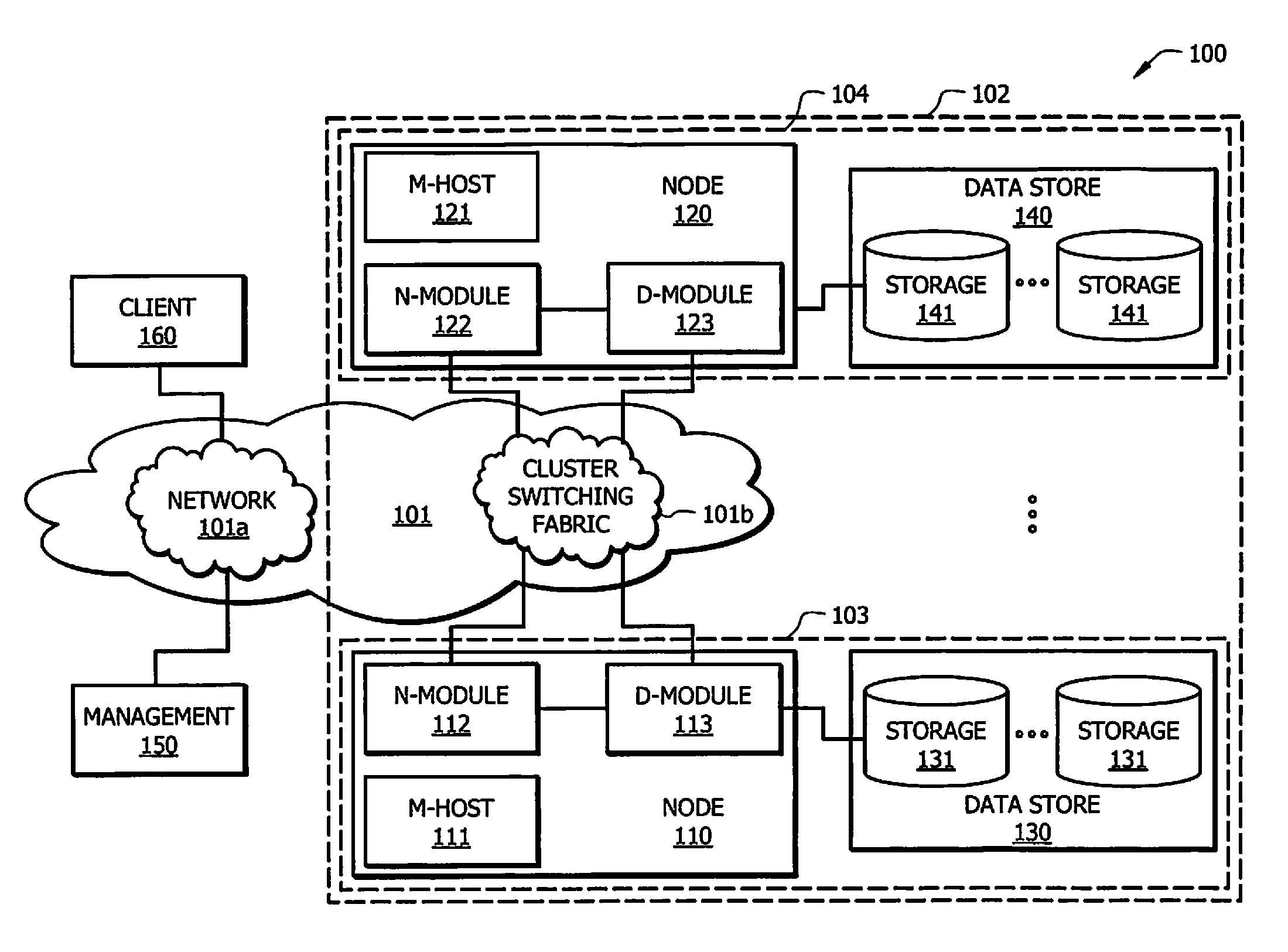
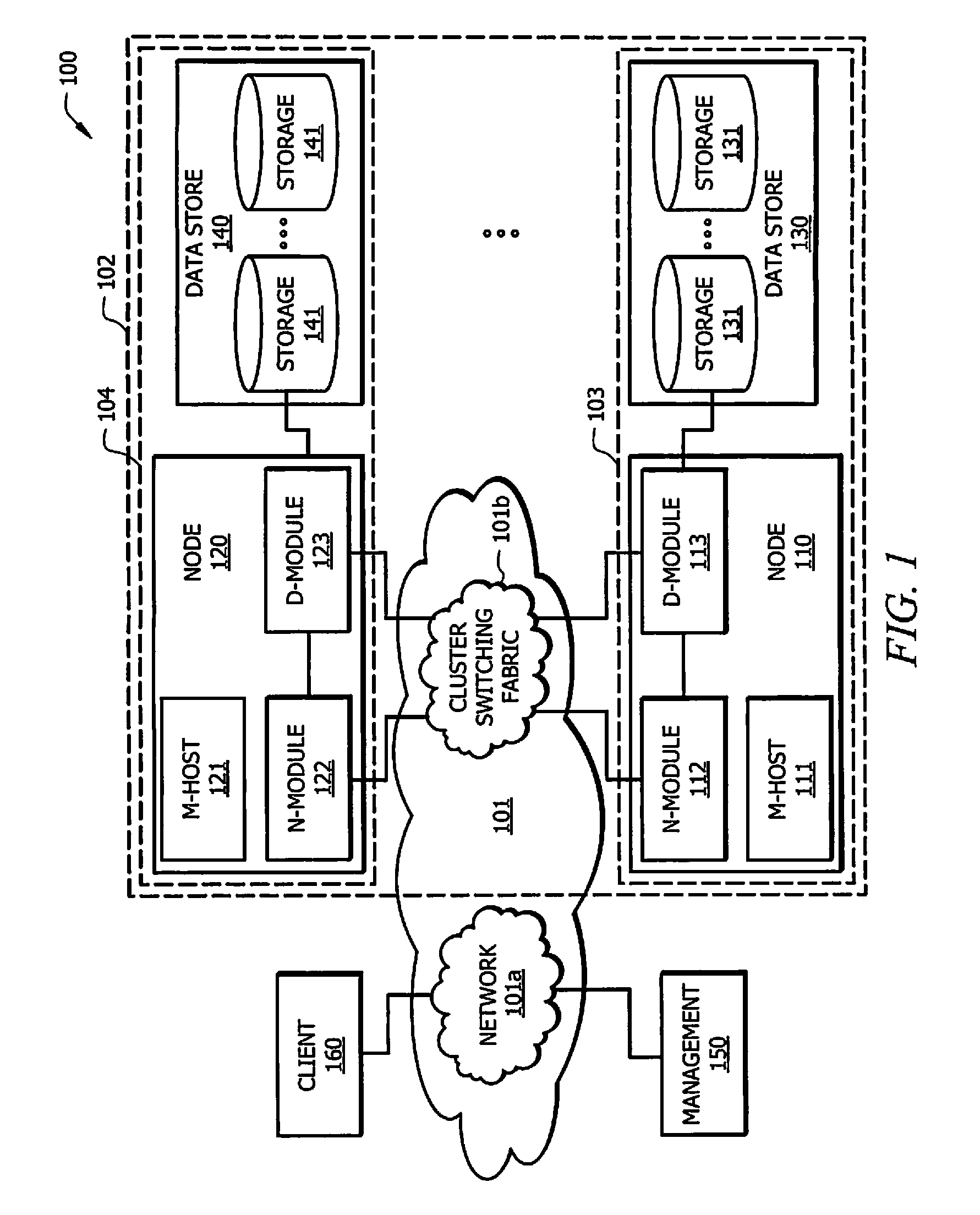
Coordinated shared storage architecture
ActiveUS8180855B2Increase the number ofOvercome disadvantagesError detection/correctionMultiple digital computer combinationsSCSIComputer module
Owner:NETWORK APPLIANCE INC
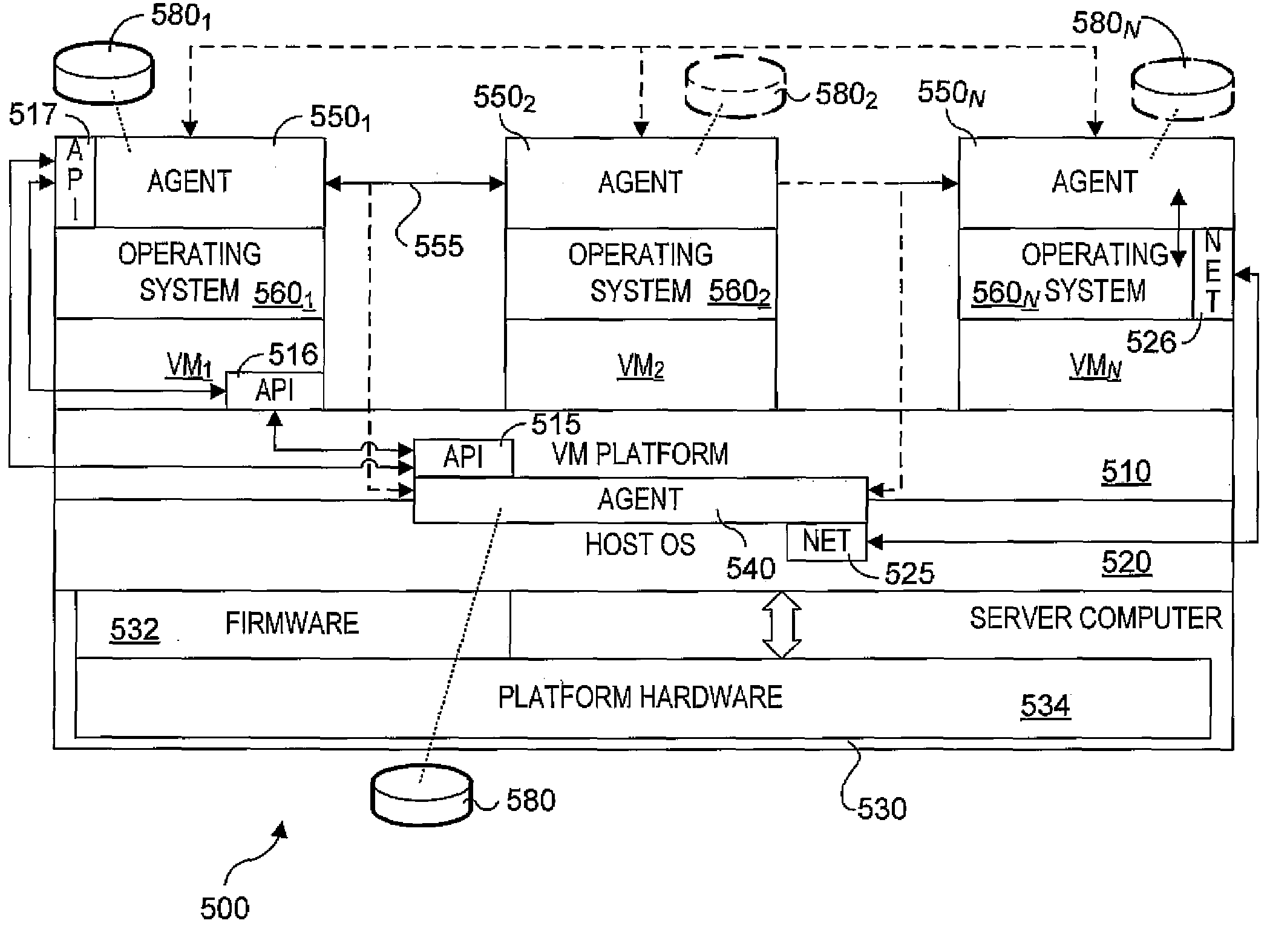
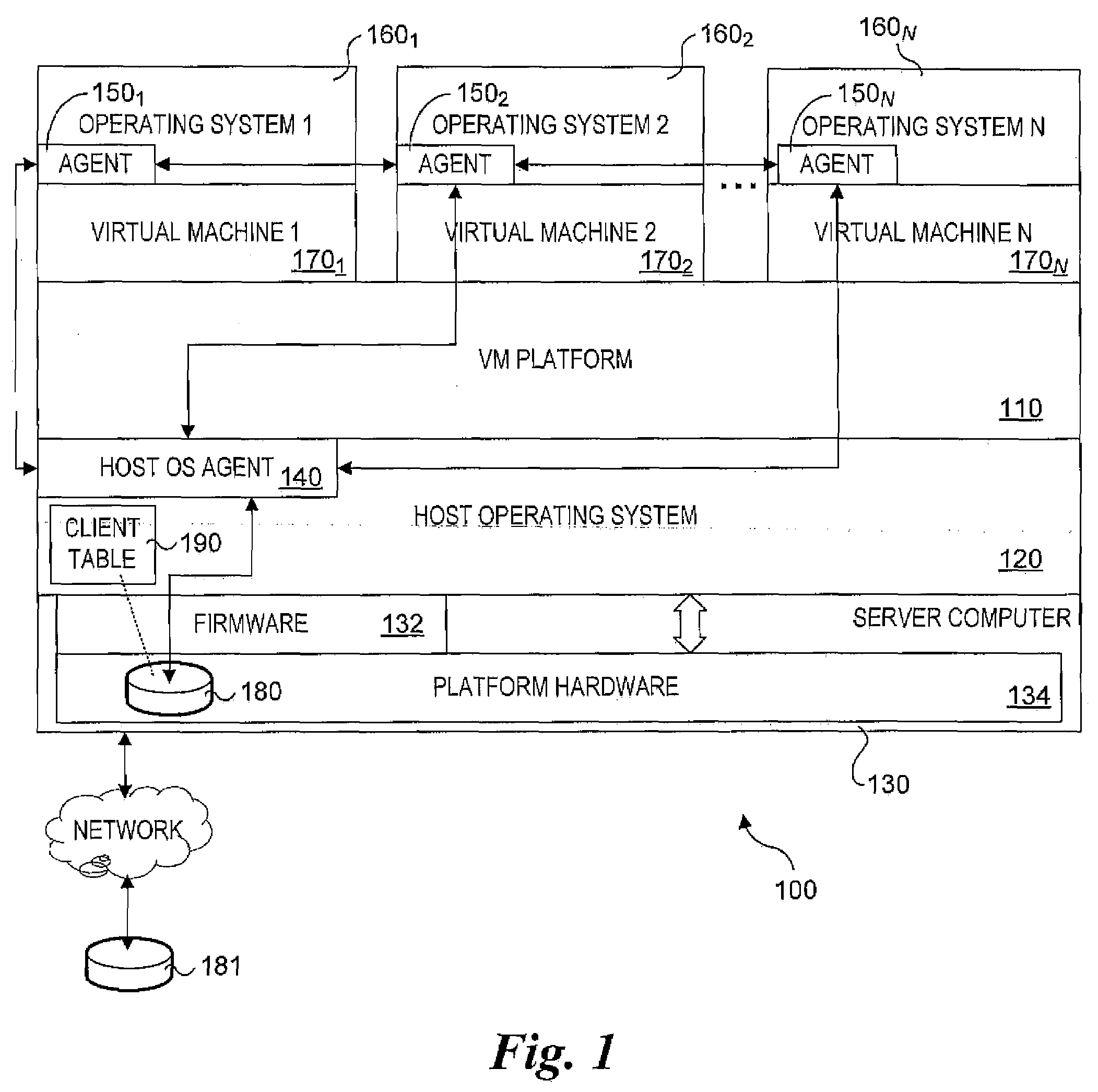
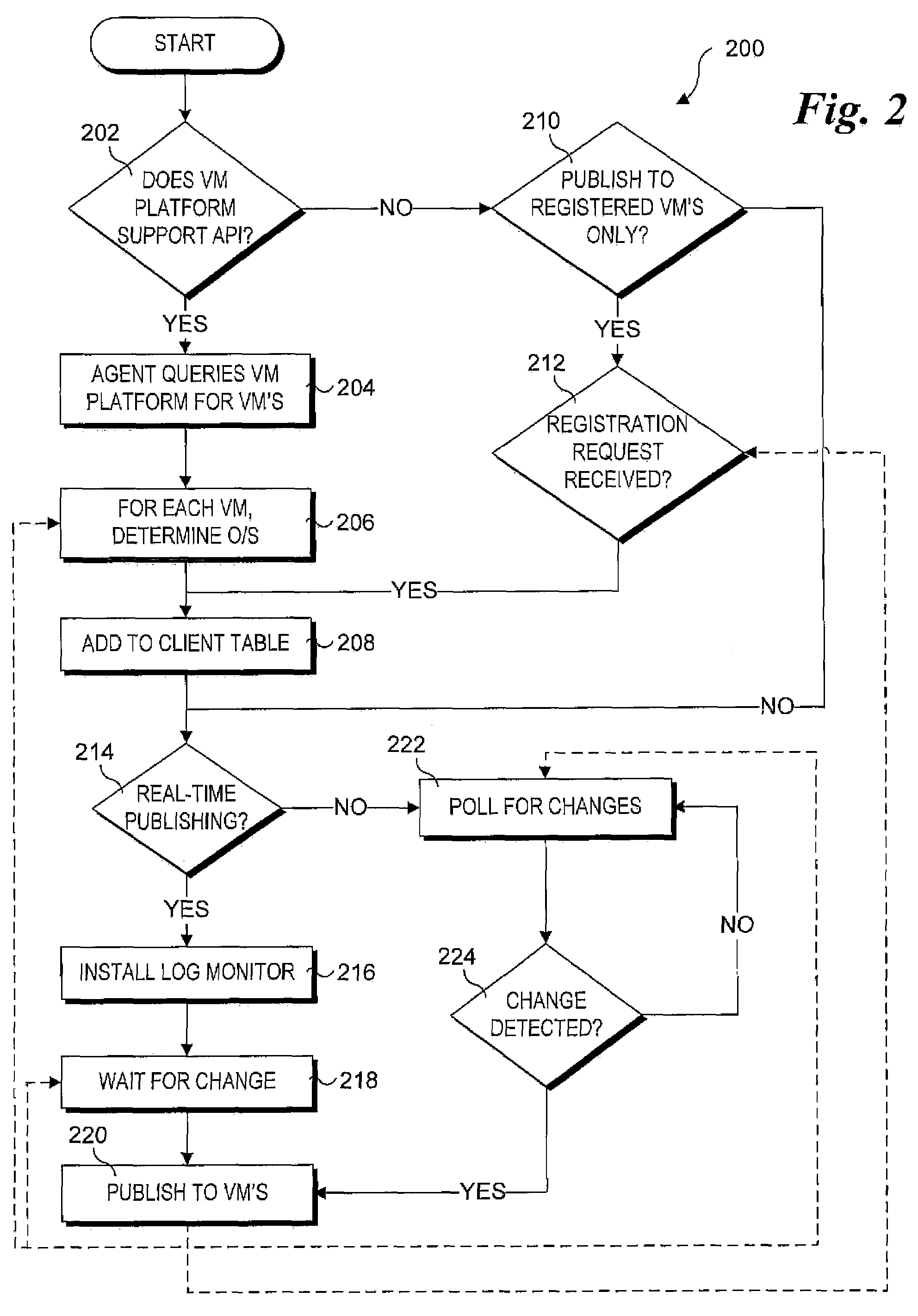
System and method for host and virtual machine administration
InactiveUS20080196043A1Reduce dependenceResource allocationError detection/correctionOperational systemEvent data
Methods, architectures, software / firmware and systems for enabling concurrent administration of host operating systems and virtual machine-hosted operating systems. Techniques are disclosed for monitoring and reporting various administrative data (e.g., performance data, event data, log data, etc.), as well as enabling allocation and reallocation of system resources, such as physical memory and disk space. The techniques support implementation of user-interfaces hosted by a virtual machine operating system or a host operating system that enable administrators and the like to manage operations of virtual machines and hosts via a unified interface. Moreover, the techniques support concurrent management of different operating system types.
Owner:FEINLEIB DAVID +2
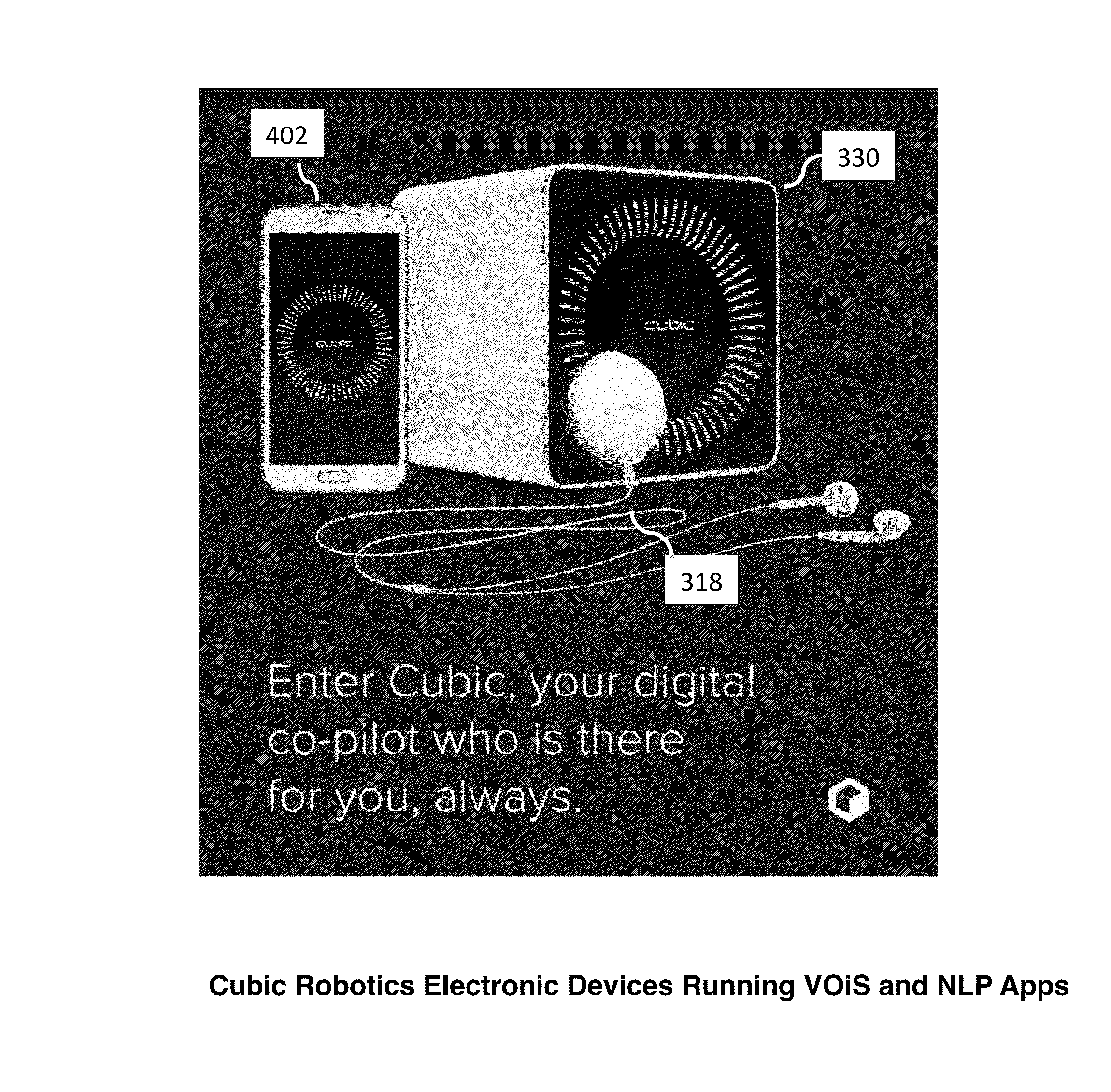
Voice driven operating system for interfacing with electronic devices: system, method, and architecture
InactiveUS20150279366A1Keep users engaged in conversationNatural language data processingProgramming languages/paradigmsOperational systemSoftware architecture
A system comprising an electronic device, a means for the electronic device to receive input text, a means to generate a response wherein the means to generate the response is a software architecture organized in the form of a stack of functional elements. These functional elements comprise an operating system kernel whose blocks and elements are dedicated to natural language processing, a dedicated programming language specifically for developing programs to run on the operating system, and one or more natural language processing applications developed employing the dedicated programming language, wherein the one or more natural language processing applications may run in parallel. Moreover, one or more of these natural language processing applications employ an emotional overlay.
Owner:CUBIC ROBOTICS
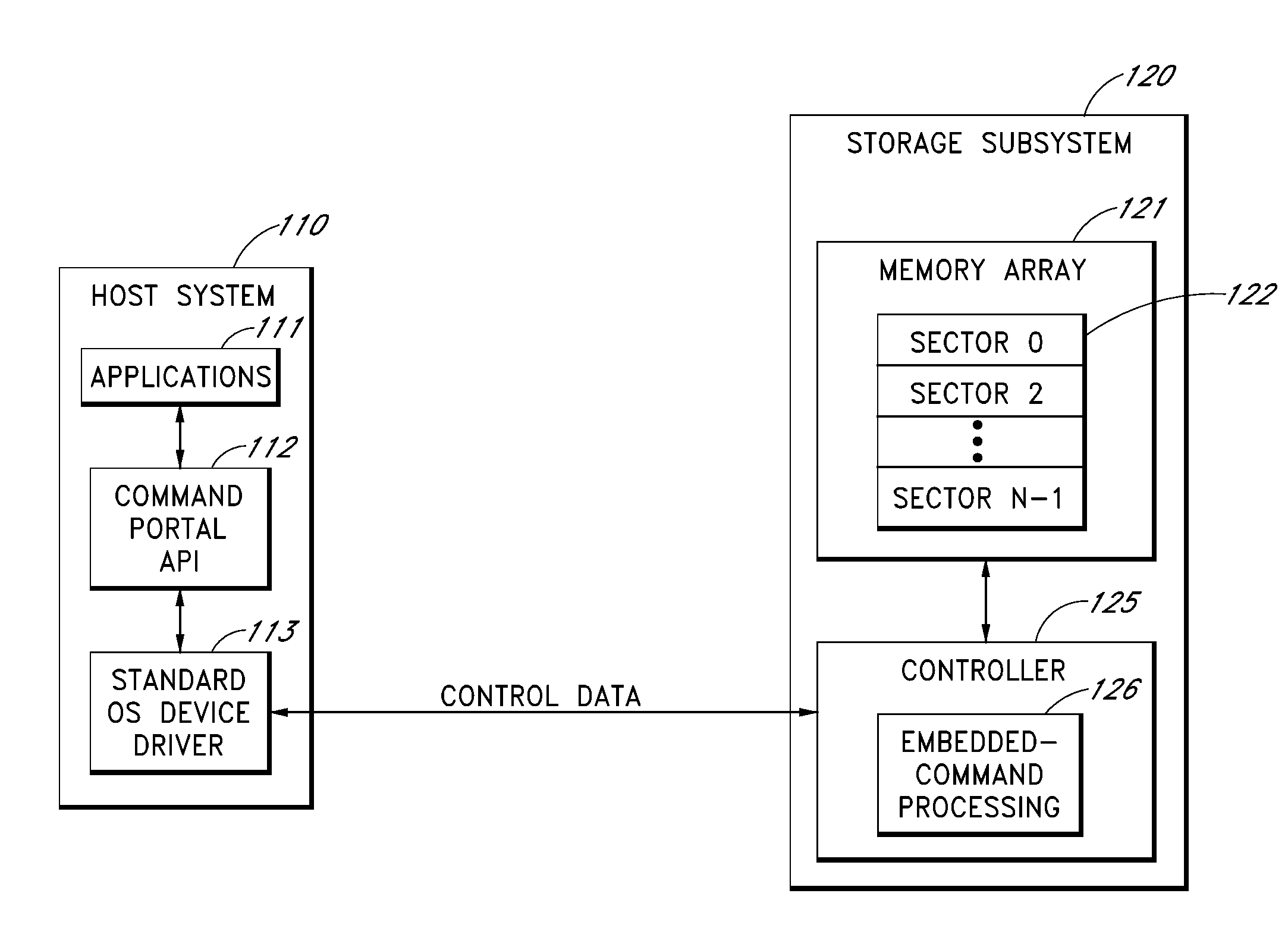
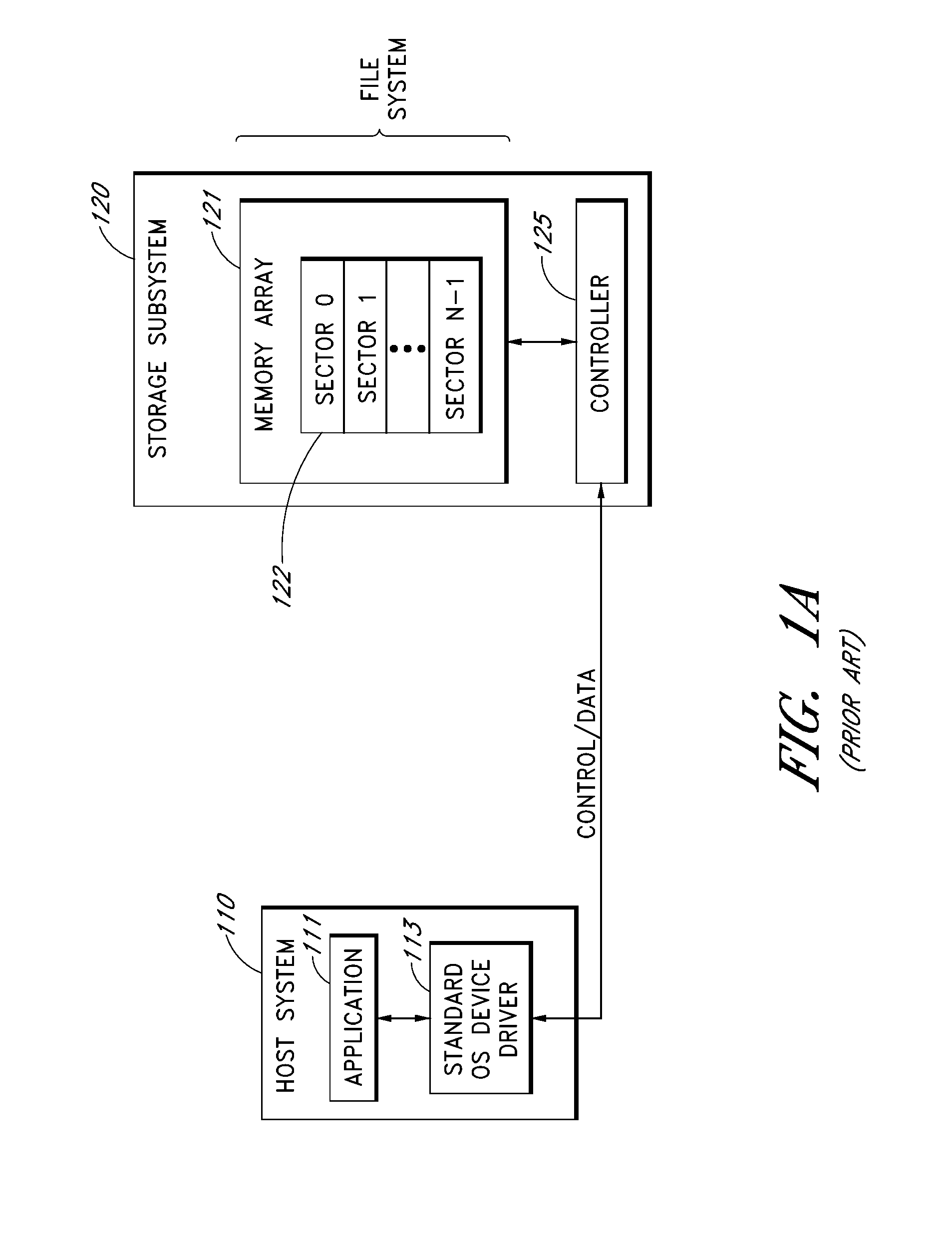
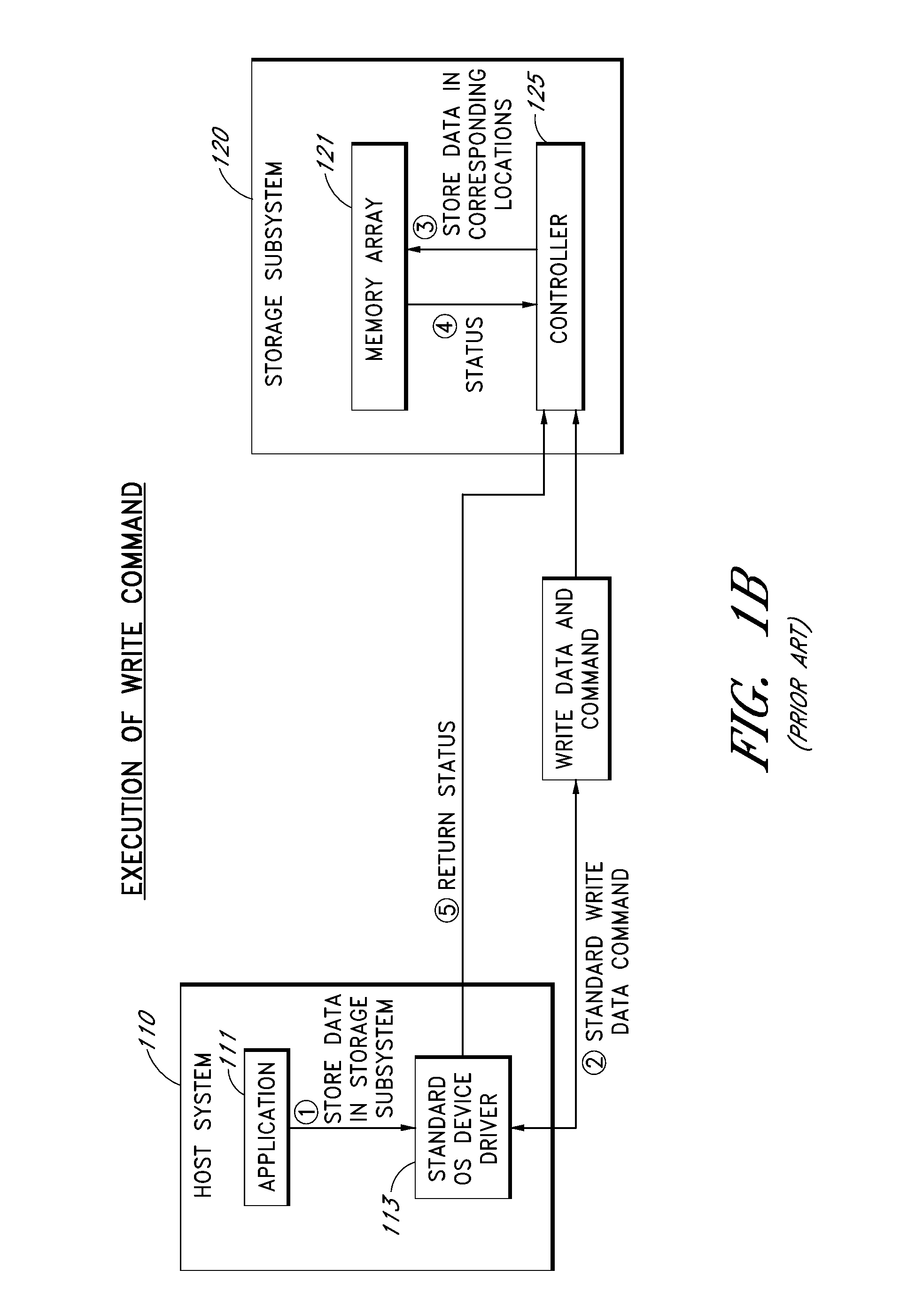
Command portal for securely communicating and executing non-standard storage subsystem commands
InactiveUS20130145106A1Reduce eliminateInput/output to record carriersMemory systemsComputer hardwareApplication software
A command portal enables a host system to send non-standard or “vendor-specific” storage subsystem commands to a storage subsystem using an operating system (OS) device driver that does not support or recognize such non-standard commands. The architecture thereby reduces or eliminates the need to develop custom device drivers that support the storage subsystem's non-standard commands. To execute non-standard commands using the command portal, the host system embeds the non-standard commands in blocks of write data, and writes these data blocks to the storage subsystem using standard write commands supported by standard OS device drivers. The storage subsystem extracts and executes the non-standard commands. The non-standard commands may alternatively be implied by the particular target addresses used. The host system may retrieve execution results of the non-standard commands using standard read commands. The host-side functionality of the command portal may be embodied in an API that is made available to application developers.
Owner:WESTERN DIGITAL TECH INC
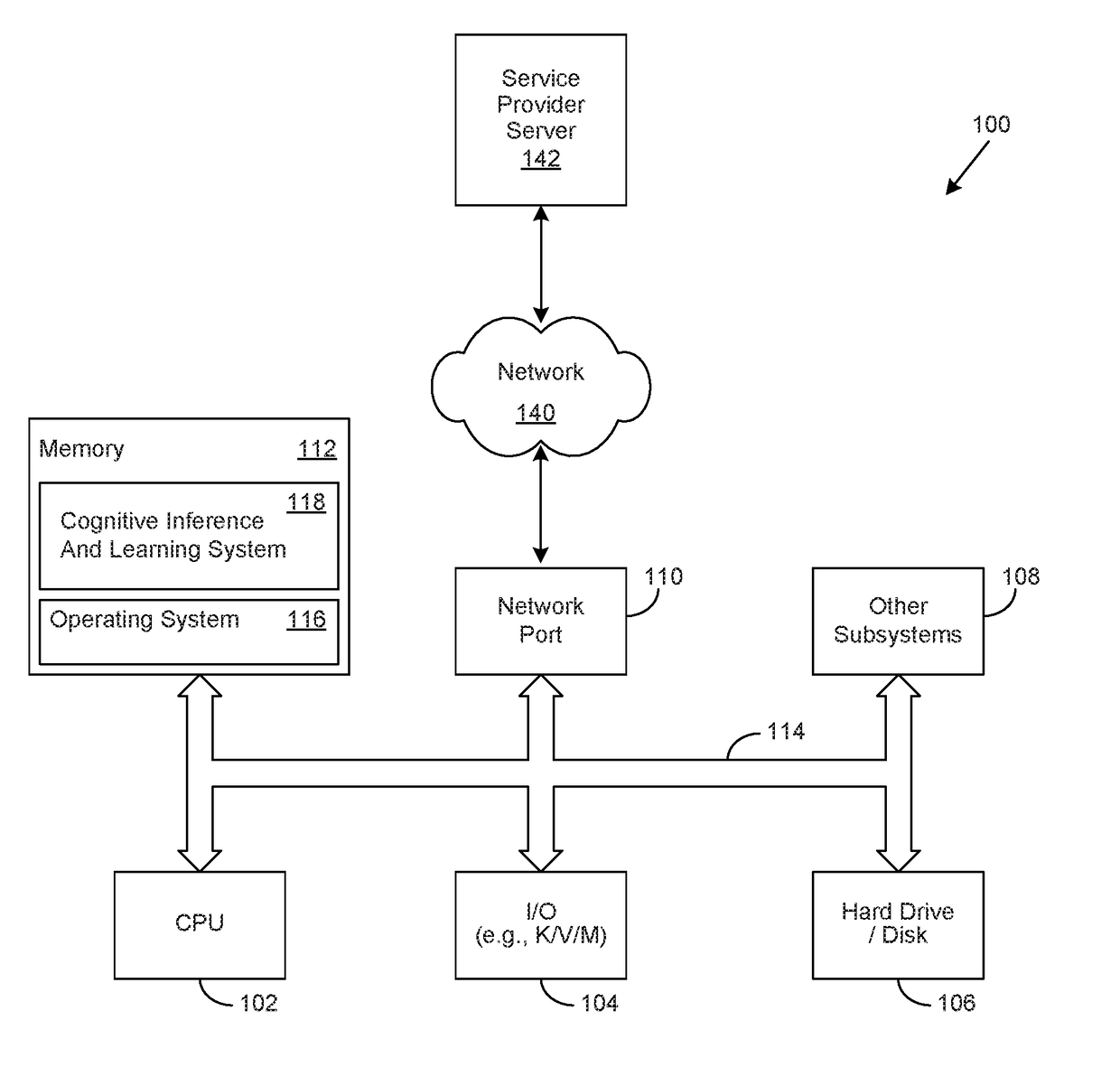
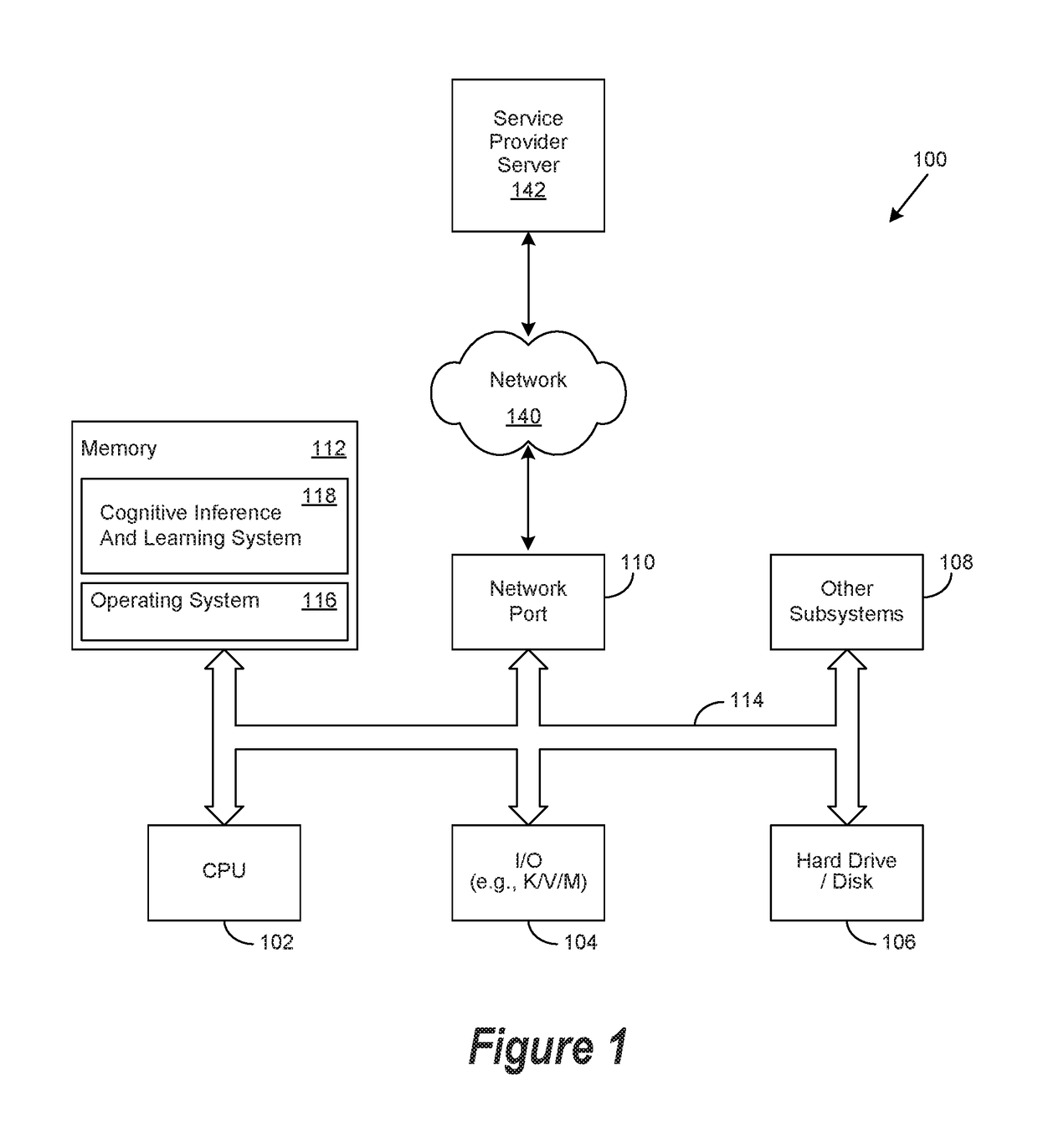
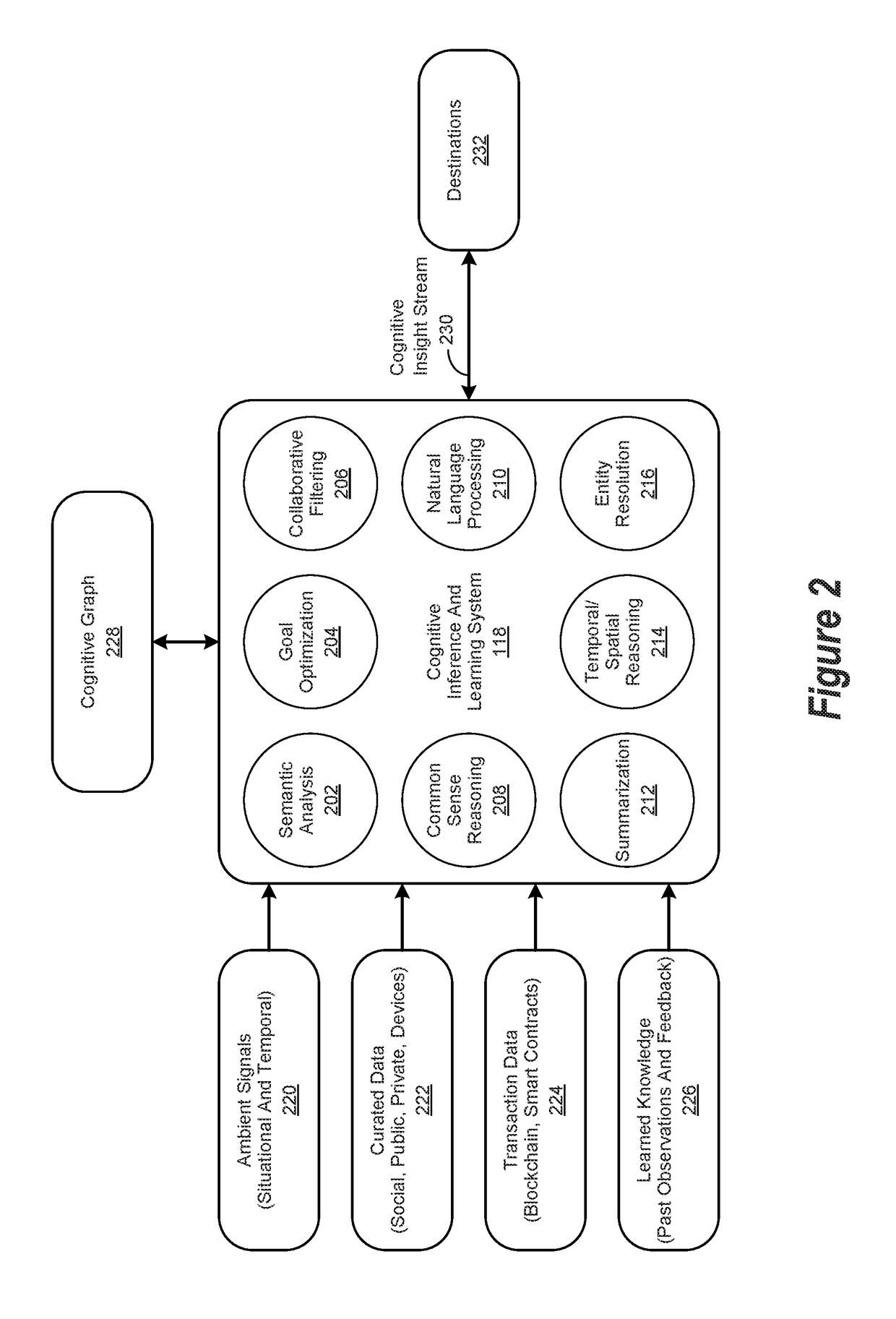
Method for Cognitive Information Processing Using a Cognitive Blockchain Architecture
A computer-implementable method for cognitive information processing comprising: receiving data from a plurality of data sources, at least one of the plurality of data sources comprising a blockchain data source having associated blockchain data; processing the data from the plurality of data sources to provide cognitively processed data; performing a learning operation to improve the cognitively processed data over time, the learning operation being based at least in part on the blockchain data from the blockchain data source; and, providing the cognitively processed data to a destination.
Owner:TECNOTREE TECH INC
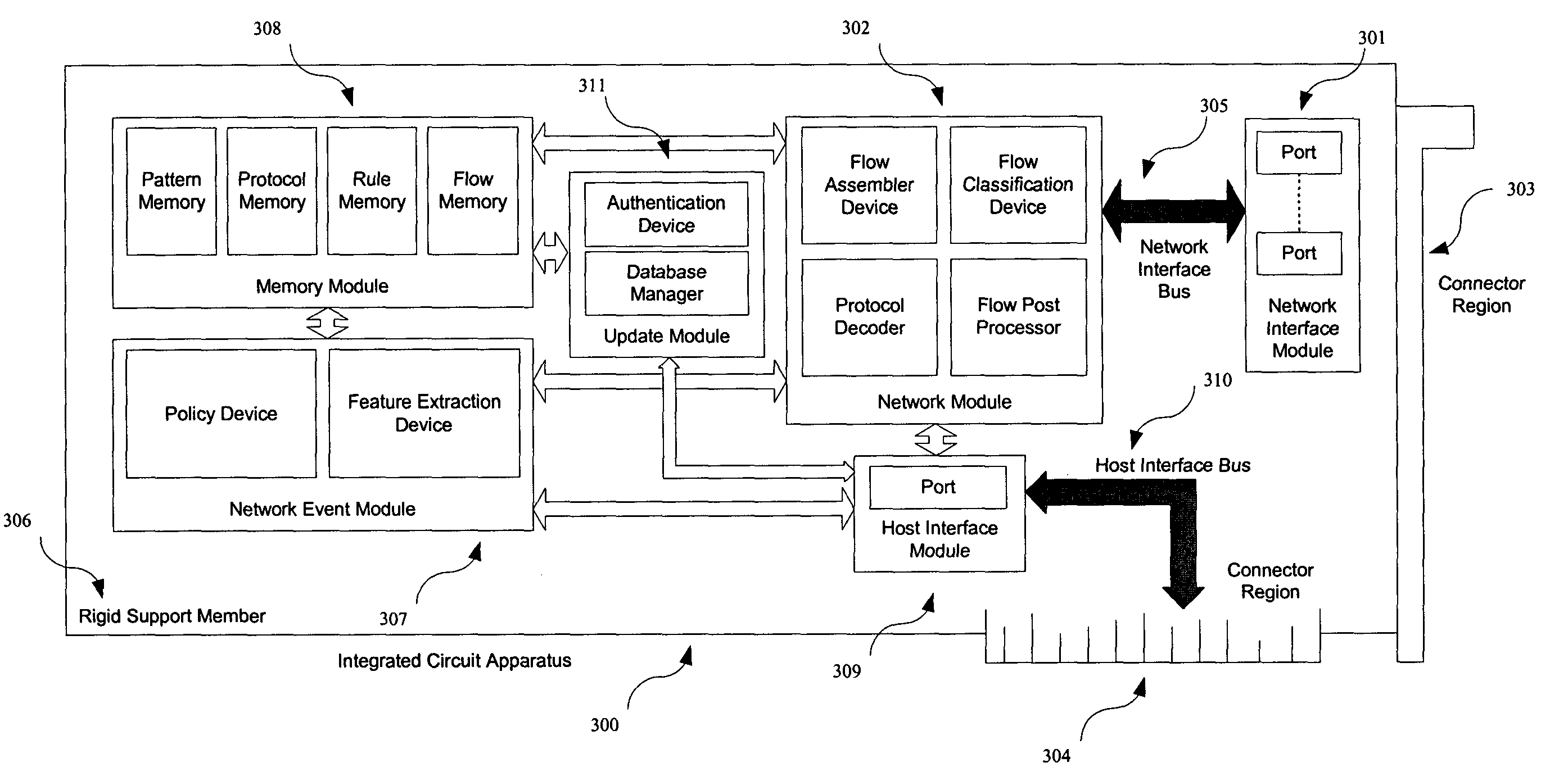
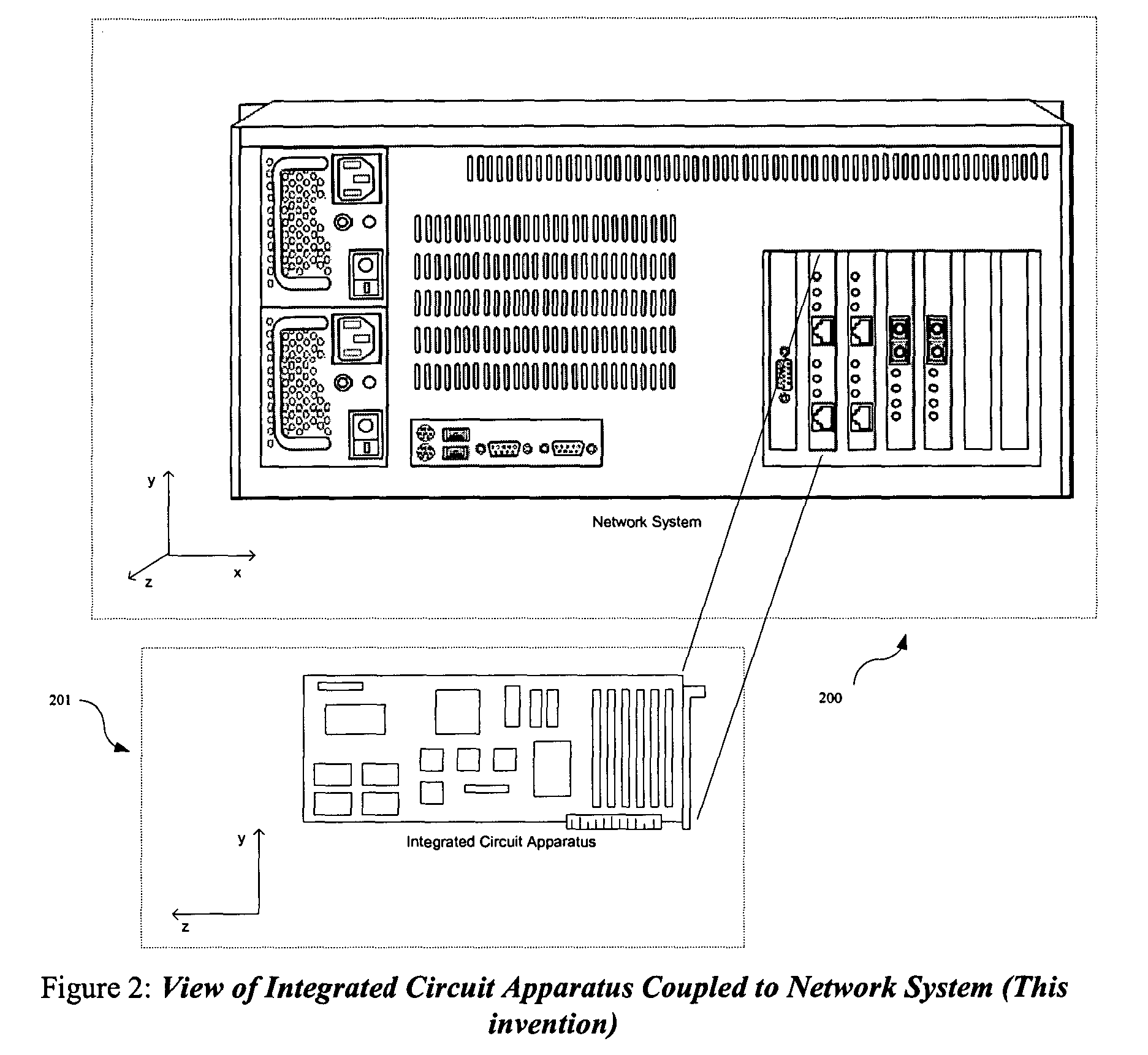
Integrated circuit apparatus and method for high throughput signature based network applications
InactiveUS20050114700A1Overcome quality of service problemOvercome deficienciesDigital data processing detailsCharacter and pattern recognitionWire speedPattern matching
An architecture for an integrated circuit apparatus and method that allows significant performance improvements for signature based network applications. In various embodiments the architecture allows high throughput classification of packets into network streams, packet reassembly of such streams, filtering and pre-processing of such streams, pattern matching on header and payload content of such streams, and action execution based upon rule-based policy for multiple network applications, simultaneously at wire speed. The present invention is improved over the prior art designs, in performance, flexibility and pattern database size.
Owner:INTEL CORP
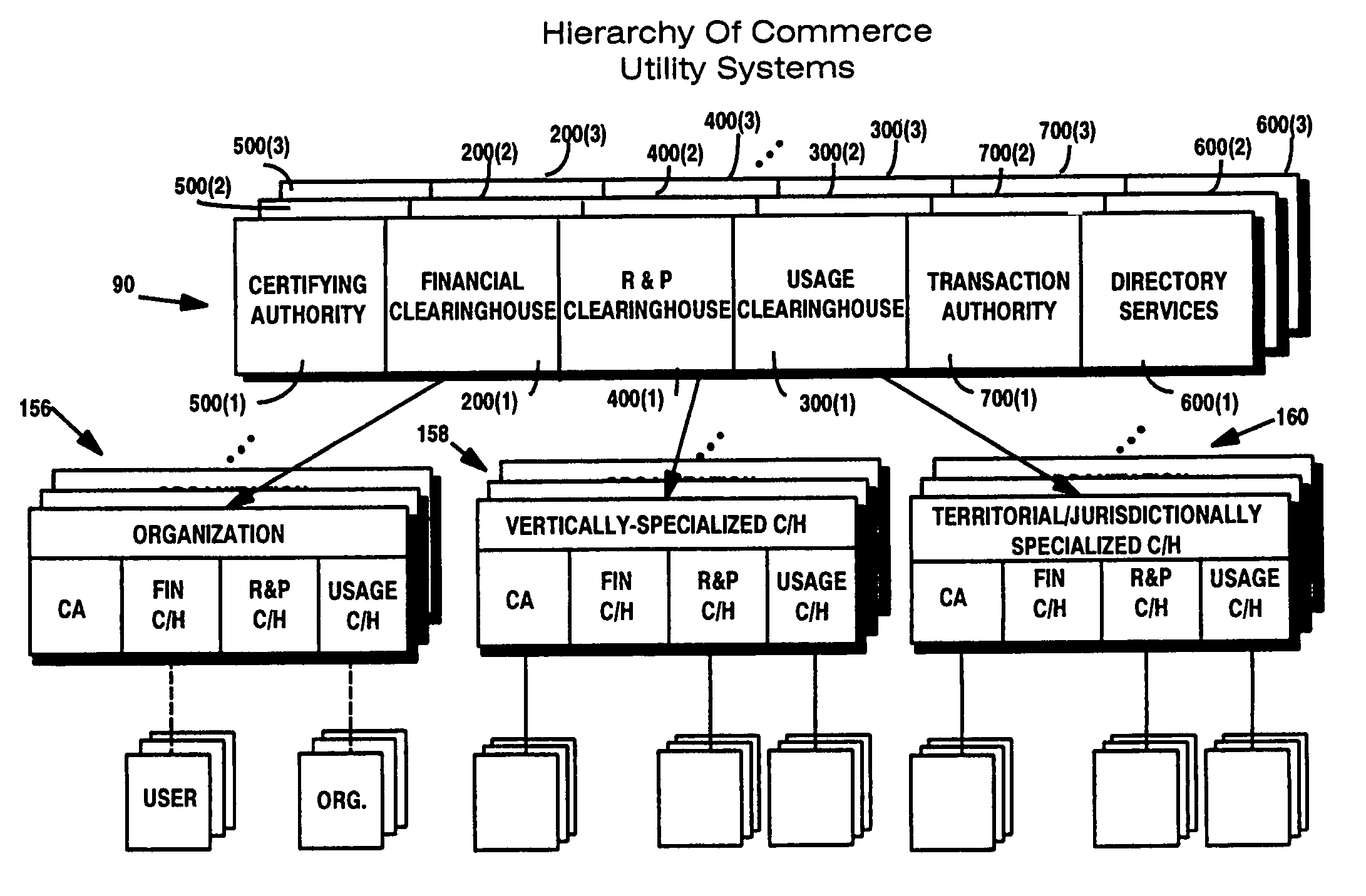
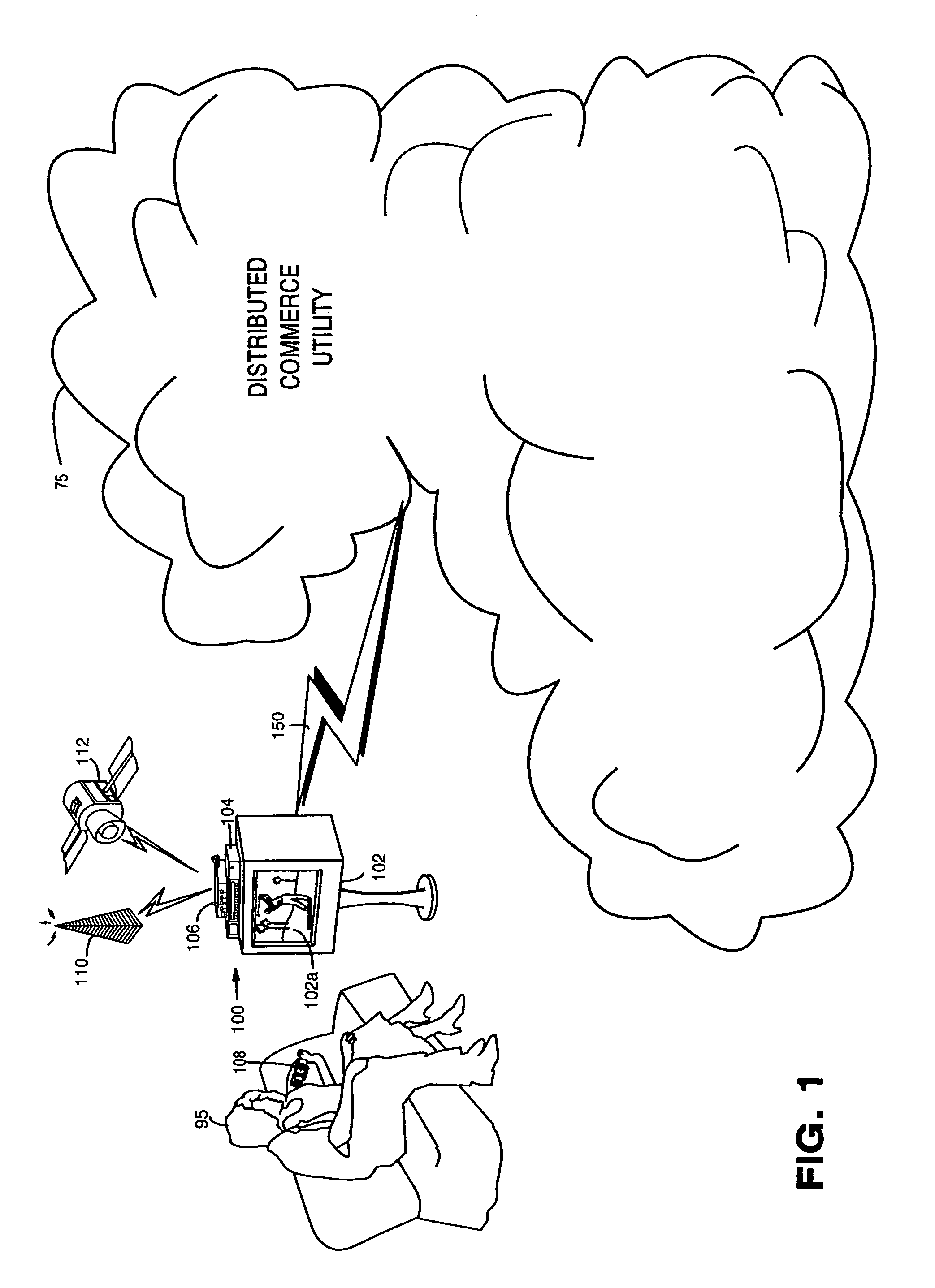
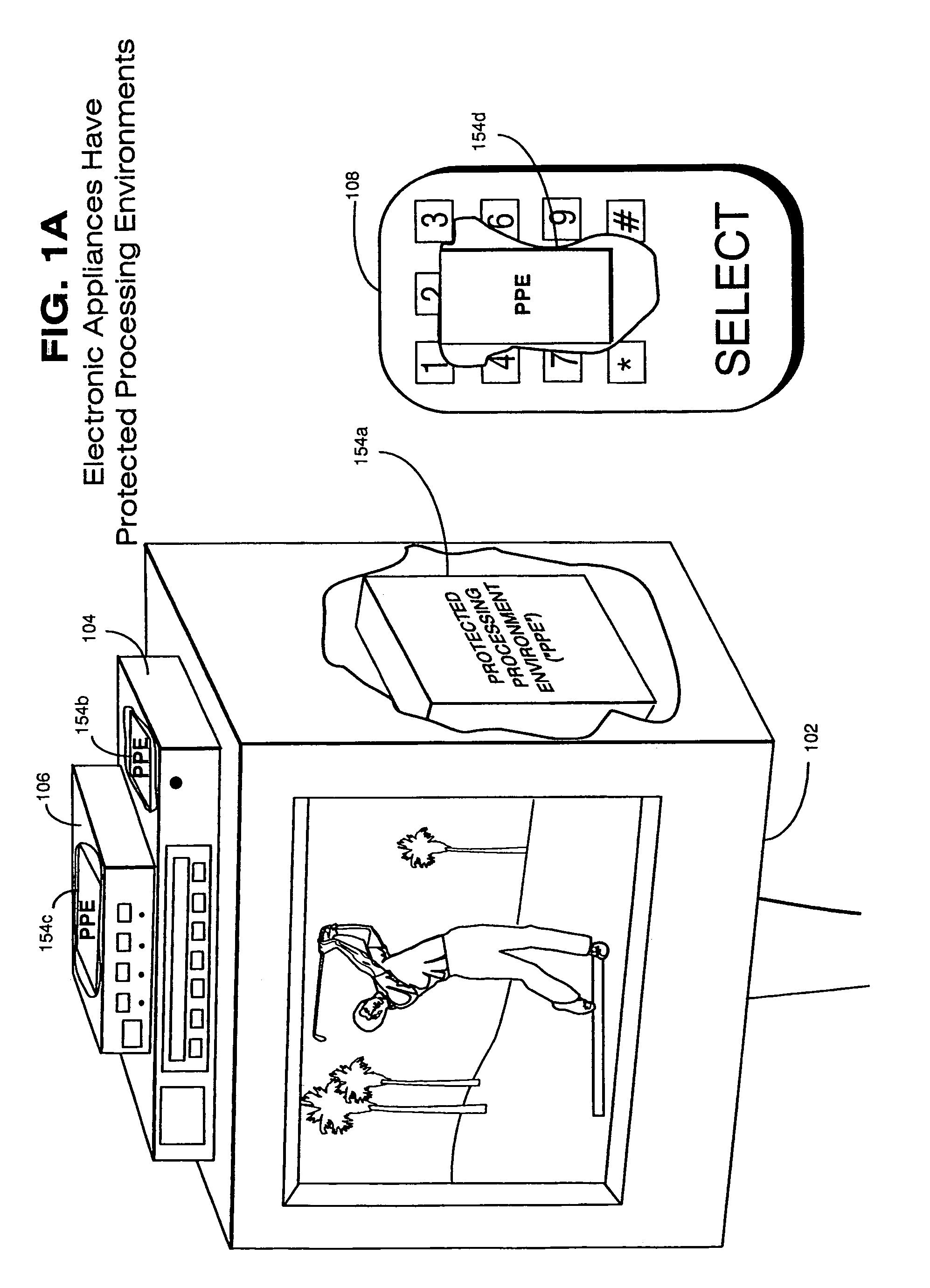
Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management
InactiveUS7415617B2Efficiently distributedDigital data processing detailsUser identity/authority verificationTransaction managementUtility industry
An integrated, modular array of administrative and support services are provided for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting transaction-related capabilities functioning over electronic network-s, and can also be adapted to the specific needs of electronic commerce value chains. In one embodiment, a Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many of its participants. Different support functions can be collected together in hierarchical and / or networked relationships to suit various business models or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes.
Owner:INTERTRUST TECH CORP
Software development process
InactiveUS20020104068A1Increase flexibilitySoftware designSpecific program execution arrangementsSoftware development processSoftware system
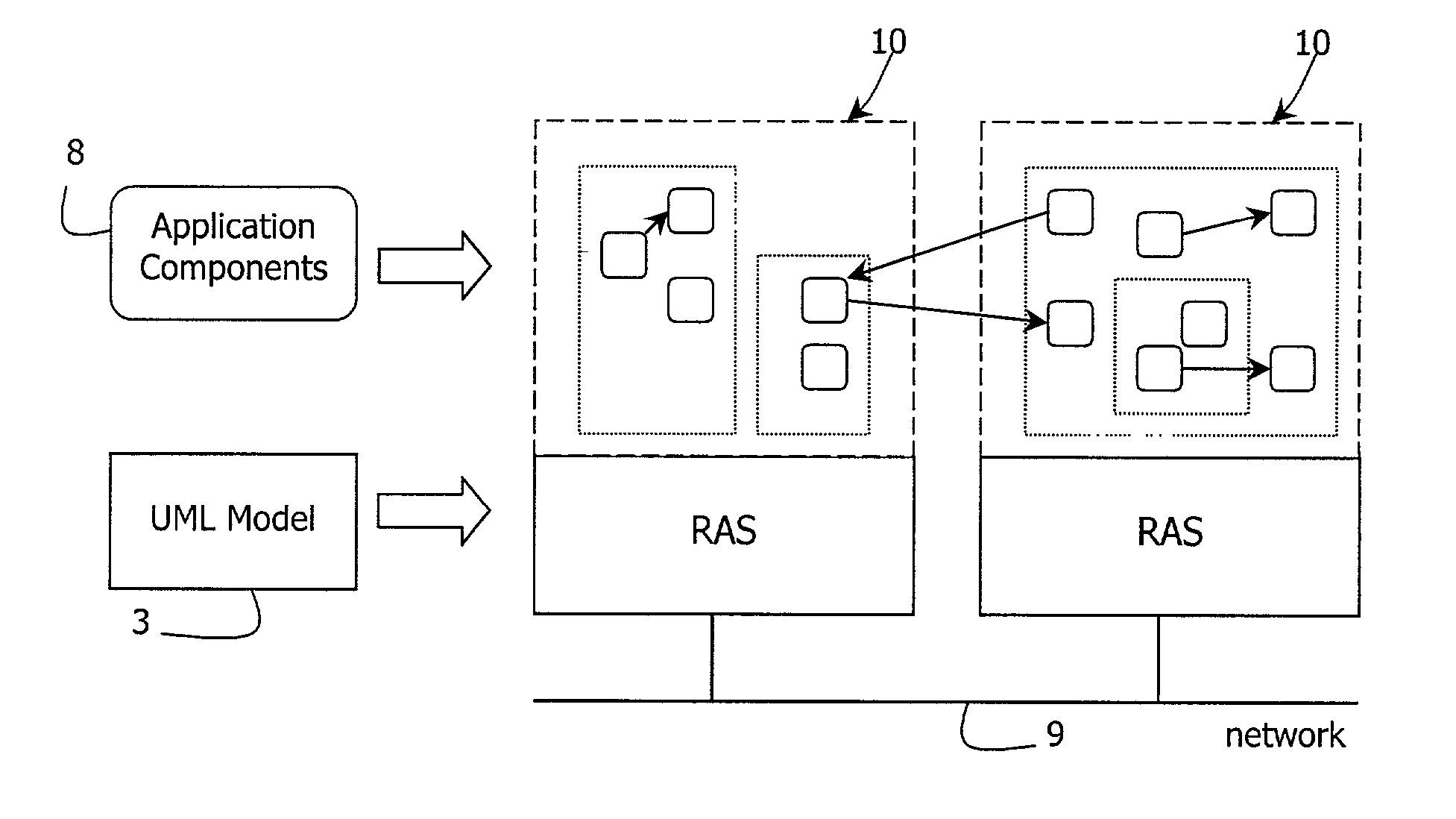
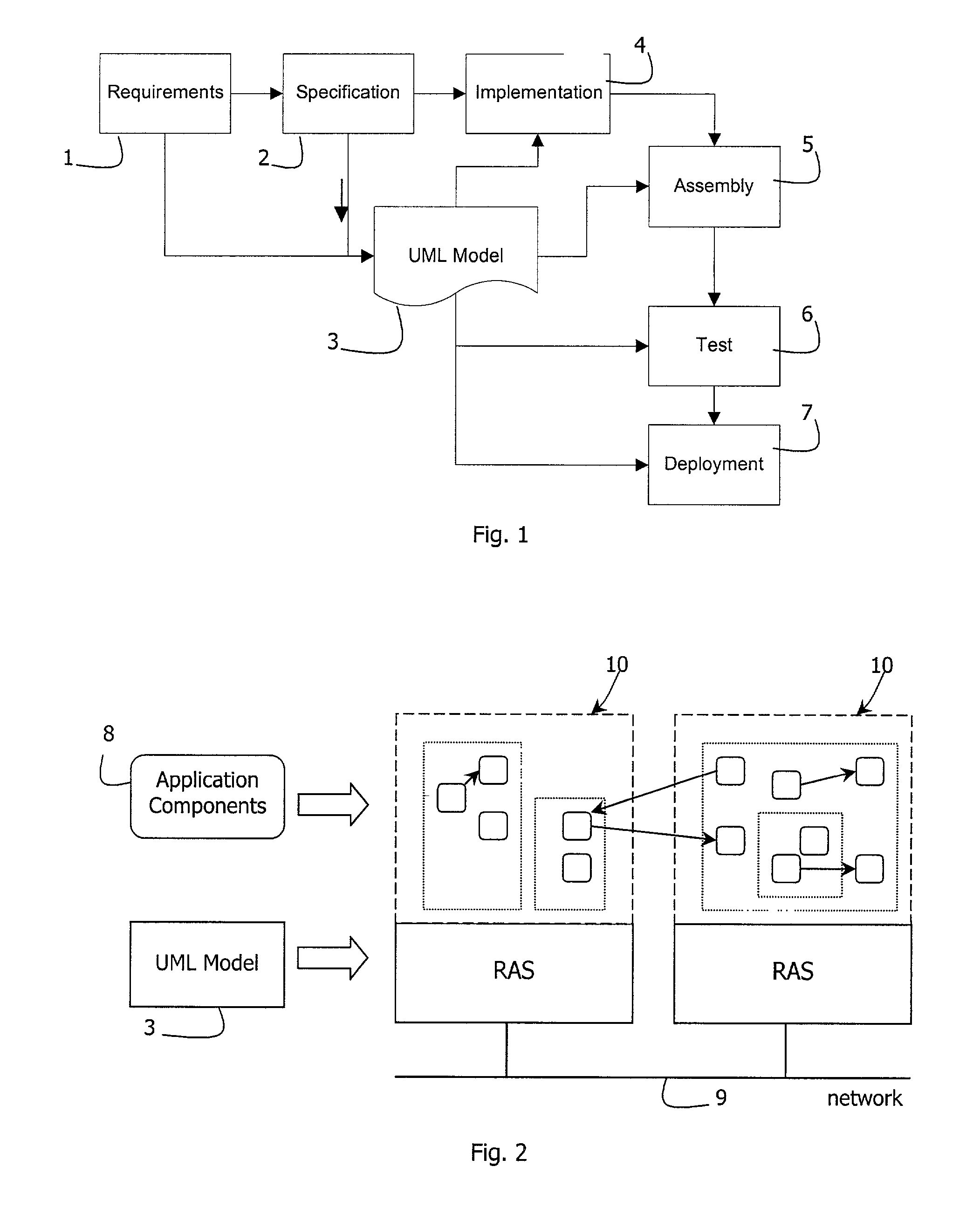
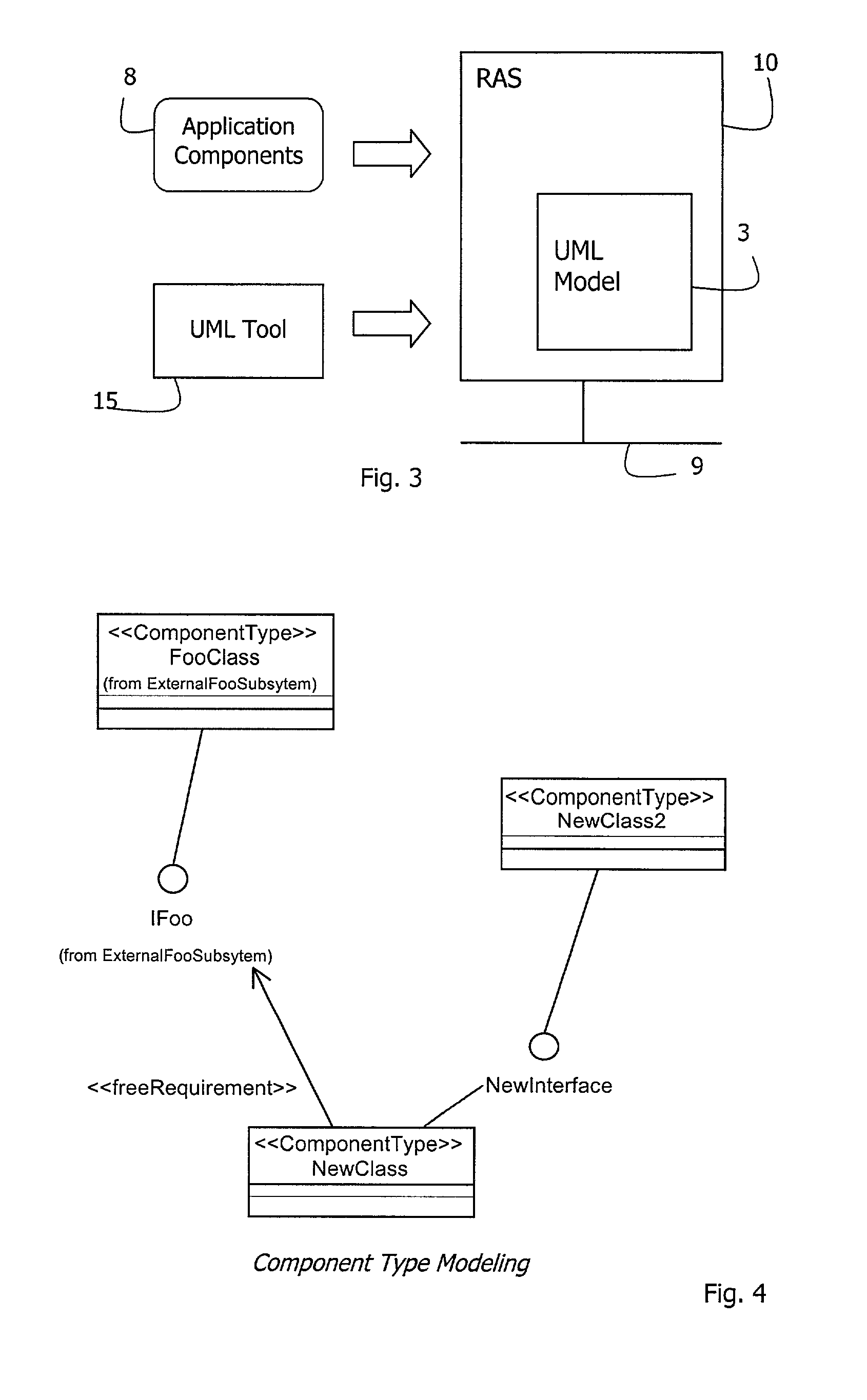
A flexible component-based software system is developed by generating a UML model (3) in a specification phase (4). Components are generated in an implementation phase (4). The UML model (3) is transformed to a meta model. A runtime architecture service (RAS, 10) dynamically assembles a system in runtime according to the meta model. A modelling tool (15) modifies the meta model via an API (34) and a meta modeller (31). This allows dynamic re-configuration of the system.
Owner:WILDE TECH
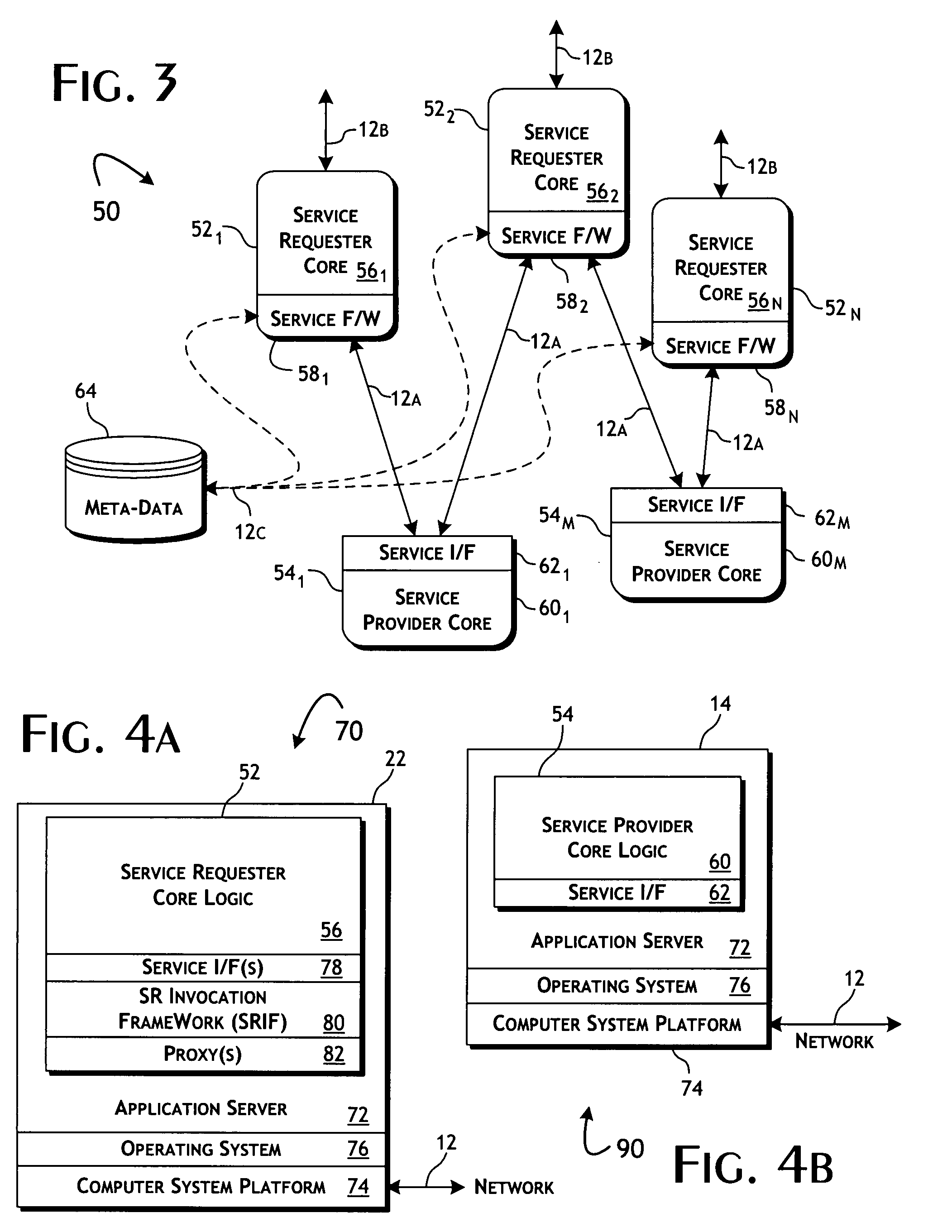
Service-oriented architecture and methods for direct invocation of services utilizing a service requestor invocation framework
InactiveUS20080140857A1Effective guidanceEfficient use ofData processing applicationsMultiple digital computer combinationsData processing systemDirect communication
A data processing system implementing a service-oriented architecture that efficiently provides for self-directed communications between service requesters and service providers. Service providers, operative to implement a predefined computing functions, are responsive to first service requests and operative to provide a first service responses. Service requesters executed remote from service providers are operative to provide second service requests and receive second service responses. A service invocation framework local to each service requester functions to convert between first and second service requests and first and second service responses and to establish direct invocation communications connection with a selected service provider for the exchange of first service requests responses. A service invocation manager provides configuration meta-data, upon dynamic request by a service invocation framework, to define the conversions and communications connection to be implemented by the service invocation framework with respect to a service provider.
Owner:PRIMITIVE LOGIC
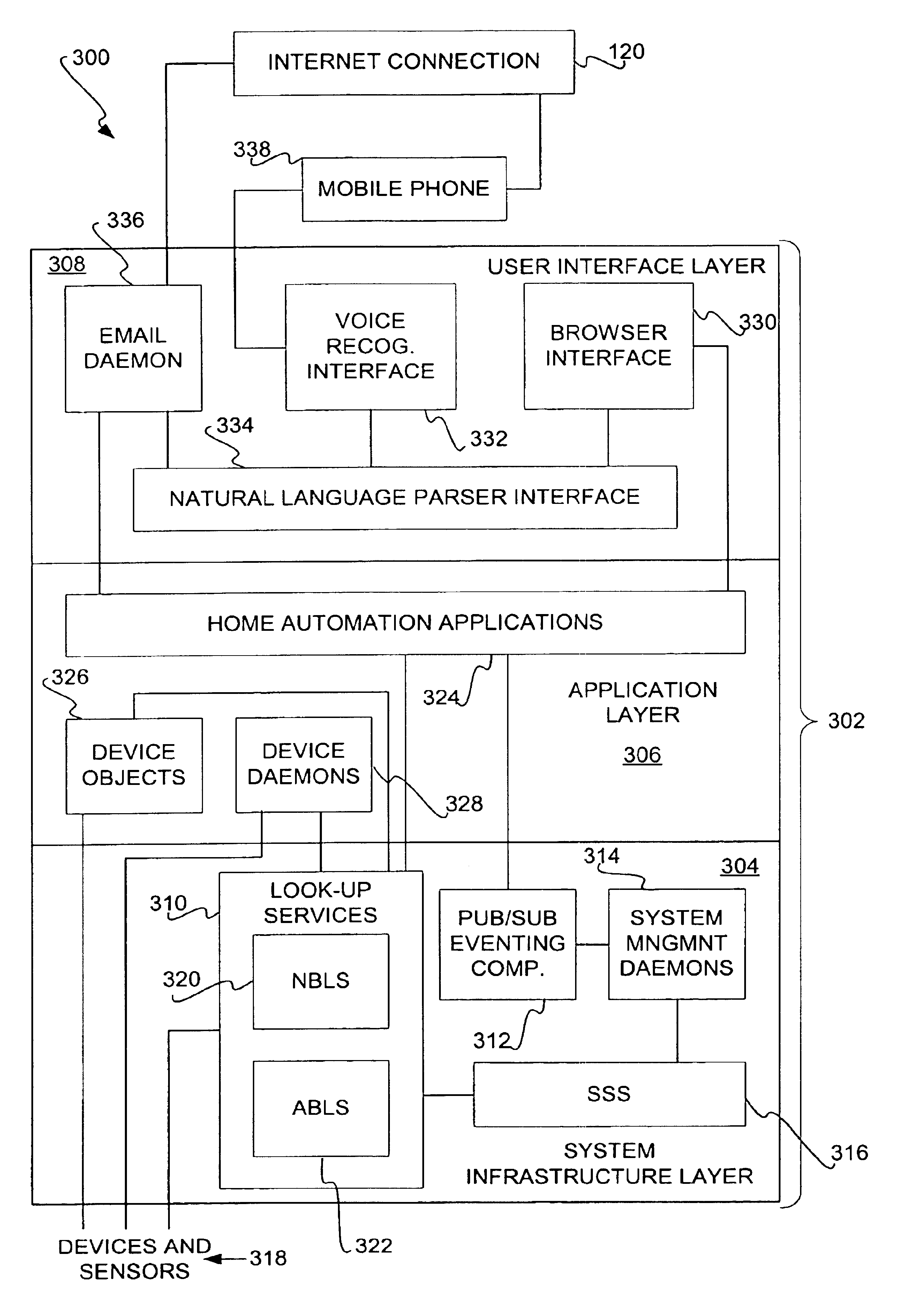
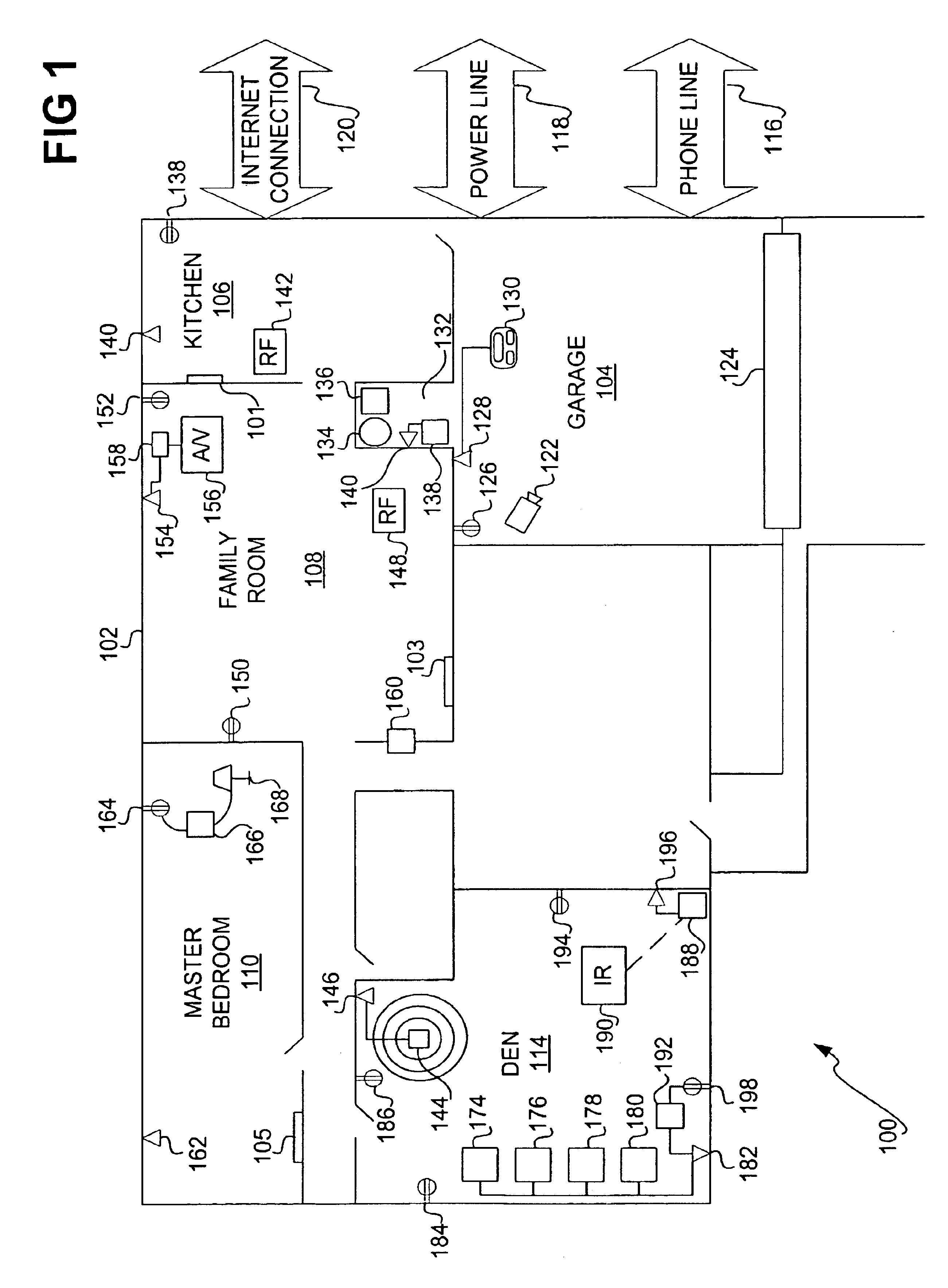
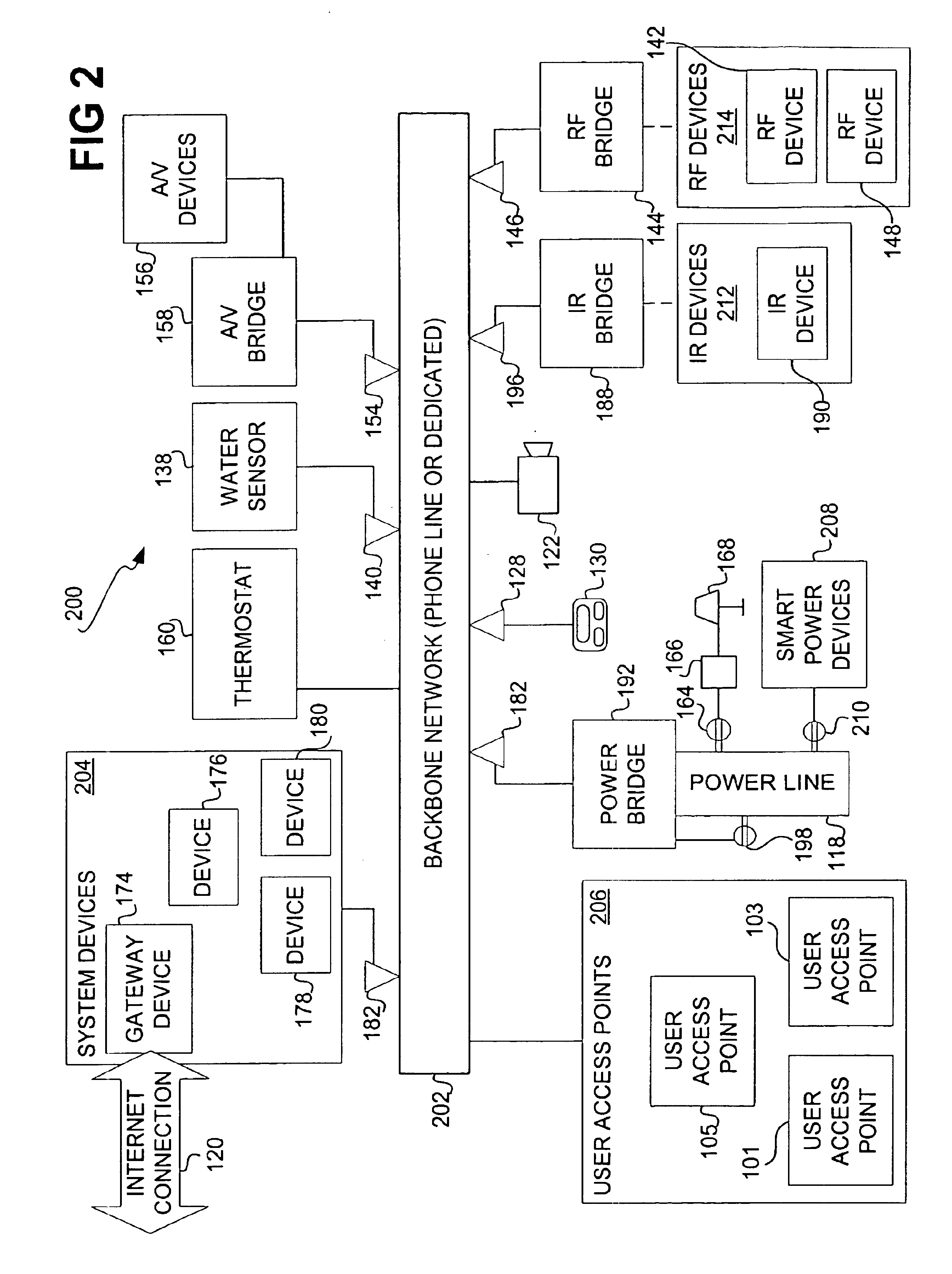
Automation system for controlling and monitoring devices and sensors
InactiveUS6961763B1Sampled-variable control systemsSafety arrangmentsSoft statePublish–subscribe pattern
An architecture for an automation system is disclosed that includes look-up services, a soft-state store, and a publication / subscription eventing component. The look-up services maintain a database of a number of devices to be controlled and monitored, and a database of a number of device objects corresponding to the devices. The services can be divided into attribute-based and name-based services. The soft-state store manages variables regarding the devices and the device objects, including heartbeats. The eventing component enables subscriptions to events related to changes in the variables. The architecture can include management daemons, such as a monitoring daemon that detects problems with power line devices.
Owner:MICROSOFT TECH LICENSING LLC
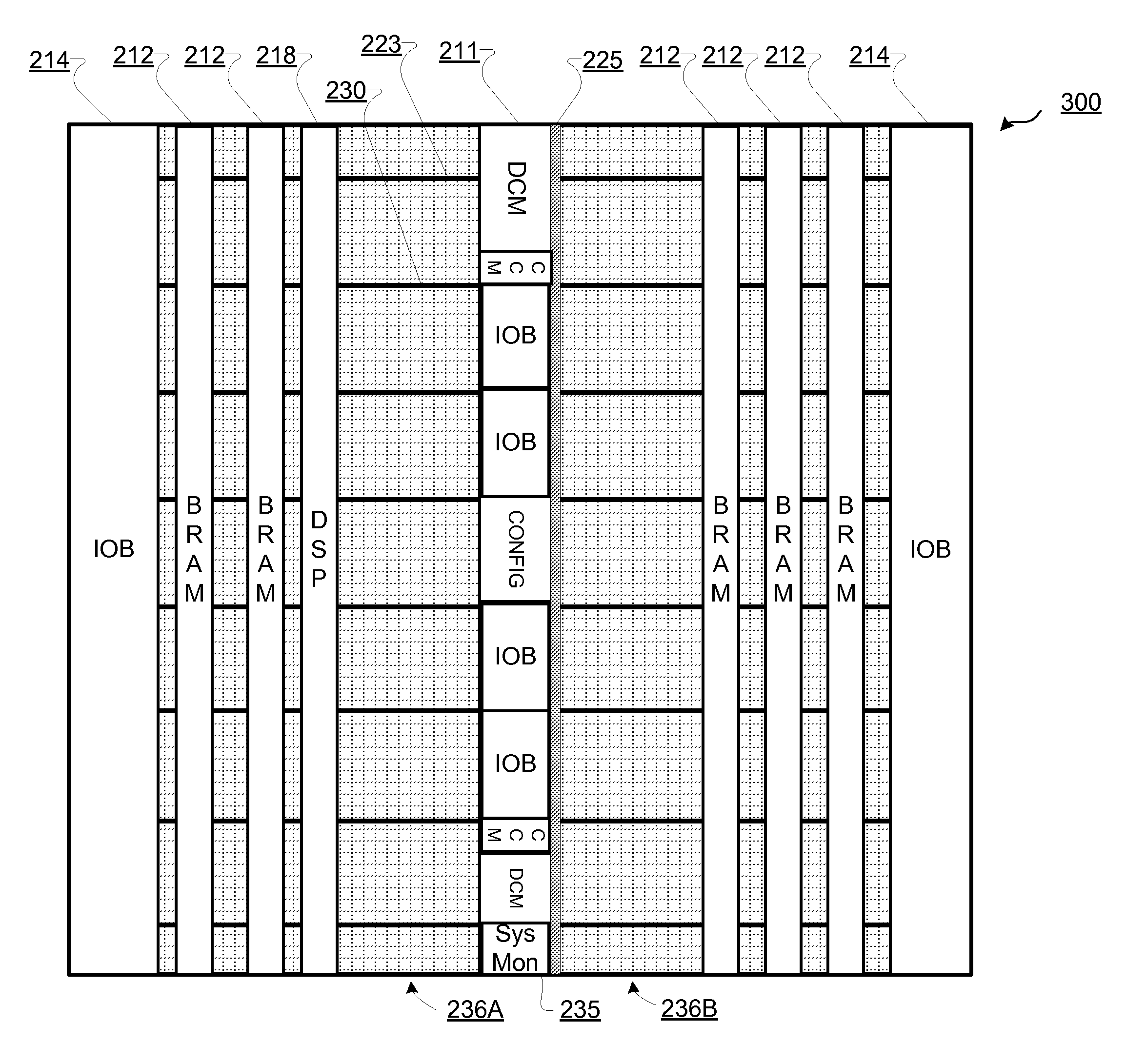
Formation of columnar application specific circuitry using a columnar programmable device
A columnar programmable device (PD) design converted to a columnar application specific integrated circuit-like (ASIC-like) design is described. A user design is instantiated in a PD having a columnar architecture associated with the columnar PD design. The columnar architecture has adjacent columns of circuitry, and one or more of the columns of circuitry as associated with instantiation of the user design in the PD are identified. At least a portion of one or more of the identified columns are swapped with application specific circuitry for implementing all or part of the user design for converting the columnar PD design to the columnar ASIC-like design.
Owner:XILINX INC
Controlled deployment of software in a web-based architecture
ActiveUS20060075398A1Digital computer detailsProgram loading/initiatingSoftware engineeringControl software
The present invention includes systems and methods for the controlled deployment of software in a web-based environment where multiple versions of a single application are supported to provide field experience of various versions before general deployment. The systems and methods of the invention support backwards compatibility, which allows older versions of the same software to be accessed concurrently with newer (revised) versions. Likewise, data item opaqueness is supported whereby data items not recognized by a software level or tier are not rejected but are passed on to another tier or level where they may be recognized.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
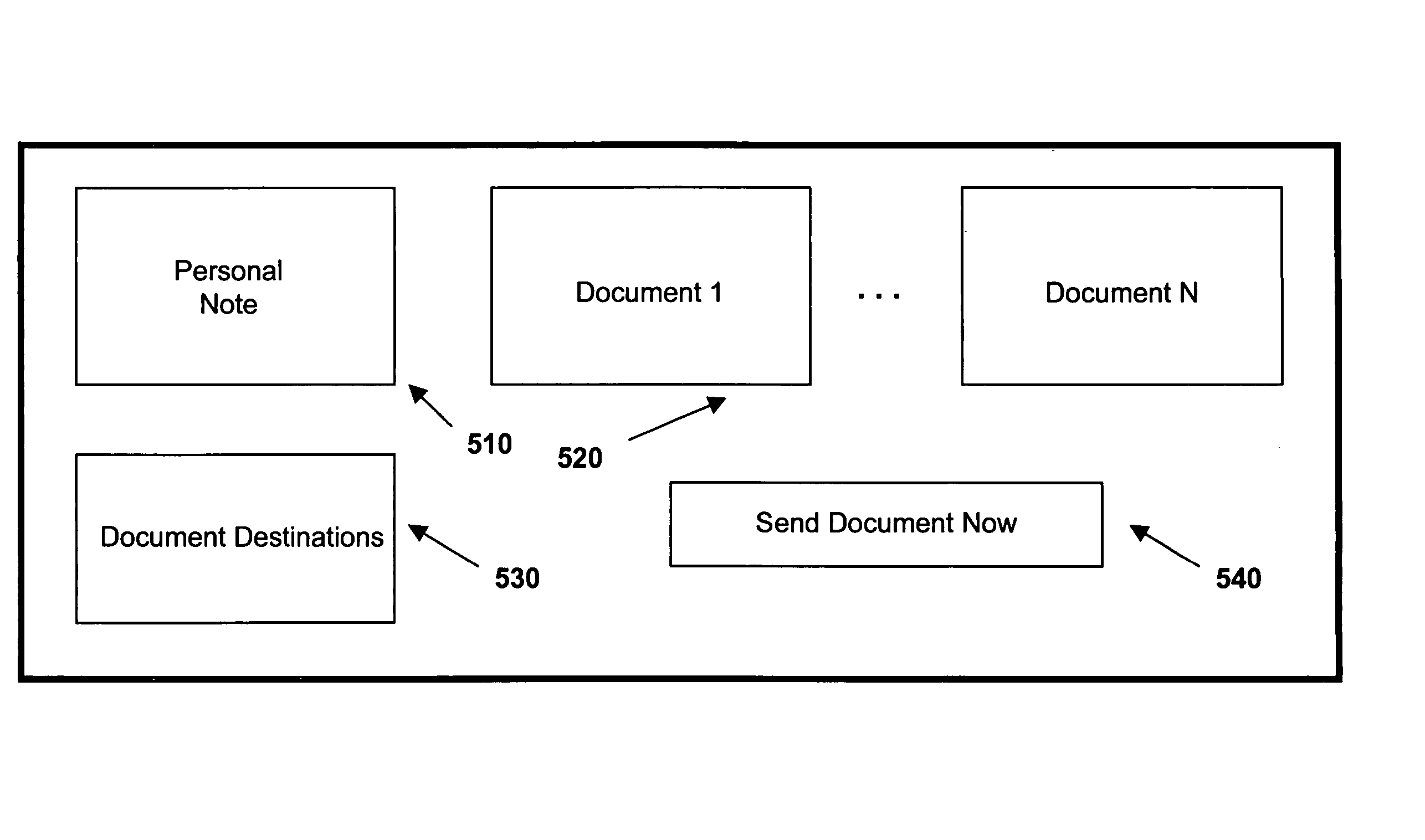
Agent architecture employed within an integrated message, document and communication system
InactiveUS20050060638A1Multiplex communicationMultiple digital computer combinationsCommunications systemAgent architecture
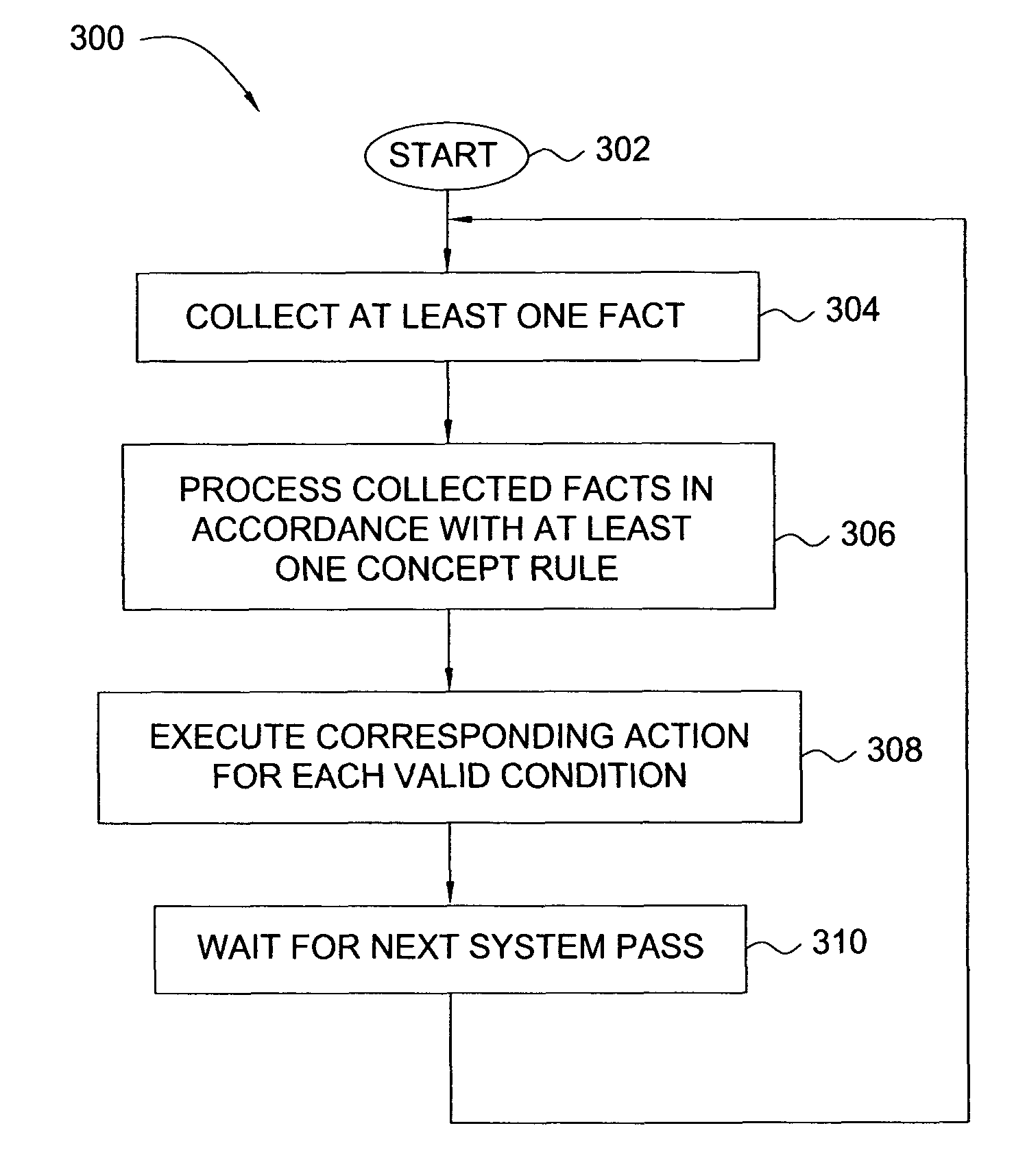
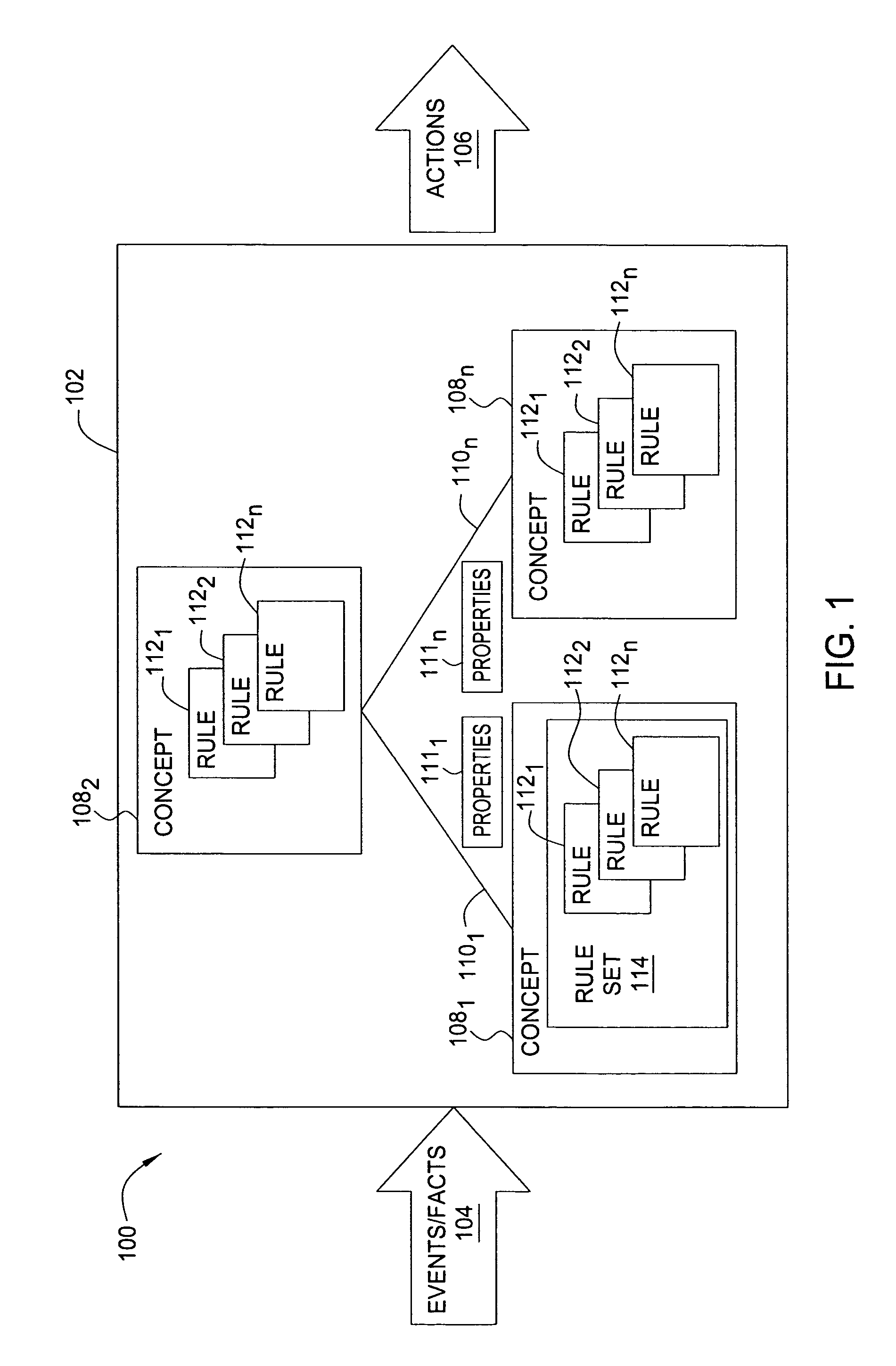
A system is described for managing messages, communications and / or documents comprising: a plurality of task agents, each task agent to perform one or more specified message processing actions, document processing actions, and / or communications processing actions on different types of messages, documents and / or communication channels, respectively; and one or more manager agents to coordinate the actions of the plurality of task agents responsive to a plurality of message and / or document processing rules.
Owner:CATALYSTWEB
Support for multiple security policies on a unified authentication architecture
ActiveUS8166304B2Digital data processing detailsUser identity/authority verificationData processing systemSecurity kernel
A method, computer program product, and data processing system are disclosed for ensuring that applications executed in the data processing system originate only from trusted sources are disclosed. In a preferred embodiment, a secure operating kernel maintains a “key ring” containing keys corresponding to trusted software vendors. The secure kernel uses vendor keys to verify that a given application was signed by an approved vendor. To make it possible for independent developers to develop software for the herein-described platform, a “global key pair” is provided in which both the public and private keys of the pair are publicly known, so that anyone may sign an application with the global key. Such an application may be allowed to execute by including the global key pair's public key in the key ring as a “vendor key” or, conversely, it may be disallowed by excluding the global public key from the key ring.
Owner:INT BUSINESS MASCH CORP
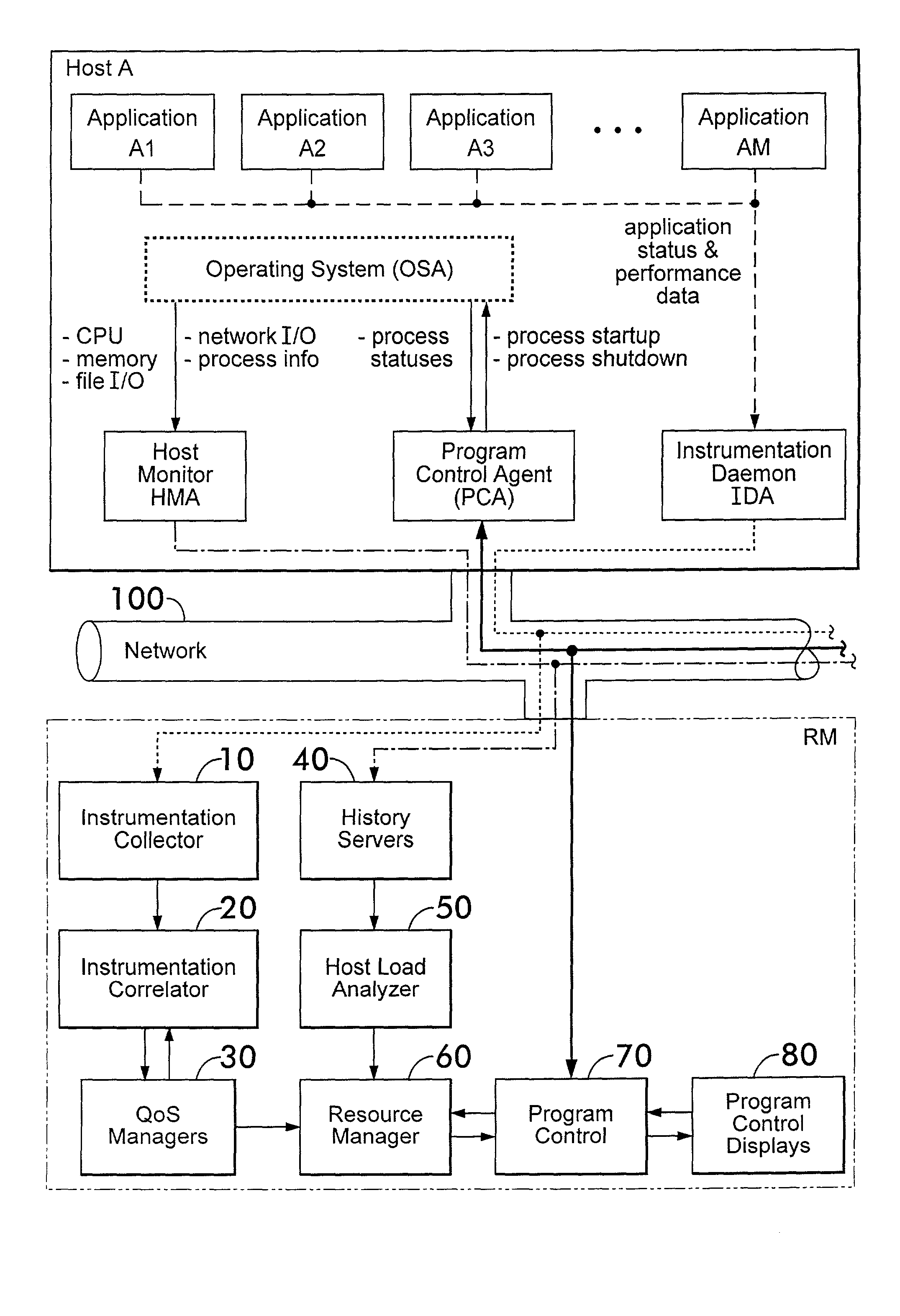
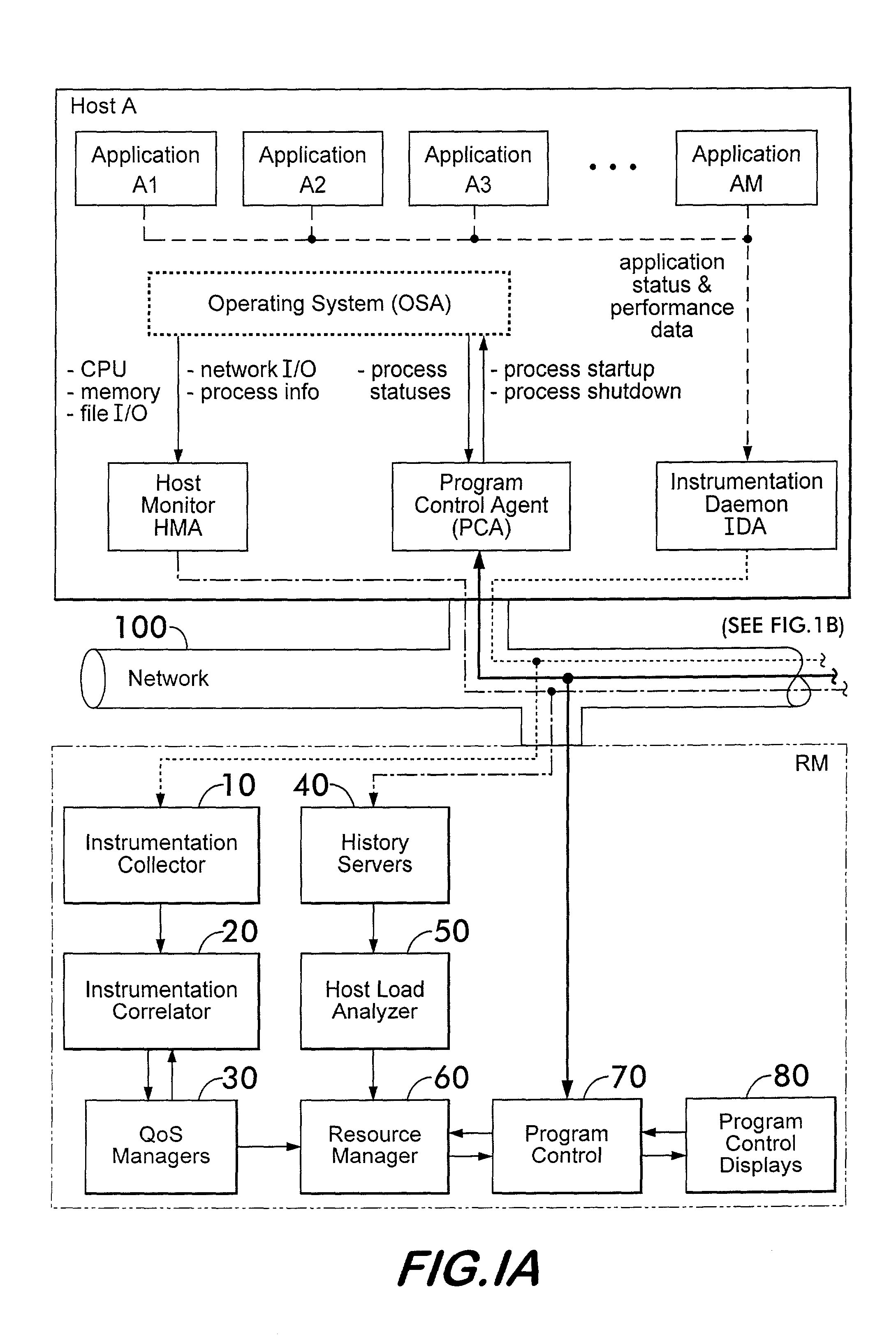
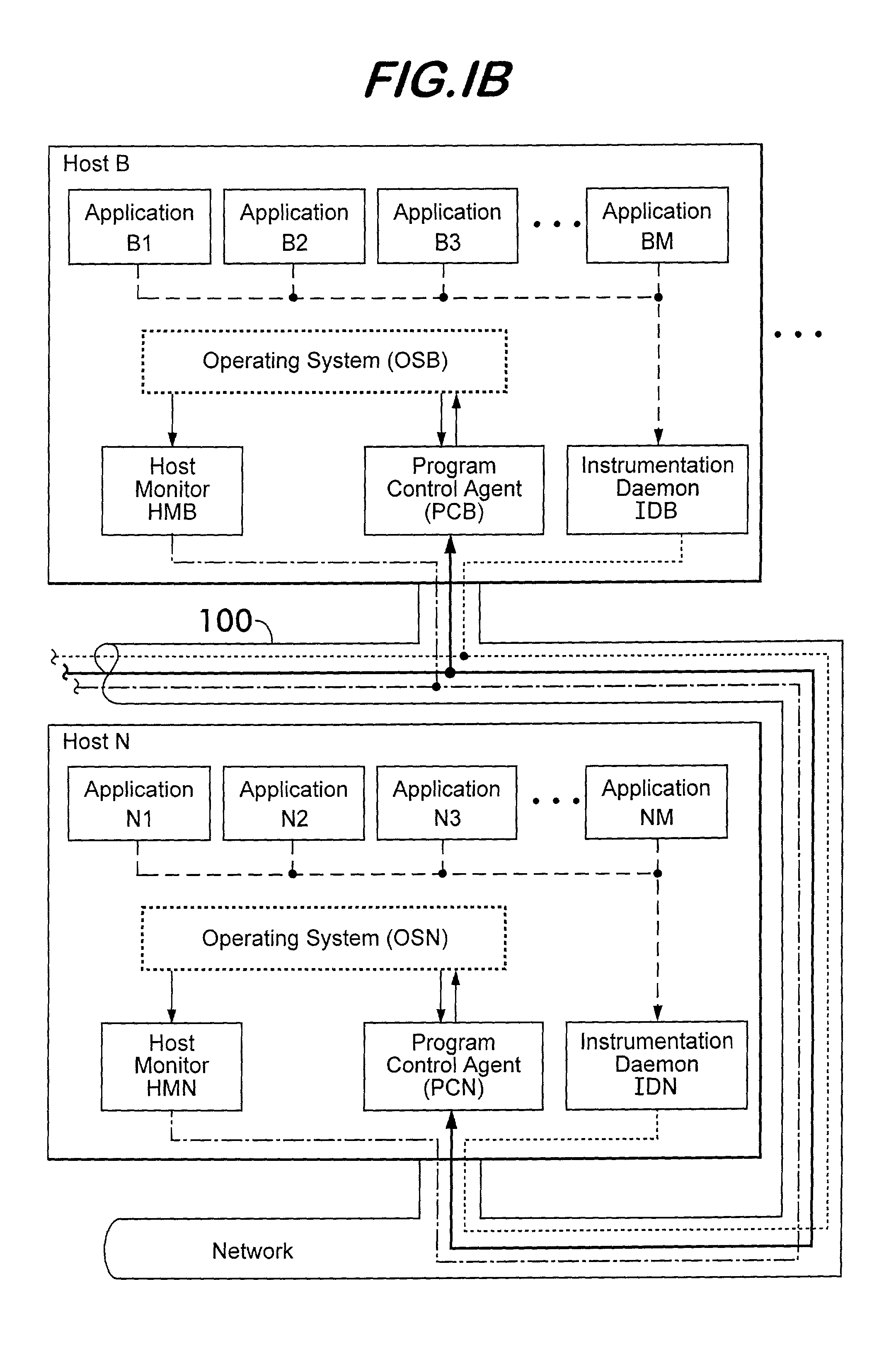
Instrumentation for resource management architecture and corresponding programs therefor
ActiveUS20050055322A1Program initiation/switchingResource allocationMonitoring systemResource management
A monitoring system for a distributed environment including a plurality of hosts capable of executing multiple copies of a scalable application includes a first device for generating first data corresponding to performance of all copies of the scalable application; a second device for generating second data corresponding to performance of all host in the distributed environment; and a third device for generating performance metrics based on the first and second data.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Remote vedio monitoring system based on next generation interconnection network and its implementing method
InactiveCN1913461ASimple structureComplete structureClosed circuit television systemsTransmission monitoringVideo monitoringDigital video
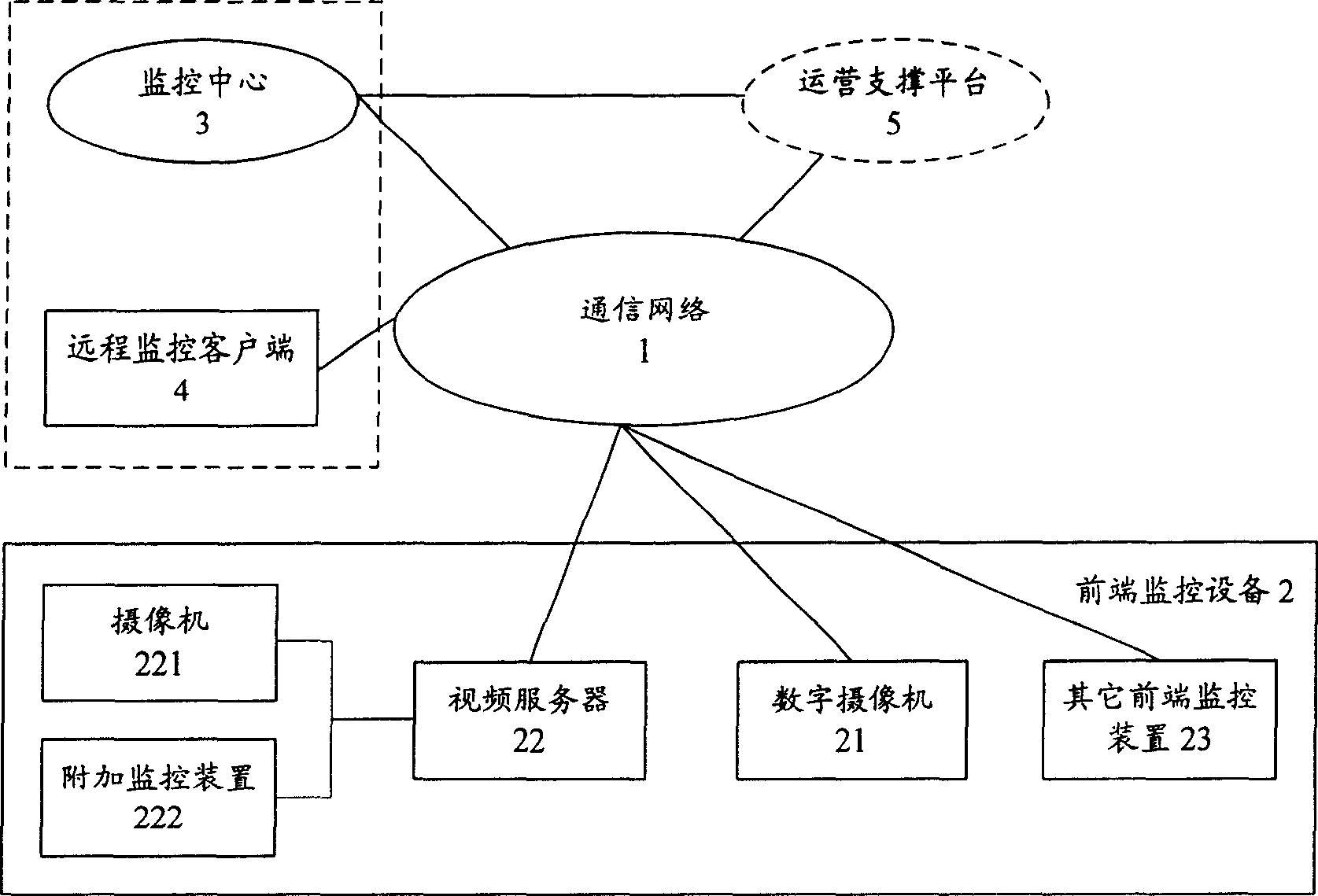
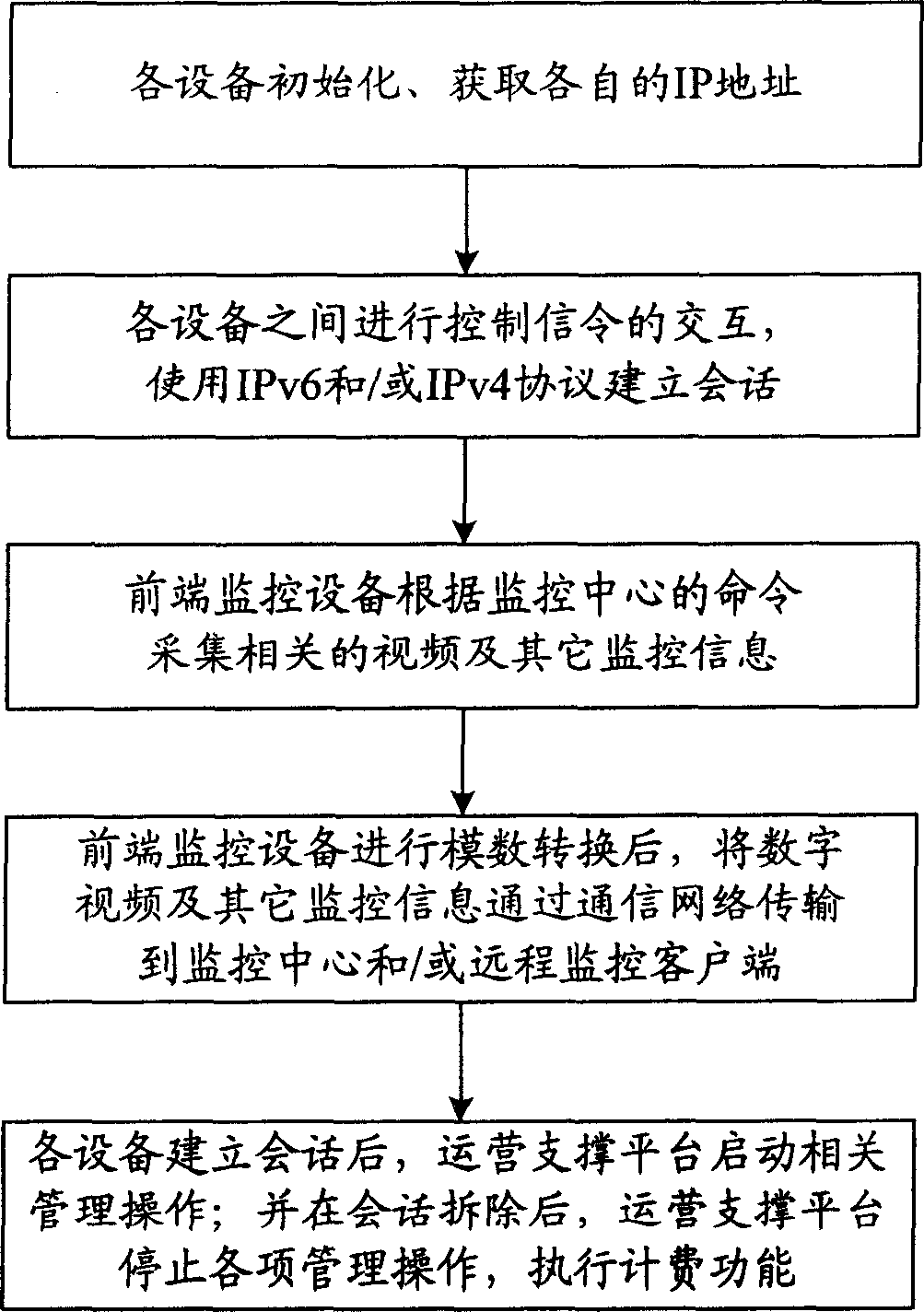
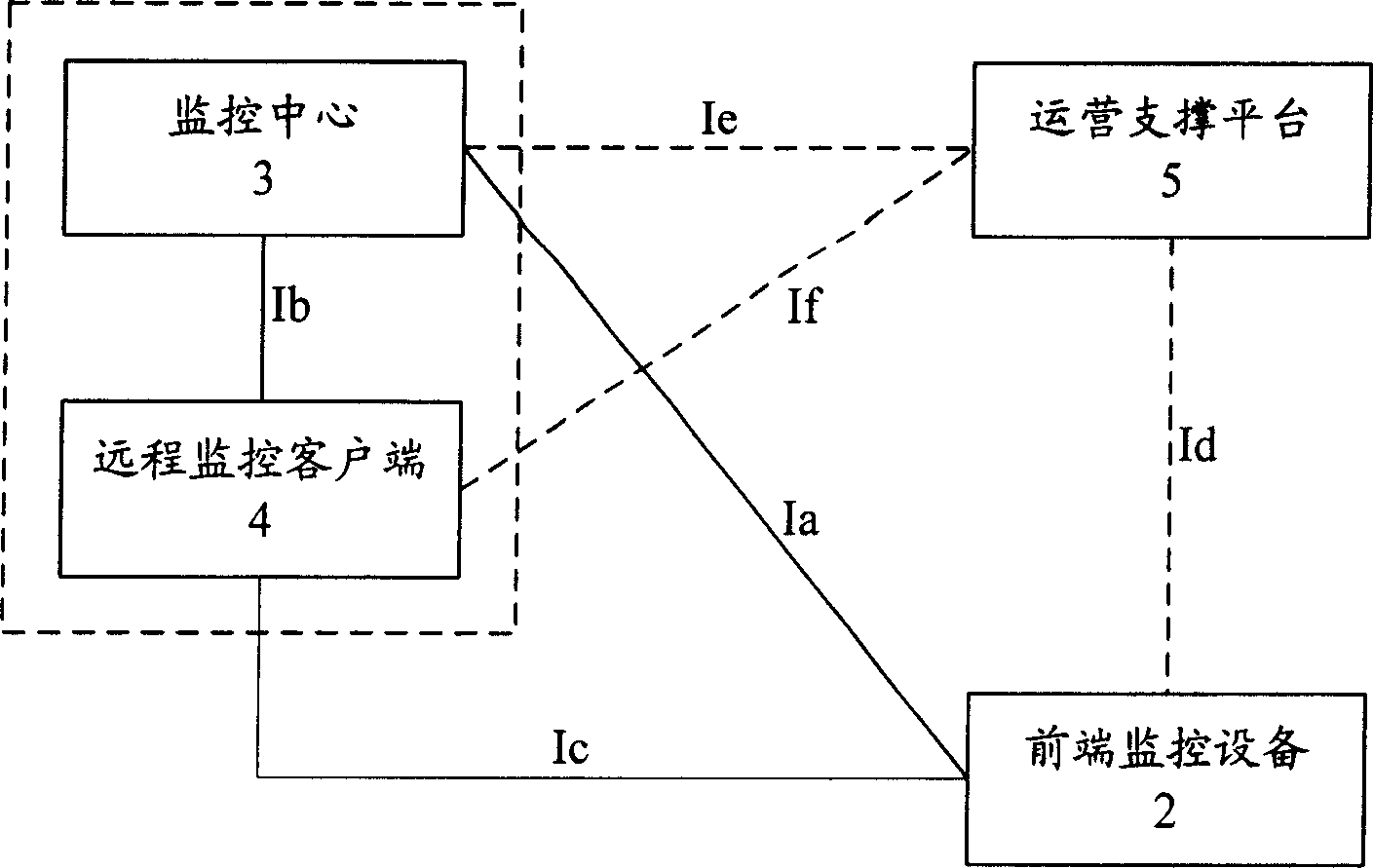
This invention relates to a remote video monitor system and a realization method based on the next generation, in which, said system is composed of a communication network, a front monitor device, a monitor center and a remote monitor customer end and a business supporting platform, provides business level remote video monitor service to the public by applying a multi-stage regional structure network topological and digital video compression coding technology, supporting two kinds of network protocols of IPv6 and IPv4 at the same time and using the IPv6 transmission data first, in which, coding addresses of the monitor nodes are ruled and unified and the monitor terminal is set with the only IP address in the world suitable for being accessed and applied at any time and any place.
Owner:BEIJING INTERNET INST
Methods and architecture for enhanced computer performance
InactiveUS20160378545A1Reducing mode switchingReduce limitationsProgram initiation/switchingHardware monitoringOperational systemComputer performance
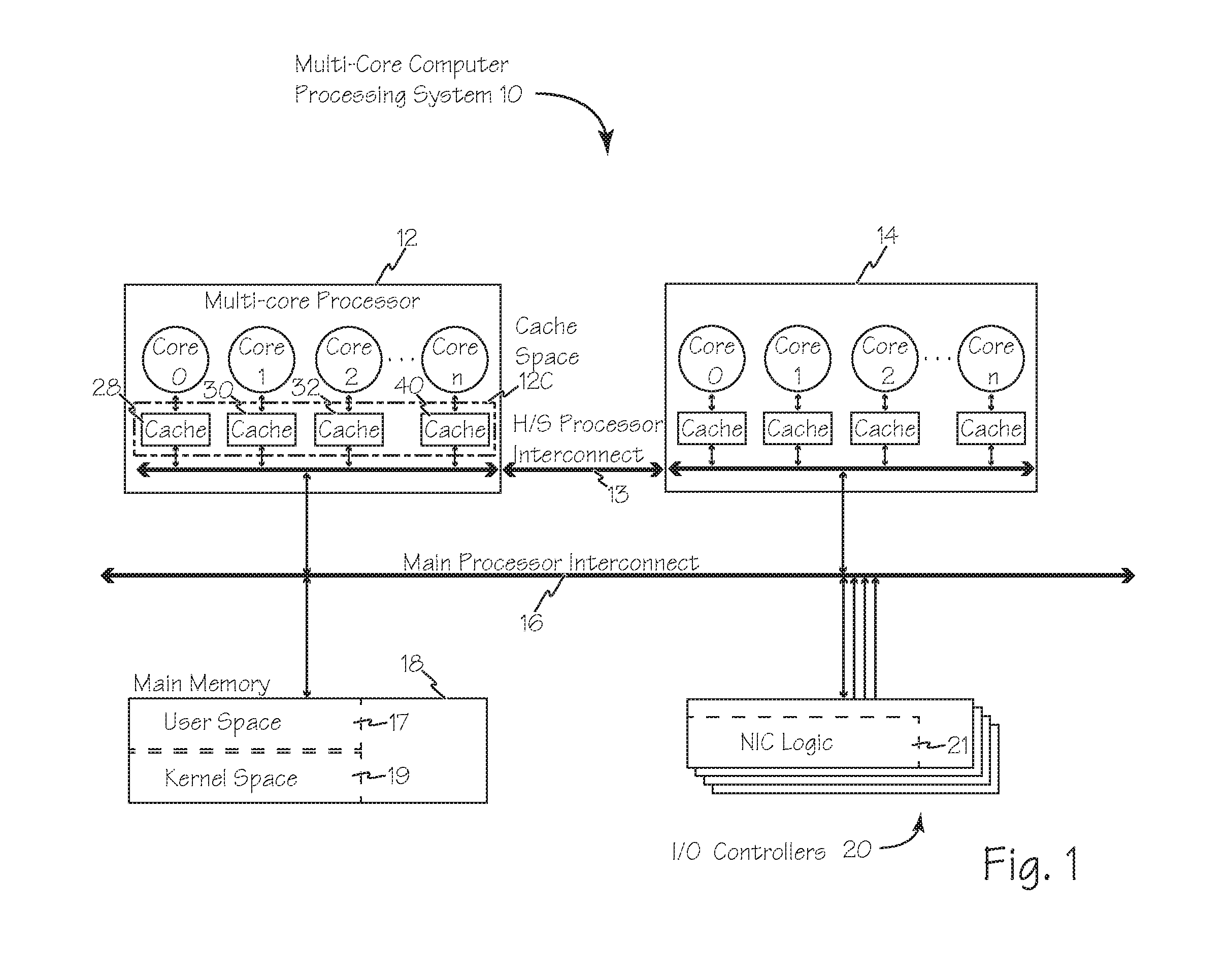
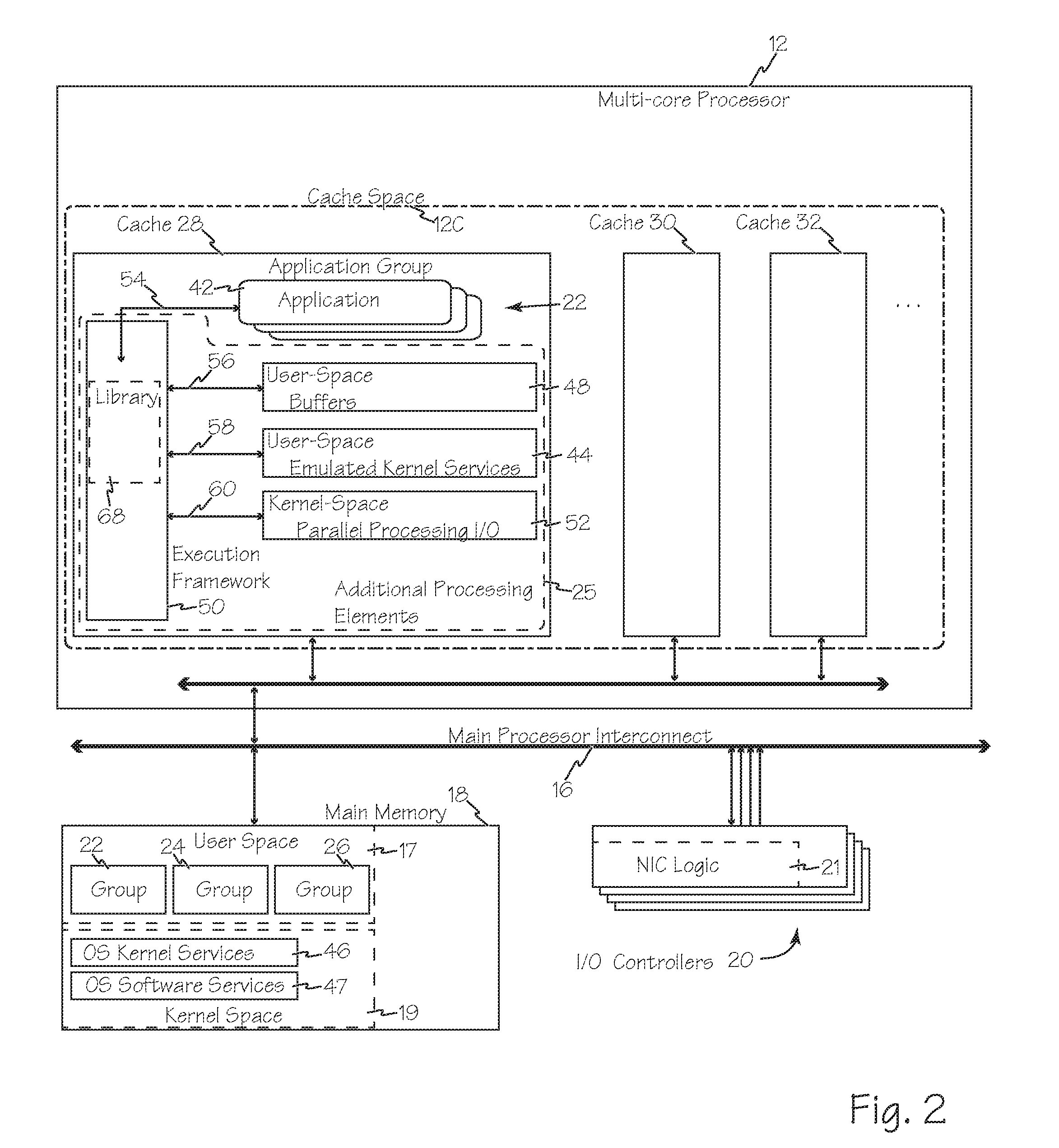
Methods and systems for enhanced computer performance improve software application execution in a computer system using, for example, a symmetrical multi-processing operating system including OS kernel services in kernel space of main memory, by using groups of related applications isolated areas in user space, such as containers, and using a reduced set of application group specific set of resource management services stored with each application group in user space, rather than the OS kernel facilities in kernel space, to manage shared resources during execution of an application, process or thread from that group. The reduced sets of resource management services may be optimized for the group stored therewith. Execution of each group may be exclusive to a different core of a multi-core processor and multiple groups may therefore execute separately and simultaneously on the different cores.
Owner:APL SOFTWARE INC
Computer-based technology for aiding the repair of motor vehicles
ActiveUS20120297337A1Easy to captureImpairing valueDetection of traffic movementCommerceRepair timeComputer-aided
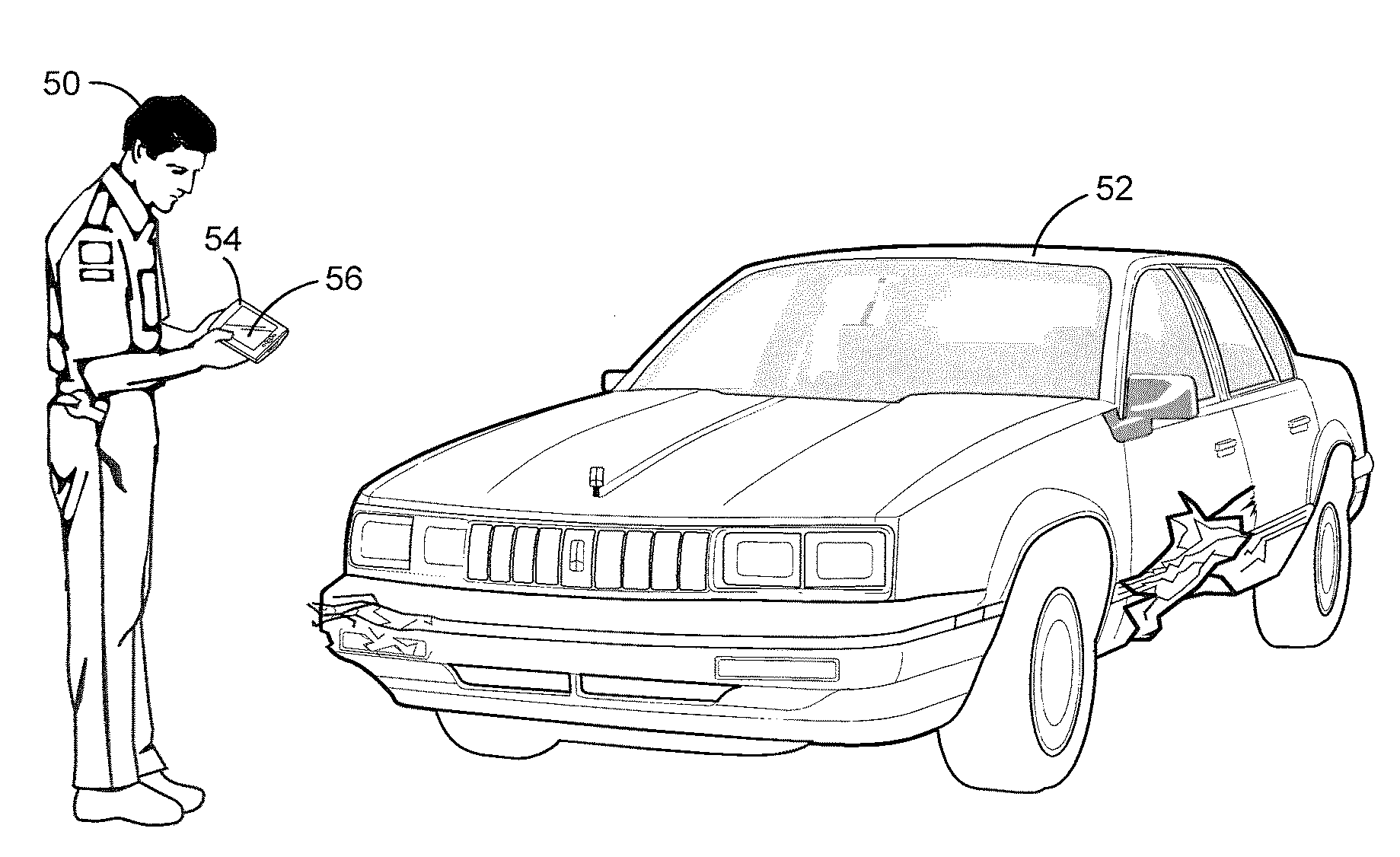
A computer-assisted inspection system provides computer architectures and software controlled algorithms to automatically provide vehicle inspections and repair recommendations including estimated repair time and cost of depression type damage such as dents. Features provided by a handheld wireless touchscreen based inspection device include flat car part picking, auto grading including seller grading, and automatic calculation of body and bumper dent repair parameters and directions.
Owner:MANHEIM INVESTMENTS
System for remote loading of objects or files in order to update software
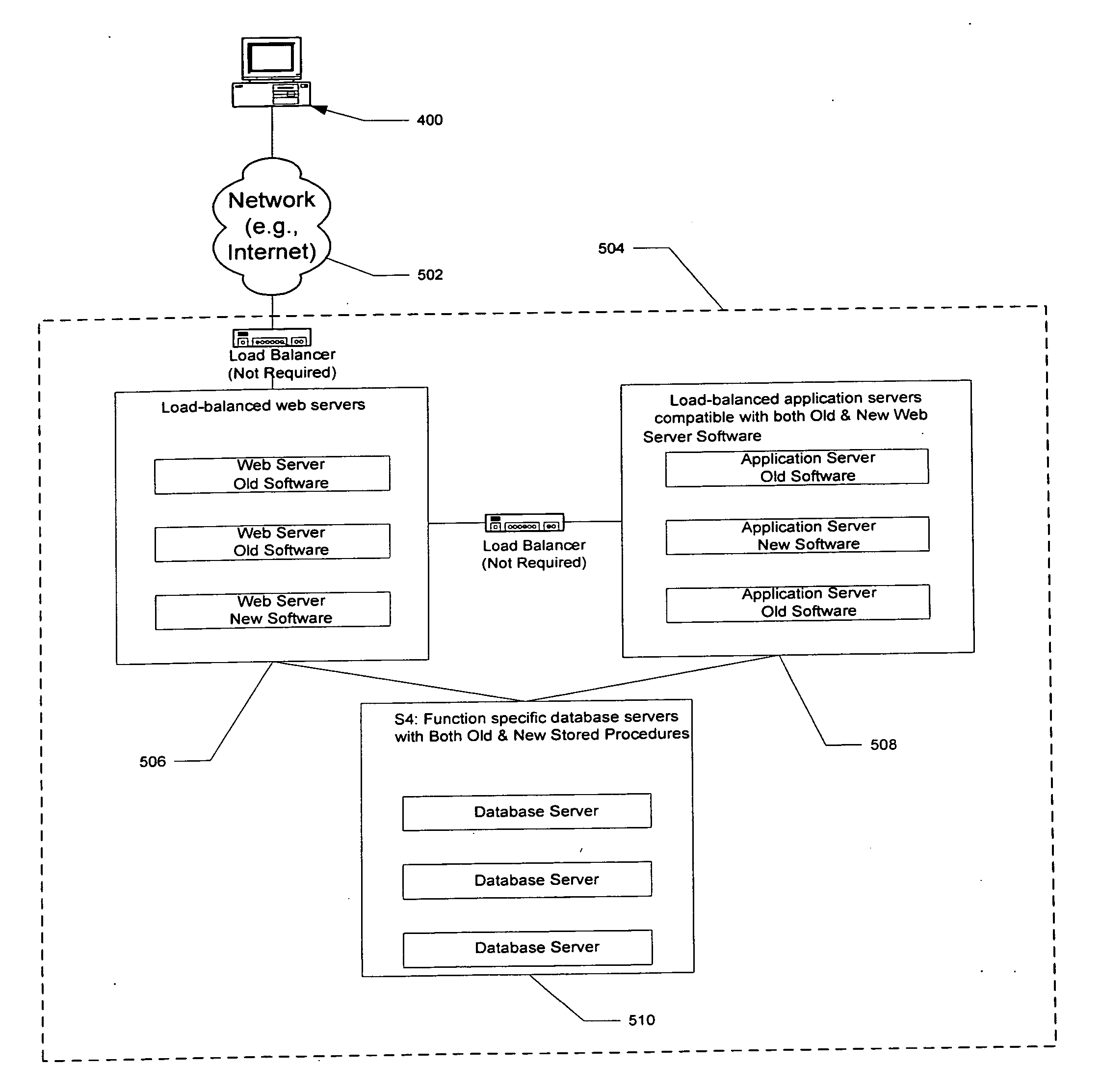
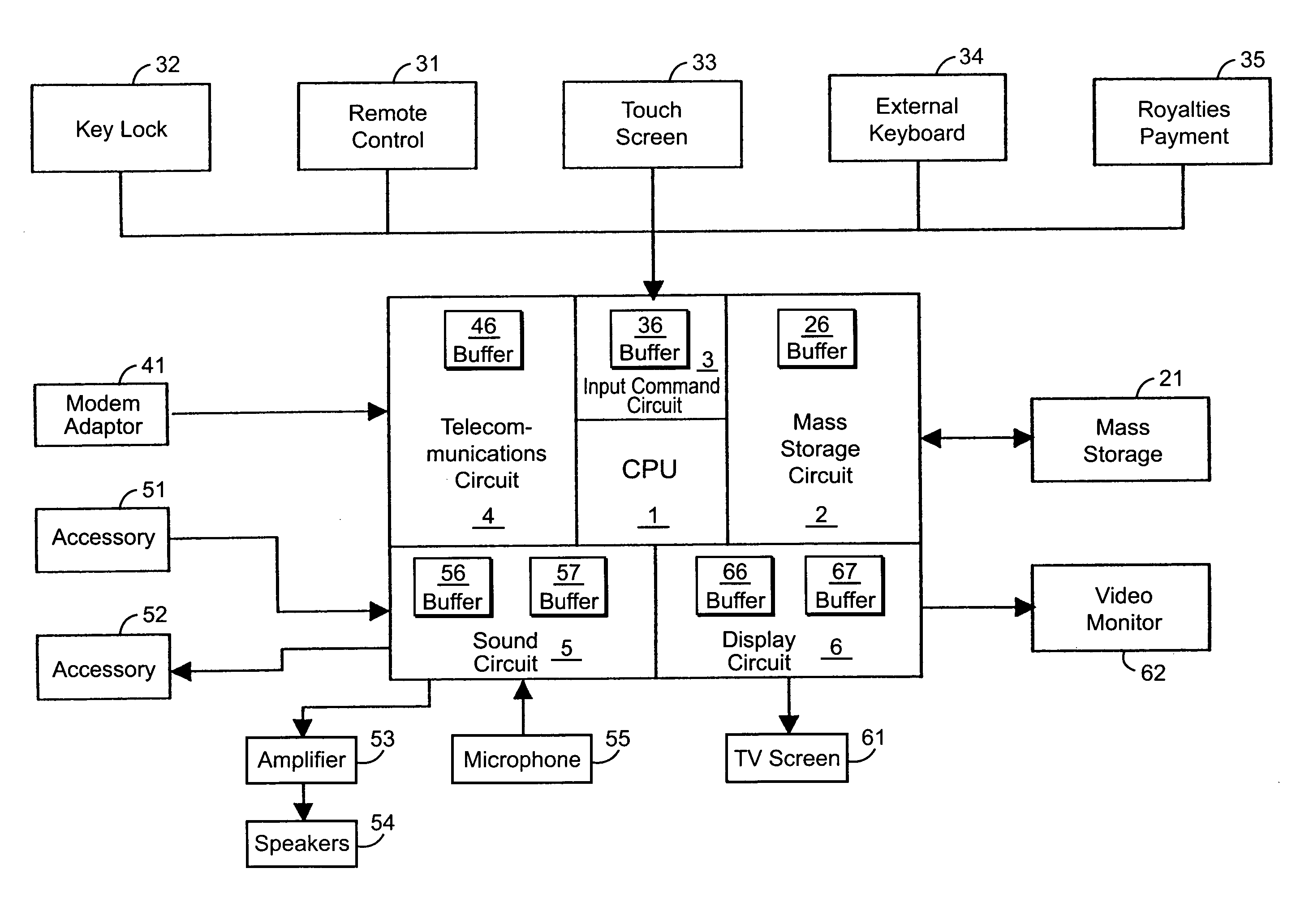
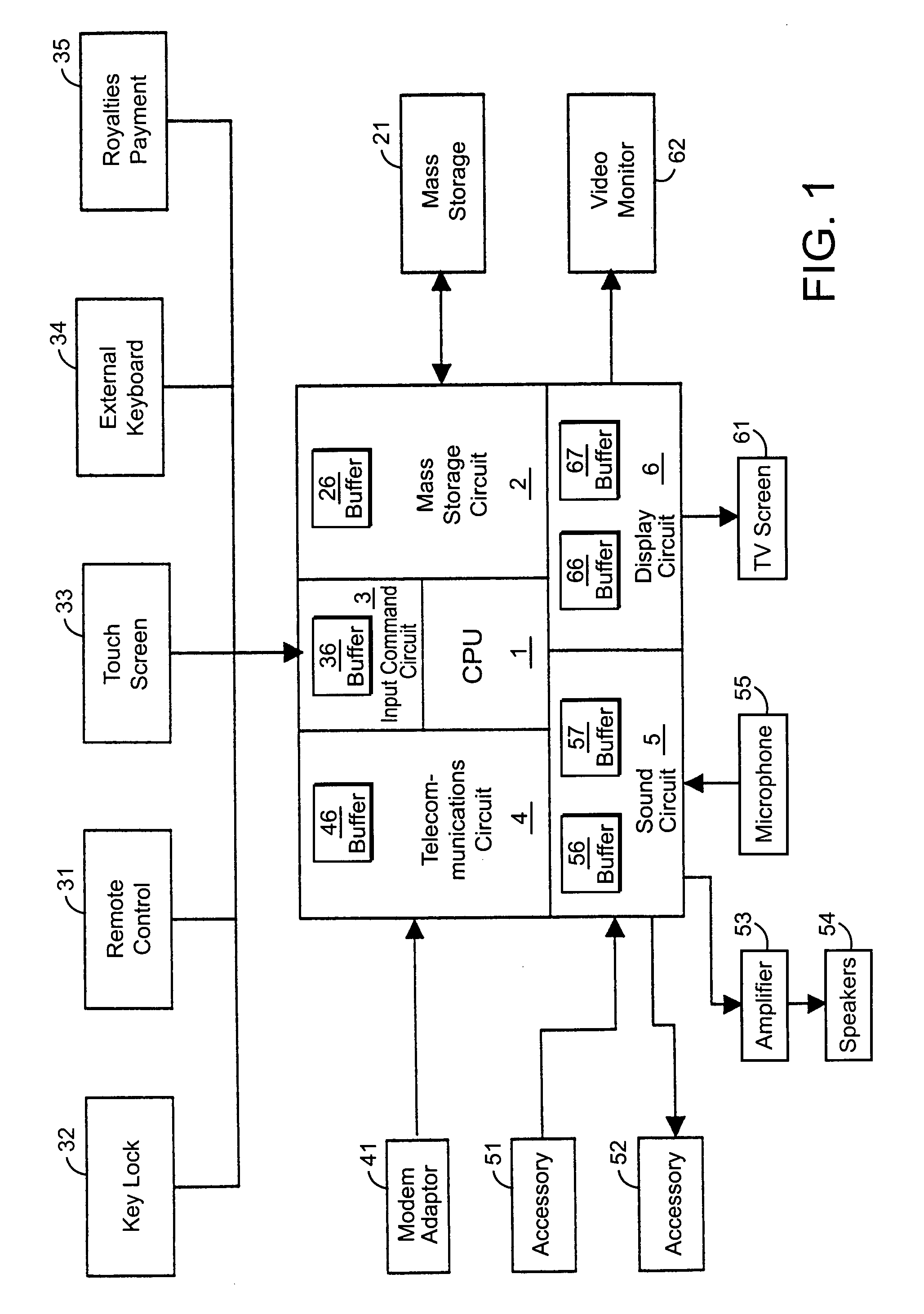
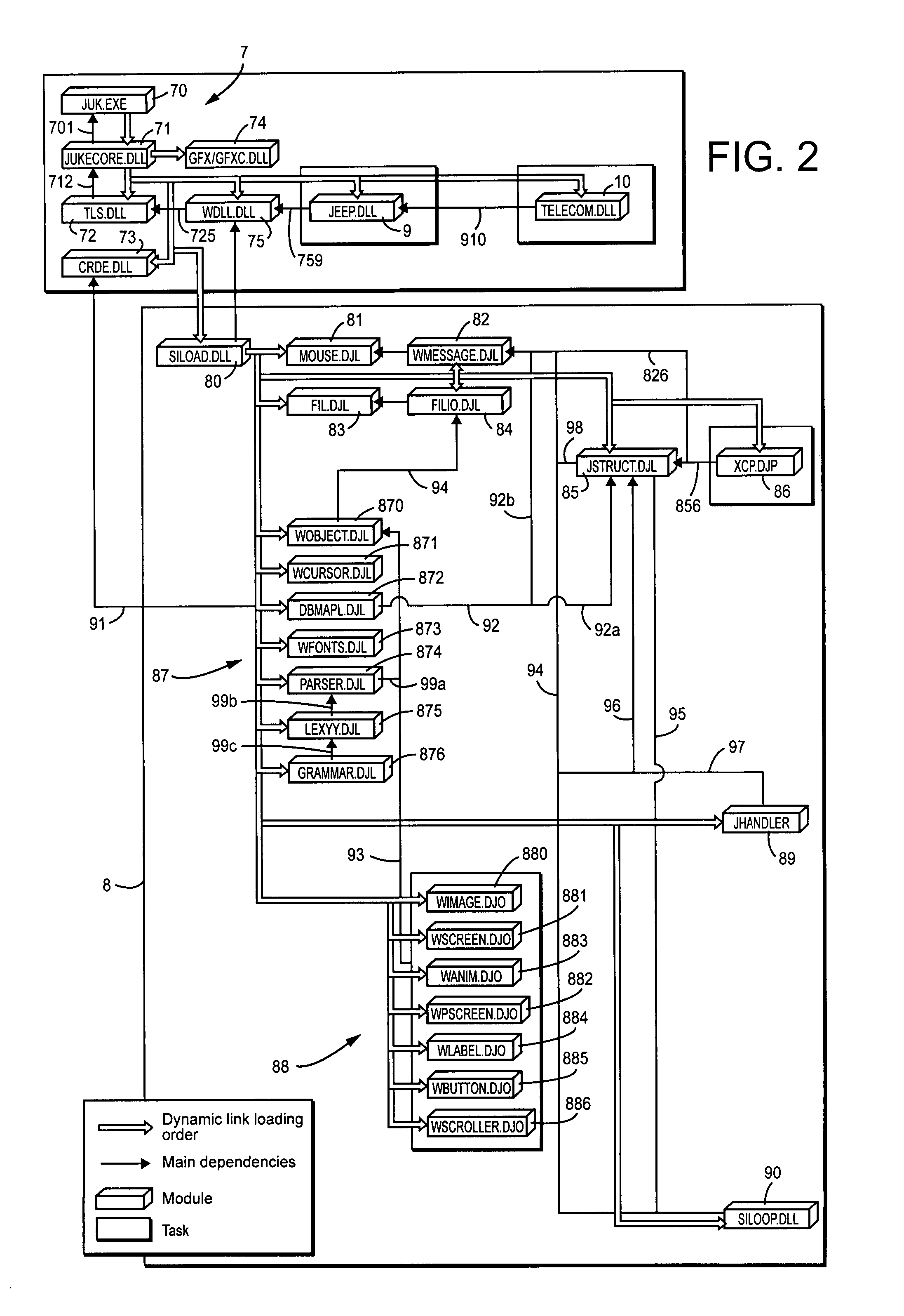
InactiveUS8032879B2Saving informationVersion controlBootstrappingComputer moduleArchitecture of Integrated Information Systems
A system for remote loading of objects or files in order to update software includes operating system architecture that calls for different tasks to be broken down into software modules that are connected to one another by dynamic links or are composed of executable subroutines that have main dependence links to other parts of the operating system. Each of the modules is composed of object files or libraries that are represented by dynamic link libraries among themselves according to a number of dependence levels that are described in their respective attributes.
Owner:TOUCHTUNES MUSIC CO LLC
Runtime adaptable security processor
InactiveUS20120117610A1Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer security arrangementsSpecial data processing applicationsInternal memoryApplication software
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
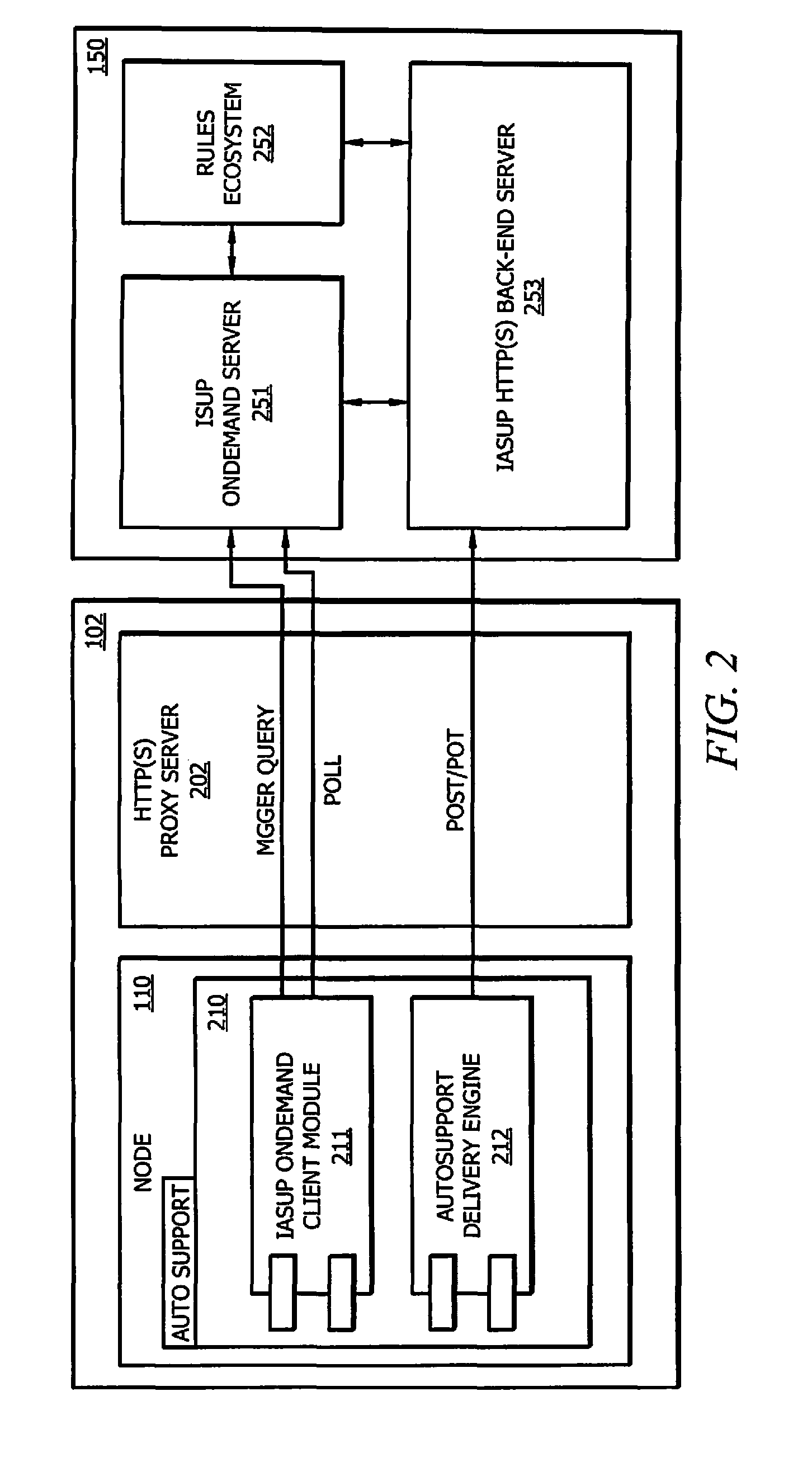
Systems and methods for providing intelligent automated support capable of self rejuvenation with respect to storage systems
ActiveUS8825752B1Facilitate IASUPEasy to collectMemory loss protectionError detection/correctionEnd systemHybrid storage system
Systems and methods which provide an intelligent automated support (IASUP) architecture in which logic is implemented to control support messaging in an automatic, timely, and meaningful fashion to imbibe intelligent automated support functionality are disclosed. Embodiments of an IASUP architecture implement bidirectional communication links between storage systems and IASUP back-end systems providing data collection. The bidirectional communication links supported by IASUP architectures of embodiments facilitate automated storage system rejuvenation functionality whereby an IASUP back-end system provides processing and analysis with respect to storage system data to initiate manipulation or control of one or more components of a storage system.
Owner:NETWORK APPLIANCE INC
Dynamic service-oriented architecture system configuration and proxy object generation server architecture and methods
InactiveUS20080140759A1Transparent managementEfficient fail-overMultiple digital computer combinationsTransmissionData processing systemSystem configuration
A data processing system implementing a service-oriented architecture that includes pluralities of service providers and service requesters, wherein each service requester includes a service invocation framework, established local to the service requester, that operatively enables direct communication of service requests between the service requester and one or more remotely distributed service providers, and wherein the service invocation framework includes a meta-data configurable mapping operator that provides for the dynamic bidirectional transformation between local service requests, as exchanged with the service requester, and remotely communicated service requests, separately exchanged with the service providers. The system further includes a service invocation manager system that monitors the execution status of the service providers, operates to resolve required associations between service requesters and service providers, and dynamically provides meta-data to the mapping operators to functionally enable the determined associations and direct communications between the service requesters and providers.
Owner:PRIMITIVE LOGIC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com