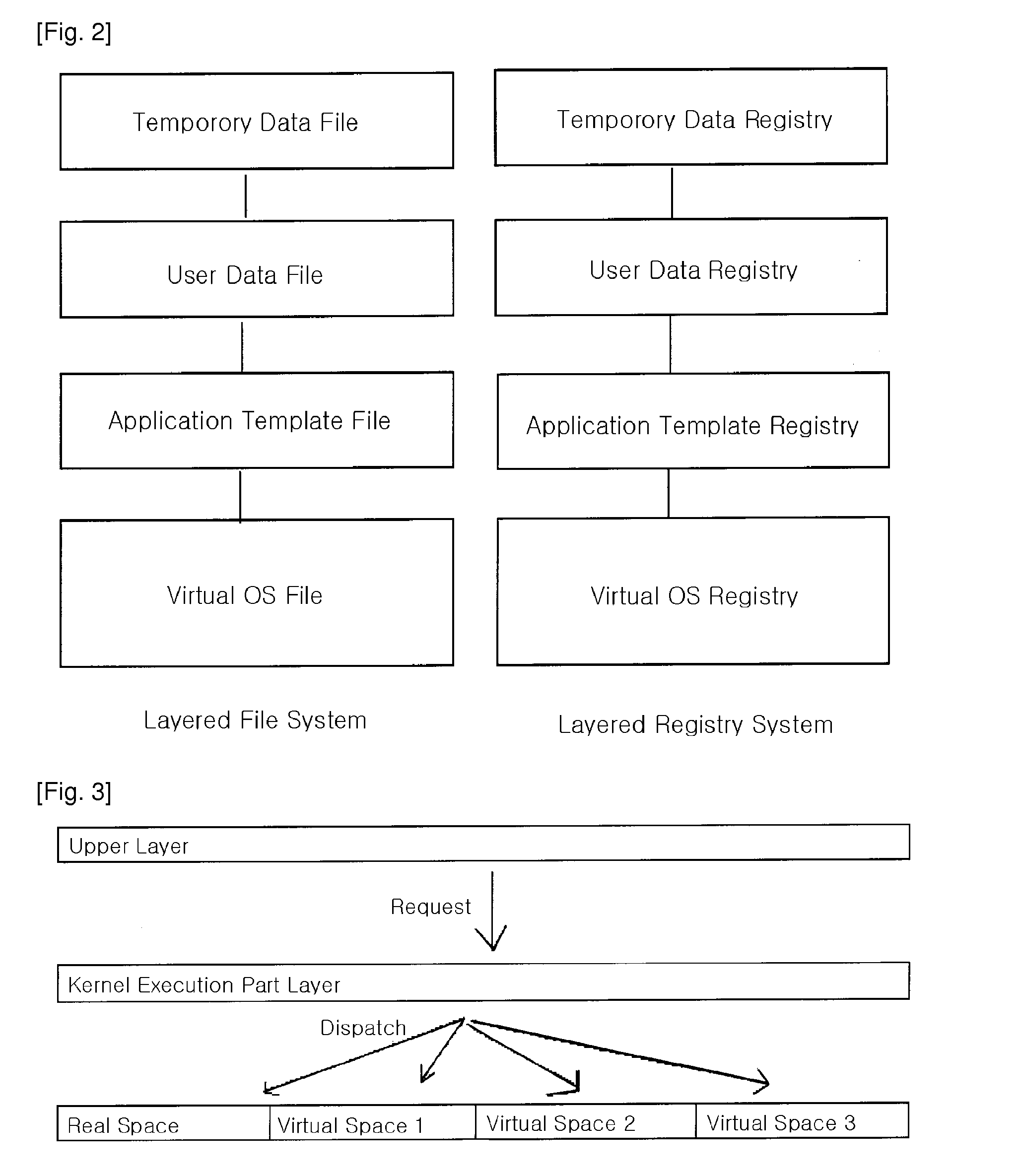
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10344results about "Bootstrapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
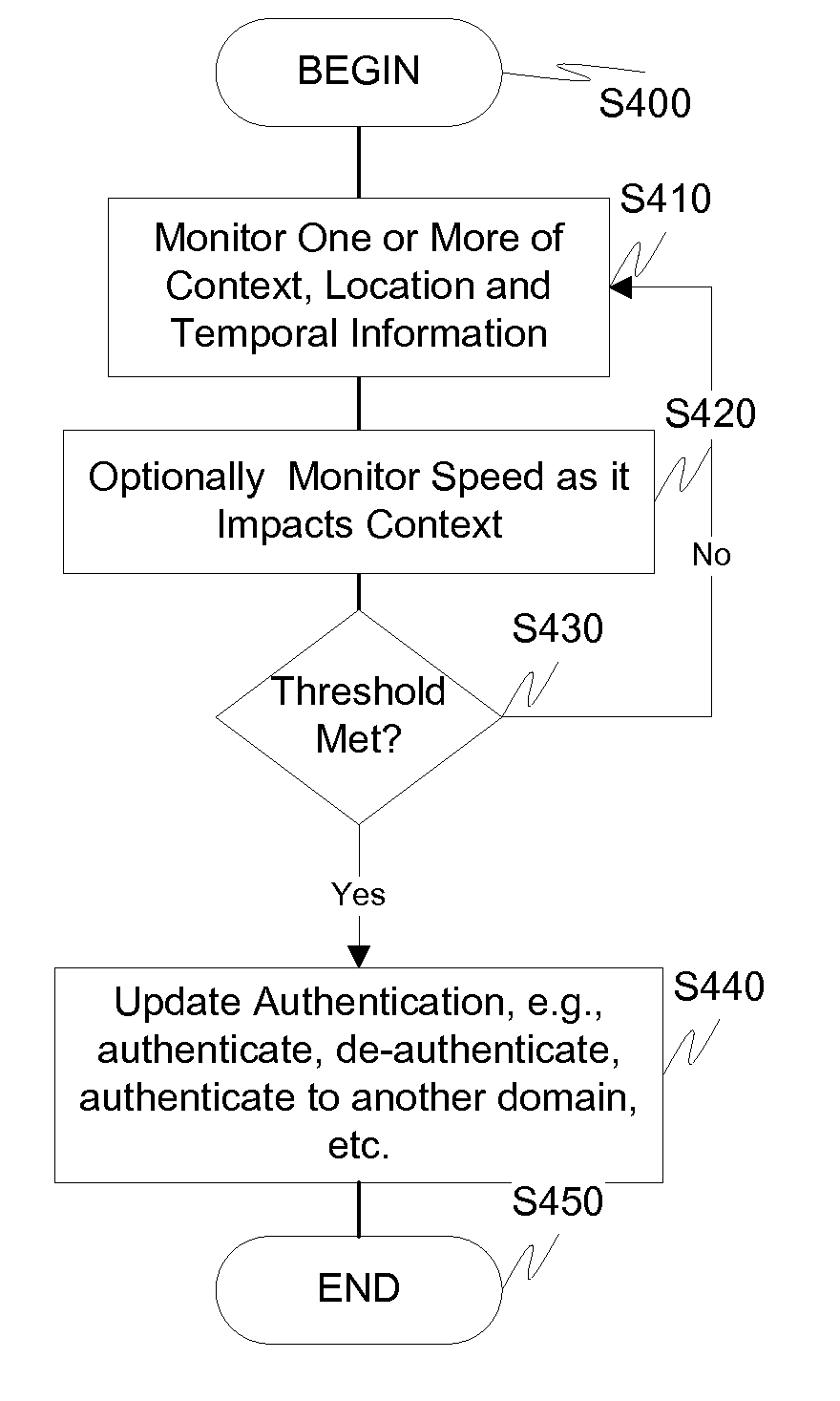
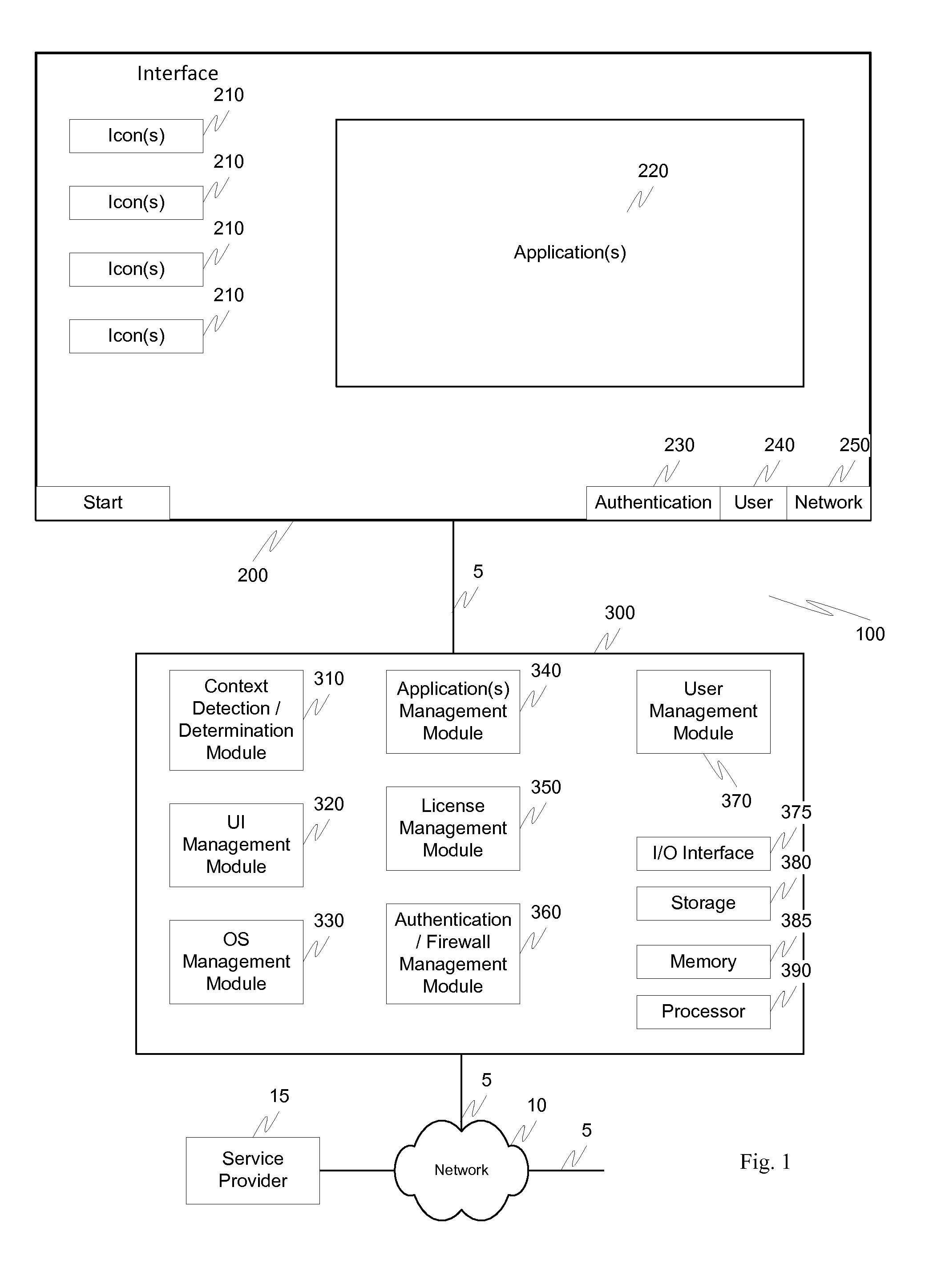
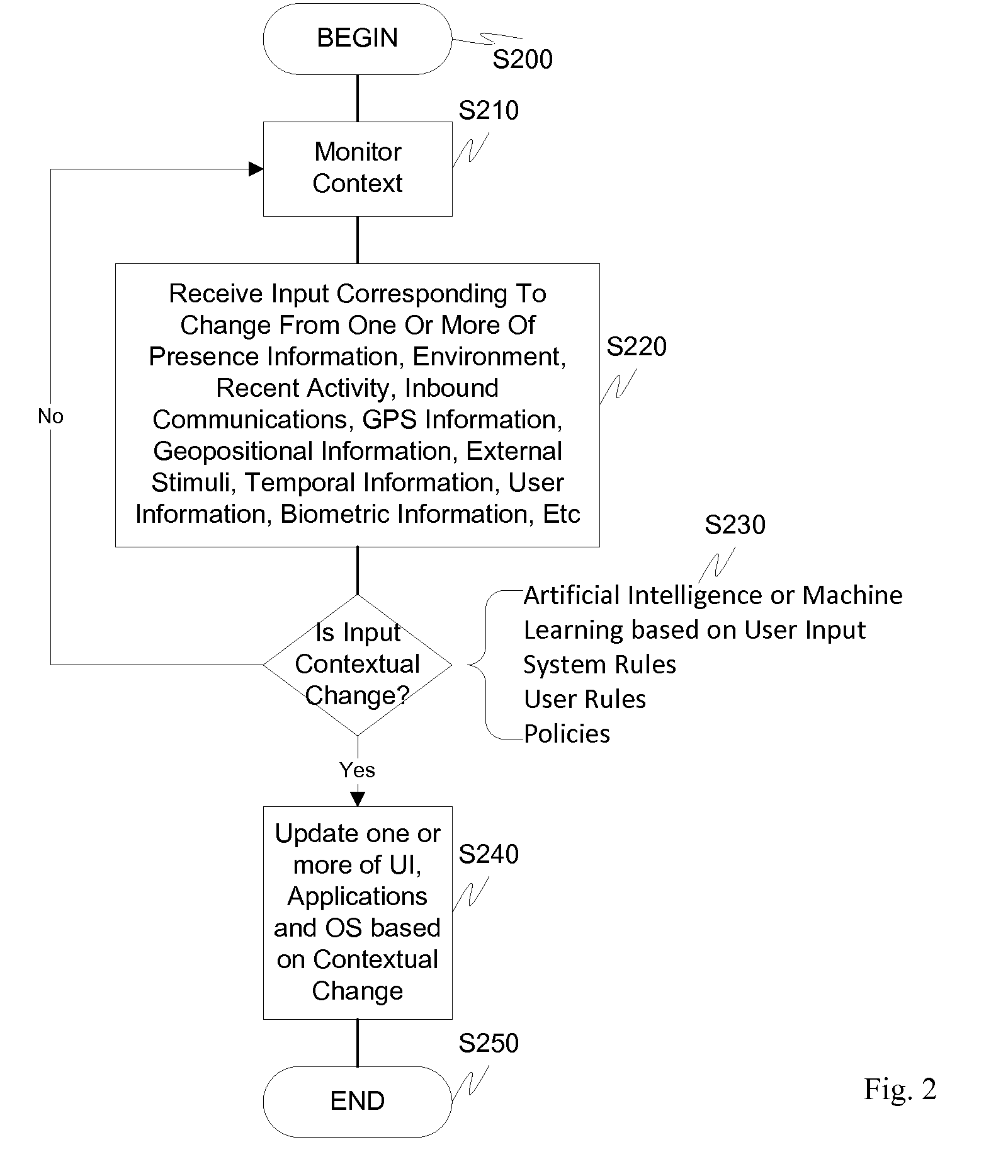
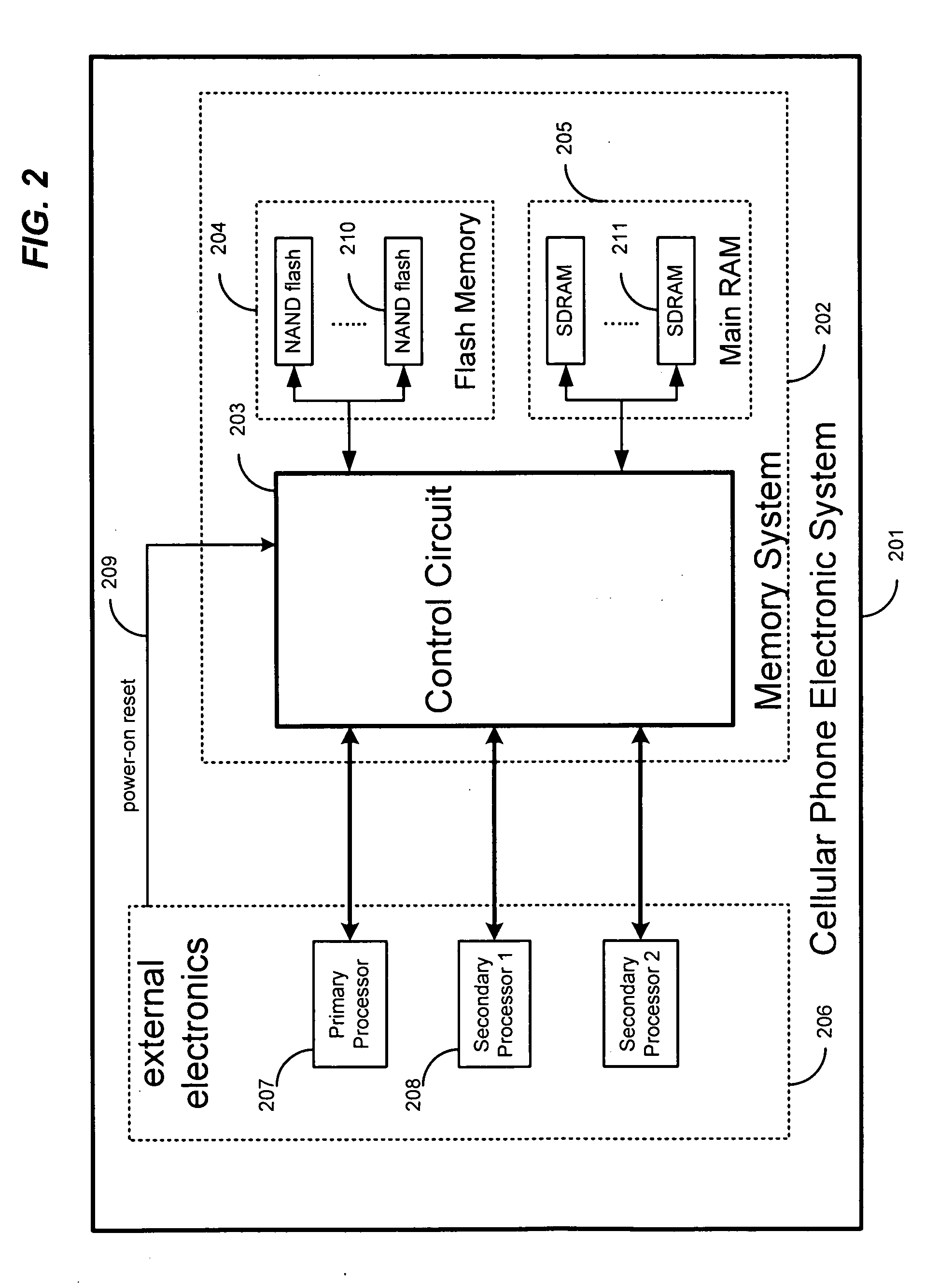
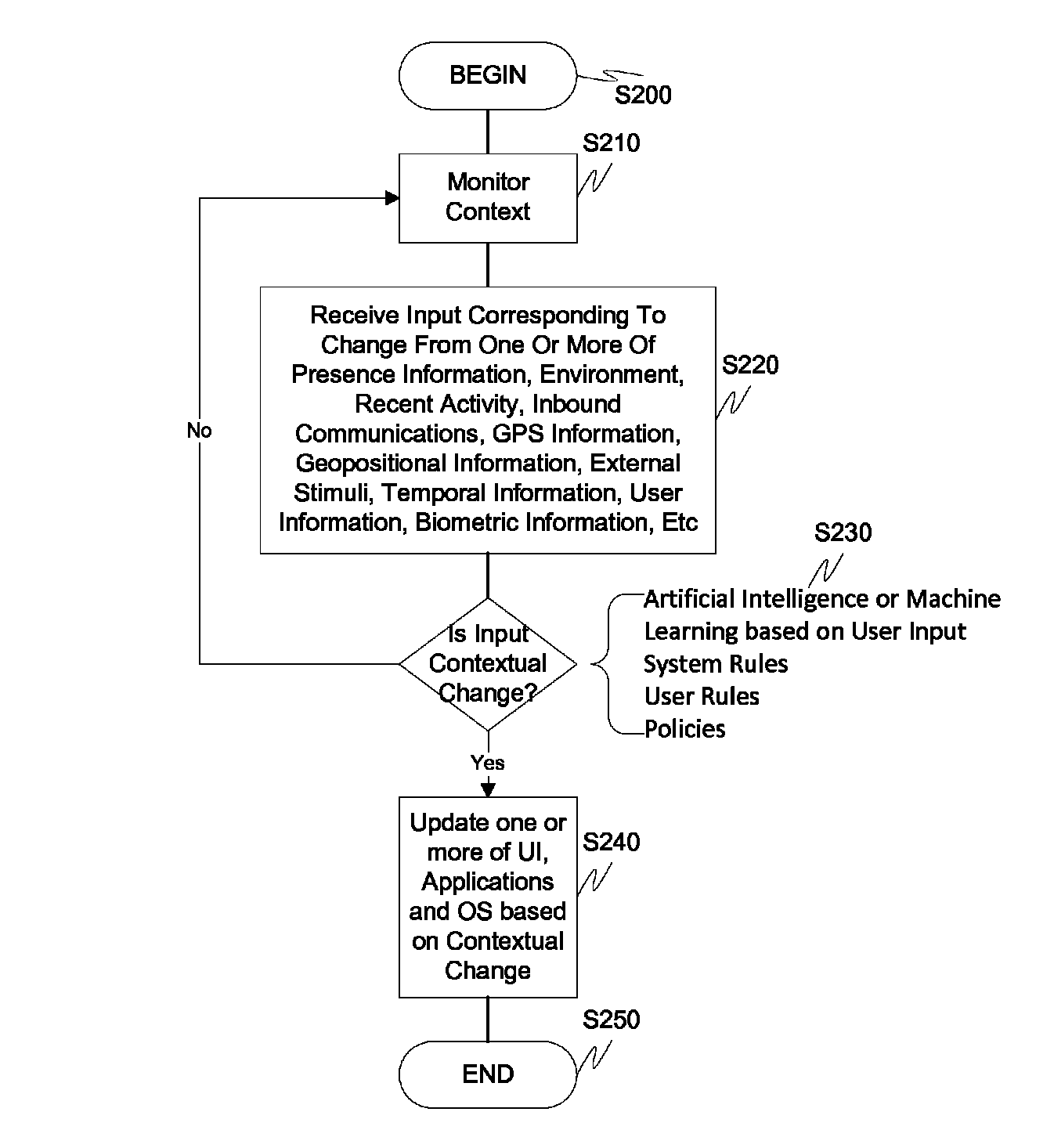
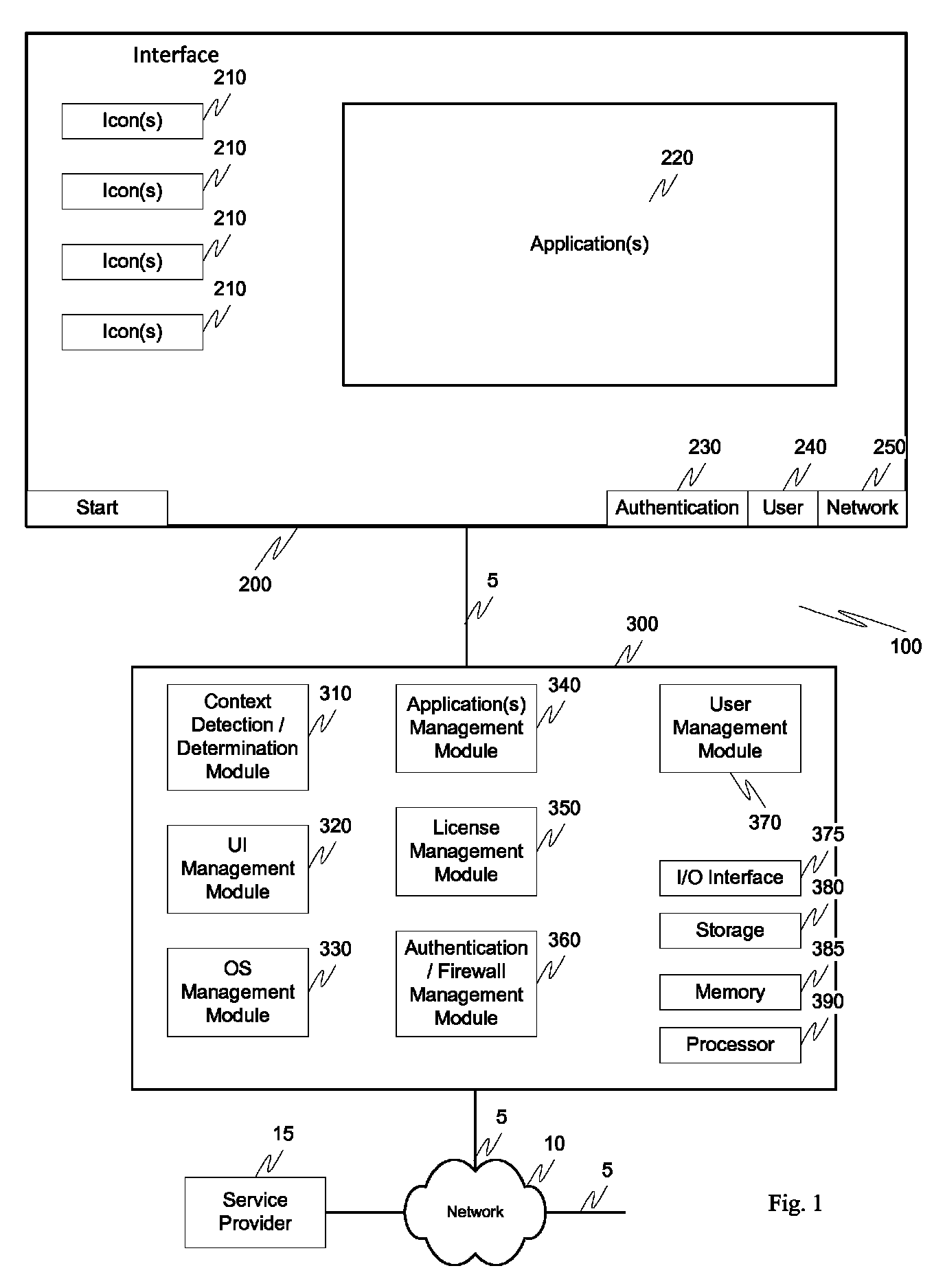
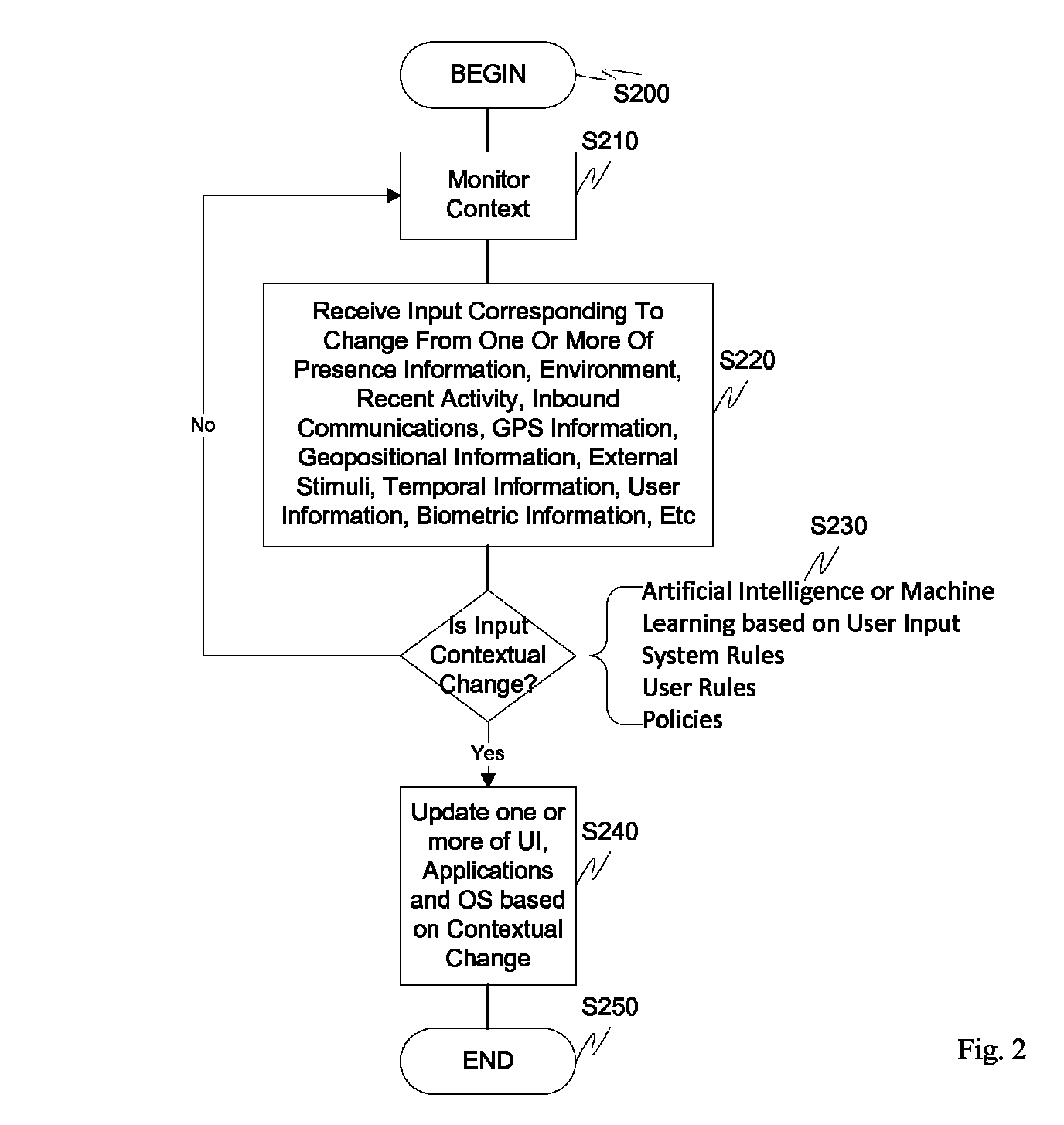
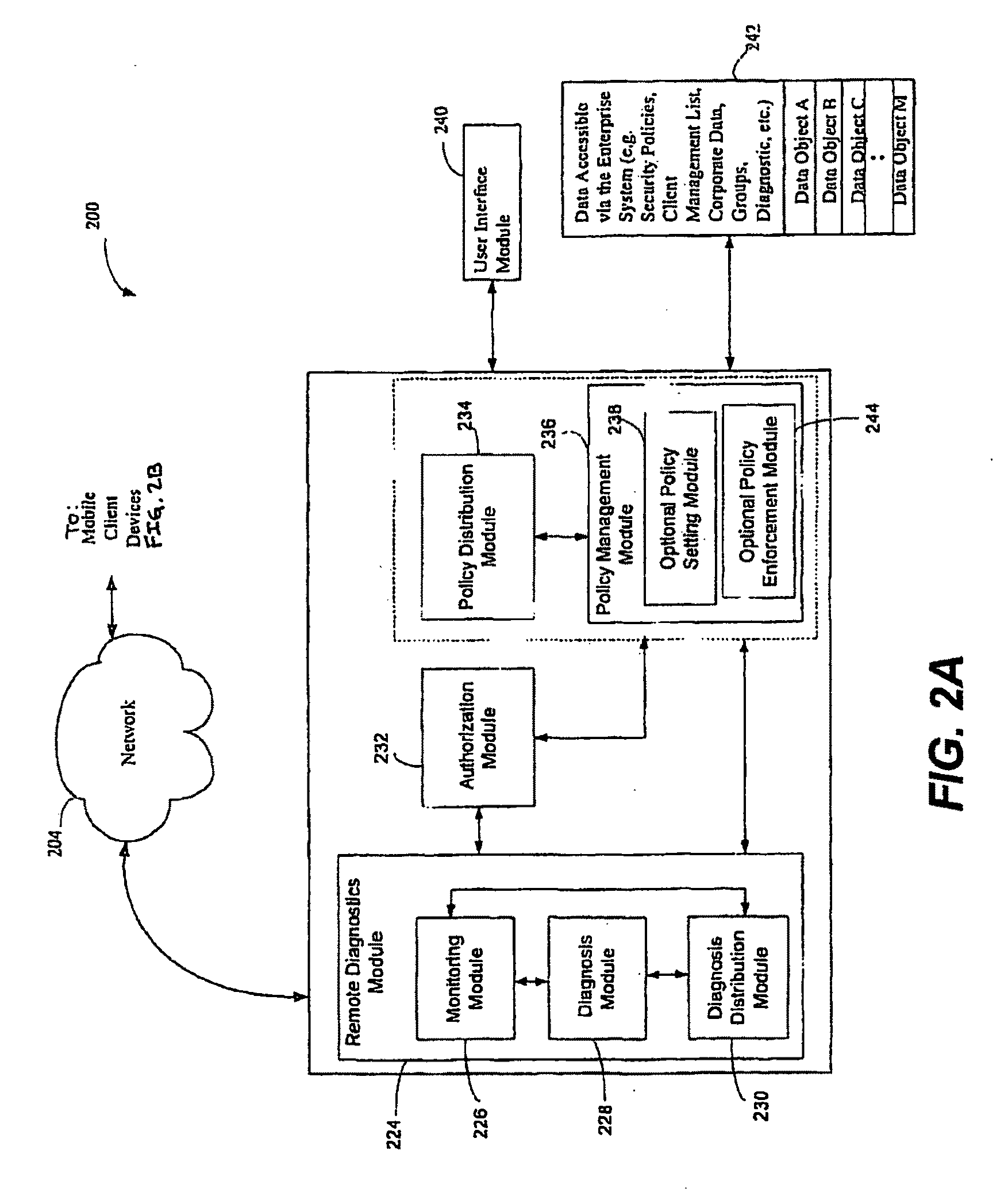
Screen icon manipulation by context and frequency of use
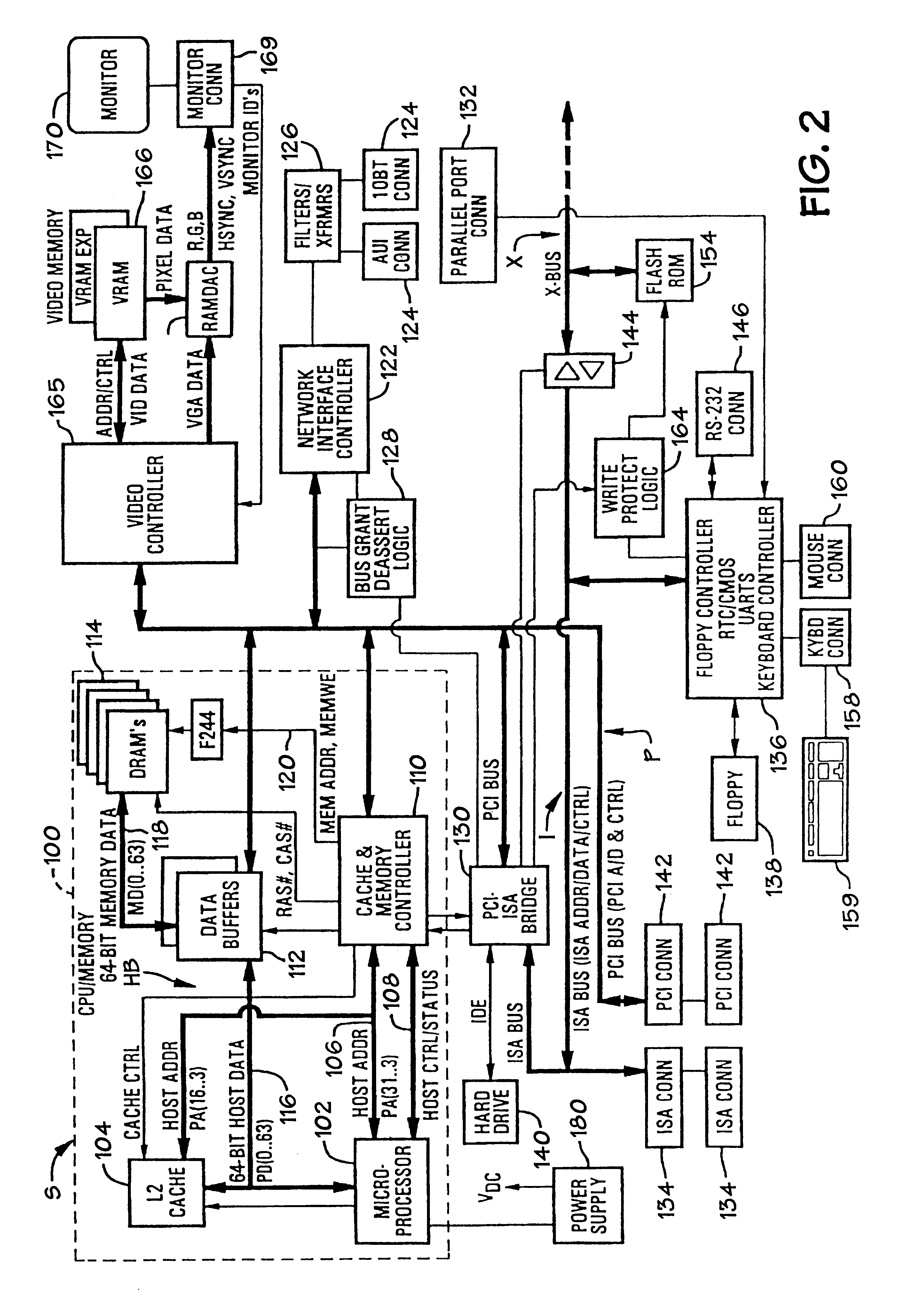
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
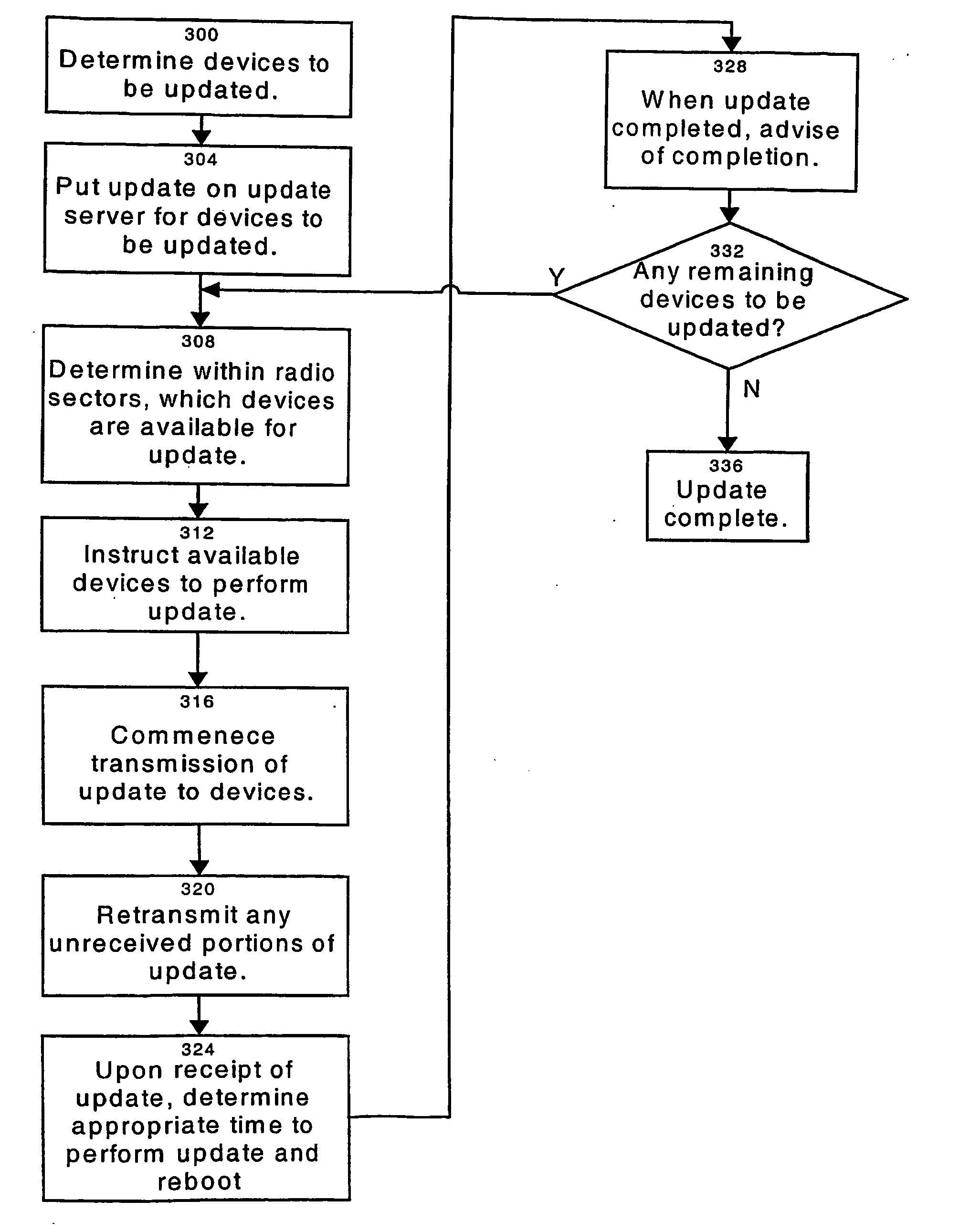
Software update method, apparatus and system
A system for remotely updating software on at least one electronic device connected to a network. The electronic devices have a non-volatile rewritable storage unit divided into at least two partitions, one of which will contain core firmware and the other of which will contain auxiliary software. When an update is received at the device, the updated core firmware is written to overwrite the partition in the rewritable storage unit that contained the auxiliary software. When this is completed and verified, the previous version of the core firmware stored in the storage unit is disabled from execution by the device. Next, the updated auxiliary software is written to overwrite the old version of the core firmware. When this write is complete, the device determines a suitable time for it to be rebooted to execute the updated software. In another embodiment, the present core firmware in the device is copied from the partition it is in to the other partition, overwriting the auxiliary software stored there. The new core firmware received to update the device is overwritten into the first partition, the old copied core firmware being present in case of an upgrade failure, and upon a successful update of the first partition, the auxiliary software is written to the second partition, overwriting the copied old core firmware. In this manner, the position of the core firmware and auxiliary software within the partitions is preserved during normal operation of the device.
Owner:WI LAN INC
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
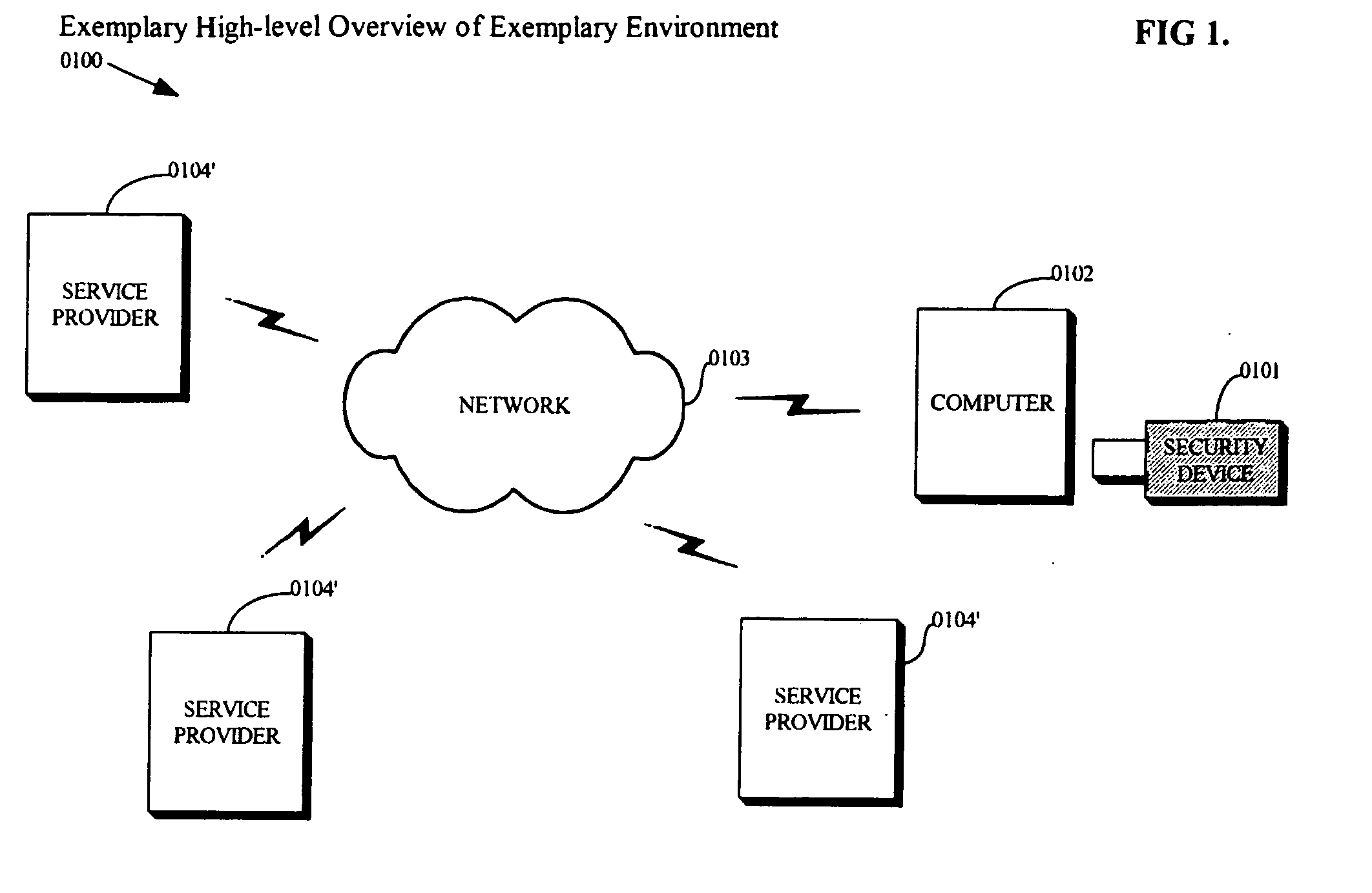
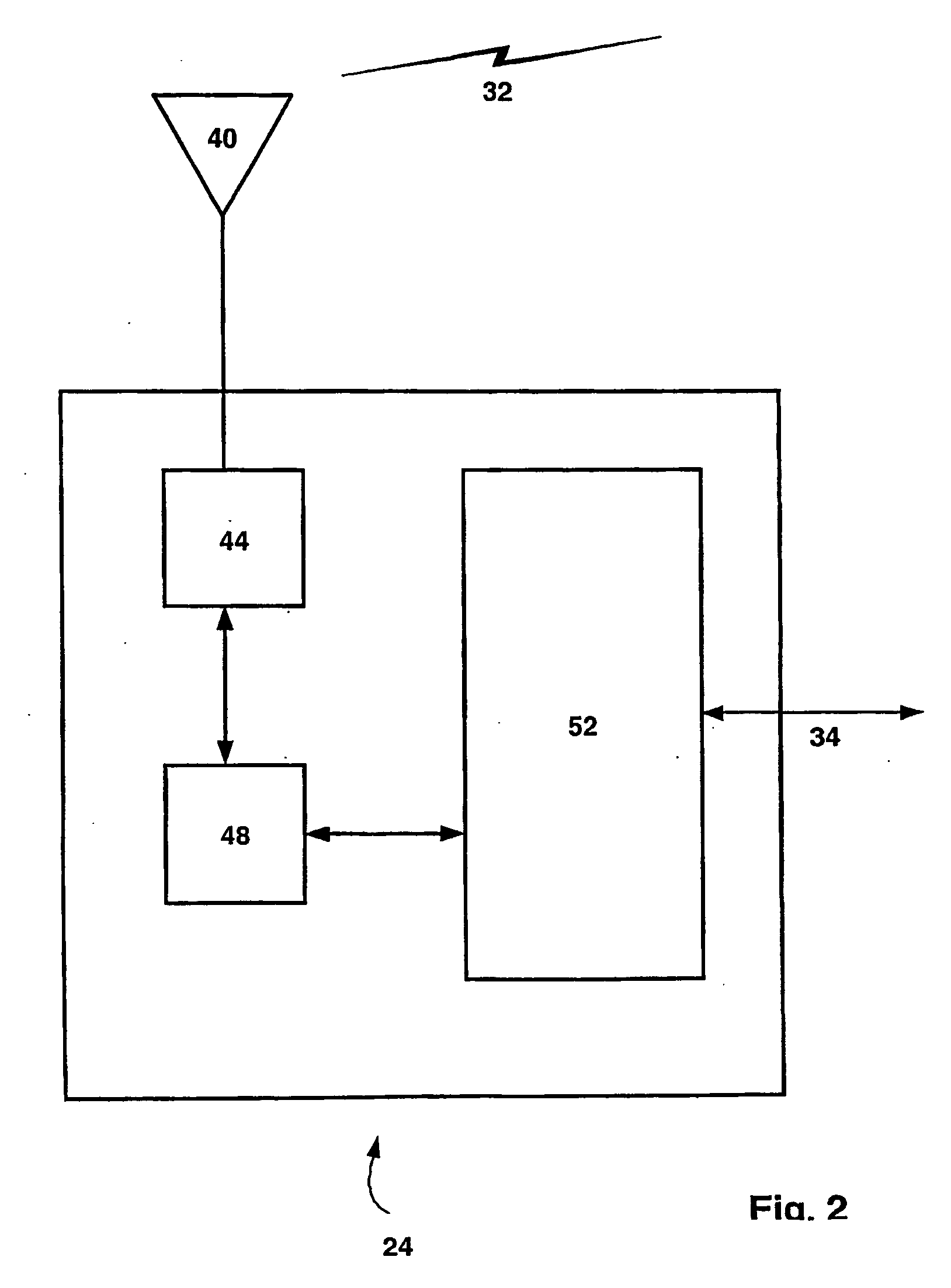
Networked computer system
InactiveUS6854009B1Multiple digital computer combinationsBootstrappingOperational systemRandom access memory
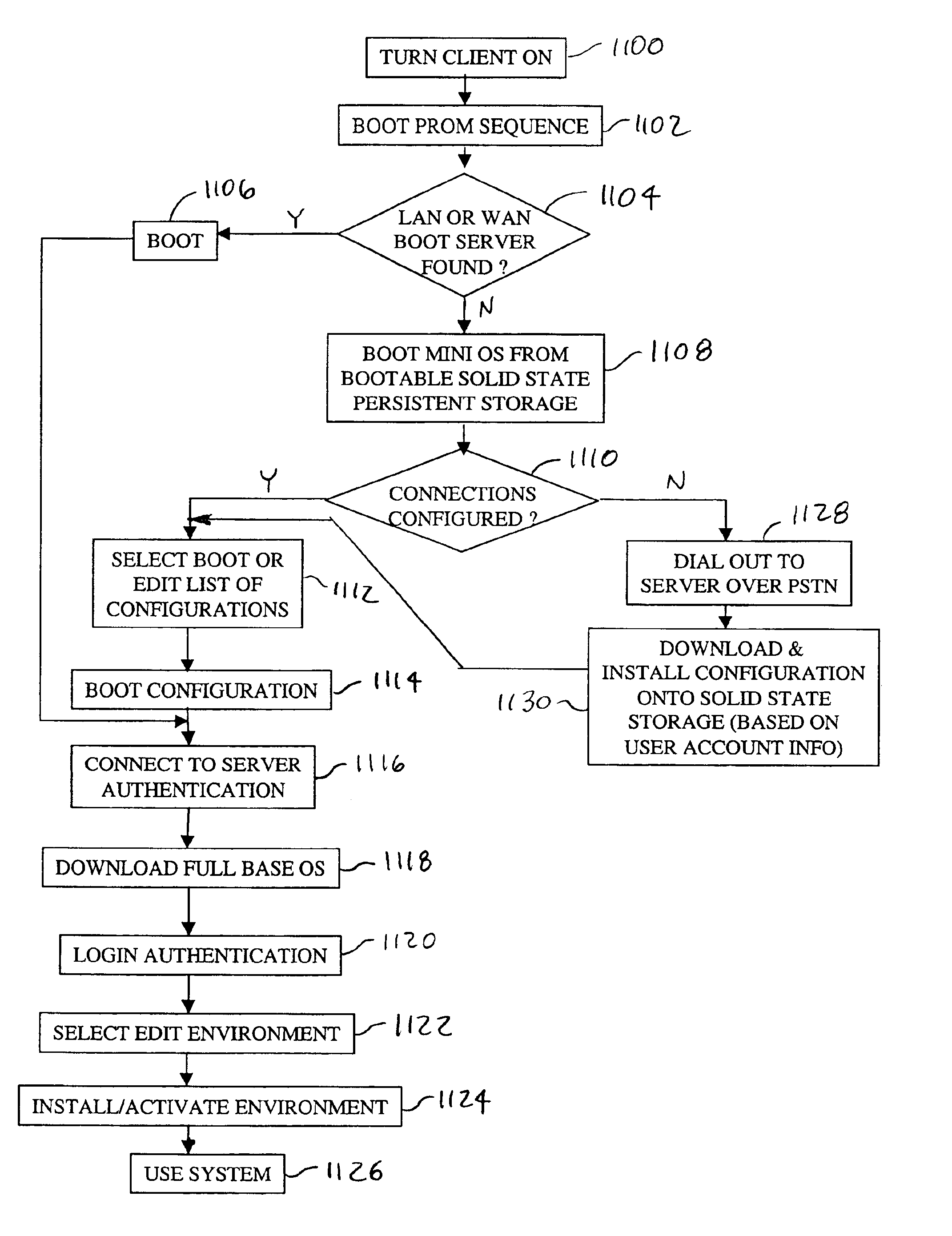
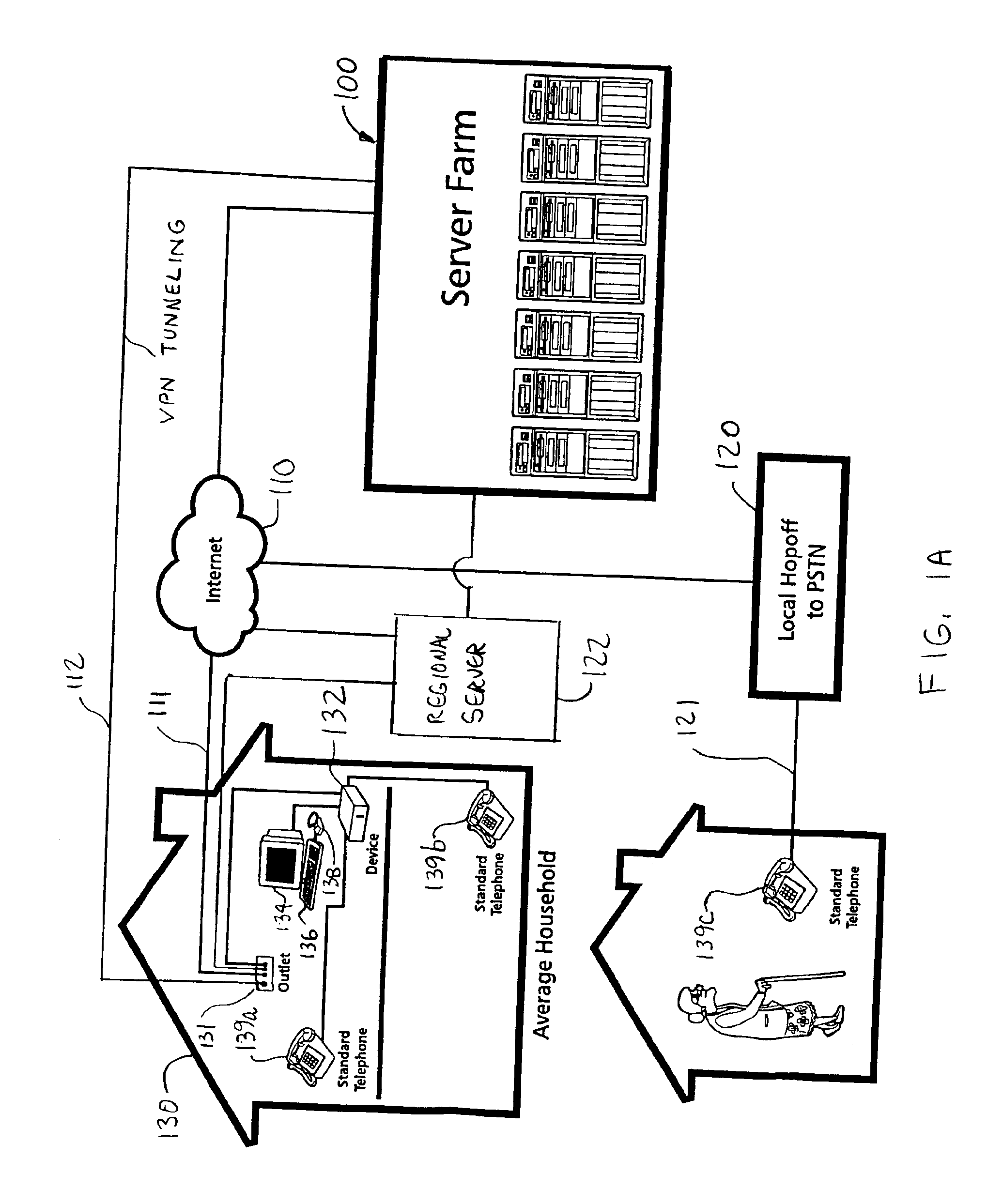
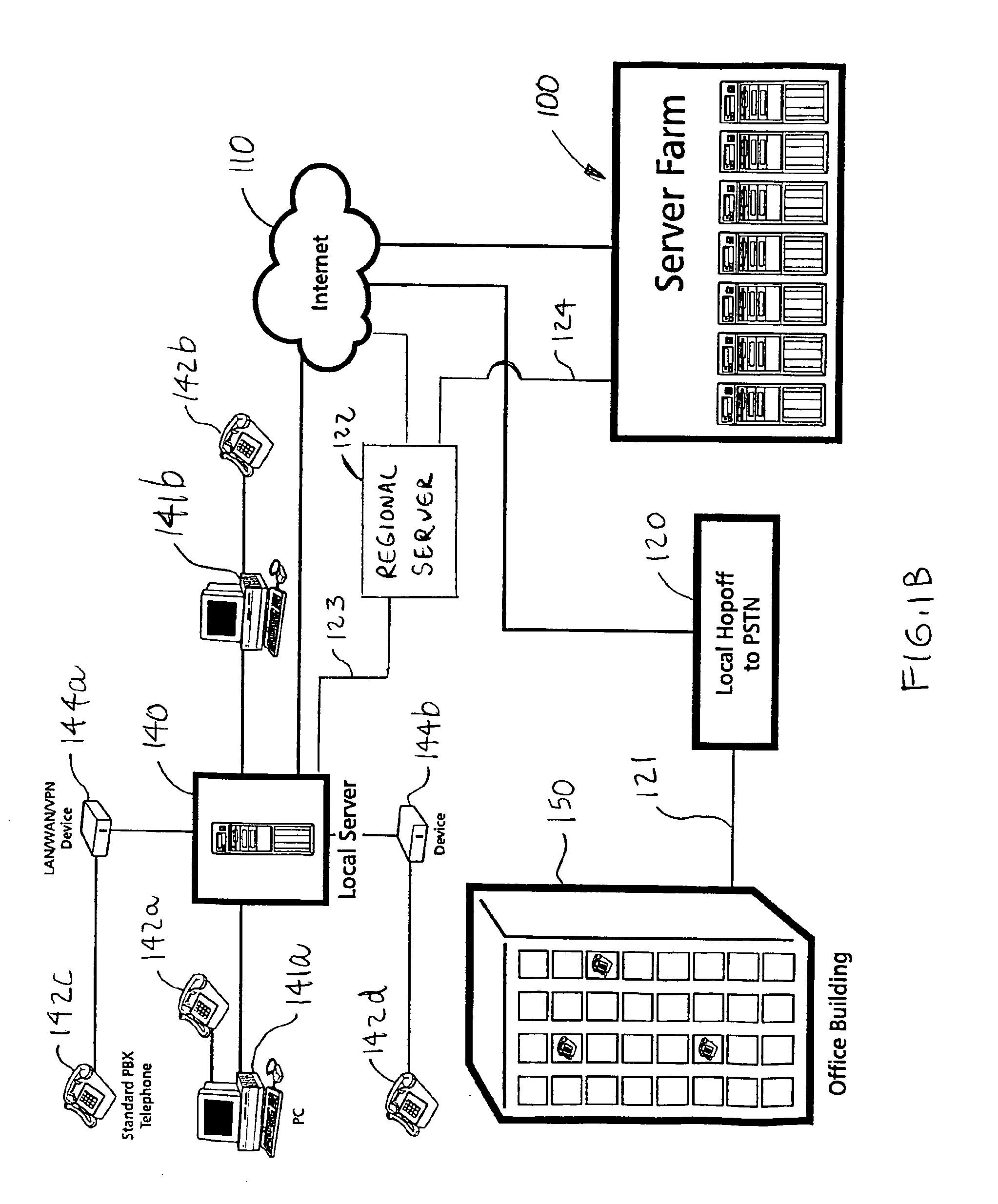
A networked computer system has a plurality of servers and a plurality of distributed clients, which may be devices or computers. Each client has a boot operating system (OS). Upon startup, the boot OS in each client automatically initiates a connection to one of the servers via the Internet. The boot OS can detect the type of medium (e.g., cable modem, DSL) to which the client is connected. The server automatically downloads a base OS and dynamically configures a suite of applications on the client without running the standard installation programs. One included application is an Internet telephony application, allowing a user to plug a standard telephone into the client appliance or computer, pick up the telephone, and automatically dial out using long distance Internet telephony. Optionally, the server may download a plurality of operating systems that are automatically initiated to run concurrently on the client. The clients use a random access memory (RAM) caching technique. A first portion of each OS or application is downloaded at startup and maintained in the client RAM, containing the files needed to launch the OS or application. If the client processes a request for an OS or application program file not in the client's RAM, the requested file is automatically downloaded from the server.
Owner:CA TECH INC
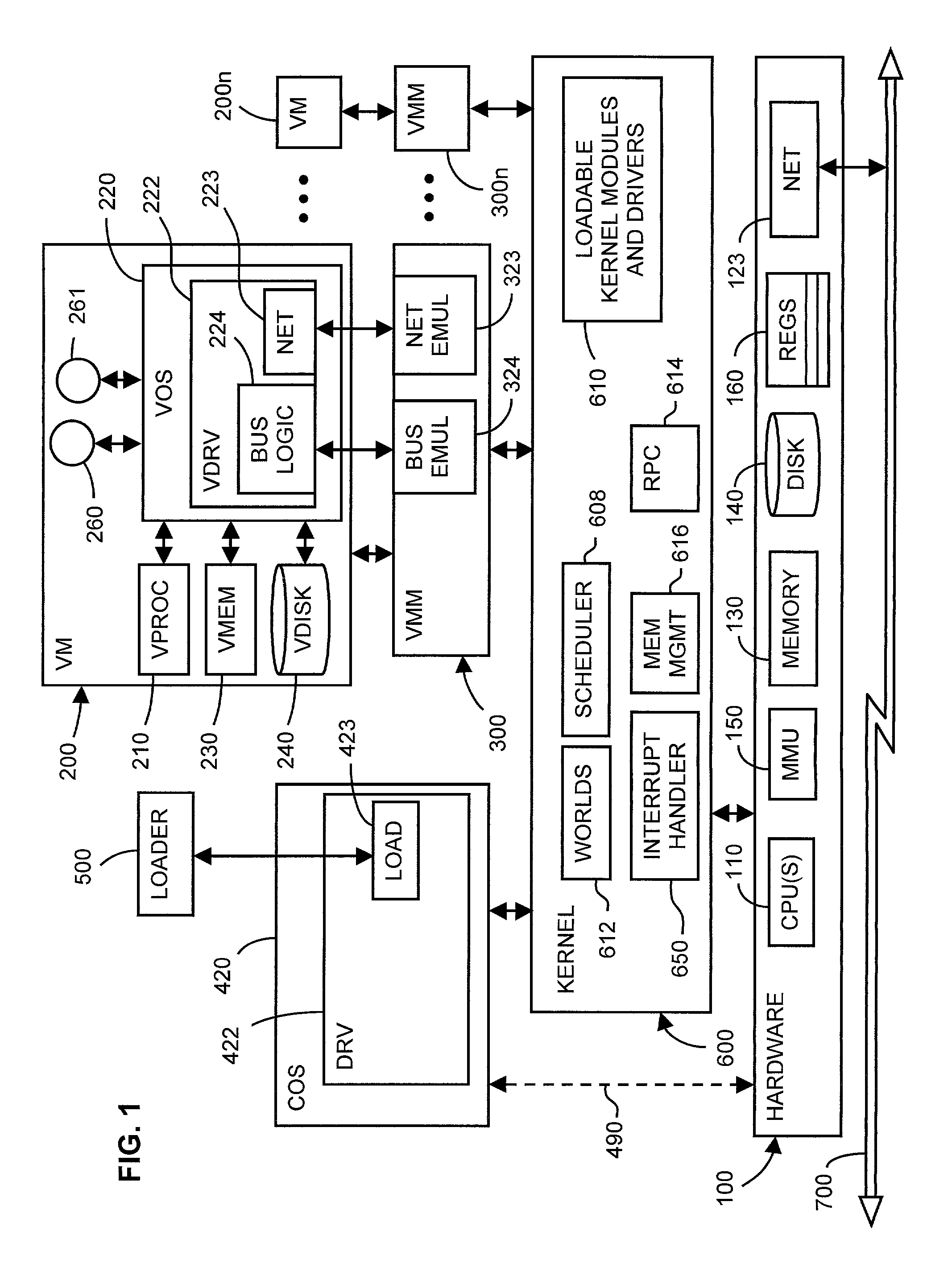
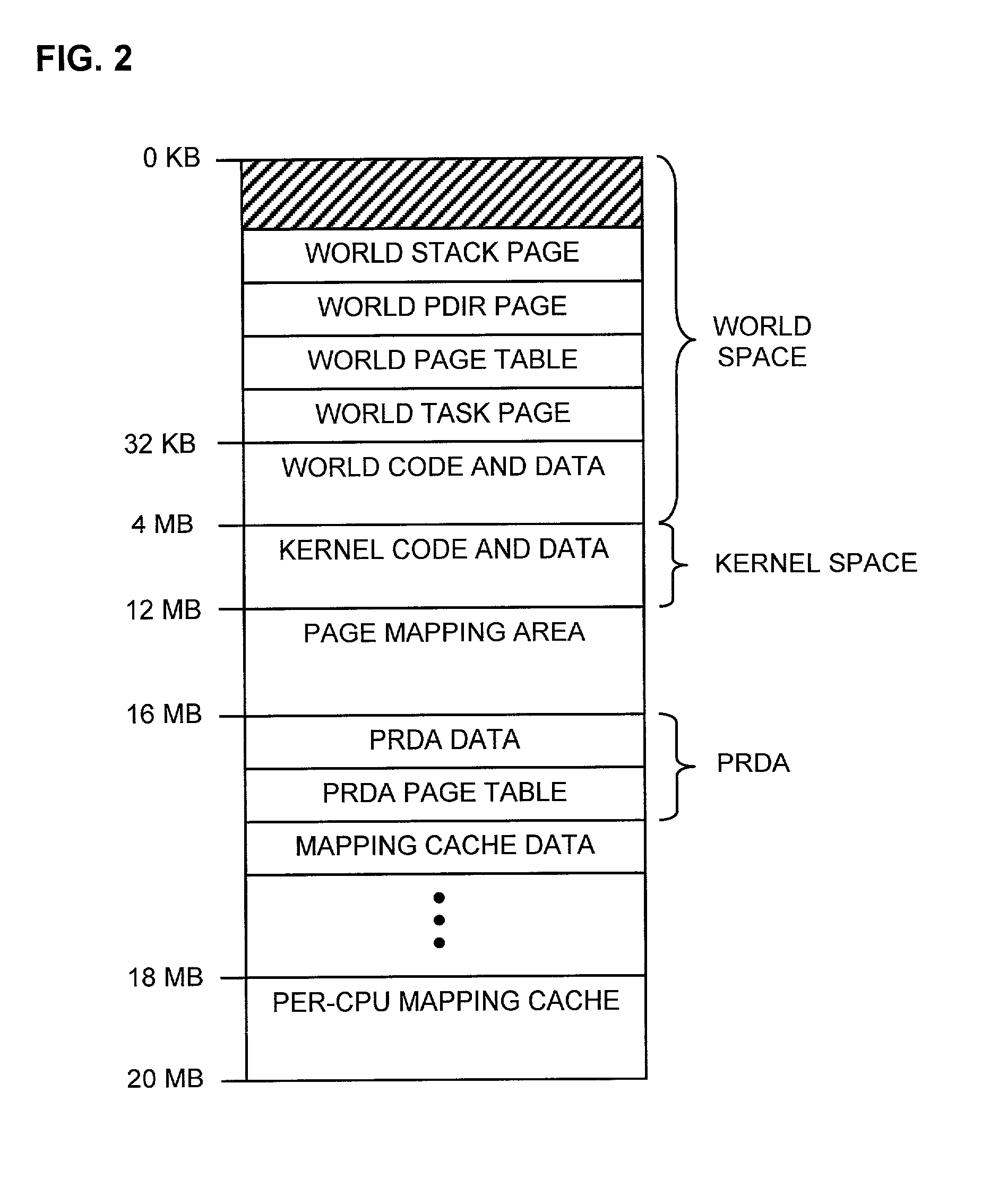
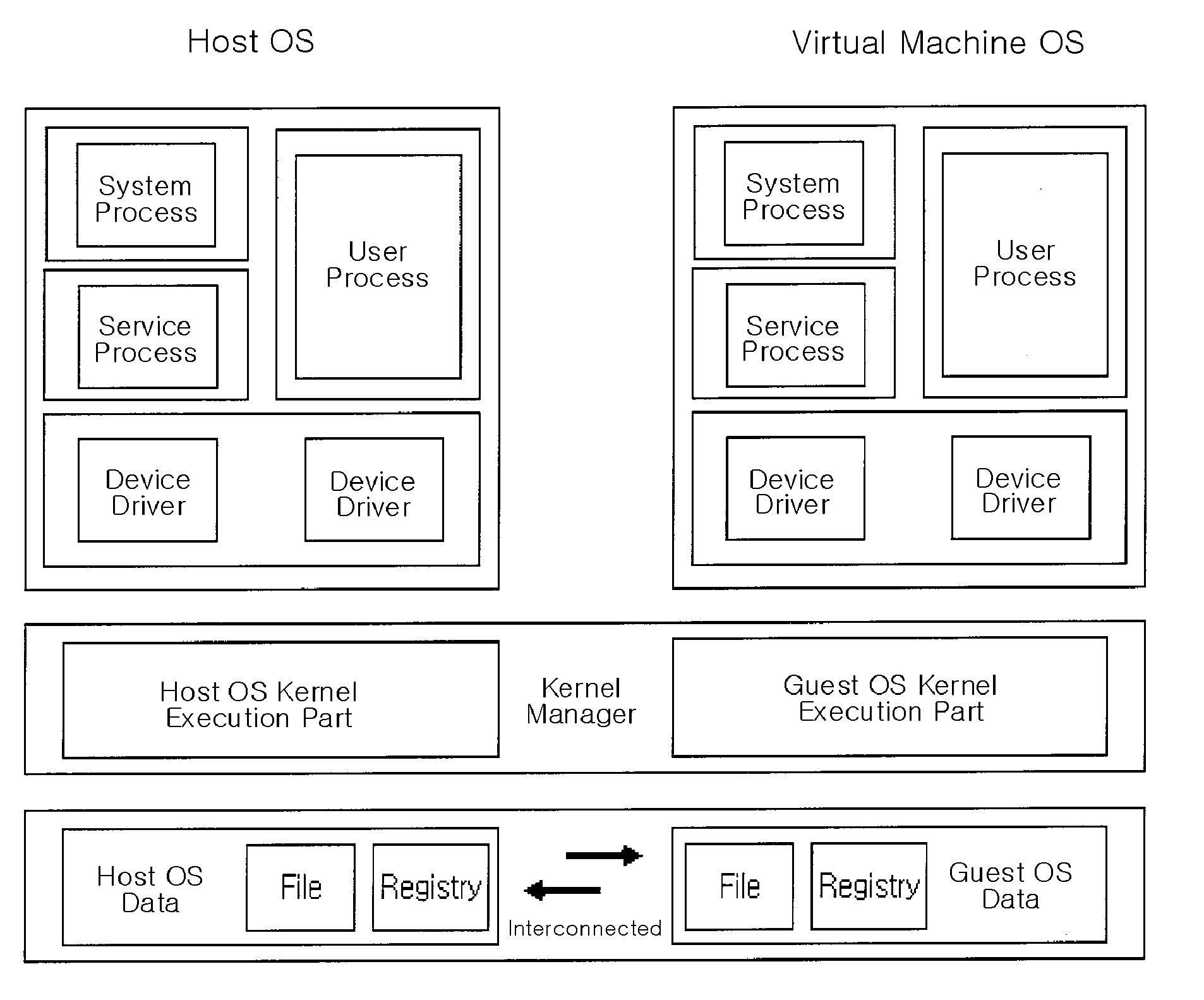
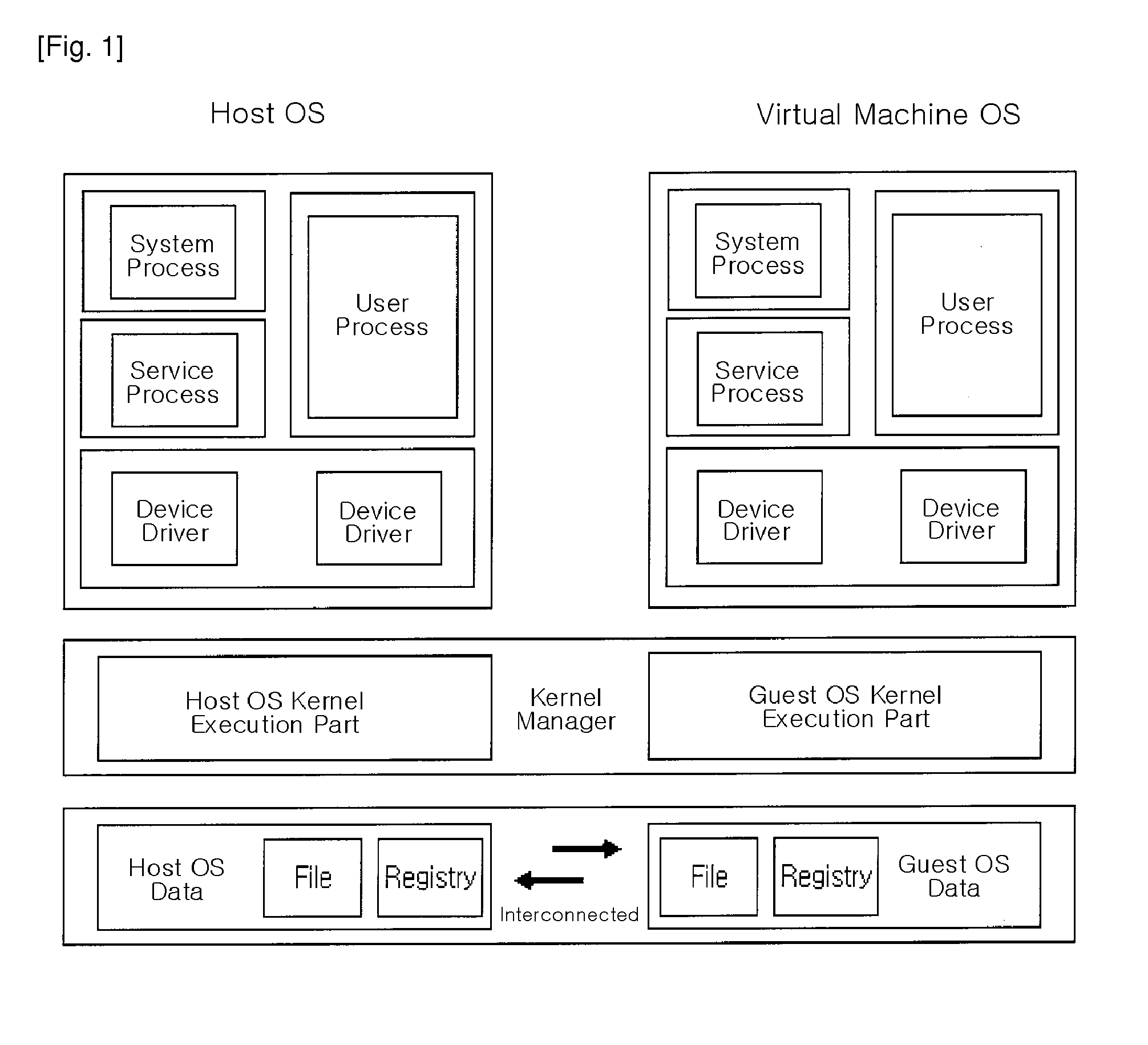
Computer configuration for resource management in systems including a virtual machine
InactiveUS6961941B1Avoiding multiple recurrenceBootstrappingSoftware simulation/interpretation/emulationOperational systemComputer configuration
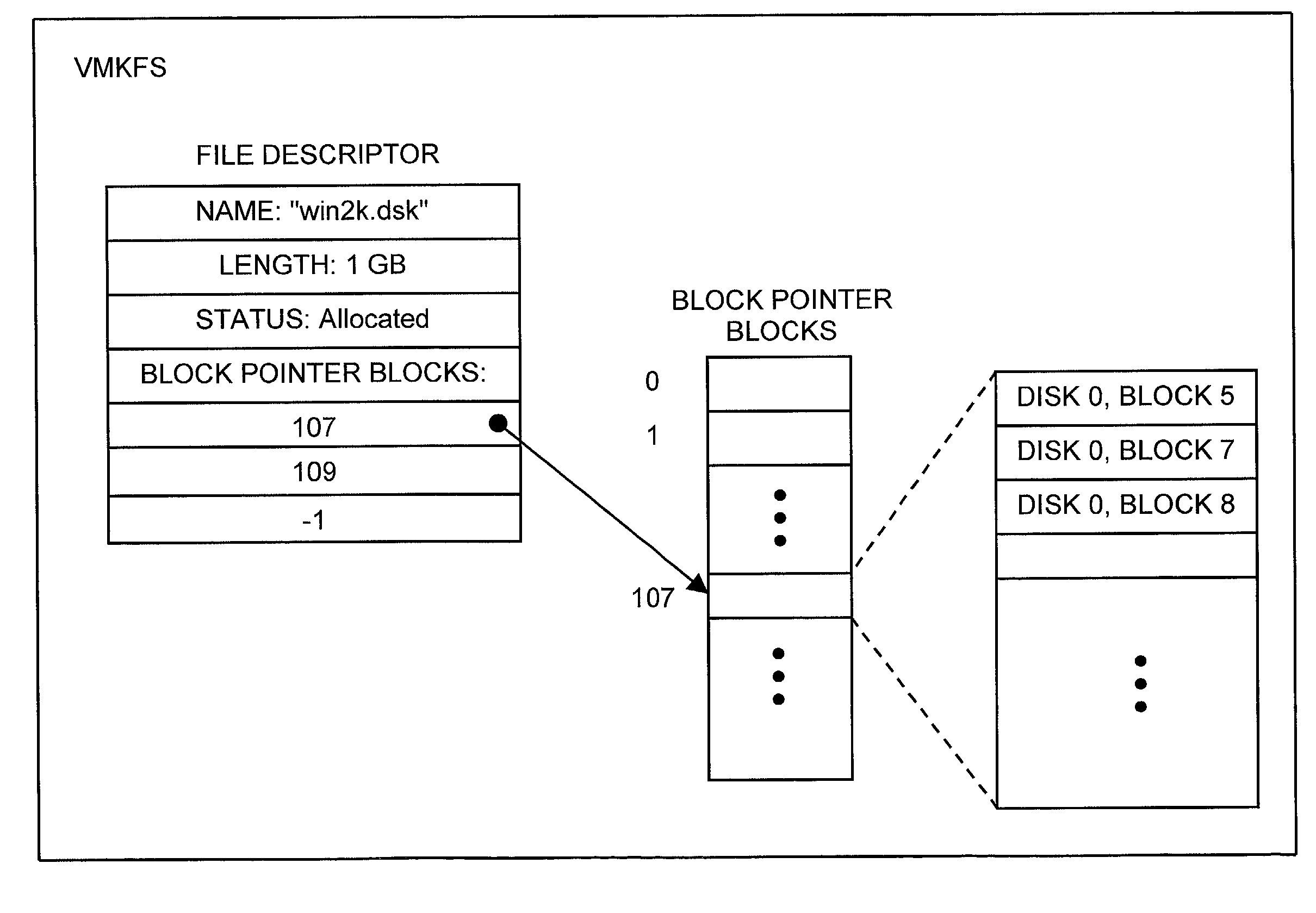
A computer architecture includes a first operating system (COS), which may be a commodity operating system, and a kernel, which acts as a second operating system. The COS is used to boot the system as a whole. After booting, the kernel is loaded and displaces the COS from the system level, meaning that the kernel itself directly accesses predetermined physical resources of the computer. All requests for use of system resources then pass via the kernel. System resources are divided into those that, in order to maximize speed, are controlled exclusively by the kernel, those that the kernel allows the COS to handle exclusively, and those for which control is shared by the kernel and COS. In the preferred embodiment of the invention, at least one virtual machine (VM) runs via a virtual machine monitor, which is installed to run on the kernel. Each VM, the COS, and even each processor in a multiprocessor embodiment, are treated as separately schedulable entities that are scheduled by the kernel. Mechanisms for high-speed I / O between VM's and I / O devices are also included.
Owner:VMWARE INC
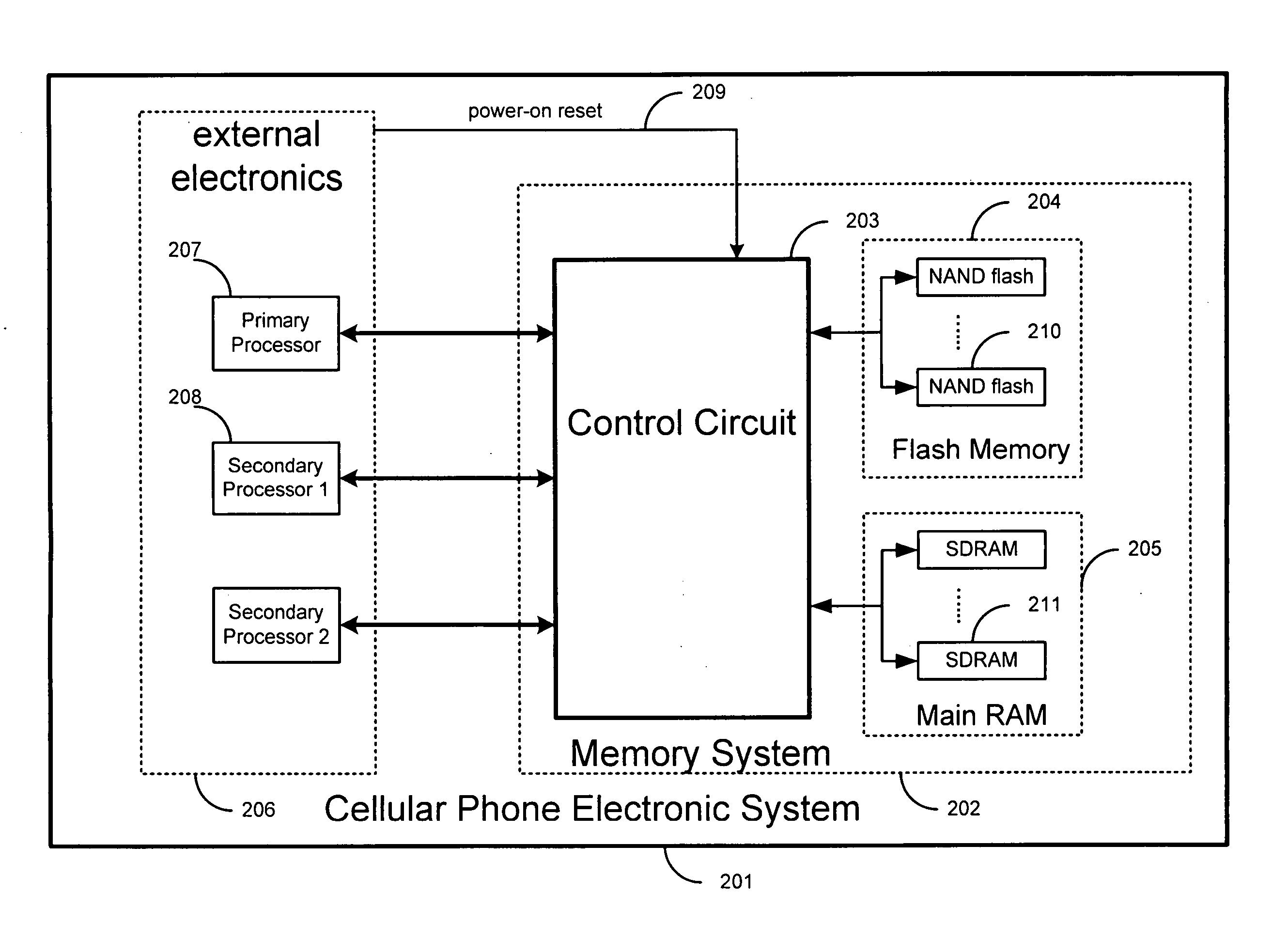
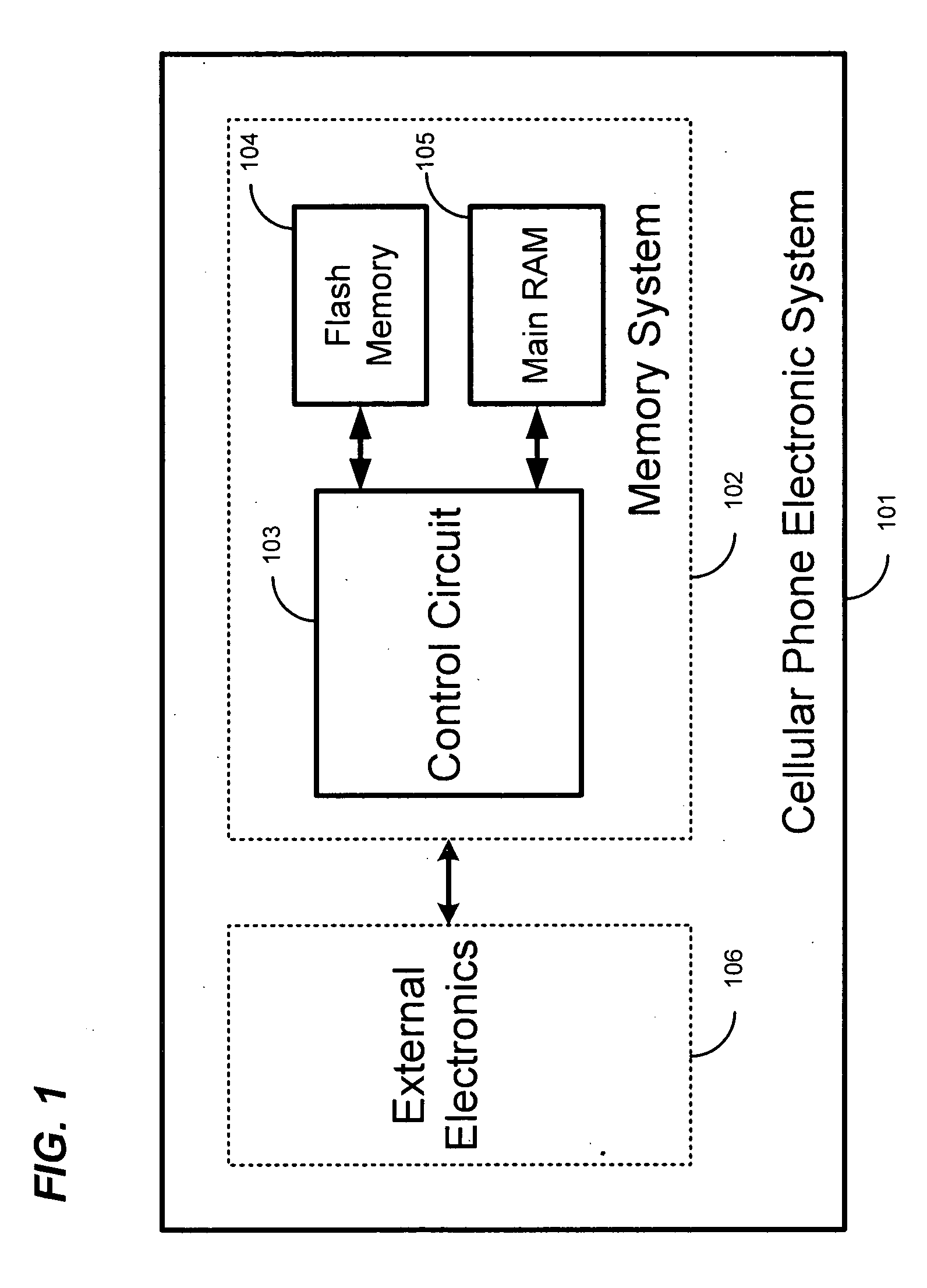
Systems and methods for providing nonvolatile memory management in wireless phones
ActiveUS20060053246A1Low costSmall sizeUnauthorized memory use protectionDigital storageMemory controllerInterface circuits
The present invention is related to memory management, and in particular, to methods and systems for accessing and managing nonvolatile, such as in a wireless phone. A wireless phone memory controller is disclosed that, comprises a first interface circuit configured to be coupled to wireless phone nonvolatile memory, a second interface circuit configured to be coupled to wireless phone volatile memory, a first processor interface configured to be coupled to a first wireless phone processor, wherein the first processor interface is configured to provide the first processor with access to the wireless phone volatile memory, a second processor interface configured to be coupled to a second wireless phone processor, and a controller circuit configured to copy at least a portion of wireless phone nonvolatile memory data to the wireless phone volatile memory.
Owner:GOOGLE LLC
Screen icon manipulation by context and frequency of Use
ActiveUS8972878B2More user confidenceDigital data authenticationSubstation equipmentTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
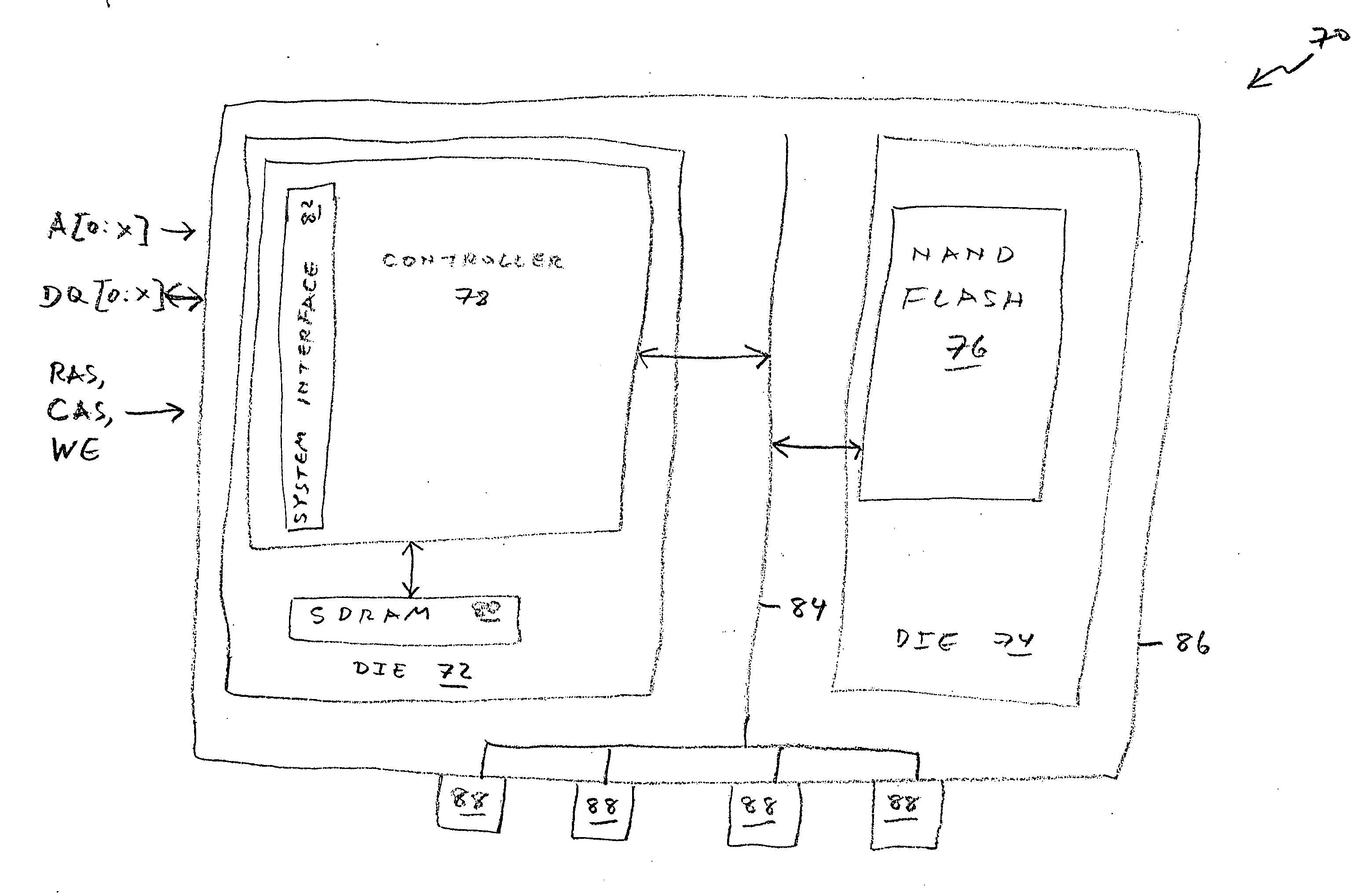
SDRAM memory device with an embedded NAND flash controller
A memory device includes two dies. A first memory is fabricated on one die. A controller of the first memory is fabricated on the other die. Also fabricated on the other die is another component, such as a second memory, that communicates with a host system using a plurality of signals different from the signals used by the first memory. The device includes a single interface for communicating with the host system using only the respective signals of the second component. In a most preferred embodiment, the first memory is a NAND flash memory and the second memory is a SDRAM.
Owner:INNOVATIVE MEMORY SYST INC
Systems and methods for accelerated loading of operating systems and application programs
InactiveUS7181608B2Easy loadingBroaden applicationInput/output to record carriersCode conversionOperational systemComputerized system
Systems and methods are provided for accelerated loading of operating system and application programs upon system boot or application launch. In one aspect, a method for providing accelerated loading of an operating system includes maintaining a list of boot data used for booting a computer system, preloading the boot data upon initialization of the computer system, and servicing requests for boot data from the computer system using the preloaded boot data. The boot data may comprise program code associated with an operating system of the computer system, an application program, and a combination thereof. The boot data is retrieved from a boot device and stored in a cache memory device. The boot data is stored in a compressed format on the boot device and the preloaded boot data is decompressed prior to transmitting the preloaded boot data to the requesting system.
Owner:REALTIME DATA
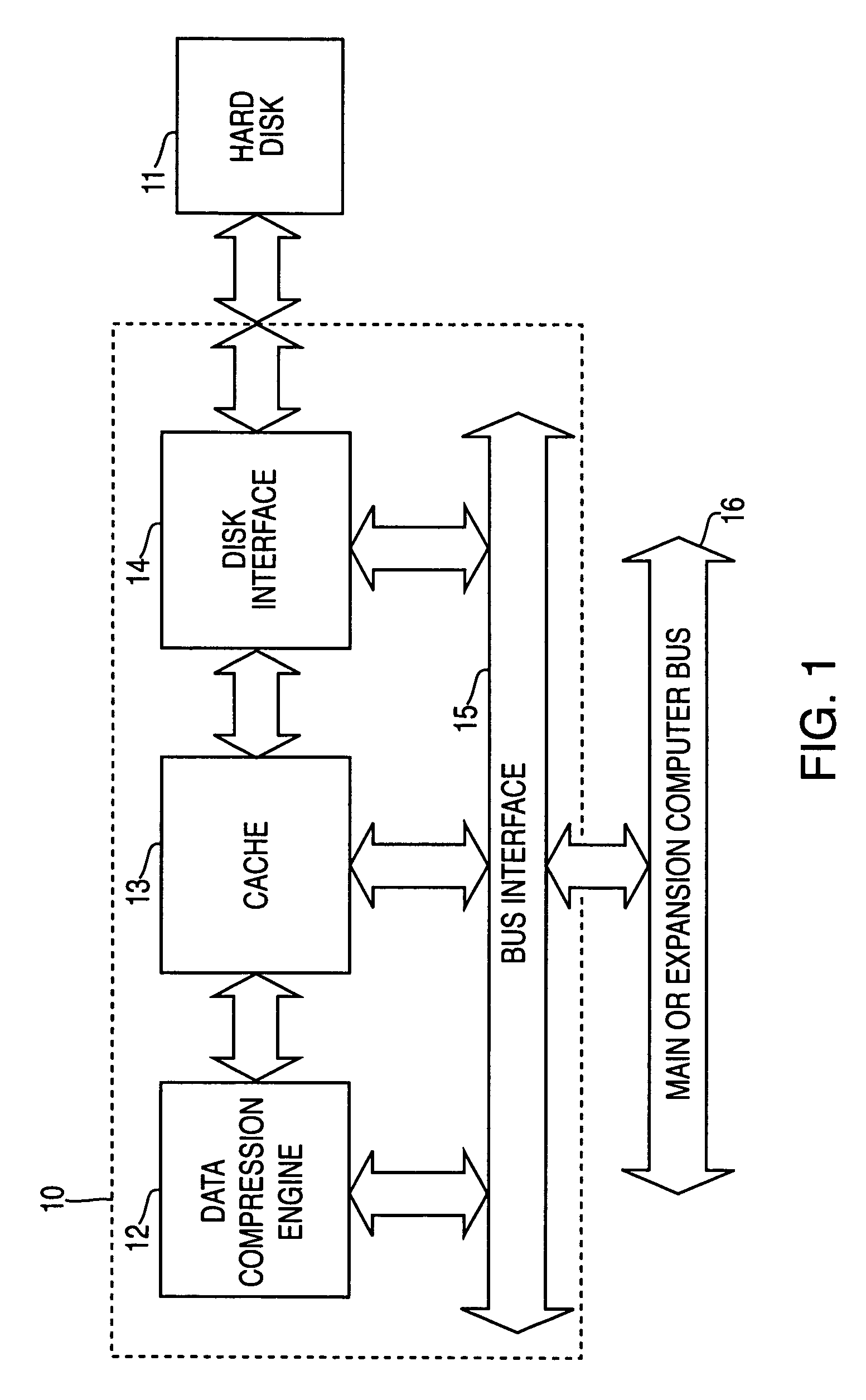
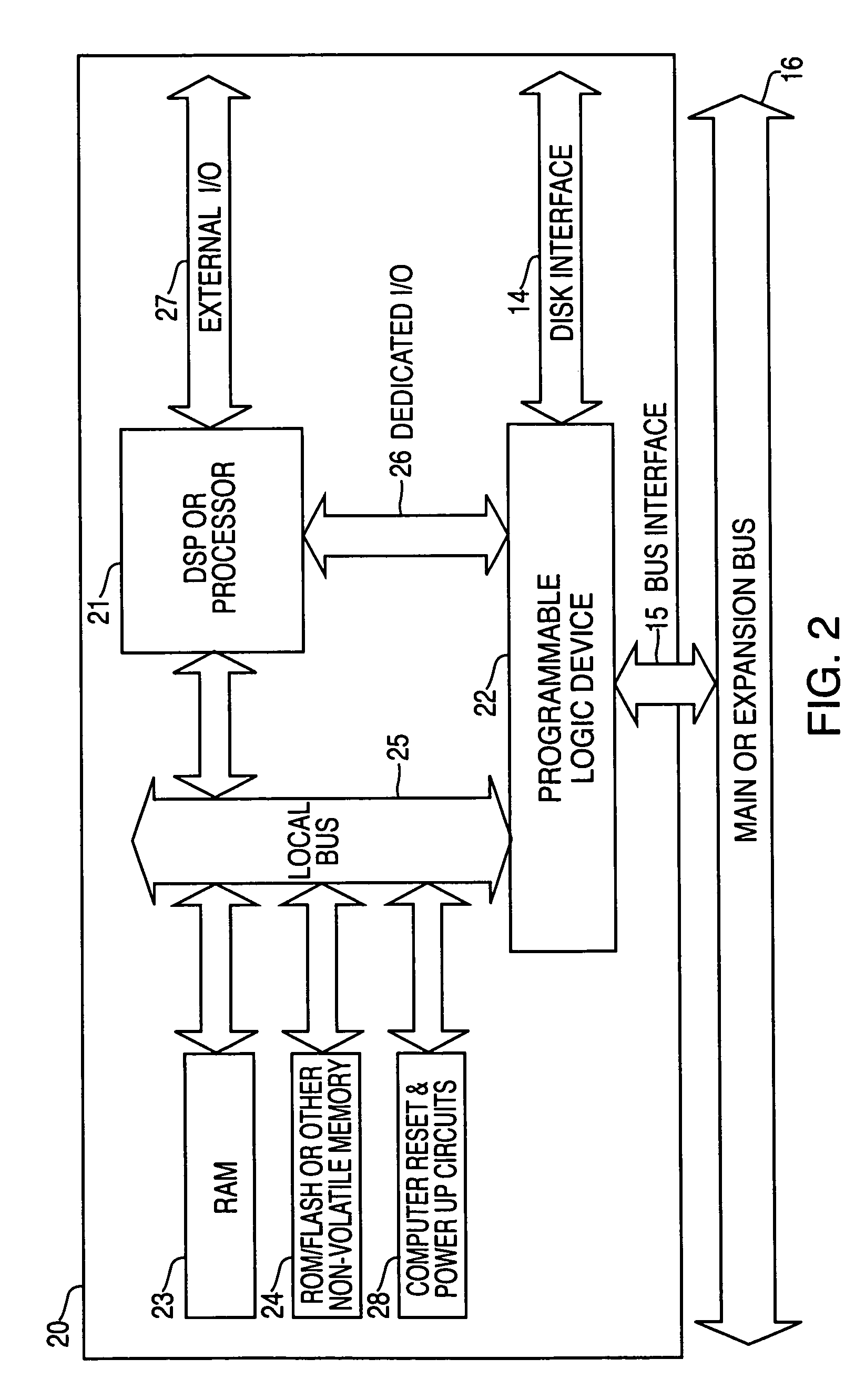
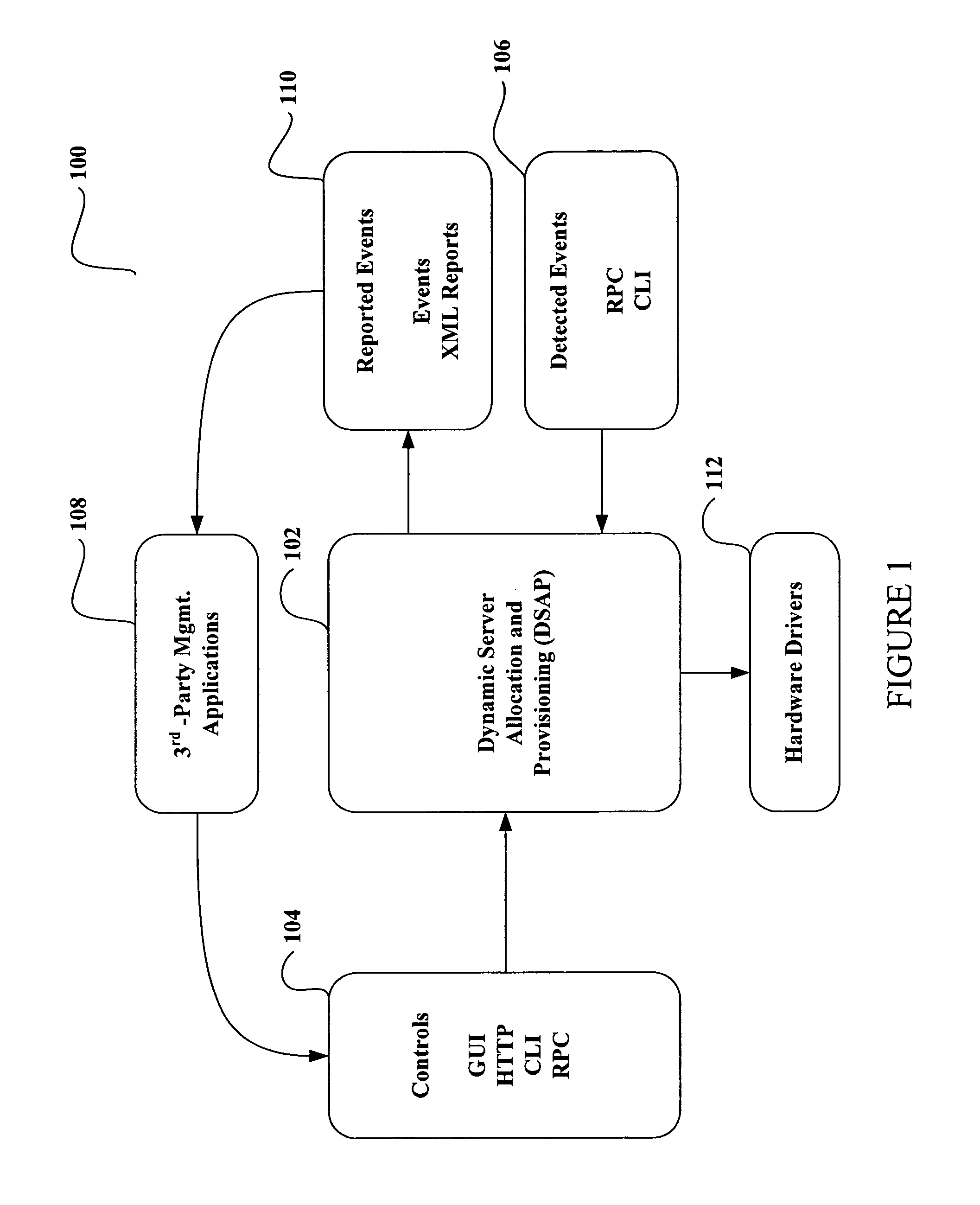
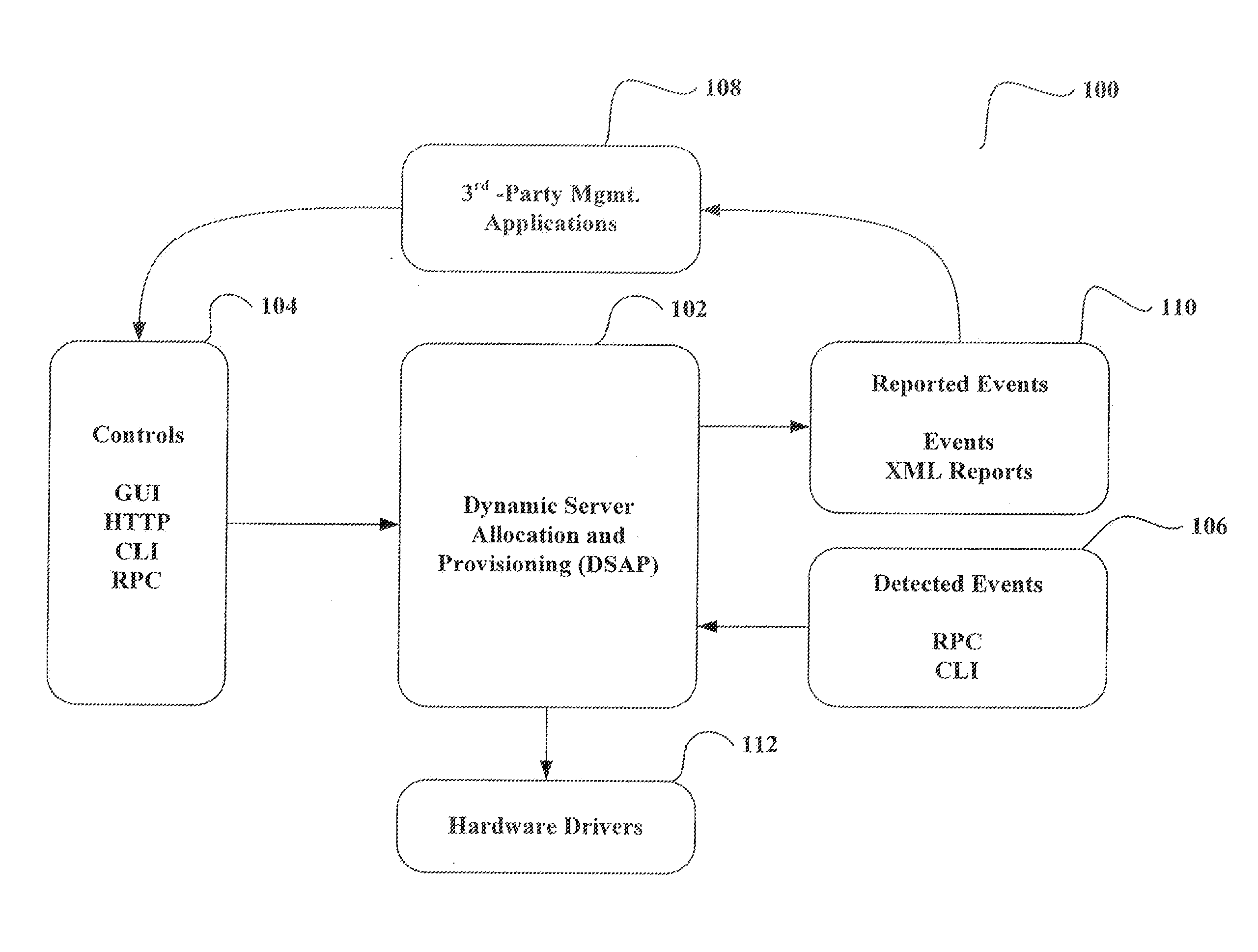
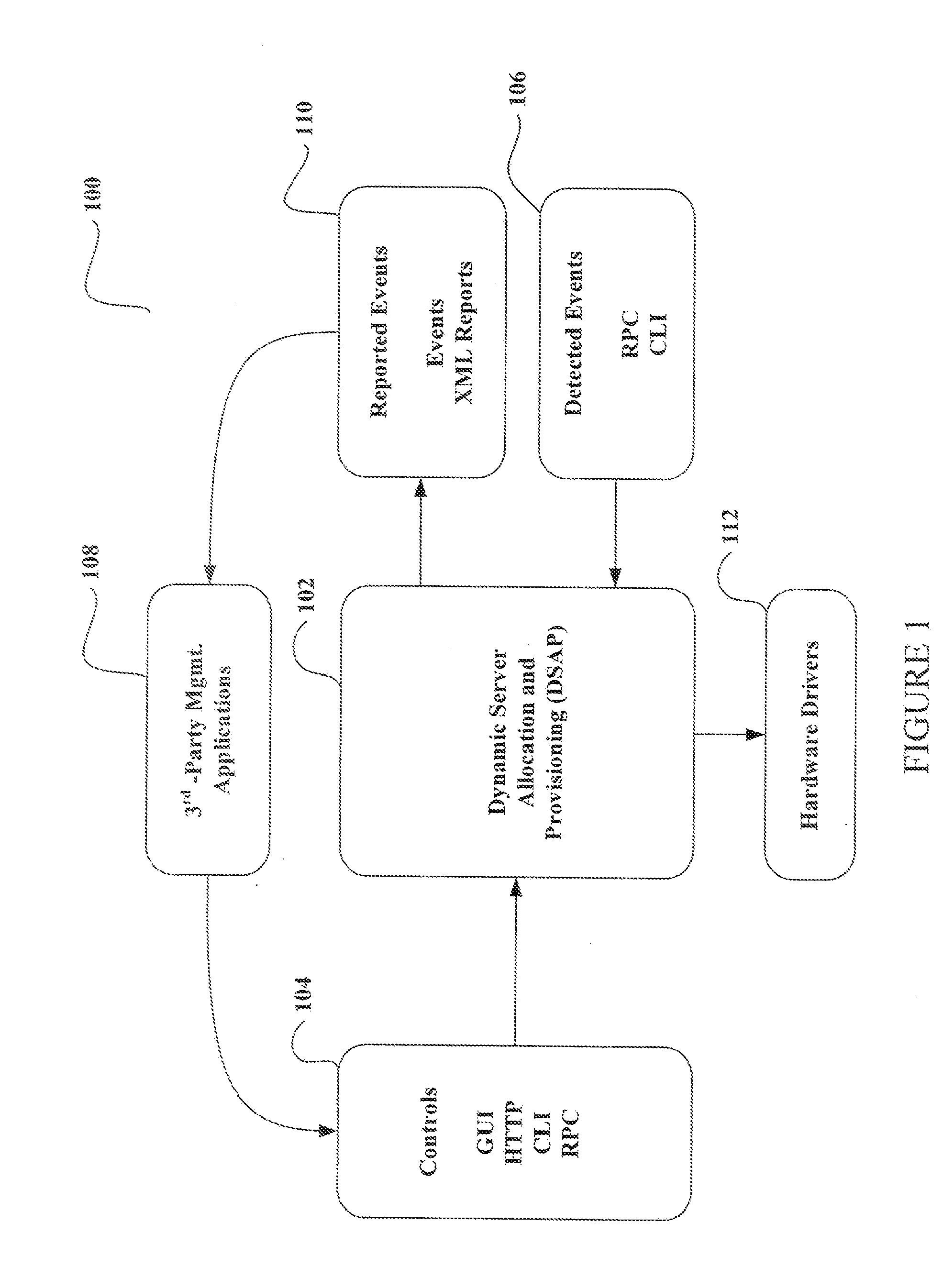
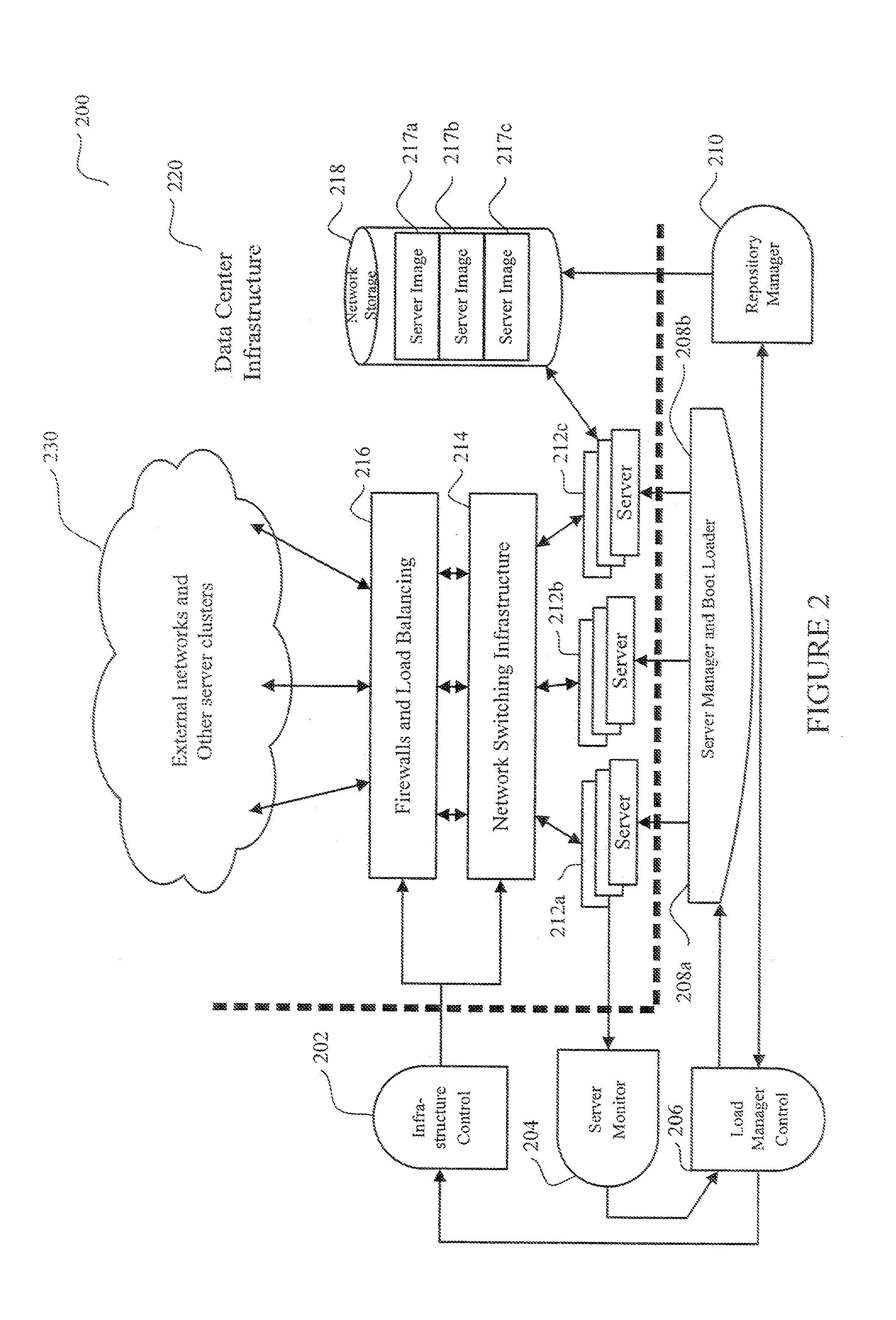
System and method for dynamic server allocation and provisioning
ActiveUS7213065B2Lower cost of capitalQuality improvementResource allocationDigital computer detailsManagement toolVirtual LAN
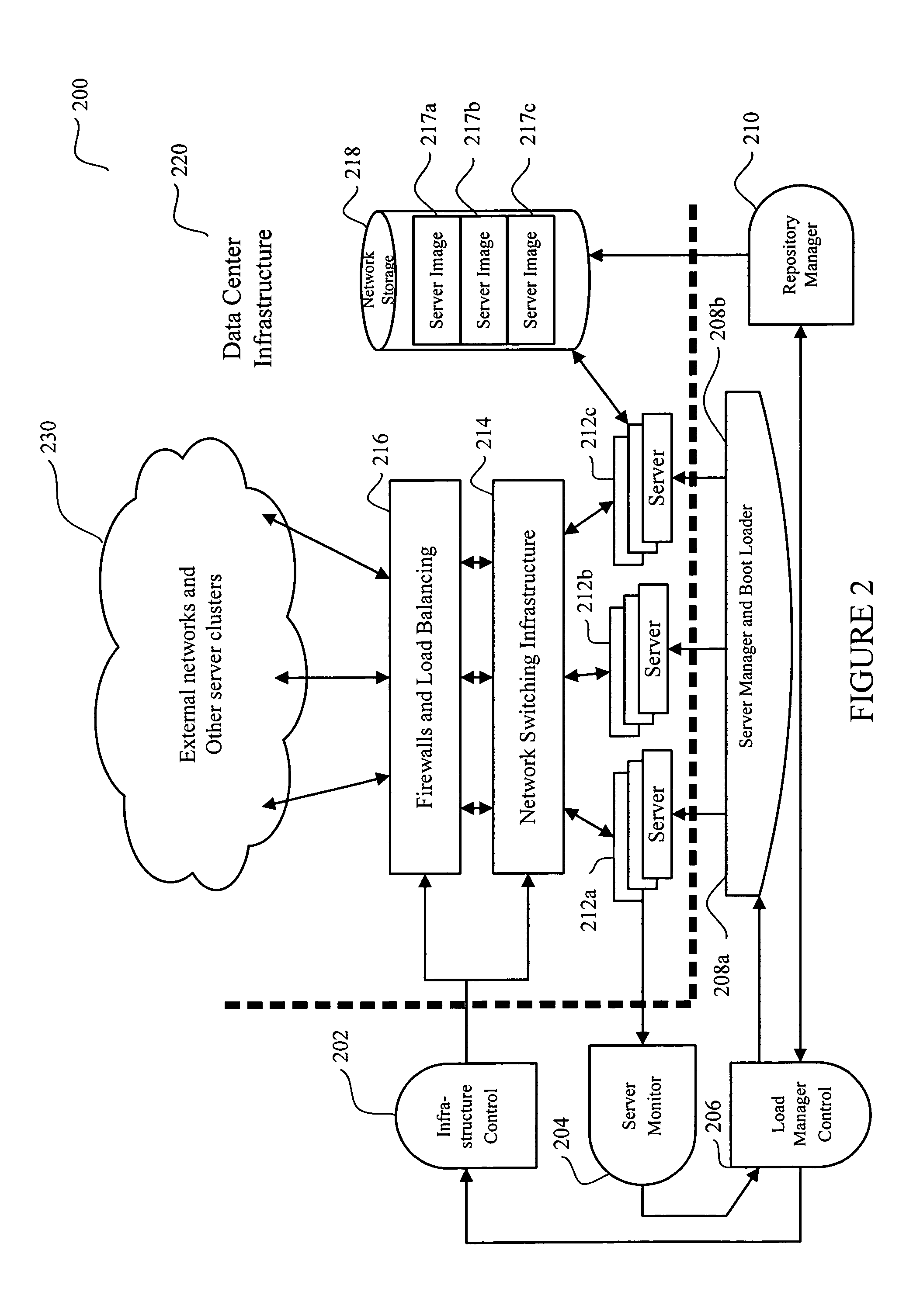
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
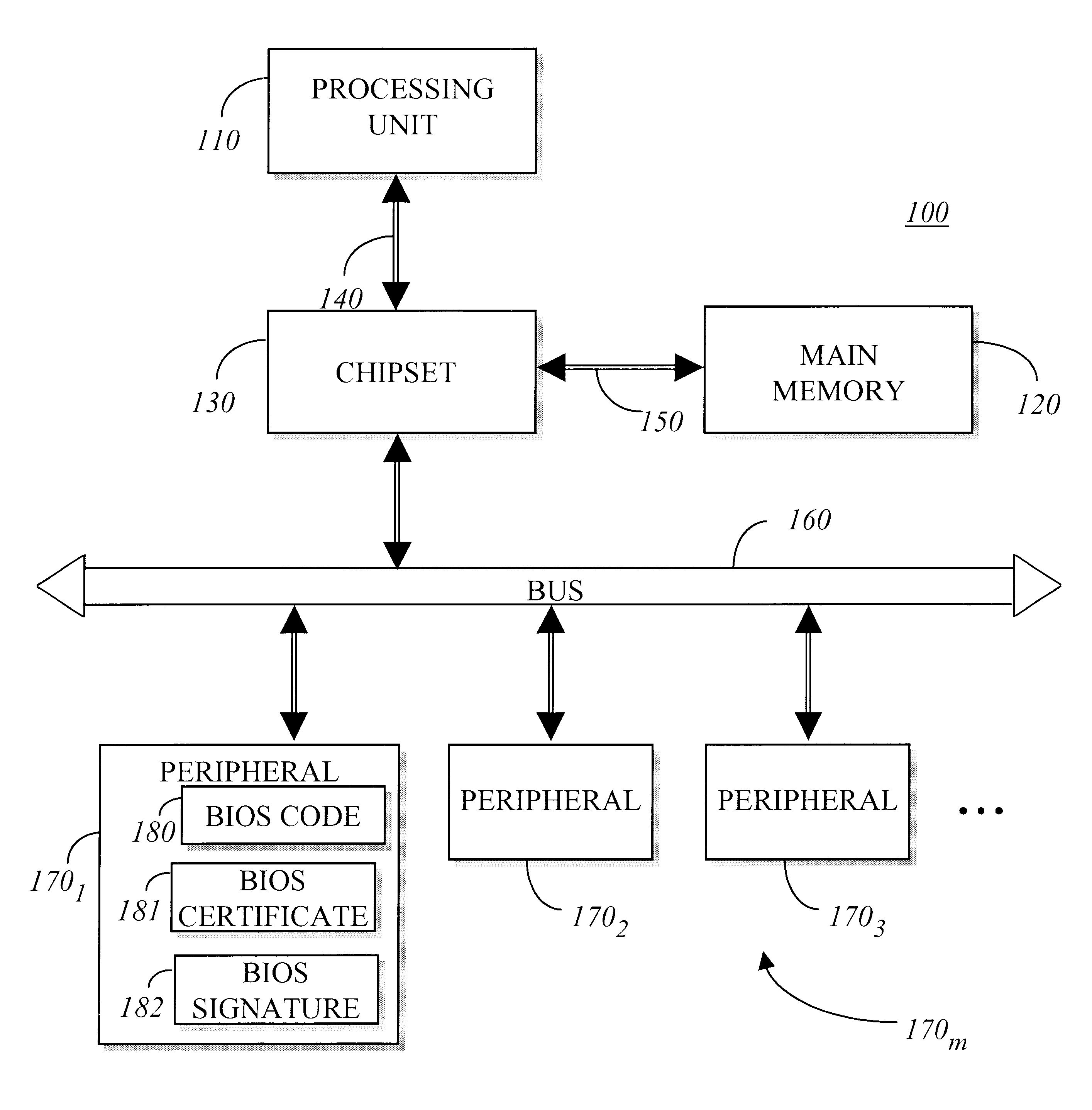
Method for BIOS authentication prior to BIOS execution
InactiveUS6401208B2User identity/authority verificationUnauthorized memory use protectionPower-on resetBIOS
Owner:INTEL CORP
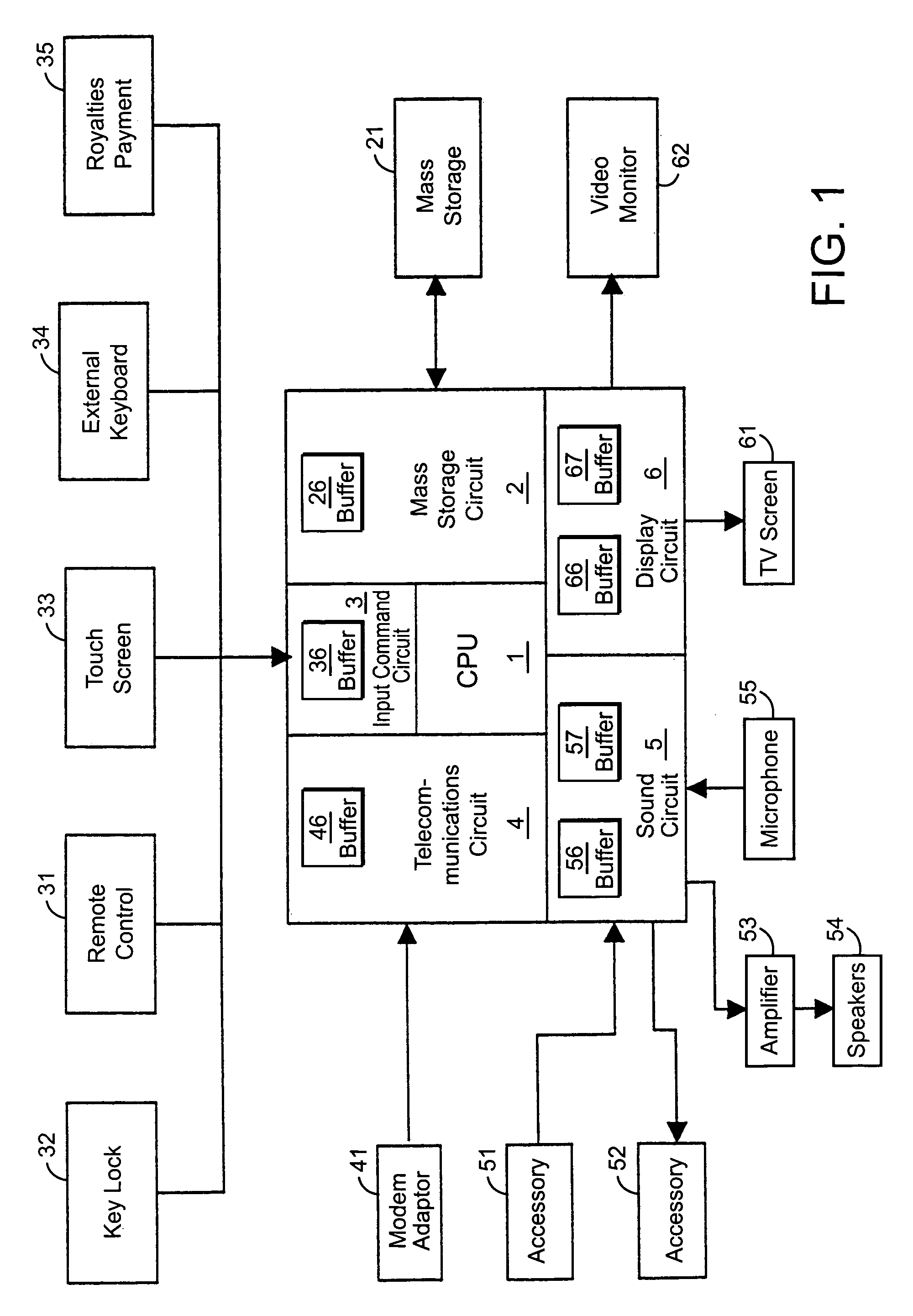
System and method of interfacing co-processors and input/output devices via a main memory system
ActiveUS20120204079A1Memory architecture accessing/allocationError detection/correctionComputer moduleMemory bus
A system for interfacing with a co-processor or input / output device is disclosed. According to one embodiment, the system includes a computer processing unit, a memory module, a memory bus that connects the computer processing unit and the memory module, and a co-processing unit or input / output device, wherein the memory bus also connects the co-processing unit or input / output device to the computer processing unit.
Owner:RAMBUS INC
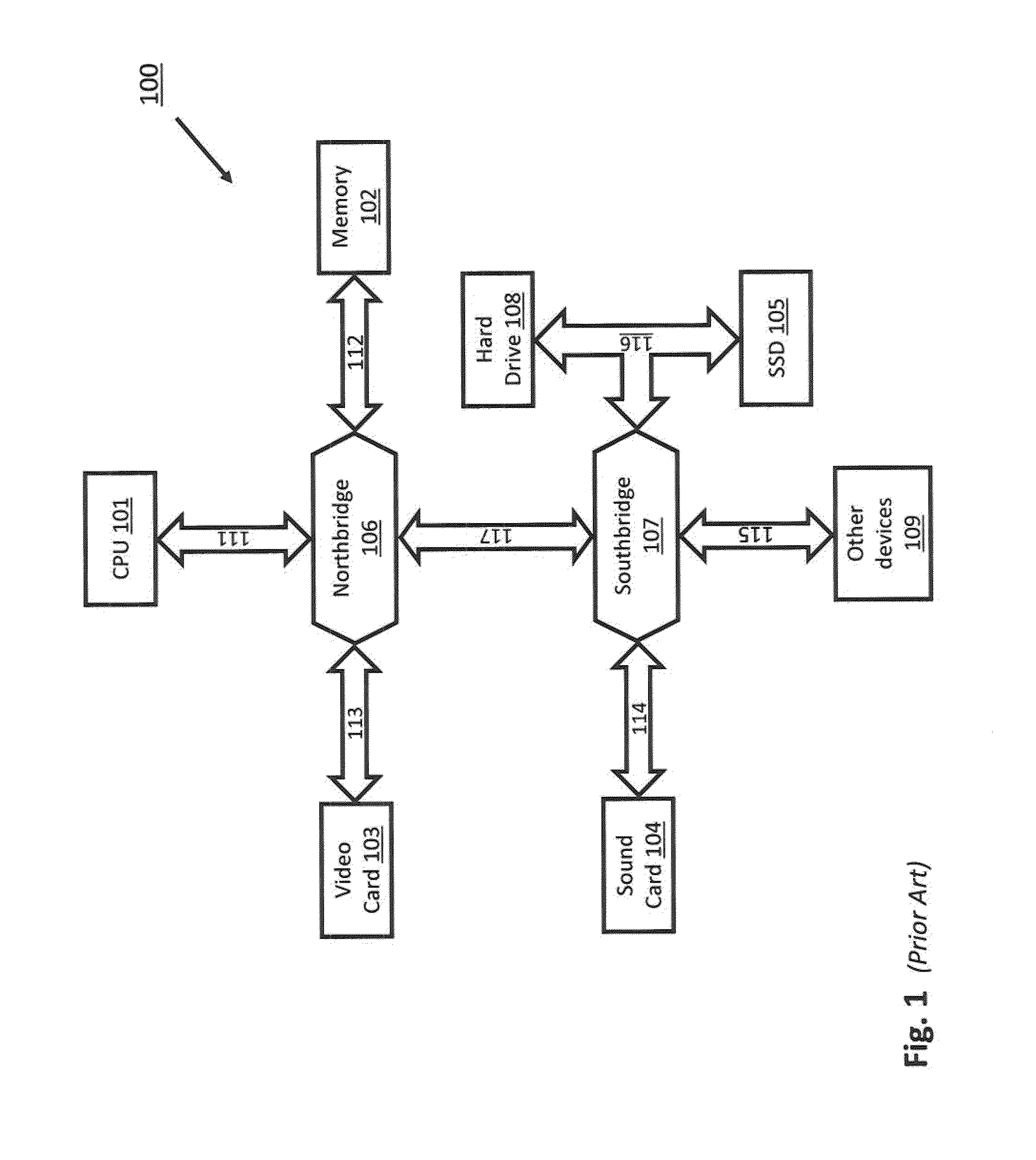
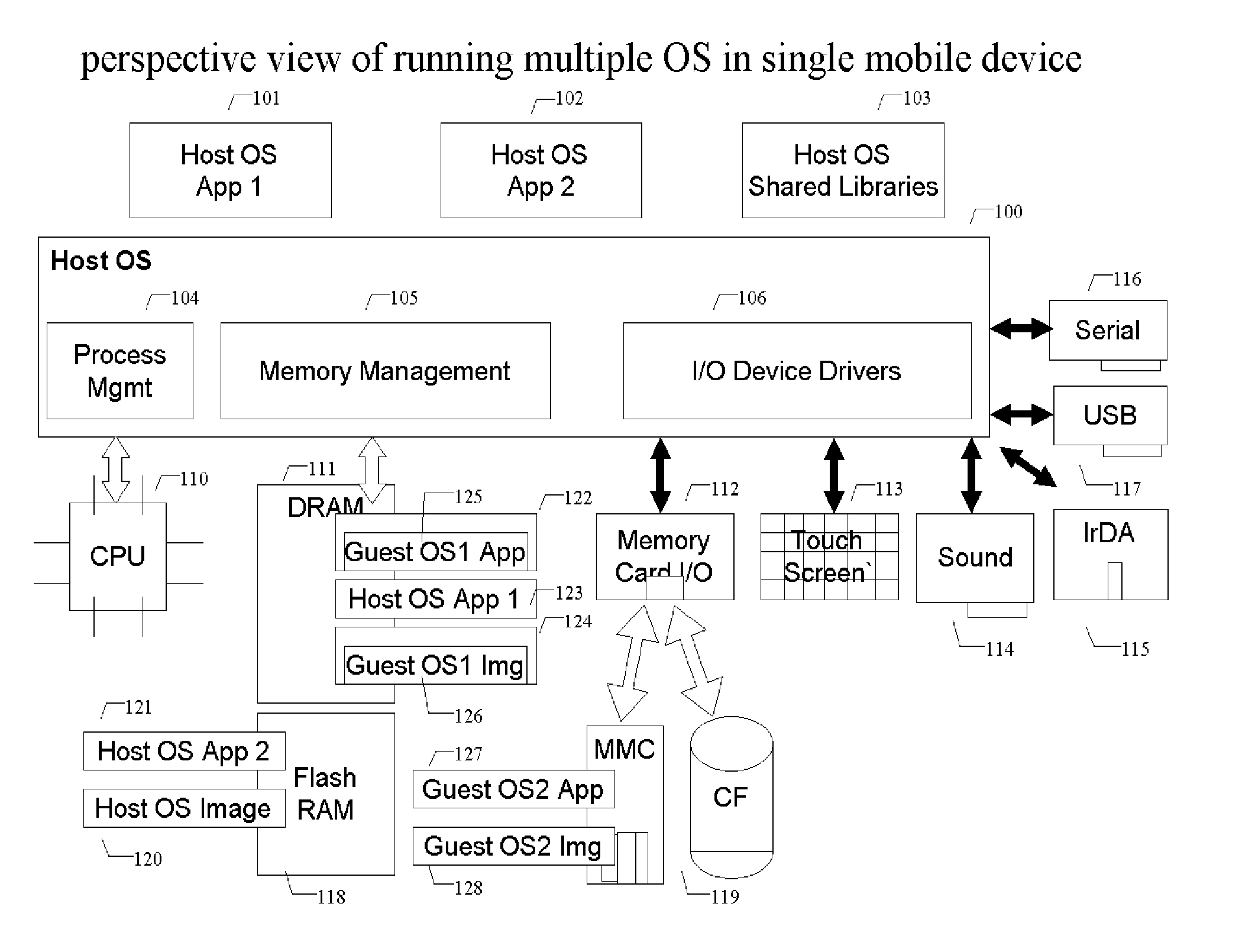
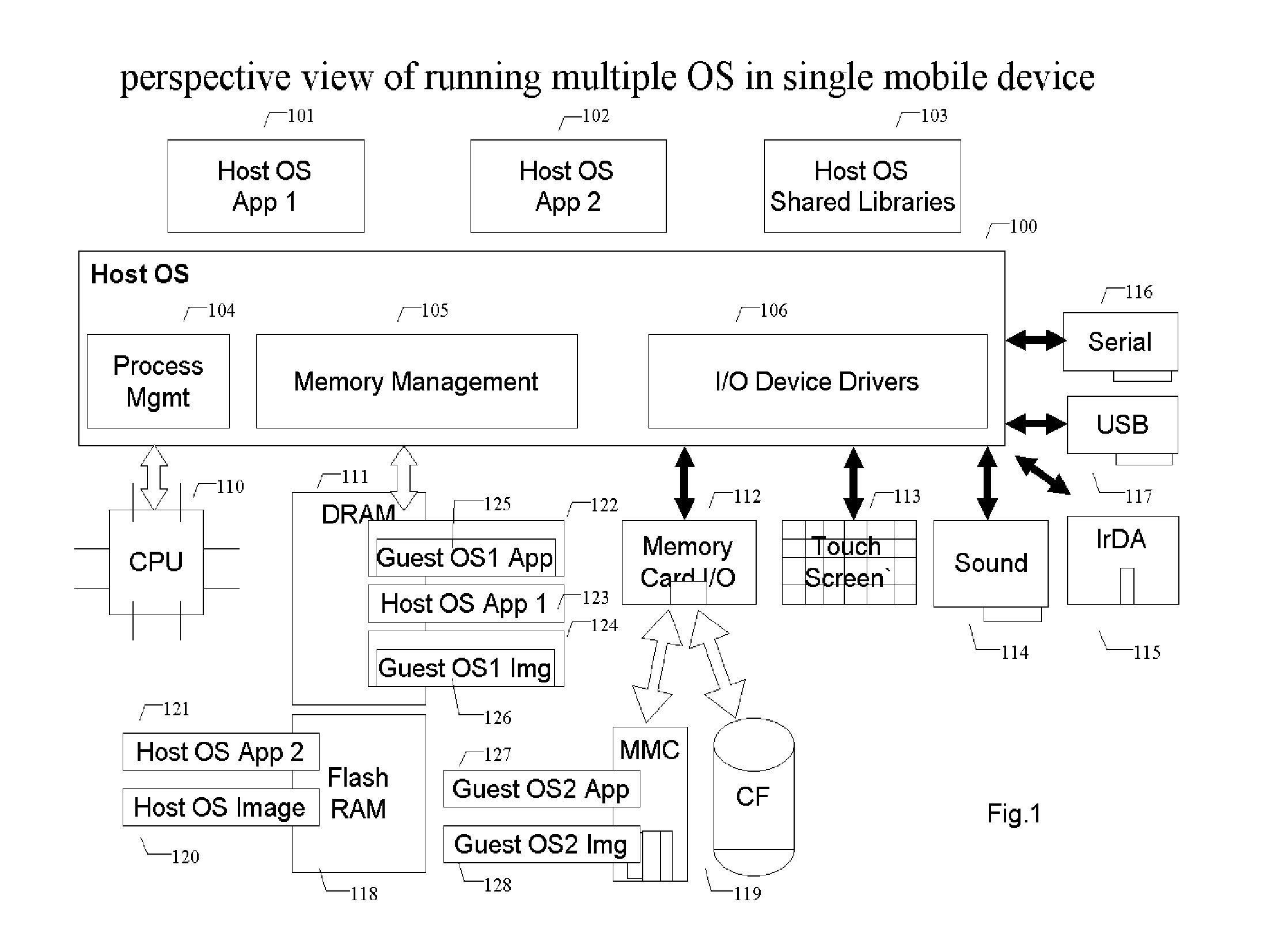
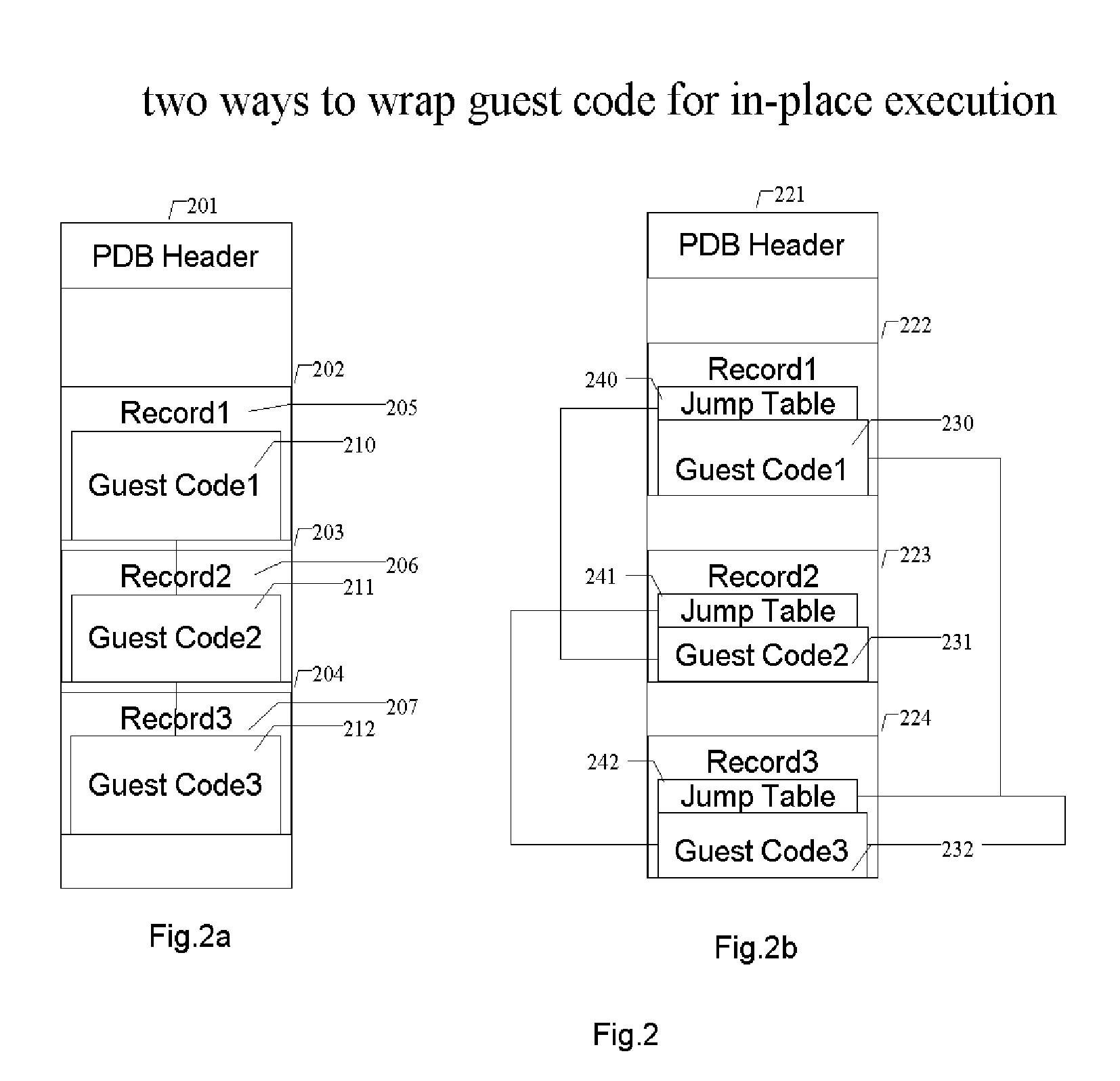
Methods and systems for running multiple operating systems in a single mobile device
ActiveUS20060010314A1Reduce memory usageError detection/correctionDigital computer detailsOperational systemEngineering
Methods and systems for running multiple operating systems in a single embedded or mobile device (include PDA, cellular phone and other devices) are disclosed. The invention allows a mobile device that normally can only run a single operating system to run another operating system while preserving the state and data of the original operating system. Guest OS is packaged into special format recognizable by the host OS that still can be executed in place by the system. The Methods include: •Change the memory protection bits for the original OS; •Fake a reduced physical memory space for guest OS; •Use special memory device driver to claim memories of host OS; •Backup whole image of the current OS and data to external memory card.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
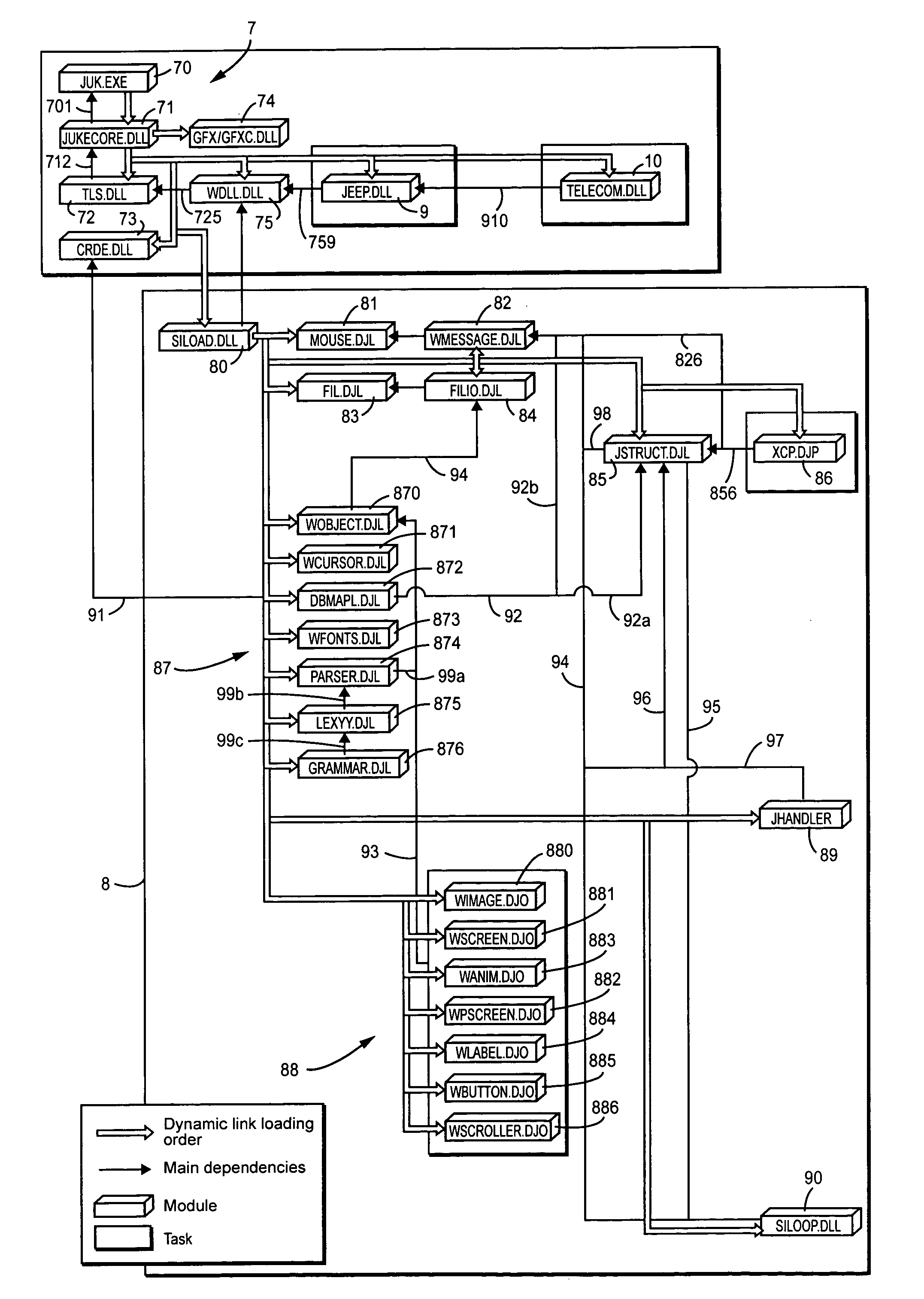
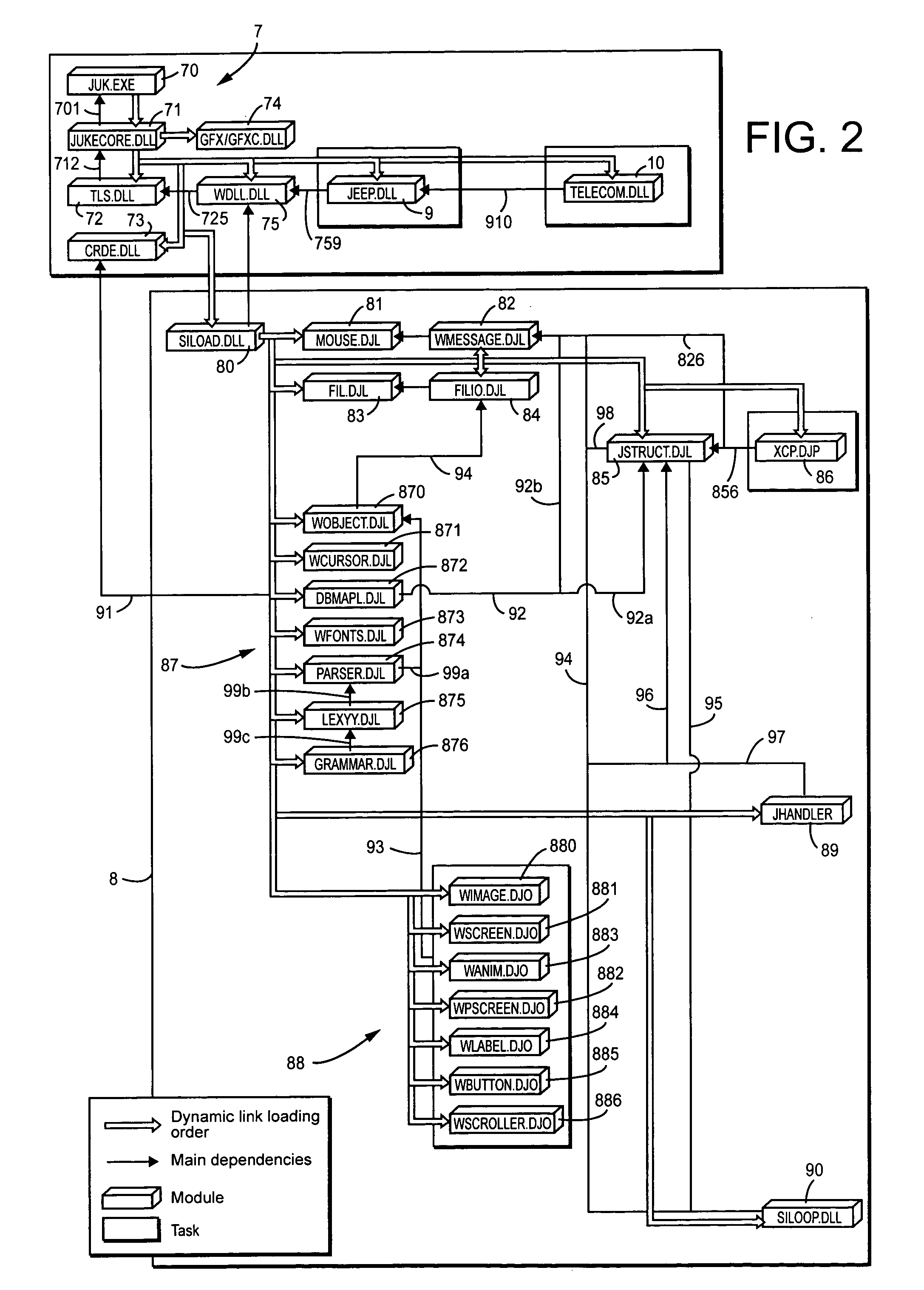
System for remote loading of objects or files in order to update software
A system for remote loading of objects or files in order to update software includes operating system architecture that calls for different tasks to be broken down into software modules that are connected to one another by dynamic links or are composed of executable subroutines that have main dependence links to other parts of the operating system. Each of the modules is composed of object files or libraries that are represented by dynamic link libraries among themselves according to a number of dependence levels that are described in their respective attributes.
Owner:TOUCHTUNES MUSIC CORP
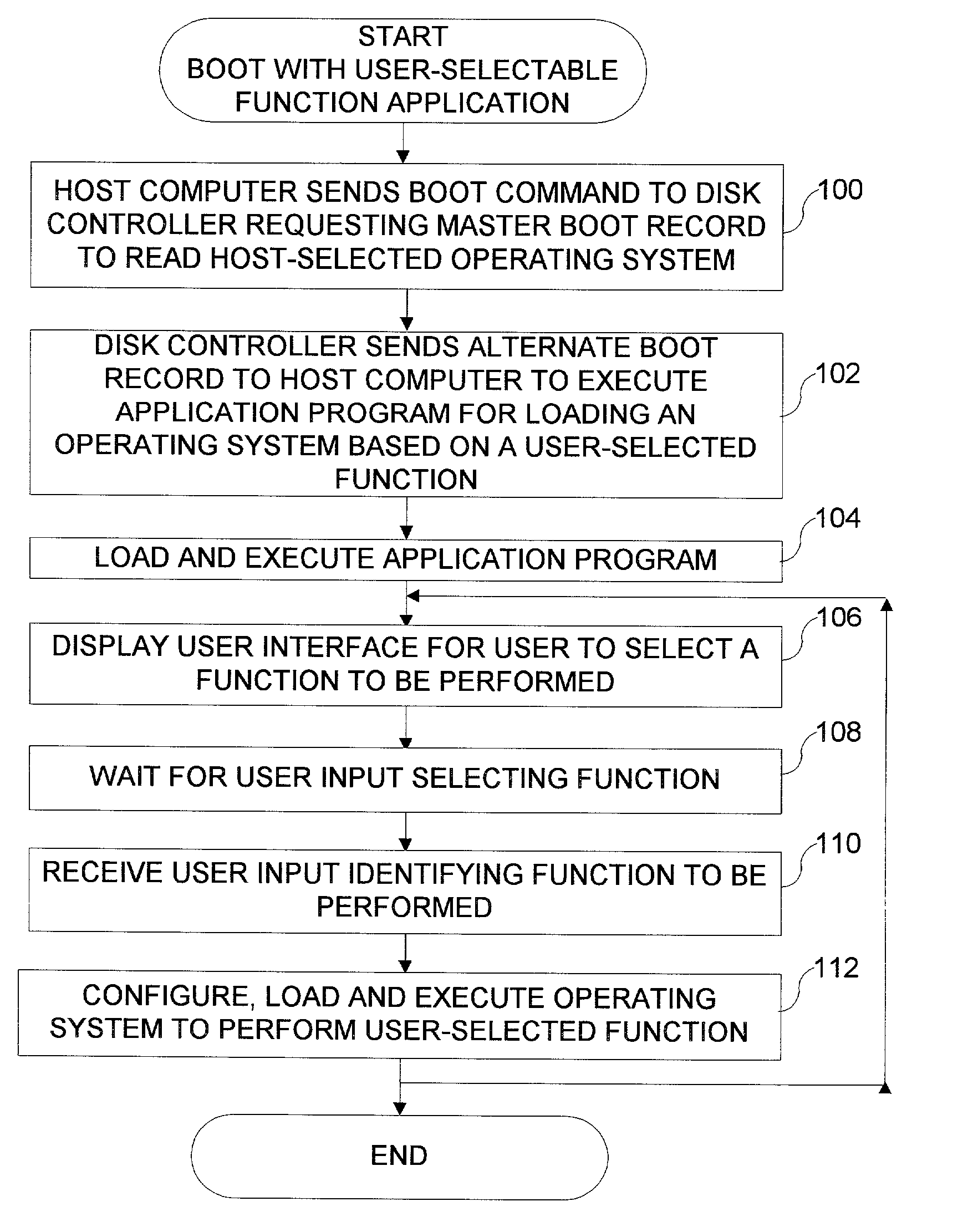
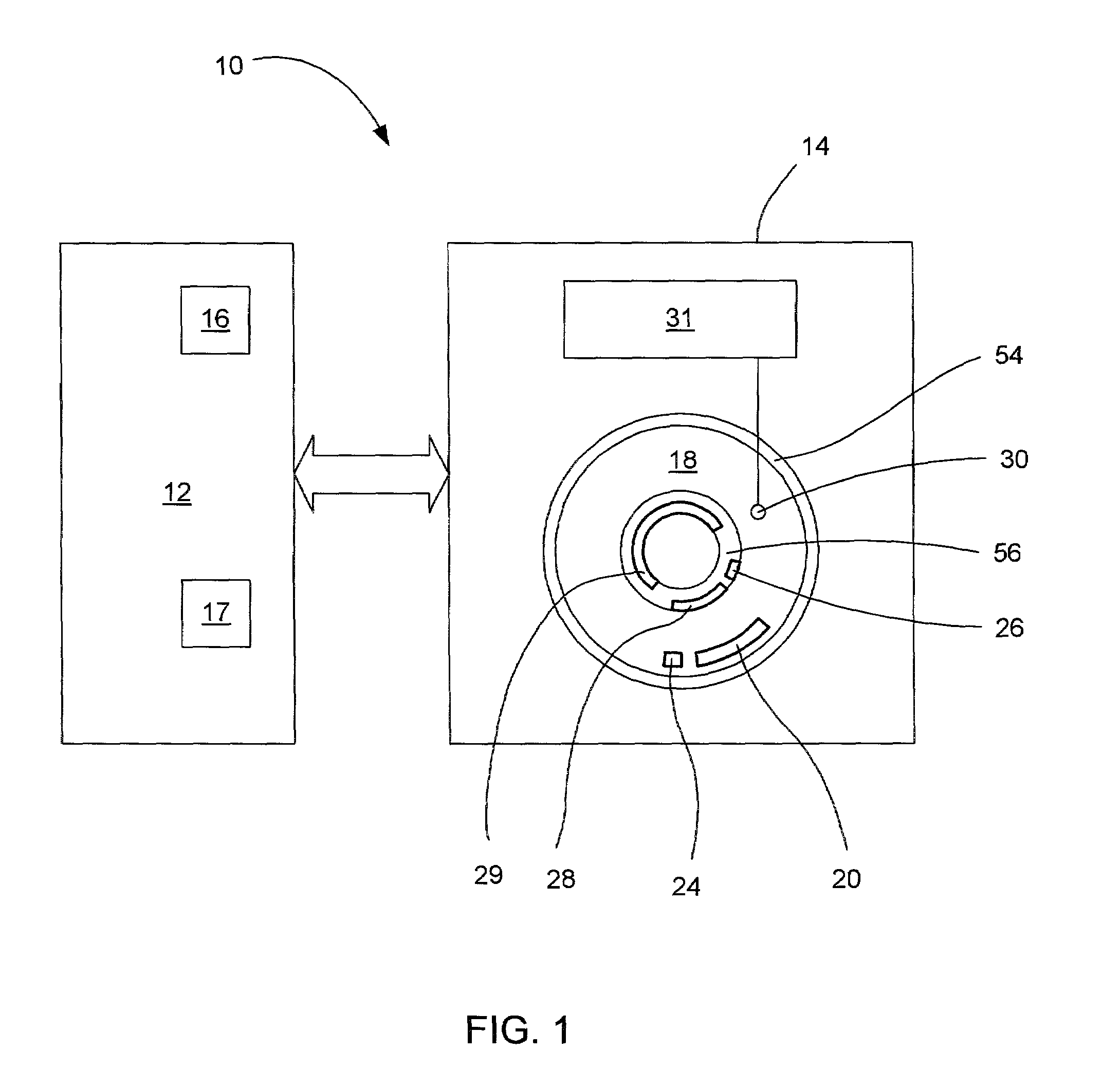
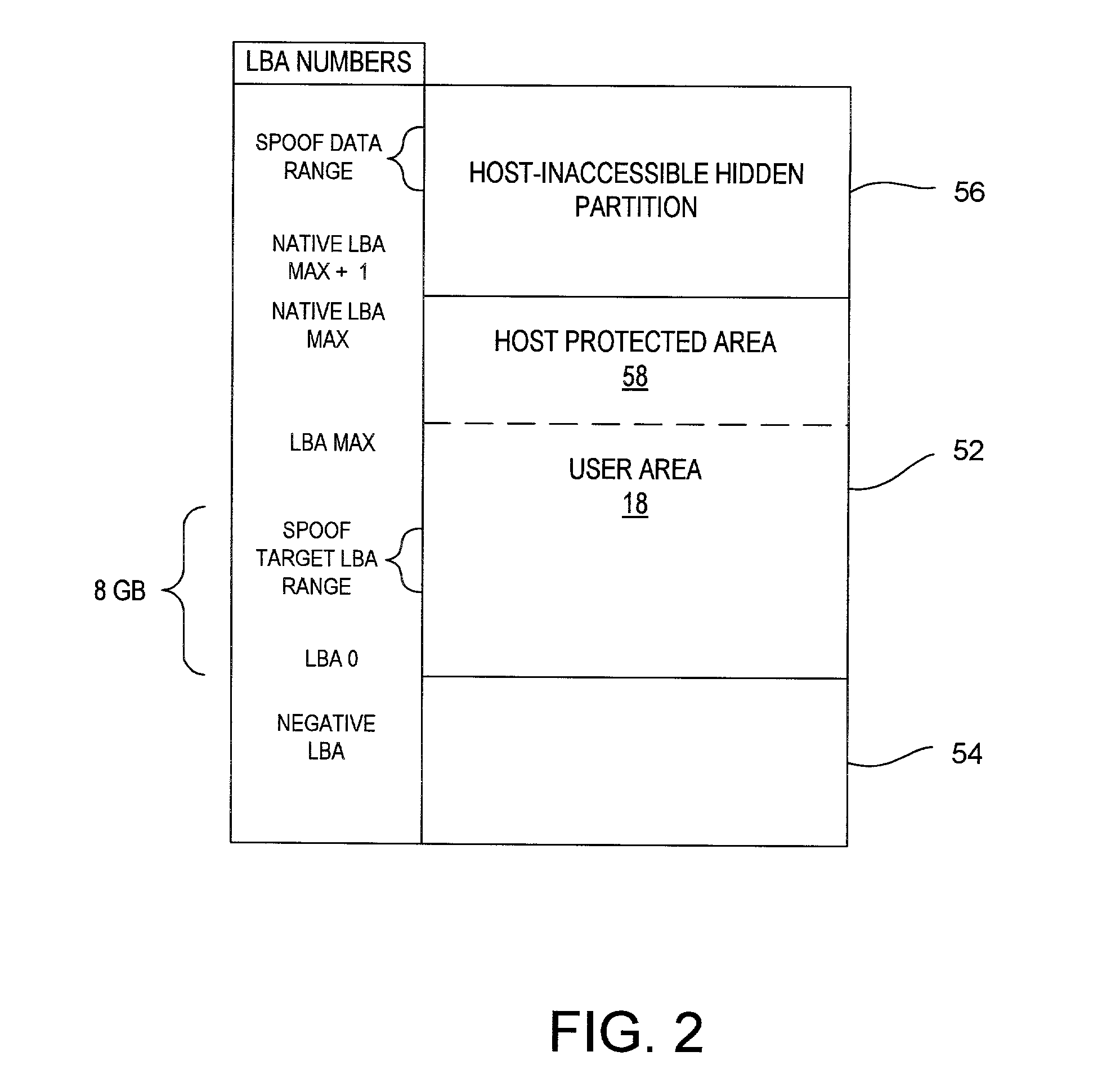
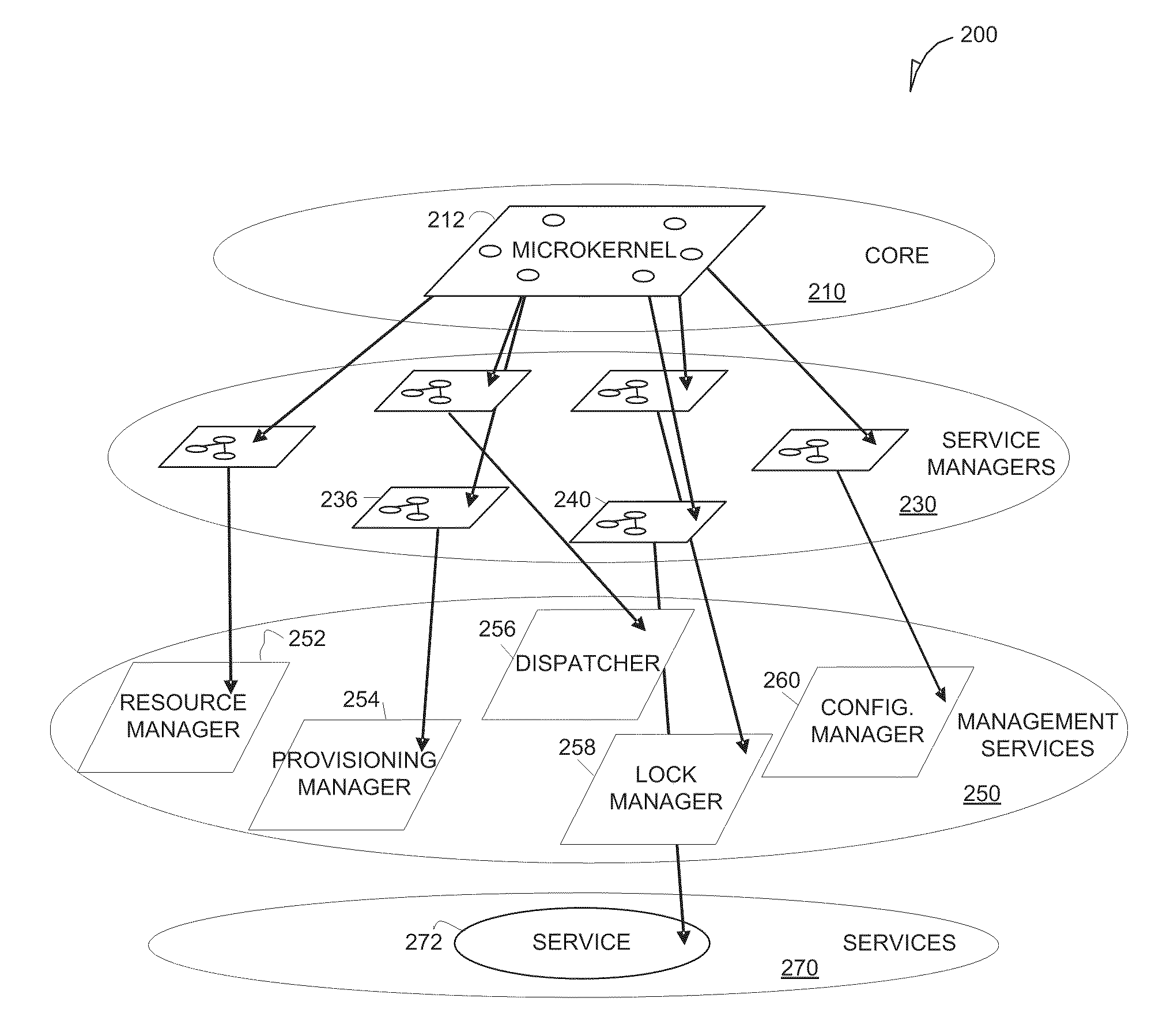
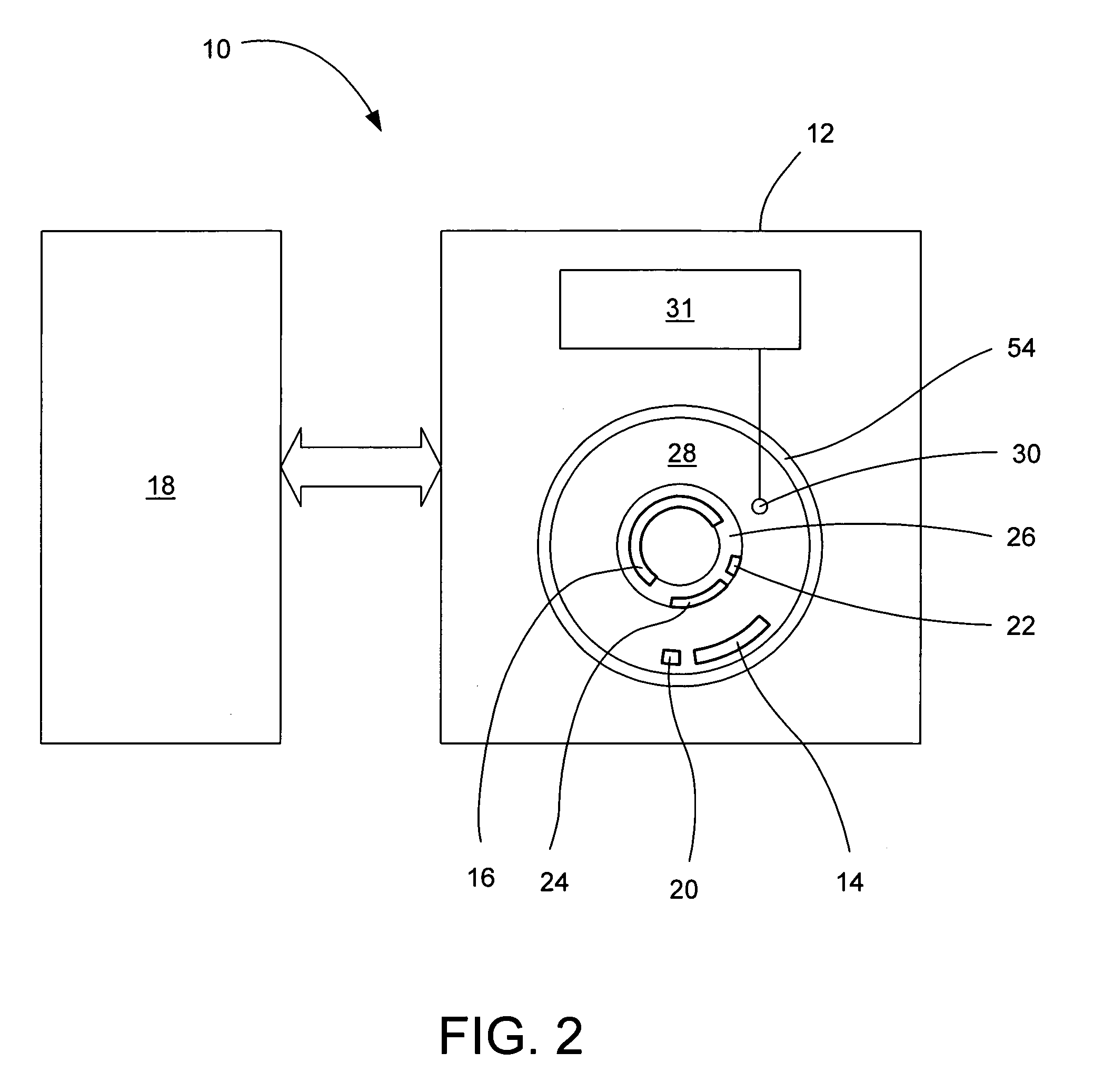
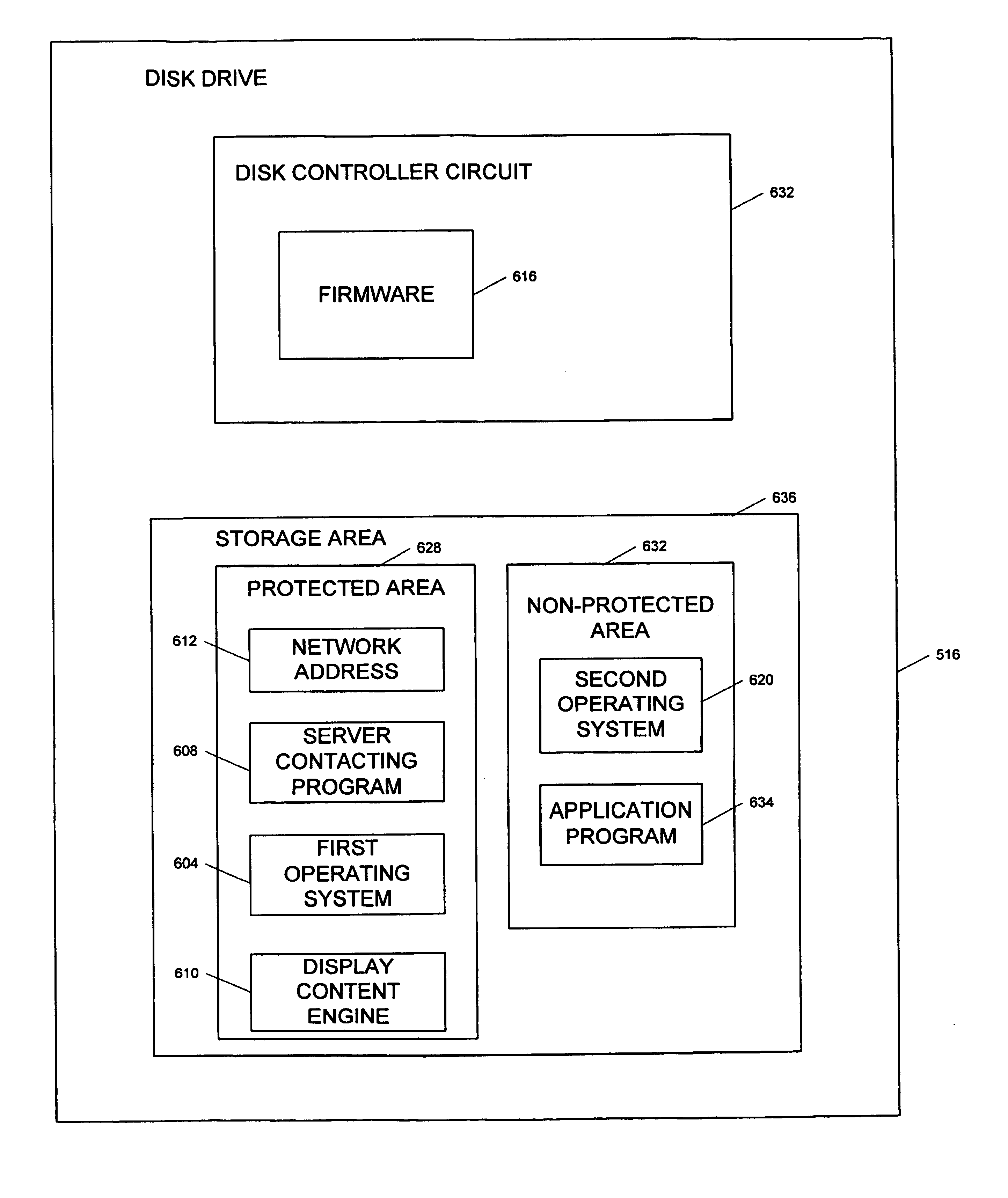
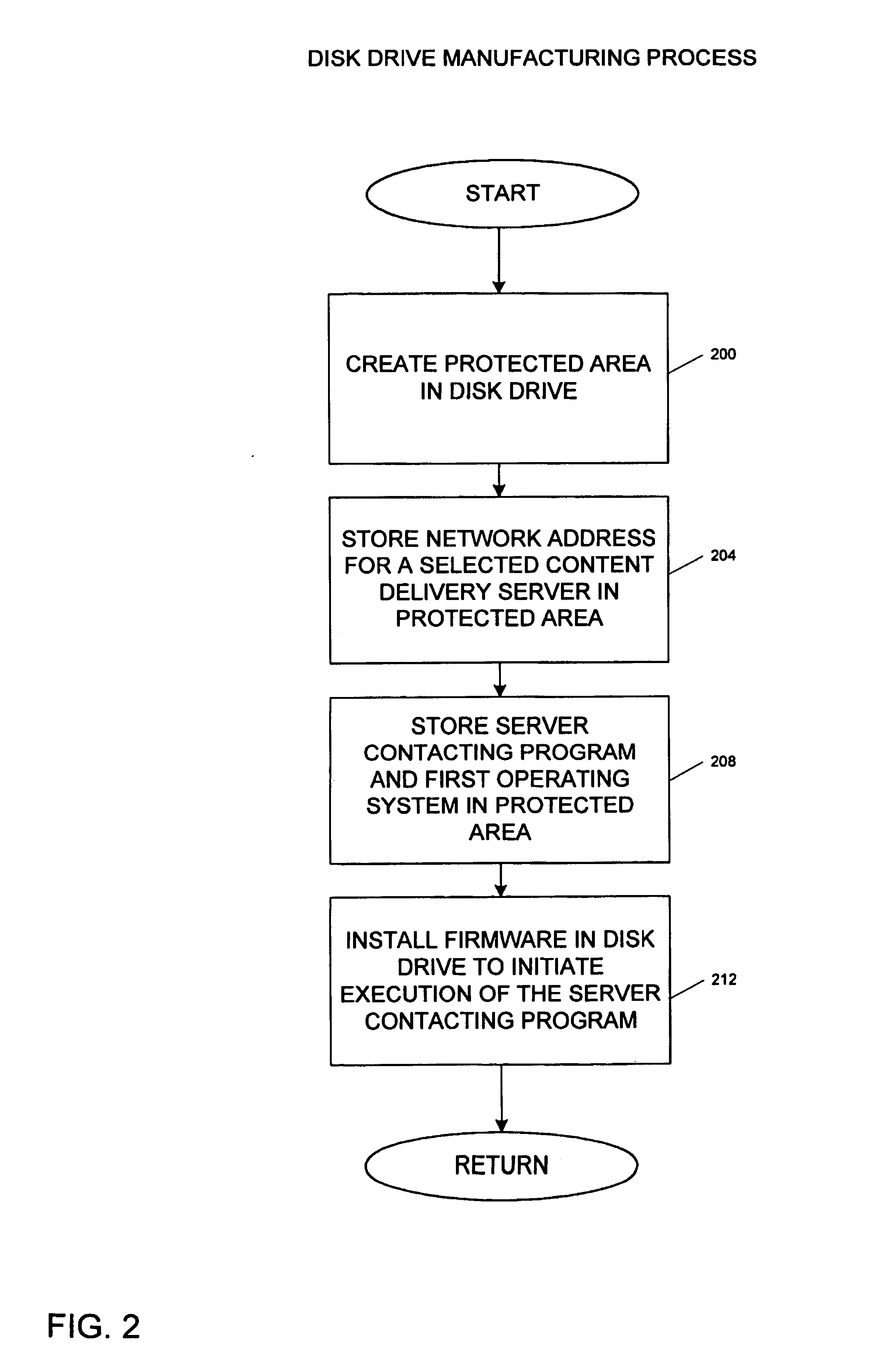
Disk drive having a protected partition configured to load an operating system for performing a user-selected function
A system for configuring, loading and executing an operating system for performing a user-selected function is disclosed. The system includes a disk drive including: a host-accessible user partition; a host-inaccessible hidden partition independent of the host-accessible user partition; and a disk controller. The user partition includes: a user partition address range; a host-selected operating system; and a host-selected master boot record. The host-inaccessible hidden partition includes: a hidden partition address range outside the user partition address range; an application program for allowing a user to select a function to perform and configuring, loading and executing an operating system to perform the selected function; and a drive-selected boot record for loading and executing the application program that allows the user to select a function and configures, loads and executes an operating system for performing the function.
Owner:WESTERN DIGITAL TECH INC
System and method for dynamic server allocation and provisioning
InactiveUS20070250608A1Lower cost of capitalQuality improvementResource allocationDigital computer detailsLoad SheddingManagement tool
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
Method and system for automatically updating operating systems
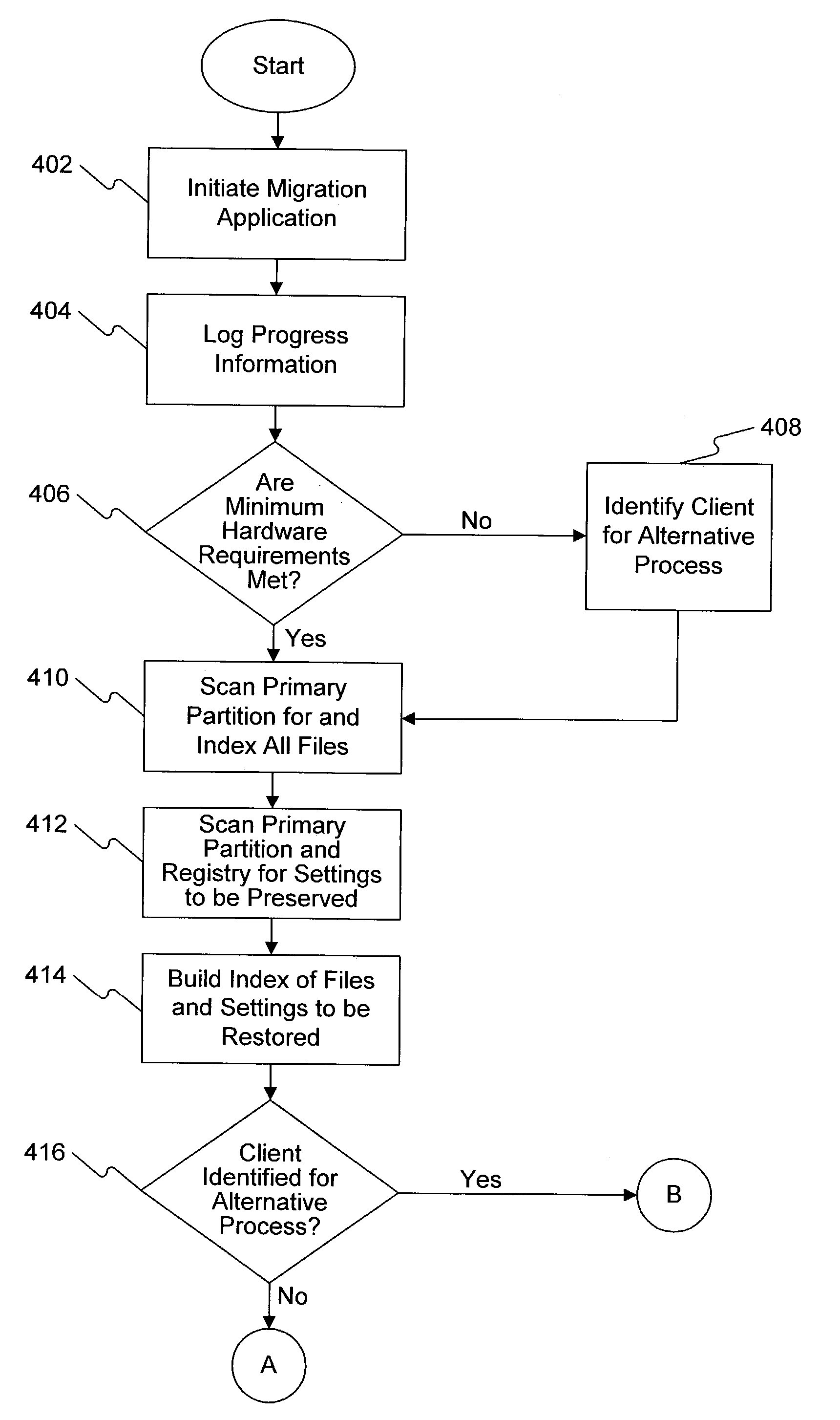
InactiveUS20040117414A1BootstrappingProgram loading/initiatingOperational systemPick operating system
Methods and systems for updating operating systems are disclosed. A computer includes a disk drive that stores an operating system to be updated. The computer creates a backup image of a first partition of the disk drive, then deletes the first partition to create free space on the disk drive. The computer also places an image of a maintenance operating system into the free space, wherein the maintenance operating system is operable to manage an operating system update. Thereafter, the computer updates the stored operating system under control of the maintenance operating system.
Owner:CAPITAL ONE FINANCIAL
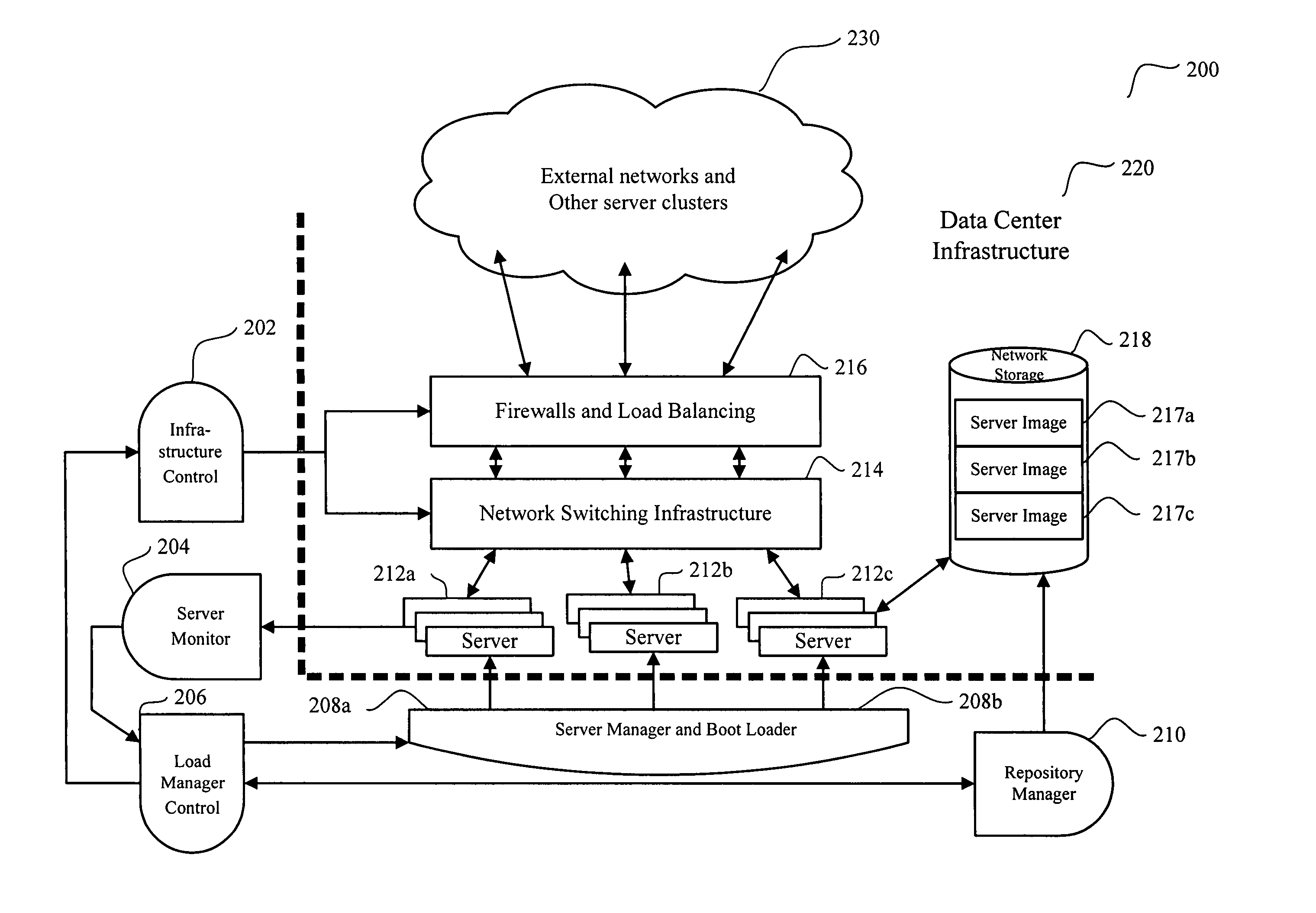
System and method to uniformly manage operational life cycles and service levels
ActiveUS20110029981A1Metering/charging/biilling arrangementsResource allocationData centerDistributed computing
A system and a method to manage a data center, the method including, for example, retrieving a physical topology of a service; determining from the physical topology a concrete type of a resource for the service; and selecting an actual instance of the resource in the data center. The actual instance having the concrete type and the actual instance selected such that a consumption of the actual instance does not violate at least one of a constraint and a policy.
Owner:PAYPAL INC
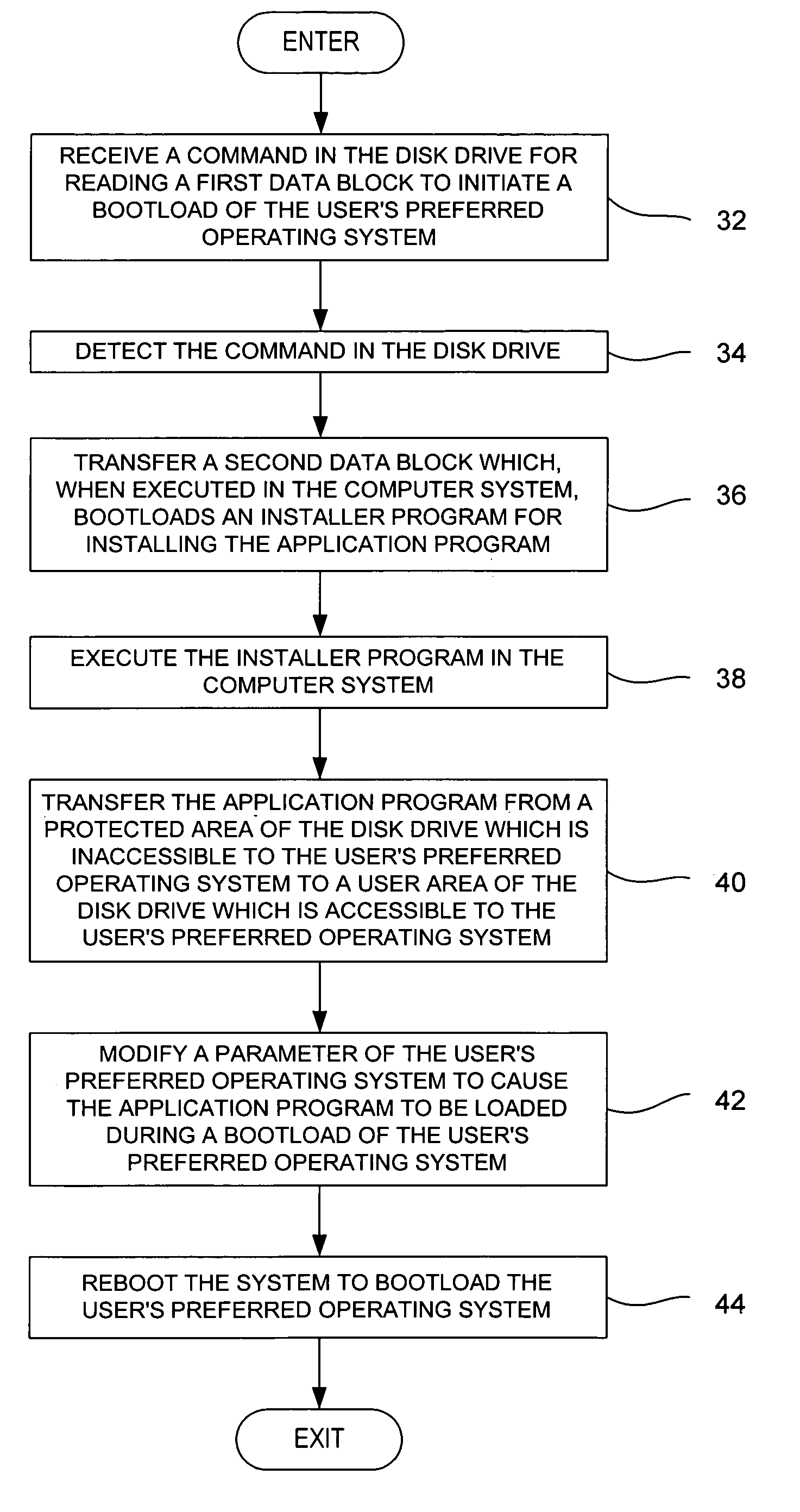
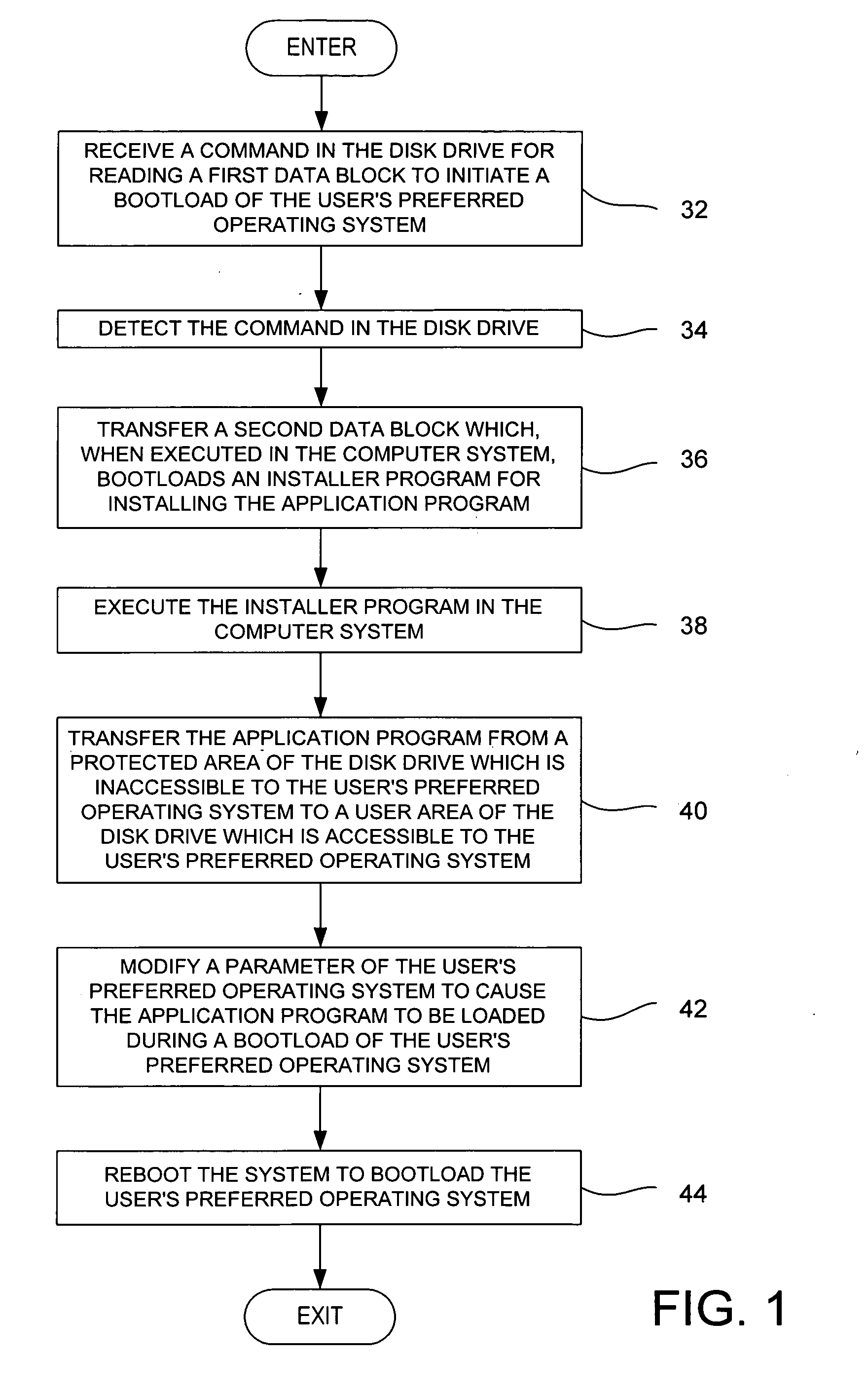
Method for installing an application program, to be executed during each bootload of a computer system for presenting a user with content options prior to conventional system startup presentation, without requiring a user's participation to install the program
The present invention may be embodied in a method, performed in a computer system having a disk drive, for installing an application program for execution under a user's preferred operating system without requiring user intervention. A command is received by the disk drive for reading a first data block to initiate a bootload of the user's preferred operating system. The disk drive detects the command and transfers a second data block which bootloads an installer program for installing the application program. The installer program is executed in the computer system to transfer the application program from a protected area of the disk drive to a user area of the disk drive, to modify a parameter of the user's preferred operating system to cause the application program to be loaded during a bootload of the user's preferred operating system, and to reboot the system to bootload the user's preferred operating system.
Owner:WESTERN DIGITAL TECH INC
Movable virtual machine image
InactiveUS20100107163A1Mobility is attainableThe process is convenient and fastDigital data processing detailsError detection/correctionComputer scienceVirtual machine
The present invention provides the movable virtual machine image using the OS level virtualization and the method for creating and utilizing the movable virtual machine image. The movable virtual machine image is independent of the hardware of PCs and easy to attach or detach from the OS, thereby presents easy and quick moving, distributing, sharing and initializing.
Owner:LEE SANGGYU
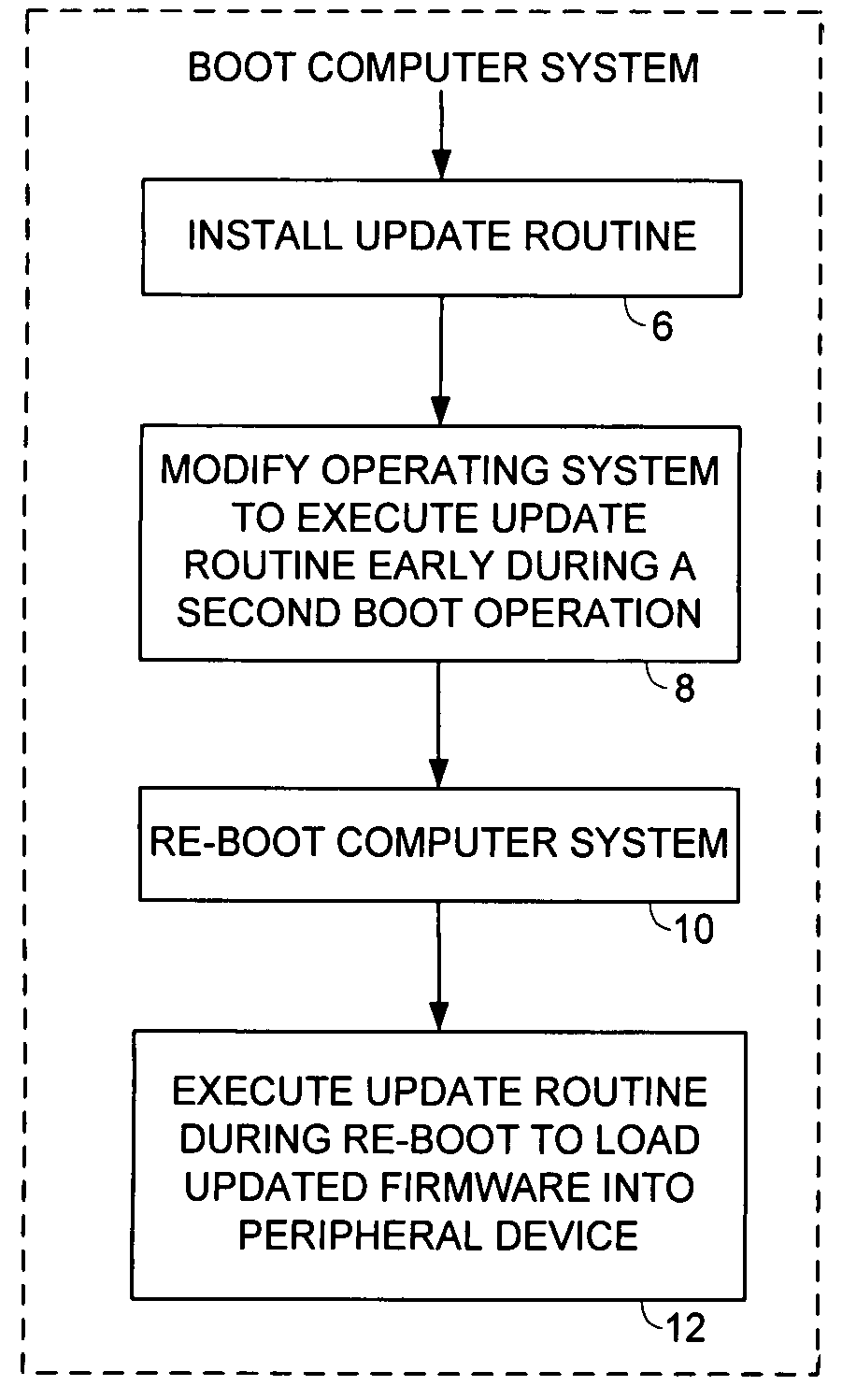
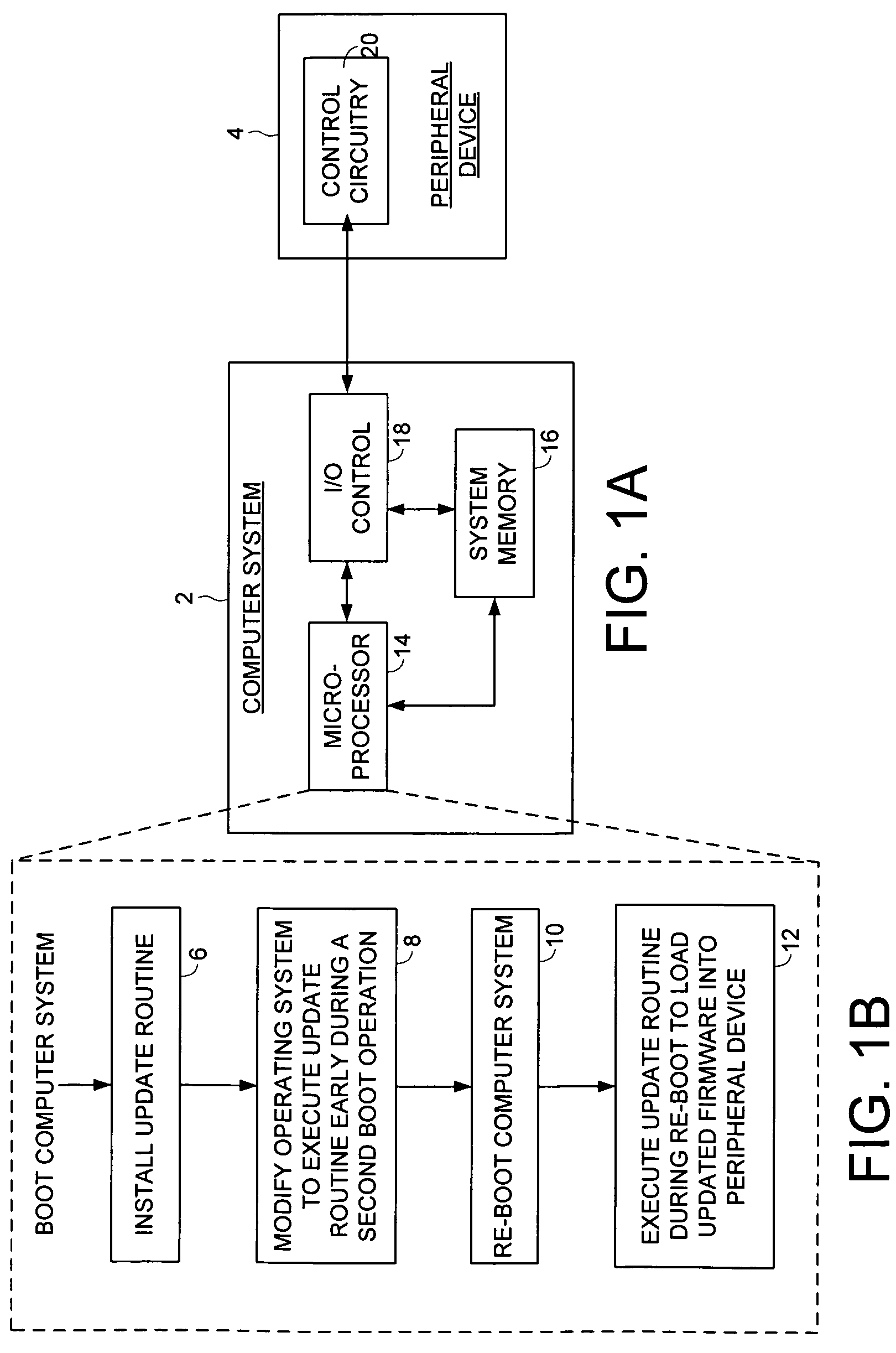
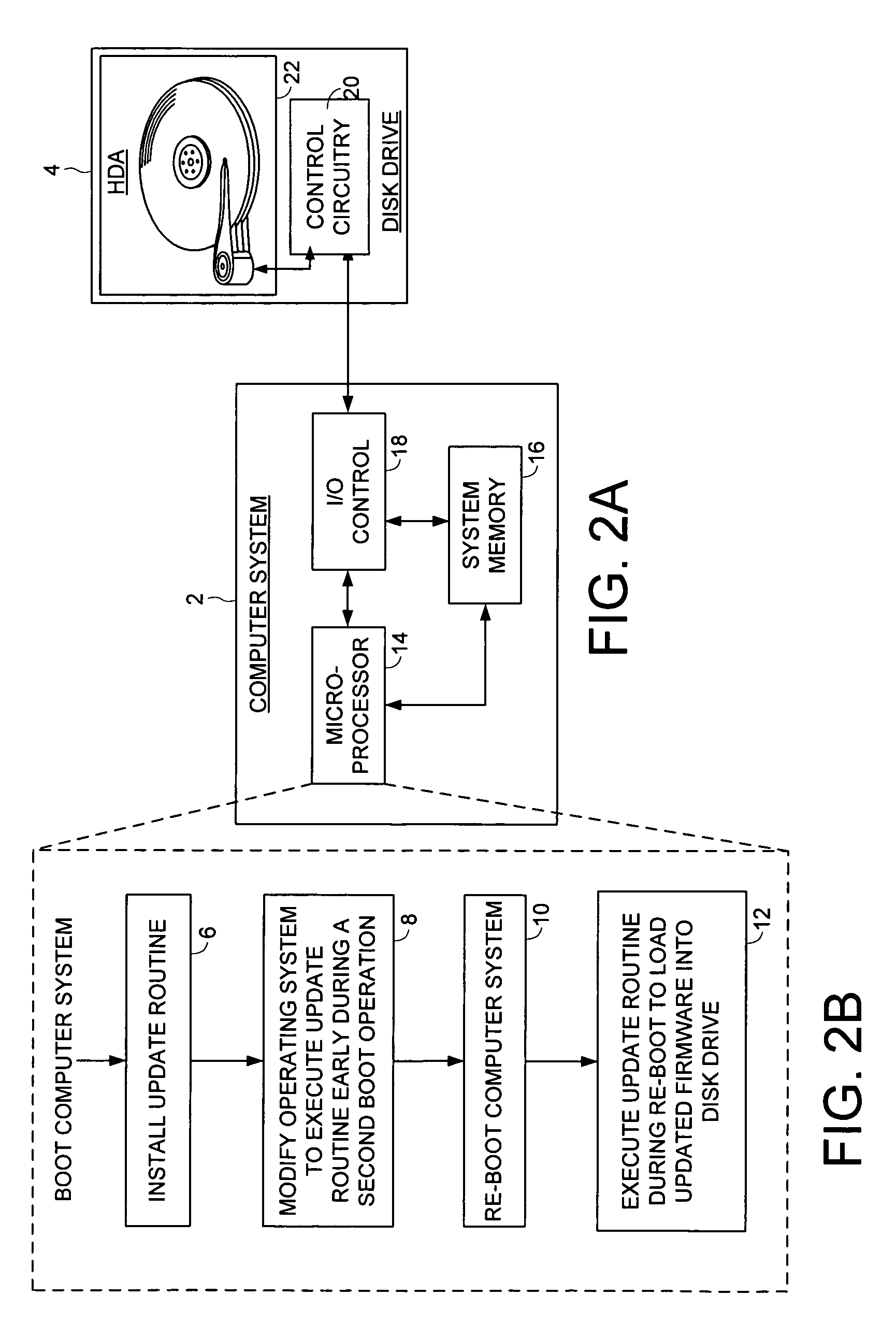
Updating firmware of a peripheral device
An embodiment of the present invention comprises a method of updating firmware of a peripheral device coupled to a computer system. A first boot operation is executed for loading an operating system into the computer system, and an update routine is installed for loading updated firmware into the peripheral device. The operating system is modified so that the update routine is executed early during a second boot operation for loading the operating system into the computer system. The second boot operation is executed, during which the update routine is executed to load the updated firmware into the peripheral device. In one embodiment, the update routine comprises an update driver having a DriverEntry code segment for loading the updated firmware into the peripheral device.
Owner:WESTERN DIGITAL TECH INC
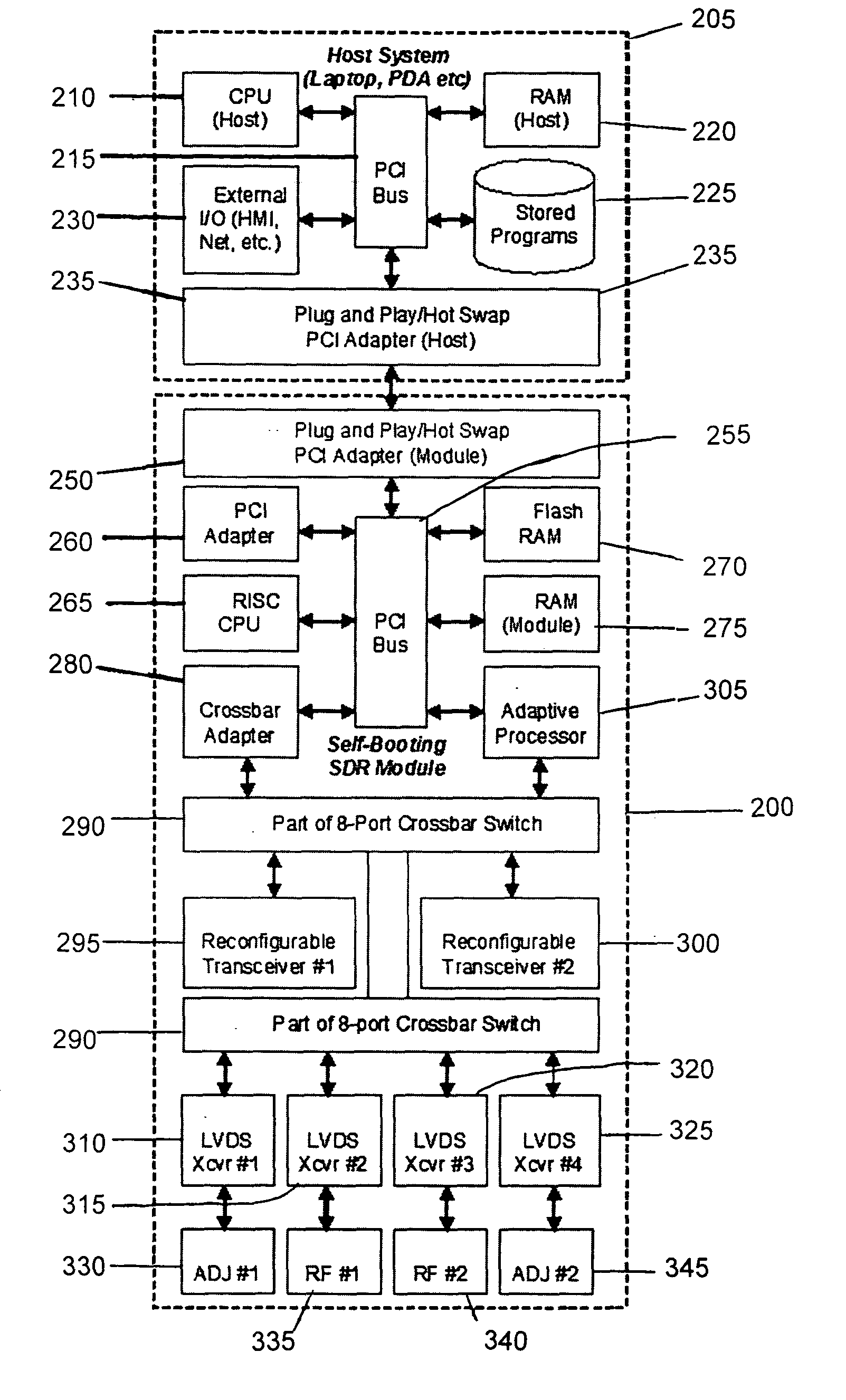
Programmable logic device with embedded switch fabric
InactiveUS20080278197A1Telephonic communicationBootstrappingCrossbar switchProgrammable logic device
The invention in the simplest form is a programmable logic device consisting of gate arrays, external I / O endpoints, and an embedded switch fabric configurable for connecting gates to gates, endpoints to endpoints and gates to endpoints. The architecture may employ a fabric interface of non-blocking crossbar switches for making complex bus connections of multiple devices to facilitate high speed processing.
Owner:TECNICA
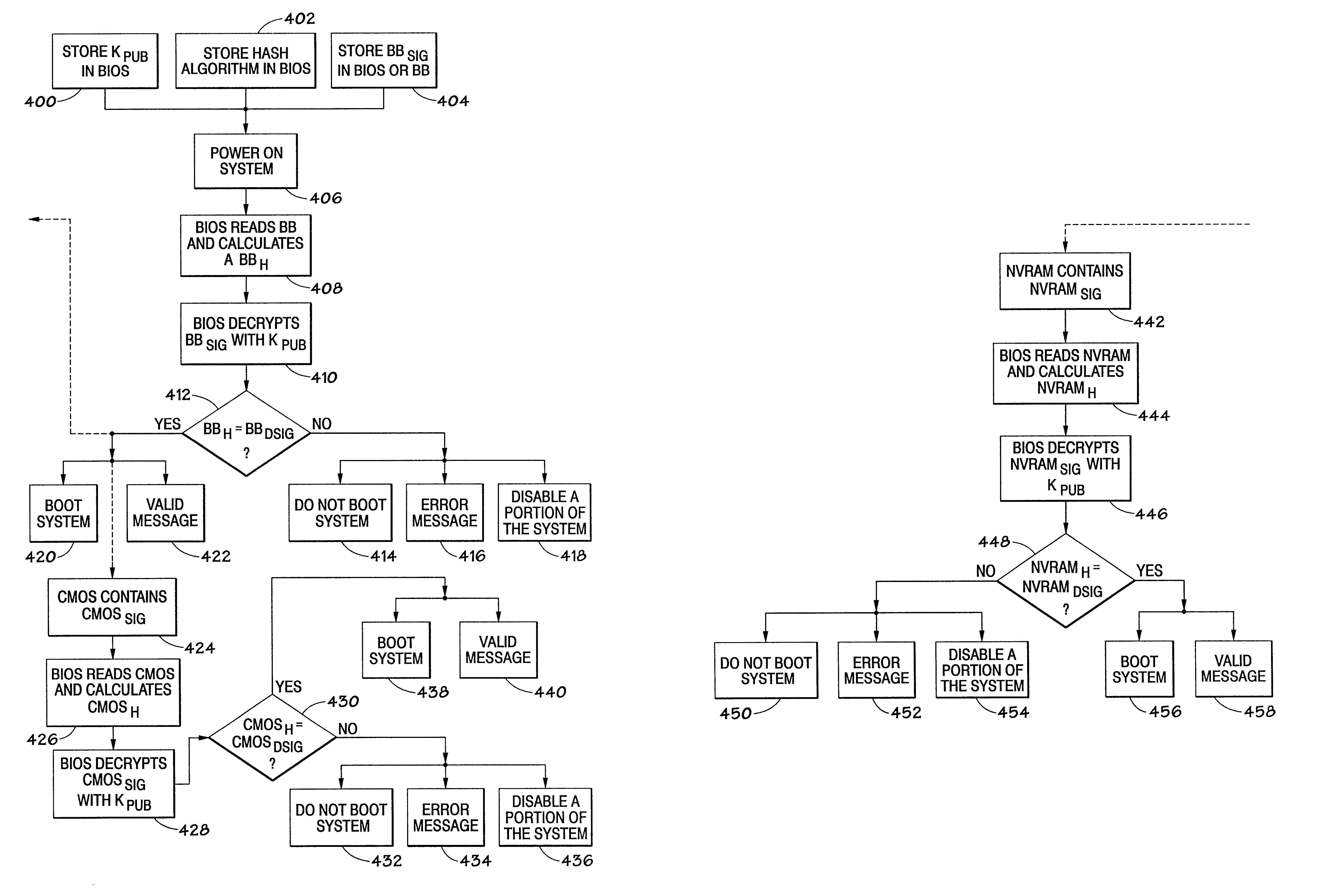
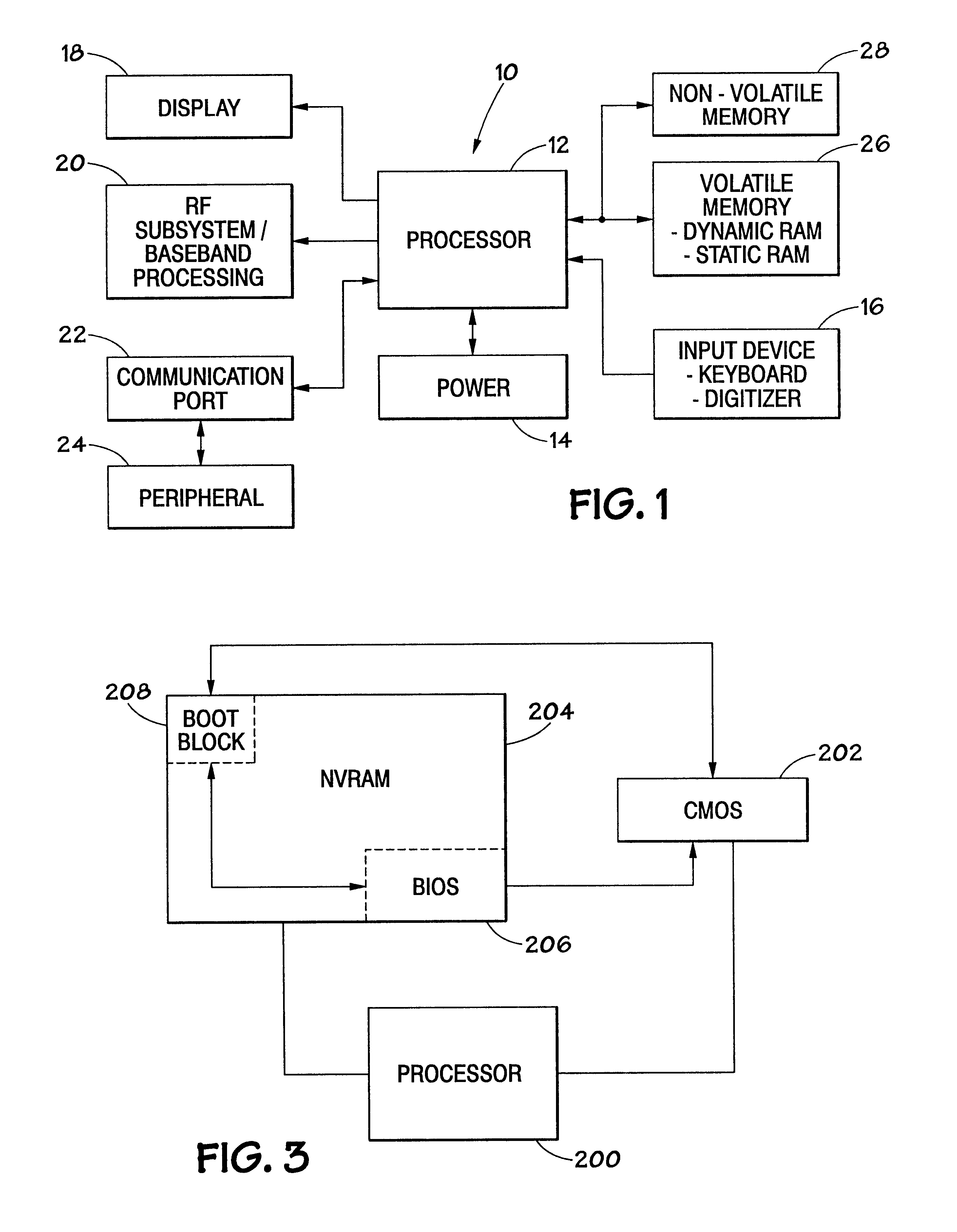
Computer system having security features for authenticating different components
InactiveUS6625729B1Digital computer detailsUnauthorized memory use protectionCMOSComputerized system
A method and apparatus for protecting a computer system. Specifically, a method and system for validating portions of memory at each power-on cycle is described. A Boot Block is used to validate the BIOS, CMOS and NVRAM of a system. The BIOS may also be used to validate the Boot Block, CMOS and NVRAM.
Owner:CONVERSANT INTPROP MANAGEMENT INC
Internet appliance
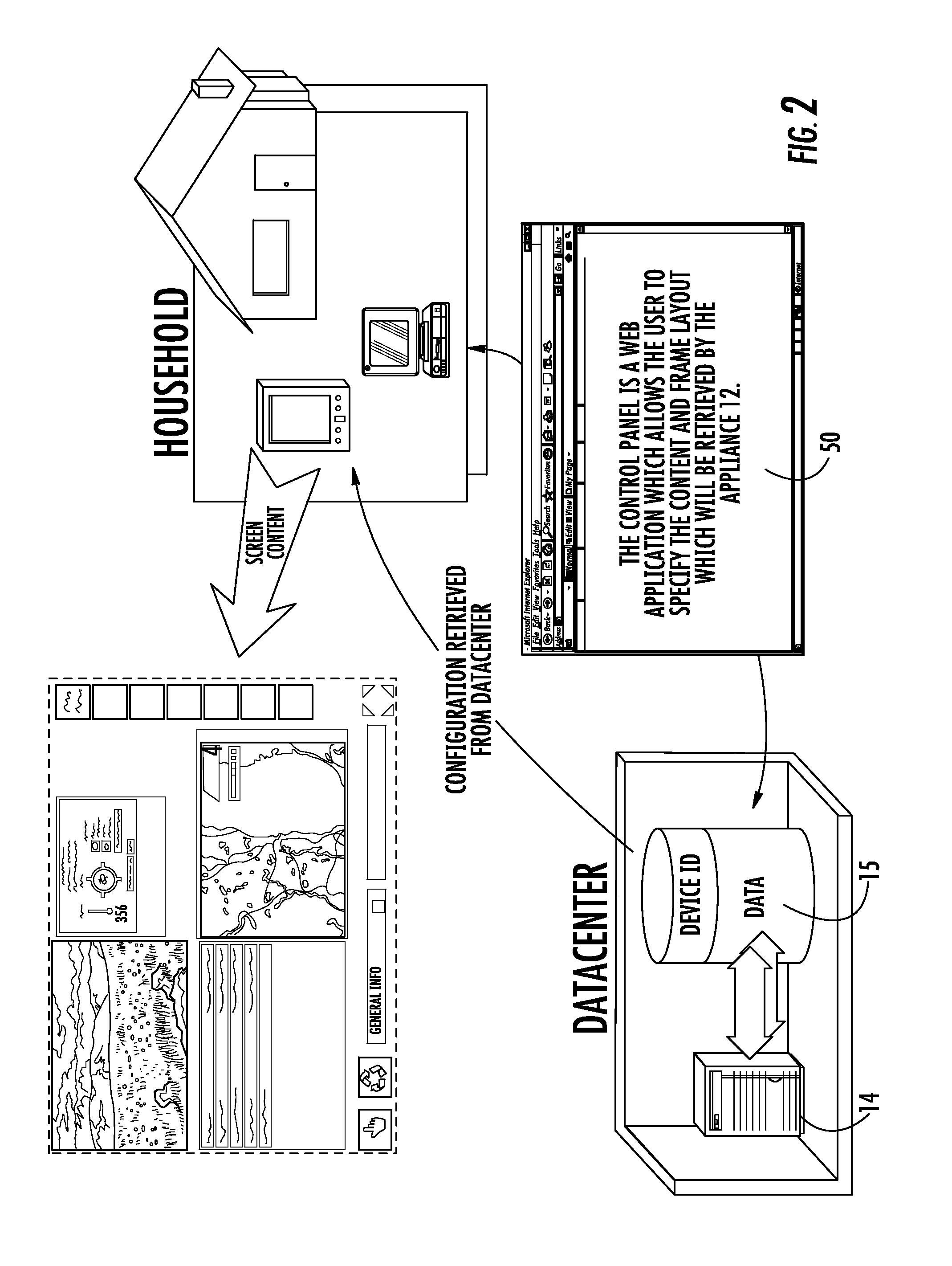
InactiveUS20090125708A1Add featureSimple and low maintenanceDigital computer detailsBootstrappingWeb browserOperational system
A system, method and apparatus dedicated to accessing certain aspects of the Internet. The system includes a hardware device having a display and firmware associated with the display. The firmware includes a web browser and an operating system, configured to automatically connect to a datacenter server using the web browser, and to receive a frameset template from the datacenter, the frameset including frames, wherein each frame includes a preset content locator, upon boot of the operating system. The data center server may have preconfigured framesets with assigned content locators, and be configured to transmit one or more of the framesets to the device. Each frame may include content from transmitted from a different internet server upon boot of the operating system.
Owner:RELATION SYST
Converting physical machines to virtual machines
ActiveUS20070260831A1Valid conversionFast copyEnergy efficient ICTResource allocationOperational systemFile system
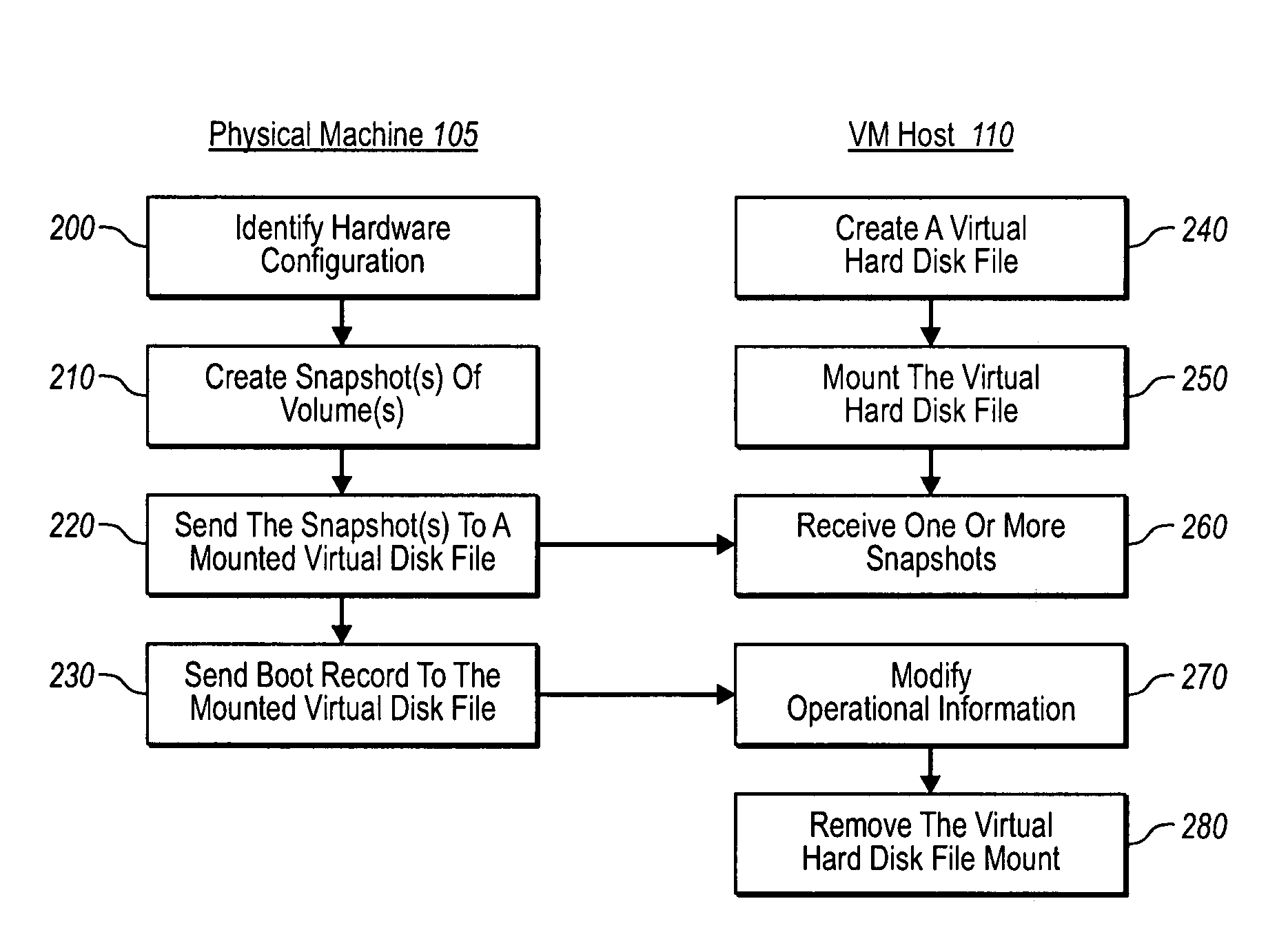
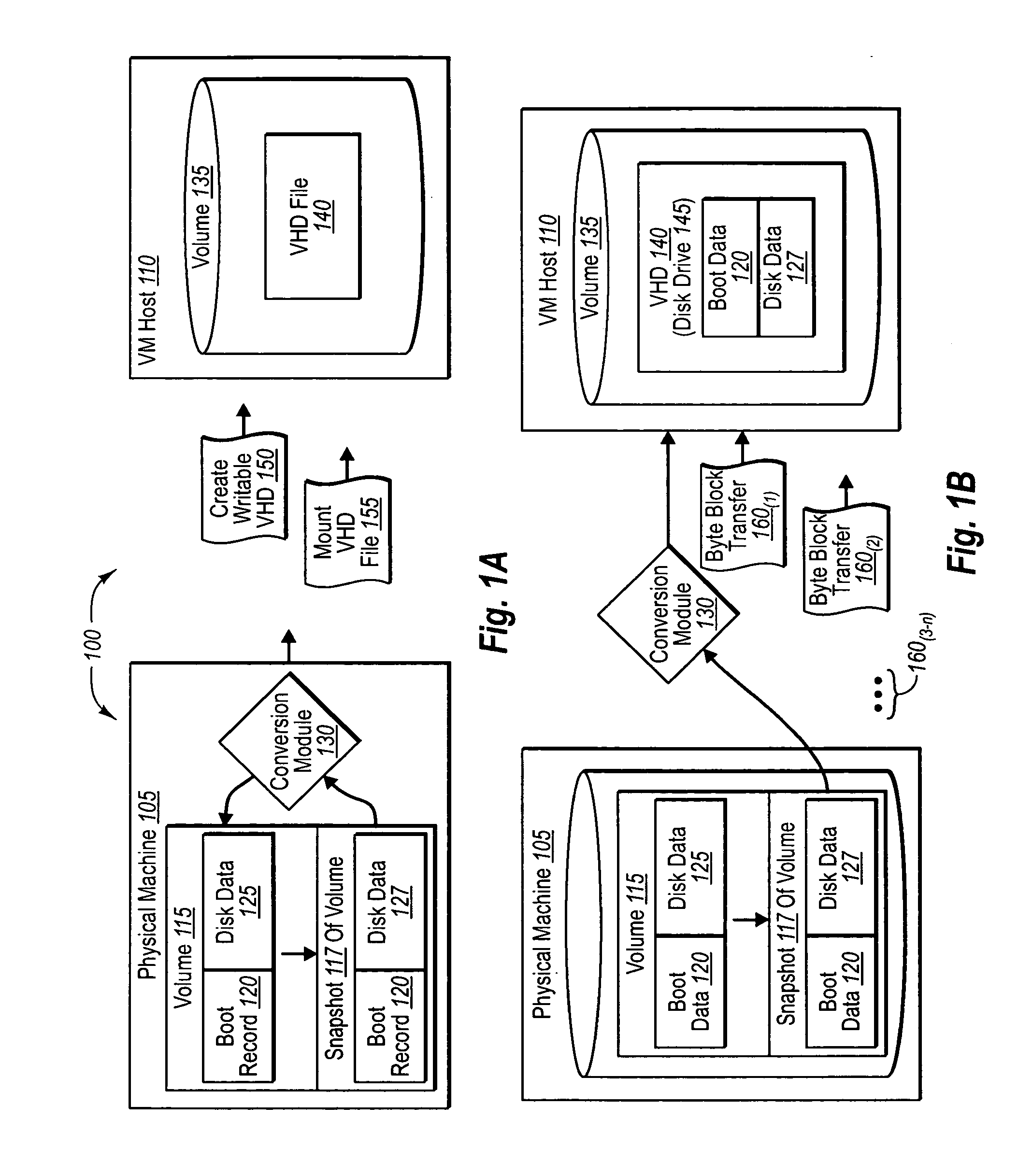
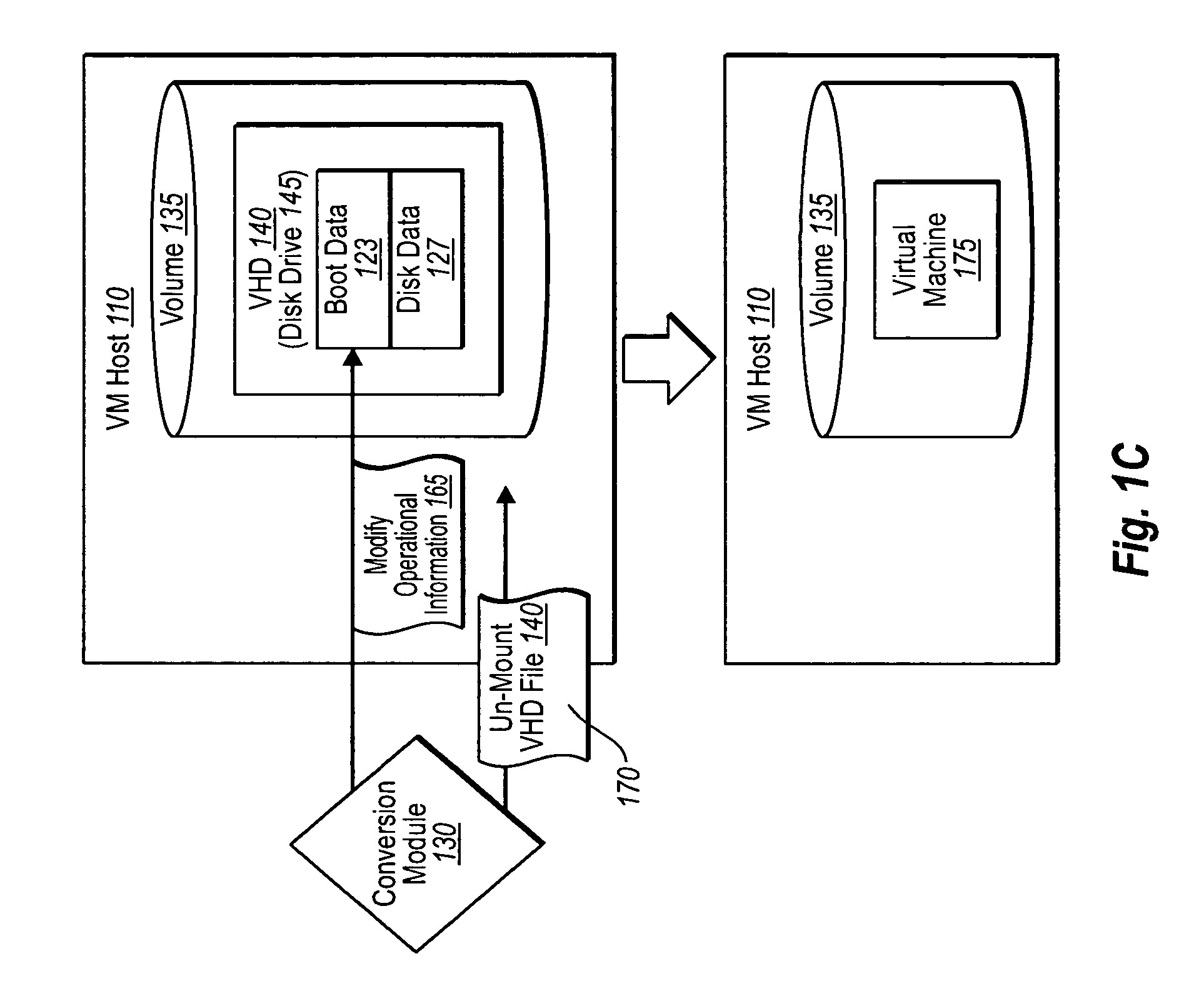
Physical (or prior virtual) machine volumes can be converted to virtual machines at a virtual machine host while the physical machines are running. In one implementation, a volume shadow copy service can be used to create an application (and / or file system)-consistent snapshot of one or more physical machine volumes while the one or more volumes are running. The snapshot data can then be transferred to a mounted virtual hard disk file (dynamic or fixed) at a virtual machine host. Operational information (e.g., boot record, system registry, drivers, devices, configuration preferences, etc.) associated with the virtual hard disk file and the operating system(s) within the virtual machine can then be modified as appropriate to ensure that the corresponding virtual machine is bootable and functional at the virtual machine host. The virtual hard disk file can then be un-mounted, and used as a new virtual machine.
Owner:MICROSOFT TECH LICENSING LLC
Data Integrity and Non-Repudiation
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
Pre-boot securing of operating system (OS) for endpoint evaluation
Methods and apparatus involve evaluating endpoint computing assets. The endpoint has both a traditional operating system for applications, and the like, and another operating system during a pre-boot phase of operation. During use, the traditional operating system identifies a last evaluation status of the computing device at a time just prior to shutting down. Upon a next booting, the pre-boot operating system loads and examines [reads] the last evaluation status. If the last evaluation status requires any completion action in order to comply with a predetermined computing policy, either or both the operating systems attend to its effectuation, including communication / handoff by way of one or more security agents. In a variety of ways, effectuation occurs by: determining a present location of the computing device, quarantining the computing device from certain network traffic; VPN enforcement; patching applications; firewall involvement; etc. Computer program products are also disclosed.
Owner:MICRO FOCUS SOFTWARE INC
Self-booting software defined radio module
ActiveUS20060015674A1Performance characteristicDigital computer detailsTelephonic communicationSoftware define radioNetworking protocol
The invention in the simplest form is a self-booting software defined radio (SDR) module which may be embodied as a PCMCIA, Compact Flash, or other plug in form factor module. The performance characteristics of the module, may include the radio frequency (RF) carrier frequency, instantaneous RF bandwidth, carrier modulation and demodulation, symbol coding and decoding, security, and network protocol that can be altered and saved by means of computer software transferred to the module from a host device such as a cellular telephone, personal digital assistant, lap top computer or other programming device
Owner:TECNICA
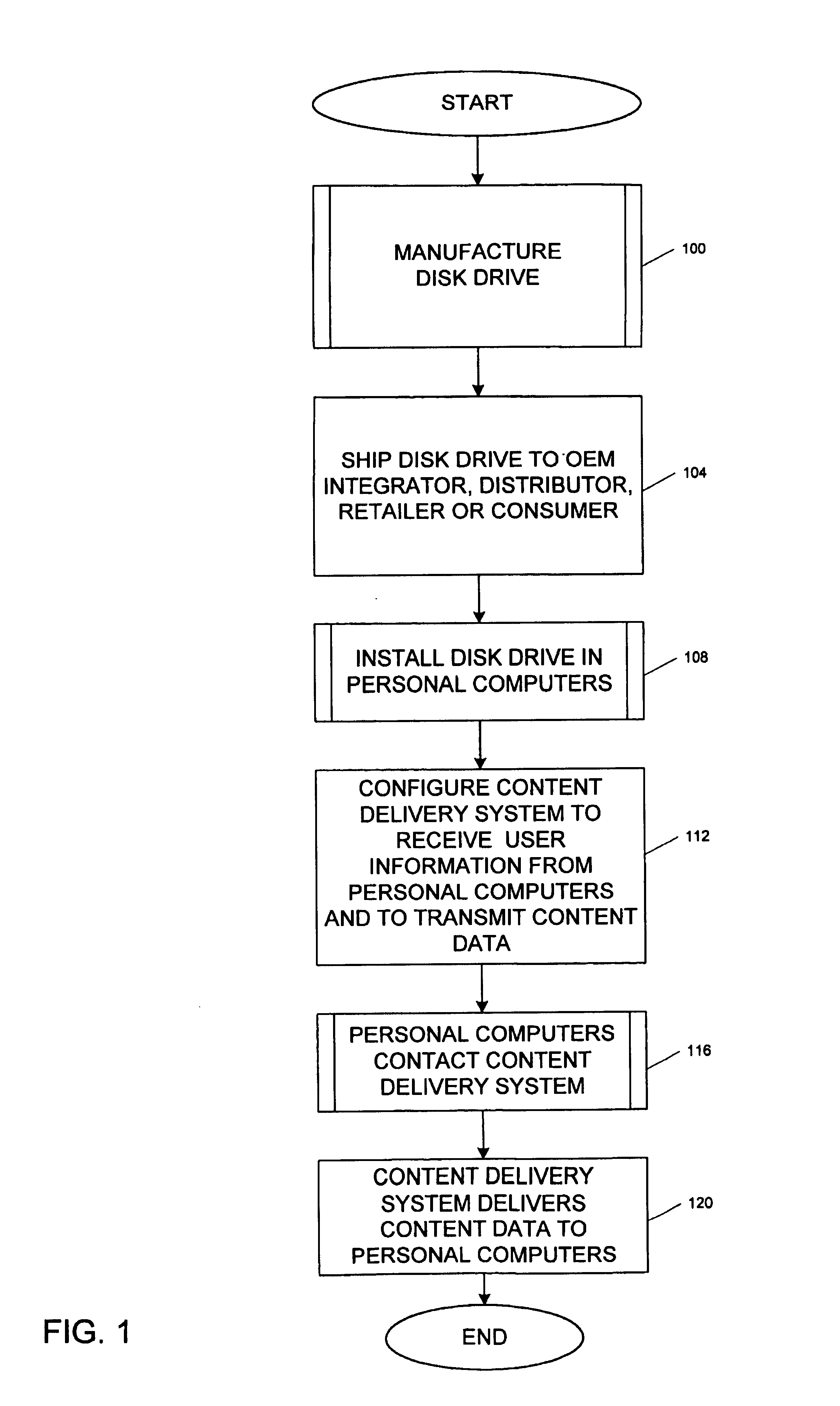
Computer network and connection method for connecting a personal computer and a content delivery system using a disk drive which includes a network address and server-contacting program
InactiveUS7054937B1Multiprogramming arrangementsMultiple digital computer combinationsNetwork connectionDigital content
A computer network connects a personal computer system to a content delivery system for delivering digital content to the personal computer. The personal computer comprises a disk drive which includes a network address for the content delivery system and a server-contacting program. The disk drive comprises firmware installed during manufacturing of the drive which initiates execution of the server-contacting program to enable the network connection and facilitate delivery of content to a large number of personal computers.
Owner:WESTERN DIGITAL TECH INC
Popular searches
Location information based service Transmission Execution for user interfaces Program/content distribution protection Special data processing applications Input/output processes for data processing Generating/distributing signals Transmission path multiple use Redundant operation error correction Synchronising arrangement
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com