Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
130 results about "Outbound communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
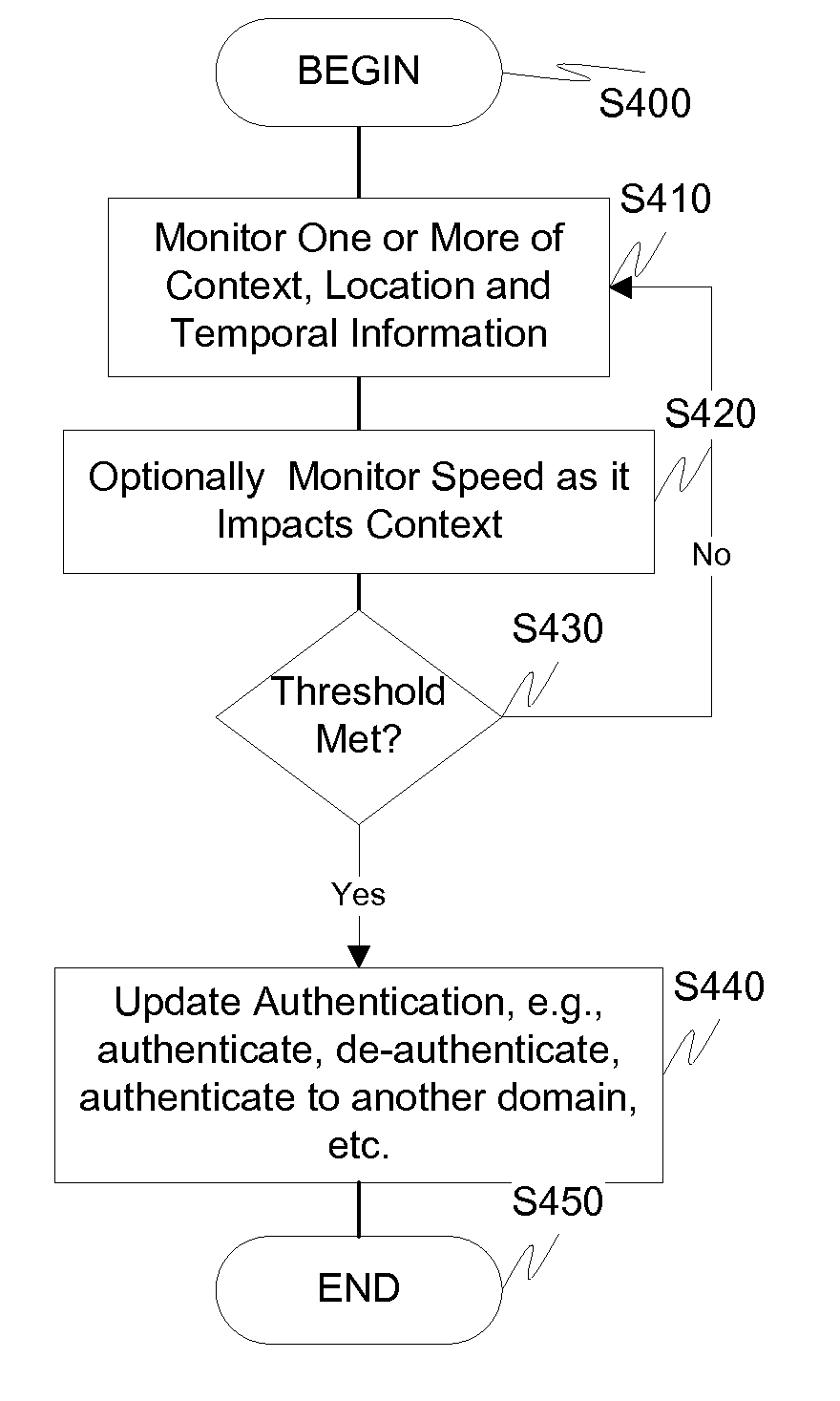
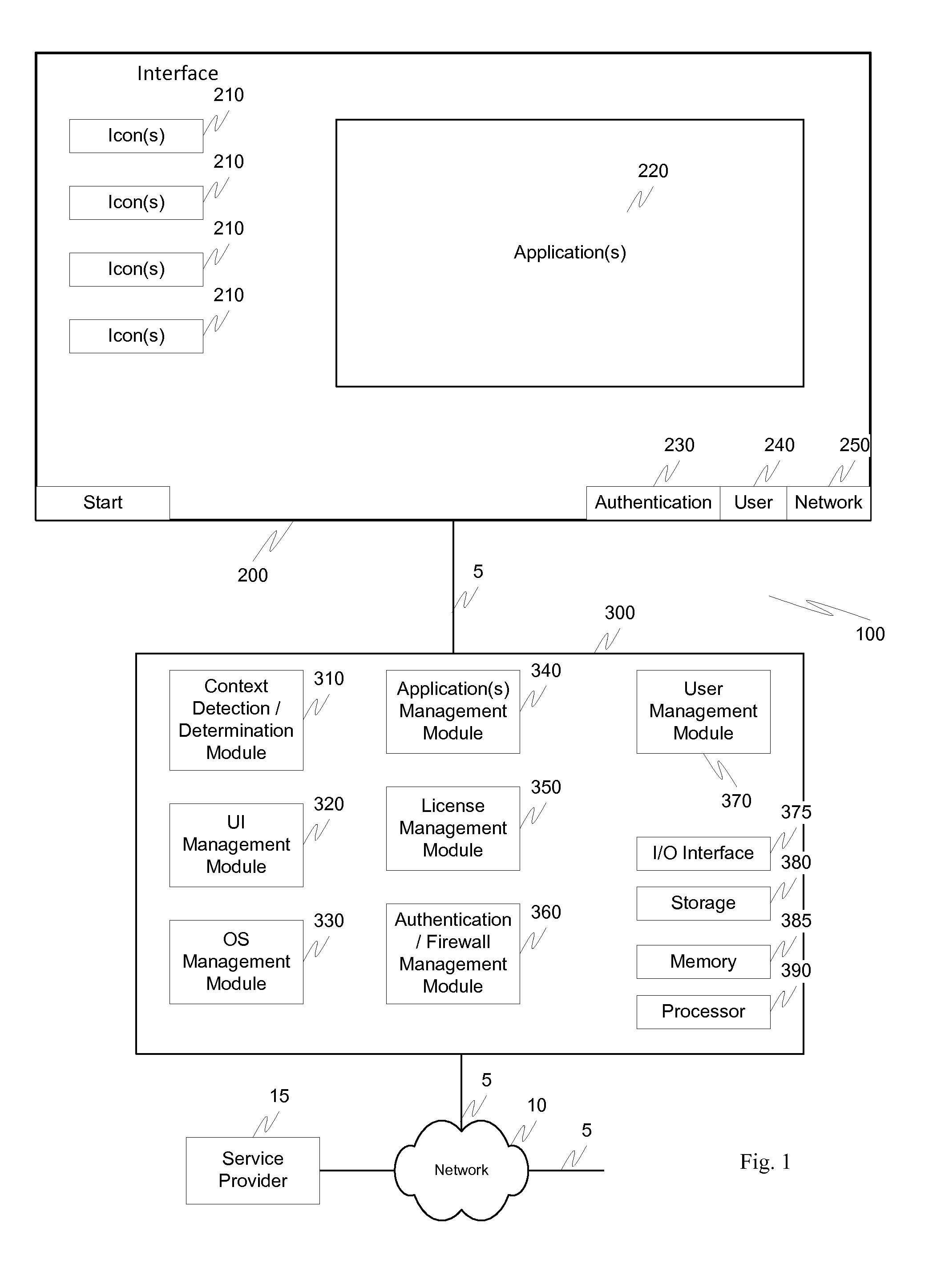
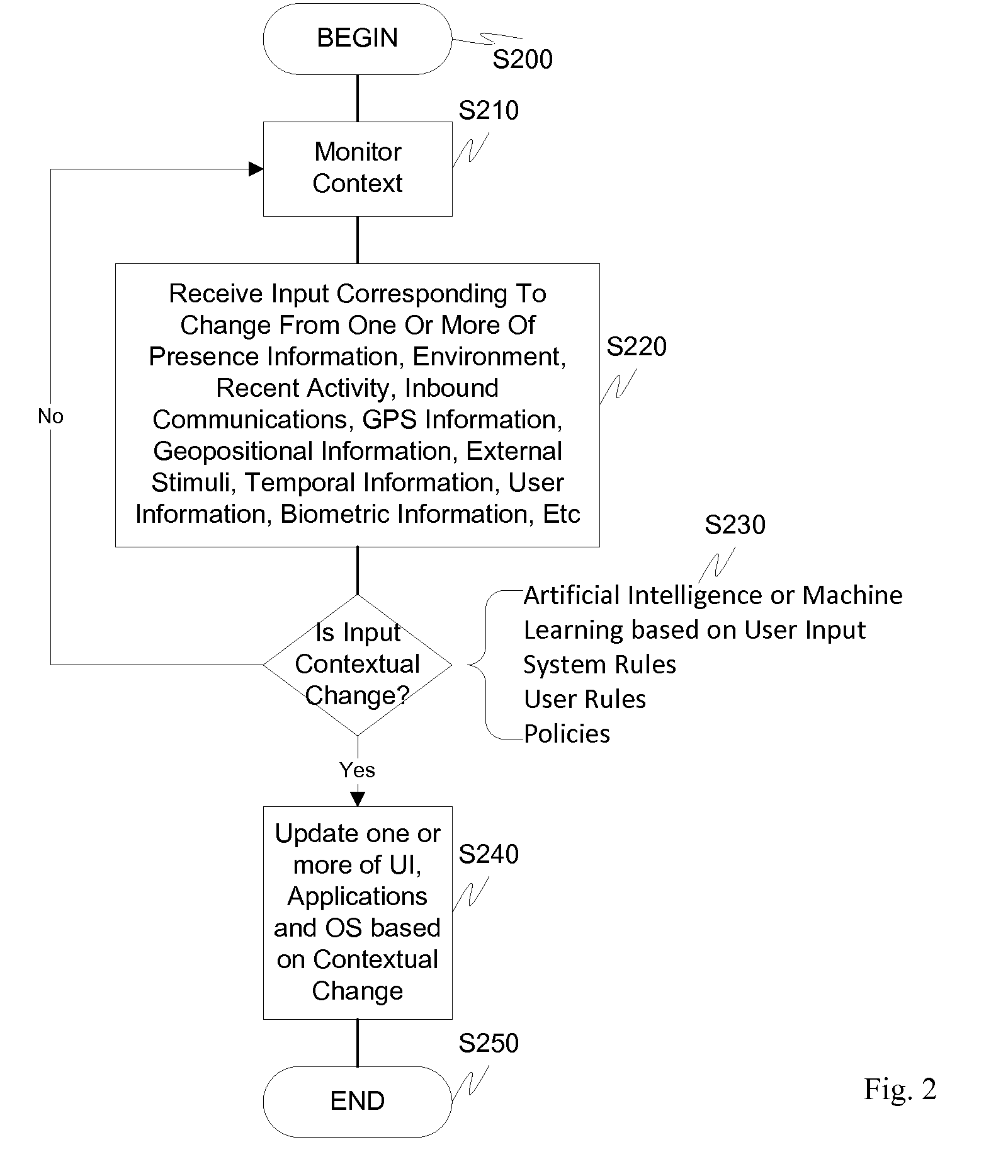
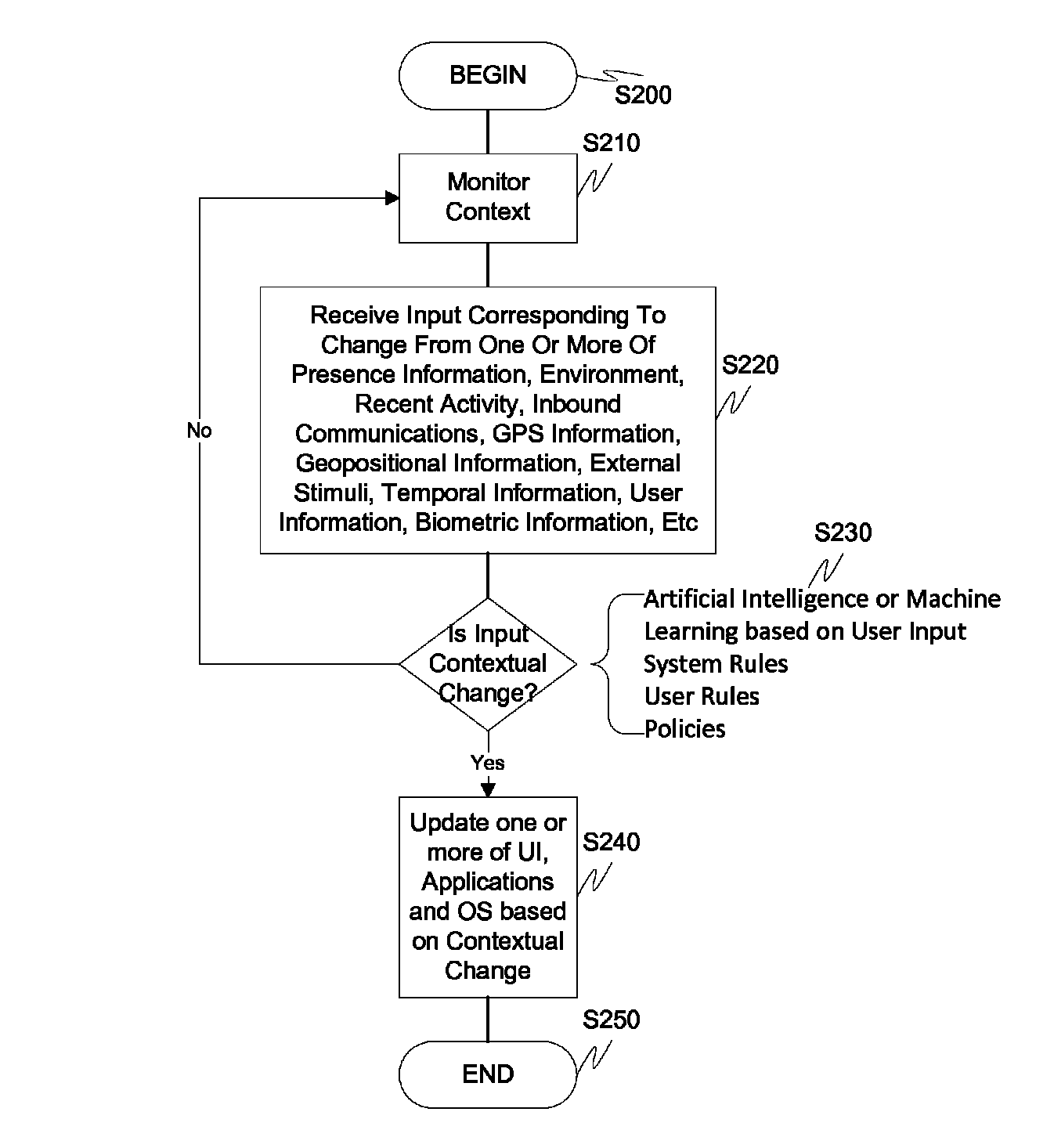
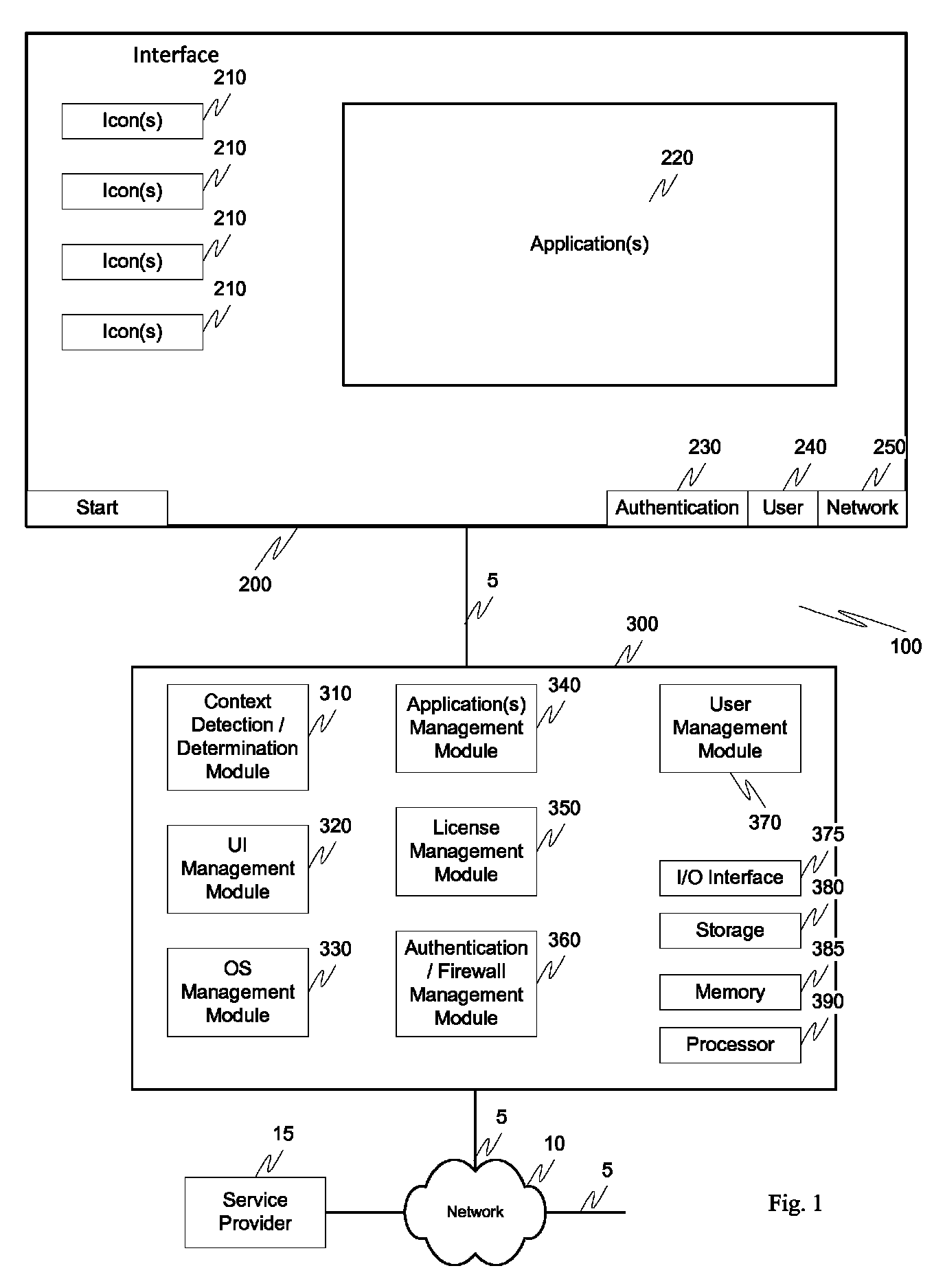
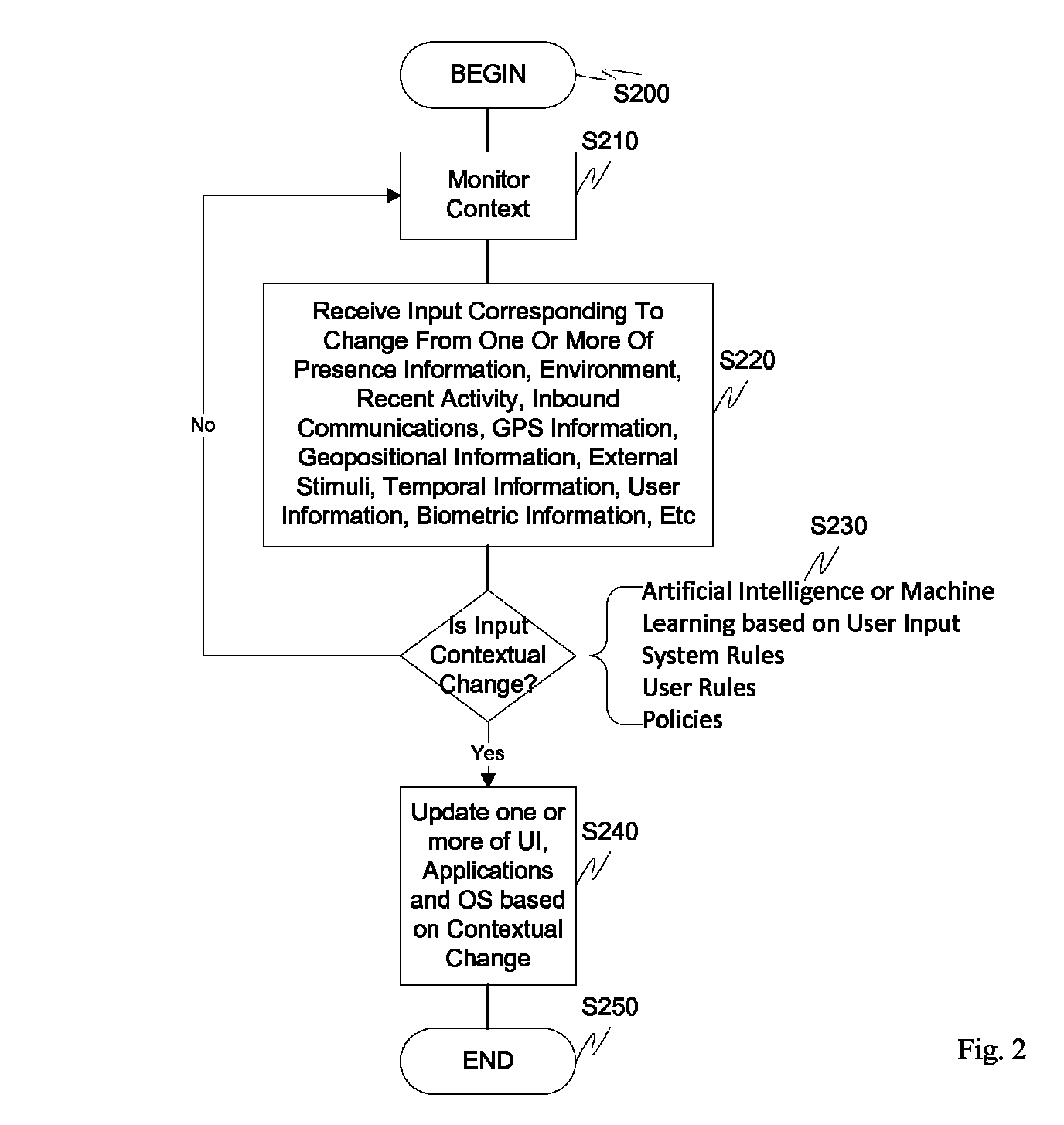
Screen icon manipulation by context and frequency of use
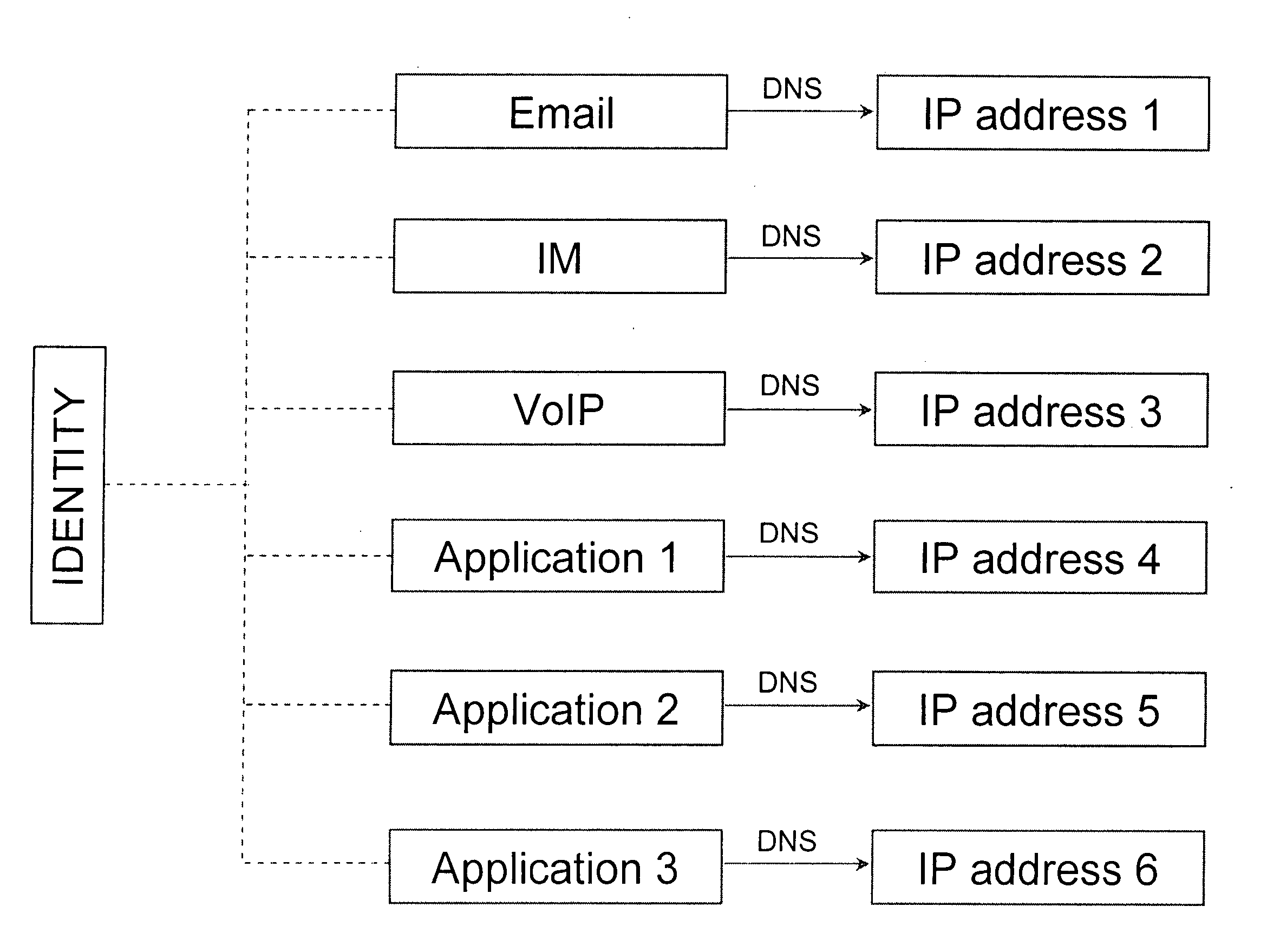
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
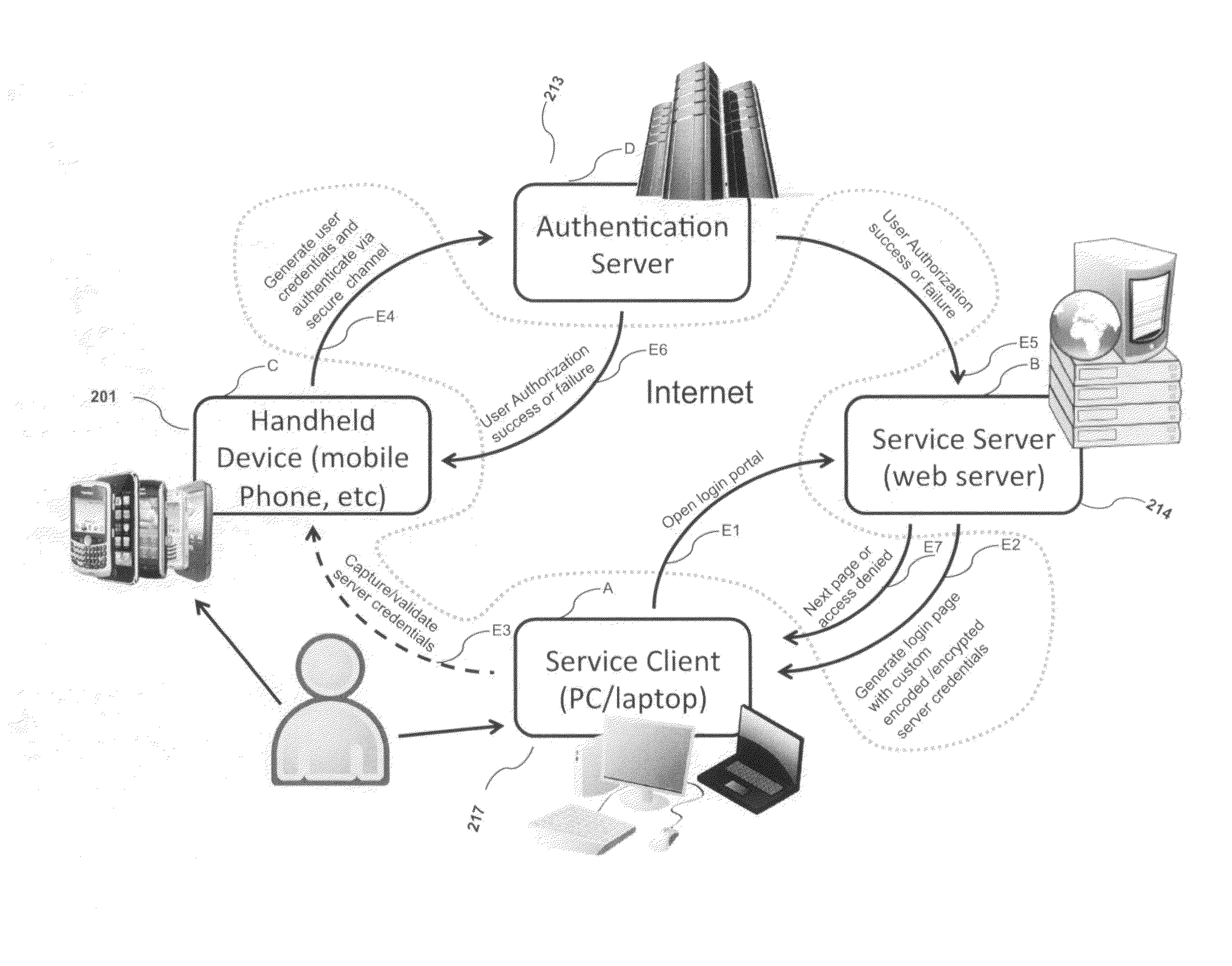
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
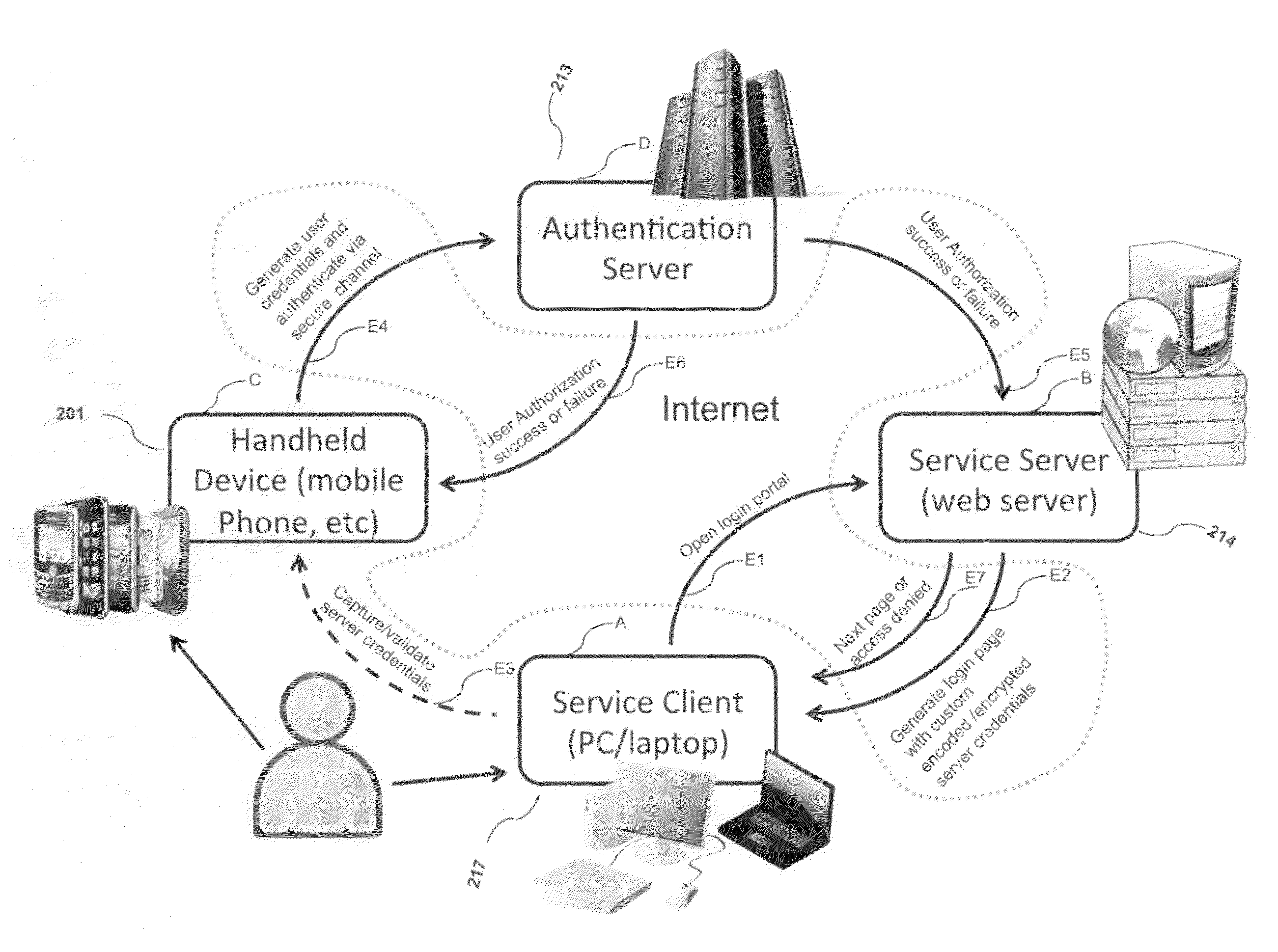
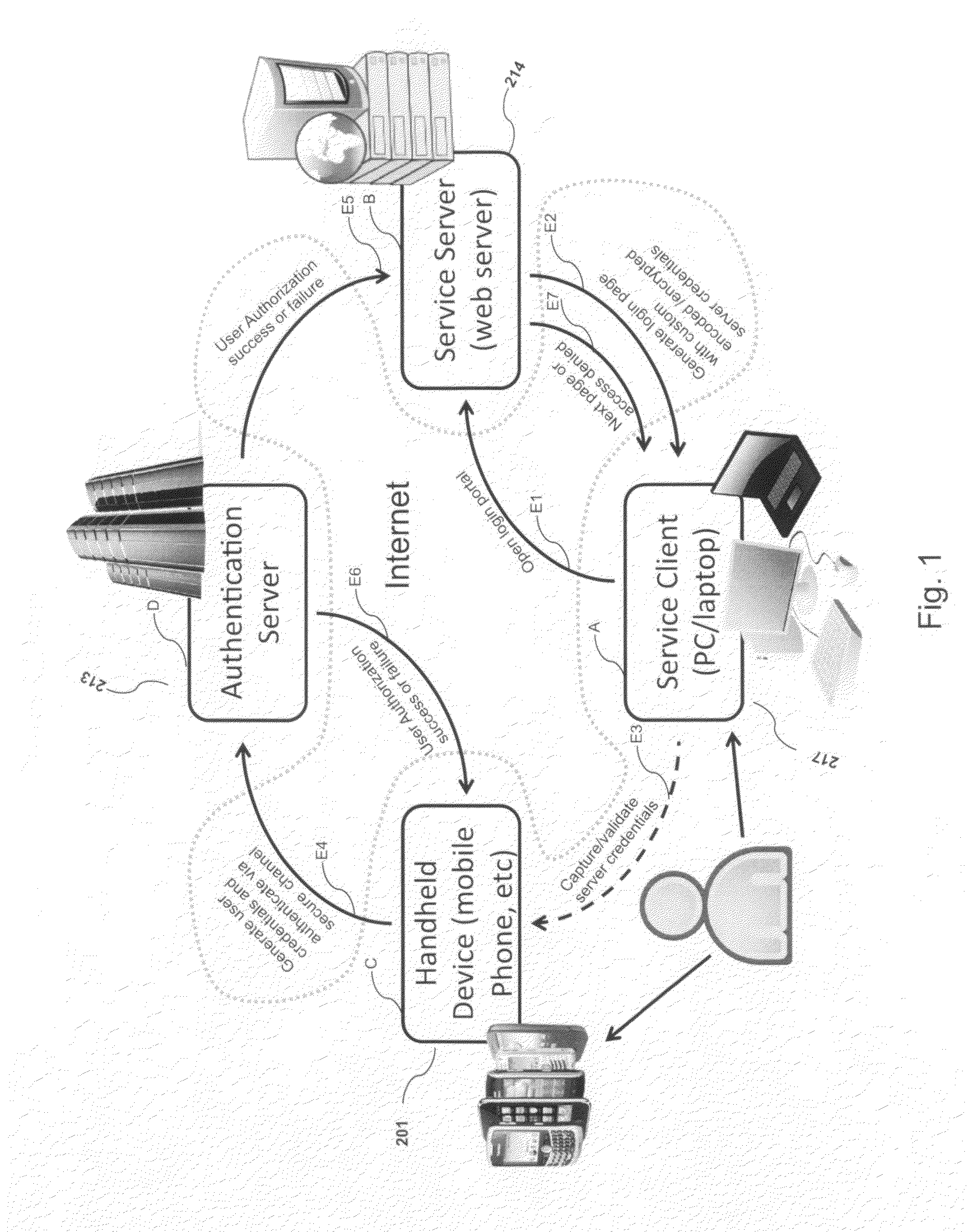
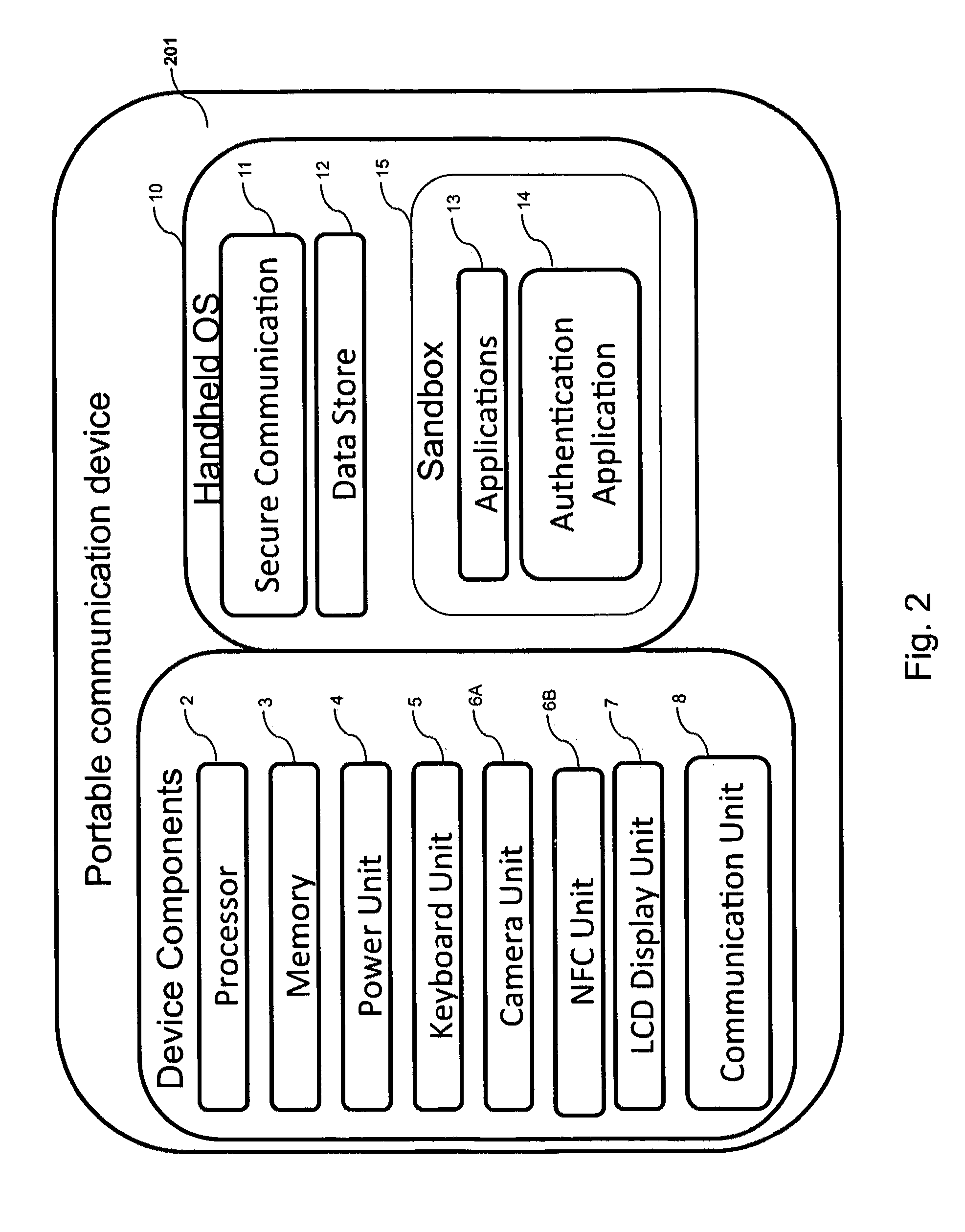
ActiveUS8763097B2Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
Owner:GCOM IP LLC
Screen icon manipulation by context and frequency of Use
ActiveUS8972878B2More user confidenceDigital data authenticationSubstation equipmentTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
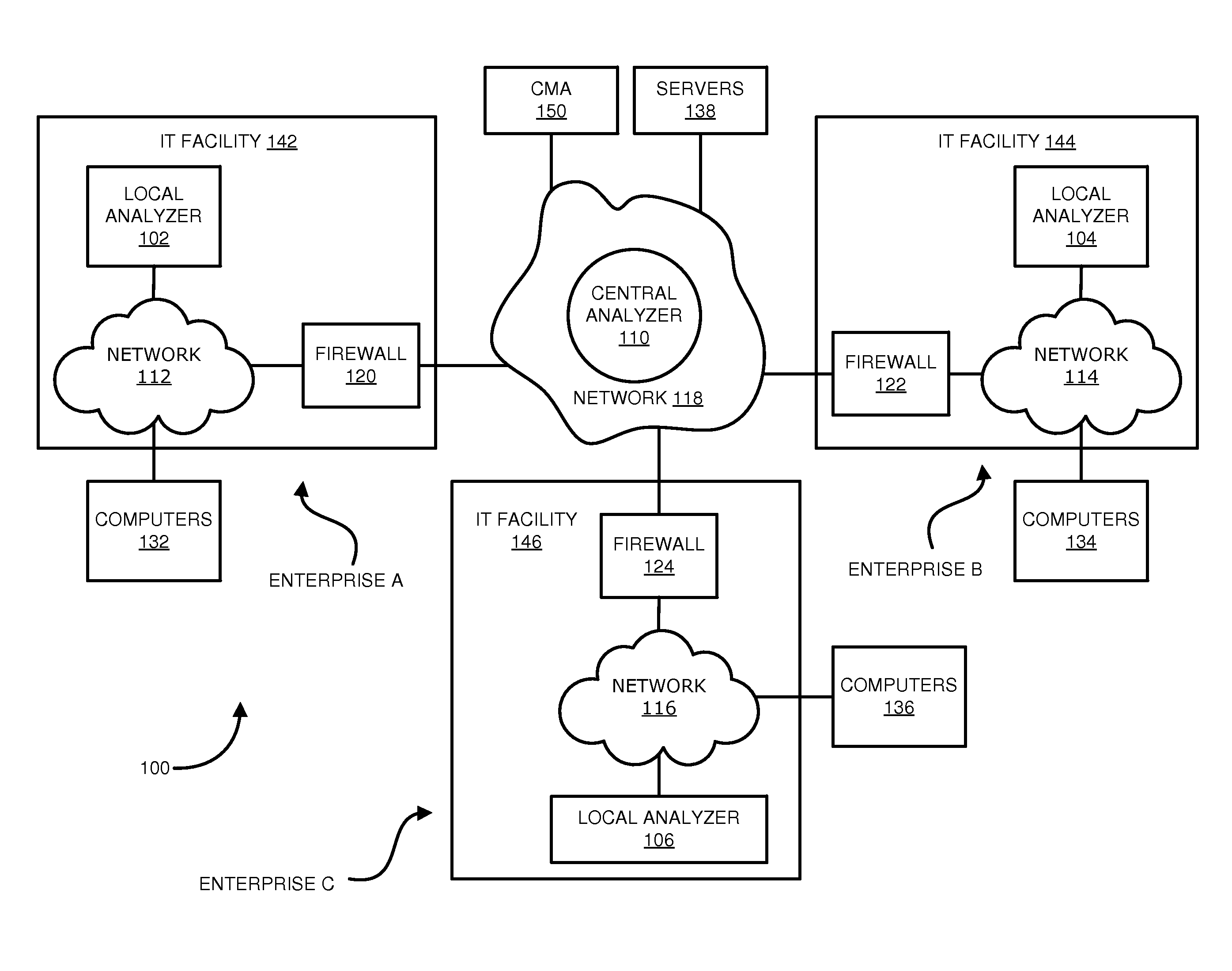
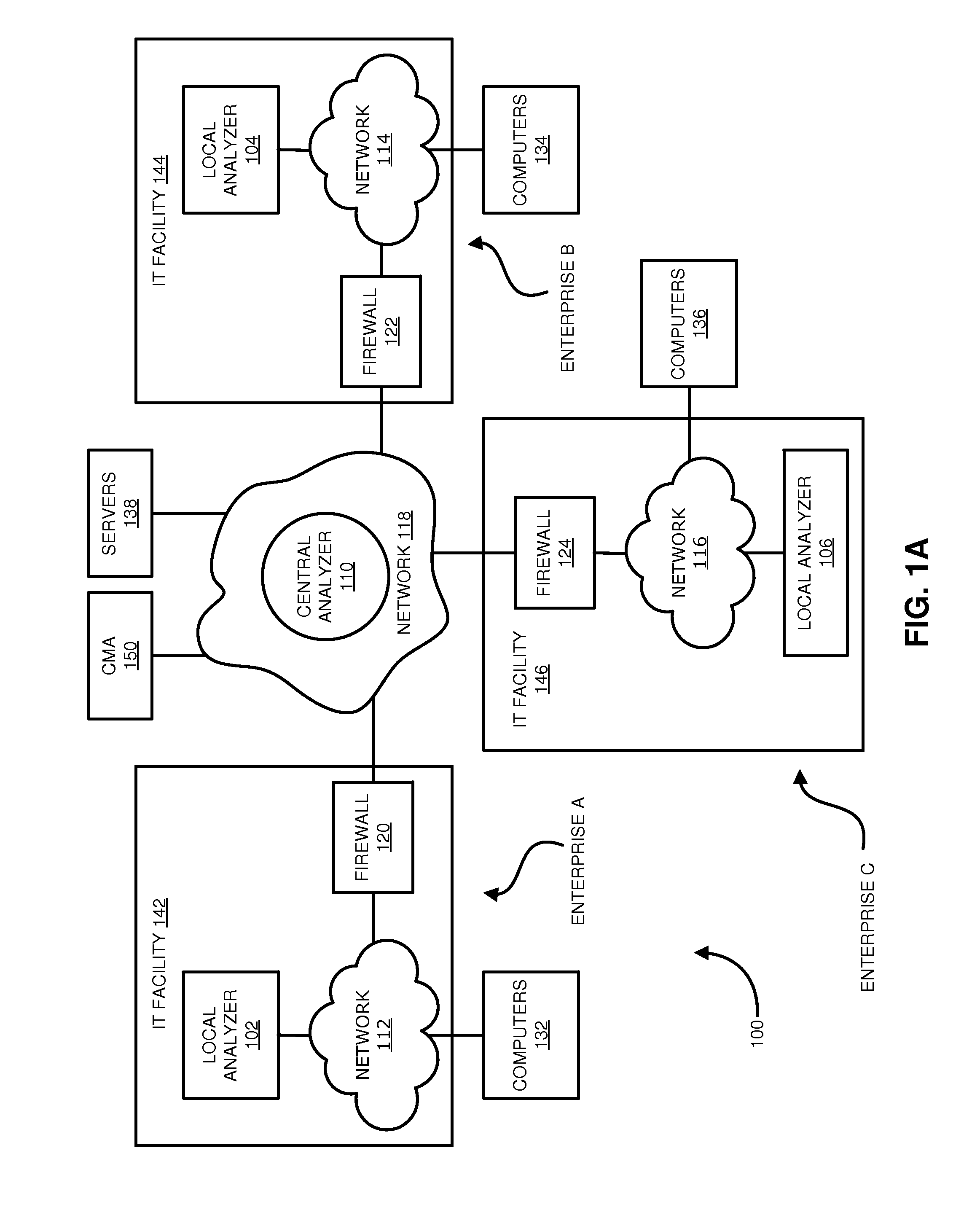
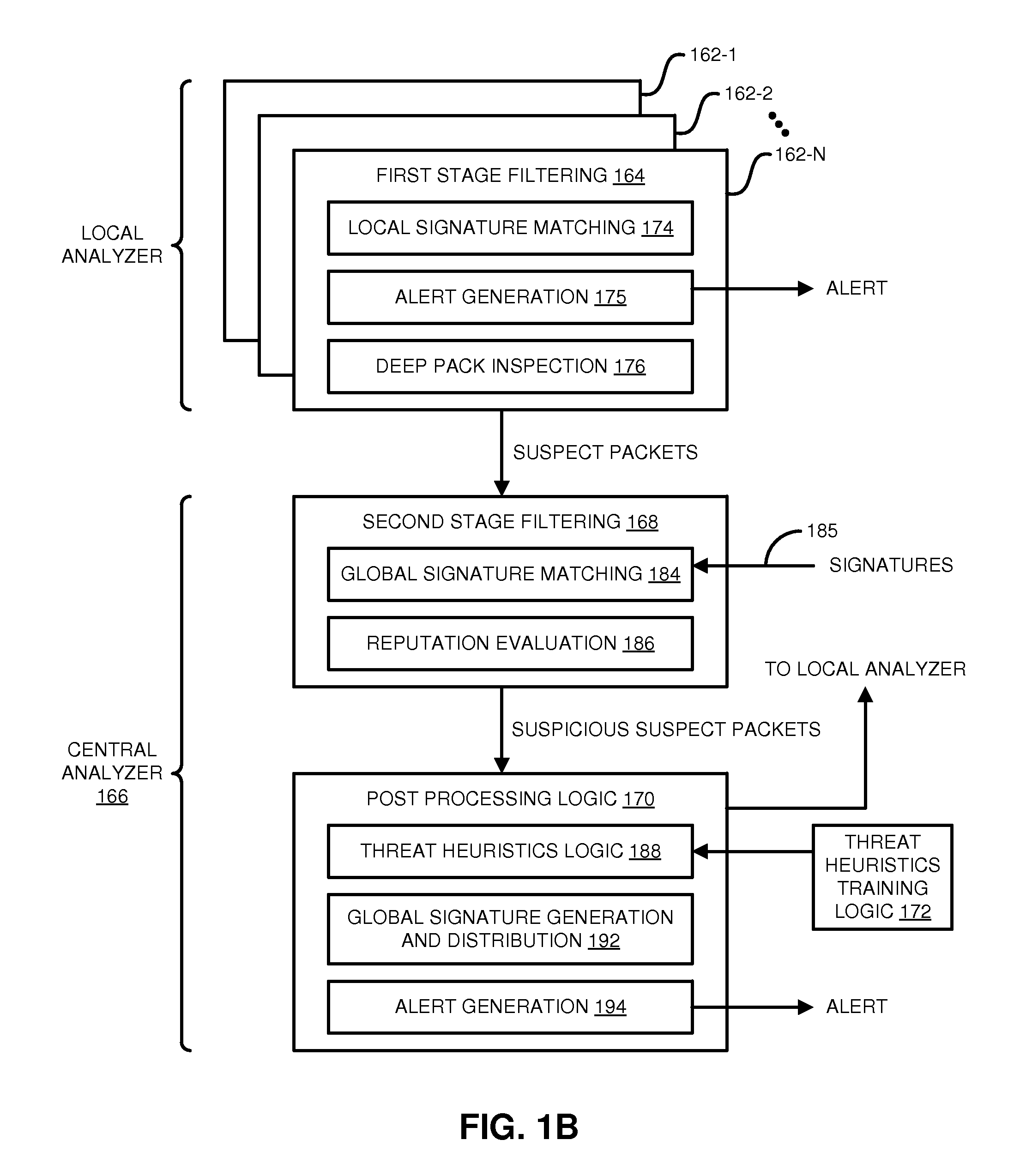
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
System and method to control transactions on communication channels based on universal identifiers
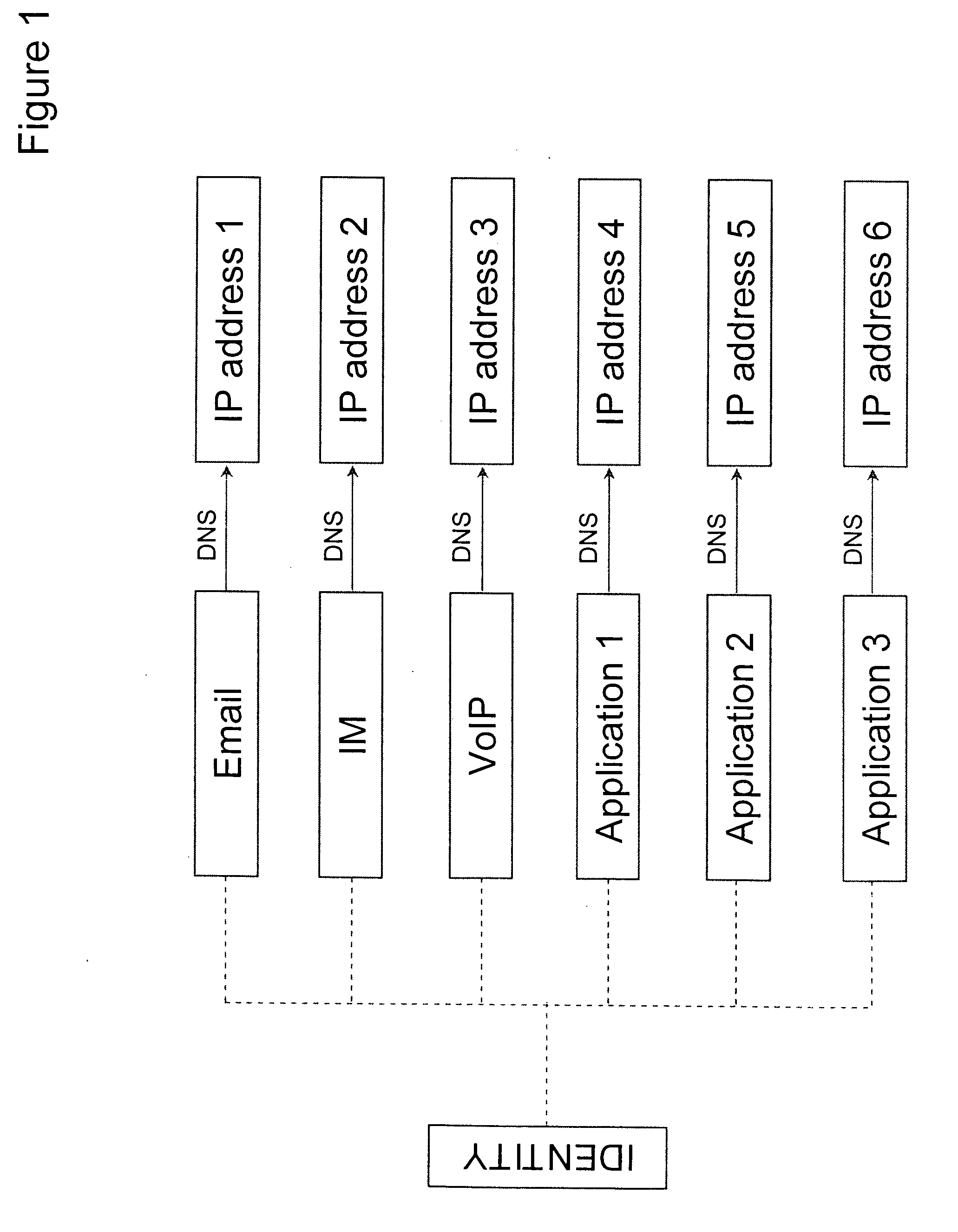
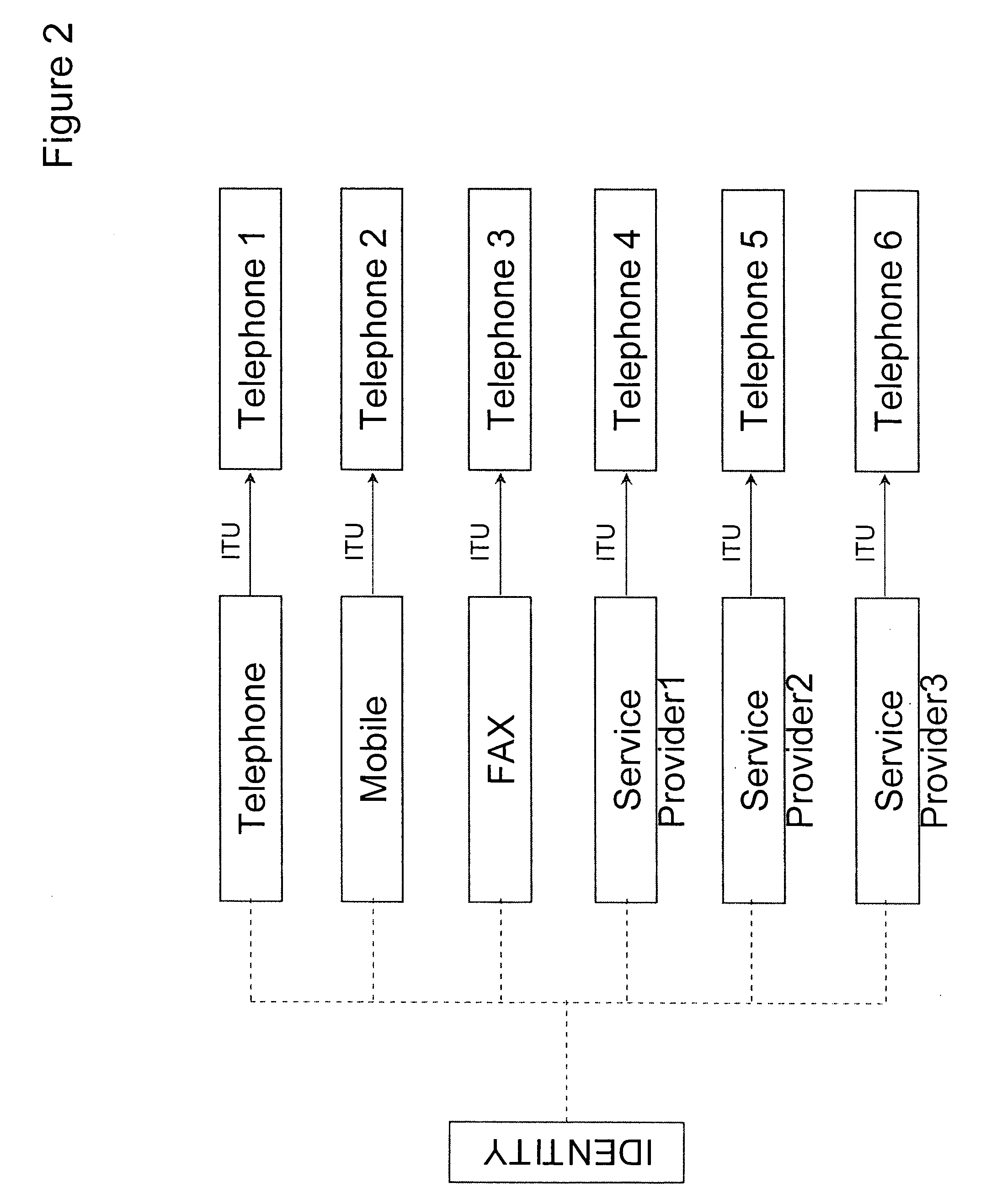
InactiveUS20070073888A1Minimizing effect of changeMultiple digital computer combinationsTransmissionOutbound communicationAutomatic routing
The present invention is a method to control communication channels using universal and persistent identifiers in circuit / packet switched or converged networks. The method involves linking domain specific addresses or concrete identifiers of communication end points within or across channels, domains and networks with an abstract, persistent and universal identifier that represents the single point of contact or principal identity of the user. The principal identity can specify parameters of inbound / outbound communication relationships with other specified / unspecified users / entities inter-alia through default / specific levels of control in communication relationships on / across / through normal or alternate channels, domains, applications, networks, etc., based on universal / persistent identifiers such as XRI. All transactions originating from, or terminating on, the principal identity are authenticated, asserted securely and routed automatically to an appropriate channel based on the principal identity's current context (state, location, presence, etc.) and privileges (or contracts) defined in rules created by the principal identity for access, usage, privacy, synchronization, compliance, expiry, etc. The principal identity is also empowered with multi-level control over attributes and metadata including rules for what data to expose / share and what data to eclipse / hide for which user. Control / user data, or traffic, and program / client / sequence logic, may be resident / executed / exchanged / carried on, or across, diverse networks / channels / media / devices / domains etc.
Owner:AMSOFT SYST PTE LTD
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS20120240204A1Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
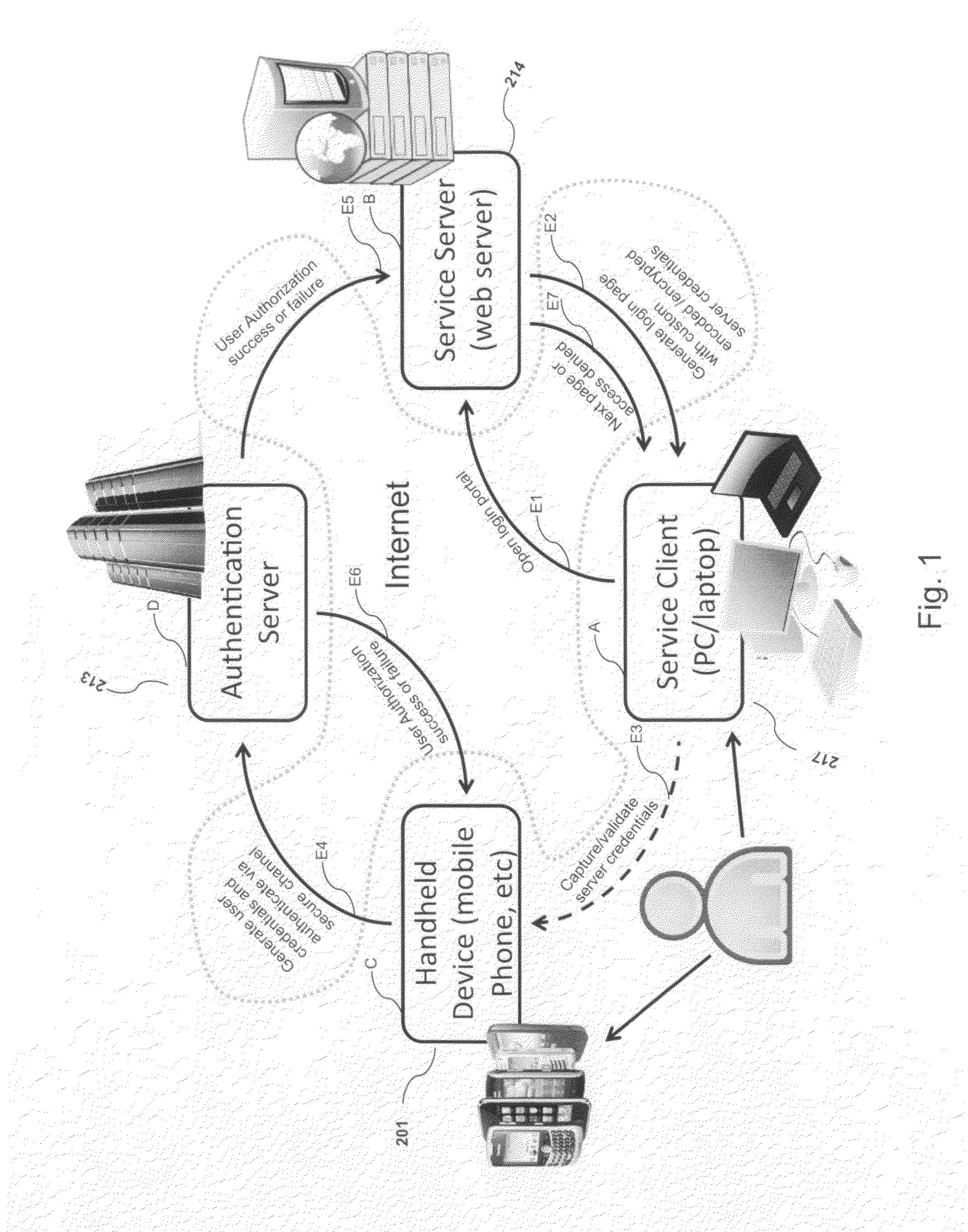
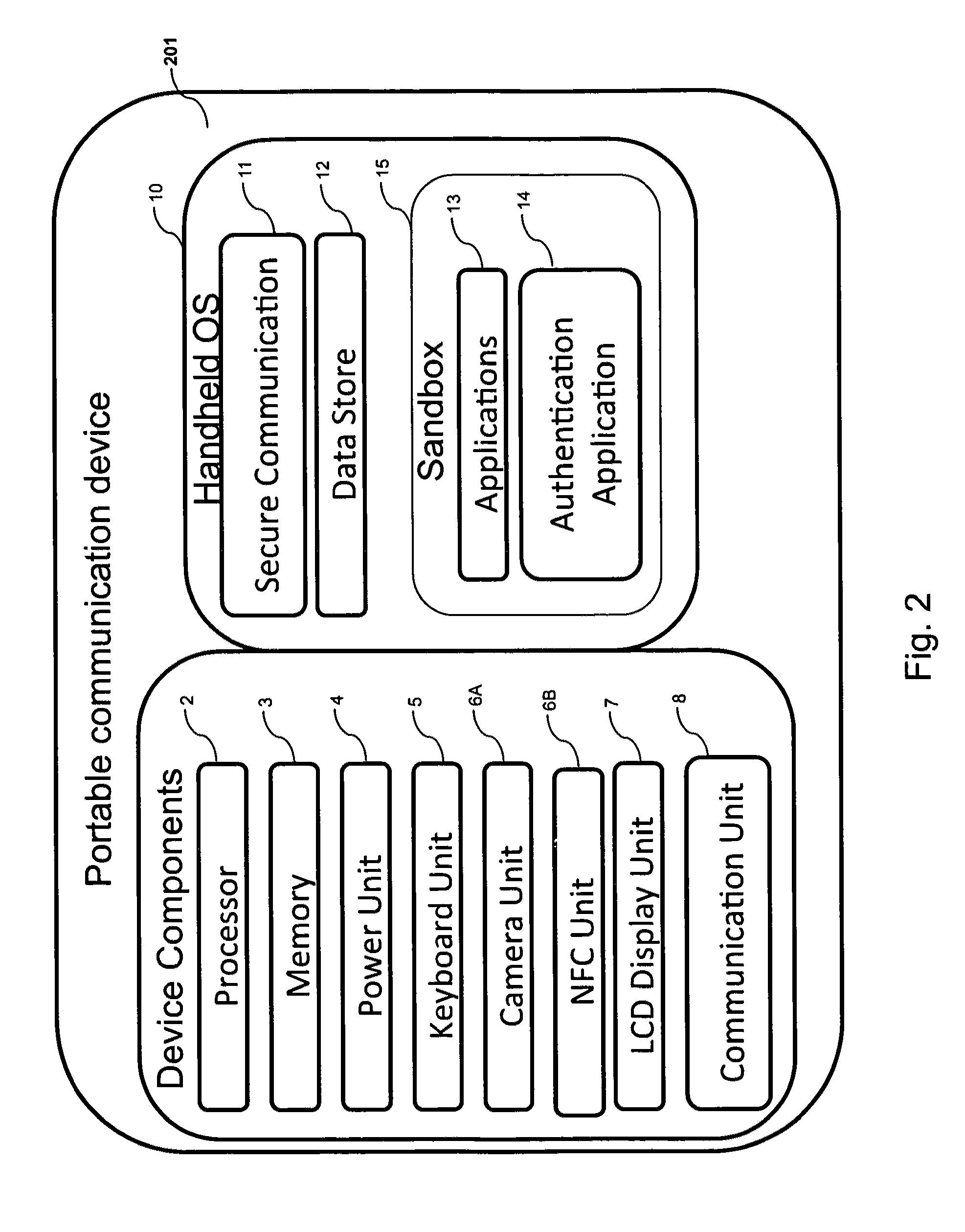
Systems and methods of authentication according to the invention are provided comprising a user, a service client, a service server, a portable communications device and an authentication server, wherein the method comprises use of one time passwords and out-of-band outbound communication channels. This system gives access to authentication seekers based on OTP out of band outbound authentication mechanism. The authentication seeker or system user scans a multi-dimensional barcode or another like encoding mechanism and validates the client and triggers the out of band outbound mechanism. The portable mobile device invokes the client server to request authentication. The client server authenticates the user based on a shared secret key and the user is automatically traversed to the next page.
Owner:GCOM IP LLC
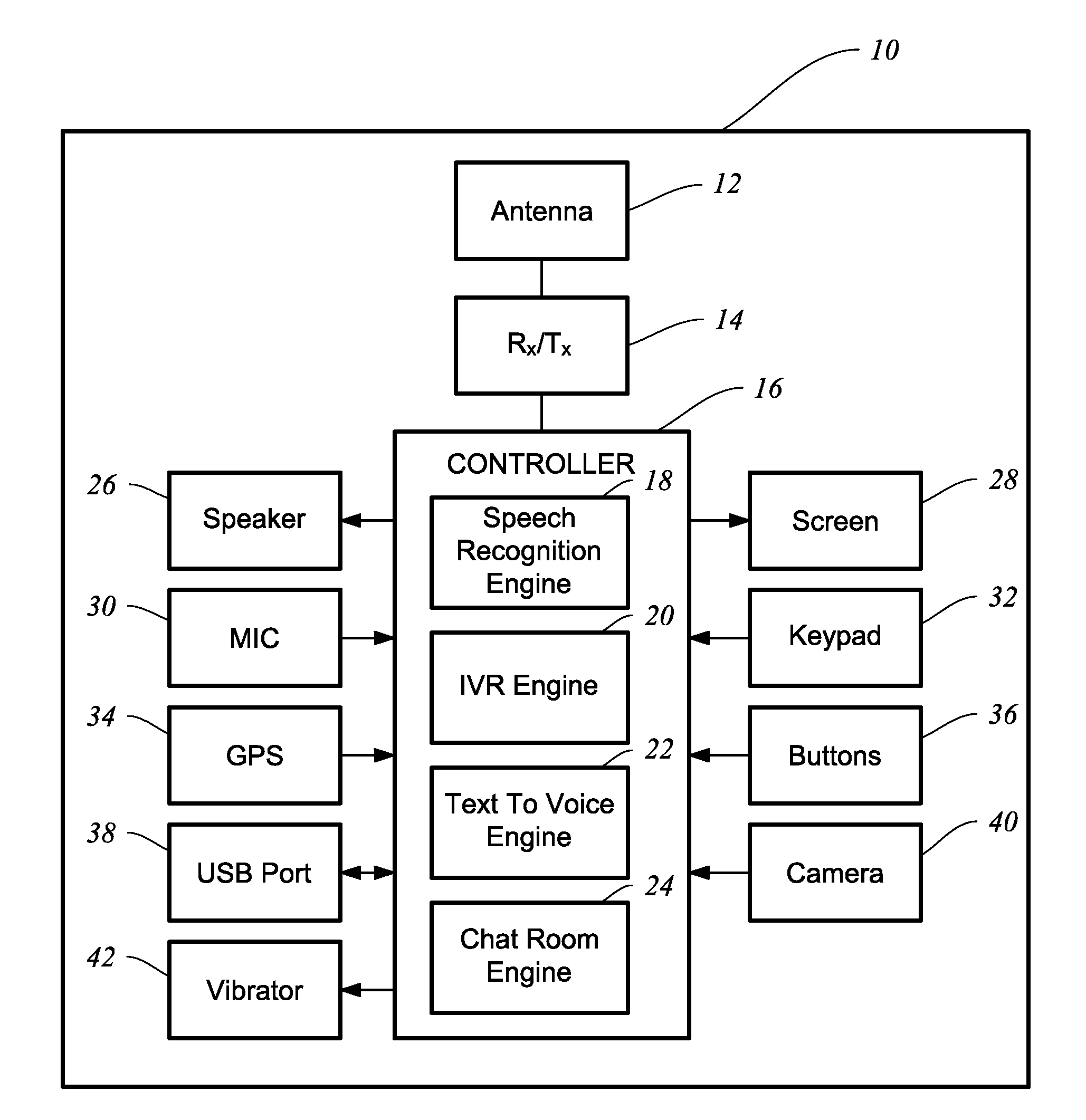
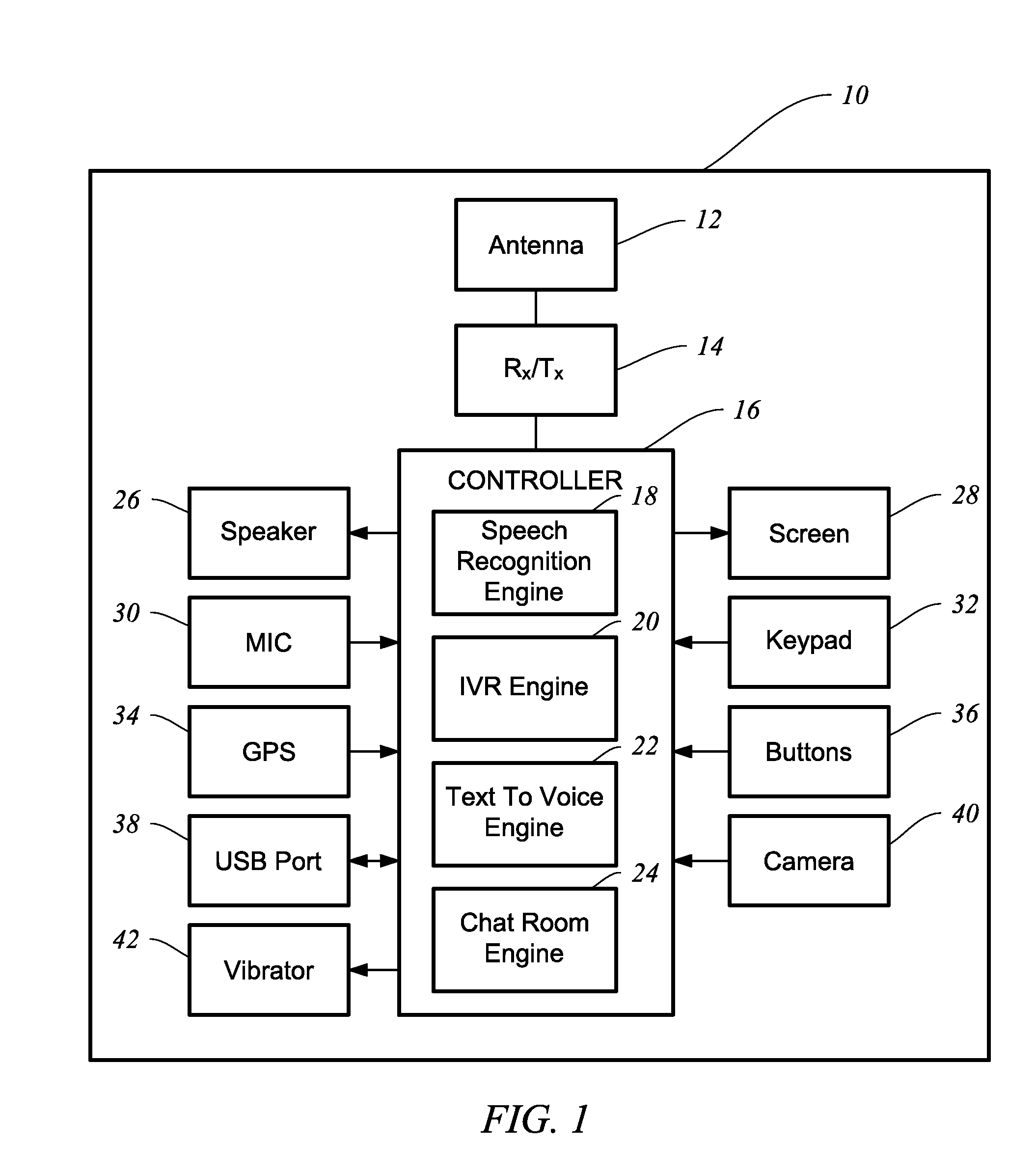
Configurable phone with interactive voice response engine
InactiveUS20110092187A1Security be importantDevices with voice recognitionSpecial service for subscribersInbound communicationOutbound communication
A land-based or mobile phone and methods are provided for receiving inbound communications as either voice or text, and then based on the user's configuration settings, the inbound communication is provided to the user as it was received or is automatically converted into a format that is desired by the user. The phone also takes voice or text that is input by the user of the phone and converts the user's input to either voice or text based on the configuration settings stored in the user's contact list or otherwise. The outbound communication is configured according to how the intended recipient wants to receive a communication based on the configuration settings stored in the user's contact list or otherwise. The phone includes a controller that determines how the phone will handle and process inbound and outbound communications. The controller includes a speech recognition engine.
Owner:MILLER LARRY
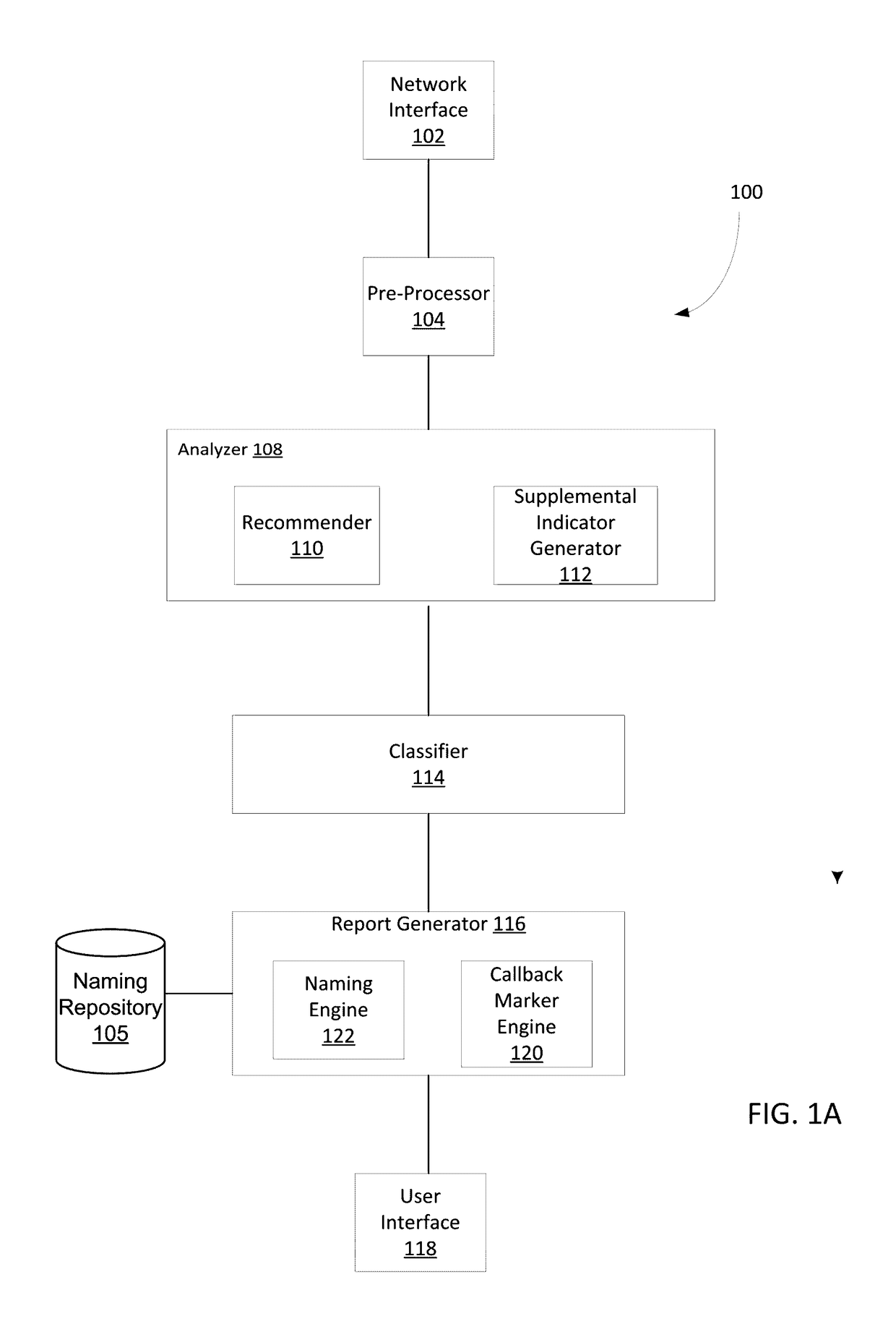
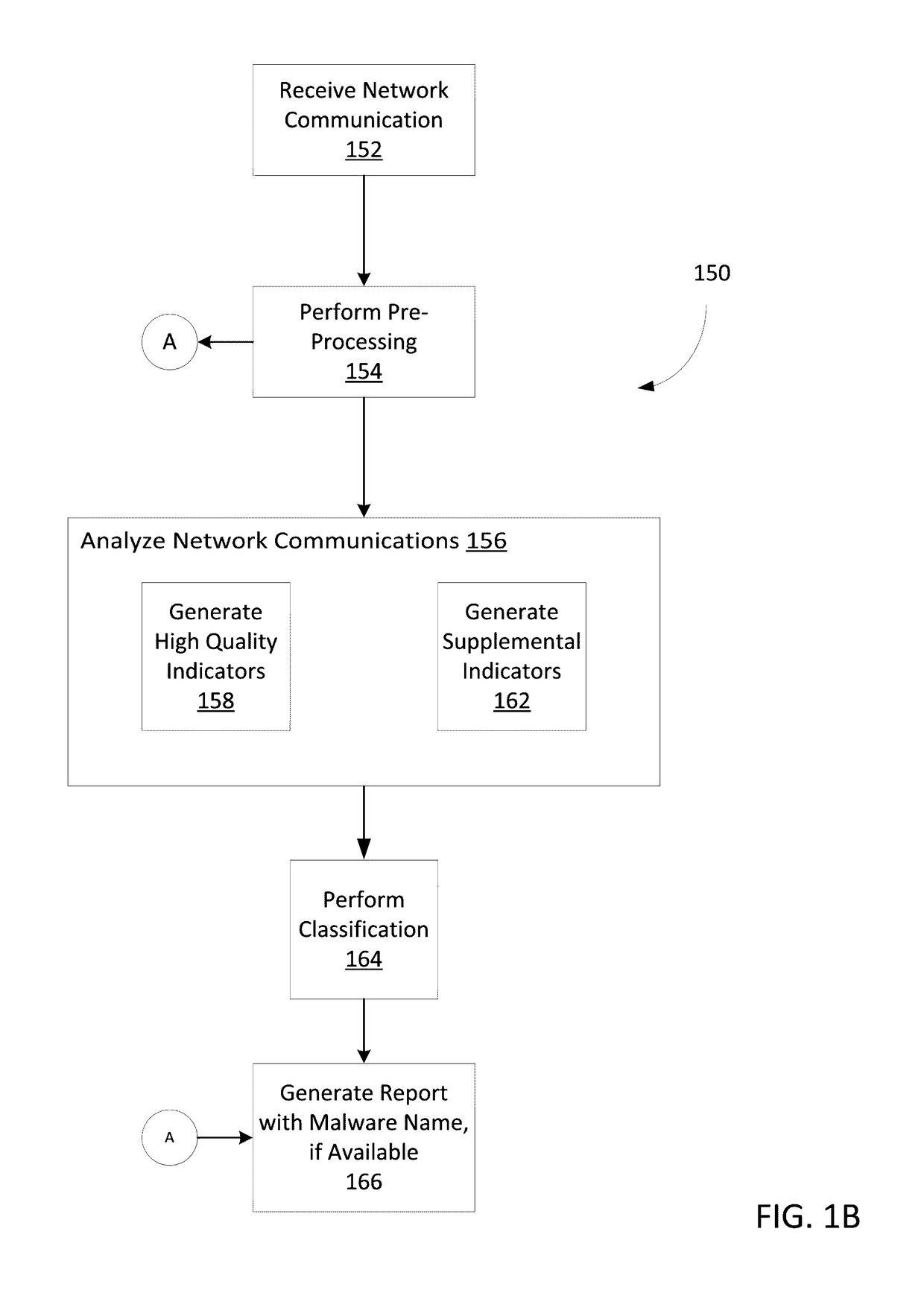
Classifying sets of malicious indicators for detecting command and control communications associated with malware
ActiveUS9635039B1Platform integrity maintainanceTransmissionOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using an approach employing both a set of high quality indicators and a set of supplemental indicators. The high quality indicators are selected since they provide a strong correlation with callbacks, and may be sufficient for the techniques to determine that the network outbound communications actually constitute callbacks. If not, the supplemental indicators may be used in conjunction with the high quality indicators to declare the outbound communications as callbacks.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for a wireless mesh network of configurable signage
One or more electronic signs each coupled to a transceiver or radio node that is communicably coupled to an access node may change its display, as directed by the access node. The access node is configured to receive data related to adjusting information displayed on one or more of the electronic signs. The access node wirelessly transmits an outbound communication to a number of radio nodes logically distributed around the access node. One or more of the radio nodes or may be configured without an electronic sign but instead be configured to repeat the outbound communication. A recipient radio node receives the outbound communication message and executes instructions contained in the outbound communication message so that its electronic sign changes the display of information, such as the price.
Owner:NIVIS
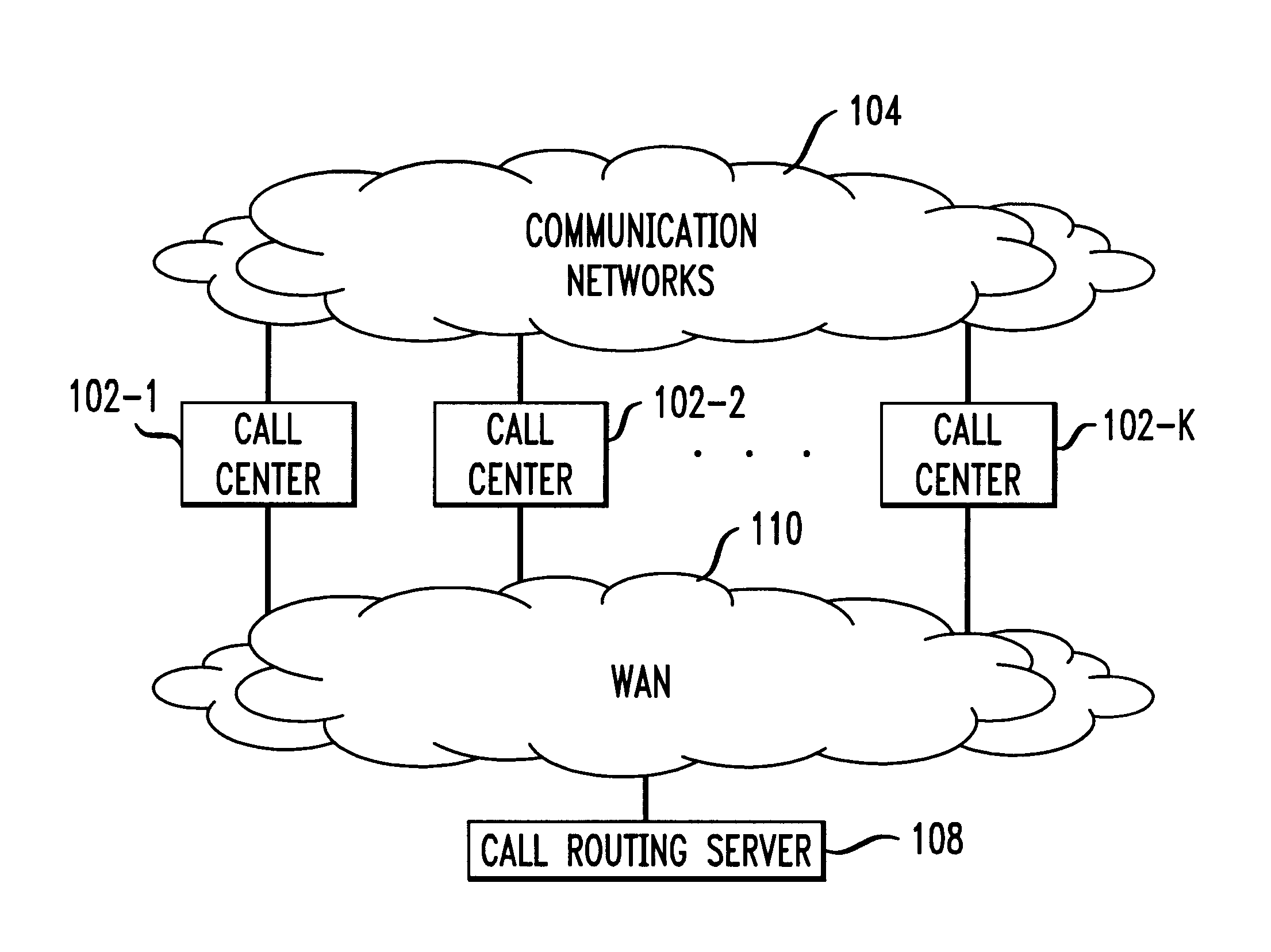
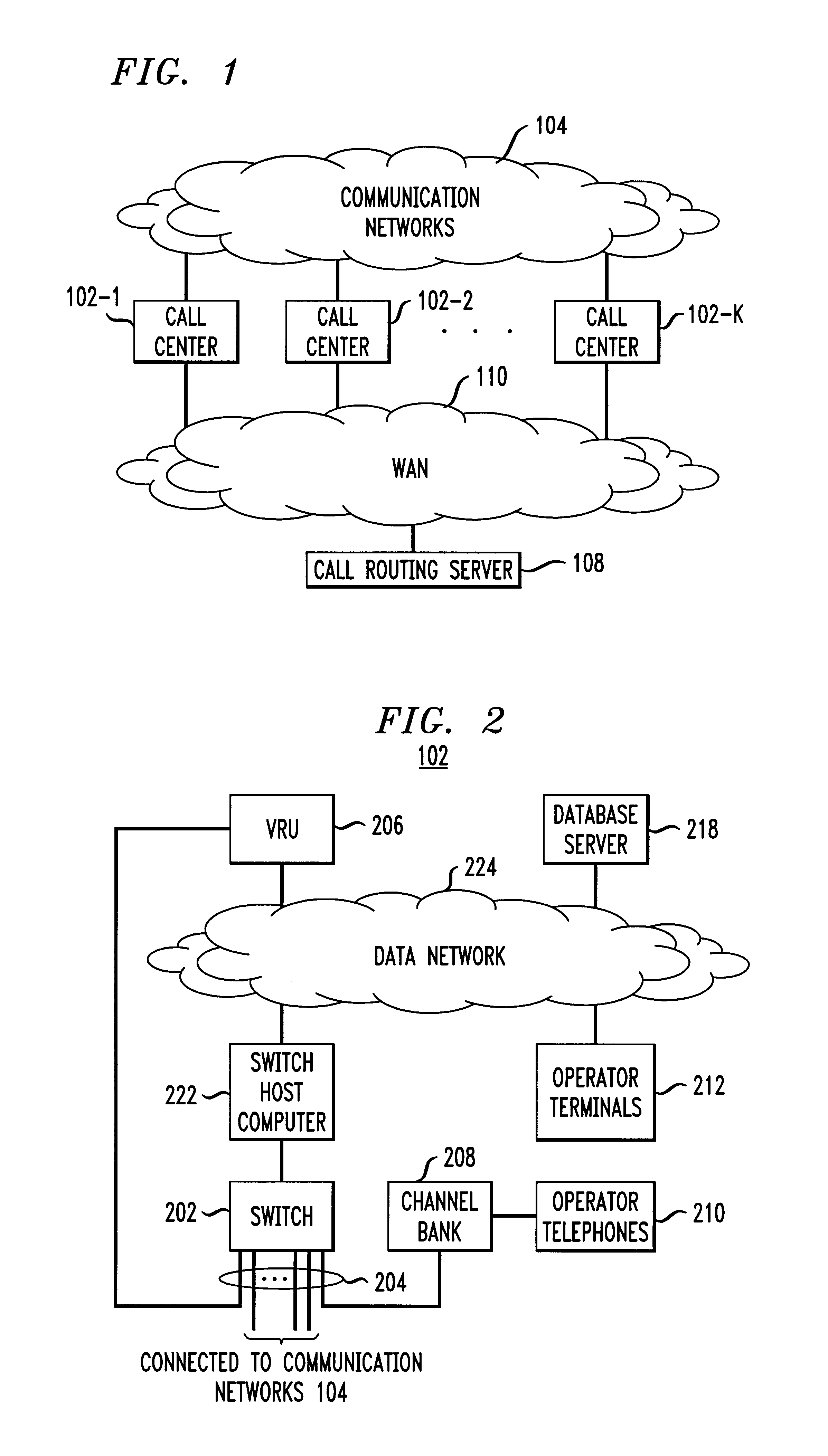
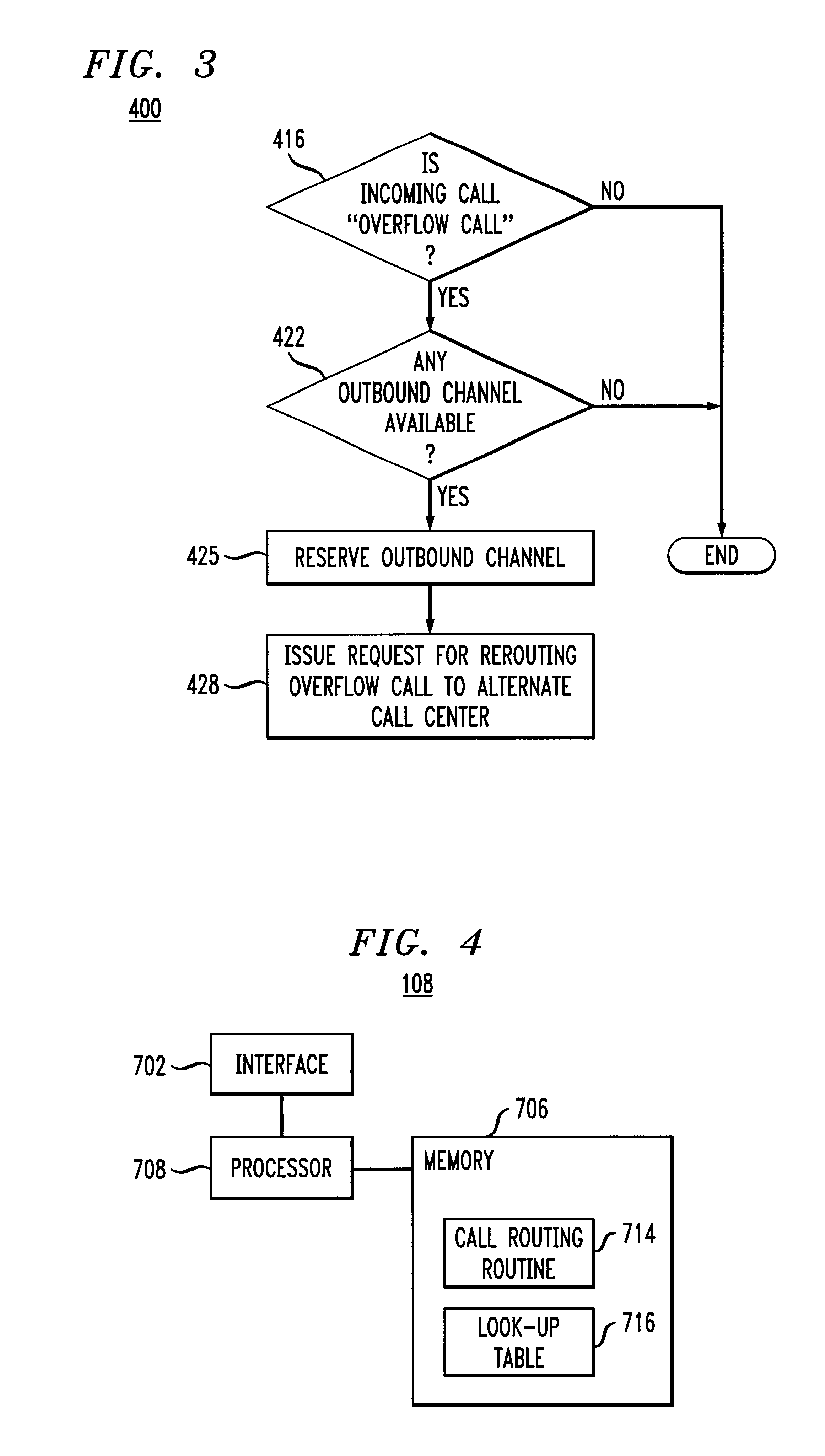
Technique for effectively processing and dynamically routing communication calls
InactiveUS6845155B2Avoid adjustmentInterconnection arrangementsSpecial service for subscribersOutbound communicationCall forwarding
In an arrangement where calls are directed to different call centers, each call center based on selected metric measures determines whether an incoming call is an “overflow” call to be rerouted to an alternate call center. These metric measures may include, e.g., the number of operators in the call center answering calls, the number of calls in queue to be answered, etc. Once an overflow call is identified, the call center reserves an outbound communication channel in anticipation of rerouting the call, and transmits a call rerouting request to a call routing server. In accordance with the invention, the server identifies an appropriate alternate call center for receiving the overflow call, and communicates routing information including an identity of the alternate call center to the overflow call center. The latter based on the received routing information transfers the call to the appropriate alternate call center.
Owner:GRAPE TECH GROUP
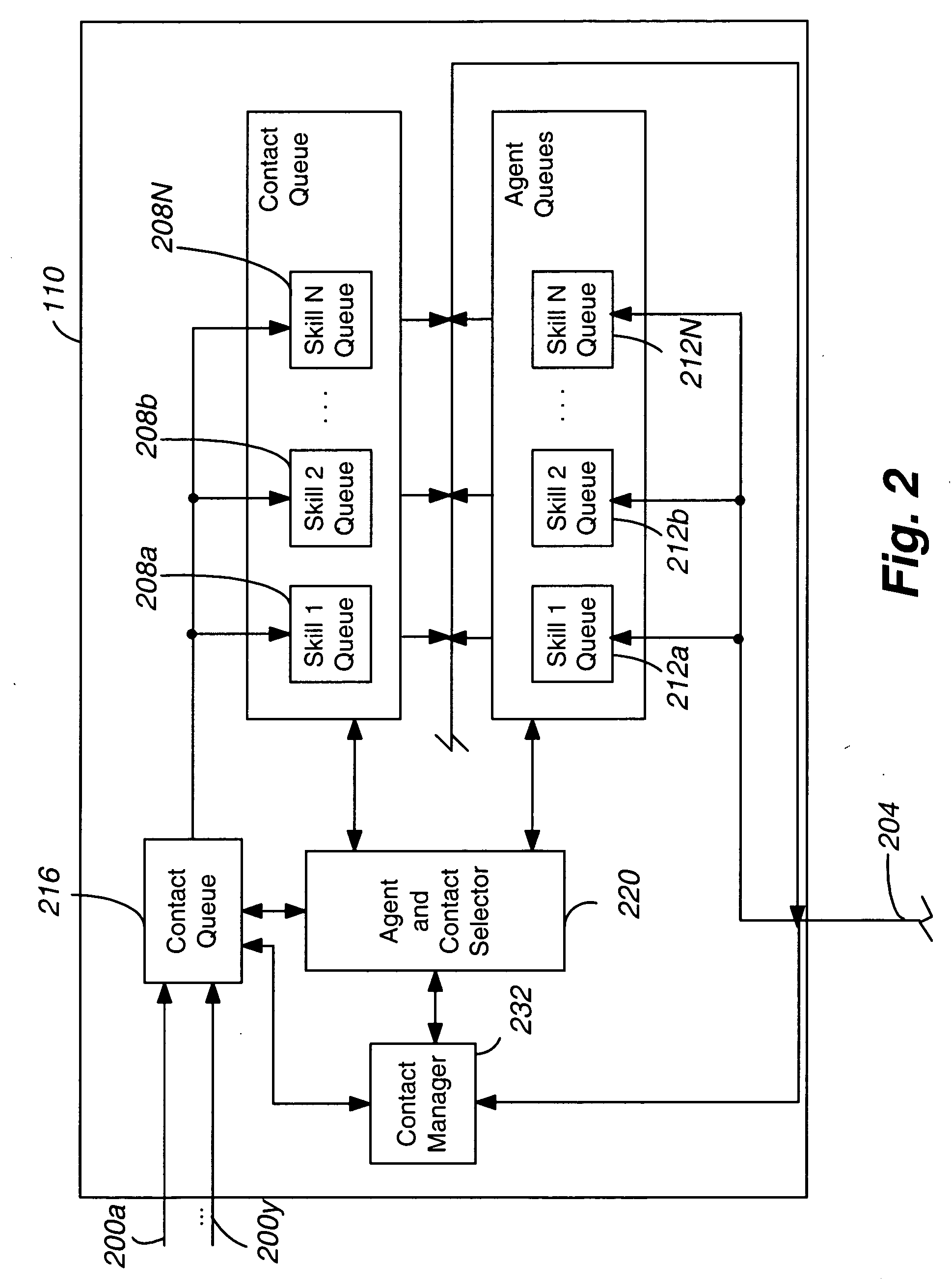
Intelligent inbound/outbound communications blending
ActiveUS7035927B2Increase speedAvoid mistakesSpecial service for subscribersDigital computer detailsOutbound communicationRest period
In a blended inbound / outbound call center (100), an outbound call-pacing function (122) decides whether or not to initiate an additional outbound call for a particular skill. It determines (206) whether the number of available agents for the skill plus the number of resting agents for the skill exceeds the number of available inbound calls for the skill plus the number of outstanding outbound calls for the skill. It also determines (312) whether a target service time for the skill exceeds an estimated wait time of each of the available inbound calls for the skill assuming that pending outbound calls for the skill plus one take precedence over the inbound calls. If both determinations are affirmative, the call pacing function initiates (318) an additional call for the skill. If either determination is negative, the function forbears (321) from initiating an additional call for the skill. The number of available and resting agents may be incremented (206) by (a) a difference between the target service time for the skill and the present waiting time of the last-enqueued inbound call for the skill divided by the average rate of advance through the skill's call queue, or (b) the average amount of time that a newly-initiated outbound call for the skill takes to become available divided by the average rate of advance, plus the number of agents for the skill who are busy but expected to become available within a time period equal to (a) or (b), less the number of those agents that will receive a rest period upon becoming idle. The number of calls may be incremented (206) by the number of inbound calls that are expected to arrive within the time period (a) or (b).
Owner:AVAYA INC
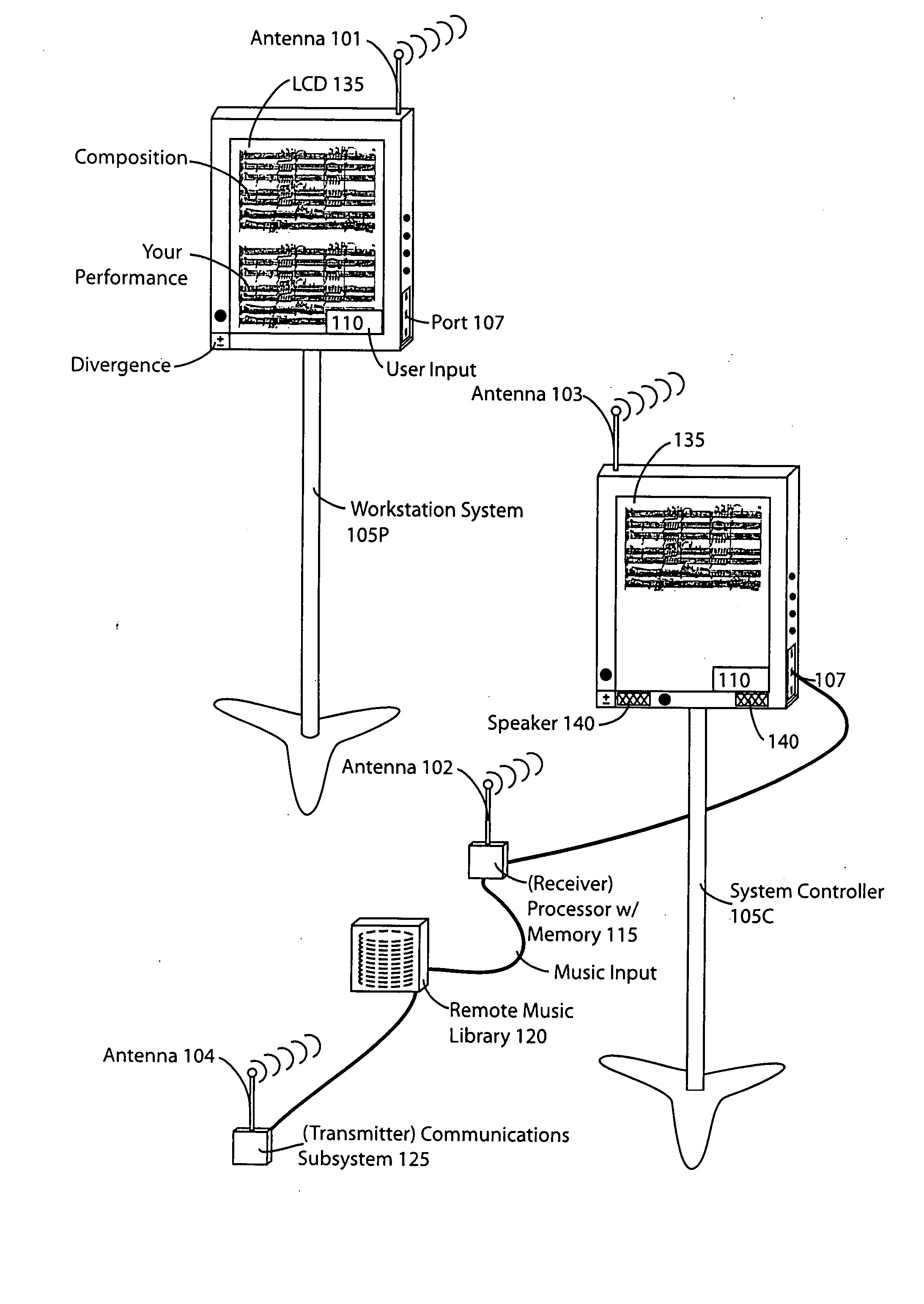
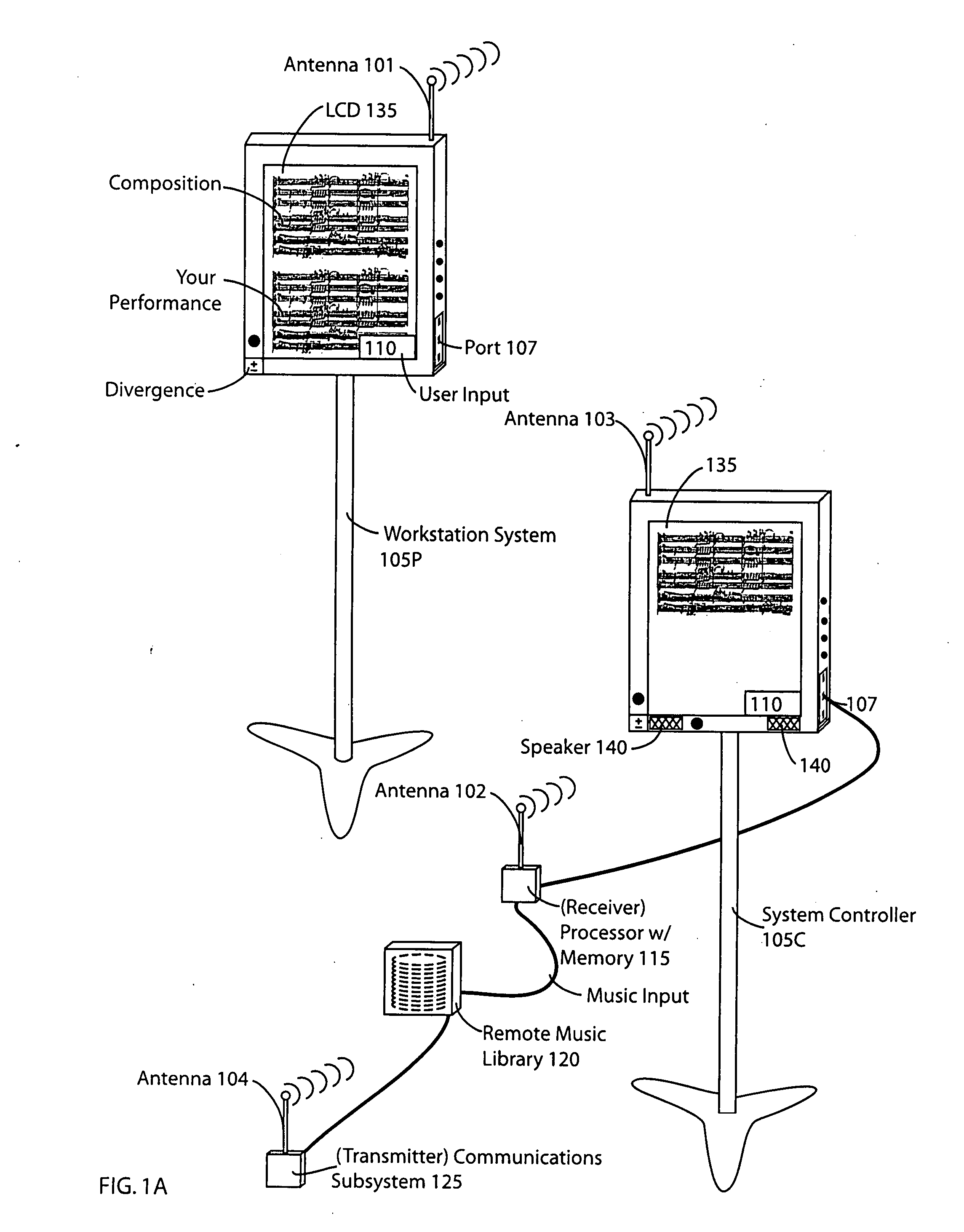
System and methodology of coordinated collaboration among users and groups
InactiveUS20080060499A1Effective versioningEffective distributionElectrophonic musical instrumentsMusicOutbound communicationCD-ROM
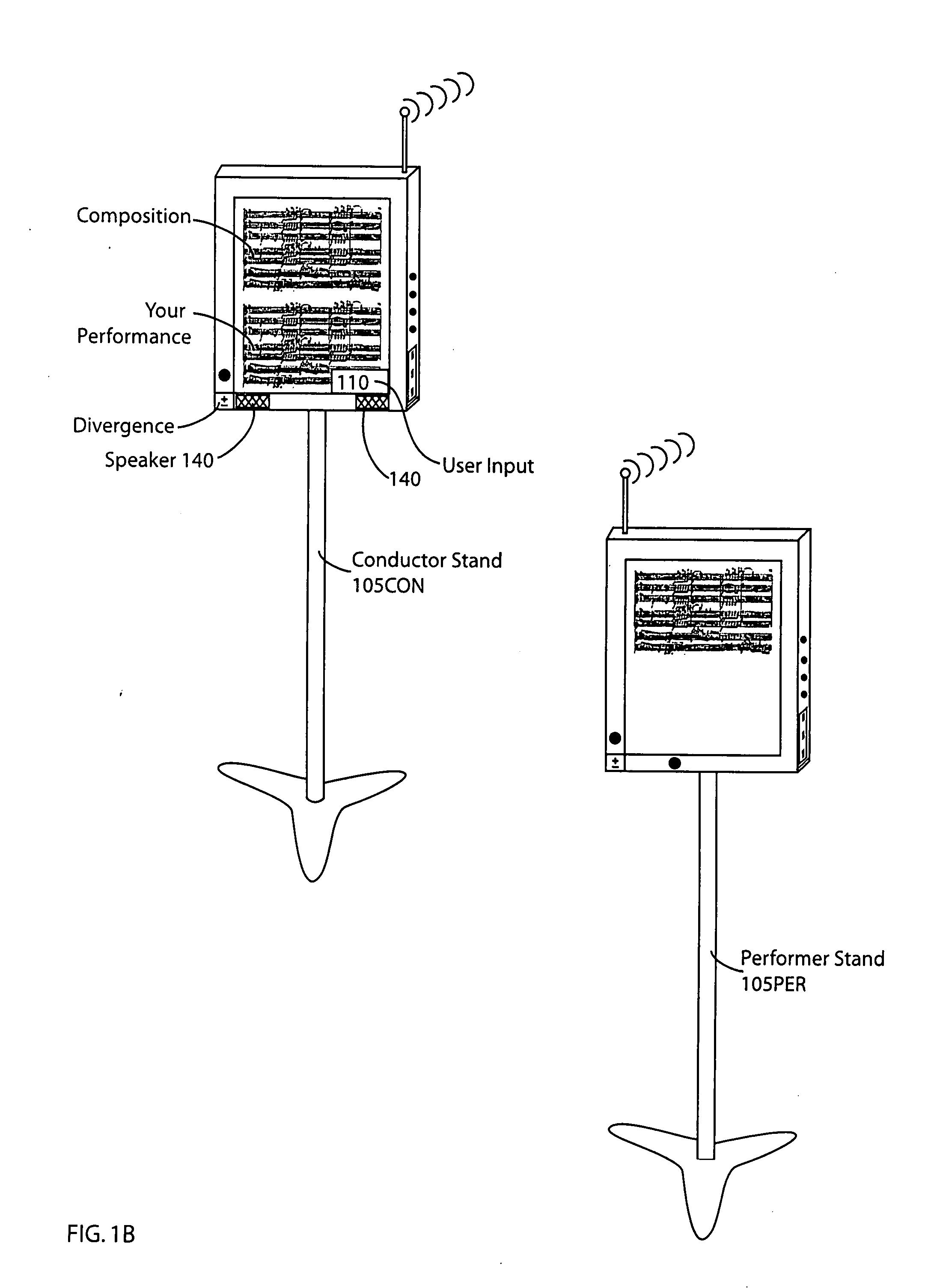
A musical workstation system produces a display presentation in one of a musical composition responsive to musical composition data and responsive to one or both of input variables and a selected operating mode. The system is comprised of (1) means to provide the musical composition data (such as local storage (ROM, RAM, CD-ROM, hard disk etc.), or via a communications interface to an external device (such as another music workstation, a master controller, a computer), a memory, a selection subsystem, a controller, and a display subsystem. The memory selectively stores the received original musical compositions. The selection subsystem determines a selected operating mode and display format. The controller, responsive to the selection subsystem, provides means for selectively controlling the storing of the musical composition data in memory and selectively processing (e.g. altering) the stored musical composition data responsive to the selected operating mode and the input variables to produce a particular one of a plurality of processed results, such as external communications, operating, mode, transformation to derivative musical compositions, etc. The music workstation can coordinate communications, or be a slave device, with one or more external devices, such as other music workstations, a master workstation, a controller, etc. The display system provides for selection of original compositions, creation of derivative compositions, distribution of compositions, monitoring of each performer's performance, group virtual performances, and also allows for local and distributed retrieval and editing of musical compositions.
Owner:BAMA GAMING +1
Apparatus, systems and methods for managing incoming and outgoing communication
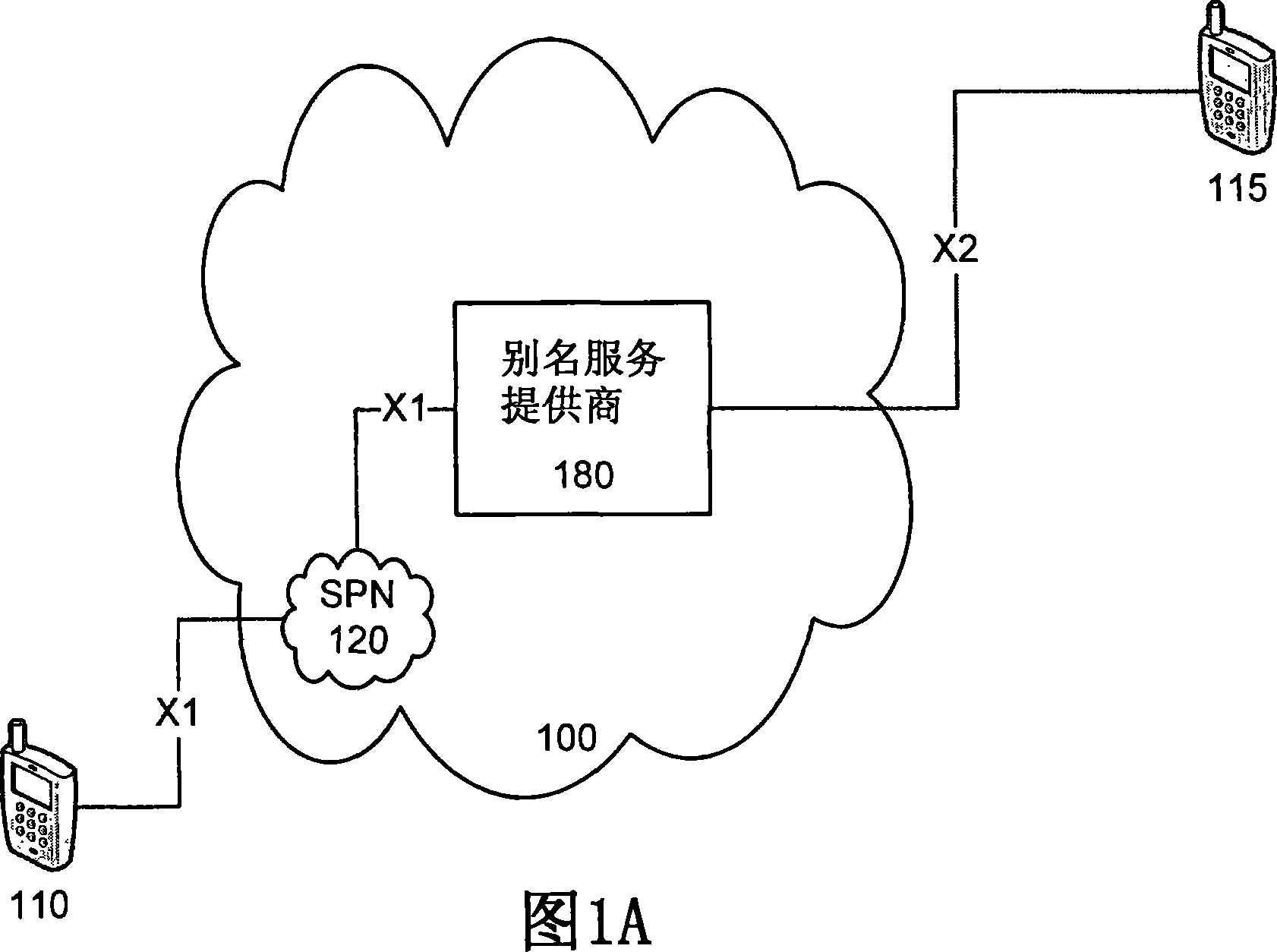
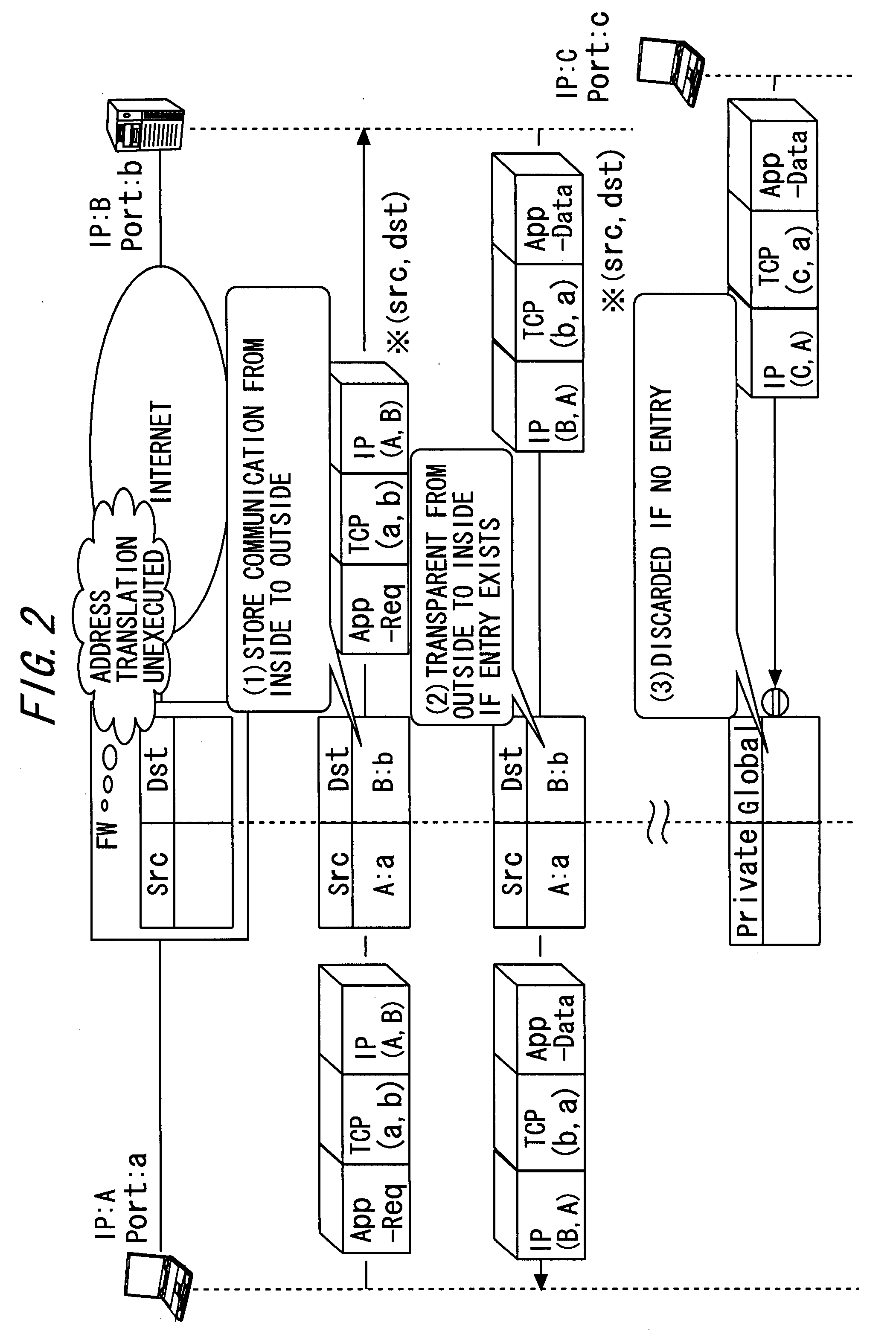
InactiveUS20070248220A1Telephone data network interconnectionsUnauthorised/fraudulent call preventionInbound communicationOutbound communication
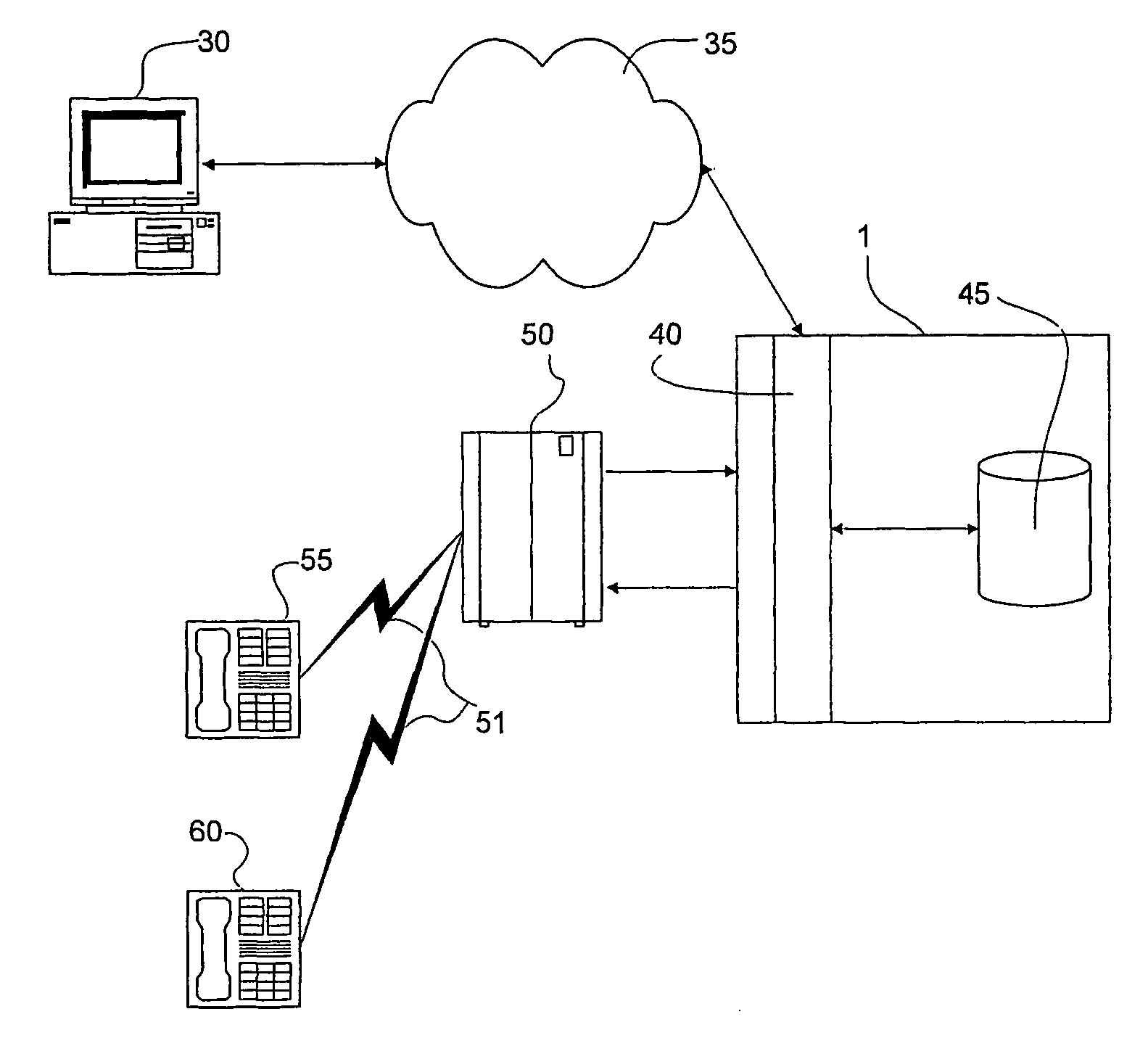
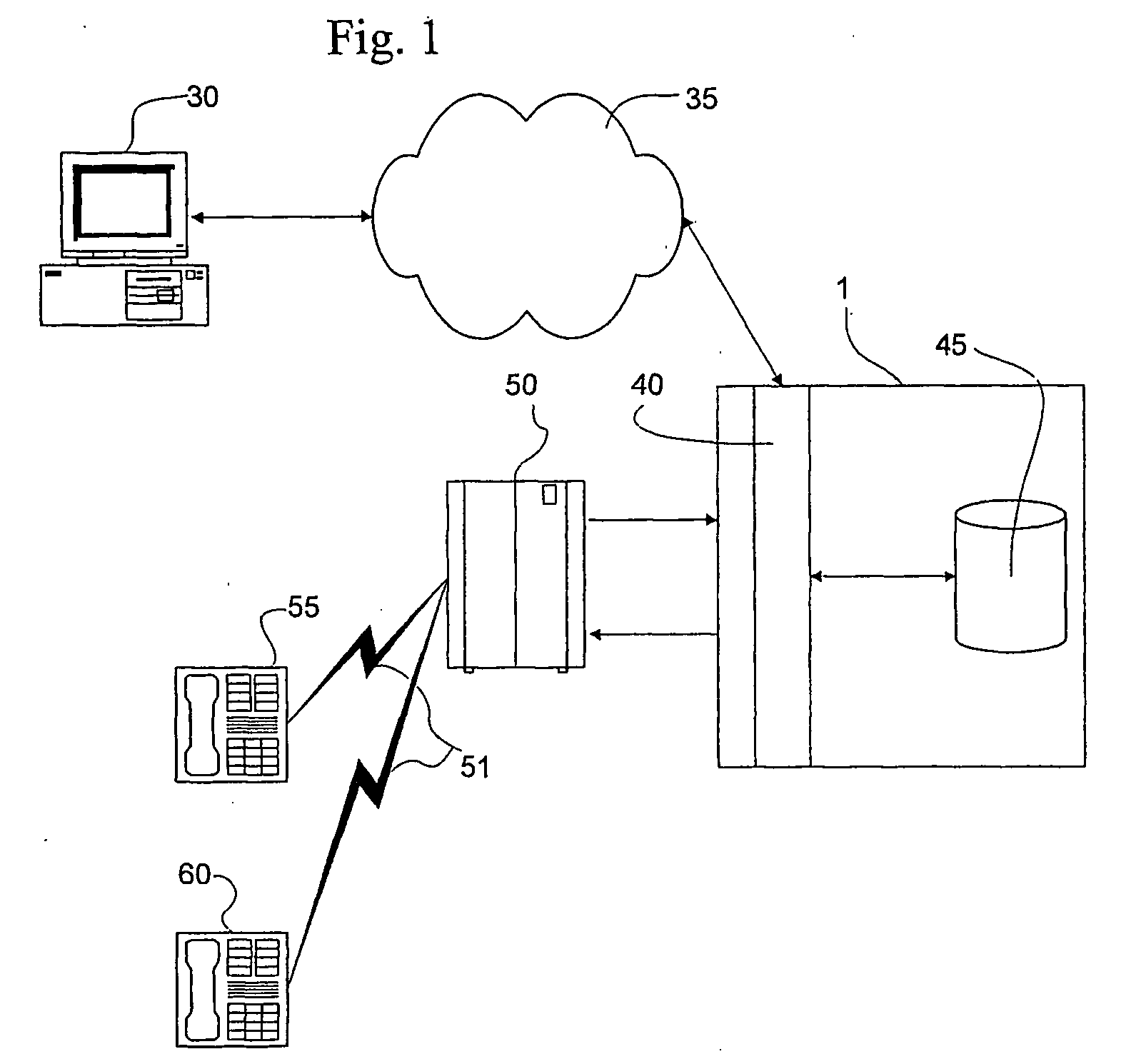
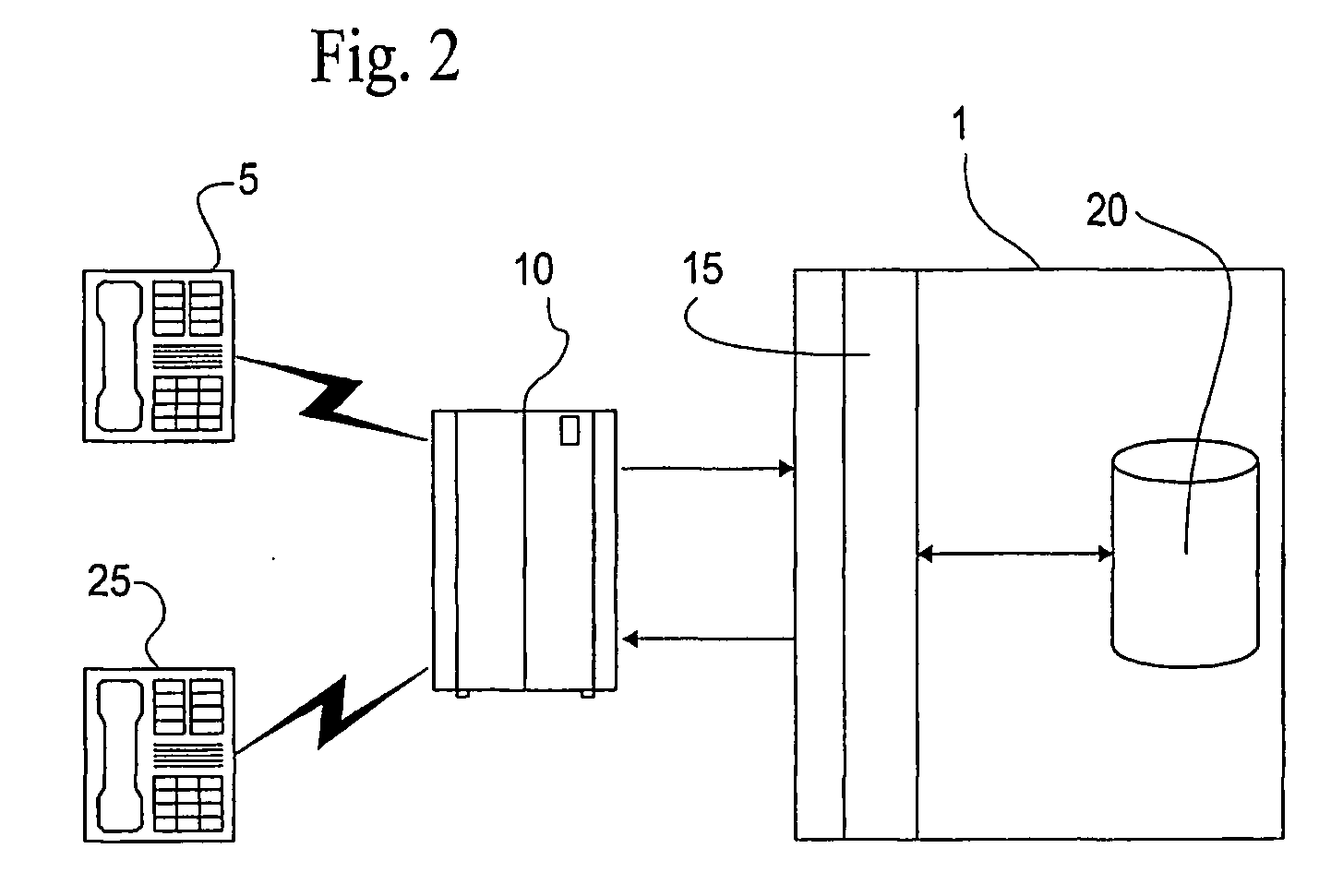
The present invention provides apparatus, systems and methods for managing incoming and outgoing communications for various communications methods. The invention provides control over inbound communications including definition of if, when, and who may communicate with a recipient. The invention also supports concealed identification communication in that no actual addresses, phone numbers, or other addressing IDs are required to be exchanged by the communication initiator and recipient. The invention also provides the capability to initiate immediate, delayed, scheduled, or recurring outbound communications. As depicted in FIG. 1, if the database (45) contains call management settings for a call recipient, the application logic (40) will evaluate the rules to determine if a particular caller is authorized to connect with the call recipient at the current time and date. If the caller is authorized by the recipient to connect to the recipient phone number, and is furthermore authorized to do so for the current time and date, the application logic (40) will connect the call utilizing the public telephone switch (50). The computer (1) passes the caller and call recipient phone numbers as stored in the database (45) to the telephone switch (50) using an application programming interface (“API”) appropriate to the service provider or telephone switch manufacturer. The exemplary embodiment of the invention utilizes an API provided by a telephone service provider as an interface to its switching infrastructure (50). The API captures both caller and recipient telephone numbers along with other variables useful for call setup and tracking. The telephone service provider then connects both parties' telephones (55), (60) to a phone call by dialing both numbers and connecting the call upon the parties' answer.
Owner:CRANDELL JEFFREY L +1
Systems and Methods for use in Marketing
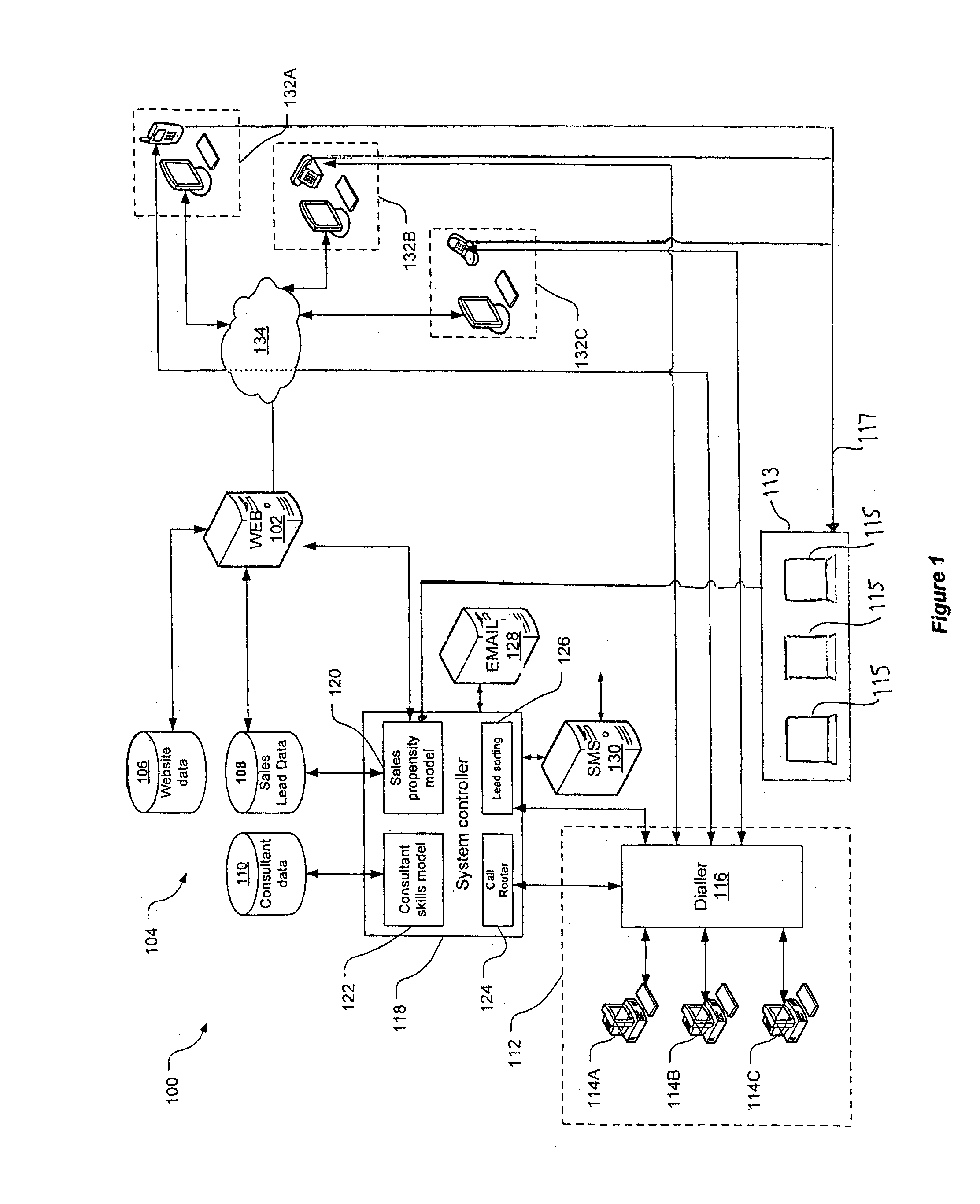
InactiveUS20150237205A1Market predictionsSpecial service for subscribersOutbound communicationElectronic communication
A method for scheduling outbound communications to sales leads based, at least partly, on a model of customer behaviour derived from (i) customer data gathered from a plurality of customers that initiated contact with an electronic communications interface, and (ii) time data recording for each of the customers a time or time period at which the customer interacted with the electronic communications interface. The model predicts, for one or more time periods and segments of a population, a likelihood of successfully engaging with a person from the segment of the population. The scheduling includes prioritising the outbound communications to the sales leads during one or more defined time periods.
Owner:ISELECT
Intelligent monitoring, repair and control method of lead-acid battery pack and system thereof
InactiveCN101894981AExtend your lifeBurn out preventionElectrical testingSecondary cells servicing/maintenanceEmbedded systemCharge and discharge
The invention relates to an intelligent monitoring, repair and control method of a lead-acid battery pack and a system thereof. In the invention, full-range real-time parameter detection, repair, analysis, control, display and external communication overall monitoring are carried out on charge and discharge processes of the lead-acid battery pack, battery performance and repaired battery. The system can enable a repair instrument to automatically repair the battery by automatically sending a repair command to a lower computer. If the battery is judged to stay in a replacement state, the battery is indicated not to be used any longer and needs to be replaced with a new one. If the battery is judged to stay in an abnormity state, people must learn about specific circumstances on site.
Owner:SHENZHEN KEYERTECH INDAL CORP
Method and apparatus for geographically regulating inbound and outbound network communications
ActiveUS20070300296A1Multiple digital computer combinationsProgram controlGraphicsGraphical user interface
A system and method for regulating and analyzing inbound and outbound communications in and between computer networks on the basis of geographic security assertions are provided. Geographic information is collected, optimized, and shared between network objects to enforce network access control on the basis of configurable security assertions. Security assertions are configured and metrics displayed using maps and other geographic data in a graphical user interface.
Owner:IORHYTHM
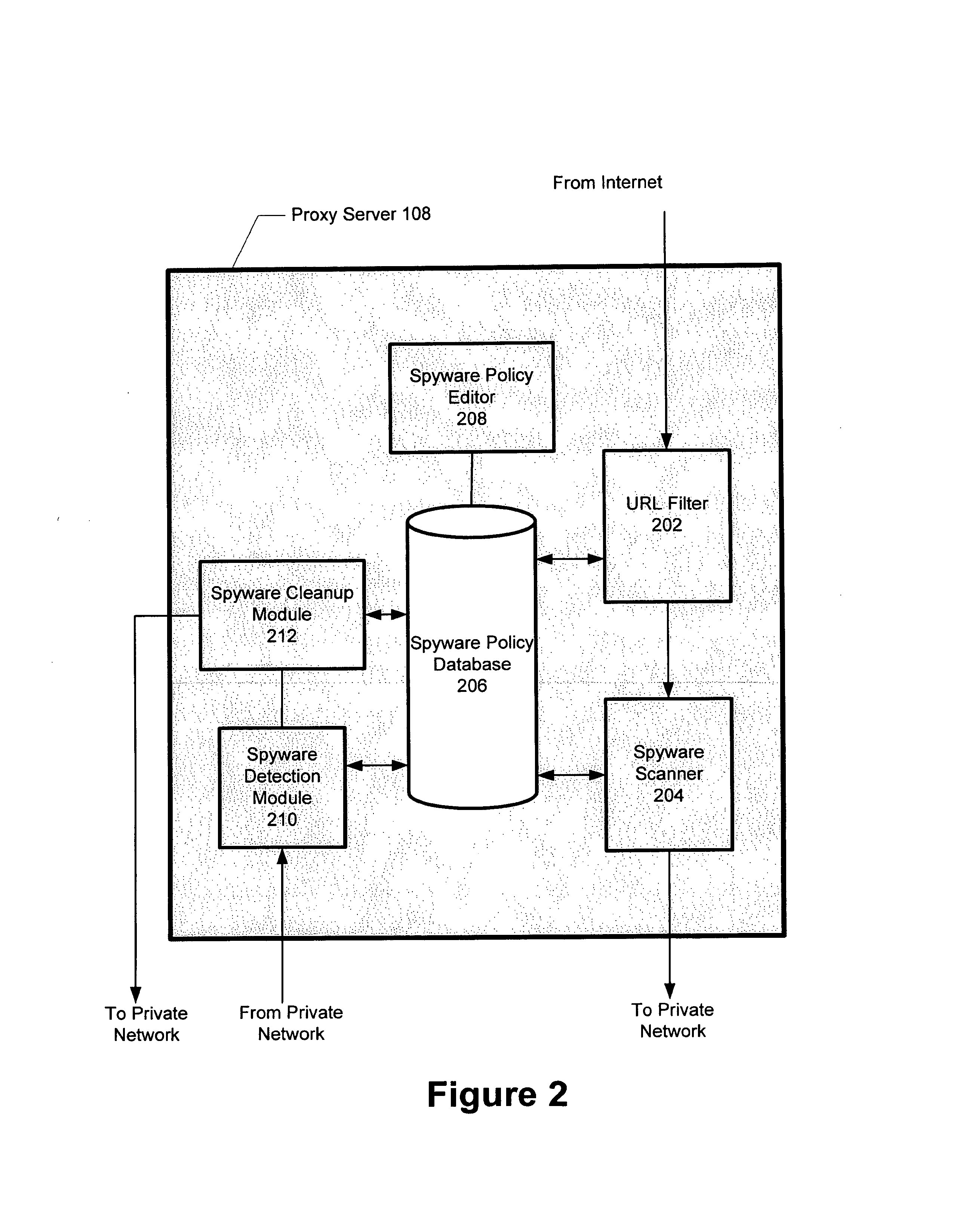
Methods and apparatus for blocking unwanted software downloads
ActiveUS20090138573A1Memory loss protectionError detection/correctionOutbound communicationComputer science
Methods and systems for blocking unwanted software downloads within a network. Such methods may thereby prevent (i) downloads of spyware from one or more identified locations, and / or (ii) certain outbound communications from the network and / or may also permit software downloads only from specified locations. In general, the policies are defined by rules specified by a network administrator or other user.
Owner:CA TECH INC
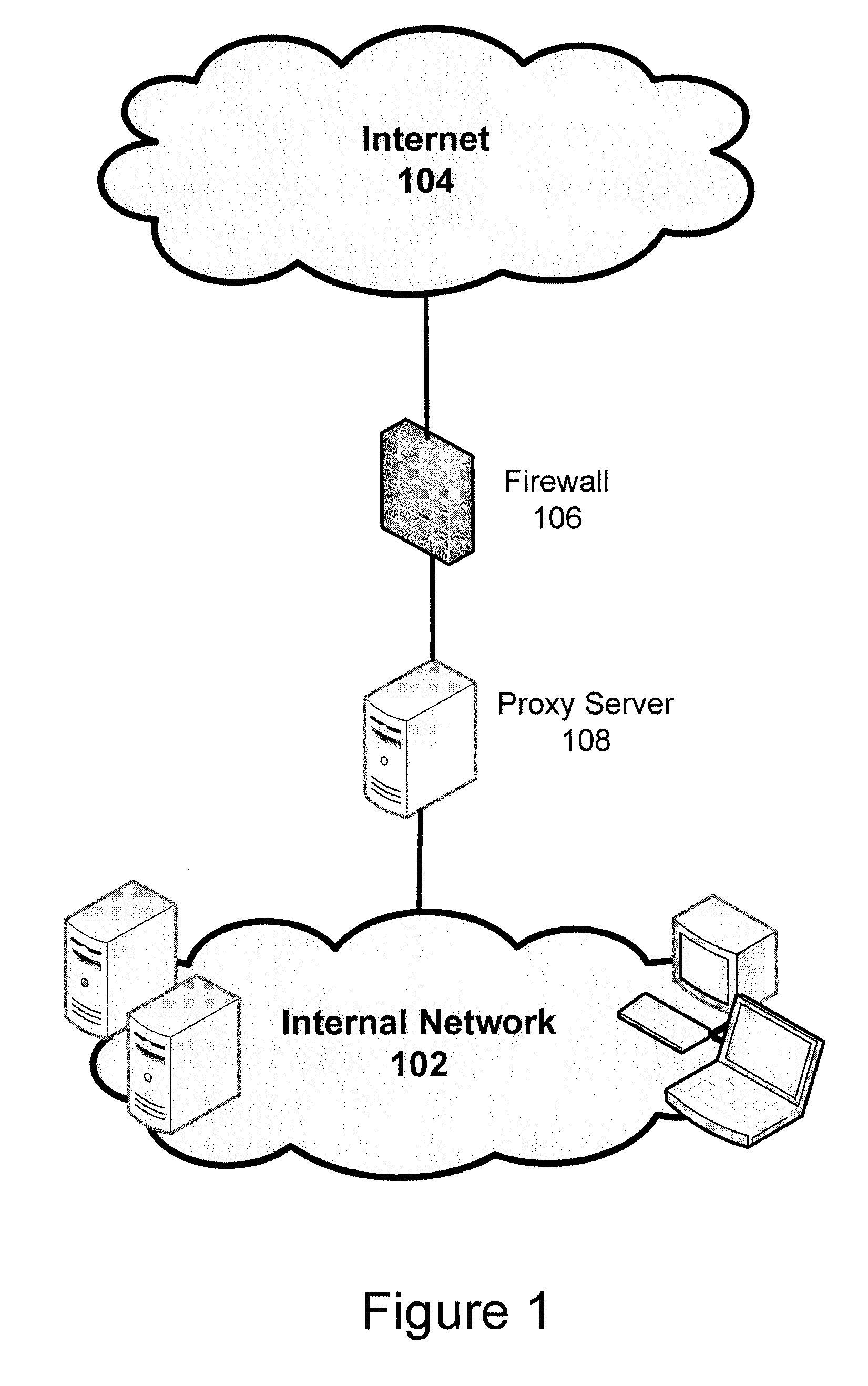
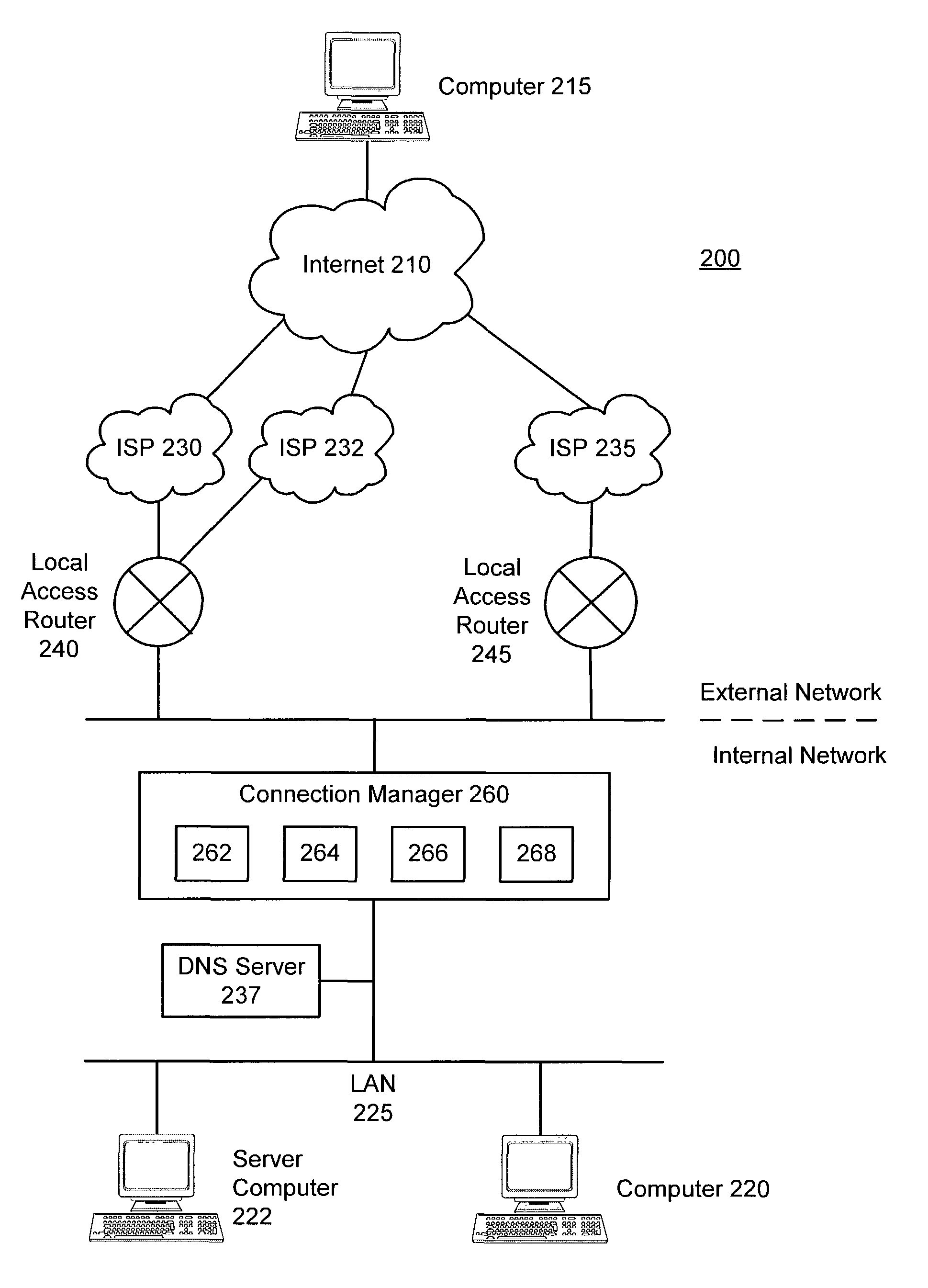
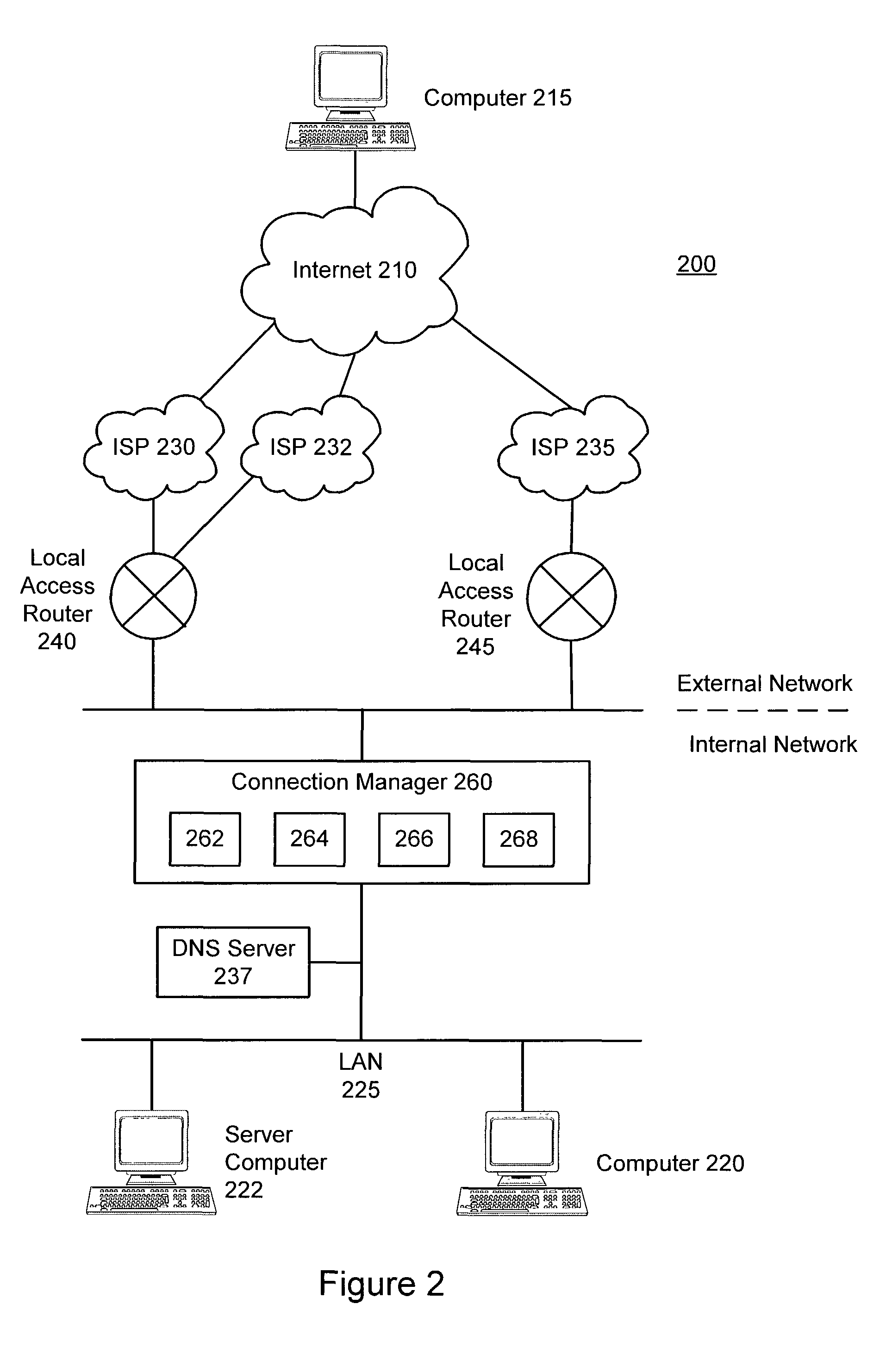
Distributed ISP load balancer
ActiveUS8145788B1Multiple digital computer combinationsTransmissionOutbound communicationService provision
The present invention relates to a device and method for managing inbound and outbound communications for a multi-homed network. A connection manager is located on a local network that is connected to an external network, such as the Internet, through multiple service provider connections. The connection manager intercepts all communication packets that are inbound to the local network from the external network and all packets that are outbound from the local network to the external network. The connection manager then associates the packets with a particular ISP connection based on the availability and bandwidth load status of the ISP connections.
Owner:EMC IP HLDG CO LLC
Post-termination contact management
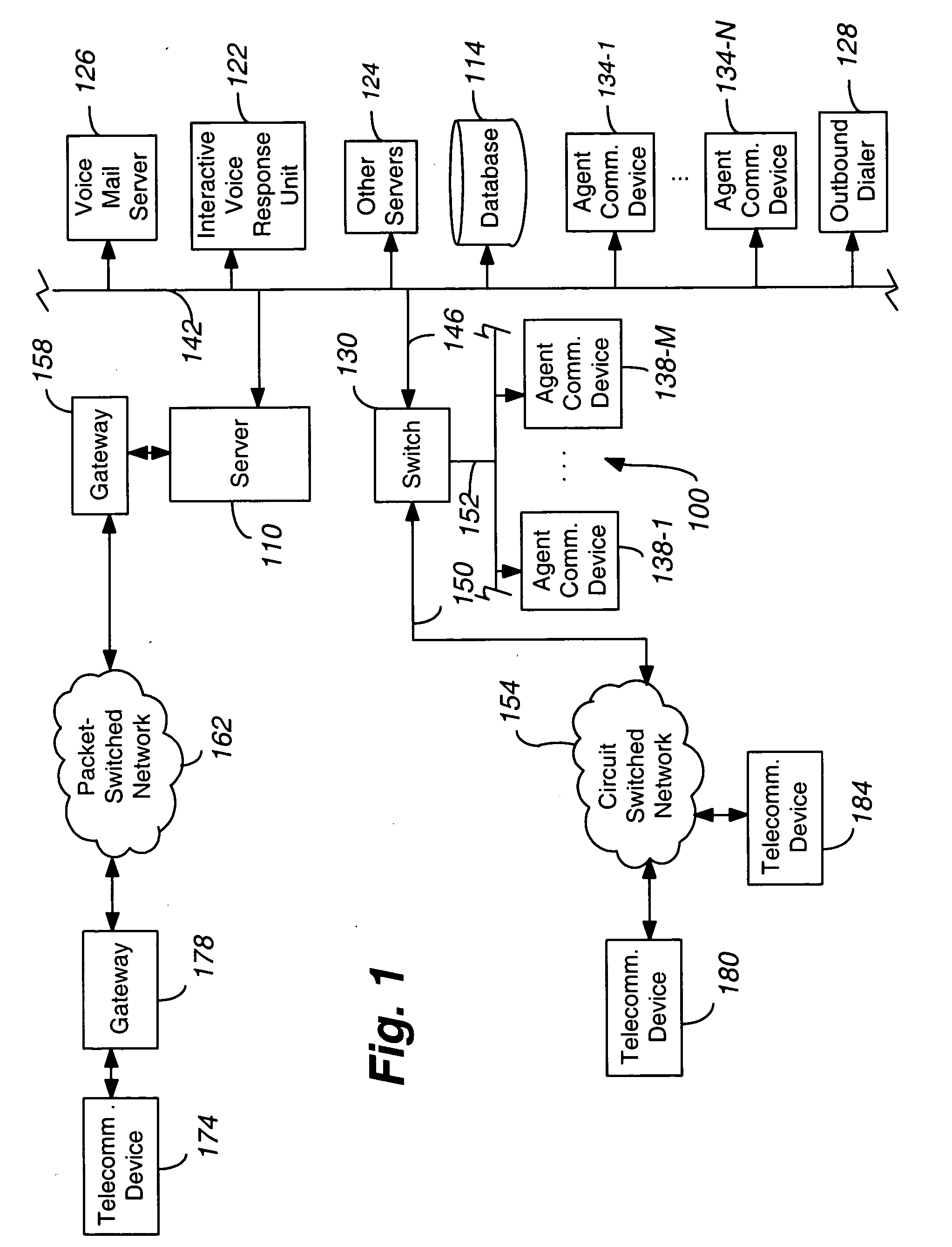
ActiveUS20050182672A1Shorten the timeSpecial service for subscribersConnection managementInbound communicationOutbound communication
The present invention is directed to a method for servicing a transaction in a contact center. When a communication associated with a transaction is terminated prematurely, special treatment may be provided to the transaction initiator. The special treatment includes: (a) maintaining, relative to other transactions, the assigned service priority for the transaction while the communication is disconnected and assigning the assigned service priority to a subsequent inbound communication from the transaction initiator; (b) scheduling a subsequent outbound communication to an external endpoint associated with the transaction initiator; (c) assigning to the transaction initiator a favored service priority when the subsequent inbound communication is received by the contact center; and (d) when, during the first communication, the transaction initiator selected at least one item as part of an electronic order and the first communication was terminated before the electronic order was completed, maintaining the item(s) in memory and providing the item(s) to the transaction initiator when the transaction initiator makes a further communication with the contact center.
Owner:AVAYA INC
Midleware broker
InactiveUS20100161821A1The method is simple and flexibleEasy and flexibleInterprogram communicationMultiple digital computer combinationsSearch data structureOutbound communication
A method of flow of an outbound communication to another module with interface using a broker which is able to review all data structures, regardless of complexity, as being comprised of a finite set of primitive data types (e.g. integer, float etc.) and with reference to the repository determine a mechanism for reading and writing these types to enable processing of structures of arbitrary complexity, wherein the rules and mechanisms for reading these basic types are defined by the protocol and once the rules are captured allow processing of any message over this protocol
Owner:SLAMKOVIC RICHARD D
Methods and apparatus for blocking unwanted software downloads
ActiveUS8316446B1Memory loss protectionUnauthorized memory use protectionOutbound communicationComputer science
Owner:CA TECH INC
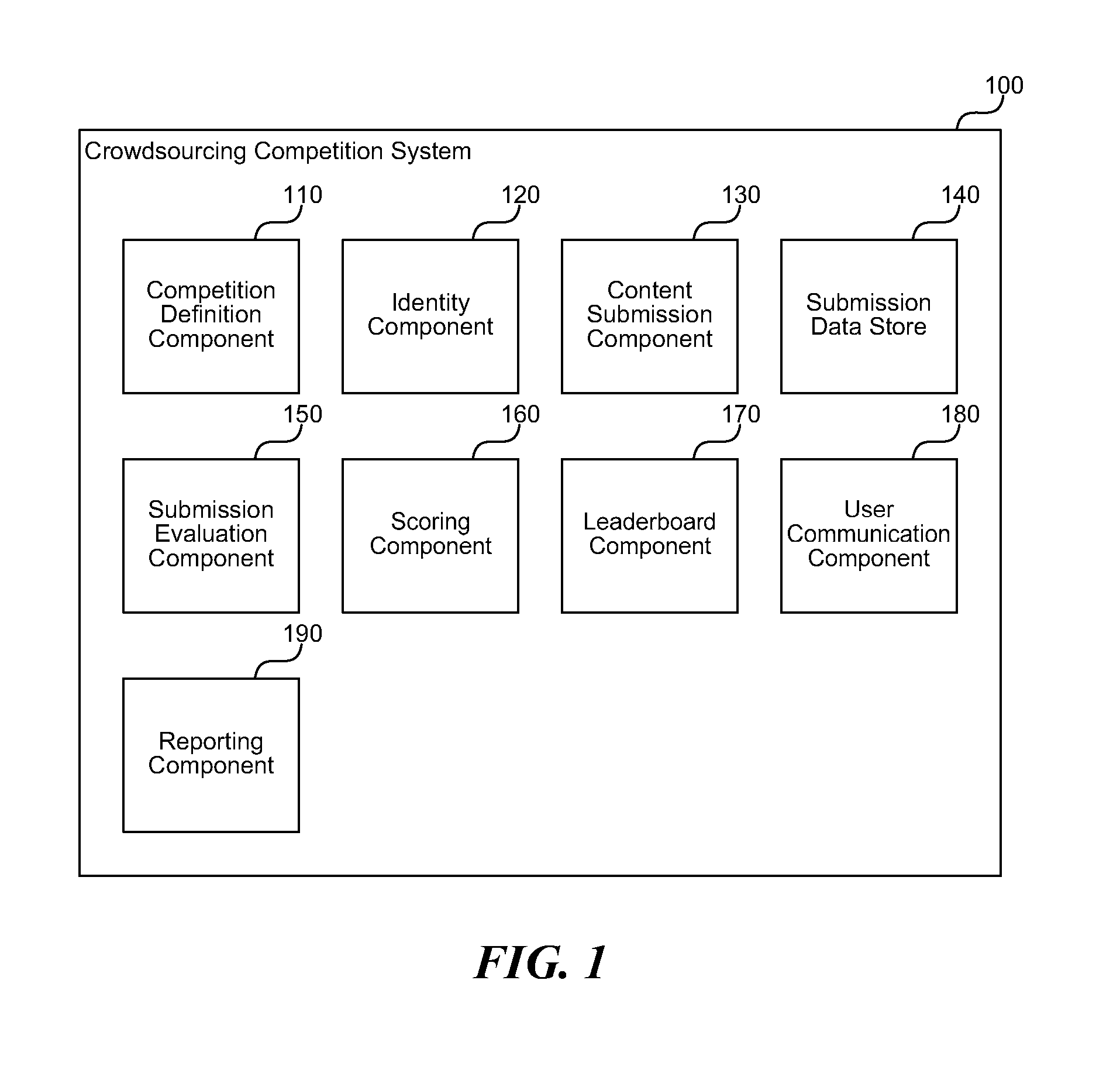
Crowd-sourced competition platform
InactiveUS20110307304A1Easy to identifyVoting apparatusDigital data processing detailsOutbound communicationWeb service
A crowdsourcing competition system is described herein that provides a reusable mechanism by which an organization can host a cloud-based crowdsourcing competition. The system facilitates identification of individuals, forums, submission of user-generated content (challenge submissions), automated scoring of user-generated content against test sets, automated outbound communication to participants, and web services for leaderboard functionality. The system provides workflows for users to submit submissions and for the system to receive and organize submissions. Thus, the crowdsourcing competition system provides a generic platform and automated workflow for holding crowd-sourced competitions and automating workflow of user generated content submissions.
Owner:MICROSOFT TECH LICENSING LLC
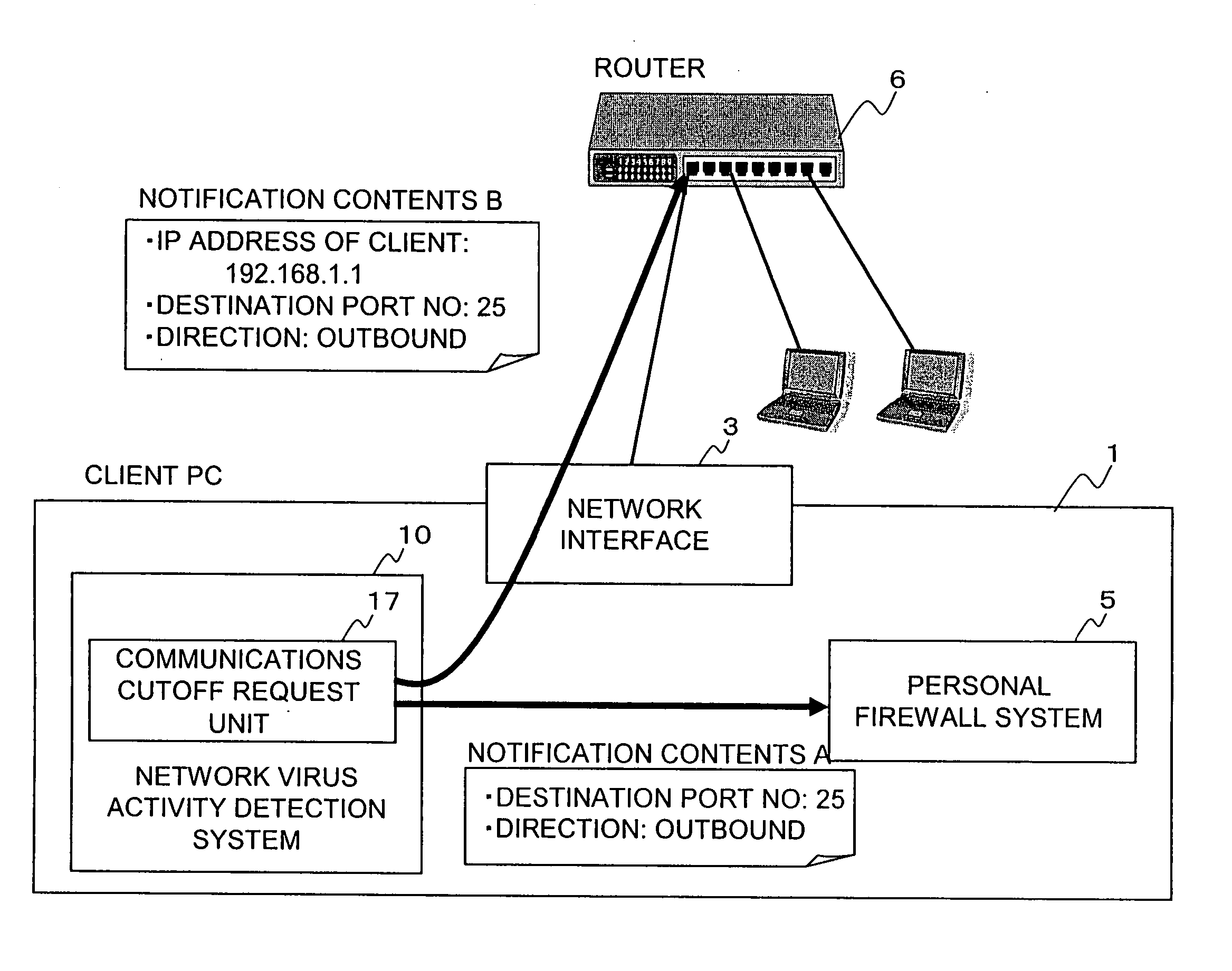
Network virus activity detecting system, method, and program, and storage medium storing said program
InactiveUS20060085857A1Efficient detectionGrowth inhibitionMemory loss protectionUser identity/authority verificationOutbound communicationData mining
In this system, a monitor unit monitors outbound communications through a network interface. A process designation unit designates a process 2X which has generated communications. A process tree obtaining unit obtains and outputs process tree information for designation of an upper process to the process 2X. A discrimination unit refers to an illegal rule file for definition of an illegal process by a combination of a process and an upper process which have generated communications, and determines whether or not a process 2X is illegal according to communications information, process information, and process tree information. A process stop unit stops a process 2X determined to be illegal. A notification unit notifies a user of the stop of the process 2X.
Owner:FUJITSU LTD
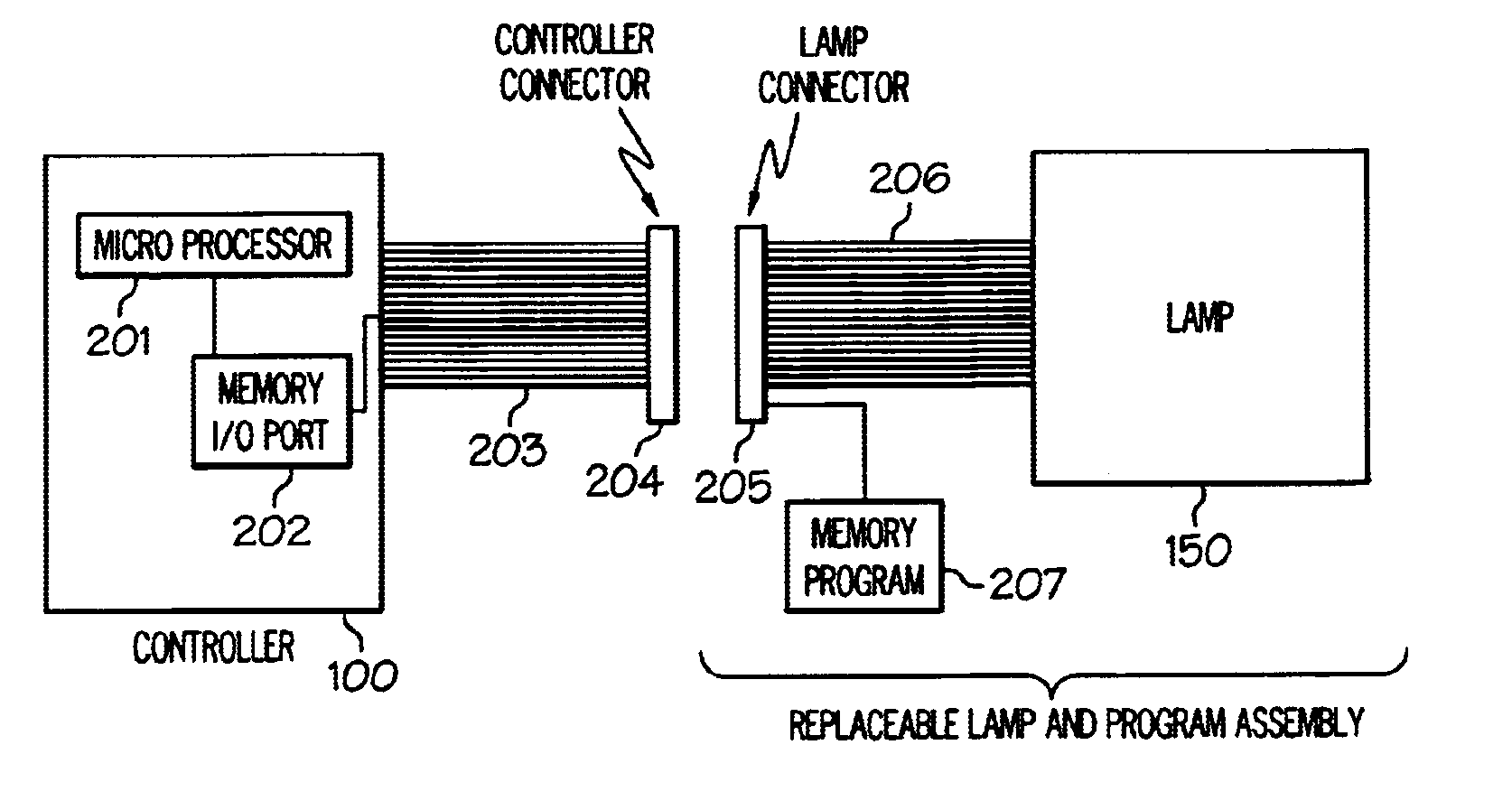
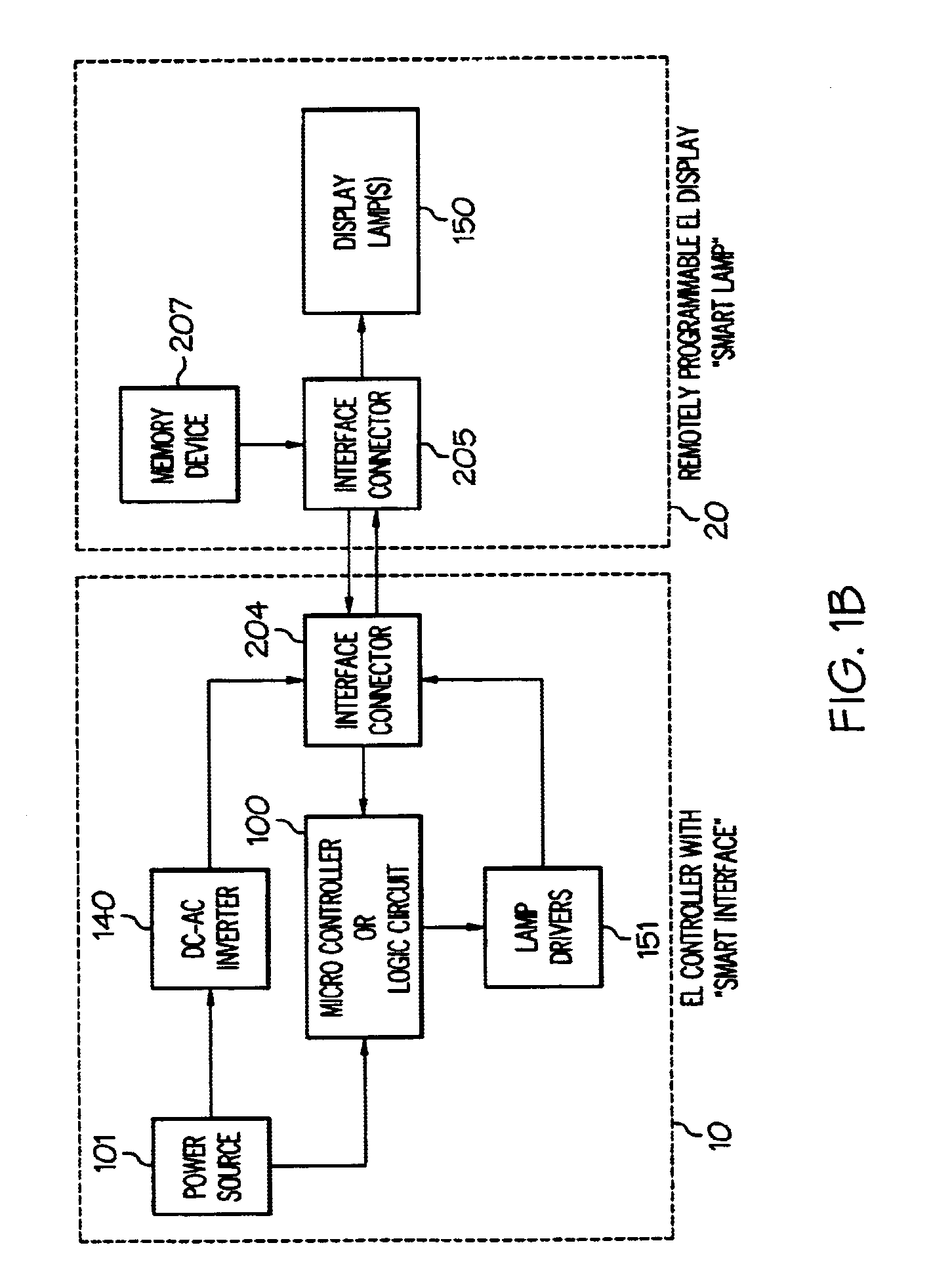
Remotely programmable control device for use in electroluminescent display and lighting applications
InactiveUS6771256B1Cathode-ray tube indicatorsInput/output processes for data processingElectricityOutbound communication
Described is a remotely programmable control device for use in electroluminescent display and lighting applications. Elements of this invention include a power supply, various inverters / wave form conditioners, a motherboard, inbound / outbound communications capability, motion-sensing devices, ambient light sensing facilities, and a floppy disk reader. Remote programmability is achieved through several methods including detecting the driving instructions from the lamp display itself, or downloading data from a remote network or a floppy disk.
Owner:IGRAPHICS
User-controlled telecommunications system
InactiveCN101112053ATime-division multiplexData switching networksTelecommunications networkOutbound communication
Disclosed are systems and methods that enable an end user to control the parameters, behavior, and identity of network communications regardless of the limitations placed upon these controls by the end user's communications device or communications service provider. An intermediate media proxy resides on a telecommunications network and accepts inbound and outbound communications to and from a network communication device. The intermediate media proxy functions as an intermediary for network communications that occur between the network communications device and other network communications devices. In this manner, the intermediate media proxy can control various features of the communications independent of limitations enacted by the end user's communications device or communications service provider.
Owner:TALKPLUS
Method and apparatus for geographically regulating inbound and outbound network communications
A system and method for regulating and analyzing inbound and outbound communications in and between computer networks on the basis of geographic security assertions are provided. Geographic information is collected, optimized, and shared between network objects to enforce network access control on the basis of configurable security assertions. Security assertions are configured and metrics displayed using maps and other geographic data in a graphical user interface.
Owner:IORHYTHM
Method for supporting high priority calls on a congested WAN link
InactiveUS6977898B1Interconnection arrangementsError preventionTelecommunications linkOutbound communication
A network node is configured to negotiate for connections for high priority calls (e.g., voice calls) received at the node in the face of otherwise congested outbound communication links. The negotiation is conducted in a fashion that will preserve connections for existing calls associated with the node. For example, the negotiation may be conducted so as to cause one or more of the existing calls to consume less bandwidth over the outbound communication links than was consumed at a time prior to reception of the high priority calls. Such negotiations may be initiated depending on the availability of codec resources and / or compression schemes at the node and may be conducted using OAM cells.
Owner:CISCO TECH INC
IP application service providing system
InactiveUS20080075097A1Easy to provideData switching by path configurationNetwork connectionsInbound communicationOutbound communication
An IP application service providing method enabling inbound communication in IP application communication intended between an internal node concealed from an outside network and belonging to an inside network and an external node belonging to the outside network through a gateway device set to permit only outbound communication, includes periodically transmitting a control packet aiming at notifying of a control channel port and at maintaining a communication permission entry of a control channel path to a connection support device on the outside network from the internal node subordinated to the gateway device; notifying the internal node of a connecting destination address / port pair associated with the external node via the control channel from the connection support device; and actively opening a data channel of an IP application to the notified connecting destination address / port pair.
Owner:FUJITSU LTD
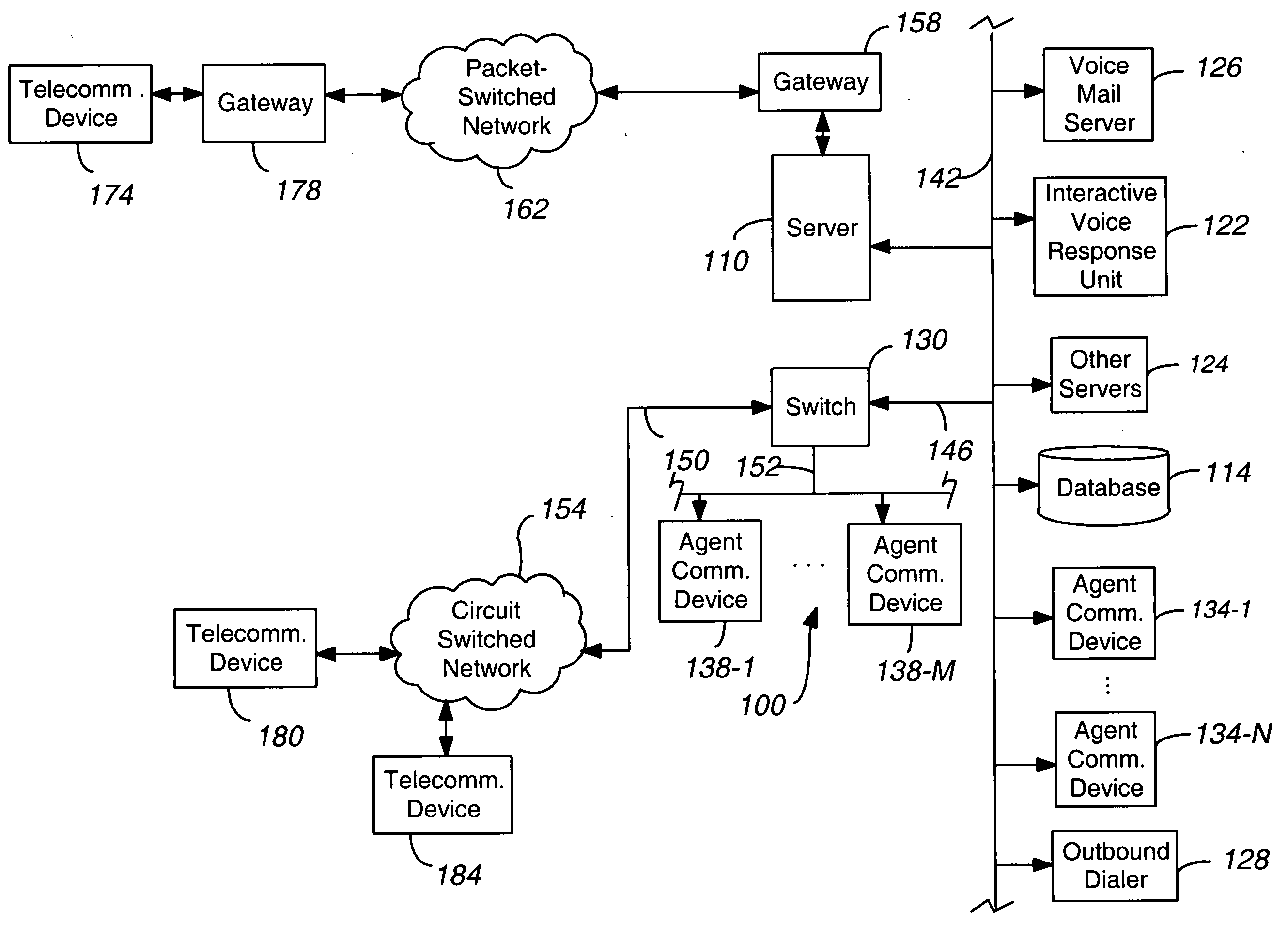
Method, device, and system for providing a survivability gateway service
A method and apparatus dynamically pair a user's communication devices with a personal survivability gateway. The gateway can support the establishment of communication services in case of a network failure between a site where the user's communication devices are located and the site that provides the user's communication services. Preferably, the survivability gateway is configured so that if a network failure occurs, the user does not experience service degradation, or at least significant service degradation. For instance, the user's inbound and outbound communications during such an outage may be routed through his personal survivability gateway and a survivability proxy to limit, if not eliminate such service degradation.
Owner:RINGCENTRAL INC
Post-termination contact management
ActiveUS7729490B2Shorten the timeSpecial service for subscribersConnection managementInbound communicationOutbound communication
The present invention is directed to a method for servicing a transaction in a contact center. When a communication associated with a transaction is terminated prematurely, special treatment may be provided to the transaction initiator. The special treatment includes: (a) maintaining, relative to other transactions, the assigned service priority for the transaction while the communication is disconnected and assigning the assigned service priority to a subsequent inbound communication from the transaction initiator; (b) scheduling a subsequent outbound communication to an external endpoint associated with the transaction initiator; (c) assigning to the transaction initiator a favored service priority when the subsequent inbound communication is received by the contact center; and (d) when, during the first communication, the transaction initiator selected at least one item as part of an electronic order and the first communication was terminated before the electronic order was completed, maintaining the item(s) in memory and providing the item(s) to the transaction initiator when the transaction initiator makes a further communication with the contact center.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com