Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
75 results about "Inbound communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
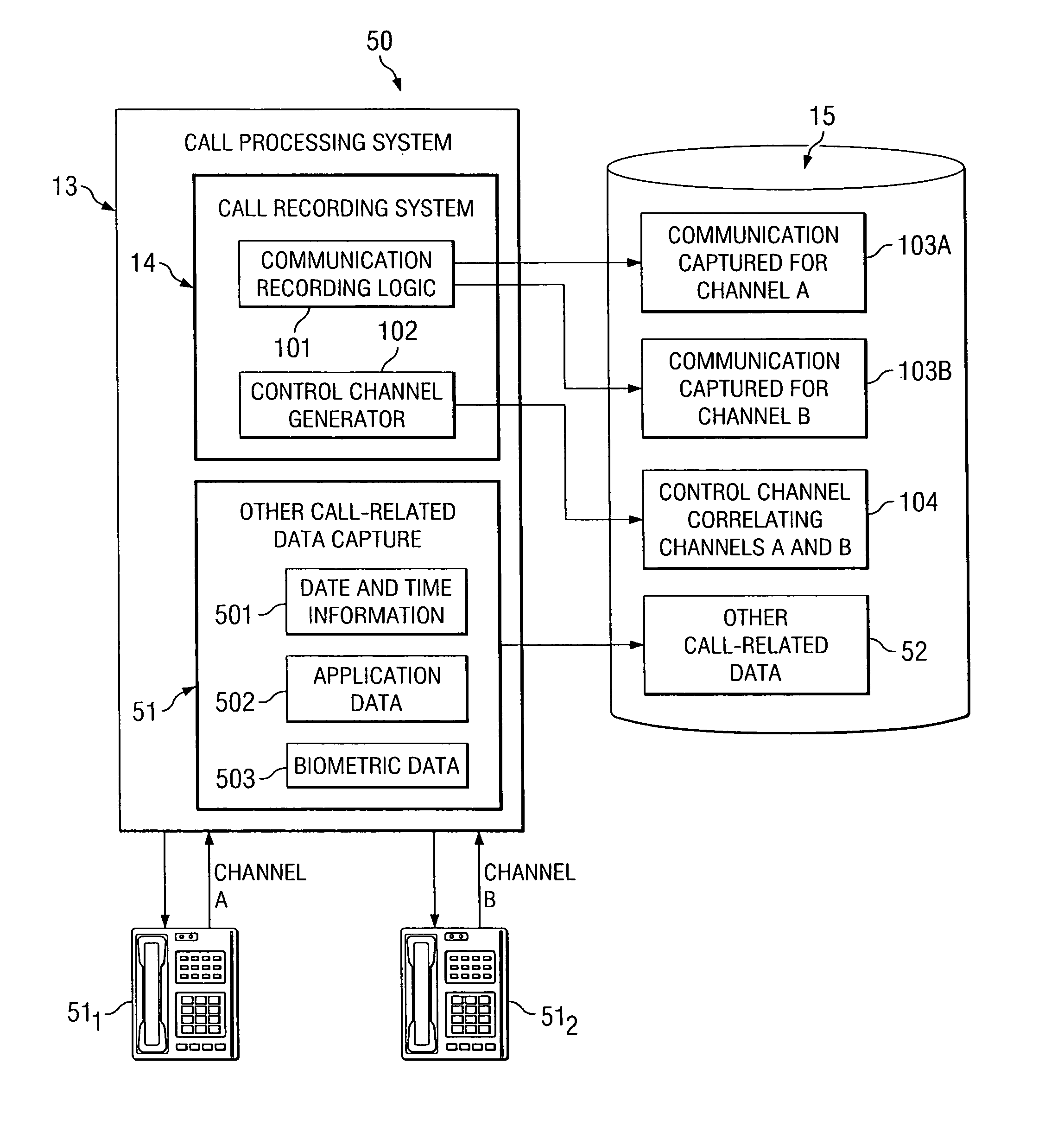
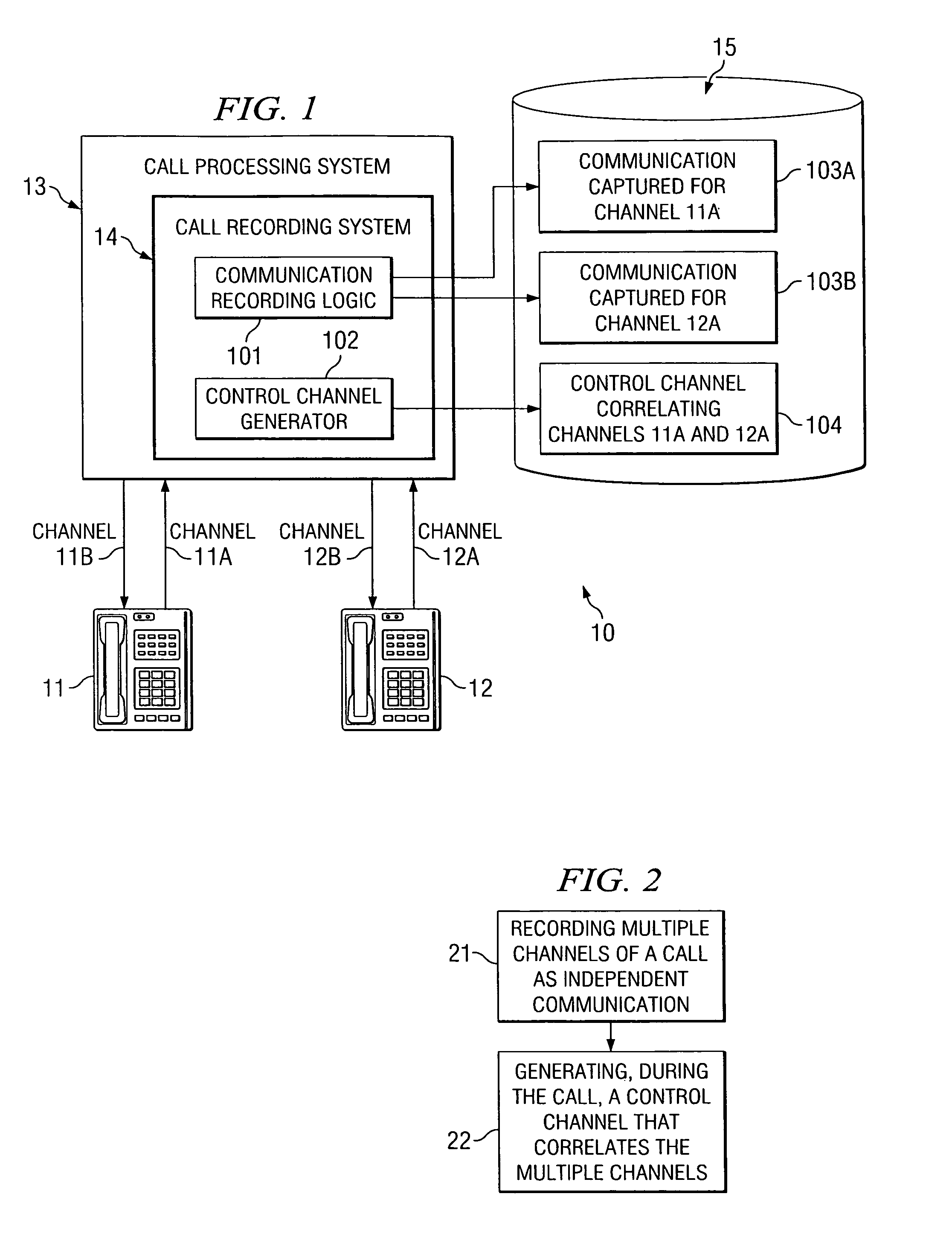
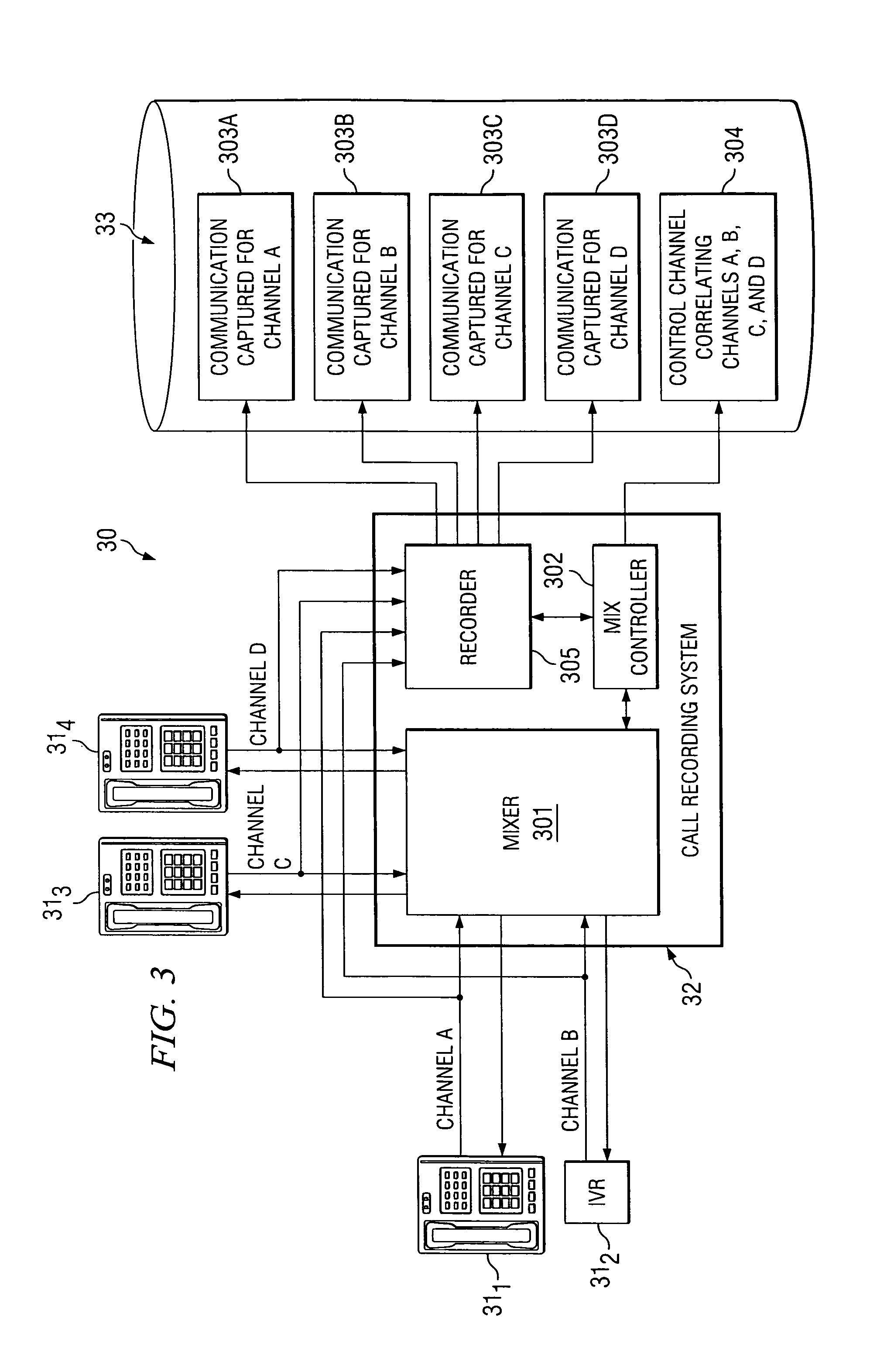
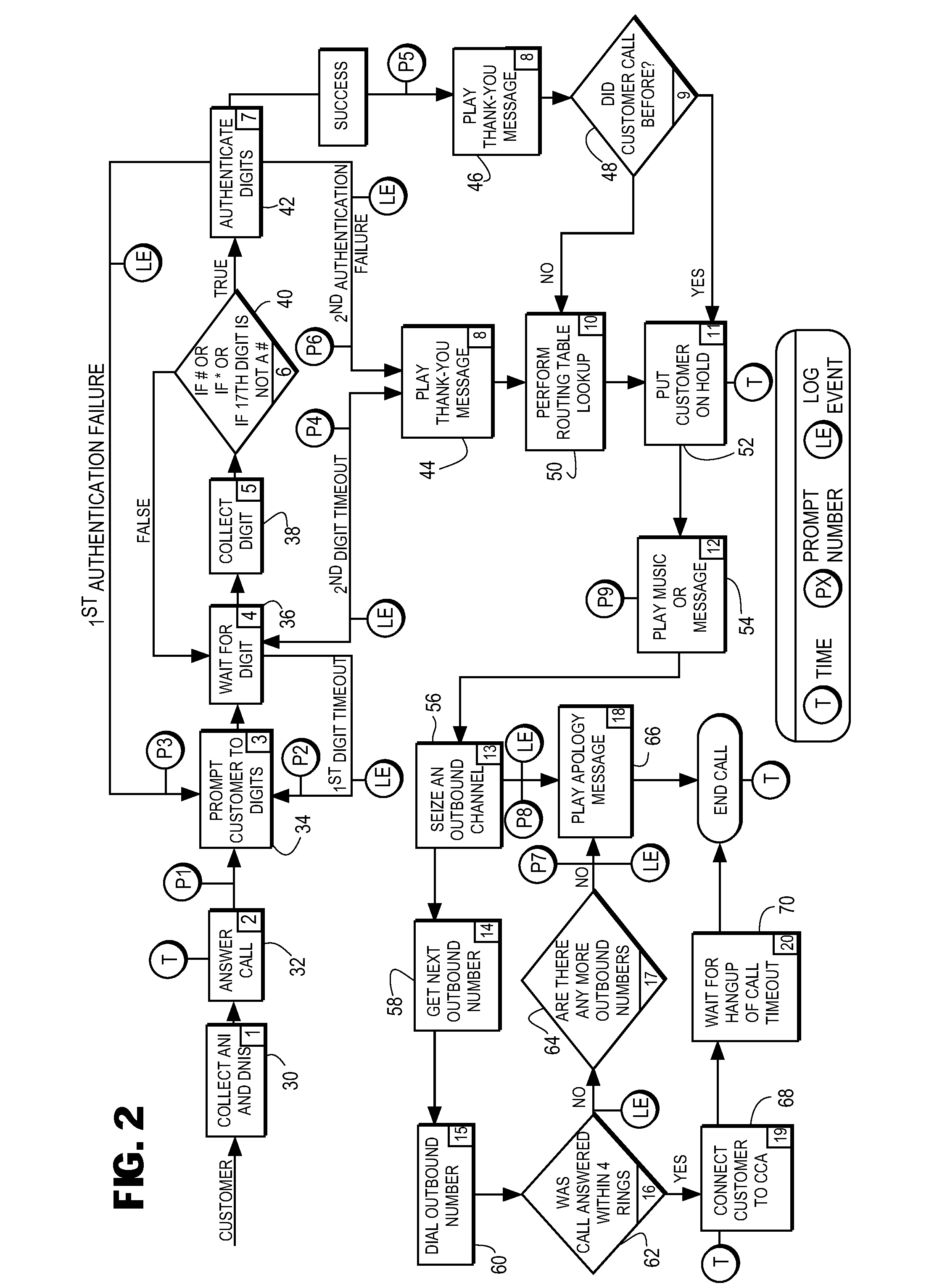
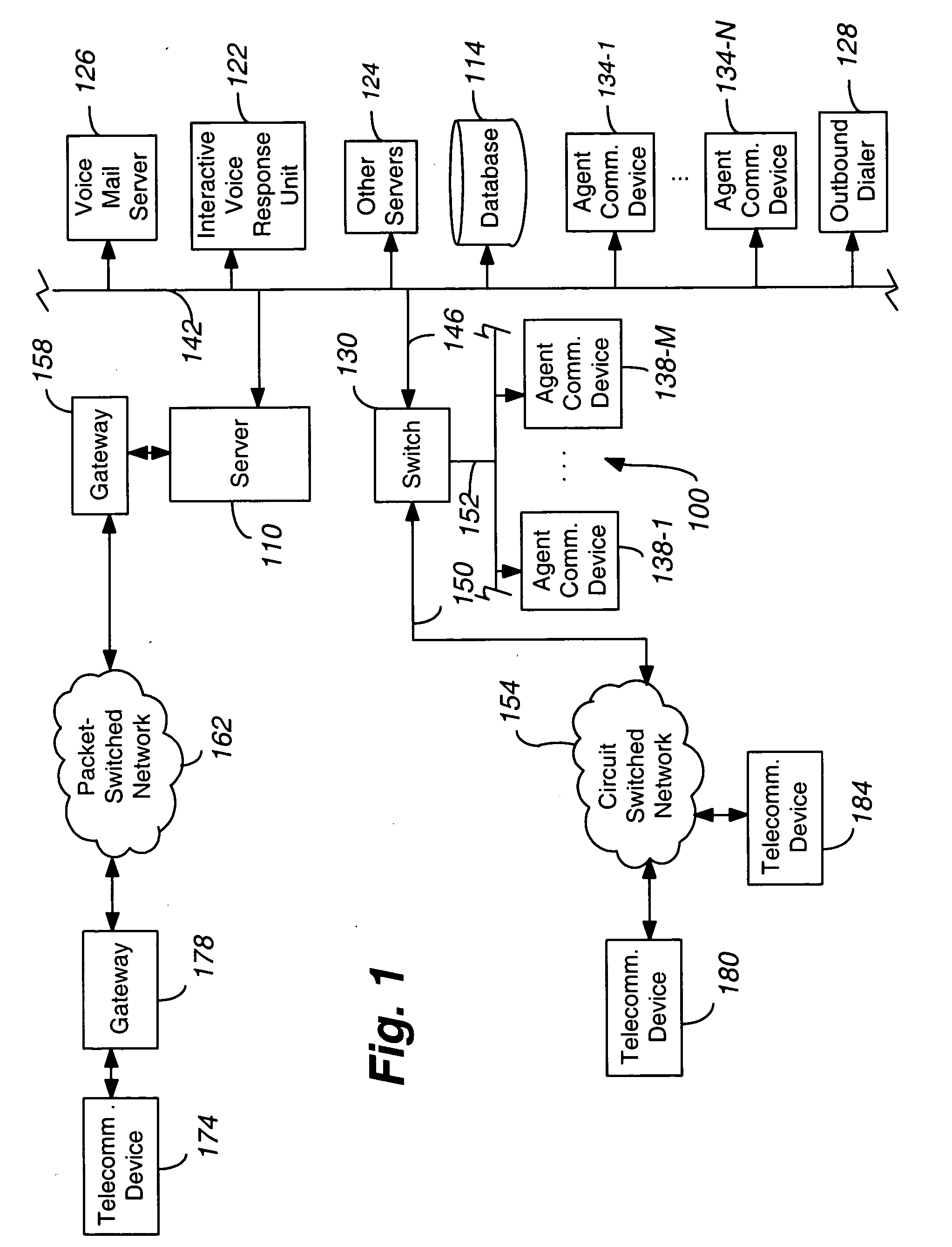
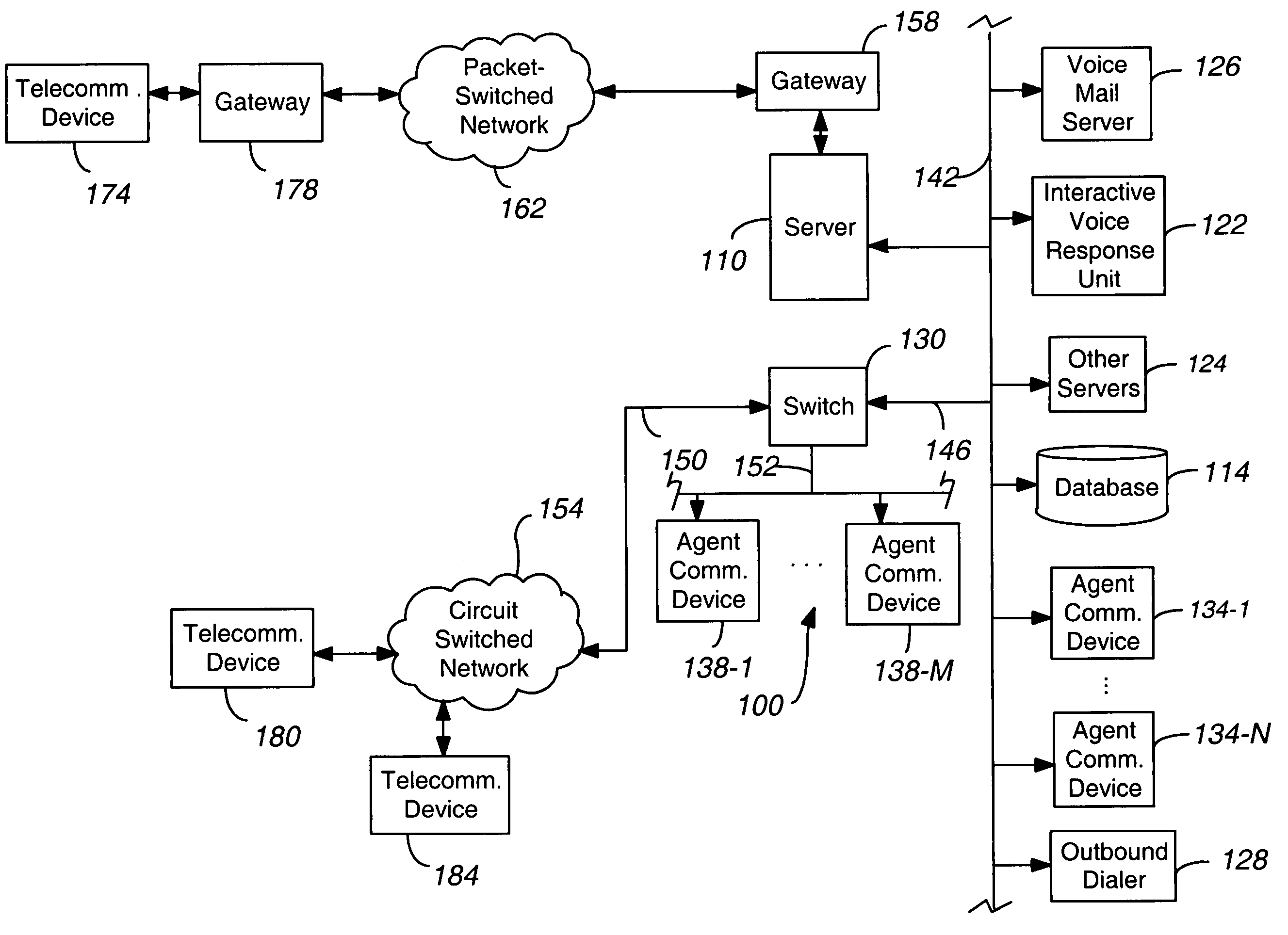
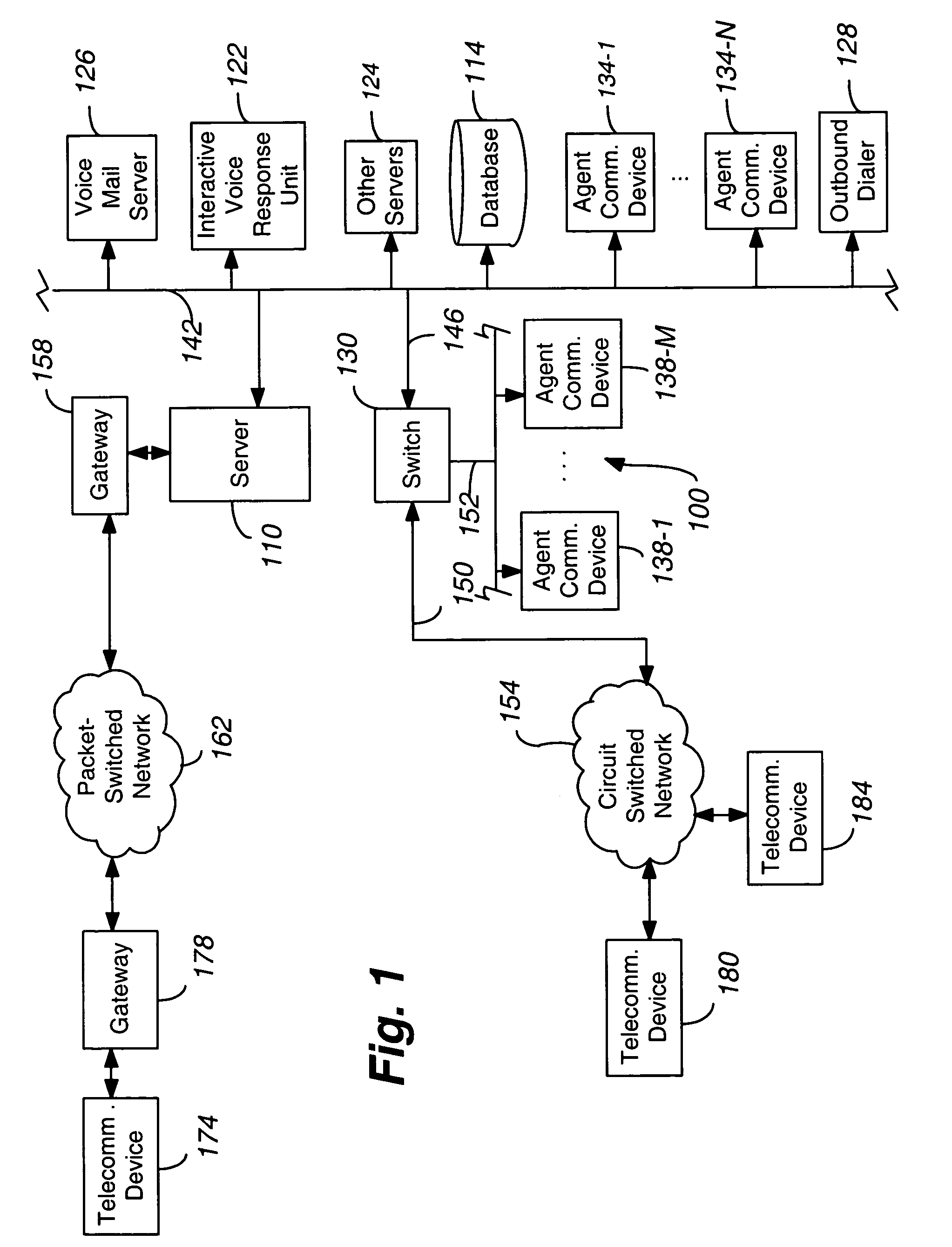
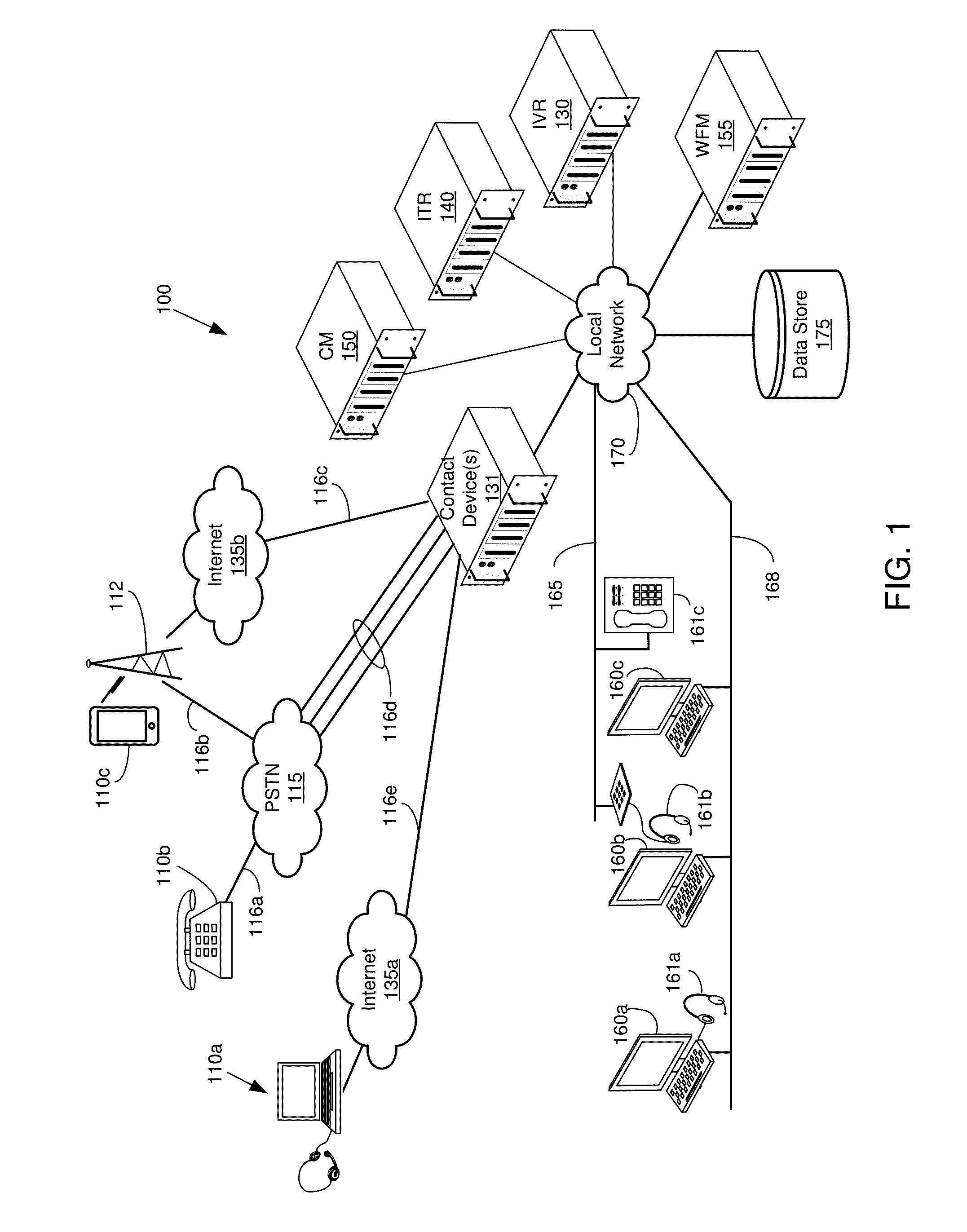
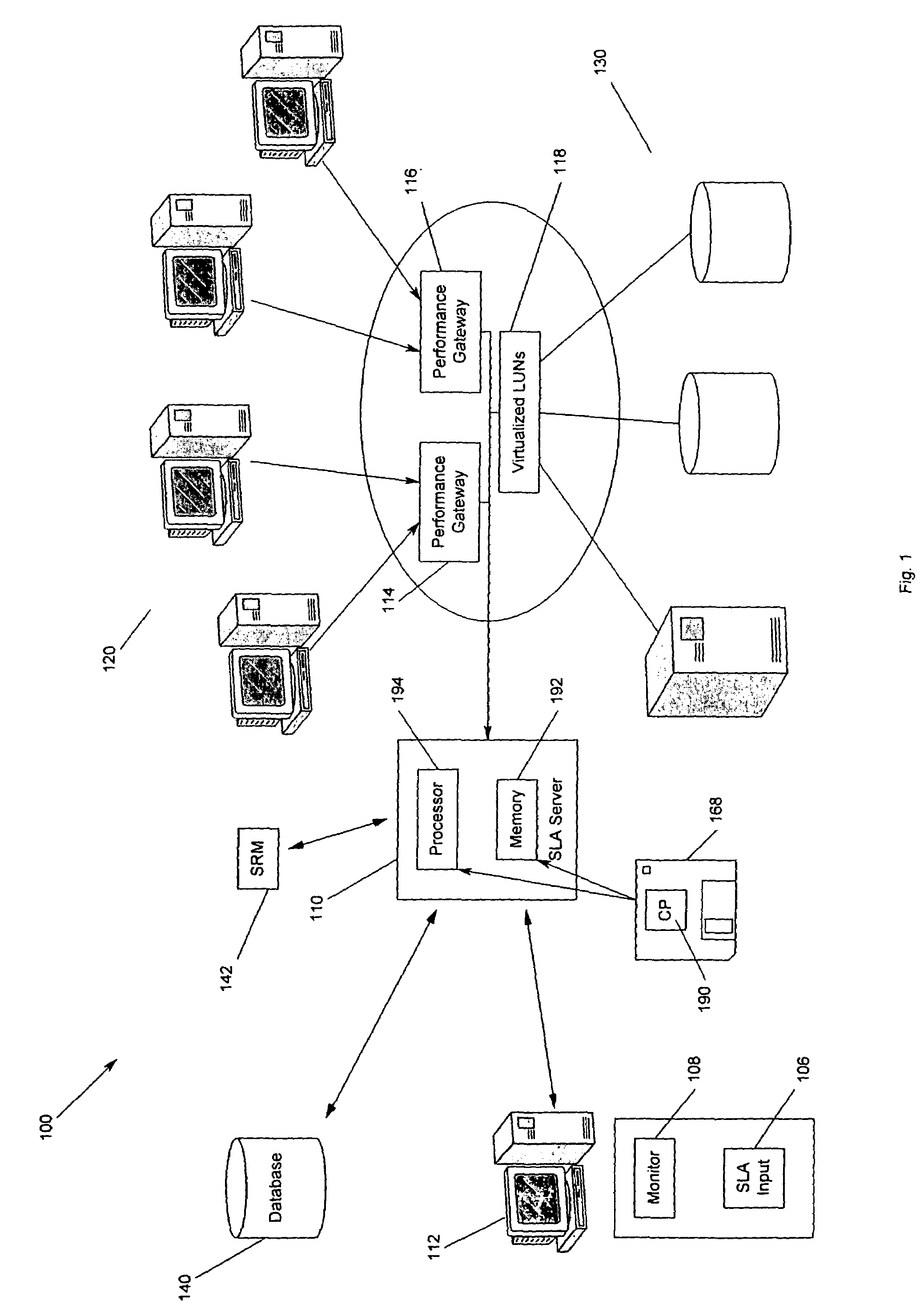
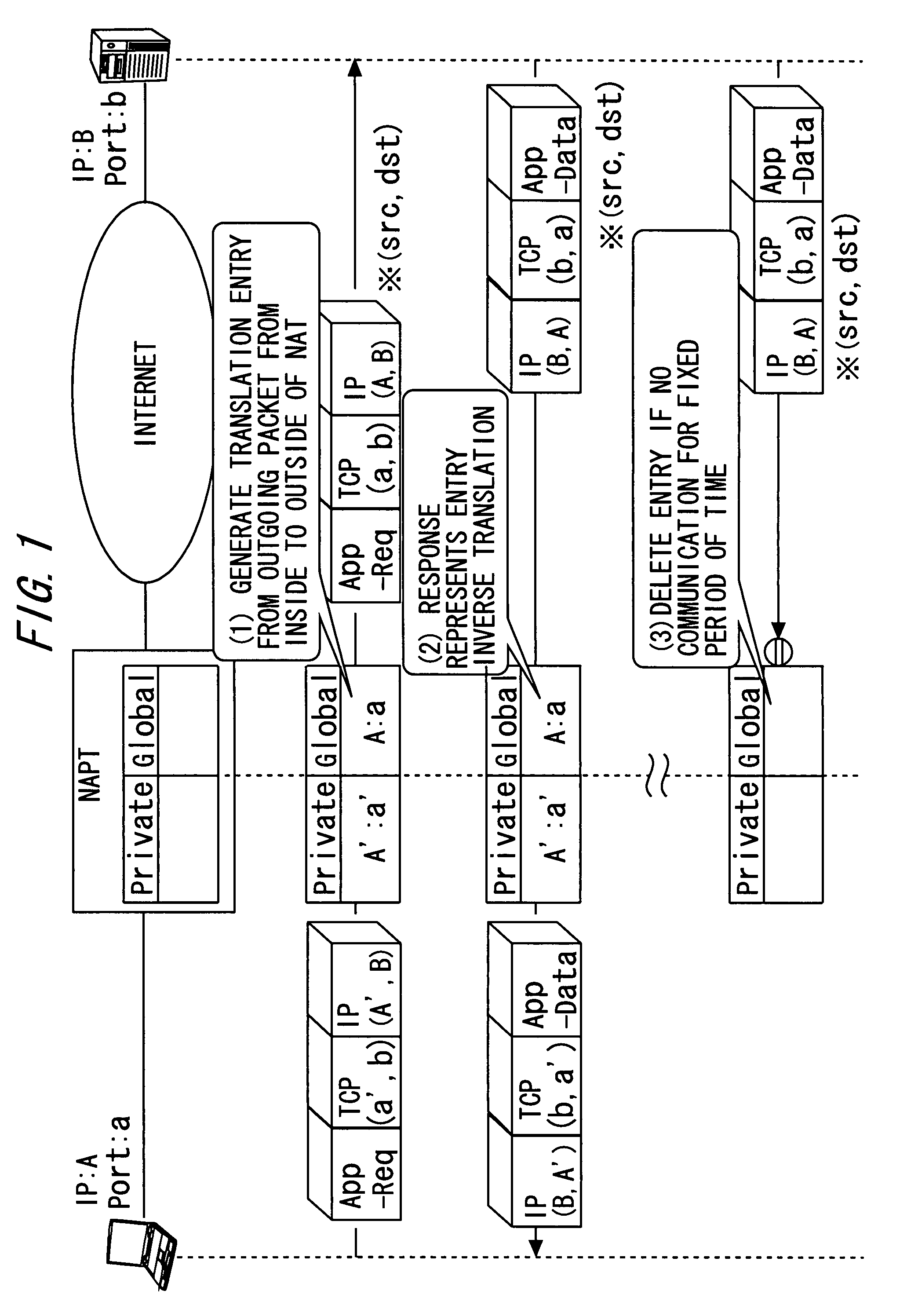
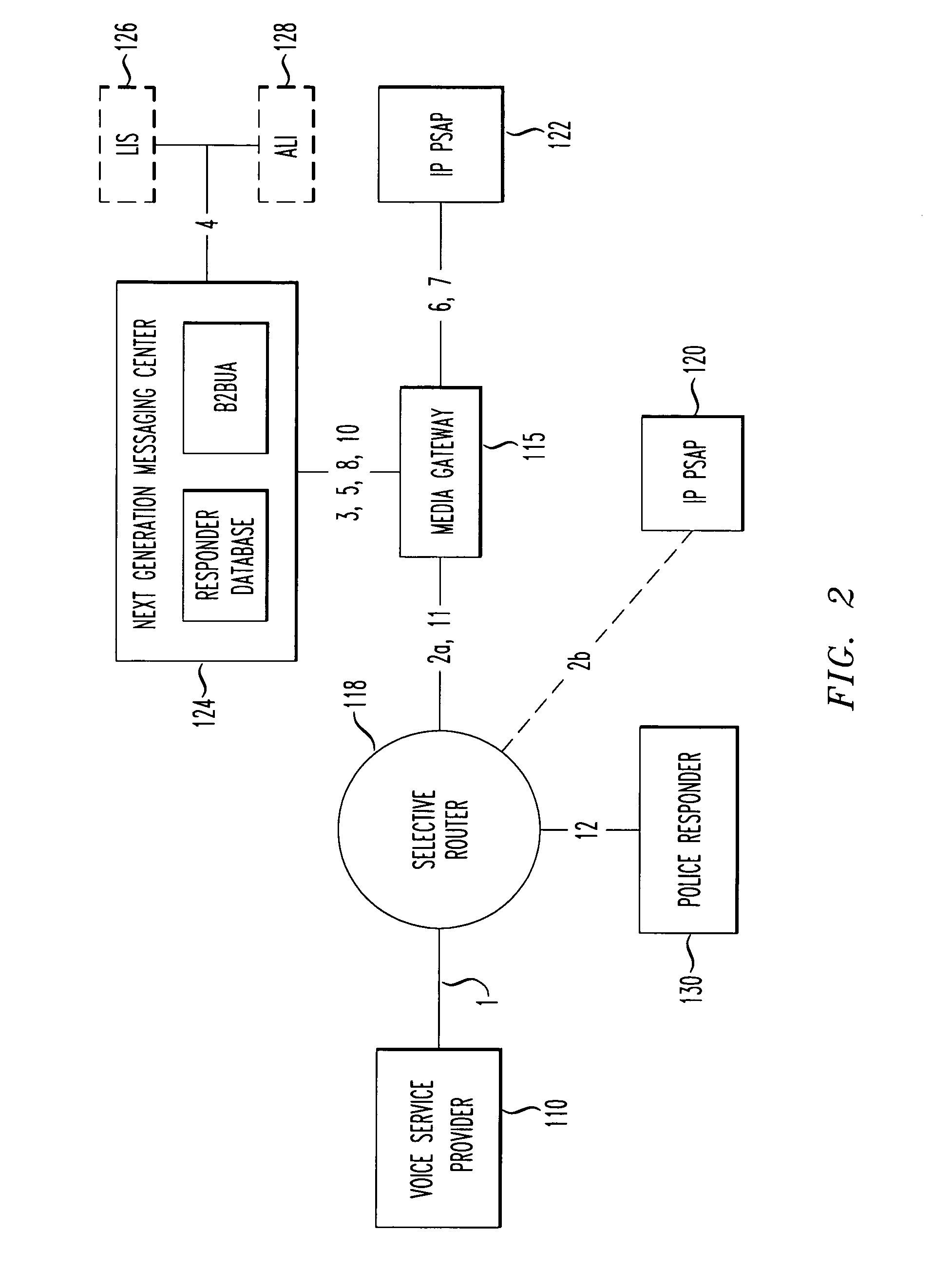
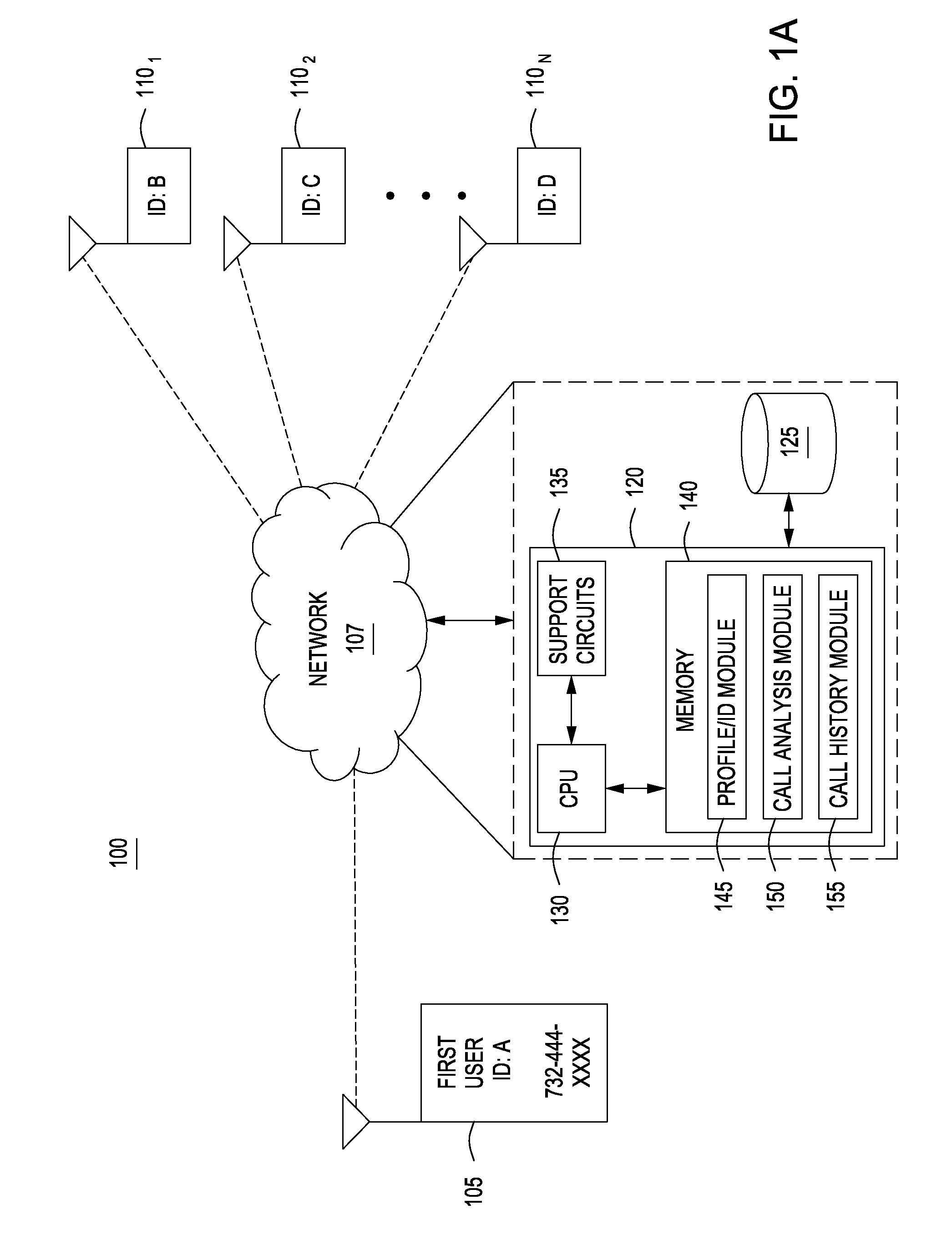
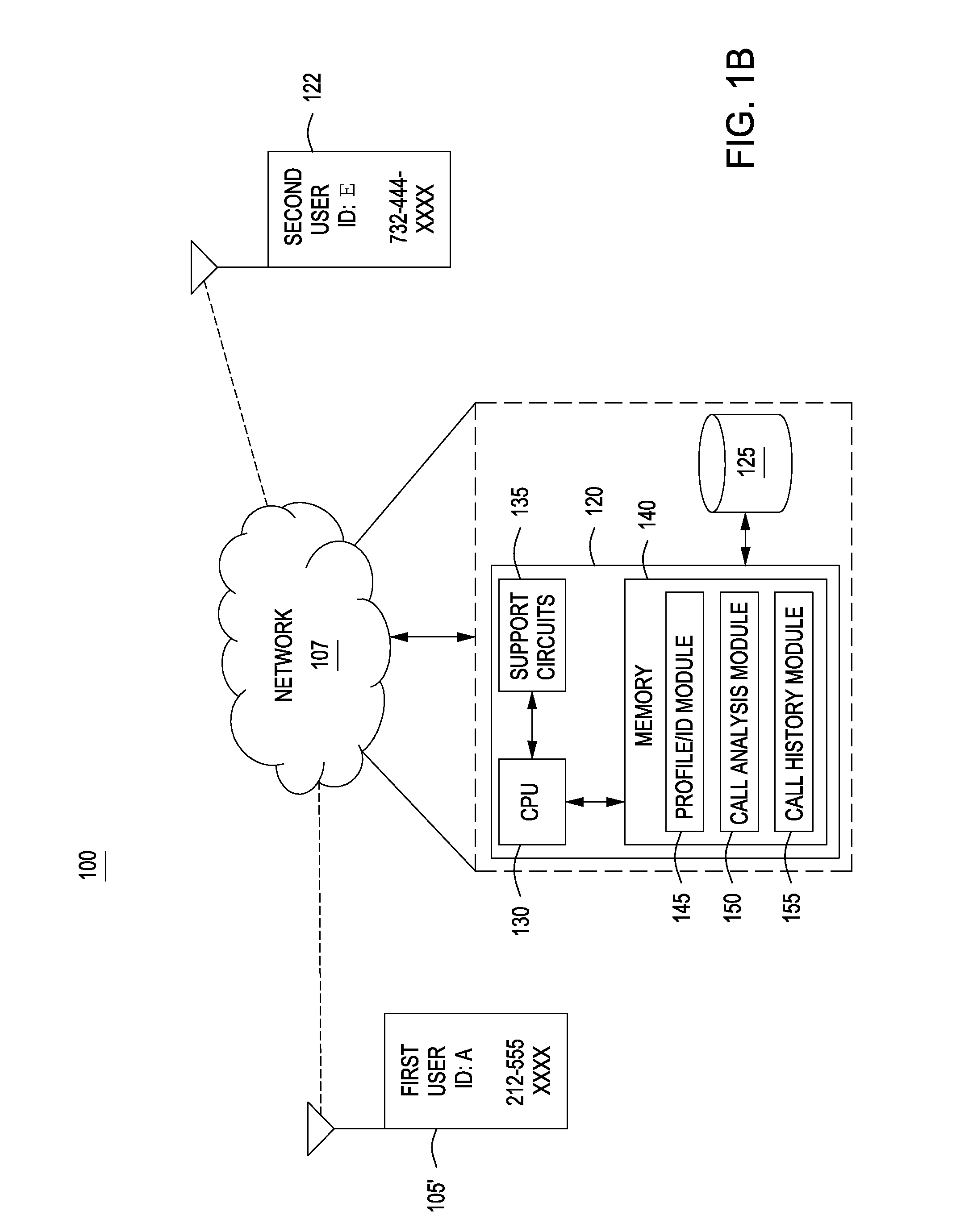
System and method for multi-channel recording
InactiveUS8135115B1Good flexibilityAccurately re-creatingSpecial service provision for substationMultiplex system selection arrangementsInbound communicationControl channel
Embodiments of the present invention are directed generally to recording communication of a call utilizing a multi-channel recording technique. According to one exemplary embodiment, inbound communication from each party to a call (e.g., from each communication device that is party to a call) to a recording system is assigned to a separate channel, and communication on each channel is independently recorded. Further, during the call, a control channel is generated that correlates the multiple communication channels. The independently recorded communication channels and control channel may be used to analyze a recorded call from any desired perspective. For instance, communication from a given party may be analyzed in isolation. Further, the control channel enables the recorded multiple communication channels to be correlated such that the communication received (e.g., heard) by any selected party may be accurately re-created for analysis thereof.
Owner:SECURUS TECH
Configurable phone with interactive voice response engine
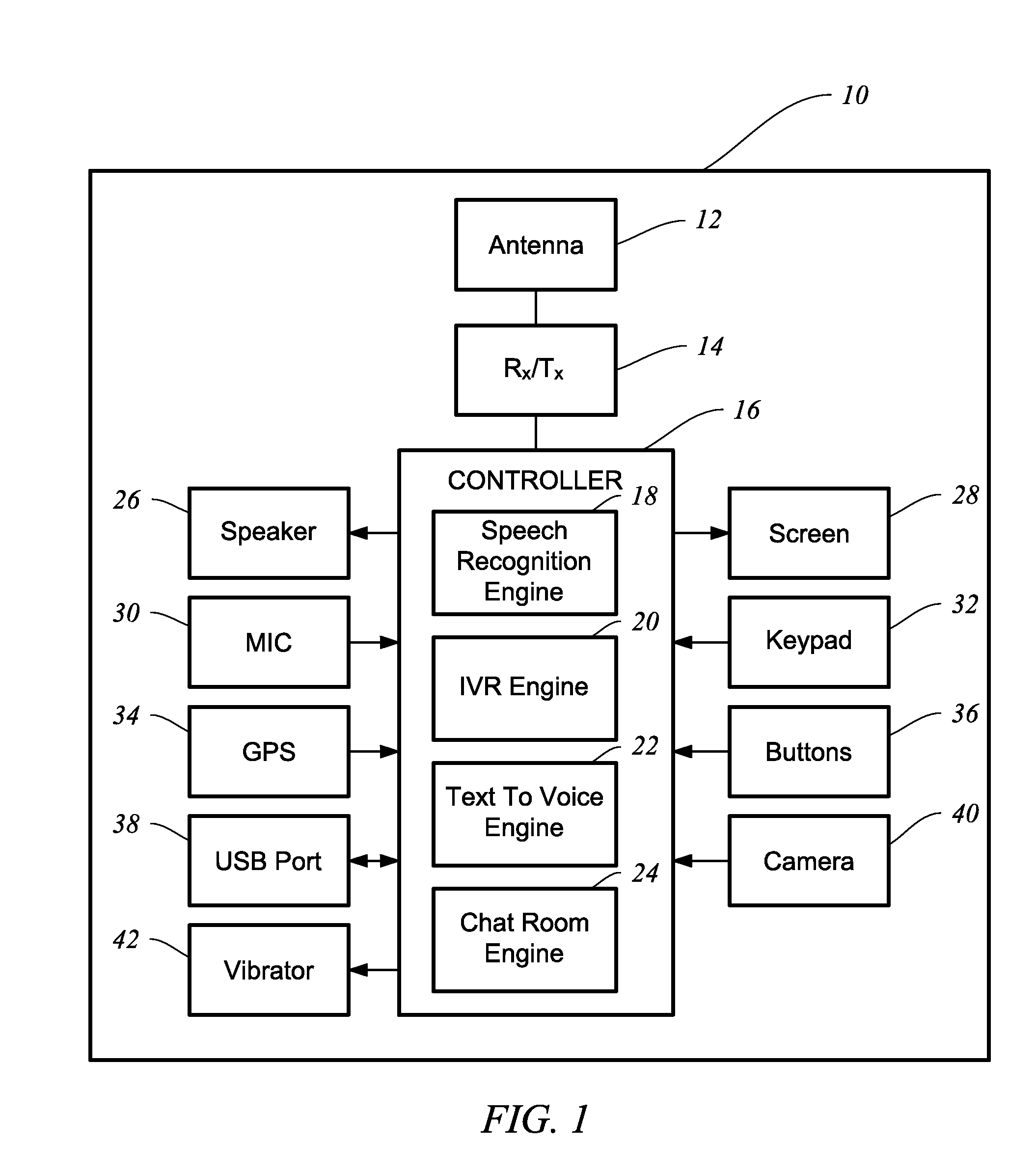
InactiveUS20110092187A1Security be importantDevices with voice recognitionSpecial service for subscribersInbound communicationOutbound communication
A land-based or mobile phone and methods are provided for receiving inbound communications as either voice or text, and then based on the user's configuration settings, the inbound communication is provided to the user as it was received or is automatically converted into a format that is desired by the user. The phone also takes voice or text that is input by the user of the phone and converts the user's input to either voice or text based on the configuration settings stored in the user's contact list or otherwise. The outbound communication is configured according to how the intended recipient wants to receive a communication based on the configuration settings stored in the user's contact list or otherwise. The phone includes a controller that determines how the phone will handle and process inbound and outbound communications. The controller includes a speech recognition engine.
Owner:MILLER LARRY
Influencing communications among a social support network
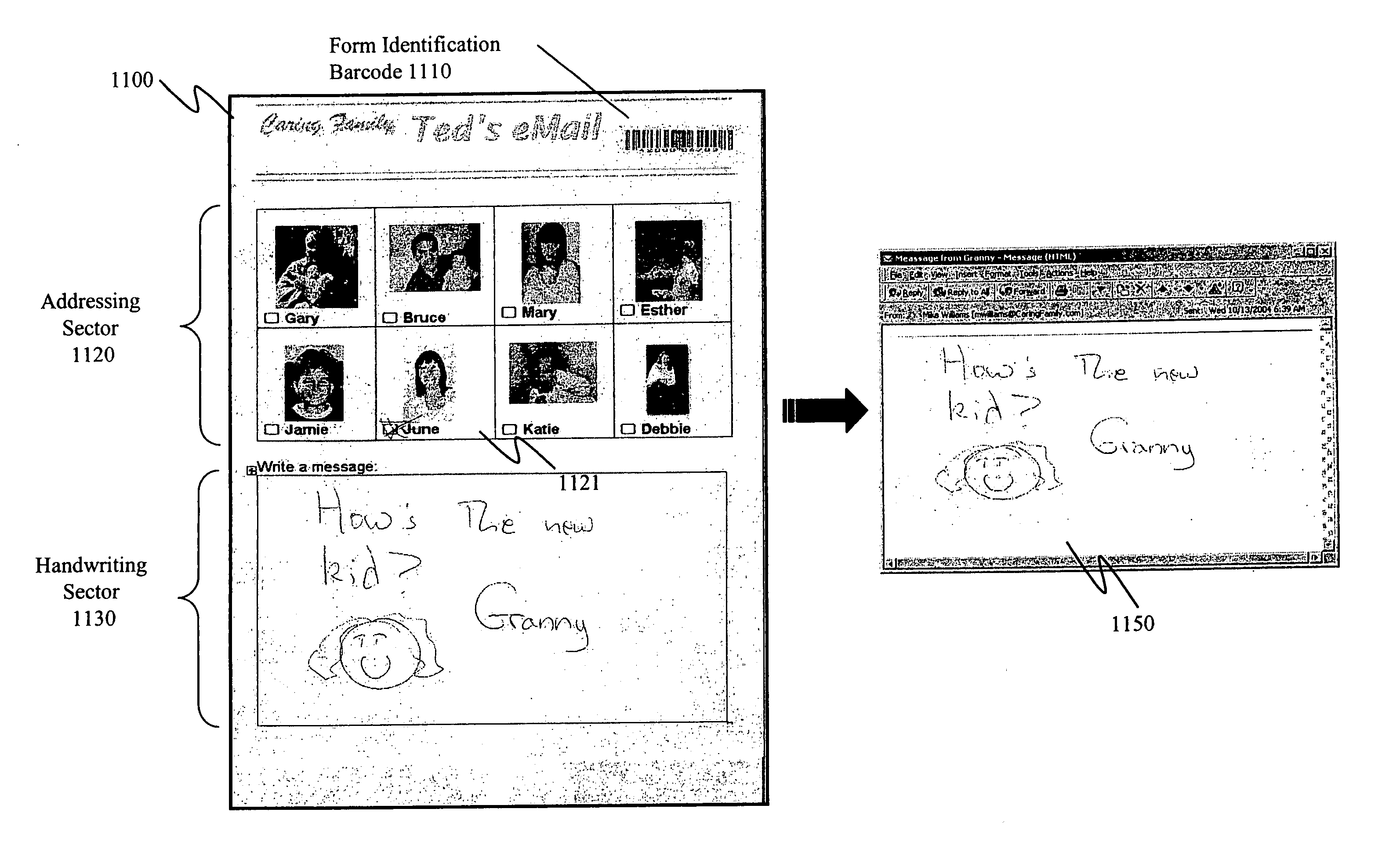
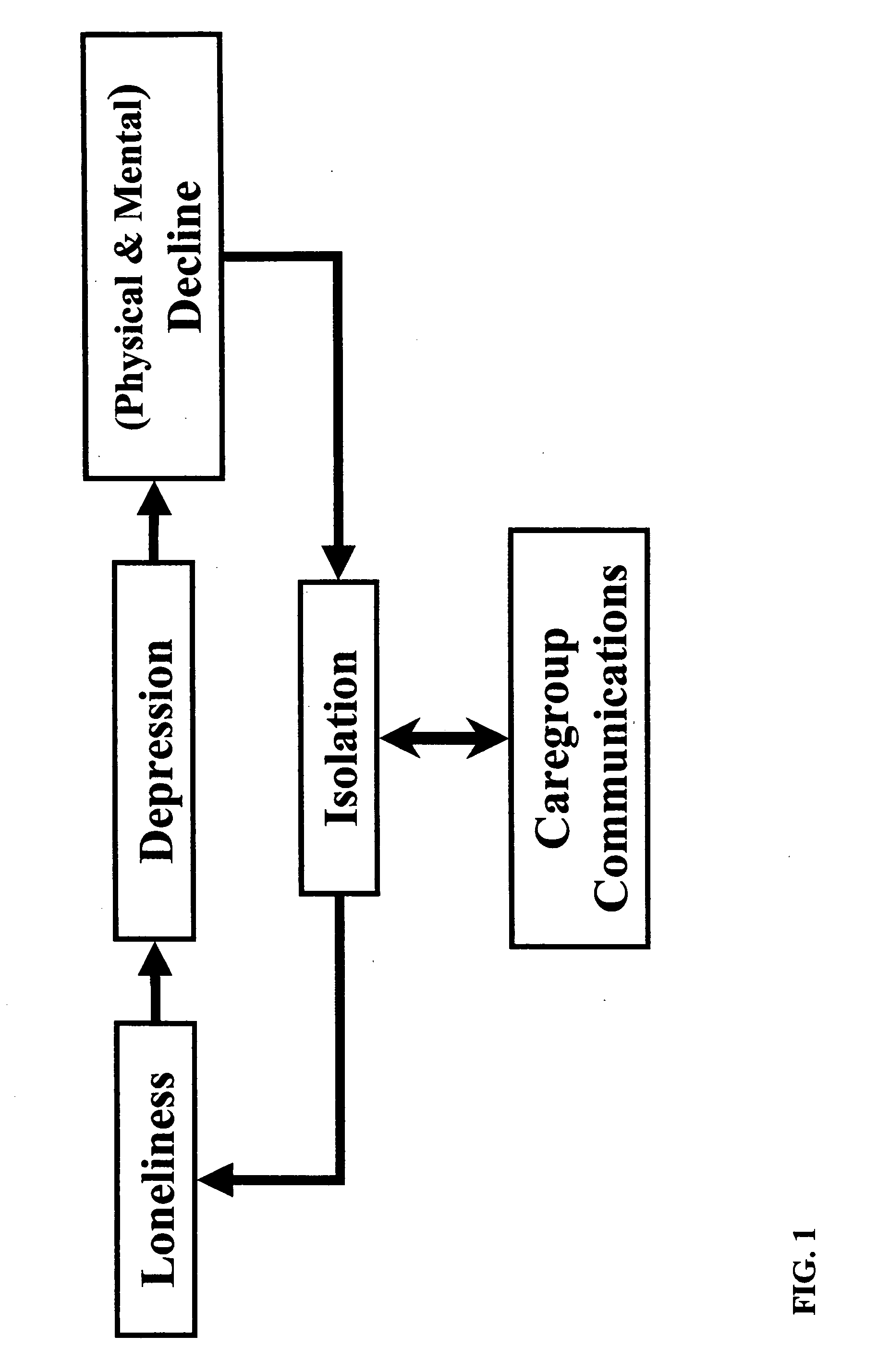
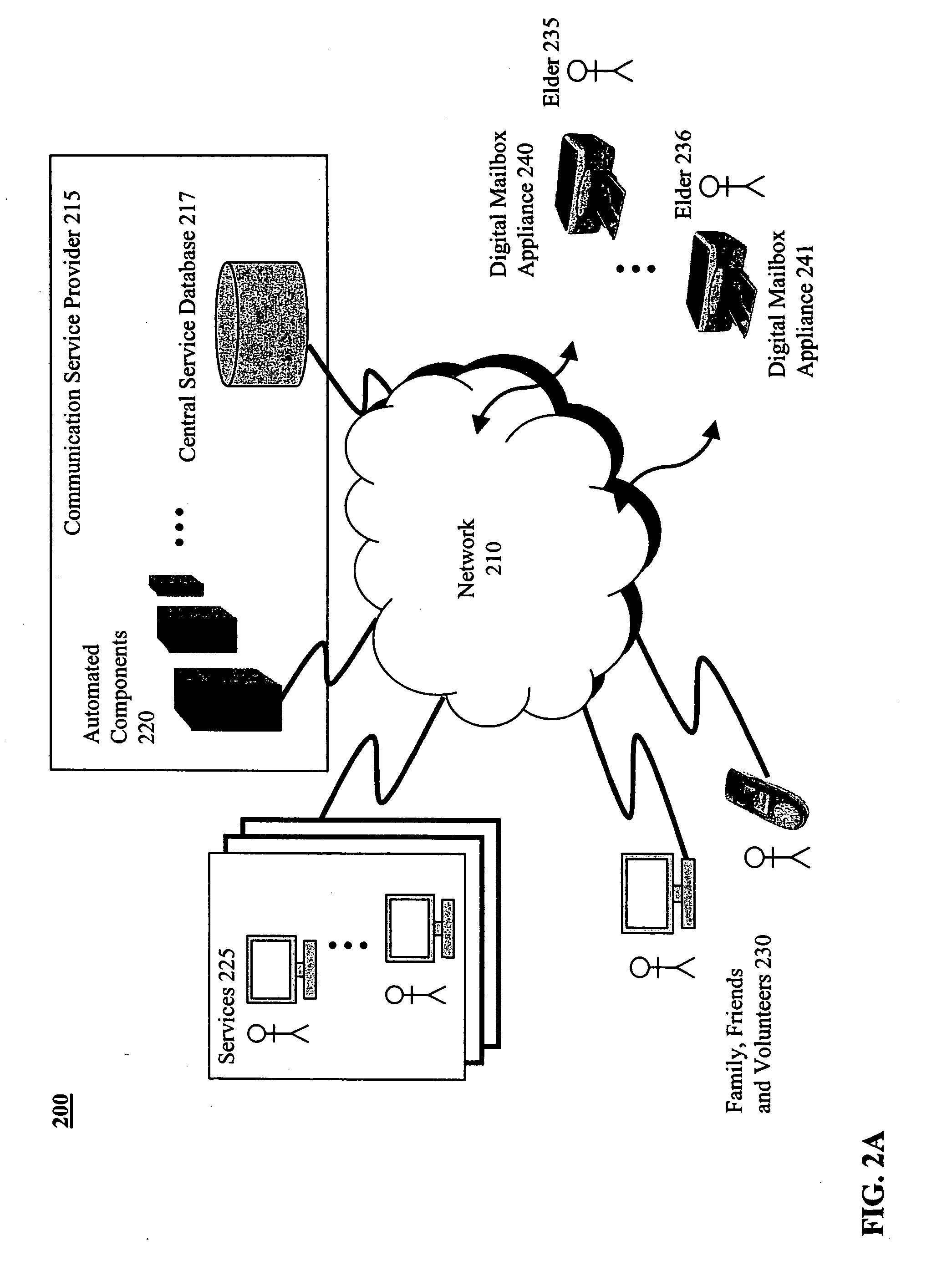
InactiveUS20050114759A1Facilitate communicationPromoting and quantitySpecial service provision for substationMedical communicationInbound communicationCommunications system
Methods and systems are provided for promoting and managing communications among a social support network. According to one embodiment, a communication system includes a closed communication service platform and a hardcopy-based communication appliance. The communication service platform provides a caregroup virtual private network (VPN) through which only registered members of the caregroup, authorized personnel of the communication service platform, processes associated with the communication service platform, and a target of the caregroup are permitted to exchange communications. The hardcopy-based communication appliance is associated with the caregroup VPN and used by the target and is operable to be communicatively coupled to the communication service platform to print inbound communications received from registered members of the caregroup, and to upload to the communication service platform outbound digital representations of annotated pages defining communications to be delivered to one or more members of the caregroup.
Owner:CARINGFAMILY
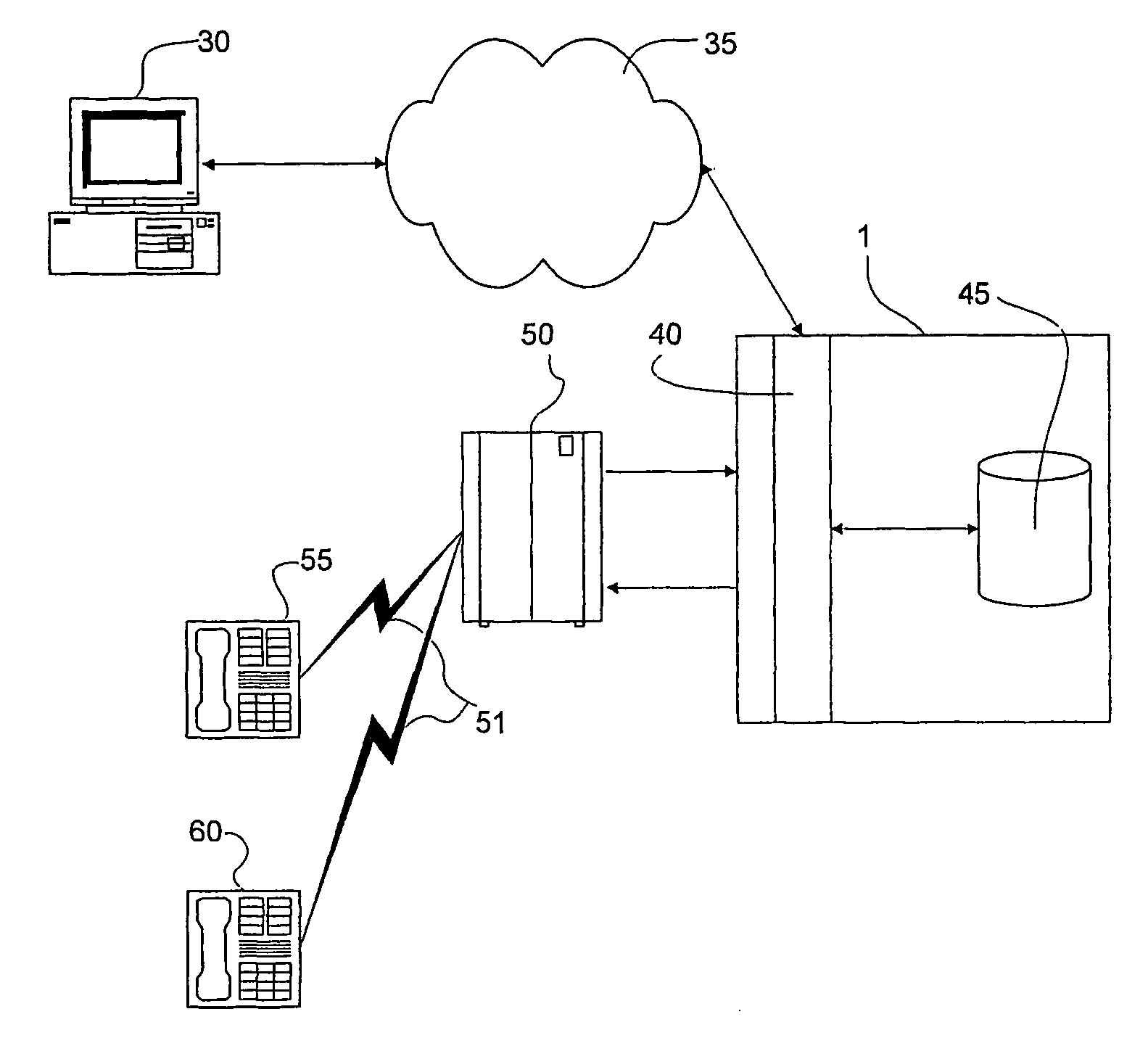
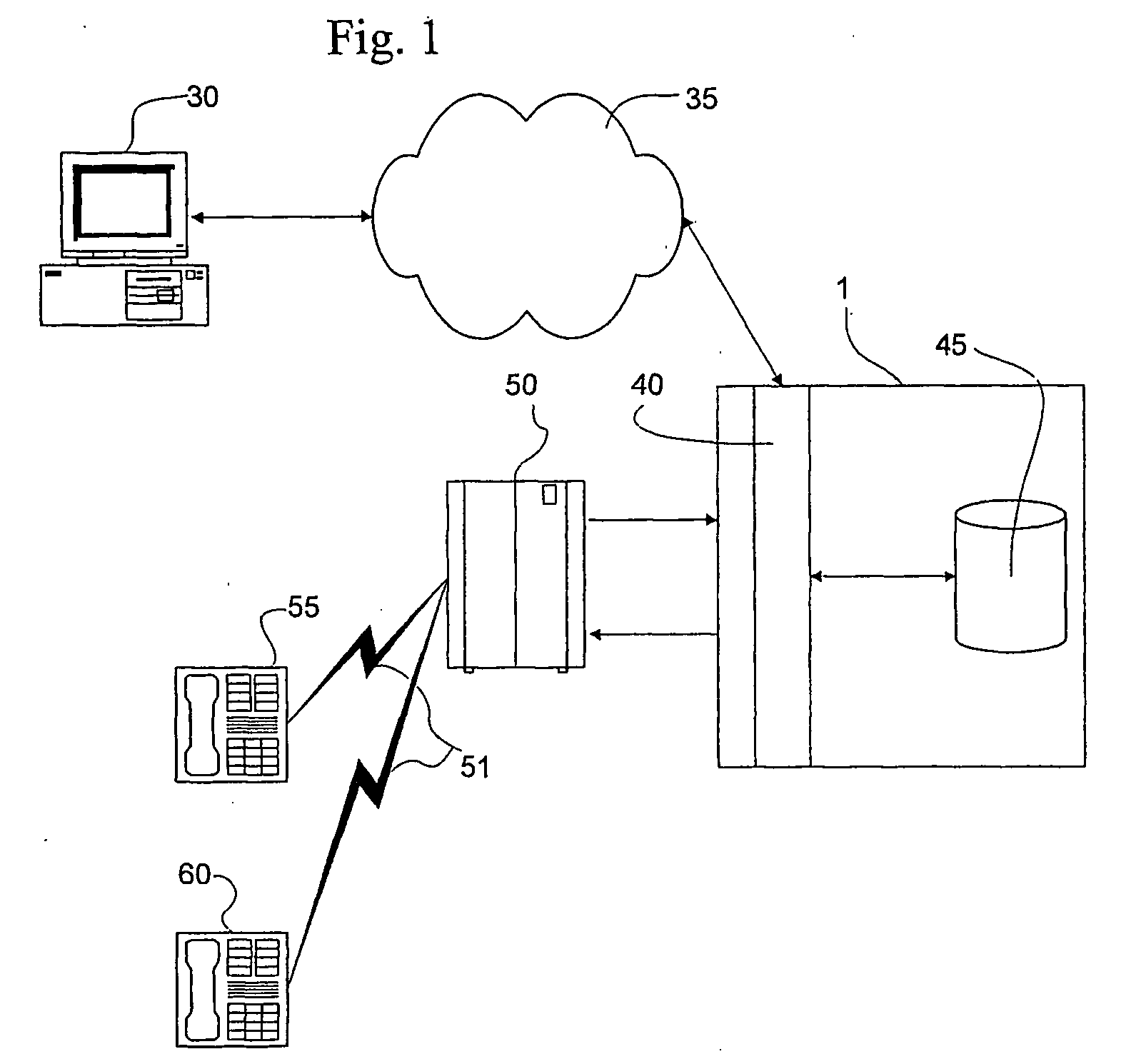
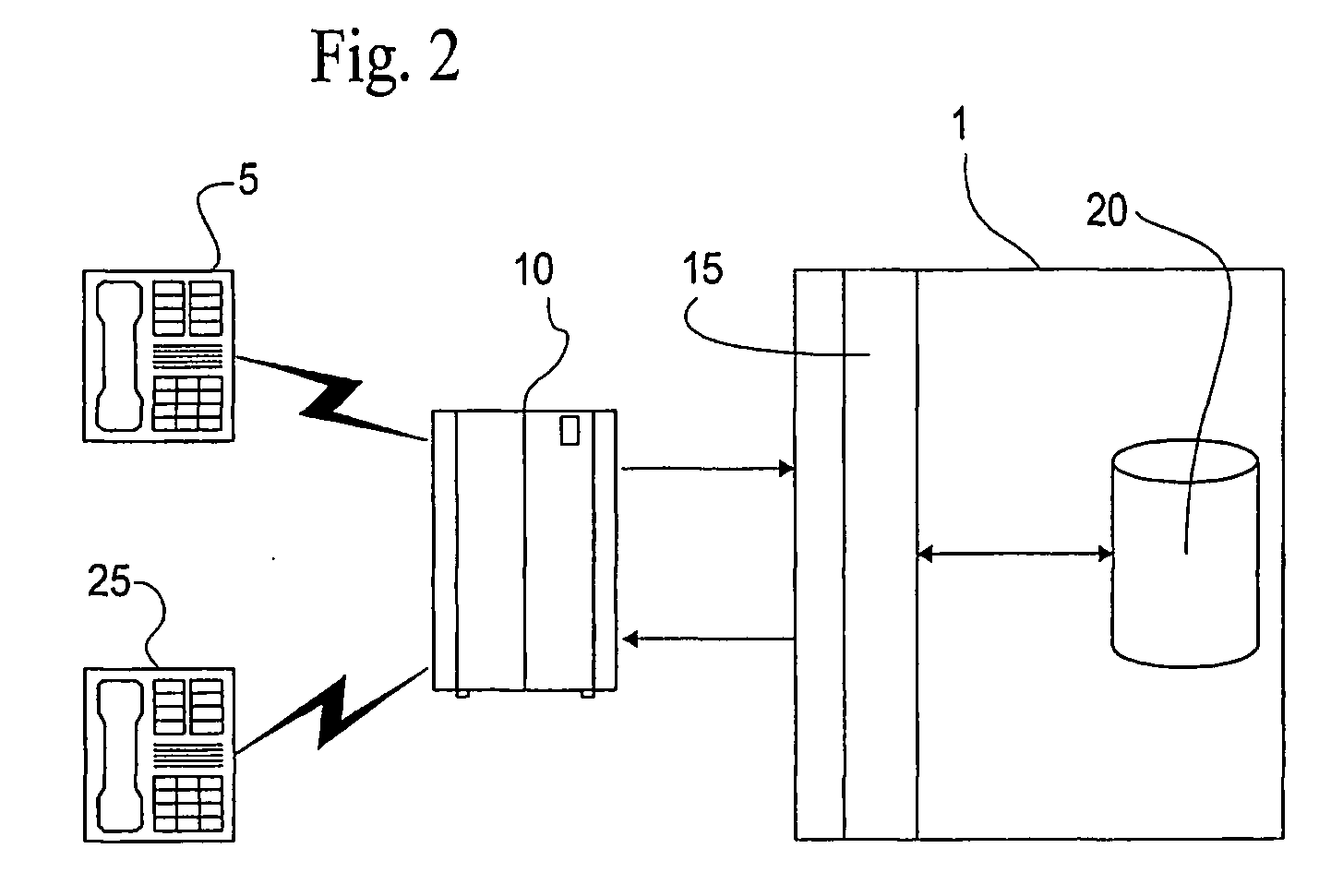
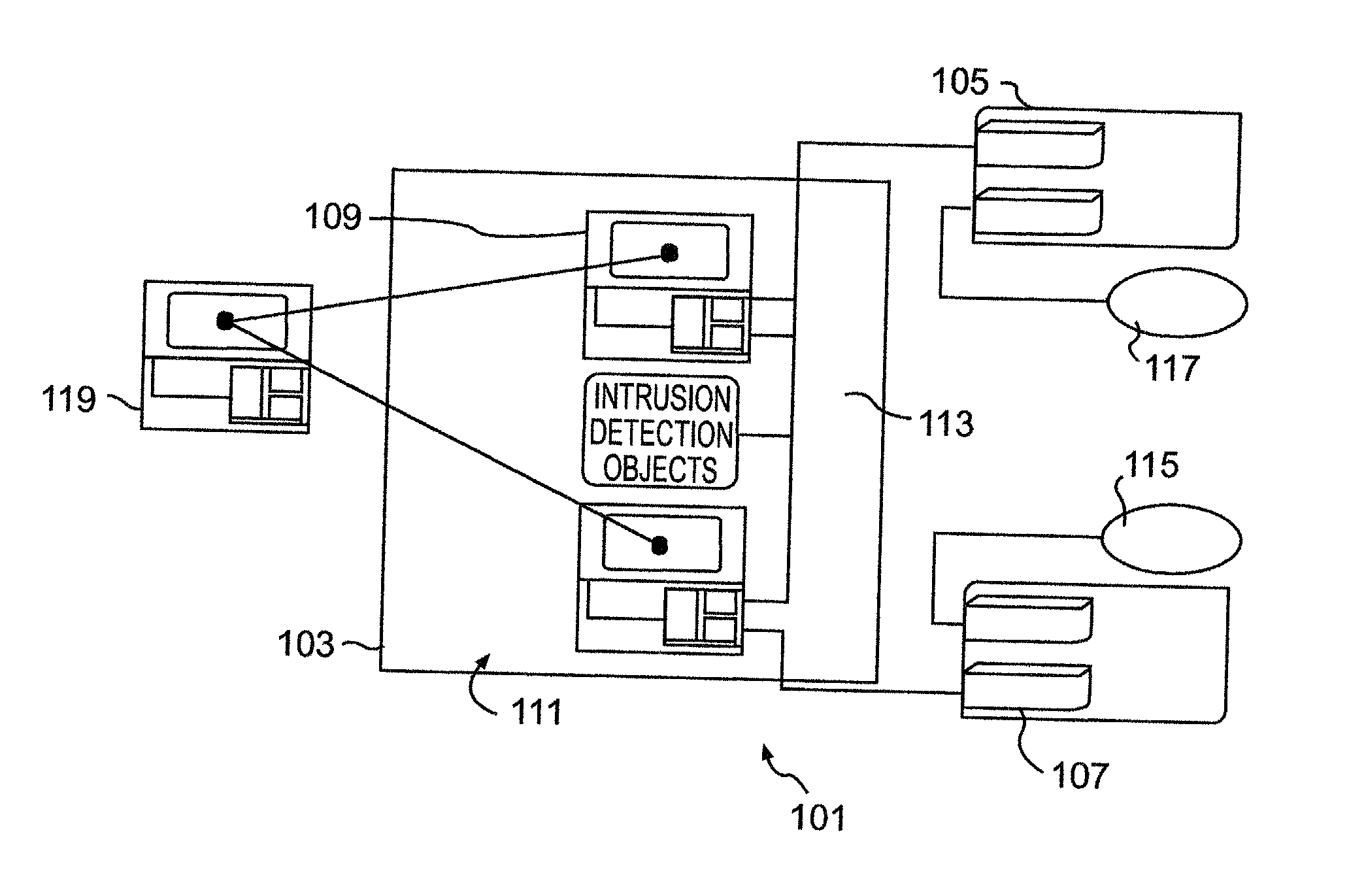
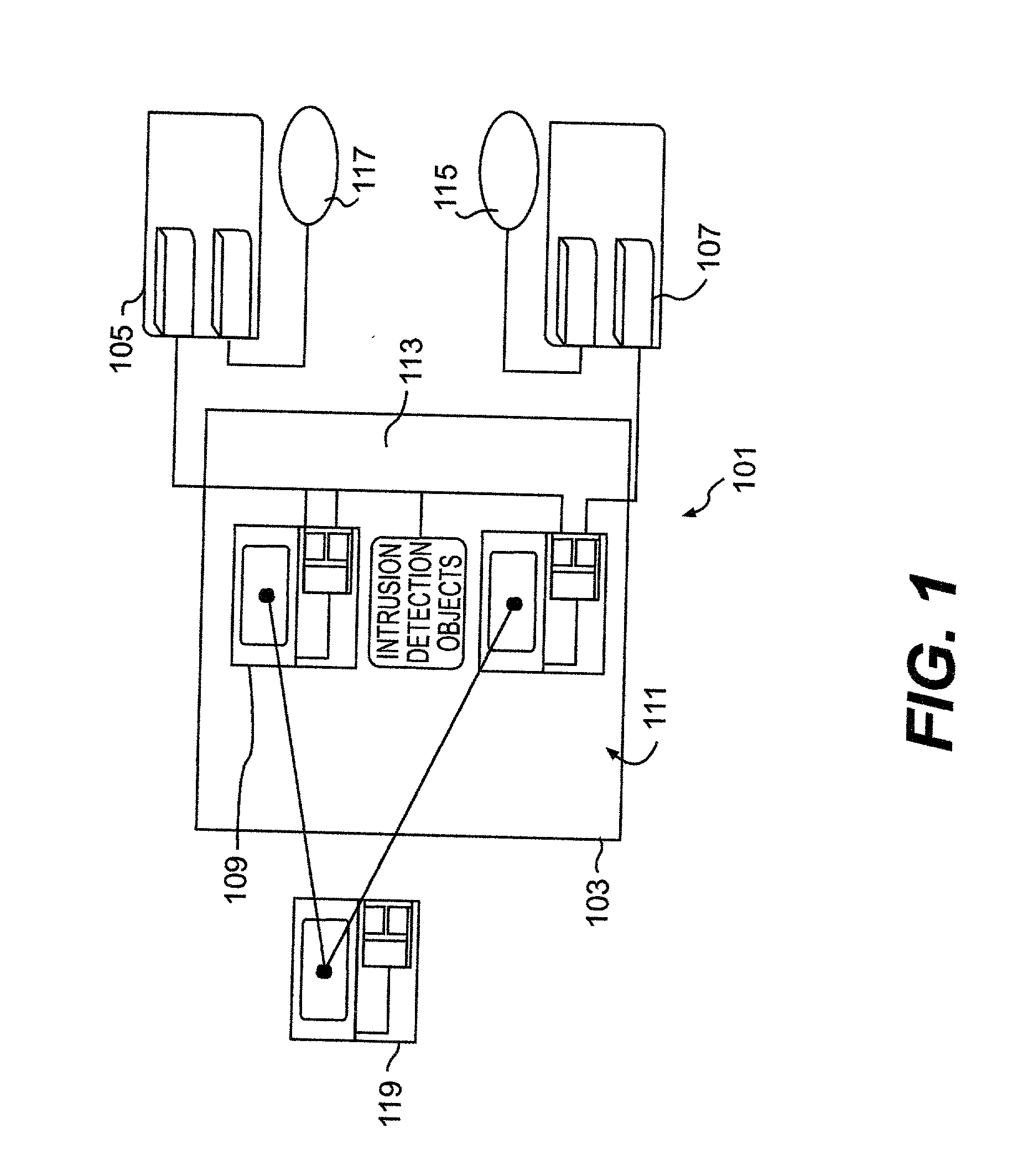
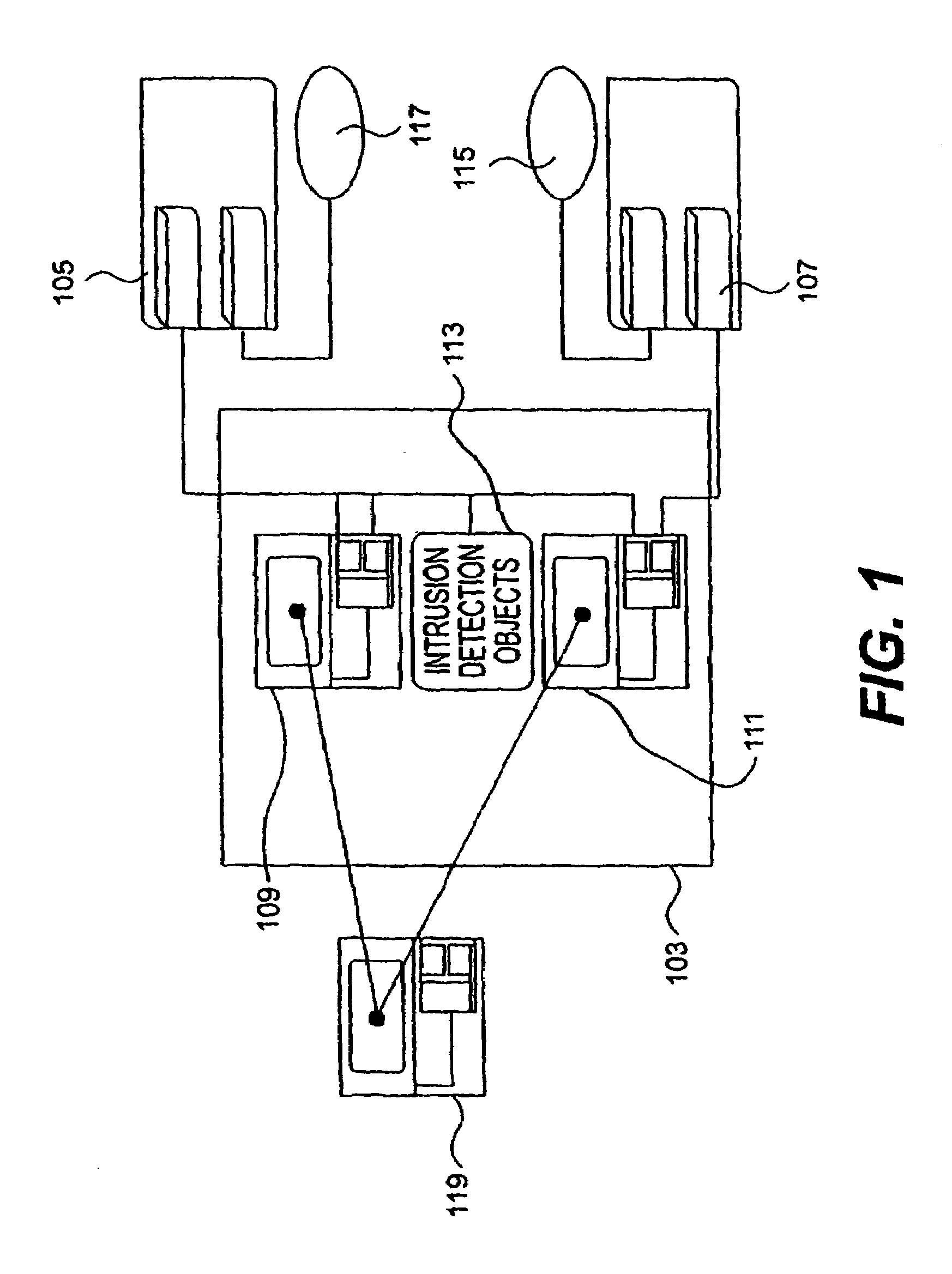
Apparatus, systems and methods for managing incoming and outgoing communication
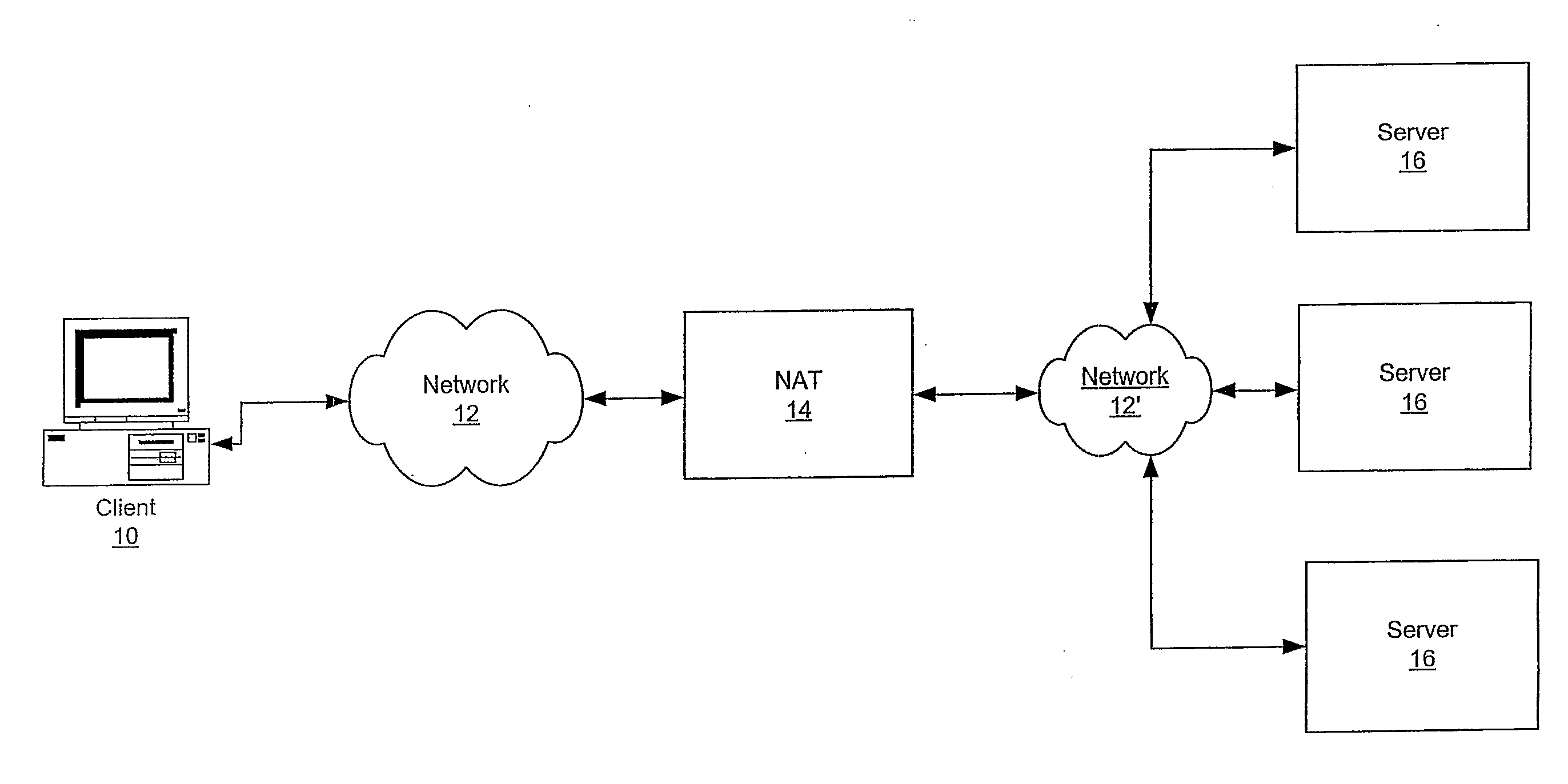
InactiveUS20070248220A1Telephone data network interconnectionsUnauthorised/fraudulent call preventionInbound communicationOutbound communication
The present invention provides apparatus, systems and methods for managing incoming and outgoing communications for various communications methods. The invention provides control over inbound communications including definition of if, when, and who may communicate with a recipient. The invention also supports concealed identification communication in that no actual addresses, phone numbers, or other addressing IDs are required to be exchanged by the communication initiator and recipient. The invention also provides the capability to initiate immediate, delayed, scheduled, or recurring outbound communications. As depicted in FIG. 1, if the database (45) contains call management settings for a call recipient, the application logic (40) will evaluate the rules to determine if a particular caller is authorized to connect with the call recipient at the current time and date. If the caller is authorized by the recipient to connect to the recipient phone number, and is furthermore authorized to do so for the current time and date, the application logic (40) will connect the call utilizing the public telephone switch (50). The computer (1) passes the caller and call recipient phone numbers as stored in the database (45) to the telephone switch (50) using an application programming interface (“API”) appropriate to the service provider or telephone switch manufacturer. The exemplary embodiment of the invention utilizes an API provided by a telephone service provider as an interface to its switching infrastructure (50). The API captures both caller and recipient telephone numbers along with other variables useful for call setup and tracking. The telephone service provider then connects both parties' telephones (55), (60) to a phone call by dialing both numbers and connecting the call upon the parties' answer.
Owner:CRANDELL JEFFREY L +1
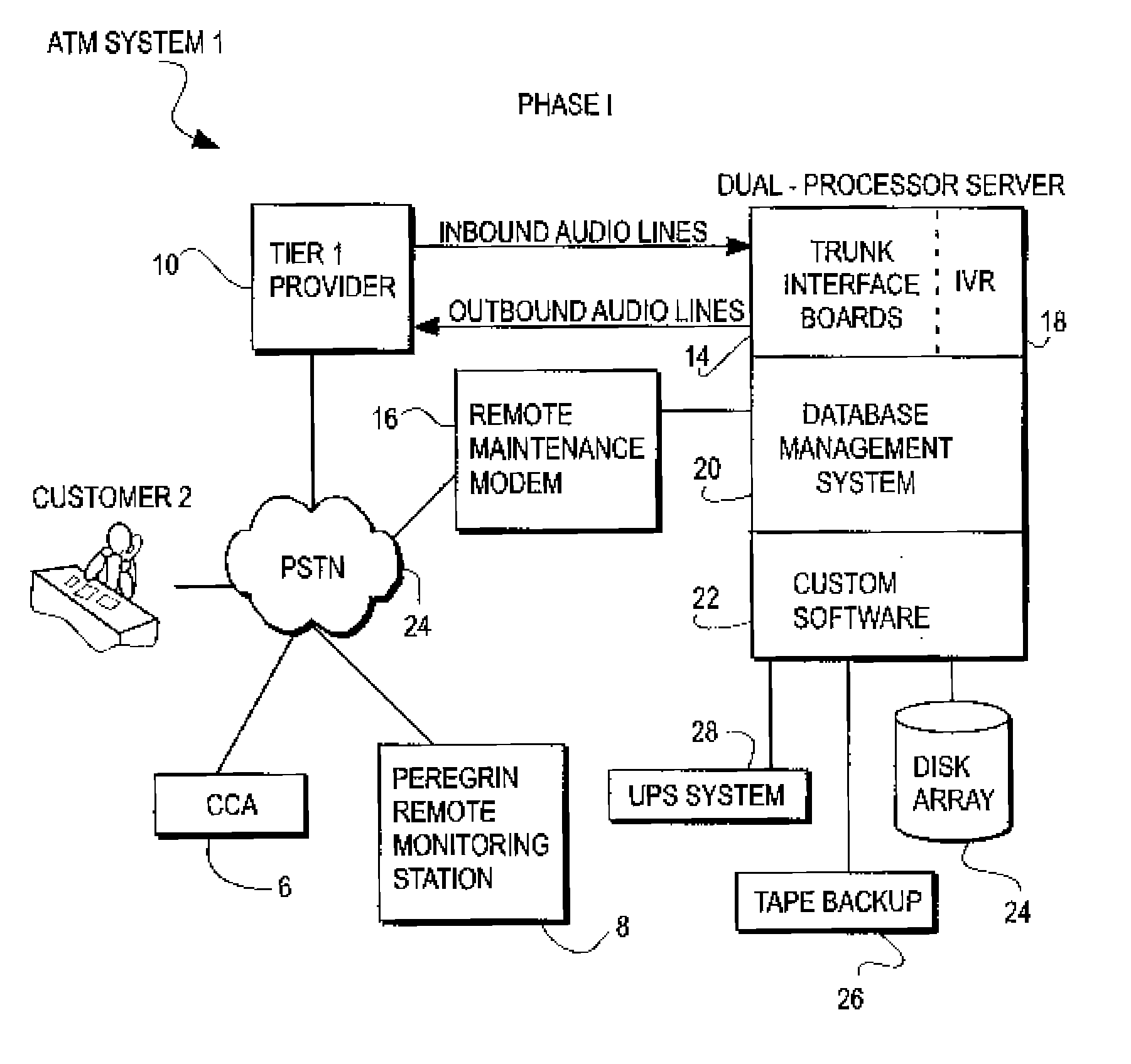
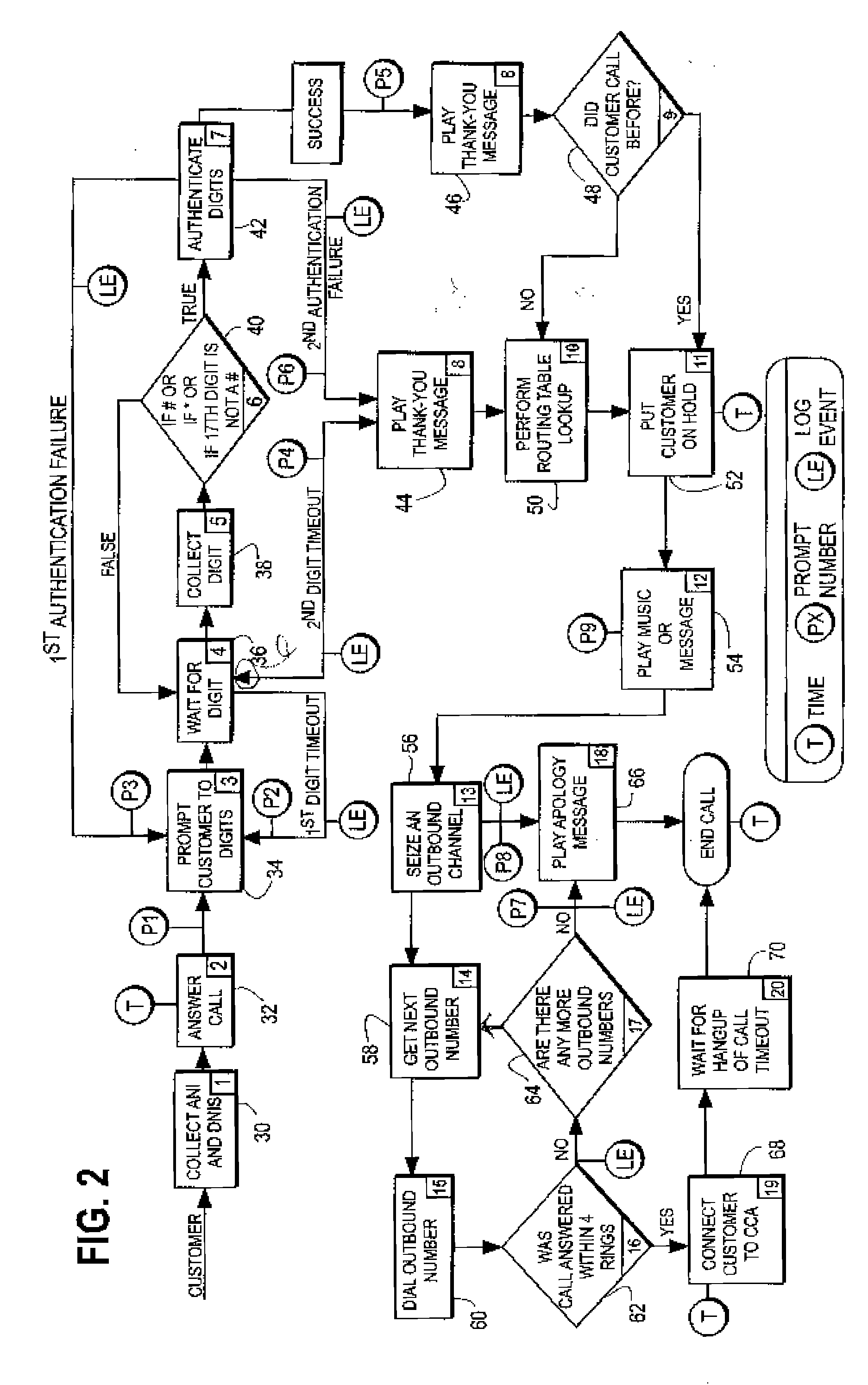
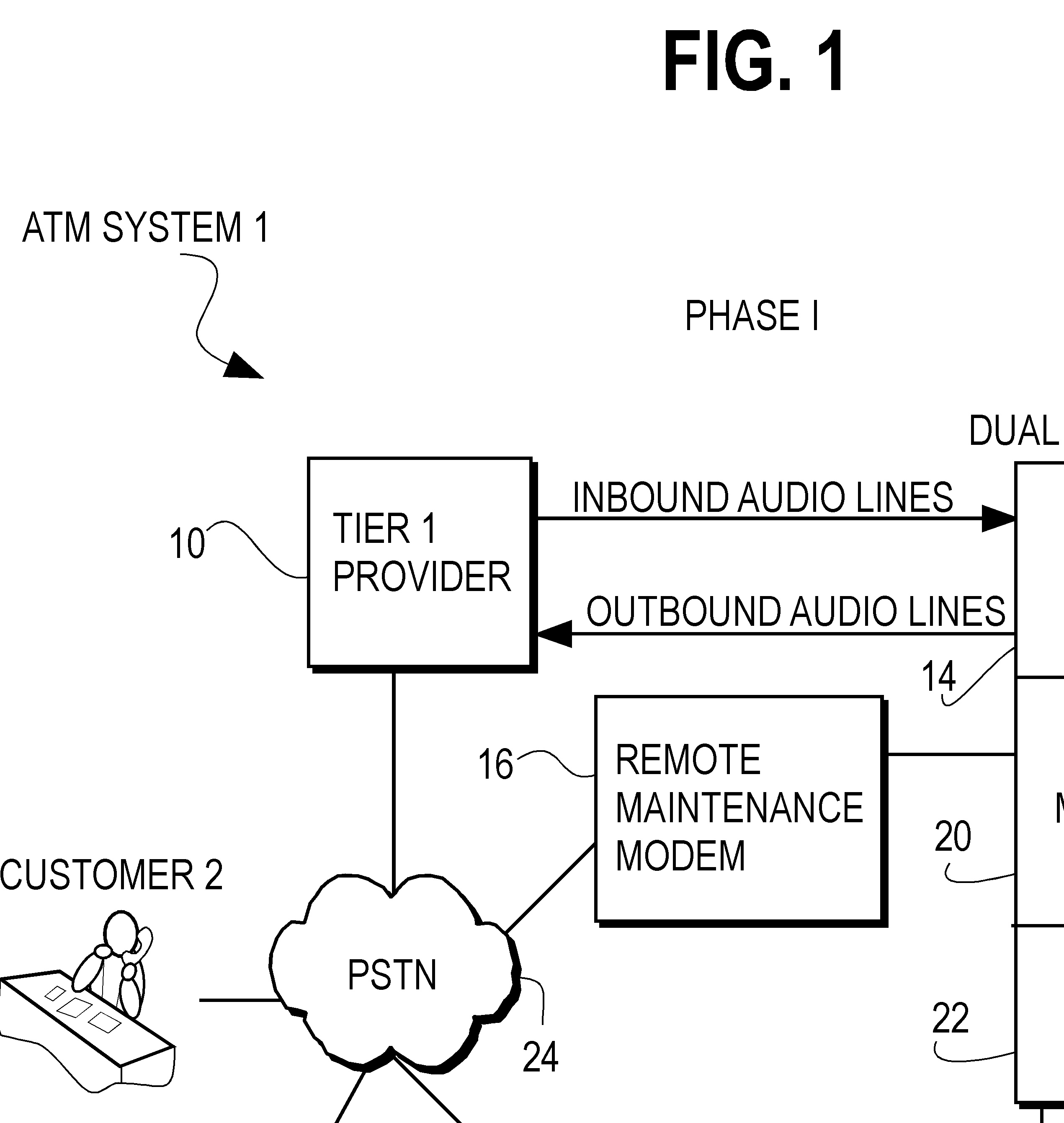
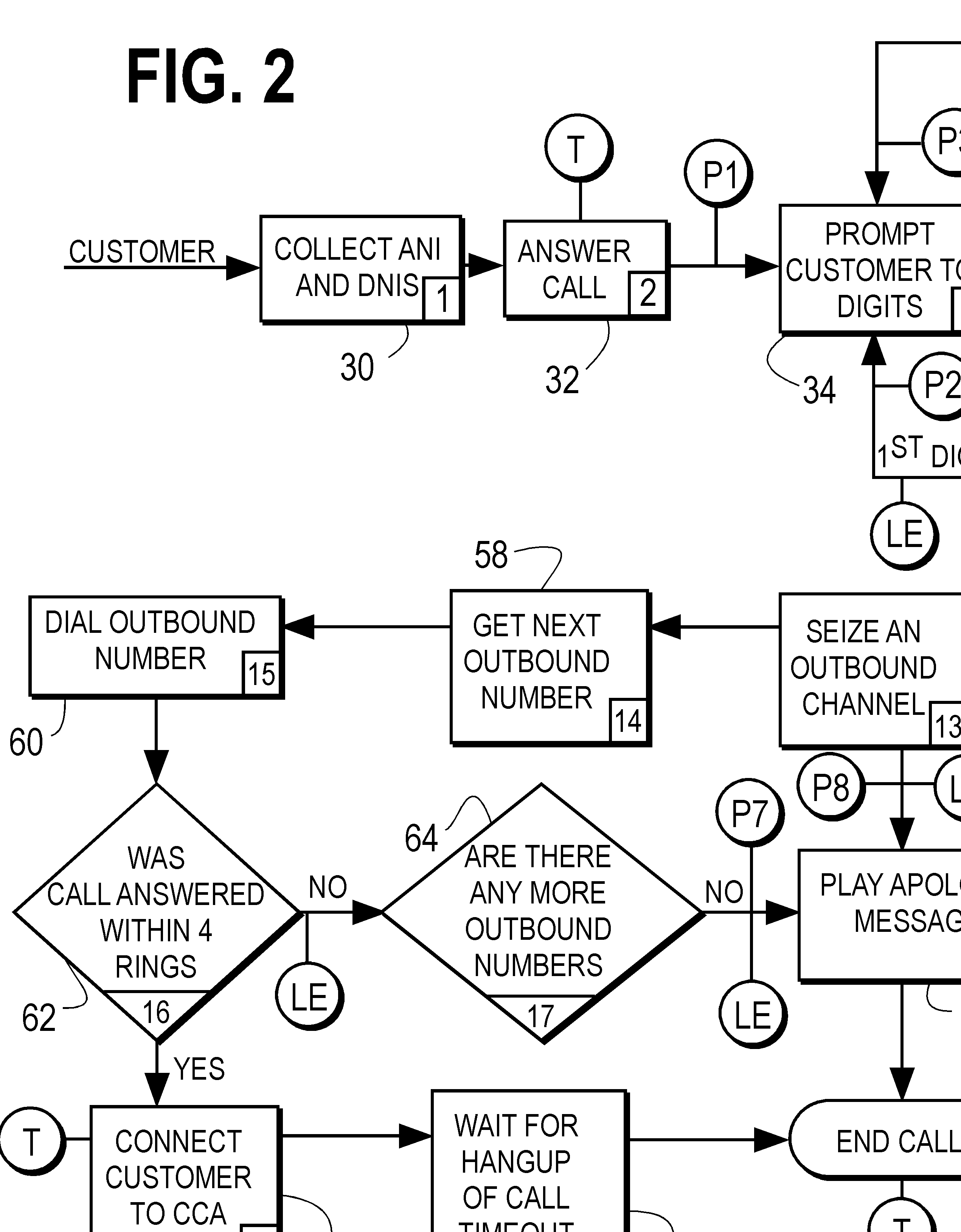
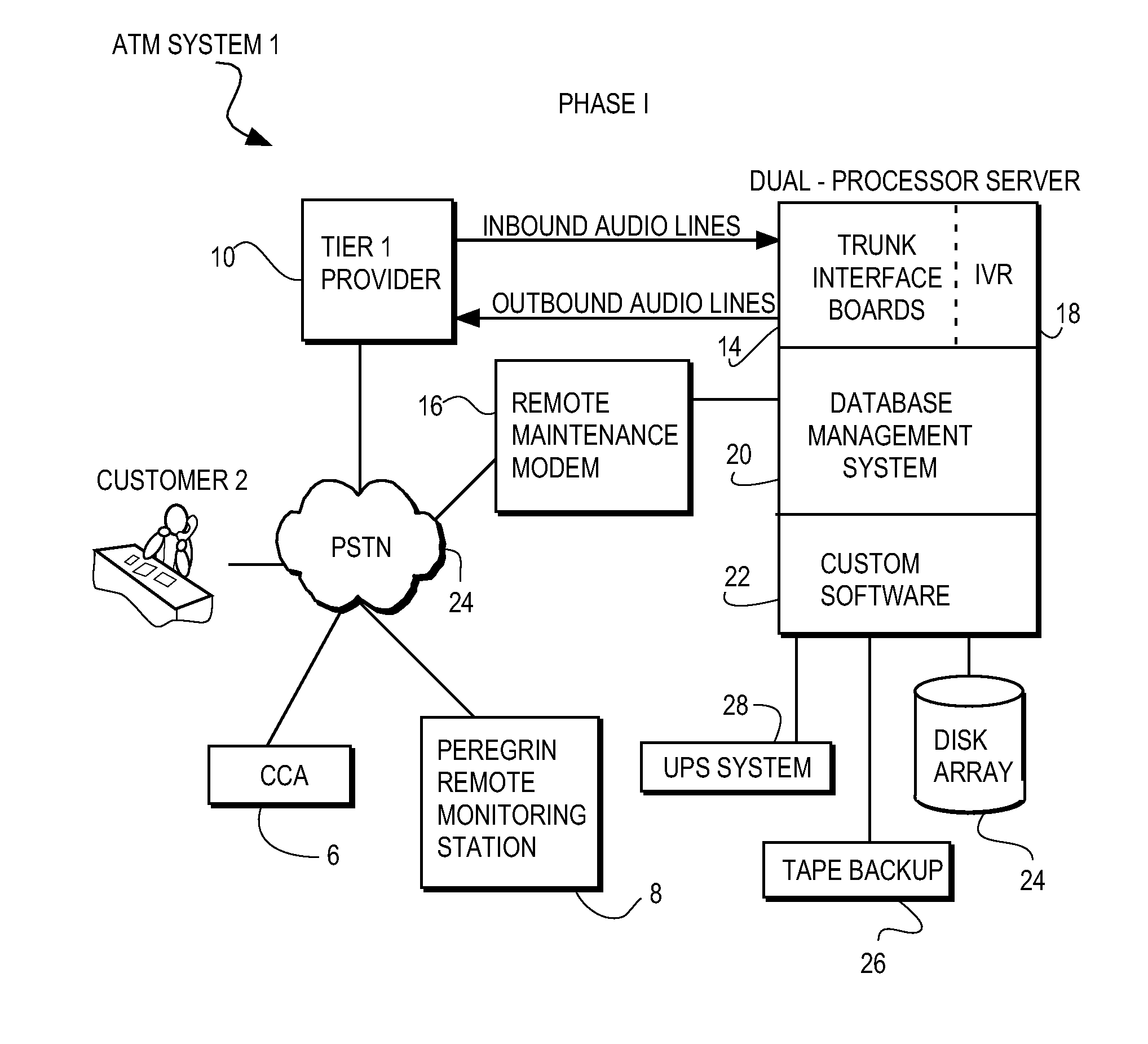
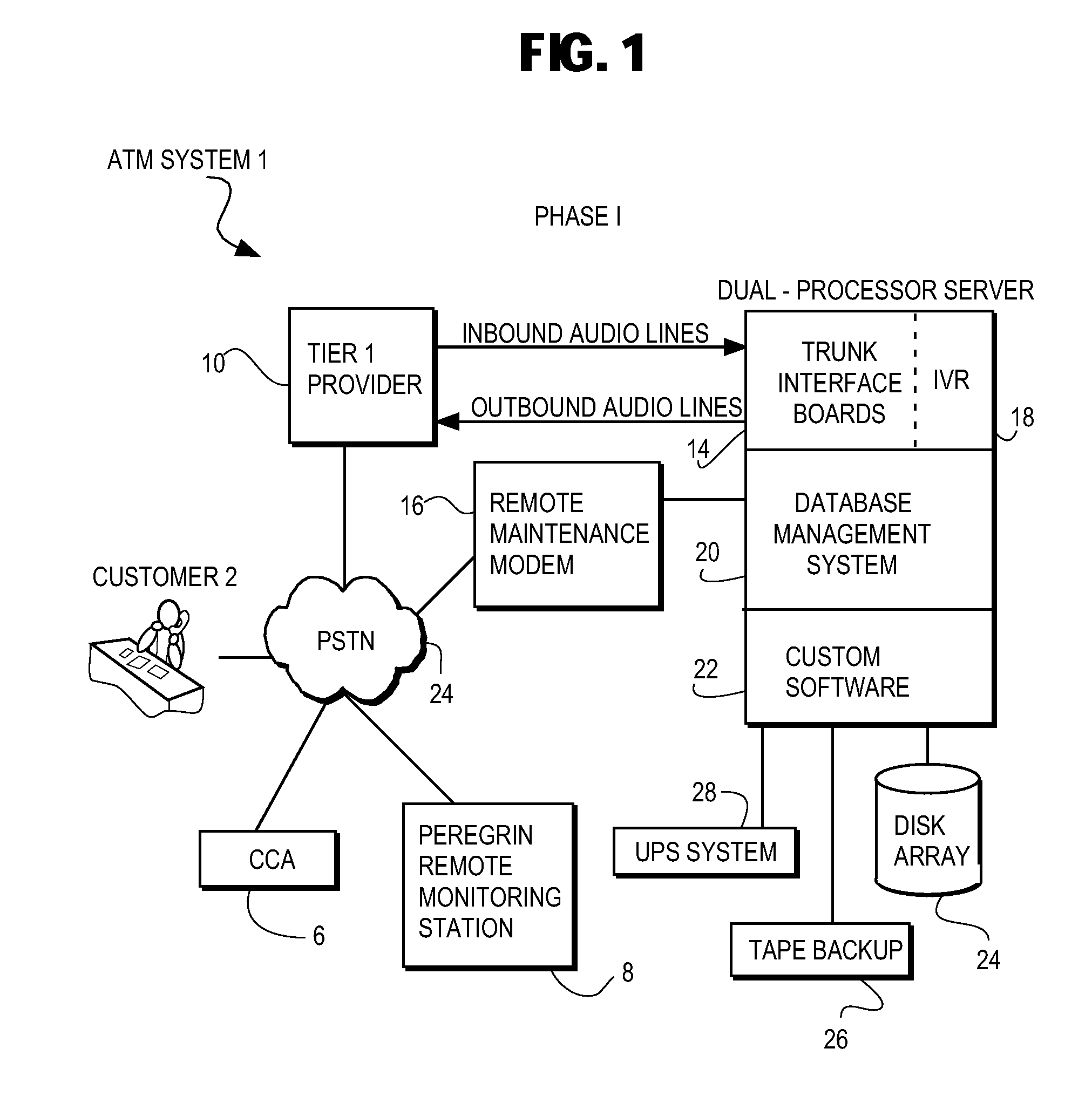
System for transfering an inbound communication to one of a plurality of credit-counseling agencies
A system for referring a telephone communication to one of a plurality of financial assistance providers based on lender criteria, the method including the steps of: storing telephone numbers for a plurality of financial assistance providers in memory accessible by a digital electrical computer; obtaining lender criteria for selecting one of the financial assistance providers; storing said criteria for access by said computer; identifying a debtor; selecting one of the financial assistance providers by accessing the criteria, applying the criteria, and accessing one of the stored telephone numbers; and connecting the debtor by telephone to the one of the stored telephone numbers. The system can be used with an intermediary that detects referring information sufficient to identify a referrer identity, to select which one of several financial assistance providers to refer the inbound communication by using a computer to look up and to apply referral criteria responsive to the referrer identity, and to form and track the call referral.
Owner:PEREGRIN LICENSING LLC
A Referrer-Controlled System for Transfering an Inbound Communication to One of a Plurality of Financial Assistance Providers
<heading lvl="0">Abstract of Disclosure< / heading> 85A system for referring a telephone communication to one of a plurality of financial assistance providers based on lender criteria, the method including the steps of: storing telephone numbers for a plurality of financial assistance providers in memory accessible by a digital electrical computer; obtaining lender criteria for selecting one of the financial assistance providers; storing said criteria for access by said computer; identifying a debtor; selecting one of the financial assistance providers by accessing the criteria, applying the criteria, and accessing one of the stored telephone numbers; and connecting the debtor by telephone to the one of the stored telephone numbers. The system can be used with an intermediary that detects referring information sufficient to identify a referrer identity, to select which one of several financial assistance providers to refer the inbound communication by using a computer to look up and to apply referral criteria responsive to the referrer identity, and to form and track the call referral.
Owner:PEREGRIN LICENSING LLC
System for transfering an inbound communication to one of a plurality of credit-counseling agencies
InactiveUS20110060673A1Additional drawbackFinanceAutomatic exchangesInbound communicationComputer access
A system for referring a telephone communication to one of a plurality of financial assistance providers based on lender criteria, the method including the steps of: storing telephone numbers for a plurality of financial assistance providers in memory accessible by a digital electrical computer; obtaining lender criteria for selecting one of the financial assistance providers; storing said criteria for access by said computer; identifying a debtor; selecting one of the financial assistance providers by accessing the criteria, applying the criteria, and accessing one of the stored telephone numbers; and connecting the debtor by telephone to the one of the stored telephone numbers. The system can be used with an intermediary that detects referring information sufficient to identify a referrer identity, to select which one of several financial assistance providers to refer the inbound communication by using a computer to look up and to apply referralcriteria responsive to the referrer identity, and to form and track the call referral.
Owner:PEREGRIN LICENSING LLC
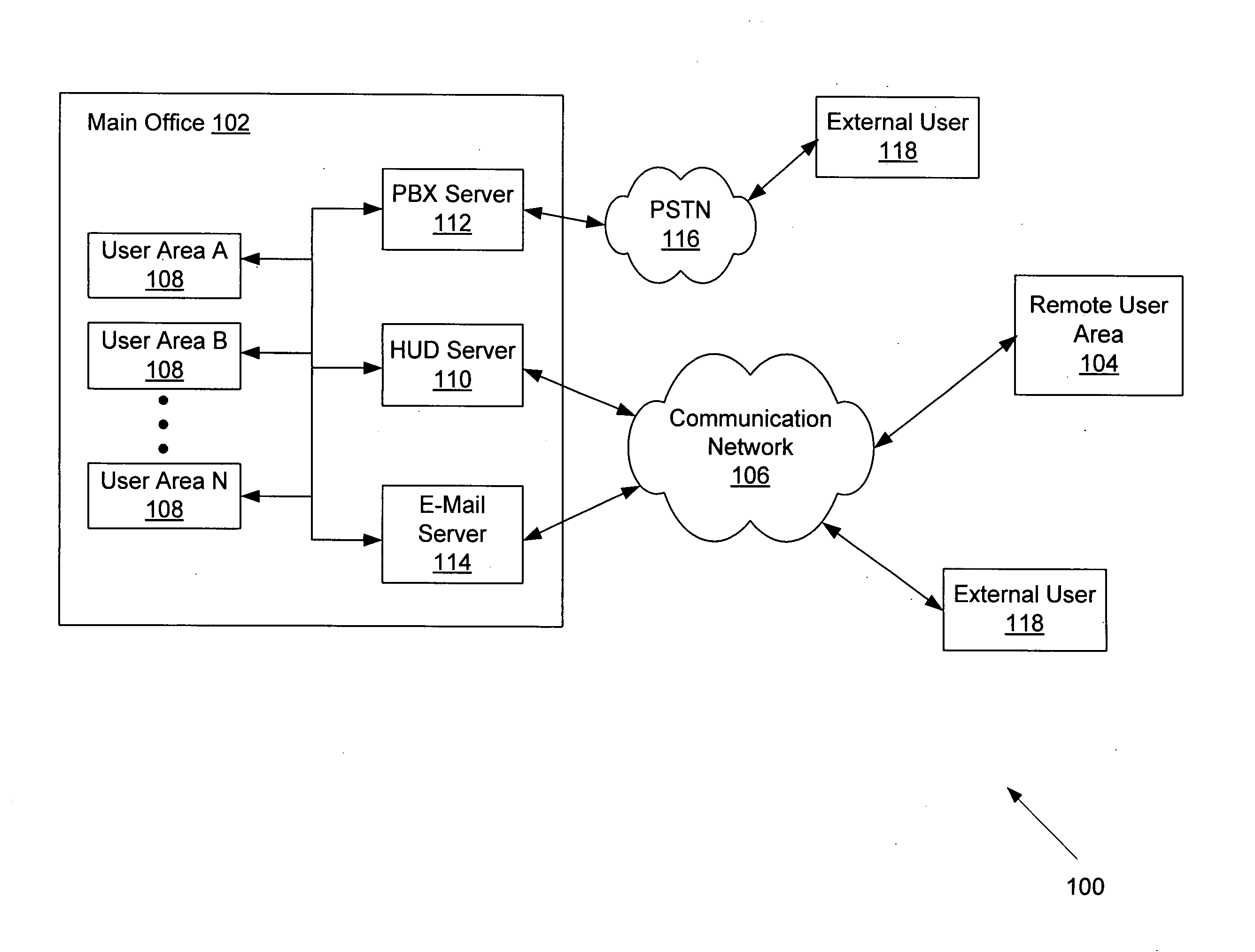
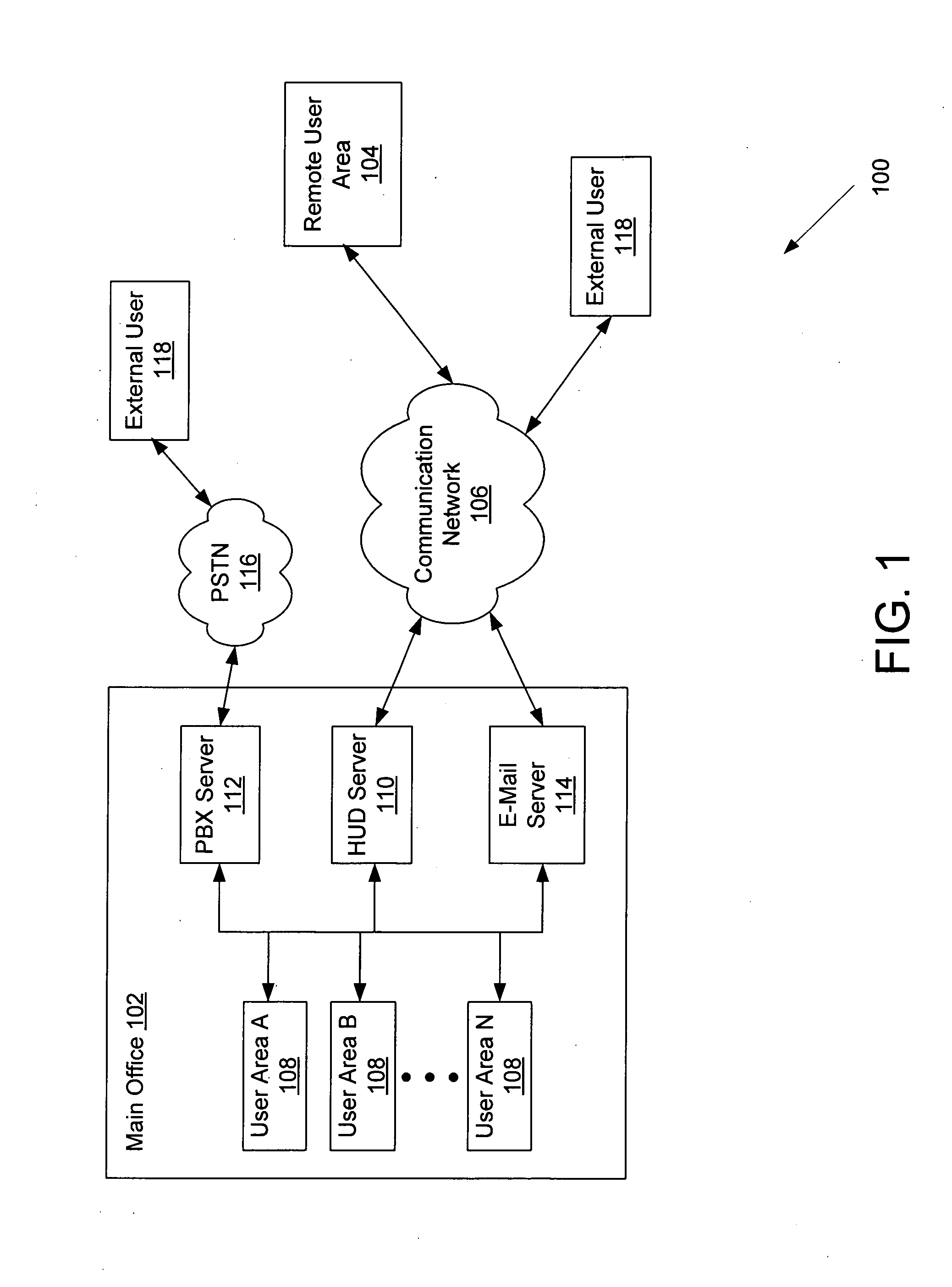
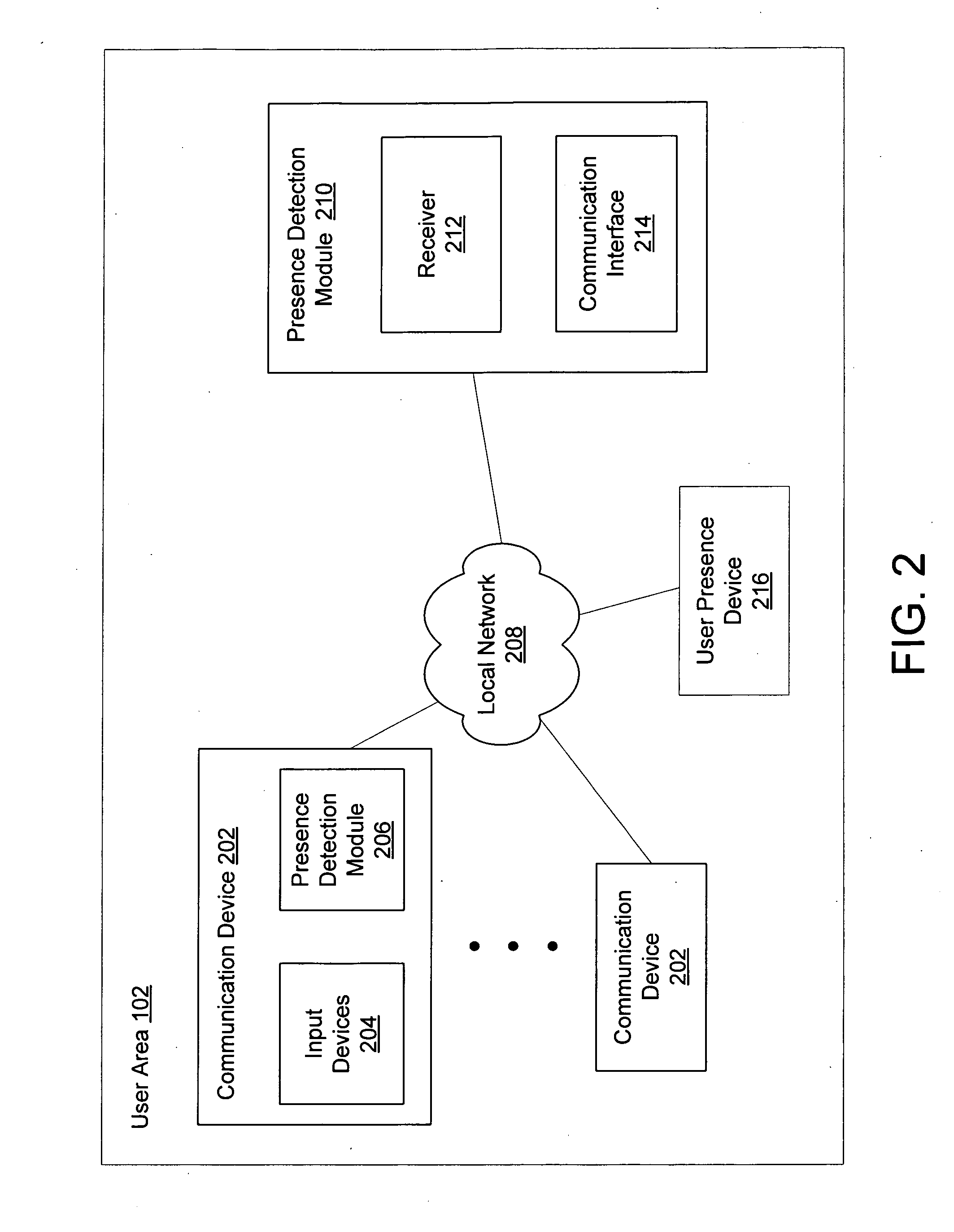
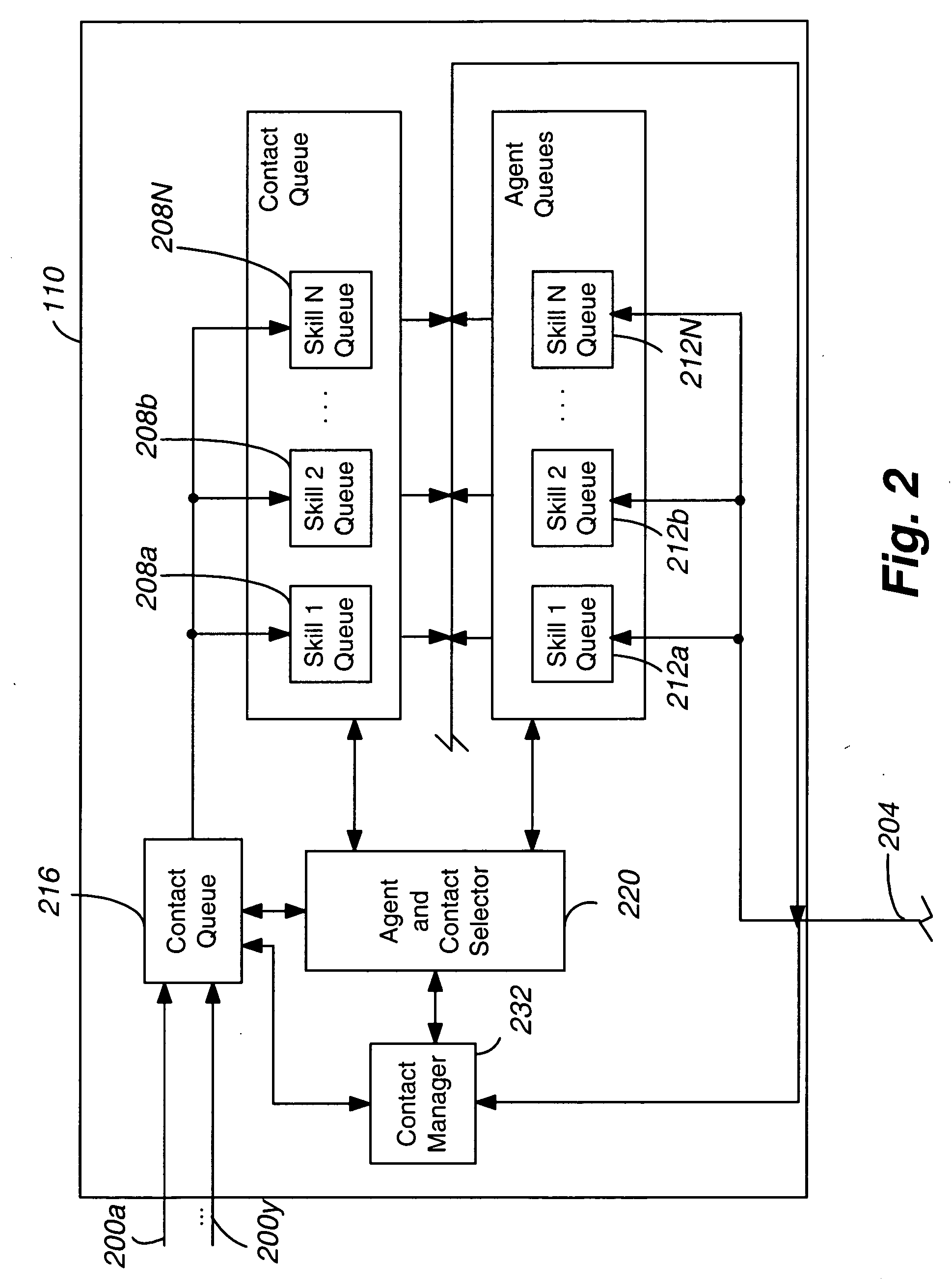
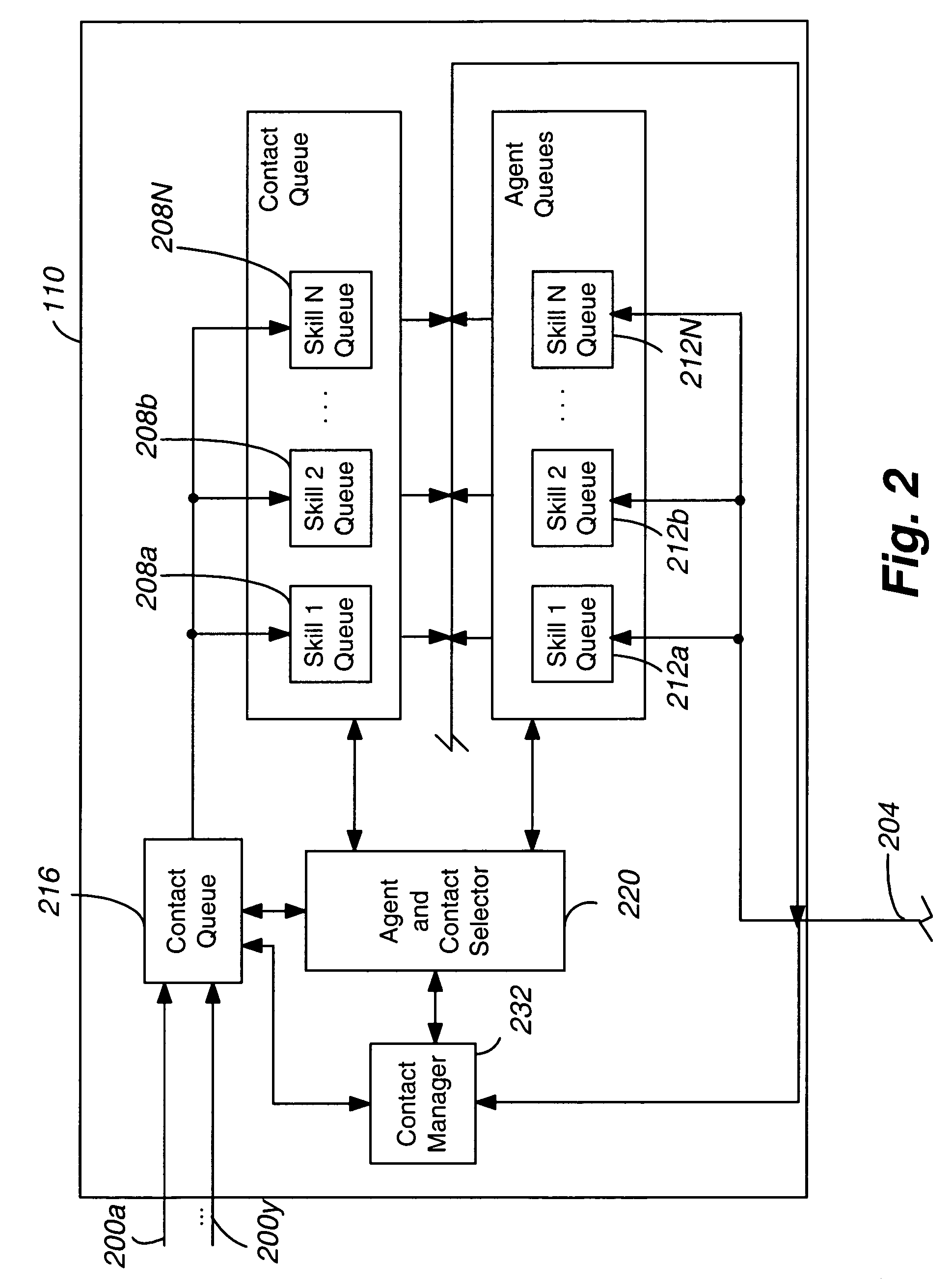
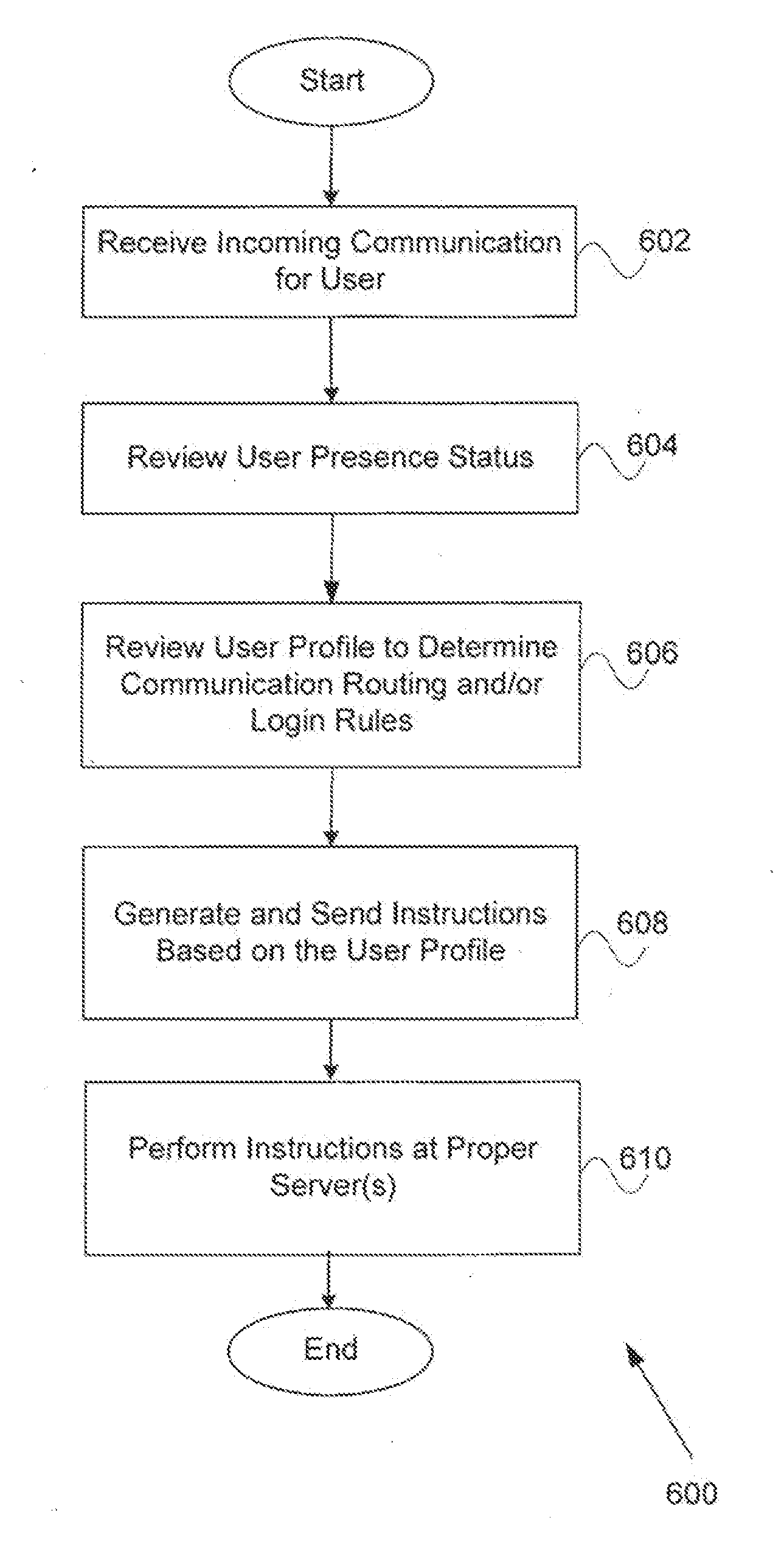
Intelligent presence management in a communication routing system
ActiveUS20090141884A1Interconnection arrangementsManual exchangesInbound communicationDistributed computing
Systems and methods for intelligent presence management in a communication routing system are provided. In exemplary embodiments, an inbound communication may be received for a user. The user's presence status is determined and a profile associated with the user is reviewed. Based on rules contained within the profile, appropriate instructions may be generated for routing the inbound communication in accordance with some embodiments. In other embodiments, instructions may be generated to log the user in or out with the communication routing system.
Owner:SANGOMA US INC
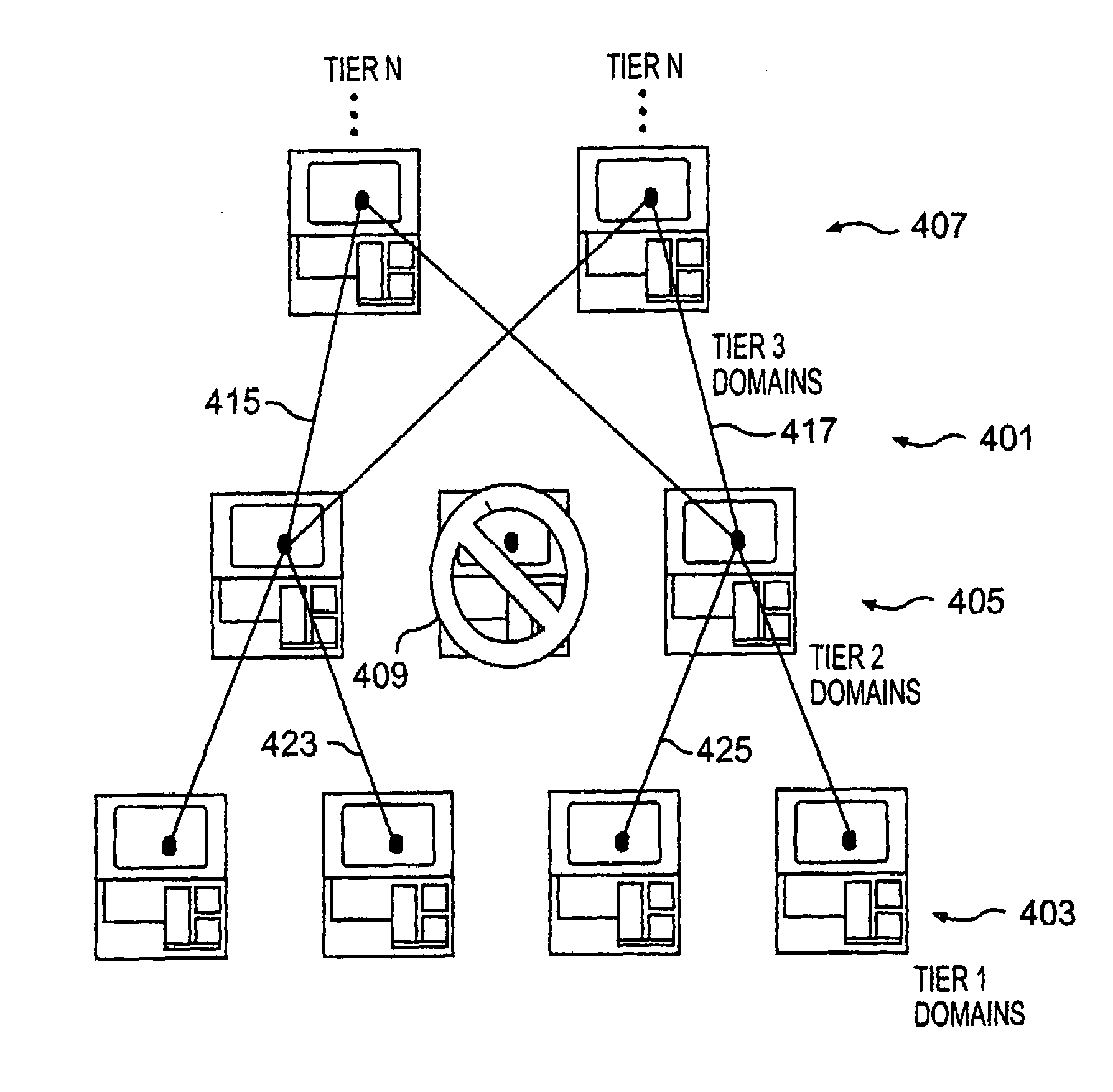
Real time active network compartmentalization
ActiveUS20020059528A1Improve functionalityMinimal disruptionError preventionFrequency-division multiplex detailsInbound communicationSecurity domain
Security policy manager devices are leveraged by manager objects to use highly secure user transparent communications to provide detection of questionable activities at every node, automatic collection of information related to any potential attack, isolation of the offending object with arbitrary flexibility of response (e.g. flexibly determining the level of certainty of an attack for initiation of a response in accordance with the number of nodes to be partitioned that is determined by the collected data concerning the potential attack), changing trust relationships between security domains, limiting the attack and launching offensive information warfare capabilities (e.g. outbound from the compromised node while limiting or eliminating inbound communications) in log time and simultaneously and / or concurrently in different but possibly overlapping sections or segments of a digital network of arbitrary configuration.
Owner:LOCKHEED MARTIN CORP
Post-termination contact management
ActiveUS20050182672A1Shorten the timeSpecial service for subscribersConnection managementInbound communicationOutbound communication
The present invention is directed to a method for servicing a transaction in a contact center. When a communication associated with a transaction is terminated prematurely, special treatment may be provided to the transaction initiator. The special treatment includes: (a) maintaining, relative to other transactions, the assigned service priority for the transaction while the communication is disconnected and assigning the assigned service priority to a subsequent inbound communication from the transaction initiator; (b) scheduling a subsequent outbound communication to an external endpoint associated with the transaction initiator; (c) assigning to the transaction initiator a favored service priority when the subsequent inbound communication is received by the contact center; and (d) when, during the first communication, the transaction initiator selected at least one item as part of an electronic order and the first communication was terminated before the electronic order was completed, maintaining the item(s) in memory and providing the item(s) to the transaction initiator when the transaction initiator makes a further communication with the contact center.
Owner:AVAYA INC
Intelligent presence management in a communication routing system
ActiveUS8098810B2Interconnection arrangementsManual exchangesInbound communicationDistributed computing
Systems and methods for intelligent presence management in a communication routing system are provided. In exemplary embodiments, an inbound communication may be received for a user. The user's presence status is determined and a profile associated with the user is reviewed. Based on rules contained within the profile, appropriate instructions may be generated for routing the inbound communication in accordance with some embodiments. In other embodiments, instructions may be generated to log the user in or out with the communication routing system.
Owner:SANGOMA US INC
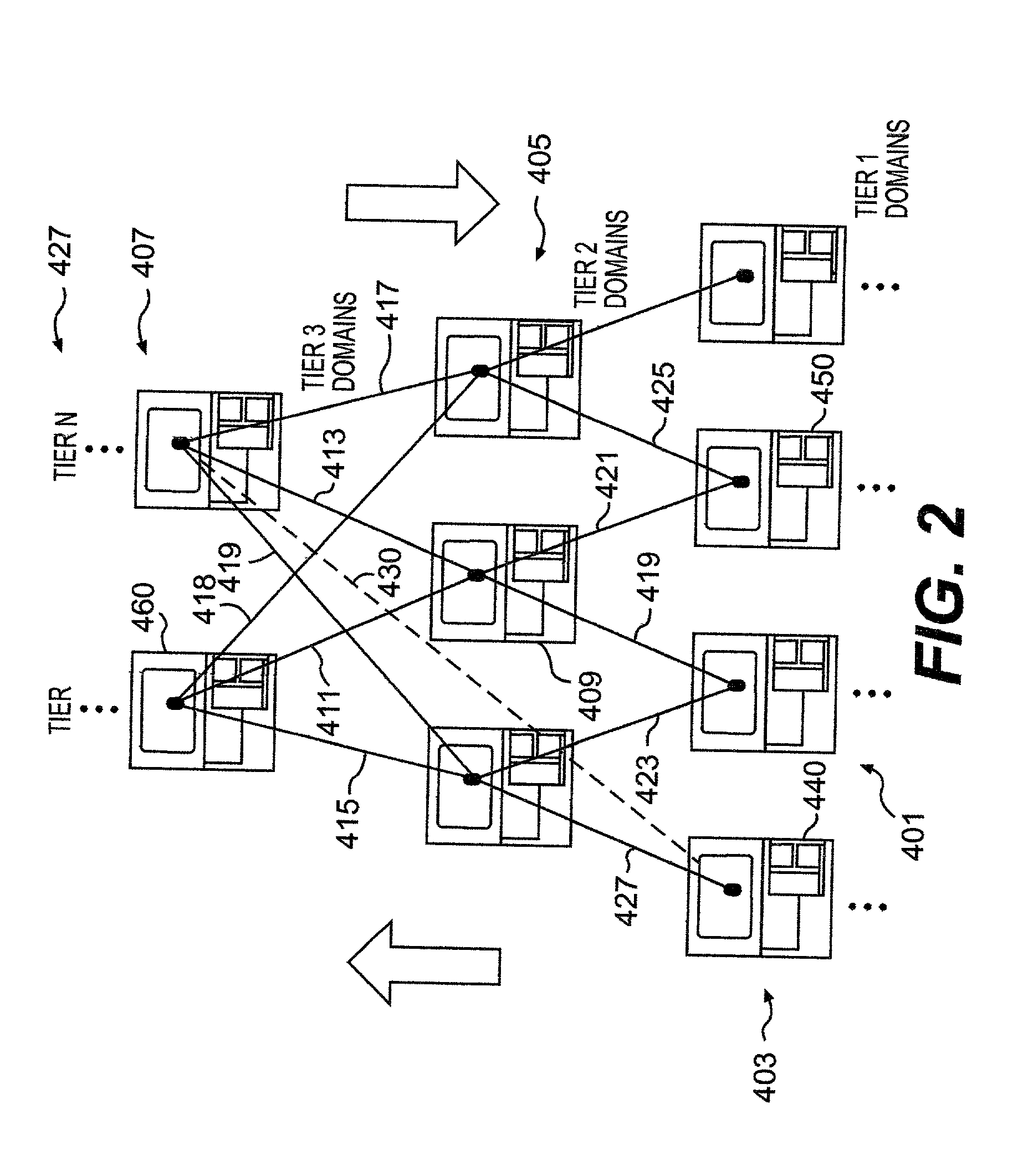
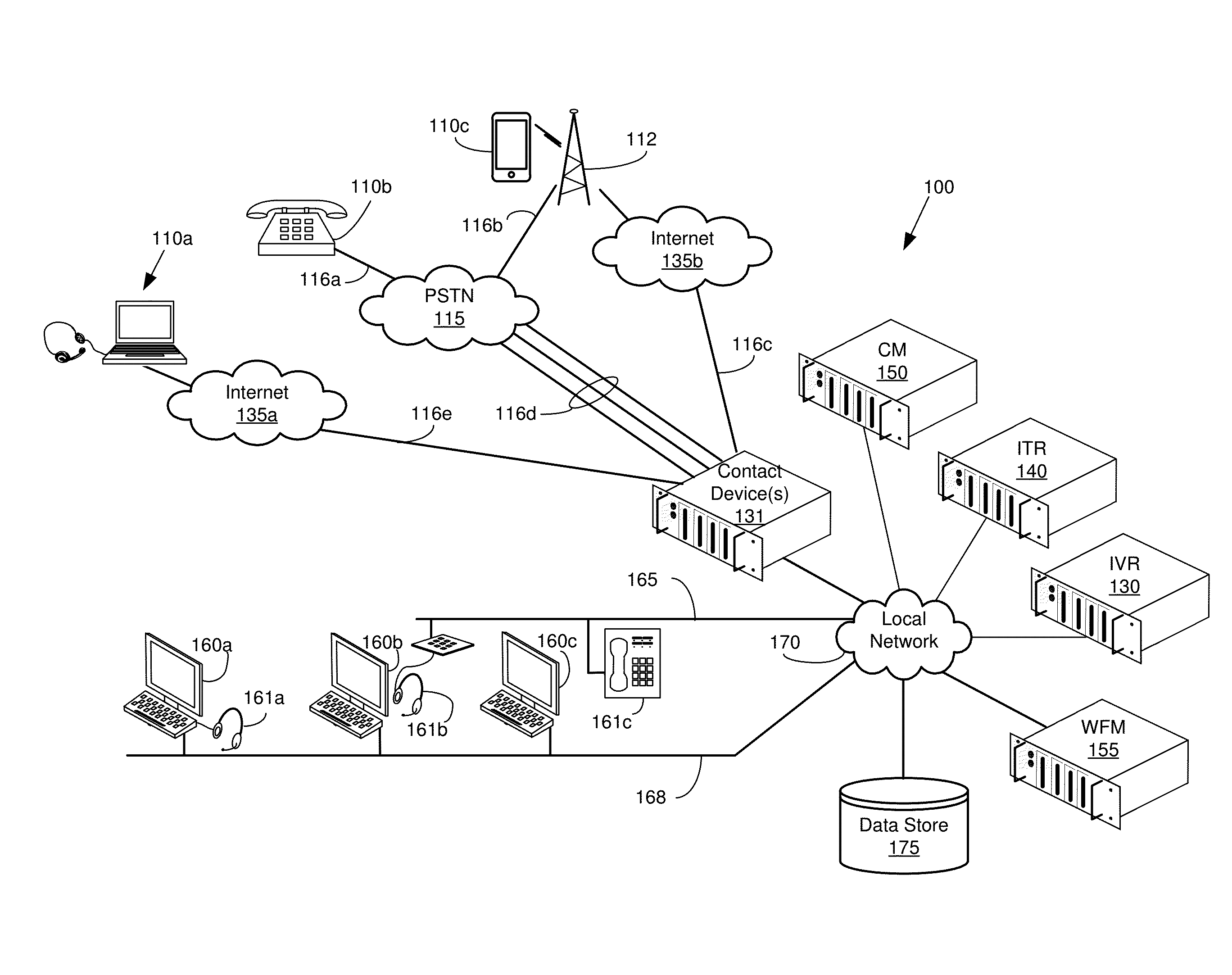
Routing inbound communications across call centers and the like
InactiveUS20110255553A1Store-and-forward switching systemsAutomatic exchangesInbound communicationRouting decision
Communications within a communication management network are routed according to a dynamic scorecard routing method in which communication routing decision attributes of communication route destinations are monitored through data feeds from the communication route destinations at a communication router. Values of the communication routing decision attributes are processed to produce processed attribute values and these processed attribute values are stored in a scorecard routing database. Thereafter, upon receipt of an indication of an inbound communication, a call controller is instructed to route the inbound communication to one of the communication route destinations according to assessed scores of the communication route destinations compiled using the processed communication routing decision attribute values stored in the scorecard routing database.
Owner:BROADSOFT
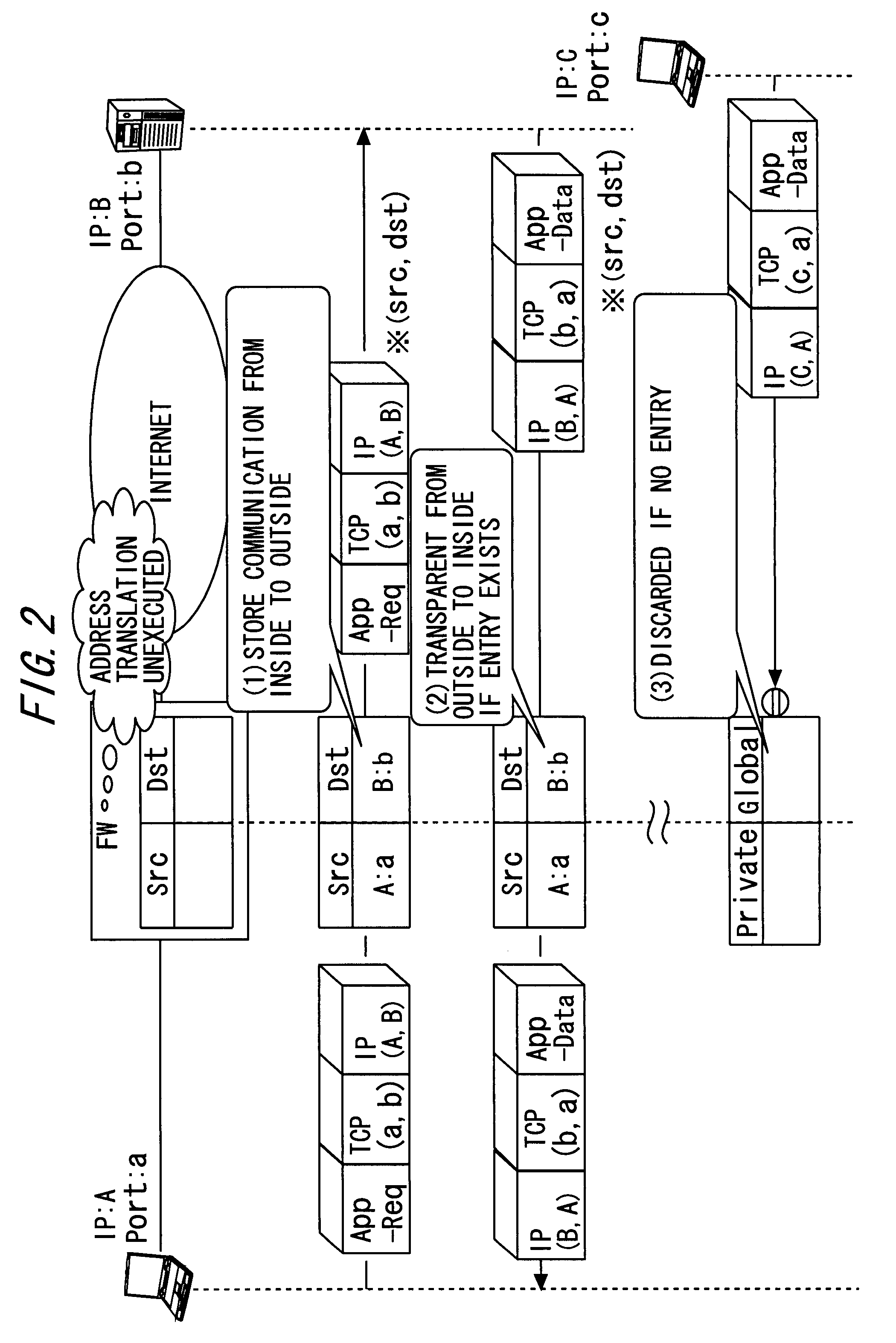
IP application service providing system
InactiveUS20080075097A1Easy to provideData switching by path configurationNetwork connectionsInbound communicationOutbound communication
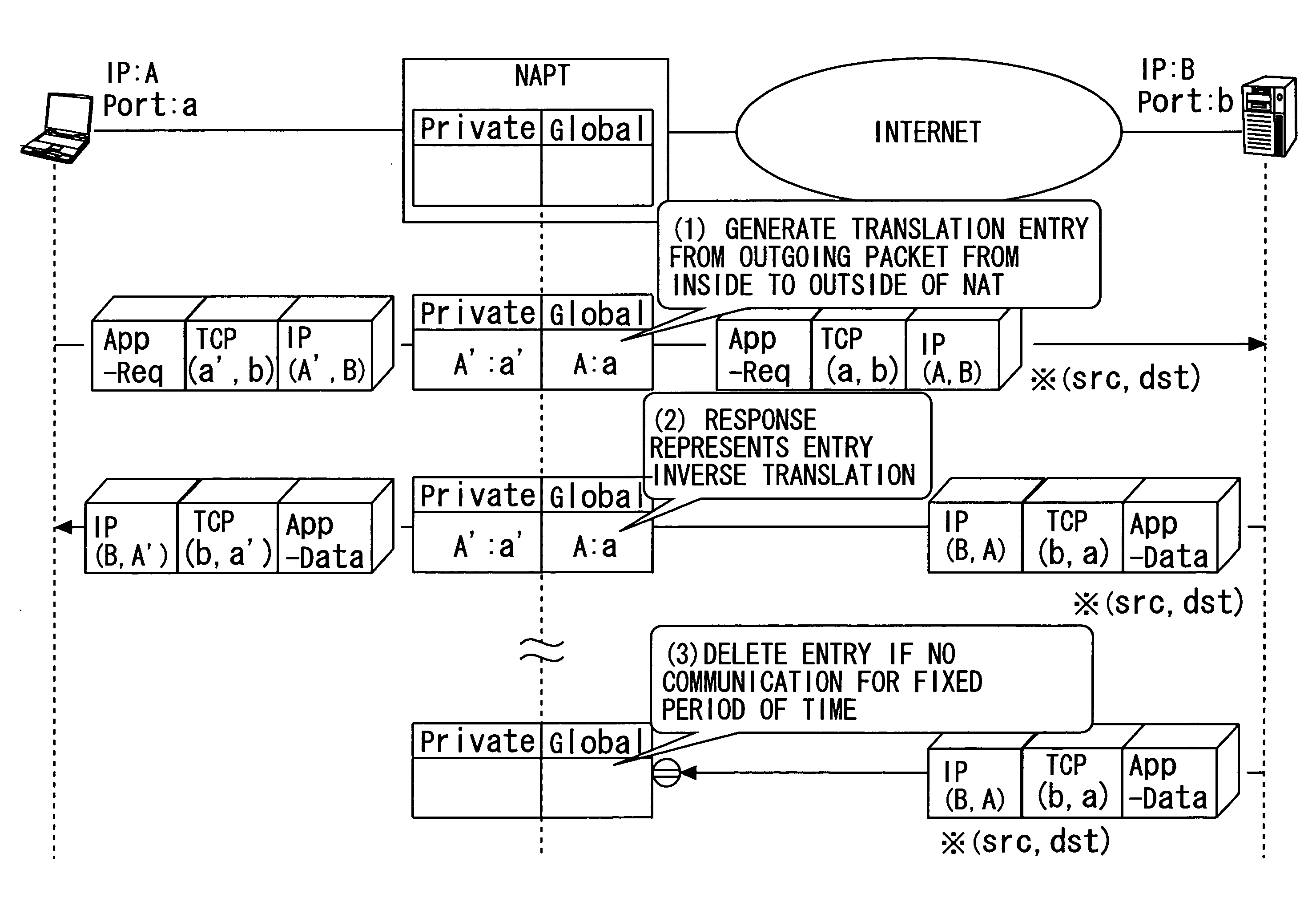
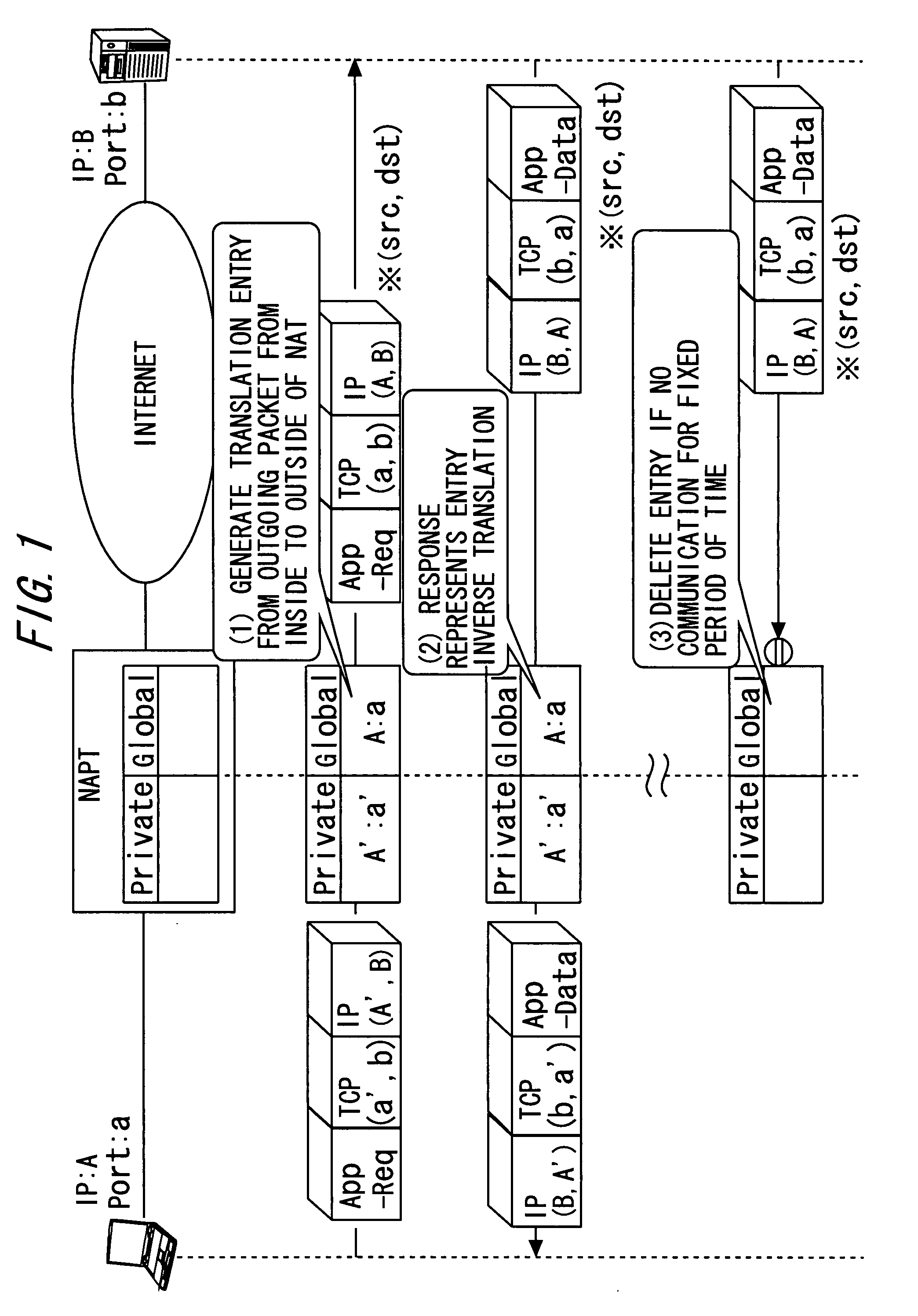
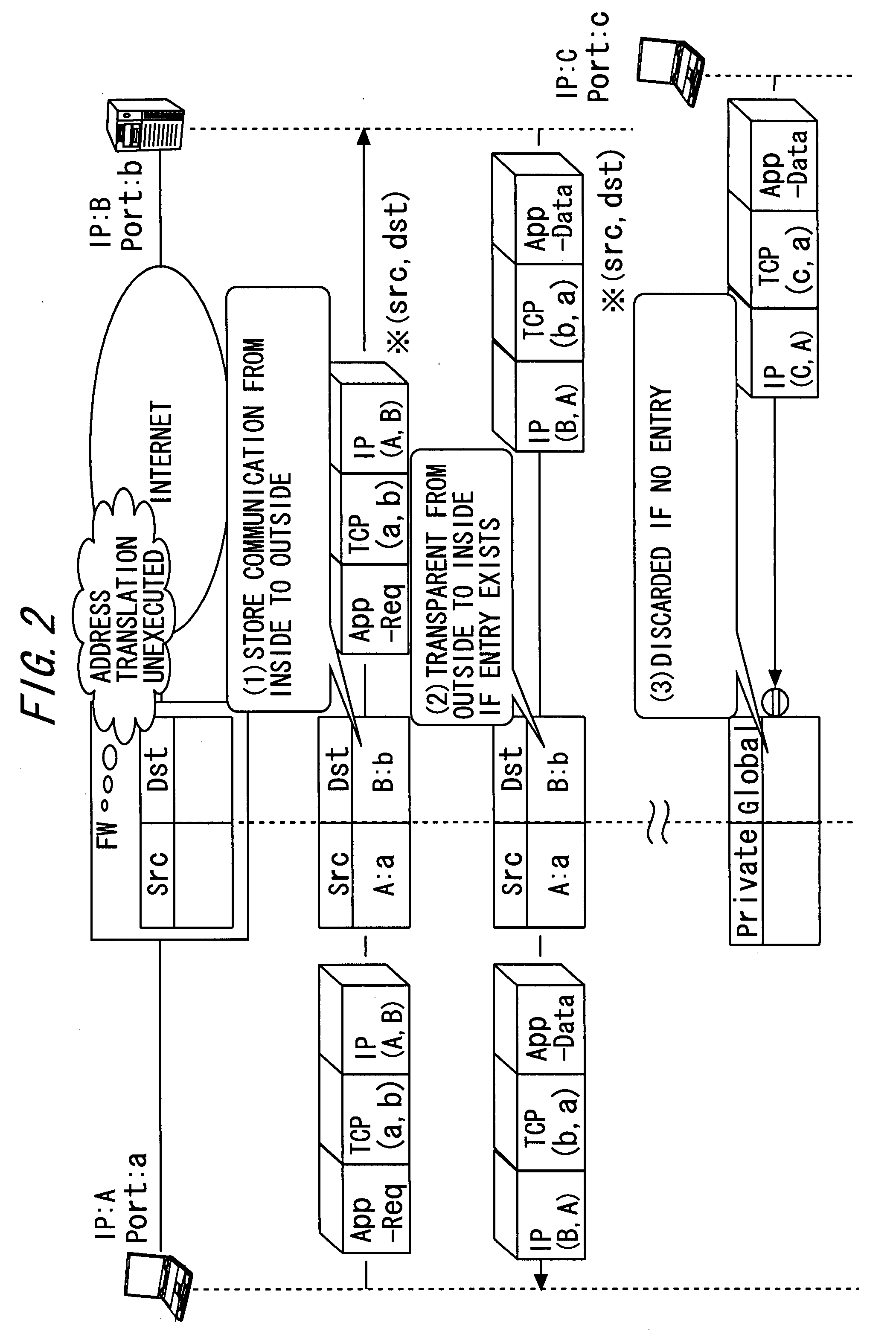
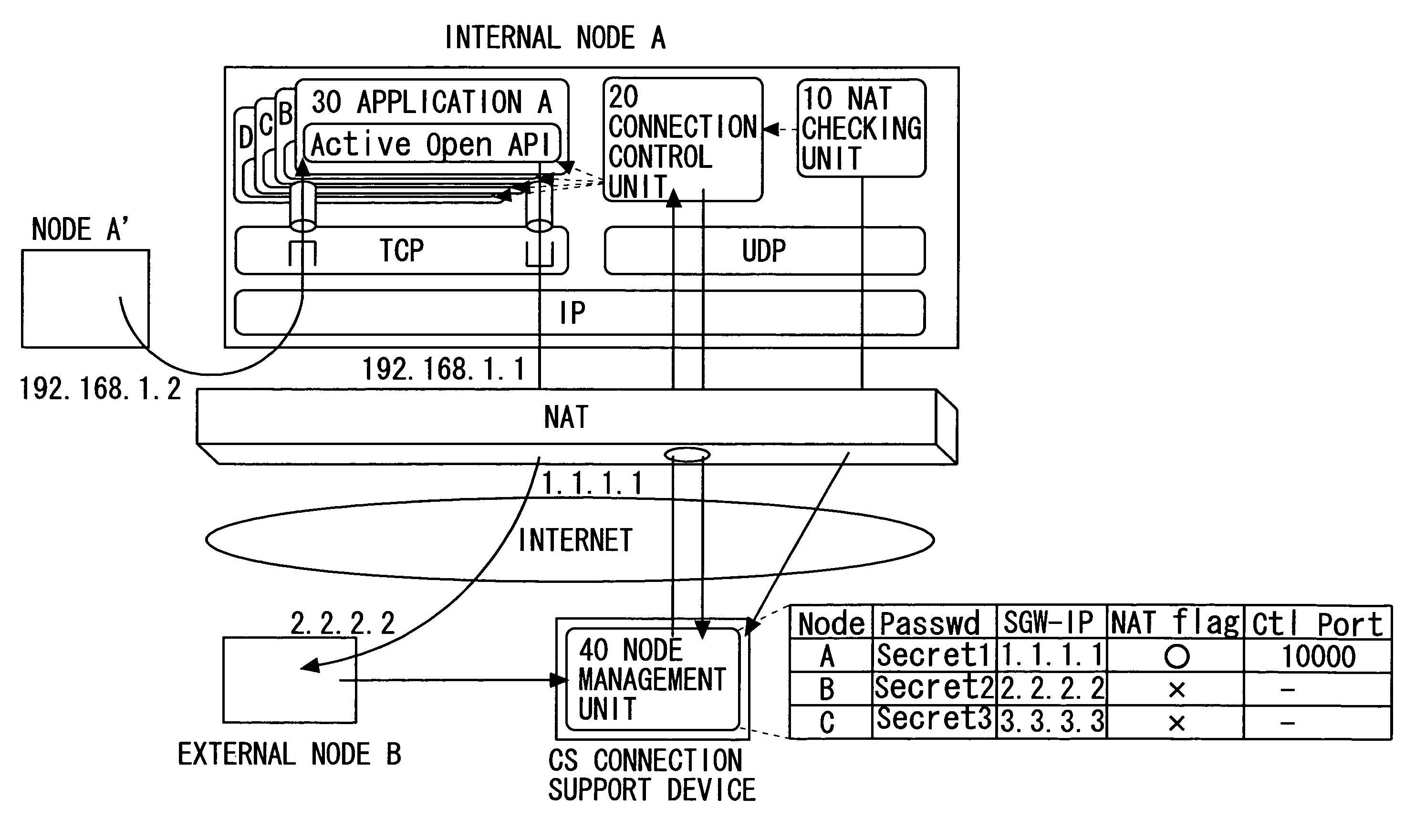
An IP application service providing method enabling inbound communication in IP application communication intended between an internal node concealed from an outside network and belonging to an inside network and an external node belonging to the outside network through a gateway device set to permit only outbound communication, includes periodically transmitting a control packet aiming at notifying of a control channel port and at maintaining a communication permission entry of a control channel path to a connection support device on the outside network from the internal node subordinated to the gateway device; notifying the internal node of a connecting destination address / port pair associated with the external node via the control channel from the connection support device; and actively opening a data channel of an IP application to the notified connecting destination address / port pair.
Owner:FUJITSU LTD
Post-termination contact management
ActiveUS7729490B2Shorten the timeSpecial service for subscribersConnection managementInbound communicationOutbound communication
The present invention is directed to a method for servicing a transaction in a contact center. When a communication associated with a transaction is terminated prematurely, special treatment may be provided to the transaction initiator. The special treatment includes: (a) maintaining, relative to other transactions, the assigned service priority for the transaction while the communication is disconnected and assigning the assigned service priority to a subsequent inbound communication from the transaction initiator; (b) scheduling a subsequent outbound communication to an external endpoint associated with the transaction initiator; (c) assigning to the transaction initiator a favored service priority when the subsequent inbound communication is received by the contact center; and (d) when, during the first communication, the transaction initiator selected at least one item as part of an electronic order and the first communication was terminated before the electronic order was completed, maintaining the item(s) in memory and providing the item(s) to the transaction initiator when the transaction initiator makes a further communication with the contact center.
Owner:AVAYA INC
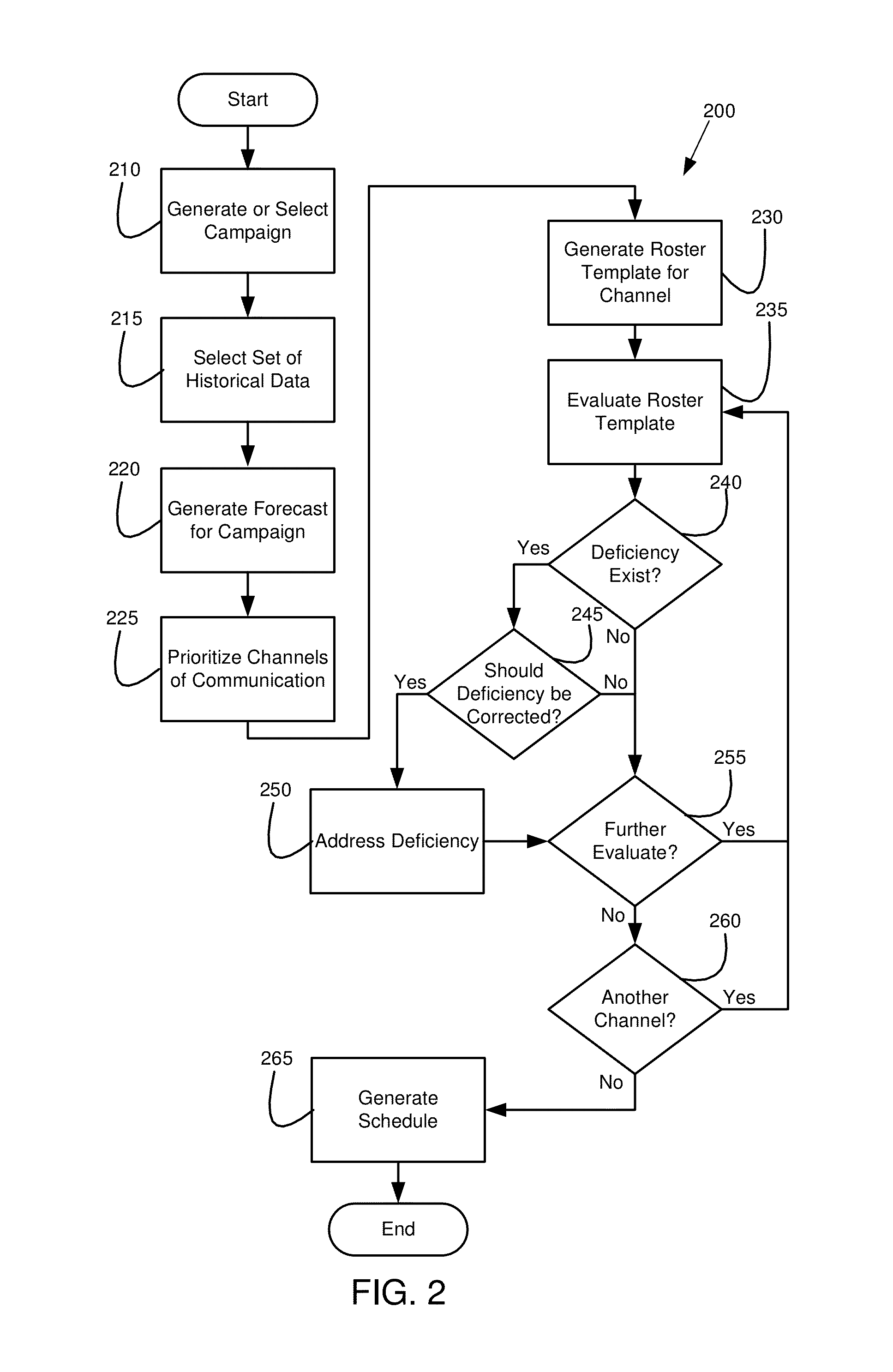
Forecasting and scheduling campaigns involving sending outbound communications that generate inbound communications
ActiveUS9426291B1Special service for subscribersManual exchangesInbound communicationOutbound communication
Various embodiments of the invention provide methods, systems, and computer program products for generating a roster template used in scheduling agent resources to conduct a campaign involving sending outbound communications using a first channel of communication to generate inbound communications using a second channel of communication. Specifically, a forecast is generated establishing a success rate for generating an inbound communication using the second channel of communication as a result of sending an outbound communication using the first channel of communication and an average response time to receive the inbound communication. Further, the forecast identifies a number of inbound communications predicted to be received for the campaign. From the forecast, a number of agent resources needed to handle the inbound communications is identified and a roster template is generated that comprises shifts identifying agent resources to schedule based on the number of agent resources needed to handle the inbound communications.
Owner:NOBLE SYSTEMS CORPORATION
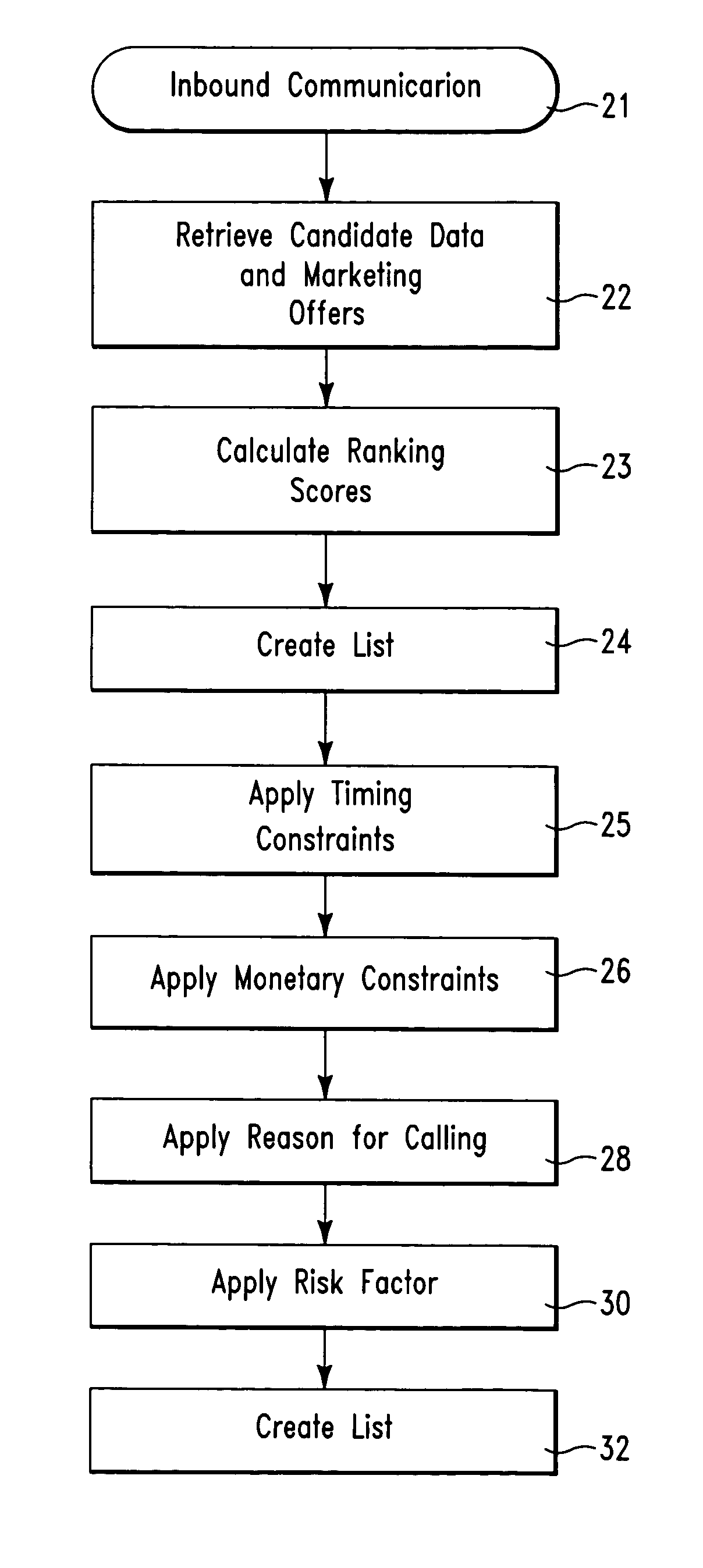
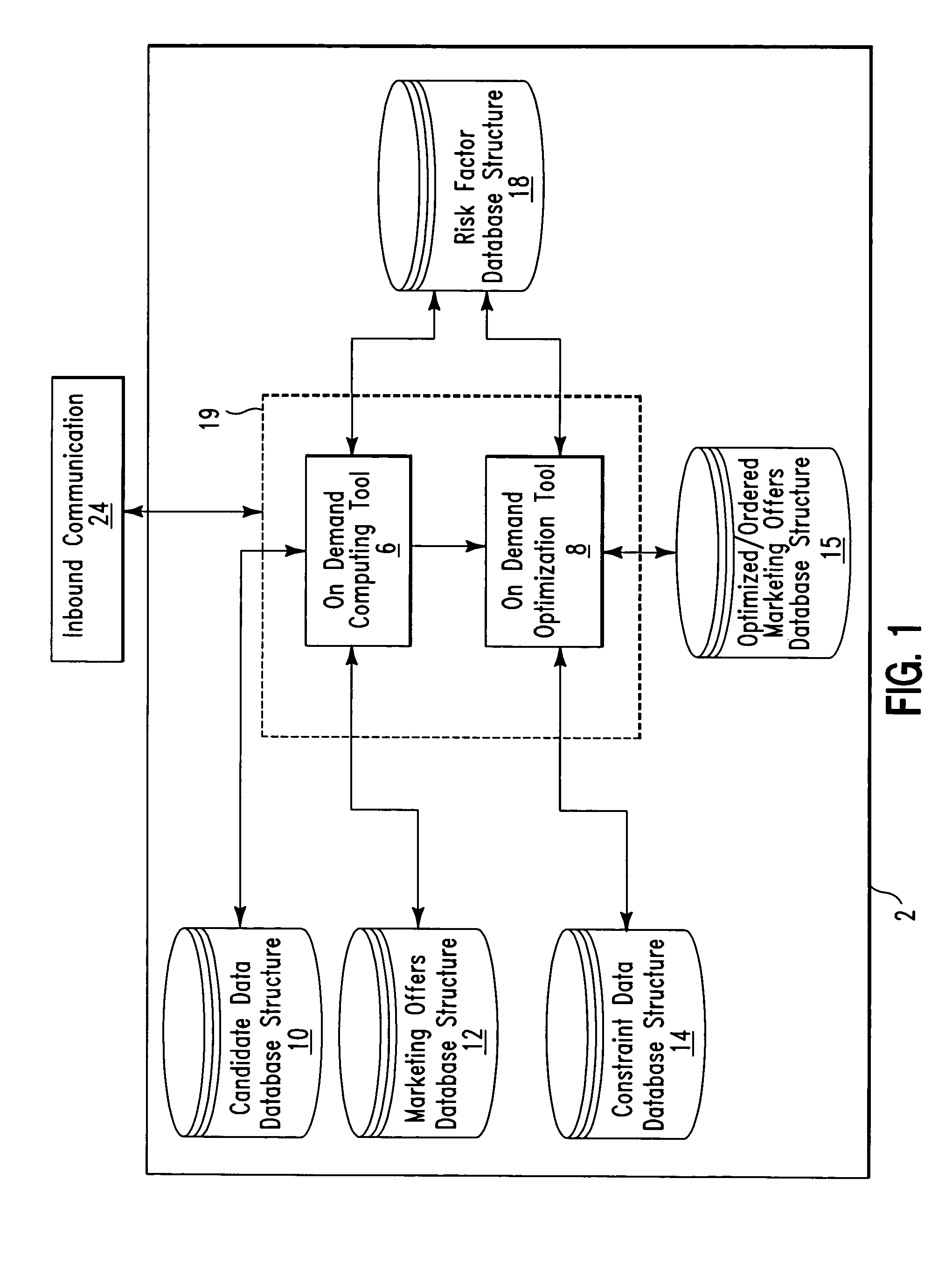
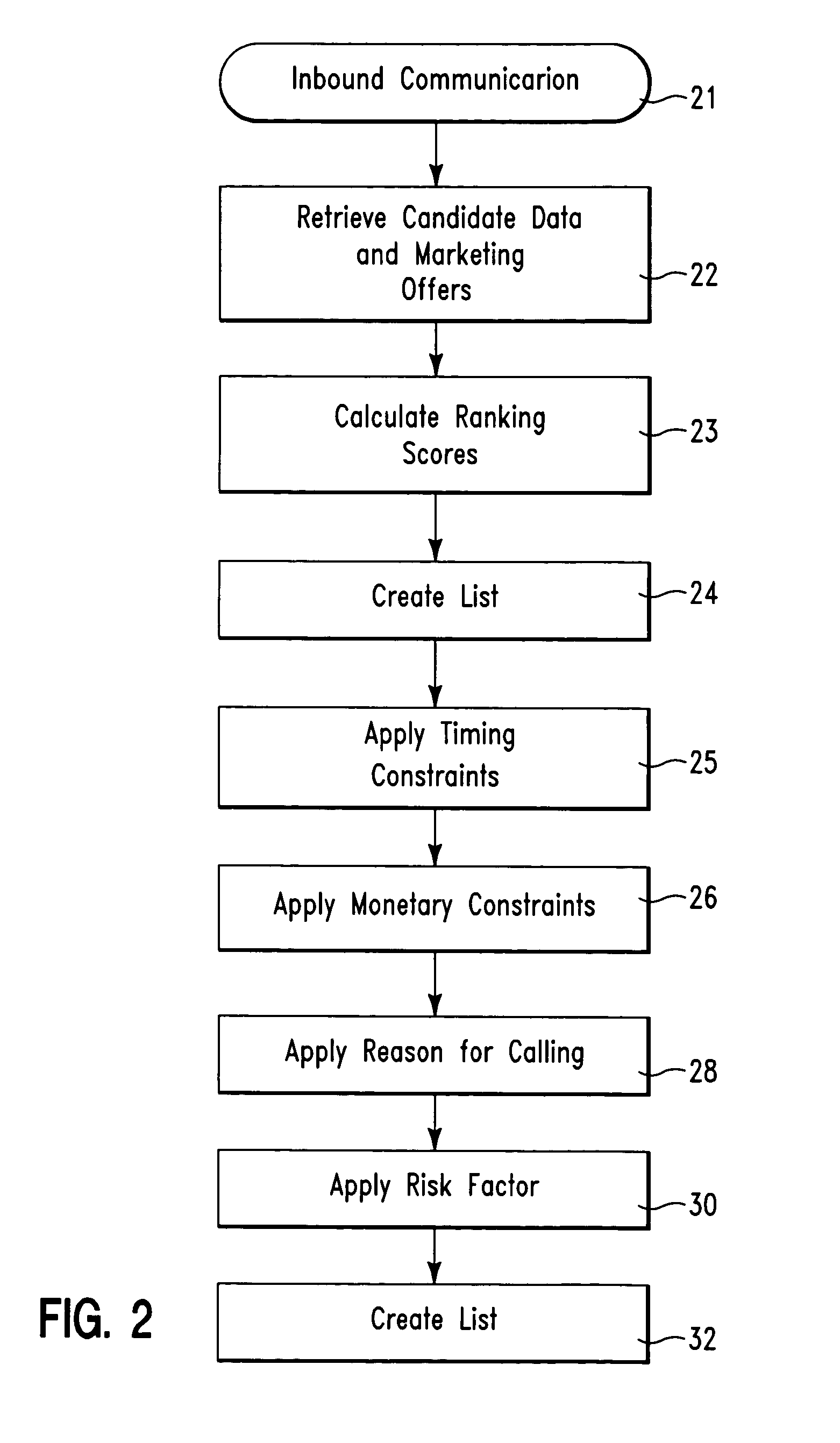
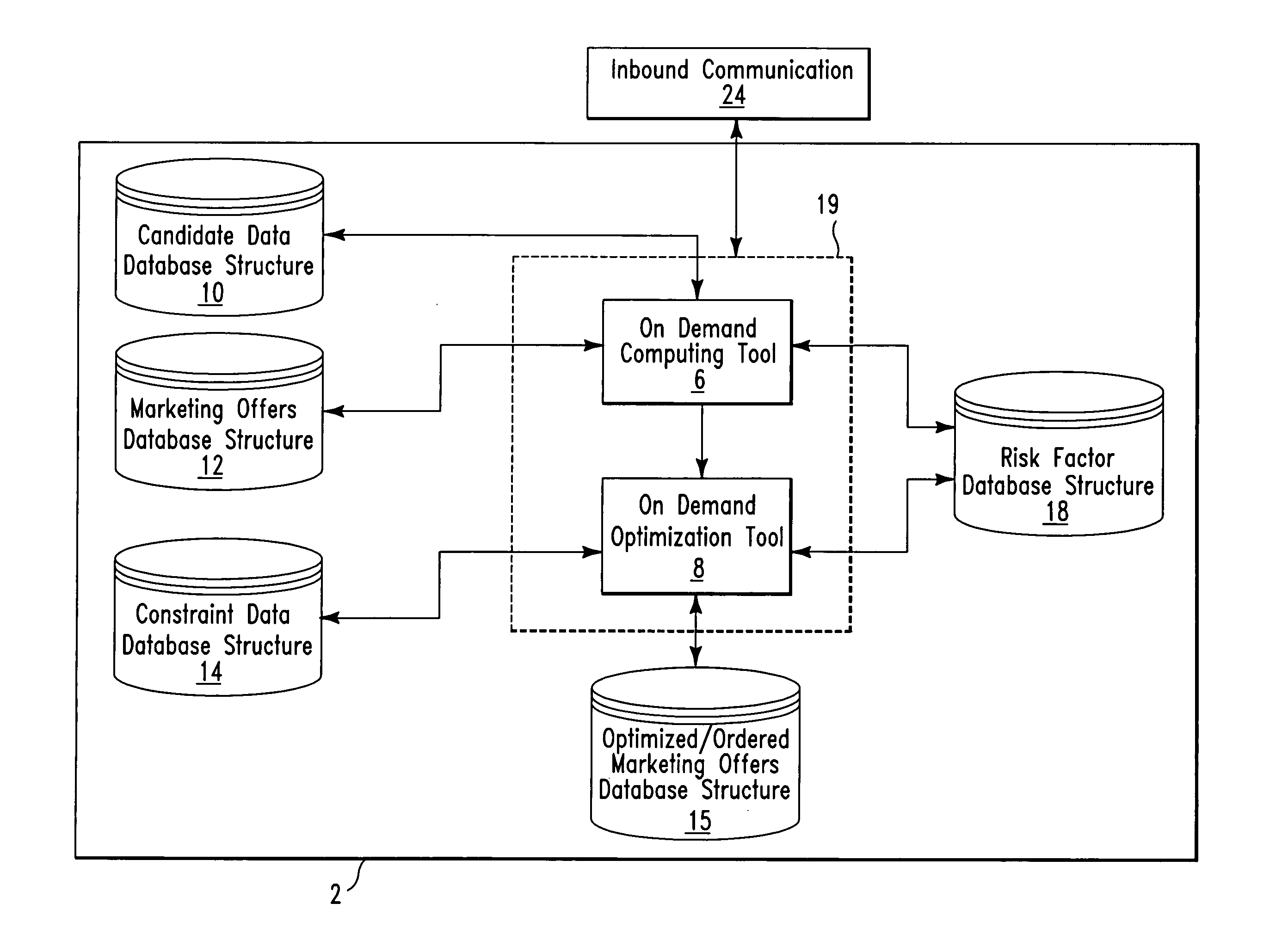
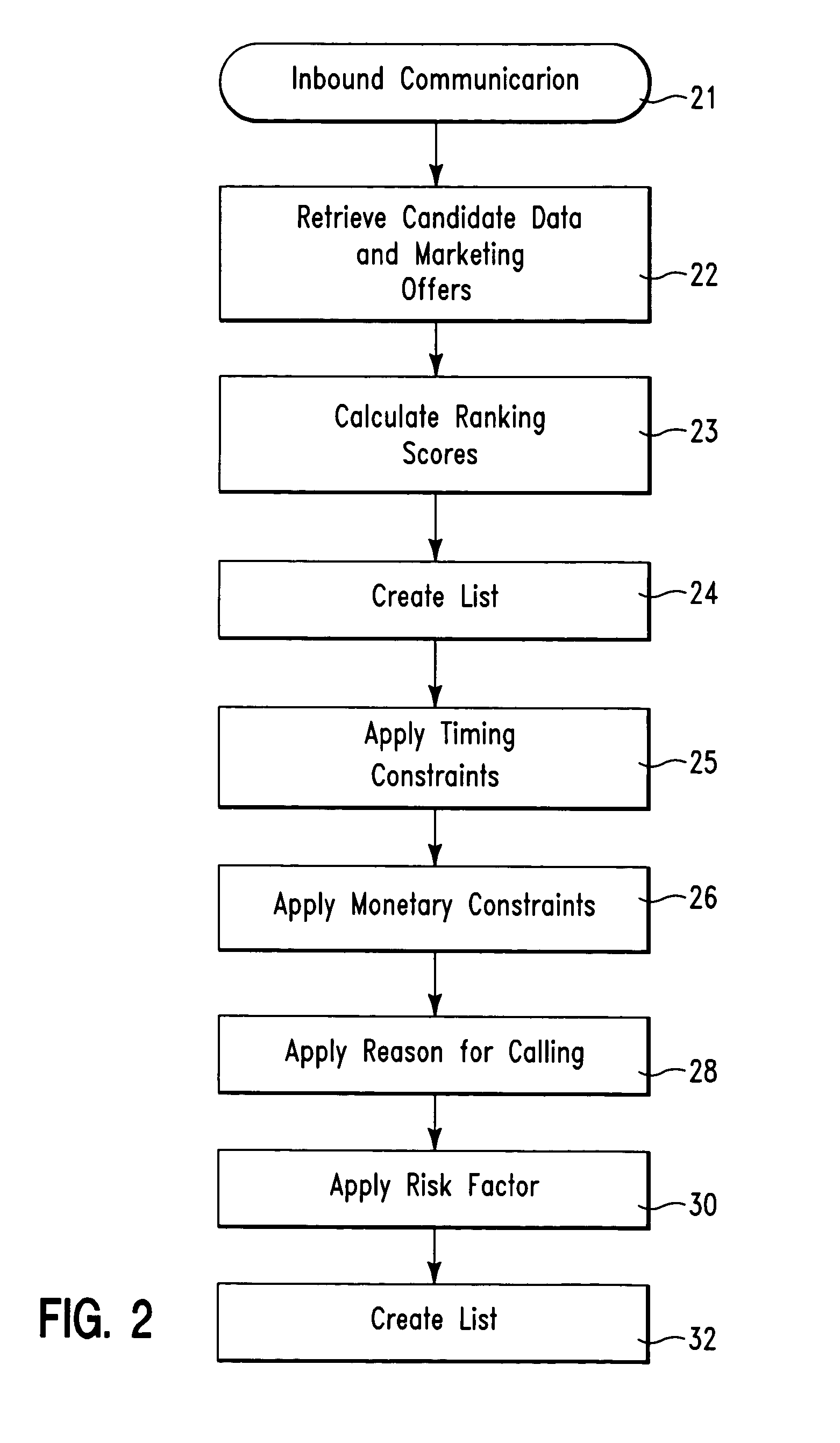
On demand selection of marketing offers in response to inbound communications
A database system and method for ordering on demand a plurality of marketing offers for offering to a candidate in response to an inbound communication from the candidate. The database system comprises a first database structure storing a first list identifying marketing offers, a second database structure storing a second list of candidates, and a database manager software application stored on a computer readable medium. The database manager software application comprises an on demand optimization tool. The on demand optimization tool is for optimizing and sorting, the marketing offers from the first list with for a first candidate from the second list in response to an inbound communication from the first candidate.
Owner:IBM CORP
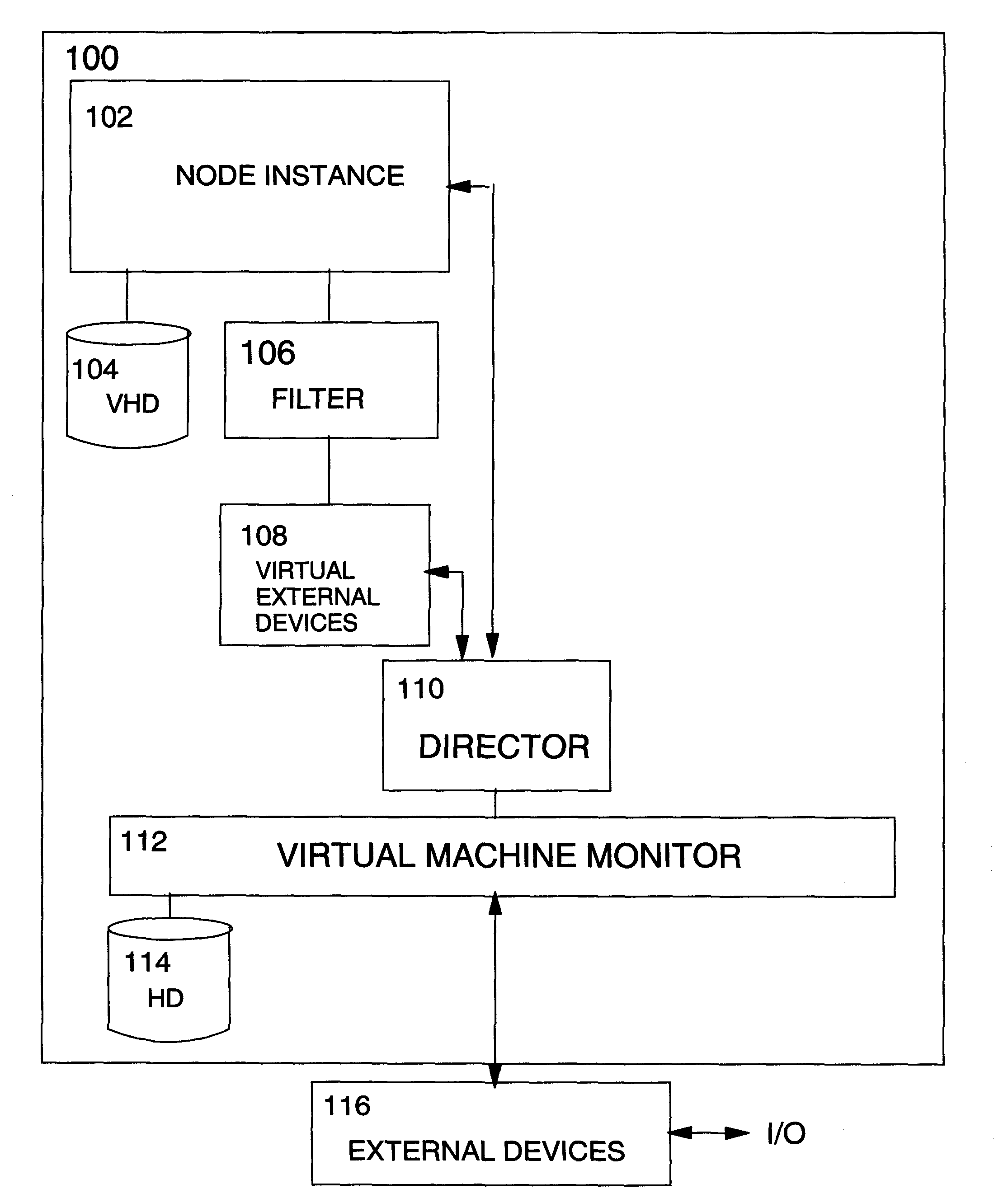
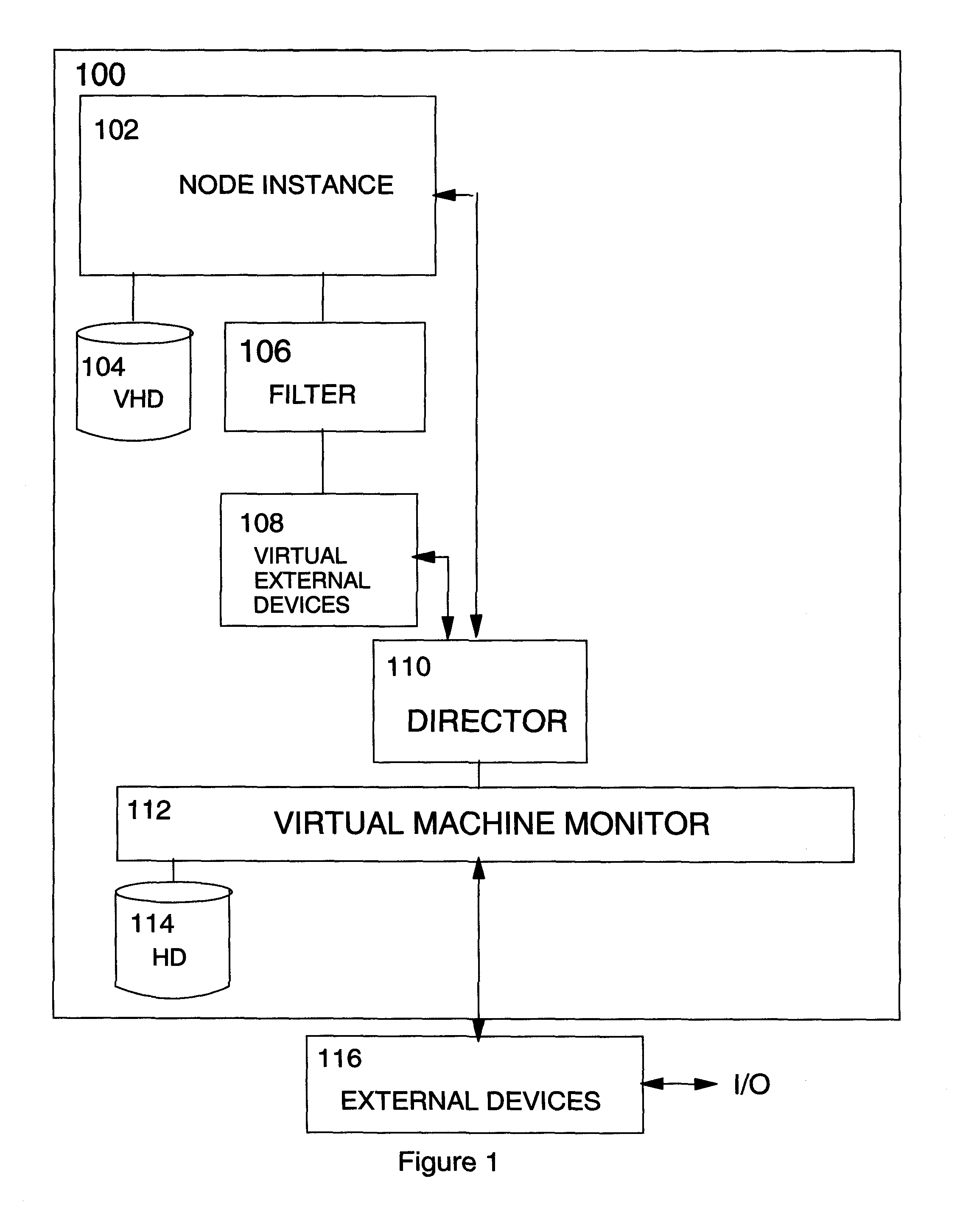
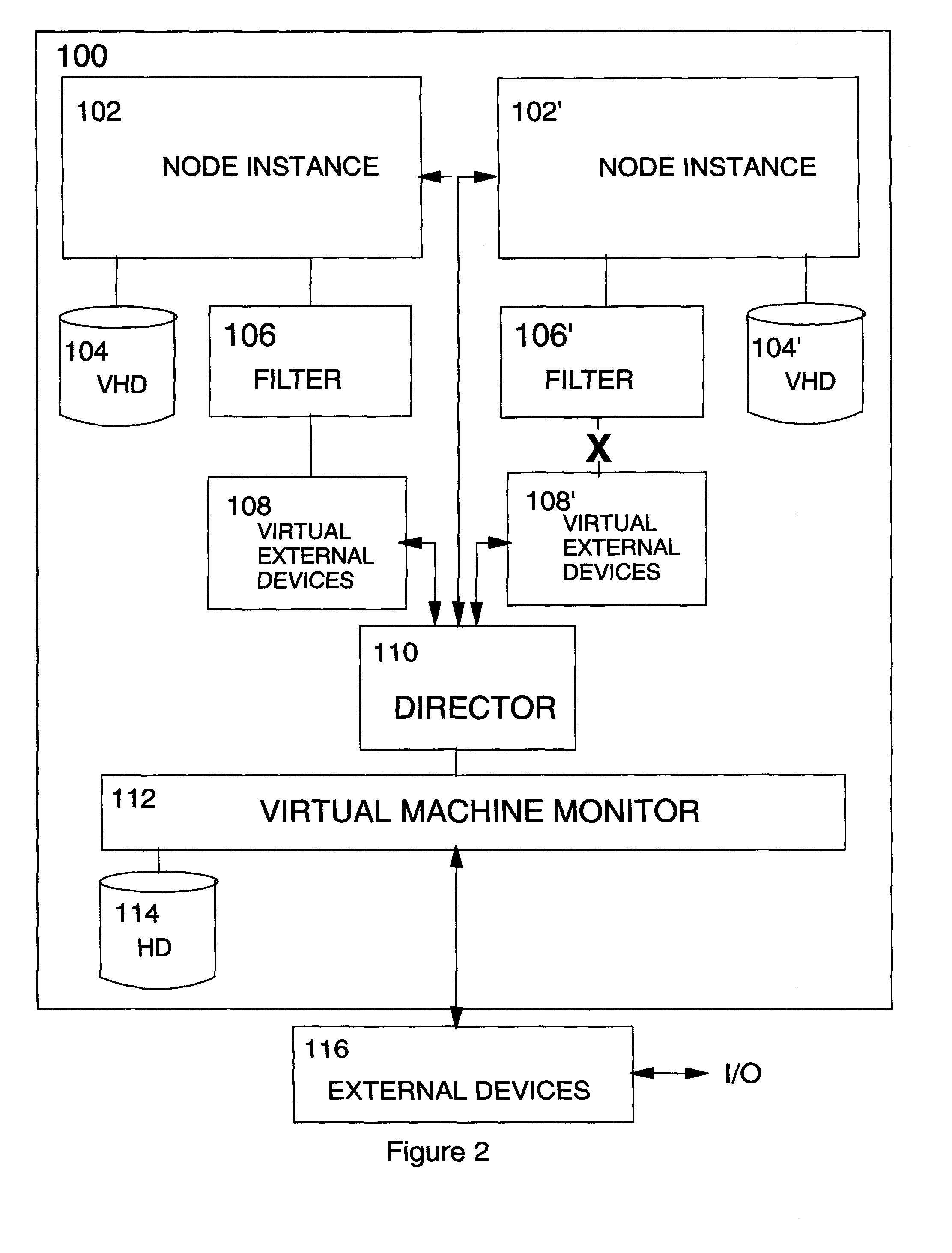
Apparatus and method for cluster recovery
InactiveUS20100054120A1Low costError preventionFrequency-division multiplex detailsInbound communicationOutbound communication
Apparatus for non-disruptive error recovery in a clustered system, comprises a node instance configuration activity quiescing component for quiescing configuration activity at a first virtual node instance; a node instance creation component for creating a second virtual node instance with I / O access blocked; a configuration transfer component for transferring configuration data from the first to the second virtual node instance; a commit component for committing the changeover from the first to the second virtual node instance; a node instance communications blocking component for blocking inbound communications to a first virtual node instance; a node instance communications unblocking component for unblocking I / O access at the second virtual node instance; a communication control component for monitoring outbound communications from the first virtual node instance and signalling completion of all pending outbound communications; and a node instance deletion component for deleting the first virtual node instance.
Owner:IBM CORP
Intelligent Presence Management in a Communication Routing System
ActiveUS20110306298A1Interconnection arrangementsSpecial service for subscribersInbound communicationComputer science
Systems and methods for intelligent presence management in a communication routing system are provided. In exemplary embodiments, an inbound communication may be received for a user. The user's presence status is determined and a profile associated with the user is reviewed. Based on rules contained within the profile, appropriate instructions may be generated for routing the inbound communication in accordance with some embodiments. In other embodiments, instructions may be generated to log the user in or out with the communication routing system.
Owner:SANGOMA US INC
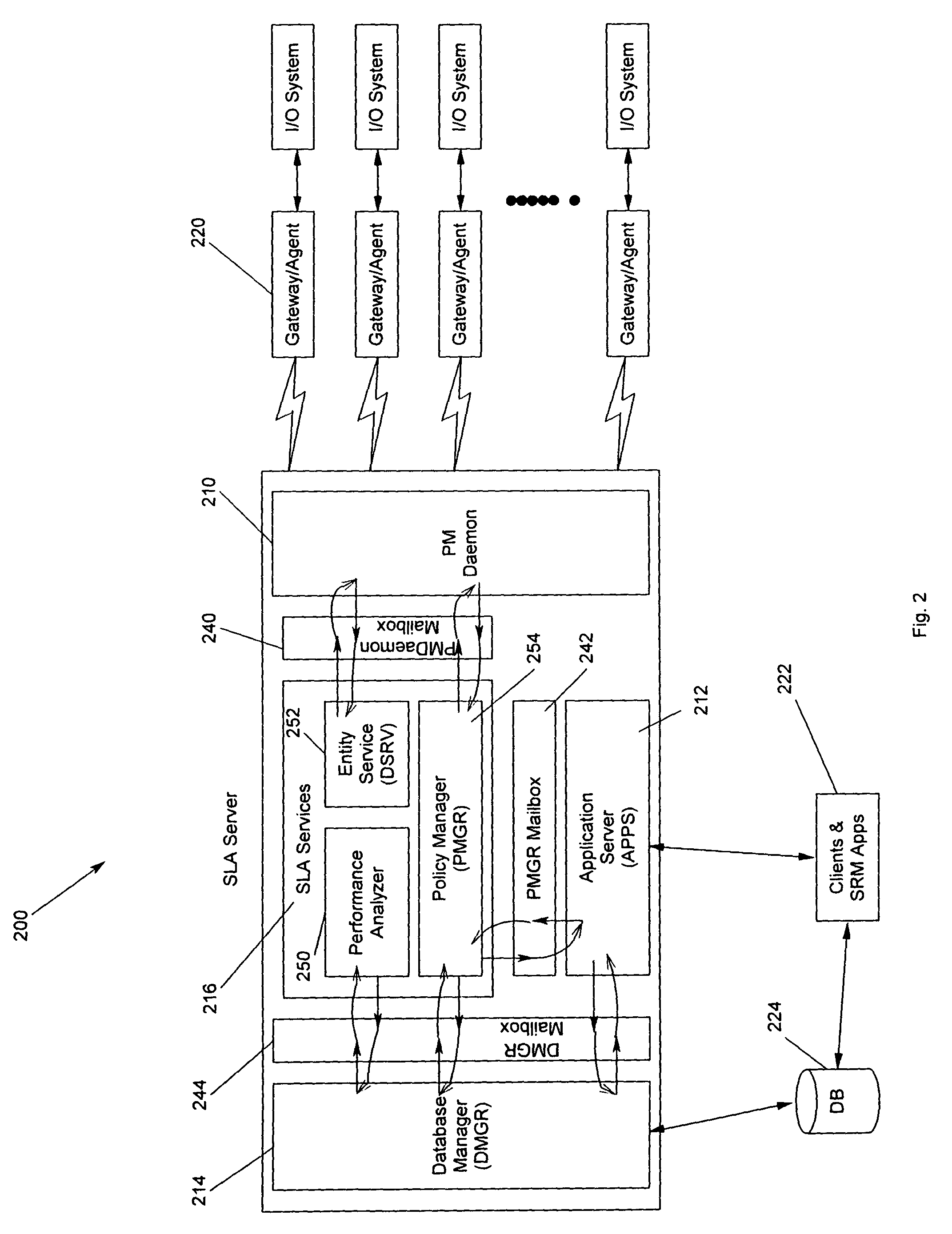
Method for improving performance in a computer storage system by regulating resource requests from clients
InactiveUS7349958B2Data processing applicationsMultiple digital computer combinationsInbound communicationOutbound communication
The present invention discloses a method, apparatus and program storage device for providing non-blocking, minimum threaded two-way messaging. A Performance Monitor Daemon provides one non-blocked thread pair per processor to support a large number of connections. The thread pair includes an outbound thread for outbound communication and an inbound thread for inbound communication. The outbound thread and the inbound thread operate asynchronously.
Owner:IBM CORP
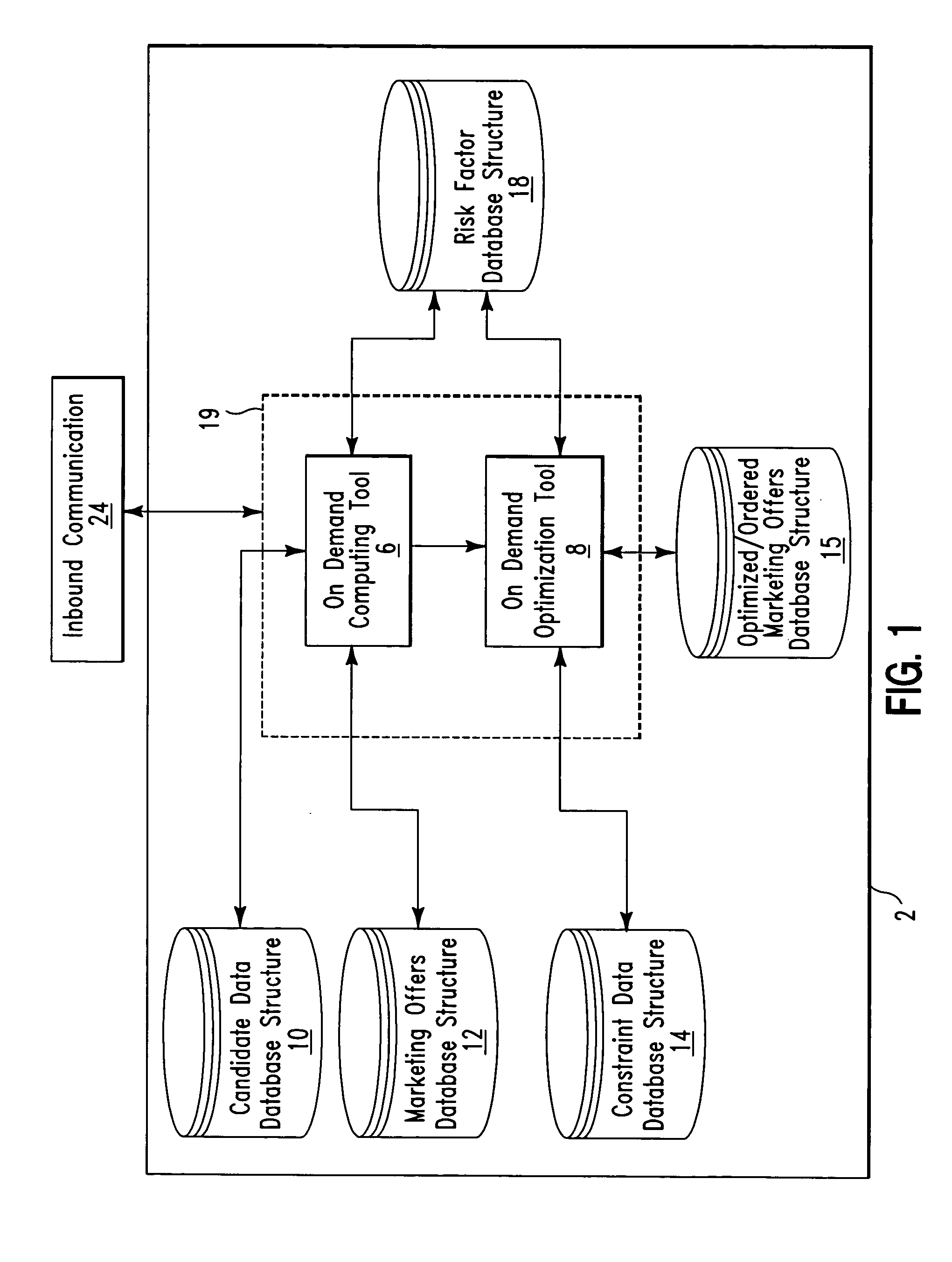
On demand selection of marketing offers in response to inbound communications
A database system and method for ordering on demand a plurality of marketing offers for offering to a candidate in response to an inbound communication from the candidate. The database system comprises a first database structure storing a first list identifying marketing offers, a second database structure storing a second list of candidates, and a database manager software application stored on a computer readable medium. The database manager software application comprises an on demand optimization tool. The on demand optimization tool is for optimizing and sorting, the marketing offers from the first list with for a first candidate from the second list in response to an inbound communication from the first candidate.
Owner:IBM CORP
Articles of manufacture, service provider computing methods, and computing service systems
Articles of manufacture, service provider computing methods, and computing service systems are described. According to one aspect, an article of manufacture includes a computer-readable storage medium storing programming configured to cause processing circuitry of a client computing device within a client network to perform processing comprising creating an outbound network connection to a service provider which is external of the client network and which is to provide computing services to the client network, accessing an inbound communication from the service provider received via the outbound network connection during the providing of the computing services by the service provider to the client network, and communicating data of the inbound communication to another client computing device within the client network.
Owner:REDWOOD TECHNOLOGY BV
Marking outgoing communications for follow-up
Responsiveness for outbound communications is monitored. An outbound communication initiated by a sender via a communications system is identified. Content of the outbound communication is analyzed to determine, using a processor of a computer, whether to monitor for a response to the outbound communication. Inbound communications to the sender are monitored for the response to the outbound communication, and a reminder is generated when a response to the outbound communication is not identified.
Owner:GOOGLE LLC
IP application service providing system
InactiveUS7706358B2Easy to provideData switching by path configurationNetwork connectionsInbound communicationOutbound communication
An IP application service providing method enabling inbound communication in IP application communication intended between an internal node concealed from an outside network and belonging to an inside network and an external node belonging to the outside network through a gateway device set to permit only outbound communication, includes periodically transmitting a control packet aiming at notifying of a control channel port and at maintaining a communication permission entry of a control channel path to a connection support device on the outside network from the internal node subordinated to the gateway device; notifying the internal node of a connecting destination address / port pair associated with the external node via the control channel from the connection support device; and actively opening a data channel of an IP application to the notified connecting destination address / port pair.
Owner:FUJITSU LTD
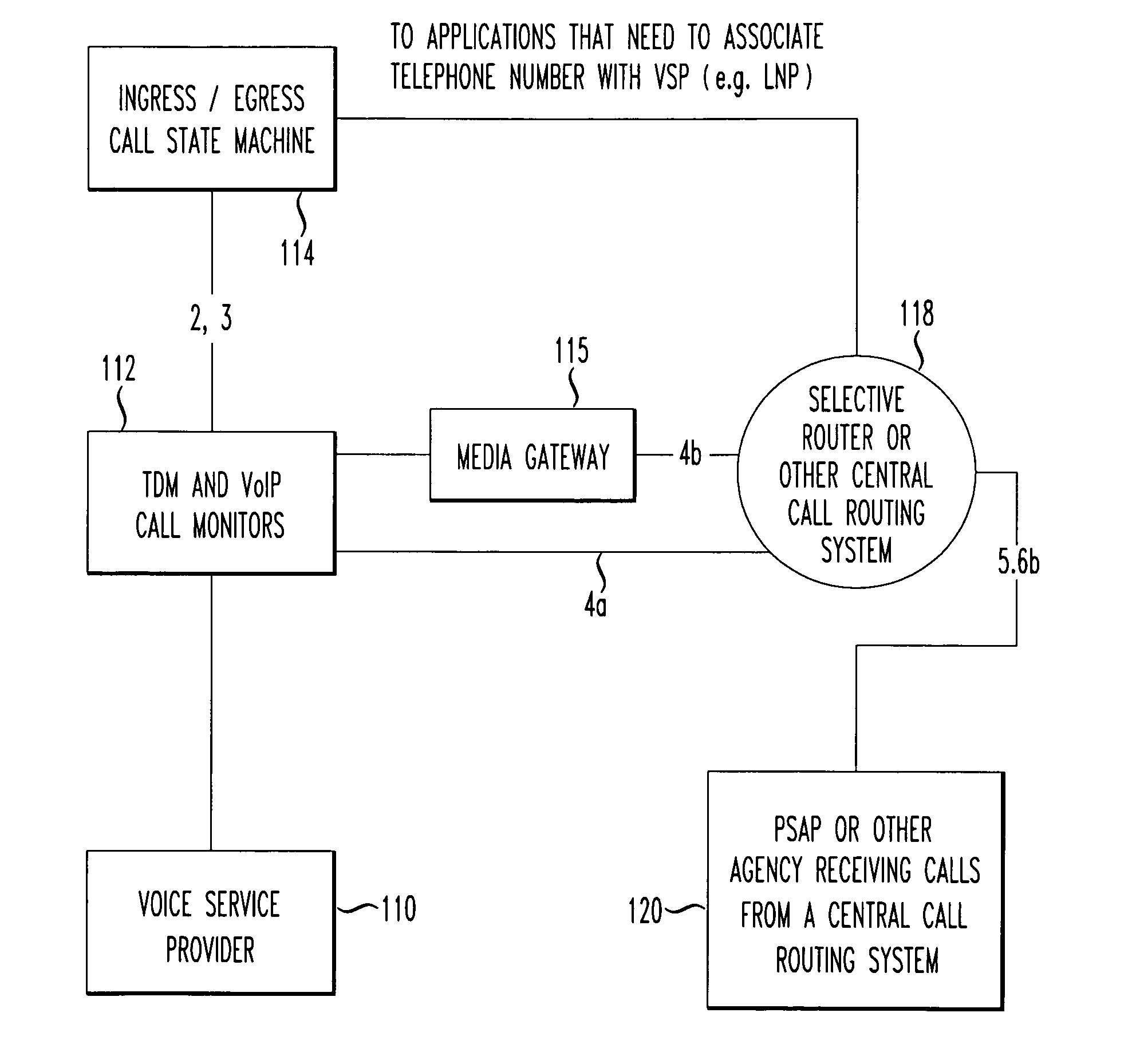
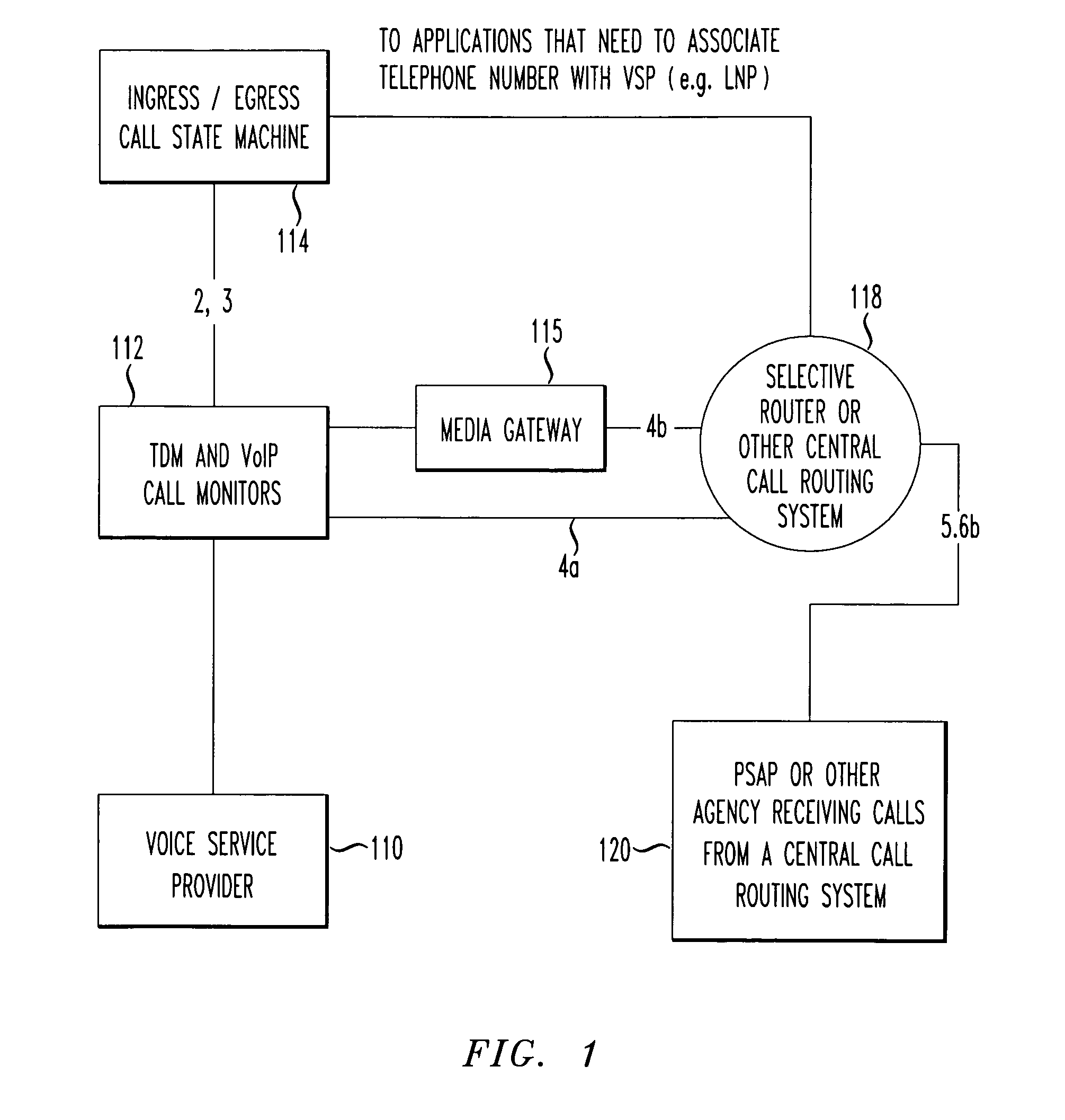
Ingress/Egress call module
ActiveUS20090275350A1Network traffic/resource managementAutomatic exchangesInbound communicationOutbound communication
A system monitors calls for a service provider. A number of simultaneous communications of a given technology type is monitored for either inbound communications and / or outbound communications associated with at least one service provider. A determination is made if the number of simultaneous communications from the service provider is in excess of a adjustable but set number of simultaneous communications of a given technology type that are permissible. A predetermined action is taken if the number of simultaneous calls or text messages (e.g., SMS, IM, email) is in excess of the set limit, e.g., the call may be terminated or other action taken. Both voice communications and / or non-voice communications (such as SMS, IM, Email, or MMS) can be monitored and throttled.
Owner:TELECOMM SYST INC
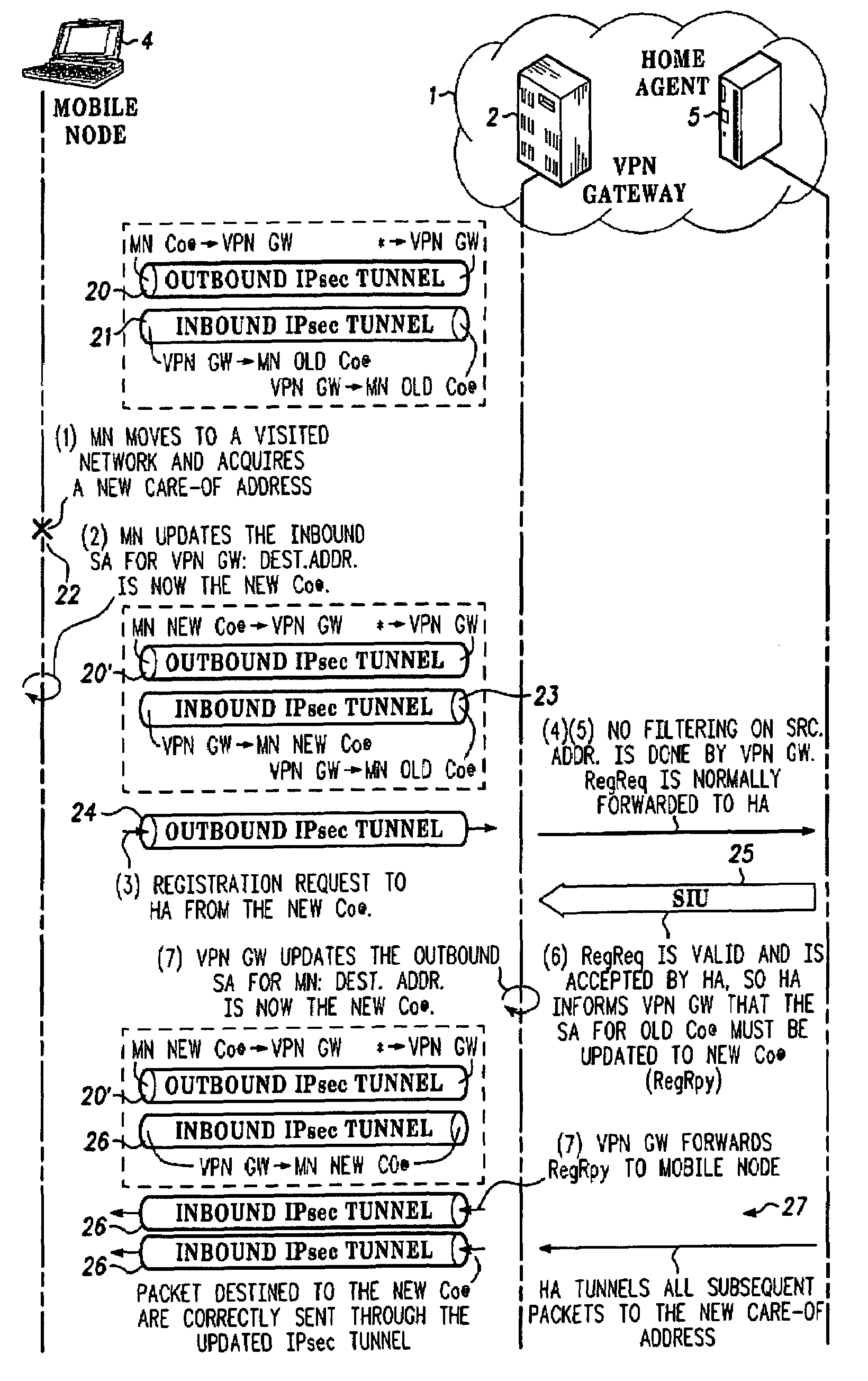
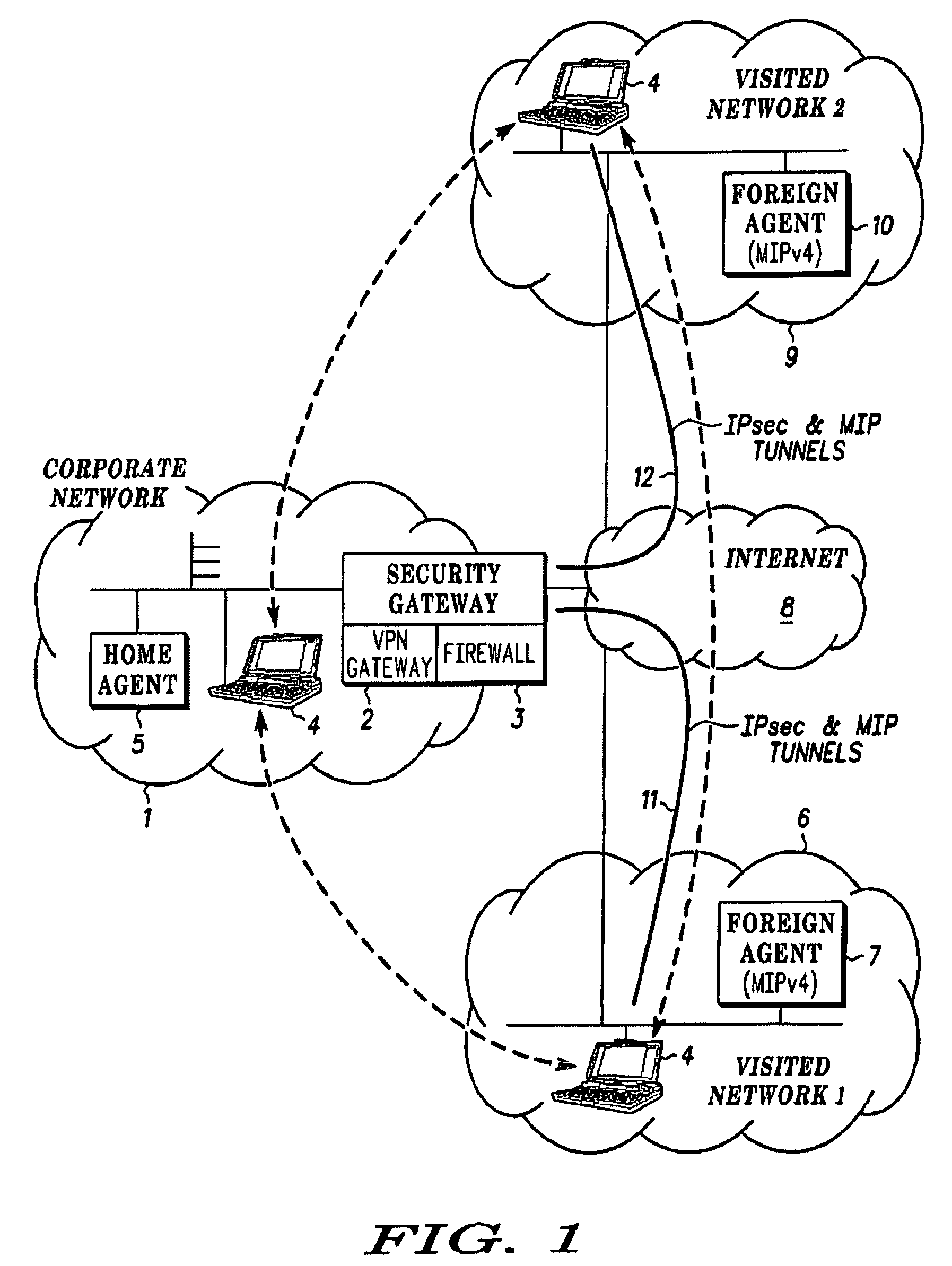
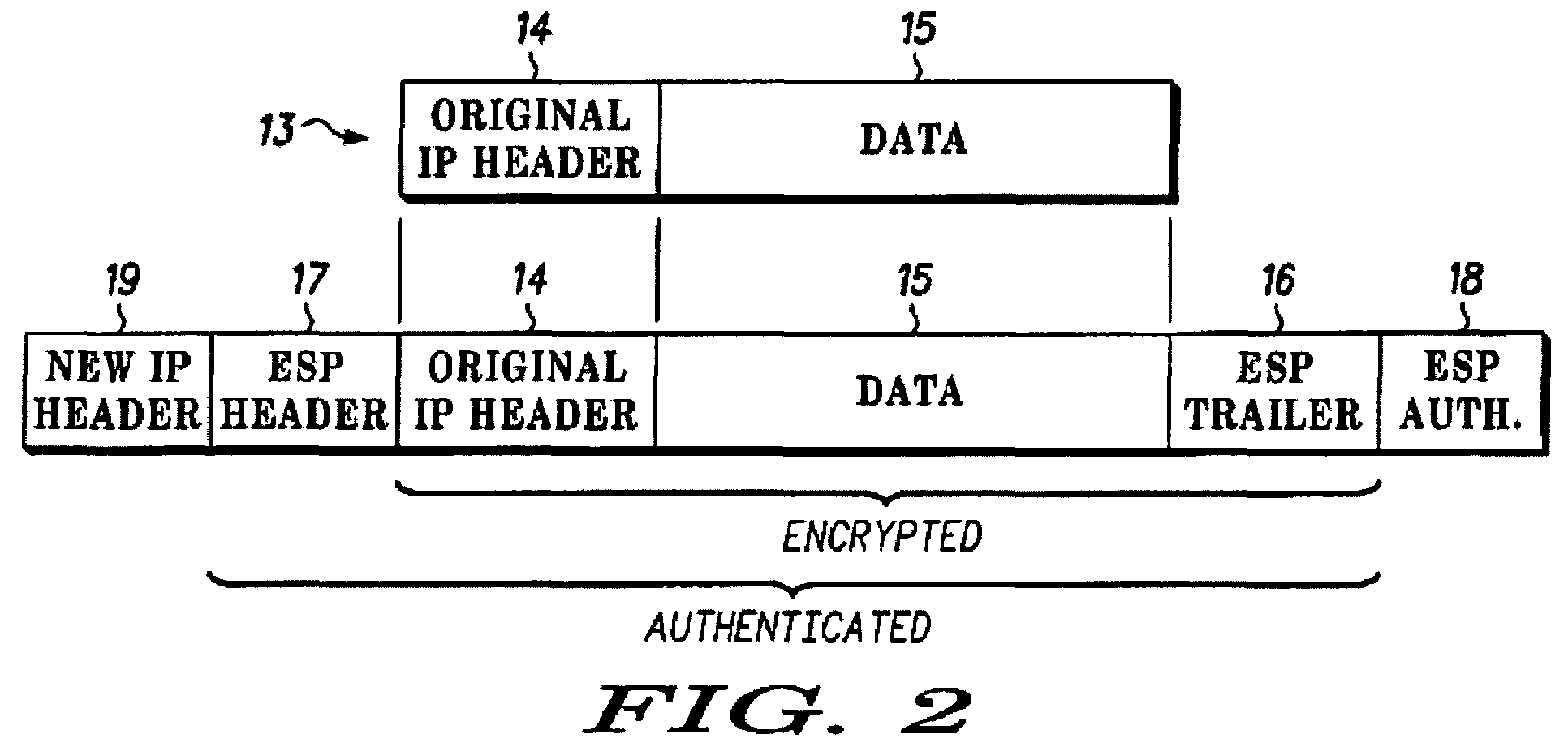
Communication between a private network and a roaming mobile terminal
ActiveUS7516486B2Computer security arrangementsMultiple digital computer combinationsInbound communicationOutbound communication
Communication between a private network (1) and a roaming mobile terminal (4), the private network (1) including a home agent (5) for the mobile terminal and a gateway (2, 3) through which, the communication passes and which-provides security protection for the private network (1). The protocols of the communication Including security association bundles each include a security association between the mobile terminal (4) and the gateway (2, 3) for inbound communication and another security association for outbound communication. In response to a handover of communication causing an IP address. (MN Co @) of the mobile terminal (4), to change to a new IP address (MN: New Co @), the mobile terminal updates its inbound security association from the, gateway (2, 3) so that it can receive packets sent to it with the new IP address (MN New Co @) as destination. It sends a first signalling message with: the home agent (5) as destination: in a secure tunnel (20′) to the gateway (2, 3), indicating the new IP address (MN, New Co @) in secure form to the home agent (5). The inbound security association of the gateway (2, 3) from the mobile terminal (4) accets, the first signalling message without cheking its source address. The gateway (2, 3) forwards the first signalling message within the private network (1) to the home agent (5), the home agent (5) checks the validity of the first signalling message and, if It is valid, updates its address data and sends a second signalling message to the gateway (2,3) indicating the new address (MN New Co @). The gateway (2, 3) updates its outbound security association with the mobile terminal (4) in response to the new address (MN New Co @) indicated. Preferably, communication between the mobile node (4) and the gateway (2, 3) is in accordance with IPsec and an Encapsulating Security Paypépad protocol used in tunnel mode. Preferably, a registration reply for the mobile node (4) is included In the second signalling message.
Owner:GOOGLE TECH HLDG LLC
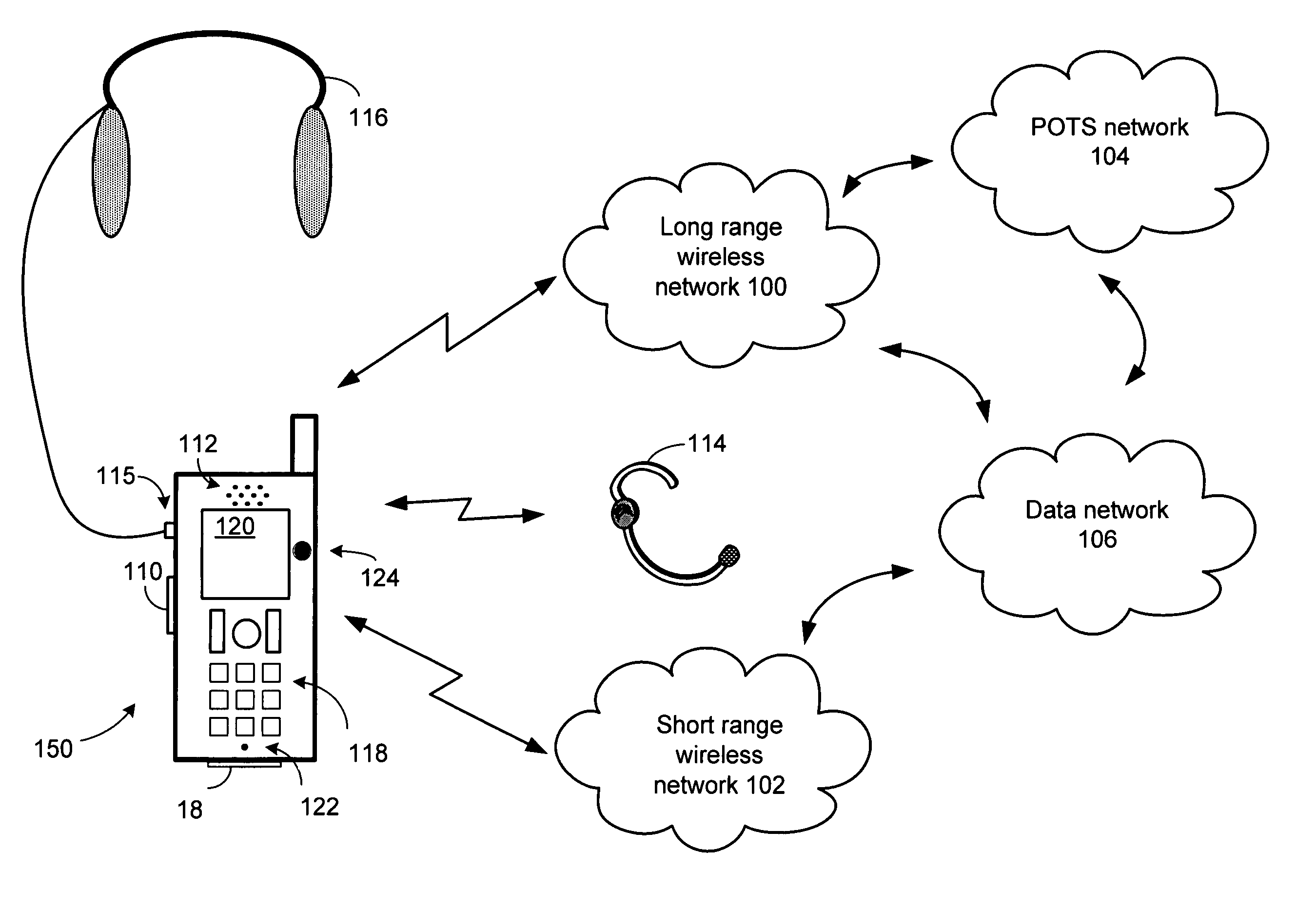
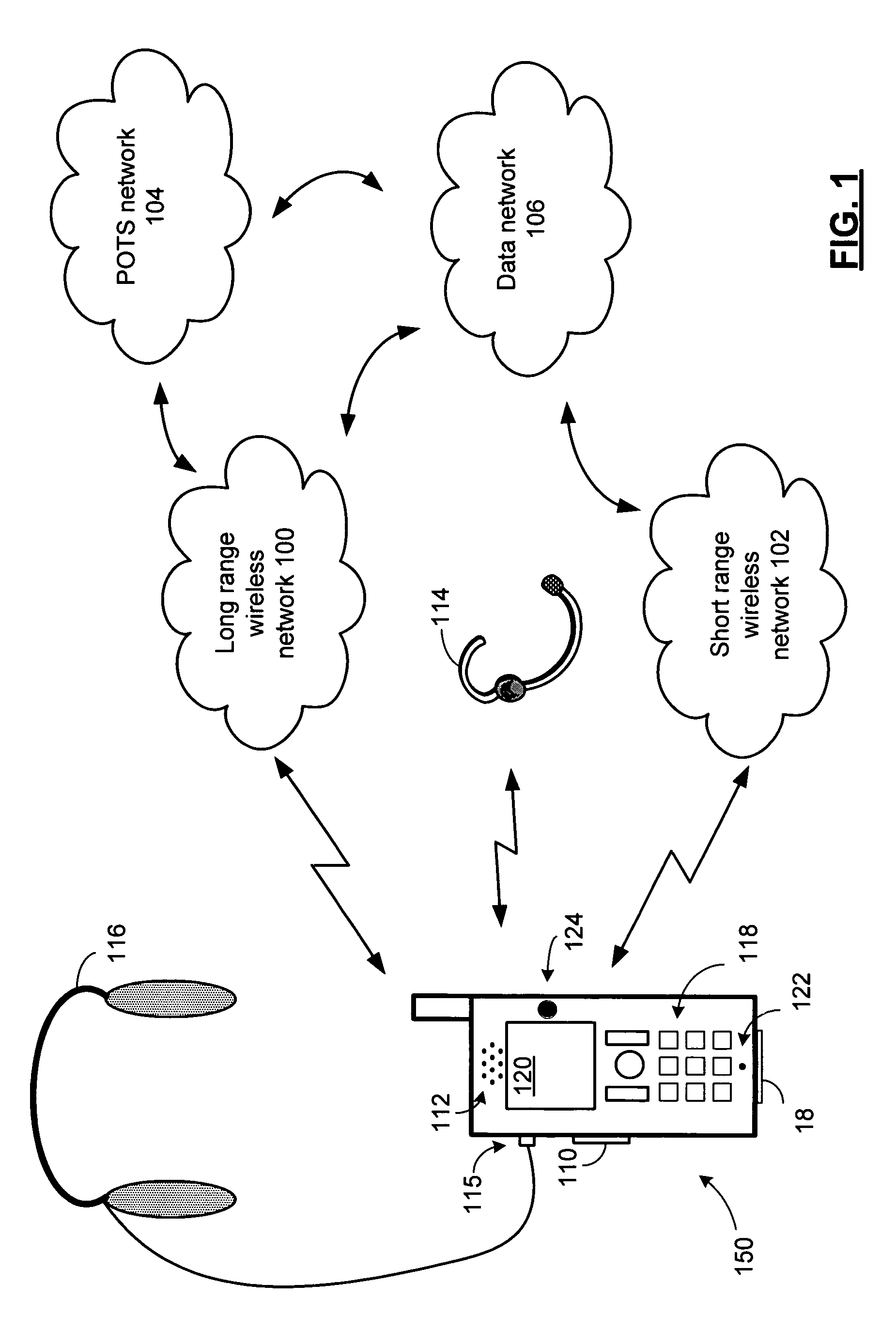
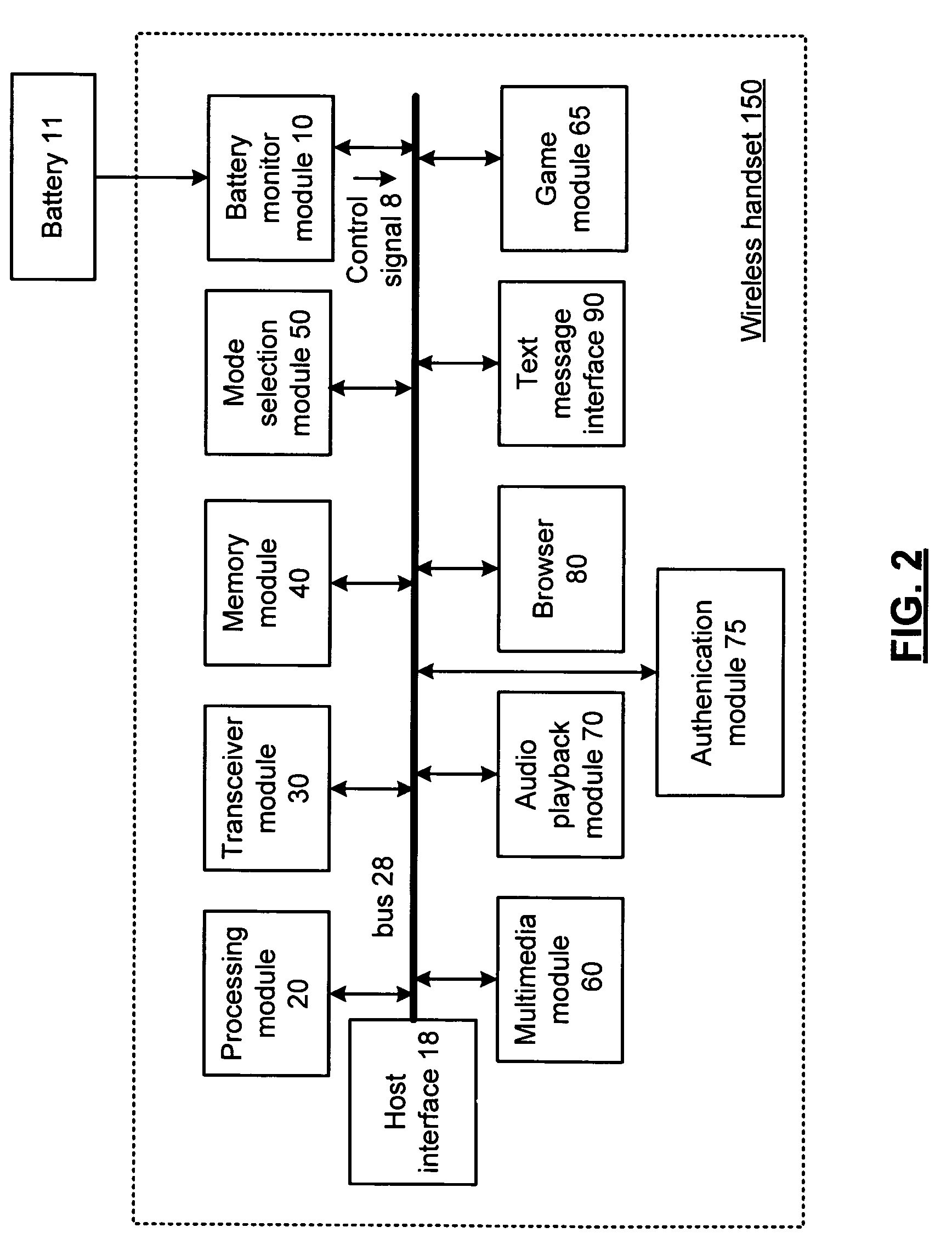
Wireless handset having selective communication control and corresponding methods
A wireless handset includes a long range wireless transceiver for selectively providing an inbound communication and an outbound communication through a wireless telephone network. A battery monitor module monitors a remaining power of a battery and produces a control signal when the remaining power compares unfavorably to a reserve power threshold. A processing module allows an outbound communication to an allowed recipient when the control signal is asserted, and prohibits an outbound communication to a disallowed recipient when the control signal is asserted.
Owner:NXP USA INC
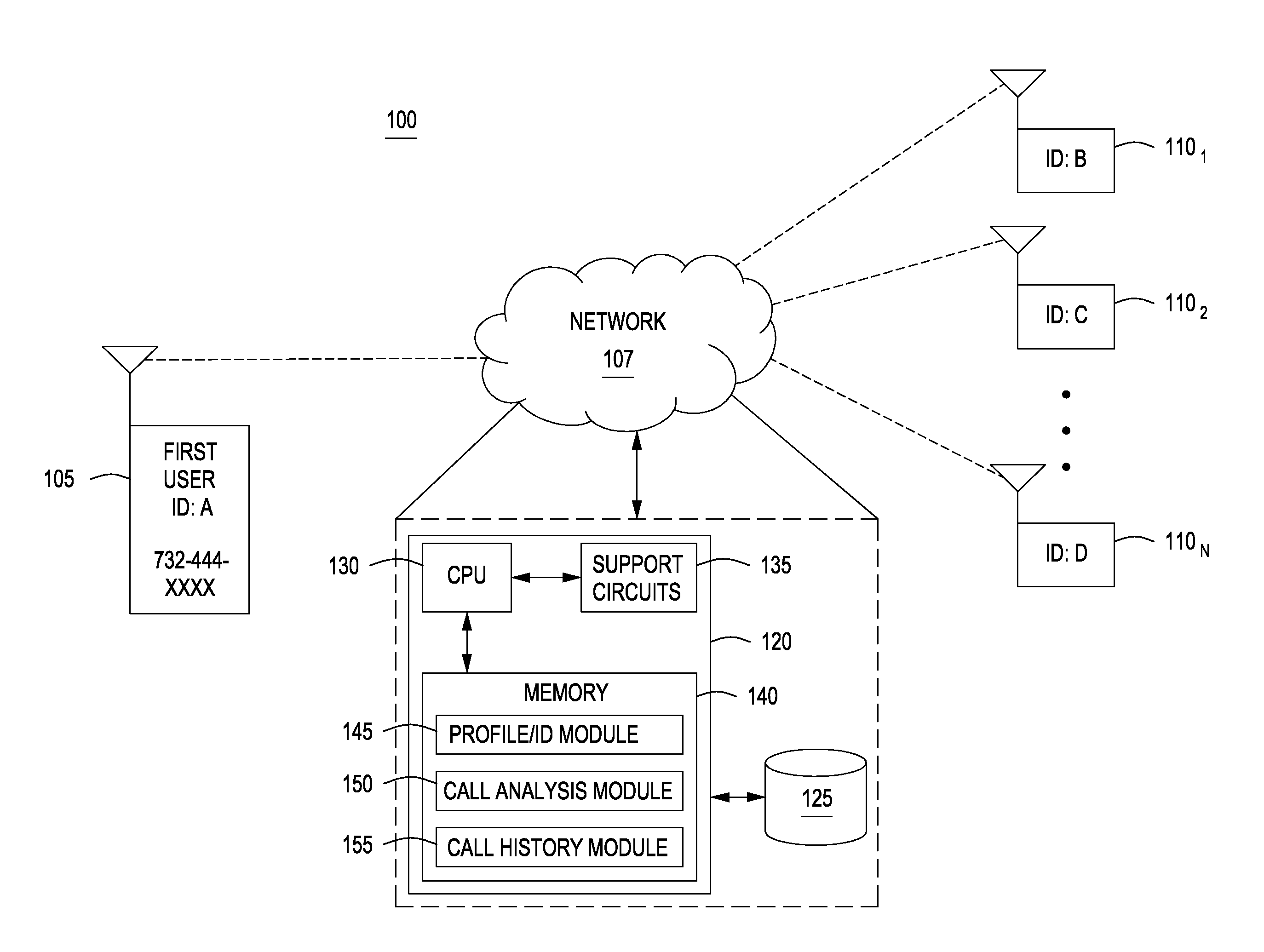
Routing communications based on history of previous communications
ActiveUS20140341081A1Special service provision for substationMultiplex system selection arrangementsInbound communicationUser profile
A method and system for routing communications includes building a first user profile for a first user based on a history of communications associated with a first communication identifier to route inbound communications. The first communication identifier is associated with the first user and subsequently, the first communication identifier may be assigned to a second user. A second communication identifier is assigned to the first user such that a received inbound communication is directed towards the first communication identifier. The method routes the inbound communication based on an analysis of the first user profile of the first user.
Owner:VONAGE AMERICA LLC
Real time active network compartmentalization
ActiveUS7213265B2Improve functionalityMinimal disruptionError preventionTransmission systemsInbound communicationSecurity domain
Security policy manager devices are leveraged by manager objects to use highly secure user transparent communications to provide detection of questionable activities at every node, automatic collection of information related to any potential attack, isolation of the offending object with arbitrary flexibility of response (e.g. flexibly determining the level of certainty of an attack for initiation of a response in accordance with the number of nodes to be partitioned that is determined by the collected data concerning the potential attack), changing trust relationships between security domains, limiting the attack and launching offensive information warfare capabilities (e.g. outbound from the compromised node while limiting or eliminating inbound communications) in log time and simultaneously and / or concurrently in different but possibly overlapping sections or segments of a digital network of arbitrary configuration.
Owner:LOCKHEED MARTIN CORP
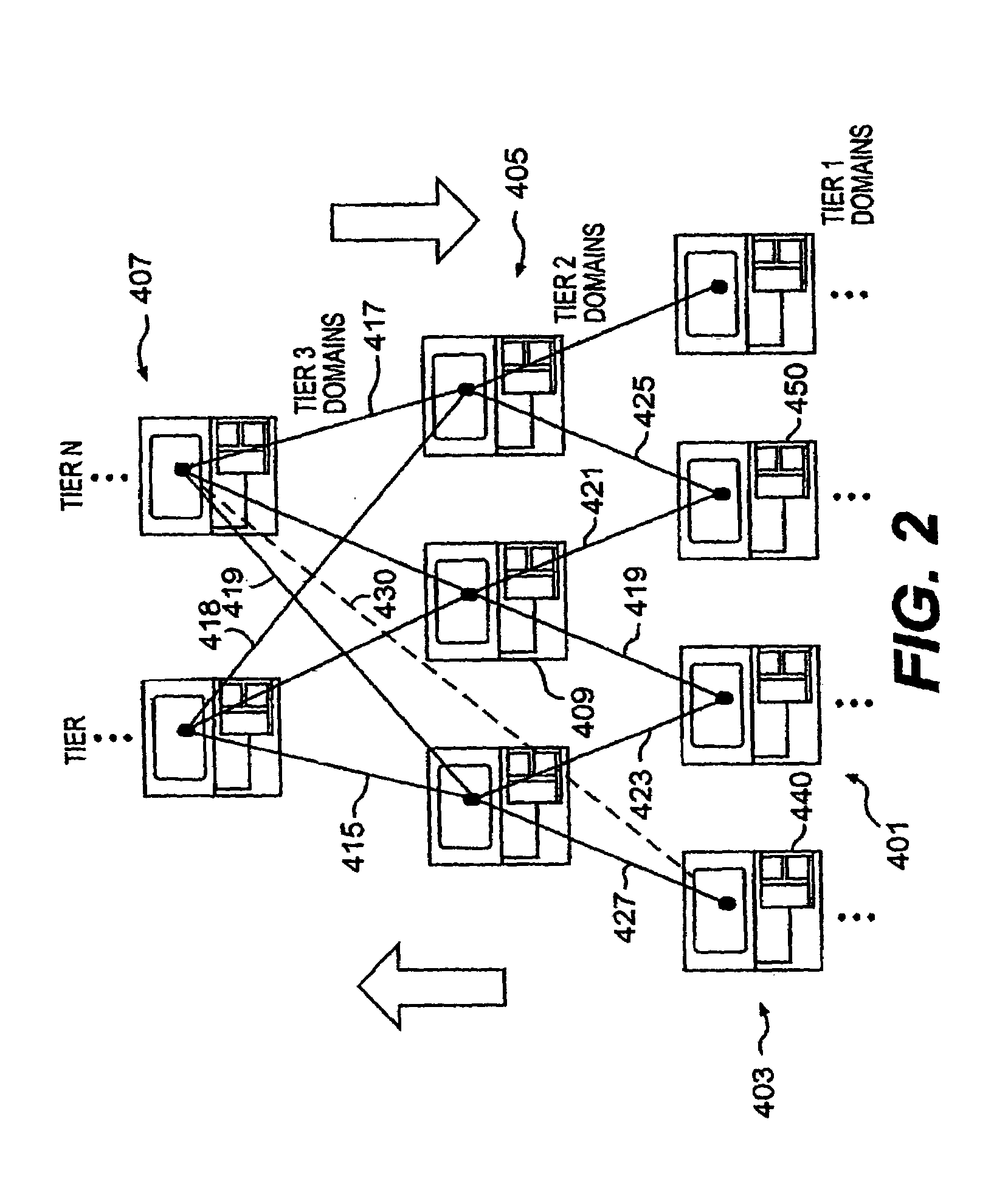
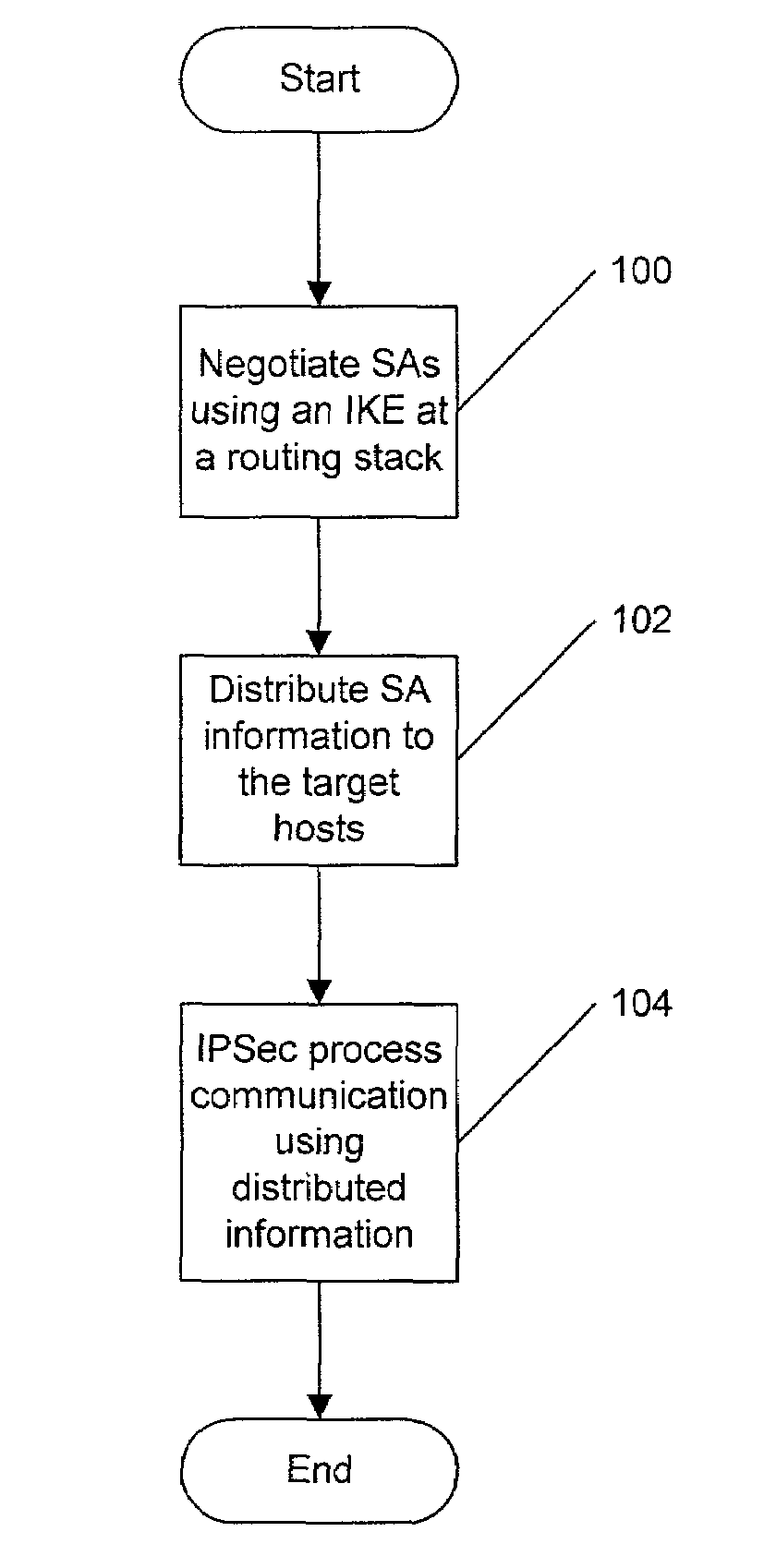
Methods, systems and computer program products for security processing inbound communications in a cluster computing environment
ActiveUS7426566B2Multiple digital computer combinationsTransmissionData processing systemInbound communication
Methods, systems and computer program products provide Internet Protocol Security (IPSec) to a plurality of target hosts in a cluster of data processing systems which communicate with a network through a routing communication protocol stack utilizing a dynamically routable Virtual Internet Protocol Address (DVIPA) by negotiating security associations (SAs) associated with the DVIPA utilizing an Internet Key Exchange (IKE) component associated with the routing communication protocol stack and distributing information about the negotiated SAs to the target hosts so as to allow the target hosts to perform IPSec processing of communications from the network utilizing the negotiated SAs.
Owner:INT BUSINESS MASCH CORP
Computer Program Products for Security Processing Inbound Communications in a Cluster Computing Environment
InactiveUS20080189428A1Multiple digital computer combinationsProgram controlInbound communicationSecurity association
Methods, systems and computer program products provide Internet Protocol Security (IPSec) to a plurality of target hosts in a cluster of data processing systems which communicate with a network through a routing communication protocol stack utilizing a dynamically routable Virtual Internet Protocol Address (DVIPA) by negotiating security associations (SAs) associated with the DVIPA utilizing an Internet Key Exchange (IKE) component associated with the routing communication protocol stack and distributing information about the negotiated SAs to the target hosts so as to allow the target hosts to perform IPSec processing of communications from the network utilizing the negotiated SAs.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com