Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4184 results about "Source address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
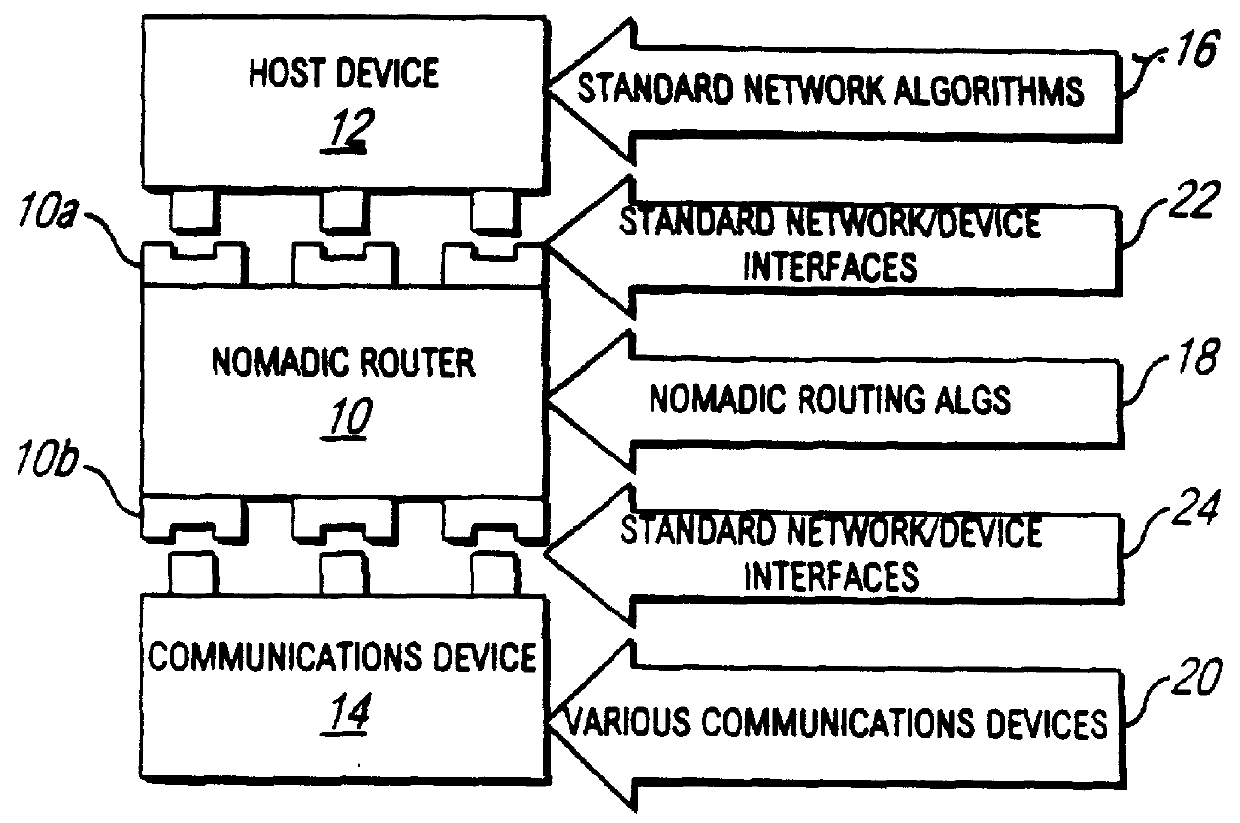
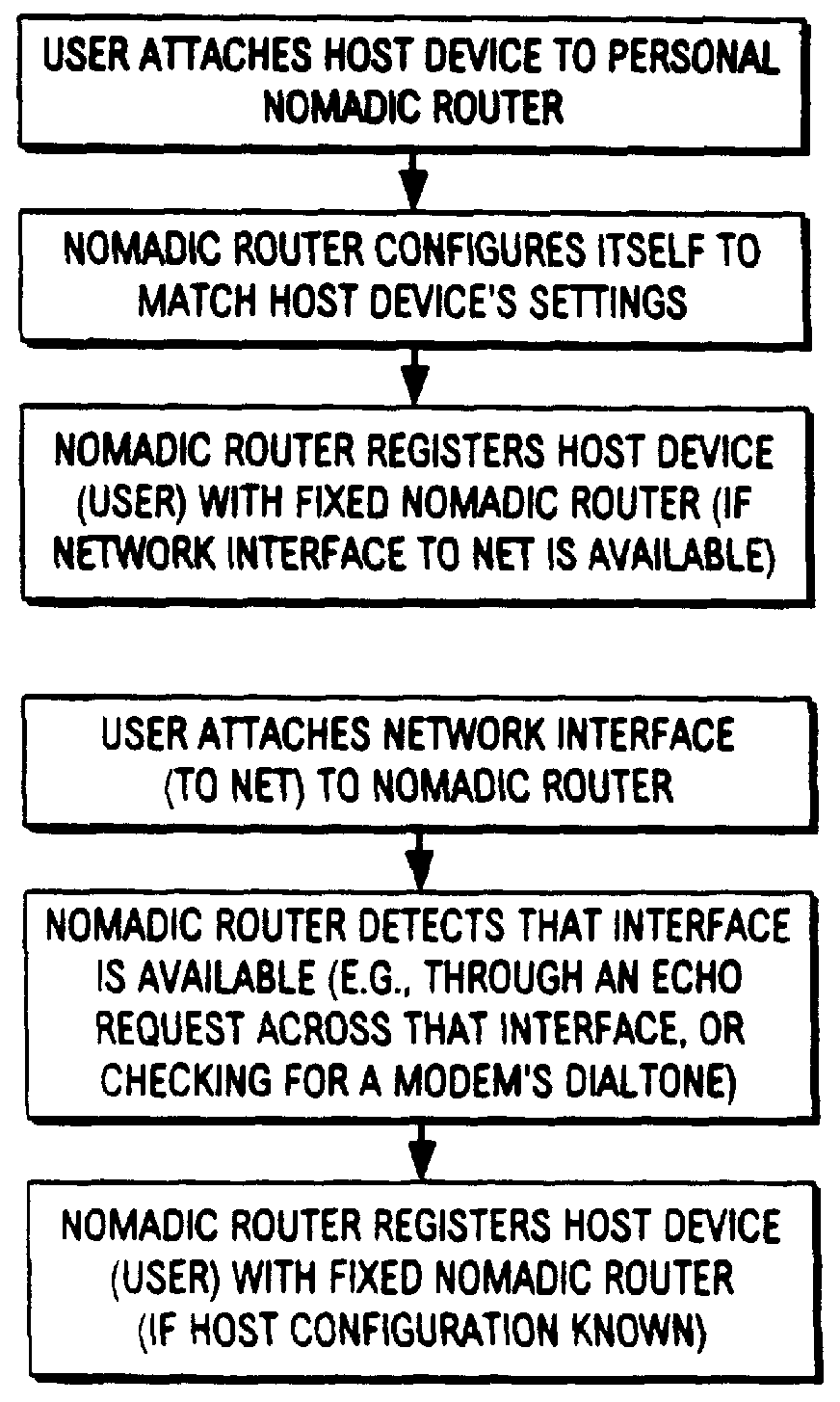
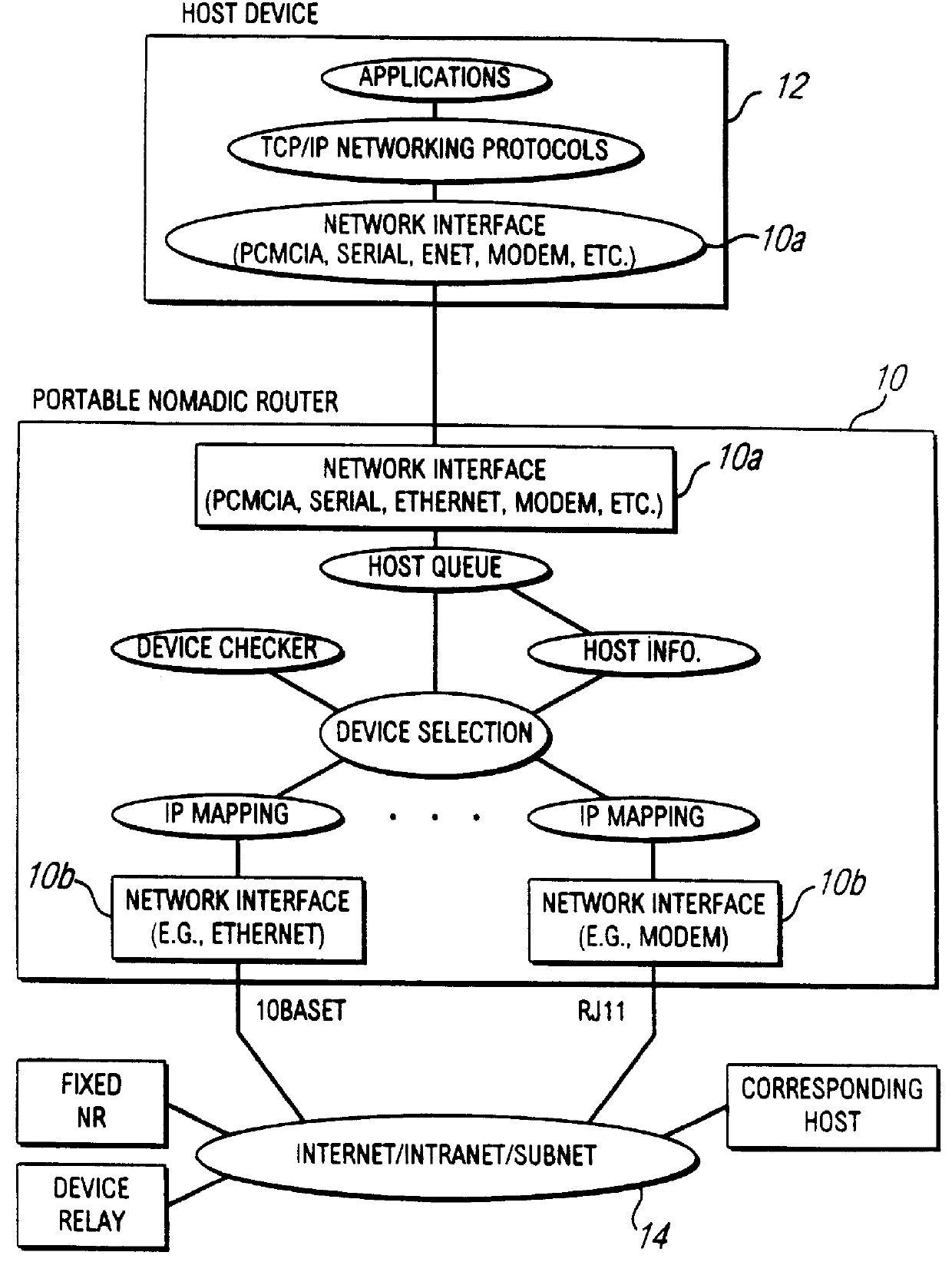
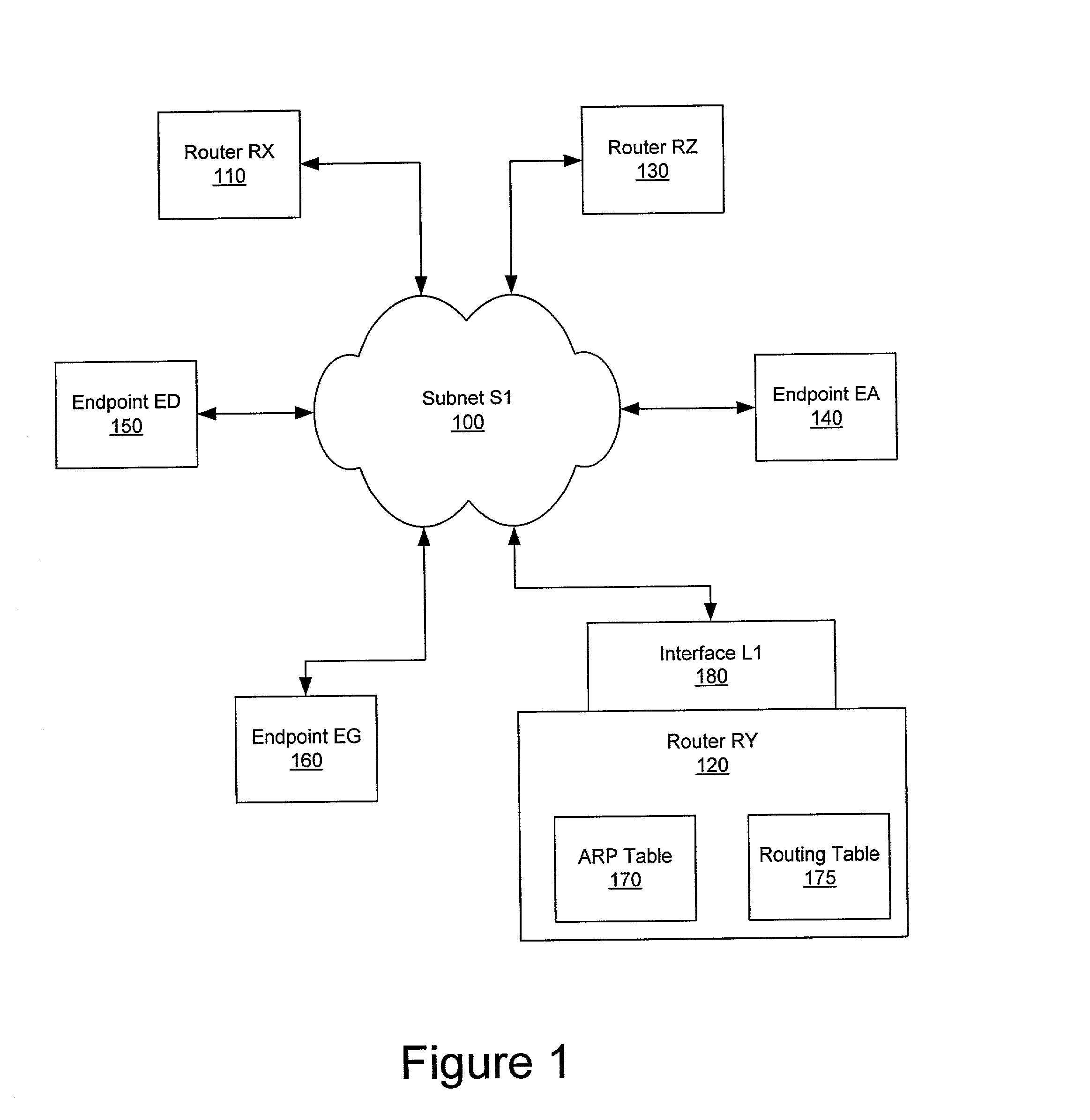
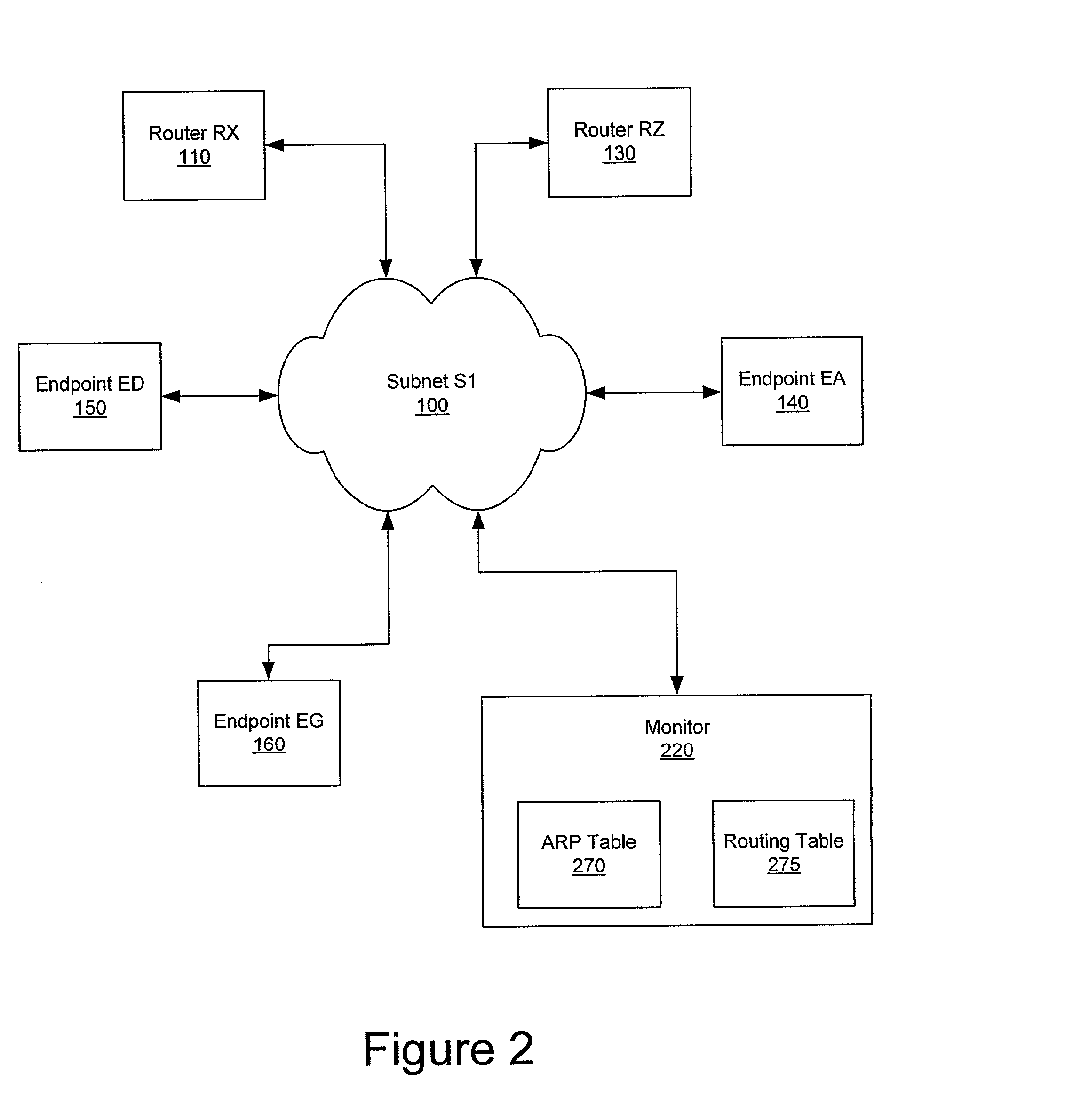
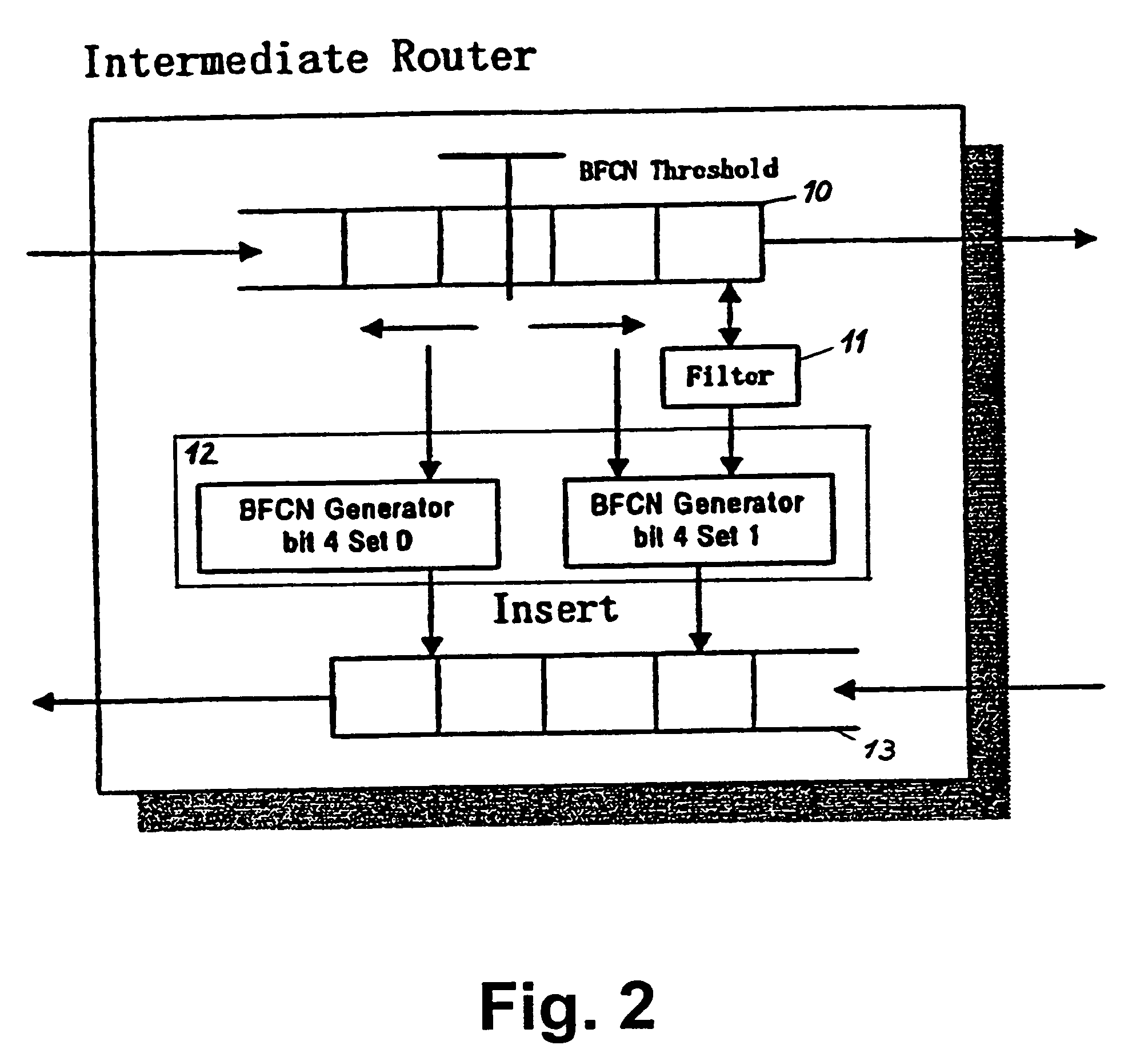
Nomadic translator or router
InactiveUS6130892ASupport mobilitySoft handoffNetwork topologiesTime-division multiplexDigital dataFile synchronization
A nomadic router or translator enables a laptop computer or other portable terminal which is configured to be connected to a home network to be connected to any location on the internet or other digital data communication system. The router automatically and transparently re-configures the terminal to its new location and processes outgoing and incoming data. The router includes a processor which appears as the home network to the terminal, and appears as the terminal to the communication system. The terminal has a permanent address, the router has a router or translator address, and the terminal transmits outgoing data to the system including the permanent address as a source address. The processor translates the outgoing data by replacing the permanent address with the router address as the source address. The terminal receives incoming data from the system including the router address as a destination address, and the processor translates the incoming data by replacing the router address with the permanent address as the destination address. Alternatively, the terminal can be directly connected to a point on a local network, and the router connected to another point on the network. The router can be employed to implement numerous applications including nomadic e-mail, network file synchronizer, database synchronizer, instant network, nomadic internet and trade show router and can also be utilized as a fixed nomadic router.
Owner:NOMADIX INC
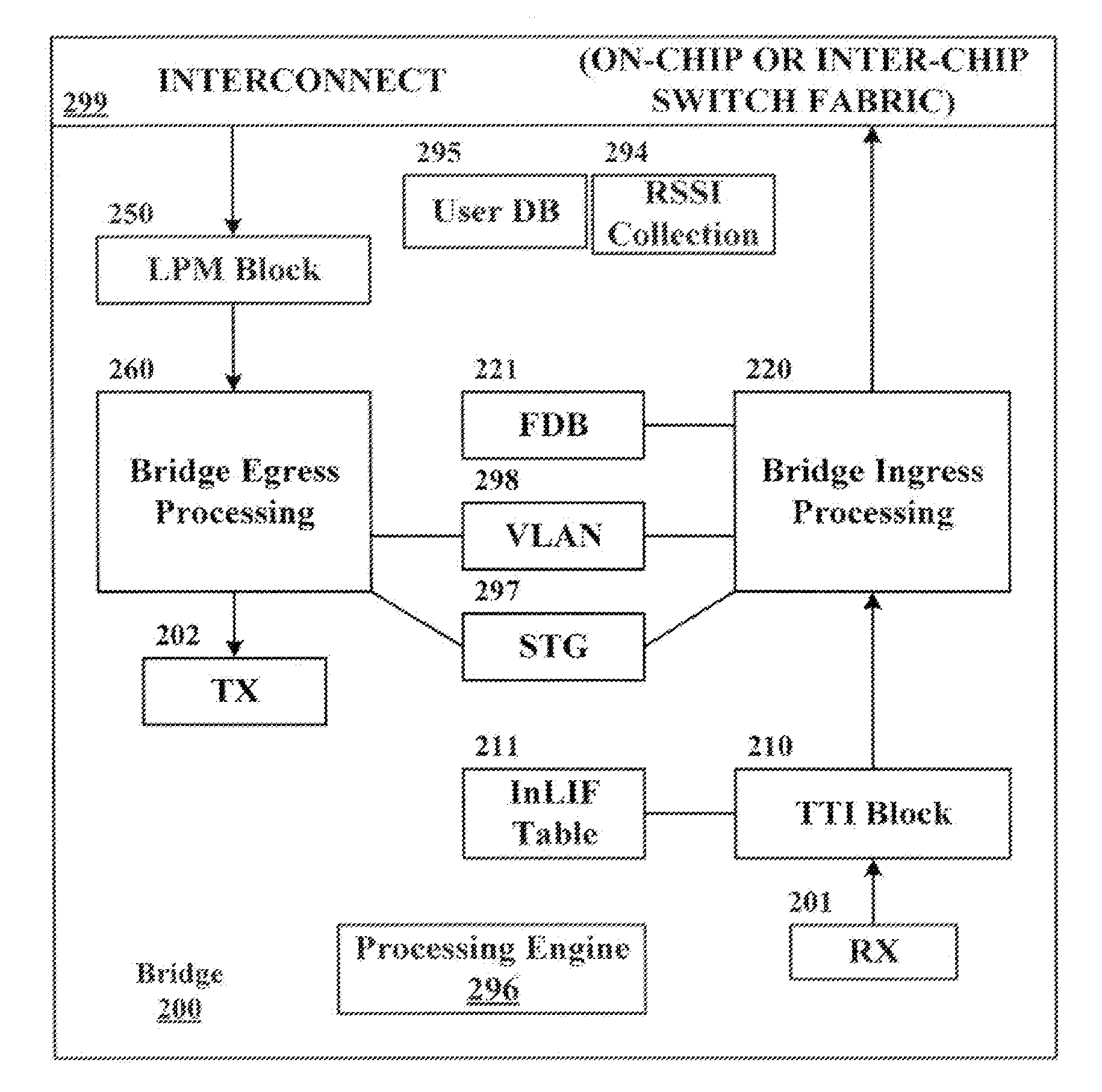
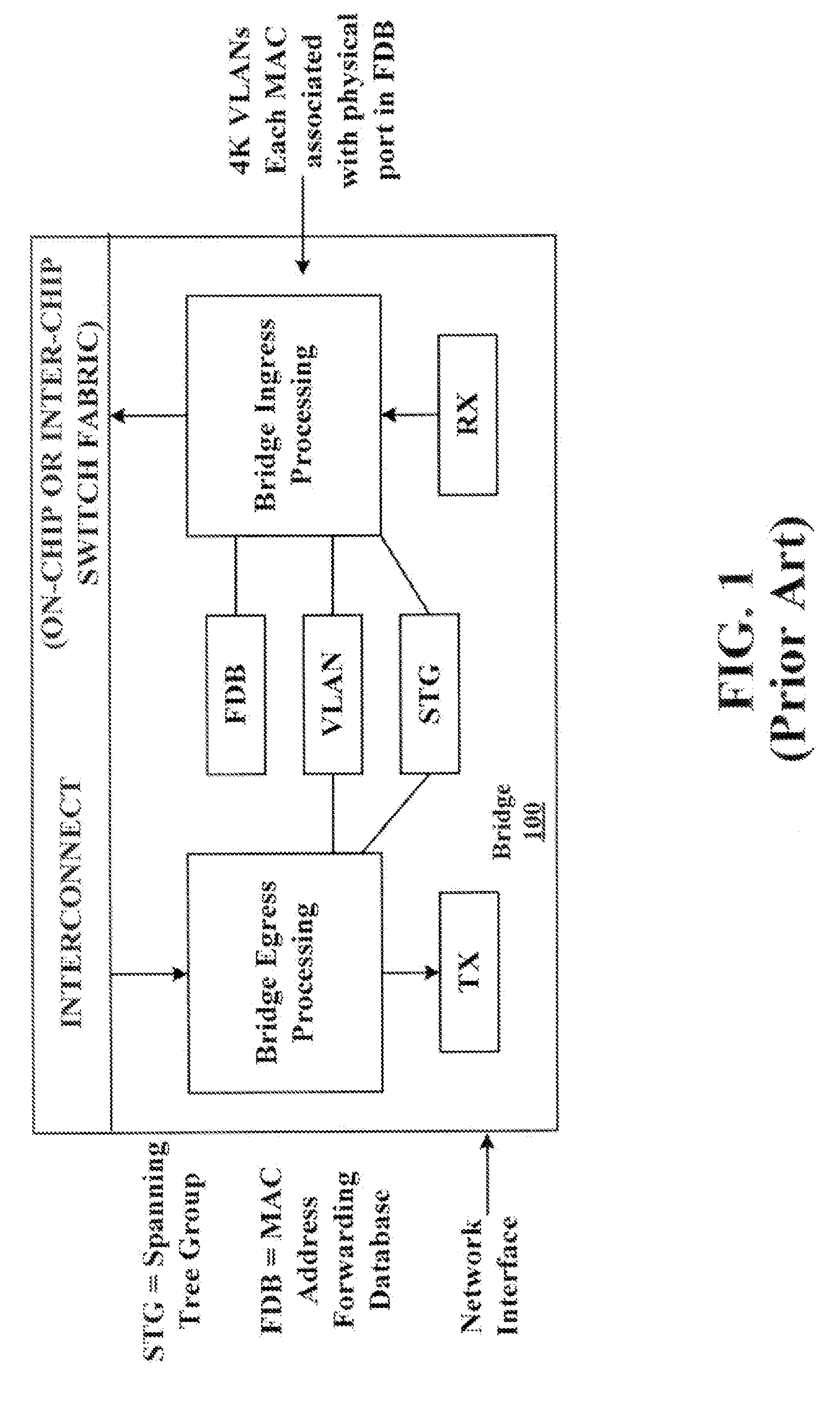
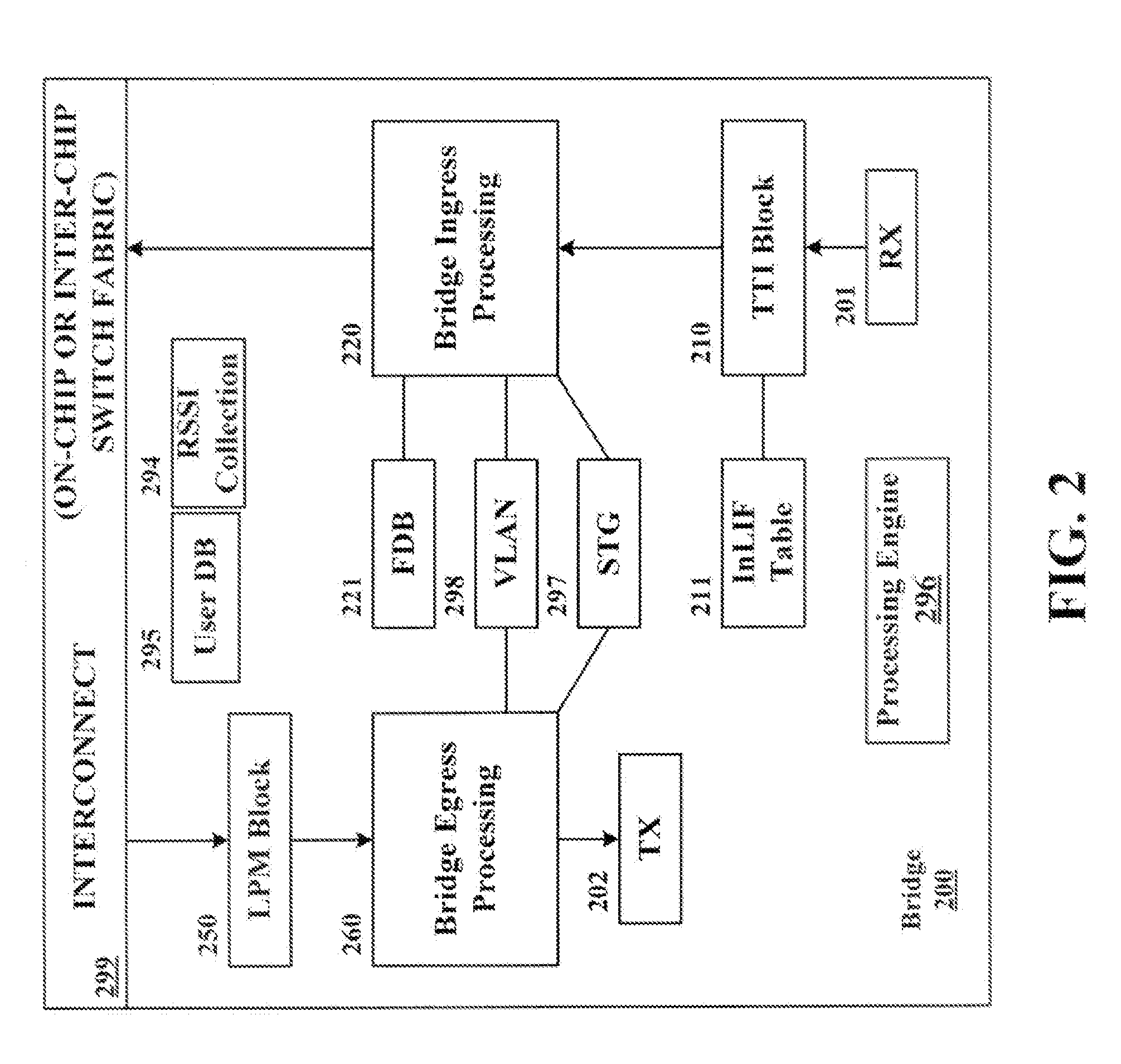
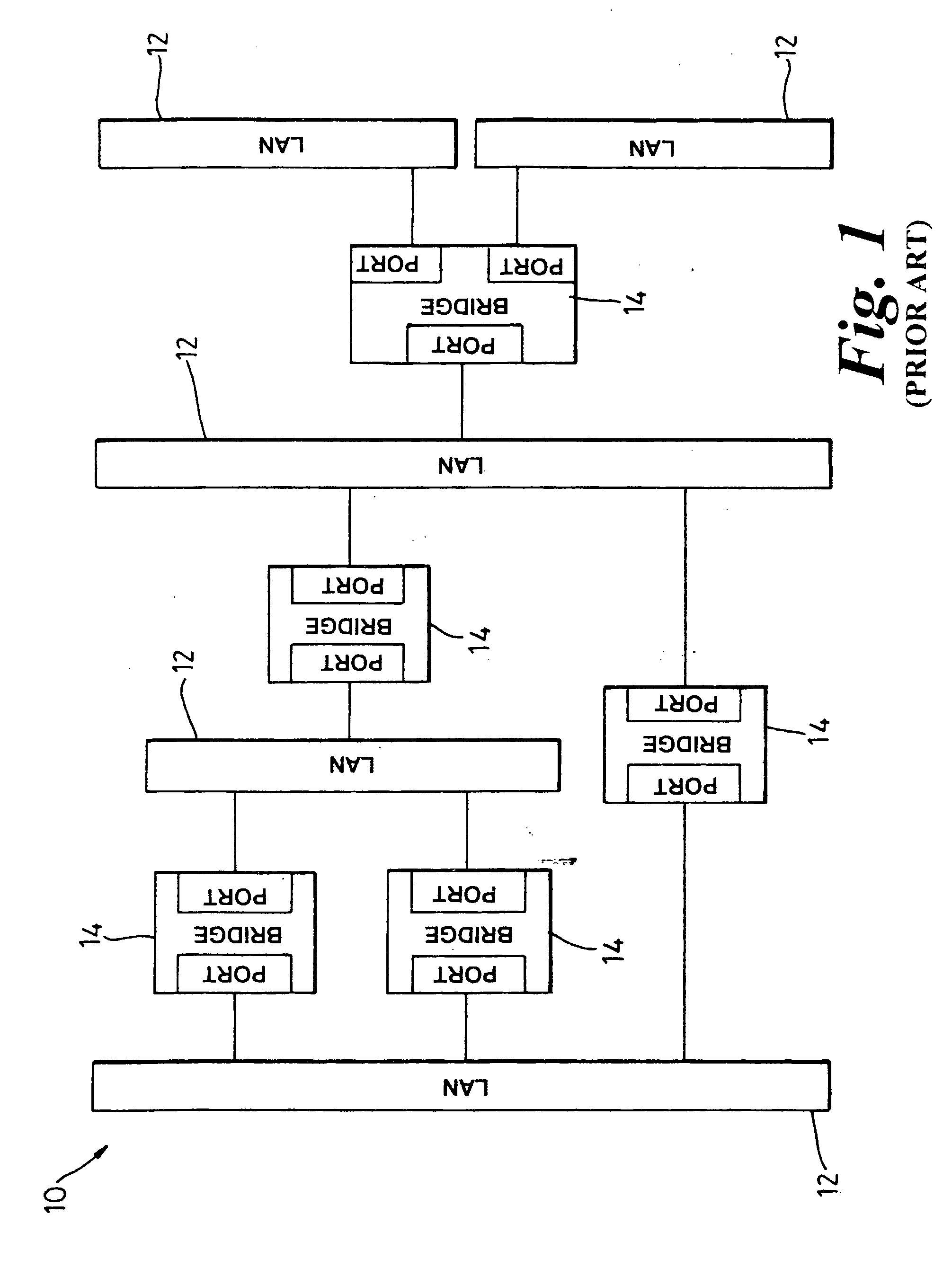
Logical bridging system and method
A system and method of extending a standard bridge to enable execution of logical bridging functionality are disclosed. In some implementations, a logical bridge may assign source logical port information to a data packet based on characteristics of the data packet, employ the source logical port information to learn the source address and to forward the data packet to a logical egress port, and map the logical egress port to a physical egress port at which the data packet is to be egressed. A tunnel interface may optionally be applied to a data packet upon egress.
Owner:MARVELL ISRAEL MISL
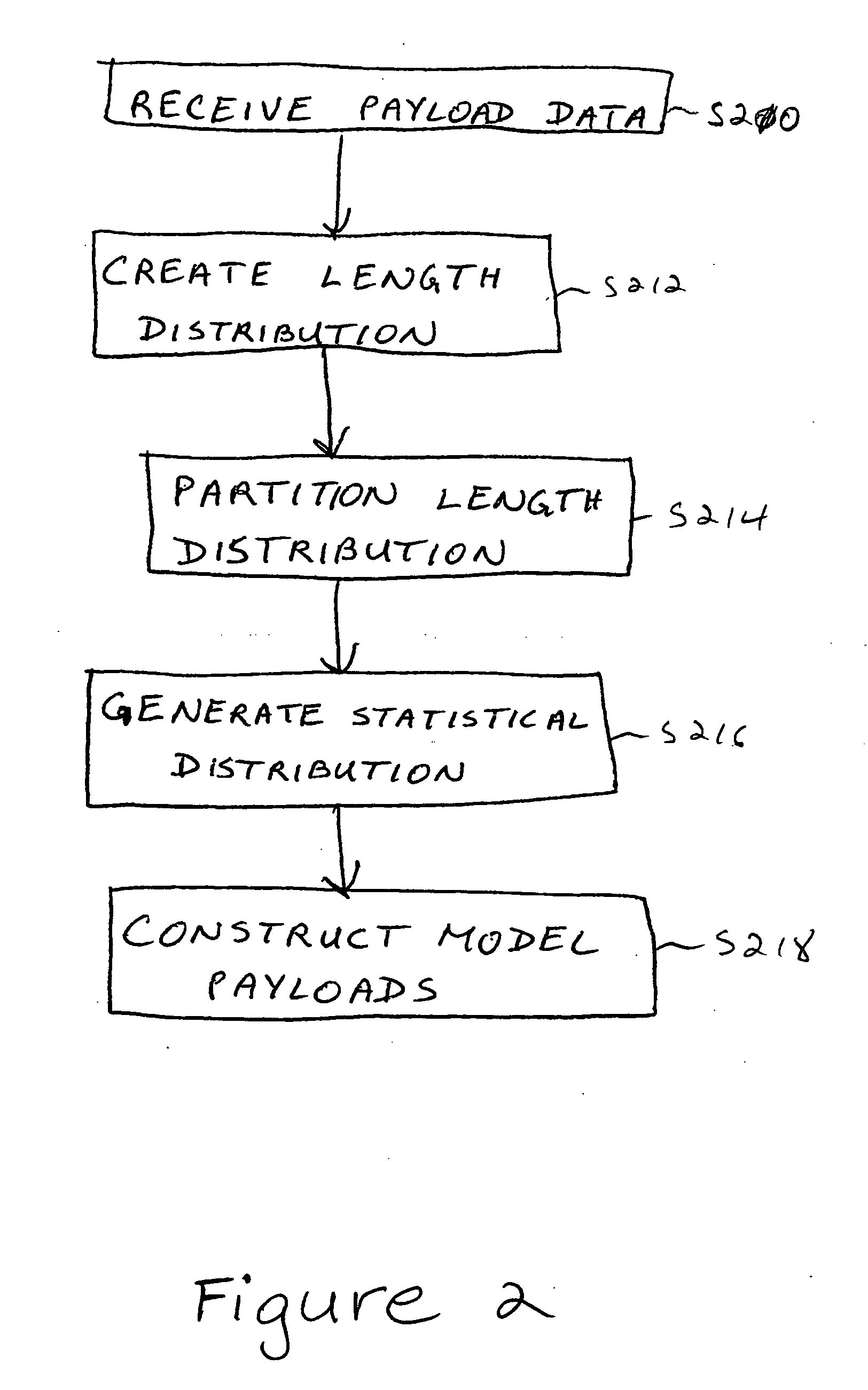
Apparatus method and medium for tracing the origin of network transmissions using n-gram distribution of data
ActiveUS20050265331A1Unauthorized memory use protectionTime-division multiplexWeb transportReal-time computing
A method, apparatus, and medium are provided for tracing the origin of network transmissions. Connection records are maintained at computer system for storing source and destination addresses. The connection records also maintain a statistical distribution of data corresponding to the data payload being transmitted. The statistical distribution can be compared to that of the connection records in order to identify the sender. The location of the sender can subsequently be determined from the source address stored in the connection record. The process can be repeated multiple times until the location of the original sender has been traced.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
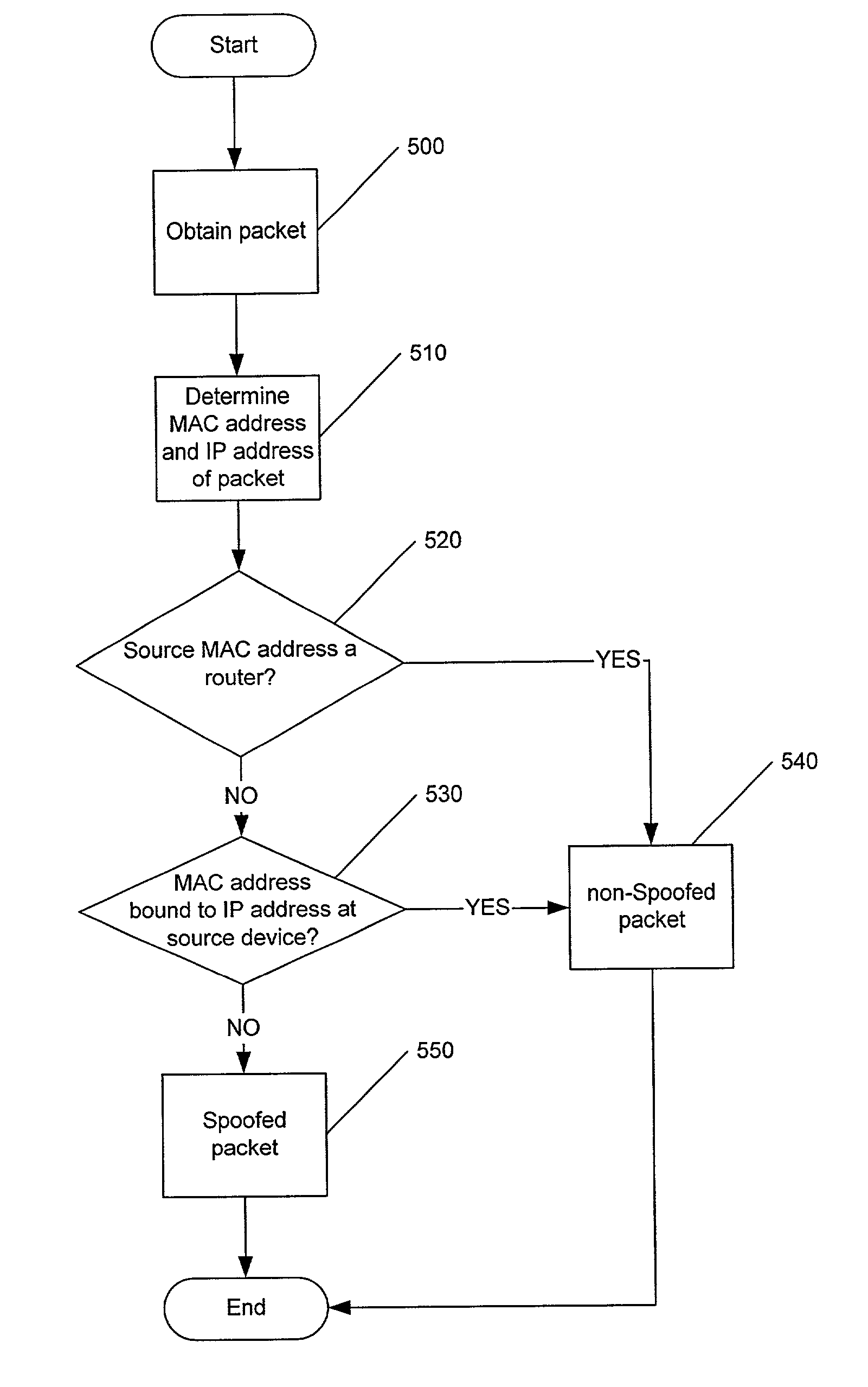
Methods, systems and computer program products for detecting a spoofed source address in IP datagrams
InactiveUS7134012B2Improve usabilityFrequency-division multiplexData switching by path configurationIp addressMedia access control
Methods, systems and computer program products are provided for determining if a packet has a spoofed source Internet Protocol (IP) address. A source media access control (MAC) address of the packet and the source IP address are evaluated to determine if the source IP address of the packet has been bound to the source MAC address at a source device of the packet. The packet is determined to have a spoofed source IP address if the evaluation indicates that the source IP address is not bound to the source MAC address. Such an evaluation may be made for packets having a subnet of the source IP address which matches a subnet from which the packet originated.
Owner:IBM CORP
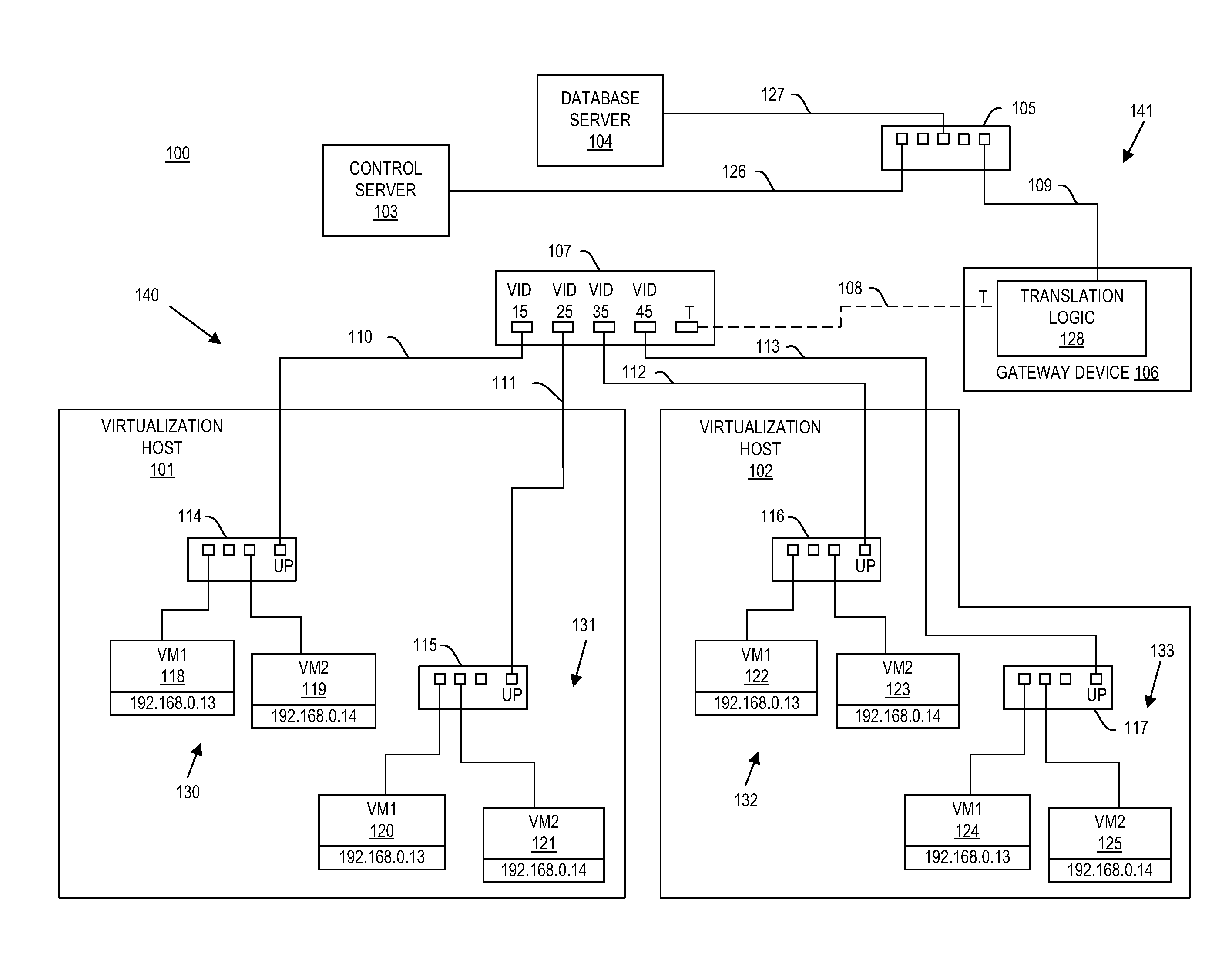
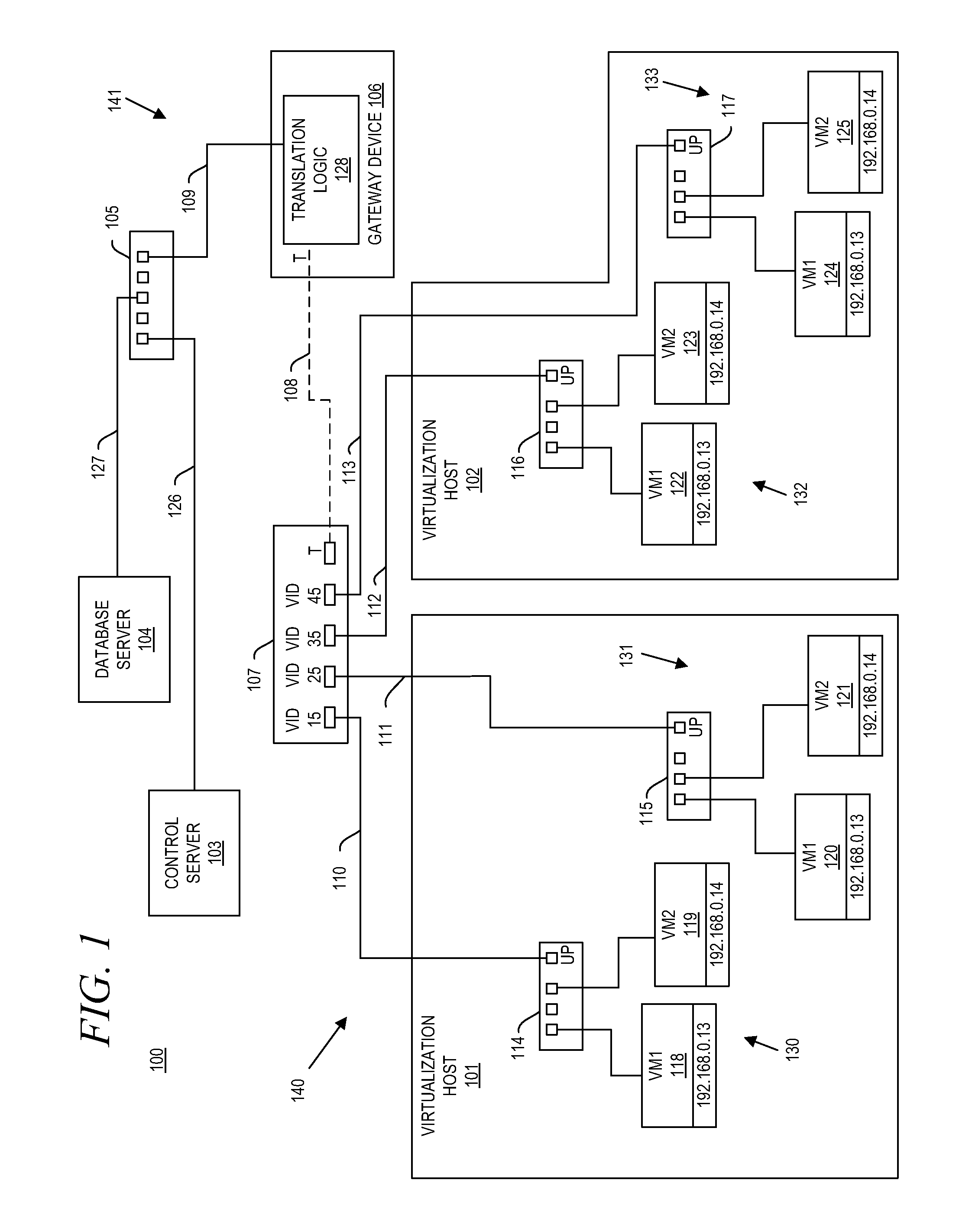
System and method for aggregating communications and for translating between overlapping internal network addresses and unique external network addresses
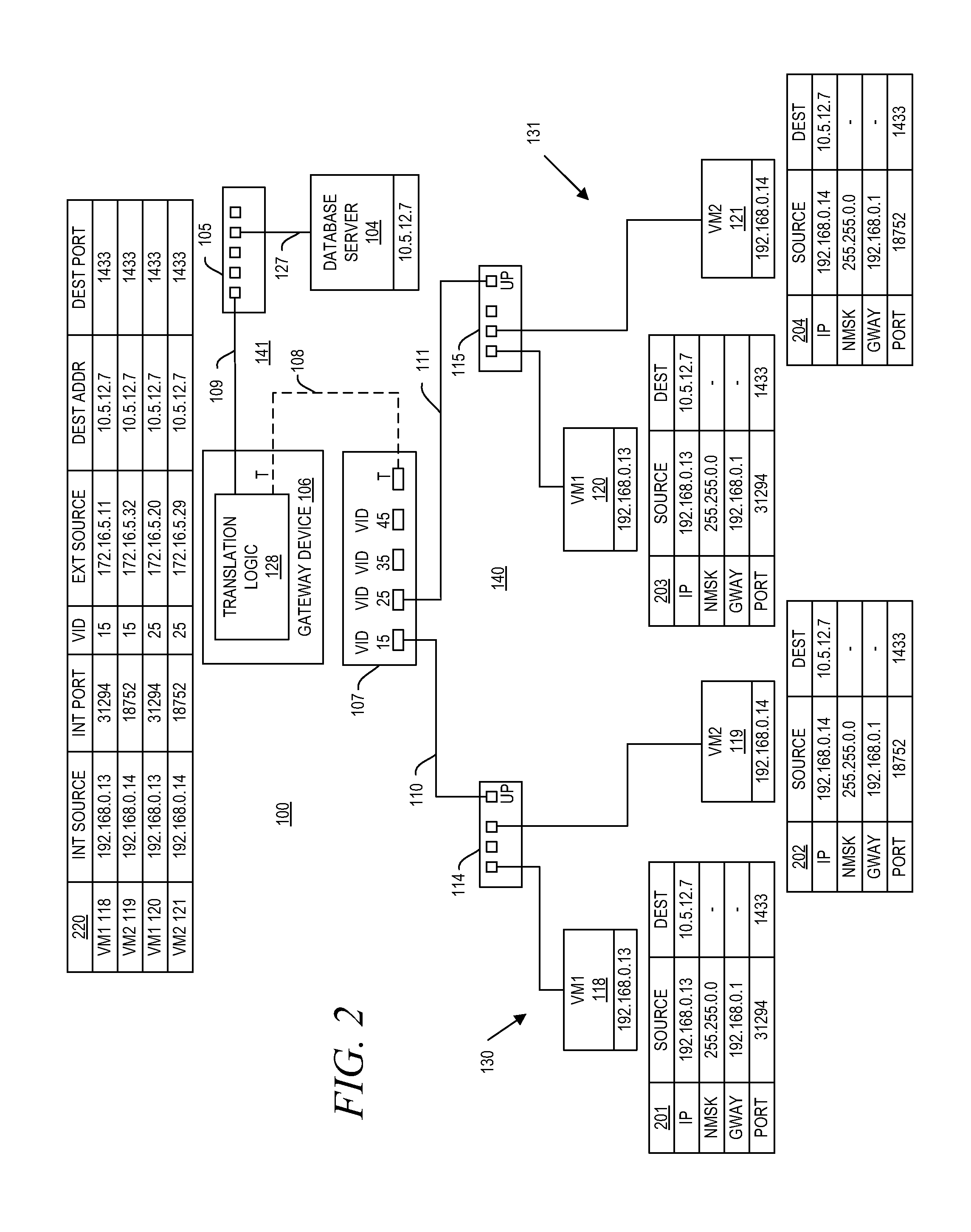
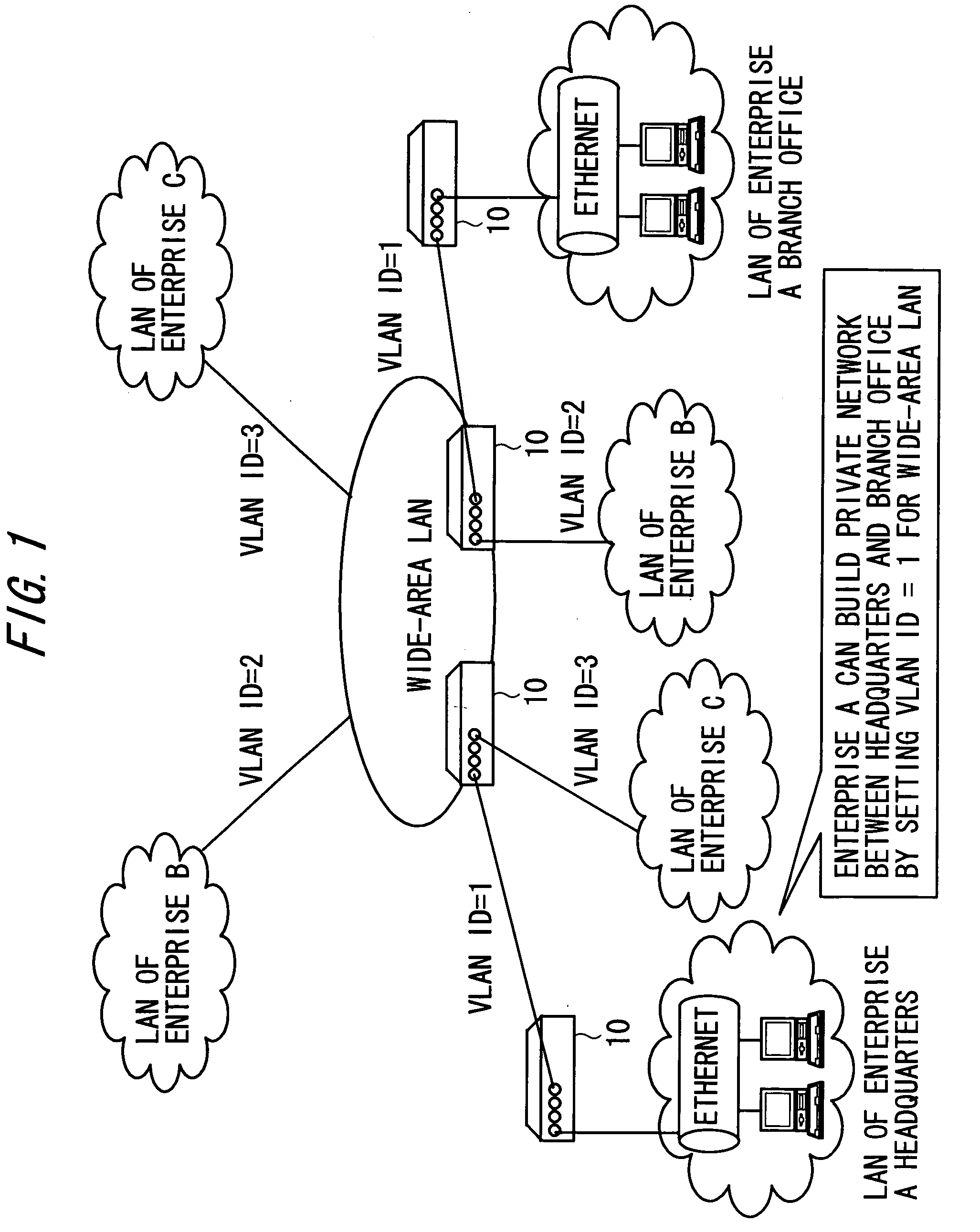
A gateway device including an access interface to an external network, a trunked interface, and translation logic. The access interface is associated with multiple external source addresses. The trunked interface is interfaced with multiple different virtual local area networks (VLANs), where each VLAN is associated with a corresponding VLAN tag and at least one of potentially overlapping internal source addresses. The translation logic translates between each external source address and each unique combination of internal source address and VLAN tag. A method of network address translation including assigning one of first network addresses to each first device of a first network, dividing the first network into a plurality of VLANs, separating the first devices with the same first network address into different VLANs, and assigning first devices with the same first address to different second network addresses.
Owner:QUEST SOFTWARE INC
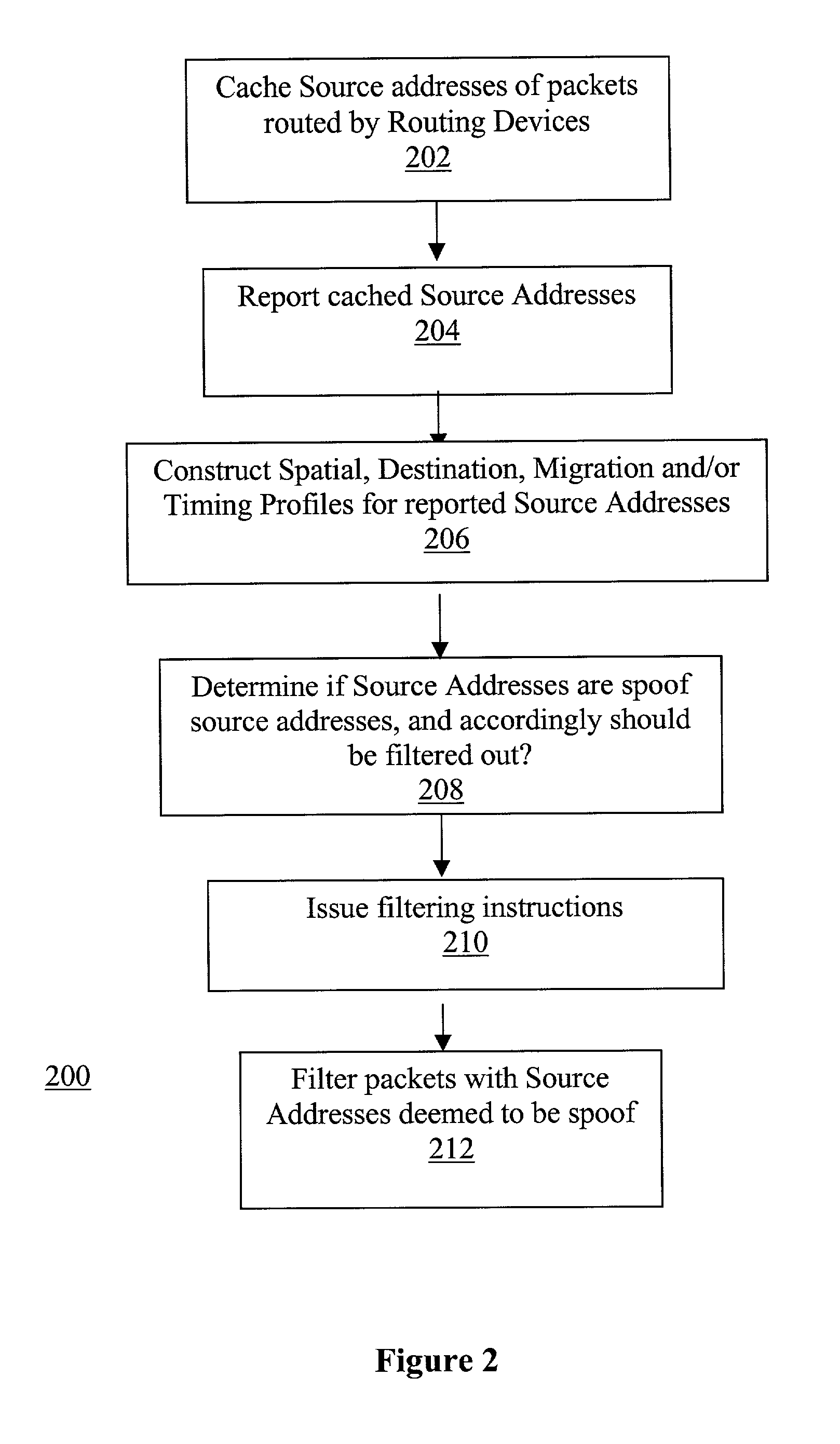
Network traffic regulation including consistency based detection and filtering of packets with spoof source addresses
InactiveUS7444404B2Ensuring quality of serviceEnsure qualityRandom number generatorsUser identity/authority verificationTraffic capacityReporting source
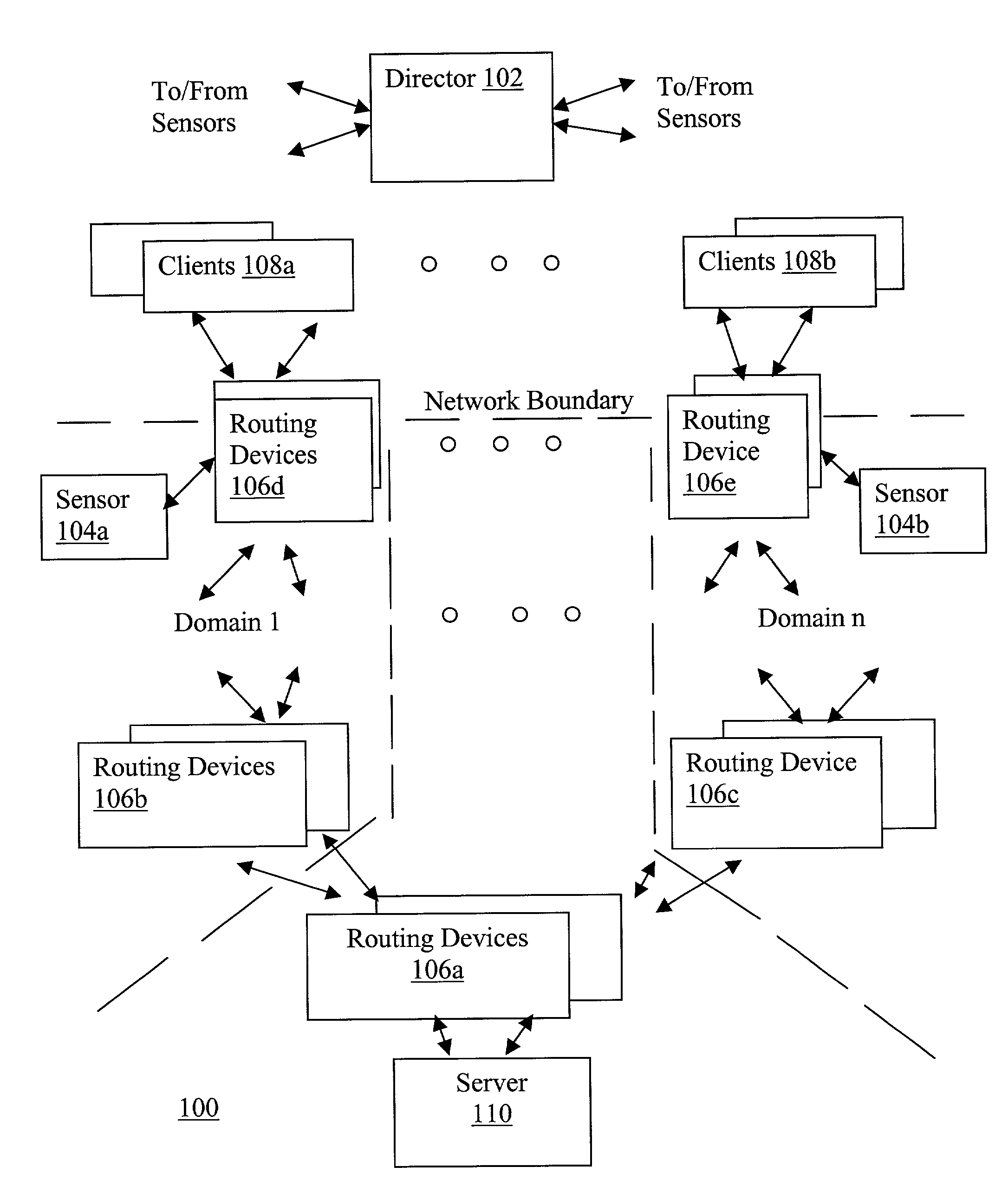
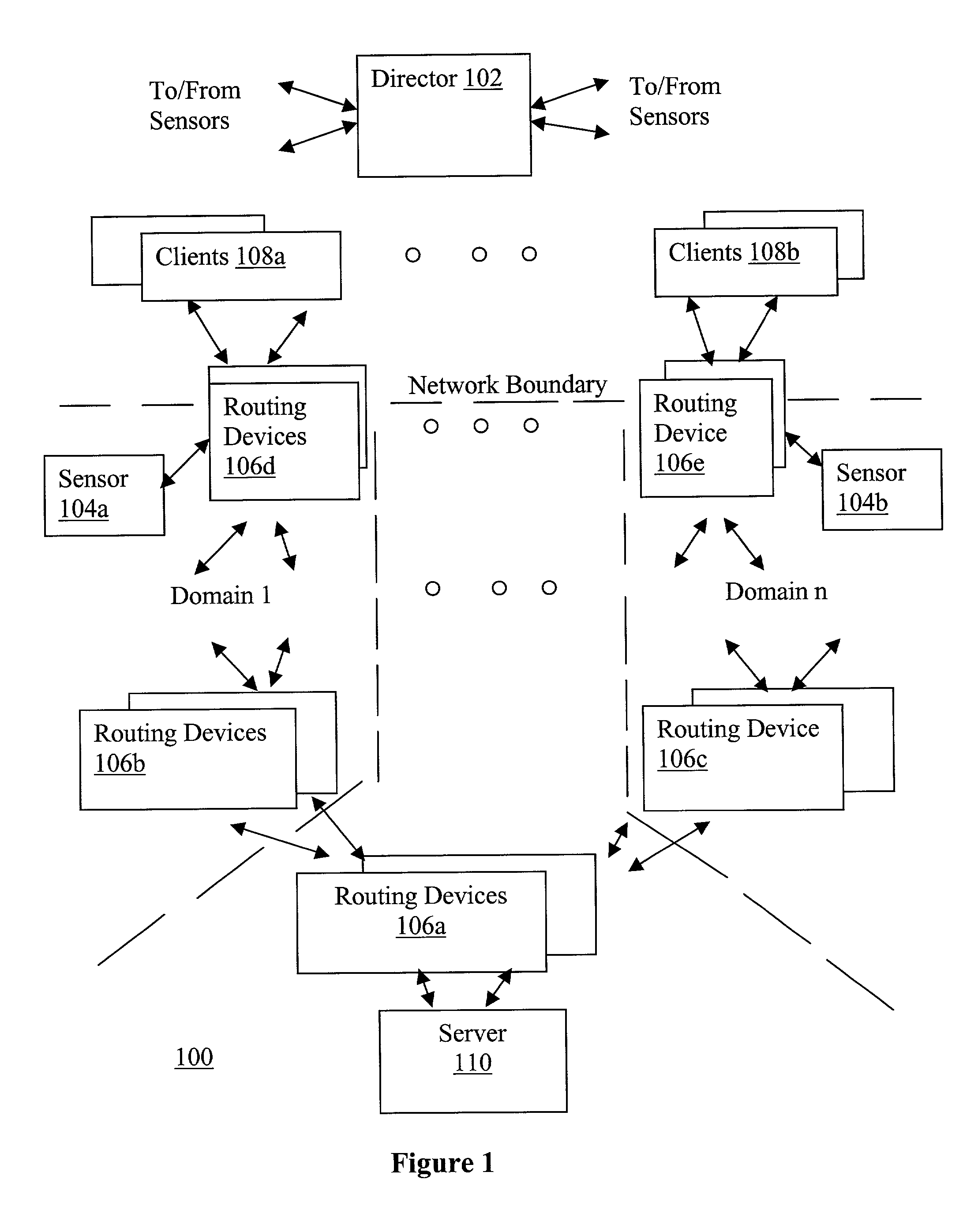
A director is provided to receive source address instances of packets routed through routing devices of a network. The director determines whether any of the reported source address instances are to be deemed as spoof source address instances. The director further determines where filtering actions are to be deployed to filter out packets having certain source addresses deemed to be spoof instances. The director makes its determinations based at least in part on a selected one of a number of consistency measures. The consistency measures may include but are not limited to spatial consistency, destination consistency, migration consistency, and temporary consistency. The consistency measures are evaluated using spatial, destination source address range, migration and timing S / D / M / T distribution profiles of the reported source addresses. In some embodiments, the determinations are based further in view of reference S / D / M / T distribution profiles, which may be an exemplary S / D / M / T distribution profile of a typical non-spoof source address or a historical S / D / M / T distribution profile of the source address.
Owner:ARBOR NETWORKS
Power line communication rate limiting system and method
InactiveUS20070002771A1Rate limiting quality of service (QoS) controlError preventionTransmission systemsQuality of serviceRate limiting
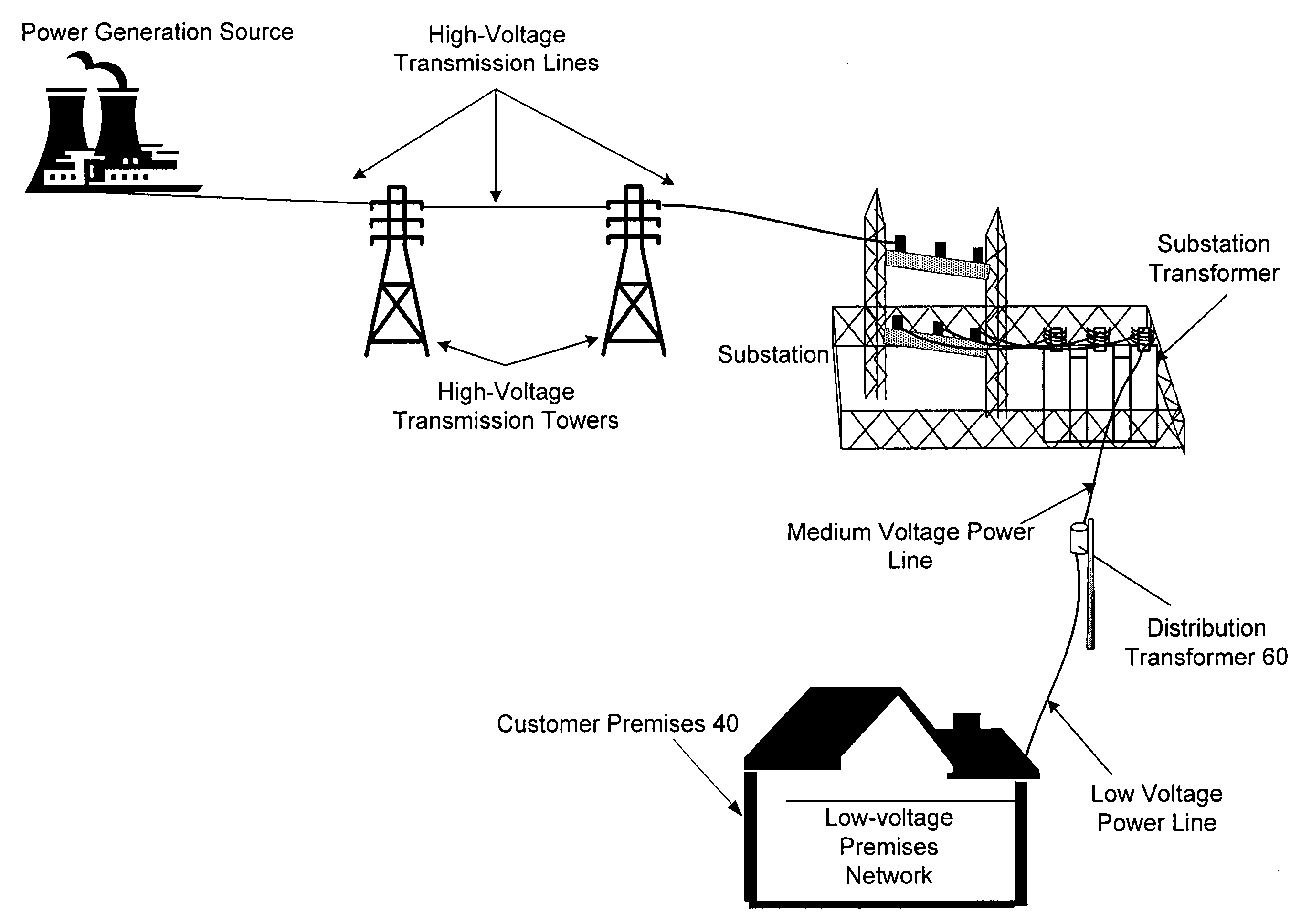
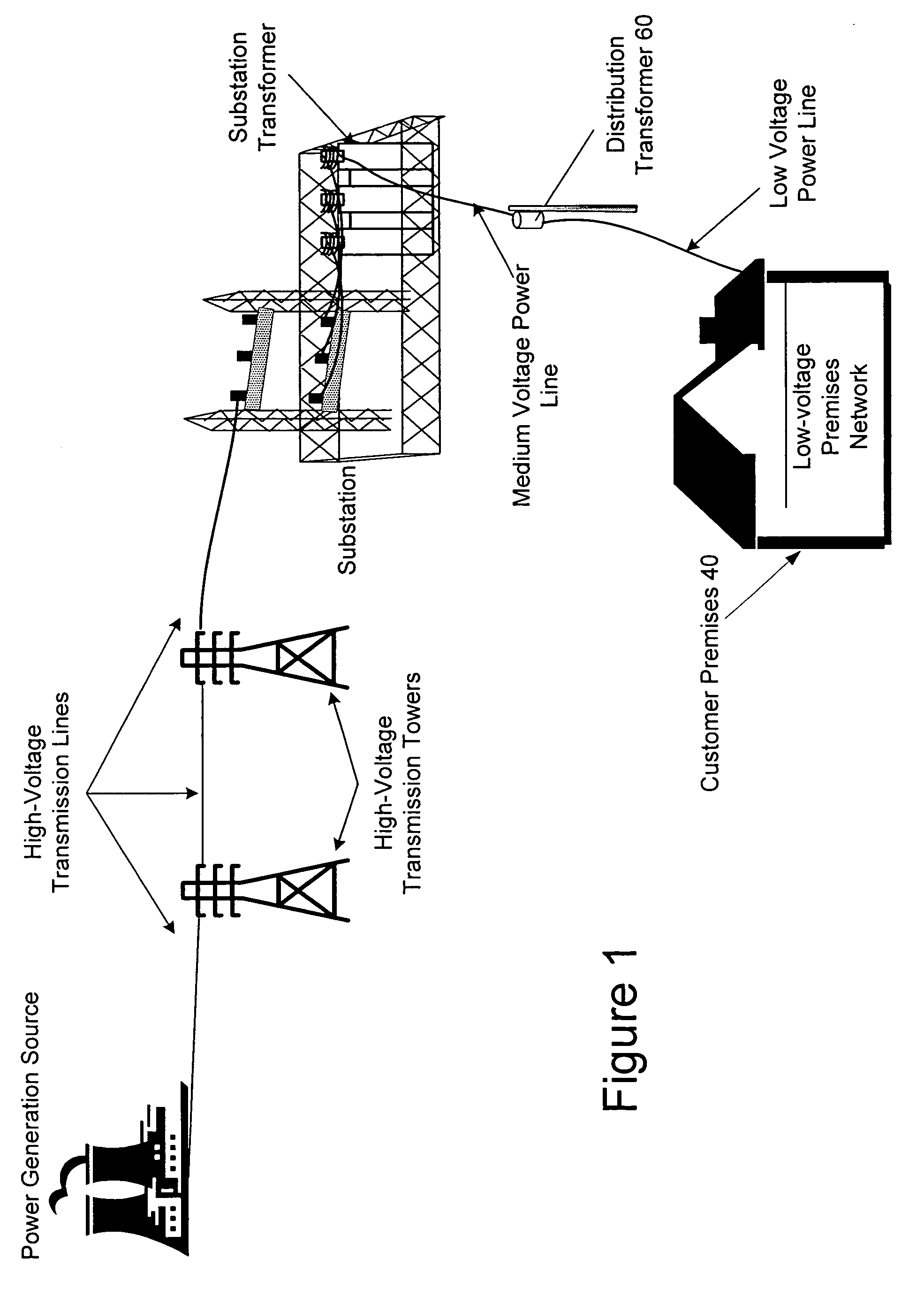
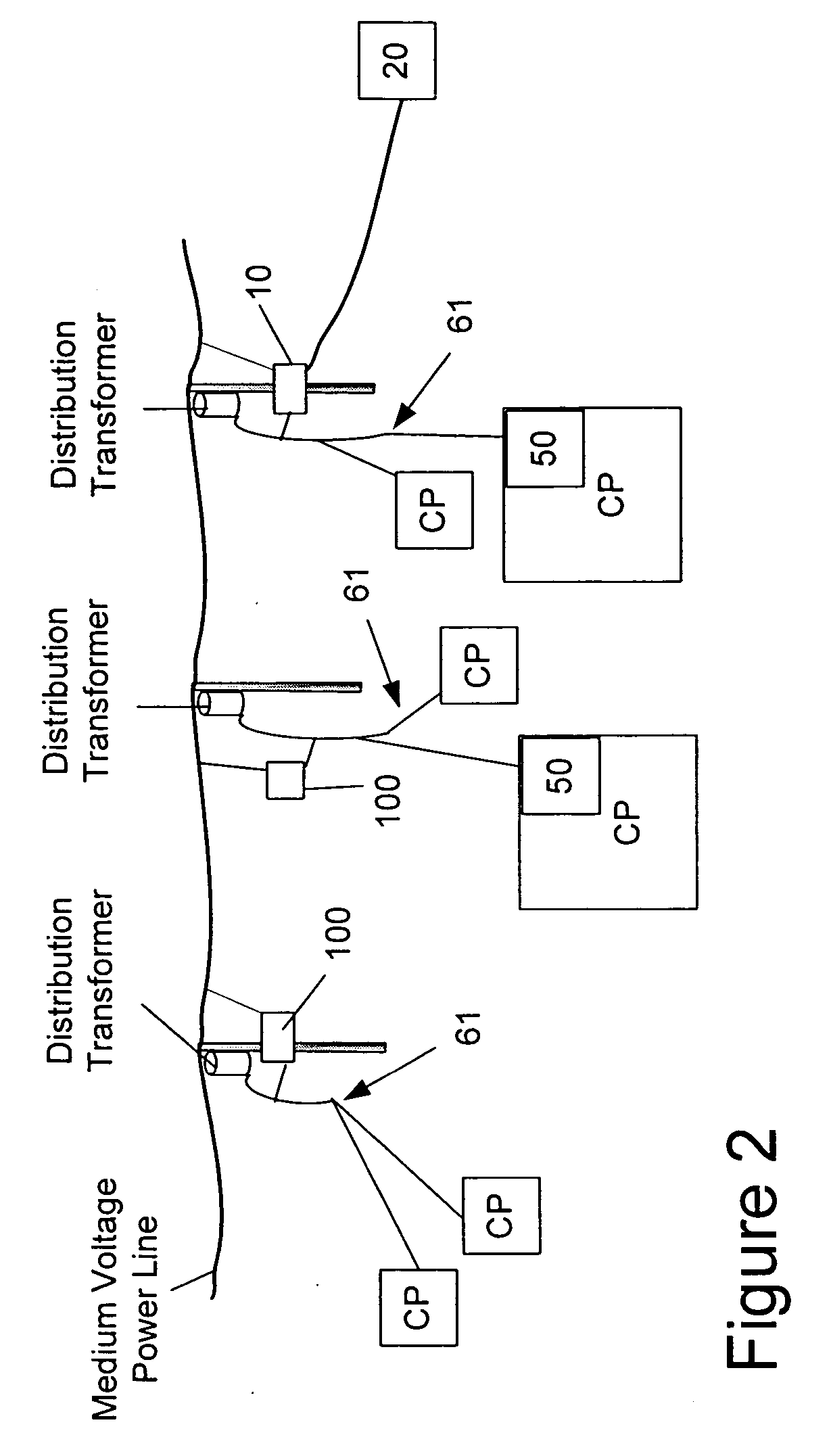
A power line communications device that may provide rate limiting and quality of service control is provided. The device may include a first modem in communication with one or more user devices via a low voltage power line subnet and a second modem communicatively coupled to a second communications medium. The device also may include a controller in communication with the first and second modems and a computer readable medium encoded with instructions to control the operation of the controller. The controller may rate limit data to and / or from a destination and / or source based one or more parameters such as the destination address, the source address, the type of data, temporal parameters, and other criteria. In addition, the controller may implement QoS for data and transmit QoS parameters to power line modems to allow the power line modems to perform QoS.
Owner:CURRENT TECH
Differential Forwarding in Address-Based Carrier Networks
InactiveUS20080279196A1Flexibility connections-egData switching by path configurationTraffic capacityFrame based
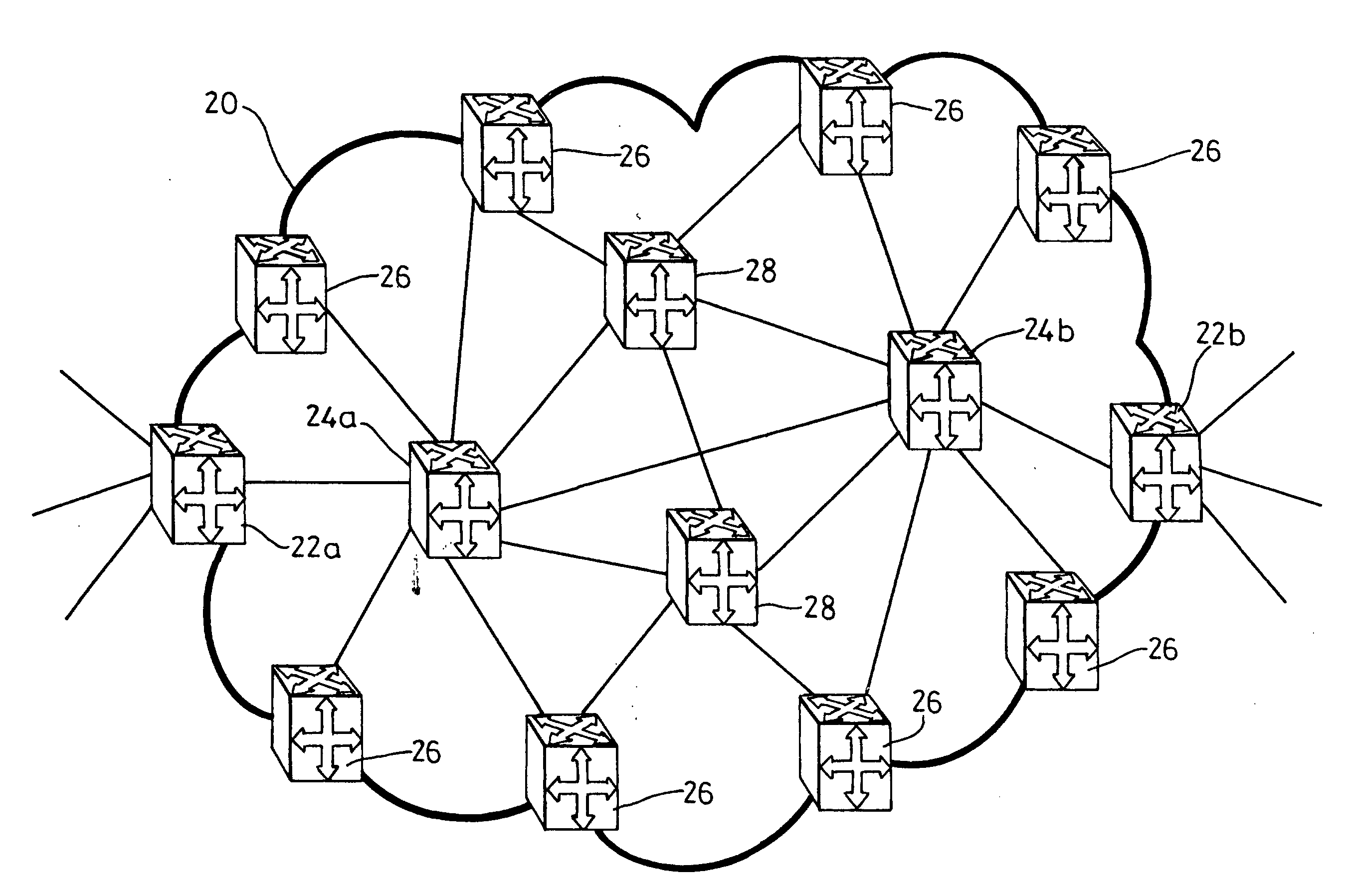
The invention relates to enabling differential forwarding in address-based carrier networks such as Ethernet networks. There is described a method of and connection controller for establishing connections (76, 77) in a frame-based communications network comprising nodes (71-75 and 78) such as Ethernet switches. The connections are established by configuring, in various of the nodes, mappings for forwarding data frames, such as Ethernet frames. The mappings are from a combination of a) a destination (or source) address corresponding to a destination (or source) node (73) of the connection and b) an identifier, such as a VLAN tag. The mappings are to selected output ports of the various nodes. By using the combination of destination (or source) address AND identifier, the mappings enable data frames belonging to different connections (76, 77) to be forwarded differentially (ie forwarded on different output ports) at a node (75) despite the different connections having the same destination node. This enables flexibility in routing connections and the ability to perform traffic engineering.
Owner:RPX CLEARINGHOUSE
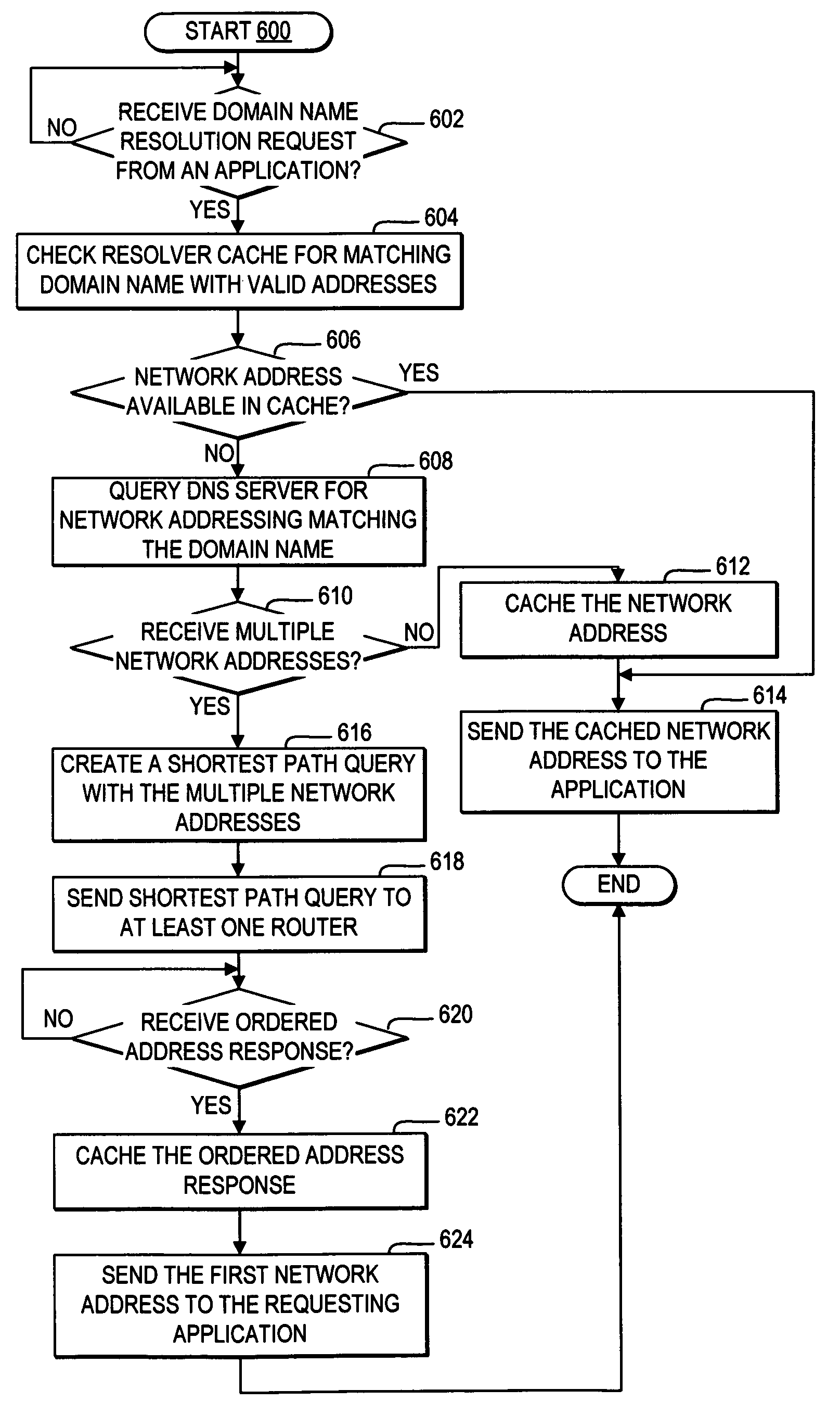
Resolver caching of a shortest path to a multihomed server as determined by a router
A resolver queries a DNS server for any network addresses associated with the particular domain name. If the resolver detects a response for the DNS server with multiple network addresses for a particular domain name, then the resolver creates and sends a shortest path query to at least one router enabled to receive and respond to shortest path queries. The shortest path query indicates at least one source address and the multiple destination addresses returned by the DNS server for the particular domain name. The router detects a separate length for each path accessible between each source address and each of the multiple destination addresses. The router then orders the destination addresses from shortest path to longest path and returns the ordered destination addresses to the requesting resolver. The resolver caches the ordered network addresses in the local cache in association with the particular domain name, such that for future requests for the particular domain name, the resolver retrieves from local cache the shortest path network address as ordered by the router. In addition, the resolver, responsive to receiving the ordered destination addresses, selects the shortest path network address for a response to an application requesting the resolution of the particular domain name.
Owner:IBM CORP
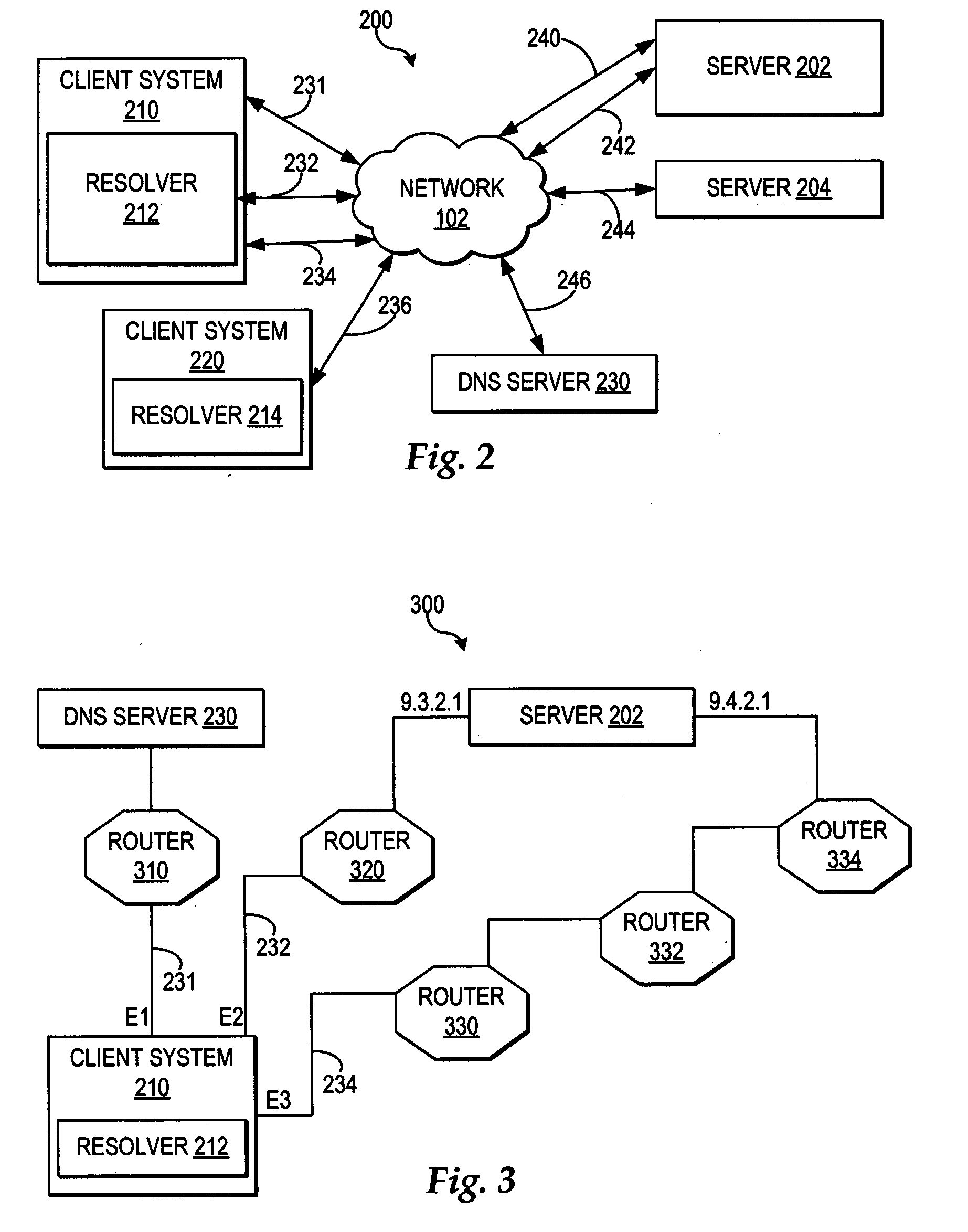
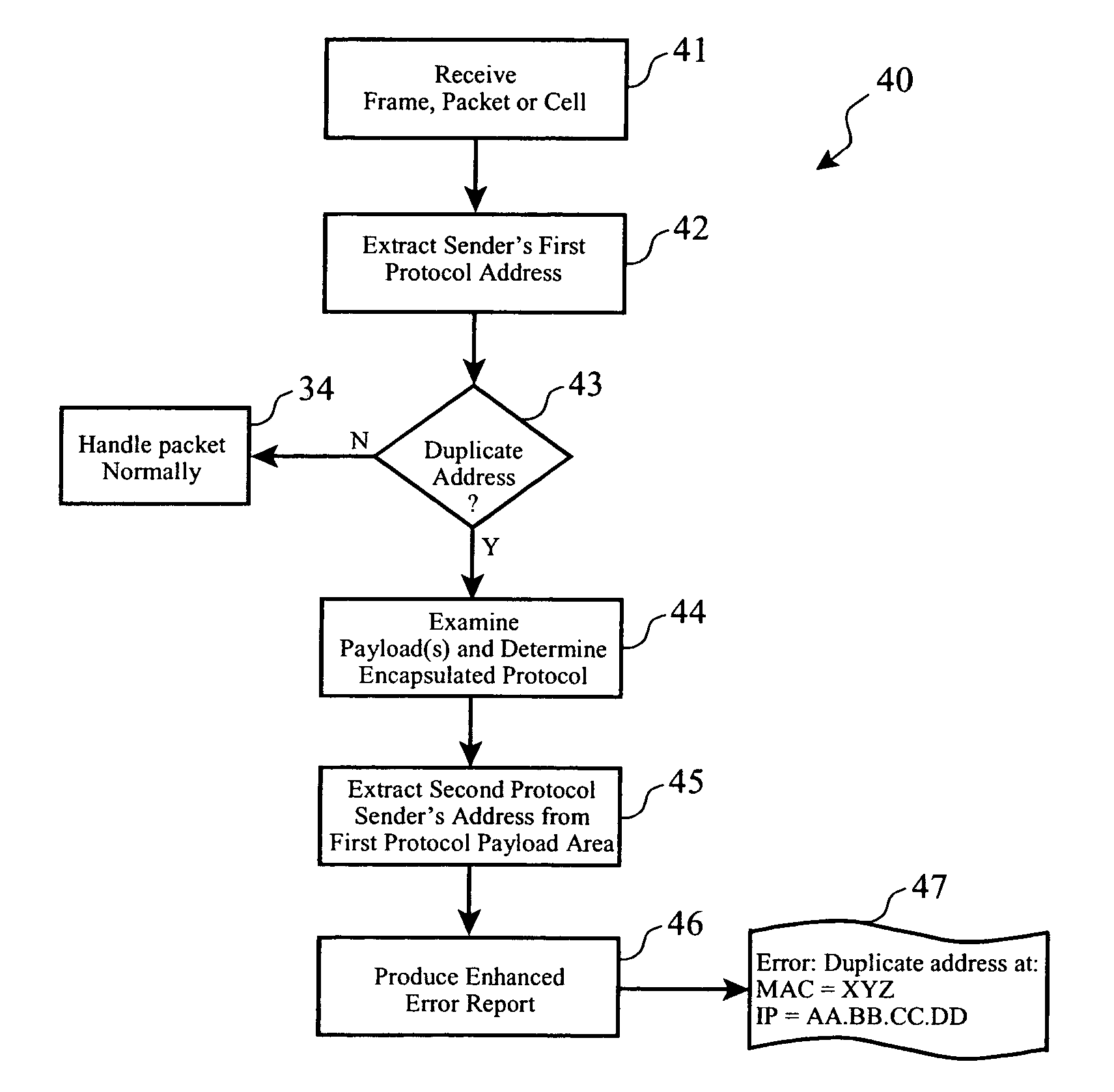
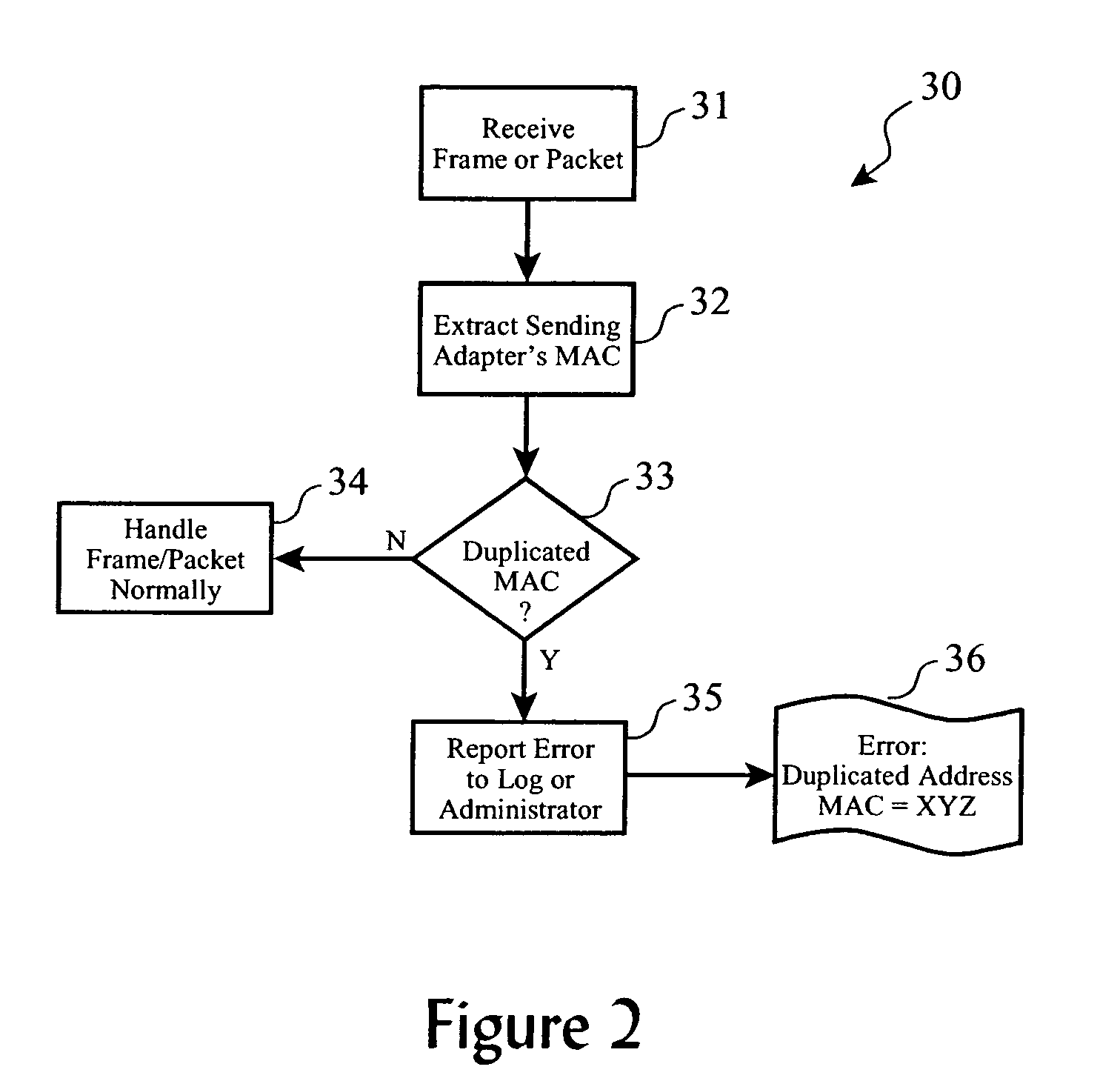
Duplicate network address detection
ActiveUS7246272B2Easy to detectError detection/correctionData switching by path configurationEncapsulated dataNetwork addressing
A plurality of data packets encoded according to a first protocol are received which encapsulate data encoded according to a second protocol. A first source address is extracted from the packets according to the first protocol, it is determined whether or not the first source address is a substantial duplicate of a known assigned address. If it is a duplicate, a second source address is extracted from the encapsulated data according to the second protocol, and the first source address and said second source address are provided in an enhanced error log so that a system administrator may correct the duplicate assigned address. Enhanced embodiments of the invention included analysis of data encapsulated by a third, fourth and subsequent protocols, and automatic determination of each protocol encoding format.
Owner:GOOGLE LLC
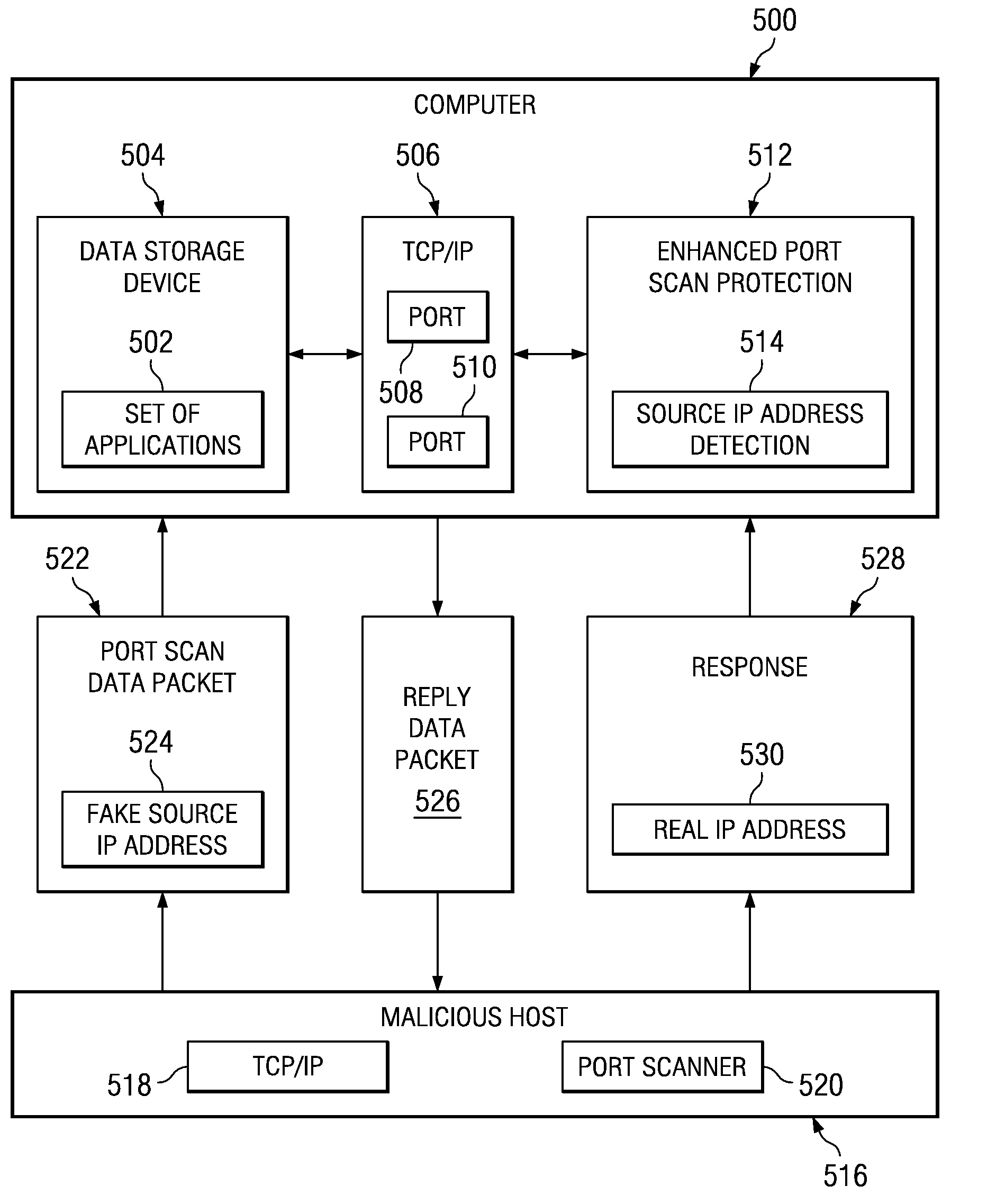
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
Multilink trunking for encapsulated traffic
InactiveUS20070098006A1Increase variabilityMinimize jitterEnergy efficient ICTTime-division multiplexFrame basedEncapsulated data
A node of a frame-based network has a group of outgoing links which are to be treated as an aggregated group of links. A frame distributor performs a distribution function on data frames which are intended for transmission on the group of links. The frame distributor determines if the data frame is an encapsulated data frame which forms part of a tunnelled traffic path across the network. If the data frame does form part of a tunnelled traffic path across the network, the frame distributor allocates the data frame to one of the group of links using at least part of an identifier from the header of the data frame. The identifier represents a service with which the data frame is associated, a customer or user of the data frame, or the tunnelled traffic path, which have greater variability than the backbone destination and source addresses.
Owner:RPX CLEARINGHOUSE
Session load balancing and use of VIP as source address for inter-cluster traffic through the use of a session identifier
InactiveUS7003574B1Improve the level ofCurrent is limitedMultiple digital computer combinationsProgram controlTraffic capacityIp address
A method and system for enhancing a load balancing network's ability to load balance sessions is presented. A session identifier is placed within the TCP packet to enable a new mechanism of load distribution and connection grouping within a load balancing system. Specifically, TCP is invoked by a user application to obtain a unique session identifier value. On receiving such a packet, the destination load balancing system hashes over at least the session identifier value, and the node corresponding to the results of the hash algorithm acquires the packet. This method of hashing ensures that the same node acquires all subsequently received TCP packets possessing the same session identifier regardless of the source IP address or source port information. The node then places an identical session identifier value in the form of a response session identifier in its TCP response packet. When the TCP packet with response session identifier is received at a load balancing system, the node whose session identifier matches the response session identifier acquires it.
Owner:MICROSOFT TECH LICENSING LLC
System and process for managing network traffic
InactiveUS20050249214A1Data switching by path configurationMultiple digital computer combinationsInternet trafficIp address
A traffic management system for use in a communications network, including a detection module for determining the source addresses of received network packets, and for comparing the source addresses with stored source address data for network packets received in a previous time period. The system monitors increases in the number of new source IP addresses of received packets to detect a network traffic anomaly such as a distributed denial of service (DDoS) attack or a flash crowd. If a traffic anomaly is detected, a filtering module performs history-based filtering to block a received packet unless one or more legitimate packets with the same source address have been previously received in a predetermined time period.
Owner:INTELLIGUARD I T
Authentication method and apparatus for detecting and preventing source address spoofing packets
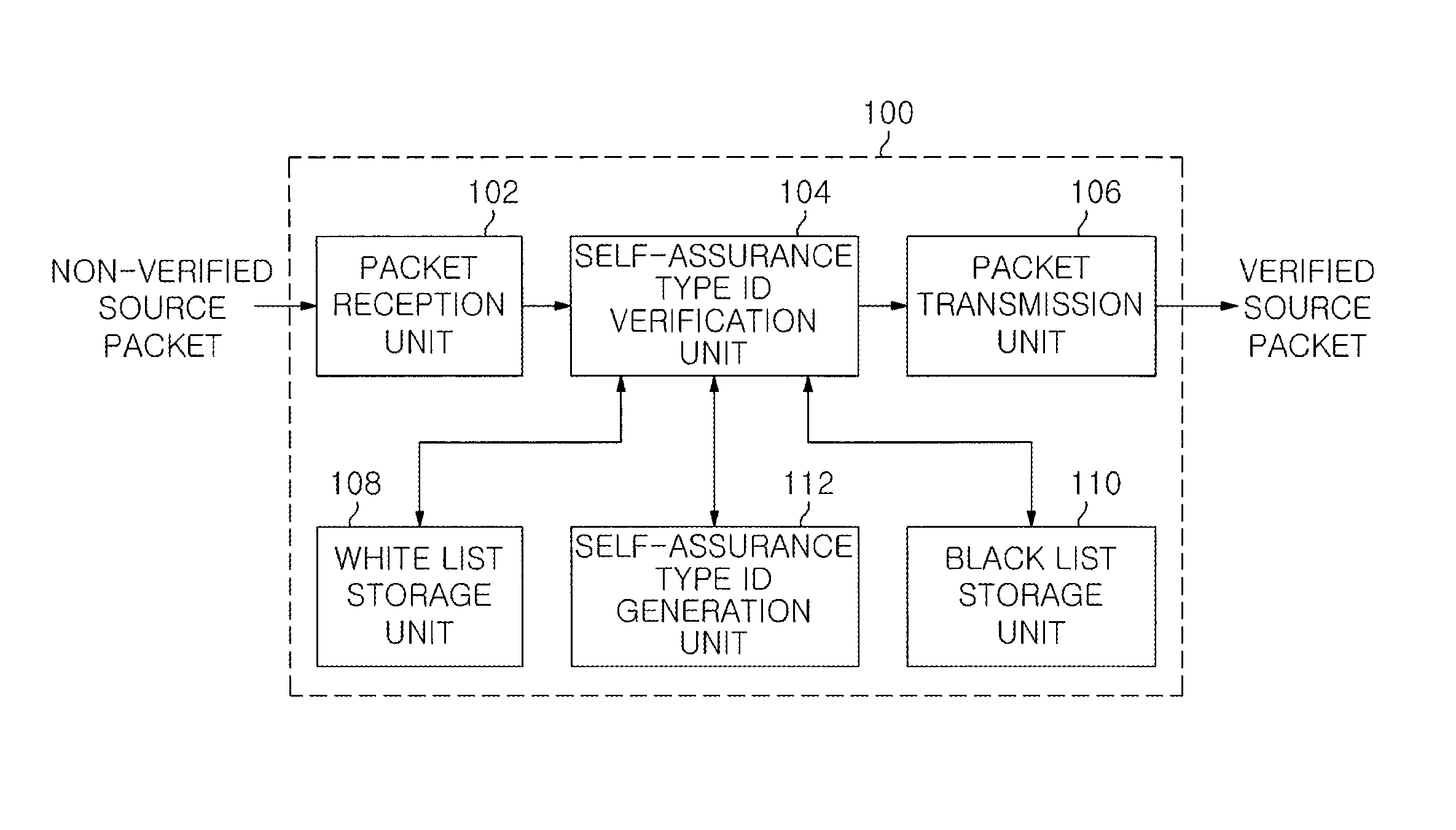
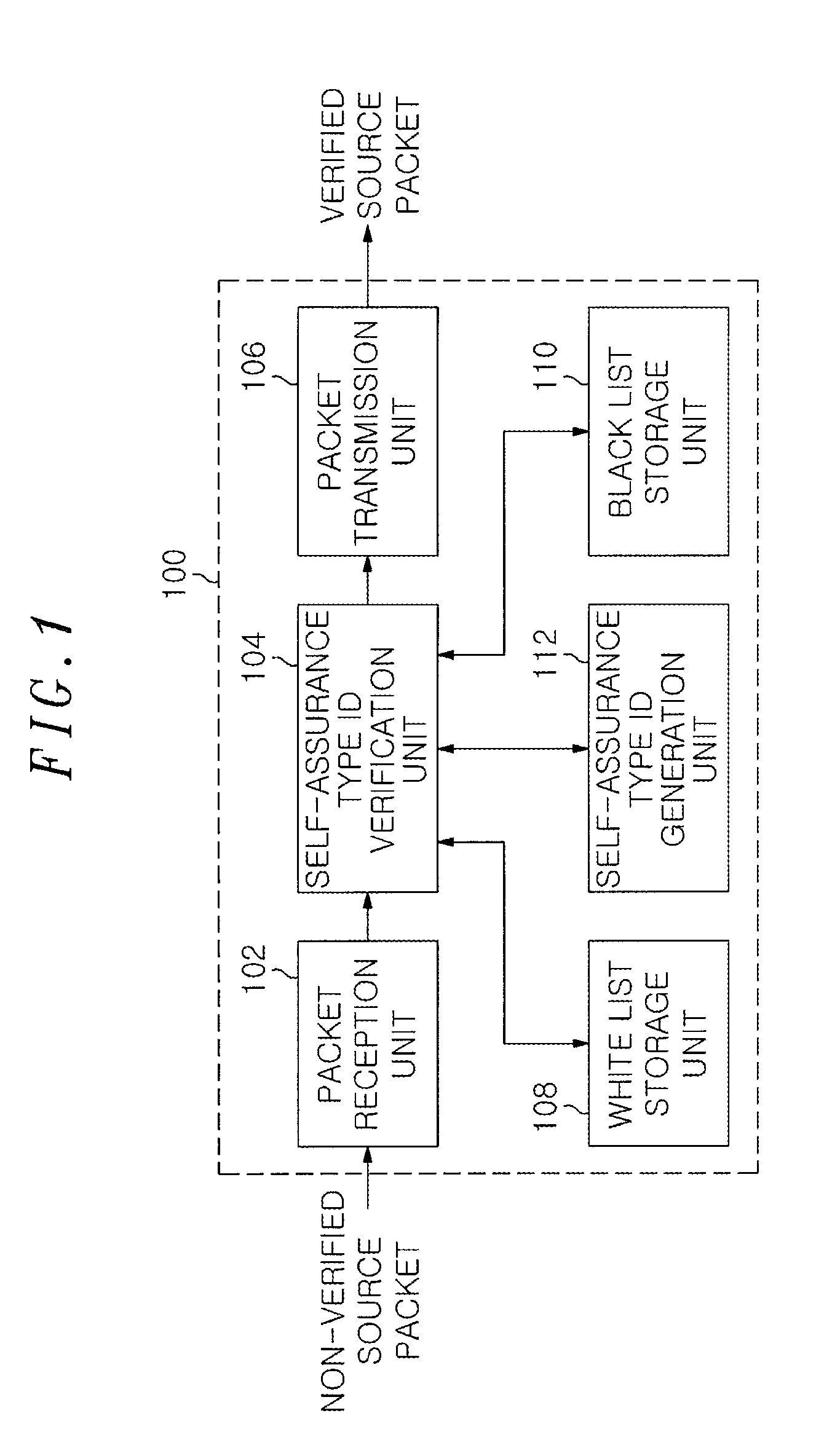
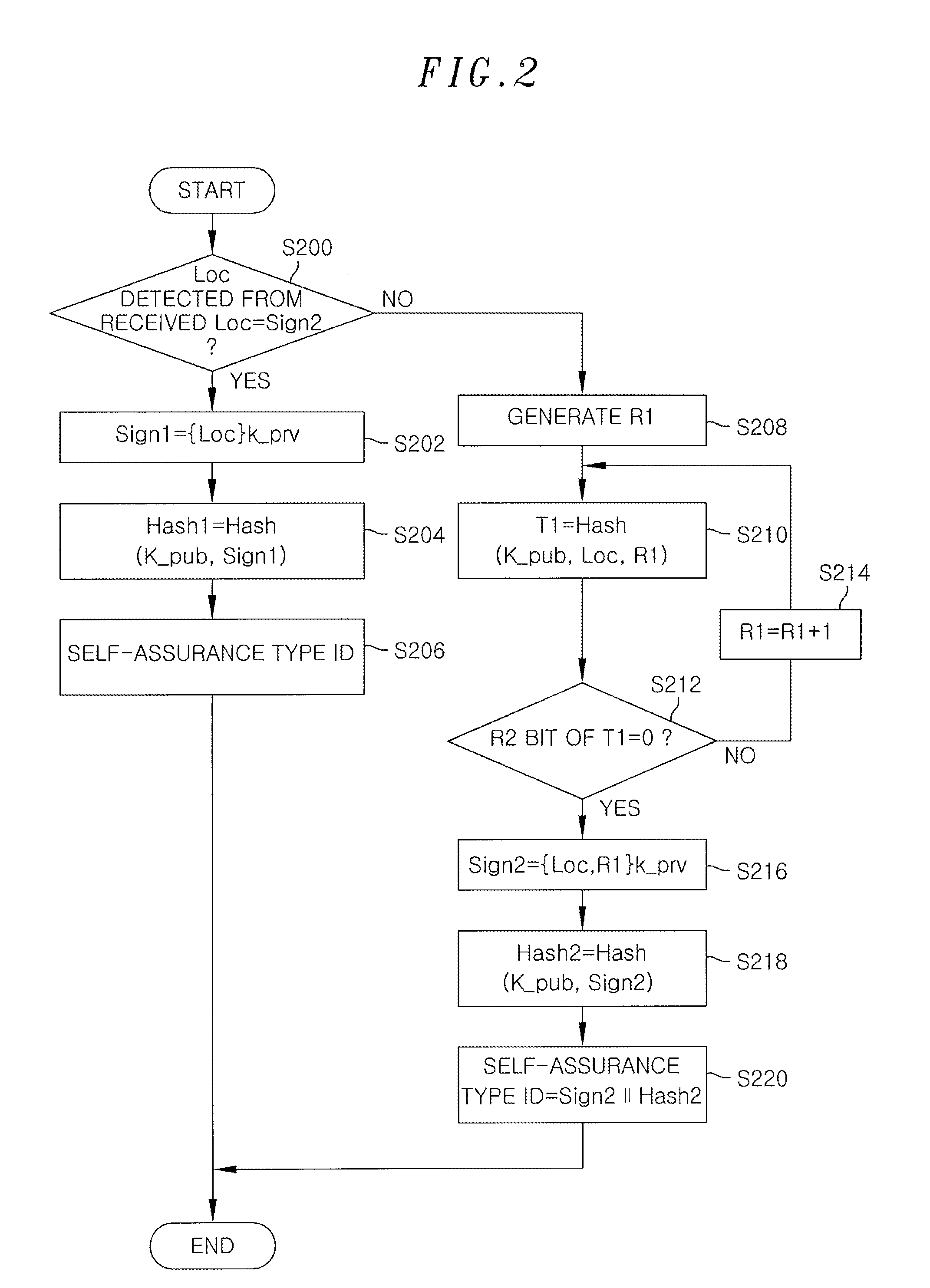
An authentication apparatus for detecting and preventing a source address spoofing packet, includes a packet reception unit configured to receive a packet from a previous node or a user host; a self-assurance type ID generation unit configured to generate a self-assurance type ID of a source node of the received packet; and a self-assurance type ID verification unit configured to determine whether the source address of the received packet has been spoofed. Further, the authentication apparatus includes a white list storage unit configured to store a reliable source node; a black list storage unit configured to store an unreliable source node; and a packet transmission unit configured to transmit the packet whose source has been verified through the self-assurance type ID verification unit to a next network node.
Owner:ELECTRONICS & TELECOMM RES INST
Traffic distribution control device
InactiveUS20050276263A1Process stabilityHigh bandwidthError preventionTransmission systemsTraffic capacityHash function
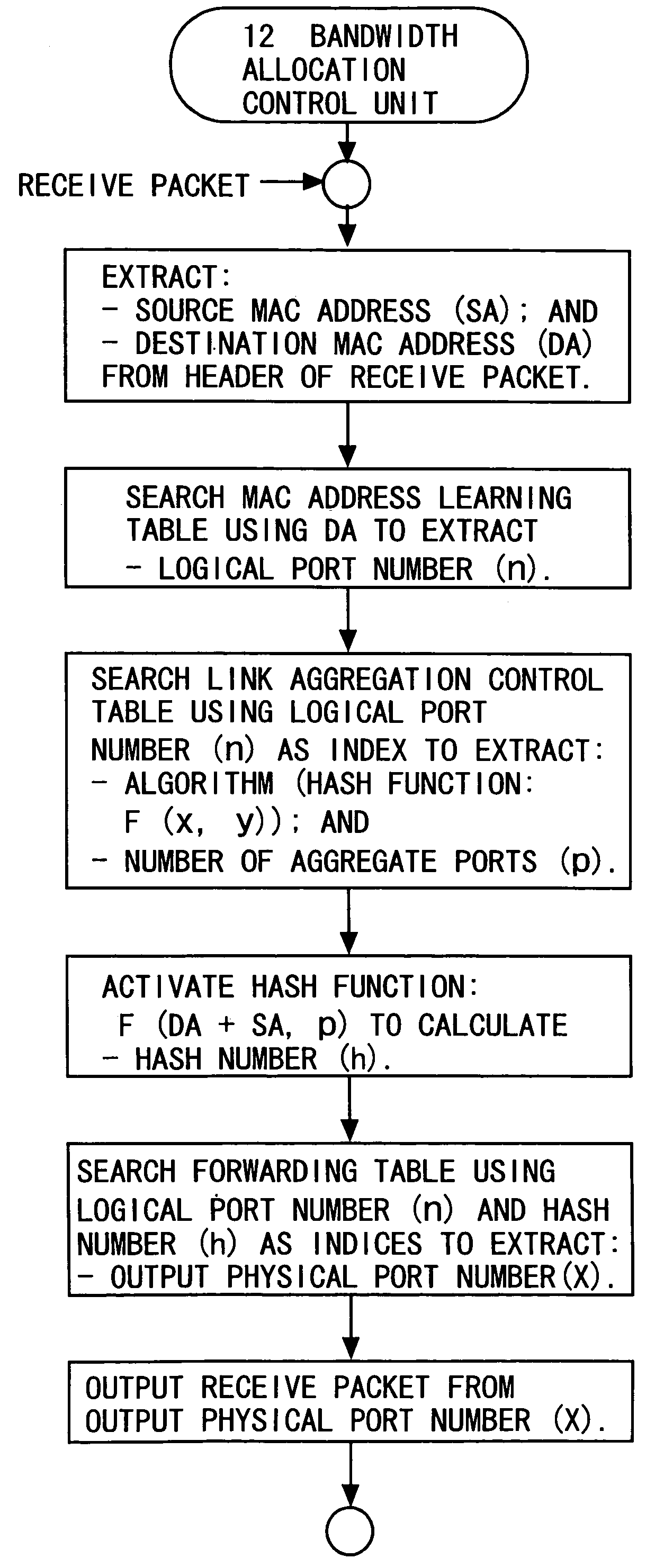
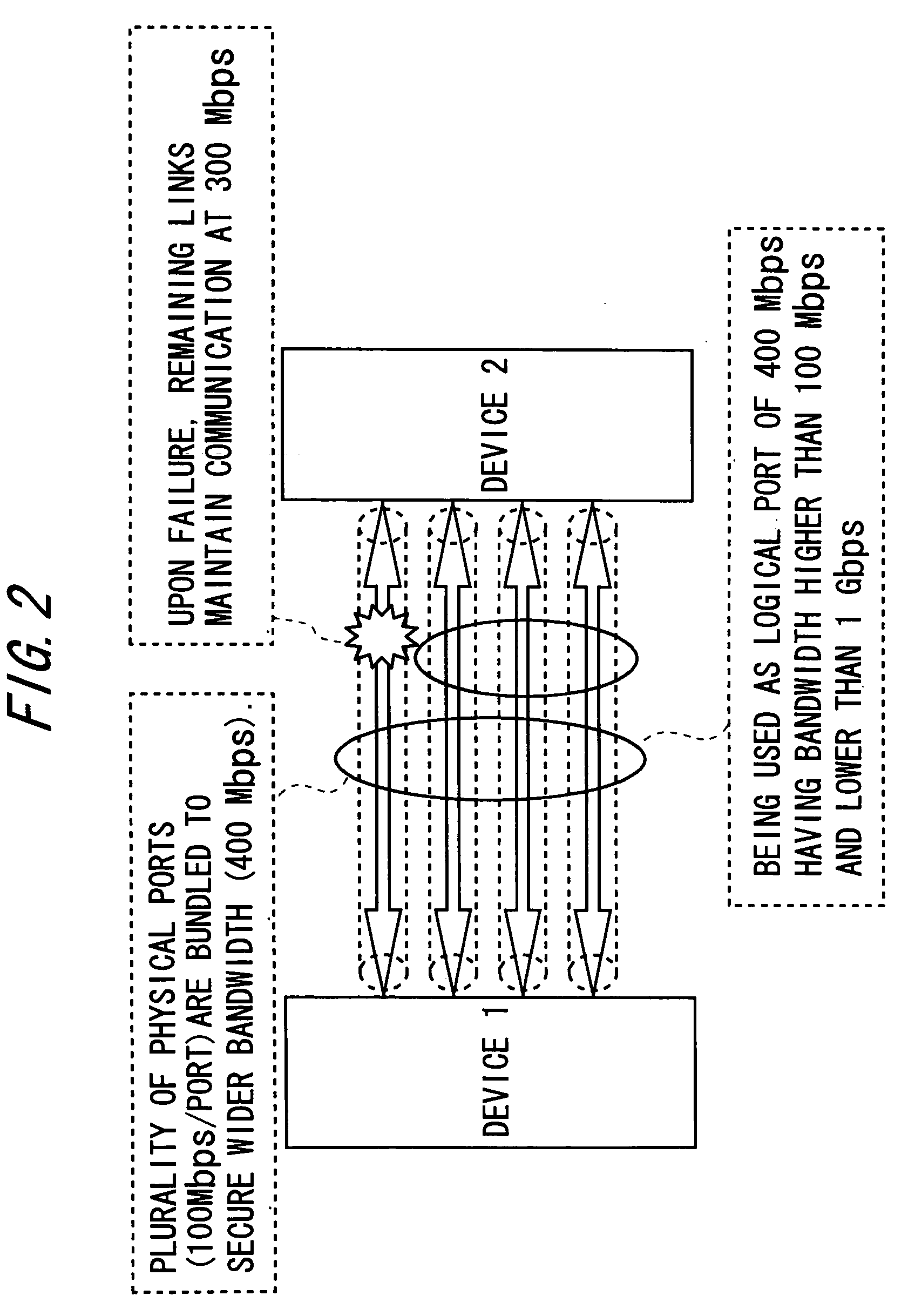
A data transmission device 10 serving as a traffic distribution control device is a device which, in order to distribute traffic across a plurality of physical ports composing a logical port for link aggregation, uses a hash function to calculate a hash value from a destination address and a source address of a receive packet, and determines a destination physical port. The traffic distribution control device includes a measuring unit 13 that measures an output flow rate of a packet outputted from each of the plurality of physical ports; a calculating unit 14 that calculates a flow rate ratio between the plurality of physical ports with respect to the measured output flow rates; and a first control unit 12 that feeds the calculated flow rate ratio back to a bandwidth distribution ratio between the plurality of physical ports to change numerical allocation of hash values for determining the destination physical port.
Owner:FUJITSU LTD
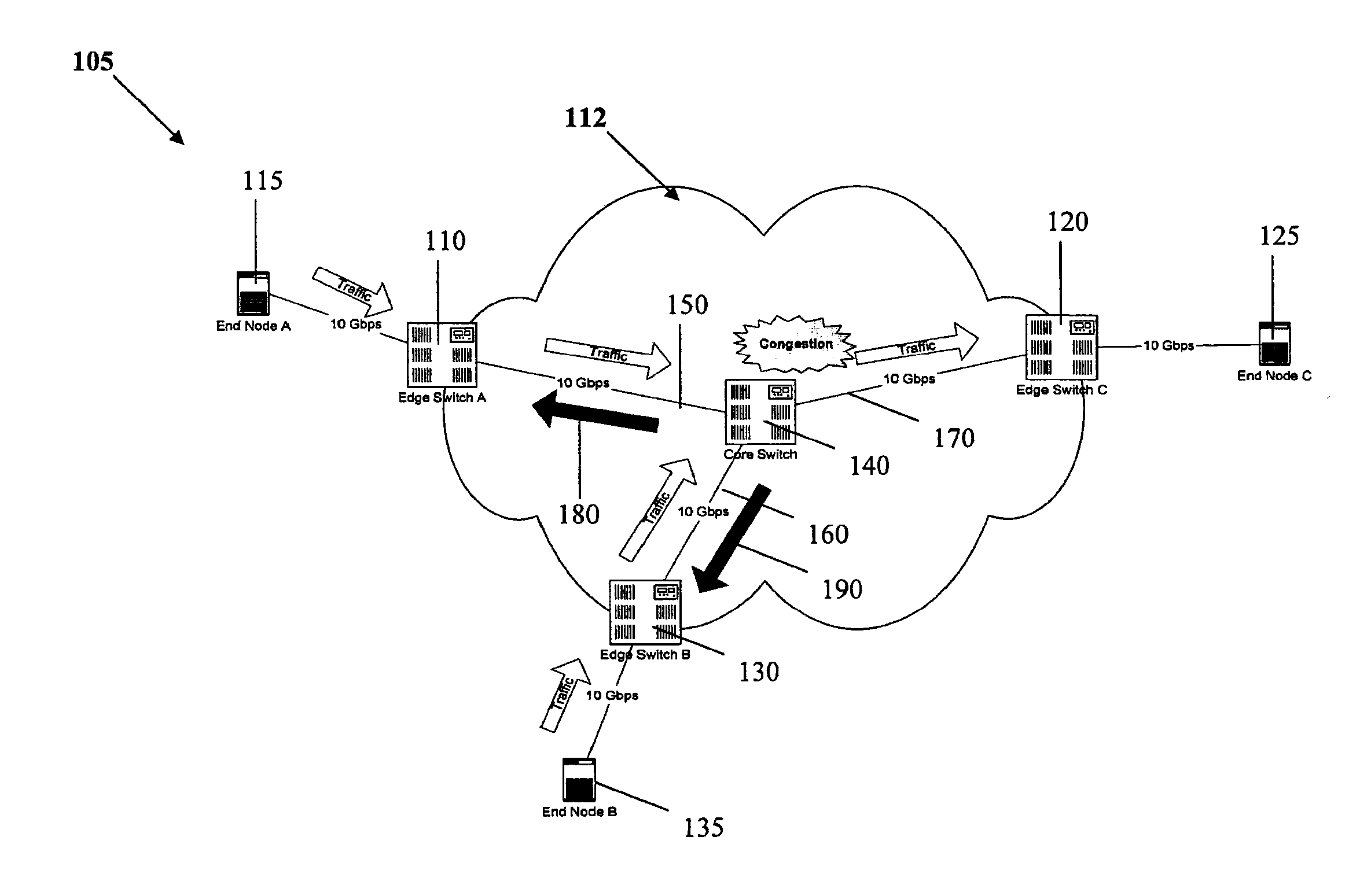
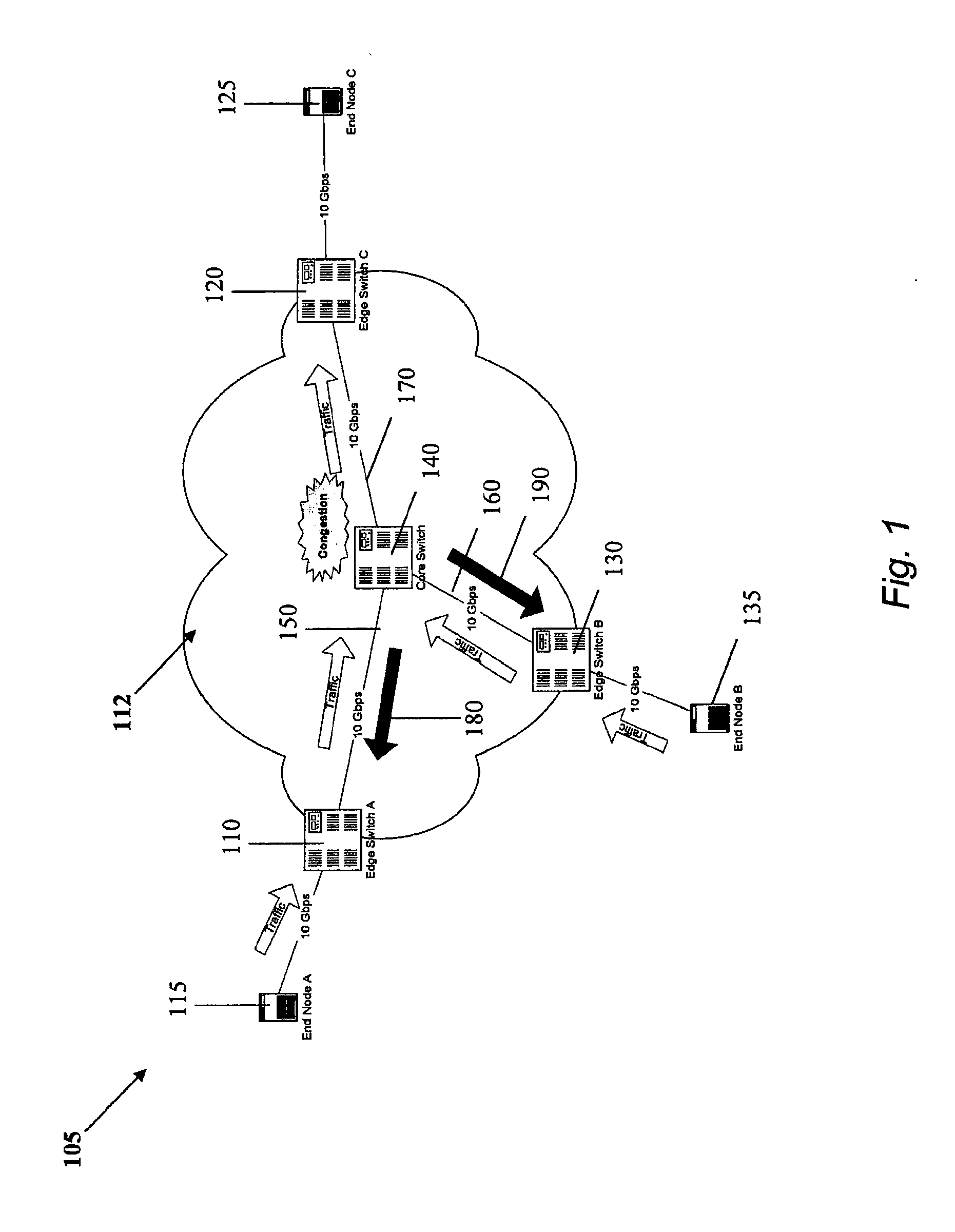
Congestion control method for a packet-switched network
InactiveUS7369498B1Increase profitError preventionFrequency-division multiplex detailsTraffic capacityPacket loss
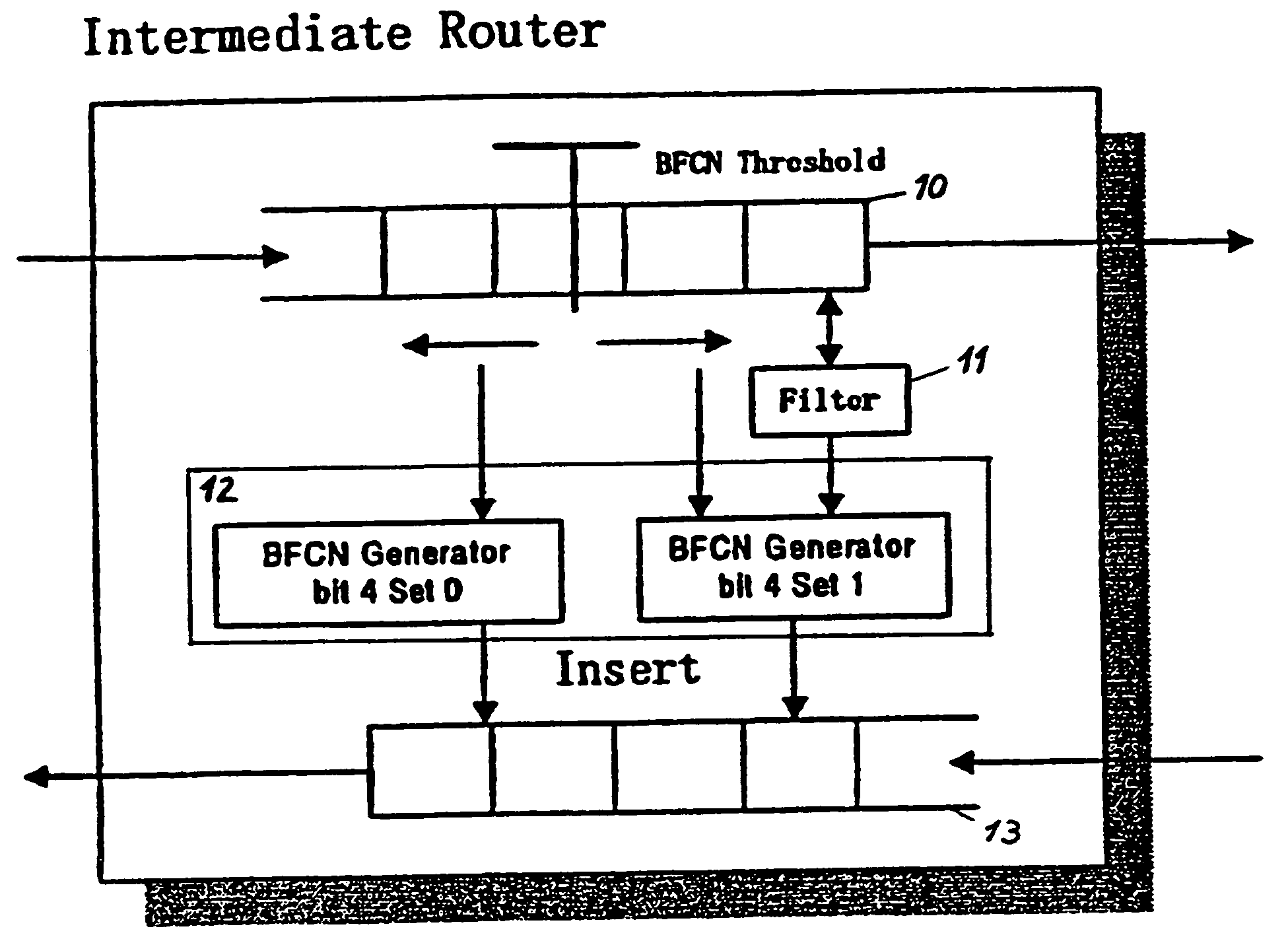
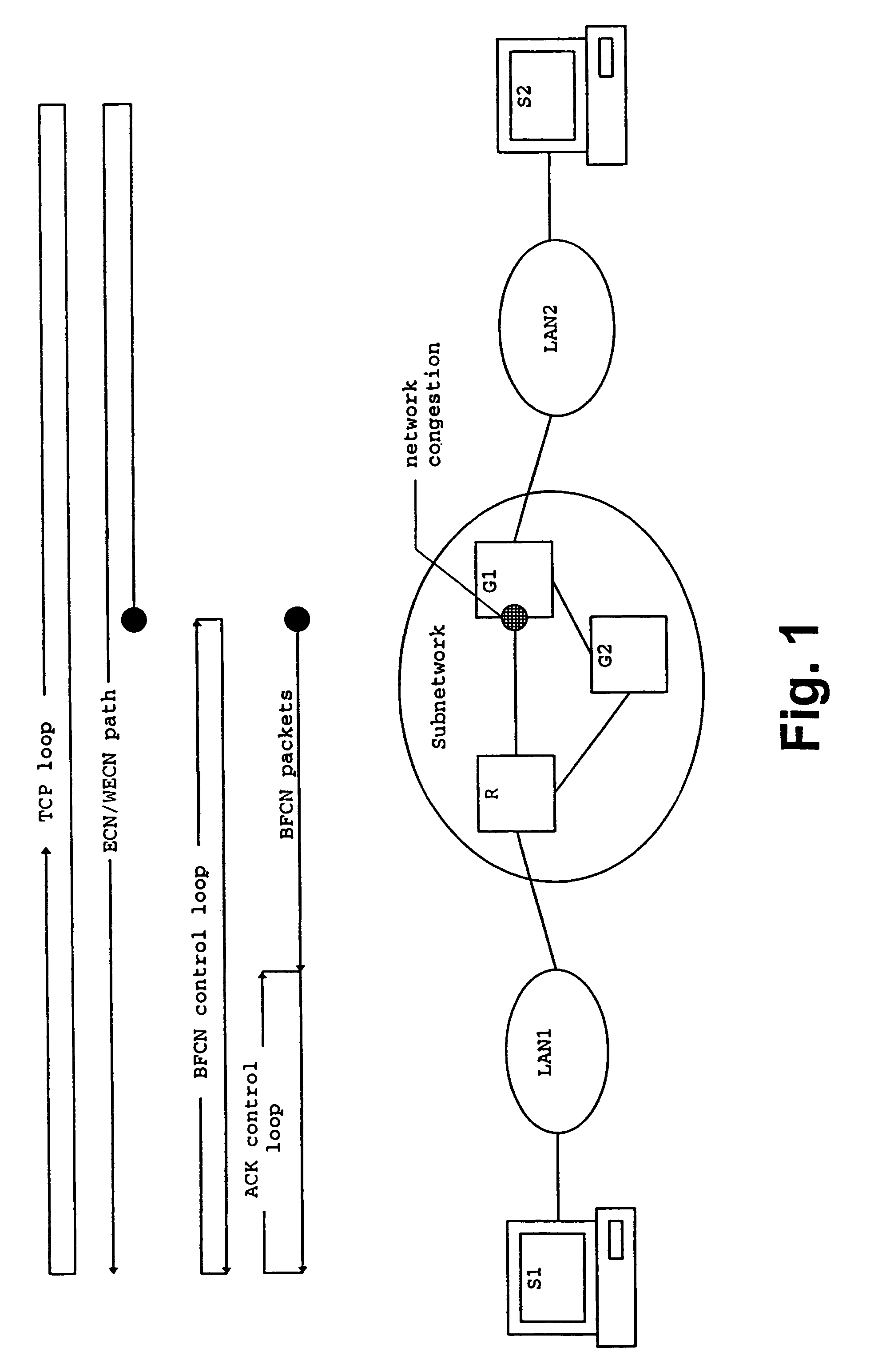
The present invention relates to a method and network for controlling congestion in a packet-switched network, comprising traffic sources, traffic destinations and network nodes, wherein a packet queue length in a network node is determined and a congestion notification is transmitted back towards the source address of an incoming data packet received at the network node, if the detected packet queue length exceeds a predetermined threshold. Then, congestion control is performed at a predetermined intermediate network node in response to the receipt of the congestion notification. Thereby, burts of source traffic can be constrained and unnecessary packet losses can be avoided already at an intermediate access node and within the network. The congestion notification message generated due to an incipient congestion is immediately routed back according to its source address. As a result, control delay time is shortened, such that buffer size requirements and number of congestion notification messages are reduced.
Owner:NOKIA CORP
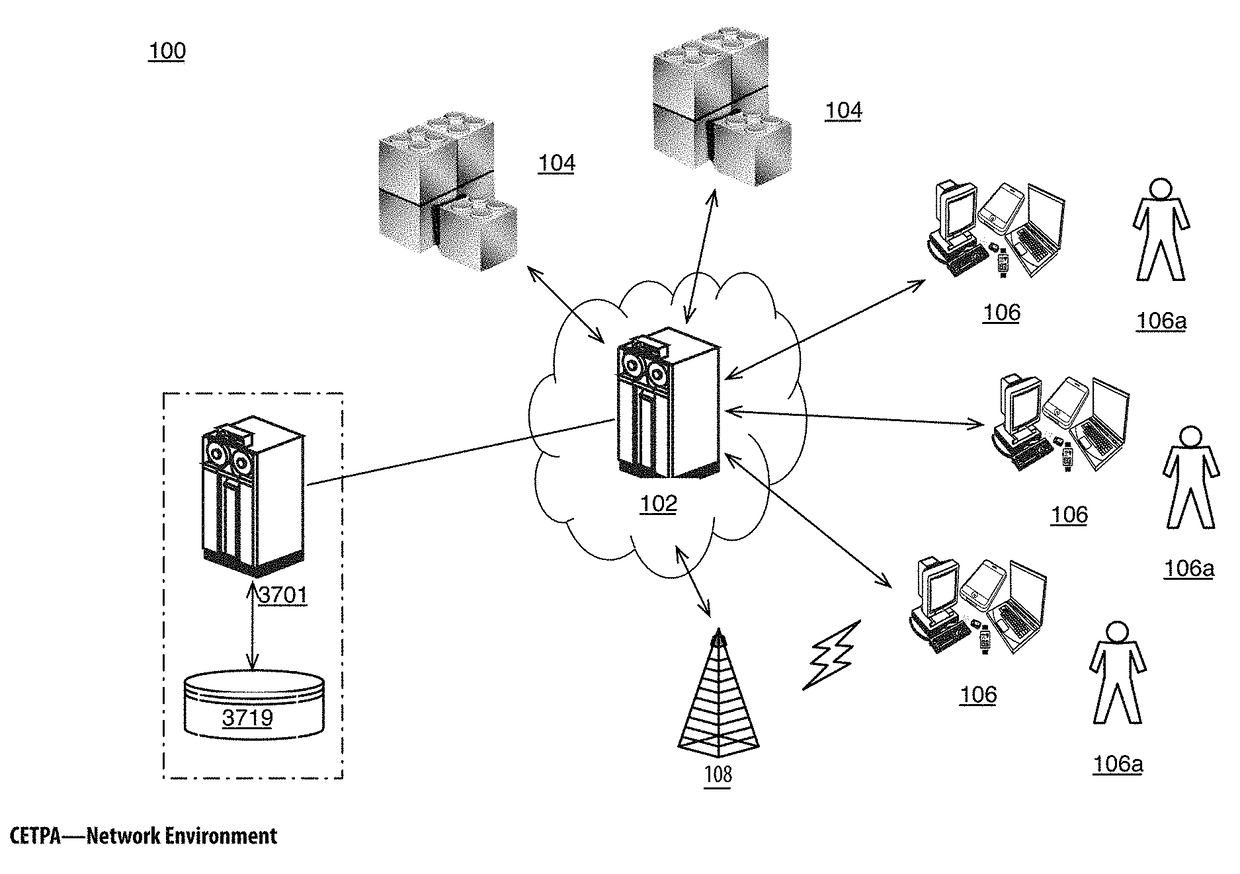
Computationally Efficient Transfer Processing and Auditing Apparatuses, Methods and Systems
The Computationally Efficient Transfer Processing and Auditing Apparatuses, Methods and Systems (“CETPA”) transforms transaction record inputs via CETPA components into matrix and list tuple outputs for computationally efficient auditing. A blockchain transaction data auditing apparatus comprises a blockchain recordation component, a matrix Conversion component, and a bloom filter component. The blockchain recordation component receives a plurality of transaction records for each of a plurality of transactions, each transaction record comprising a source address, a destination address, a transaction amount and a timestamp of a transaction; the source address comprising a source wallet address corresponding to a source digital wallet, and the destination address comprising a destination wallet address corresponding to a destination virtual currency wallet; verifies that the transaction amount is available in the source virtual currency wallet; and when the transaction amount is available, cryptographically records the transaction in a blockchain comprising a plurality of hashes of transaction records. The Bloom Filter component receives the source address and the destination address, hashes the source address using a Bloom Filter to generate a source wallet address, and hashes the destination address using the Bloom Filter to generate a destination wallet address. The Matrix Conversion component adds the source wallet address as a first row and a column entry to a stored distance matrix representing the plurality of transactions, adds the destination wallet address as a second row and column entry to the stored distance matrix representing the plurality of transactions, adds the transaction amount and the timestamp as an entry to the row corresponding to the source wallet address and the column corresponding to the destination wallet address; and generate a list representation of the matrix, where each entry in the list comprises a tuple having the source wallet address, the destination wallet address, the transaction amount and the timestamp.
Owner:FMR CORP
System and method for providing rapid rerouting of real-time multi-media flows
A system and method for providing rapid rerouting of real-time transport protocol (RTP) multi-media flows is disclosed. Generally, a first endpoint is connected to a second endpoint, wherein the first endpoint comprises a transceiver, software stored within the first endpoint defining functions to be performed by the first endpoint, and a processor configured by the software. The processor is configured to perform the steps of, performing flow processing on a data packet received at a first endpoint, from a second endpoint, removing a multi-protocol label switching (MPLS) tag from the data packet, translating a source address and destination address of the data packet, and determining a forwarding destination if more than one destination address of the data packet is provided.
Owner:PRIMARY NETWORKS +1
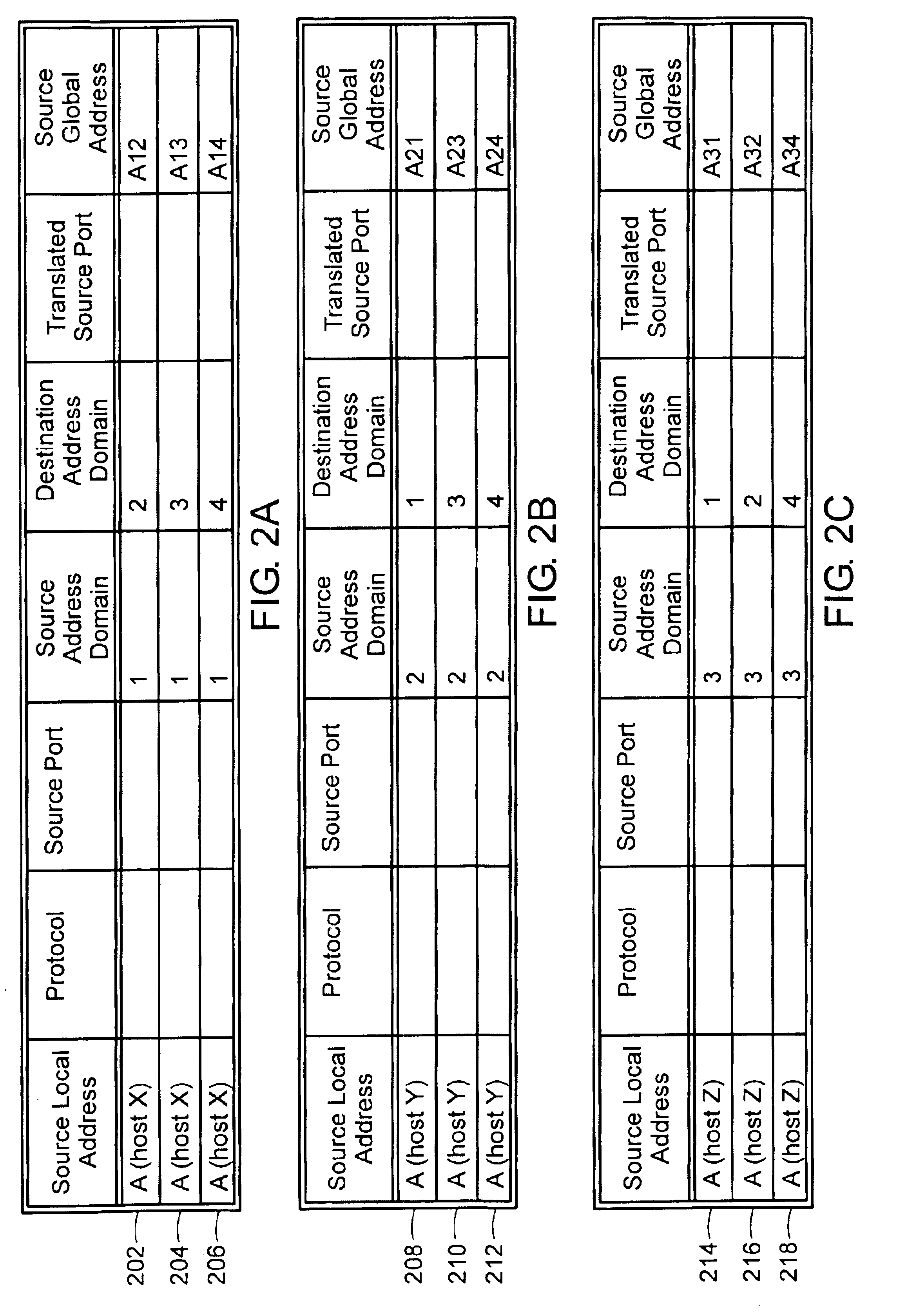
Management information base for a multi-domain network address translator
InactiveUS6892245B1Interconnection arrangementsMultiple digital computer combinationsManagement information baseInformation repository
A management information base (MIB) for a multi-domain network address translator provides management objects for configuring and controlling the multi-domain network address translator. The MIB includes management objects for defining a domain-specific source address filter range, which is a range of addresses used to detect domain-specific packets that require domain-specific network address translation forwarding. The domain-specific source address filter management objects include a beginning address, a prefix length, a domain indicator, and a domain-specific translation pool indicator. The MIB also includes management objects for defining a domain-specific translation pool, which is a range of addresses from which domain-specific translation addresses are selected for domain-specific network address translation forwarding. The domain-specific translation pool management objects include a beginning address, a prefix length, and a domain indicator.
Owner:RPX CLEARINGHOUSE
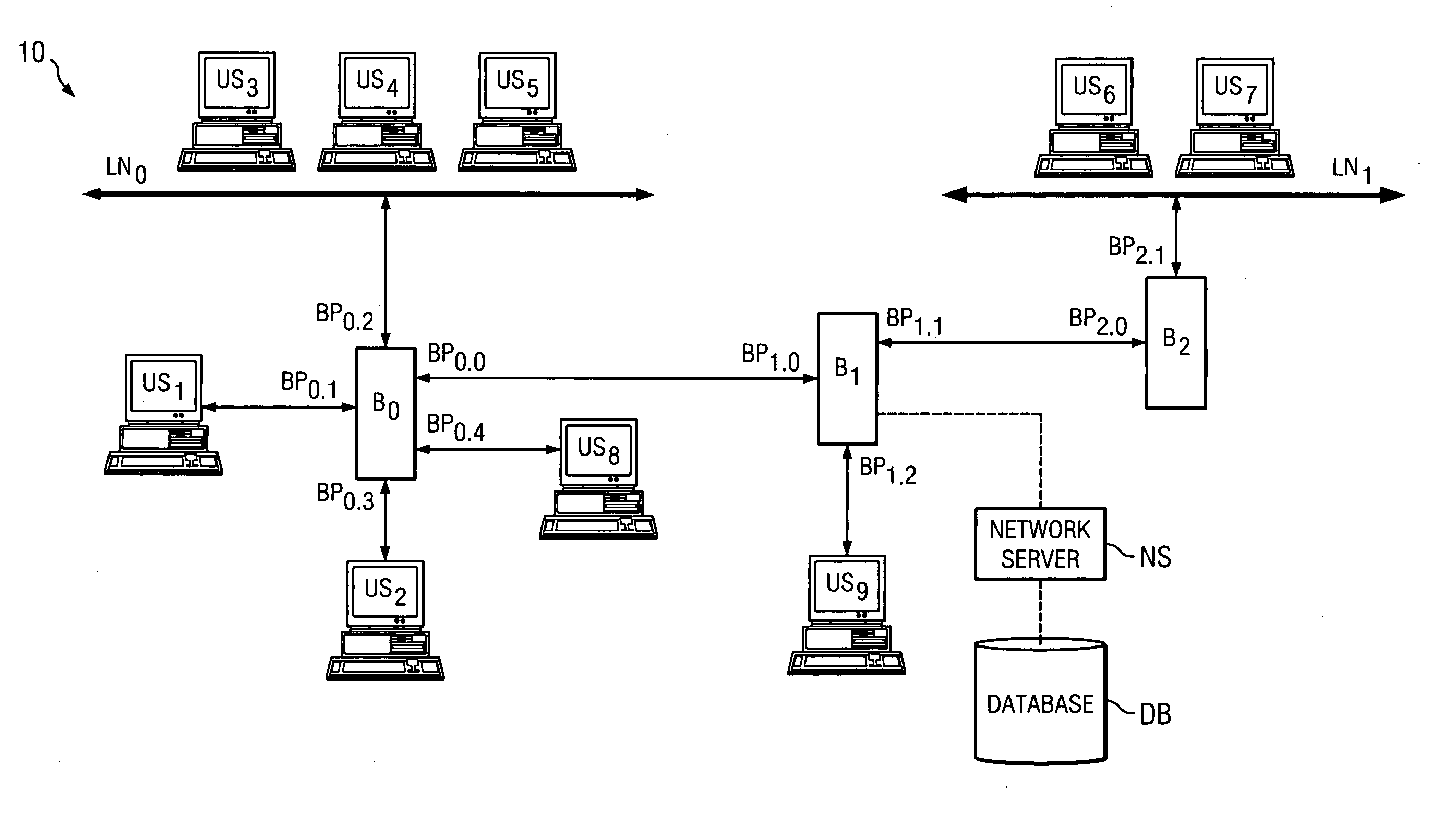
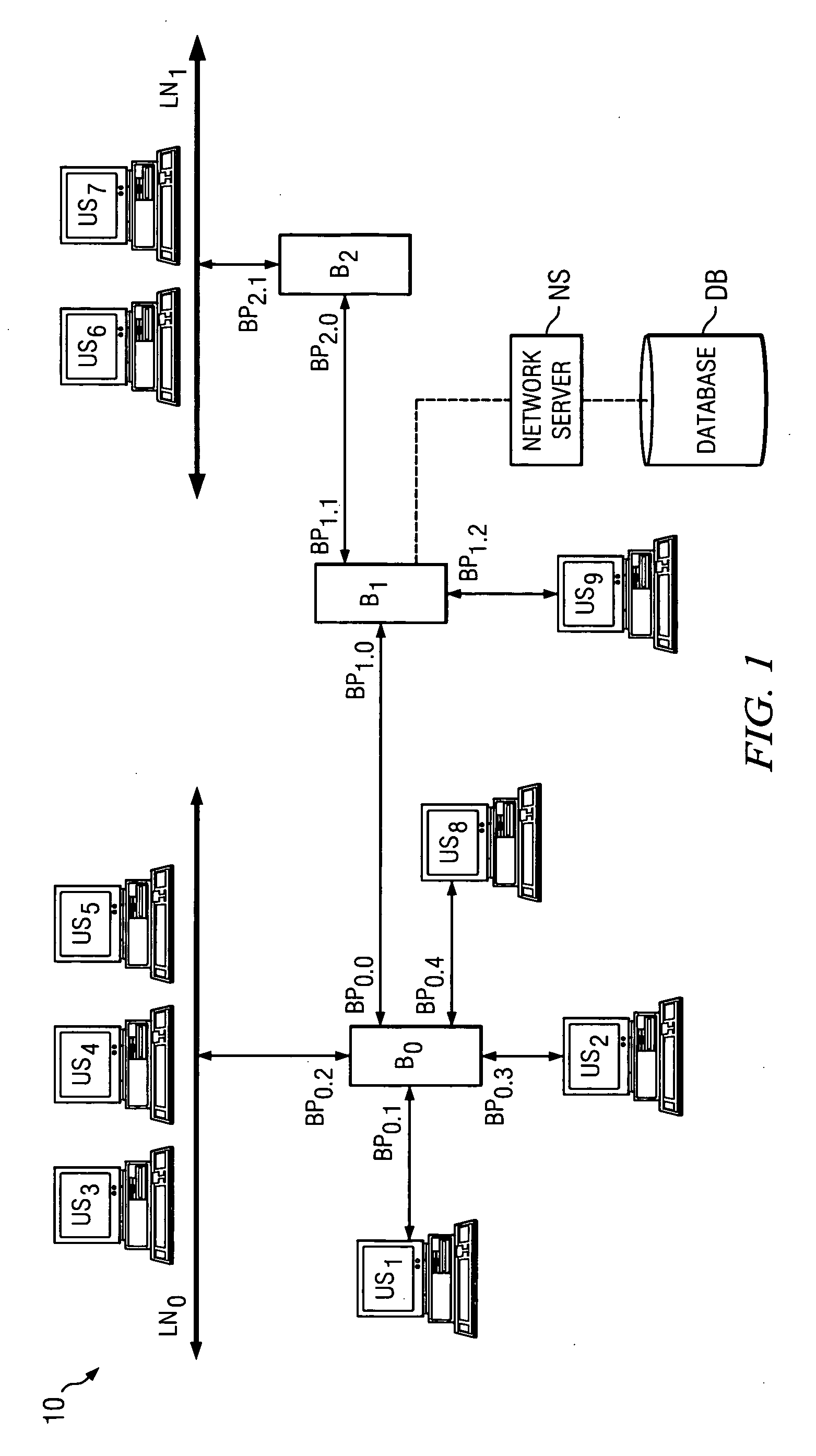
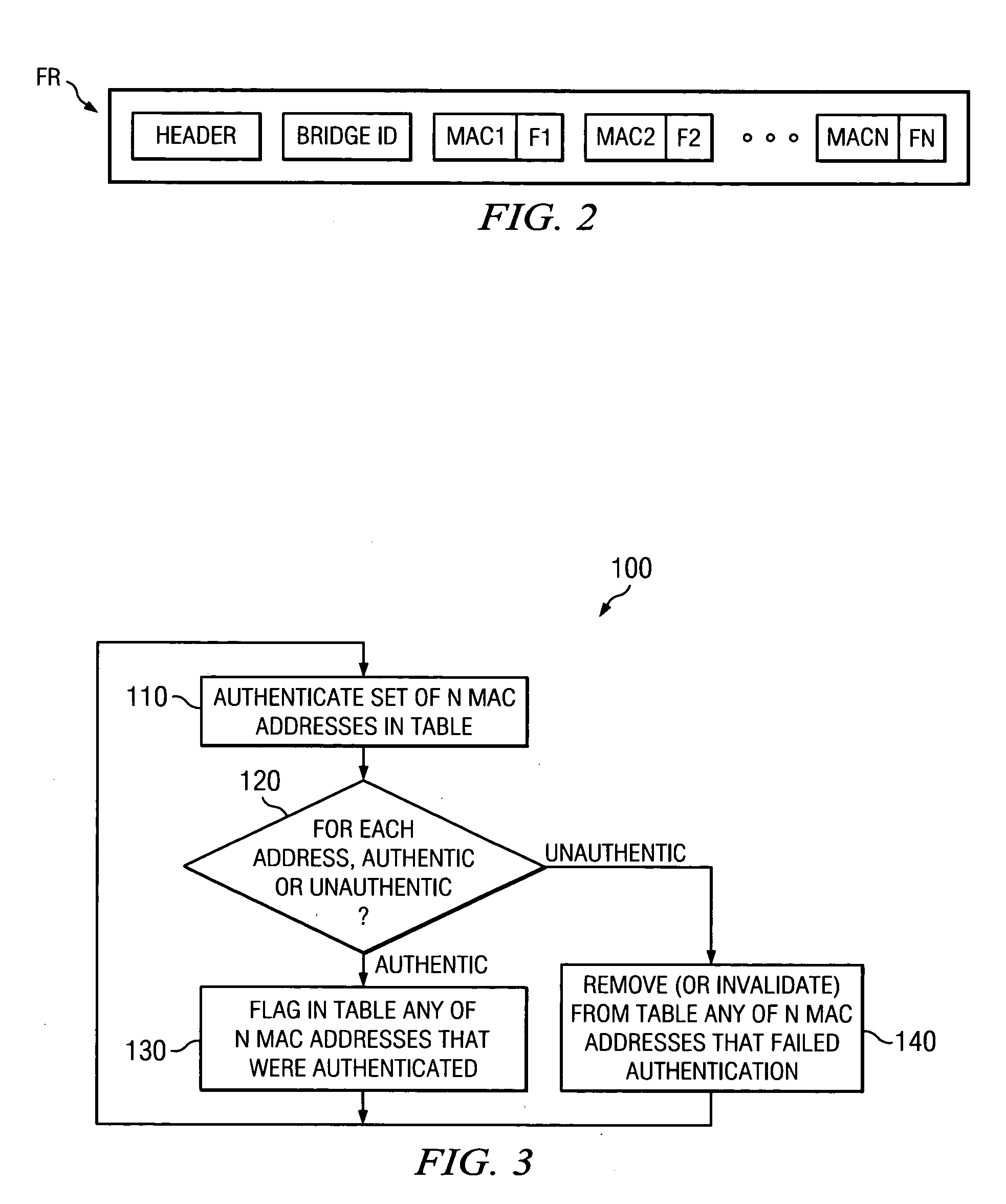
Network with MAC table overflow protection
A method of operating a bridge node (B0) in a network system. The bridge node comprises a plurality of ports (BP0.x). The method comprises a step of receiving a frame (240), from a device in the network system and other than the bridge node, at a port in the plurality of ports. The frame comprises a source network address. The method is also responsive to at least one condition (250, 260) associated with the port in that the method stores the source address in a forwarding table associated with the bridge if the at least one condition is satisfied. The at least one condition comprises whether the frame was received within a time window Tw of when a threshold number of previous frames were received at the port and their respective source network addresses were stored in the table.
Owner:PROVEN NETWORKS LLC
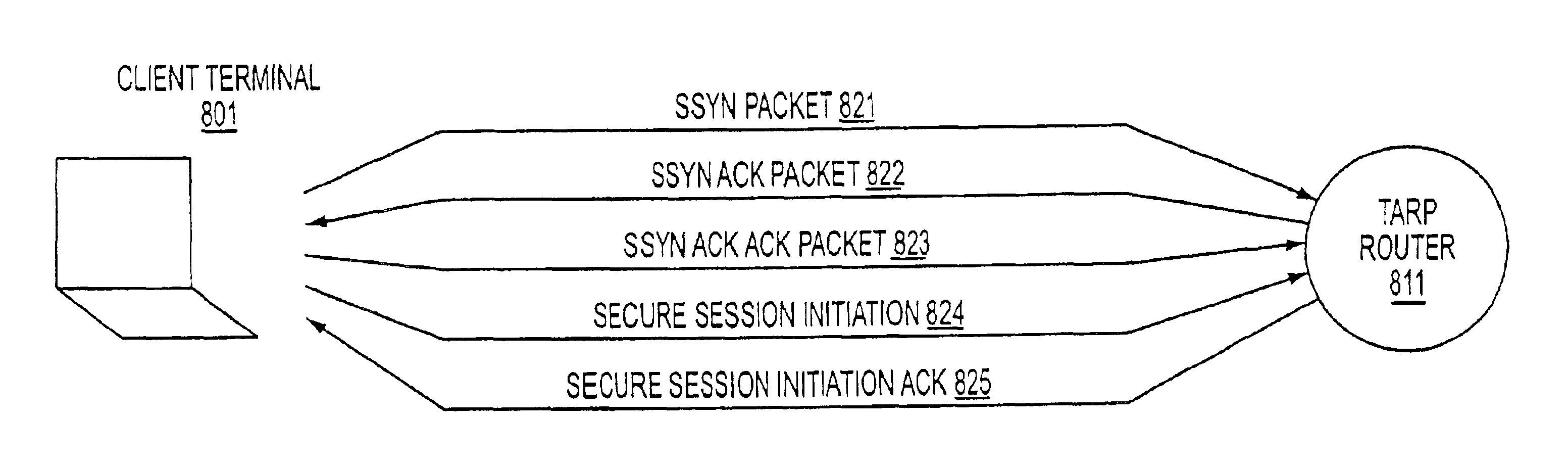
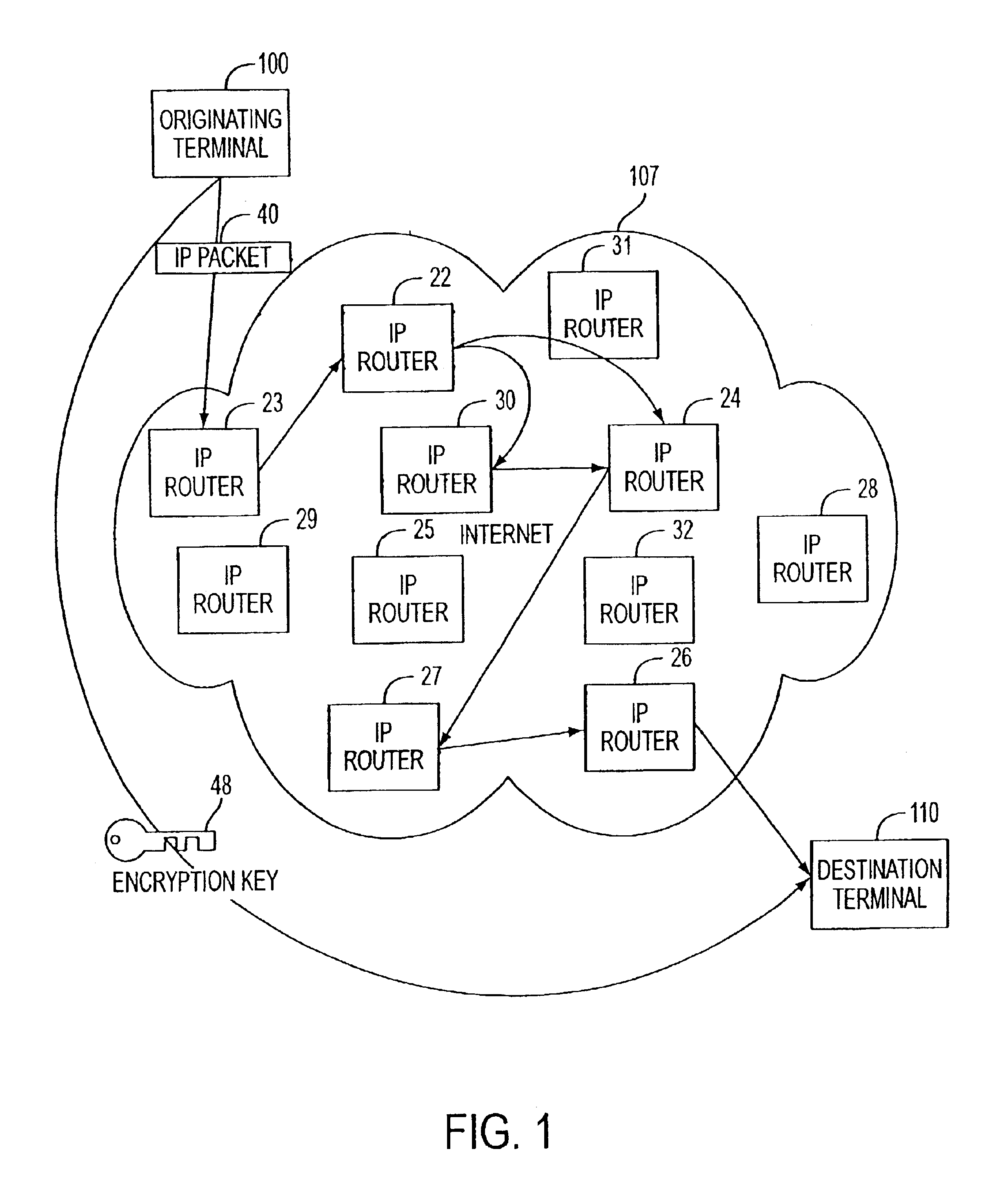
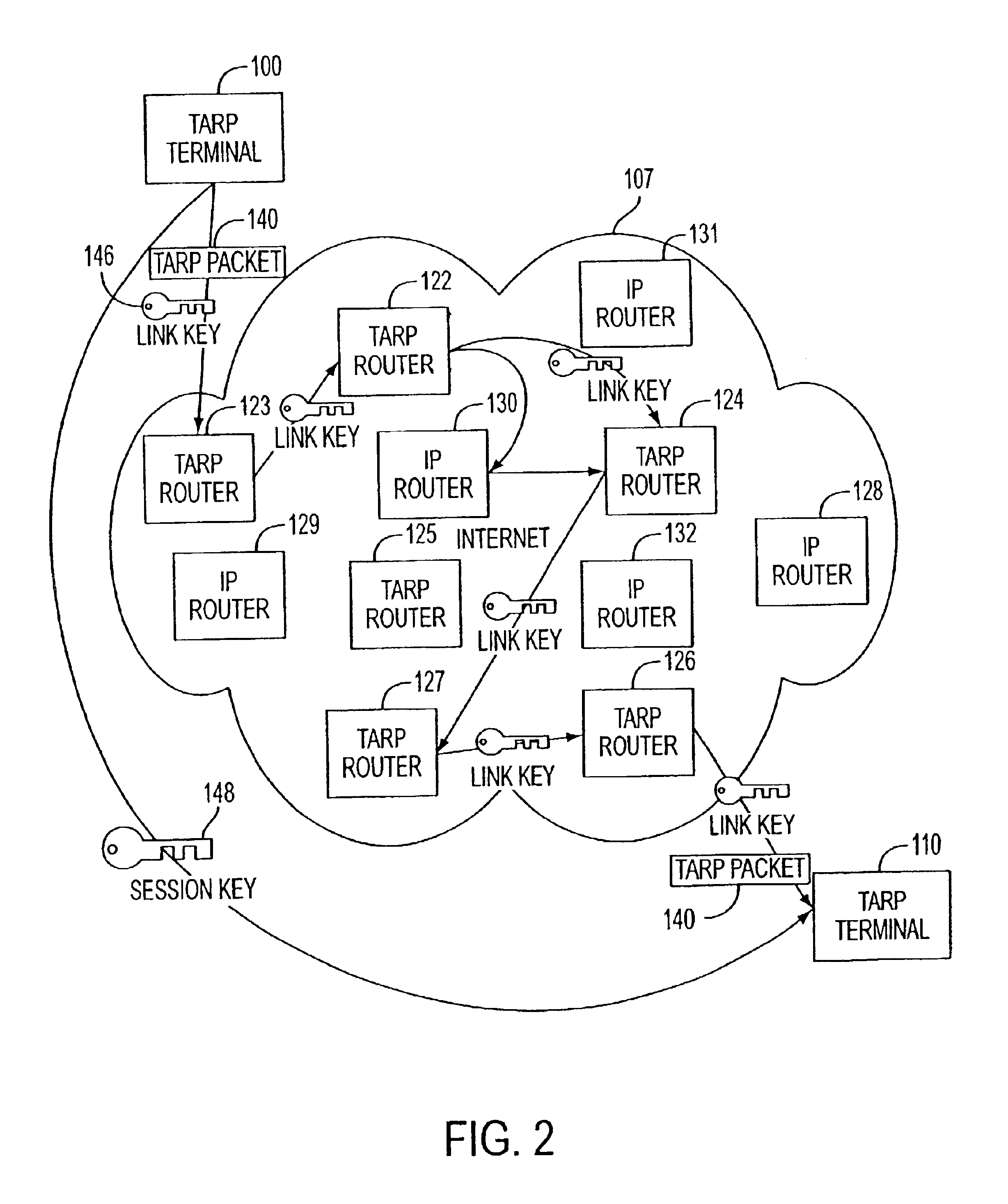
Agile network protocol for secure communications with assured system availability
InactiveUS6907473B2Prevents denial-of-service attackAvoid attackError detection/correctionMultiple digital computer combinationsSecure communicationPrivate network
A plurality of computer nodes communicate using seemingly random Internet Protocol source and destination addresses. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are quickly rejected. Improvements to the basic design include (1) a load balancer that distributes packets across different transmission paths according to transmission path quality; (2) a DNS proxy server that transparently creates a virtual private network in response to a domain name inquiry; (3) a large-to-small link bandwidth management feature that prevents denial-of-service attacks at system chokepoints; (4) a traffic limiter that regulates incoming packets by limiting the rate at which a transmitter can be synchronized with a receiver; and (5) a signaling synchronizer, that allows a large number of nodes to communicate with a central node by partitioning the communication function between two separate entities.
Owner:VIRNETX
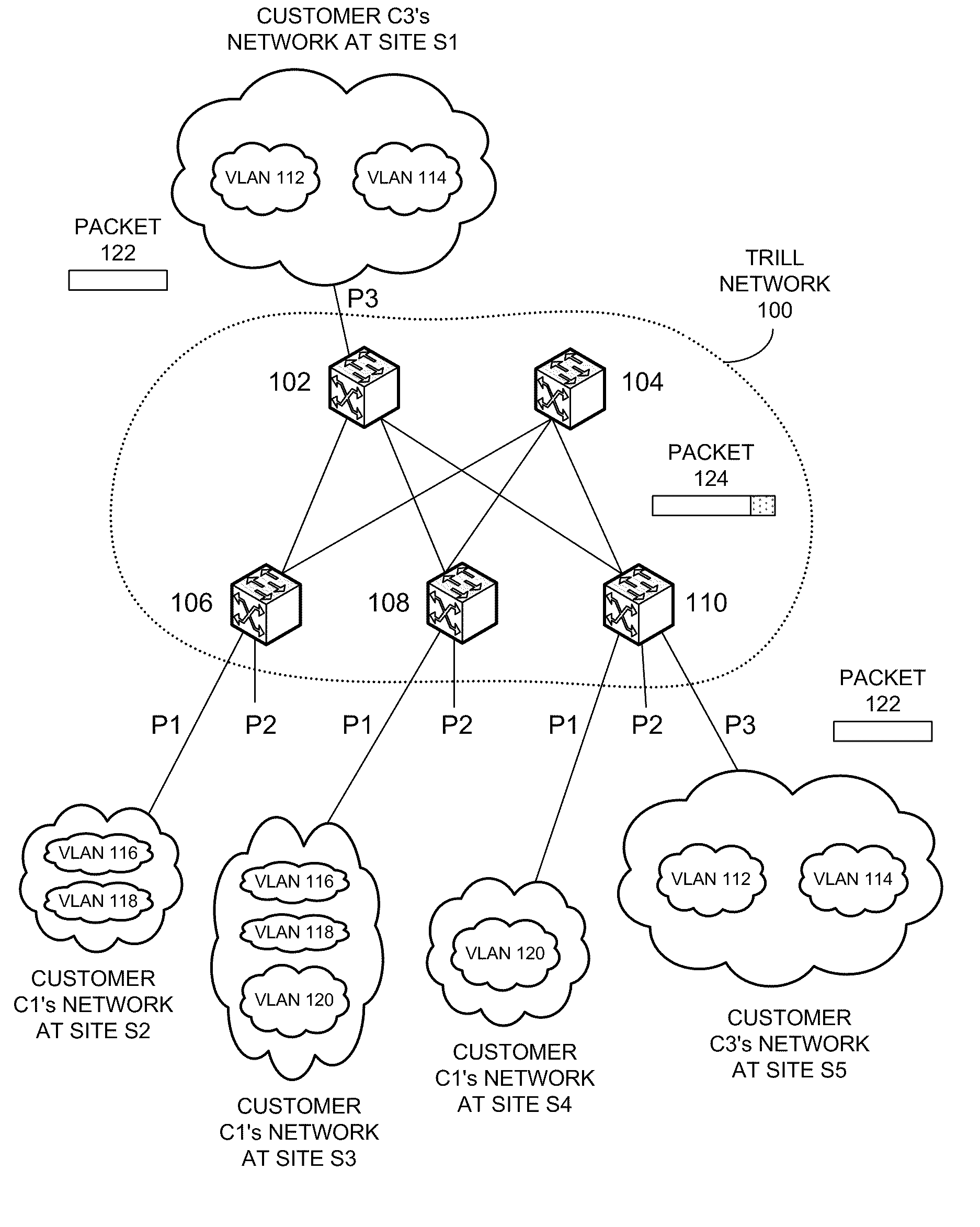
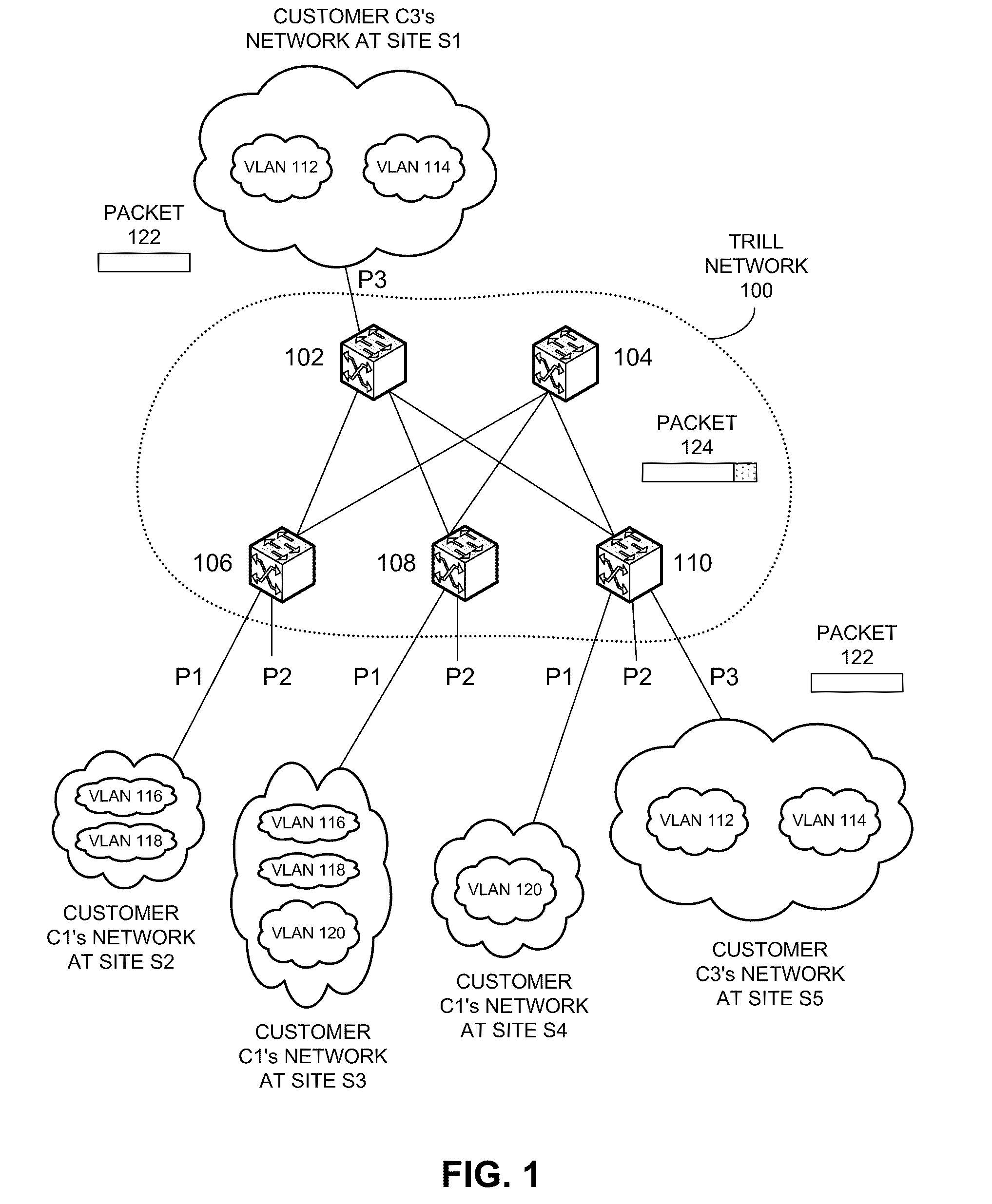
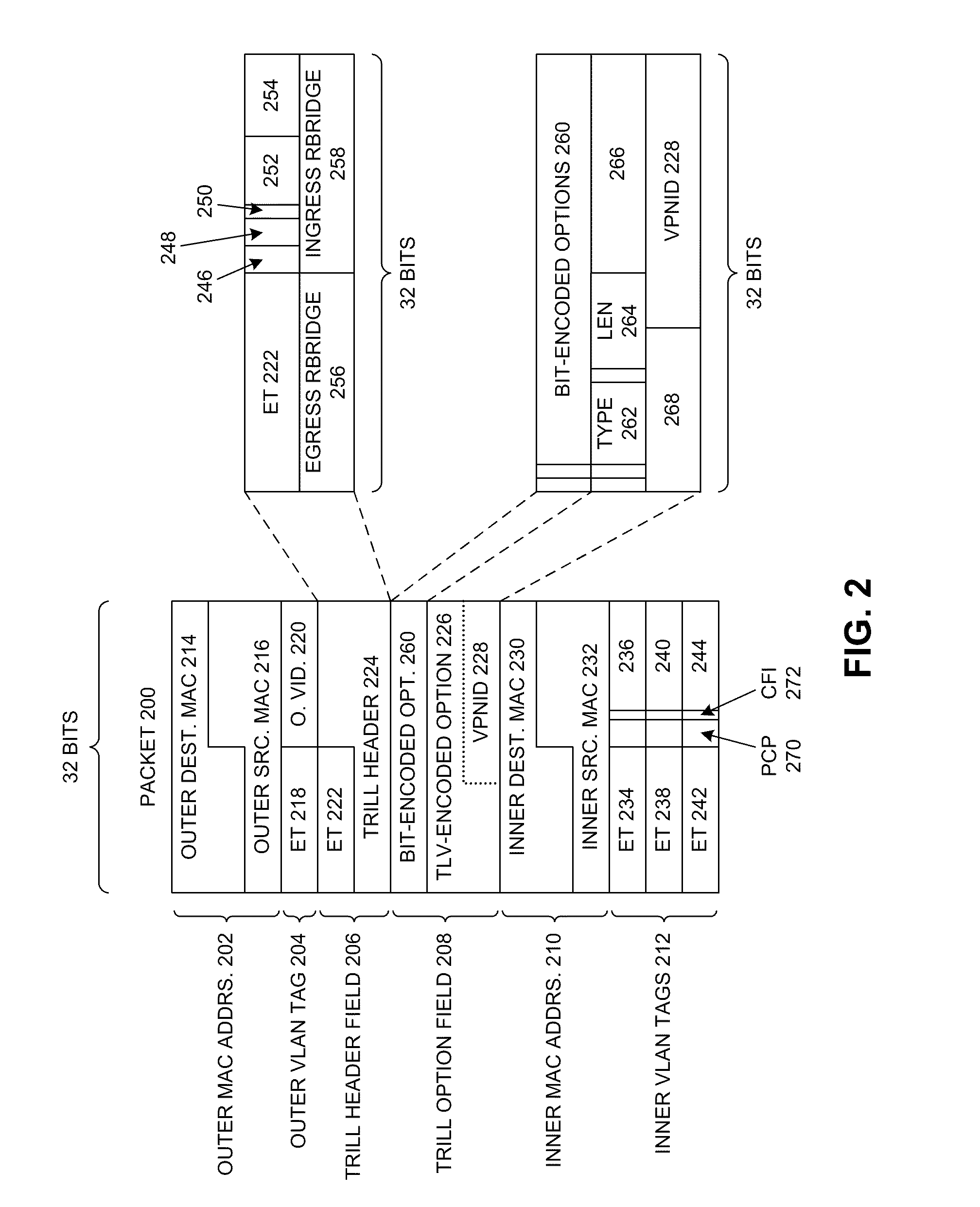
Supporting multiple multicast trees in trill networks
Systems and techniques for supporting multiple multicast trees are described. Some embodiments provide a system that determines an internal multicast group identifier based on a source address, a multicast address, and a multicast tree identifier field associated with a multicast packet. The system can then forward the multicast packet based on the internal multicast group identifier. Specifically, the system can determine a first set of bits based on the source address and the multicast address of the multicast packet. The system can determine a second set of bits based on the multicast tree identifier field of the multicast packet. Next, the system can combine the first set of bits and the second set of bits to obtain the internal multicast group identifier. In some embodiments, the scope of an internal virtual network identifier does not extend beyond a switch or a forwarding module within a switch.
Owner:AVAGO TECH INT SALES PTE LTD
Method of determining the topology of a network of objects
InactiveUS6411997B1Reduce complexityImprove accuracyMultiple digital computer combinationsData switching networksTraffic countData source
A method of determining a connection between a data emitting device and a network device which may carry the data, wherein the network device is comprised of a store for a data source address of a last frame transmitted to the network device and an input traffic count comprising (a) periodically reading the data source address, (b) periodically reading the input traffic count, (c) determining whether the data source address has always stayed the same, (d) in the event the data source address has always stayed the same, determine whether the traffic count has exceeded a predetermined threshold, (e) in the event the result of step (d) is true, indicate that the data source address identifies with acceptable probability a data emitting device directly connected to the network device.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
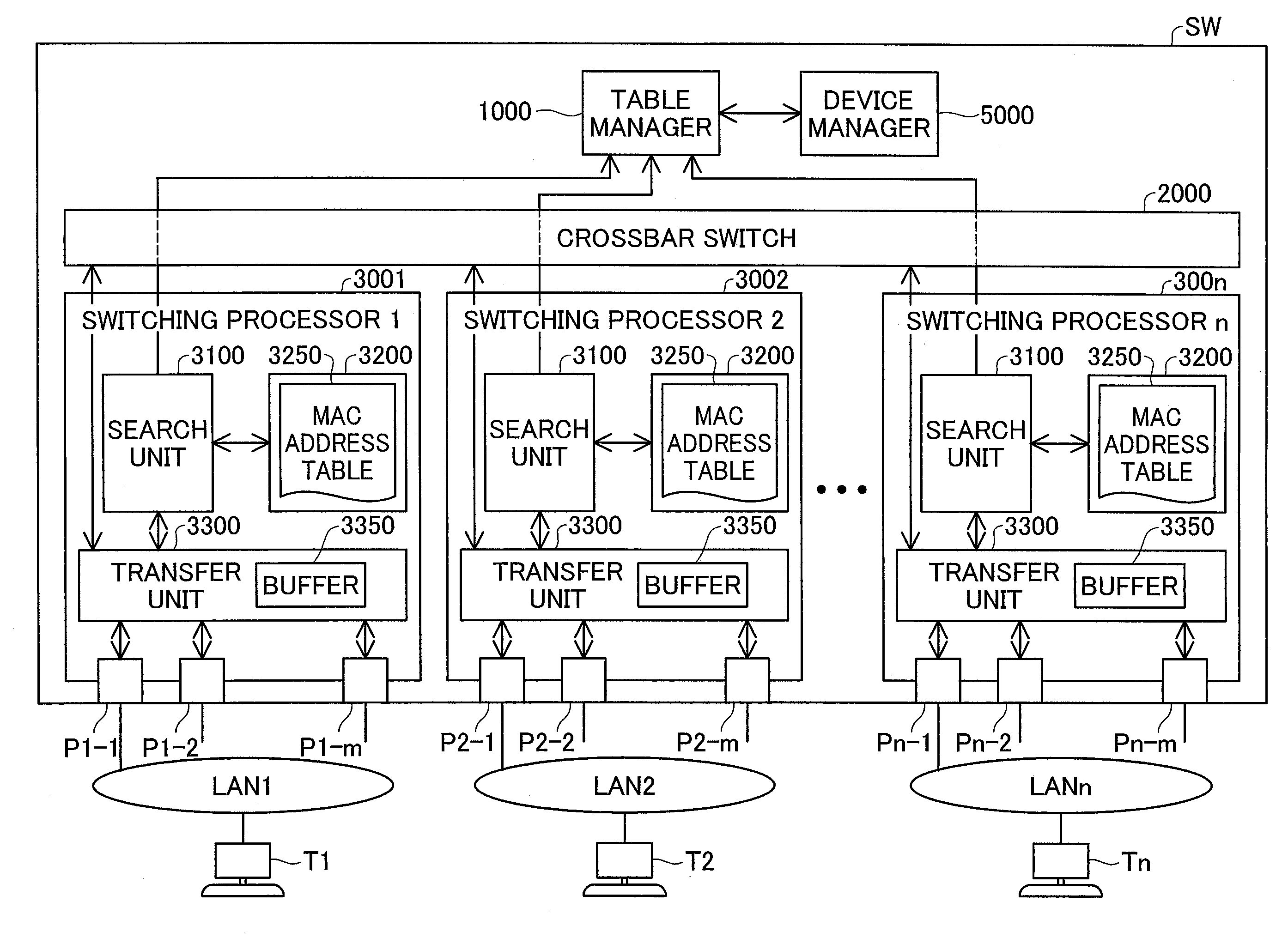
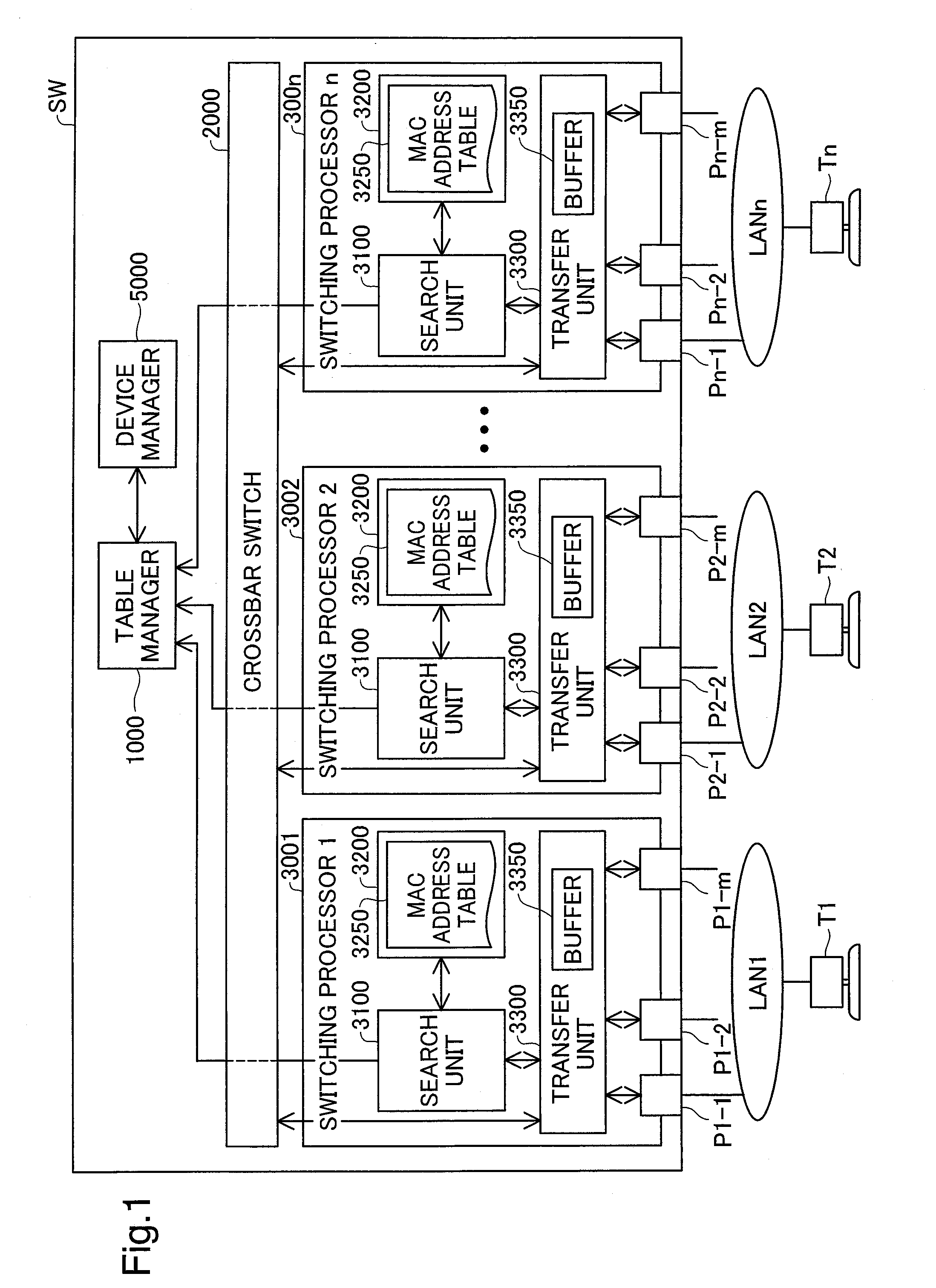
Network switching device and control method of network switching device
InactiveUS20080052487A1Effectively be standardizedReduce processing loadMemory adressing/allocation/relocationData switching by path configurationNetwork switchComputer engineering
A network switching device includes multiple ports, multiple switching processors, and a table manager. The switching processors respectively have an address table, a output port specification module, an update requirement determination module, and a table update module. The output port specification module refers to a destination address in received data and the address table and specifies a output port for sending the data among the multiple ports. The update requirement determination module determines requirement for update of the address table with regard to a source address in the data. The table manager has an update detail acquisition module and an update request module. Upon determination of the requirement for update of the address table, the update detail acquisition module obtains an update detail of the address table from one of the switching processors. The update request module sends an update request to the switching processors, based on the update detail.
Owner:ALAXALA NETWORKS
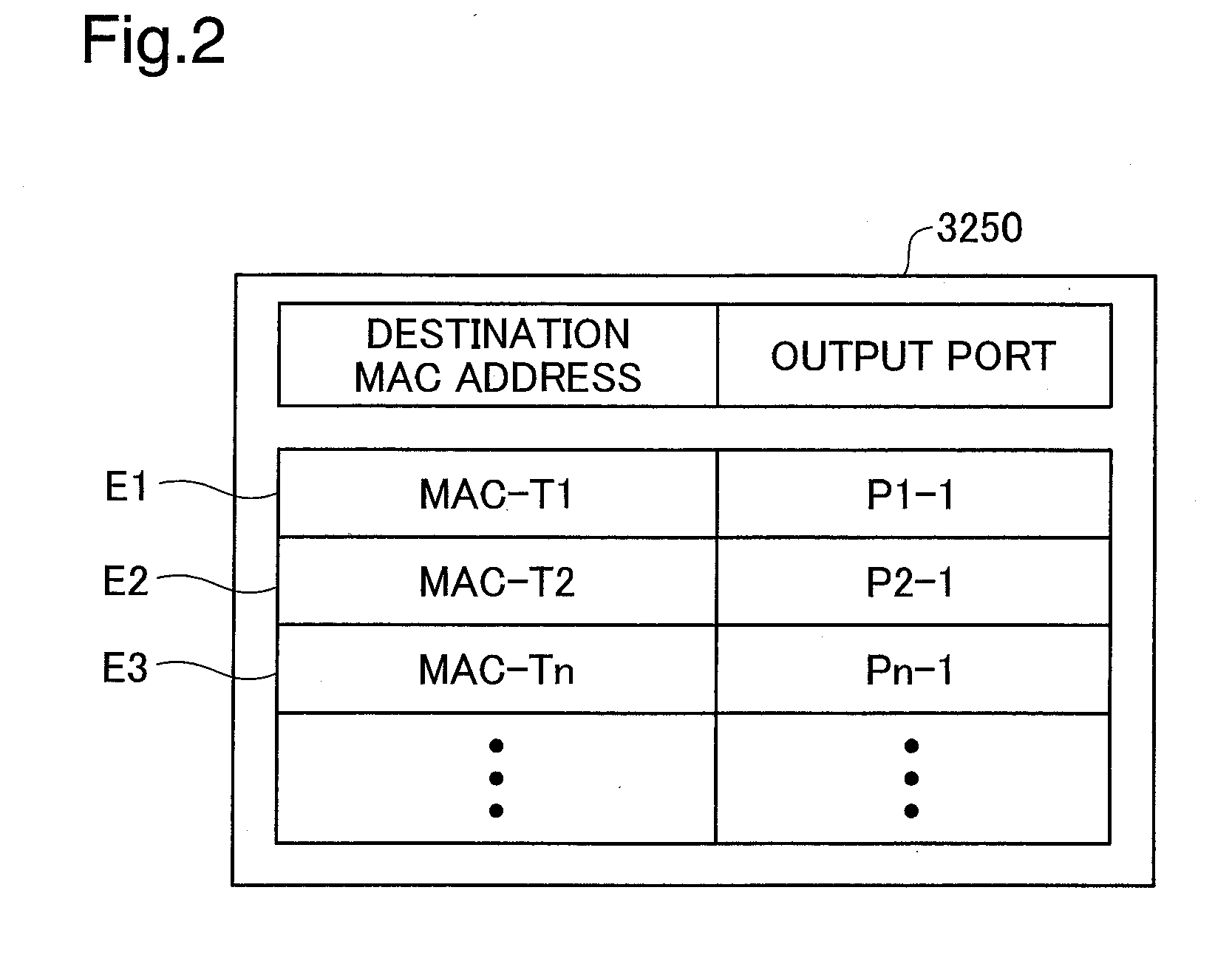
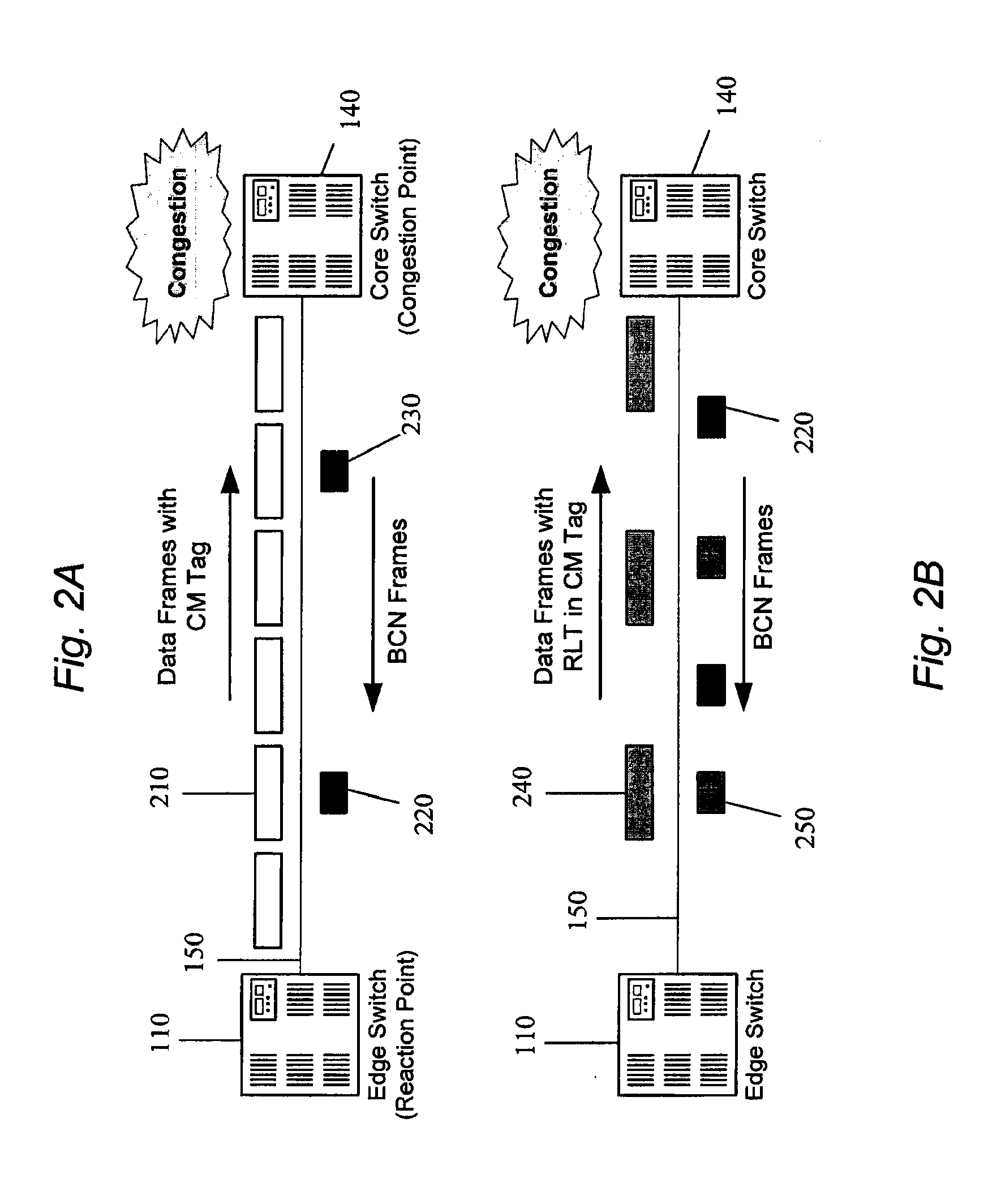
Backward congestion notification
In one embodiment, an apparatus comprises a network interface system having at least one input port configured for receiving frames and a logic system comprising at least one logic device. The logic system may be configured to perform the following functions: determining a source address and a destination address of a frame received at an ingress port; calculating a flow hash based at least upon the source address and the destination address; forming a congestion management (“CM”) tag that includes the flow hash; inserting the CM tag in the frame; and forwarding the frame to the destination address.
Owner:CISCO TECH INC
Method and apparatus for order independent processing of virtual private network protocols
InactiveUS20020129271A1Multiple digital computer combinationsProgram controlDiscriminatorProtocol processing
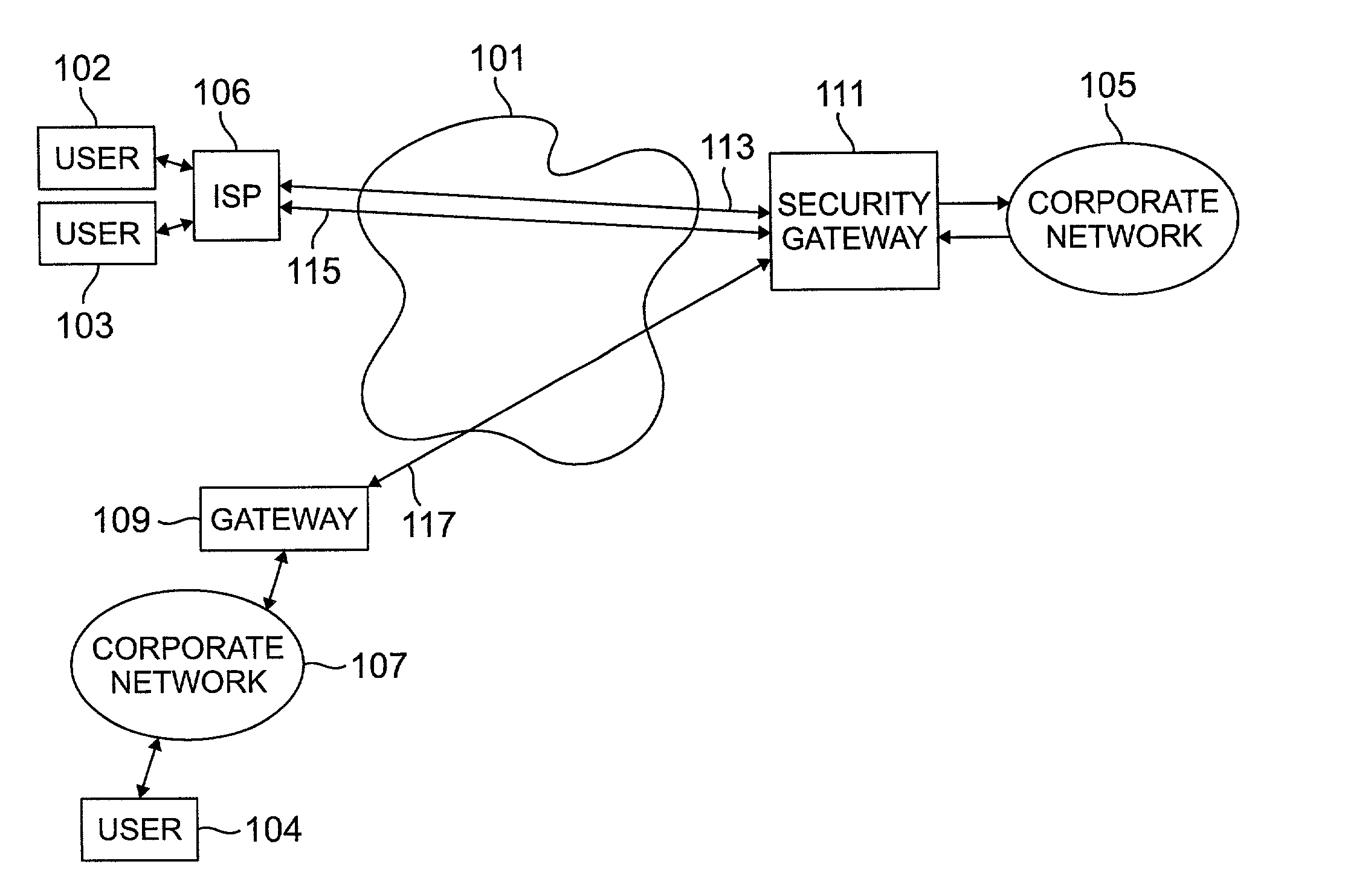
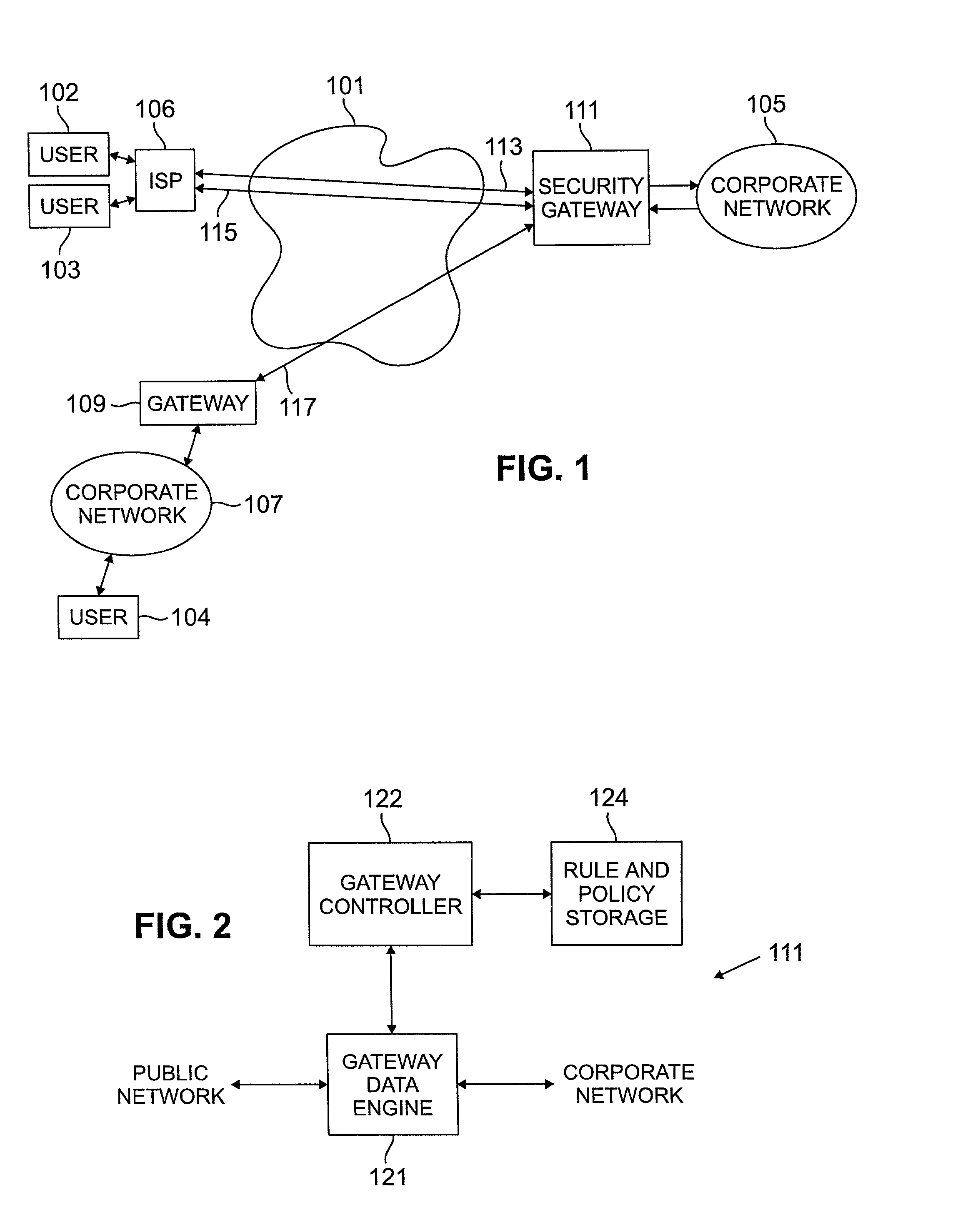
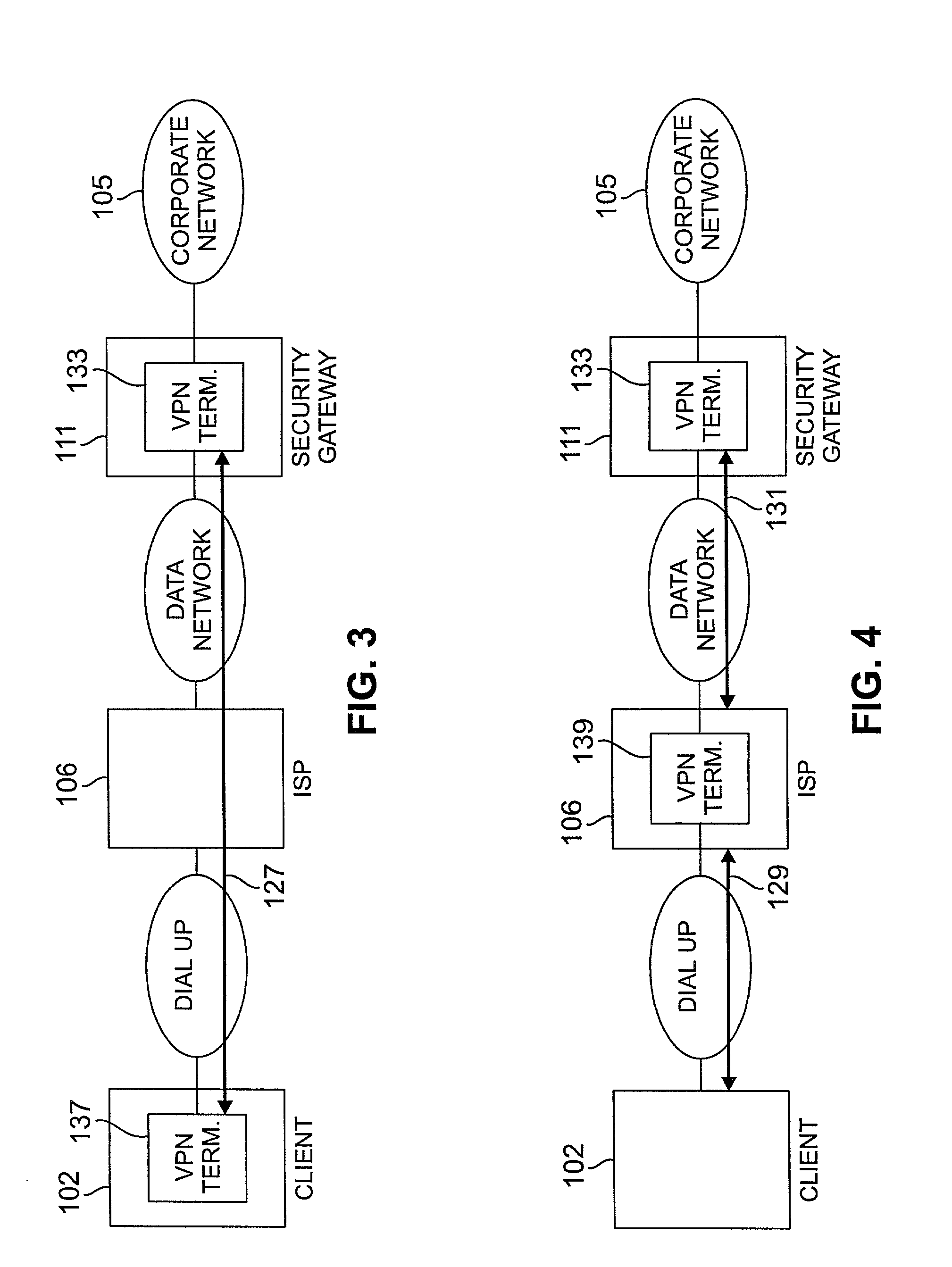
Methods and arrangements for virtual private network (VPN) data packets are disclosed. VPN packets include a payload having Internet Protocol (IP) addresses which guide the packet through a network to a security gateway. The payload may be encrypted and / or compressed and may include internal addresses to denote the real source and destination for a data portion of the payload. As initial control packets are received they are authenticated and rules and procedures are identified for proper treatment of VPN data packets bearing the same source IP address. The rules and procedures are stored in a gateway data engine having a plurality of protocol processing modules. VPN data packets are received by a protocol discriminator which reads the stored rules and procedures identified for the source IP address of the received packet. The discriminator passes the received packet to a first protocol module as identified in the stored rules and procedures. After the first module completes processing, the packet is passed back to the protocol discriminator which determines whether further protocol processing is required. When further protocol processing is required, the packet is passed to another protocol module for processing in accordance with another protocol. At the completion of processing, the second protocol module returns the packet to the protocol discriminator.
Owner:LUCENT TECH INC
Fast stack save and restore system and method
InactiveUS6449709B1Memory adressing/allocation/relocationDigital computer detailsData accessParallel computing
A processor includes a stack that operates as a circular stack and appears to the address space in the memory of the processor as a single point address location. The stack supports read and write data access functions in addition to CALL (push) and RETURN (pop) programming operations. The processor may be programmed to save the stack in a typical manner with one instruction atomically transferring each element in the stack directly from the stack to a save storage. To restore the stack, the processor may be programmed to individually restore each element. The processor supports a special MOV instruction that transfers a plurality of bytes in a single operation. The special MOV instruction has one argument that identifies the beginning transfer source address, another argument defines the byte count indicating the number of bytes to be transferred, and a beginning transfer destination address. The processor may be programmed to perform a stack save operation with only a single instruction that moves the contents of the stack to the save storage. To further reduce context switching time and reduce the stack save and restore operation to a minimum number of instructions while maintaining the proper entry relationship for both stack read and write operations, the processor includes a "stack read forward" option to the special MOV instruction. The option to the special MOV instruction operates to read data in a forward direction even when no valid data is stored in the locations. The read operation begins at the start address specified by an argument to the MOV instruction, reads forward, and wraps around in a binary fashion back to the start address.
Owner:PMC-SIERRA
System and method for routing network messages
InactiveUS20060182103A1Facilitates duplex communicationRelieving of riskData switching by path configurationTraffic capacityVirtual address space
A network routing system is provided that may establish a communication session between a local device and a remote destination. To establish a communication session, the local device generates a message directed to the remote destination. A traffic processor intercepts the message and redirects the message to a predefined network server in a secure fashion. The network server receives the message, and extracts the address for the remote destination, as well as message data. The network server has a pool of available virtual address that are registered with the network server. The network server associates a virtual source address with the real address of the local device or traffic processor, and opens a communication session. The virtual address is set as the source address for the message, and the message is sent to the remote destination. Since the source address is virtual, the real address for the local device or traffic processor are not sent to the remote location. If the remote location sends a return message, the return message will be directed to the virtual address. The network server receives the return message, and using the virtual address information, redirects the message to the real address for the traffic processor in a secure fashion. The traffic processor sets the address on the message to show it was sent from the remote destination, and forwards the message to the local device.
Owner:IBOSS
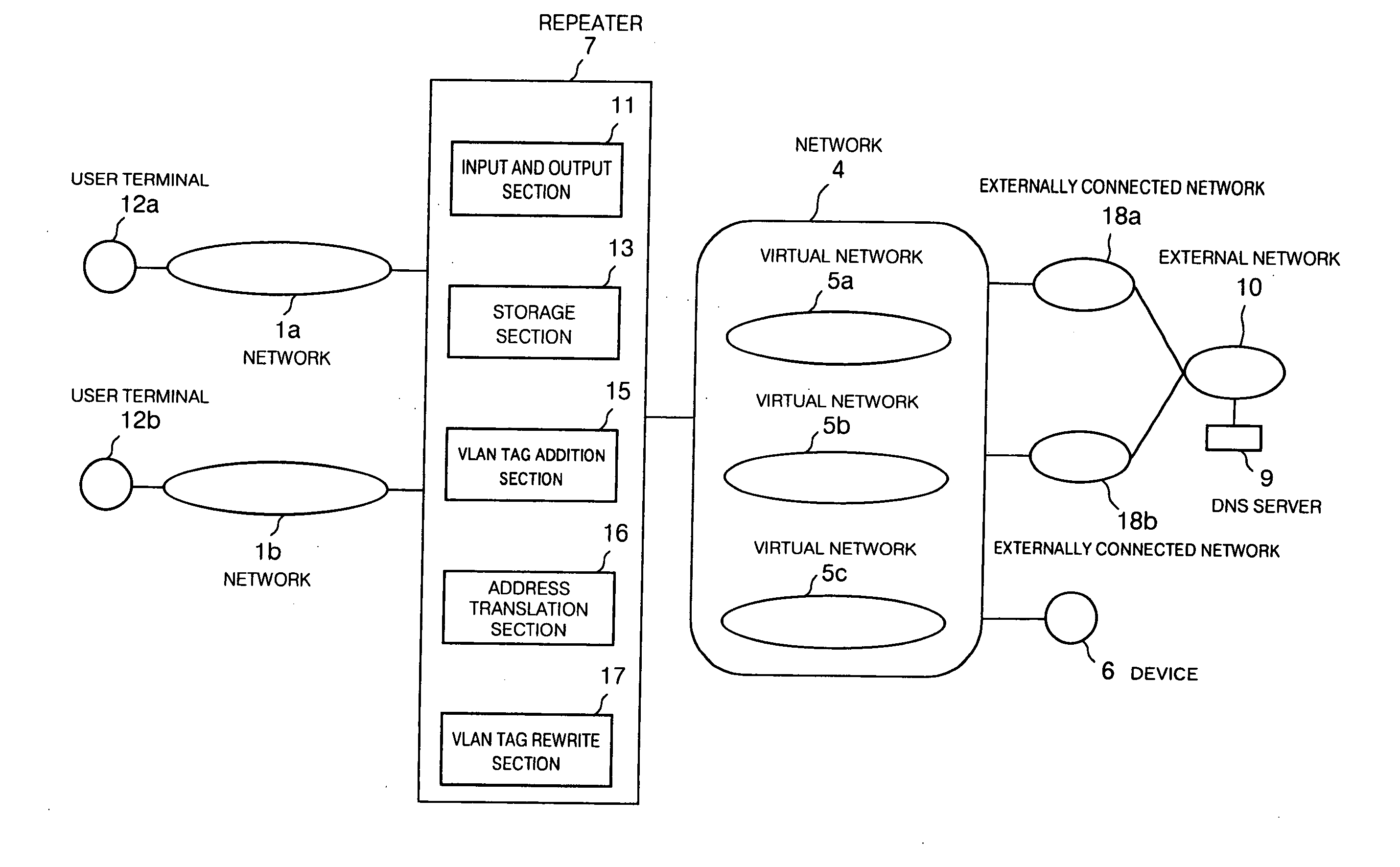
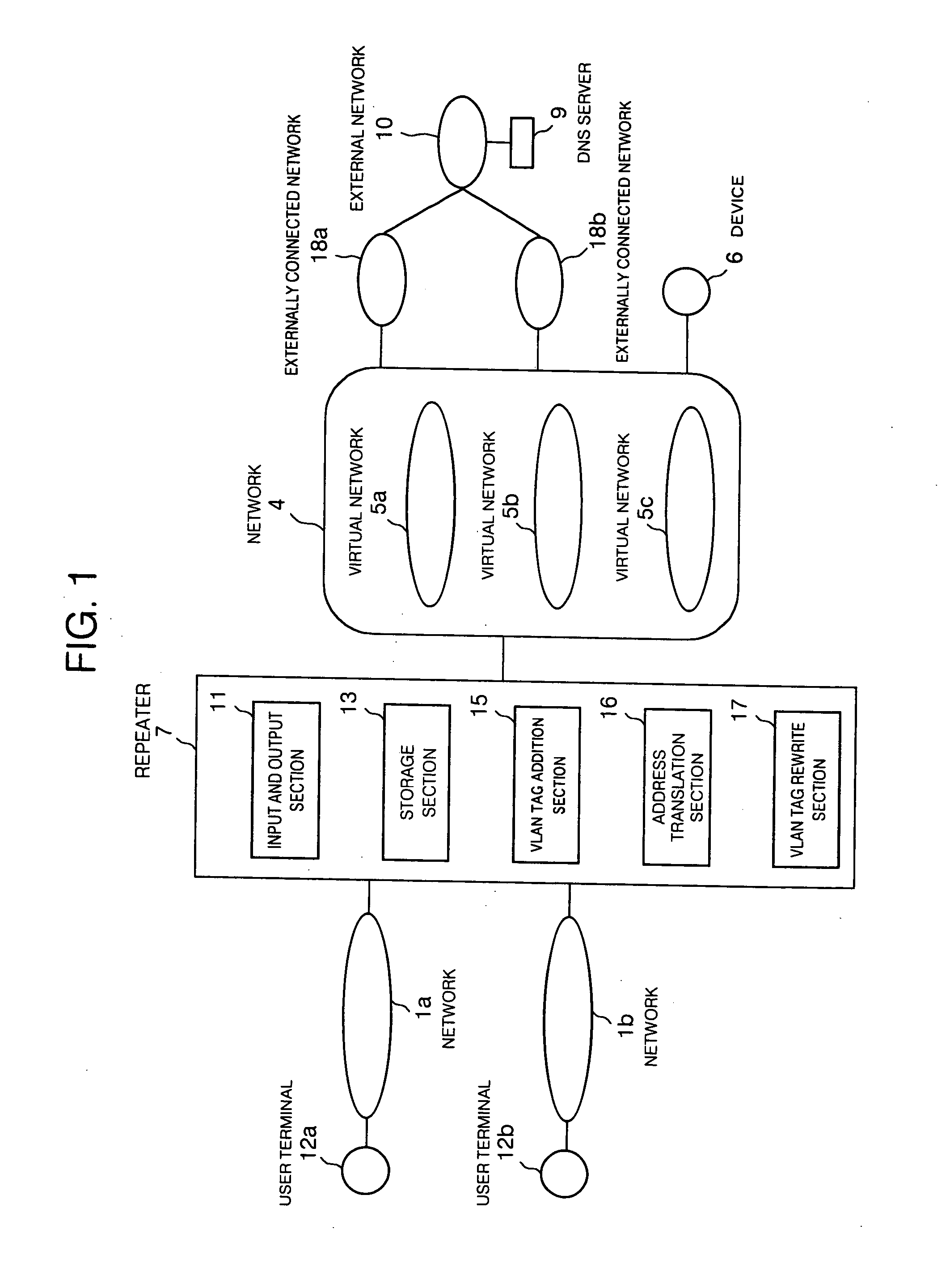
Network repeater apparatus, network repeater method and network repeater program
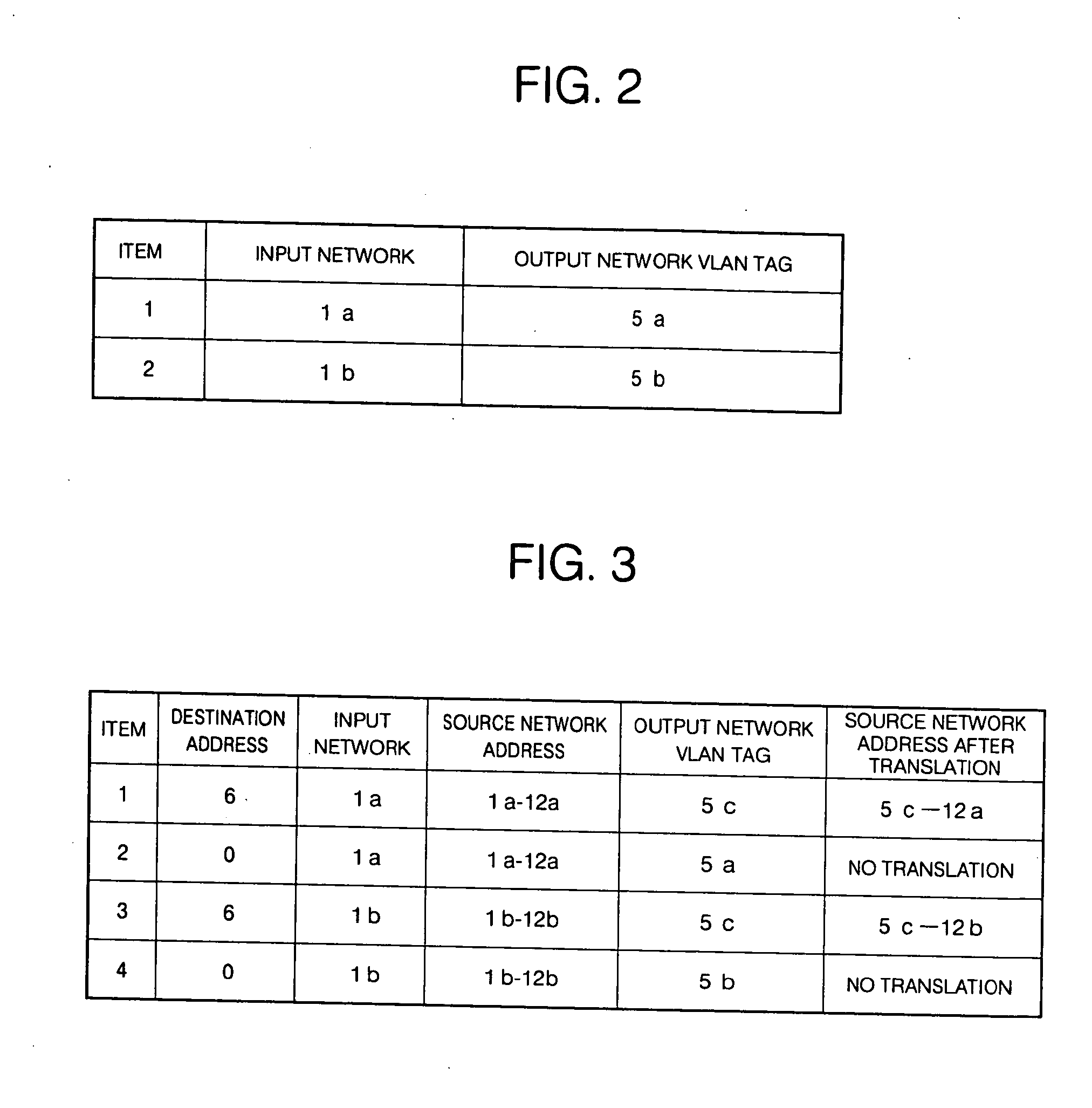
InactiveUS20050058132A1Generation of unnecessary and wastefulUnnecessary and wasteful trafficTime-division multiplexNetworks interconnectionRepeaterVirtual network
A network repeater apparatus connected to a plurality of networks is provided which includes a VLAN tag addition section (15) or a VLAN tag rewrite section (17) that performs prescribed VLAN tag processing with respect to a communication packet based on prescribed information of the communication packet when the communication packet is input from any one among a plurality of networks, an address translation section (16) that translates a source address of the communication packet based on the prescribed information, and an input and output section (11) that outputs to a prescribed virtual network a communication packet which has been subjected to at least either one of processing by the VLAN tag addition section (15) or the VLAN tag rewrite section (17) or address translation by the address translation part (16), whereby access can be made to a common device while ensuring security between the networks.
Owner:FUJITSU LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com