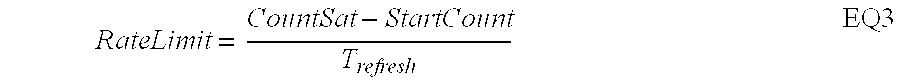Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
586 results about "Rate limiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networks, rate limiting is used to control the rate of traffic sent or received by a network interface controller and is used to prevent DoS attacks.
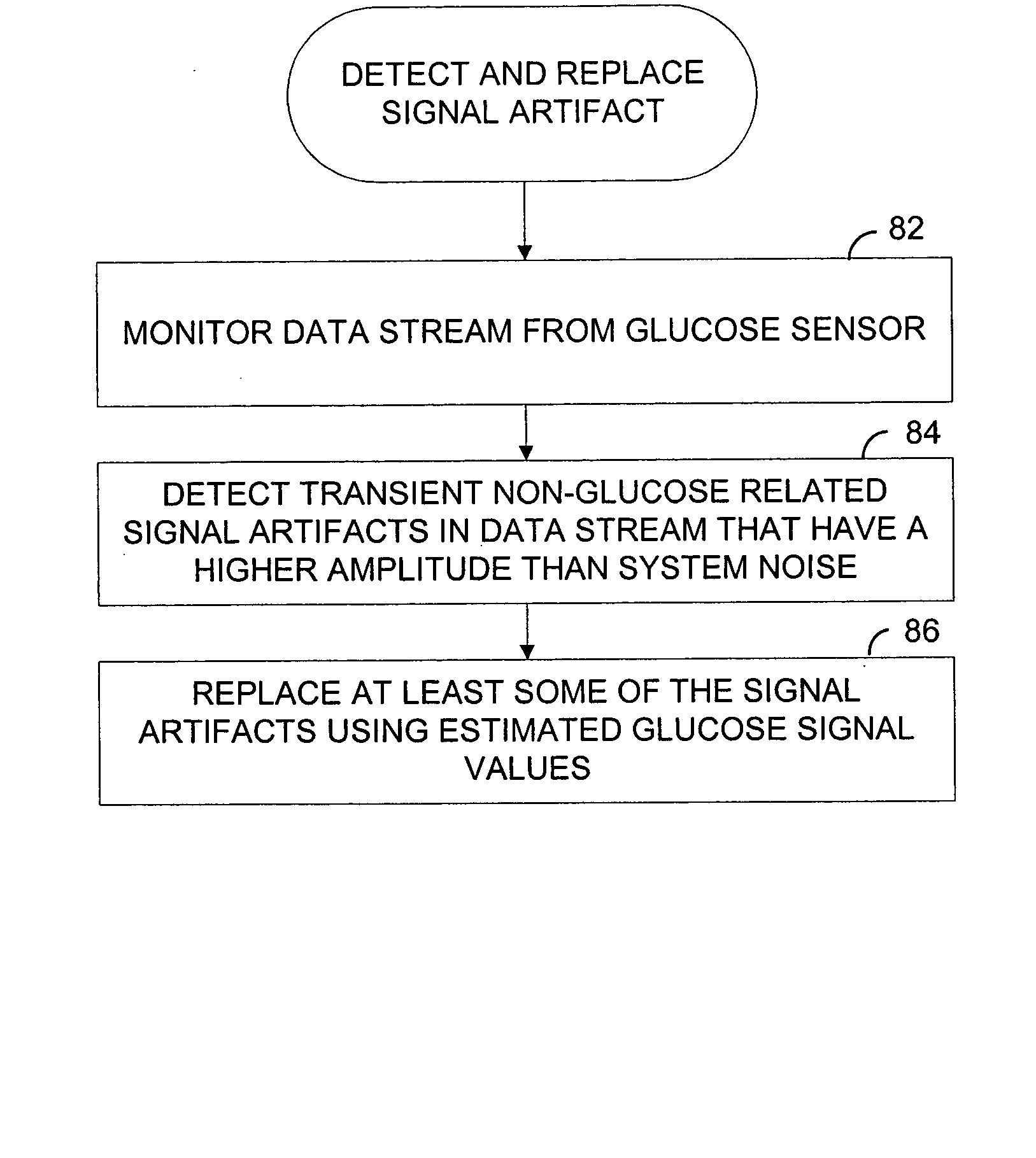
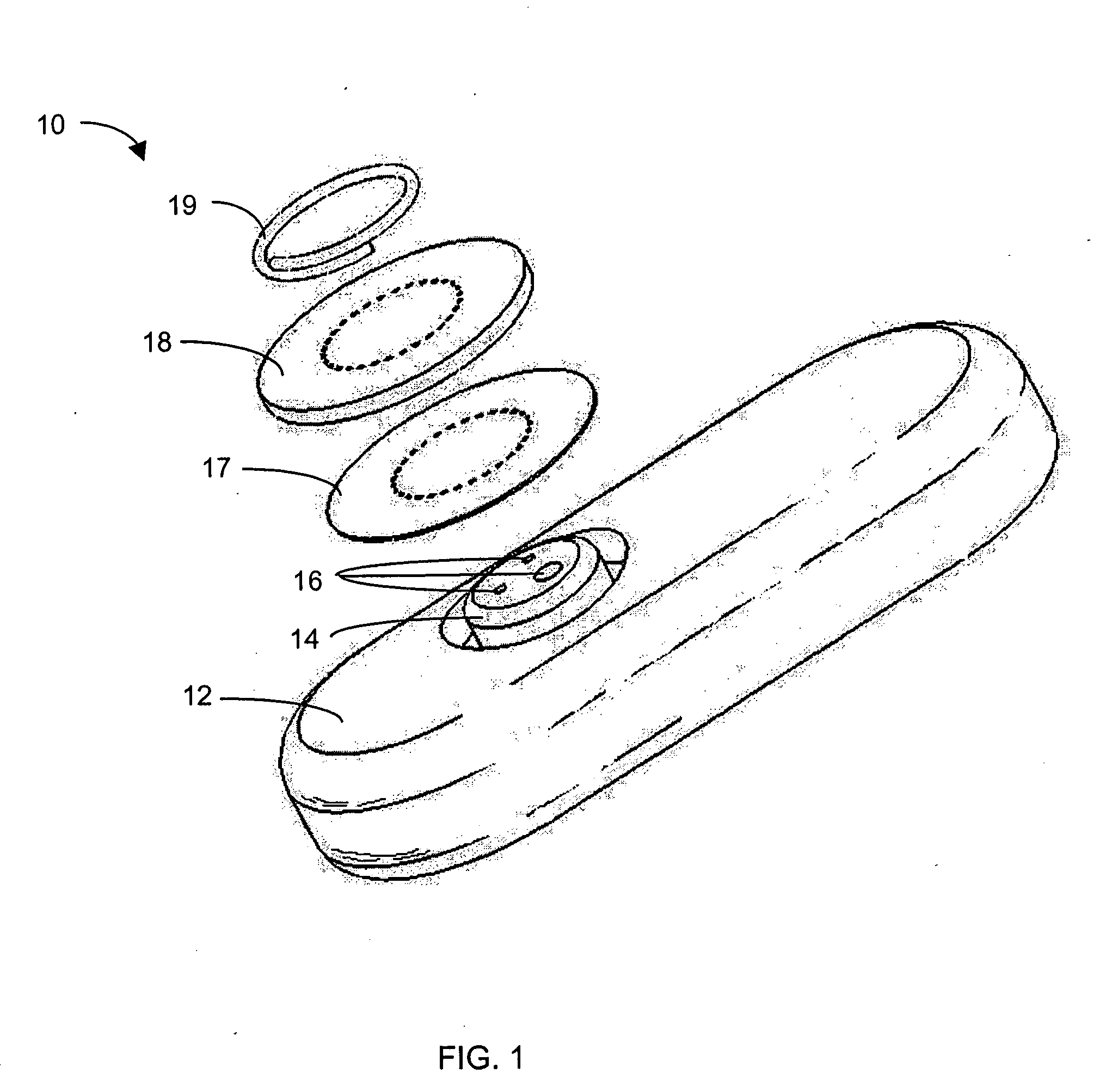
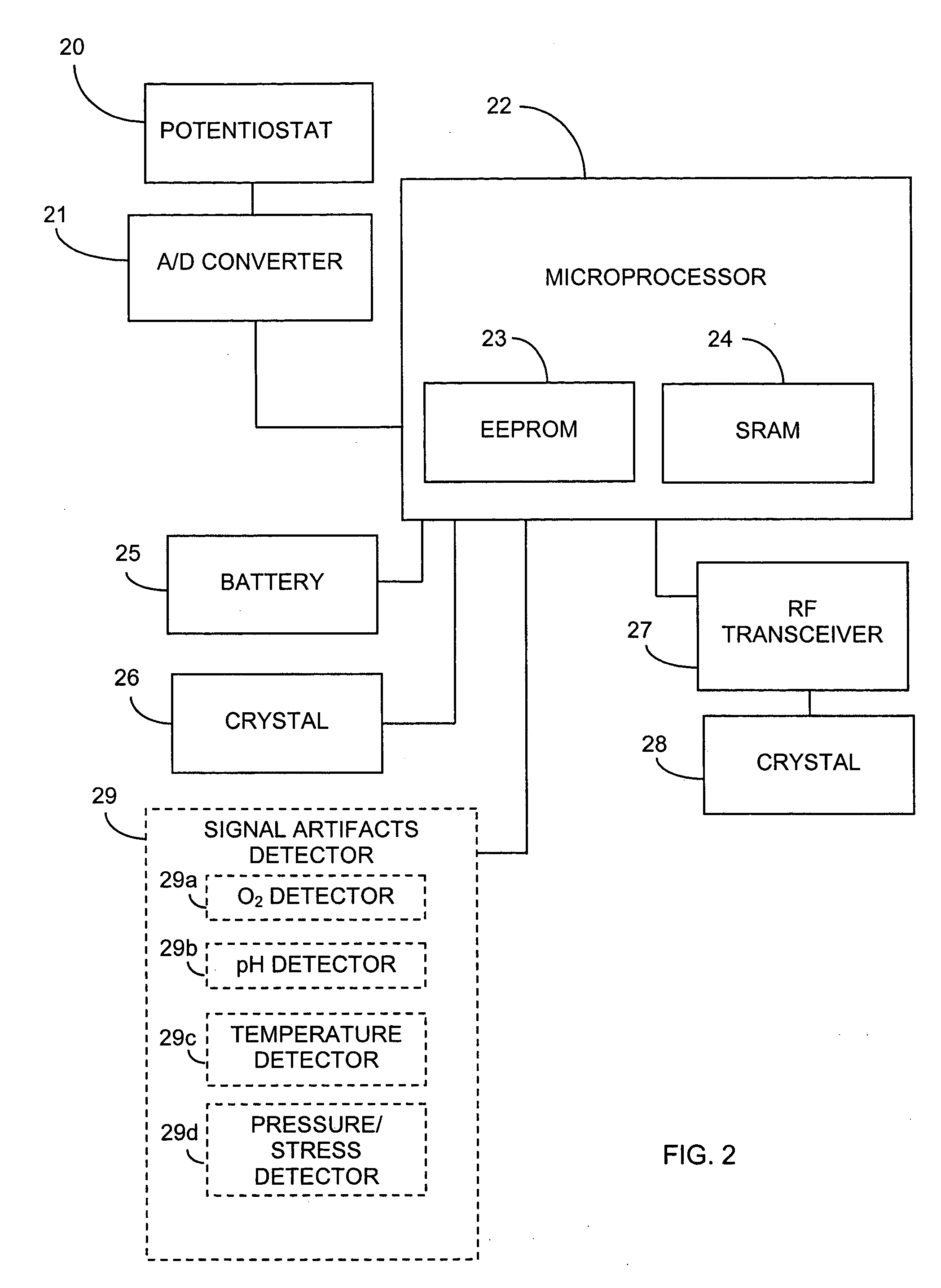
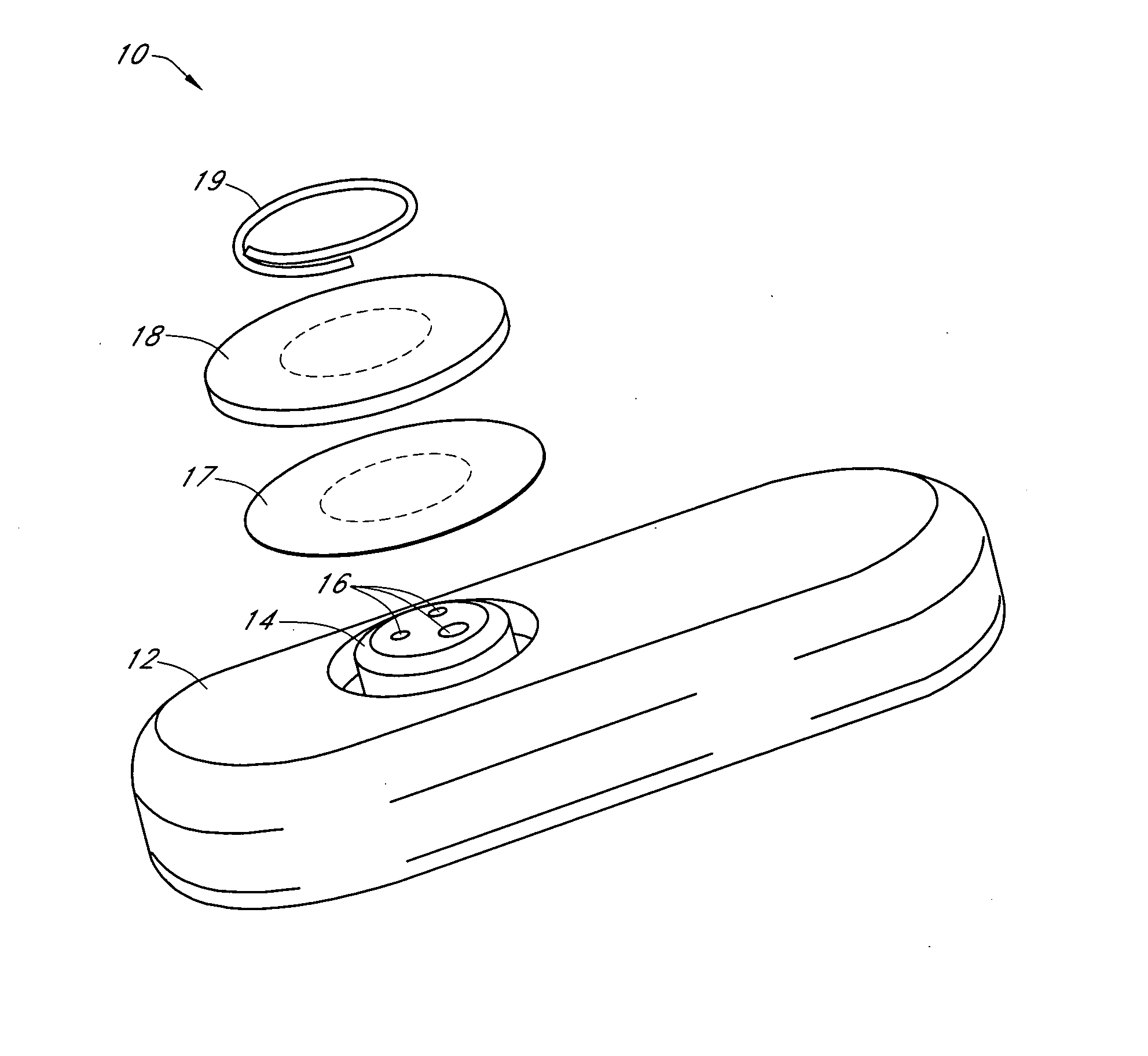
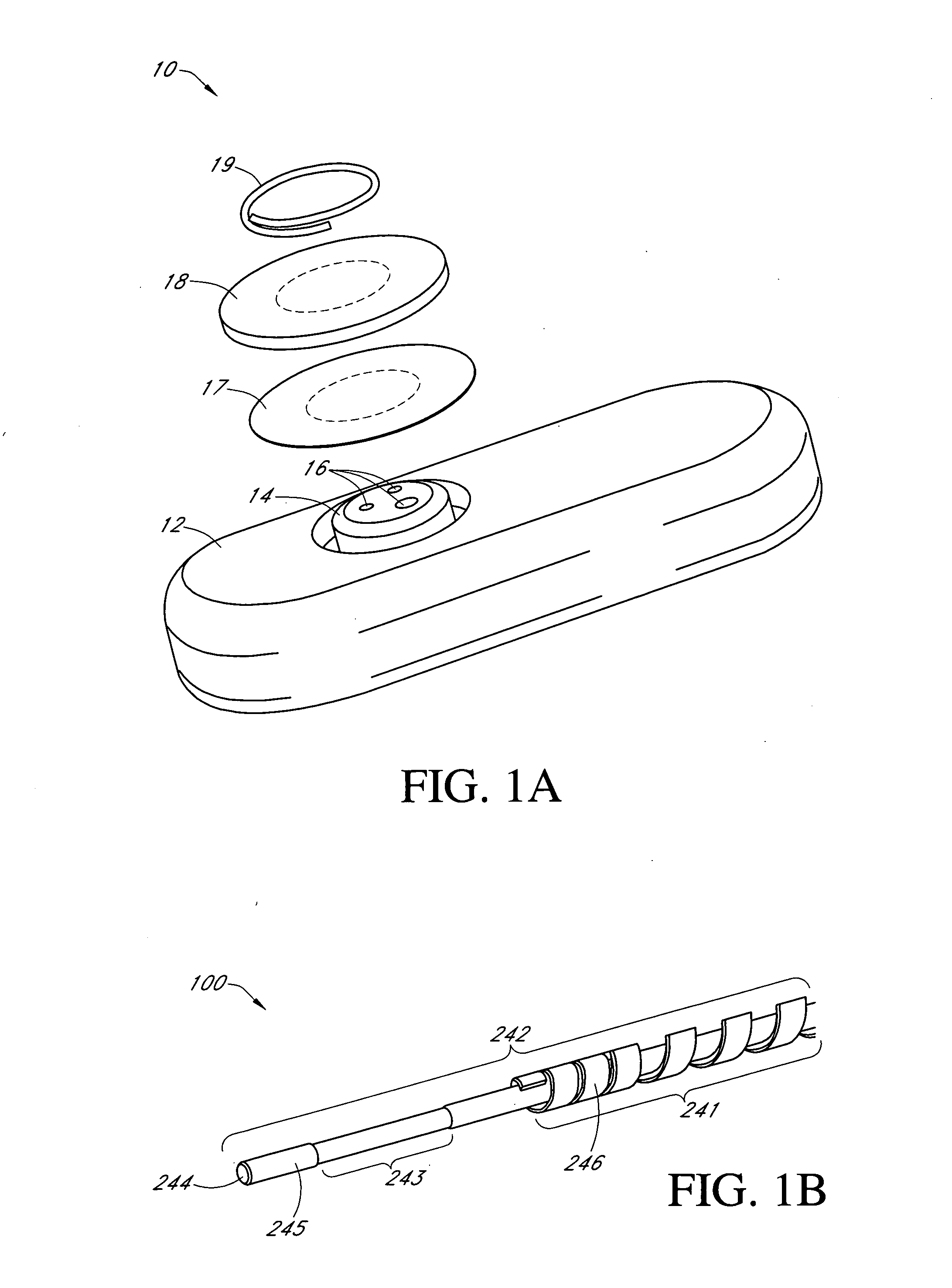
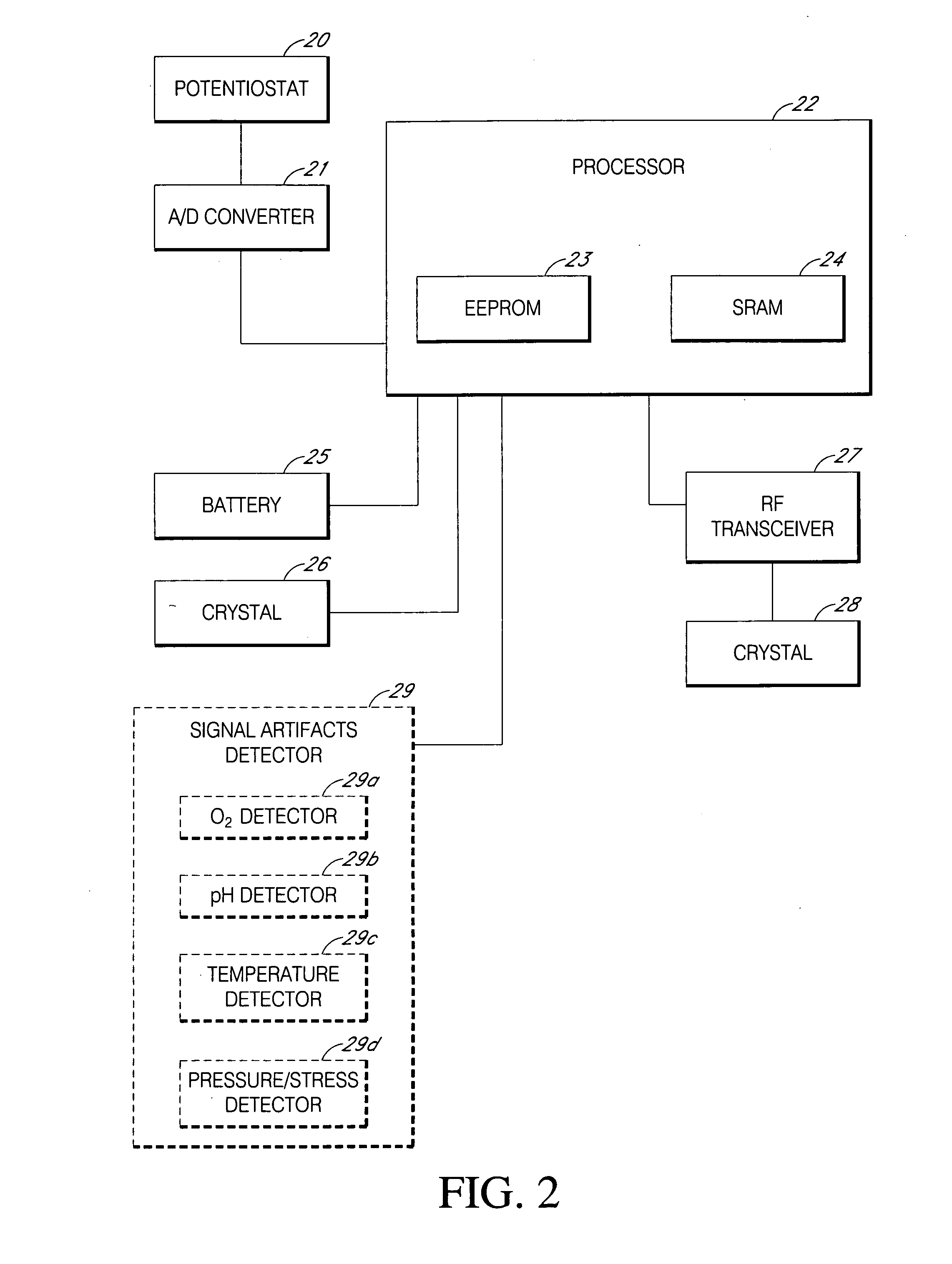
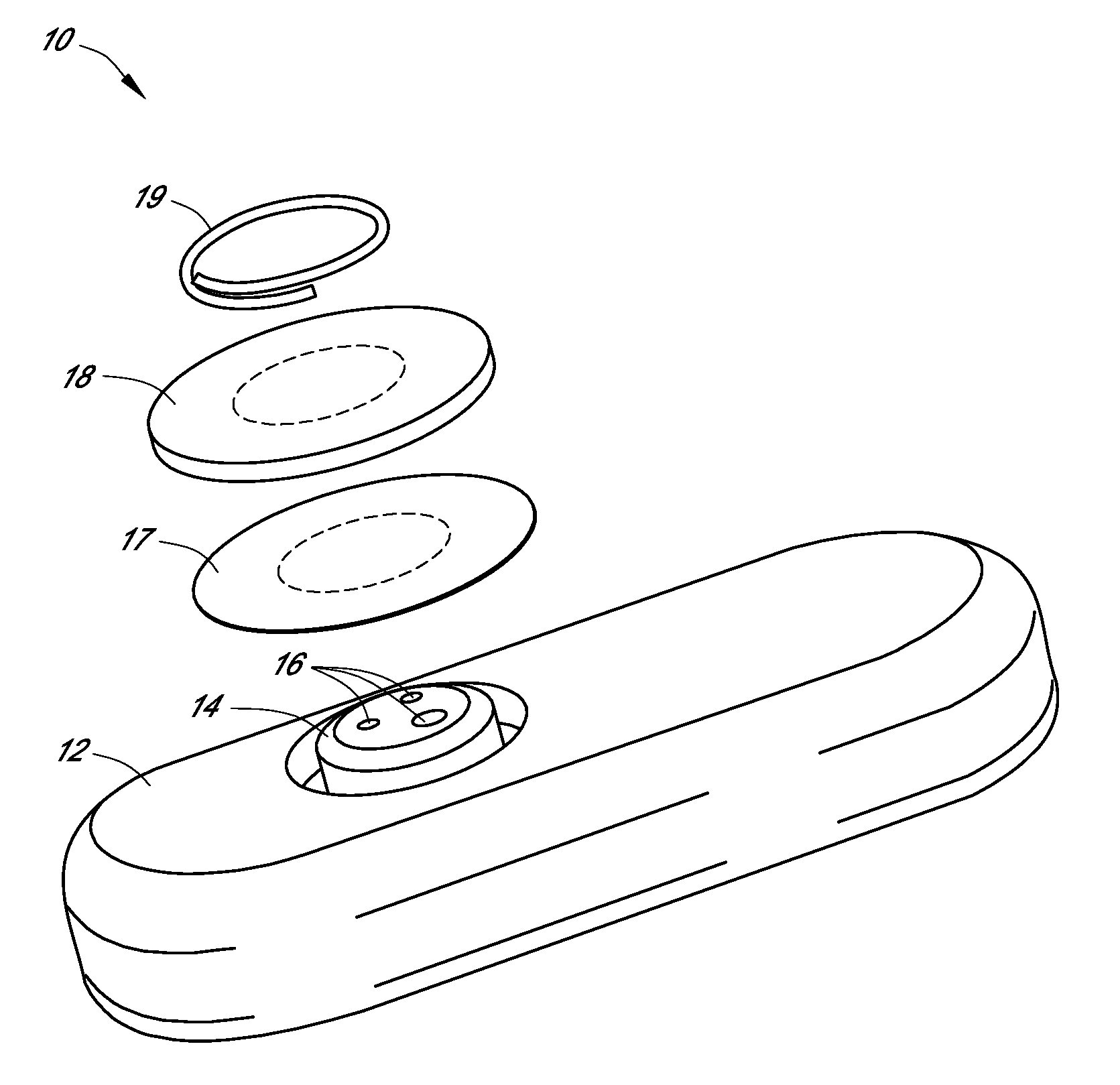
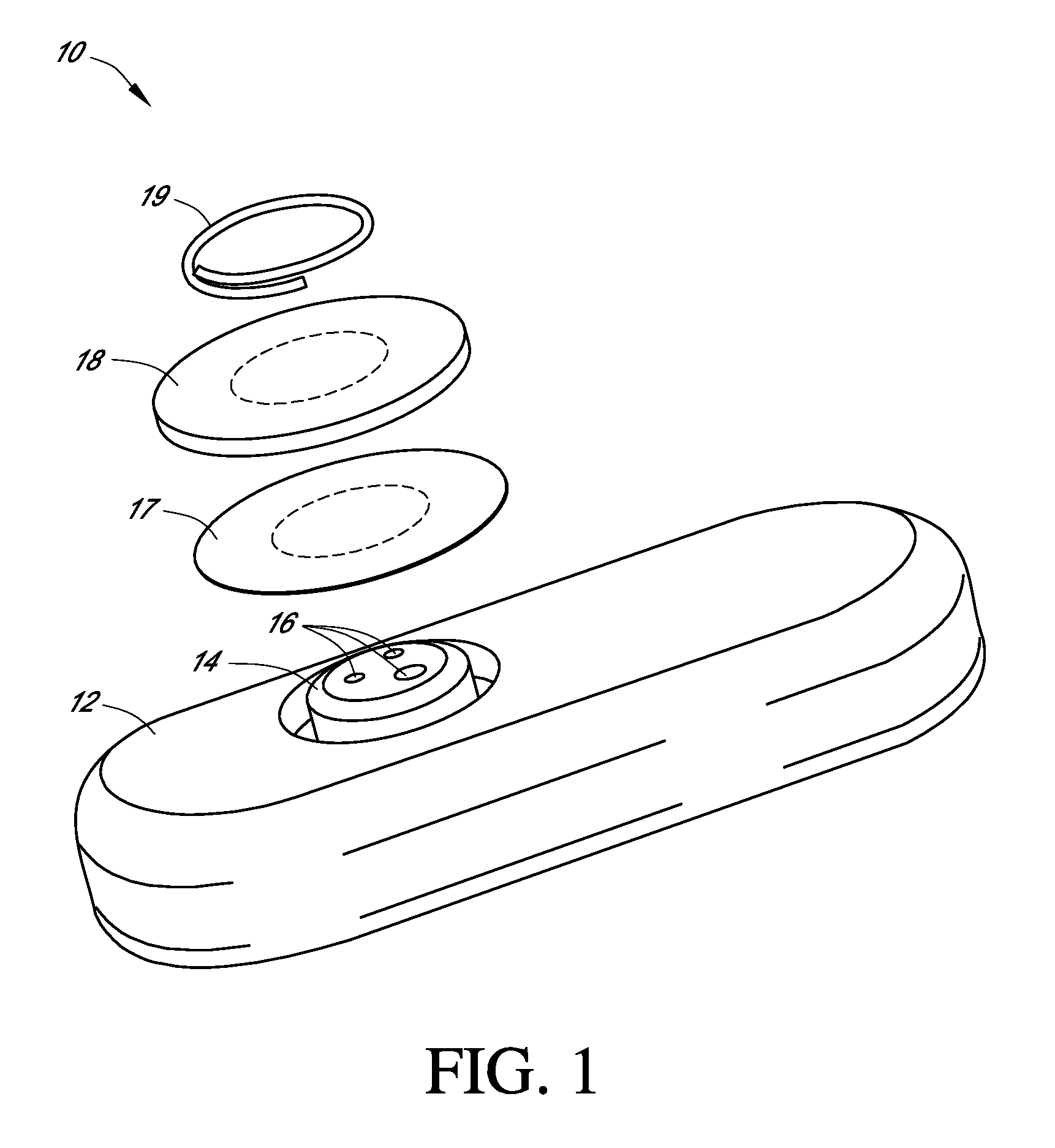
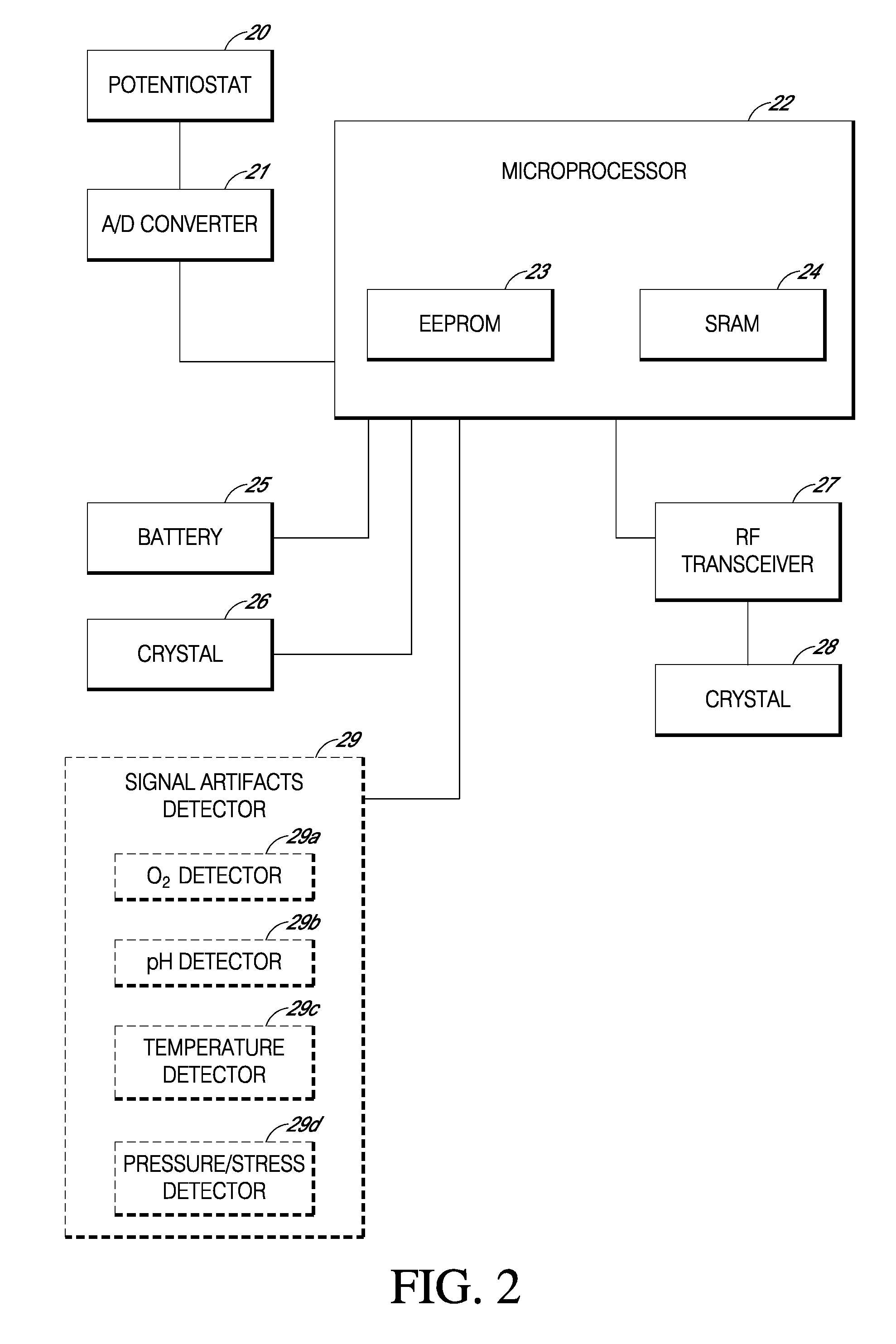
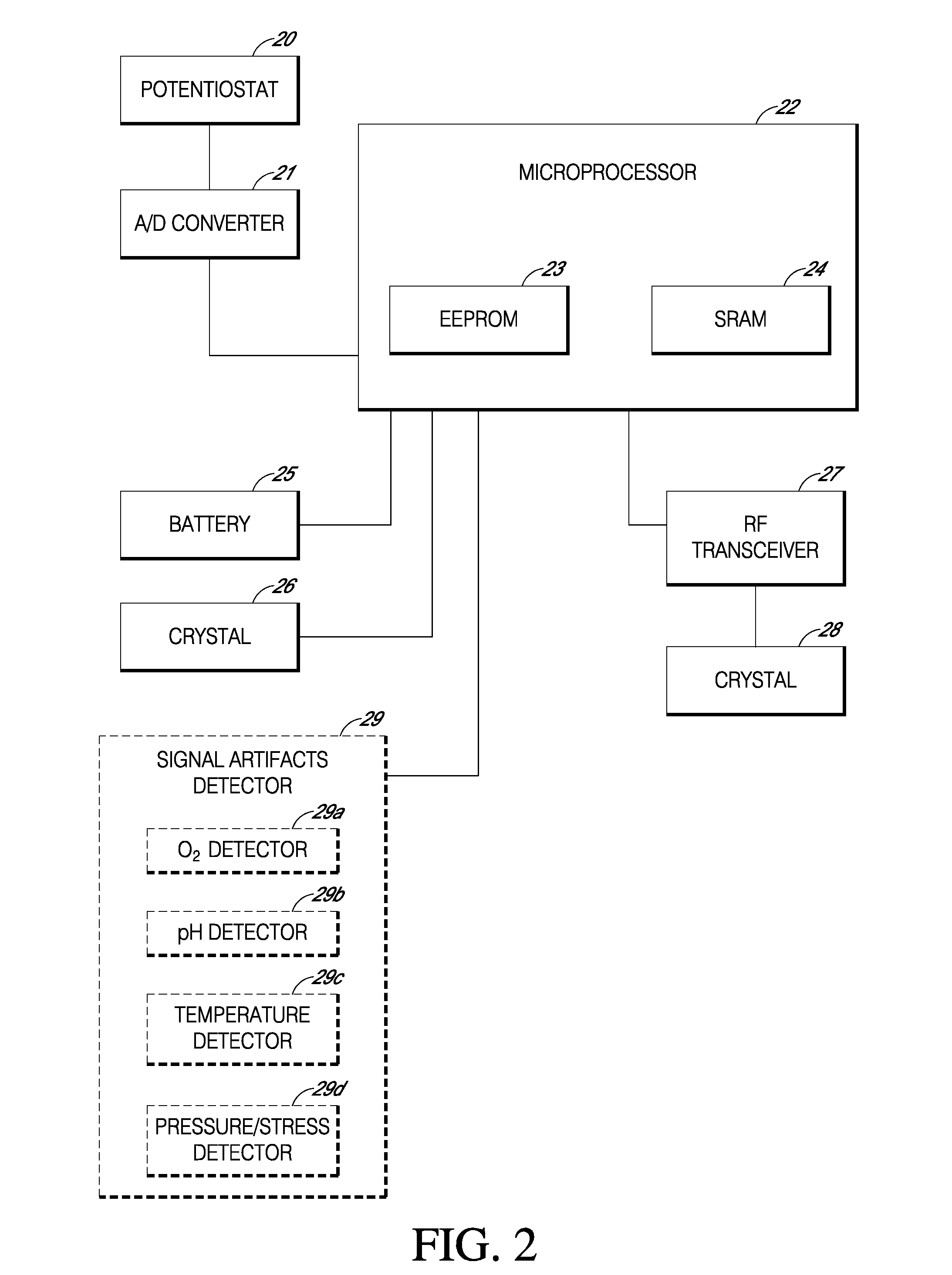
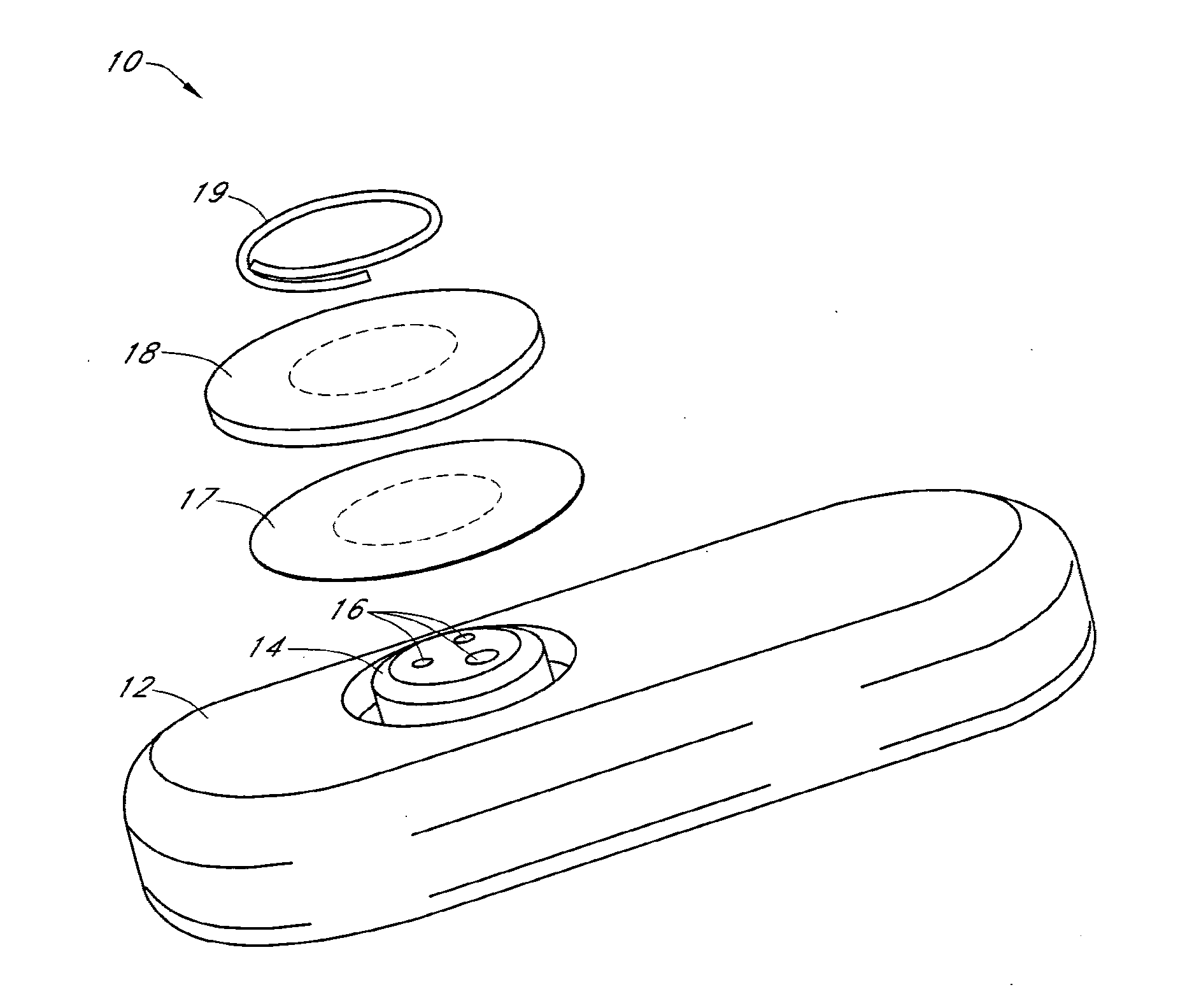
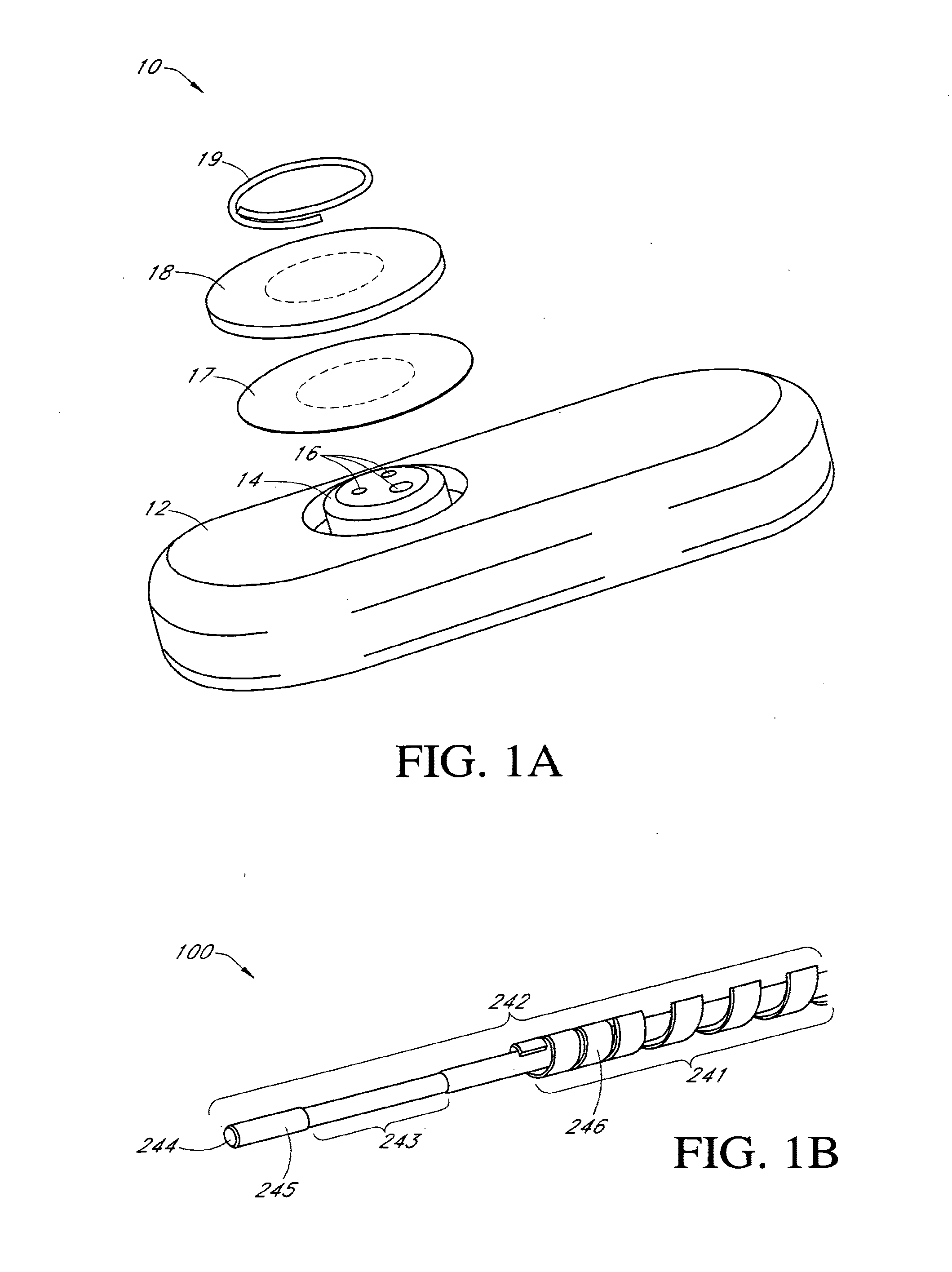
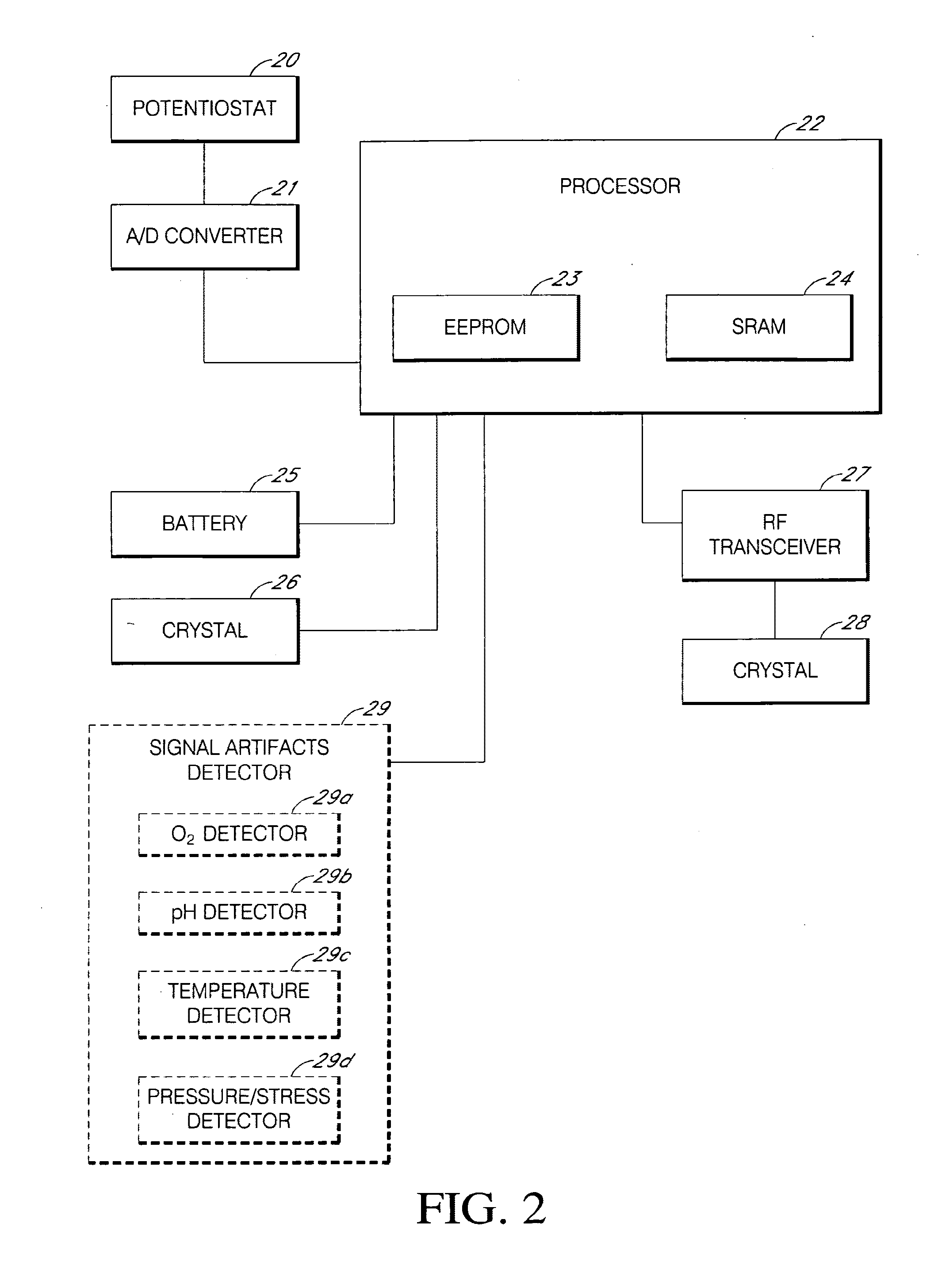
Systems and methods for replacing signal artifacts in a glucose sensor data stream
ActiveUS20050043598A1Accurate detectionAccurate replacementCatheterTemperature sensorsRate limitingData stream
Systems and methods for minimizing or eliminating transient non-glucose related signal noise due to non-glucose rate limiting phenomenon such as ischemia, pH changes, temperatures changes, and the like. The system monitors a data stream from a glucose sensor and detects signal artifacts that have higher amplitude than electronic or diffusion-related system noise. The system replaces some or the entire data stream continually or intermittently including signal estimation methods that particularly address transient signal artifacts. The system is also capable of detecting the severity of the signal artifacts and selectively applying one or more signal estimation algorithm factors responsive to the severity of the signal artifacts, which includes selectively applying distinct sets of parameters to a signal estimation algorithm or selectively applying distinct signal estimation algorithms.
Owner:DEXCOM
Systems and methods for replacing signal artifacts in a glucose sensor data stream
ActiveUS20070032706A1Accurate detectionAvoid adjustmentMedical automated diagnosisCatheterRate limitingData stream
Systems and methods for minimizing or eliminating transient non-glucose related signal noise due to non-glucose rate limiting phenomenon such as interfering species, ischemia, pH changes, temperatures changes, known or unknown sources of mechanical, electrical and / or biochemical noise, and the like. The system monitors a data stream from a glucose sensor and detects signal artifacts that have higher amplitude than electronic or diffusion-related system noise. The system processes some or the entire data stream continually or intermittently based at least in part on whether the signal artifact event has occurred.
Owner:DEXCOM
Systems and methods for replacing signal artifacts in a glucose sensor data stream
ActiveUS20090124877A1Accurately detect and replaceAvoid adjustmentCatheterTemperature sensorsRate limitingGlucose sensors
Systems and methods for minimizing or eliminating transient non-glucose related signal noise due to non-glucose rate limiting phenomenon such as ischemia, pH changes, temperatures changes, and the like. The system monitors a data stream from a glucose sensor and detects signal artifacts that have higher amplitude than electronic or diffusion-related system noise. The system replaces some or the entire data stream continually or intermittently including signal estimation methods that particularly address transient signal artifacts. The system is also capable of detecting the severity of the signal artifacts and selectively applying one or more signal estimation algorithm factors responsive to the severity of the signal artifacts, which includes selectively applying distinct sets of parameters to a signal estimation algorithm or selectively applying distinct signal estimation algorithms.
Owner:DEXCOM INC
Systems and methods for replacing signal artifacts in a glucose sensor data stream
ActiveUS20090124878A1Accurately detect and replaceAvoid adjustmentCatheterTemperature sensorsRate limitingData stream
Systems and methods for minimizing or eliminating transient non-glucose related signal noise due to non-glucose rate limiting phenomenon such as ischemia, pH changes, temperatures changes, and the like. The system monitors a data stream from a glucose sensor and detects signal artifacts that have higher amplitude than electronic or diffusion-related system noise. The system replaces some or the entire data stream continually or intermittently including signal estimation methods that particularly address transient signal artifacts. The system is also capable of detecting the severity of the signal artifacts and selectively applying one or more signal estimation algorithm factors responsive to the severity of the signal artifacts, which includes selectively applying distinct sets of parameters to a signal estimation algorithm or selectively applying distinct signal estimation algorithms.
Owner:DEXCOM INC
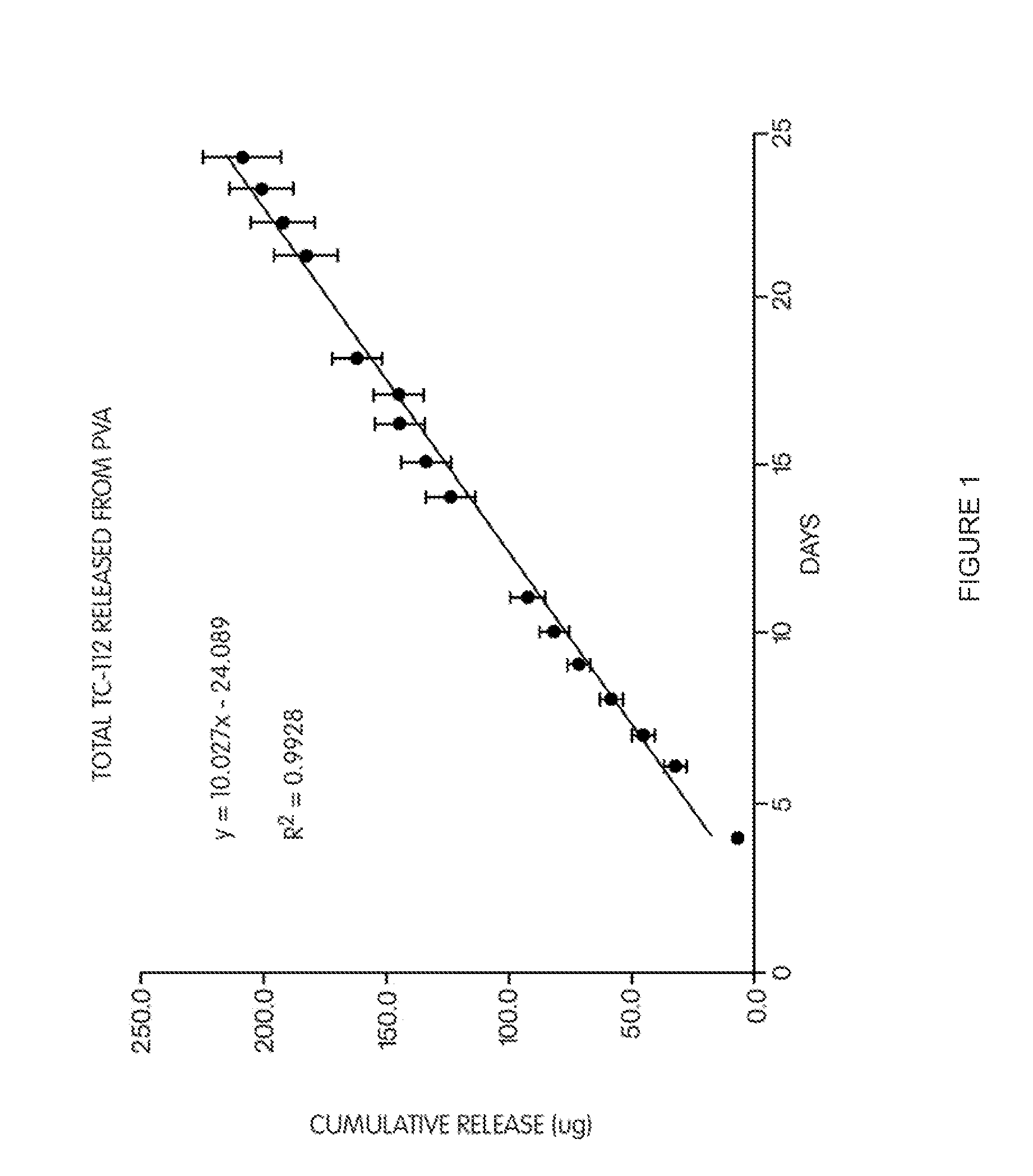
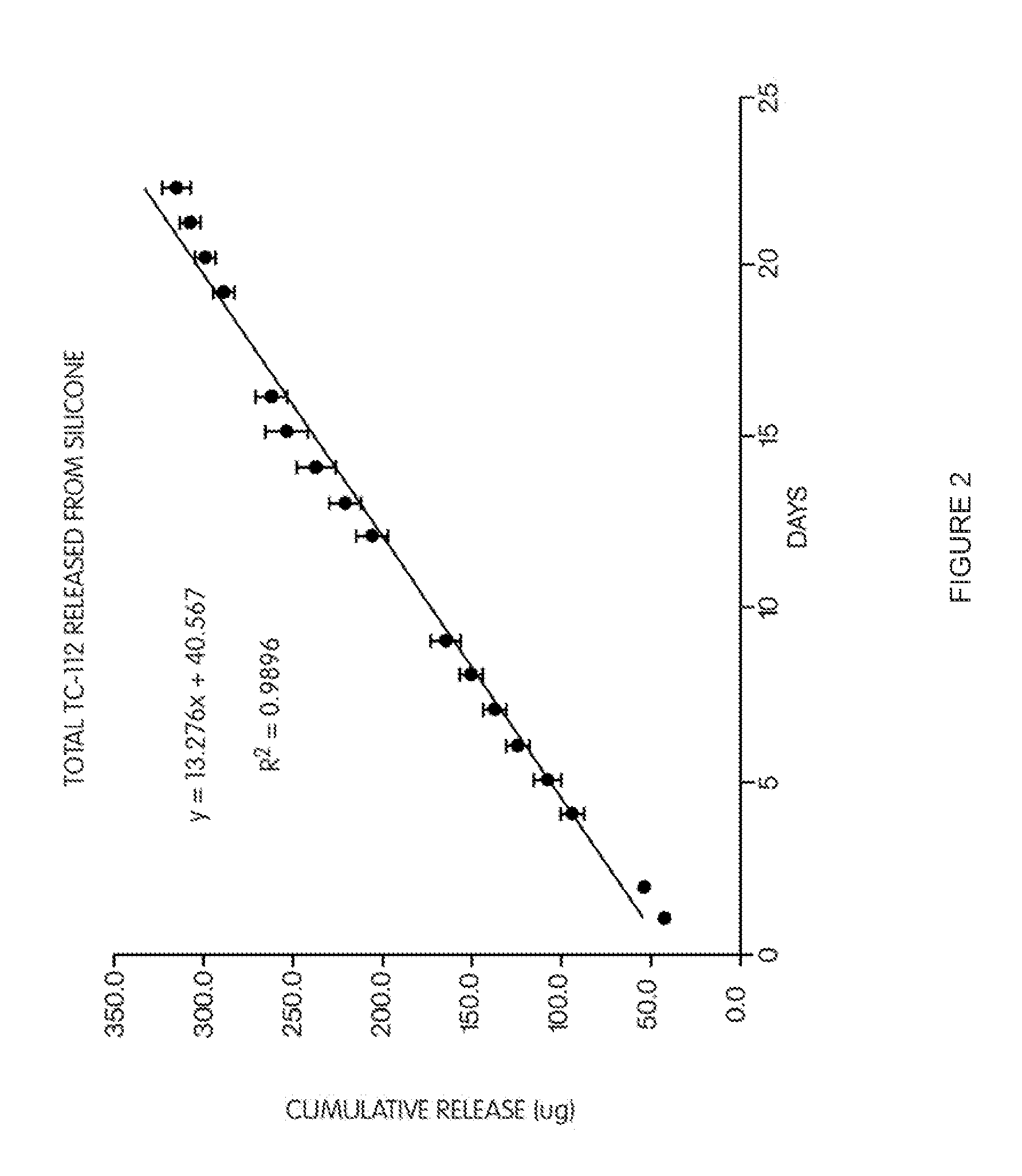
Polymer-based, sustained release drug delivery system
InactiveUS20120016467A1Reduce interactionSuture equipmentsAntibacterial agentsRate limitingSolubility
Disclosed is a sustained release system that includes a polymer and a prodrug having a solubility less than about 1 mg / ml dispersed in the polymer. Advantageously, the polymer is permeable to the prodrug and may be non-release rate limiting with respect to the rate of release of the prodrug from the polymer. This permits improved drug delivery within a body in the vicinity of a surgery via sustained release rate kinetics over a prolonged period of time, while not requiring complicated manufacturing processes.
Owner:PSIVIDA INC
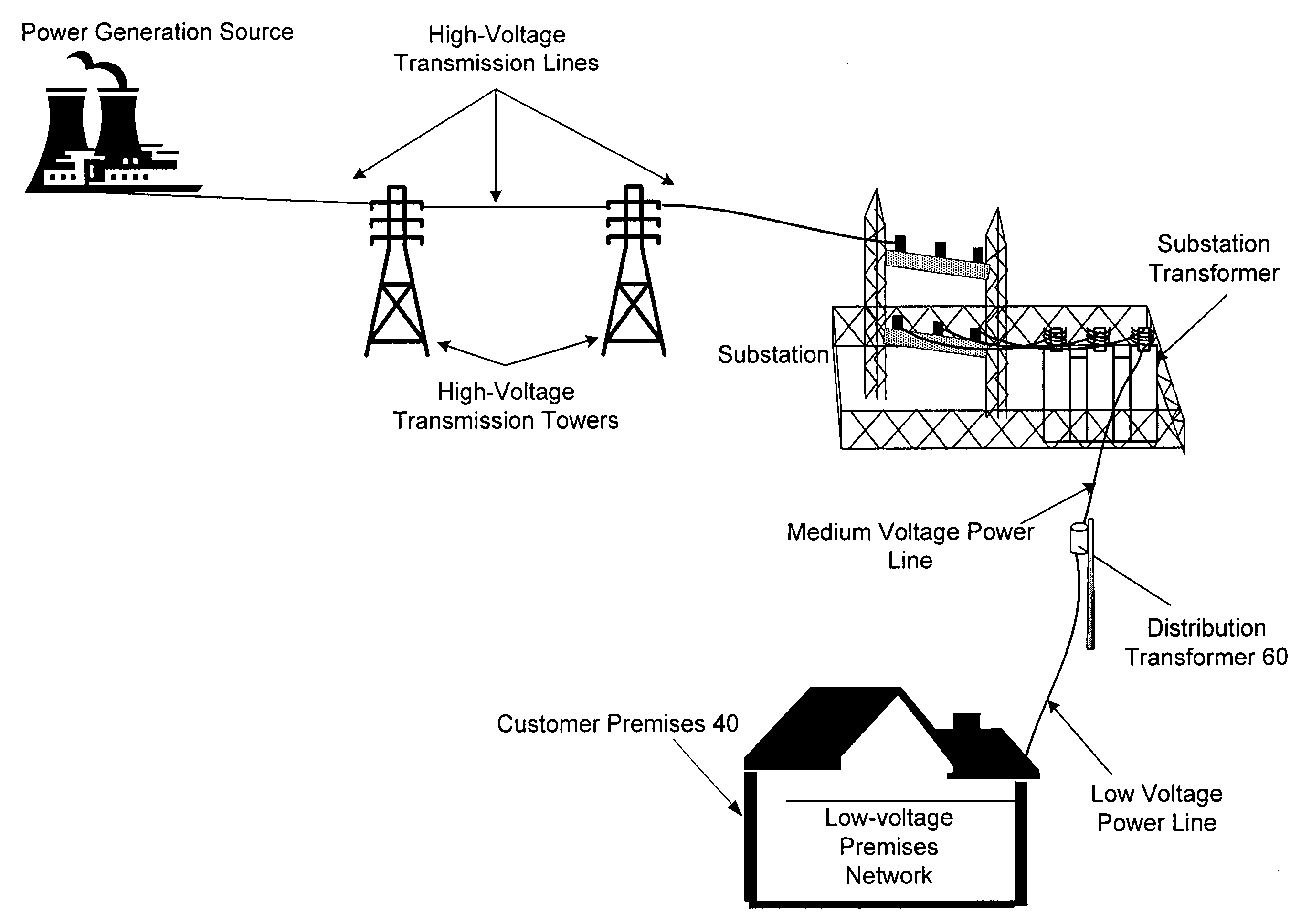
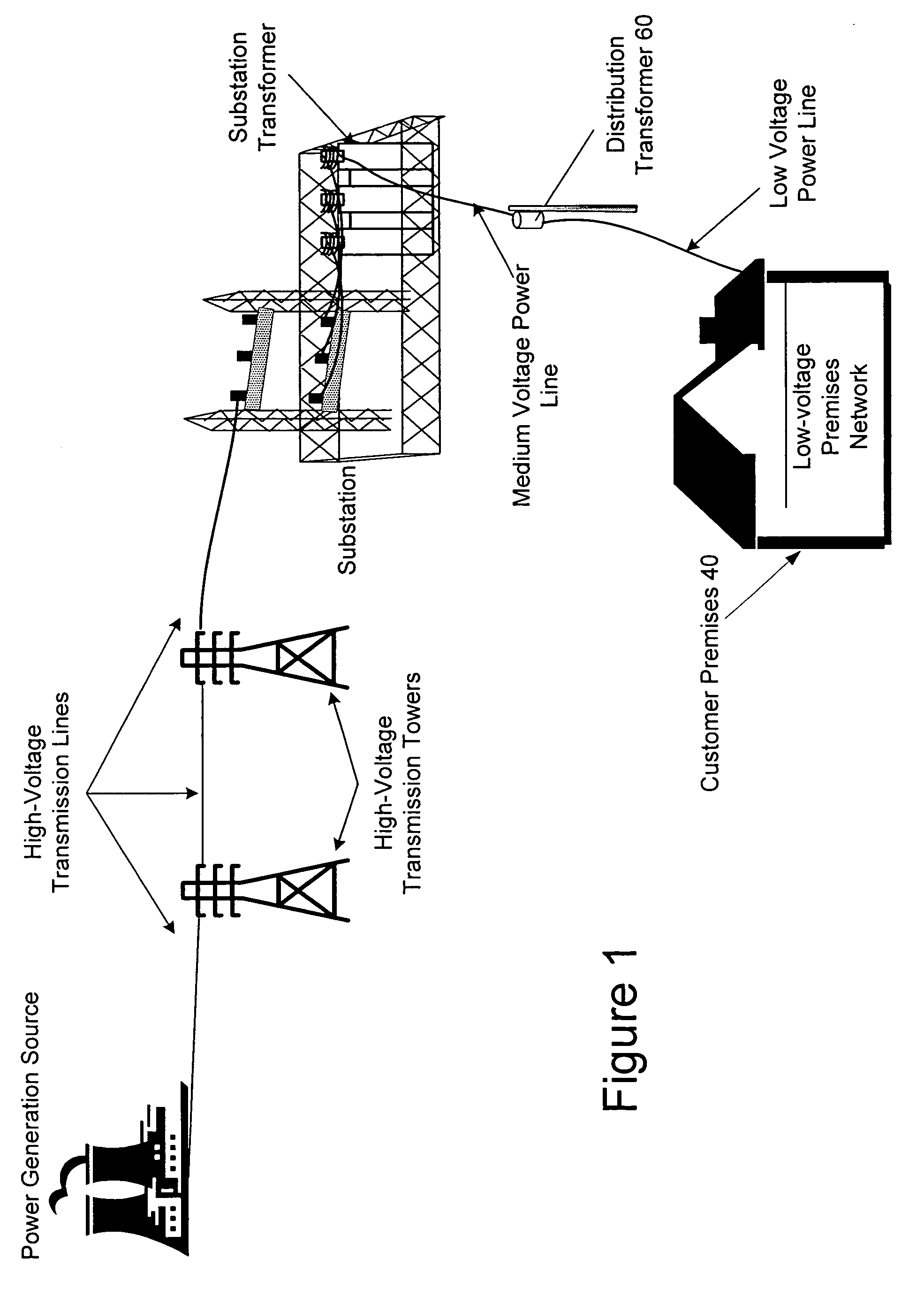
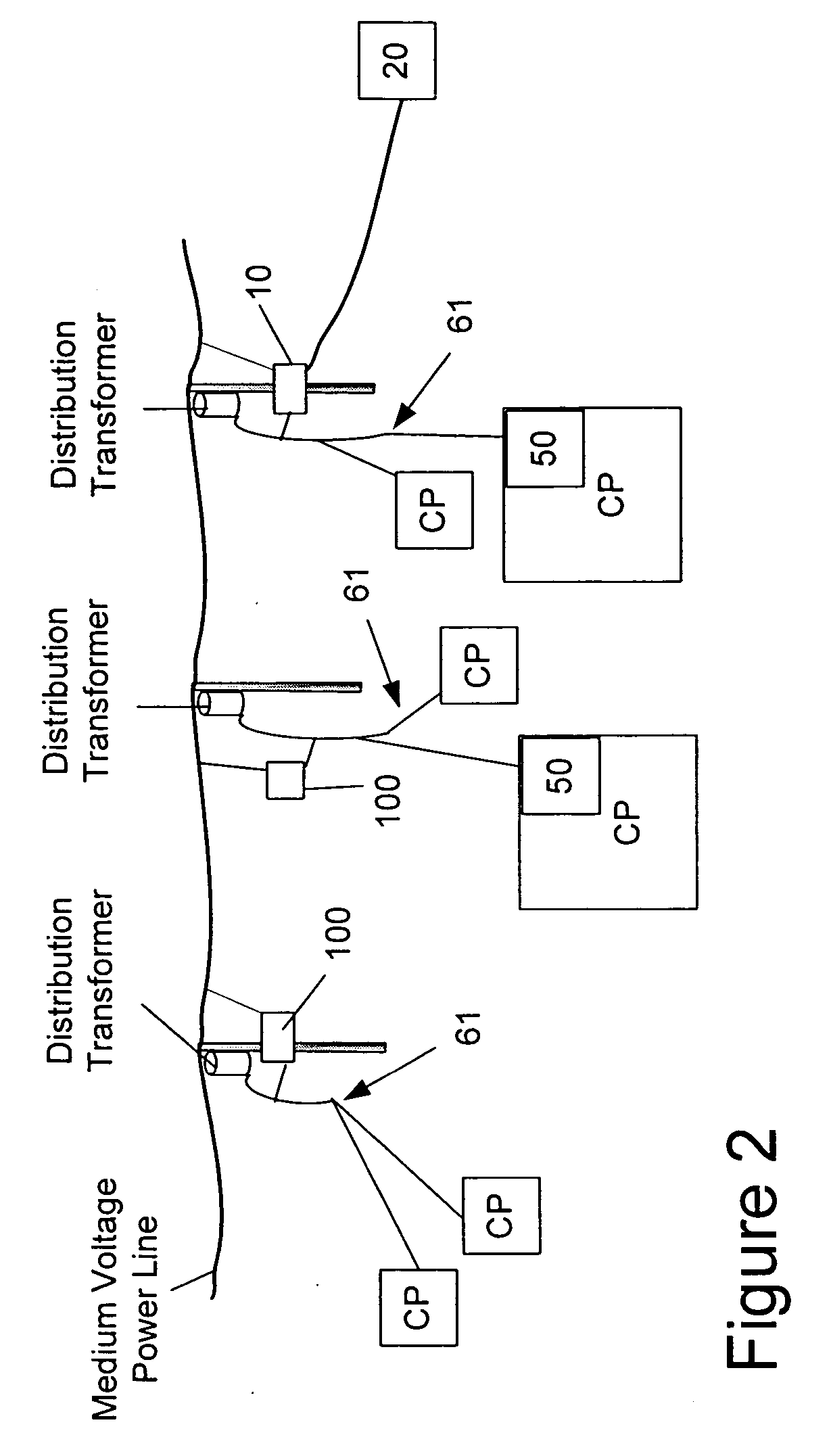
Power line communication rate limiting system and method
InactiveUS20070002771A1Rate limiting quality of service (QoS) controlError preventionTransmission systemsQuality of serviceRate limiting
A power line communications device that may provide rate limiting and quality of service control is provided. The device may include a first modem in communication with one or more user devices via a low voltage power line subnet and a second modem communicatively coupled to a second communications medium. The device also may include a controller in communication with the first and second modems and a computer readable medium encoded with instructions to control the operation of the controller. The controller may rate limit data to and / or from a destination and / or source based one or more parameters such as the destination address, the source address, the type of data, temporal parameters, and other criteria. In addition, the controller may implement QoS for data and transmit QoS parameters to power line modems to allow the power line modems to perform QoS.
Owner:CURRENT TECH
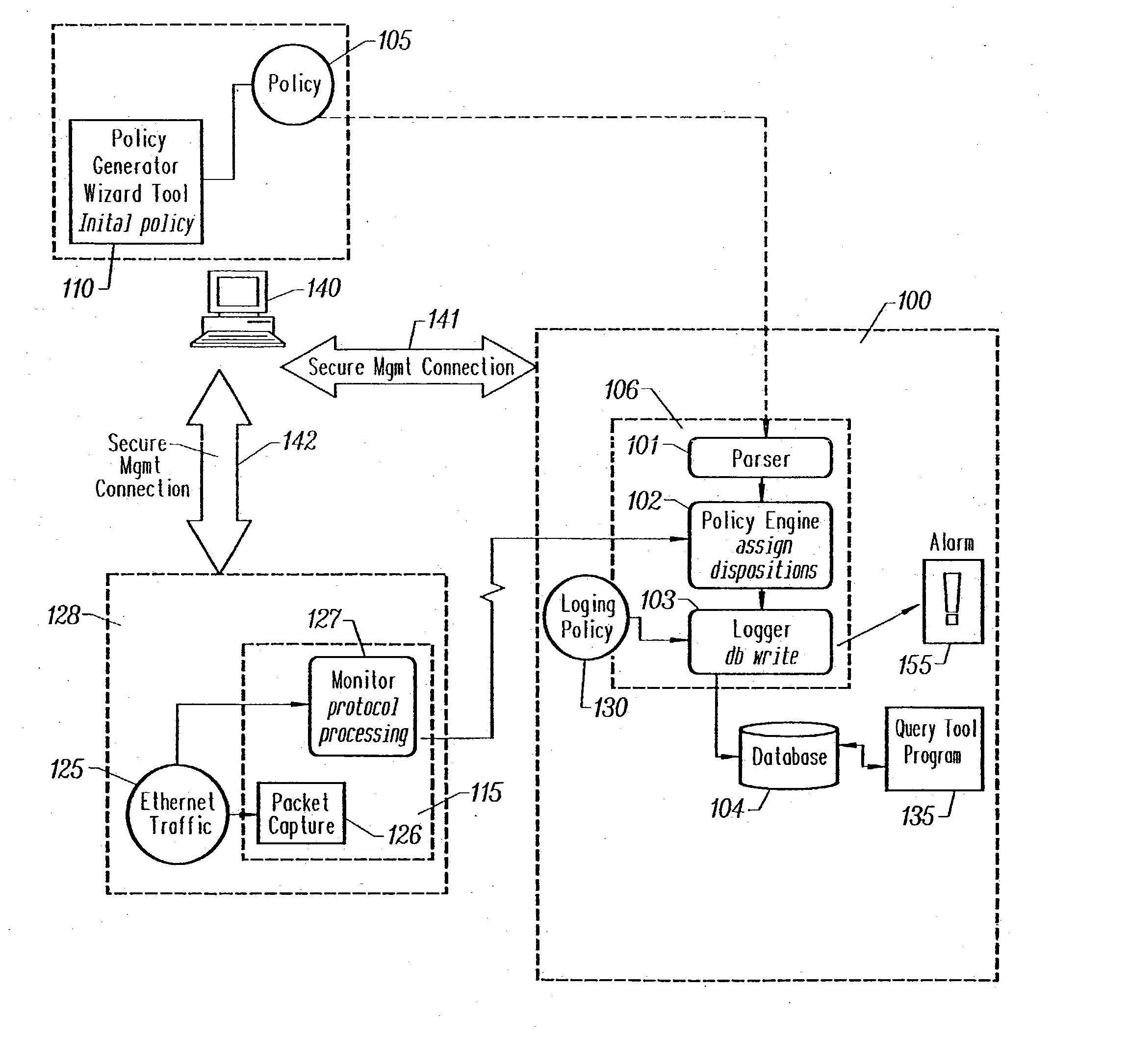
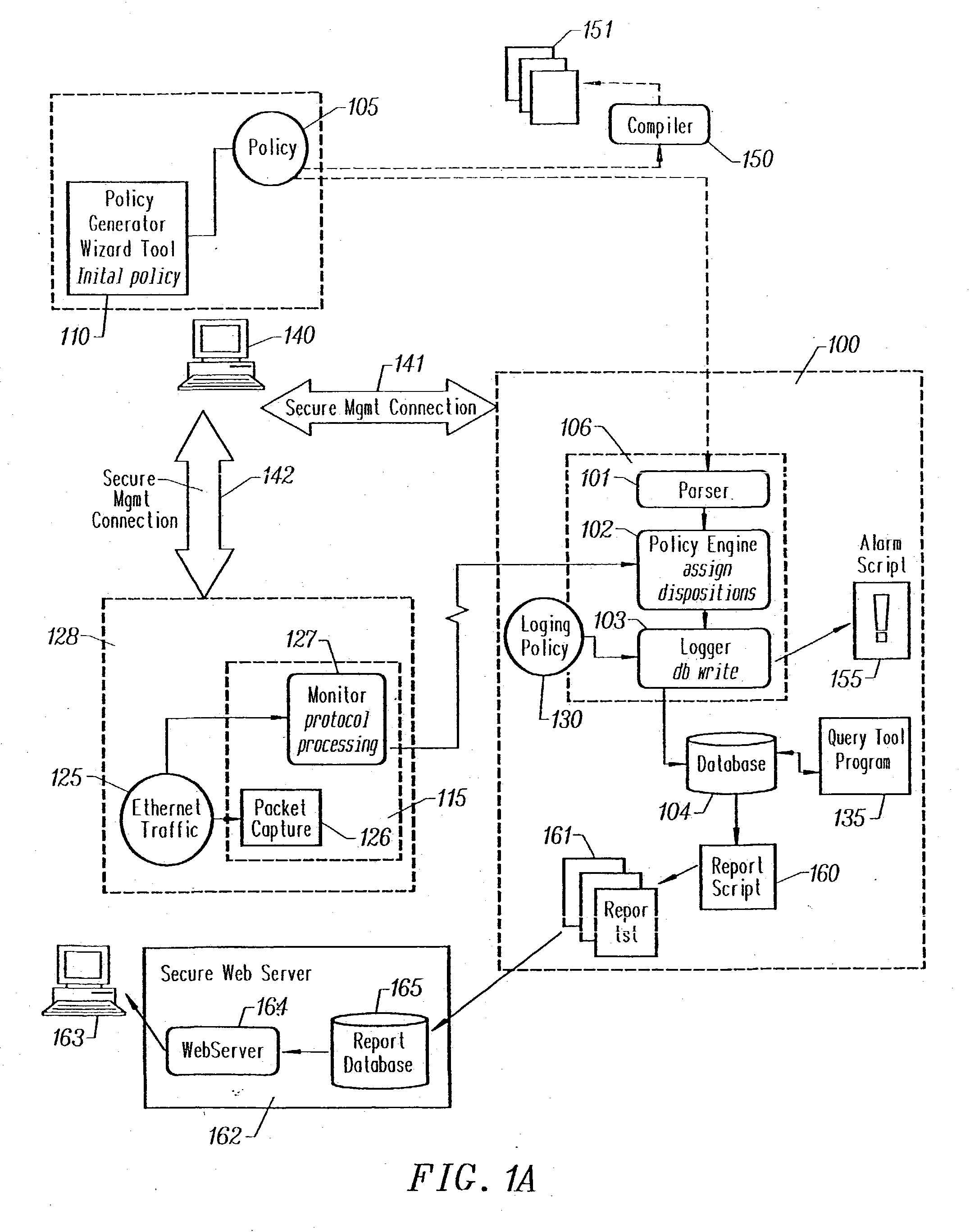
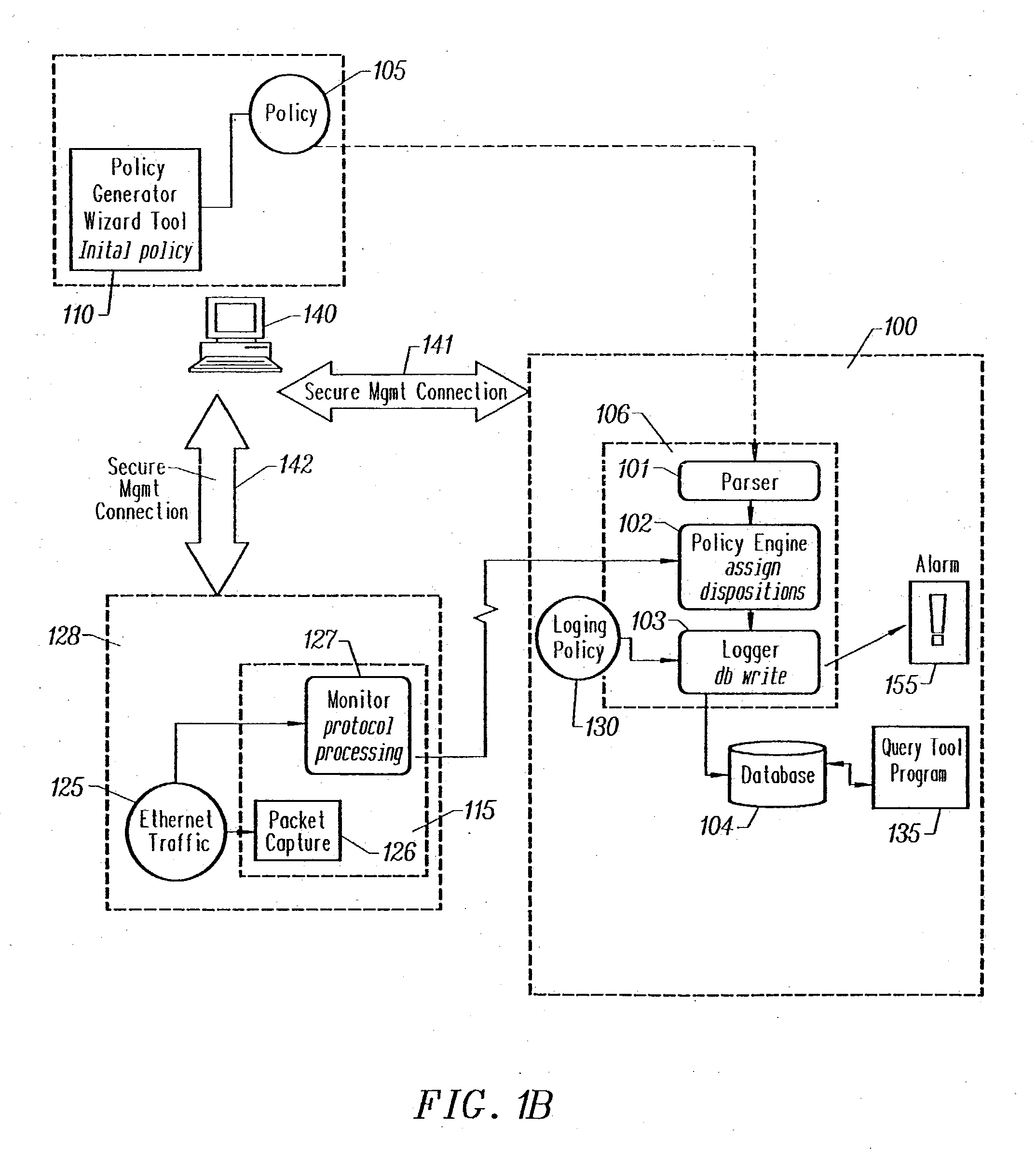
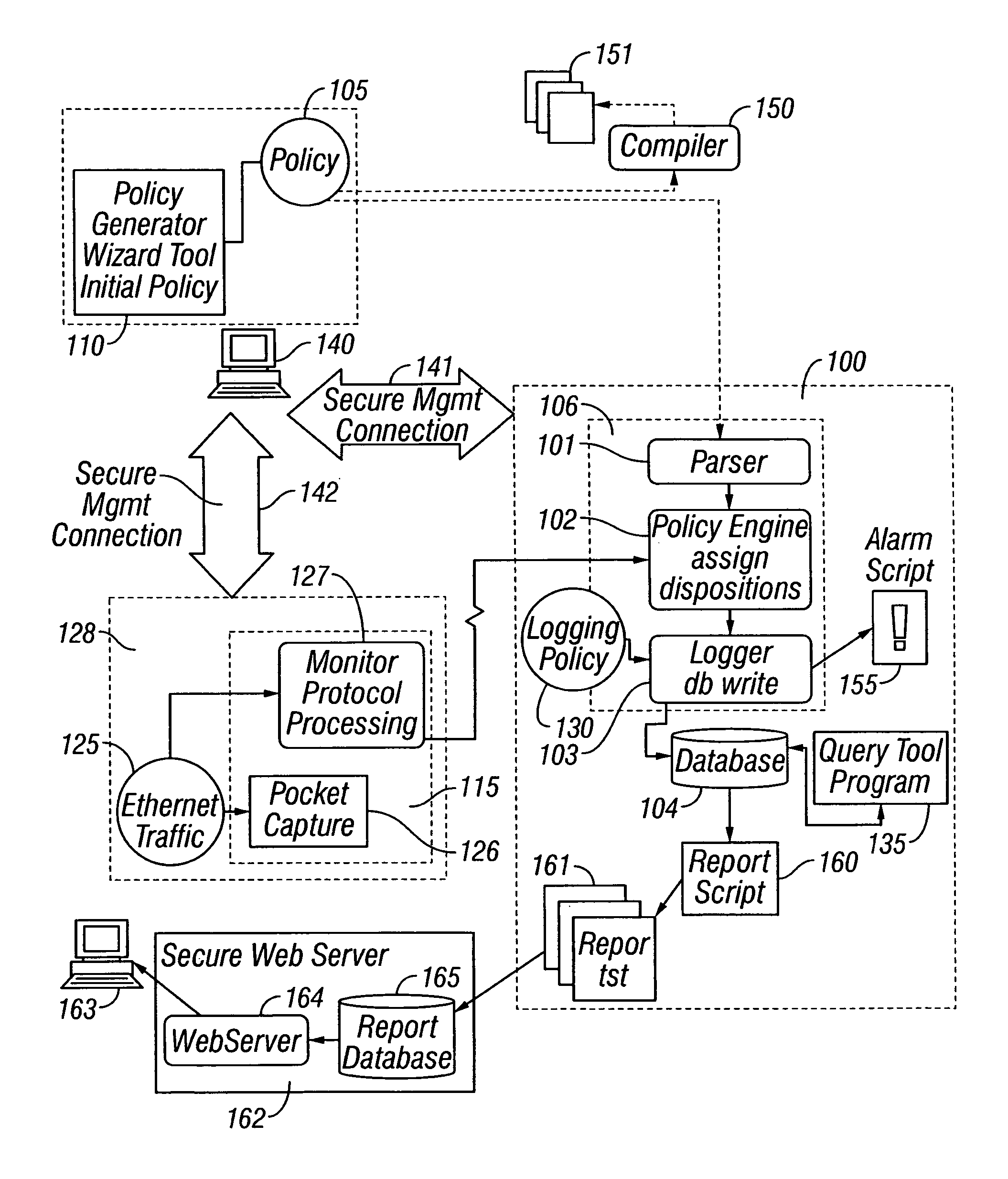
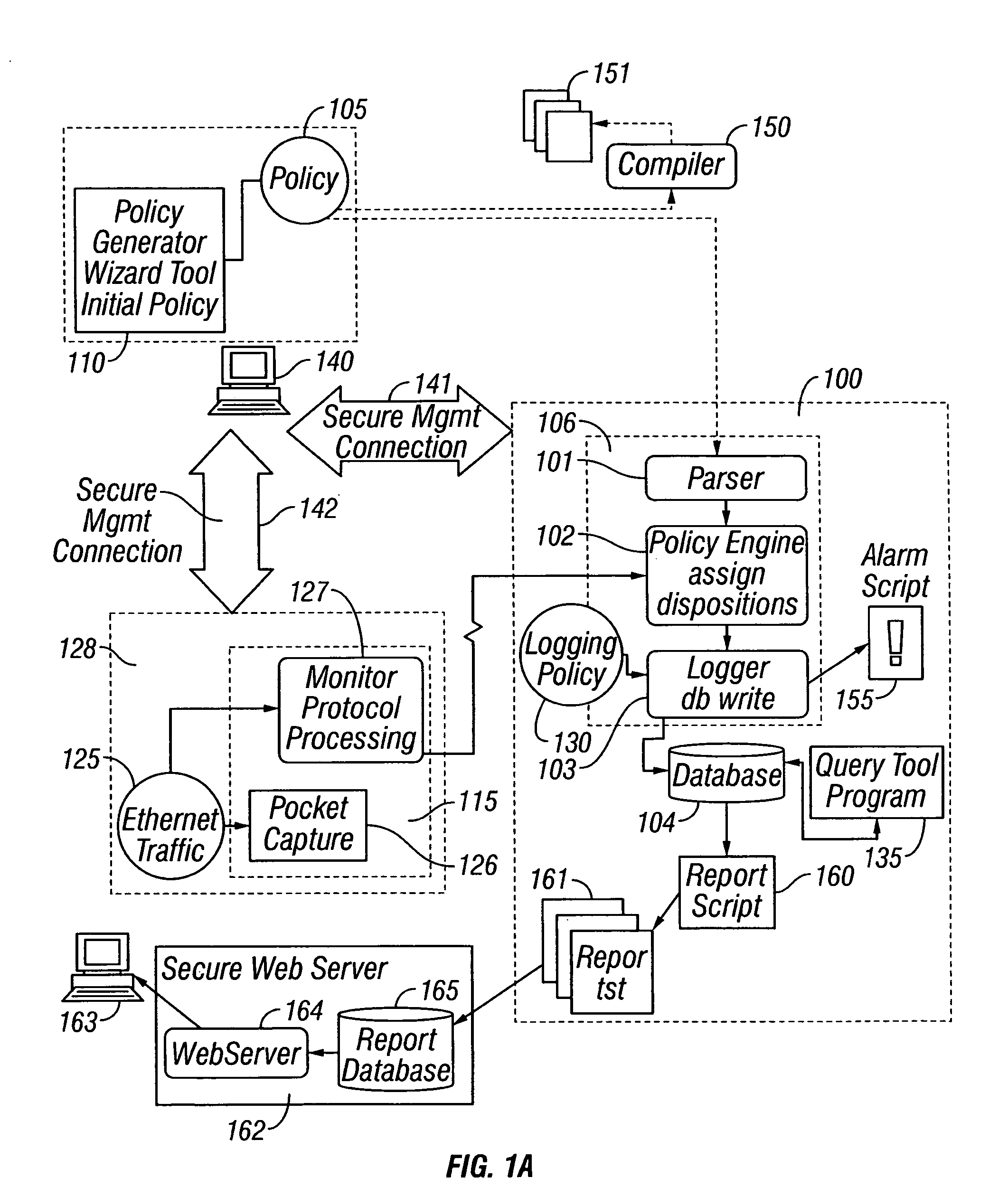
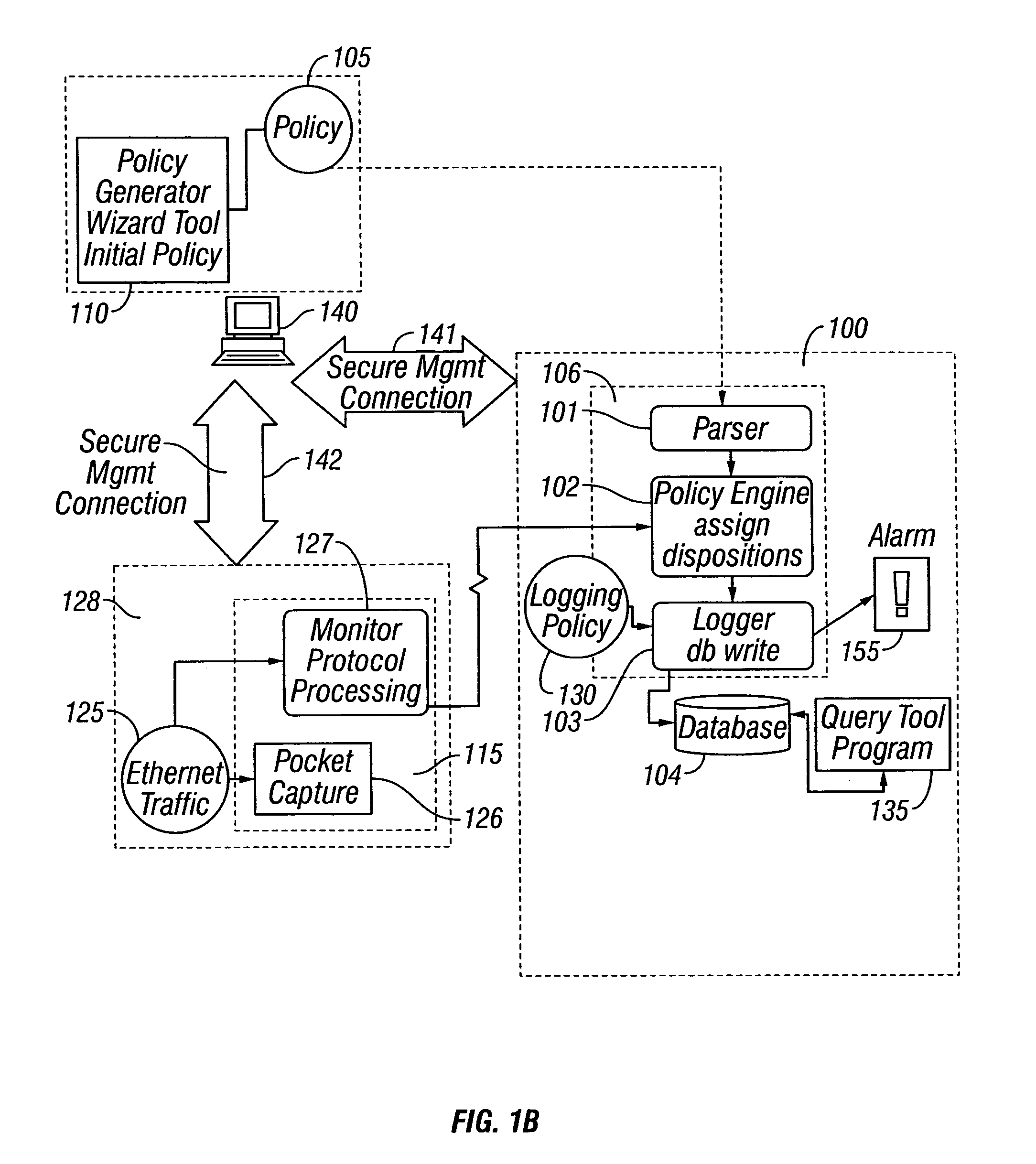
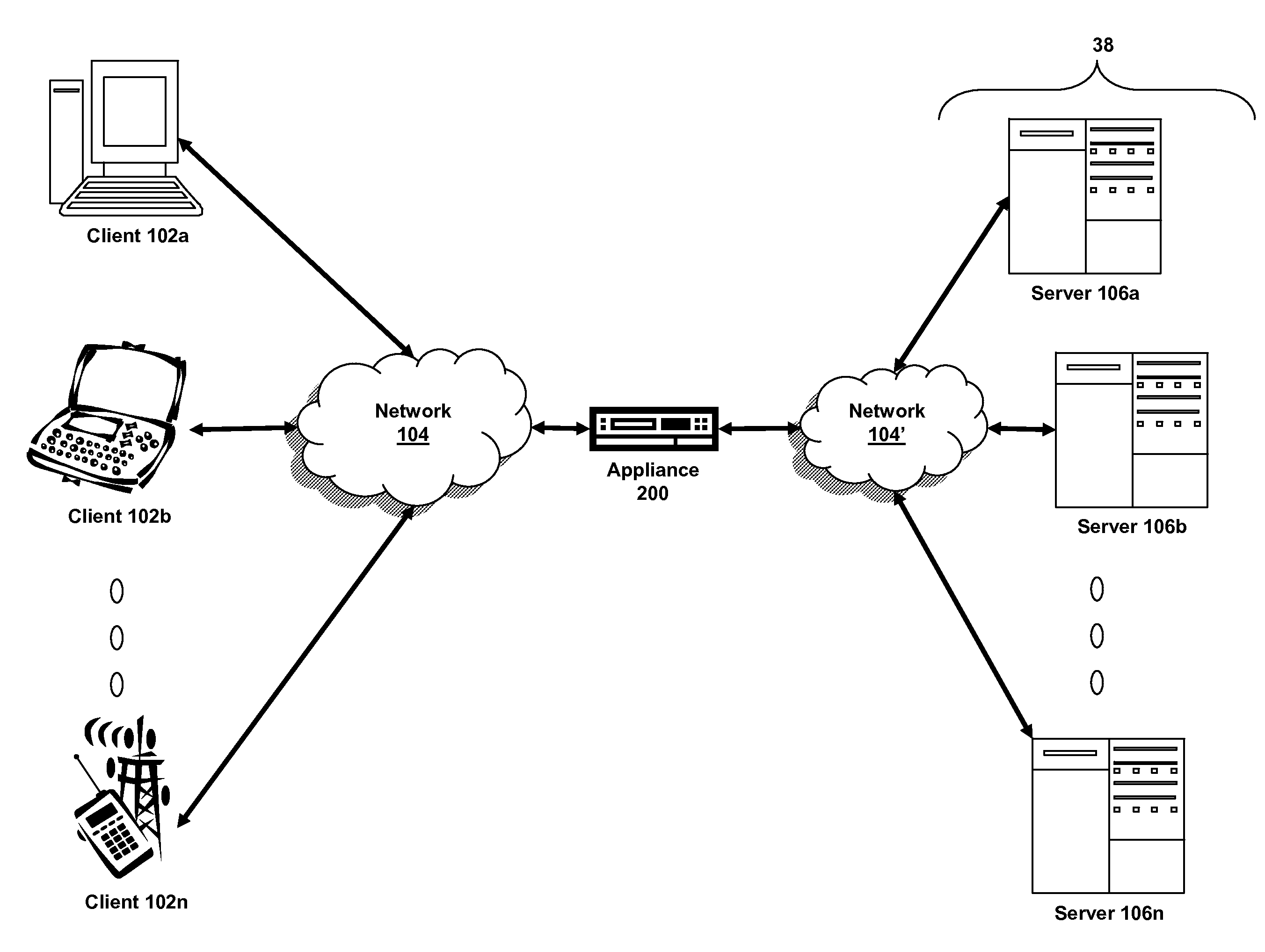
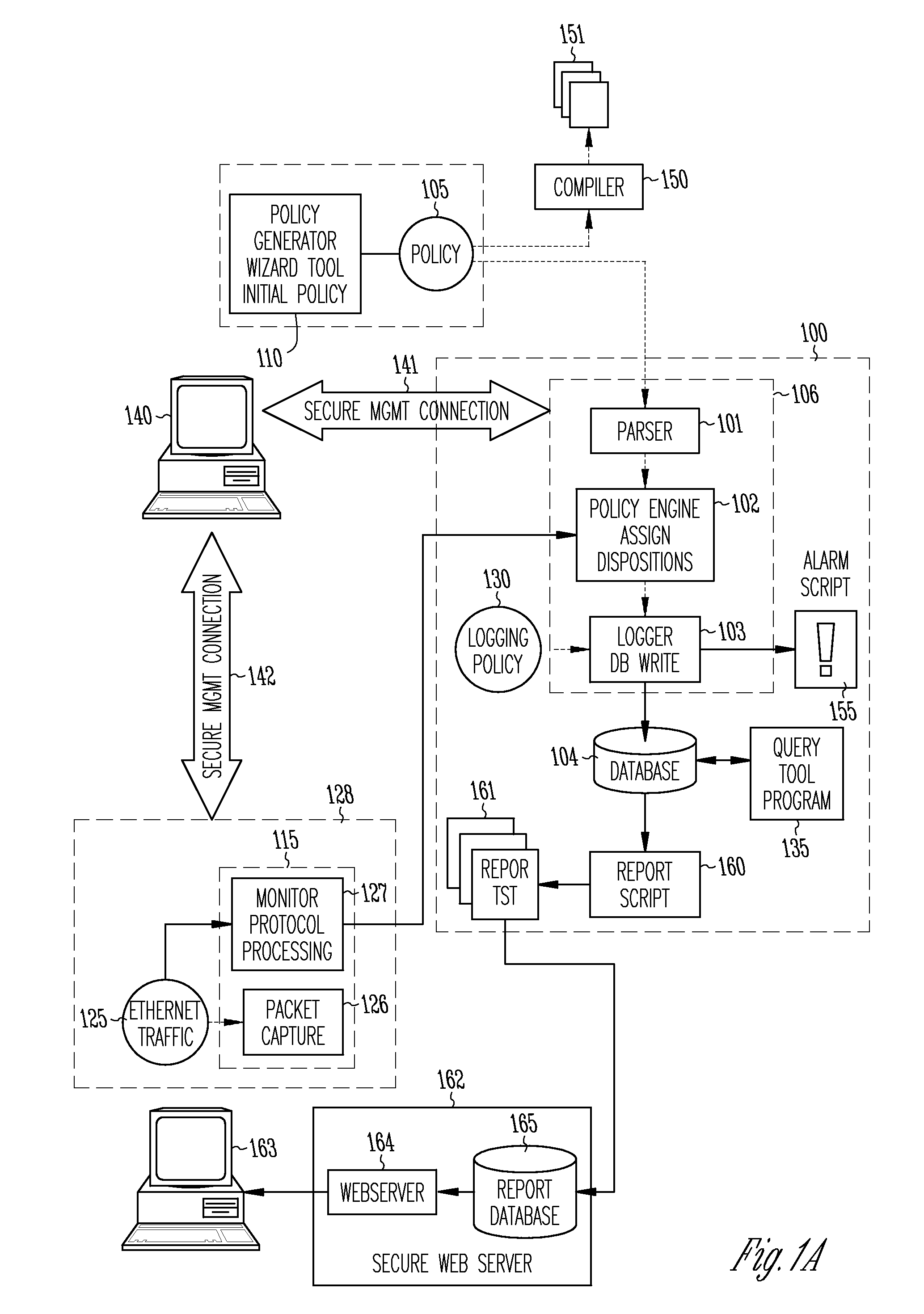
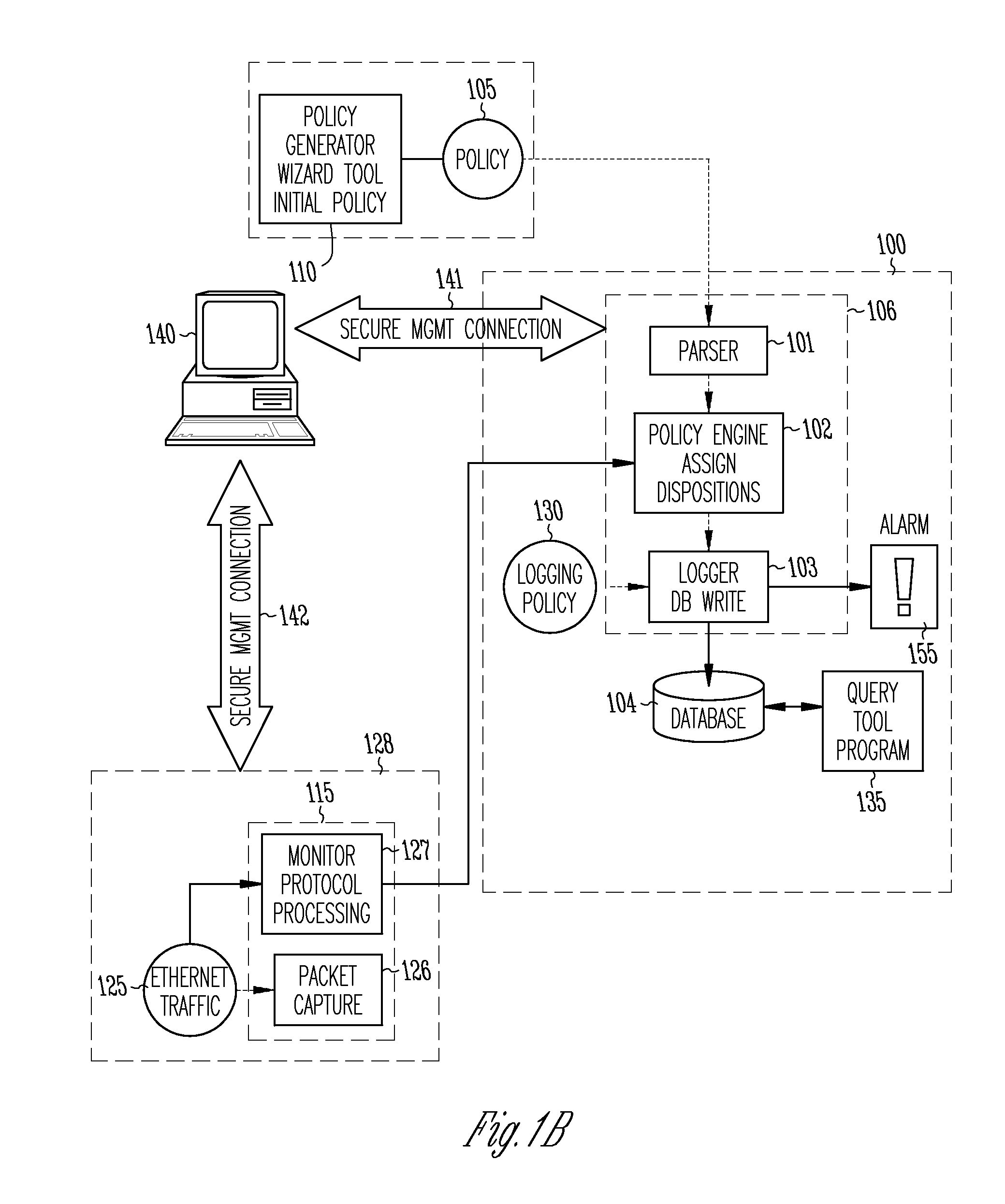
Method and apparatus for enterprise management
A method and apparatus for a network monitor internals mechanism, which serves to translate packet data into multiple concurrent streams of encoded network event data, to contribute to enterprise management, reporting, and global mechanisms for aggregating monitors at a centralized aggregation point, and to facilitate rate limiting techniques because such monitors are not in control (i.e. cannot back pressure flow) is provided.
Owner:SECURIFY
Method and apparatus for rate limiting
A method and apparatus for a network monitor internals mechanism, which serves to translate packet data into multiple concurrent streams of encoded network event data, to contribute to enterprise management, reporting, and global mechanisms for aggregating monitors at a centralized aggregation point, and to facilitate rate limiting techniques because such monitors are not in control (i.e. cannot back pressure flow) is provided.
Owner:MCAFEE LLC
Systems and methods for object rate limiting in multi-core system
The present invention is directed towards systems and methods for managing a rate of request for an object transmitted between a server and one or more clients via a multi-core intermediary device. A first core of the intermediary device can receive a request for an object and assume ownership of the object. The first core can store the object in shared memory along with a rate-related counter for the object and generate a hash to the object and counter. Other cores can obtain the hash from the first core and access the object and counter in shared memory. Policy engines and throttlers in operation on each core can control the rate of access to the stored object.
Owner:CITRIX SYST INC
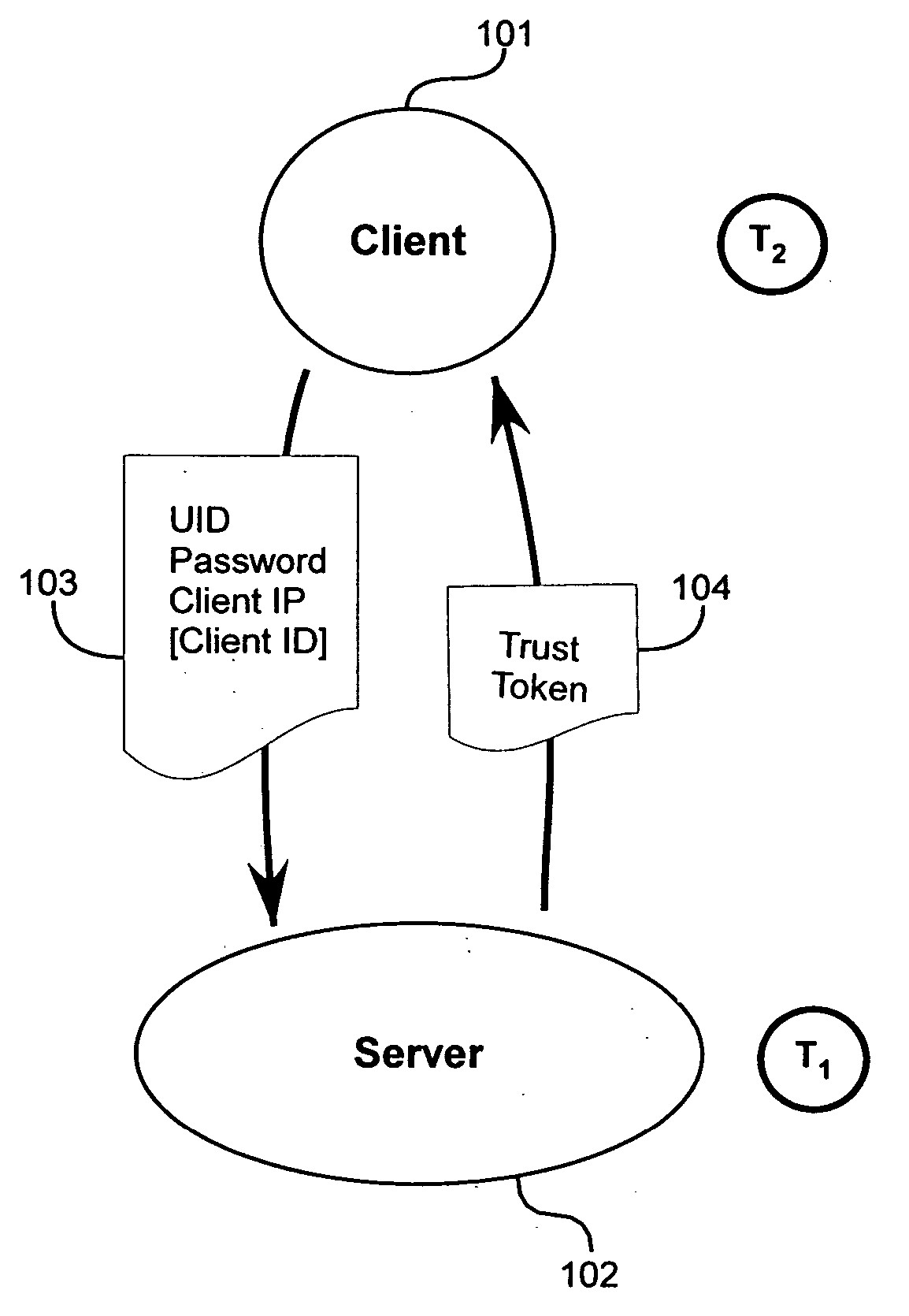
Method and apparatus for trust-based, fine-grained rate limiting of network requests
ActiveUS20050108551A1Digital data processing detailsUser identity/authority verificationRate limitingInternet traffic
A method and apparatus for fine-grained, trust-based rate limiting of network requests distinguishes trusted network traffic from untrusted network traffic at the granularity of an individual user / machine combination, so that network traffic policing measures are readily implemented against untrusted and potentially hostile traffic without compromising service to trusted users. A server establishes a user / client pair as trusted by issuing a trust token to the client when successfully authenticating to the server for the first time. Subsequently, the client provides the trust token at login. At the server, rate policies apportion bandwidth according to type of traffic: network requests that include a valid trust token are granted highest priority. Rate policies further specify bandwidth restrictions imposed for untrusted network traffic. This scheme enables the server to throttle untrusted password-guessing requests from crackers without penalizing most friendly logins and only slightly penalizing the relatively few untrusted friendly logins.
Owner:META PLATFORMS INC
Method and system for mitigating denial of service in a communication network
InactiveUS20060174324A1Mitigating denial of serviceDigital data processing detailsUser identity/authority verificationRate limitingReal-time computing
Certain aspects of a method and system for mitigating denial of service may comprise determining whether at least a first connection identifier of a received incoming packet matches at least a second connection identifier stored in memory. A screening mechanism and a rate limiting mechanism may be utilized to regulate the received incoming packet based on determining whether at least the first connection identifier of the received incoming packet matches at least the second connection identifier stored in memory.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
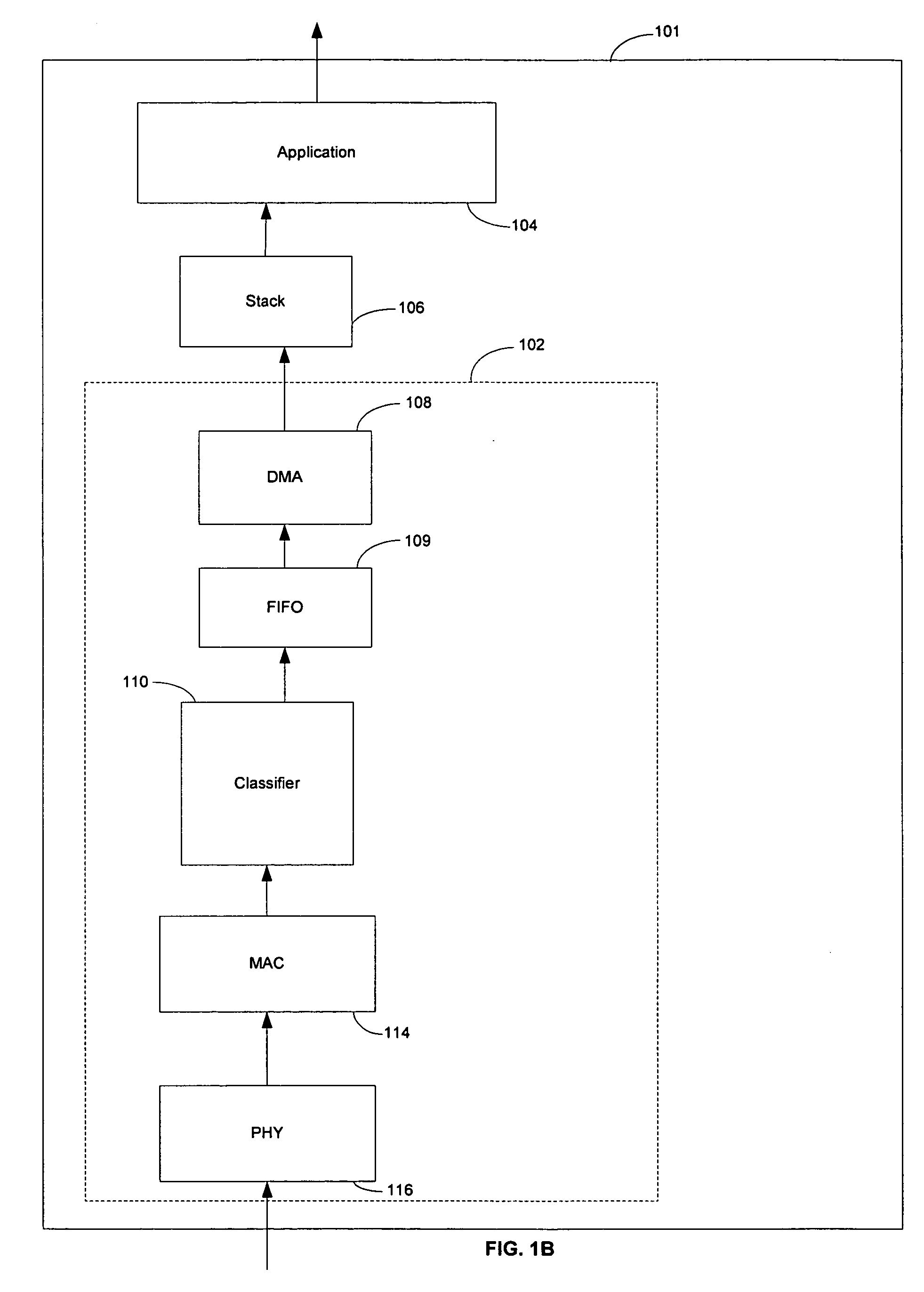
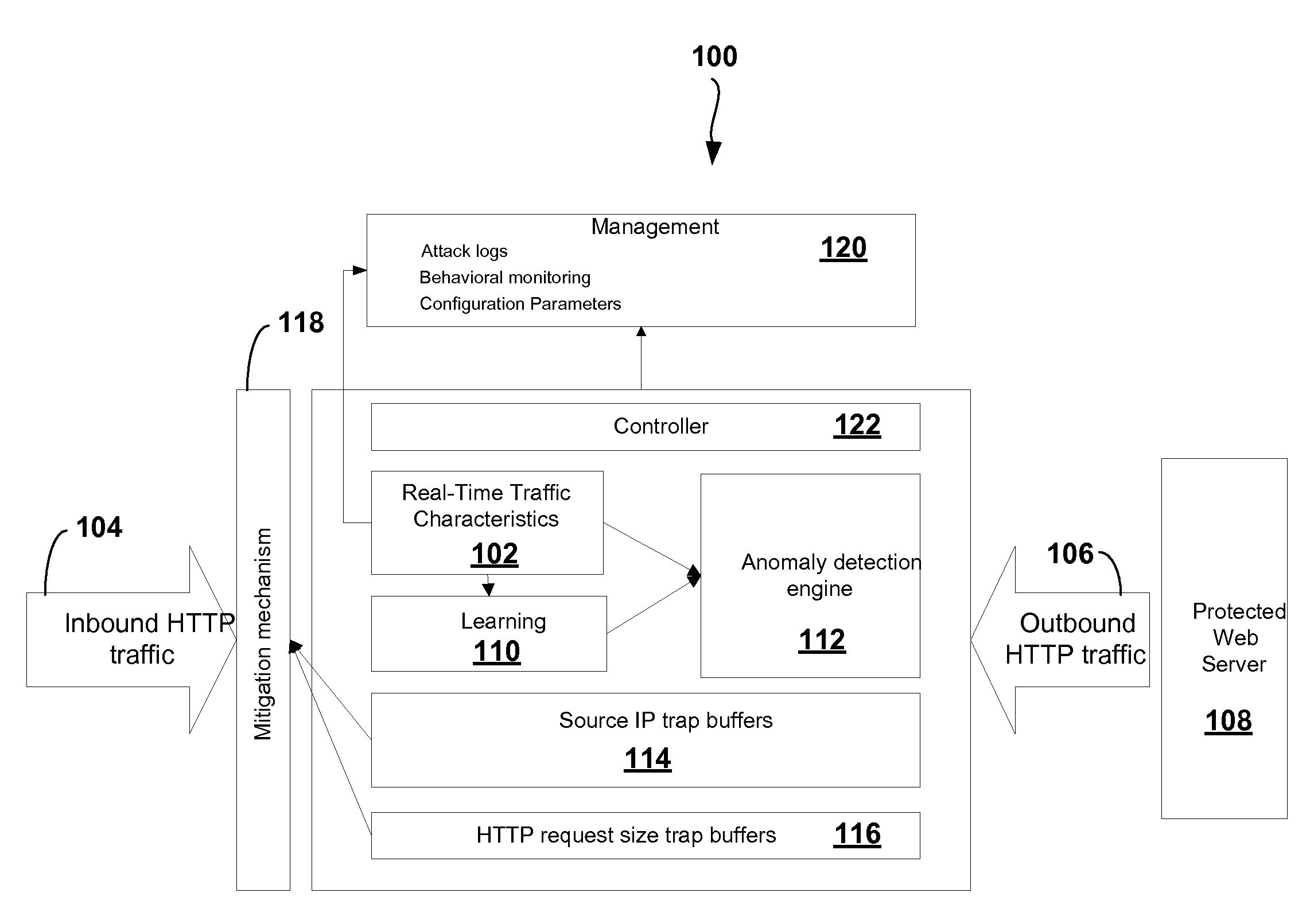
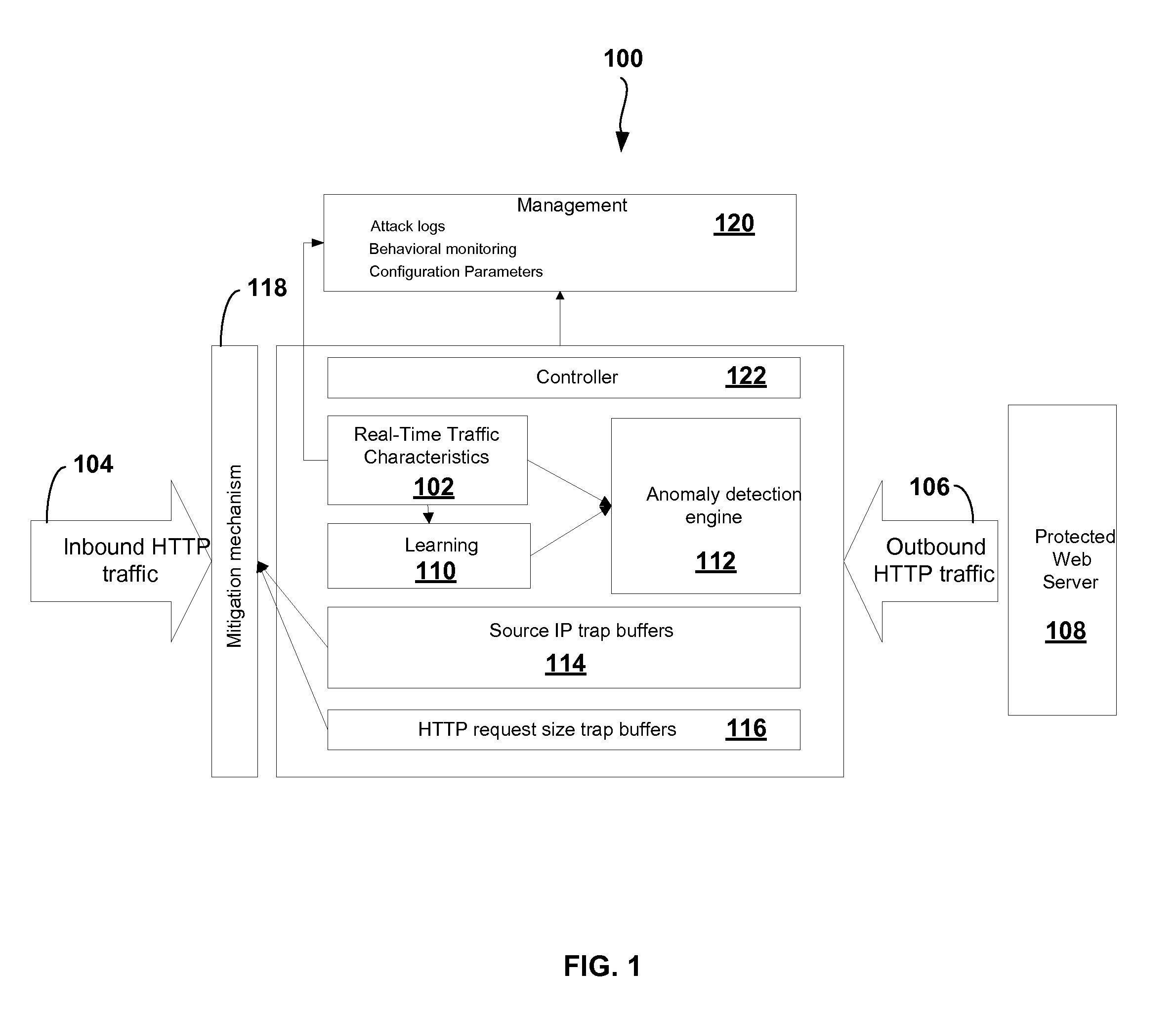
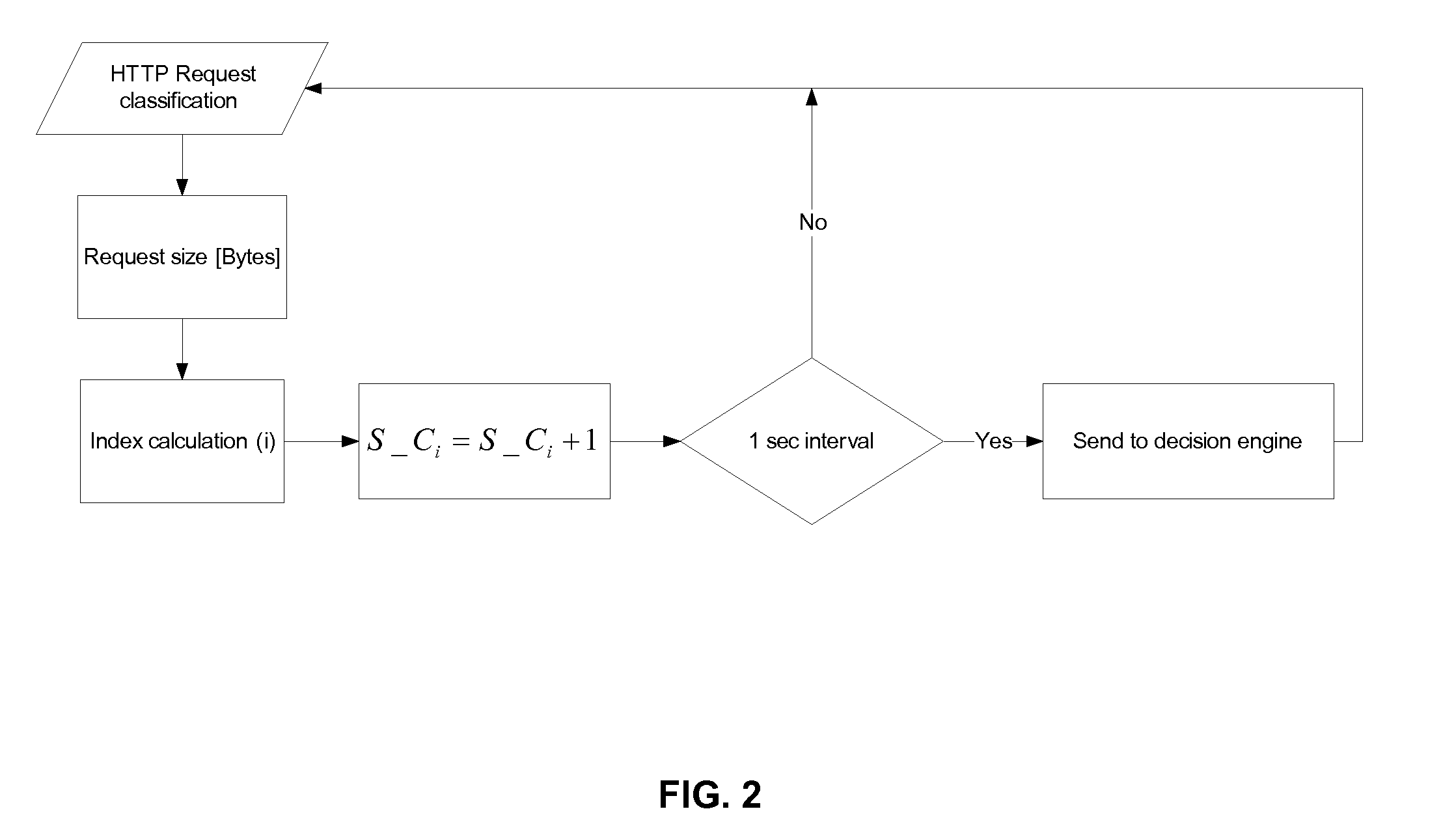
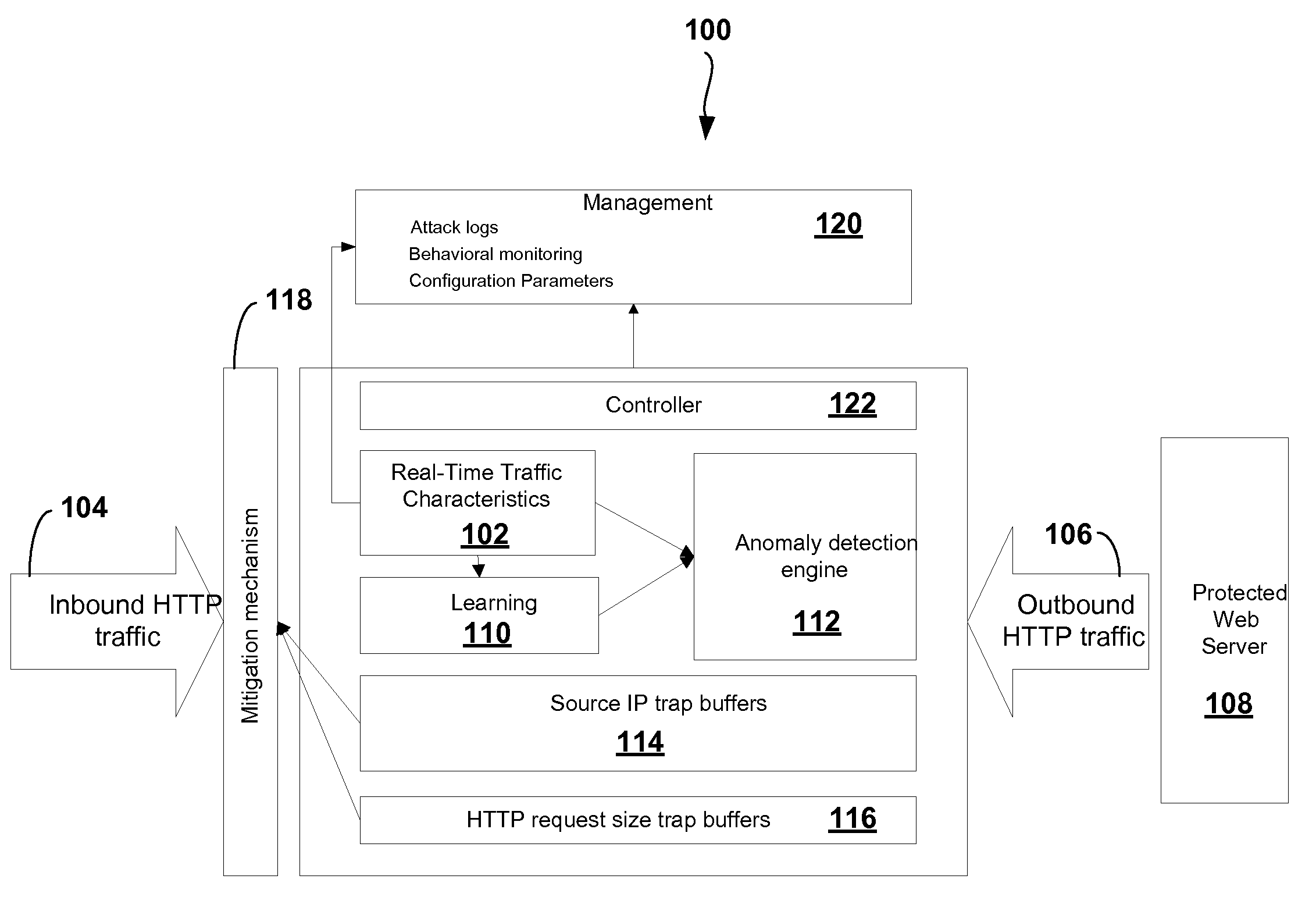
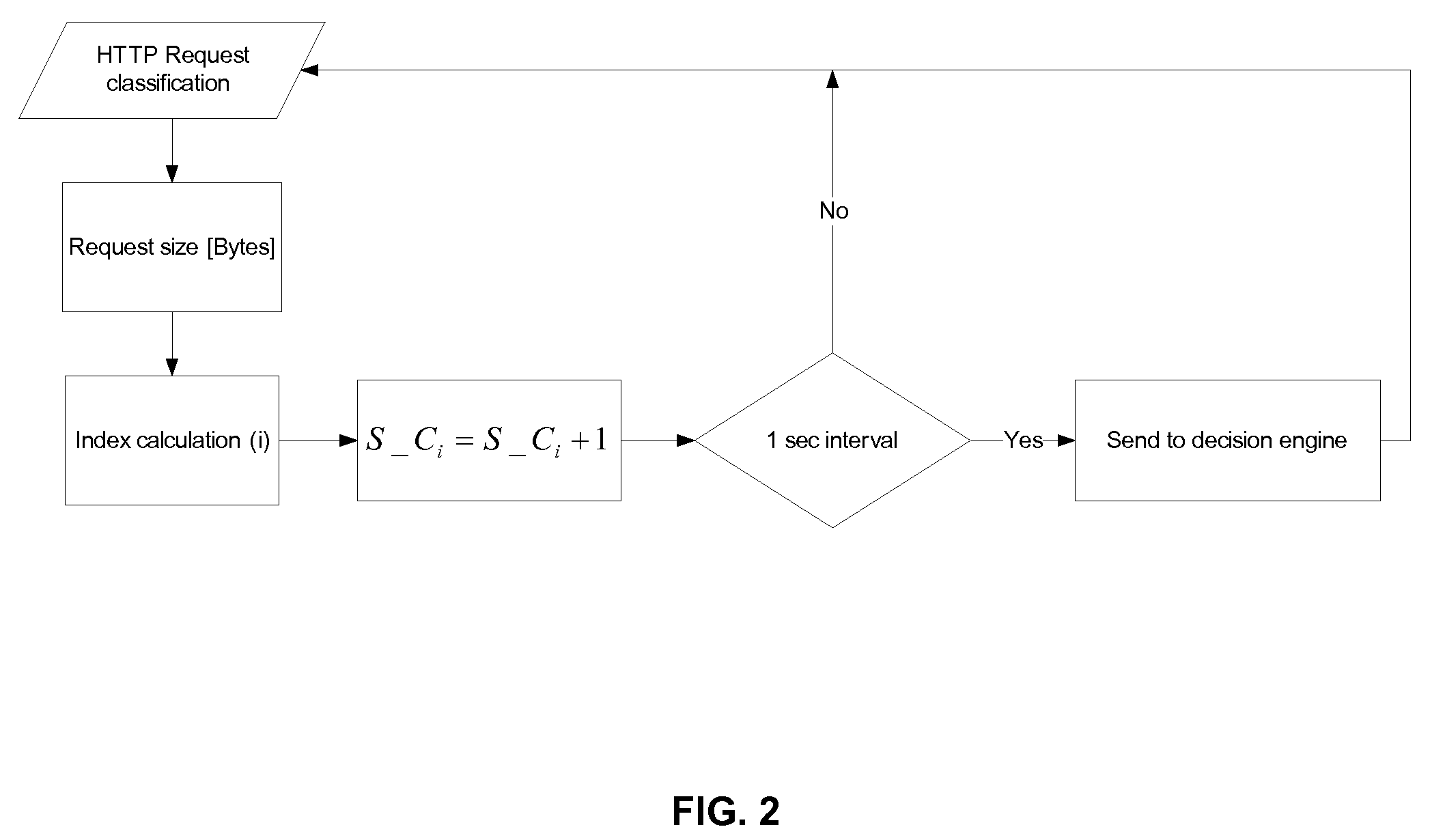
Adaptive Behavioral HTTP Flood Protection
A system and method to detect and mitigate denial of service and distributed denial of service HTTP “page” flood attacks. Detection of attack / anomaly is made according to multiple traffic parameters including rate-based and rate-invariant parameters in both traffic directions. Prevention is done according to HTTP traffic parameters that are analyzed once a traffic anomaly is detected. This protection includes a differential adaptive mechanism that tunes the sensitivity of the anomaly detection engine. The decision engine is based on a combination between fuzzy logic inference systems and statistical thresholds. A “trap buffer” characterizes the attack to allow an accurate mitigation according to the source IP(s) and the HTTP request URL's that are used as part of the attack. Mitigation is controlled through a feedback mechanism that tunes the level of rate limit factors that are needed in order to mitigate the attack effectively while letting legitimate traffic to pass.
Owner:RADWARE
BFD rate-limiting and automatic session activation
A system and method for bidirectional forwarding detection (BFD) rate-limiting and automatic BFD session activation includes tracking a total bidirectional forwarding detection (BFD) packet rate for a line card (LC) of the node, and rejecting operations associated with creation of a new BFD session that would cause the total BFD packet rate to exceed a predetermined maximum rate. The new BFD session is stored in a state on the node and the operations of the new BFD session are automatically retried at a time when doing so would not exceed the predetermined maximum rate. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
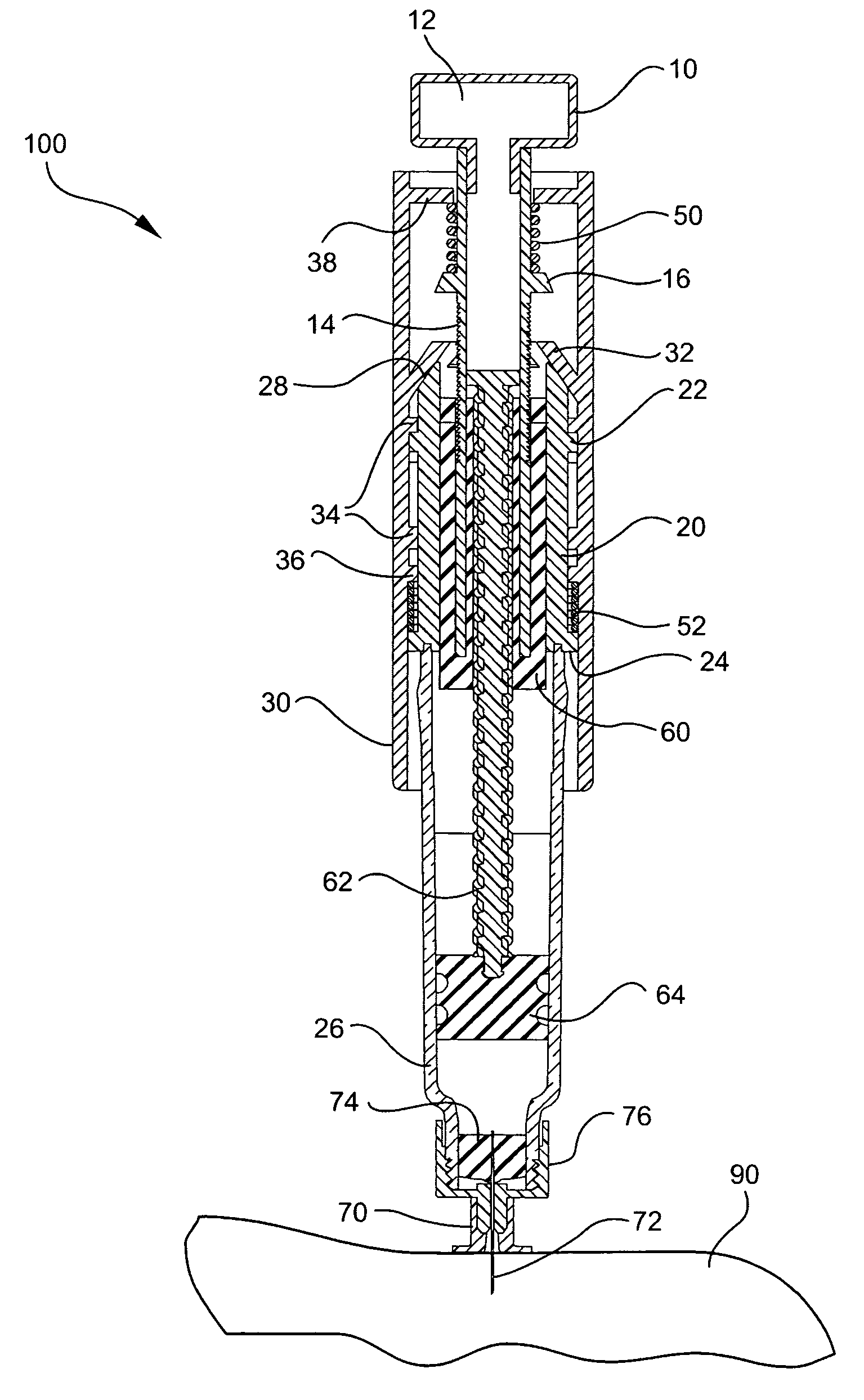
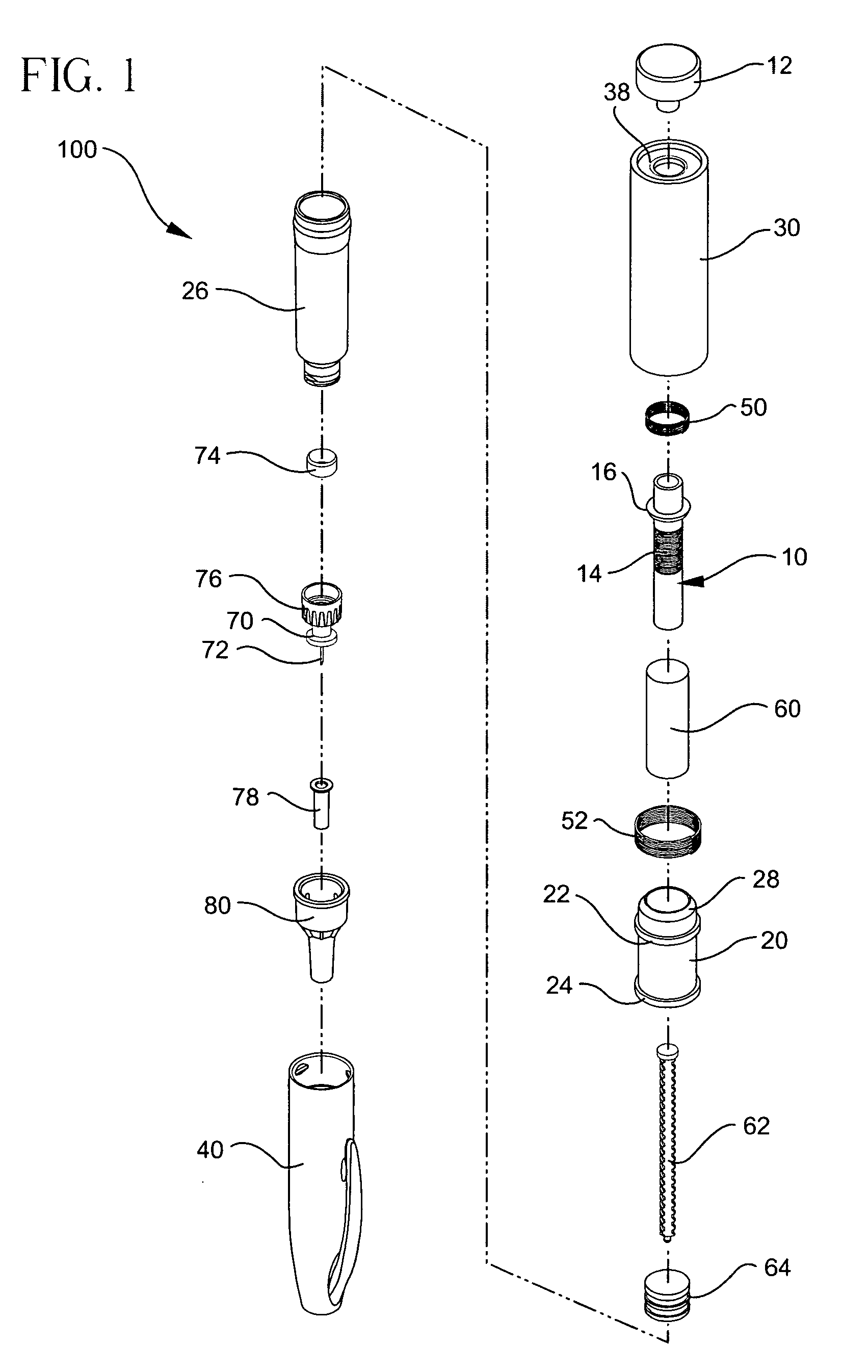
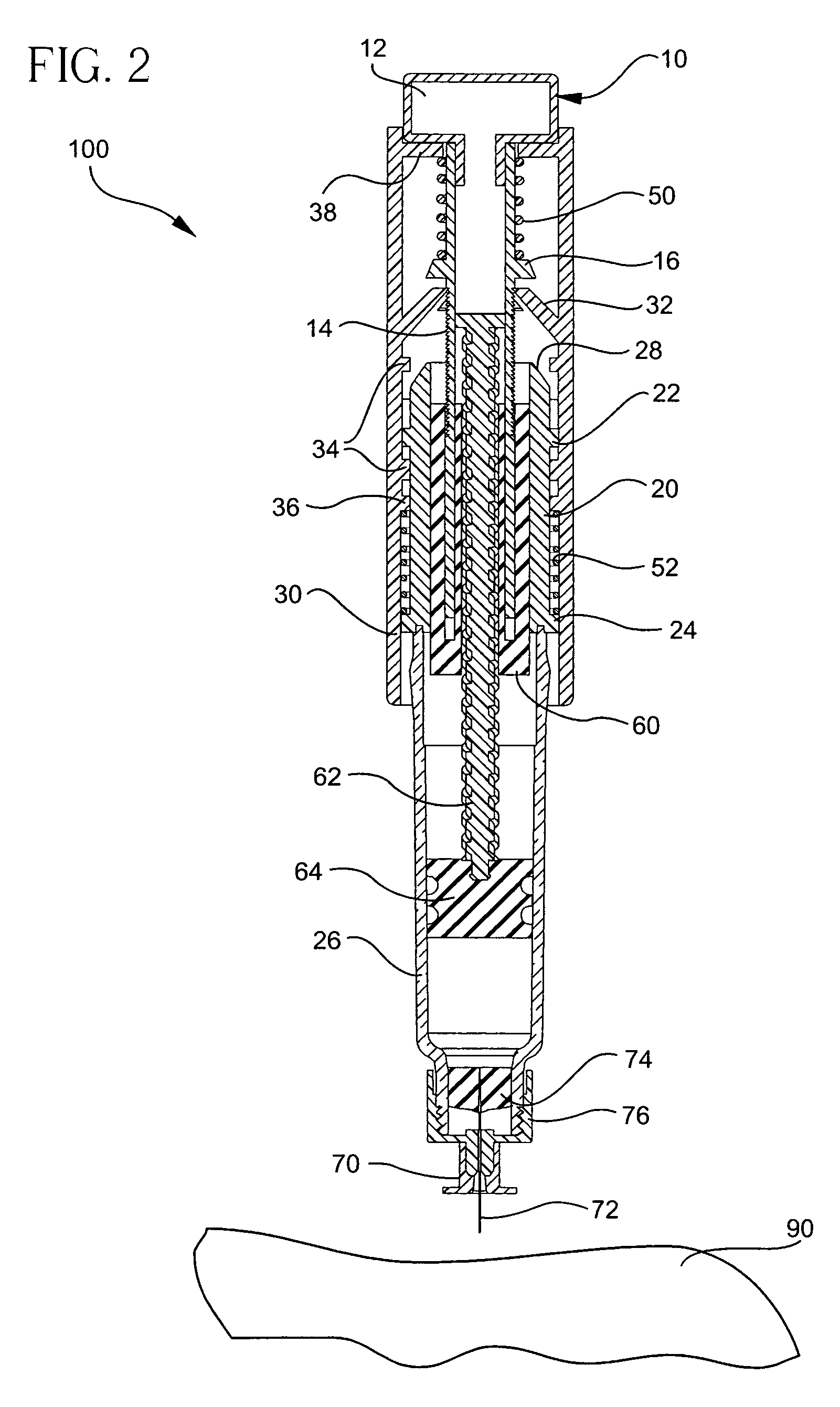
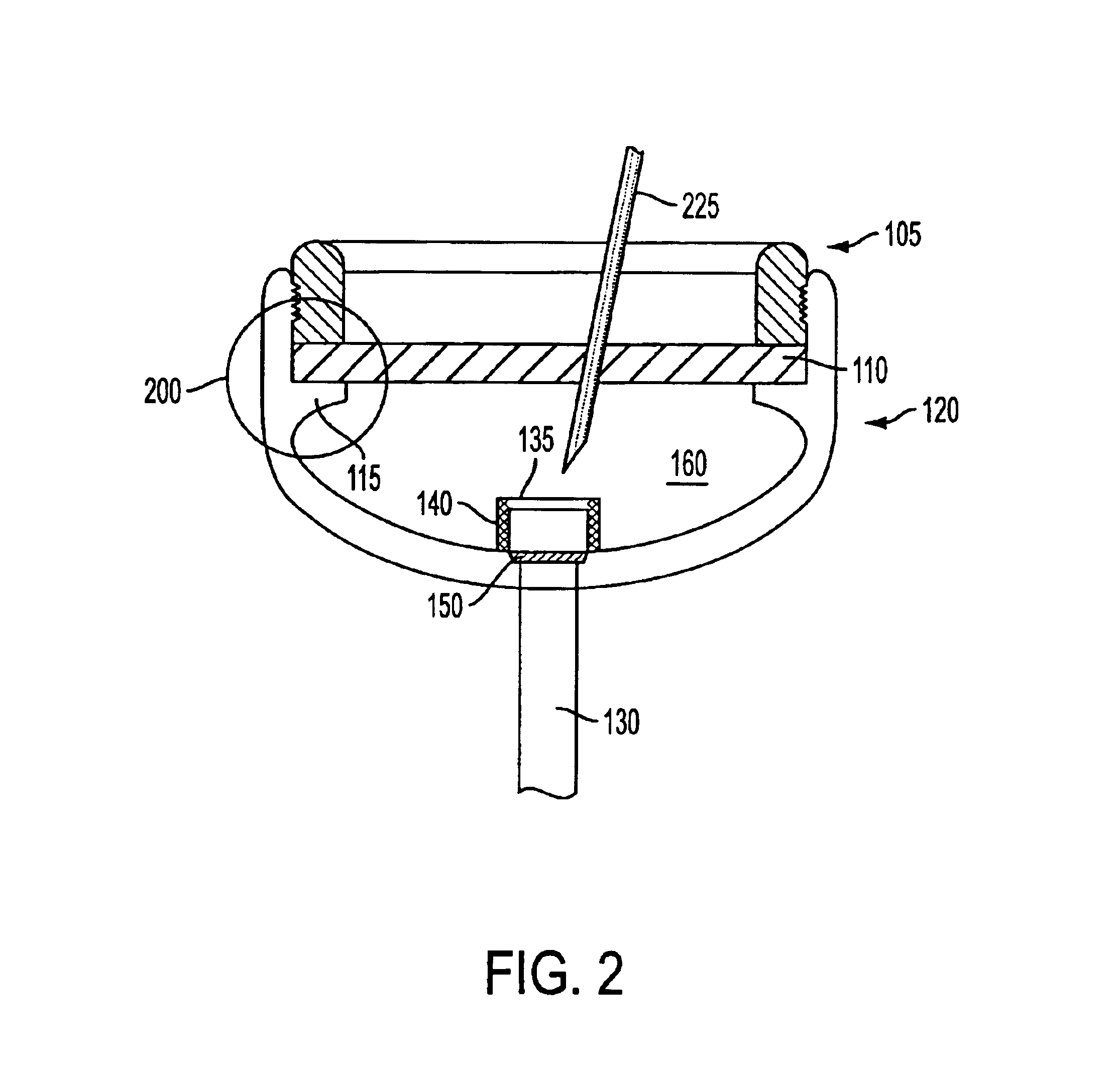
Injector device with force lock-out and injection rate limiting mechanisms
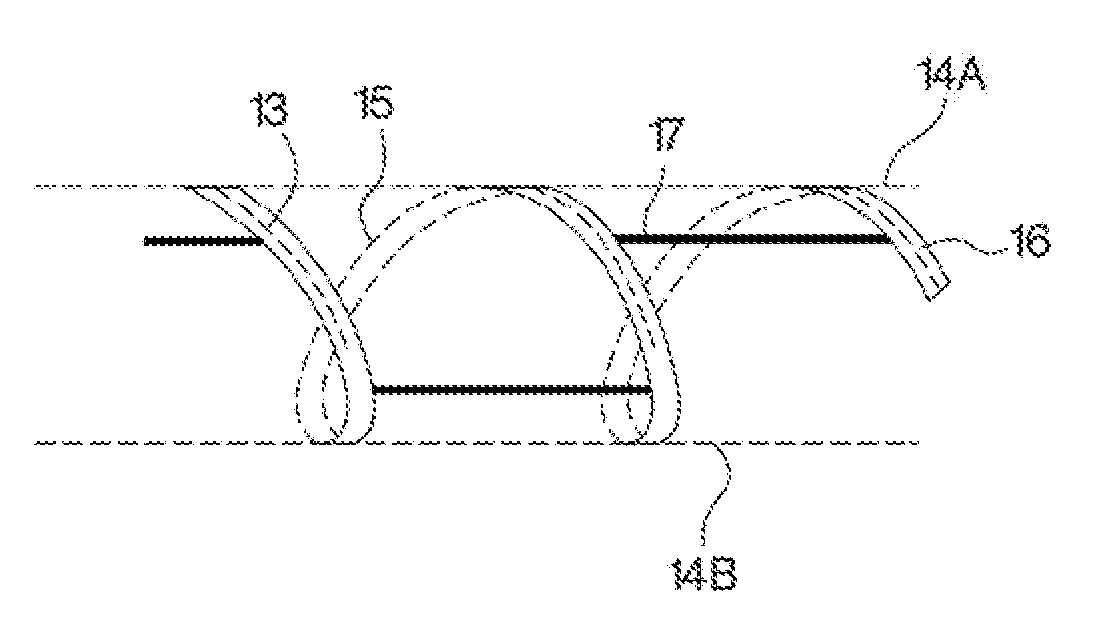
ActiveUS20060229570A1Inhibit injectionEliminate and minimize leakageAmpoule syringesAutomatic syringesRate limitingNeedle puncture
An injectable substance delivery device comprising a pen device body, a cartridge, a plunger, a drive mechanism, and at least one of a lock-out mechanism and a rate-limiting mechanism. The lock-out mechanism is provided through a ratchet engagement between the body and the plunger to restrict plunger movement and to ensure that the required needle puncture depth is realized prior to injection by locking out the injection mechanism from advancing until a specified force is applied to the skin. A rate-limiting mechanism is also provided through a user compressed plunger drive spring to ensure that a specific rate of injection is realized during the injection of a medicament.
Owner:BECTON DICKINSON & CO
Method and apparatus for rate limiting
A method and apparatus for a network monitor internals mechanism, which serves to translate packet data into multiple concurrent streams of encoded network event data, to contribute to enterprise management, reporting, and global mechanisms for aggregating monitors at a centralized aggregation point, and to facilitate rate limiting techniques because such monitors are not in control (i.e. cannot back pressure flow) is provided.
Owner:MCAFEE LLC
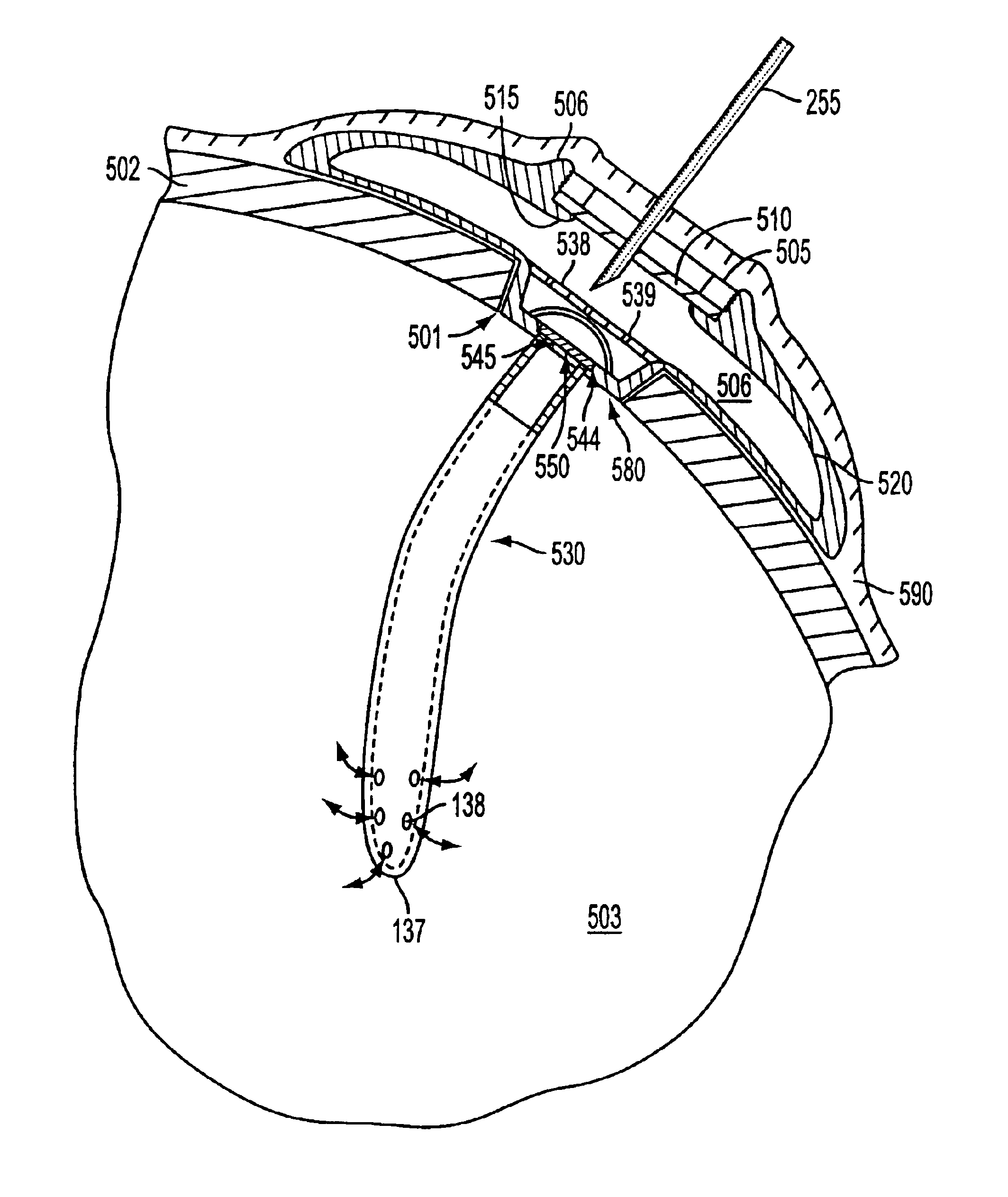
Implantable refillable and ported controlled release drug delivery device
InactiveUS6852106B2Prevent leakageEnhanced advantageSurgeryMedical devicesRate limitingDifferential pressure
An implantable, refillable, rate controlled drug delivery device is disclosed that includes a base structure having at least a first opening and a second opening, the base structure defining a chamber, a septum covering the first opening and configured to substantially prevent leakage from the first opening to an exterior of the device, a drug delivery tube comprising a first and second distal end, wherein the first distal end of the tube communicates with the chamber through the second opening, and at least one rate-limiting permeable membrane disposed across a passage between the base structure and the second distal end of the drug delivery tube, which membrane passively regulates drug delivery. The drug delivery device is used to provide controlled drug delivery to an internal portion of the body and is advantageously leak-proof and does not rely on a pressure differential to drive the drug from the device.
Owner:CONTROL DELIVERY SYST
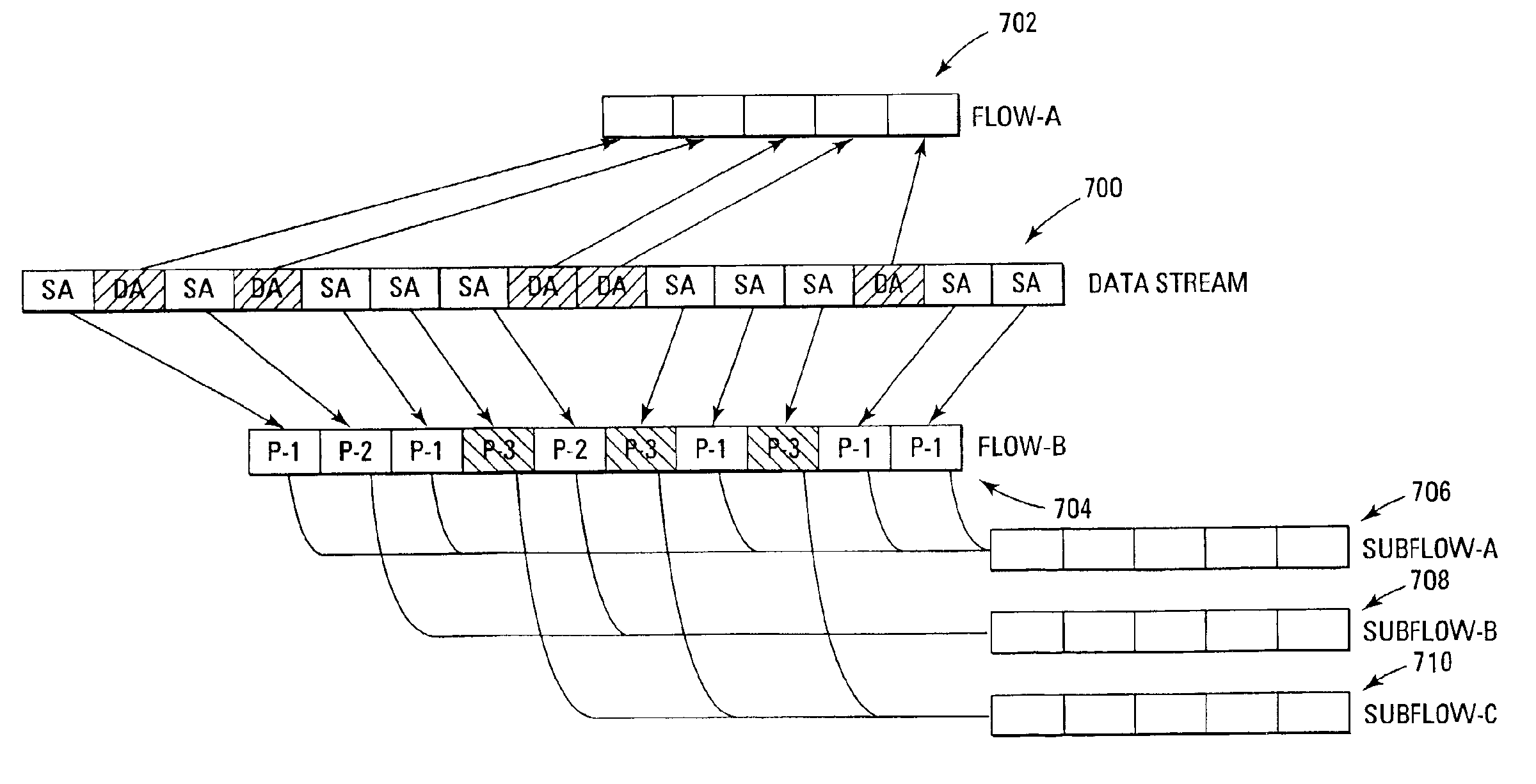
System and method for hierarchical policing of flows and subflows of a data stream
ActiveUS7042848B2Facilitating layered policingMaximizing exploitationError preventionTransmission systemsRate limitingData stream
A system and method for policing individual flows and subflows of a data stream. Data traffic streams are classified into separate traffic flows, which in turn can be further classified into subflows, thereby providing for different priority levels of subsets of the flow. The subflows may be still further classified into additional subflows, creating a hierarchical, layered prioritization that can be metered at each vertical and horizontal level of the hierarchy. A packet flow rate of each of the subflows is compared to a predefined rate limit to allow subflows of a flow to have different priorities therebetween.
Owner:RPX CORP
Hierarchical metering in a virtual router-based network switch
Owner:GOOGLE LLC
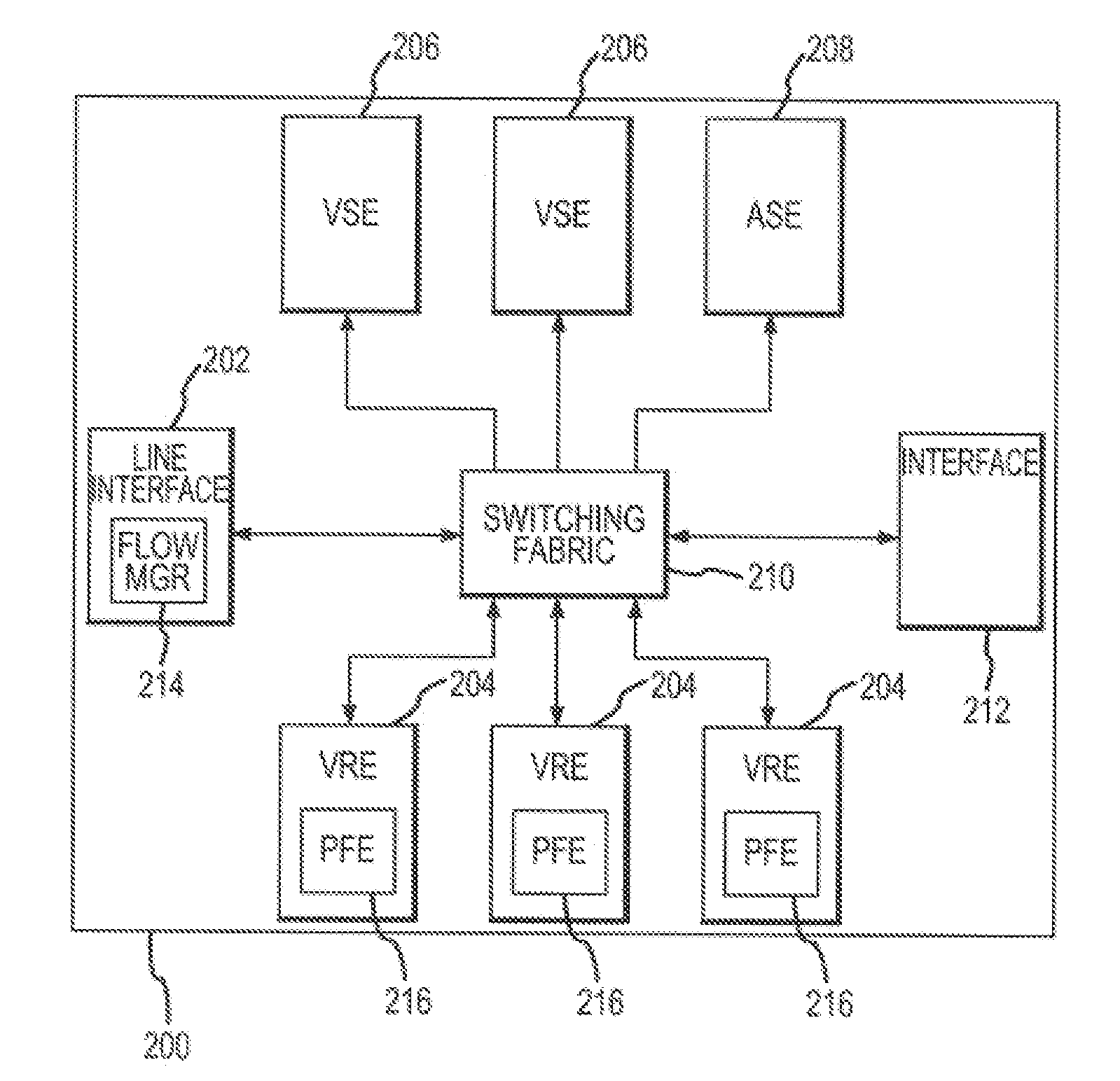
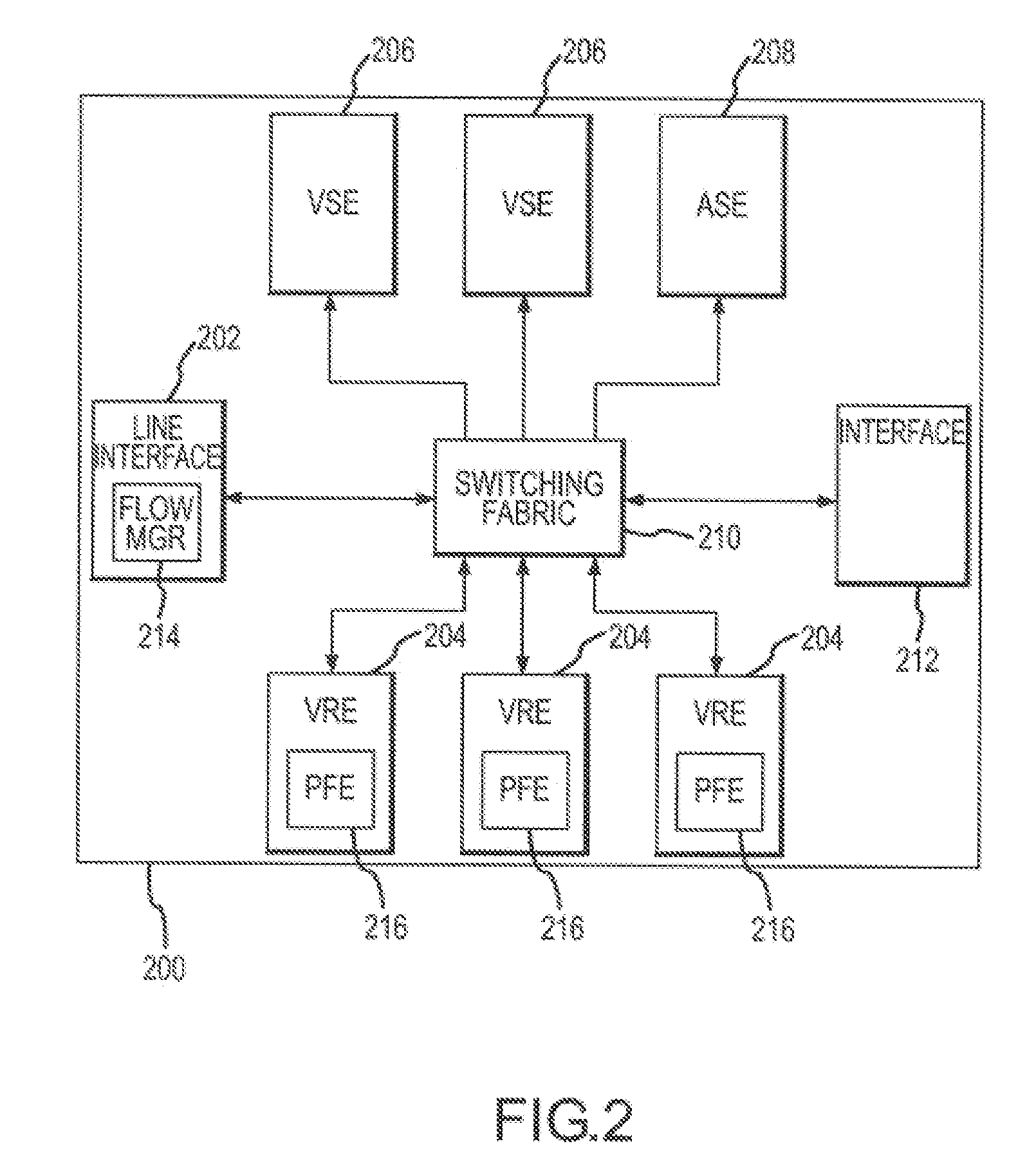
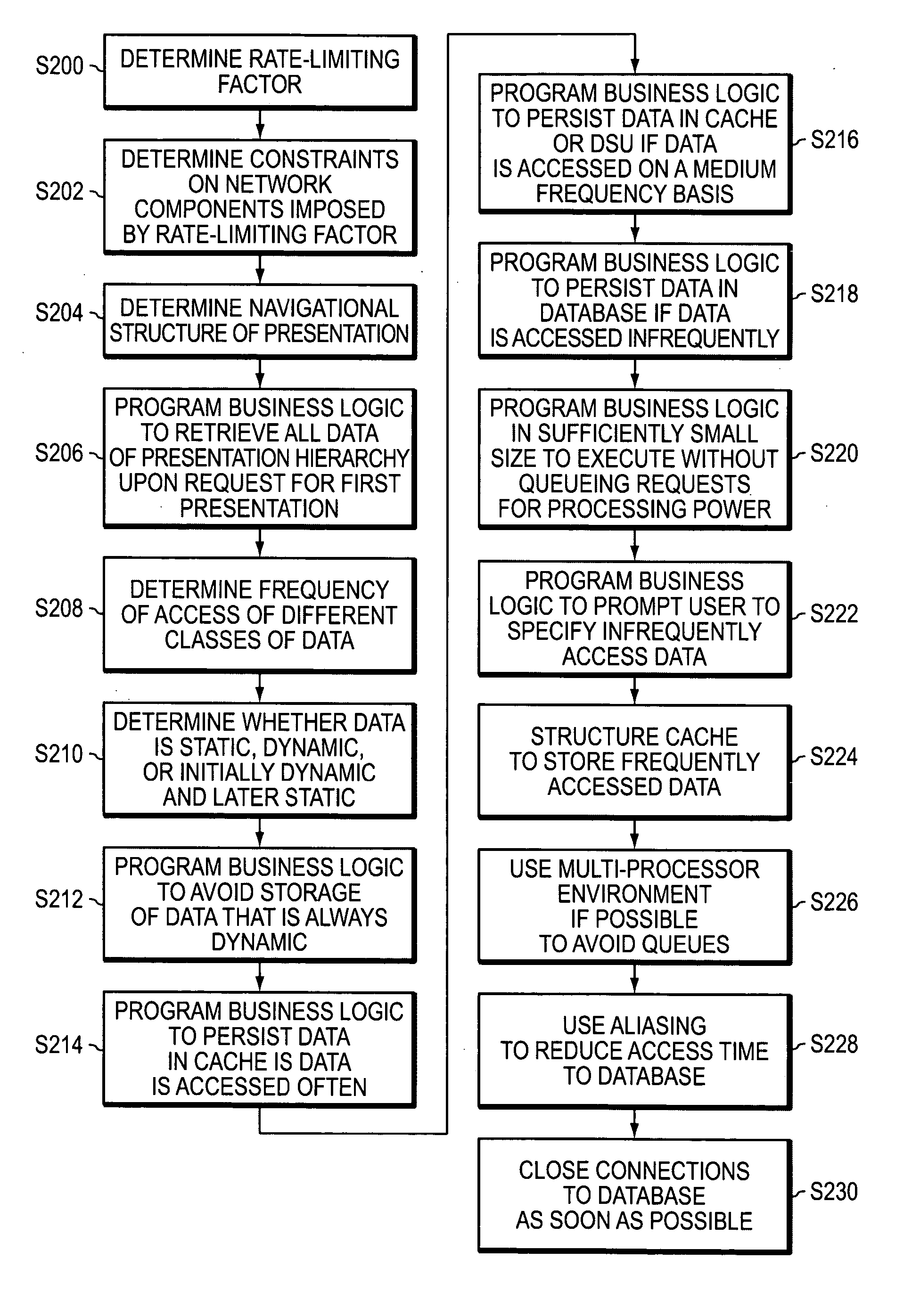
Methods, apparatuses, systems, and articles for determining and implementing an efficient computer network architecture
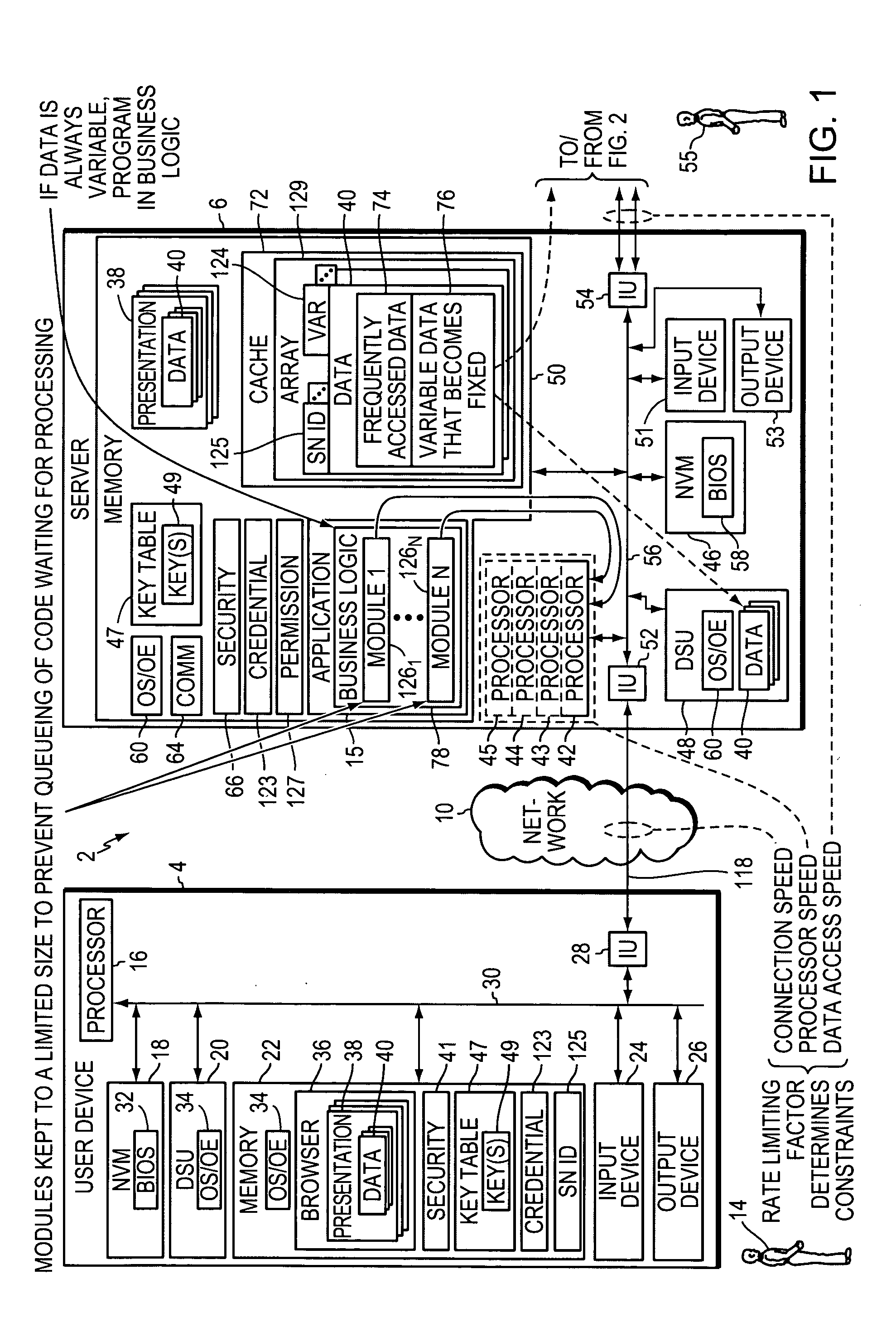
InactiveUS20050138198A1Reduce system performanceAvoid queuingMultiple digital computer combinationsTransmissionRate limitingNetwork architecture
Methods, apparatuses, systems, and articles of the invention are used to enhance the efficiency of a computing environment, and to improve its responsiveness to one or more users. In the invention, queuing of data or computer instructions is avoided since this would detract from best case performance for a network environment. The rate-limiting factor for the network is determined, and all constraints imposed by the rate-limiting factor are determined. Business logic is programmed in modules sufficiently small to avoid queuing of instructions. Data is stored by frequency of access and persistence to increase responsiveness to user requests. Requests for data from a data storage device are fulfilled not only with the requested data, but also additional data which is likely to be requested in the navigational hierarchy of presentations to which the requested data belongs.
Owner:IT WORKS
Systems and methods for replacing signal artifacts in a glucose sensor data stream
ActiveUS20120203467A1Accurate detectionAvoid adjustmentMedical automated diagnosisCatheterRate limitingDiffusion
Systems and methods for minimizing or eliminating transient non-glucose related signal noise due to non-glucose rate limiting phenomenon such as interfering species, ischemia, pH changes, temperatures changes, known or unknown sources of mechanical, electrical and / or biochemical noise, and the like. The system monitors a data stream from a glucose sensor and detects signal artifacts that have higher amplitude than electronic or diffusion-related system noise. The system processes some or the entire data stream continually or intermittently based at least in part on whether the signal artifact event has occurred.
Owner:DEXCOM INC
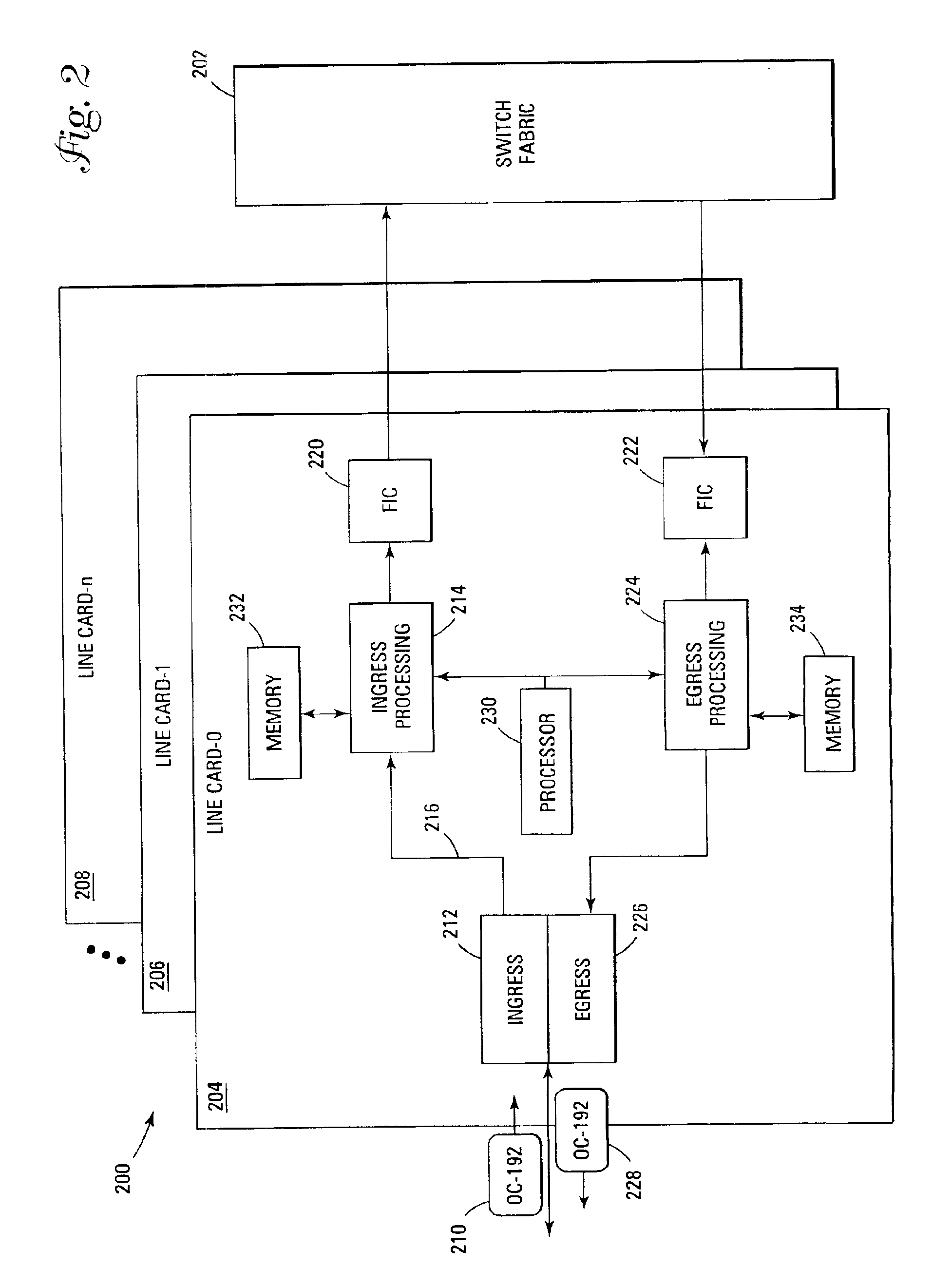
Method and system for controlling traffic over a computer network
ActiveUS20100128605A1Not negatively affect performanceShort amount of timeEnergy efficient ICTError preventionRate limitingTraffic capacity
A rate limiter incorporated in a server connected to a network. The rate limiter is adapted to reduce congestion in the network in response to a congestion notification message. The server is adapted to send packets over the network. The rate limiter includes at least one of: a server rate limiter engine adapted to rate limit the packets in response to the server; a virtual machine rate limiter engine adapted to rate limit the packets in response to a virtual machine associated with the packets, the virtual machine hosted by the server; a flow rate limiter engine adapted to rate limit the packets in response to a flow associated with the packets; the flow being one of a plurality of flows transporting packets over the network; and a transmit engine adapted to rate limit the packets in response to a virtual pipe of the network for transmitting the packets.
Owner:AVAGO TECH INT SALES PTE LTD
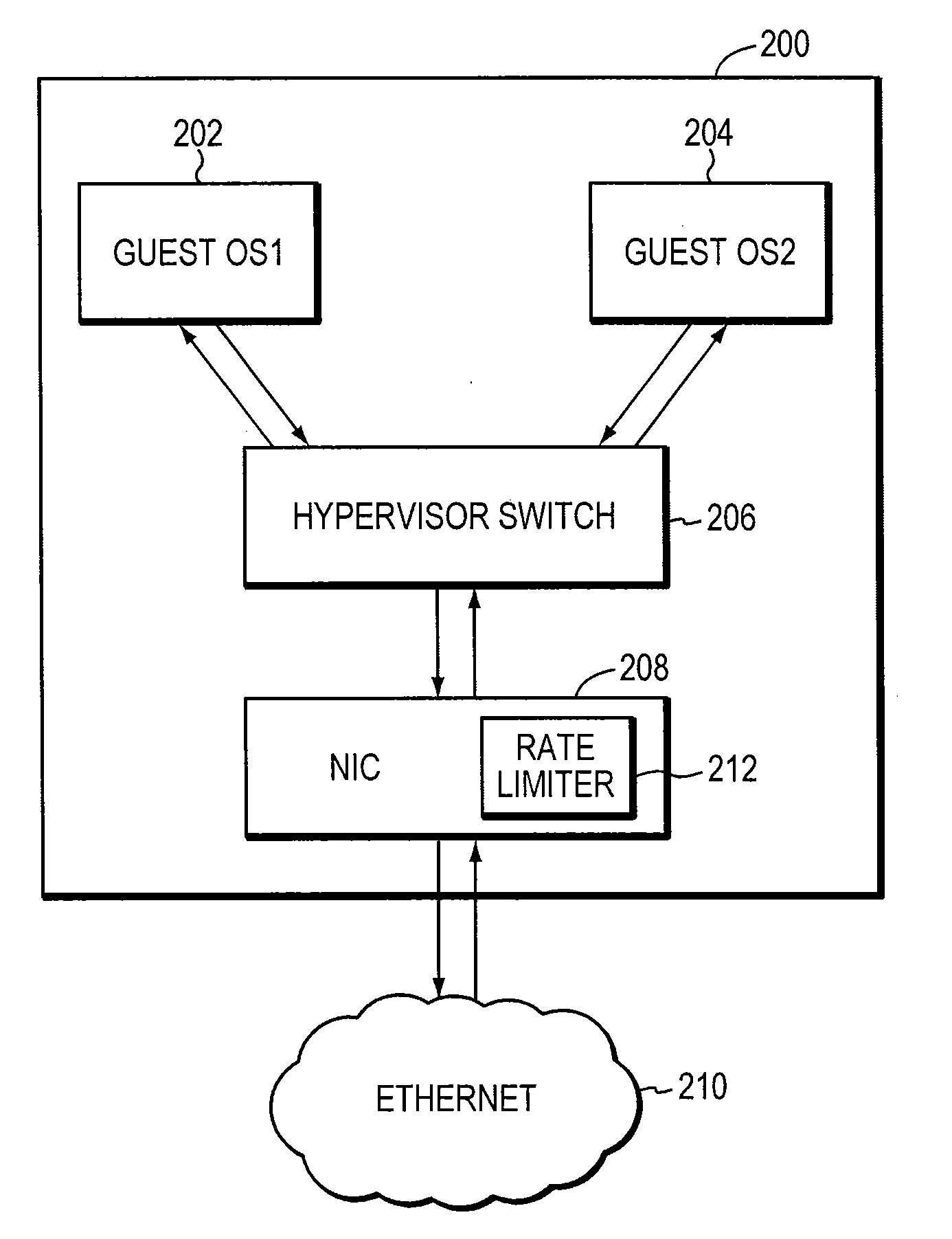
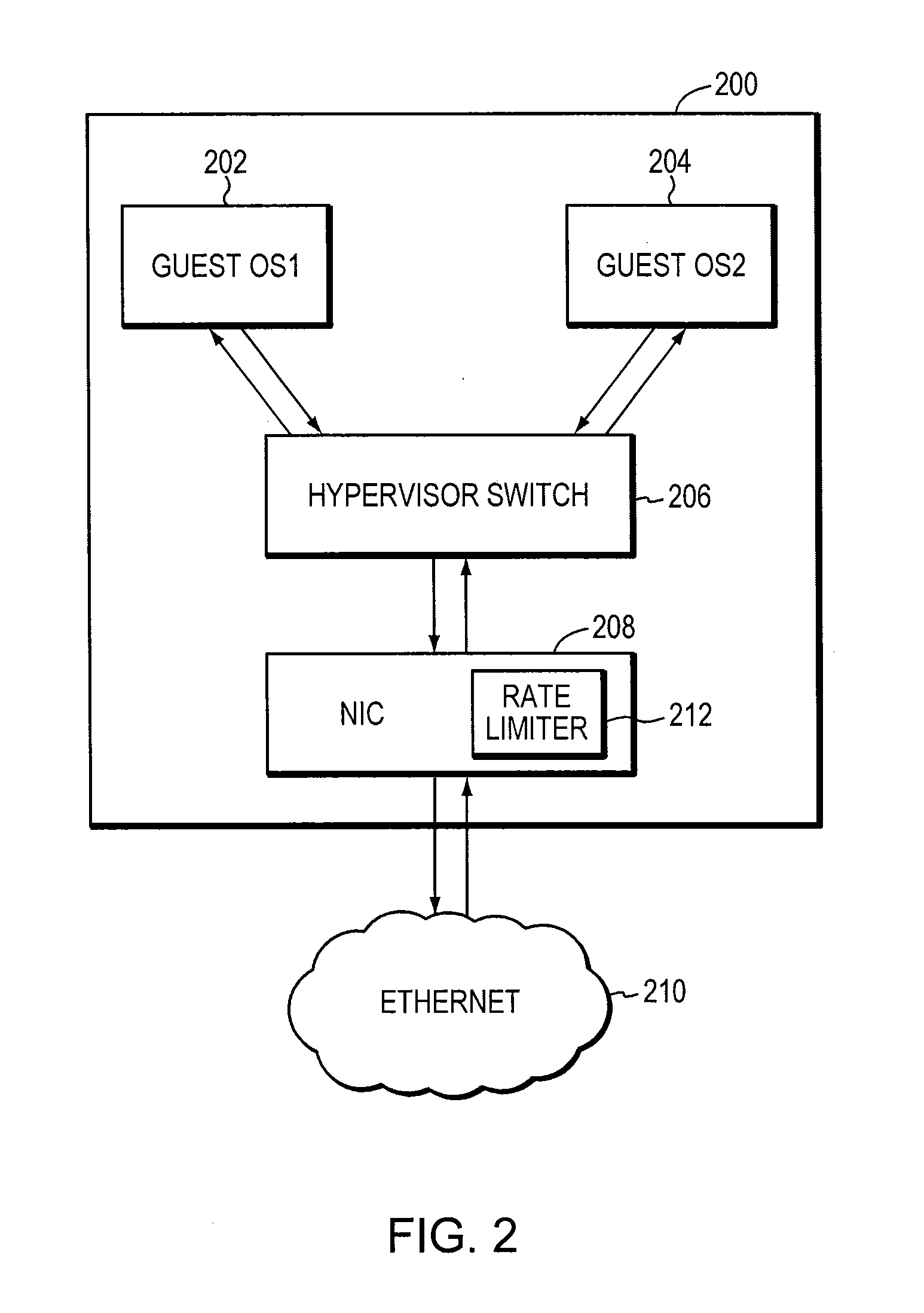
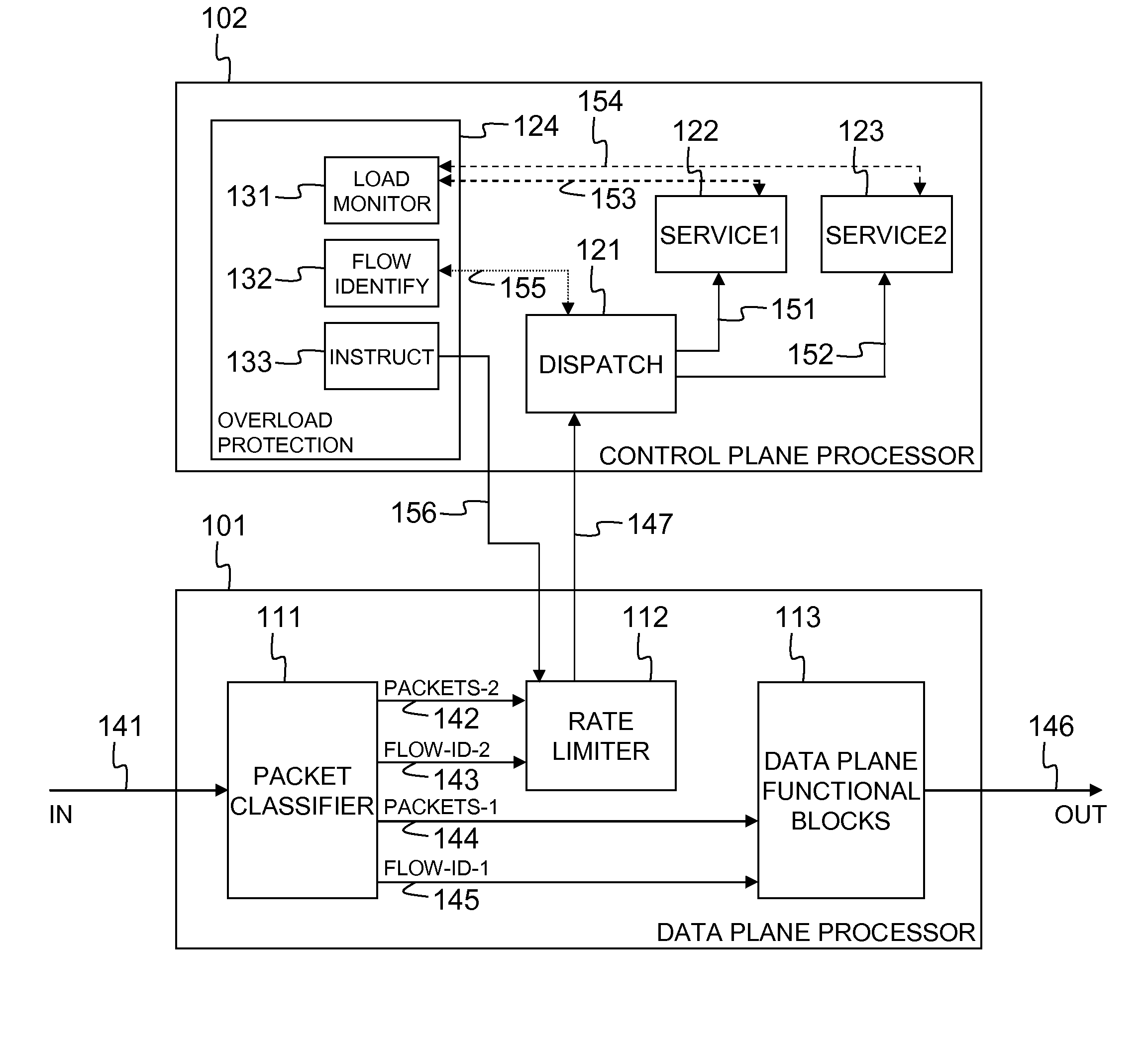
Network node with control plane processor overload protection
InactiveUS20070127491A1Easy to controlIncrease flexibilityError preventionTransmission systemsRate limitingEngineering
Owner:ALCATEL LUCENT SAS
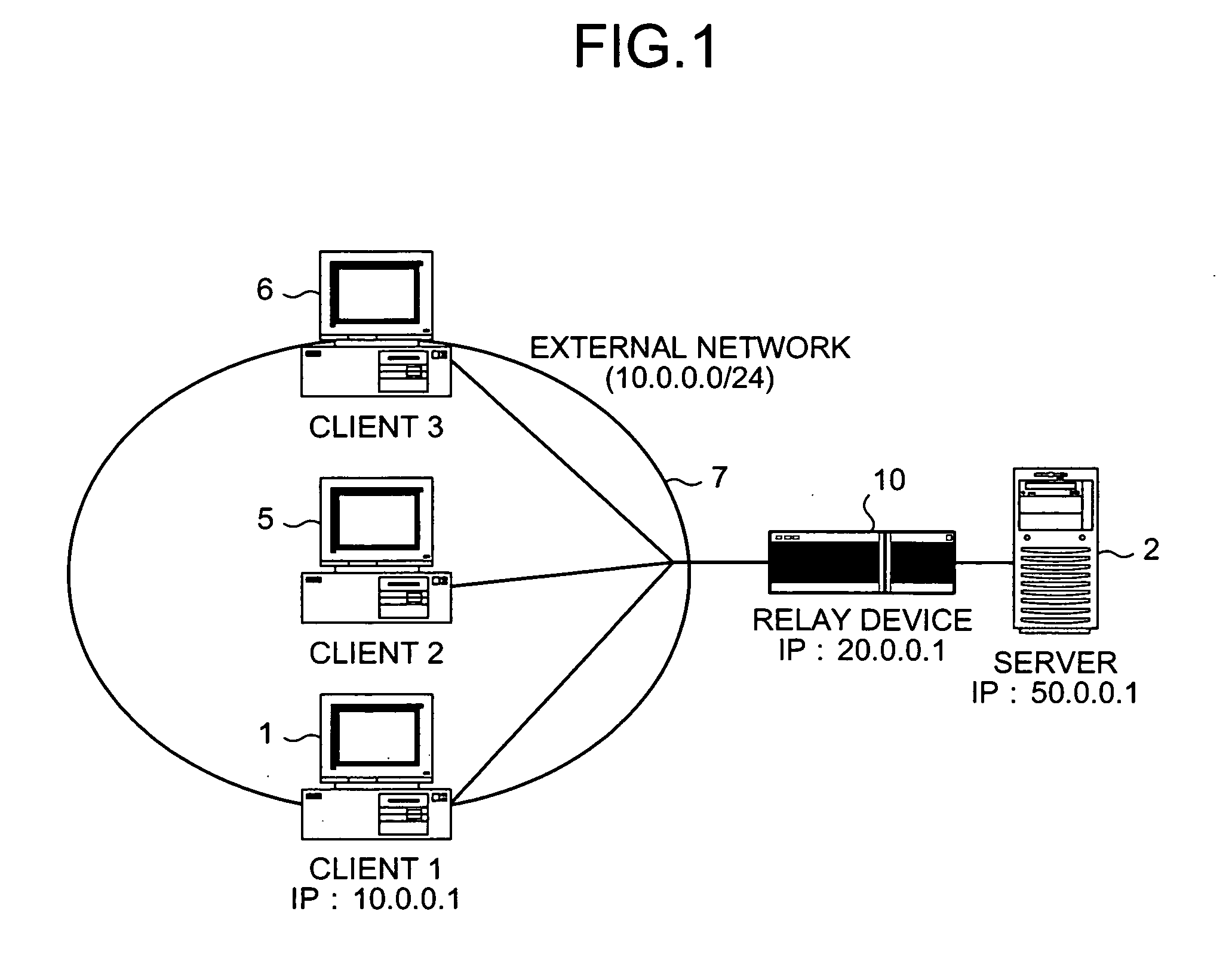
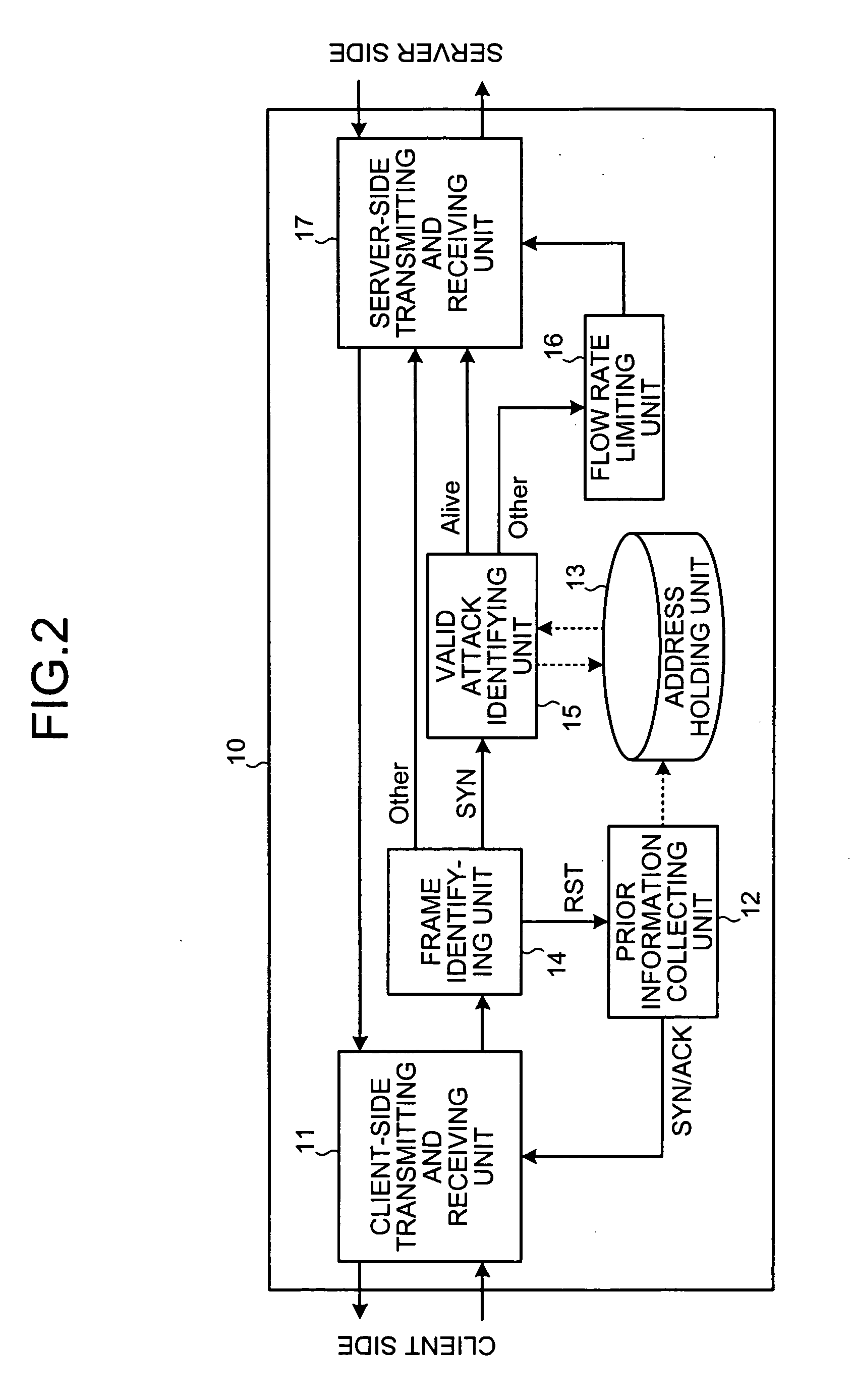
Frame-transfer control device, DoS-attack preventing device, and DoS-attack preventing system
InactiveUS20060280121A1Protection attackControl flowError preventionTransmission systemsRate limitingPrior information
A prior information collecting unit transmits in advance a SYN / ACK frame to an address of a client in an external network, and monitors a response to the SYN / ACK frame. If there is no response, the prior information collecting unit determines that the address is a valid attack address. If there is a response with a RST frame, the prior information collecting unit determines that the address is an invalid attack address. An address holding unit stores a responding state of the client. A valid attack identifying unit detects a valid attack frame having a valid attack address as a source address from among frames addressed to the server, based on information stored in the address holding unit. A flow rate limiting unit limits a flow rate at the time of transferring the valid attack frames to the server.
Owner:FUJITSU LTD
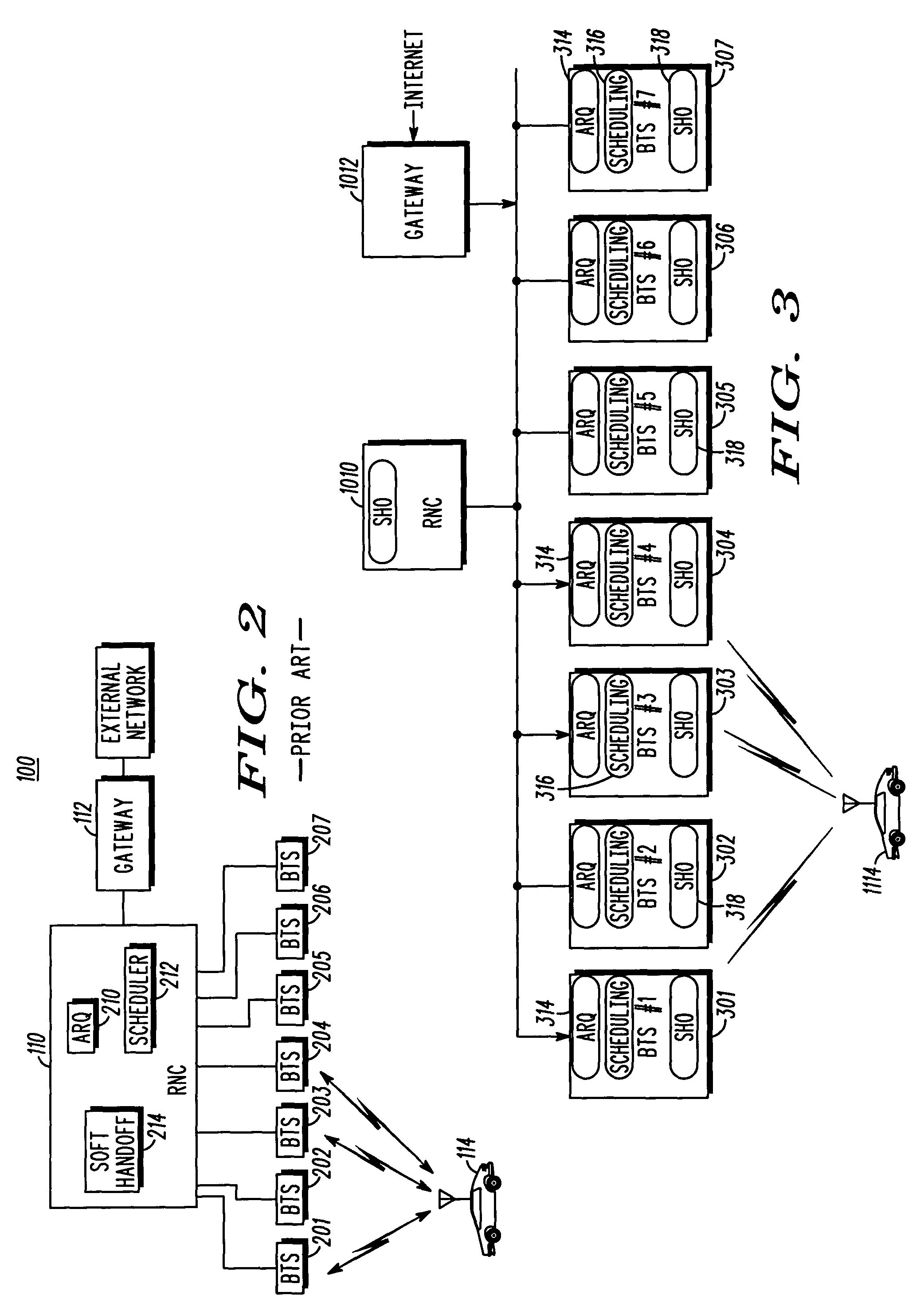
Enhanced uplink rate selection by a communication device during soft handoff
InactiveUS7321780B2Error prevention/detection by using return channelPower managementRate limitingCommunications system
A method for rate selection by a communication device for enhanced uplink during soft handoff in a wireless communication system includes a first step of receiving information from a scheduler. This information can include one or more of scheduling, a rate limit, a power margin limit, and a persistence. A next step includes determining a data rate for an enhanced uplink during soft handoff using the information. A next step includes transmitting to a serving base station on an enhanced uplink channel at the data rate determined from the determining step.
Owner:GOOGLE TECH HLDG LLC
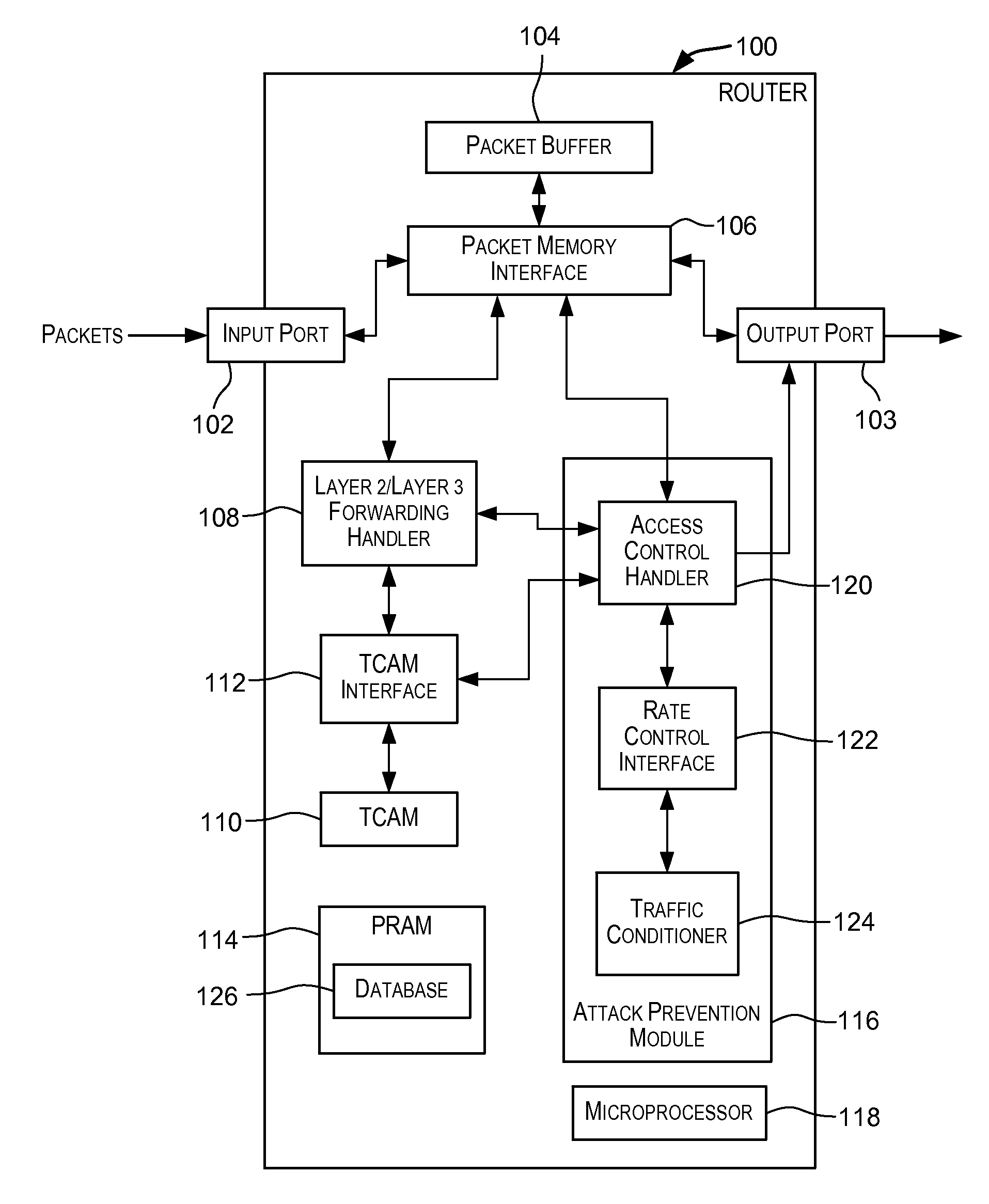
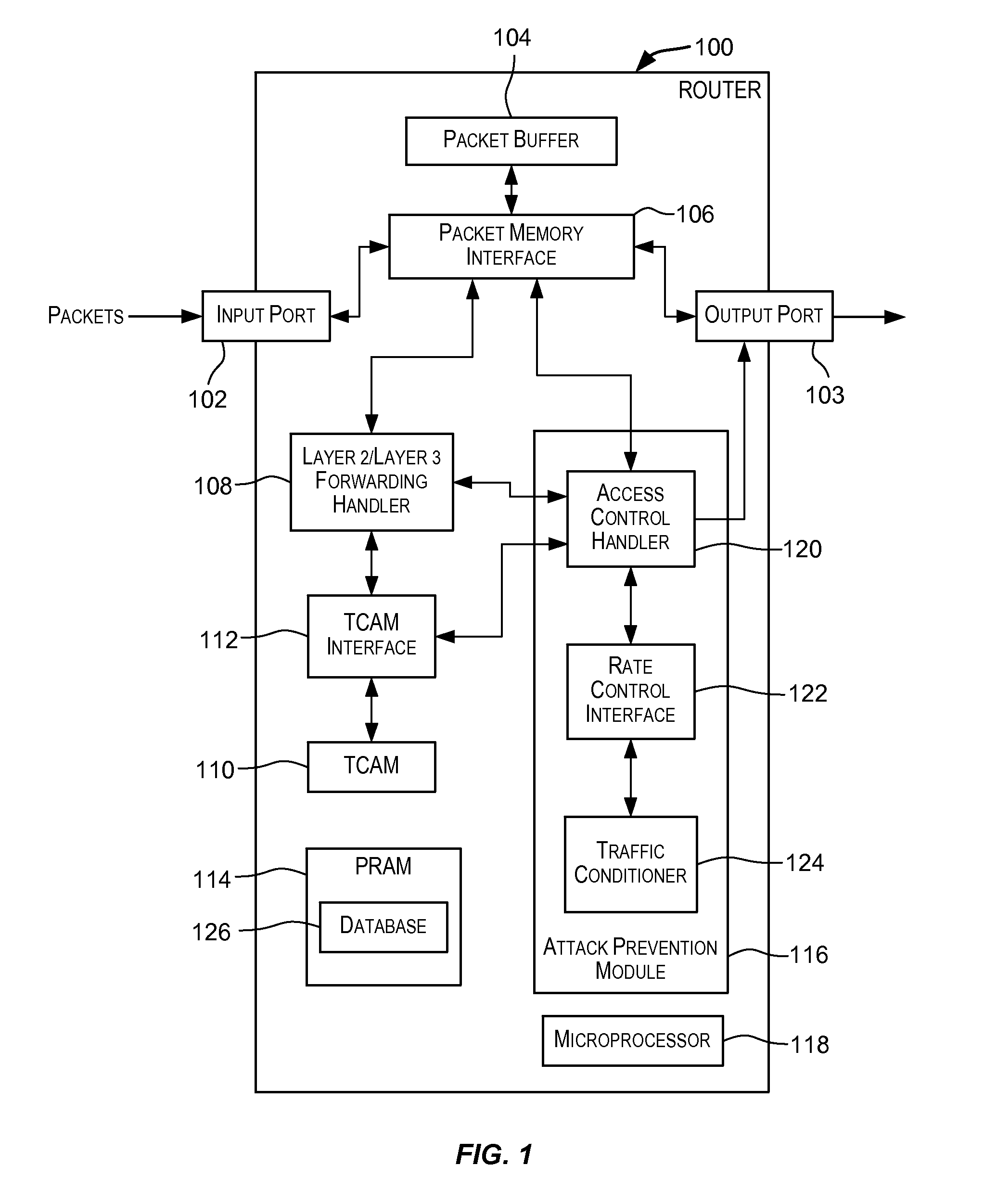
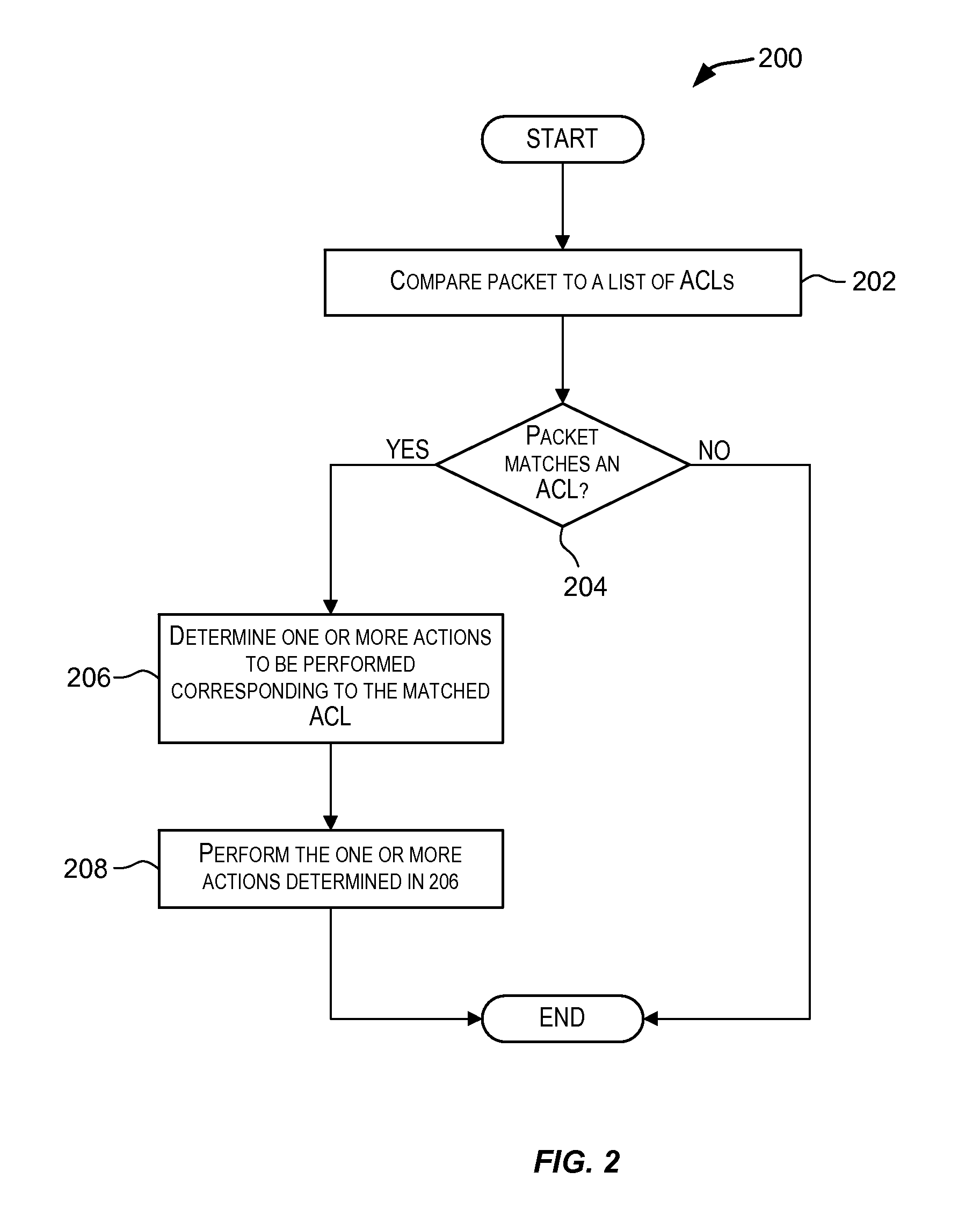
Attack prevention techniques
Techniques for detecting and responding to attacks on computer and network systems including denial-of-service (DoS) attacks. A packet is classified as potentially being an attack packet if it matches an access control list (ACL) specifying one or more conditions. One or more actions may be performed responsive to packets identified as potential attack packets. These actions may include dropping packets identified as potential attack packets for a period of time, rate limiting a port over which the potential attack packets are received for a period of time, and other actions.
Owner:AVAGO TECH INT SALES PTE LTD
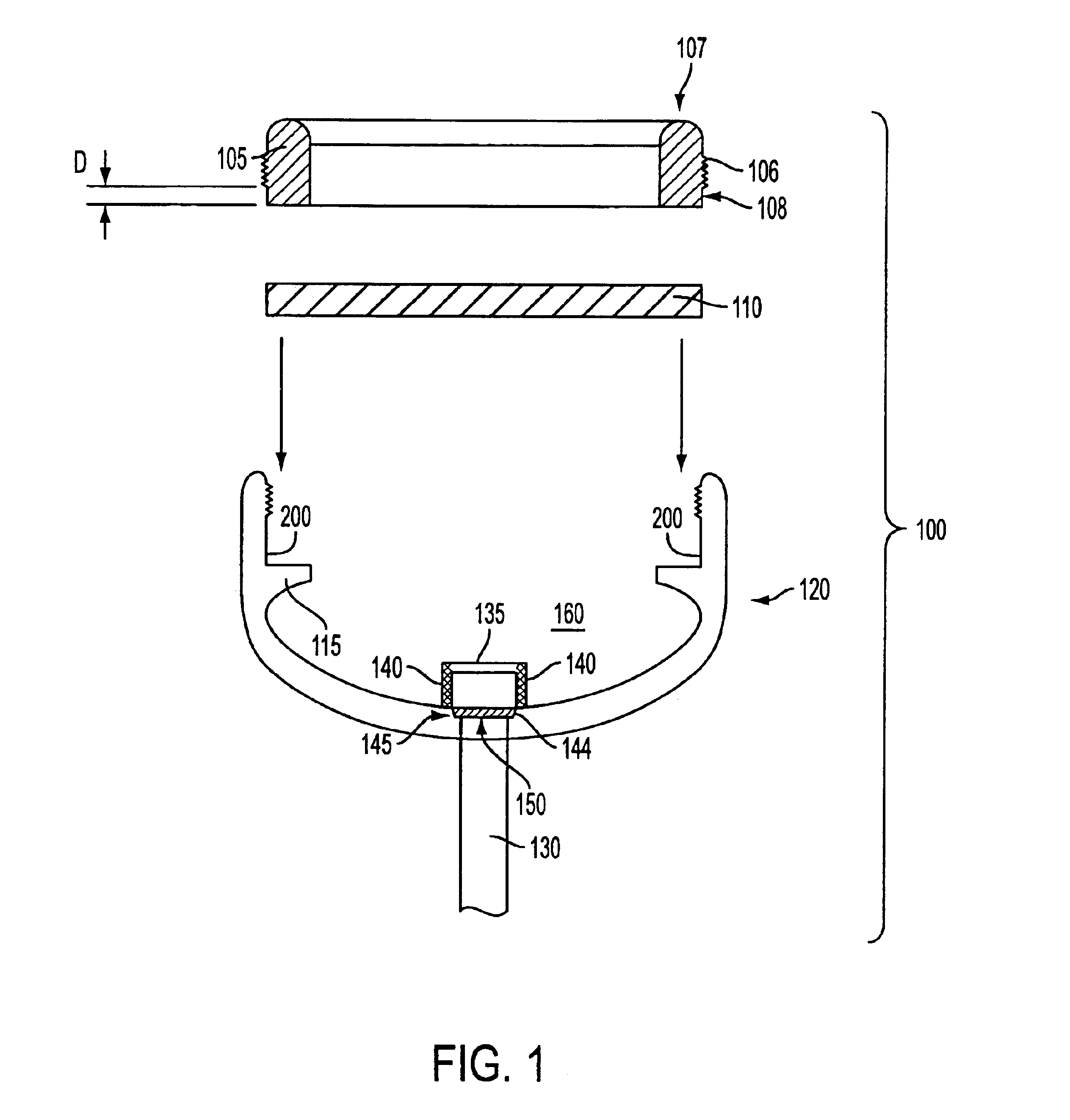
Rate limiting barriers for implantable devices and methods for fabrication thereof
InactiveUS7175873B1Solution value is not highIncrease valueSurgeryPharmaceutical containersRate limitingHydrophobic polymer
A method of coating an implantable medical device, such as a stent, is disclosed. The method includes applying a formulation on a first polymer layer containing a therapeutic substance to form a second layer. The formulation can contain a highly hydrophobic polymer or a solvent which is a poor solvent for the drug or the polymer of the first layer. The formulation can have a low surface tension value or a high Weber number value.
Owner:ABBOTT CARDIOVASCULAR
Rate limiting barriers for implantable devices
A coating for implantable medical devices including an interpenetrating polymer network serving as a rate limiting barrier.
Owner:ABBOTT CARDIOVASCULAR
Metering packet flows for limiting effects of denial of service attacks
ActiveUS20050157647A1Simple and fast implementationError preventionTransmission systemsRate limitingData pack
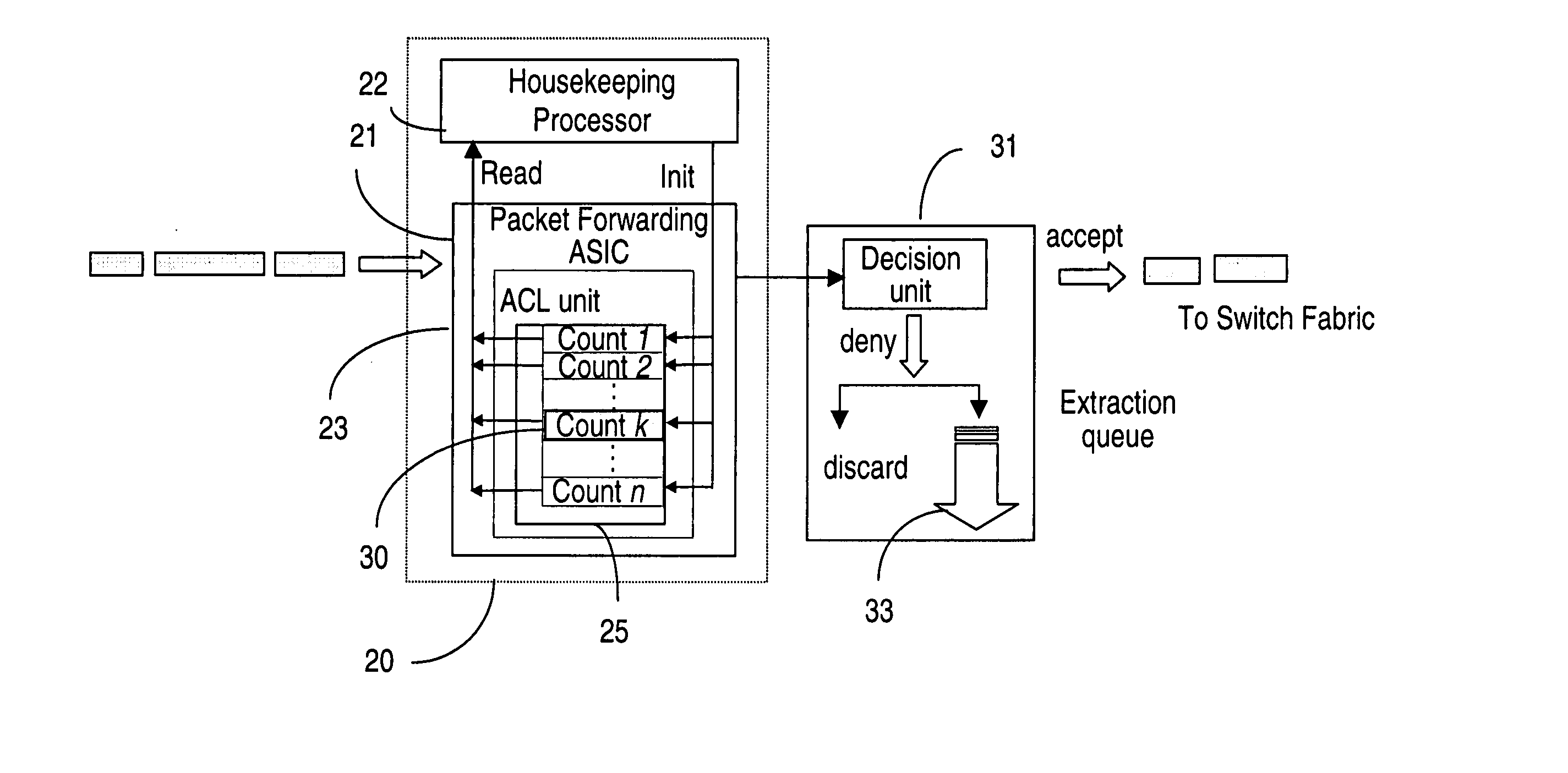
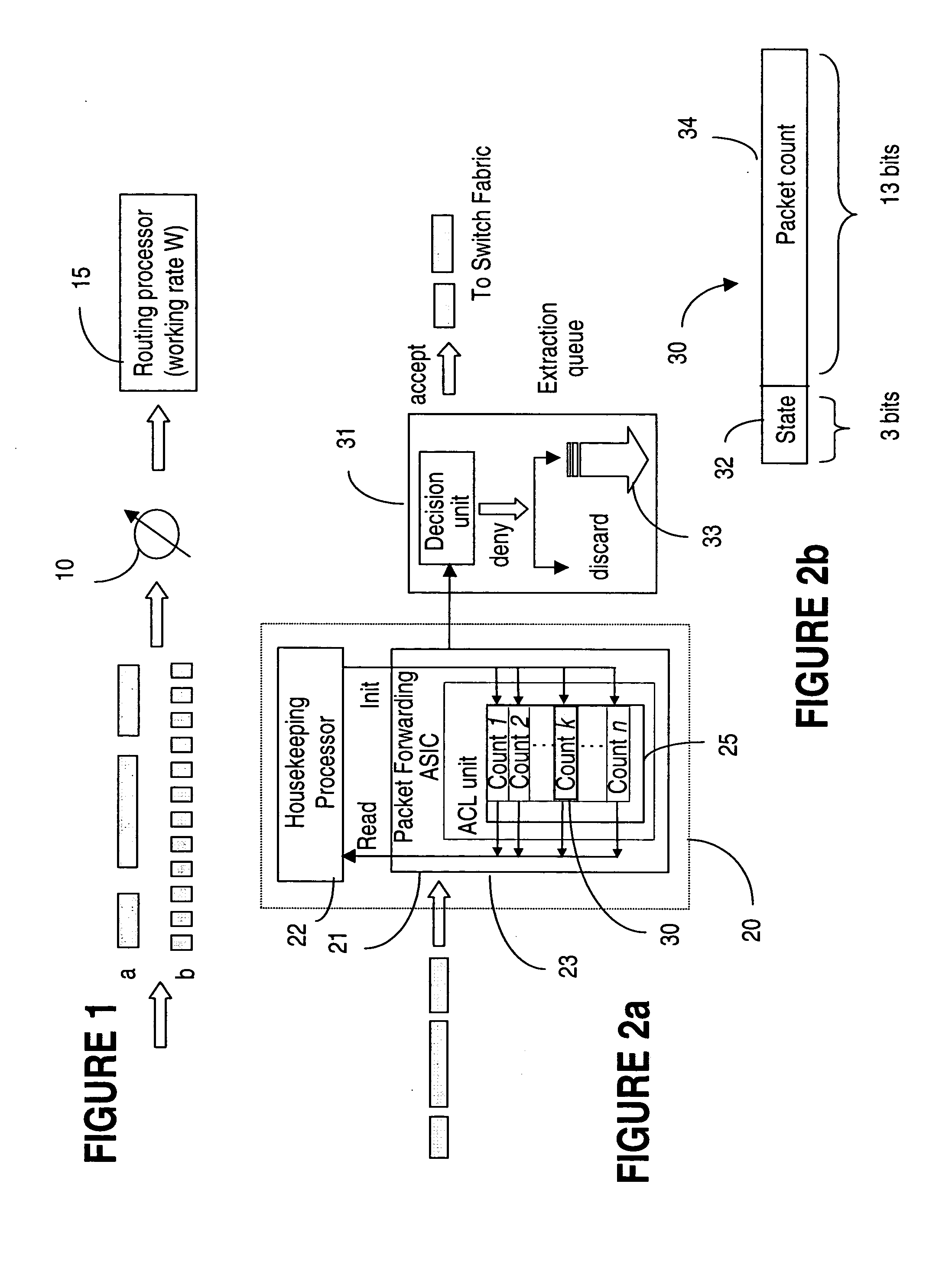
The packet rate limiting method and system is used for detecting and blocking the effects of DoS attacks on IP networks. The method uses an ACL counter that stores an action parameter in the first 3 most significant bits and uses 13 bits as a packet counter. A rate limit is enforced by setting the packet counter to an initial value, and resetting this value at given intervals of time. The action parameter enables the ACL to accept or deny packets based on this rate limit. If the number of packets in the incoming flow saturates the packet counter before the reset time, the packets are denied access to the network until the counter is next reset. The denied packets may be just discarded or may be extracted for further examination.
Owner:RPX CORP
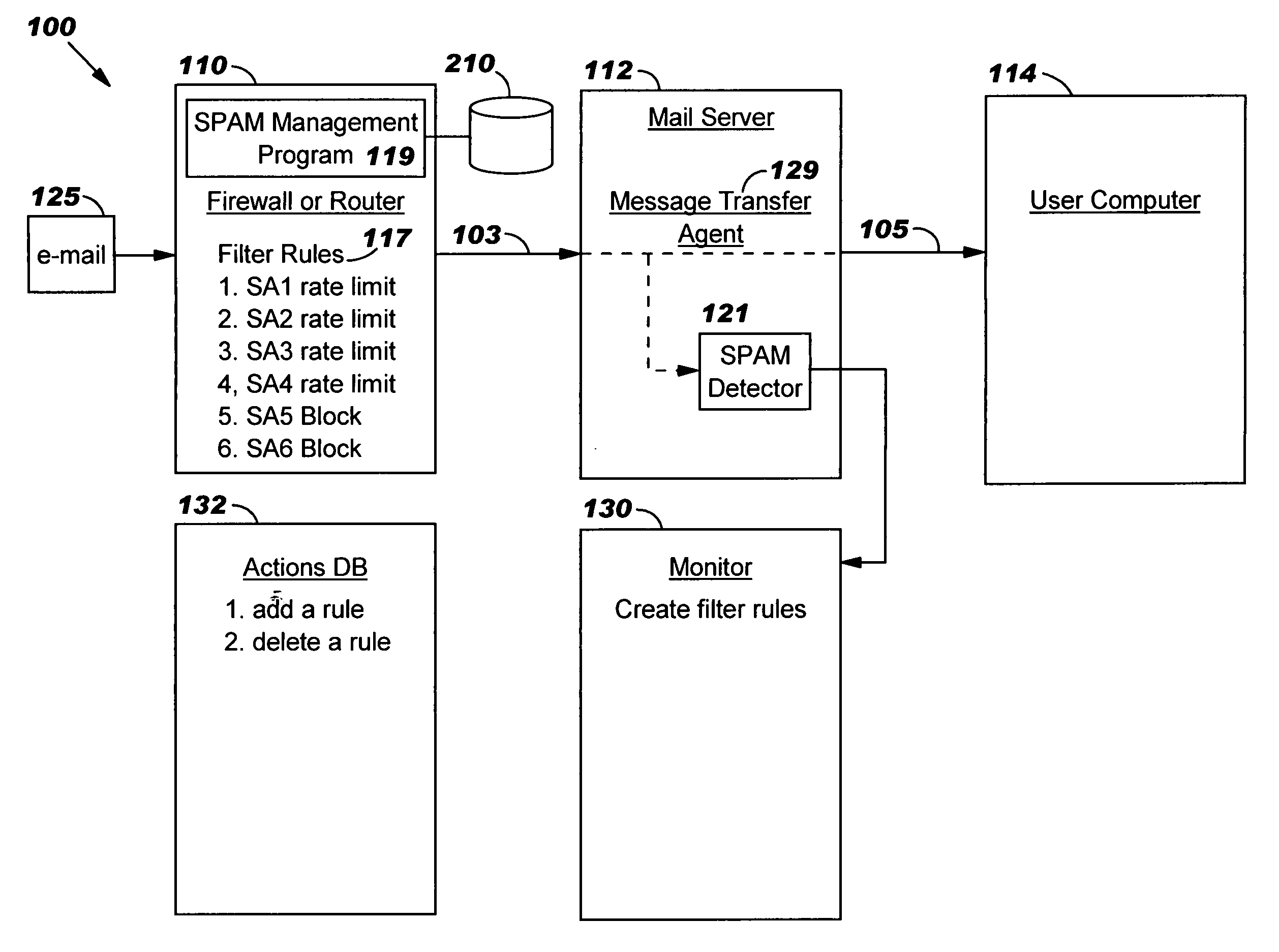
System, method and program to limit rate of transferring messages from suspected spammers
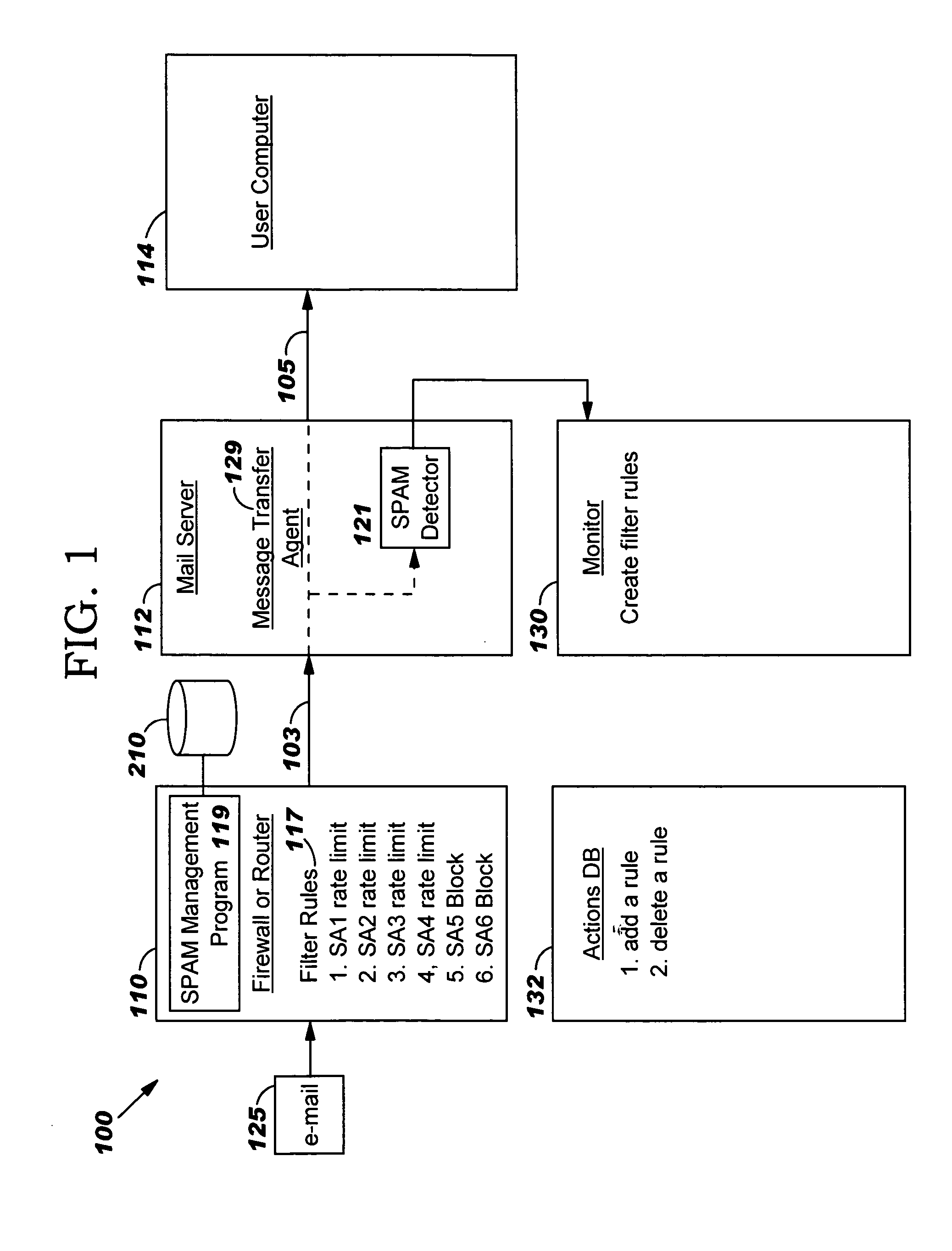
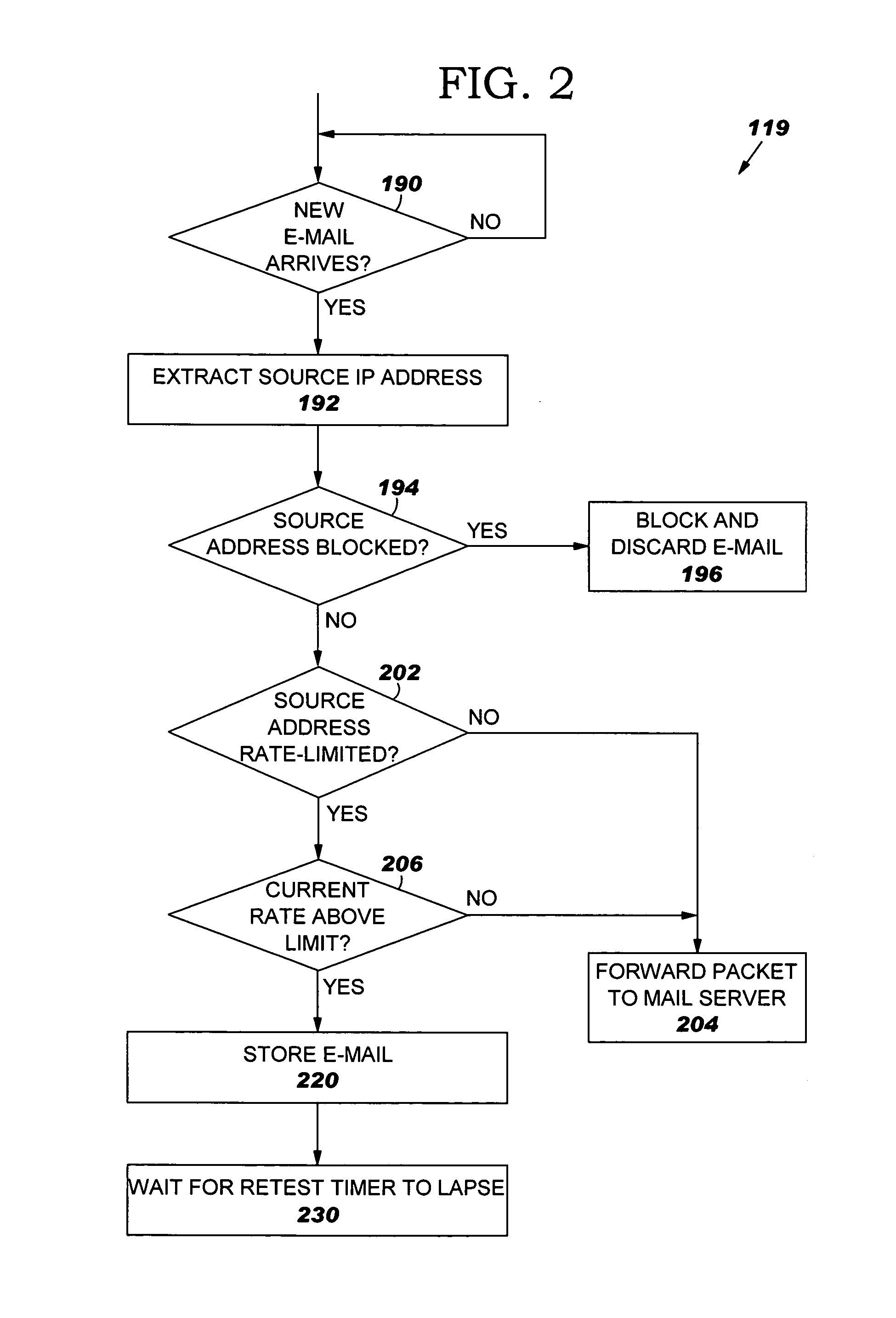
InactiveUS20060047769A1Multiple digital computer combinationsData switching networksRate limitingUnit of time
A system, method and program product for managing e-mails from a source suspected of sending spam. The e-mails are received at a firewall or router en route to a mail server. A determination is made whether a source has sent an e-mail which exhibits characteristics of spam. In response, subsequent e-mails from the source destined for the mail server are rate-limiting at the firewall or router such that the firewall or router limits a rate at which the subsequent e-mails are forwarded from the firewall or router to the mail server. The rate is predetermined and less than a maximum rate at which the firewall or router can physically forward e-mails to the mail server absent the rate limit. A determination is made whether another source has sent another e-mail which exhibits more characteristics of spam than the first said e-mail. In response, subsequent e-mails from this other source are blocked at the firewall or router. The rate limit can be a limit on a number of e-mails per unit of time from the source that will be forwarded from the firewall or router to the mail server.
Owner:IBM CORP
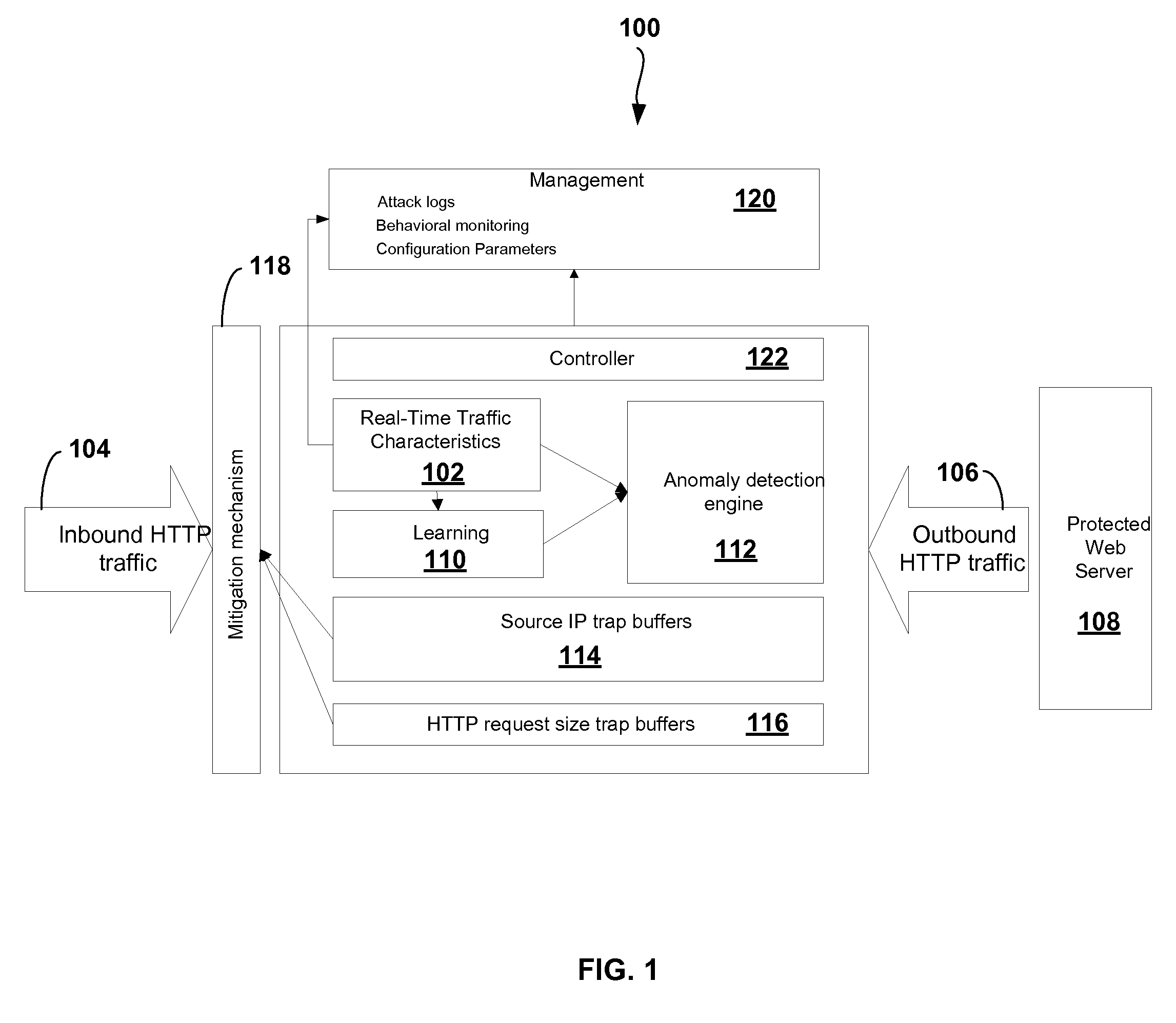
Adaptive Behavioral HTTP Flood Protection
A system and method to detect and mitigate denial of service and distributed denial of service HTTP “page” flood attacks. Detection of attack / anomaly is made according to multiple traffic parameters including rate-based and rate-invariant parameters in both traffic directions. Prevention is done according to HTTP traffic parameters that are analyzed once a traffic anomaly is detected. This protection includes a differential adaptive mechanism that tunes the sensitivity of the anomaly detection engine. The decision engine is based on a combination between fuzzy logic inference systems and statistical thresholds. A “trap buffer” characterizes the attack to allow an accurate mitigation according to the source IP(s) and the HTTP request URL's that are used as part of the attack. Mitigation is controlled through a feedback mechanism that tunes the level of rate limit factors that are needed in order to mitigate the attack effectively while letting legitimate traffic to pass.
Owner:RADWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com