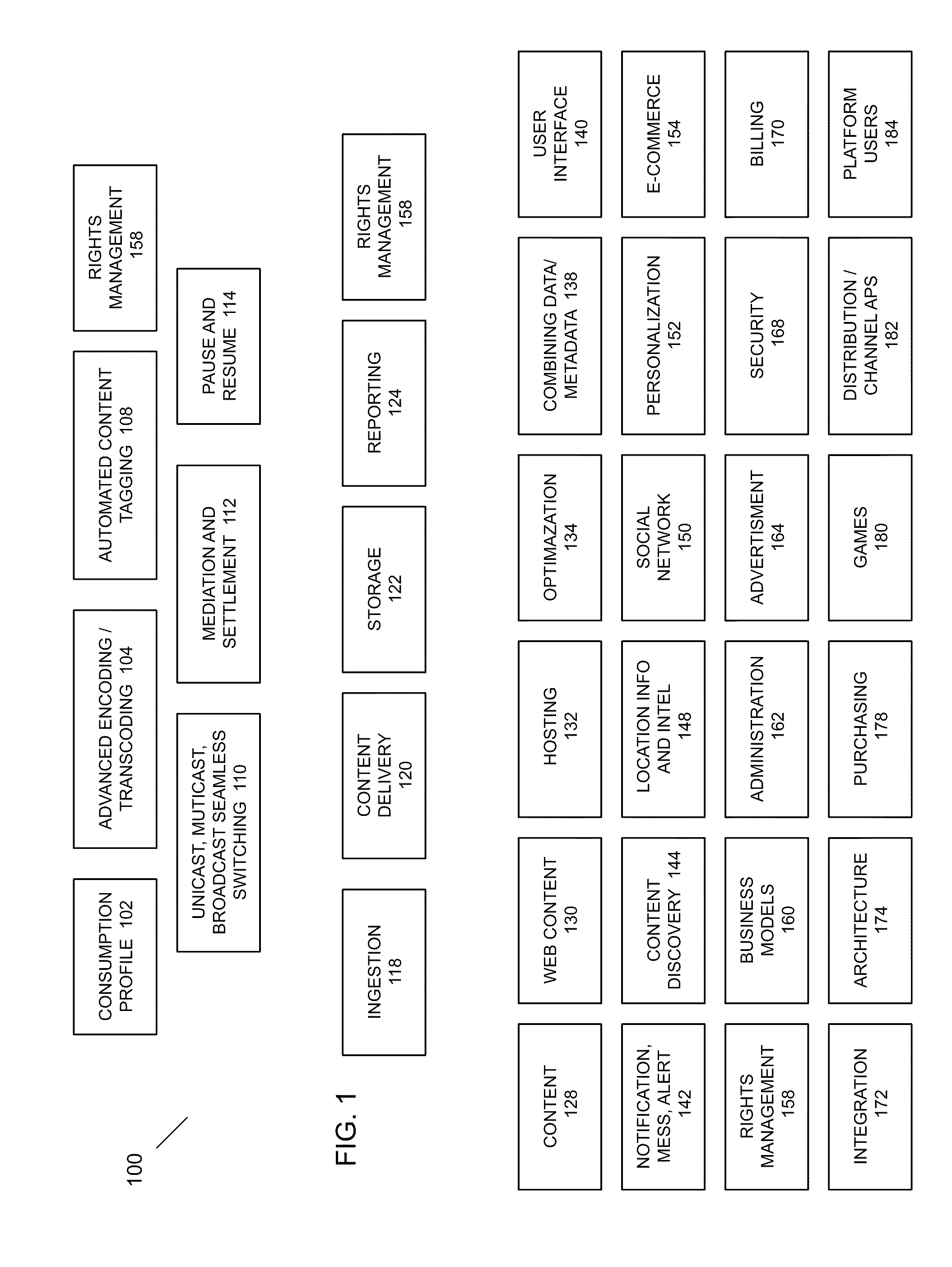
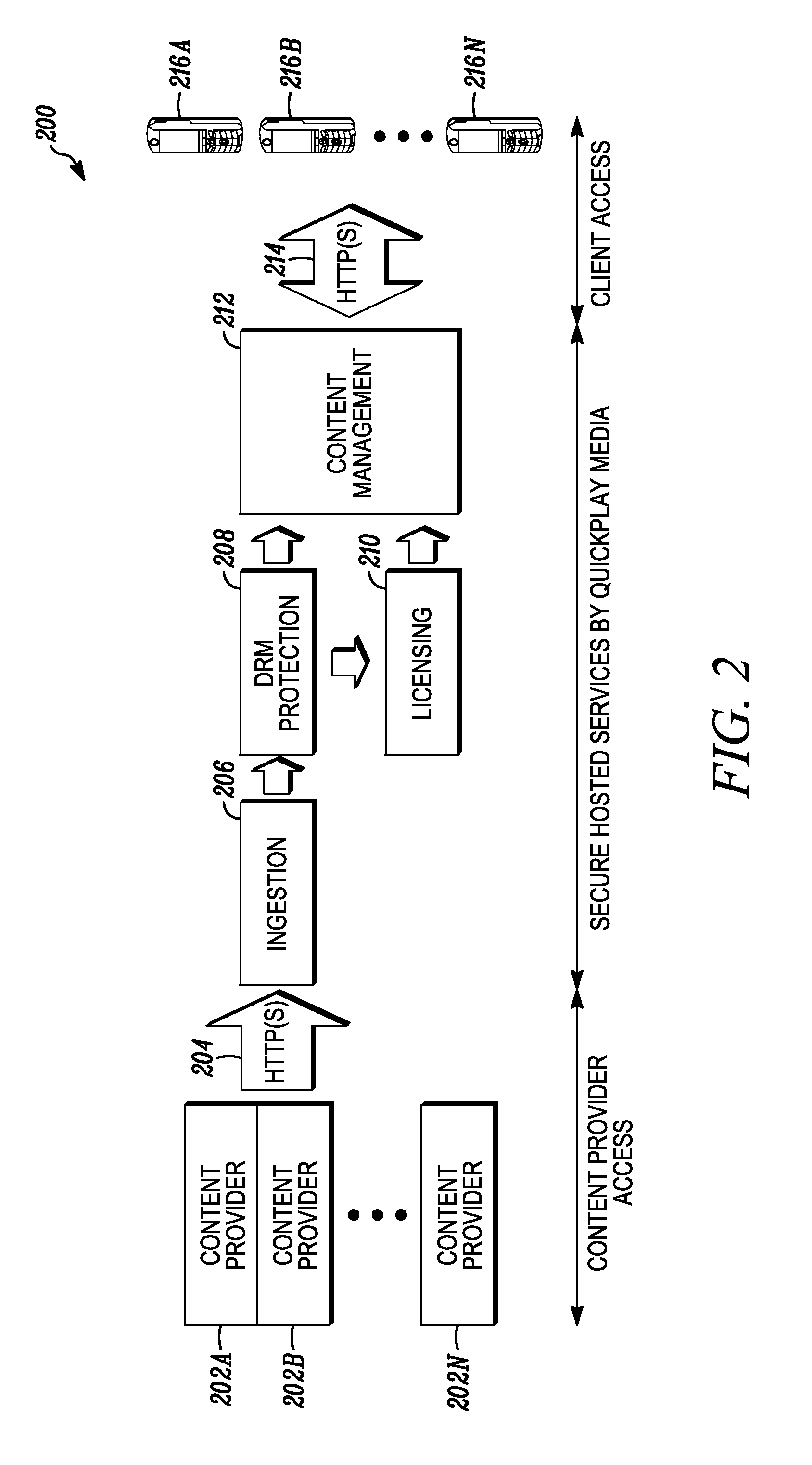
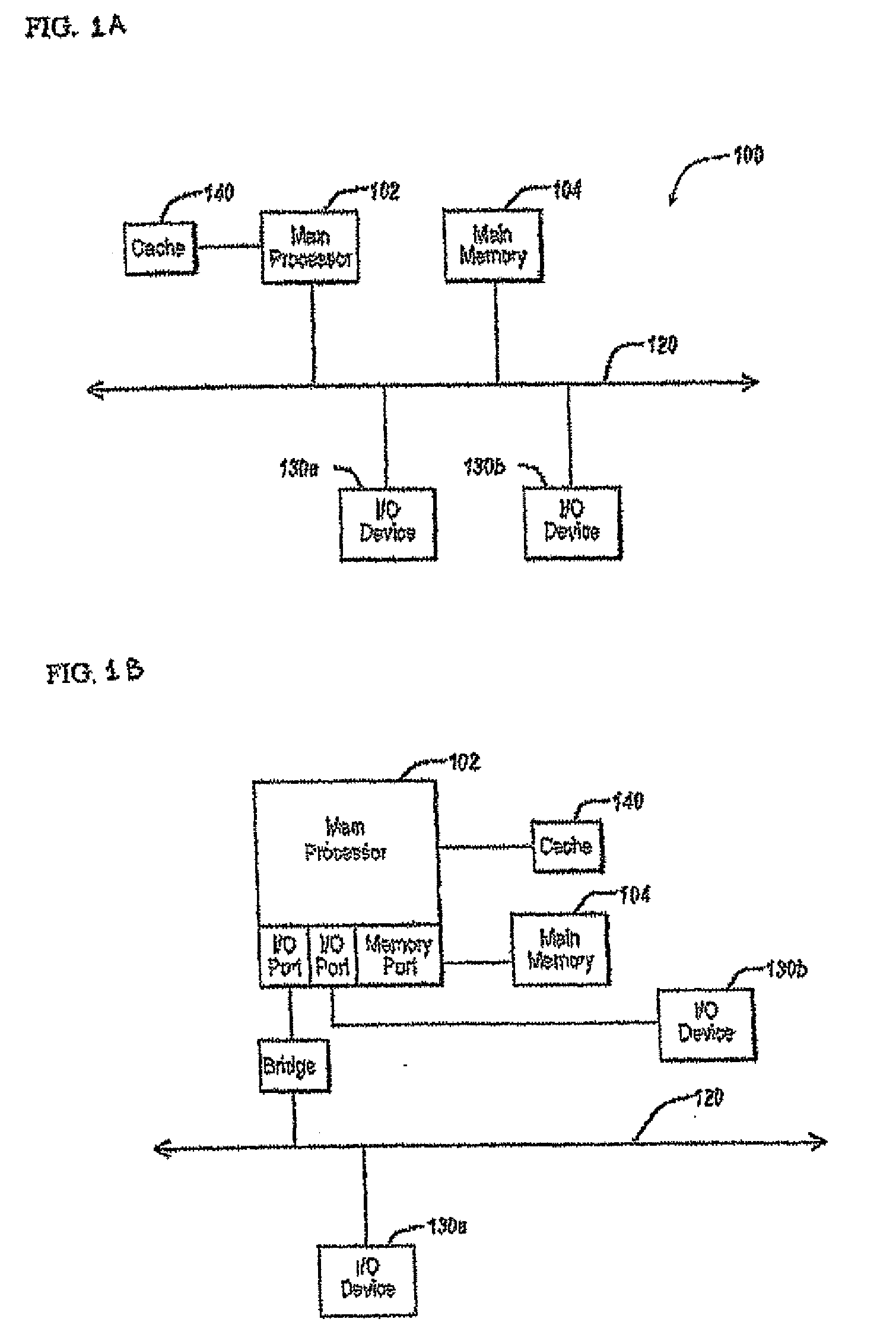
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
18413 results about "Virtual machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
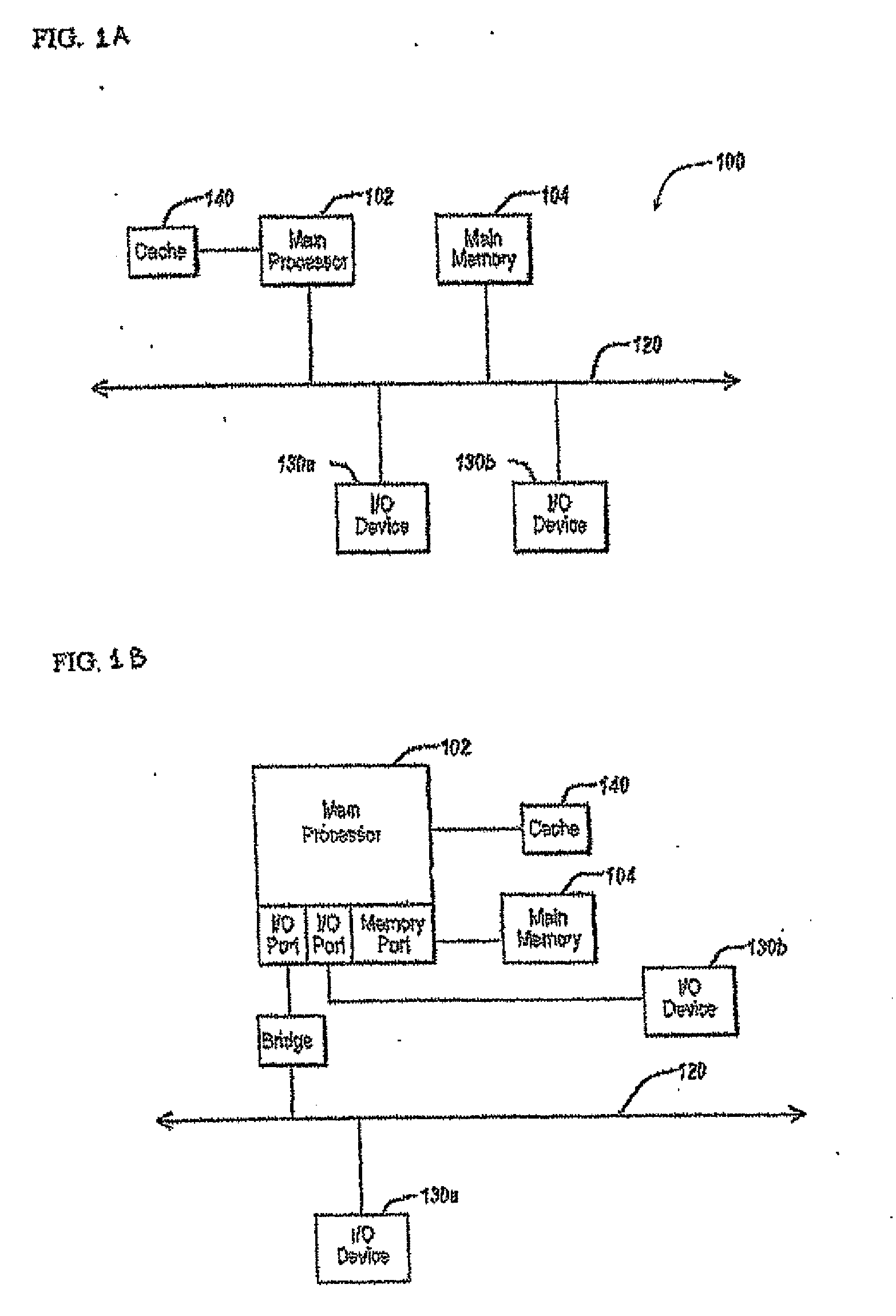
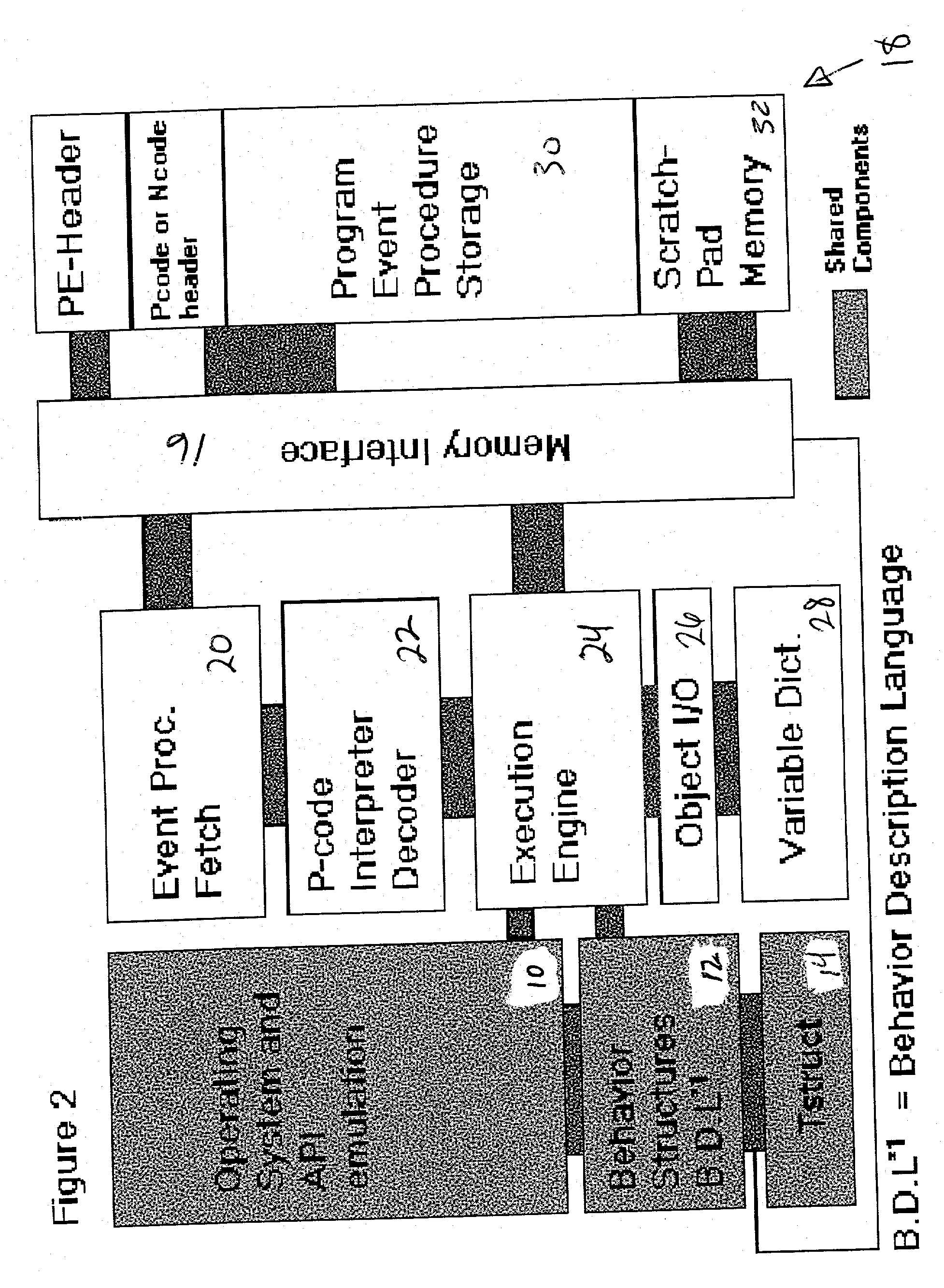
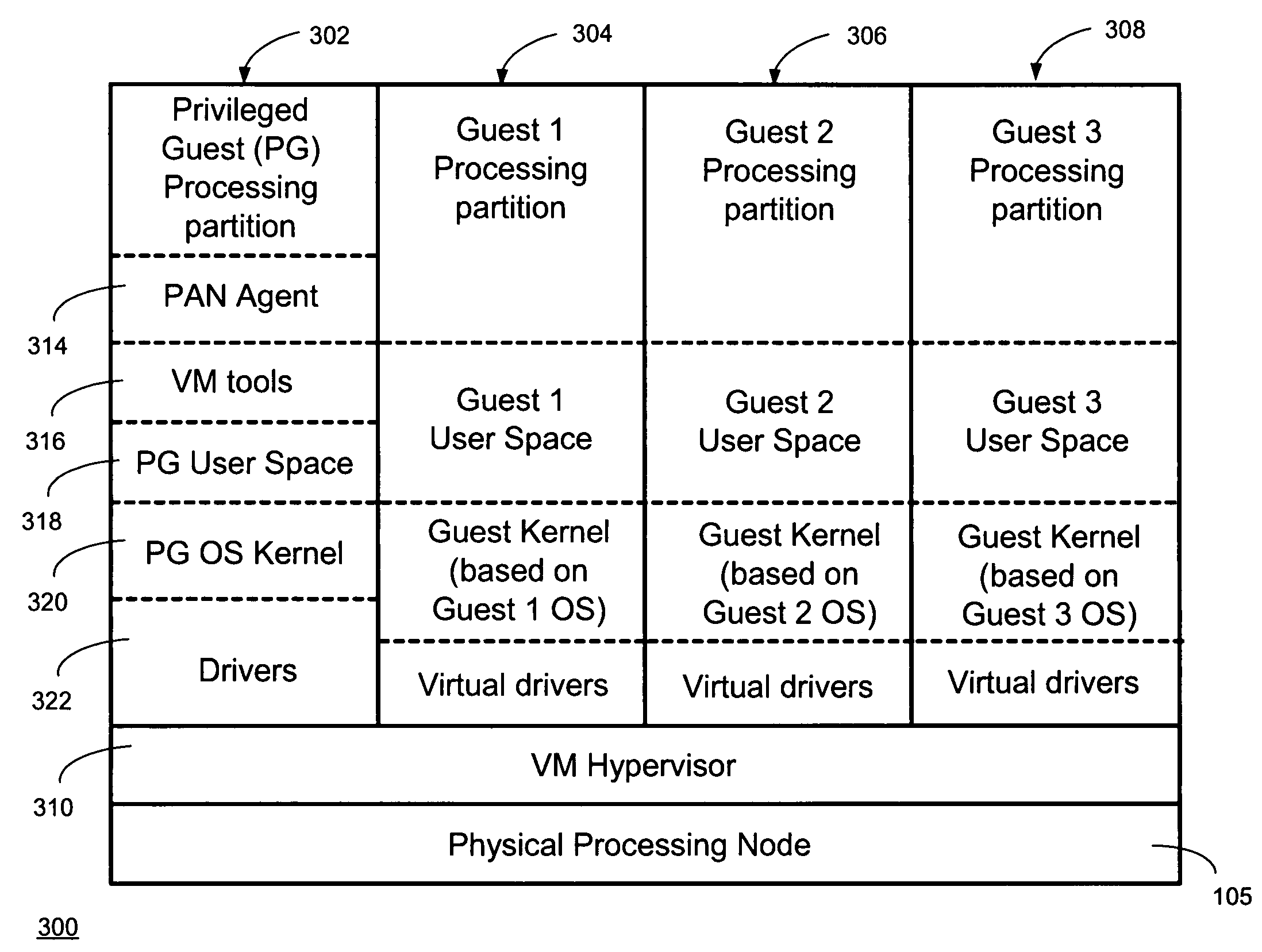
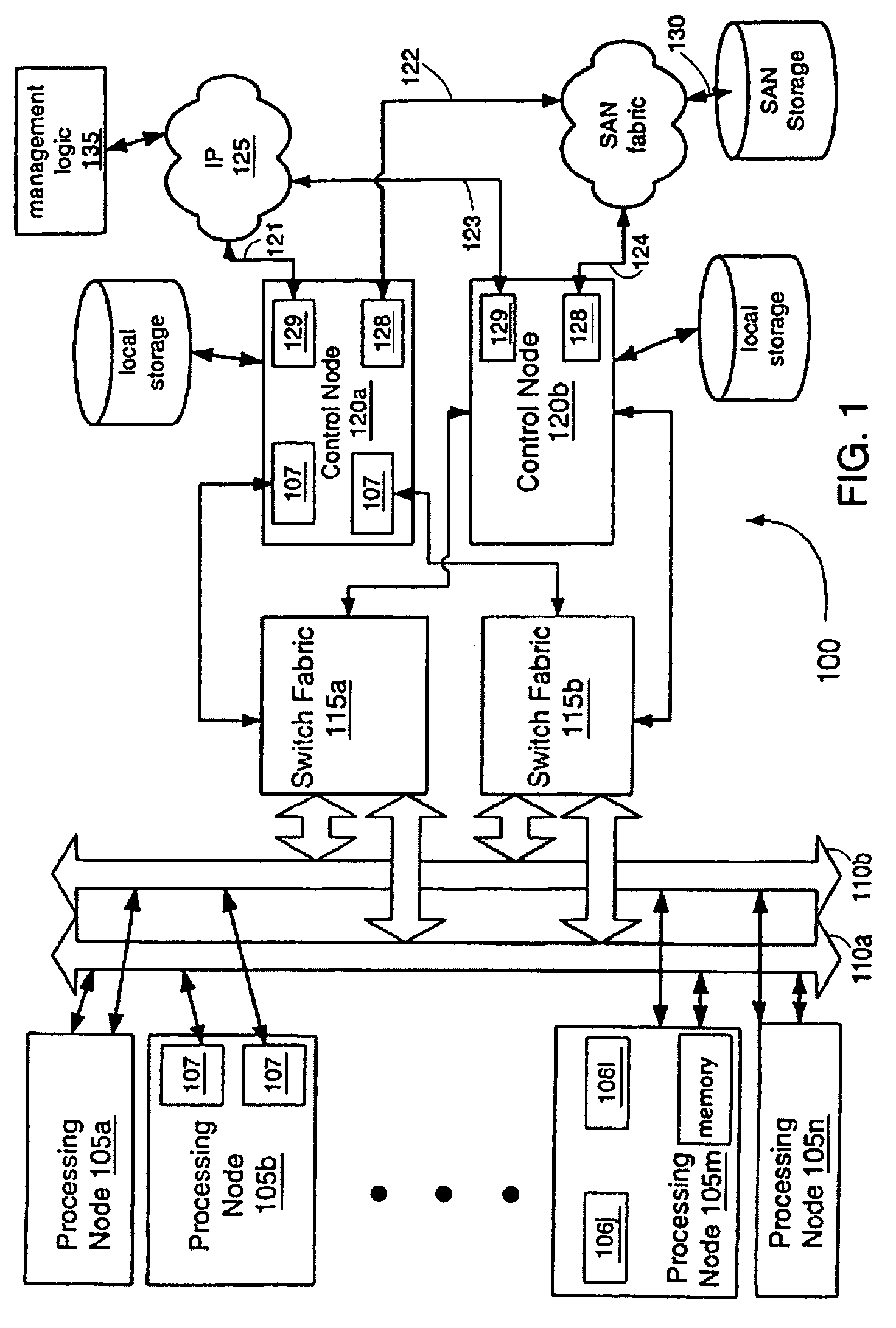
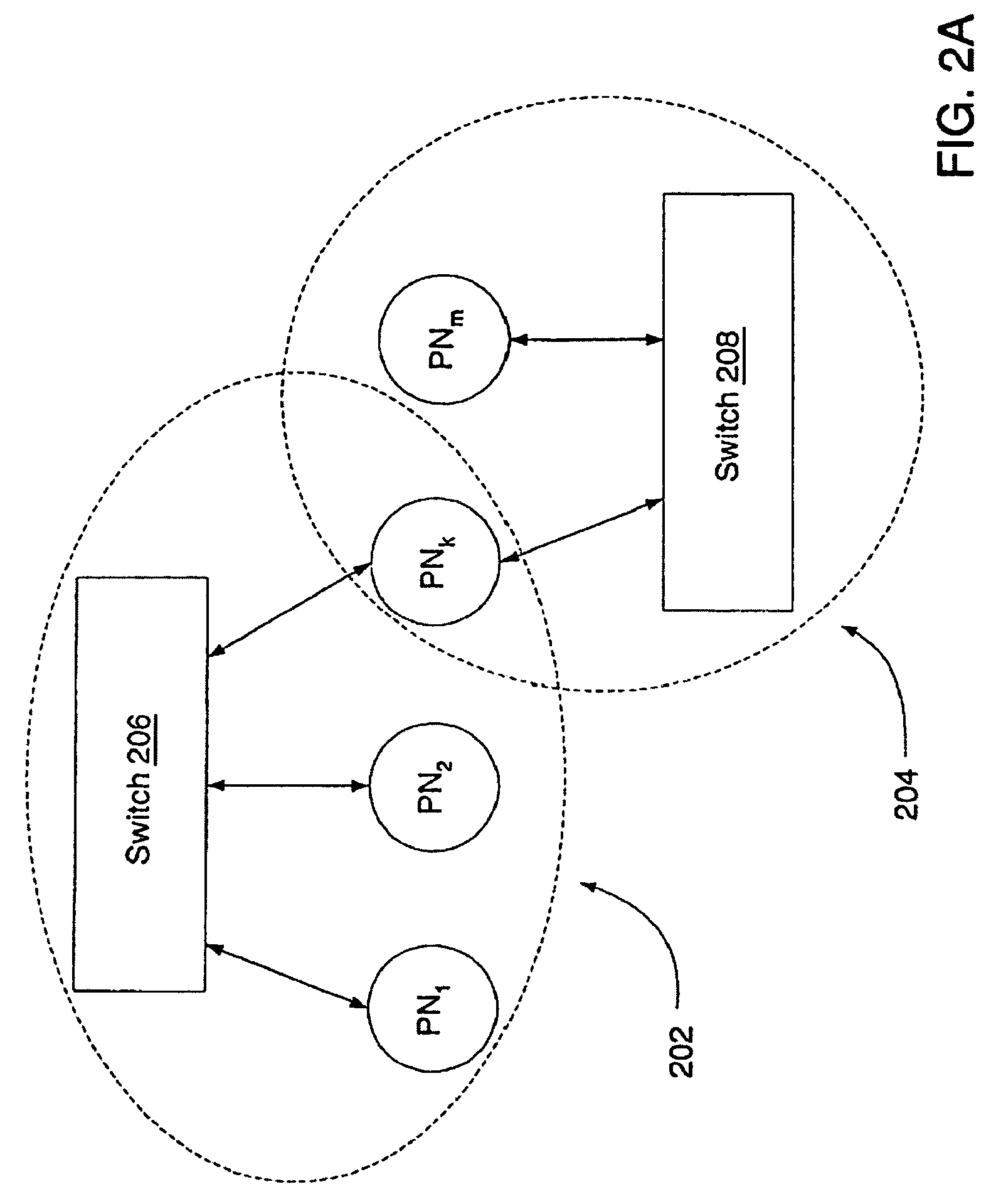
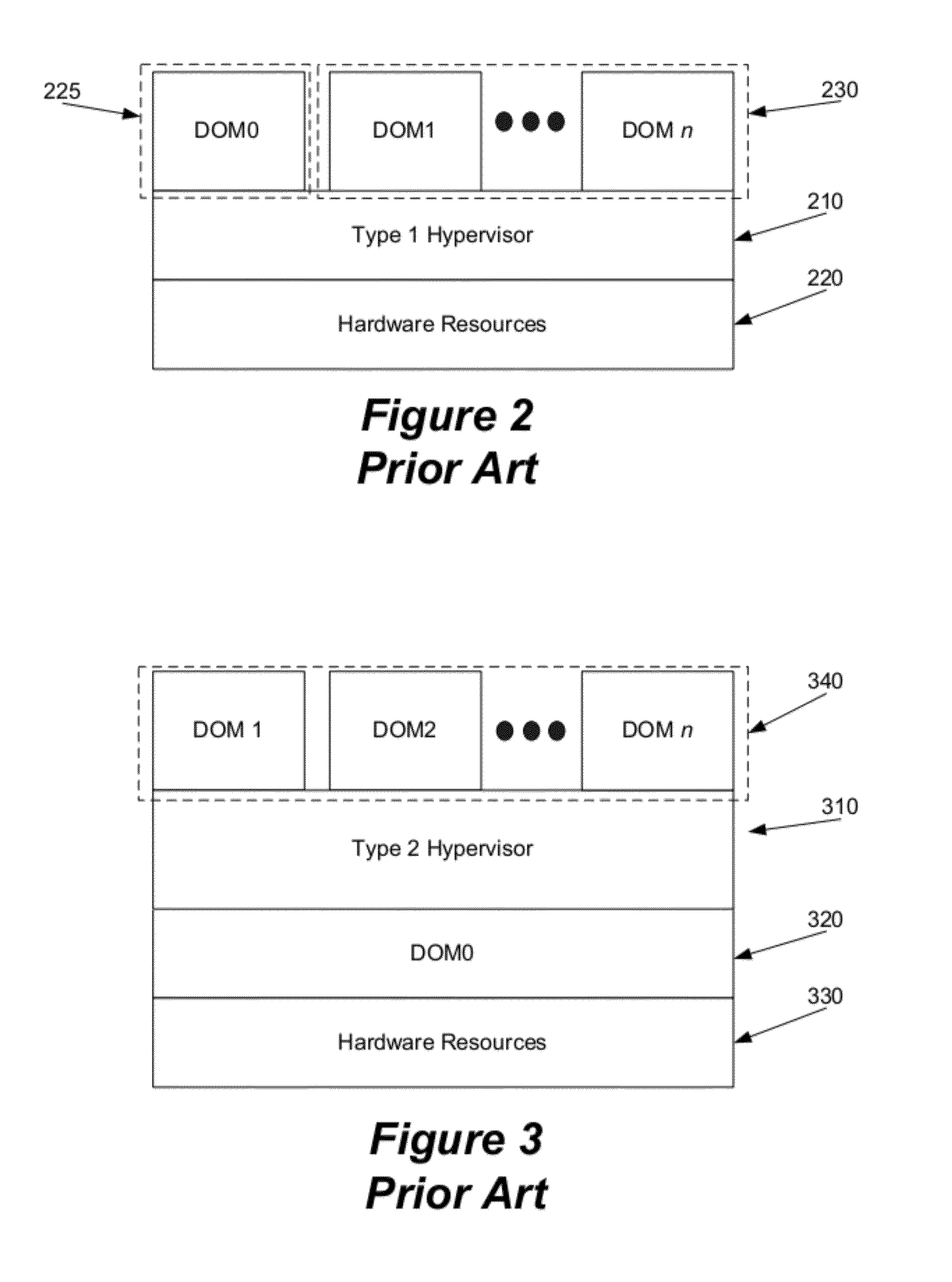
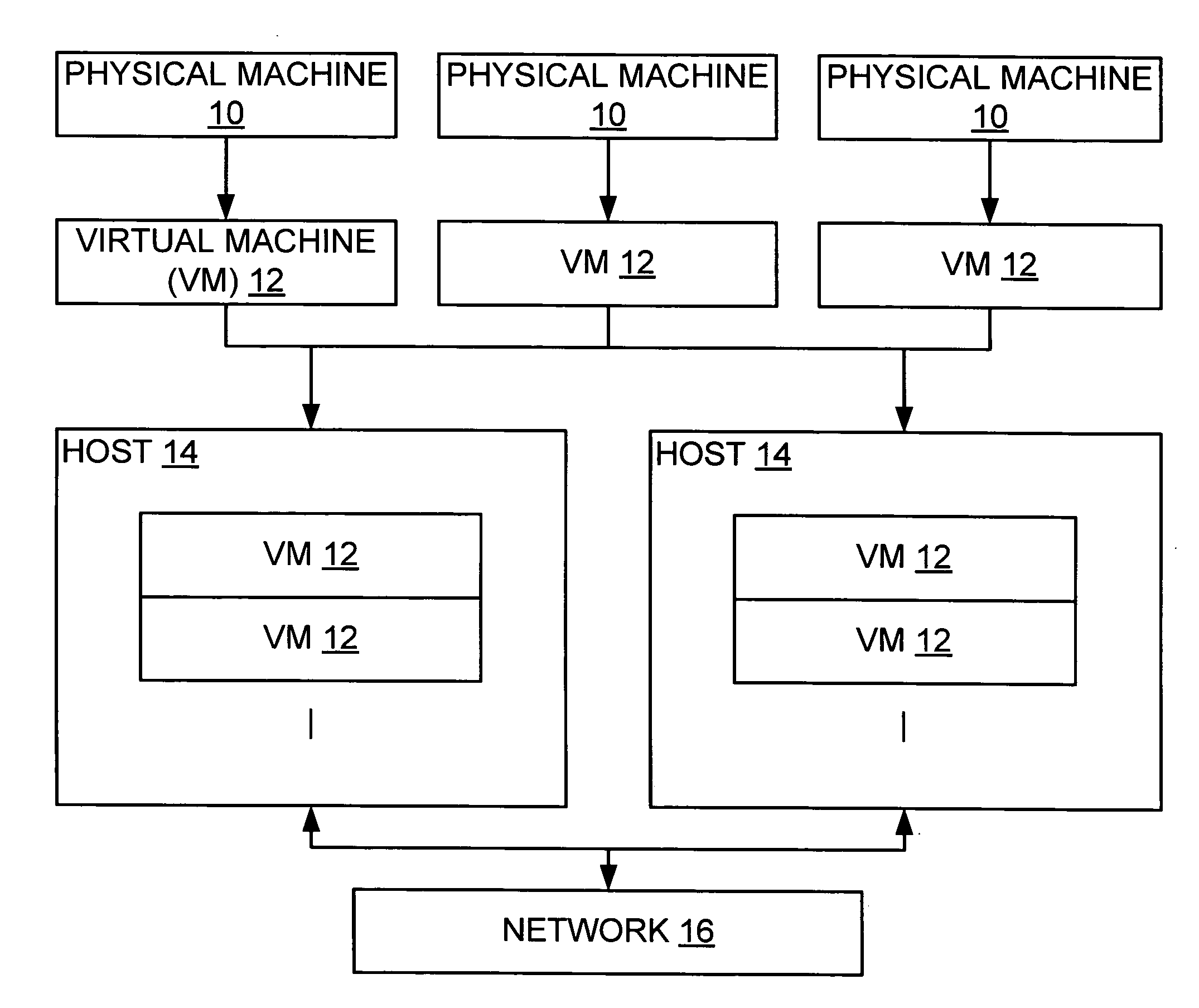
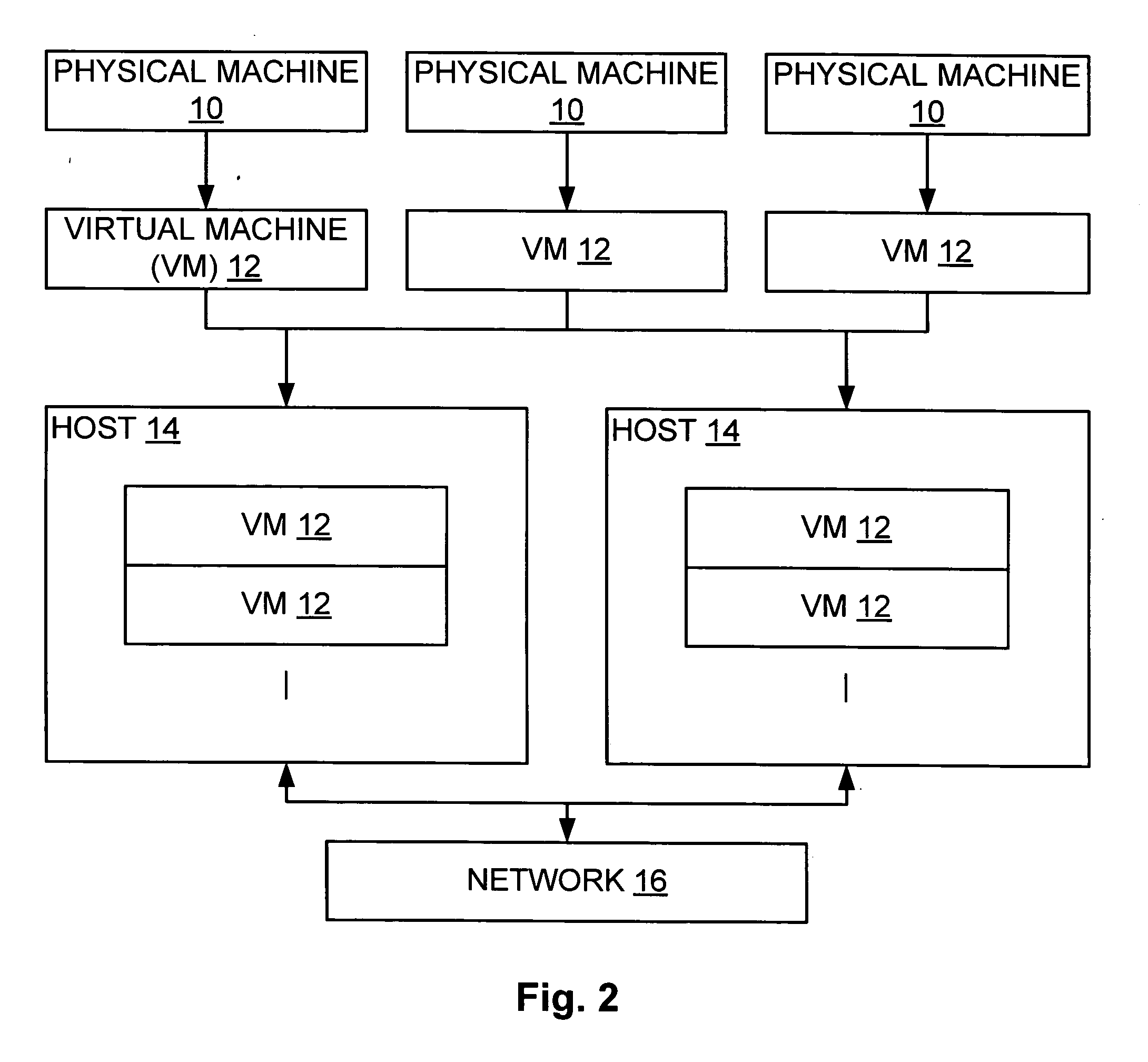
In computing, a virtual machine (VM) is an emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination.
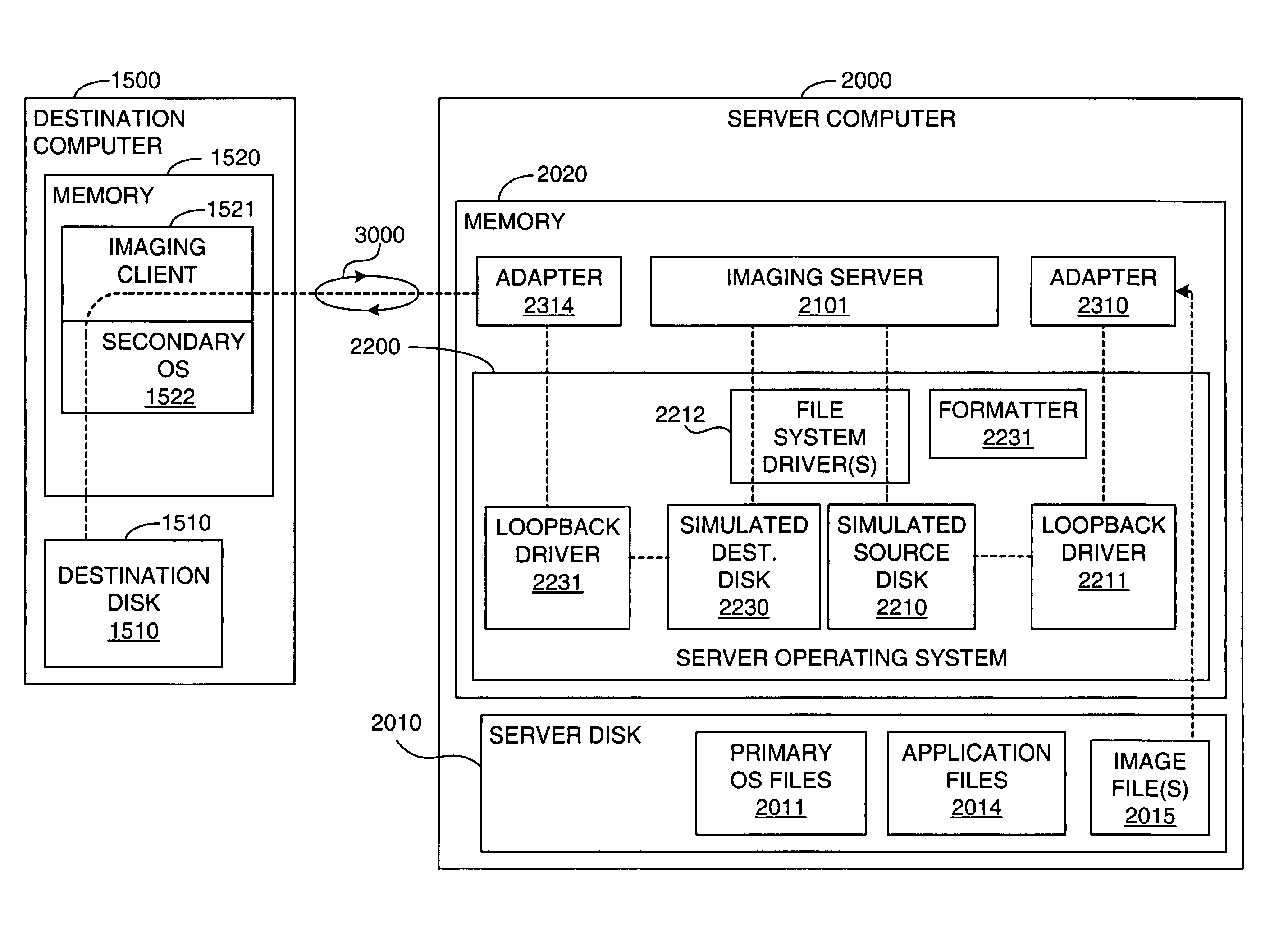
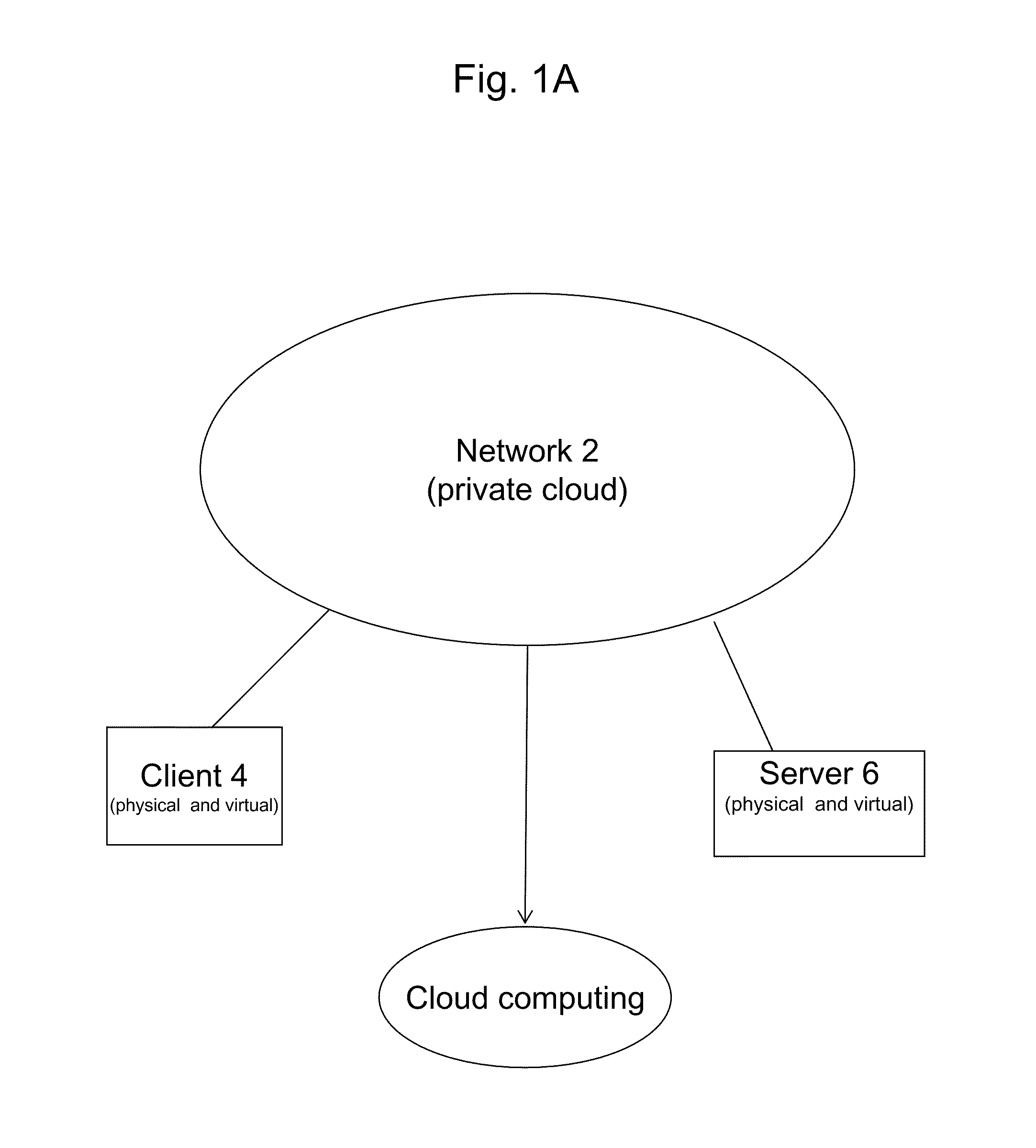
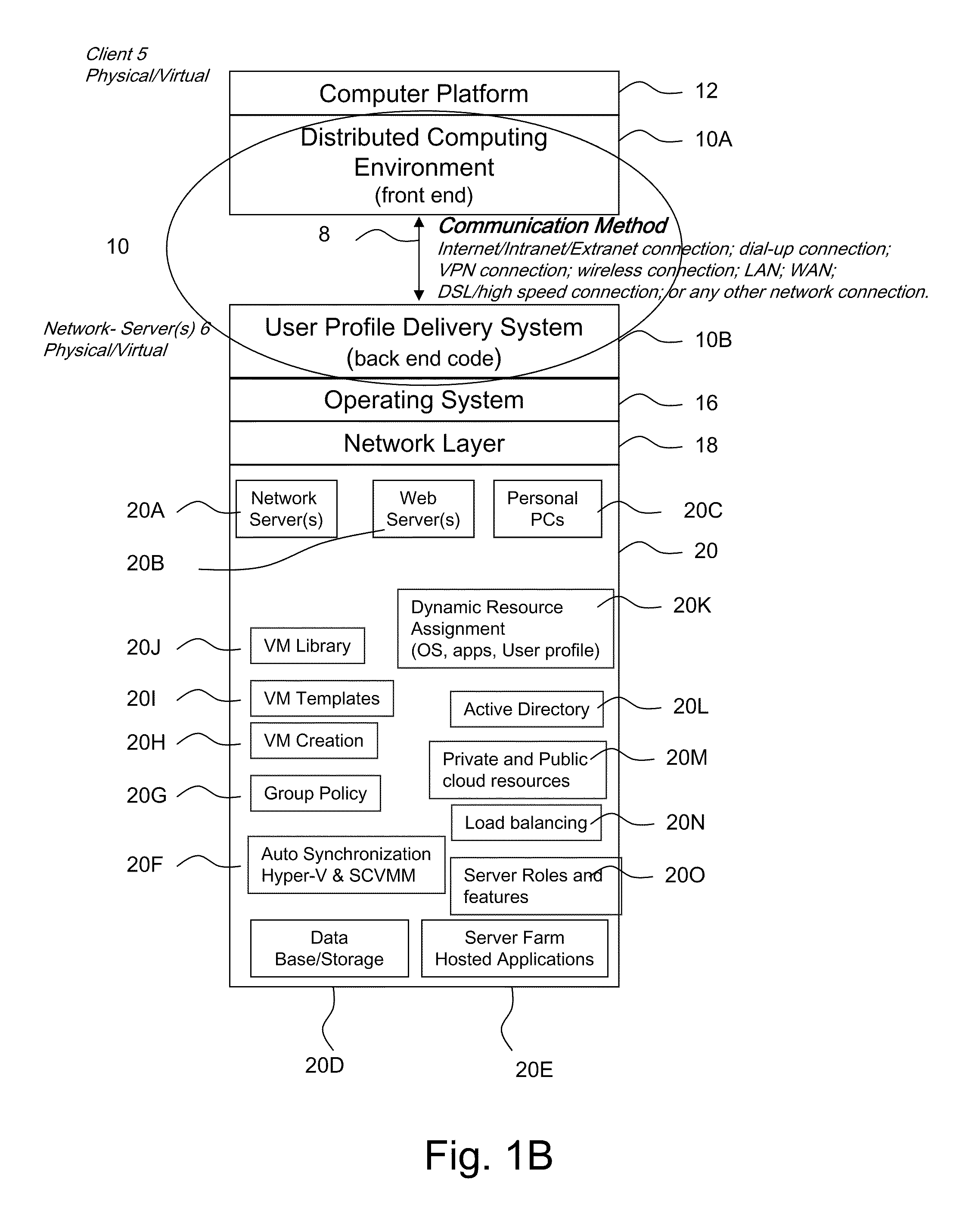
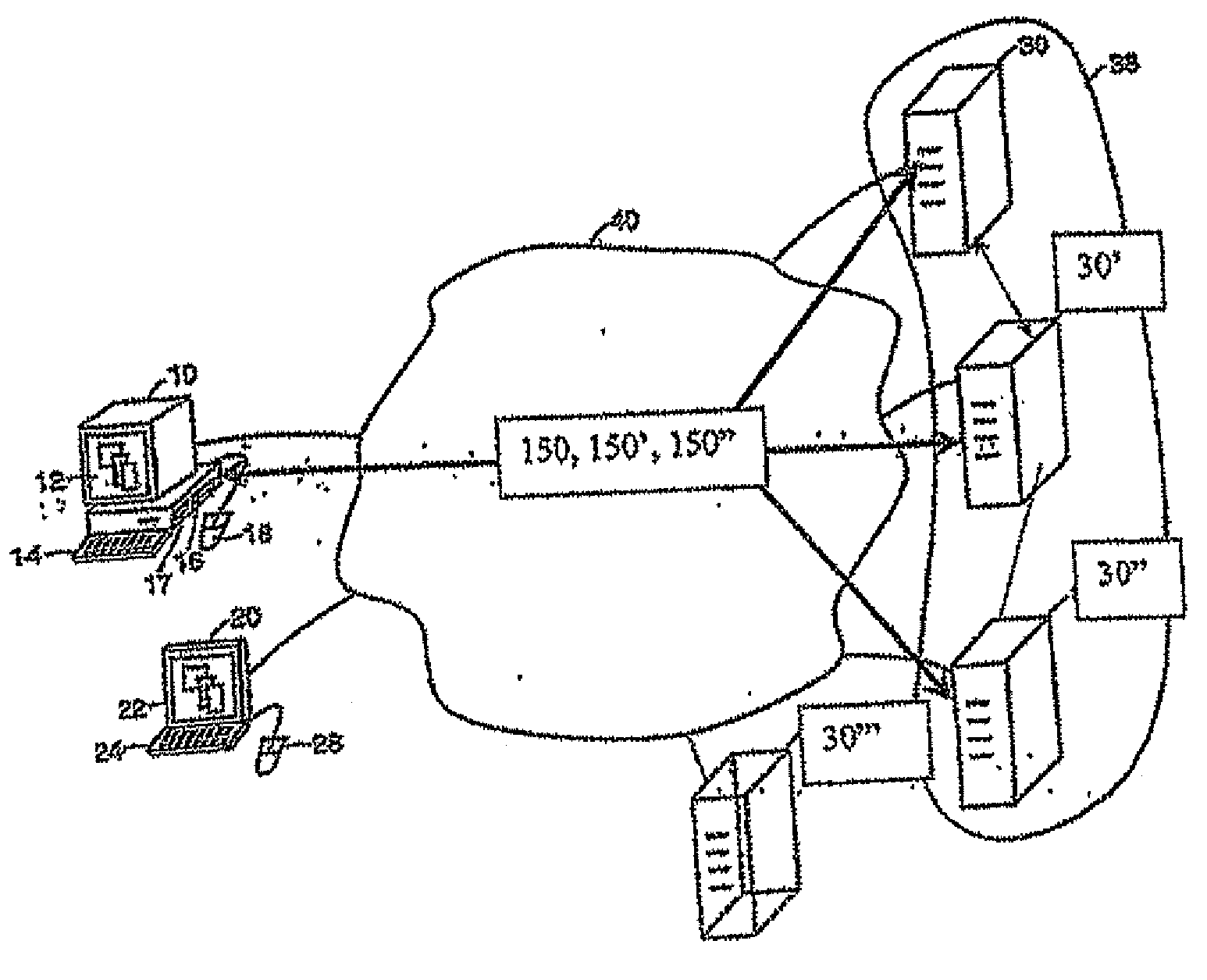
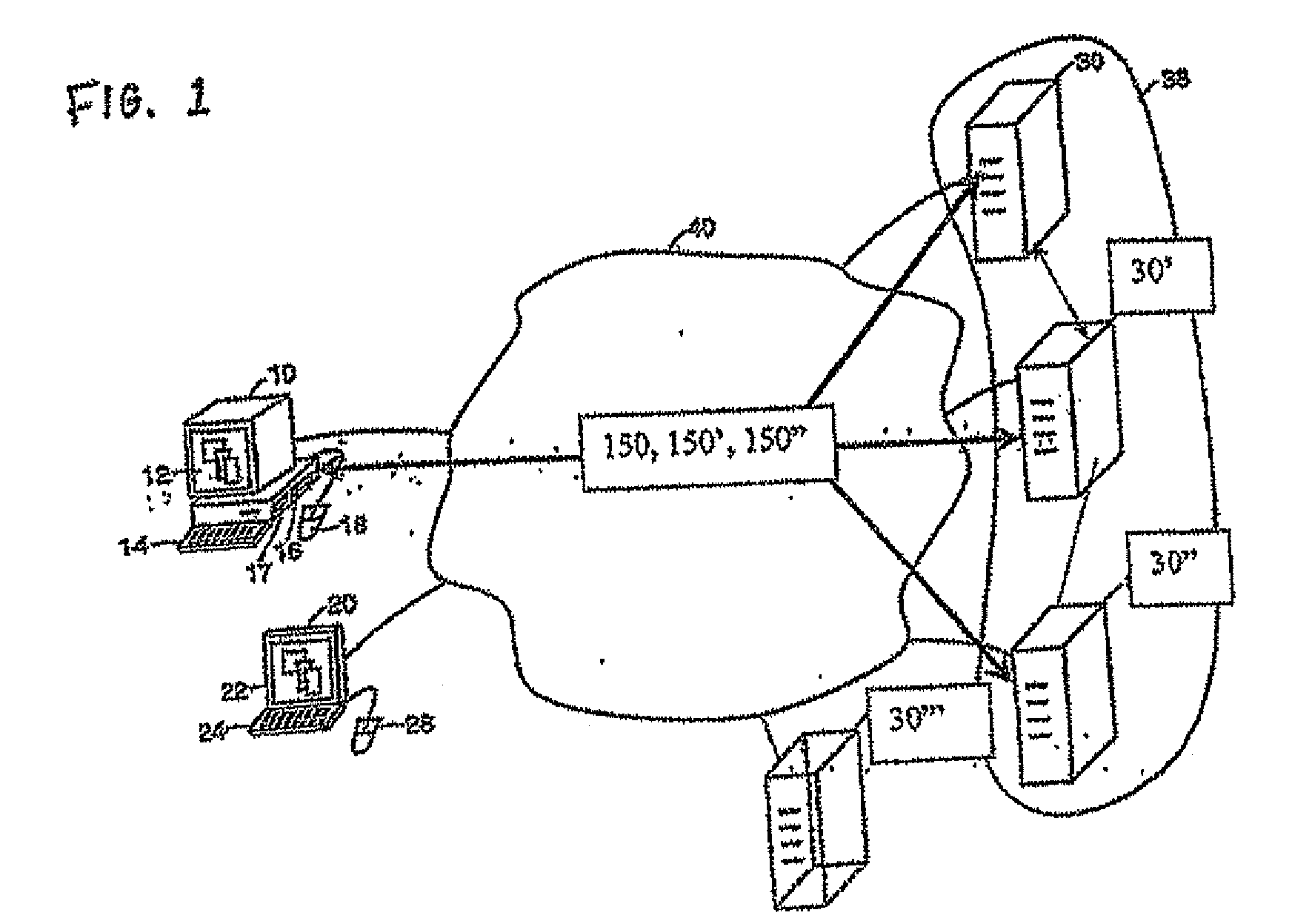
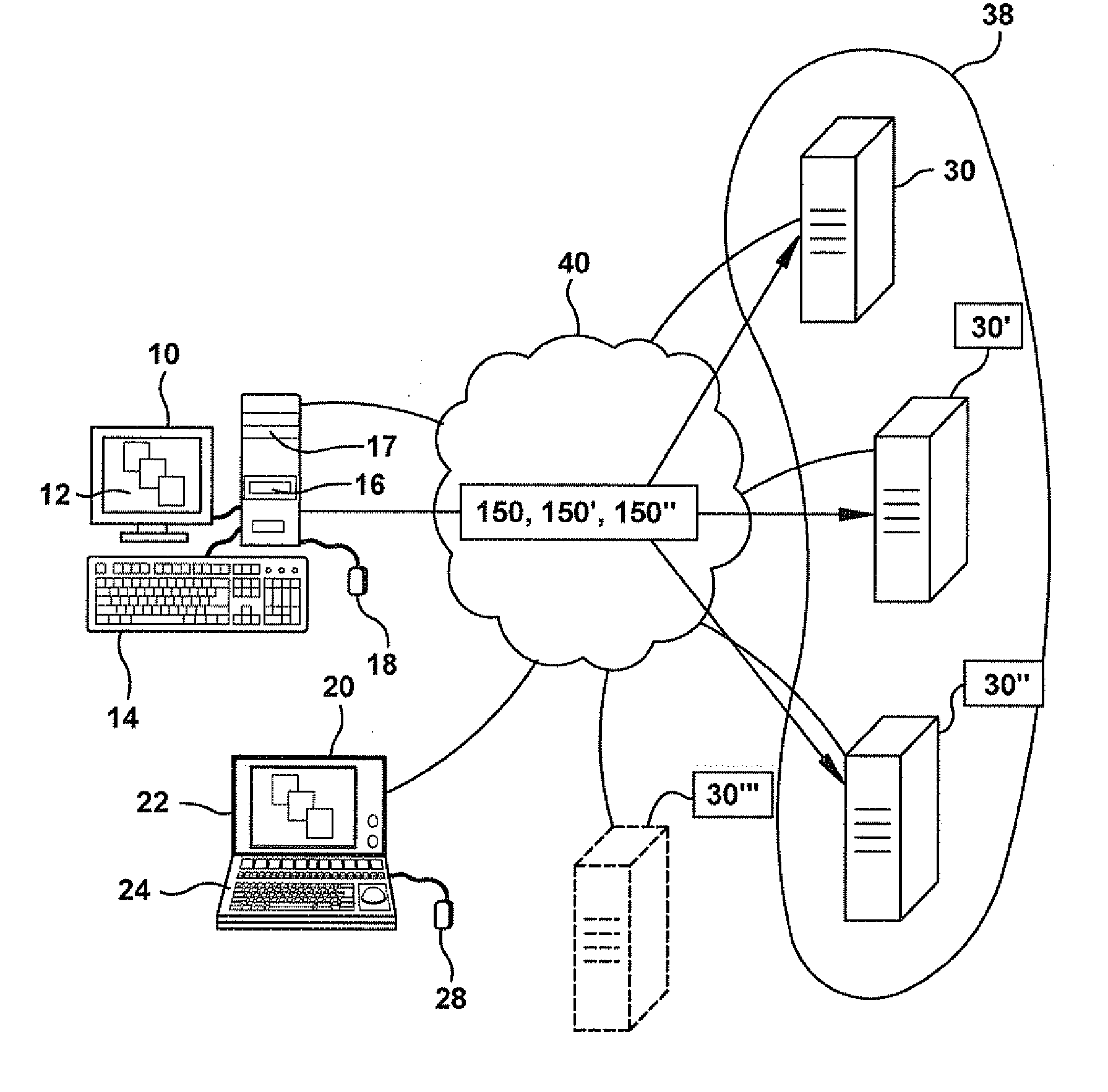
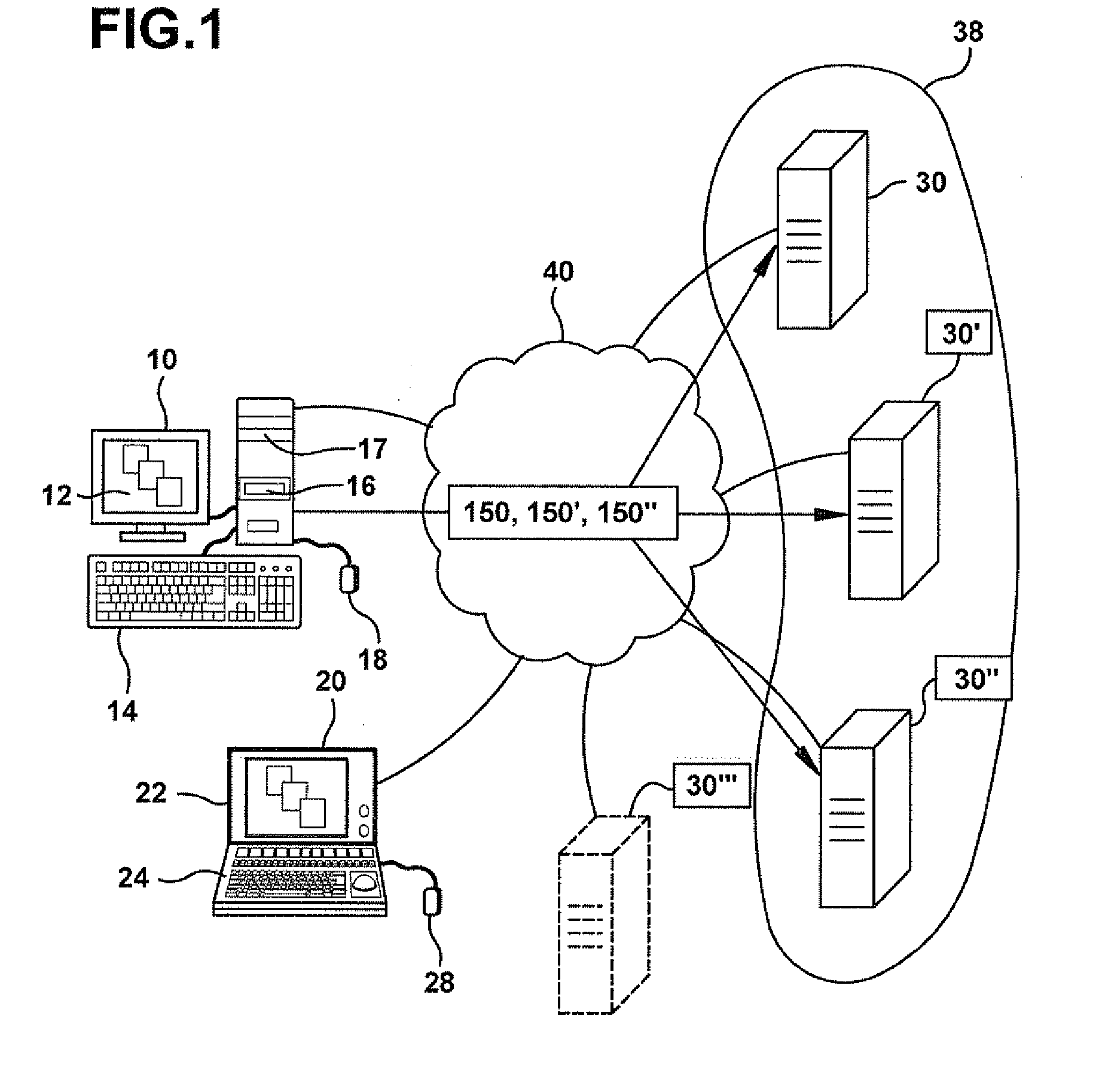
Computer image capture, customization and deployment
ActiveUS7356679B1Increased riskDigital computer detailsProgram loading/initiatingVirtual machineSoftware
Owner:VMWARE INC
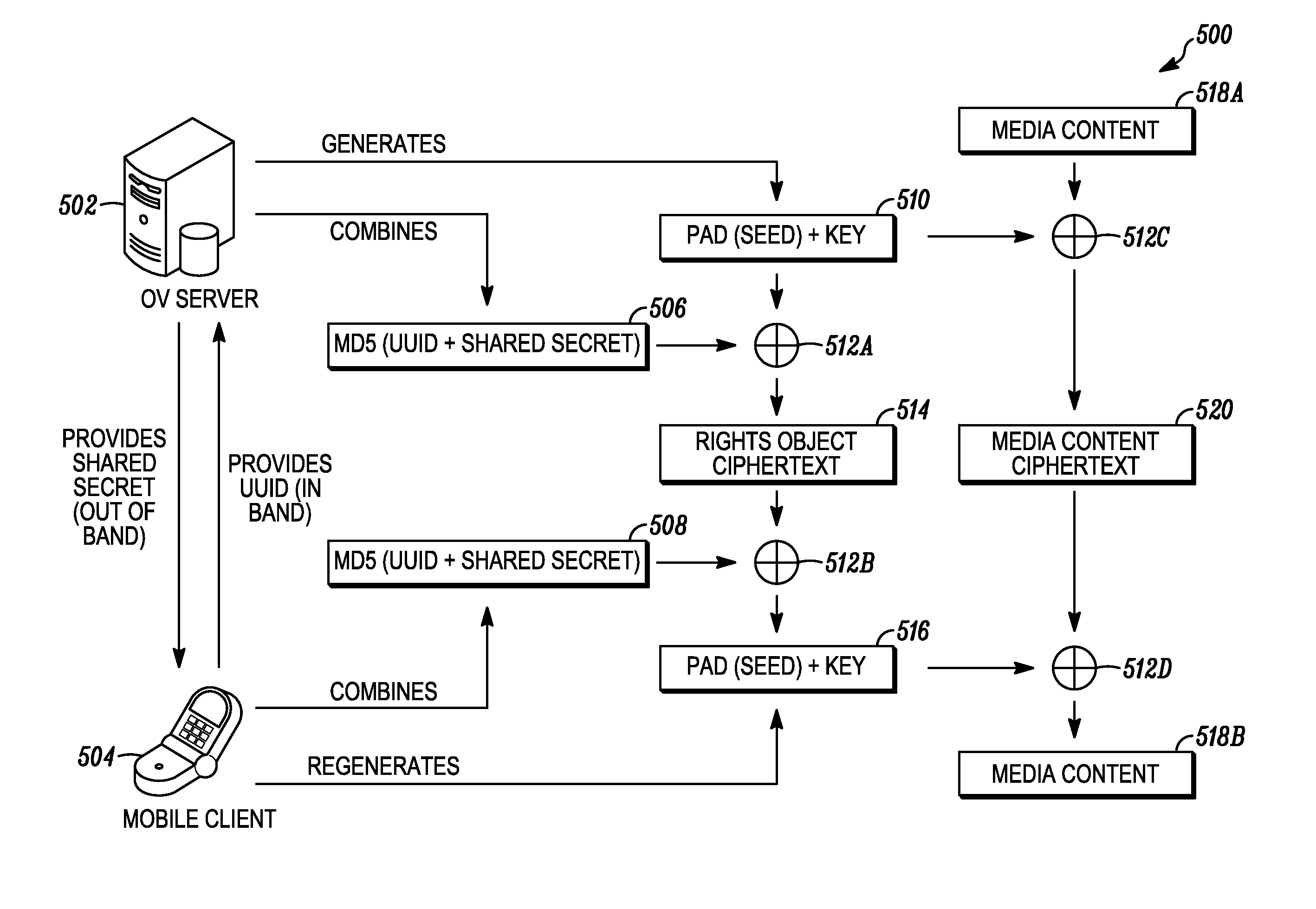
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
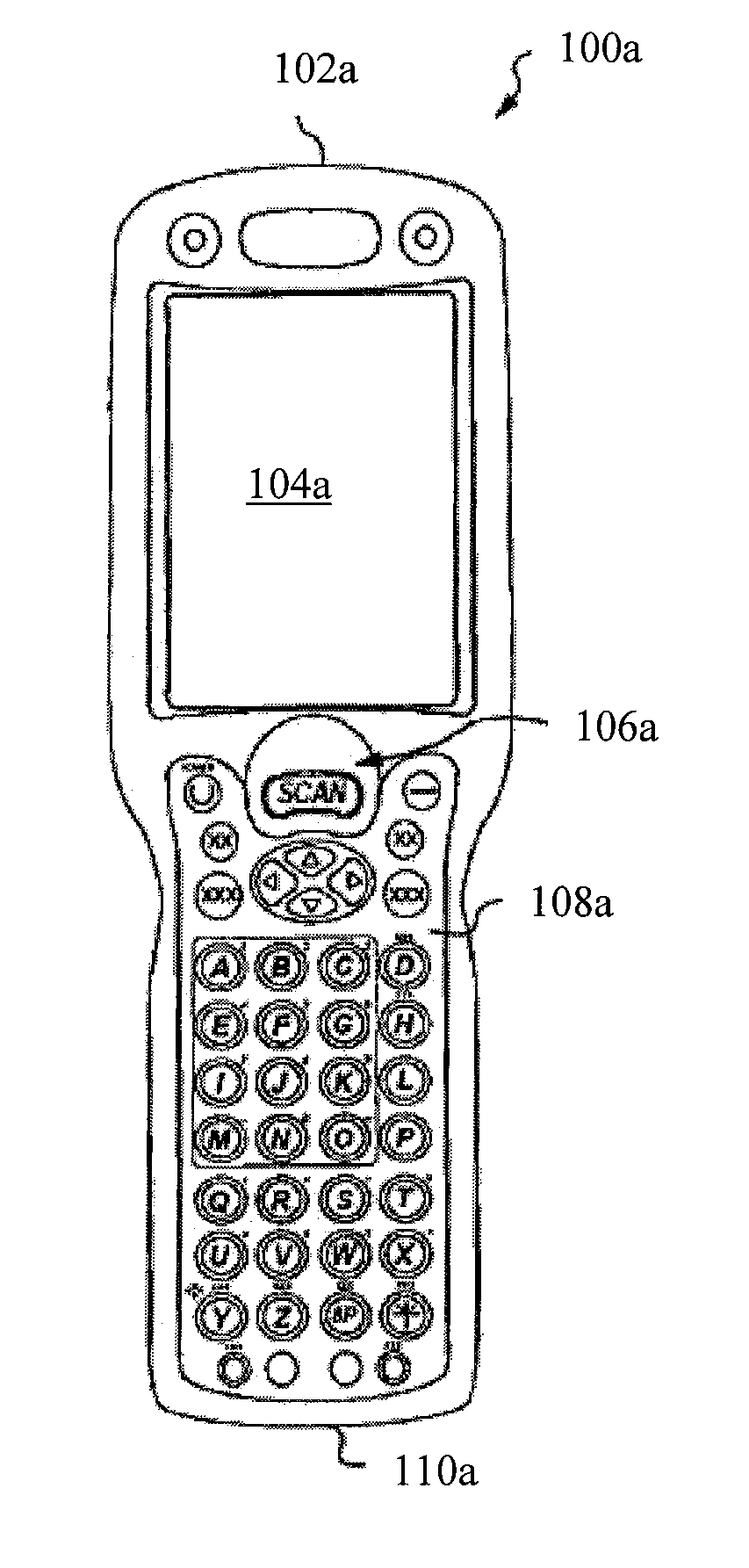
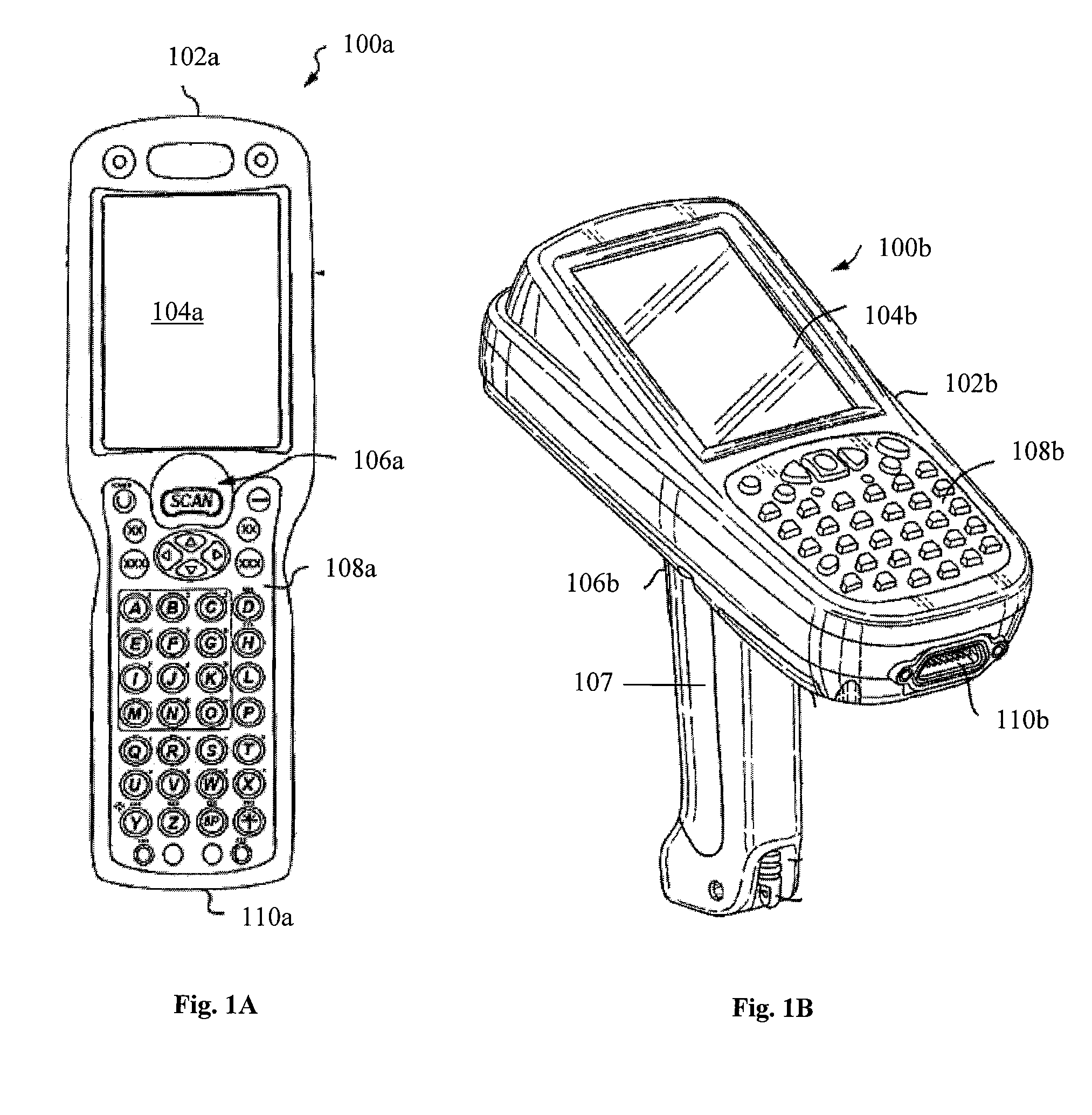
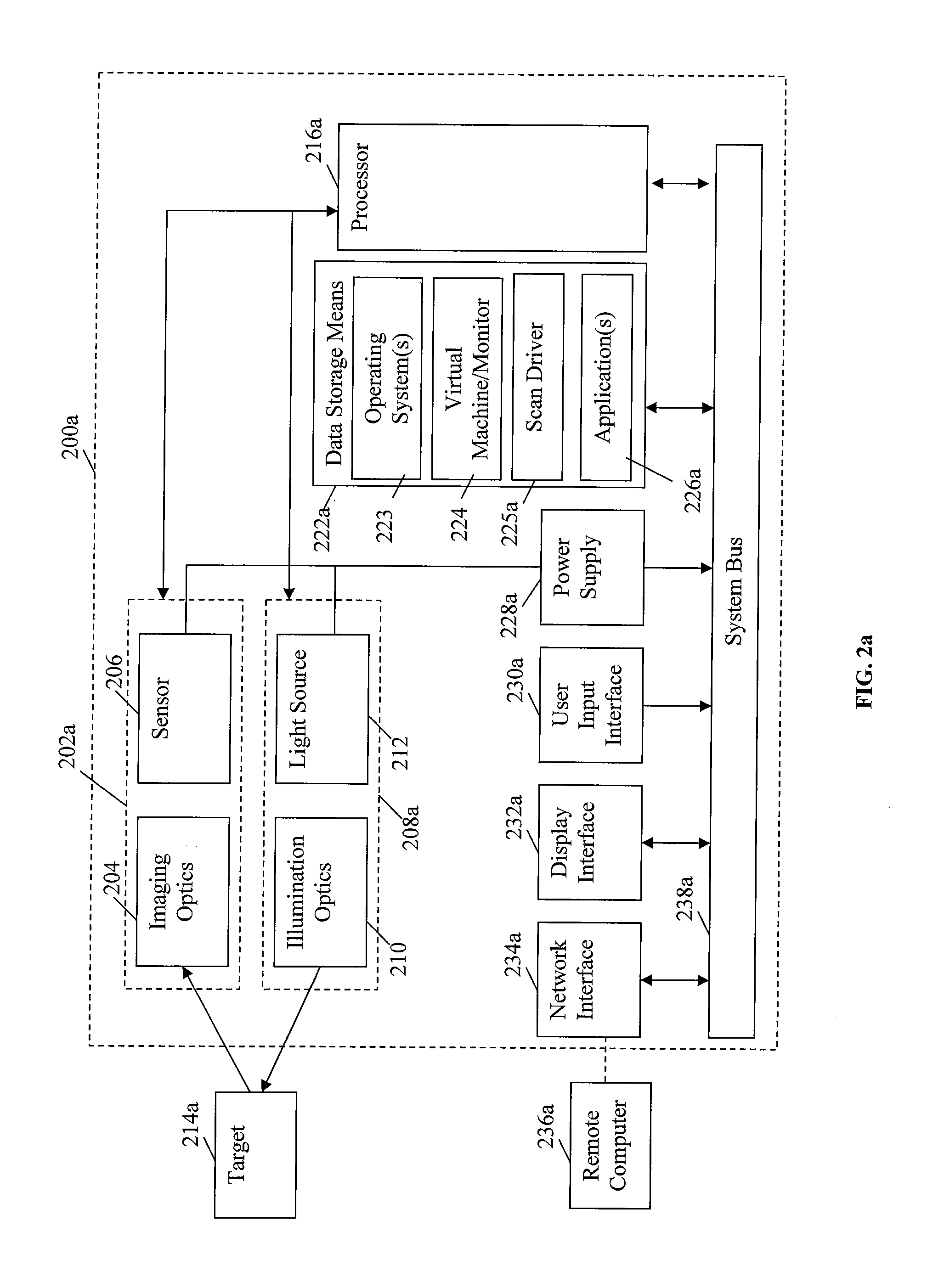
Multiple platform support system and method
InactiveUS9010641B2Software simulation/interpretation/emulationSpecial data processing applicationsSupporting systemData terminal
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
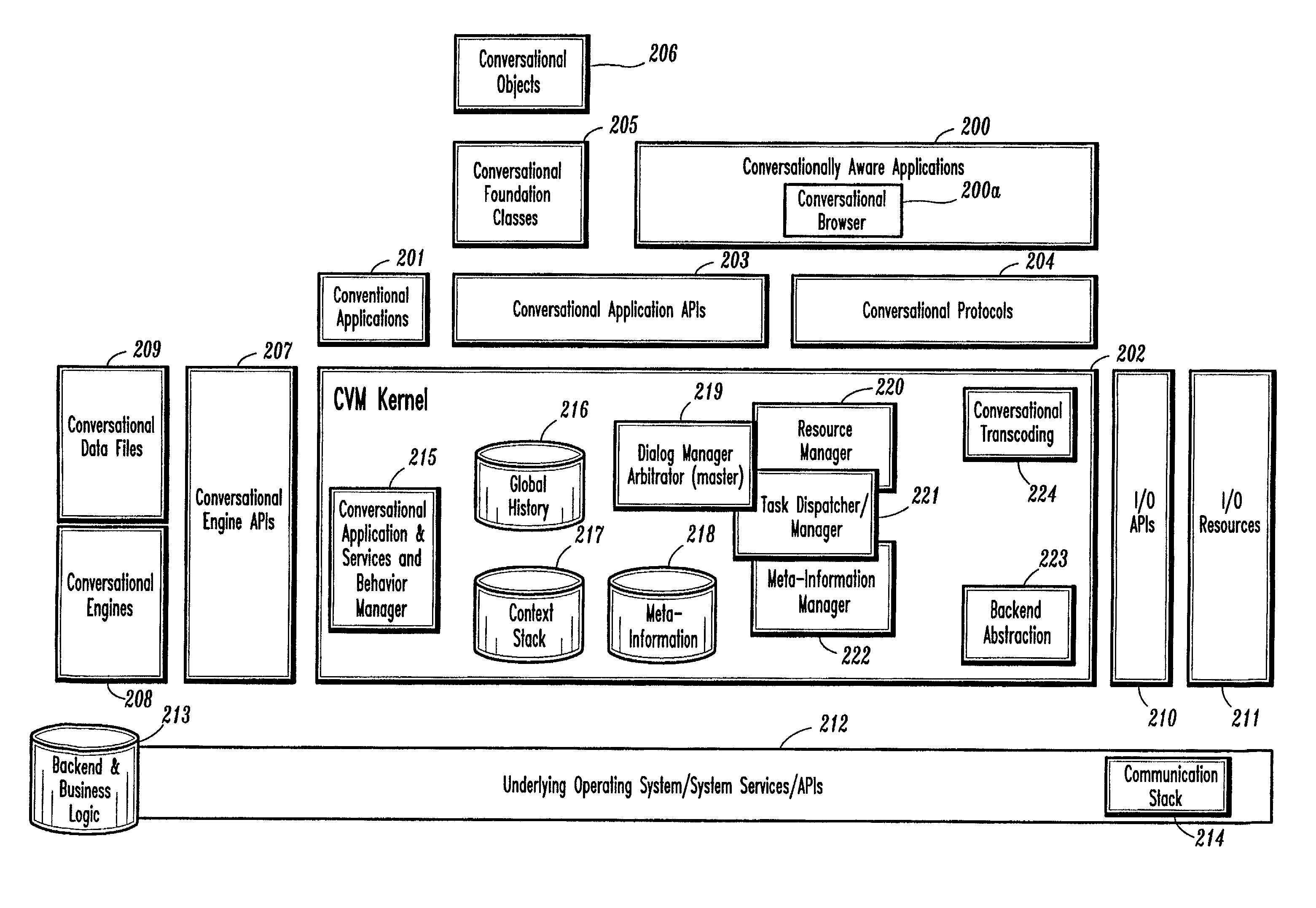
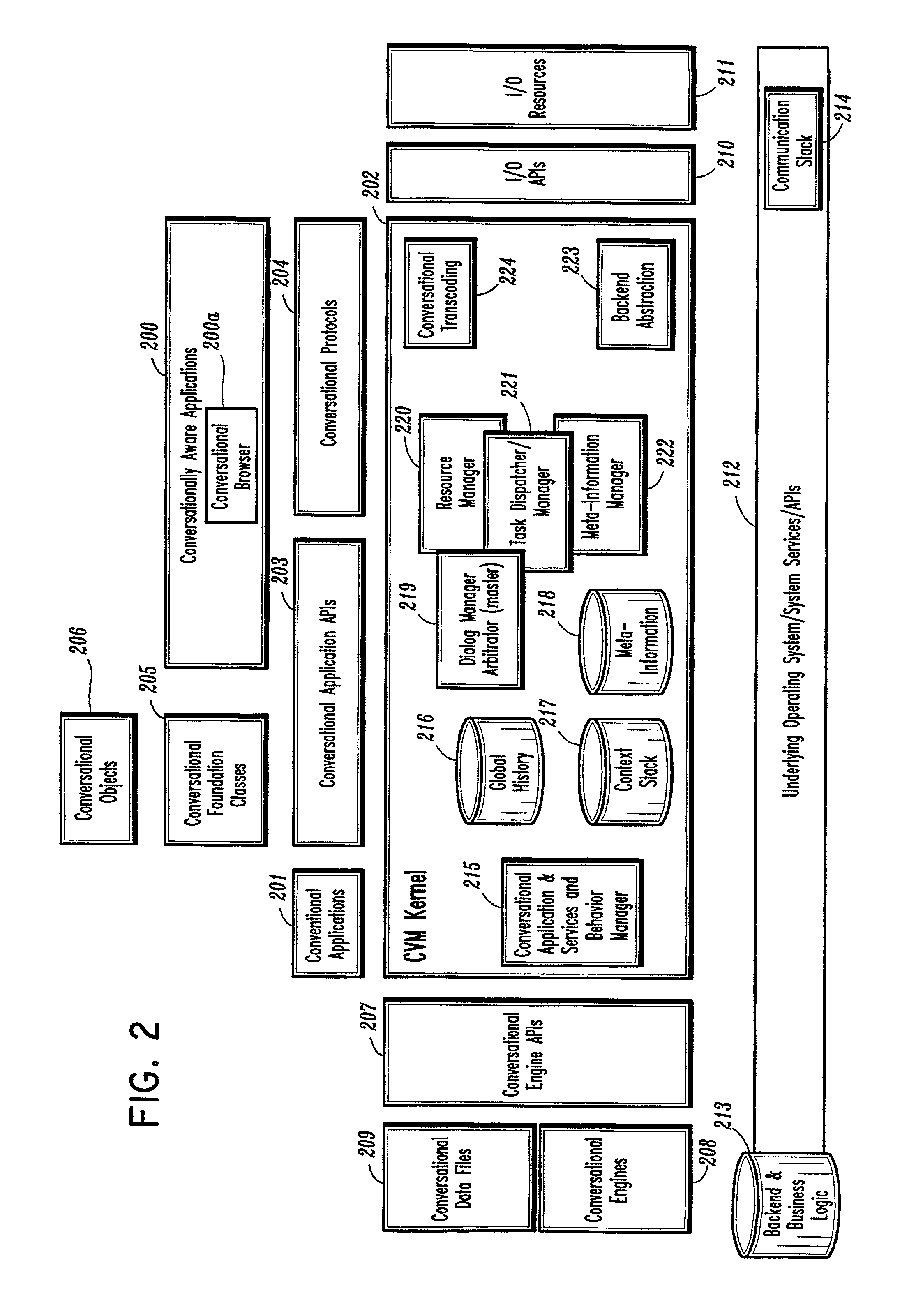
Conversational computing via conversational virtual machine
InactiveUS7137126B1Limitation for transferReduce degradationInterconnection arrangementsResource allocationConversational speechApplication software
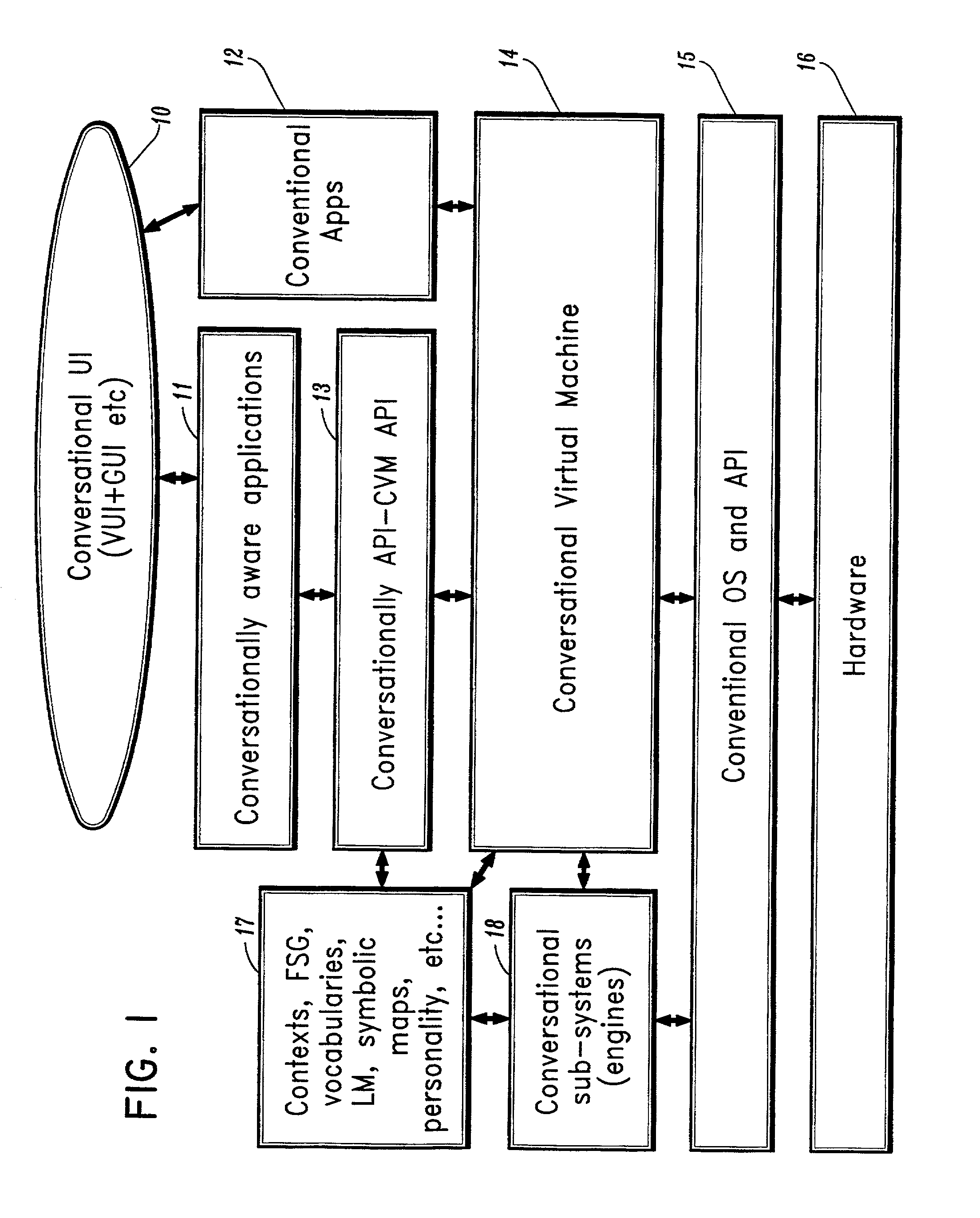
A conversational computing system that provides a universal coordinated multi-modal conversational user interface (CUI) (10) across a plurality of conversationally aware applications (11) (i.e., applications that “speak” conversational protocols) and conventional applications (12). The conversationally aware maps, applications (11) communicate with a conversational kernel (14) via conversational application APIs (13). The conversational kernel (14) controls the dialog across applications and devices (local and networked) on the basis of their registered conversational capabilities and requirements and provides a unified conversational user interface and conversational services and behaviors. The conversational computing system may be built on top of a conventional operating system and APIs (15) and conventional device hardware (16). The conversational kernel (14) handles all I / O processing and controls conversational engines (18). The conversational kernel (14) converts voice requests into queries and converts outputs and results into spoken messages using conversational engines (18) and conversational arguments (17). The conversational application API (13) conveys all the information for the conversational kernel (14) to transform queries into application calls and conversely convert output into speech, appropriately sorted before being provided to the user.
Owner:UNILOC 2017 LLC
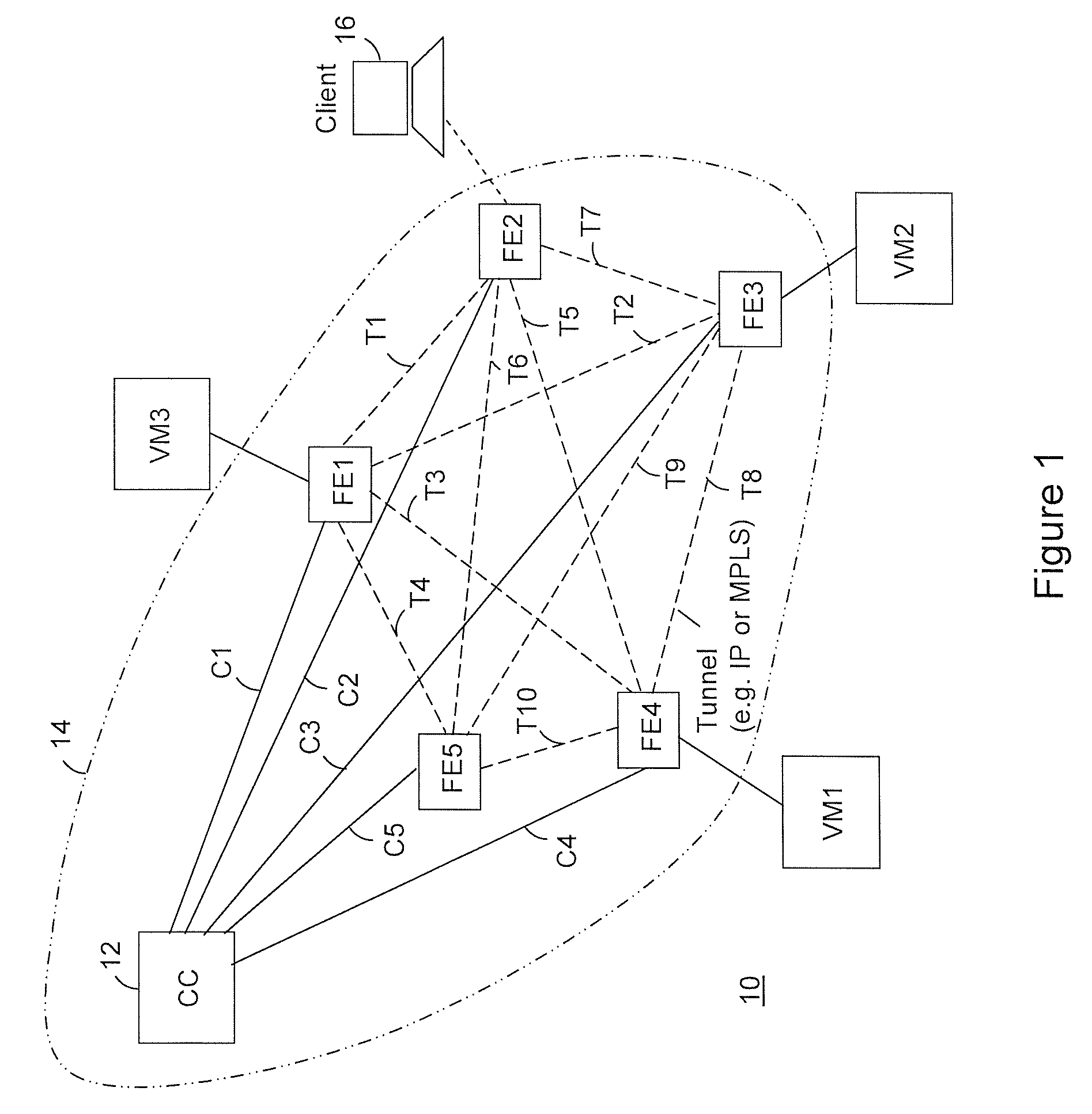
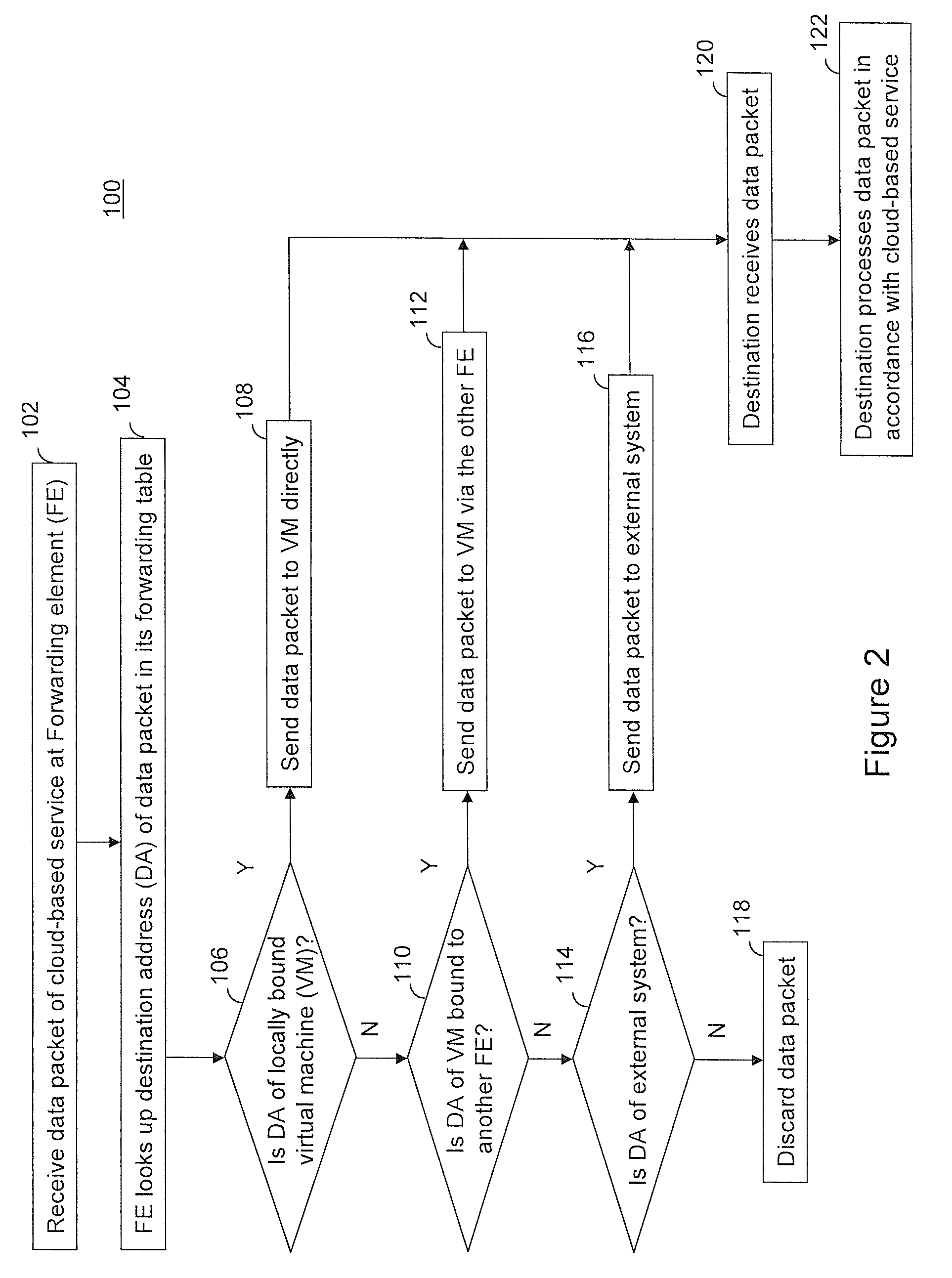
Providing cloud-based services using dynamic network virtualization
ActiveUS20100322255A1Network supportFaster service provisioningData switching by path configurationProgram controlCloud baseIp address
The invention is directed to providing cloud-based services using dynamic network virtualization. Embodiments of the invention provide a cloud-based service over a system that has a dynamic network virtualization architecture. The architecture includes a set of distributed forwarding elements with centralized control, and at least one virtual machine that is bound to one of the forwarding elements. These features enable the virtual machine to be migrated across a wide area network while maintaining its original IP address and service continuity.
Owner:ALCATEL LUCENT SAS
Virtual machine with dynamic data flow analysis
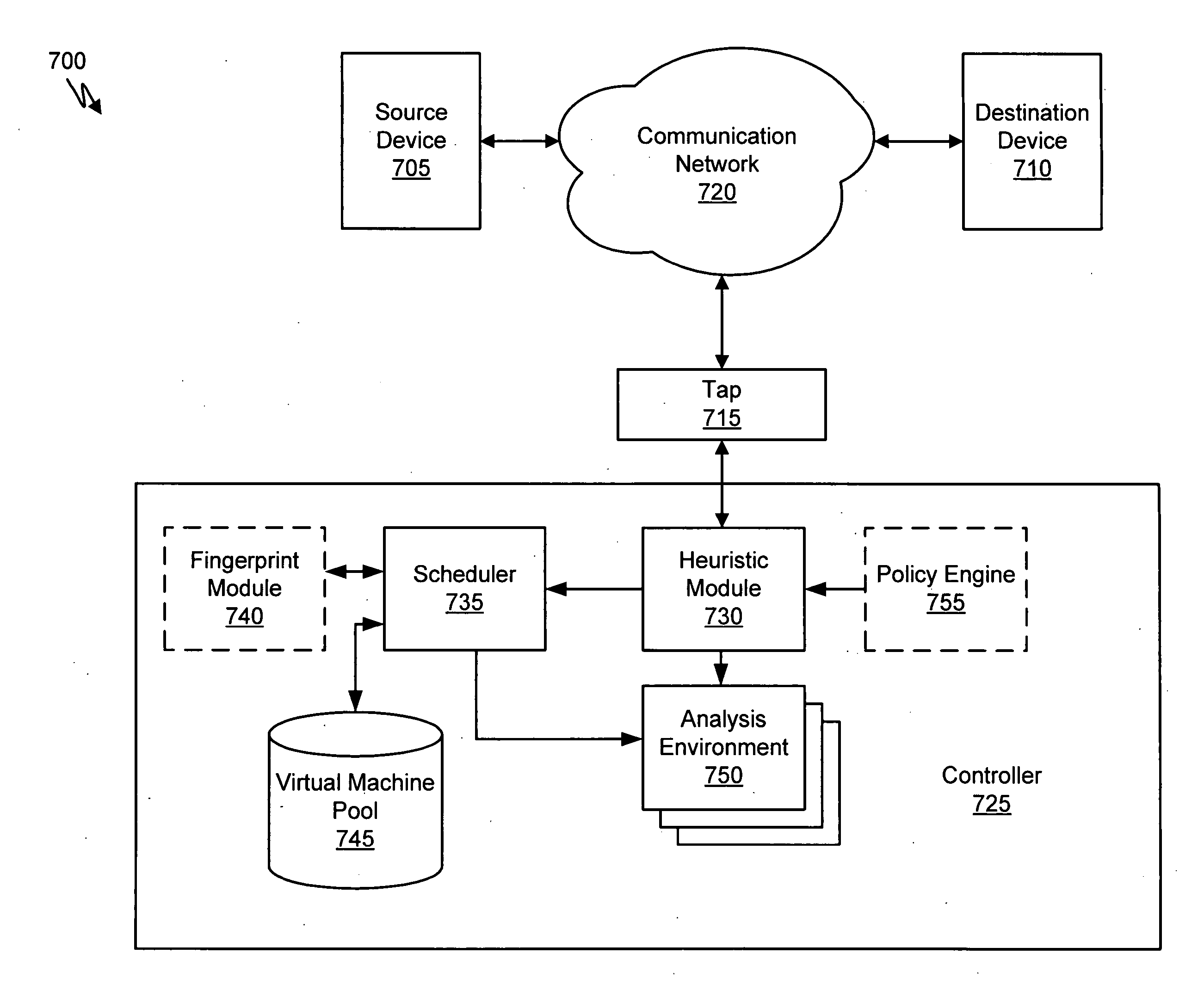
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
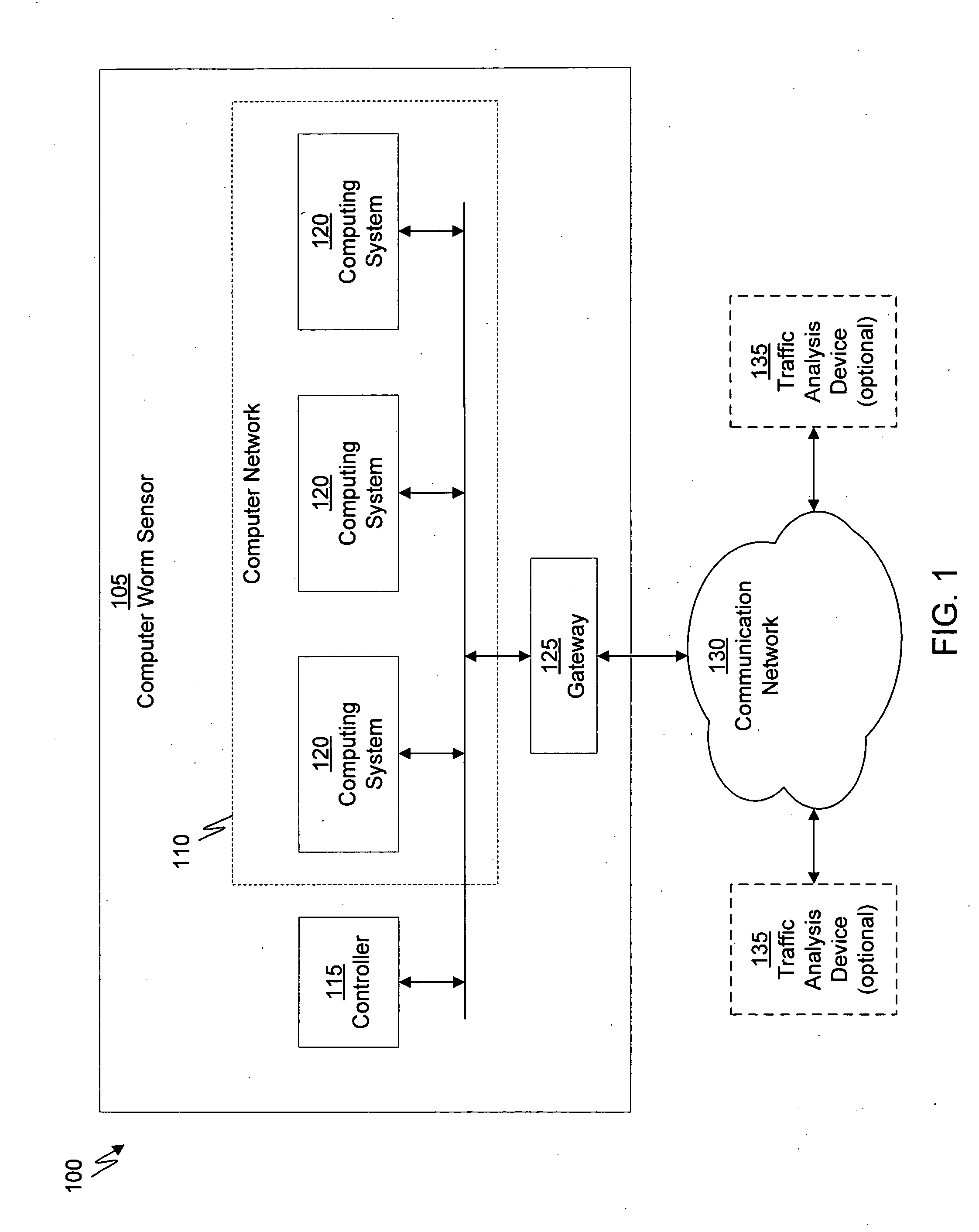
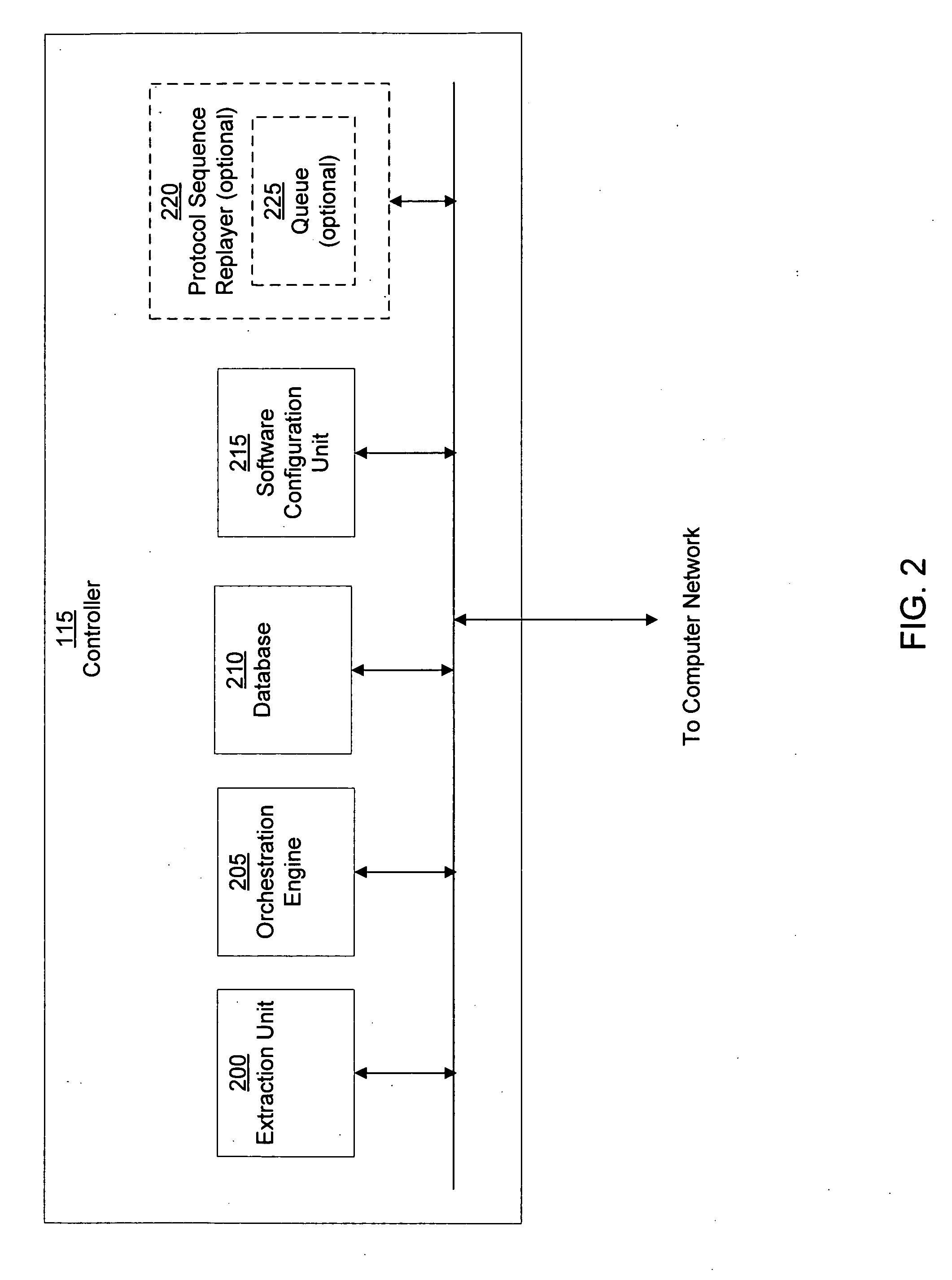
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
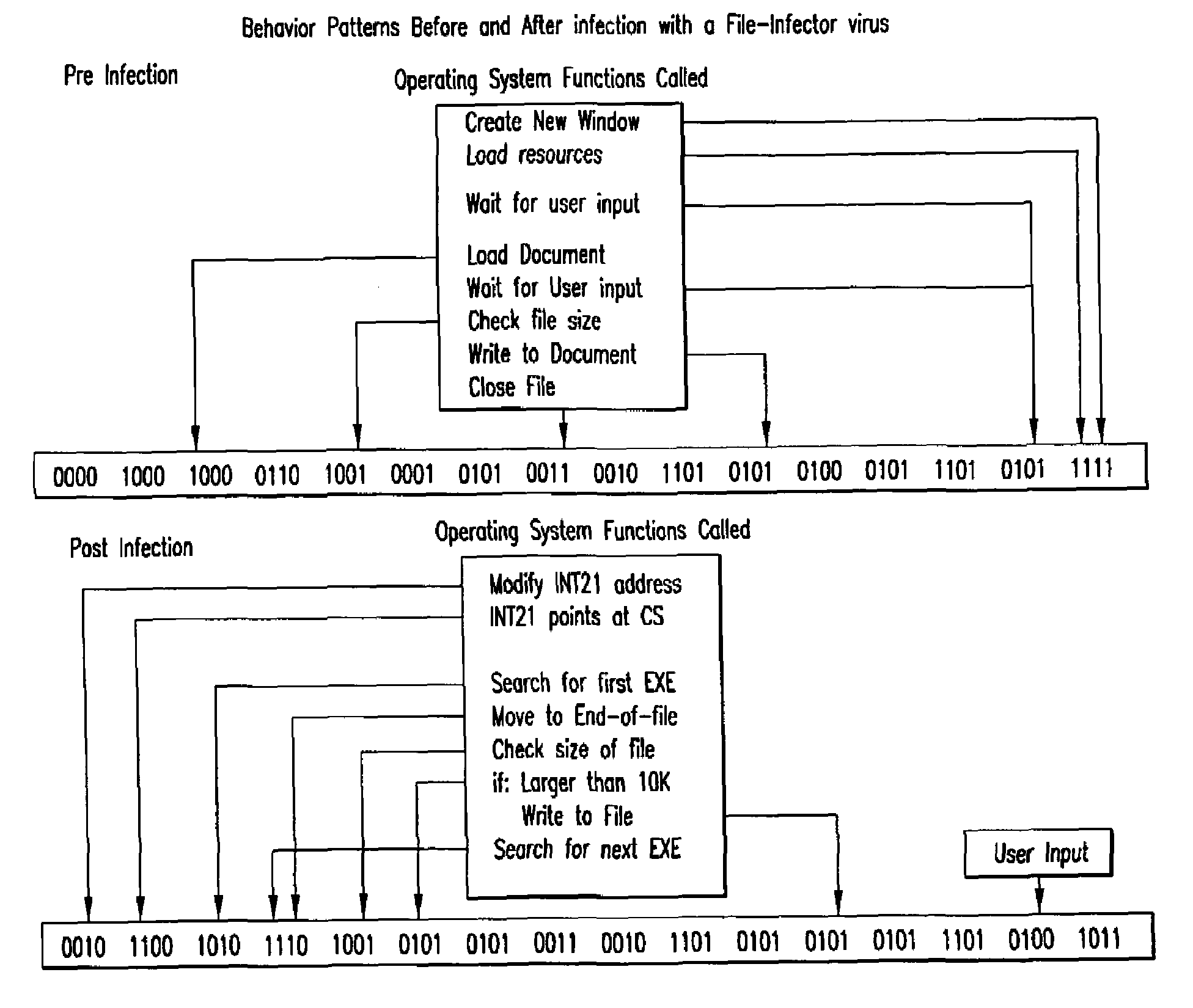
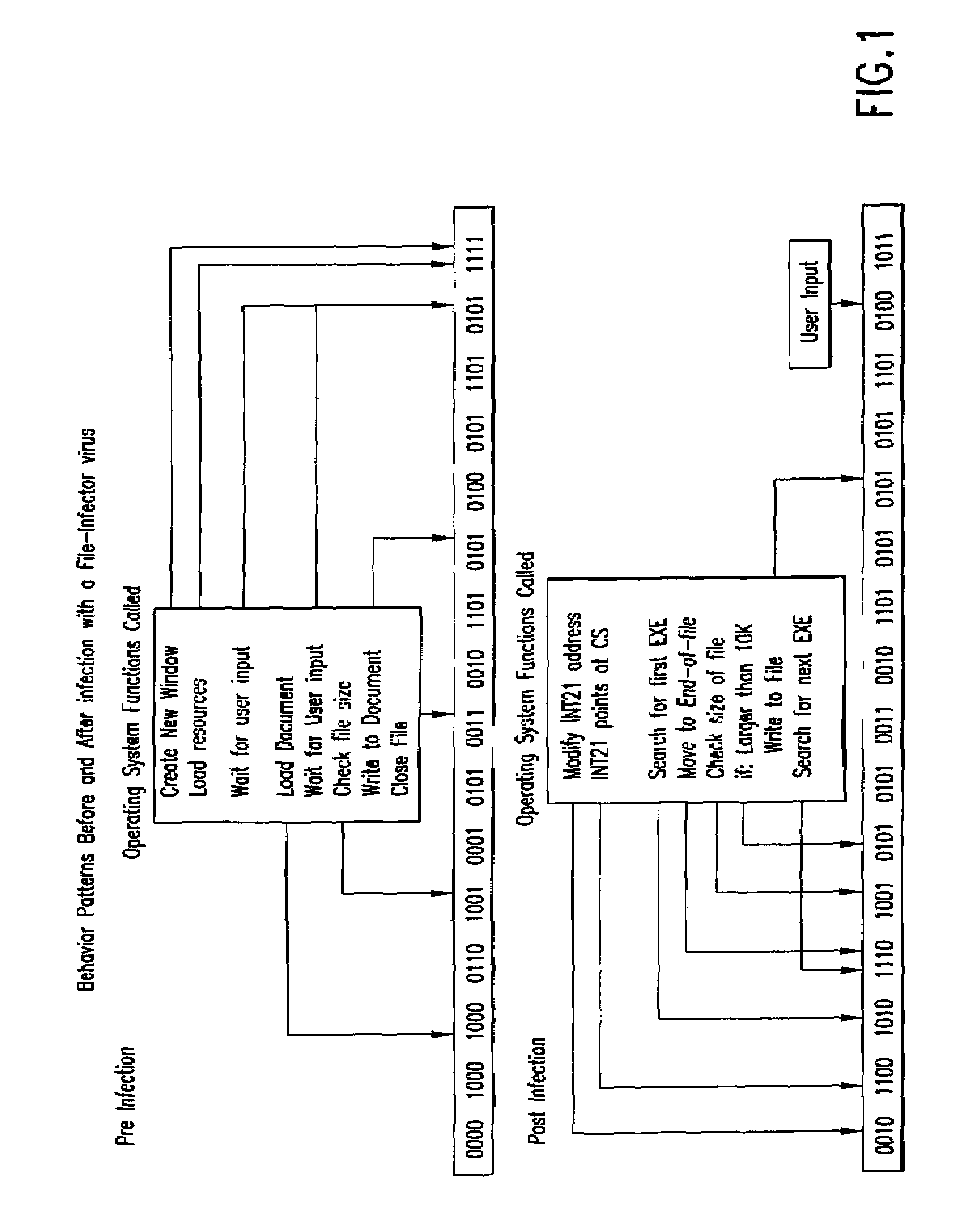
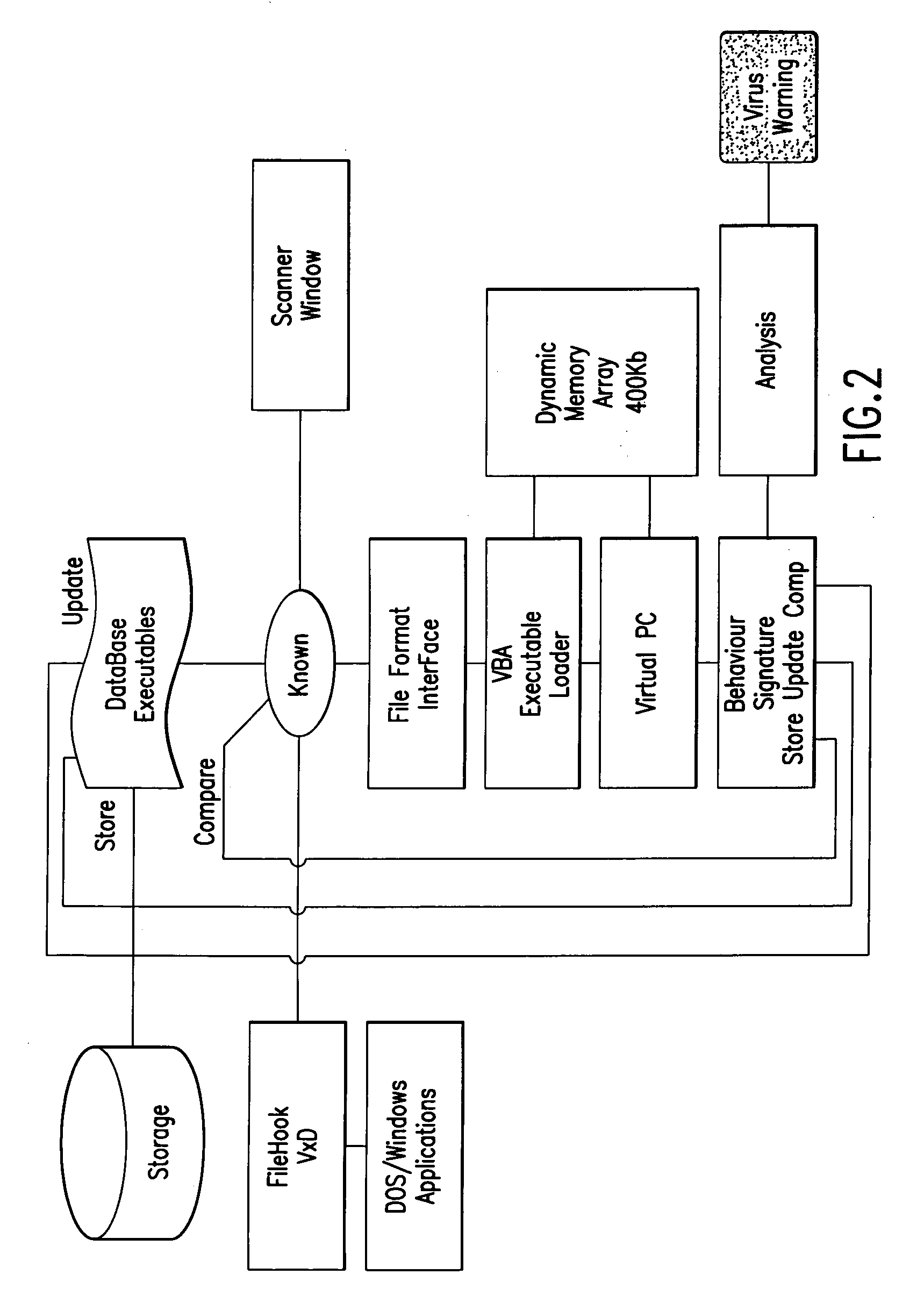
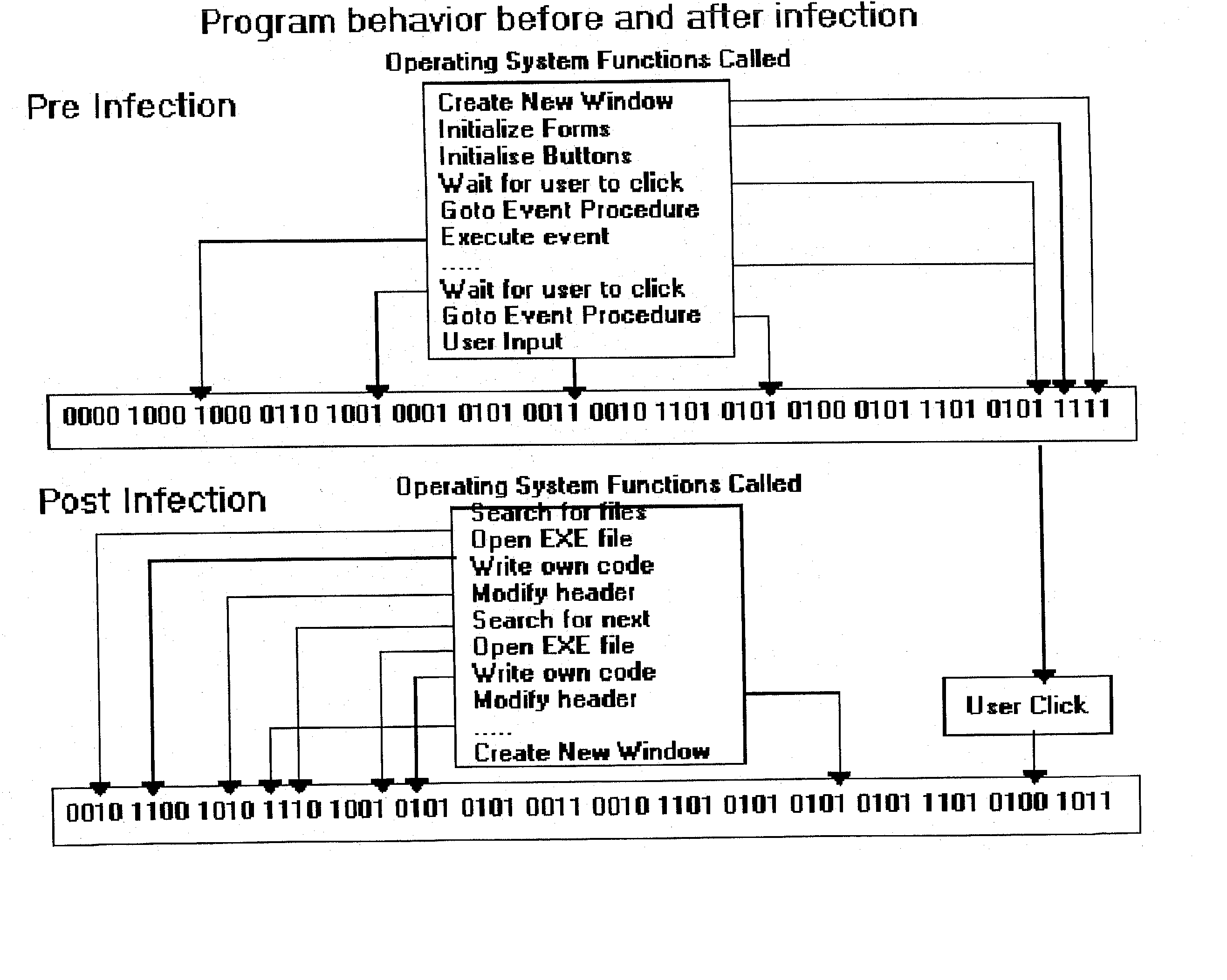
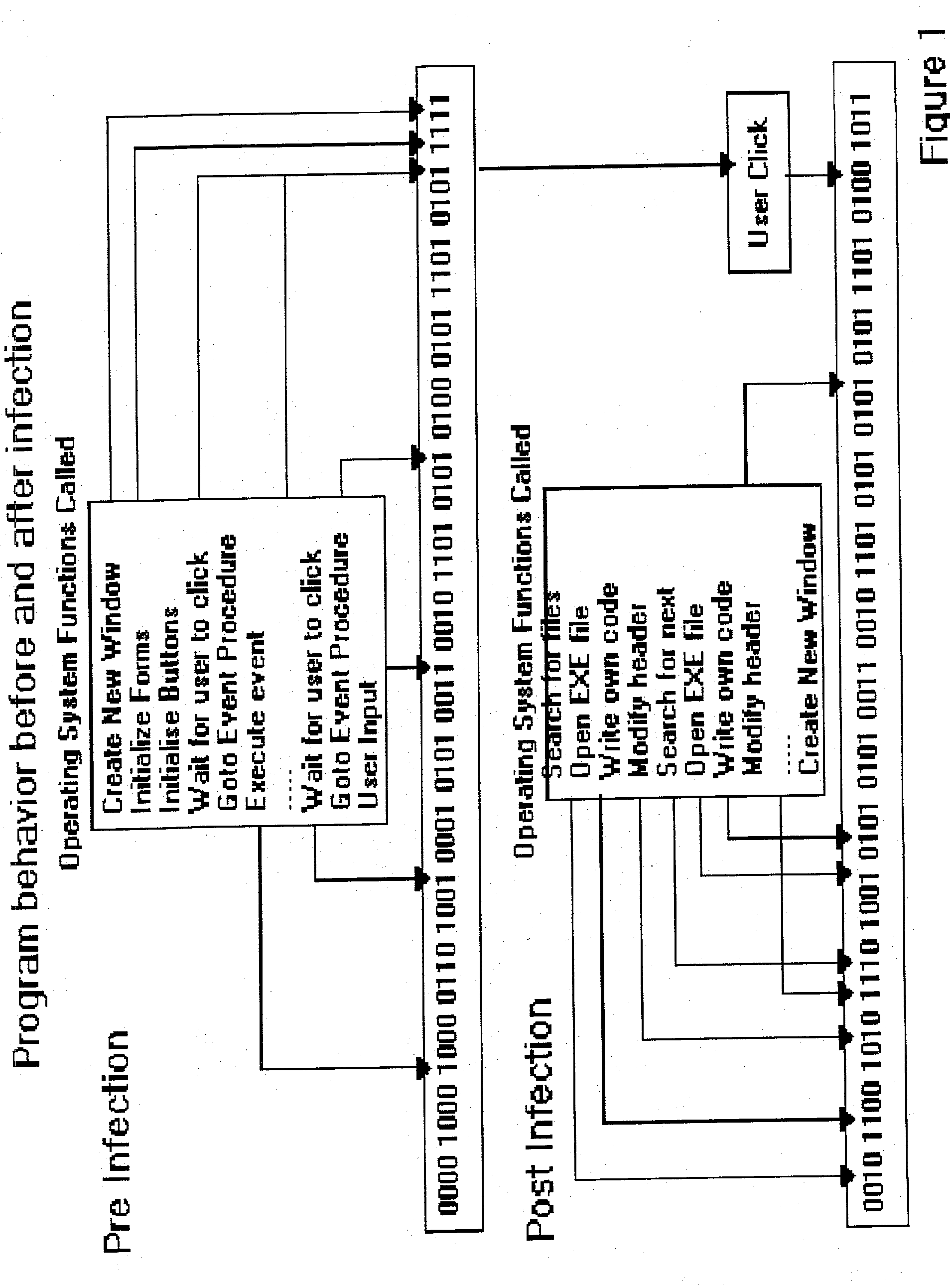
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
System and method for centralized software management in virtual machines
InactiveUS20060184937A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
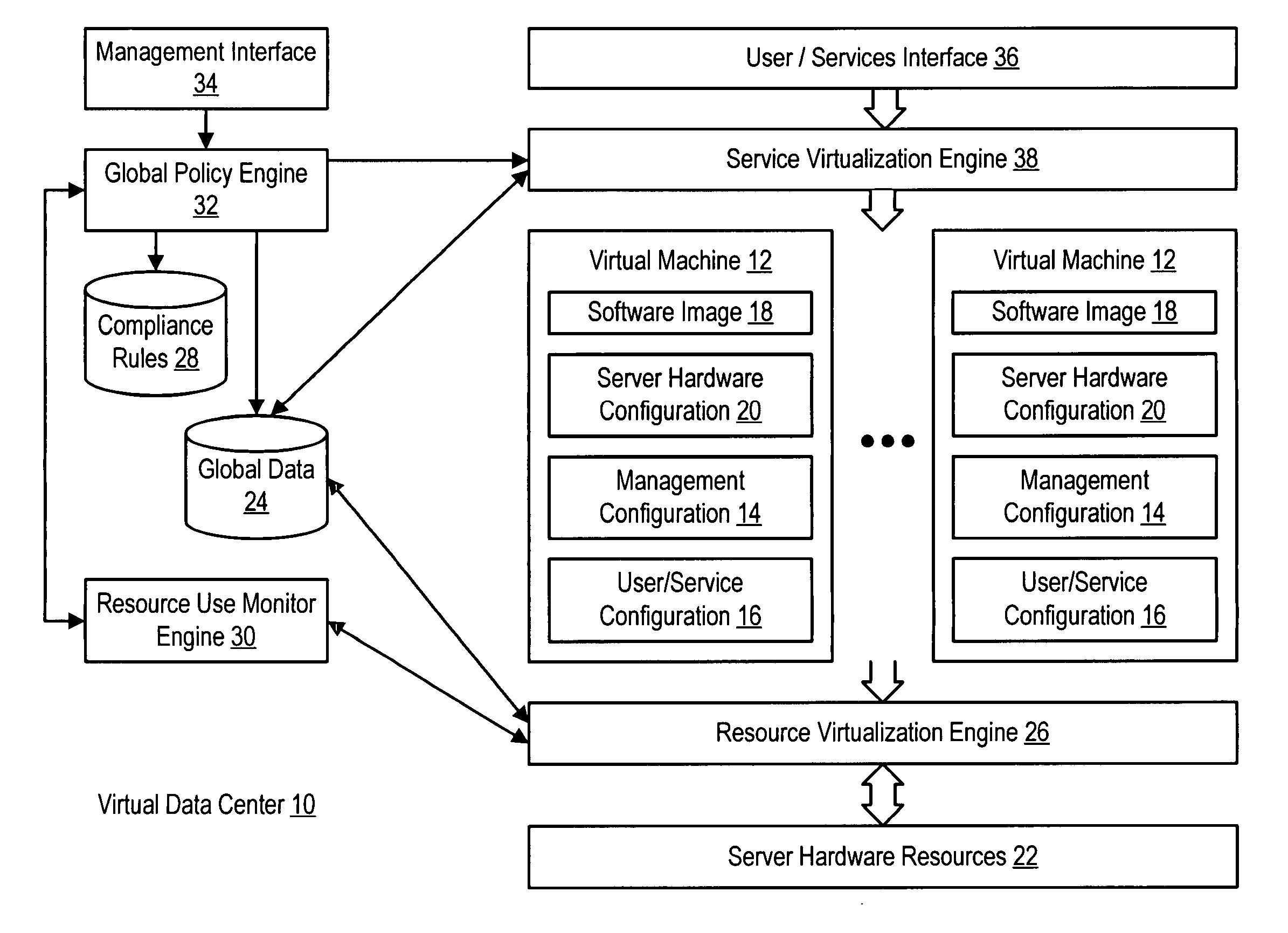
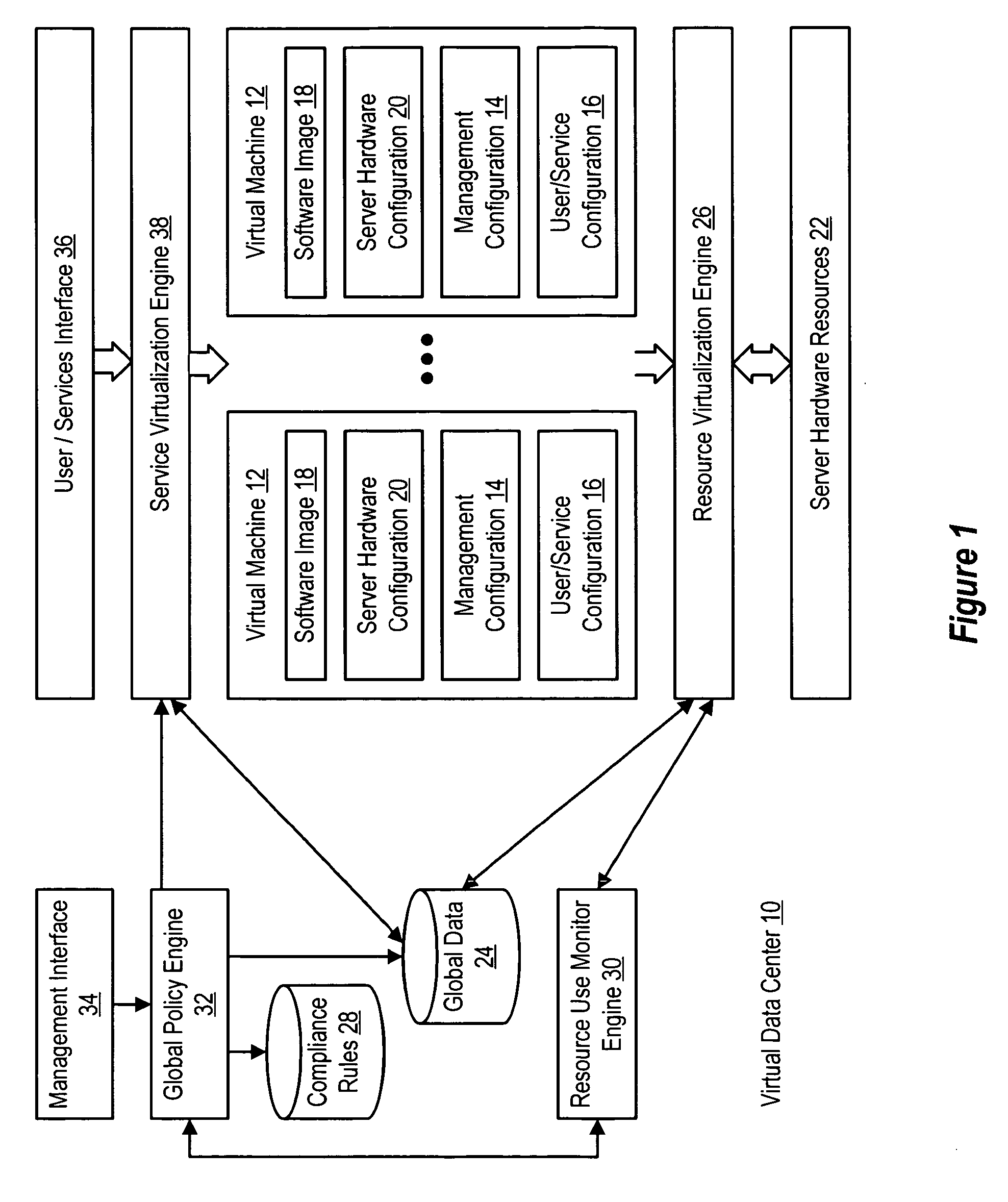
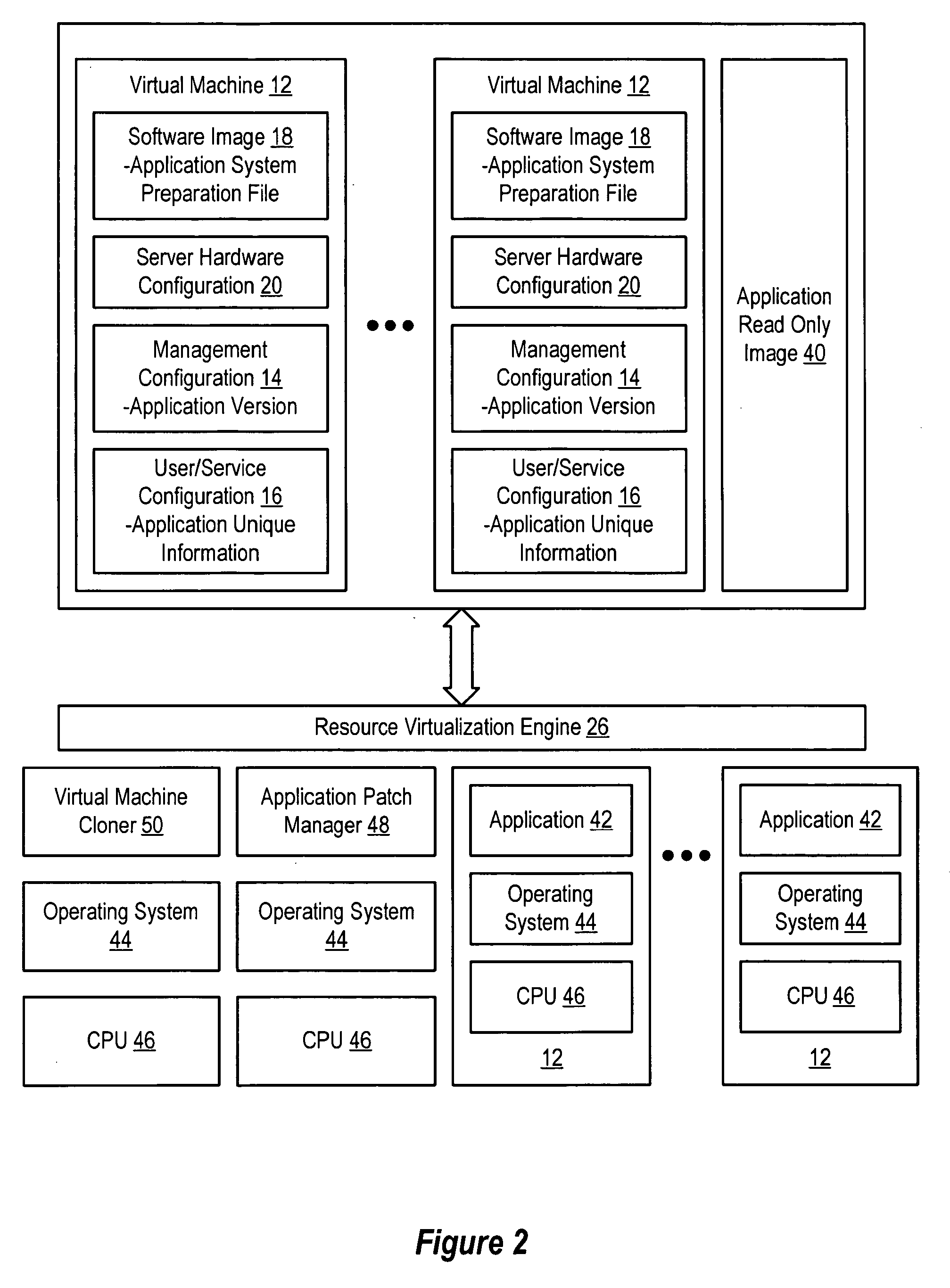
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
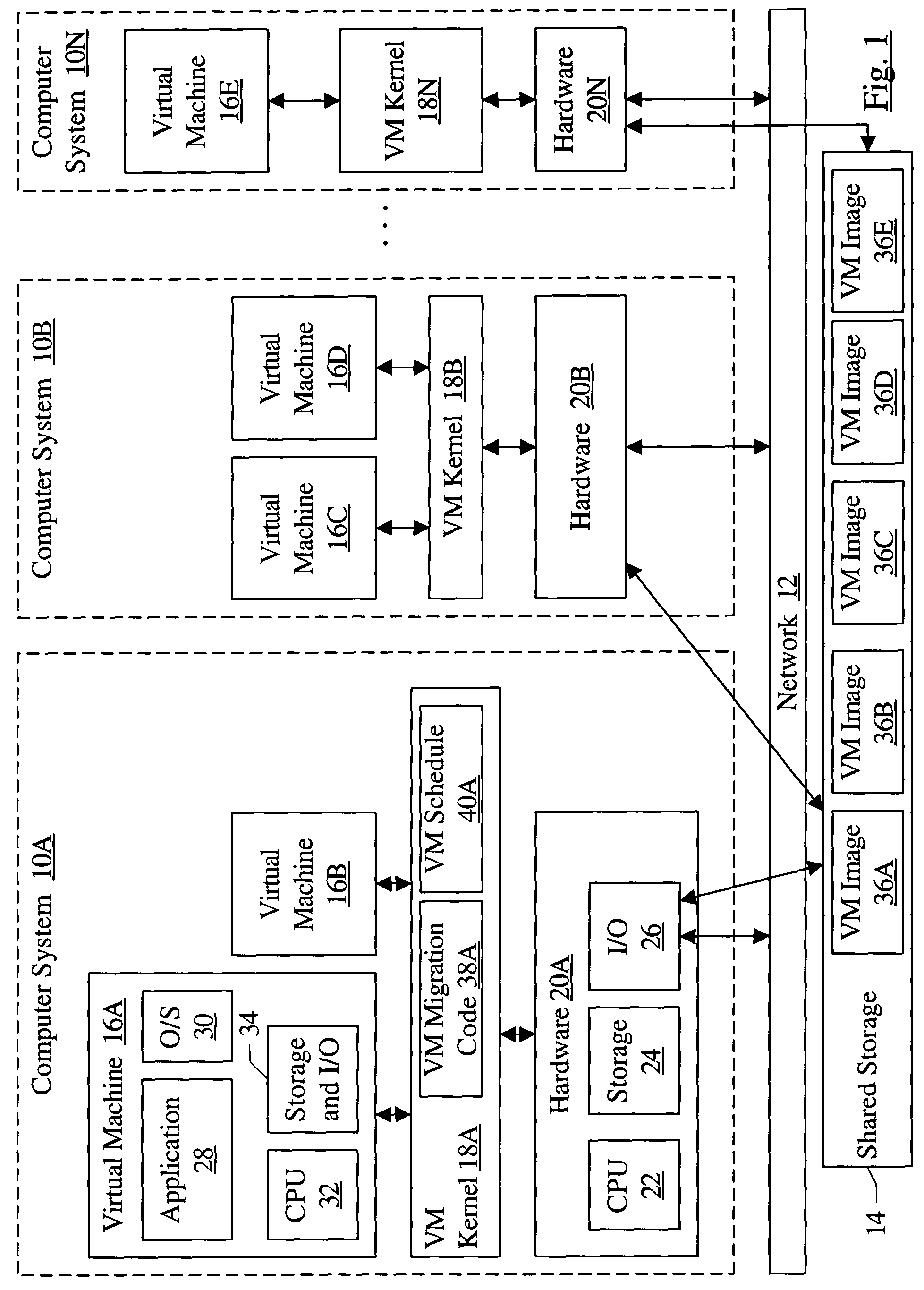
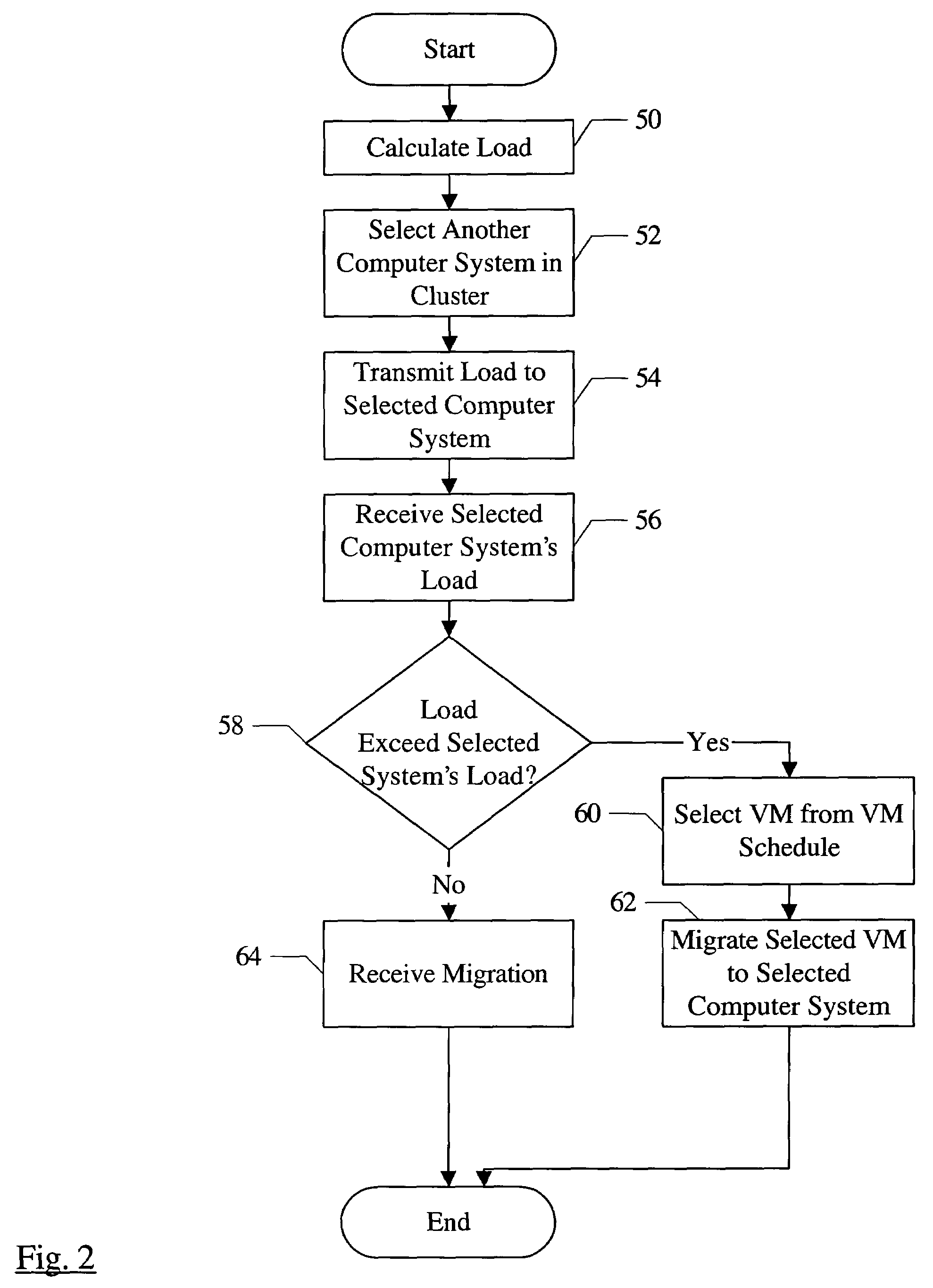
Migrating virtual machines among computer systems to balance load caused by virtual machines
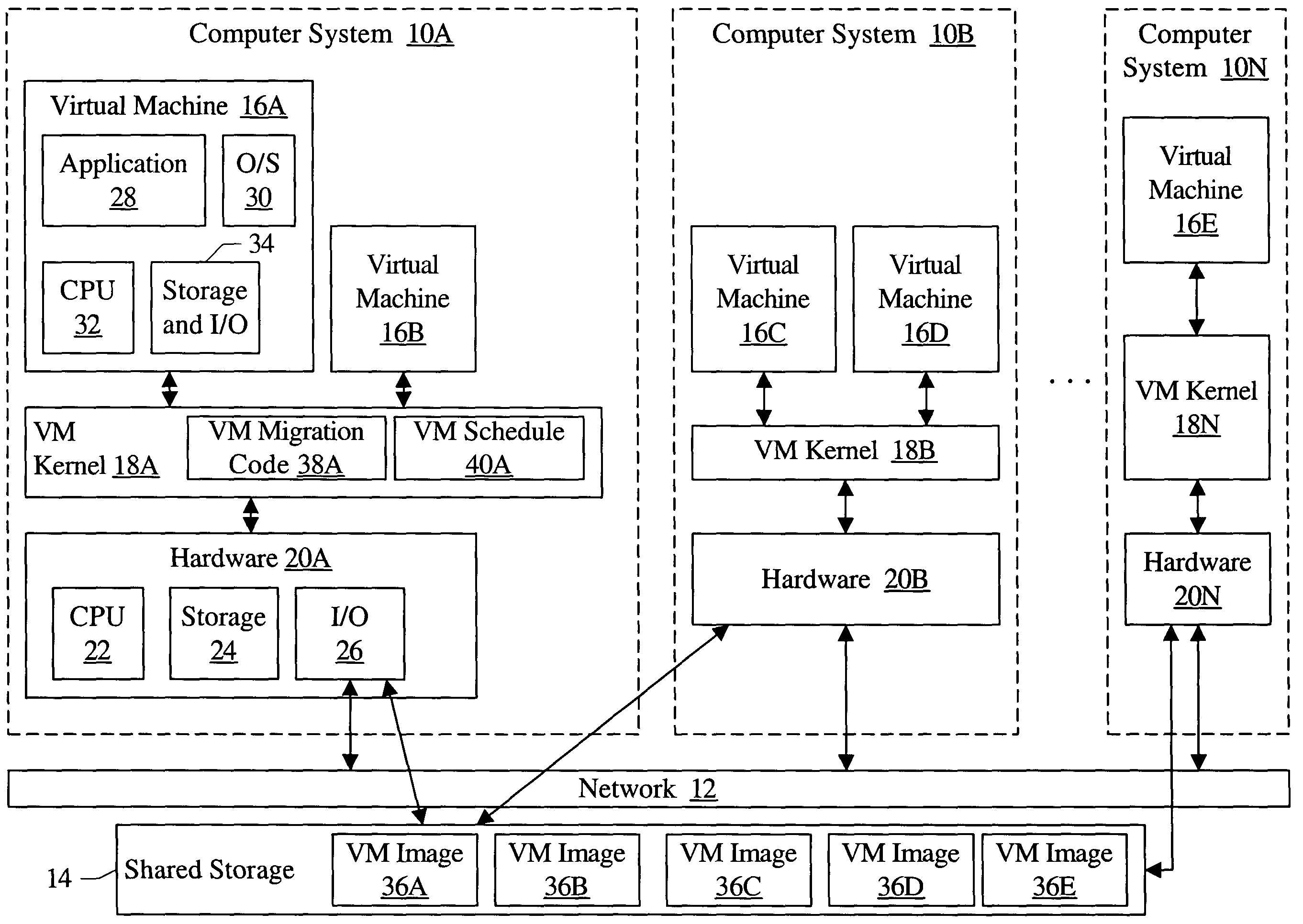
InactiveUS7203944B1Multiprogramming arrangementsSoftware simulation/interpretation/emulationComputerized systemVirtual machine
A cluster comprises a plurality of computer systems, wherein each of the plurality of computer systems is configured to execute one or more virtual machines. Each of the plurality of computer systems comprises hardware and a plurality of instructions. The plurality of instructions, when executed on the hardware, migrates at least a first virtual machine executing on a first computer system of the plurality of computer systems to a second computer system of the plurality of computer systems. The plurality of instructions migrates the first virtual machine responsive to a first load of the first computer system prior to the migration exceeding a second load of the second computer system prior to the migration.
Owner:SYMANTEC OPERATING CORP
Dynamic virtual machine service provider allocation
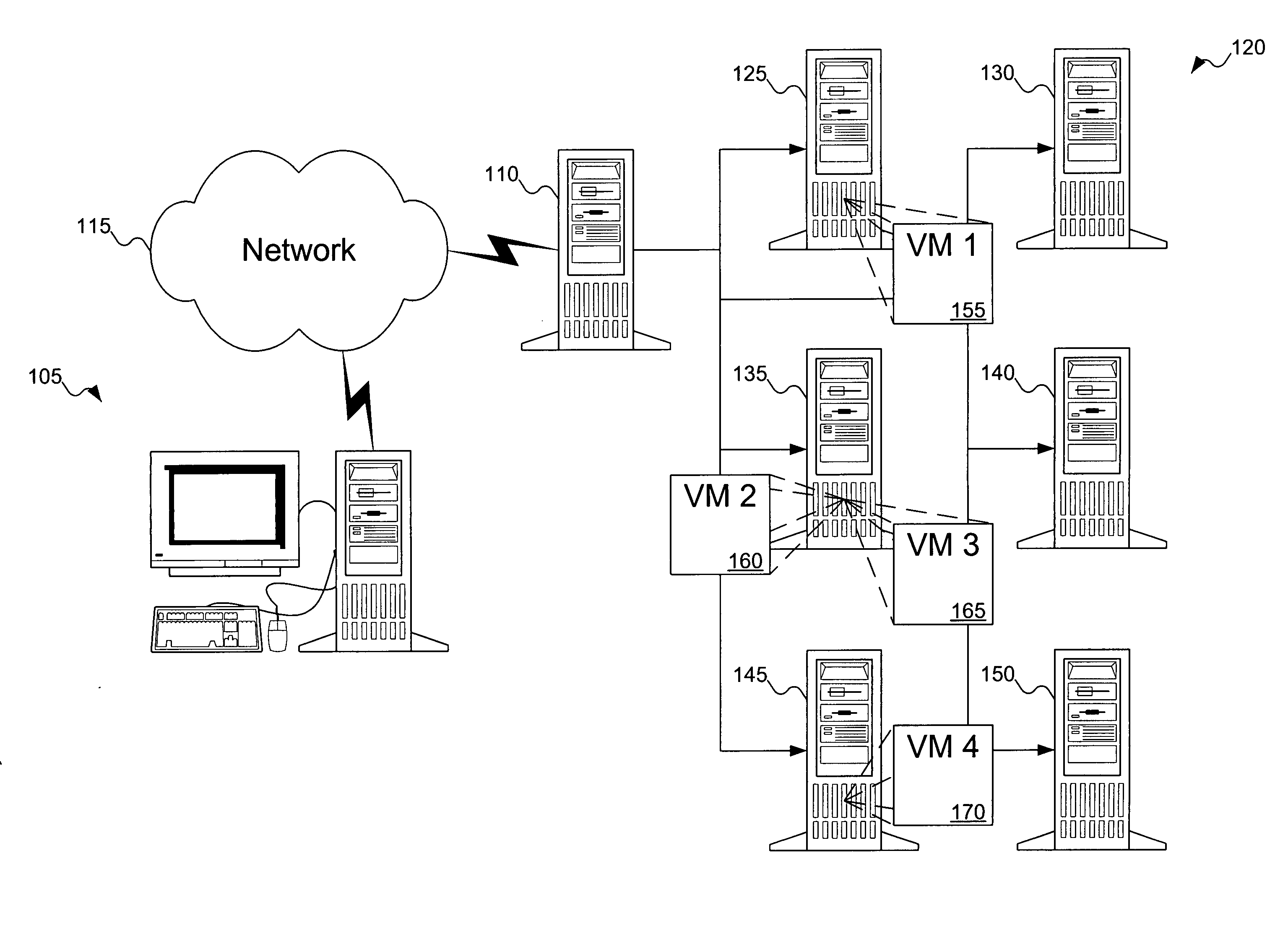
InactiveUS20050198303A1Multiple digital computer combinationsProgram controlClient-sideVirtual machine
A server receives a request for a service. The server determines if a virtual machine already exists that offers the service. If so, the server returns an identifier of the virtual machine to the requesting client so that the client may access the service from the virtual machine. Otherwise, the server attempts to create an image of a virtual machine offering the service. If successful in creating the image, the image is installed as a new virtual machine in a host machine, and the server returns an identifier of the newly created virtual machine to the client.
Owner:KNAUERHASE ROBERT +4
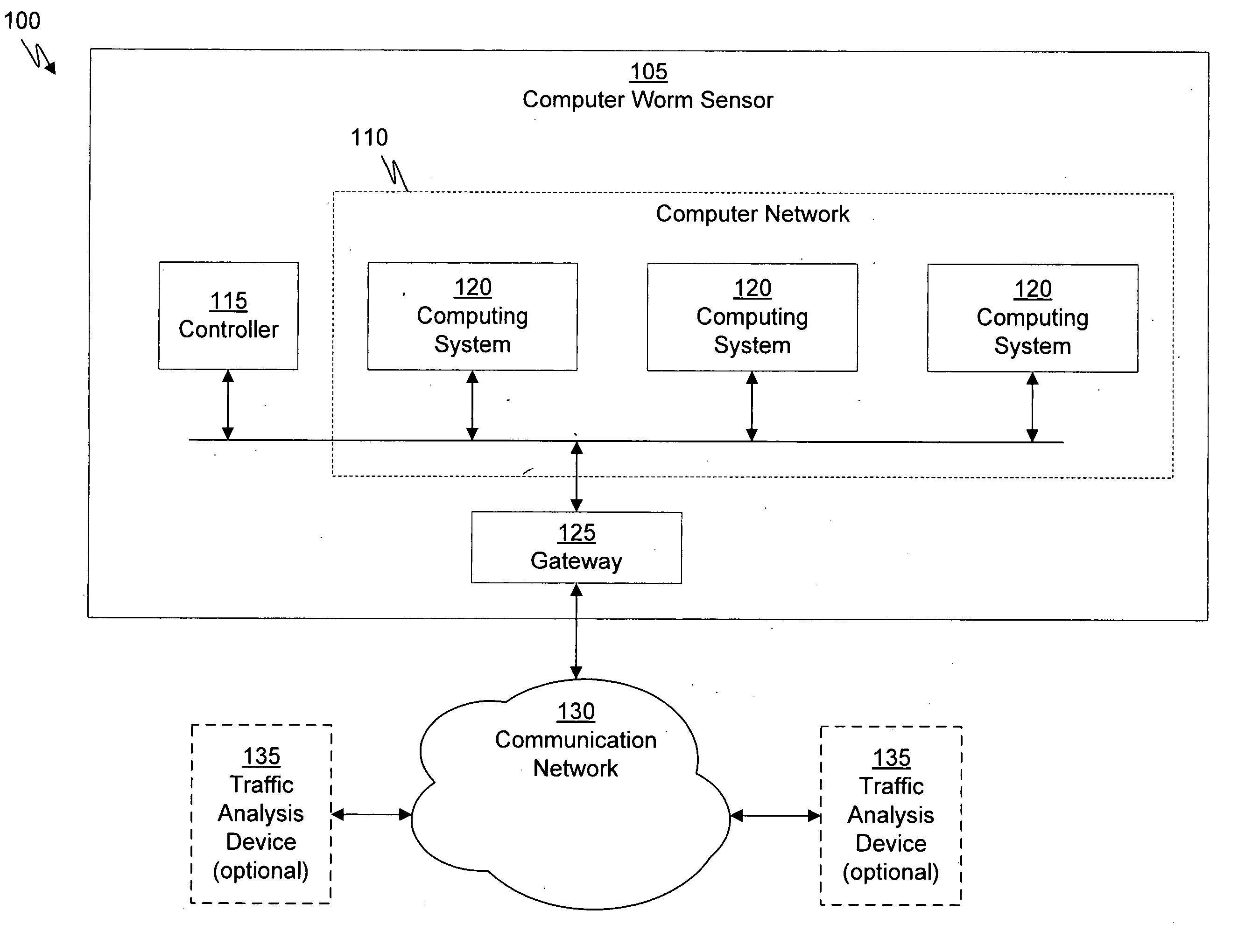
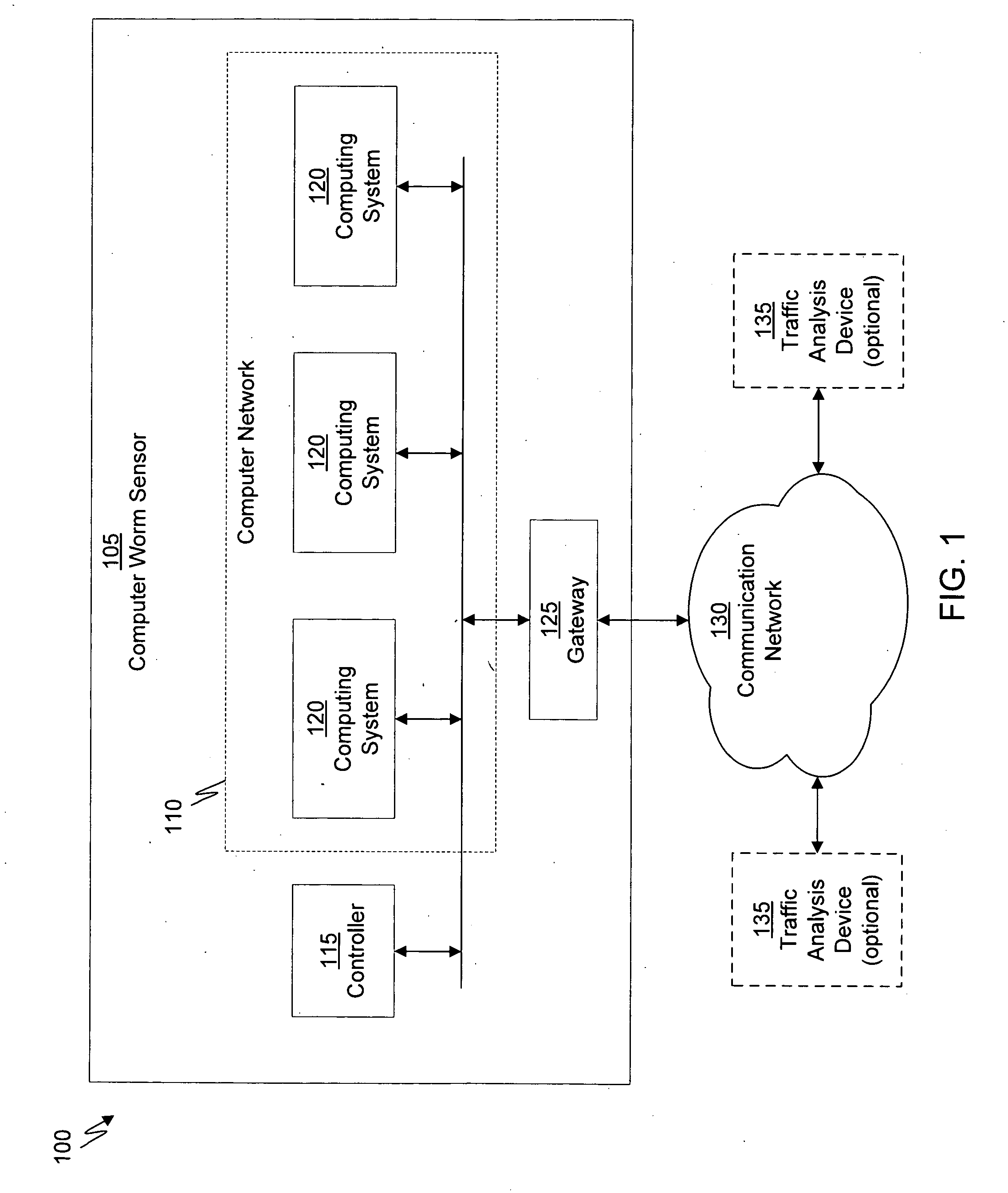
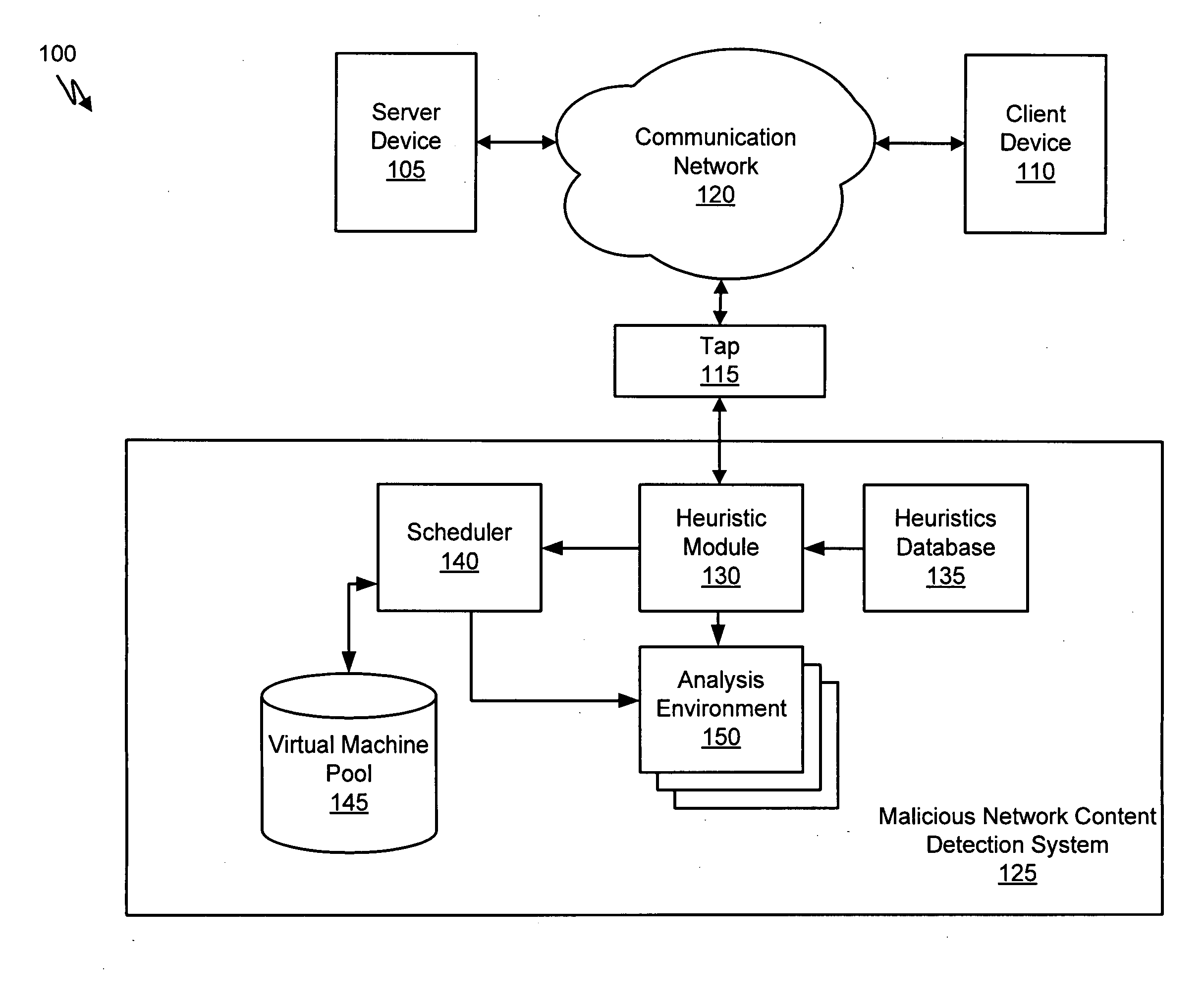
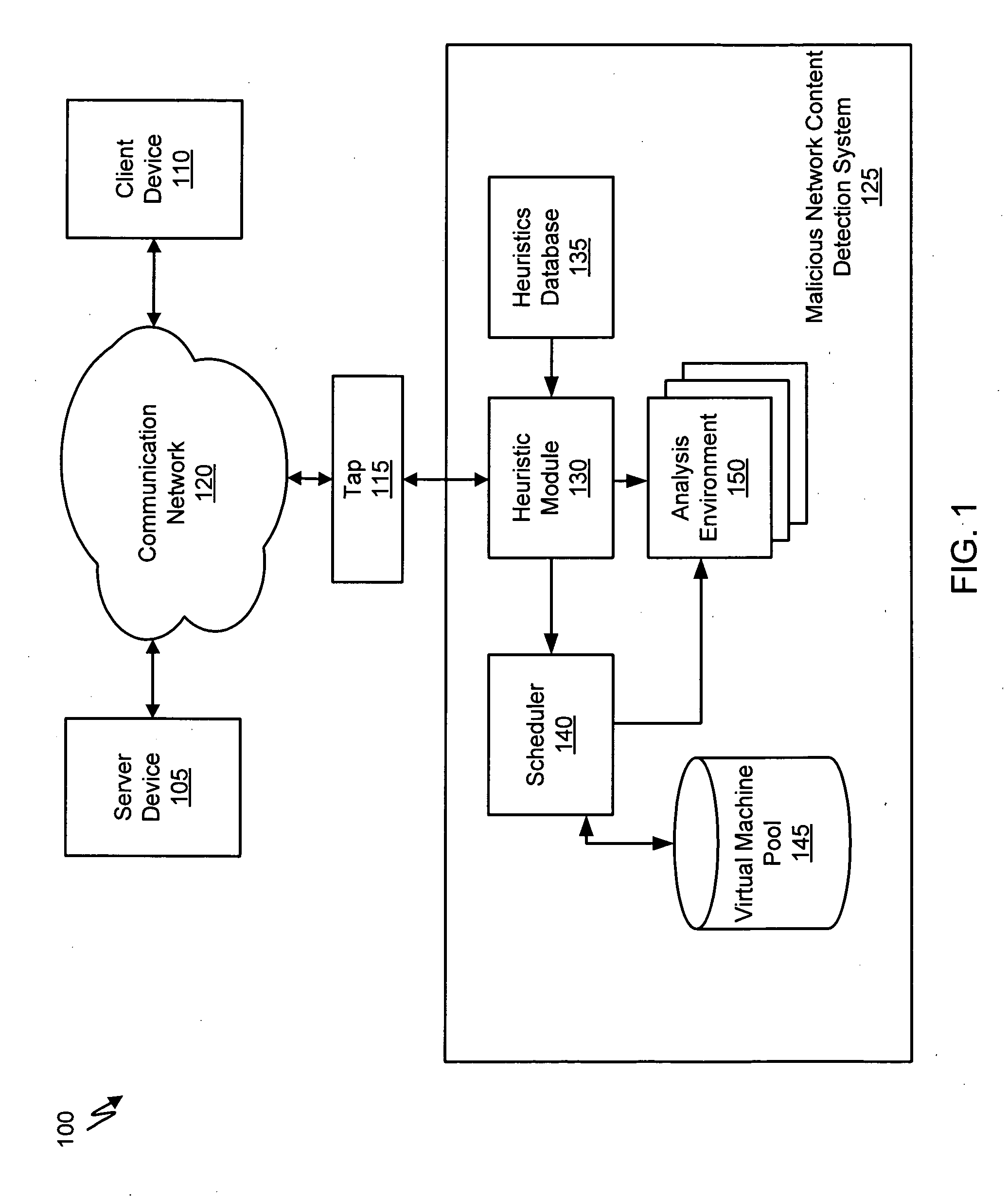
Systems and Methods for Detecting Malicious Network Content
A method for detecting malicious network content comprises inspecting one or more packets of network content, identifying a suspicious characteristic of the network content, determining a score related to a probability that the network content includes malicious network content based on at least the suspicious characteristic, identifying the network content as suspicious if the score satisfies a threshold value, executing a virtual machine to process the suspicious network content, and analyzing a response of the virtual machine to detect malicious network content.
Owner:FIREEYE SECURITY HLDG US LLC
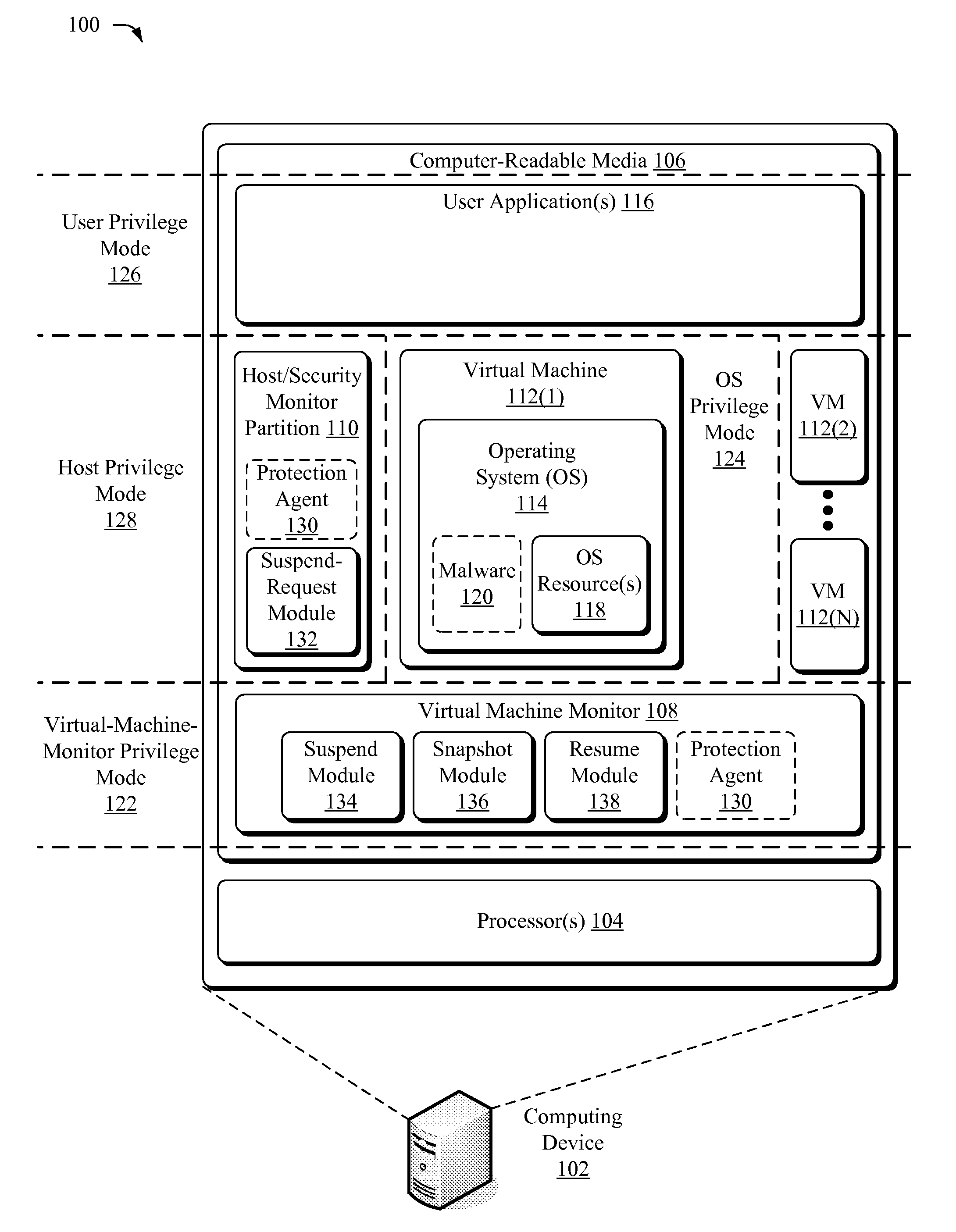
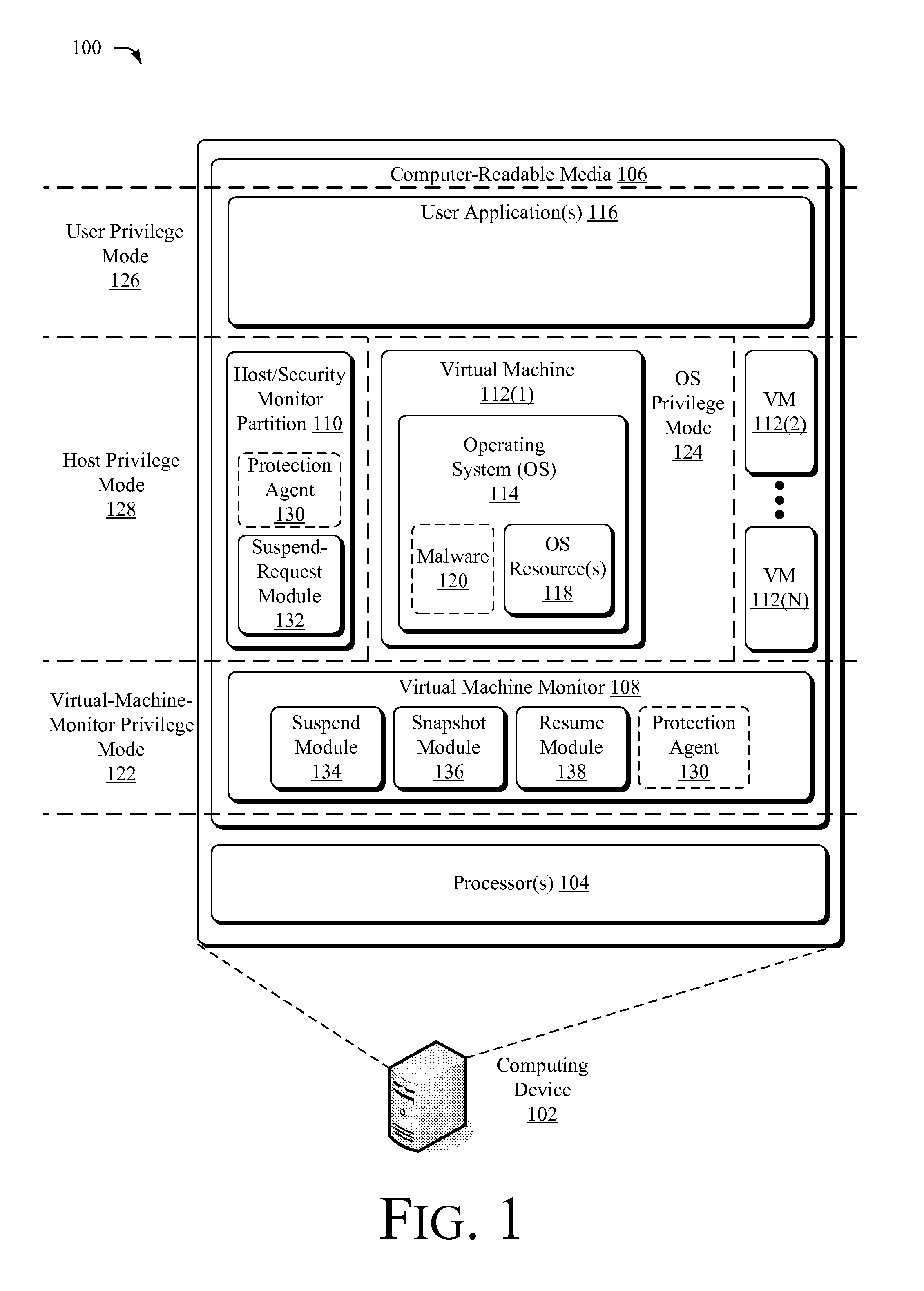
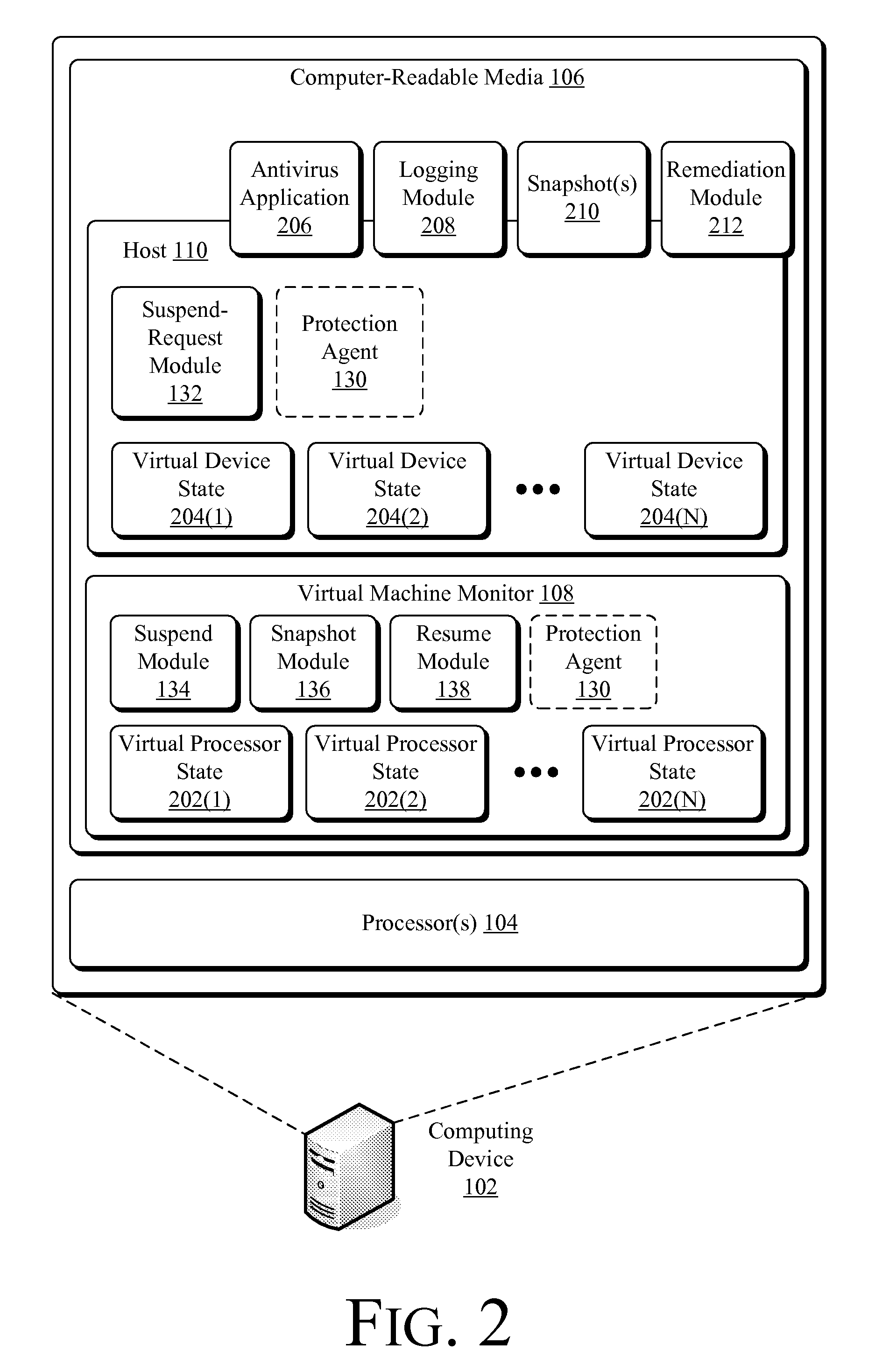
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
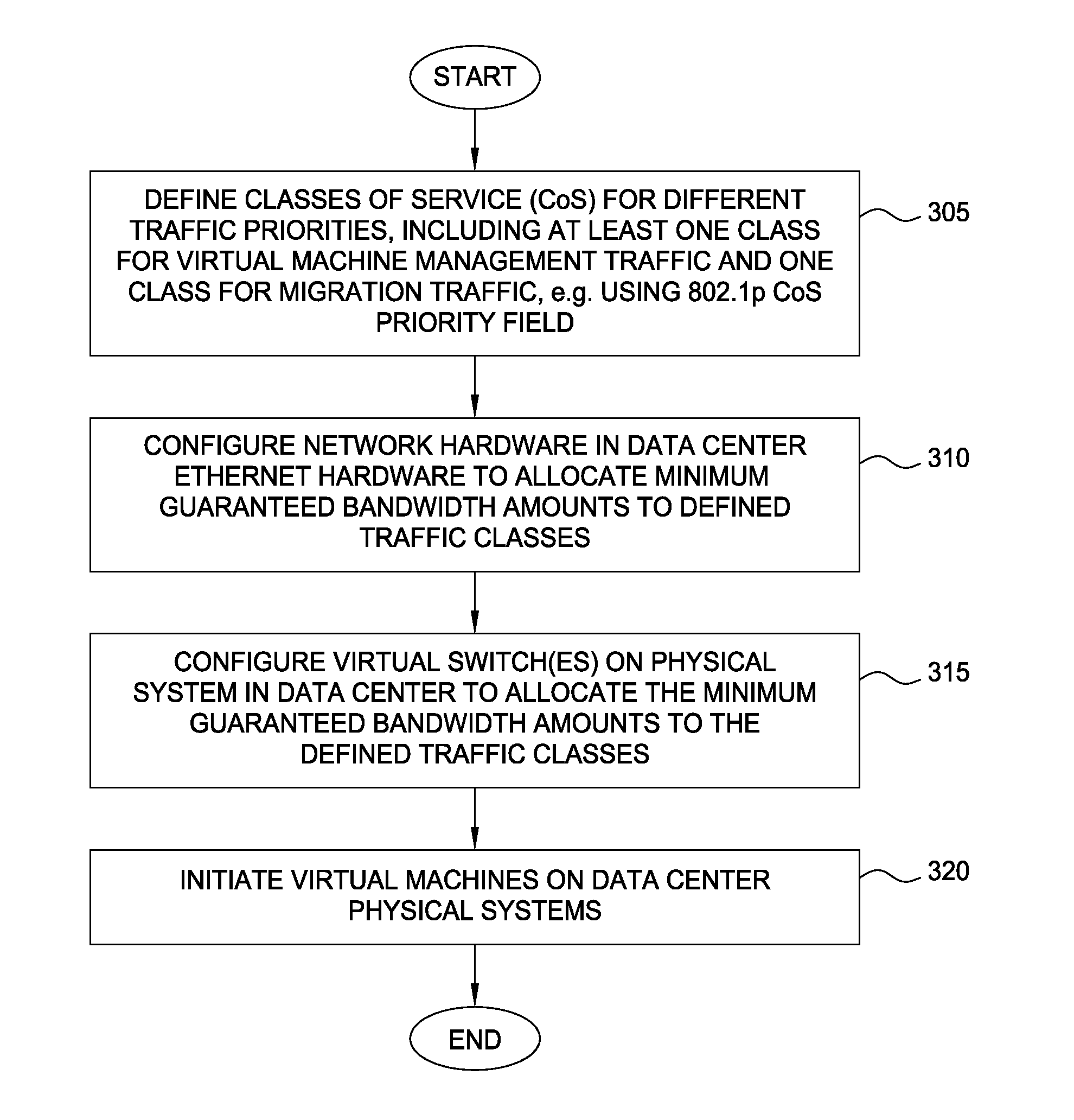
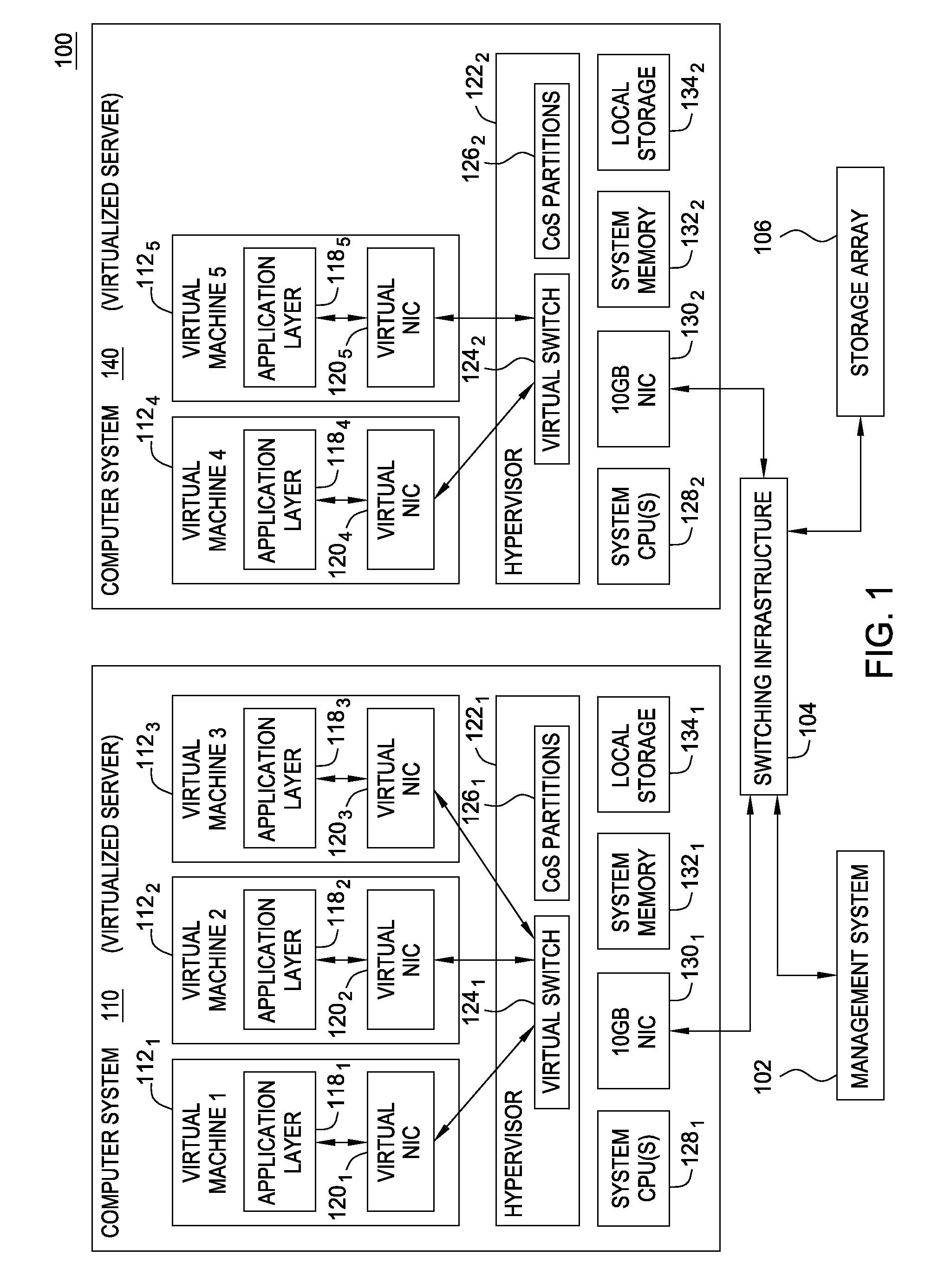
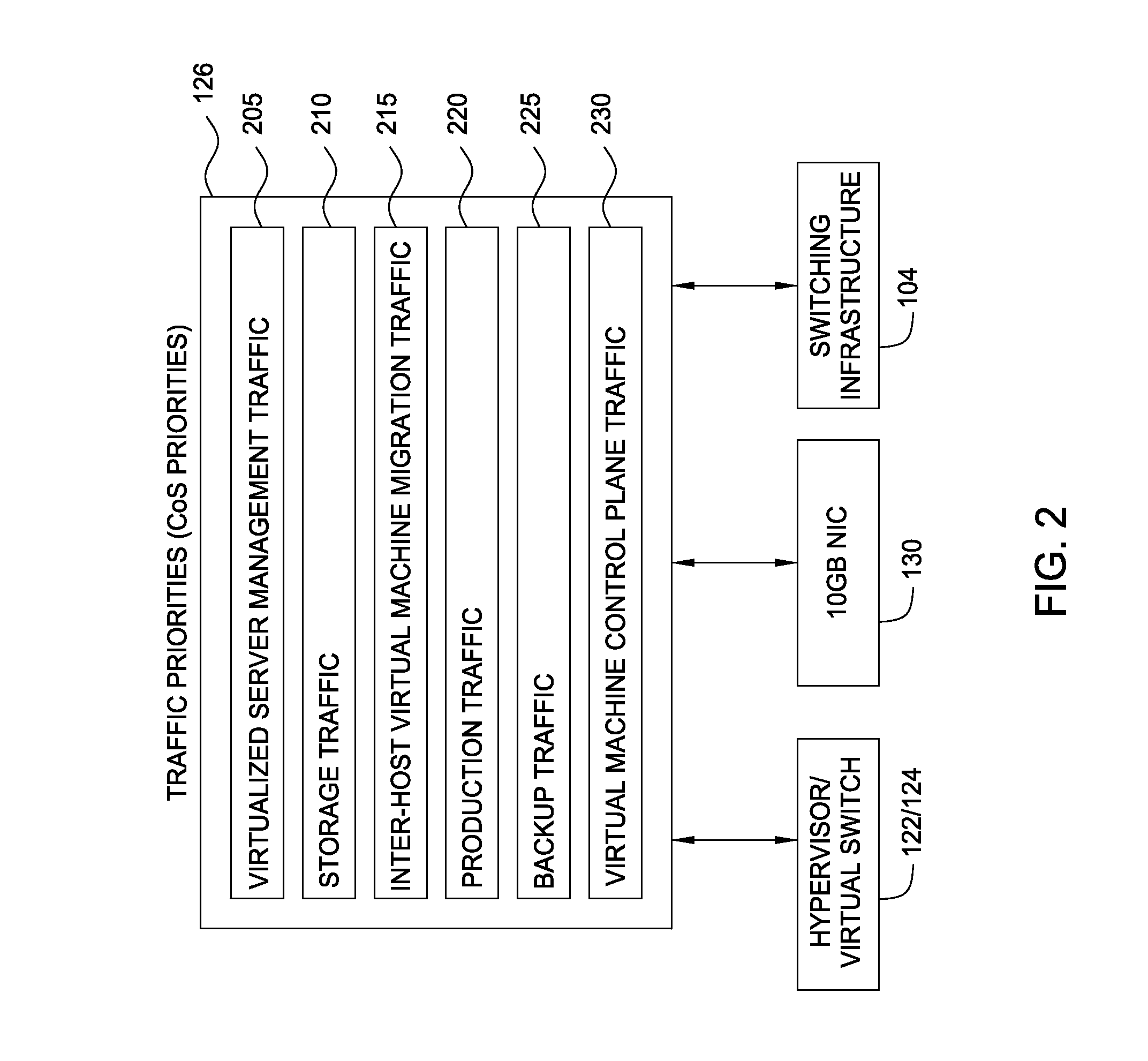
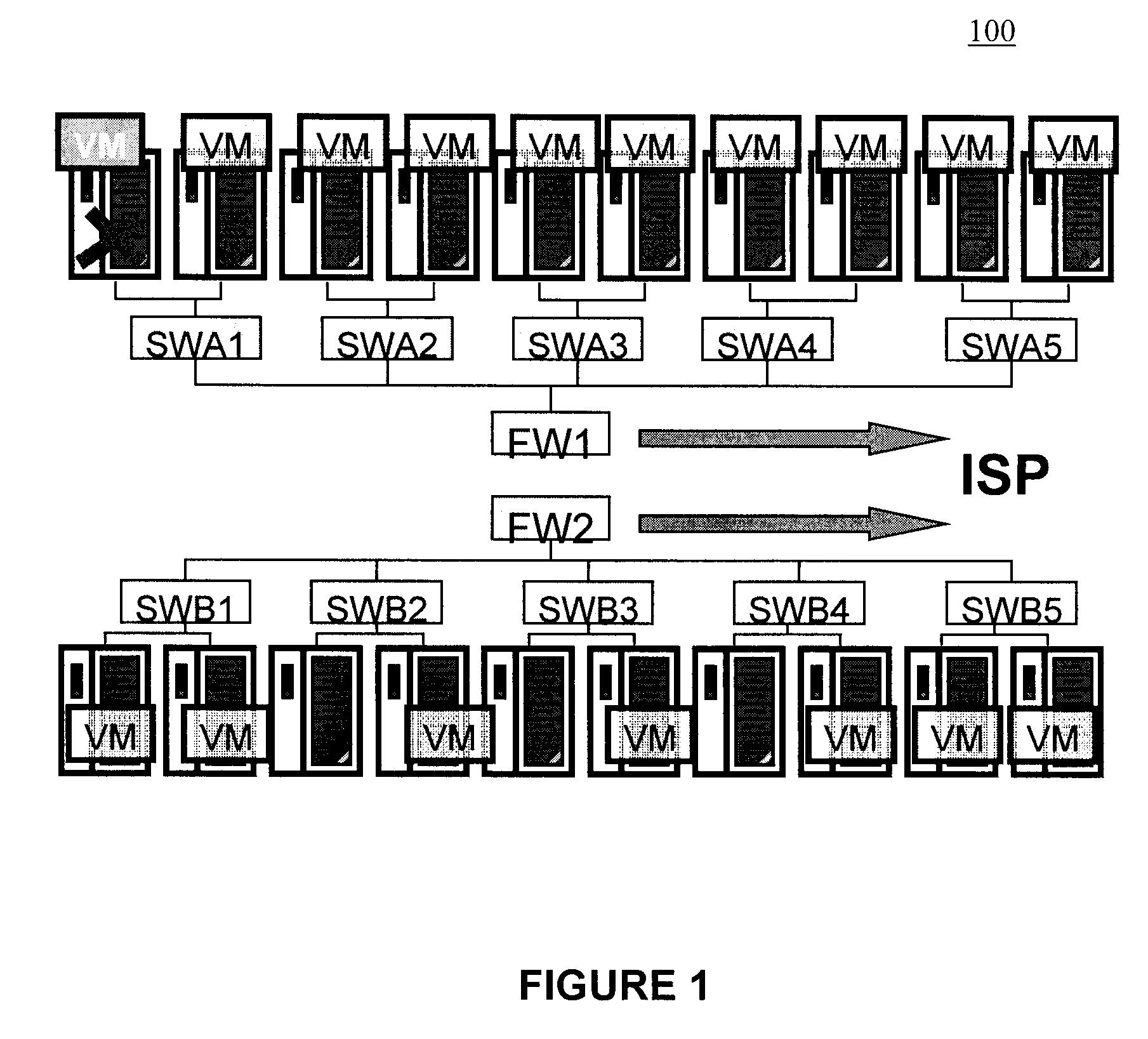
Network consolidation for virtualized servers
Techniques are disclosed for virtualized server kernel and virtual networks consolidation. The network consolidation allows a data center to migrate from an infrastructure that uses multiple dedicated gigabit Ethernet Network Adapters to manage system virtualization and migration to an infrastructure using consolidated, redundant, 10 gigabit Ethernet adapters. Different priority classes may be defined for different classes of network traffic such as hypervisor management traffic, inter-host virtual machine migration traffic, virtual machine production traffic, virtualized switching control plane traffic, etc. Further, an enhanced transmission standard may be used to specify a minimum bandwidth guarantee for certain traffic classes. Thus, the hypervisor management and inter-host virtual machine migration traffic may be transmitted, even the presence of congestion.
Owner:CISCO TECH INC
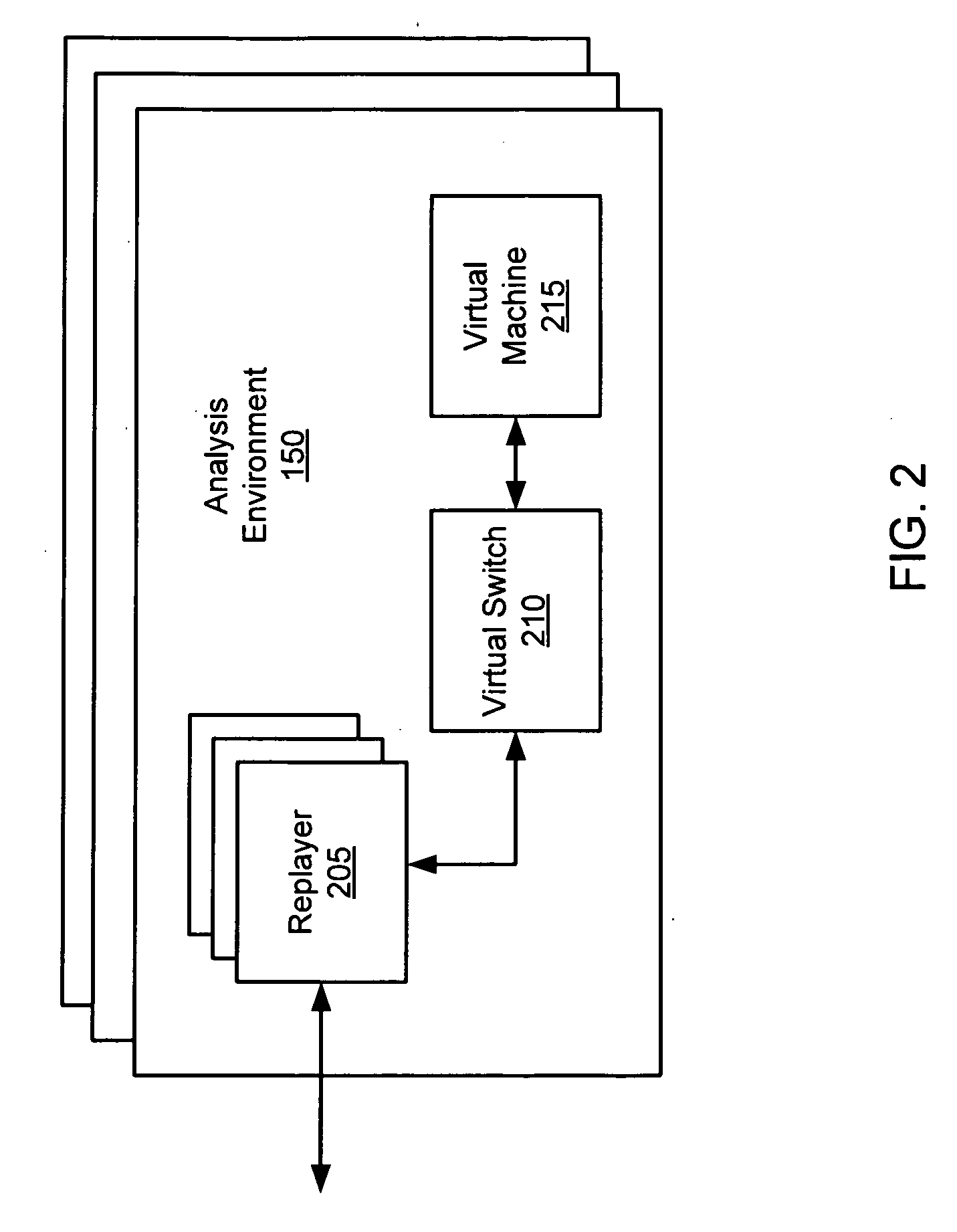
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
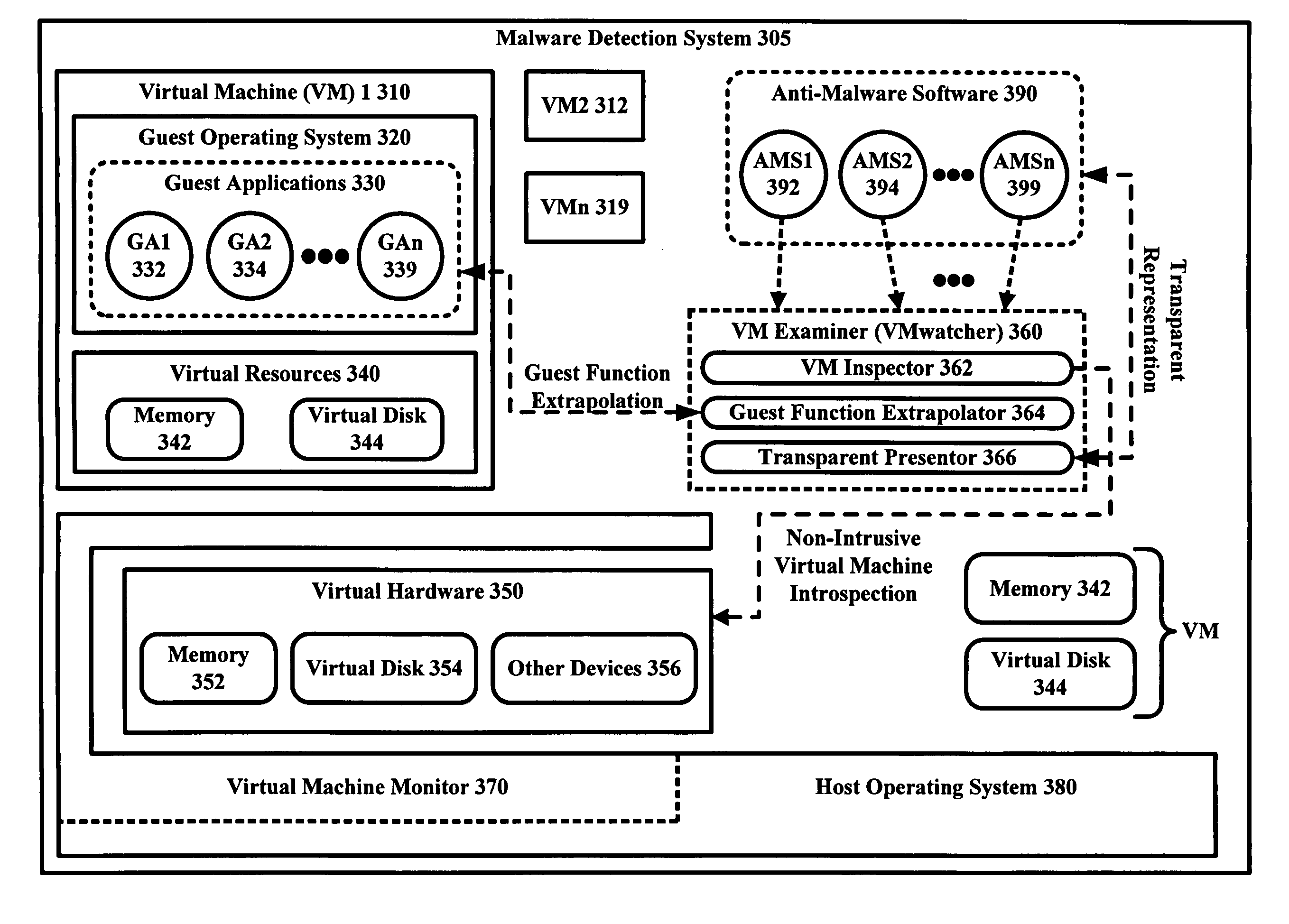
Malware Detector
InactiveUS20080320594A1Memory loss protectionError detection/correctionVirtual memoryOperational system
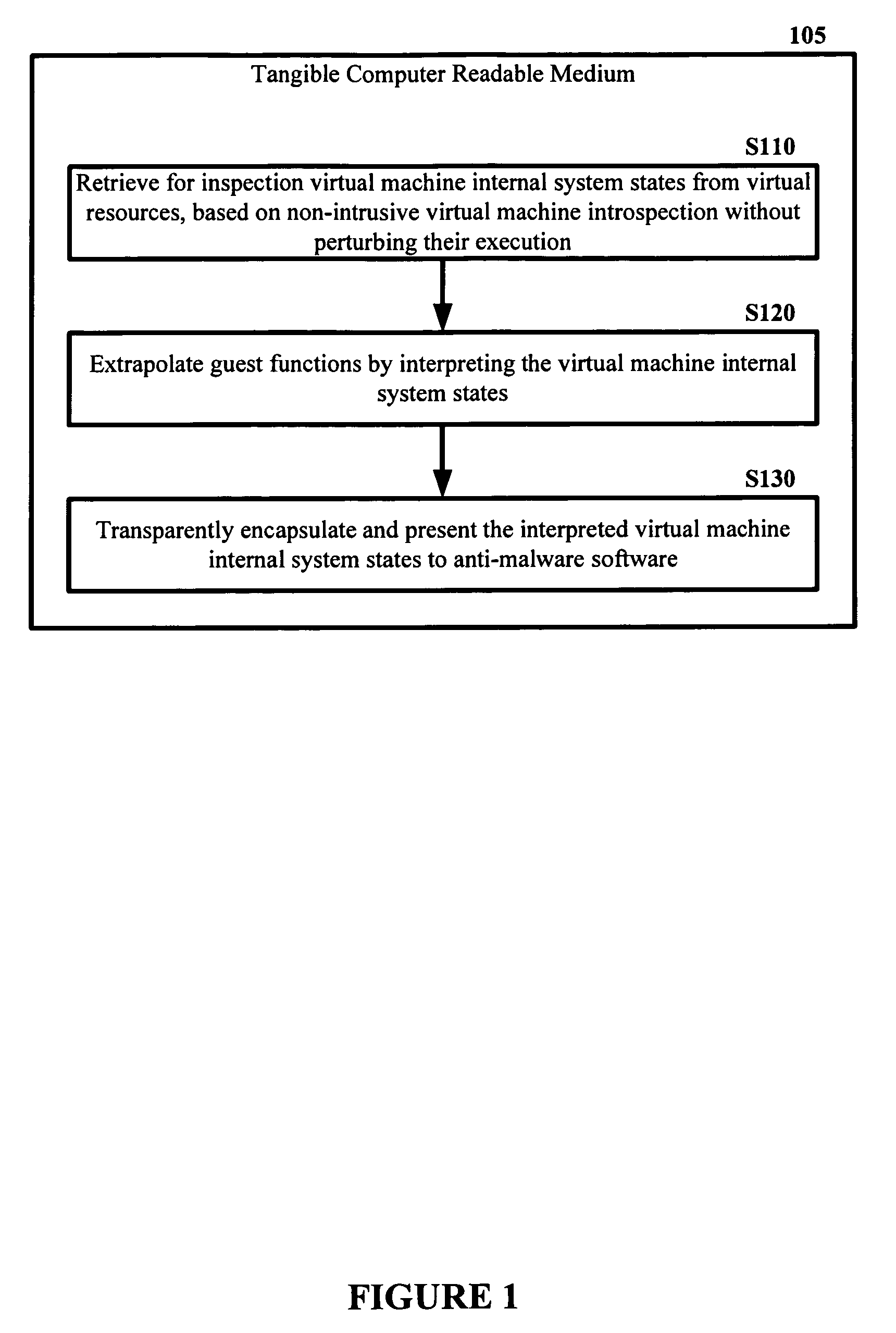
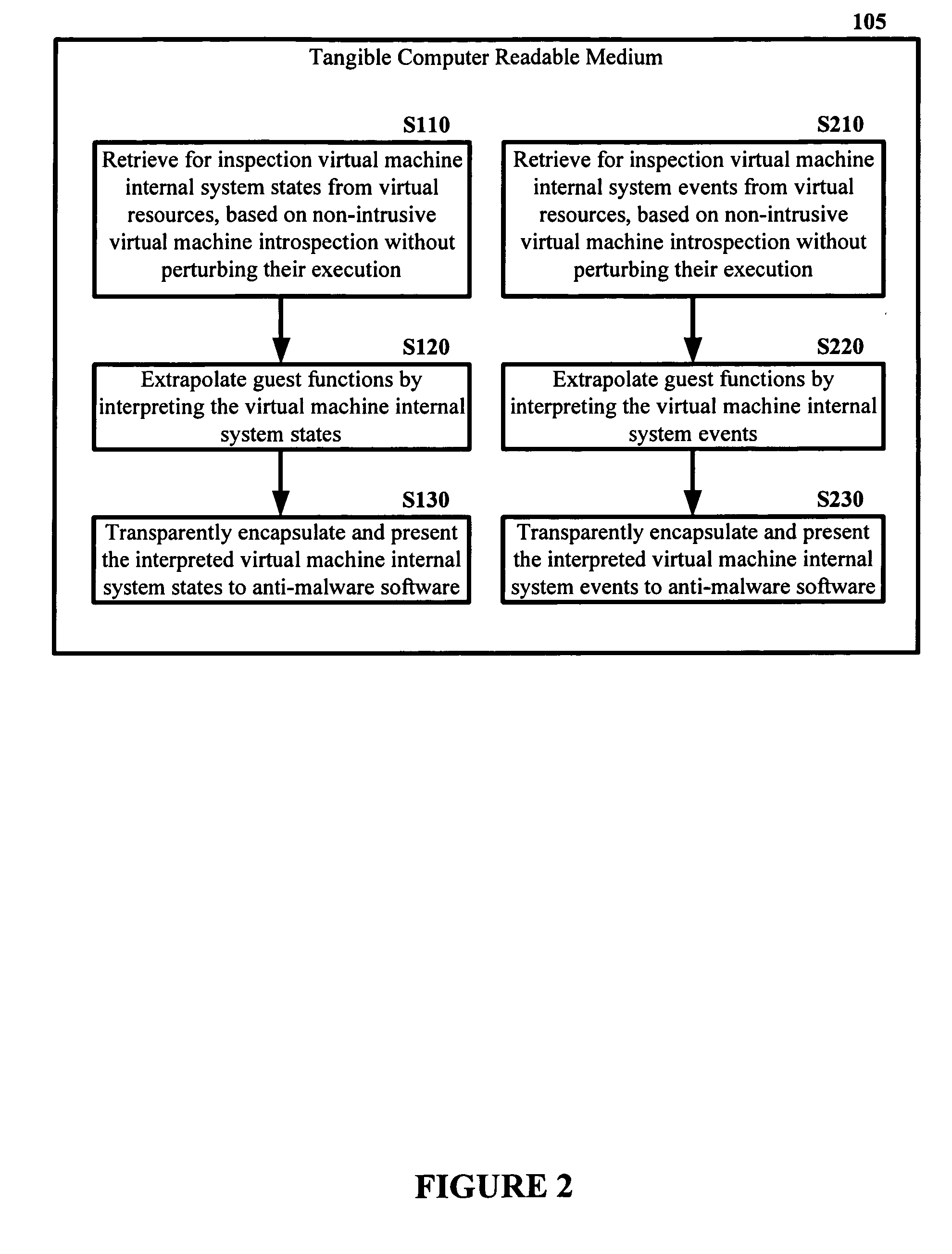
The malware detection system enables out-of-the box, tamper-resistant malware detection without losing the semantic view. This system comprises at least one guest operating system and at least one virtual machine, where the guest operating system runs on the virtual machine. Having virtual resources, the virtual machine resides on a host operating system. The virtual resources include virtual memory and at least one virtual disk. A virtual machine examiner is used to examine the virtual machine. With a virtual machine inspector, a guest function extrapolator, and a transparent presenter, the virtual machine examiner resides outside the virtual machine. The virtual machine inspector is configured to retrieve virtual machine internal system states and / or events. The guest function extrapolator is configured to interpret such states and / or events. The transparent presenter is configured to present the interpreted states and / or events to anti-malware software. The anti-malware software is configured to use the interpreted states and / or events to detect any system compromise.
Owner:GEORGE MASON INTPROP INC
Computer immune system and method for detecting unwanted code in a P-code or partially compiled native-code program executing within a virtual machine
InactiveUS20030212902A1Memory loss protectionDigital data processing detailsComputerized systemBehaviour pattern
An automated analysis system identifies the presence of malicious P-code or N-code programs in a manner that limits the possibility of the malicious code infecting a target computer. The target computer system initializes an analytical virtual P-code engine (AVPE). As initialized, the AVPE comprises software simulating the functionality of a P-code or intermediate language engine as well as machine language facilities simulating the P-code library routines that allow the execution of N-code programs. The AVPE executes a target program so that the target program does not interact with the target computer. The AVPE analyzes the behavior of the target program to identify occurrence of malicious code behavior and to indicate in a behavior pattern the occurrence of malicious code behavior. The AVPE is terminated at the end of the analysis process, thereby removing from the computer system the copy of the target program that was contained within the AVPE.
Owner:PALO ALTO NETWORKS INC
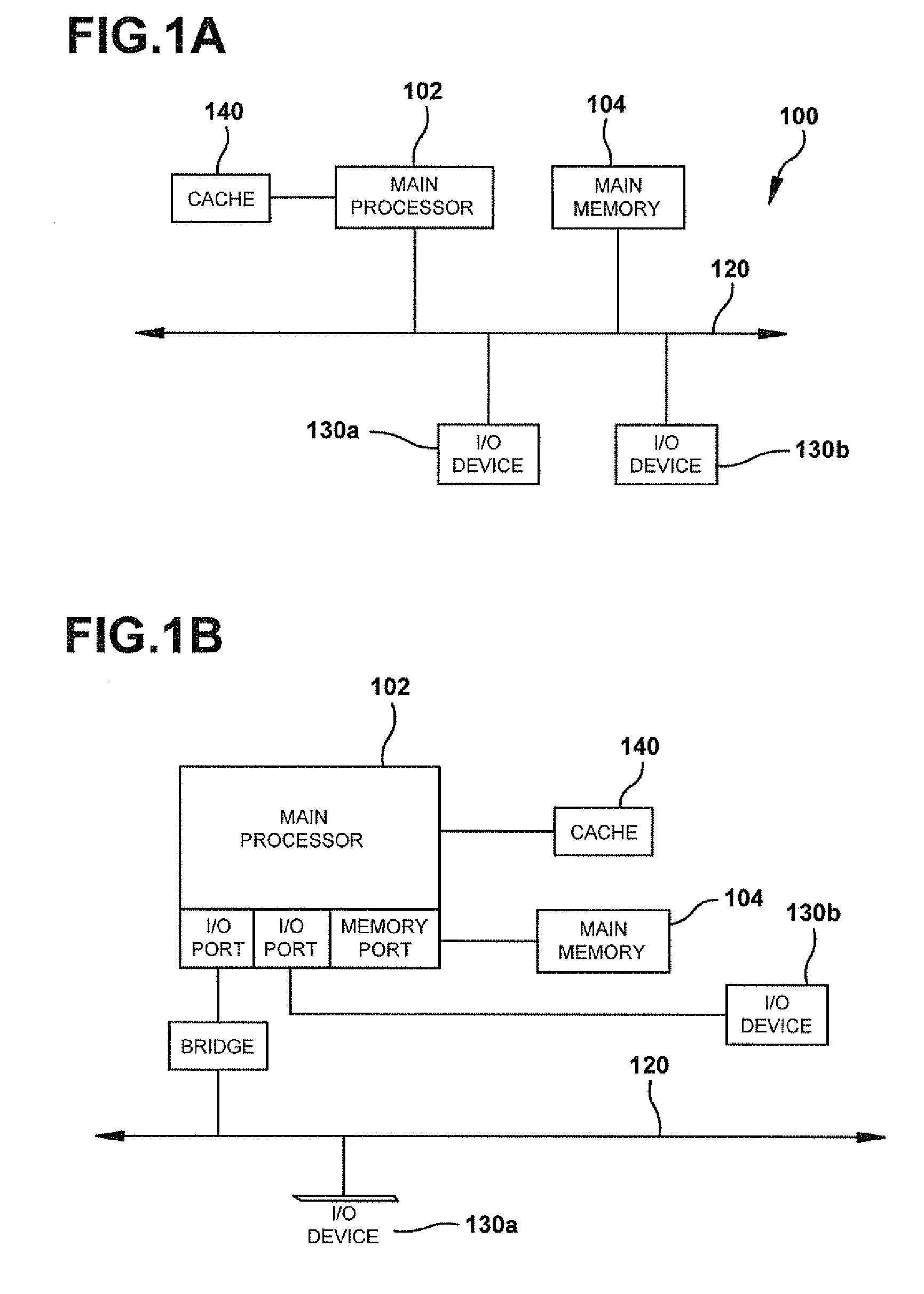
Providing virtual machine technology as an embedded layer within a processing platform
InactiveUS20080059556A1Satisfies specificationMultiple digital computer combinationsProgram controlAuto-configurationProcessor node
A platform, method, and computer program product, provides virtual machine technology within a processing platform. A computing platform automatically deploys one or more servers in response to receiving corresponding server specifications. Each server specification identifies a server application that a corresponding server should execute and defines communication network and storage network connectivity for the server. The platform includes a plurality of processor nodes and virtual machine hypervisor. The virtual machine hypervisor logic has logic for instantiating and controlling the execution of one or more guest virtual machines on a computer processor. In response to interpreting the server specification, control software deploys computer processors or guest virtual machines to execute the identified server application and automatically configures the defined communication network and storage network connectivity to the selected computer processors or guest virtual machines to thereby deploy the server defined in the server specification.
Owner:EGENERA
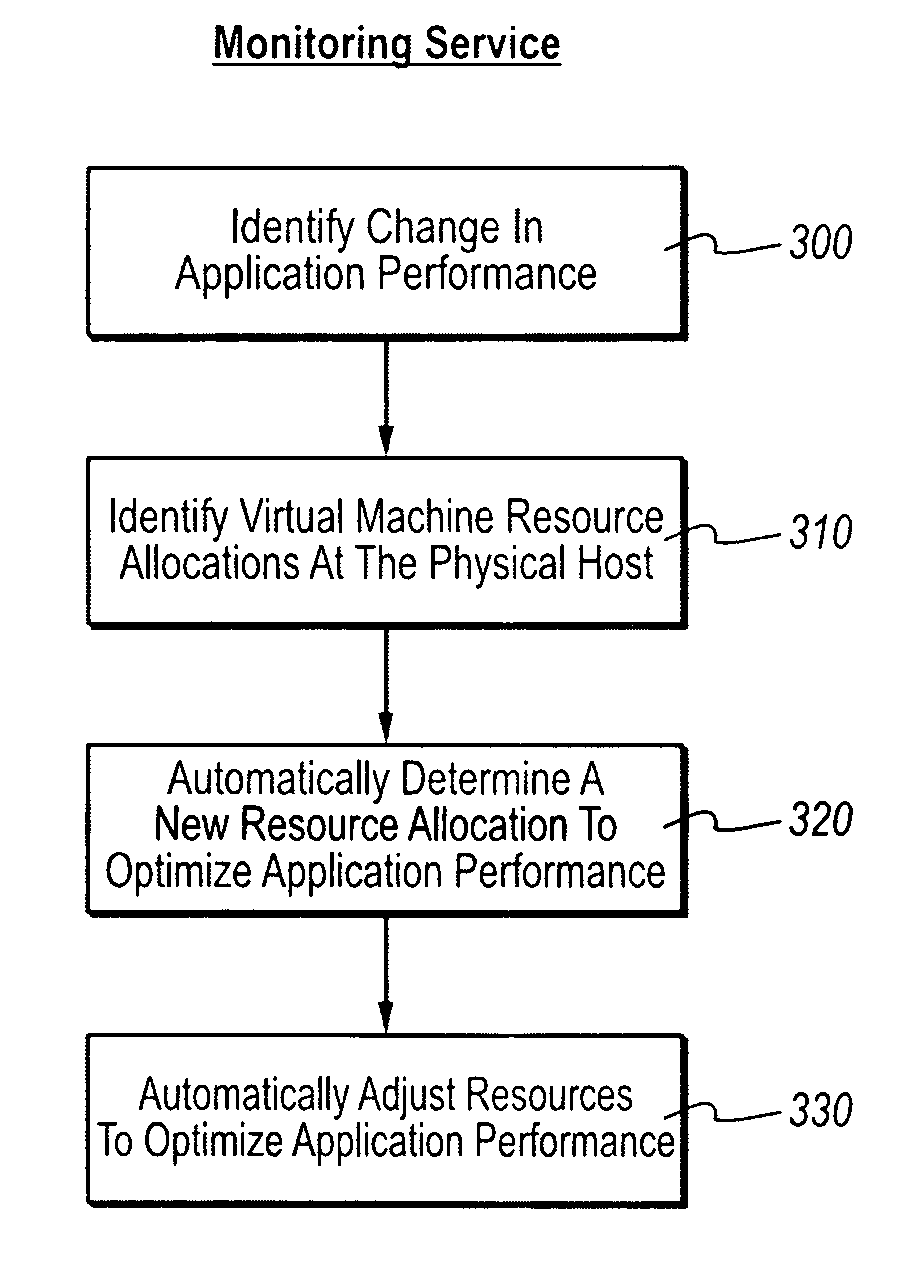
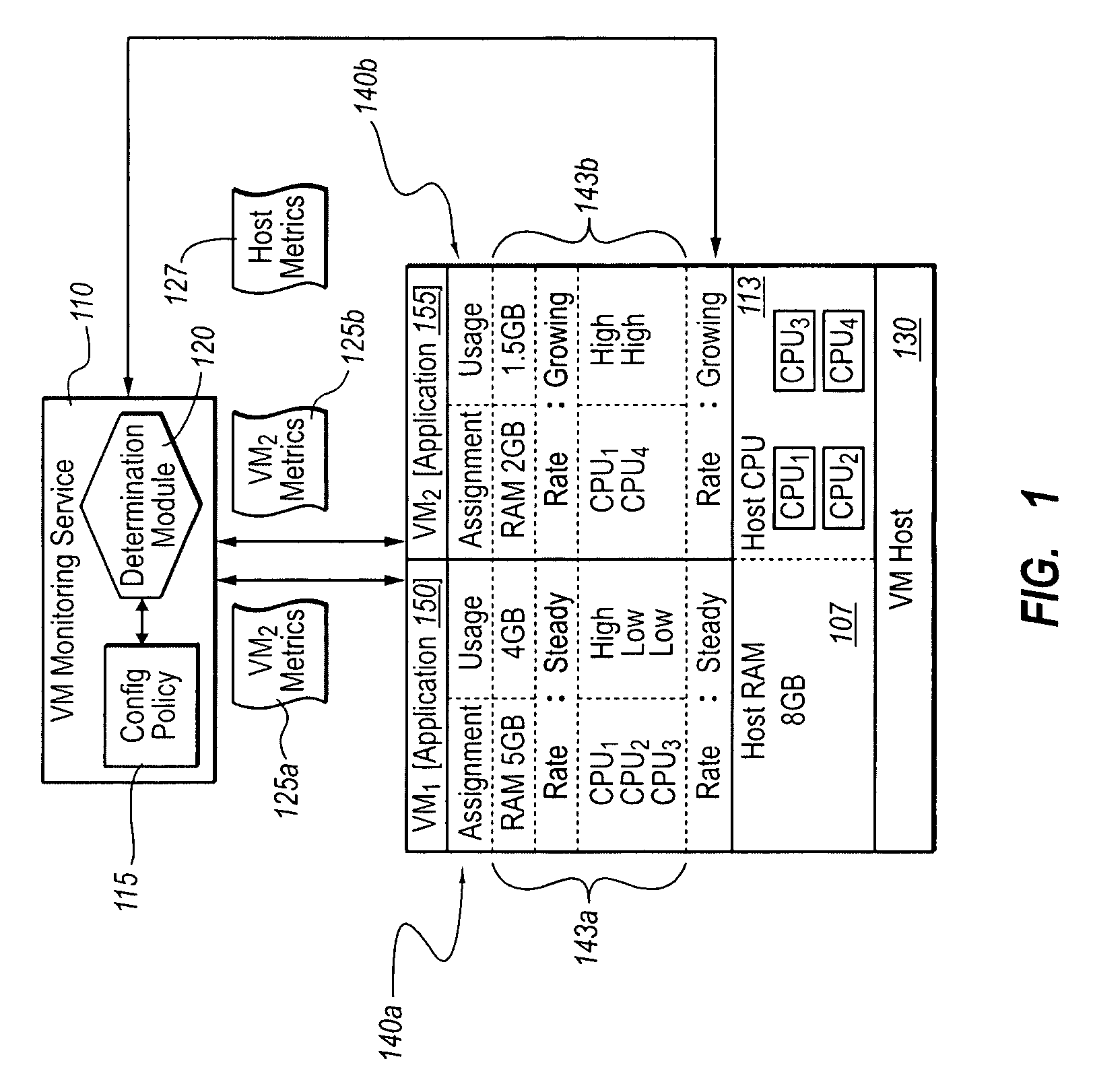
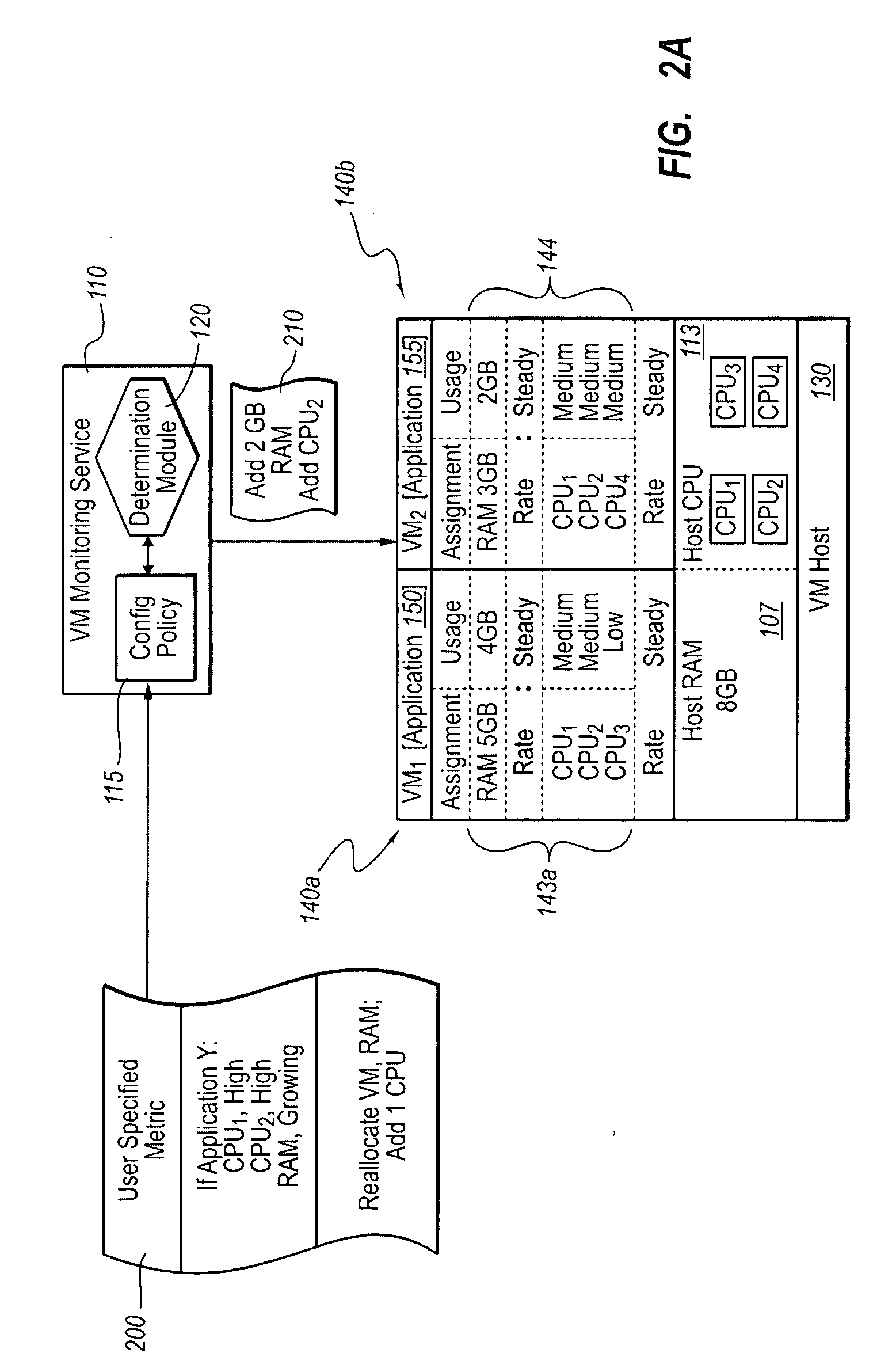
Optimizing application performance on virtual machines automatically with end-user preferences
InactiveUS20090265707A1Improve performanceError detection/correctionMultiprogramming arrangementsUser inputResource utilization
A virtual machine management / monitoring service can be configured to automatically monitor and implement user-defined (e.g., administrator-defined) configuration policies with respect to virtual machine and application resource utilization. In one implementation, the monitoring service can be extended to provide user-customized alerts based on various particularly defined events that occur (e.g., some memory or processing threshold) during operation of the virtual machines and / or application execution. The user can also specify particularly tailored solutions, which can include automatically reallocating physical host resources without additional user input on a given physical host, or moving / adding virtual machines on other physical hosts. For example, the monitoring service can be configured so that, upon identifying that a virtual machine's memory and processing resources are maxed out and / or growing, the monitoring service adds memory or processing resources for the virtual machine, or adds a new virtual machine to handle the load for the application program.
Owner:MICROSOFT TECH LICENSING LLC
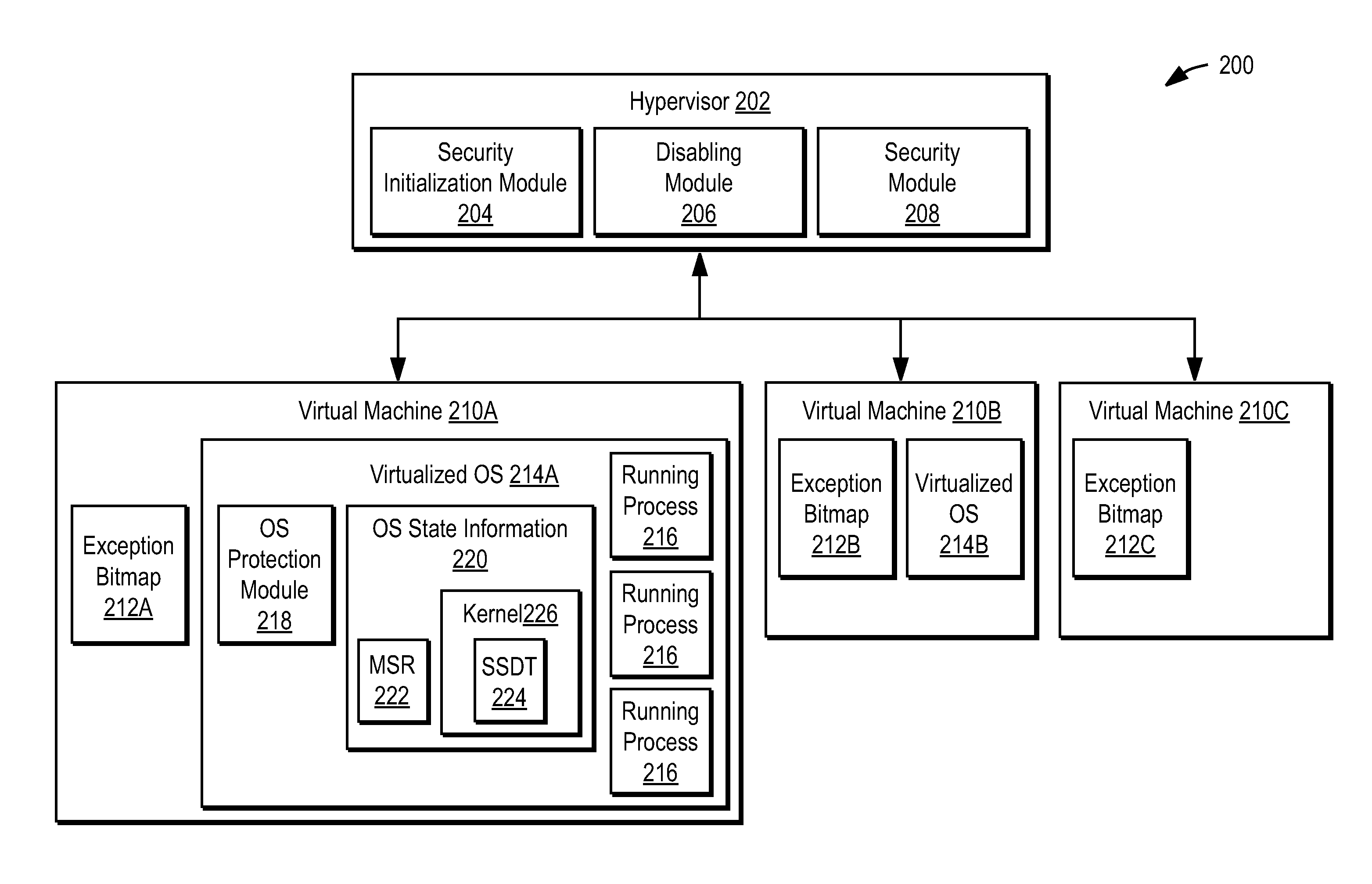
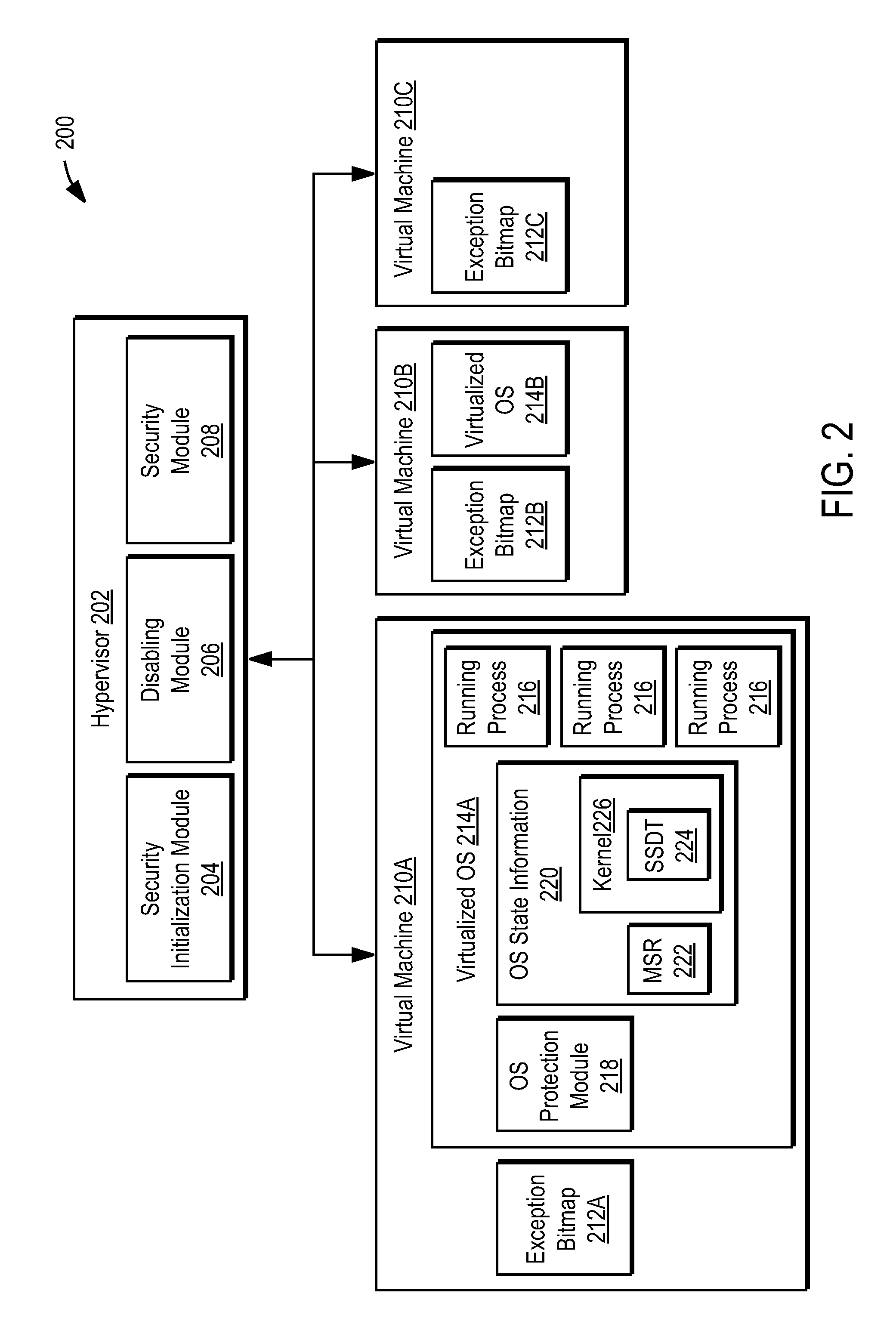
Using a hypervisor to provide computer security
ActiveUS7996836B1Provide securityMemory loss protectionError detection/correctionRemedial actionVirtual machine
A computer includes a virtual machine controlled by a hypervisor. The virtual machine runs a virtualized operating system with running processes. A security initialization module sets the state in the virtual machine to pass execution from the virtual machine to the hypervisor responsive to a process making a system call in the virtualized operating system. Responsive to execution being passed from the virtual machine to the hypervisor, a security module analyzes the process making the system call to determine whether it poses a security threat. If a security threat is found, the security module takes remedial action to address the threat.
Owner:NORTONLIFELOCK INC
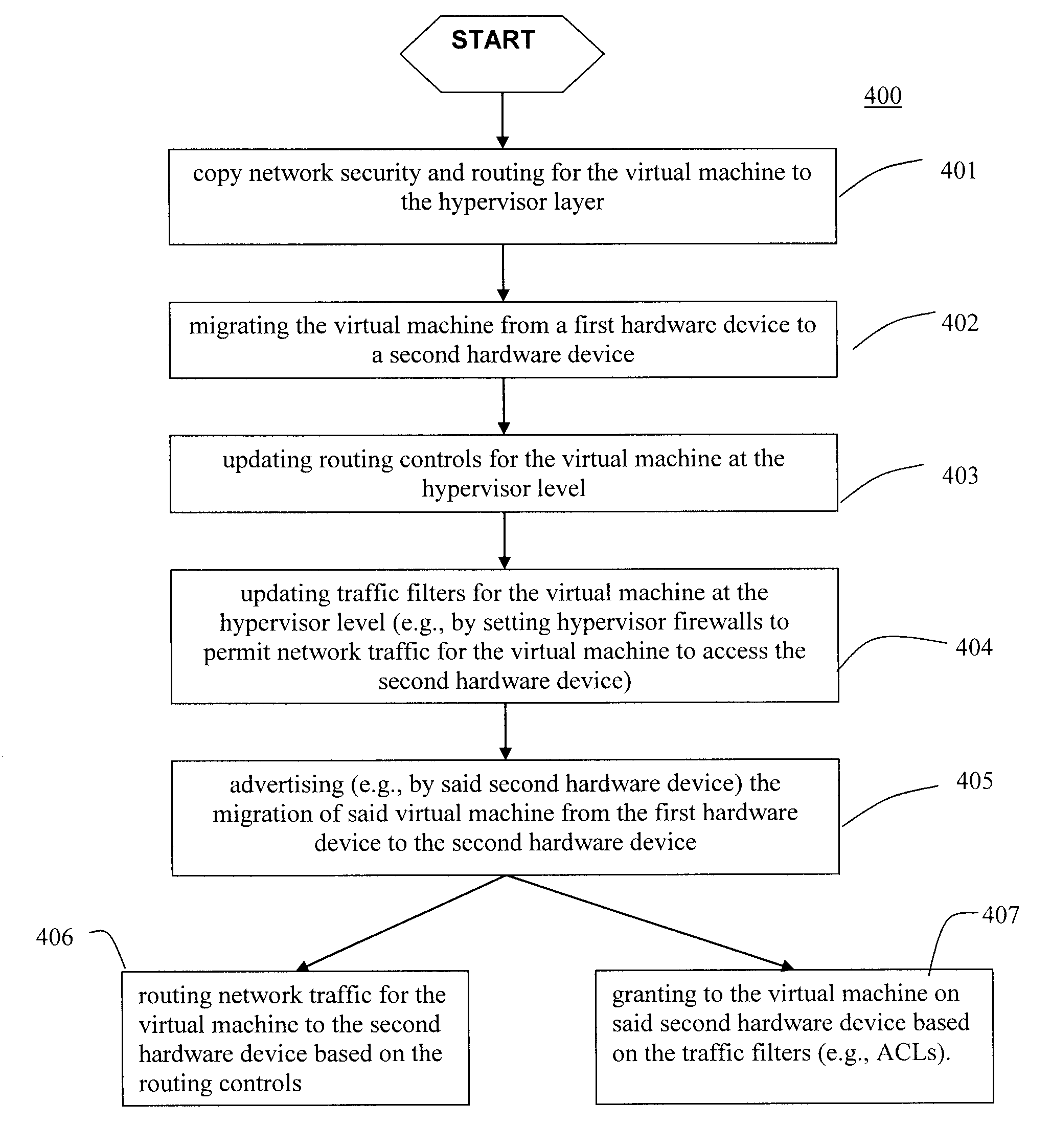
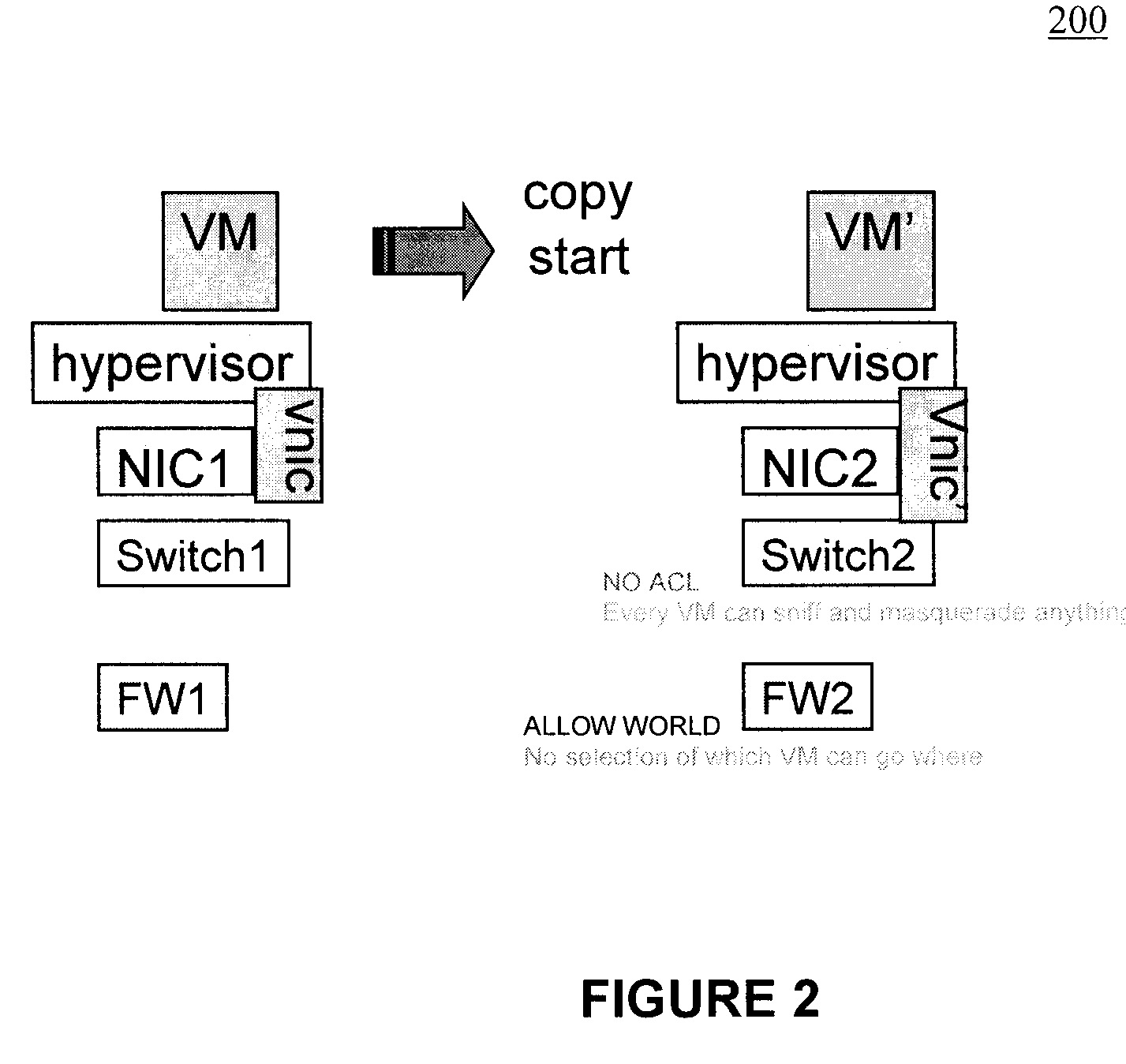
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
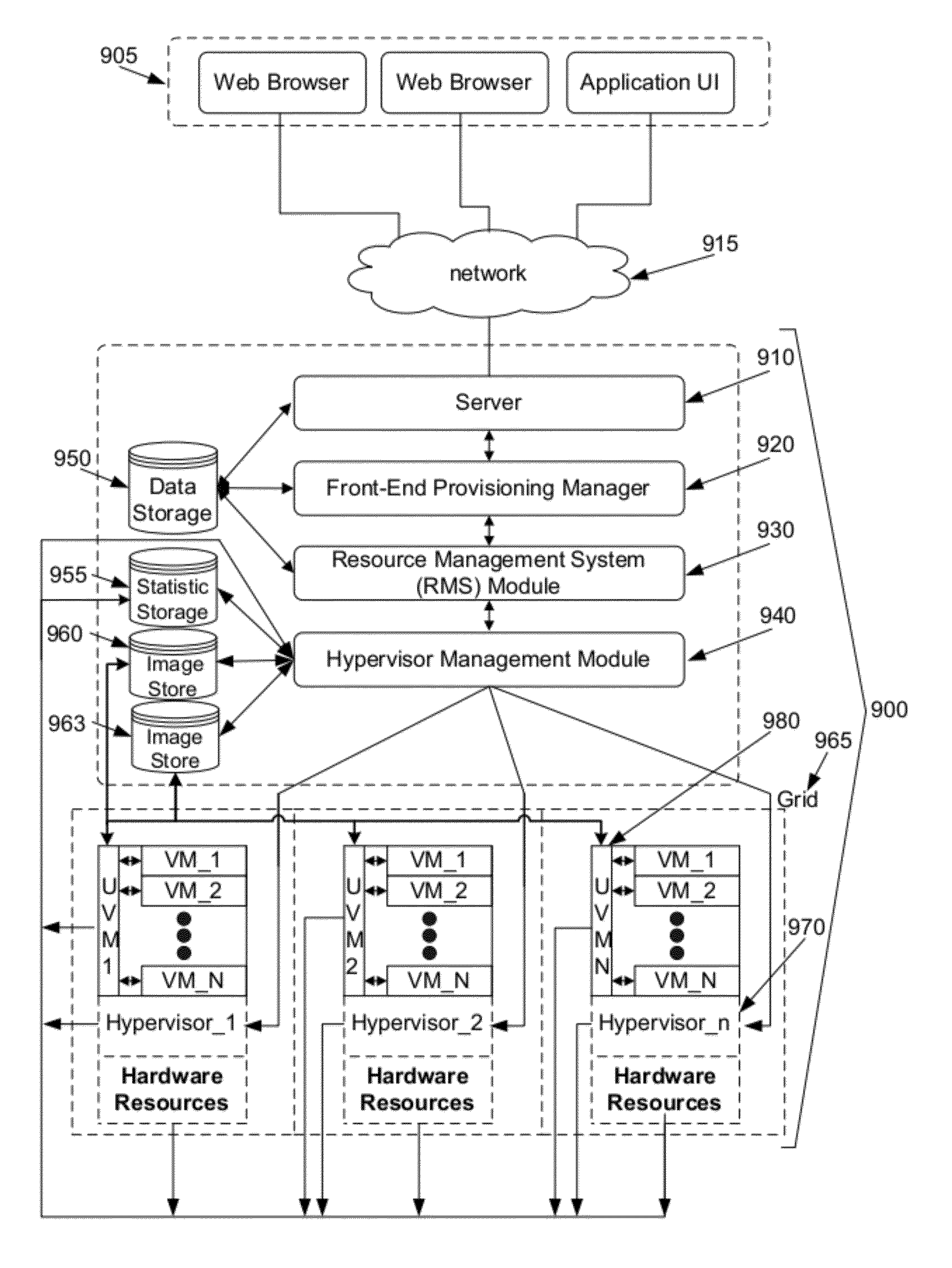
System and method for automated configuration of hosting resources
ActiveUS8352608B1Facilitate efficient deploymentMaximize useDigital computer detailsProgram controlAuto-configurationFile system
Some embodiments provide a method for automated configuration of a set of resources for hosting a virtual machine at a particular node in a hosting system. The hosting system includes several nodes for hosting several virtual machines. The method, at a first virtual machine operating using a first set of resources of the particular node, receives a configuration for a second virtual machine to be hosted on a second set of resources of the particular node. The method, from the first virtual machine, accesses the second set of resources to partition a file system for storing the second virtual machine. The method modifies the file system to configure the second virtual machine as specified by the configuration.
Owner:GOOGLE LLC
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
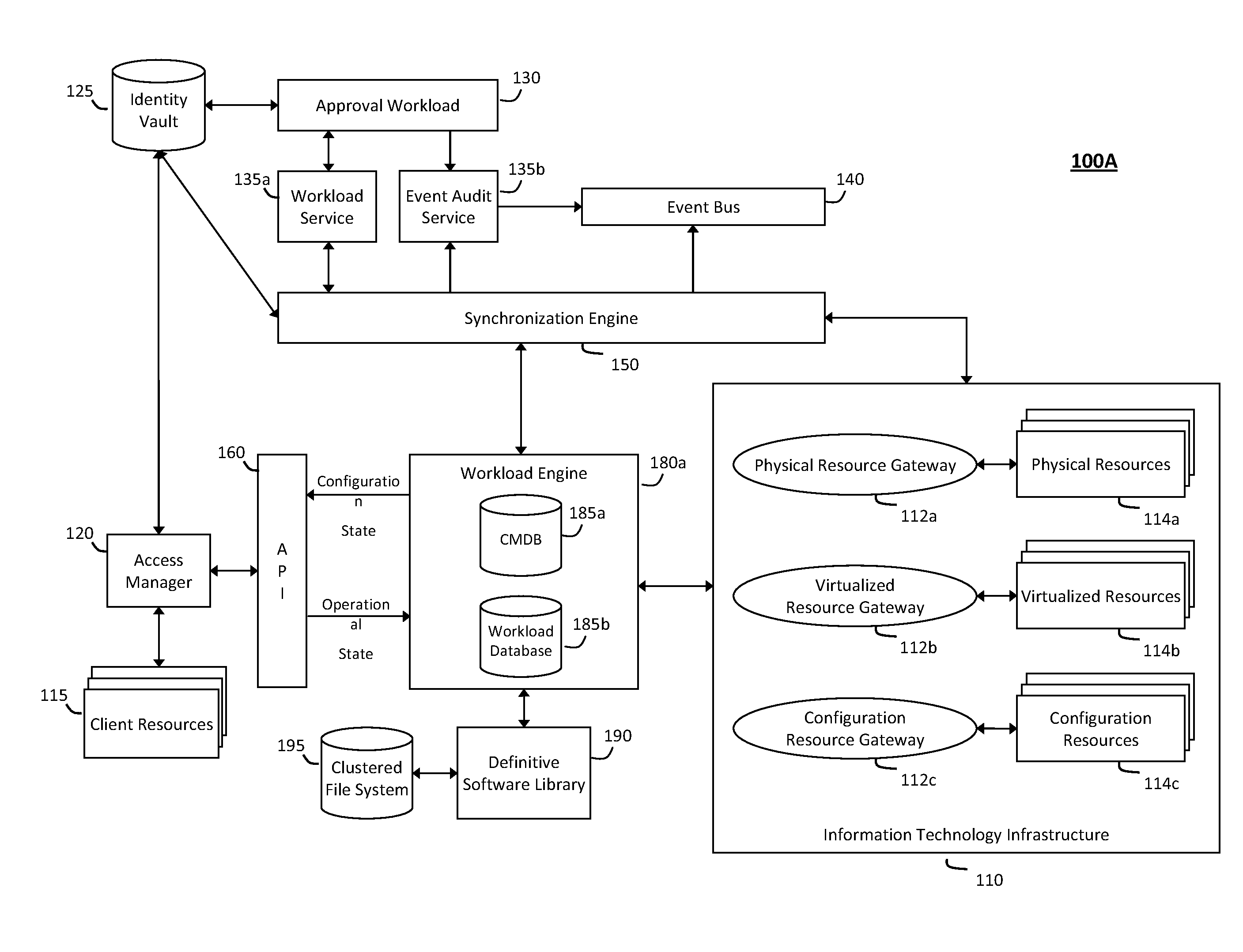
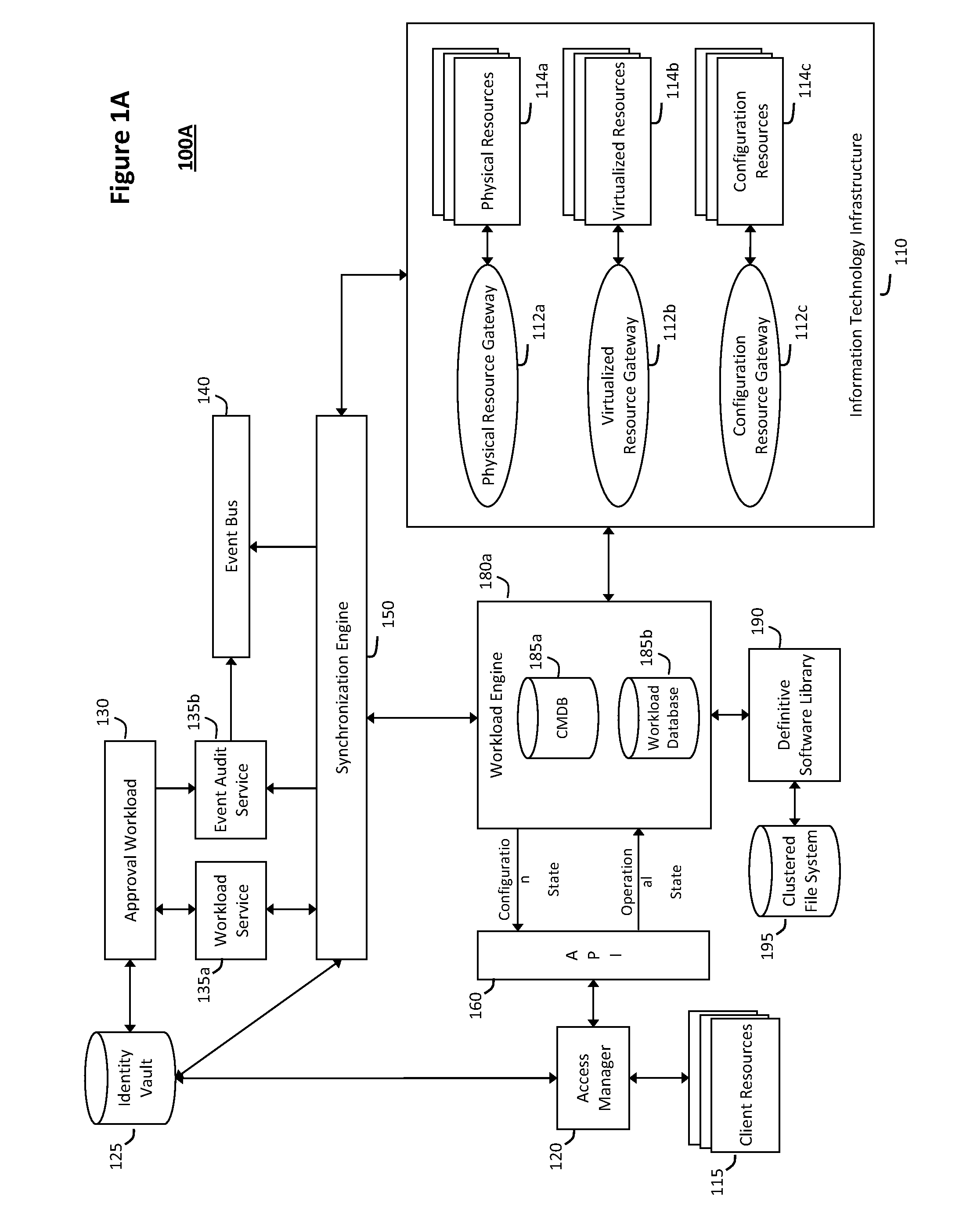
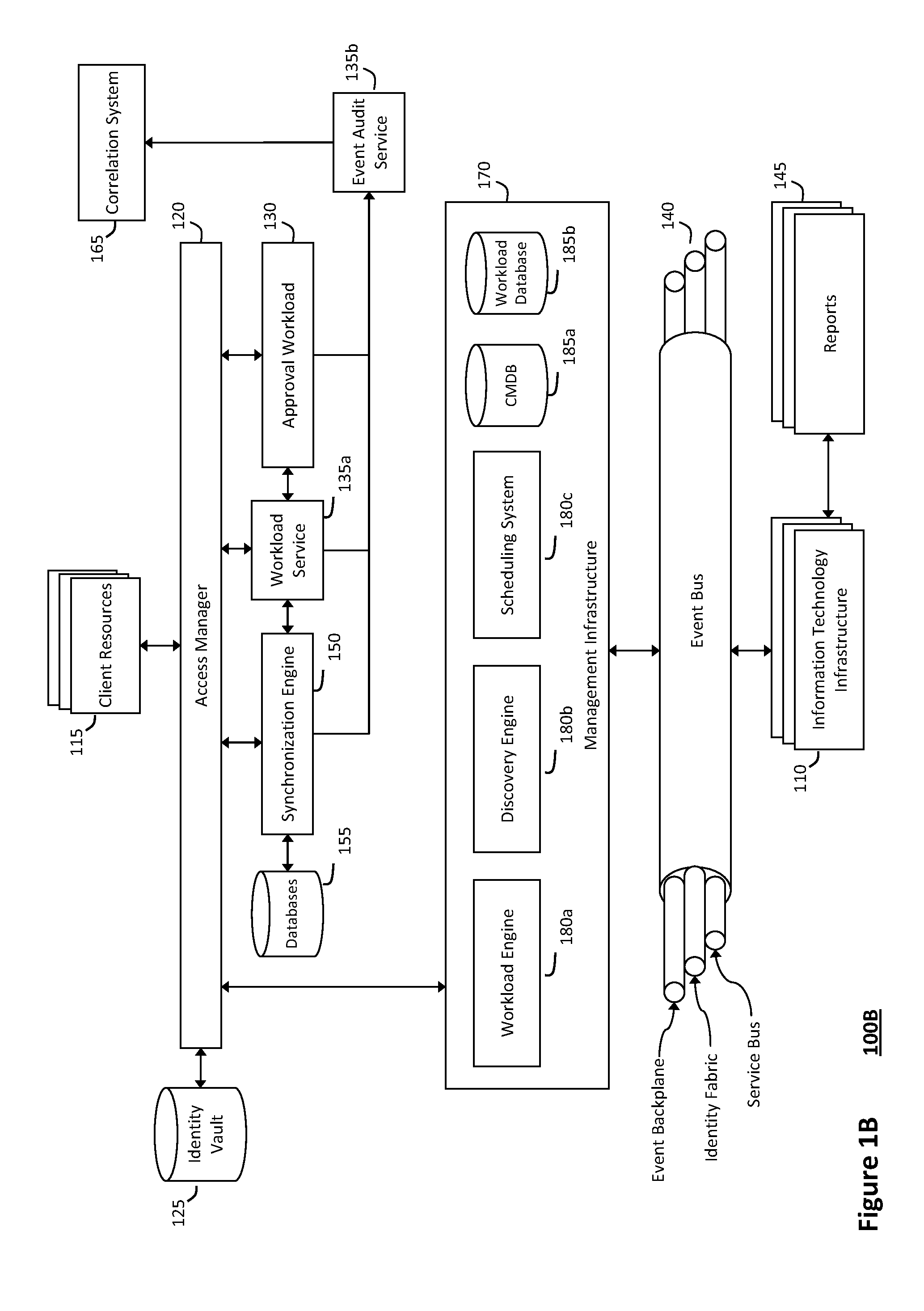
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
System and method for launching a resource in a network
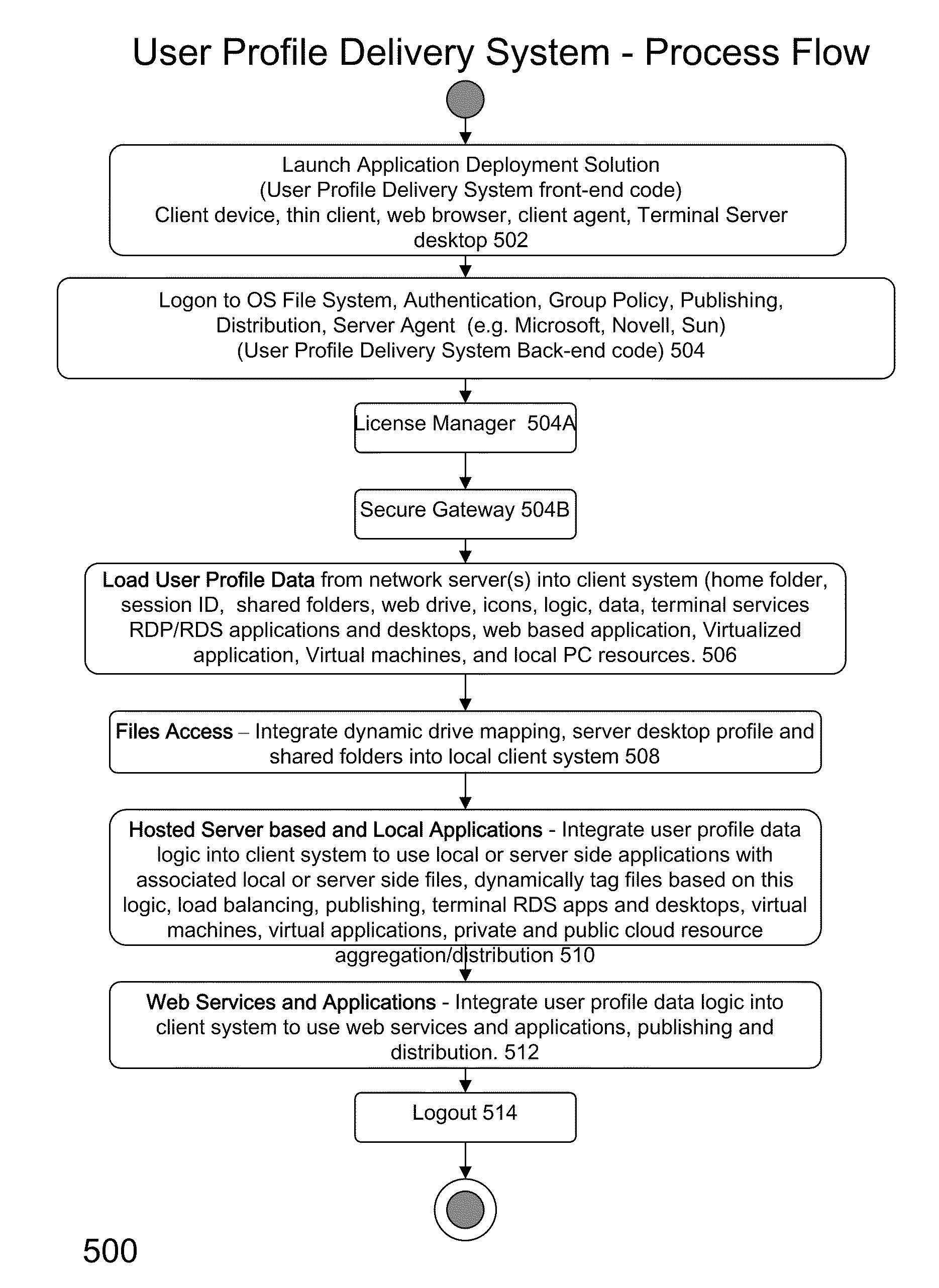
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
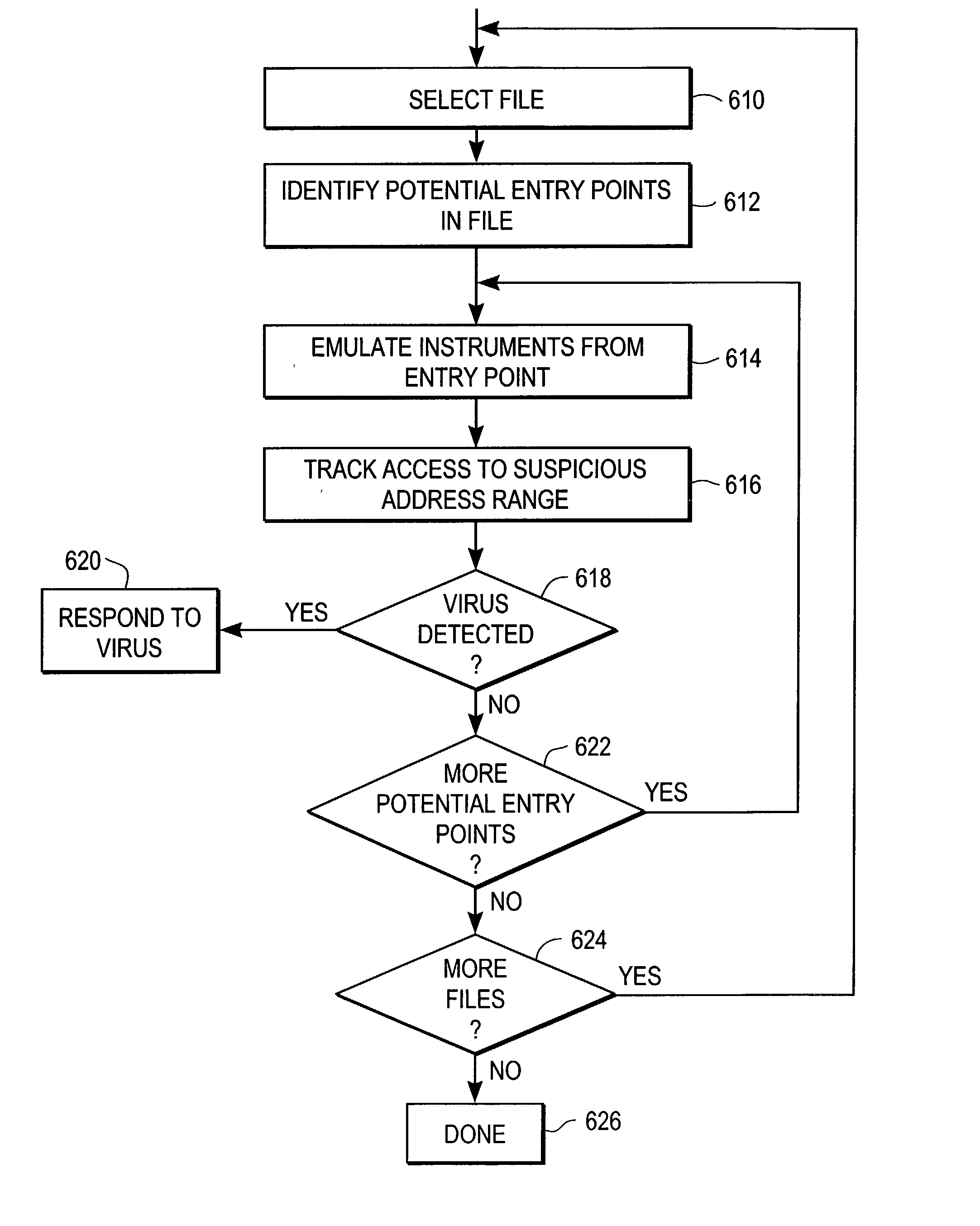
Heuristic detection of malicious computer code by page tracking
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
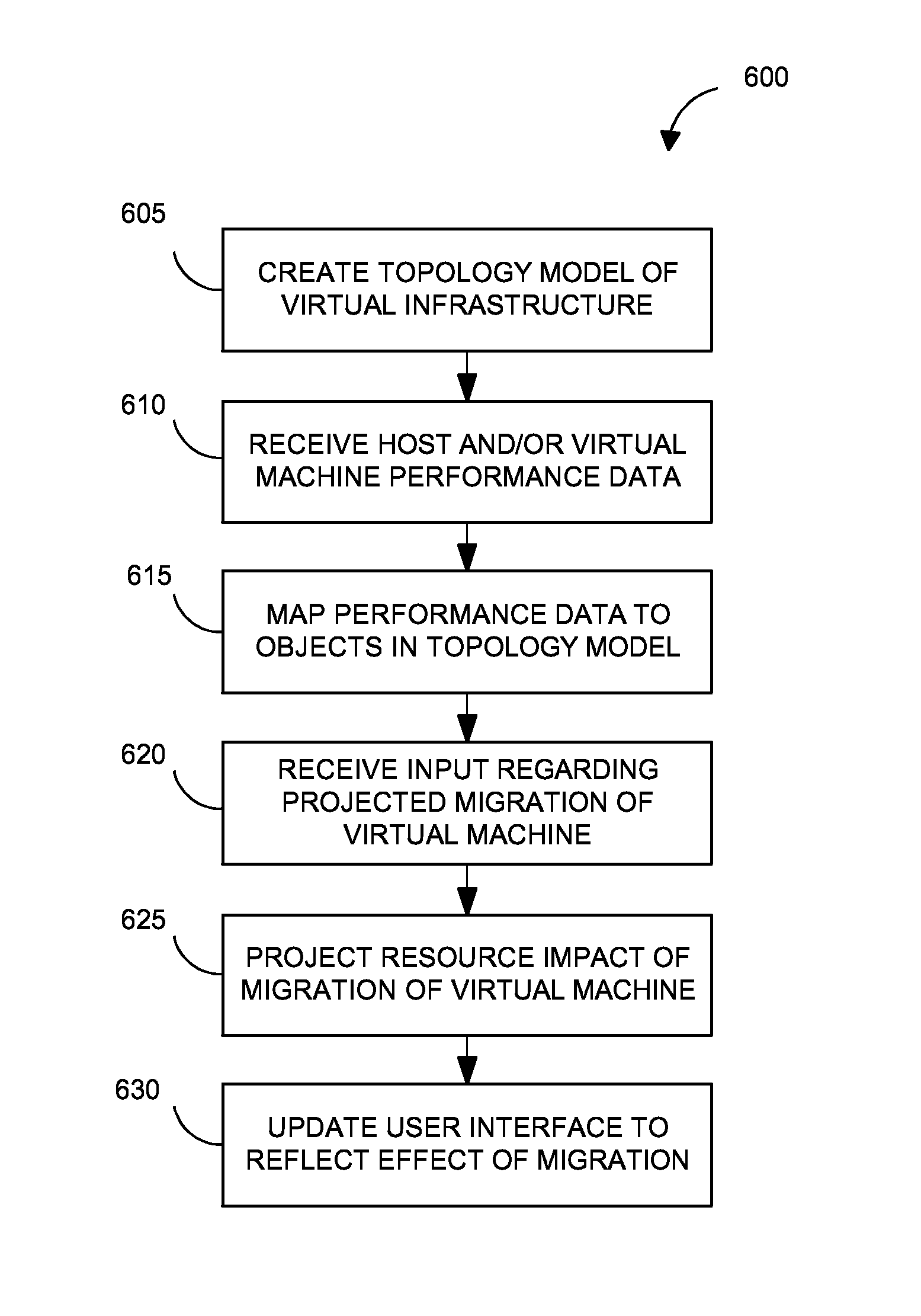
Systems and methods for analyzing performance of virtual environments
InactiveUS8175863B1Effective and efficient diagnosisResource allocationError detection/correctionMonitoring systemSmart surveillance
Intelligent monitoring systems and methods for virtual environments are disclosed that understand various components of a virtual infrastructure and how the components interact to provide improved performance analysis to users. In certain examples, a monitoring system assesses the performance of virtual machine(s) in the context of the overall performance of the physical server(s) and the environment in which the virtual machine(s) are running. For instance, the monitoring system can track performance metrics over a determined period of time to view changes to the allocation of resources to virtual machines and their location(s) on physical platforms. Moreover, monitoring systems can utilize past performance information from separate virtual environments to project a performance impact resulting from the migration of a virtual machine from one physical platform to another.
Owner:QUEST SOFTWARE INC
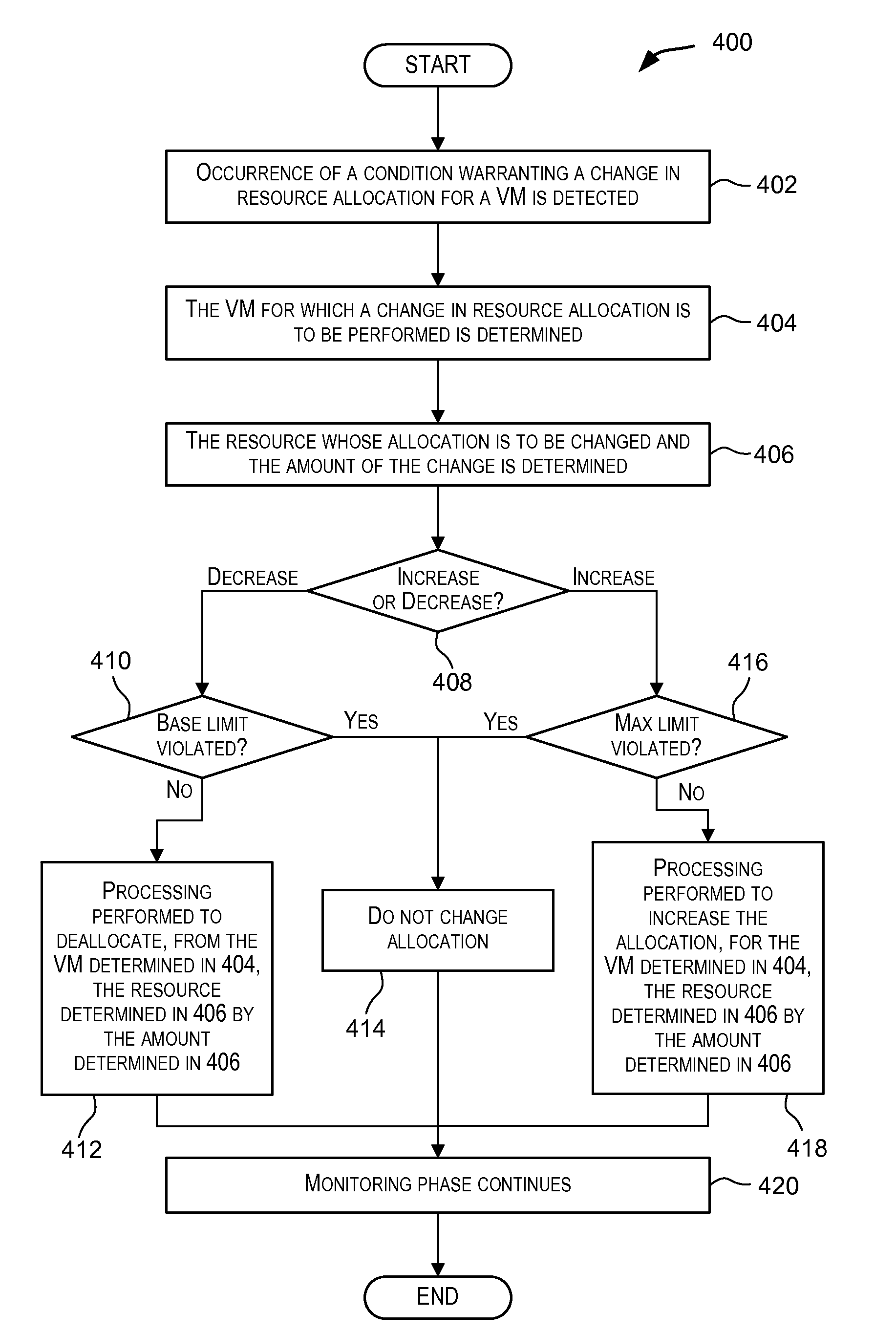
Dynamic resource allocation for virtual machines
InactiveUS20140007097A1Increase the amount of resourcesReduce the amount of solutionSoftware simulation/interpretation/emulationMemory systemsFailoverService-level agreement
Certain embodiments enable resources assigned or allocated to an operating virtual machine (VM) to be modified while the VM is operating and without having to stop, restart, or reboot the VM. The modification may correspond to increasing or decreasing the amount of a resource being assigned to the VM. In this manner, resources assigned to a VM at the time of creation of the VM are not static and can instead be dynamically changed while the VM is operating without having to stop, reboot, or restart the VM. In some embodiments, the changes to the resources allocated to one or more VMs provided for a user (e.g., a customer) may be made according to or in response to a Service Level Agreement (SLA) entered into by the user, in response to an event such as a failover or switchover event, and the like.
Owner:AVAGO TECH INT SALES PTE LTD
Deploying virtual machine to host based on workload characterizations
InactiveUS20070271560A1Convenient to accommodateSoftware simulation/interpretation/emulationMemory systemsWorkloadVirtual machine
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com