Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
629results about How to "Provide security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
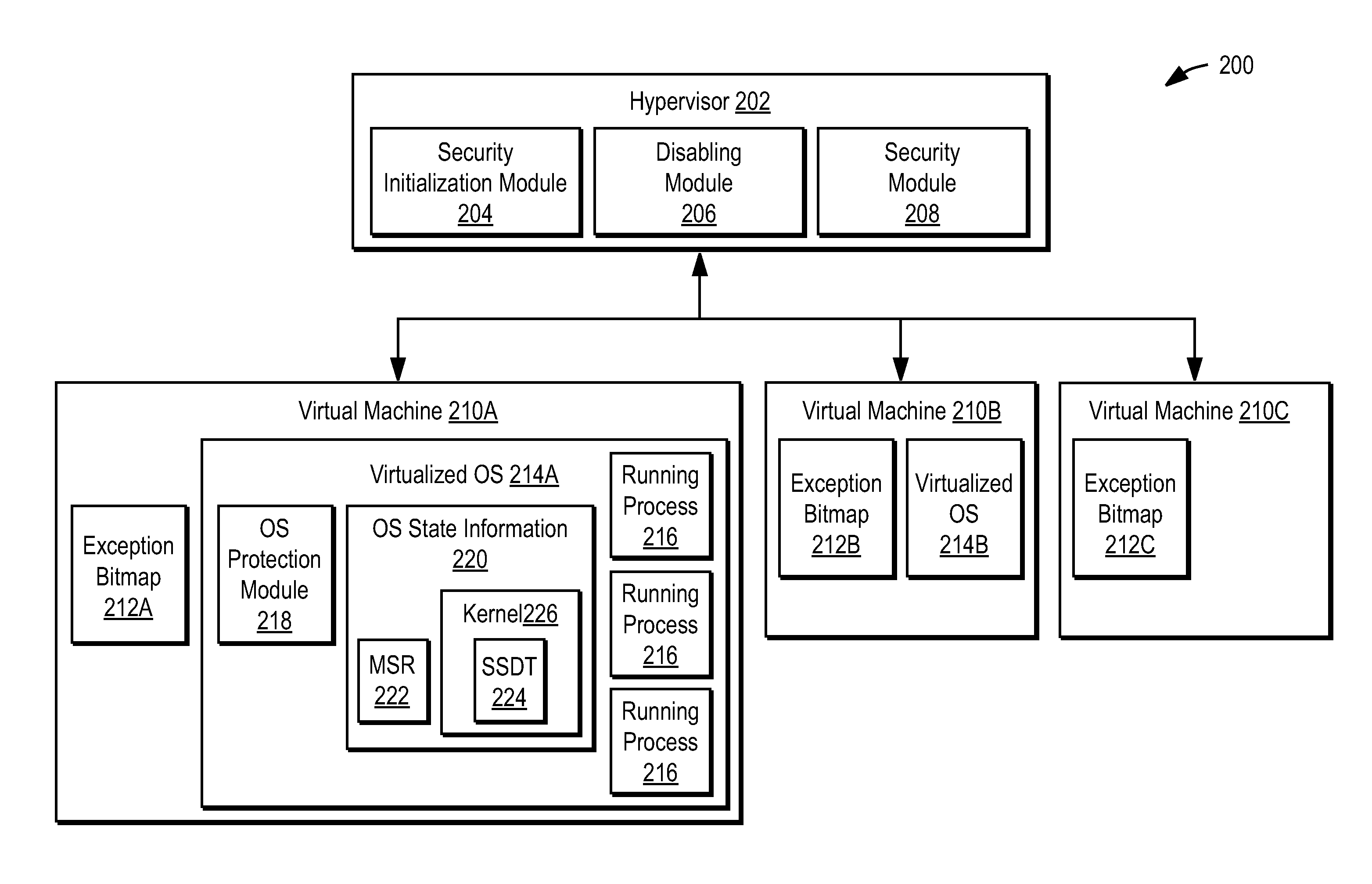
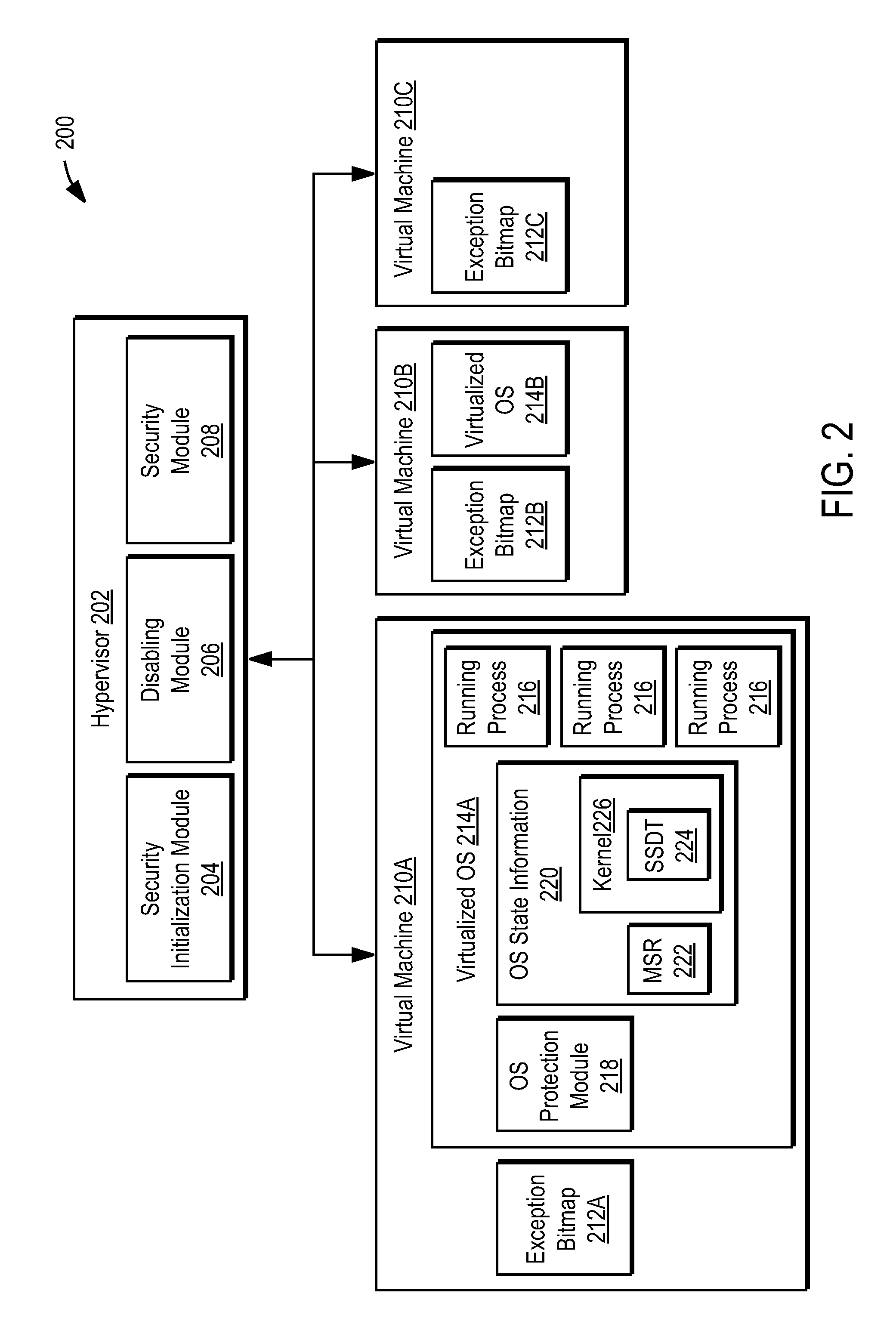
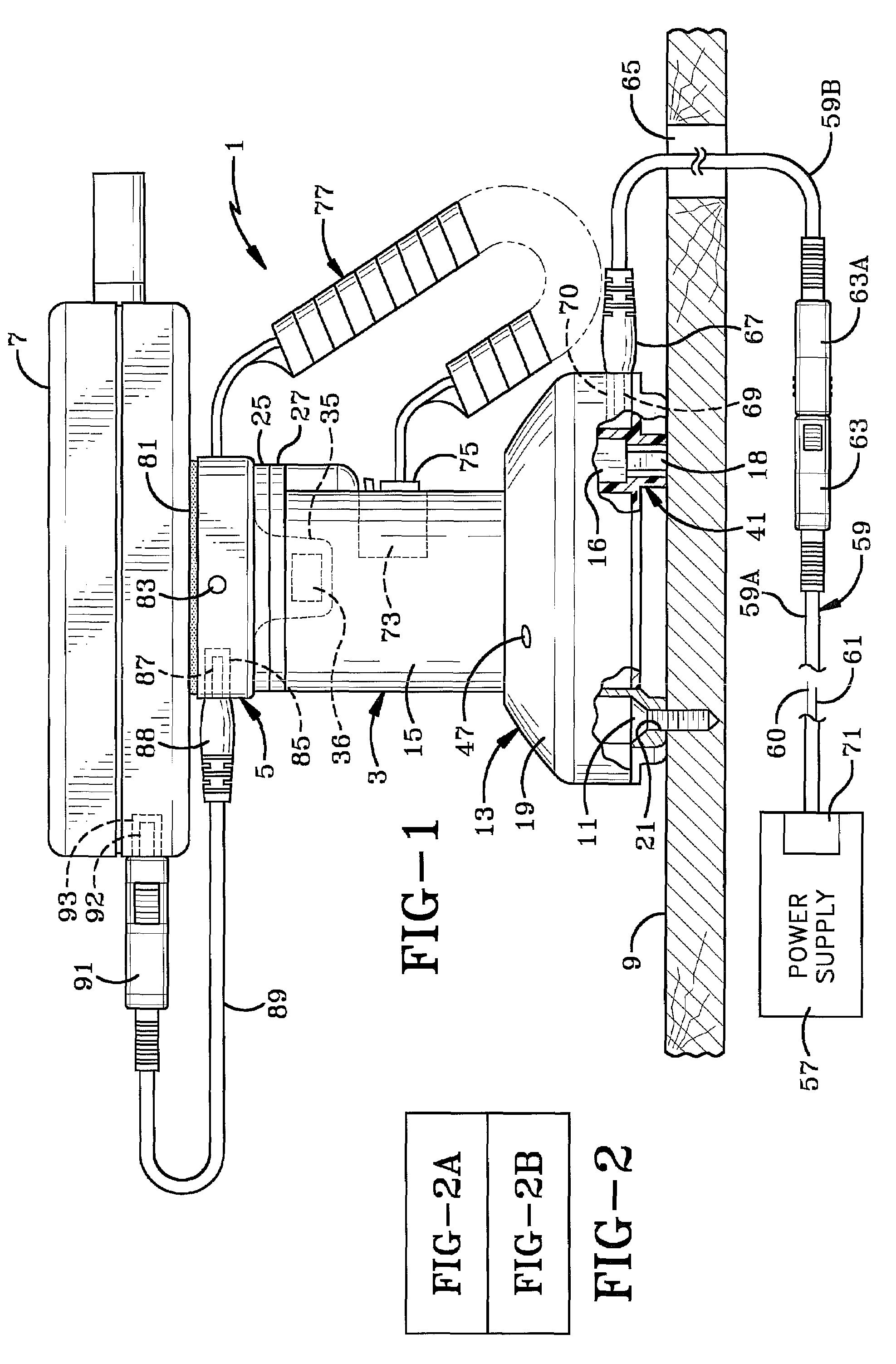
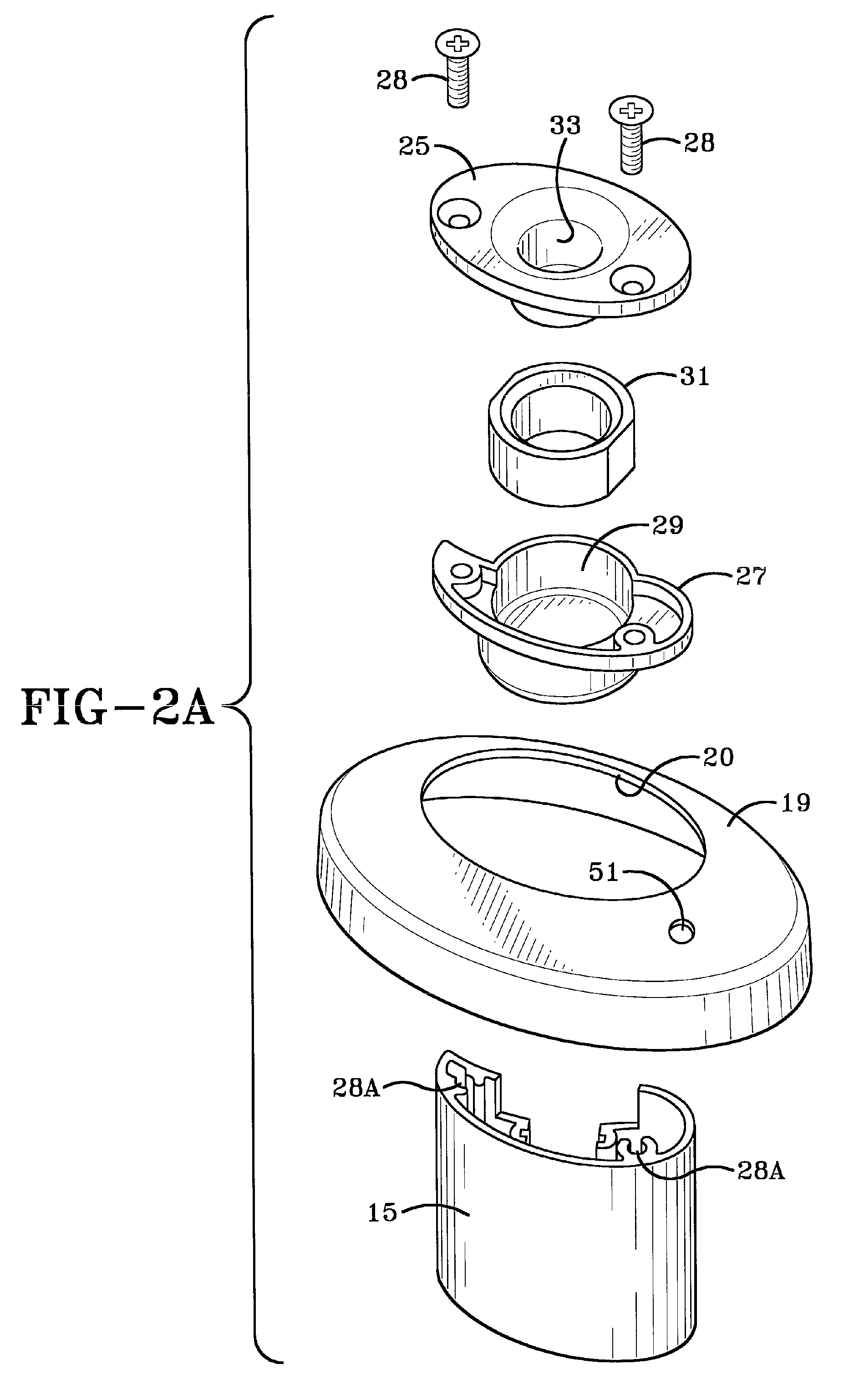
Using a hypervisor to provide computer security
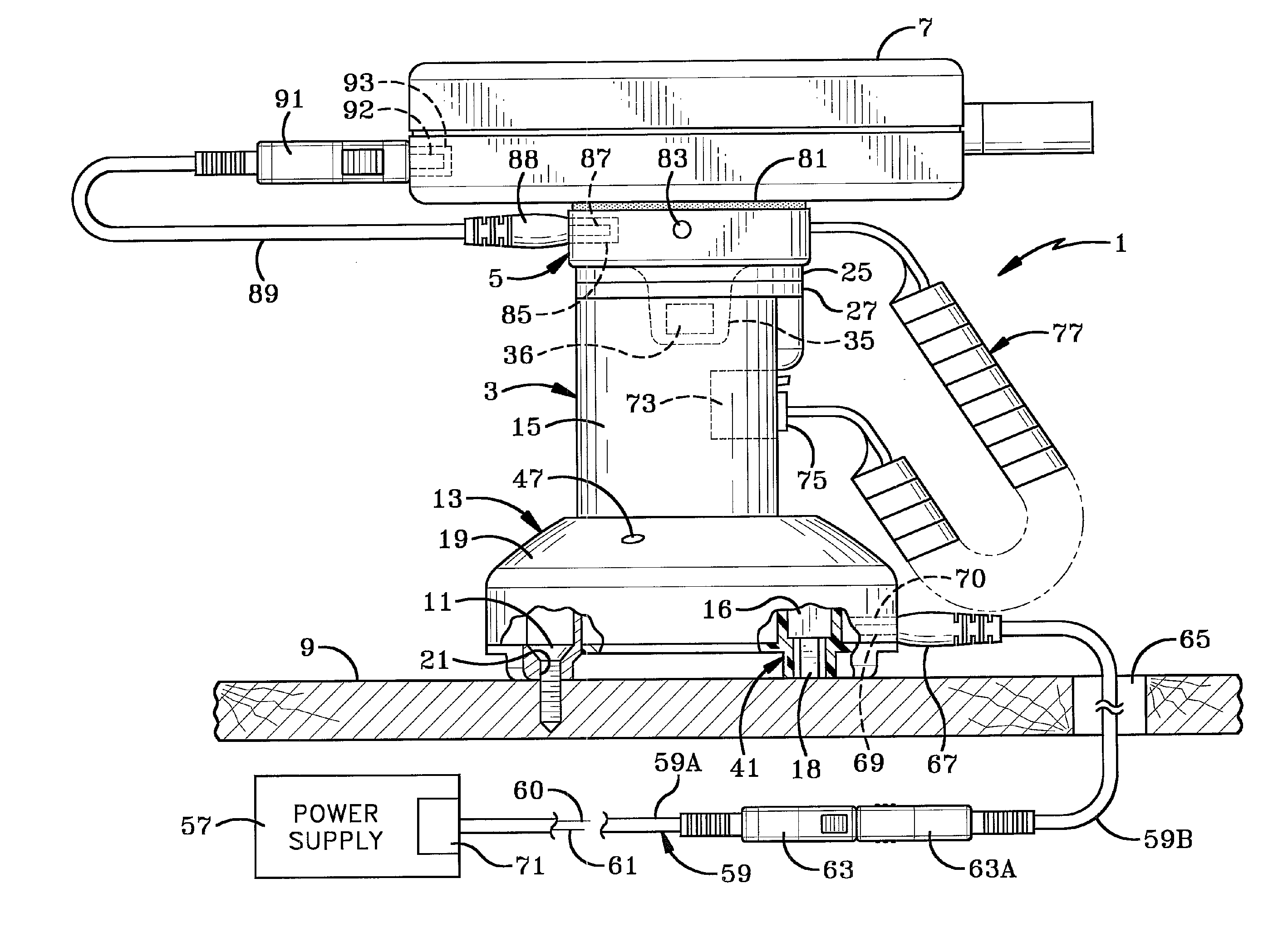
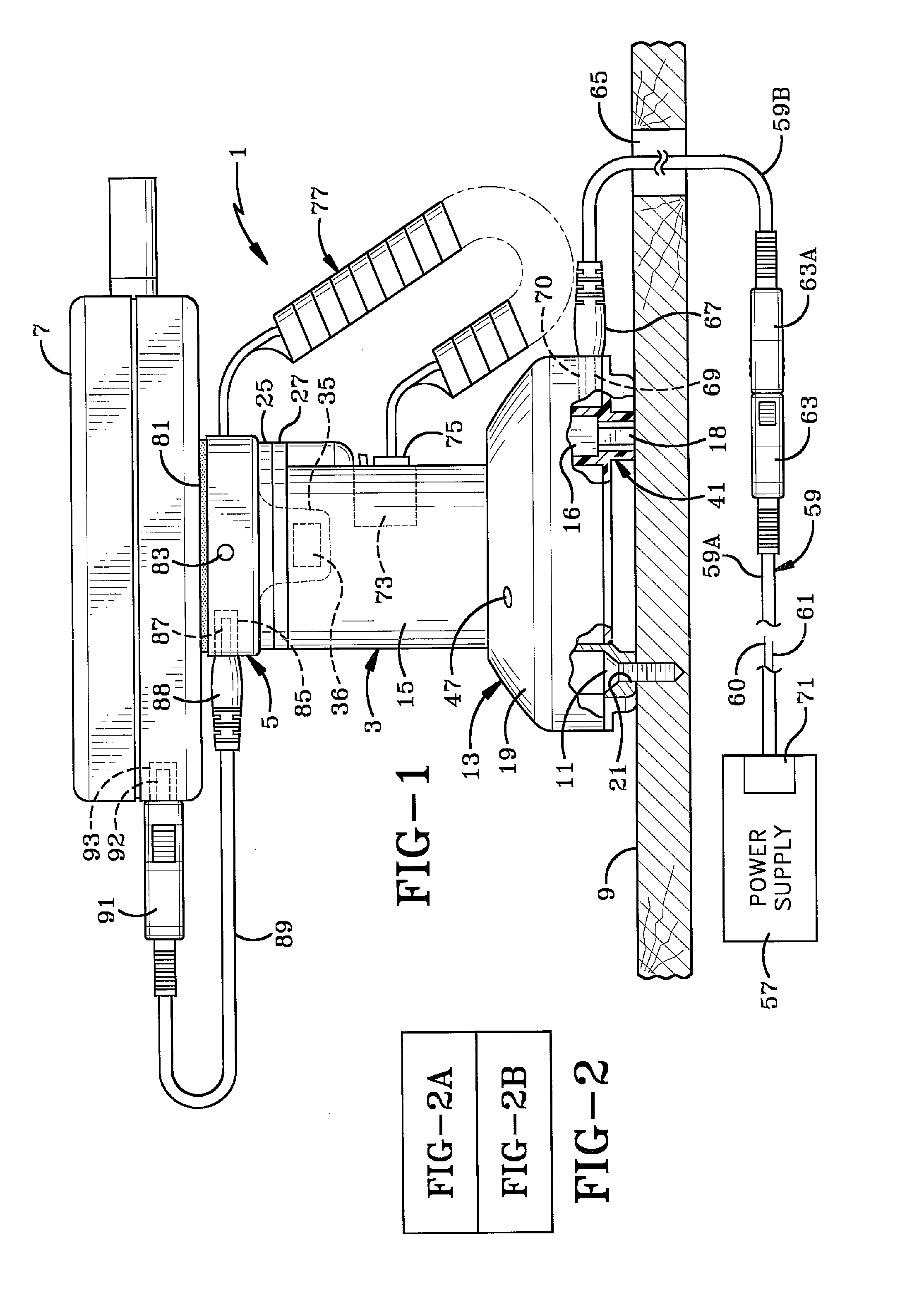
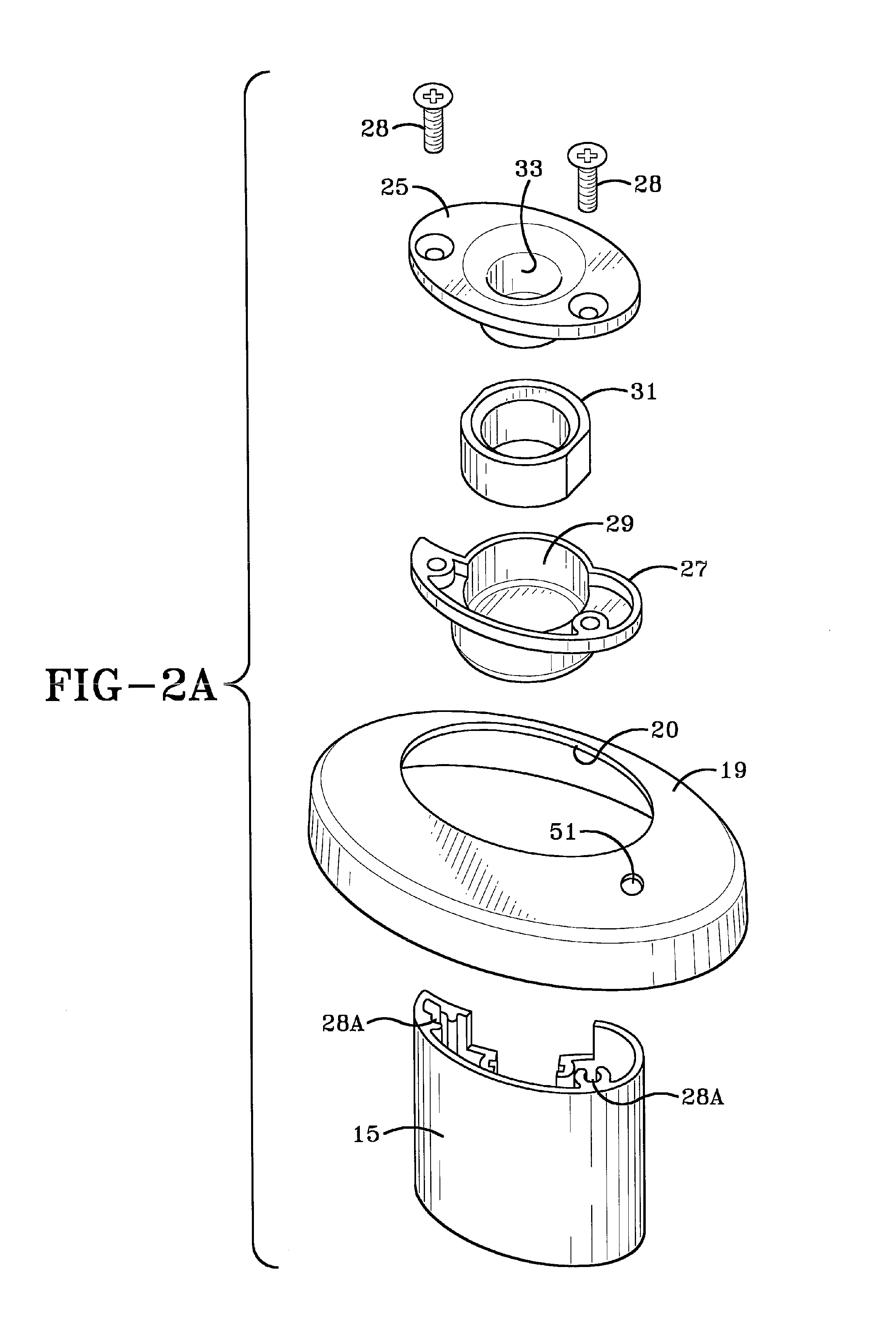
ActiveUS7996836B1Provide securityMemory loss protectionError detection/correctionRemedial actionVirtual machine
A computer includes a virtual machine controlled by a hypervisor. The virtual machine runs a virtualized operating system with running processes. A security initialization module sets the state in the virtual machine to pass execution from the virtual machine to the hypervisor responsive to a process making a system call in the virtualized operating system. Responsive to execution being passed from the virtual machine to the hypervisor, a security module analyzes the process making the system call to determine whether it poses a security threat. If a security threat is found, the security module takes remedial action to address the threat.
Owner:NORTONLIFELOCK INC
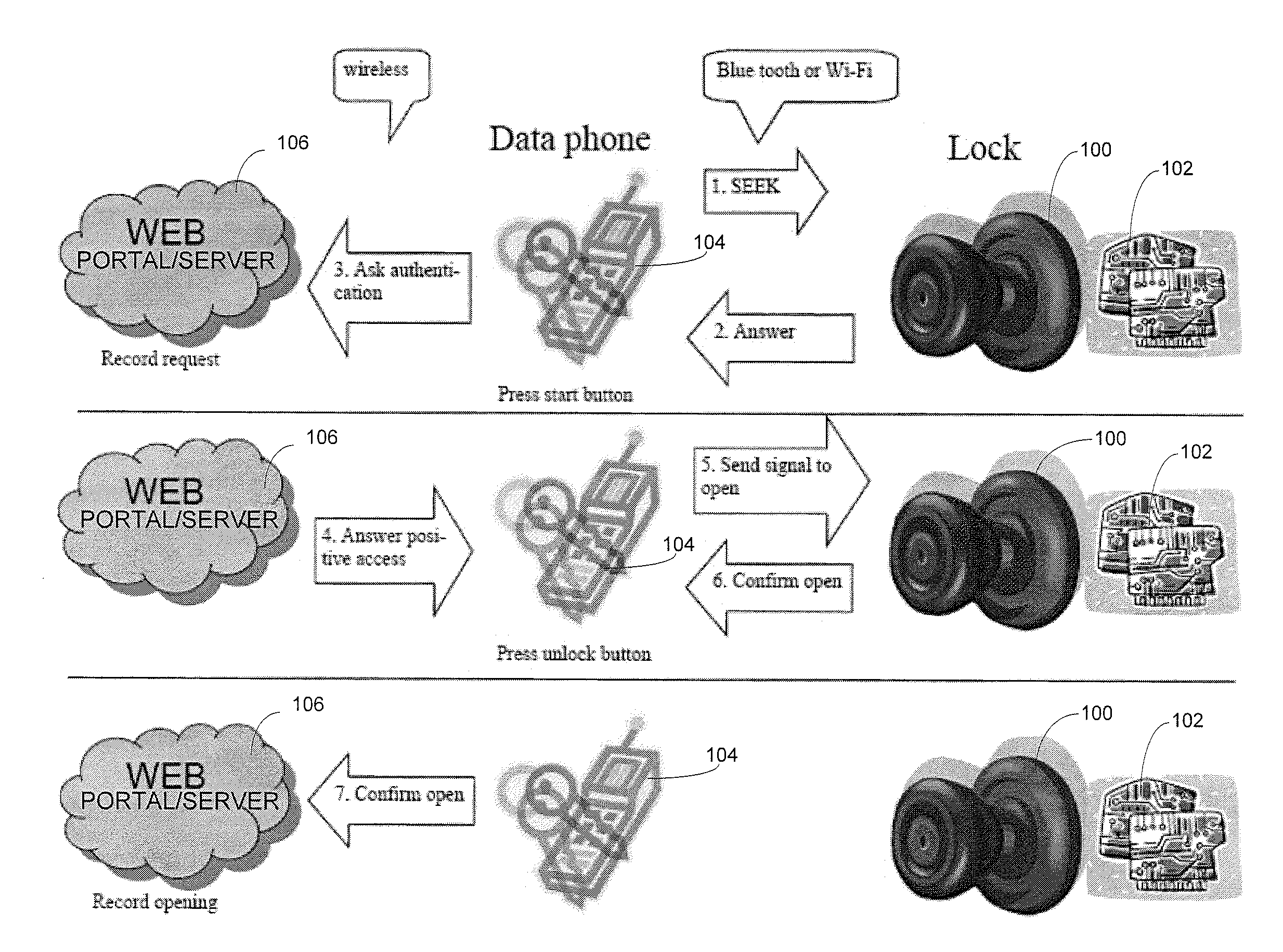
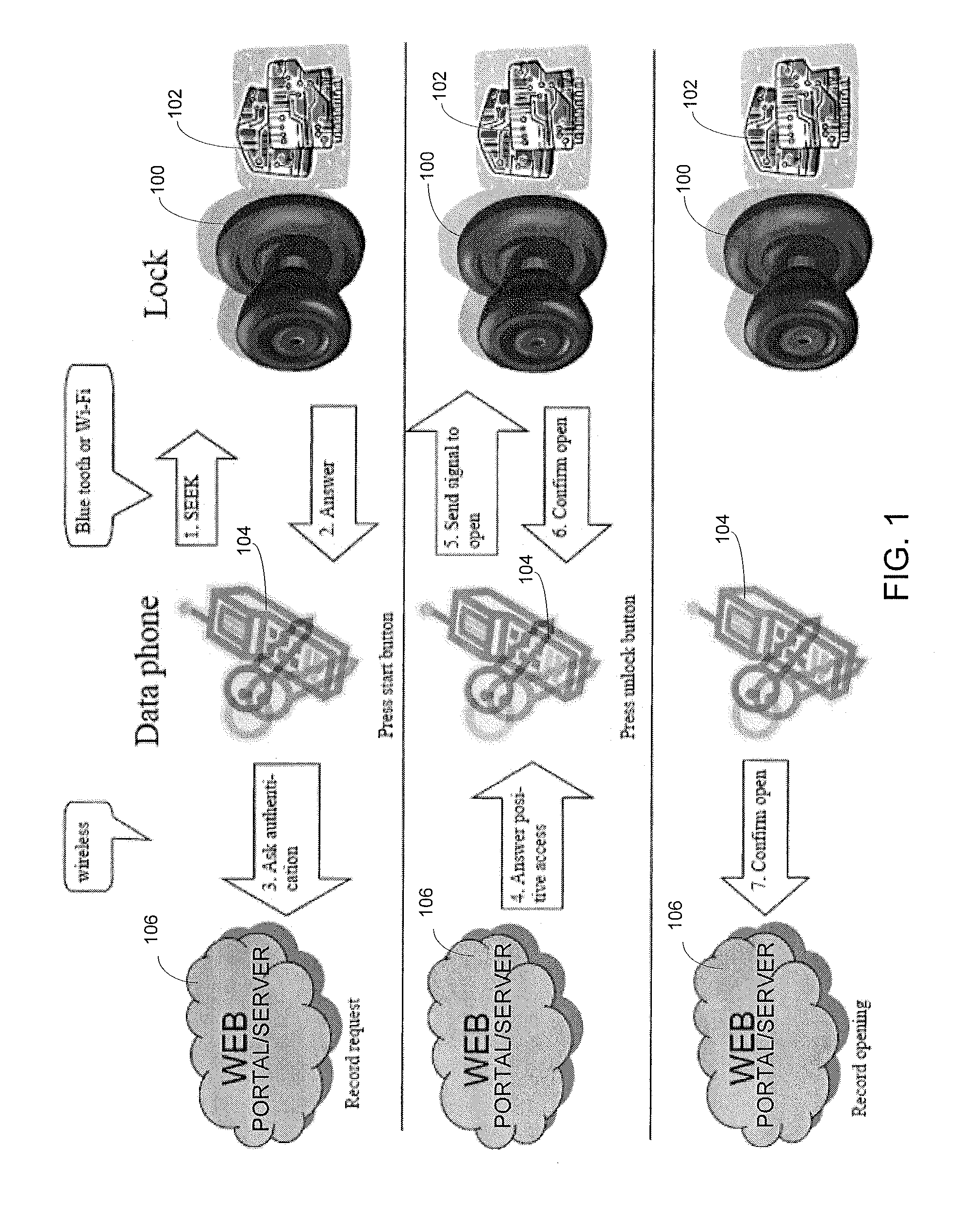
Wireless Device Enabled Locking System
ActiveUS20110311052A1Provide securityDigital data authenticationSecret communicationUnique identifierMobile device
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
Location Dependent Control Access in a Process Control System
ActiveUS20090065578A1Avoid changeProvide securityIndividual entry/exit registersTotal factory controlControl systemPosition dependent
A method of accessing an element in a process control environment using a portable communicator includes defining a plurality of control areas within the process control environment, determining a position of a user operating a portable communicator with respect to one or more of the control areas, establishing an identity of the user, and selectively allowing the user to access an element within the process control environment via the portable communicator depending on the determined position of the user with respect to the one or more control areas and on the identity of the user.
Owner:FISHER-ROSEMOUNT SYST INC
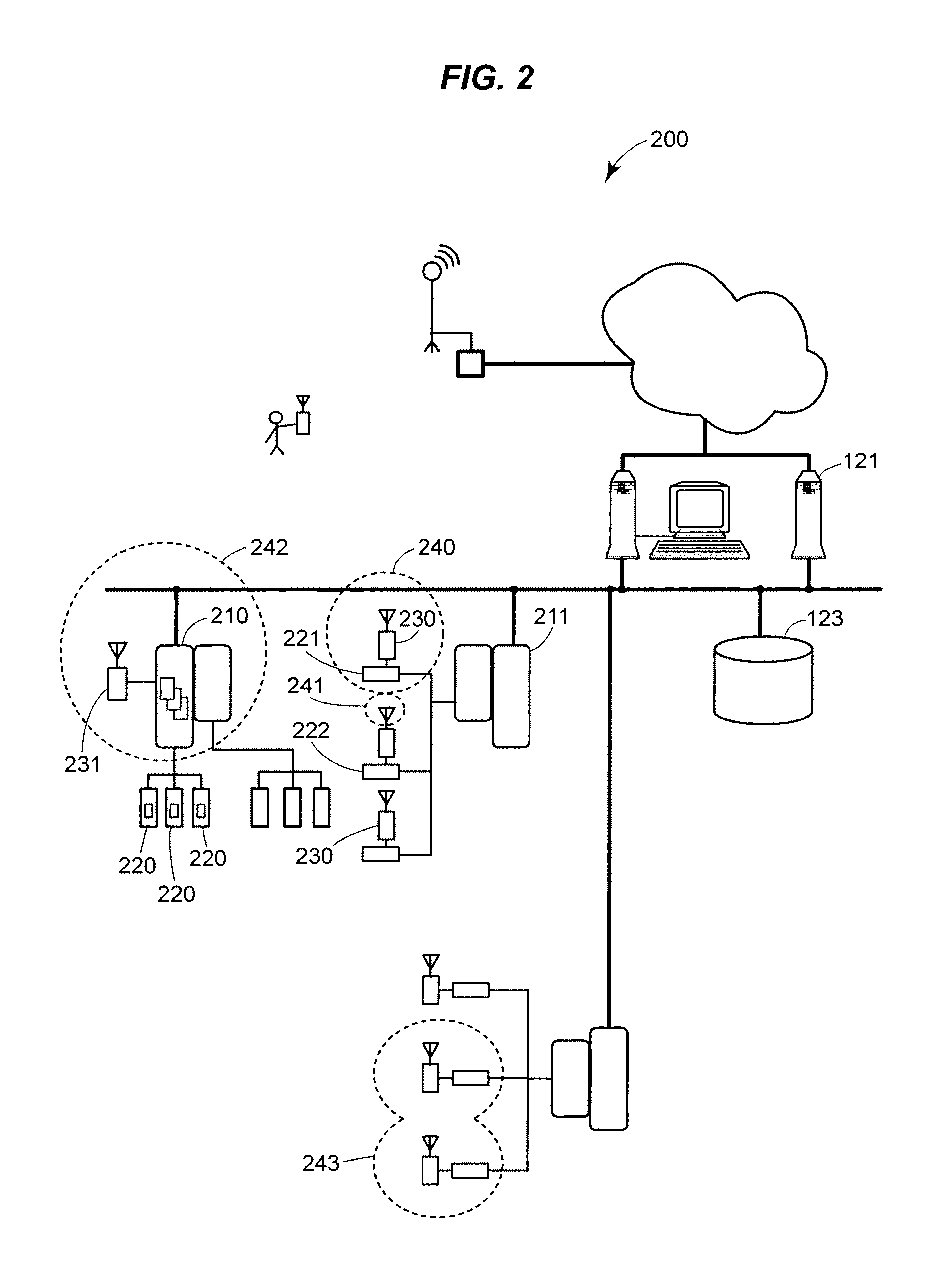
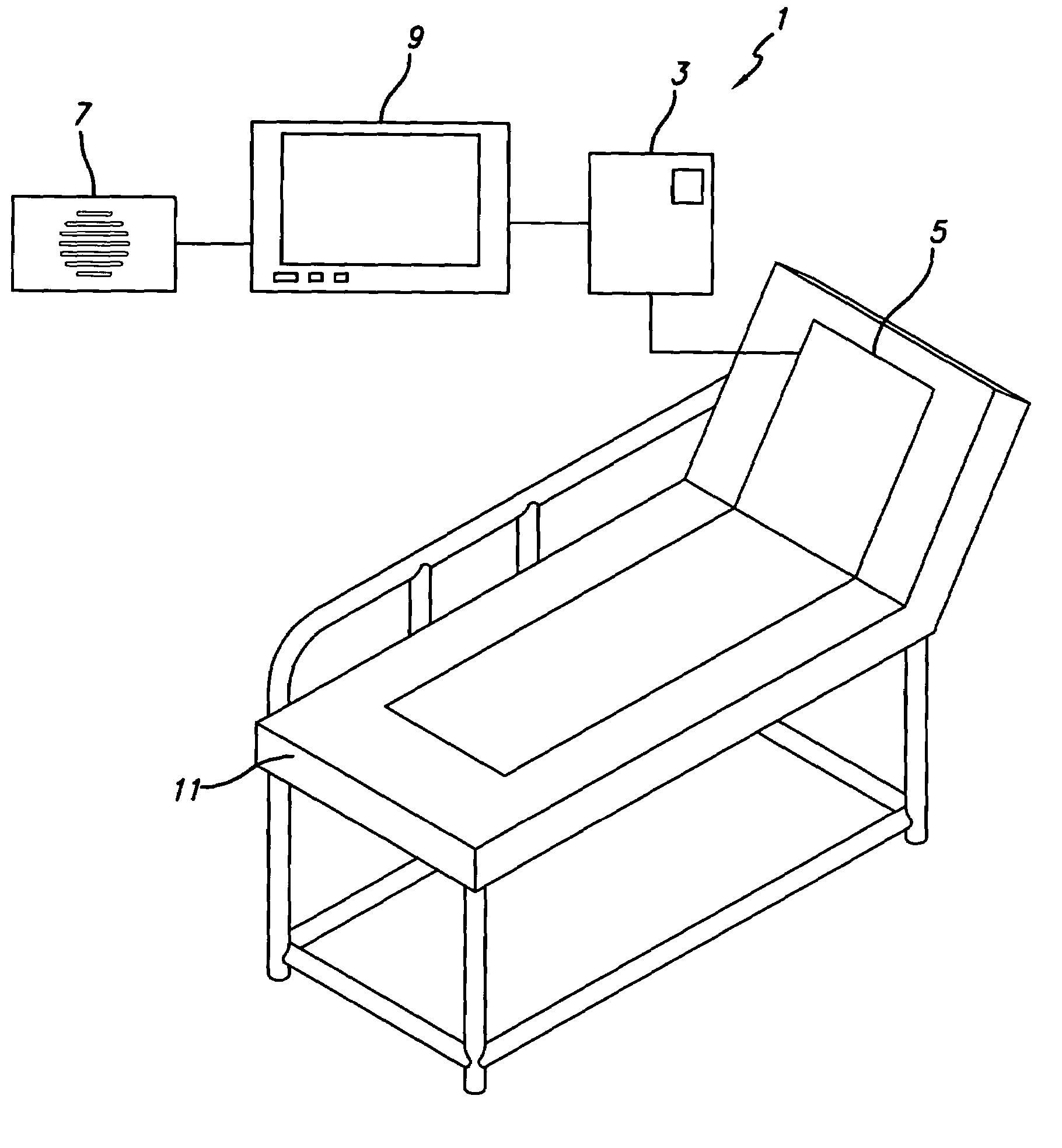
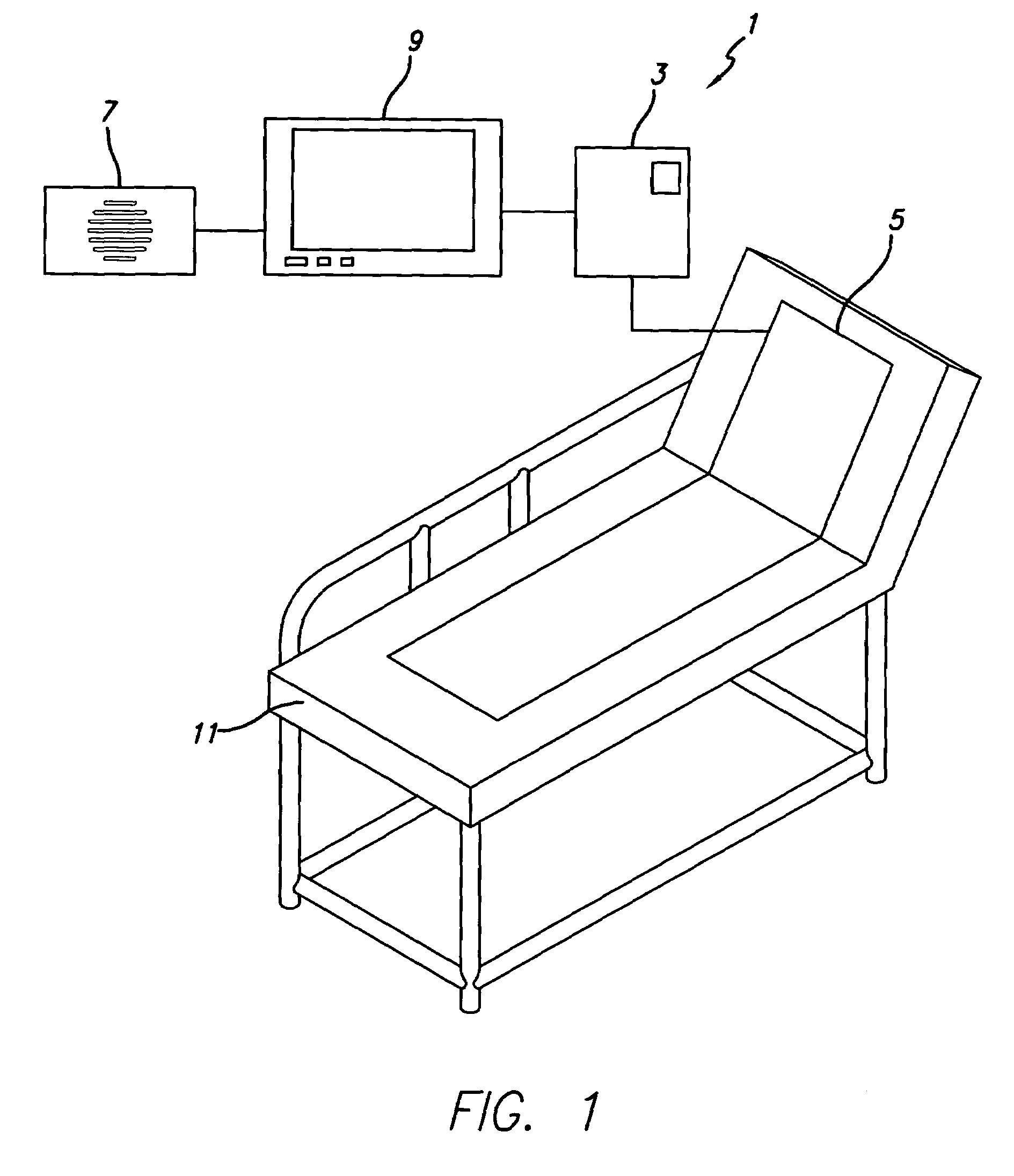
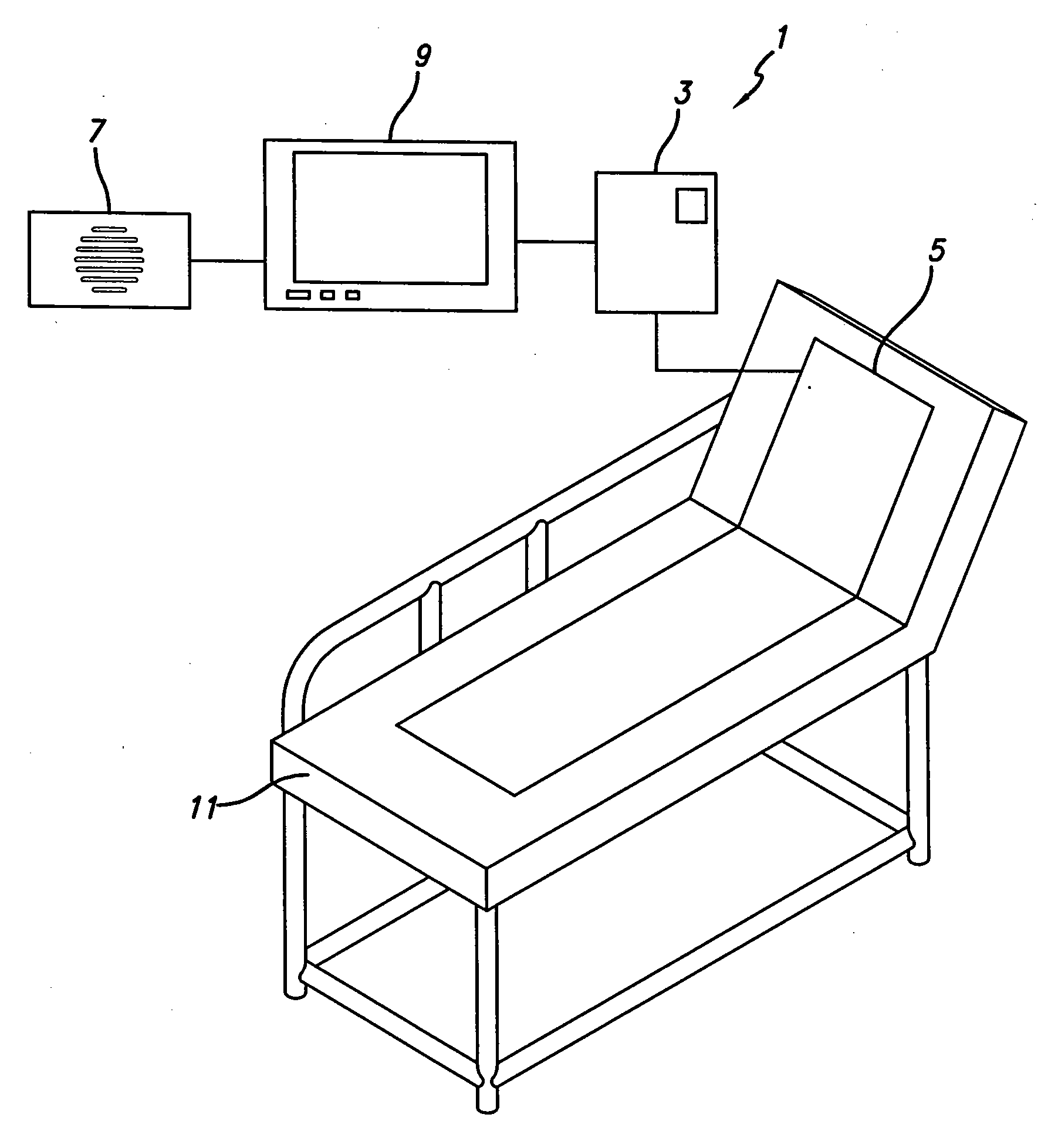
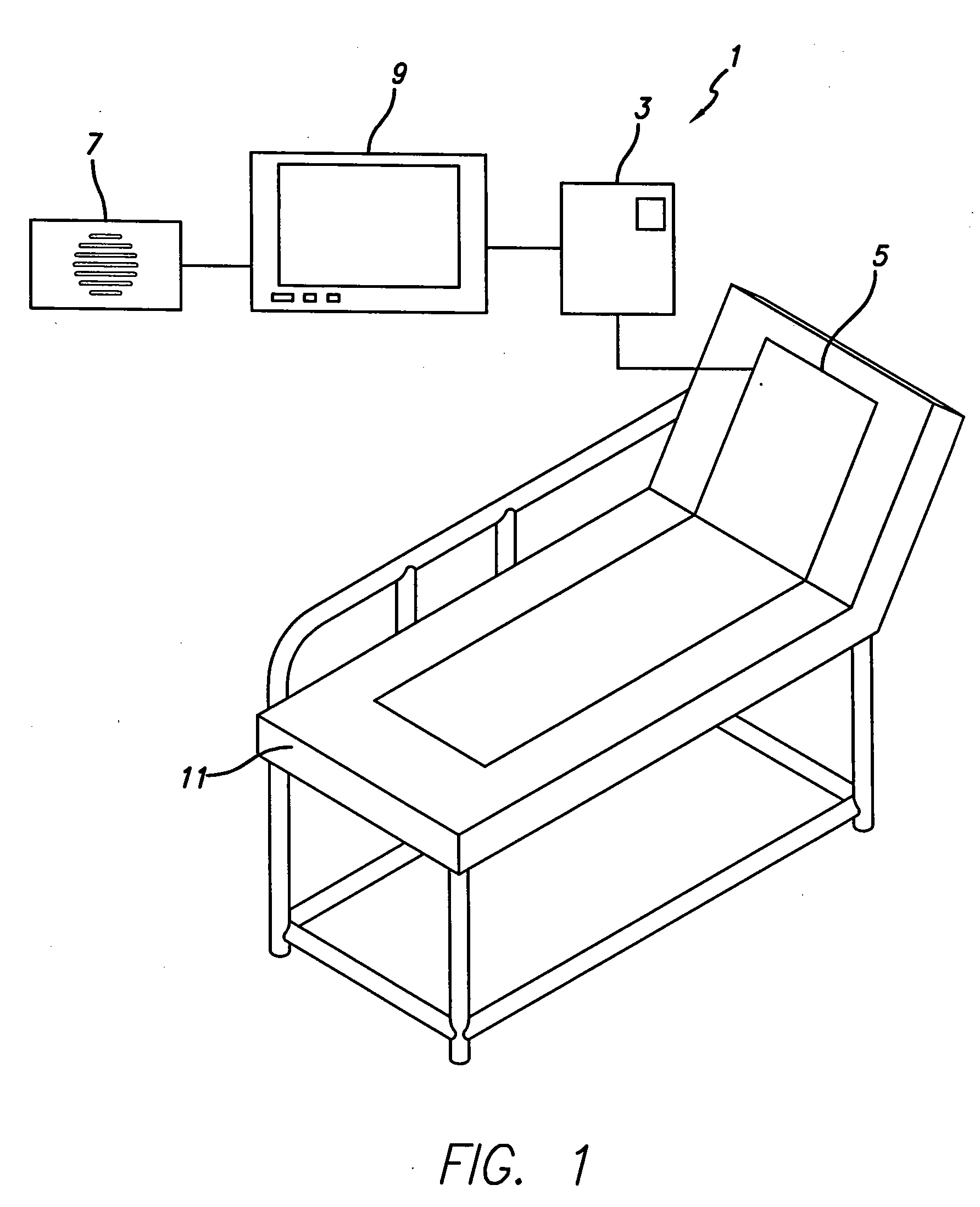
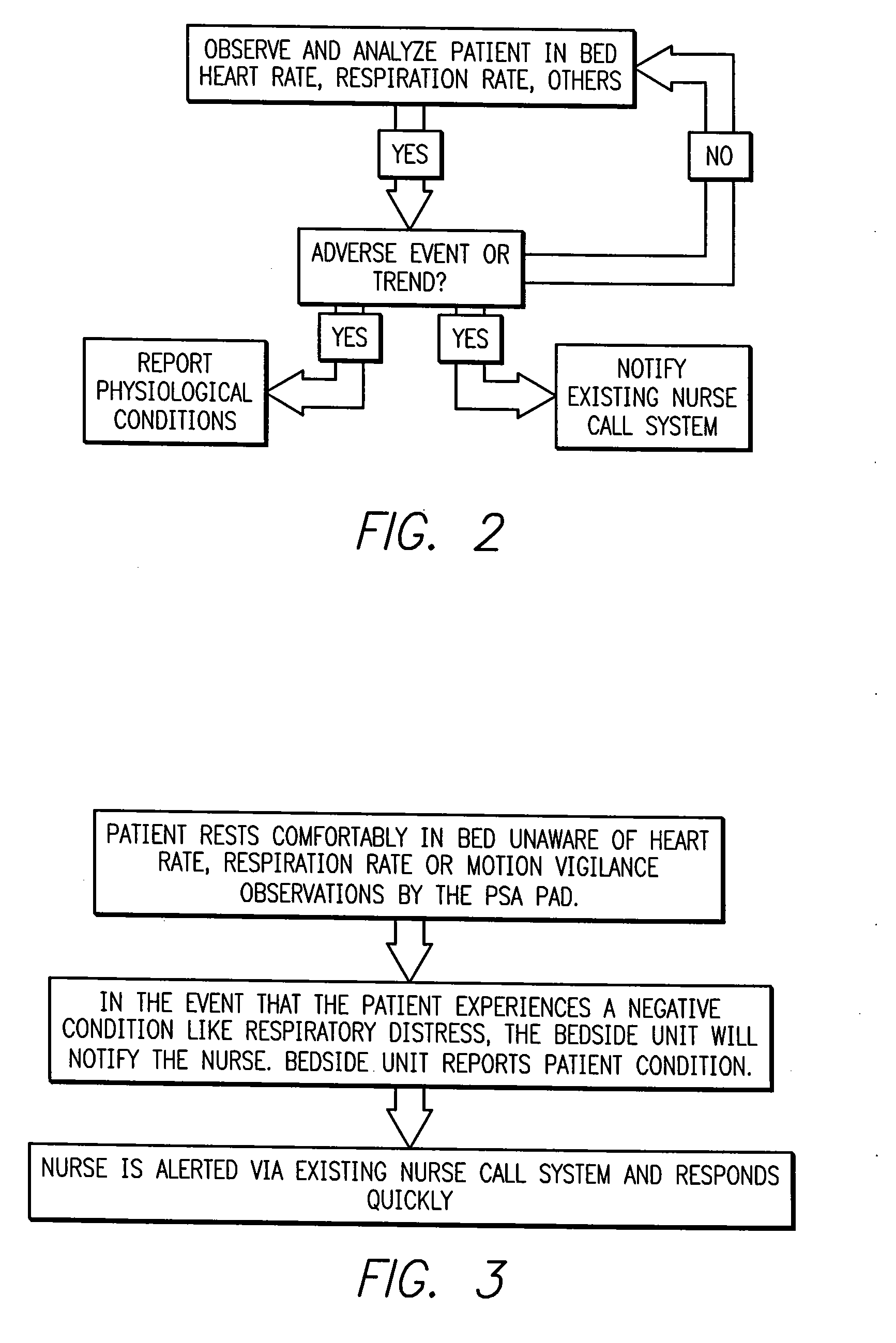
Intelligent medical vigilance system
InactiveUS7304580B2Improve abilitiesEffective resourcesAcoustic sensorsTelemedicineSensor arrayDisplay device
An intelligent medical vigilance system that observes and analyzes, and, only in the event of a clinically significant negative condition, notifies and reports the event to the care staff utilizing the hospital's existing nurse call system. The device includes a bedside unit connected to a pad or coverlet with a sensor array (placed under the patient) and also to an existing hospital nurse call system via an interface. Within the physical bedside unit are a signal processor and an alarm processor that measure data and evaluate whether a clinically significant event is occurring. The bedside unit is a wall-mounted unit with a display that becomes active when an alarm condition is enabled. The sensing pad or coverlet is a thin, piezoelectric film, or other similar sensing technology, with an array of sensors sheathed in soft padding and is not directly in contact with the skin of the patient. The nurse call feature is made up of hardware, software and cabling to connect to the nurse call system already installed in the hospital or care facility. The monitoring system can also be installed in vehicles to monitor operator physiological conditions.
Owner:HOANA MEDICAL
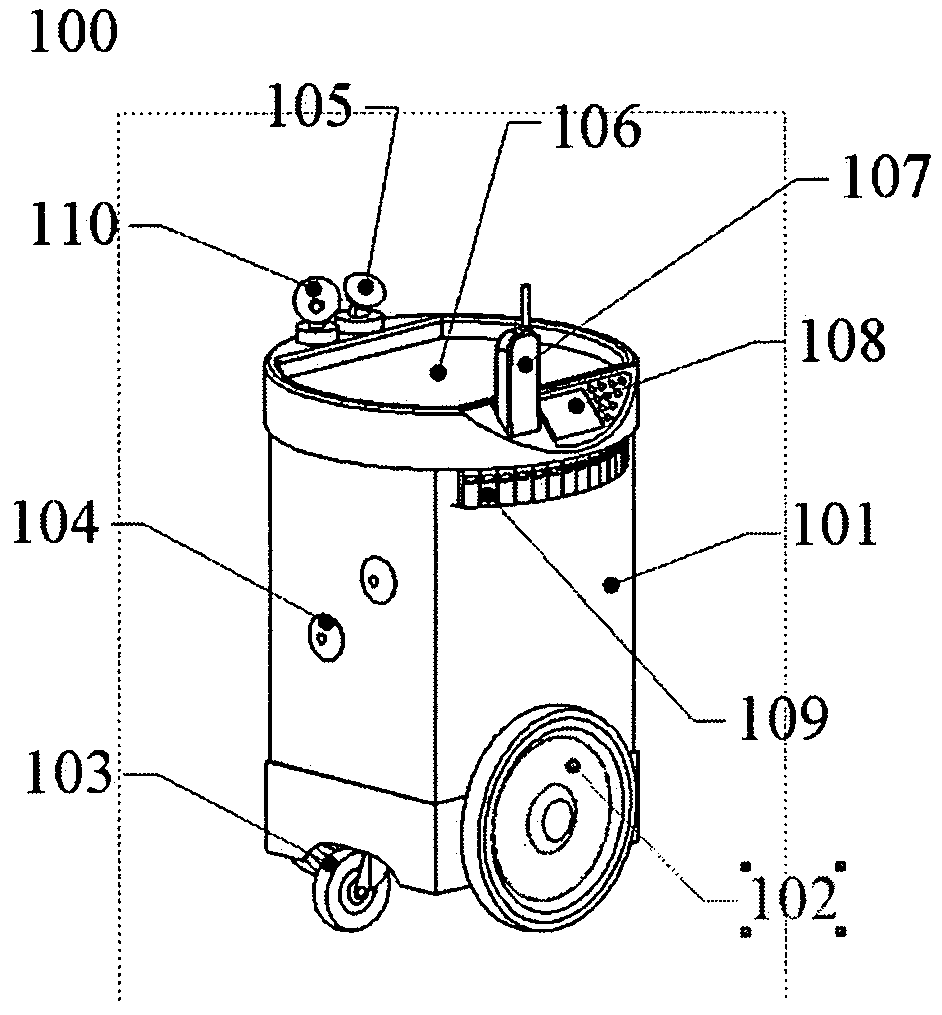
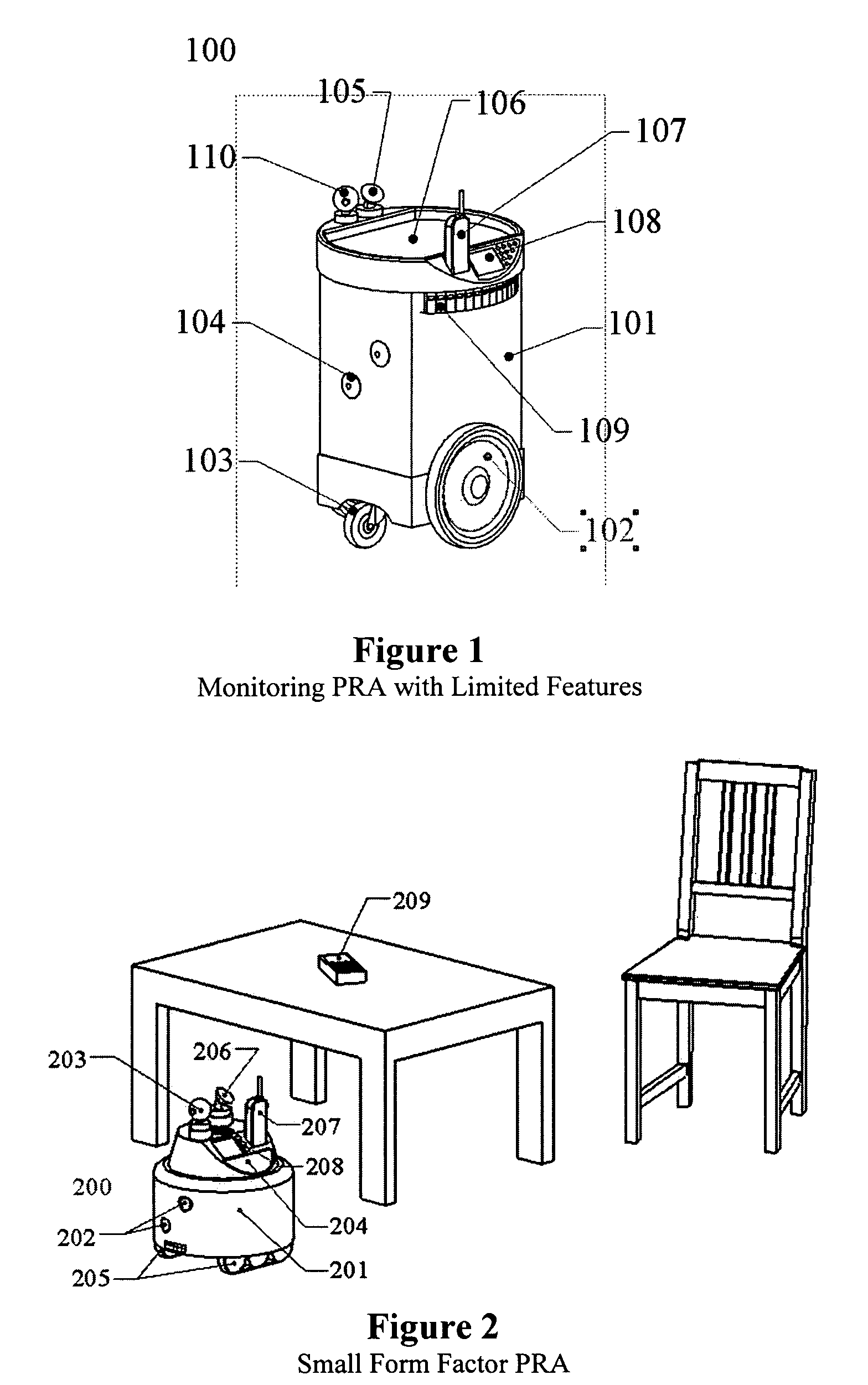
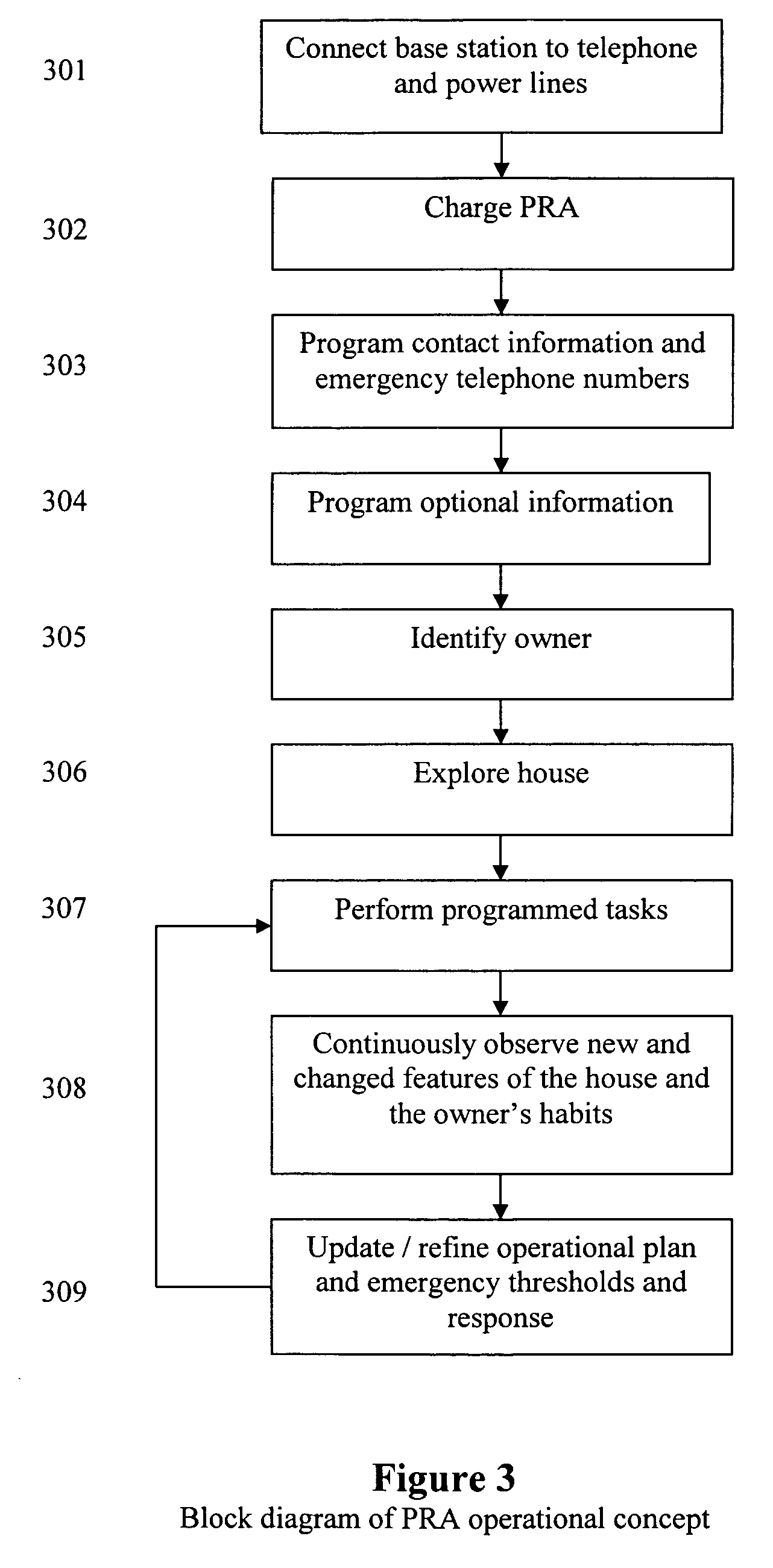
Autonomous personal service robot
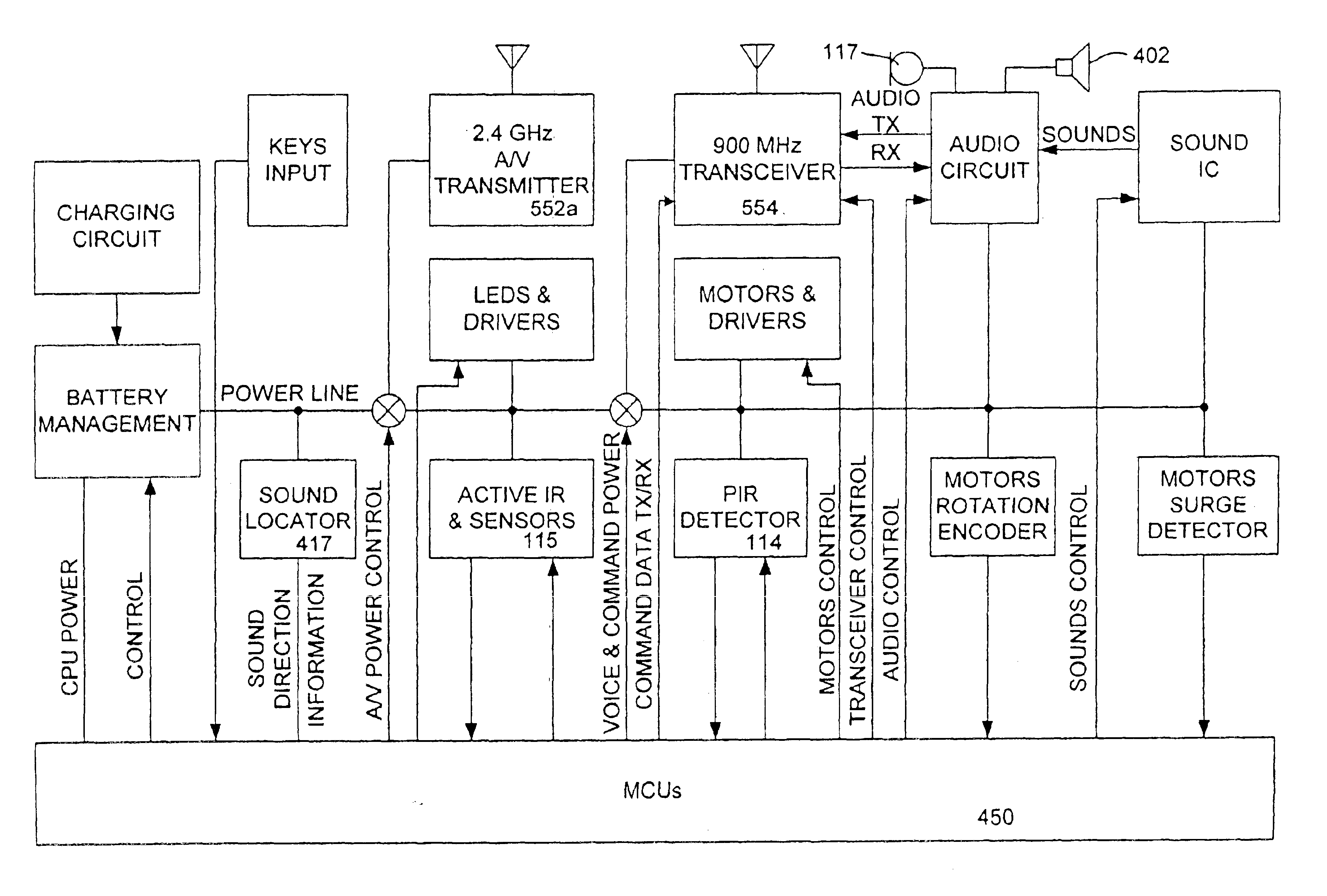
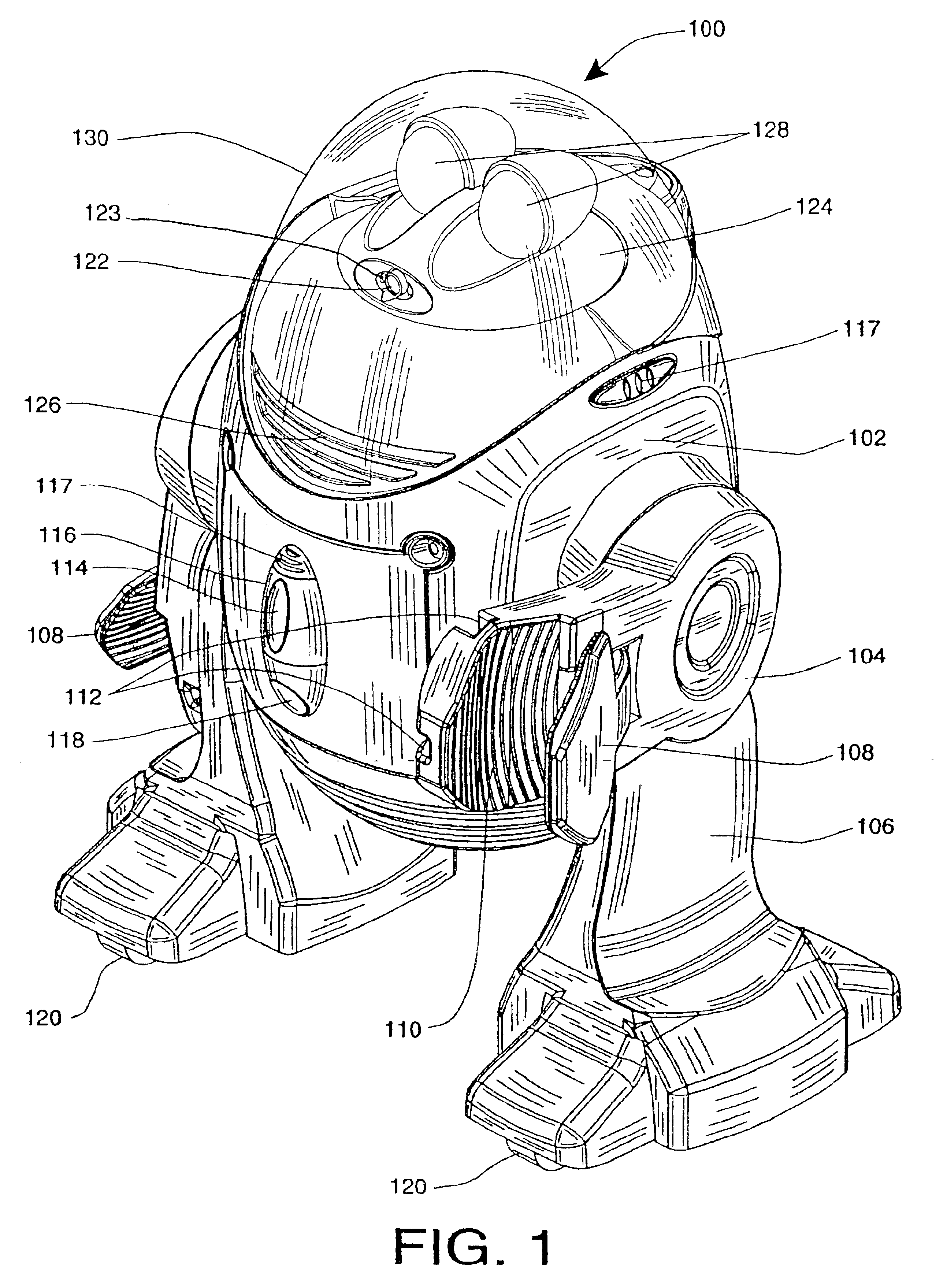
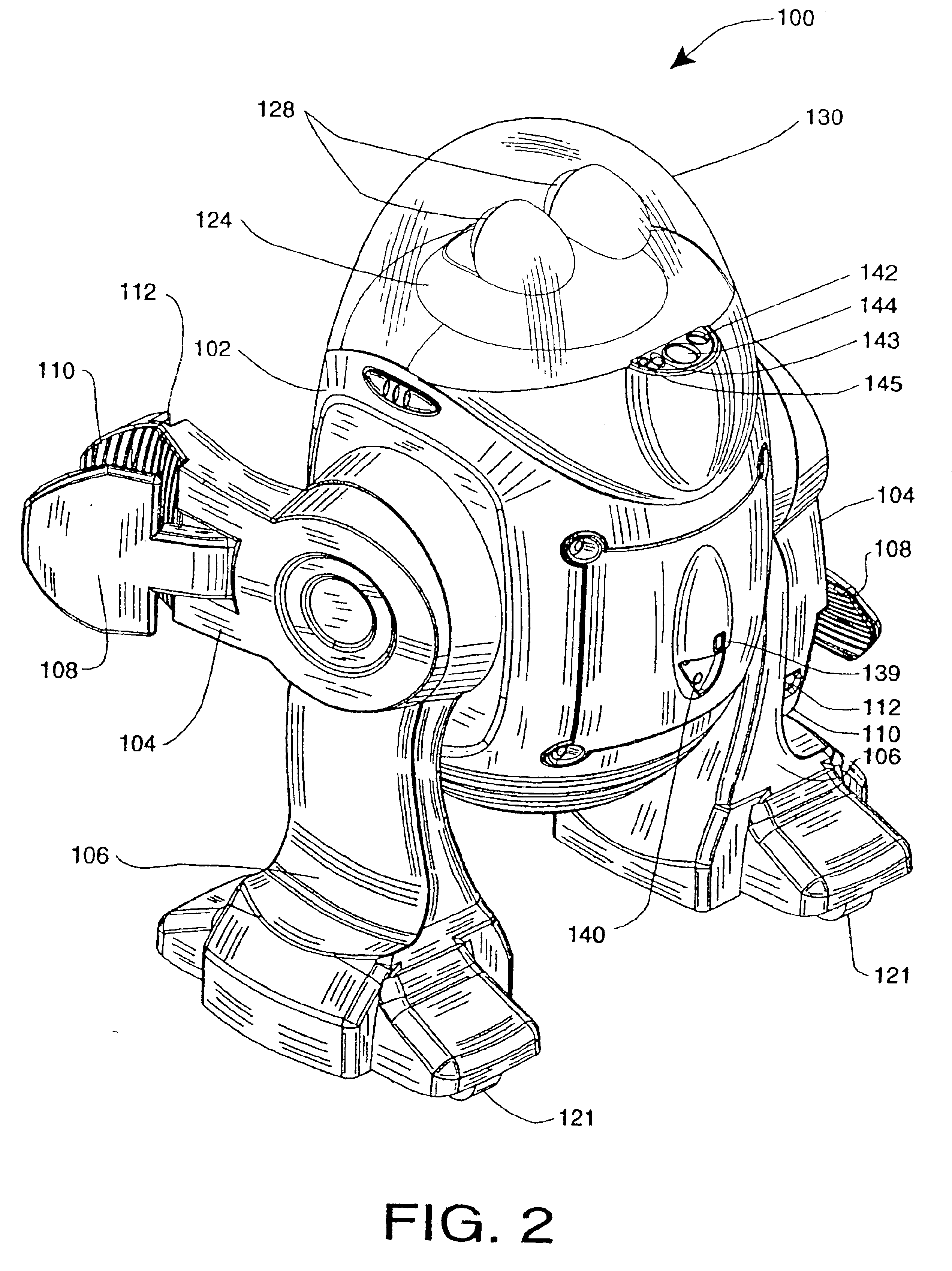
InactiveUS20050216126A1Low costReduced versatilityProgramme controlProgramme-controlled manipulatorAutomatic controlBlood pressure cuffs
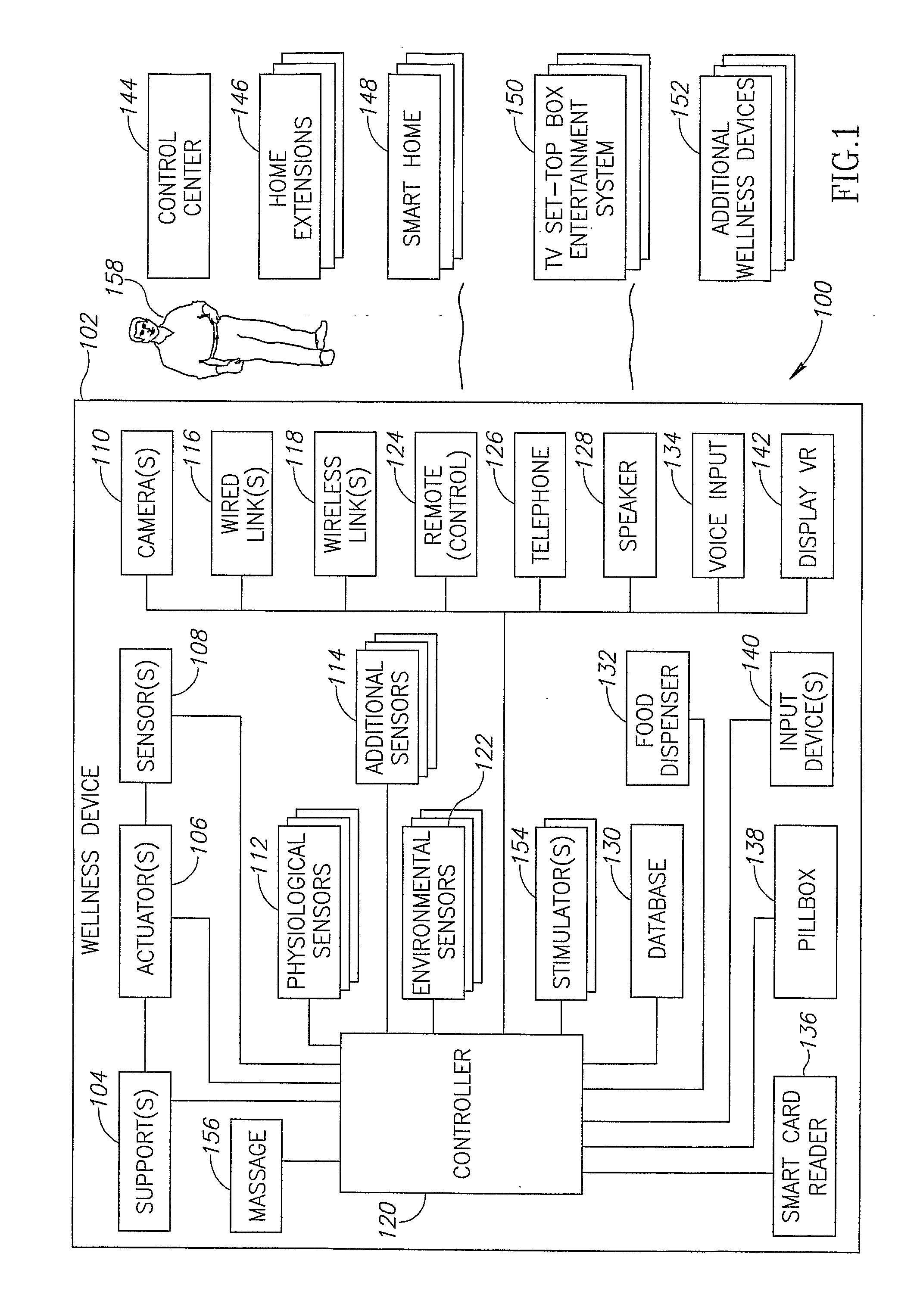
Autonomous personal service robot to monitor its owner for symptoms of distress and provide assistance. The system may include sensors to detect situations before they affect people such as smoke, heat, temperature and carbon monoxide sensors. The system can provide security for the home. The PRA may comprise features such as a medicine dispenser and blood pressure cuff. Features such as broadband internet, MP3 player, reading lights and eye glass tracker provide butler type capabilities that enable the system to appeal to markets beyond the elderly and infirmed. The system may also include an X10 transmitter / receiver to automatically control various household lights and appliances. Equipping the system with a robot arm enables the robot to fetch items, turn on and off wall switches and open the refrigerator.
Owner:VISION ROBOTICS
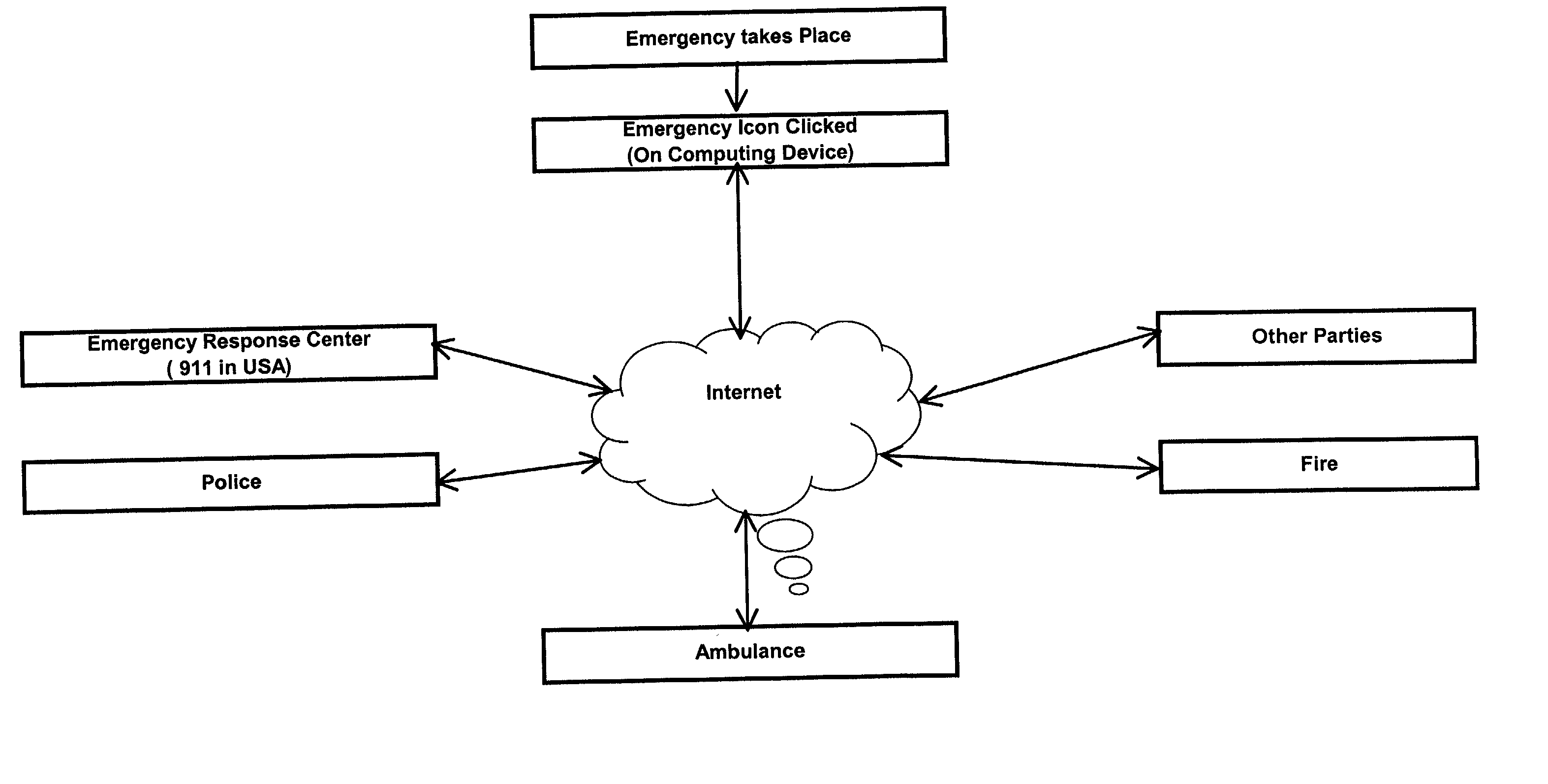
System and a method for emergency services
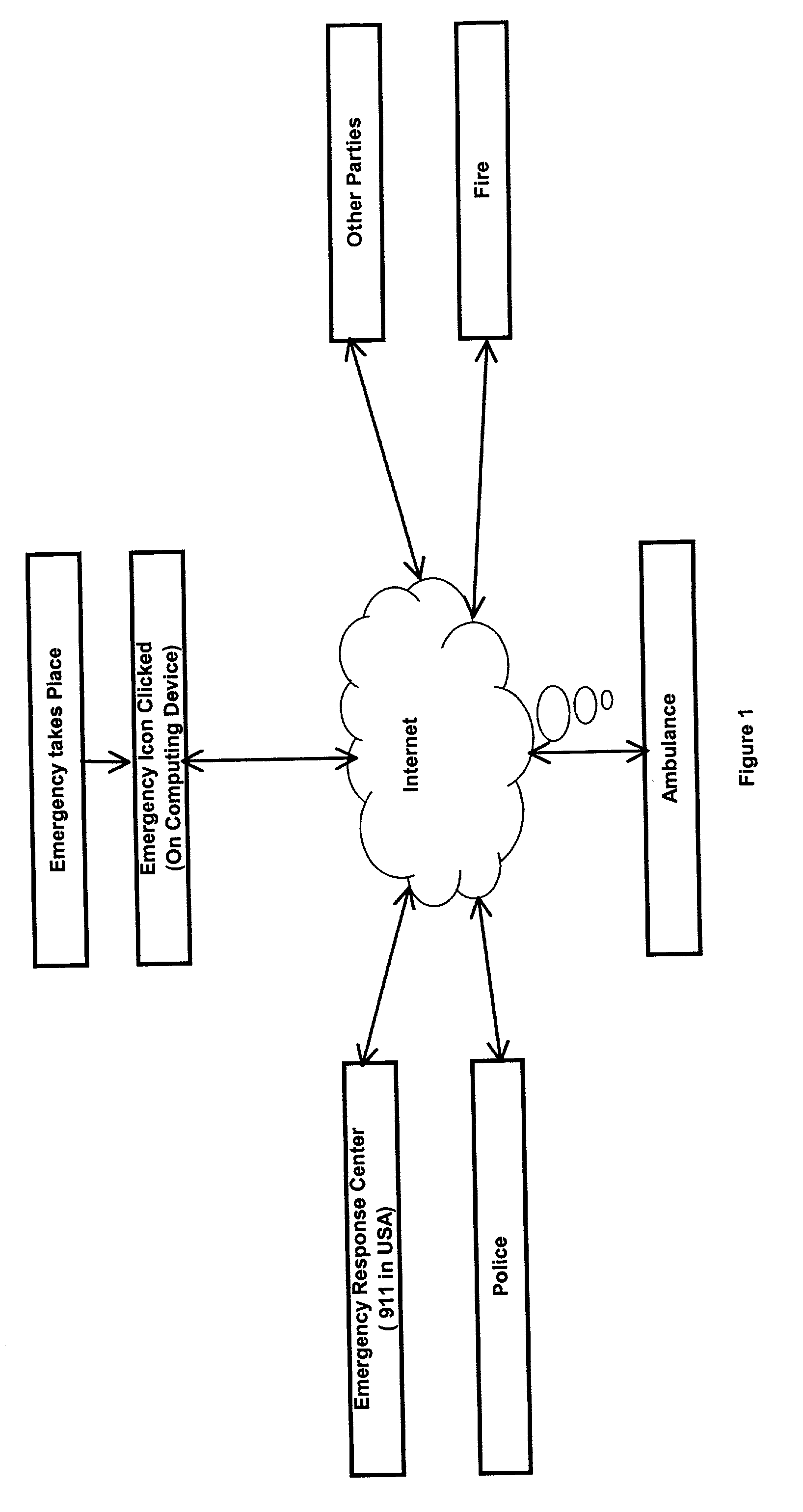
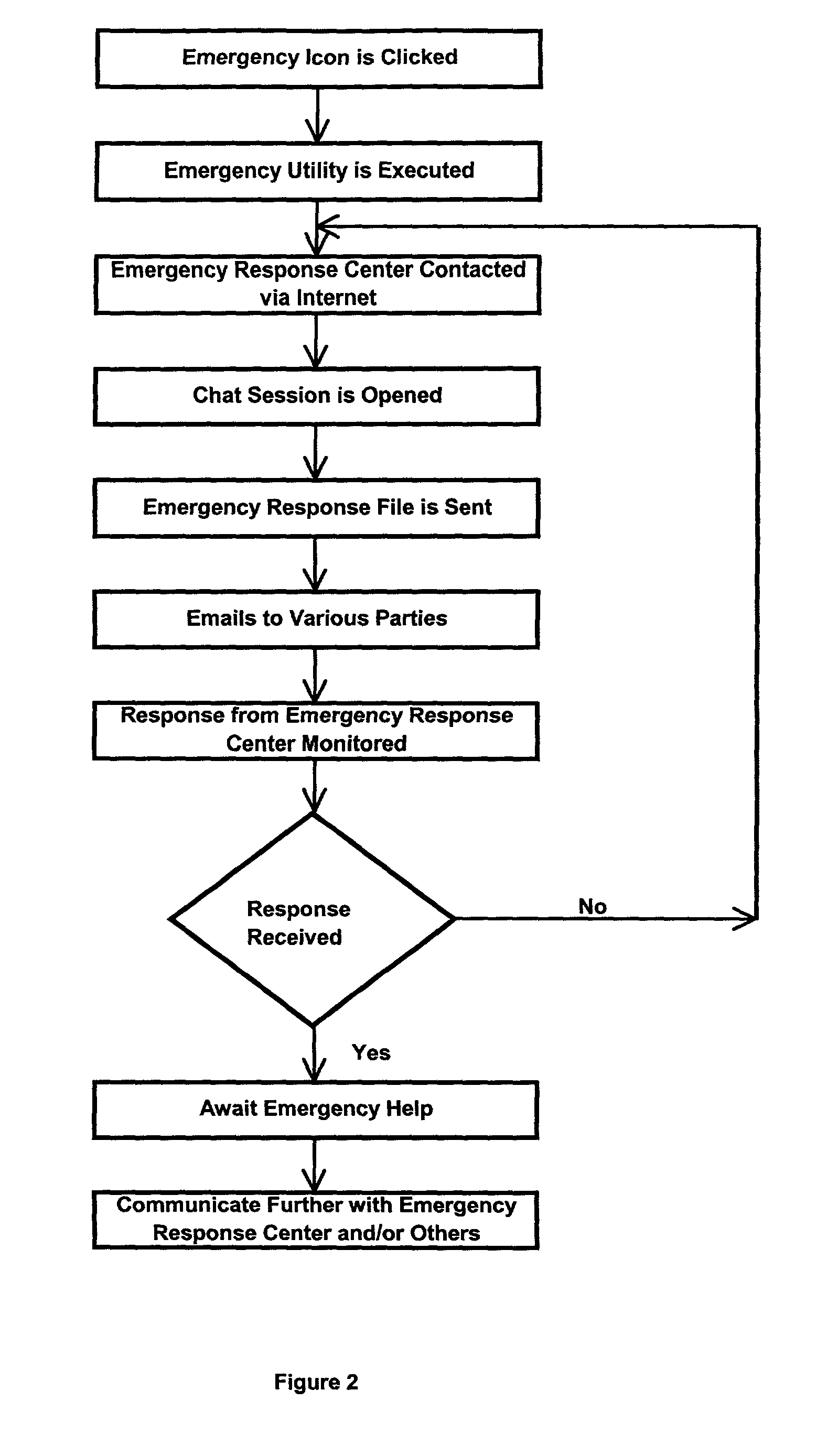
InactiveUS20030012344A1Providing privacyProvide securityEmergency connection handlingTelephonic communicationHand heldEngineering
A system and a method for communicating information concerning required emergency services including a software Emergency Utility that may reside on any home, office, automobile or hand-held device, or internet website, that can, when activated, automatically communicate emergency information to emergency service facilities and to other desired persons or devices. A ubiquitous Emergency icon is also provided for the activation of the Emergency utility.
Owner:AGARWAL RITA +1
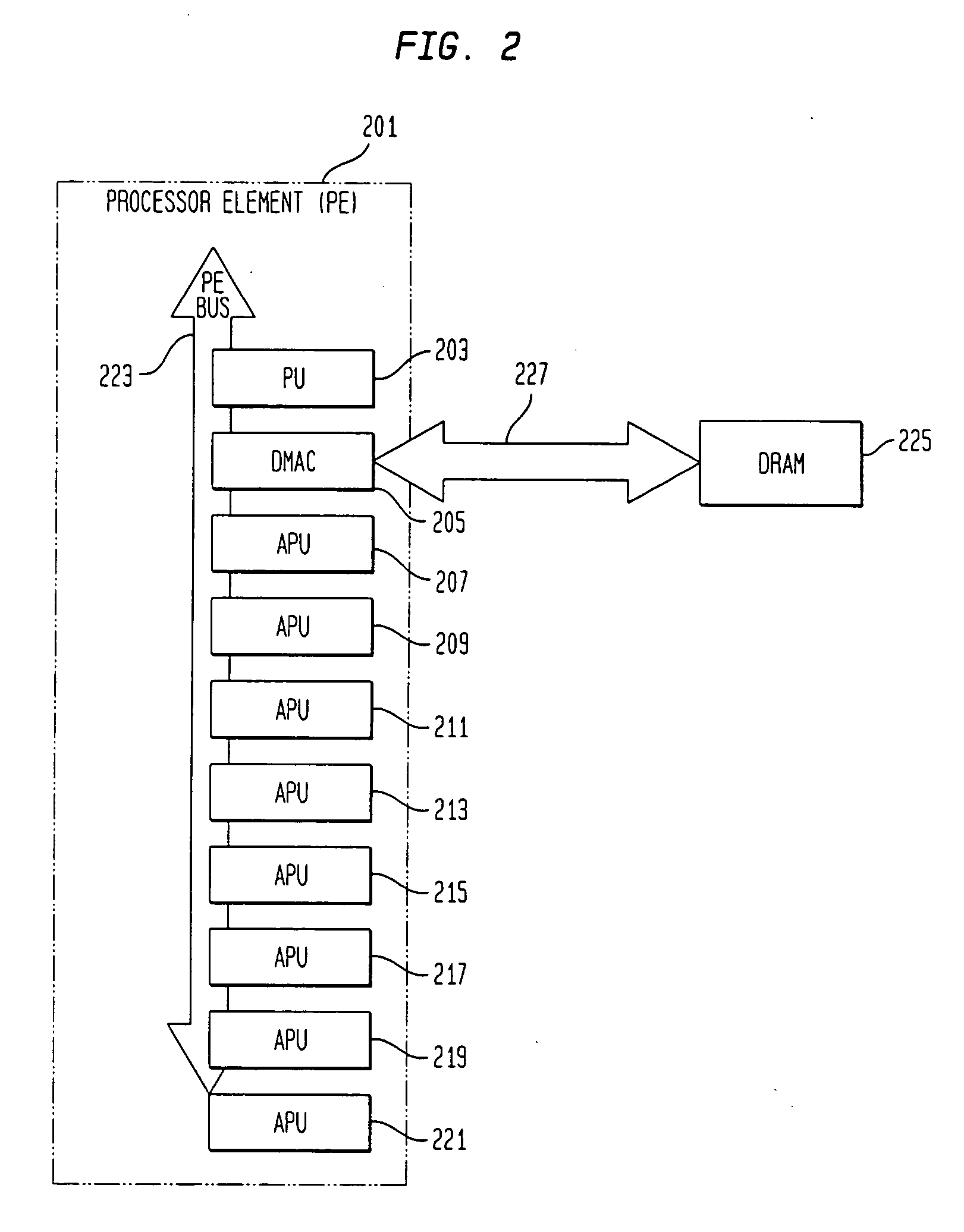
System and method for data synchronization for a computer architecture for broadband networks
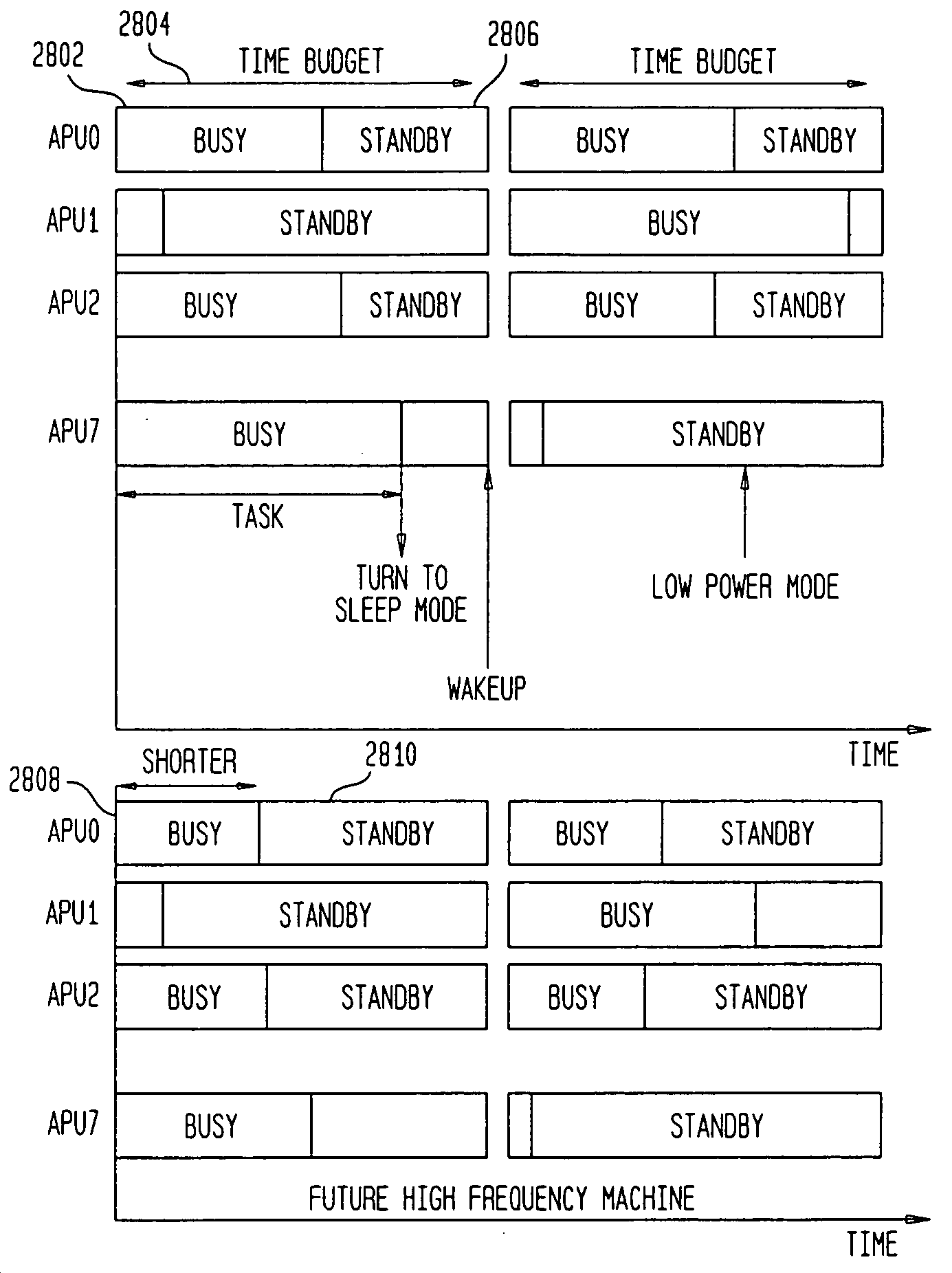
ActiveUS20050081213A1Avoid confictAvoid computational overheadVolume/mass flow measurementUnauthorized memory use protectionModular structureBroadband networks
A computer architecture and programming model for high speed processing over broadband networks are provided. The architecture employs a consistent modular structure, a common computing module and uniform software cells. The common computing module includes a control processor, a plurality of processing units, a plurality of local memories from which the processing units process programs, a direct memory access controller and a shared main memory. A synchronized system and method for the coordinated reading and writing of data to and from the shared main memory by the processing units also are provided. A processing system for processing tasks is also provided. The processing system includes processing devices and an absolute timer. The absolute timer defines a time budget. The time budget provides a time period for the completion of tasks by selected processing devices independent of clock frequencies employed by the processing devices for processing the tasks.
Owner:SONY COMPUTER ENTERTAINMENT INC
Truncated transcriptionally active cytomegalovirus promoters
InactiveUS6156567AProvide securityIncrease capacitySsRNA viruses negative-senseGenetic material ingredientsBiotechnologyEukaryotic plasmids
Recombinant adenoviruses, methods of making them, uses for them, including in immunological, immunogenic, vaccine or therapeutic compositions, or, as a vector for cloning, replicating or expressing DNA and methods of using the compositions and vector, expression products from them, and uses for the expression products are provided. More particularly, recombinant canine adenoviruses (CAV) and methods of making them, uses for them, expression products from them, and uses for the expression products, including recombinant CAV2 viruses are provided. Additionally, truncated promoters, expression cassettes containing the promoters, and recombinant viruses and plasmids containing the promoters or expression cassettes are provided.
Owner:VIROGENETICS
Recombinant canine adenoviruses, method for making and uses thereof
InactiveUS6090393AProvide securityIncrease capacitySsRNA viruses negative-senseVectorsBiotechnologyImmunogenicity
Disclosed and claimed are recombinant adenoviruses, methods of making them, uses for them (including in immunological, immunogenic, vaccine or therapeutic compositions, or, as a vector for cloning, replicating or expressing DNA and methods of using the compositions and vector), expression products from them, and uses for the expression products. More particularly, disclosed and claimed are recombinant canine adenoviruses (CAV) and methods of making them, uses for them, expression products from them, and uses for the expression products, including recombinant CAV2 viruses. Additionally, disclosed and claimed are truncated promoters, expression cassettes containing the promoters, and recombinant viruses and plasmids containing the promoters or expression cassettes.
Owner:VIROGENETICS +1
Device And Method For Training, Rehabilitation And/Or Support
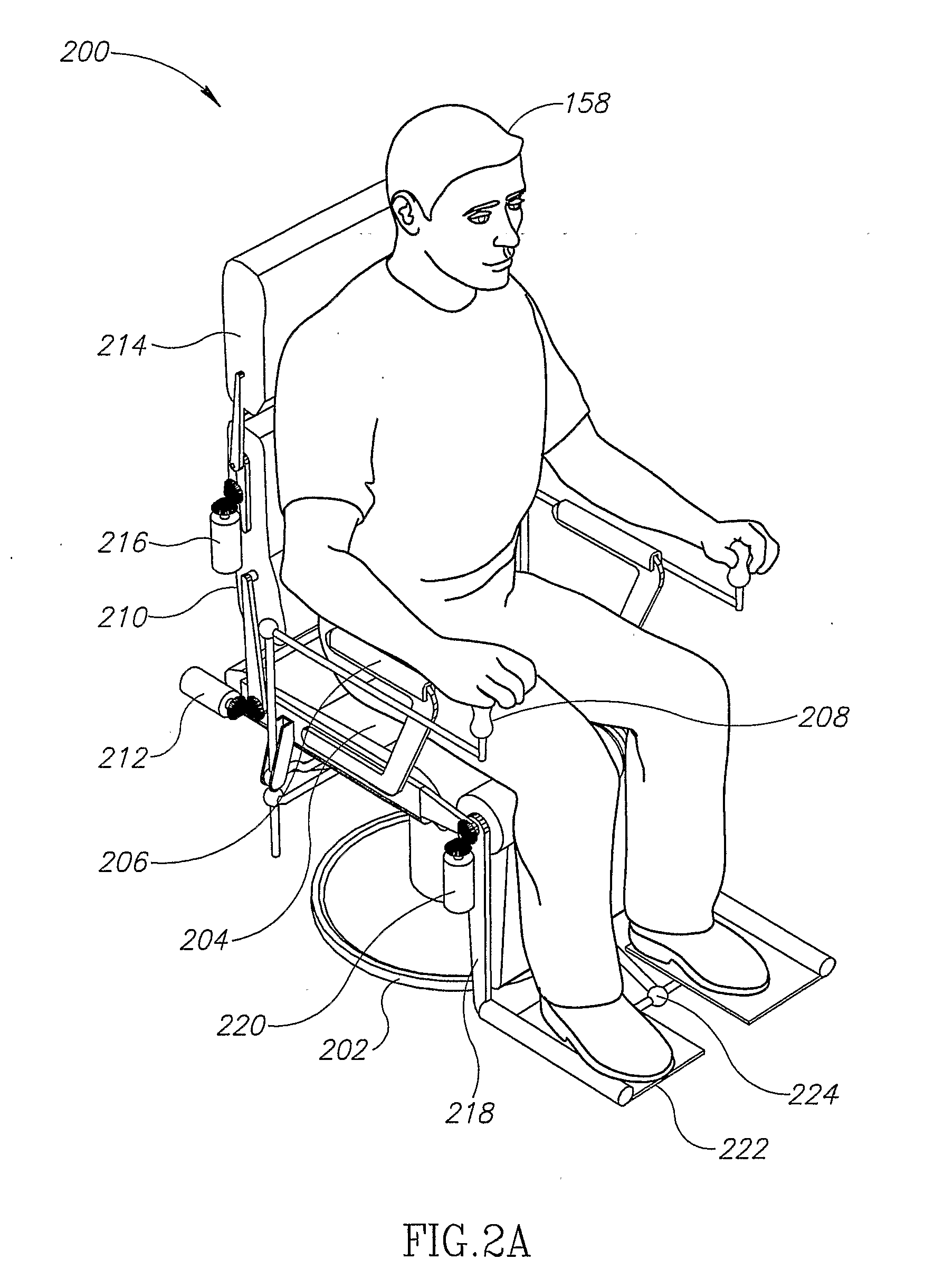
InactiveUS20080132383A1Great level of securityProvide securityUltrasonic/sonic/infrasonic diagnosticsElectrotherapyPhysical exerciseEngineering
A wellness apparatus, comprising: at least one support for a body portion of a user of the apparatus; at least one robotic actuator adapted to move the body portion; and a controller configured to control the actuator in accordance with needs of the user for physical exercise, the controller also adapted for assisting the user with primarily non-physical exercise activity.
Owner:TYLERTON INT INC
Secure card-based transactions using mobile phones or other mobile devices
InactiveUS20120284194A1Easily and quickly encodedProvide securityFinancePayment architectureSmart cardMobile device
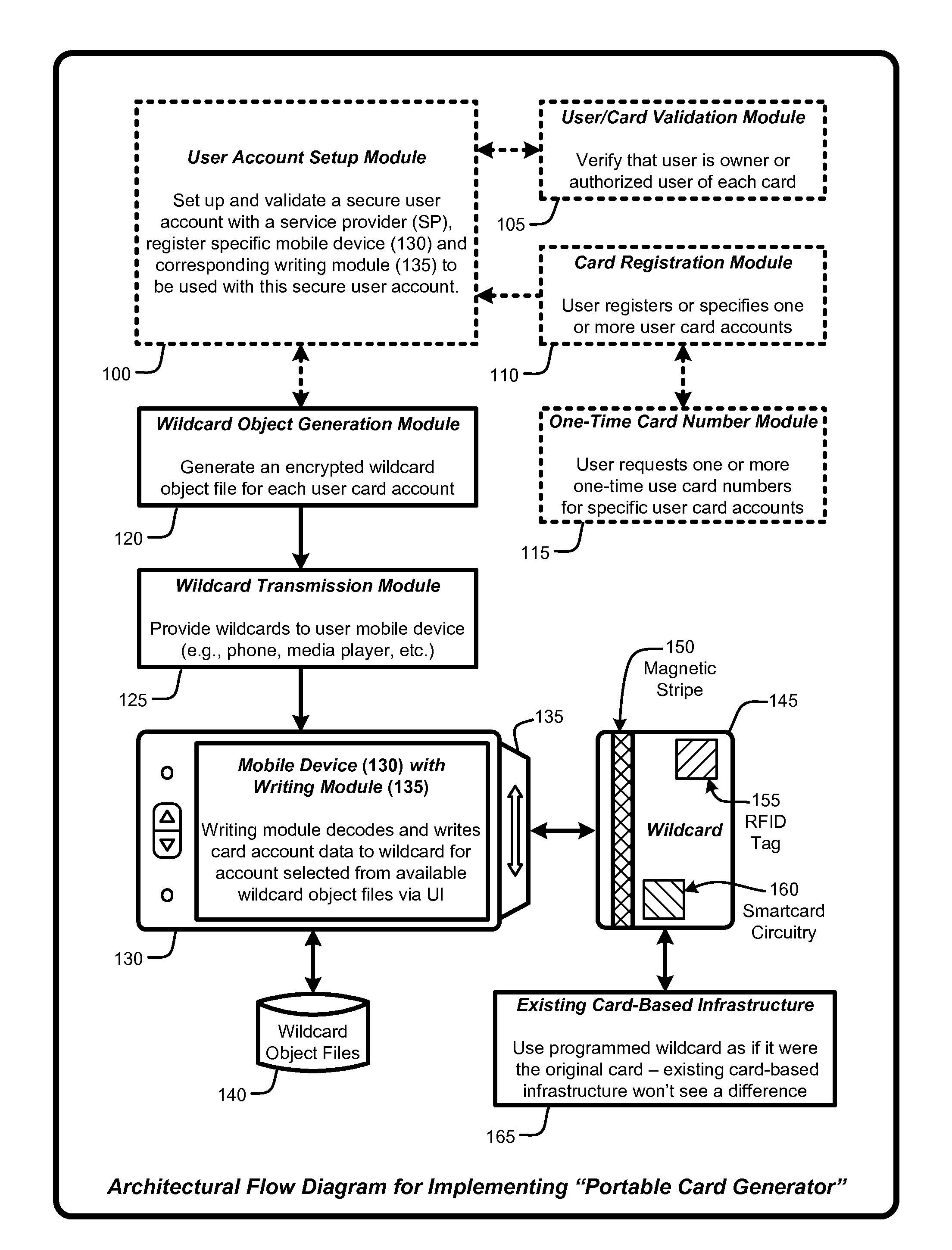
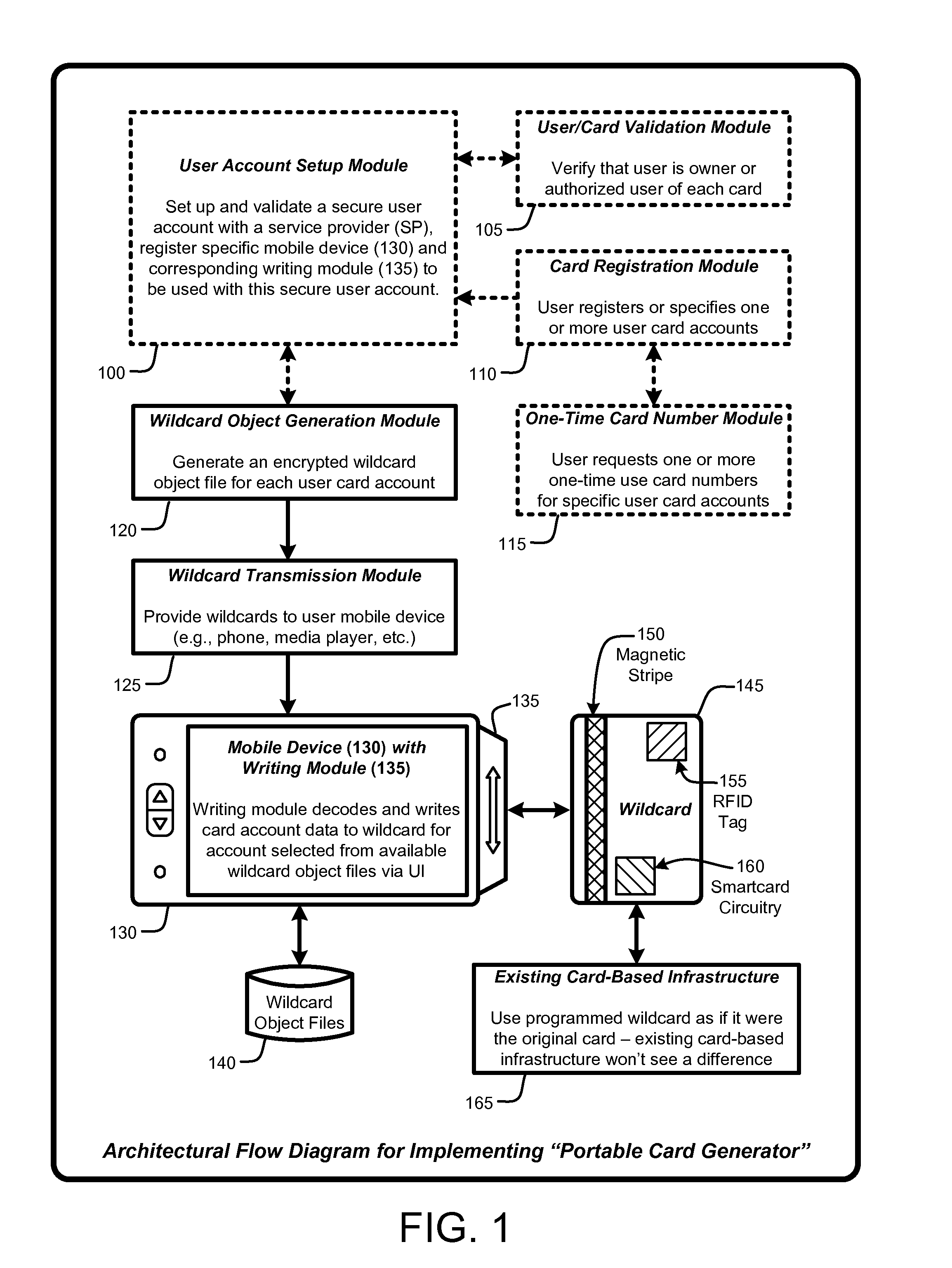
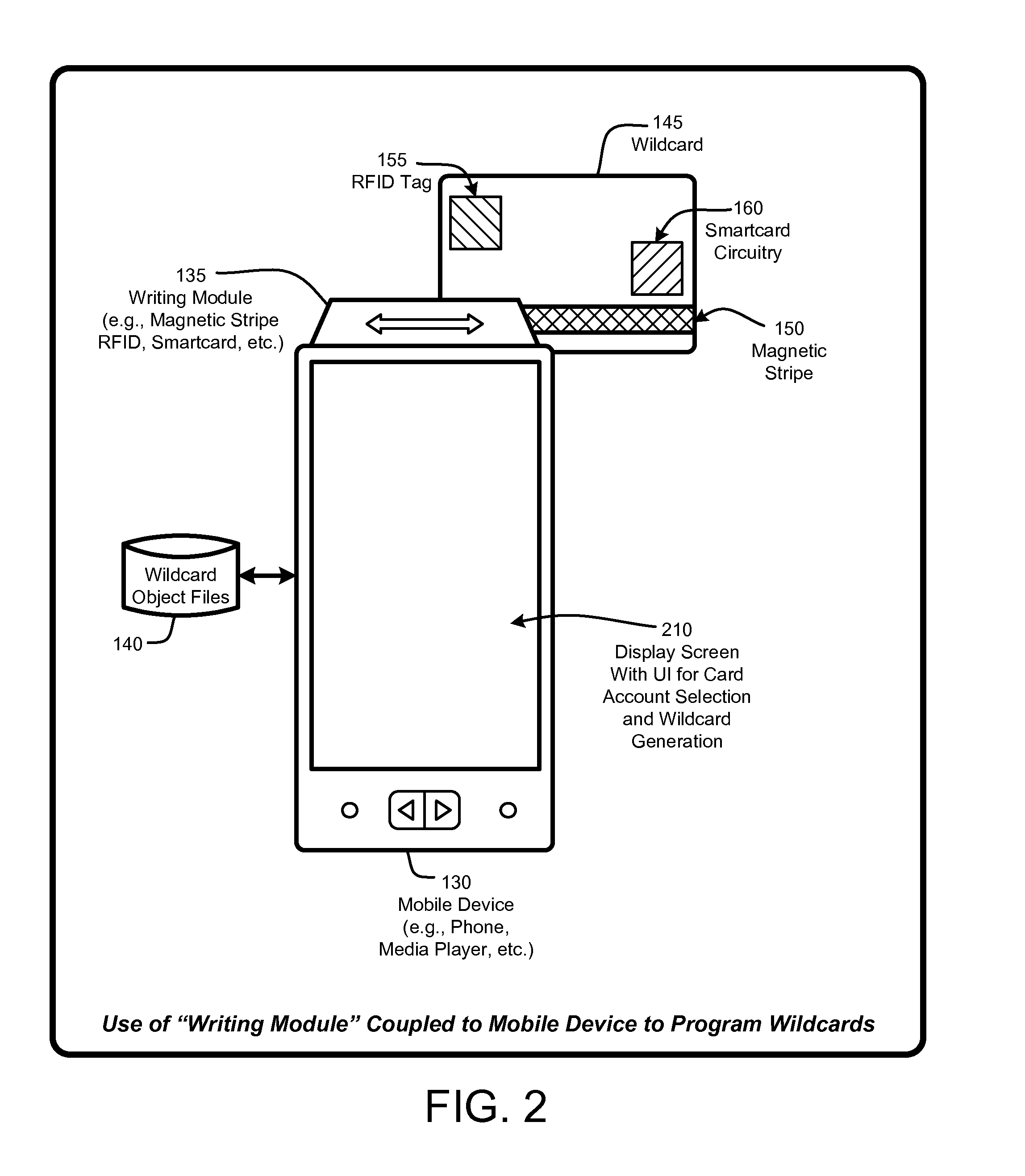
A “Portable Card Generator” is implemented within a portable device, such as a mobile phone, and provides various techniques for writing secure account information from user selected accounts to a “wildcard” having rewritable magnetic stripes, rewritable RFID tags, and / or rewritable smartcard circuitry. The account information is retrieved by the portable device from local or remote stores of user accounts. Once that account information is written, the wildcard is then available for immediate use for credit card or debit-type payments, loyalty card use, etc. Consequently, by providing a credit card sized object having a rewriteable magnetic stripe, RFID tag, and / or smartcard circuitry, in combination with account information for various credit cards, debit cards, consumer loyalty cards, insurance cards, ID cards or badges, etc., the user is no longer required to physically carry those cards in order to use the corresponding accounts within existing card-based infrastructures.
Owner:MICROSOFT TECH LICENSING LLC
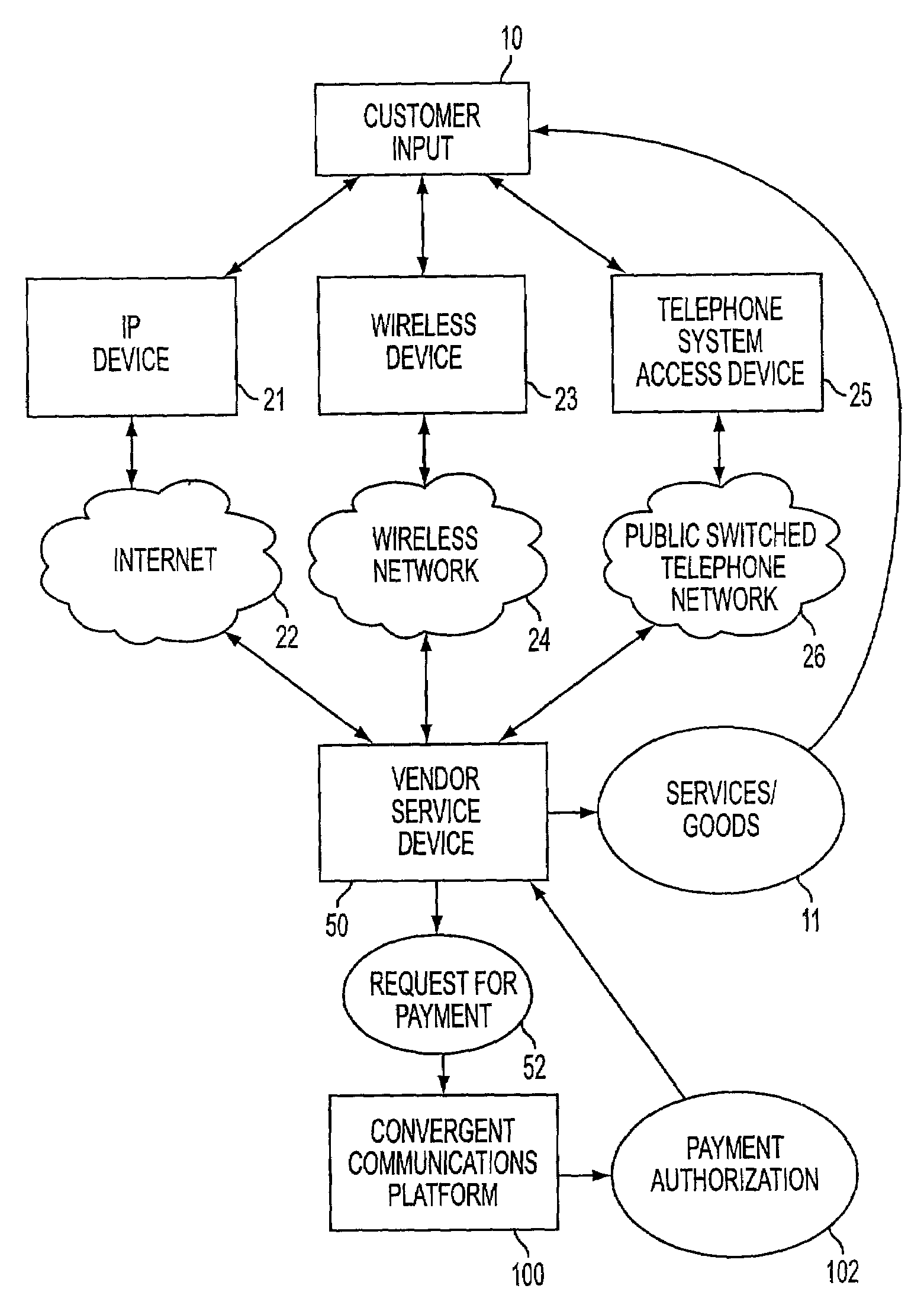
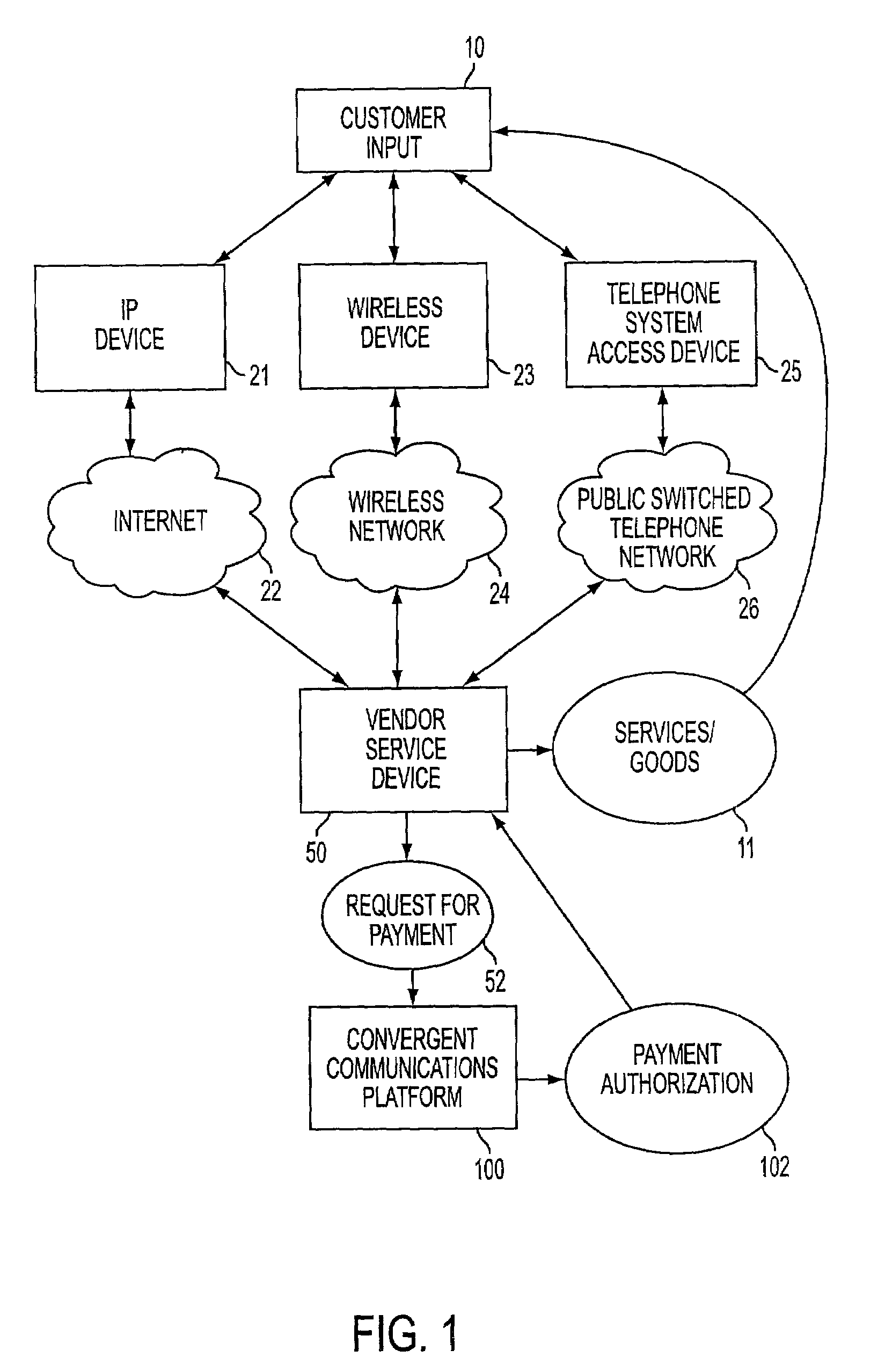
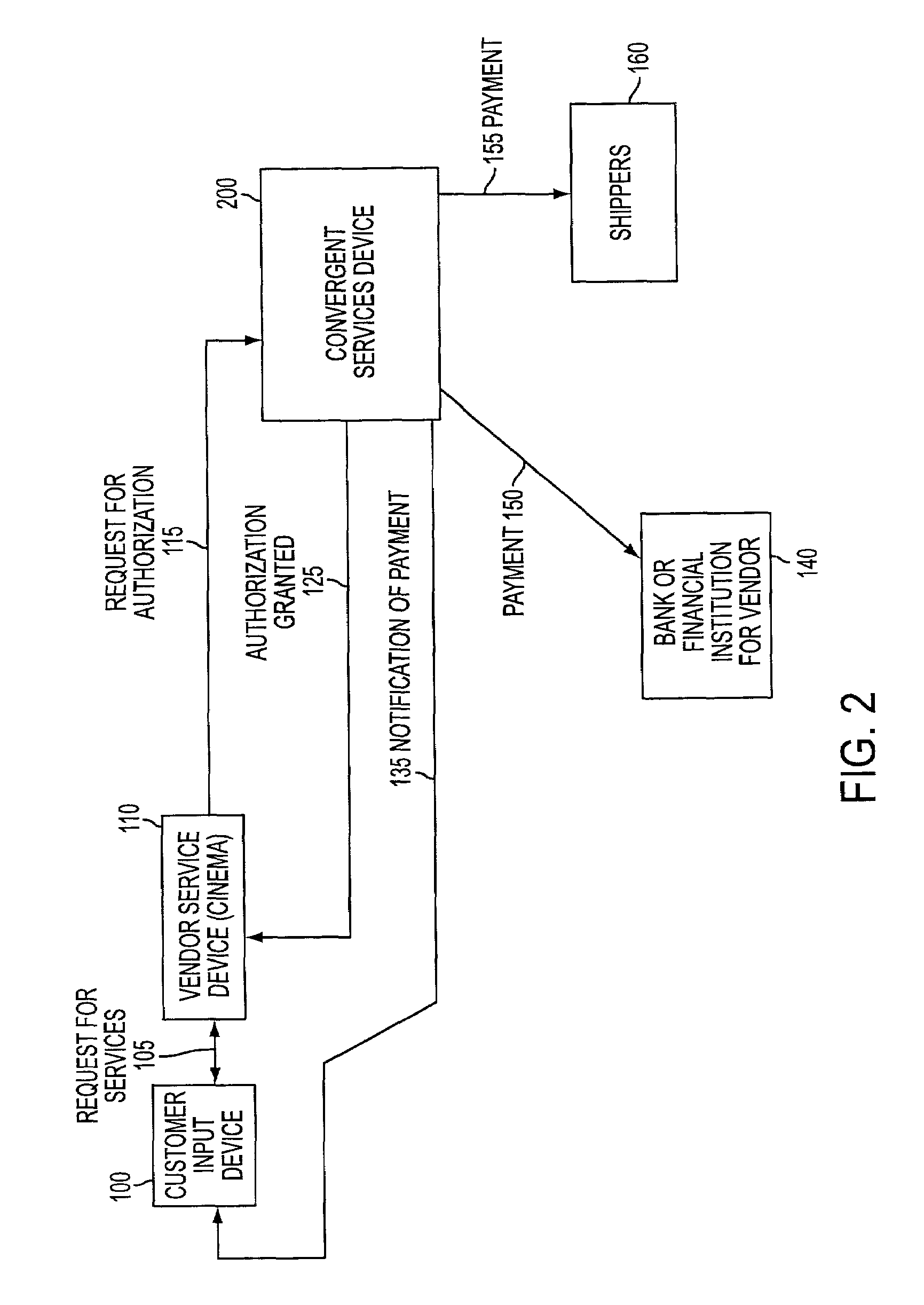
Convergent communications system and method with a rule set for authorizing, debiting, settling and recharging a mobile commerce account
InactiveUS7248855B2Low costImprove adaptabilityDigital data authenticationBuying/selling/leasing transactionsCommunications systemHeterogeneous network
A rule set is used to determine at least one rule for authorizing a transaction debiting an account of an authorized user. Subsequently, the account is debited, according to the at least one rule, in real time if the transaction is authorized. The real time debit is settled with transaction providers in accordance with at least one settlement rule. If it is determined that the authorized user does not have sufficient funds in an authorized user account to debit for the transaction, the authorized user account may be recharged by a recharge routine that includes determining a recharge user account to transfer funds from and authorizing the transfer by at least one of referring to a pre-authorized transfer and requesting authorization from the authorized user. The transaction may be requested and the transaction providers may be connected via heterogeneous networks.
Owner:UPAID SYST LTD
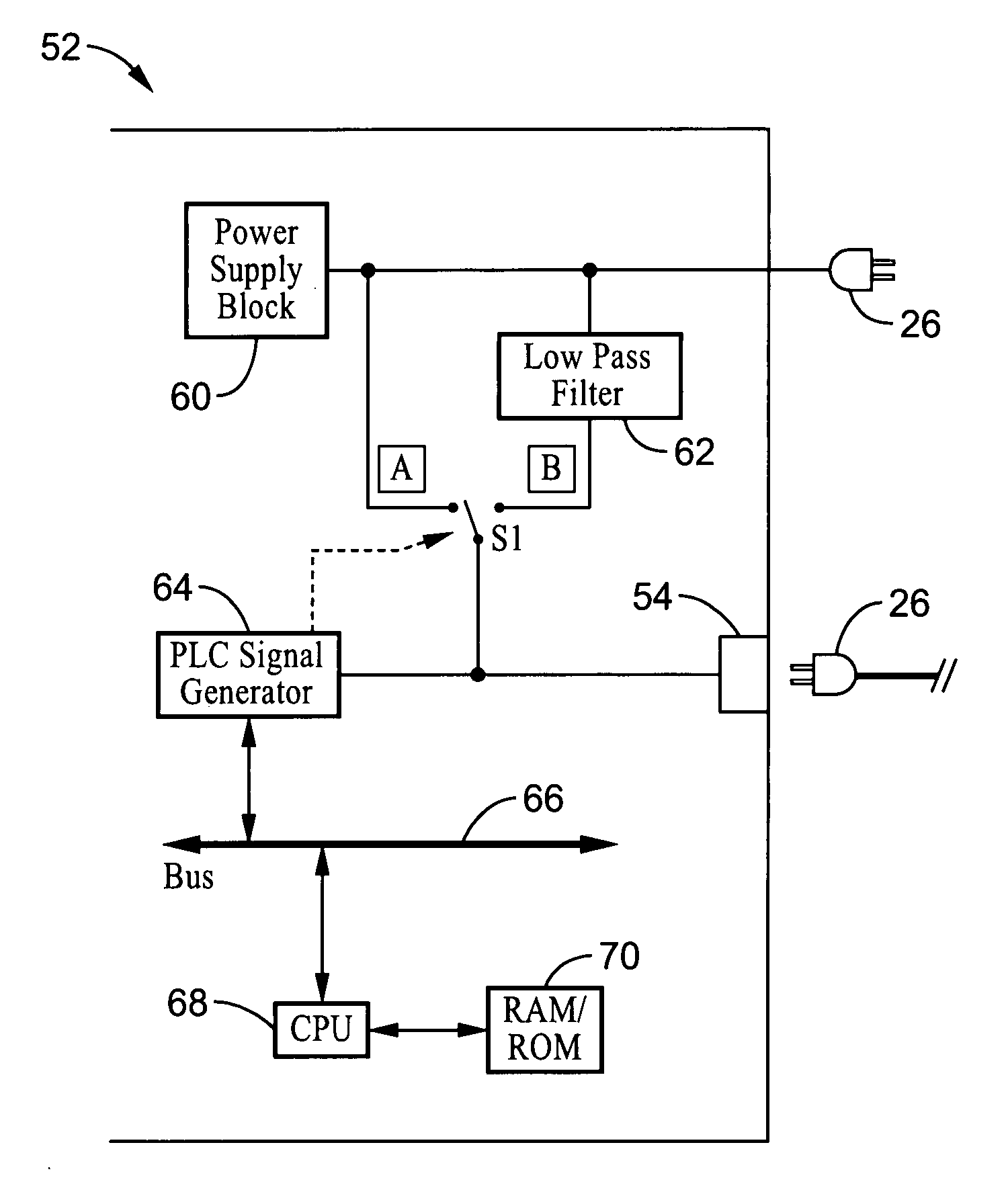
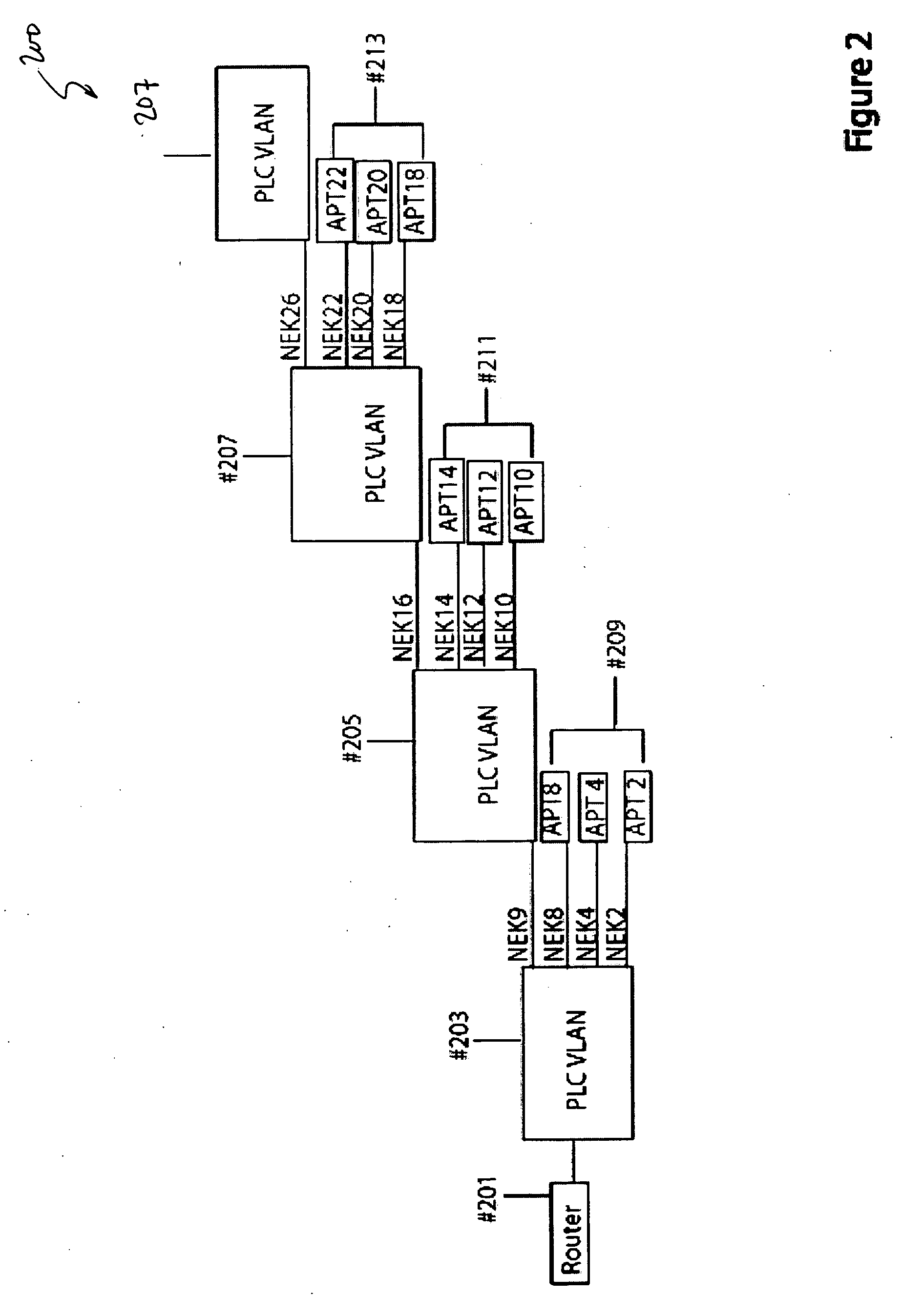
System and method for authenticating/registering network device in power line communication (PLC)
ActiveUS20060038660A1Avoid sharingProvide securitySystems using filtering and bypassingPower distribution line transmissionNetwork keyElectric power
A method and apparatus for protecting privacy in power line communication (PLC) networks. Data transmitted on a PLC network is encrypted according to a network key and can be properly received only by registered devices that have the proper network ID and network key value so that proper decryption can be performed. According to the invention a streaming media device is provided with a compatible network ID and network key during a registration process facilitated by coupling the device (applicant) to a direct power line connection associated with another device (administrator). The network key, and optionally network ID, are then shared over the direct connection without being distributed over the PLC network at large. By way of example, the data is prevented from being distributed across the PLC network in response to using selectable filtering of PLC data, and preferably a secure data communication mechanism, such as public-private key encoding.
Owner:SONY CORP +1
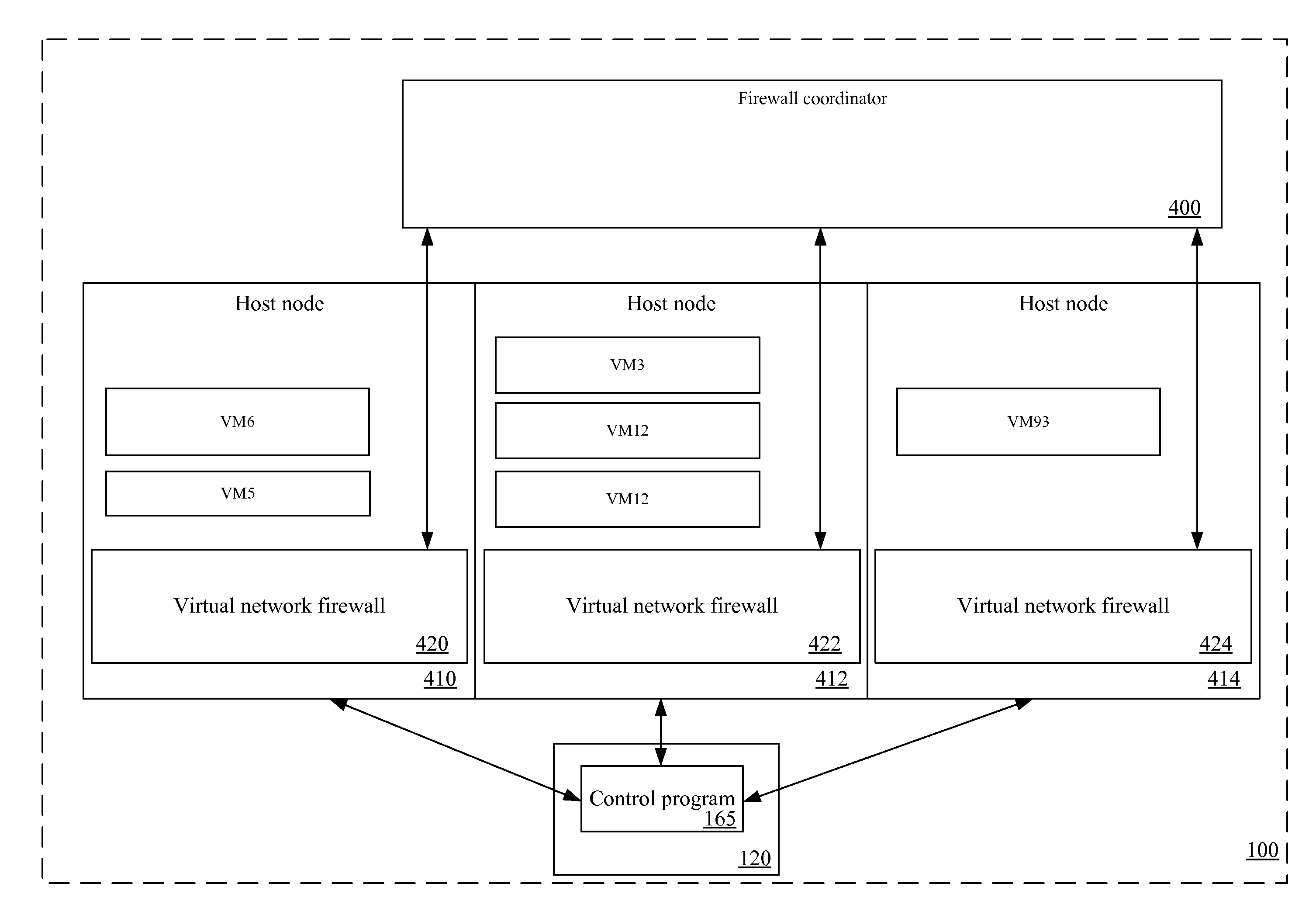
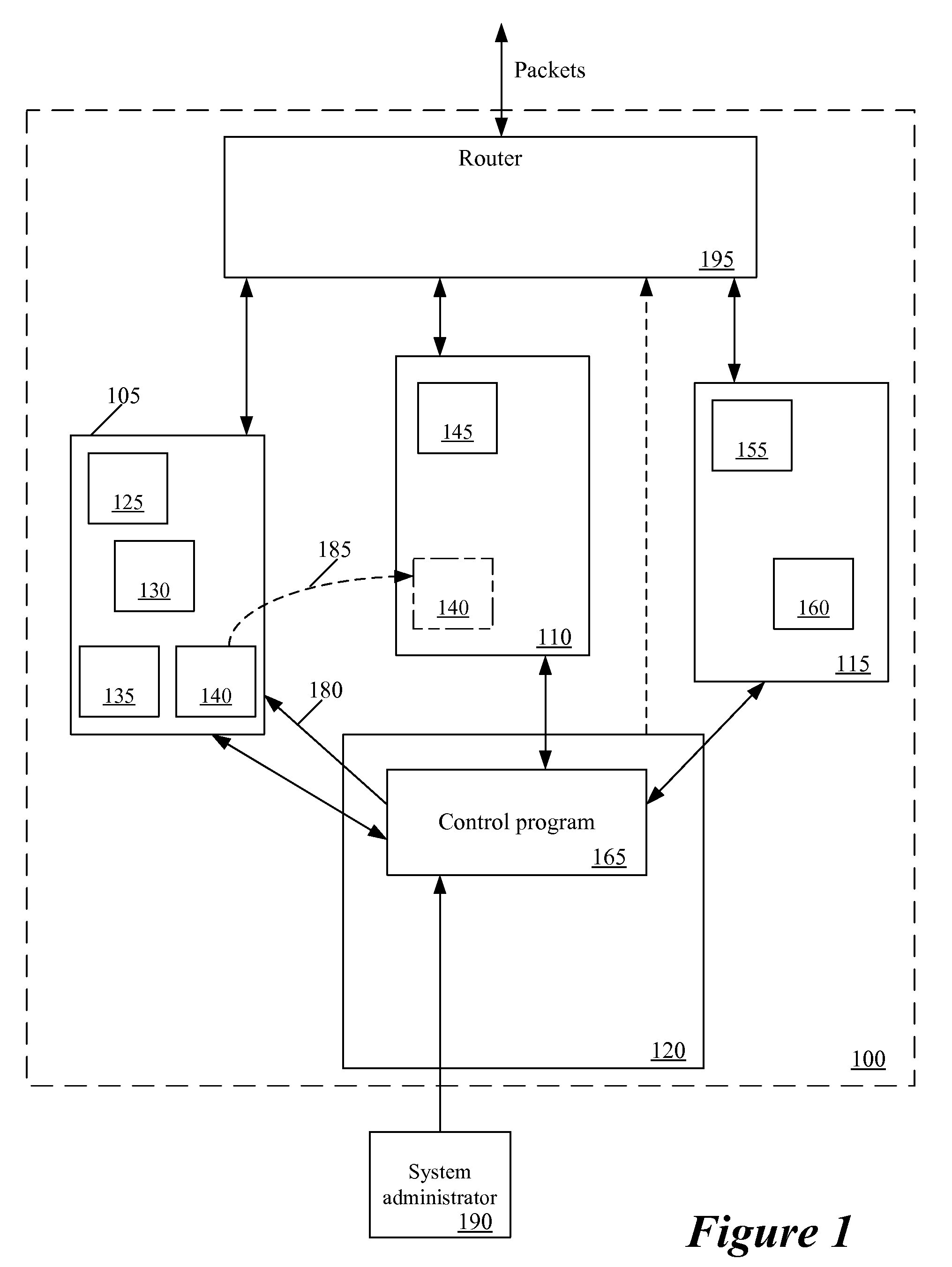
Moving security for virtual machines
InactiveUS20090249438A1Provide securityError preventionFrequency-division multiplex detailsVirtual machineHost machine
A method of maintaining multiple firewalls on multiple host nodes. Each host node runs one or more virtual machines. For at least a first host node, the method maintains multiple sets of policies for multiple virtual machines that run on the first host node. The method, upon detecting that a particular virtual machine has been moved from the first host node to a second host node, removes a set of policies associated with the particular virtual machine from the first host node and supplies the set of policies to the second host node.
Owner:JUMIPER NETWORKS INC
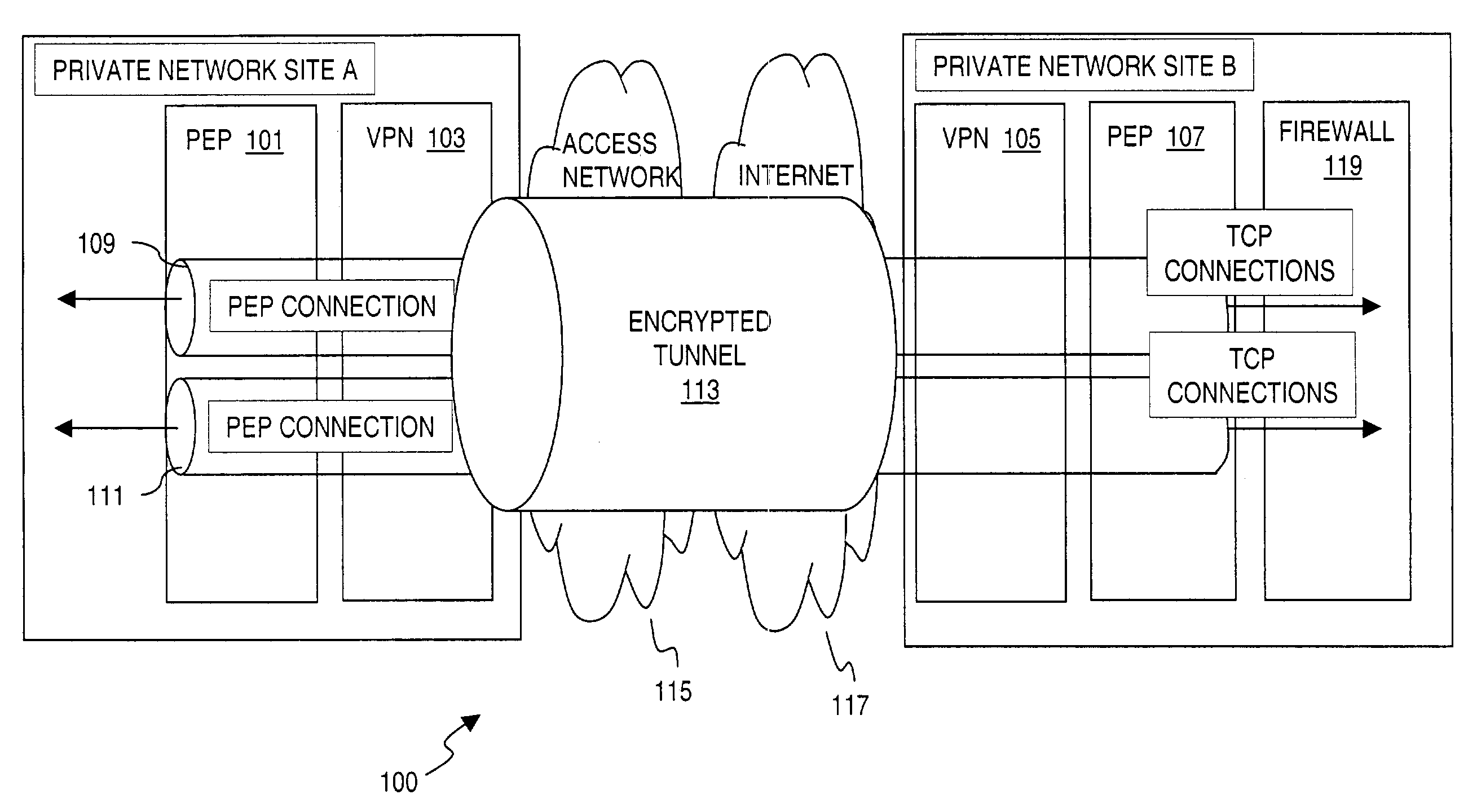
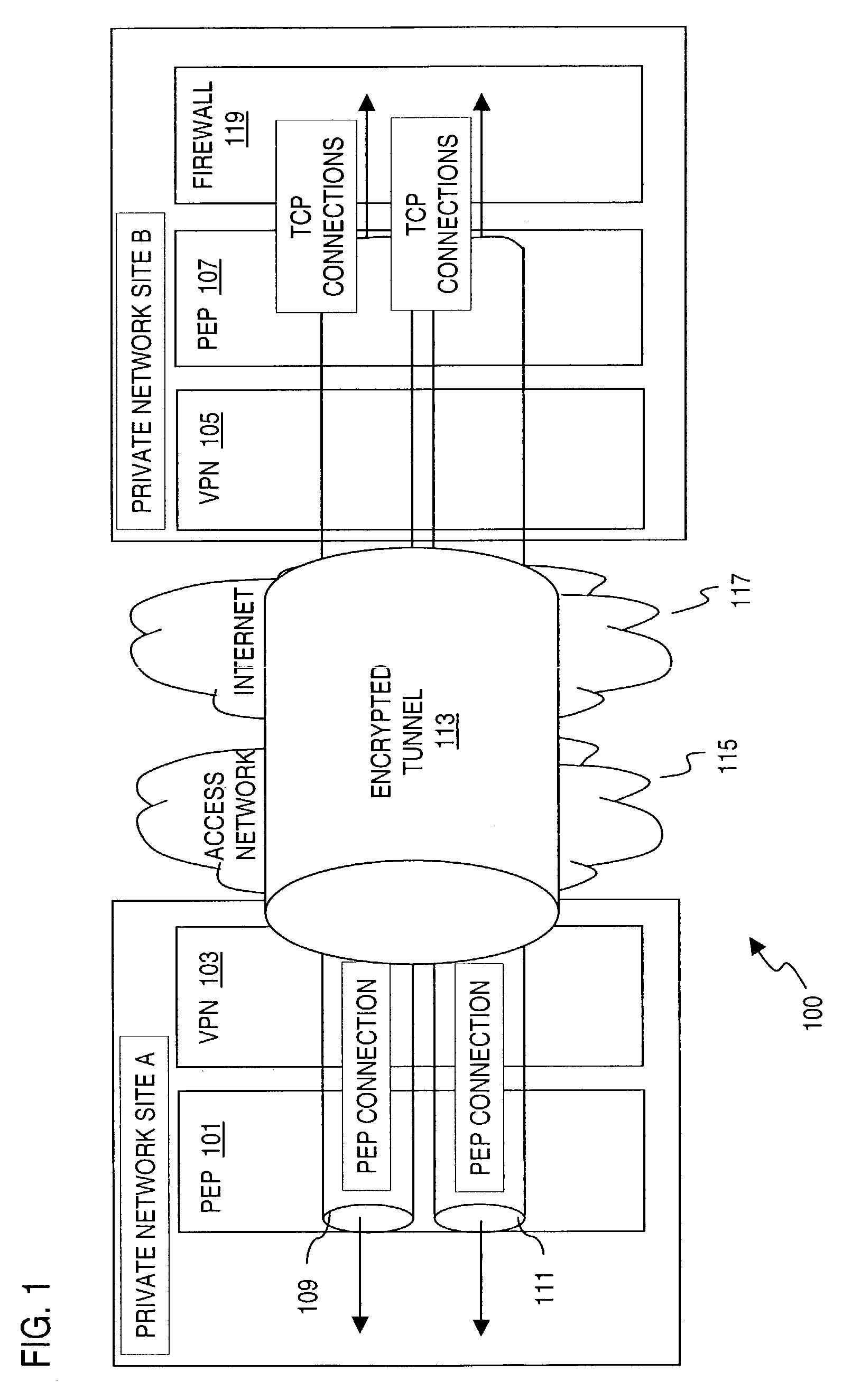
Method and system for integrating performance enhancing functions in a virtual private network (VPN)
ActiveUS7398552B2Increase delayImprove network performanceMultiple digital computer combinationsProgram controlTraffic capacityPrivate network
An approach for supporting security in a communications network is disclosed. A network device includes a security peer that establishes a secure tunnel over a data network (e.g., satellite network) for transport of encrypted traffic. The device also includes a performance peer for establishing a connection supported by the secure tunnel. The performance peer includes a plurality of modules for providing respective performance enhancing functions to minimize performance impact of latency of the network.
Owner:HUGHES NETWORK SYST
Safety Accommodation Arrangement in LED Package/Secondary Lens Structure
ActiveUS20080273327A1Achieves electrical product safetyAchieve securityPlanar light sourcesMechanical apparatusEngineeringSafety barrier
An LED apparatus including (a) a mounting board, (b) a plurality of LED packages thereon, (c) a lens member over each LED package, and (d) a safety barrier positioned over the mounting board, the barrier having sufficient thickness for enclosure of electrical elements on the mounting board and including a plurality of openings each sized to permit light from an LED package to pass therethrough and through a light-transmission portion of the lens member over such LED package to prevent finger-contact of electrical elements on the mounting board when the light-transmission portion is not present.
Owner:IDEAL IND LIGHTING LLC
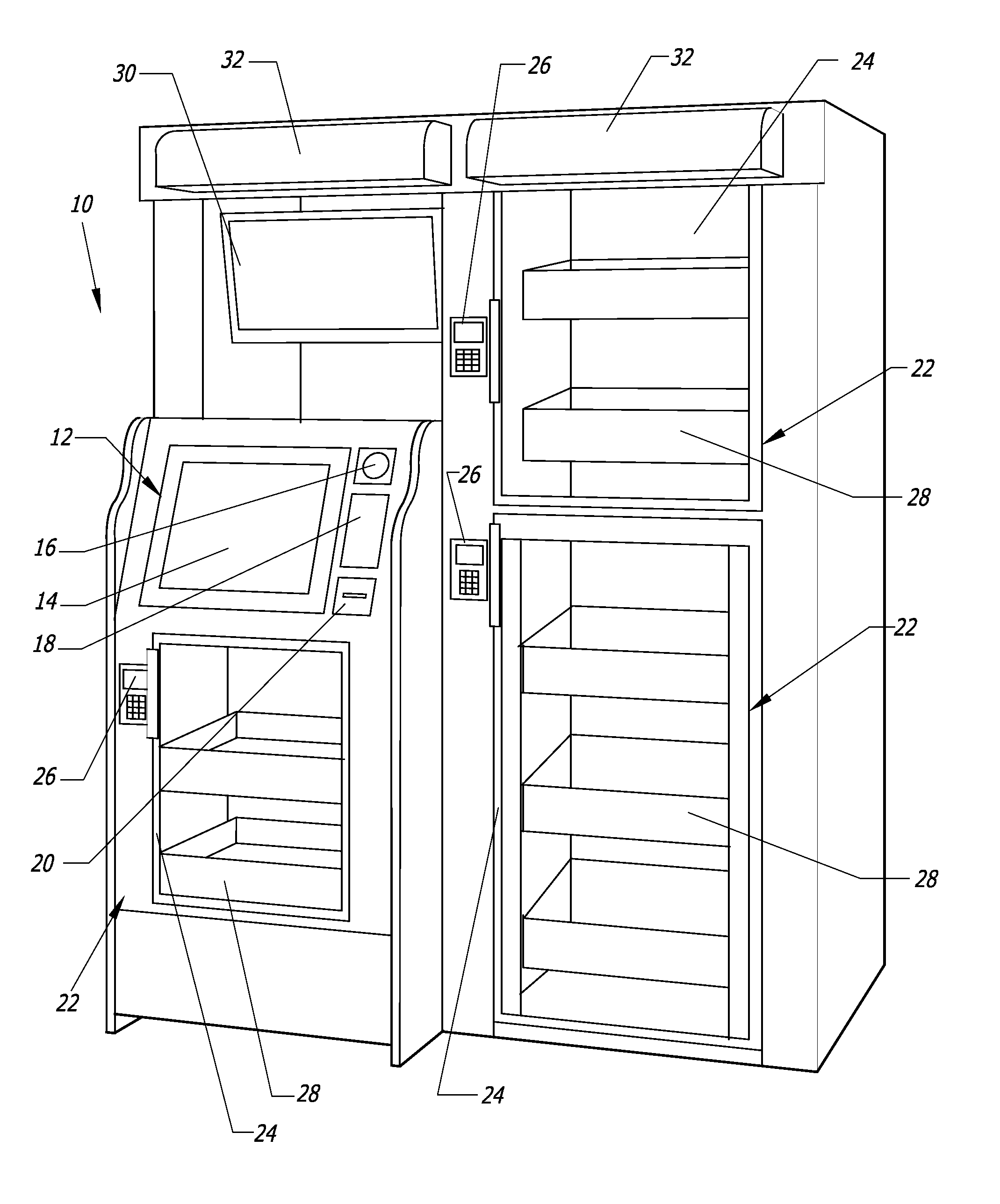
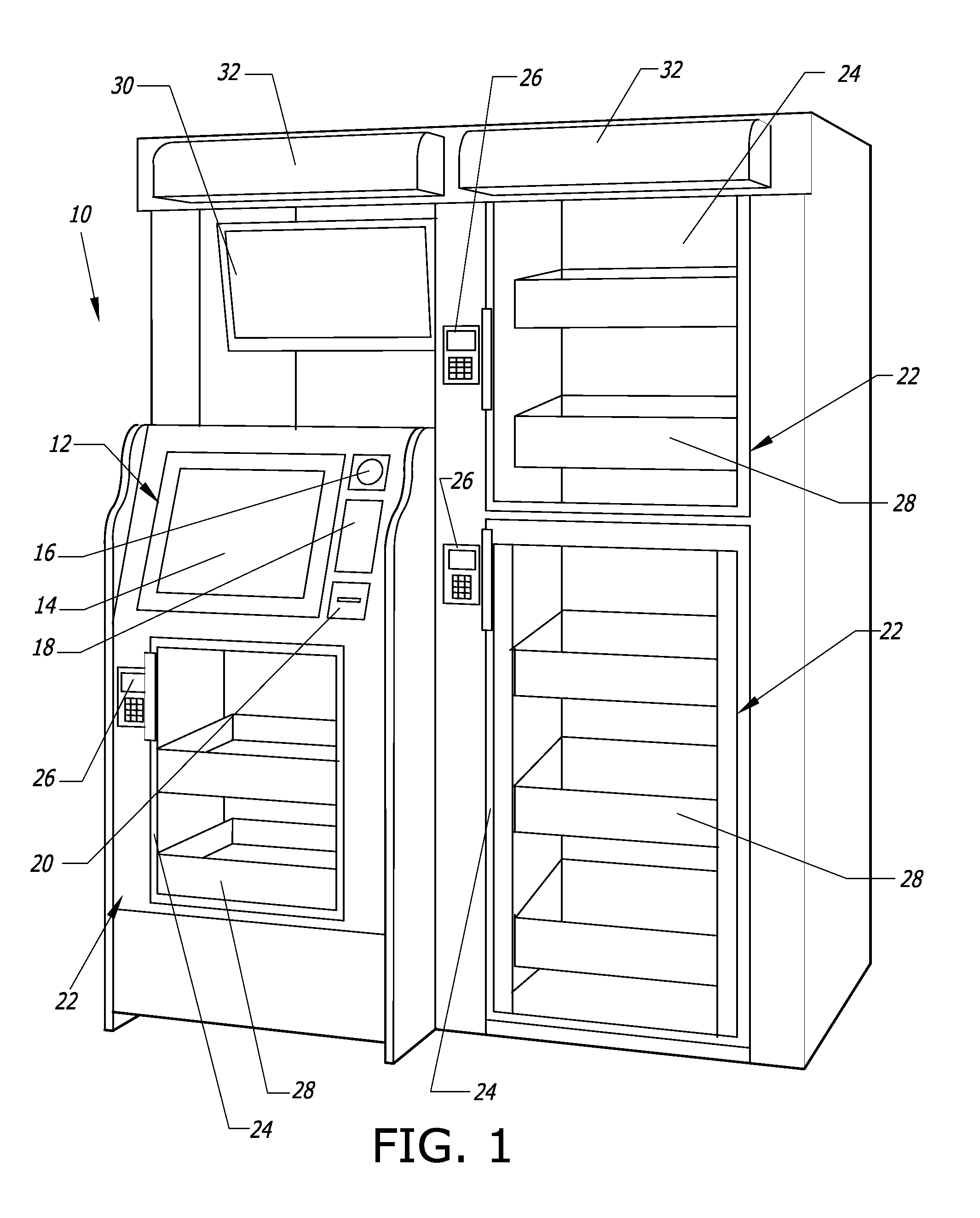
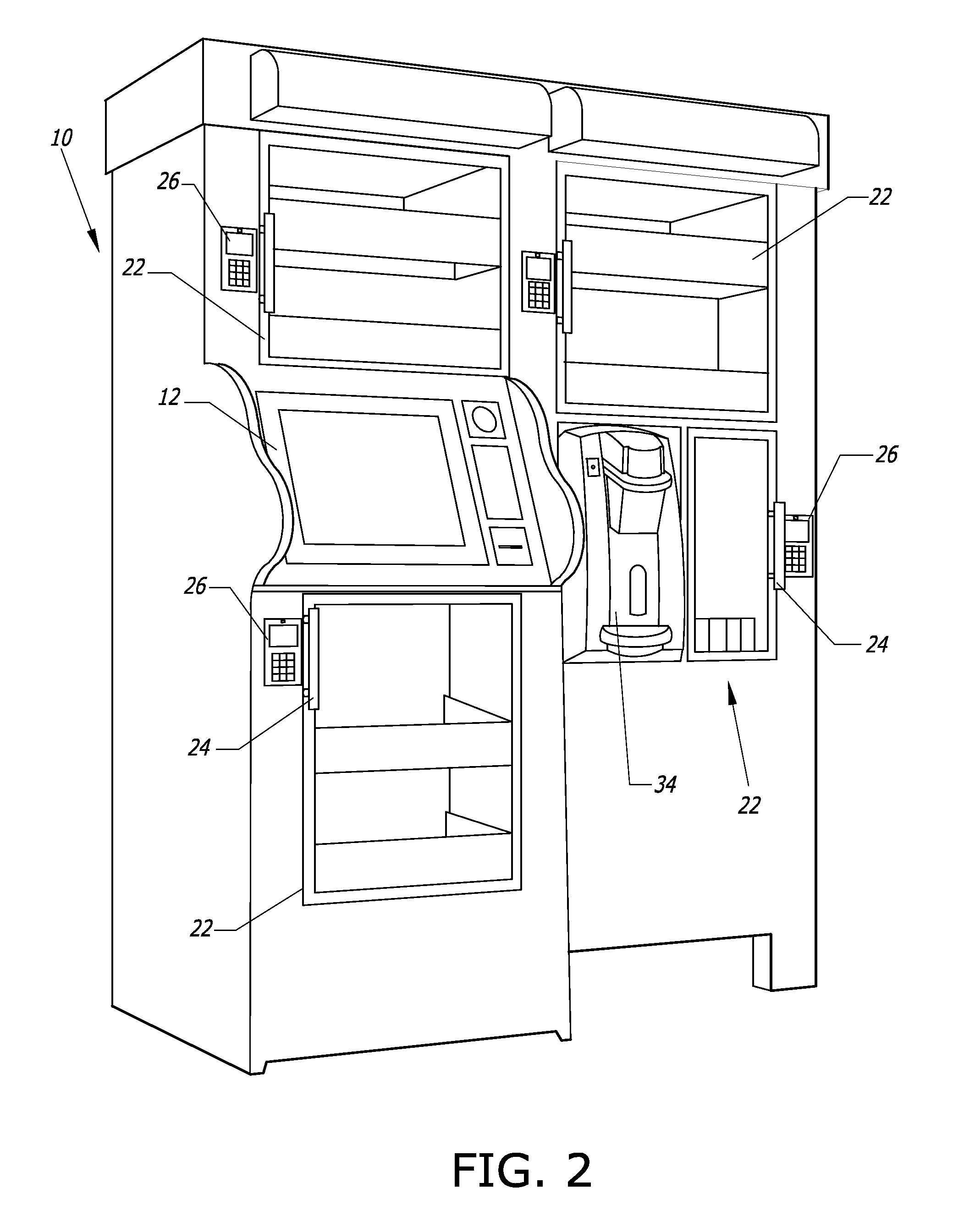
Computer-controlled, unattended, automated checkout store outlet and related method
ActiveUS20140316916A1Provide securityPrevent theftHand manipulated computer devicesCoin-freed apparatus detailsEngineeringSensor system
A computer-controlled, automated checkout store outlet comprises at least one bay. A normally locked door is associated with each bay, and provides access to items within the bay by customers approved by a computer of the automated store outlet. At least one tray is disposed within at least one bay, and adapted to hold items to be stocked by the bay. A sensor system is configured to detect the removal of an item from the bay and identify the removed item, such as when a customer is removing the item for purchase.
Owner:HAY RONNY
System and method of secure login on insecure systems
InactiveUS20060206919A1Little overheadEasy to addDigital data processing detailsUser identity/authority verificationKey imagesSafe system
A method for authenticating a user for use of a server computing device wherein the server computing device is connected by a network to a host device. Generating a key representation image having thereon a plurality of individual key images placed at random positions, each corresponding to a possible character value in an authentication phrase. Accepting a sequence corresponding to locations of mouse clicks representing user selections of character values in an attempted authentication phrase. Verifying that the sequence of location values corresponds to a correct authentication phrase by mapping the locations of the mouse clicks to the locations of the randomly placed key images. Alternatively, accepting a sequence corresponding to a transformation of personal identification number based on a random number and a numerical operation or selection in a matrix.
Owner:AXALTO SA
Method and system for virtual powerline local area networks
InactiveUS20050076148A1Easy to implementSelective connectionSystems using filtering and bypassingPower distribution line transmissionVirtual LANModem device
A system for powerline networking. The system has an external data source, which is derived from a world wide networks of computers. A router is coupled to the external data source and coupled to a first datasource connection. A powerline network switch apparatus is coupled to the first datasource connection. The apparatus has a second datasource connection, which is coupled to the first data source connection. The apparatus also has a powerline device coupled to the second datasource connection. Preferably, the powerline device is adapted to receive and transmit information in a first format from the second data source connection and adapted to receive and transmit information in a second format. The apparatus also has a virtual local area network device including a first input / output port and a plurality of second input / output ports. Each of the second input / output ports is numbered from 1 through N, where N is an integer greater than 1. A plurality of modem devices are coupled to the virtual local area network device. The plurality of modem devices are numbered from 1 through N, where each of the plurality of modem devices being coupled respectively to one of the plurality of second input / output ports and where each of the plurality of modem devices also being coupled to one of a plurality of power lines numbered from 1 through N, each of the power lines being capable of communicating information to and from the second data source connection.
Owner:ASOKA USA CORP
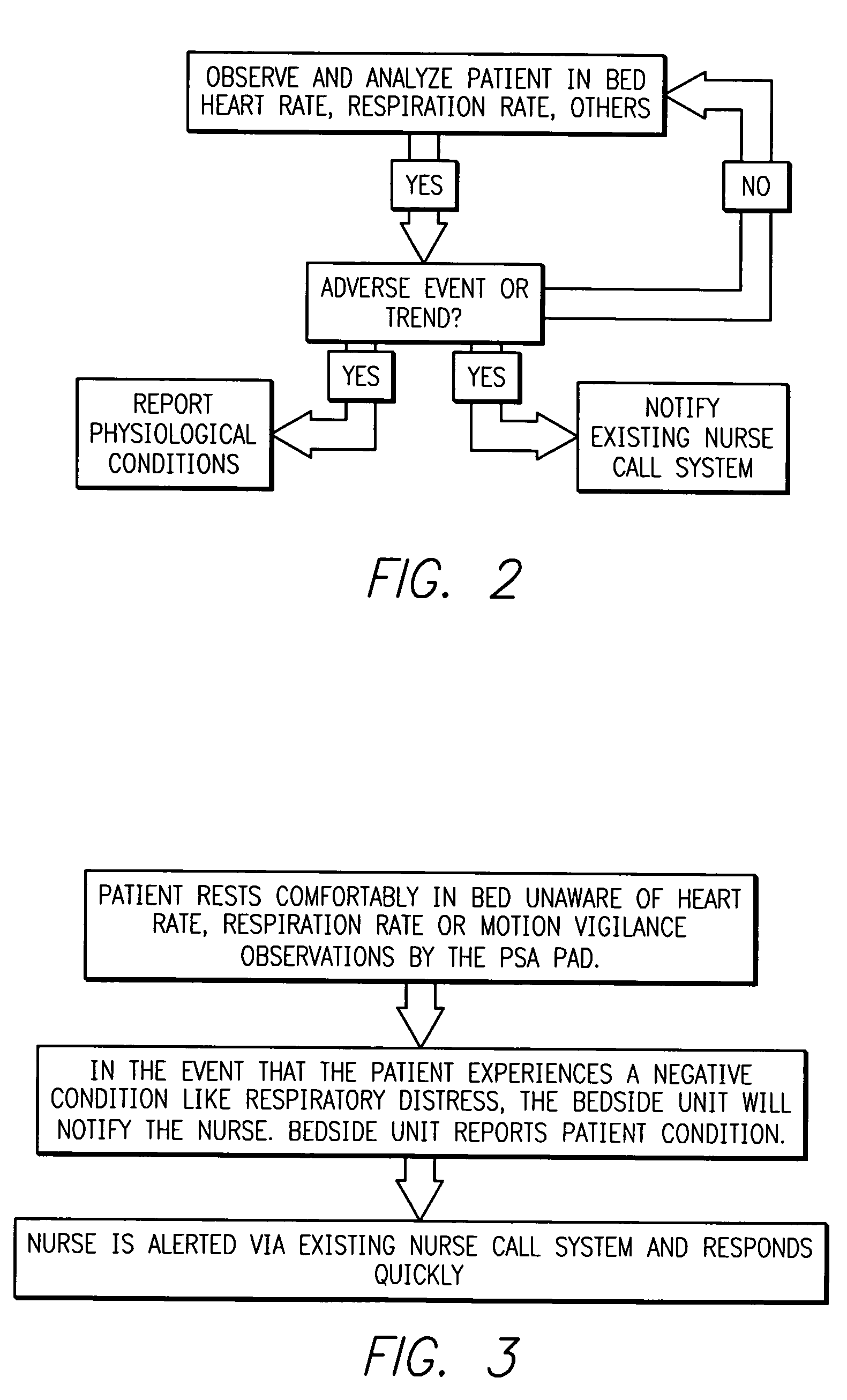
Systems and methods for intelligent medical vigilance
InactiveUS20070156031A1Improve abilitiesEffective resourcesCatheterRespiratory organ evaluationSensor arrayDisplay device
An intelligent medical vigilance system that observes and analyzes, and, only in the event of a clinically significant negative condition, notifies and reports the event to the care staff utilizing the hospital's existing nurse call system. The device includes a bedside unit connected to a pad or coverlet with a sensor array (placed under the patient) and also to an existing hospital nurse call system via an interface. Within the physical bedside unit are a signal processor and an alarm processor that measure data and evaluate whether a clinically significant event is occurring. The bedside unit is a wall-mounted unit with a display that becomes active when an alarm condition is enabled. The sensing pad or coverlet is a thin, piezoelectric film, or other similar sensing technology, with an array of sensors sheathed in soft padding and is not directly in contact with the skin of the patient. The nurse call feature is made up of hardware, software and cabling to connect to the nurse call system already installed in the hospital or care facility. The monitoring system can also be installed in vehicles to monitor operator physiological conditions. Vigilance alarms are suspended if a patient is detected out of bed. An unable-to-measure alert is provided if the system is unable to reliably monitor. Bed exit alarms can be placed into a pause mode for supervised bed exit of patients on bed restriction. An alert message is generated and maintained on the display screen to inform a responding caregiver of the time and reason for any alarm.
Owner:HOANA MEDICAL
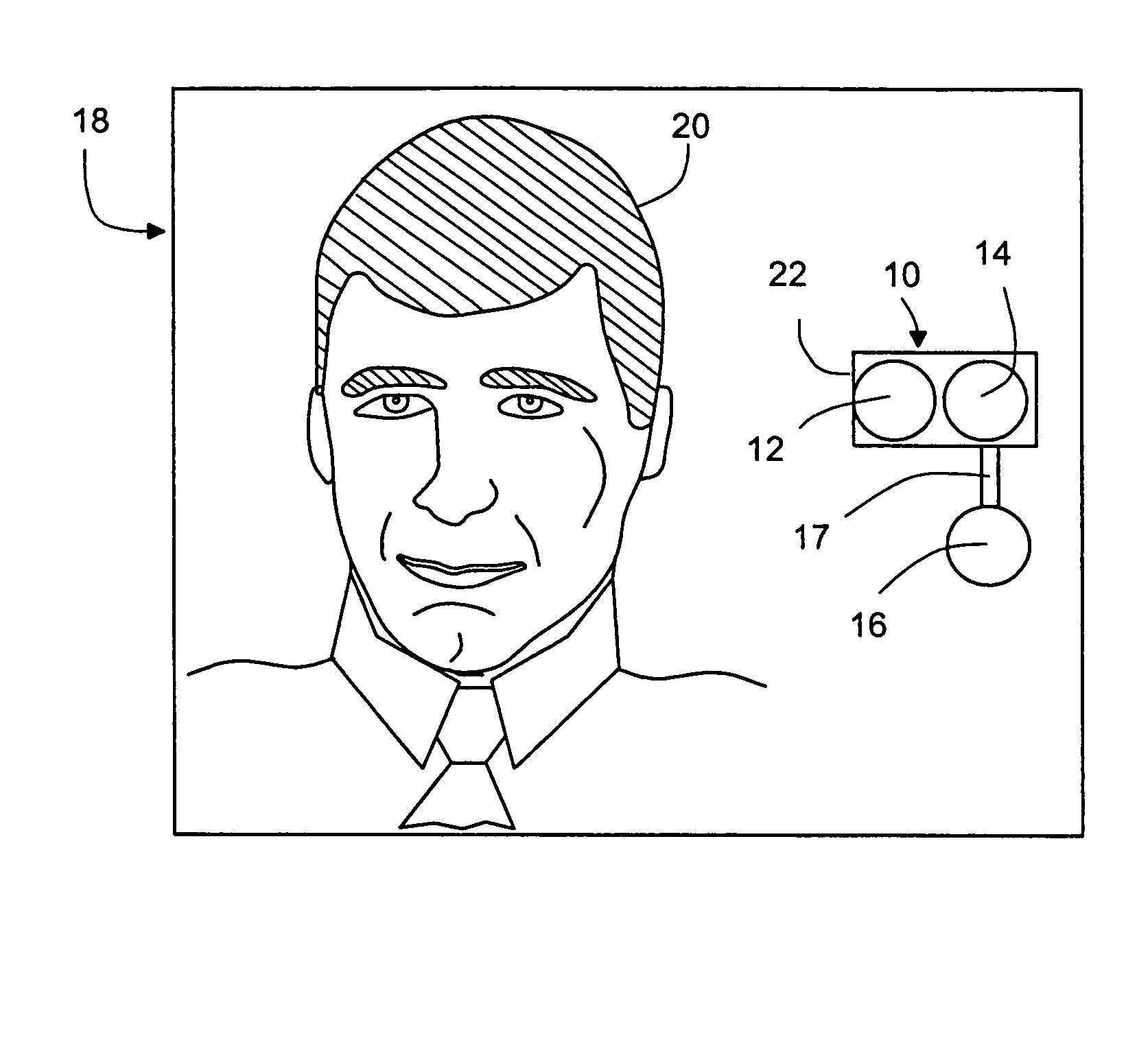
Robot capable of detecting an edge
InactiveUS6865447B2Provide securityEasy to operateProgramme controlComputer controlEngineeringEdge based
Owner:SHARPER IMAGE ACQUISITION LLC A DELAWARE LIMITED LIABILITY
Security system with product power capability
ActiveUS7710266B2Firmly connectedProlong lifeElectric connection structural associationsBurglar alarm by hand-portable articles removalElectricityPower capability
A security system and display module therefore protects an item of merchandise mounted on the display module in a retail environment. The item of merchandise is electrically and mechanically connected to a sensor which is removably mounted on the display module by a first power cord. A second power cord connects the display module to the sensor and a third power cord connects the display module to a source of electricity for supplying electric power to the sensor through the display module and then to the displayed item for maintaining the charge on a battery of the displayed item. The display module contains an alarm unit having an audible alarm which is actuated if the integrity of either of the first or second power cords is compromised. A plunger switch and LED may be contained in the sensor and in a base of the display module and connected to the internal alarm to provide additional security for the protected item of merchandise. The alarm is powered from the source of electricity but is automatically switched to the battery upon interruption of this power source.
Owner:INVUE SECURITY PROD INC
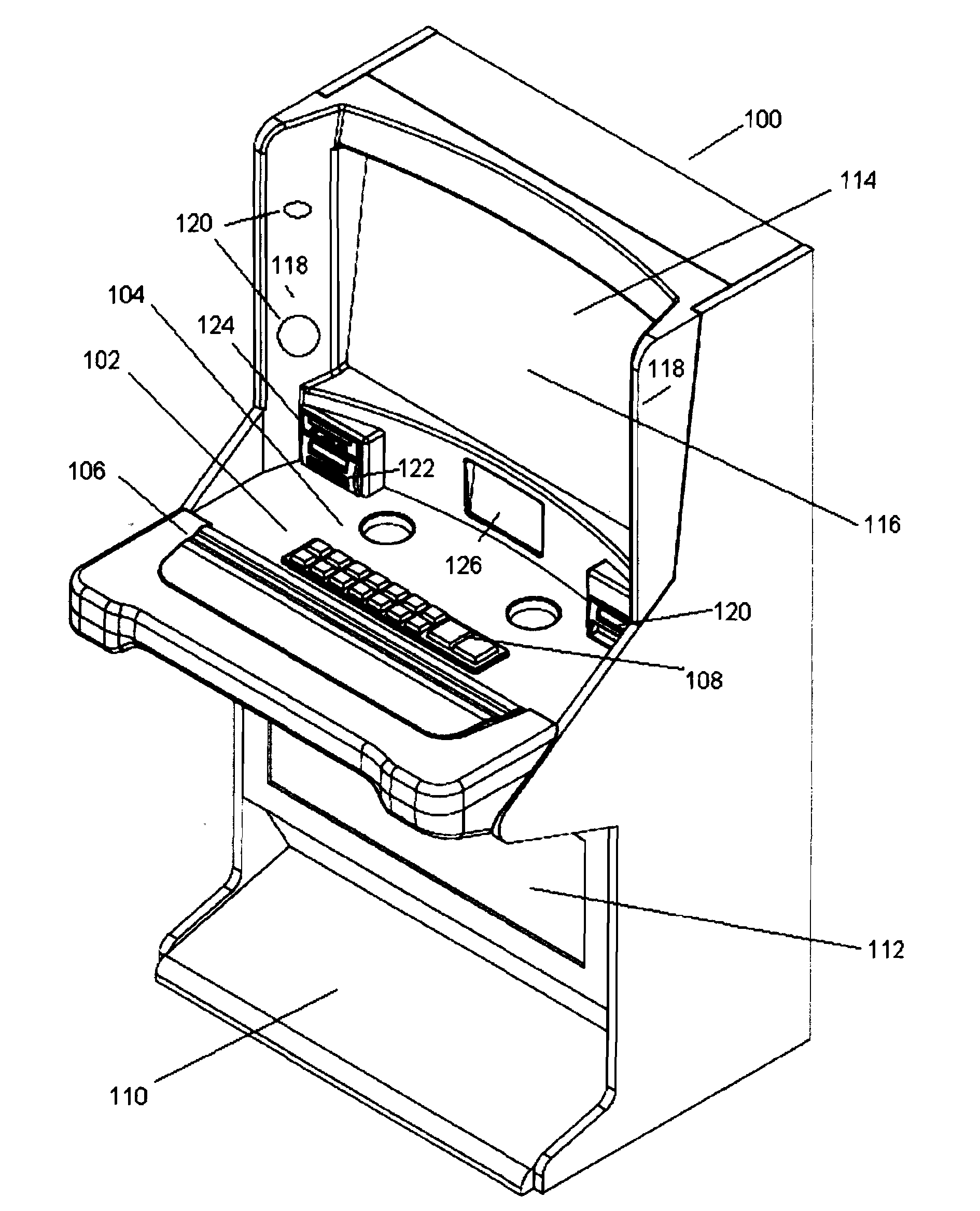
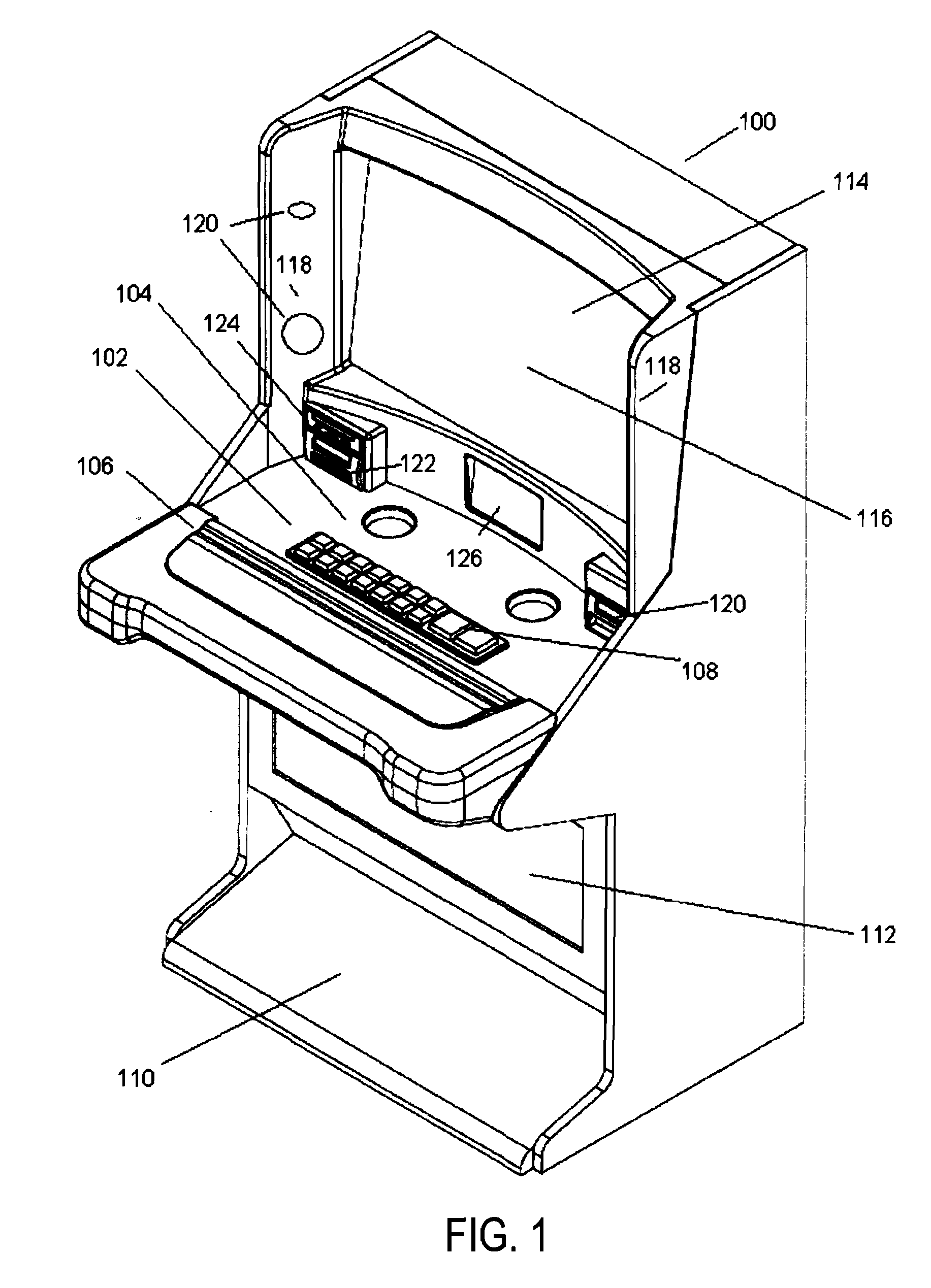
Ergonomic gaming cabinet
InactiveUS20060281559A1Effectively discourage subtle or passive thievingProvide securityApparatus for meter-controlled dispensingVideo gamesVisual distractionDisplay device
A new ergonomic game cabinet with a unique layout is disclosed. The gaming machine cabinet includes a display mounted nearly vertically, combined with a player deck extending towards a player having more space at a more useful angle than previously available. The player deck will have open space usable by a player for small items (wallets, purses, chips, etc.), a player device area (typically buttons), and then a further area where a player can rest their arms, wrists, or elbows and comfortably reach the player device area. This further area may also be used for small player items, such as chips, tickets, etc. In addition, the new cabinet provides side panels on each side of the gaming machine cabinet that creates a feeling of being “surrounded” by the game experience due to reduced noise and visual distractions from nearby gaming machines, other patrons, waitrons, and the like.
Owner:BALLY GAMING INT
Mobile terminal
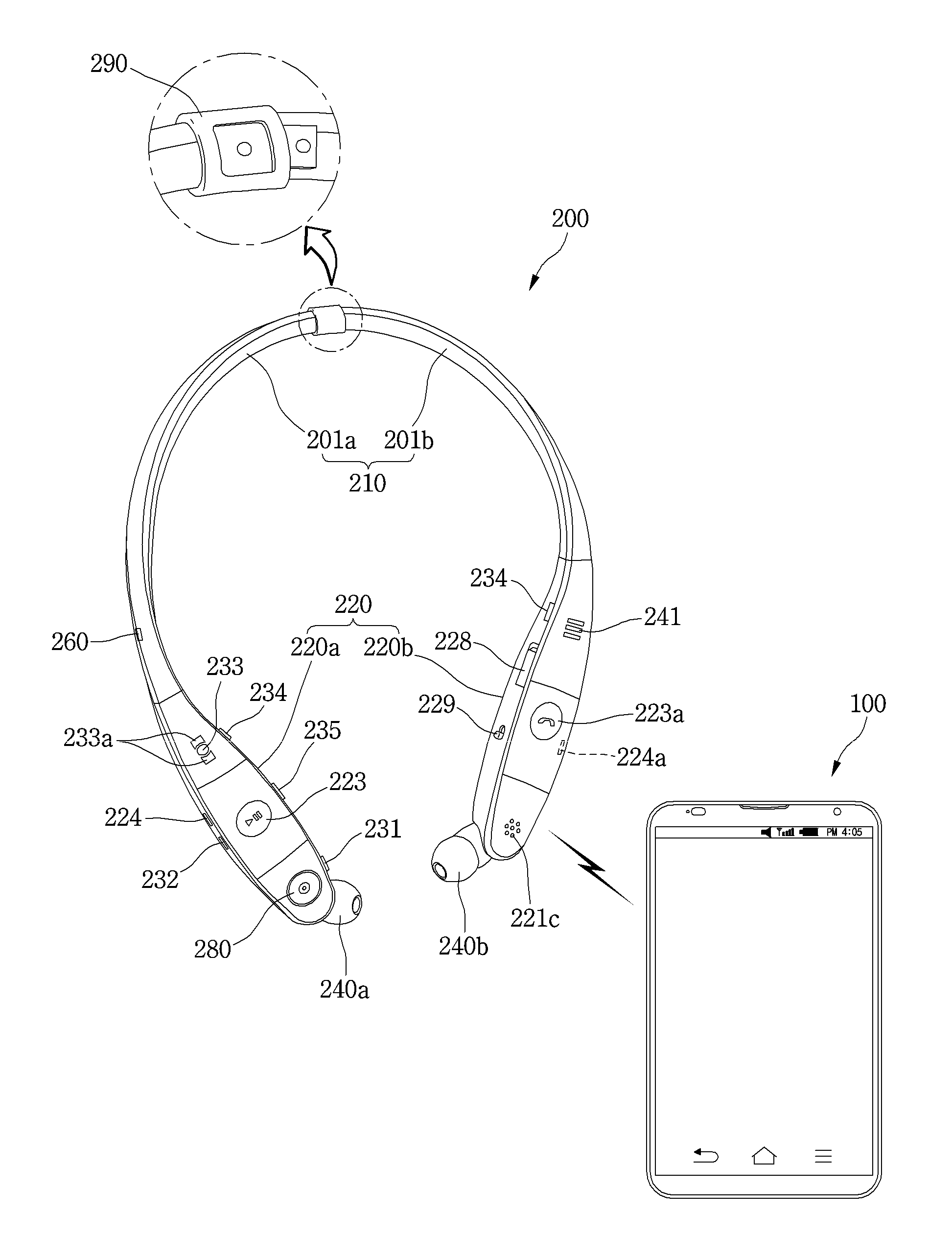
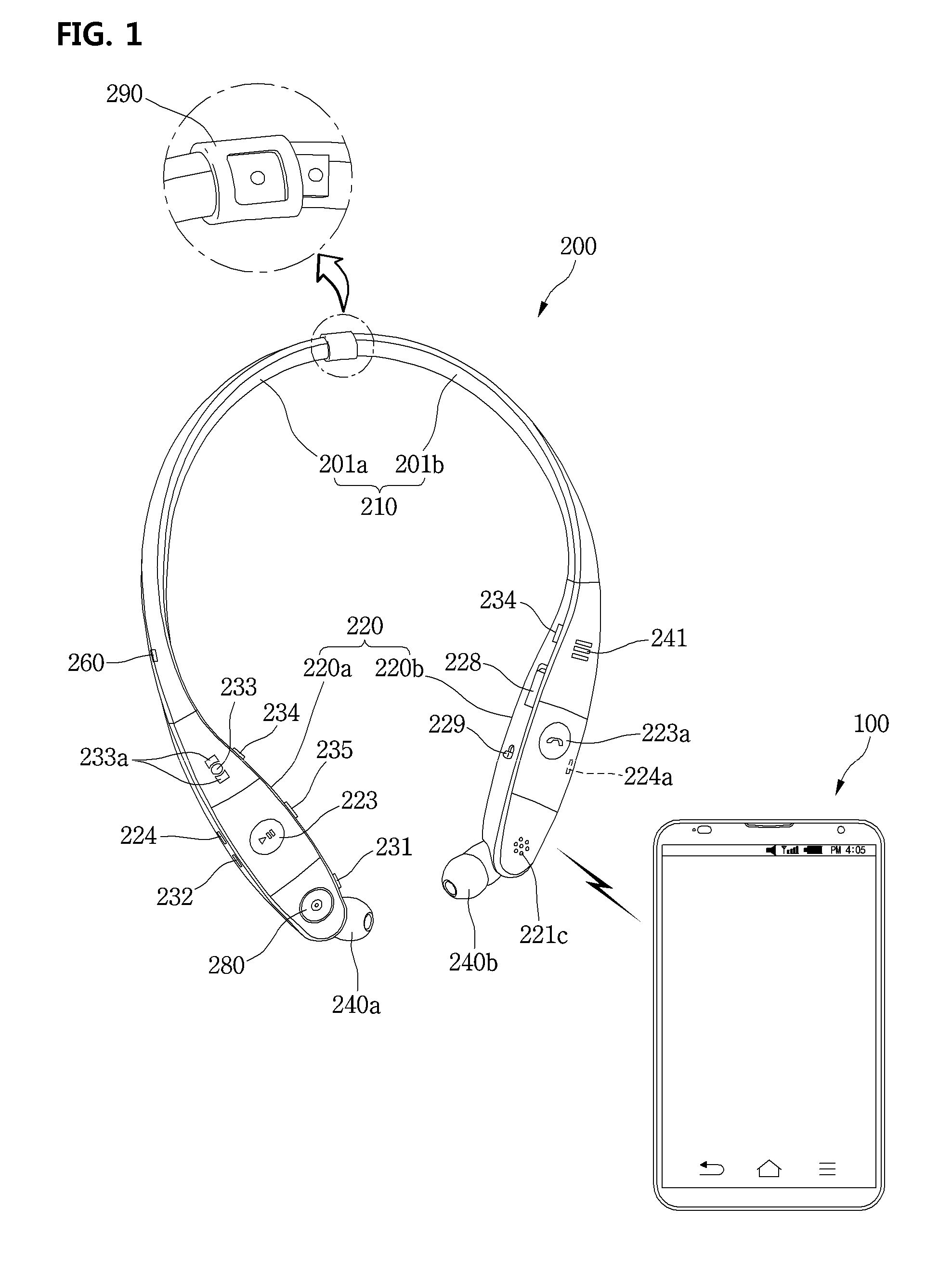
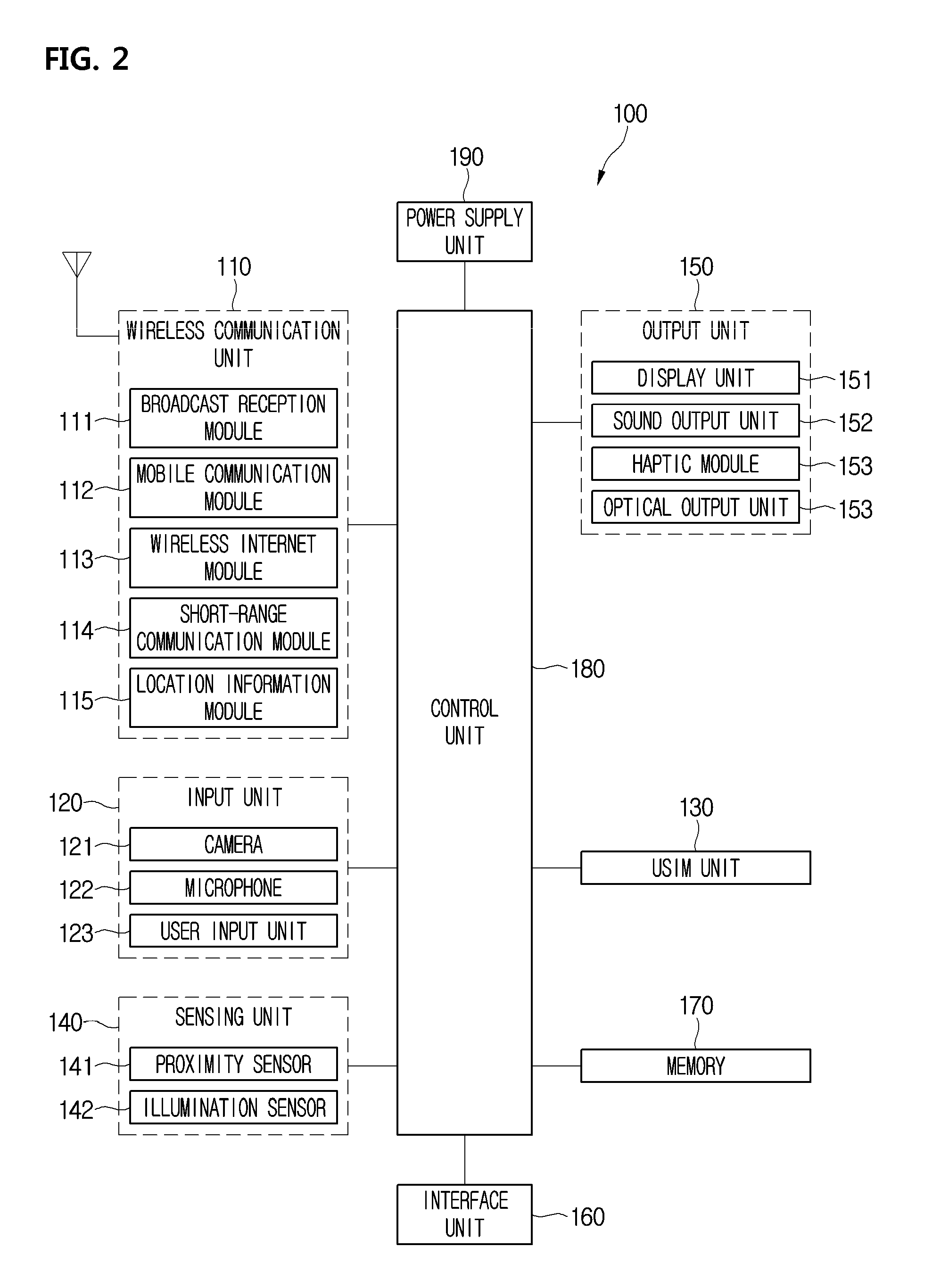
ActiveUS20160098138A1Improve user convenienceProvide securityTelevision system detailsDevices with rotatable cameraCamera controlMobile end
A mobile terminal including a wearable device including a first wireless communication device, a sound output unit, and at least one camera; a second wireless communication device configured to perform wireless communication with the wearable device via the first wireless communication device; a touch screen configured to display information; and a control unit configured to display an icon on the touch screen for controlling the wearable device, and display a control screen including both a first control area including at least one sound control object for controlling sound output by the mobile terminal and a second control area including at least one camera control object for controlling the at least one camera of the wearable device, in response to a selection of the displayed icon.
Owner:LG ELECTRONICS INC
Online Protection Of Information And Resources
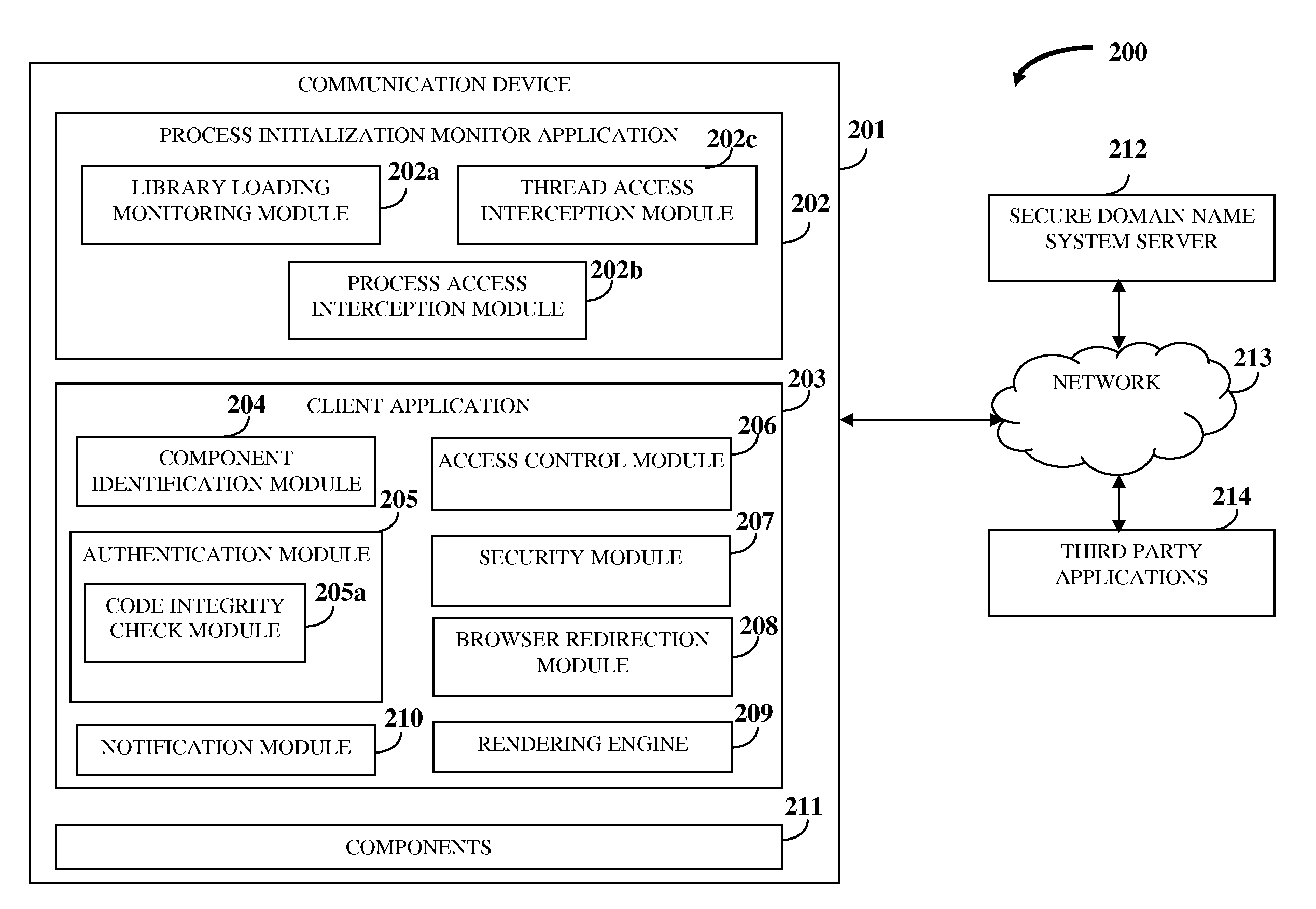
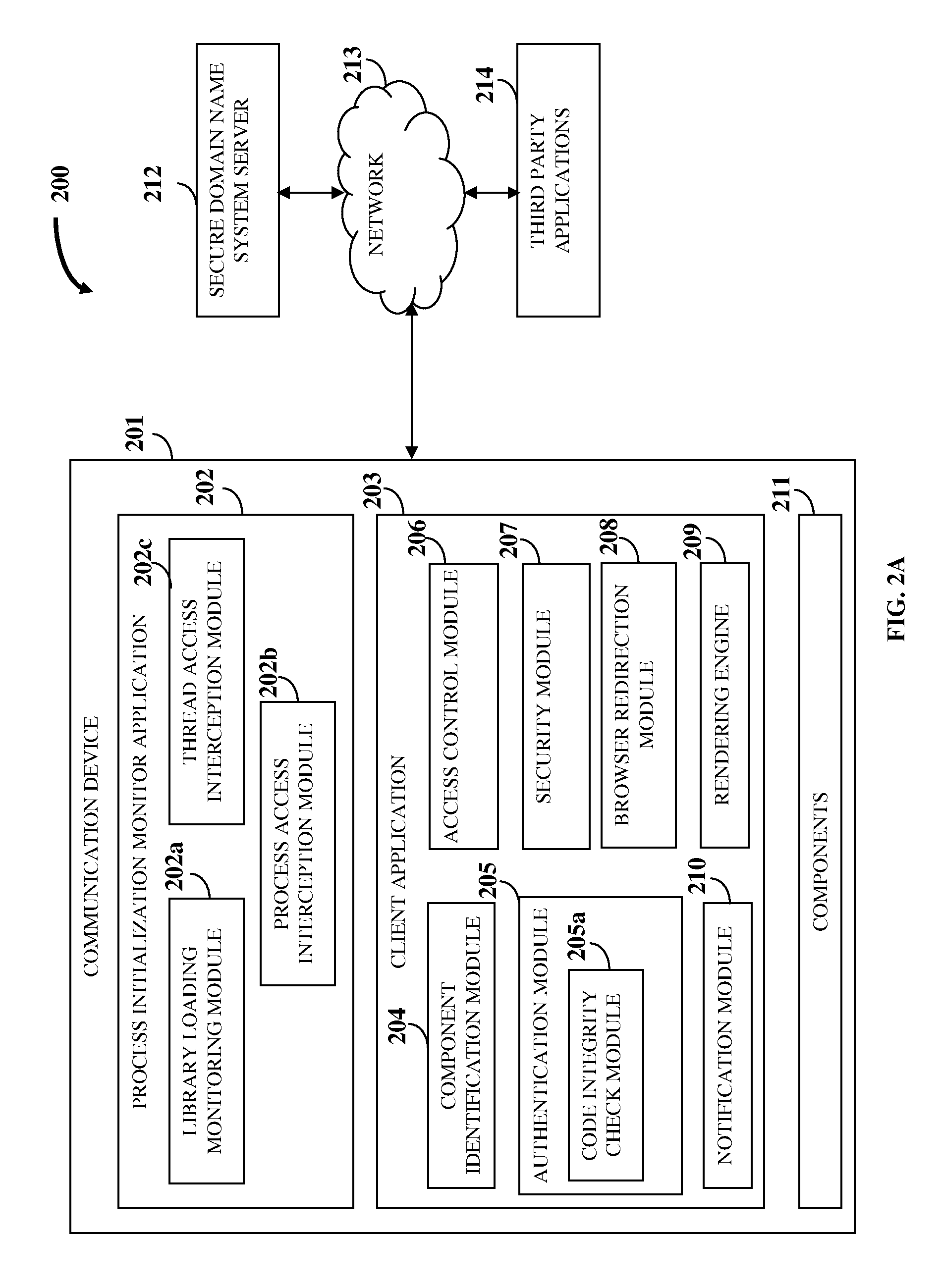
InactiveUS20110321139A1Avoid interceptionAvoid manipulationDigital data processing detailsMultiple digital computer combinationsThird partyApplication software
A computer implemented method and system for protecting information and resources in an online environment is provided. A process initialization monitor application monitors process initialization of a client application provided on a user's communication device. The client application identifies and authenticates one or more components operating on the communication device and one or more third party applications attempting to access the client application. The client application performs the authentication by performing a code integrity check integrated in the client application independent of the communication device, and grants access to the authenticated components and the authenticated third party applications. The client application protects information being processed, exchanged, stored, and displayed within the client application. The client application masks input information, encrypts a communication channel that transfers the input information, blocks attempts to monitor, intercept and manipulate information by unauthorized entities, and prevents access of certificates, resources, etc., by unauthorized entities.
Owner:K7 COMPUTING PRIVATE
Distributive access controller
ActiveUS20040025052A1Provide securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionComputer resourcesComputerized system
A device for securely controlling communications among or within computers, computer systems, or computer networks, comprising: (a) a primary access port to which an "owner" computer program, computer, computer system, or computer network is connectable to access shared computer resources; (b) a secondary access port to which a non-owner computer program, computer, computer system, or computer network is connectable to access the shared computer resources; (c) a transfer port to which a shared computer resource is connectable to provide controlled access to that computer resource from computer programs, computers, computer systems, or computer networks connected to the access ports; and (d) a separate physical communication path to and from each access port and each transfer port, where access permissions and restrictions for each communication path are set by the owner of the device through the primary access port.
Owner:SECUREEDEN LLC
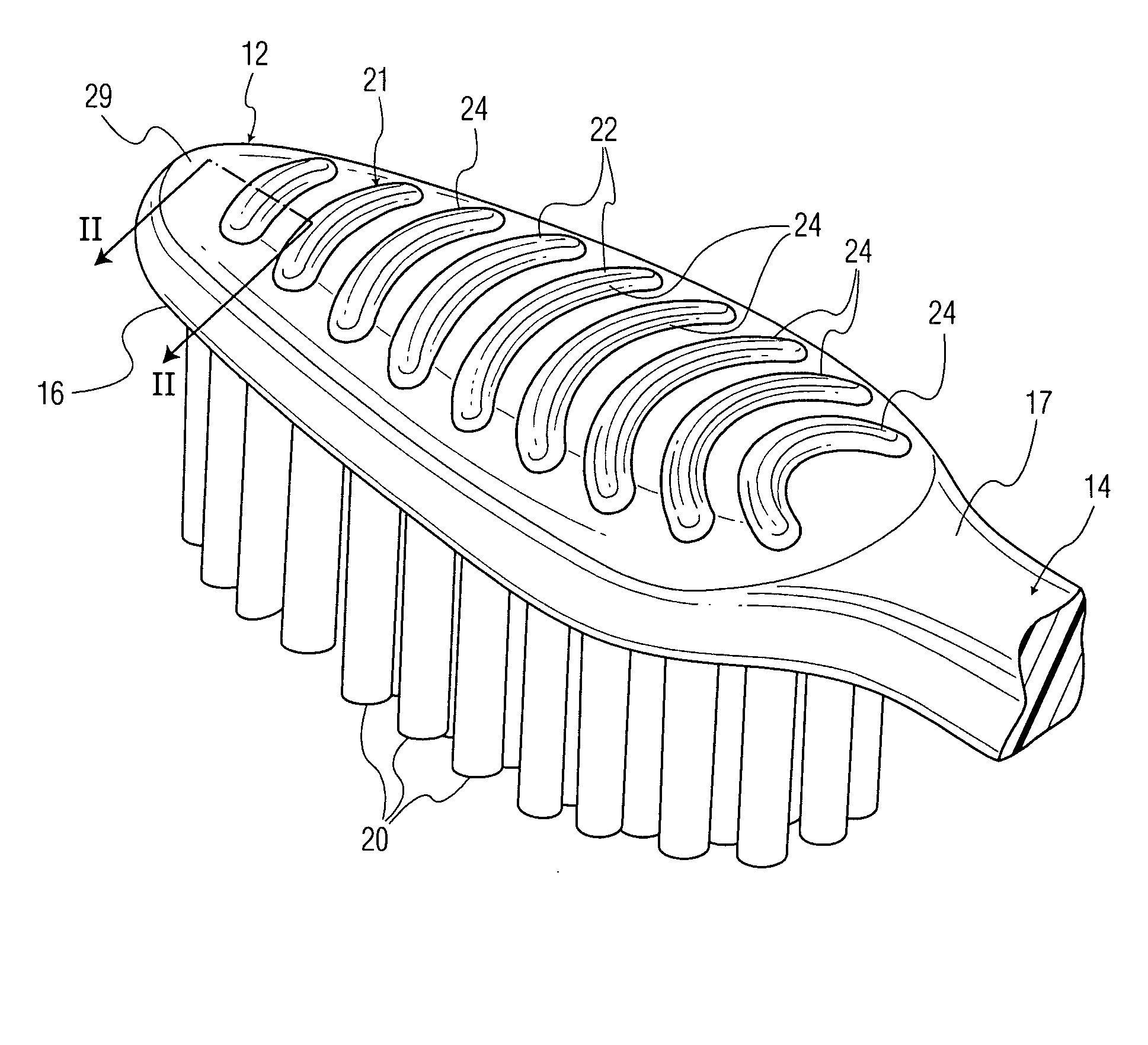
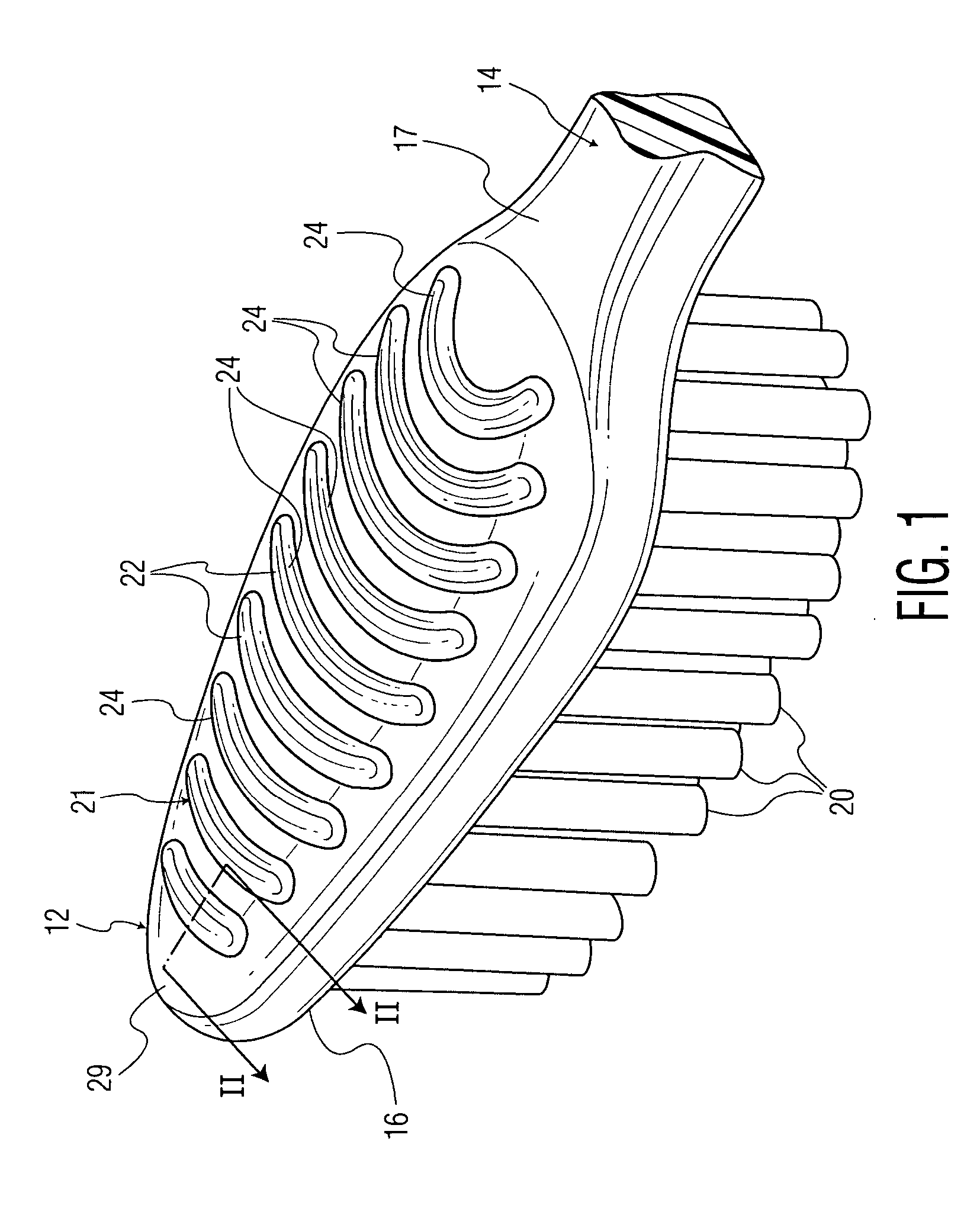
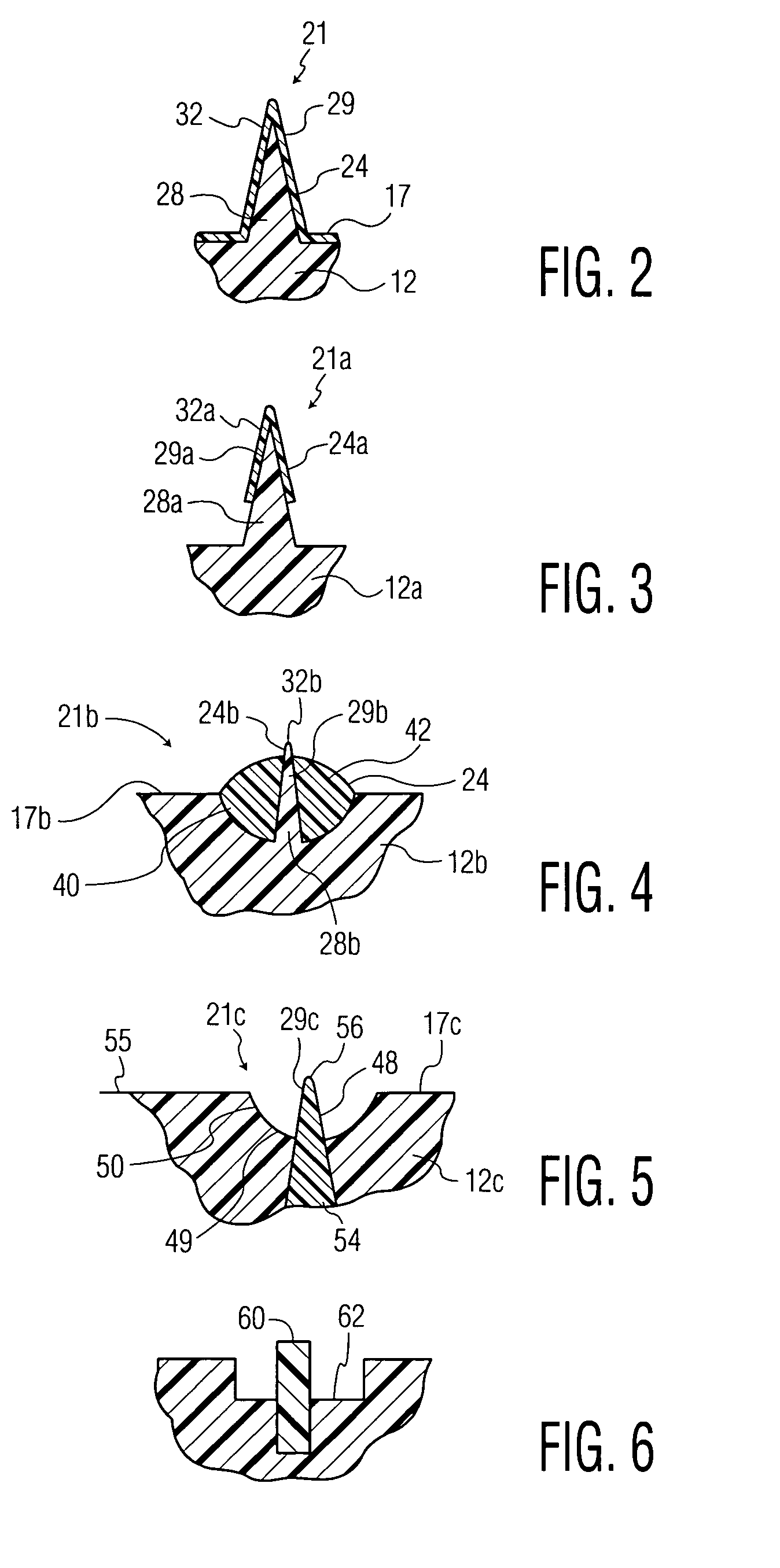
Oral care implement
ActiveUS20060052806A1Reduce the risk of injuryEffectively cleanse the tongue and other soft tissueEar treatmentBrush bodiesSoft materialsDentistry
An oral care implement with a soft tissue cleanser is provided to effectively cleanse the soft tissue of the mouth with comfort and a reduced risk of injury to the user. In one construction, a projection is formed of a combination of a hard material and a soft material. The hard material provides good stability for cleaning debris from the tongue or other tissue while the soft material provides comfort and a reduced risk of injury.
Owner:COLGATE PALMOLIVE CO
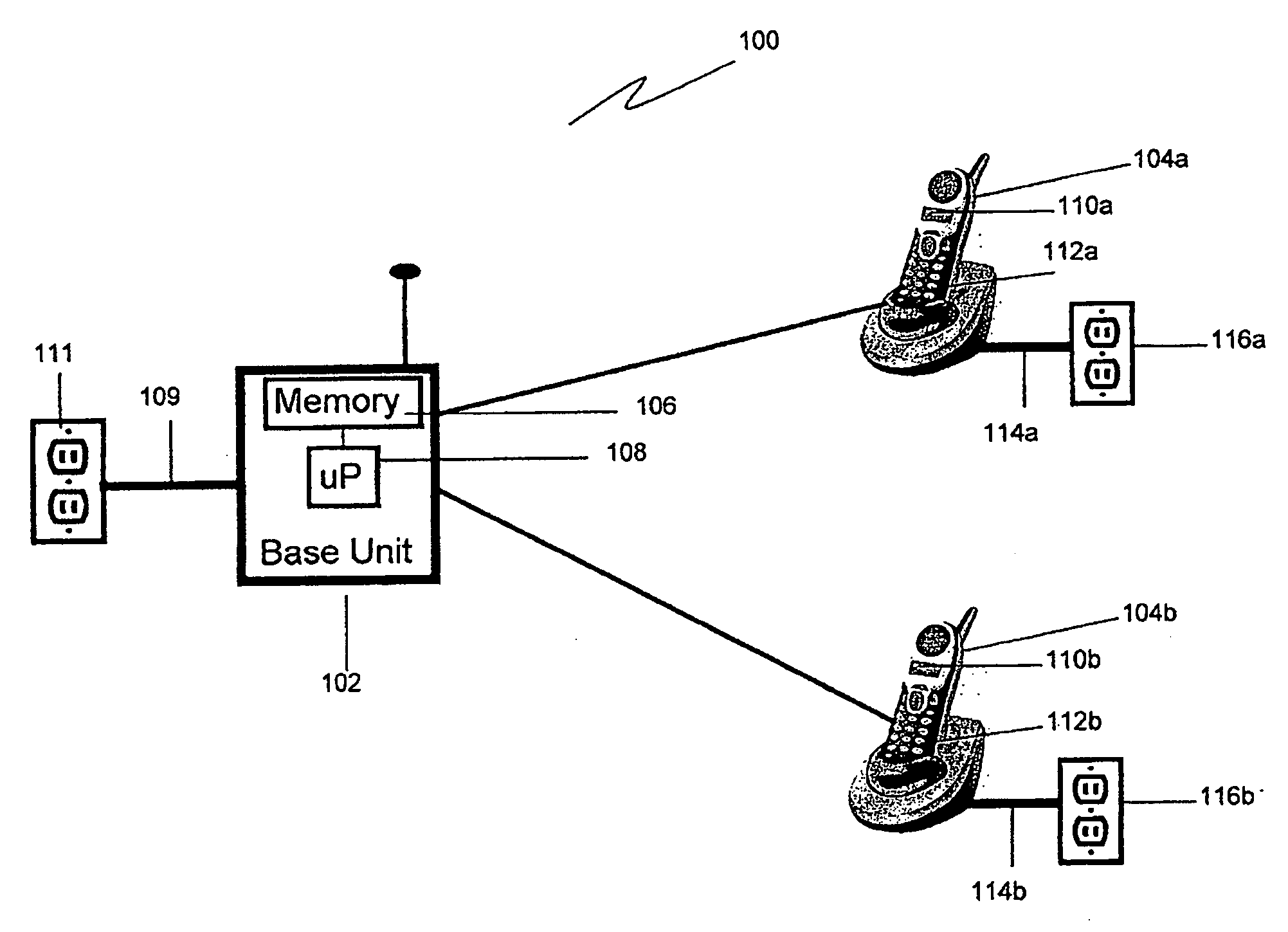
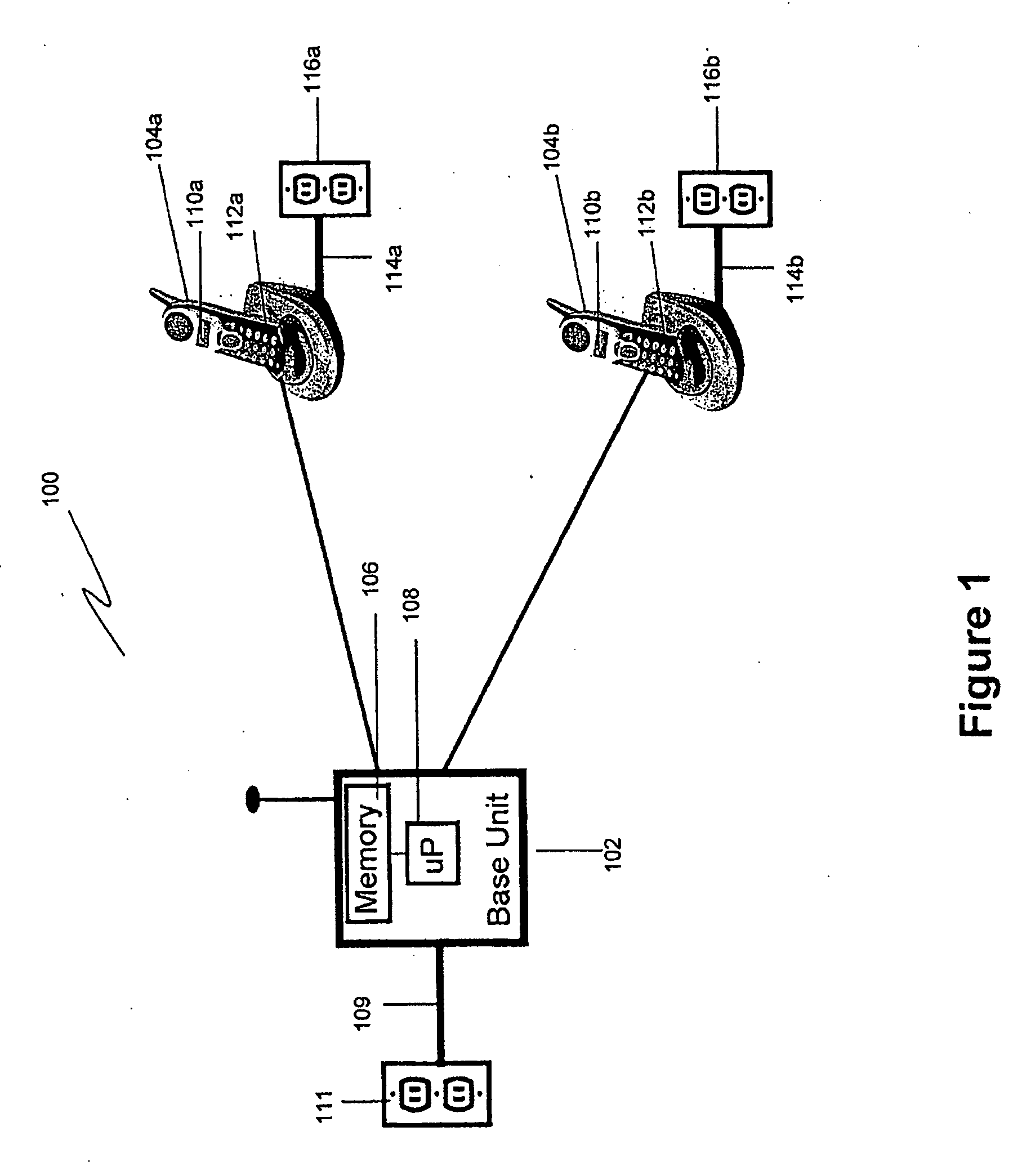
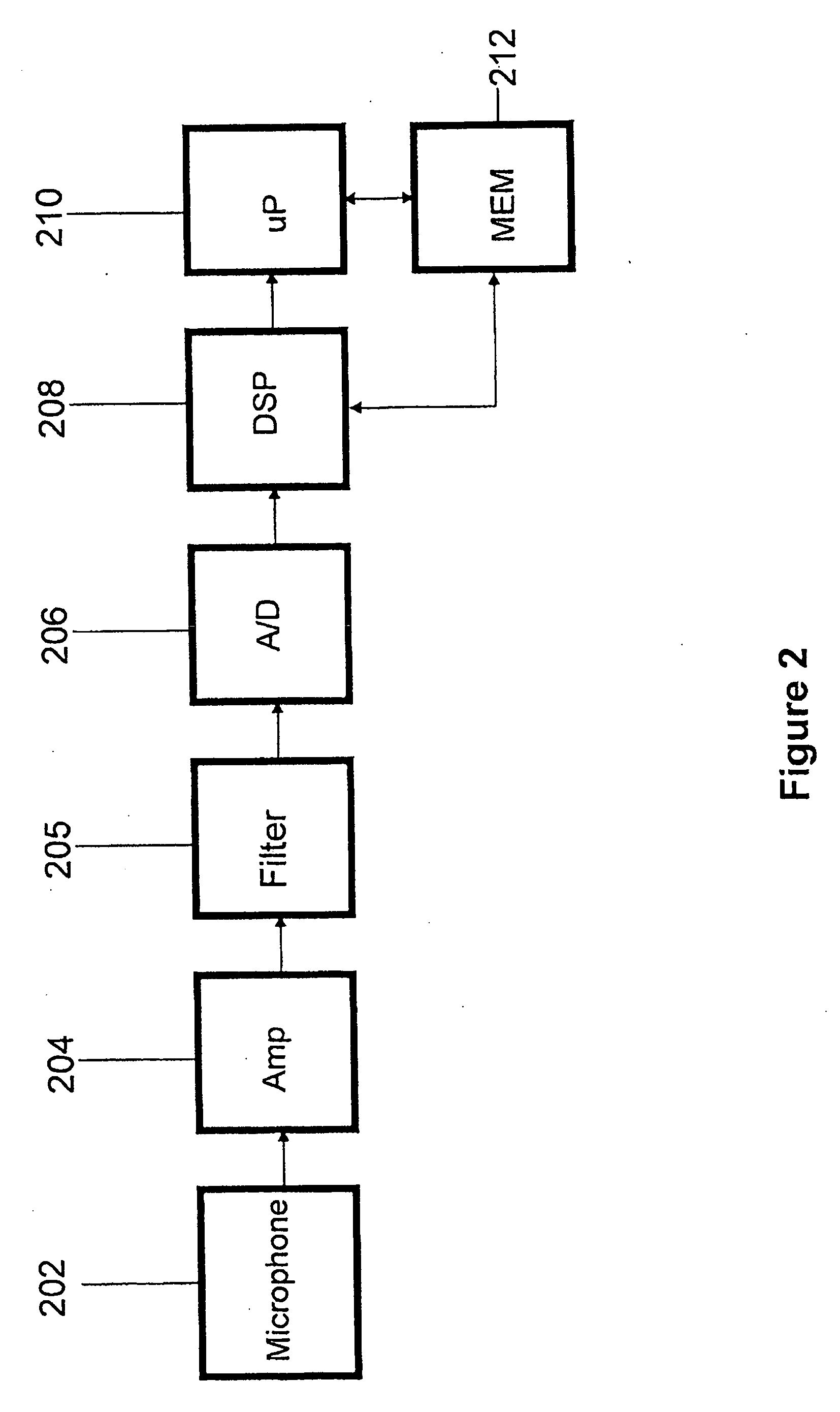
Cordless phone system with integrated alarm & remote monitoring capability
InactiveUS20070161372A1Affordable home securityProvide securityDevices with sensorRadio/inductive link selection arrangementsHandsetNoise level
A cordless telephone system provides home security. Each handset associated with the cordless telephone system detects a noise level. If the detected noise level exceeds a threshold level, the handset detecting the noise level exceeding the threshold level initiates a telephone call through the base unit to an alert telephone number. When the telephone call to the alert telephone number is established, a message is played to provide notification of a possible home security breach, such as an intruder.
Owner:VTECH TELECOMM
Security system with product power capability
ActiveUS20080169923A1Firmly connectedProlong lifeElectric connection structural associationsBurglar alarm by hand-portable articles removalElectricityPower capability
A security system and display module therefore protects an item of merchandise mounted on the display module in a retail environment. The item of merchandise is electrically and mechanically connected to a sensor which is removably mounted on the display module by a first power cord. A second power cord connects the display module to the sensor and a third power cord connects the display module to a source of electricity for supplying electric power to the sensor through the display module and then to the displayed item for maintaining the charge on a battery of the displayed item. The display module contains an alarm unit having an audible alarm which is actuated if the integrity of either of the first or second power cords is compromised. A plunger switch and LED may be contained in the sensor and in a base of the display module and connected to the internal alarm to provide additional security for the protected item of merchandise. The alarm is powered from the source of electricity but is automatically switched to the battery upon interruption of this power source.
Owner:INVUE SECURITY PROD INC
Methods and apparatus for a remote, noninvasive technique to detect core body temperature in a subject via thermal imaging
ActiveUS7340293B2Accurate of core body temperatureConvenience and securitySensing radiation from moving bodiesDiagnostic recording/measuringDiseaseEngineering
An approach to noninvasively, remotely and accurately detect core body temperature in a warm-blooded subject, human or animal, via thermal imaging. Preferred features such as the use of in-frame temperature references, specific anatomical target regions and a physiological heat transfer model help the present invention to overcome pitfalls inherent with existing thermal imaging techniques applied to physiological screening applications. This invention provides the ability to noninvasively, remotely and rapidly screen for diseases or conditions that are characterized by changes in core body temperature. One human application of this invention is the remote screening for severe acute respiratory syndrome (SARS), since fever is a common, early symptom. Other diseases and conditions that affect the core body temperature of humans or animals may also be noninvasively and remotely detected with this invention.
Owner:CARDIOWAVE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com