Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2935 results about "Credit card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
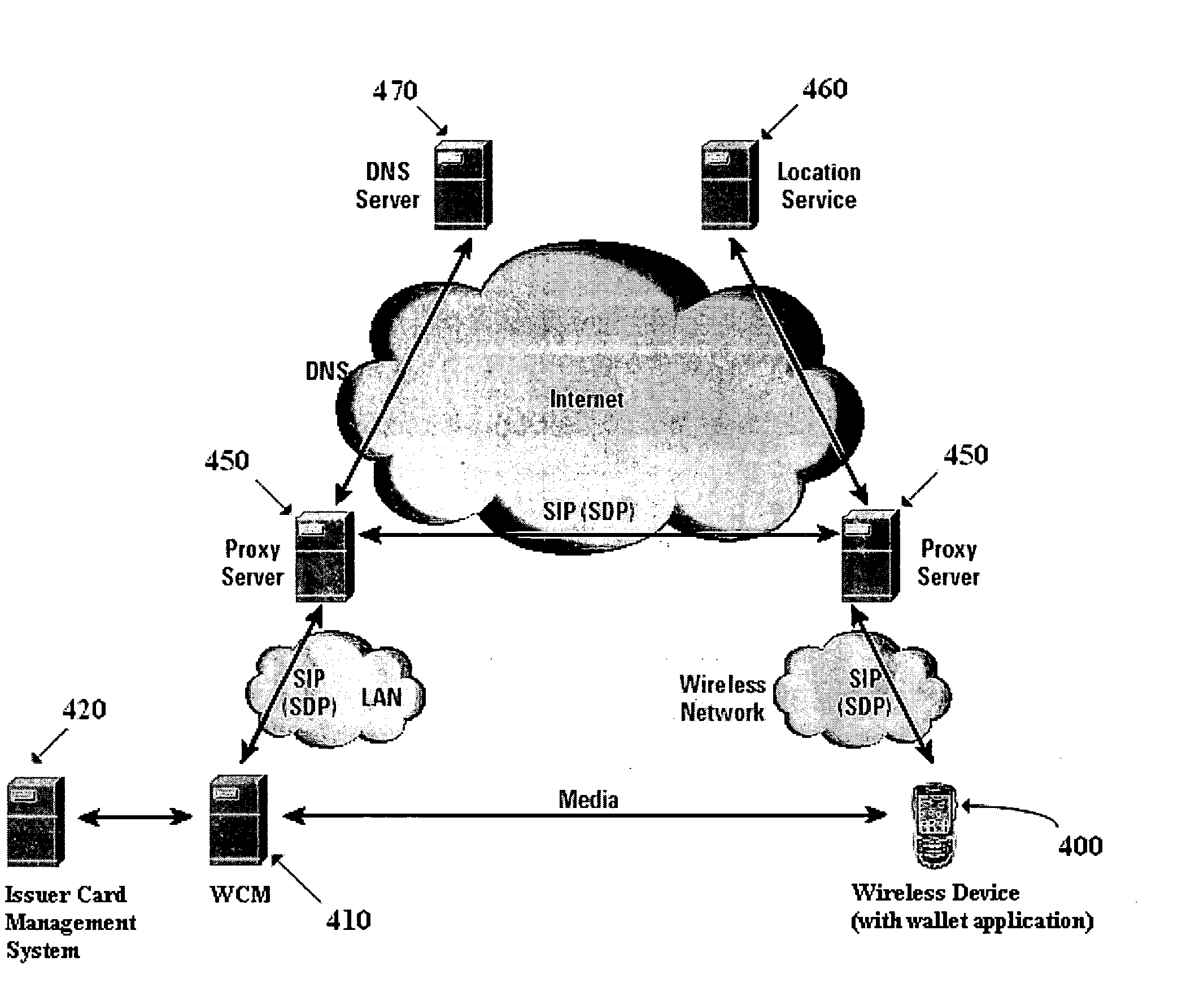
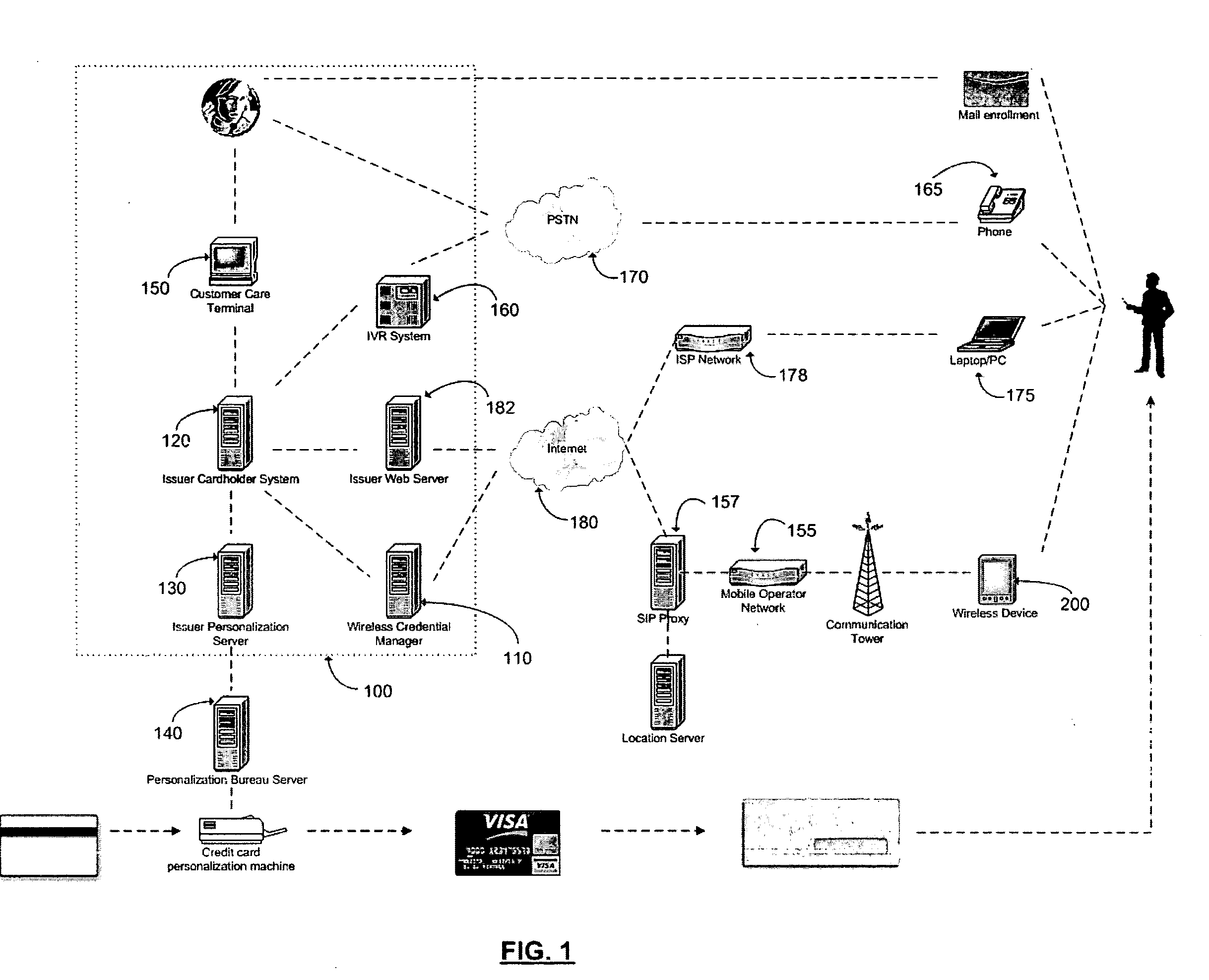
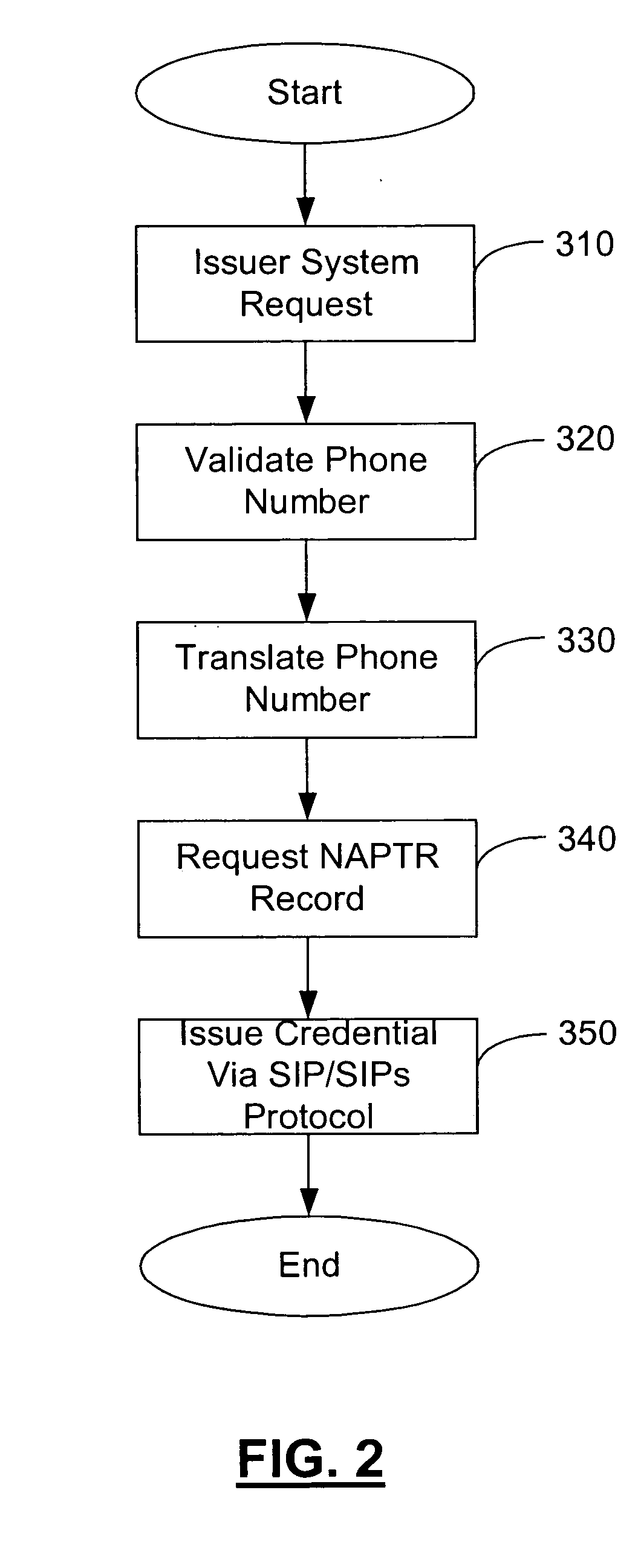
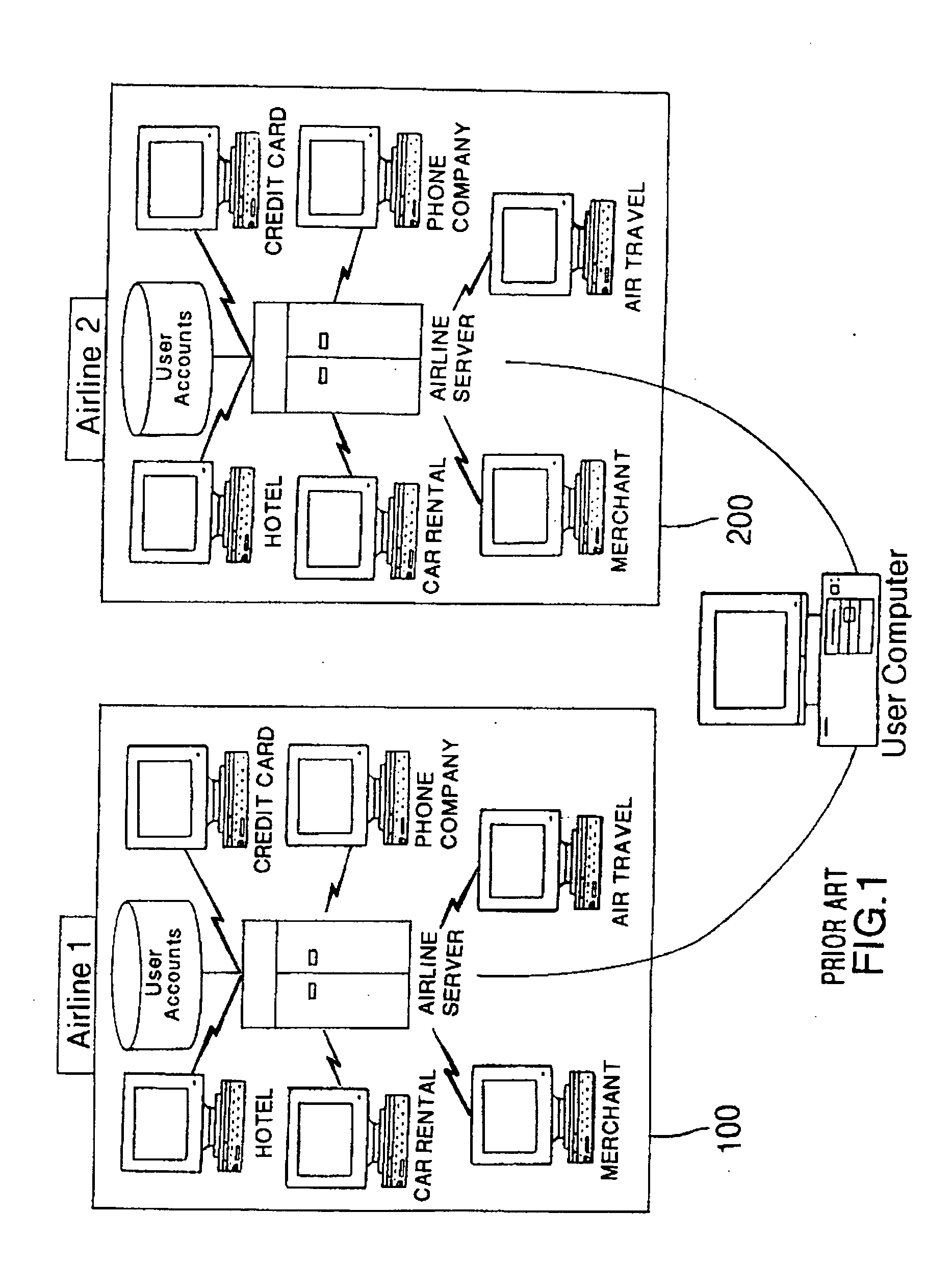
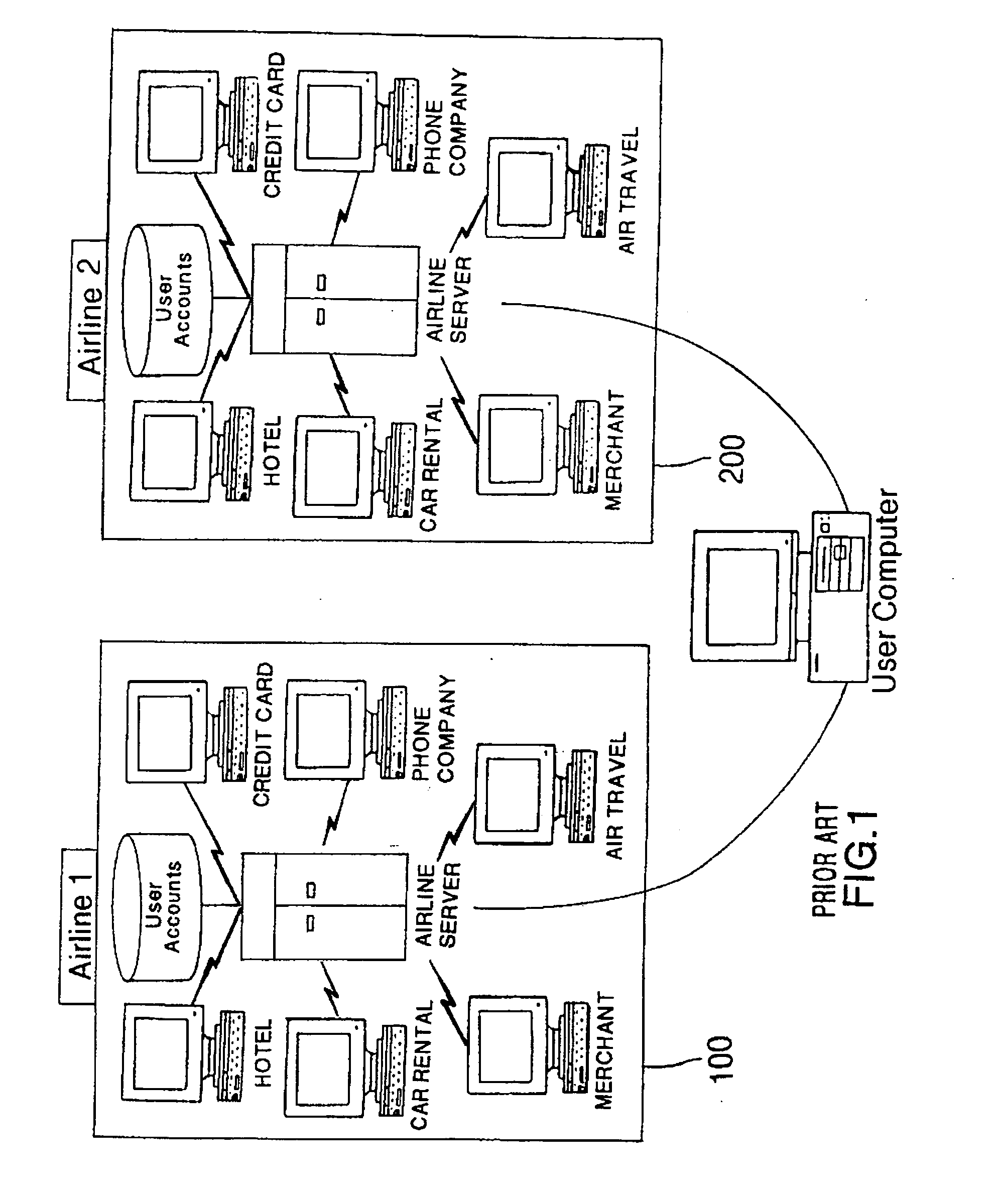
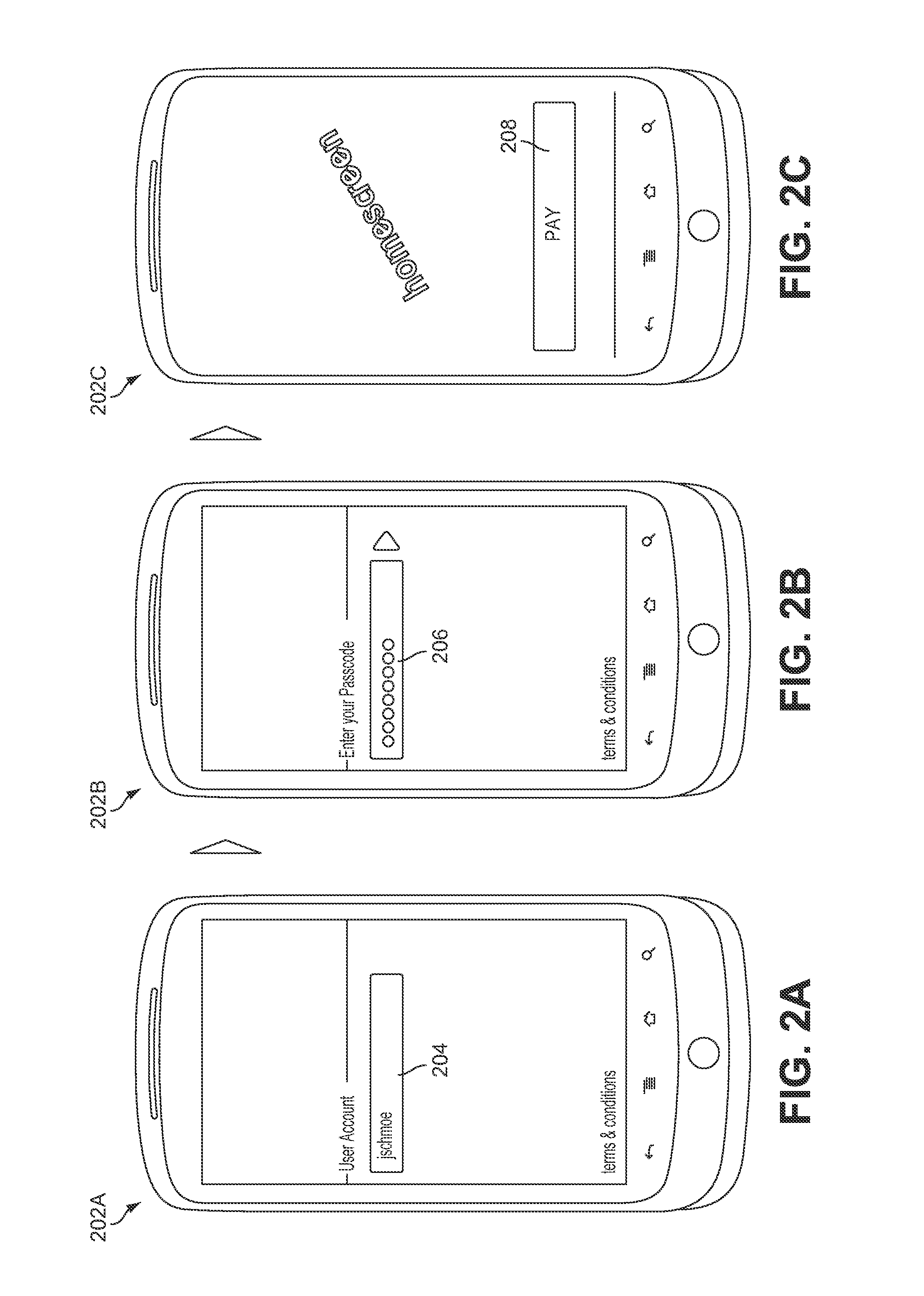
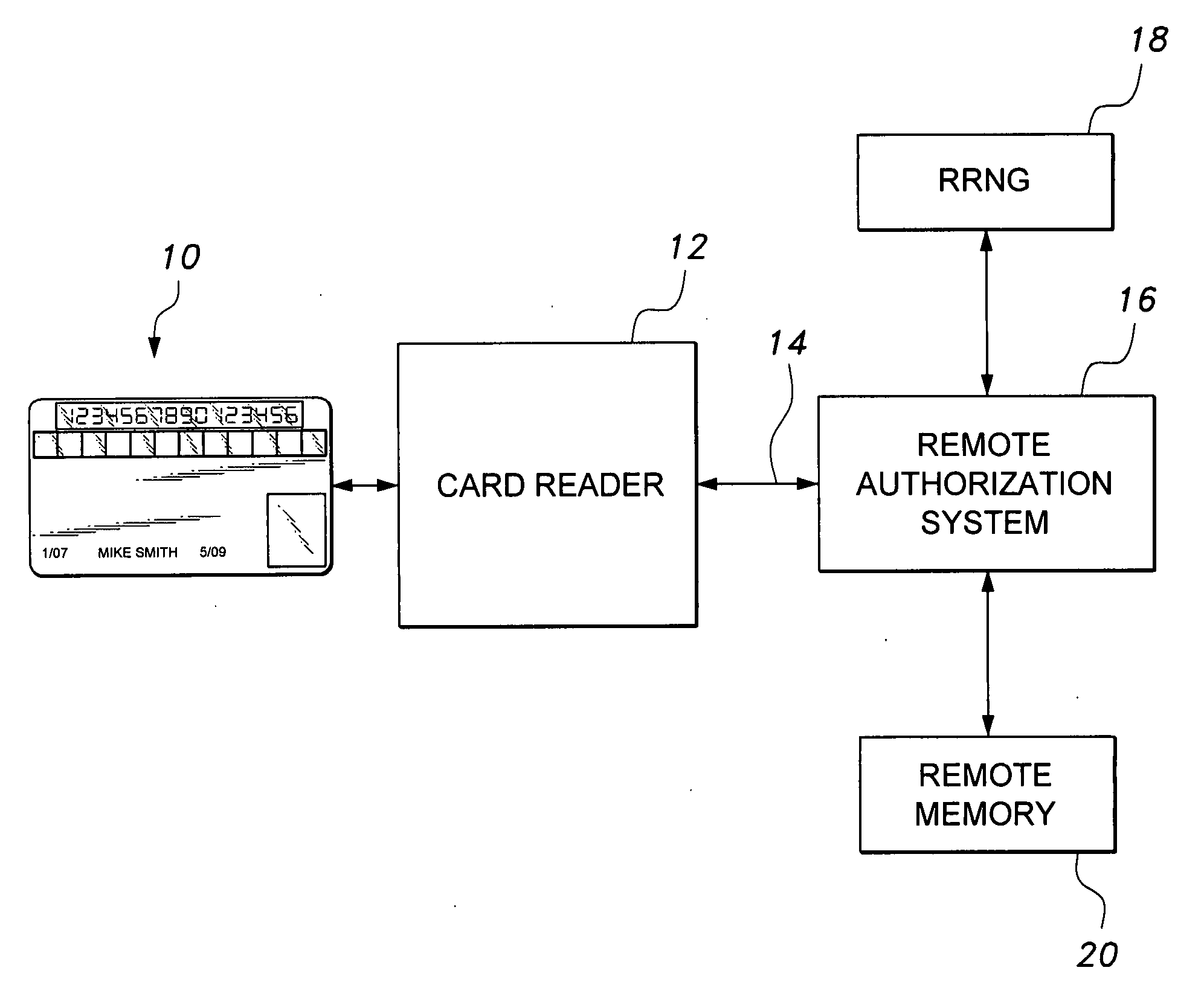
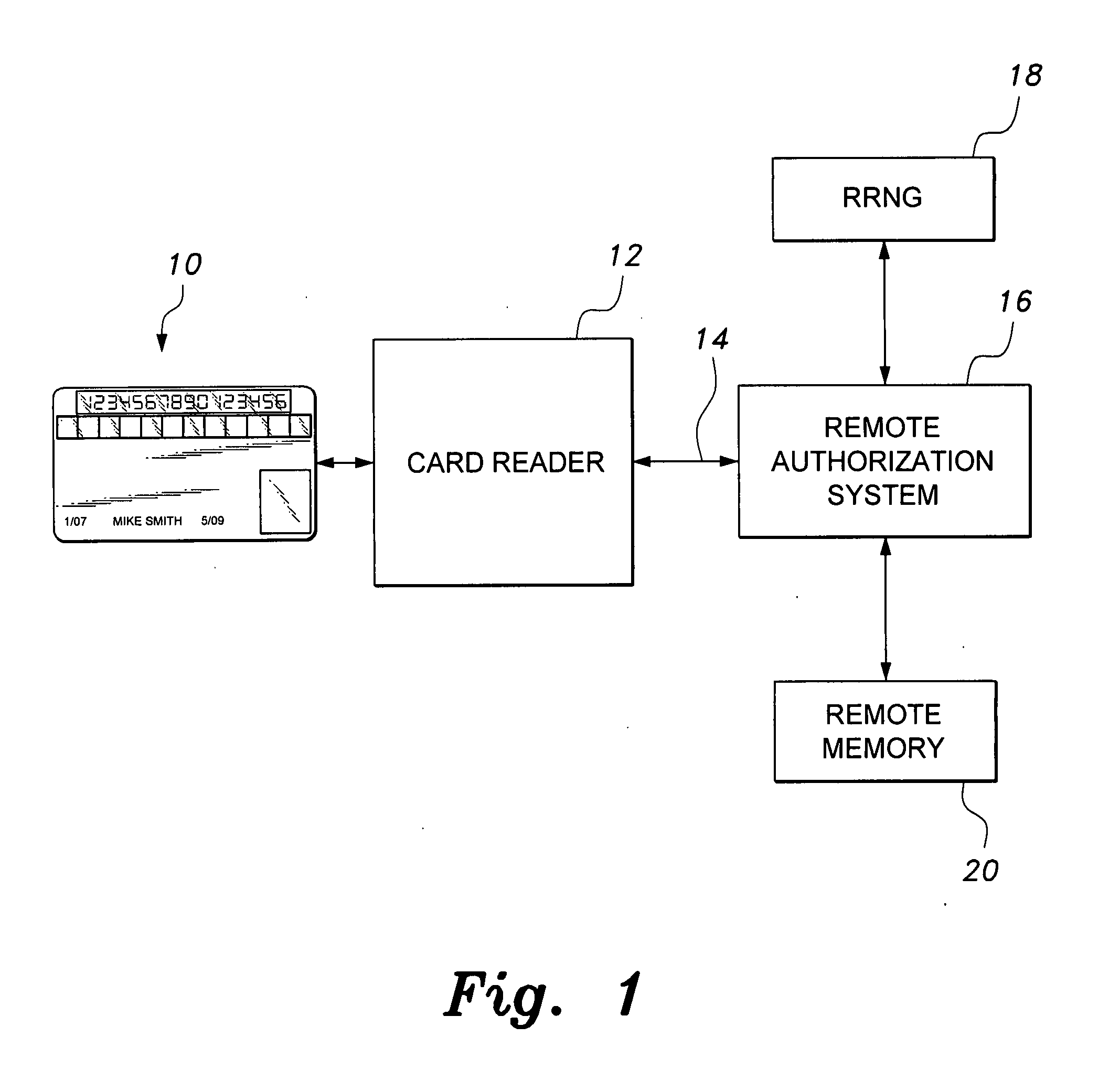
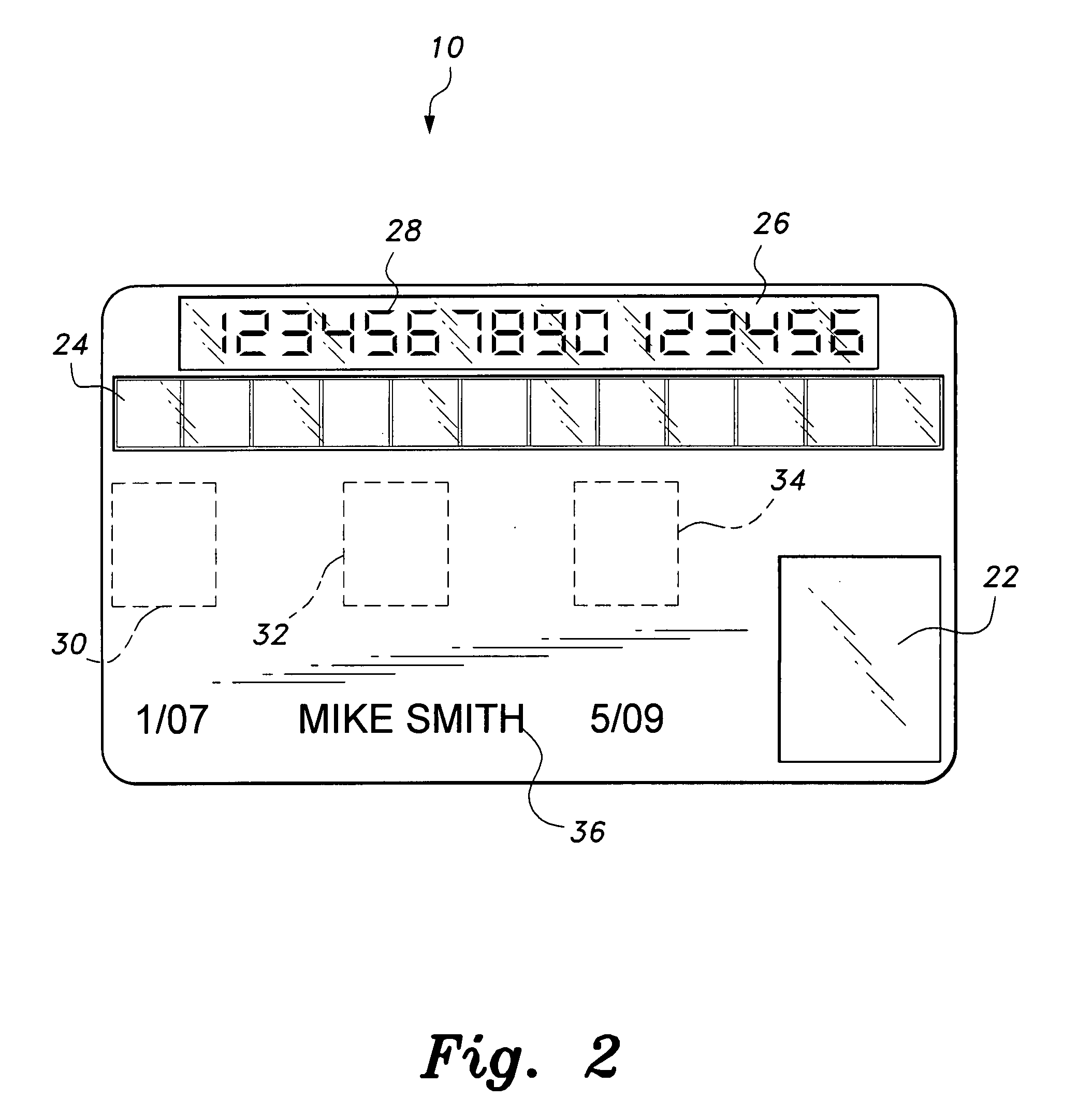
Method and apparatus for managing credentials through a wireless network
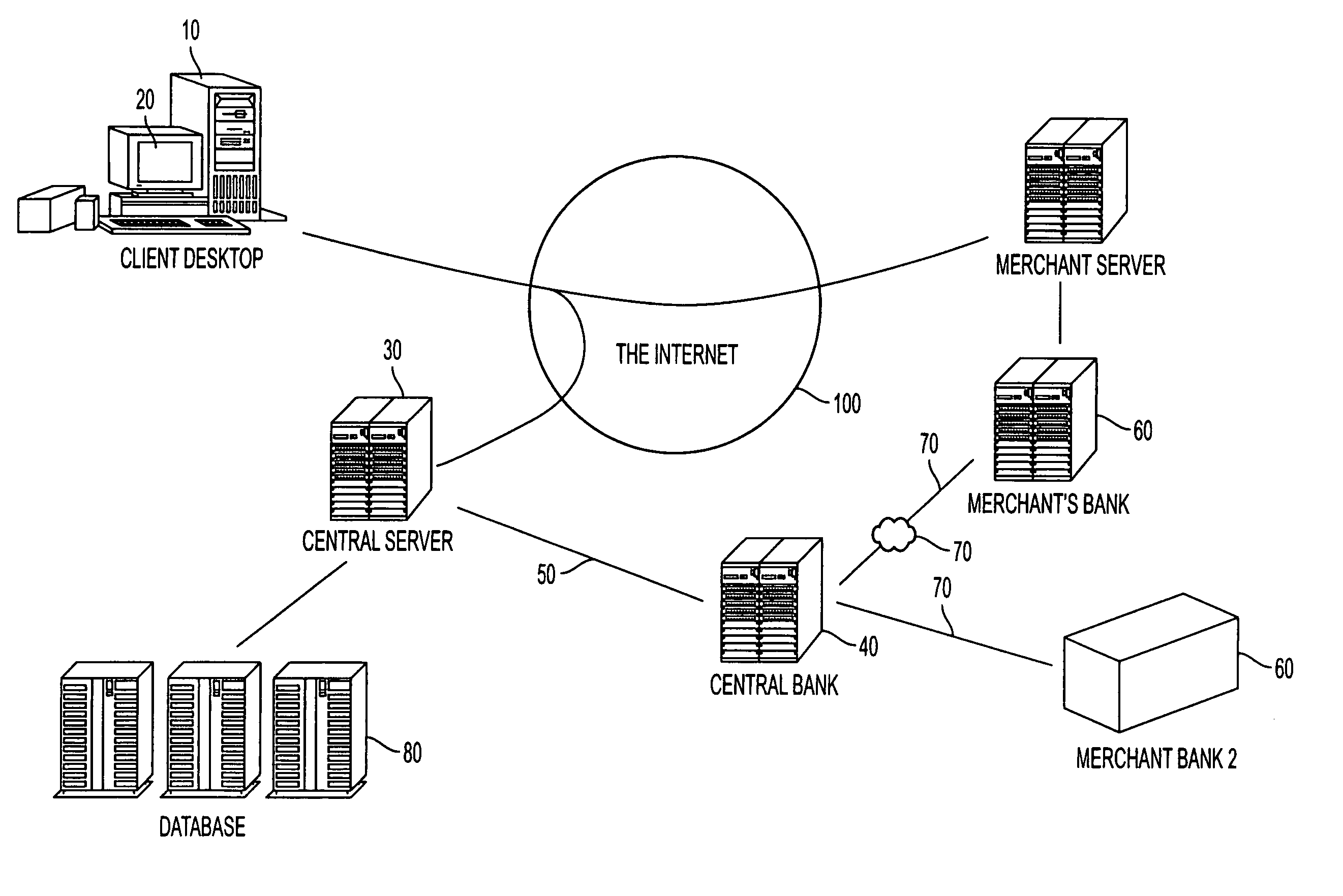
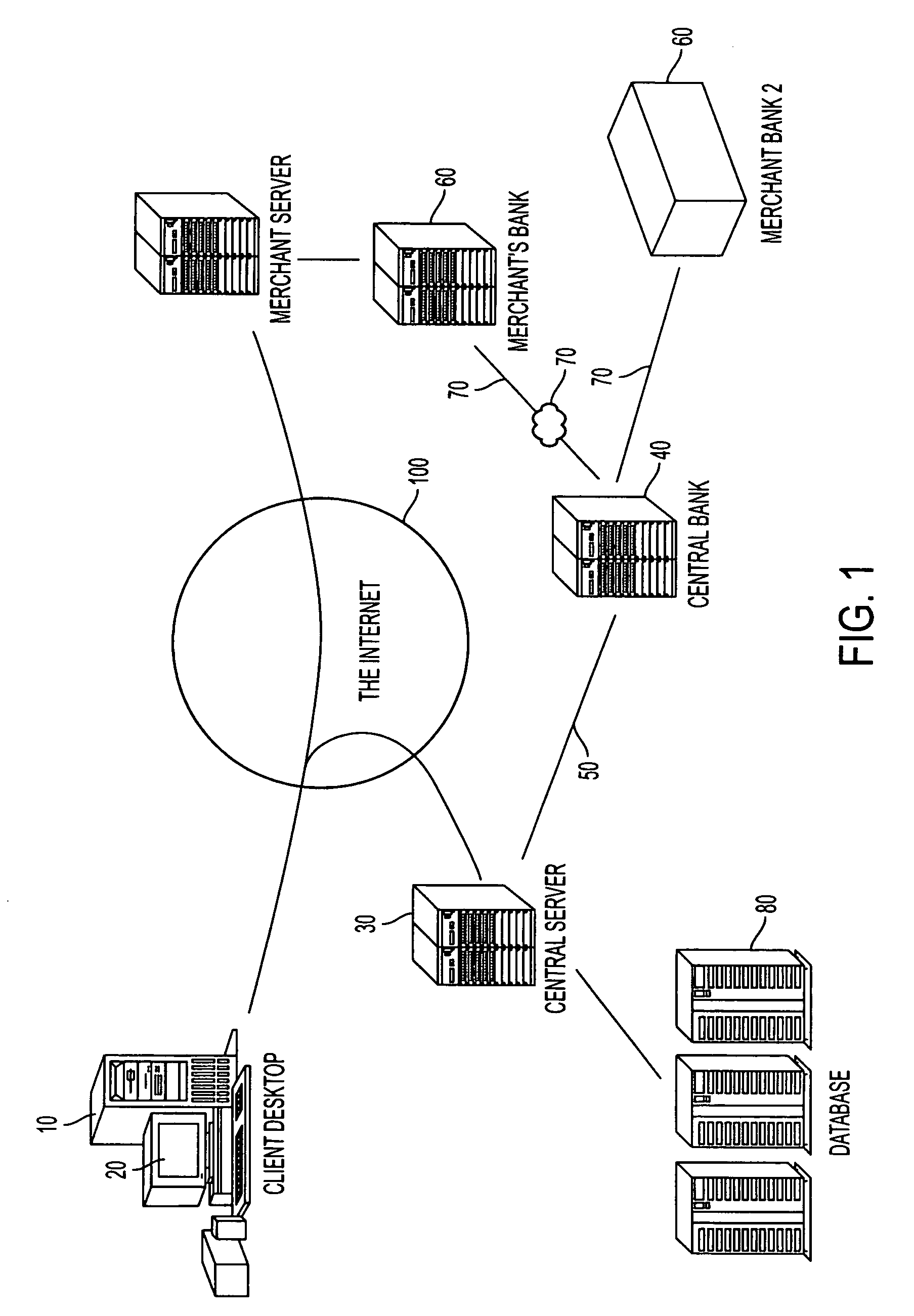
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
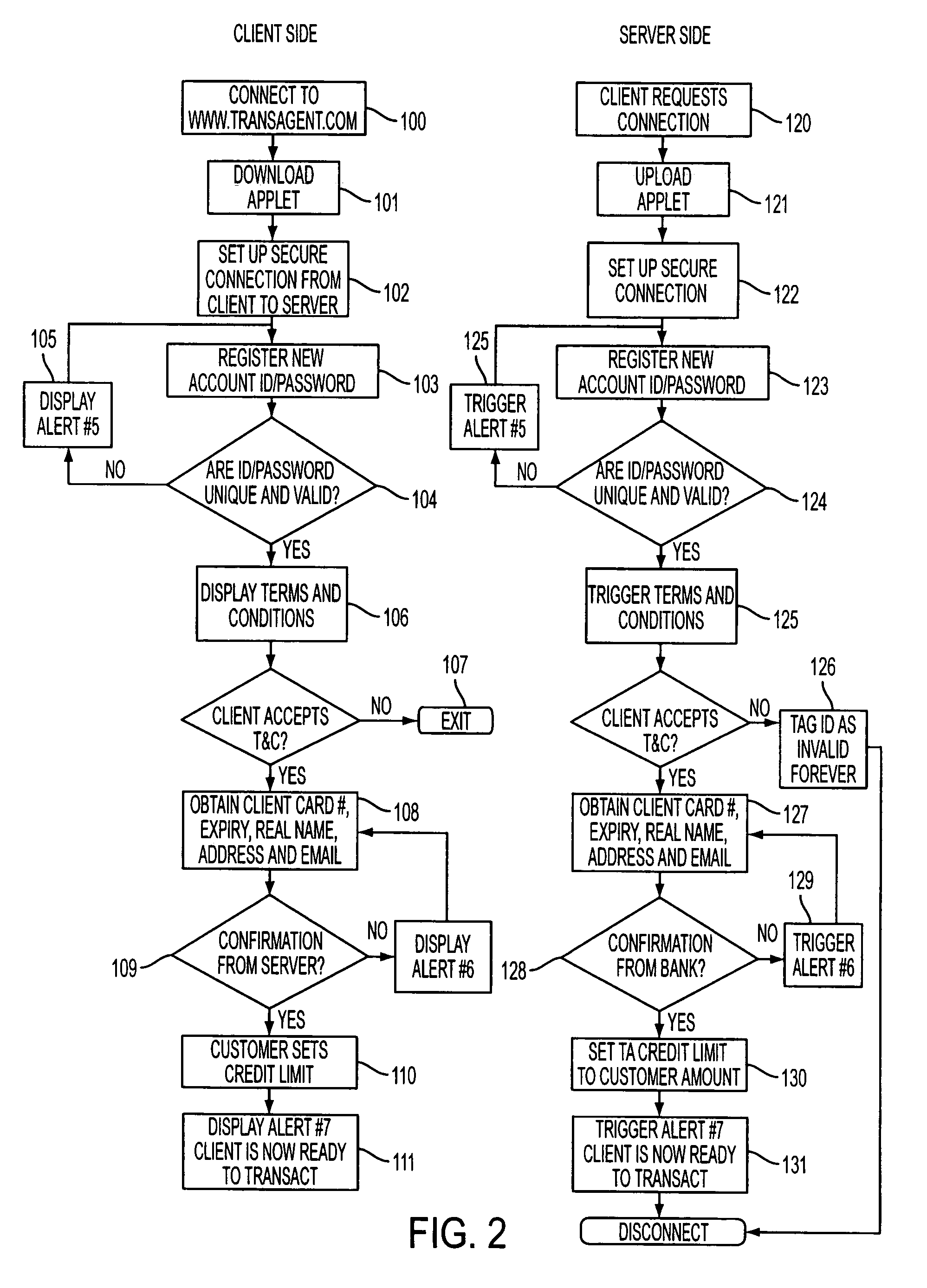
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
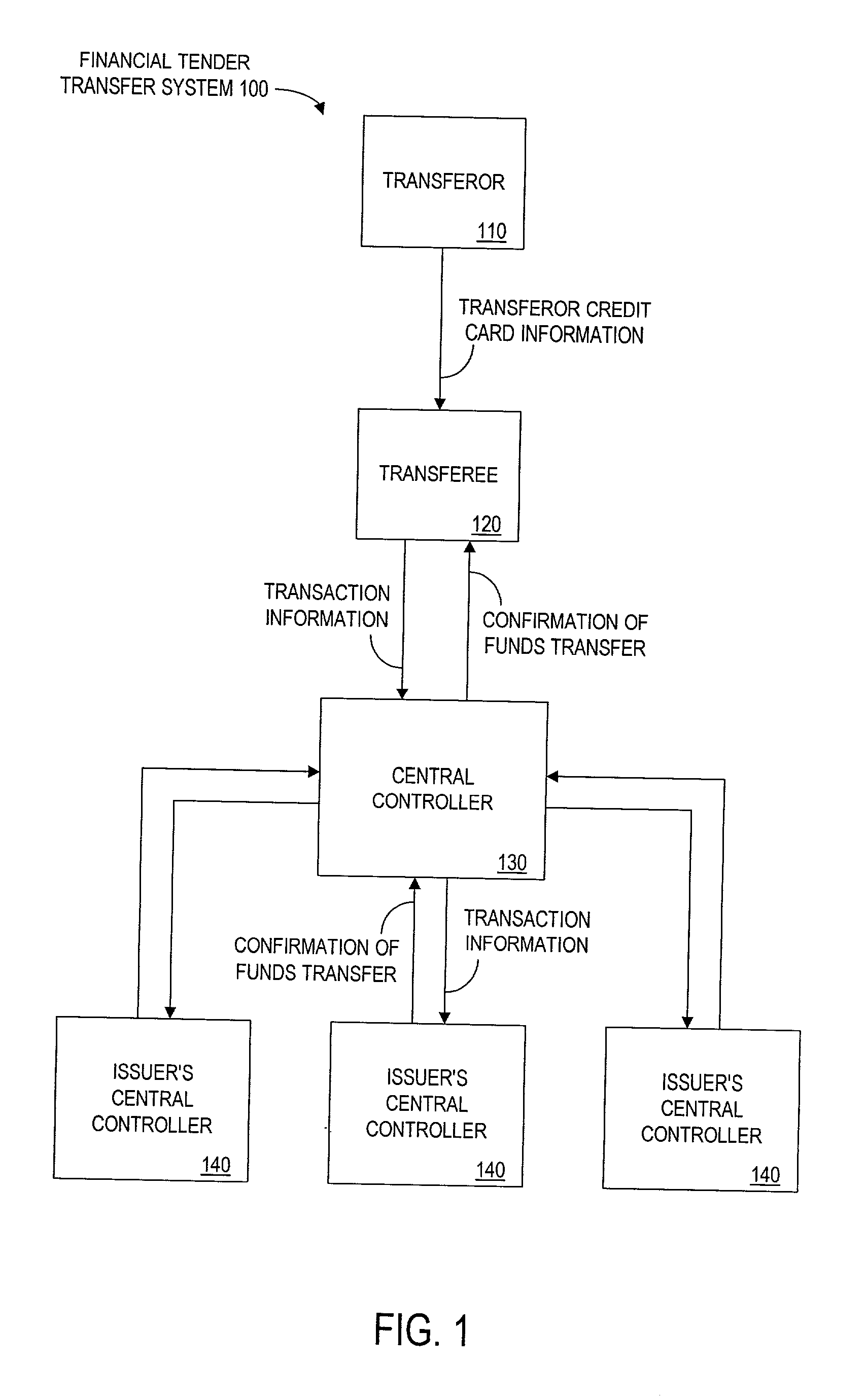
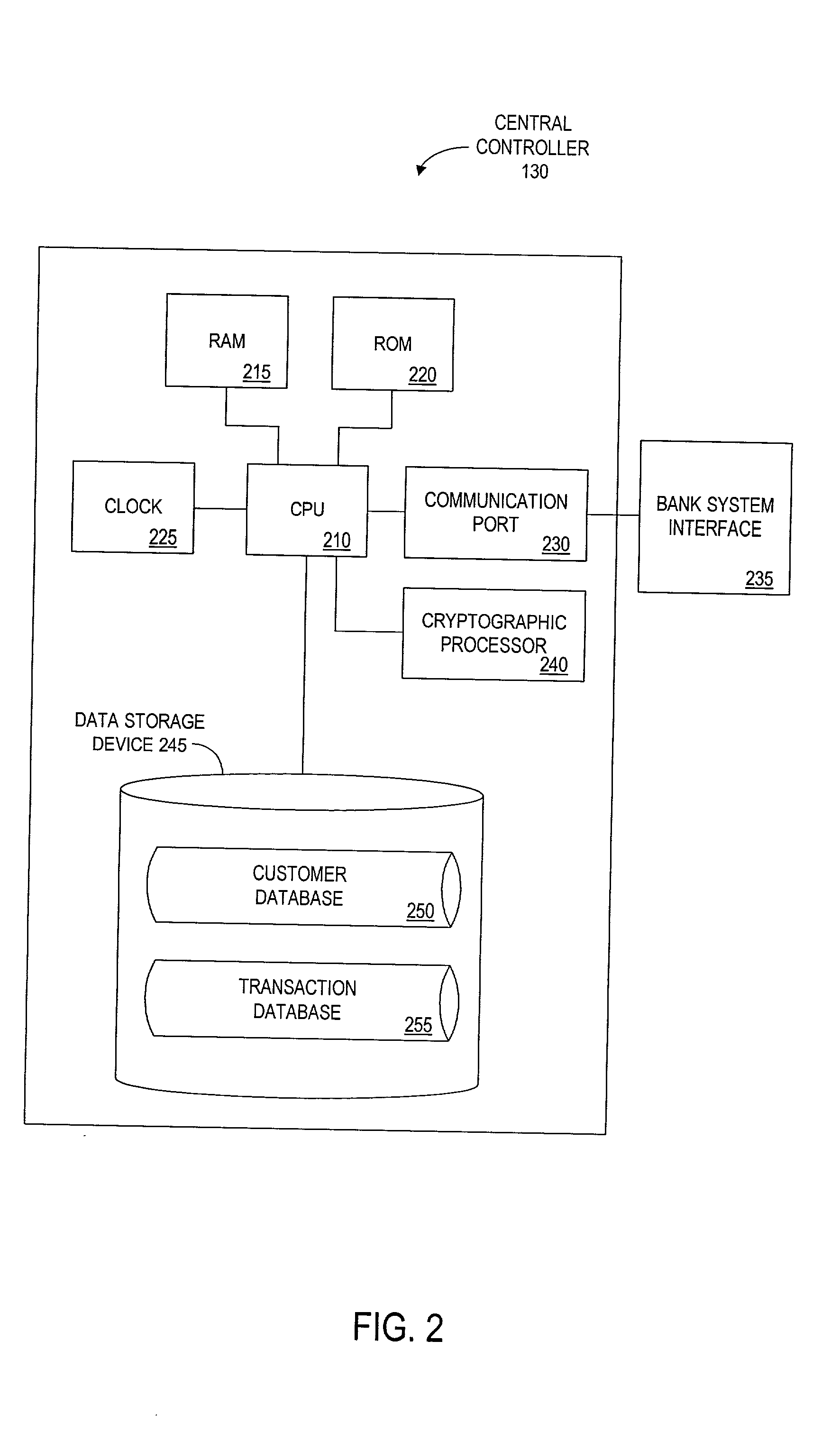
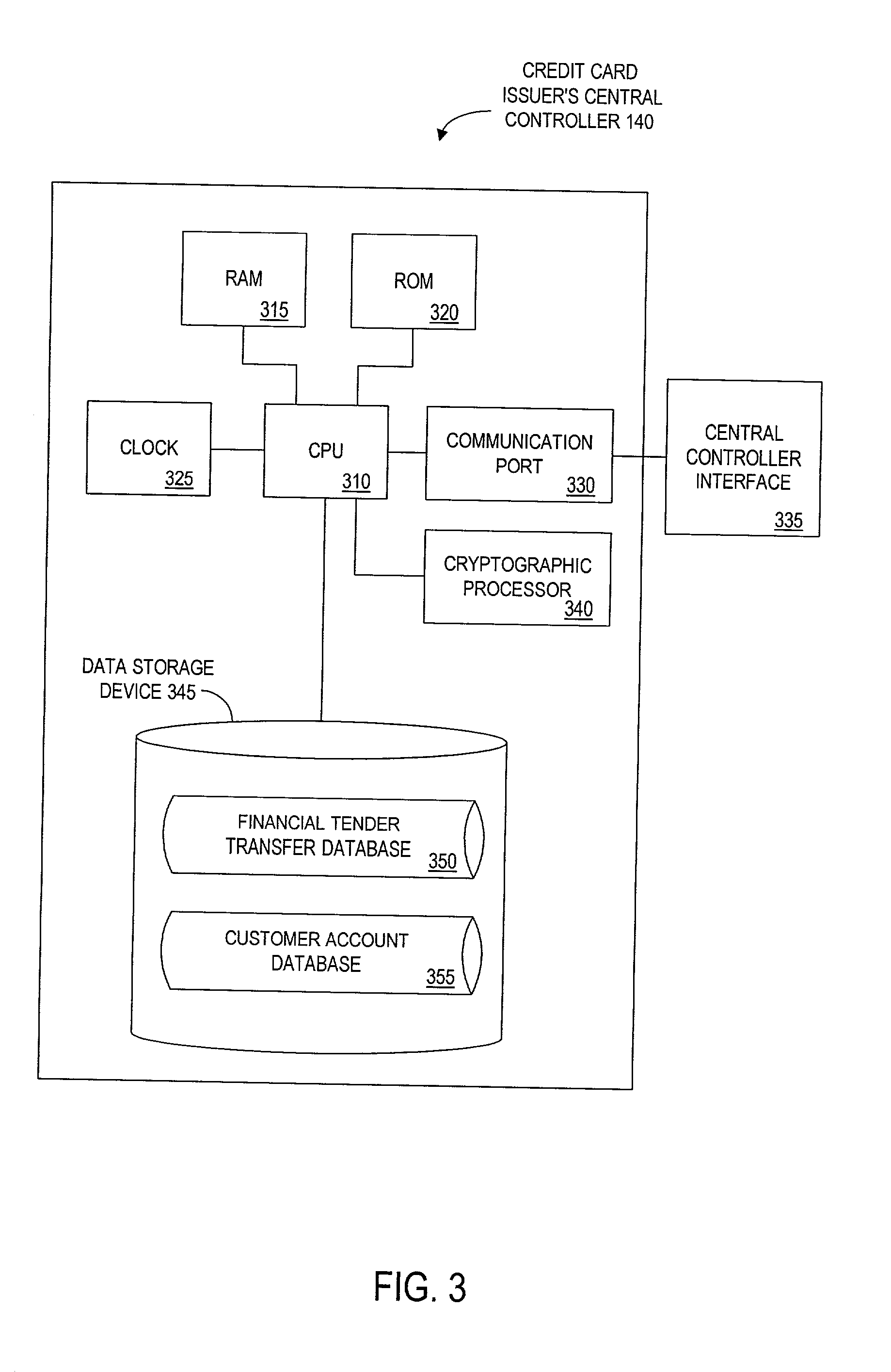
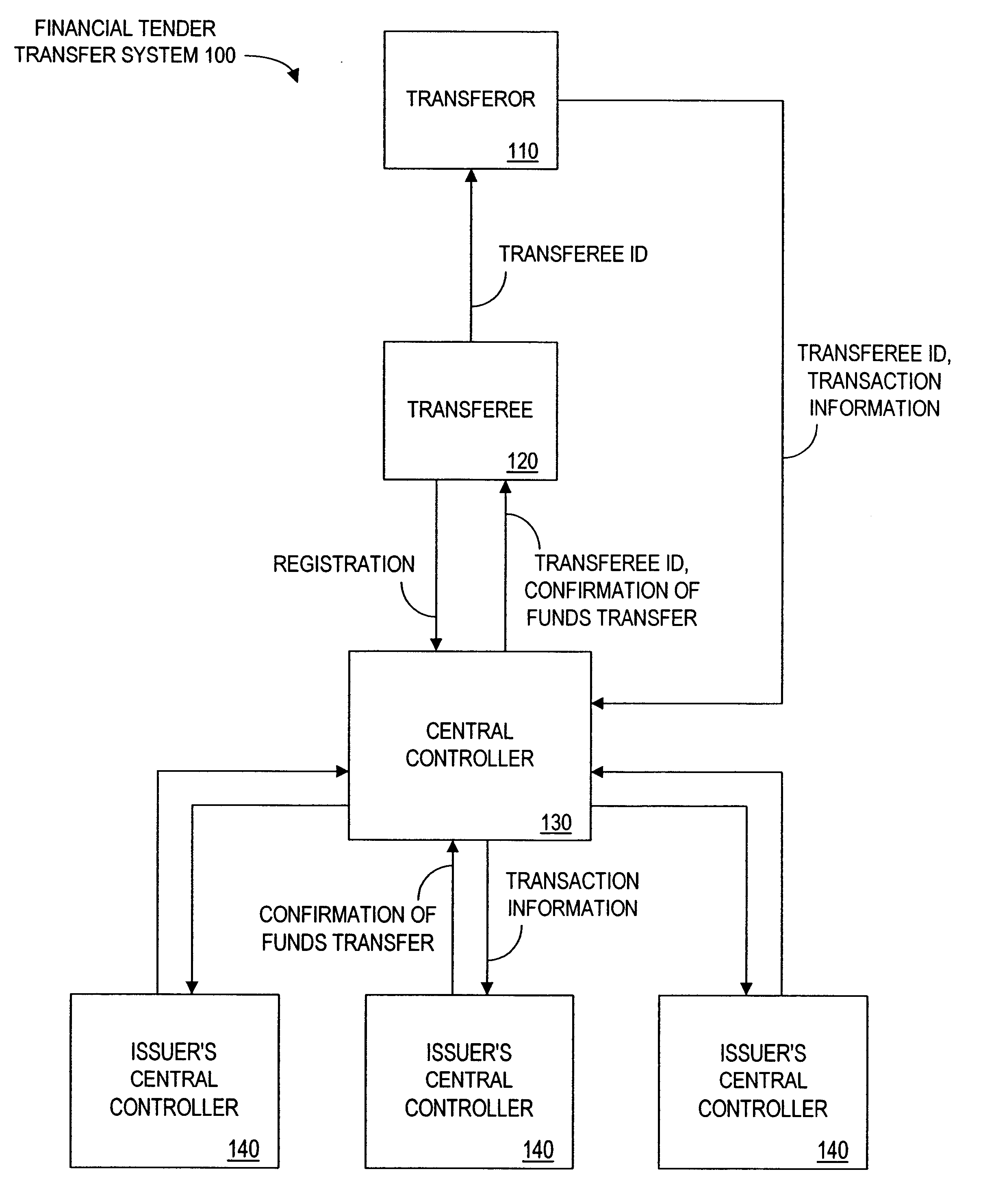
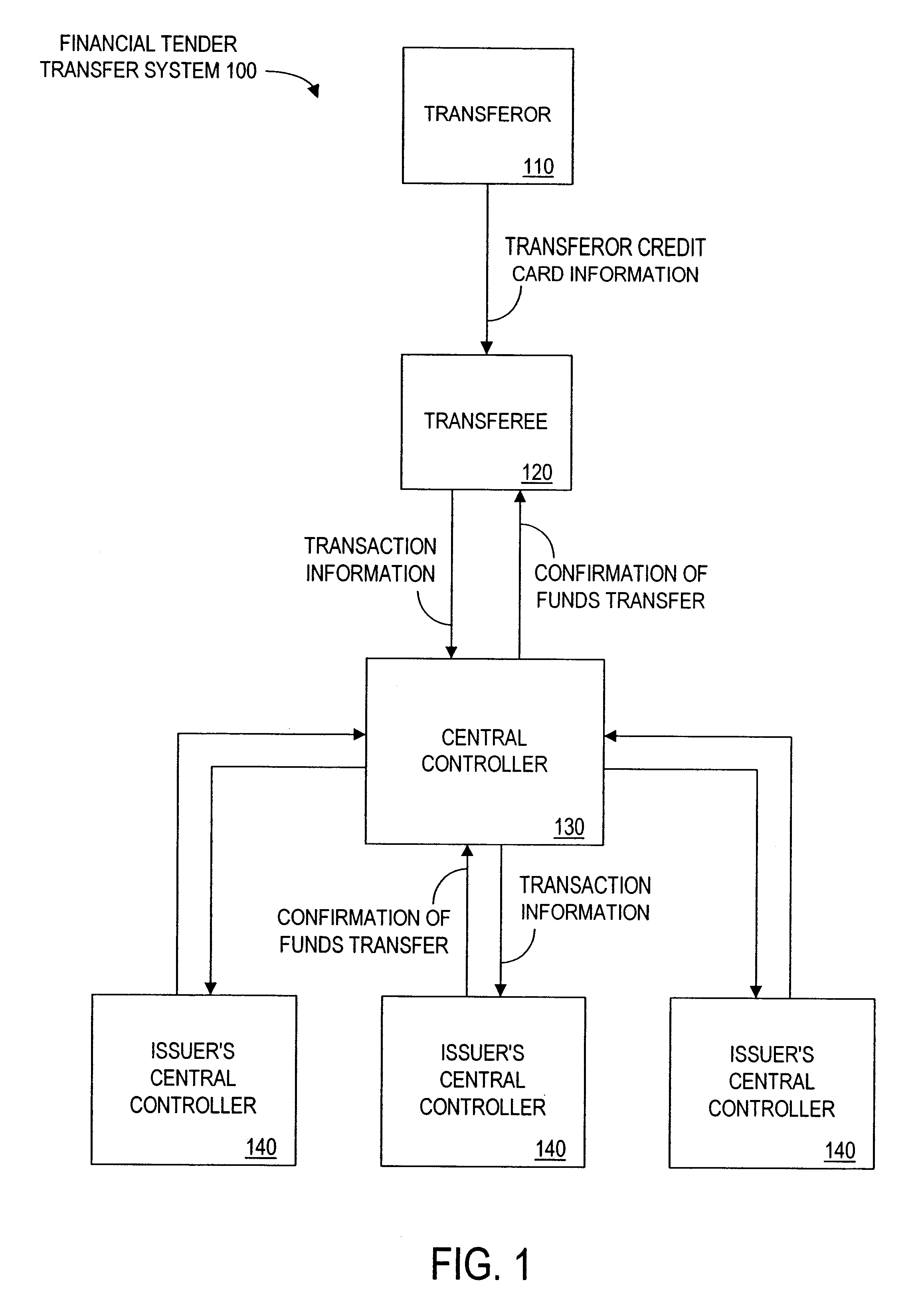
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
System and method for use of distributed electronic wallets
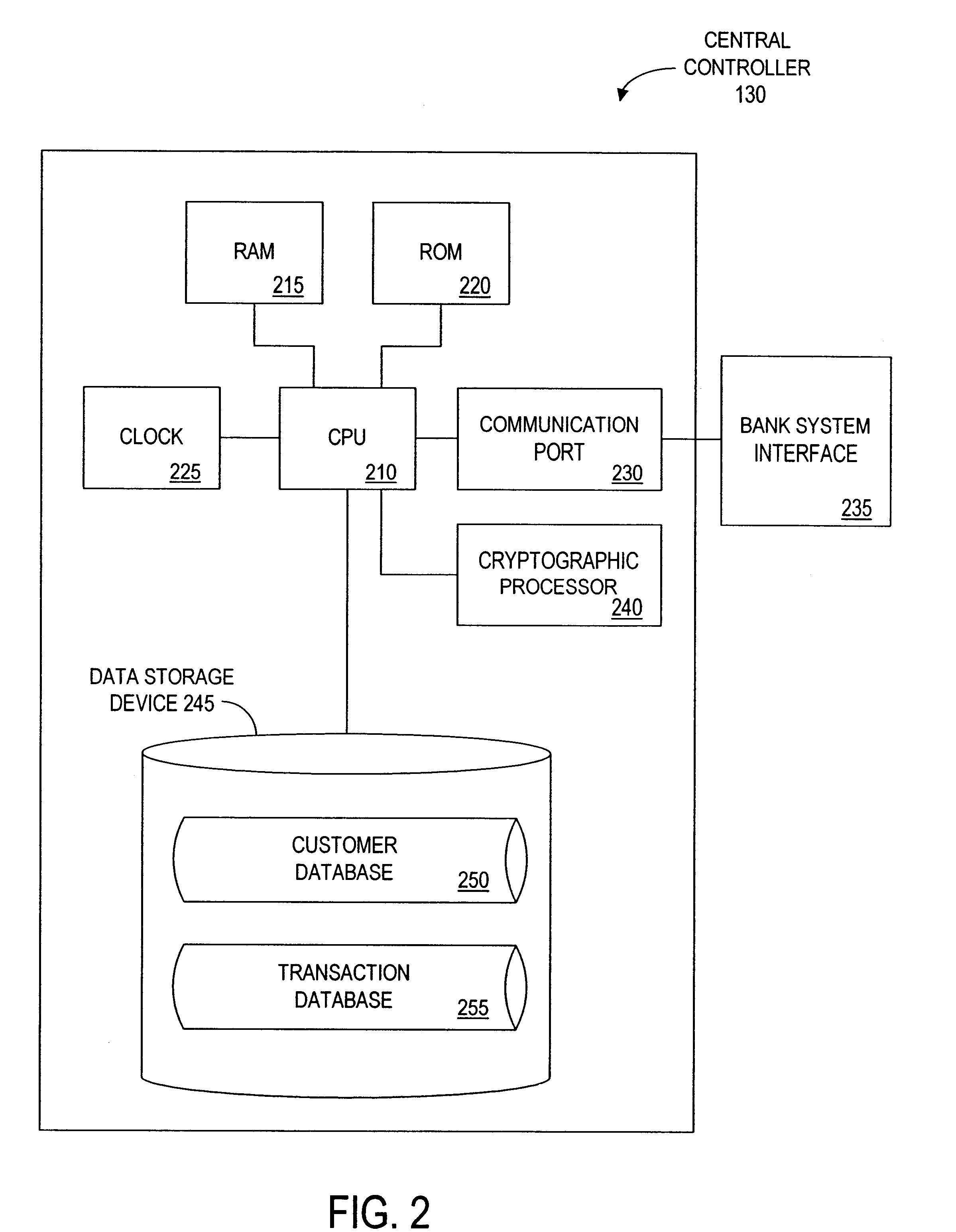
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
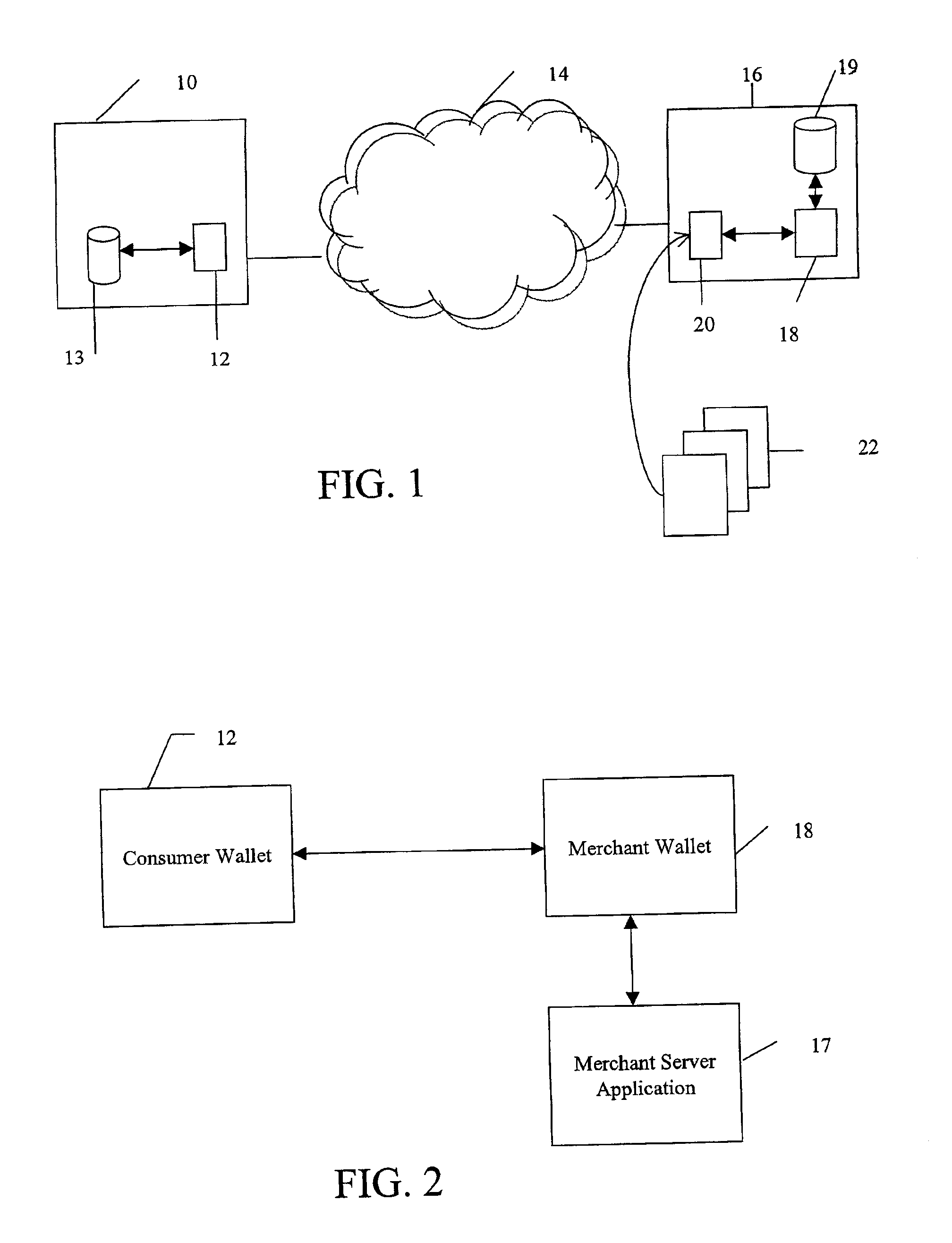
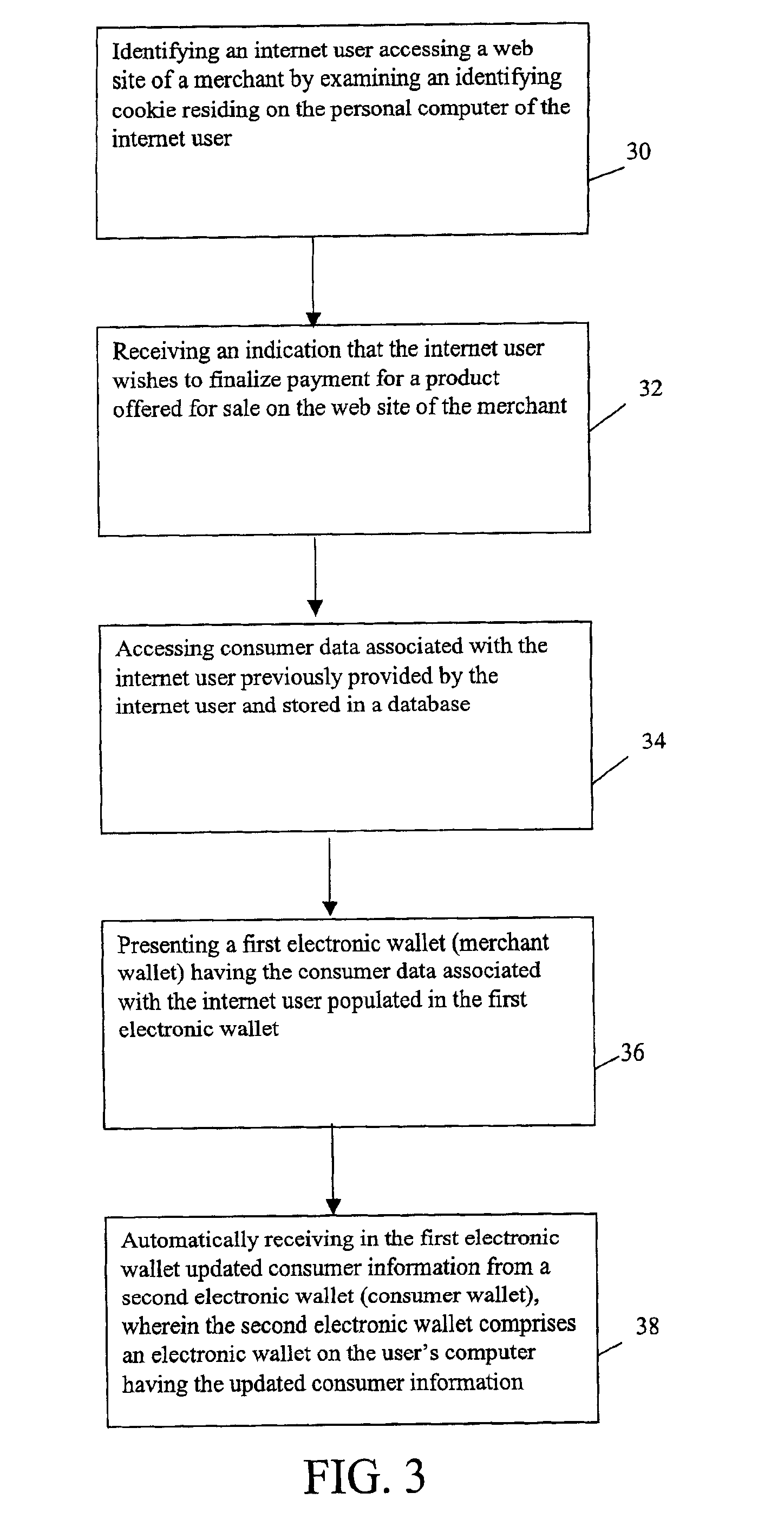
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
Transaction security method and apparatus
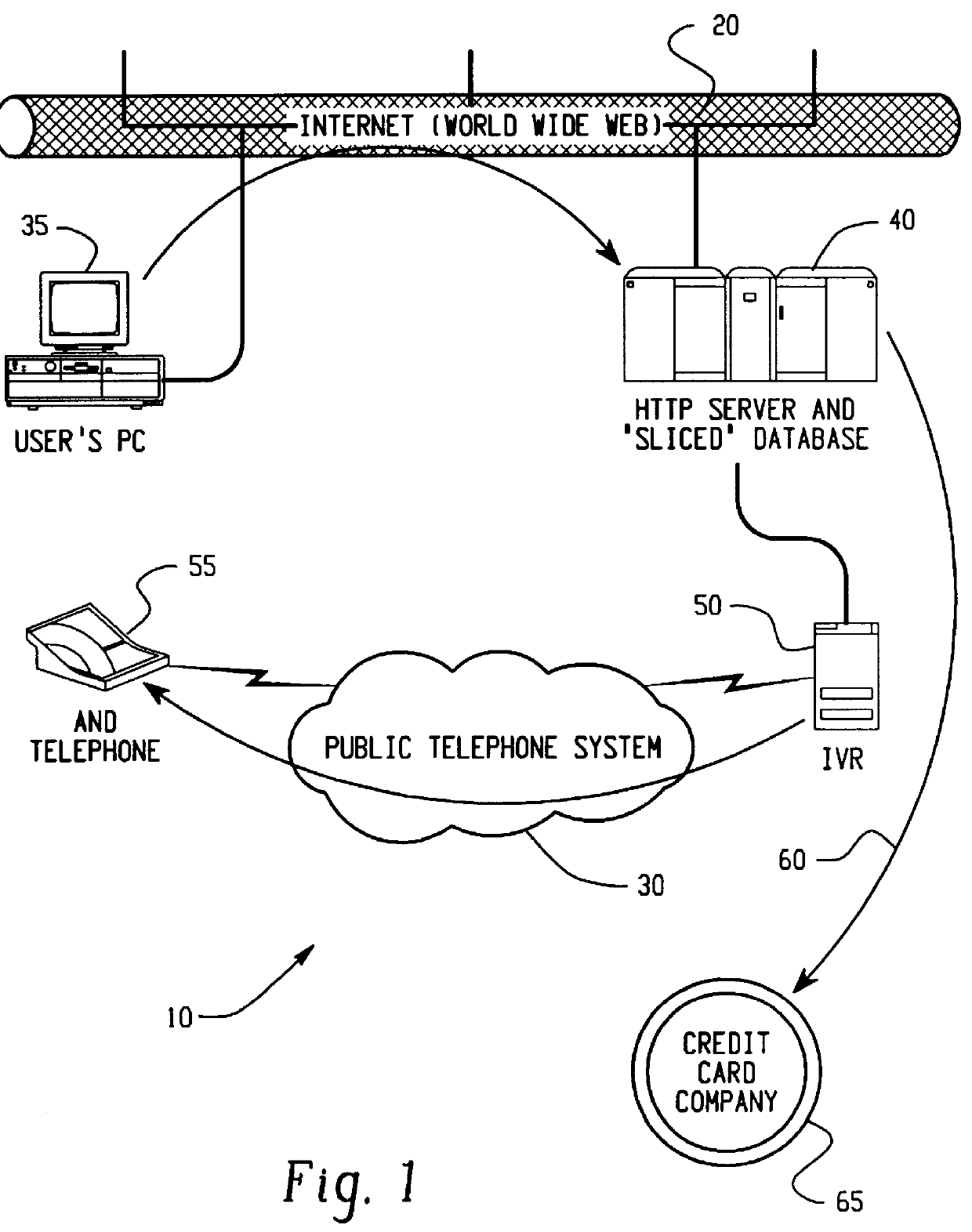
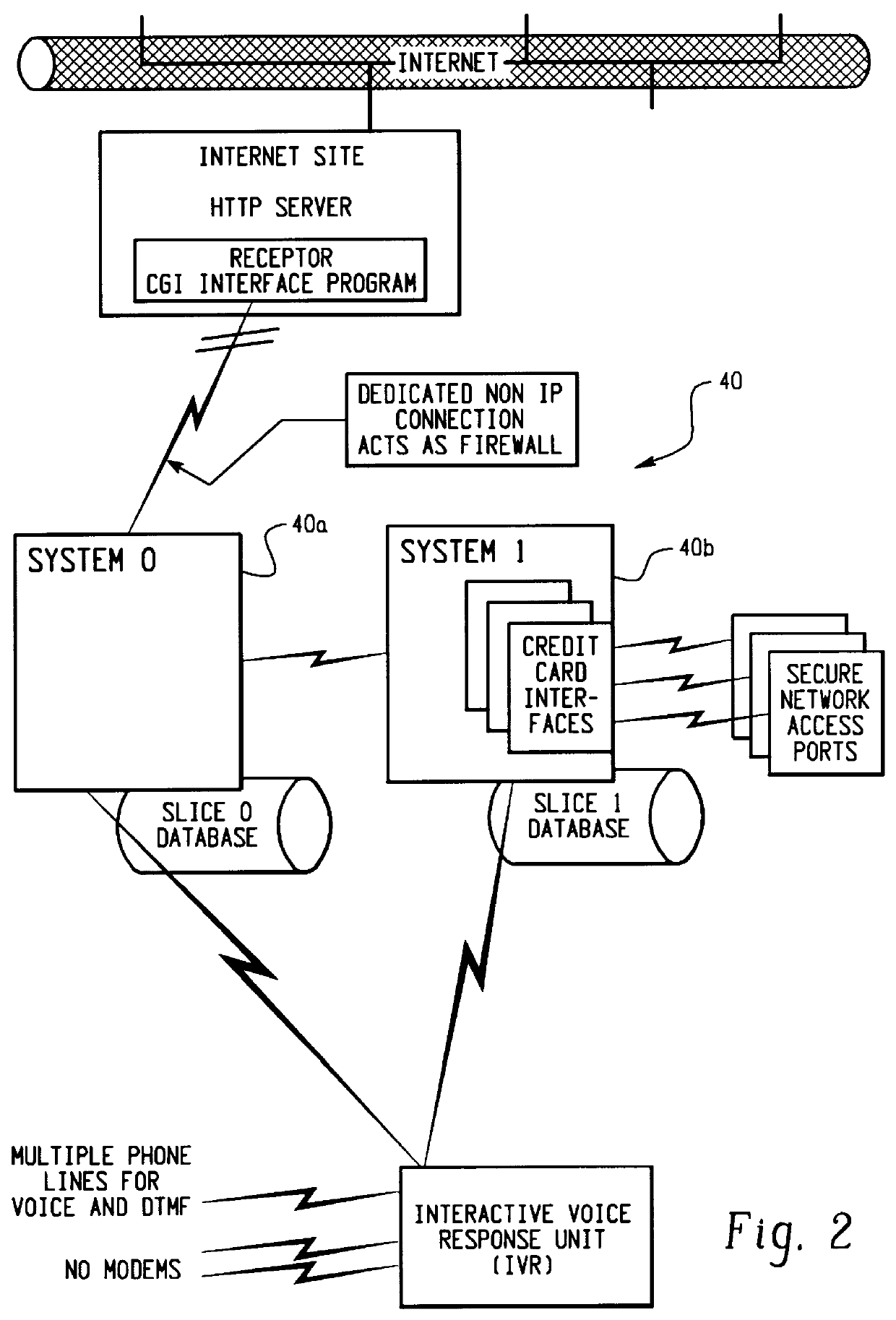
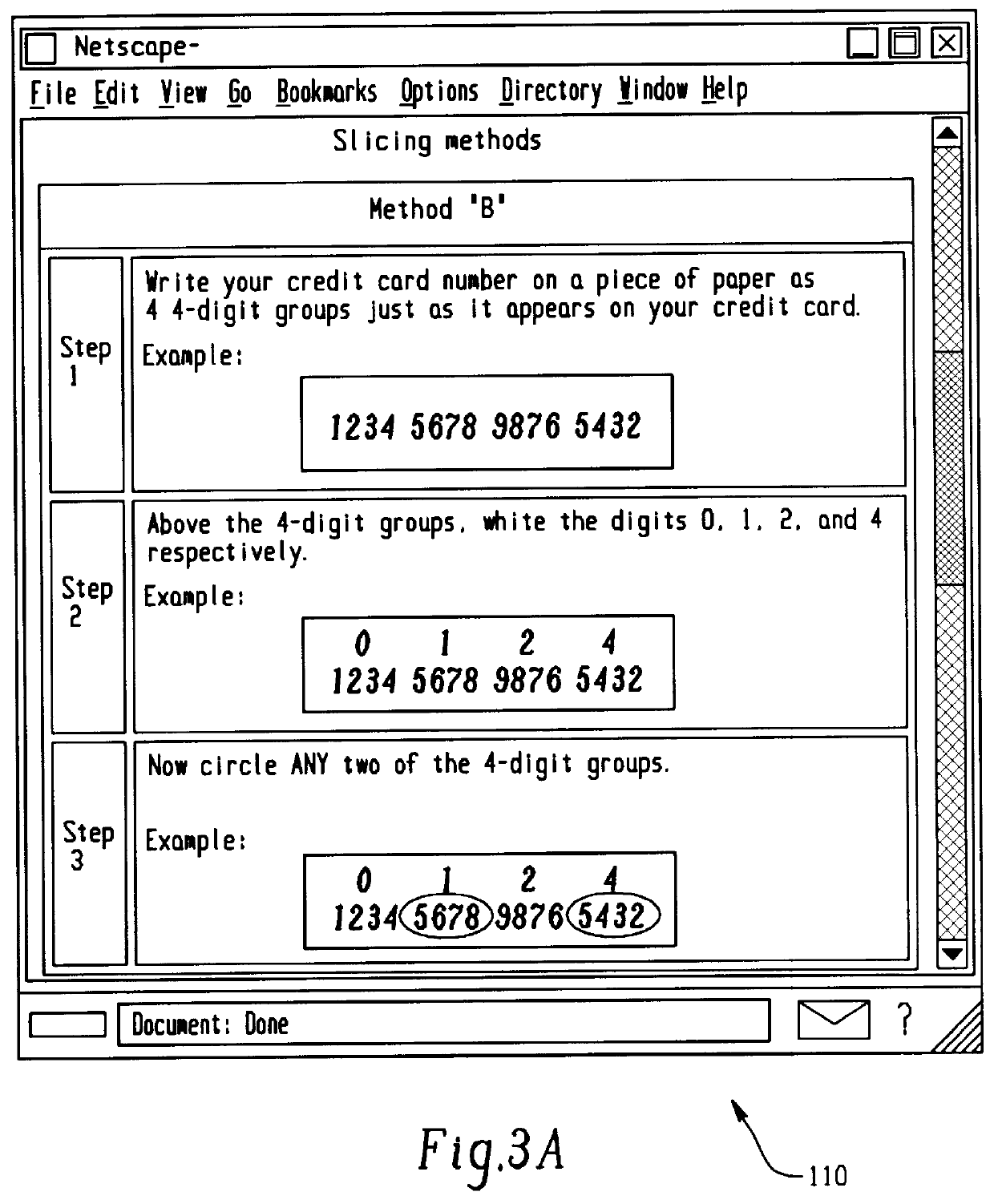
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
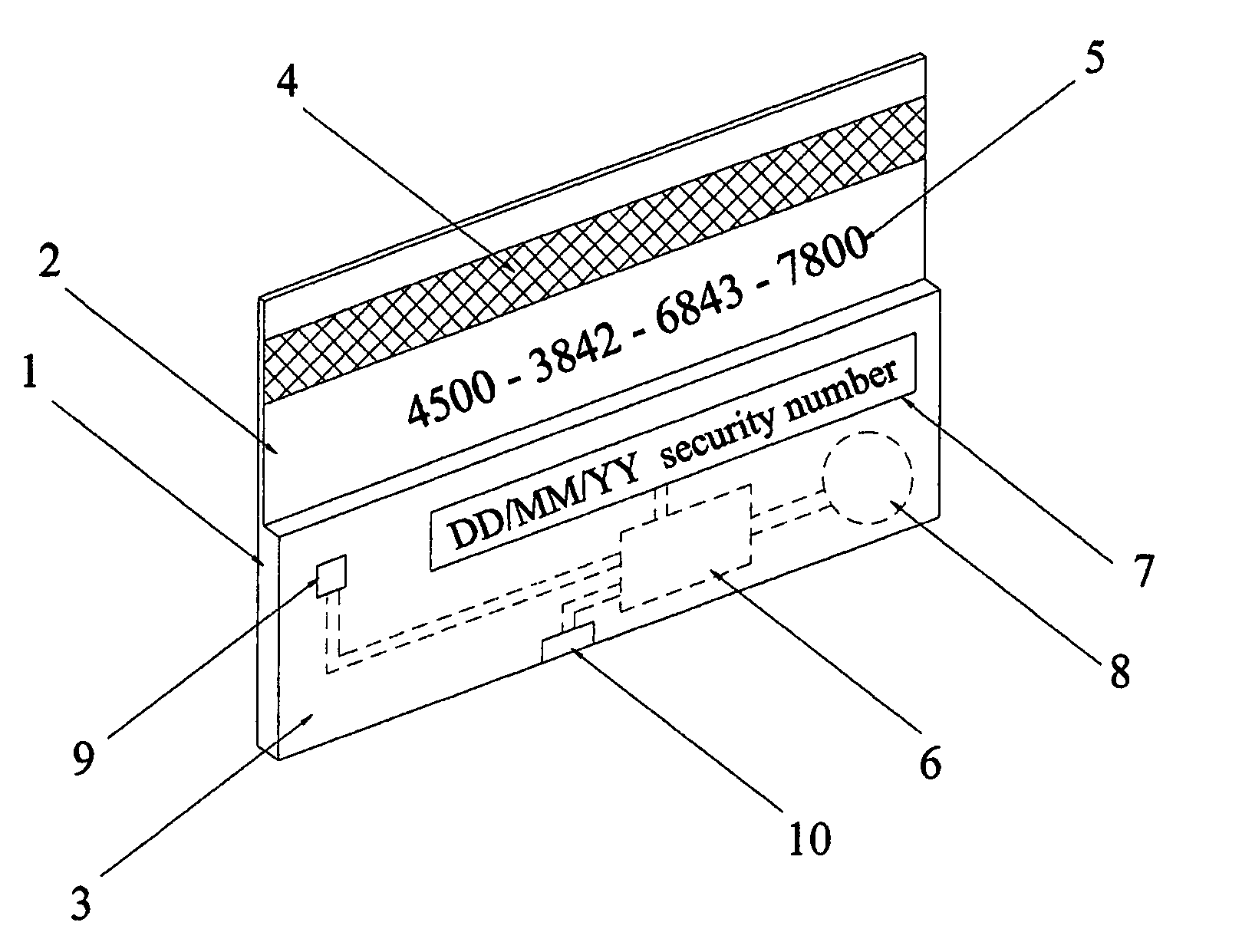
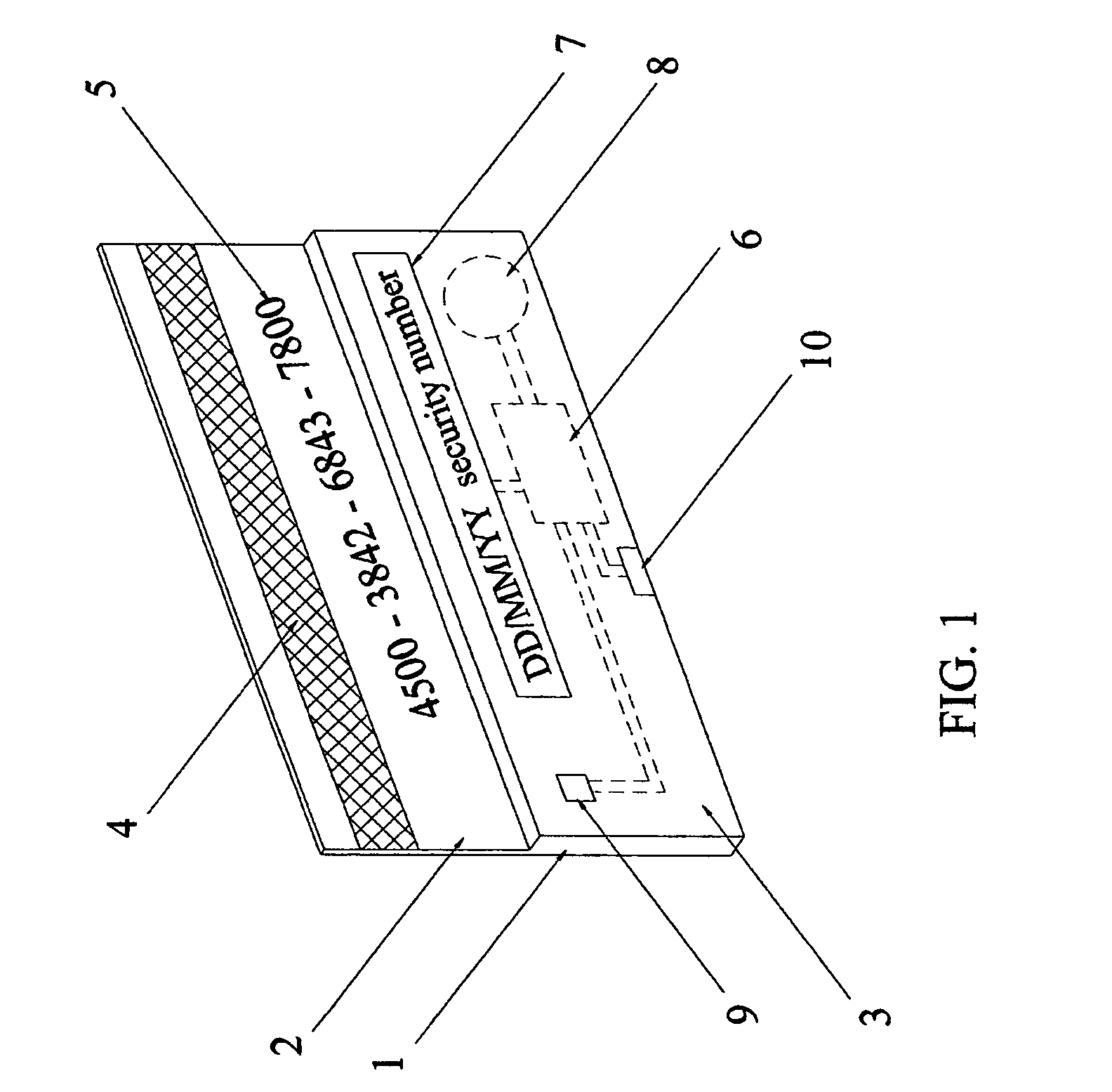
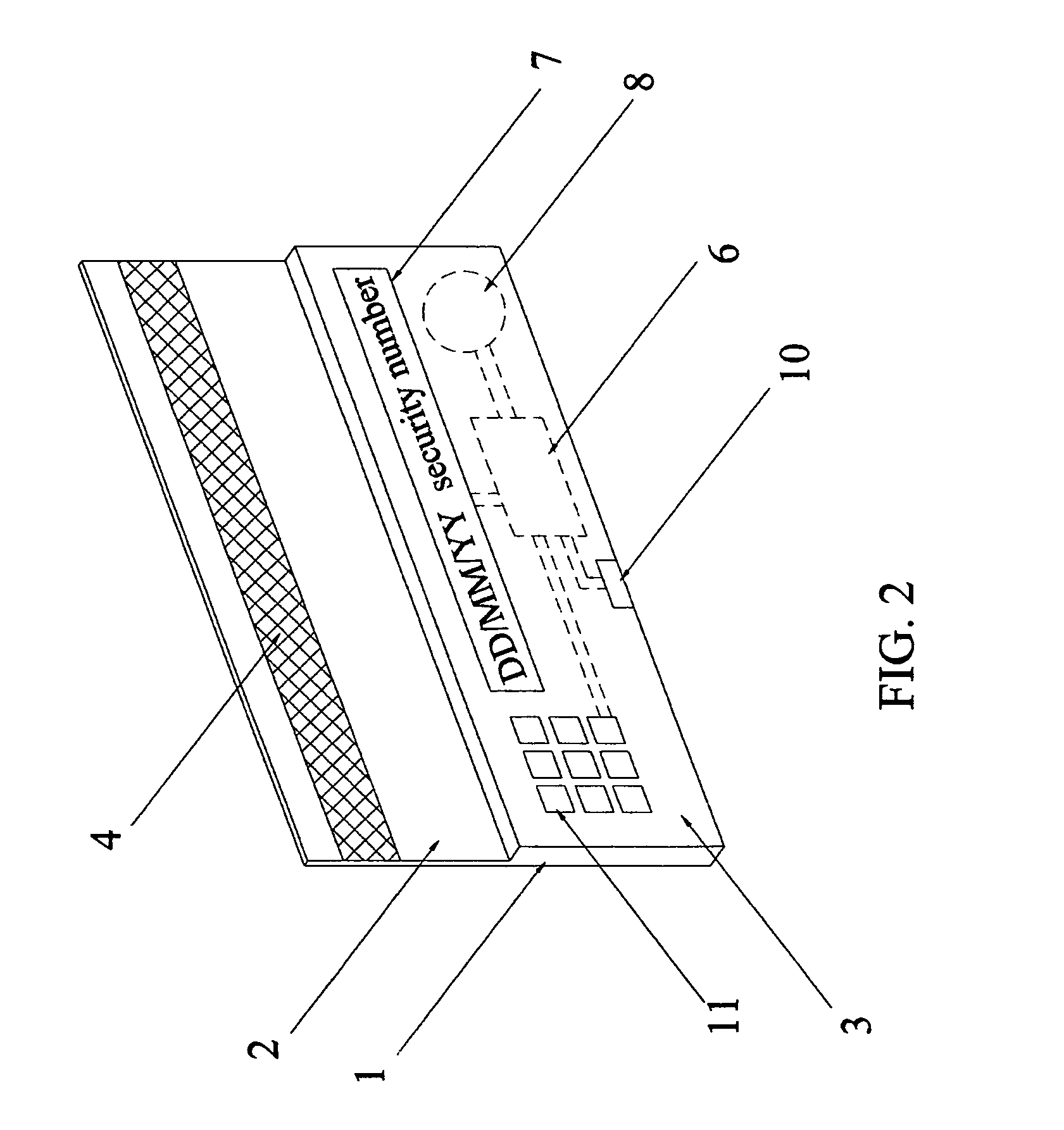
Secure credit card having daily changed security number
InactiveUS7051929B2Enhance memorySimple technologyPayment architectureRecord carriers used with machinesCredit cardThe Internet
Owner:LI GONGLING
Score based decisioning
InactiveUS7251624B1Reduce riskReduce the possibilityFinanceDigital computer detailsCredit cardThe Internet
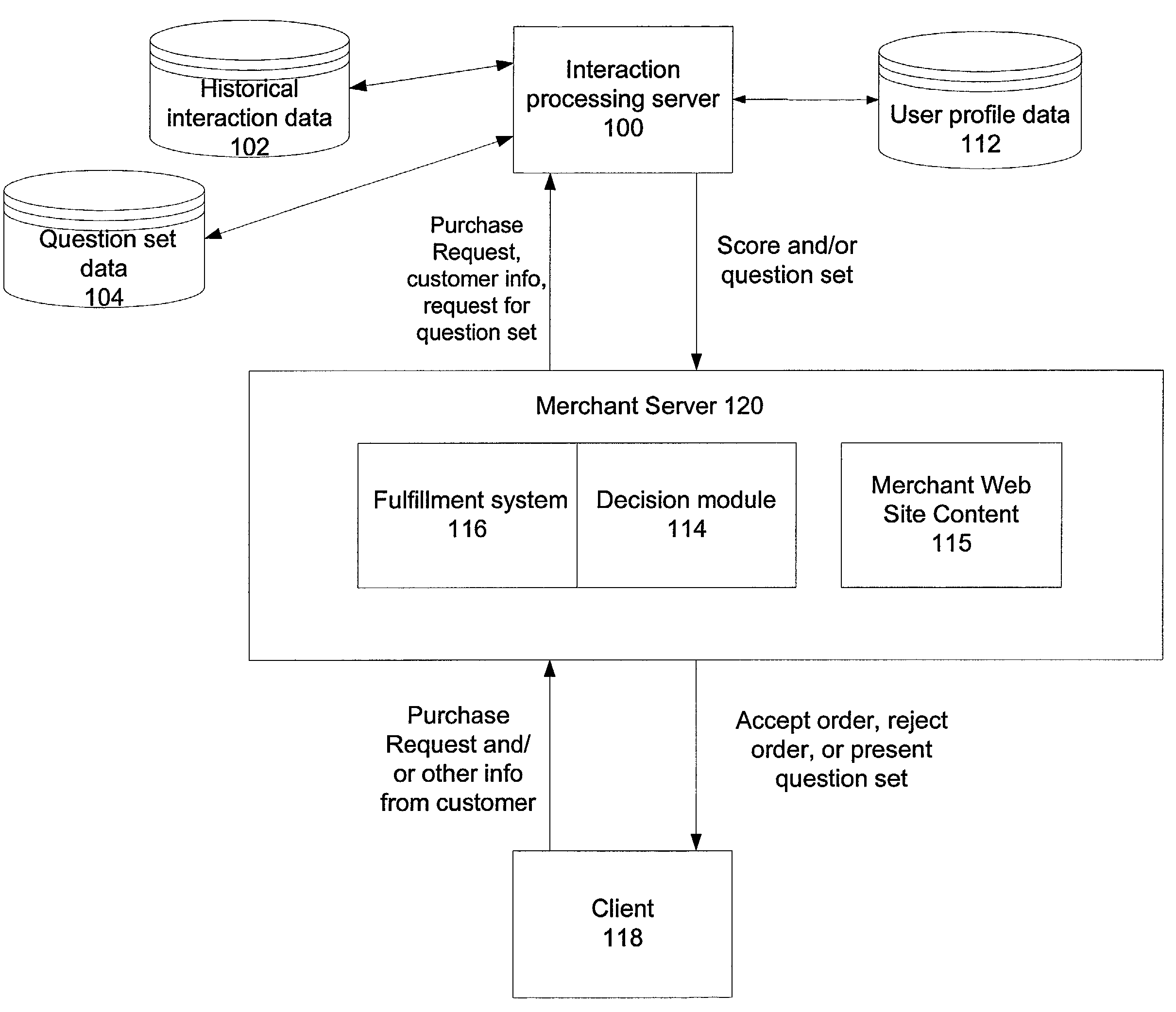
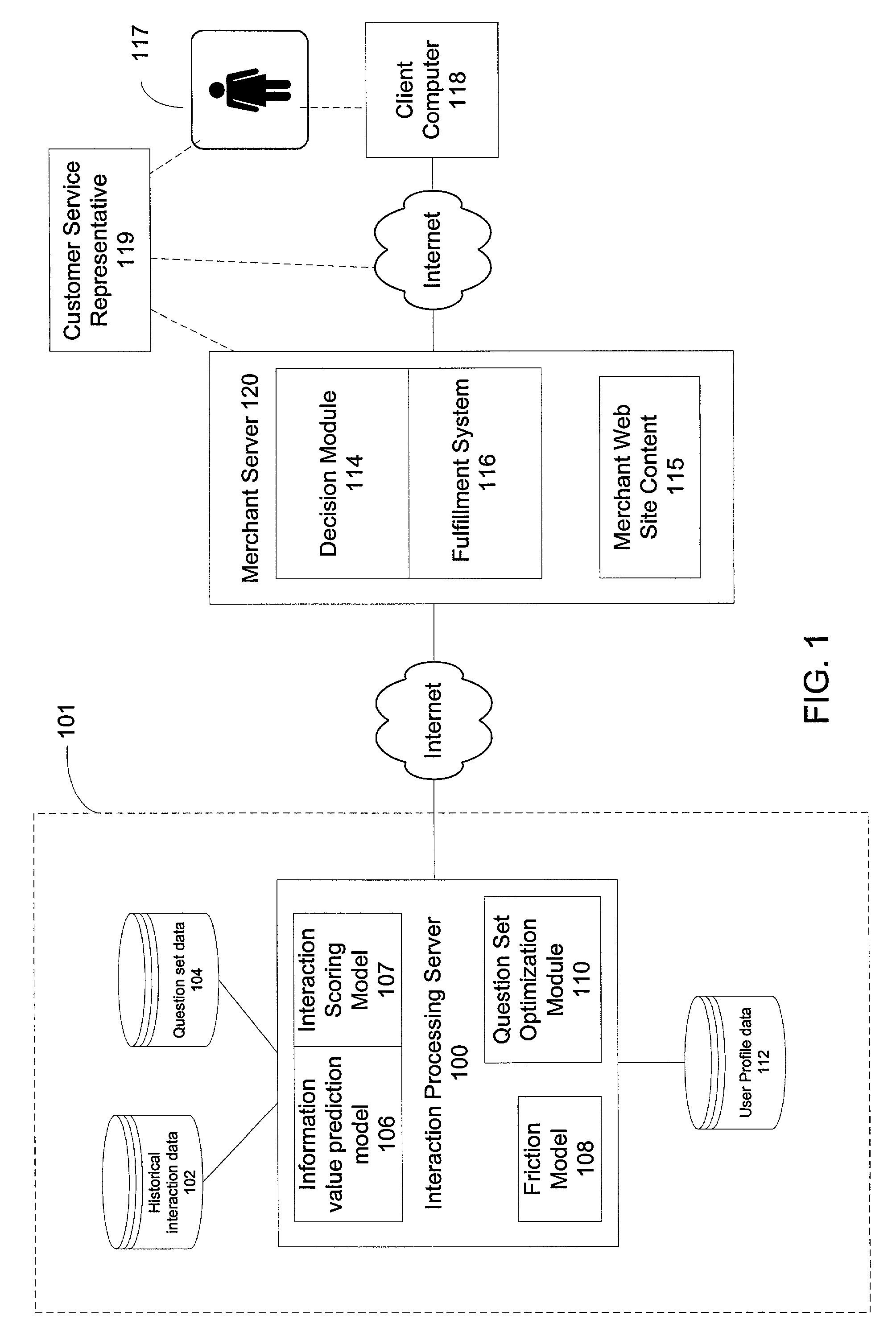
The invention aids an entity to selectively request additional data about a user to serve the needs of the entity without causing the user to have an adverse reaction. The invention helps an entity to determine the condition under which to request additional data so as to reduce the likelihood of causing the user to have an adverse reaction, e.g., terminate the interaction. One embodiment of the invention concerns customers requesting transactions with on-line merchants. More specifically, this embodiment aids merchants by detecting Internet credit card transactions that are likely to be fraudulent, and providing the merchants with mechanisms for managing a suspected transaction as it occurs to obtain additional information that can be useful to reducing the likelihood of fraud.
Owner:FAIR ISAAC & CO INC
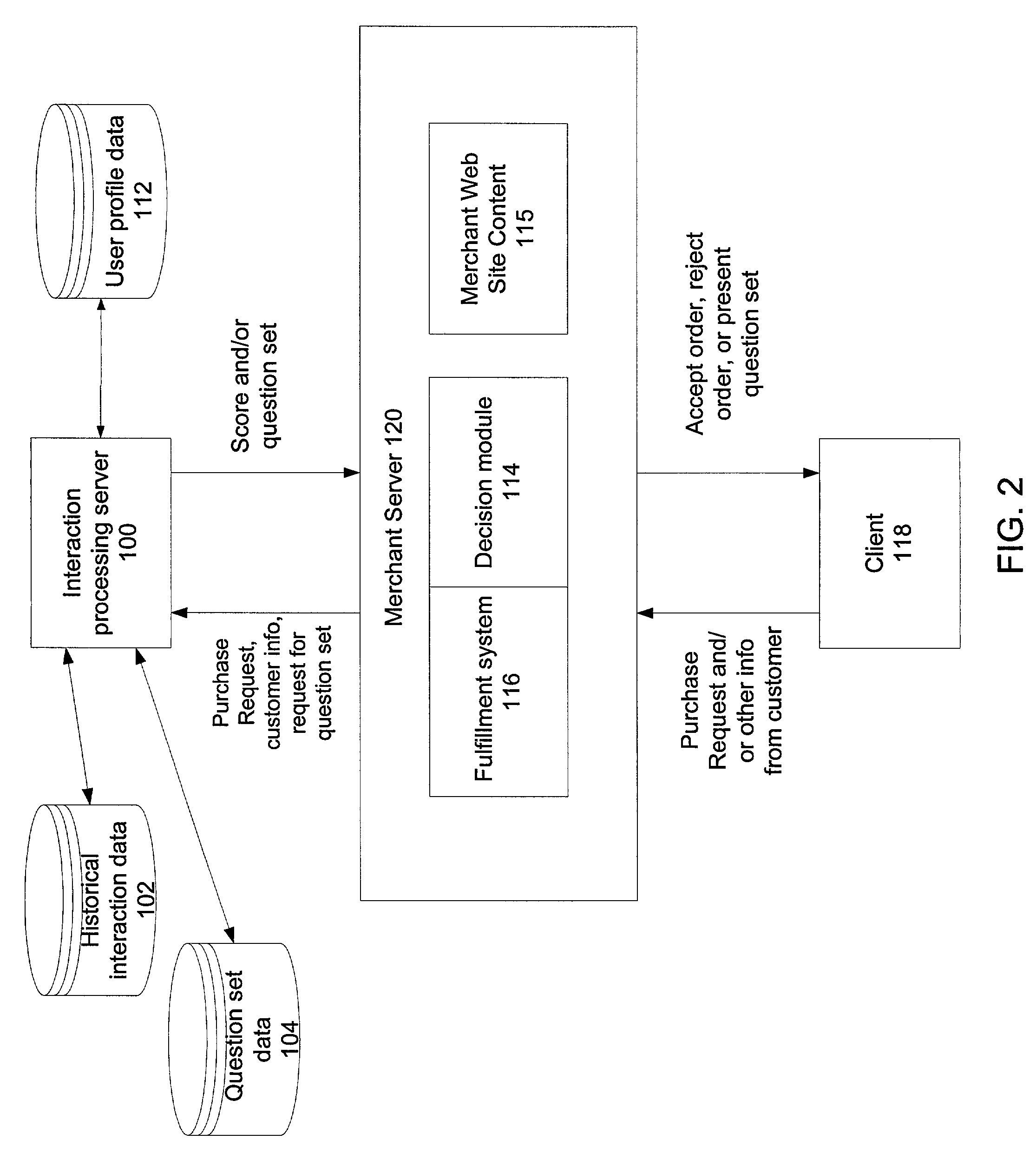
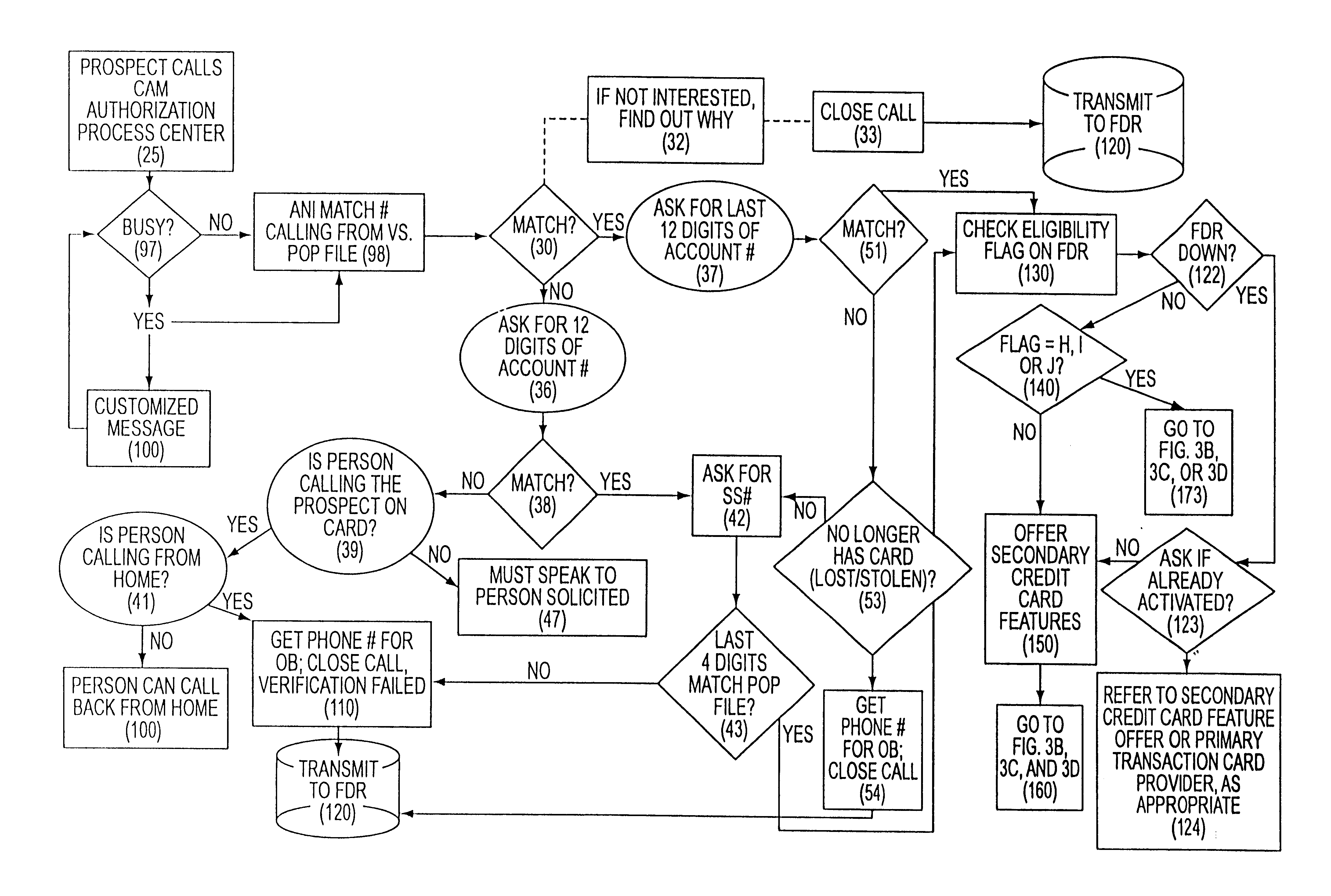
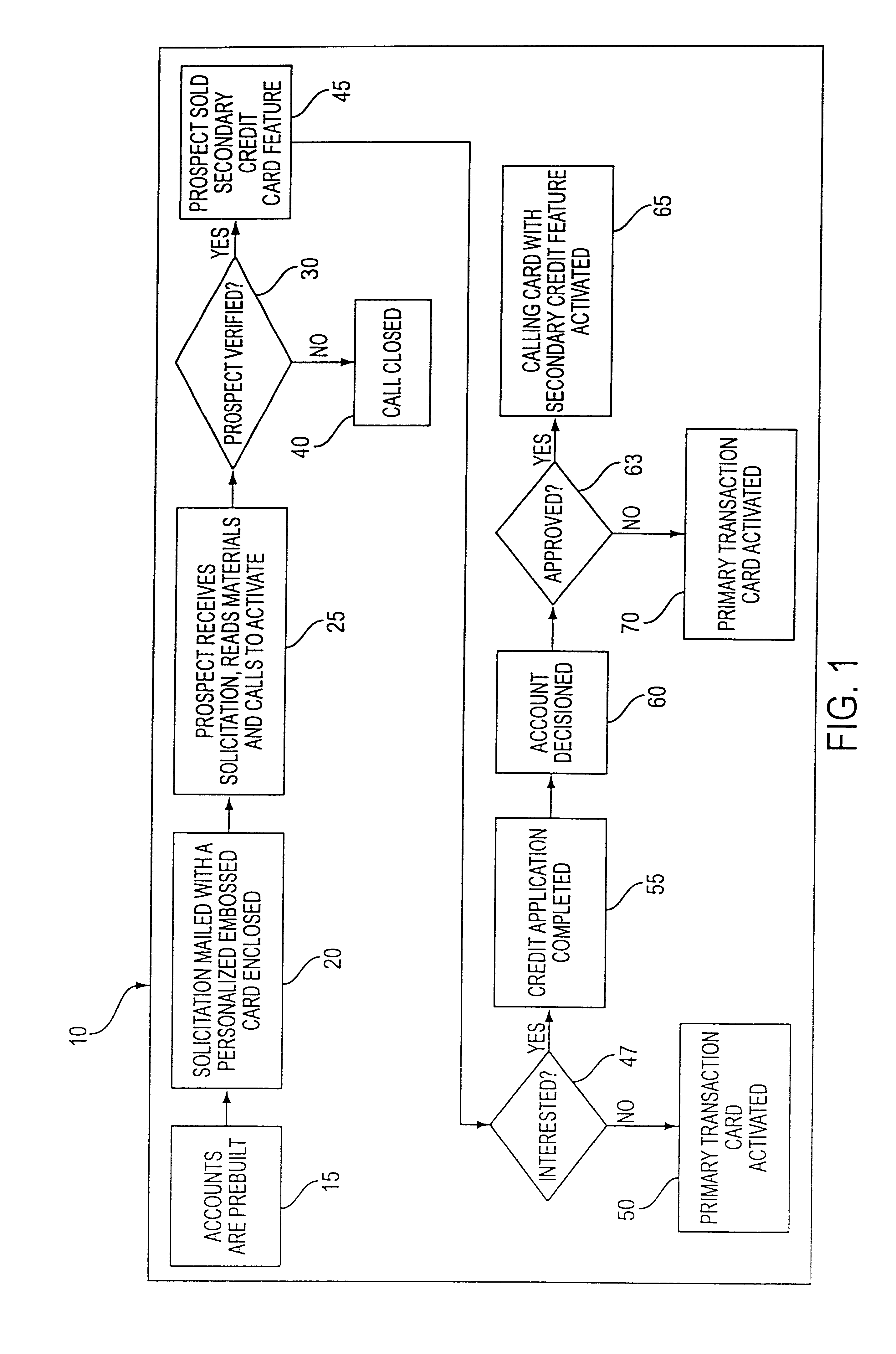
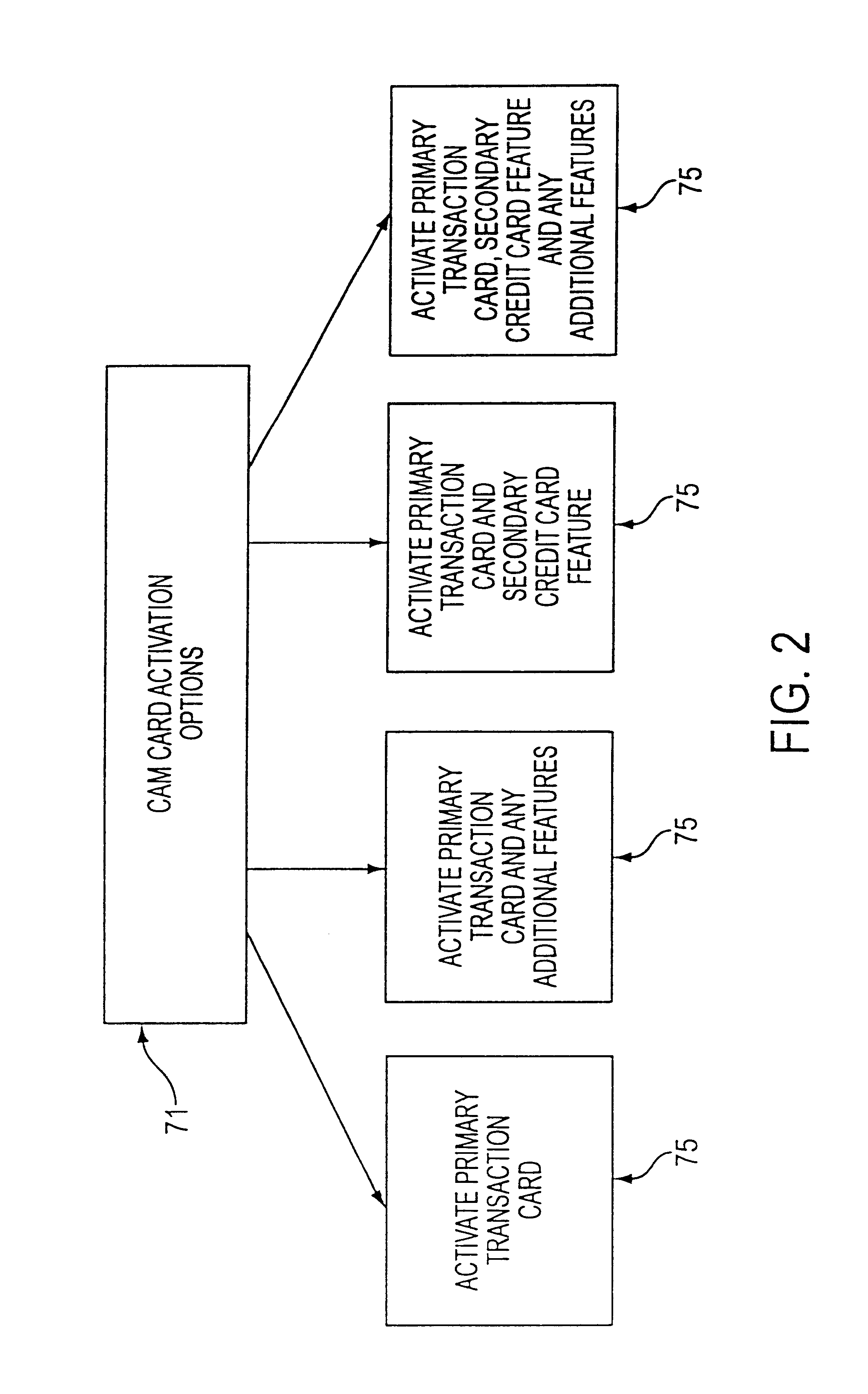
Customer activated multi-value (CAM) card
InactiveUS6865547B1Easy to useCredit registering devices actuationDiscounts/incentivesCredit cardGasoline
The Customer Activated Multi-Value (CAM) card provides a customer with a primary use as a transaction card which can be further activated to have a secondary use as a credit card. The CAM card can be activated as a transaction card or as a transaction card with a credit card feature. Activation of the CAM card as a transaction card allows the customer to purchase goods and services from one specific vendor and to establish a relationship with that vendor for the goods or services rendered (for example, telephone calling card or gasoline product purchasing card) while enjoying reward benefits based on those purchases. Activation of the credit feature of the card allows the customer to interact with any merchant that accepts traditional credit cards such as VISA®, MASTERCARD®, AMERICAN EXPRESS®, or DISCOVER®. The combination of features allows a customer to purchase various goods and services from several different merchants. If the customer chooses to activate the CAM card as both a transaction card and a credit card, the customer is given the benefit of using the card in both manners described above.
Owner:JPMORGAN CHASE BANK NA
Secure credit card
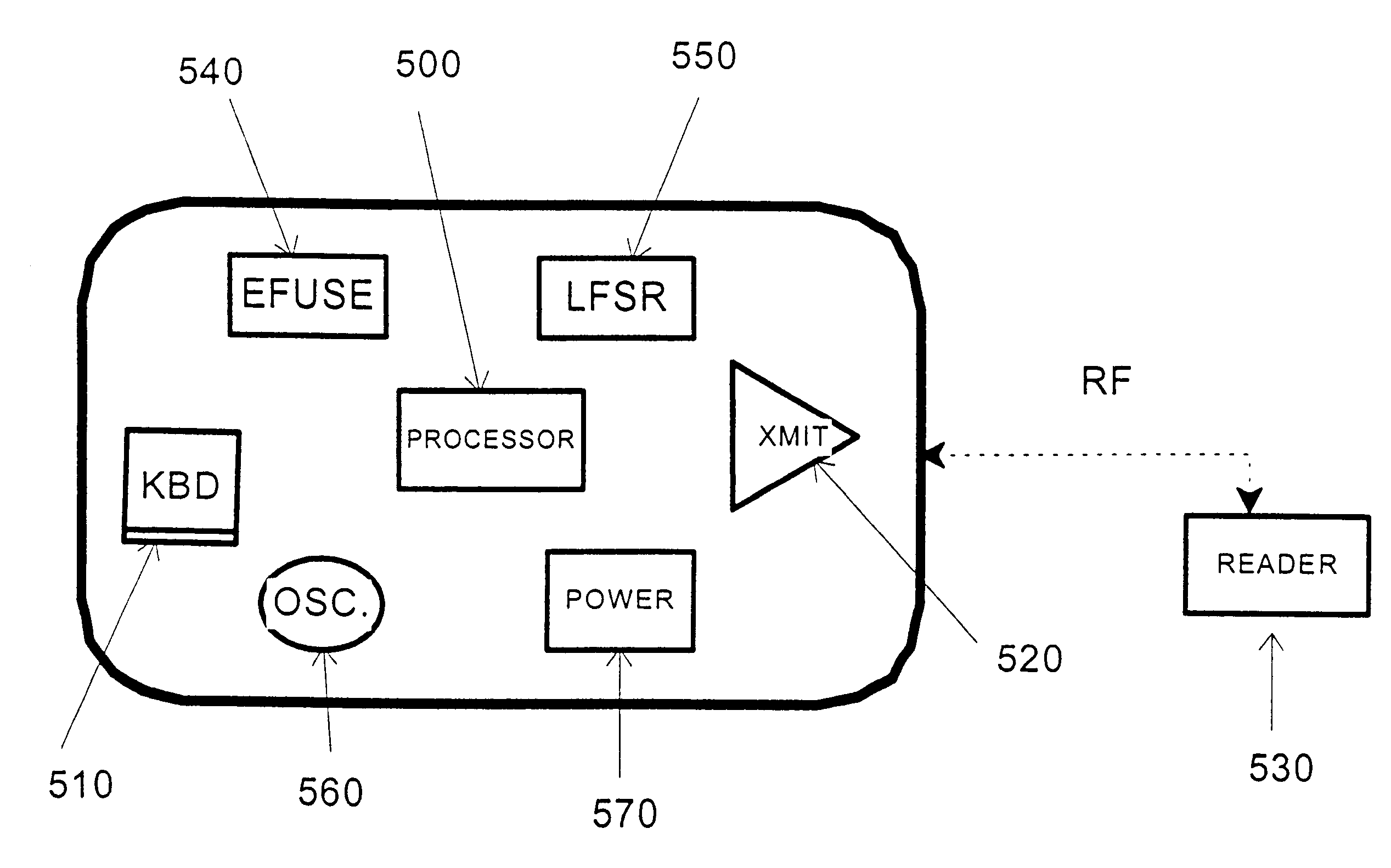
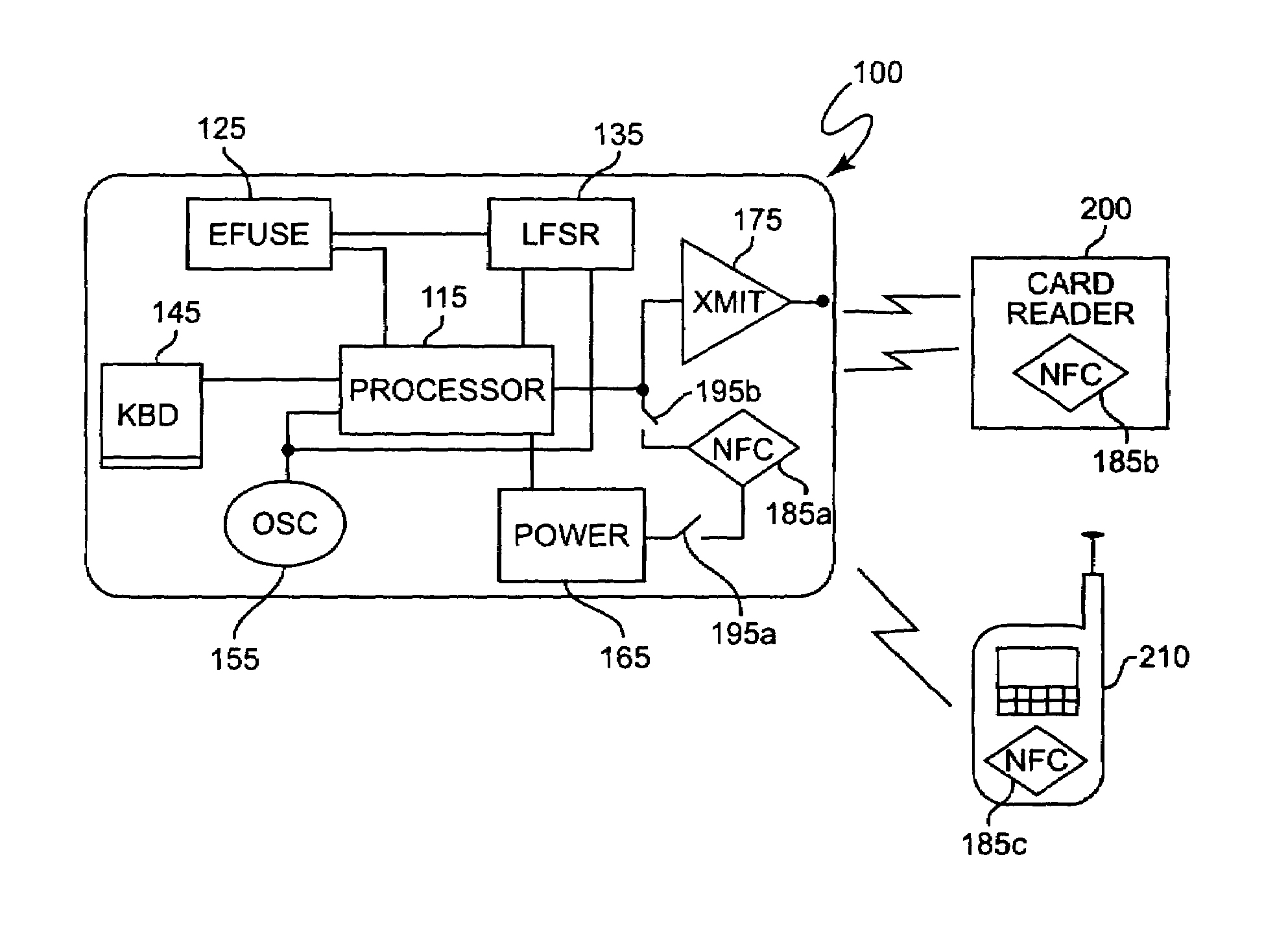
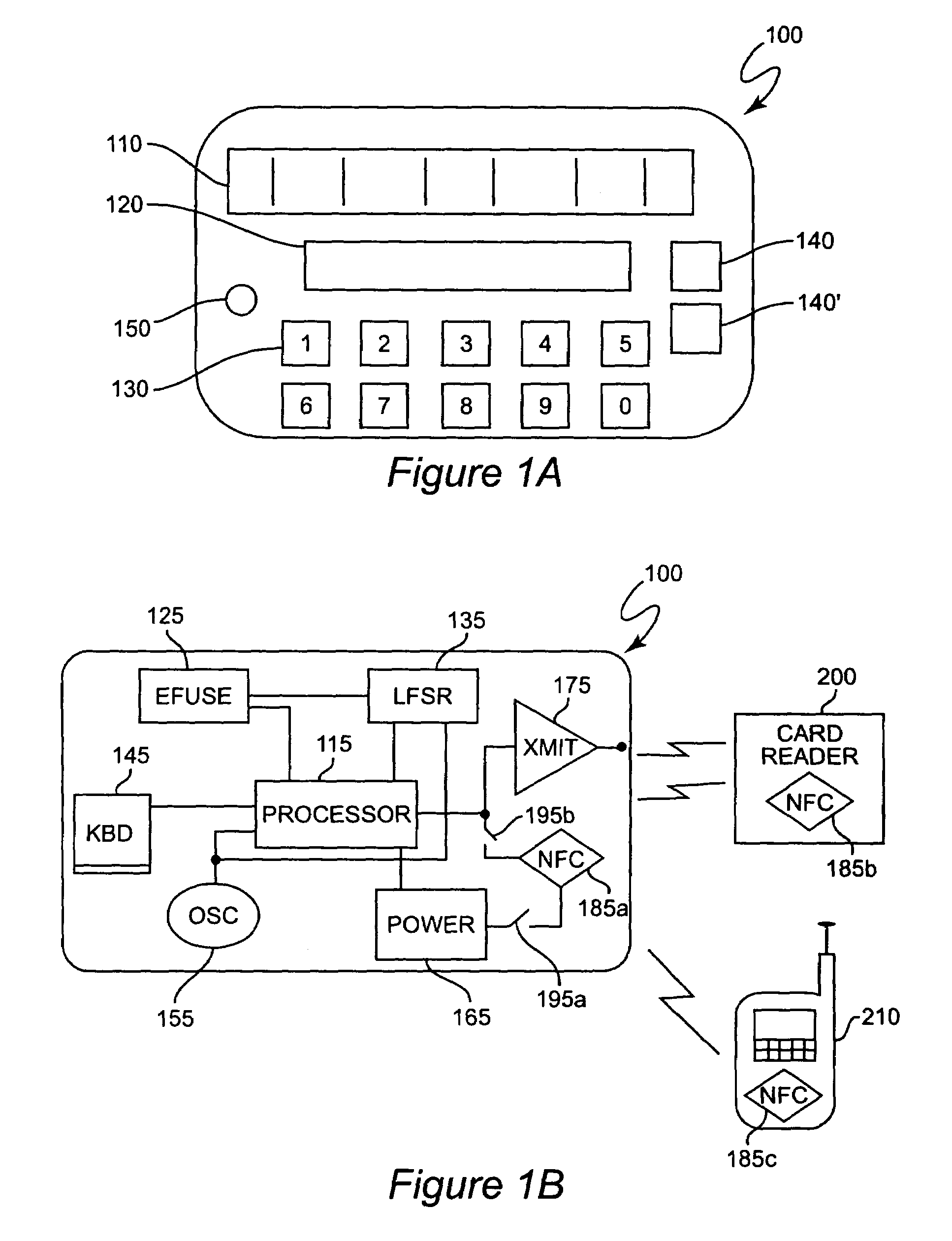
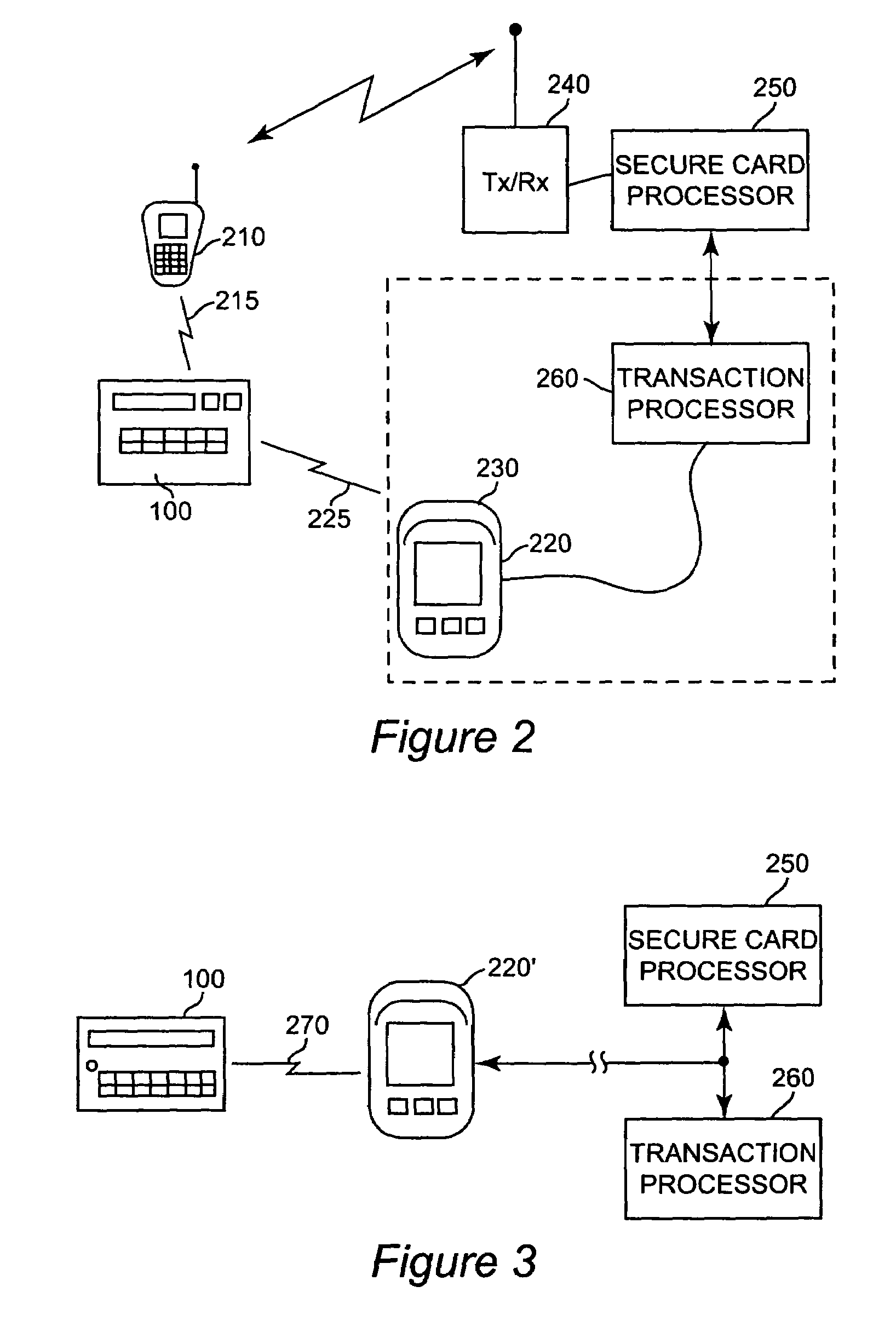
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with an LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo-random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card provide a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number permits the card owner to activate the card for a predetermined length of time while processing a transaction. The card dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
Method and system for using multi-function cards for storing, managing and aggregating reward points
InactiveUS20050021400A1Decreasing (if not eliminating) reliance on a central server systemDiscounts/incentivesFinanceCredit cardMultimedia
A system and method for operating a reward points accumulation and redemption program wherein a user earns reward points from a plurality of independent reward points issuing entities, with each tracking the user's earned reward points in a user reward point account stored on a multi-function card (such as a frequent flyer account or a credit card loyalty account). The multi-function card is adapted to aggregate some or all of the user's earned reward points from the reward accounts and credit the aggregated points into a single reward exchange account on the multi-function card. The user may then select an item for purchase with the accumulated reward points from the multi-function card. The item is provided to the user in exchange for a subset or all of the reward points from the multi-function card.
Owner:SIGNATURE SYST
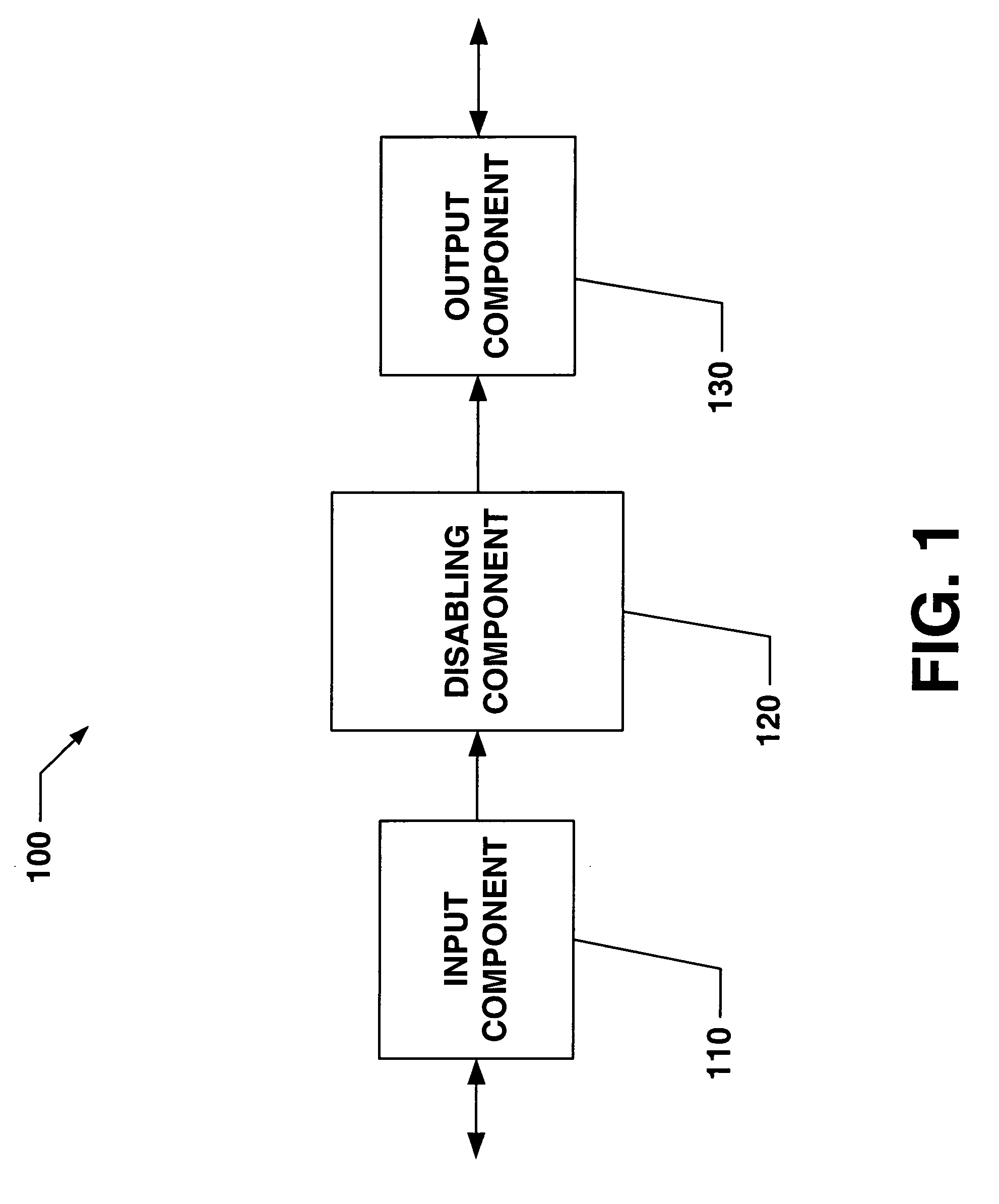
Systems and methods that provide user and/or network personal data disabling commands for mobile devices
InactiveUS20050186954A1Reduce harmPrevent unauthorized accessUnauthorised/fraudulent call preventionUnauthorized memory use protectionCredit cardInternet privacy
The present invention relates to systems and methods that employ various mechanisms to selectively disable mobile device functionality. In general, mobile devices can be utilized to store personal and / or highly sensitive information such as bank account numbers, social security numbers, credit card numbers and the like. If the mobile device is lost or stolen, data stored within the device can be accessed by an unauthorized user; and, thus, any personal and / or highly sensitive information can be obtained. In order to mitigate unauthorized access, the subject invention provides a disabling component that communicates with the lost or stolen device to render data stored thereon inaccessible. Further, the data can be stored in local or remote locations to backup stored information, thereby creating a more robust and reliable method of storing information important to the device owner. These features provide enhancements over conventional mobile device security techniques.
Owner:NOKIA CORP
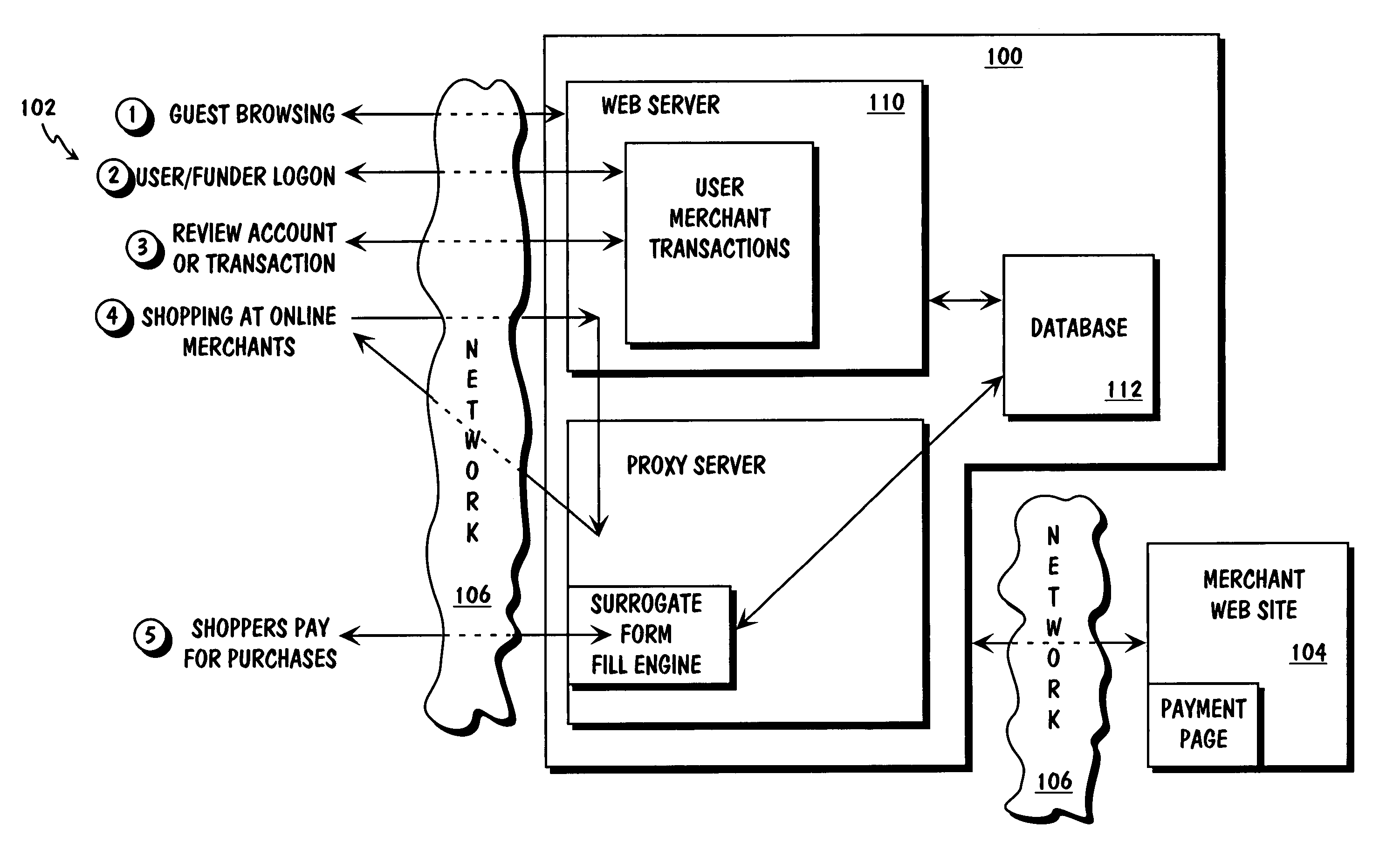
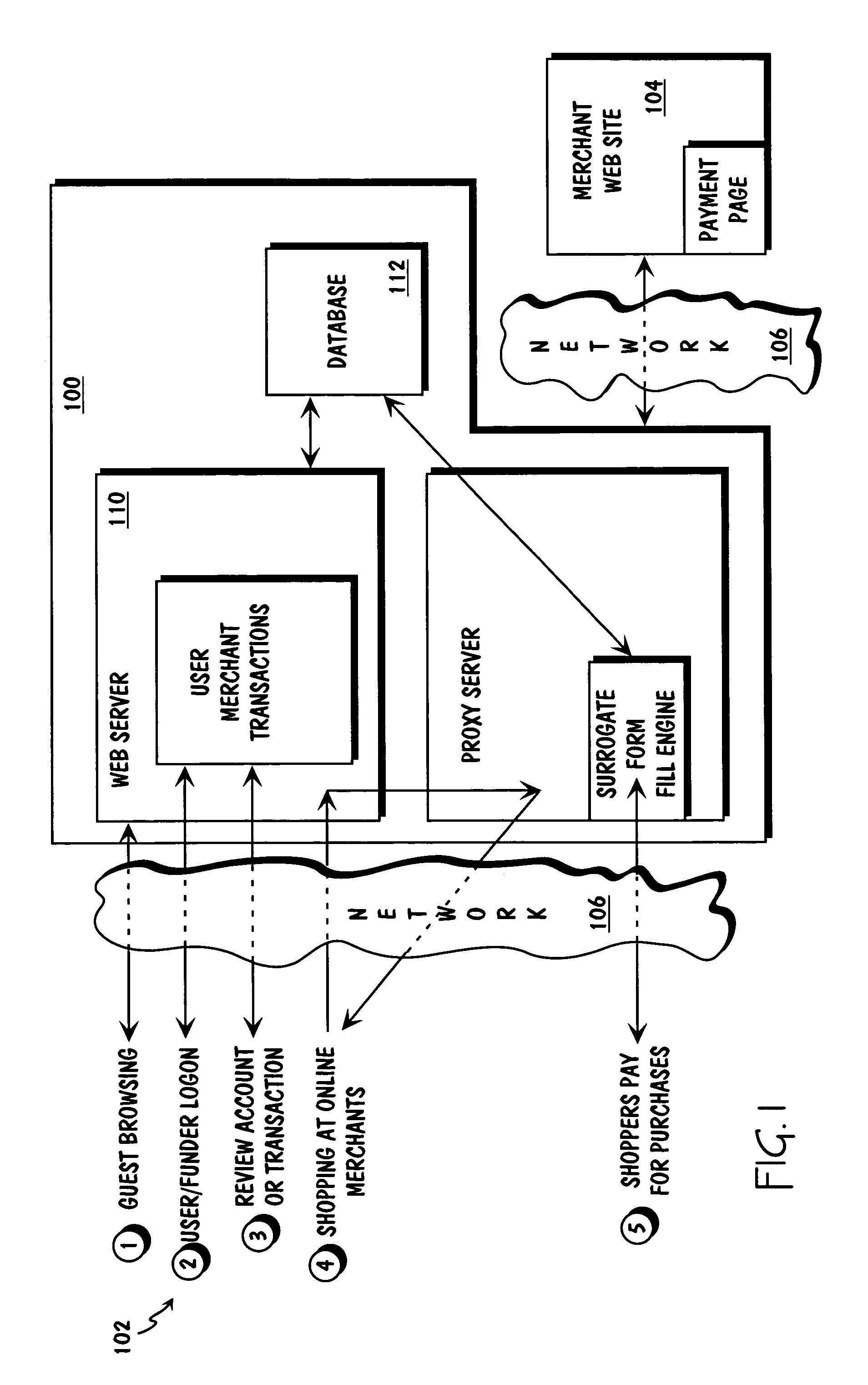
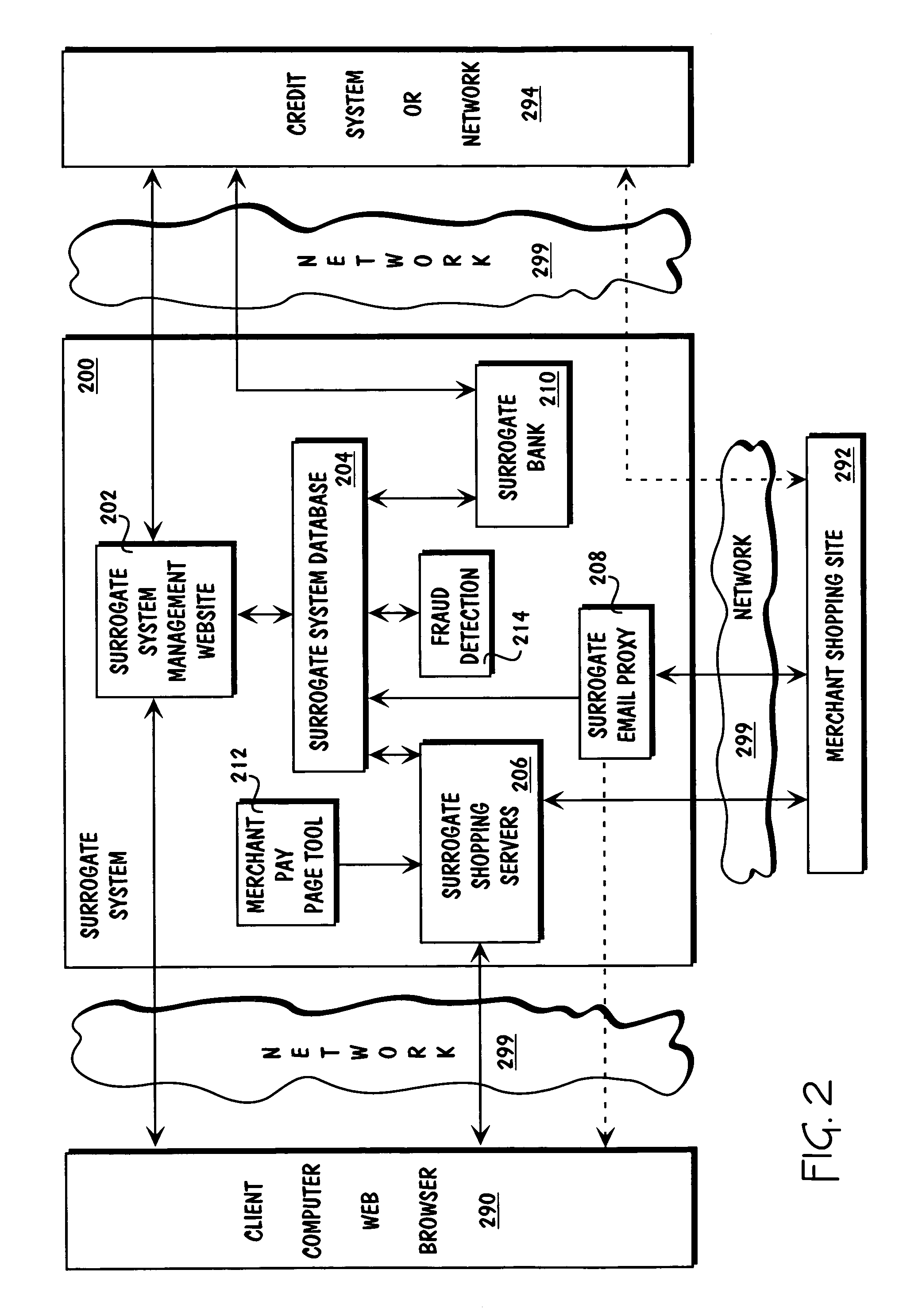
Method and apparatus for surrogate control of network-based electronic transactions
A surrogate system for the transparent control of electronic commerce transactions is provided through which an individual without a credit card is enabled to shop at online merchant sites. Upon opening an account within the surrogate system, the account can be funded using numerous fund sources, for example credit cards, checking accounts, money orders, gift certificates, incentive codes, online currency, coupons, and stored value cards. A user with a funded account can shop at numerous merchant web sites through the surrogate system. When merchandise is selected for purchase, a purchase transaction is executed in which a credit card belonging to the surrogate system is temporarily or permanently assigned to the user. The credit card, once loaded with funds from the user's corresponding funded account, is used to complete the purchase transaction. The surrogate system provides controls that include monitoring the data streams and, in response, controlling the information flow between the user and the merchant sites.
Owner:THE COCA-COLA CO
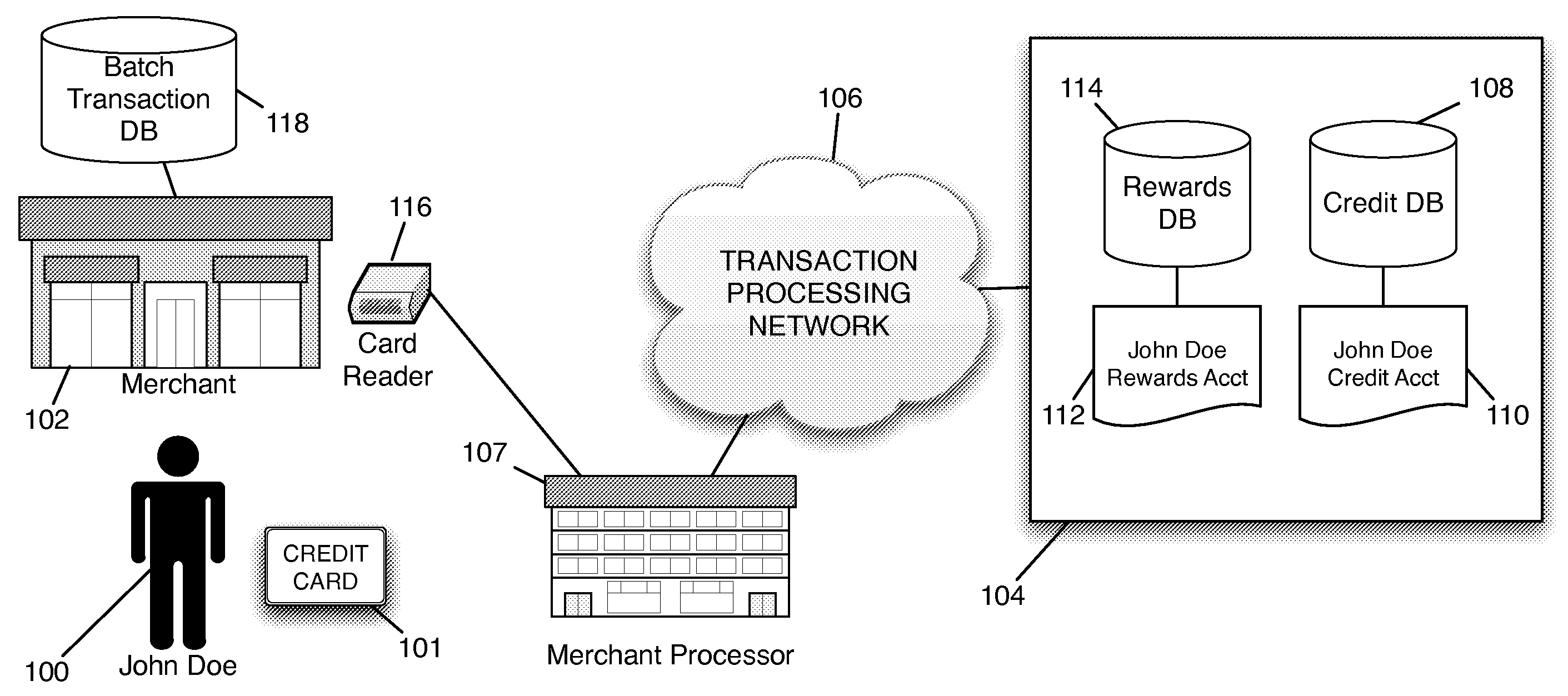
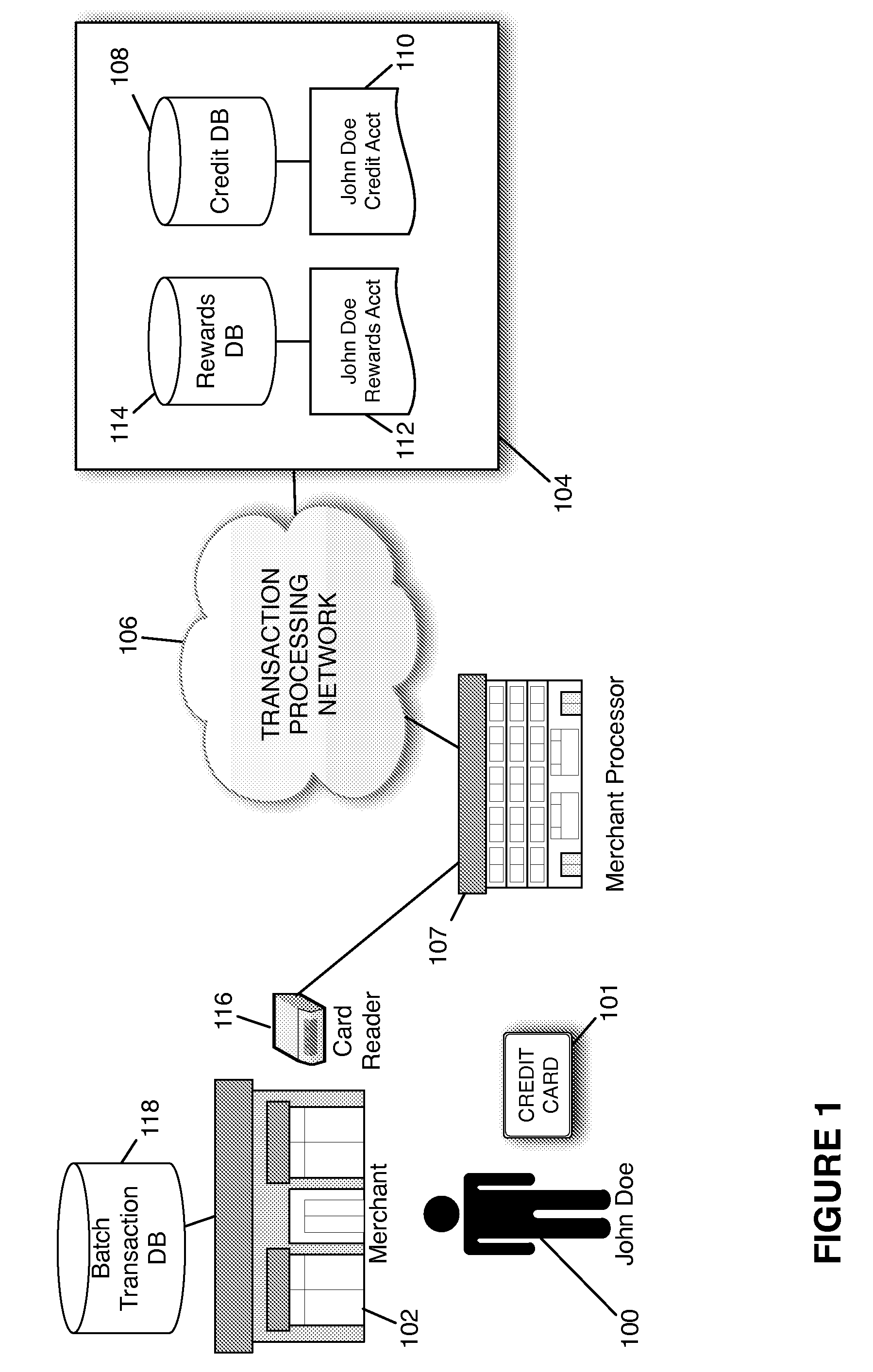
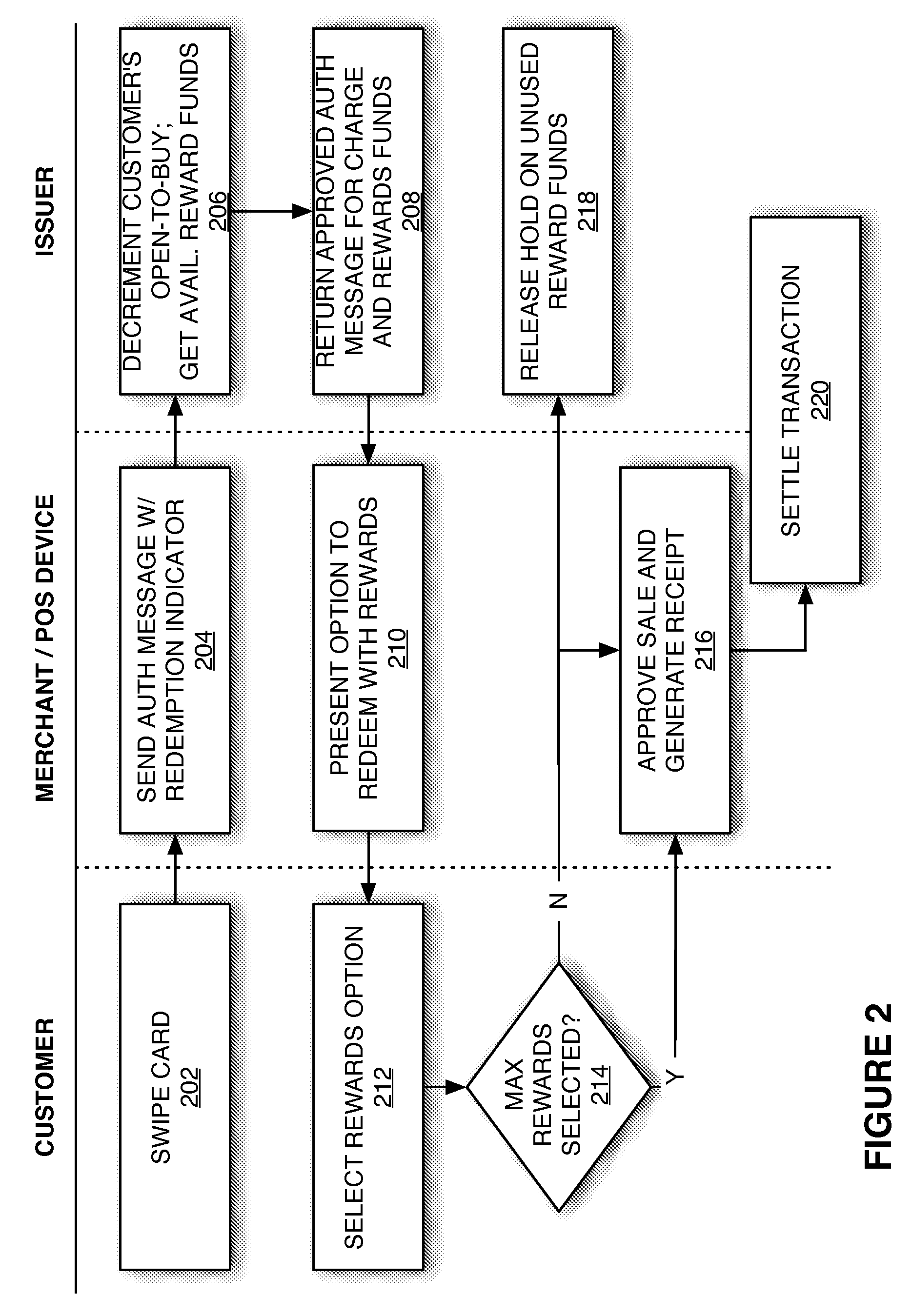
Redemption of Credit Card Rewards at a Point of Sale
Systems and methods are described for redeeming rewards at a merchant's point-of-sale. The reward redemption takes place in real time and can be accomplished without the active participation of the merchant. A single credit card with no additional information may be used with a single swipe from the consumer to access both credit and rewards accounts, such that a single authorization request is made to encompass both rewards and credit. Merchants can be fully compensated for transactions by the issuer despite the customer's choice to redeem rewards.
Owner:DFS SERVICES
Credit cards system and method having additional features
InactiveUS20090037333A1Complete banking machinesCredit registering devices actuationCredit cardComputer hardware
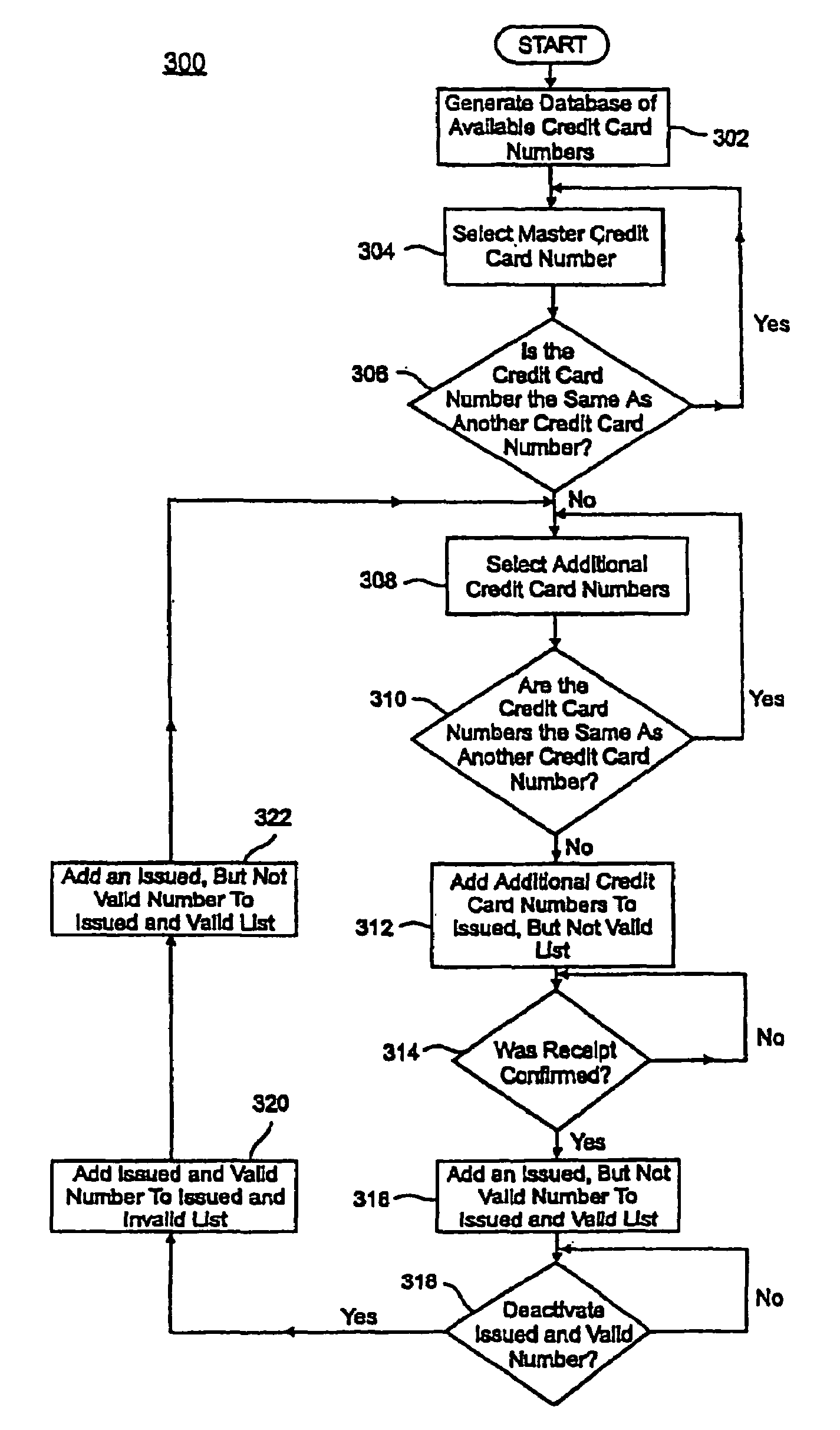
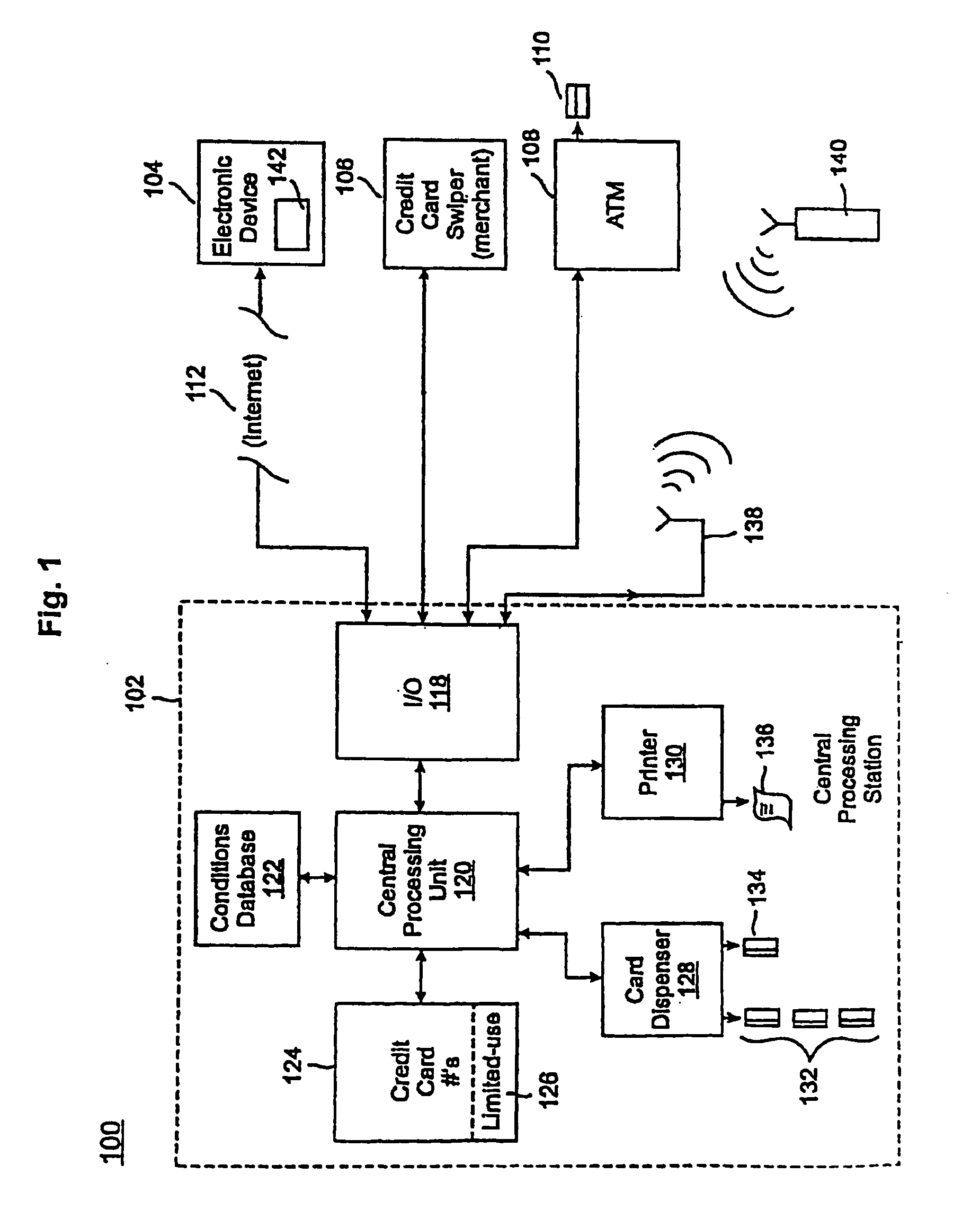
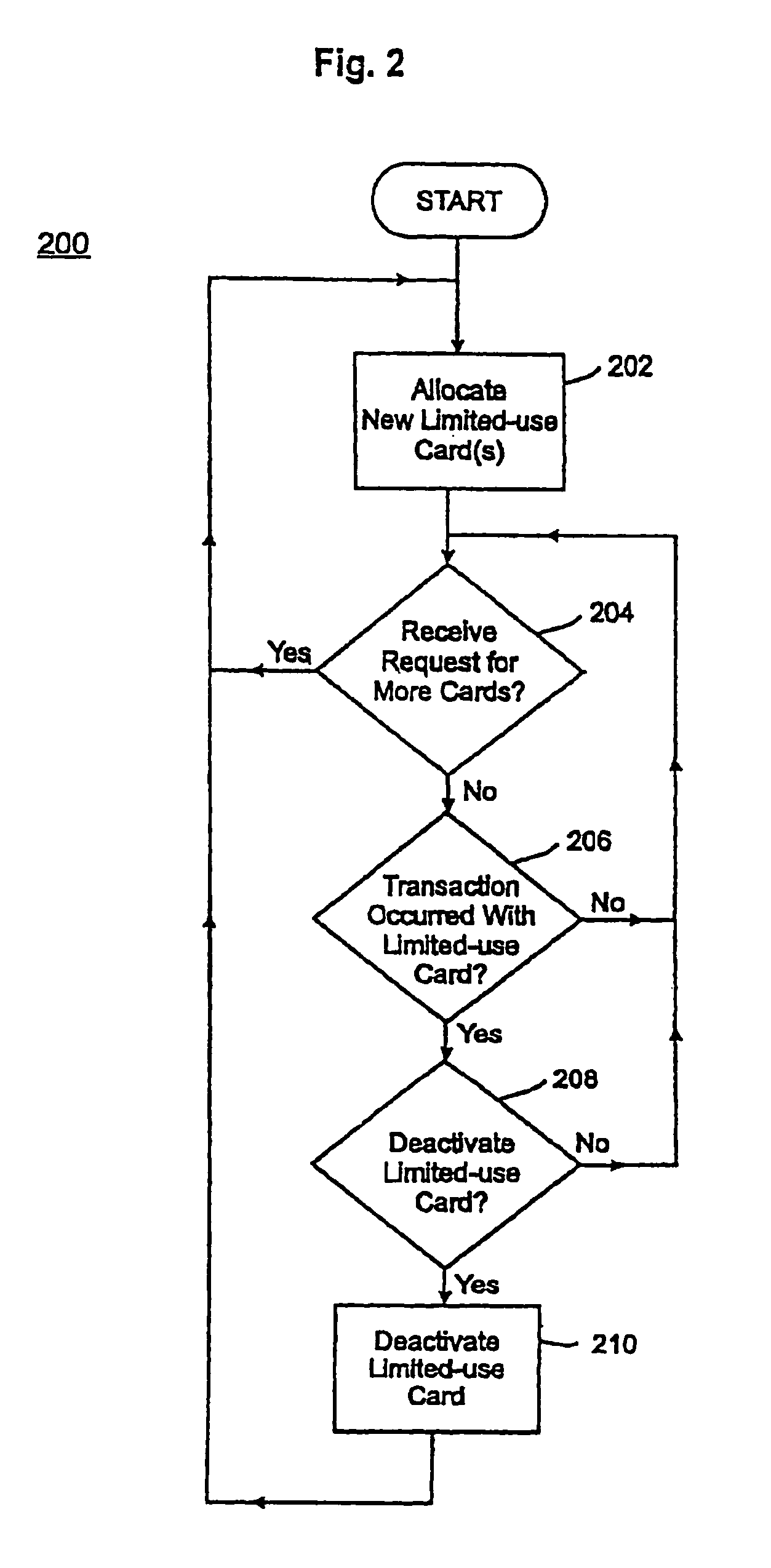
A credit card system is provided which has the added feature of providing additional limited use credit card numbers and / or cards. These numbers and / or cards can be used for a single or limited use transaction, thereby reducing the potential for fraudulent reuse of these numbers and / or cards. The credit card system finds application to “card remote” transactions such as by phone or Internet. Additionally, when a single use or limited use credit card is used for “card present” transactions, so called “skimming” fraud is eliminated. Various other features enhance the credit card system, which will allow secure trade without the use of elaborate encryption techniques. Methods for limiting, distributing and using a limited use card number, controlling the validity of a limited use credit card number, conducting a limited use credit card number transaction and providing remote access devices for accessing a limited use credit card number are also provided.
Owner:ORBIS PATENTS
Method for implementing anonymous credit card transactions using a fictitious account name
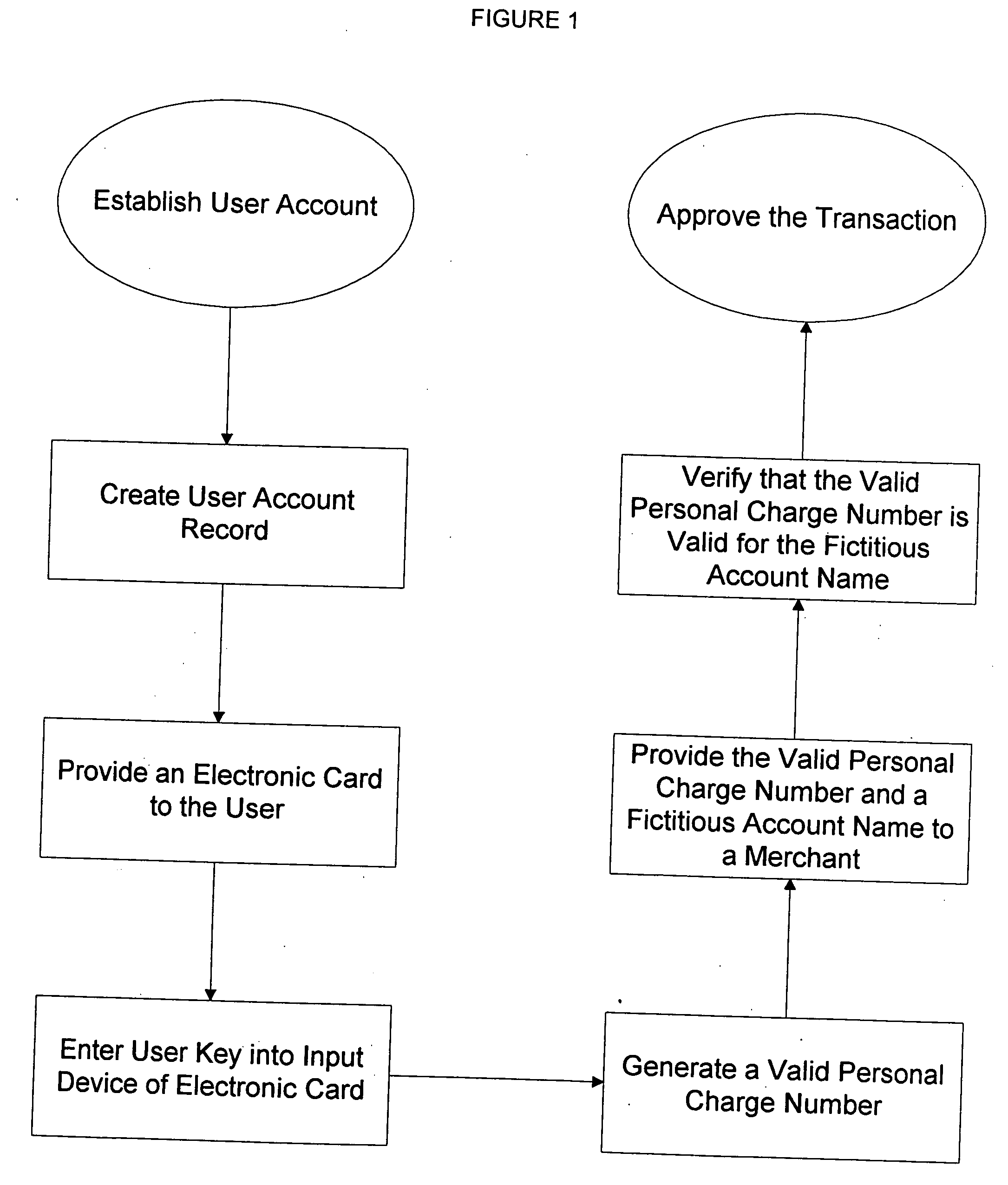
InactiveUS20050086160A1Electric signal transmission systemsDigital data processing detailsCredit cardInternet privacy
A method for implementing an anonymous face to face or Mail Order Telephone Order credit card transaction by a user who has established a user account associated with a fictitious name. The user generates a valid personal charge number by executing an algorithm in a computer affixed to the electronic credit card that uses a user key and a card number as input variables. A merchant is provided with the valid personal charge number and the fictitious name that is submitted for approval to a credit approval center. The electronic credit card is sized such that a standard magnetic stripe reader can read it.
Owner:WONG JACOB Y +1
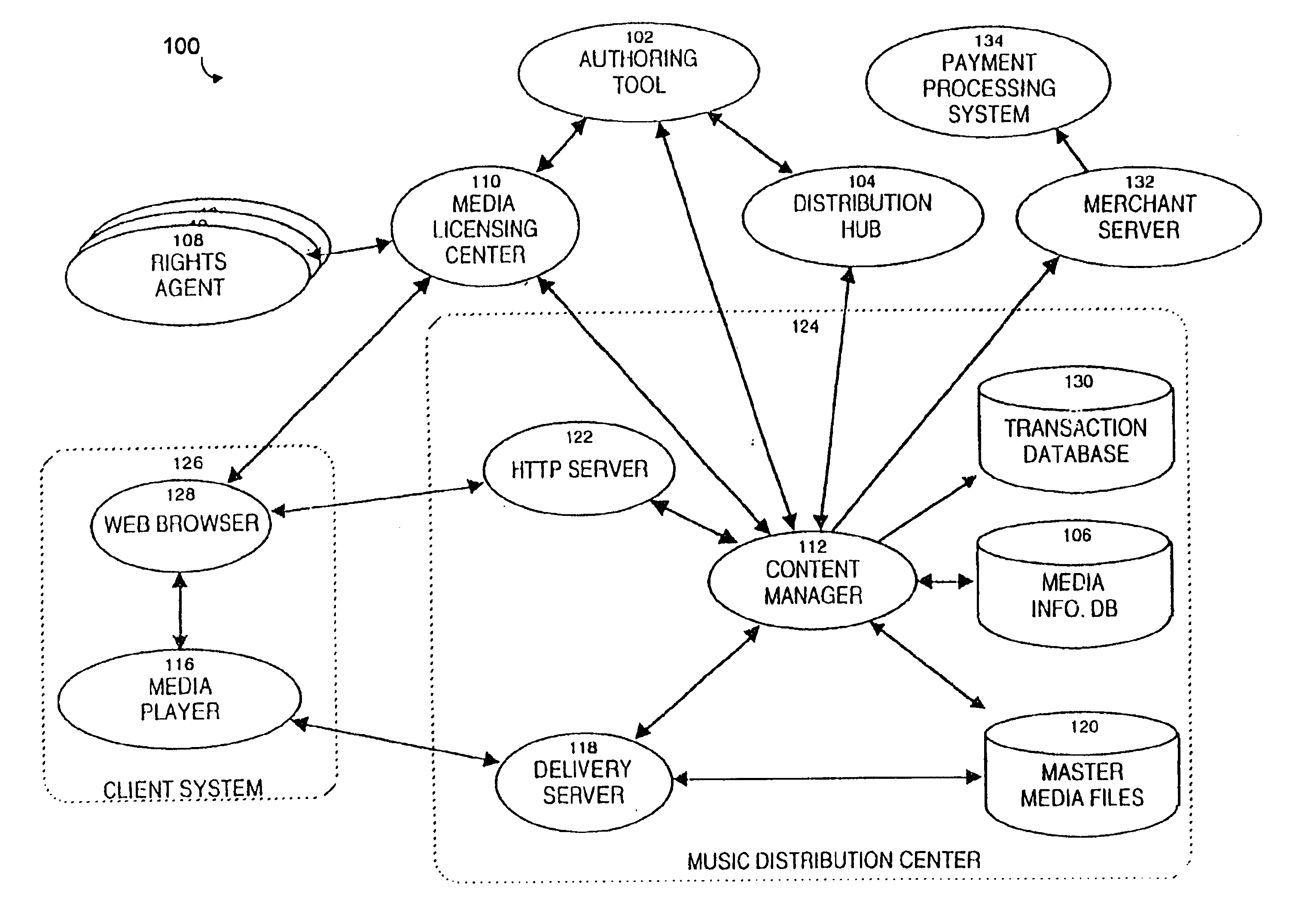
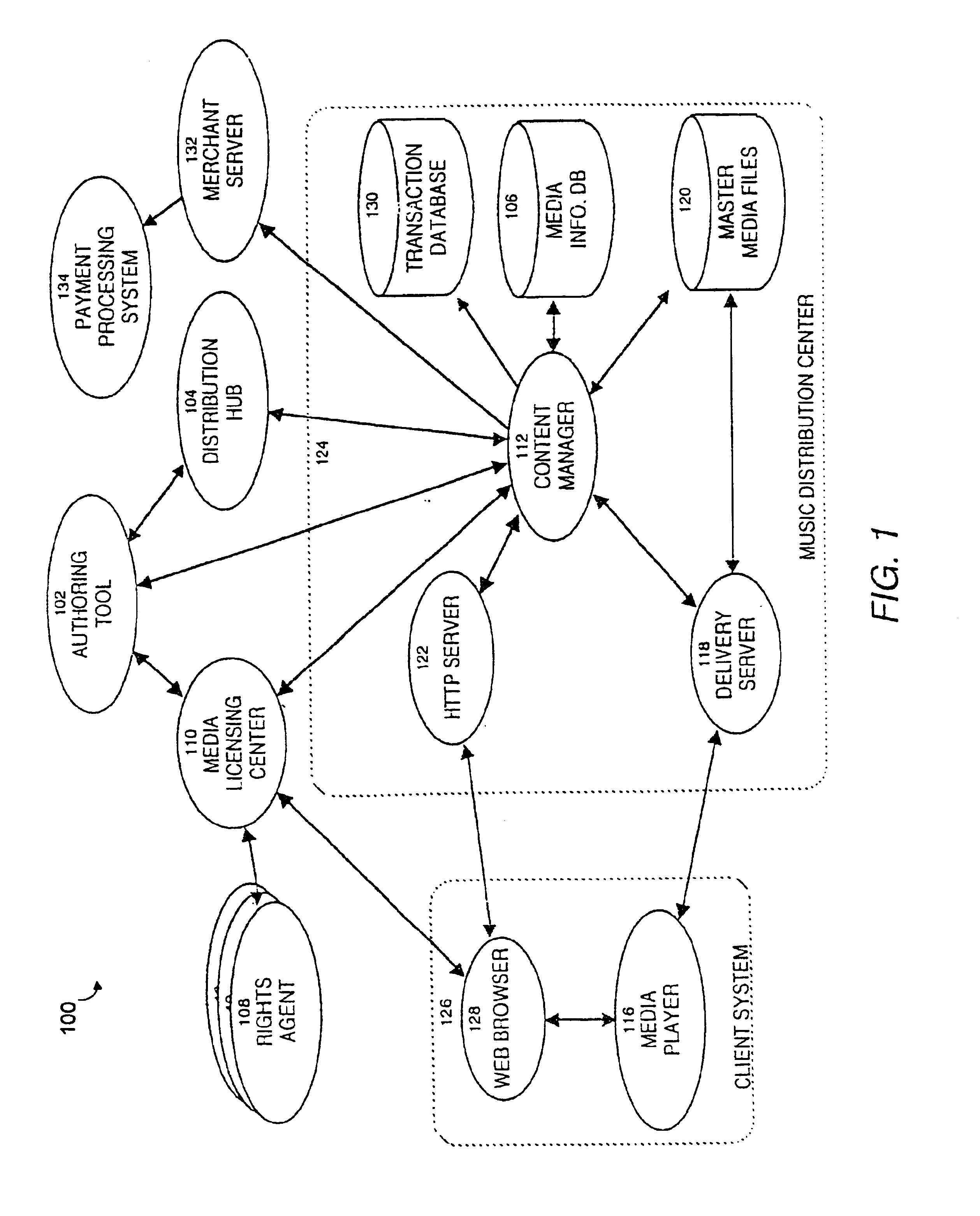
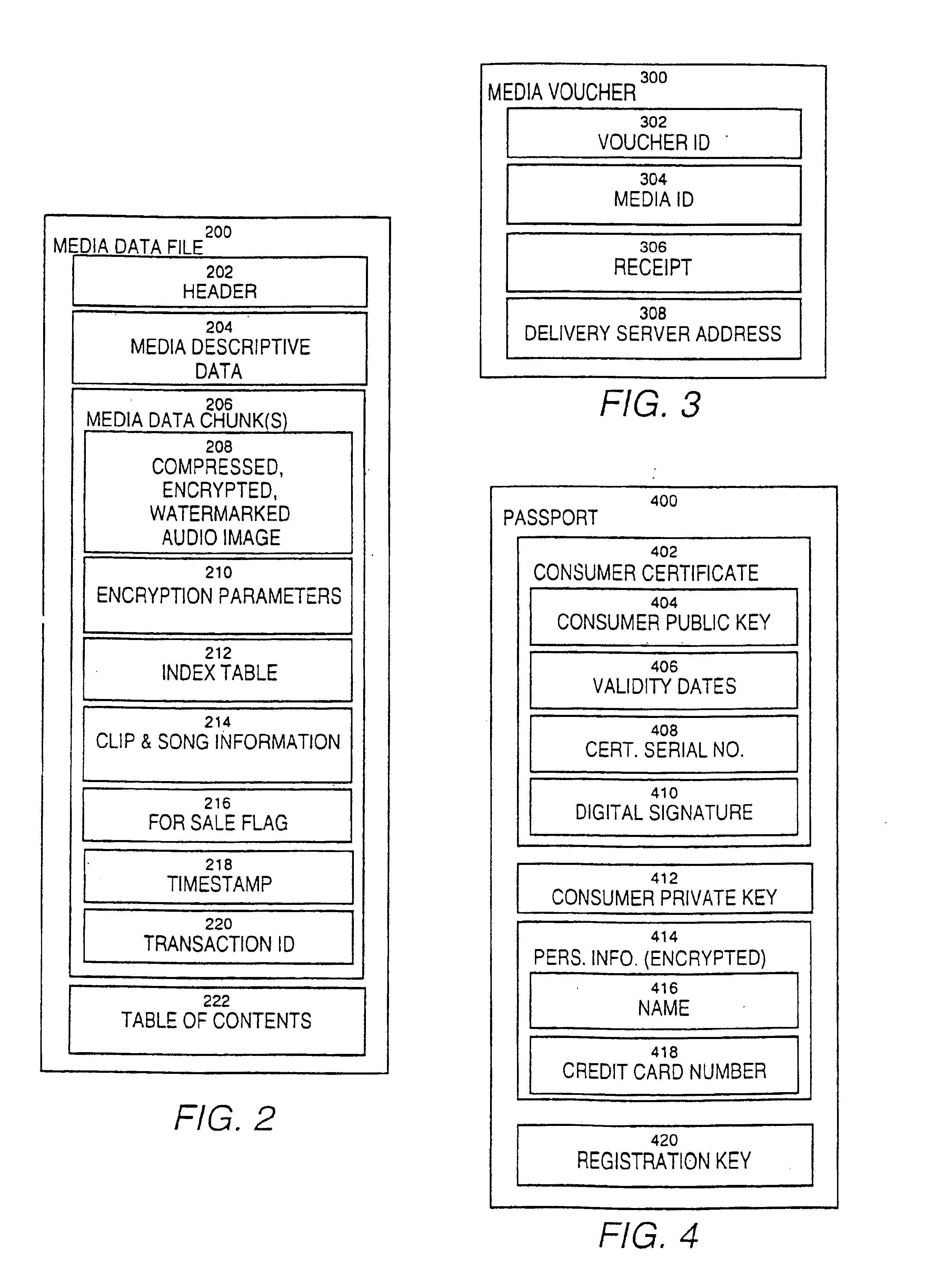
Secure online music distribution system
InactiveUS6868403B1Ease of useFlexibilityReservationsPayment architectureCredit cardClient server systems
A computer implemented online music distribution system provides for the secure delivery of audio data and related media, including text and images, over a public communications network. The online music distribution system provides security through multiple layers of encryption, and the cryptographic binding of purchased audio data to each specific purchaser. The online music distribution system also provides for previewing of audio data prior to purchase. In one embodiment, the online music distribution system is a client-server system including a content manager, a delivery server, and an HTTP server, communicating with a client system including a Web browser and a media player. The content manager provides for management of media and audio content, and processing of purchase requests. The delivery server provides delivery of the purchased media data. The Web browser and HTTP server provide a communications interface over the public network between the content manager and media players. The media player provides for encryption of user personal information, and for decryption and playback of purchased media data. Security of purchased media data is enhanced in part by the use of a personal, digital passport in each media player. The digital passport contains identifying information that identifies the purchaser, along with confidential information, such as credit card number, and encryption data, such as the media player's public and private keys. The media player encryption data is used to encrypt purchased media data, which is decrypted in real time by the media player. The media player also displays confidential information, such as the purchaser's credit card number, during playback.
Owner:MICROSOFT TECH LICENSING LLC
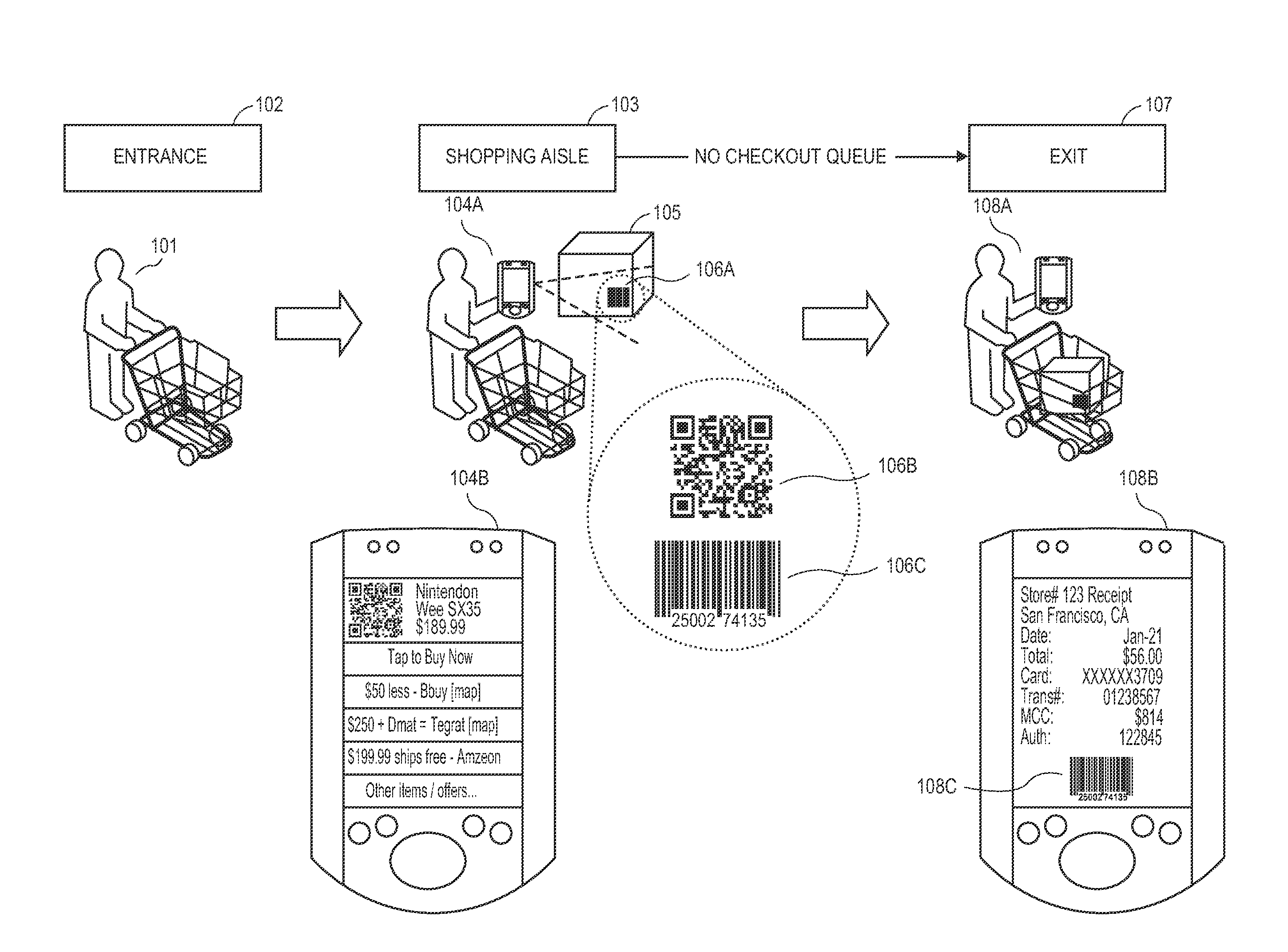
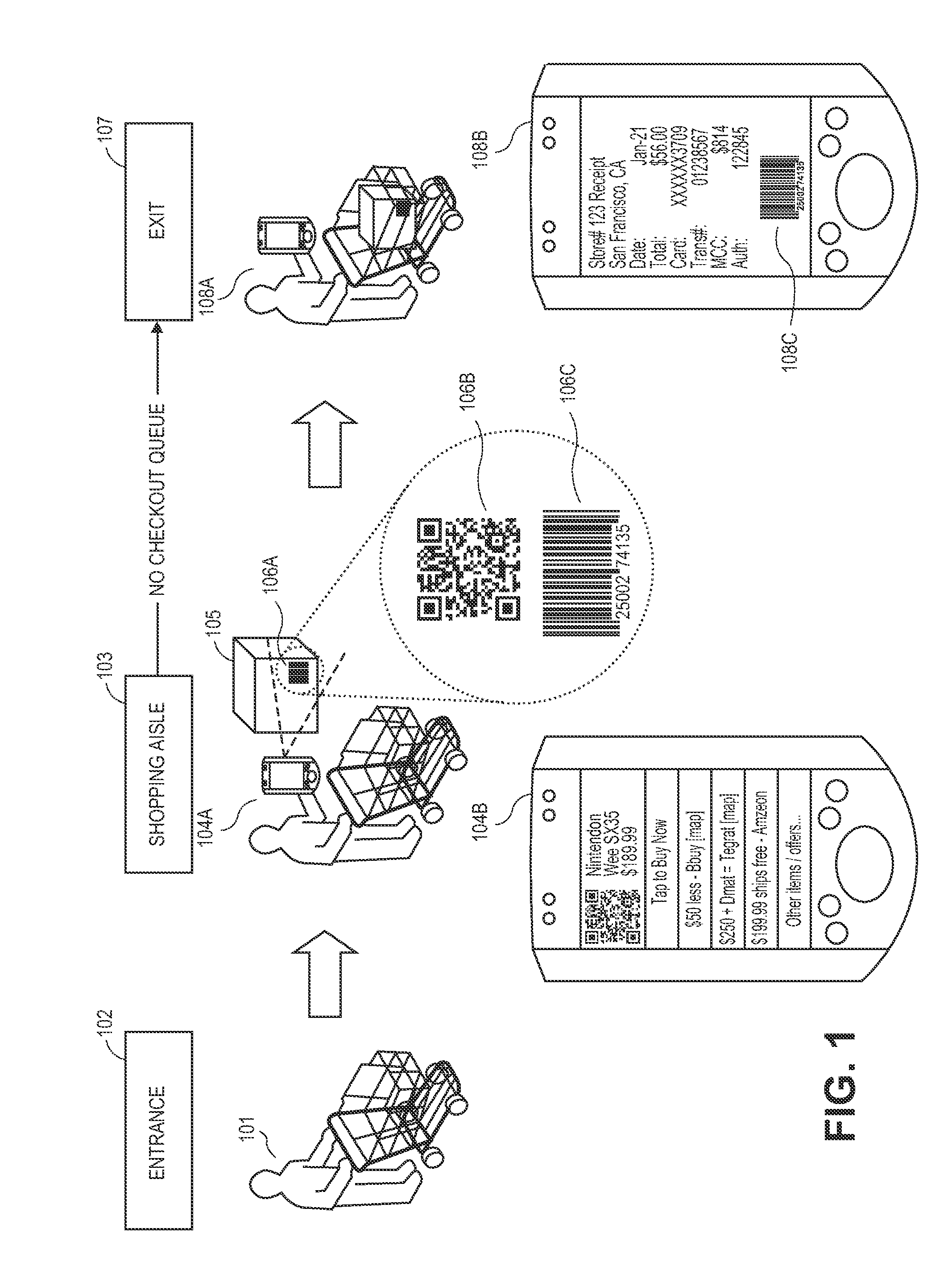
In-person one-tap purchasing apparatuses, methods and systems
Methods, systems, and devices are disclosed for transforming product code snapshots into real-time, offer-driven electronic purchase transaction notifications that minimize fraud. In one embodiment, a smart phone scans a product identifier from a product package, a server accesses a products database for product purchase offers associated with the product identifier, a user authorizes a credit card from his or her wallet to charge, and then product purchase offers or other credit card offers (for loyalty points or otherwise) are provided to the user mobile device. After a user has purchased an item while in the aisle of the store, the user's smart phone displays a barcoded electronic receipt that can be scanned by the exit so that the consumer can walk out with the produce. In some embodiments, a video chat is requested by a customer service representative and a transaction risk score is lowered based on acceptance of the video chat.
Owner:VISA INT SERVICE ASSOC
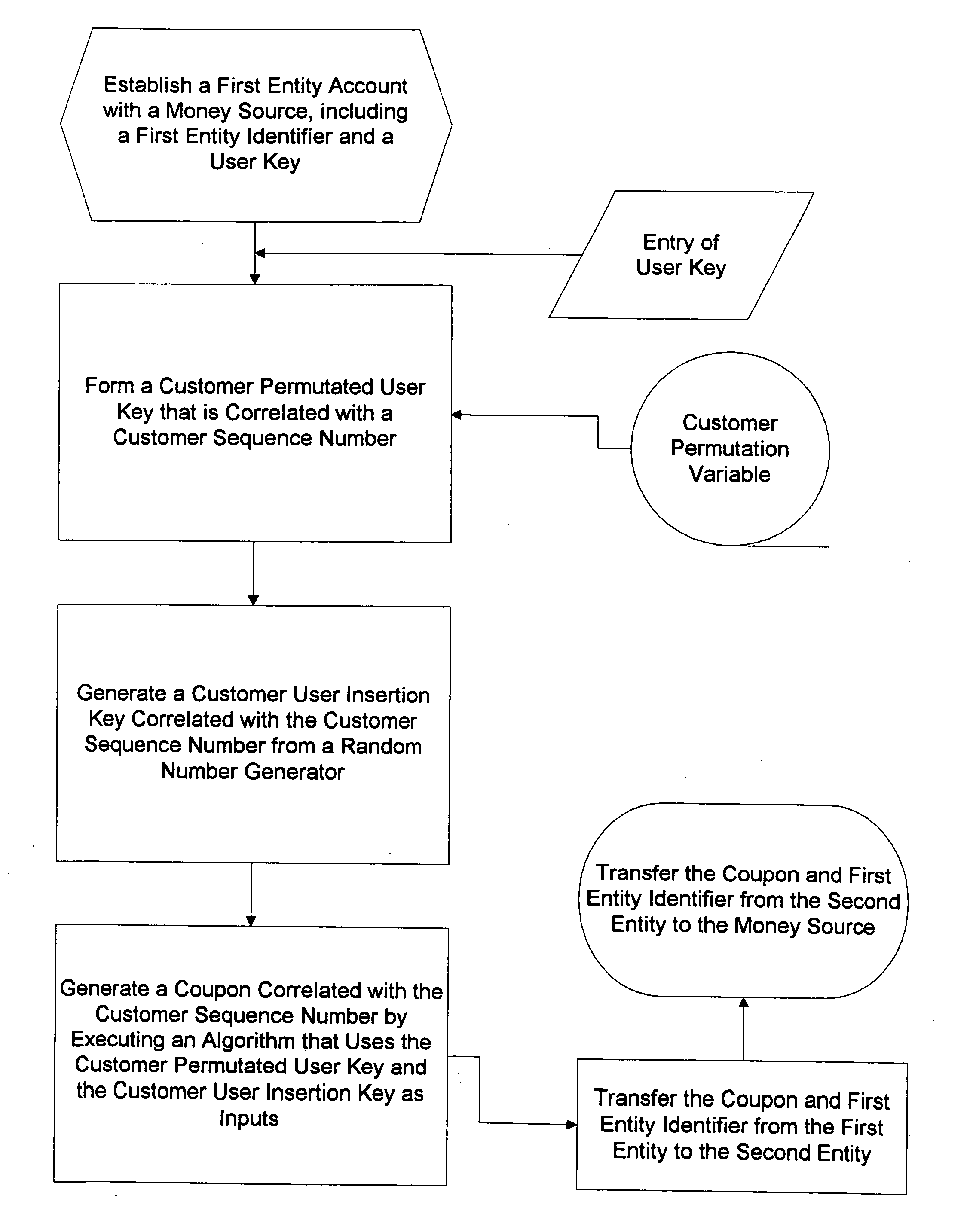
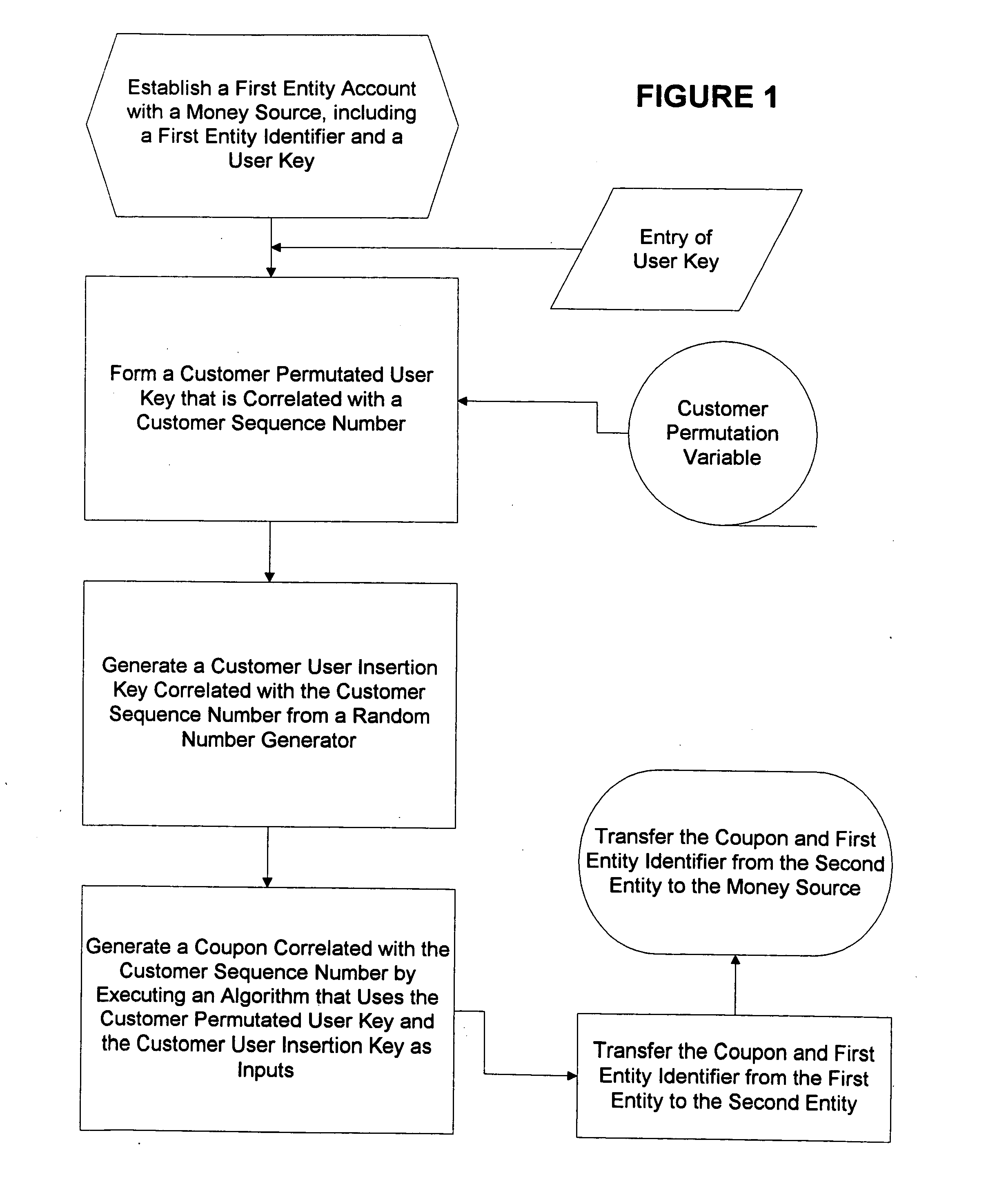
Method for generating customer one-time unique purchase order numbers
InactiveUS20050080747A1Anonymous user systemsRecord carriers used with machinesCredit cardPersonal identification number
Multiple secure transactions are provided through use of a method that uses customer one-time unique purchase order numbers (“Coupons”) generated by an algorithm that uses a permutated user key and a user insertion key as input variables. A user key (such as a Personal Identification Number, or “PIN”) is combined with a permutation variable that is correlated with a customer sequence number to create the permutated user key. A random number generator is used to generate the user insertion key correlated with the customer sequence number. The algorithm can insert the permutated user key into a user account number through use of the user insertion key. A Coupon is validated by confirming that it is contained in a set of money source Coupons generated by a money source using the user key and a random number generator that is synchronized with the random number used to generate Coupons. Once a Coupon is validated, the matching money source Coupon and all earlier generated money source Coupons are deleted from the set, and a new set is generated. If a preselected number of Coupons are not validated for a chosen entity, an invalid user account number will be set. Coupons can be used for credit card or bank card transactions, and they can be generated without changing fixed digits of traditional twenty digit account numbers.
Owner:PRIVASYS
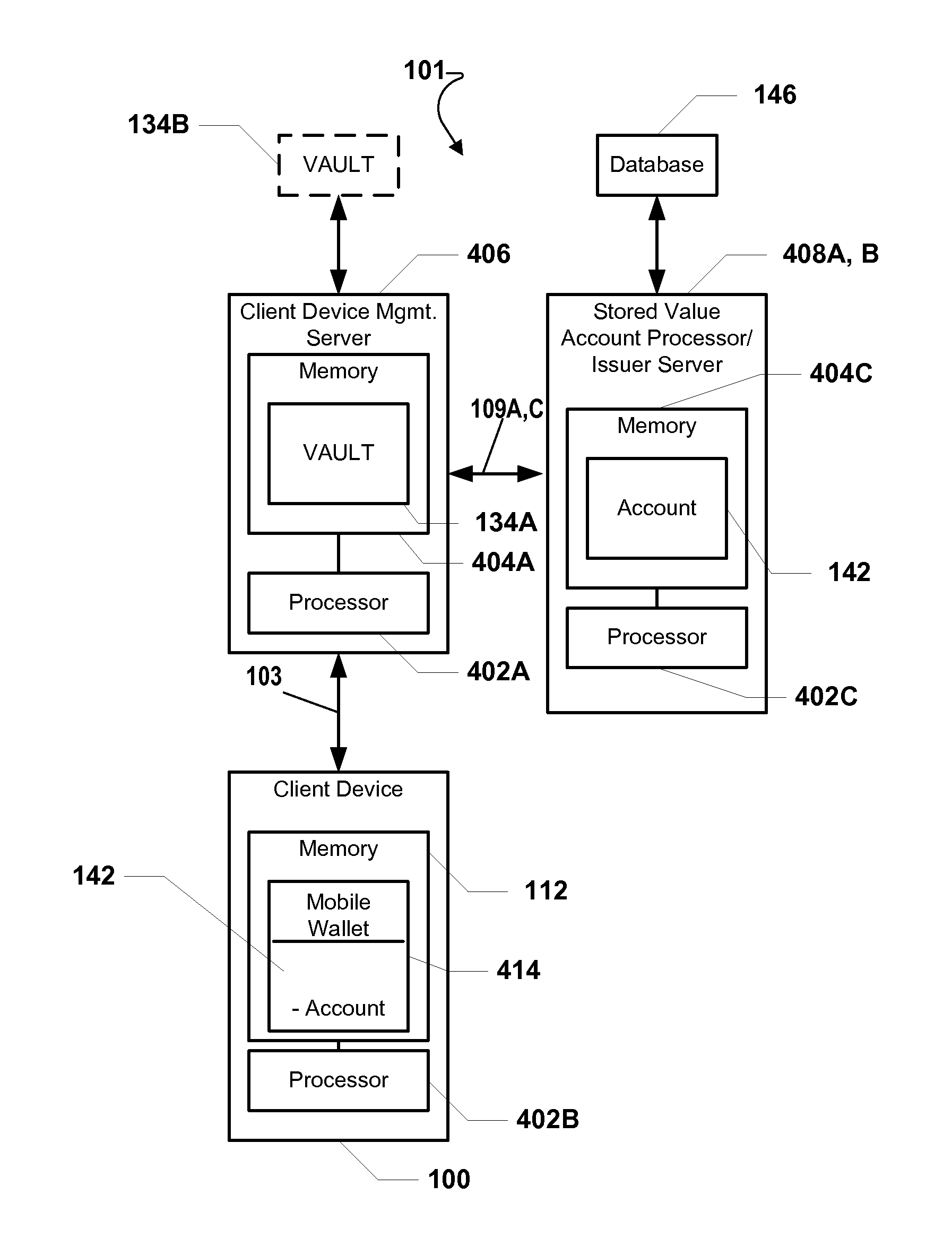
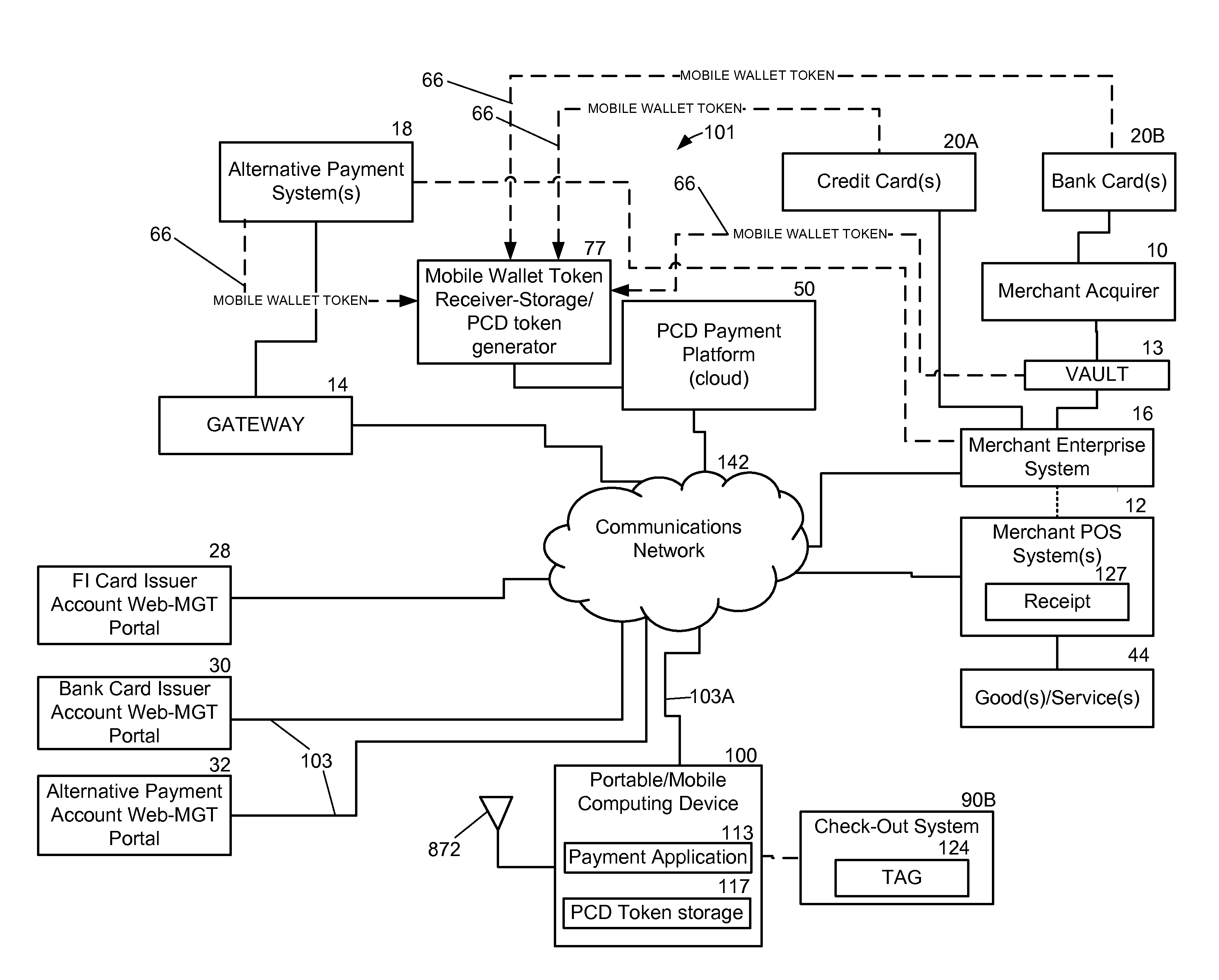
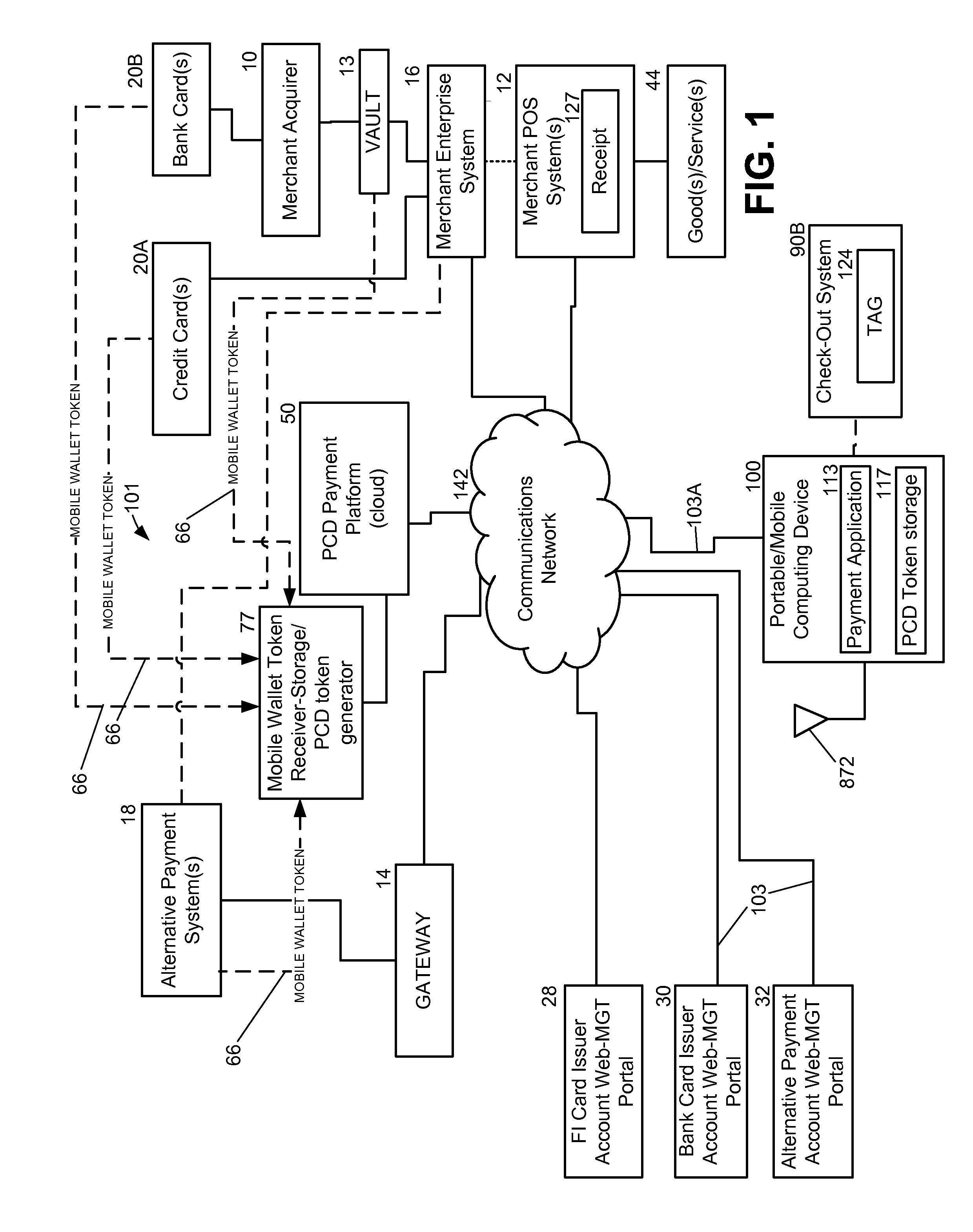
System and Method For Loading A Virtual Token Managed By A Mobile Wallet System
A method and system include receiving a payment account number from a token, such as a traditional credit card. Either the payment account number or a token is communicated over a communications network to a mobile wallet system and / or a vault. A first authorization code may be generated in response to receiving the payment account number or token. Next, the first authorization code is then transmitted over the communications network for relaying the first authorization code to a portable computing device, such as a mobile phone. The portable computing device receives the authorization code and re-transmits the code (as a second authorization code) over the communications network. Subsequently, the first and second code from the portable computing device are compared to determine if a match exists. If a match exists, then the payment account number is loaded into the mobile wallet system for use as a virtual token.
Owner:QUALCOMM INC
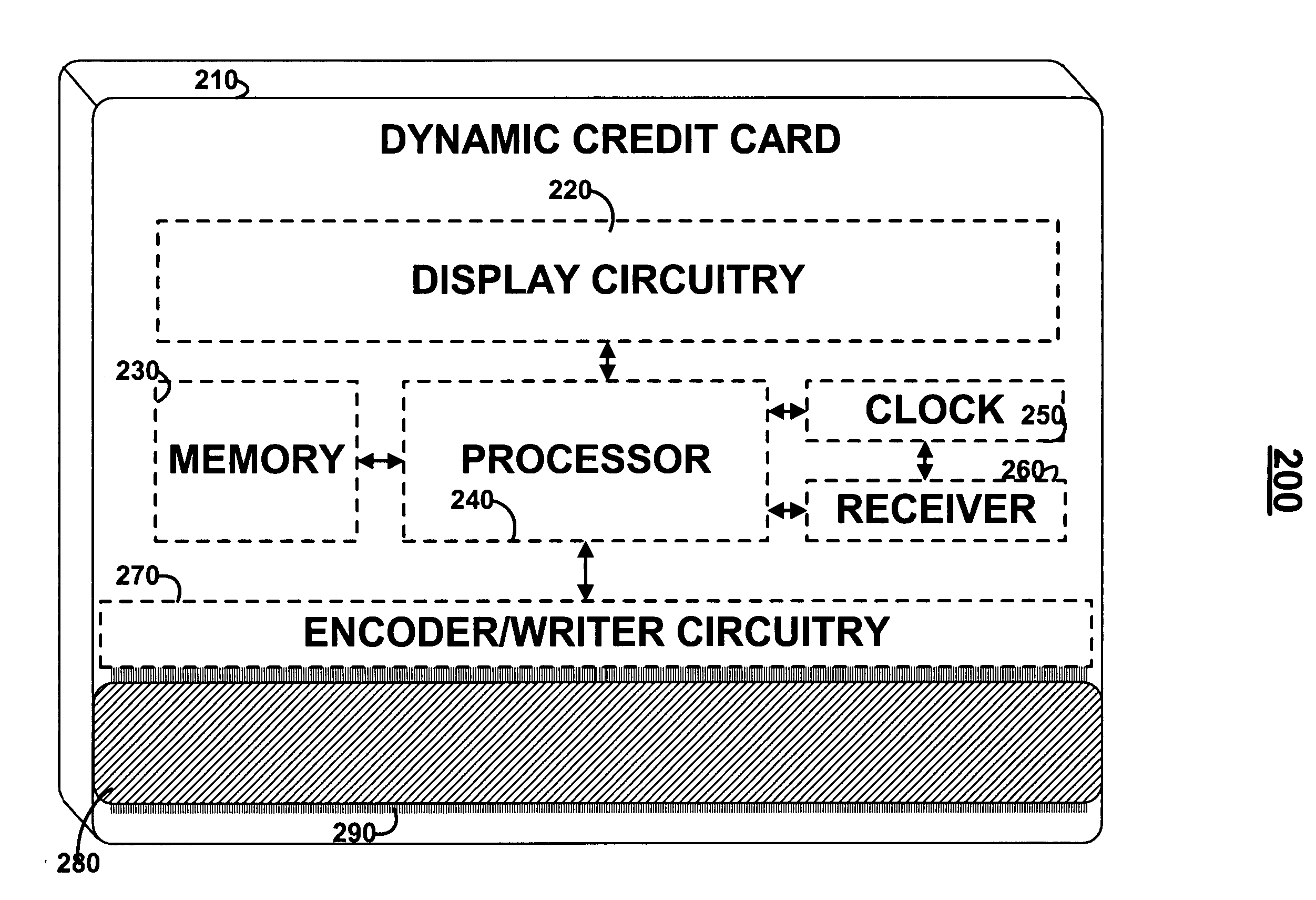
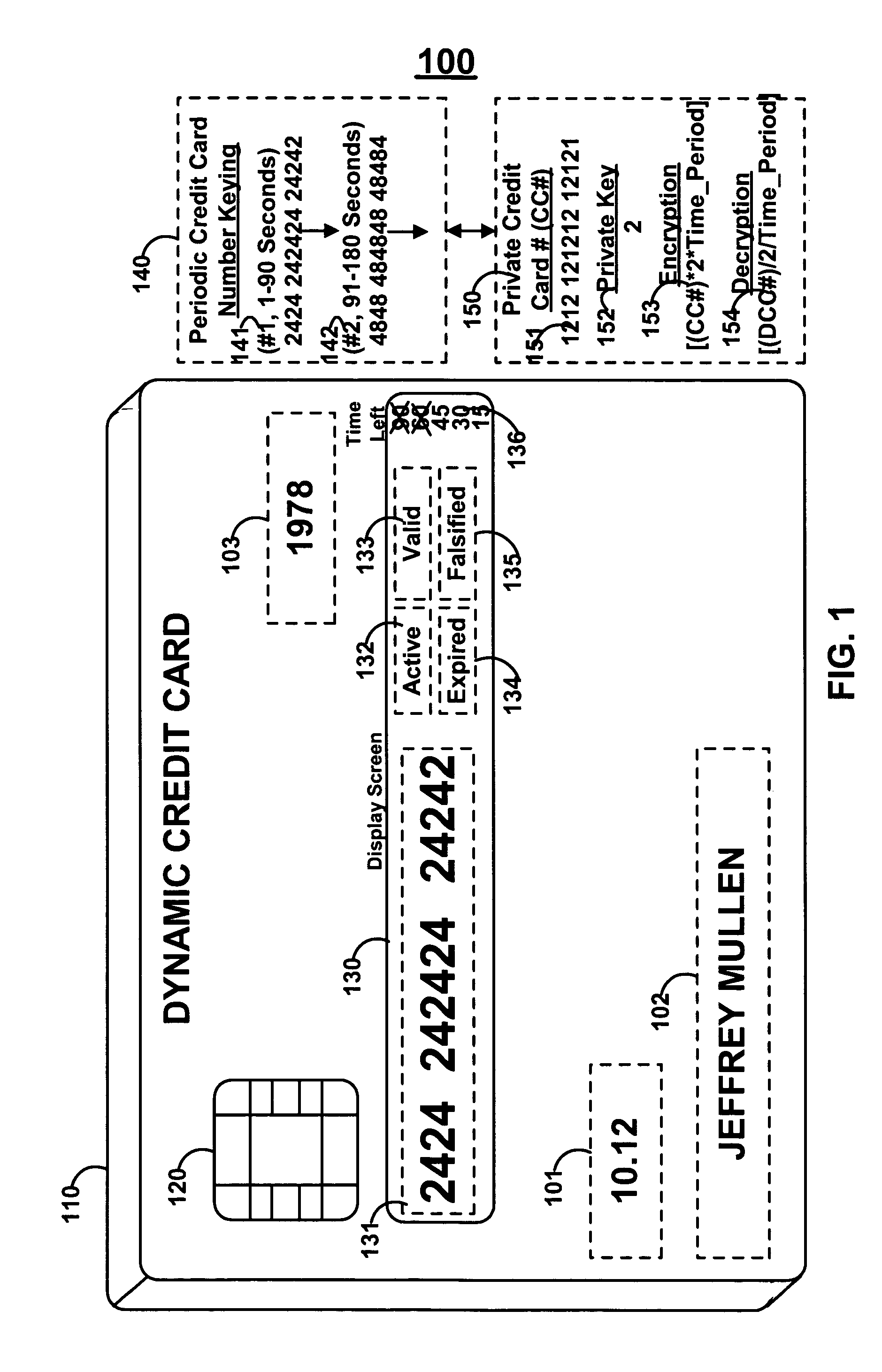
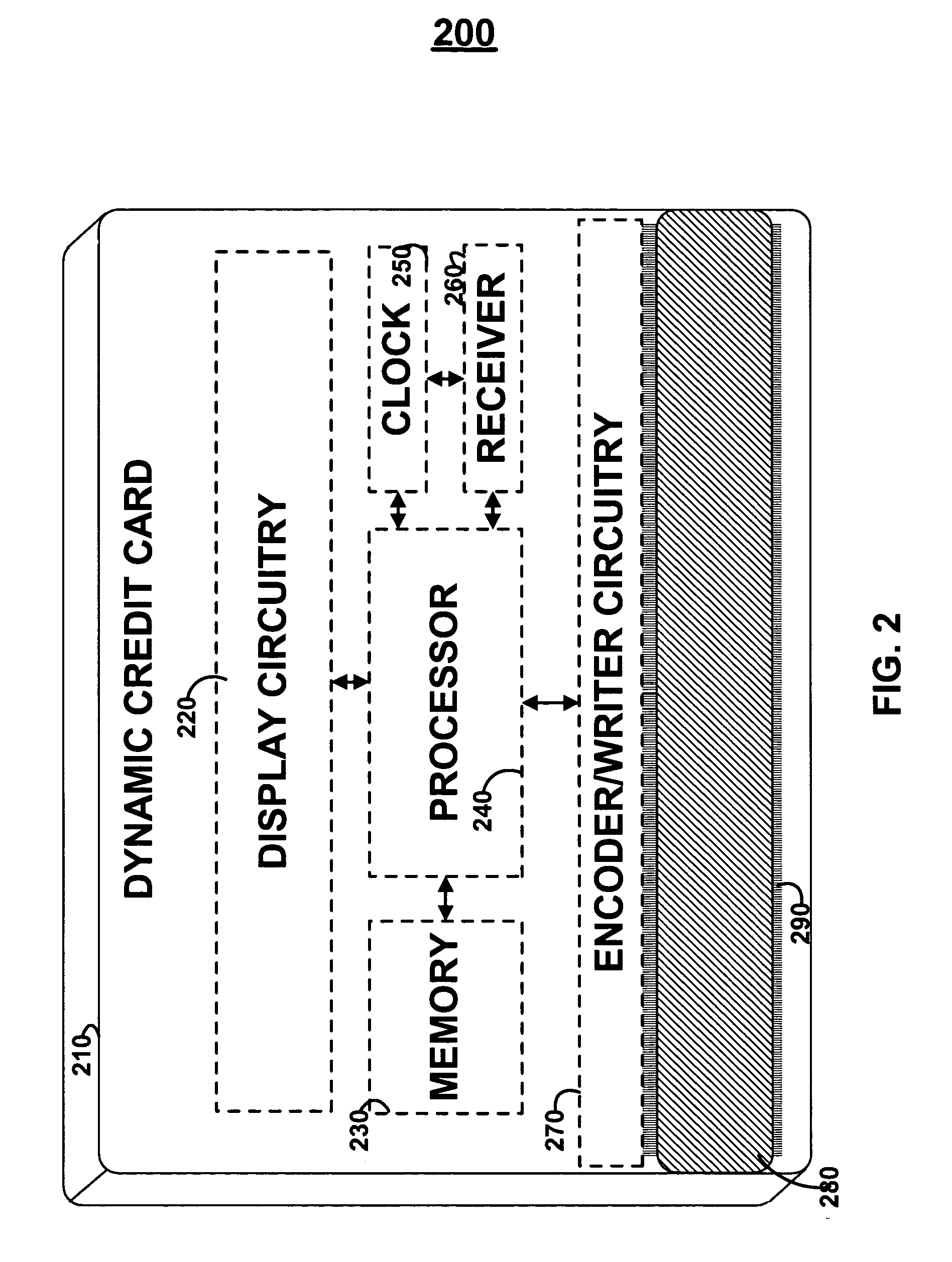
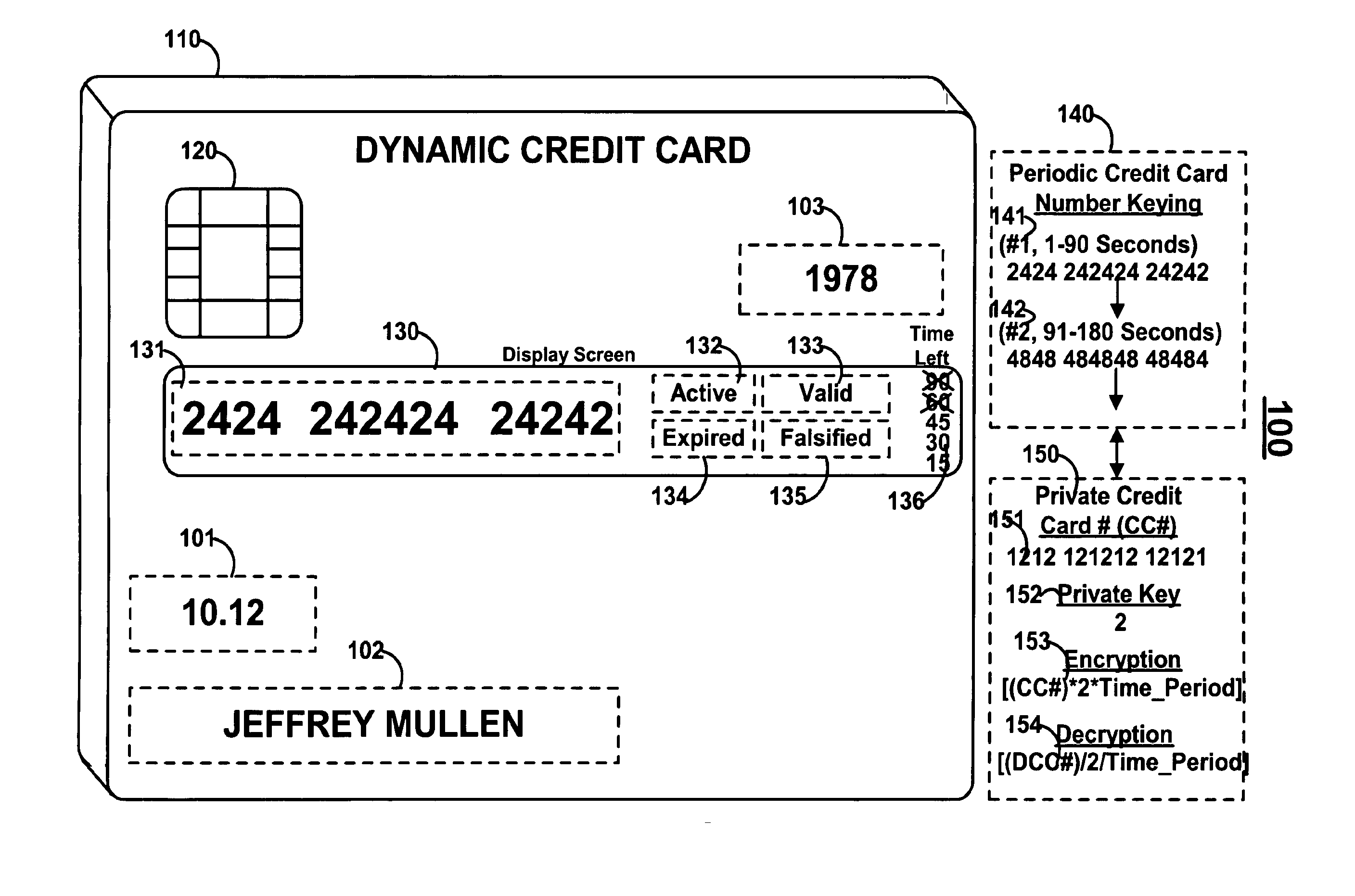
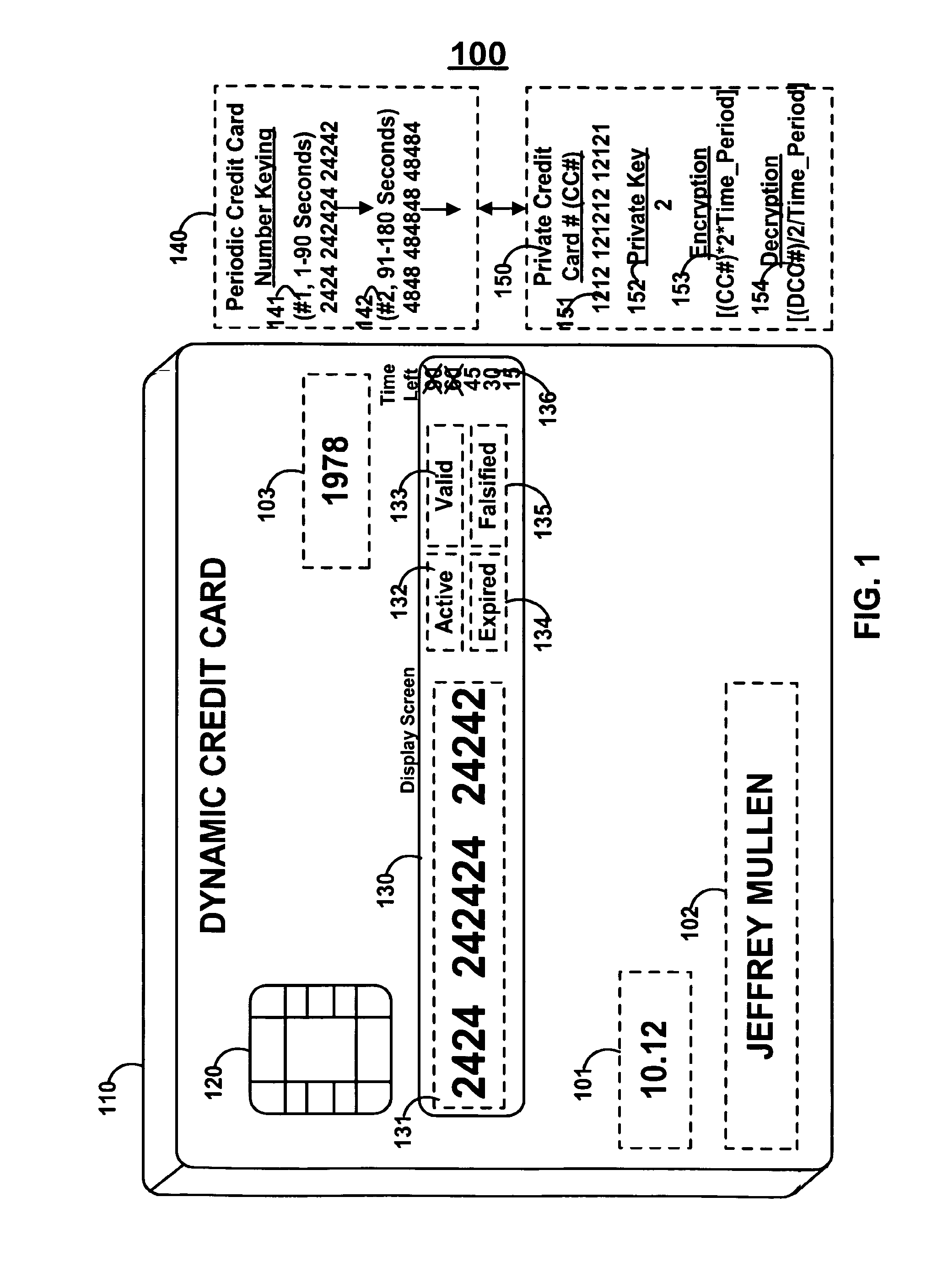
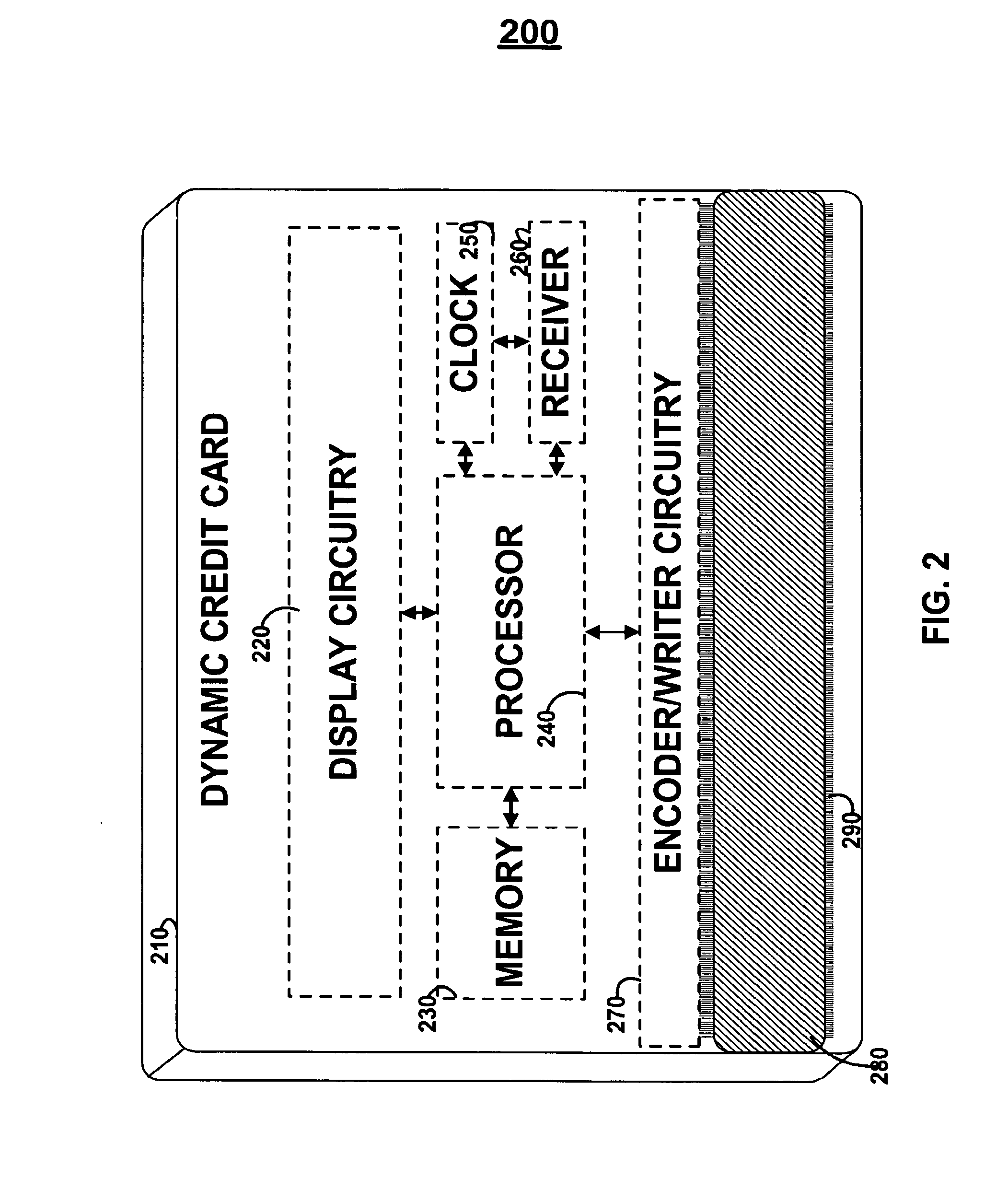
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
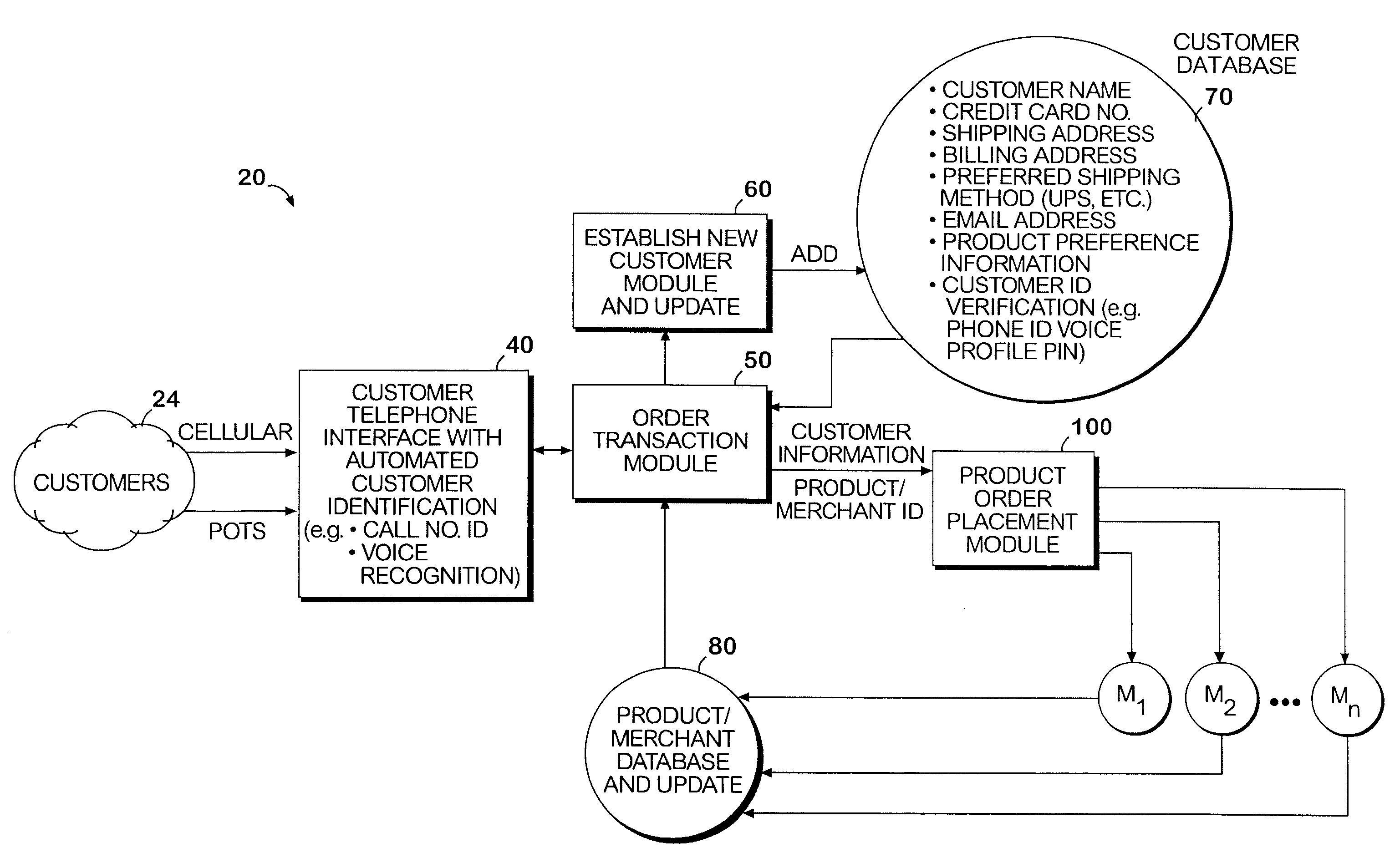
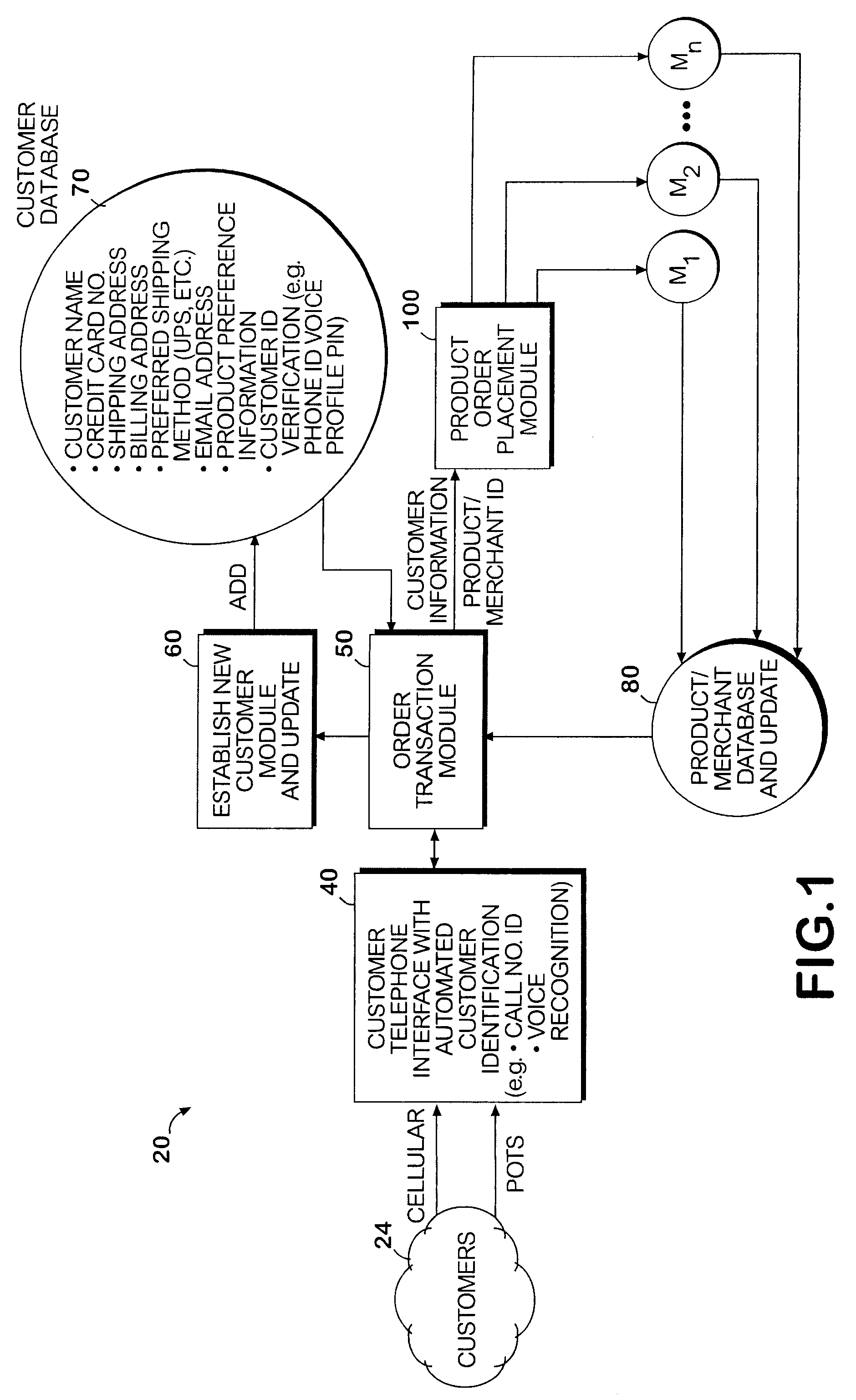
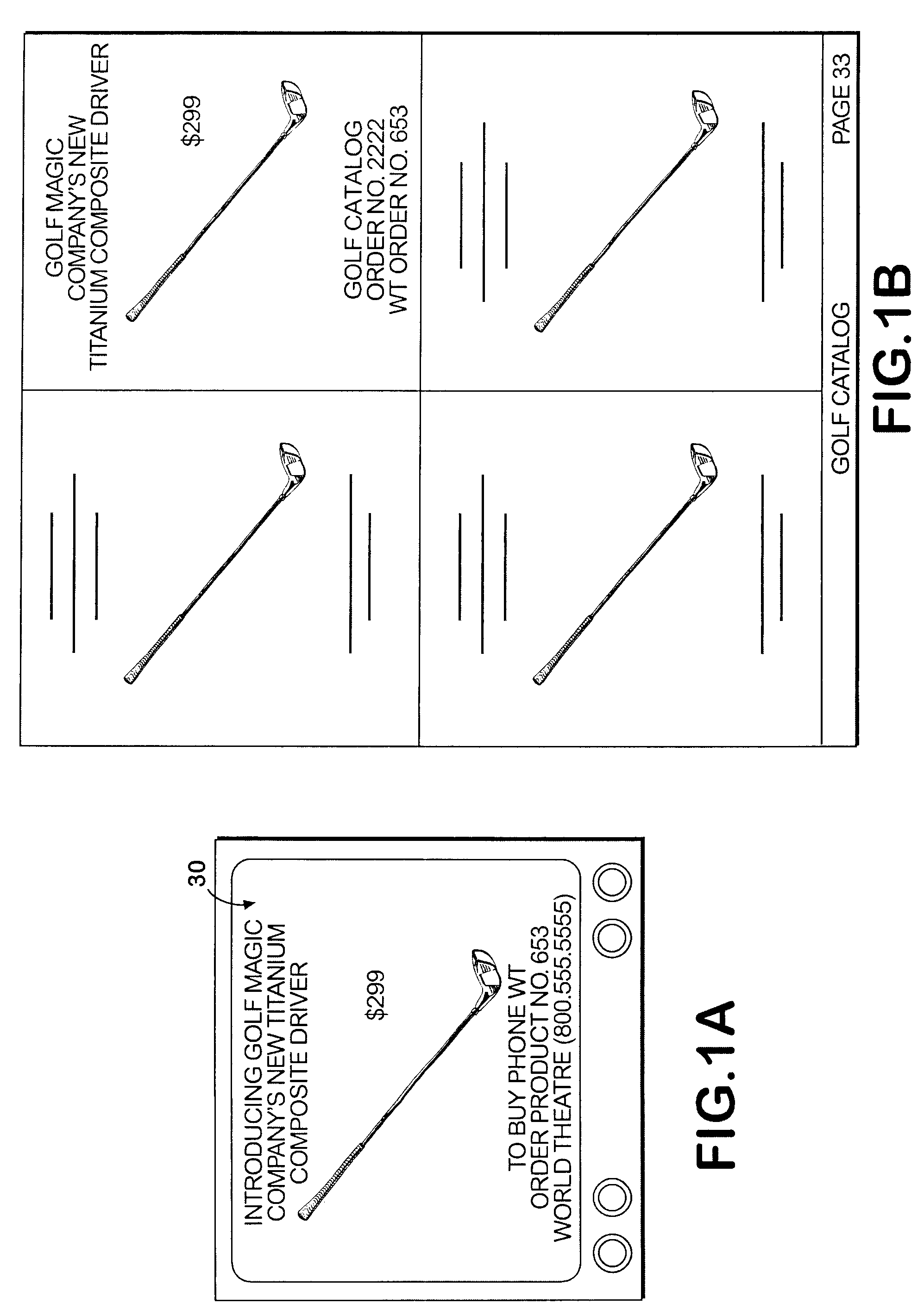
System and method permitting customers to order products from multiple participating merchants
A universal automated order processing system represents multiple (e.g., hundreds or thousands) participating merchants who offer their products through the system. Customers become qualified for using the system by supplying a set of information (e.g., name, credit card number, shipping address) that is stored in a customer database. When a customer wishes to order a product, the customer calls the system, customer identity is automatically confirmed, the customer enters a product order number and the complete order is routed to the appropriate merchant with the information necessary for the merchant to fulfill the order. Available credit verification and other aspects of credit card transactions may be handled by either the system operator or the merchant. The system operator may offer revolving credit. The system may also be used to provide potential customers of the merchants with free product information.
Owner:WORLD THEATRE INC +1
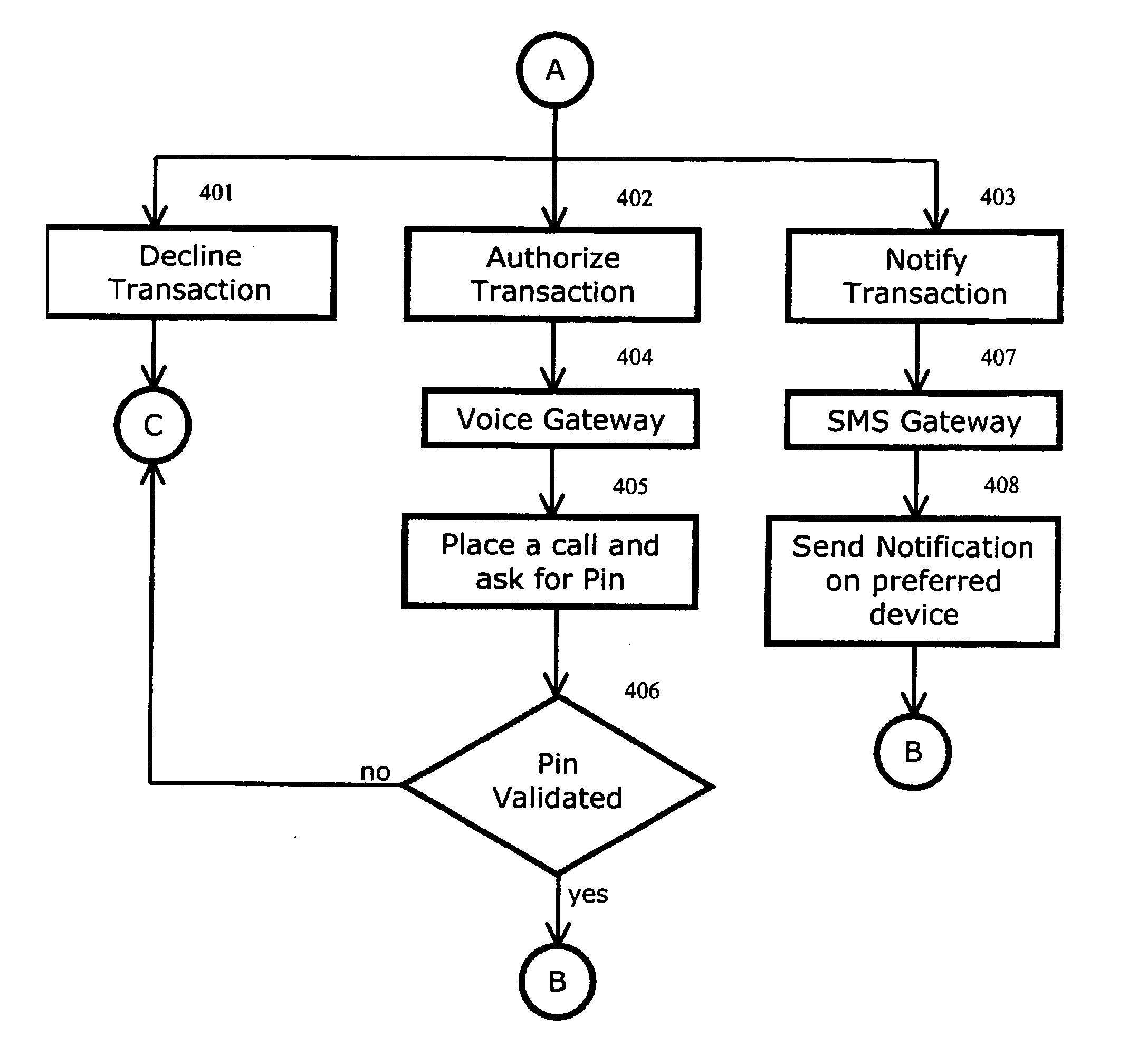
System and method for detecting card fraud
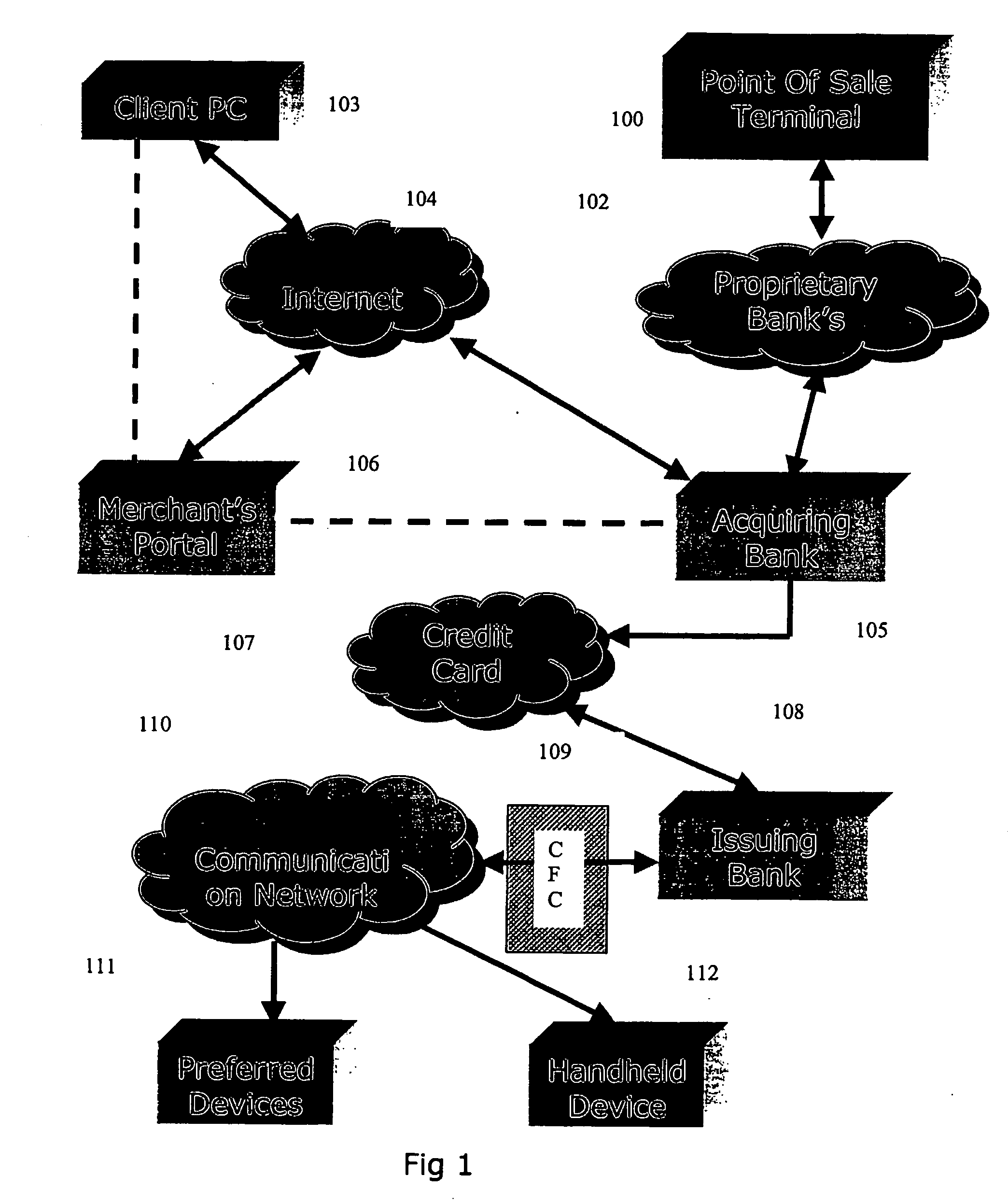
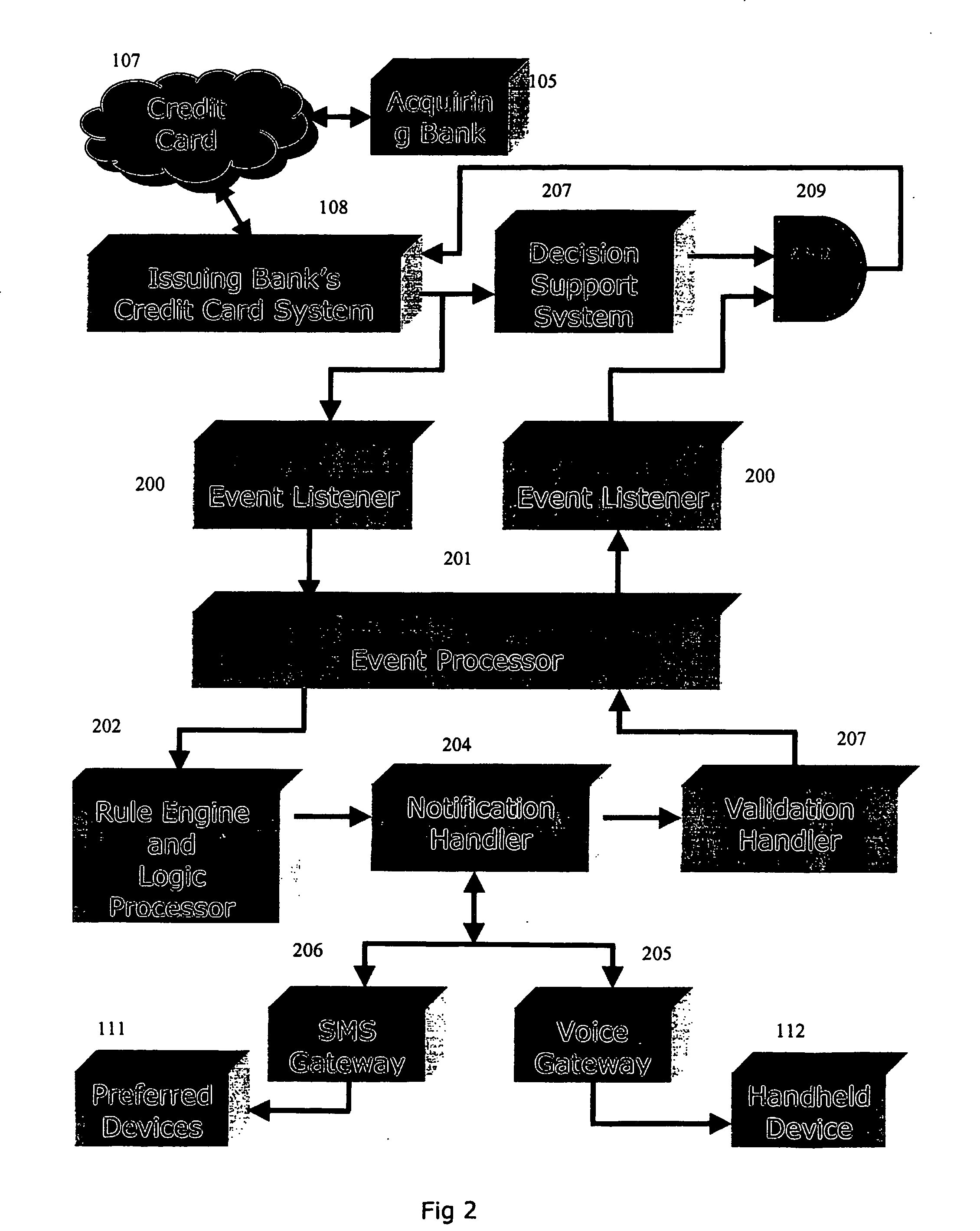
The invention discloses a system and method for notifying and authorizing card transaction by a user. The notifying and authorizing a card is done by a card fraud control system. The card user is notified on his hand held device by a short message service that a card transaction is taking place. The card user can also authorize the credit card transaction by keying in a personal identification number from his hand held device. The system also enables the user to change the rule-based system for a credit card transaction using voice and text inputs from a hand held device.
Owner:MADHOK AJAY +2
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
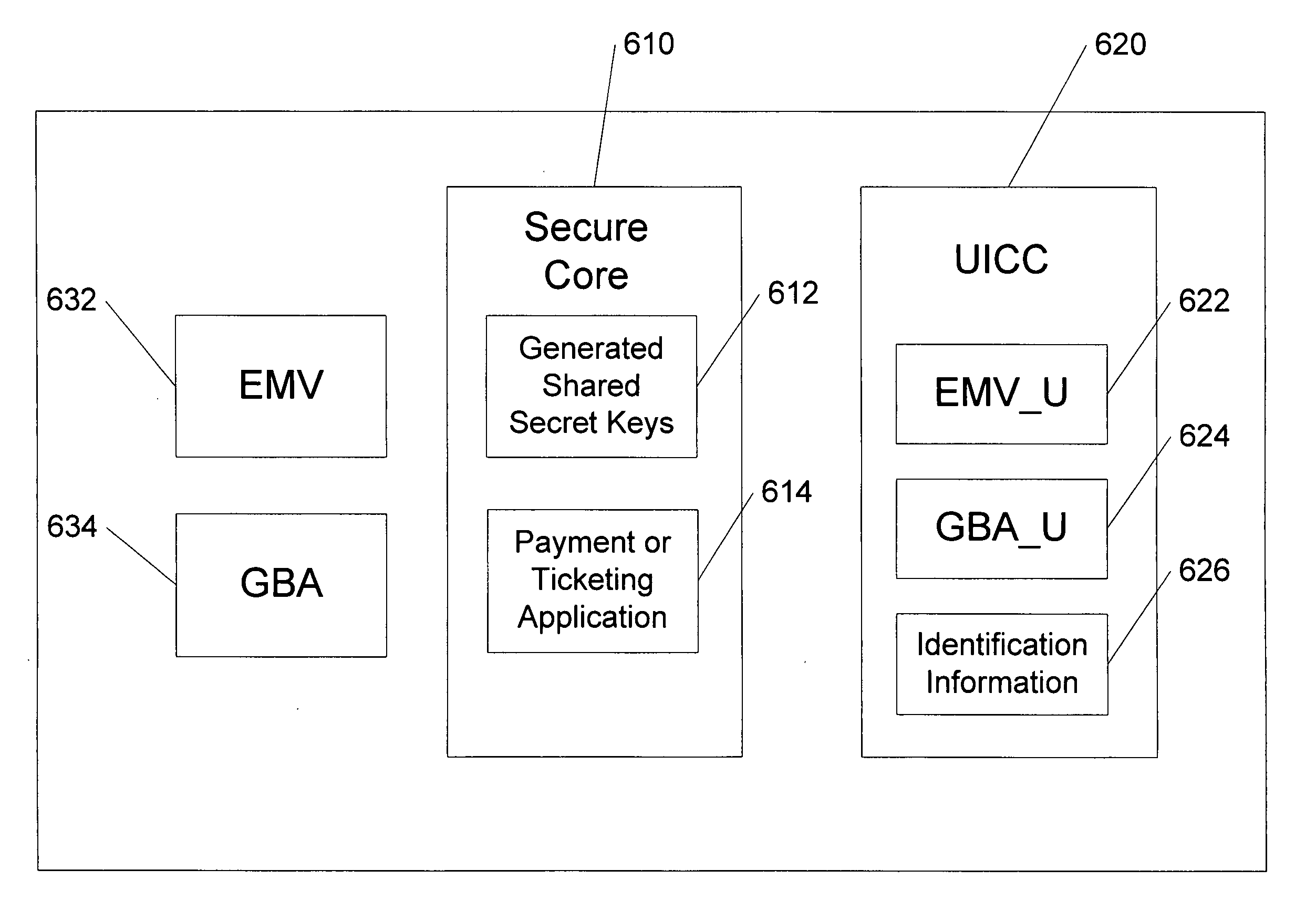
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
Secure credit card with near field communications
ActiveUS7128274B2Facilitate communicationIncrease speedAcutation objectsMemory record carrier reading problemsComputer hardwareCredit card
A near field communication device included in a secure transaction card provides an addition and / or transitional communication link for communicating secure transaction information. The near field communication device may be selectively engaged or disengaged and, when engaged, either active or passive modes of operation of the near field communication device can be selected. in the active mode, secure transaction information is transmitted upon establishment of a communication link with a complementary near field communication device. In the passive mode, secure transaction information is transmitted upon interrogation from a complementary near field communication device. Secure transaction information is generated and stored for transmission in a memory and at least a portion of the memory is erased or nulled upon transmission or upon expiration of a selected period of time.
Owner:EBAY INC
Enabling use of smart cards by consumer devices for internet commerce
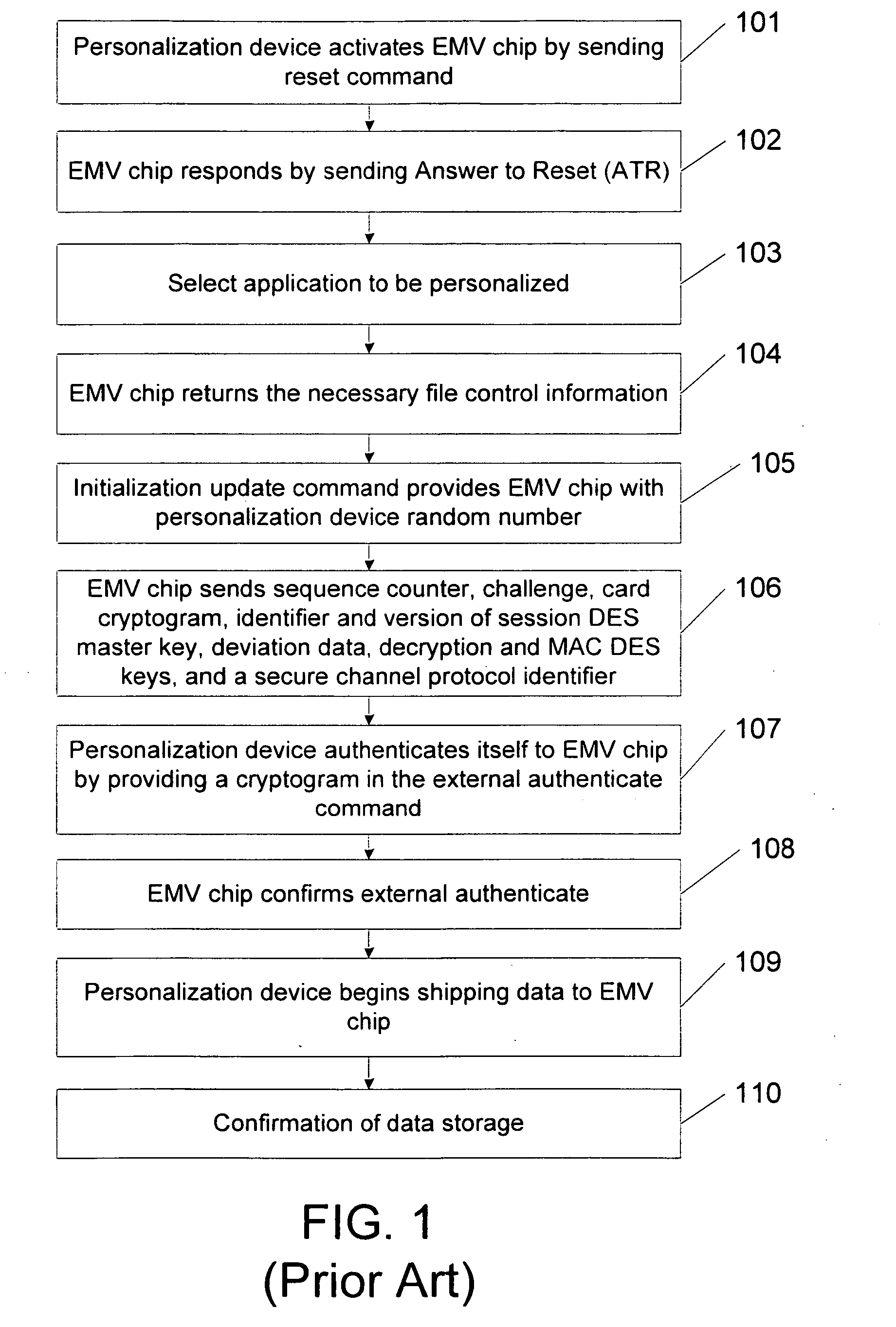
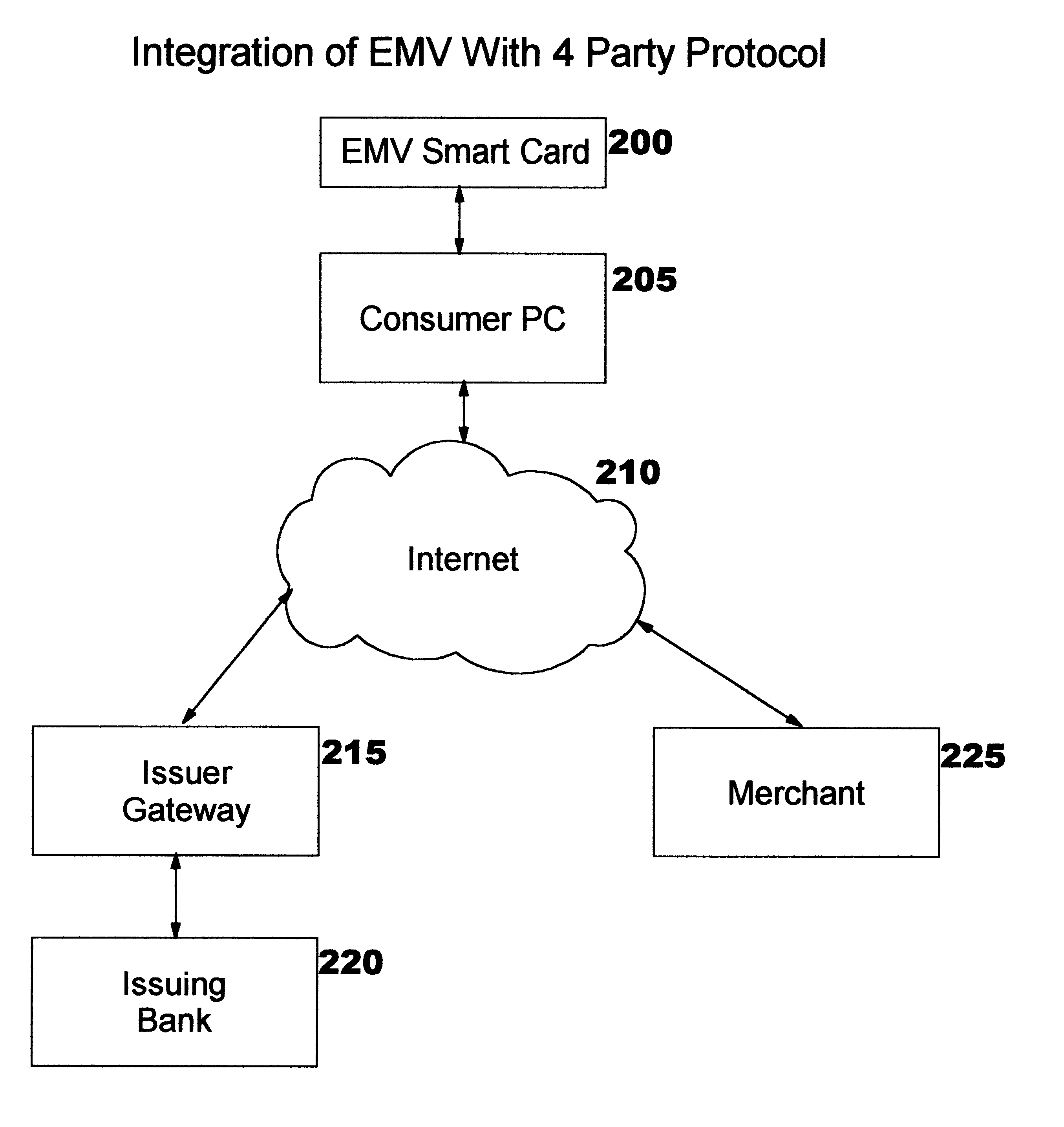
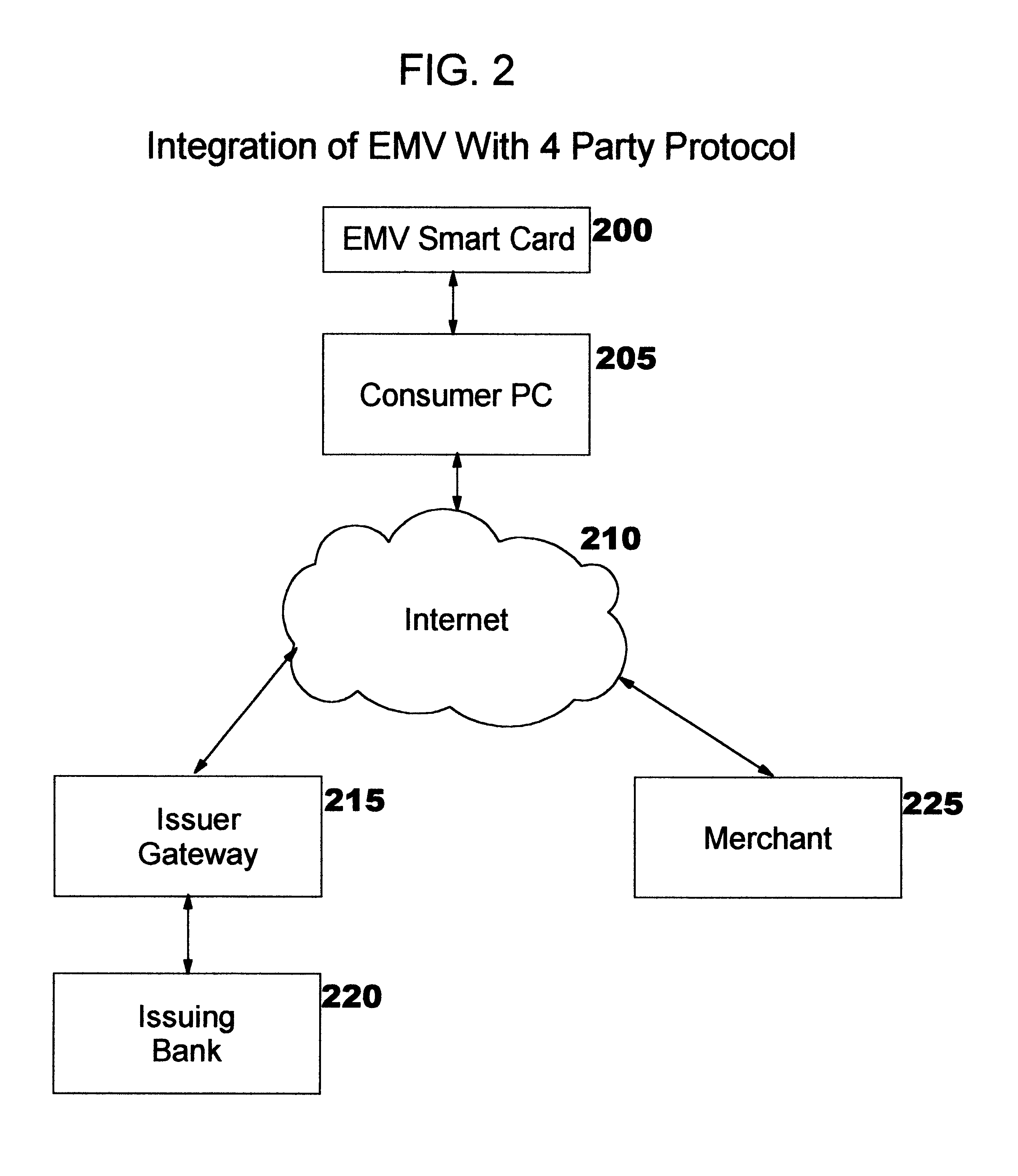
A method, system, and computer readable code for enabling use of smart cards by consumer devices for Internet commerce. This is achieved by integrating an existing “Integrated Circuit Card Specification for Application Payment Systems” standard (commonly known as the “EMV” standard) with an augmented version of the Four-Party Credit / Debit Payment Protocol which was disclosed in U.S. Pat. No. 6,327,578. The result of the integration allows a consumer to use a smart card from a personal computer system for credit or debit transactions, while preserving the level of security and other features required by the credit card associations and banks. No modifications are required to the existing EMV standard or existing EMV smart cards.
Owner:IBM CORP
Method and system for issuing, aggregating and redeeming merchant loyalty points with an acquiring bank
InactiveUS20050021401A1High cost of administrationHigh cost of setupPayment architectureMarketingCredit cardComputer science
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by the acquiring bank. The reward account is maintained on the acquiring bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
System and method for managing payment in transactions with a pcd
A system and method for managing payment in a transaction using a portable computing device (“PCD”) includes a mobile wallet token being received from an account issuing entity. Next, the mobile wallet token is stored in memory within a PCD payment platform (i.e., a cloud payment solution). A PCD token that corresponds with the mobile wallet token is generated by the PCD payment platform. The PCD token is transmitted over a communications network to a PCD. The mobile wallet token corresponds to at least one of: a credit card account, an alternative or non-traditional payment account, a stored value account, an account from a financial institution, and a merchant based card account. A mobile wallet token may be generated in response to receiving input from an on-line portal that future use of a payment account with a PCD is desired or in response to input received from a point-of-sale terminal.
Owner:QUALCOMM INC
Smart card with random temporary account number generation
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
Secure online commerce transactions
A method of enabling electronic commerce transactions is provided by a service, the service giving to users a disposable credit card or other indicia of credit for a particular transaction or amount. The service receives registration information from the user and authorizes the user. The service establishes an account for the user and issues a disposable (one use) credit card number to the user which has the same format as a permanent credit card number, is acceptable to the user and the institution with whom the user is transacting business. The system incorporates various security features.
Owner:ACEINC PTY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com