Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
219 results about "Public access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
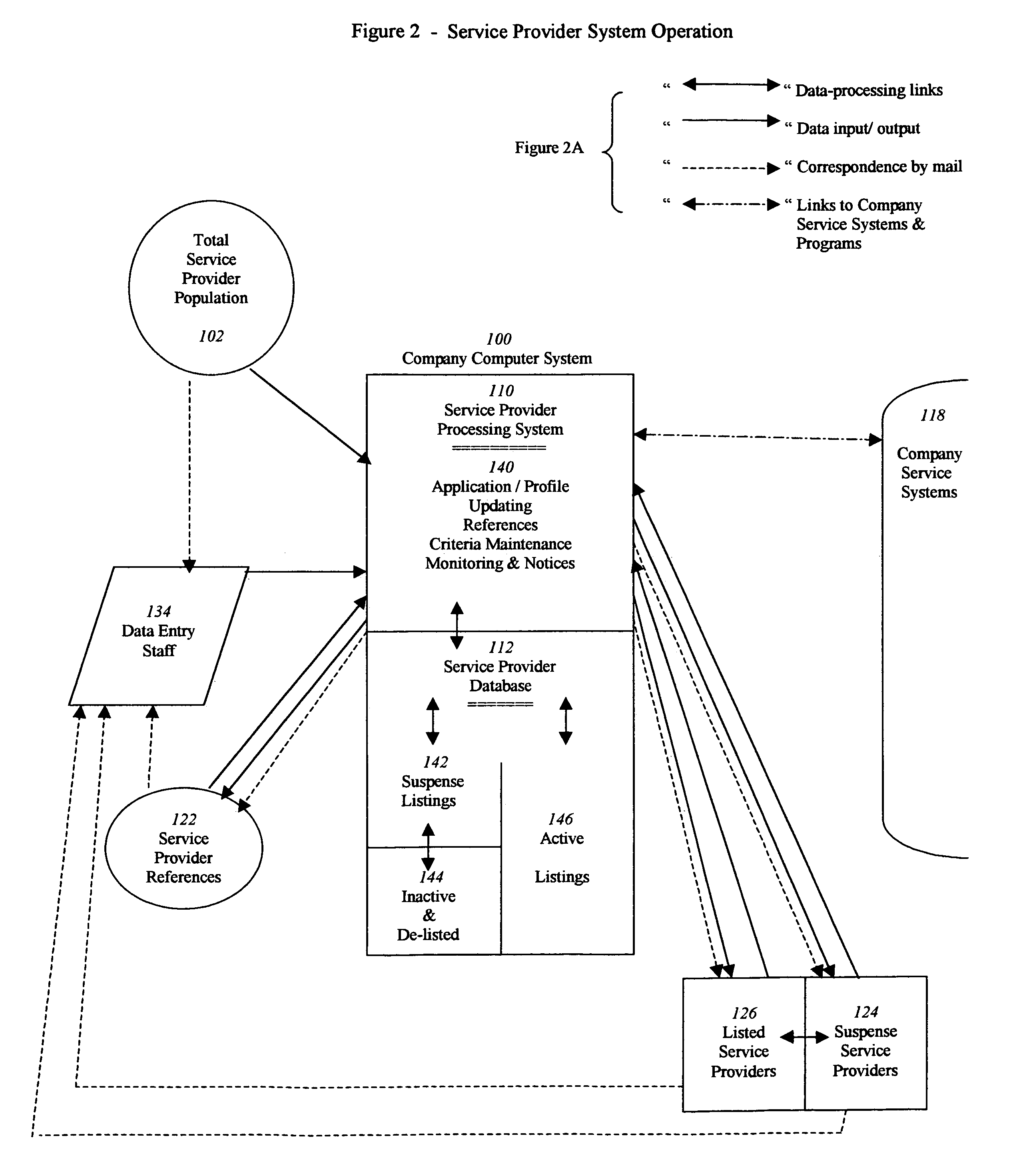
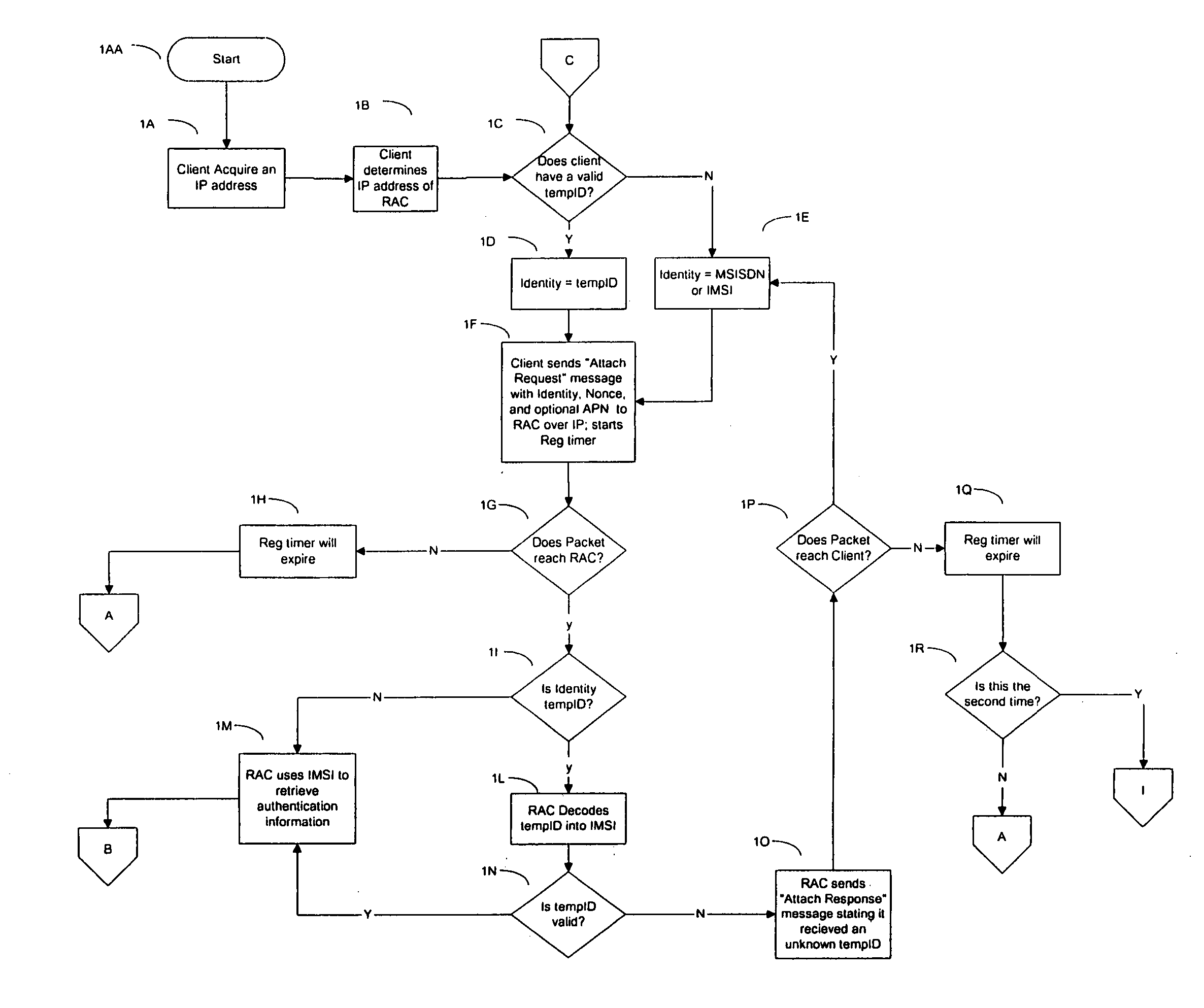
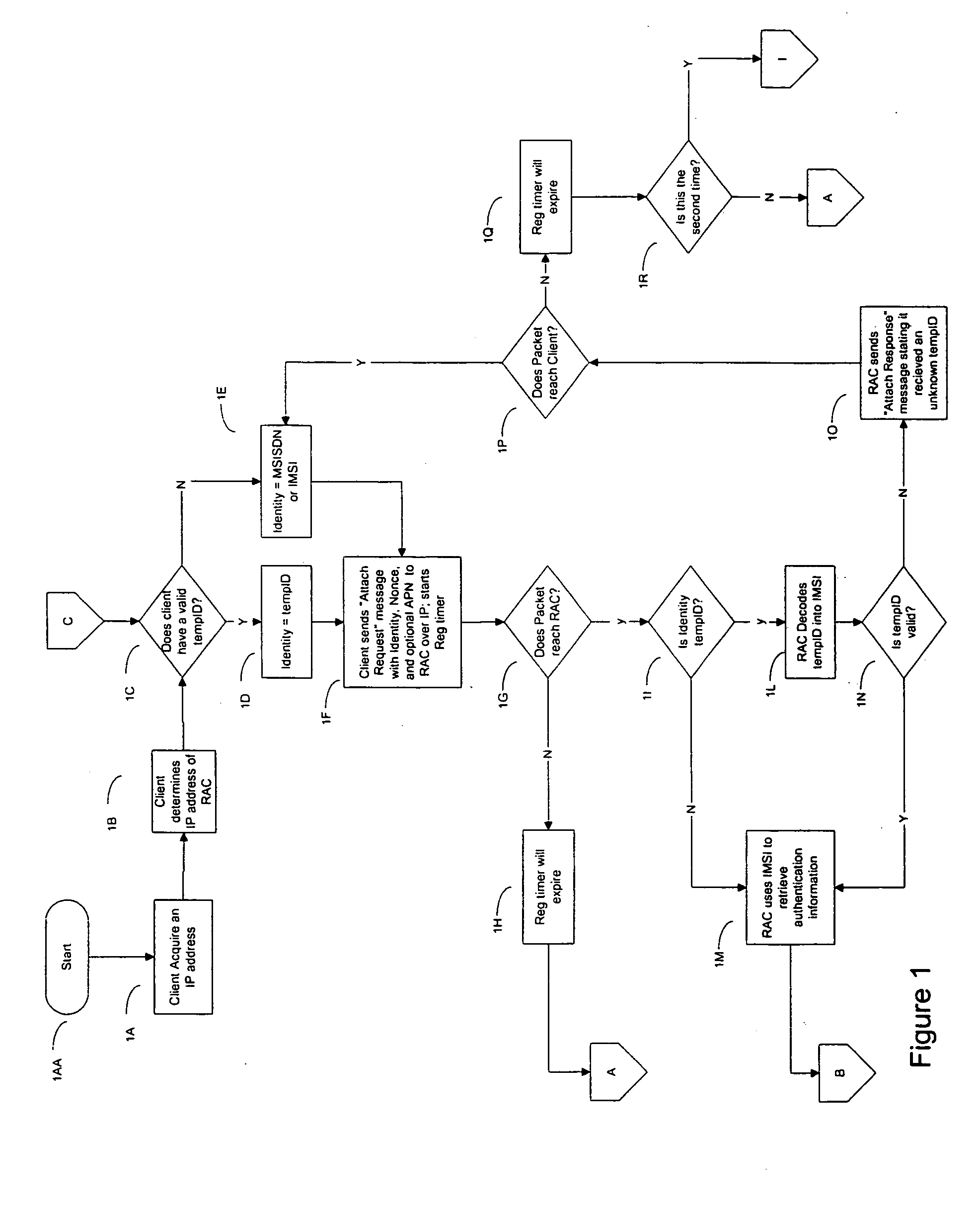
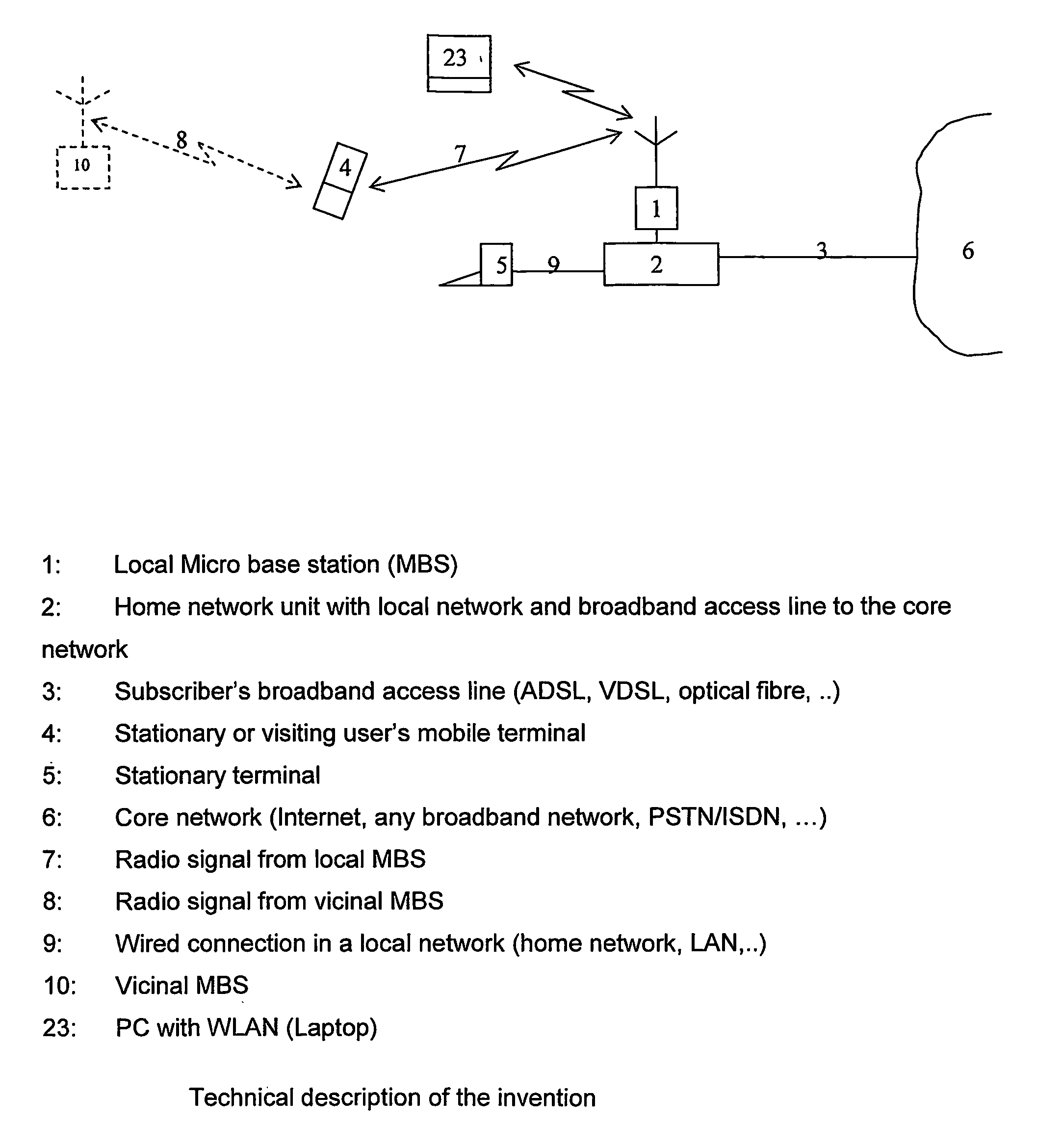
Method and apparatus for managing credentials through a wireless network
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
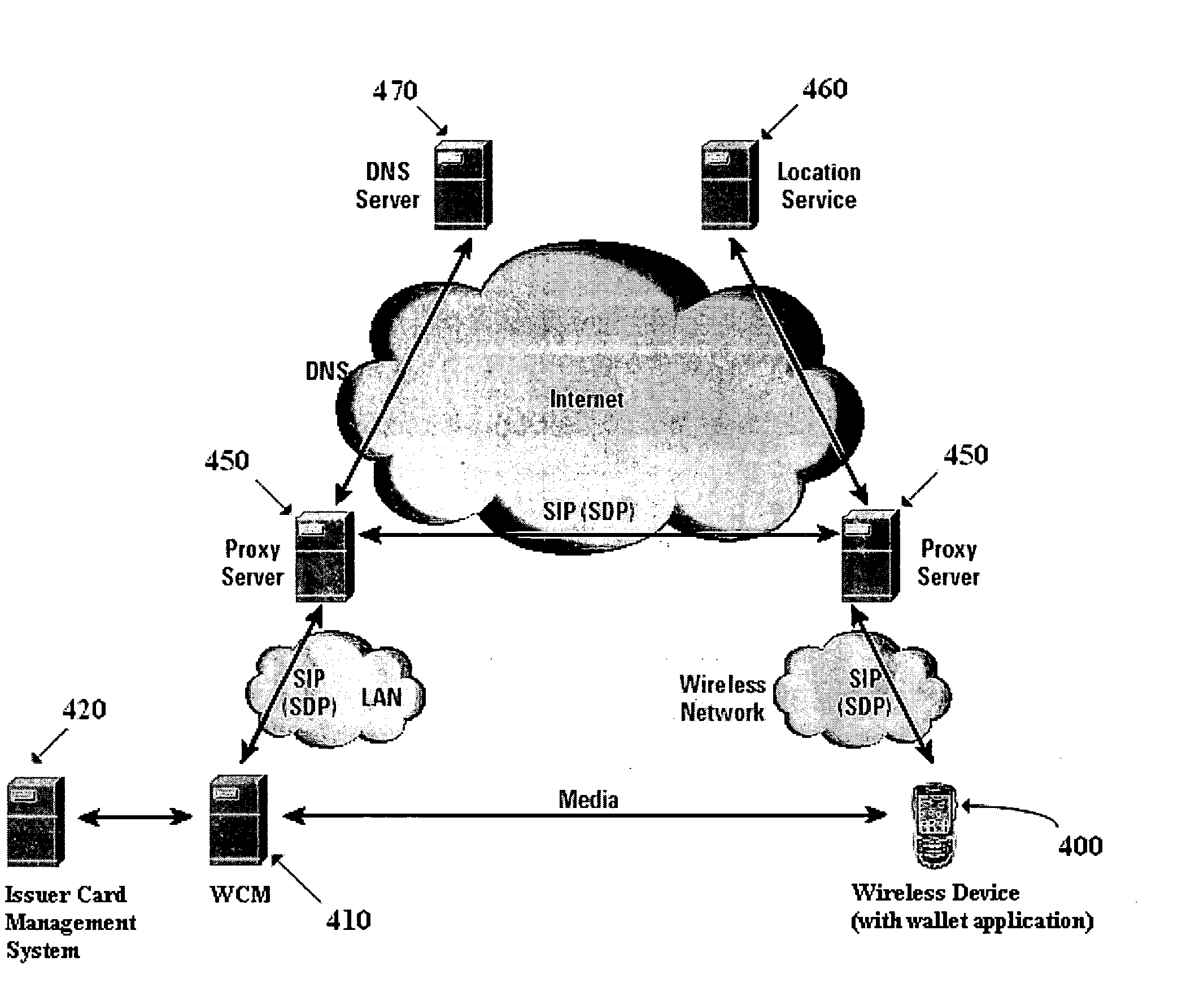
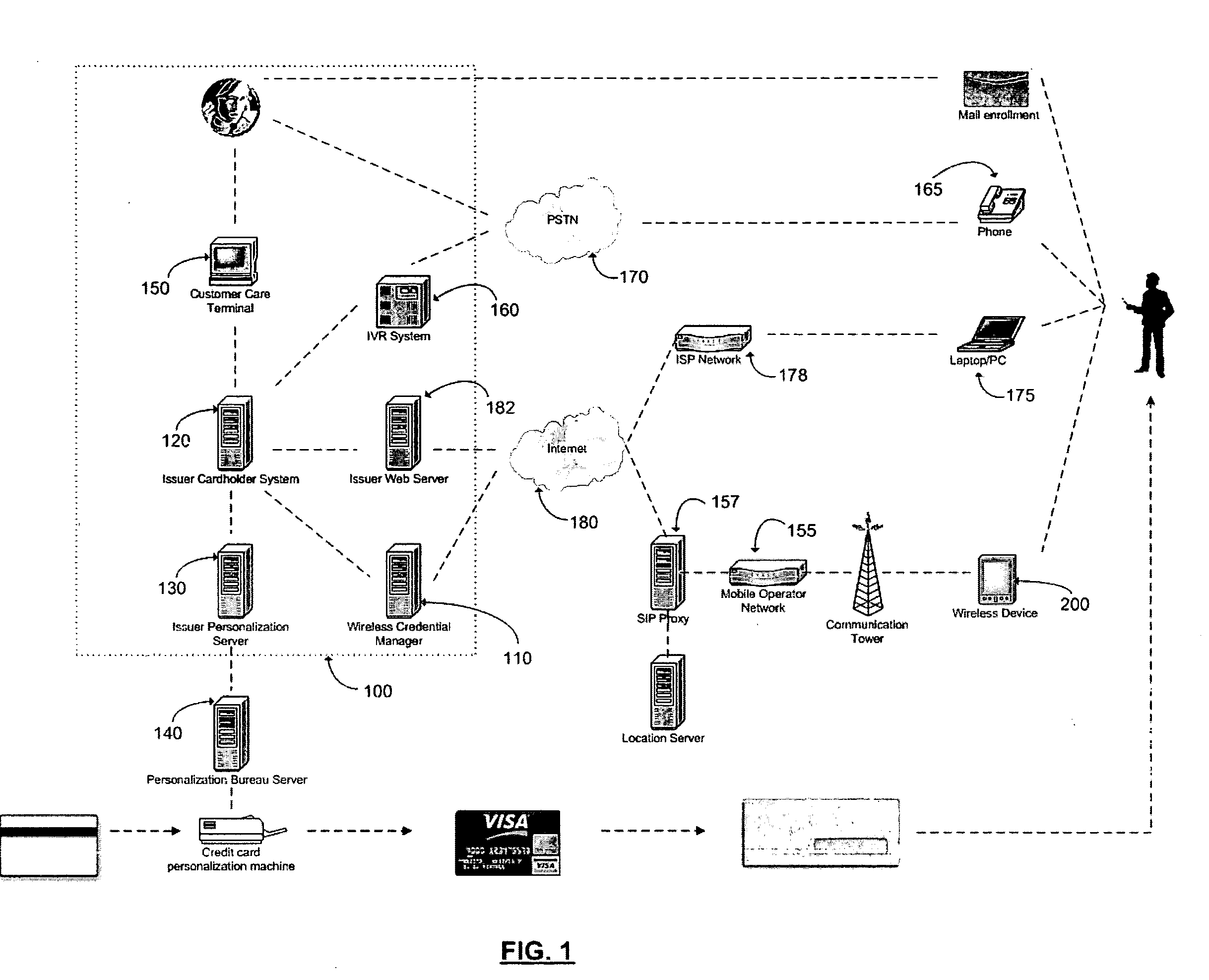
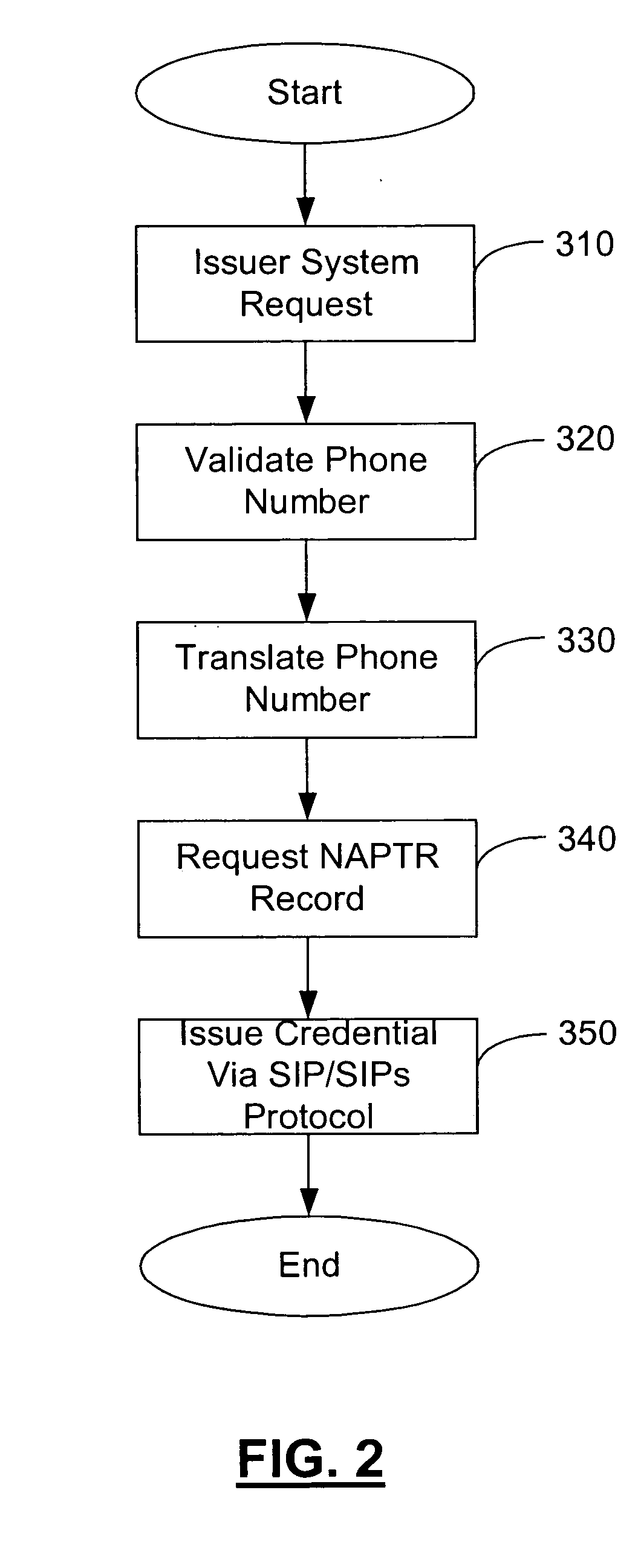
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
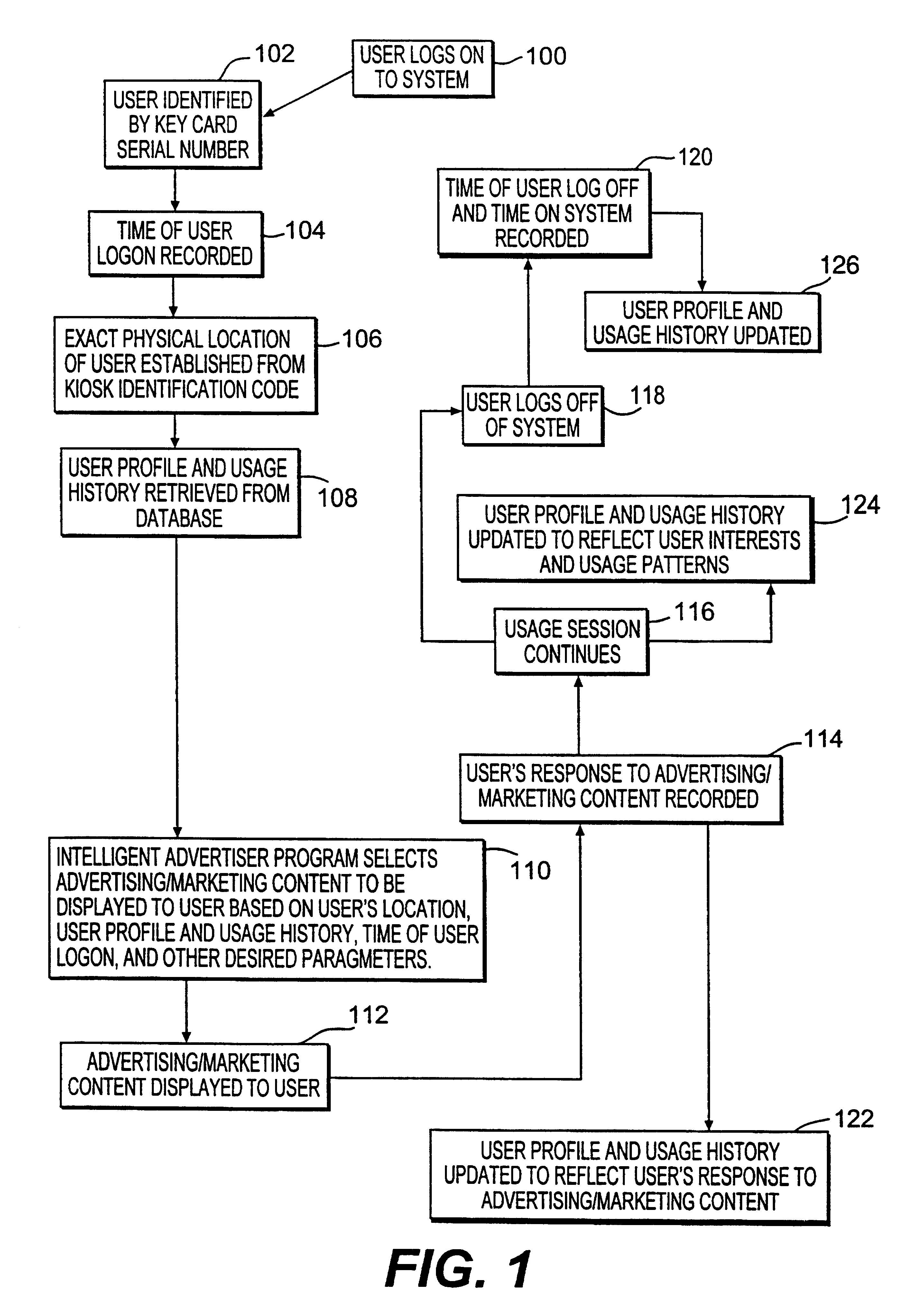
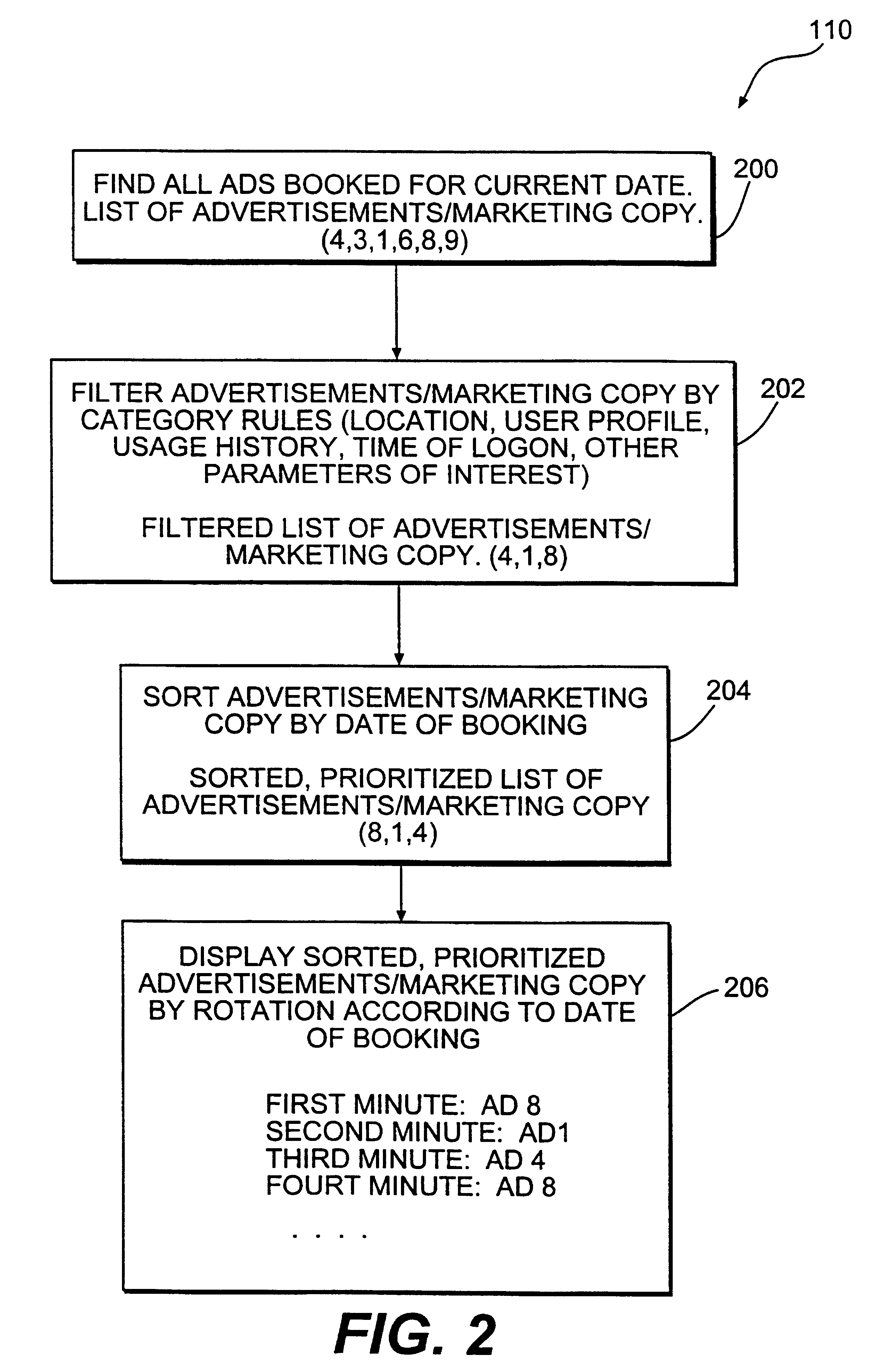
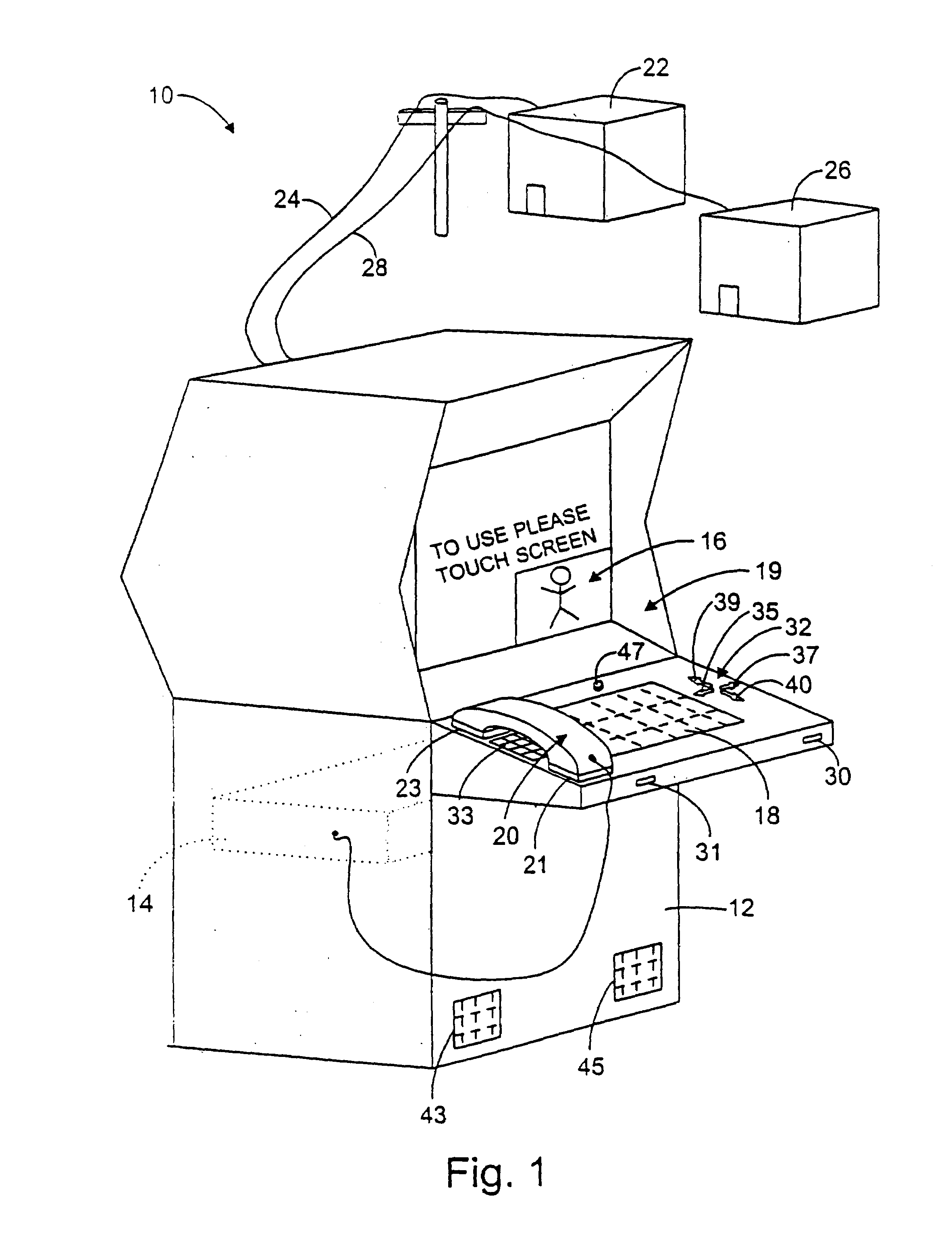
Method and system for providing personalized online services and advertisements in public spaces
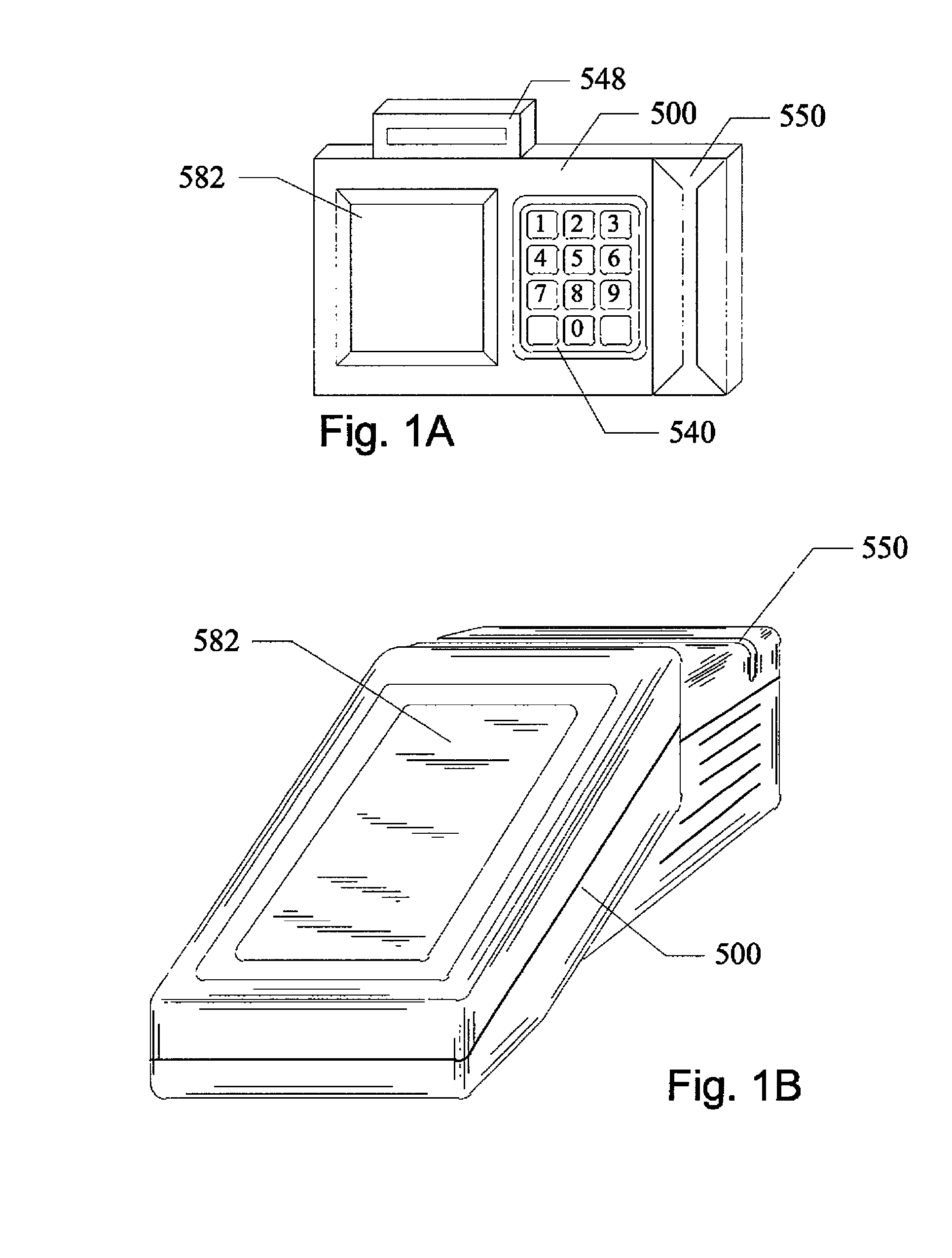
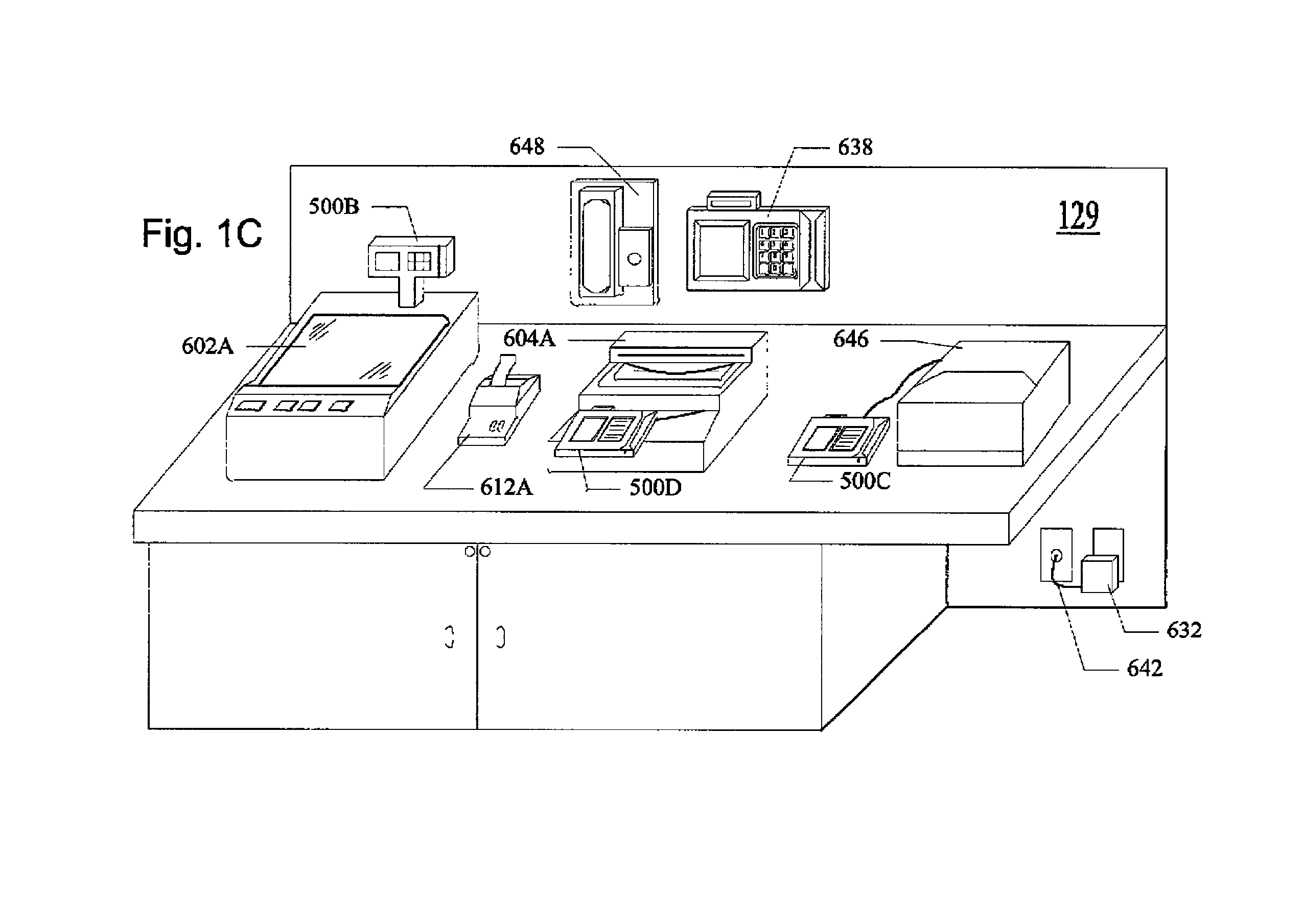
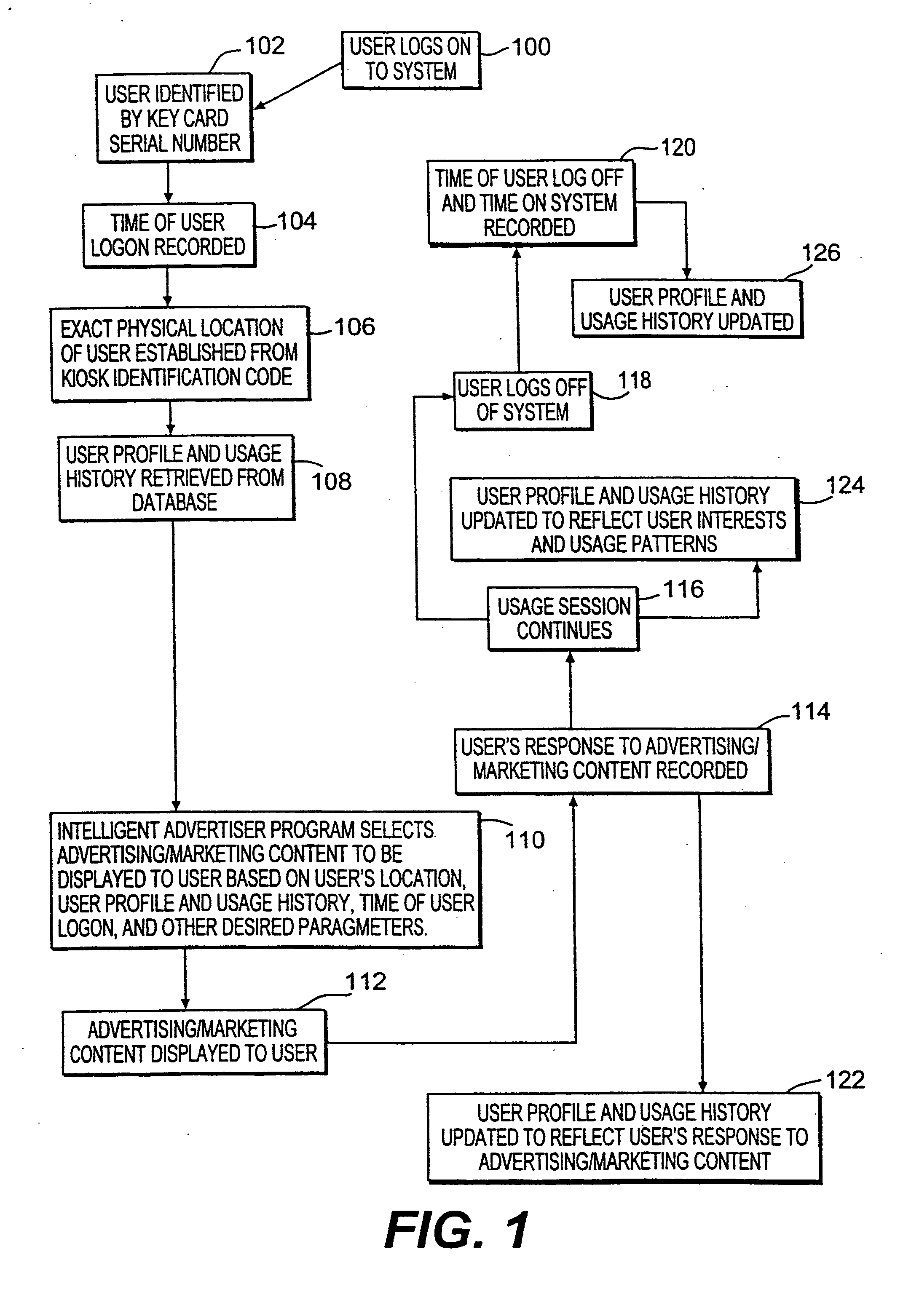
InactiveUS6847969B1Without time-consuming searchingComplete banking machinesAcutation objectsPersonalizationPersonal details
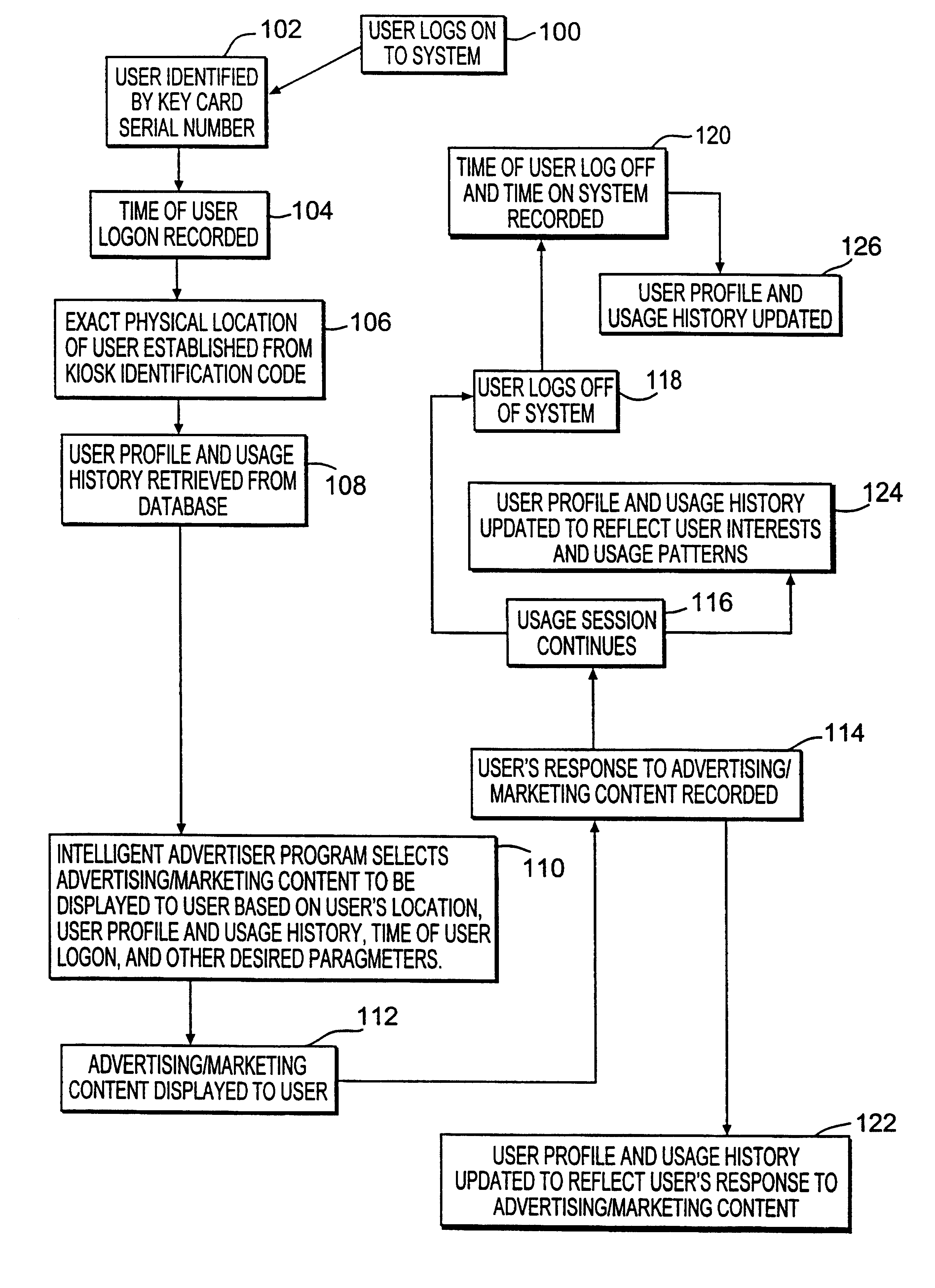
A method and system for providing, personalized and integrated online services for communications and commercial transactions both in private and public venues. The invention provides personalized information that is conveniently accessible through a network of public access stations (or terminals) which are enabled by a personal system access card (e.g., smart card). The invention also provides advertisers the opportunity to directly engage action; and potential user-consumers with selected advertising or marketing content based on each user's profile and usage history.
Owner:STREETABPACE
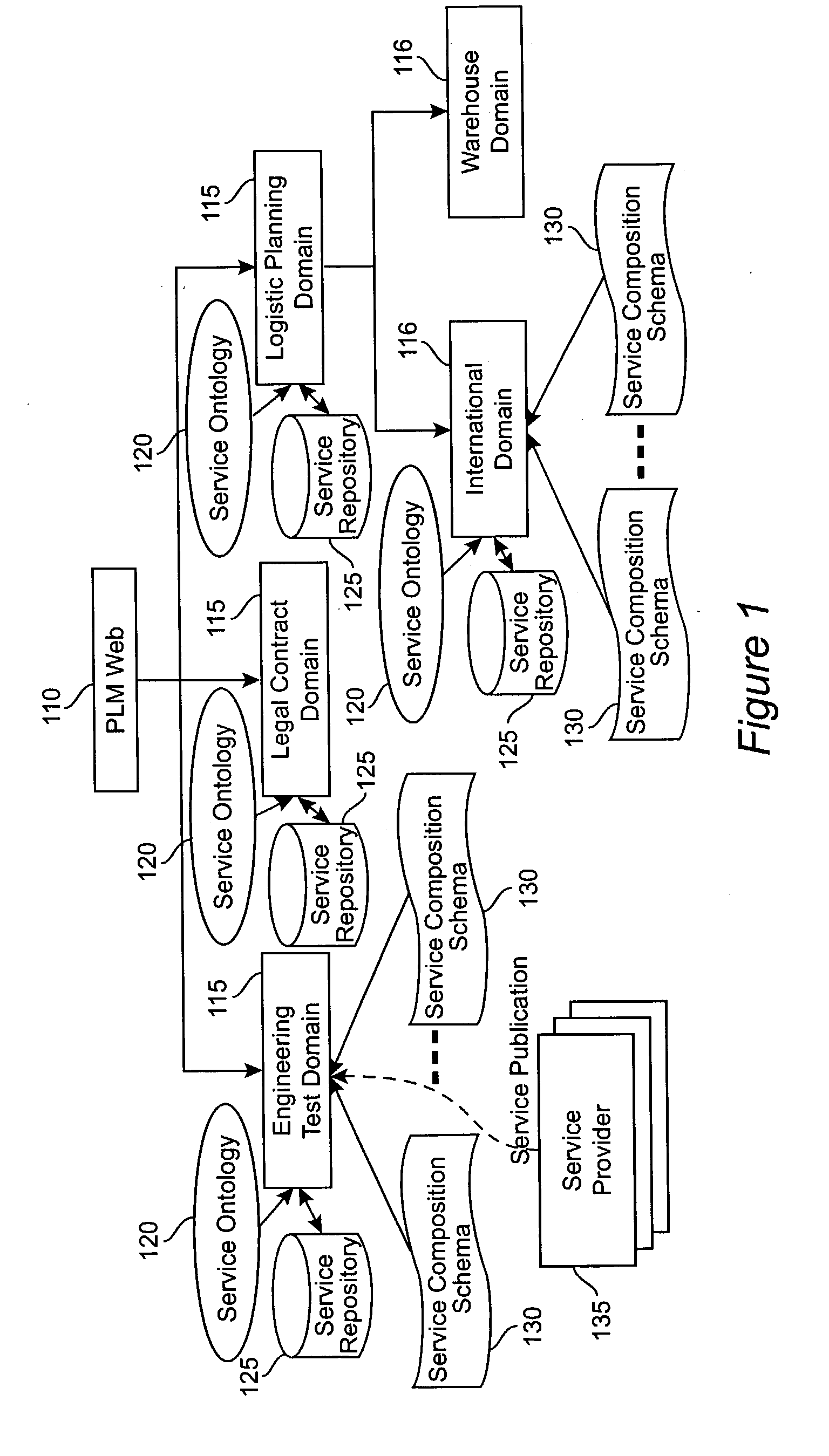
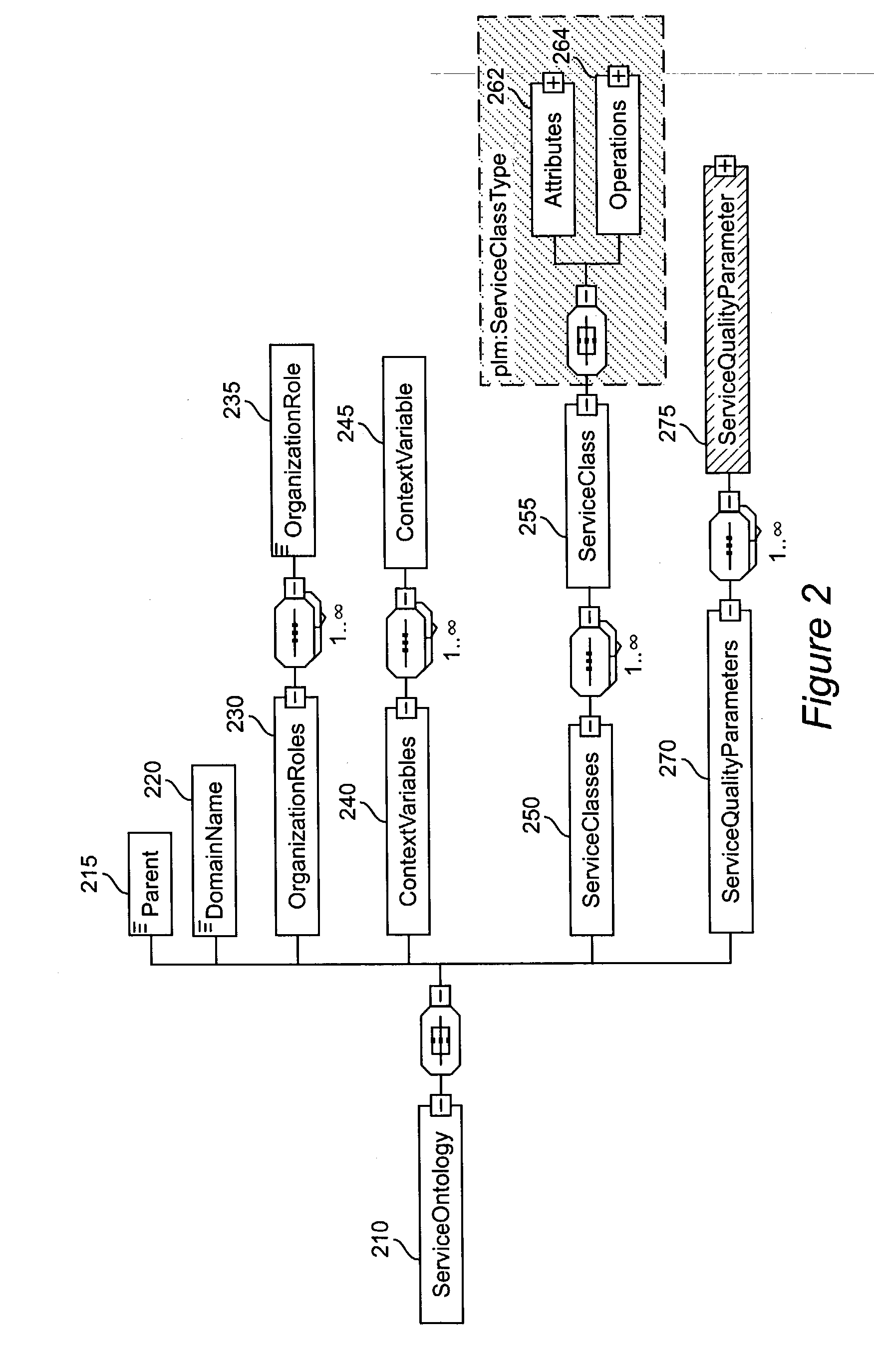
Method and apparatus for product lifecycle management in a distributed environment enabled by dynamic business process composition and execution by rule inference
InactiveUS20040162741A1Detect and resolve conflictOffice automationResourcesDistributed servicesNetwork topology
A system and method for supporting Product Lifecycle Management over a distributed service network topology that connects a hierarchy of functional domains, each domain having a service ontology and one or more service composition schemas defined by the service ontology. Each service composition schema models a business process in its domain. Descriptions of services provided to each domain are published to a service repository by providers of the services, in conformity with one of the service composition schemas. There is a business process proxy provided by the service provider for each service description, which encapsulates for public access the internal processes of the service provider. The invention makes use of an event messaging protocol that enables service collaboration and ad-hoc workflow composition. Each business process is implemented by an ad-hoc workflow comprised of one or more tasks connected by one or more business rules. For each business process there is a business flow manager that dynamically composes ad-hoc workflow prior to execution and dynamically modifies the ad-hoc workflow as the business process executes. The business flow manager uses backward-chain inferencing and then forward-chain inferencing to generate the ad-hoc workflows, based on user identification of a target task. The business flow manager is able to stop execution of the workflow and regenerate a workflow for remaining tasks in response to events received over the network from service providers, and is also able to detect conflicts in the workflows at composition time and at execution time.
Owner:IBM CORP
Voice-activated call placement systems and methods
InactiveUS7127046B1Easily reachableEasy to adaptIntelligent networksAutomatic call-answering/message-recording/conversation-recordingSpoken languageService control
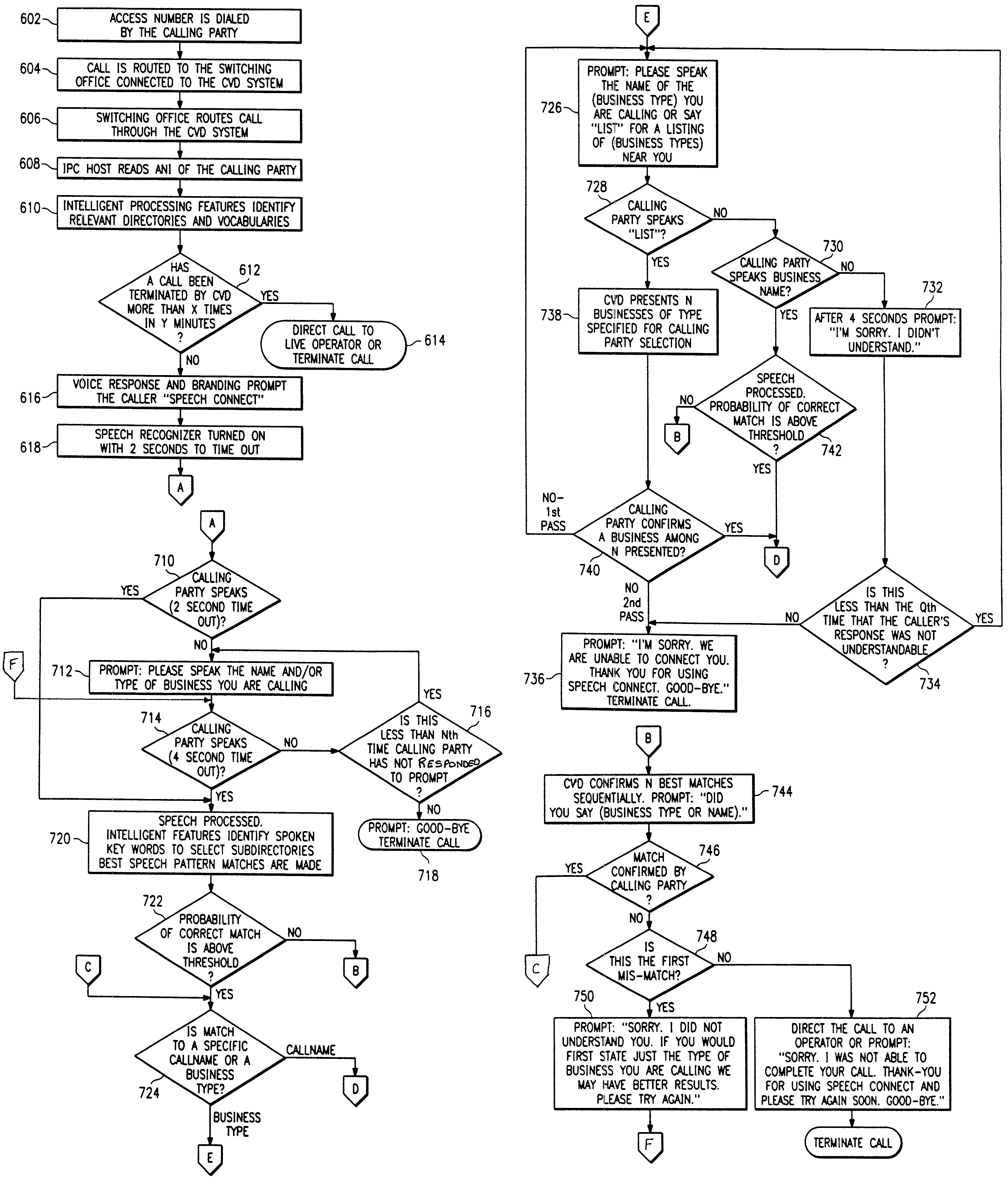
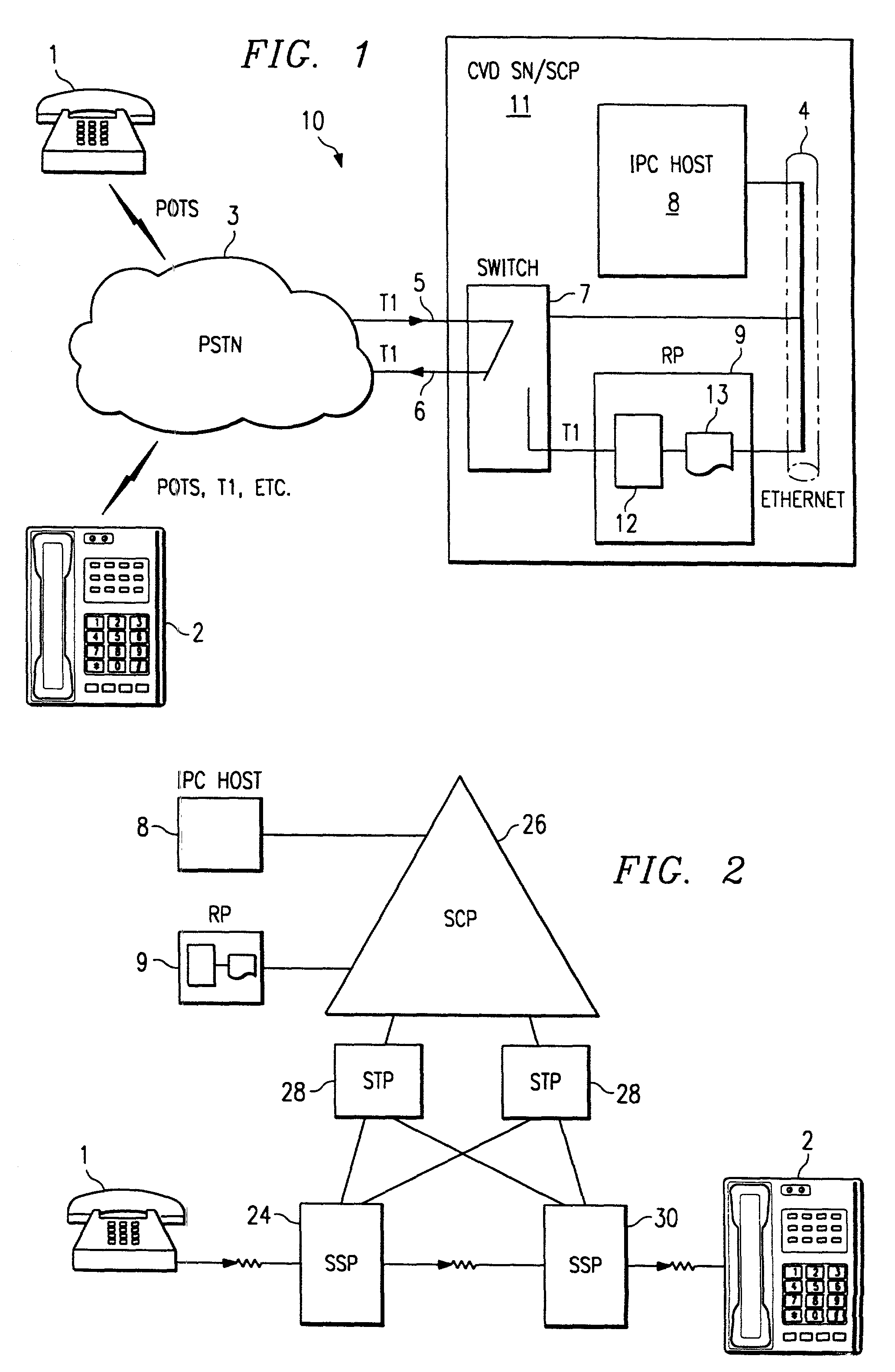
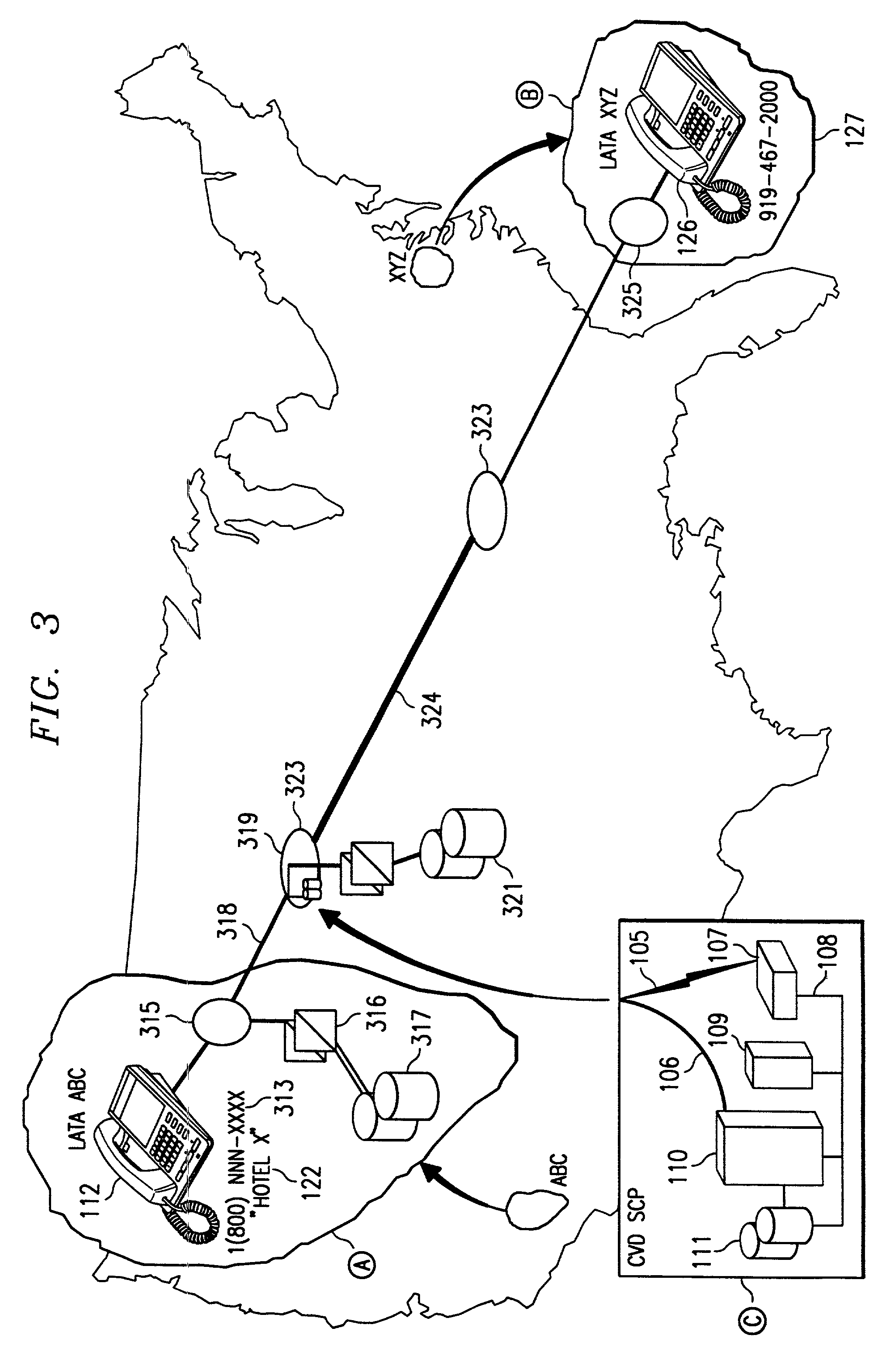
System and method for deriving call routing information utilizing a network control data base system and voice recognition for matching spoken word sound patterns to routing numbers needed to set up calls. Public access is provided to a common database via a common access number or code. Terminating parties sponsor the call and originating parties need not be pre-subscribed to use the service. The common access number is used to initiate or trigger the service. The system advantageously operates under the direction of a service control point, which combines technologies for switching, interactive voice response, and voice recognition with the data base to automate the processes of assisting callers in making calls for which they do not know the phone number. Usage information is gathered on completed calls to each terminating party for billing. Three alternative deployments in the U.S. telephone network are described, and vary based on the location of the service control points or intelligent processors and the degree of intelligence within the network.
Owner:GOOGLE LLC
Networked personal customized information and facility services
InactiveUS6055512AMultiple digital computer combinationsBuying/selling/leasing transactionsData displayPersonal details
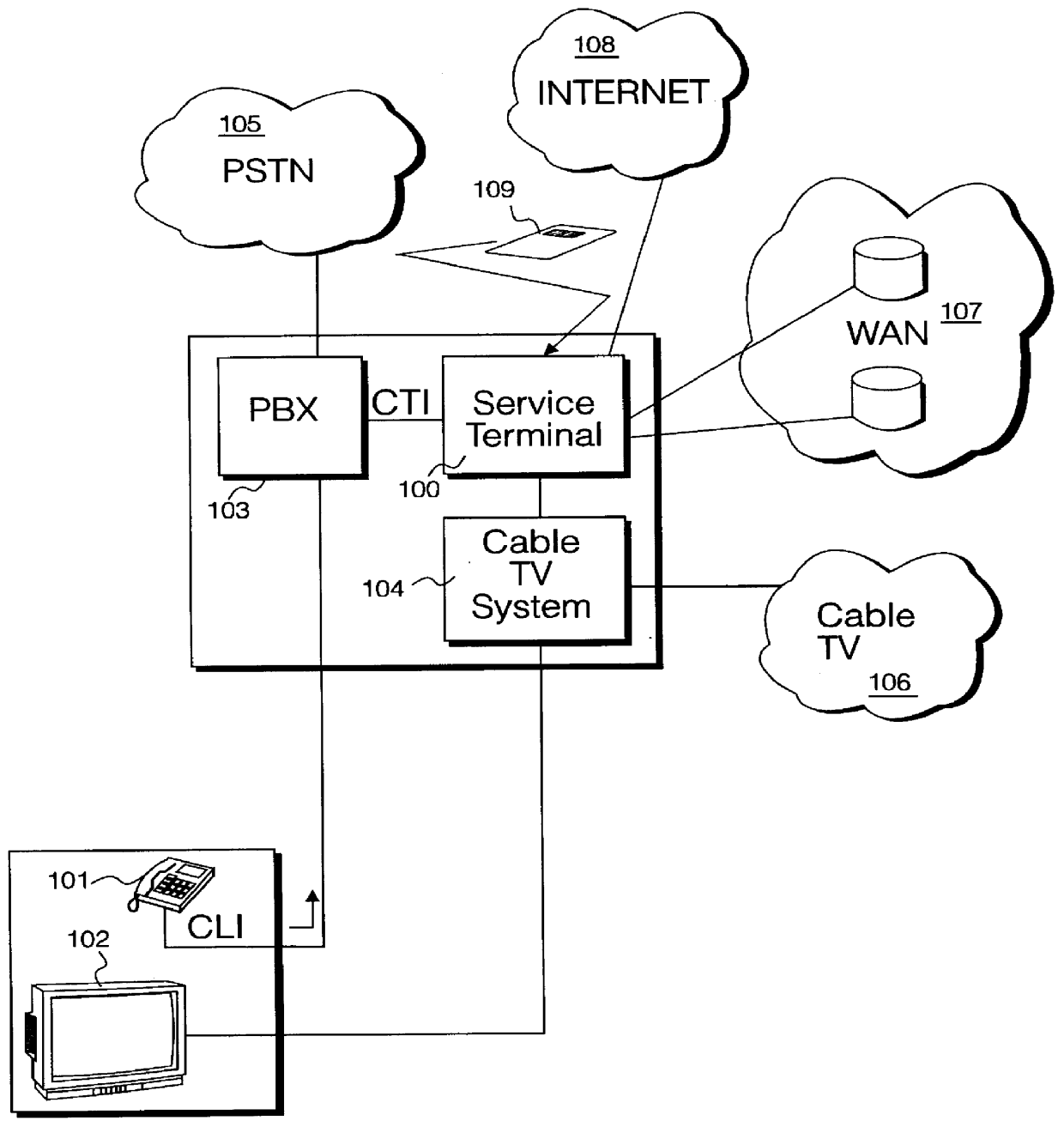
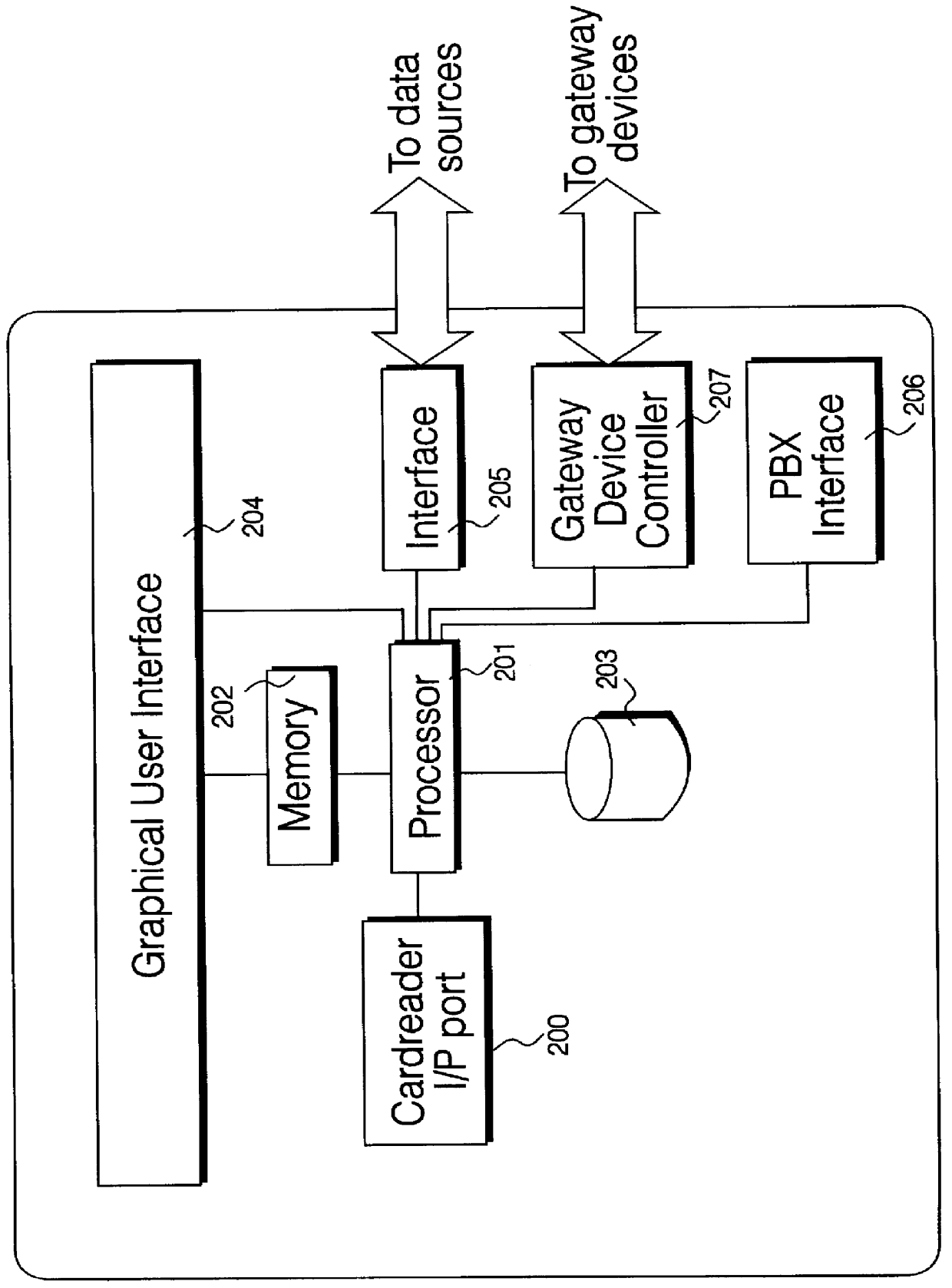
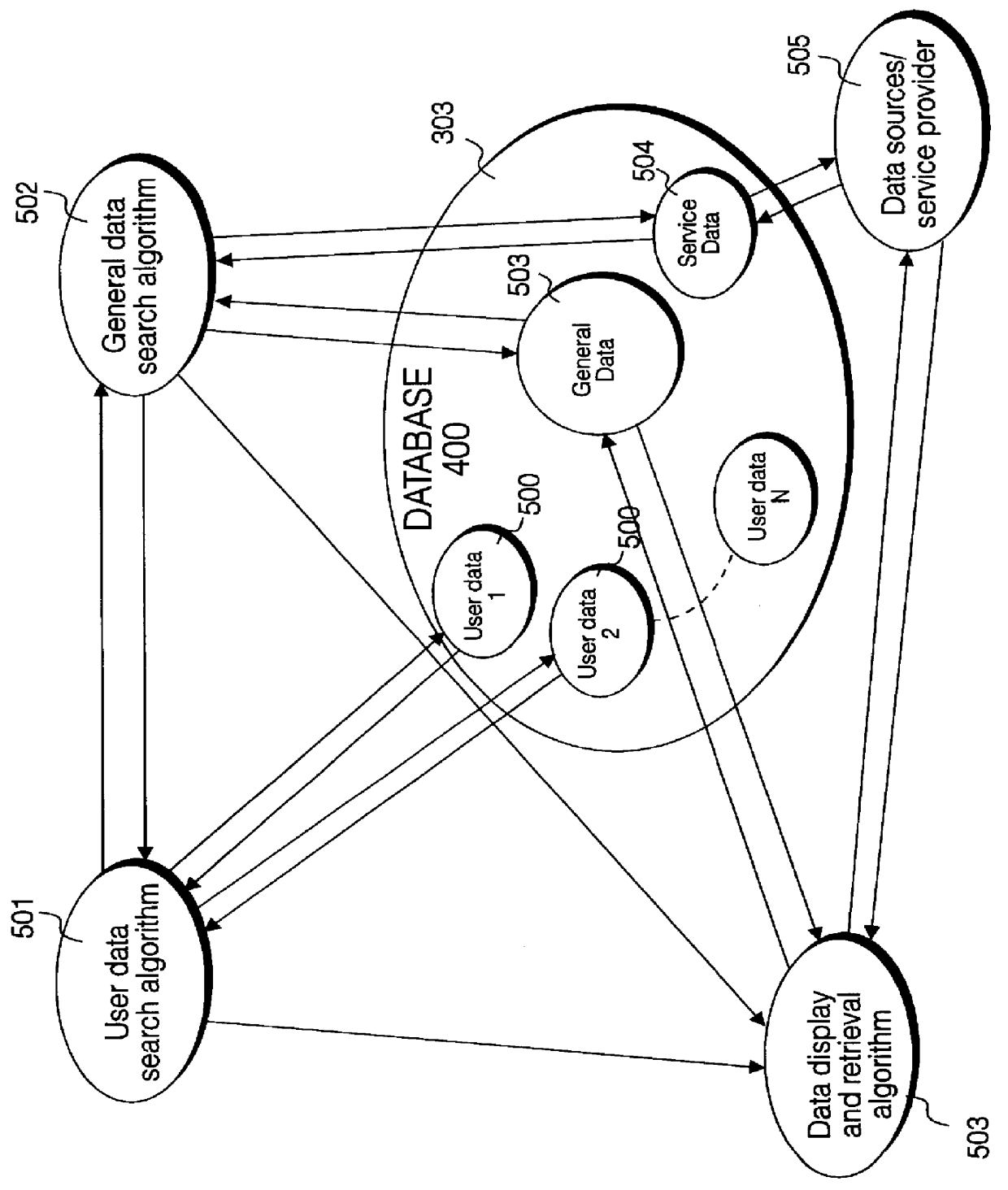
A service terminal facility is provided at a public access location, for example in a hotel, hospital or airport, the service terminal facility available for providing electronic information services to users, in response to input of a portable data storage medium, for example a smart card or the like. A smart card contains stored data describing user specified information such as contacts names, personal details and medical information and personal interest information. The service terminal comprises a search engine for searching the user data and comparing data types within the user data with general data stored locally at the service terminal. The service terminal selects data corresponding to data types specified in the user data and displays these on the graphical user interface at the service terminal, or at a user interface connected with the service terminal. The user data may specify one or more data sources or service providers from which electronic data services of interest to the user can be obtained. The service terminal may obtain listings of data from remote data sources and / or service providers and display these on the graphical user interface and / or user interface. The user may instruct downloading of electronic data or electronic information services from remote data sources or service providers from the service terminal for delivery to the graphical user interface or the user interface.
Owner:NORTEL NETWORKS LTD
Operating system extension to provide security for web-based public access services
InactiveUS7171686B1Improve securityDigital data processing detailsUser identity/authority verificationOperational systemPassword
Owner:RPX CLEARINGHOUSE
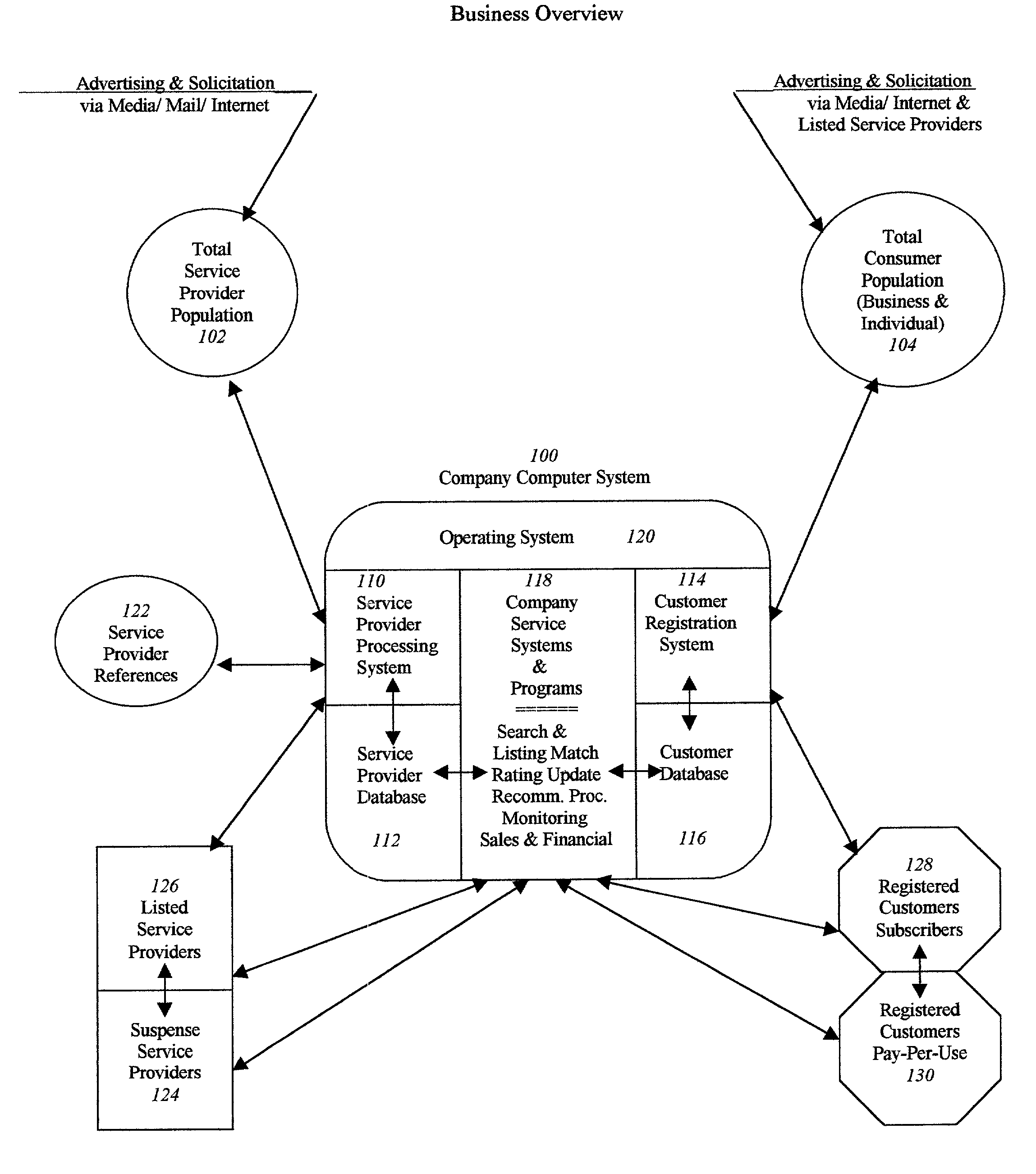
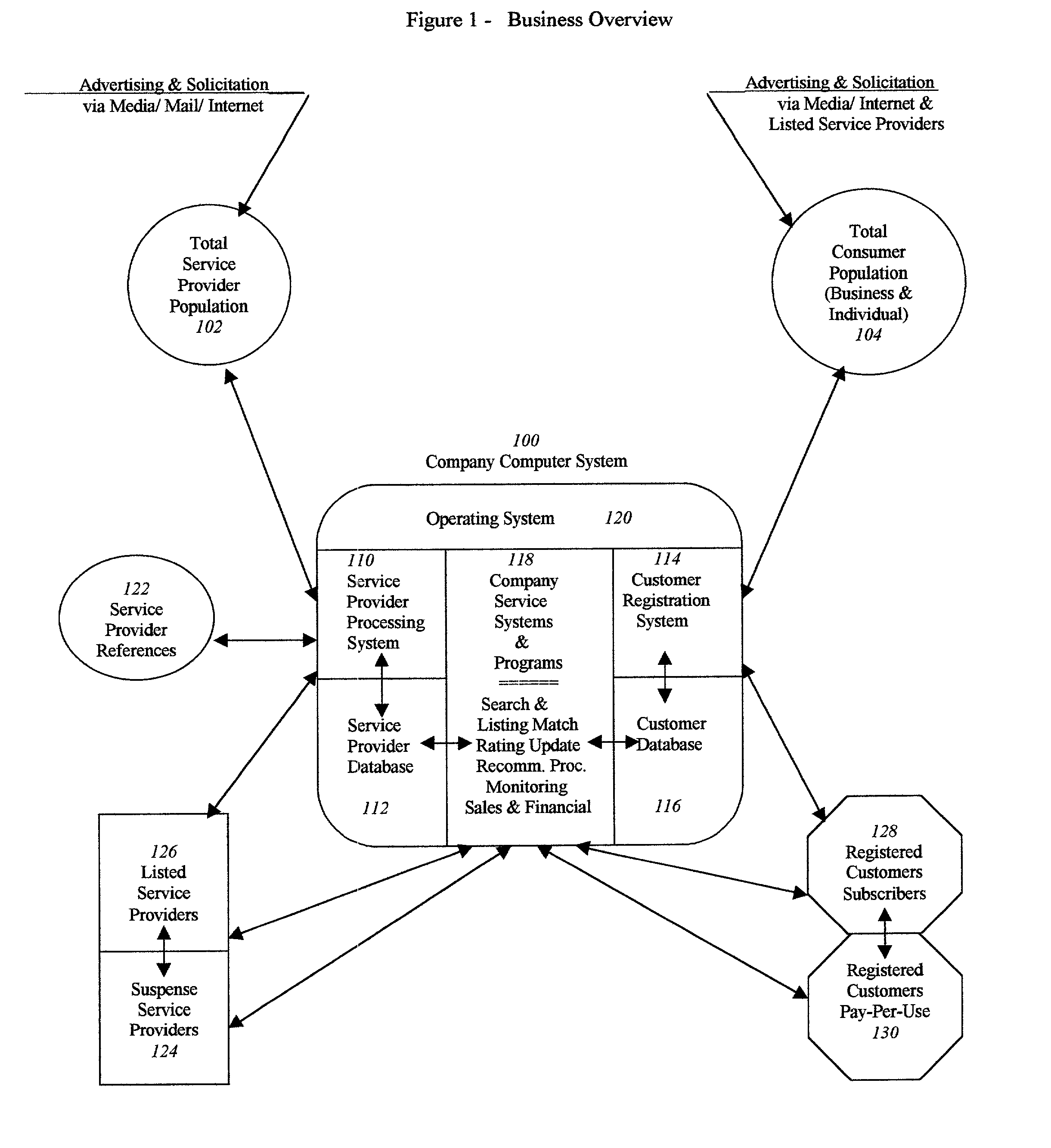
Accessible service provider clearinghouse
A service that maintains a minimum criteria level for service providers to be listed and available for public access. It can list not only the service provider's credentials and insurance support (with monitored expiration dates), but may also provide a current up-to-date rating system by the users themselves, as to the satisfaction level of the quality and reliability of the work performed. It can also offer a double-check of the credentials by customer verification input. Furthermore, the example service can be easily accessible by the general public (for individual or business use) on the Internet, or by printed text directories sold direct or in bookstores.
Owner:LOKITZ SHEILA
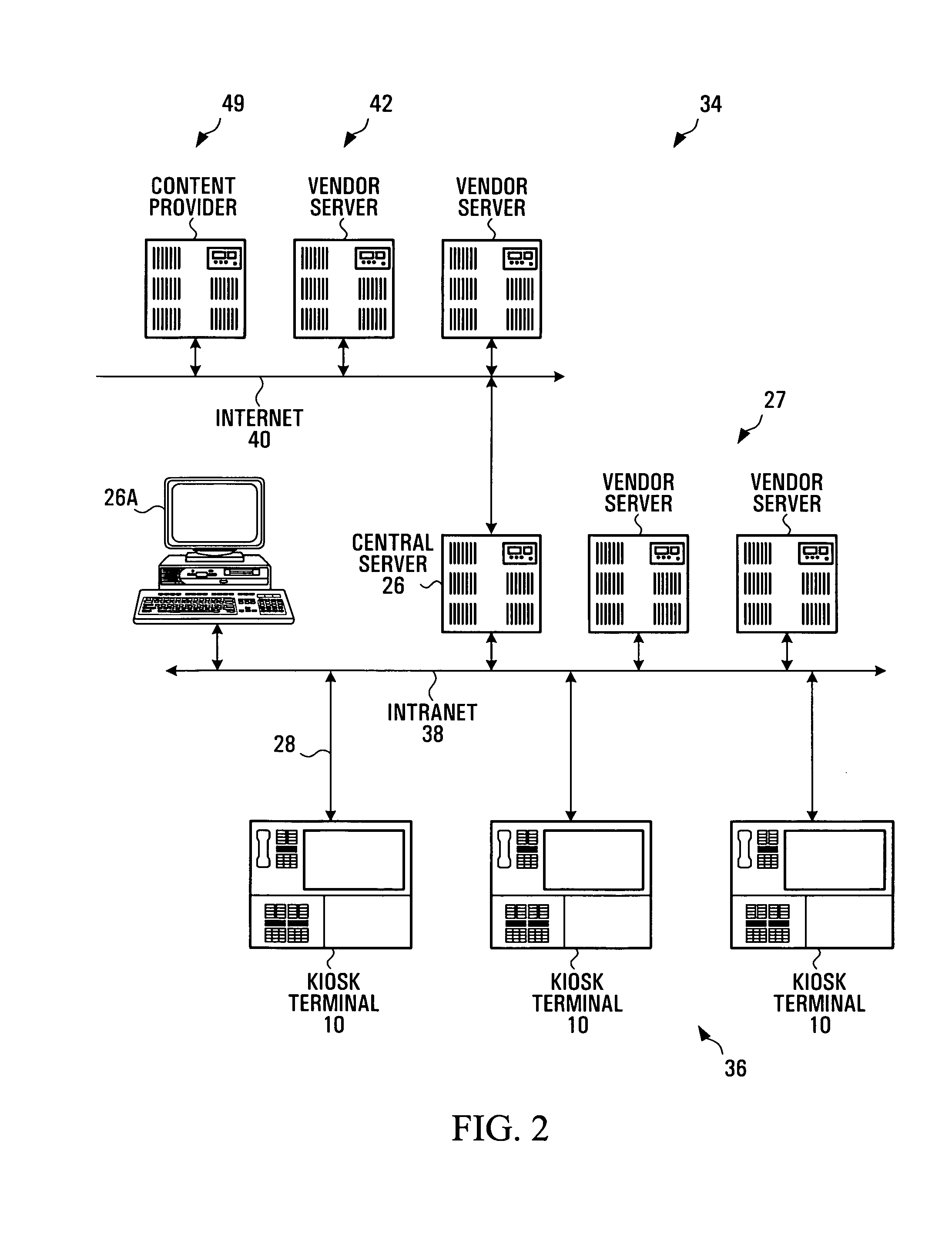
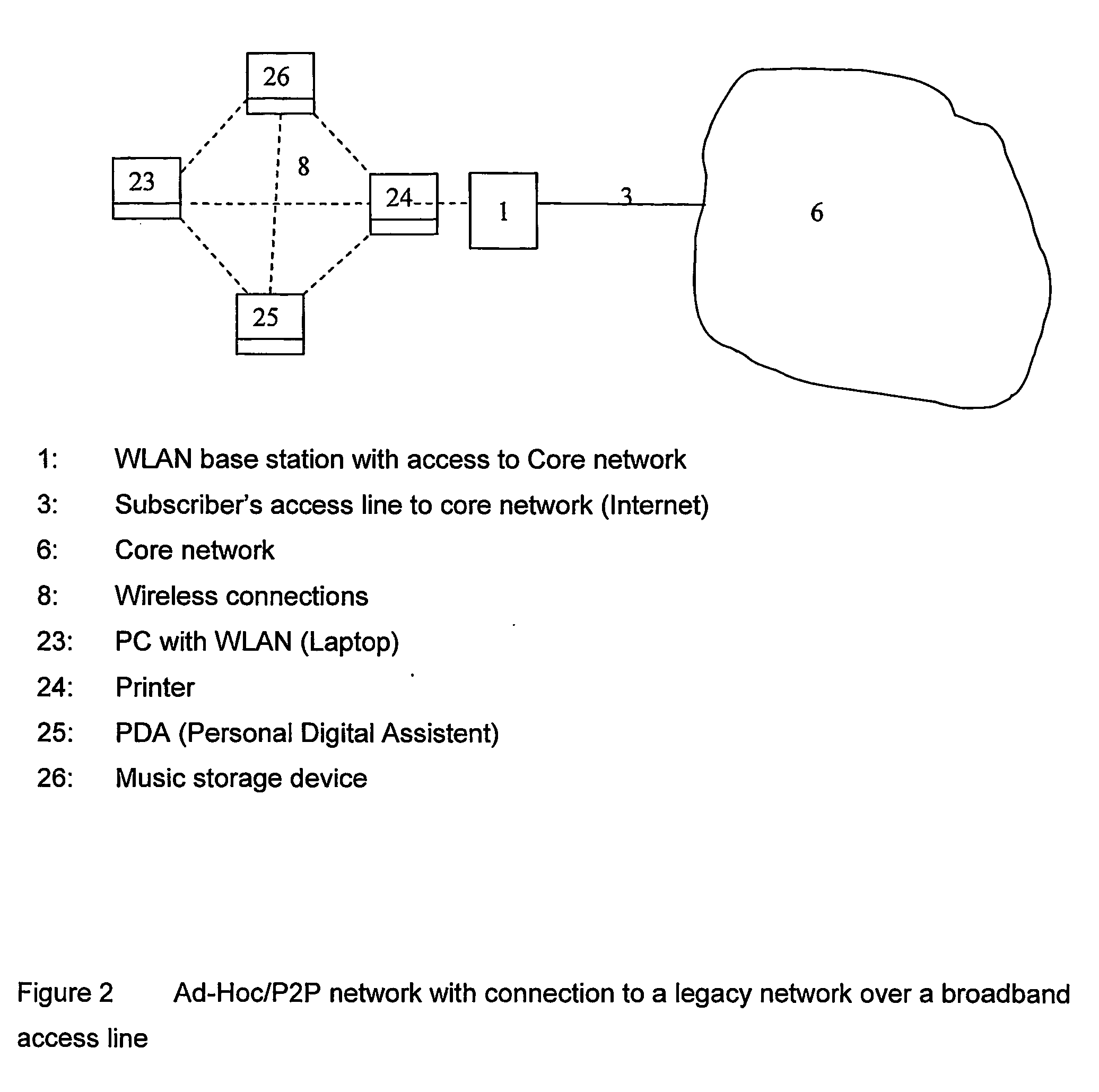
E-commerce development intranet portal
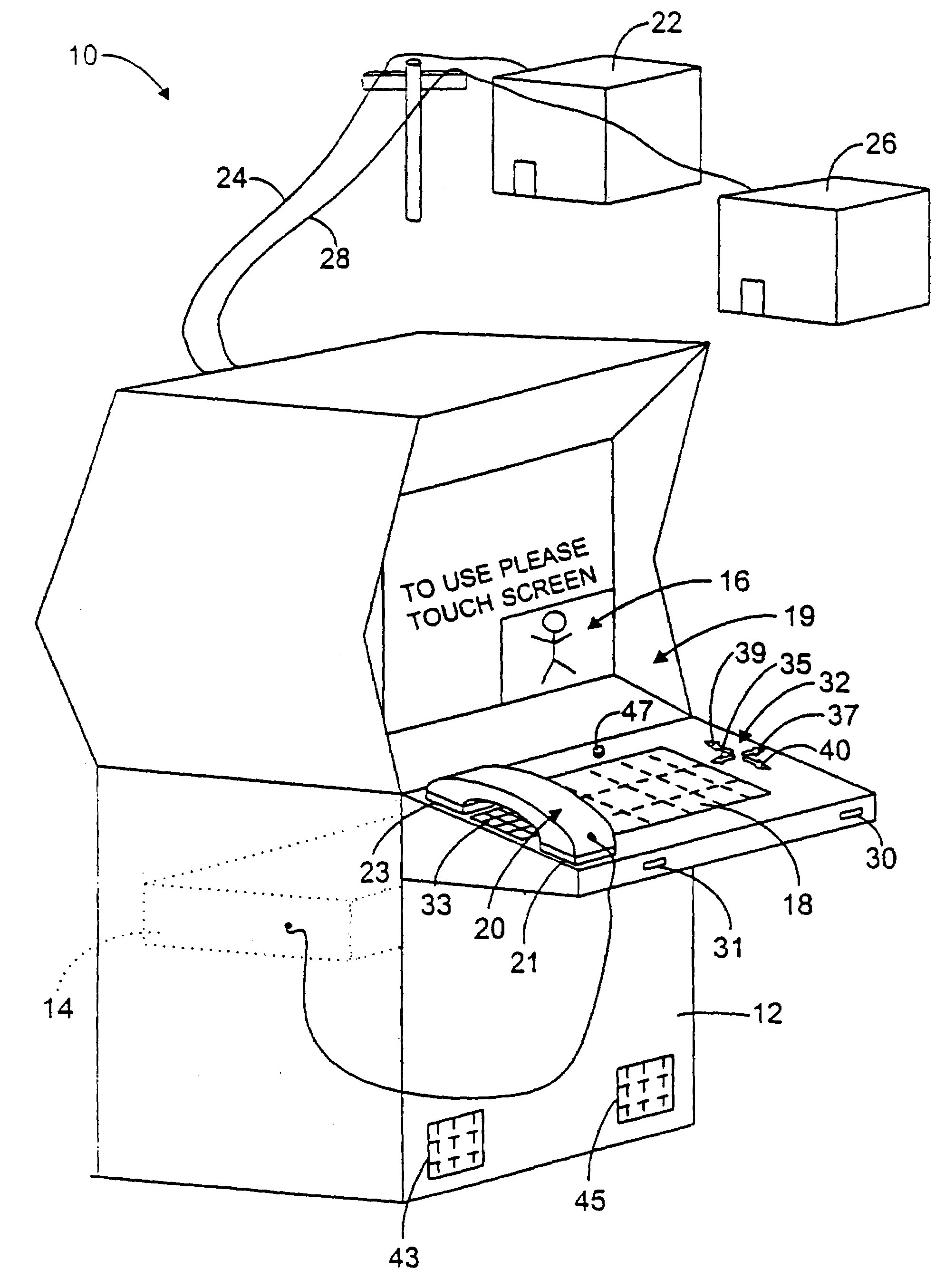
An intranet providing a multiple-carrel public-access kiosk is disclosed. The intranet provides free access to foreign and domestic informational e-commerce intranet sites as well as e-mail and public service educational and informational materials. The kiosk accepts anonymous pre-paid cards issued by a local franchisee of a network of c-commerce intranets that includes the local intranet. The franchisee owns or leases kiosks and also provides a walk-in e-commerce support center where e-commerce support services and goods, such as pre-paid accounts for access to paid services at a kiosk, can be purchased. The paid services provided by the carrel include video-conference and chat room time, playing and / or copying audio-visual materials such as computer games and music videos, and international e-commerce purchase support services such as customs and currency exchange. The third-party sponsored public service materials include audio-visual instructional materials in local dialects introducing the user to the use of the kiosks services and providing training for using standard business software programs. Sponsors include pop-up market research questions in the sponsored public service information and receive clickstream date correlated with the user's intranet ID and answers to the original demographic questions answered by the user.
Owner:DE FABREGA INGRID PERSCKY
Open registry for provenance and tracking of goods in the supply chain
InactiveUS20180108024A1Avoid flowEncryption apparatus with shift registers/memoriesCryptography processingThird partyThe Internet
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with items / goods without relying on a third-party-controlled authentication service. The system includes tags having alphanumeric values and coupled to items / goods and an open registry database and ledger where digital records associated with the items / goods is able to be stored. The open registry enables public access to the items / goods and data combined with item registration anonymity.
Owner:CHRONICLED INC
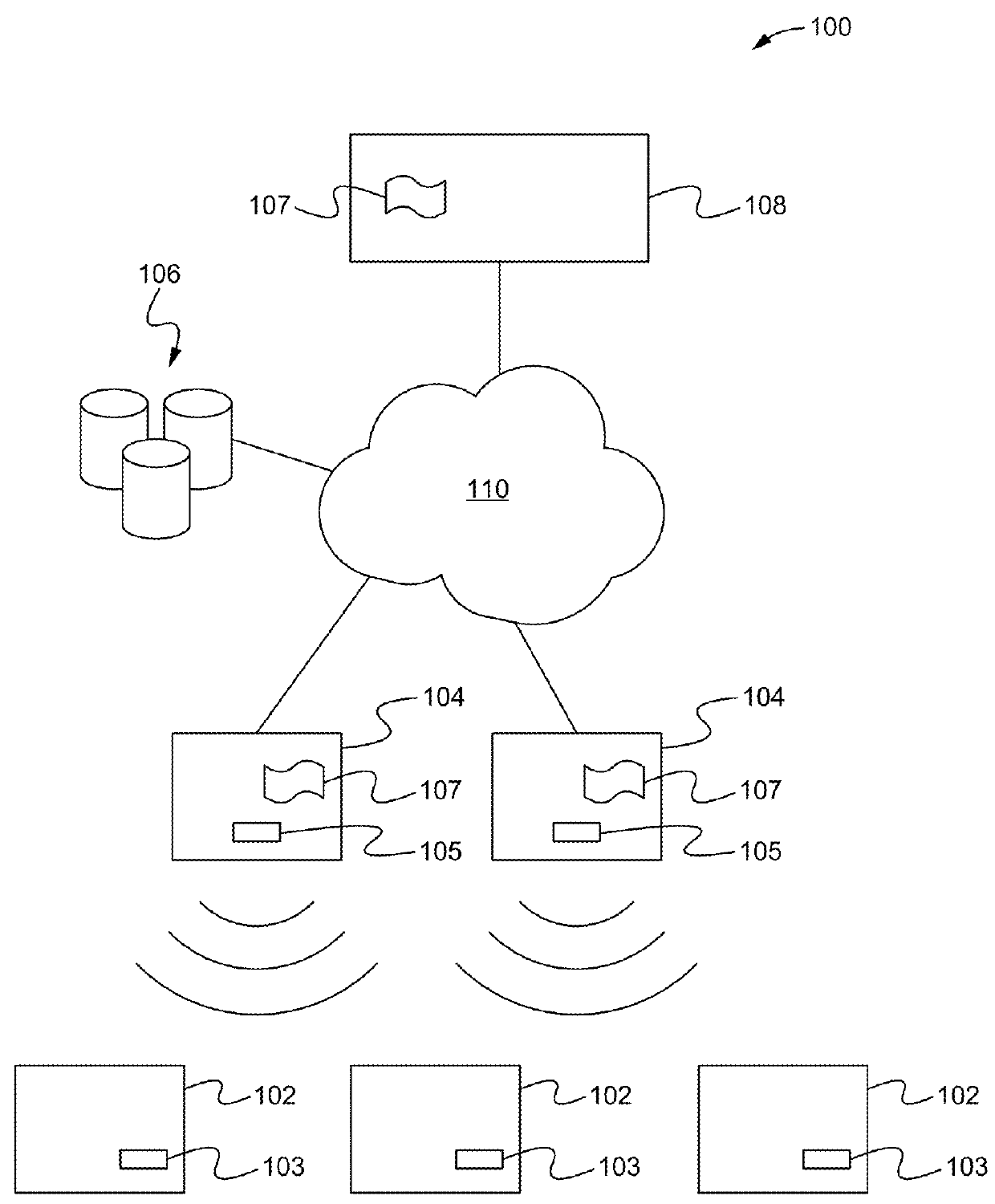
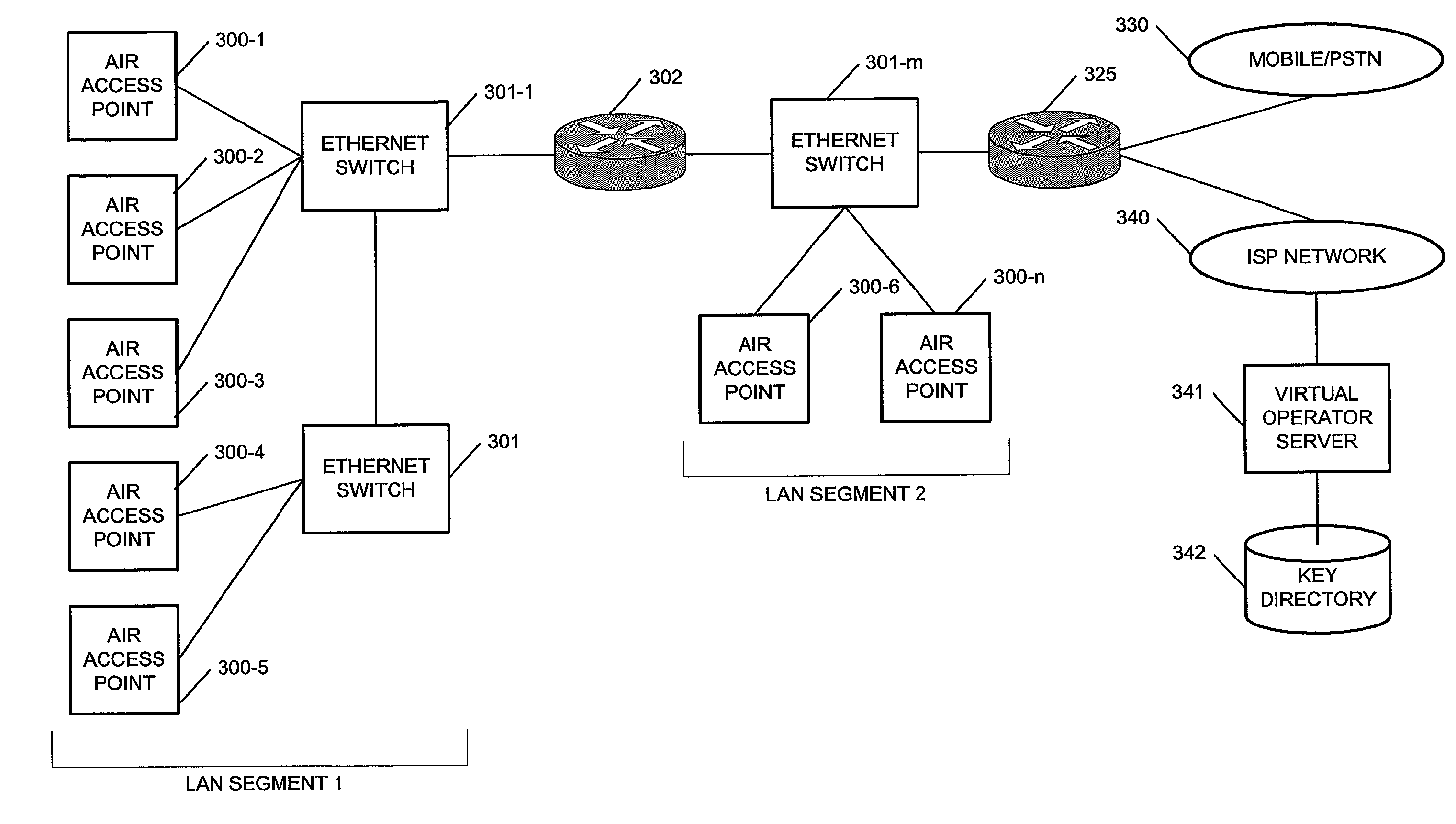
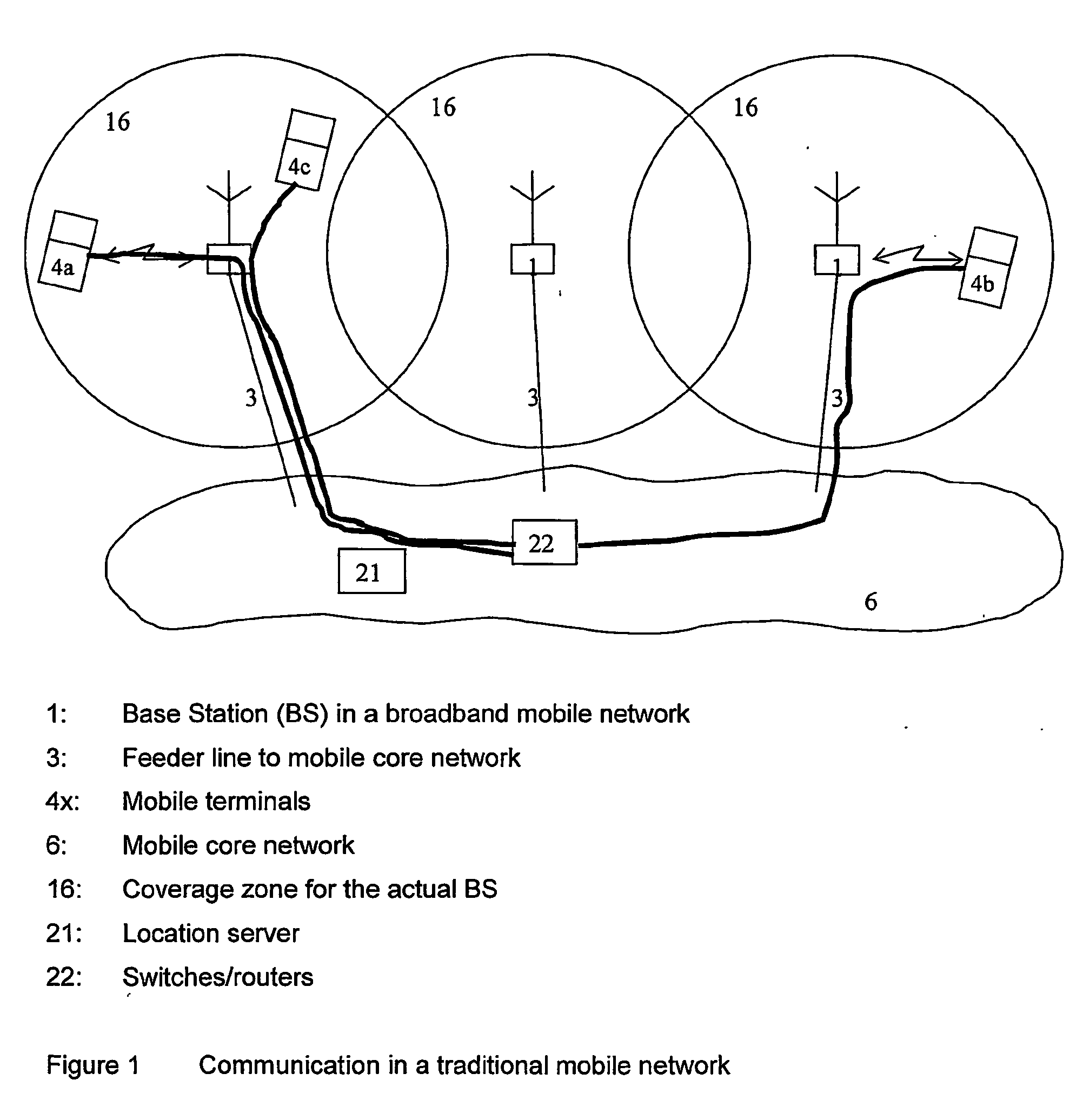
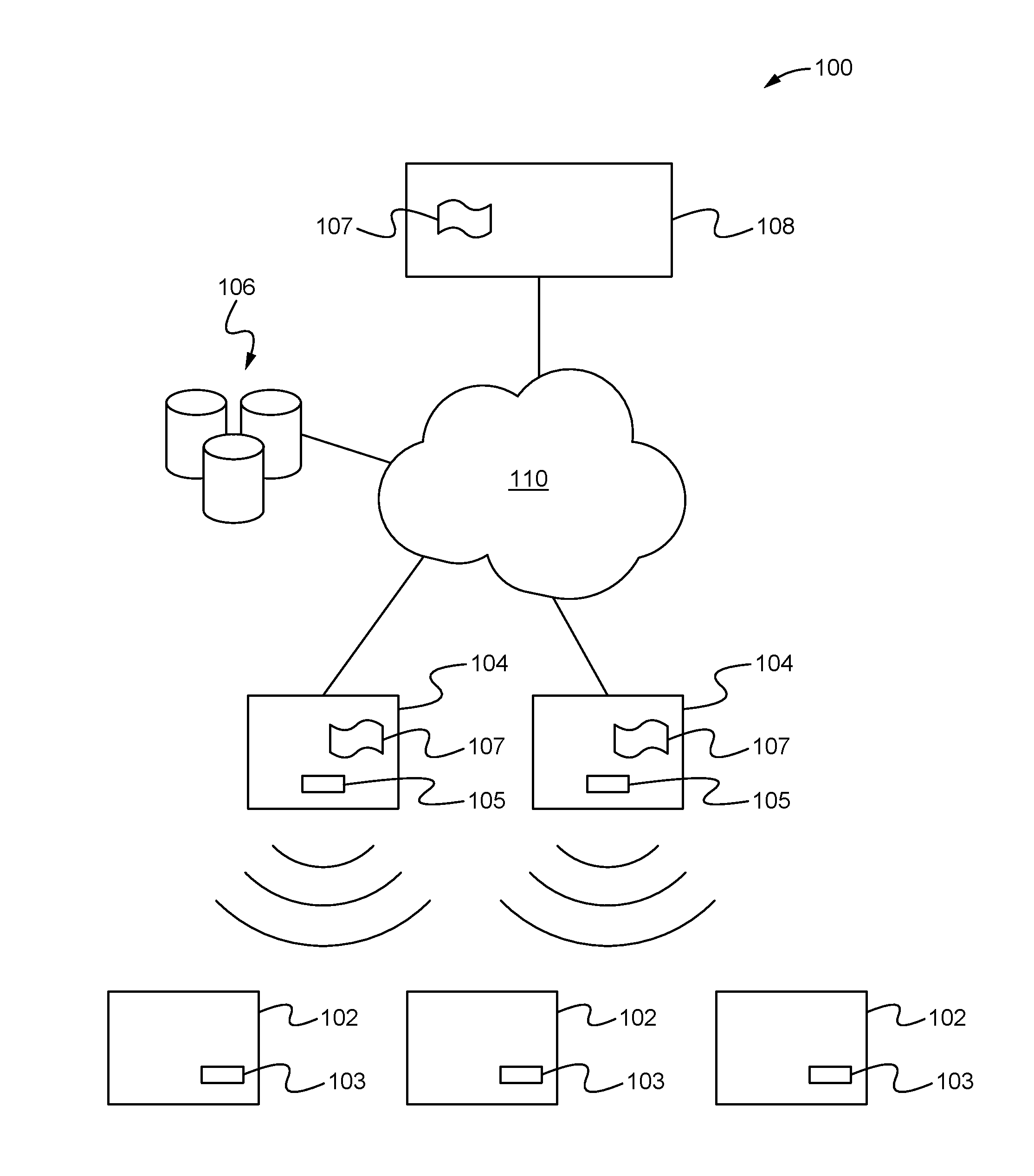
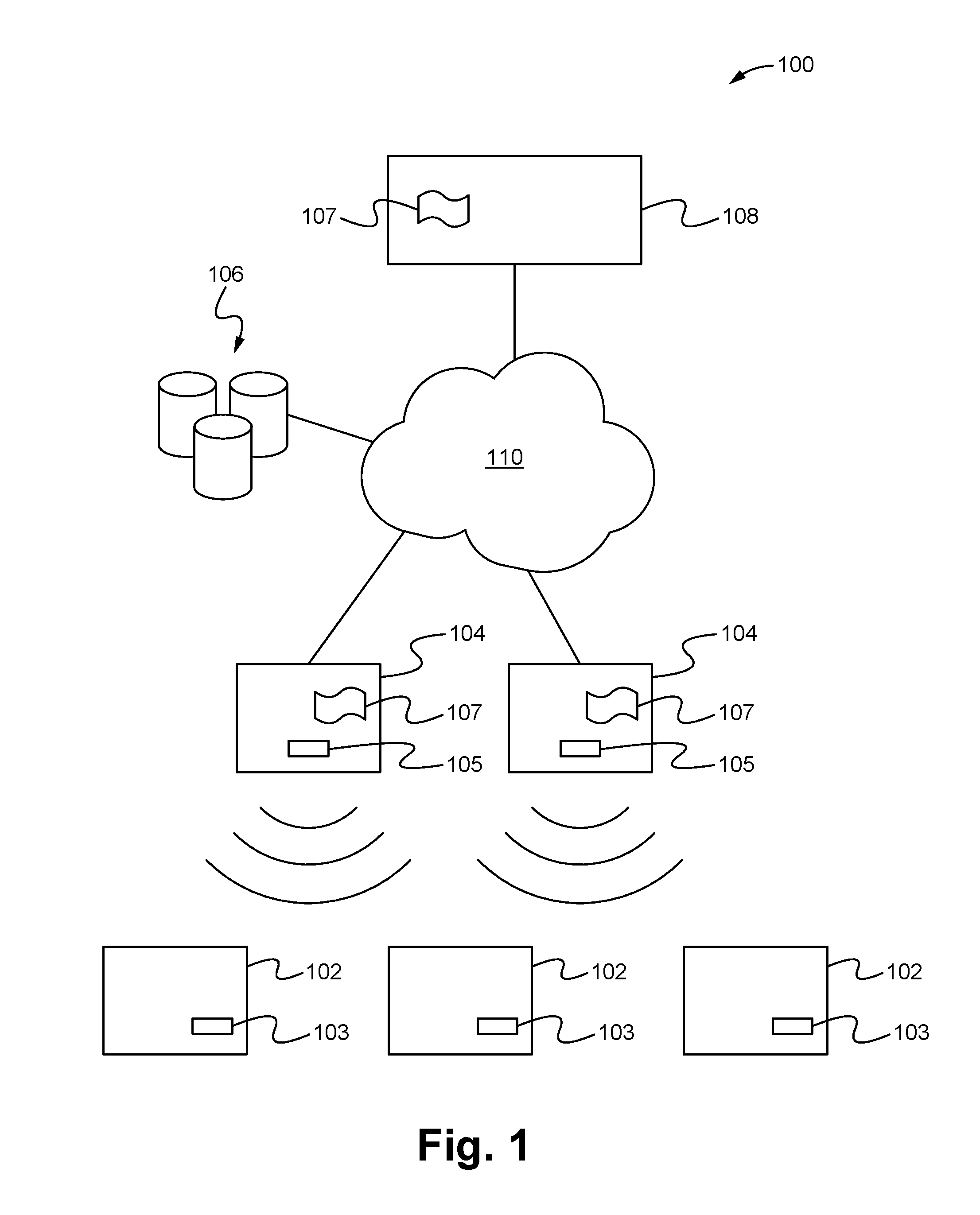
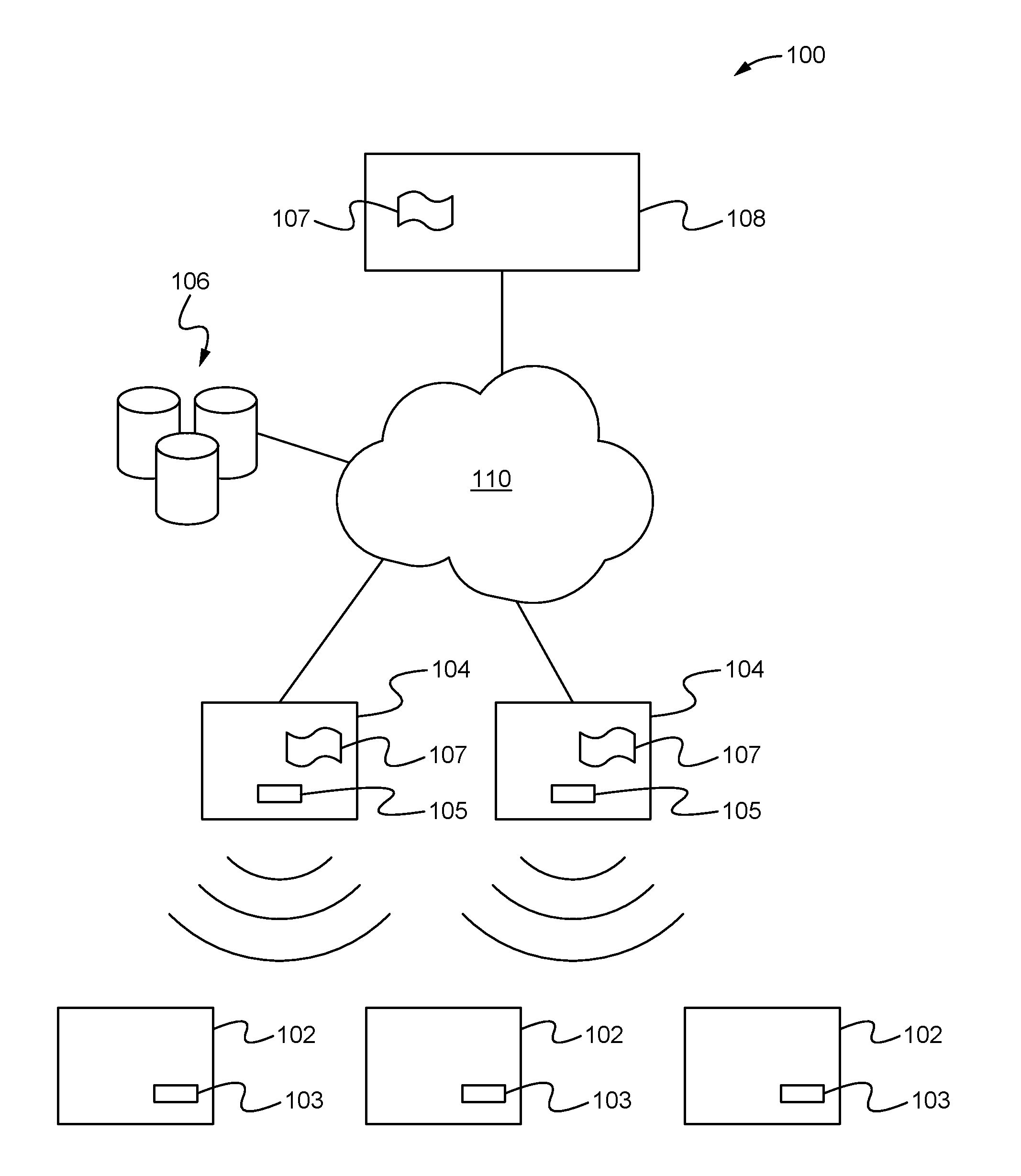
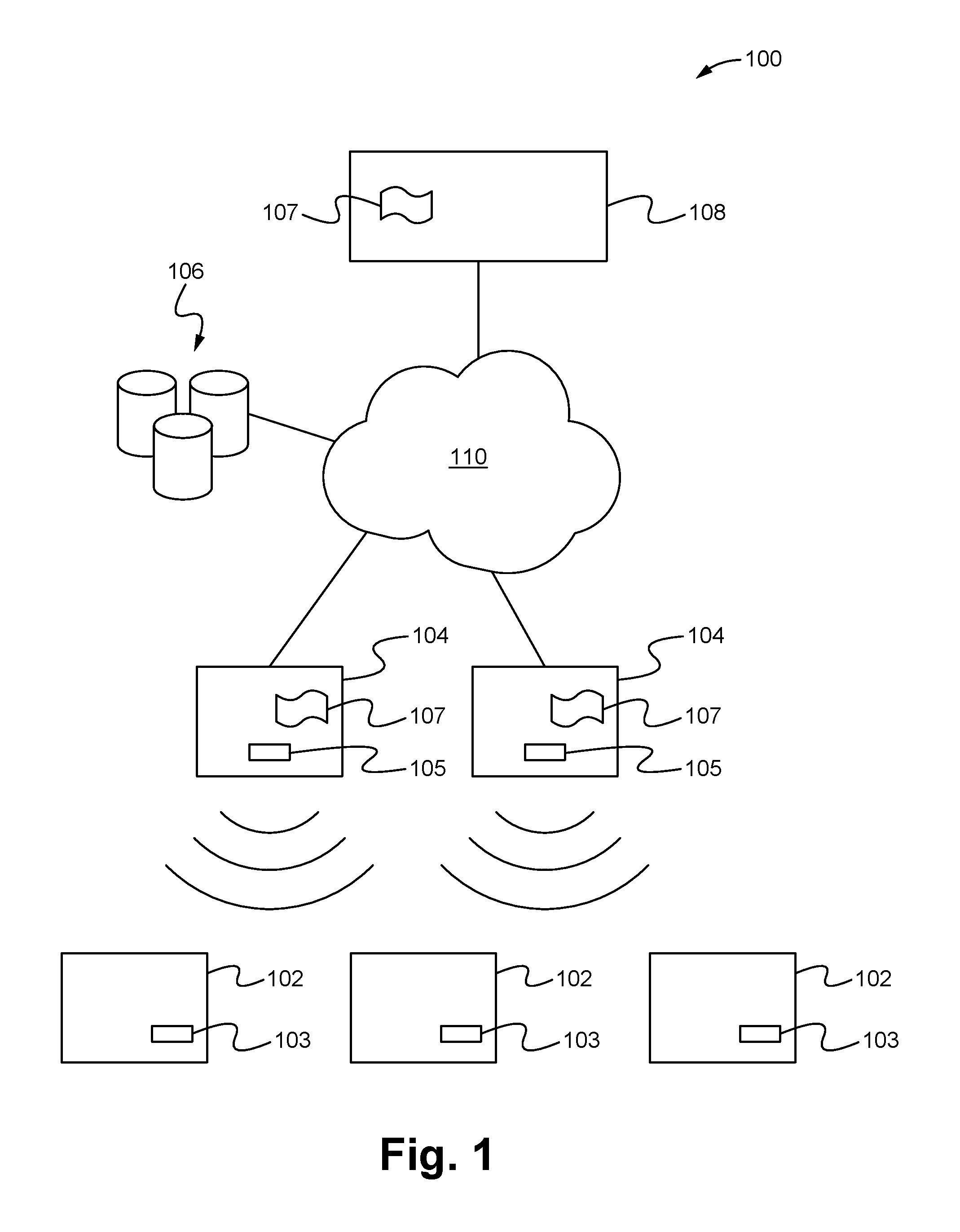
Apparatus for public access mobility LAN and method of operation thereof
ActiveUS7483411B2Key distribution for secure communicationAccounting/billing servicesAir interfaceThe Internet
Public wireless communications will increasingly extend into wireless LAN (WLAN) environments in order to meet the ubiquitous access, high data rate, and local services demands of future Internet appliances. By relying on IP-level services mechanisms, the Public Access Mobility LAN (PAMLAN) can simultaneously support different air interfaces, franchises for multiple services providers, and a multi-segment LAN environment including handoffs. The PAMLAN supports virtual operator LANs representing different network services providers, authorization and accounting mechanism, support of multiple air interfaces, and local IP mobility. A router associated with each base station realizes this highly distributed IP networking environment, and a QoS-enabled switched Ethernet core supports virtual networks and QoS services.
Owner:NEC CORP
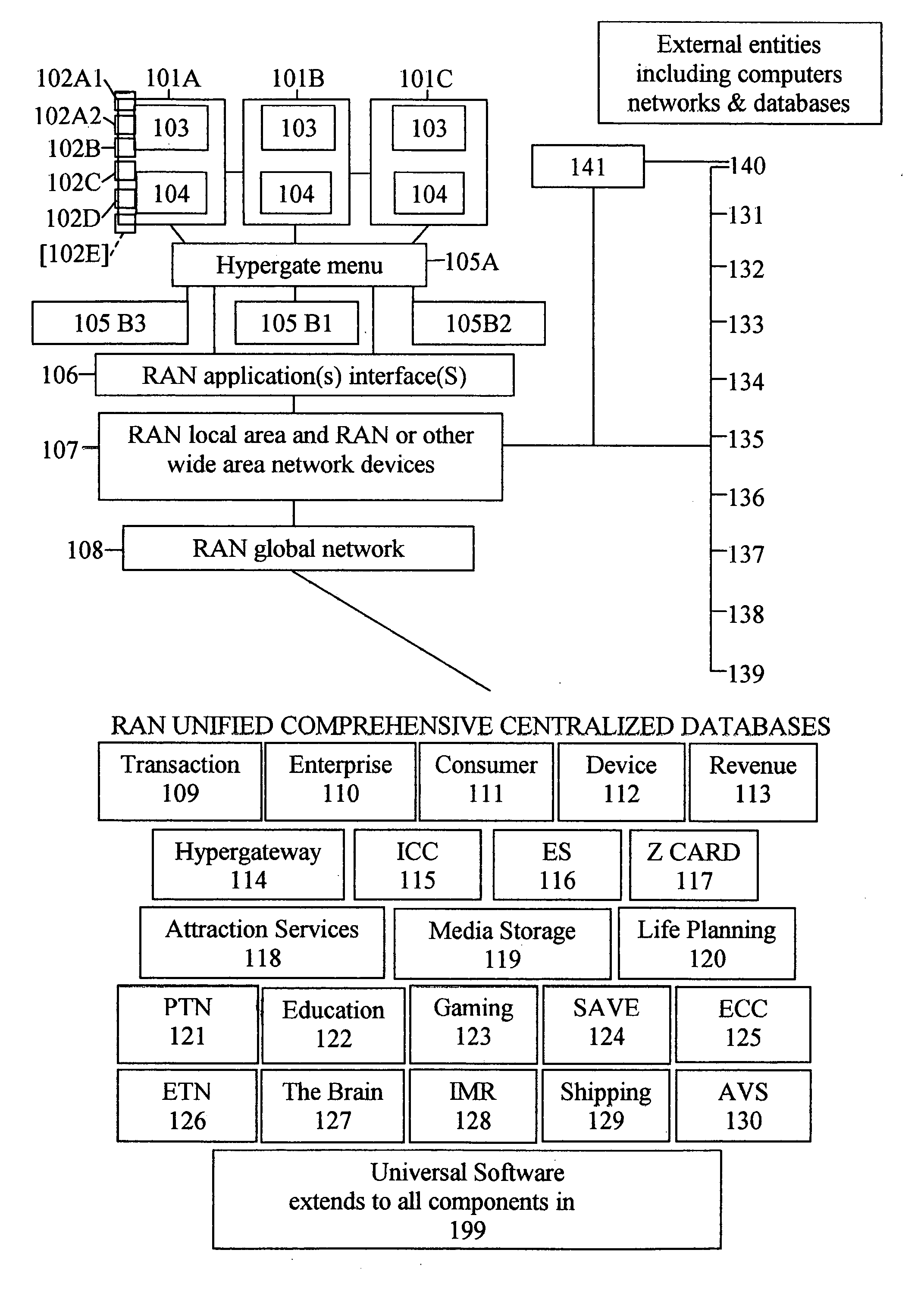
System and method for integration of a universally publicly accessible global network
InactiveUS20050102374A1Improve efficiencySignificant financial magnitudeMultiple digital computer combinationsData switching networksIntegrated softwareApplication software
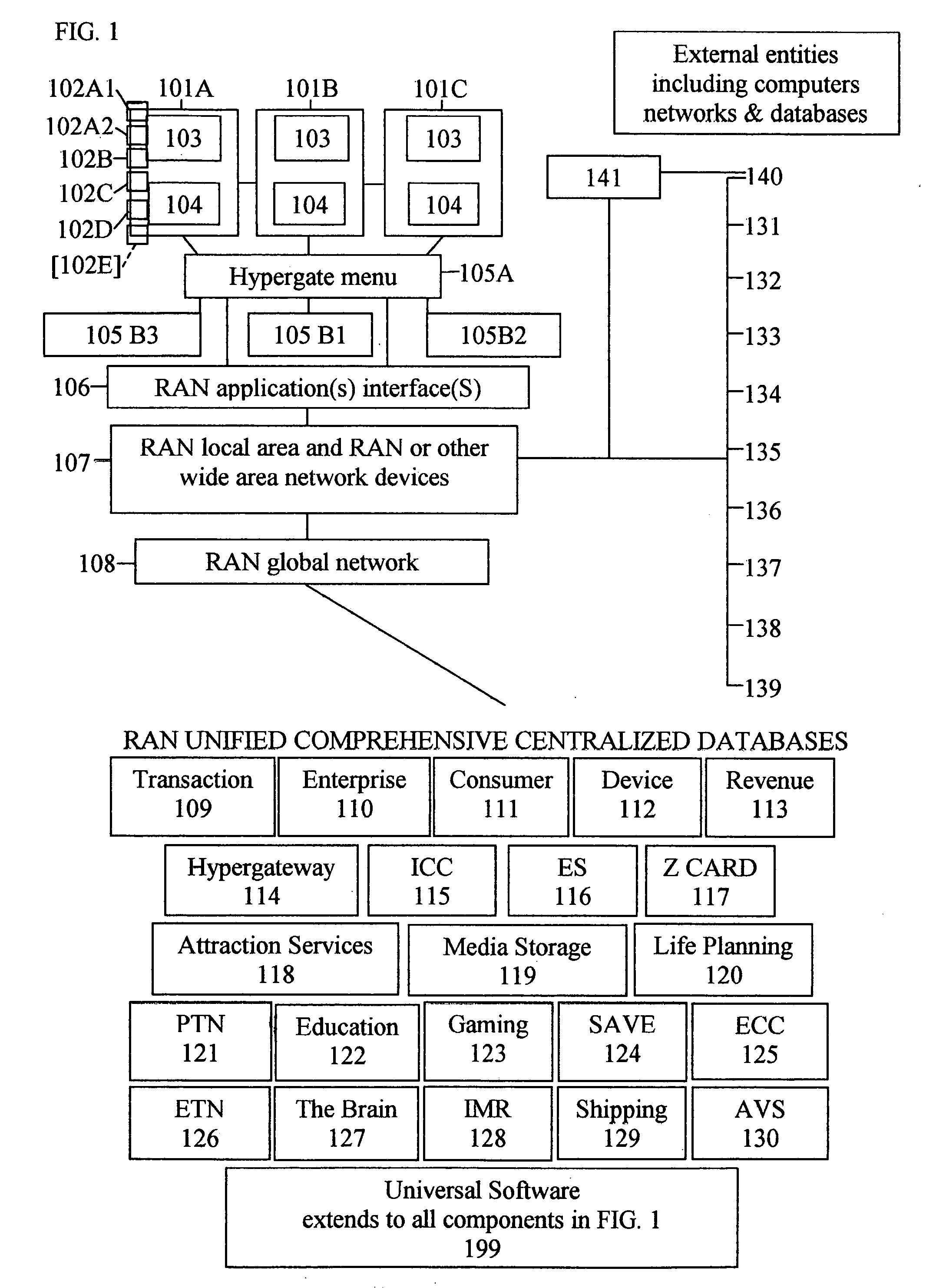
The present invention is a system and method for integrated operation, provision of user services, and management and control, for a publicly accessible global network. The global network has one or more horizontal levels for the provision of user services, network operation, overall management and control in a vertical hierarchy, and one or more horizontal levels of data management, including data capture, processing, analysis, reporting, etc. The system further includes Universal Software which integrates the functionalities of various software platforms into one unified integrated software. The system incorporates a plurality of components for connecting any user directly to applications, and enterprise sites and consumer sites for connecting users via the global network directly to other networks, data bases and computer devices, of emergency services personnel / agencies, for performing simultaneously mathematical formulae, algorithms or procedures, and for displaying and updating advertisements appearing at specific points in a software operation.
Owner:ZEPHYR MEDIA
System and use for correspondent banking
InactiveUS6947908B1Reduce the amount requiredImprove Internet efficiencyComputer security arrangementsPayment circuitsFinancial transactionPersonal computer
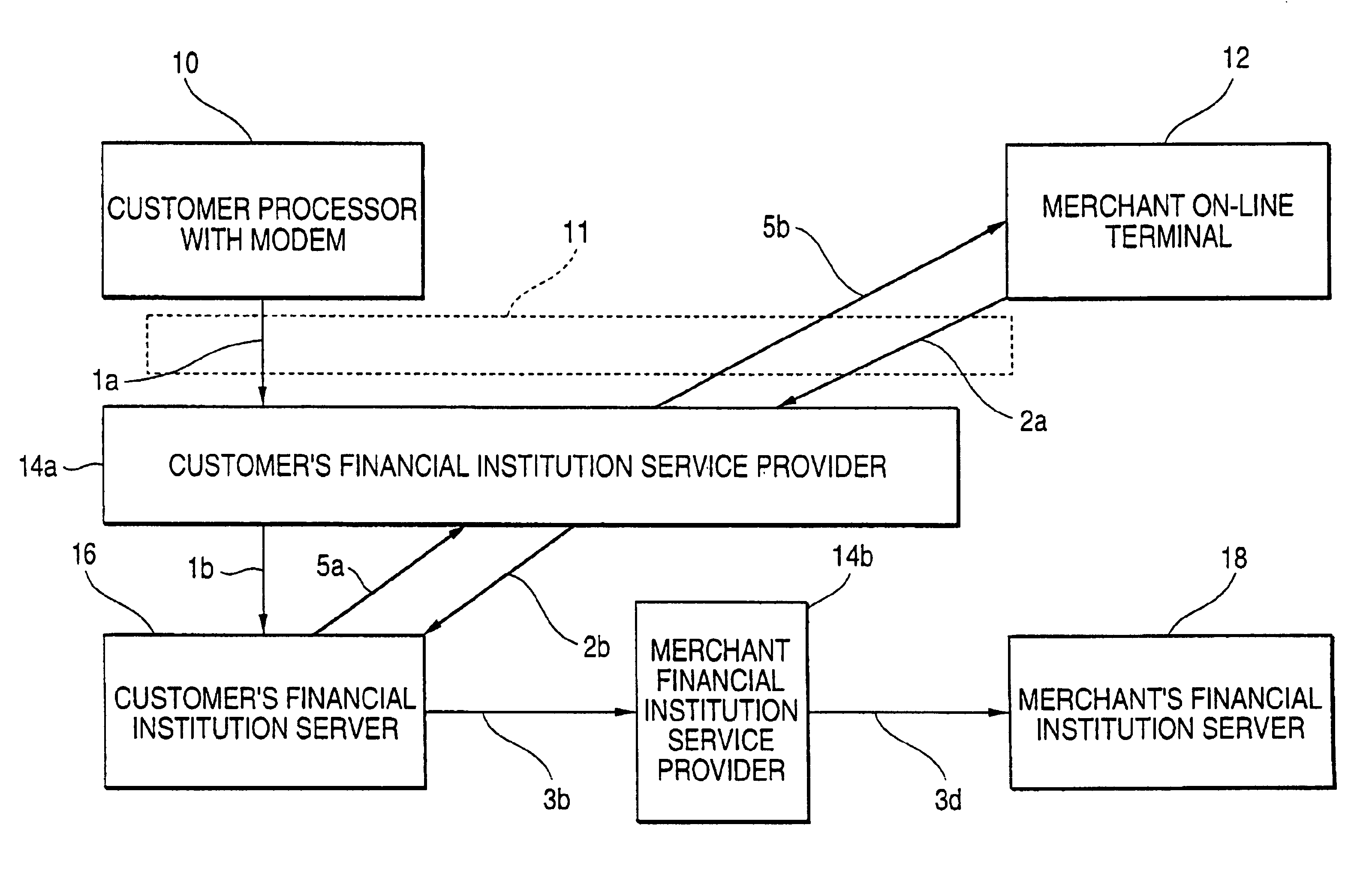
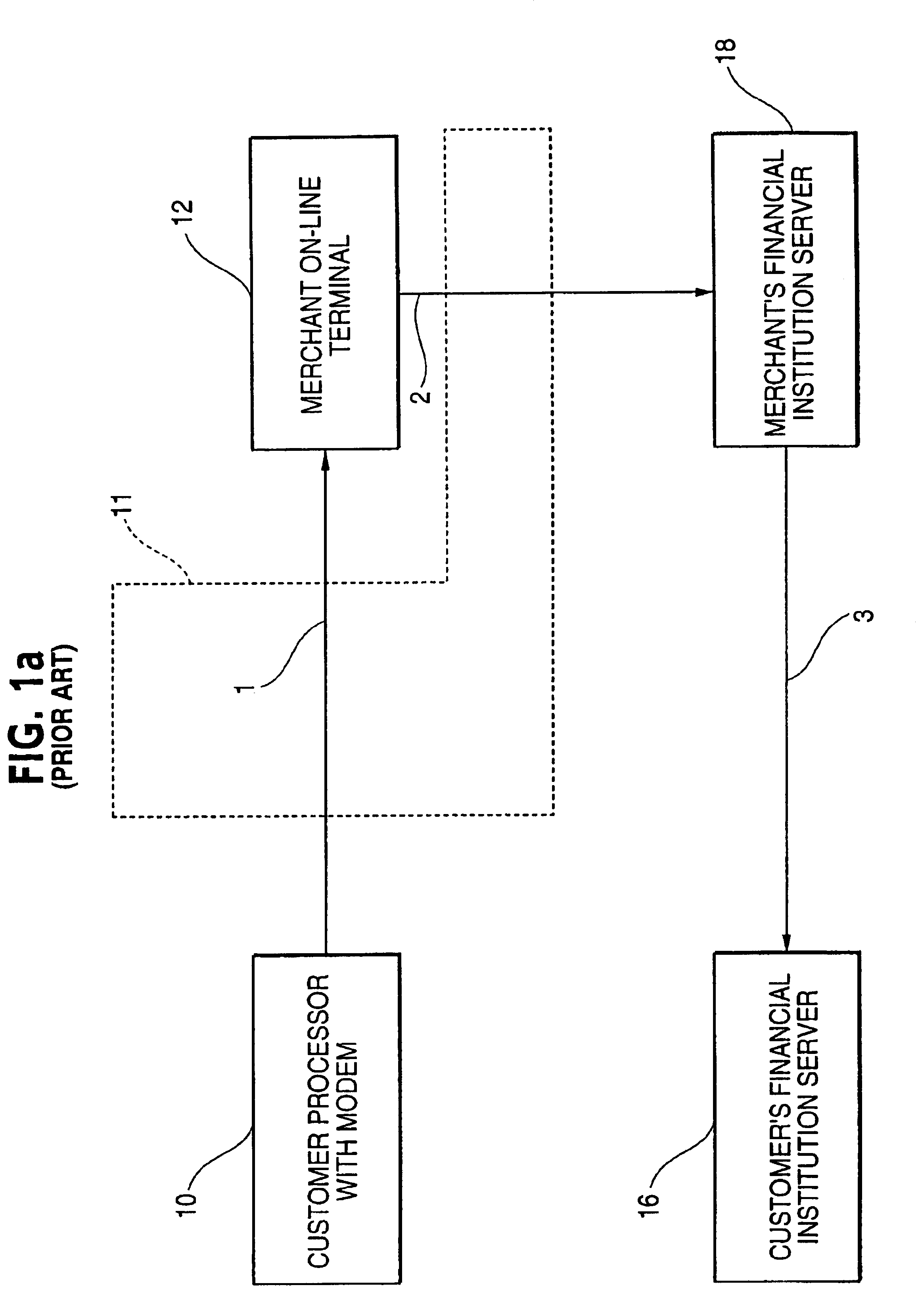
The present invention comprises a system and method for a customer and merchant to perform an on-line, and in some cases, real-time financial transaction from a personal computer or similar processing terminal over a public access communications network utilizing a universally acceptable electronic financial transaction instruction that debits a customer's selected account and notifies a merchant that a credit is due or forthcoming and a service provider. The financial transaction instruction is provided in a secured format for transactions sent over the public access communications network, which is external from any other conventional open or closed communication channels used for performing financial transactions.
Owner:CITIBANK
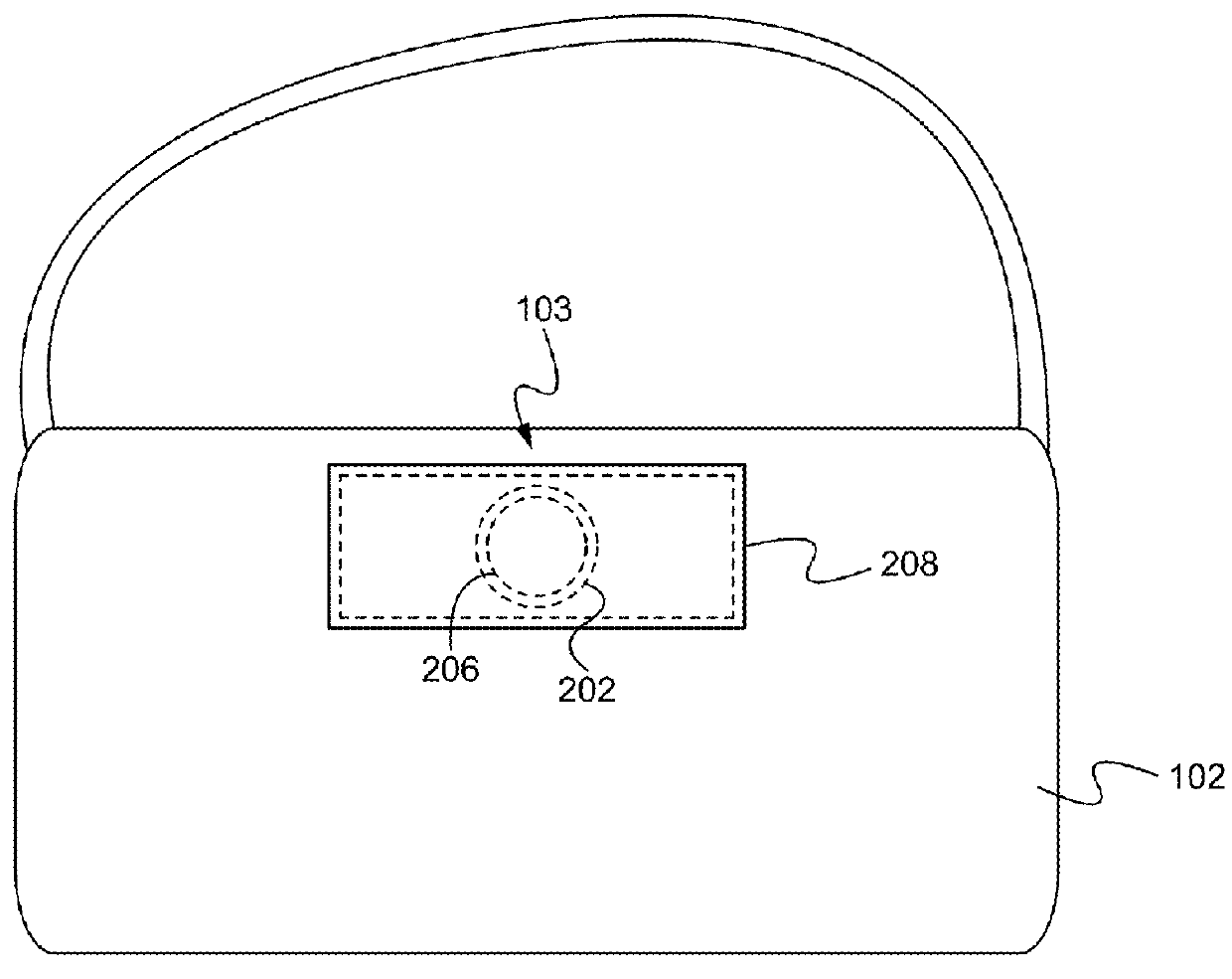
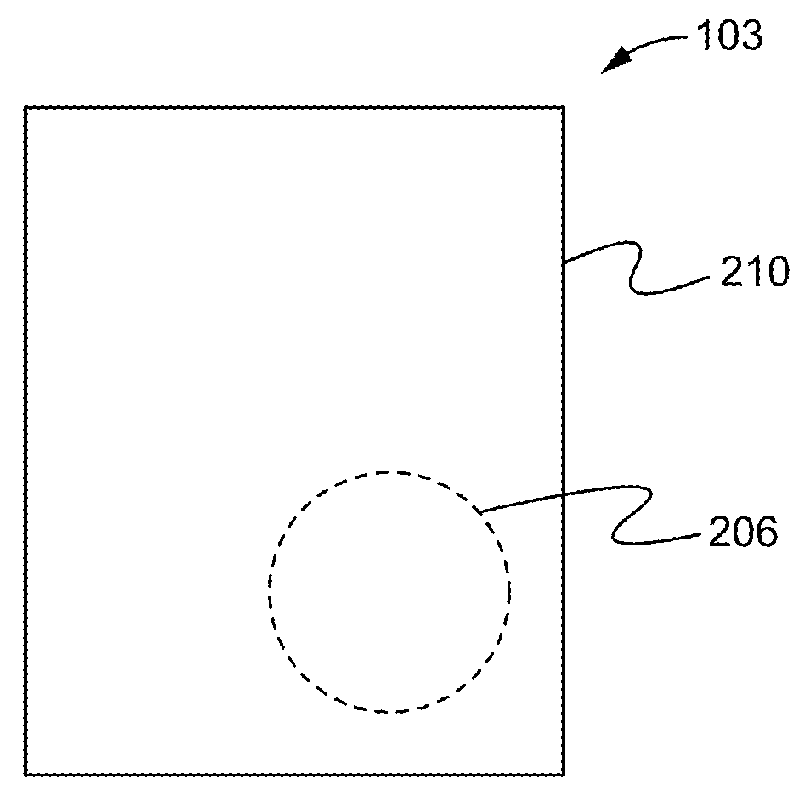
Public access defibrillator
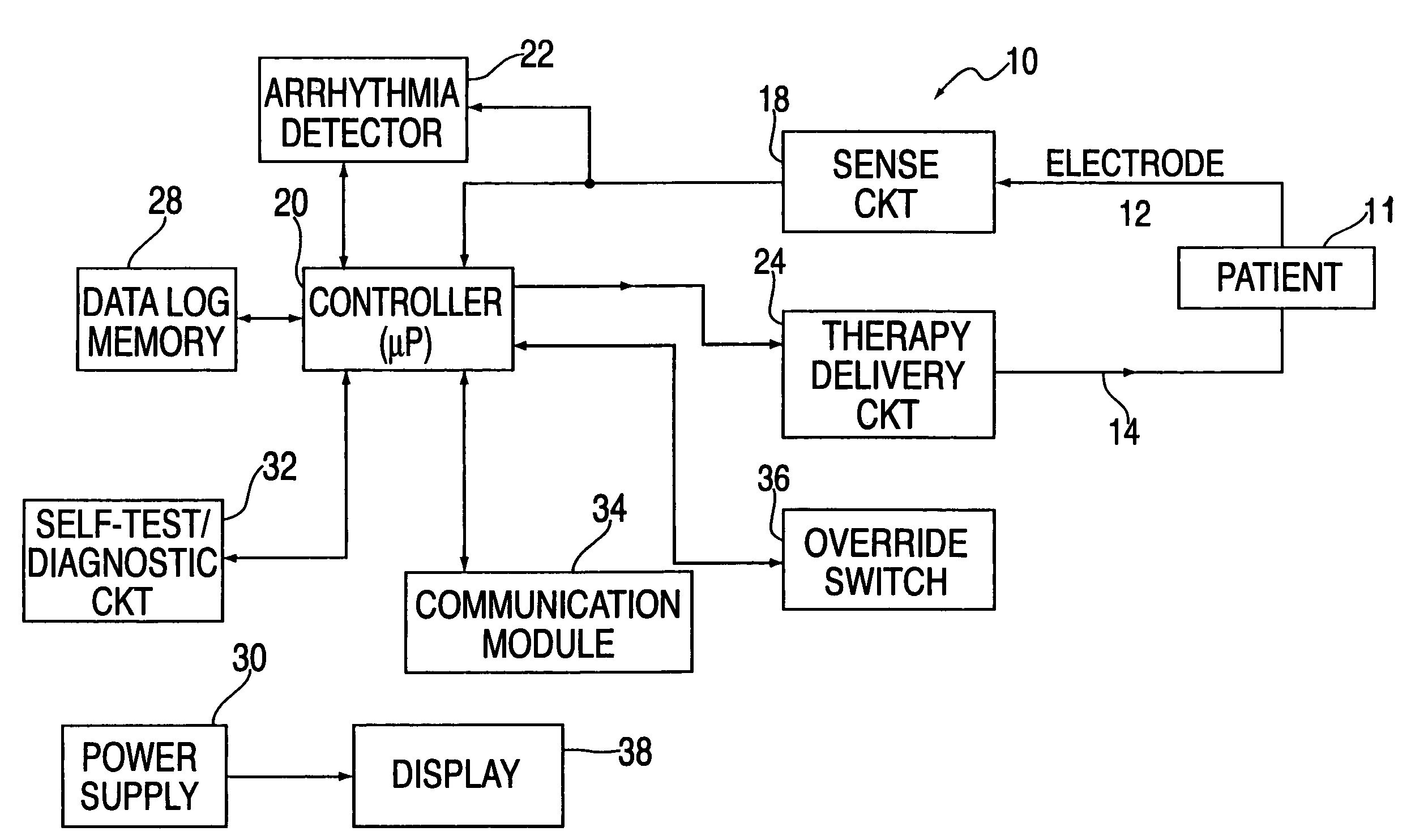
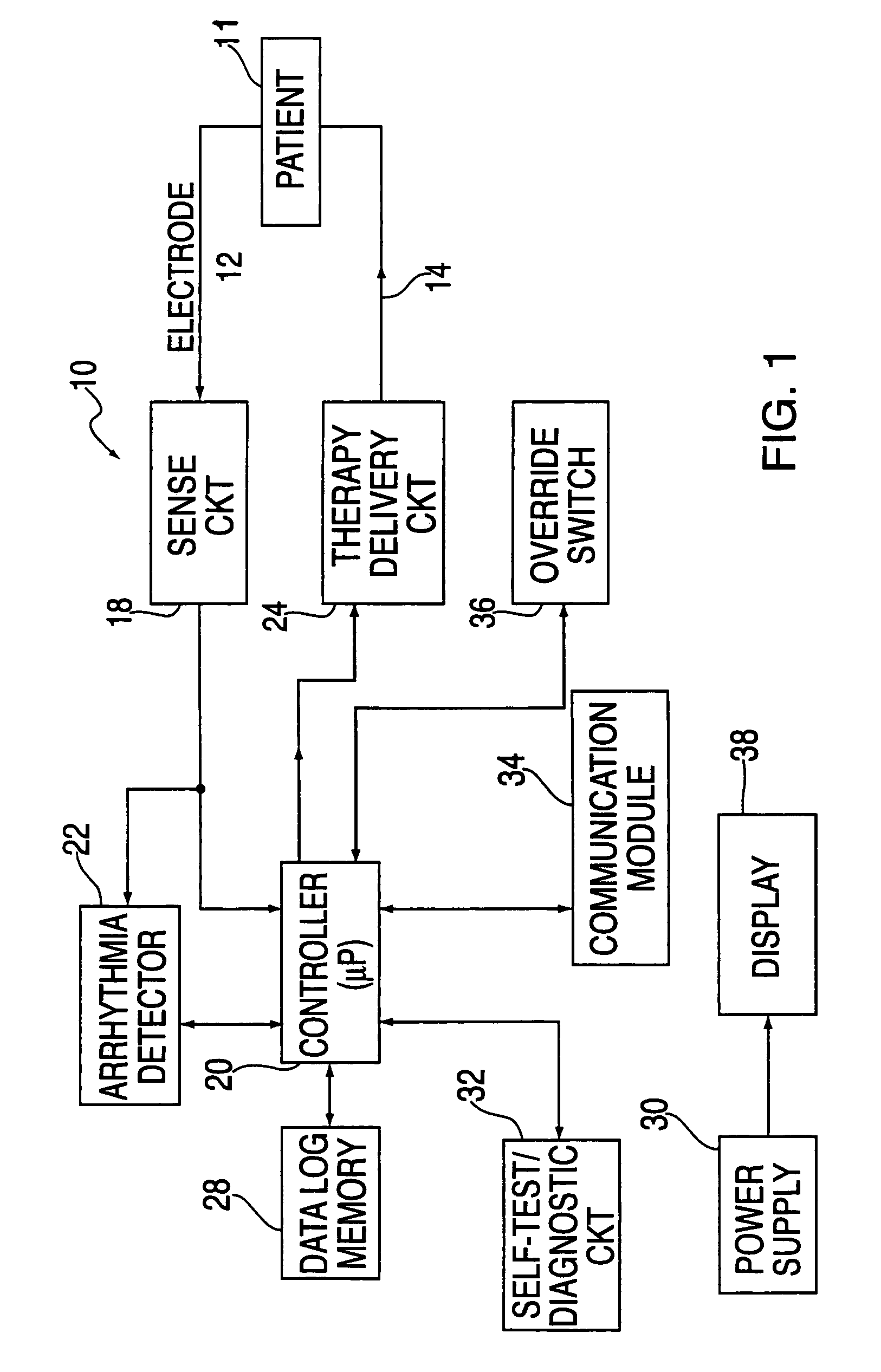
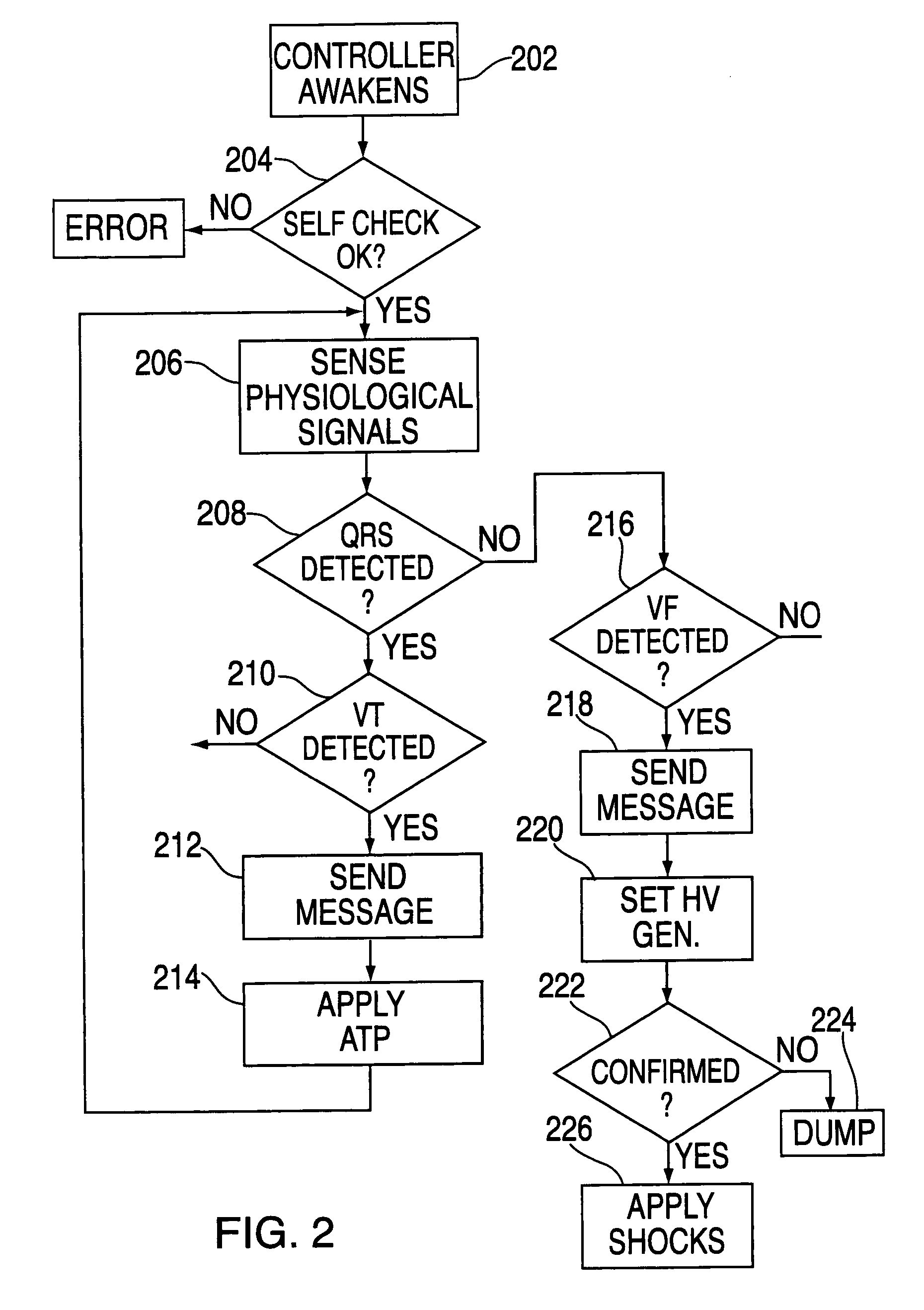
InactiveUS6993386B2Easy to useProviding therapyHeart defibrillatorsPublic access defibrillatorMedical emergency
A publically available external defibrillator includes a detector used to detect a life threatening condition of a patient, a controller operating the defibrillator automatically and a therapy delivery circuit that delivers appropriate therapy. The defibrillator is attached to a patient by any attendant or bystander and once it is attached, the defibrillator is adapted to monitor the patient and when a life threatening condition is detected, to apply therapy automatically, i.e., without any involvement by the patient or the attendant.
Owner:ZOLL MEDICAL CORPORATION
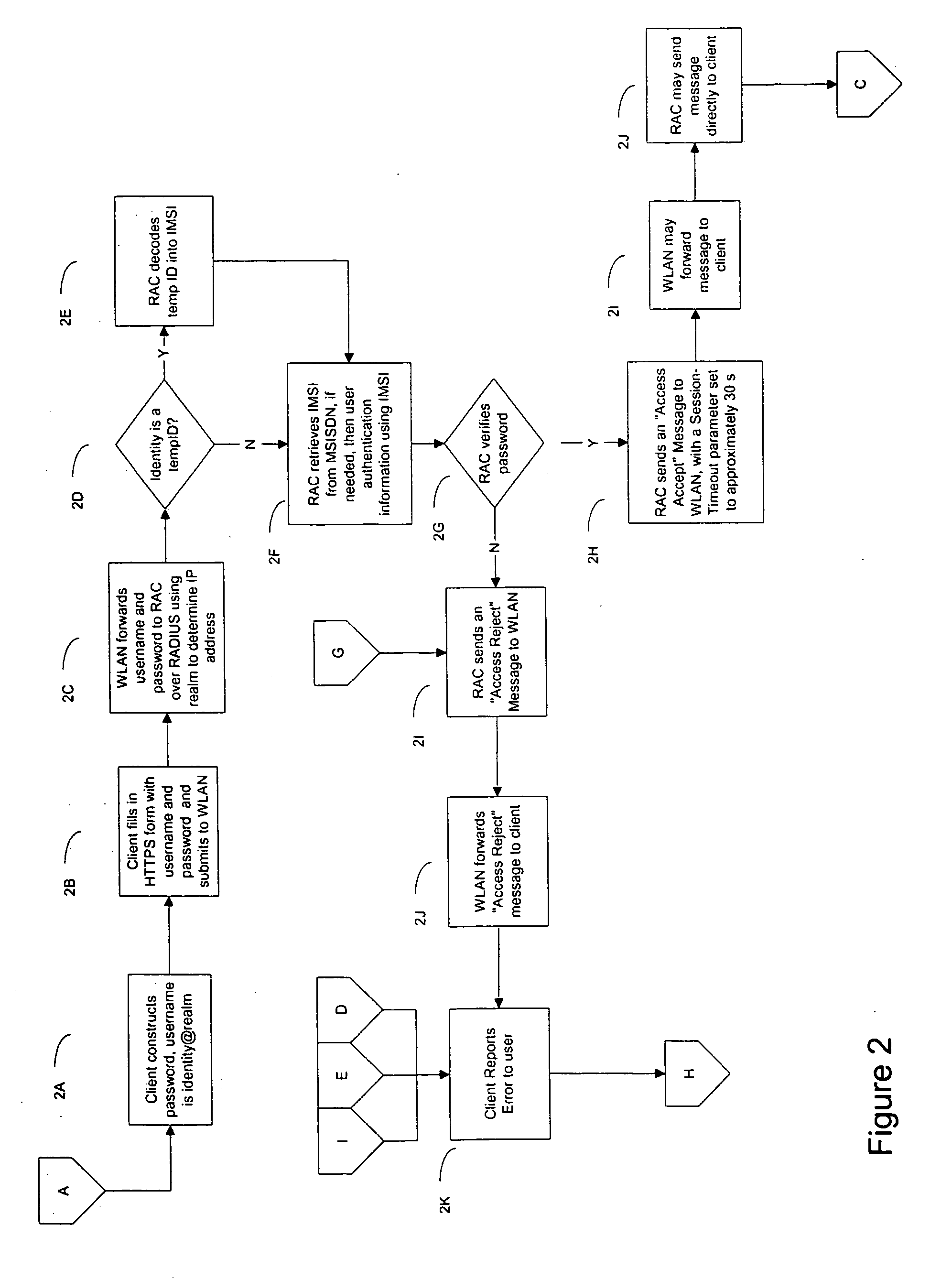
Method and system for providing SIM-based roaming over existing WLAN public access infrastructure
InactiveUS20050114680A1Prevent replay attacksUser identity/authority verificationNetwork topologiesWeb authenticationAccess method
A method and apparatus for performing SIM-based authentication and authorization in a WLAN Internet Service Provider (WISP) network supporting the universal access method (UAM) of authentication and authorization enabling roaming for customers of mobile service providers onto said networks. In addition, the invention provides a secure way of authenticating the customer's client device to the mobile service provider's network by employing temporary credentials for authentication that provide privacy of the user's identity and prevent replay attacks. Finally, if the WISP network supports the ‘pass-through’ facility, the authentication can be done more securely and quickly.
Owner:AZAIRE NETWORKS
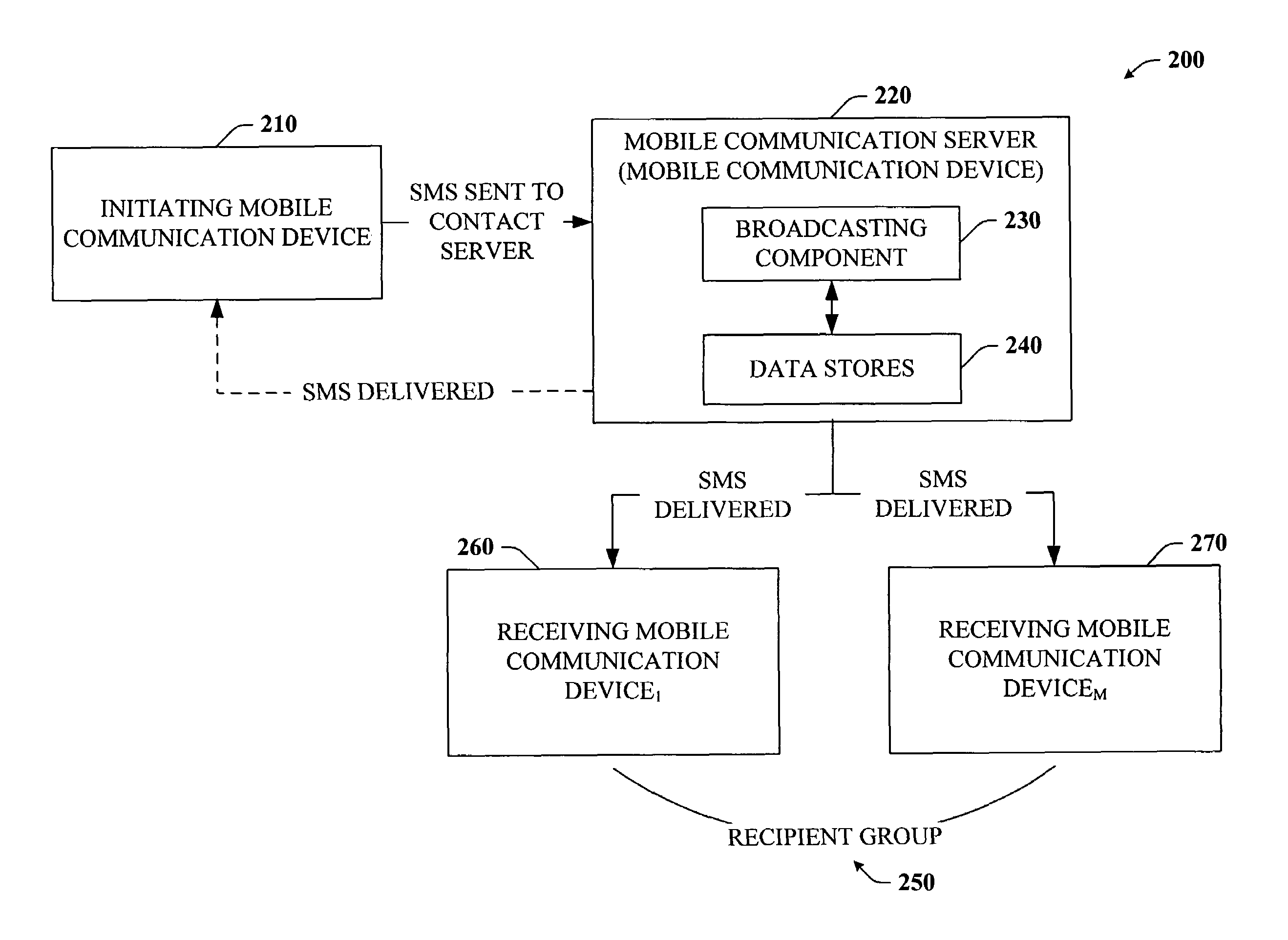
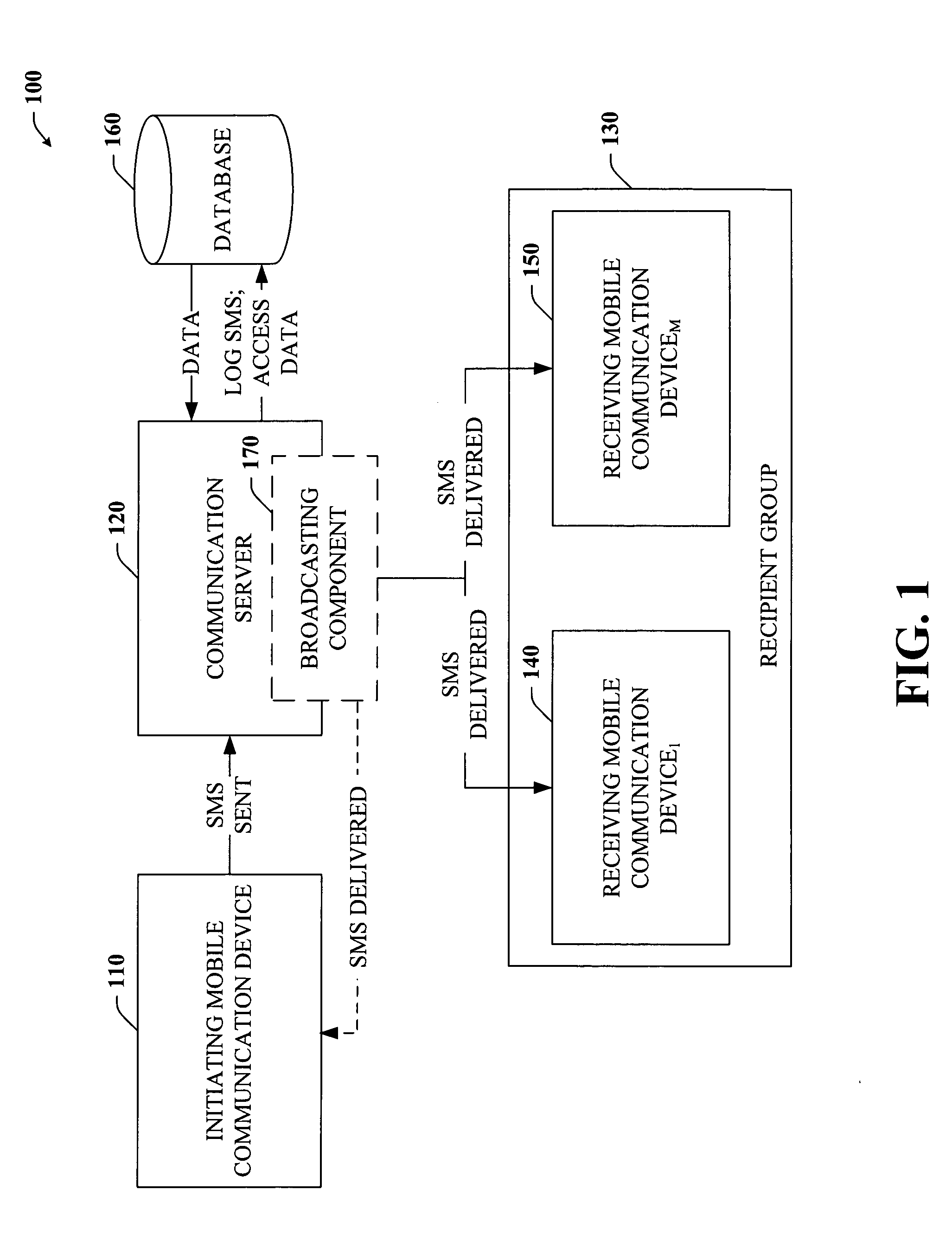
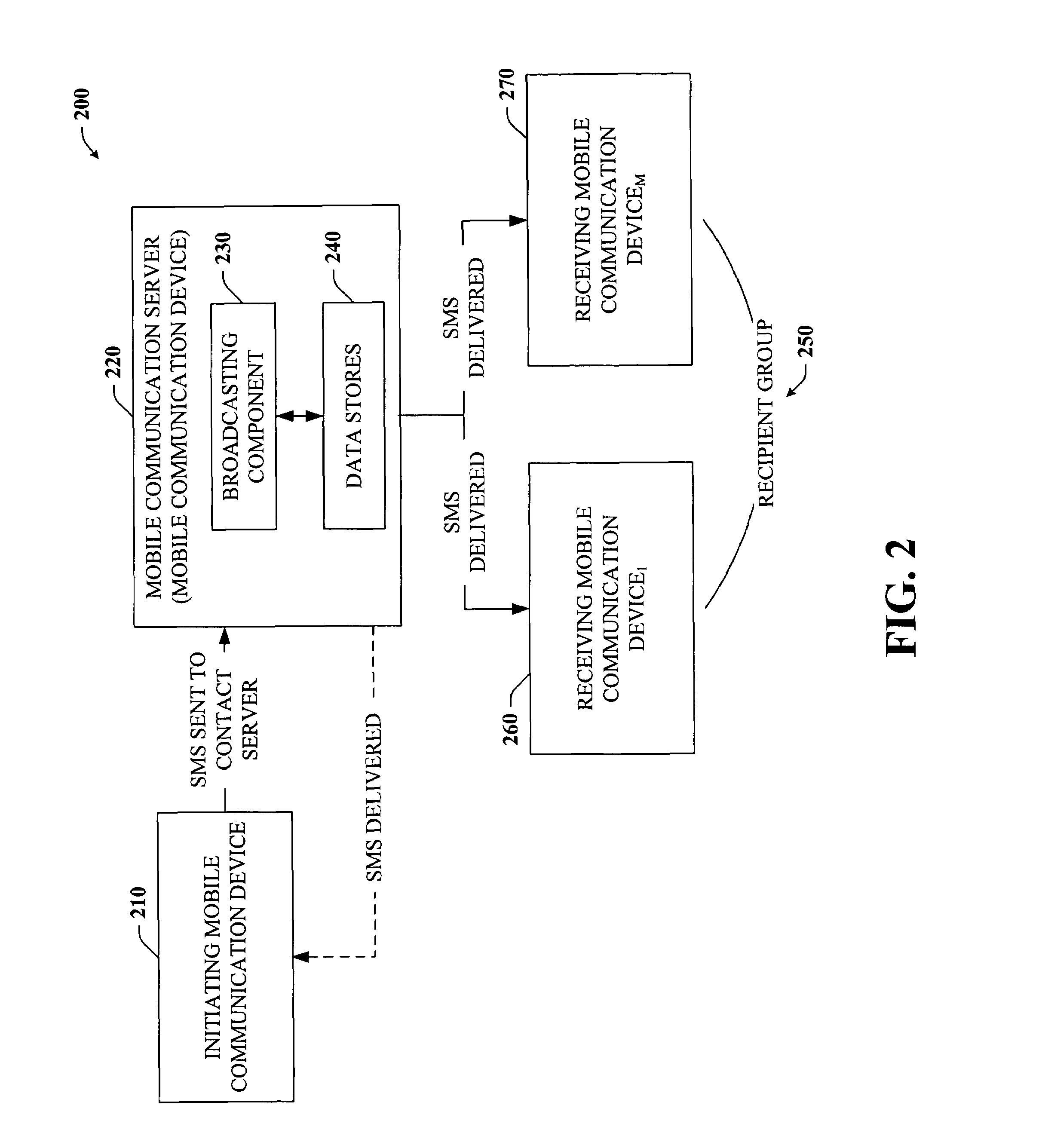
Command based group SMS with mobile message receiver and server
InactiveUS7251495B2Facilitate communicationEasy to manufactureOperating means/releasing devices for valvesSpecial service for subscribersPublic accessBroadcasting
Disclosed is a unique system and method that facilitate group communication using SMS text messaging and a plurality of SMS based commands. More specifically, the system and method make use of mobile communication devices such as mobile or cellular phones, smart phones, and / or PDAs which are equipped with SMS capabilities. Communication within a group of users can be accomplished in part by creating a text message and sending it to at least one communication server by way of at least one common access number. The communication server can analyze the message to determine the recipient group and broadcast the message to the members of the group in real-time or near real-time. Groups can be user-defined and managed dynamically by users using either a website interface or a mobile communication device interface at any time or anywhere. The communication server can be a suitably equipped mobile communication device or a separate server can be employed.
Owner:MICROSOFT TECH LICENSING LLC
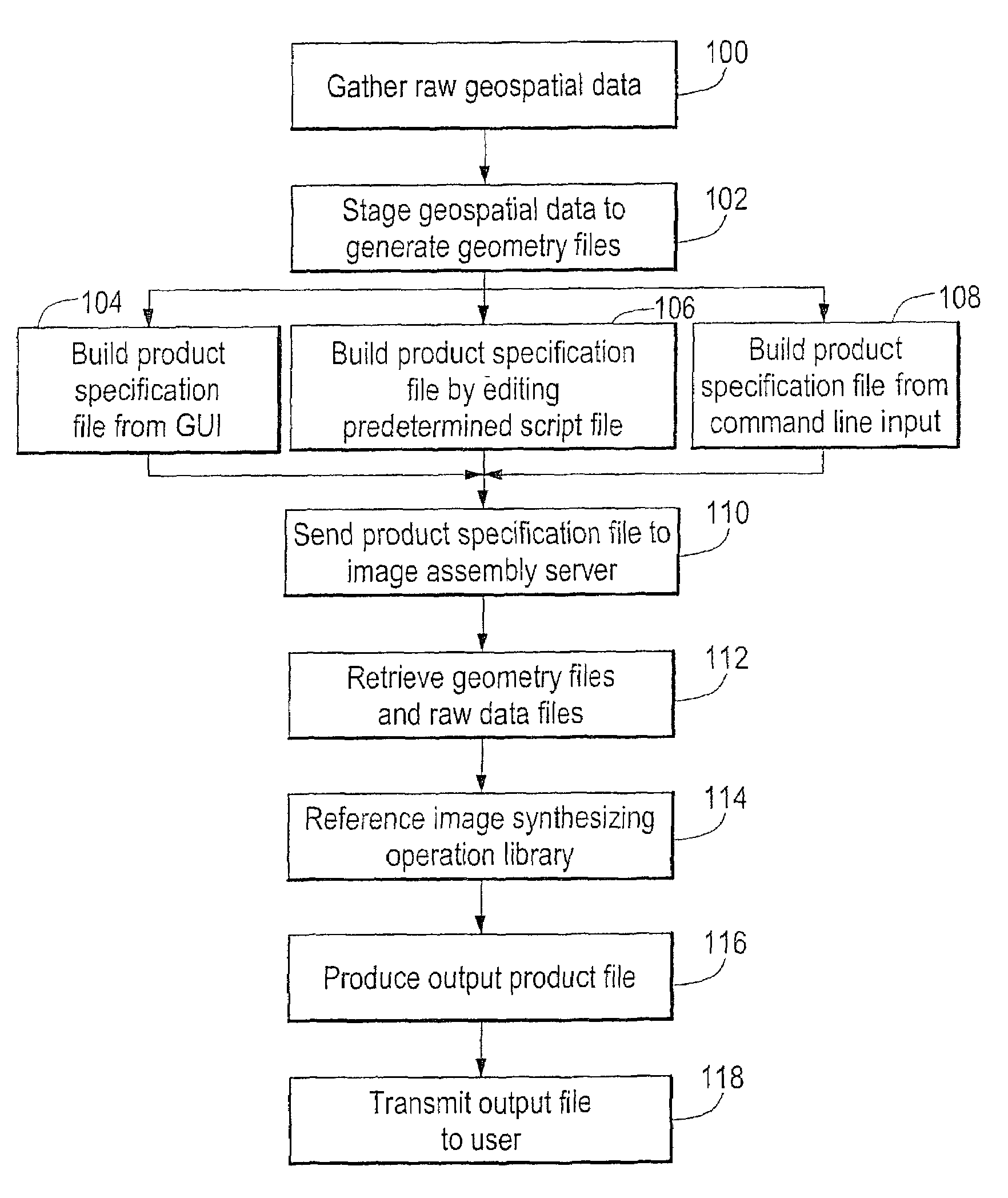
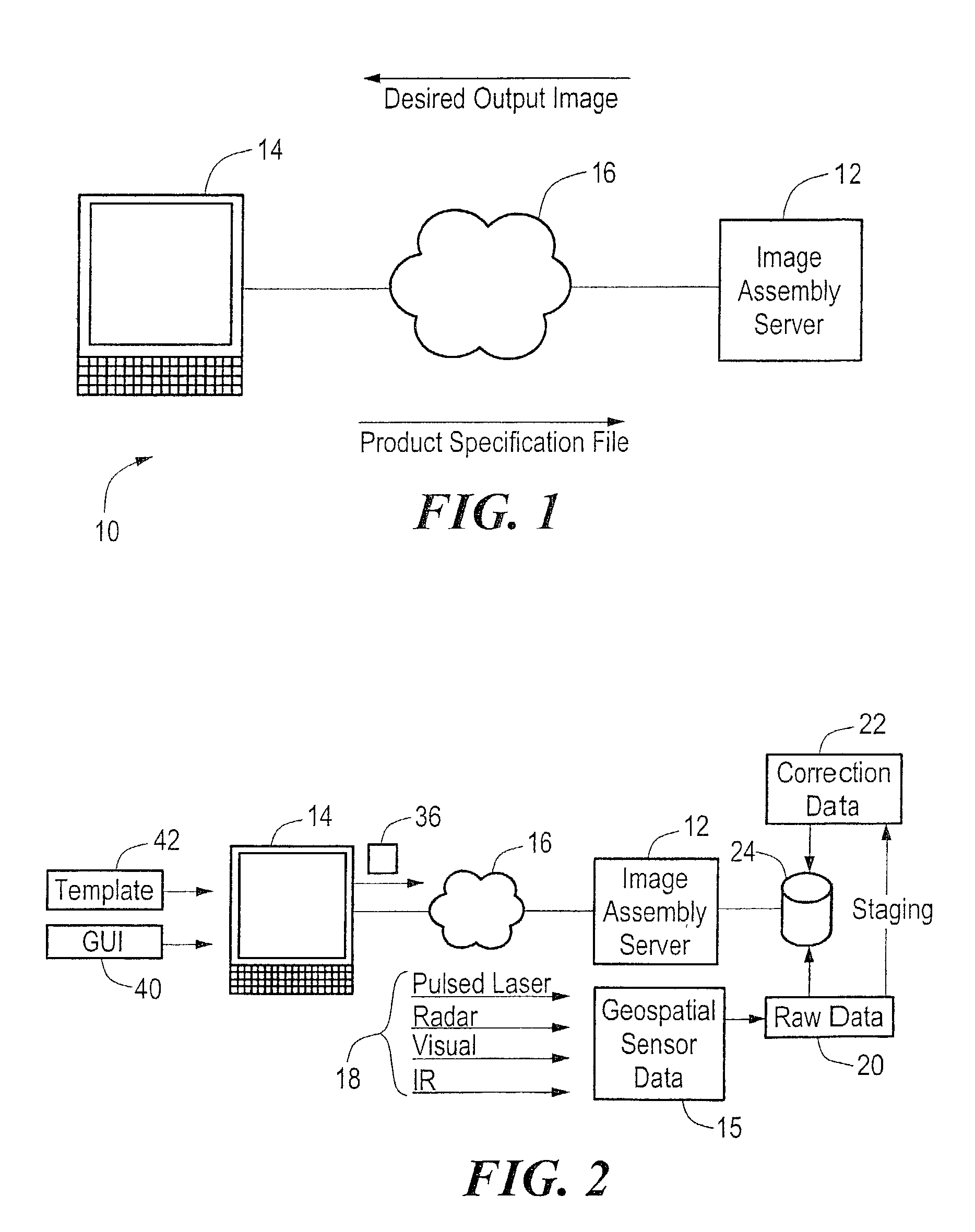
3-dimensional interactive image modeling system
InactiveUS7457706B2Easy to identifyCharacter and pattern recognitionSpecial data processing applicationsThe InternetInformation product
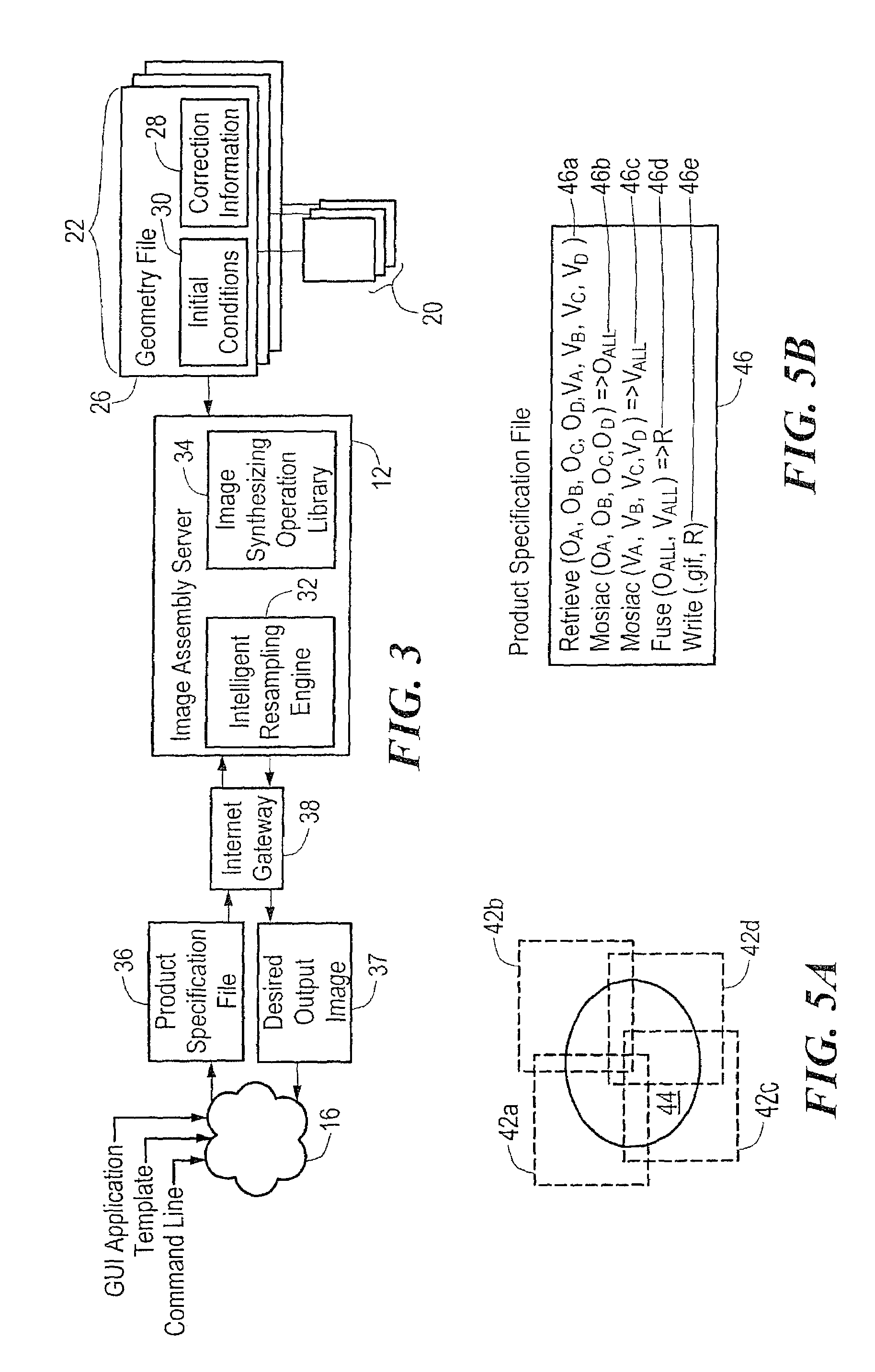
A system and method for generating custom geospatial information maps and precision corrected images allows real-time interactive production of a desired output image by incorporating user selectable parameters that define various image synthesizing operations. A graphical user interface allows a user to specify parameters that define the desired output image via a remote computing device over a public access network such as the Internet. The parameters define image synthesizing operations such as area, projection, datum, fusion, masking, blending, mosaiking, resampling, and others. The desired output image is processed by an image assembly server according to the parameters and a variety of geospatial image data sources, and electronically delivered to a user via a public access network. The geospatial information may also be correlated with non-georeferenced data such that relevant associations between non-georeferenced data and the geospatial data are integrated in the output information product.
Owner:IMAGELINKS
Systems, methods, and computer-readable media for backup and restoration of computer information
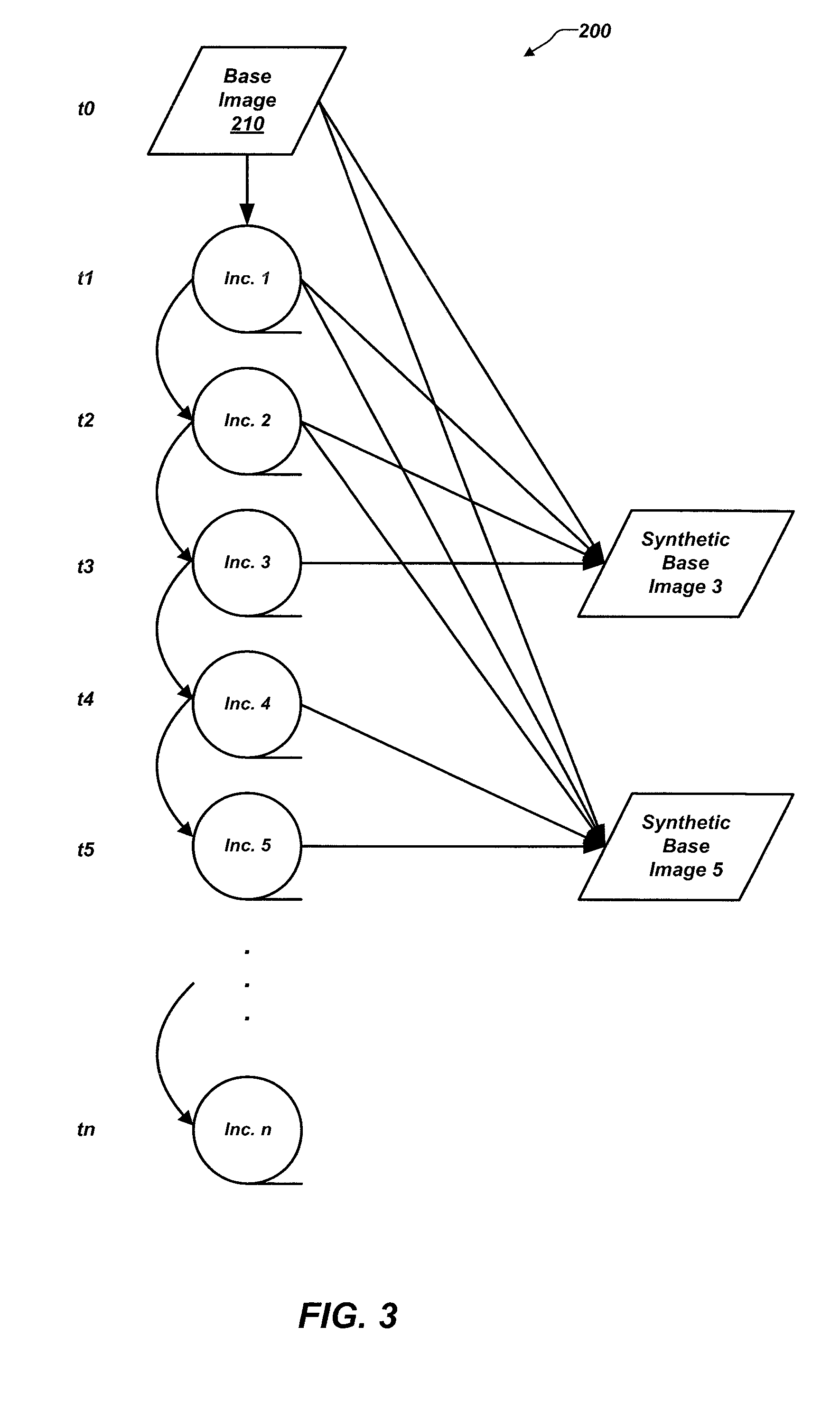
ActiveUS20110218966A1Reduce downtimeDigital data information retrievalMemory loss protectionFile systemPublic access
A computer creates a full backup of a target volume by copying sectors of the target volume. Incremental backups are created by copying modified sectors that have changed since a preceding backup. Public accesses to a restore volume are prevented by modifying a volume boot record (VBR) of the restore volume to prevent file systems from recognizing the restore volume or by filtering public accesses while allowing private block accesses to the restore volume. Sector data are copied from the backup files to the restore volume while the public accesses are being prevented. The restore can begin, using previously created backup files, while the backup is still in process creating new incremental backups for the target volume. The restore volume is finalized after restoring the full or any number of incremental backups by restoring the VBR to indicate the restore volume is valid or stopping the filtering of public accesses.
Owner:STORAGECRAFT TECH CORP
Open access network architecture
InactiveUS20060098593A1Increase in sizeGreat advantageRadio/inductive link selection arrangementsWireless commuication servicesAccess networkNetwork architecture
Owner:TELENOR AS
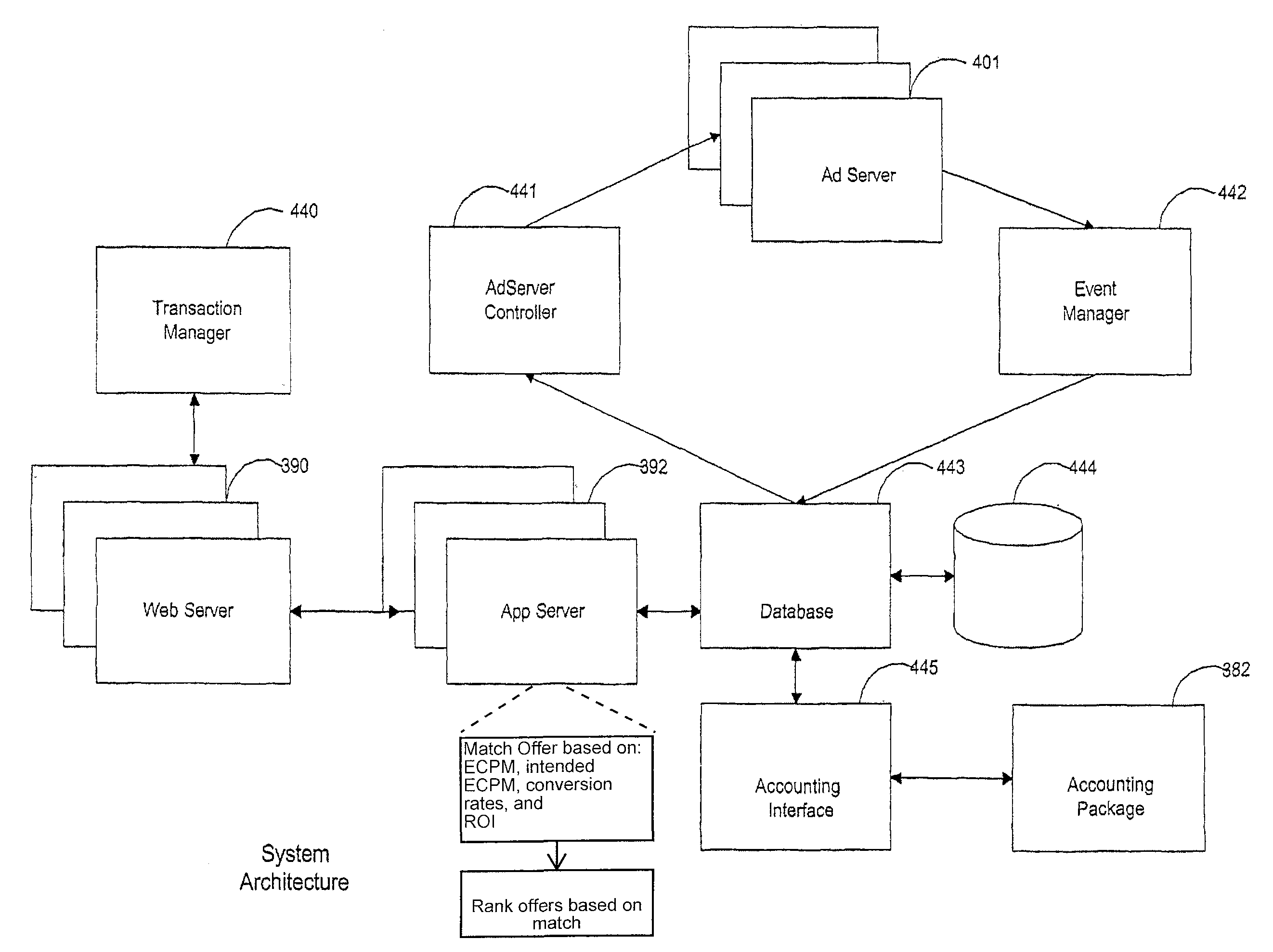
Online media exchange
InactiveUS7962363B2Time-consume and expensiveReduce fragmentationBacterial antigen ingredientsAdvertisementsData processing systemData treatment
A data processing system enables a network of interconnected public access computers (250) to act as a continuous transactional exchange for electronic advertising. The system customizes paid advertising, enabling dynamic pricing and price discovery. The system provides extensive real-time tracking which supports a hybrid pay for performance model as well as a process for multi-stage optimization.
Owner:R2 SOLUTIONS
Frictionless Access System for Public Access Point
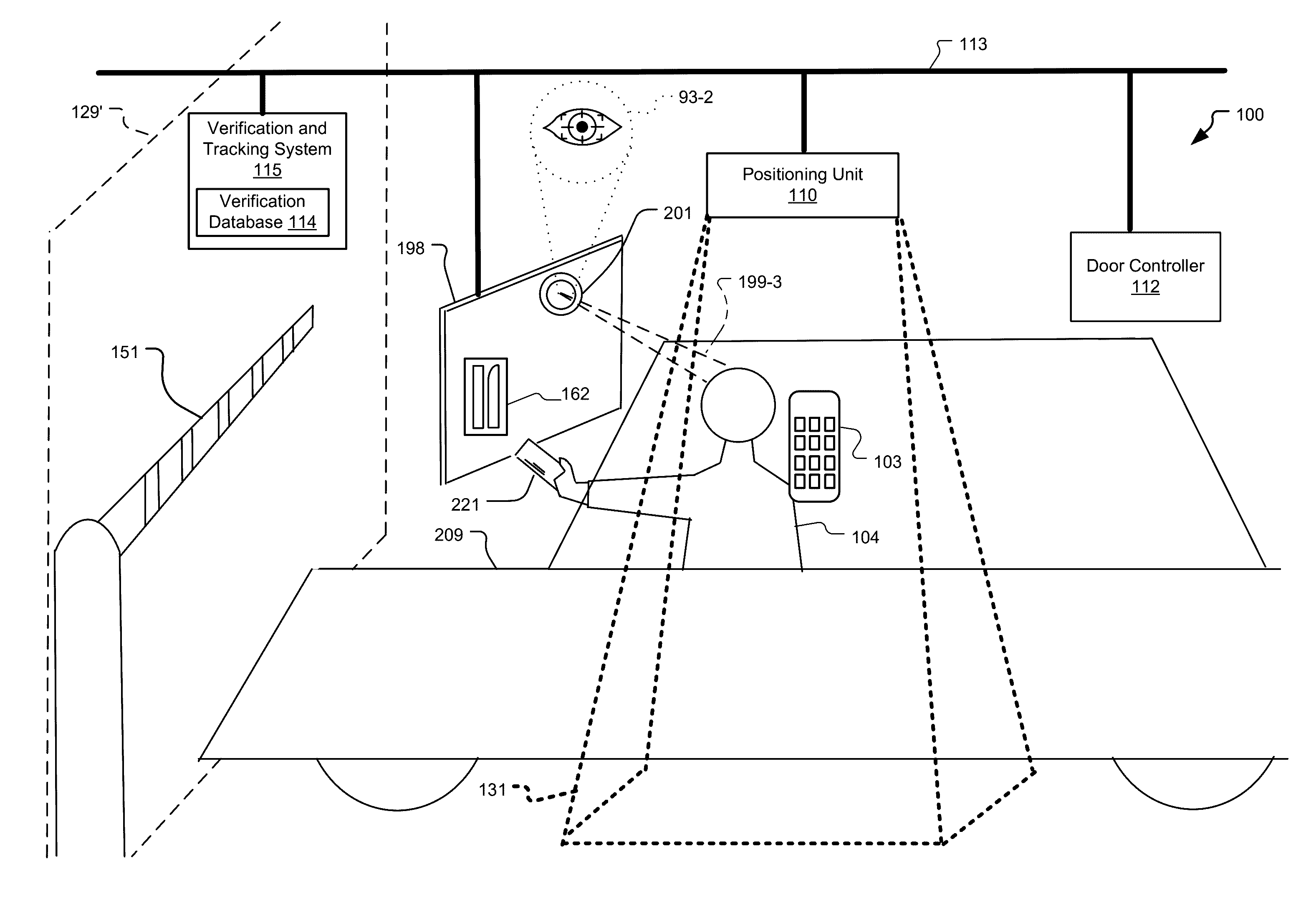
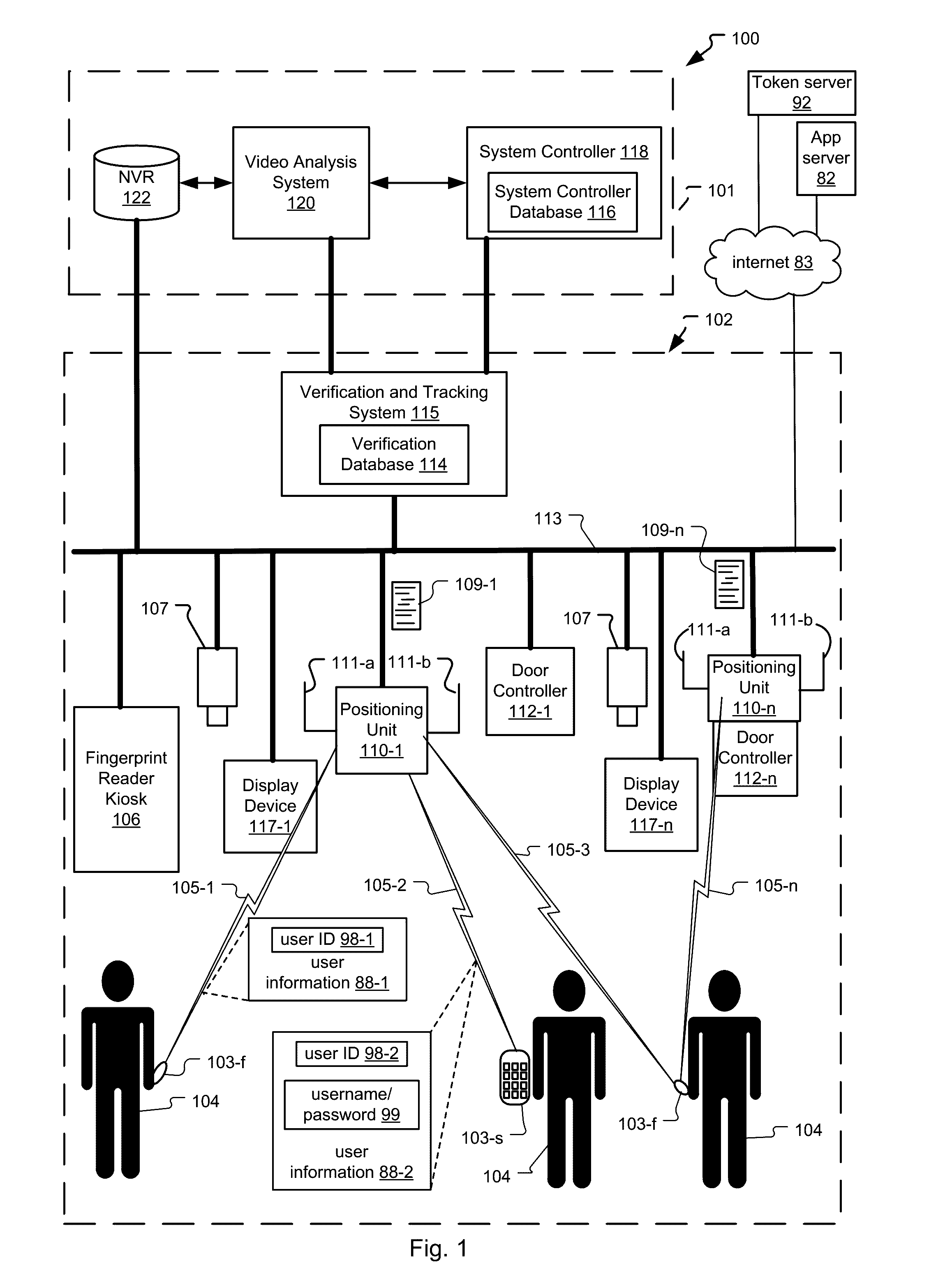
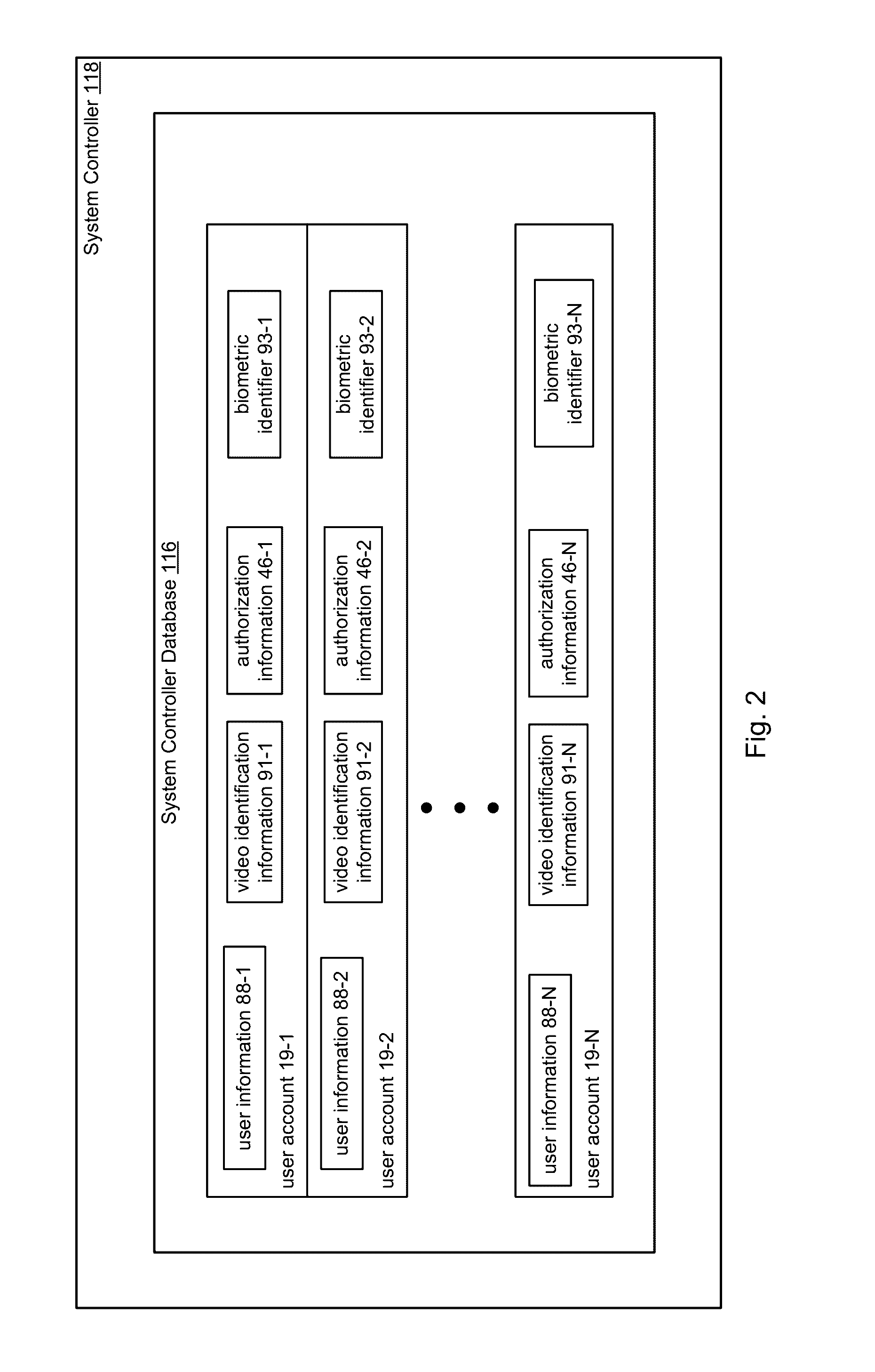
ActiveUS20160343187A1Improve securityContinuous trackingAntenna arraysRadiating elements structural formsUser deviceControl system
An access control system and method for monitoring a public access point are disclosed. The system includes a positioning unit that tracks locations of users carrying user devices relative to the public access point, where the user devices transmit user information identifying the users via wireless signals. The system determines whether the users are authorized to pass through the access point based on the wireless signals from the user devices. Public access points include security checkpoints at government buildings, airports, amusement parks, and universities, in examples. In embodiments, biometric identifiers are obtained from the users when the users are preferably located within a threshold area of the public access points, and the system confirms the identity of the authorized users via the biometric identifiers to enable the users to pass through the public access points. Additionally, the system can assist in evacuation of users based on their tracked locations.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
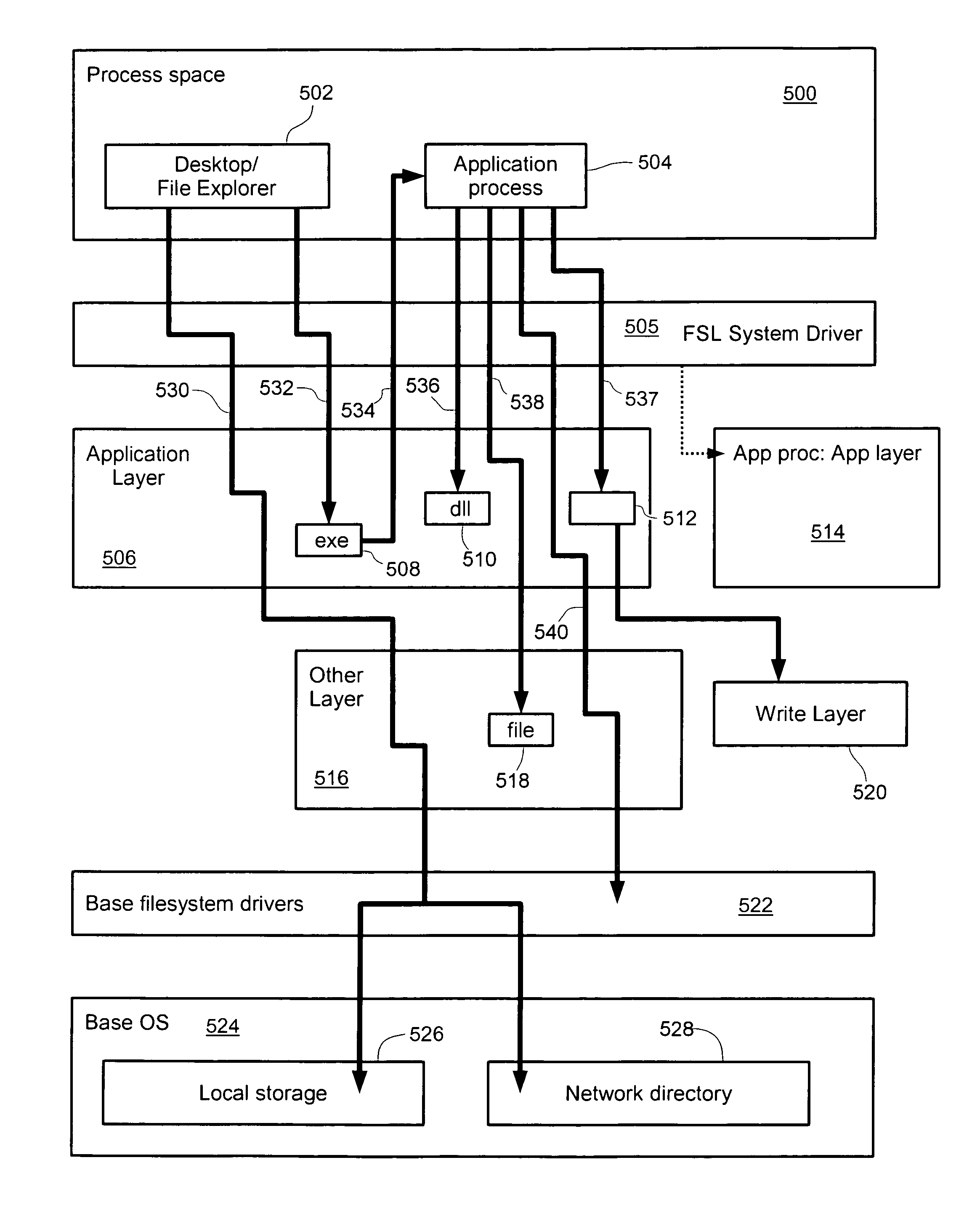
Sublayered application layered system
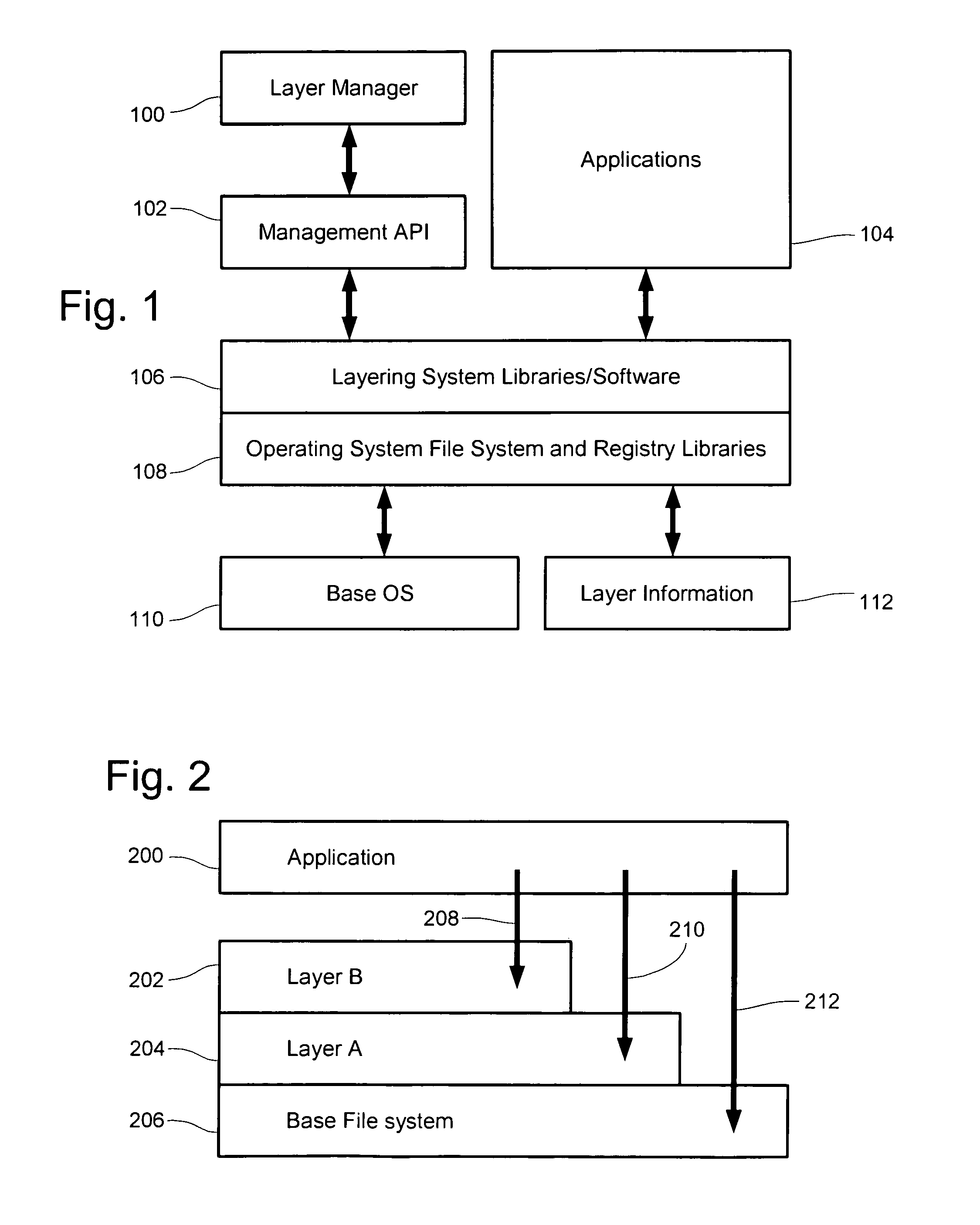
InactiveUS7970789B1Digital data processing detailsSoftware simulation/interpretation/emulationService provisionTheoretical computer science
The inventions relate generally to layered computing systems that provide public access to the content of the layers. Also disclosed herein are prioritization schemes usable in a layered computing system, including prioritization by layer type, by assigned priority weights, by access type, by sub-layers and by read-write indicators. Processes may further be associated to layers from which they originate, and priority given to associated layers thereby. Association may also be provided for installer services, thereby depositing an applications updates into its layer. Layers may also contain file reference information including exclusion or inclusion entries indicating what files may be written thereto. Paths recorded in layers may also embed variables to true paths on a layered system. Detailed information on various example embodiments of the inventions are provided in the Detailed Description below, and the inventions are defined by the appended claims.
Owner:CA TECH INC
Access retry method for shared channel wireless communications links
InactiveUS6333937B1Lower performance requirementsAccurate informationNetwork traffic/resource managementTime-division multiplexAccess methodTelecommunications link
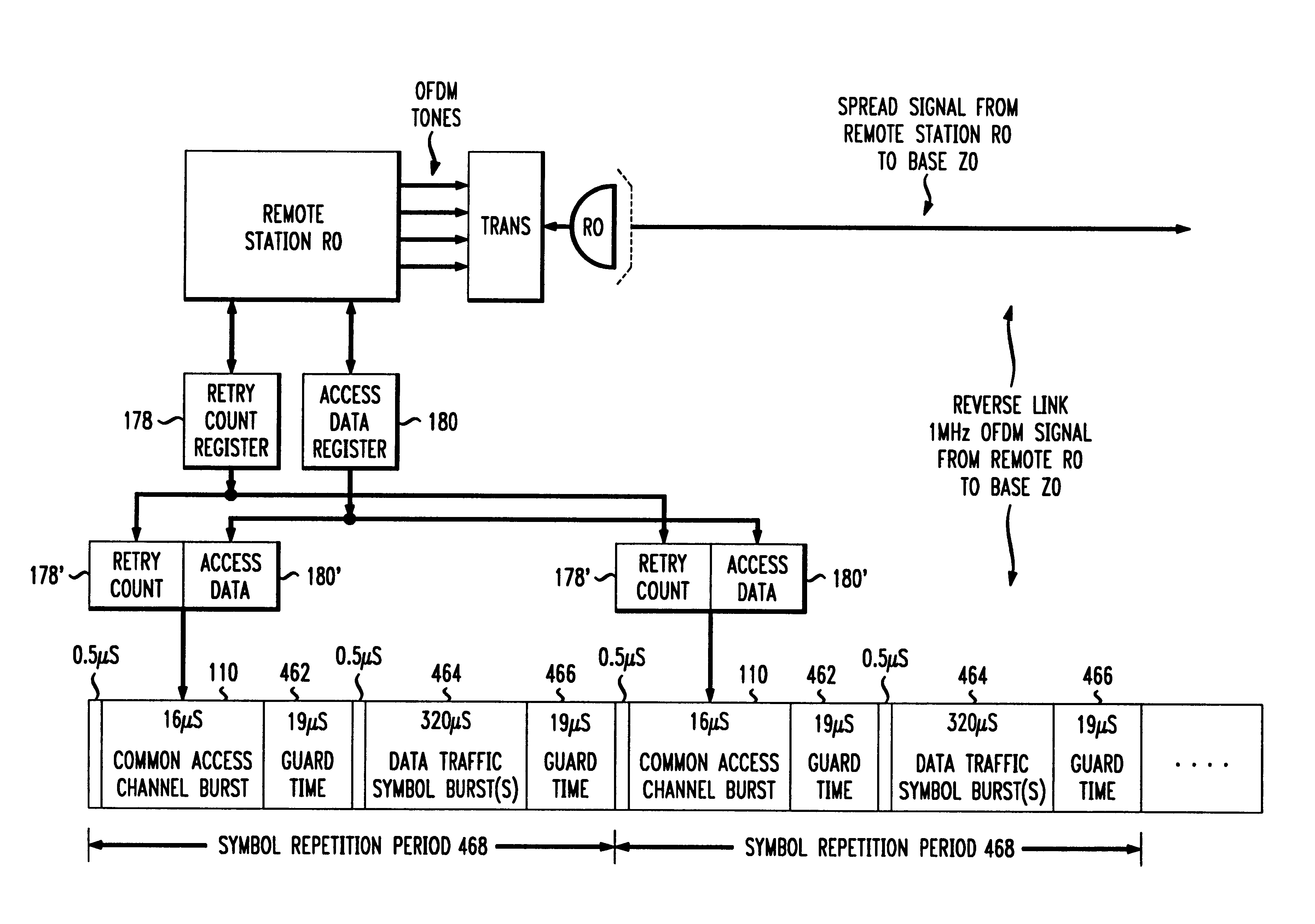
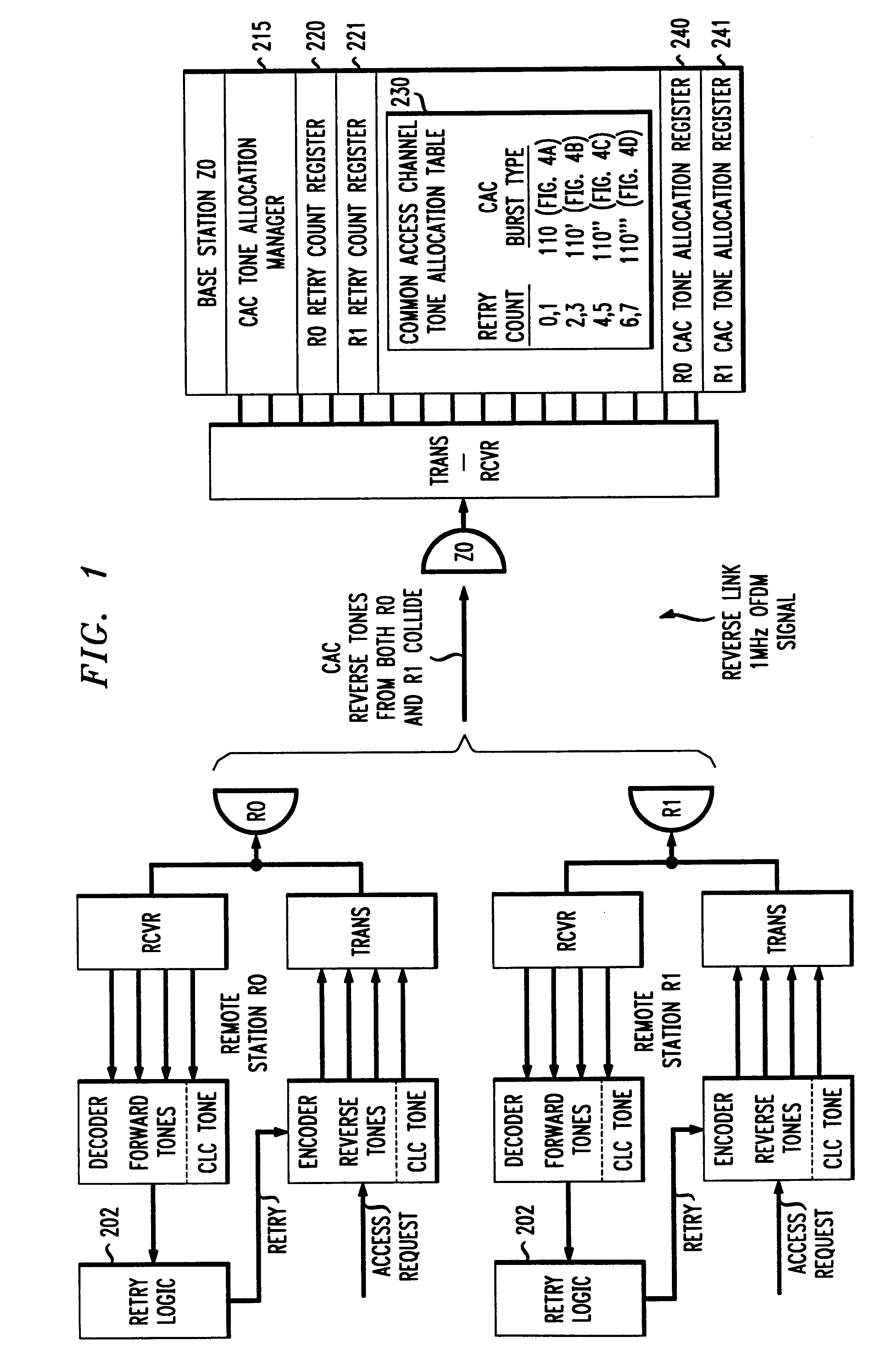
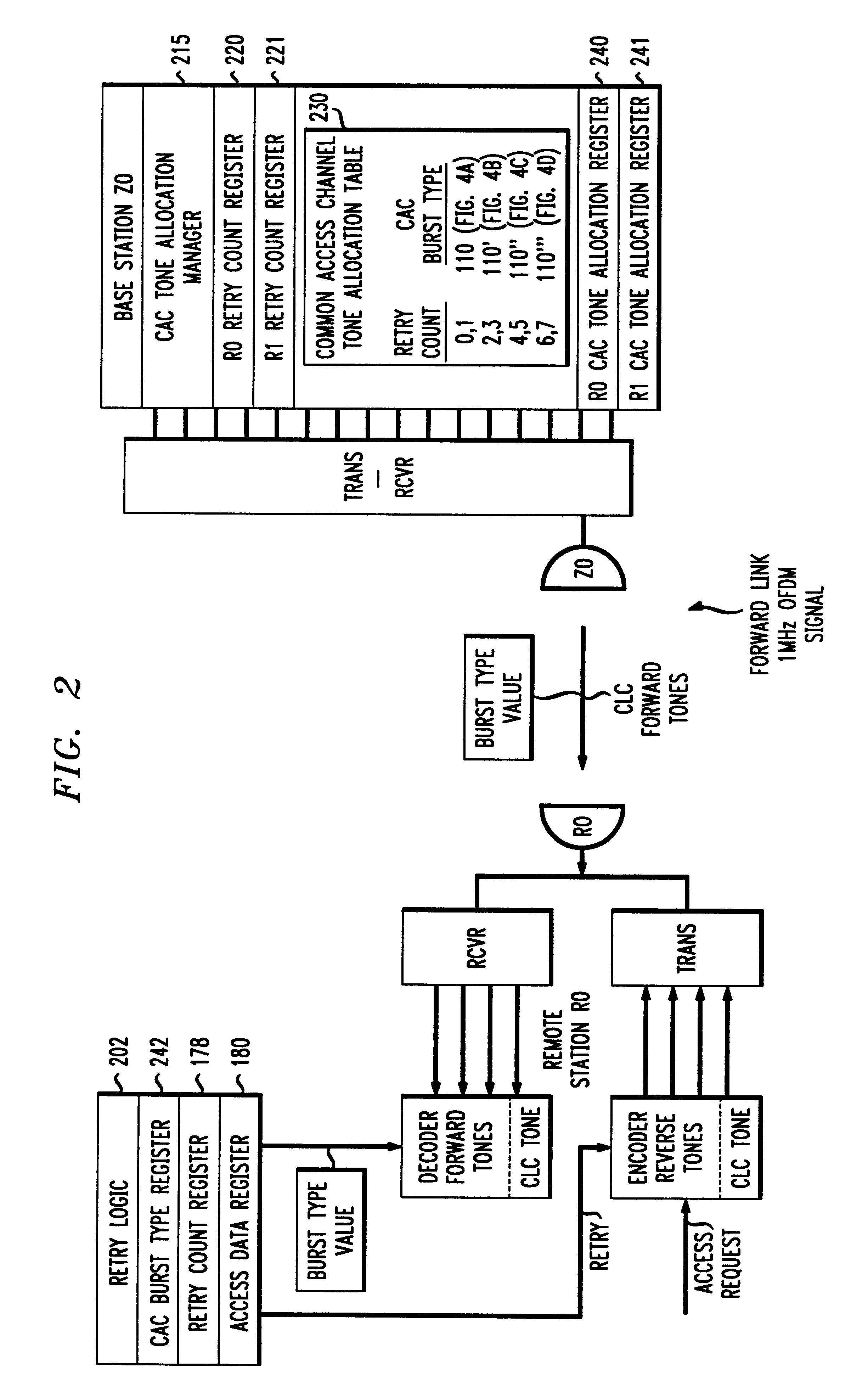
Each remote station in a wireless network cell that uses a collision oriented multiple access scheme, counts the number of retries attempted to gain access to the base station for a particular message. The accumulated value of the number of retries is then inserted in a retry count field of the access request message. After one or more retries, the base station successfully receives the access request message. The base station runs a common access channel allocation manager program that adaptively provides additional channels to the remote station, depending on the number of retries the remote station required to successfully transmit the access request message. In this manner, the base station has accurate information about the reduced performance that the remote stations suffer during an interval of high usage, to enable the base station to adaptively provide additional channels to the remote stations.
Owner:CLEARWIRE IP HLDG
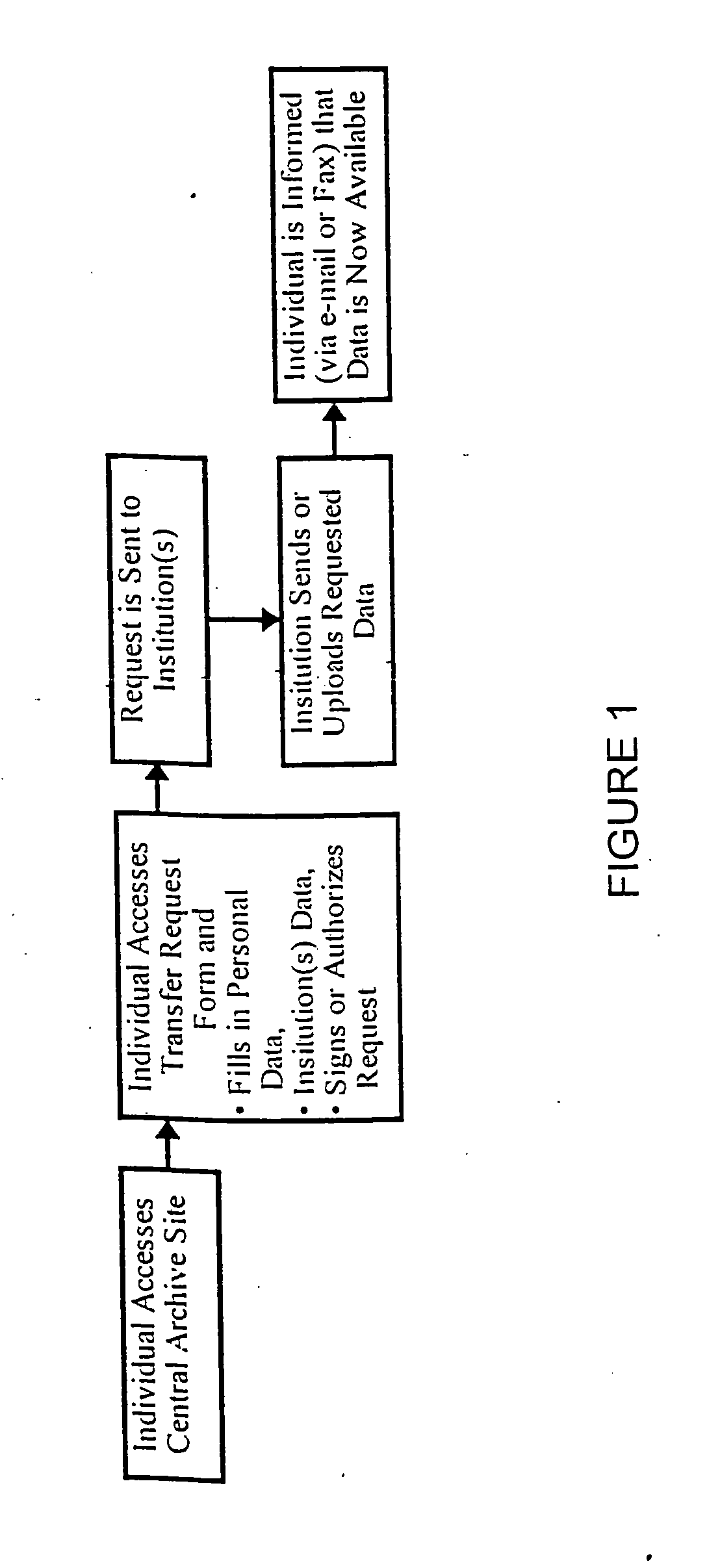
Method for consolidatin medical records through the world wide web
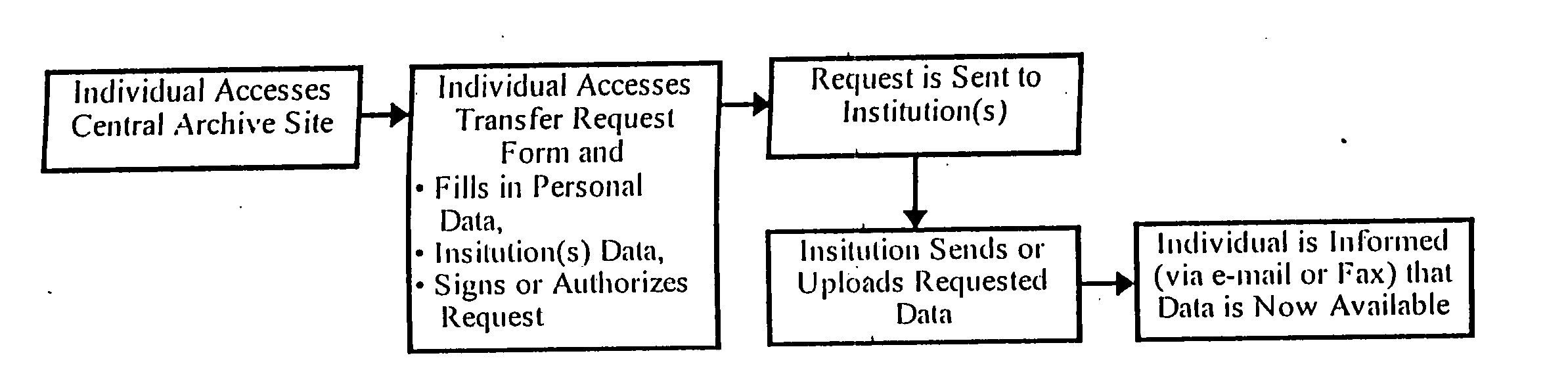
Medical records, clinical observations, and medical imagery are organized and aggregated into a common database, enabling the data to be viewed and / or updated by medical practitioners world-wide. The information may also be viewed and monitored by patients or their relatives for accuracy, also regardless of their location. The invention further allows the records to be updated by manually controlled or automated instrumentation which measures medical parameters whether located in a doctors office, in a hospital setting, in the patient's home, or worn by the patient. Common access and point-to-point data transmission is via the global grid, or over public access common data networks supporting TCP / IP, most often referred to as the Internet. The same approach can be using insider an organization over an internal network or Intranet.
Owner:CYBERNET SYST
Open registry for identity of things
ActiveUS20160358186A1Avoid readingMultiple keys/algorithms usageCryptography processingThird partyRegistry data
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
Open registry for internet of things
ActiveUS20170345019A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesThird partyThe Internet
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
Run-time application installation application layered system
InactiveUS7461086B1Data processing applicationsProgram controlService provisionTheoretical computer science
The inventions relate generally to layered computing systems that provide public access to the content of the layers. Also disclosed herein are prioritization schemes usable in a layered computing system, including prioritization by layer type, by assigned priority weights, by access type, by sub-layers and by read-write indicators. Processes may further be associated to layers from which they originate, and priority given to associated layers thereby. Association may also be provided for installer services, thereby depositing an applications updates into its layer. Layers may also contain file reference information including exclusion or inclusion entries indicating what files may be written thereto. Paths recorded in layers may also embed variables to true paths on a layered system. Detailed information on various example embodiments of the inventions are provided in the Detailed Description below, and the inventions are defined by the appended claims.
Owner:CA TECH INC
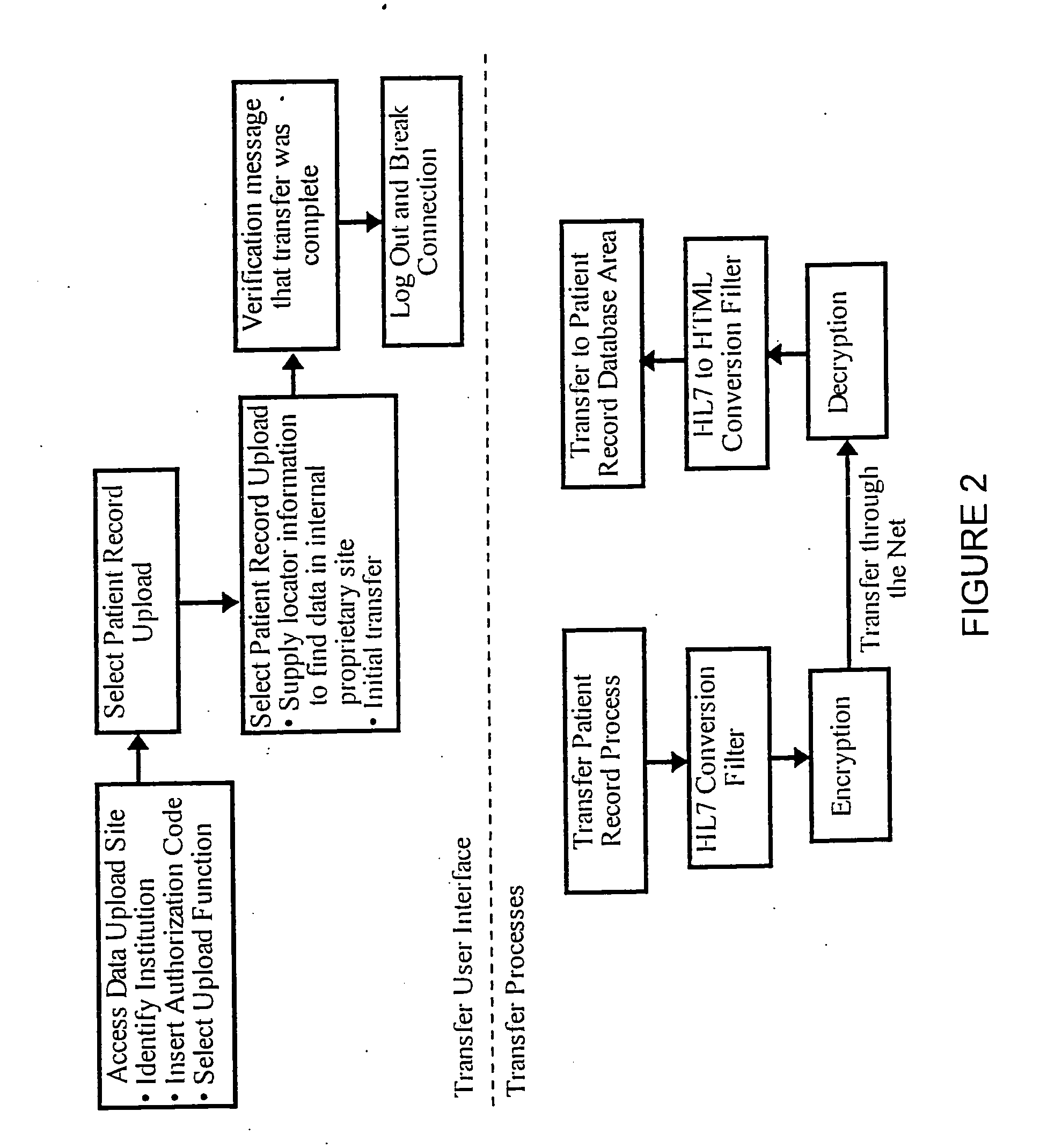
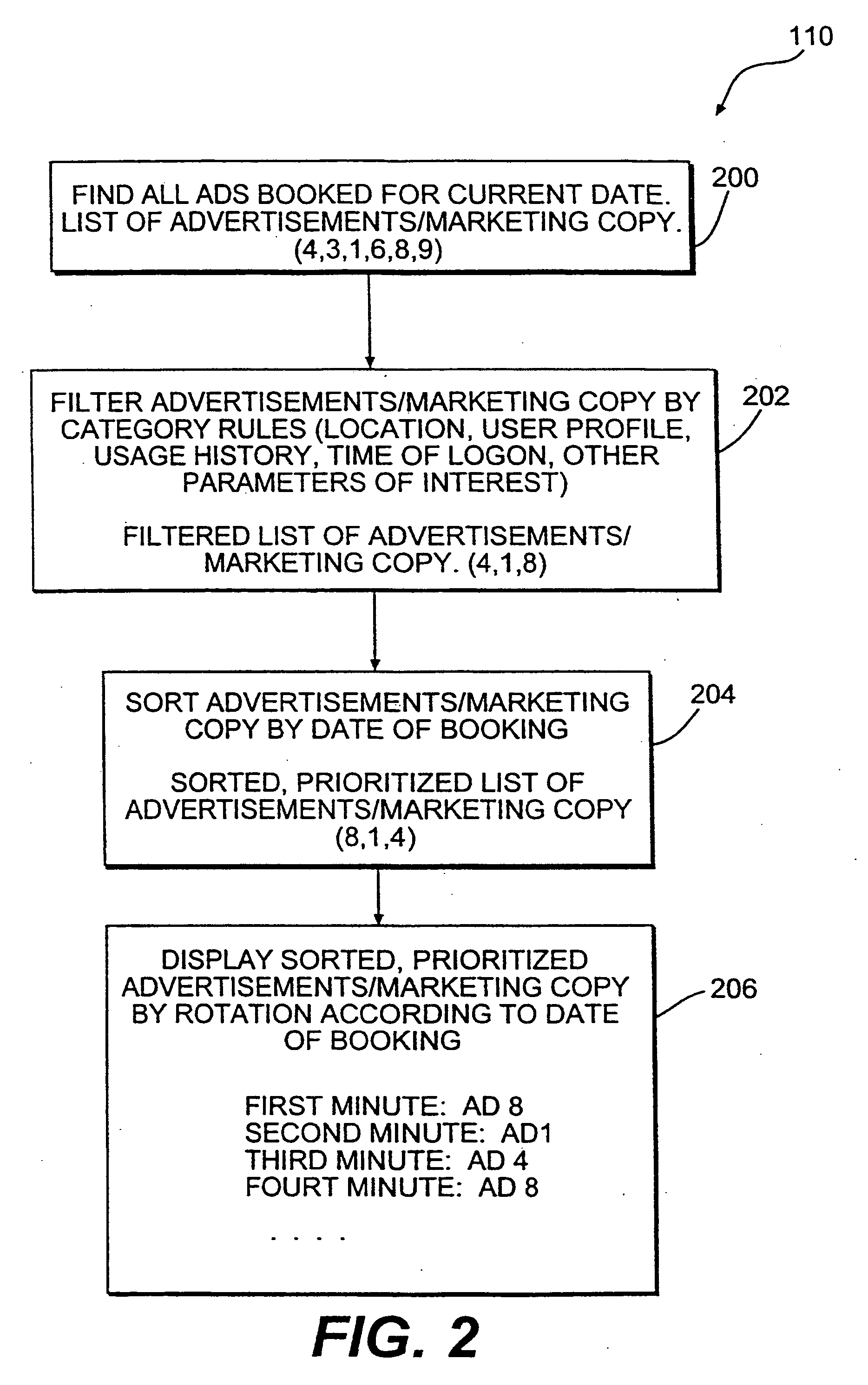
Method of constructing a digital content play list for transmission and presentation on a public access electronic terminal
ActiveUS7805338B2Cathode-ray tube indicatorsBuying/selling/leasing transactionsVirtual terminalDigital content
The present invention relates to a method of constructing a play list of a plurality of digital content for transmission and presentation on a public access electronic terminal for use with various data processing resources. The method establishes a virtual terminal on a play list server; selects the plurality of digital content at the virtual terminal; appends a digital content header to each of the plurality of digital content included in the play list; stores the play list in association with said virtual terminal; transmits the play list from the virtual terminal to the public access electronic commerce terminal; selectively receives the play list from the public access electronic commerce terminal; generates an activity report in the public access electronic commerce terminal based on the play list transmission; and selectively updates the data processing resources to reflect the activity report.
Owner:CANTALOUPE INC
Method and system for providing personalized online services and advertisements in public spaces
Owner:STREETABPACE
Open registry for identity of things including social record feature
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
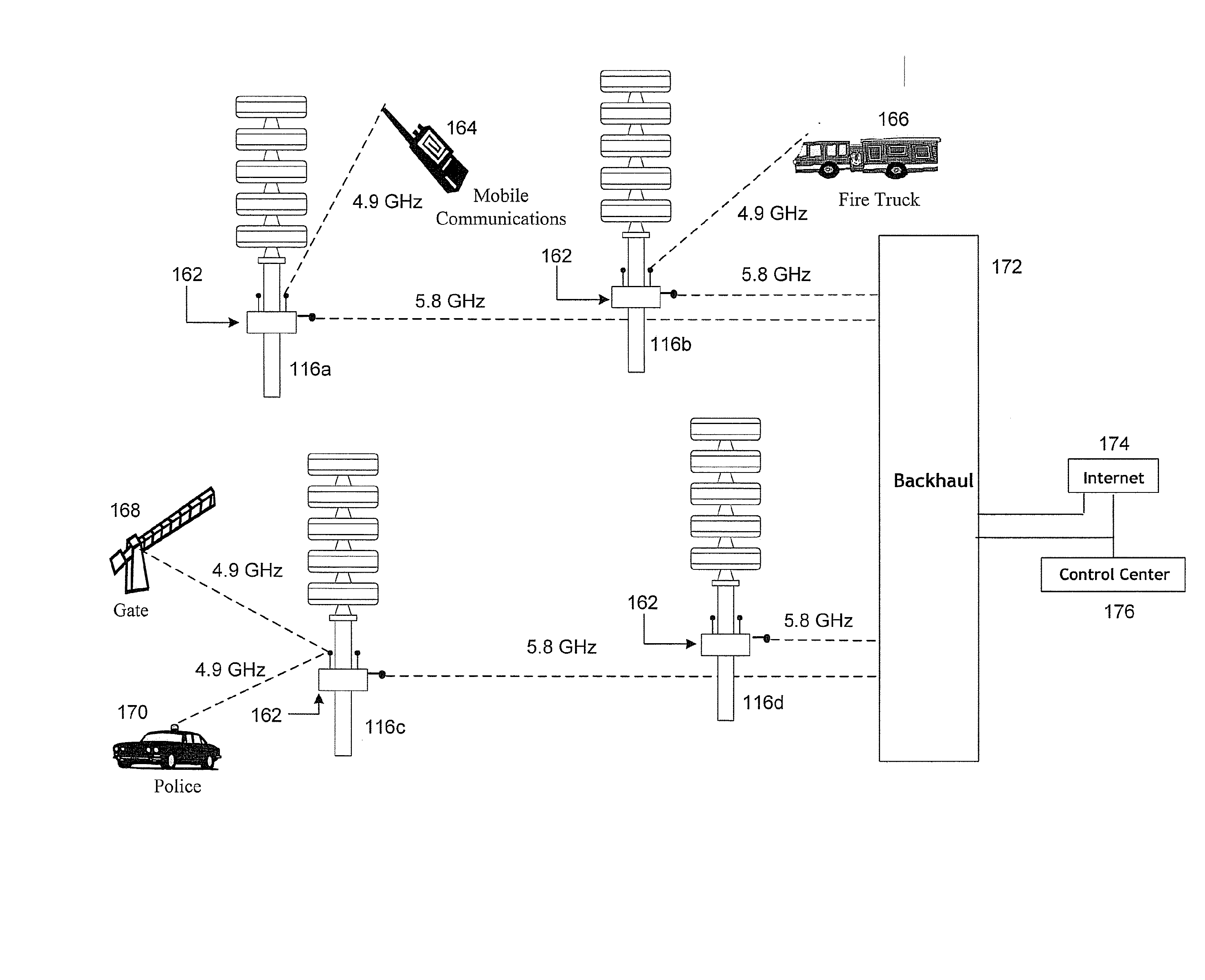
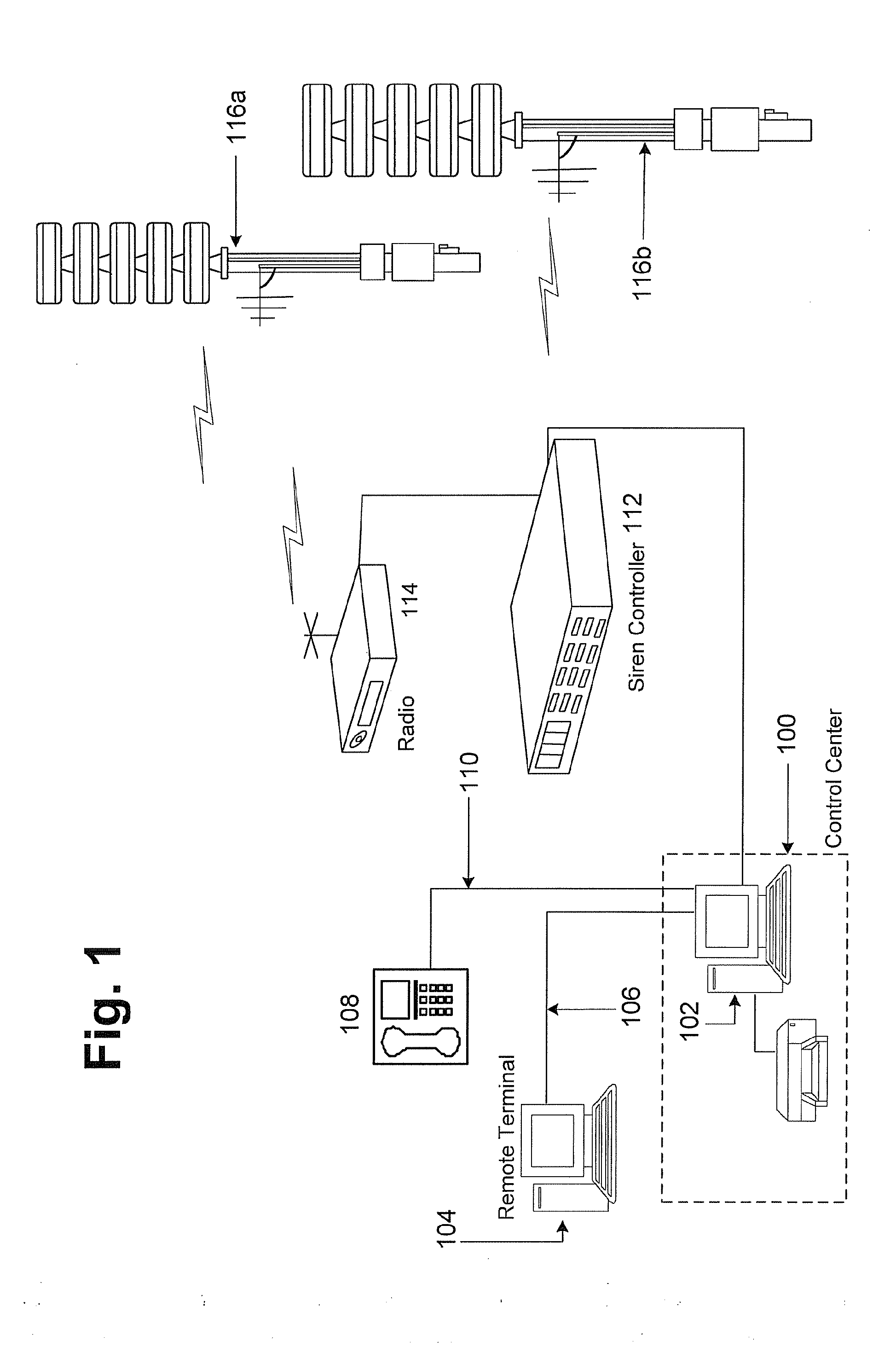
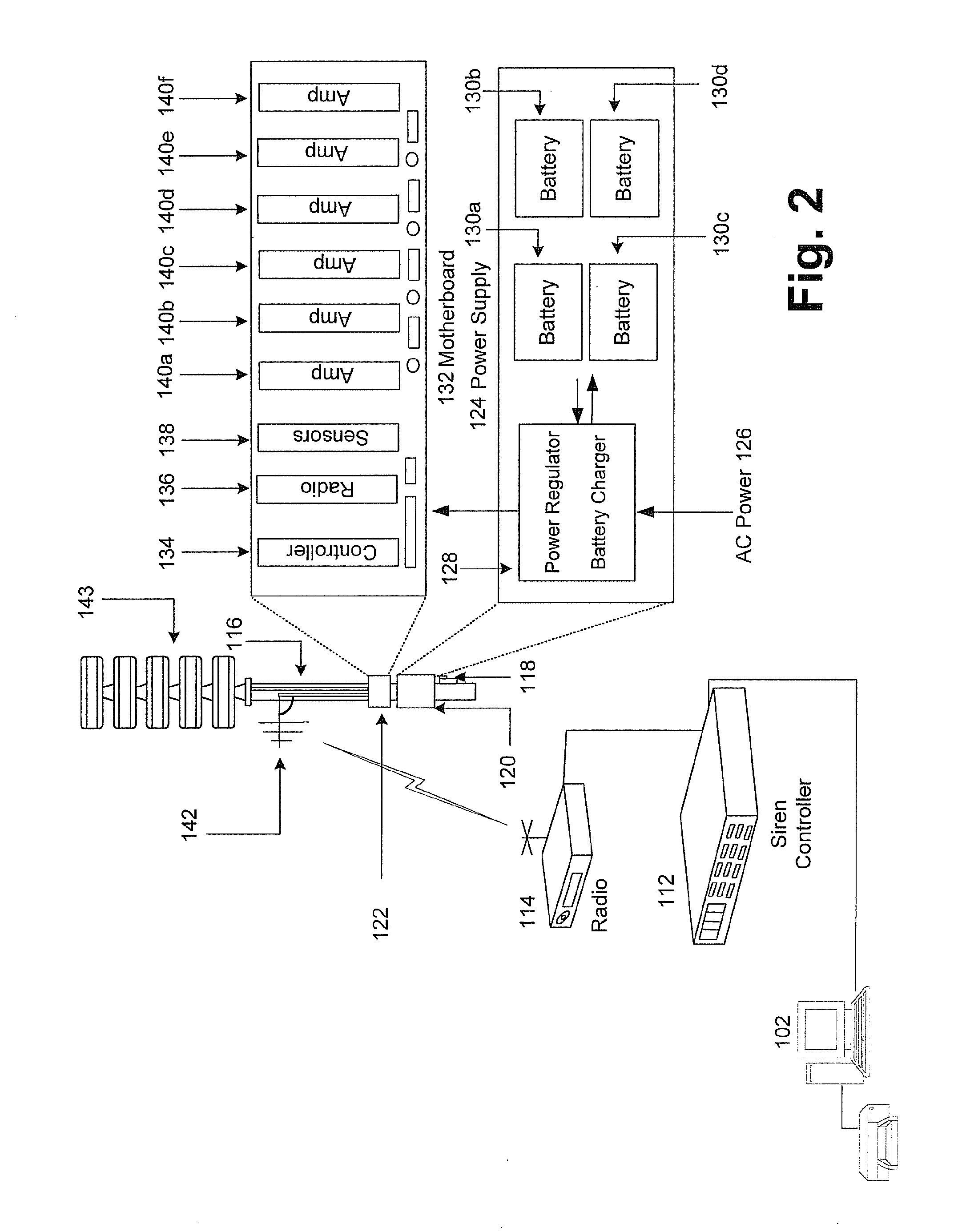
Public safety warning network
A communications infrastructure is upgraded to a public safety network that supports wireless communications of emergency information. Communities have installed public safety communications systems such as community warning siren systems that rely on point-to-point communications systems. Each site in the system is upgraded to a node in a wireless network that provides the communications infrastructure for a network-enabled public safety communications system that enables trusted resources such as warning sirens to access the network and communicate with other trusted resources across the network. Additionally, the public safety network may be patched using mobile transceivers to form an ad hoc network in the event part of the infrastructure supporting the emergency response network is lost. Additionally, the upgrading of the communications system may include a public access network that relies on at least some of the same communications sites or nodes employed by the public safety network.
Owner:FEDERAL SIGNAL CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com