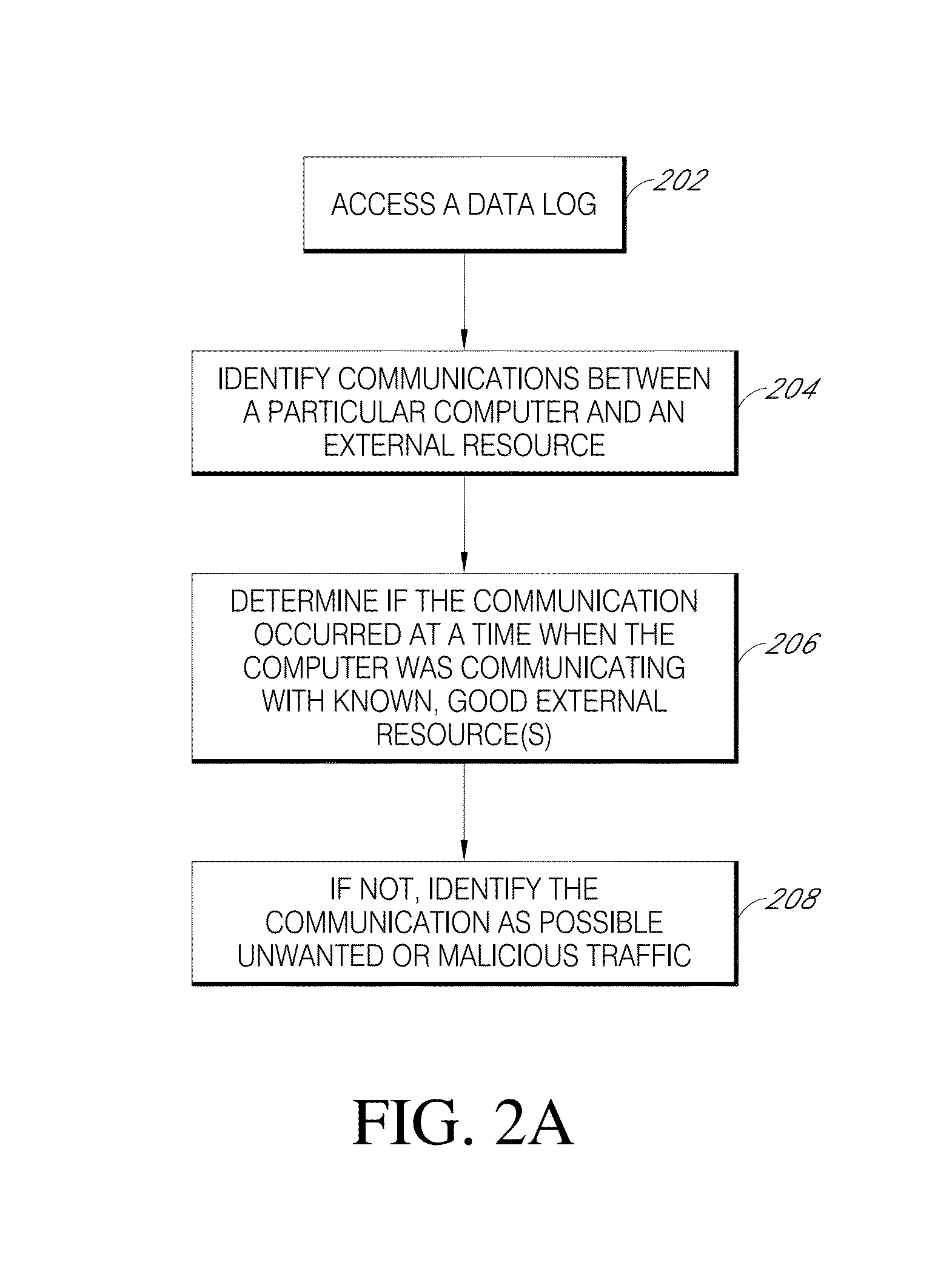
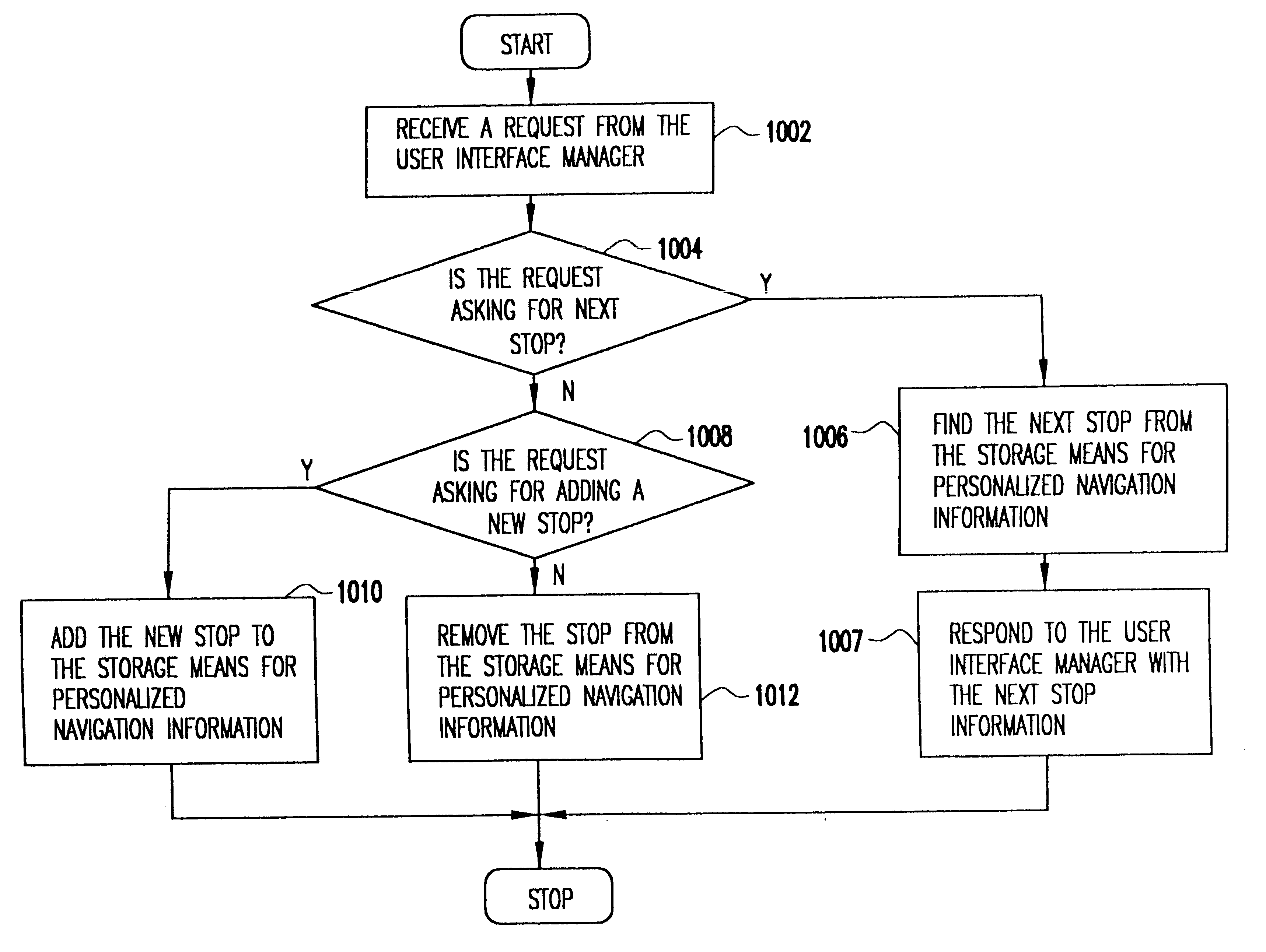
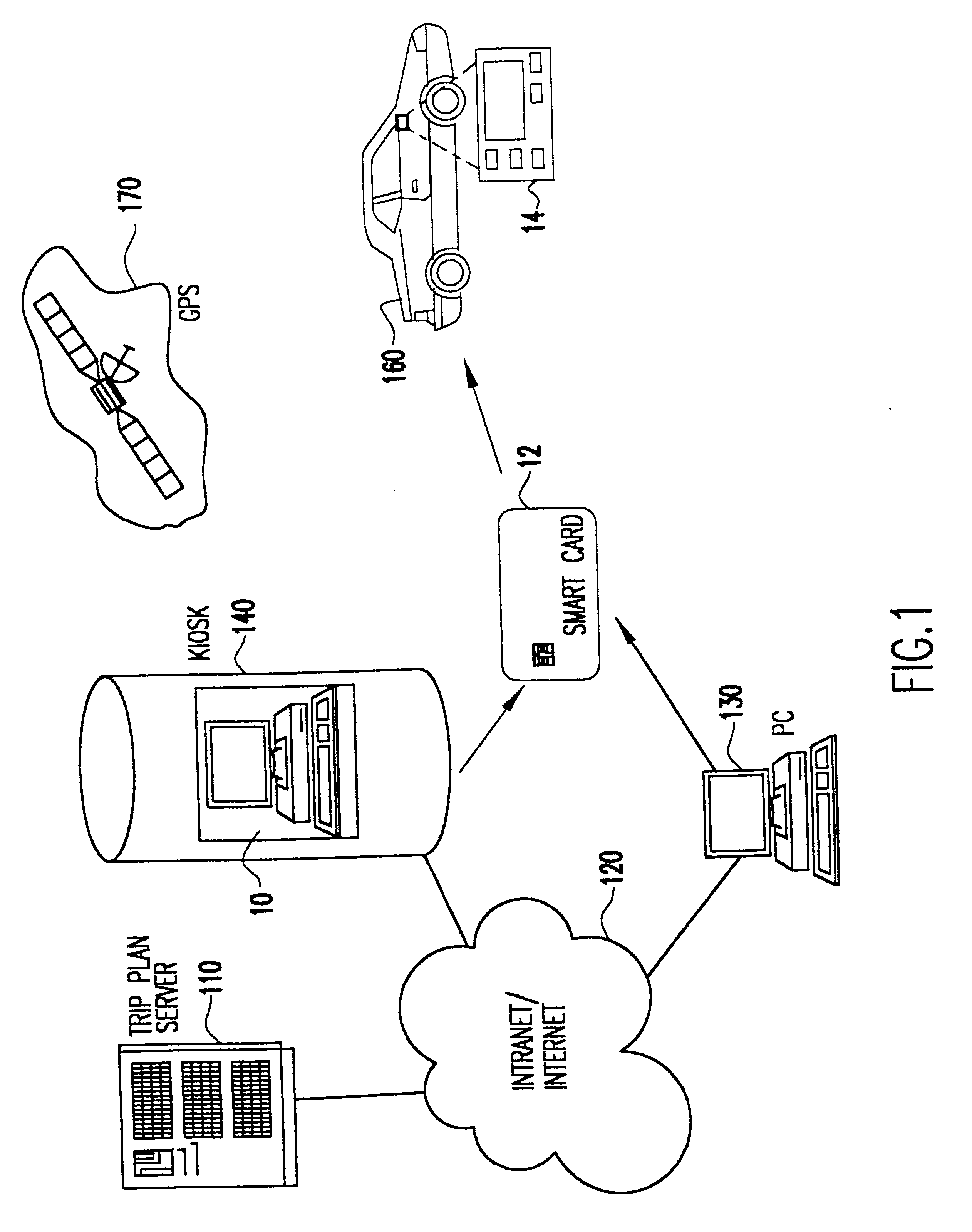
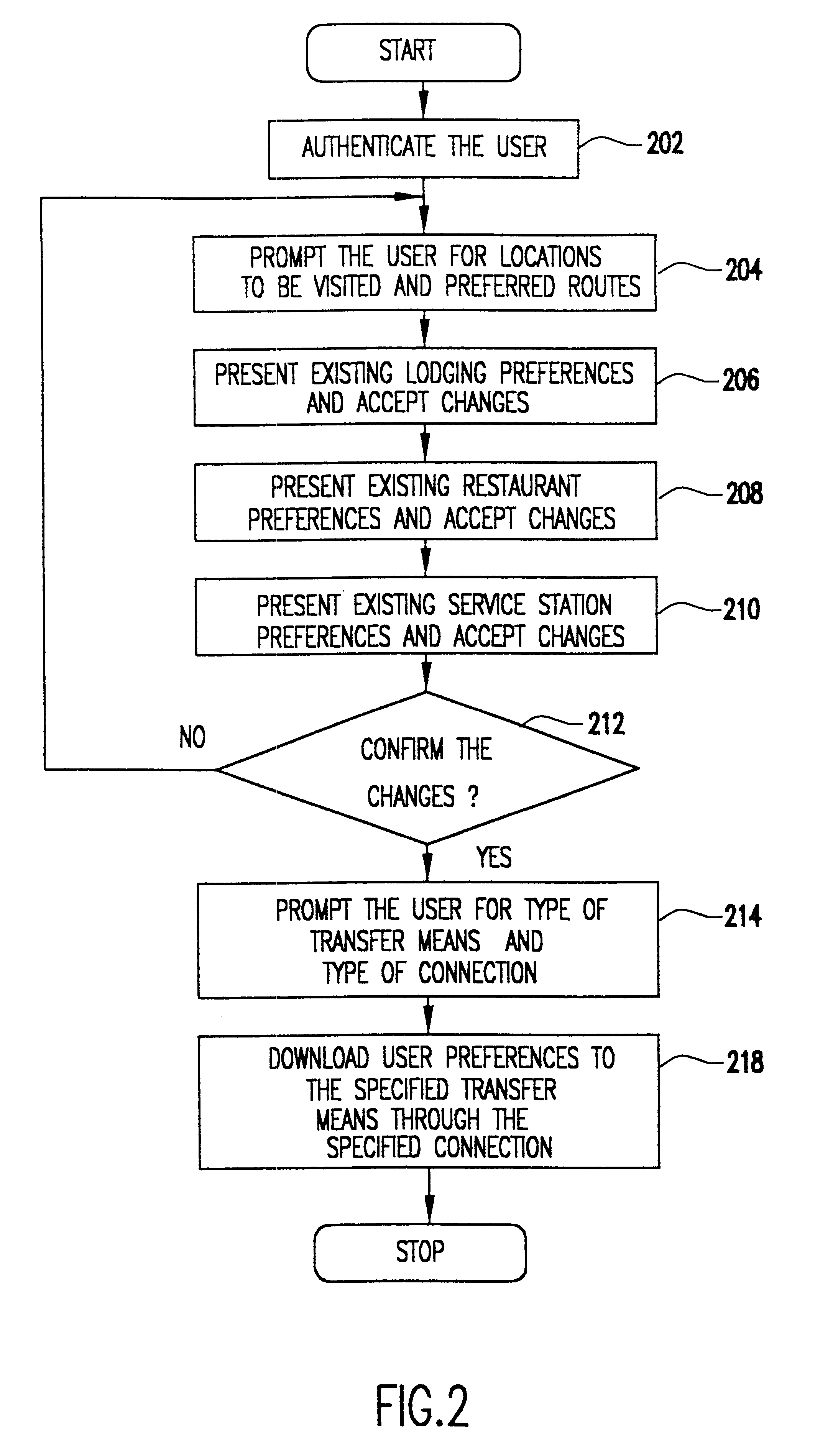
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10397 results about "Computing systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computing system - a system of one or more computers and associated software with common storage. ADP system, ADPS, automatic data processing system, computer system. backup system - a computer system for making backups.
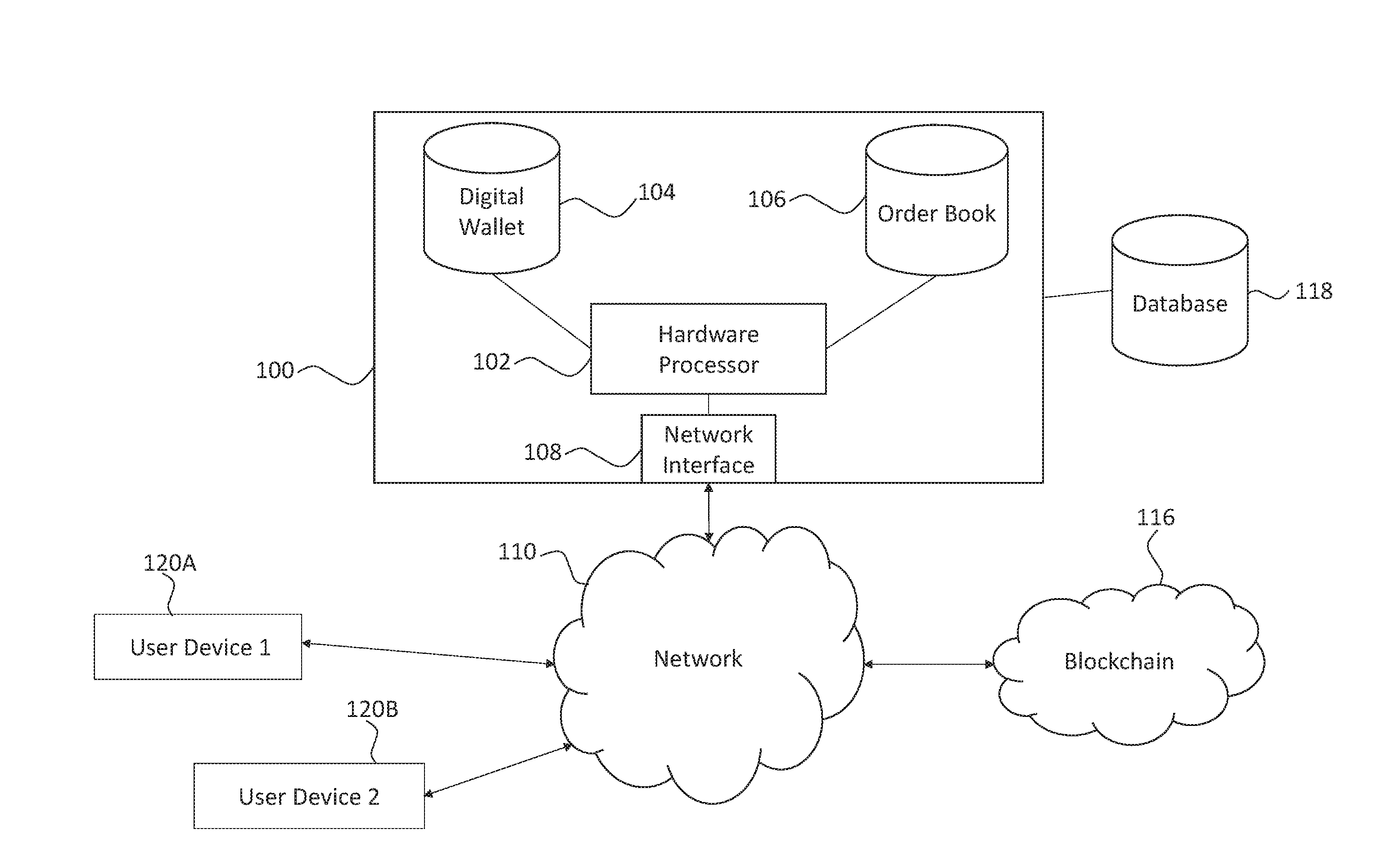
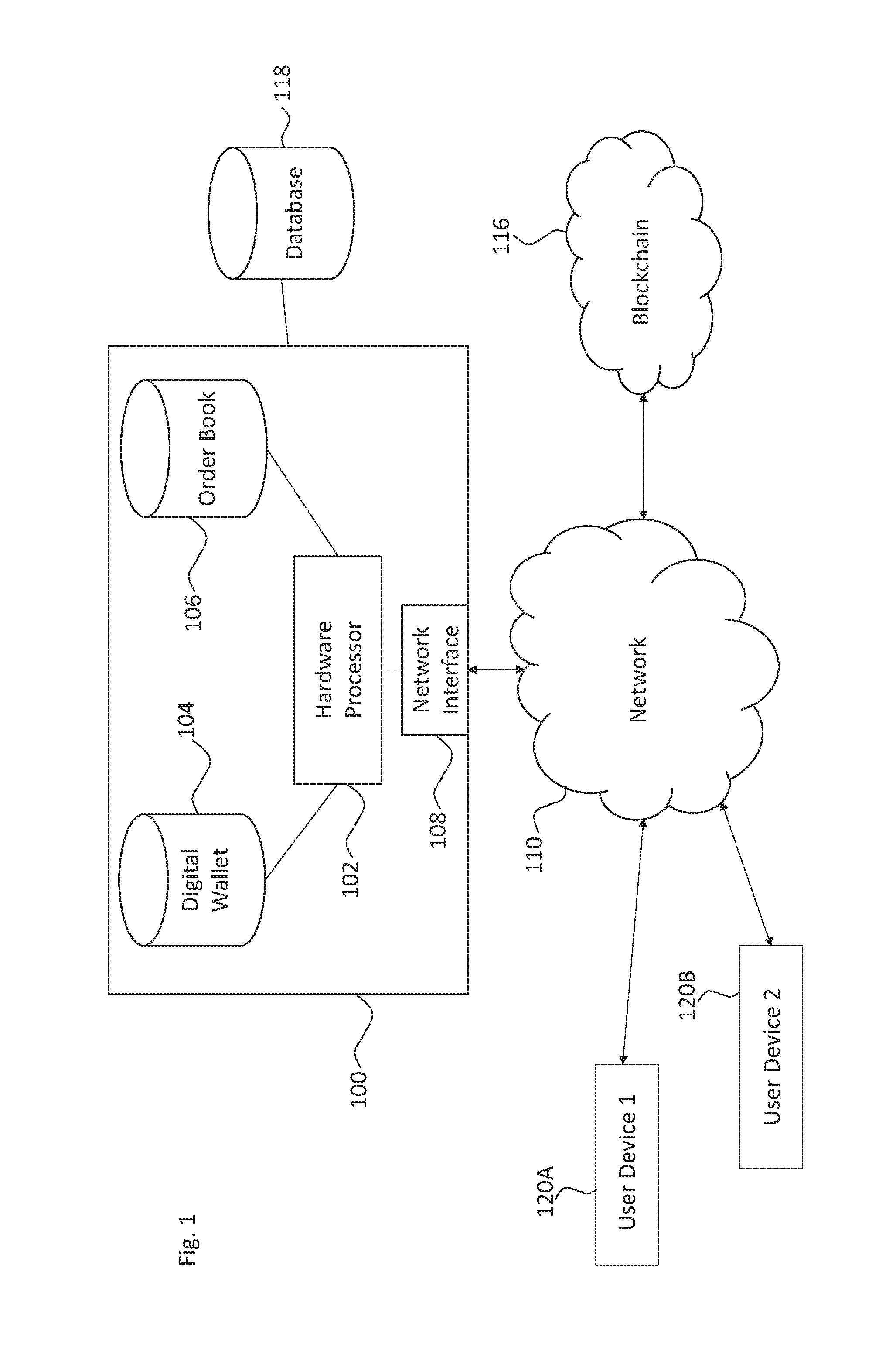
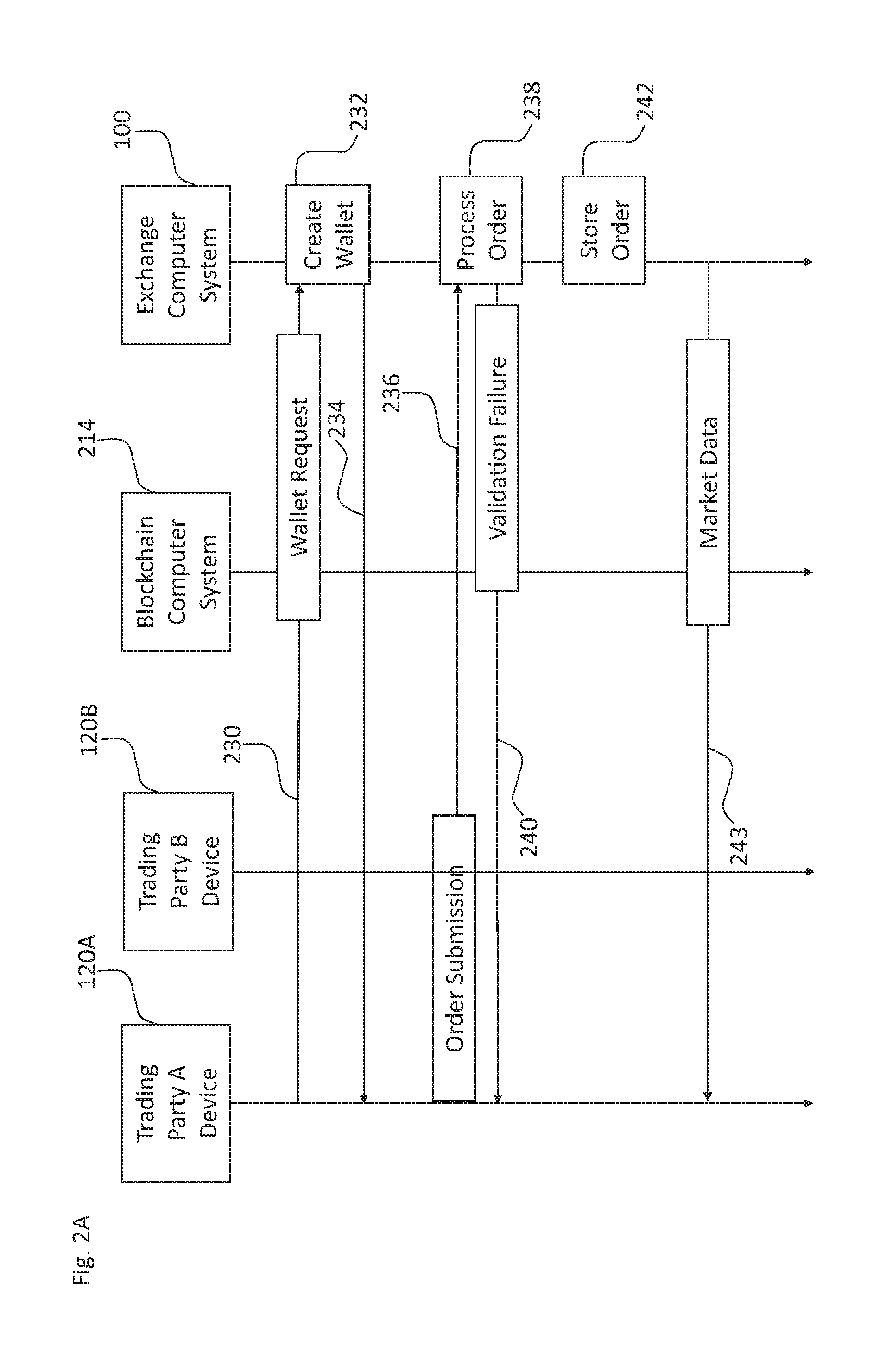
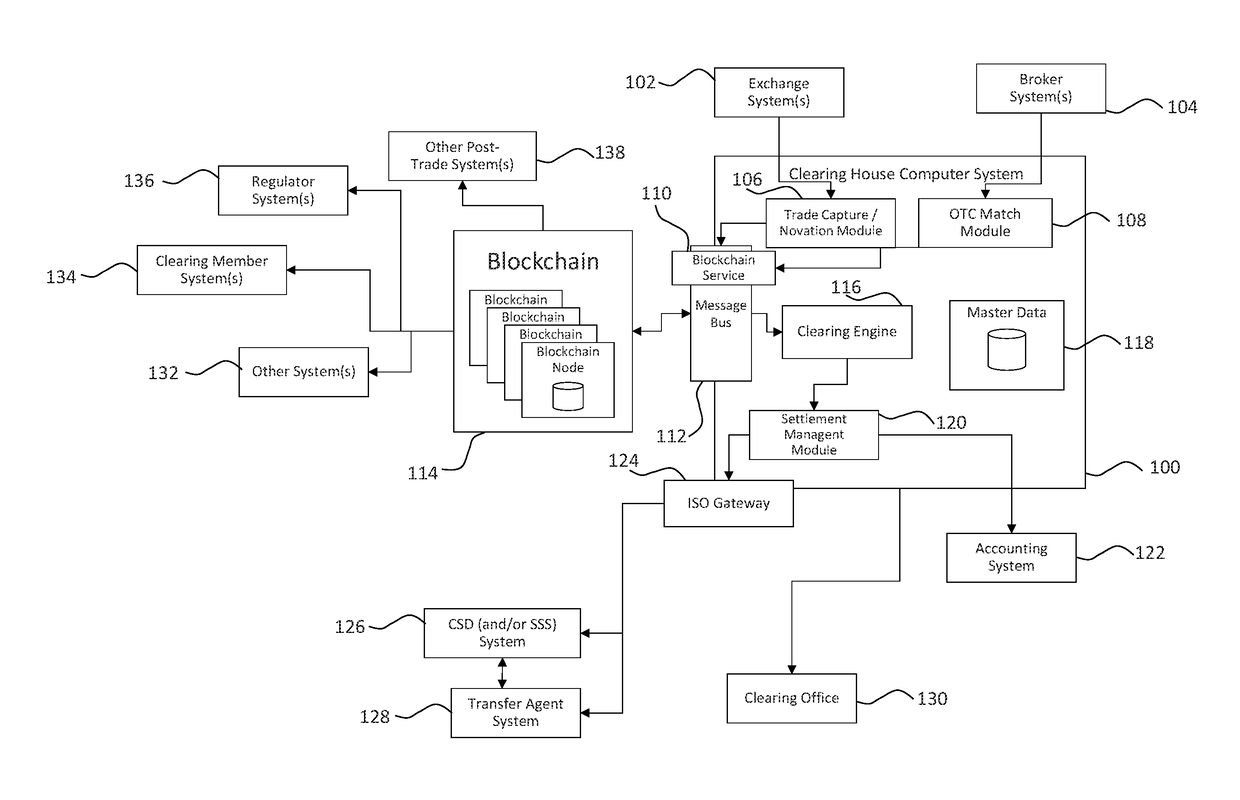
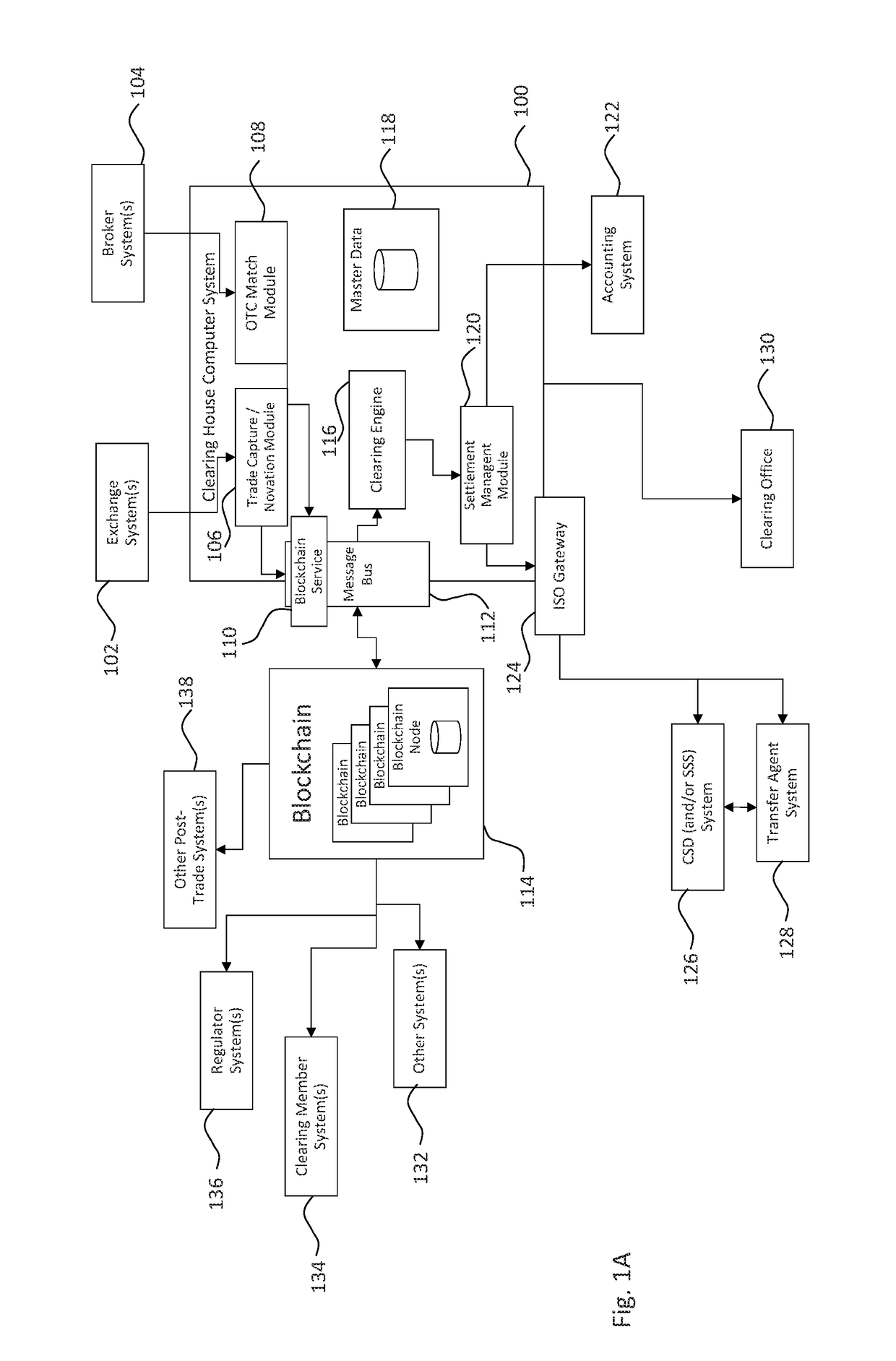
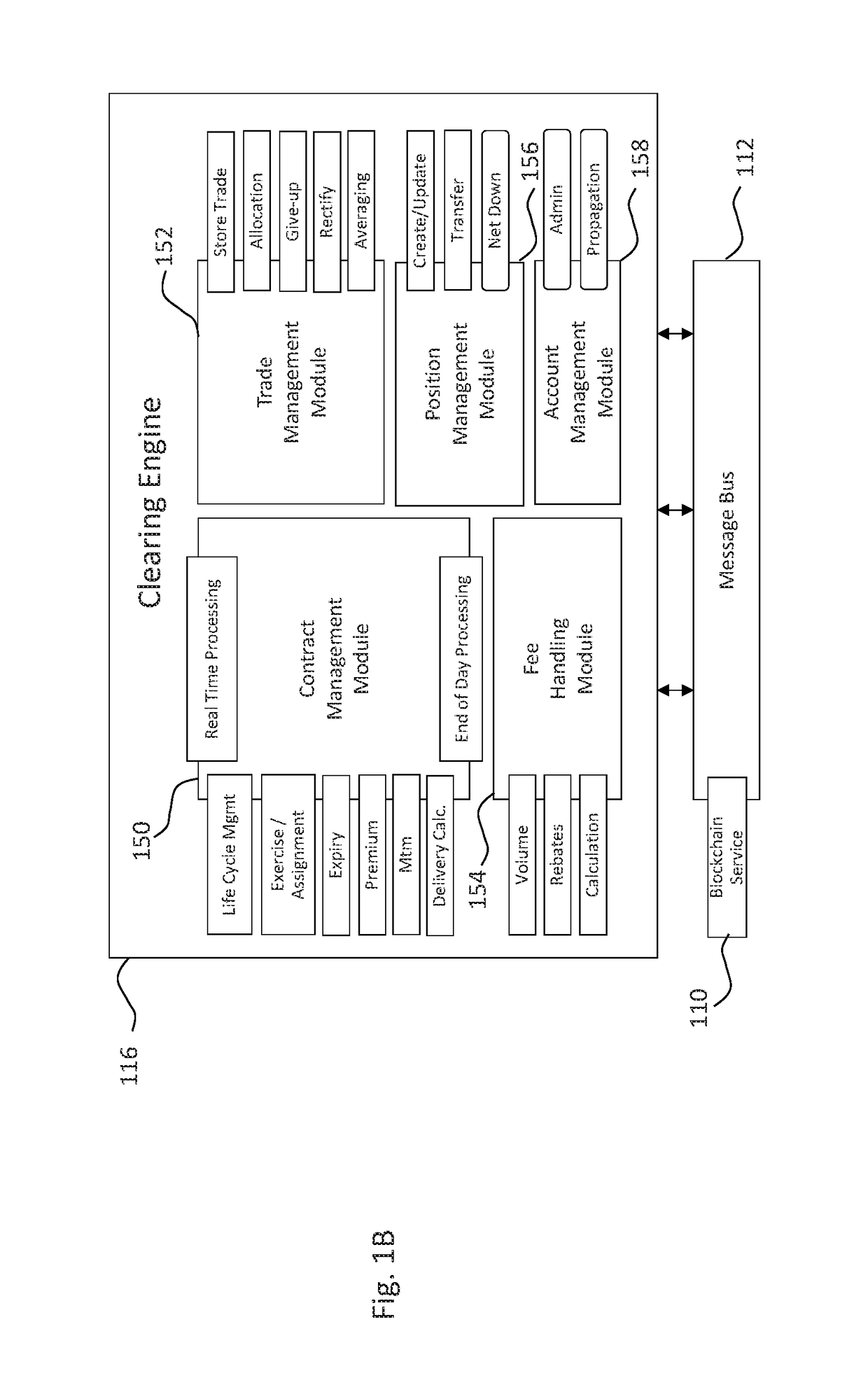
Systems and methods of blockchain transaction recordation
Owner:NASDAQ INC
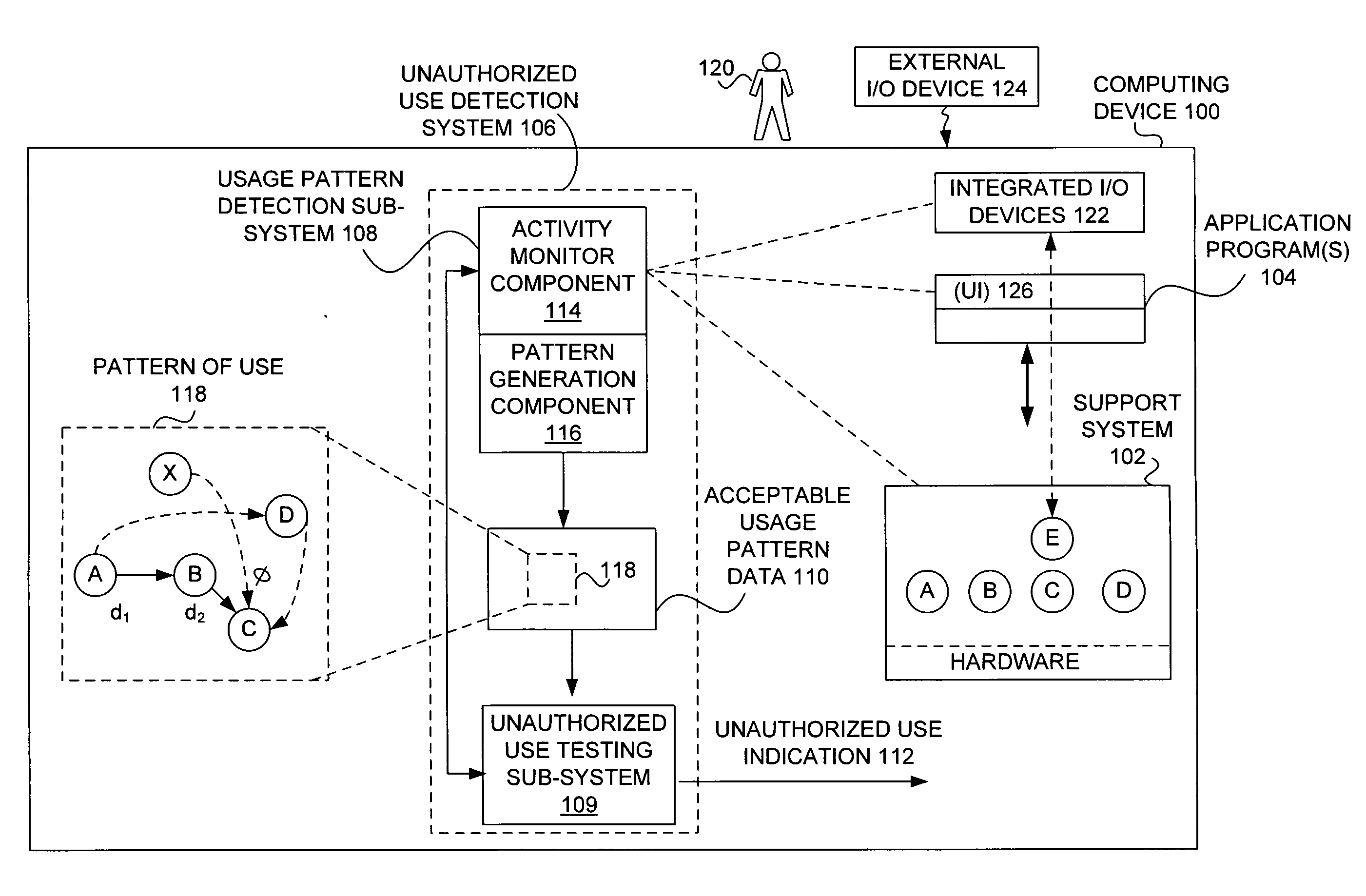
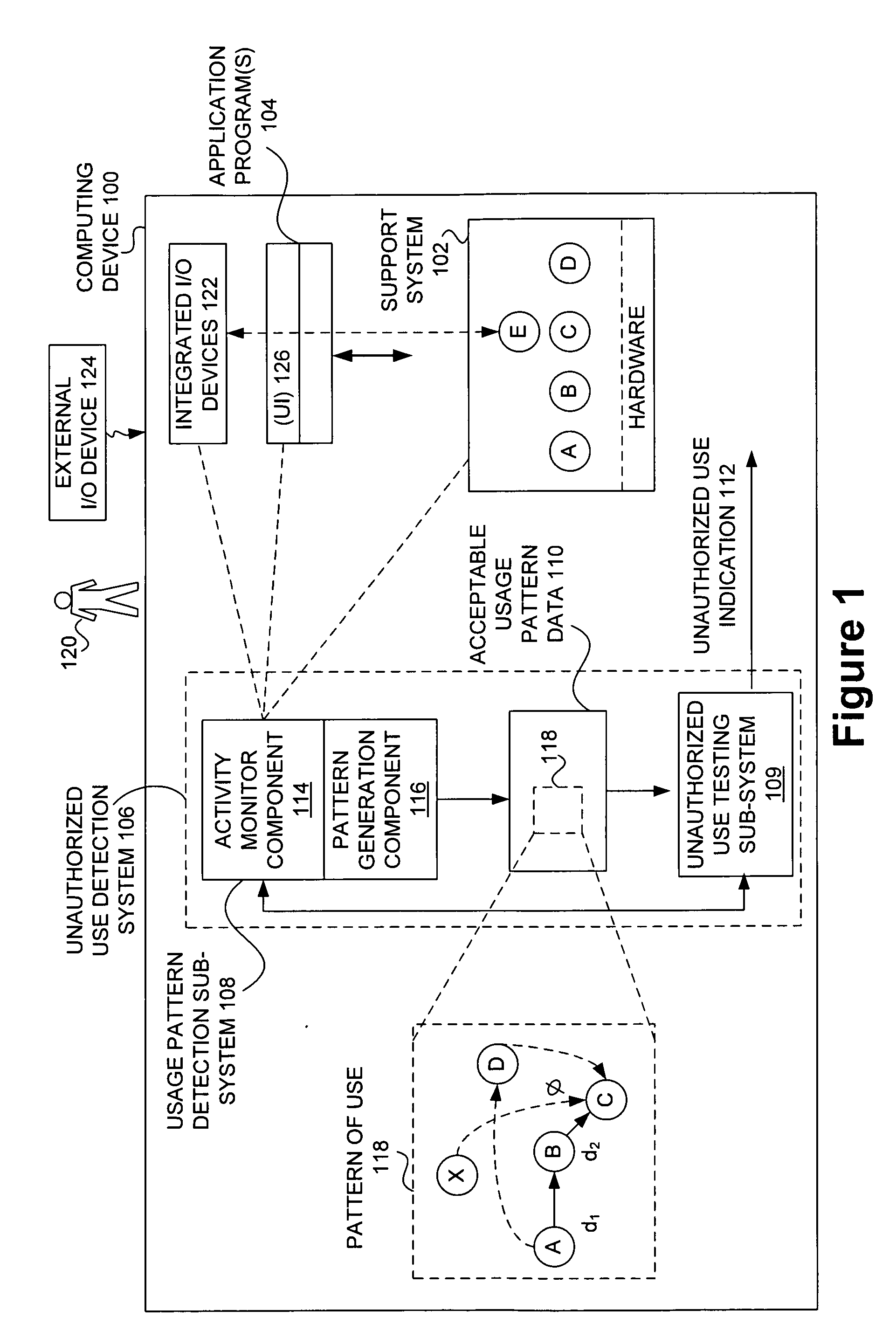
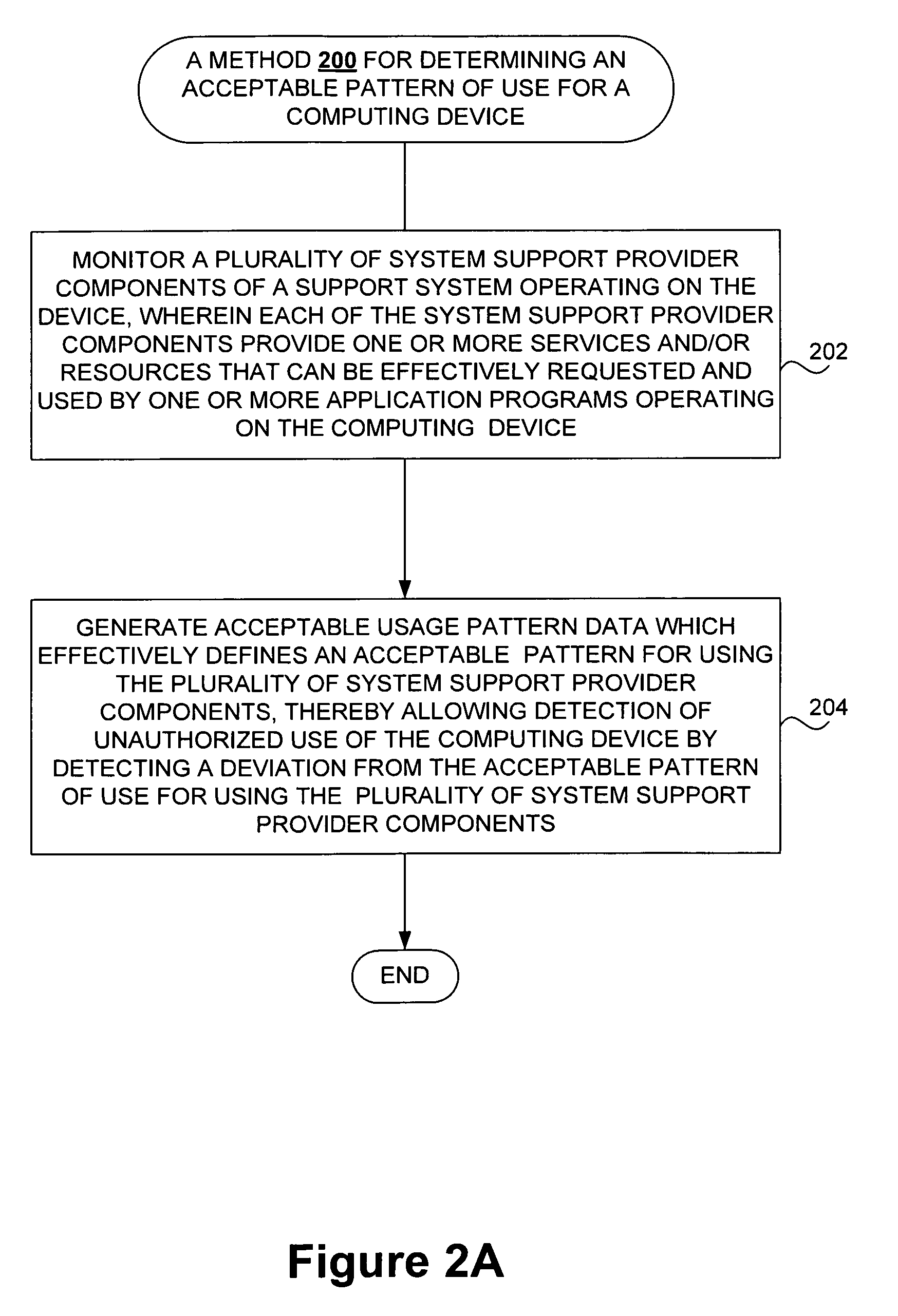
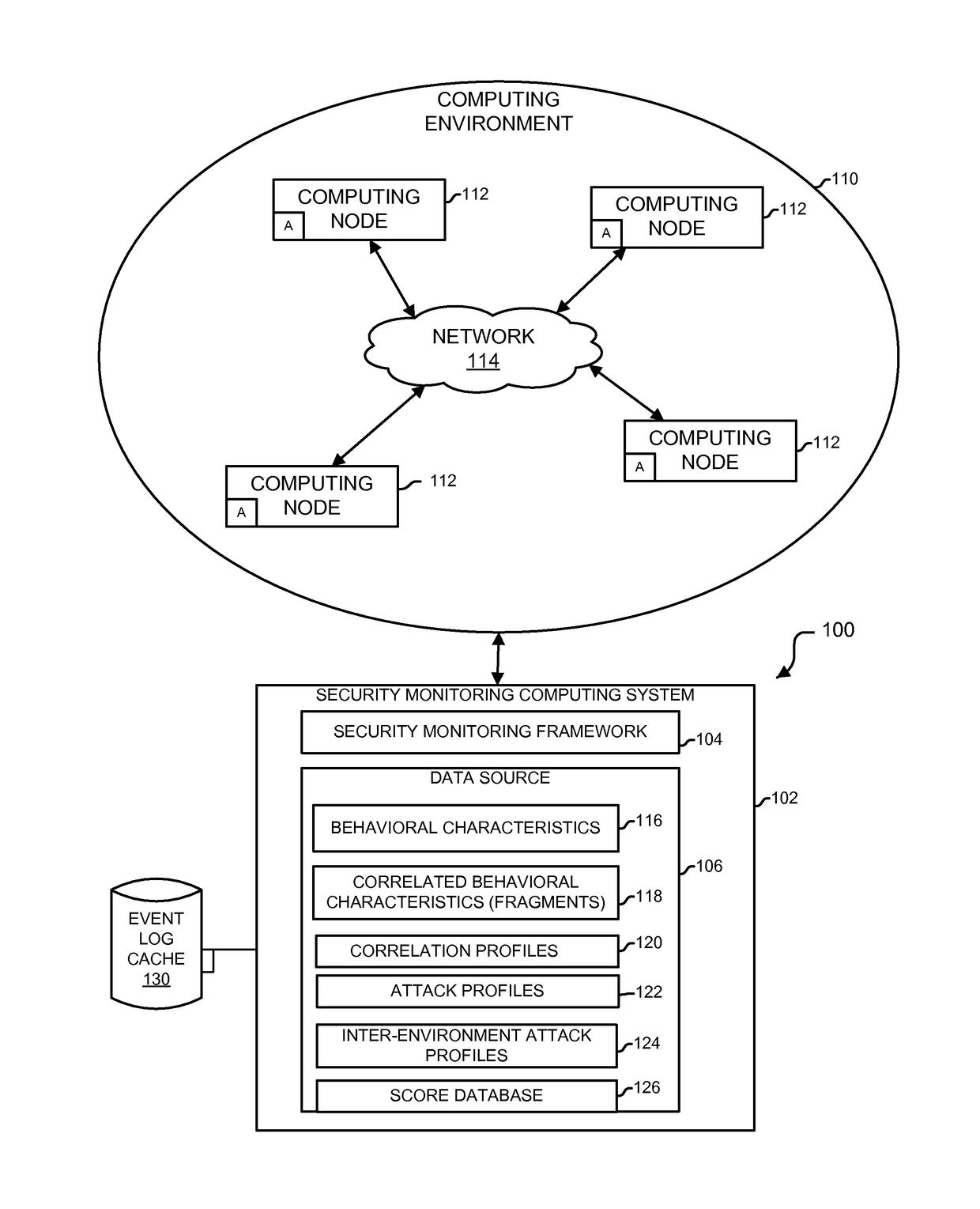
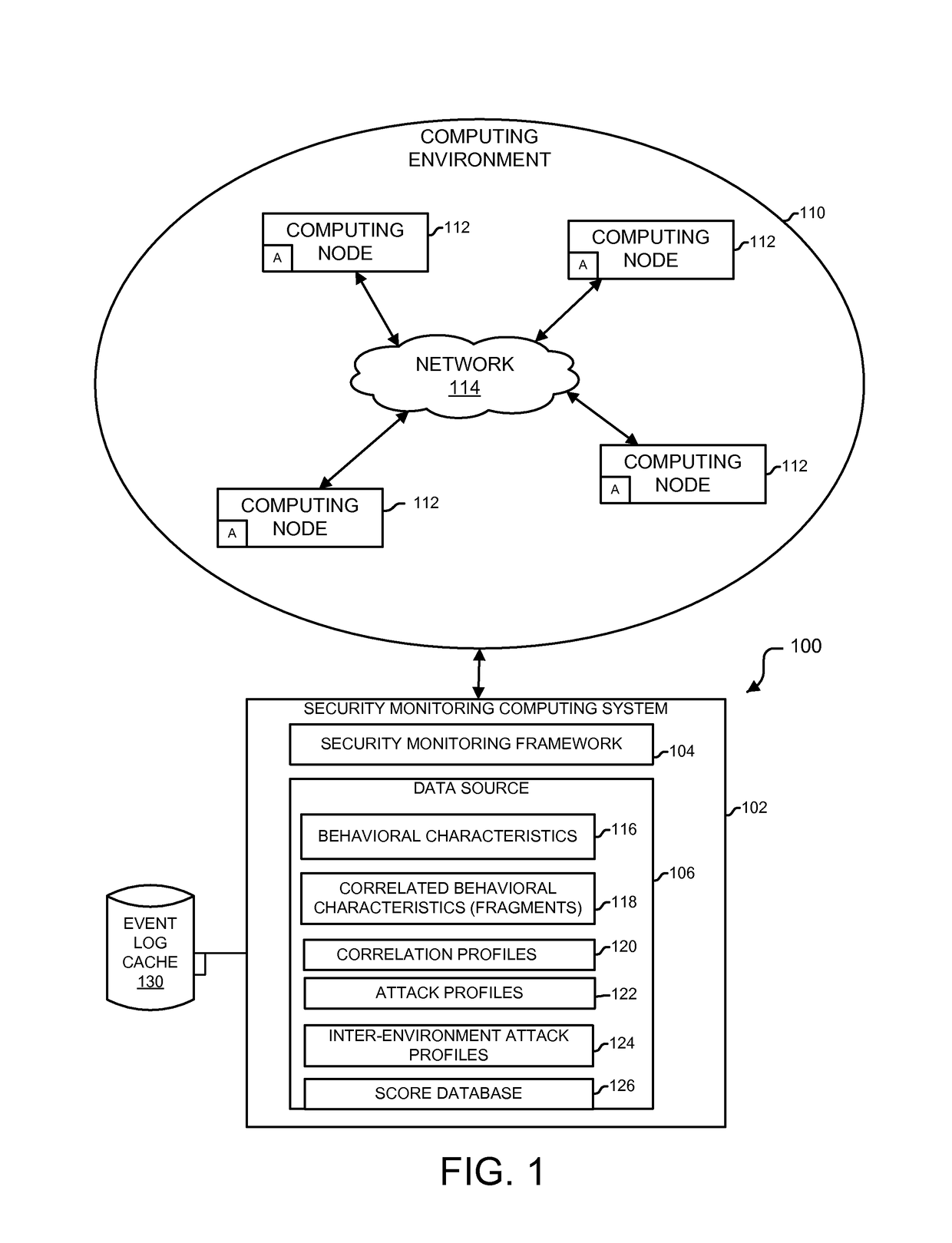
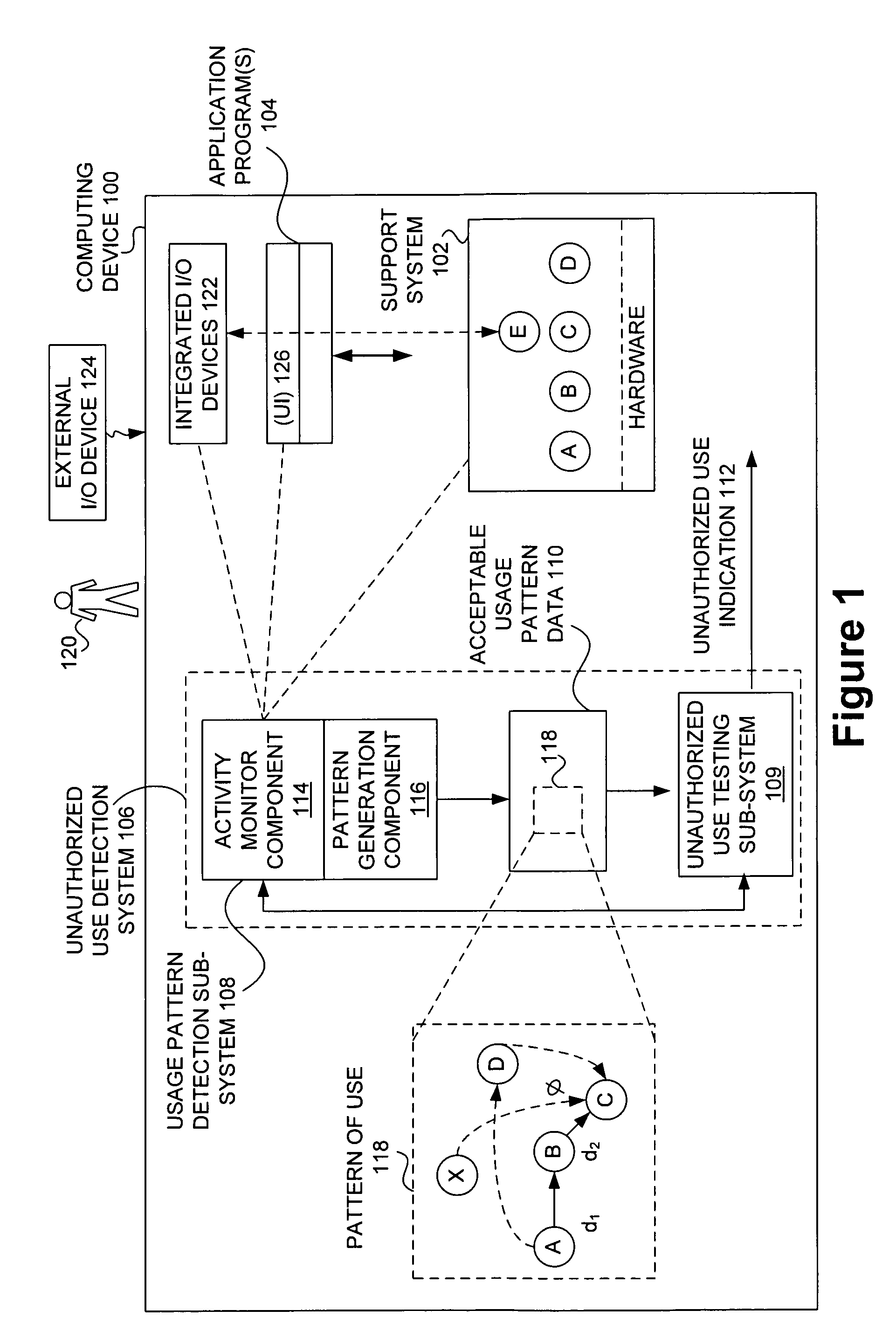
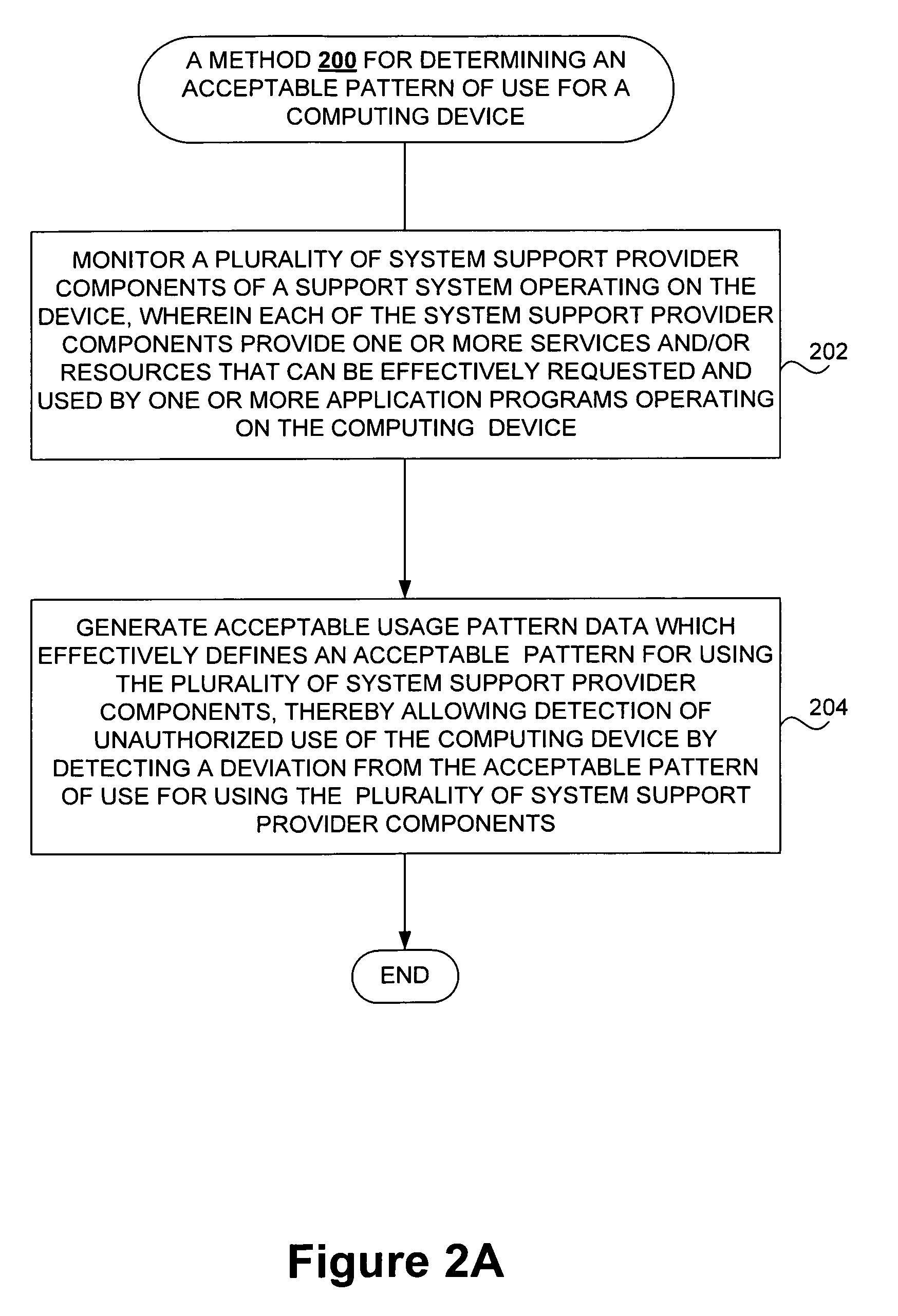
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS20090199296A1Efficiently definedMemory loss protectionError detection/correctionSupporting systemOperational system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
Modular data center
Modular data centers with modular components suitable for use with rack or shelf mount computing systems, for example, are disclosed. The modular center generally includes a modular computing module including an intermodal shipping container and computing systems mounted within the container and configured to be shipped and operated within the container and a temperature control system for maintaining the air temperature surrounding the computing systems. The intermodal shipping container may be configured in accordance to International Organization for Standardization (ISO) container manufacturing standards or otherwise configured with respect to height, length, width, weight, and / or lifting points of the container for transport via an intermodal transport infrastructure. The modular design enables the modules to be cost effectively built at a factory and easily transported to and deployed at a data center site.
Owner:GOOGLE LLC
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
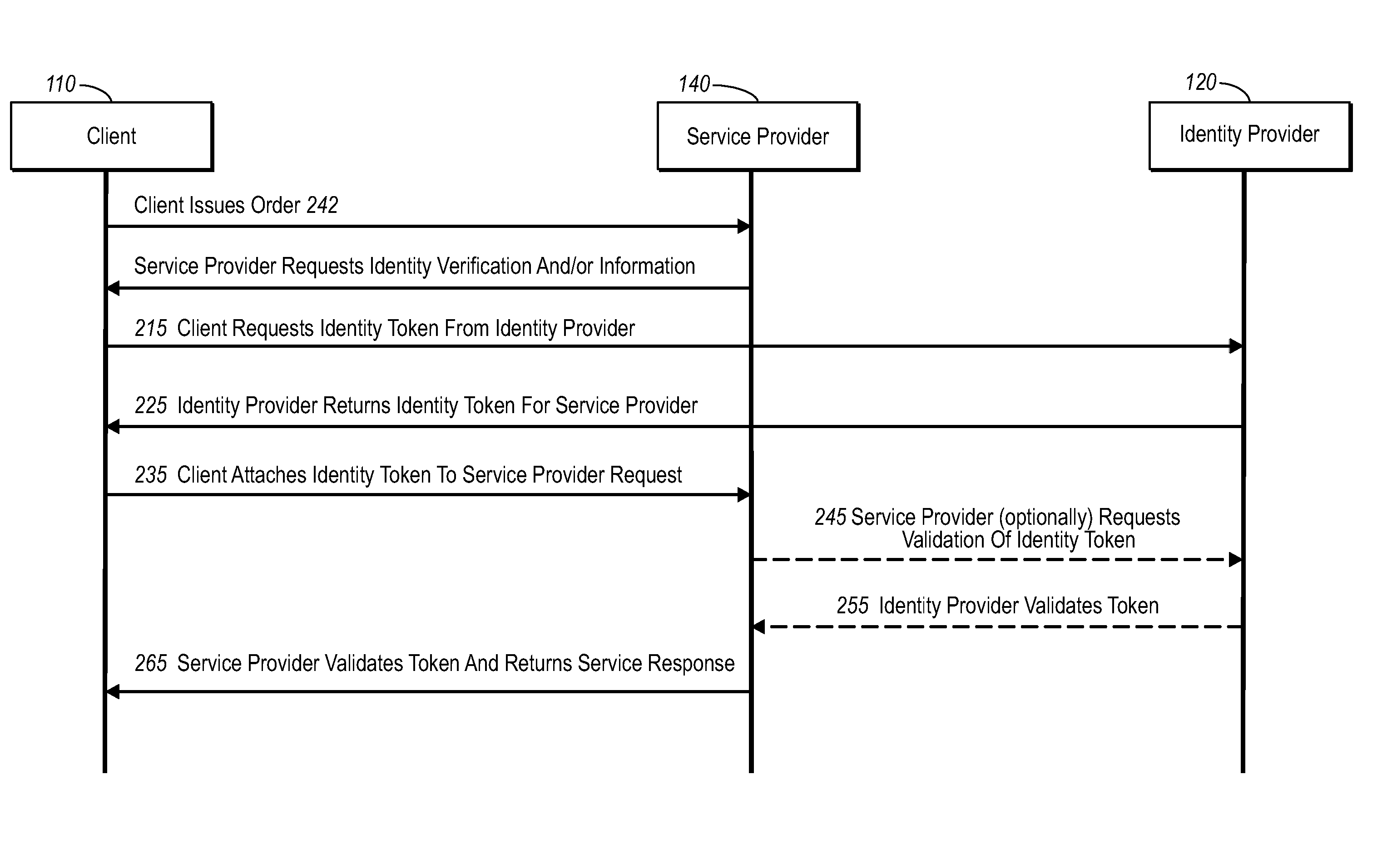
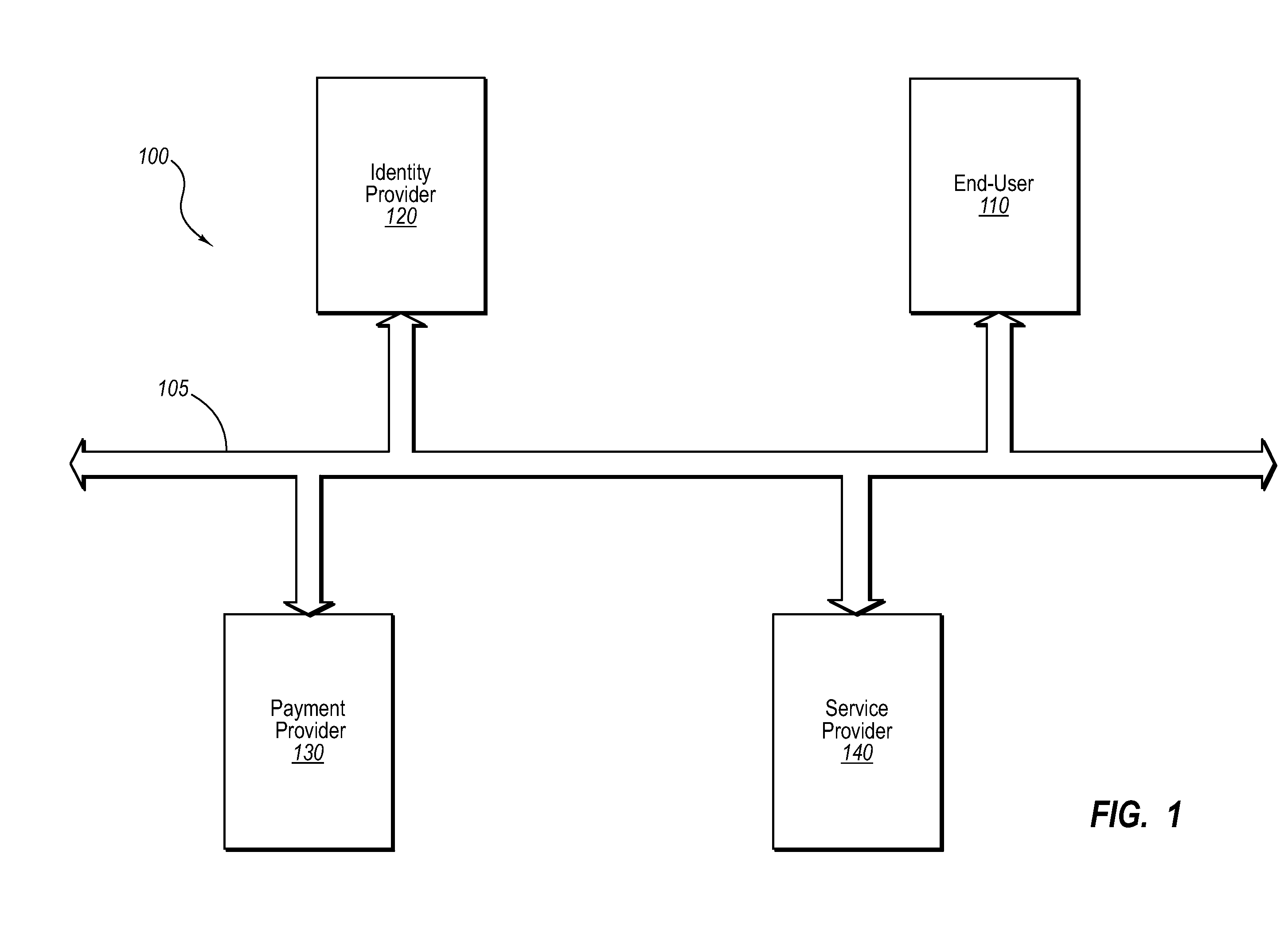
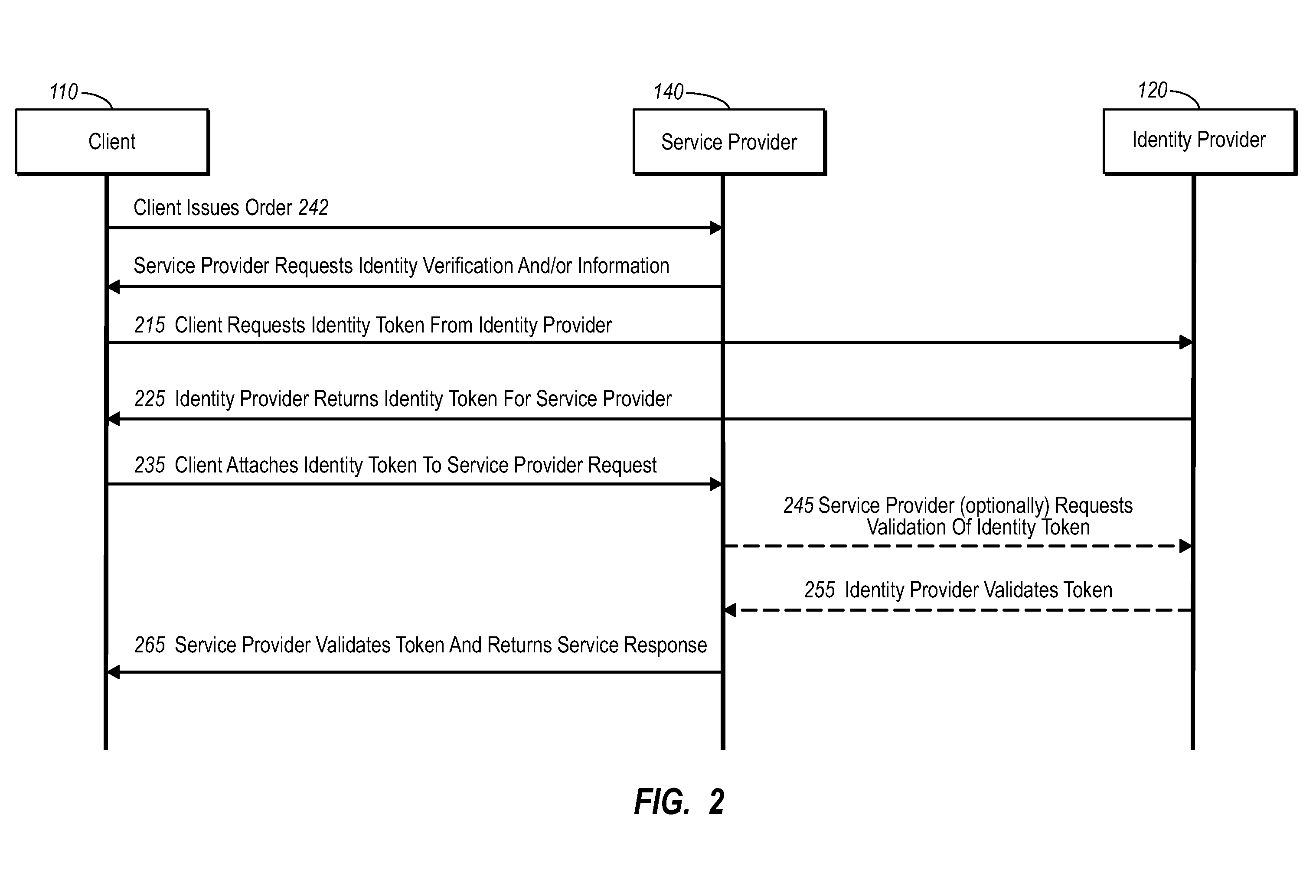
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
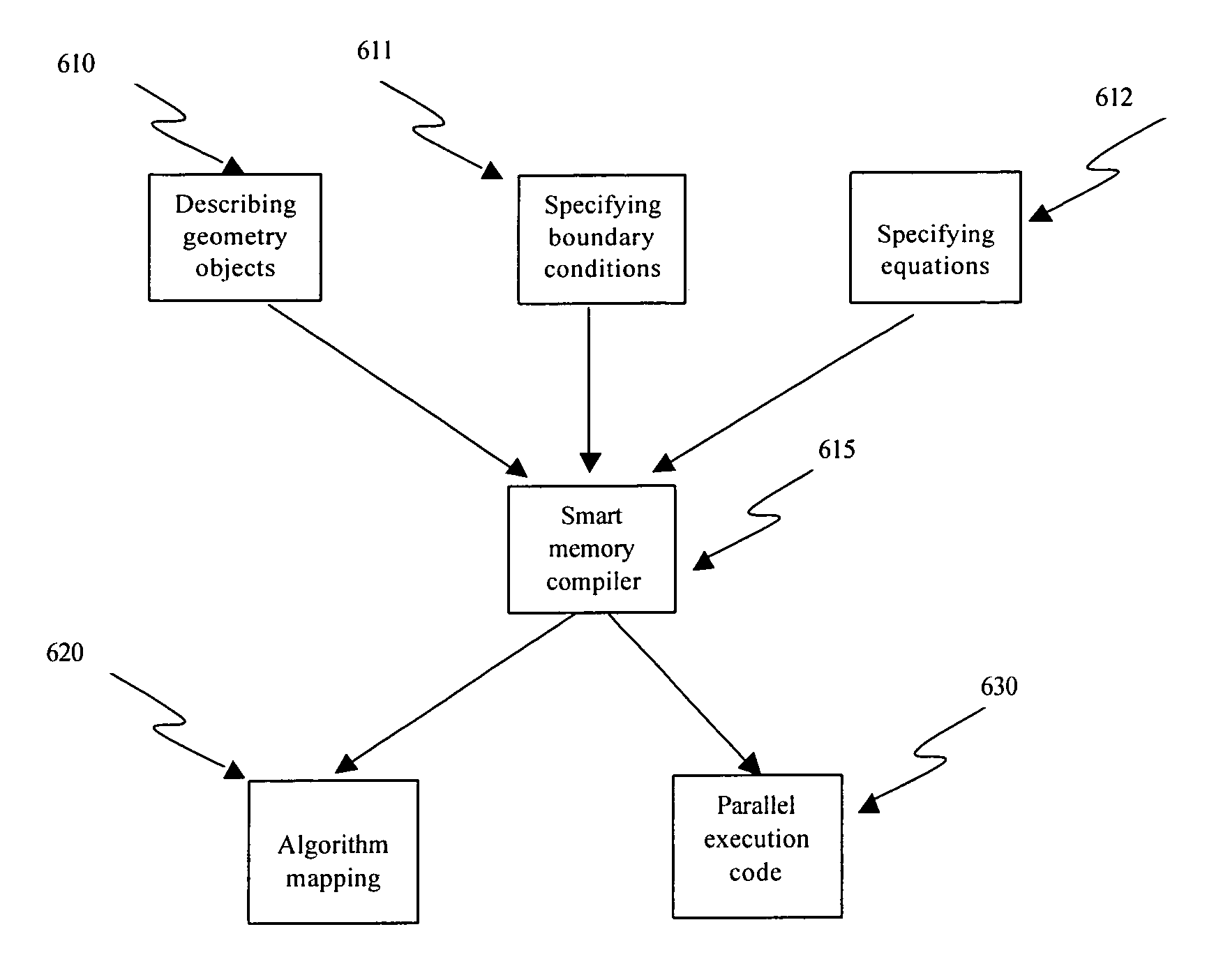
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS7546438B2Improve performanceLow costMultiplex system selection arrangementsDigital computer detailsSmart memoryExecution unit
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
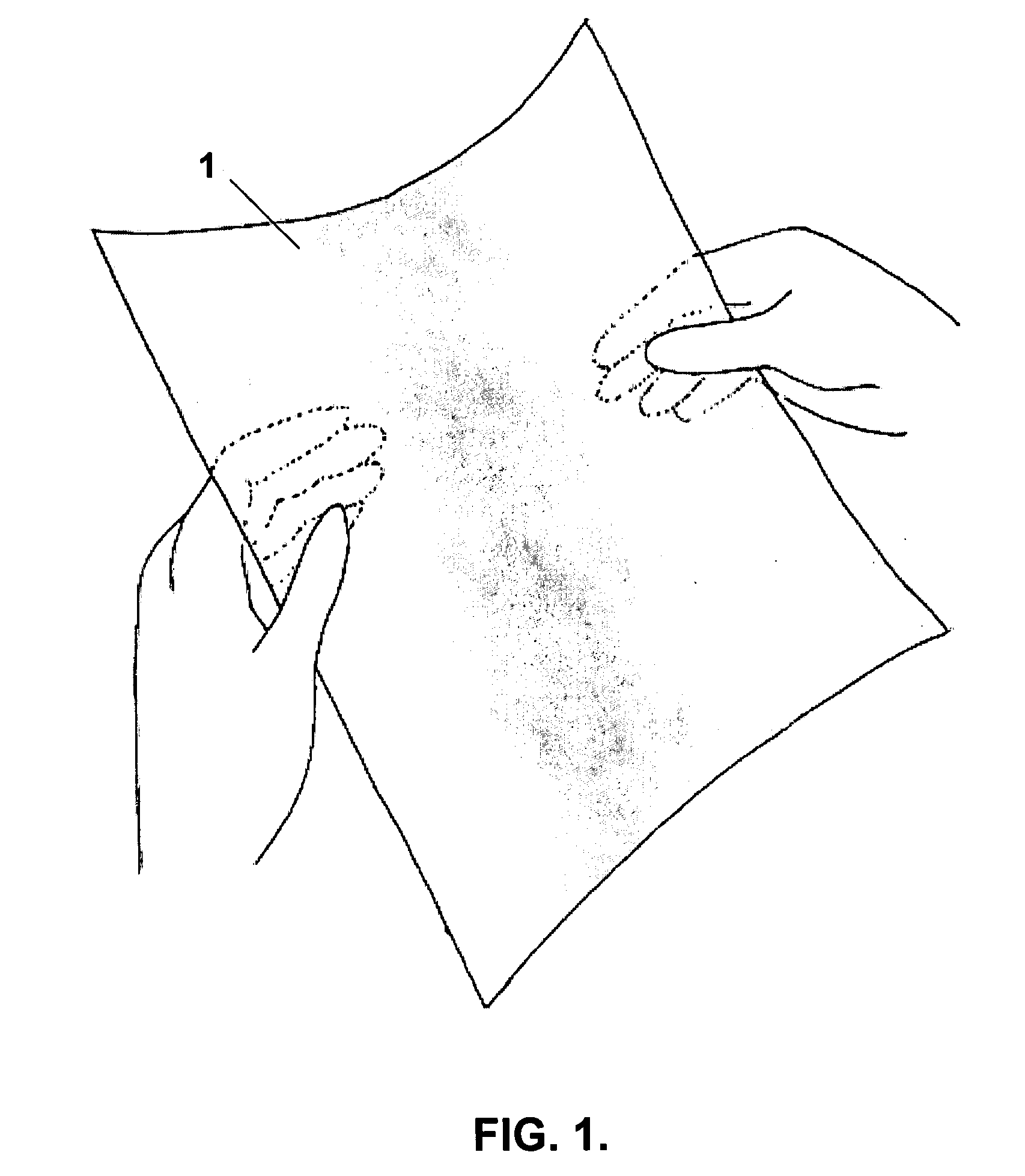
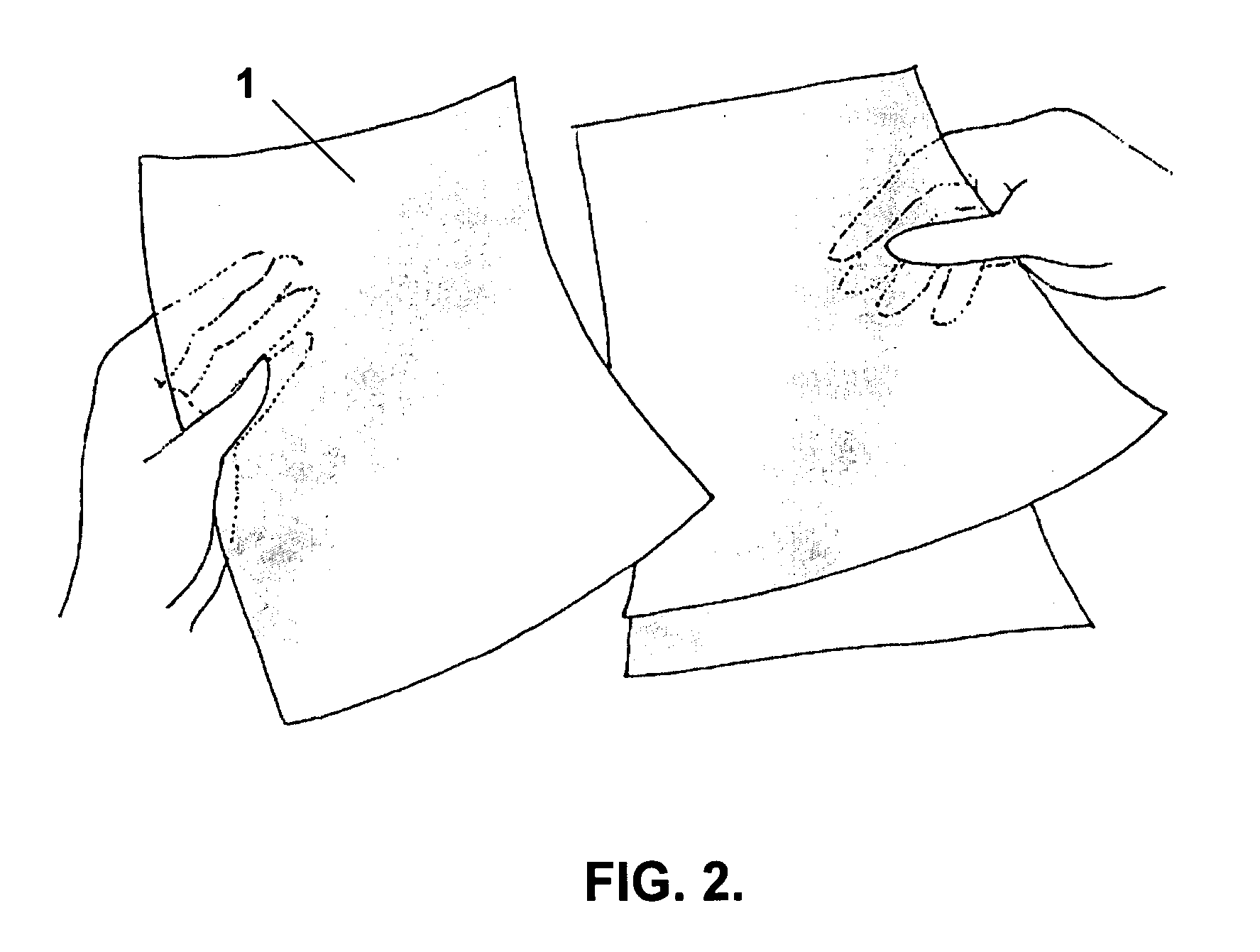
Interaction techniques for flexible displays
InactiveUS20070247422A1Input/output for user-computer interactionDigital data processing detailsGraphicsGraphical content
The invention relates to a set of interaction techniques for obtaining input to a computer system based on methods and apparatus for detecting properties of the shape, location and orientation of flexible display surfaces, as determined through manual or gestural interactions of a user with said display surfaces. Such input may be used to alter graphical content and functionality displayed on said surfaces or some other display or computing system.
Owner:XUUK
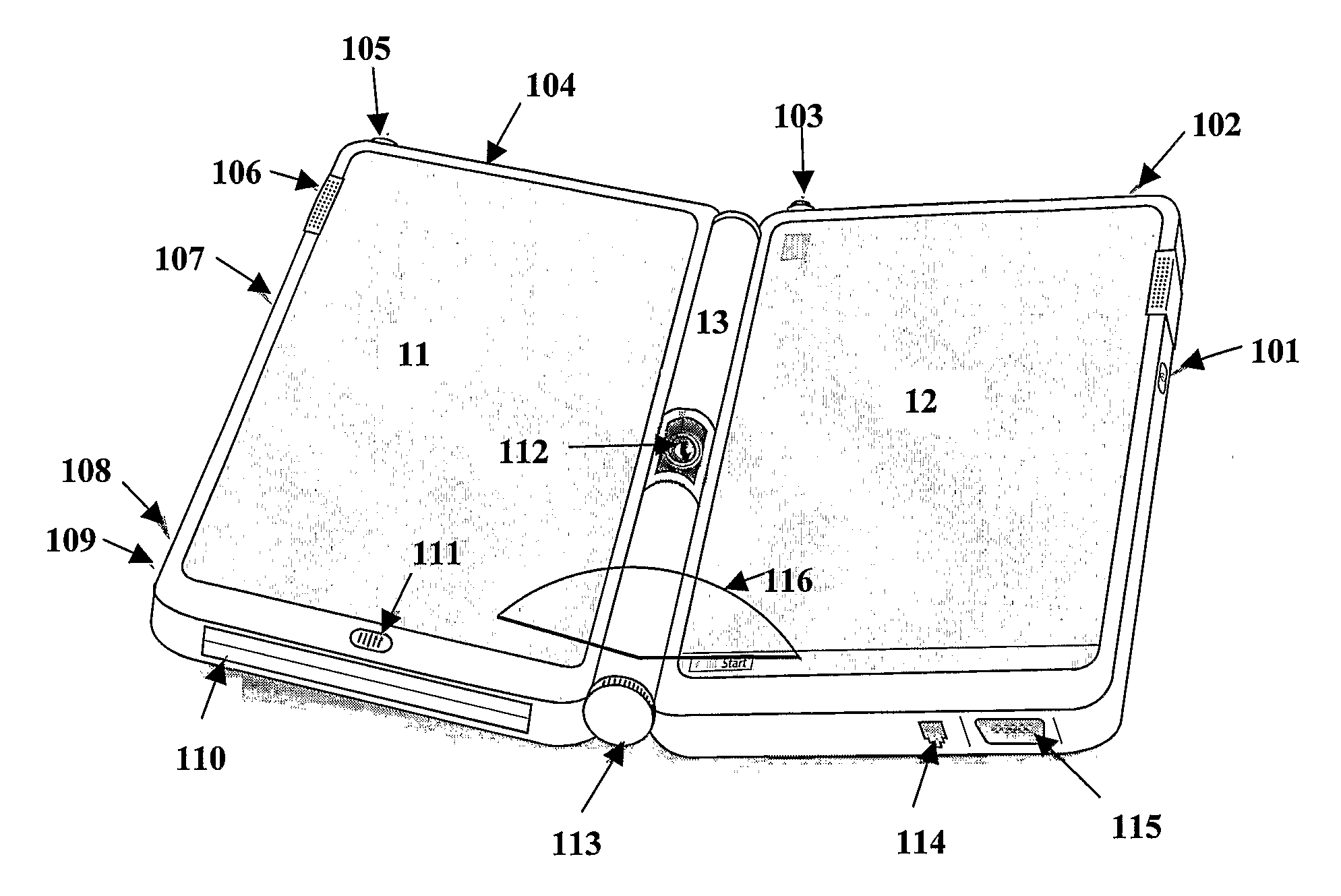
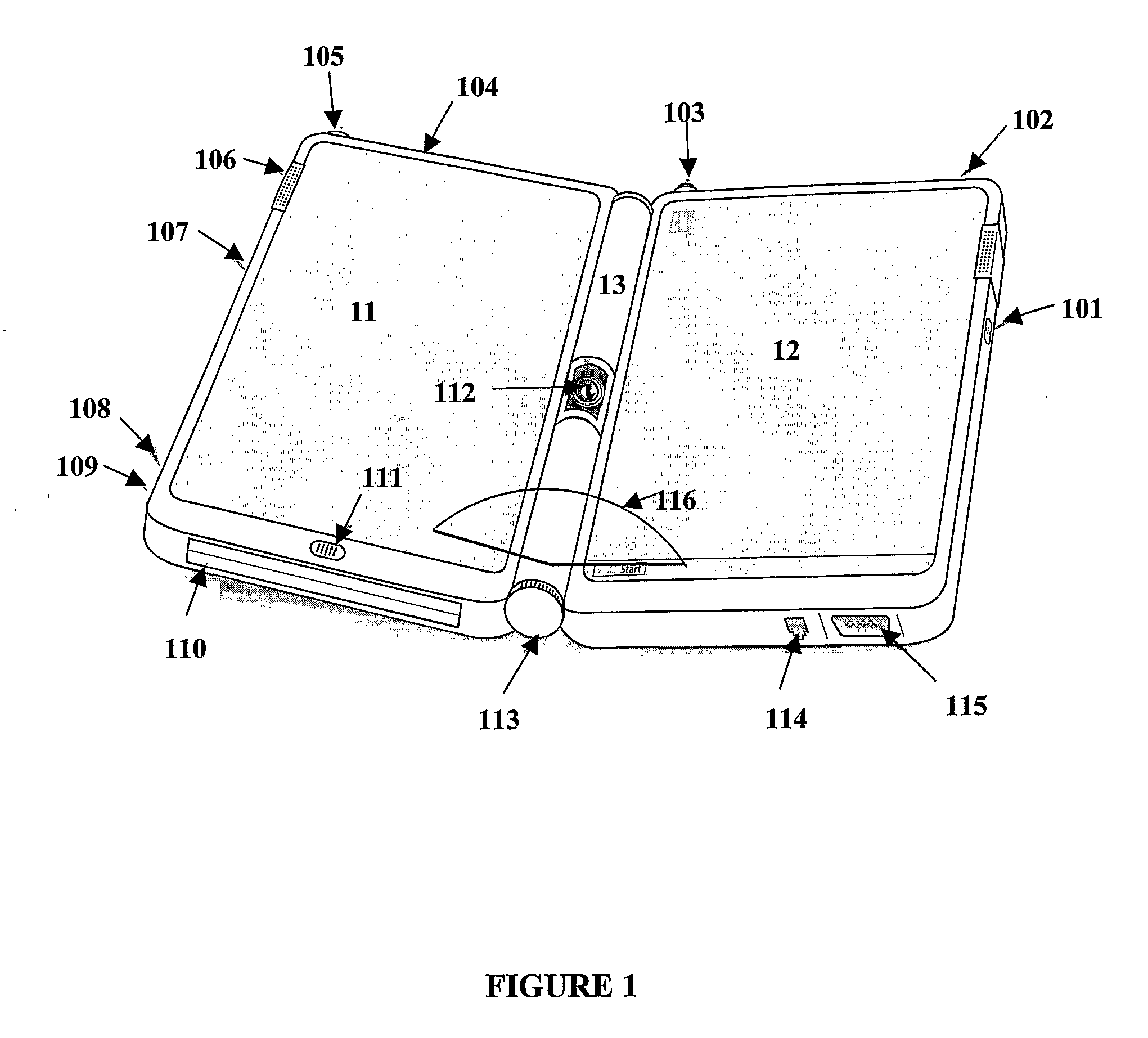
Portable, folding and separable multi-display computing system
InactiveUS20070182663A1Volume/mass flow measurementDigital computer detailsComputer monitorDisplay device
The present invention provides a coupling mechanism between a primary computing device and a secondary computing device, wherein each computing device may be physically separated from each other while continuing to communicate with each other. The primary computing device has the minimum functionality of a complete computing system such as a Tablet PC™, for example, and the secondary computing device has the minimum functionality of a hand-held computer monitor. The secondary computing device may also however, have the functionality of a complete computing system, or other level of functionality therebetween. The primary computing device may act as a master and control the functionality of the secondary computing device via a network or data bus connection, for example. The secondary computing device may be toggled between computer monitor functionality and secondary computer functionality regardless of whether or not the two computers are physically connected.
Owner:BIECH GRANT STEVEN
System and method for malicious software detection in multiple protocols
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
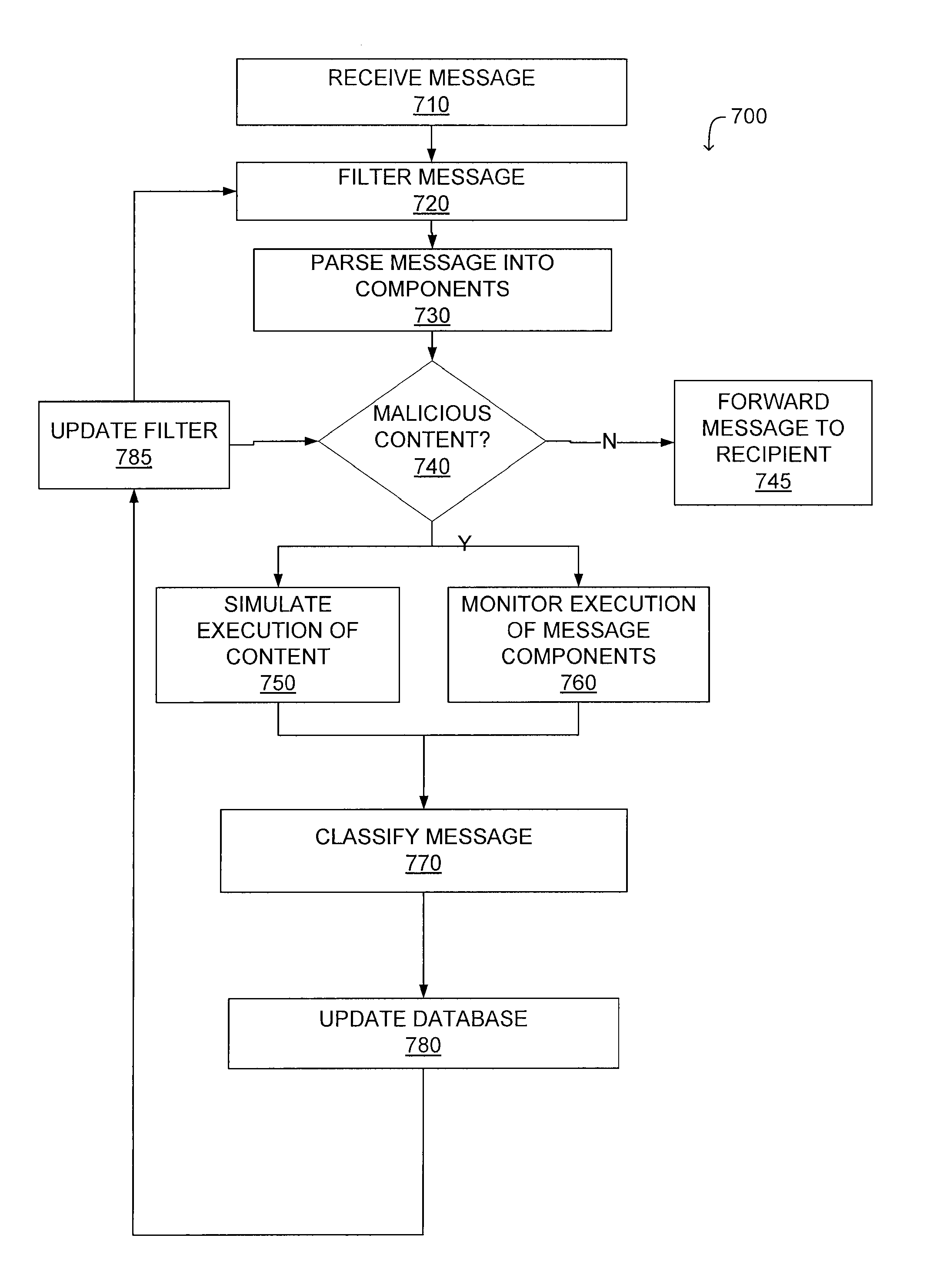
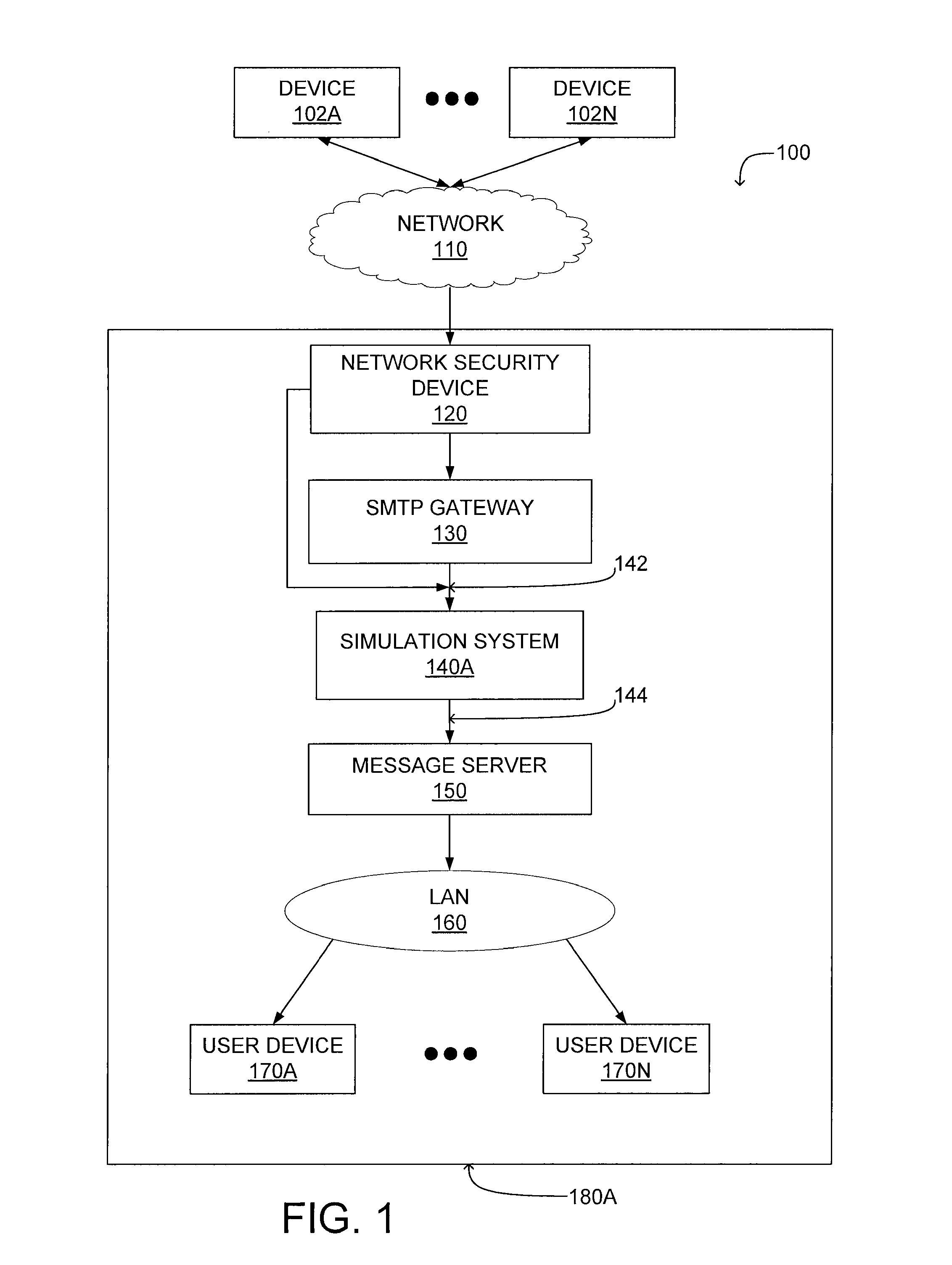
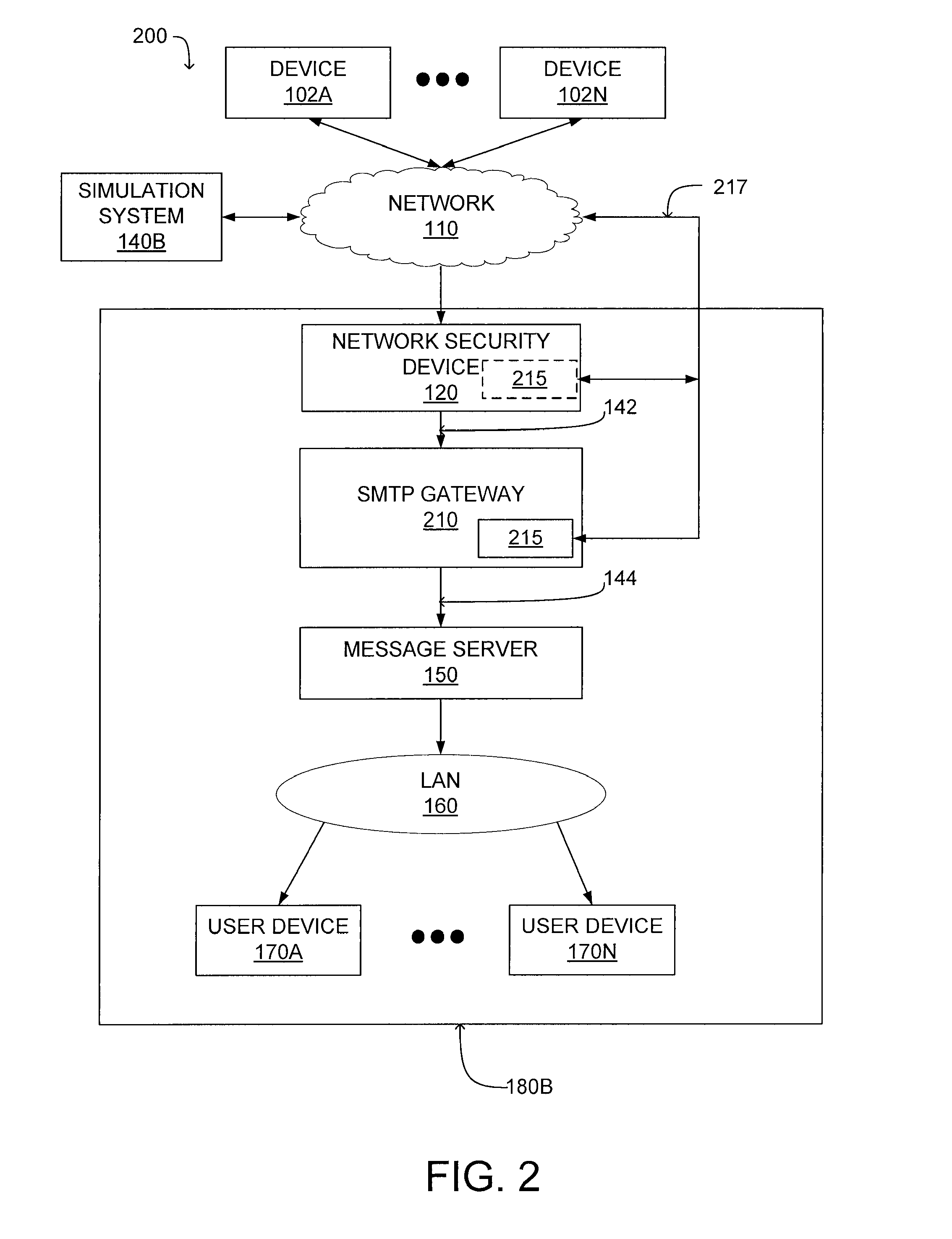
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
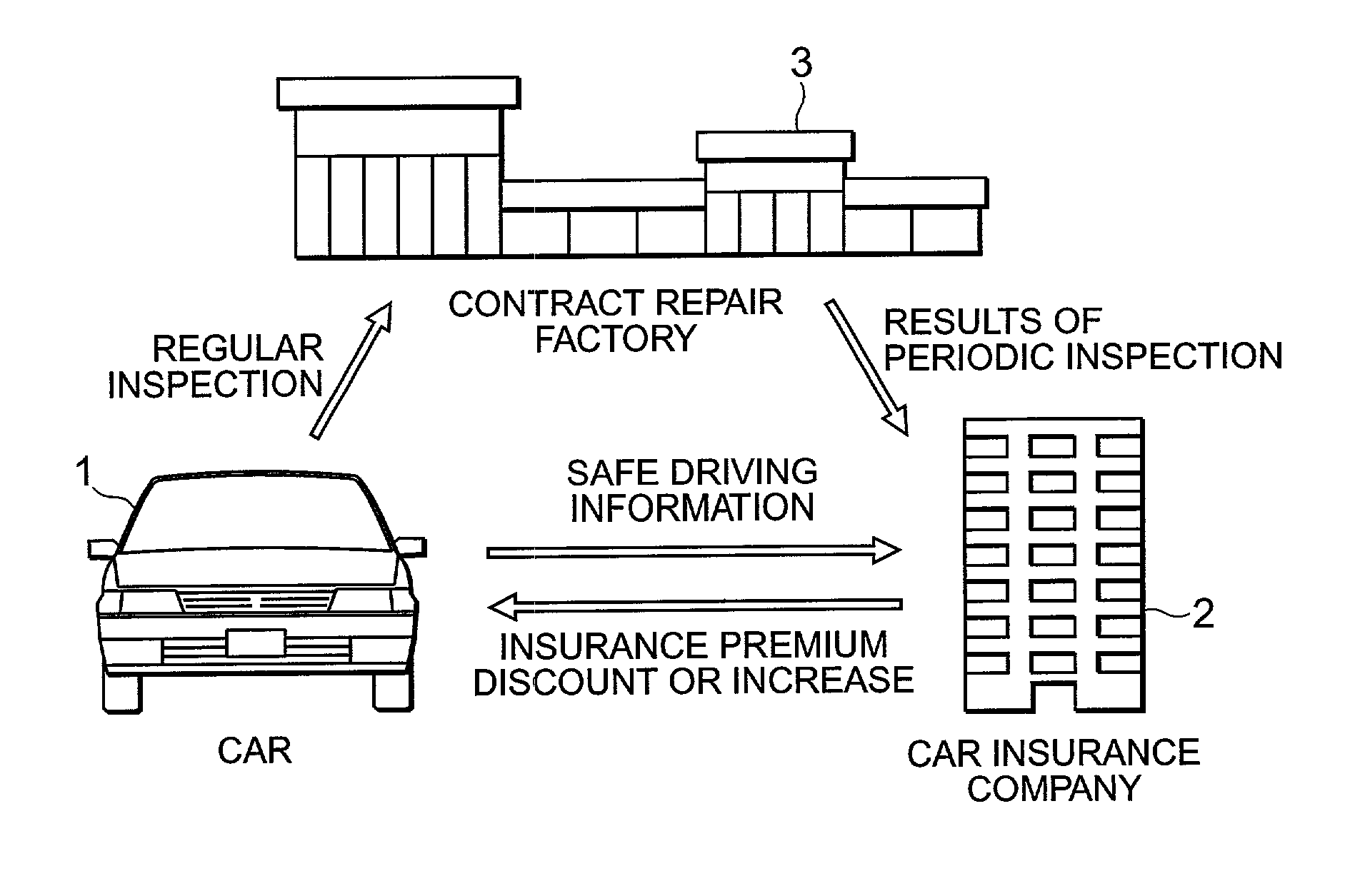
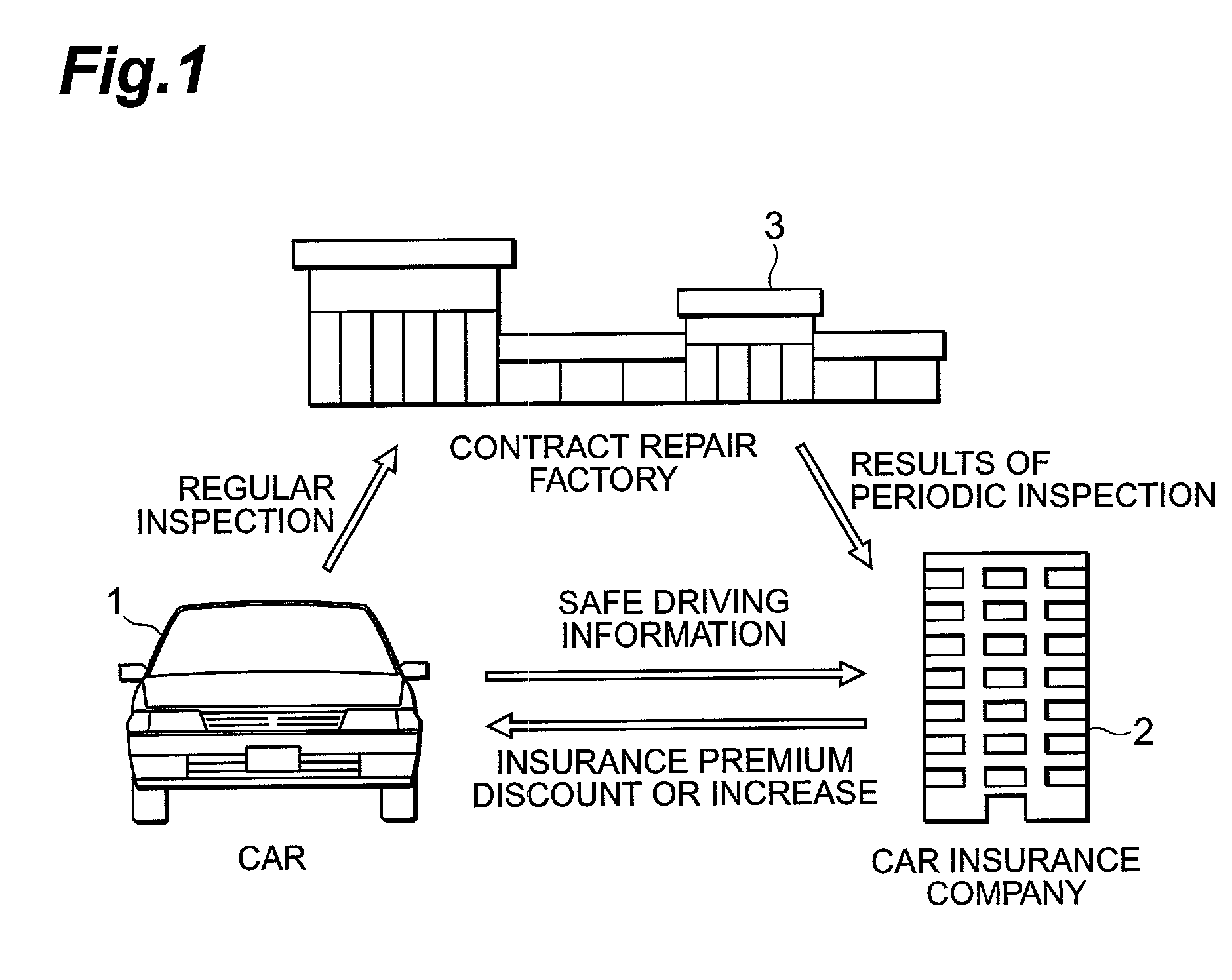
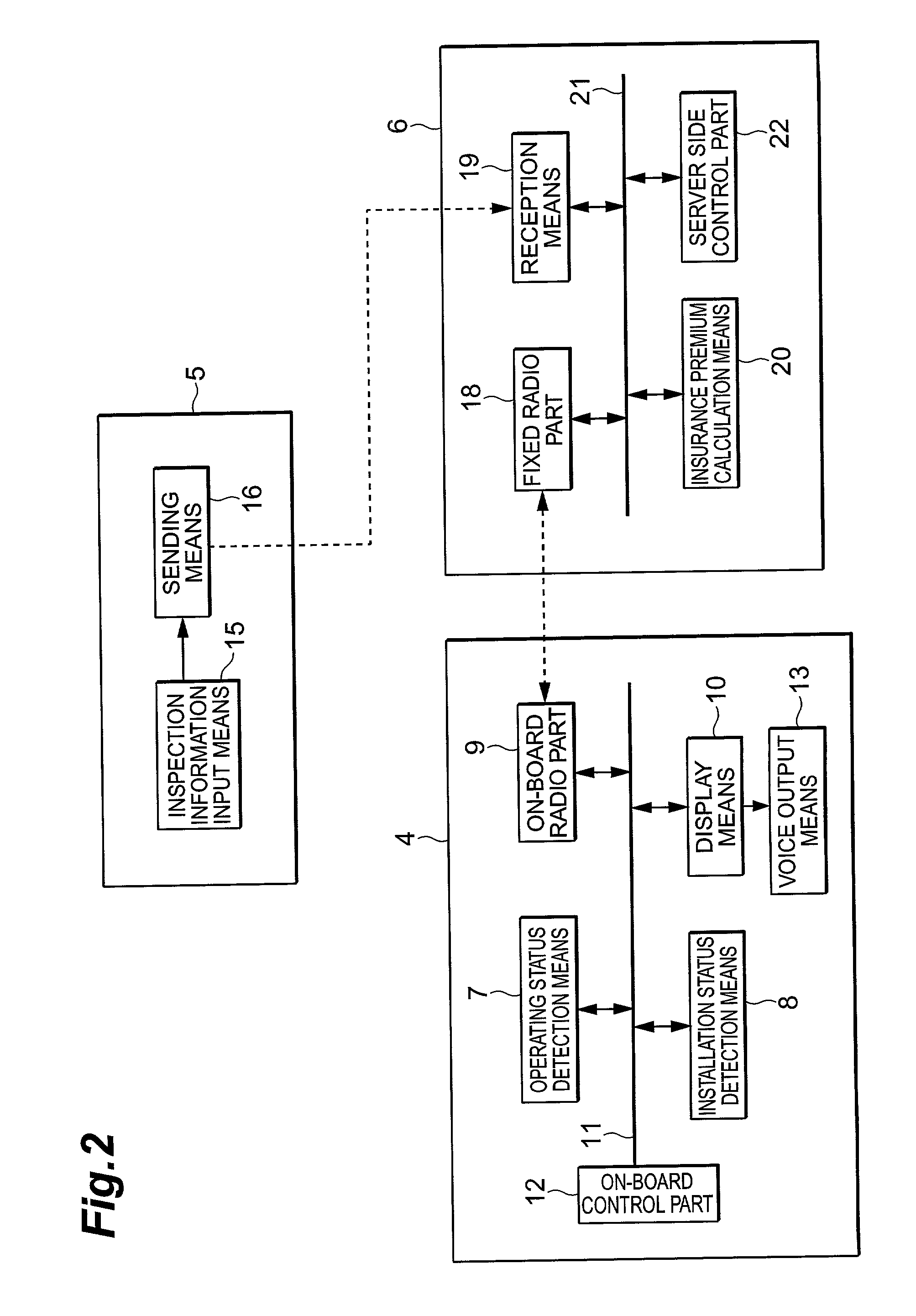
Vehicle insurance premium calculation system, on-board apparatus, and server apparatus
This system comprises a usage status detection means for detecting the usage status of a vehicle, data input means for inputting data relating to the maintenance or management of a vehicle, and insurance premium calculation means for calculating vehicle insurance premiums based on detection results and inputted data.
Owner:TOYOTA JIDOSHA KK +1
Market-Based Virtual Machine Allocation
InactiveUS20130304903A1Program control using stored programsDigital computer detailsMarket placeMarket based
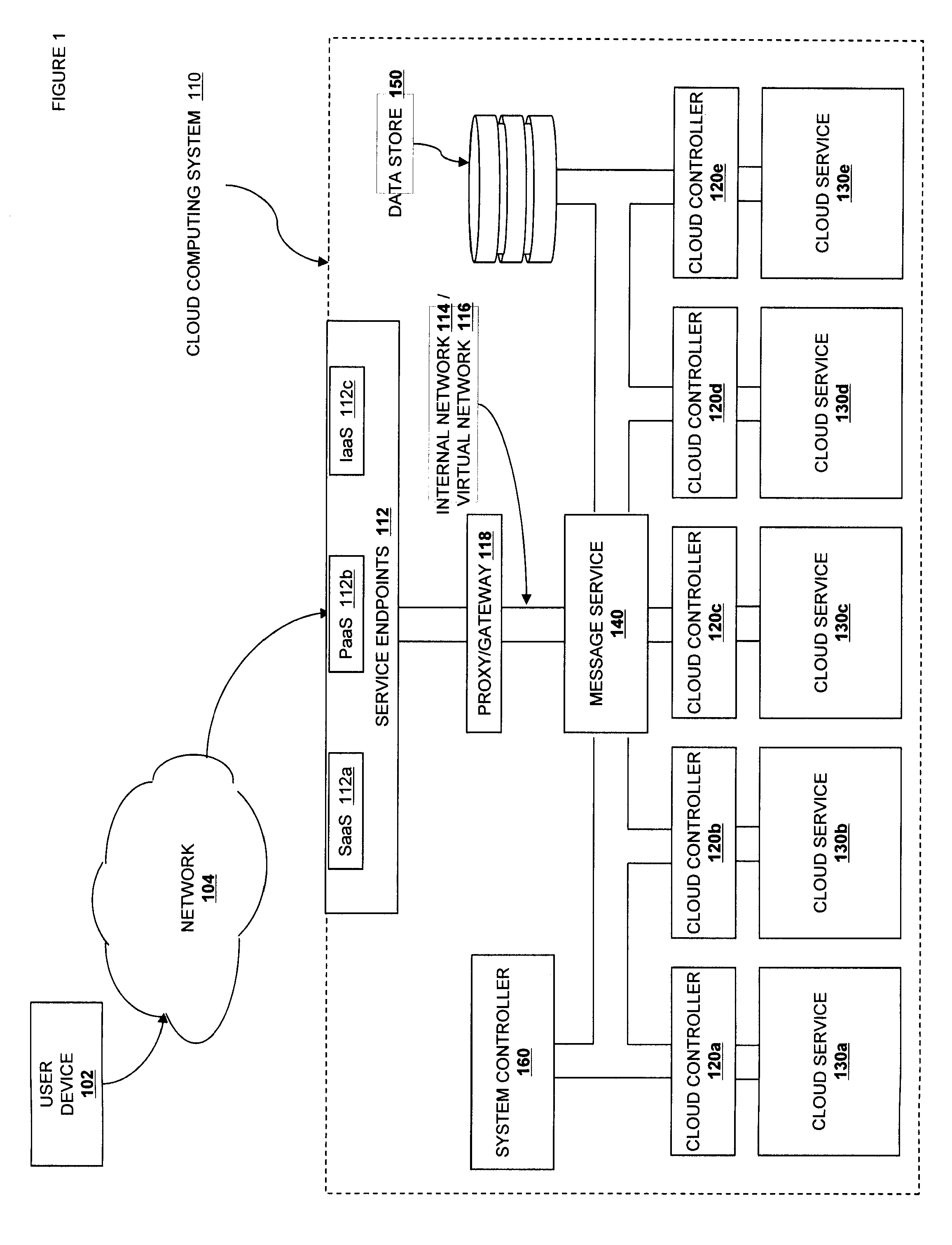
A cloud computing system management system including a plurality of computing devices configured to host virtual machine instances, each computing device in the plurality of computing devices including a local agent that continuously evaluates the observed load relative to a utility maximization function. If observed load is higher than a calculated optimal level, individual loading processes are offered for “sale” via a market scheduler. If observed load is lower than a calculated optimal level, then available capacity is offered as a bid via the market scheduler. The market scheduler matches bids with available processes and coordinates the transfer of load from the selling device to the buying device. The offered prices and utility maximization functions can be employed to optimize the performance of the cloud system as a whole.
Owner:RACKSPACE US
Malicious software detection in a computing system
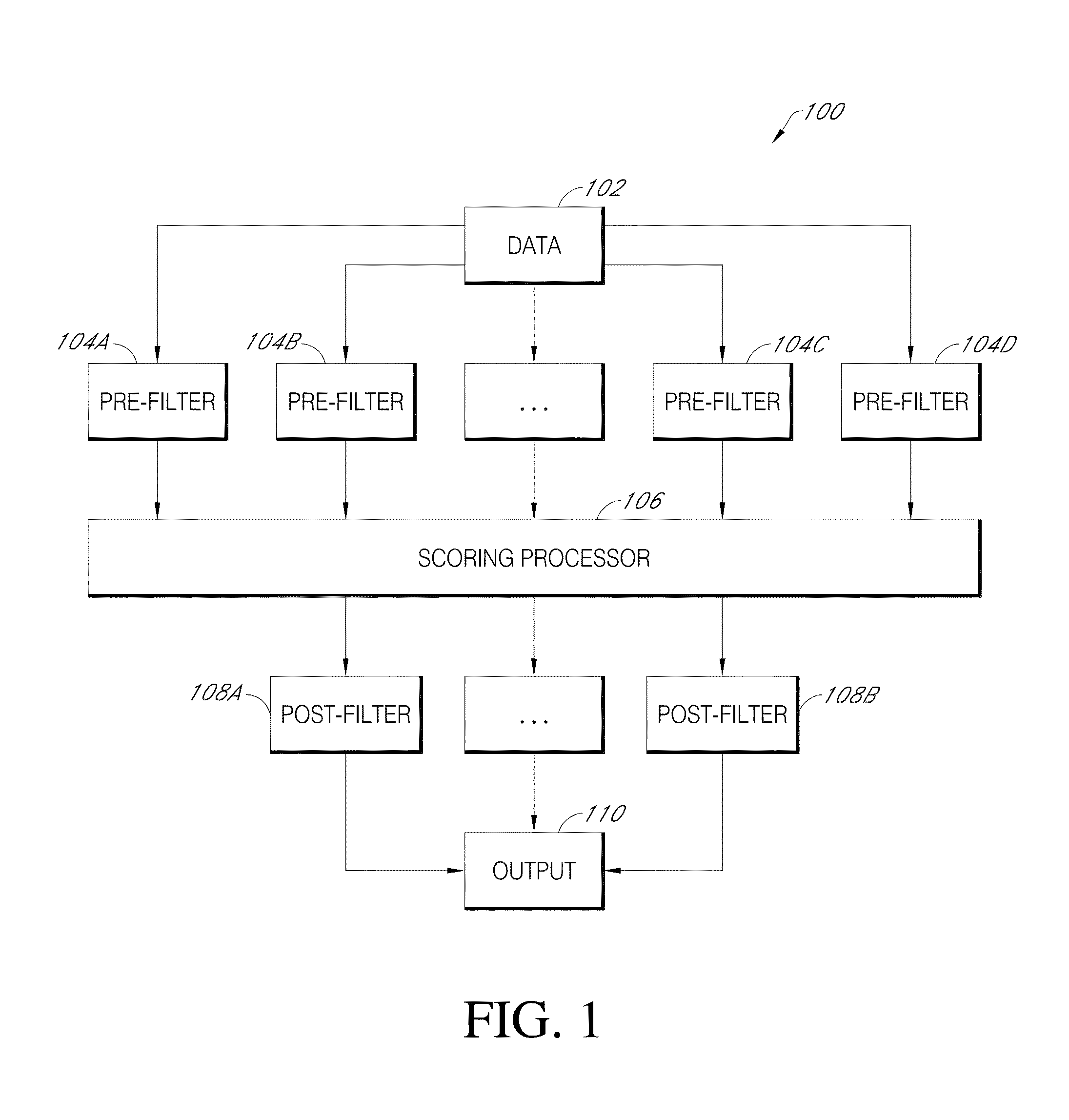
ActiveUS9043894B1Function increaseConsume significant storageComputer security arrangementsMultiple digital computer combinationsComputerized systemMalware
A computer system identifies malicious Uniform Resource Locator (URL) data items from a plurality of unscreened data items that have not been previously identified as associated with malicious URLs. The system can execute a number of pre-filters to identify a subset of URLs in the plurality of data items that are likely to be malicious. A scoring processor can score the subset of URLs based on a plurality of input vectors using a suitable machine learning model. Optionally, the system can execute one or more post-filters on the score data to identify data items of interest. Such data items can be fed back into the system to improve machine learning or can be used to provide a notification that a particular resource within a local network is infected with malicious software.
Owner:PALANTIR TECHNOLOGIES
System for personalized mobile navigation information
InactiveUS6349257B1Analogue computers for vehiclesElectric signal transmission systemsPersonalizationMobile navigation
A mobile navigation system implemented as an embedded system in a vehicle is easy to use, does not detract the driver's attention from the road, and limits the number of choices presented to the user of the navigation system according to a predetermined set of preferences or personalized information. Choices are filtered according to a set of driver preferences, according to the vehicle's geographic position, direction of motion, and the driver's intended itinerary. The itinerary, including intermediate stops, is calculated on an external computing system. The information is downloaded from the computing system to a memory device such as, for example, a smart card. The information is then transferred from the smart card to the embedded vehicle navigation system. In one application of the invention, a kiosk located at a car rental agency may be used to create and store personalized navigation information onto a smart card which the customer then inserts into the vehicle navigation system that is installed in the rental car.
Owner:IBM CORP
Method and System for Identity-Based Authentication of Virtual Machines
ActiveUS20140282889A1Specific access rightsDigital data processing detailsComputing systemsAuthentication
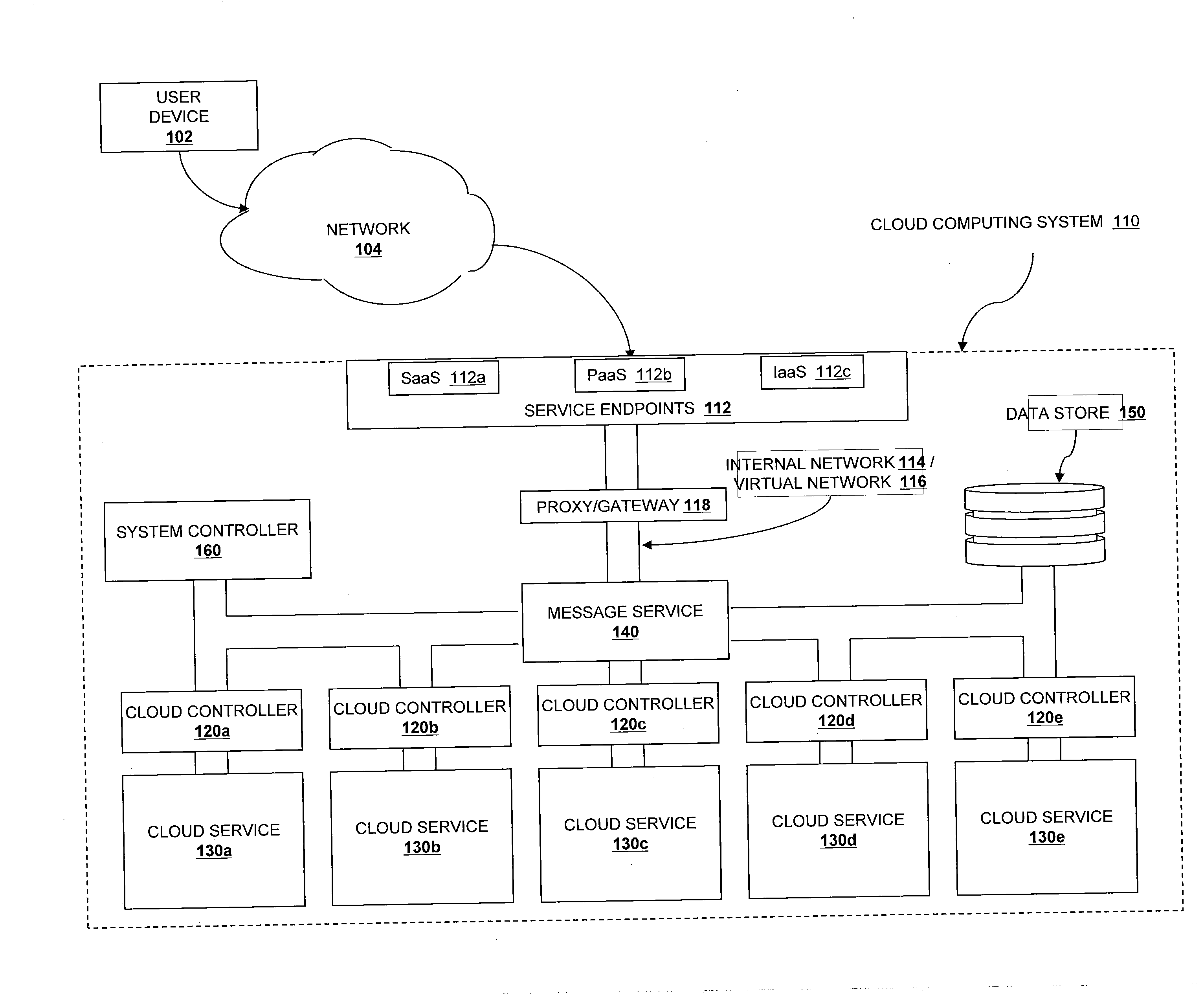
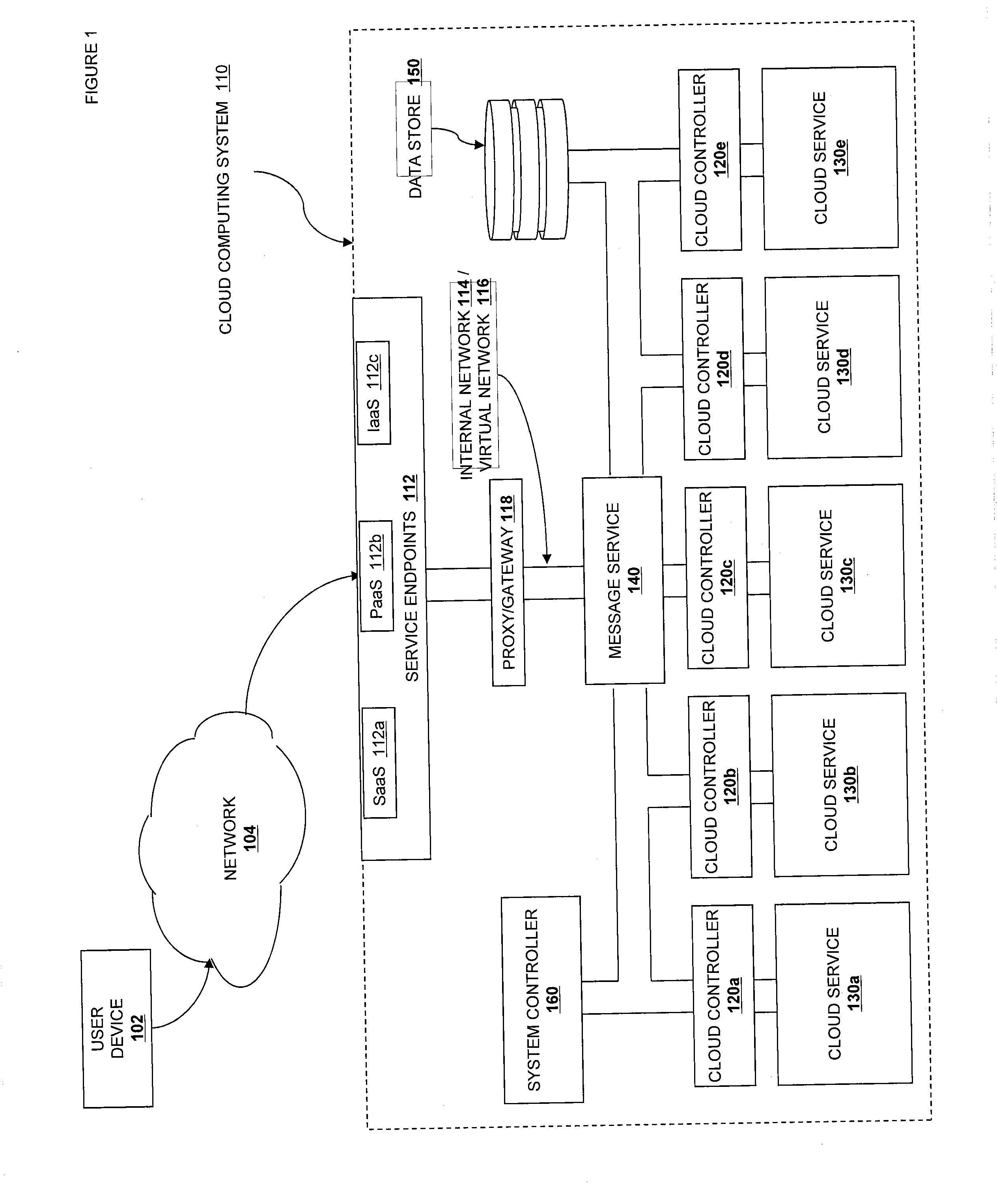
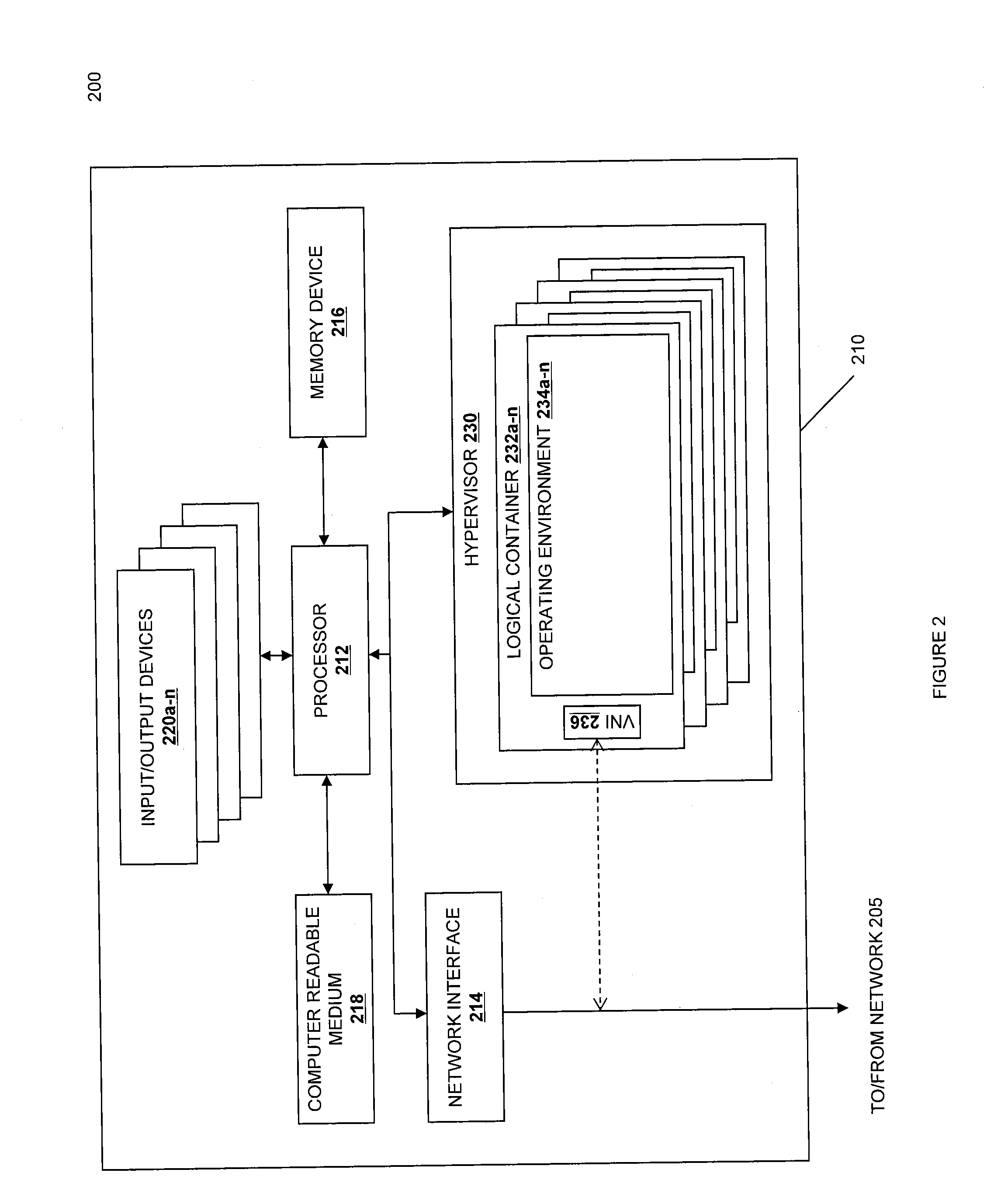
A cloud computing system configured to run virtual machine instances is disclosed. The cloud computing system assigns an identity to each virtual machine instance. When the virtual machine instance accesses initial configuration resources, it provides this identity to the resources to authenticate itself. This allows for flexible and extensible initial configuration of virtual machine instances.
Owner:RACKSPACE US
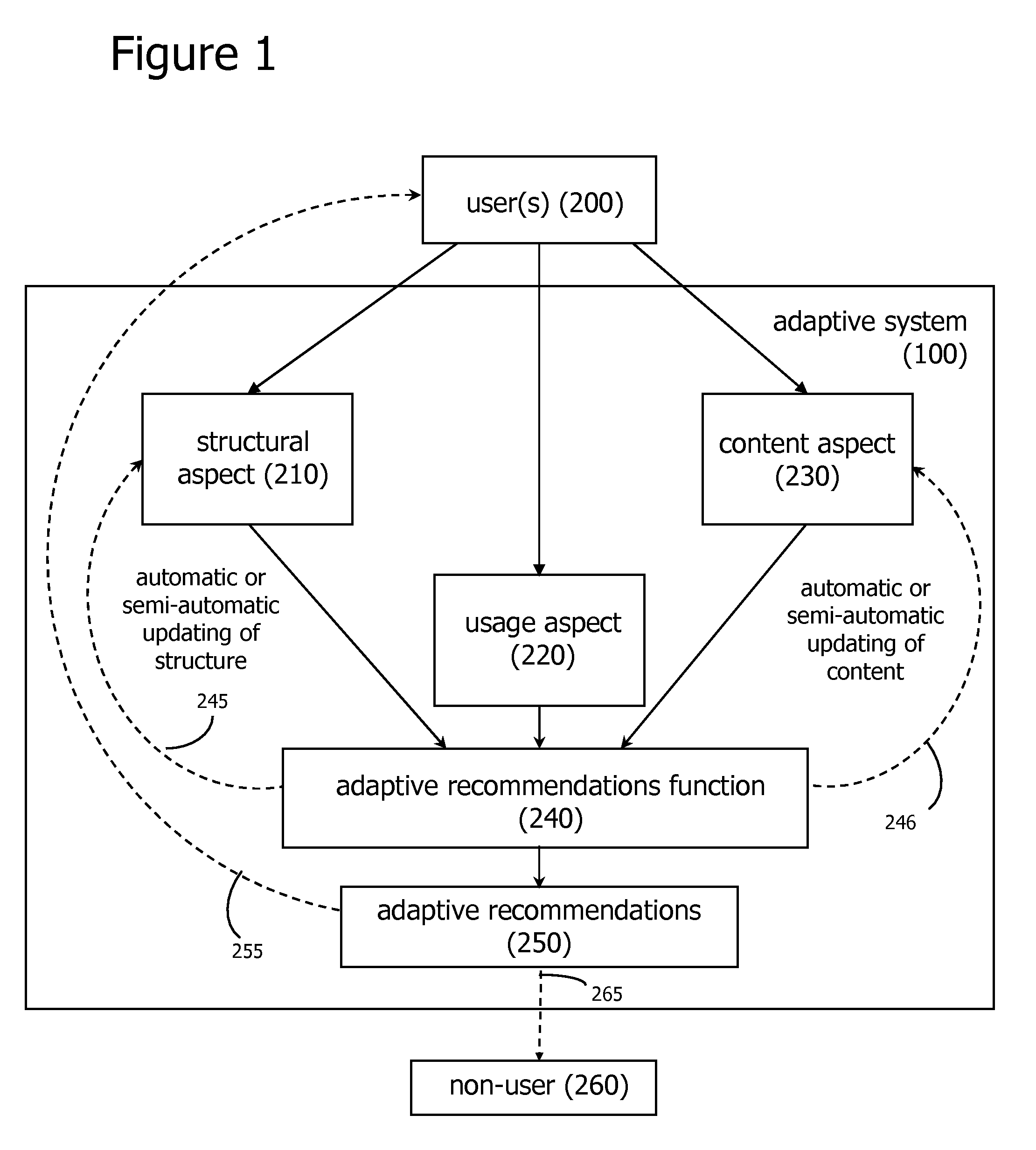
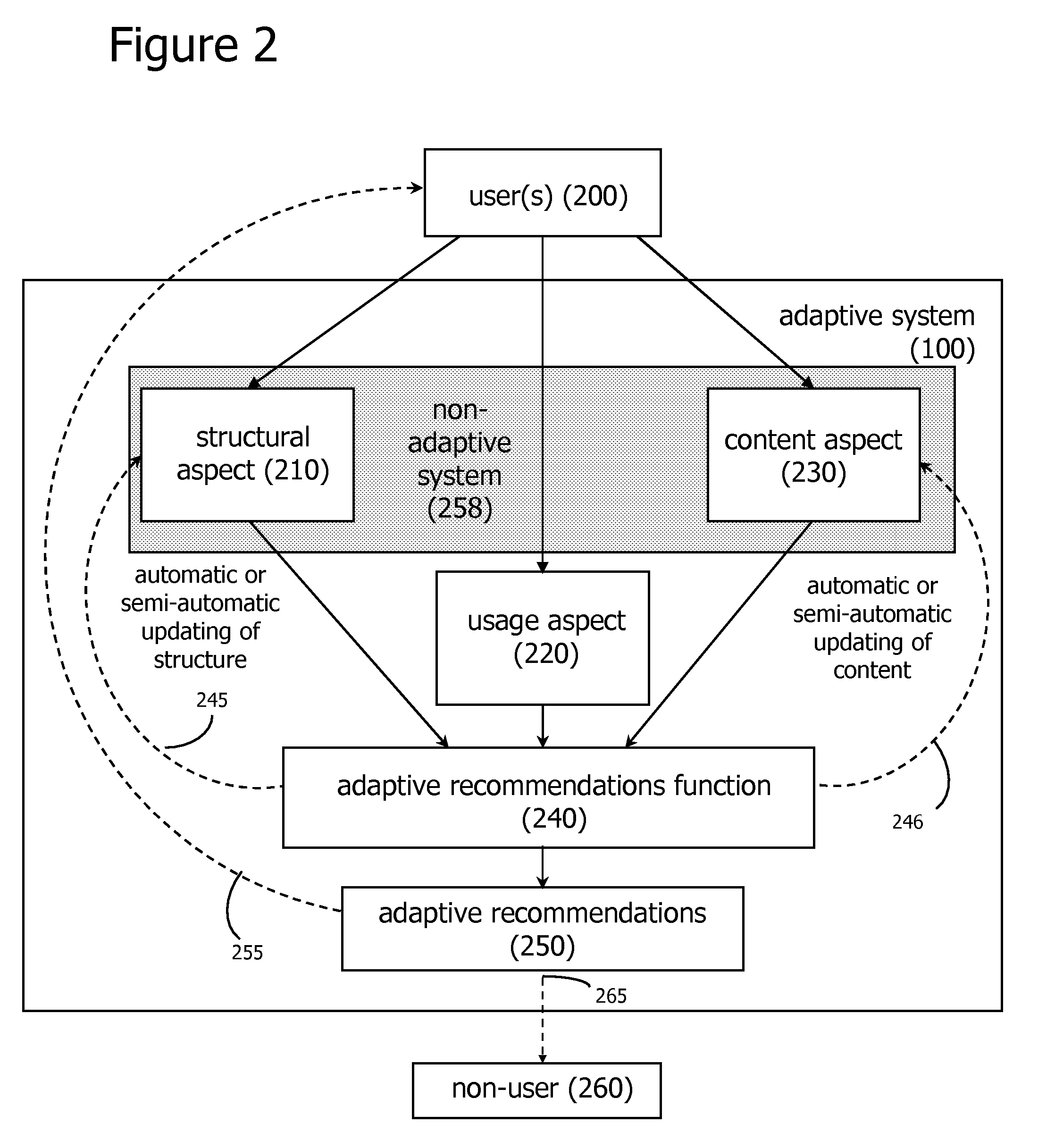
Adaptive Social Computing Methods
ActiveUS20060200435A1Easy to adaptEfficiently navigateDigital computer detailsMachine learningVision basedSelf adaptive
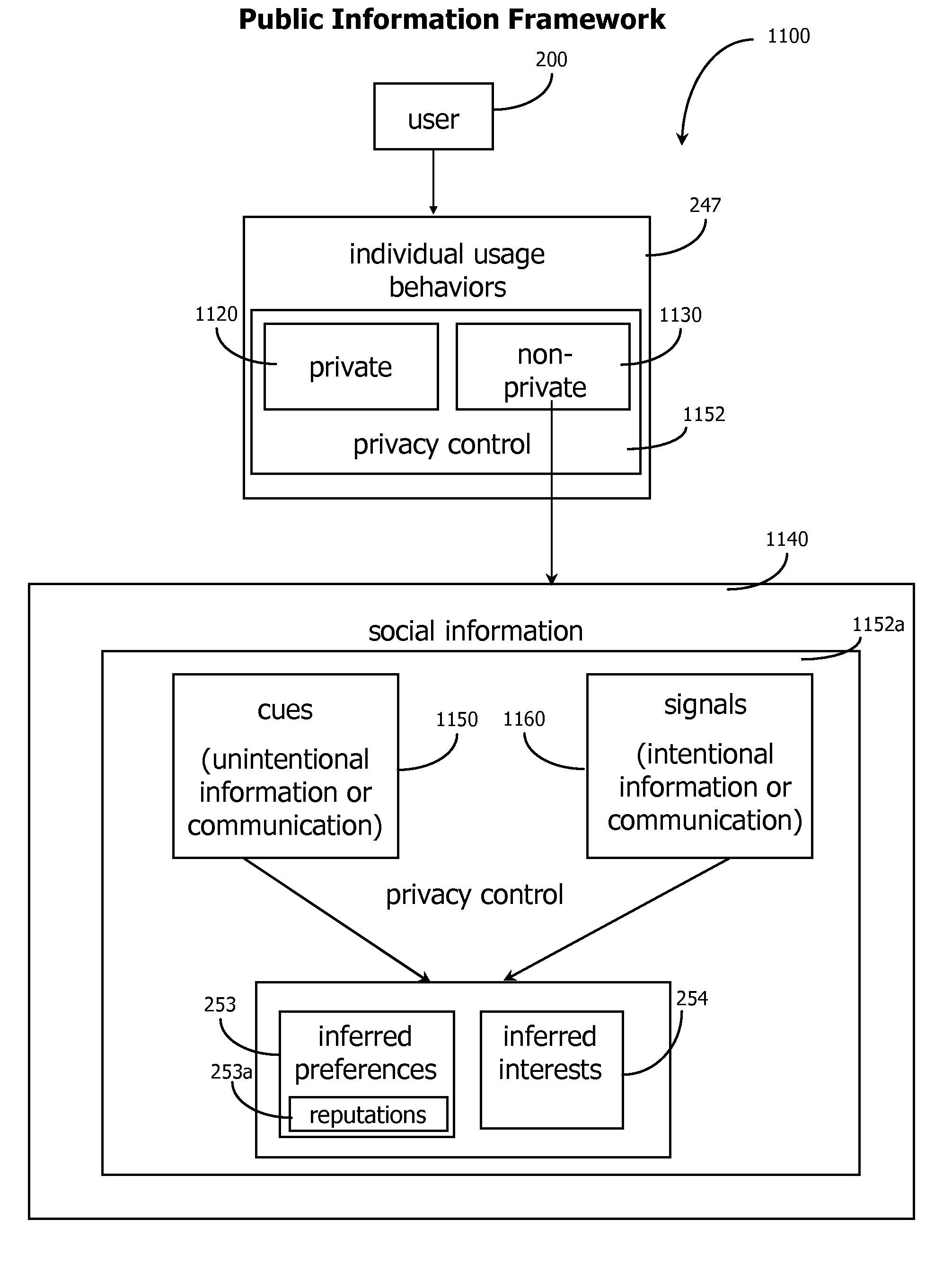
Methods of applying adaptive social computing systems are disclosed. The social computing systems include capabilities to generate adaptive recommendations and representations of social networks derived, at least in part, from inferences of the preferences and interests of system users based on a plurality of usage behaviors, spanning a plurality of usage behavior categories. The behavioral categories include system navigation behaviors, content referencing behaviors, collaborative behaviors, and the monitoring of physical location and changes in location. Privacy control functions and compensatory functions related to insincere usage behaviors can be applied. Adaptive recommendation delivery can take the form of visual-based or audio-based formats.
Owner:WORLD ASSETS CONSULTING AG
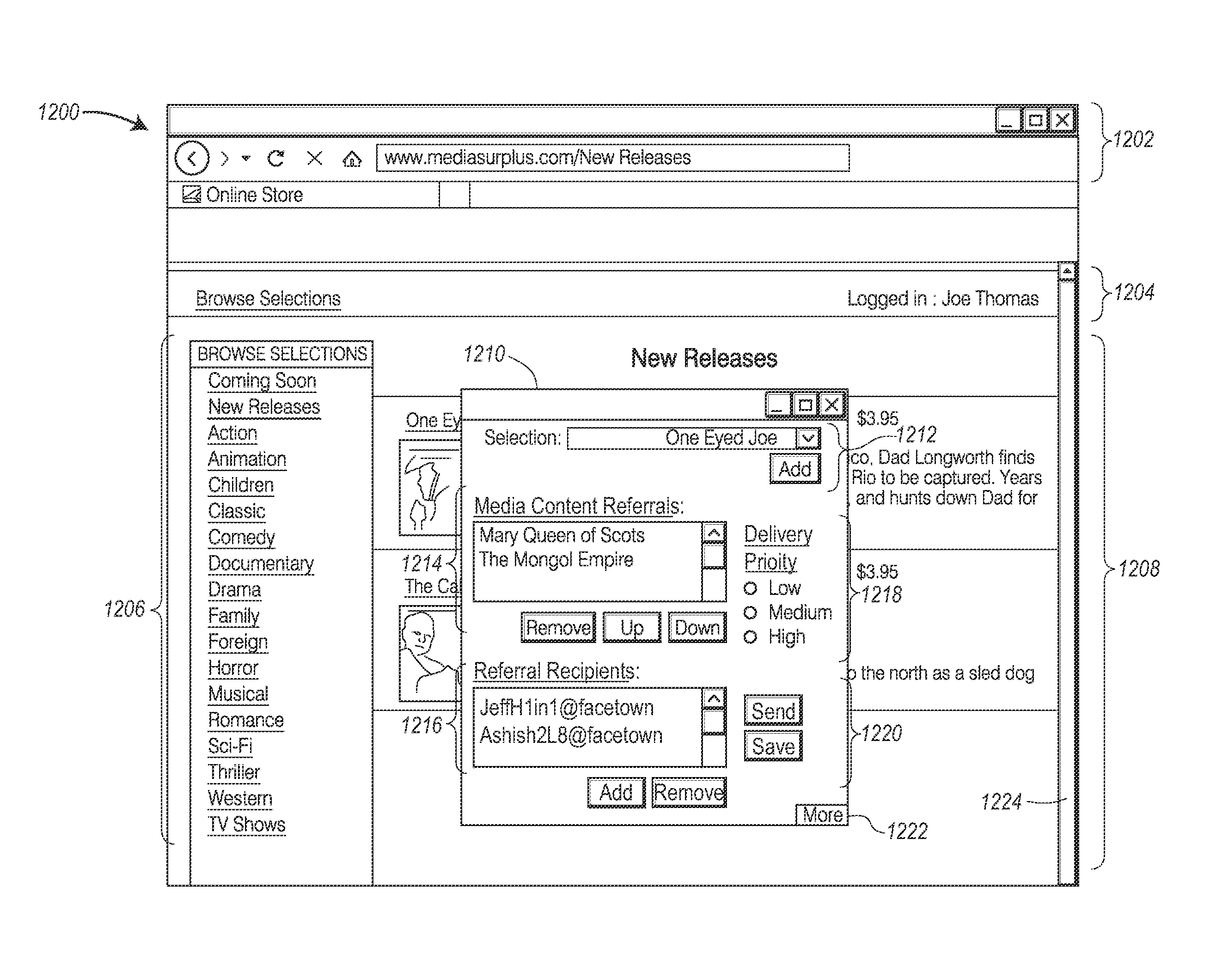
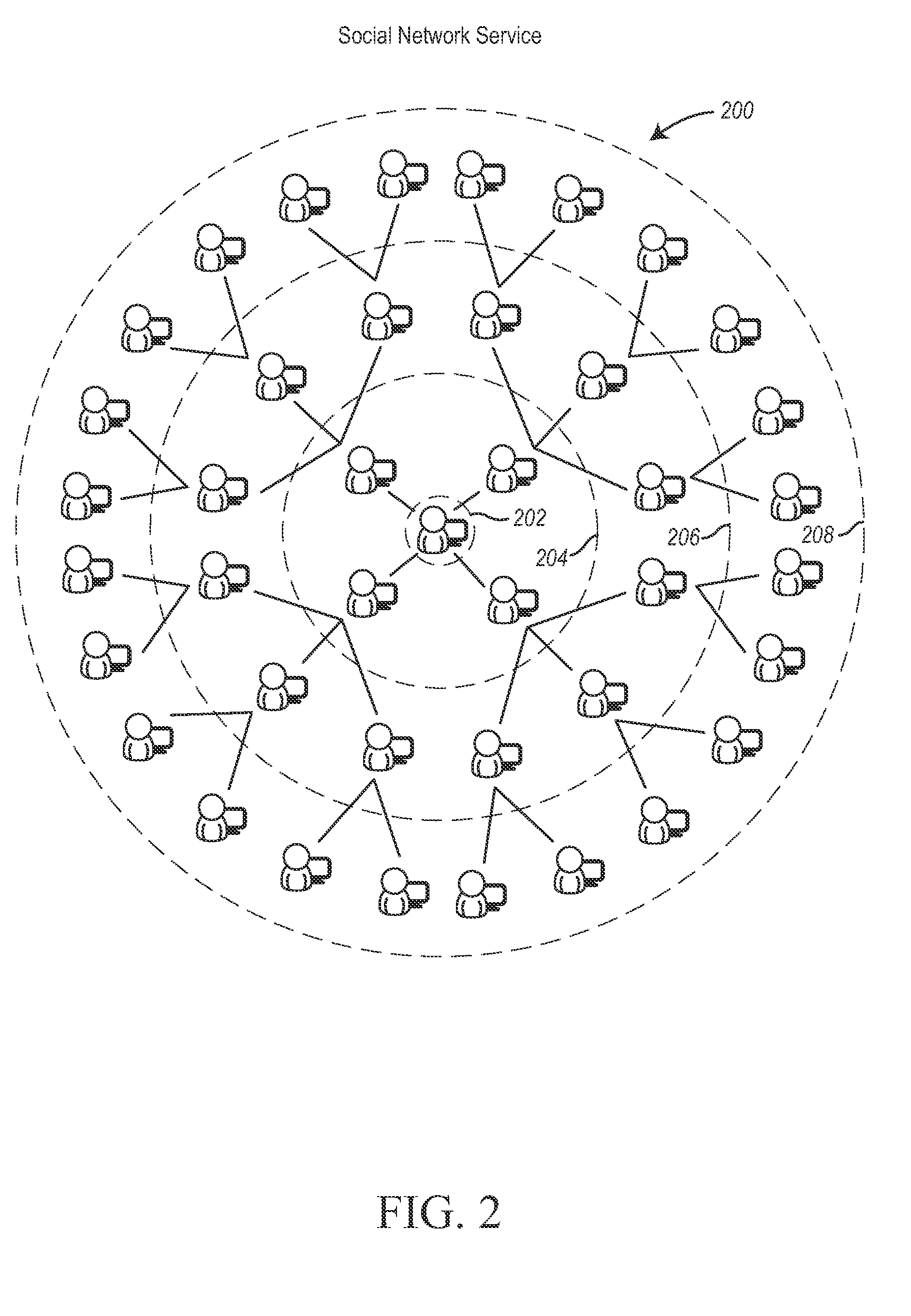
Systems and methods for distribution of digital media content utilizing viral marketing over social networks
InactiveUS20100131385A1AdvertisementsMultiple digital computer combinationsViral marketingDigital content
A networked computing system capable of distributing commercial digital media content utilizing existing interpersonal resources of a social network service (SNS). The networked computing system includes a media content provider (MCP), multiple personal computing devices (PCDs), a SNS and a data communications network that facilitates data communications amongst the MCP, the PCDs, and the SNS. A registered user of the SNS at a first PCD is able to access media content emanating from a MCP based on a media content referral from a registered user of the same SNS at a second PCD. The SNS may operate as an agent for the MCP so that the MCP can use the SNS as a viral media content marketing utility.
Owner:OPANGA NETWORKS
Systems and methods for storing and sharing transactional data using a distributed computing systems
ActiveUS20170230189A1FinanceEncryption apparatus with shift registers/memoriesComputerized systemComputing systems
A computer system that interfaces with a blockchain is provided. The computer system receives match data for a match between a first data transaction request that is associated with a first identifier and a second data transaction request that is associated with a second identifier. A first blockchain transaction is generated based on the match data and stored to a blockchain. At least one further blockchain transaction is generates that splits the match into two different transactions—one between the first identifier and an intermediary and the second between the intermediary. These are recorded to the blockchain via the further blockchain transactions.
Owner:NASDAQ TECHNOLOGY AB
Virtual input device for computing
InactiveUS20080136775A1Efficient methodComfortable sittingIndoor gamesCathode-ray tube indicatorsElectronic systemsDisplay device
A virtual input device or apparatus that replaces the typical mouse, keyboard or other finger manipulated inputs currently used as inputs for any type of computing system such as signals used to control computers, PDAs, Video Games, Multimedia Displays and other similar electronic systems whether of a desktop or mobile configuration.
Owner:MEDIAFLY INC
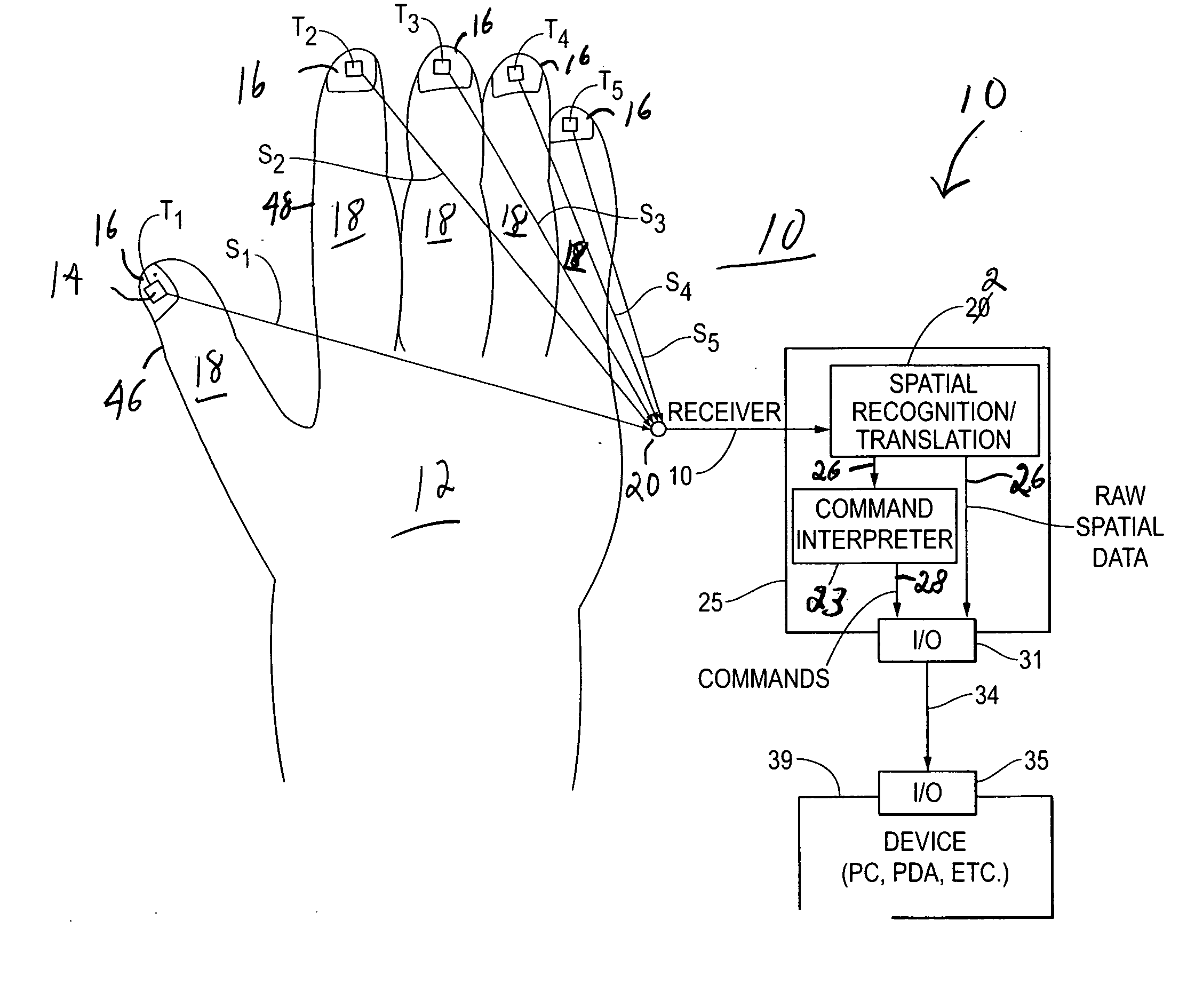
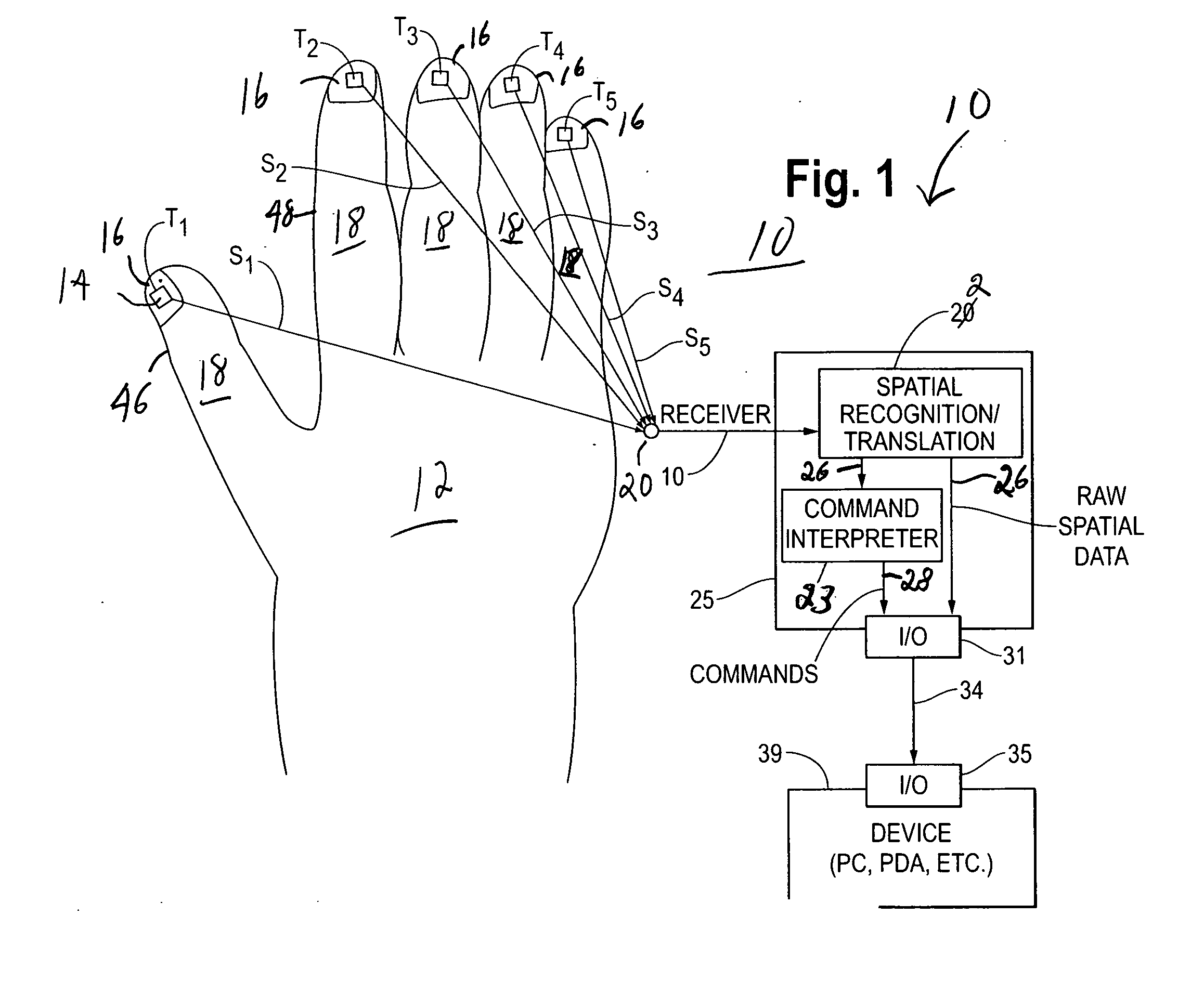
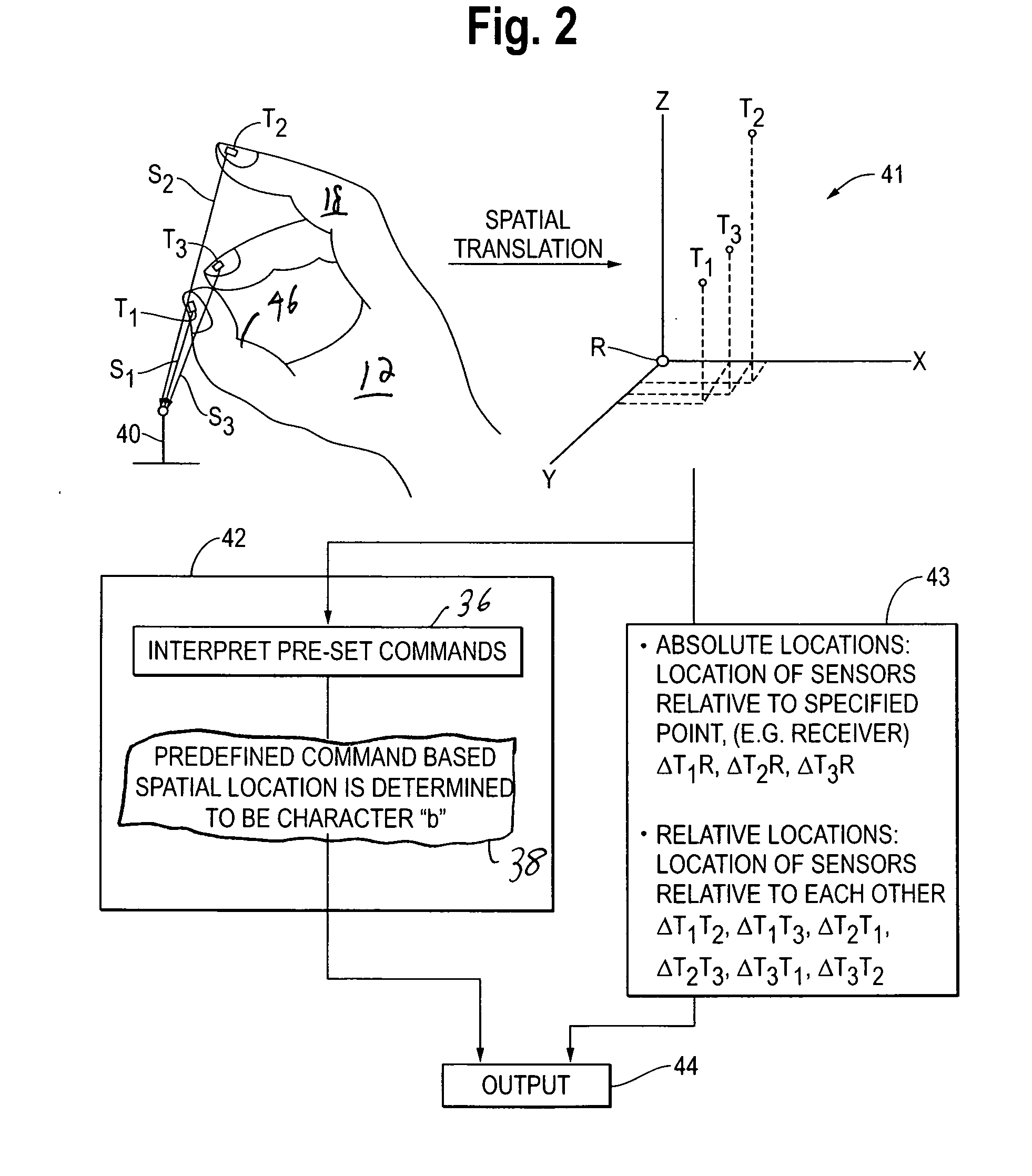
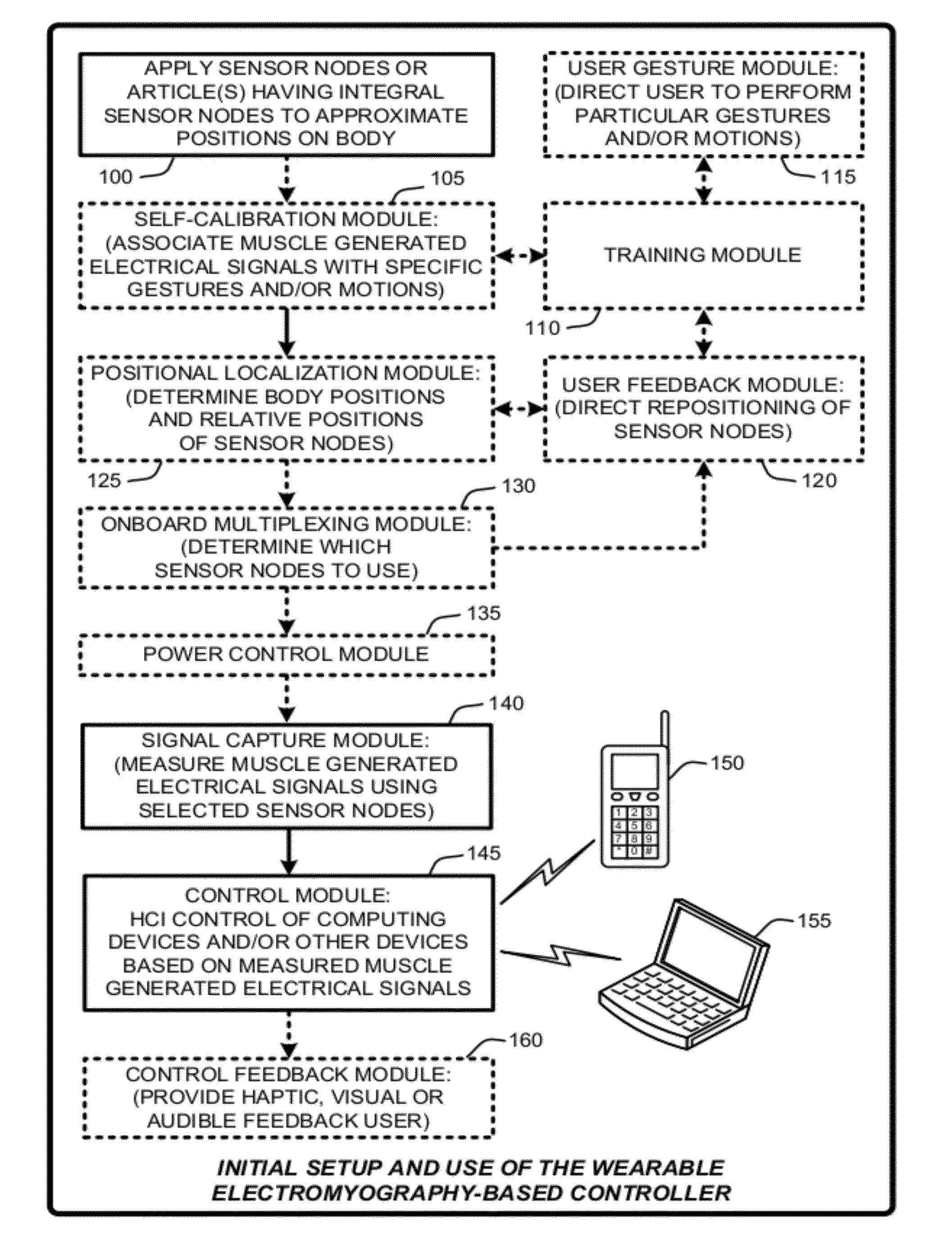
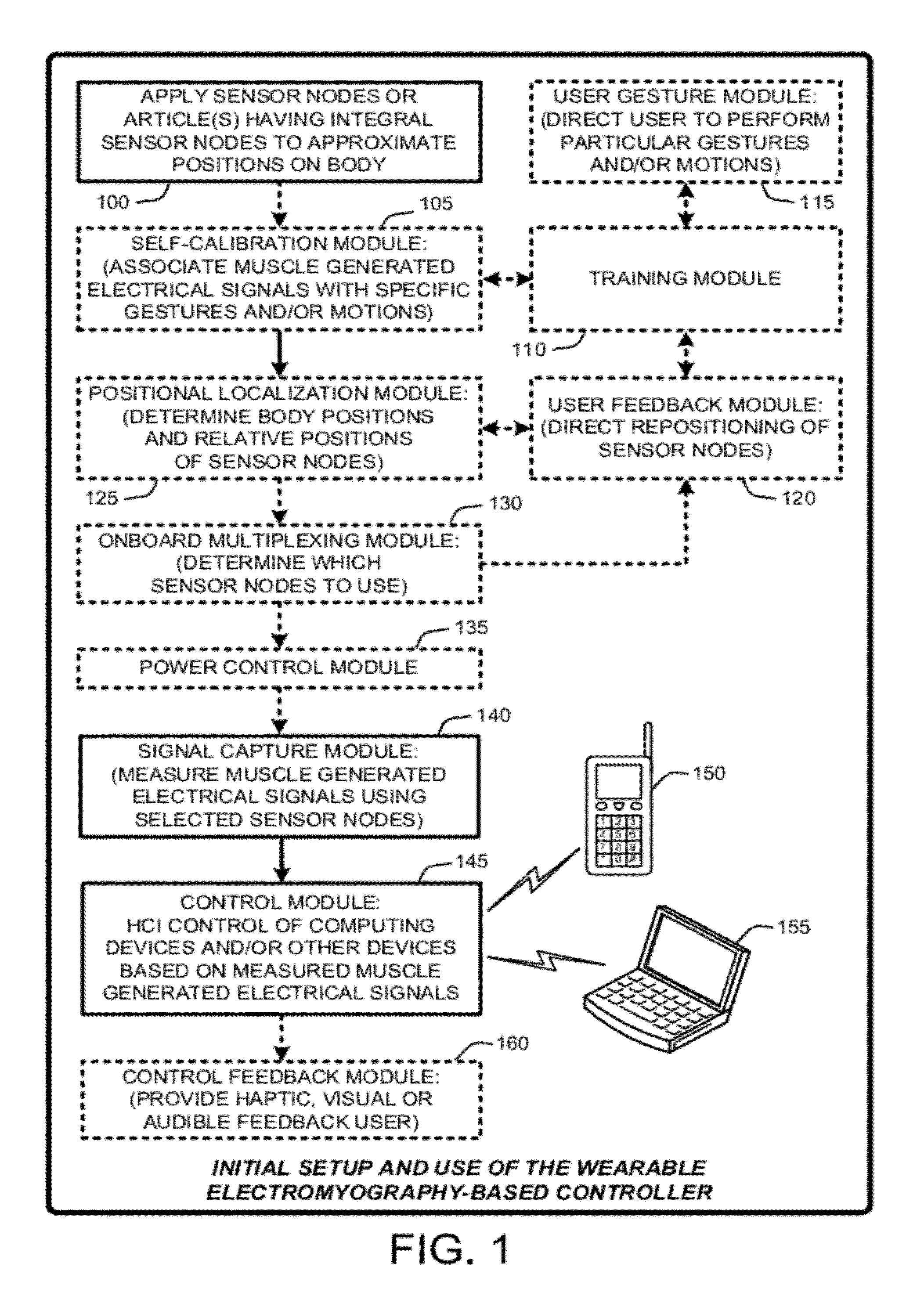
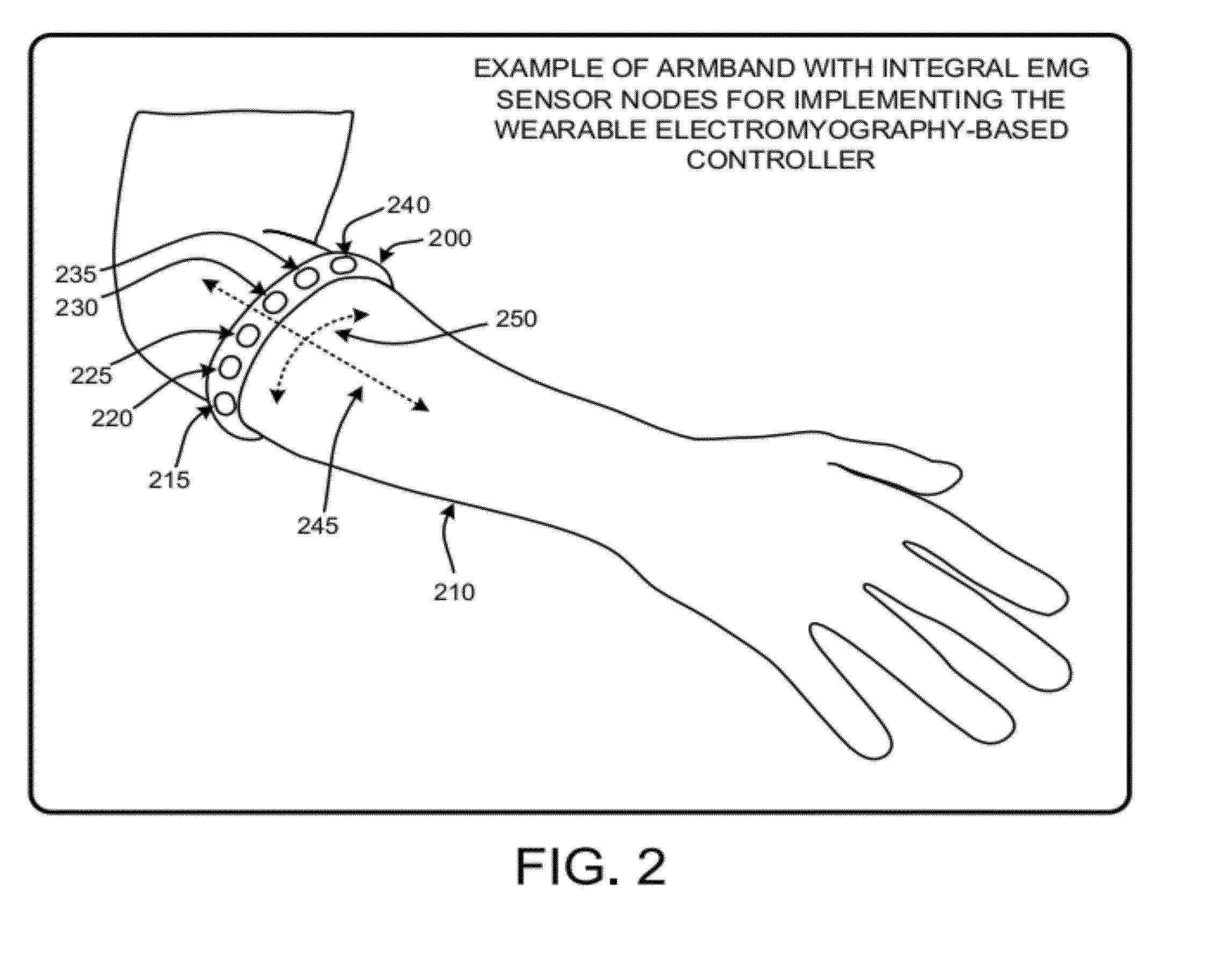
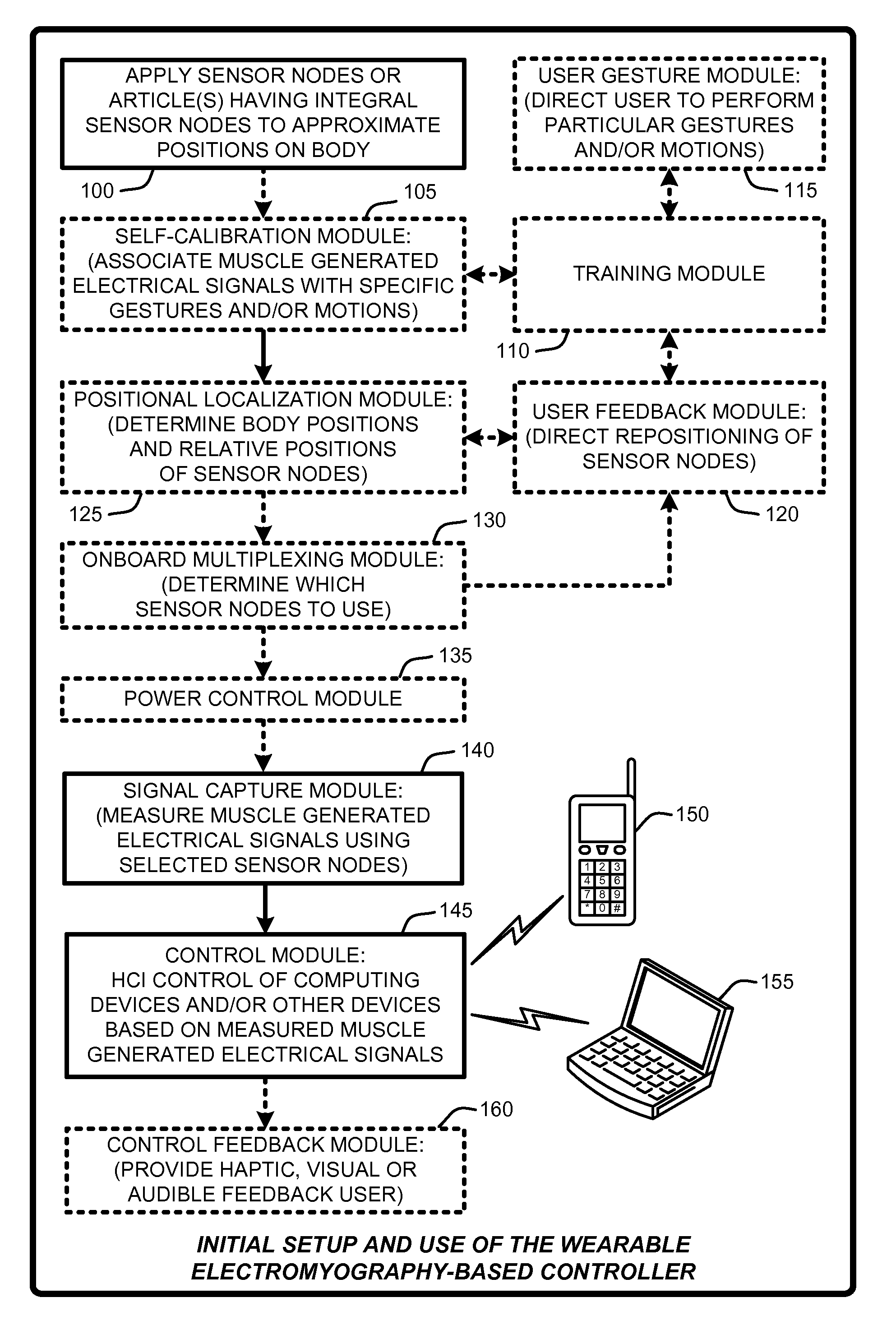
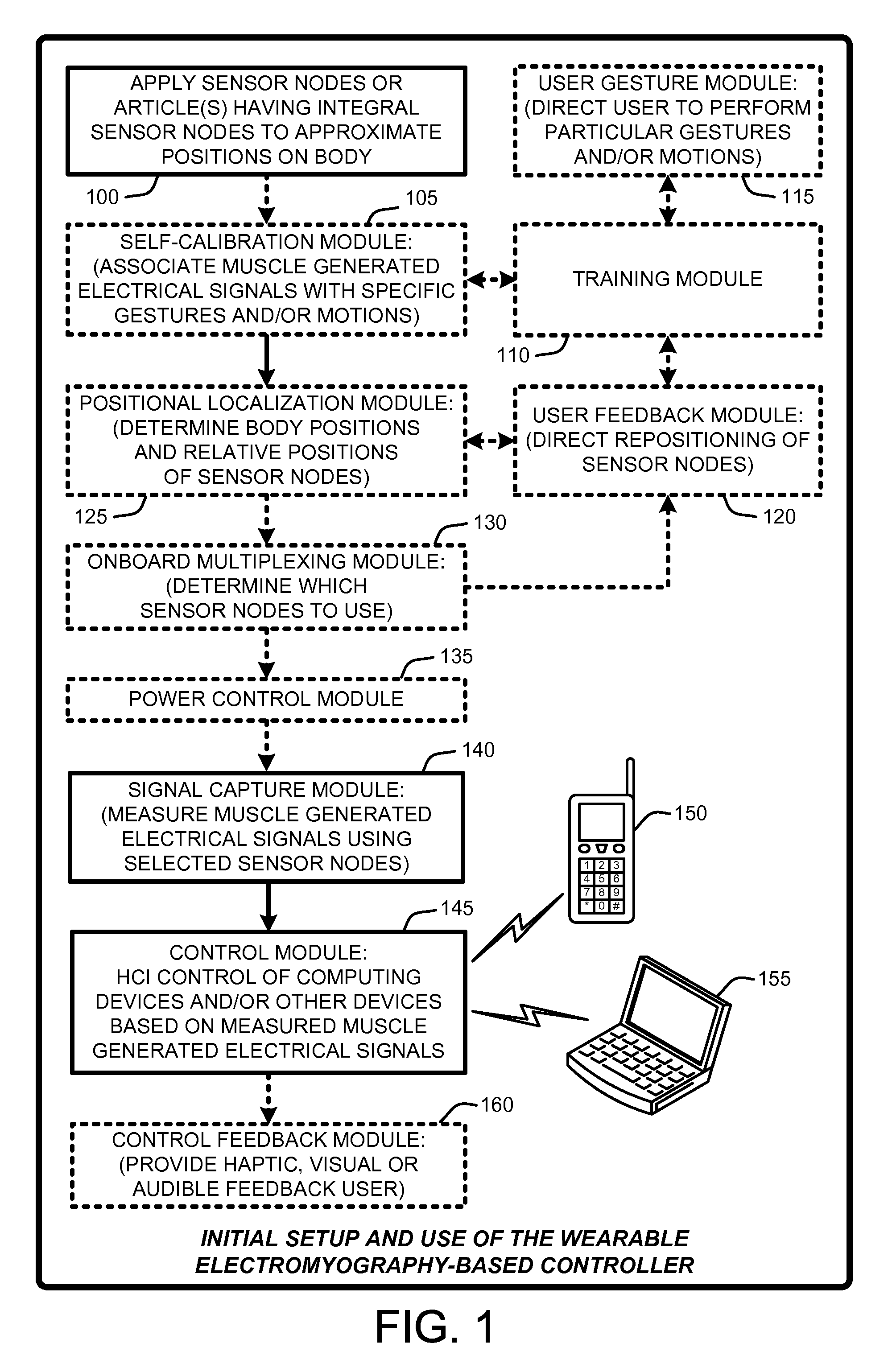
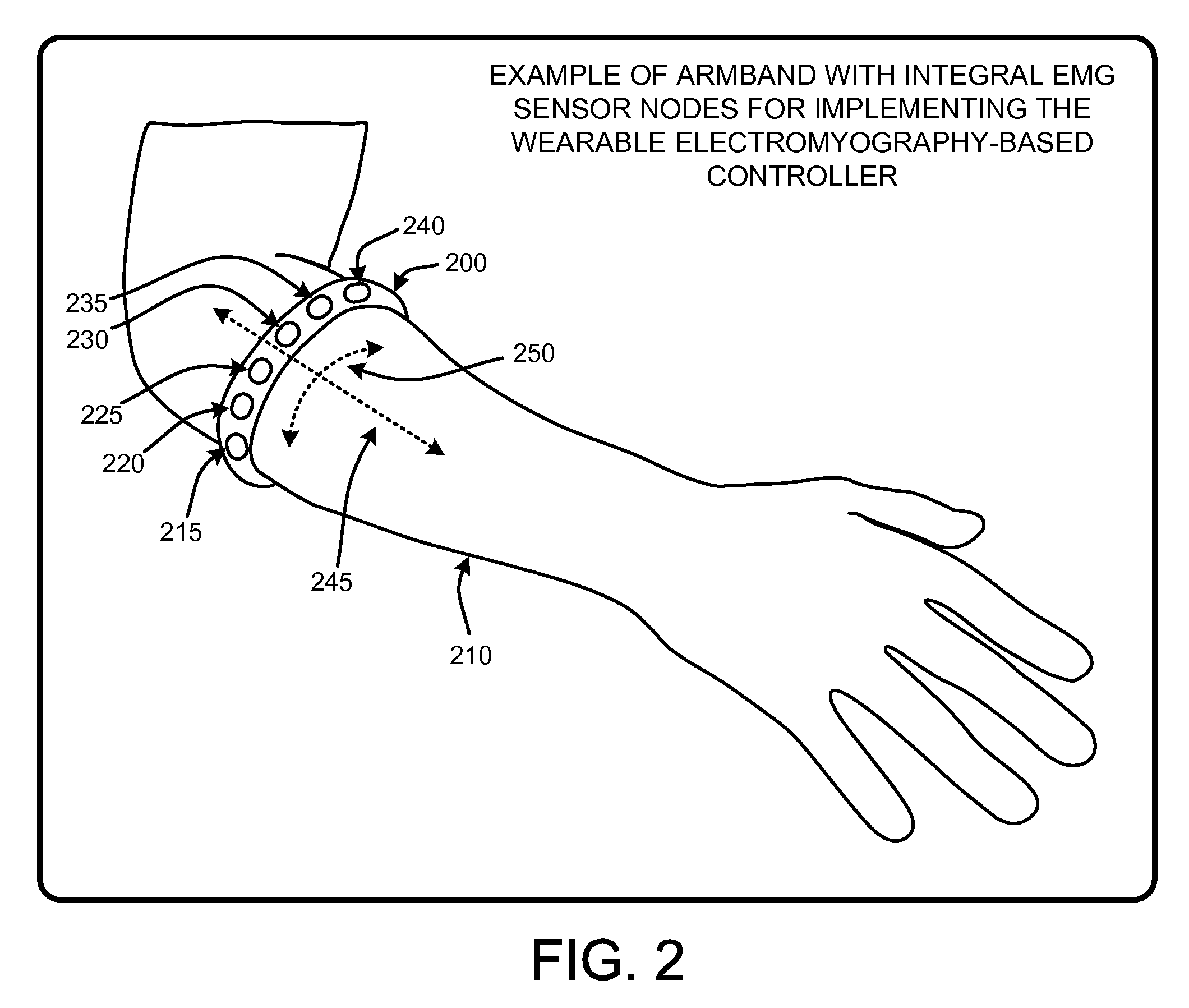
Wearable electromyography-based human-computer interface
ActiveUS20120188158A1Input/output for user-computer interactionElectromyographyHuman–machine interfacePhysical medicine and rehabilitation
A “Wearable Electromyography-Based Controller” includes a plurality of Electromyography (EMG) sensors and provides a wired or wireless human-computer interface (HCl) for interacting with computing systems and attached devices via electrical signals generated by specific movement of the user's muscles. Following initial automated self-calibration and positional localization processes, measurement and interpretation of muscle generated electrical signals is accomplished by sampling signals from the EMG sensors of the Wearable Electromyography-Based Controller. In operation, the Wearable Electromyography-Based Controller is donned by the user and placed into a coarsely approximate position on the surface of the user's skin. Automated cues or instructions are then provided to the user for fine-tuning placement of the Wearable Electromyography-Based Controller. Examples of Wearable Electromyography-Based Controllers include articles of manufacture, such as an armband, wristwatch, or article of clothing having a plurality of integrated EMG-based sensor nodes and associated electronics.
Owner:MICROSOFT TECH LICENSING LLC
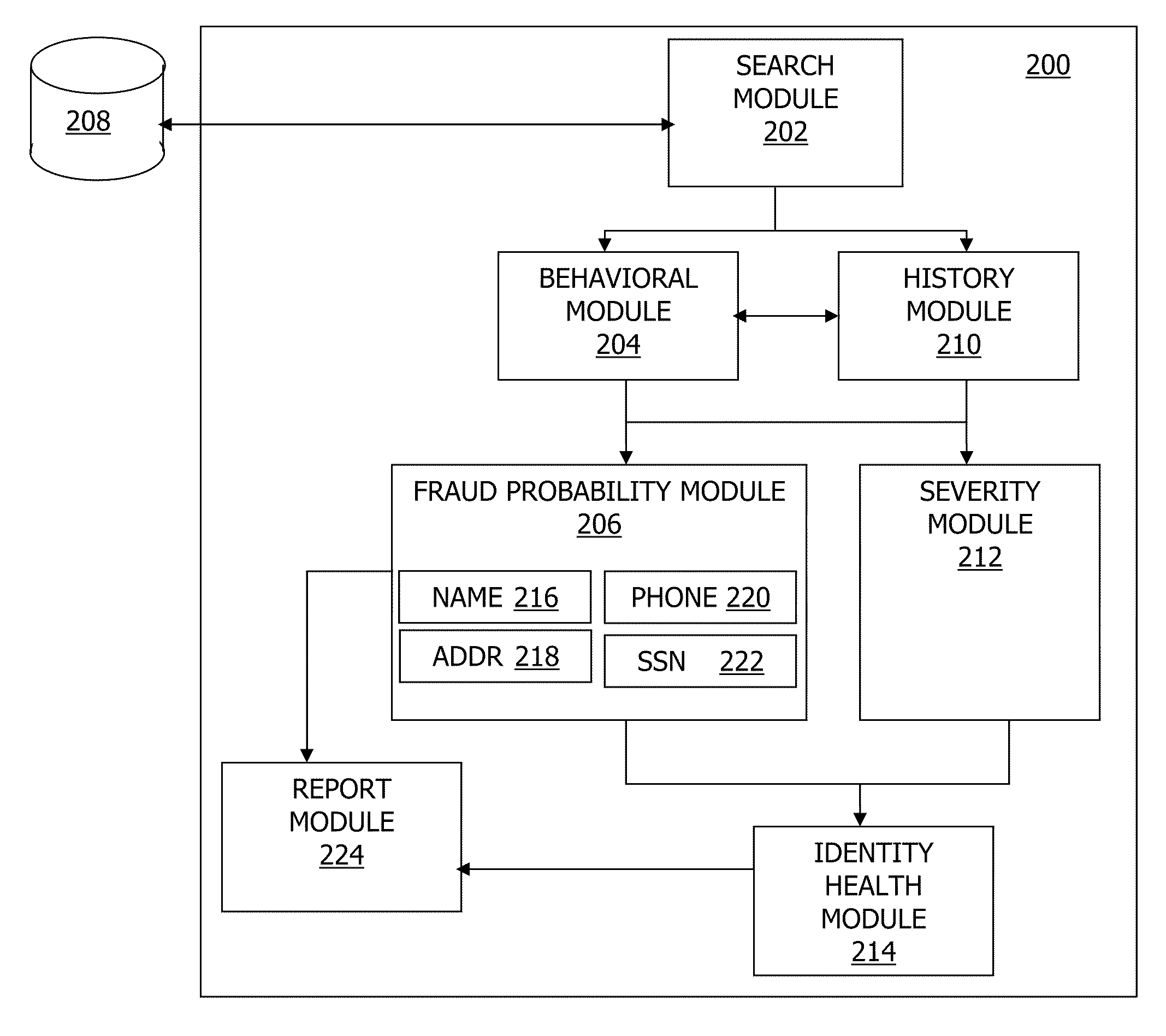
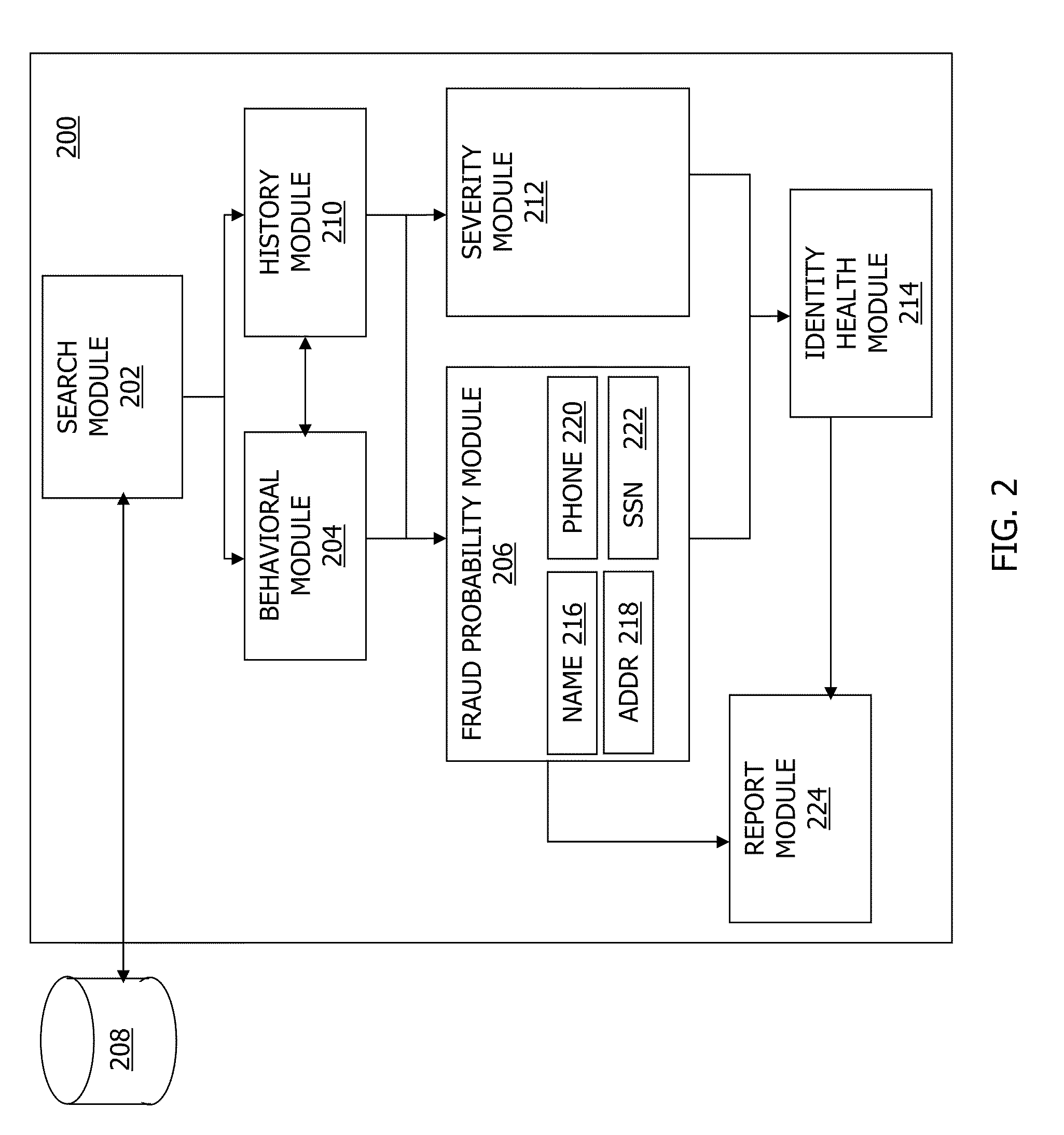
Systems, methods, and apparatus for determining fraud probability scores and identity health scores
In general, in one embodiment, a computing system that evaluates a fraud probability score for an identity event relevant to a user first queries a data store to identify the identity event. A fraud probability score is then computed for the identity event using a behavioral module that models multiple categories of suspected fraud.
Owner:IDENTITYTRUTH
QoS channels for multimedia services on a general purpose operating system platform using data cards
InactiveUS7609700B1Increase data rateMultiplex system selection arrangementsSpecial service provision for substationComputer hardwareSession Initiation Protocol
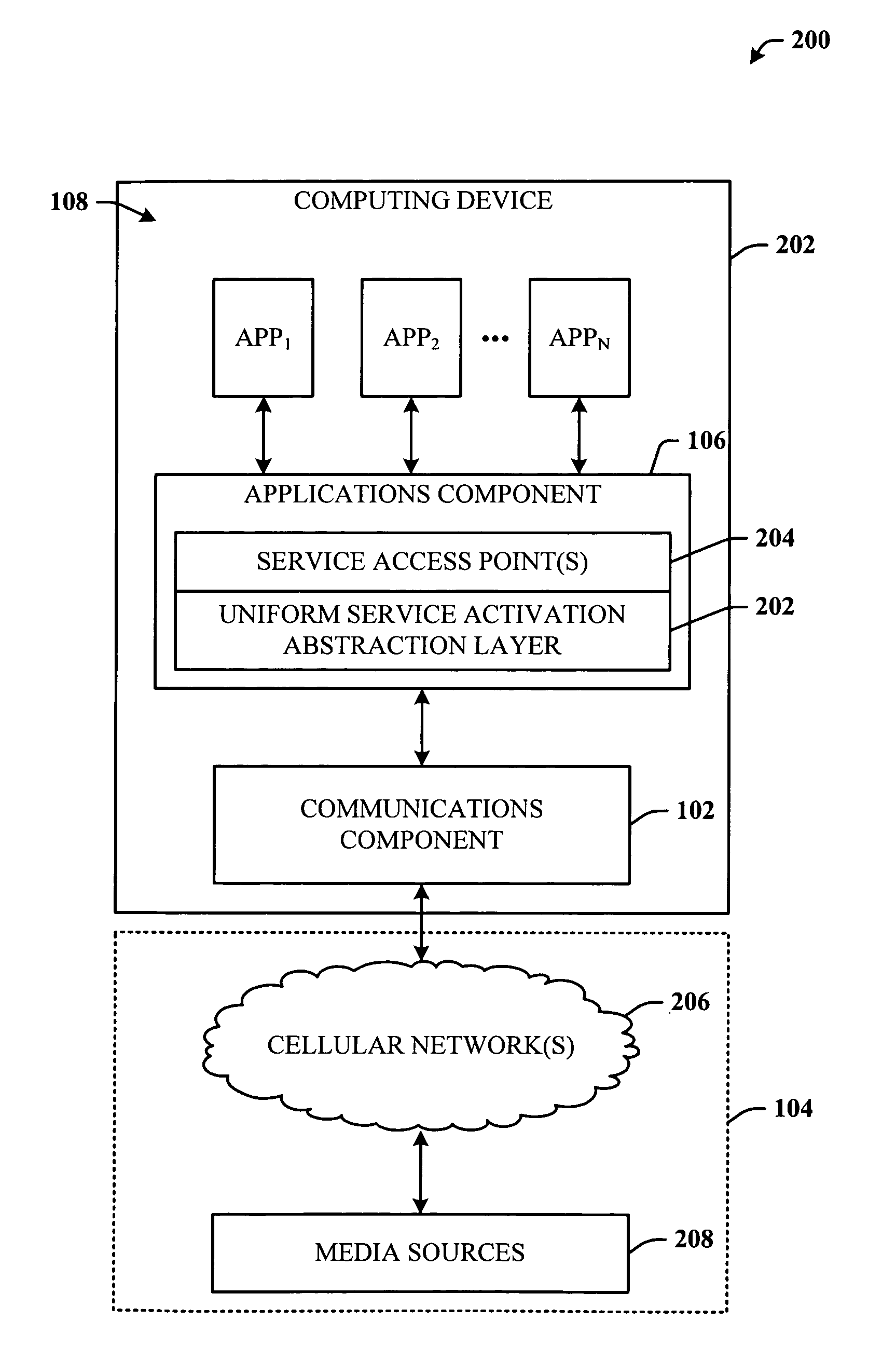
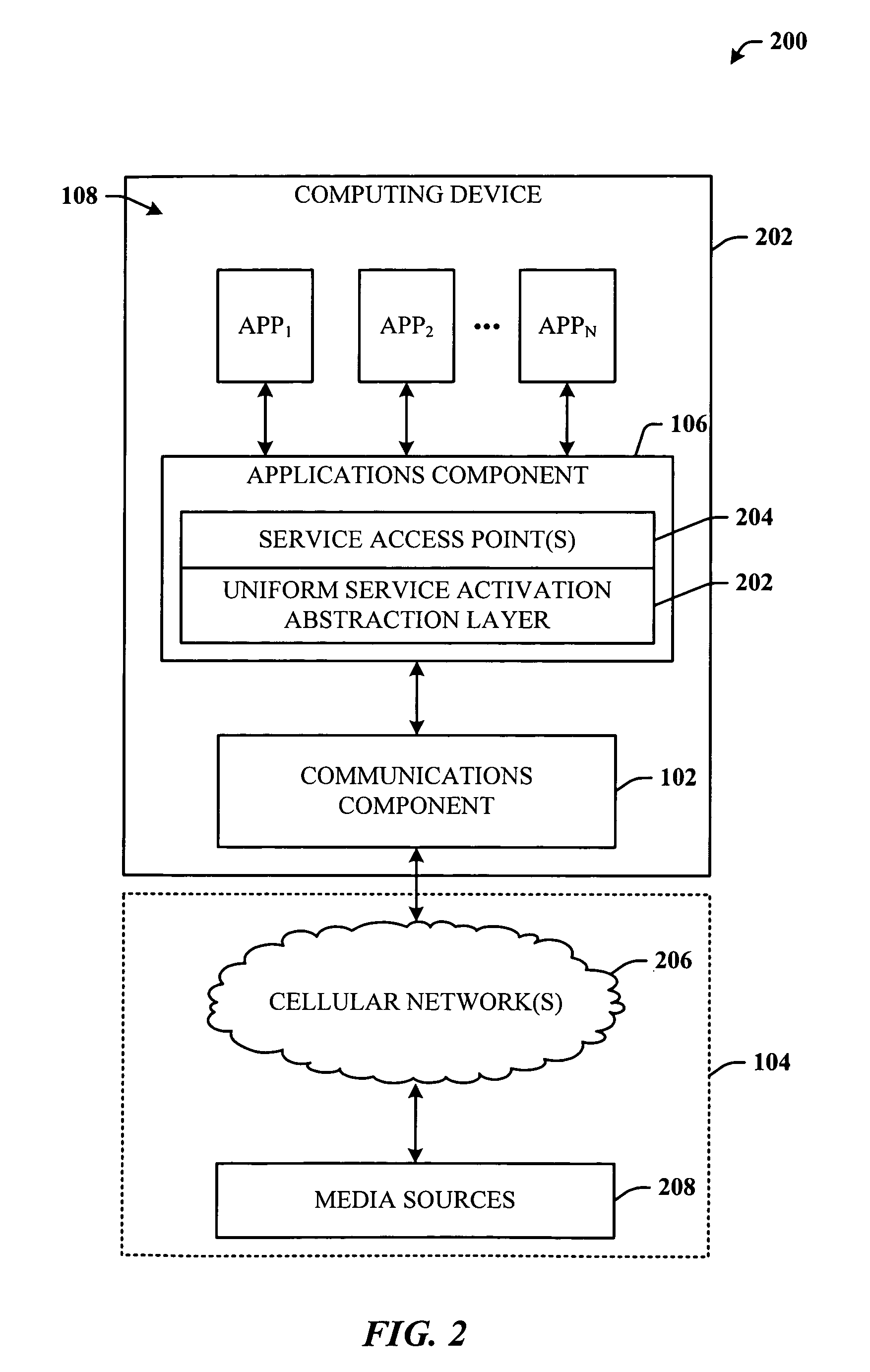
Upper layer applications discover, establish and manage the QoS connectivity through a SIP (session initiation protocol) that serves as a unified interface. In one implementation, this is IP Multimedia Subsystem-centric, further supporting applications that utilize SIP for session control. This capability extends to the data card universe allowing UMTS data card vendors to establish concurrent QoS-based sessions using multiple primary PDP (packet data protocol) contexts based on a set of SIP triggers, further allowing applications running on a computing system to transparently utilize the established pipes based on the individual QoS requirements.
Owner:CINGULAR WIRELESS LLC
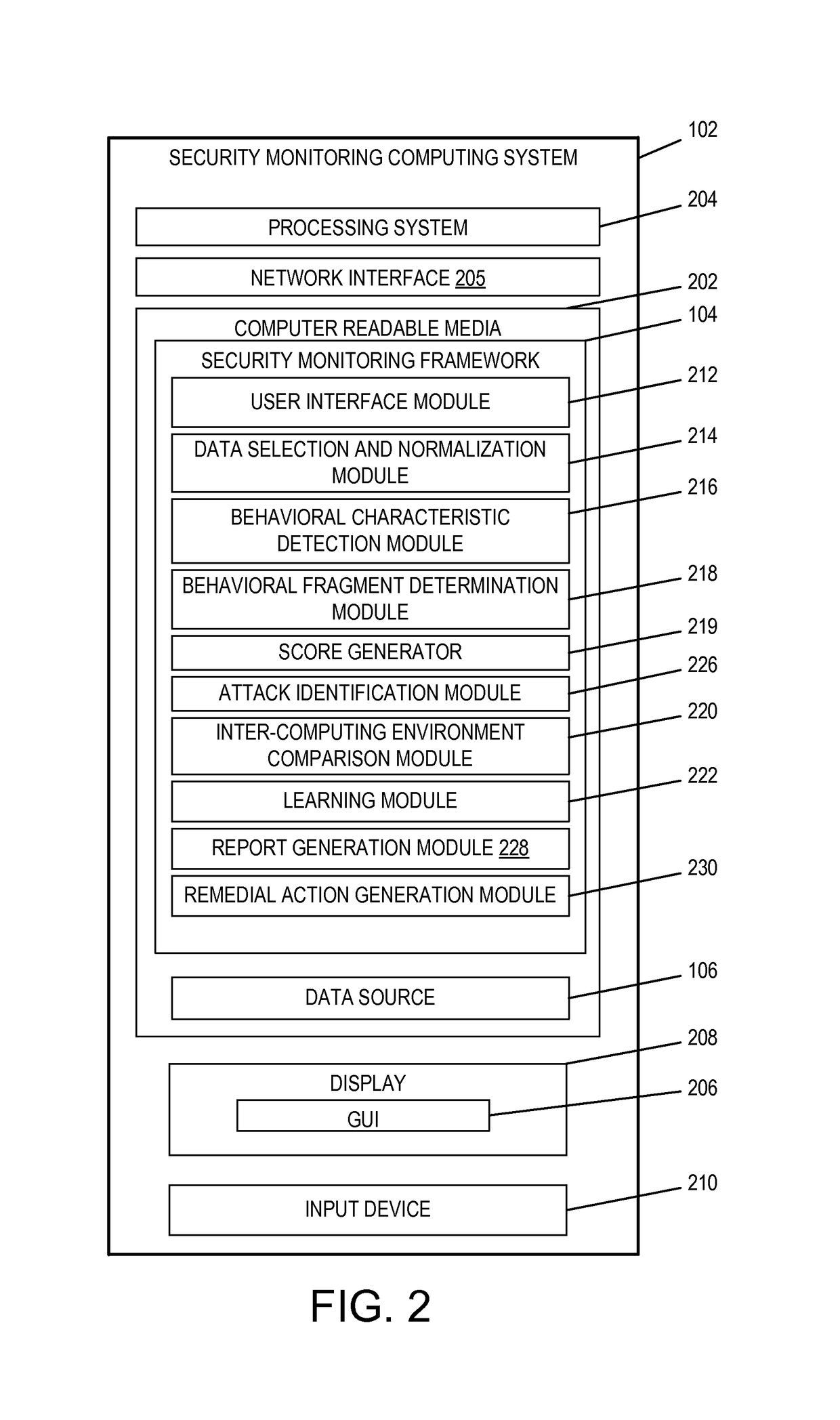
Analytics-based security monitoring system and method
ActiveUS9654485B1Reduce size (quantity)Easy to analyzeMemory loss protectionError detection/correctionRemedial actionSecurity monitoring
An analytics-based security monitoring system includes instructions that may be executed by a computing system to receive data in the form of event logs from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:MANDIANT +1
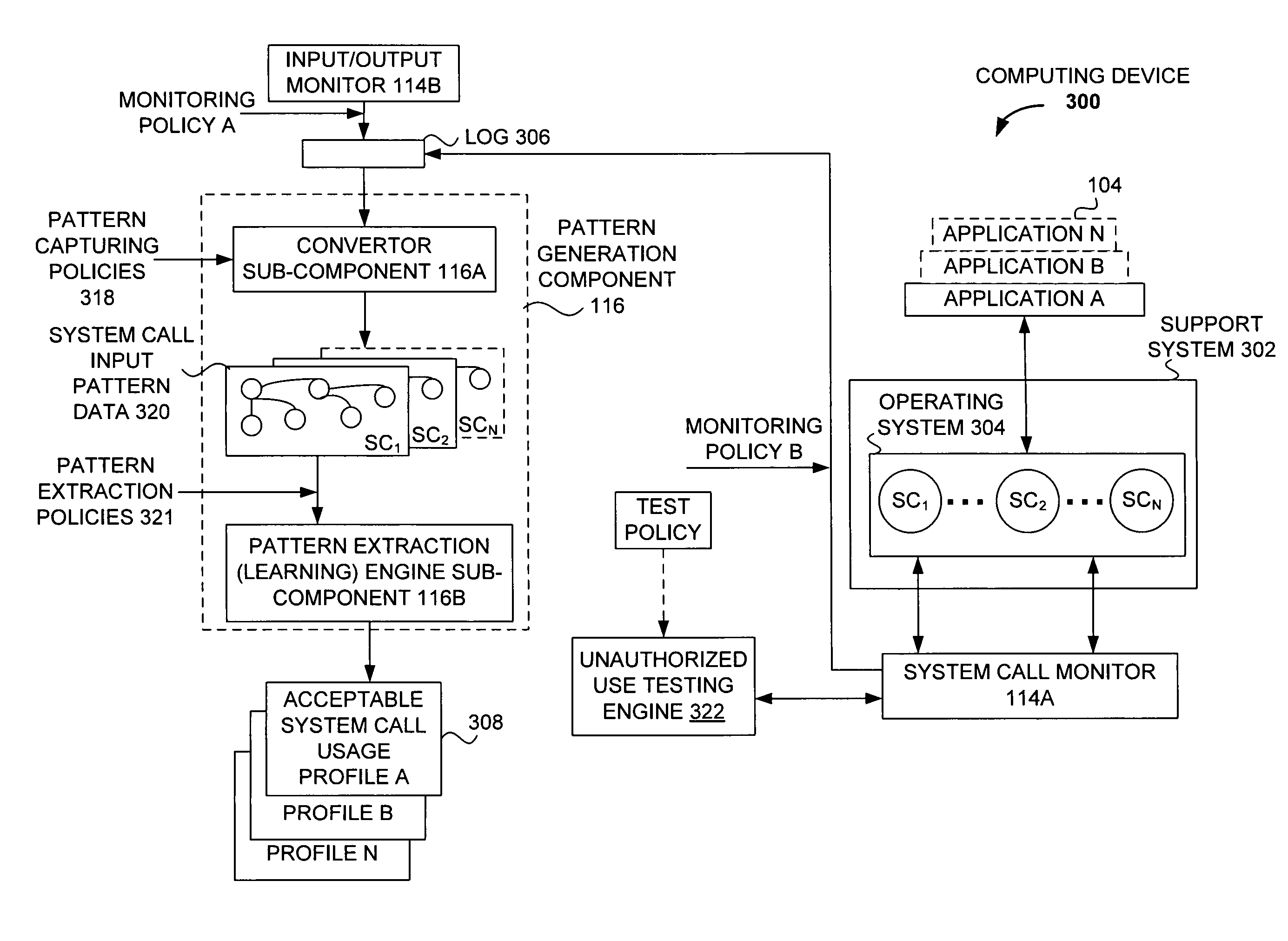
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS8595834B2Memory loss protectionError detection/correctionSupporting systemMonitoring system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
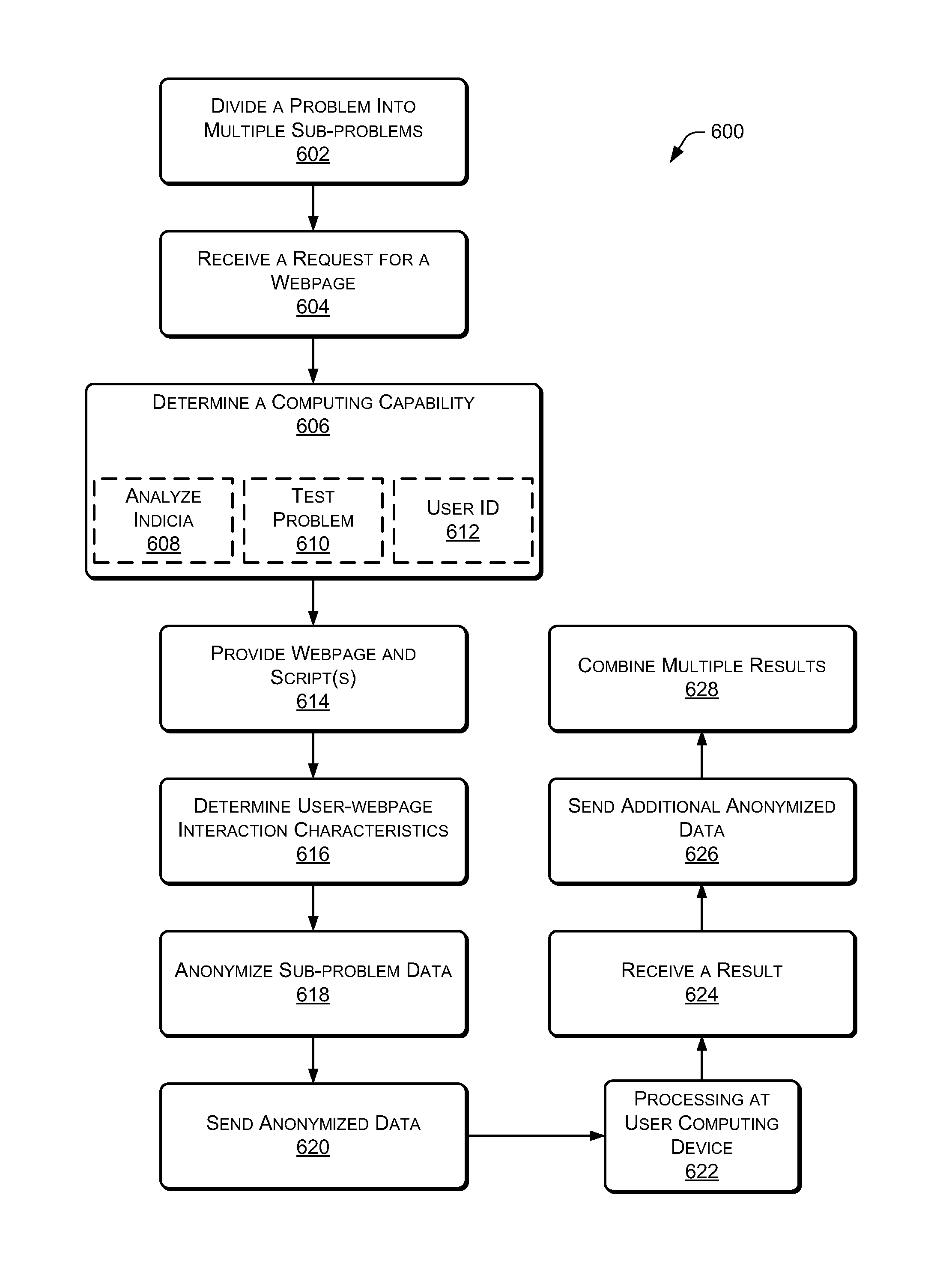
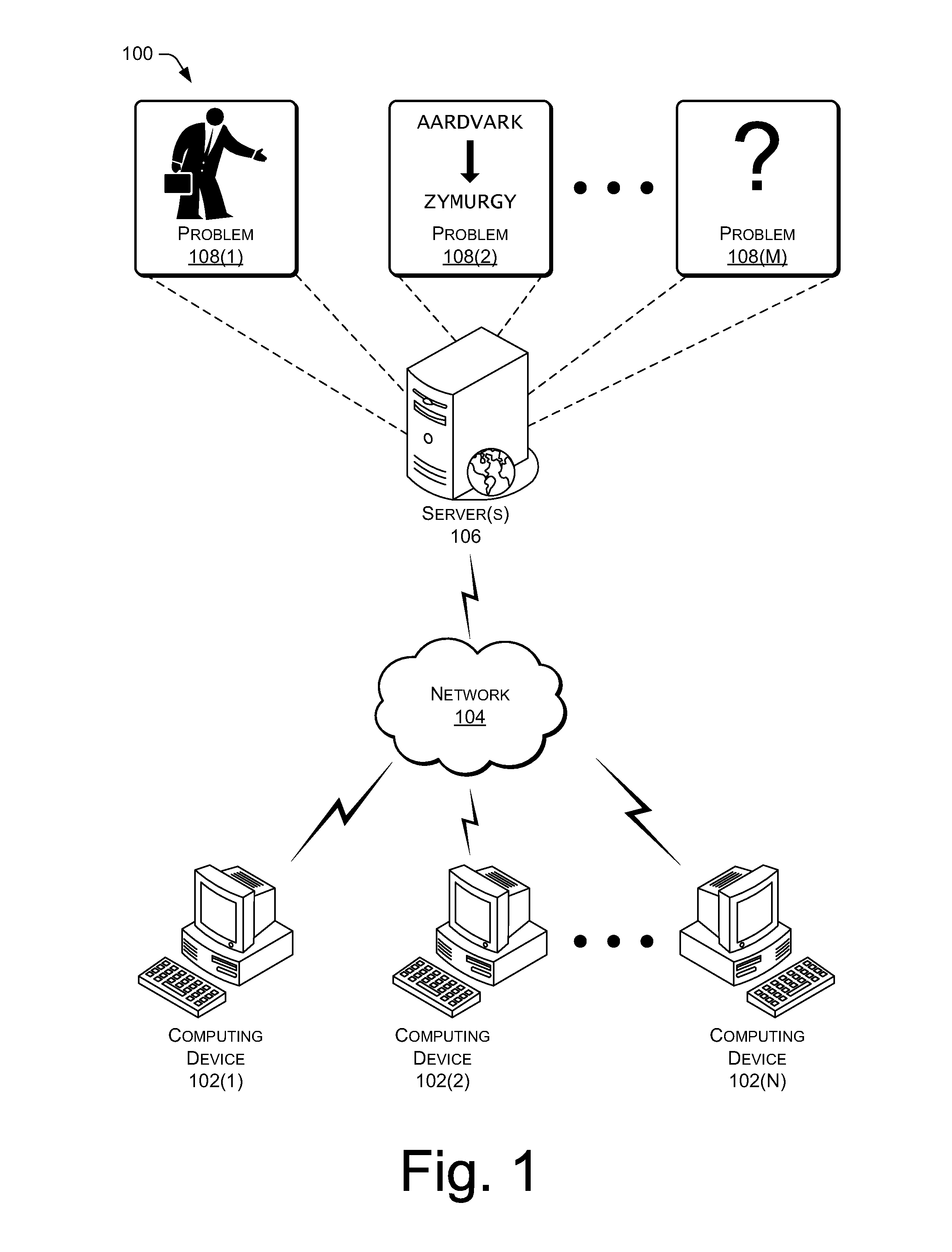
Data anonymity and separation for user computation
InactiveUS8930896B1Computer security arrangementsTransmissionScripting languageComputational problem
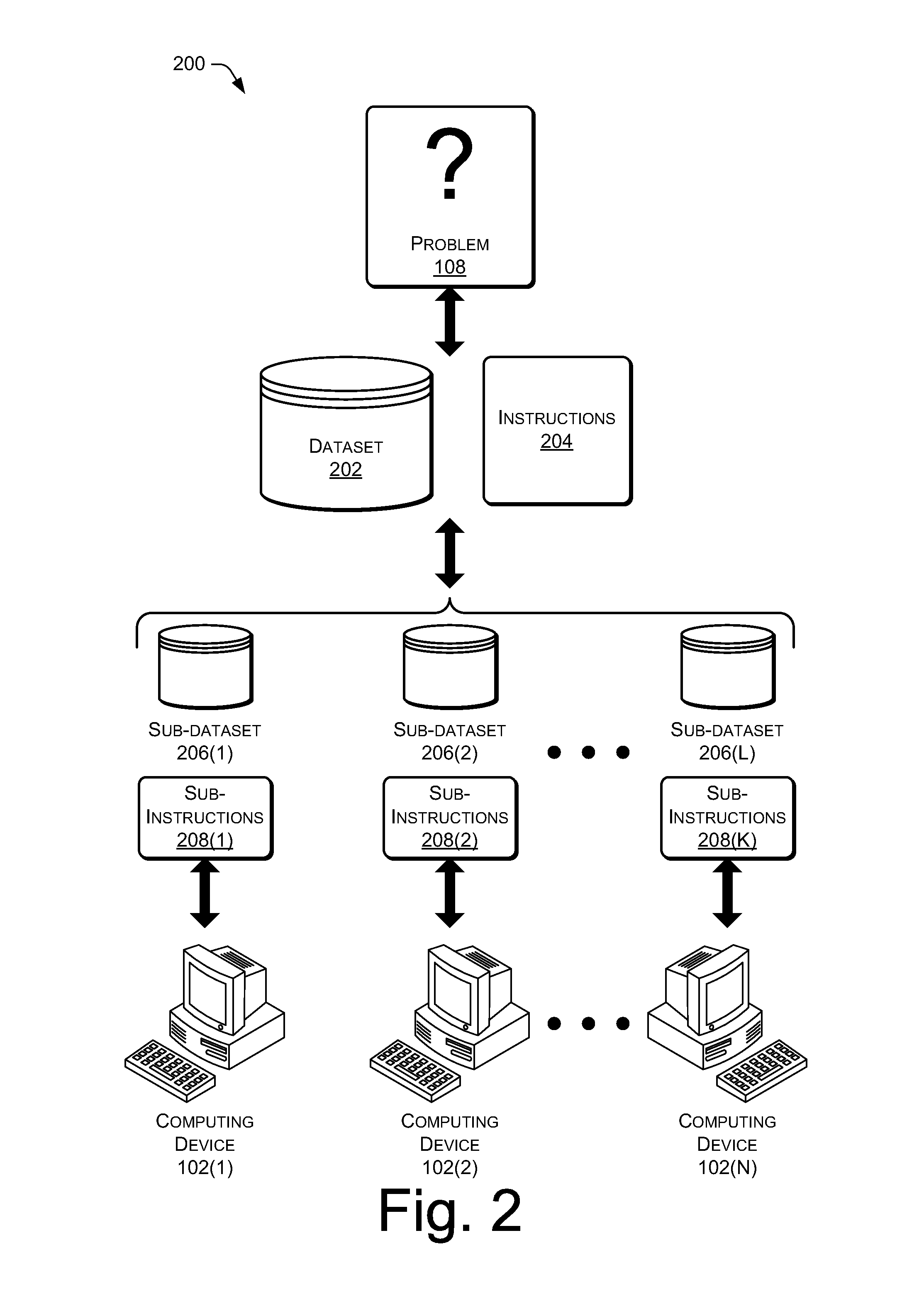
This disclosure includes techniques for using distributed computing over a network to resolve difficult computational problems. Anonymization of the data allows computing devices in the distributed computing system to solve the computational problem without exposing private aspects of the data. Individual computing devices receive instructions and data that correspond to a piece of a larger computational problem. In one implementation, a user may request a webpage from a web server and receive the webpage along with commands in a scripting language that instructs the user's computer to process a piece of the larger computational problem. The web server may assign the piece of the problem to the user's computer based on processing capabilities of the user's computer. Combining solutions received from multiple distributed computing devices and reversing the anonymization process yields a solution to the computational problem.
Owner:AMAZON TECH INC
Method and system for a multitenancy telephone network
ActiveUS20100232594A1Energy efficient ICTSpecial service for subscribersTelephone networkMultitenancy
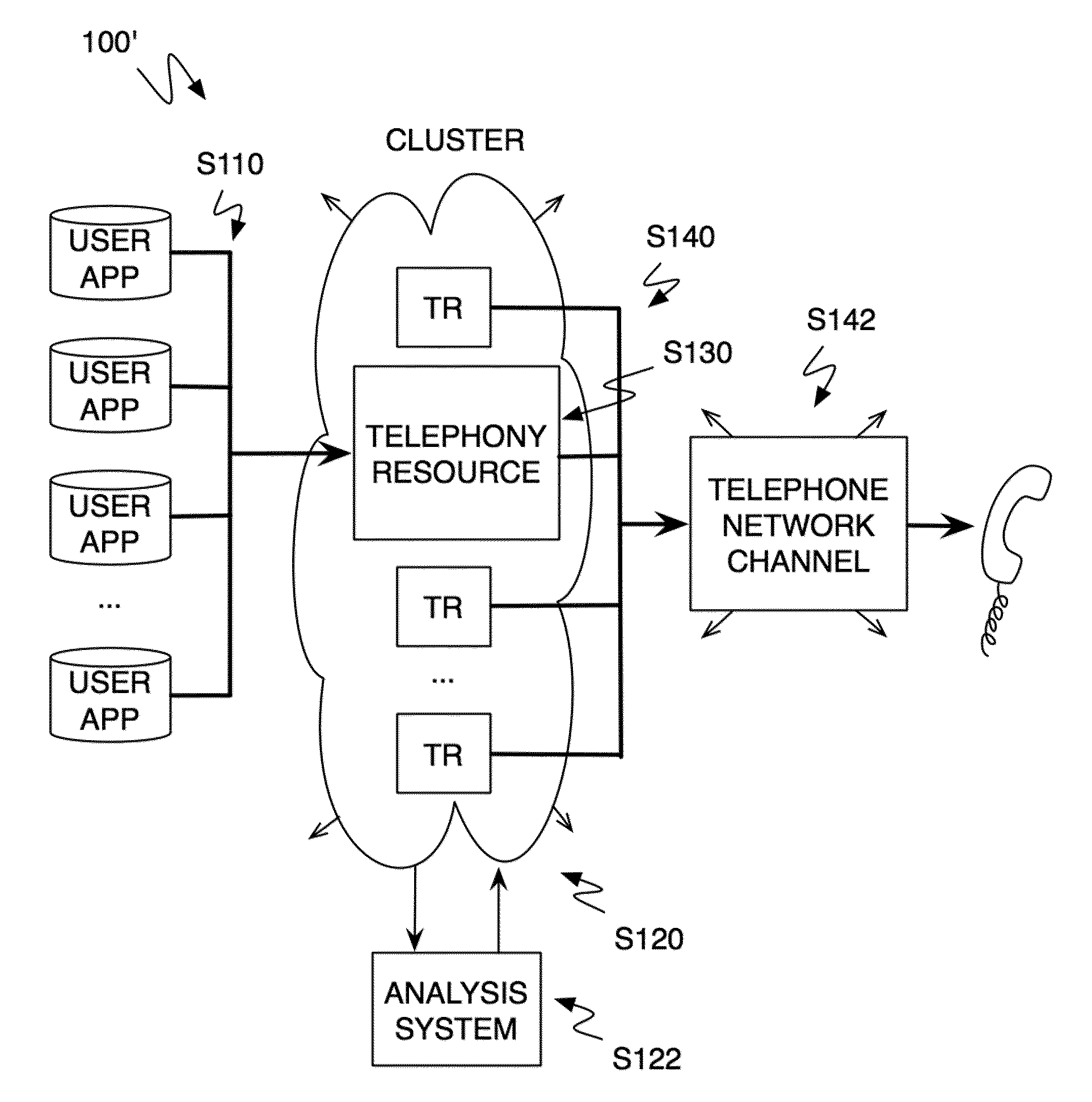
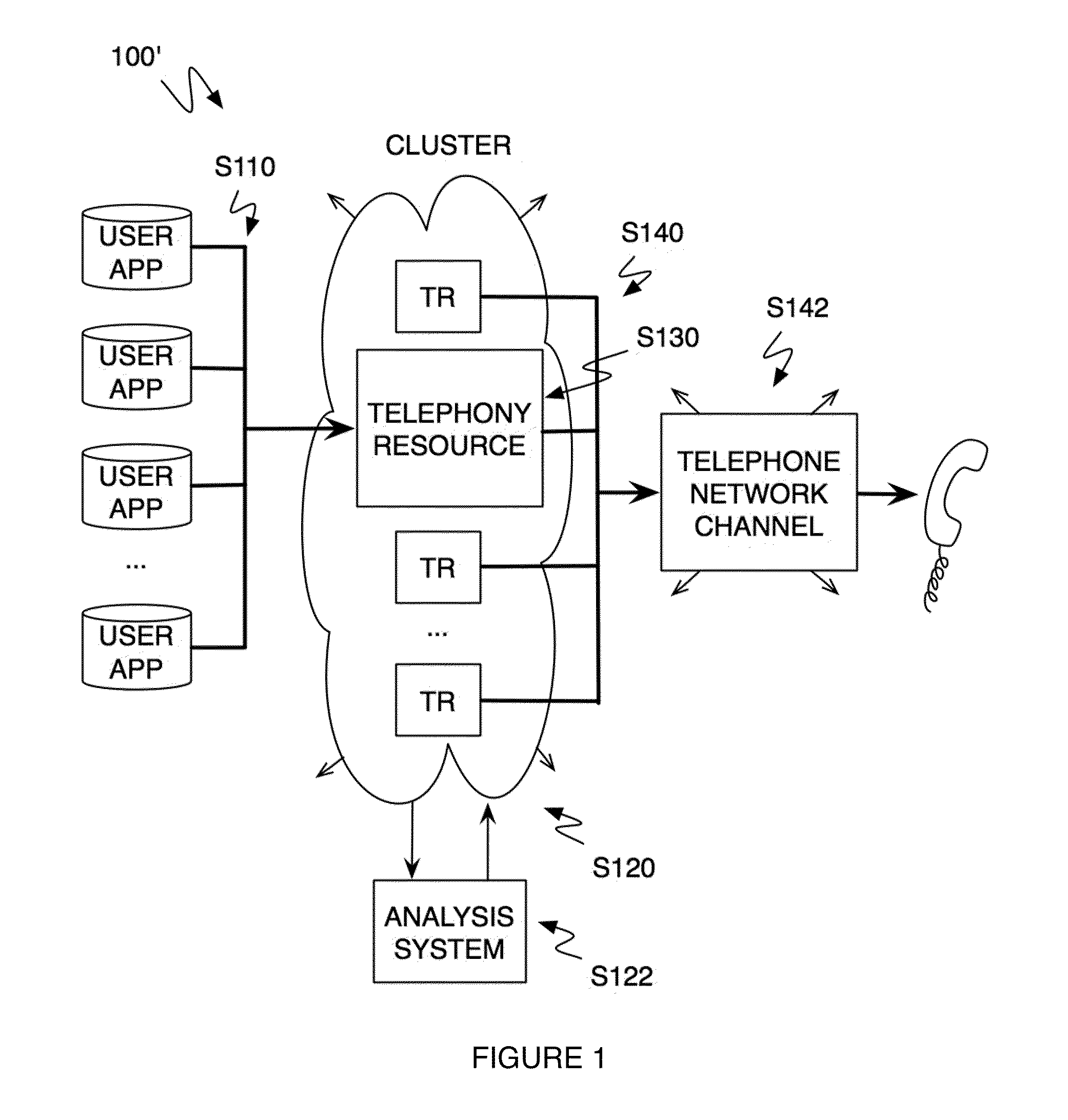
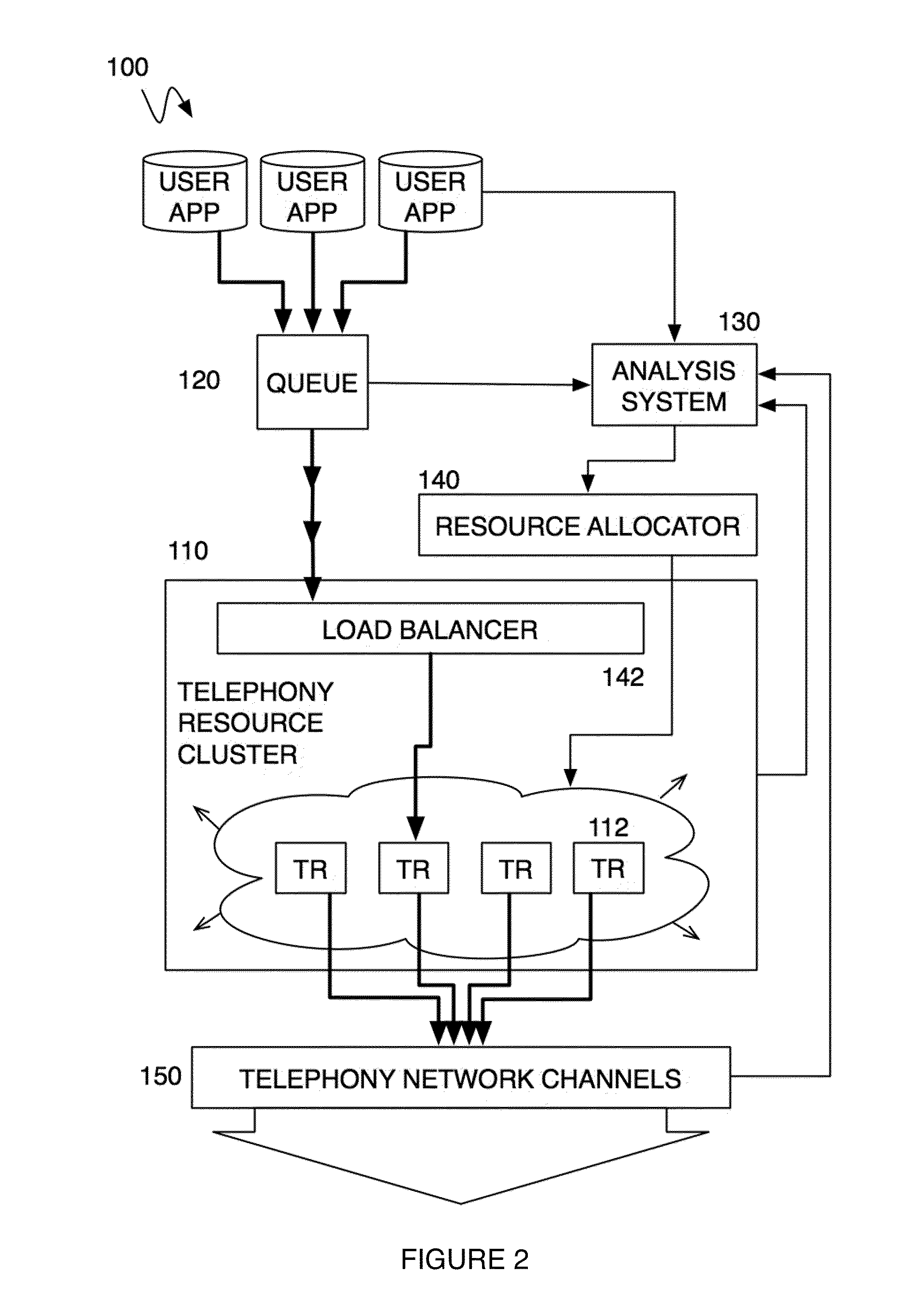
A method and system for operating a multitenancy telephony system including a call queue that stores call requests received from a plurality of users; an expandable and contractible telephony resource cluster that establishes call sessions for call requests; a analysis system that calculates capacity requirements of the system; a resource allocator that manages the scaling and operation of the telephony resource cluster; and a plurality of telephony network channels that are used as telephony communication channels for call sessions.
Owner:TWILO INC
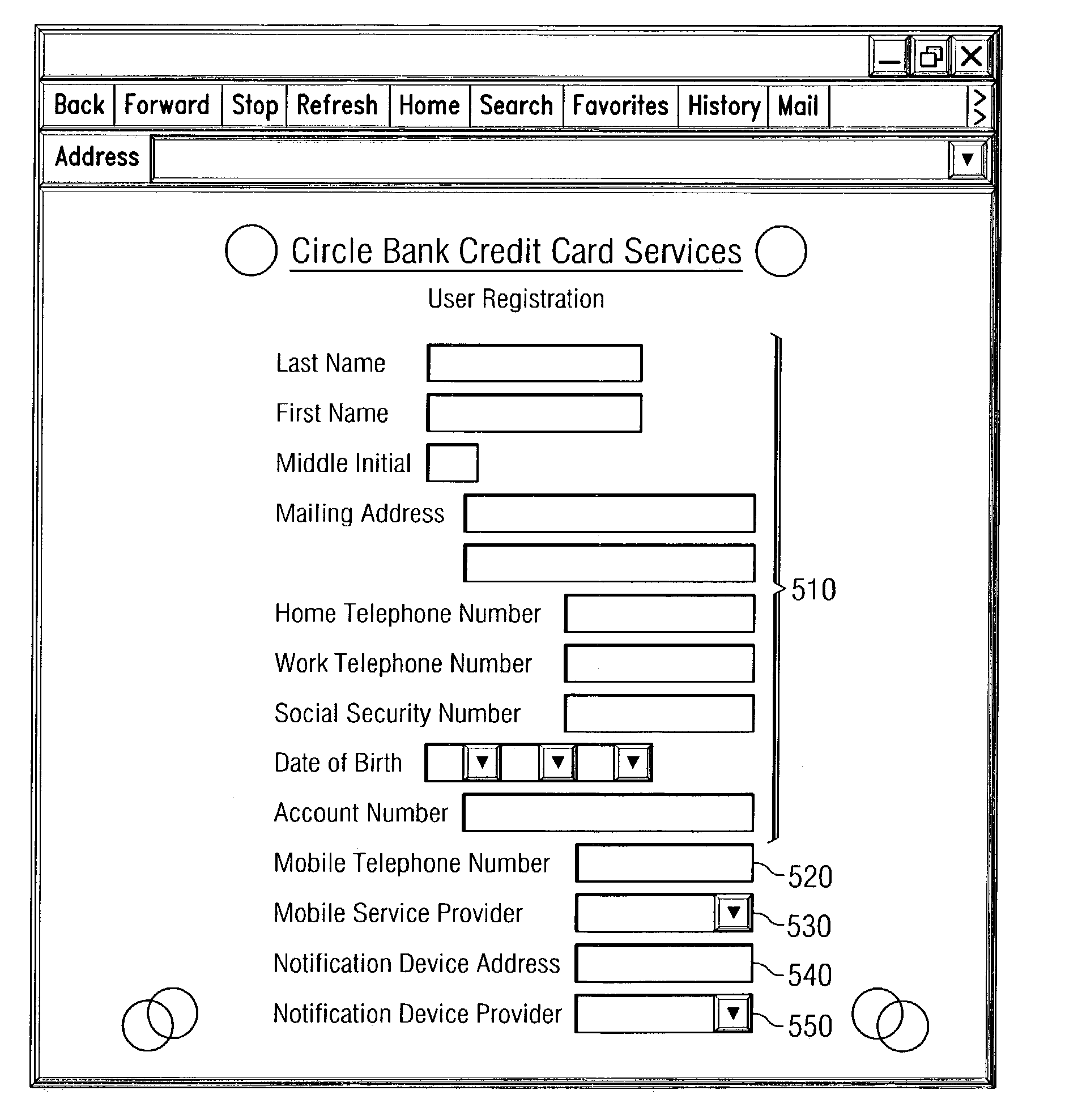
System and method for early detection and prevention of identity theft
InactiveUS7548886B2Identity theft has increasedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsIdentity theftMobile device
A system and method for early detection of identity theft are provided. An authorized user establishes an identity with an organization's computing system and registers a mobile device and a notification device with the organization's computing system. When a use of the identity is attempted, a record associated with the identity is retrieved and a request is sent to the registered mobile device for location information. The current location of the mobile device is compared to the location of the source of the request for authorization. If the current location of the mobile device is not within an area of the source of the authentication request, information about the attempted use is compared with the registered notification criteria. If the conditions of the attempted use fall within the notification criteria, a notification message is sent to the notification device.
Owner:PAYPAL INC
Wearable electromyography-based controllers for human-computer interface
A “Wearable Electromyography-Based Controller” includes a plurality of Electromyography (EMG) sensors and provides a wired or wireless human-computer interface (HCl) for interacting with computing systems and attached devices via electrical signals generated by specific movement of the user's muscles. Following initial automated self-calibration and positional localization processes, measurement and interpretation of muscle generated electrical signals is accomplished by sampling signals from the EMG sensors of the Wearable Electromyography-Based Controller. In operation, the Wearable Electromyography-Based Controller is donned by the user and placed into a coarsely approximate position on the surface of the user's skin. Automated cues or instructions are then provided to the user for fine-tuning placement of the Wearable Electromyography-Based Controller. Examples of Wearable Electromyography-Based Controllers include articles of manufacture, such as an armband, wristwatch, or article of clothing having a plurality of integrated EMG-based sensor nodes and associated electronics.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for Metadata Discovery and Metadata-Aware Scheduling
InactiveUS20130238785A1Efficient use ofDigital computer detailsSoftware simulation/interpretation/emulationMetadata discoveryComputing systems
A cloud computing system including a plurality of computing devices configured to host virtual machine instances, each computing device in the plurality of computing devices including a monitor operable to collect metadata about the associated computing device. The system also includes a registry operable to receive and store the metadata from the plurality of computing devices and a scheduler operable to select a host computing device out of the plurality of computing devices on which to instantiate a virtual machine instance based on the metadata stored in the registry.
Owner:RACKSPACE US
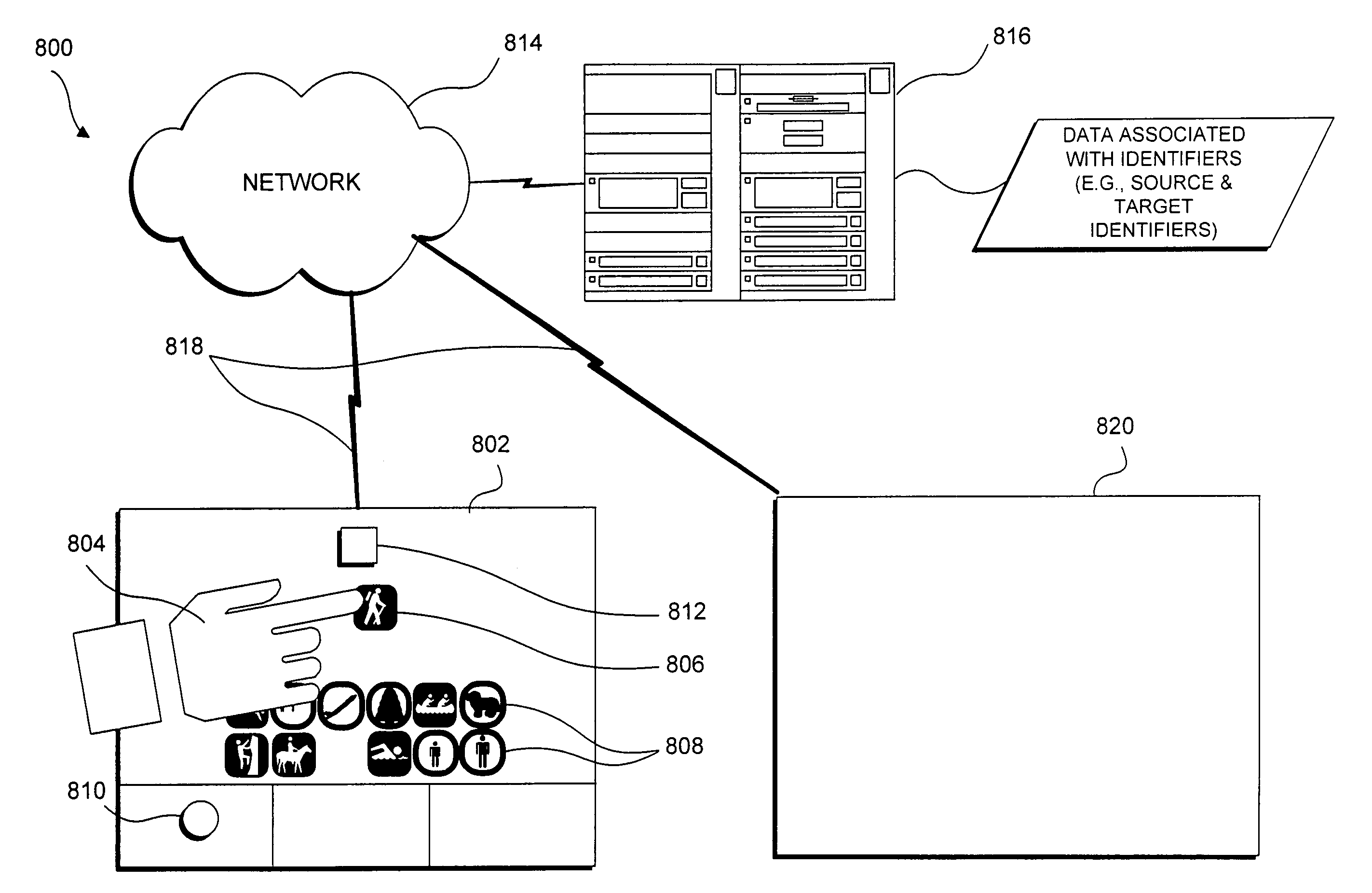
Manipulating association of data with a physical object
InactiveUS20050275636A1Easy retrievalSimple methodInput/output for user-computer interactionCathode-ray tube indicatorsWeb environmentComputing systems
Data elements stored in a computing system and associated with a physical object are reassociated with the same or another physical object. An identifying characteristic presented by the physical object, such as a reflective pattern applied to the object, is detected when the object is positioned adjacent to the interactive display surface. Images or other files associated with the identifying characteristic are accessed and displayed on the interactive display surface. A gesture by a user adjacent to the interactive display surface is detected to reassociate a selected representation. For example, the user can change where the selected element fits in a sequence of data elements, or reassociate the selected element with a second object placed on the interactive display surface. In a networked environment, the reassociated element can be stored on a server and subsequently accessed from a different interactive surface via the network using the second physical object.
Owner:MICROSOFT TECH LICENSING LLC
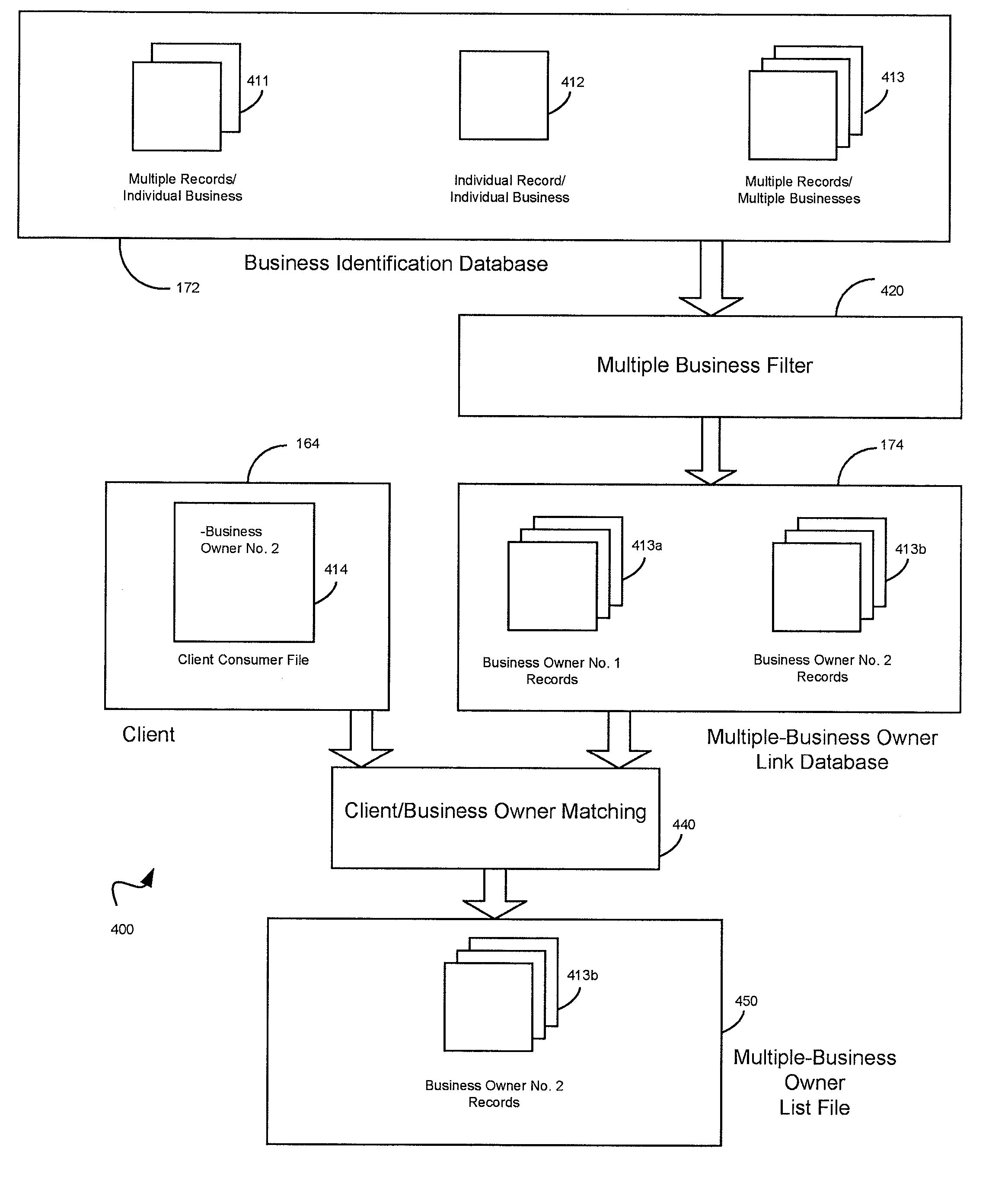
System and method for linking multiple entities in a business database
Embodiments of a system and method are described for determining whether an applicant is a multiple-business owner and for providing information related to multiple-business owners to a financial service provider or other client. According to one embodiment, a computing system is provided to collect and store business data and identify business owners associated with multiple business records.
Owner:EXPERIAN MARKETING SOLUTIONS
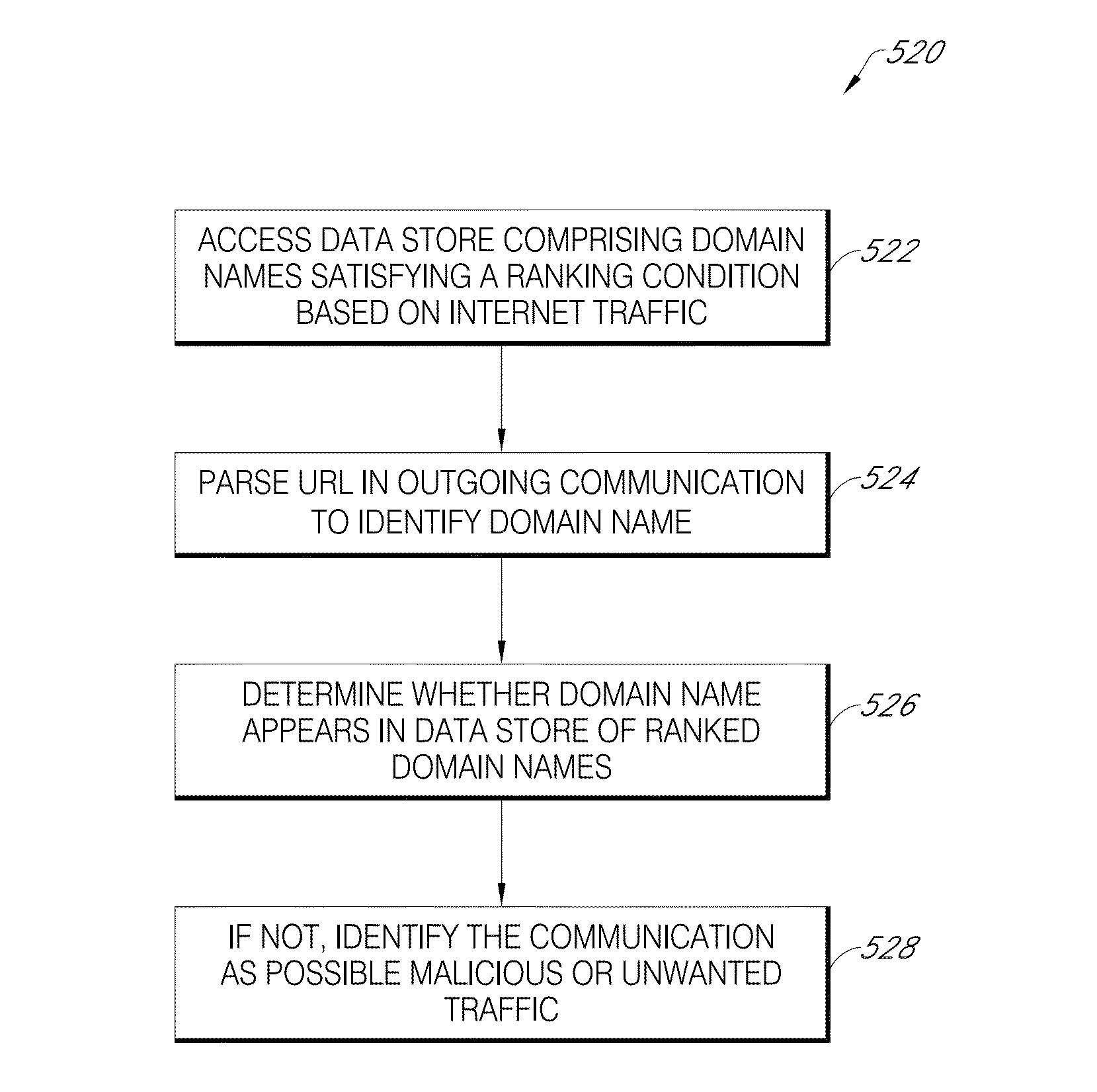
Filter-based identification of malicious websites
A candidate suspicious website is identified. A plurality of lightweight features associated with the candidate suspicious website is identified. A filter score is determined based on the plurality of lightweight features, wherein the filter score indicates a likelihood that the candidate suspicious website is a malicious website. Whether the filter score exceeds a threshold is determined. Responsive at least in part to the filter score exceeding the threshold it is determined that the candidate suspicious website is a suspicious website. Whether the suspicious website is a malicious website is determined by identifying software downloaded to the computing system responsive to accessing the suspicious website and determining whether the software downloaded to the computing system is malware based on characteristics associated with the downloaded software.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com