Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
227 results about "Identity theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identity theft is the deliberate use of someone else's identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other person's name, and perhaps to the other person's disadvantage or loss. The person whose identity has been assumed may suffer adverse consequences, especially if they are held responsible for the perpetrator's actions. Identity theft occurs when someone uses another's personally identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term identity theft was coined in 1964. Since that time, the definition of identity theft has been statutorily prescribed throughout both the U.K. and the United States as the theft of personally identifiable information, generally including a person’s name, date of birth, social security number, driver’s license number, bank account or credit card numbers, PIN numbers, electronic signatures, fingerprints, passwords, or any other information that can be used to access a person’s financial resources.
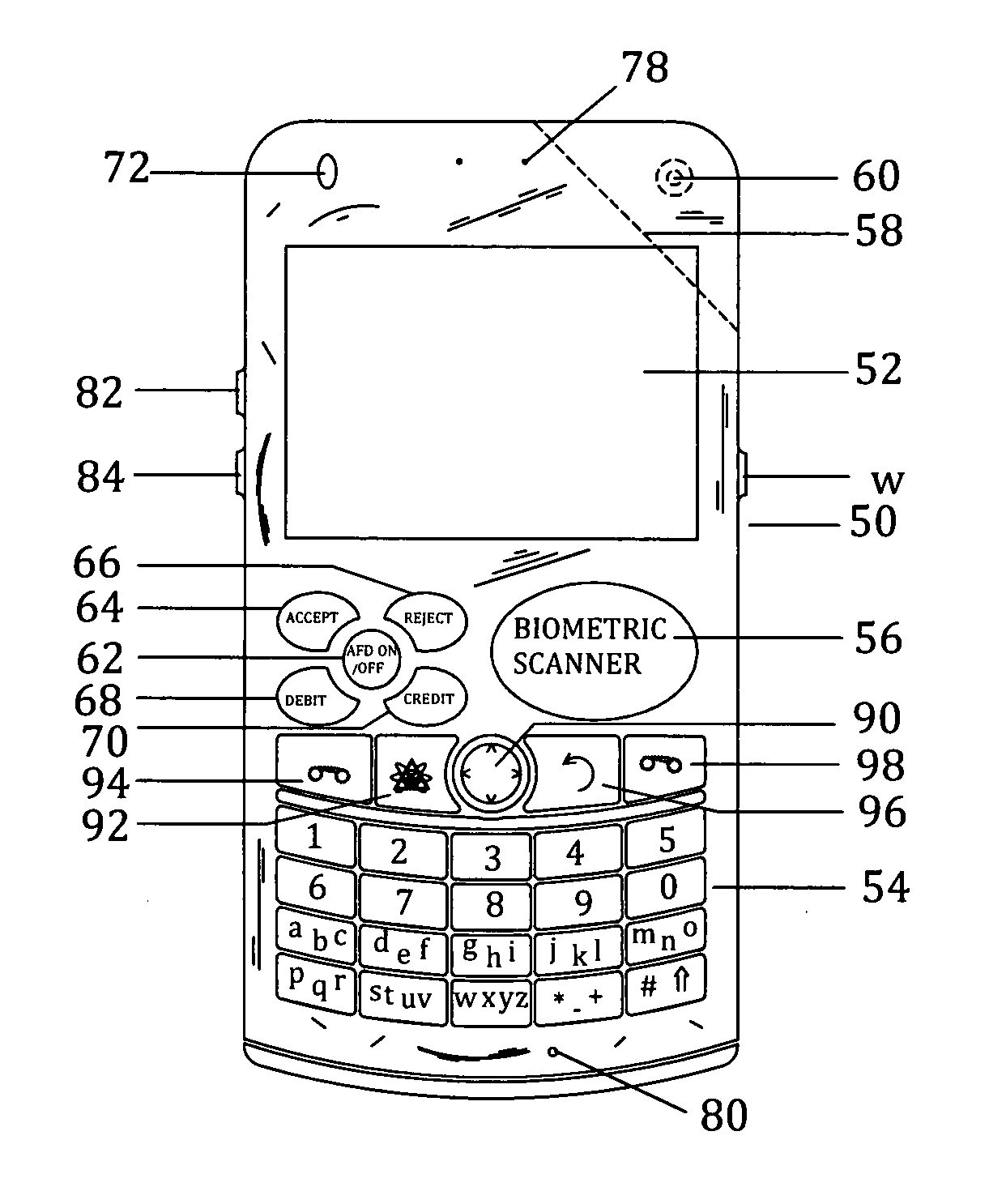
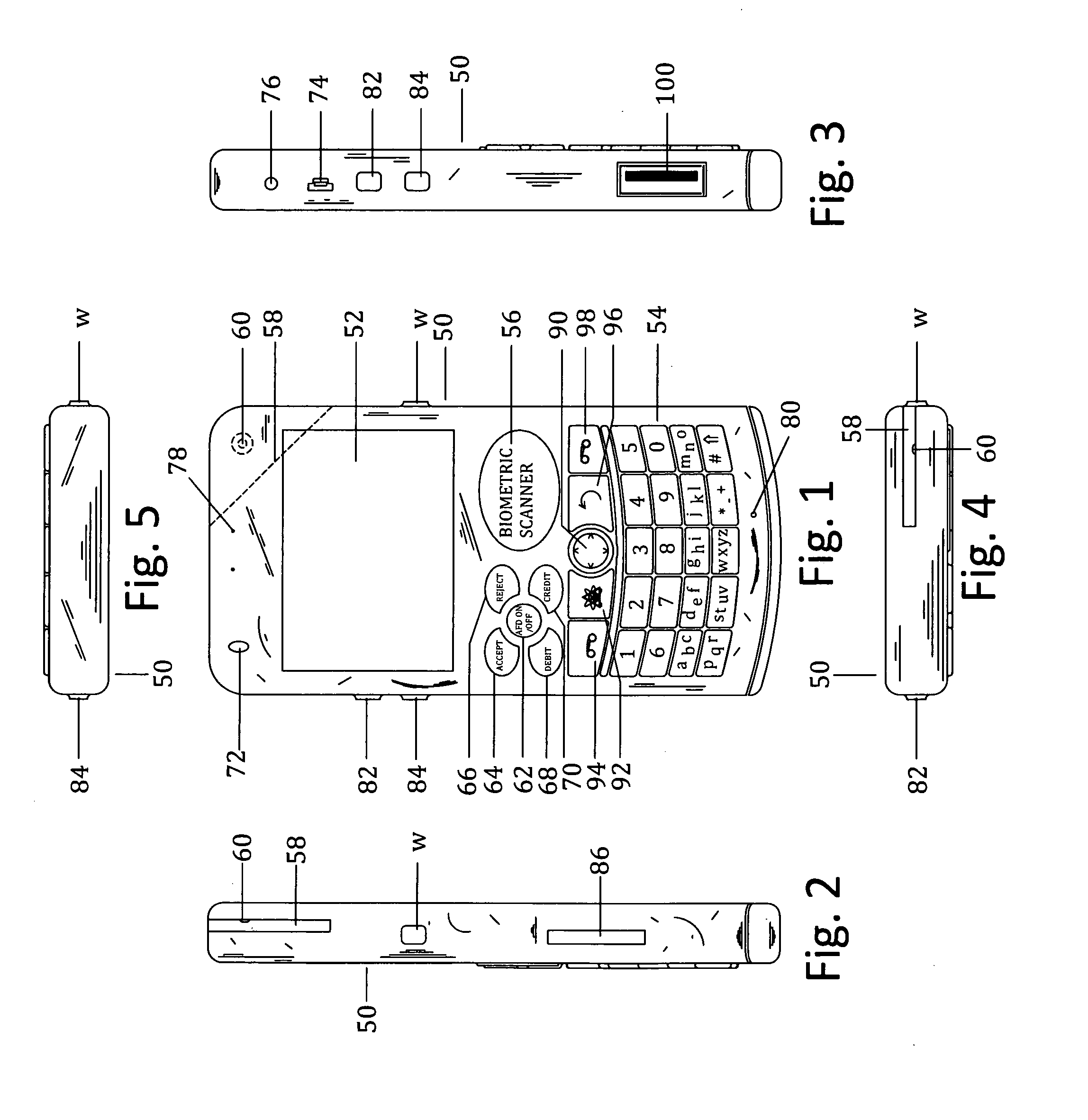
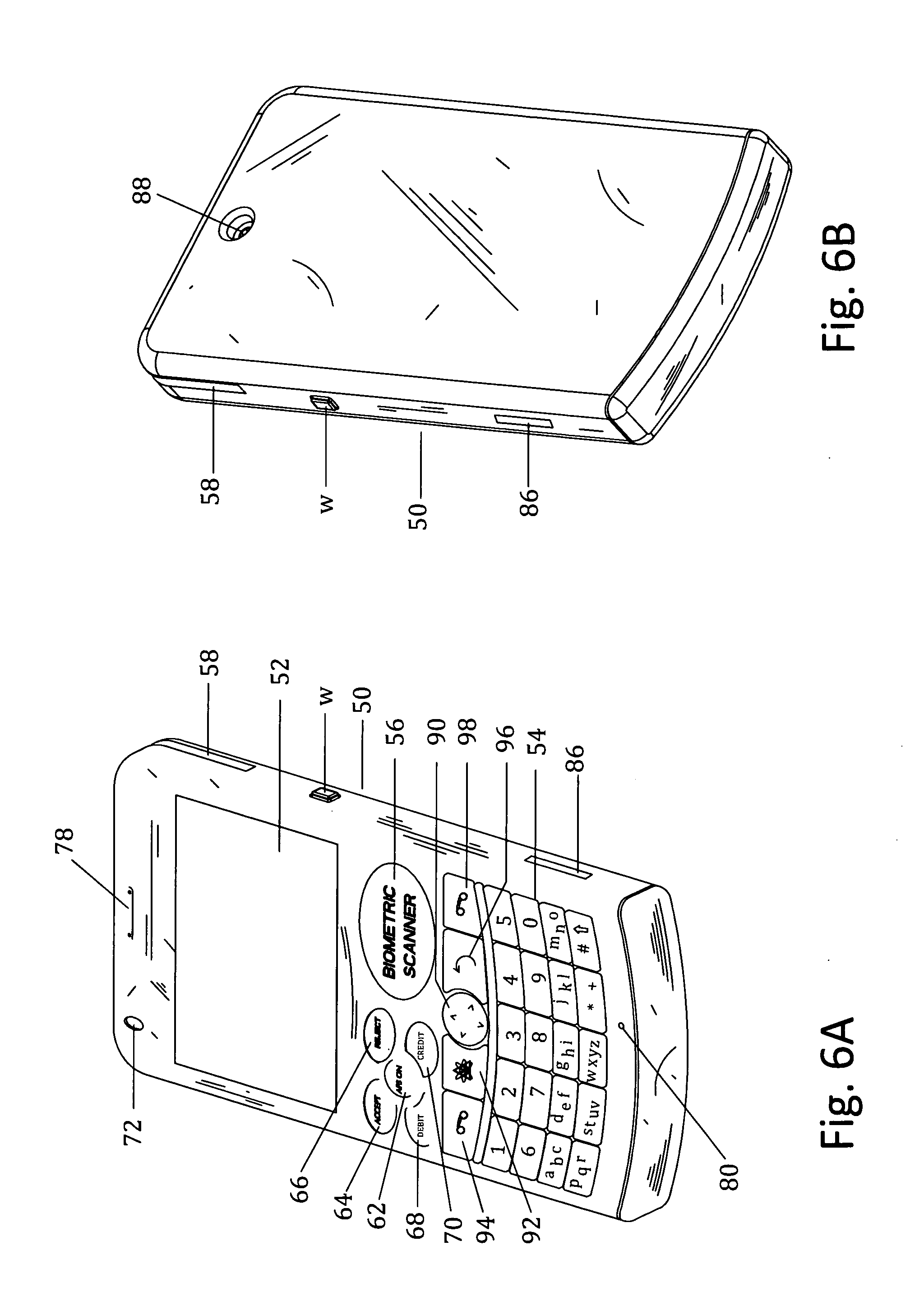
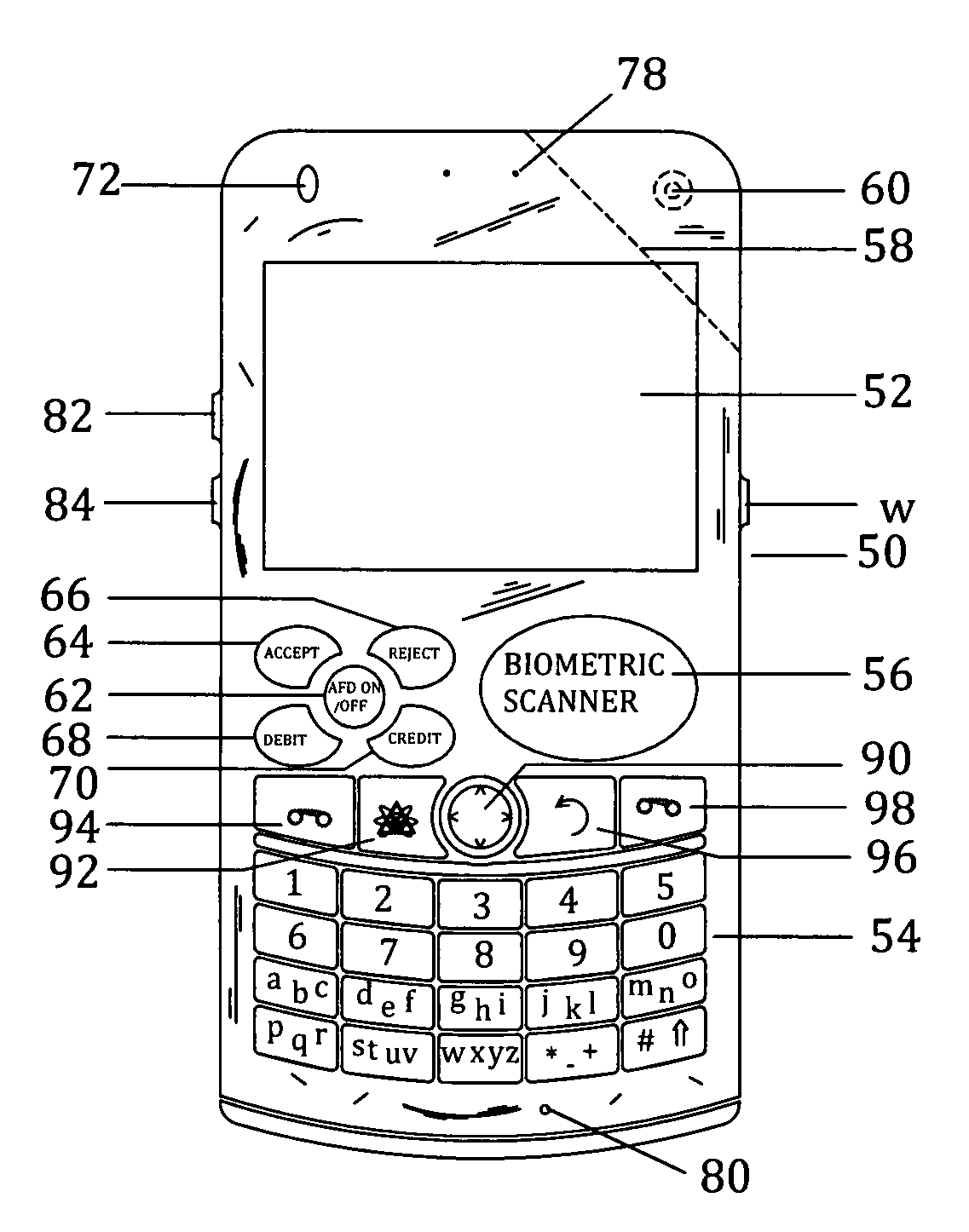
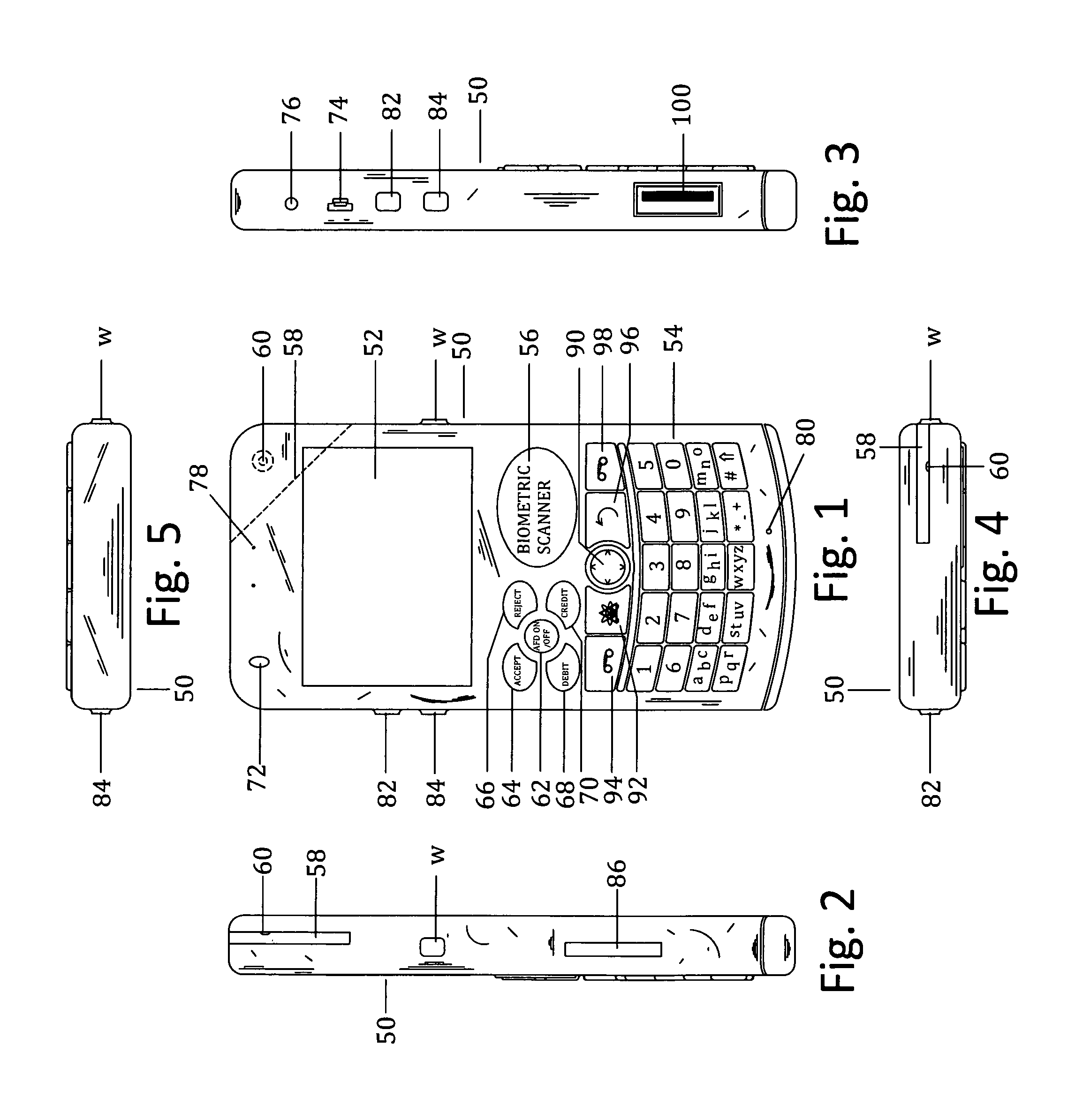
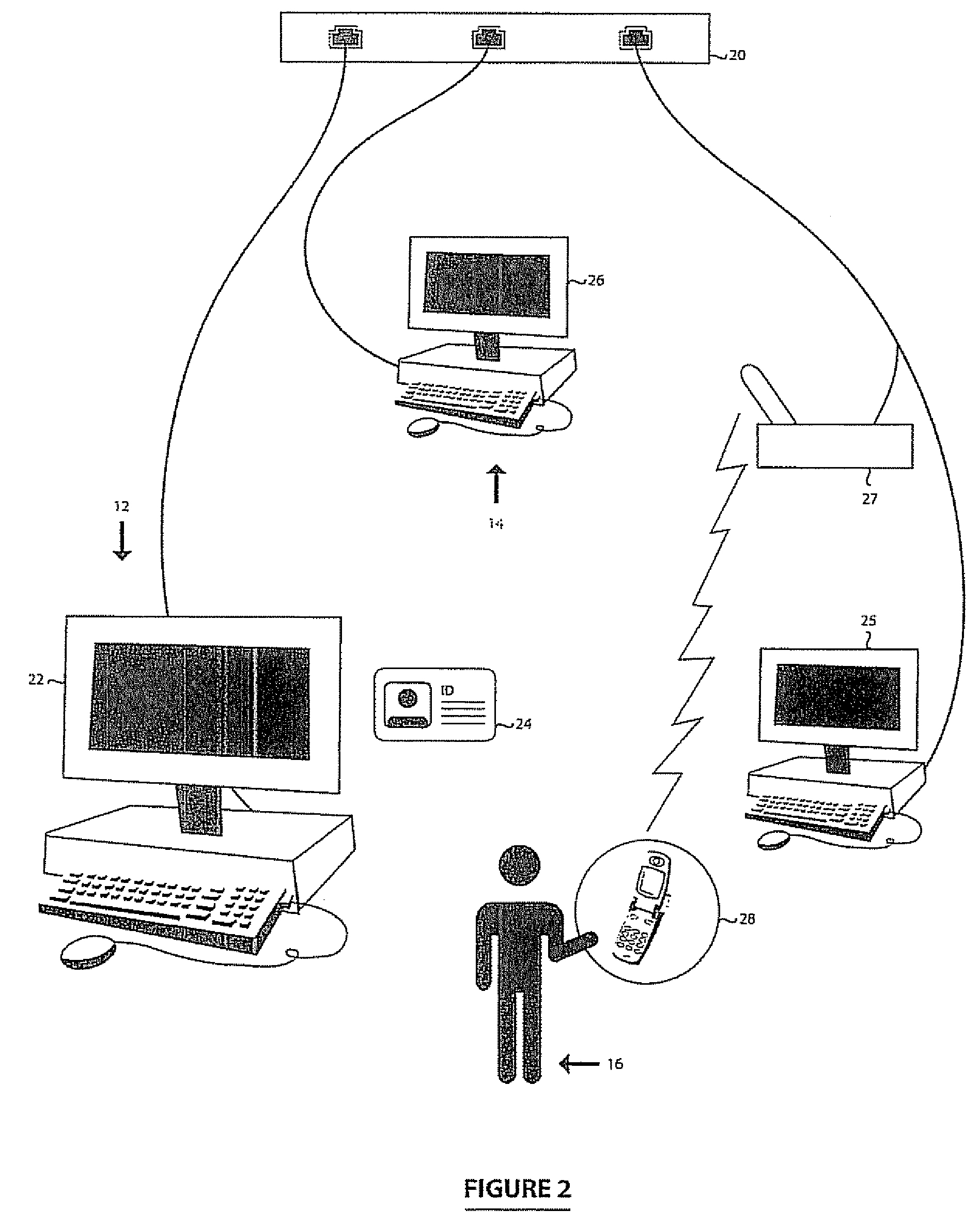
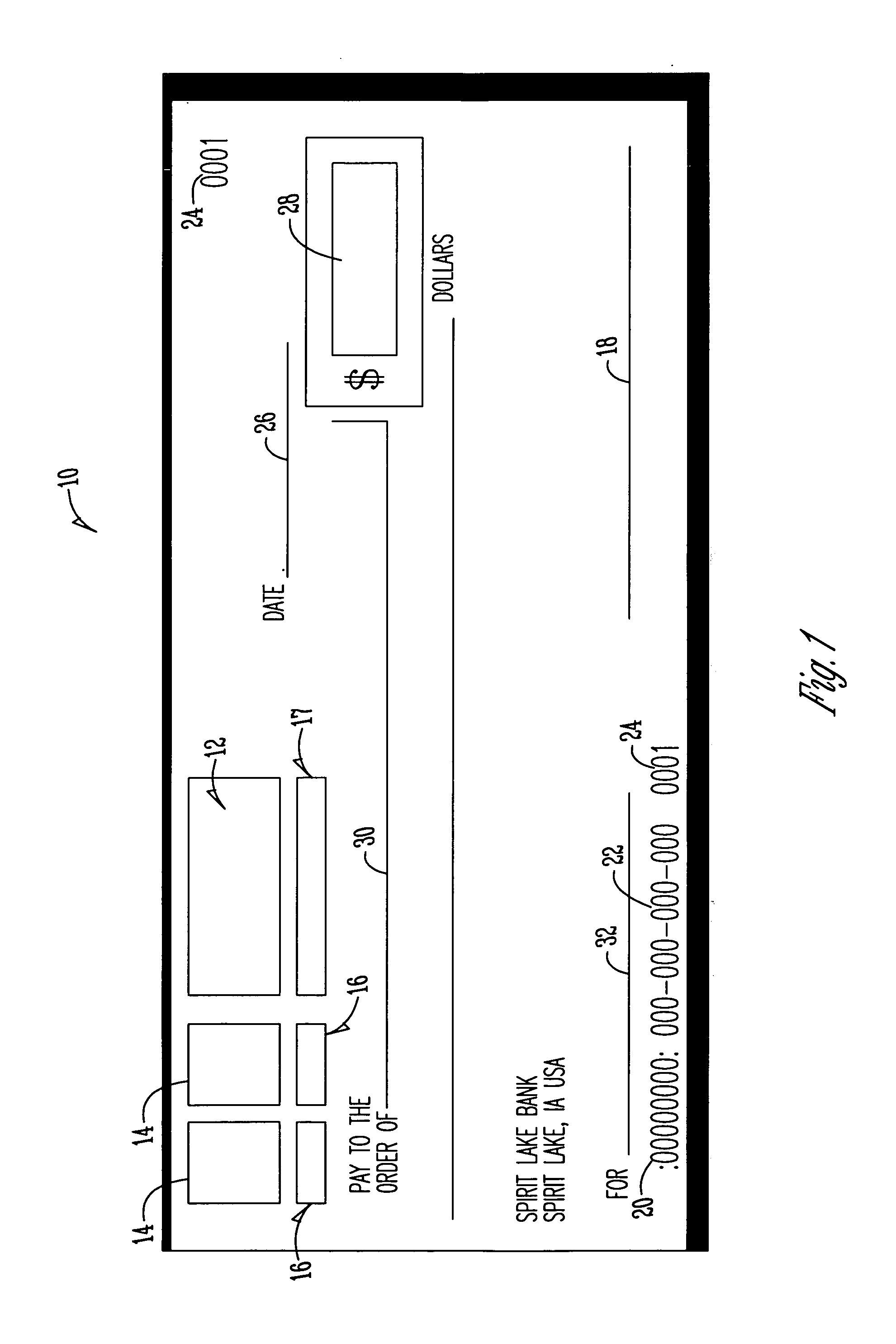
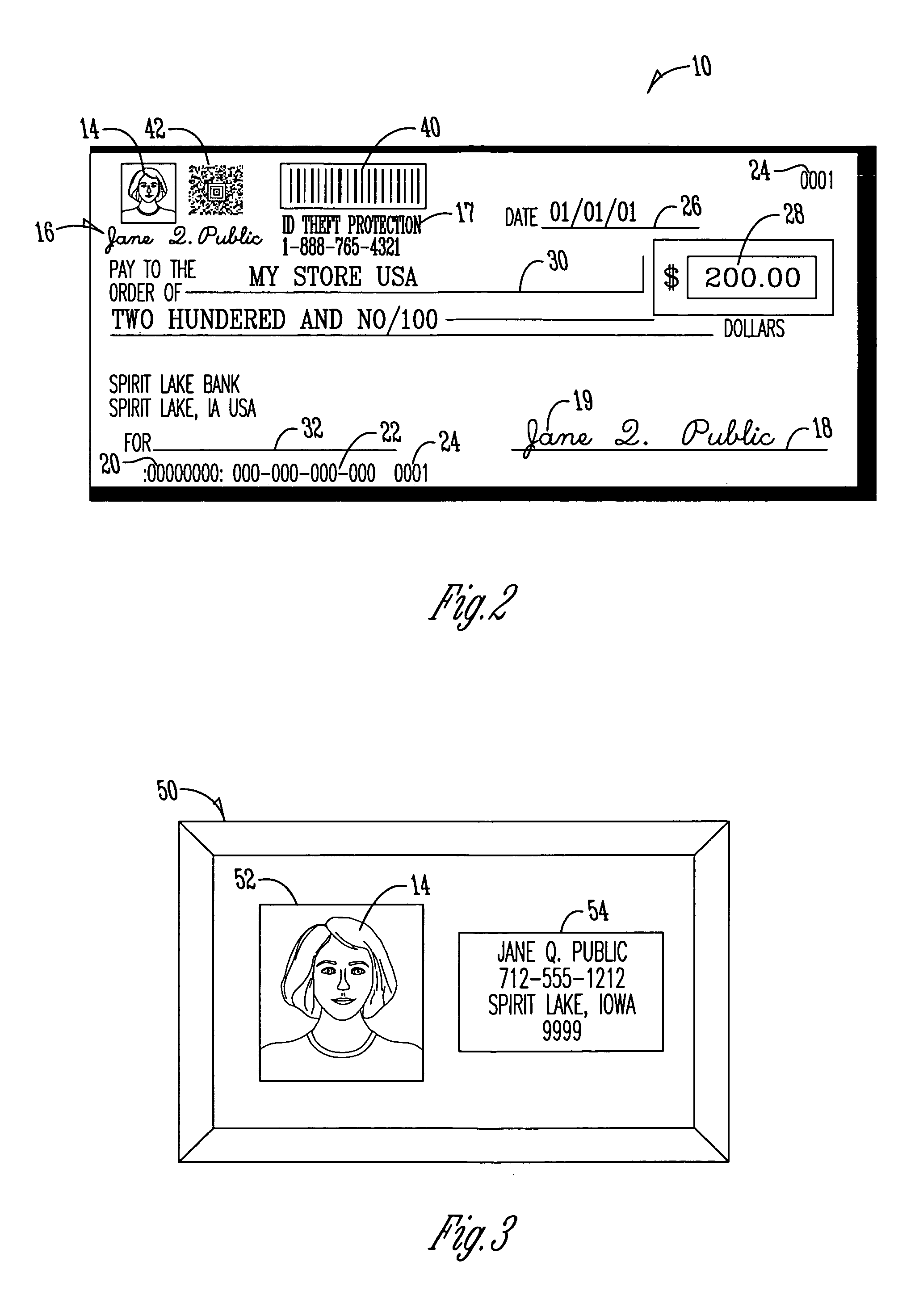
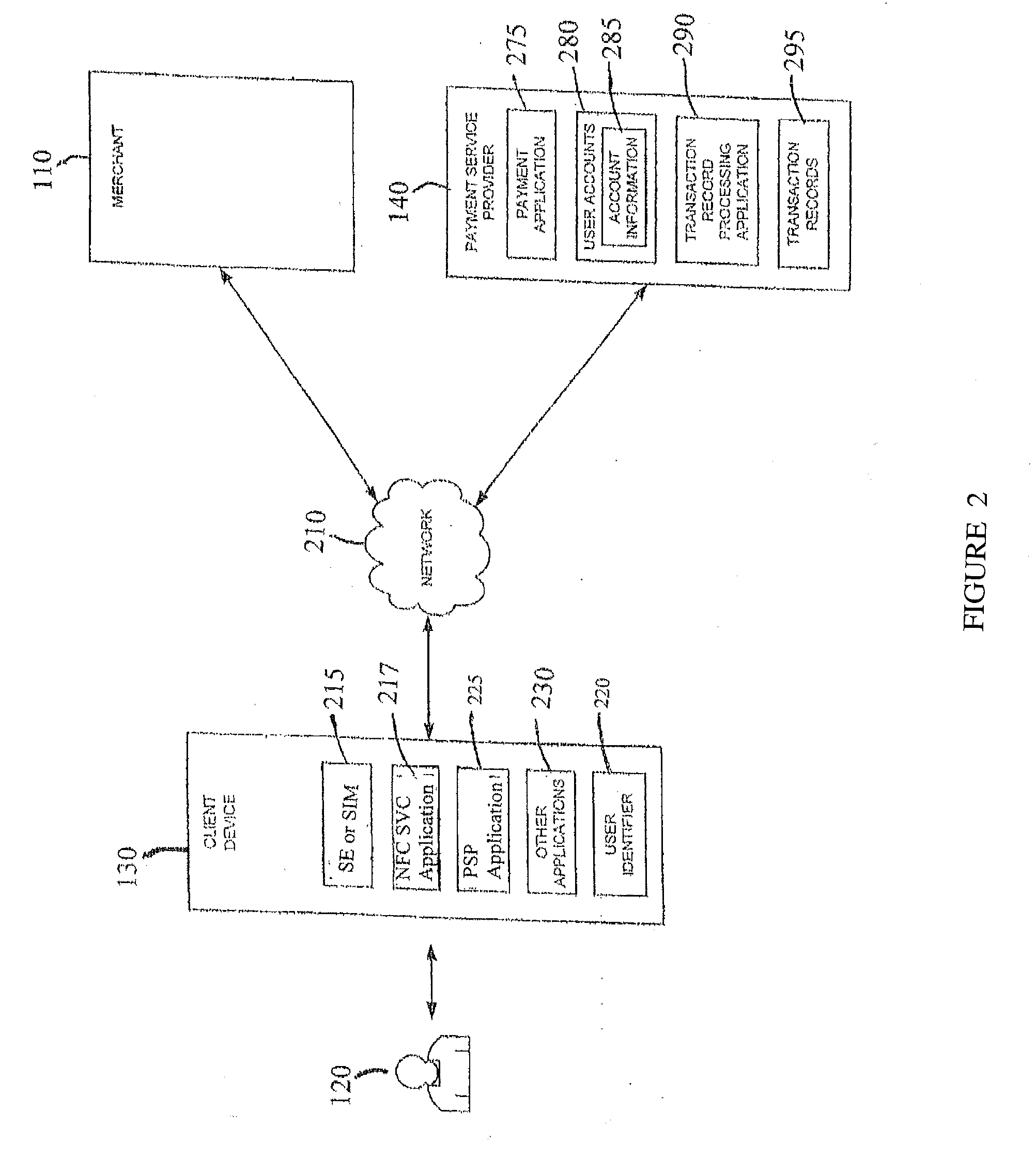
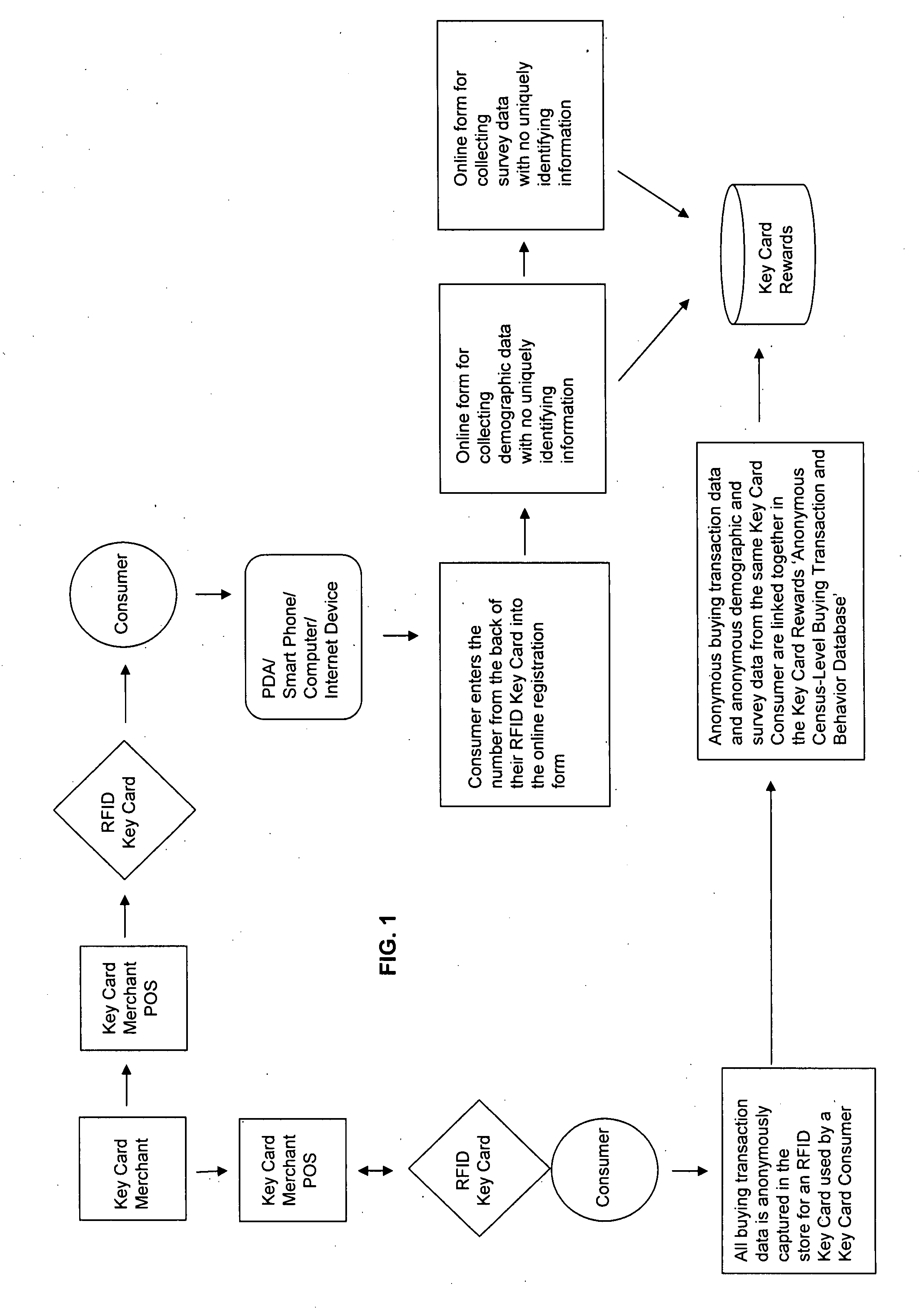
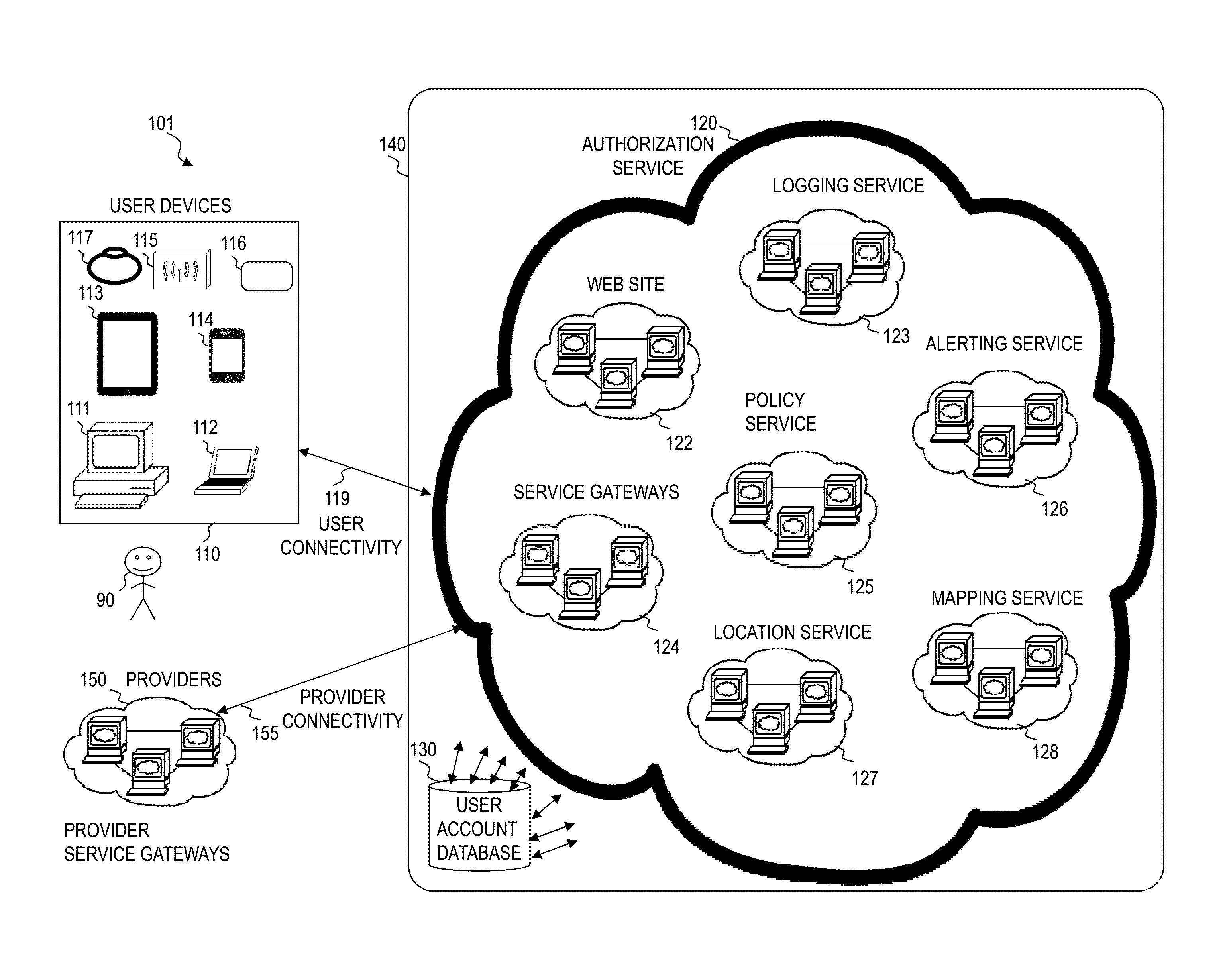
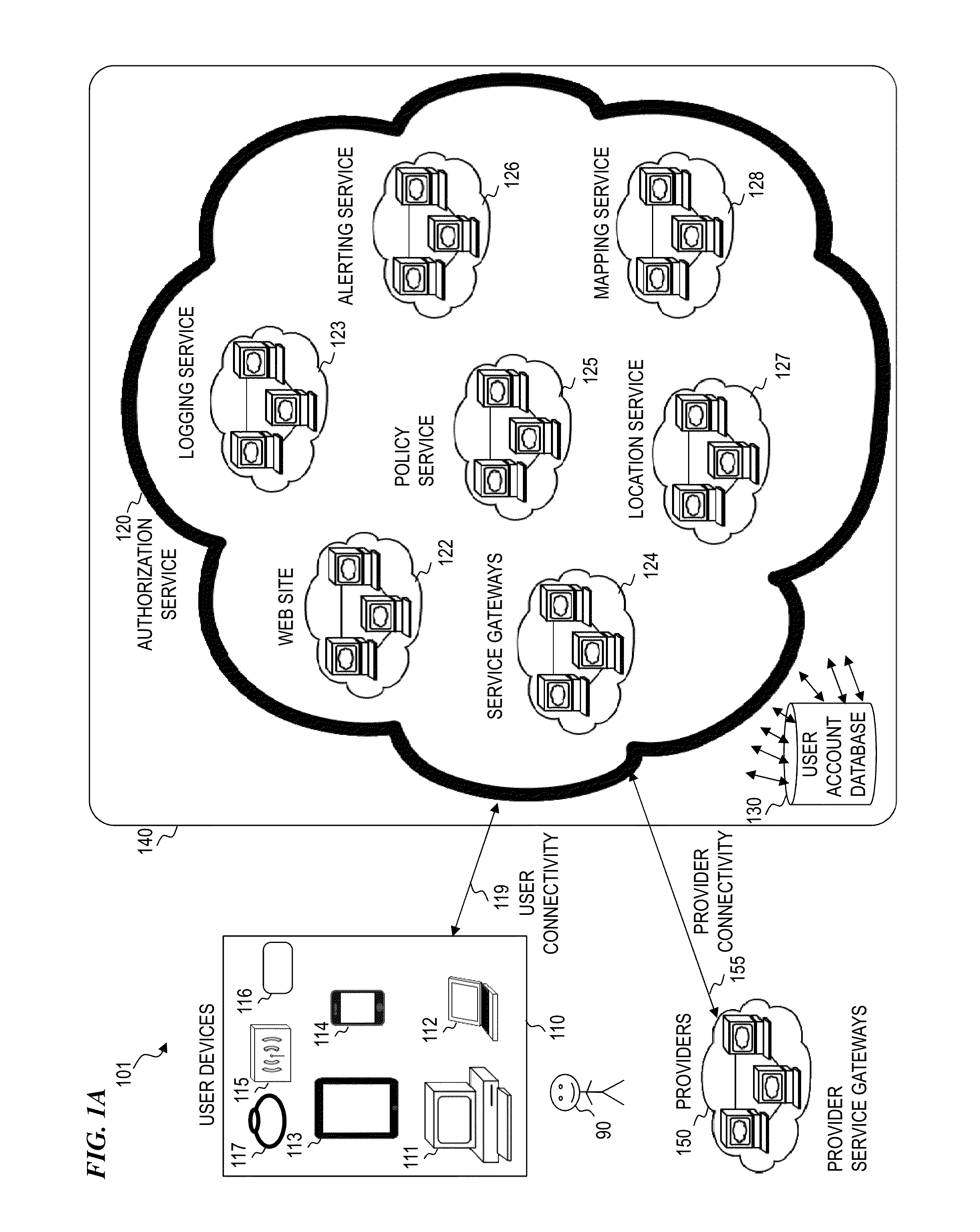
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true-personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with checks anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
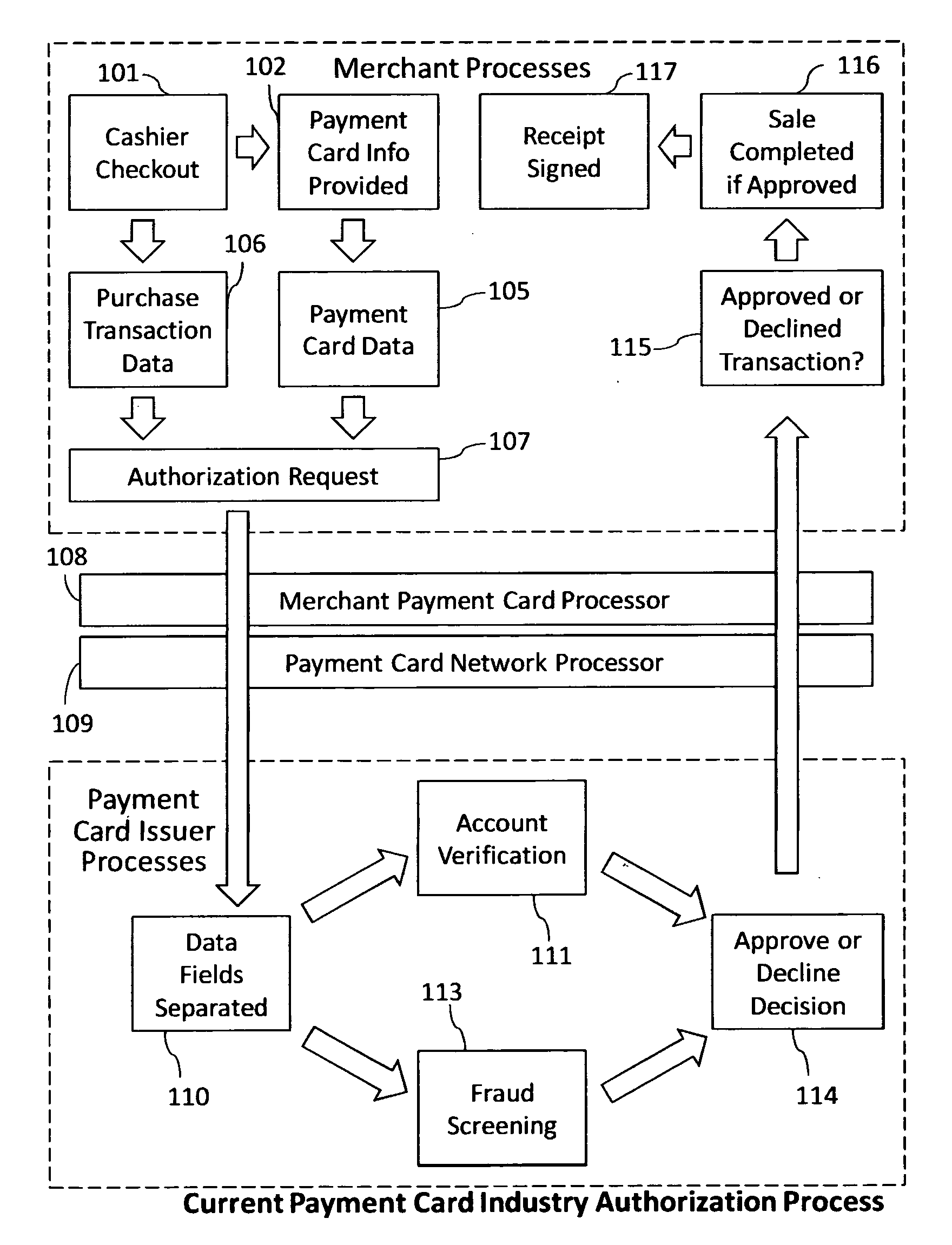
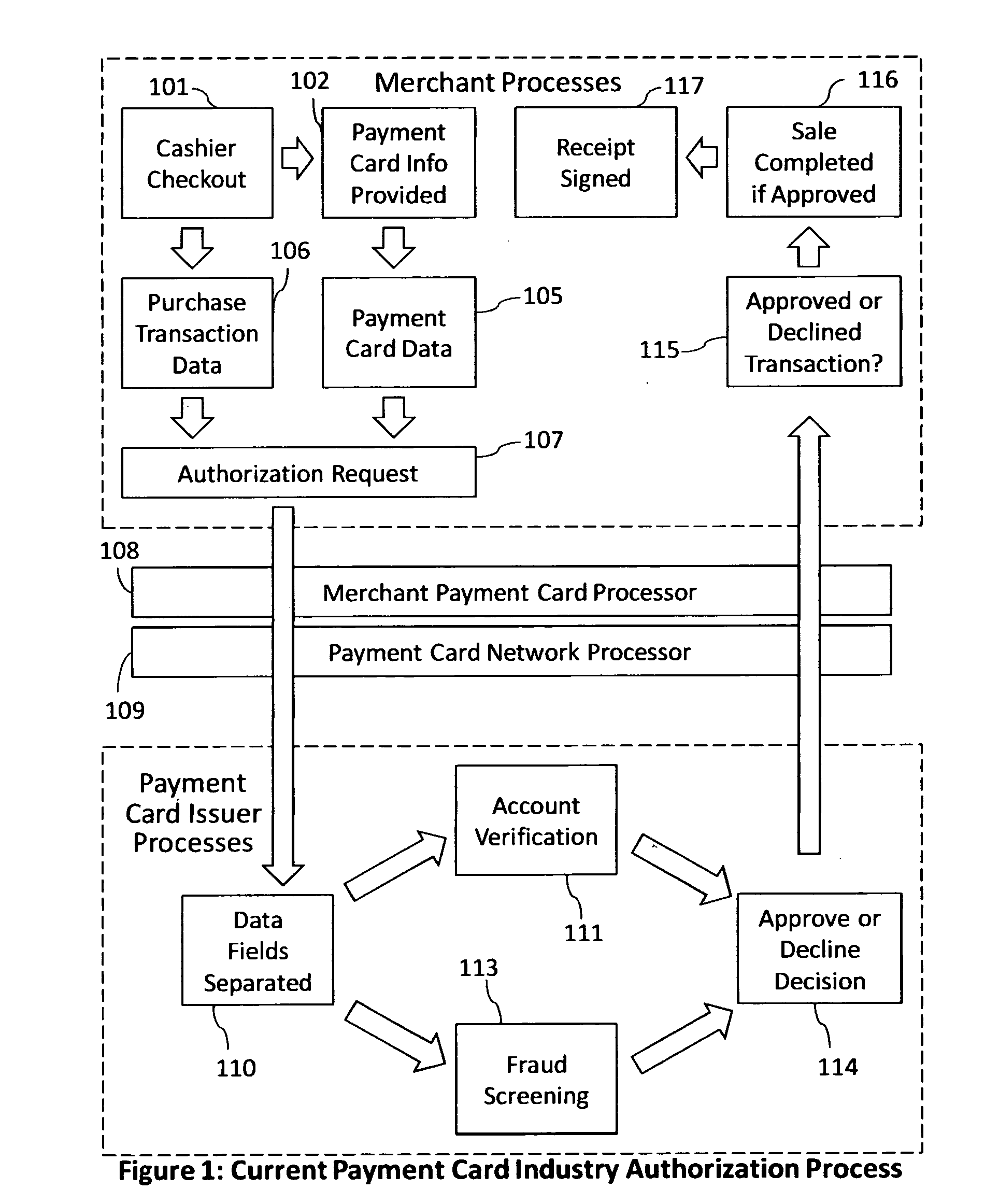
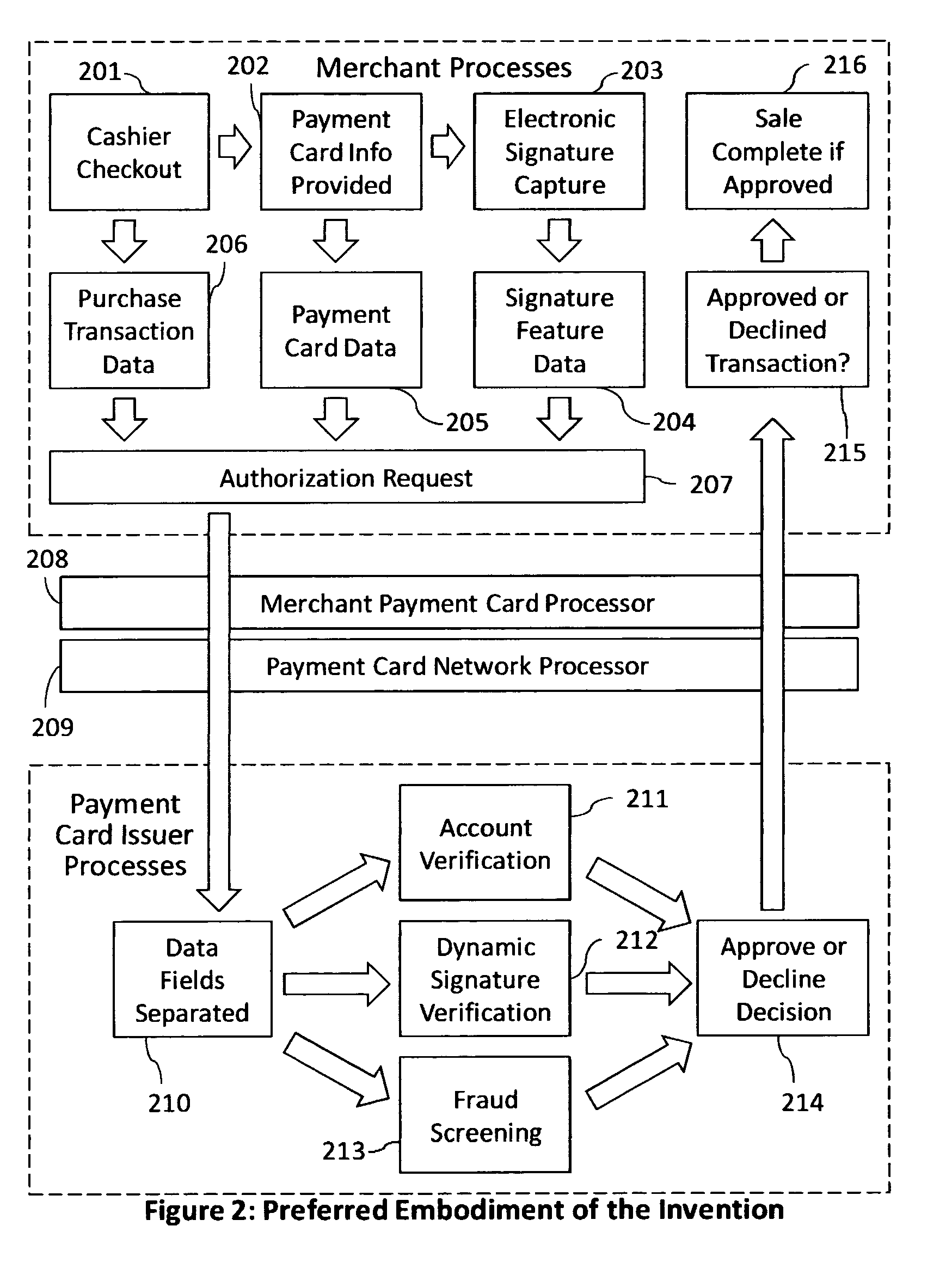
Reduction of transaction fraud through the use of automatic centralized signature/sign verification combined with credit and fraud scoring during real-time payment card authorization processes
InactiveUS20110238510A1Reduce payment card industry fraud lossReduce the amount of dataFinanceCharacter and pattern recognitionDigital signatureIdentity theft
A dynamic signature / sign biometric verification system for detecting and preventing fraudulent transactions is described. The system comprises remote digital signature / sign input devices, a means to extract spatial and temporal features from the signature, a means to transmit the signature / sign features along with customer identifier information to a centralized signature / sign verification authority, a means for combining signature / sign feature verification with other forms of fraud detection technology, and a means for transmitting the results of a signature / sign verification back to the remote location where the signature / sign was captured. The system was primarily developed for use in payment card industries (e.g. credit cards, debit cards) but has applicability to other centralized signature / sign verification applications such as Automated Teller Machine authorizations and other identity theft detection and monitoring services.
Owner:BIOCRYPT ACCESS LLC
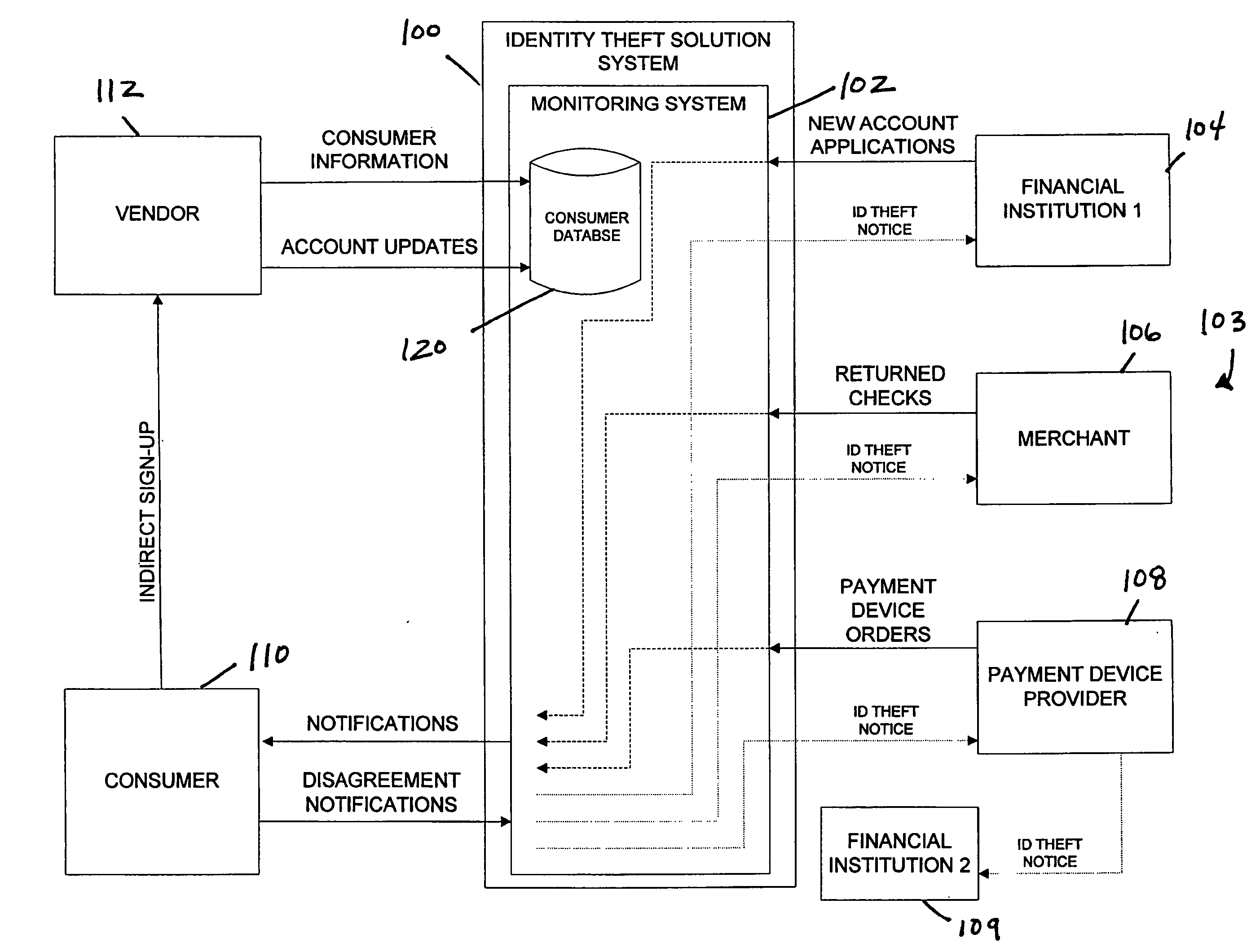
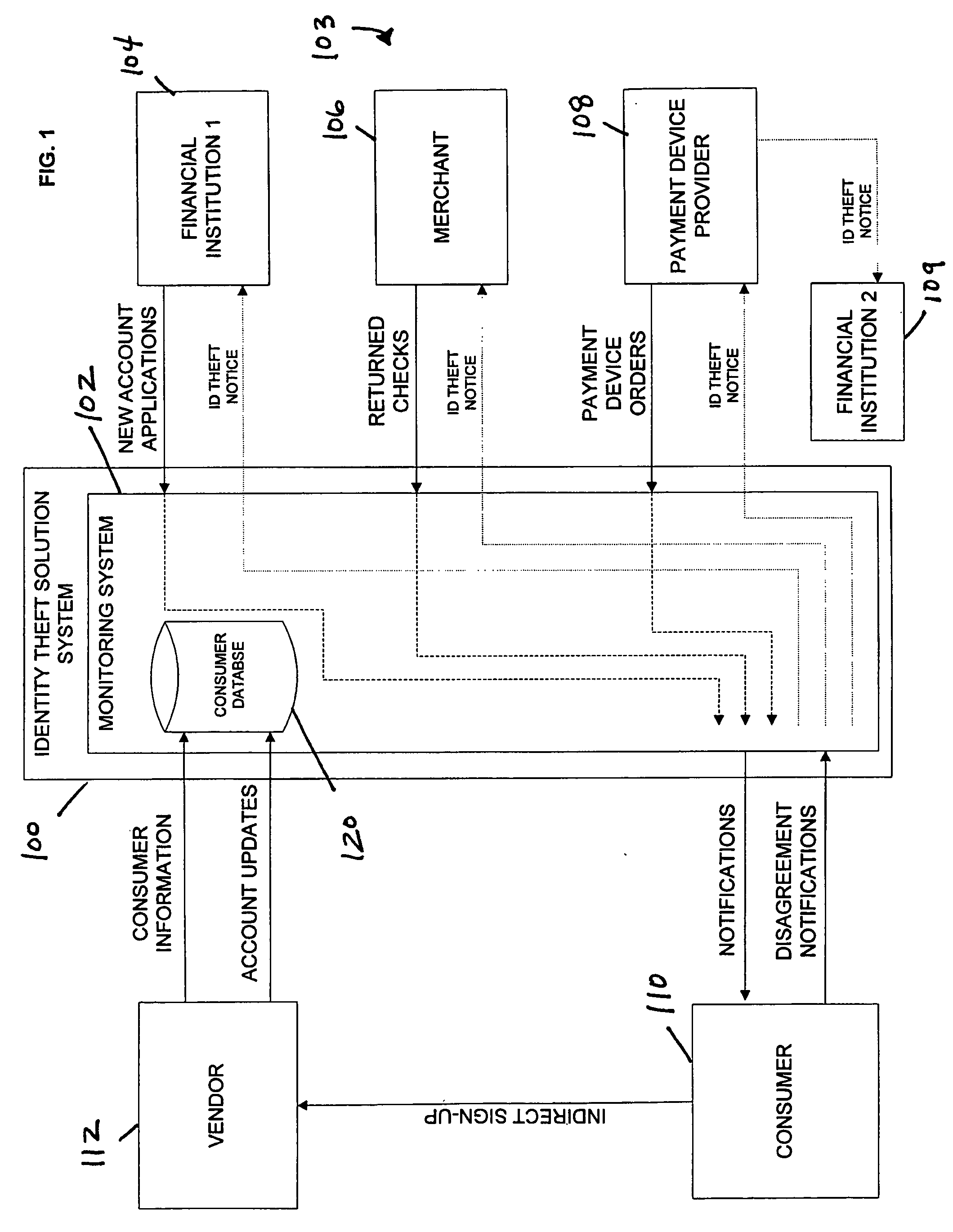
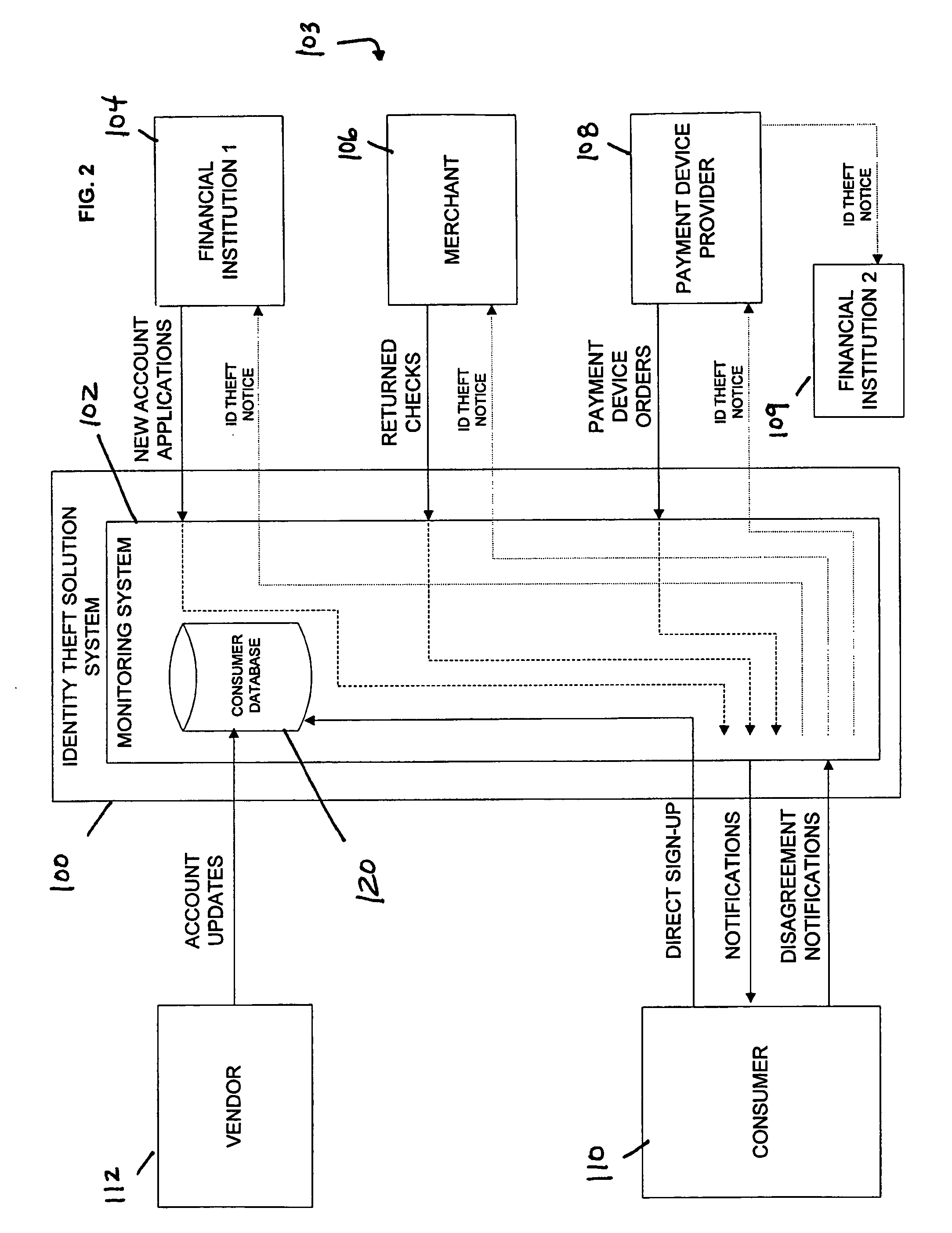
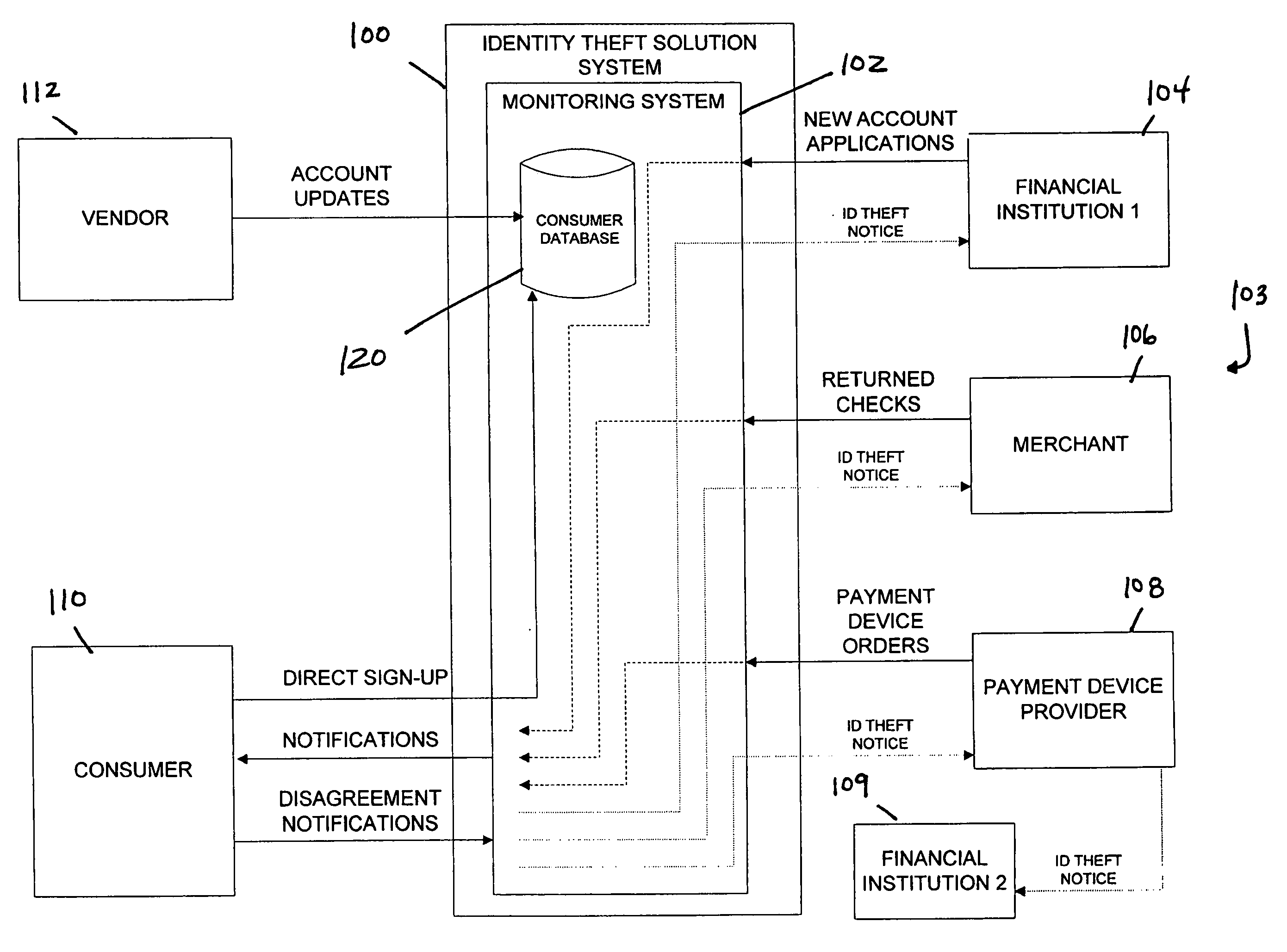
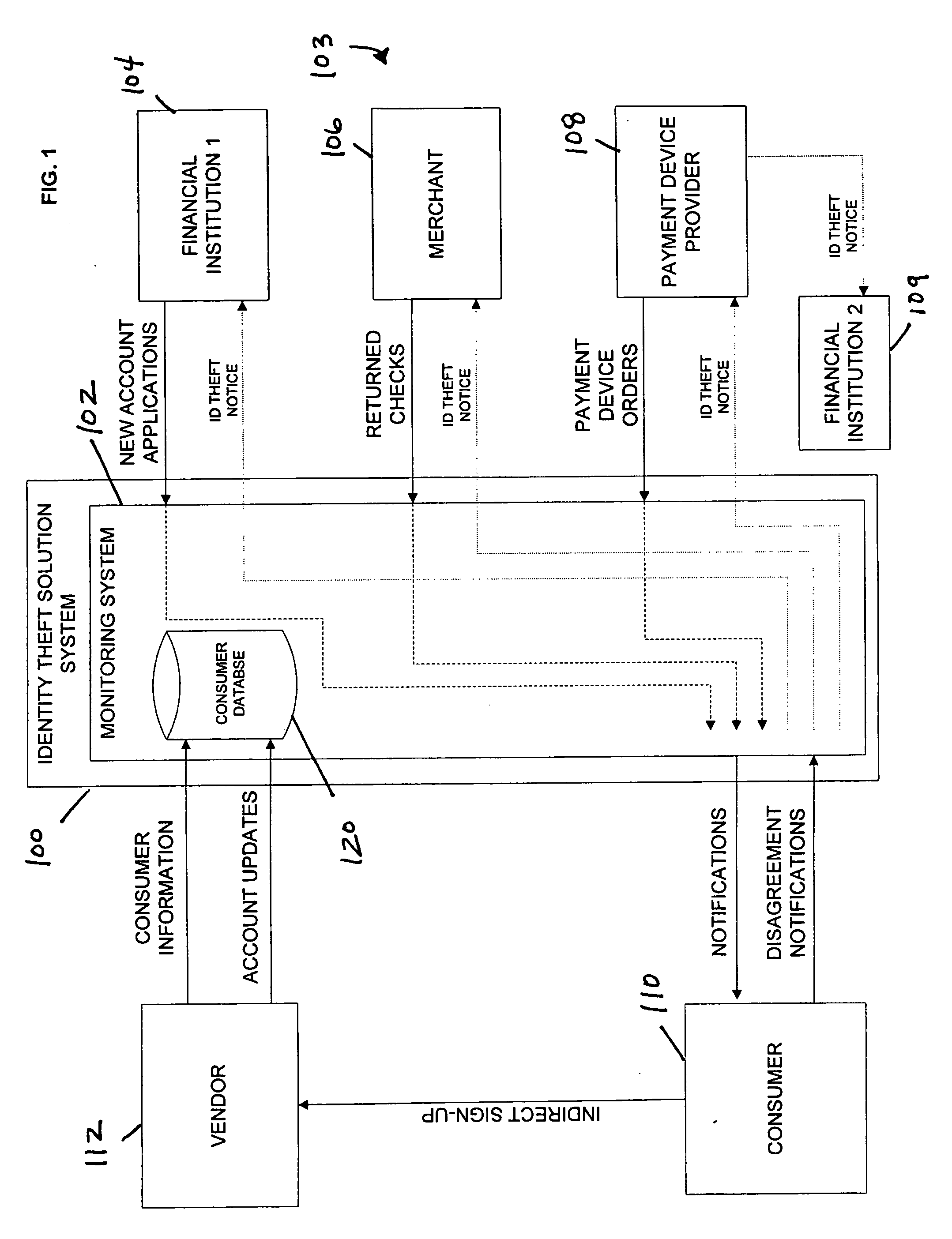
Identity theft monitoring and prevention
InactiveUS20060271457A1Prevent and limit potential financialPrevent and limit and reputation lossFinanceSecret communicationIdentity theftSystem configuration
Systems and methods of monitoring financial information of a consumer for fraudulent activity. One system can include an identity verification system configured to verify an identity of a consumer. The system can include a new account identity theft detection system configured to determine a first score for a new account application submitted by the consumer, the first score indicating likelihood that the new account application is fraudulent, and an address analyzer configured to determine a second score for an address modification submitted by the consumer, the second score indicating likelihood that the address modification is fraudulent.
Owner:EFUNDS CORP
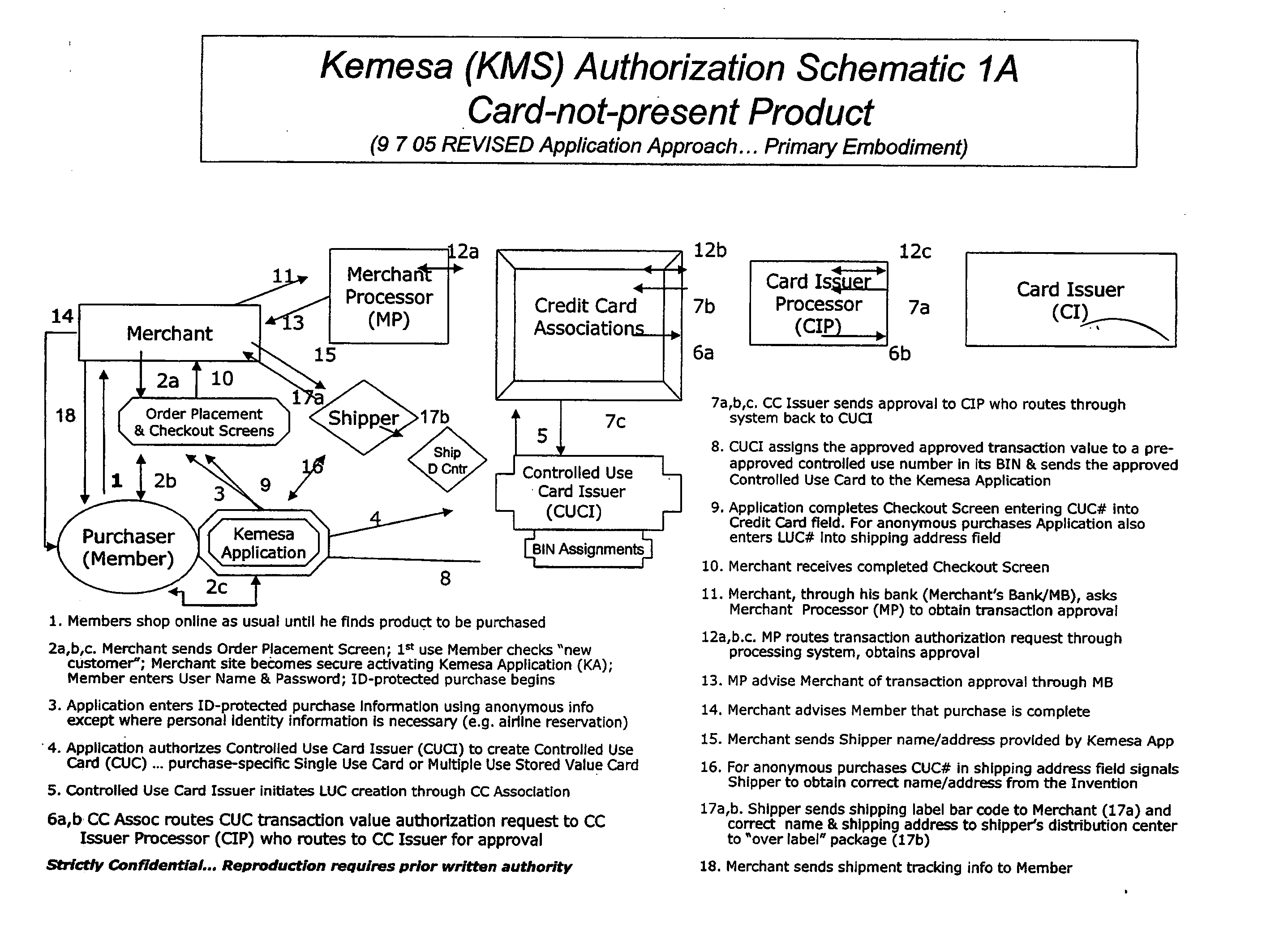
Identity theft and fraud protection system and method
ActiveUS20070083460A1Prevent theftMaximum anonymityFinanceDigital data protectionCredit cardEmail address
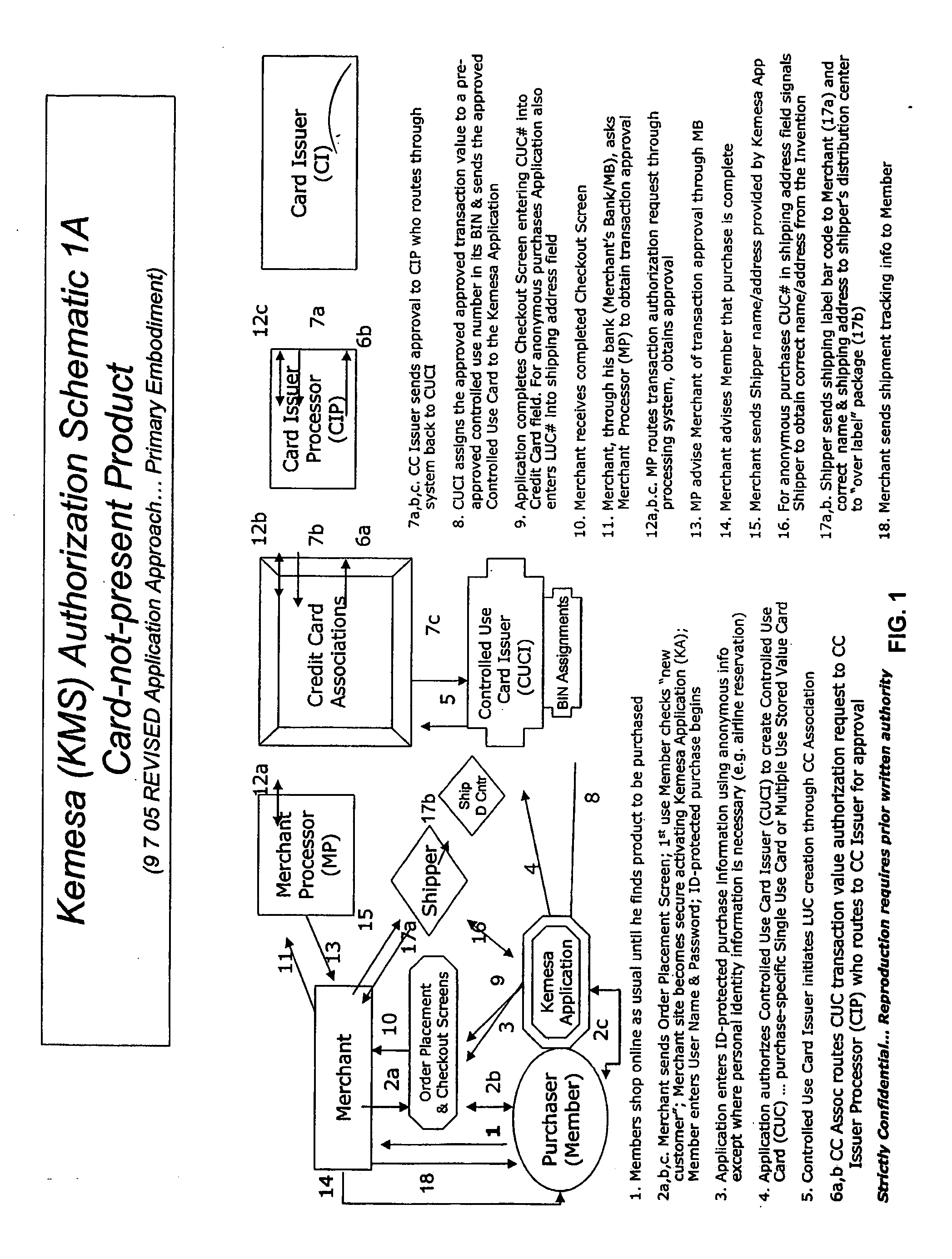
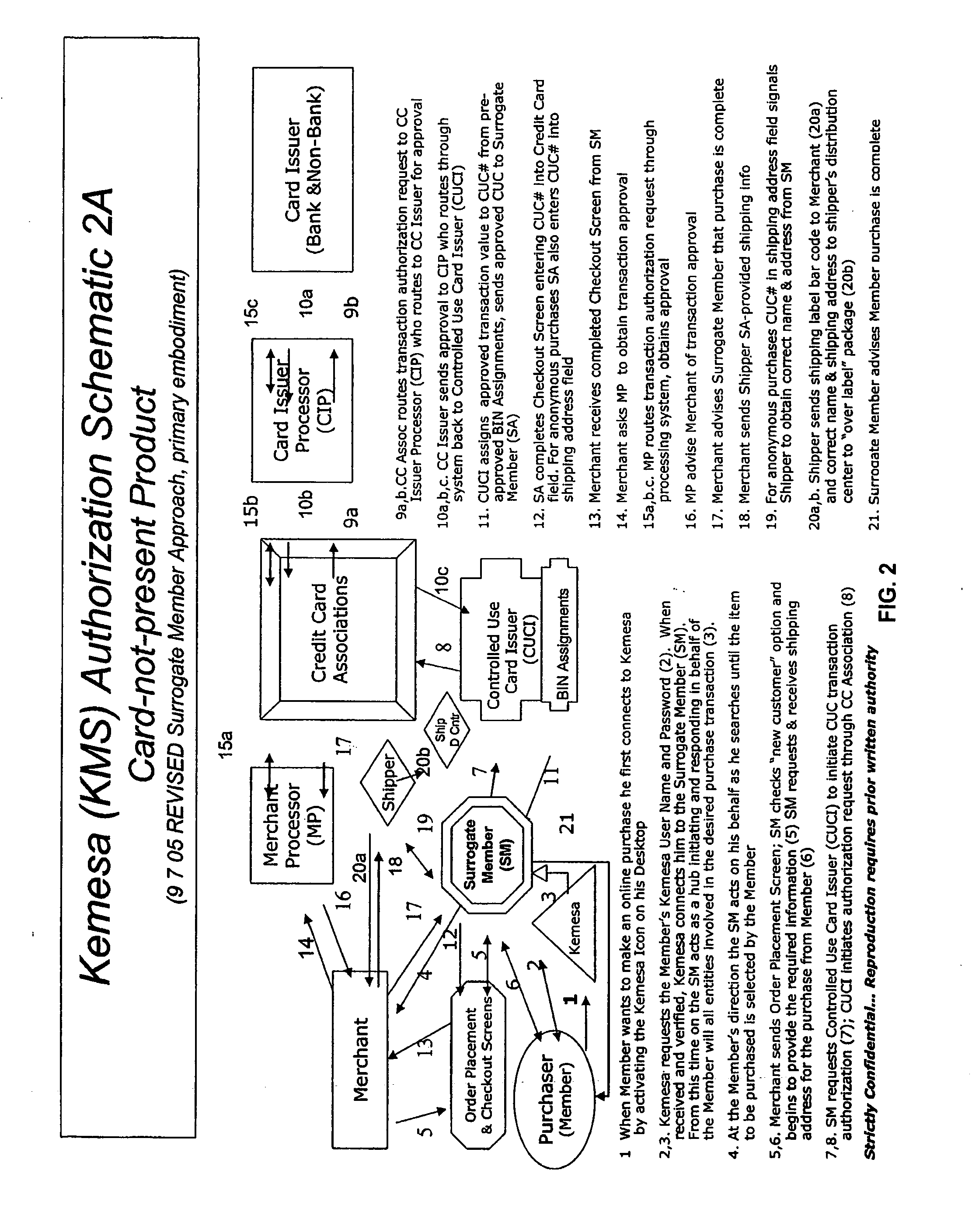
A system and method for preventing personal identity theft when making online and offline purchases requires a purchaser to first subscribe and become a member user by registering and providing relevant personal identity information. Once registered, the member is assigned a user name and a password. The subscribing member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the member for use to make each purchase transaction. The CUC is anonymous with respect to user (member) identity and may be a purchase-specific single-use card or a multiple-use stored value card with no traceable connection to any other financial account. When the member makes a secure online purchase, the system software enters anonymous information (i.e. not revealing the member's real name, email address, billing information, etc.) on the merchant's order placement screen, except in instances where the member's real identity information is required (e.g. airline tickets). The merchant receives the completed checkout screen, obtains credit approval through a credit card association, and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s).
Owner:VIPR SYST +1
System and method for early detection and prevention of identity theft
InactiveUS7548886B2Identity theft has increasedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsIdentity theftMobile device
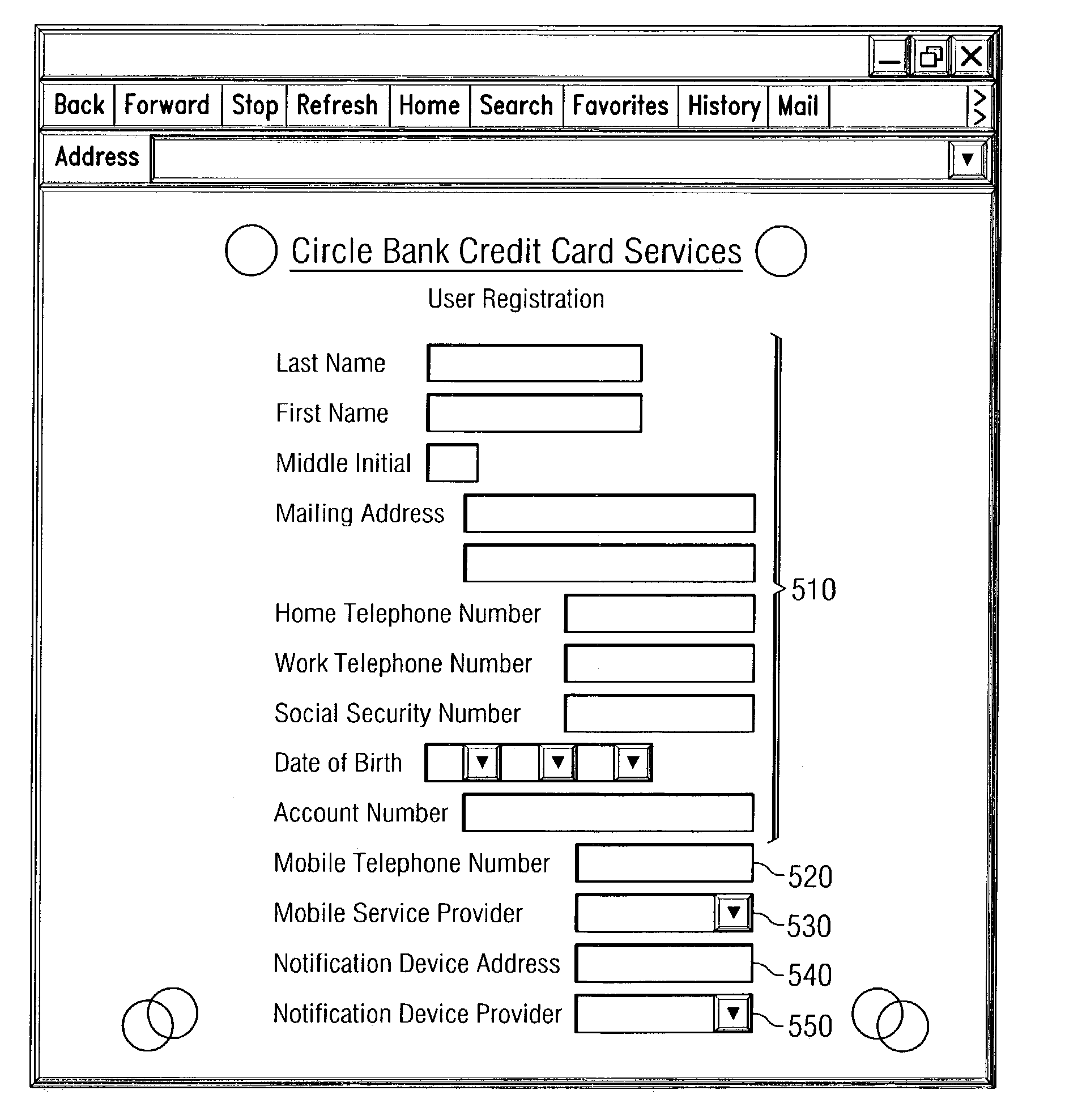
A system and method for early detection of identity theft are provided. An authorized user establishes an identity with an organization's computing system and registers a mobile device and a notification device with the organization's computing system. When a use of the identity is attempted, a record associated with the identity is retrieved and a request is sent to the registered mobile device for location information. The current location of the mobile device is compared to the location of the source of the request for authorization. If the current location of the mobile device is not within an area of the source of the authentication request, information about the attempted use is compared with the registered notification criteria. If the conditions of the attempted use fall within the notification criteria, a notification message is sent to the notification device.
Owner:PAYPAL INC
System and method for preventing identity theft using a secure computing device
ActiveUS20050071282A1Secure transmissionDigital data processing detailsMultiple digital computer combinationsSecure transmissionIdentity theft
A system and method for effecting secure transactions over a computer network in a manner designed to foil identity theft perpetrated from an untrusted computer. A connection from a client computer to the network wherein the client computer provides a user interface for a user, a connection from a server computer to the network, and a connection from a portable secure computing device to the network provides for secure transmission of private confidential user information from the user to a server. The private information is transmitted directly from the secure computing device to the server over the secure connection without possibility of capture on the computer with which the user is interacting.
Owner:GEMPLU
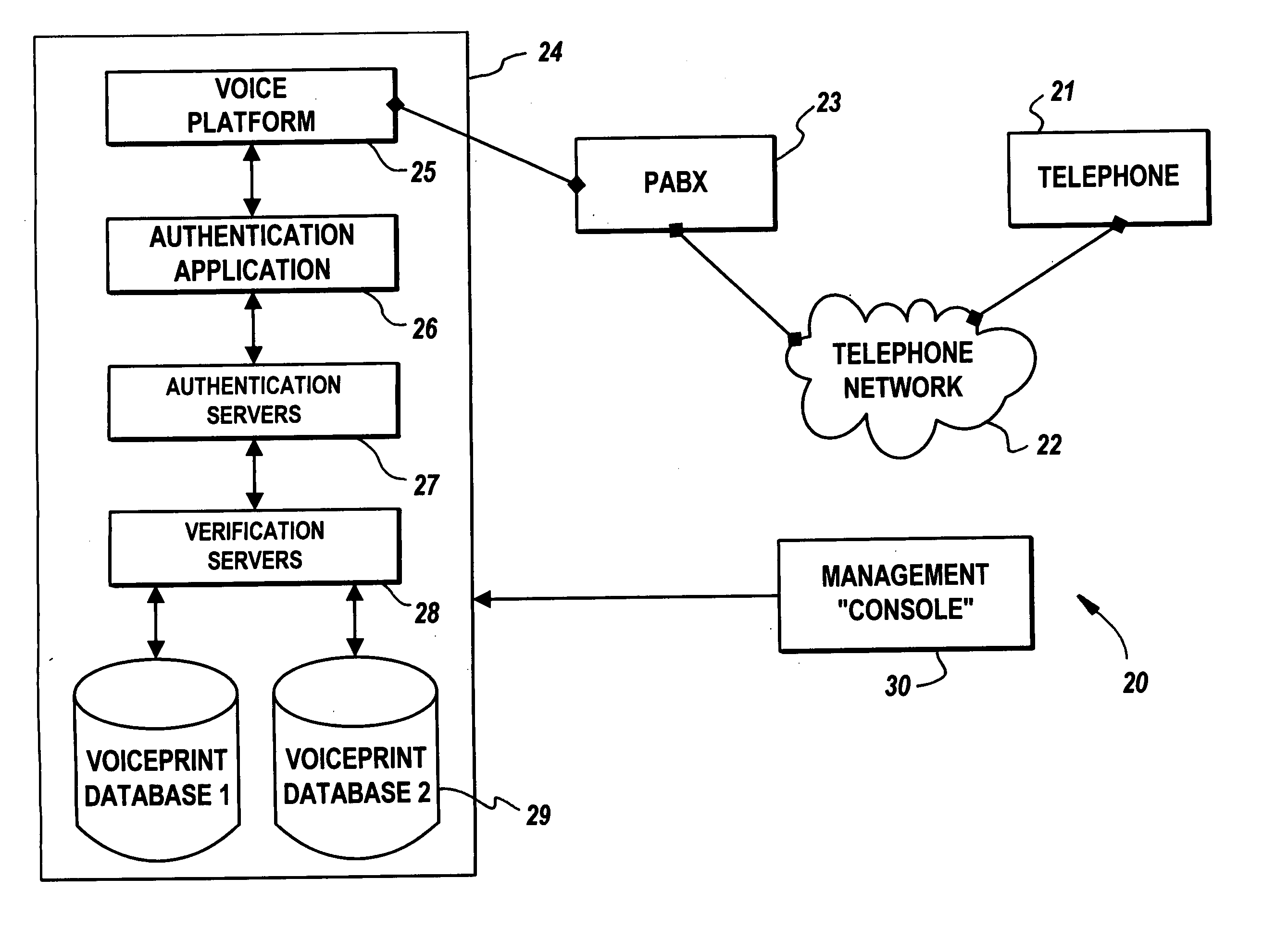
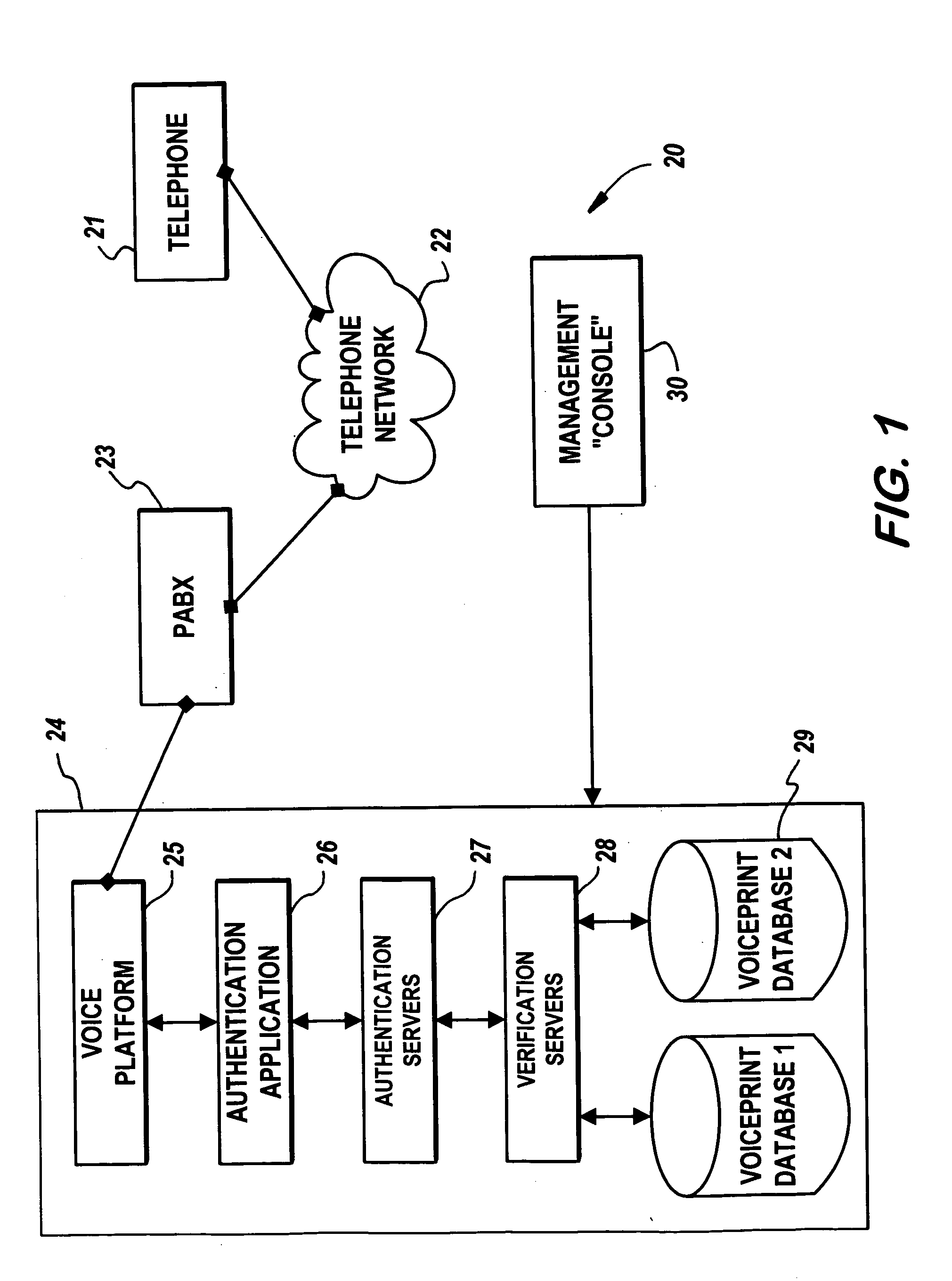
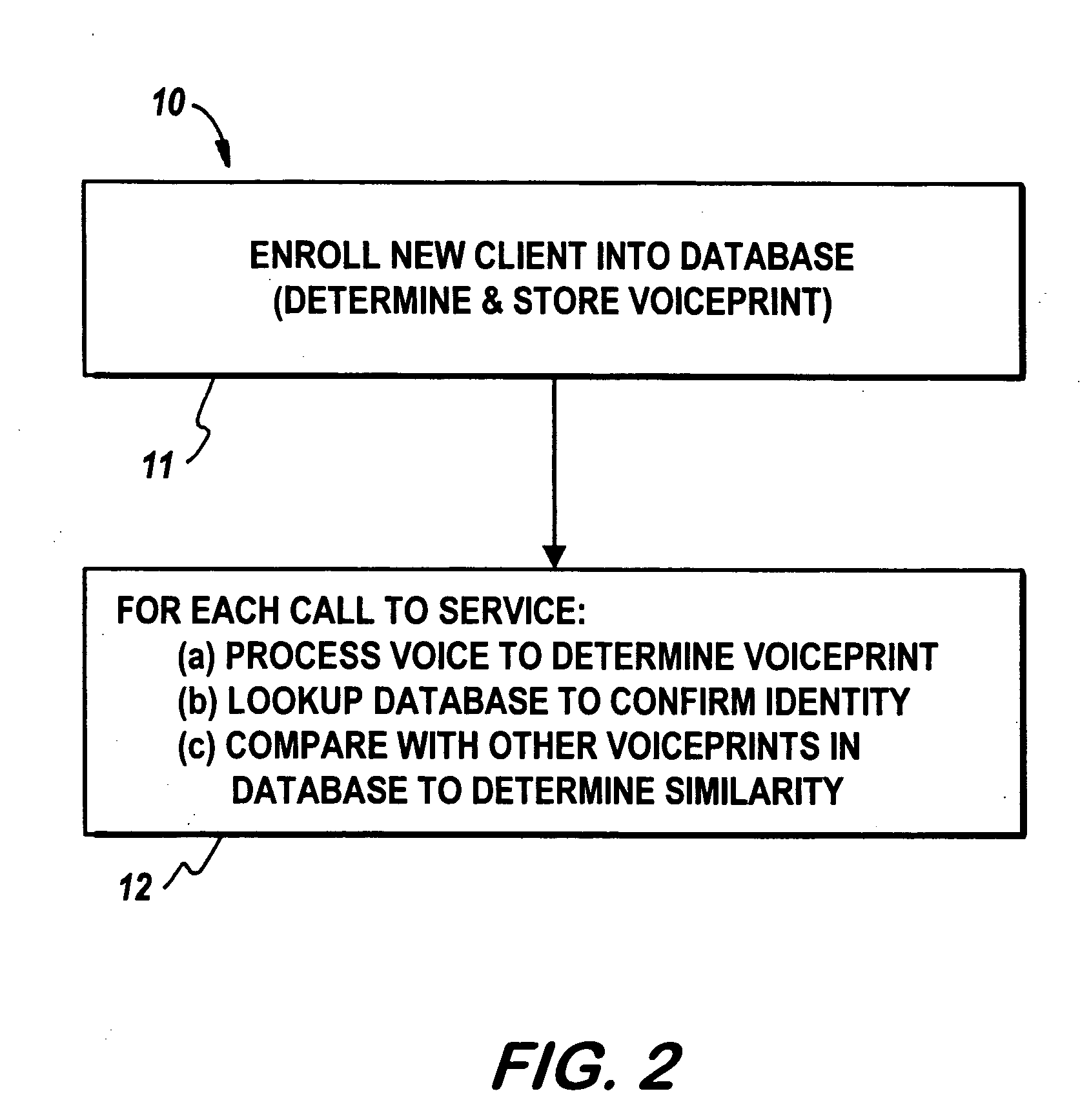
Voice recognition system and method
InactiveUS20050125226A1Reduce the possibilityDigital data authenticationIndividual entry/exit registersIdentity theftSpeech identification
In a voice transmission system, a method of reducing the likelihood of identity theft, the method including the steps of: (a) recording the voice of a series of users and deriving a corresponding voiceprint from each voice, the voiceprint having at least a corresponding first series of measurable identification features associated with the voice. (b) —for a new voice introduced to the authentication system: deriving a new voiceprint for the new voice; and comparing the new voiceprint with voiceprints stored in the database to determine correlations there between.
Owner:VECOMMERCE
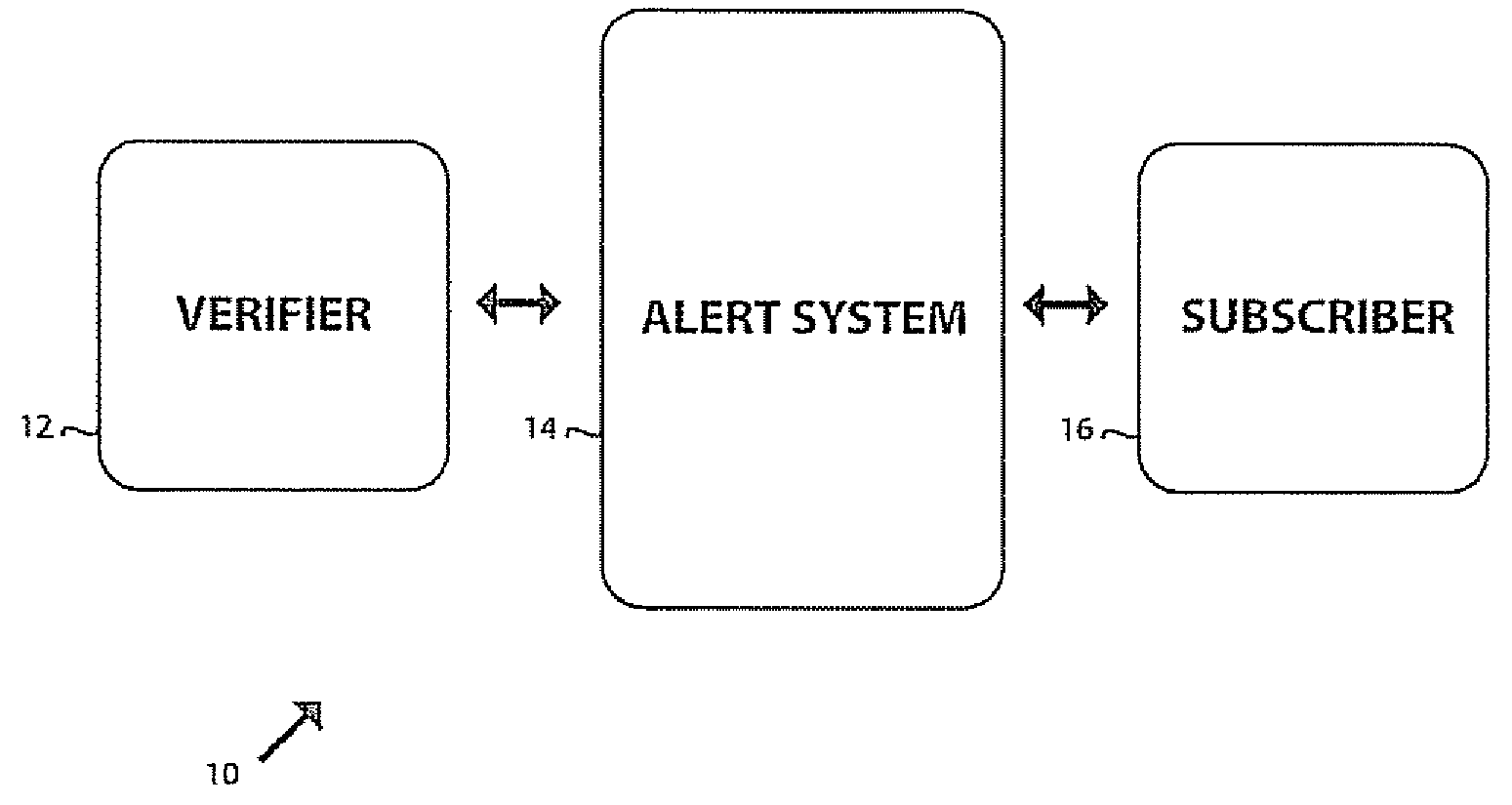
Identify theft protection and notification system
InactiveUS20070093234A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsIdentity theftData mining
An information monitoring and alert system is provided which registers subscribers and verifiers with a central alert system. The alert system provides an interface for the verifiers to submit queries relating to identification information. Information in this query is compared to the stored data submitted by the subscriber during registration and if a match occurs the subscriber is notified that the identification has been used for a certain purpose. The alert system only stores an encrypted value of the identification with only contact information which is preferably anonymous. Any other information is deleted after registration. The subscriber upon being alerted of the use of the identification is instructed to authorize or reject the transaction pertaining to the query.
Owner:WILLIS GROUP +2
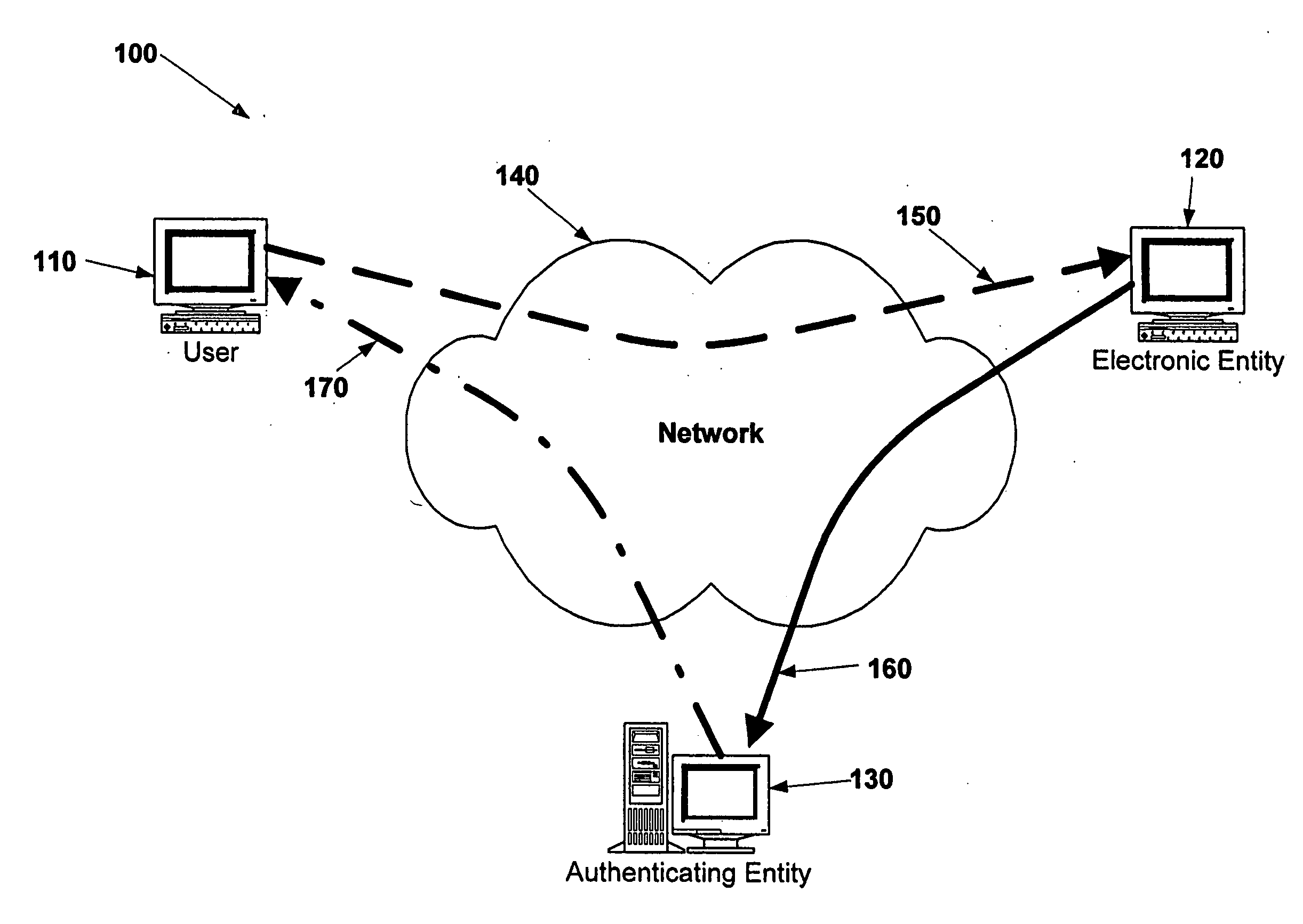
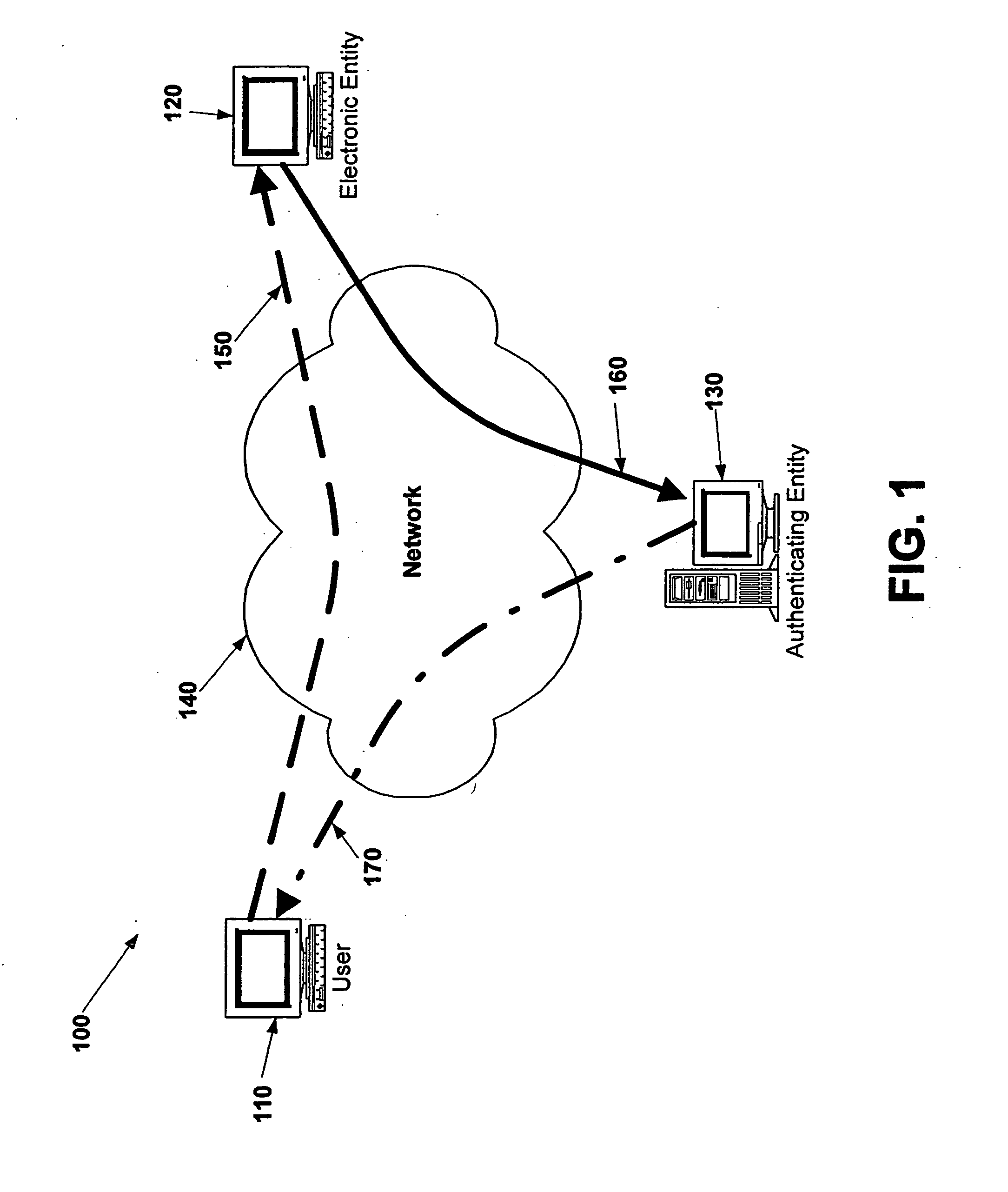
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
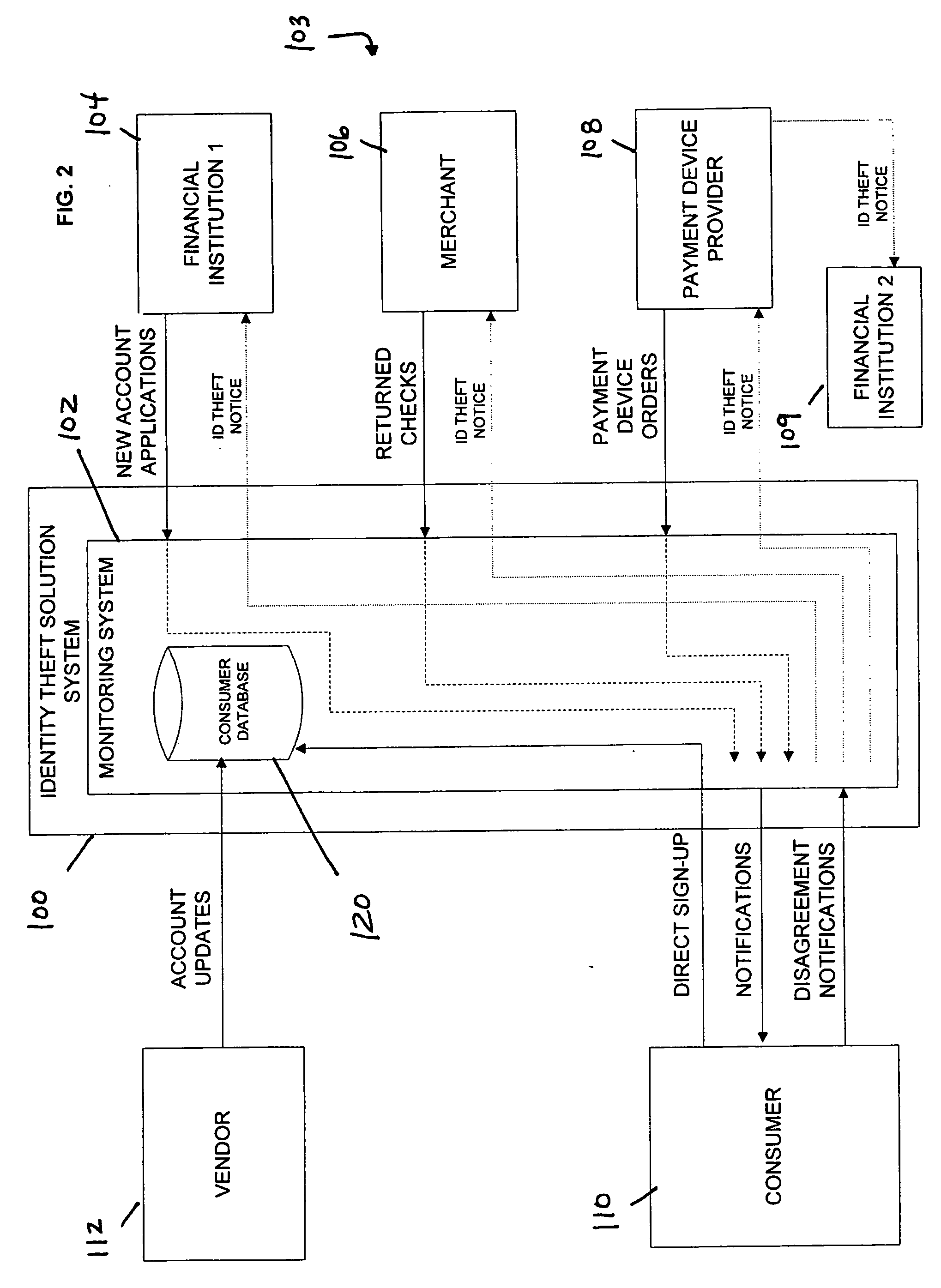
Debit-based identity theft monitoring and prevention
ActiveUS20060271456A1Prevent and limit potential financialPrevent and limit and reputation lossFinancePayment architectureIdentity theftCheque
Systems and methods of monitoring financial information of a consumer for fraudulent activity. One method can include receiving an account closure event from an event provider, determining if the account closure event is associated with financial information of the consumer, generating a notification, and providing the notification to the consumer. Another method can include receiving a returned check event from an event provider, determining if the returned check event is associated with financial information of the consumer, generating a notification, and providing the notification to the consumer.
Owner:FIDELITY INFORMATION SERVICES LLC
Anti-identity theft system and method
InactiveUS20060239512A1Reduce and eliminate identity theftEliminate needElectric signal transmission systemsDigital data processing detailsIdentity theftData bank
A method of entering information for identity validation of an individual is provided, where an individual enters their personal information and biometric information that is compared to one or more databases to verify the identity of the individual. Once the identity is verified, the individual selects one or more random biometrics that are stored as random biometric information on a database for later identity verification purposes. When the individual later wants to review or change his personal information, or when the individual wants to perform or consummate a transaction, the individual simply submits his / her one or more random biometrics that were previously selected and stored in the database. The biometrics are compared with the random biometric information in the database, and if the one or more random biometrics match the random biometric information in the database, then the identity is verified.
Owner:IMME
Method and system for preventing and detecting identity theft
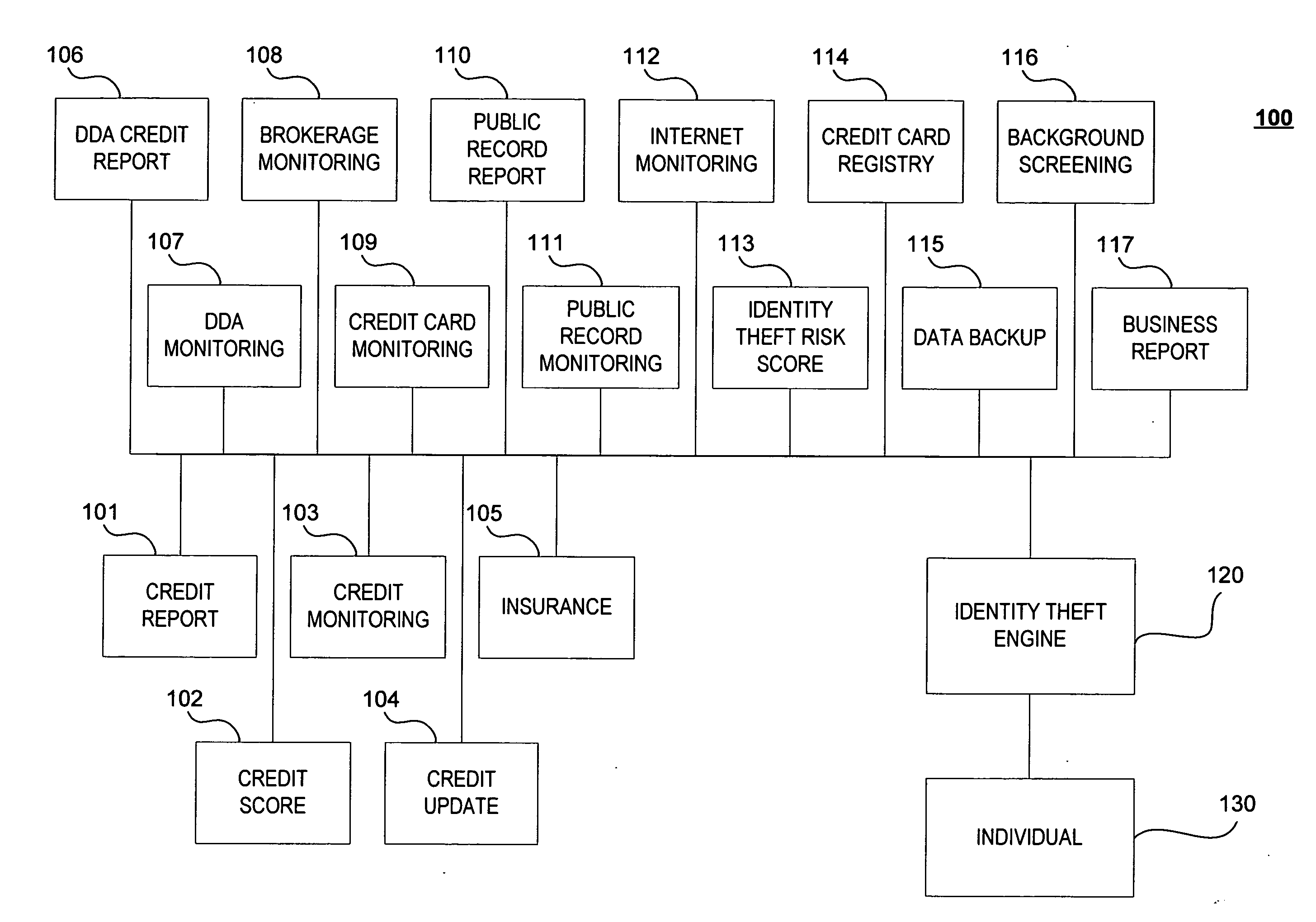
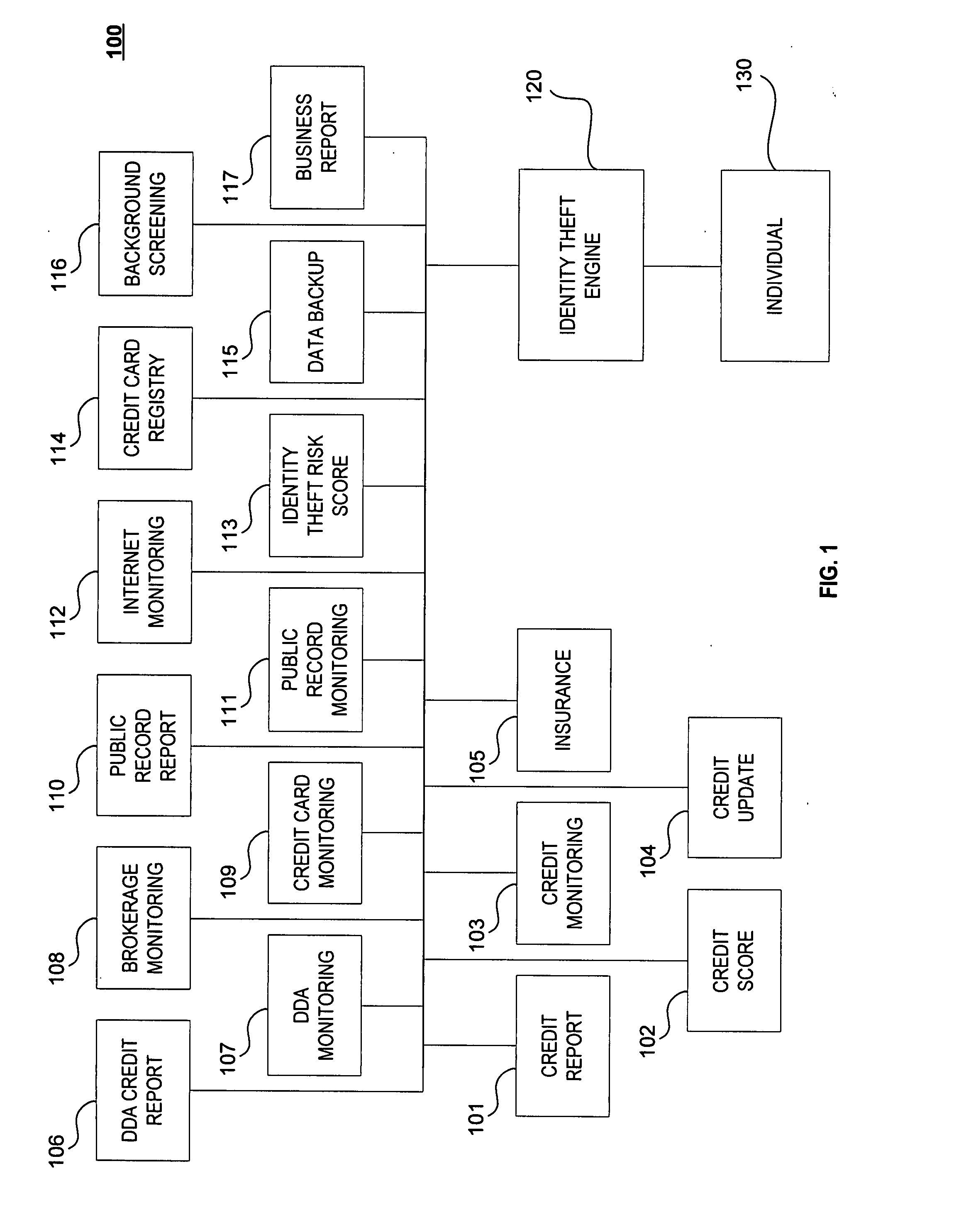
ActiveUS20070244807A1Preventing and detecting identity theftStop in trackFinanceCredit cardData provider
A system, method and computer program product for receiving information relating to a financial account of an individual from at least one first data provider; receiving information relating to at least one of an identity theft expense reimbursement insurance policy of the individual, a public information relating to the individual, an identity theft risk score of the individual, a credit card registry of the individual, a backup data relating to the individual, a background information of the individual, and a business report relating to the individual, from at least one second data provider; and preparing a report relating to the individual's identity theft based on the information.
Owner:AURA SUB LLC +1
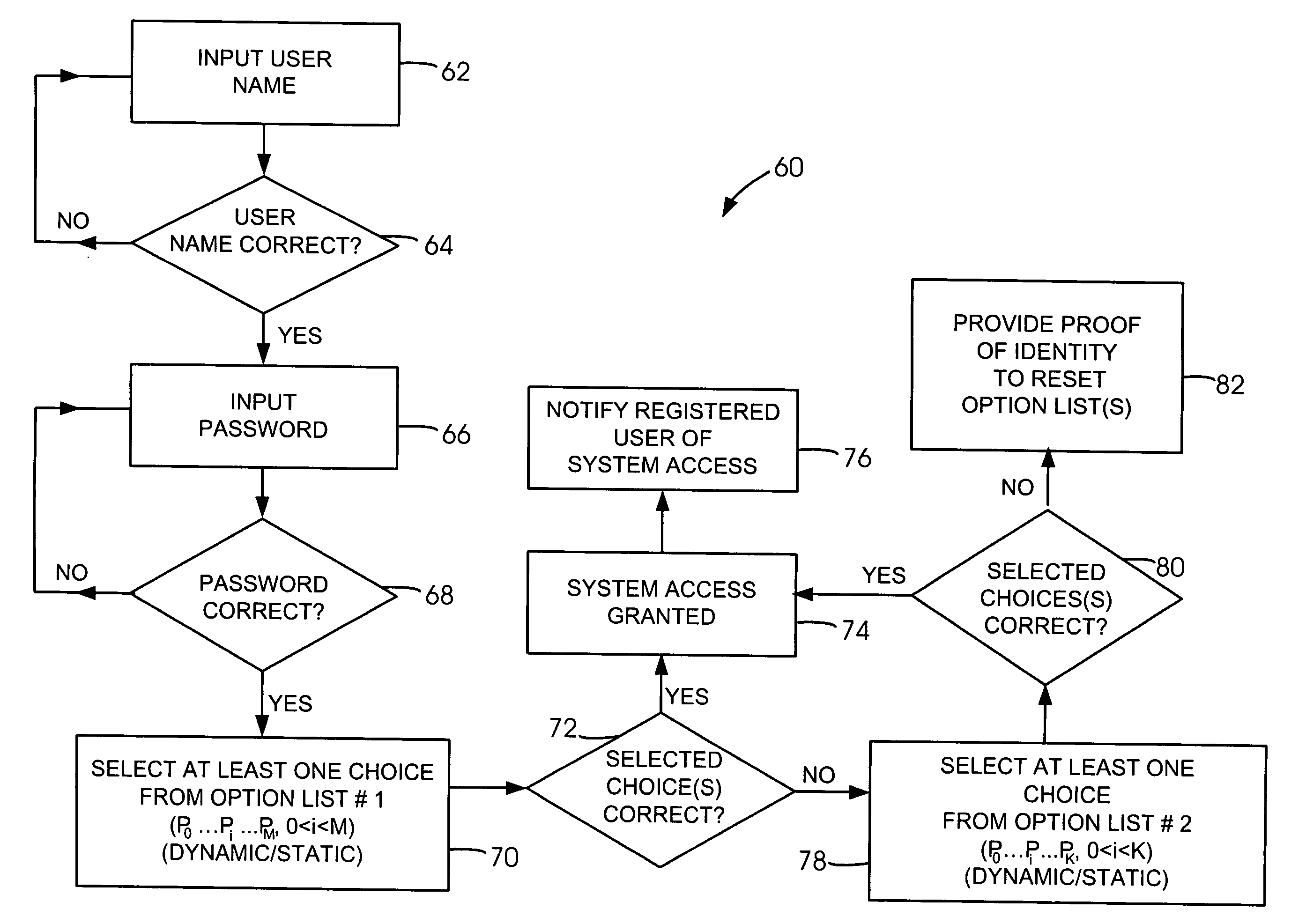
Strategy-driven methodology for reducing identity theft
A strategy-driven methodology for reducing identity theft comprises the steps of attempting to gain system access, and presenting at least one list of user choices instead of granting system access, as practiced conventionally. The presented list contains at least one choice that is preset by a registered user. Other steps include selecting at least one choice from the presented list, and granting system access if the selected choice matches the preset choice.
Owner:MADHOGARHIA SUSHIL
Negotiable instrument with fraud protection
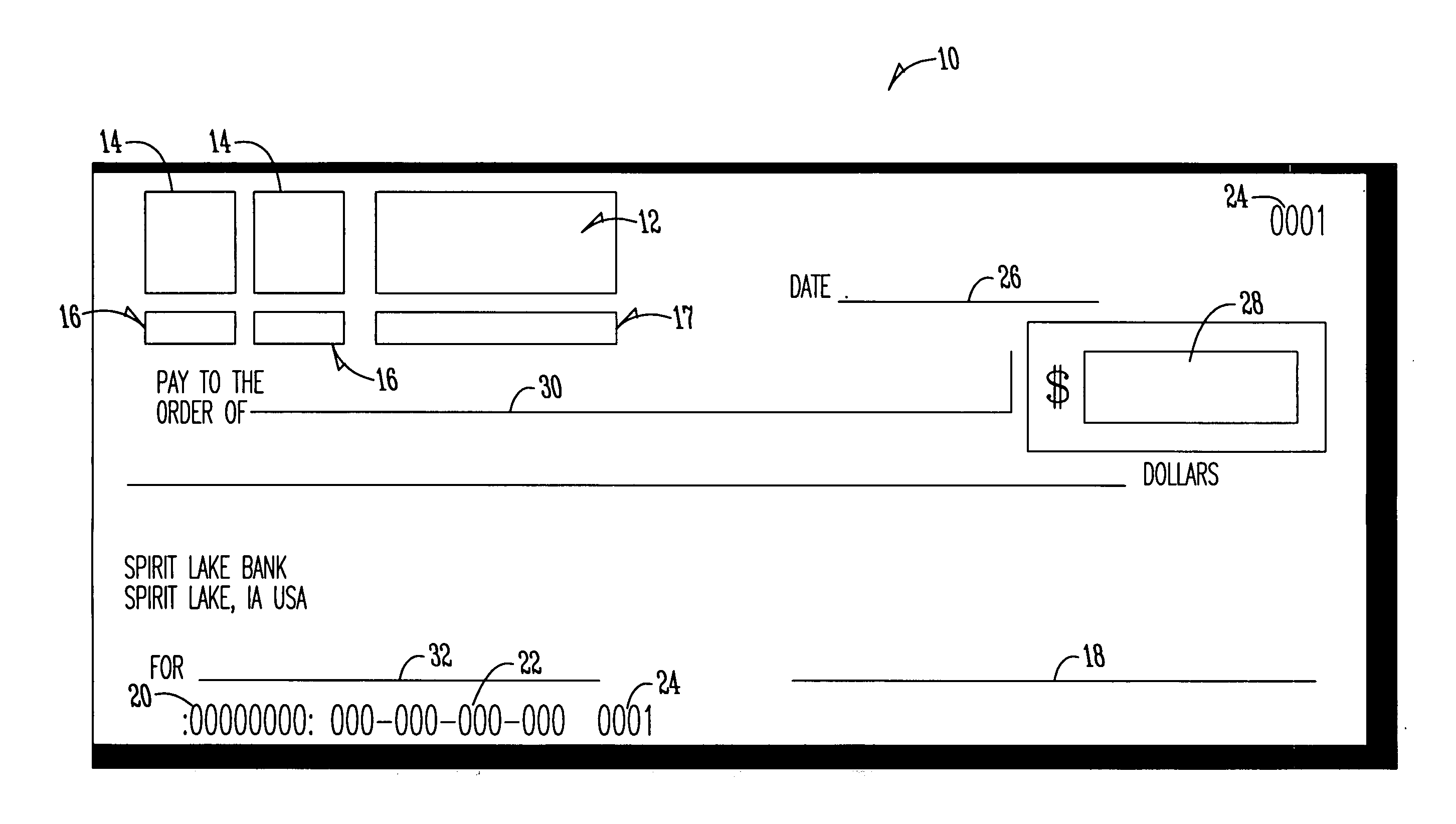
ActiveUS20060144924A1Effective positioningMaximize deterrence effectComplete banking machinesFinanceBarcodeIdentity theft
A negotiable instrument with fraud and identity theft protection and method of use is provided. The method includes step accepting a negotiable instrument having a pre-printed bar code, reading the bar code on a negotiable instrument using a bar code scanner, and receiving from the writer a code presented to the merchant for deriving personal information associated with the account holder and banking information associated with the account from the bar code. The method also having the step of comparing the personal identification information from the bar code with information provided by the writer. The merchant using the bank processing information derived from the bar code to process the negotiable instrument.
Owner:STOVER MERLIN D
Mobile User Identify And Risk/Fraud Model Service
InactiveUS20090307778A1Risk dataGeneration of riskDigital data processing detailsAnalogue secracy/subscription systemsIdentity theftBluetooth
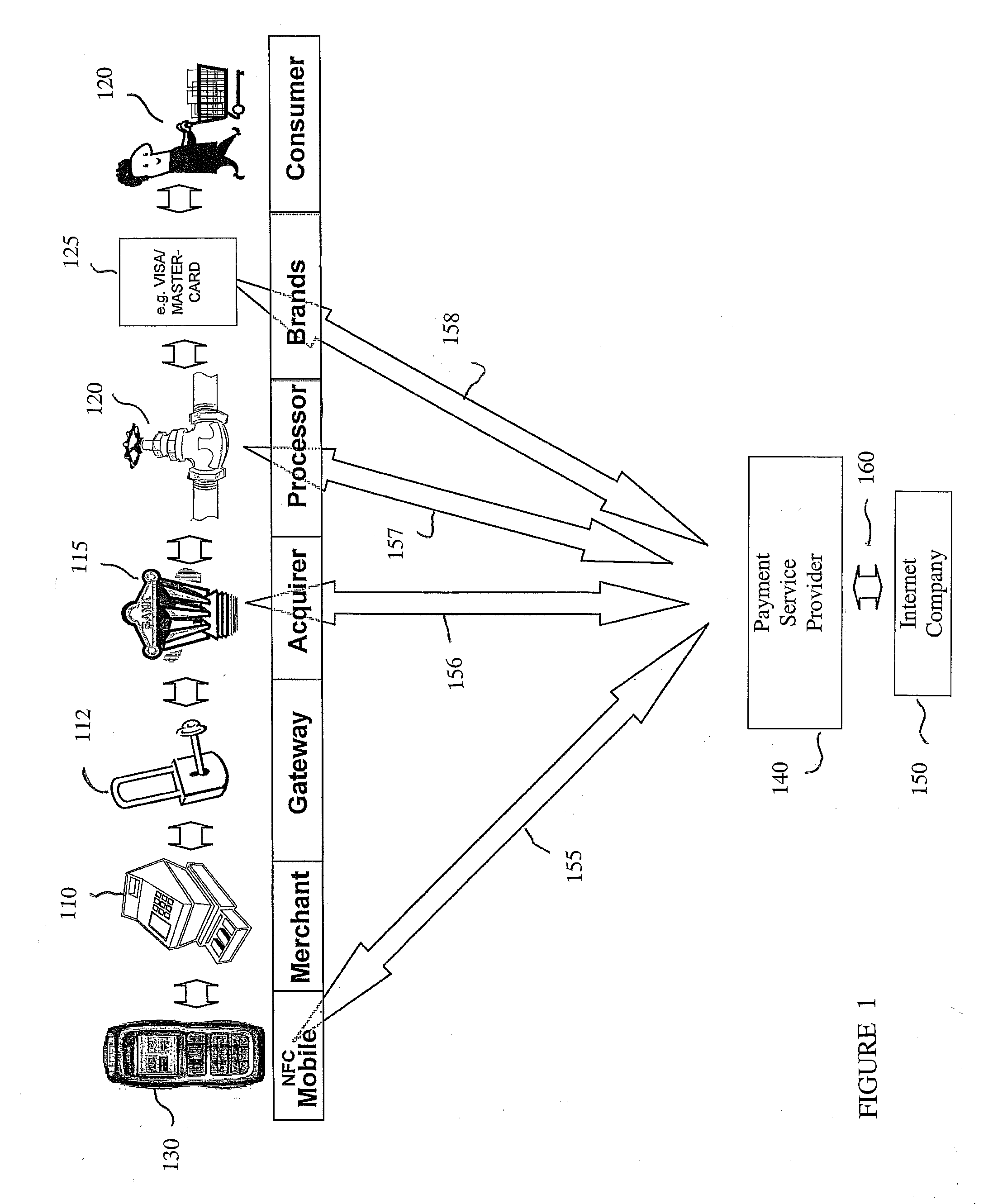
Transactions using, for example, Near Field Communication (NFC), Bluetooth, online, or other applications, may pose a risk of fraud or identity theft. According to an embodiment, a method of evaluating transaction information in view of potential fraud and / or risk includes receiving transaction information at a remote location. The method also includes correlating the received transaction information with user data maintained at the remote location. The method further includes generating a score and / or risk or fraud data based on the correlating. Such transactions may be facilitated by a payment service provider. Related methods, devices, and systems are also disclosed.
Owner:PAYPAL INC
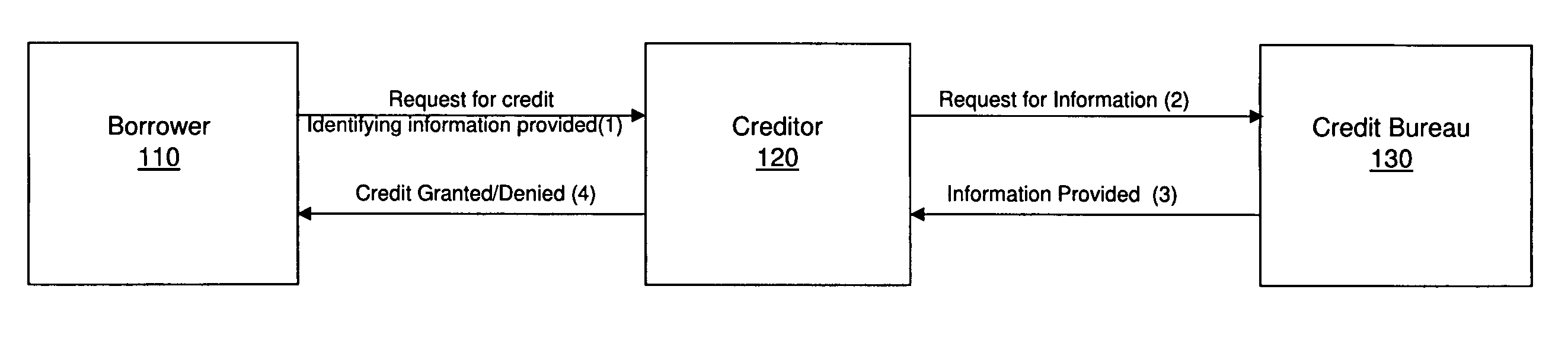
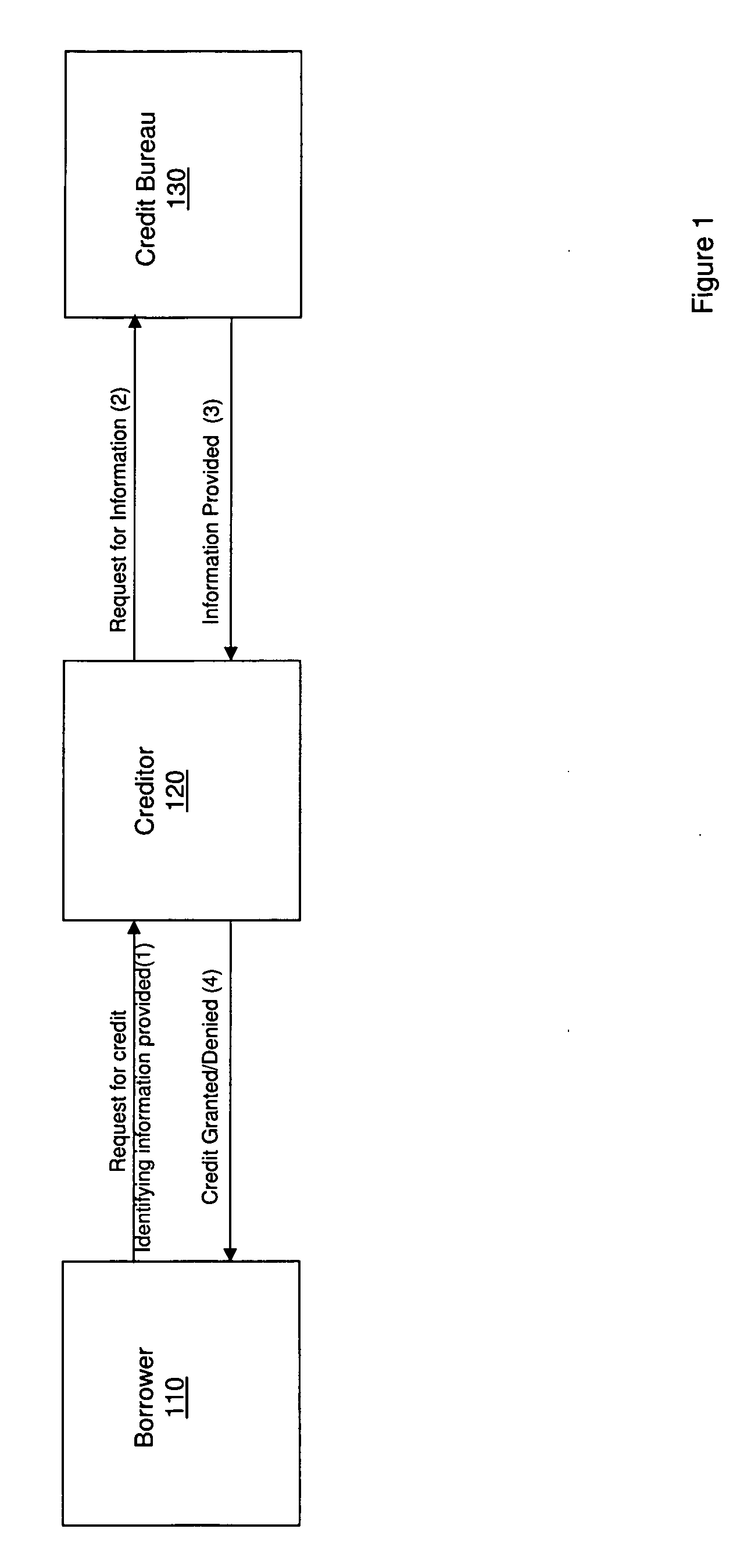
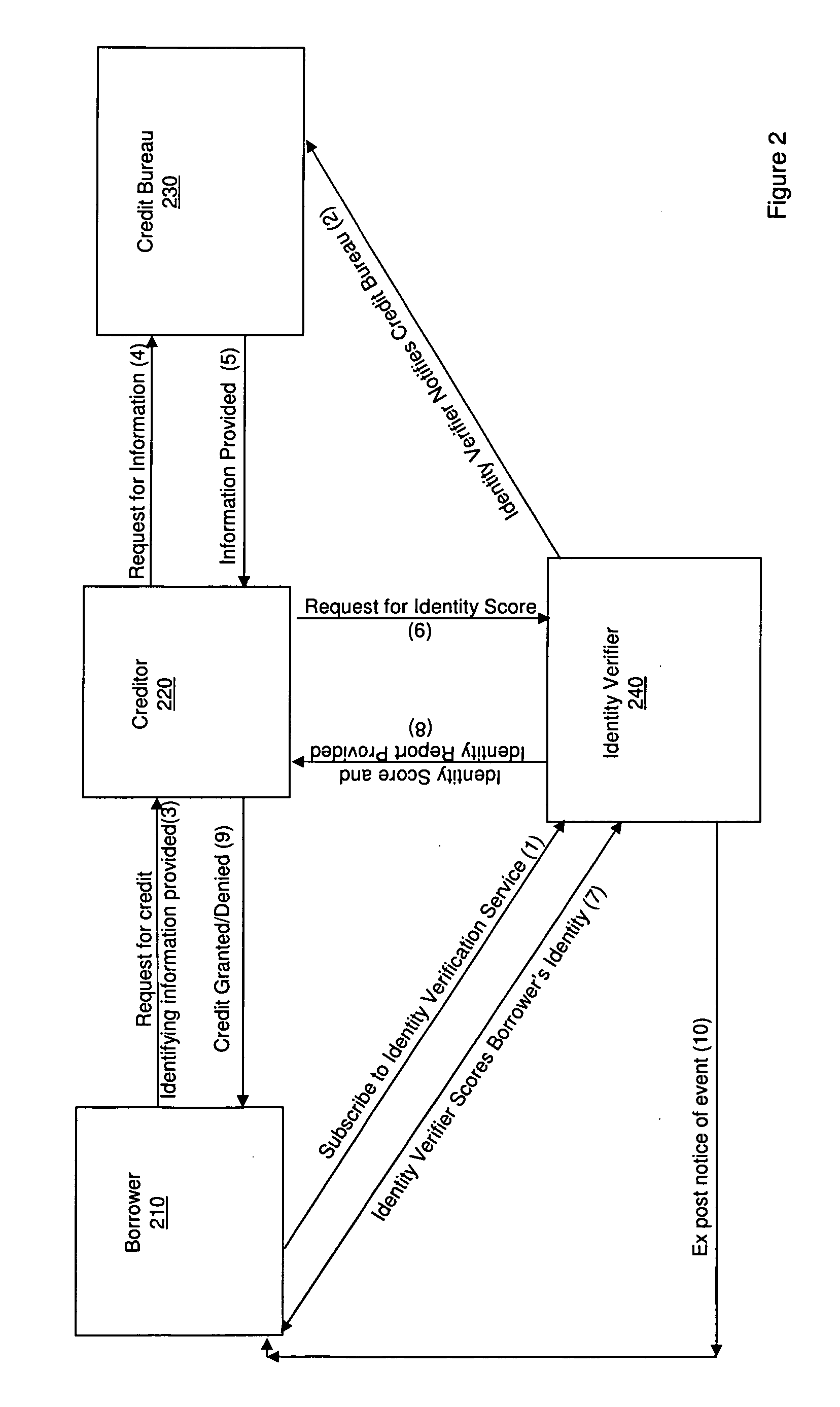
Methods, systems, and apparatus for lowering the incidence of identity theft in consumer credit transactions
InactiveUS20080162383A1Reduce morbidityFinanceSpecial data processing applicationsIdentity scoreBackground information
A process, system, and apparatus are may lower the incidence of identity theft in consumer credit transactions through the use of an identity score. In a representative context, the entities involved include a prospective debtor, a prospective creditor, and a credit bureau. The credit bureau provides background information to the prospective creditor regarding the prospective debtor's credit risk. A process provides certain additional information to enhance this value and make it more resistant to misuse by fraudulent parties who stand in the shoes of prospective debtors. The process will also be used in conjunction with other current methods that prospective creditors employ in making such determinations, such as credit scores.
Owner:MYPUBLICINFO
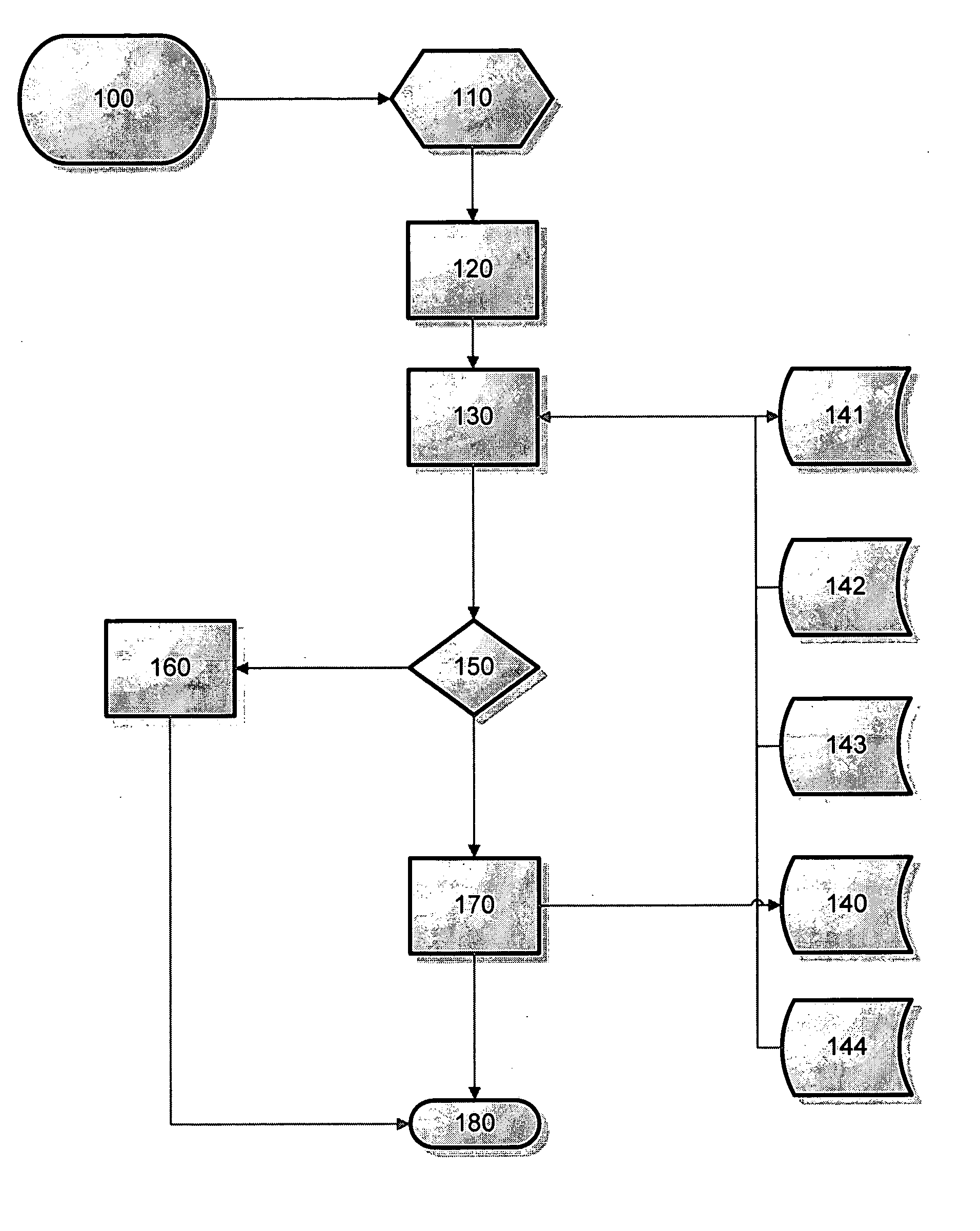
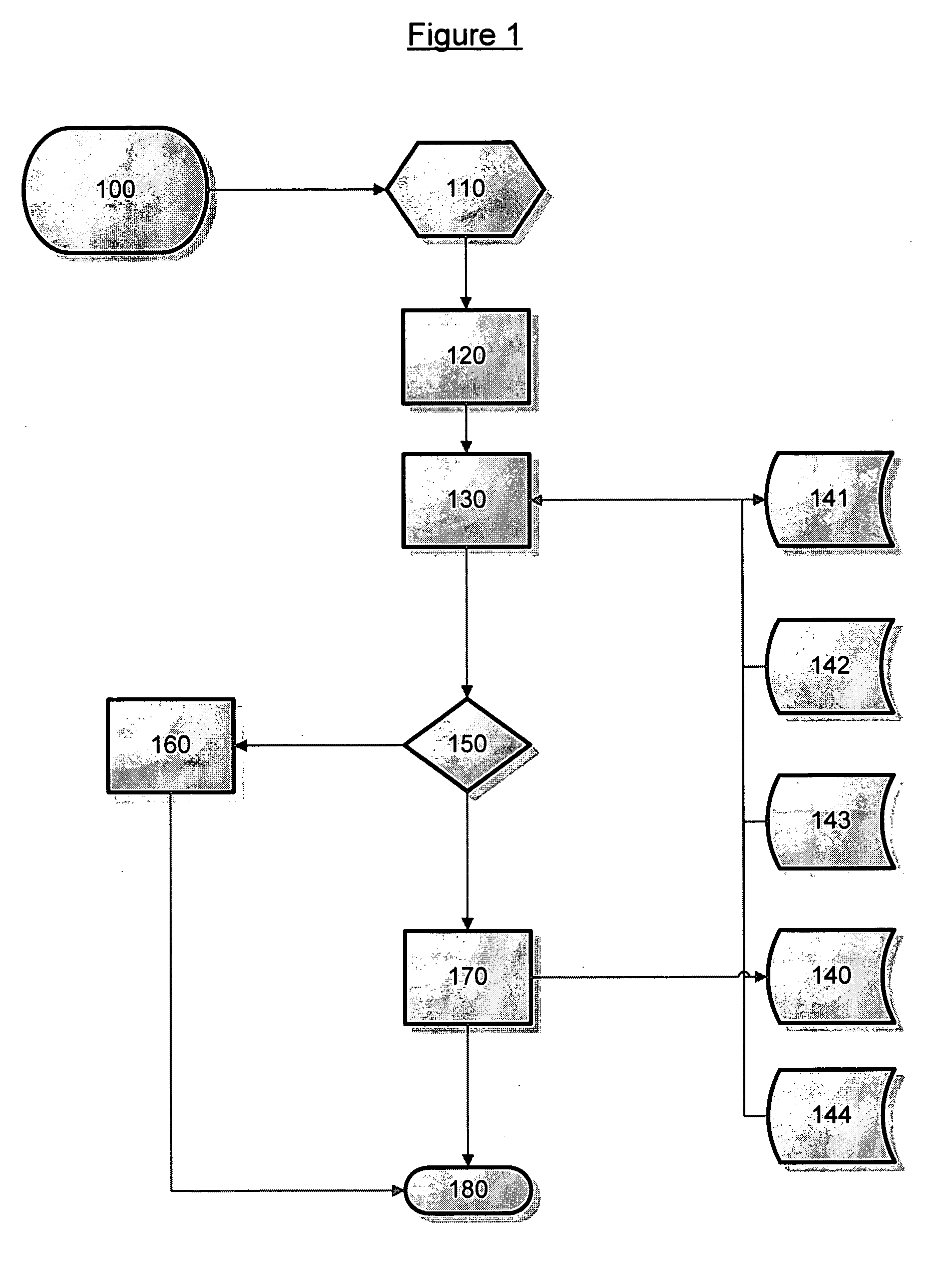
Method and system for preventing identity theft in electronic communications
ActiveUS20050125686A1Memory loss protectionDigital data processing detailsThird partyElectronic communication
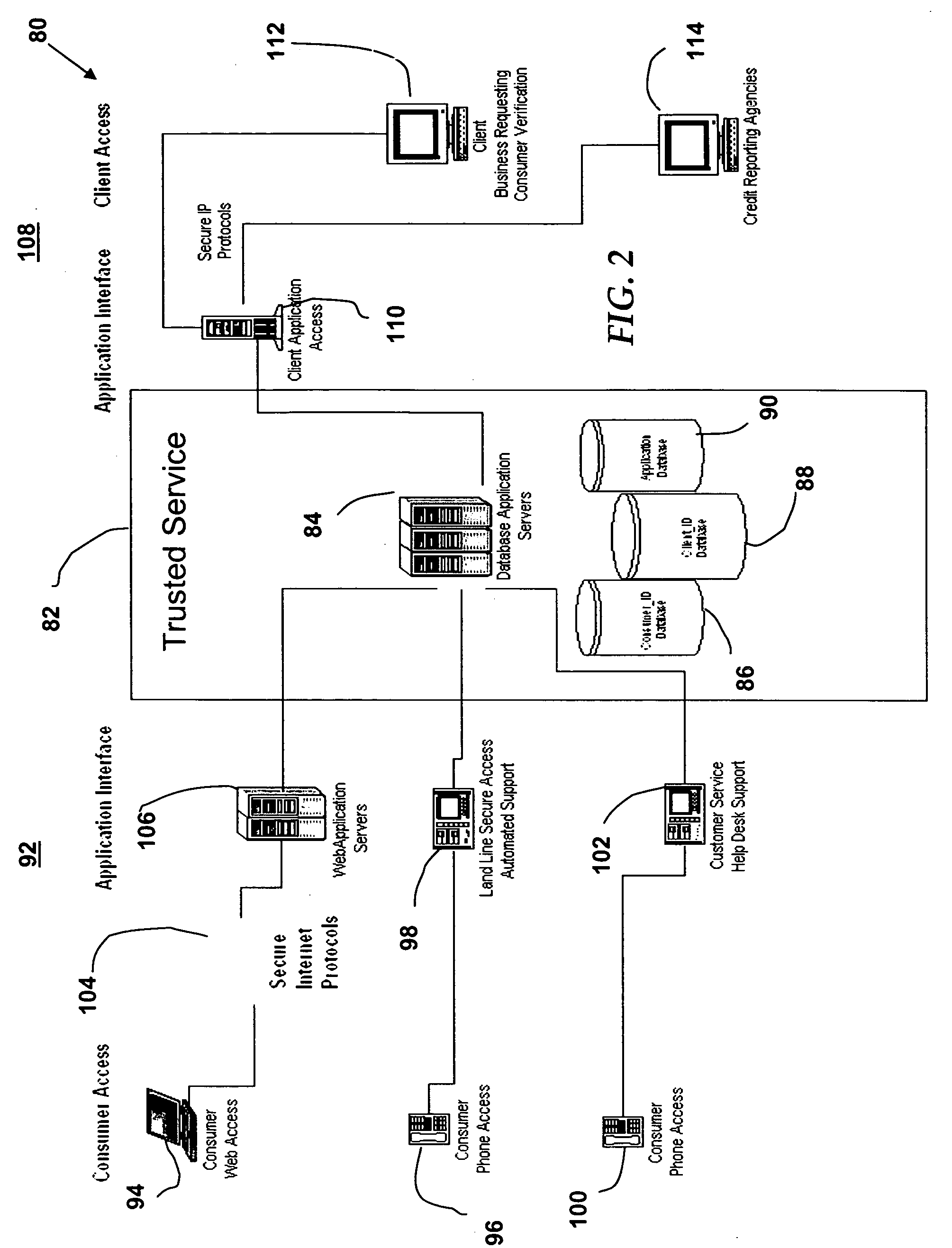
Preventing identity theft in electronic communications sequences (180) involves generating a consumer identifier (126) for an individual (92) from a trusted service (82), including a primary key (128), a unique identifier (130), and a consumer-defined sequence (132). The consumer-defined sequence (132) allows the individual (92) to control use of the consumer identifier (126) by third parties, such as business entities (112). The method and system further allows business entities (114) to verify use of the consumer identifier (126) by first initiating a verification process (196) via a secure connection (110). Verification includes comparing (200) the consumer identifier (126) with a pre-determined set of database records (86, 88, and 90). If the requesting business (108) has registered with the trusted service (82), the invention presents a positive or negative confirmation (208) to the requesting business (108) according to the inquiry (204). Then, the invention permits confirming (210) the requested information relating to the individual (92) via the secure connection (98, 102, 106), conditioned upon the requested information having previously been authorized by the individual for presenting to the requesting business (108).
Owner:MARQETA
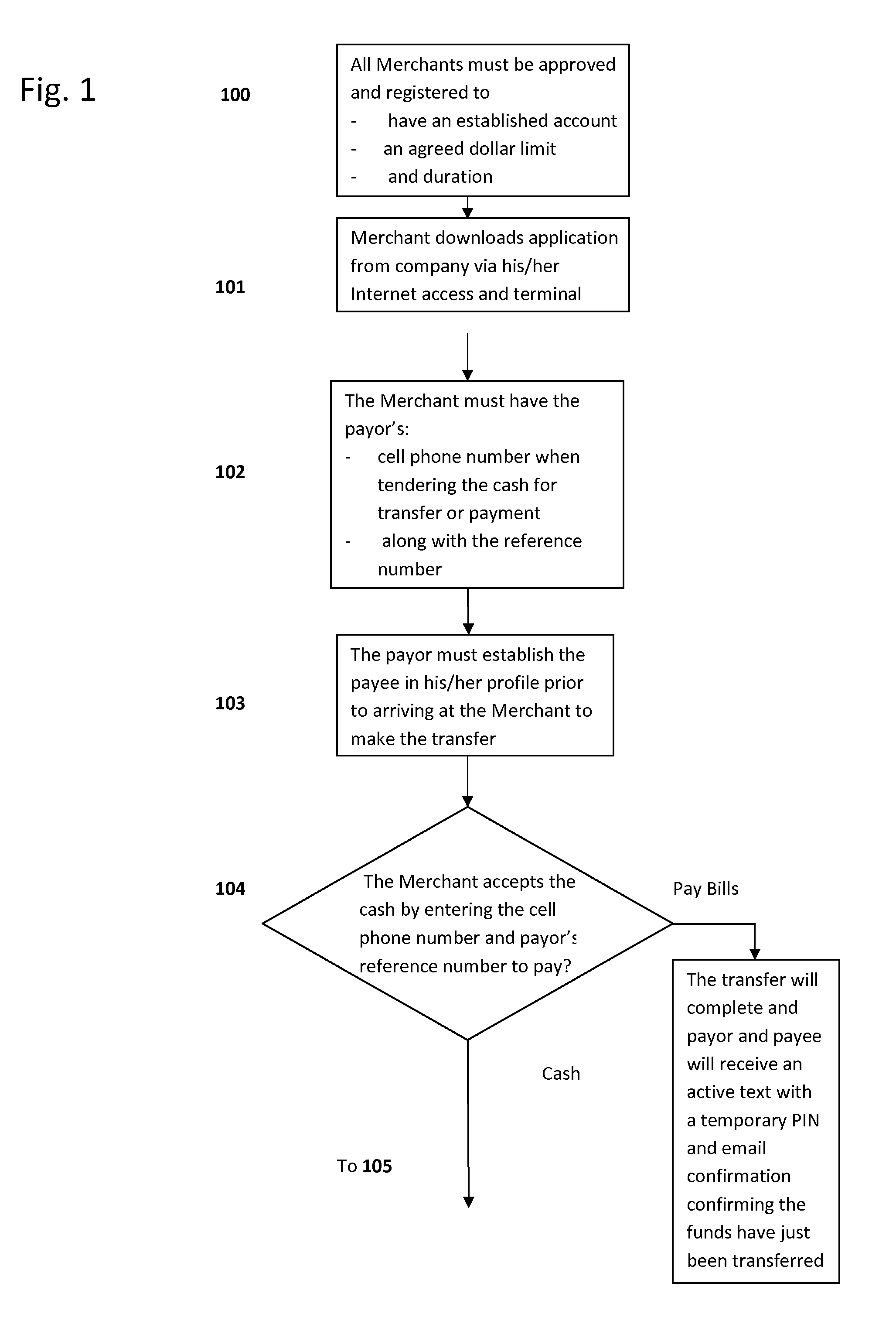
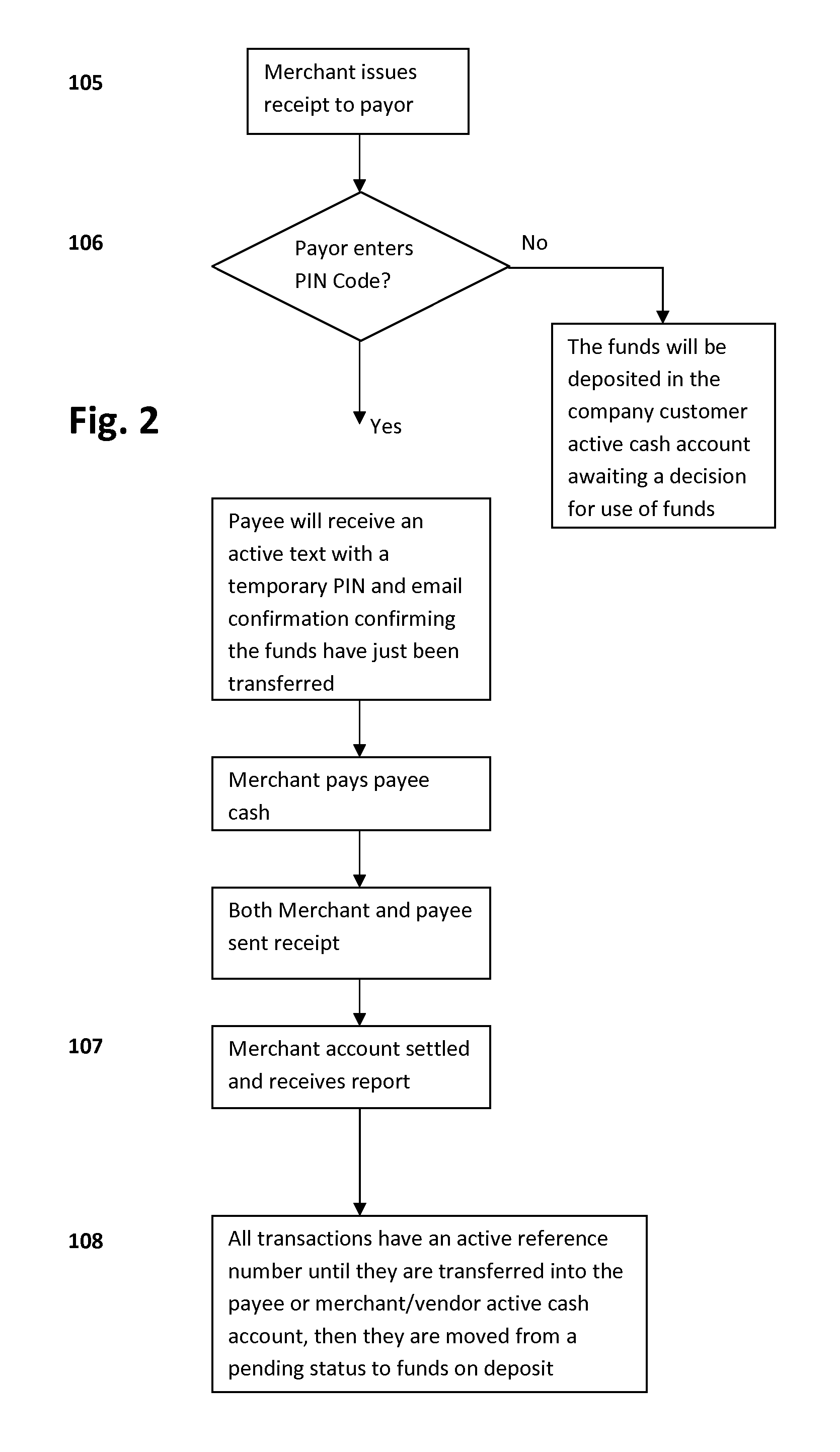
ATM/KIOSK Cash Acceptance
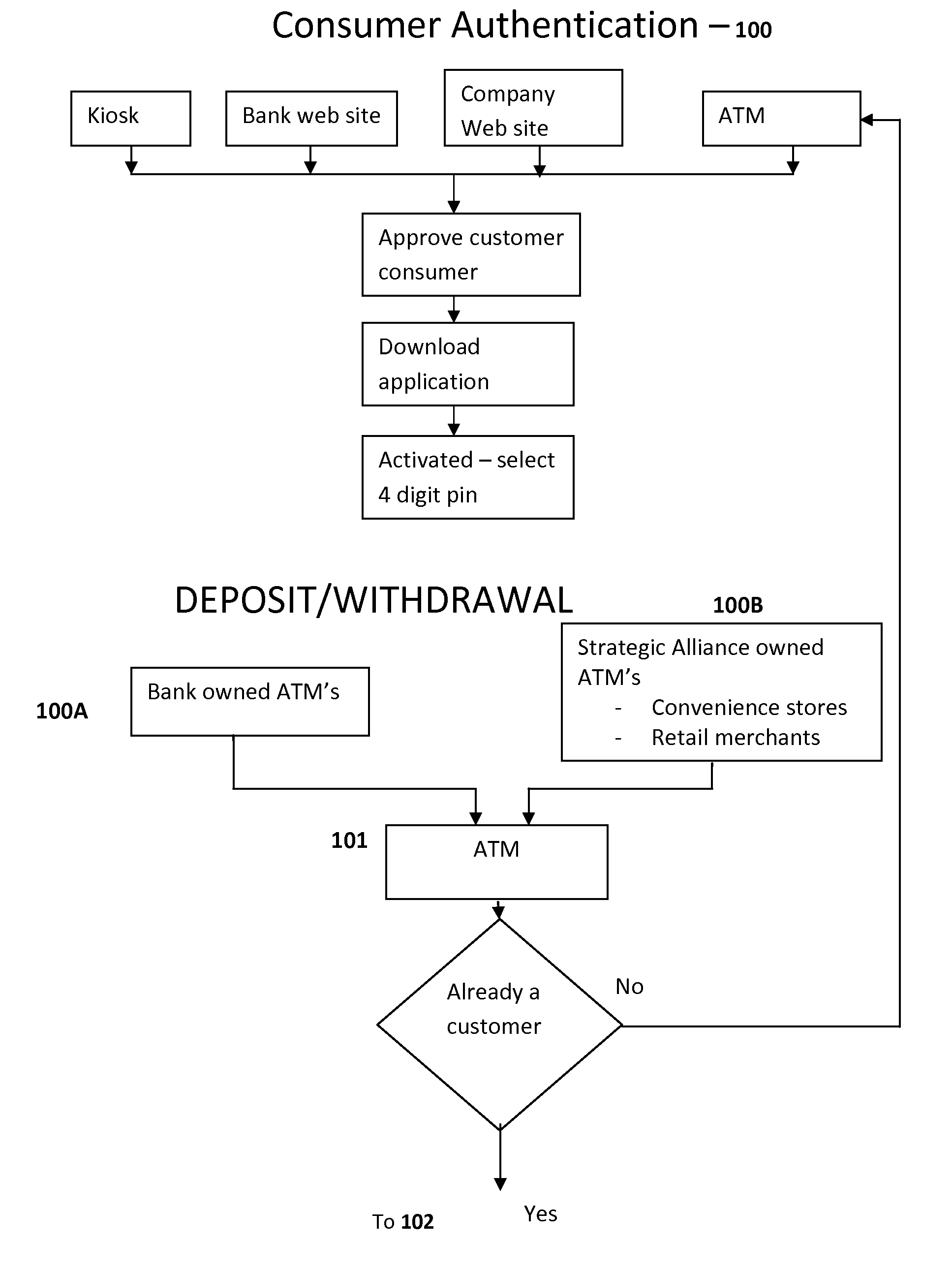
In one aspect, this invention relates to a new method for using a mobile telephone, in conjunction with a payment transaction server, as an authentication and cash payment device of a cash deposit made into an ATM / KIOSK for a variety of financial transactions where a cash payment is desired. Further, the transaction systems and methods for mobile telephone devices described herein allow a mobile telephone to participate in payment transactions in a manner that helps prevent identify theft and without relying on transferring amounts to / from one stored value account to another. It is emphasized that this abstract is provided to enable a searcher to quickly ascertain the subject matter of the technical disclosure and is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:GLOBAL 1 ENTERPRISES
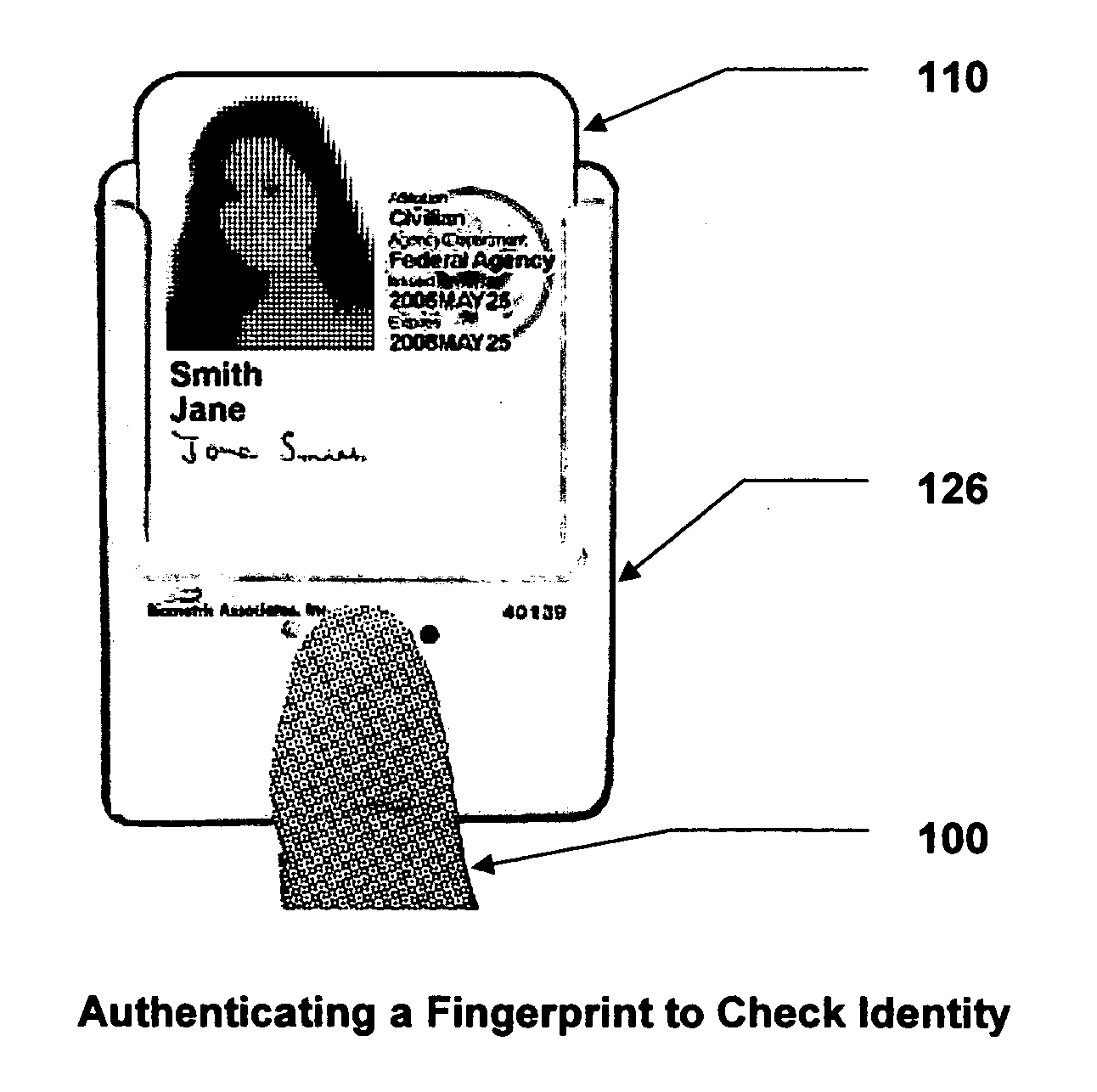
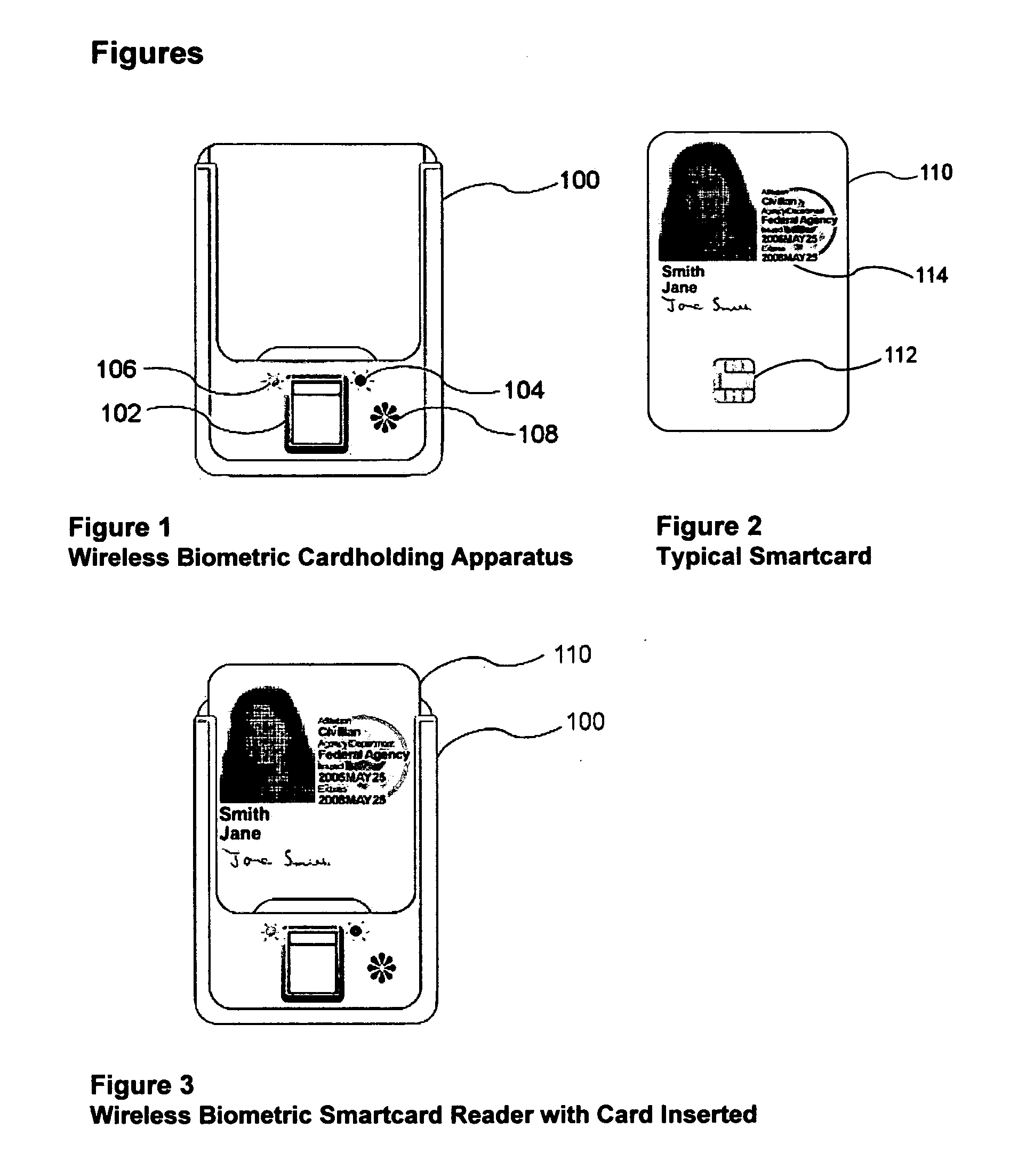
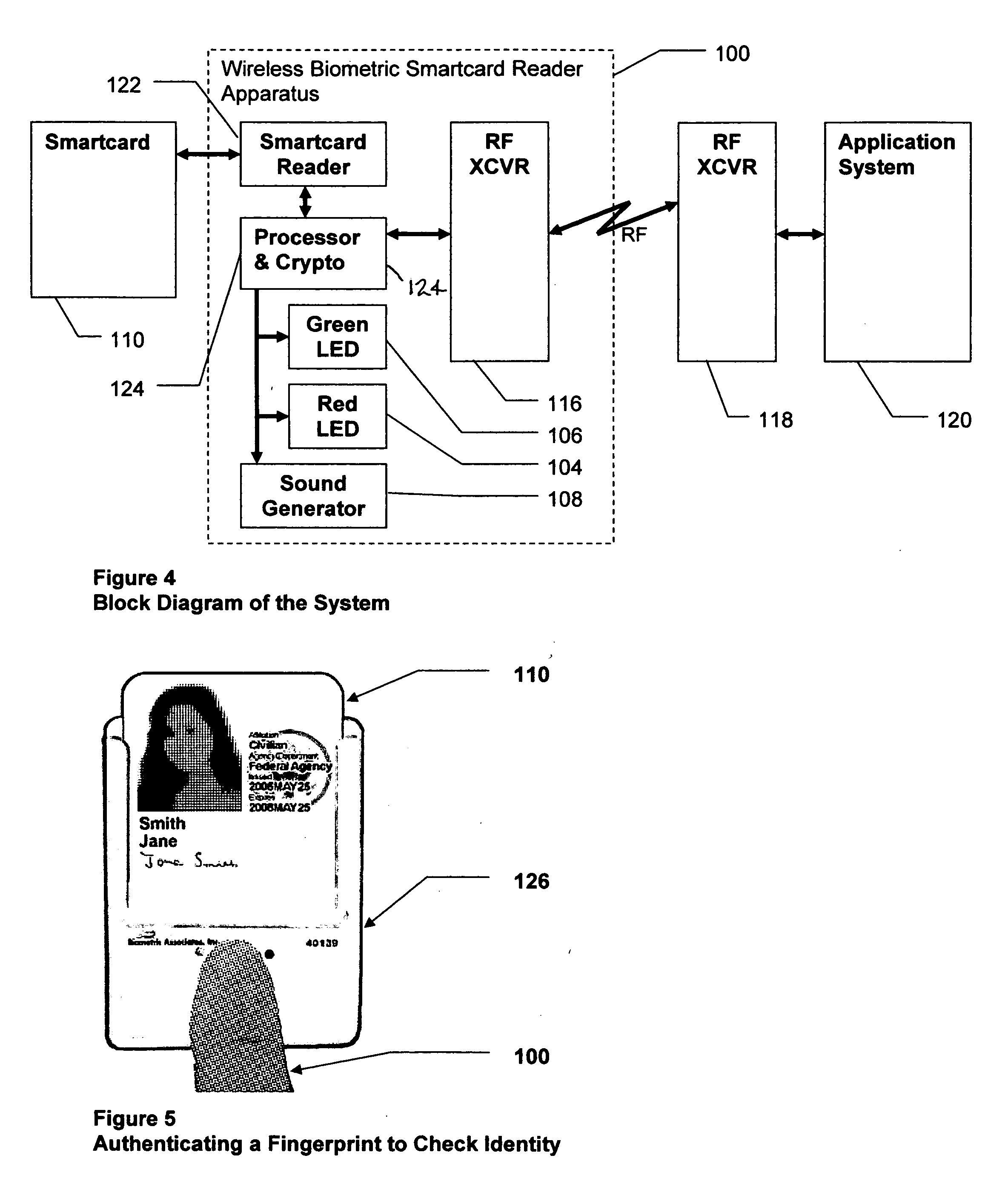
Wireless biometric cardholder apparatus, method, & system
InactiveUS20070040017A1Easy to checkSensing record carriersRecord carriers used with machinesTransceiverIdentity theft
A wireless biometric cardholding apparatus is disclosed. The invention facilitates remote reading and writing smartcards after a user has been biometrically authenticated. The invention promotes secure, wireless exchange of data between standard smartcards and an application, via a remote external RF transceiver. This invention enables enrolled users to access physical, logical, or financial resources and / or other protected assets. The cardholding apparatus holds a conventional identifying card, badge, or smartcard. One preferred embodiment is constructed of clear plastic and / or is of sufficiently open design that it displays visible ID credentials. The invention actively reads identification data from the smartcard, cryptographically protects data, and transmits it by means of radio or other wireless communications to a reader terminal. The cardholding apparatus also contains a biometric authenticator that positively identifies the cardholder, and inhibits transmission until after successful authentication completion. The apparatus protects the cardholder from identity theft by preventing unauthorized tracking.
Owner:BIOMETRIC ASSOCS LP
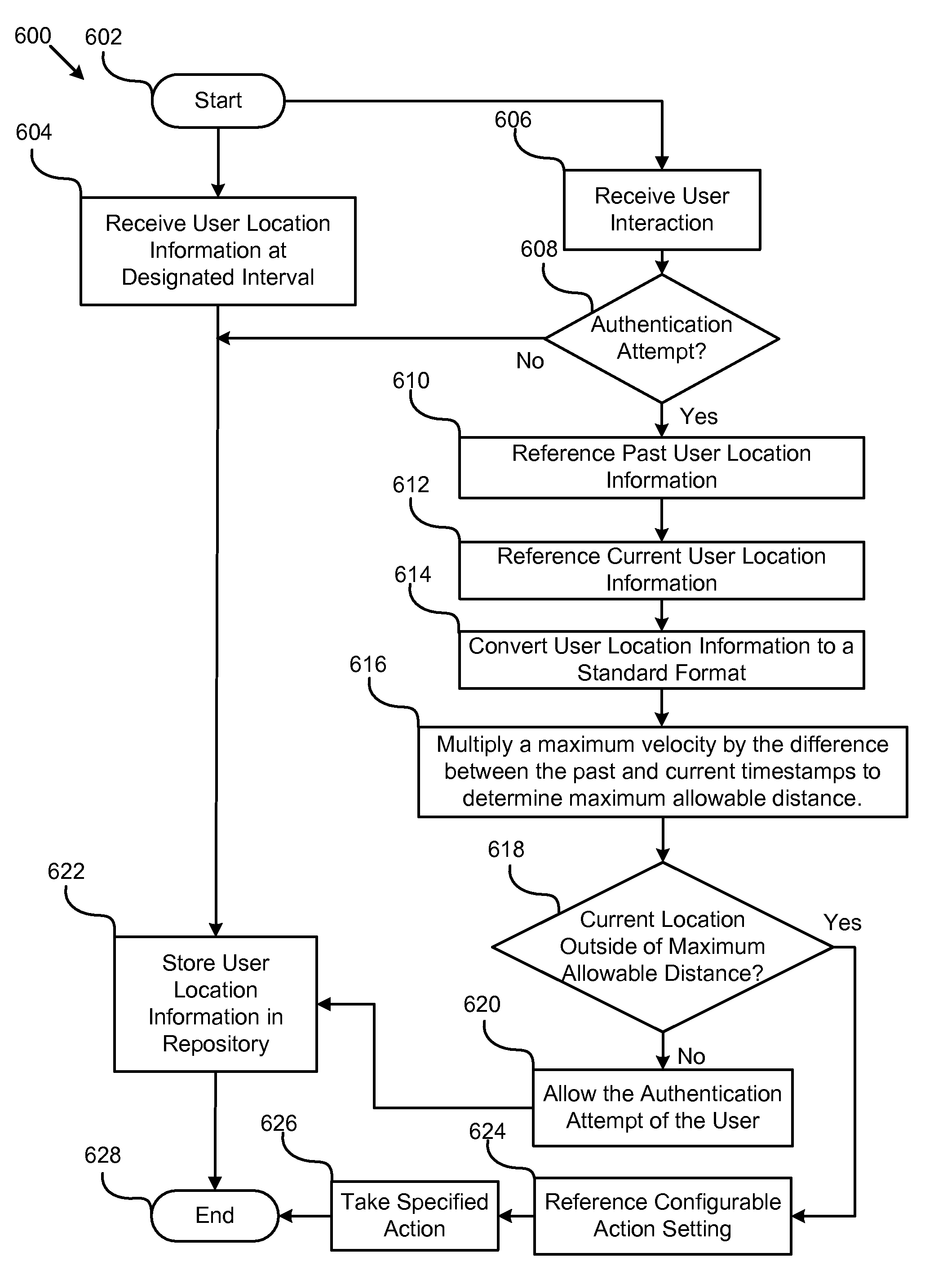
Apparatus, system, and method for user authentication based on authentication credentials and location information
ActiveUS20090158404A1Digital data processing detailsUser identity/authority verificationReference currentIdentity theft
A computer program product, apparatus, and system, are disclosed for user authentication based on authentication credentials and location information. A computer program product performs operations for such authentication. These operations of the computer program product include referencing past user location information in response to an authentication validation request and referencing current user location information. These operations also include determining a maximum allowable distance between an authentication attempt location associated with the authentication attempt location identifier and a past location associated with the past user interaction location identifier, and managing the authentication attempt, in response to determining that the physical authentication attempt location is outside the maximum allowable distance. The computer program product, apparatus, and system thereby reduce the possibility of identity theft by adding an element of location awareness to the authentication process.
Owner:IBM CORP
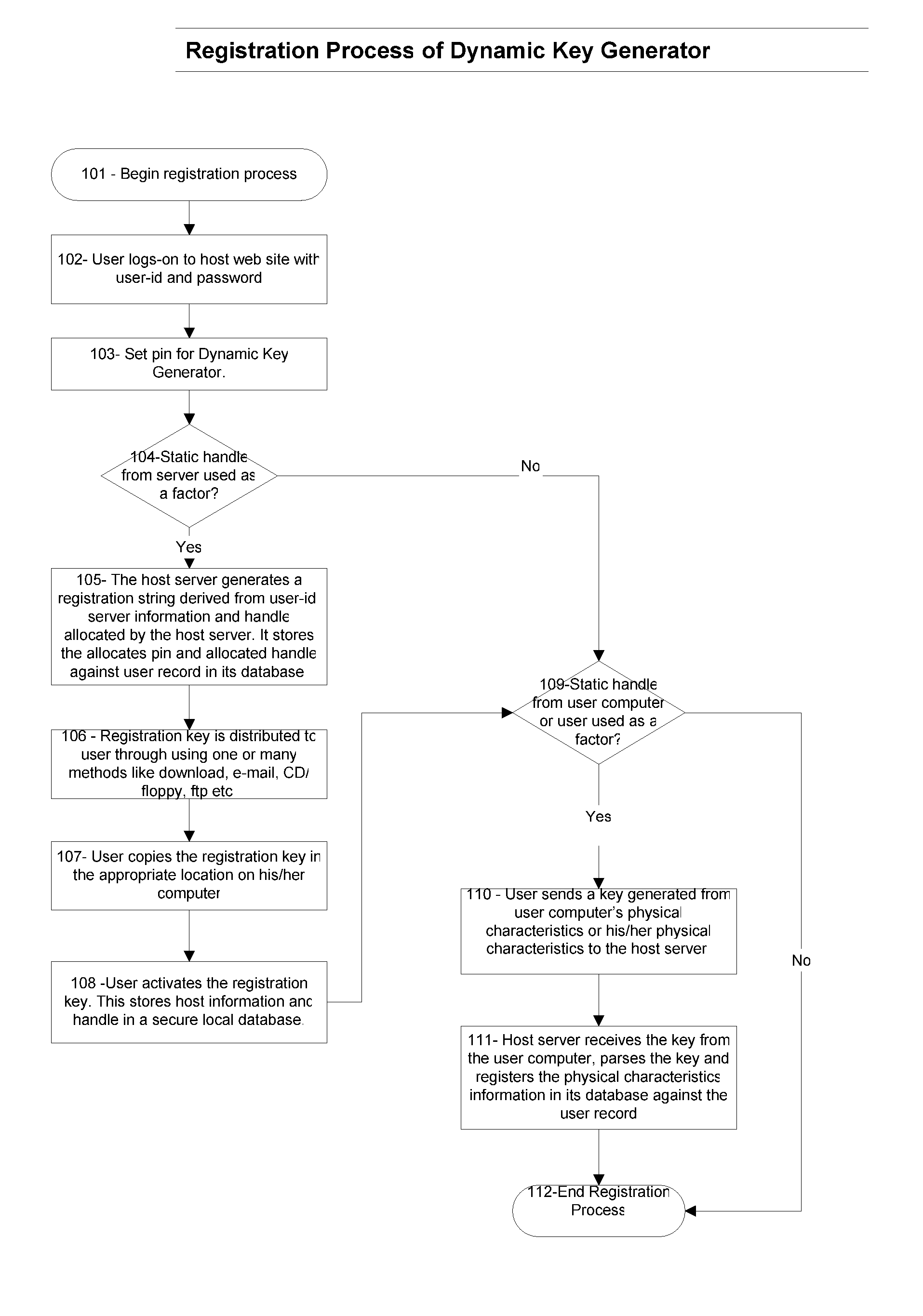
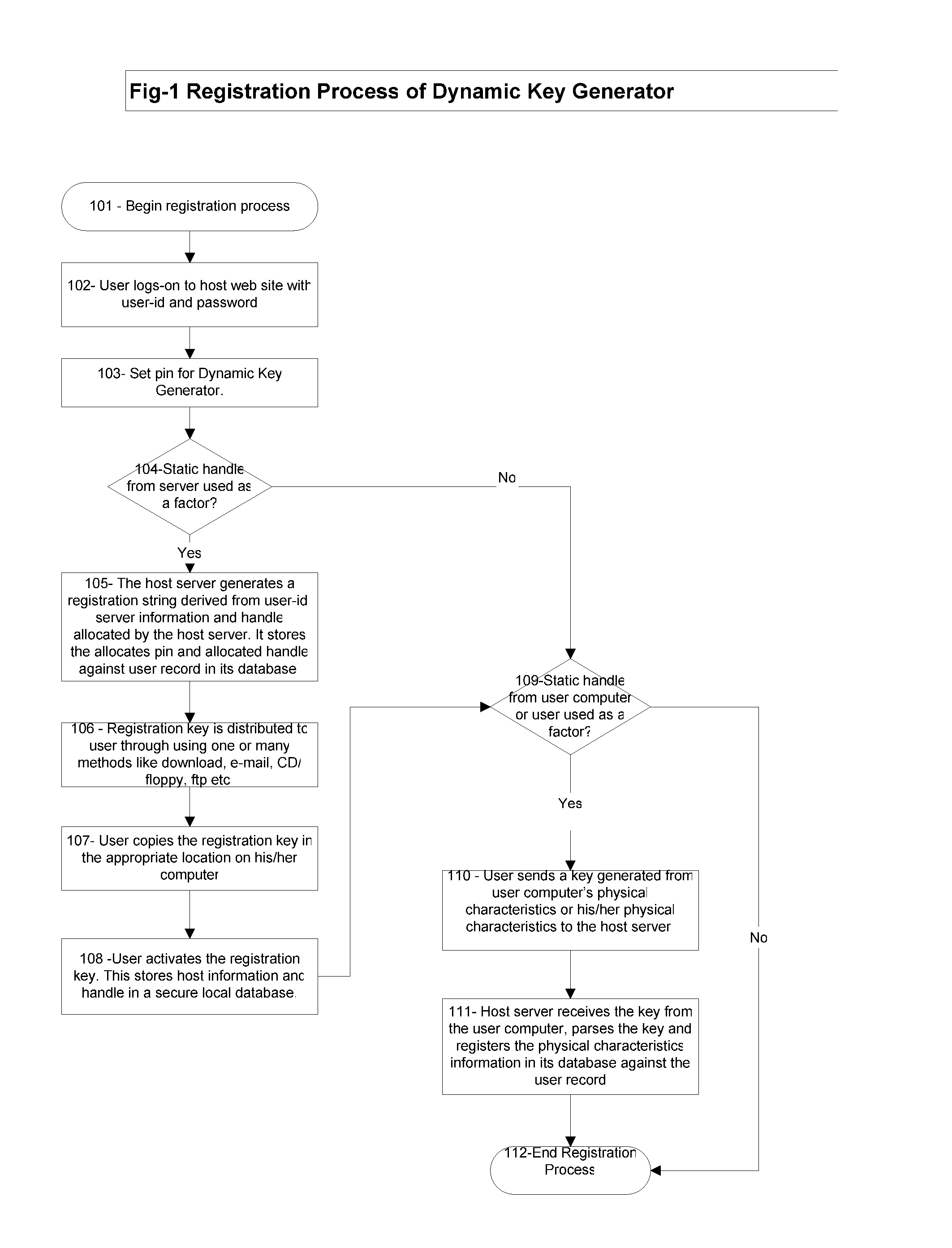
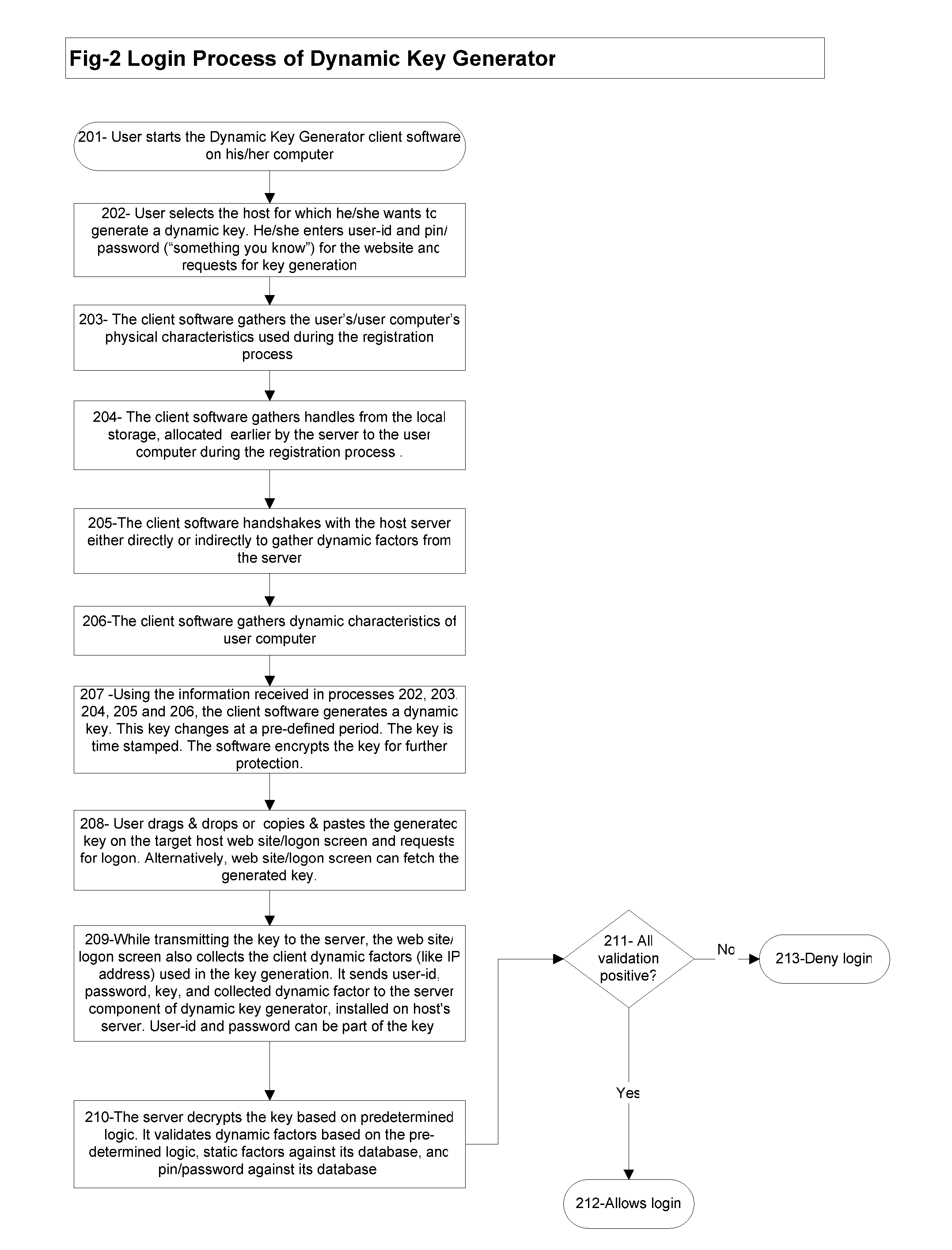
Software based Dynamic Key Generator for Multifactor Authentication
InactiveUS20070220594A1Reduce chanceEasy to useDigital data processing detailsUser identity/authority verificationFactor baseIdentity theft
A software based method and system providing secure and robust multifactor authentication of internet users using at least one factor each of 1) Something you know; 2) Something you have; and 3) Something you are—A physical characteristic of the user or his / her computer / device. This method of authenticating the identity of a user to determine access to a host includes providing an encrypted key string based on one or more static and dynamic factors corresponding the data instances of a user or his / her computer / device, one or more static and dynamic factors corresponding the data instances of the host, and user input factors; evaluating the factor-based data instances to determine if the user's identity is authenticated; and granting or restricting the user's access to the host based on authentication results. The provider generates a key string based on the inputs gathered / provided, time stamps the key, encrypts the key and sends it to the host. The host in turns decrypts the key string, evaluates the static factors against its database, and evaluates the dynamic factors based on pre-defined logic. The user is successfully authenticated if all validations are positive. Based on the authentication results the user is granted or restricted an access to the host resources. This method and system significantly reduces the chances of identity theft occurring from phishing, pharming, man-in-middle theft, spy-ware, and key stroke logger in everyday consumer e-commerce by deploying multifactor authentication based on static and dynamic factors stored / generated at multiple places, key encryption, key time stamping, and elimination of key strokes.
Owner:TULSYAN SURENDRA KUMAR
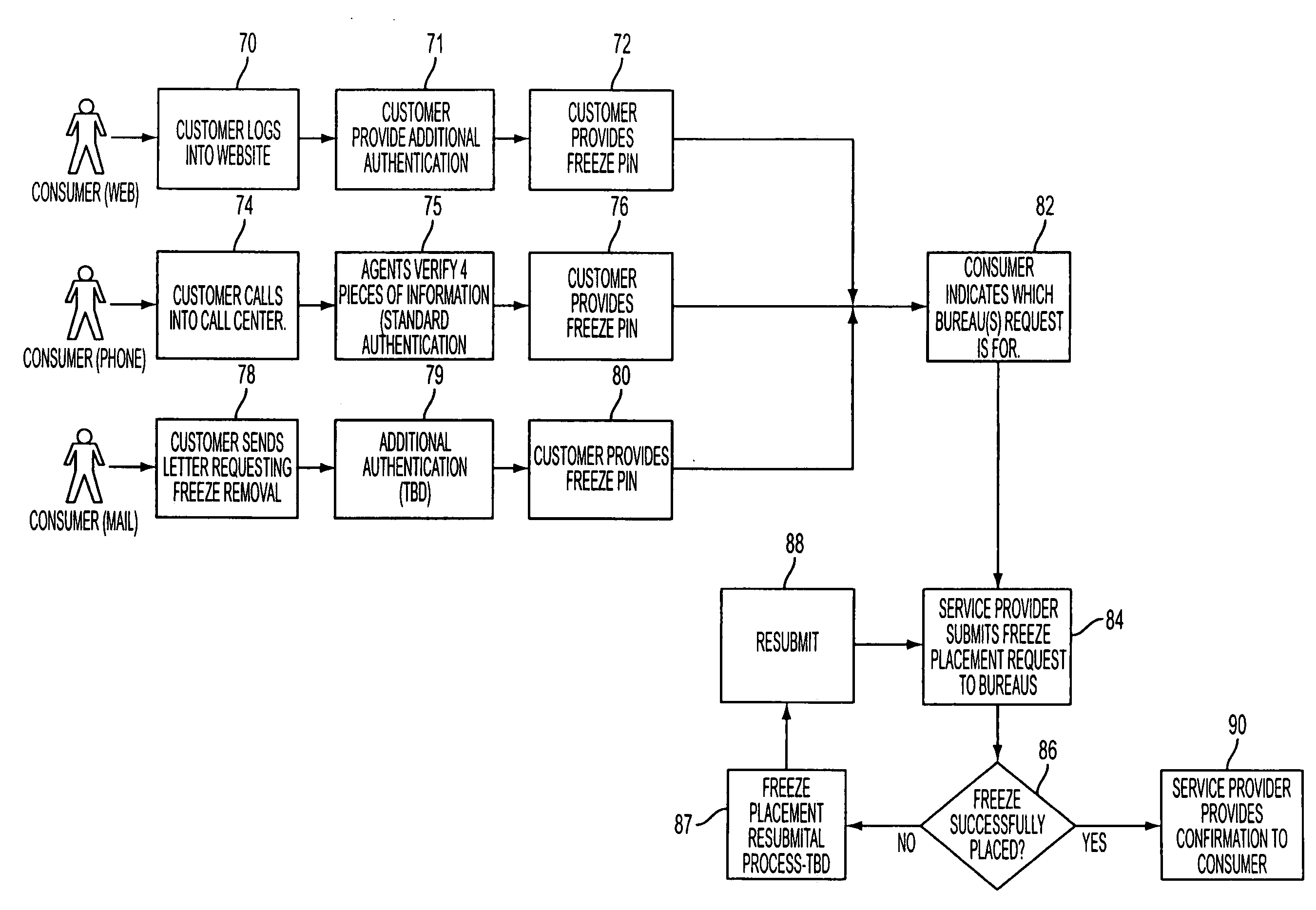
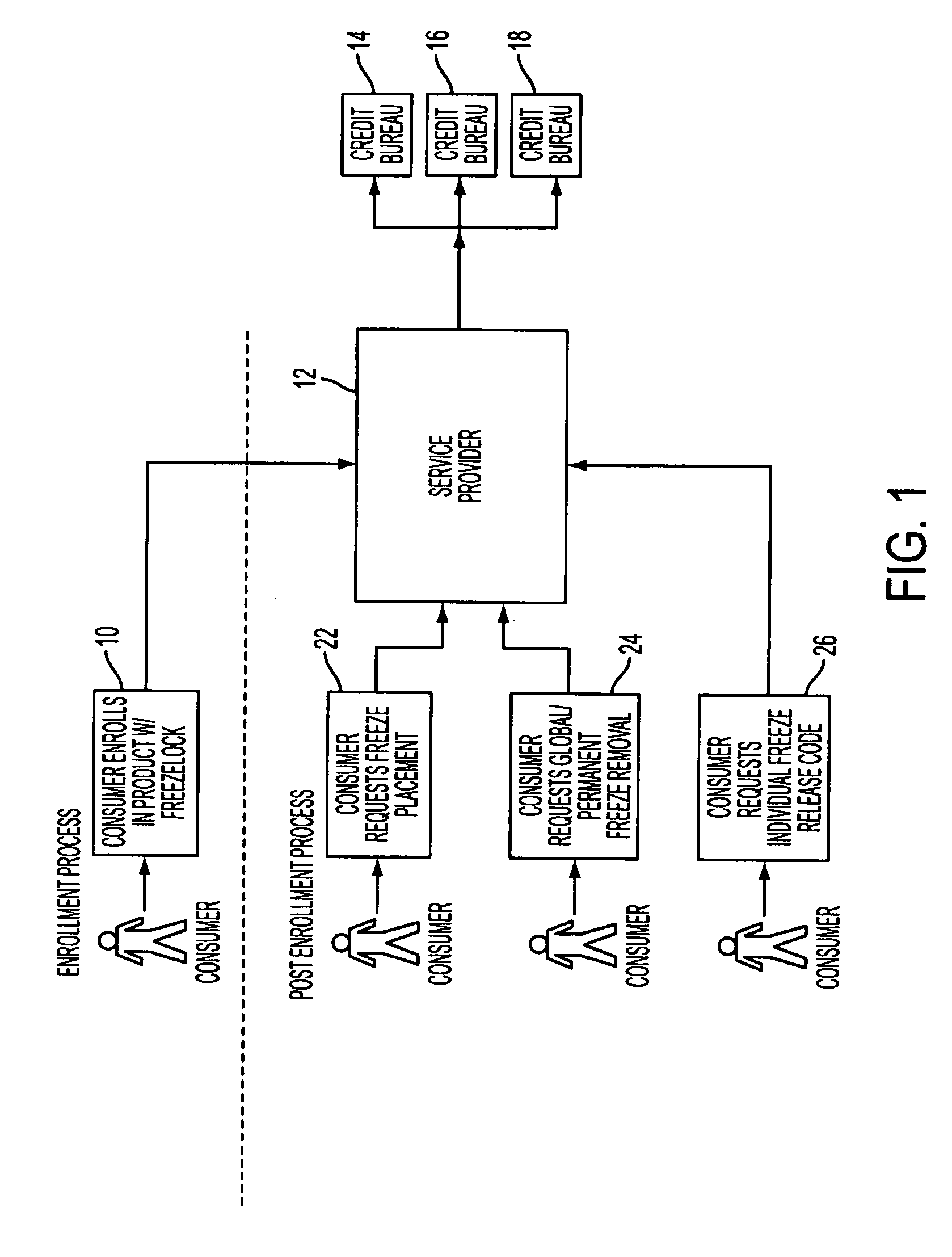
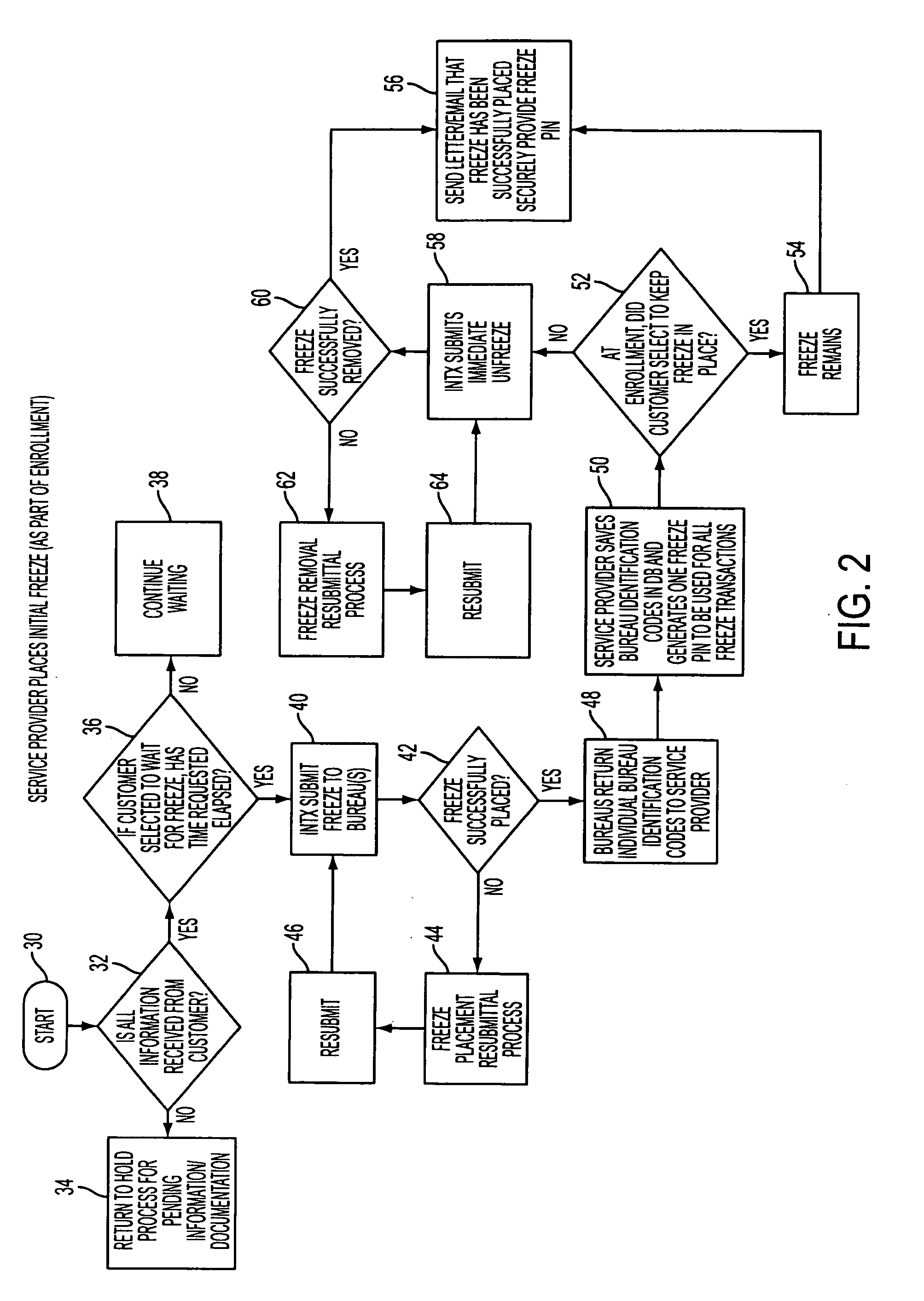
Method and system for securing credit accounts
An enterprising identity thief may open new credit accounts in a consumer's name and then place a credit freeze on a consumer's credit file, thus making it more difficult to detect or remedy the identity theft. This problem may be solved by automatically requesting a security freeze at each of the three main credit bureaus upon the enrollment of a consumer with the service provider. The requesting of the security freeze may result in the credit bureau generating an identification code for the consumer at each of the credit bureaus. The service provider then may immediately request that the security freeze be removed. Accordingly, the consumer may gain control of the security freeze credentials from each credit bureau before the identity thief.
Owner:AURA SUB LLC +1
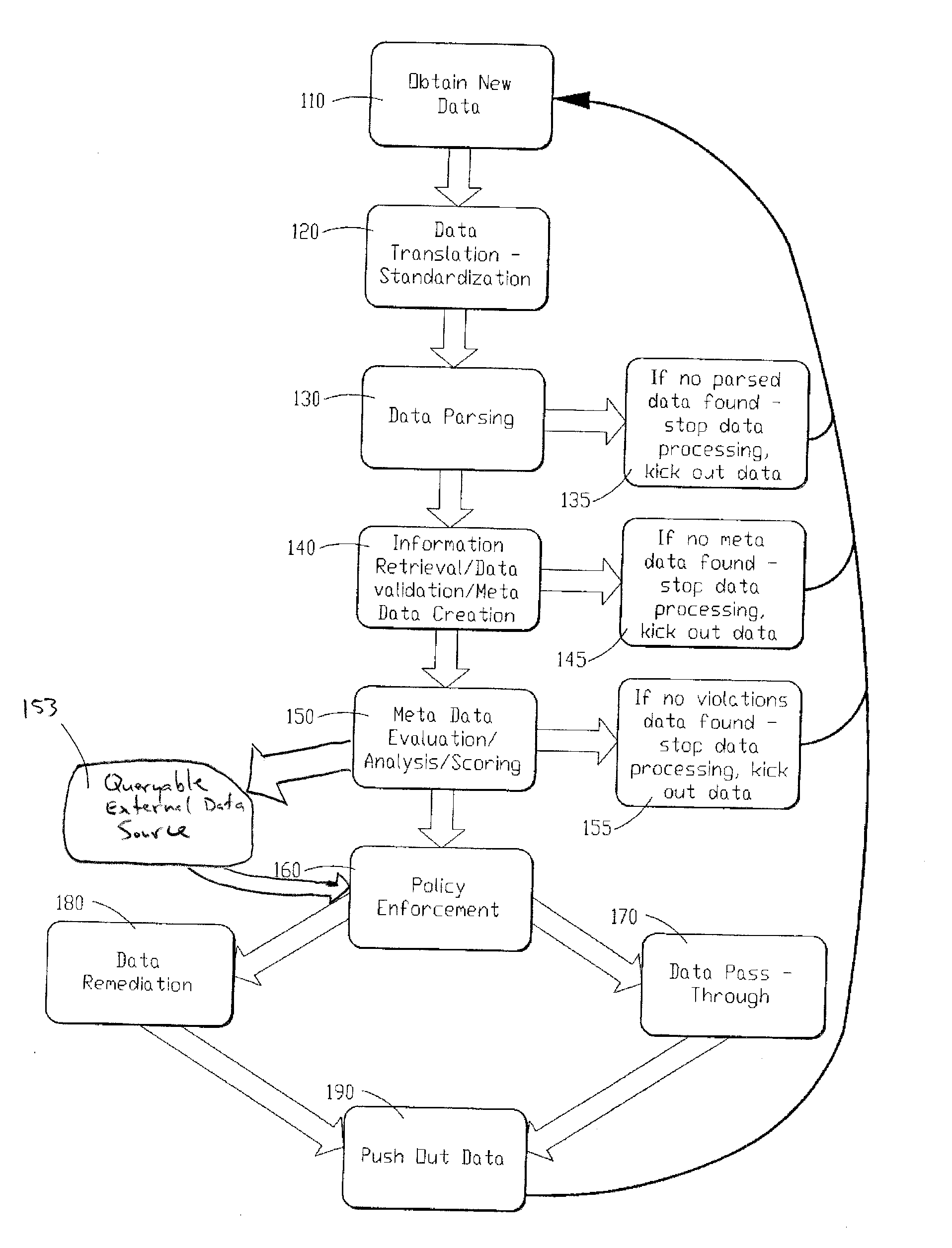
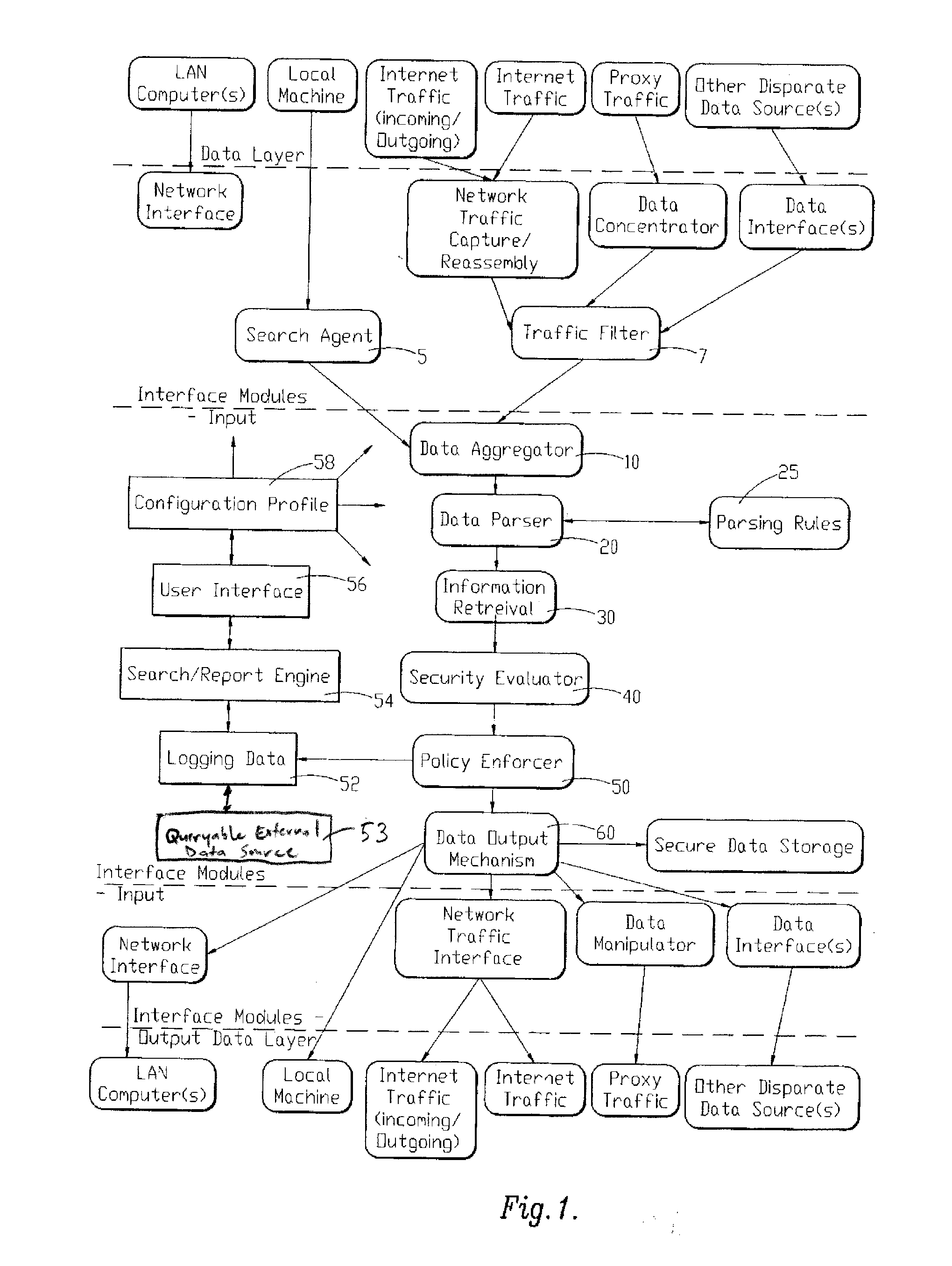
System and method for providing identity theft security
InactiveUS20110040983A1Reduce the burden onMinimal effortDigital data processing detailsUnauthorized memory use protectionIdentity theftComputerized system
A system and method of providing identity theft security is provided. The system and method utilizes a computer program that identifies, locates, secures, and / or removes from computers, computer systems and / or computer networks personally identifying and / or other sensitive information in different data formats. The computer program utilizes a multi-tiered escalation model of searching / identifying sensitive information. The computer program of the instant invention utilizes a self-learning process for fine-tuning a level of scrutiny for identifying potentially sensitive information.
Owner:TOUCHNET INFORMATION SYST
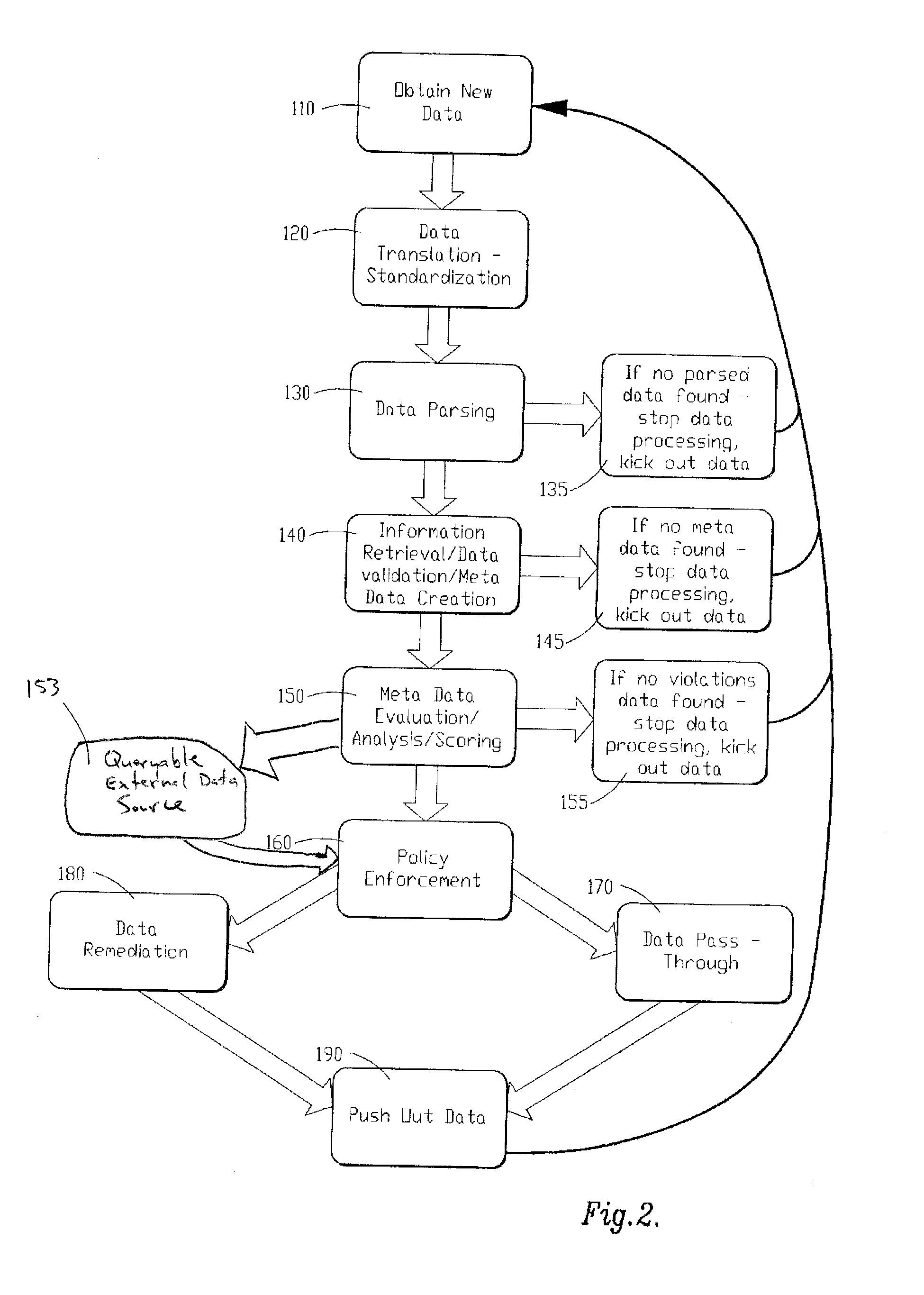
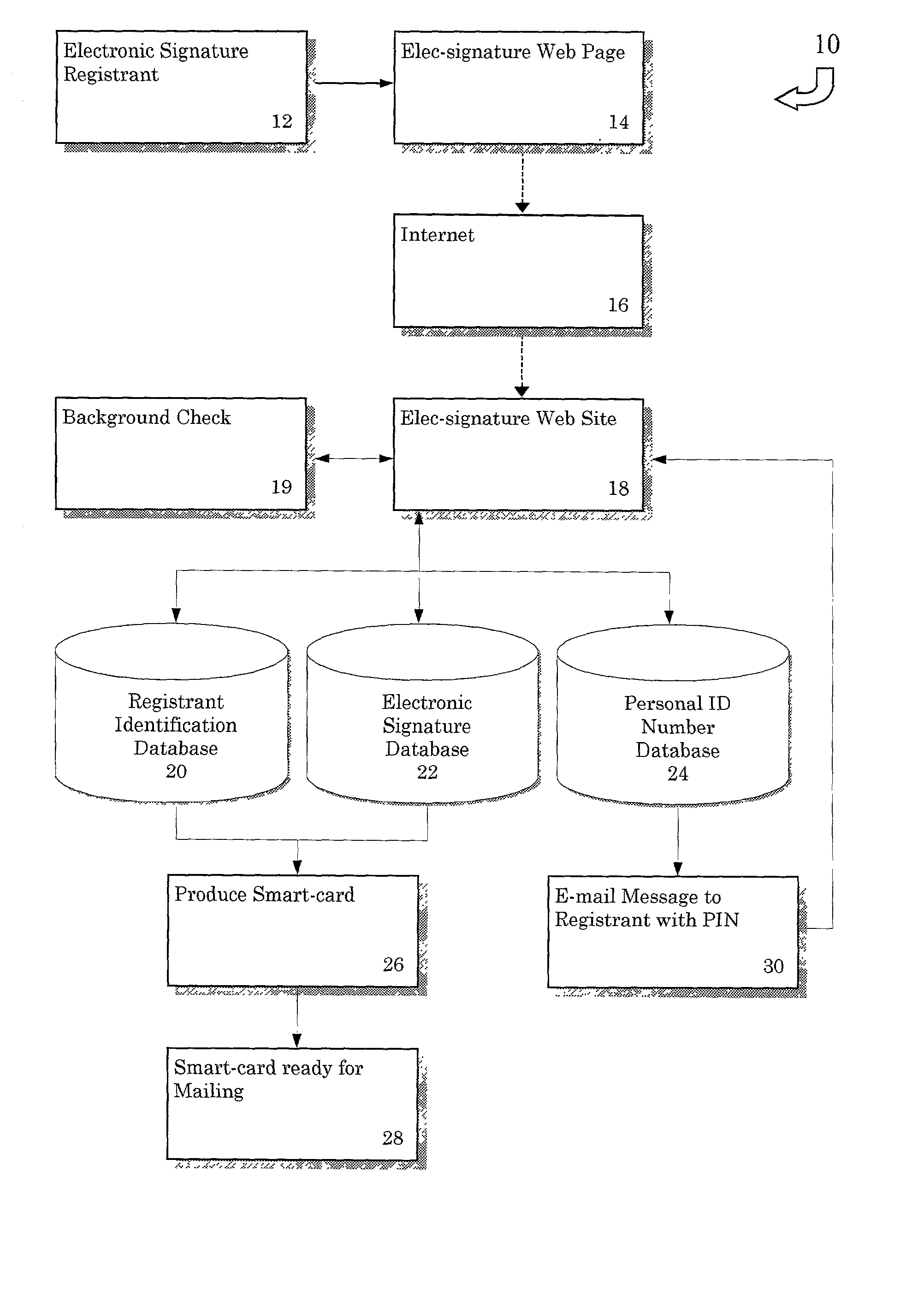
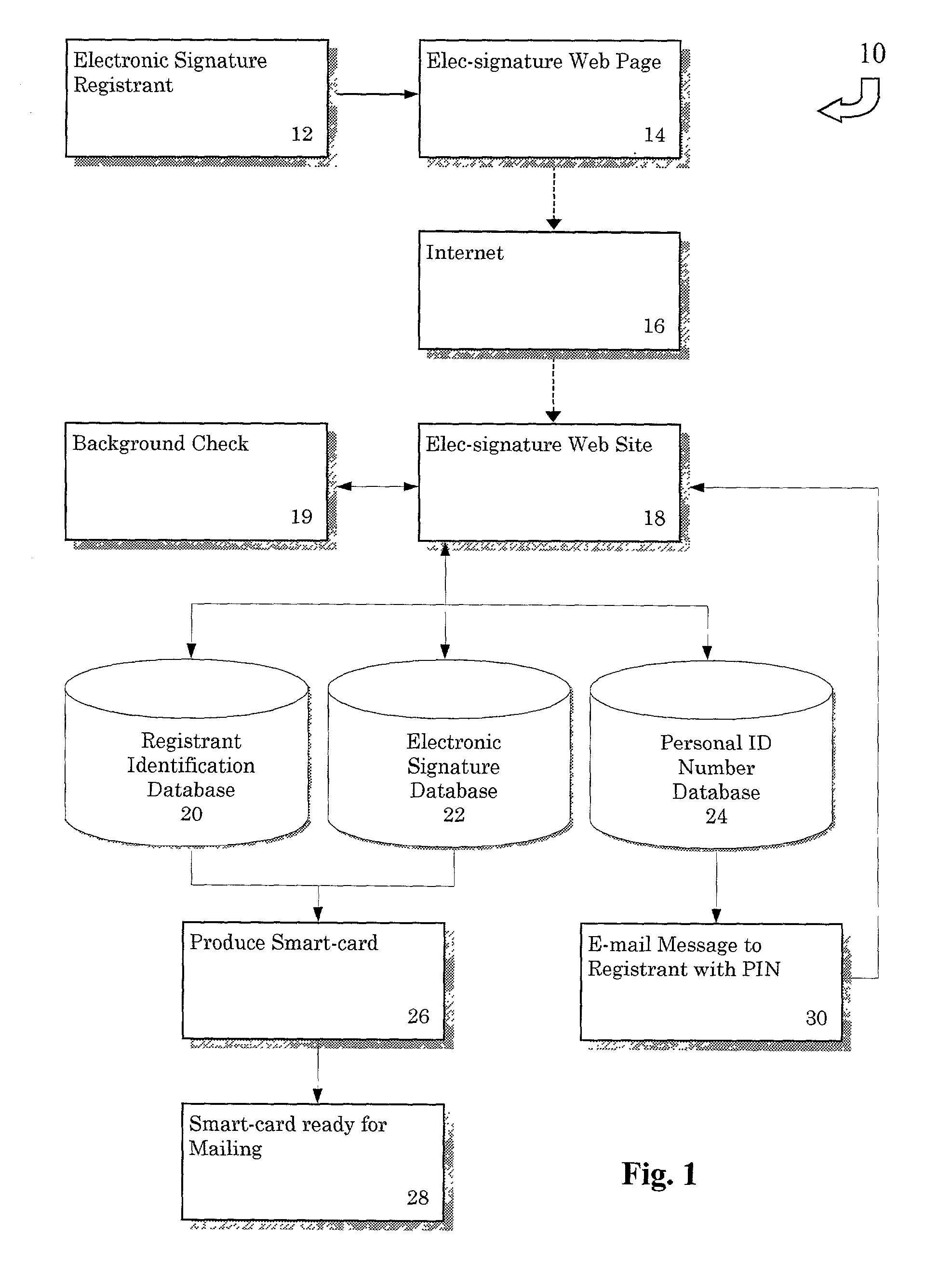
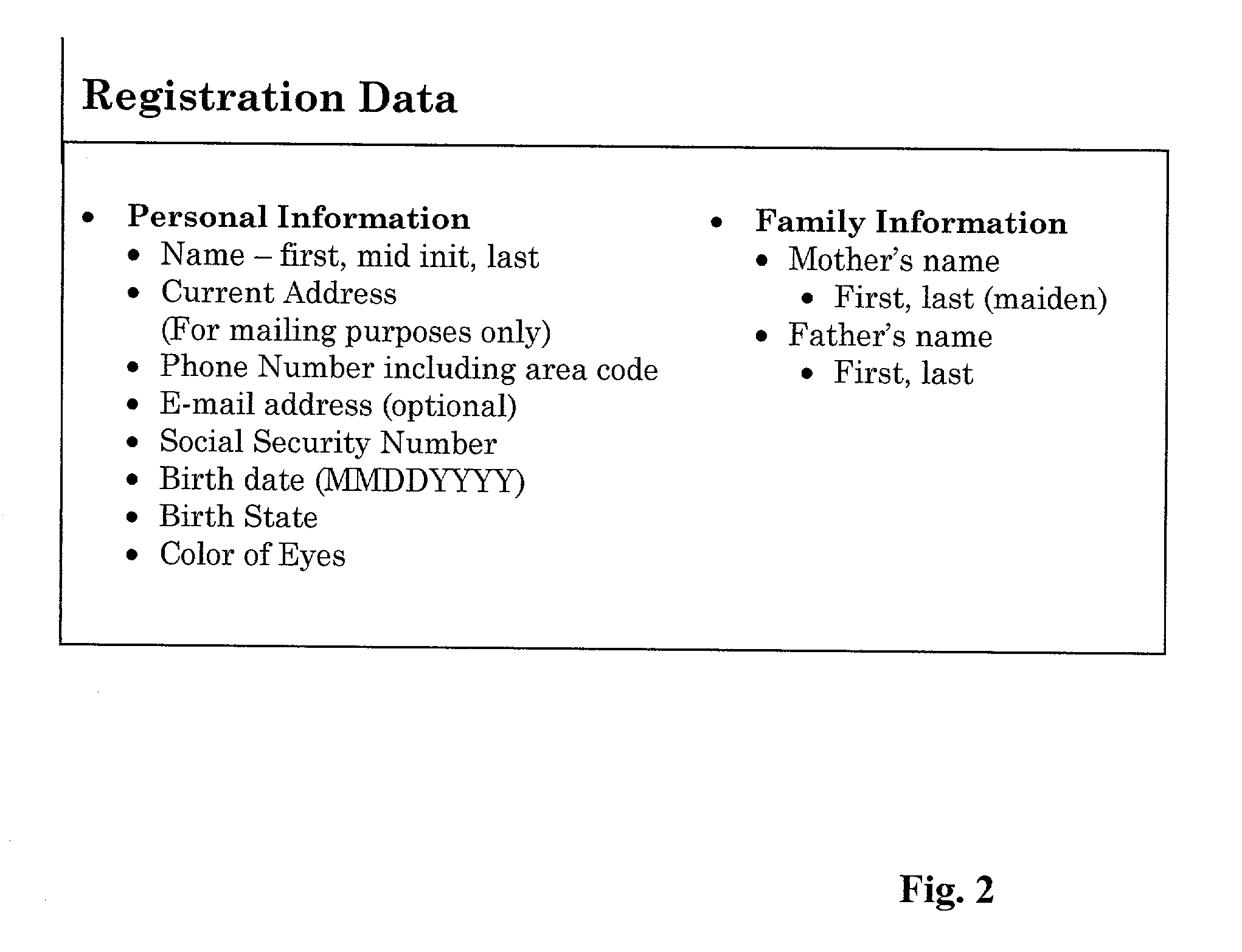
Electronic signature system
InactiveUS20020042879A1User identity/authority verificationPayment architectureIdentity theftCard reader
A method of producing an electronic signature and a system for verifying that signature by a licensed vendor. Personal information is received by an individual wishing to utilize this system. This personal information would be used to produce an electronic signature, including an authentication number. The electronic signature, as well as the means for producing the authentication number, can be created through the use of a electronic signature card. This card can be inserted into a reader and the licensed vendor can compare the generated authentication number with an authentication number associated with the individual. Once the electronic signature is verified, a particular commercial transaction can be completed. Additionally, the present invention can be used to ensure the integrity of the document after the electronic signature has been attached thereto. This invention prevents identity theft, as well as minimizing the risk of unauthorized use of the signature card to sign a document in another person's name.
Owner:LEGACY SYST DEV
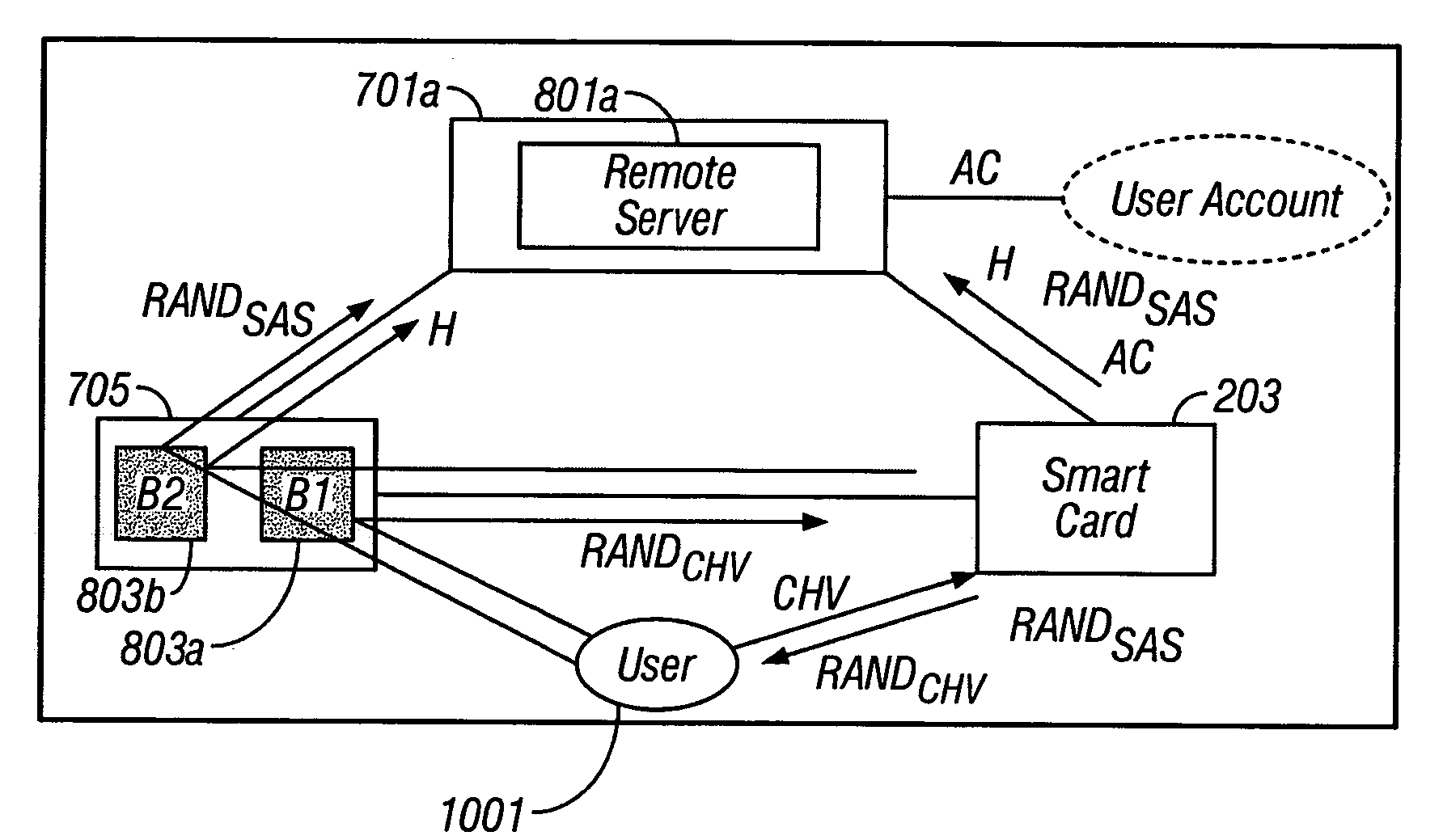
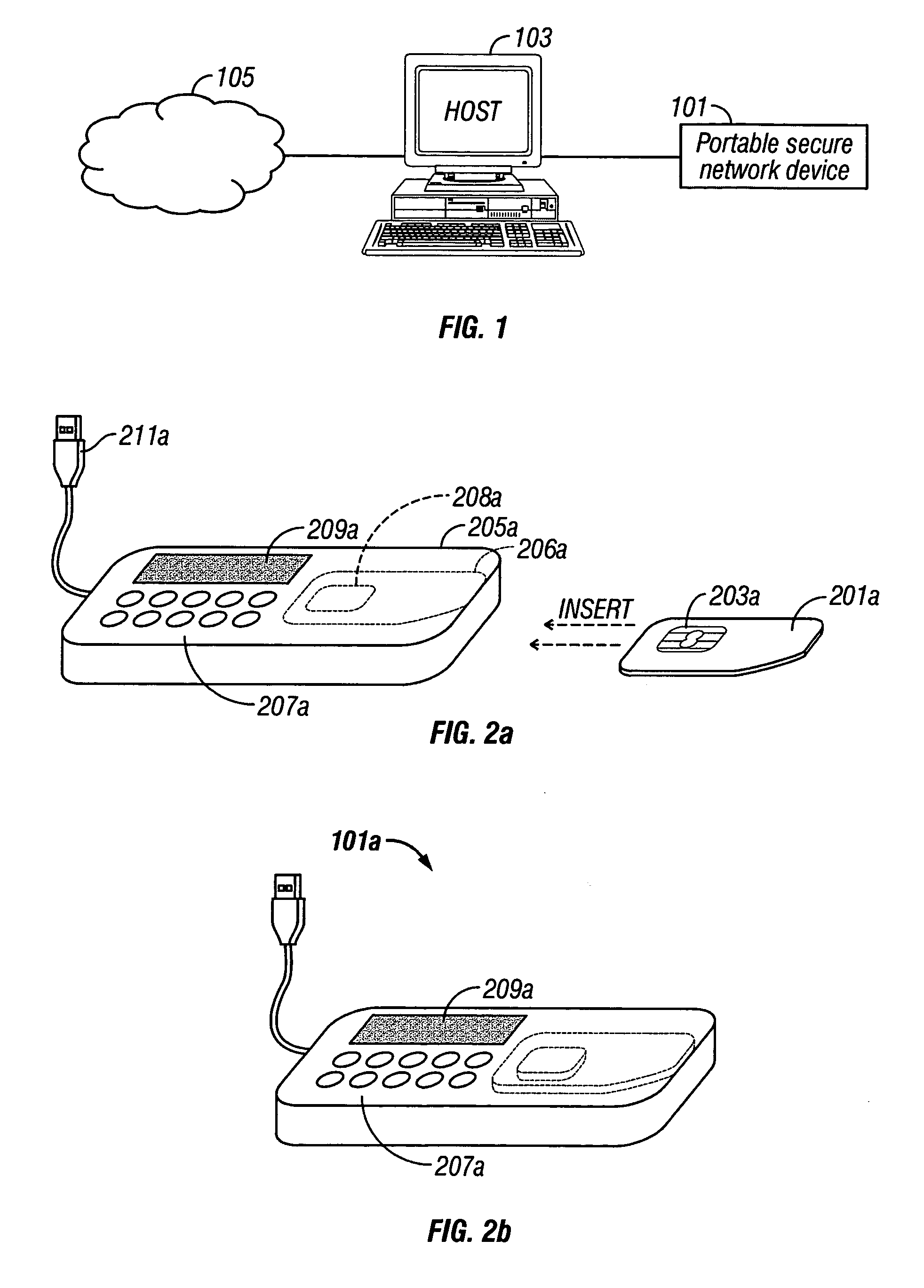
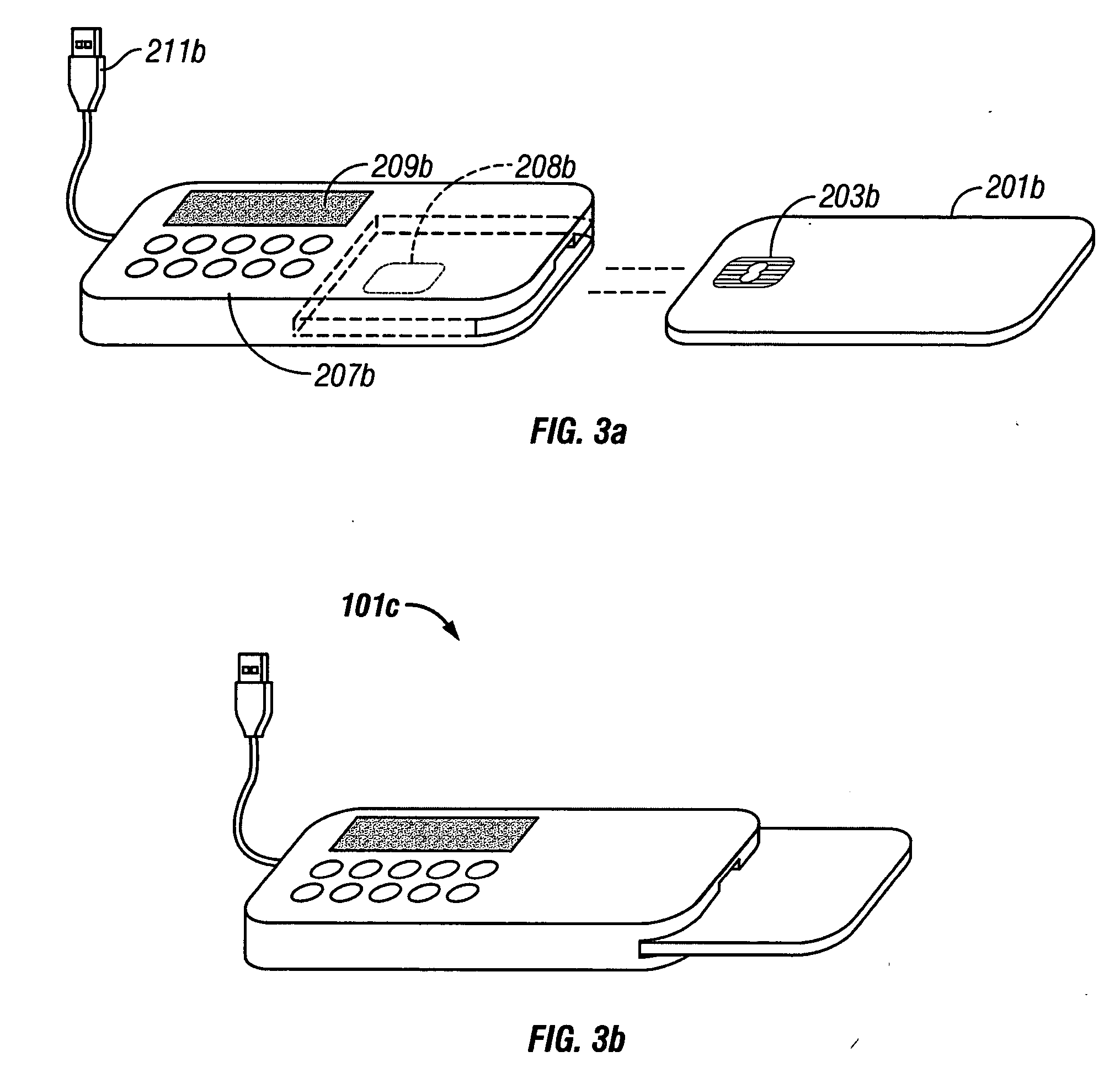
System and method for secure online transactions using portable secure network devices
InactiveUS20060294023A1Prevent online identity theftPrevent theftPayment architectureDigital data authenticationIdentity theftSmart card
A portable secure network device and method to operate such a device to provide secure login, secure online transactions, and to prevent online identity theft. An embodiment of the invention may be constructed by inserting a network smart card into a card reader, wherein either the card reader or the card itself has an output device and input device wherein the processor is programmed to execute according to instructions to cause the microprocessor: to produce a shared association secret; to display the shared association secret on the output device; and to transmit the shared association secret to the remote server; thereby ensuring that a user observing the output device and the remote server computer both possess the shared association secret.
Owner:AXALTO INC
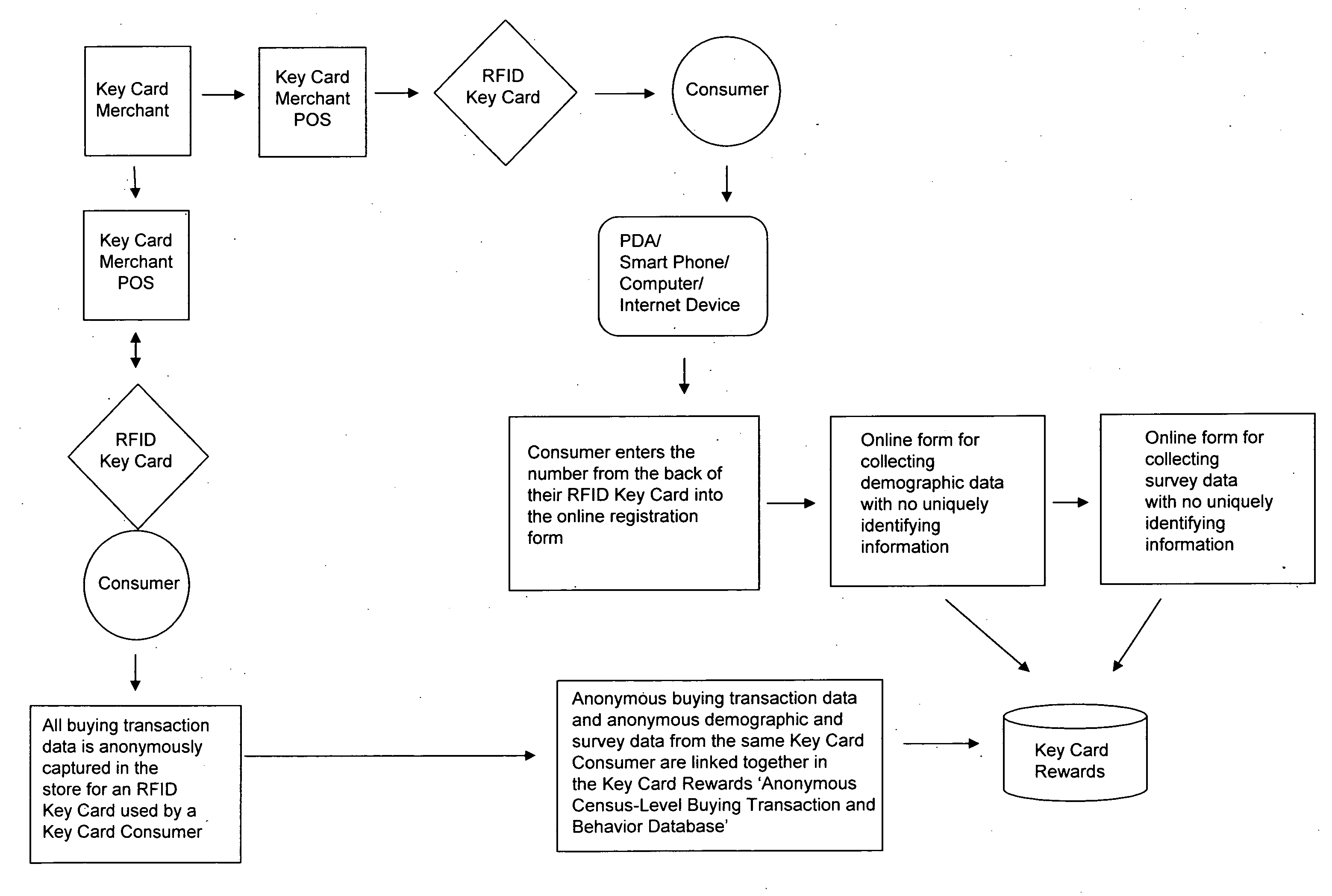
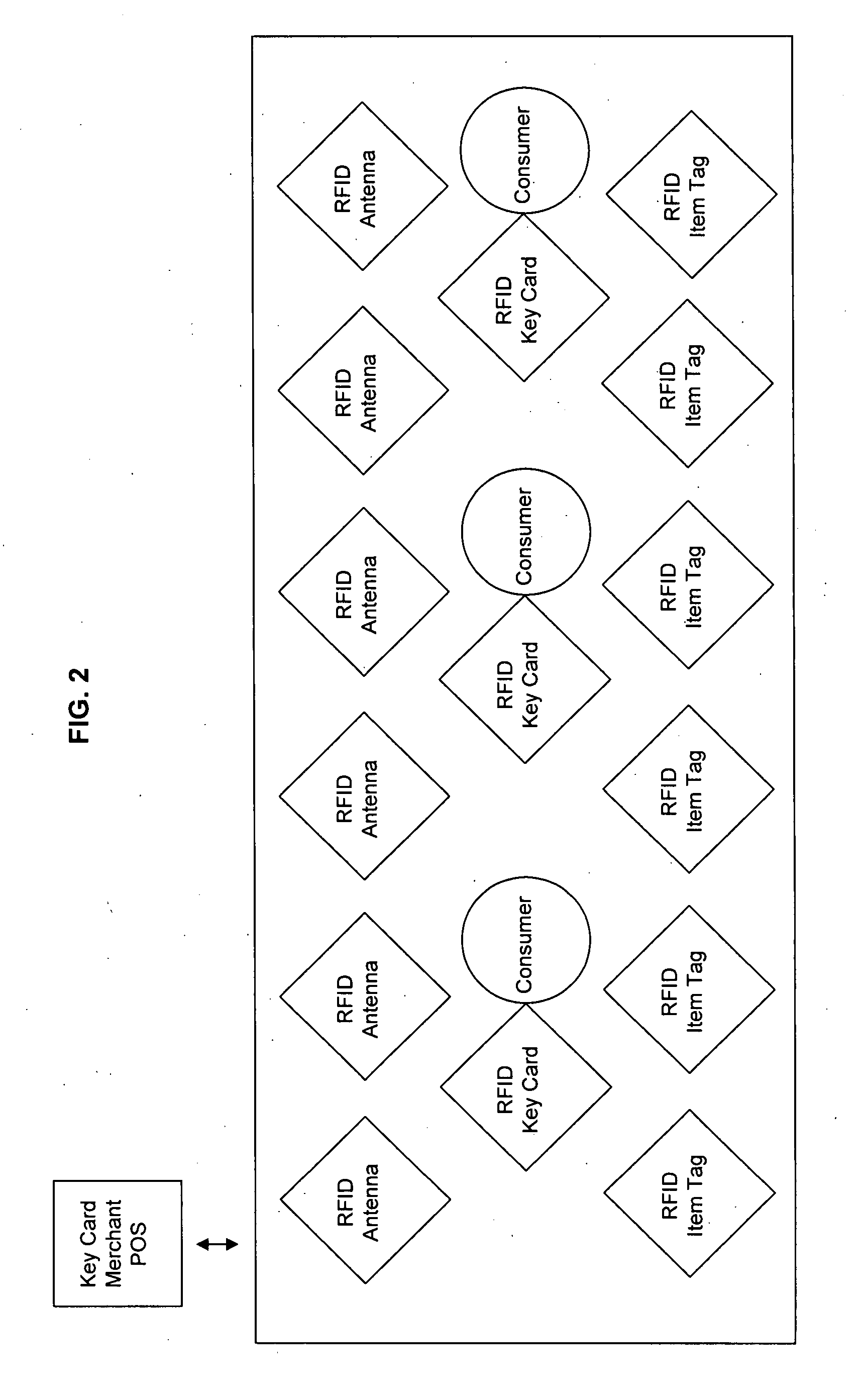
System and method of obtaining and using anonymous data
InactiveUS20070214037A1Improve identityPrivacy protectionMarket predictionsCash registersThird partyMarket place
A system and method that anonymously collects and uses consumer purchase data, including radio frequency metrics, linked to individual characteristics, including demographic and attitudinal profiles of each user, while protecting individual user's identities. Uniquely identifying information about the user is not requested or recorded, keeping individual users anonymous and protected from unrequested solicitations, identity theft, and disclosure of individually identifying information to any third party. This data can then be used for a variety of purposes, including mass marketing, individually targeted marketing, and market research.
Owner:SHUBERT ERIC +1
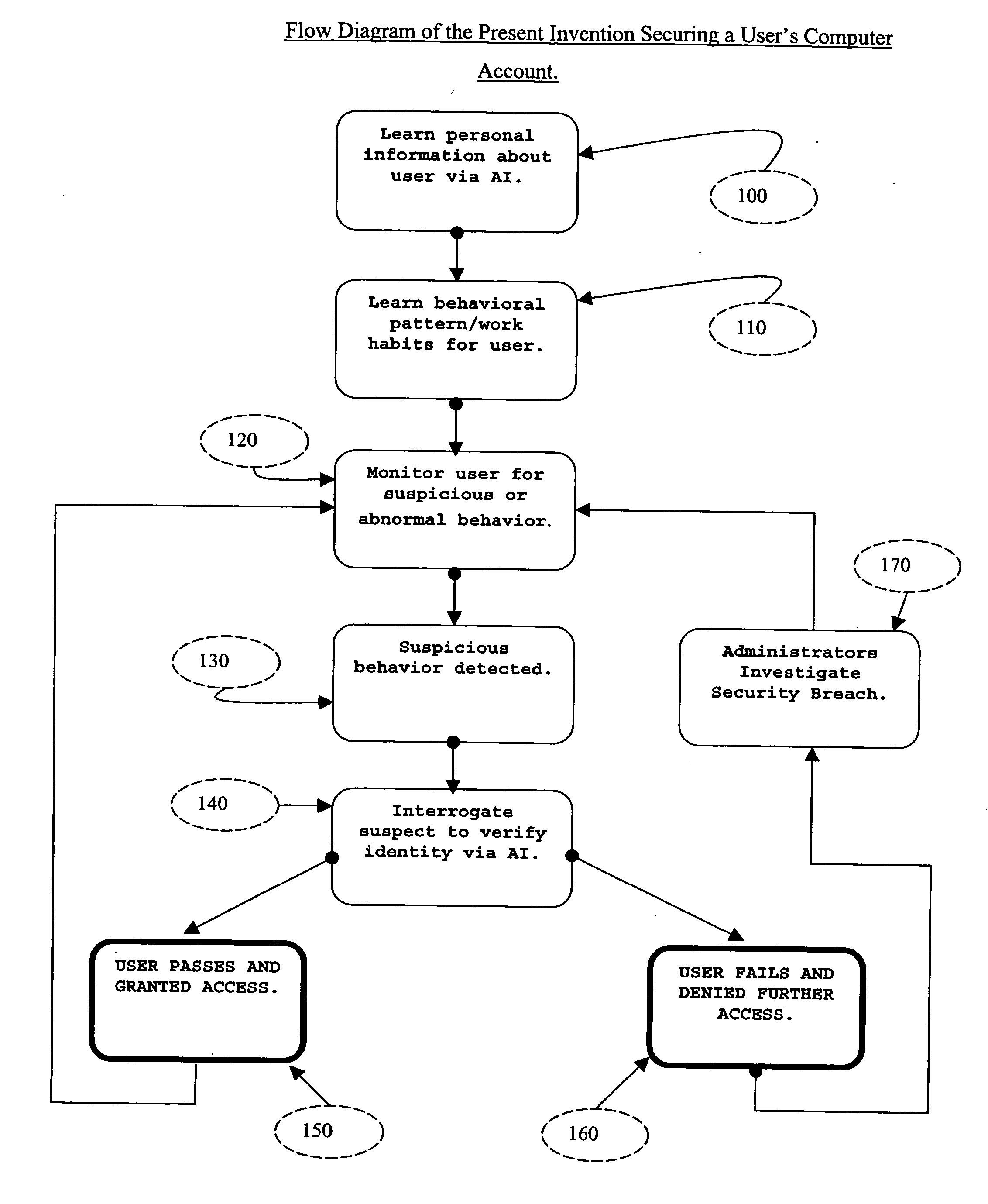
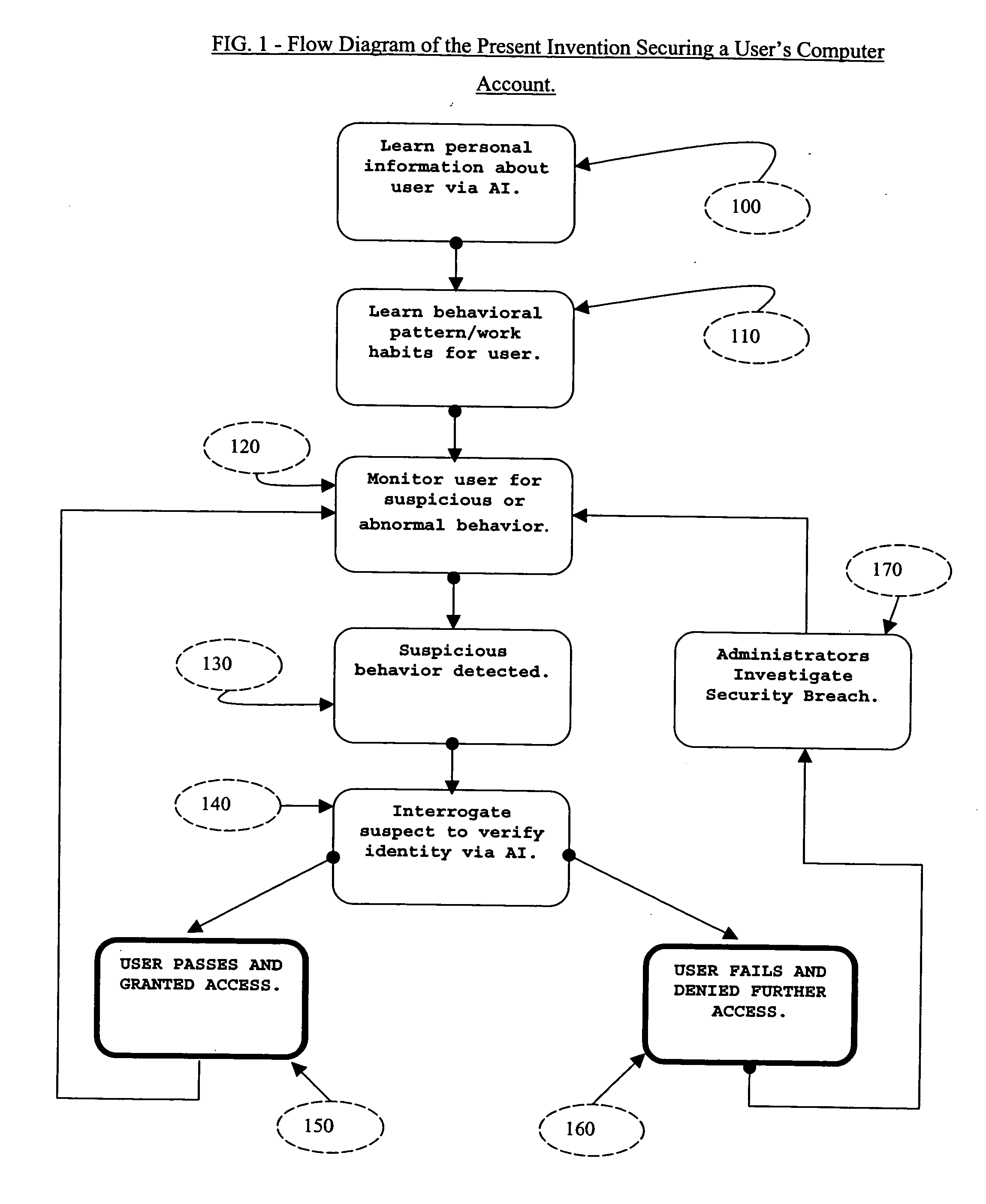
System and method for securing computer system against unauthorized access
ActiveUS20050097364A1Defeat computer security breachSecurity breachMemory loss protectionDigital data processing detailsComputer usersIdentity theft
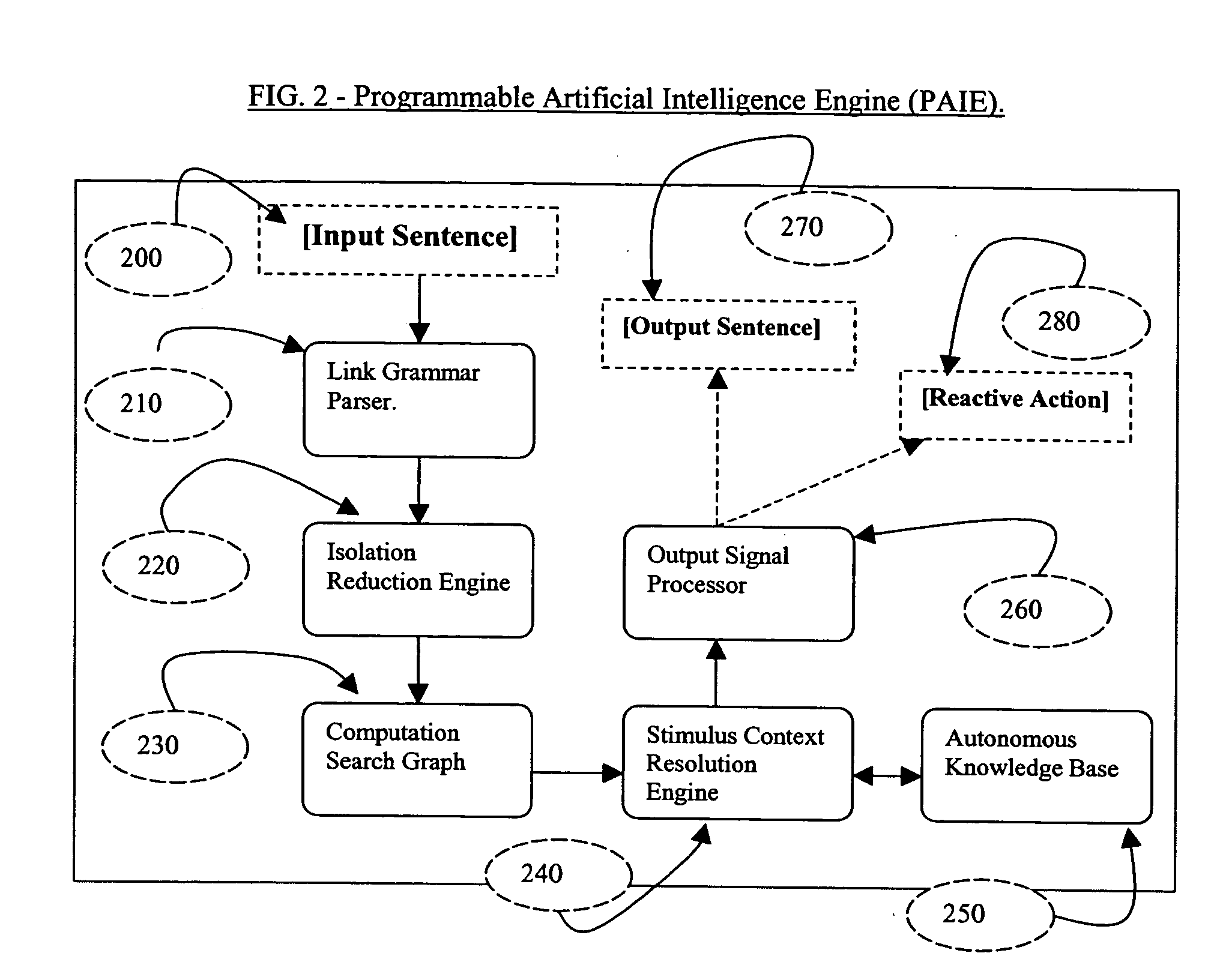
The present invention described secures a computer account against unauthorized access caused as a result of identity-theft, and insider-espionage using artificial intelligence and behavioral modeling methods. The present invention has the ability to detect intruders or impersonators by observing “suspicious” activity under a computer account. When it sees such suspicious behavior, it uses artificial intelligence to authenticate the suspect by interrogation. The present invention asks the suspect questions that only the legitimate computer account owner can verify correctly. If the suspect fails the interrogation, that proves that he / she is an impersonator and therefore further access to the computer account is denied immediately. On the other hand if the suspect passes, access to the computer account is restored. The present invention uses a Programmable Artificial Intelligence Engine (PAIE) to interact with computer users in human natural language. The PAIE can also be programmed to suit other applications where natural language interaction with humans is helpful.
Owner:EDEKI OMON AYODELE +2
System and method for providing identity theft security
InactiveUS20100024037A1Reduce the burden onMinimal effortDigital data processing detailsDigital computer detailsComputerized systemIdentity theft
A system and method of providing identity theft security is provided. The system and method utilizes a computer program that identifies, locates, secures, and / or removes from computers, computer systems and / or computer networks personally identifying and / or other sensitive information in different data formats. The computer program utilizes a multi-tiered escalation model of searching / identifying sensitive information. The computer program of the instant invention utilizes a self-learning process for fine-tuning a level of scrutiny for identifying potentially sensitive information.
Owner:TOUCHNET INFORMATION SYST
Method and system for preventing identity theft and increasing security on all systems
The present invention provides a method and system for preventing identity theft and increasing security on systems. Some embodiments include receiving, into a computer system, a request to perform an electronic transaction for an identified human user at a remote location; accessing, by the system, a set of authentication criteria of the identified user; retrieving, into the system, a plurality of real-time authentication parameters relevant to the user and to the transaction; and comparing, by the system, the plurality authentication criteria to the accessed set of authentication parameters of the user and either authorizing an action to complete the electronic transaction or not. Some embodiments include displaying, on a first personal electronic device of the user, an indication of the real-time alert of the request to perform the electronic transaction; and eliciting and receiving a real-time authorization indication from the user using the first personal electronic device of the user.
Owner:CANNON ROYCE E
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com