Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
409 results about "Electronic identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
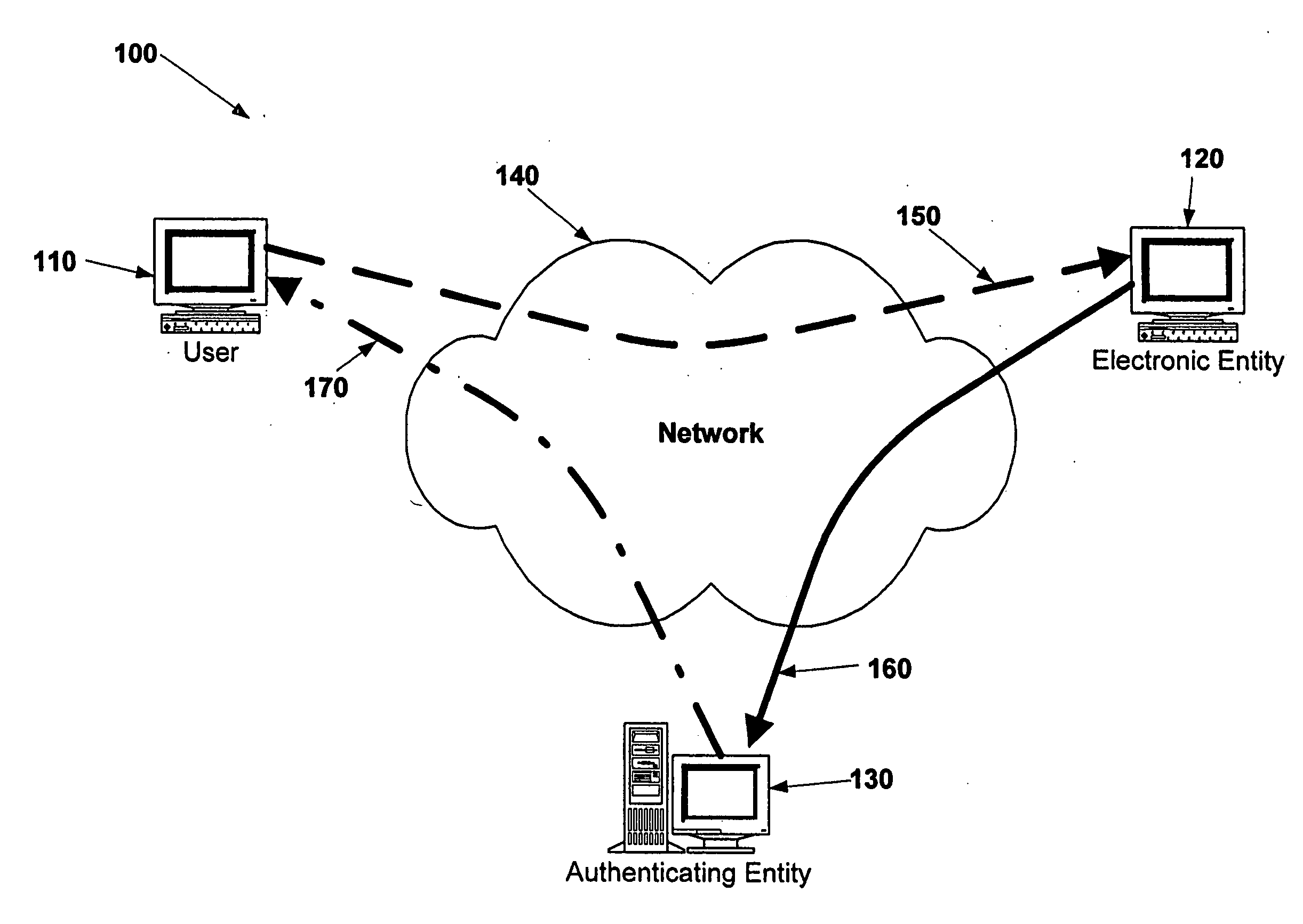
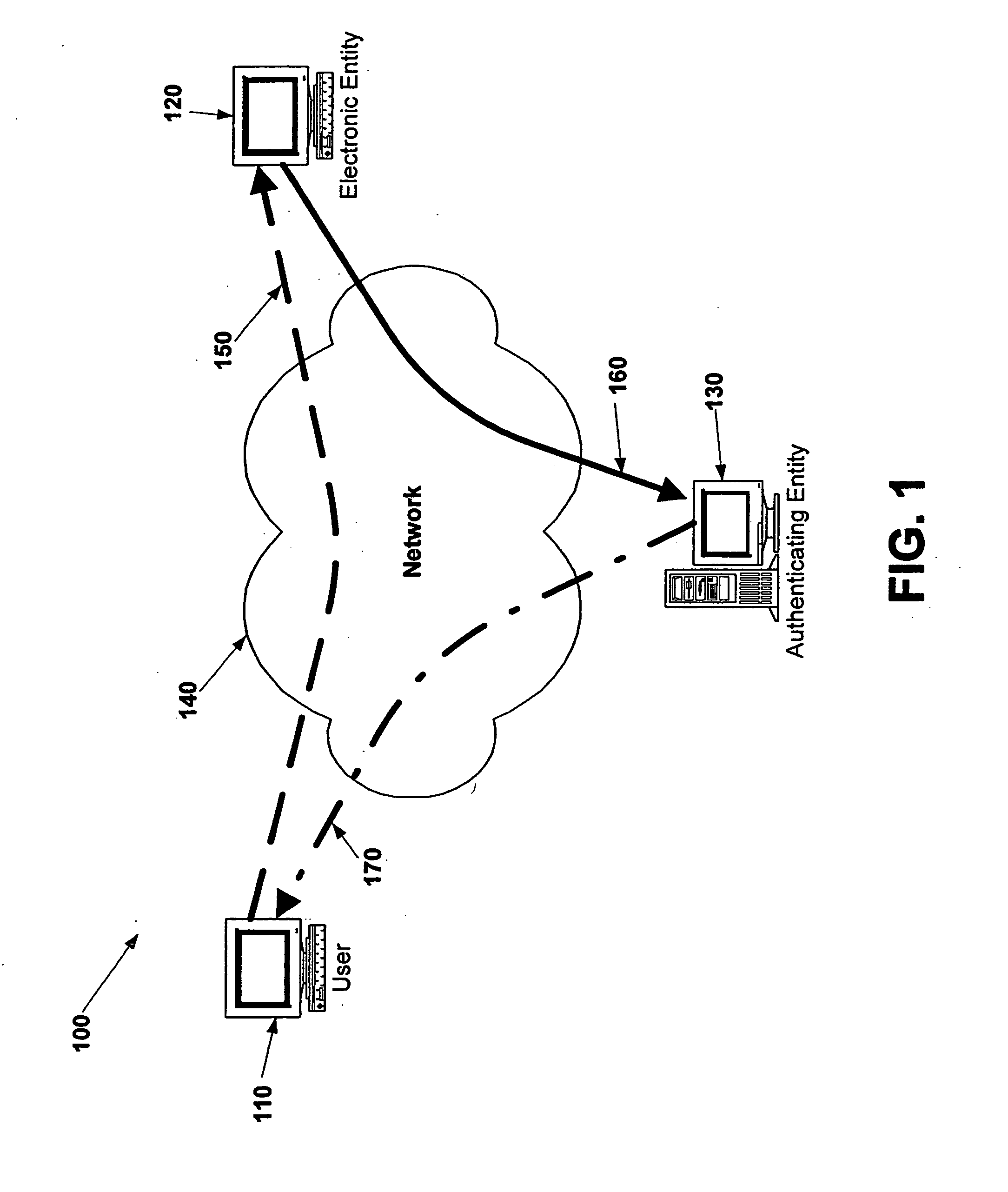
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
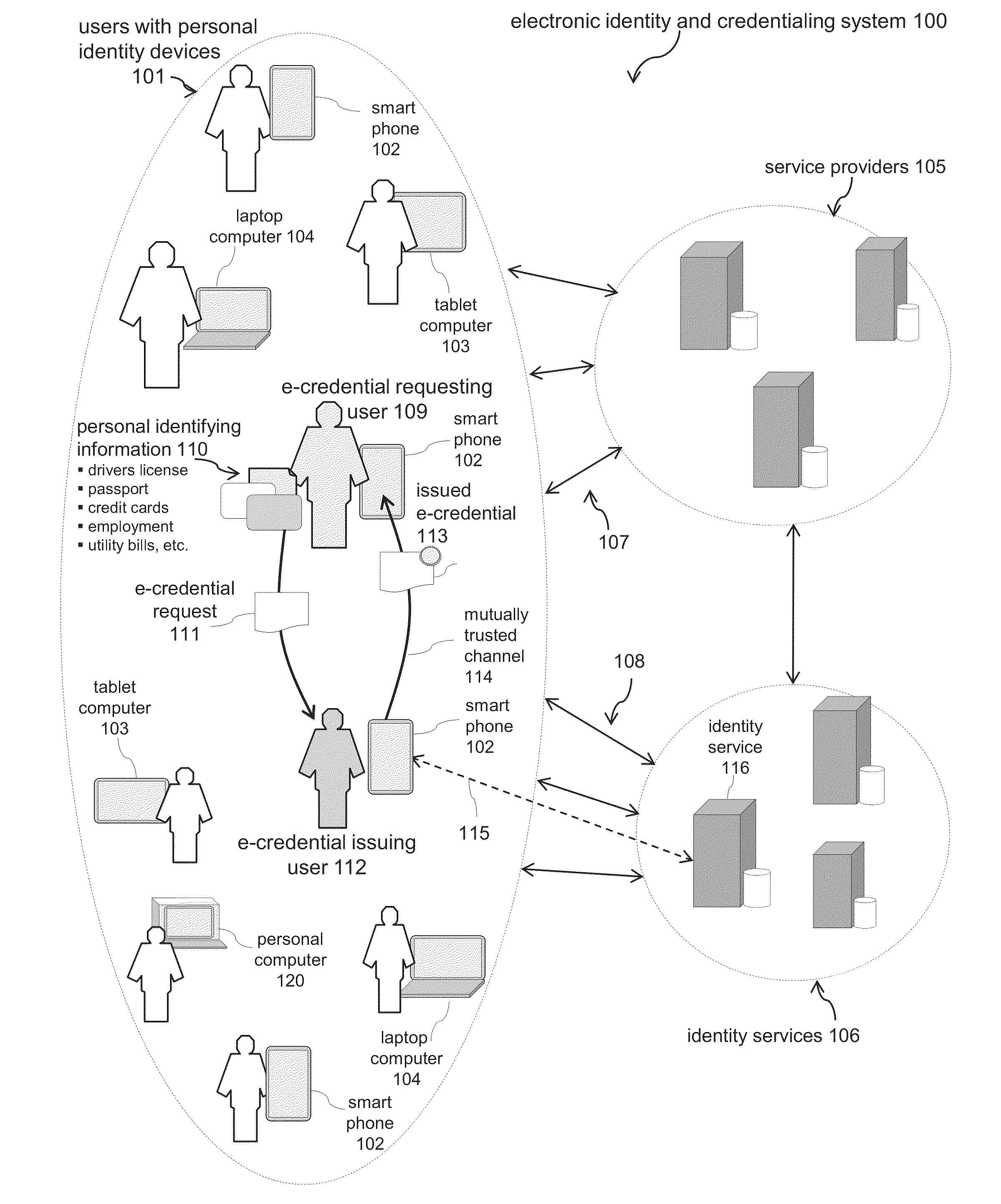
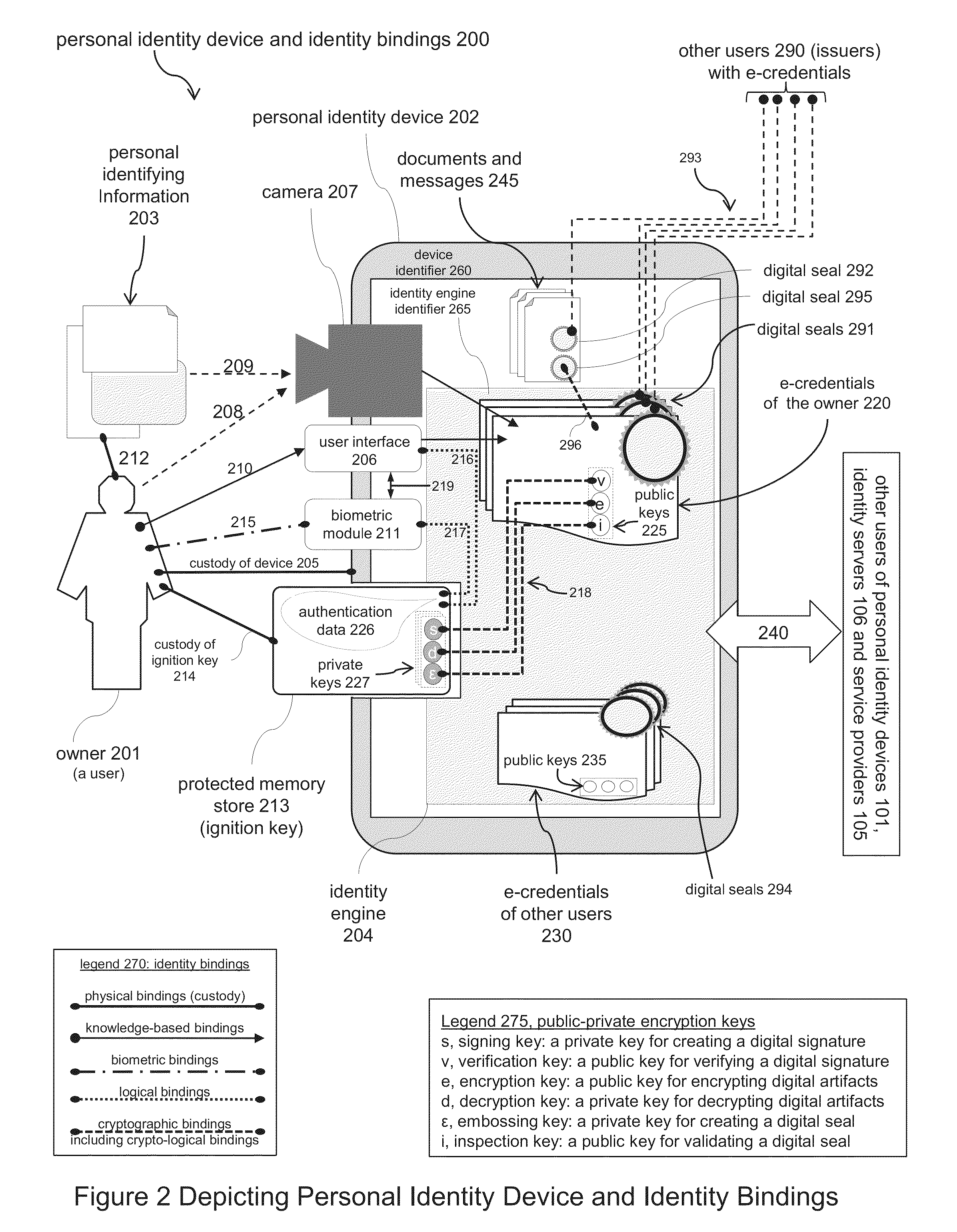
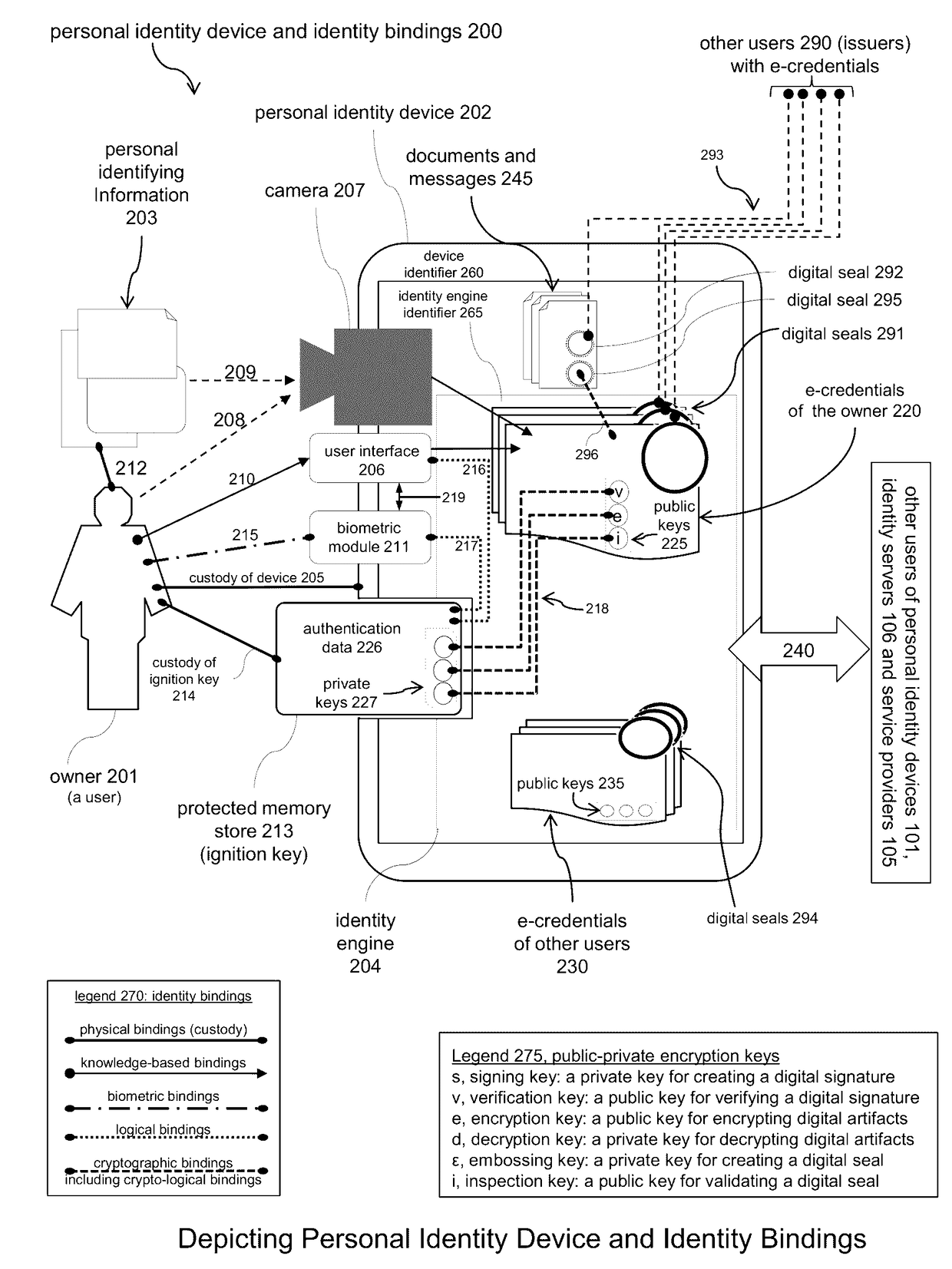
Electronic Identity and Credentialing System
ActiveUS20150095999A1Reduce riskAvoid attenuationDigital data processing detailsUser identity/authority verificationTablet computerCredentialing
Described is an electronic credentialing system that allows personal identity devices to interact; each interacting device has an installed identity engine that acquires, holds, issues and uses electronic credentials (e-credentials), these electronic credentials can be installed on personal identity devices, such as: smart phones, tablets, laptops, embedded systems, and / or personal computers.
Owner:TOTH KALMAN CSABA
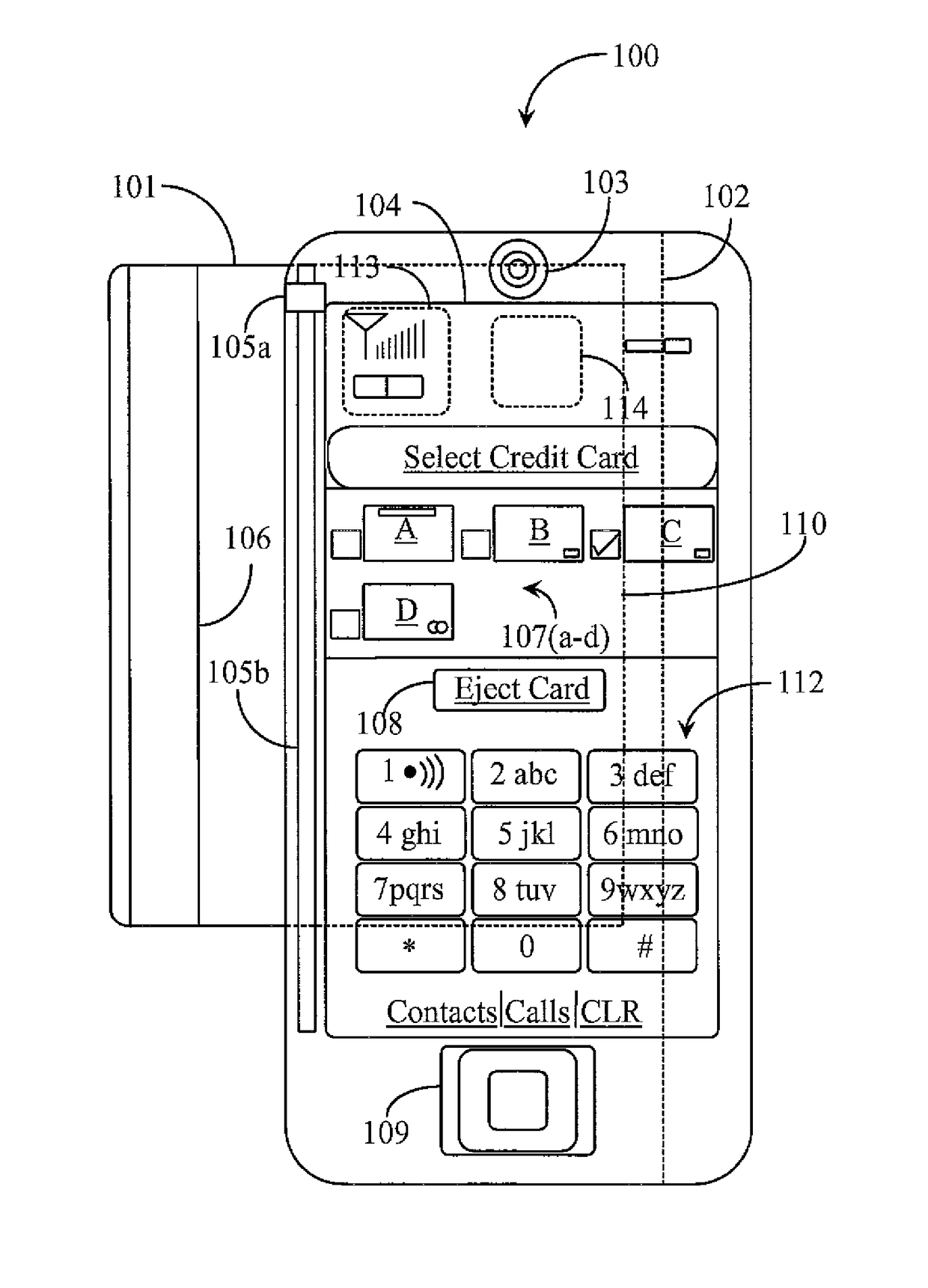
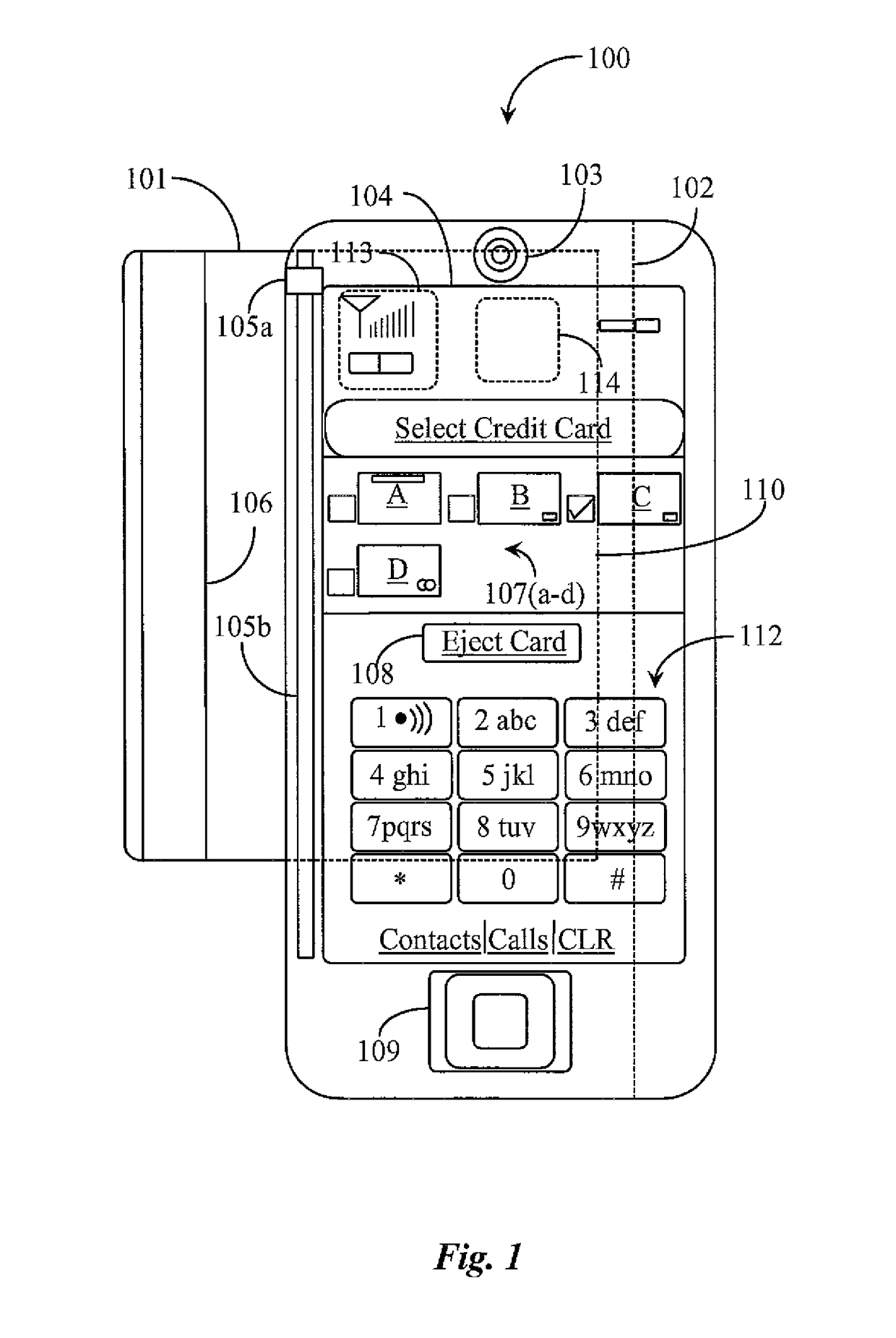
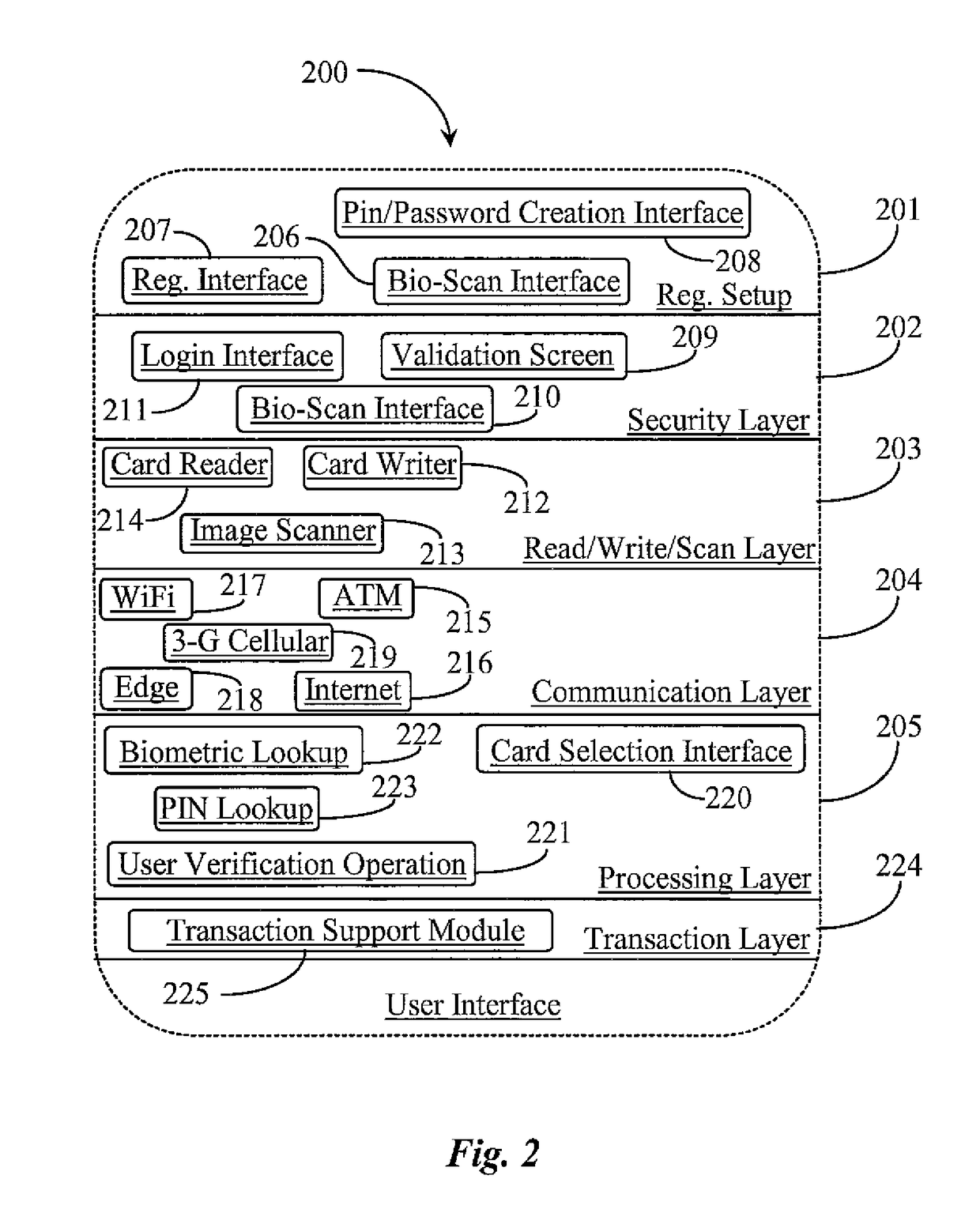
Hand-held electronics device for aggregation of and management of personal electronic data
A readable and rewriteable card blank for use with a hand-held electronics device having a card reading and writing interface for aggregation of and management of personal electronic data sets is provided including a readable and rewriteable media disposed on a credit card form factor, a first touch enabled display, internal micro-circuitry such as an embedded smart chip, a proximity sensing capability characterized in that the personal electronic data sets are read into the card form factor selectively or collectively via a personal electronics device enabled as a smart phone for use in electronic transacting or fulfillment of electronic identification queries.
Owner:EDGE MOBILE PAYMENTS LLC
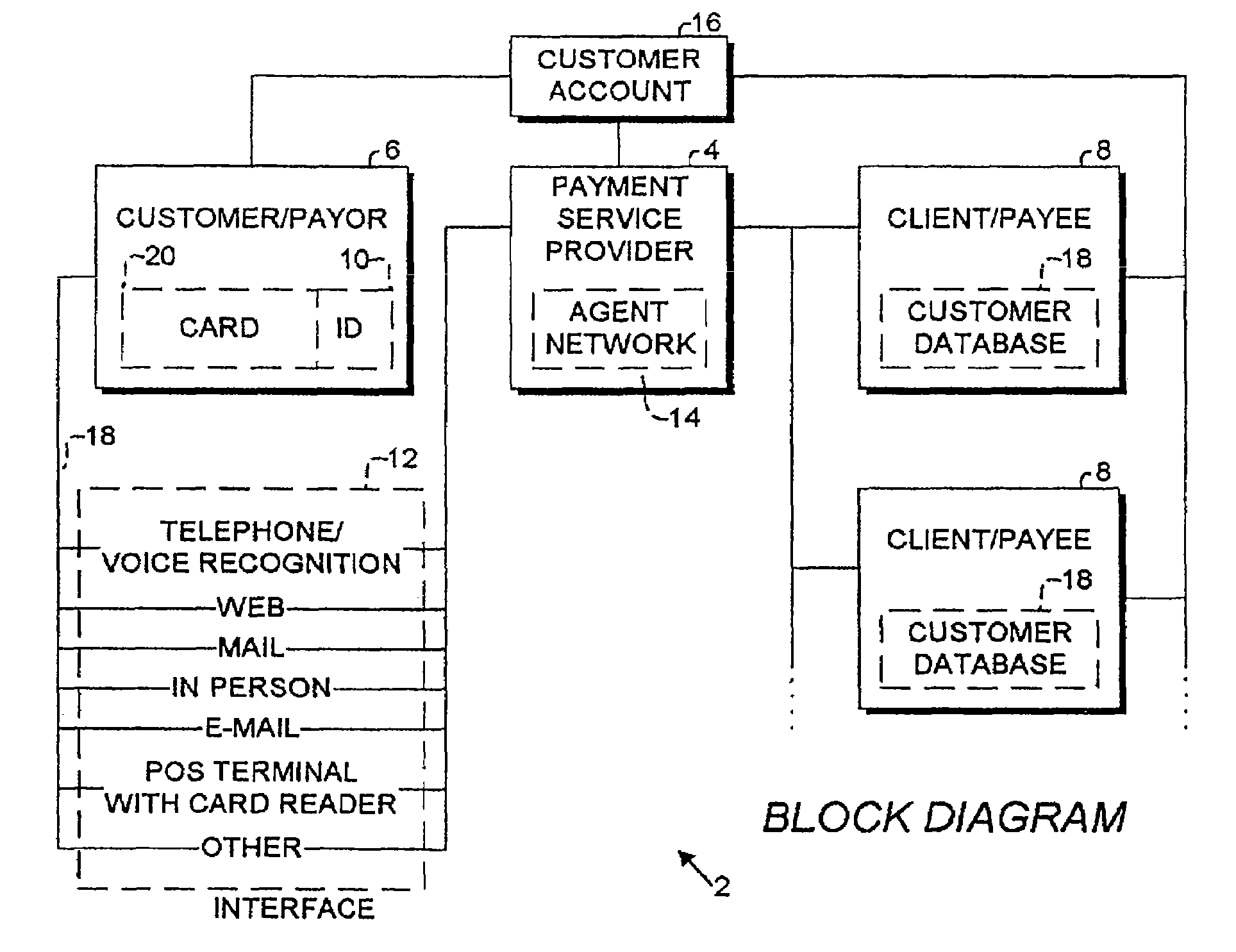
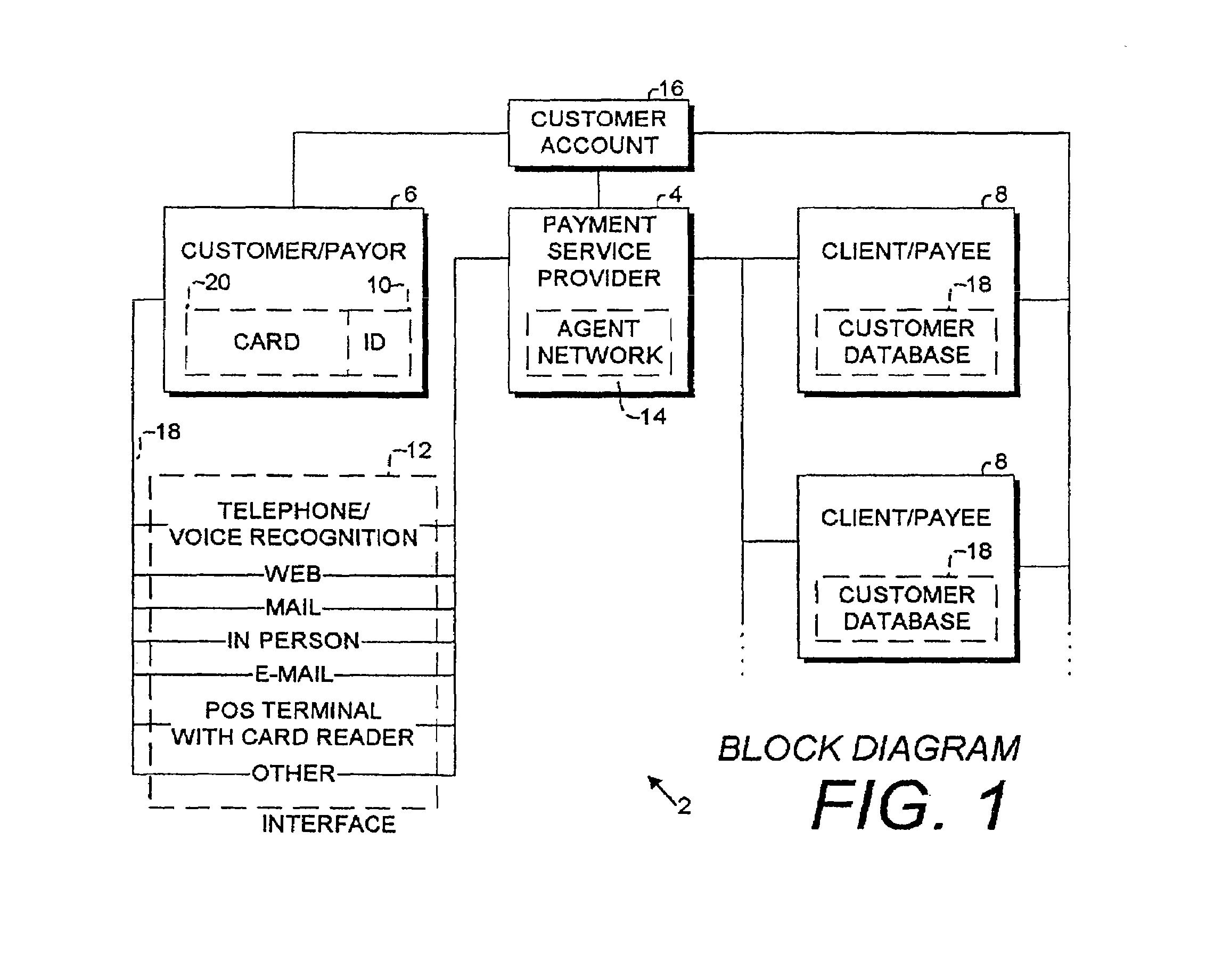
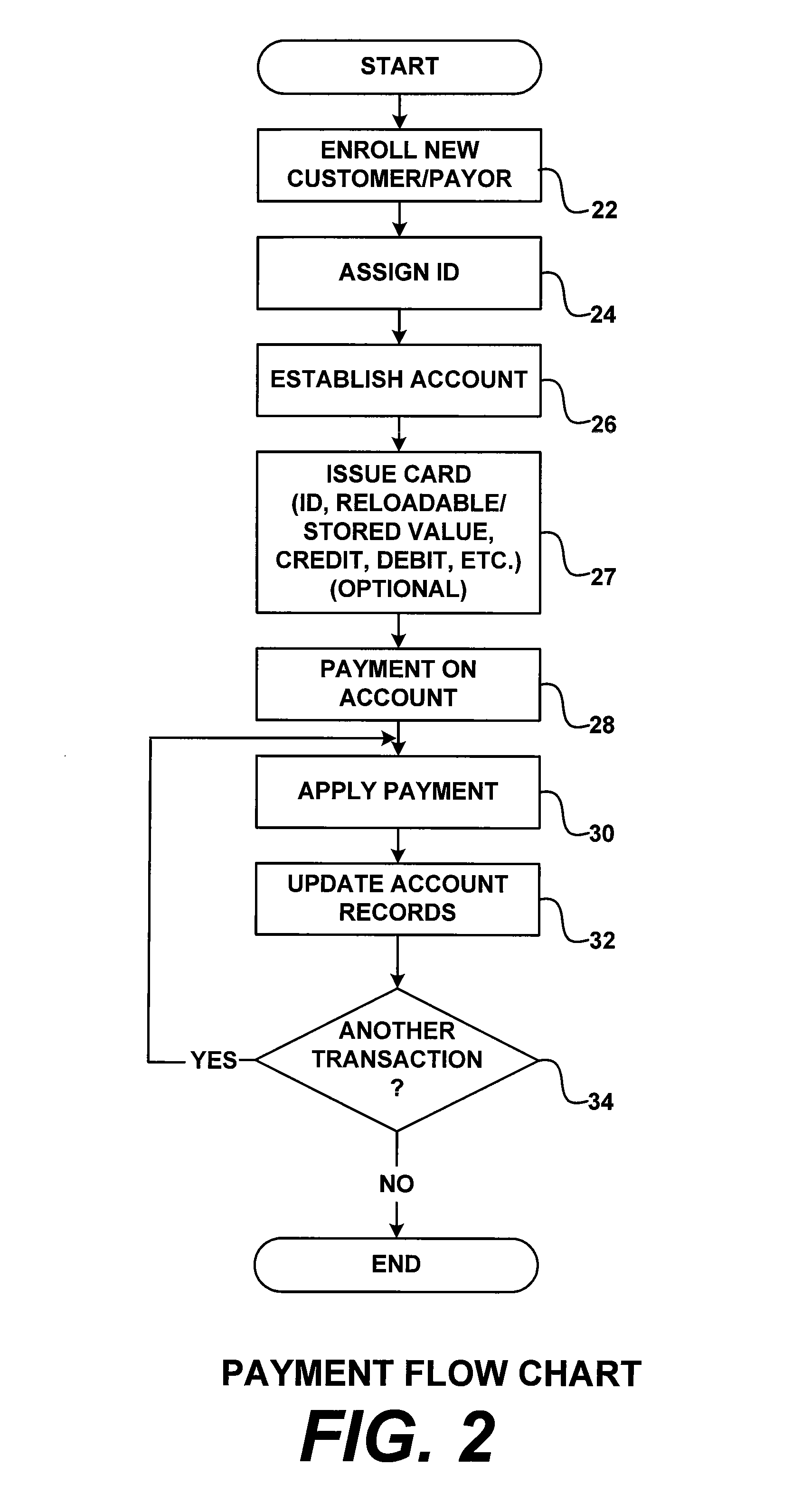
Electronic identifier payment system and methods
InactiveUS7092916B2Credit registering devices actuationAdvertisementsElectronic identificationUnique identifier
A payment service method and system involve a payment service provider, a customer / payor and a consumer provider / payee. The customer / payor enrolls in the service and is provided a unique identifier that enables the customer to conduct transactions with the payment service provider. The customer / payor interfaces with the payment service provider through various forms of communication, and can facilitate payments to the consumer providers / payees through the payment service provider while remaining anonymous.
Owner:THE WESTERN UNION CO
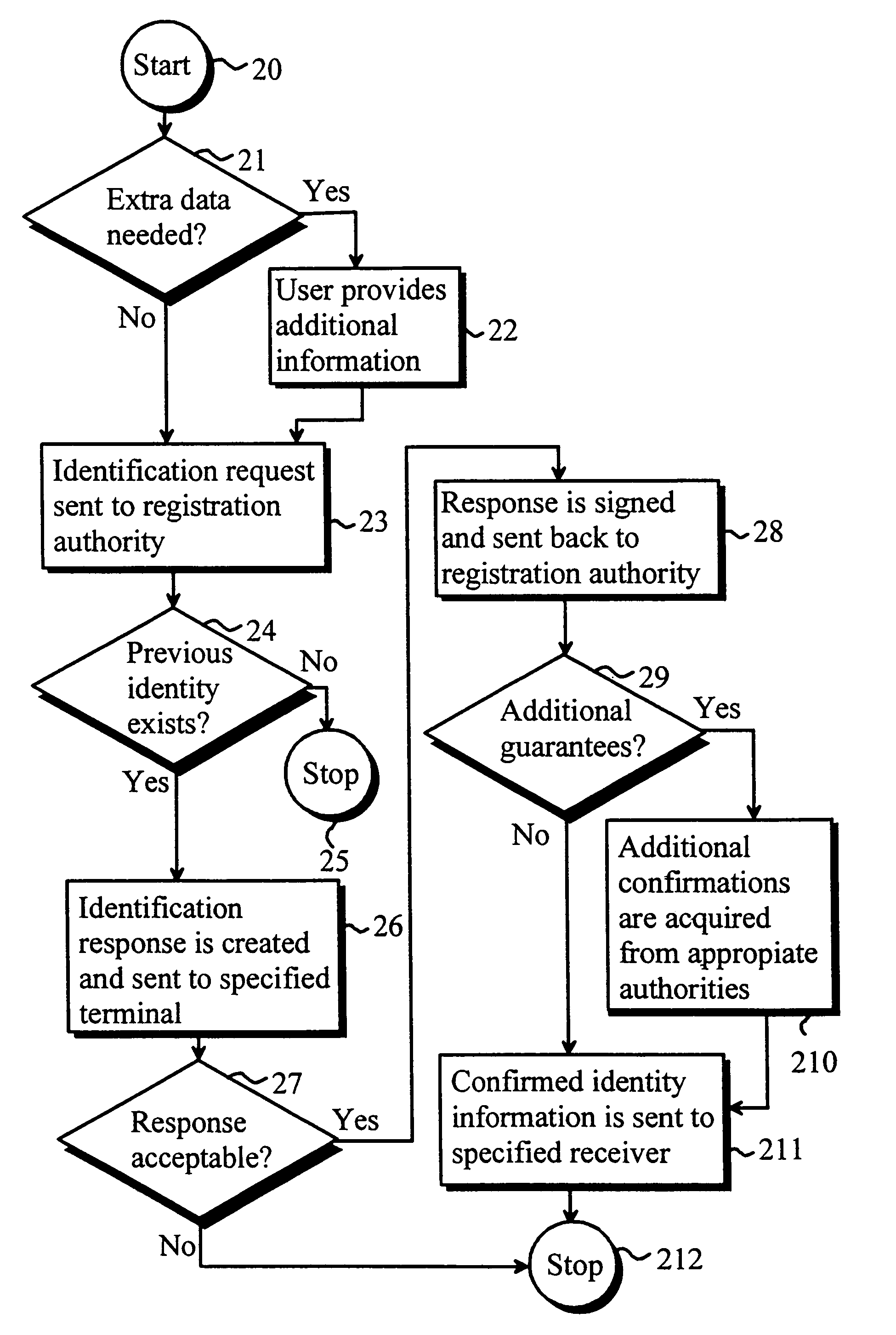
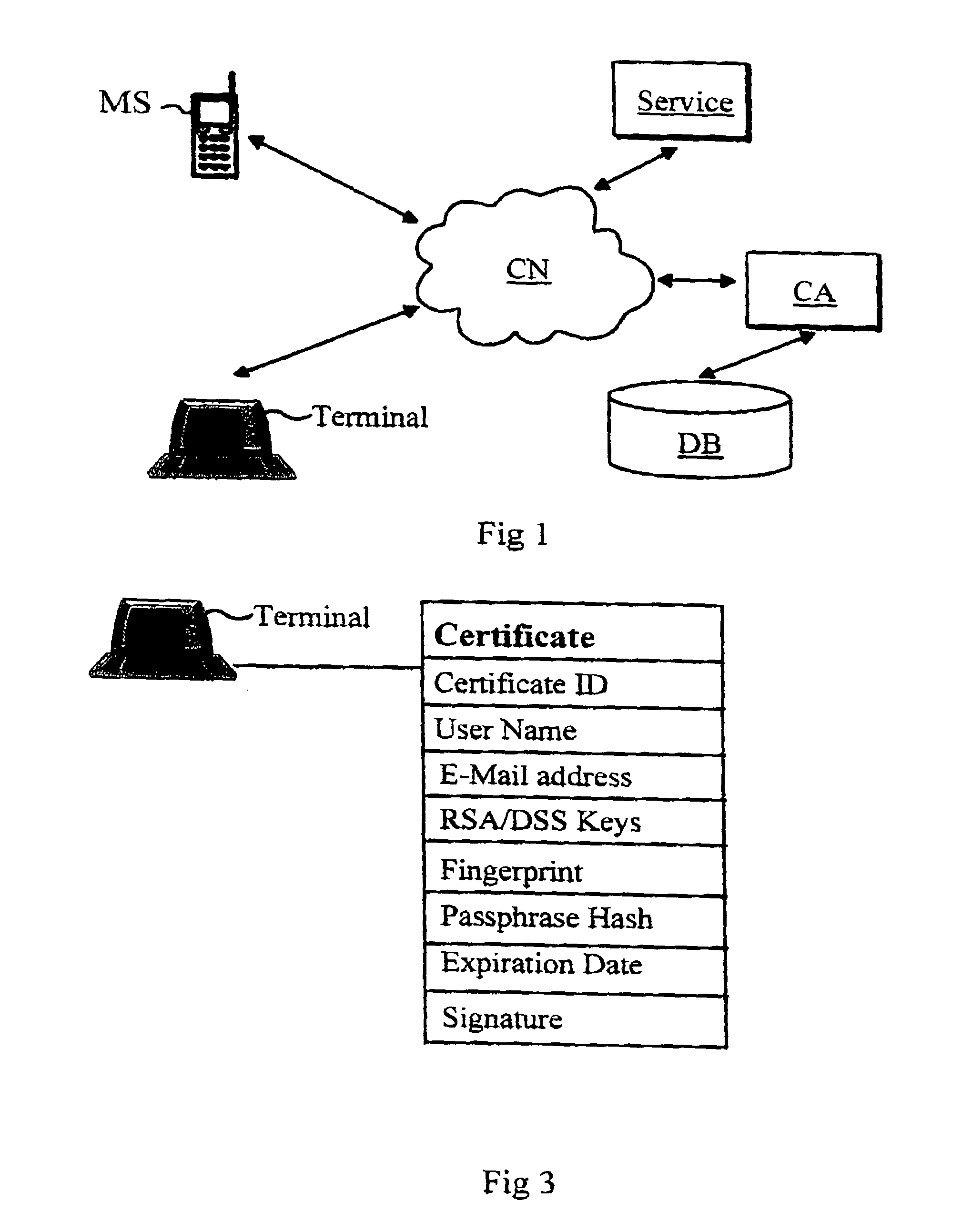
Method for issuing an electronic identity
InactiveUS7020778B1Improve identityData processing applicationsDigital data processing detailsDigital signatureComputer terminal
A method for issuing an electronic identity based on previously certified electronic identity. This is accomplished by providing a method to use a previously certified identity to create another representational form for the same identity. This way the holder of a certificate can extend his or her already verified identity for other uses. The previously certified identity can be for instance so called mobile identity which is associated to a person's mobile terminal such as mobile phone. The person can show to certificate be his / her own by using the digital signature feature of the mobile terminal.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
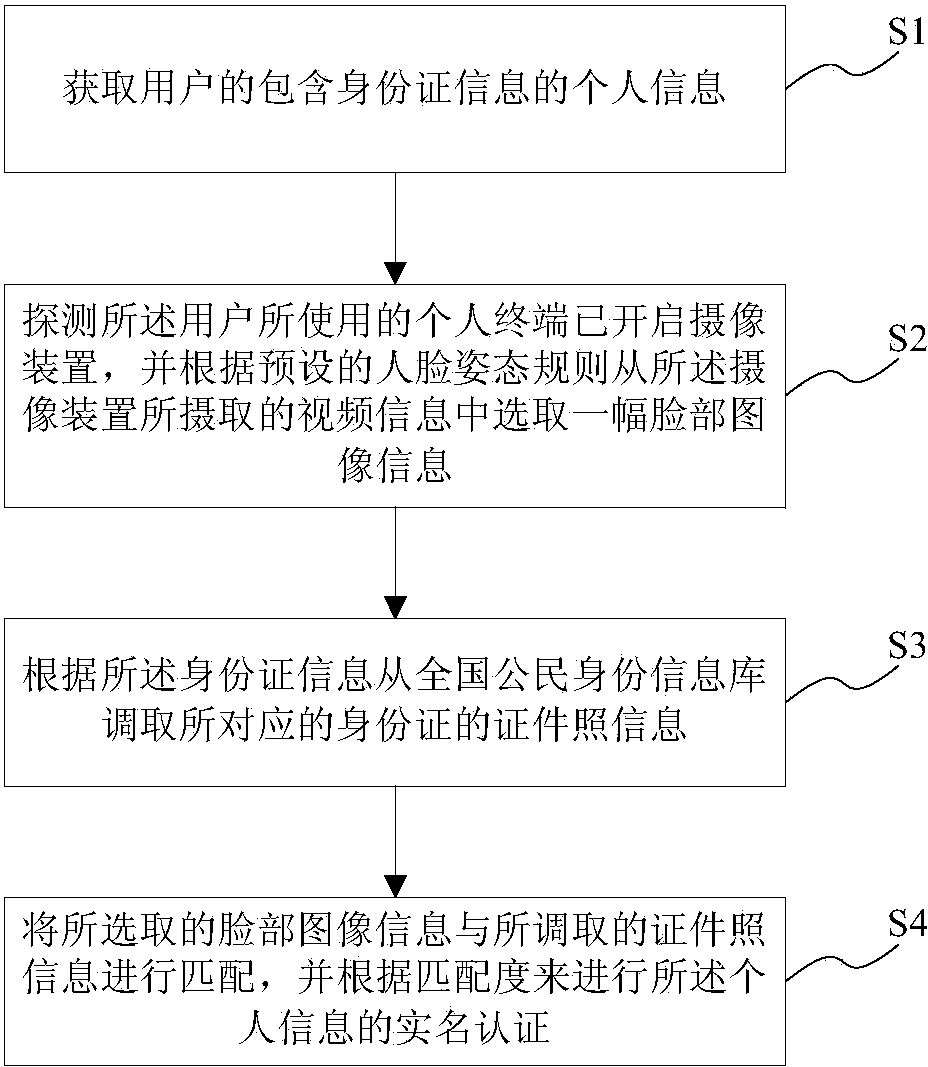
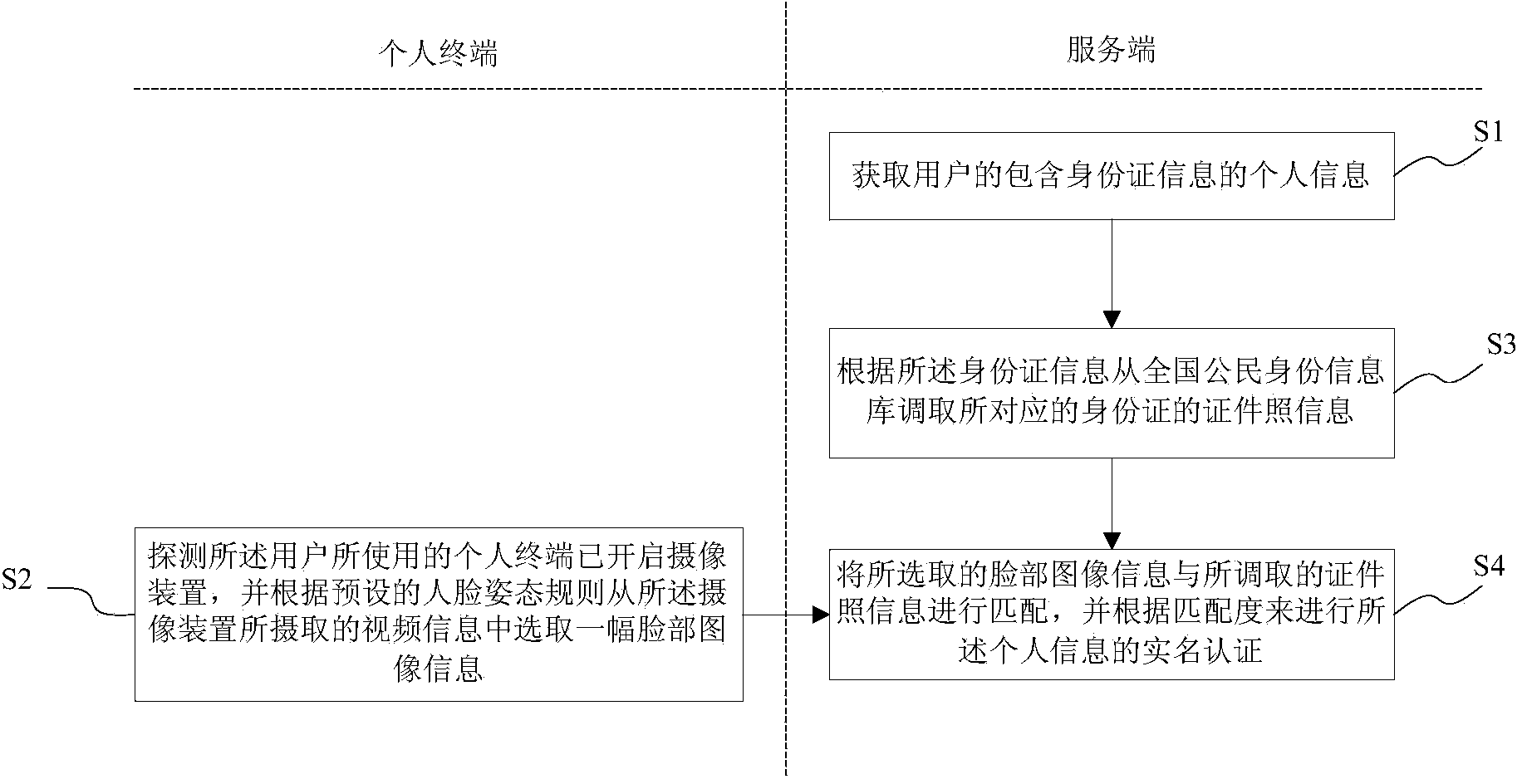
Method and system for real-name authentication based on face recognition
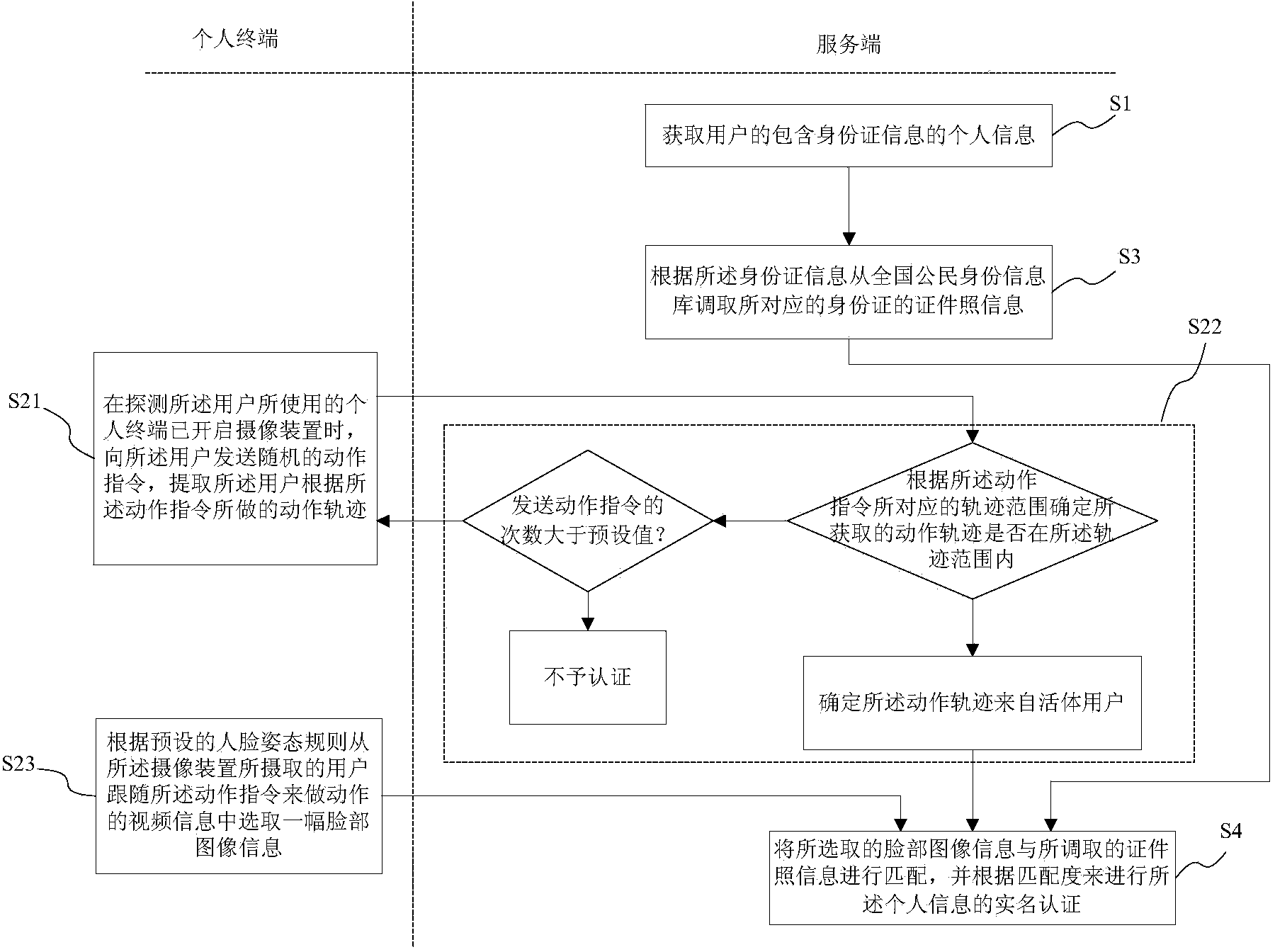
InactiveCN103634120ASolve the problem of identificationPrevent fraudulent useUser identity/authority verificationDigital data authenticationInformation repositoryInternet privacy
The invention provides a method and a system for real-name authentication based on face recognition. According to the method, personal information of a user including identity card information is acquired by the system, the condition that a personal terminal used by the user starts a camera device is detected, the information of a facial image from video information picked up by the camera device is selected according to a preset face posture rule, the identification photo information of a corresponding identity card is retrieved from the national citizen identity information database according to the identity card information, the selected information of the facial image is matched with the retrieved identification photo information, and real-name authentication of the personal information is performed according the matching degree. According to the method and the system disclosed by the invention, the difficult problem of non-face-to-face personal network identity identification is solved to ensure that a user can quickly finish real-time authentication anytime and anywhere, and meanwhile, because the user dose not need to provide an electronic identity card, the phenomena of falsely use and embezzlement of identity cards can be effectively prevented.
Owner:上海市数字证书认证中心有限公司
Method and system for eID authentication on mobile terminal
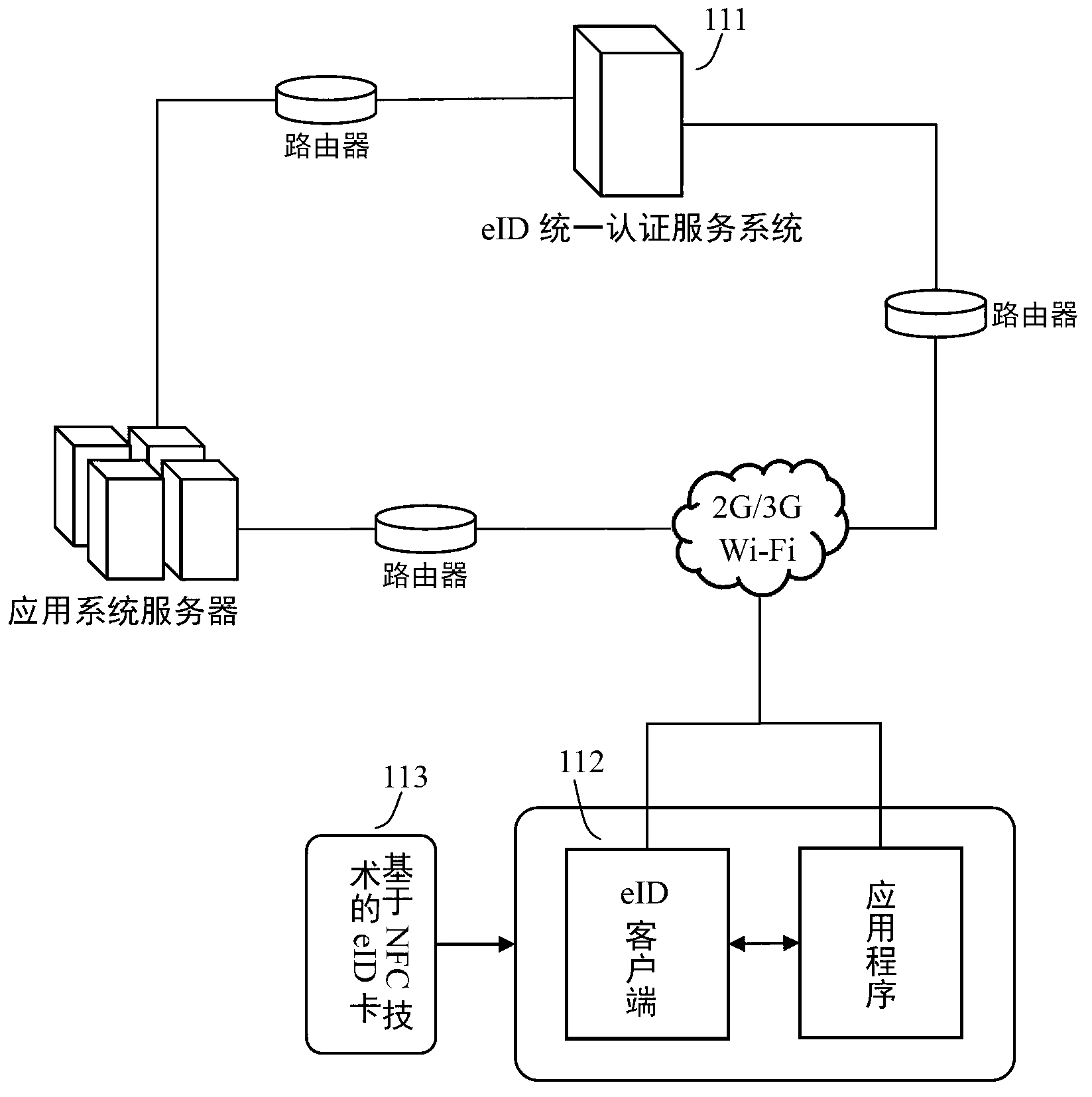
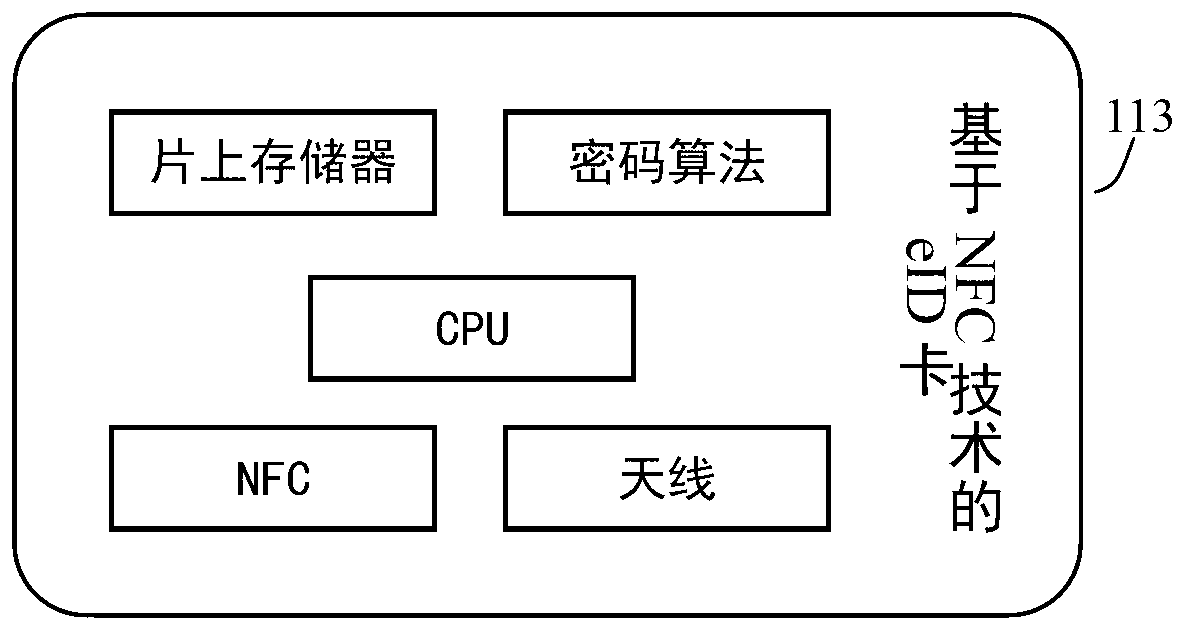
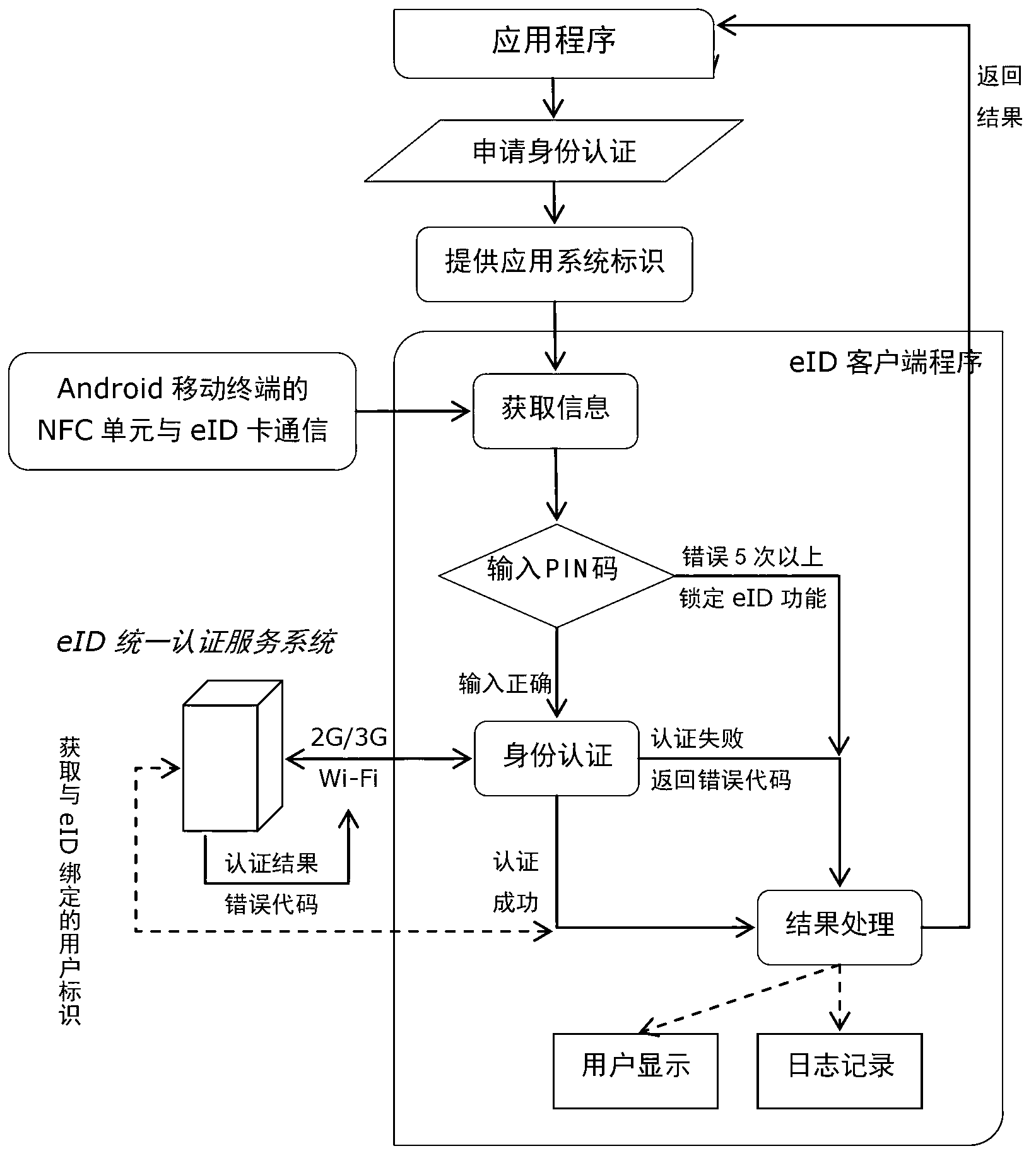
InactiveCN103259667AWon't leakPrevent the risk caused by cookies being stolen and used by othersNear-field transmissionUser identity/authority verificationComputer terminalUser authentication
The invention relates to the technical field of wireless communication, and provides a method and a system for eID (electronic identity) authentication on a mobile terminal. The system comprises an eID terminal carrier, an eID client and an eID unified authentication service system, wherein the eID client acquires relevant eID information from the eID terminal carrier; and the eID client and the eID unified authentication service system perform information exchange and user identity verification. The information transferred by the system does not contain personal information, and leakage of the personal information cannot be caused; With the adoption of an NFC (Near Field Communication) technology, an applicable occasion of the eID authentication is expanded; and the eID unified authentication service system is required to be accessed twice in the whole authentication process, so that the security of the system is improved, and a risk due to the fact that a browser cookies is stolen and utilized by others is prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
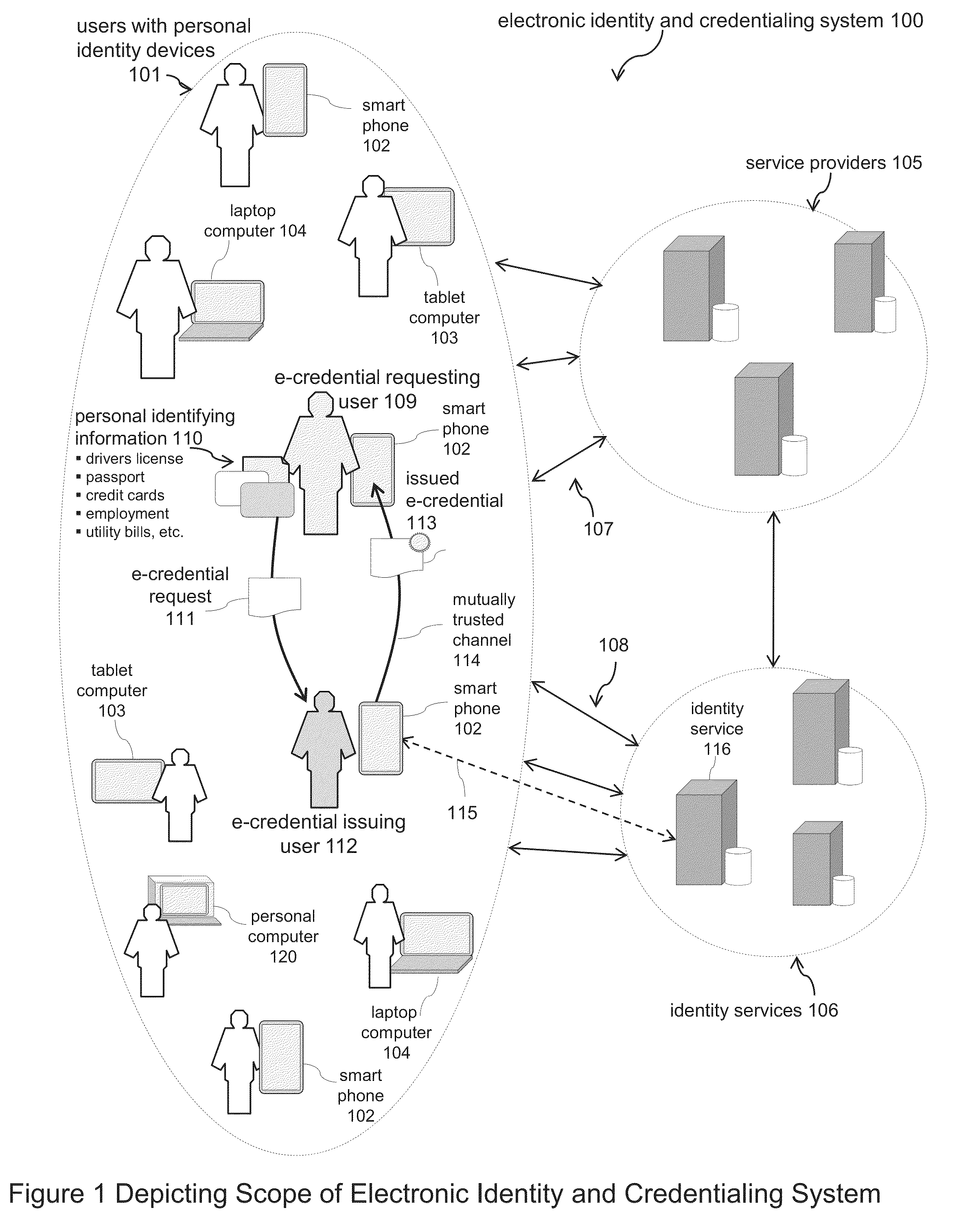
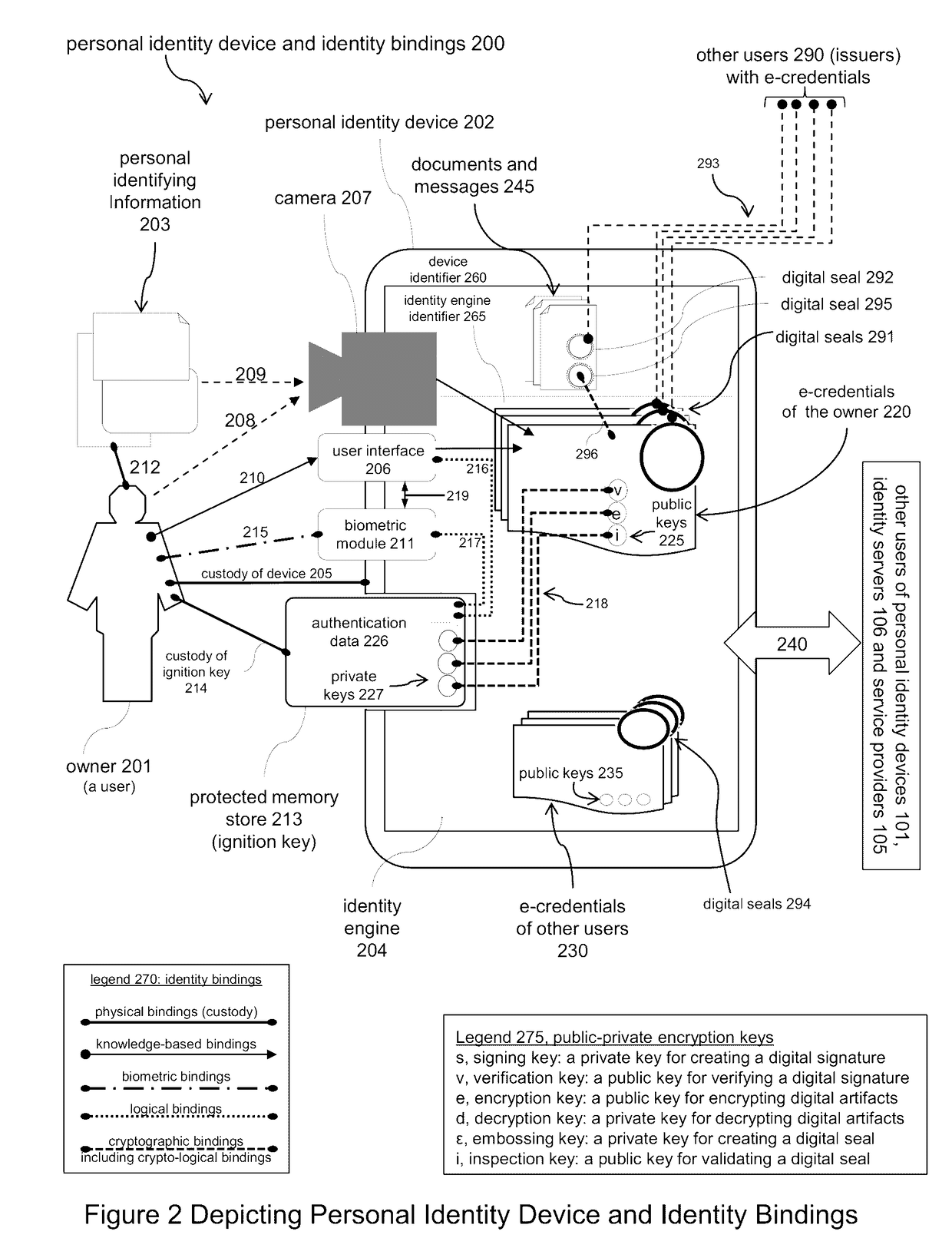
Electronic identity and credentialing system
ActiveUS9646150B2Reduce riskAvoid attenuationUser identity/authority verificationDigital data authenticationTablet computerCredentialing
Described is an electronic credentialing system that allows personal identity devices to interact; each interacting device has an installed identity engine that acquires, holds, issues and uses electronic credentials (e-credentials), these electronic credentials can be installed on personal identity devices, such as: smart phones, tablets, laptops, embedded systems, and / or personal computers.
Owner:TOTH KALMAN CSABA
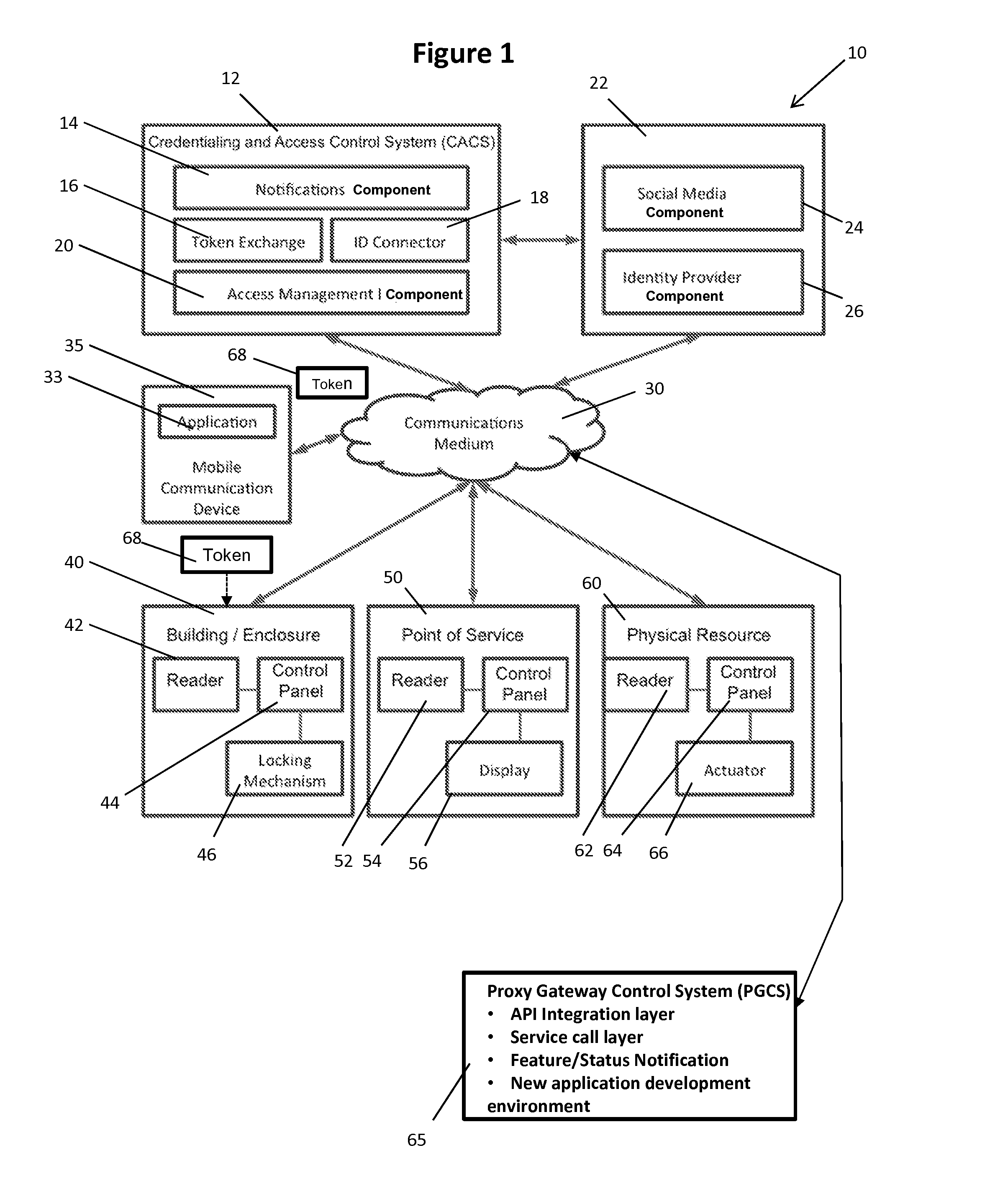
System and Method for Physical Access Control
ActiveUS20140282993A1Minimize duplicationImprove consistencyDigital data processing detailsMultiple digital computer combinationsIdentity providerSocial web
The present invention provides, in one aspect, a system and method for managing authentication tokens that operate across multiple types of physical resources binding the tokens to one or more external electronic Identity Providers; generating tokens; authenticating the tokens at multiple physical resources; managing access to physical resources by linking the tokens to the electronic identities; translating the tokens to the appropriate physical token type based on infrastructure services available at the point of service; validating tokens at the physical resource; tracking and conveying usage information; and making use of social group relationships and other data defined by individual usage to, among other things, simplify the process of granting user-generated credentials to persons connected to a given individual via the Identity Provider or an external social network, for example.
Owner:BRIVO SYST LLC
Method for carrying out electronic identity recognition by utilizing two-dimensional code
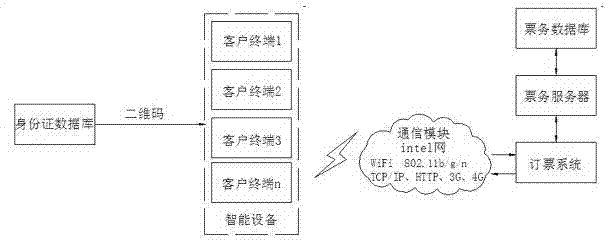
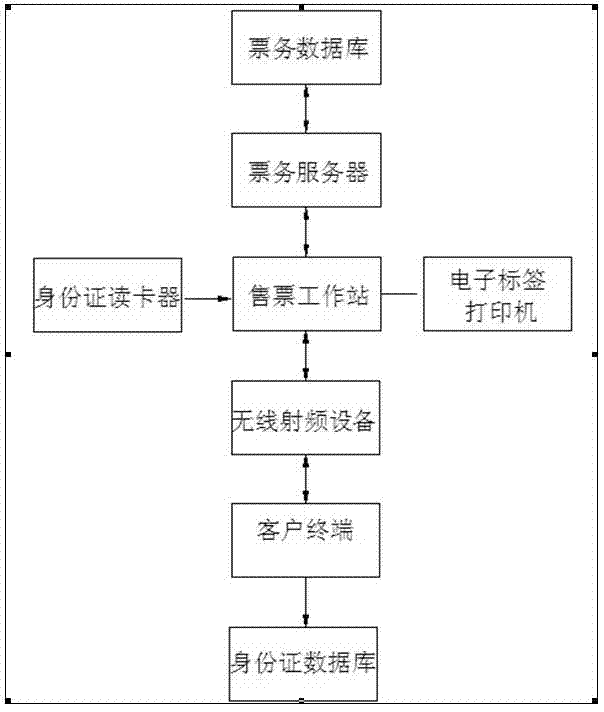
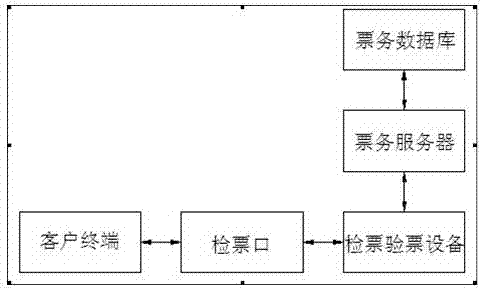
InactiveCN103177297ARealize online managementConducive to the efficiency of pit stopsTicket-issuing apparatusReservationsElectronic taggingTerminal equipment
The invention relates to the field of identification, and particularly relates to a method for carrying out electronic identity recognition by utilizing two-dimensional codes. The method is characterized in that at least one client terminal, a ticket reservation system, a ticket business server, a ticket business database, a ticket selling workstation, an electronic tag printer, an identity card reader, a ticket checking entrance, wireless radio-frequency equipment and an identity card database are adopted in the method, wherein the client terminal refers to a passenger, namely a person who needs to purchase a ticket for taking a bus and acquires a two-dimensional code electronic tag through intelligent terminal equipment during ticket purchasing; the ticket reservation system refers to a network ticket reservation system; and the ticket selling workstation refers to the existing station ticket window and various agent ticket offices. The method for fast and conveniently carrying out the electronic identity recognition, which is provided by the invention, mainly aims at overcoming the defects of the existing paper ticket and solving the problem of difficult queuing during the ticket purchasing and can reduce the labor intensity of ticket checking personnel, improve the incoming efficiency of the passengers and realize the high security and the high antifalsification through the uniqueness of a second-generation identity card.
Owner:JINHUA INFORMATION DIGITAL TECH
Portable verifiable credentials and methods thereof
InactiveUS20170324750A1Reduce restrictionsUser identity/authority verificationSecurity arrangementElectronic documentDocument preparation
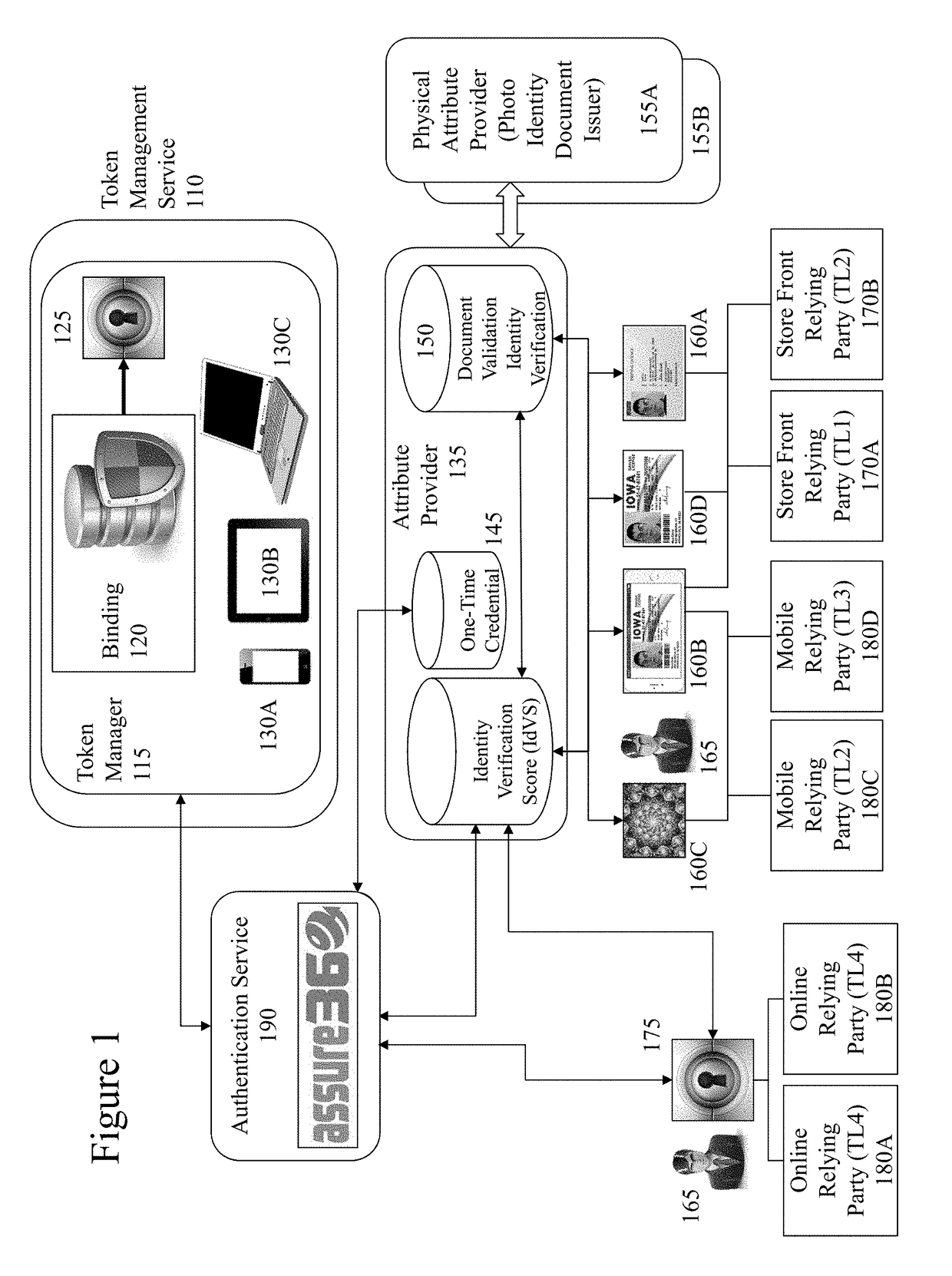
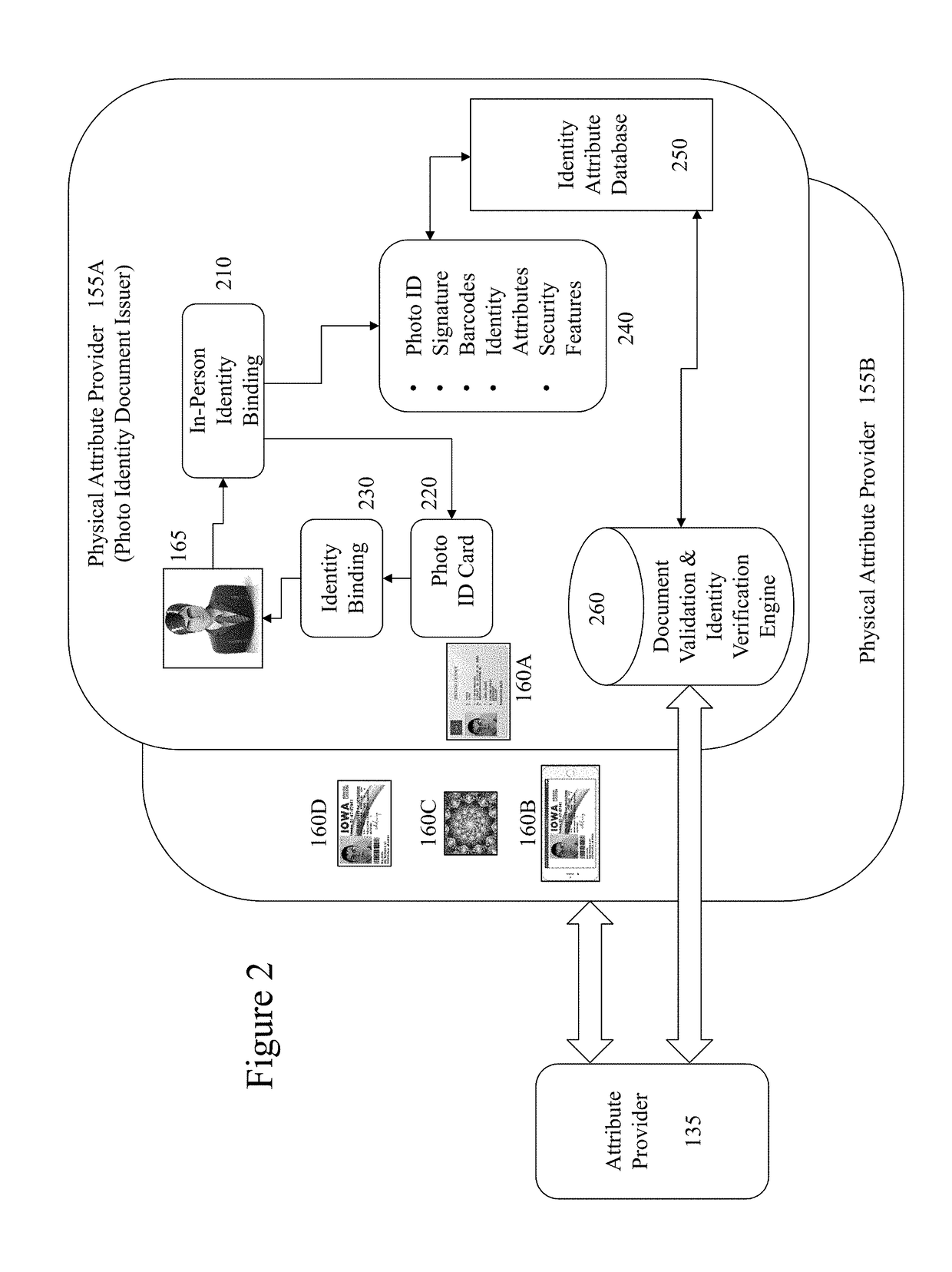
The migration of identity documents, such as driving licenses, from physical documents to electronic documents creates new problems for those seeking to verify the identity of an individual based upon the electronic document they provide. However, the inventors have established a means of binding electronic documents and electronic representations of physical documents to individuals at issuance of the document(s). Accordingly, the inventors address identity verification by providing to those seeking to verify the individual's identity data allowing them to verify the presented electronic ID document. For example, a police officer requesting a driving license can obtain on their own electronic device through the methods of the invention the issued driving license associated with identifier information on the license provided by the individual. As such tampering with the license to change a name, date of birth, photo etc. will result in a visible mismatch to the police officer in comparing them.
Owner:KHAN SAL
Techniques for securing electronic identities
ActiveUS20050071687A1Digital data processing detailsUser identity/authority verificationInternet privacyData storing
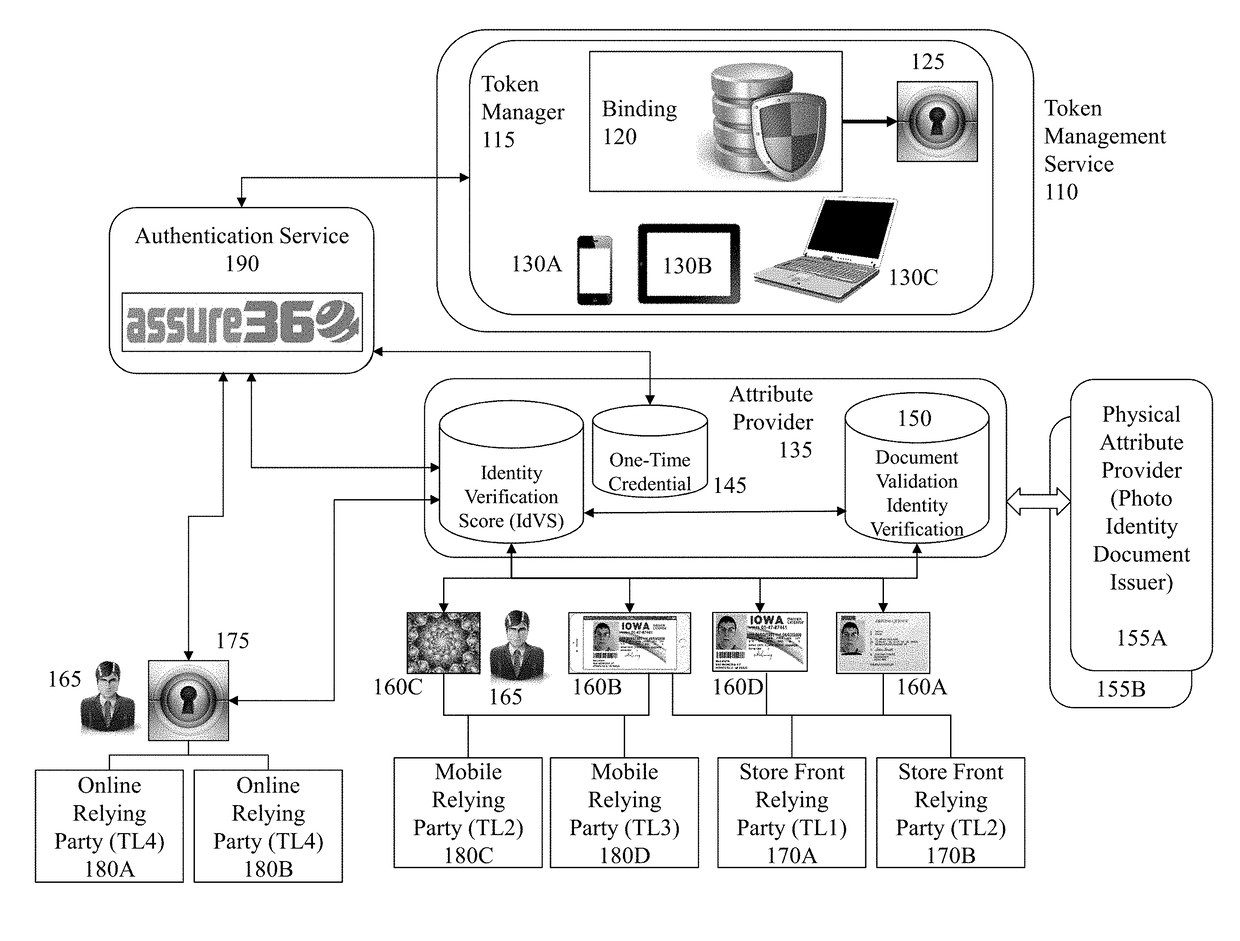
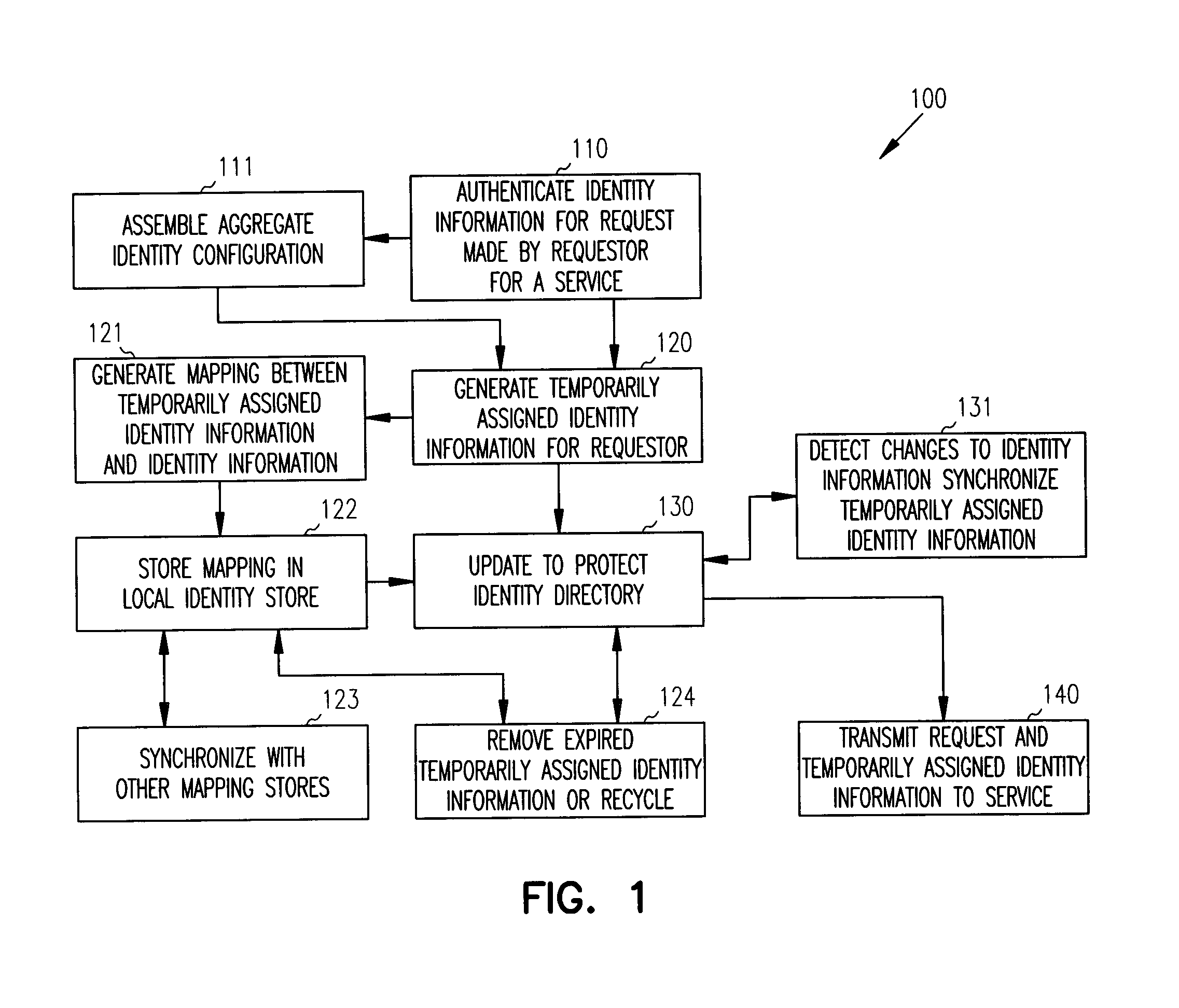
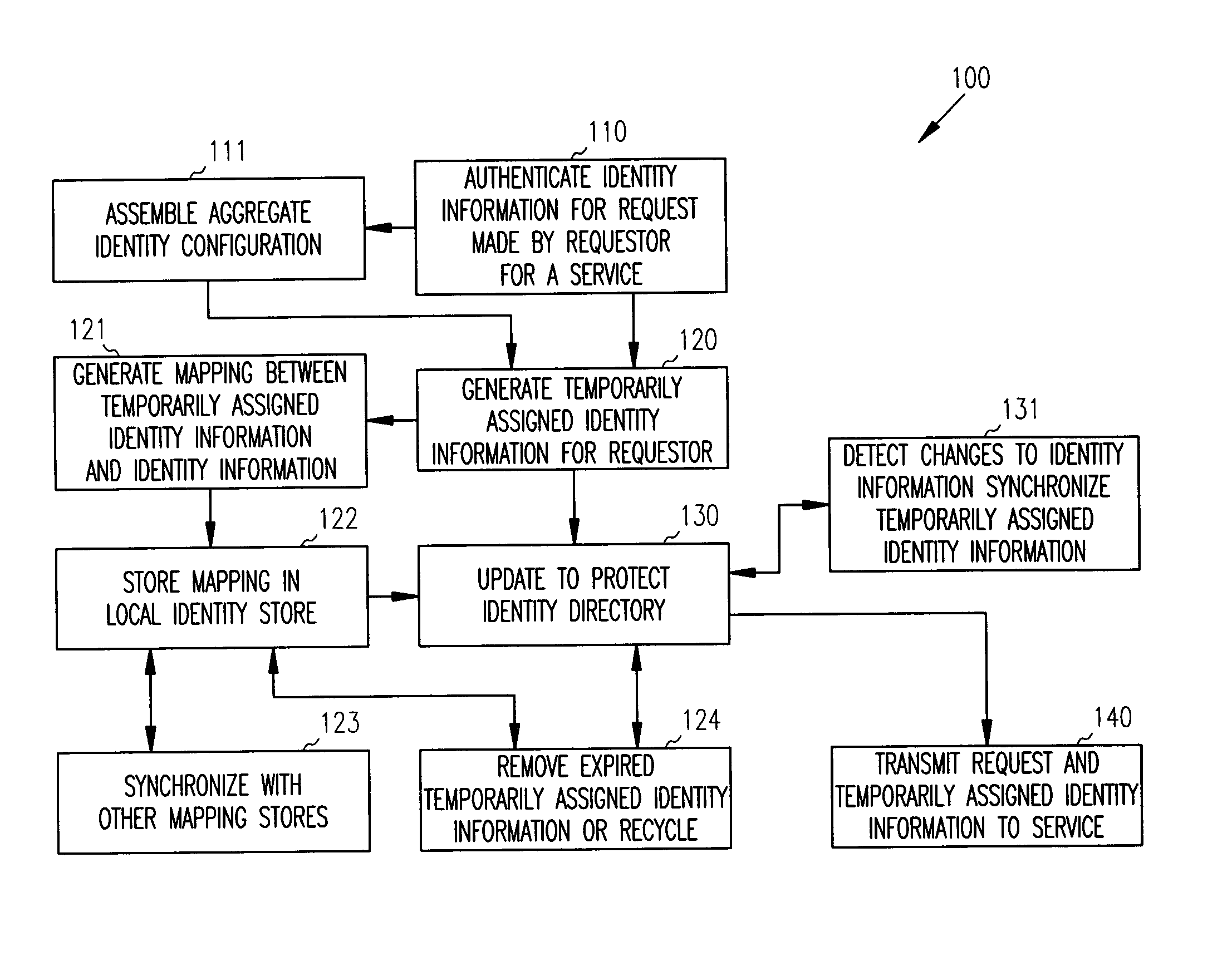
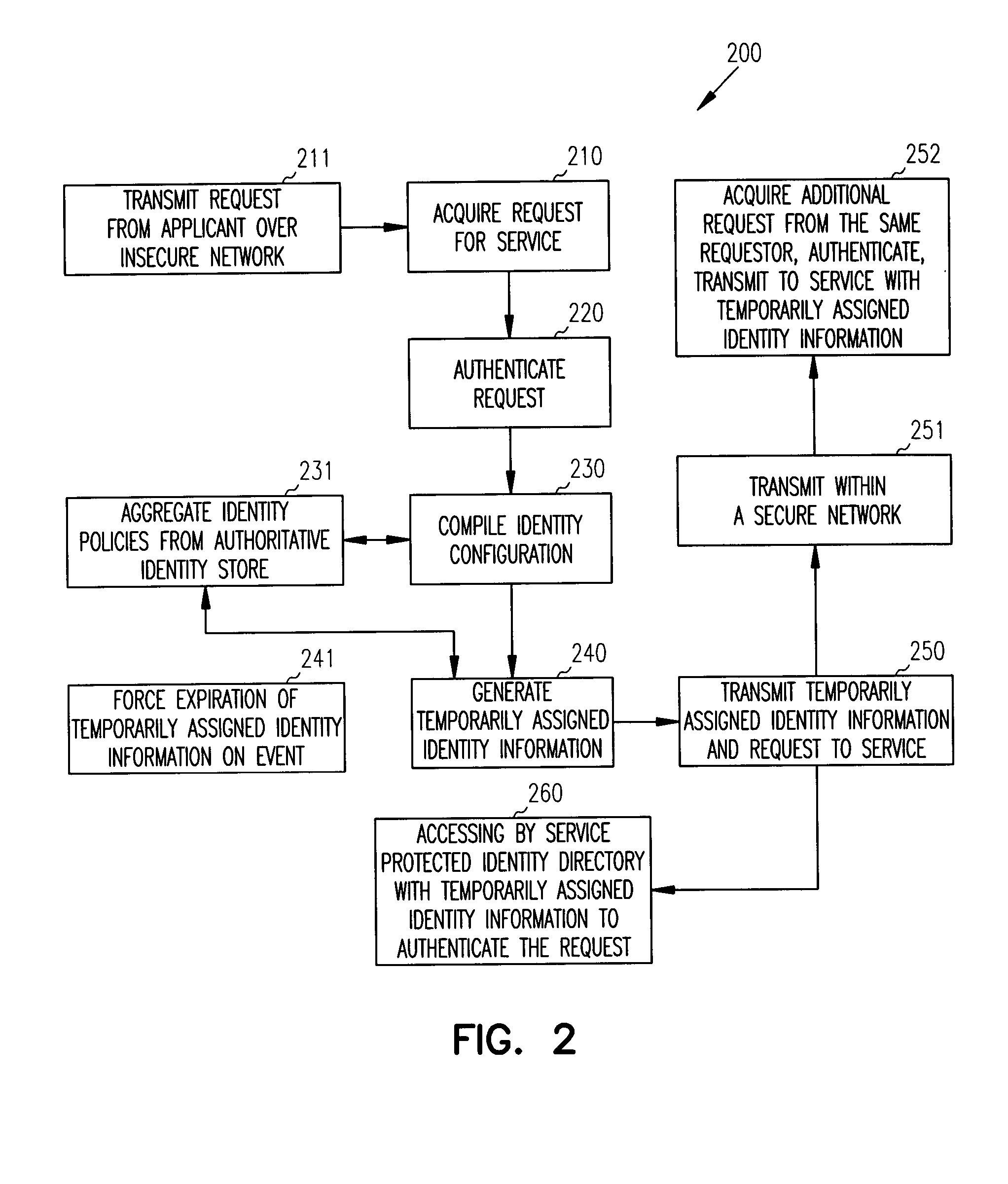
Methods, systems, and data stores generate and manage temporarily assigned identities. A requestor issues a request for a service. The request includes an identity used for authenticating the requestor. The identity is used for generating an identity configuration and for generating a temporarily assigned identity that is updated to a protected identity directory. The request and the temporarily assigned identity are transmitted to the service. The service uses the temporarily assigned identity to access the protected identity directory for purposes of authenticating the request. The service uses the authenticated request to access attributes associated with the temporarily assigned identity.
Owner:EMC IP HLDG CO LLC
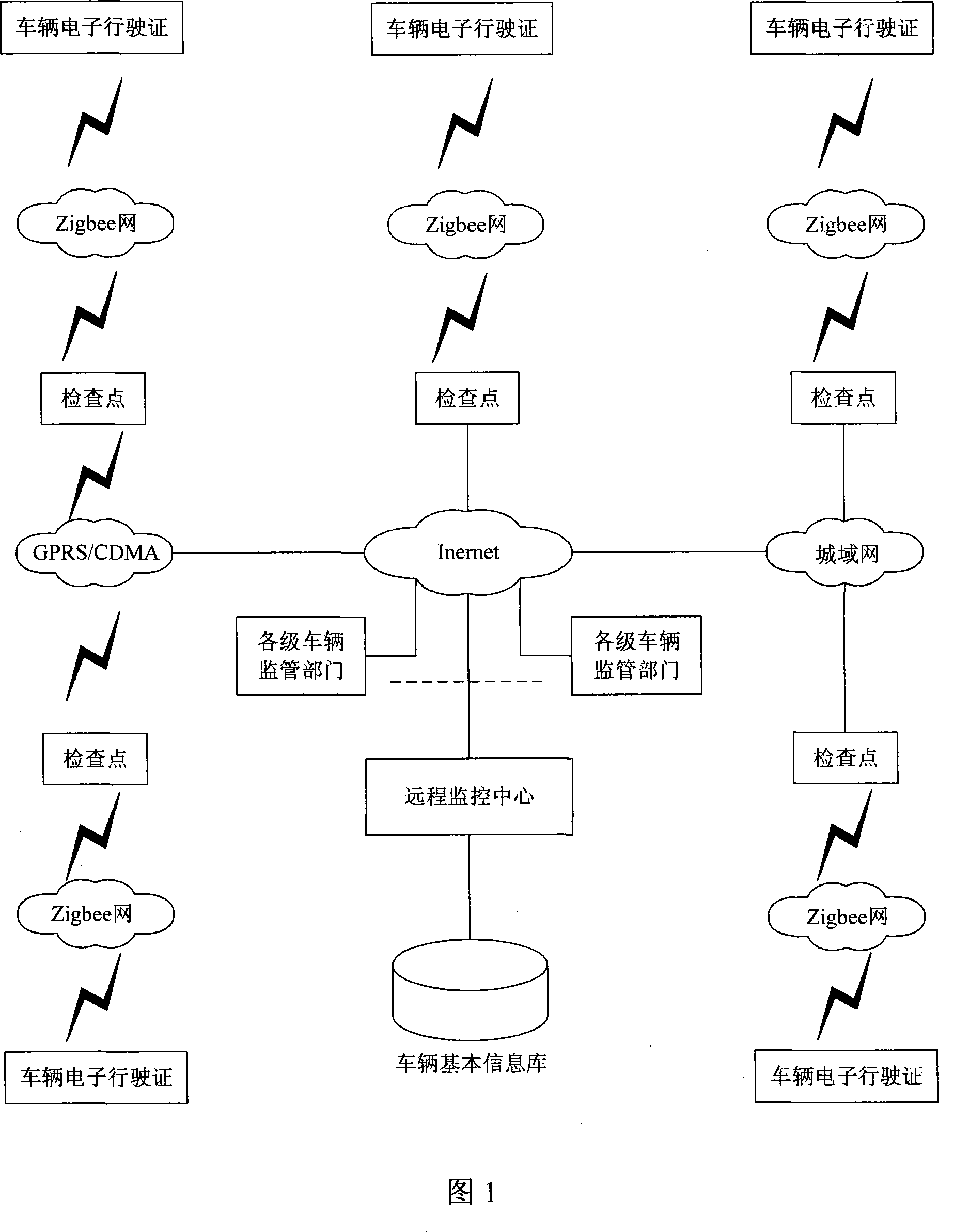
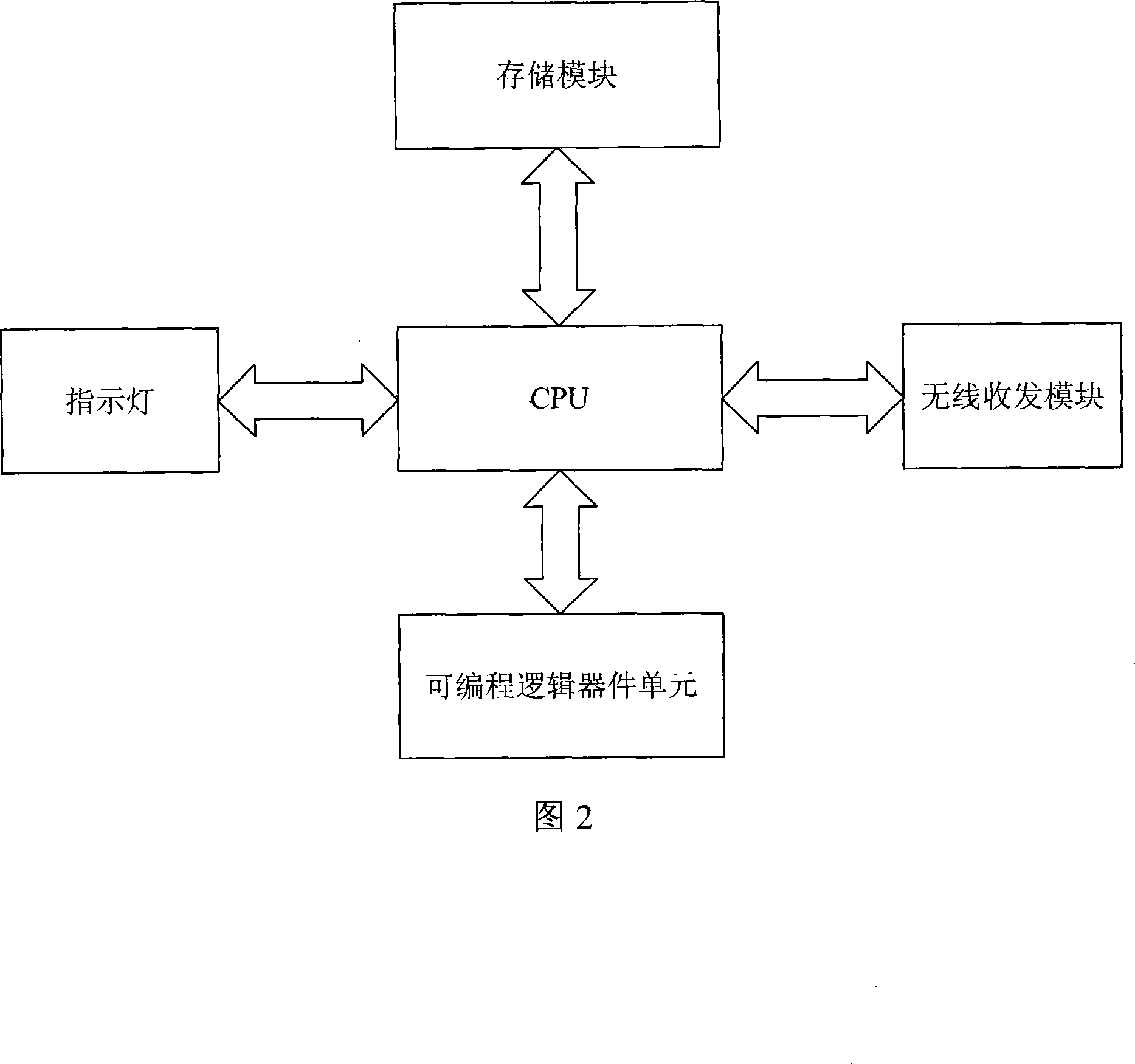
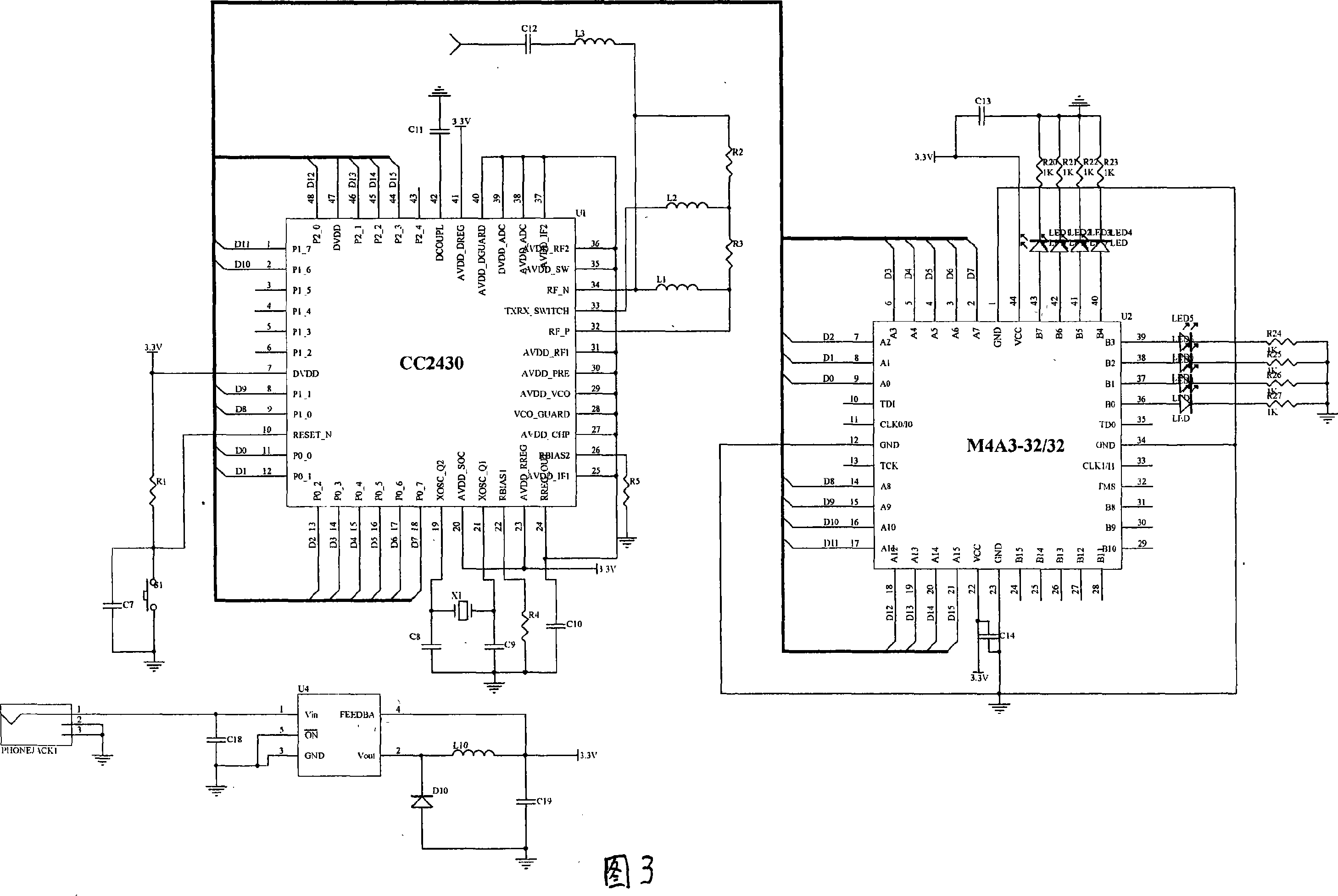
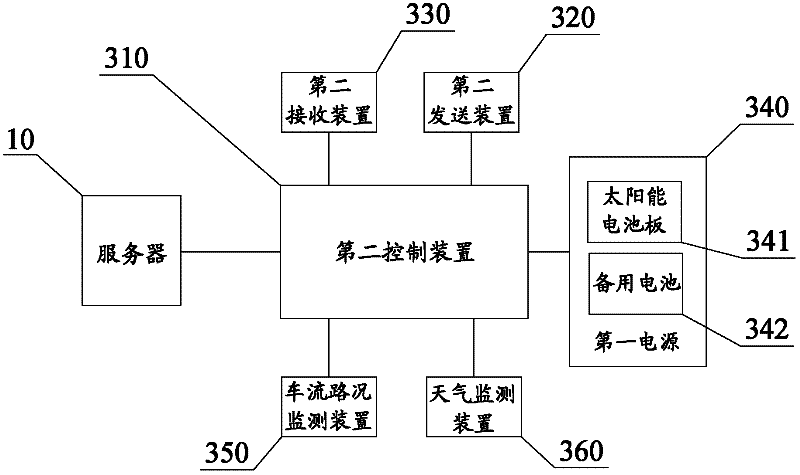
Car monitoring system based on electronic identity recognition
InactiveCN101127660AImprove reliabilityImprove accuracyDetection of traffic movementData switching by path configurationLine sensorLicense control
The utility model relates to an electronic personal identification system used in car, and comprises an electronic driving license, a checkpoint and a remote monitoring centre, wherein the electronic driving license is arranged in the car, and comprises a driving license control unit, a radio frequency module of a radio sensor which is connected with the control unit and a programmable logic device which is connected with the control unit and used for encrypting the hardware; the checkpoint can be arranged in the urban highway and the checkpost; the radio frequency module is used for receiving the personal identification information sent from the electronic driving license and the programmable logic device is used for decrypting the cryptograph sent from the electronic driving license; a remote transferring unit is connected with the data end of a checkpoint control unit and the personal identification information sent from the electronic driving license is transferred to the remote monitoring centre by the remote transferring unit; the remote monitoring centre comprises a database management system and a remote monitoring system, wherein the car identification information is stored in the database management system. The remote monitoring system receives the information sent from the checkpoint in real time and then sends the final data back to the checkpoint.
Owner:陈洪 +1
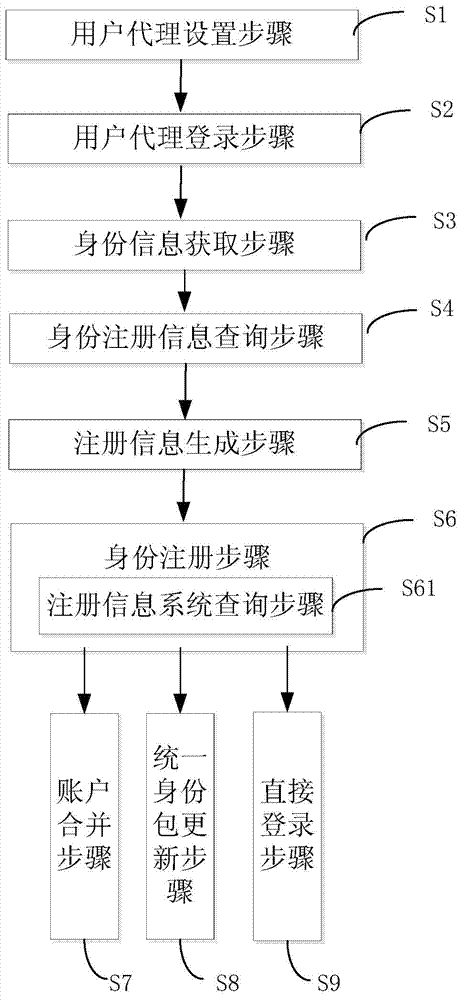
A method and system of electronic identity registration and authentication login
The invention discloses a method of electronic identity registration and authentication login. The method of electronic identity registration and authentication login comprises: an identity information acquisition step, wherein a user agent on a mobile terminal acquires encrypted identity information on a system and encrypted session information between a system agent and the system through the system agent; a registration information generation step, wherein the user agent executes decryption according to reception of the encrypted identity information and the encrypted session information to generate automatically a uniform identity code, encrypts registration login information containing the uniform identity code, and sends the encrypted registration login information to the system for identity registration; and an identity registration step, wherein the system executes decryption after reception of the encrypted registration login information containing the uniform identity code, and automatically executes identity registration operation. The invention also discloses a system of electronic identity registration and authentication login.
Owner:登录(北京)科技有限公司
System and method for effecting secure online payment using a client payment card
InactiveUS20030069792A1Alleviate, the drawbacks and deficienciesImprove securityCredit schemesPayment circuitsThe InternetInformation networks
Payment using a payment card for goods and / or services ordered online via an information network such as the Internet is implemented in a notably secure manner without the need to transmit the client's payment card number over the data transmission network. A separate confirmation for effecting the payment for an order is requested from the client. The information to be confirmed is transmitted to the terminal device of the client, such as a mobile station, by means of which the client confirms the order by digitally signing the confirmation request. The digitally signed confirmation and the electronic identity information associated with the client are then returned to the payment service equipment, which verifies the client's identity, checks the validity of the client's payment card, and then transmits the necessary payment information to the payment system.
Owner:SMARTTRUST SYST
Secure biometric authentication using electronic identity
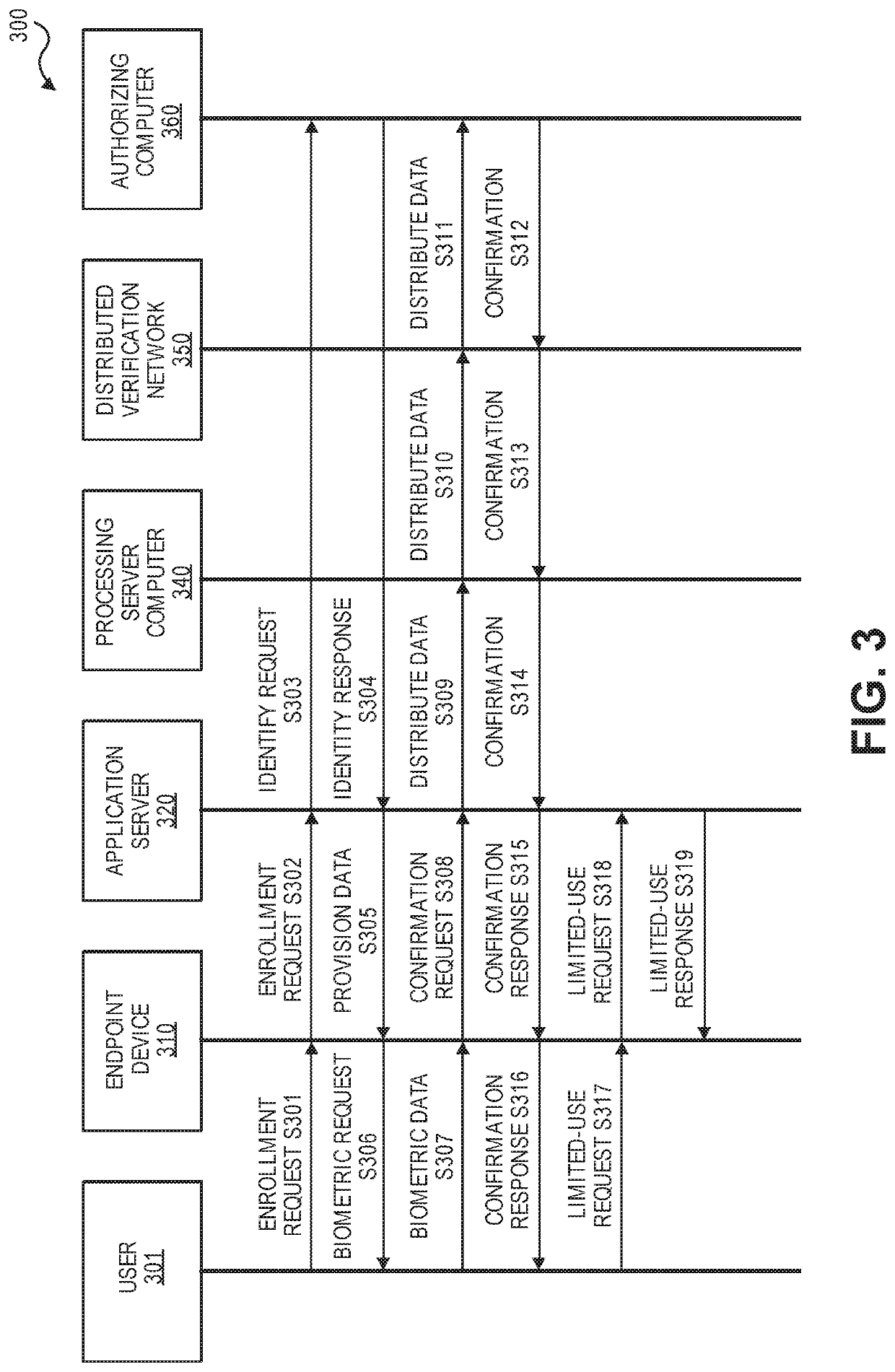
ActiveUS20200092102A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesUser deviceInternet privacy
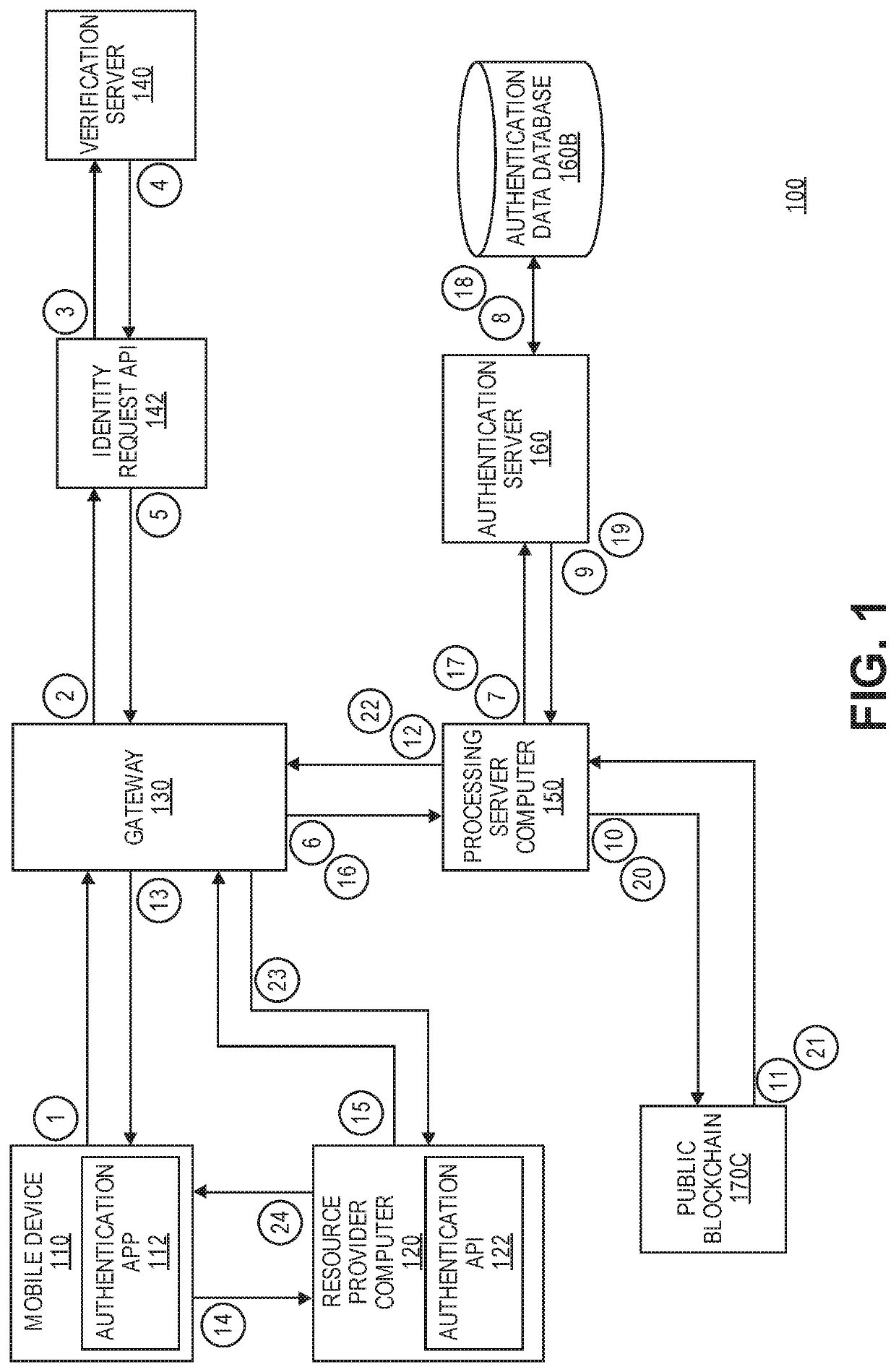
Embodiments of the invention are directed to a method. The method may comprise receiving a second biometric template of a user, and providing an authentication request message comprising an electronic identity and a derivative of the second biometric template of the user to a resource provider computer to conduct an interaction. The authentication request may be forwarded to a processing server computer by the resource provider computer, and the user device may receive an authentication response message comprising an authentication result from the processing server computer. The authentication result may be determined by the processing server computer based on a comparison of the derivative of the second biometric template to a derivative of a first biometric template accessible to the processing server computer. The authentication result may also be based on the validity of the electronic identity.
Owner:VISA INT SERVICE ASSOC
System and method for securely processing an electronic identity
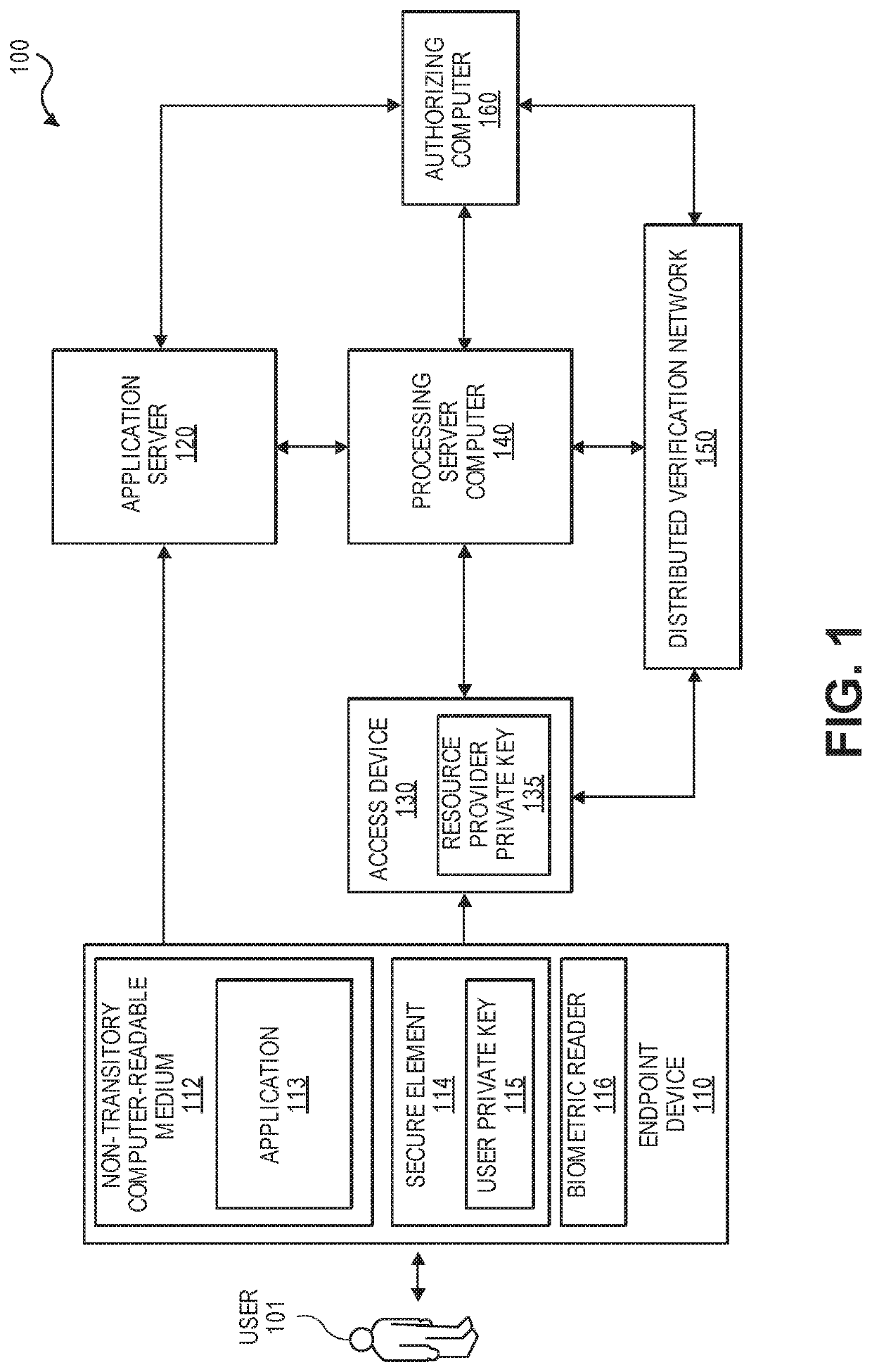
ActiveUS20190363889A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptogramAuthorization
A method for providing identification using an endpoint device is disclosed. The endpoint device may include an electronic identity that is unique and can be securely stored. The electronic identity may be passed to an access device along with signed interaction data and a cryptogram. The access device may generate an authorization request with the cryptogram and may send it to a remote server computer for further processing.
Owner:VISA INT SERVICE ASSOC
Intelligent tracking transport case
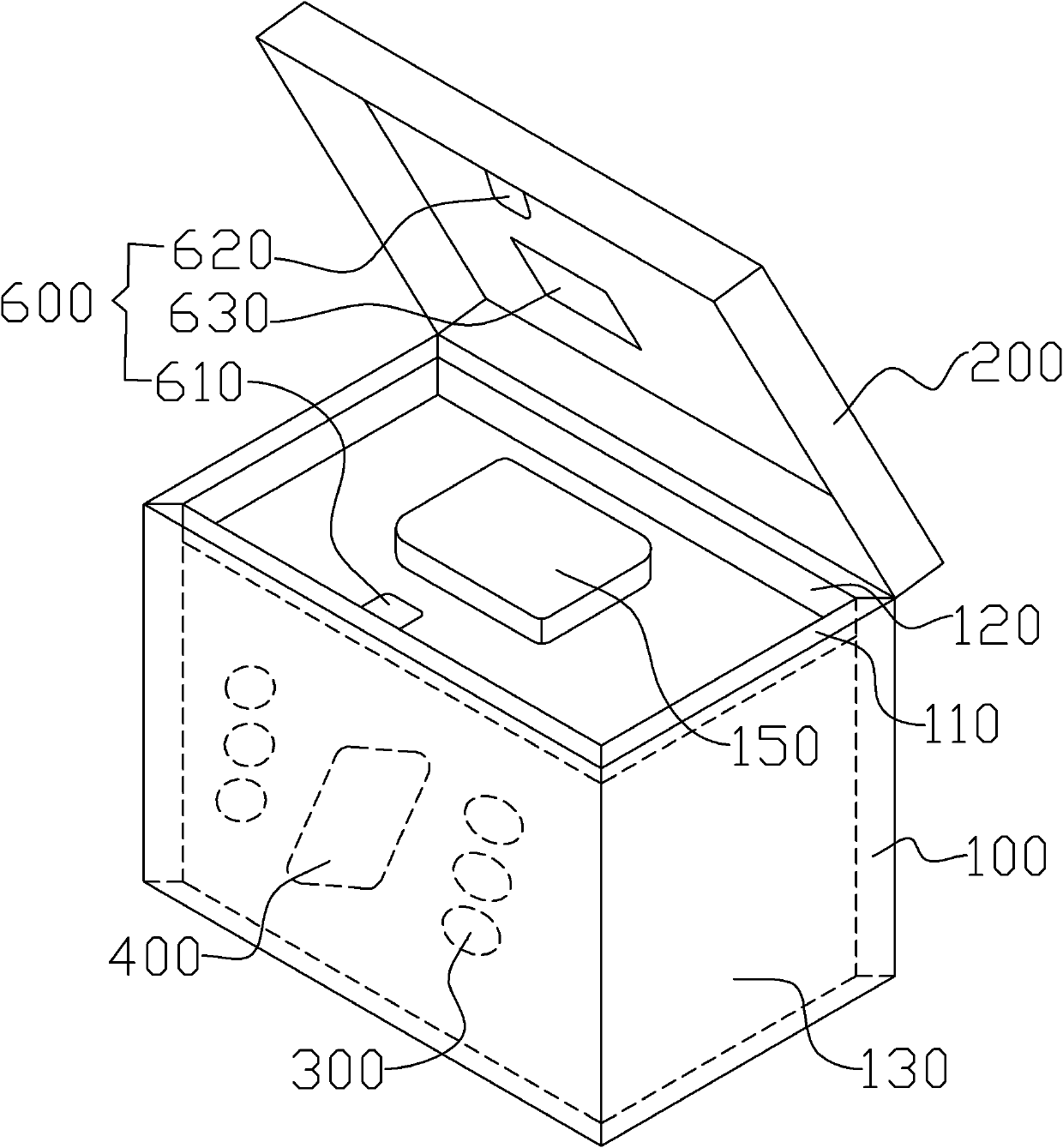
InactiveCN102167182AGrasp the storage conditions in timeCo-operative working arrangementsRecord carriers used with machinesElectricityThermal insulation
The invention discloses an intelligent tracking transport case which comprises a thermal insulation case body and a thermal insulation case cover, wherein a tray is arranged inside the thermal insulation box body; the inner cavity of the thermal insulation case body is divided into an upper cavity and a lower cavity by the tray; and the lower cavity is used for placing ice cubes and a sample. The intelligent tracking transport case further comprises an intelligent tracking controller and an intelligent electronic identity card, wherein the intelligent electronic identity card comprises a magnetic material, a switch circuit and an RFID (radio frequency identification) electronic tag; the RFID electronic tag is encapsulated into the thermal insulation box cover; the switch circuit is arranged on the inner cover surface of the thermal insulation box cover and is electrically connected with the RFID electronic tag; and the magnetic material is arranged on the case opening of the thermal insulation case body and is opposite to the switch circuit. The intelligent tracking controller is mounted in the tray, and is communicated and connected with the RFID electronic tag in the intelligent electronic identity card. The intelligent tracking transport case can be used for carrying out whole-process monitoring on the transport process of a biological sample.
Owner:SHANGHAI MUNICIPAL CENT FOR DISEASE CONTROL & PREVENTION +1
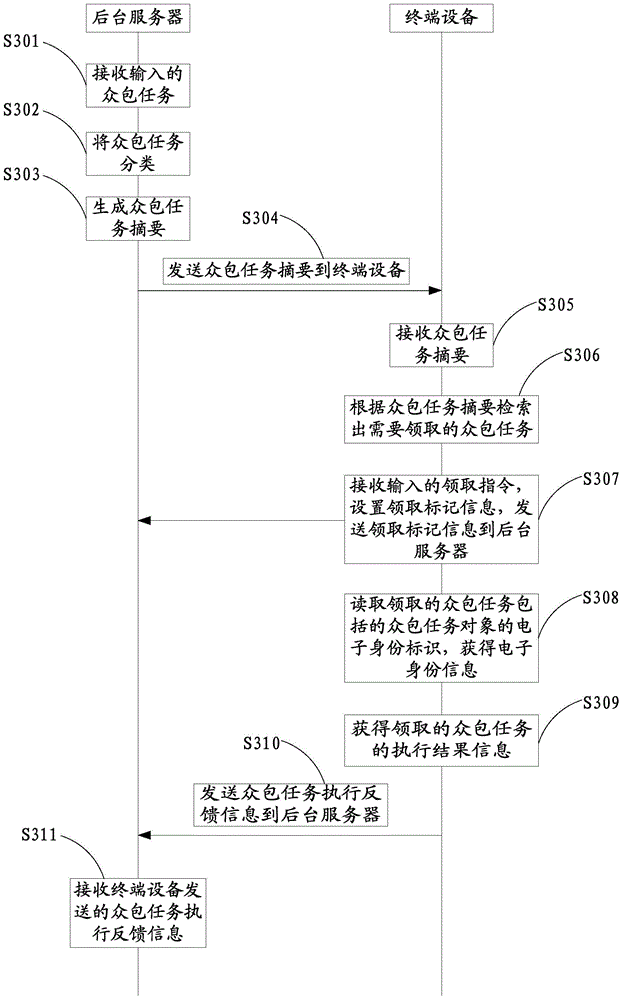
Crowdsourcing task release and execution methods and devices
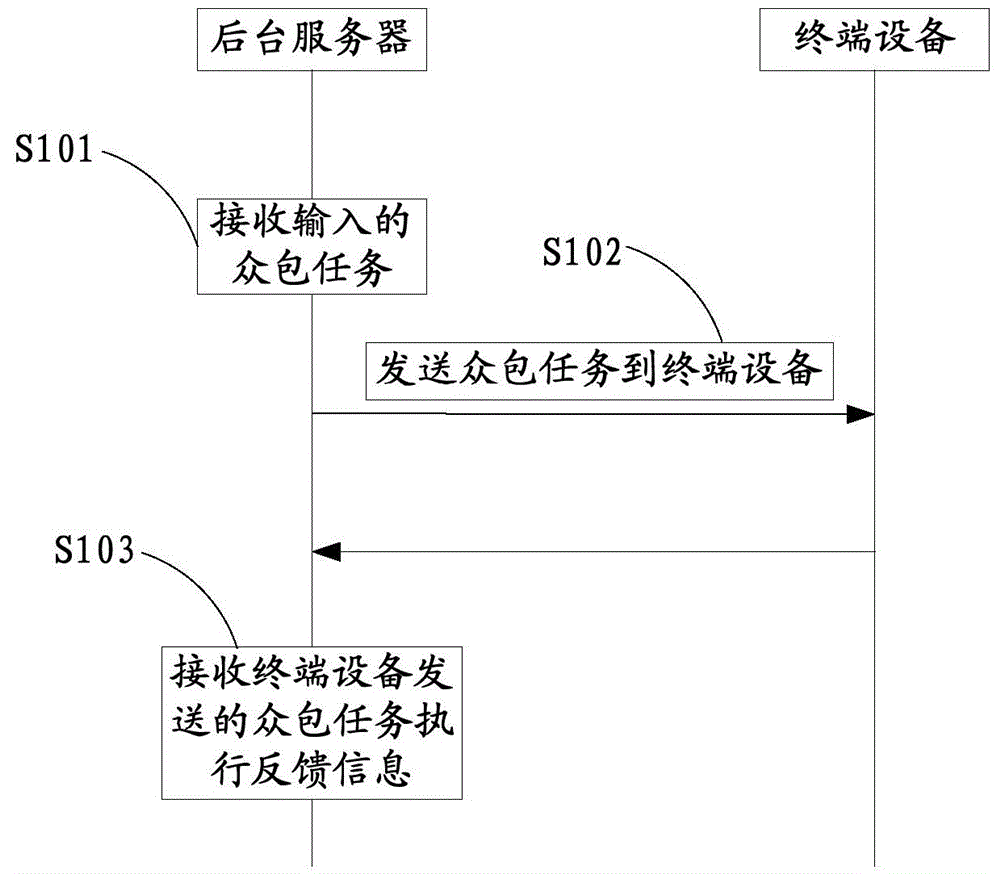
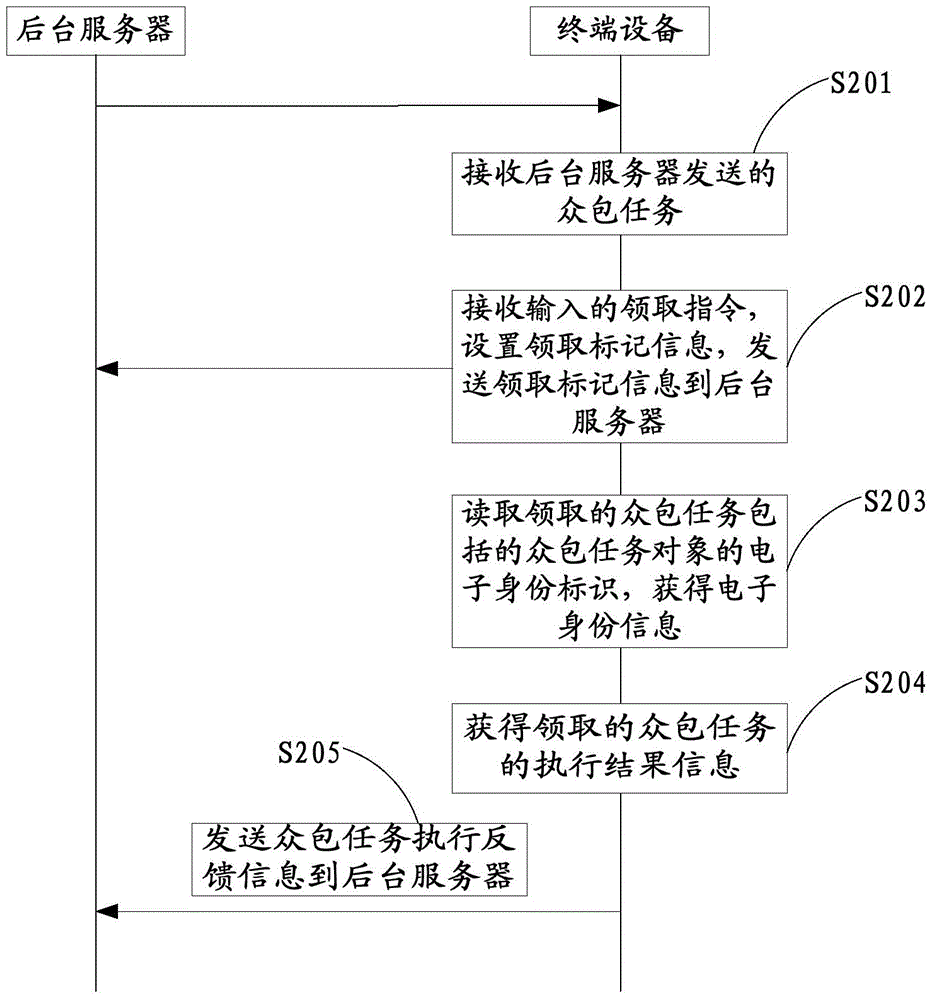
InactiveCN104573995AFully mobilize idle labor in societyResourcesCommerceTerminal equipmentThe Internet
The invention relates to the technical field of internet and provides crowdsourcing task release and execution methods and devices. The release method includes the steps: allowing a background server to receive a crowdsourcing task input; transmitting the crowdsourcing task to a terminal device; receiving crowdsourcing task execution feedback information transmitted by the terminal device. The execution method includes the steps: allowing the terminal device to receive the crowdsourcing task transmitted; receiving a collecting command input, setting collecting mark information for the crowdsourcing task collected, and transmitting the collecting mark information to the background server; reading an electronic identifier of a crowdsourcing task object included in the crowdsourcing task collected to acquire electronic identity information of the crowdsourcing task object; acquiring execution result information of the crowdsourcing task collected; sending crowdsourcing task execution feedback information to the background sever. The crowdsourcing task release and execution methods and devices have the advantages that execution results and processes of crowdsourcing tasks can be effectively monitored and social idle labor can be made full use to serve multiple industries.
Owner:CHONGQING RUANWEN TECH
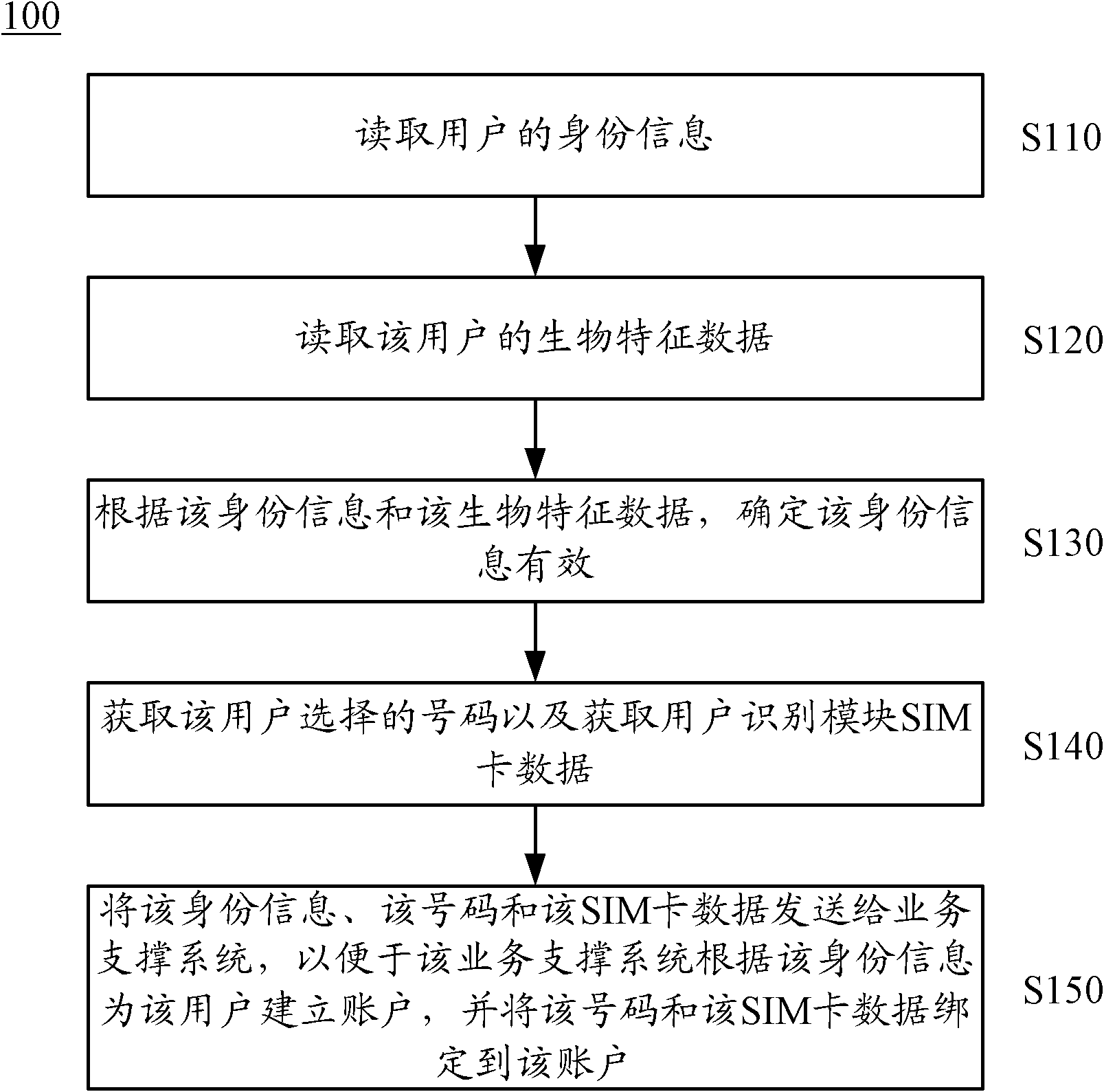
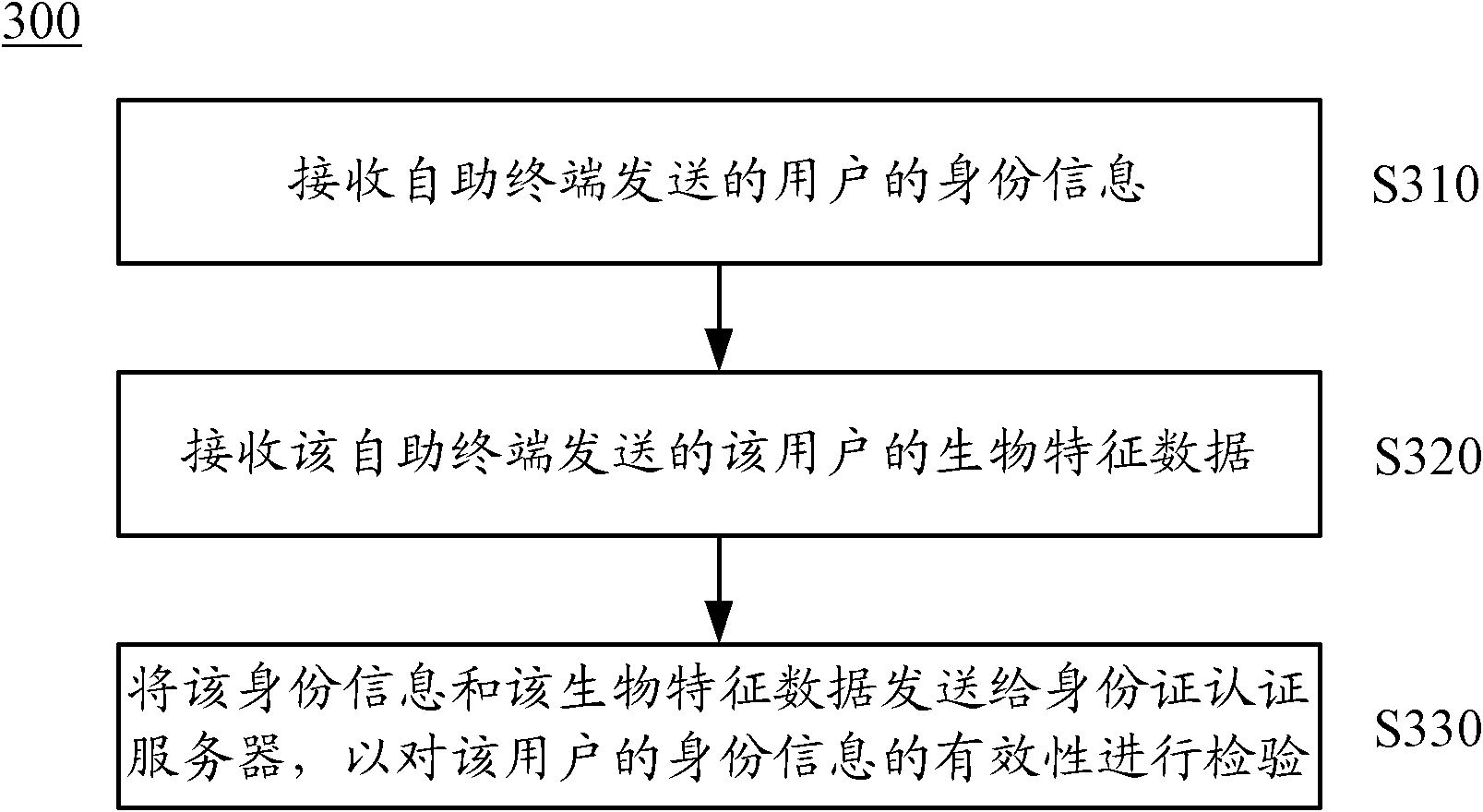
Real-name account-opening method based on self-help terminal and terminal thereof
The invention discloses a real-name account-opening method based on a self-help terminal and the terminal thereof. The method comprises: reading the identity information of a user; reading the data on the biological features of the user; determining the validness of the user identity information based on the identity information and the data on biological features; acquiring the number selected by the user and the data of SIM card; forwarding the identity information, the number and the data of SIM card to a business support system for the support system to establish an account for the user according to the identity information; and binding the number and the data of SIM card to the account. The self-help terminal consists of an electronic ID card reader, a biological feature reading module, a determining module, a first acquiring module, a second acquiring module, and a first forwarding module. The invention embodiment provides a real-name account-opening method based on a self-help terminal. Based on the user identity information and the data on biological features, the user identity can be checked, thereby providing real-name account-opening service to clients.
Owner:HUAWEI TECH CO LTD
Electronic number plate free flow charge payment method
InactiveCN104112296AImprove transportation efficiencySimplify the payment processTicket-issuing apparatusPaymentEngineering
The invention discloses an electronic number plate free flow charge payment method. The electronic number plate free flow charge payment method is characterized by comprising an electronic number plate tag, an electronic number plate read-write base station and a background software processing system, wherein the electronic number plate tag is installed on a vehicle, the electronic number plate read-write base station is mounted on a charge road, the background software processing system performs information records in a background and operates charge rules, and the free flow charge payment method supports a prepayment method and a post-payment method. The charge payment method relies on support of the background software processing system, a lane where a vehicle is located, front and back positions, passing time or speed is not required to be confirmed, multiple electronic number plate tags can be read simultaneously on multiple lanes, and electronic identity verification and charge payment processes of multiple vehicles can be achieved simultaneously.
Owner:JIANGSU BELLON TECH
Vehicle electronic identity recognition information network system
InactiveCN102402858AAvoid robberyAvoid applyingRoad vehicles traffic controlTransmissionPaymentInformation networks
The invention relates to a vehicle electronic identity recognition information network system, which comprises a vehicle electronic identity vehicle-mounted terminal, a vehicle identity information acquisition terminal, a handheld vehicle information management terminal and a server; the vehicle electronic identity vehicle-mounted terminal records and stores vehicle identity information in the form of electronic data; and the vehicle identity information acquisition terminal can check vehicle identities of passing vehicles in real time and automatically give an alarm when checking illegal vehicles. Illegal activities such as vehicle robbing and stealing, indiscriminate use of license plate of others, arrear and evasion of various fees, illegal vehicle transportation, illegal business and the like can be effectively avoided; and the vehicle identity information can be recorded in the vehicle electronic identity vehicle-mounted terminal by handholding the vehicle information management terminal, can be checked randomly anytime and is connected with a server, so that payment and non-payment information of various fees, records breaking rules and regulations and the like for vehicle can be retrieved and looked up.
Owner:SHENZHEN TDF TAI INTELLIGENT TECH CO LTD
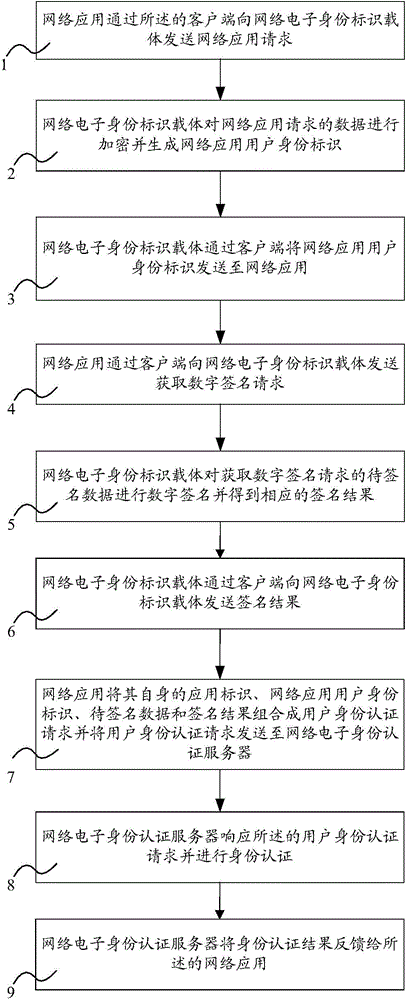
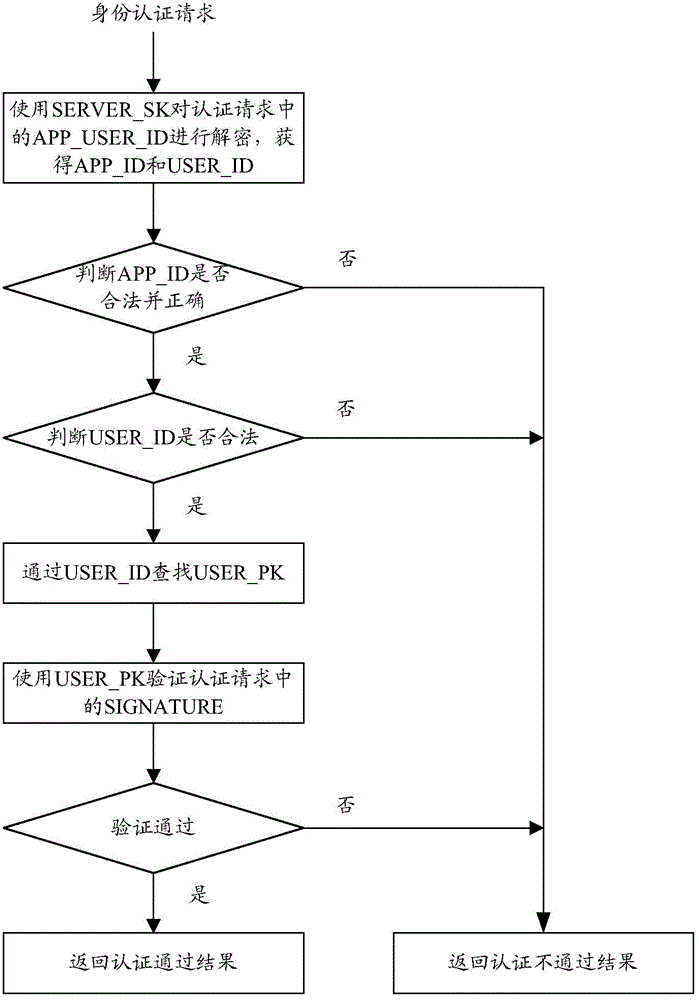
Anti-tracking method in network electronic identity authentication process based on challenge modes
ActiveCN104601593AImprove safety and reliabilityPrevent leakageTransmissionDigital signatureDual purpose
The invention relates to an anti-tracking method in a network electronic identity authentication process based on challenge modes. The anti-tracking method includes that a network electronic identity label carrier encrypts data of network application requests, generates a network application user identity label and transmits the network application user identity label to network application; the network electronic identity label carrier performs digital signature on data to be signed of an acquired digital signature request to obtain corresponding signature results; the network electronic identity label carrier transmits the signature results; the network application combines its application label, the network application user identity label, the data to be signed and the signature results into the user identity authentication request, and the user identity authentication request is transmitted to a network electronic identity authentication server; the network electronic identity authentication server can perform identity authentication. By the anti-tracking method, dual purposes for effectively managing the network identity and sufficiently protecting privacy are achieved, safety and reliability in identity authentication are improved, and the anti-tracking method has wider application range.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
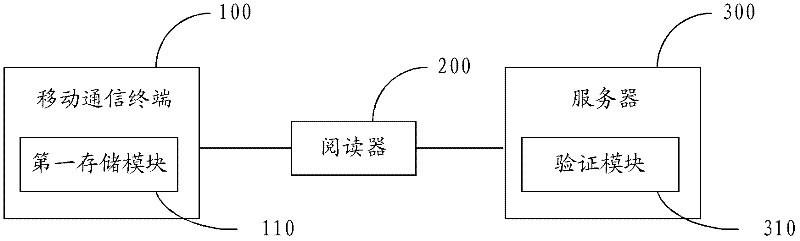
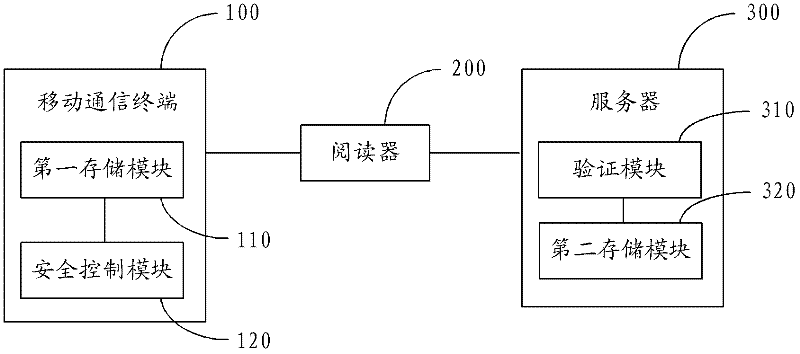
Electronic identity card verification system
ActiveCN102404328AImprove portabilityPrevent leakageUser identity/authority verificationDigital data authenticationComputer terminalVerification system
The invention discloses an electronic identity card verification system, which comprises a mobile communication terminal, wherein the mobile communication terminal comprises a first storing module used for storing user identity information; a reader used for reading the user identity information from the first storing module and sending the user identity information to a server; the server which comprises a verification module used for verifying the user identity information and returning the verification information to the reader, wherein the reader is further used for displaying the corresponding information according to the verification result returned by the server. The system stores the user identity information in the mobile communication terminal; namely, the mobile communication terminal has the function of the electronic identity card; the user does not need to take resident identity card after taking the mobile communication terminal, so that the convenience for operation of the user is increased; besides, after the user identity information is verified, the corresponding information is displayed according to the verification result; and the user identity information is not easy to be leaked, thus the safety of the user identity information is increased.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
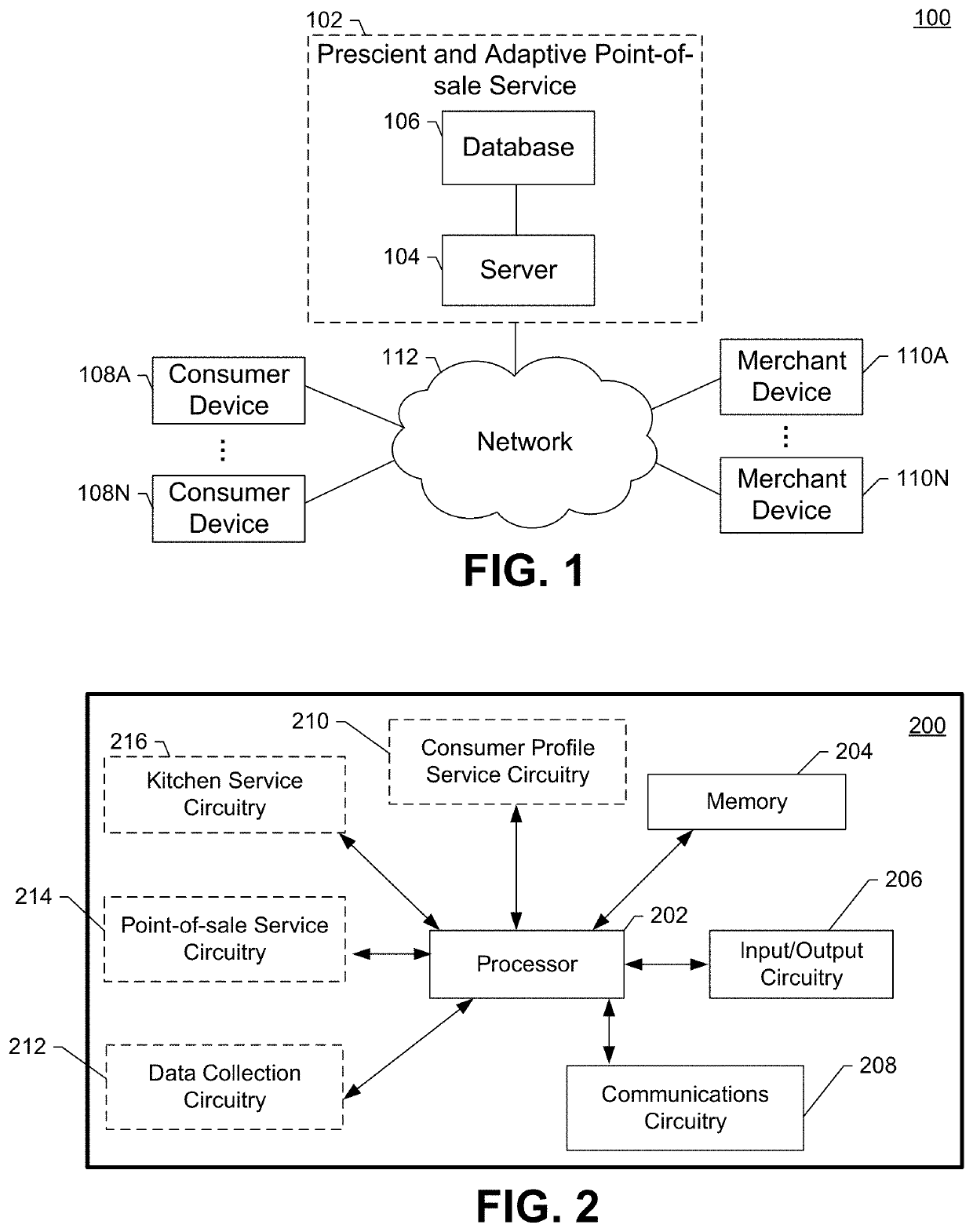
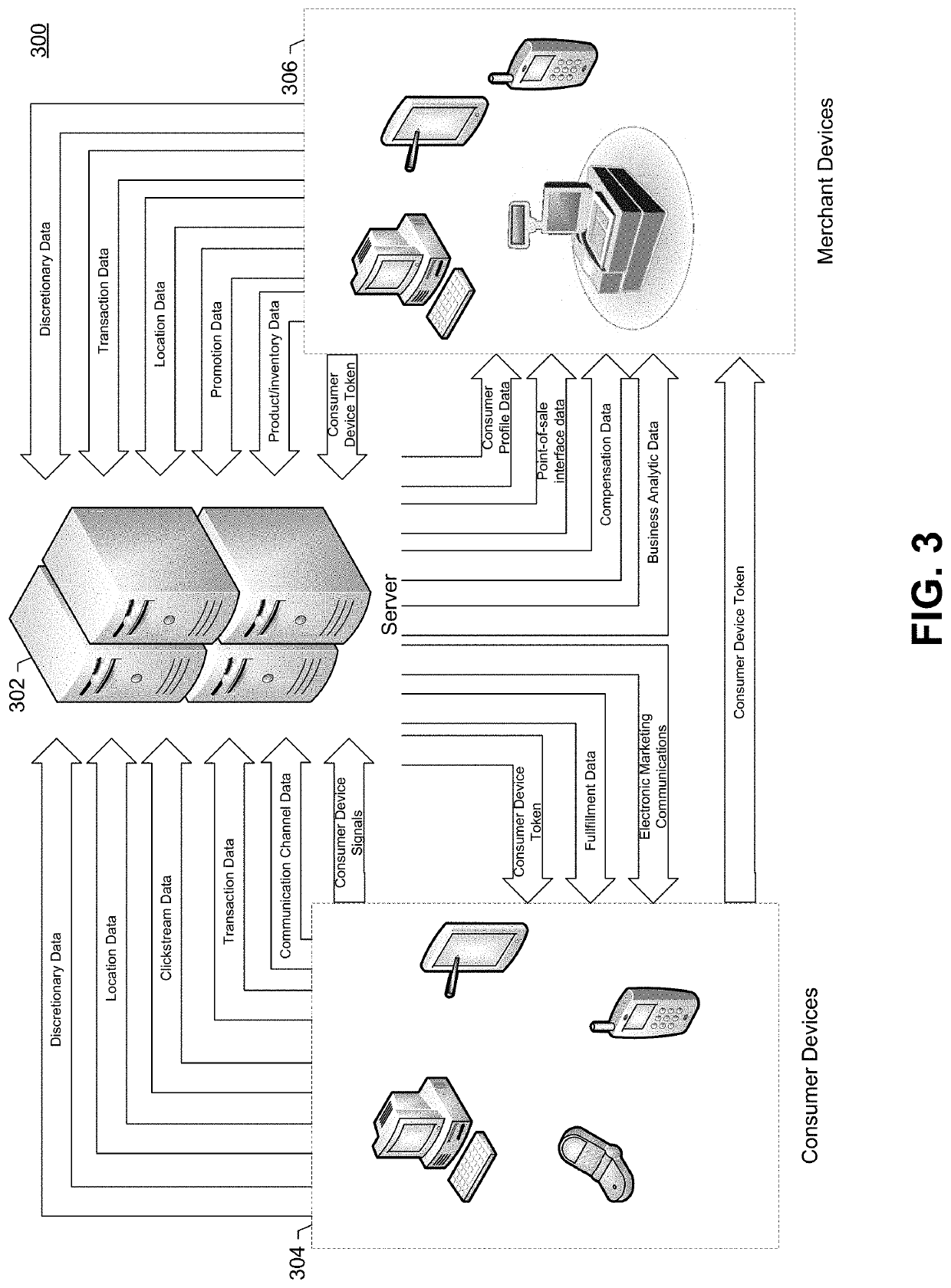
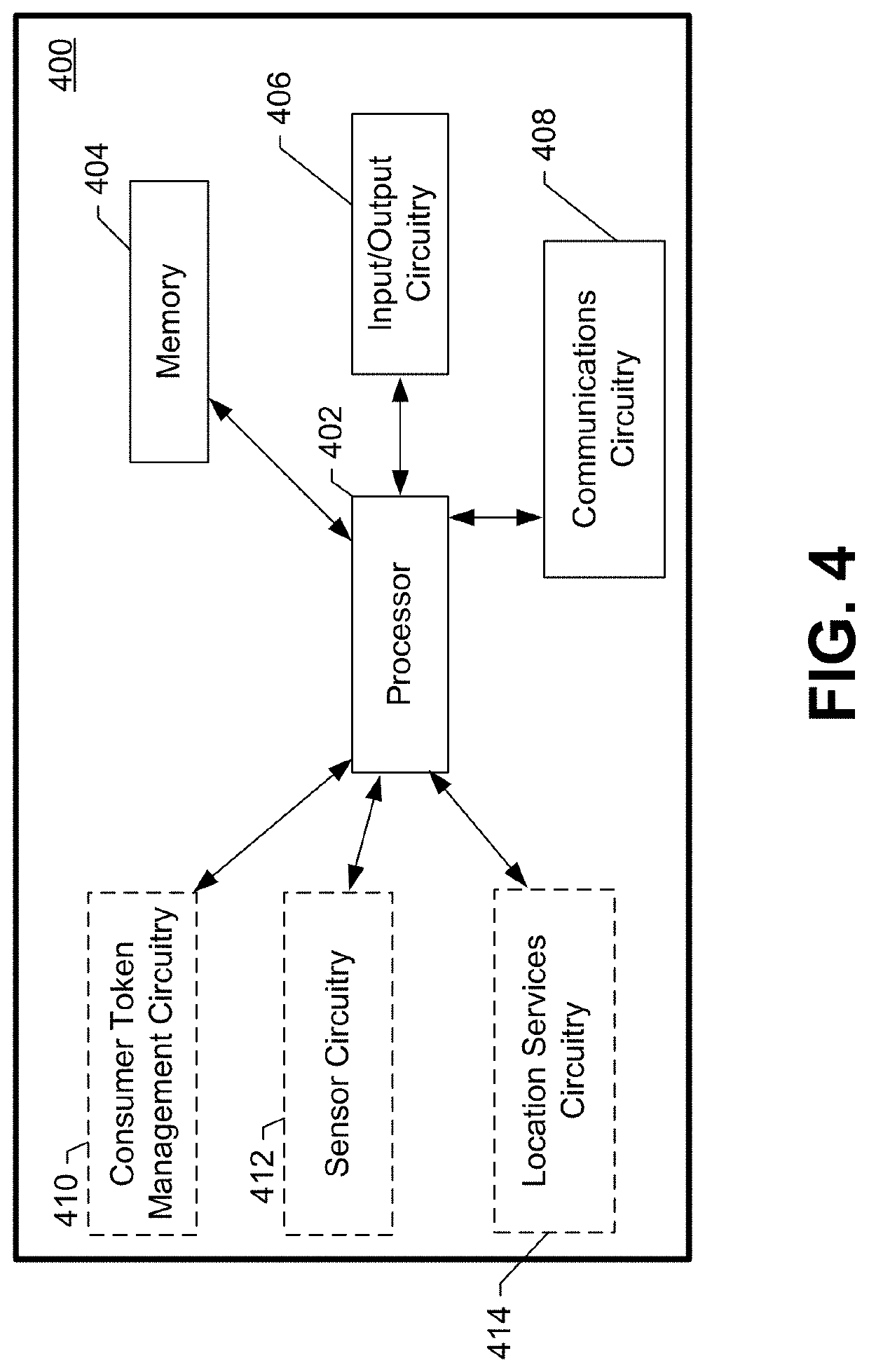
Prescient and adaptive point-of-sale systems
ActiveUS10592882B1Enhanced interactionTransmissionPoint-of-sale network systemsTelecommunicationsElectronic network
Systems, apparatus, methods, and non-transitory media for providing prescient and adaptive point-of-sale services via electronic networks are discussed herein. Some embodiments may include a system with one or more servers. The one or more servers may be configured to generate digital consumer tokens and provide the digital consumer tokens to consumer devices for sharing with merchant devices. When a merchant device receives the digital consumer token, the merchant device may forward the digital consumer token to the one or more servers in exchange for consumer data to facilitate consumer service. In some embodiments, the one or more servers may be configured to provide point-of-sale interfaces that adapt to different consumer preferences or consumer device signals. Some embodiments may provide for consumer interfaces that allow consumers to manage their electronic identity at various (e.g., merchant) locations.
Owner:GROUPON INC
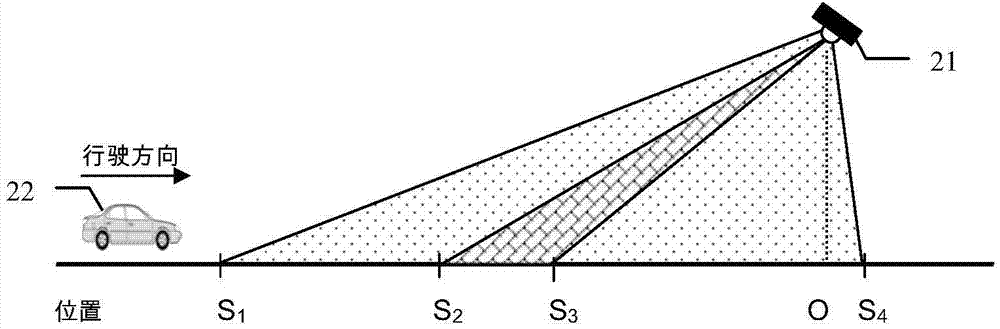
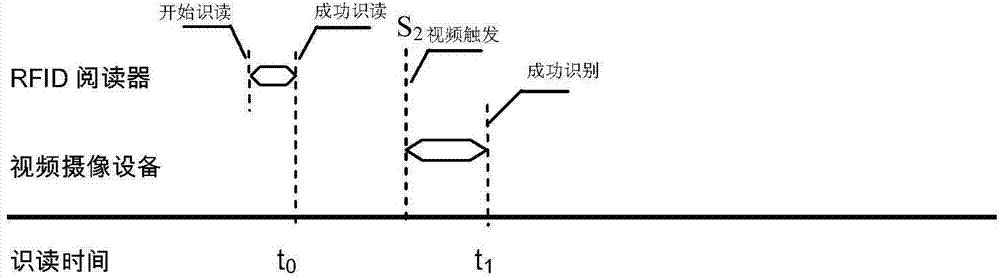
Automobile identity recognition method and device based on ultrahigh frequency radio frequency and video image dual-recognition matching
InactiveCN104766479AImprove integrityAchieve accuracyRoad vehicles traffic controlCharacter and pattern recognitionElectronic identificationIdentity recognition
The invention relates to an automobile identity recognition method and device based on ultrahigh frequency radio frequency and video image dual-recognition matching. The method includes the steps of unceasingly matching automobile identity information with vehicle track records captured and recognized by a video camera shooting device within the time period from t[0]-delta t[02] to t[0]+delta t[01] on the basis of the vehicle identity information recognized by an automobile electronic identification RFID reader at a certain moment t[0], outputting the vehicle identity information and corresponding video image information and removing the vehicle track records which are successfully matched if the vehicle identity information is successfully matched with the record, read at a certain moment t[1], of a video image, and outputting the vehicle identity information and video image information not matched within the time duration through the device after waiting for alpha seconds if matching does not succeed. By means of the method and the device, the electronic identity and vehicle types of vehicles running on roads can be accurately and rapidly recognized, and meanwhile corresponding video image evidence obtaining is achieved.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY +1
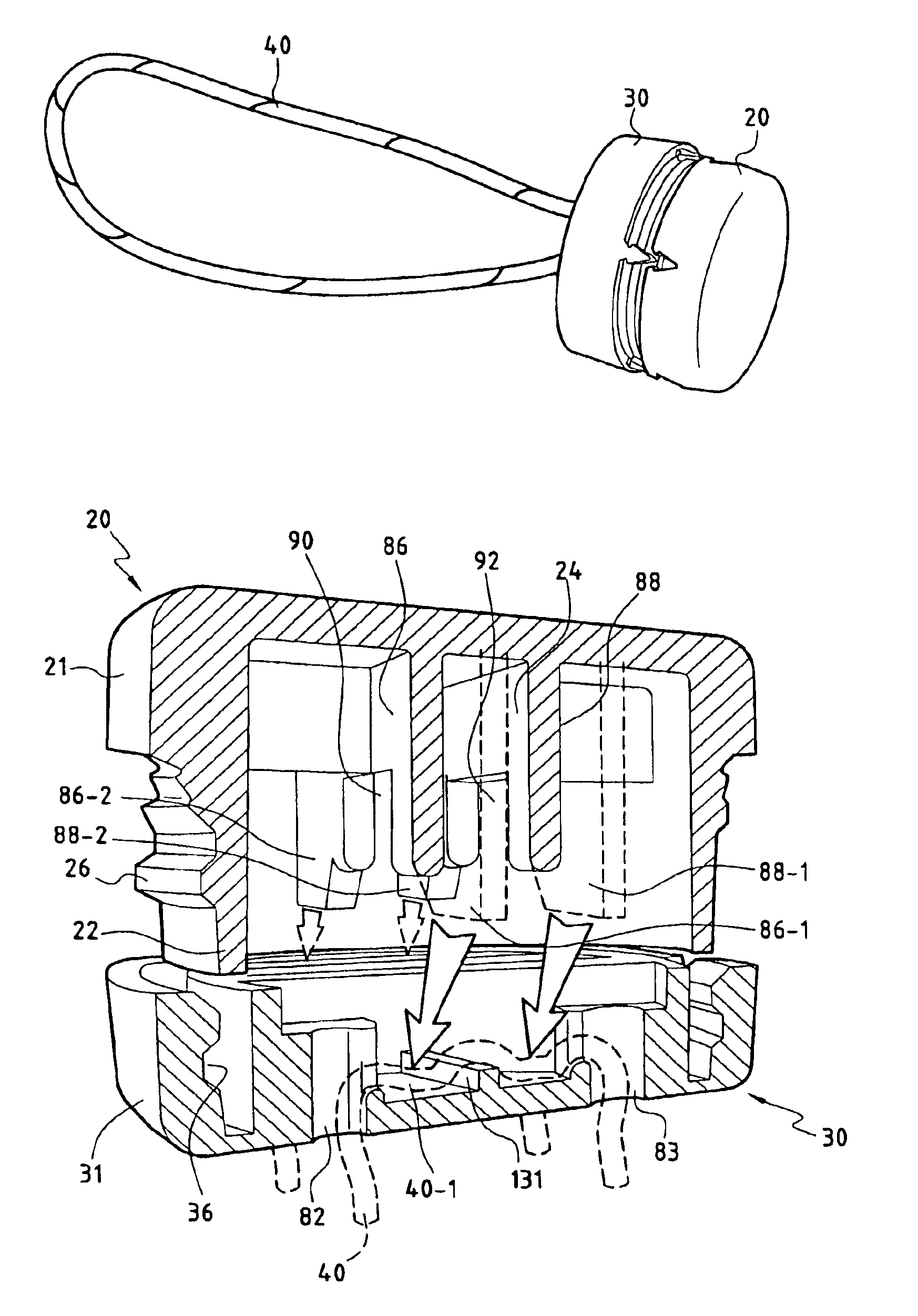
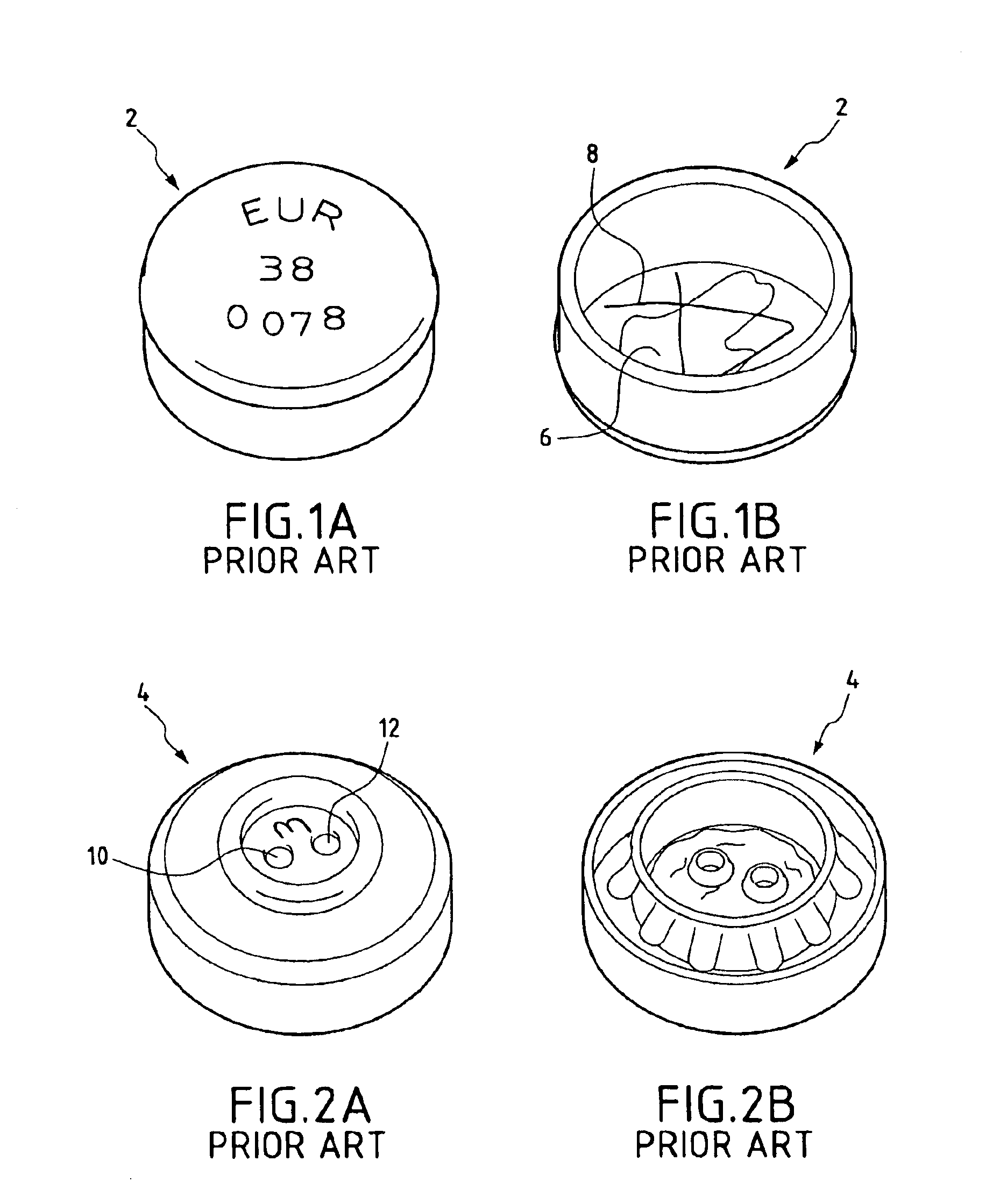
Electronic multipurpose seal with passive transponder
InactiveUS6888241B1Convenient verificationReduce extra spaceStampsSemiconductor/solid-state device detailsBiomedical engineeringElectronic identity
The invention provides a system for sealing, comprising:a first capsule (20);a second capsule (30);electronic means (23, 33), for placing in at least one of the capsules, and capable of containing an electronic identity that is remotely interrogatable; andclosure means (25-1, 25-2, 25-3, 25-4; 35-1, 35-2, 35-3, 35-4) to seal the two capsules together.
Owner:EURON COMMUNITY EC
User identity certificate storage and verification method and device based on block chain and verification system
ActiveCN109889479AGet goodWill not be tampered withDigital data protectionDigital data authenticationValidation methodsUser identifier
The invention discloses a user identity certificate storage and verification method and device based on a block chain and a verification system. The user identity certificate storage method based on ablock chain comprises the following steps: distributing a user identifier for representing a user identity to a user according to a storage request, wherein the unique private key and the unique public key are associated with the user identifier; obtaining identity information of a user, performing Hash calculation on the identity information of the user to generate a digital fingerprint, sendingthe digital fingerprint to a block chain, encrypting a user identifier, the identity information of the user, a storage identifier of a block chain distribution user and the digital fingerprint according to a unique private key, and generating a user identification code representing the identity information. By implementing the method and the device, the identity information of the user is storedby utilizing the identity information storage platform on the basis of the blockchain technology, so that the stored identity information cannot be tampered once the stored identity information is online, the credibility of the electronic identity storage information is enhanced, and meanwhile, the identity information is acquired more conveniently and quickly.
Owner:中积教育科技有限公司
Techniques for securing electronic identities
ActiveUS7770204B2Digital data processing detailsDigital computer detailsInternet privacyData storing
Methods, systems, and data stores generate and manage temporarily assigned identities. A requestor issues a request for a service. The request includes an identity used for authenticating the requestor. The identity is used for generating an identity configuration and for generating a temporarily assigned identity that is updated to a protected identity directory. The request and the temporarily assigned identity are transmitted to the service. The service uses the temporarily assigned identity to access the protected identity directory for purposes of authenticating the request. The service uses the authenticated request to access attributes associated with the temporarily assigned identity.
Owner:EMC IP HLDG CO LLC
Fully electronic identity authentication
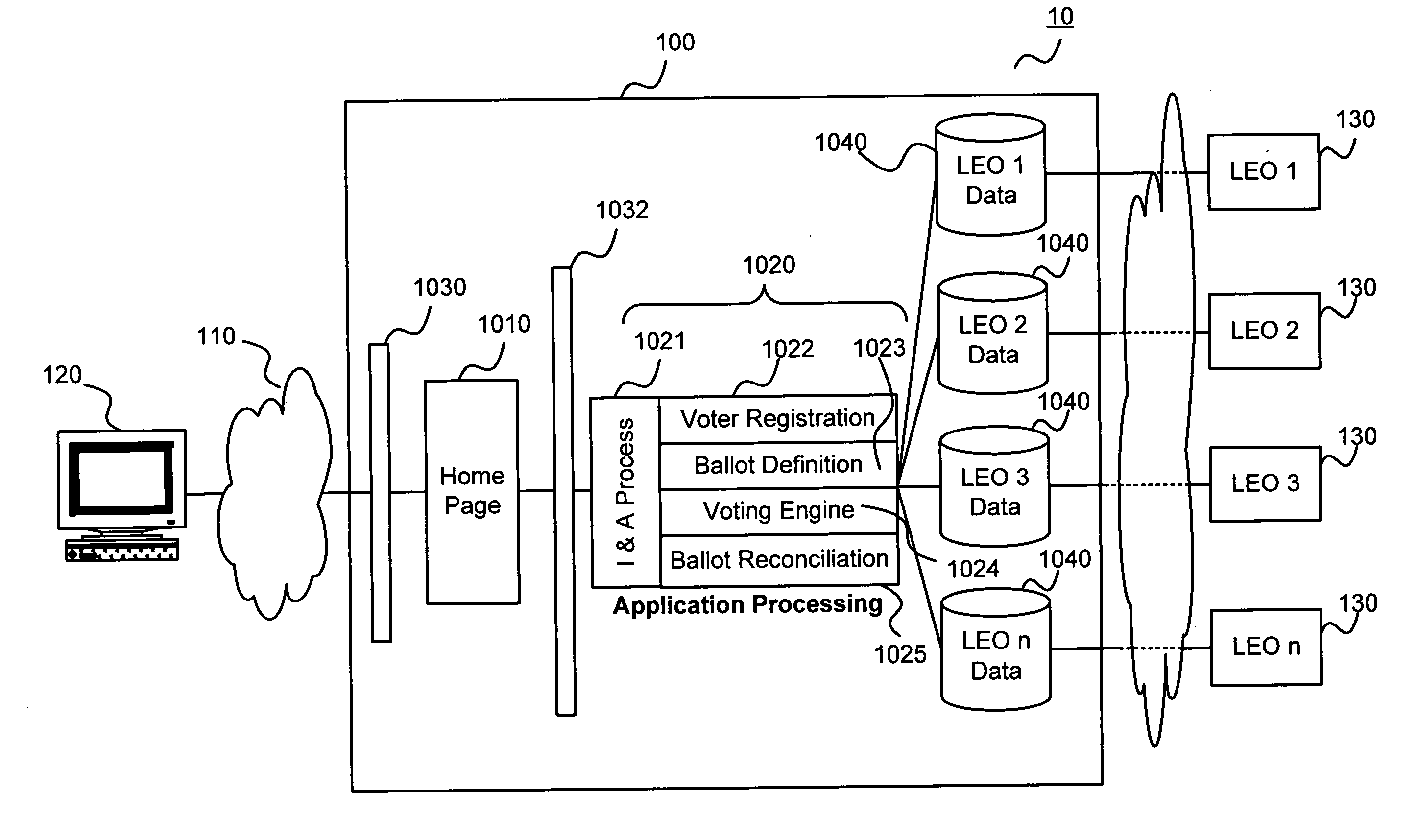
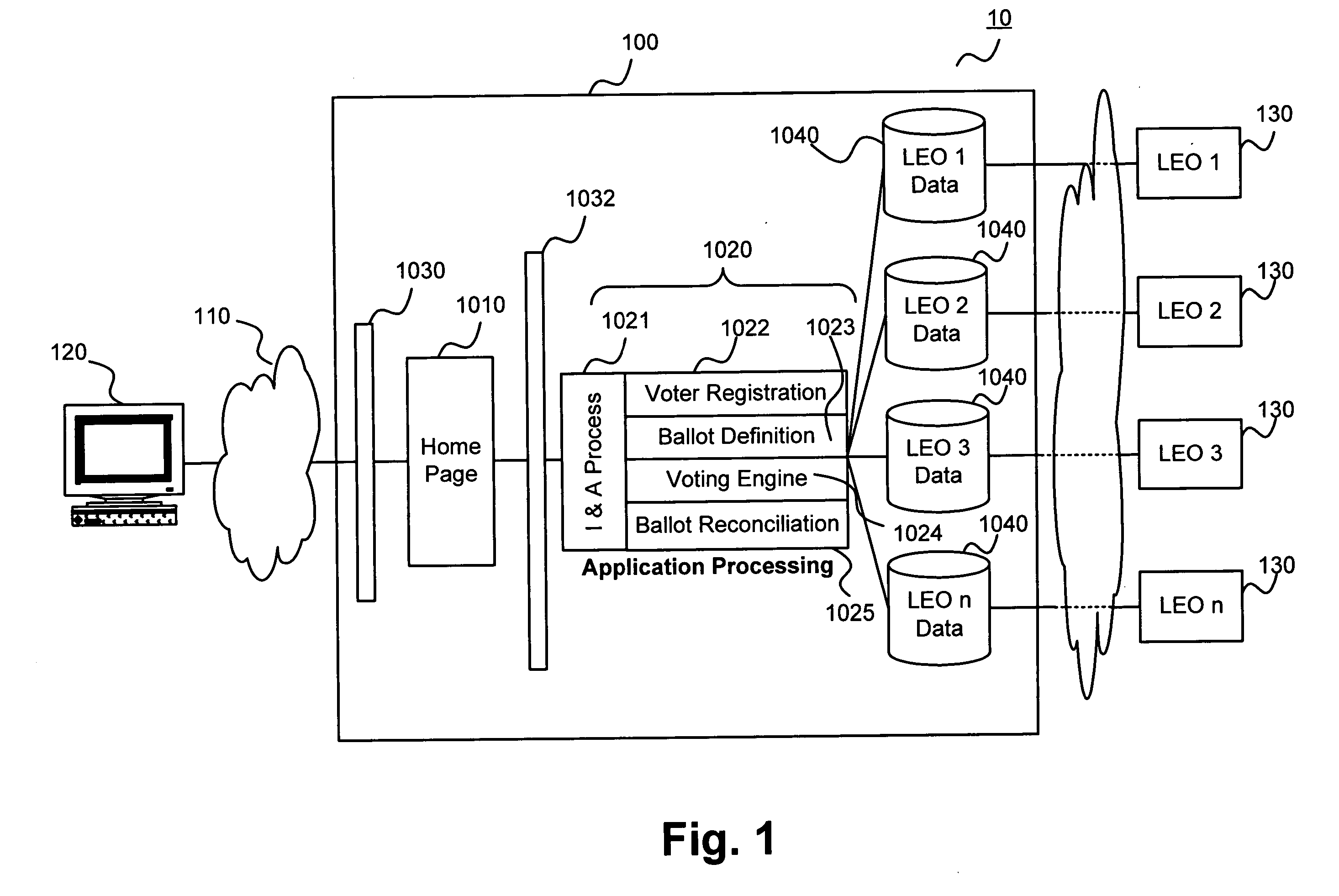
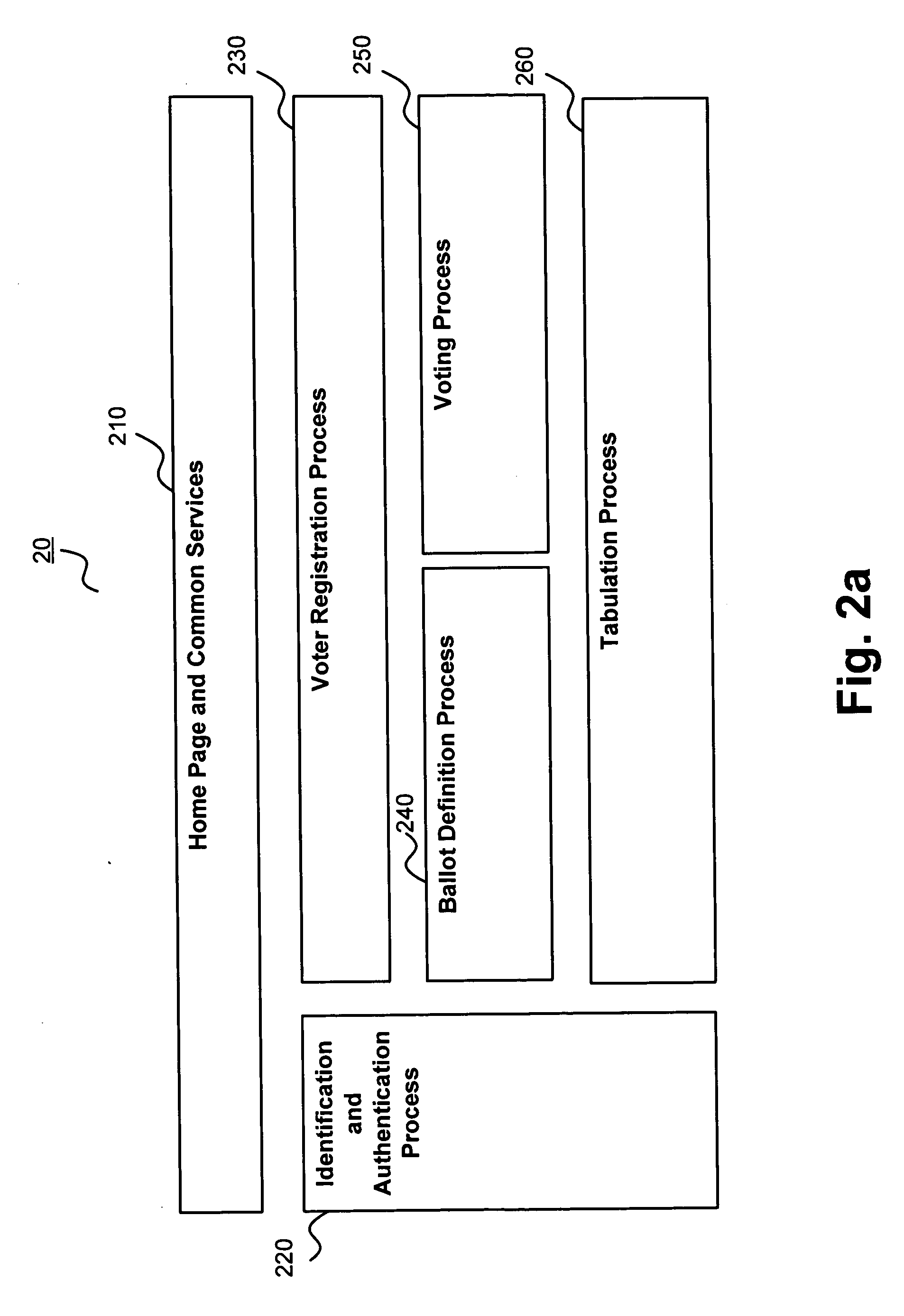
ActiveUS20060031116A1Voting apparatusError detection/correctionAuthentication systemElectronic identity
The present invention relates to a system and method for fully electronic identity authentication, with particular application to electronic election registration and voting. In particular, the present invention provides an authentication system that operates in conjunction with a secure server to authenticate users to provide access information as needed for the authenticated users to access the secure server.
Owner:ACCENTURE GLOBAL SERVICES LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com