Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
772 results about "Payment card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
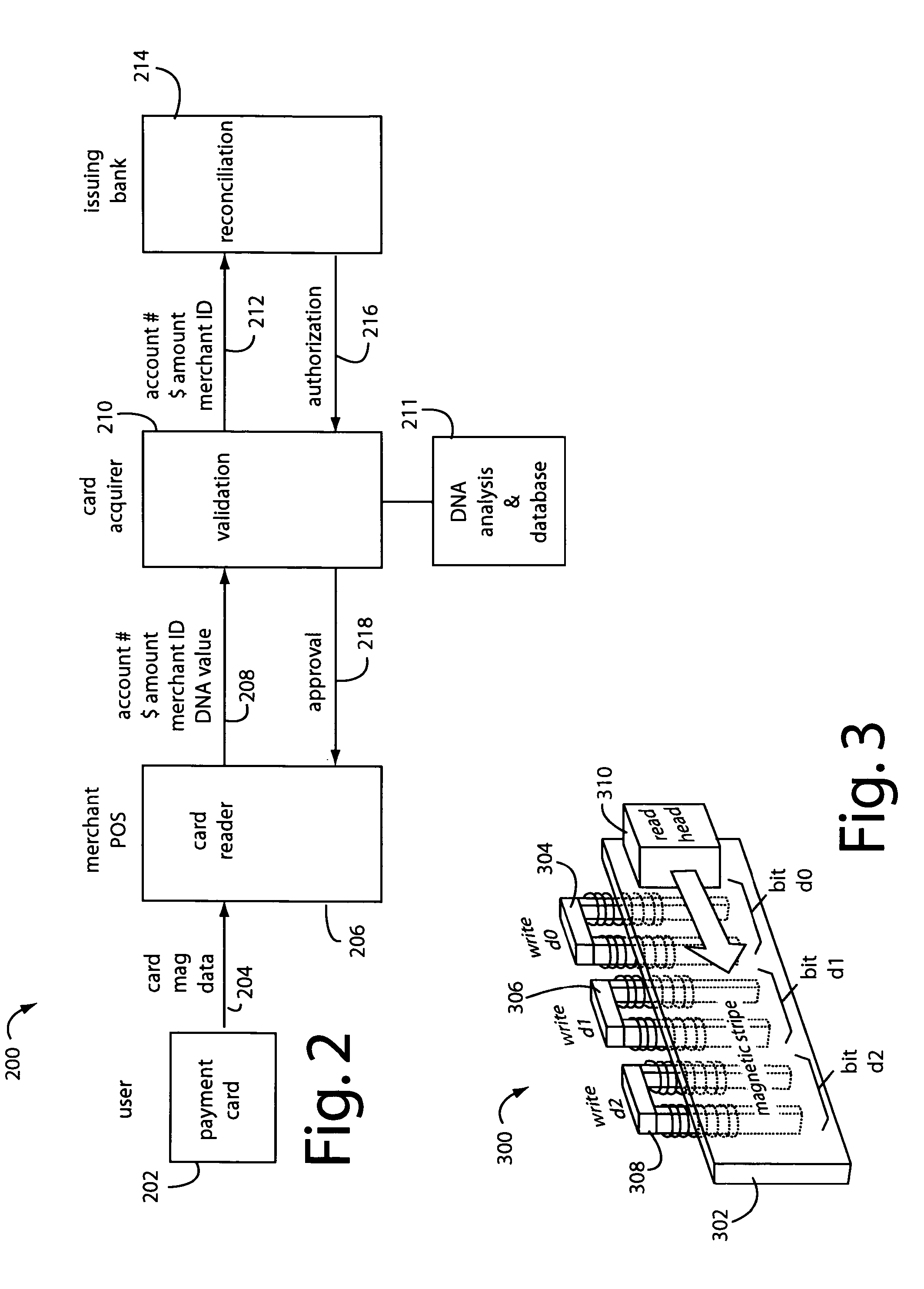
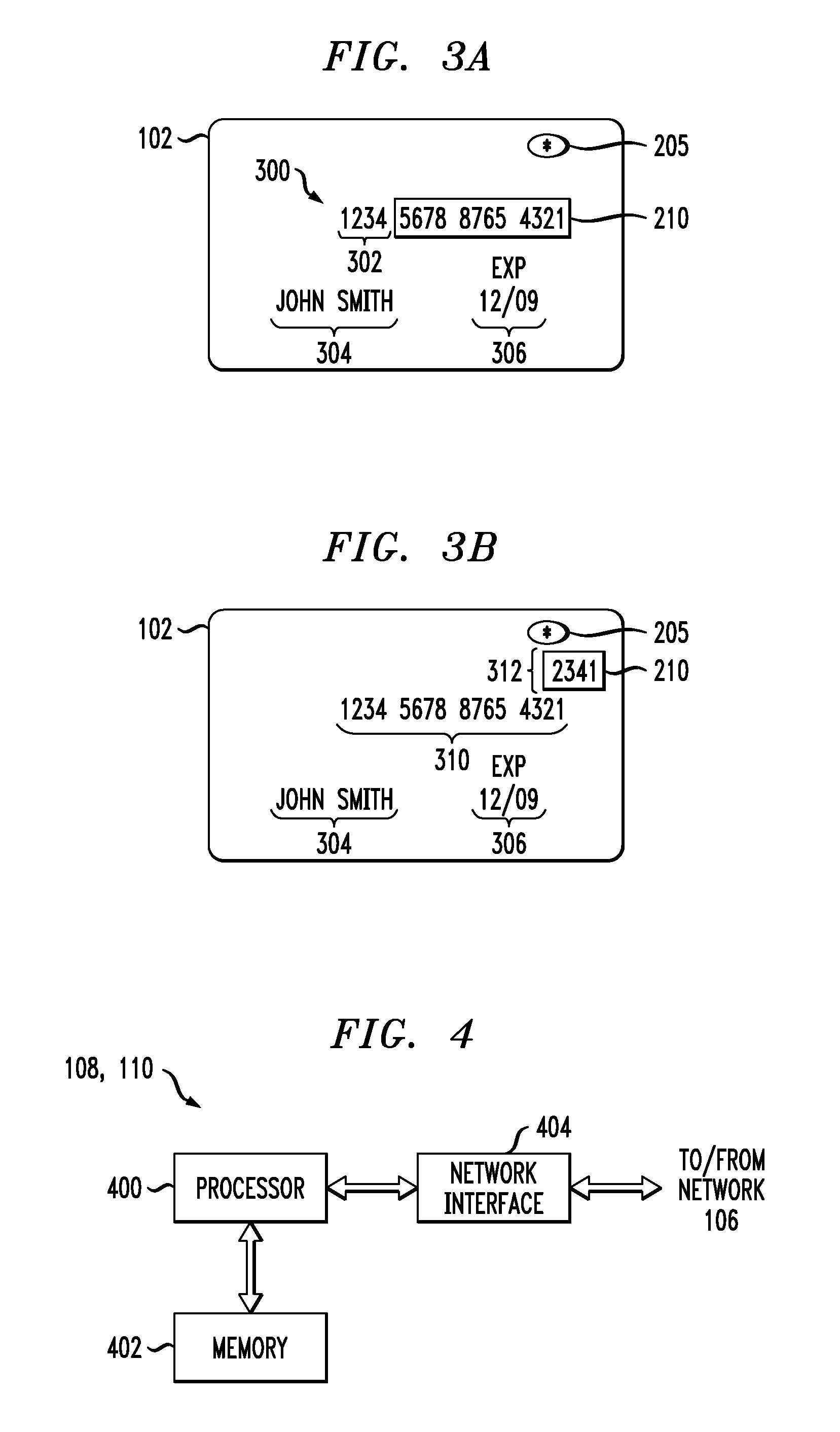
An ATM card is a payment card or dedicated payment card issued by a financial institution which enables a customer to access automated teller machines (ATMs). ATM cards are payment card size and style plastic cards with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVVC (CVV). ATM cards are known by a variety of names such as bank card, MAC (money access card), client card, key card or cash card, among others. Most payment cards, such as debit and credit cards can also function as ATM cards, although ATM-only cards are also available. Charge and proprietary cards cannot be used as ATM cards. The use of a credit card to withdraw cash at an ATM is treated differently to a POS transaction, usually attracting interest charges from the date of the cash withdrawal. Interbank networks allow the use of ATM cards at ATMs of private operators and financial institutions other than those of the institution that issued the cards.
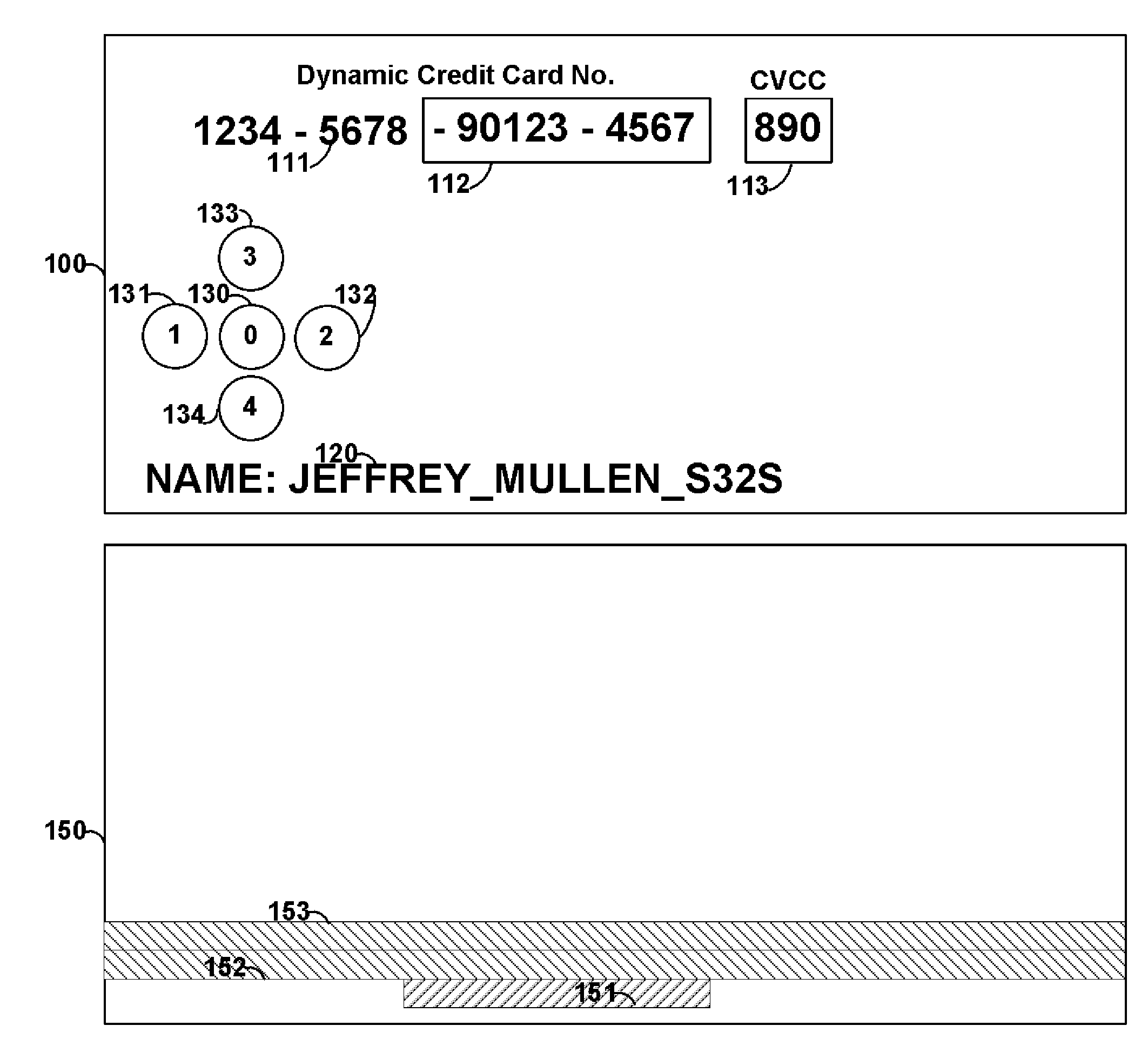
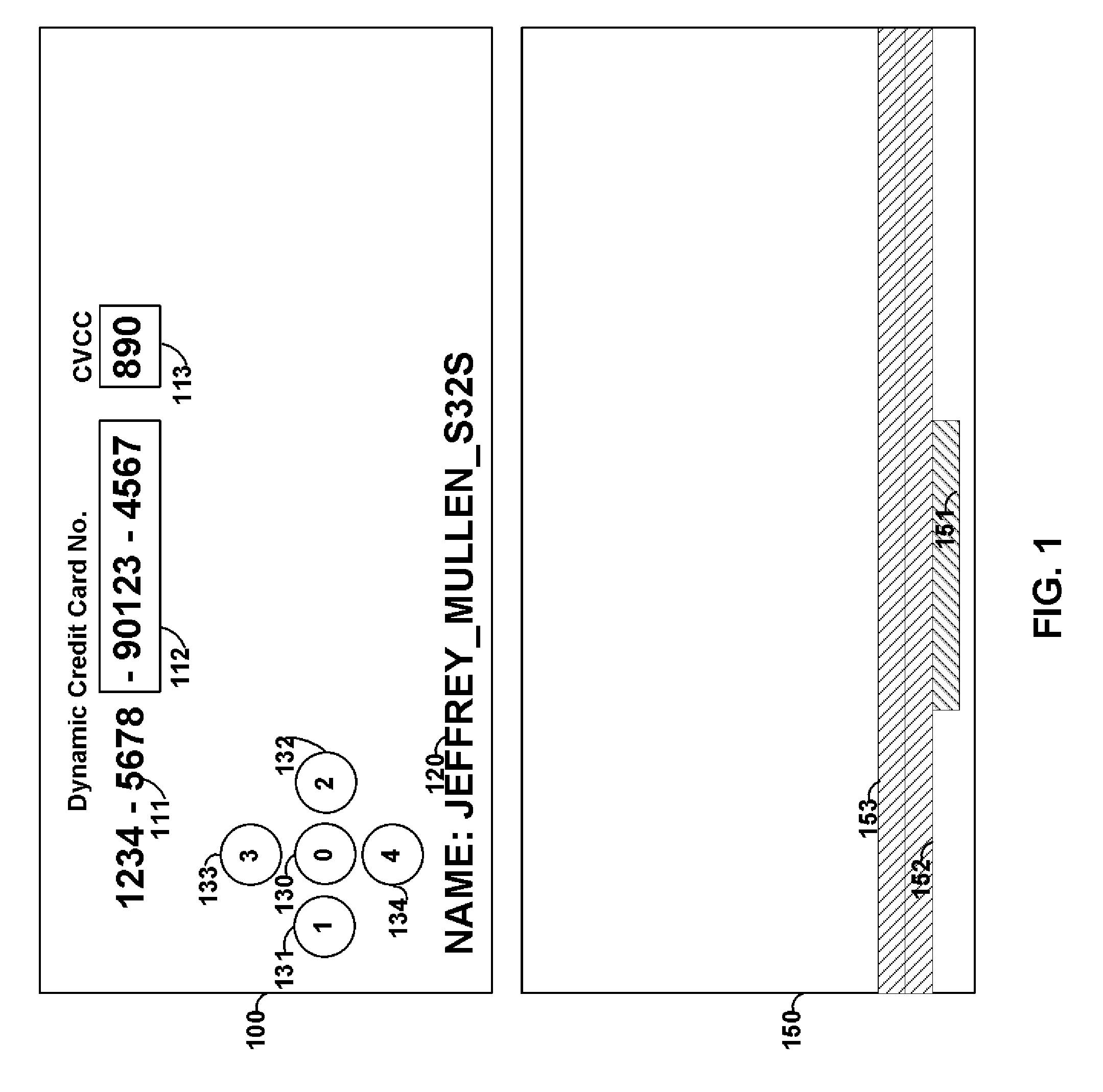
Financial transactions with dynamic card verification values
ActiveUS7584153B2Sufficient dataComputer security arrangementsPayment architectureUser needsDisplay device
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the user when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
Secure interactive electronic account statement delivery system
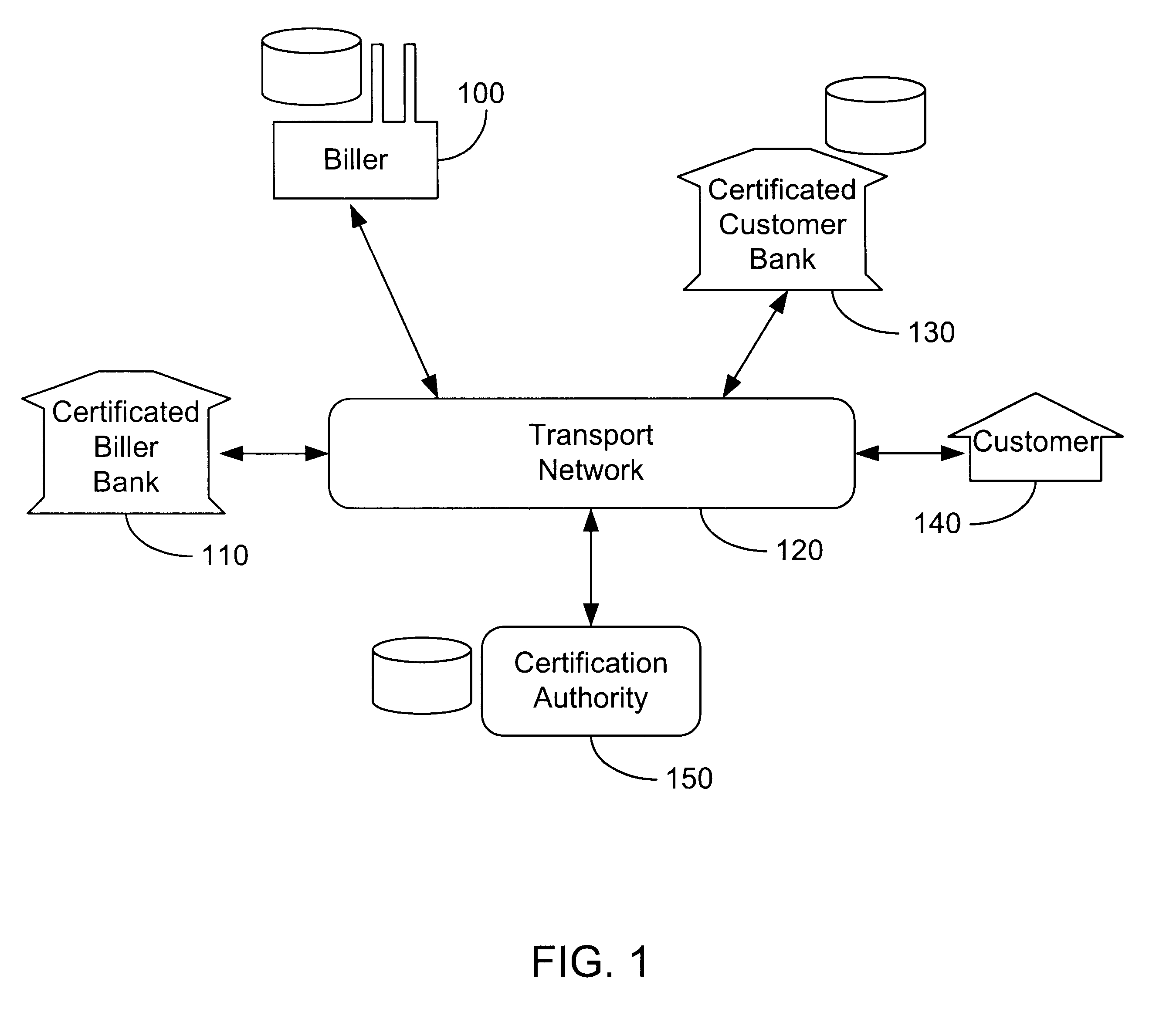
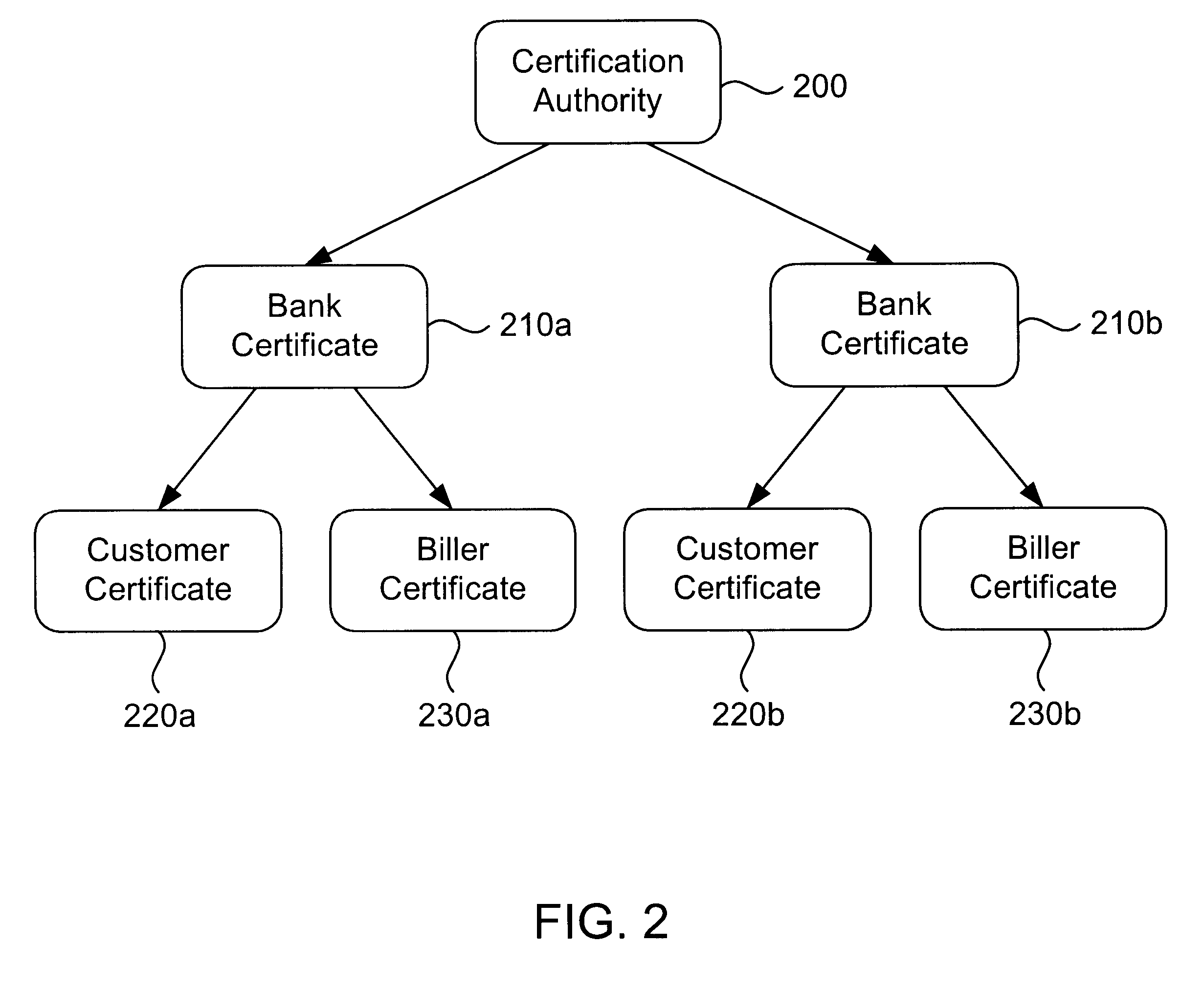
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
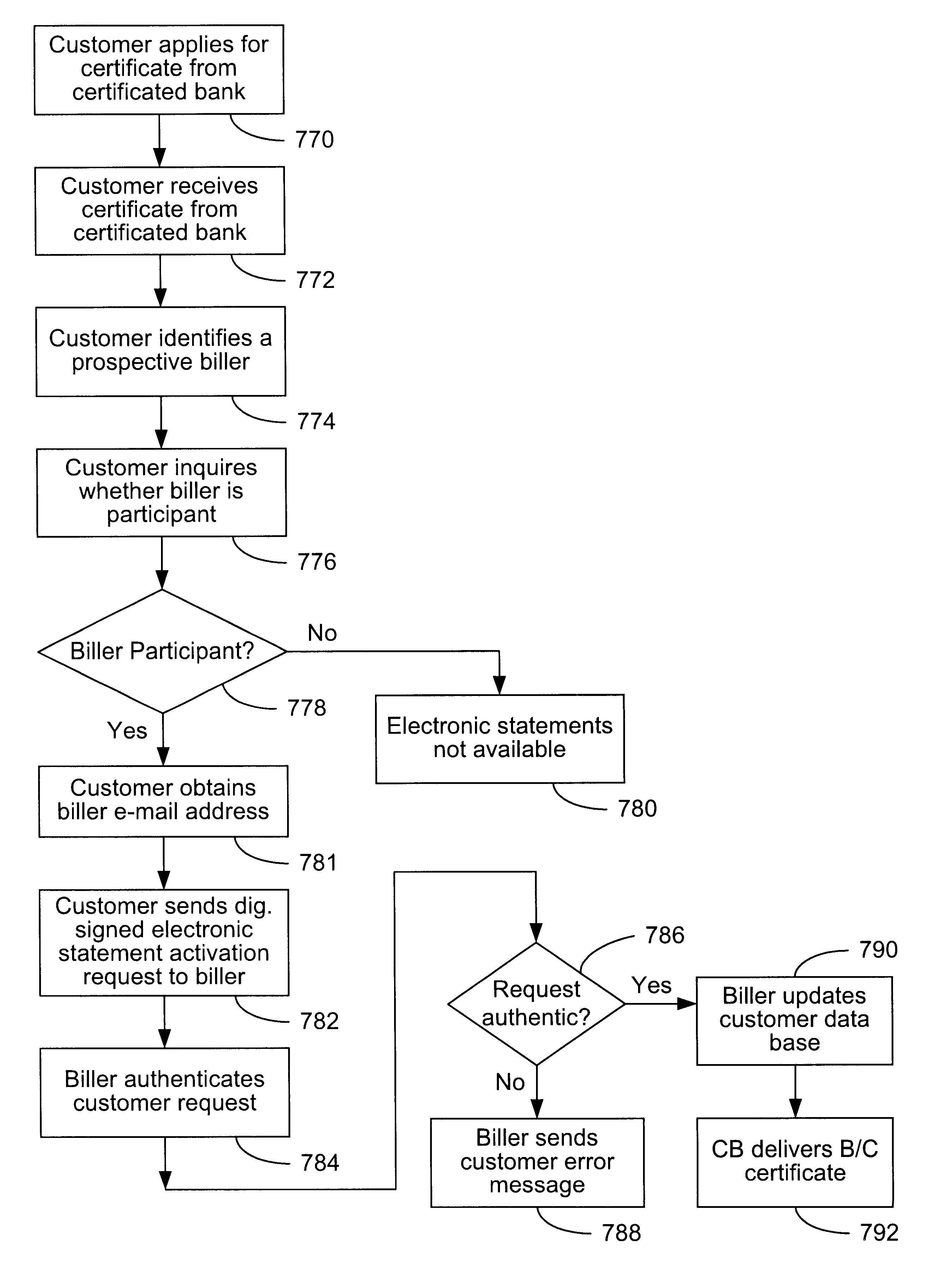
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
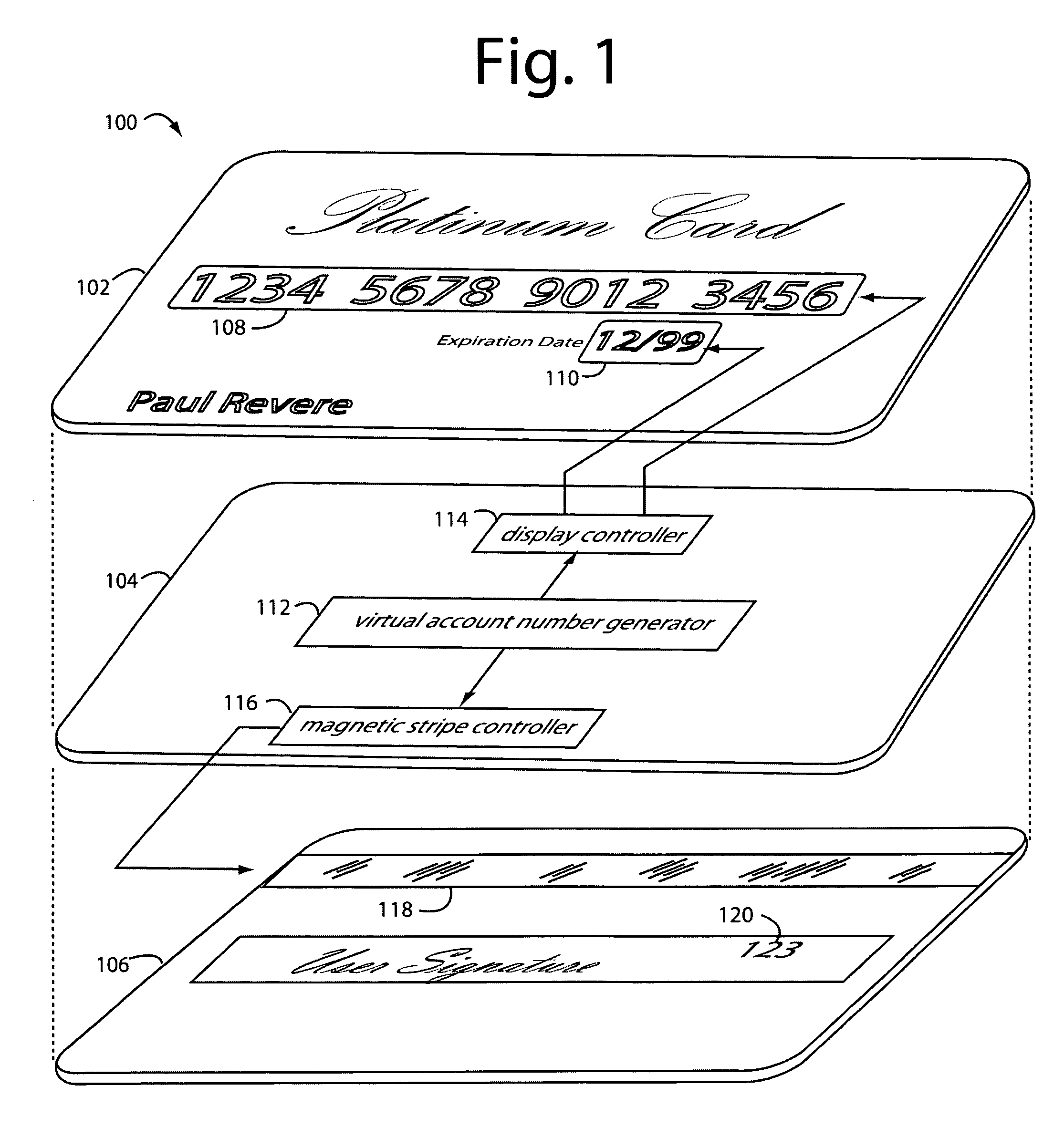
Payment card with internally generated virtual account numbers for its magnetic stripe encoder and user display
A payment card comprises an internal virtual account number generator and a user display for online transactions. Offline transactions with merchant card readers are enabled by a magnetic array positioned behind the card's magnetic stripe on the back. The internal virtual account number generator is able to program the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, it is discarded and put on an exclusion list.
Owner:FITBIT INC
Financial transactions with dynamic personal account numbers
ActiveUS7580898B2Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
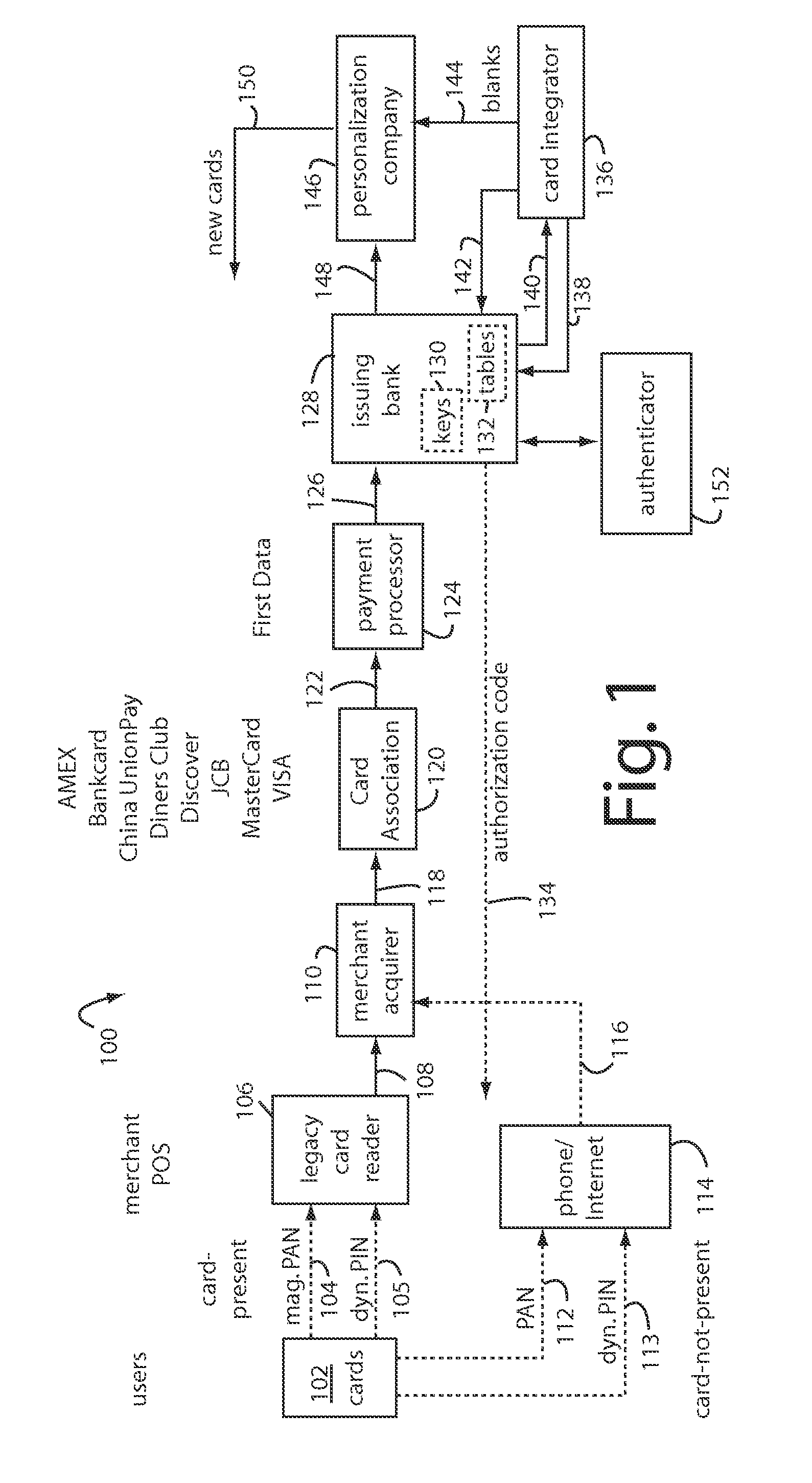
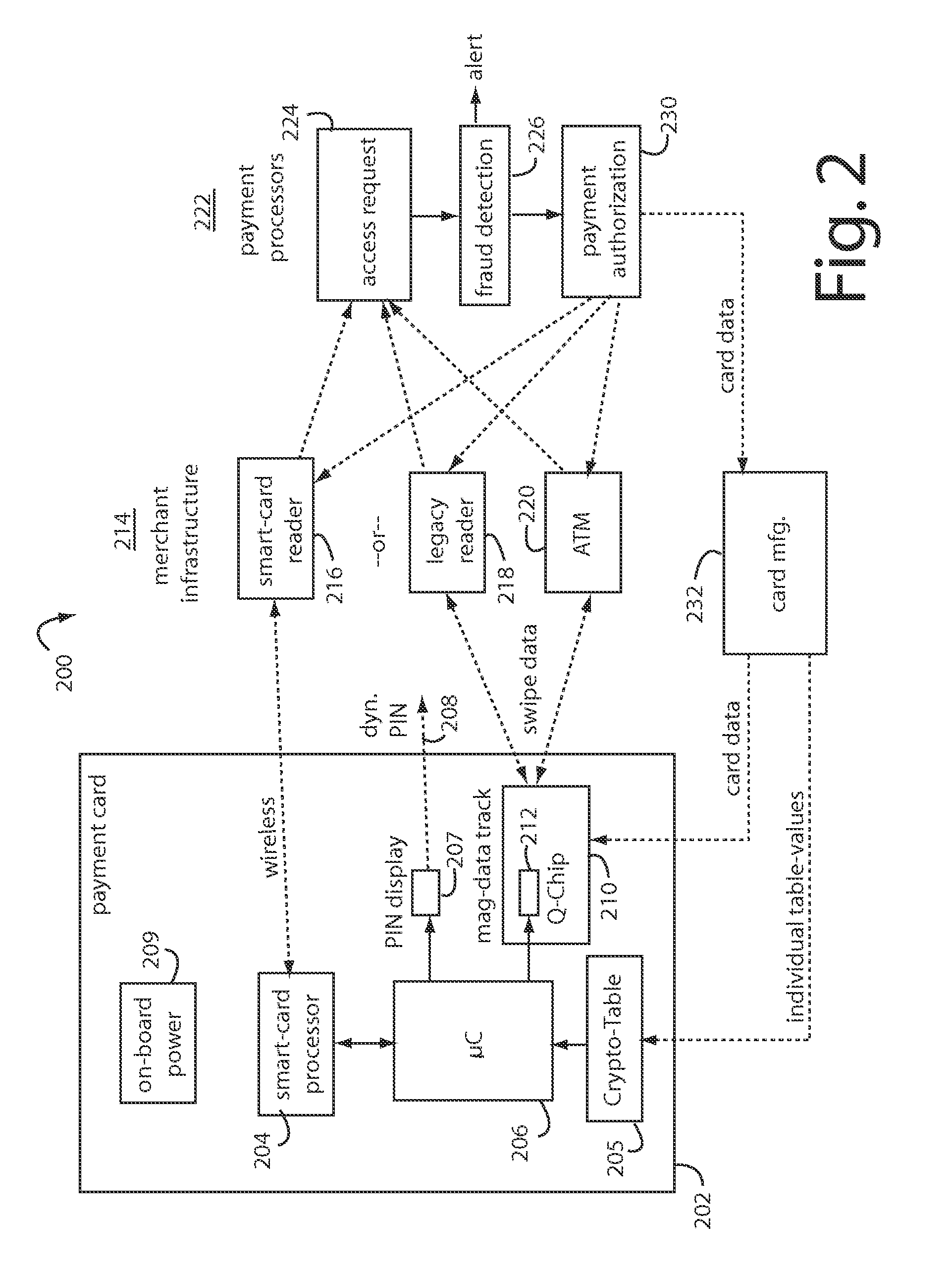
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
Financial transactions with dynamic card verification values
ActiveUS20070136211A1Sufficient dataComputer security arrangementsPayment architectureUser needsPower user
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the suer when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
Payment card financial transaction authenticator
InactiveUS20080201264A1Sufficient dataAcutation objectsFinanceCryptographic nonceFinancial transaction
A payment card financial transaction authenticates for providing overall financial network security computes a number of results from a cryptographic key that match values that were selectively used to personalize individual payment cards with their individual user identification and account access codes. An account access code is later presented daring a financial transaction involving at least one of those individual payment cards. A dynamic portion is included in a merchant's magnetic reading of the payment card. Then authenication can proceed by matching it with values computed from the cryptographic key.
Owner:FITBIT INC
Automated payment card fraud detection and location
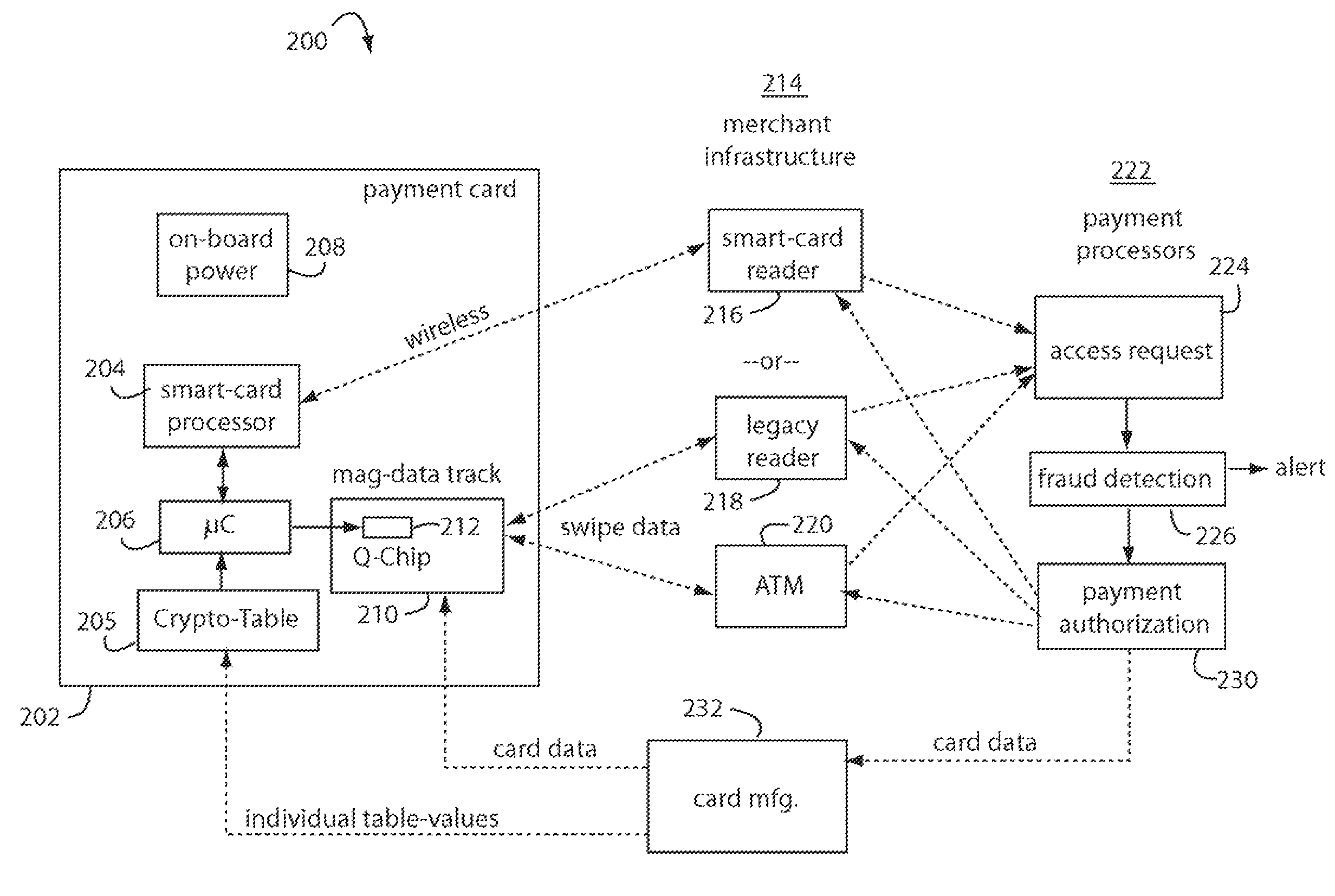
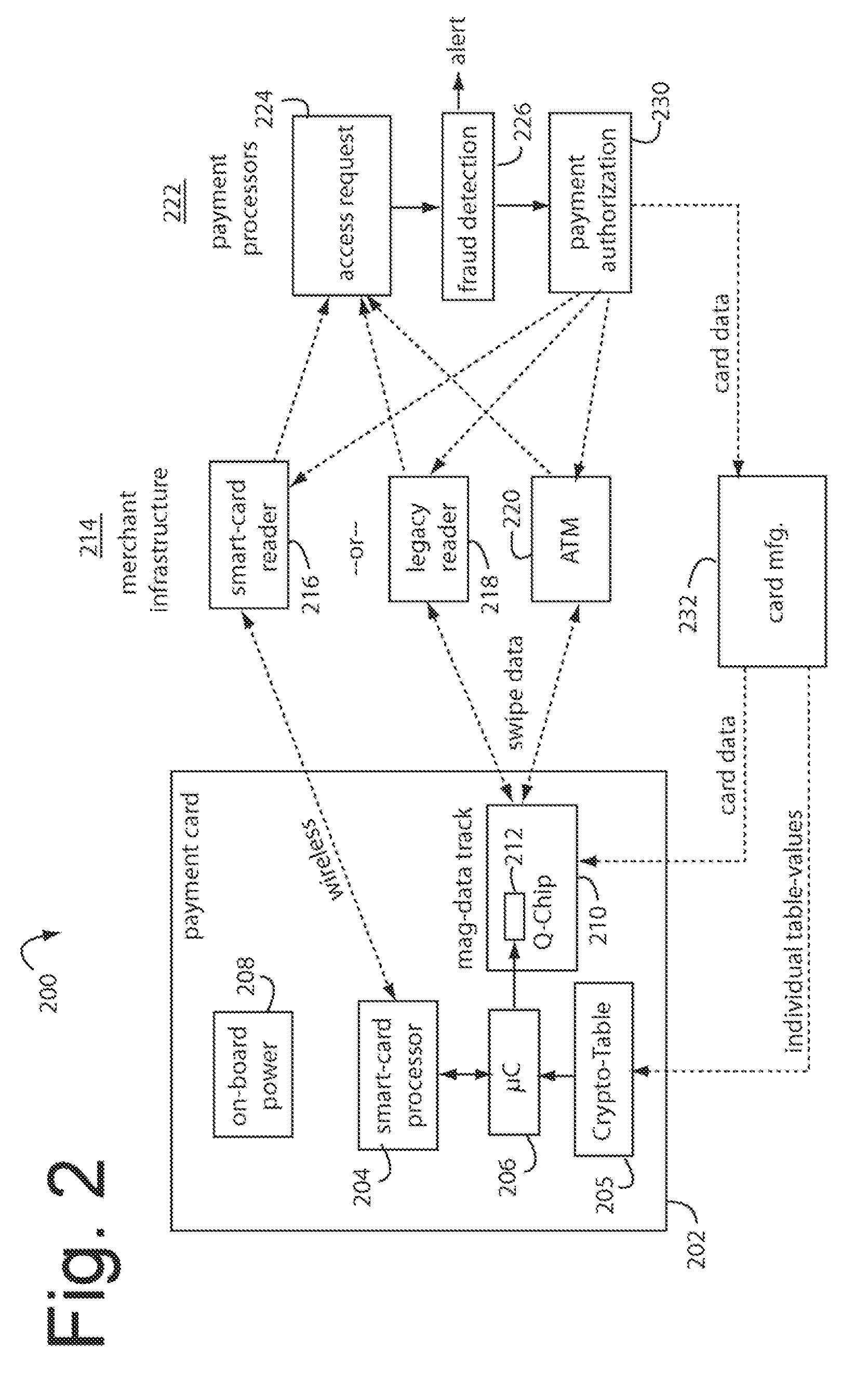
A payment card fraud detection business model comprises an internal virtual account number generator and a user display for Card-Not-Present transactions. Card-Present transactions with merchant card readers are enabled by a magnetic array internally associated with the card's magnetic stripe. The internal virtual account number generator is able to reprogram some of the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, such is discarded and put on an exclusion list or reserved for a specific merchant until the expiration date. A server for the issuing bank logs the merchant locations associated with each use or attempted use, and provides real-time detection of fraudulent attempts to use a virtual account number on the exclusion list. Law enforcement efforts can then be directed in a timely and useful way not only where the fraud occurs but also at its origination.
Owner:FITBIT INC
Financial transactions with dynamic personal account numbers
ActiveUS20070208671A1Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
Payment card preloaded with unique numbers
ActiveUS7380710B2Reduce financial riskSimple and inexpensive and effectiveFinancePayment architectureFinancial transactionPayment order
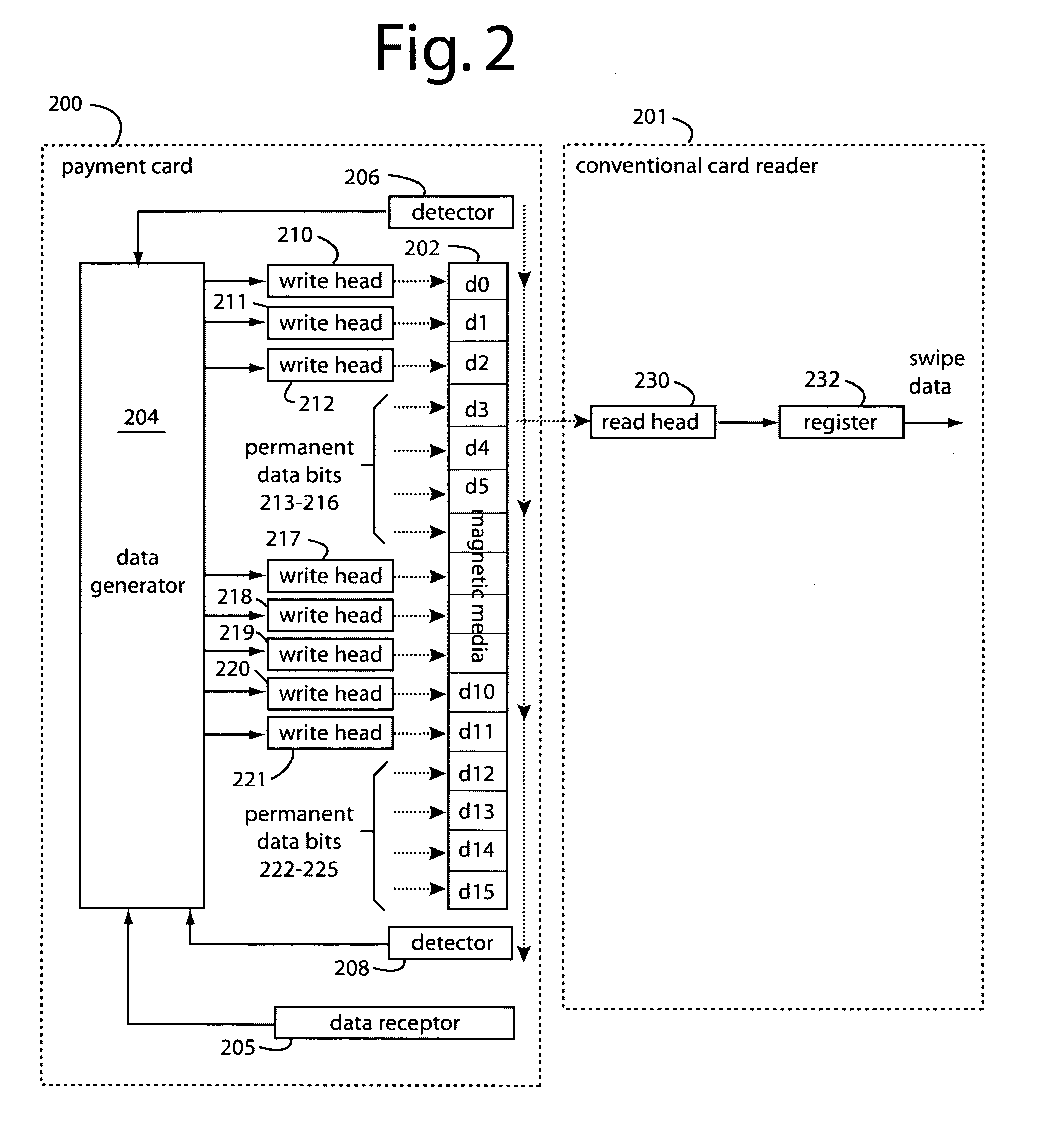
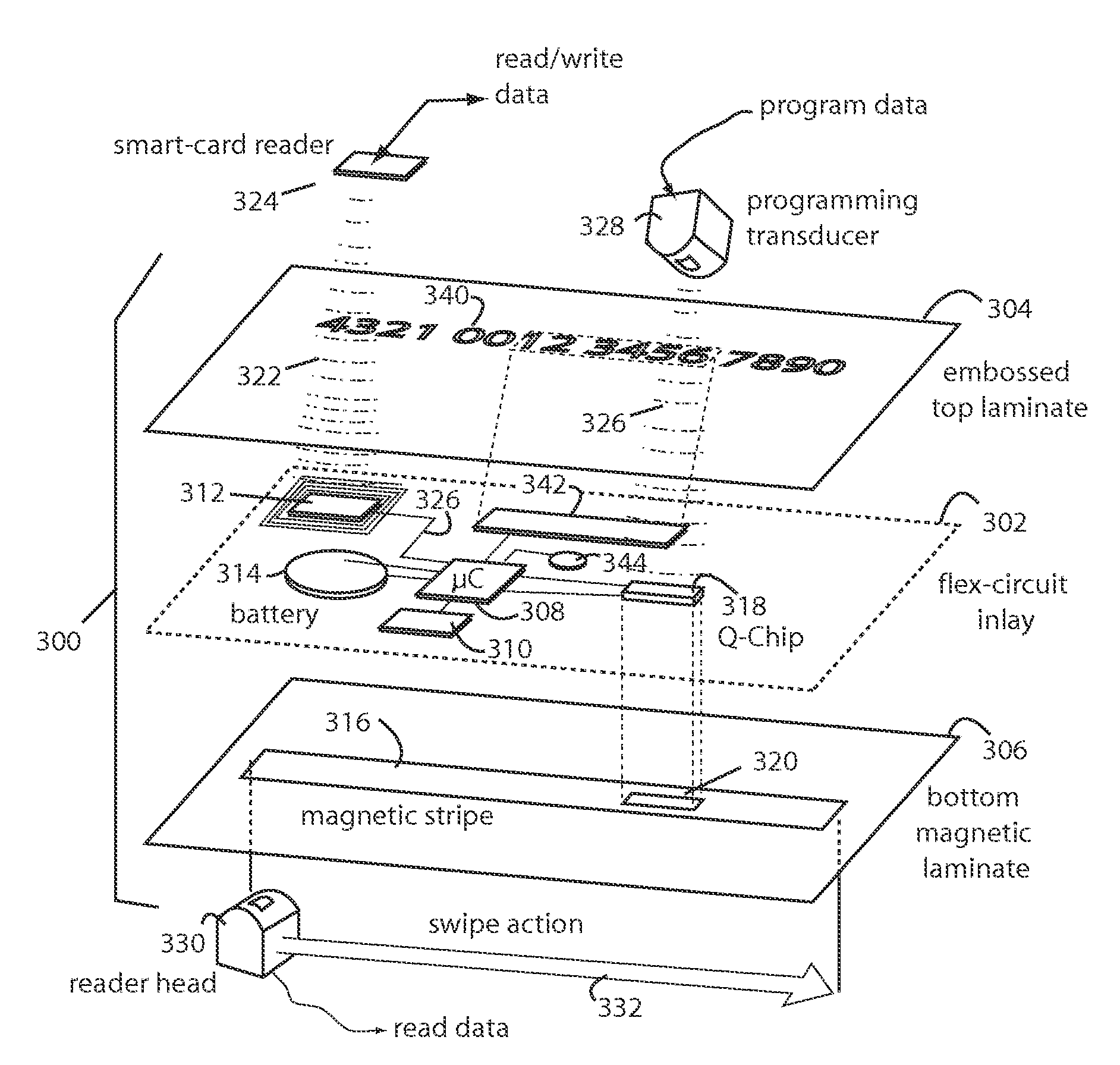
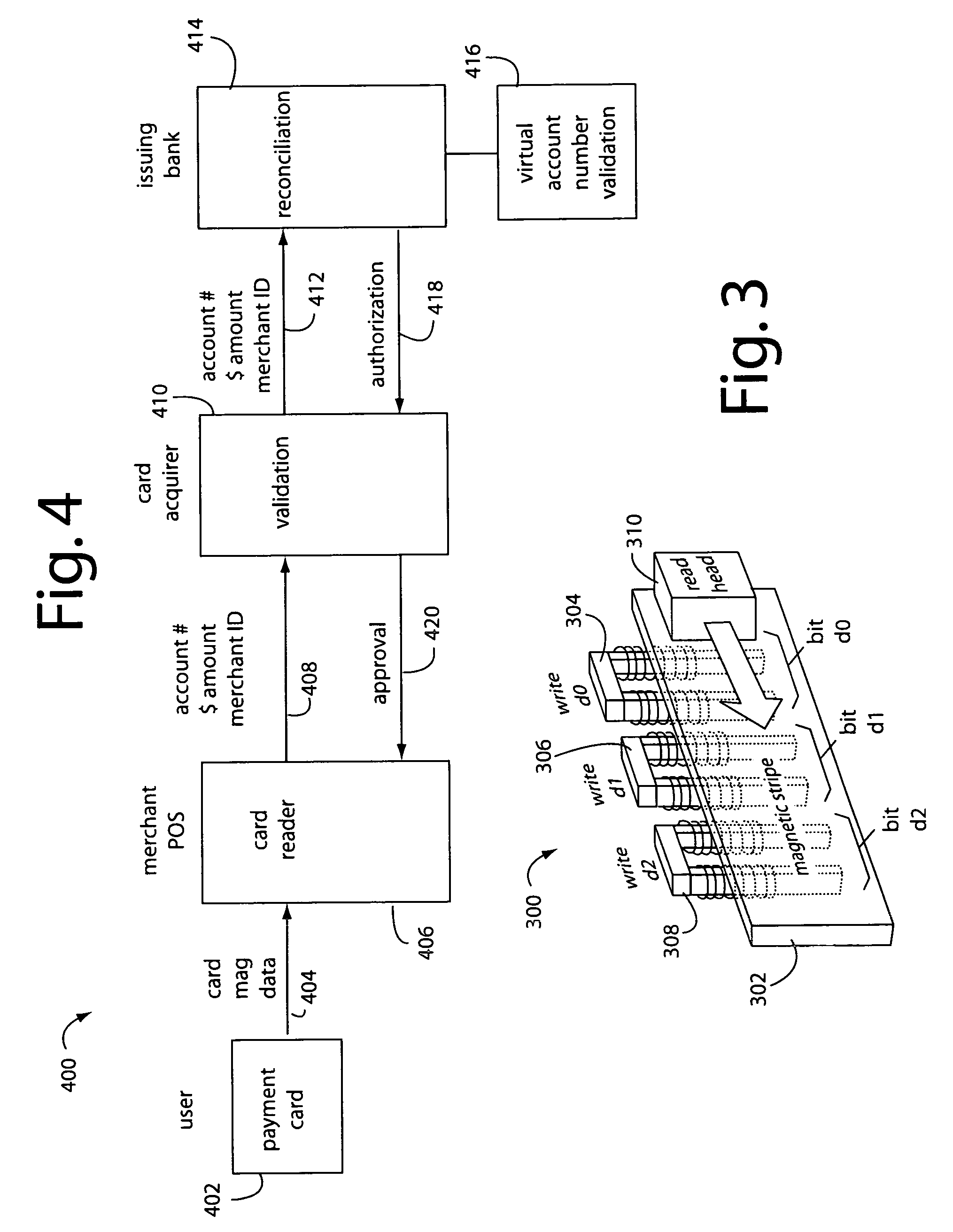
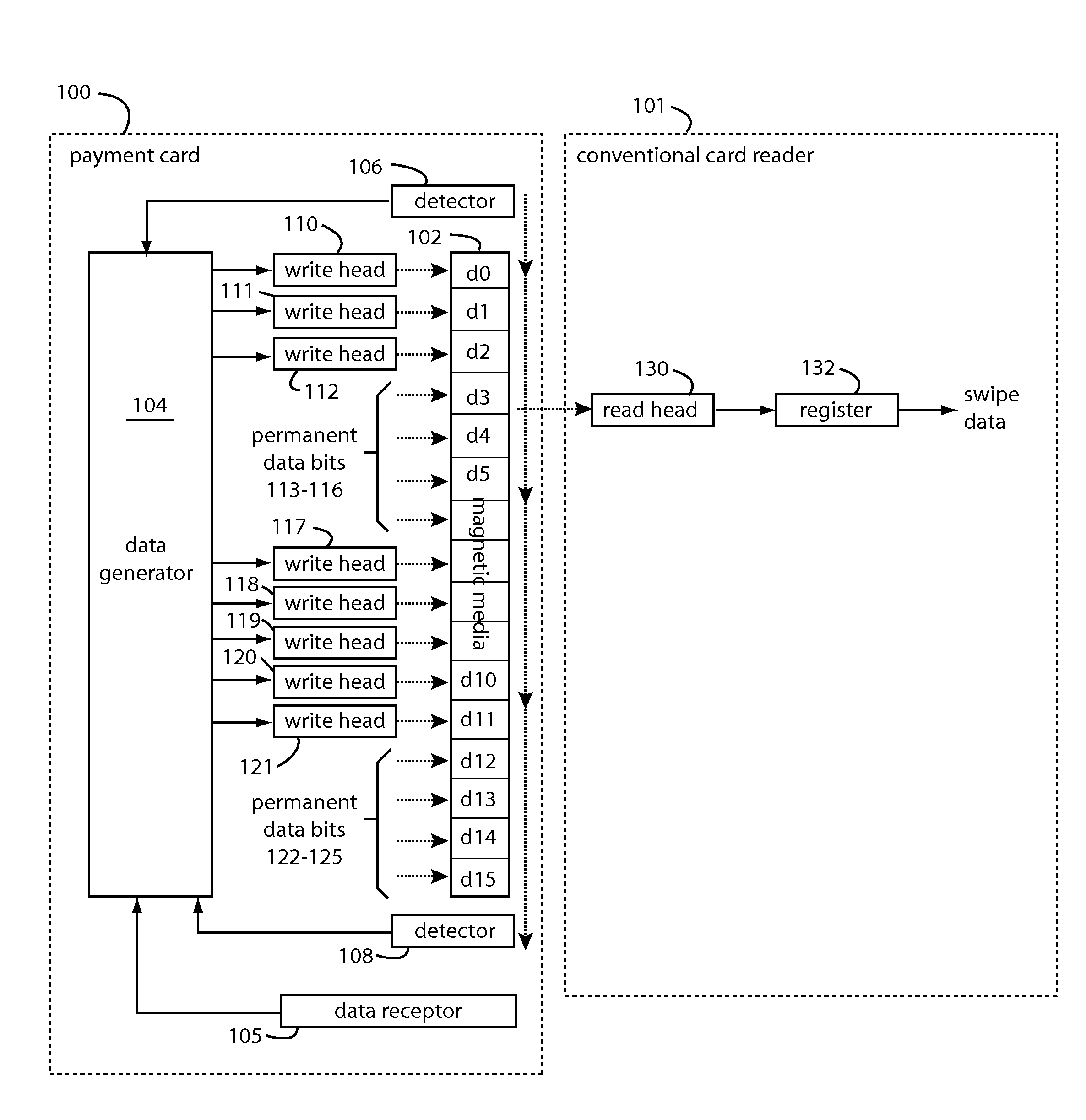
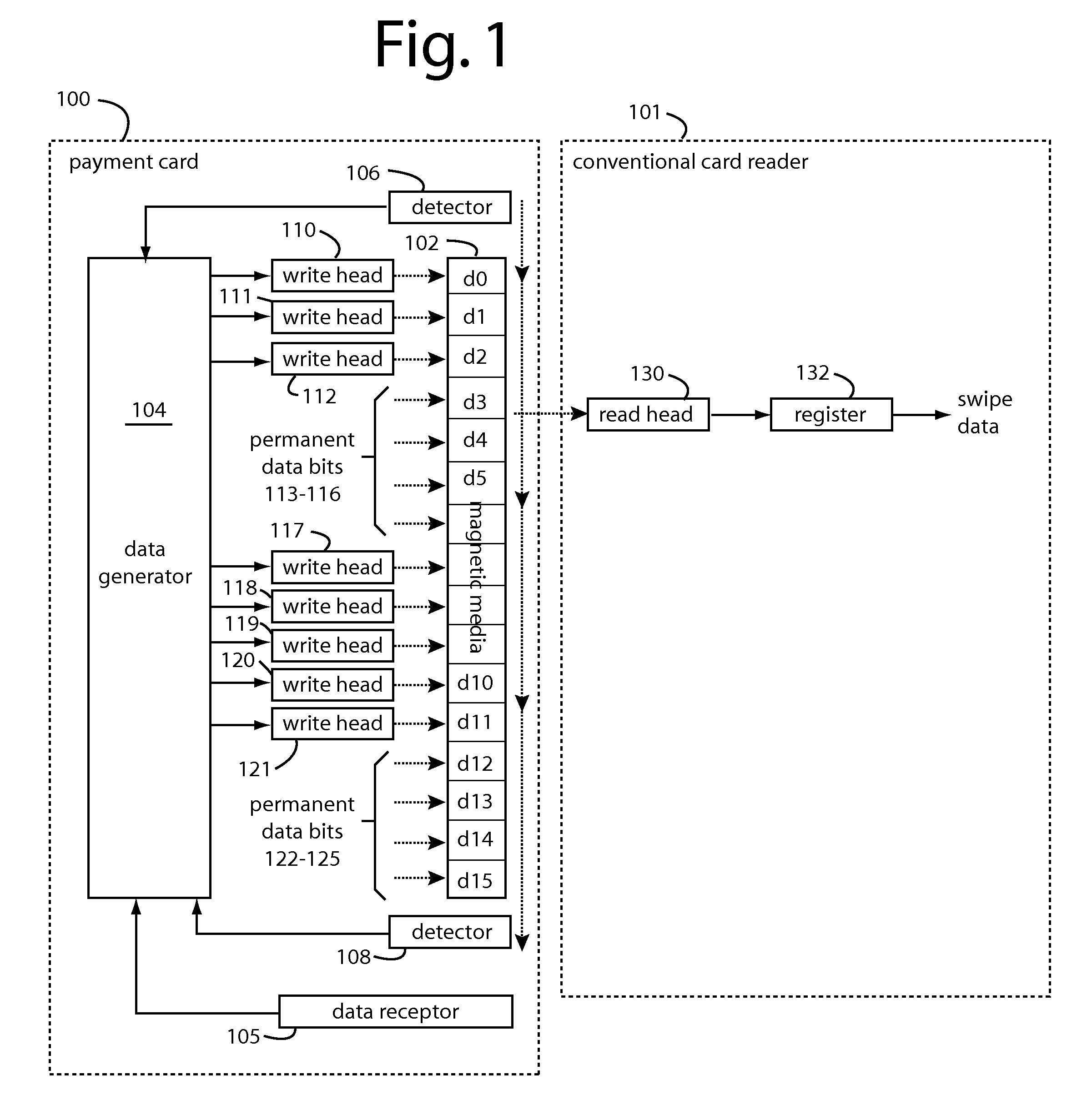
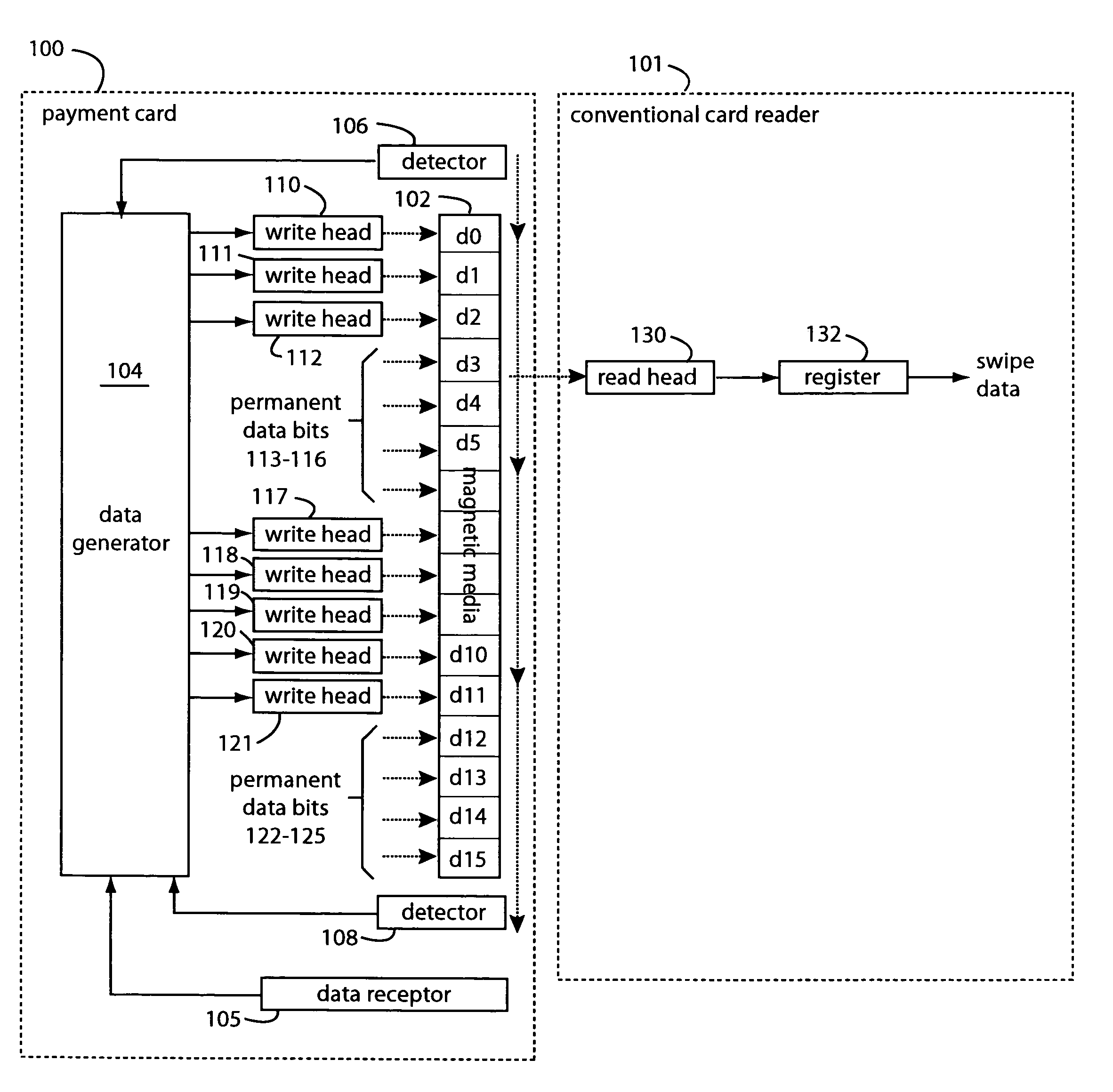
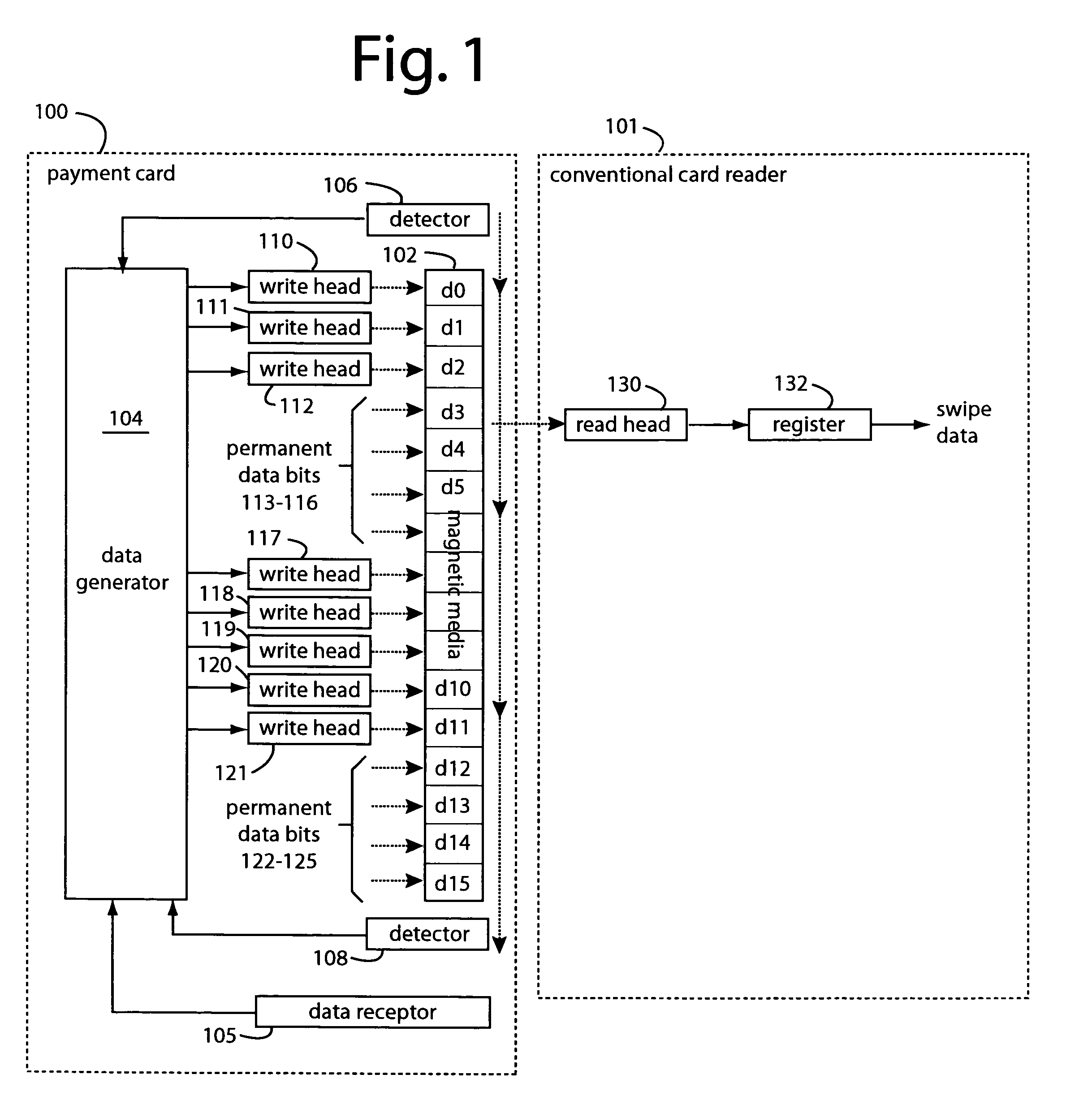
A conventional looking payment card comprises a plastic card with a legacy card reader compatible magnetic stripe for dynamic user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be modified autonomously. Electronics within the card are pre-loaded with many unique numbers that are selected for one-time use in financial transactions. A payment processing center keeps track of the unique numbers used, and knows which numbers to expect in future transactions. It will not authorize transaction requests if the unique number read during a magnetic card swipe is not as expected. A card-swipe detector embedded in the plastic card detects each use in a scanner, so changes can be made to the data bits sent to the write heads.
Owner:FITBIT INC
Financial transaction payment processor
InactiveUS20090006262A1Sufficient dataAcutation objectsSynchronising transmission/receiving encryption devicesPayment orderFinancial transaction
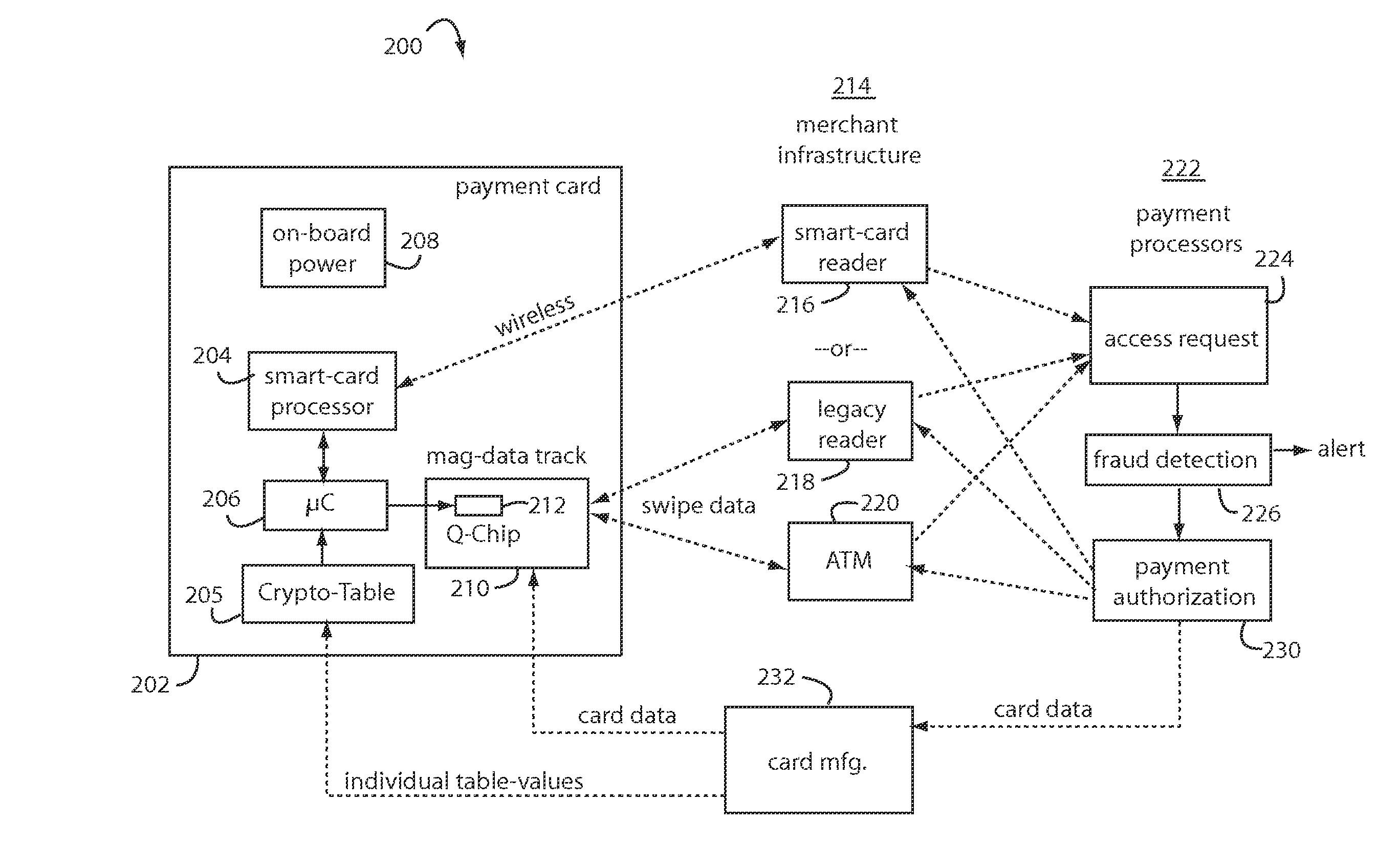
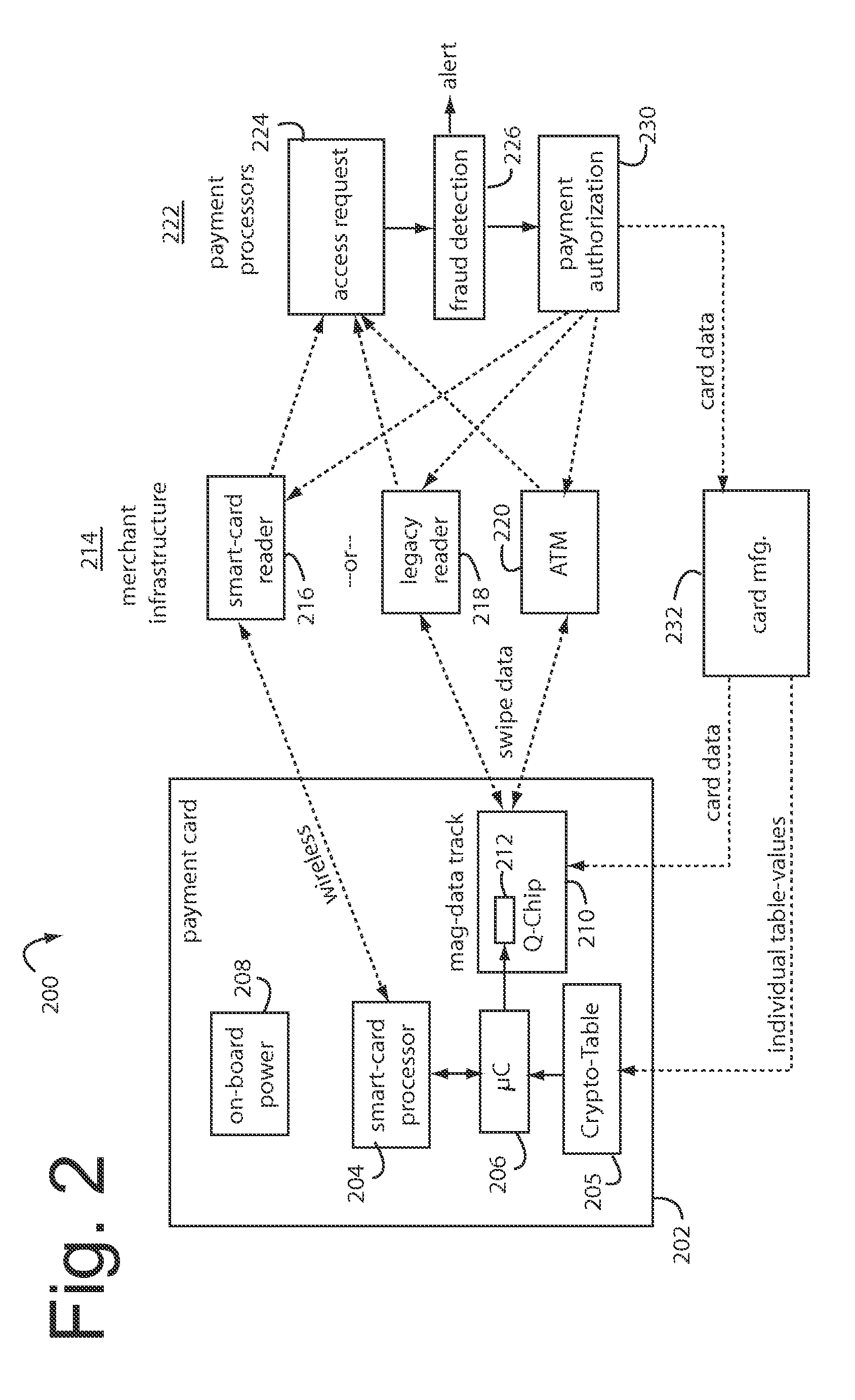
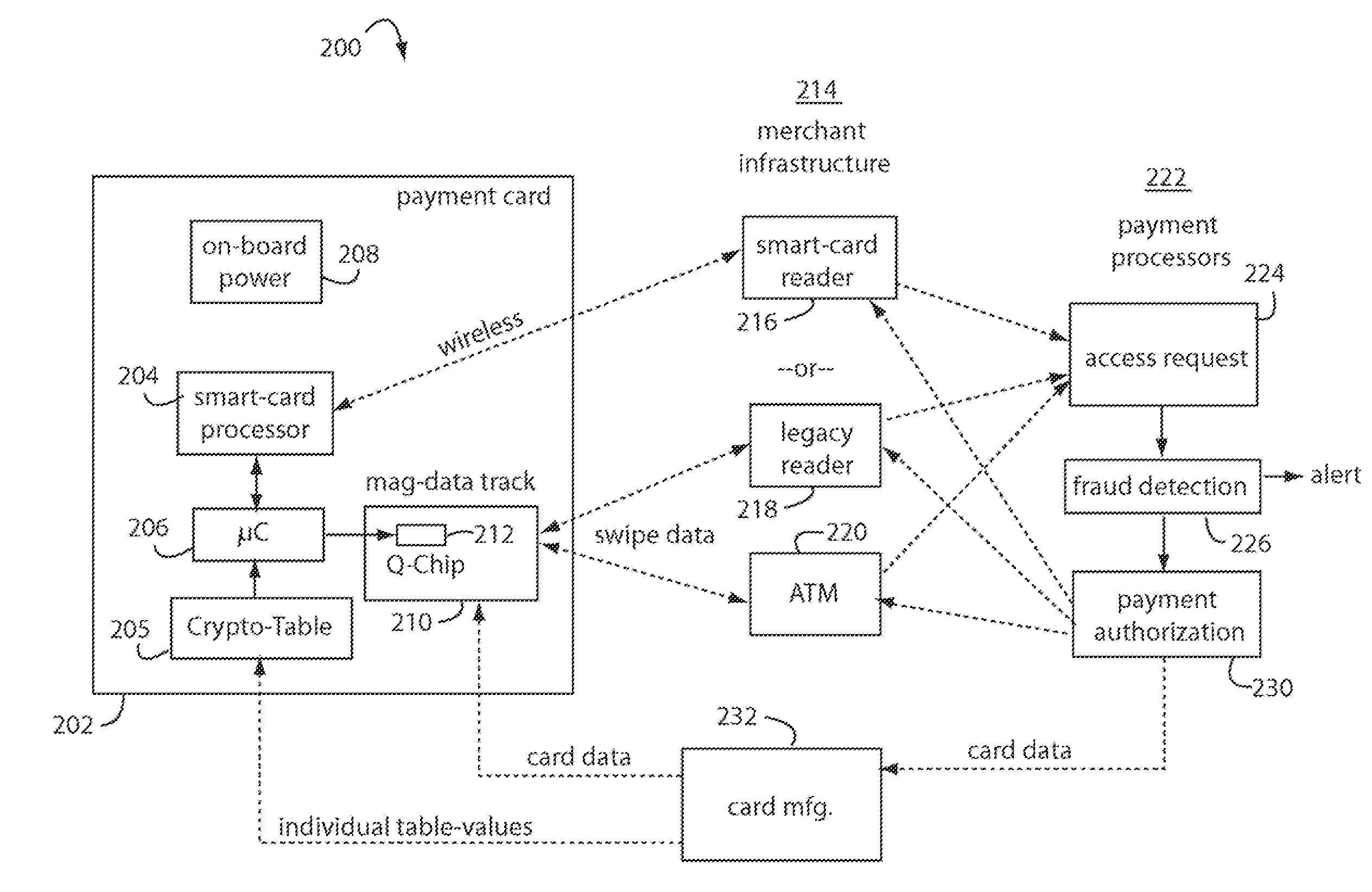
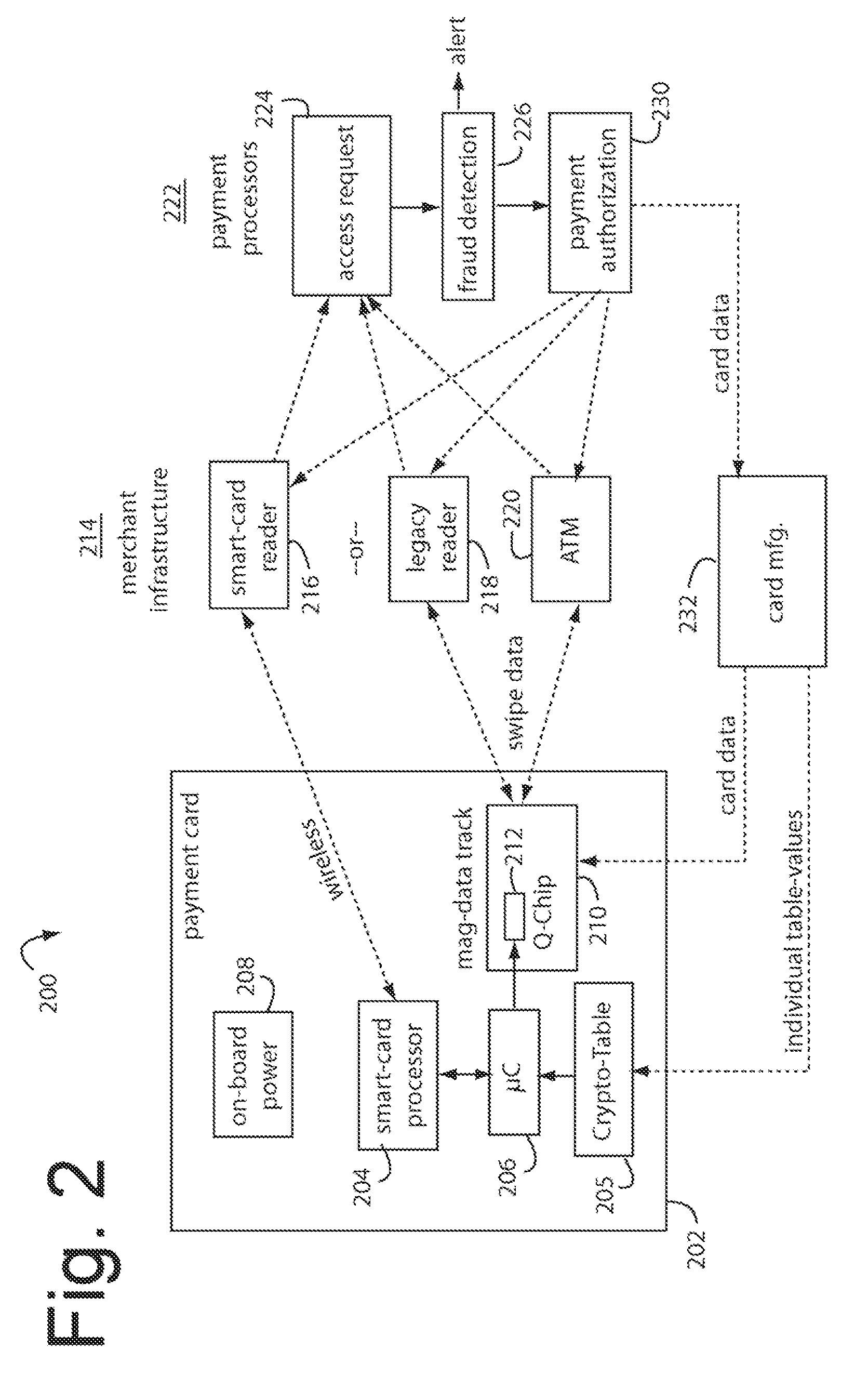
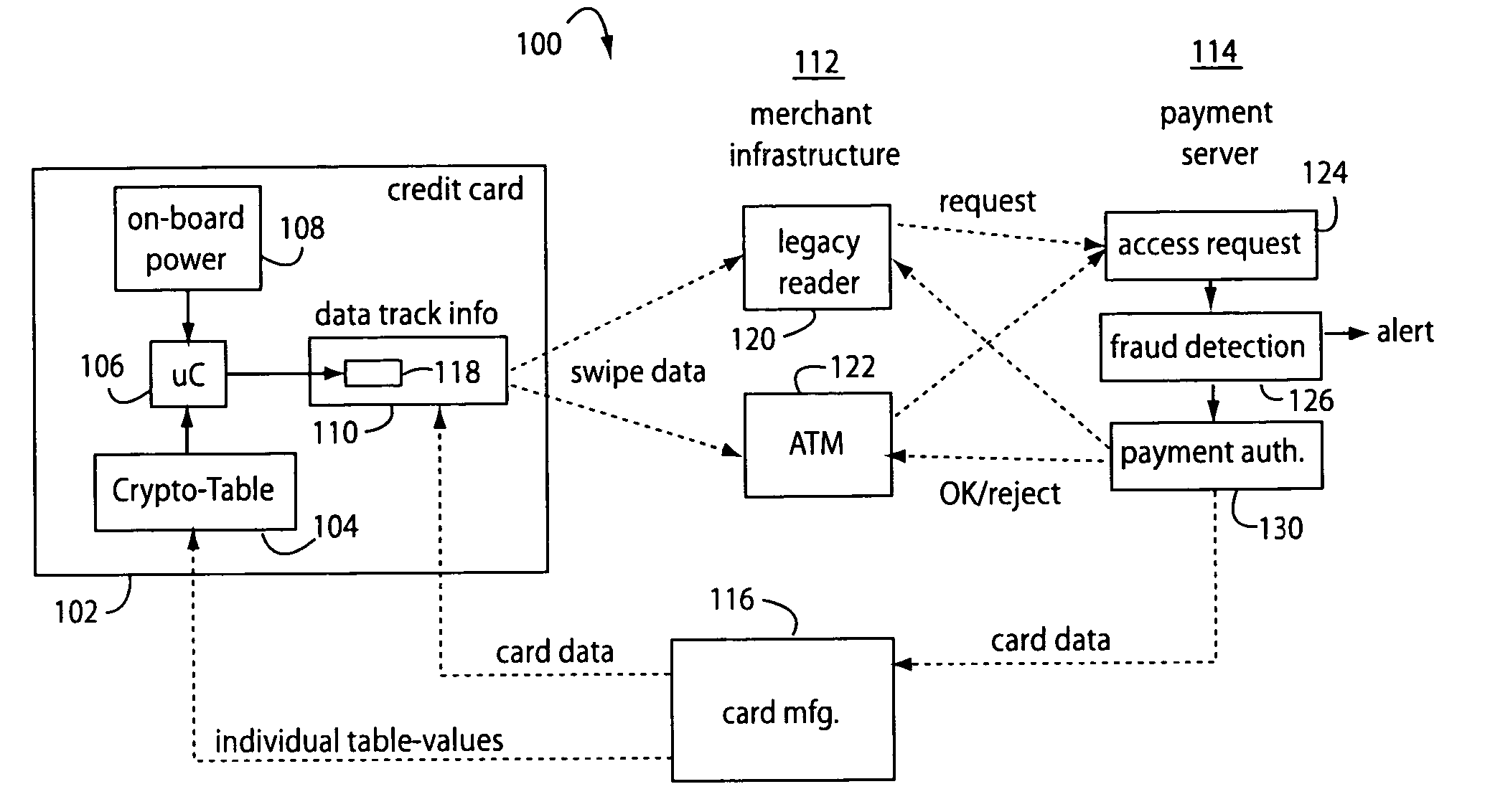
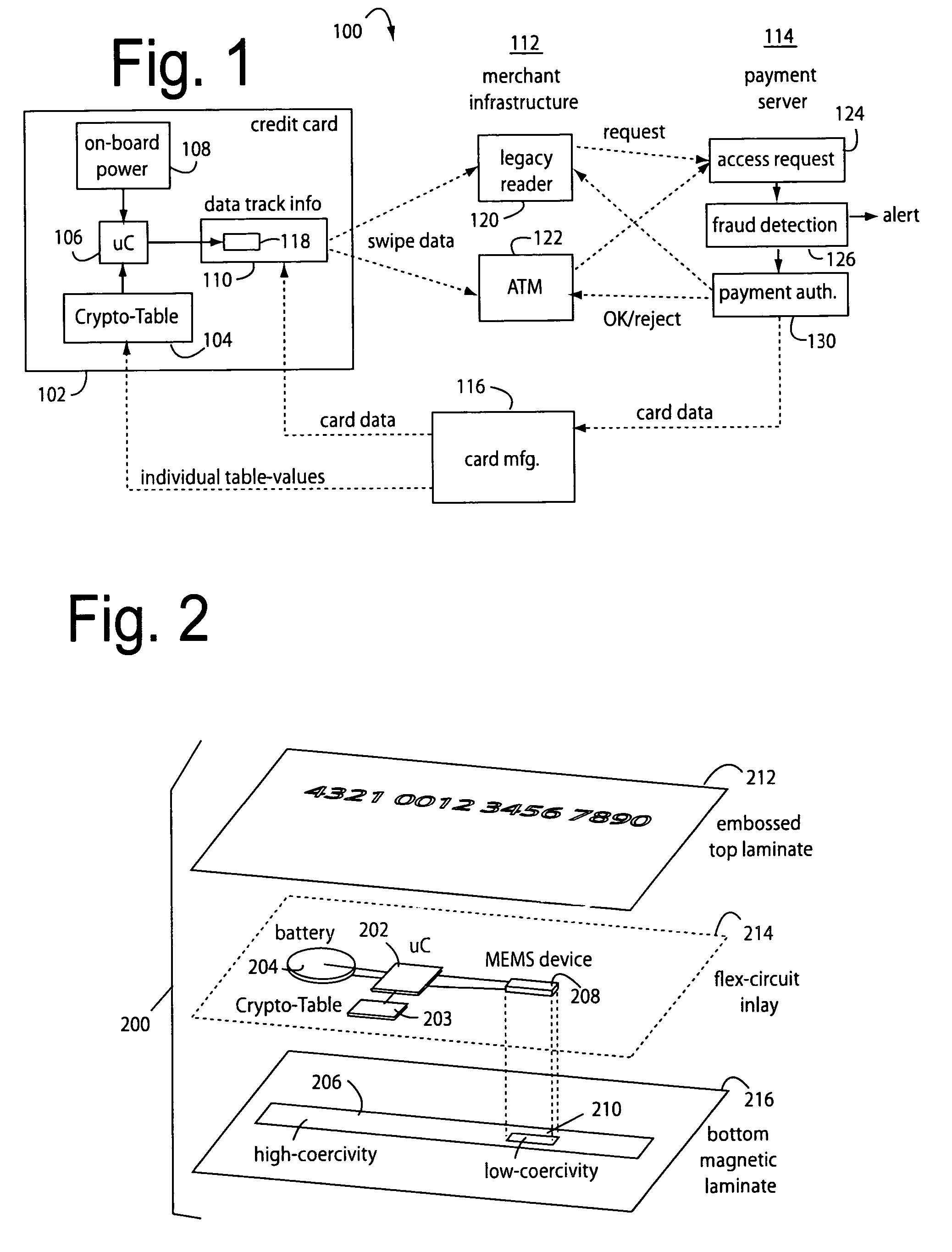
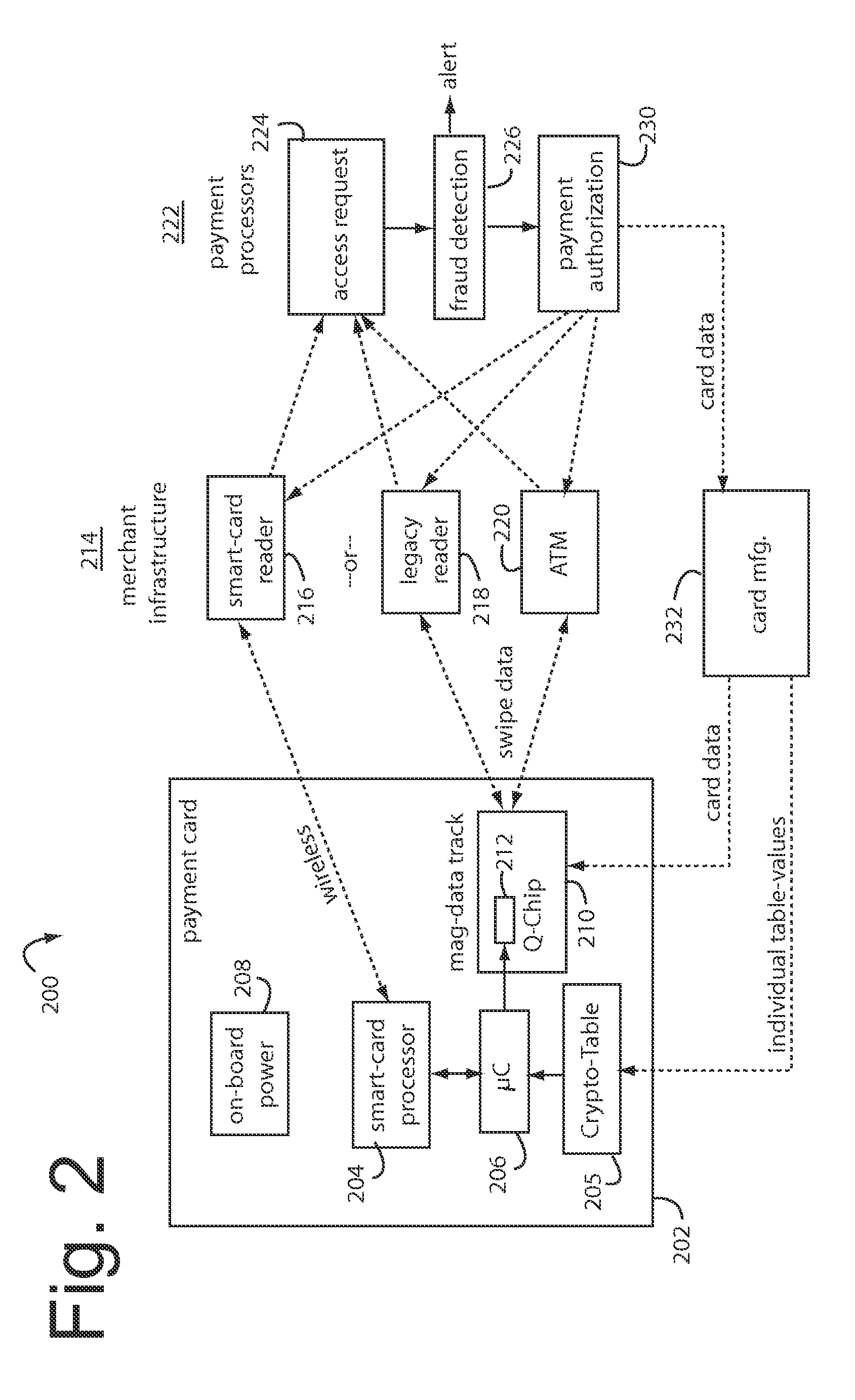
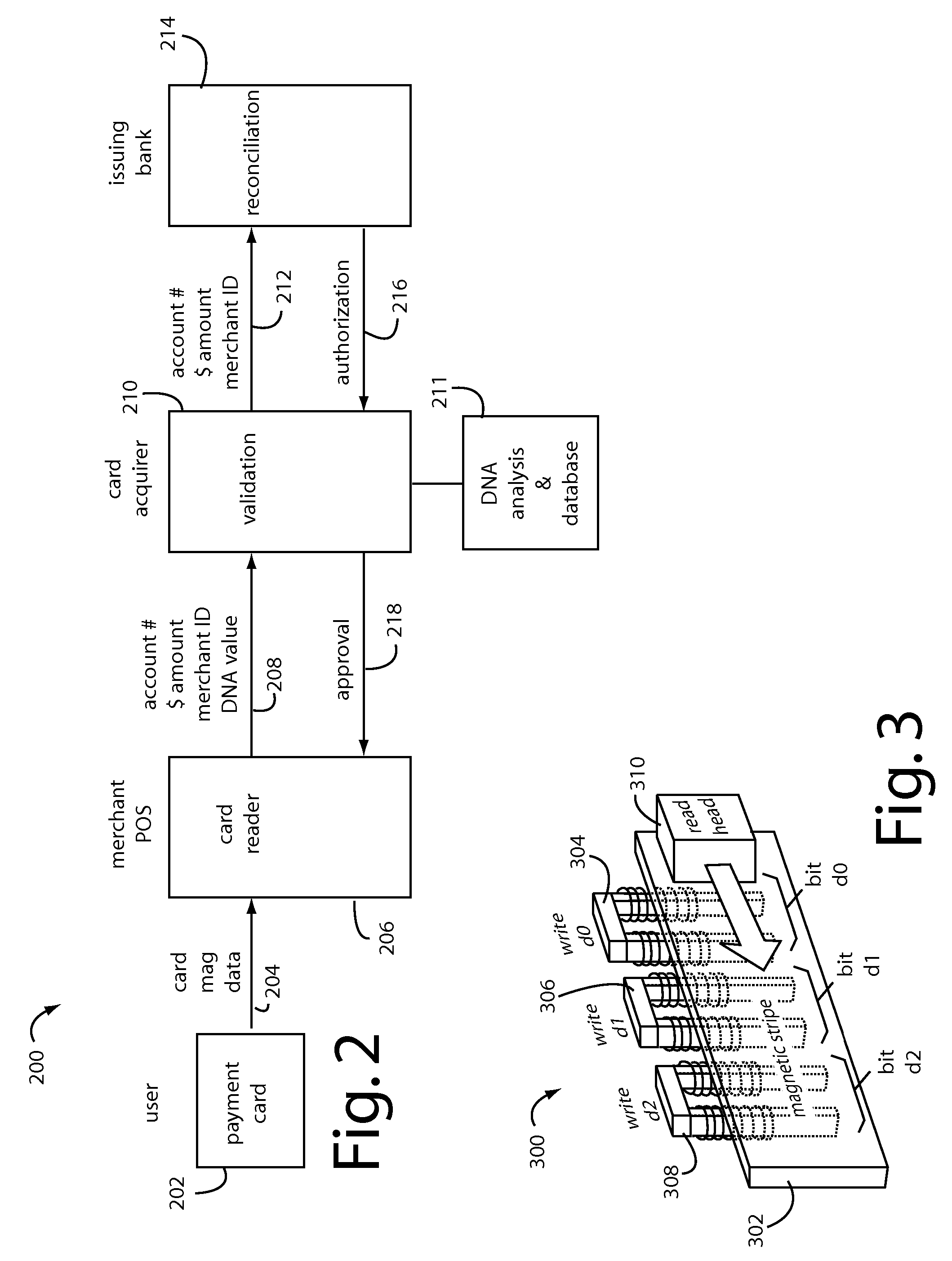
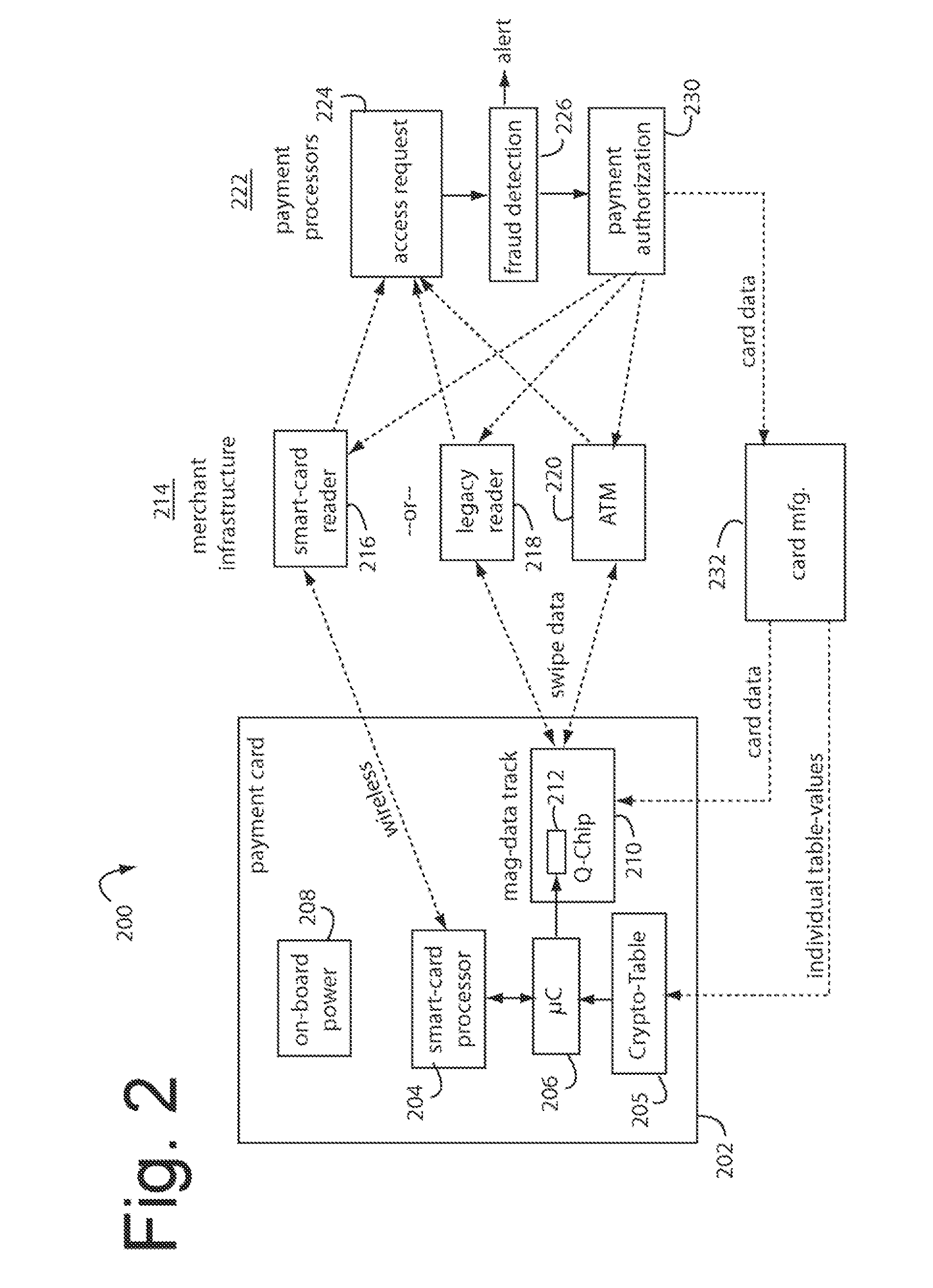
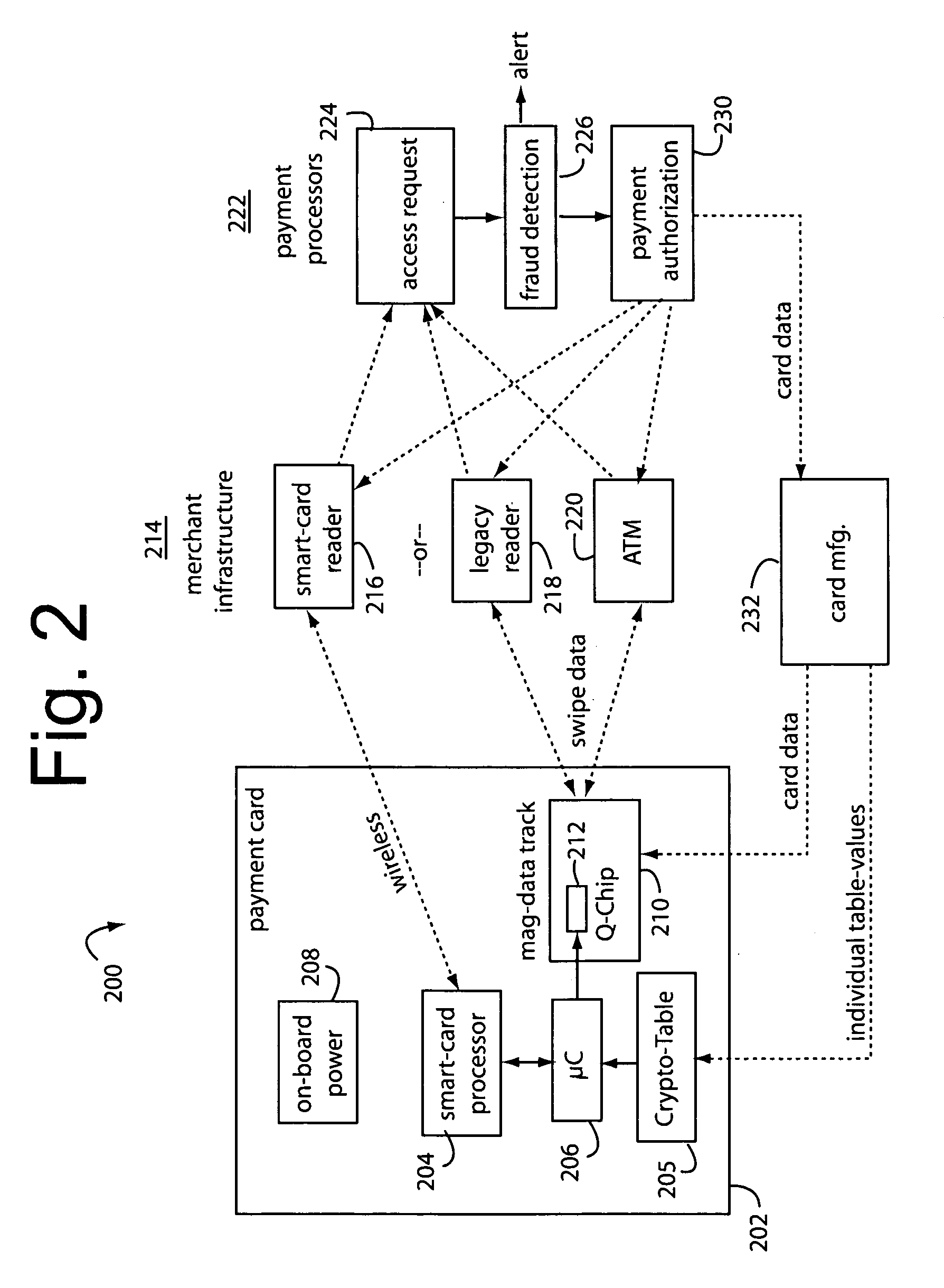
A financial transaction payment processor includes an account access request processor for receiving dynamic swipe data from a payment card through a merchant infrastructure. A fraud detection processor is connected to analyze a dynamic data obtained by the account access request processor that should agree with values pre-loaded in a Crypto-Table by a card manufacturer. A payment authorization processor is connected to receive a message from the fraud detection processor and to then forward a response to the merchant infrastructure.
Owner:FITBIT INC
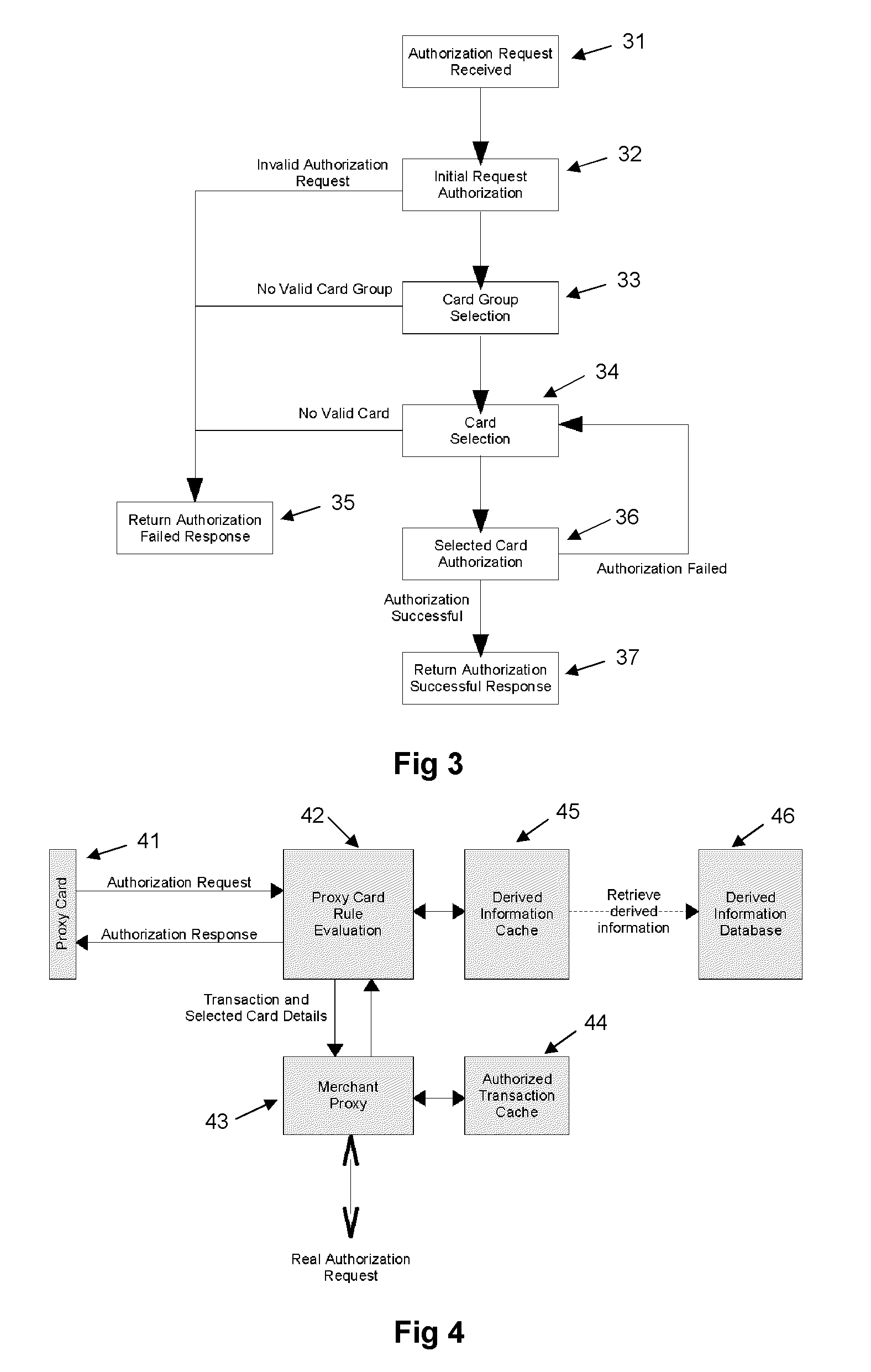
Proxy card authorization system
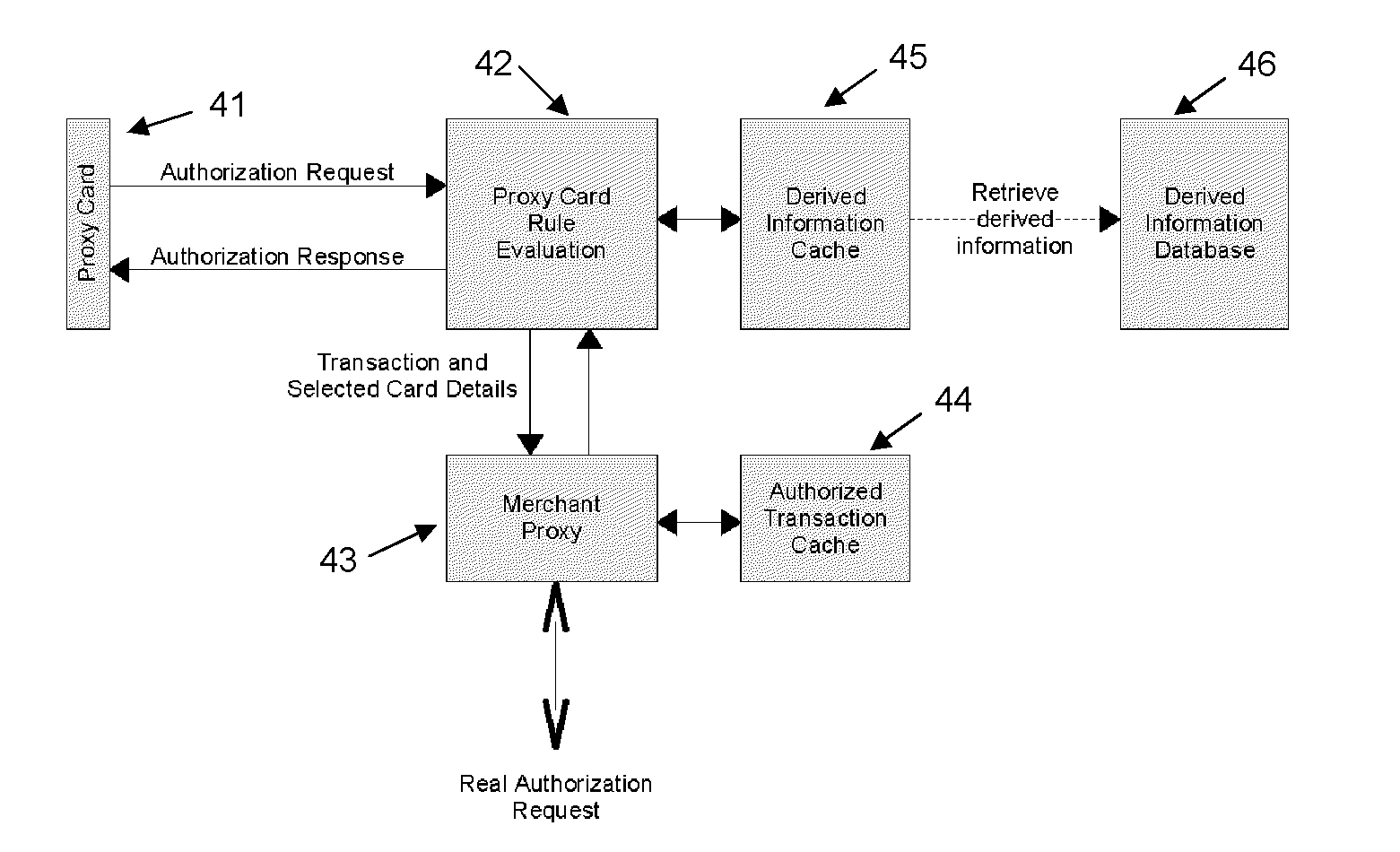
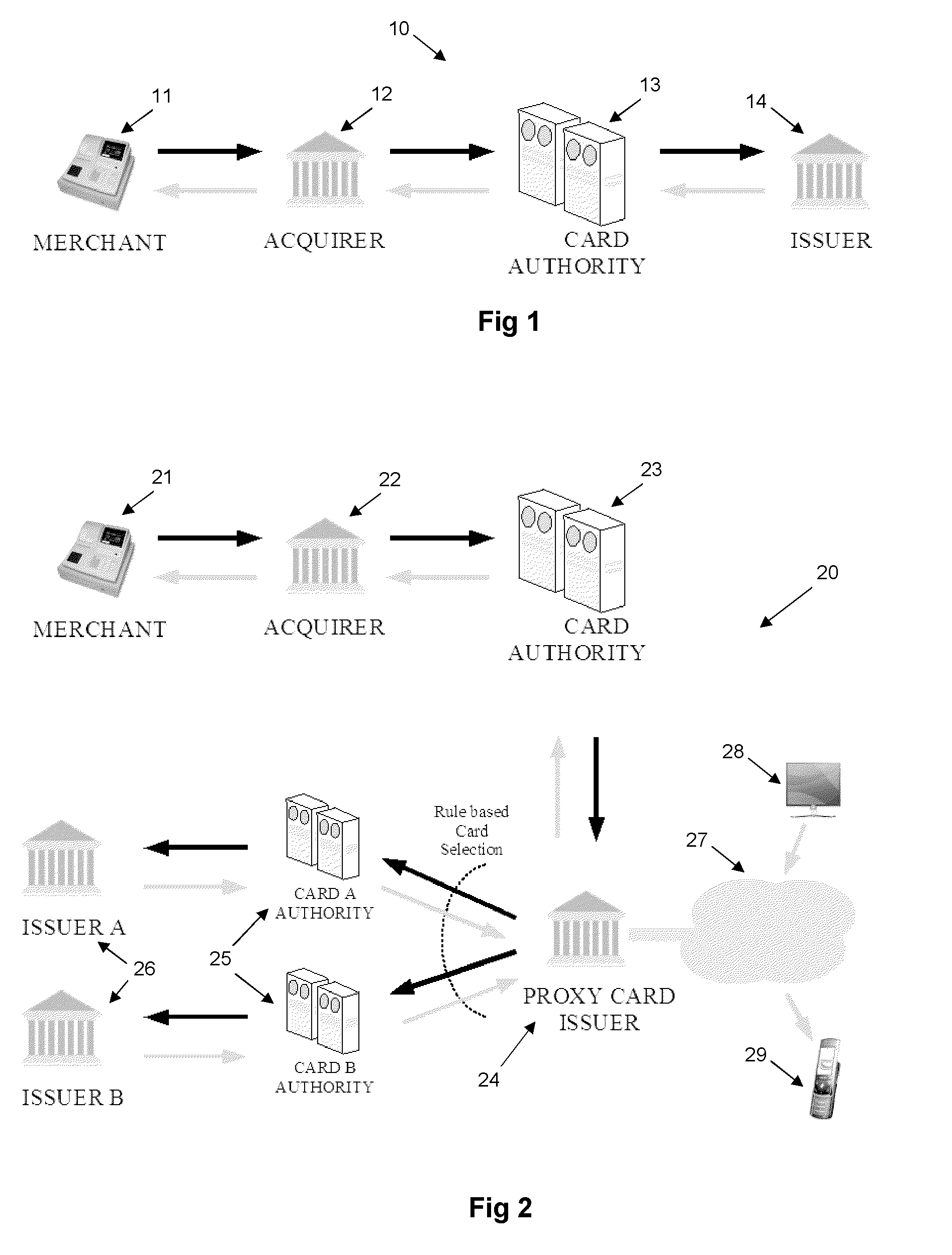
A system and method is provided for providing proxy access to a set of resources subject to constraints specified by the primary party having access to the resources. The system comprises one or more proxy cards associated with a proxy account that contains details on the resources available and also configurable rules for processing proxy authorization requests and returning an authorization response in dependence on the rules. The system has a particular application to payment cards and accounts, whereby the proxy card can act as proxy for one or more of the real payment cards and the proxy card authentication service may operate in a transparent manner as part of a normal overall payment authorization process.
Owner:BROWN GARY +1
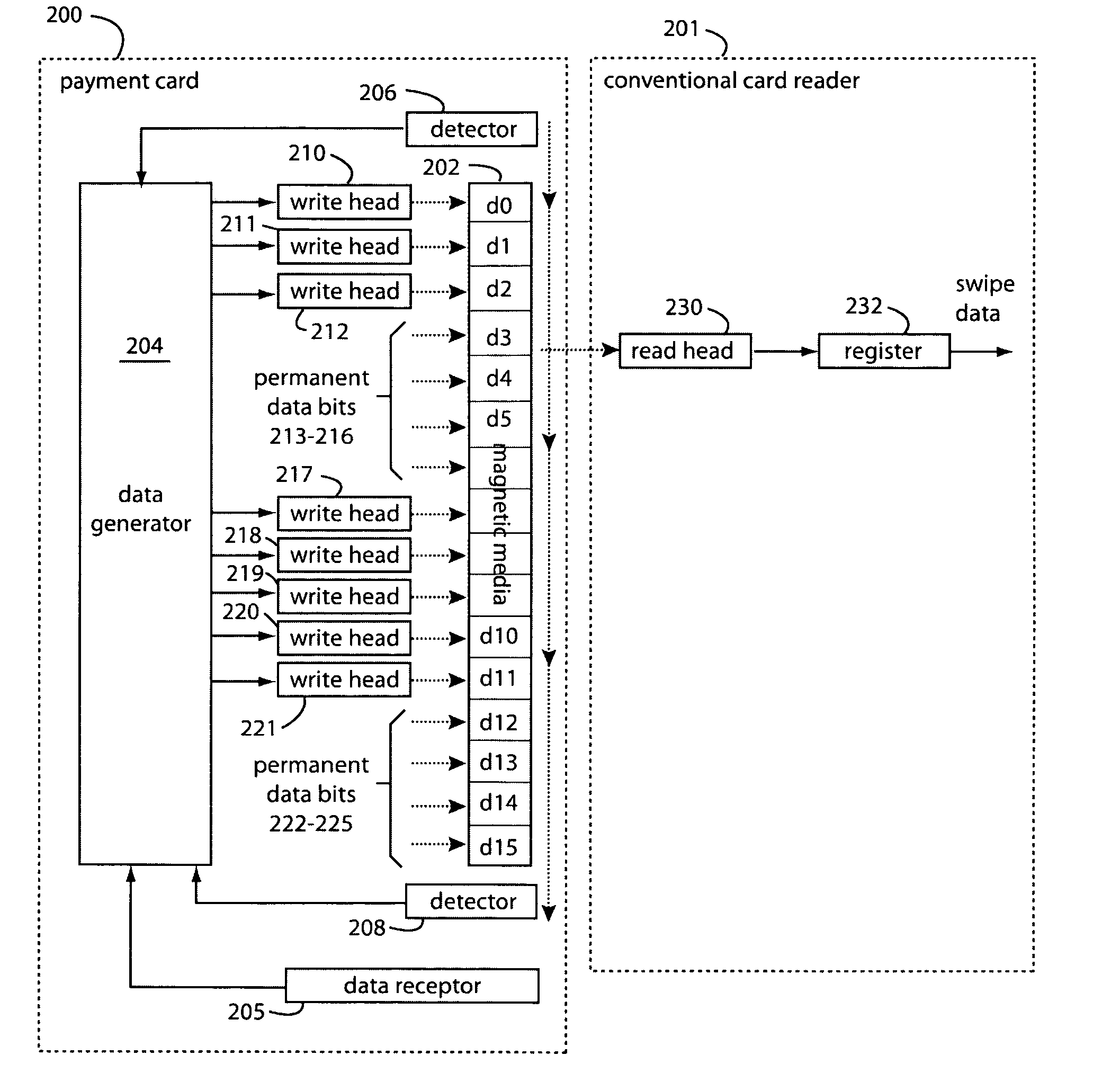
Programmable magnetic data storage card
ActiveUS7044394B2Reduce financial riskSimple and inexpensive and effectiveAcutation objectsApparatus for flat record carriersMicrocomputerComing out
A payment card comprises a plastic card with a magnetic stripe for user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be automatically modified. For example, a data field that counts the number of times the card has been scanned is incremented. A payment processing center keeps track of this usage-counter data field, and will not authorize transaction requests that come out of sequence. For example, as can occur from a magnetic clone of a card that has been skimmed and tried later. A card-swipe detector embedded in the plastic card detects each use in a scanner, and it signals an internal microcomputer which changes data bits sent to the write heads. Once scanned, the payment card can also disable any reading of the user account data for a short fixed period of time.
Owner:FITBIT INC
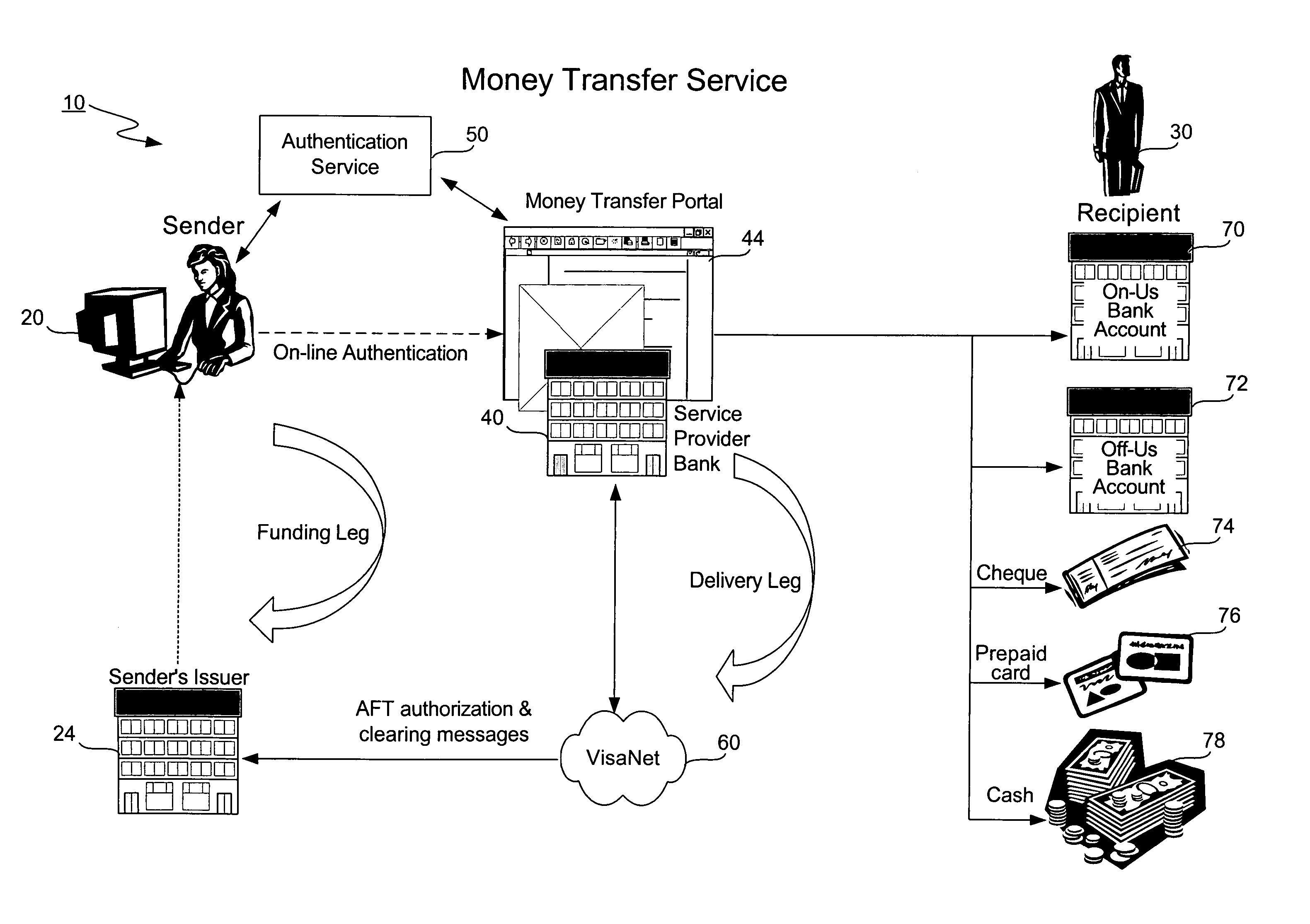
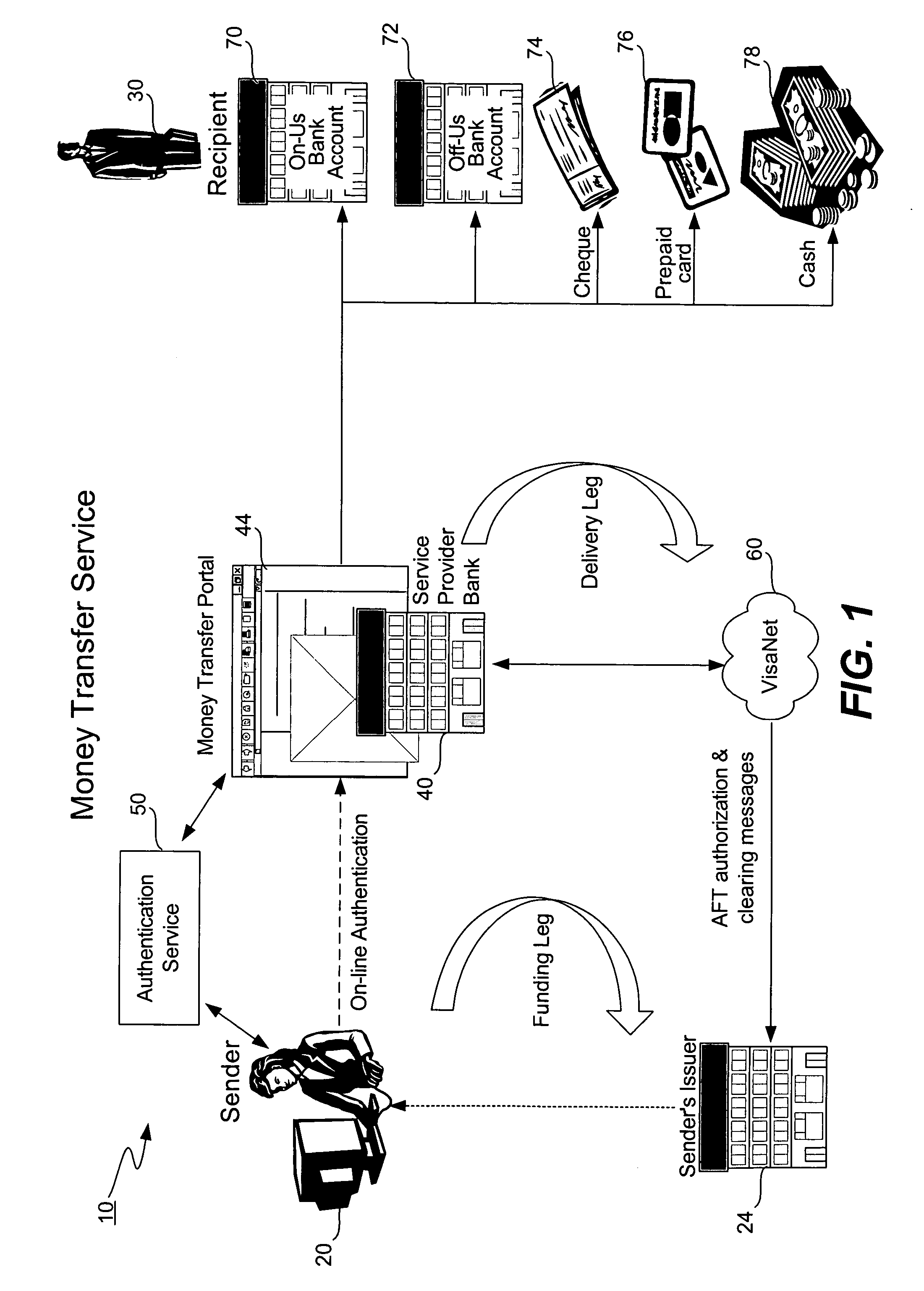
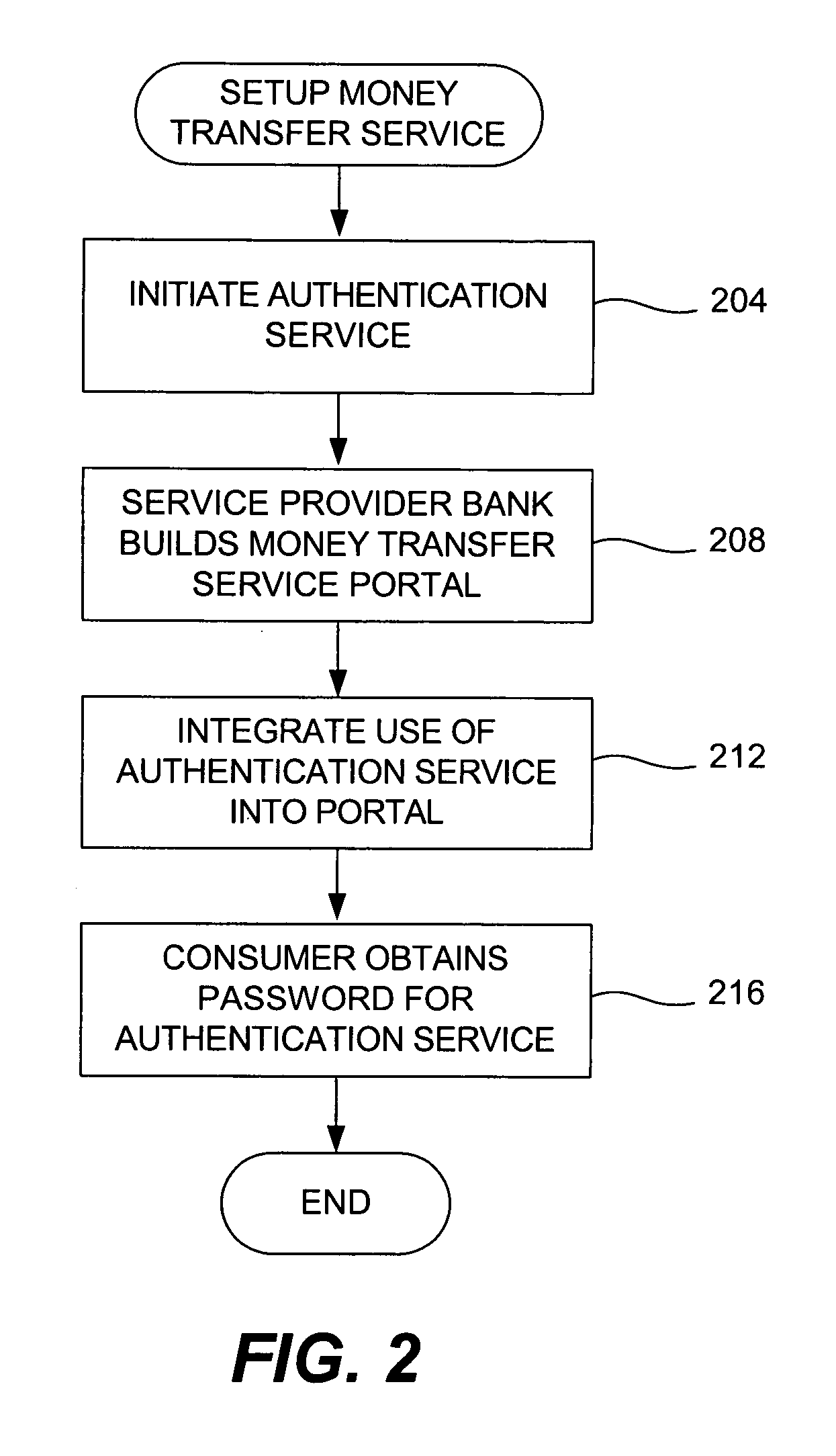
Money transfer service with authentication
ActiveUS20060006224A1Good serviceAvoids cash handling costComplete banking machinesFinancePasswordUse of services
A bank (or merchant) hosts and operates an online money transfer service (or “portal”). A sender logs into the portal and enters payment card and money transfer details and then submits the transaction. An authentication window appears displaying the sender's transaction details and the sender is prompted to enter his or her password. Upon successful authentication, the bank seeks authorization from the card issuer. Upon successful authorization, the bank credits the recipient's local bank account or existing payment card. The recipient can also receive a check, a draft, a prepaid card or cash. The money transfer service is used both cross-border and domestic to effect person-to-person money transfer. The money transfer service uses the “Verified by Visa” authentication service and VisaNet for authorization. Messages over VisaNet are used to deliver funds to a recipient.
Owner:VISA INT SERVICE ASSOC
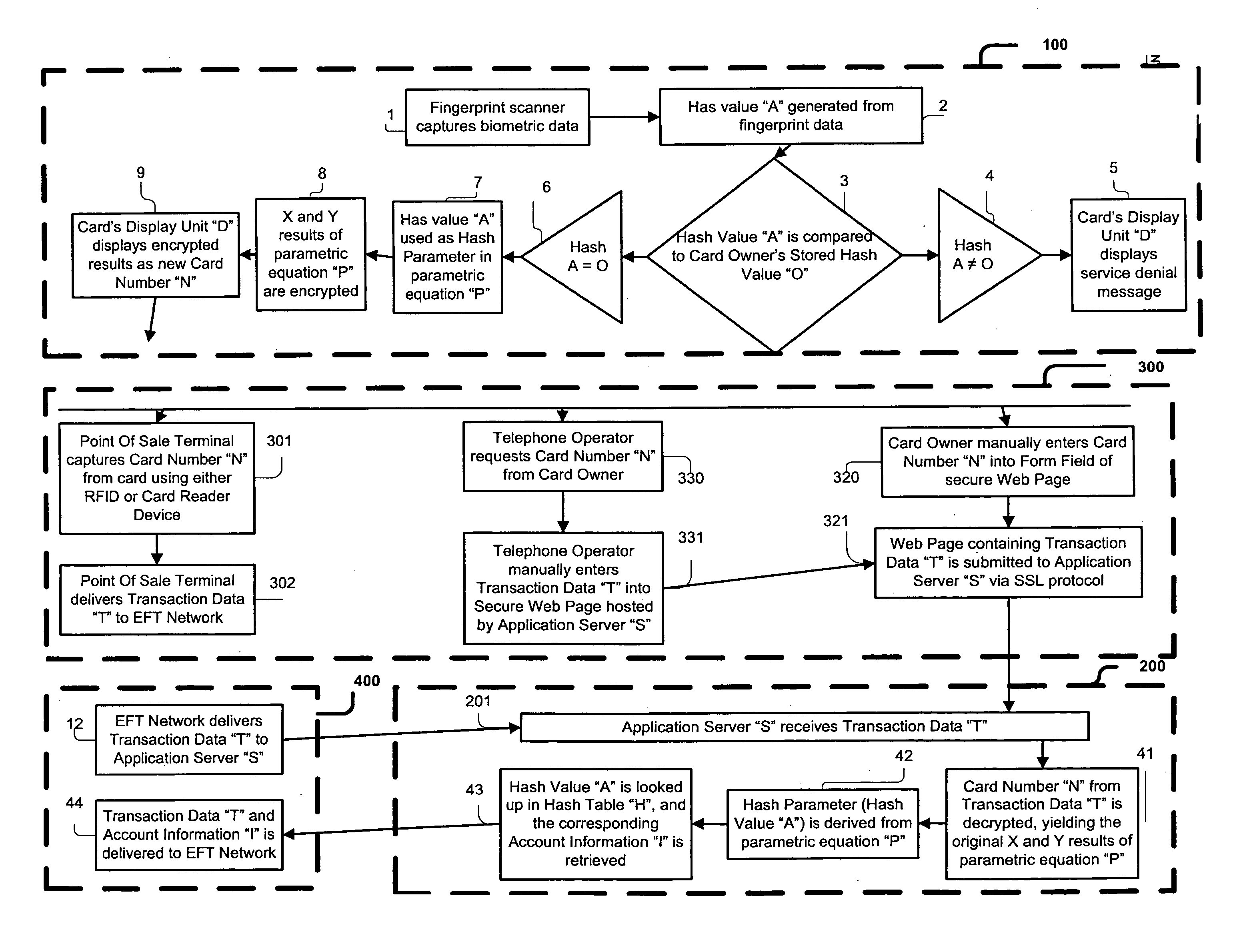
System, Method, and Apparatus for Preventing Identity Fraud Associated With Payment and Identity Cards
InactiveUS20070291995A1Easy and efficient to manufactureDurable and reliable constructionCharacter and pattern recognitionInternal/peripheral component protectionIdentity fraudDriver's license
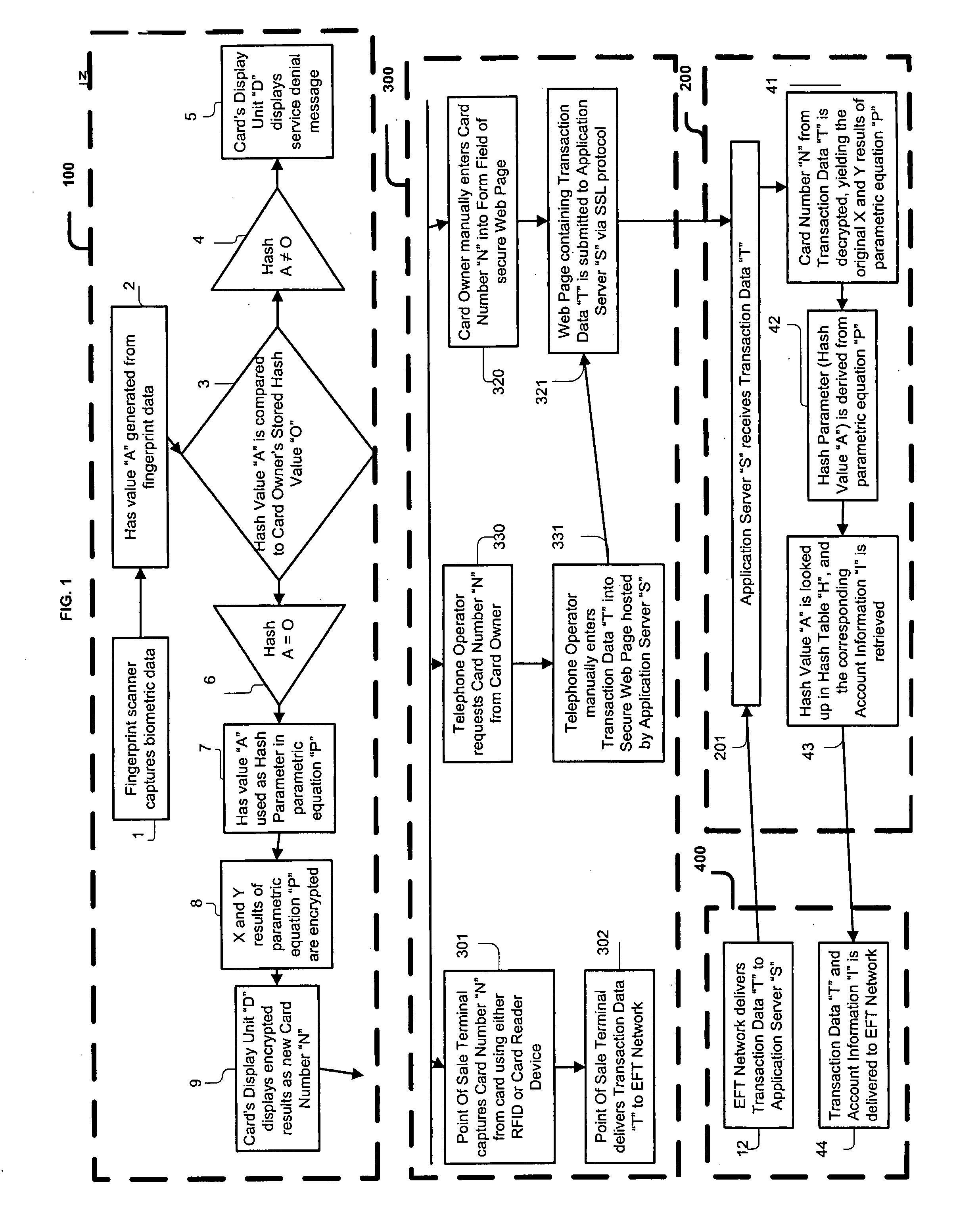
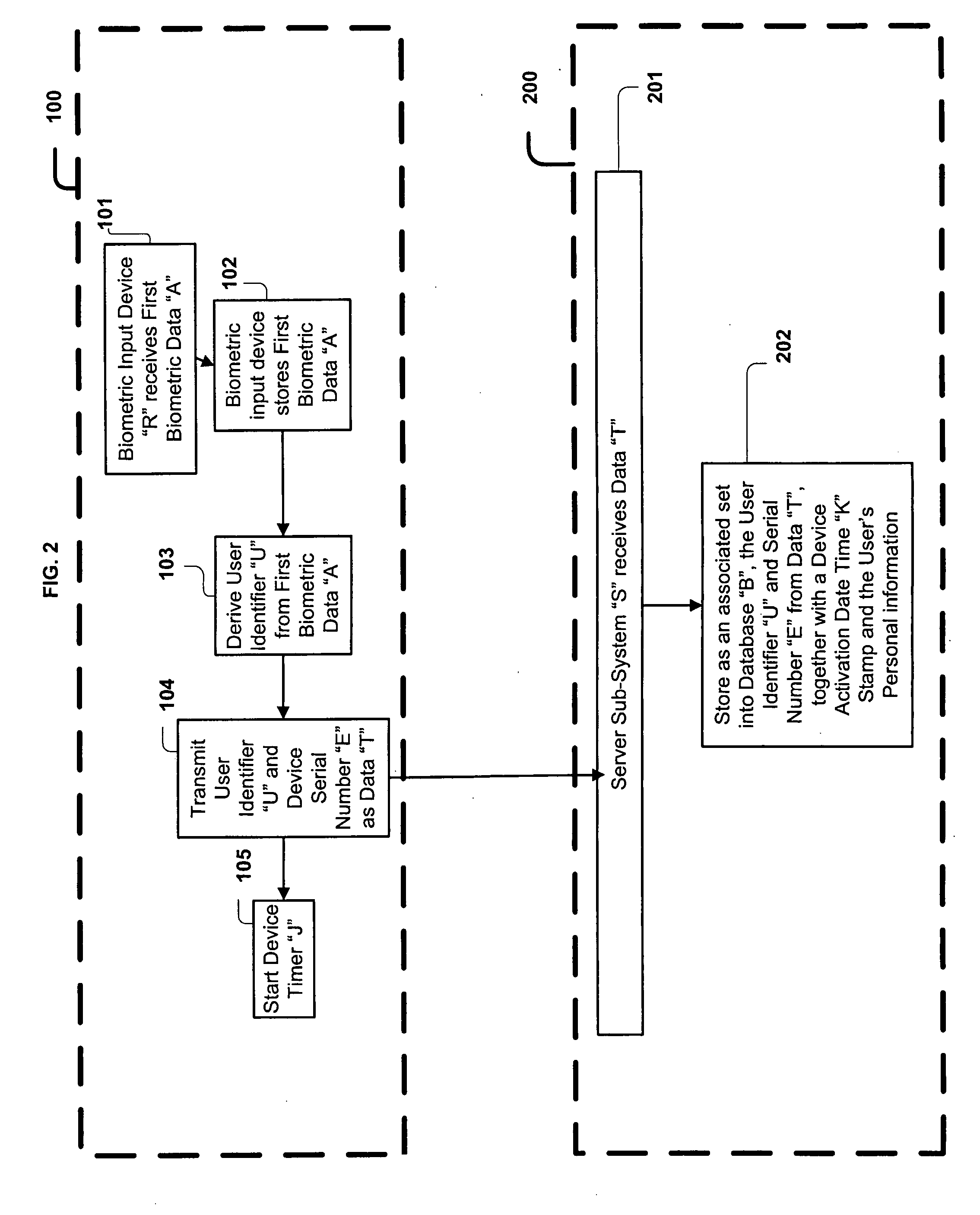
The system, method, and apparatus of the present invention, address the problem of identity theft associated with the use of payment cards such as credit and debit cards, as well as identity theft associated with the use of identity cards such as driver's licenses and social security cards. An apparatus including a biometric input component that authenticates a system user is disclosed herein. Upon authentication, a proxy account number and a time varying security code are generated and displayed on the apparatus. The dynamically generated number and security code are then used to validate the user's identity within the system. Furthermore, the system, method, and apparatus of the present invention can be used to consolidate into one instrument, several payment and identity instruments.
Owner:RIVERA PAUL G
Transfer instrument
InactiveUS7010512B1Easy to controlLow costFinanceBuying/selling/leasing transactionsInternet privacyEngineering
A method is disclosed involving acquiring a plurality of charge accounts. The accounts are of a type normally issued with an associated physically producible card which may be presented as evidence of an existing charge account, the physically producible cards bearing human readable account numbers and expiration dates. The plurality of charge accounts are capable of being gifted to a party, after acquisition. A request is received from a first party to gift a charge account to a second party having a name, without both the issuance and provision of a physical card for the charge account to the second party. The first party and the second party are different from each other. The charge account is usable in the name of the second party at any merchant who is capable of seeking authorization, using an authorization infrastructure, for purchases involving charge accounts for which the physically producible cards are issued, whether or not the physical cards evidencing the accounts are presented by purchasers when a purchase is made. An account parameter, selected by the first party, is accepted. The second party is informed of the account, by sending an e-mail to the second party. The e-mail contains a greeting selected by the first party and directs the second party to perform a specified action in order to cause an activation of the account. The account is activated for usage by the second party according to the account parameter. An indication that the second party has made a purchase from a merchant using the account is received and a settling transaction involving the account is undertaken after the usage by the second party. A system is also disclosed having a database with at least one table and a processor coupled to the database. The database is configured to, under control of the processor, maintain a record of a payment card account registered to a first person at the request of a second person, and for which, at no time at or before a time the second person buys from a merchant and provides payment by referencing the payment card account, no physical card for the payment card account will have been provided to the second person.
Owner:CITIBANK
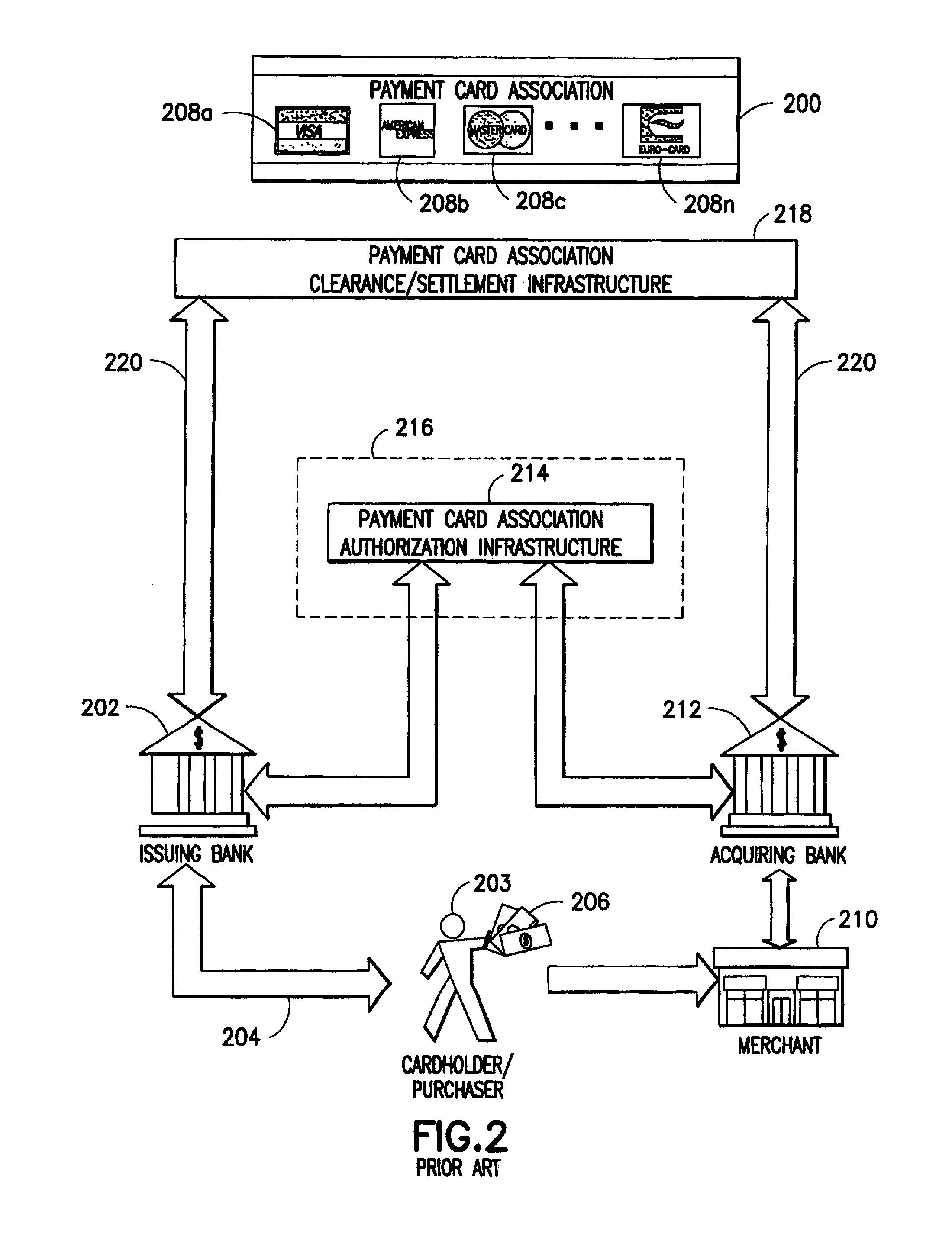
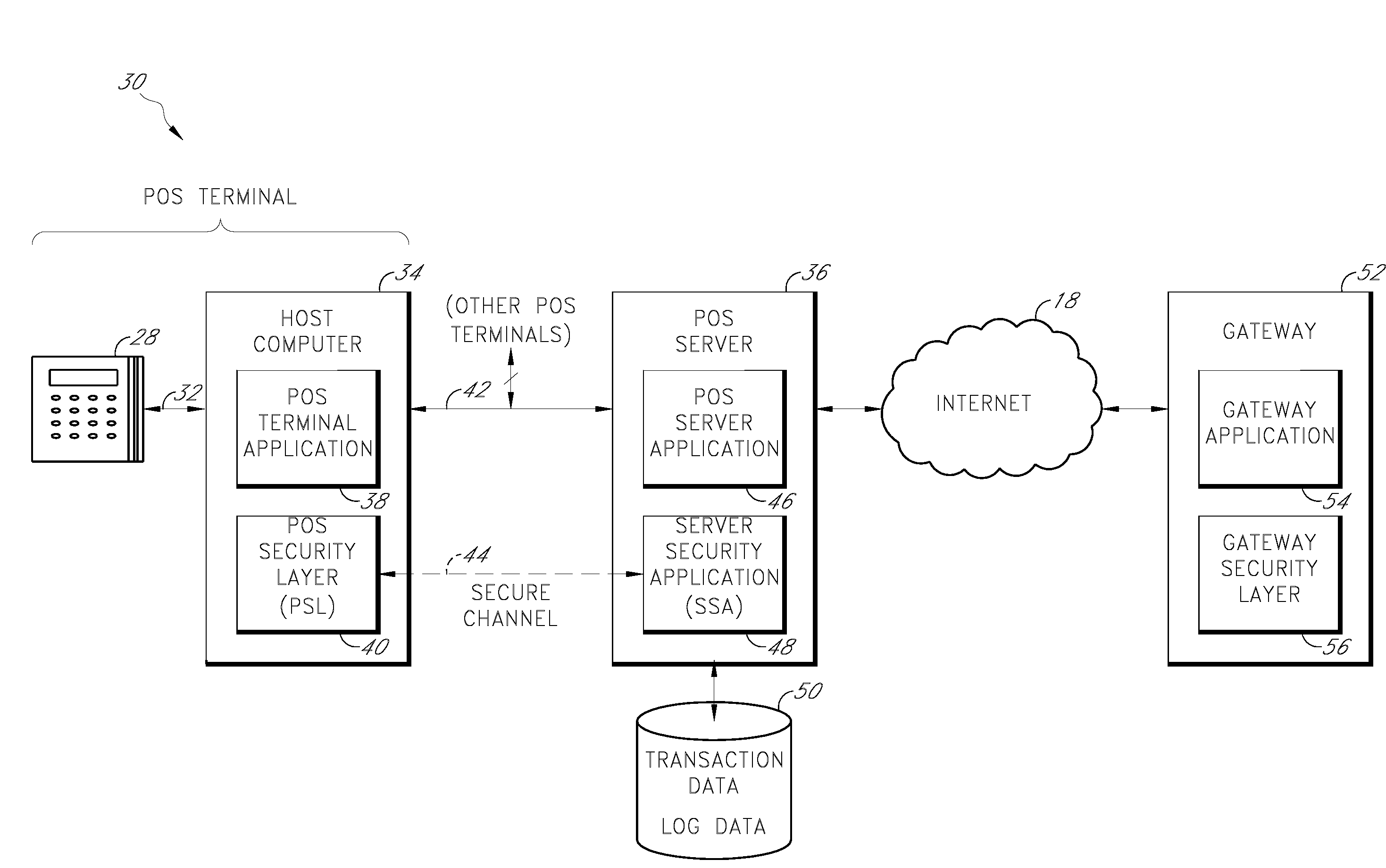
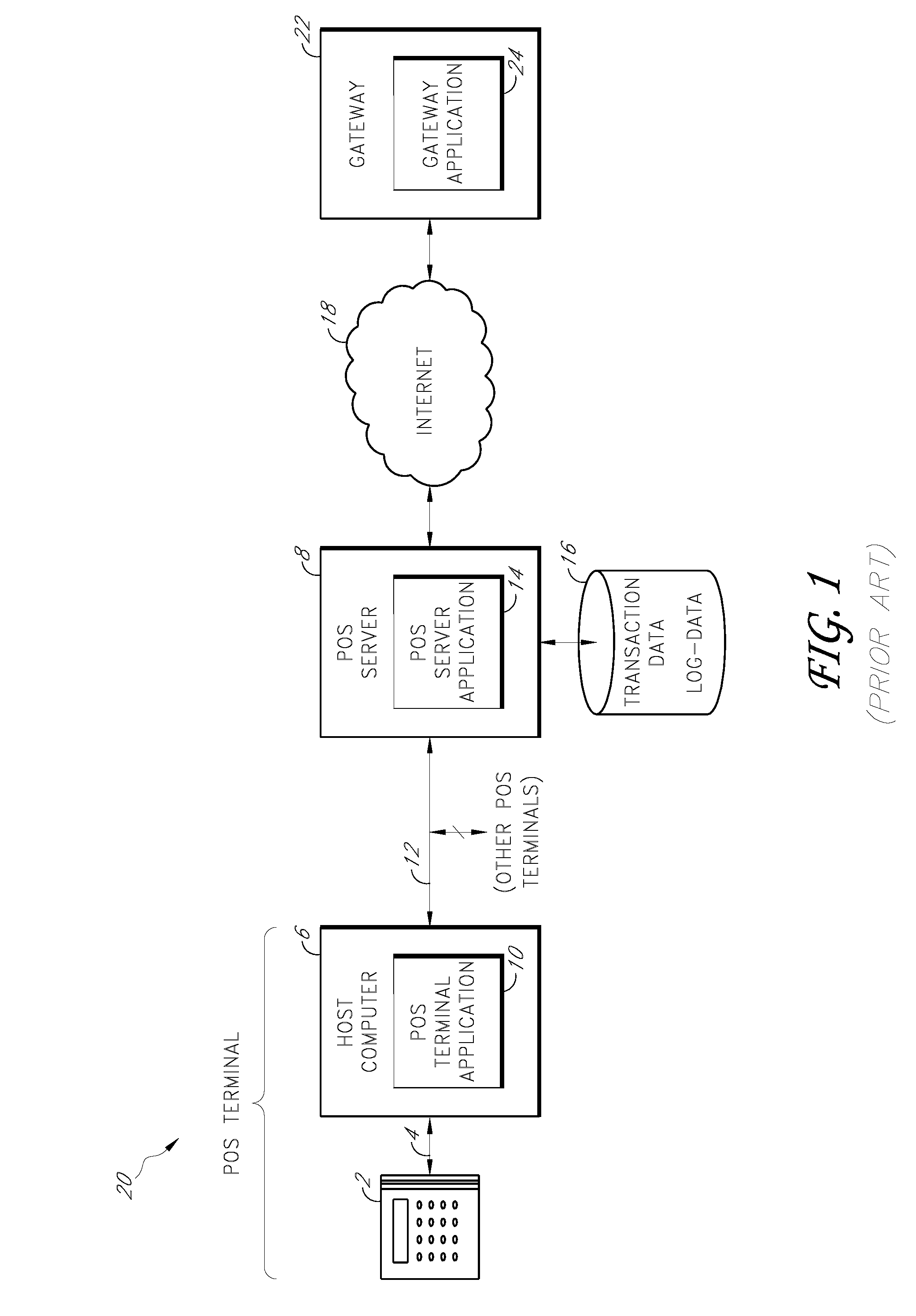
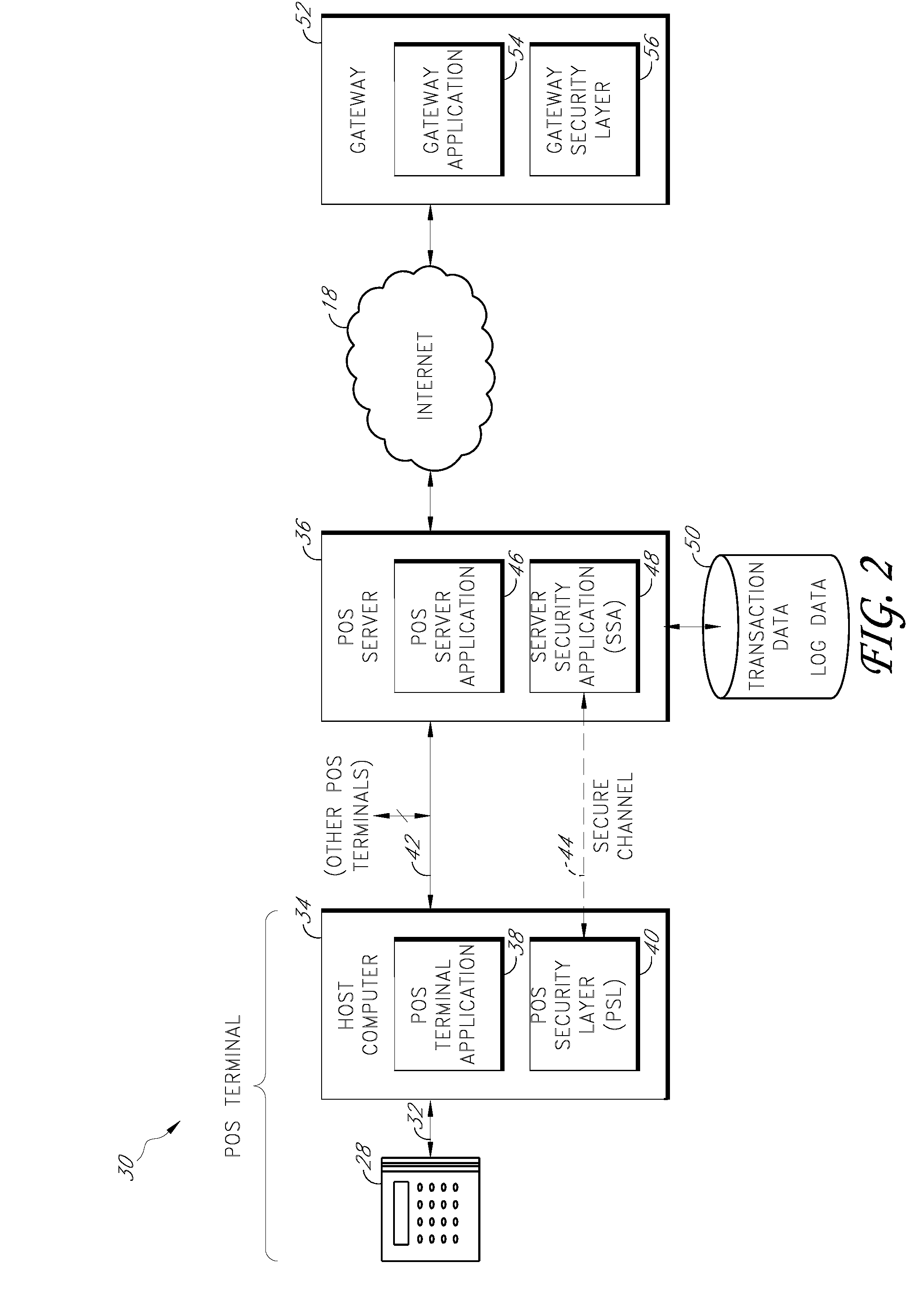
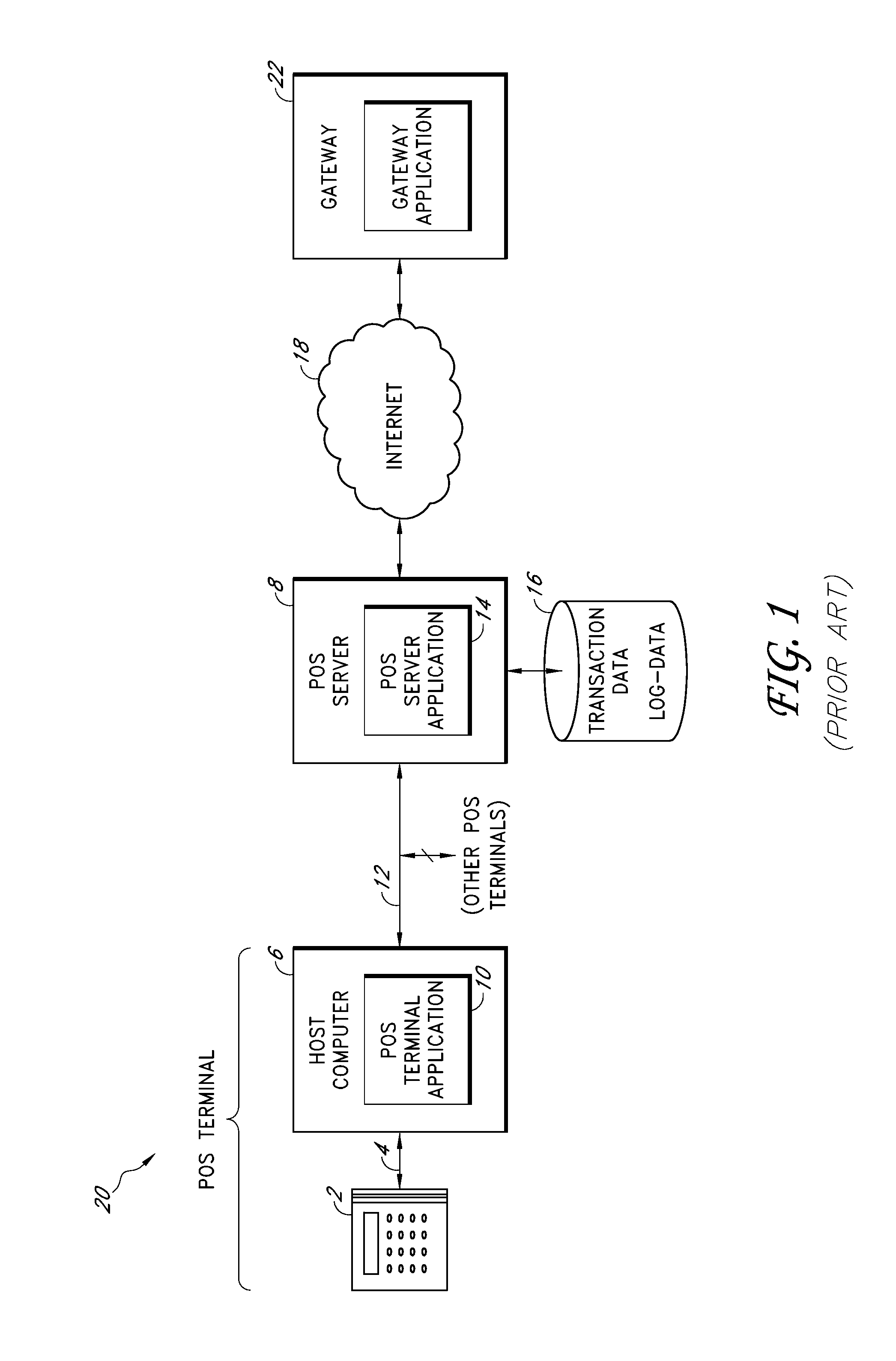
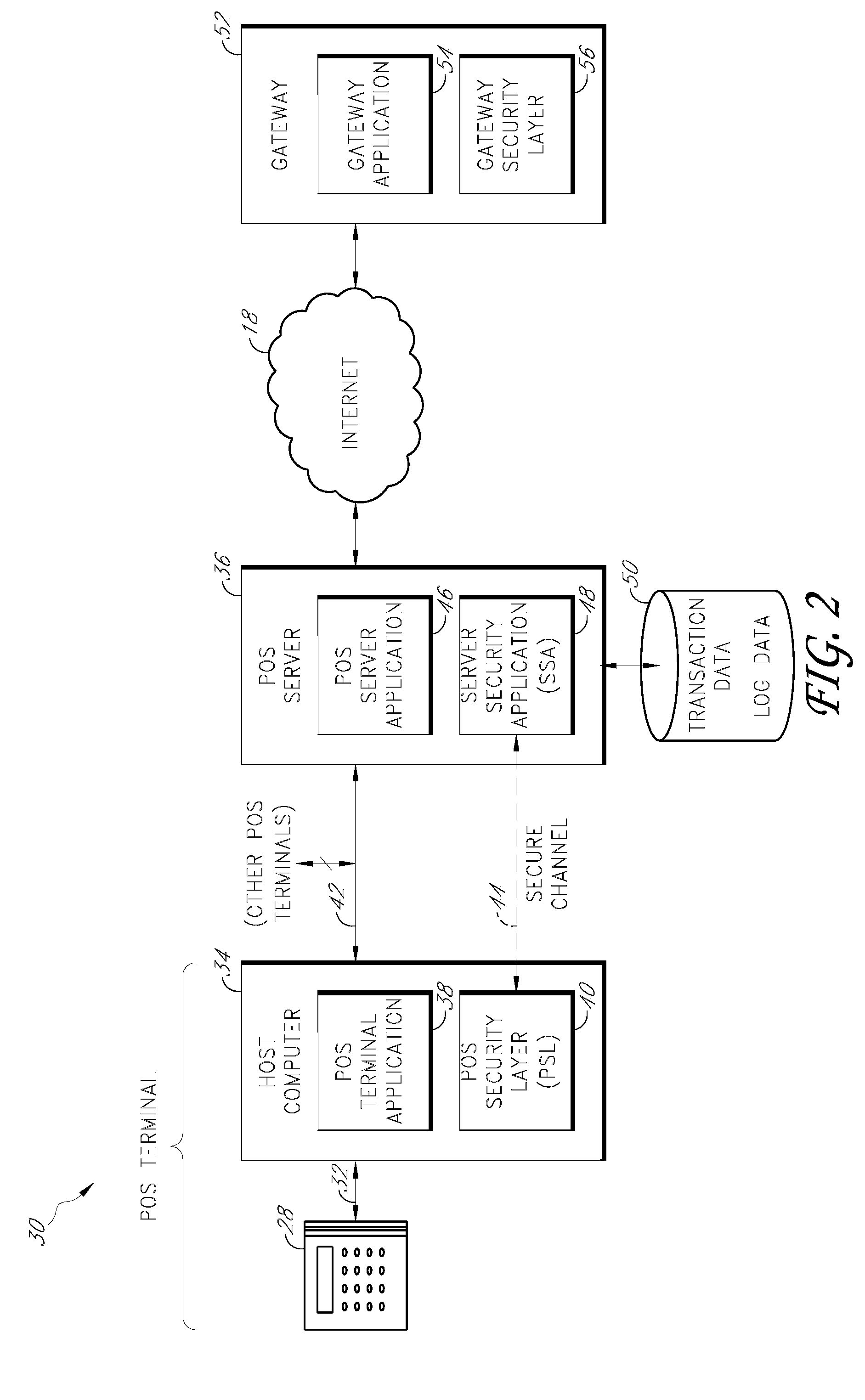
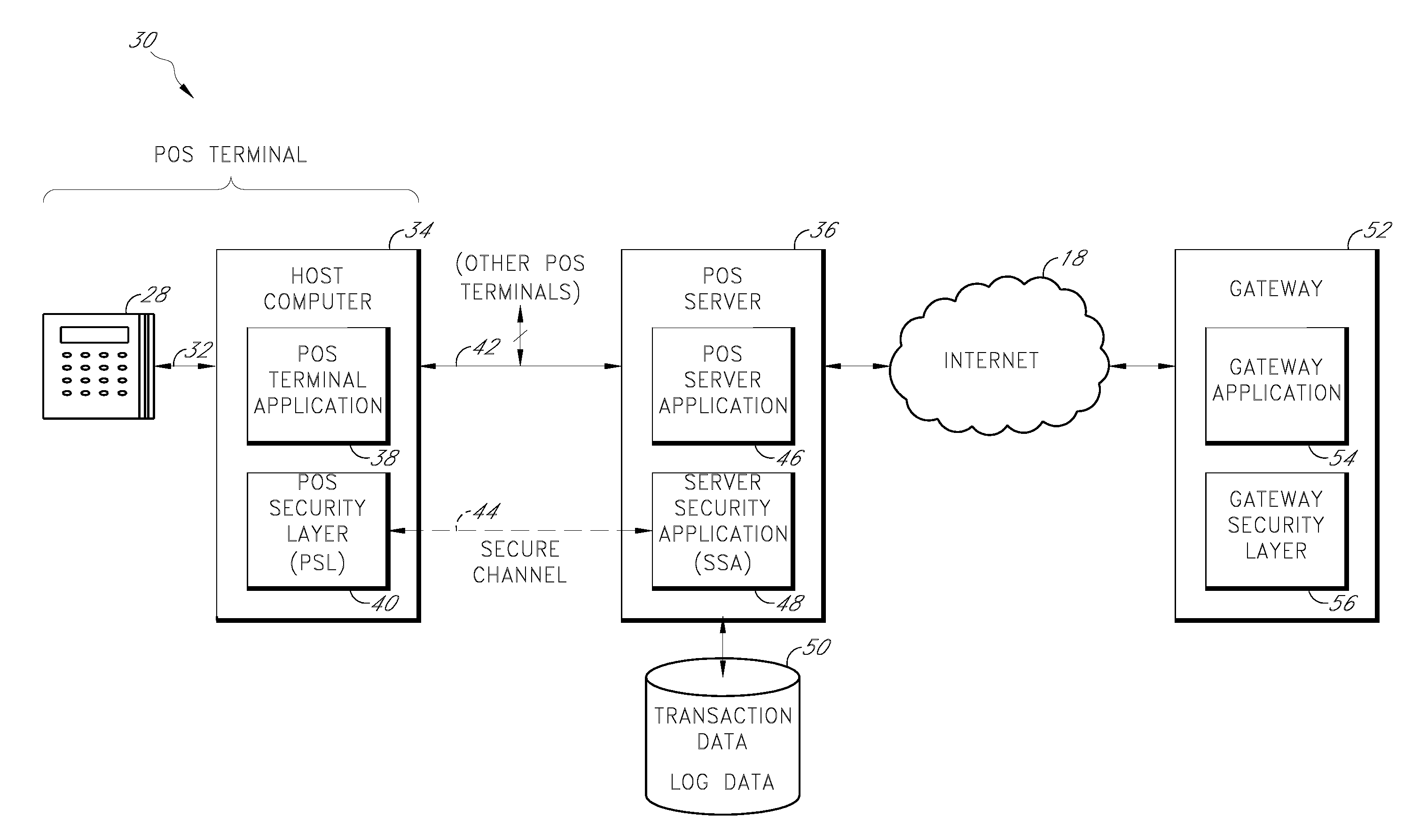
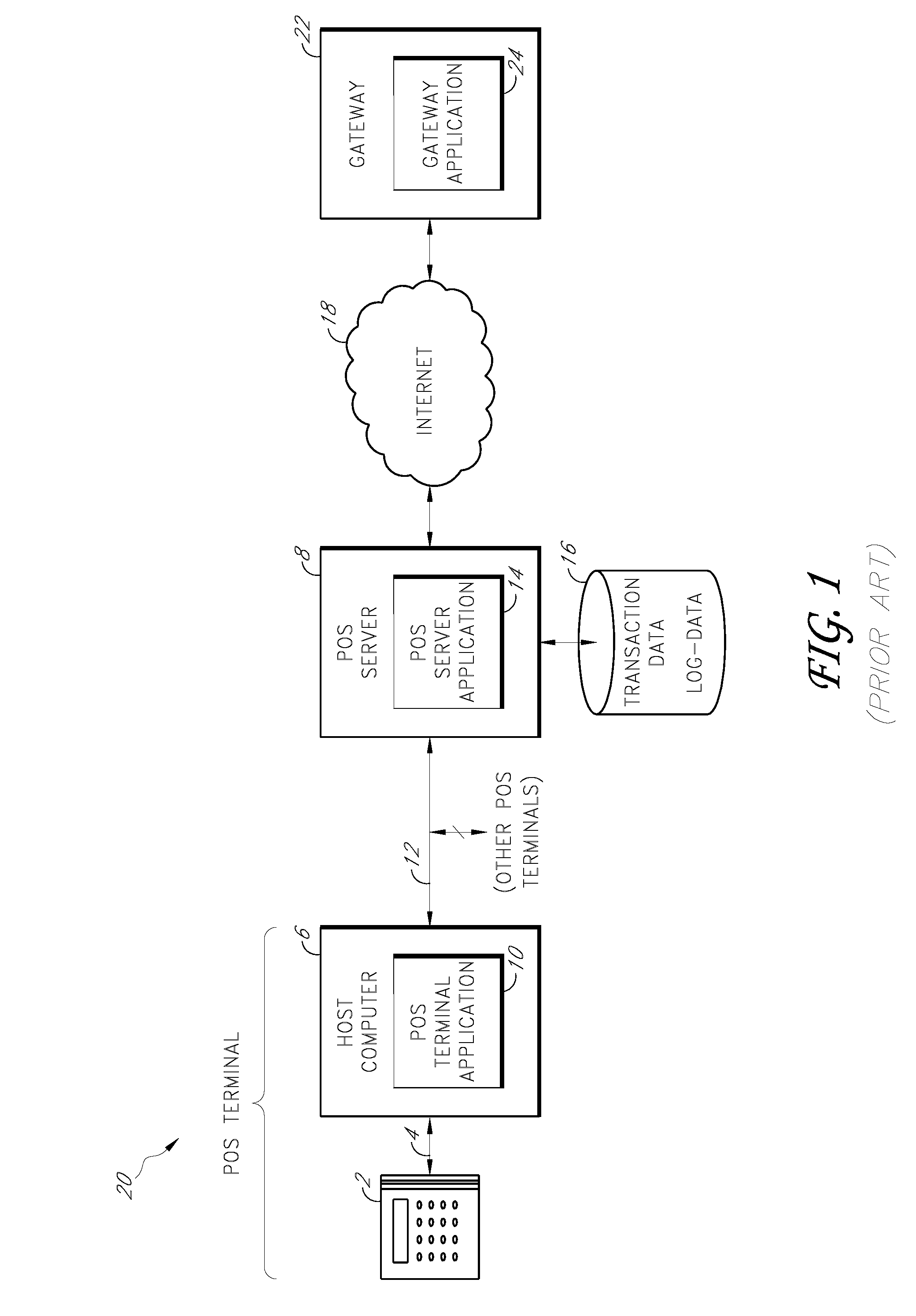
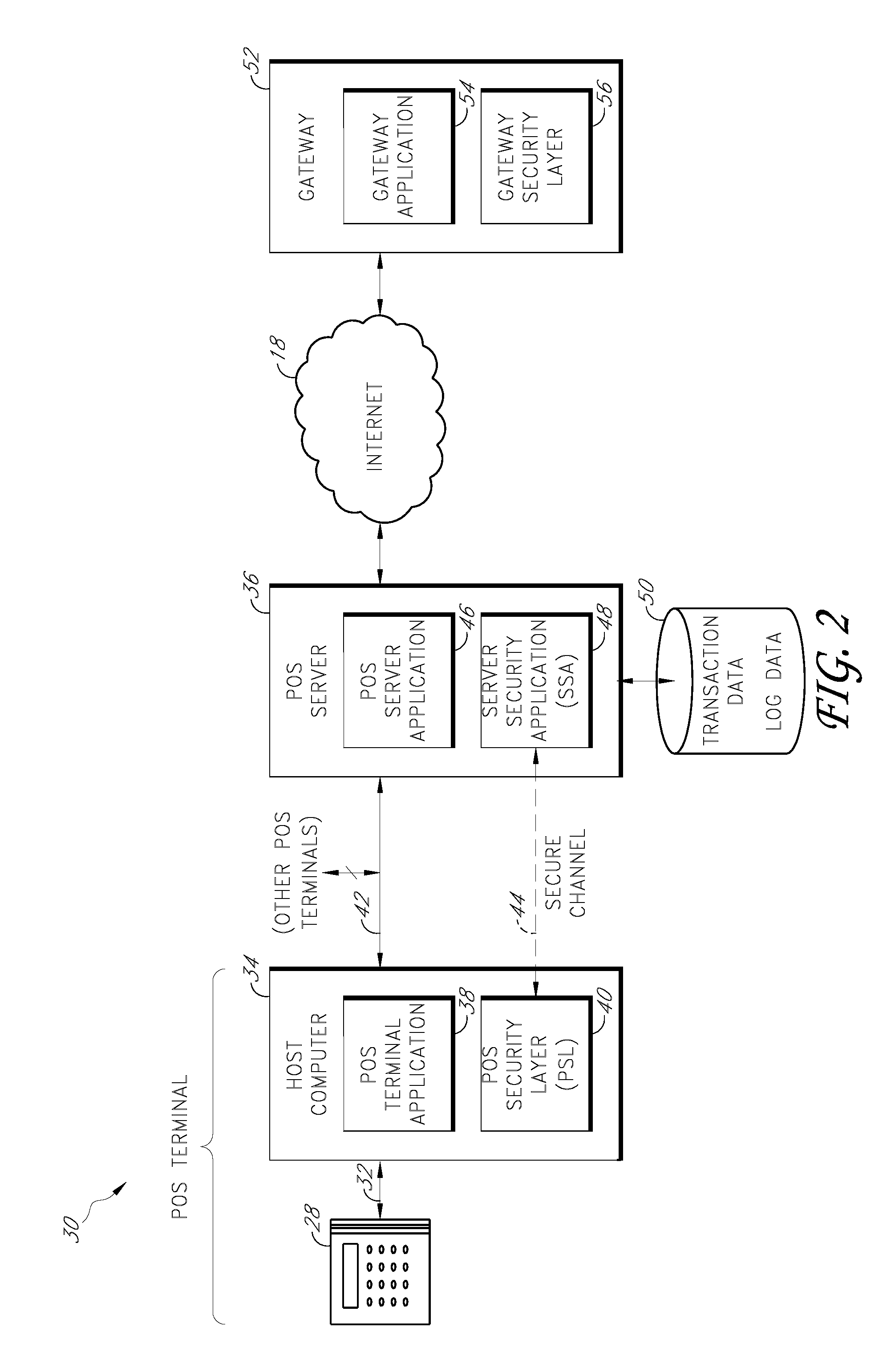
Secure payment card transactions
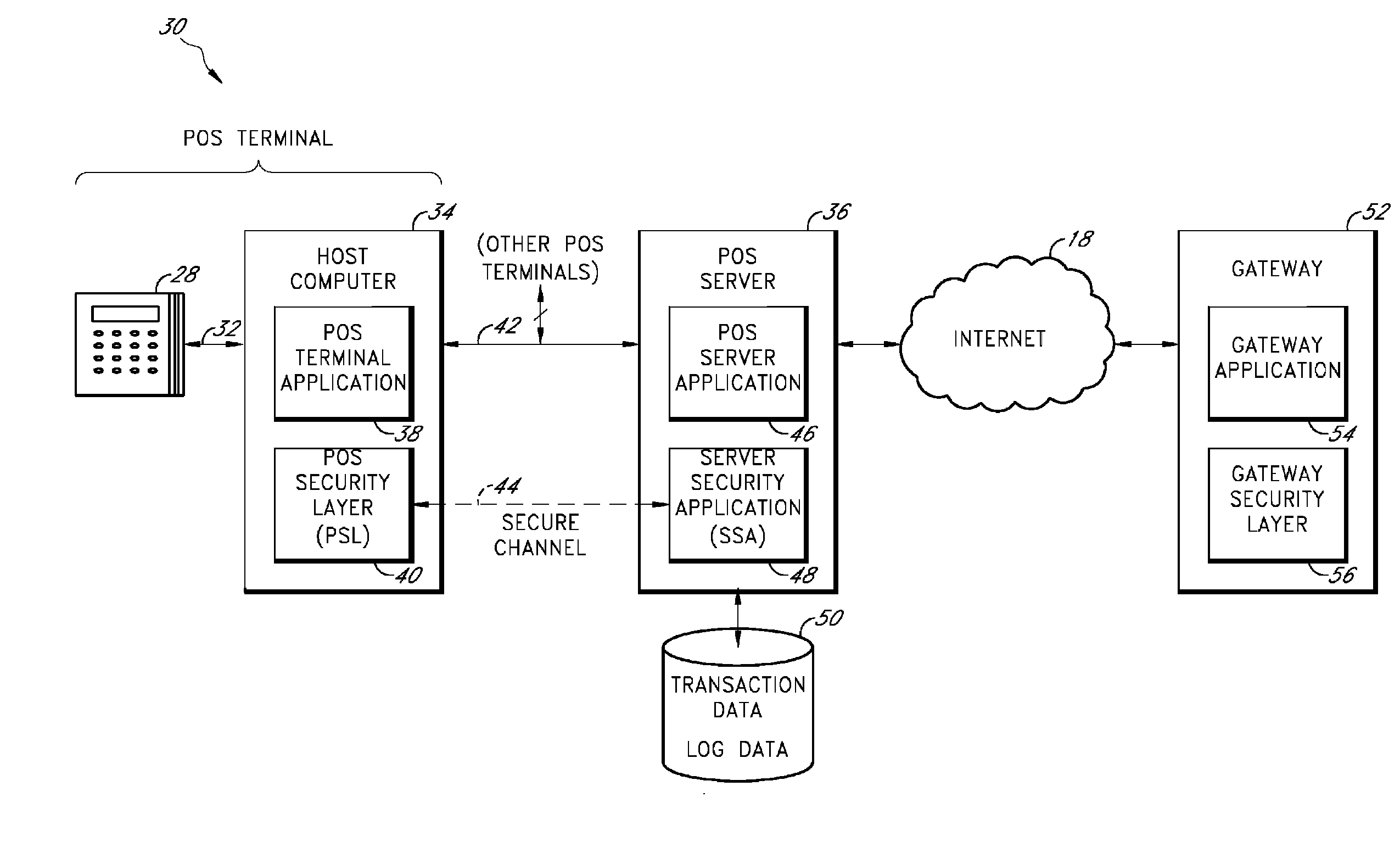
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
Method and system for identity and know your customer verification through credit card transactions in combination with internet based social data
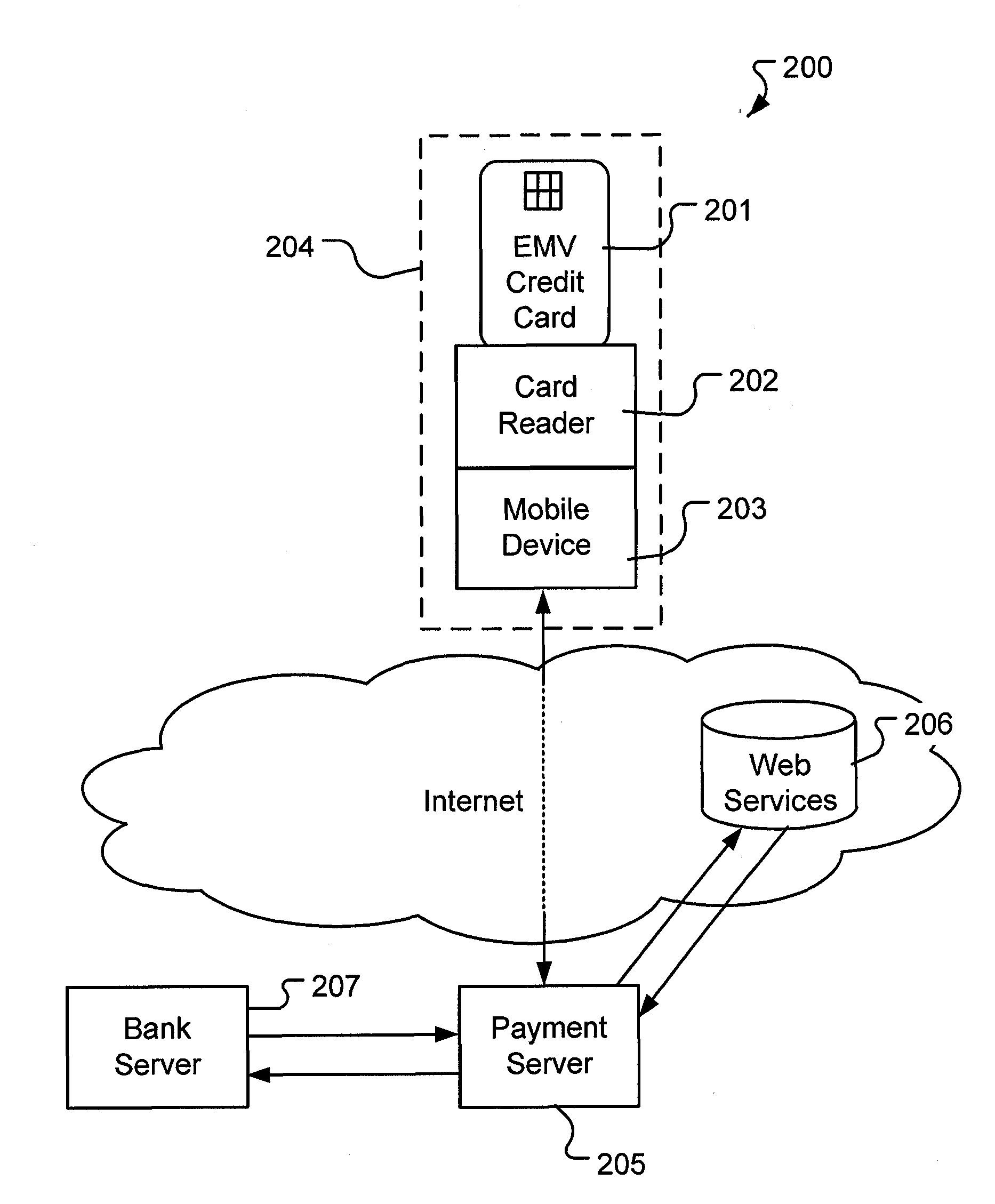
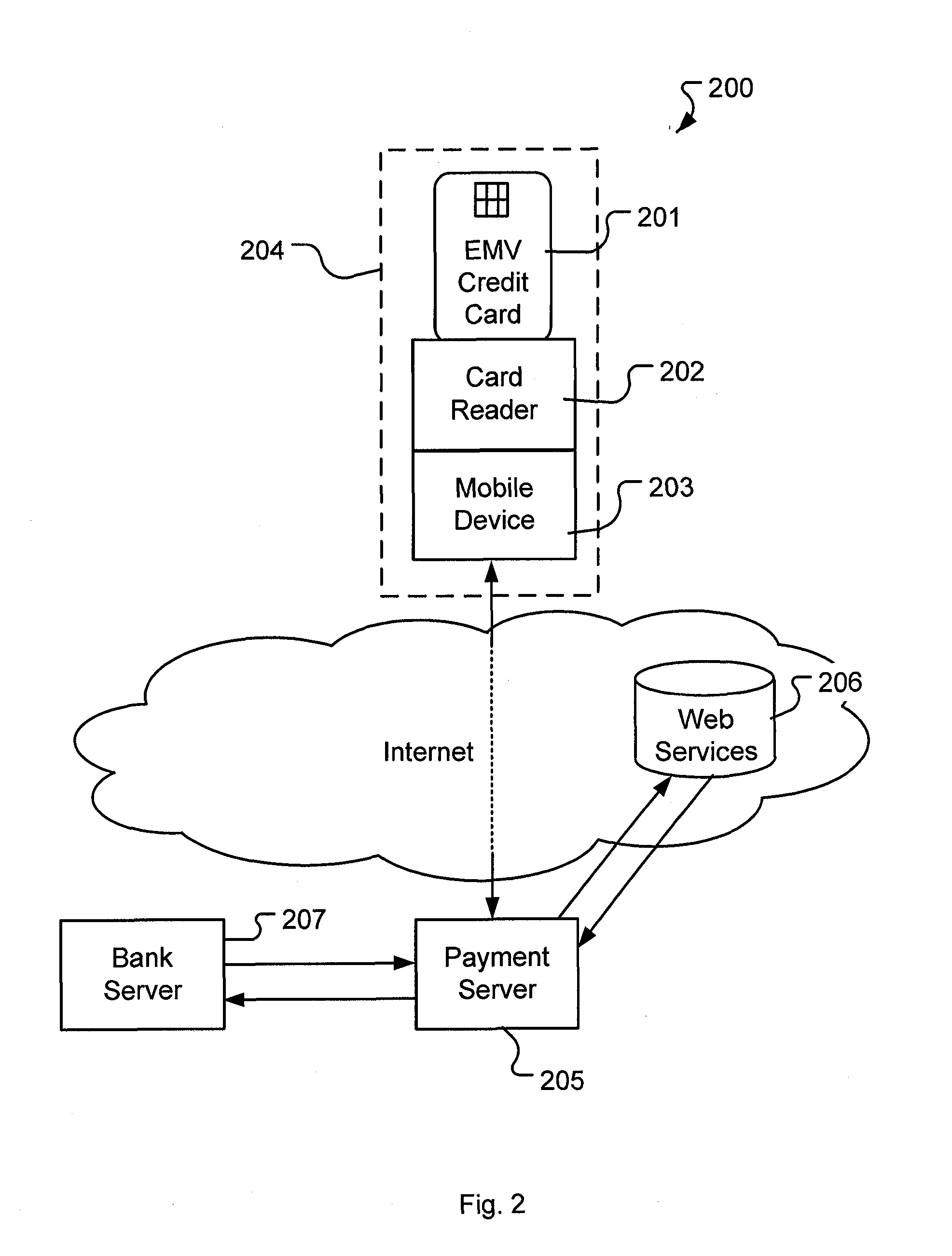
A method and system for verifying an identity of a card holder associated with a payment card using a payment device comprising a card reader and a mobile device. The method comprising the steps of initiating verification of identity of the card holder by inserting the payment card in the card reader of the payment device, reading card information from the payment card communicating the card information from the mobile device to a payment server, comparing received card information with stored card information in the payment server and accessing at least one web service. The account activity is analysed in the at least one web service and in that way verifying that the identity of the card holder is the same as the identity associated with the payment card, based on the analysis of information from the at least one web service and from the comparison of card information with stored card information. Terminating the verification process by communicating the result of the verification process from the payment server to the payment device.
Owner:IZETTLE MERCHANT SERVICES
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
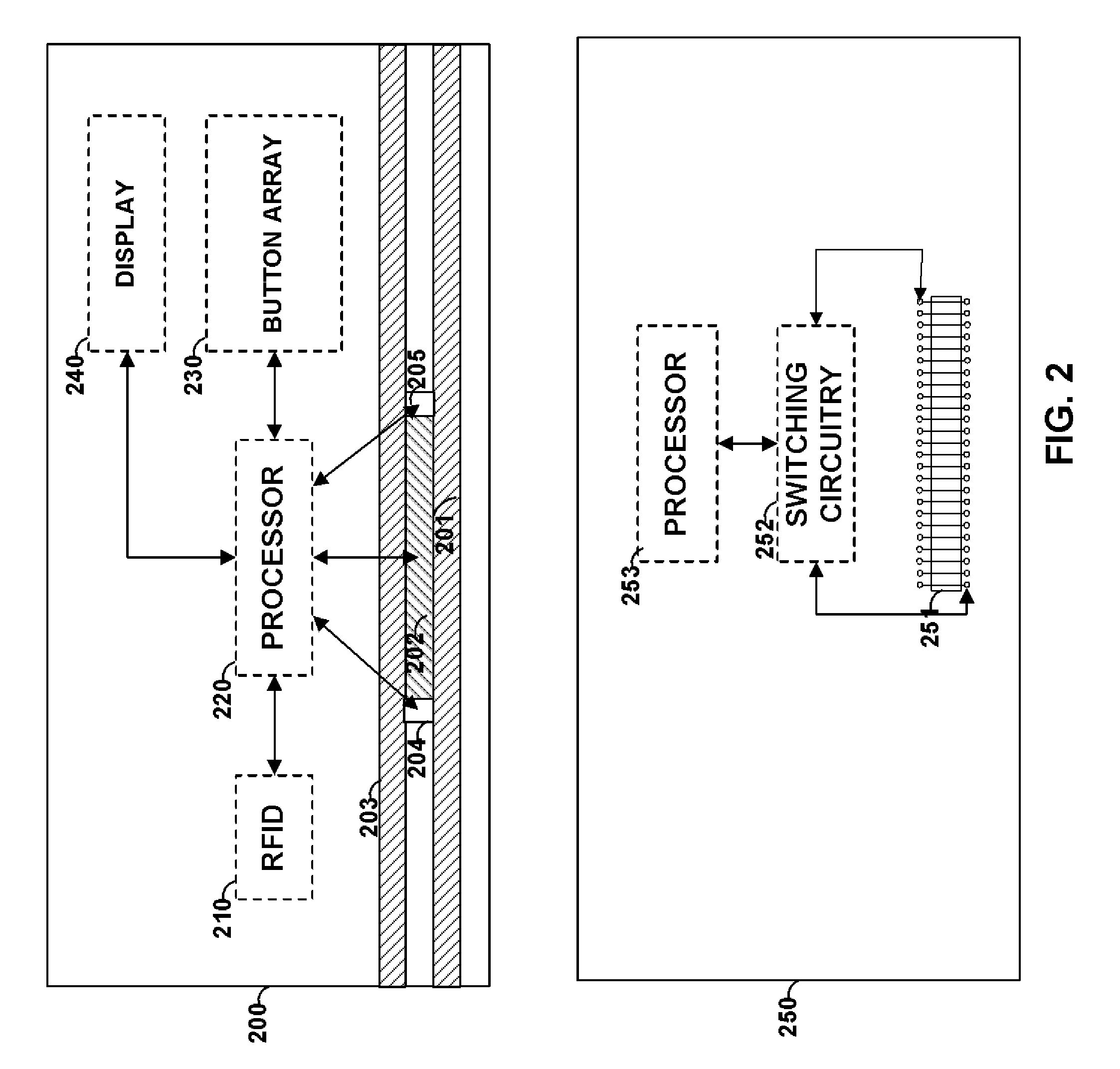
Payment card with dynamic account number
ActiveUS8494959B2Avoid processing delaysOvercomes drawbackAcutation objectsFinanceDisplay devicePayment order
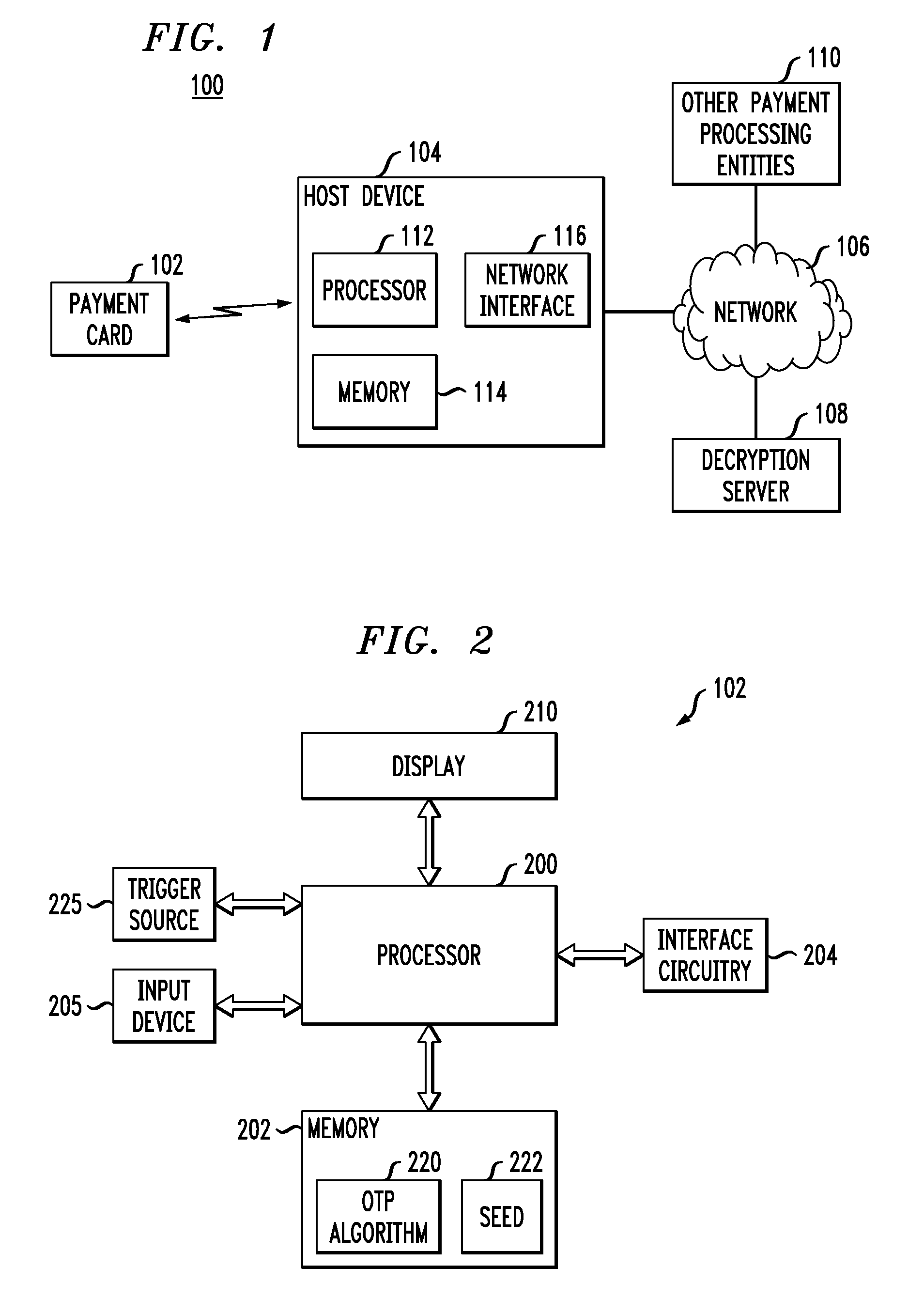
A payment card comprises a processor, a trigger source coupled to the processor, and a display for outputting at least a portion of a dynamic account number under control of the processor responsive to the trigger source. The dynamic account number is determined based at least in part on a seed stored in the payment card and an output of the trigger source. In an illustrative embodiment, the dynamic account number is generated utilizing a time-based or event-based one-time password algorithm. For example, in a time-based embodiment, the trigger source may comprise a time of day clock, with the dynamic account number being determined based at least in part on the seed and a current value of the time of day clock. In an event-based embodiment, the trigger source may comprise an event counter, with the dynamic account number being determined based at least in part on the seed and a current value of the event counter.
Owner:EMC IP HLDG CO LLC
Method and system for conducting secure payments over a computer network
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:HOGAN EDWARD J +1
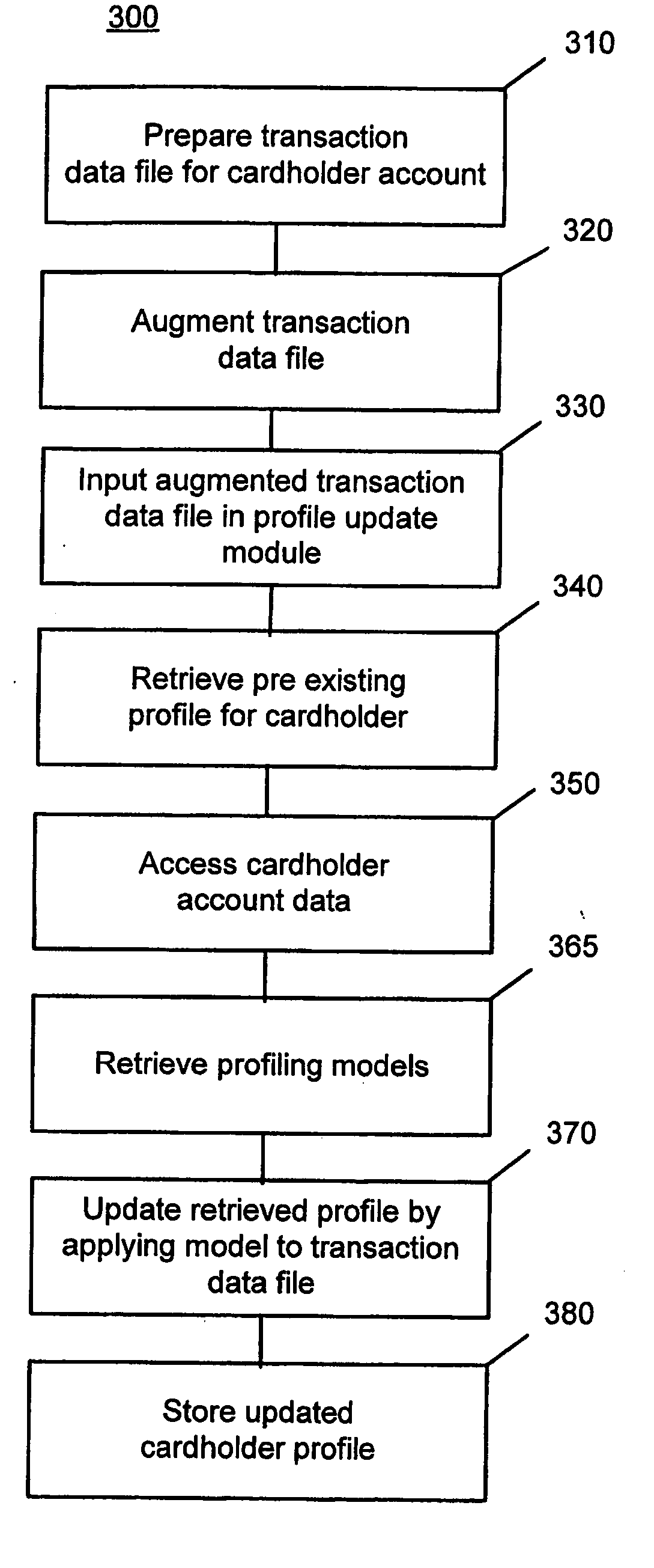
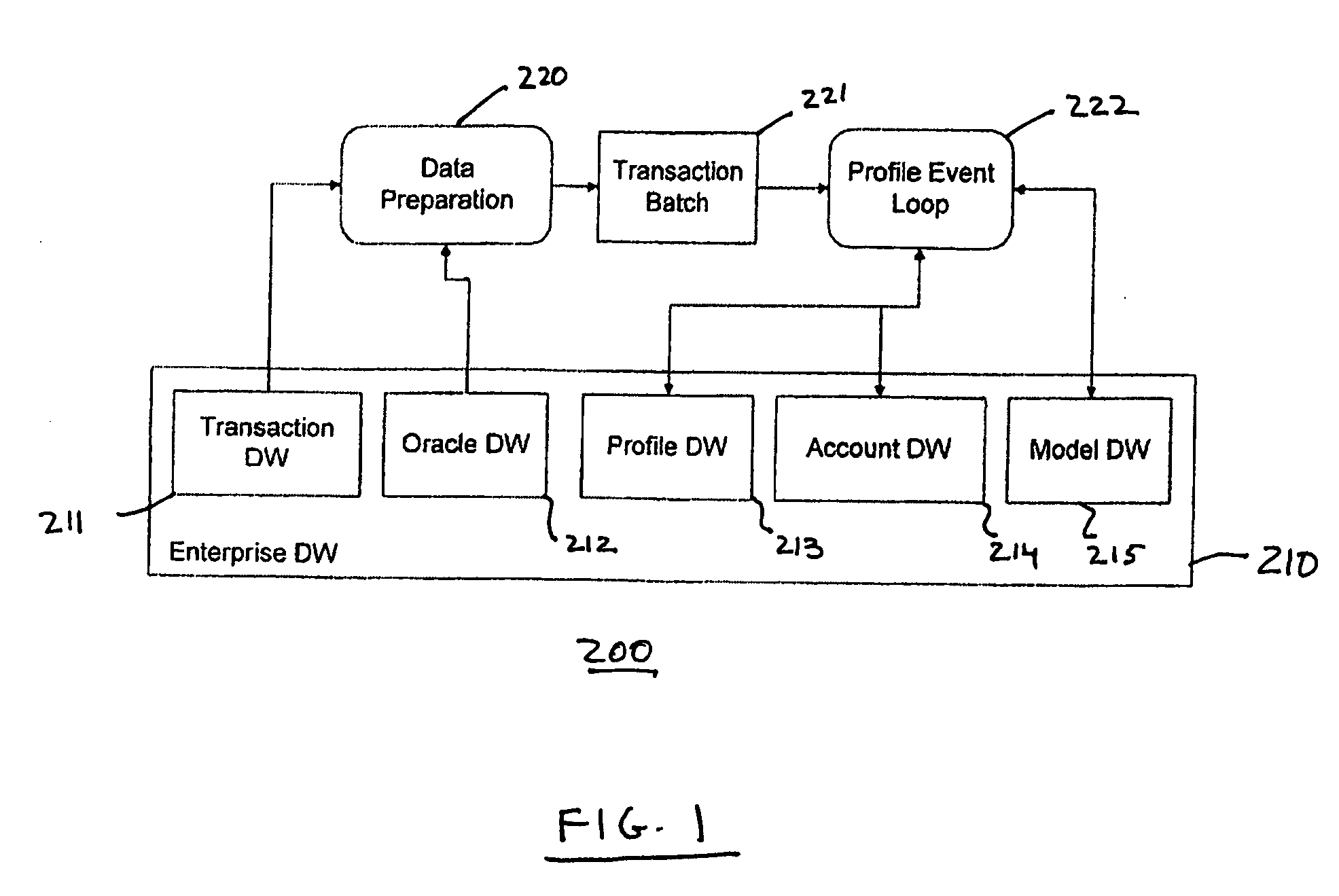
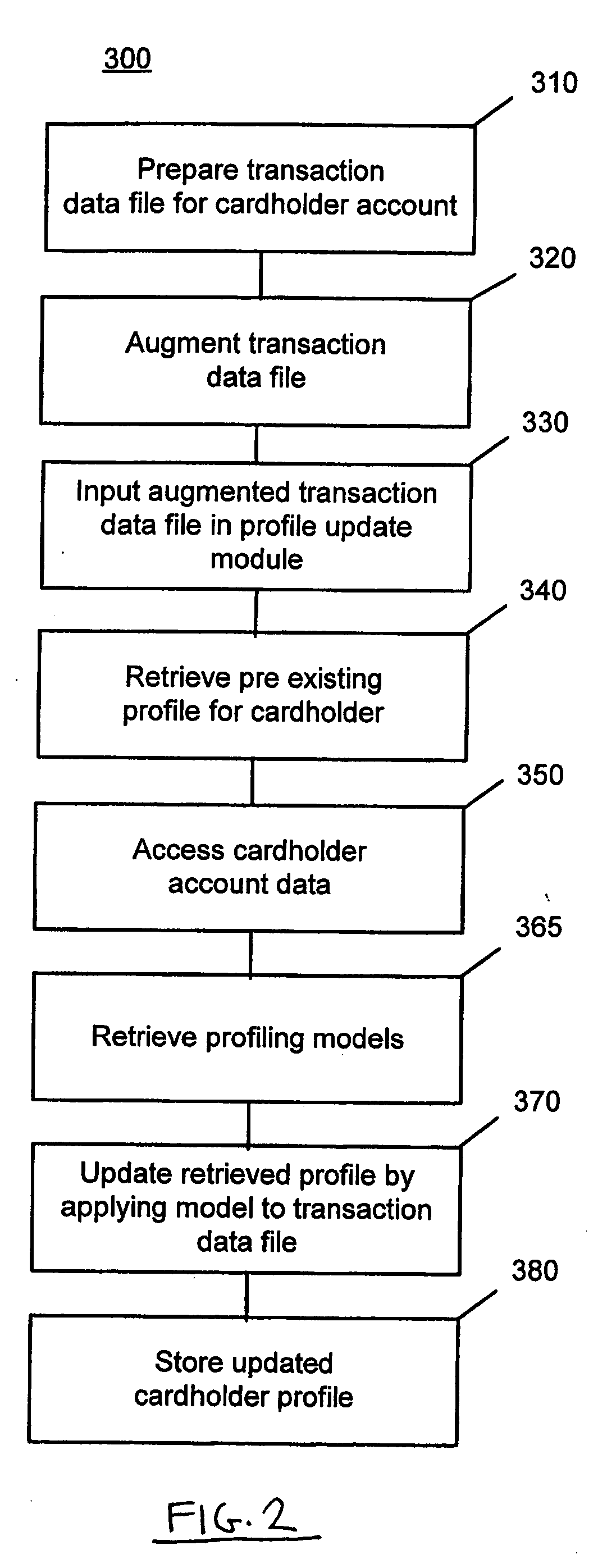
Methods and systems for predicting business behavior from profiling consumer card transactions
A system and method are provided for predicting small business behavior by analysis of consumer payment card transaction data. Transaction and amount velocity analysis of industry categories and / or real-time transaction-based profiling is employed to identify those consumer payment card accounts that are being inappropriately used to make small business purchases. A small business behavior predictor model is used to score transaction data and update cardholder profiles according to the likelihood that the transaction data represents small business activity.
Owner:MASTERCARD INT INC
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
Method and system for managing a non-changing payment card account number
The present invention provides a method and system for managing a cardholder's payment card account having a non-changing account number associated with a payment card, the method comprising the steps of assigning a series of dynamic attributes to an account number, identifying the payment card account, and changing the dynamic attributes of the account number without changing the account number.
Owner:MASTERCARD INT INC
Transactions using temporary credential data
A method is disclosed. The method includes receiving a credential request message requesting a temporary credential associated with a payment account, and then determining, by a server computer, using a routing table and data associated with the payment card, a third-party computer associated with the payment account. The method also includes transmitting the credential request message to the third-party computer, and receiving, by the server computer, the temporary credential from the third-party computer. The method also includes determining, by the server computer, the communication device associated with the requested temporary credential and transmitting, by the server computer, the temporary credential to the communication device.
Owner:VISA INT SERVICE ASSOC
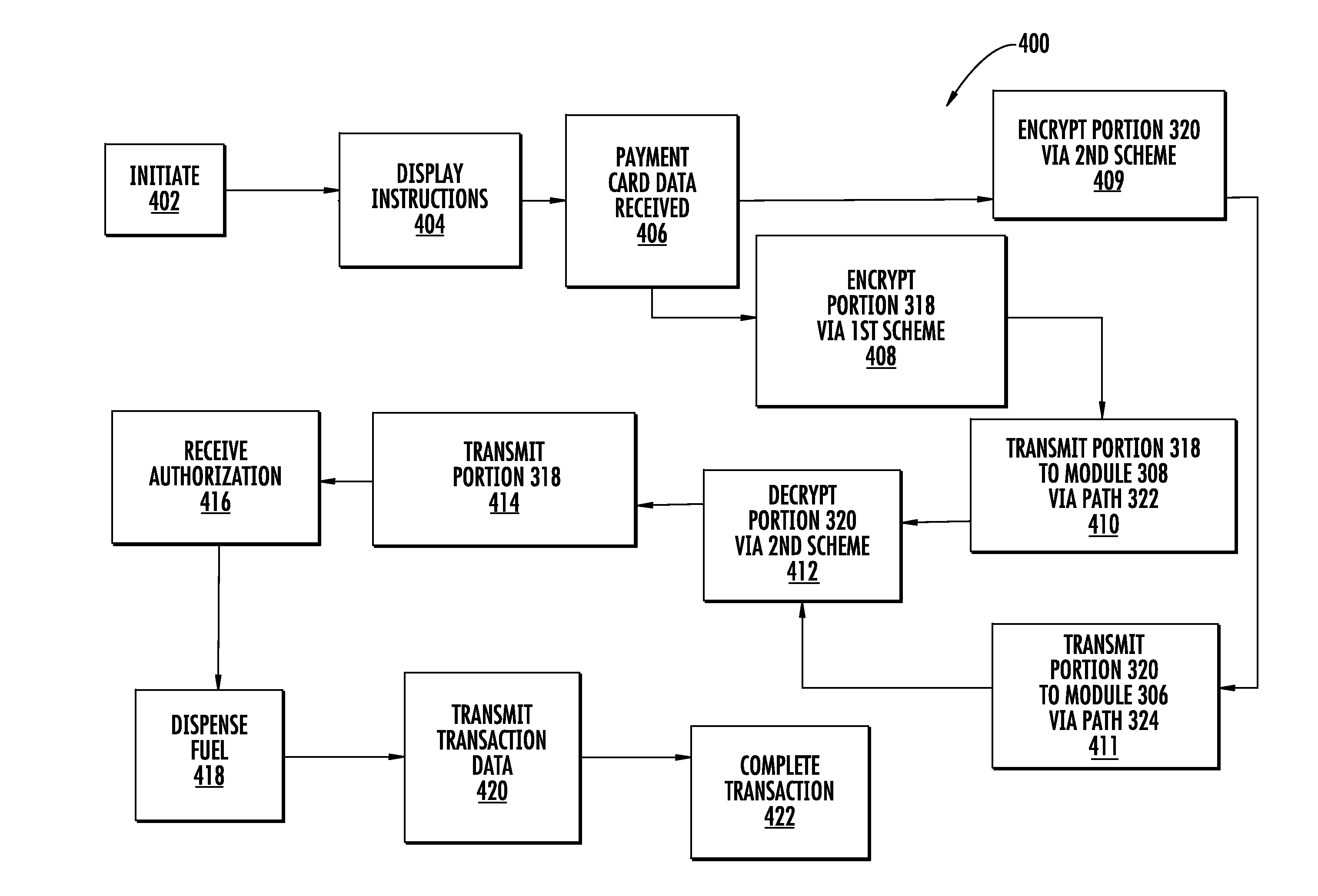
Fuel dispenser payment system and method
A system and method for effecting payment transactions comprising a card reader configured to encrypt a first portion of payment card data received by the card reader from a payment card according to a first encryption scheme associated with the financial institution responsible for an account associated with the payment card and to encrypt a second portion of the payment card data according to a second encryption scheme, where the first portion is sufficient to identify the payment card or account number and to effect a payment transaction involving the payment card or account and where the second portion is sufficient to identify the financial institution but insufficient to identify the payment card or account number.
Owner:GILBARCO
Payment cards and devices operable to receive point-of-sale actions before point-of-sale and forward actions at point-of-sale
PendingUS20090159663A1Shorten the timeEasy to changeImage enhancementImage analysisWaiters/waitressesUser input
A payment card or other device (e.g., mobile telephone) is provided with a magnetic emulator operable to communicate data to a magnetic stripe read-head. A user can utilize buttons located on the card to perform activities that would otherwise be performed at an ATM, payment card reader, or by a waitress. A user can provide instructions on a card to accelerate a transaction. The information a user enters can be communicated to a point-of-sale device. For example, a user can enter into his / her card that the user desires $100 withdrawal from a checking account. The user can also enter his / her PIN into the card. The user can swipe his / her card into an ATM and instantly be provided with the desired $100.
Owner:DYNAMICS
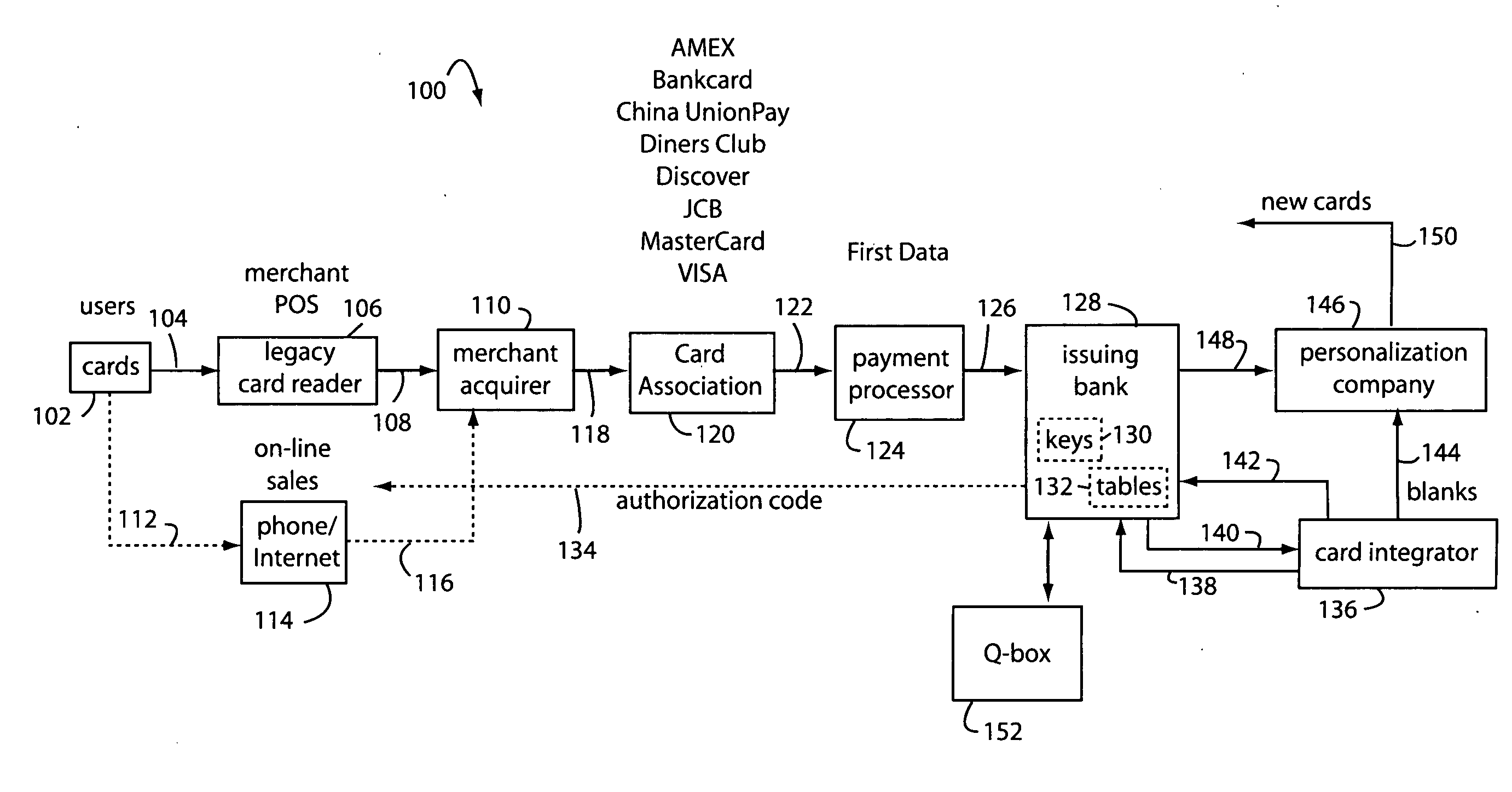
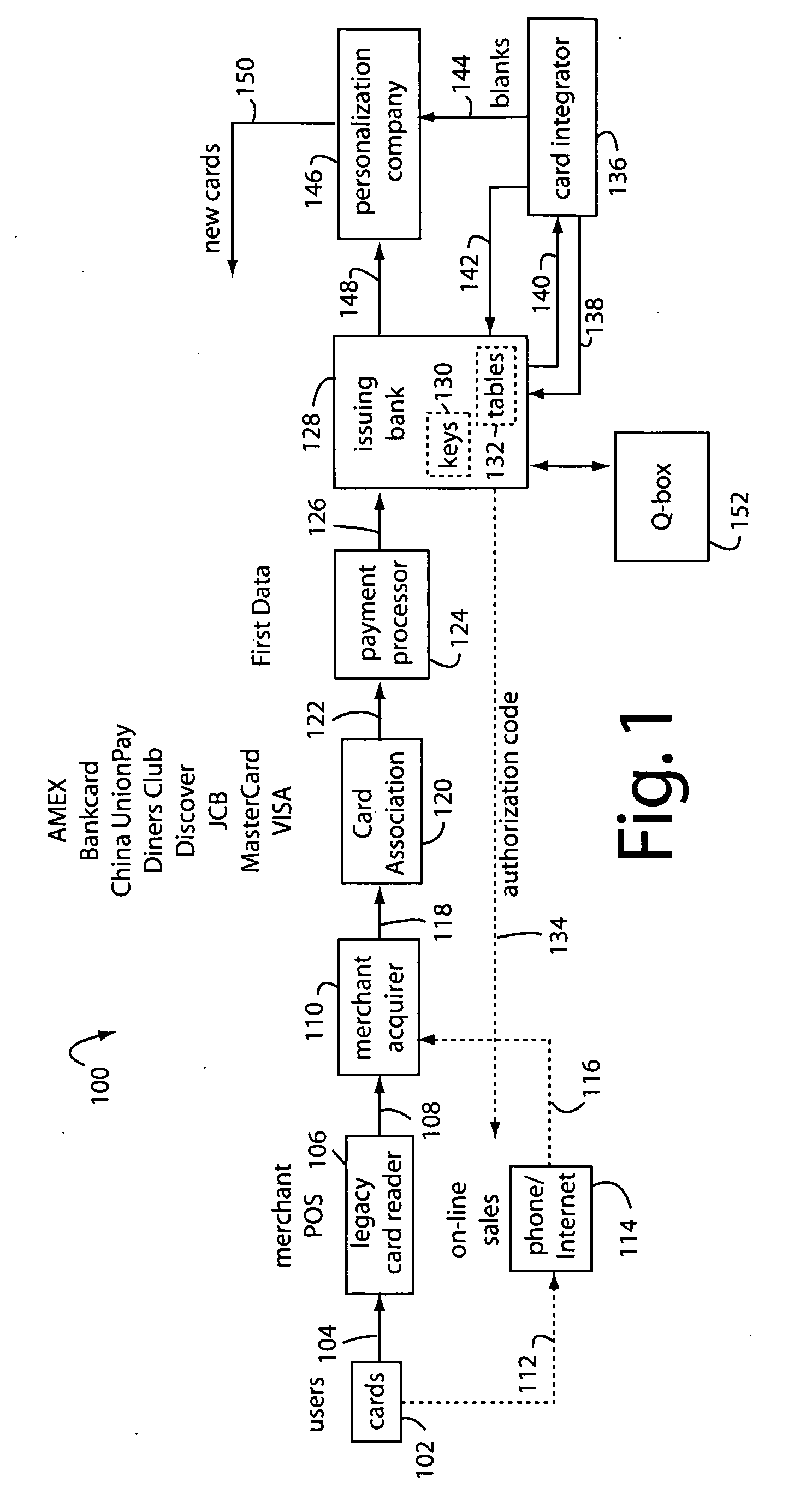
Financial transaction network
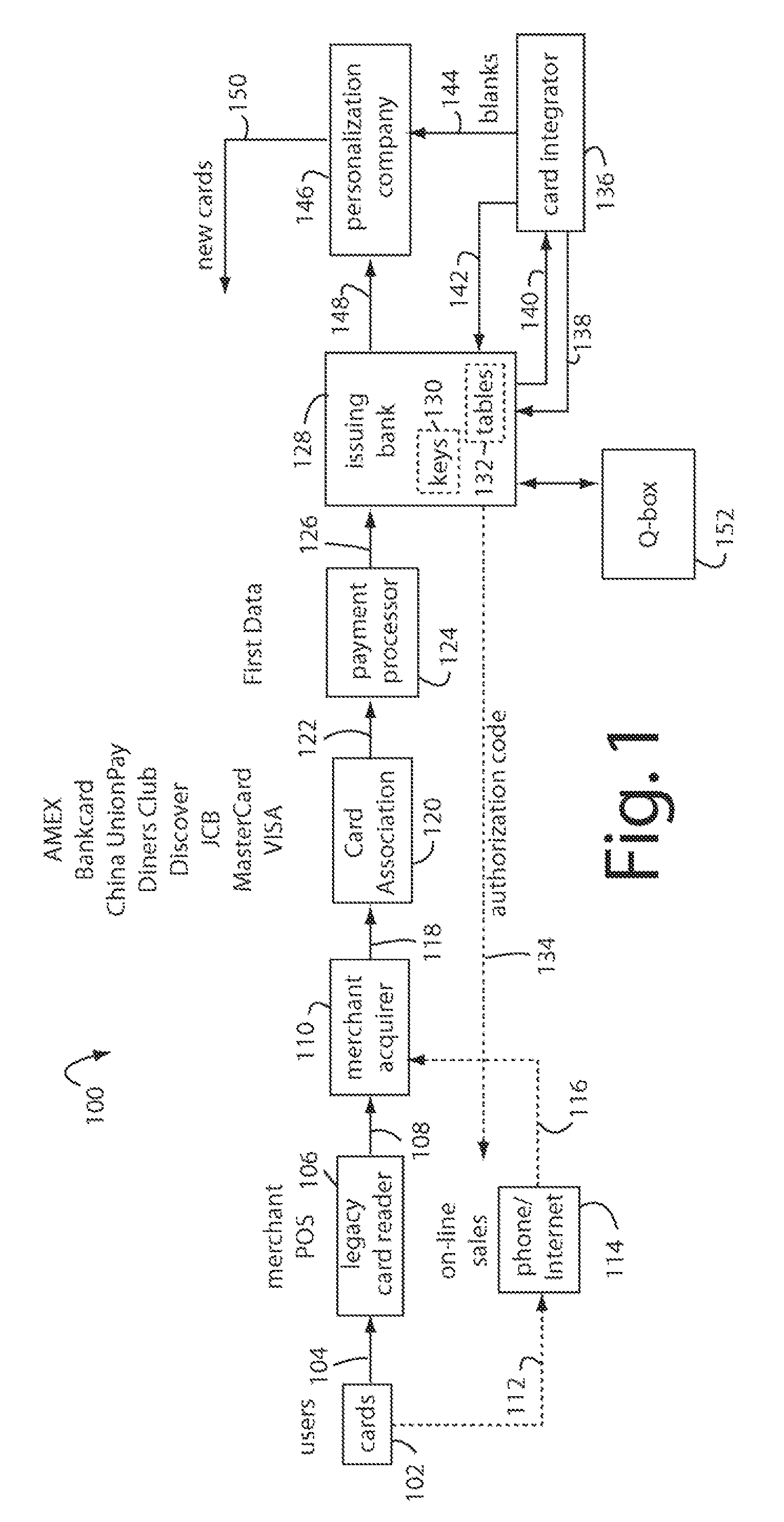
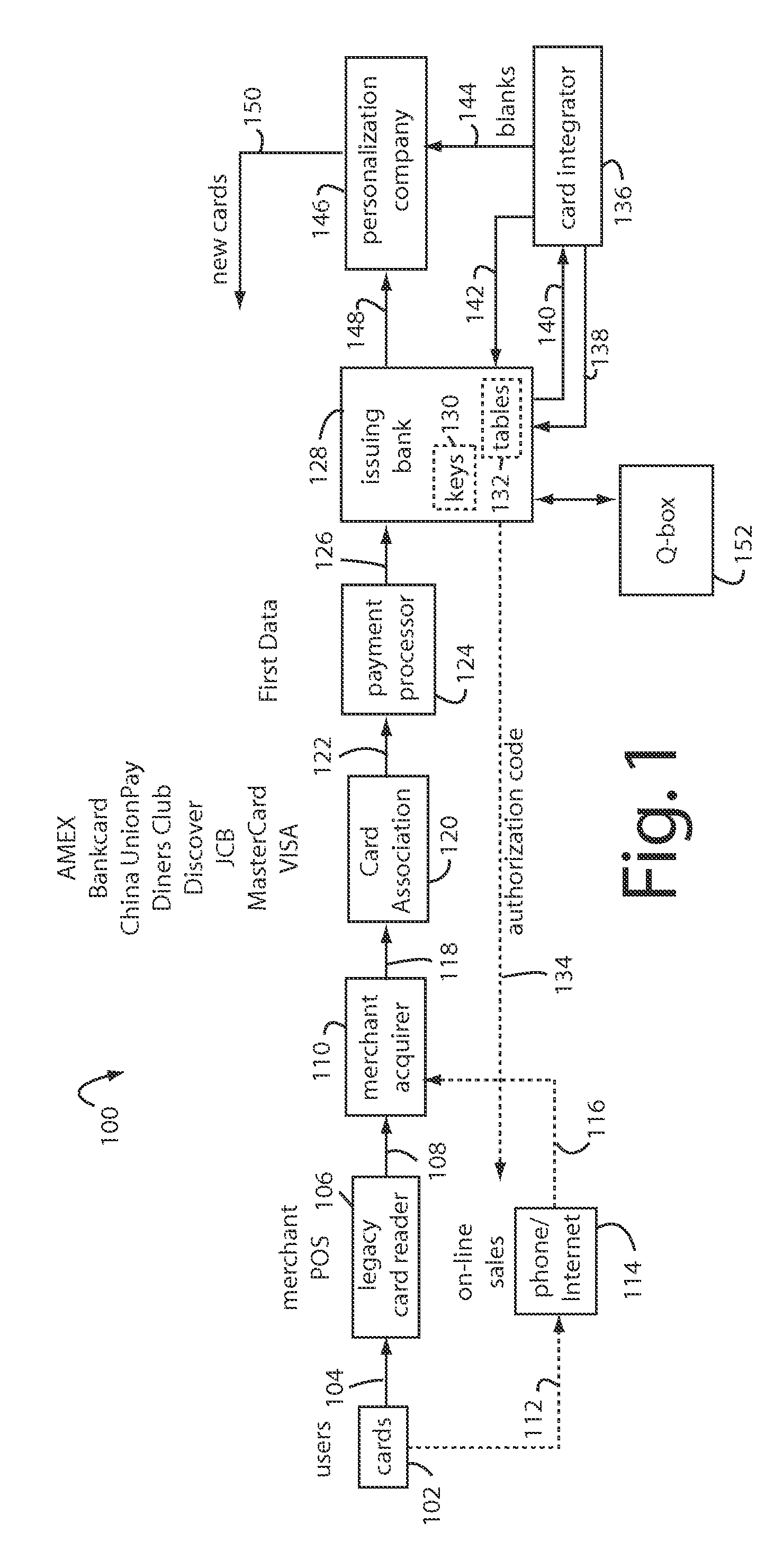
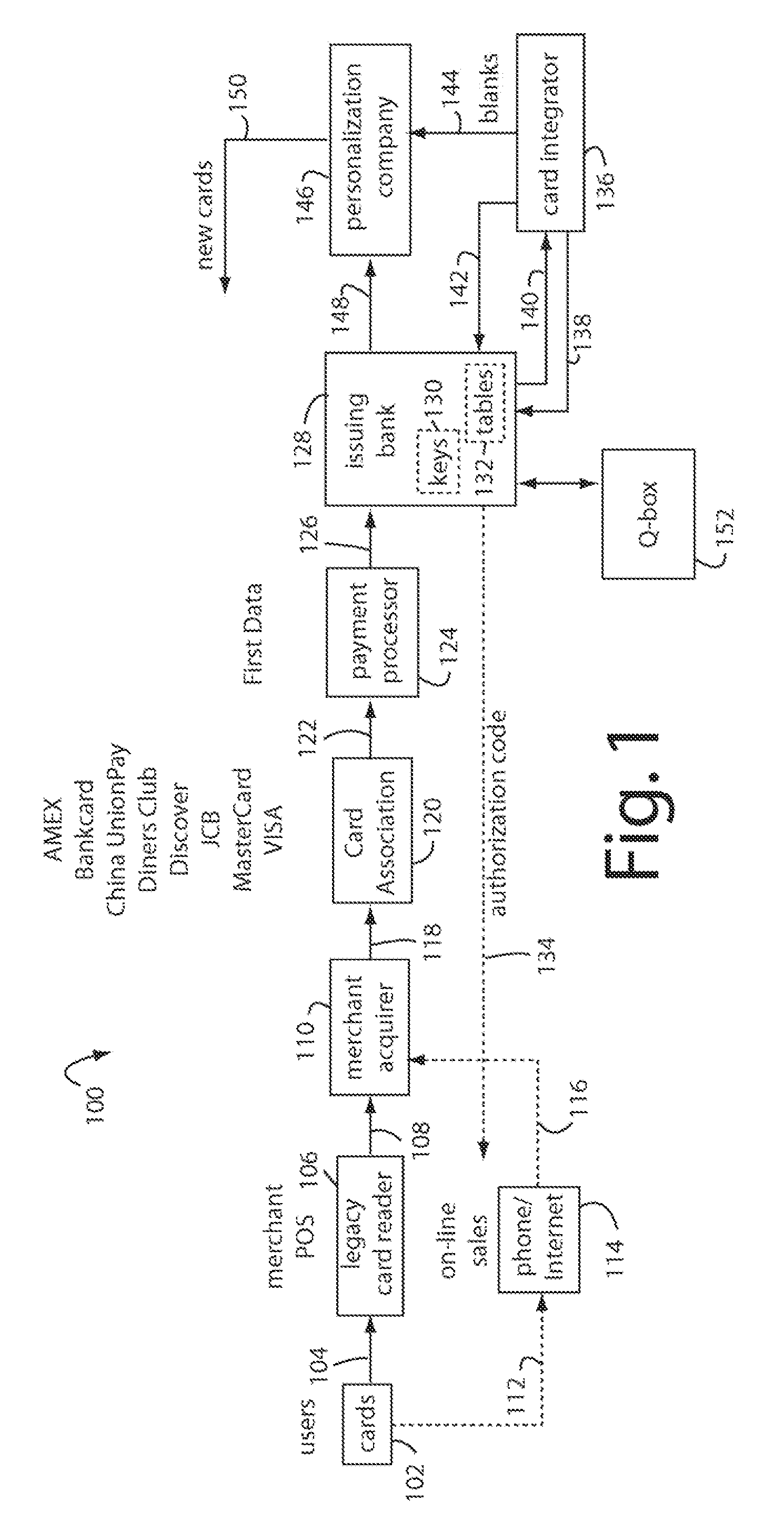
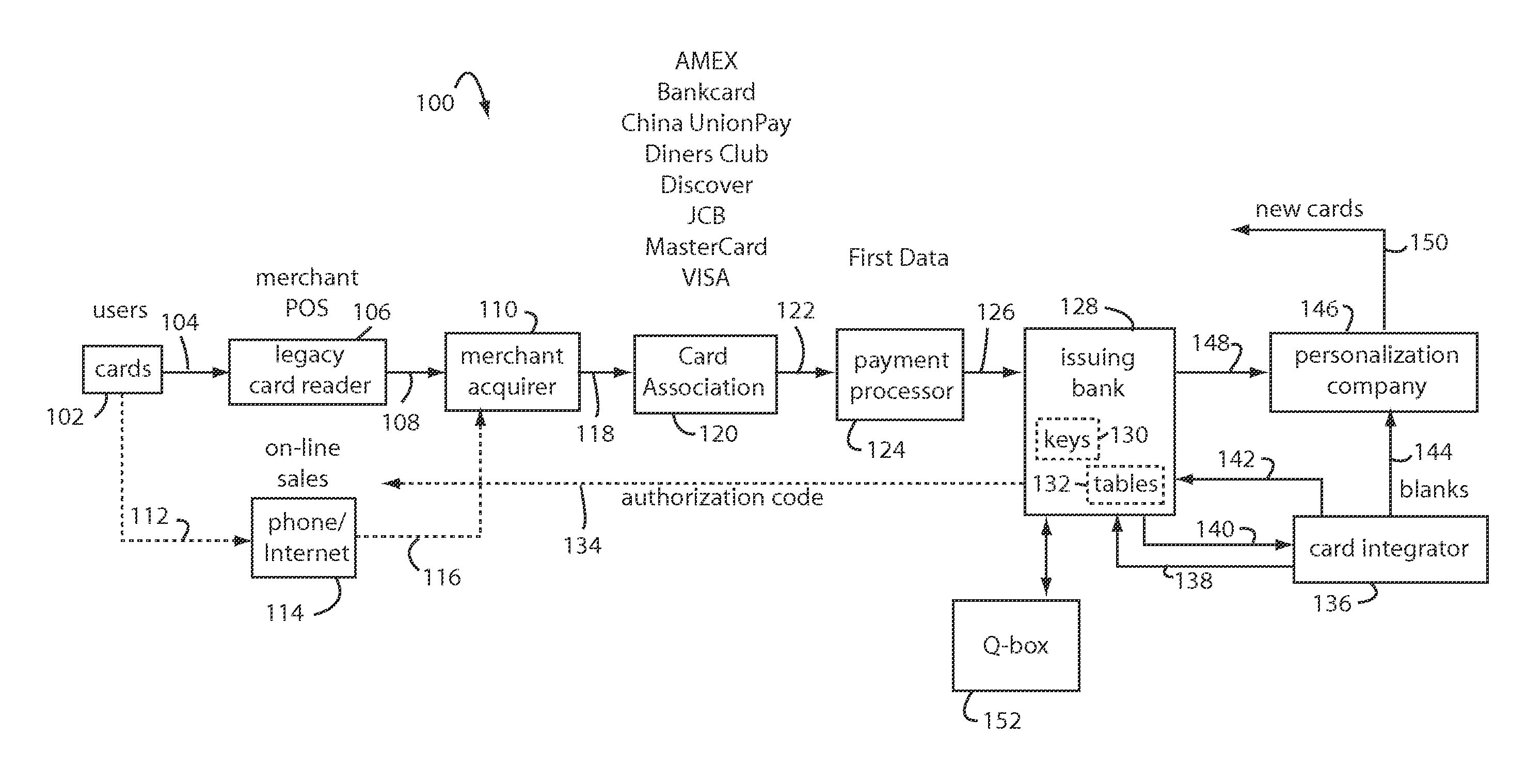
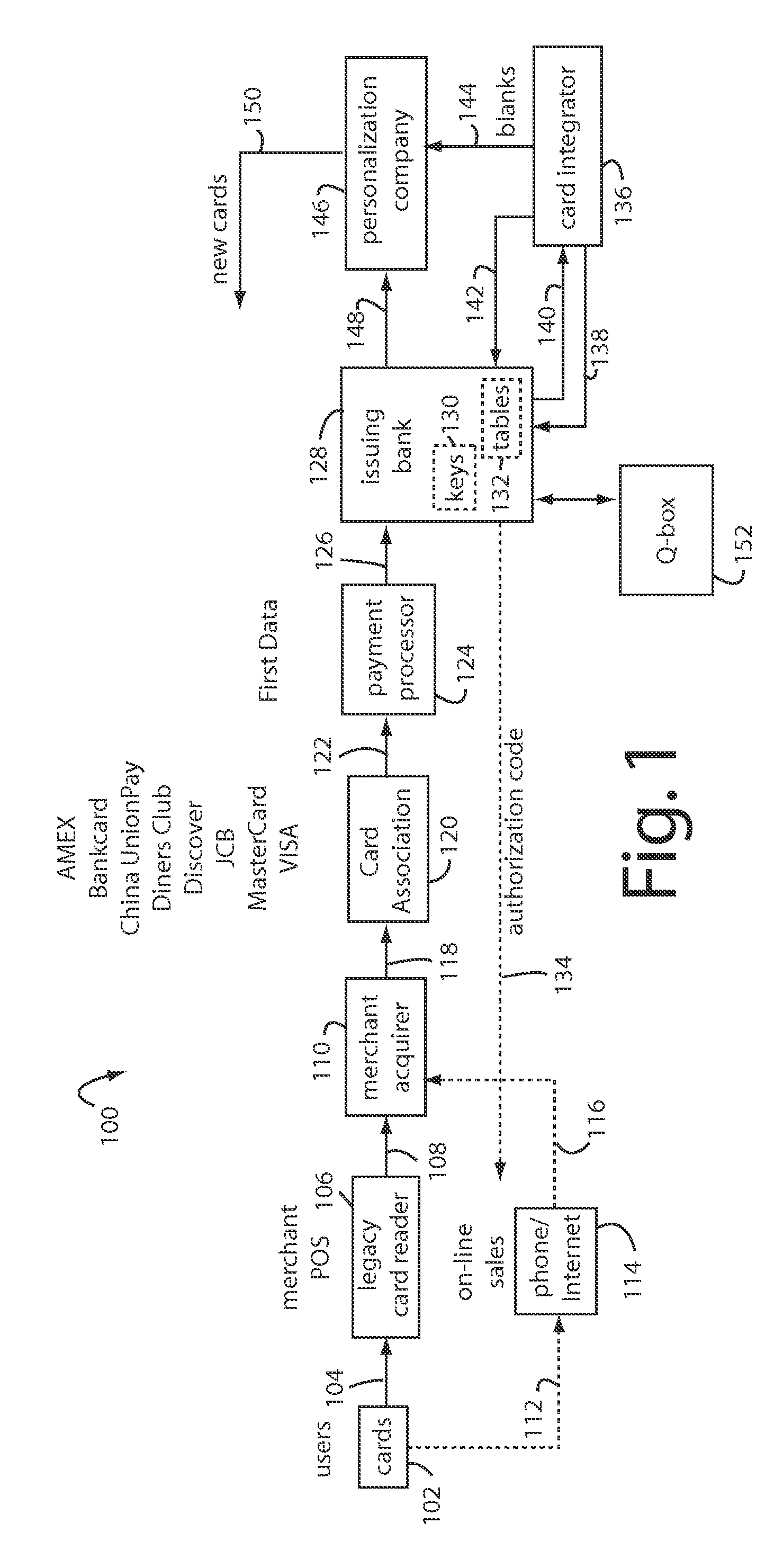
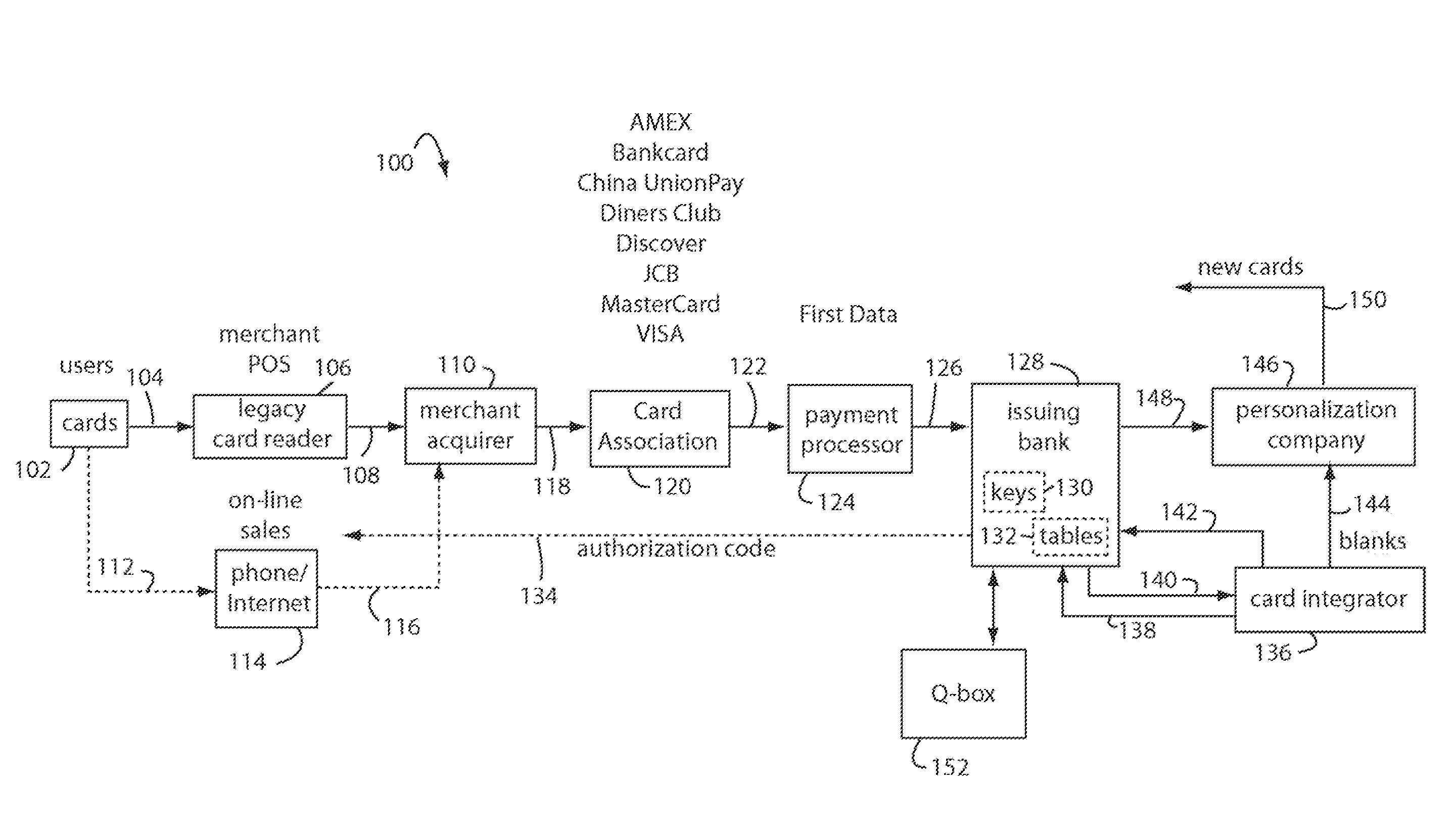
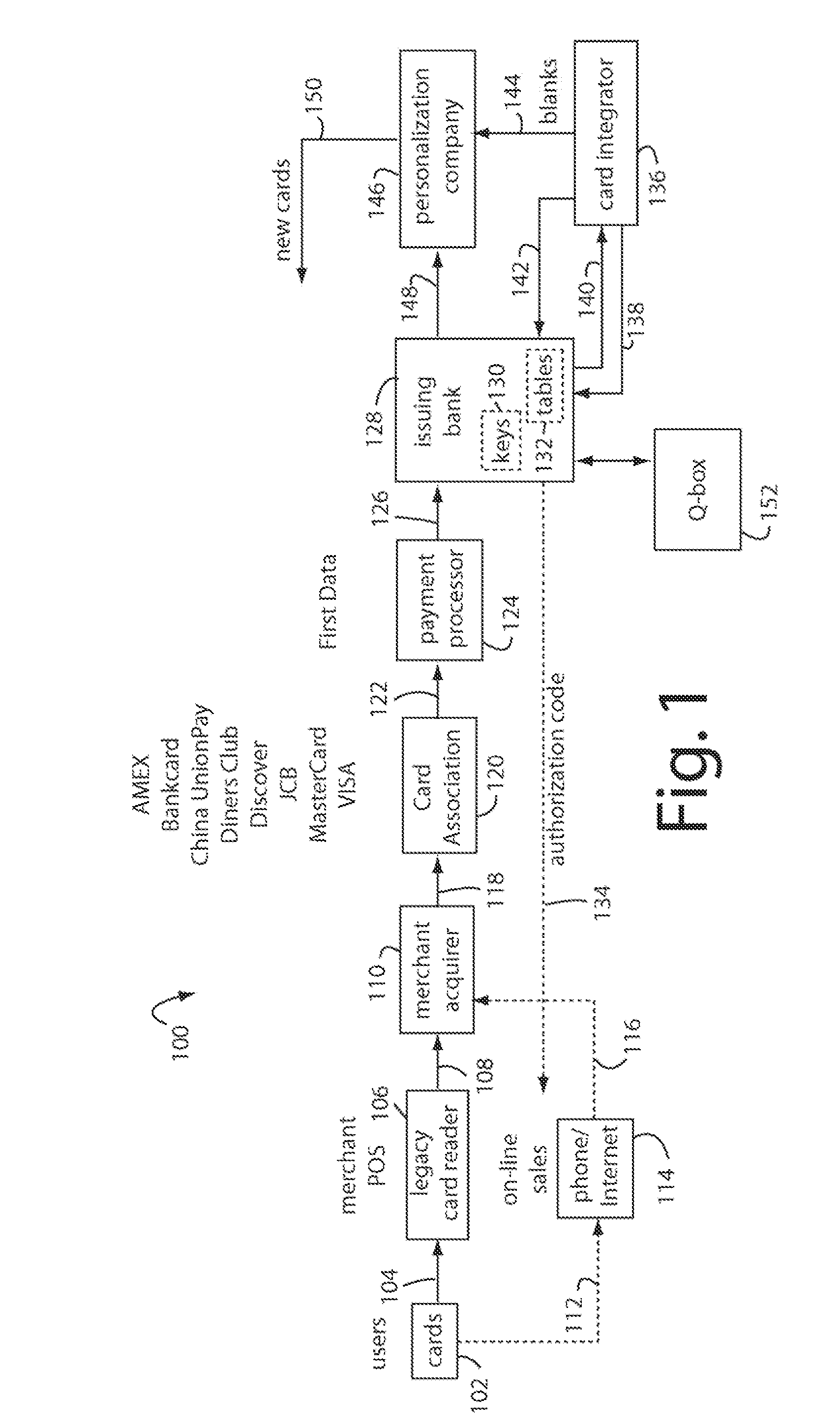
The manufacture and control of payment cards used in consumer financial transactions circulates a population of payments cards with user identification and account access codes. Each use of an individual card produces a variation of its user access code according to an encryption program seeded with encryption keys or initialization vectors. A portion of the magnetic stripe is made dynamic with a Q-Chip magnetic MEMS device. The job of personalizing payment cards with the user identification and account access codes is outsourced to a personalization company. The encryption keys and initialization vectors are kept private from the personalization company by using the encryption program to generate tables of computed results. Respective ones of the tables of computed results are sent for loading by the personalization company into new members of the population of payments cards. New payment cards are manufactured and distributed that include and operate with the tables of computed results.
Owner:FITBIT INC
Communication system and method for narrowcasting
A system includes an offer datastores including one or more offers from one or more merchants, a registered card module to register one or more payment cards to be used for a purchase transaction, a transaction matching module to identify the one or more merchants from a collection of purchase transaction data and to match the purchase transaction of the identified one or more merchants with one or more offers in the offer datastore from the identified one or more merchants, and a rewards module to determine an incentive to be applied to the one or more payment cards based on any offer associated with the matched merchant and generate a qualified transaction data to be transmitted to an issuer of the one or more payment cards.
Owner:NEXT JUMP INC
System and method for an authenticating and encrypting card reader
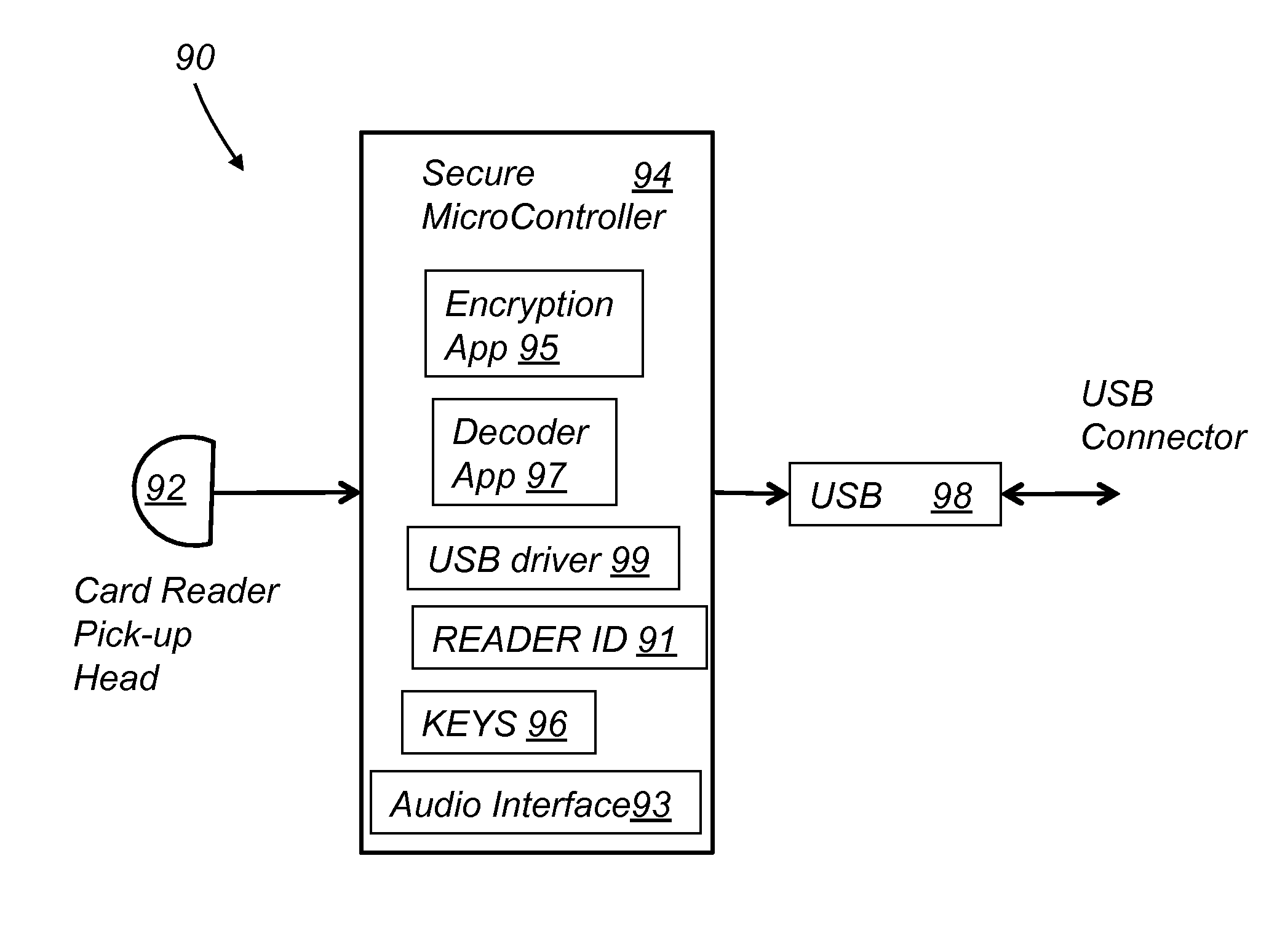
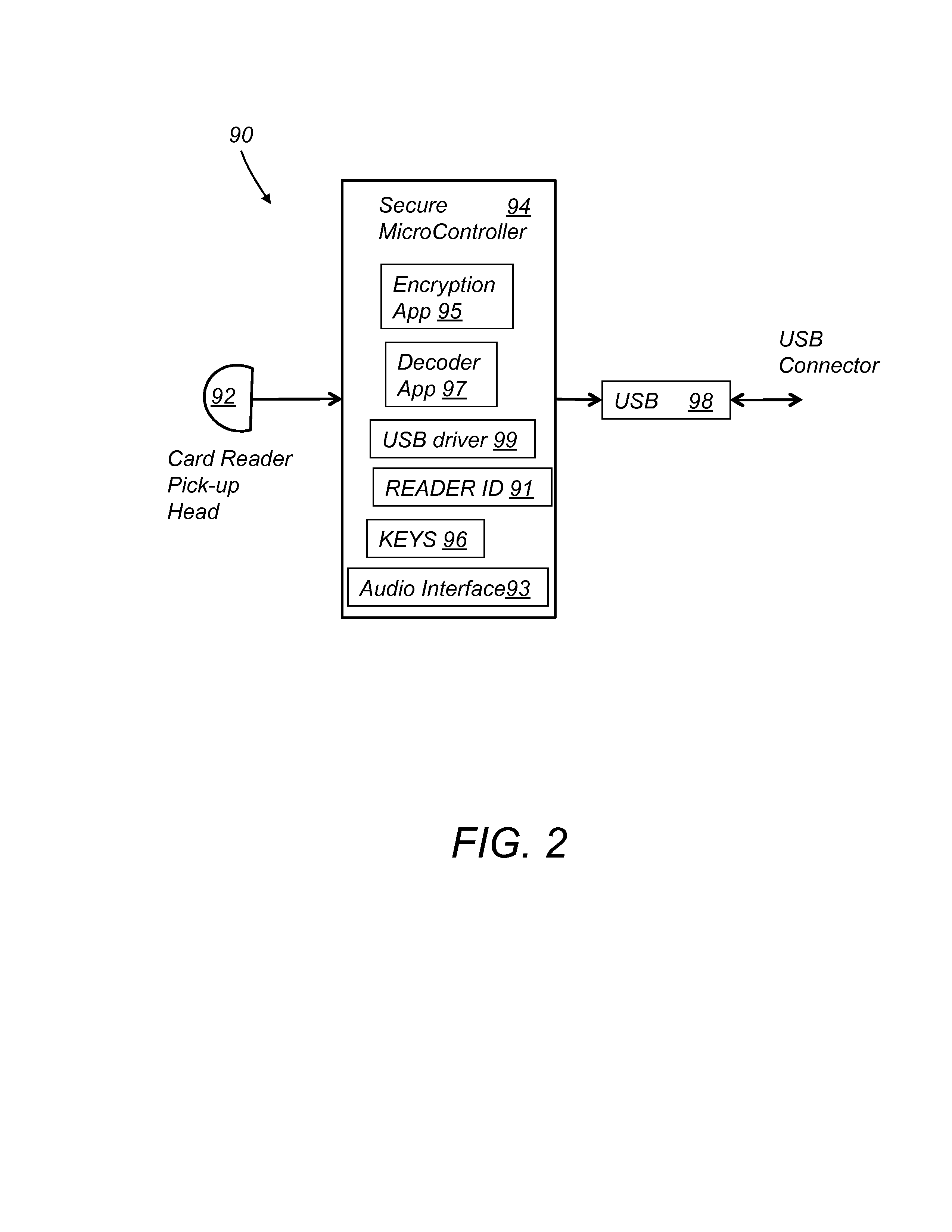
InactiveUS20130179351A1Easy checkoutLow InterchangeAcutation objectsPoint-of-sale network systemsMicrocontrollerPayment transaction
A system for encrypting and authenticating a payment transaction includes a card reader, a computing device, a card swipe application and a checkout application. The card reader includes a reader head, a secure microcontroller, and an interface. The reader head reads payment card data from a payment card. The secure microcontroller stores a unique reader identification (reader ID), and at least a first encryption key, and includes a payment card decoder application and an encryption application. The encryption application encrypts the payment card data and produces encrypted payment card data. The encryption application further encrypts the transaction data with the first encryption key and produces encrypted transaction data. The checkout application receives the encrypted payment card data and the encrypted transaction data and forwards them to a payment server for processing of the payment transaction.
Owner:WALLNER GEORGE
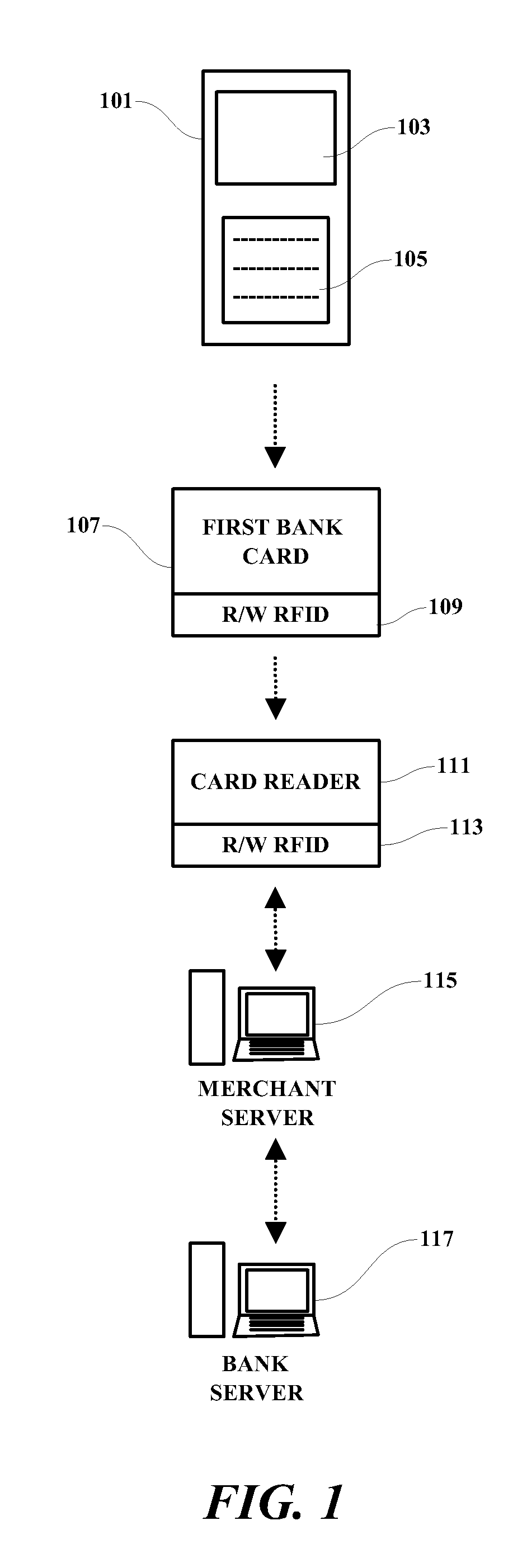
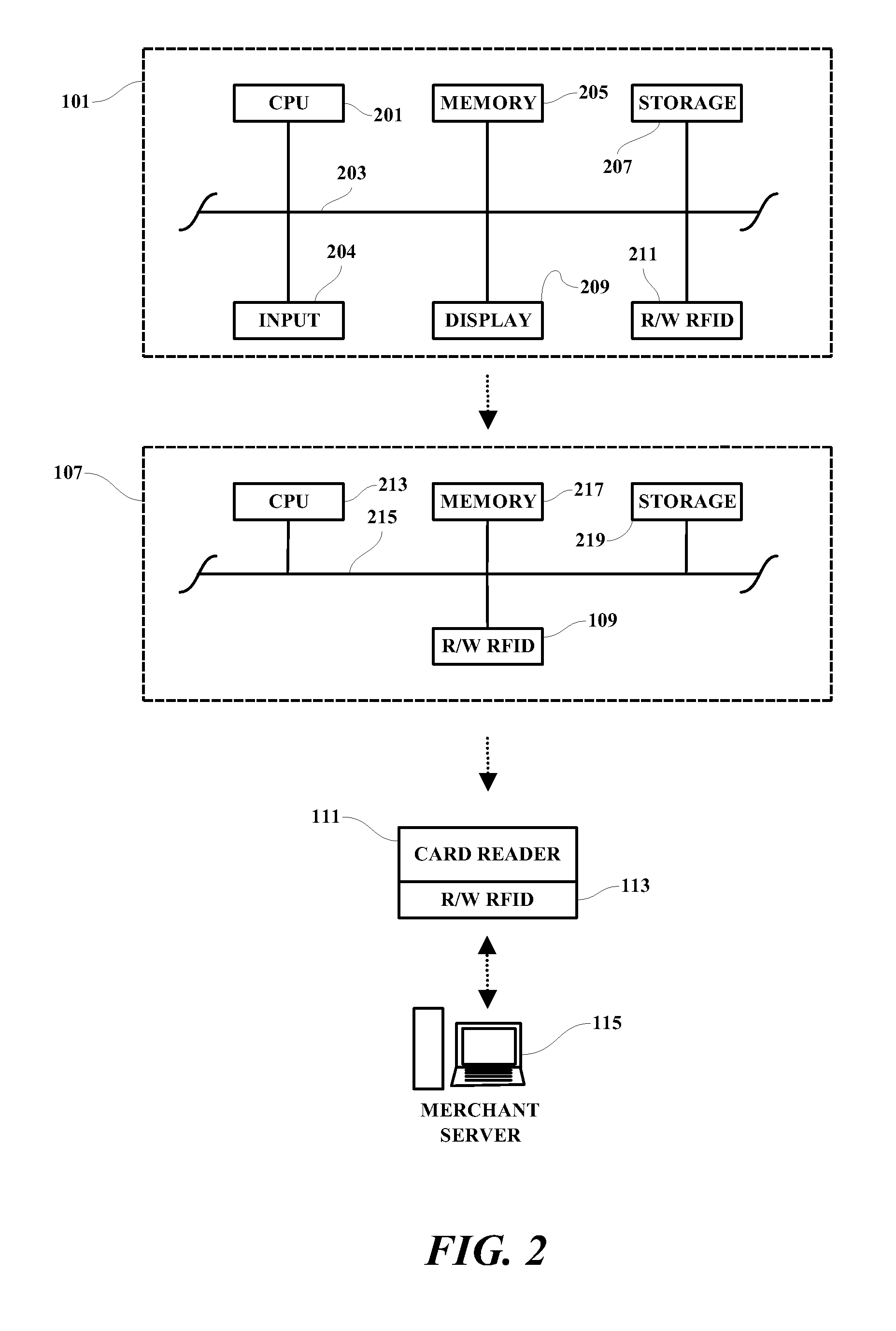
Payment card processing system
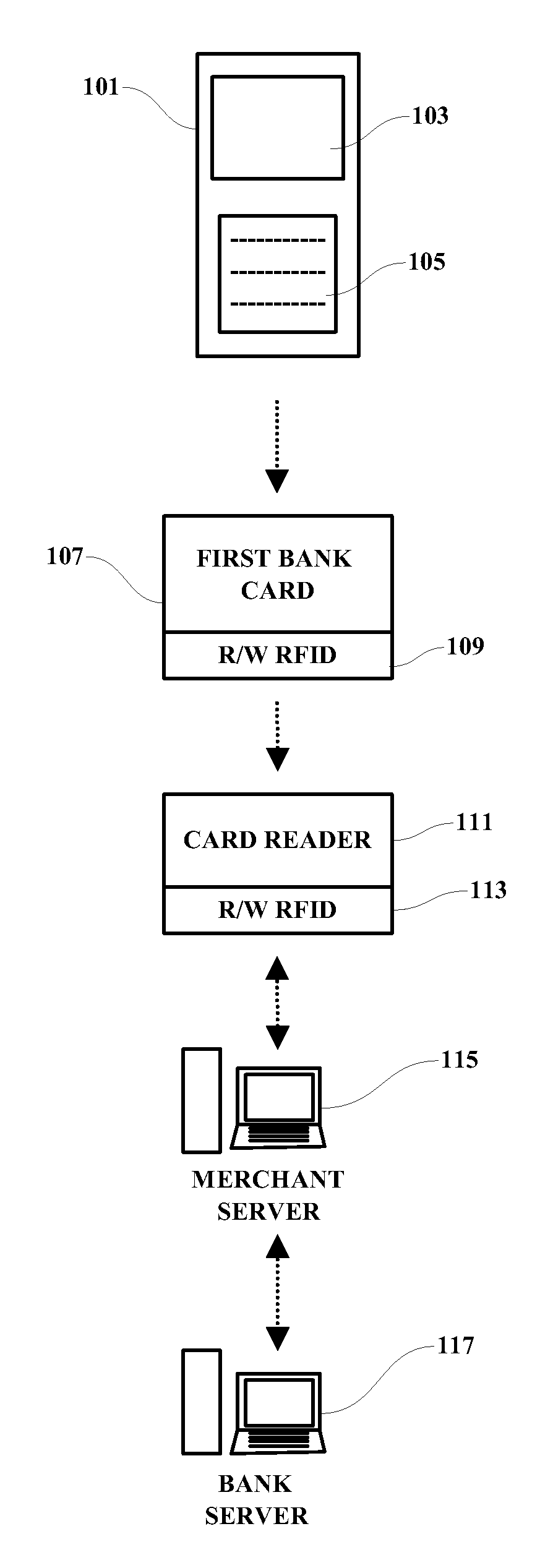
A method, programmed medium and system are provided for using a payment card with an embedded RFID device. In one example, a cellular telephone or other wireless device is used to generate a one-time password (OTP), which is then transmitted by a read-write RFID in the wireless device to the read-write RFID which is embedded within a payment card. The user's phone or other wireless device then activates the writing of the OTP to the RFID of the payment card. The payment card, with the one time password now saved in the card, is then handed to the waiter or store clerk for payment approval and / or further processing. The user's OTP is then read by the merchant's RFID reader and transmitted to an approving agency / server for approval or disapproval of the user's purchase.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com