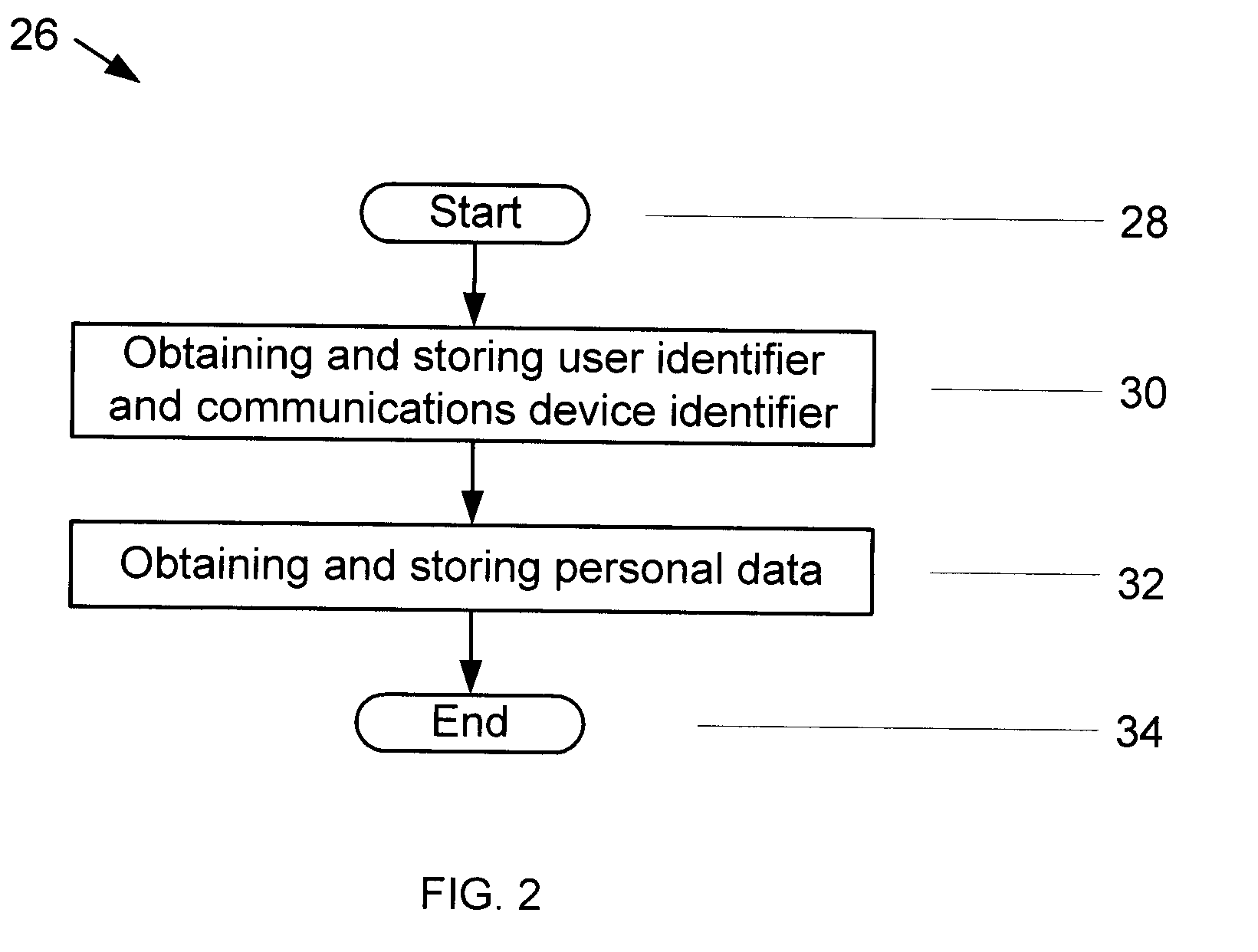
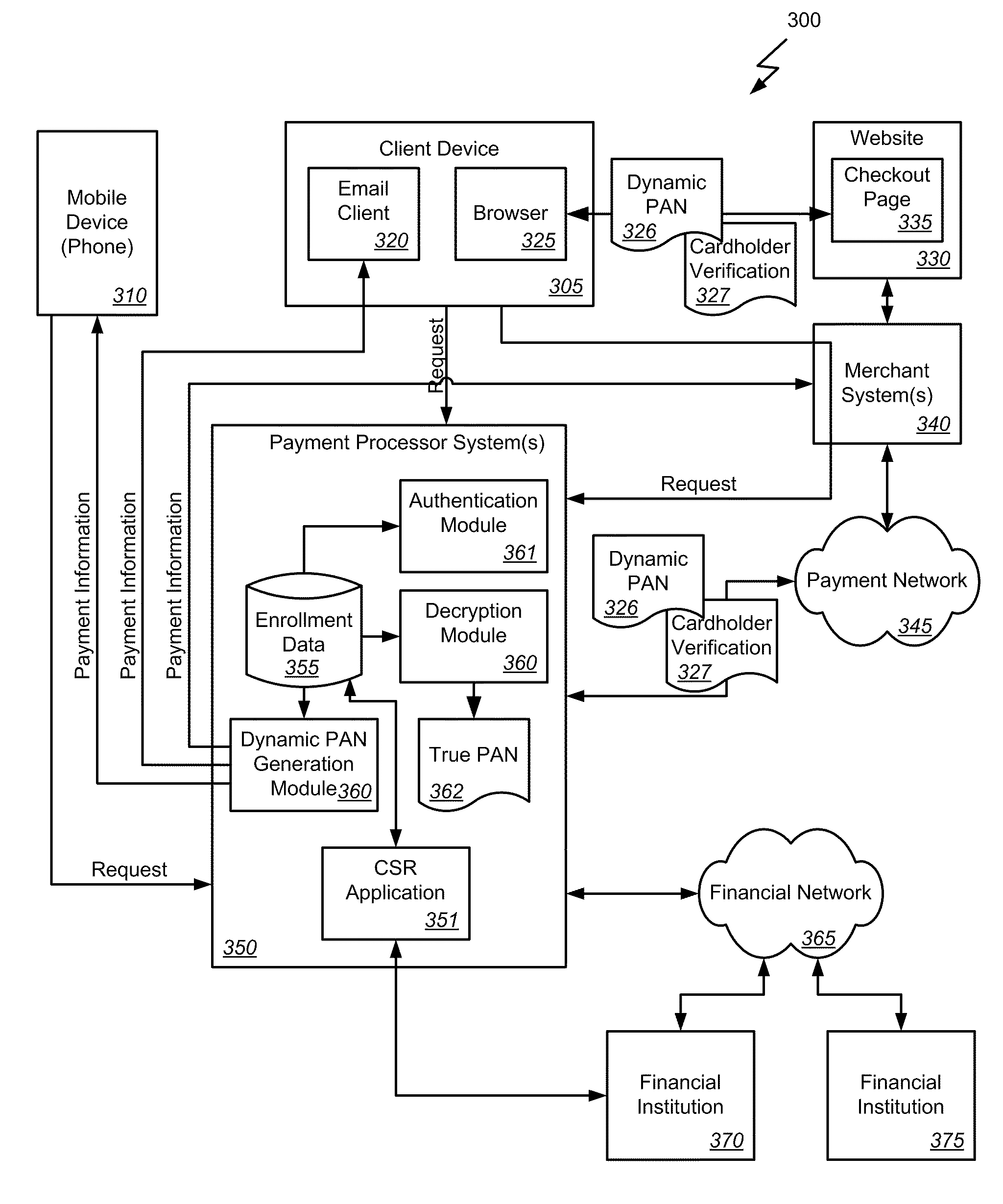
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
723 results about "One-time password" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
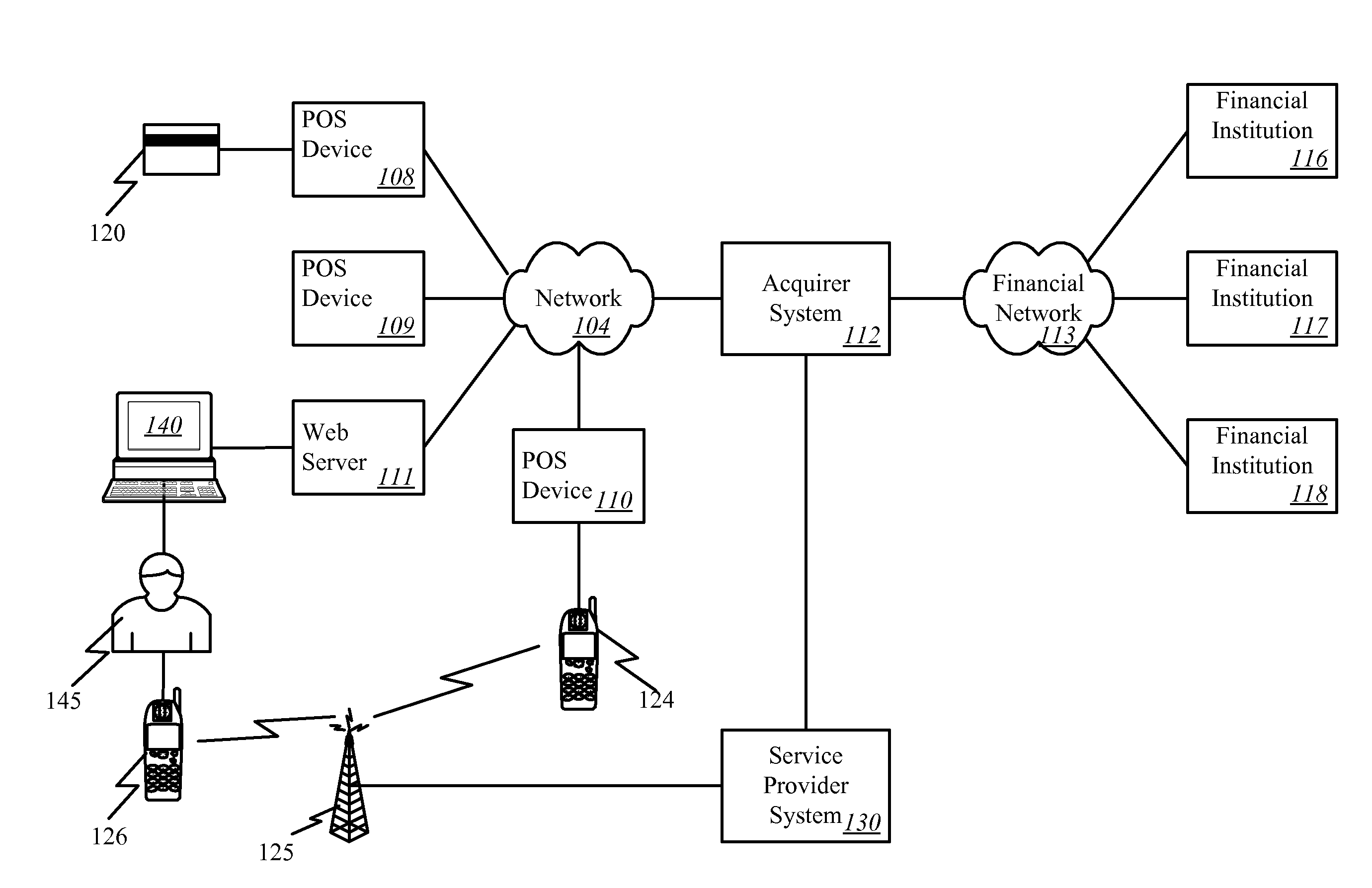
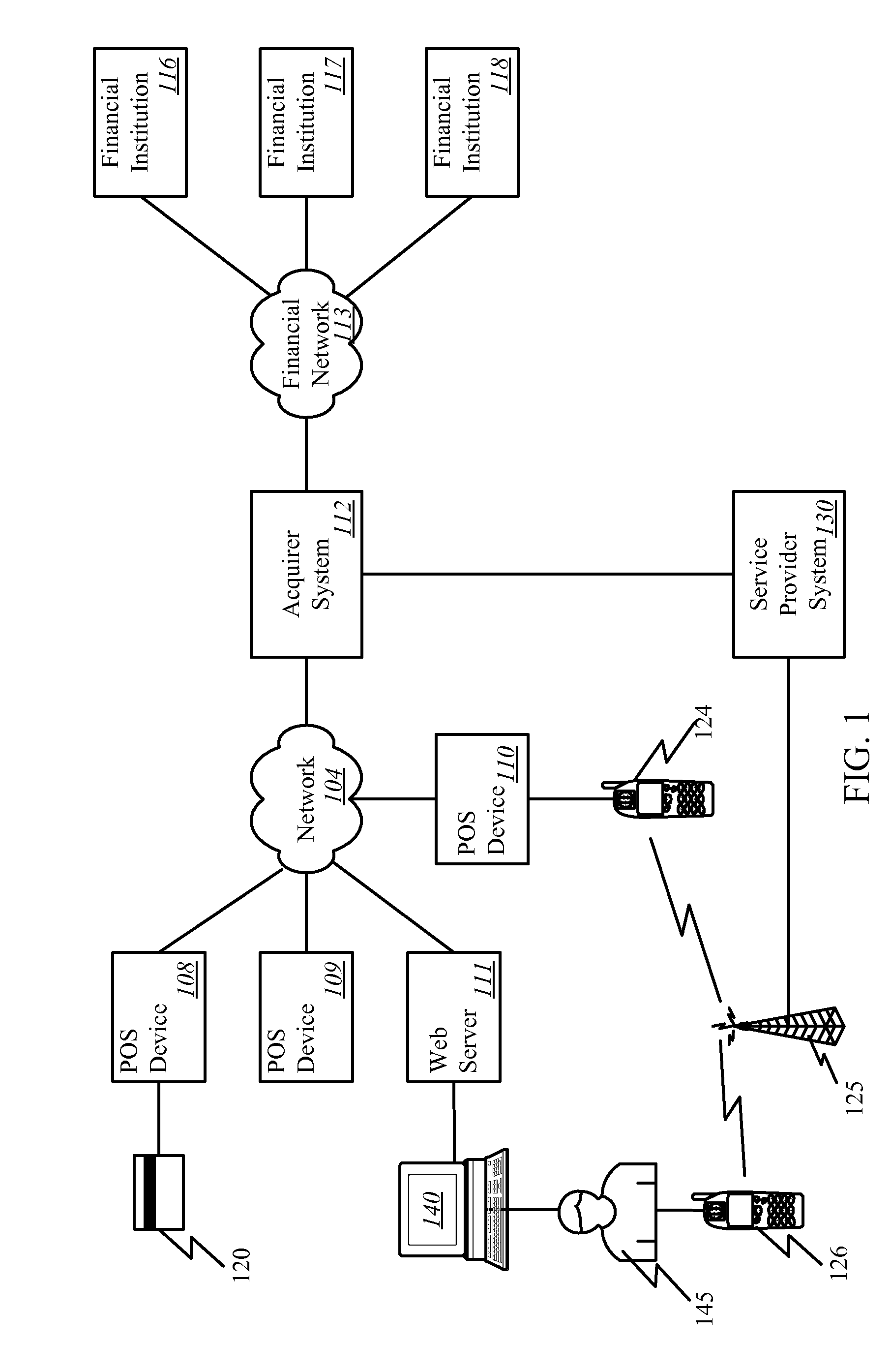
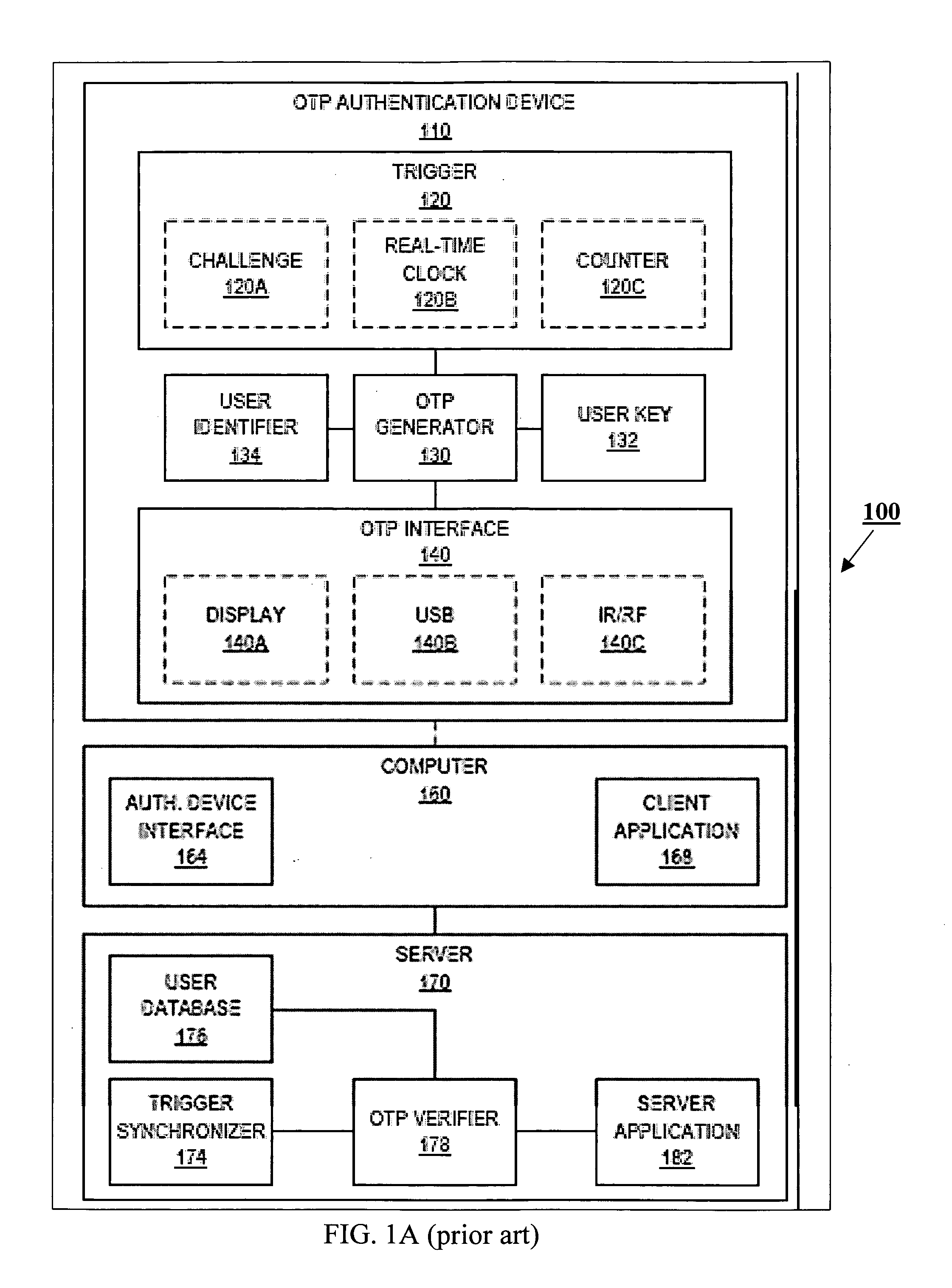
A one-time password (OTP), also known as one-time pin or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid a number of shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to something a person has (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as something a person knows (such as a PIN).
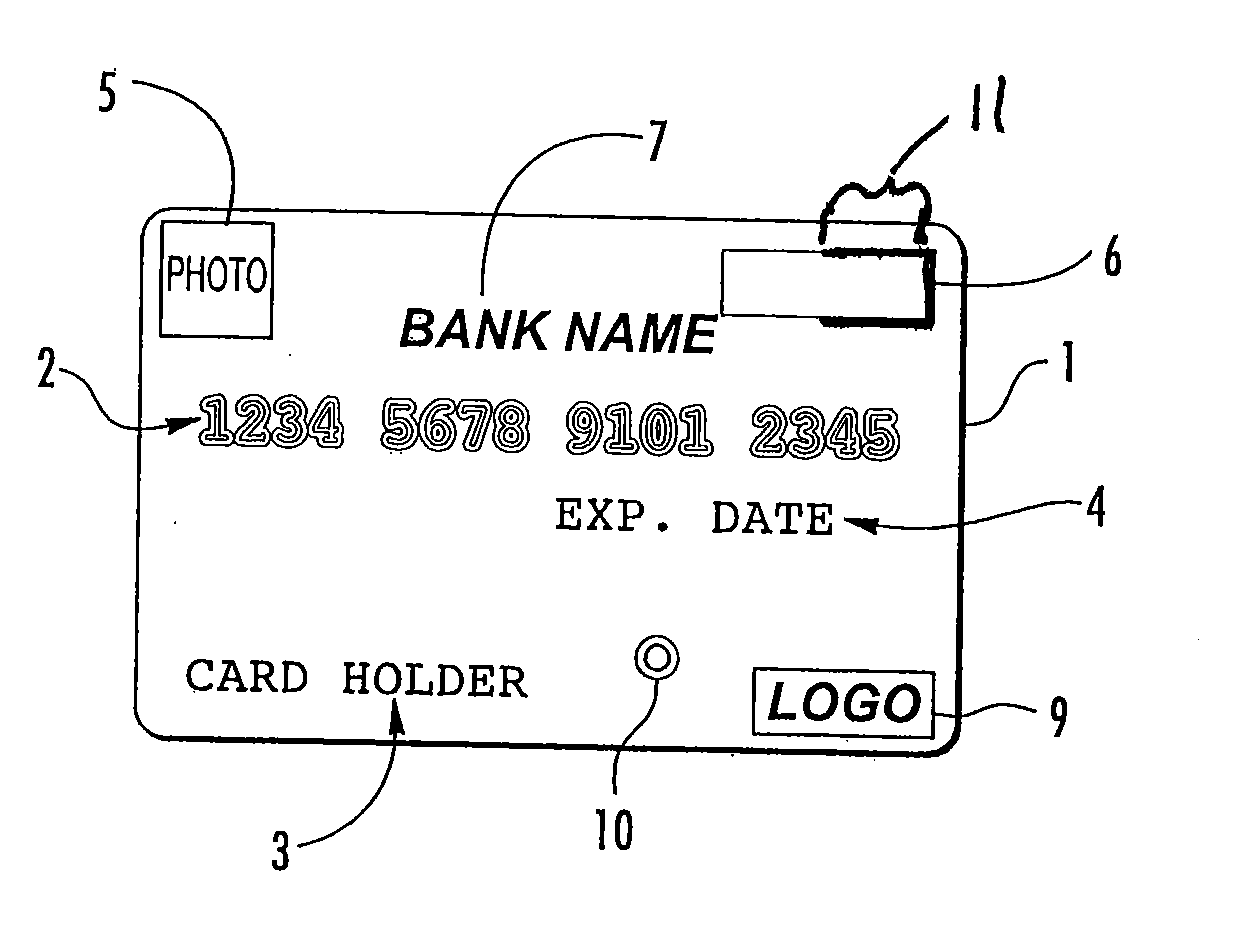
Onetime passwords for smart chip cards
ActiveUS8095113B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
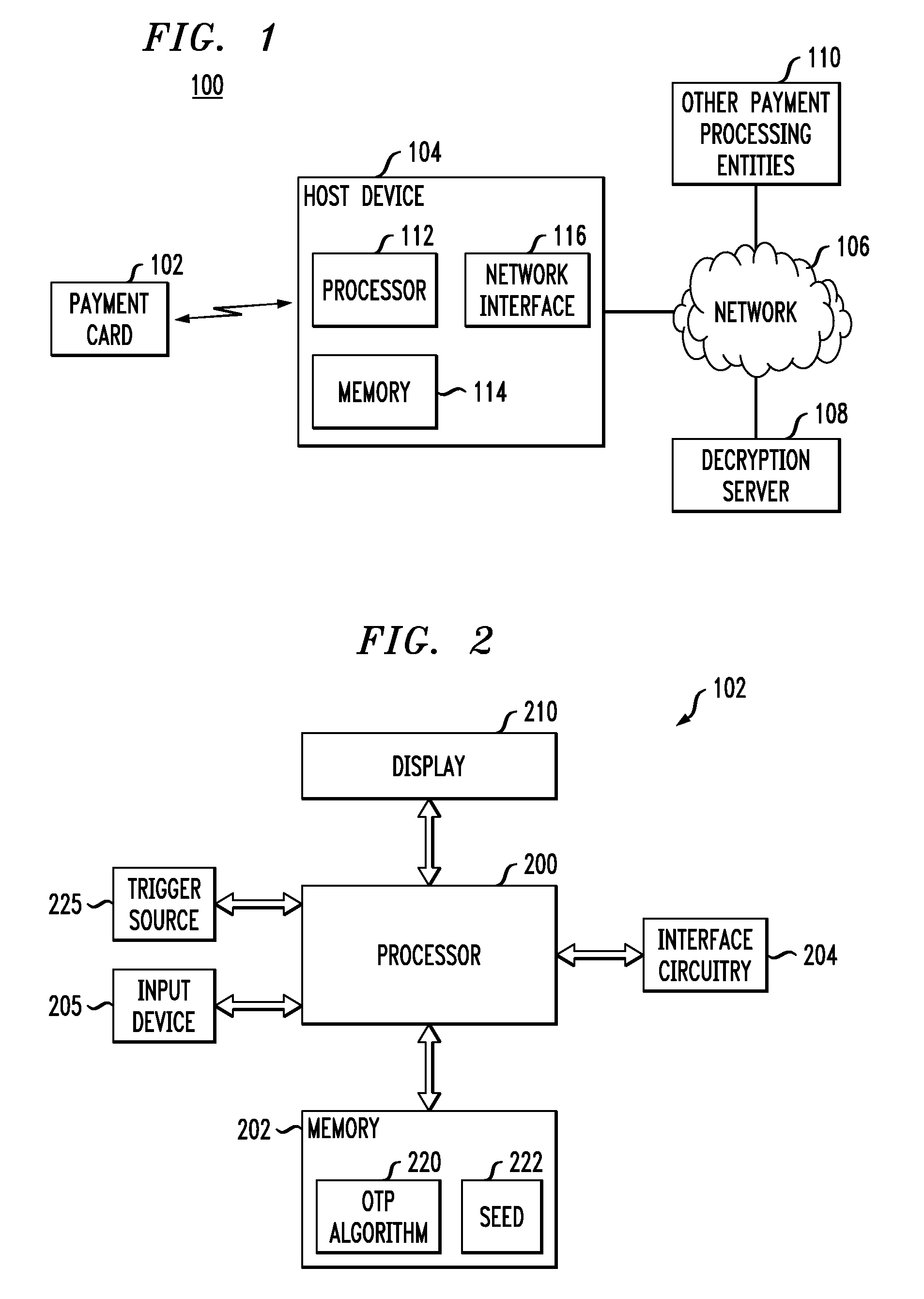
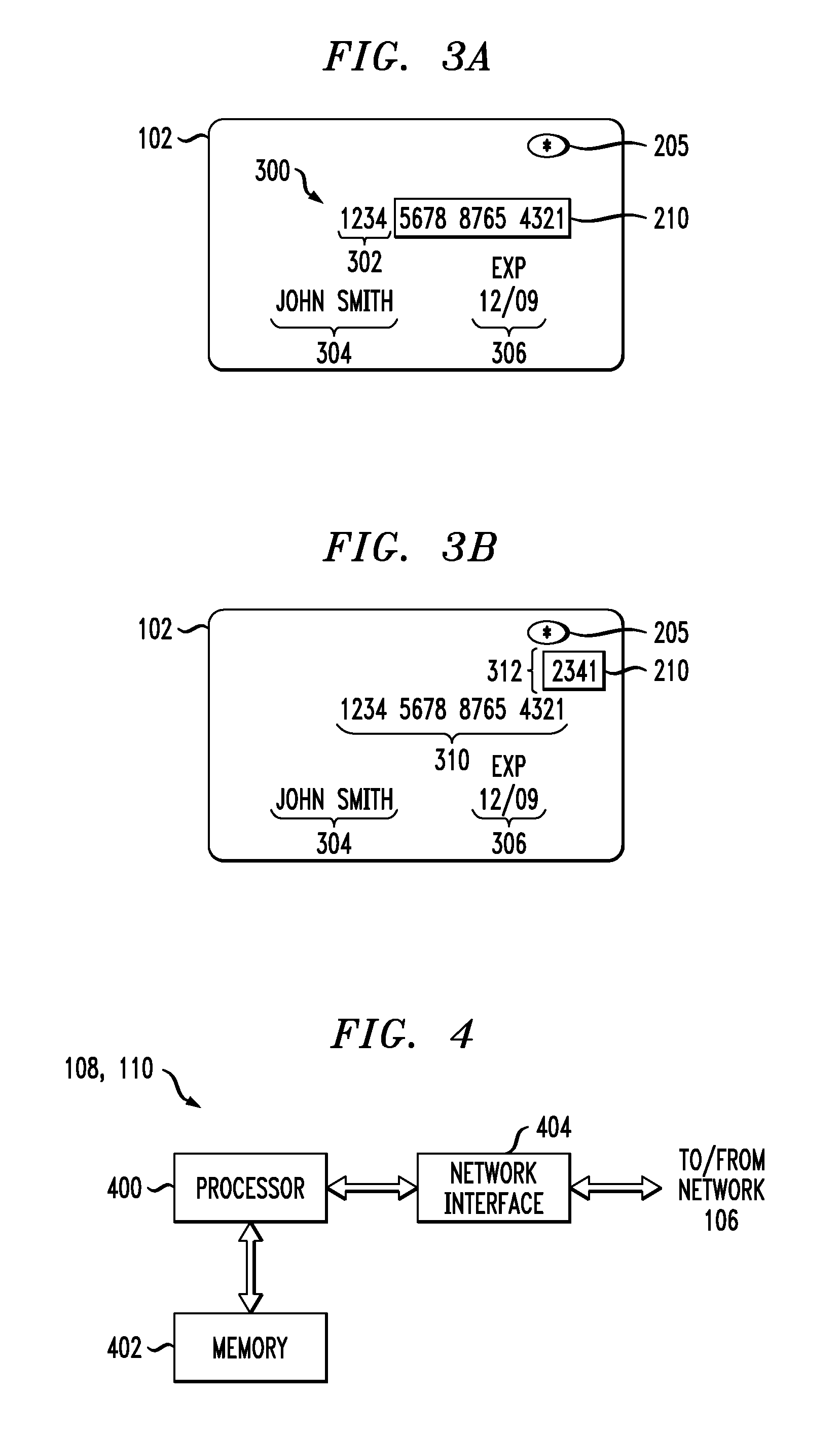
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
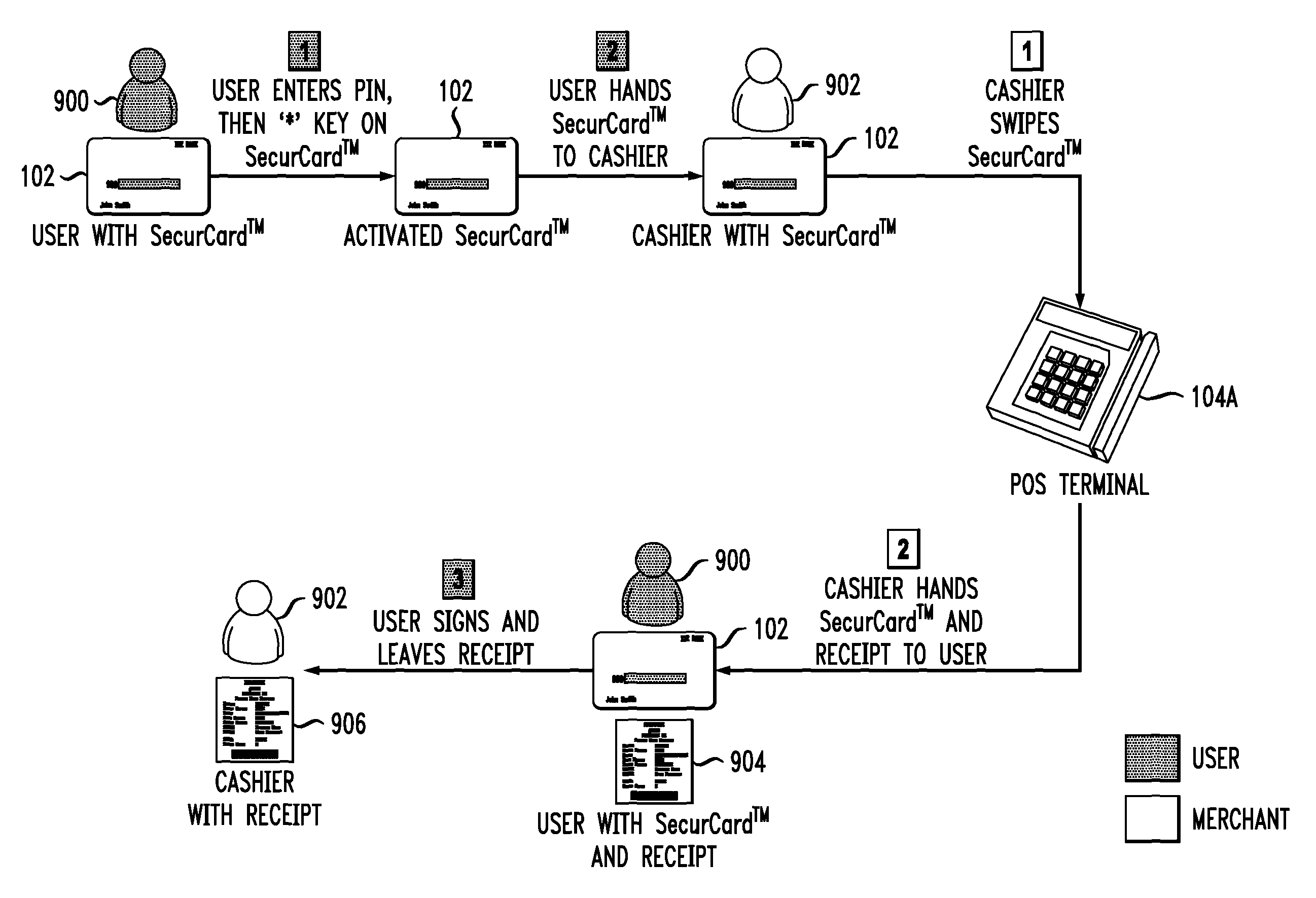
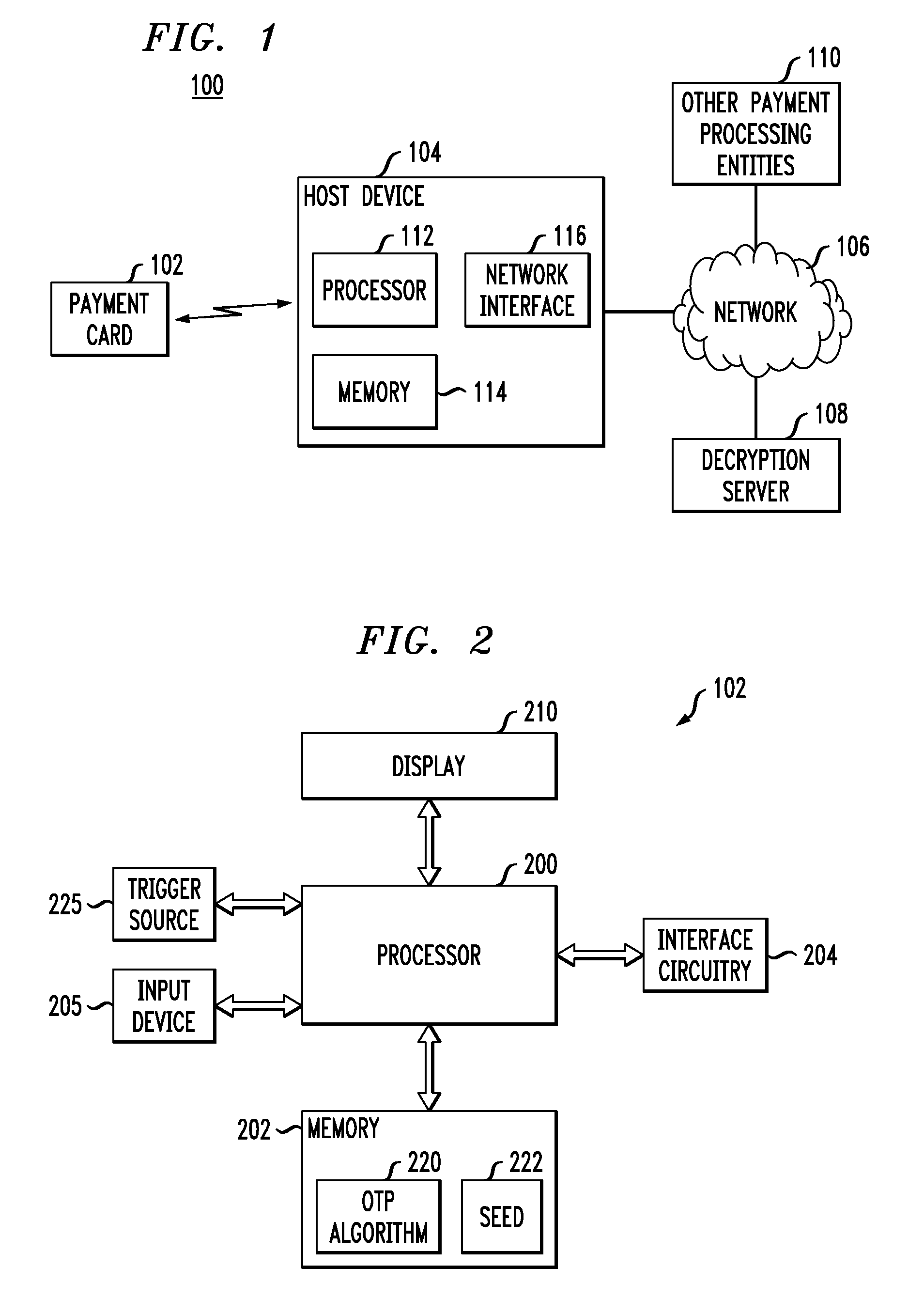
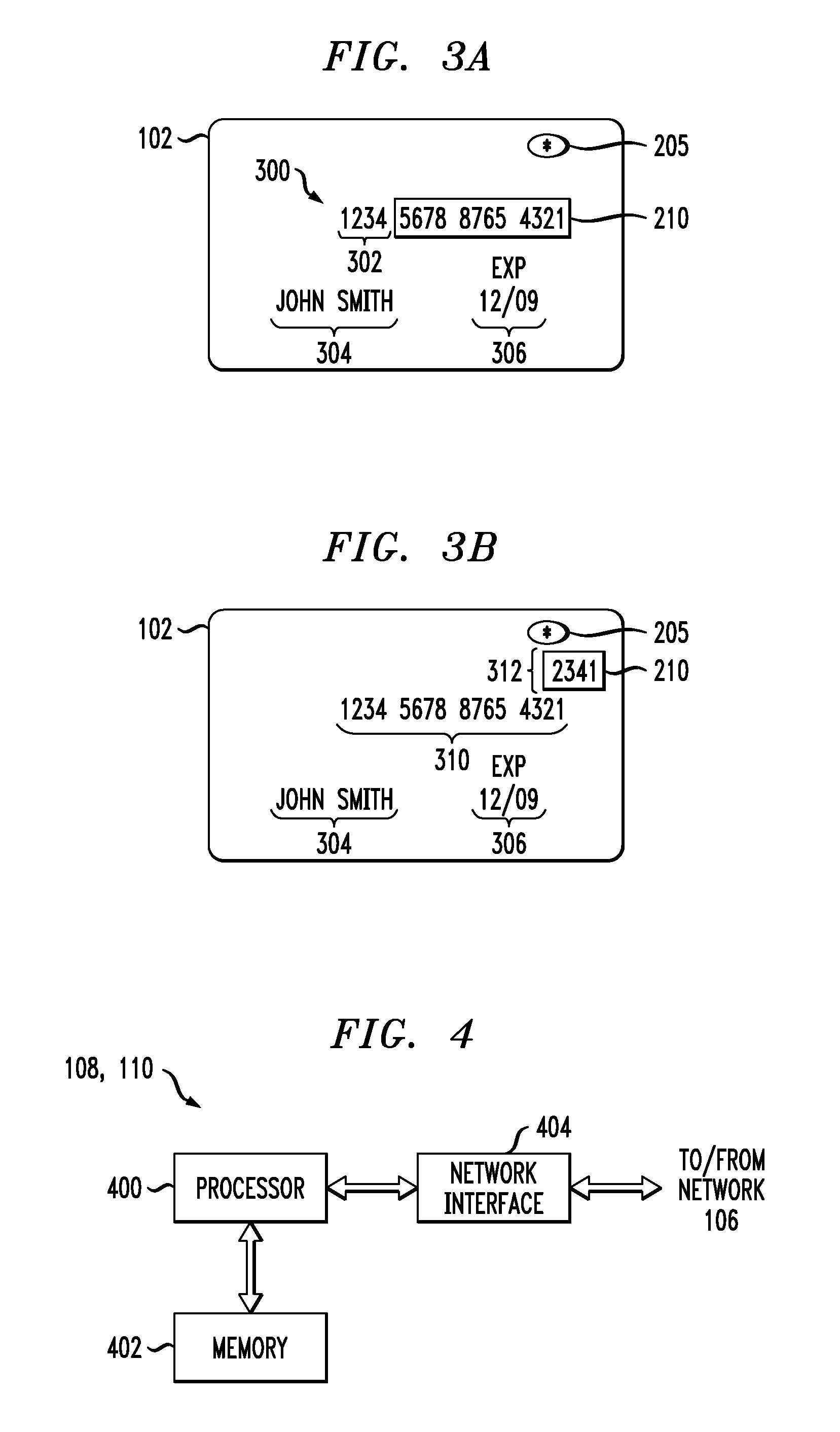
Payment Card with Dynamic Account Number
ActiveUS20090048971A1Avoid processing delaysOvercomes drawbackAcutation objectsFinanceDisplay devicePayment order
A payment card comprises a processor, a trigger source coupled to the processor, and a display for outputting at least a portion of a dynamic account number under control of the processor responsive to the trigger source. The dynamic account number is determined based at least in part on a seed stored in the payment card and an output of the trigger source. In an illustrative embodiment, the dynamic account number is generated utilizing a time-based or event-based one-time password algorithm. For example, in a time-based embodiment, the trigger source may comprise a time of day clock, with the dynamic account number being determined based at least in part on the seed and a current value of the time of day clock. In an event-based embodiment, the trigger source may comprise an event counter, with the dynamic account number being determined based at least in part on the seed and a current value of the event counter.
Owner:EMC IP HLDG CO LLC
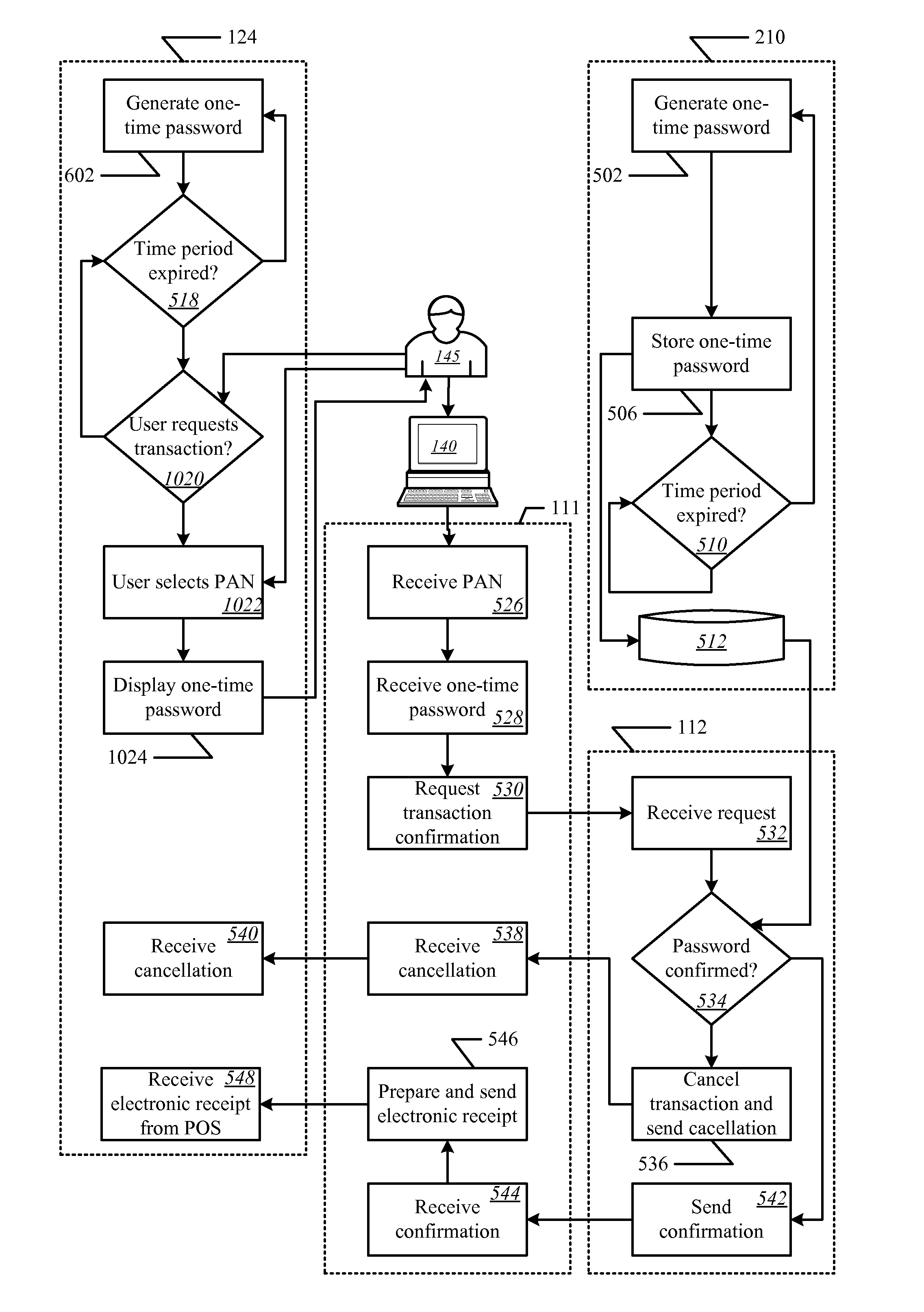
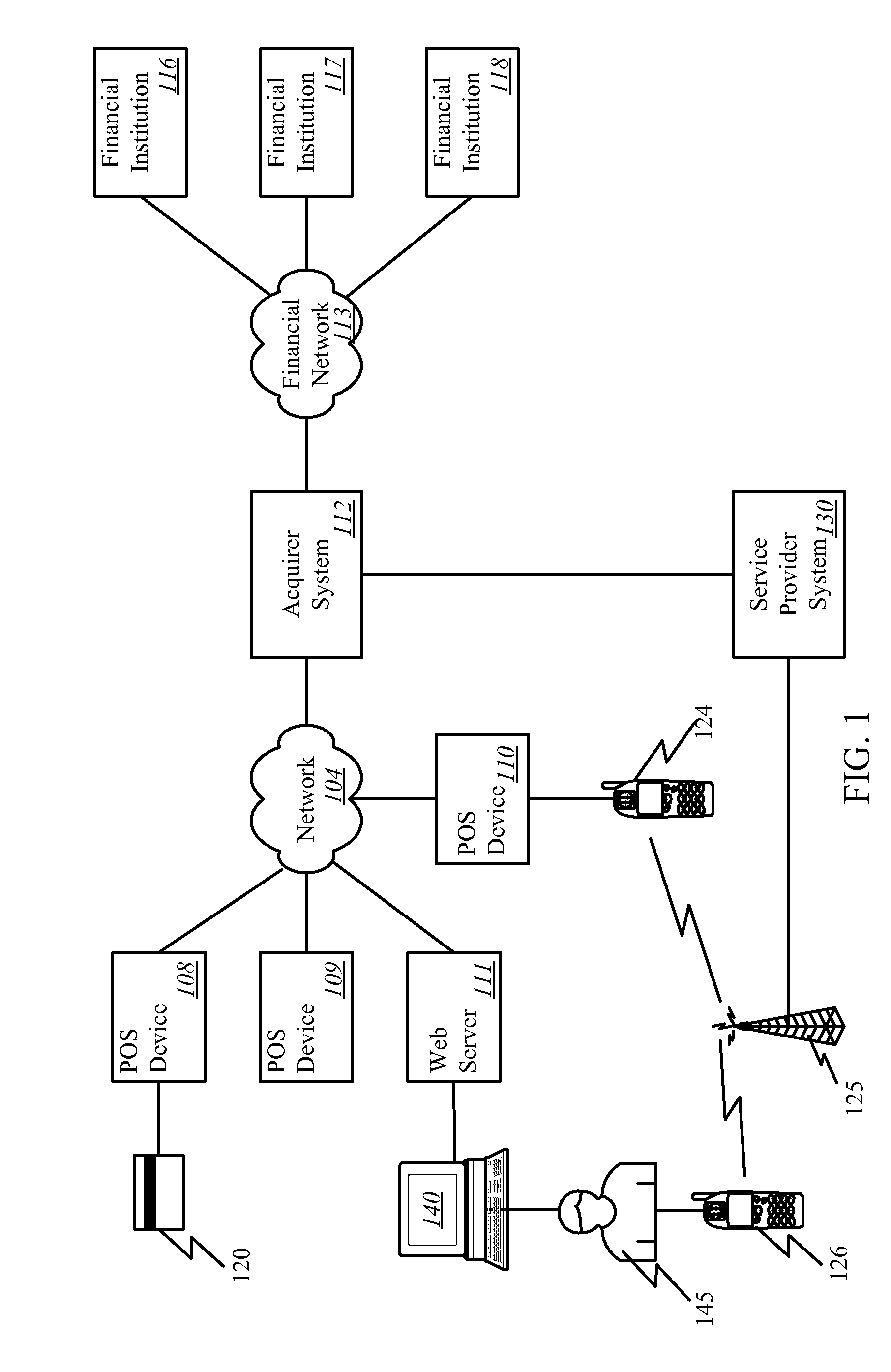
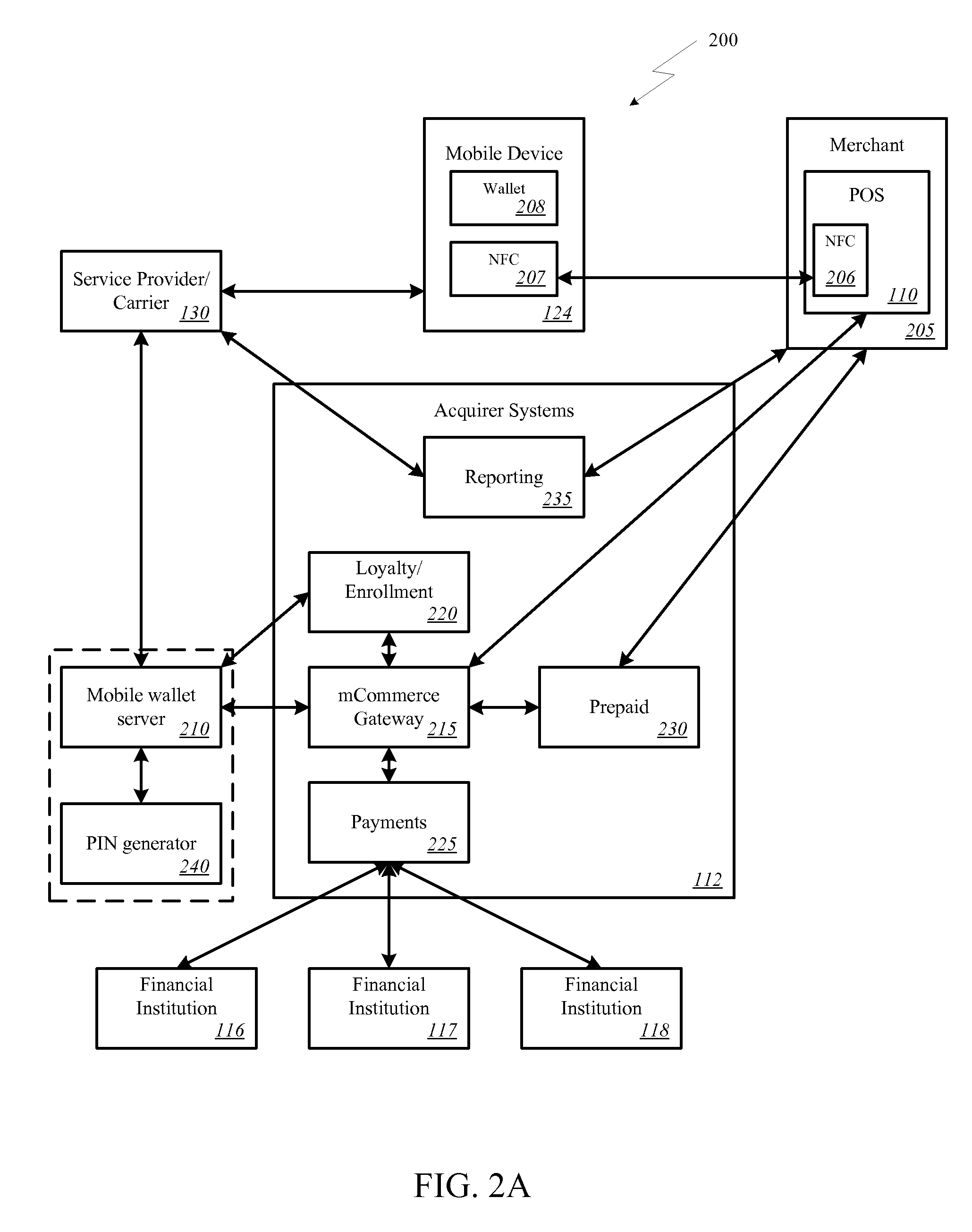
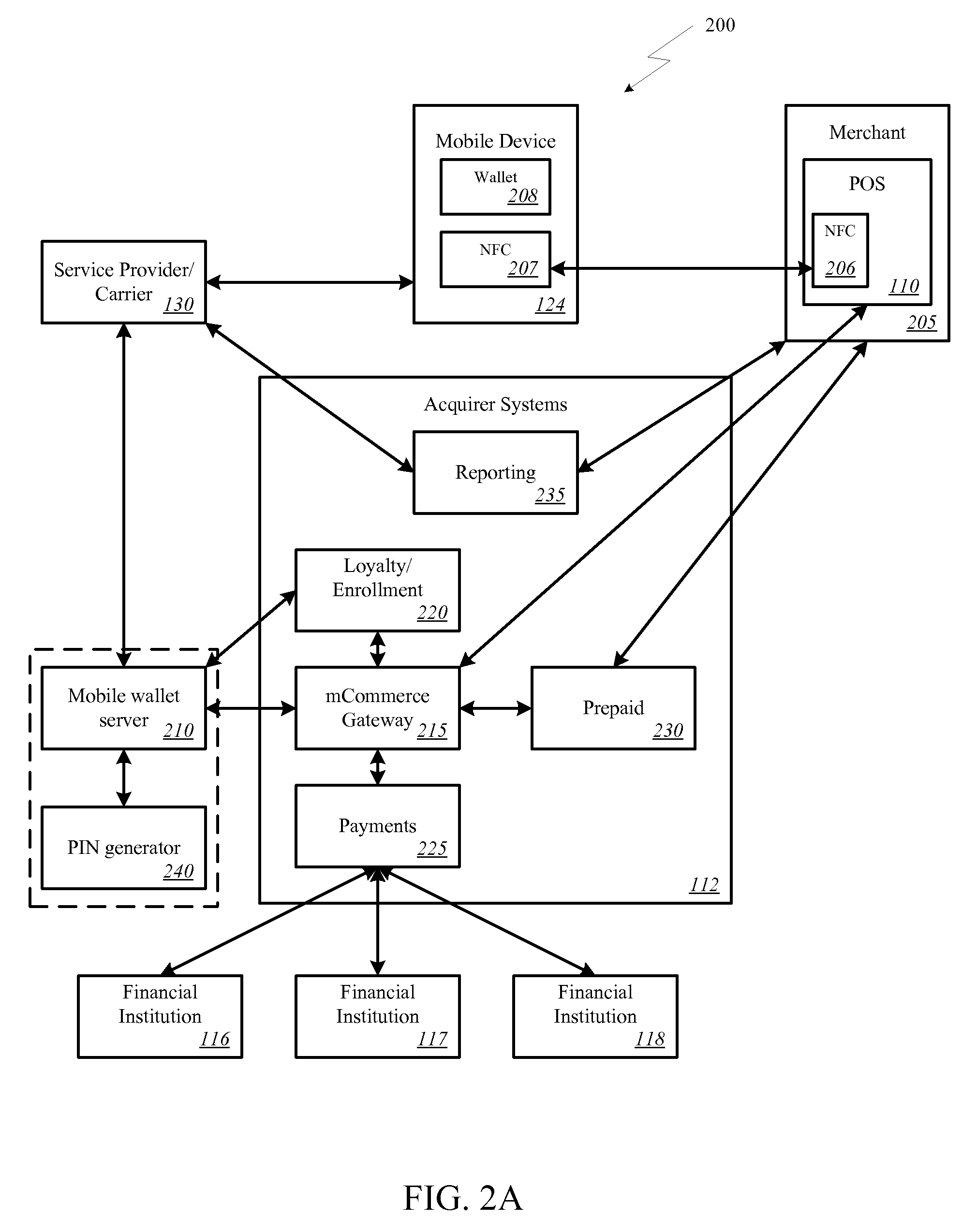
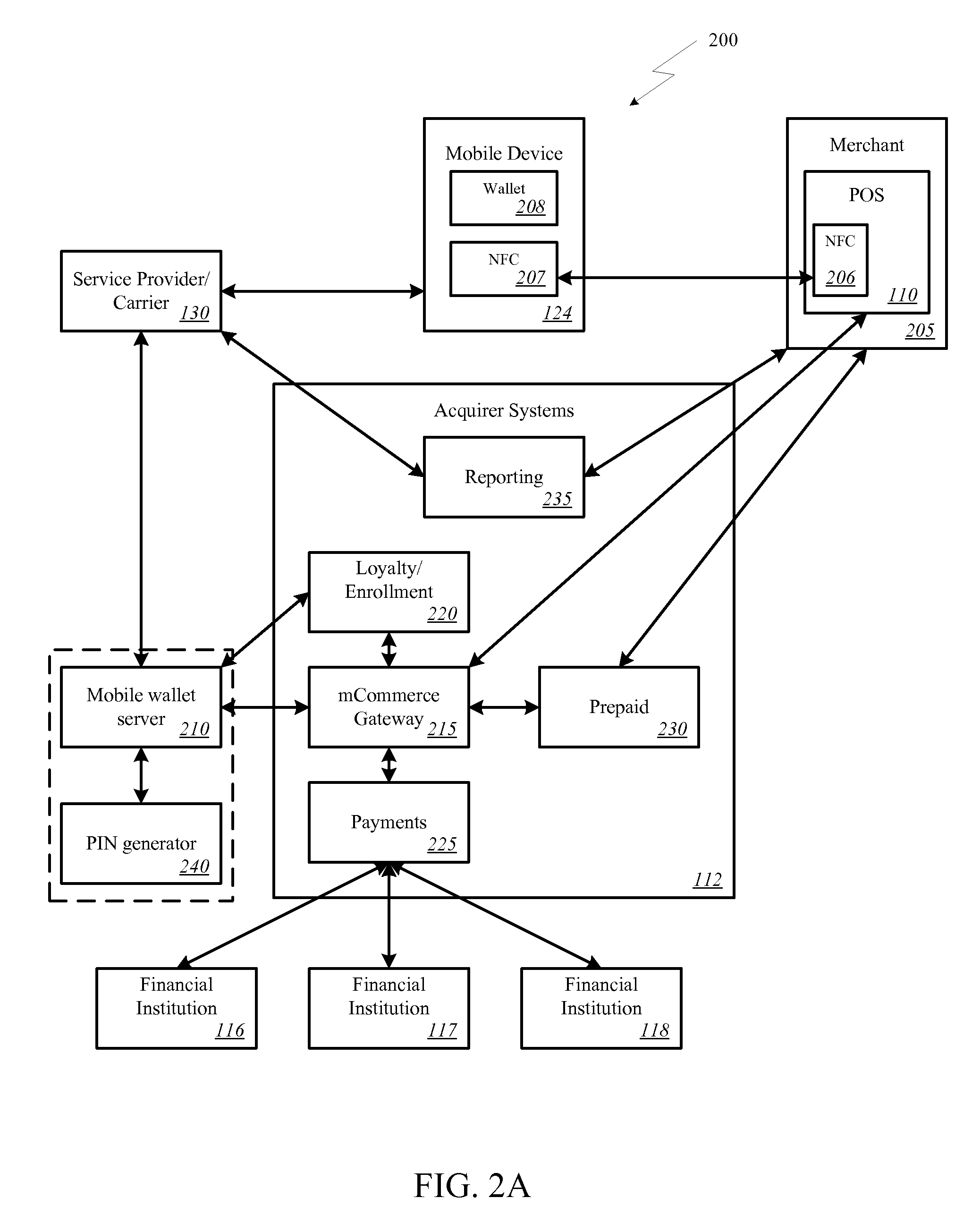
Onetime Passwords For Mobile Wallets
ActiveUS20090104888A1Near-field transmissionUnauthorised/fraudulent call preventionNetworked systemOne-time password
A mobile wallet and network system using onetime passwords for authentication is disclosed according to one embodiment of the invention. A onetime password may be generated at a mobile wallet server and transmitted to the mobile device. The onetime password may then be used to authenticate the user of the mobile wallet when completing a transaction. Authentication may require entry of the onetime password and confirmation that the onetime password entered matches the onetime password sent by the mobile wallet server. In other embodiments of the invention, a mobile wallet and a mobile wallet server are in sync and each generate the same onetime password at the same time. These onetime passwords may then be used to authenticate the user of the mobile wallet.
Owner:FIRST DATA
Onetime passwords for smart chip cards
ActiveUS20090200371A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
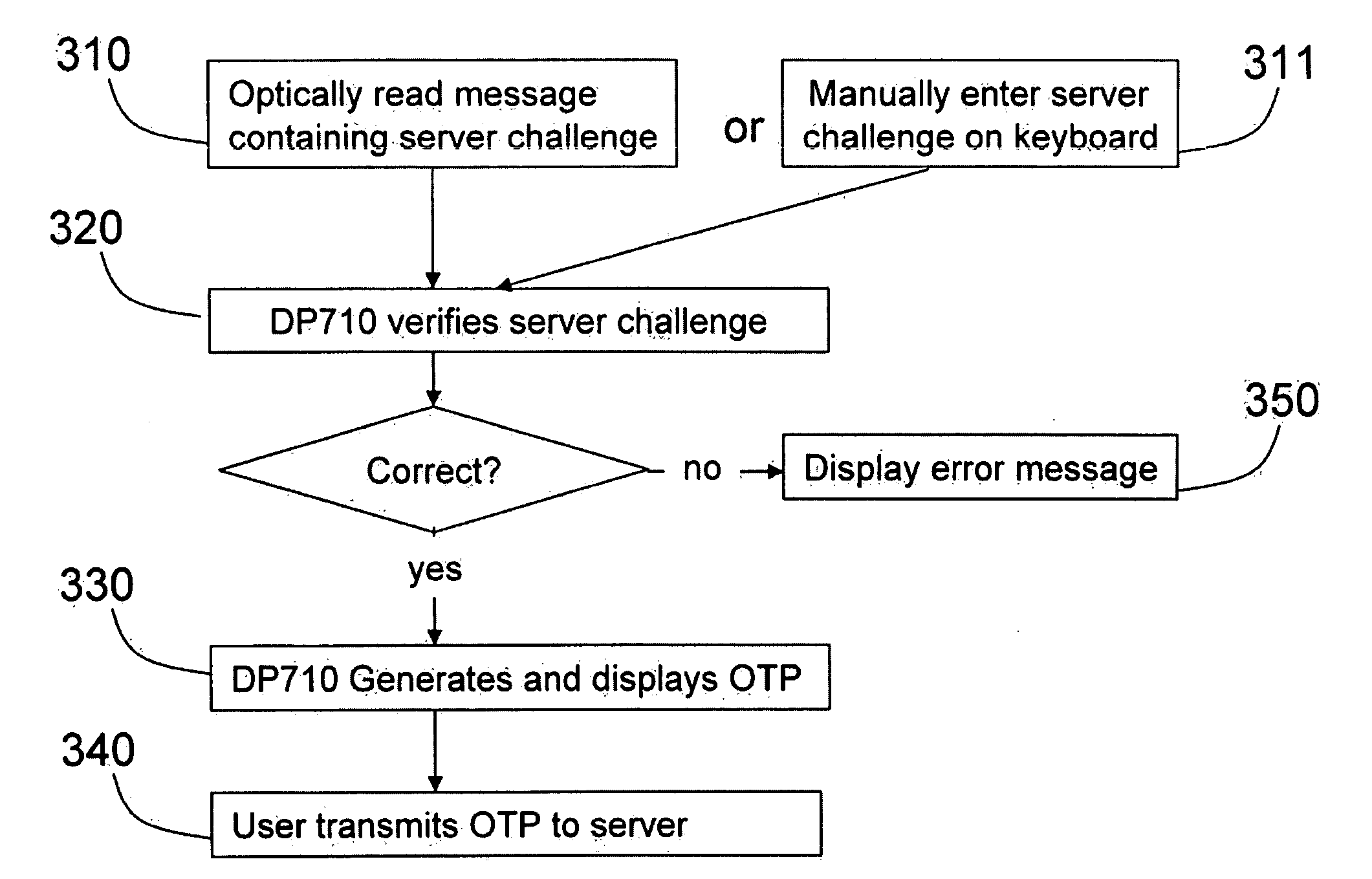
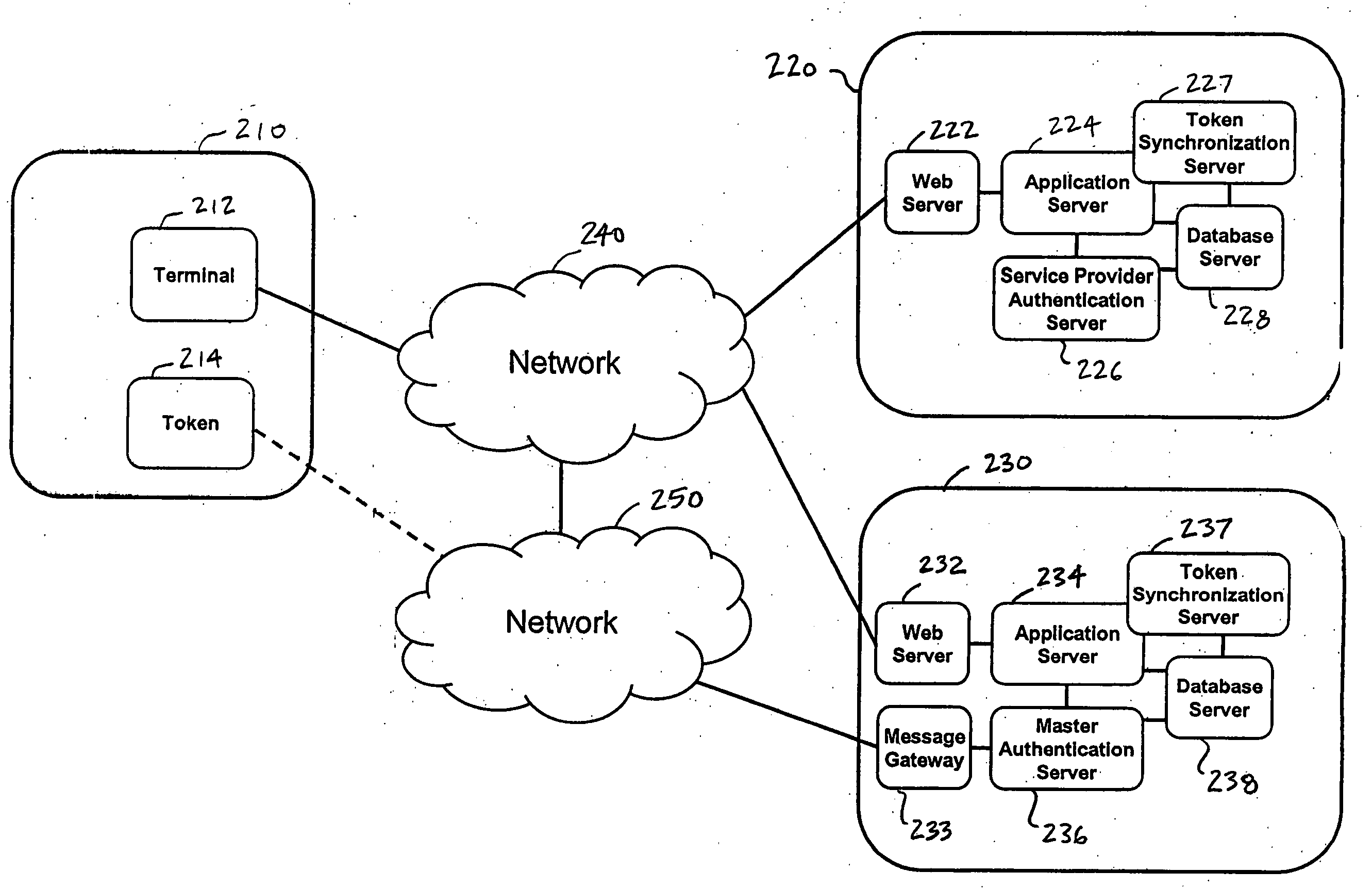
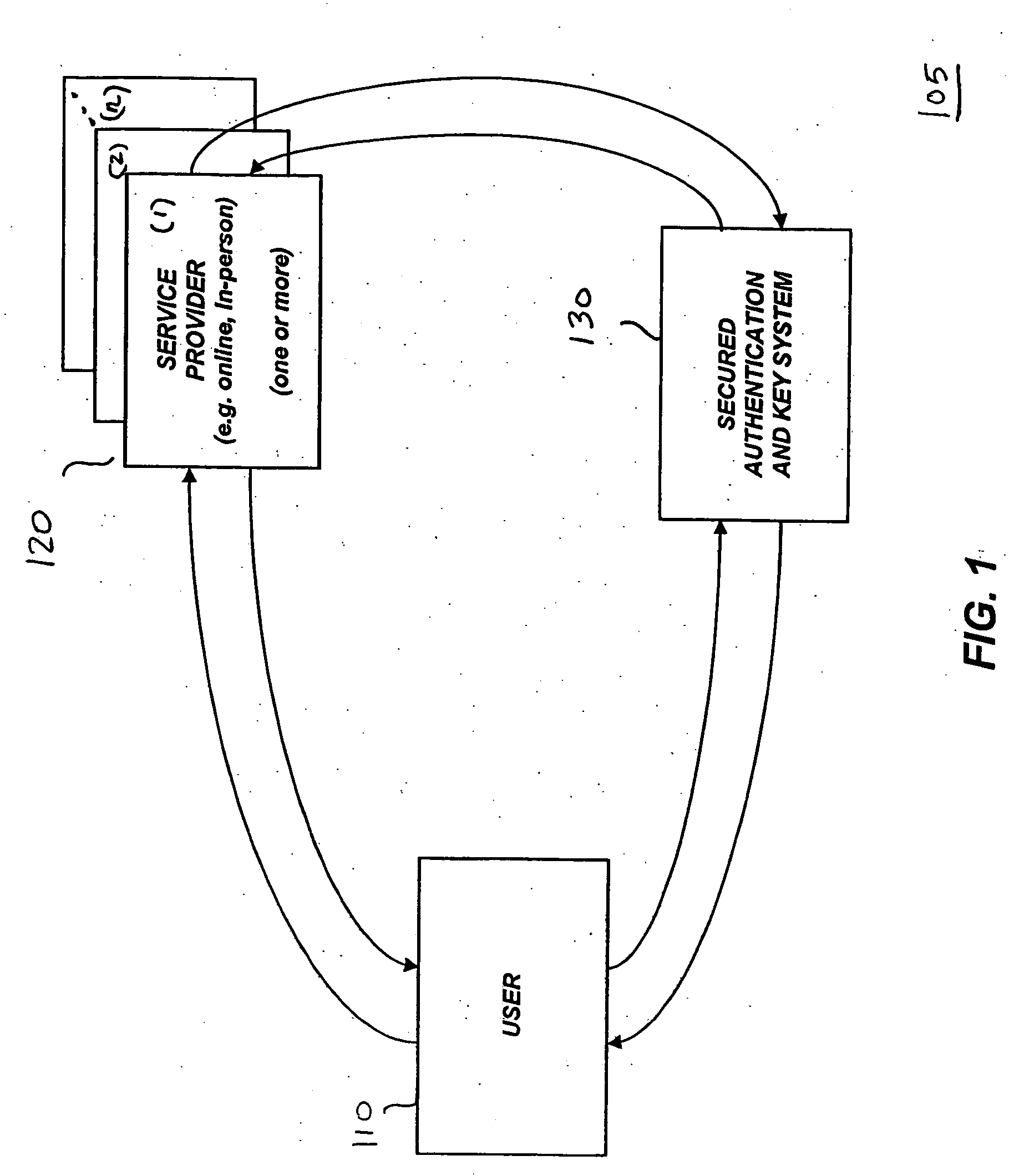
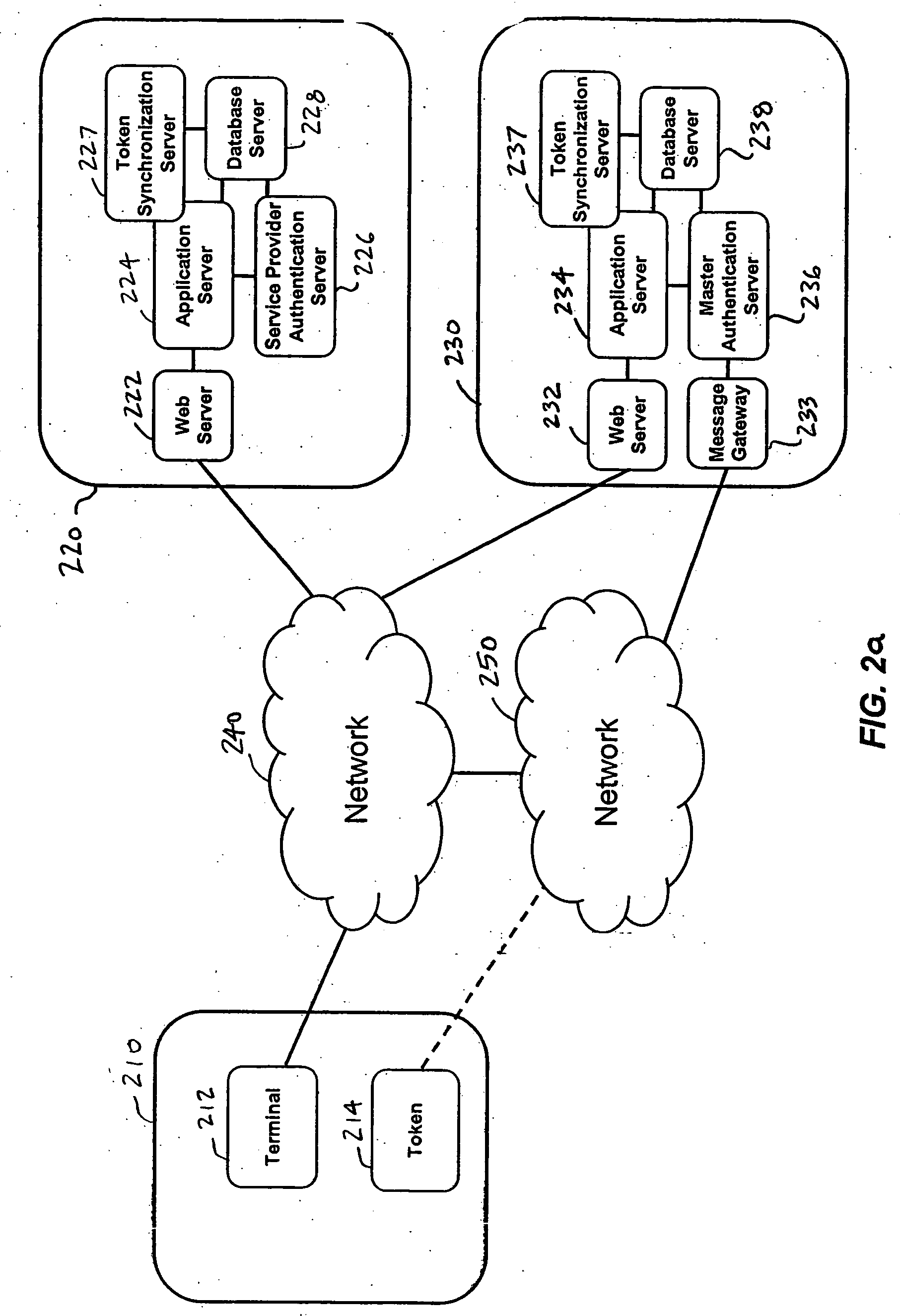
Single one-time password token with single PIN for access to multiple providers
InactiveUS20070130463A1Centralized managementEasy to useUser identity/authority verificationDigital data authenticationThird partyPersonal identification number
A system and a method are disclosed that includes a first party with a terminal and a one-time password token, one or more second parties, each with a host application system and a service provider authentication server, and a third party with a host application system and a master authentication server. The first party uses a single one-time password token with a single personal identification number (PIN) to access the one or more second parties. A third party issues the token to the first party and synchronizes token secrets and parameters with the one or more second parties. This offloads token management from the second parties and allows the second parties to directly authenticate the first party. The authentication of the first party by the second party does not involve the third party.
Owner:BONCLE
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS8763097B2Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
Owner:GCOM IP LLC
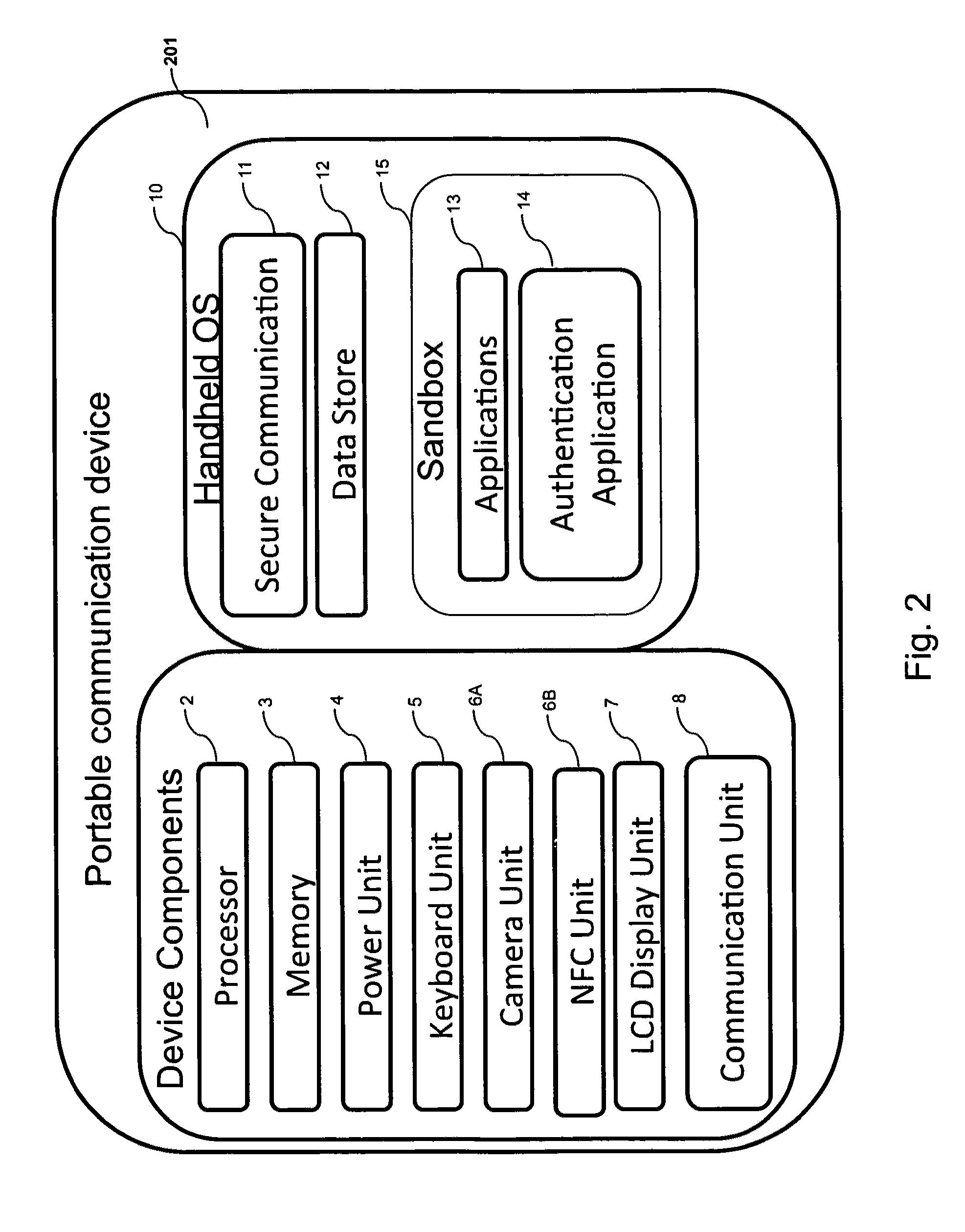
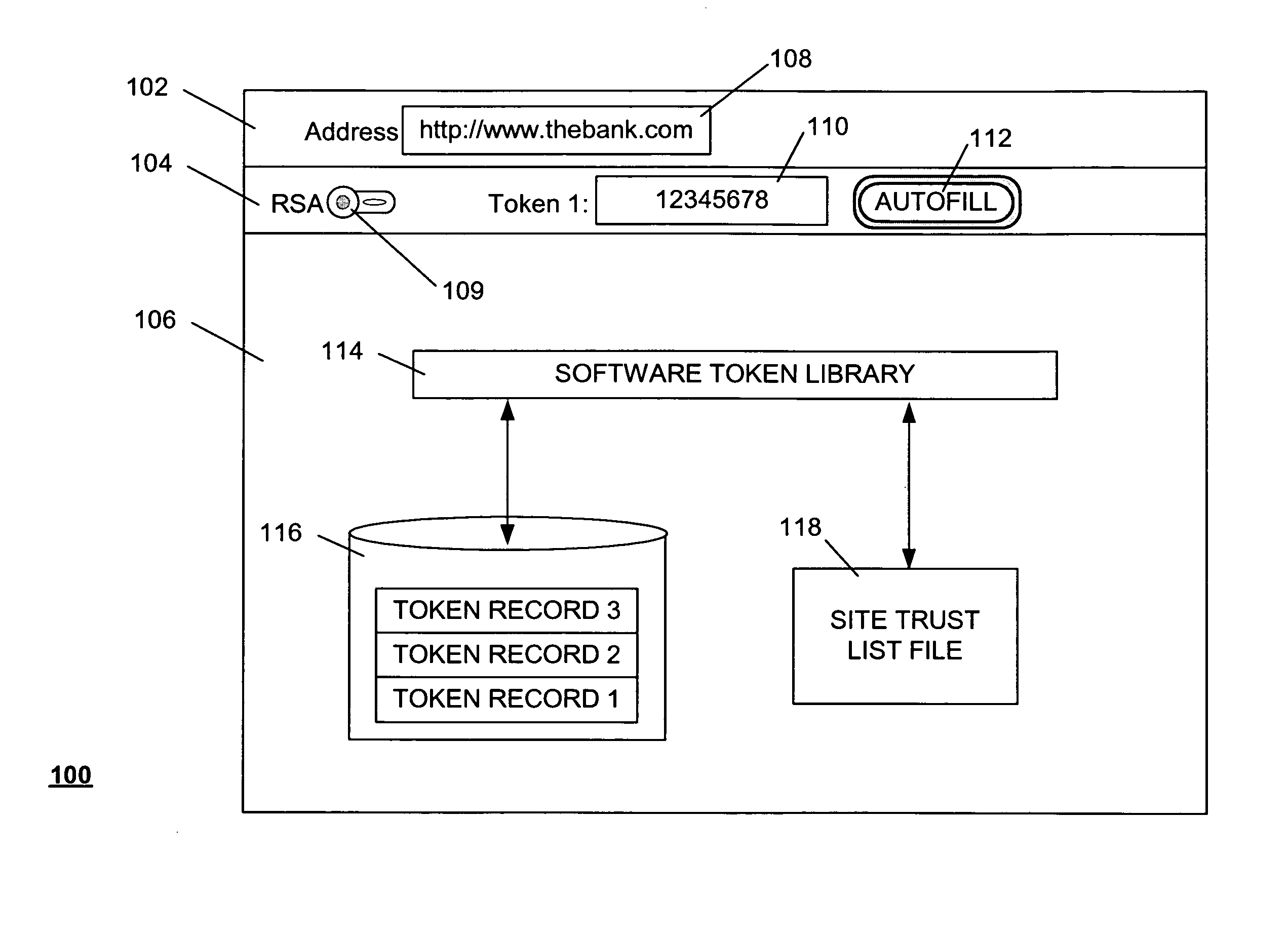
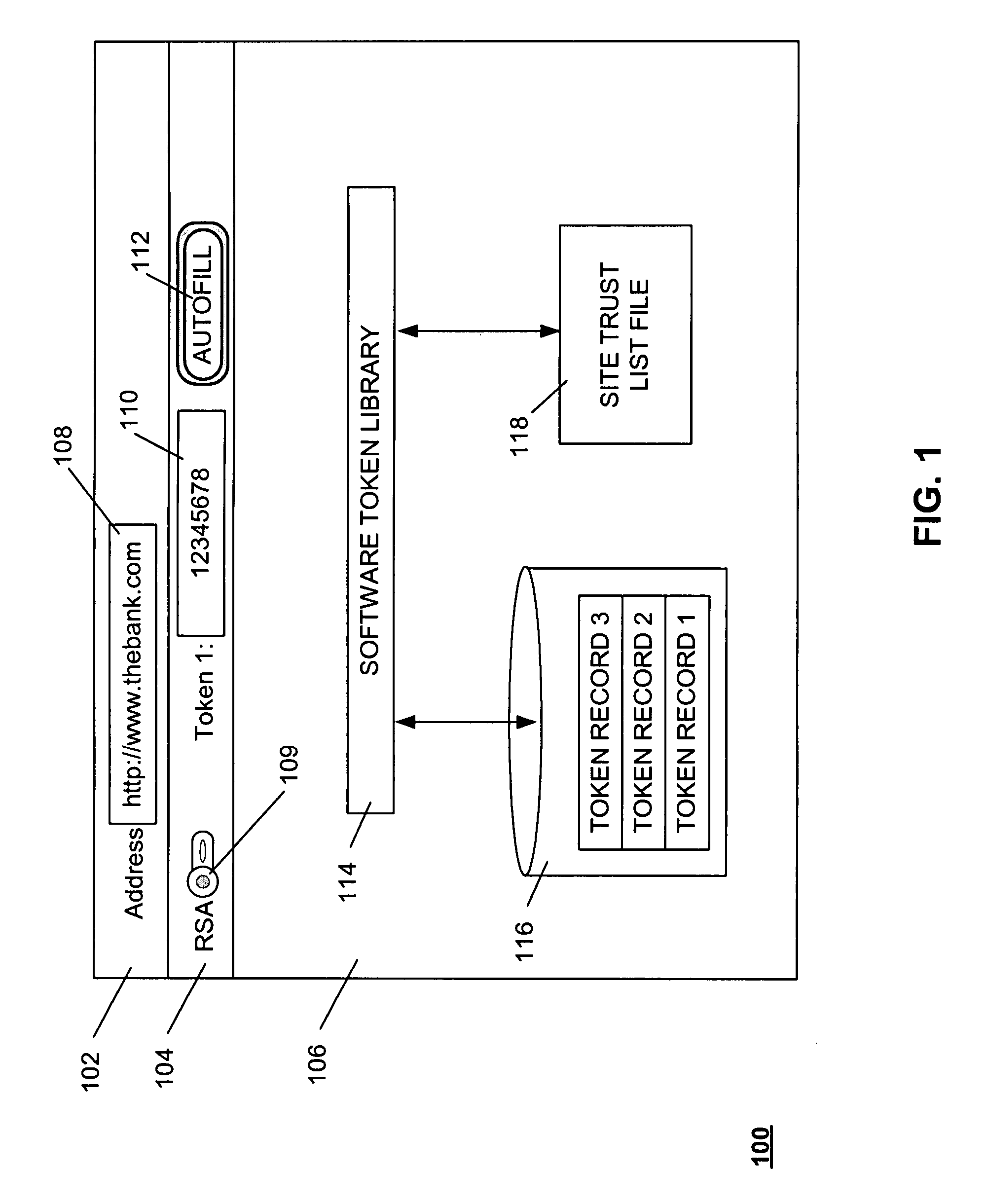
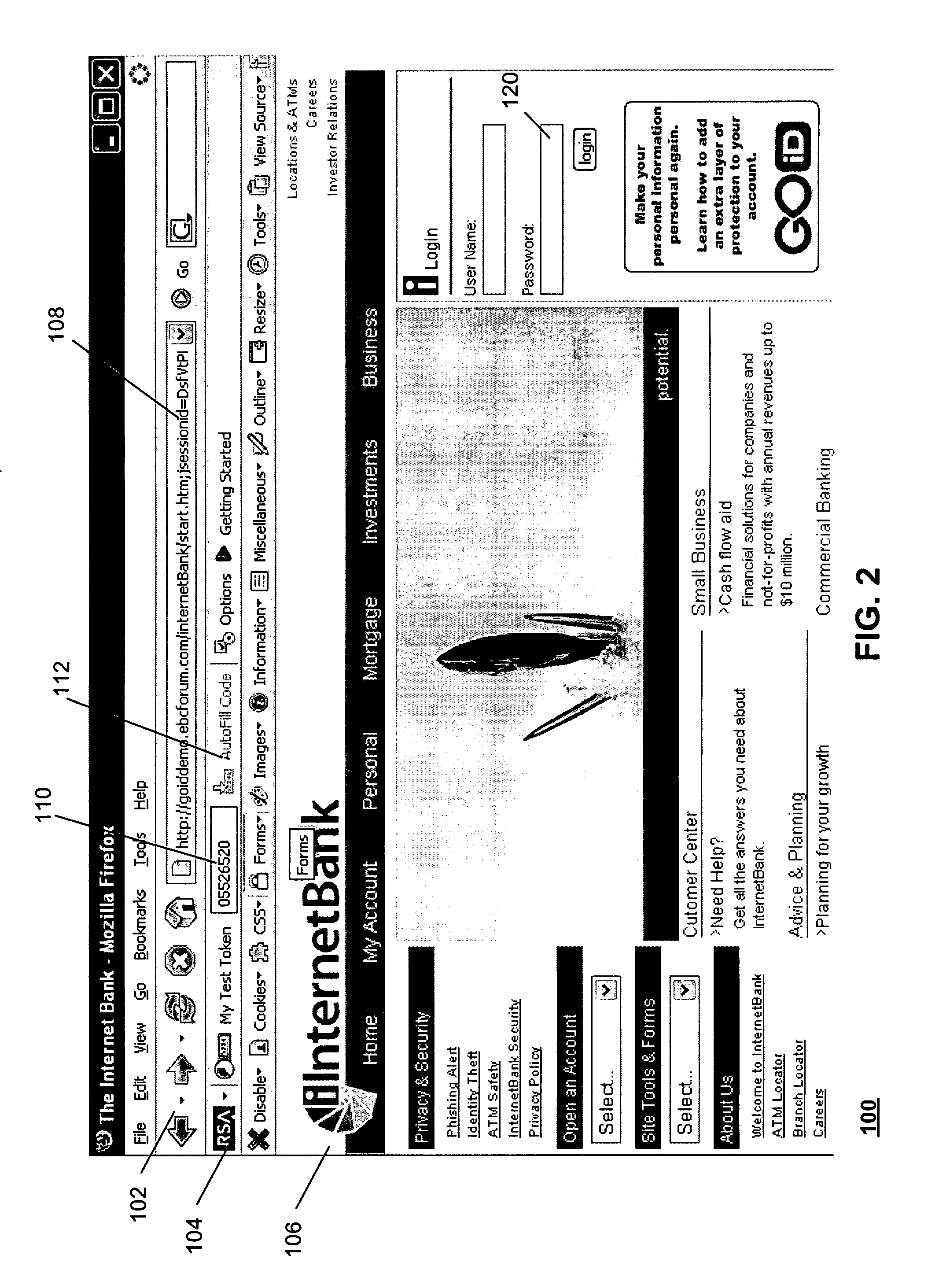
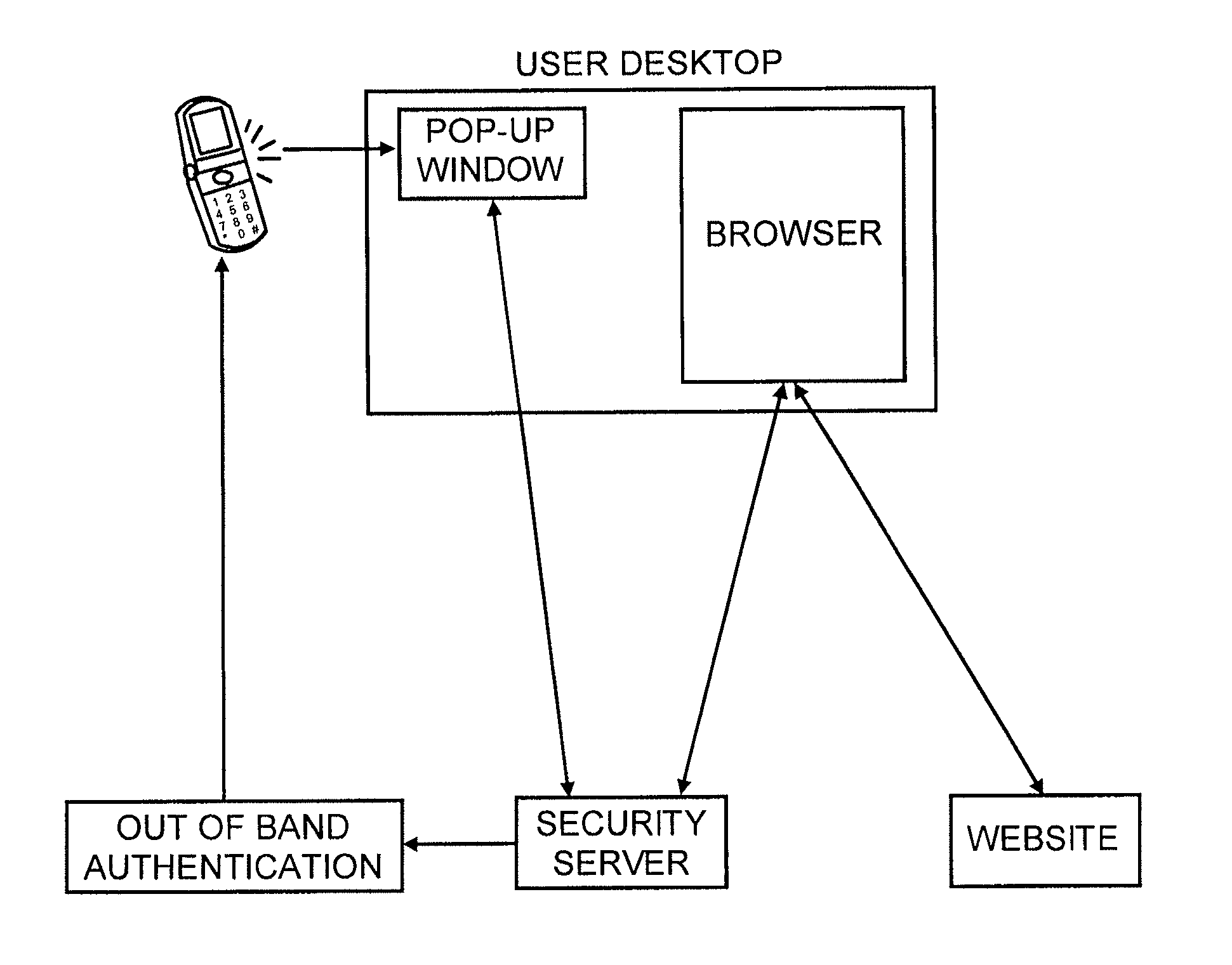
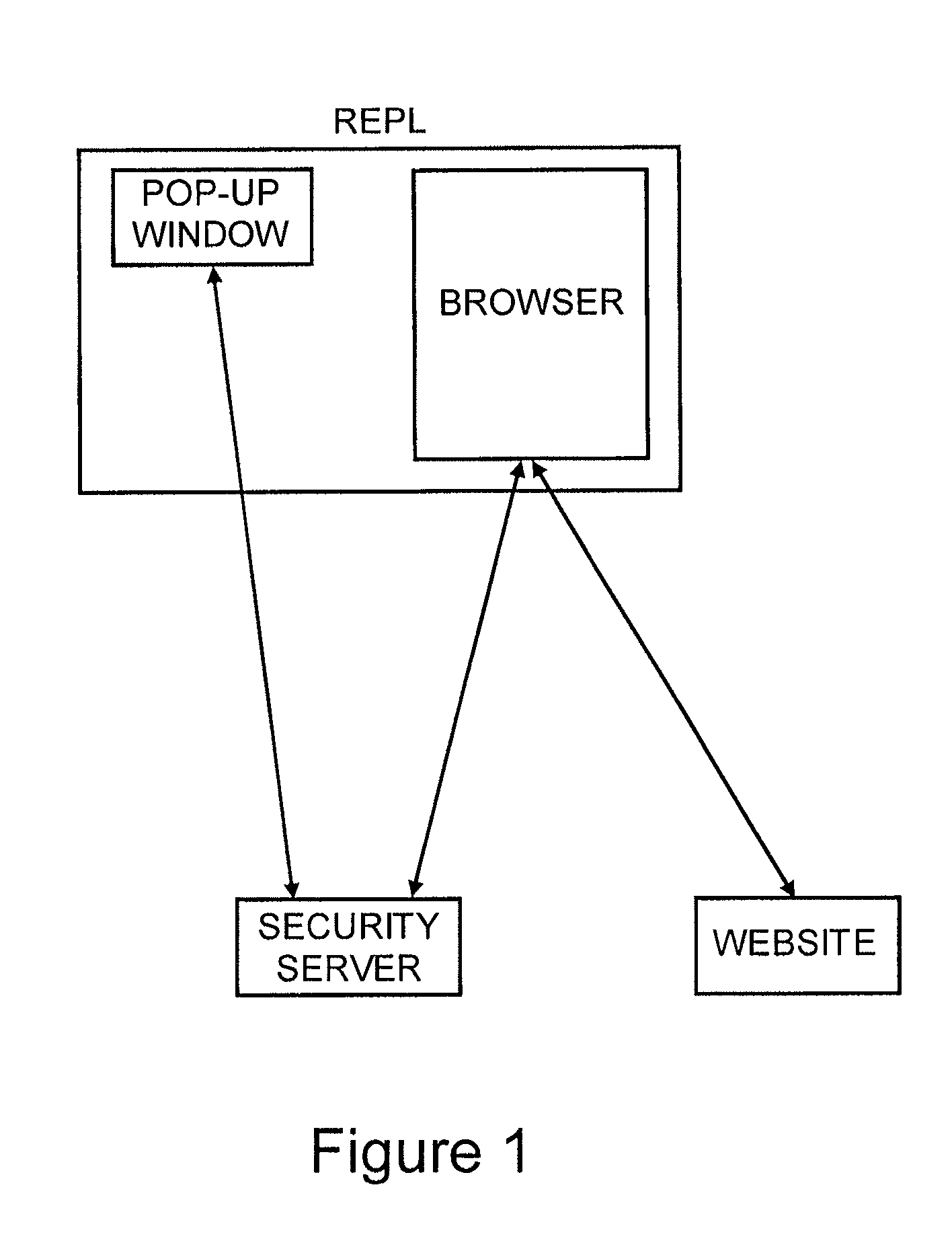
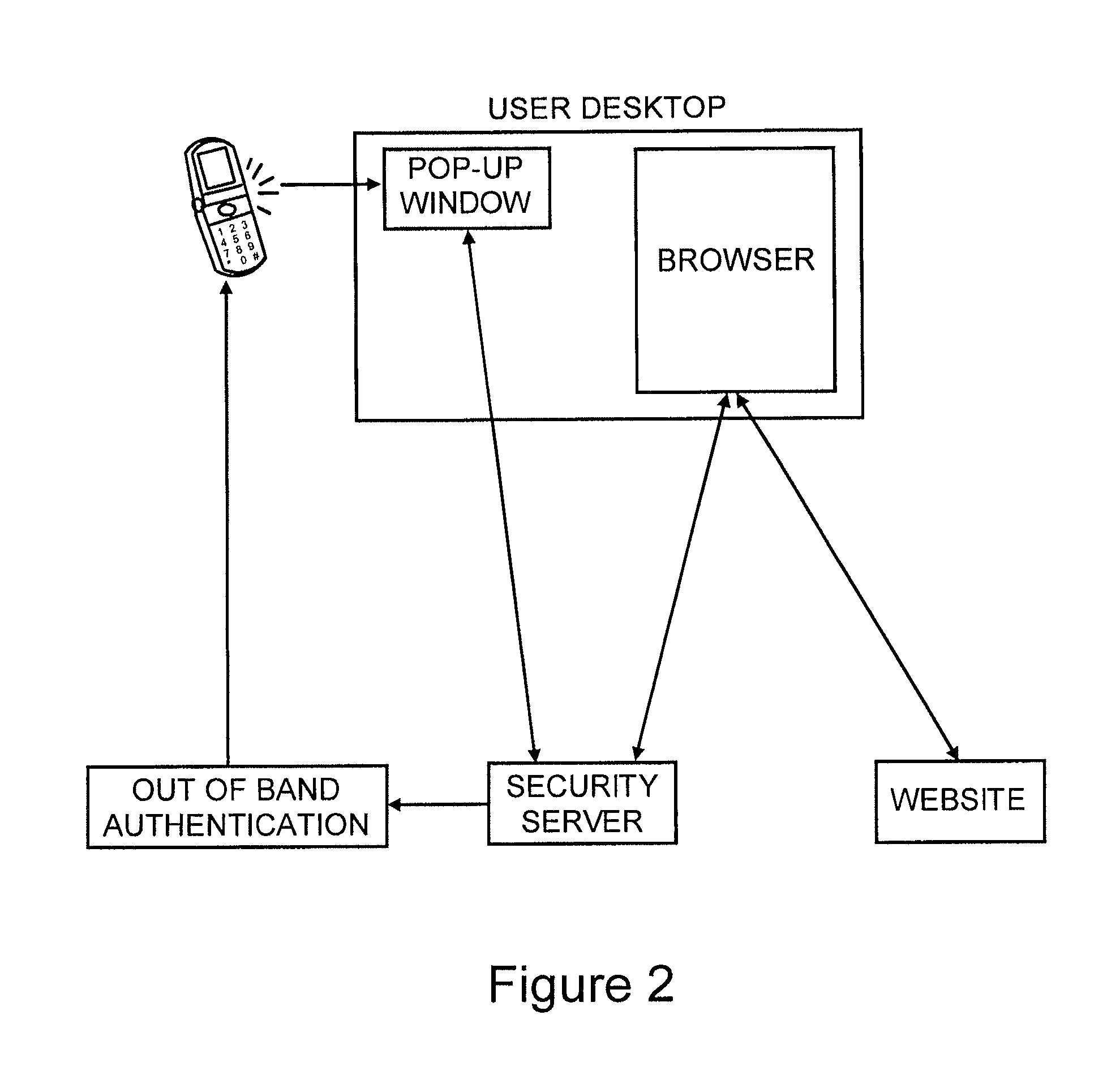
Method and system for providing a one time password to work in conjunction with a browser
ActiveUS20080028447A1Digital data processing detailsUser identity/authority verificationOne-time passwordAuthentication system
A method of submitting information as part of an authentication operation includes generating a one time password that is intended for use in an authentication operation. The method further includes providing the one time password in a display field, wherein the display field is adapted to work in conjunction with a browser to submit the one time password in response to a request for the one time password. A method of controlling submission of identity information within an authentication system includes receiving a trust list from the authentication system. The trust list identifies entities that are authorized to receive the identity information. The method further includes receiving a request to submit the identity information to a candidate entity for an authentication operation, and providing the identity information to the candidate entity if the trust list indicates that the candidate entity is authorized to receive the identity information.
Owner:EMC IP HLDG CO LLC
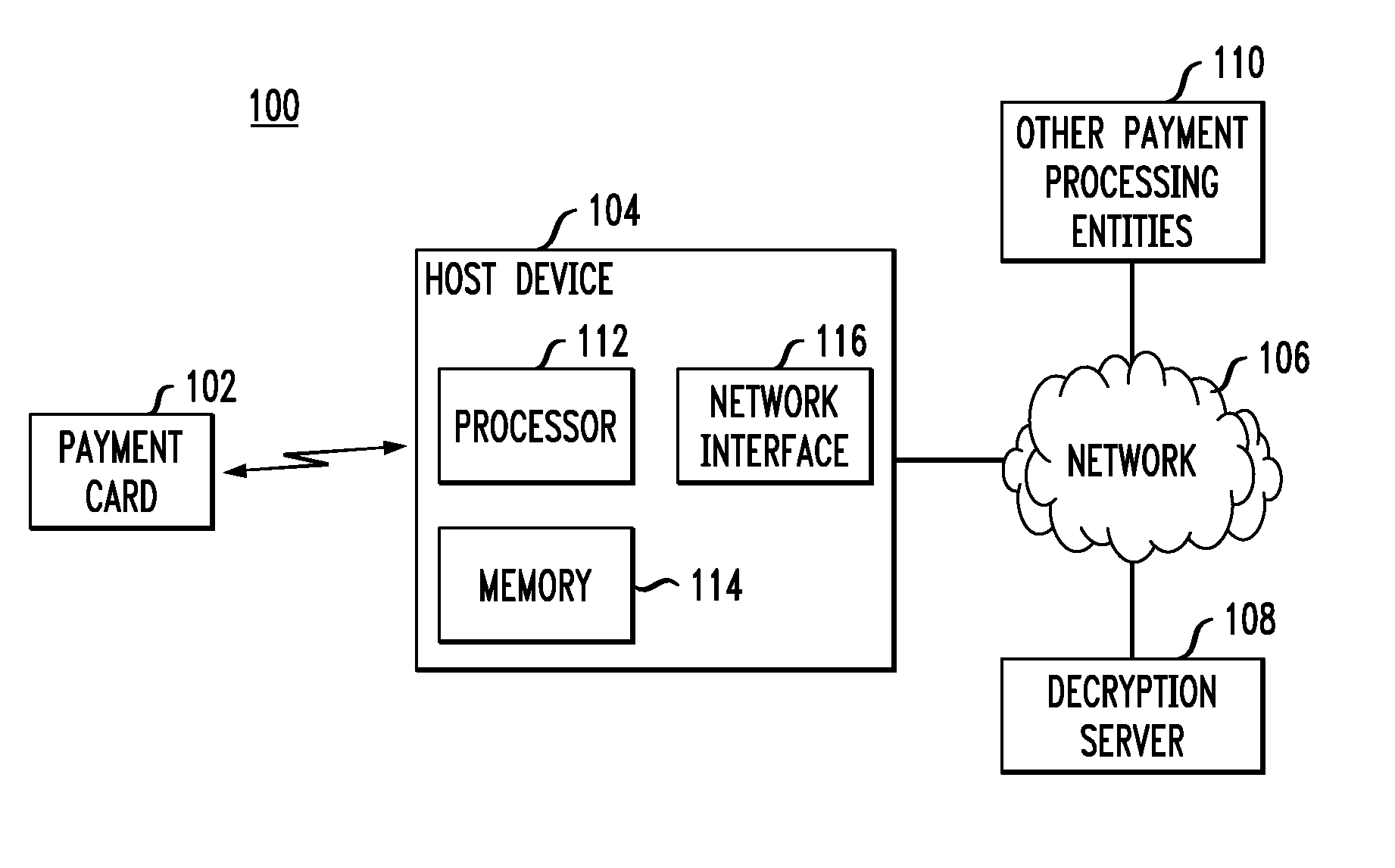
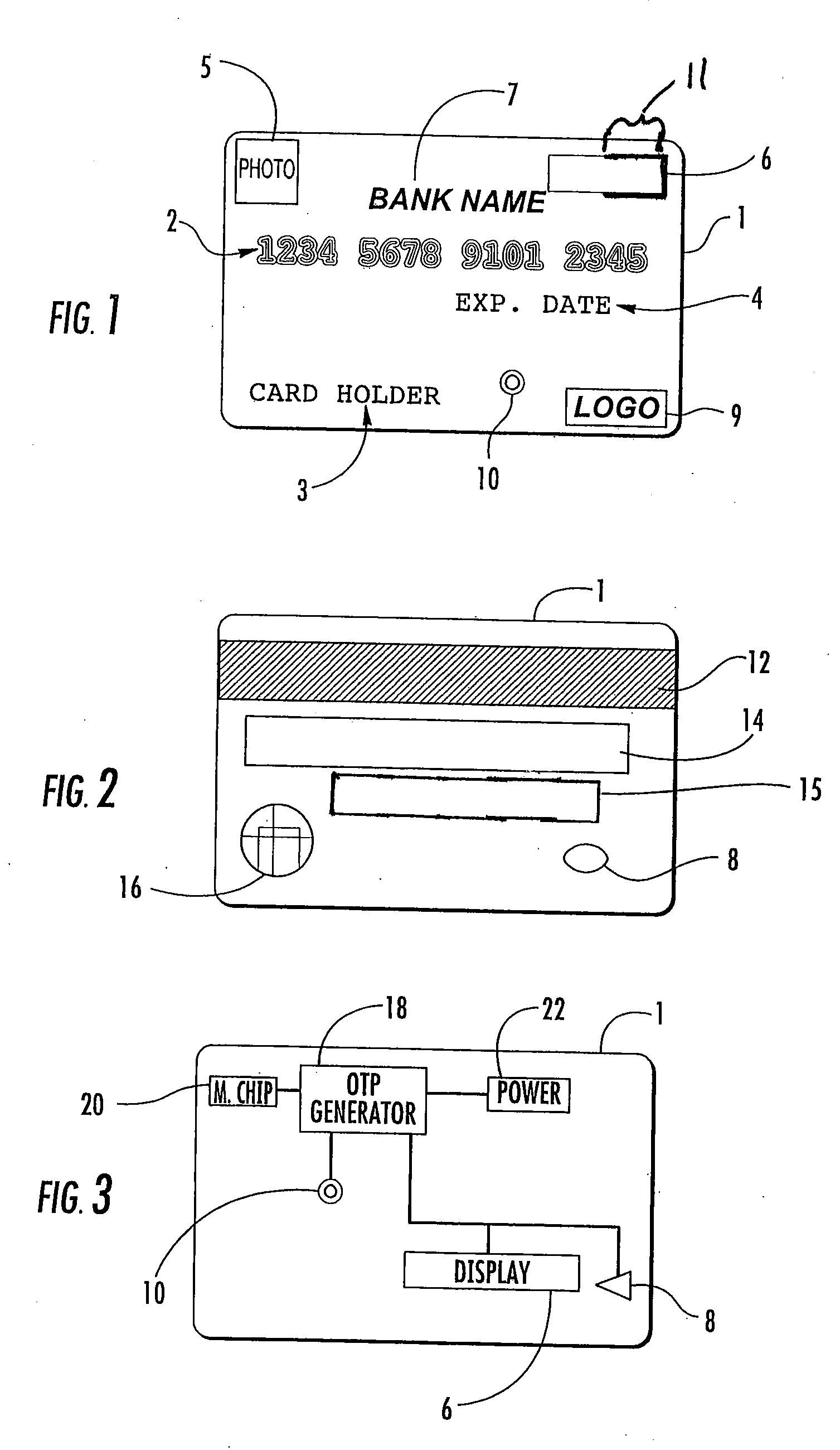
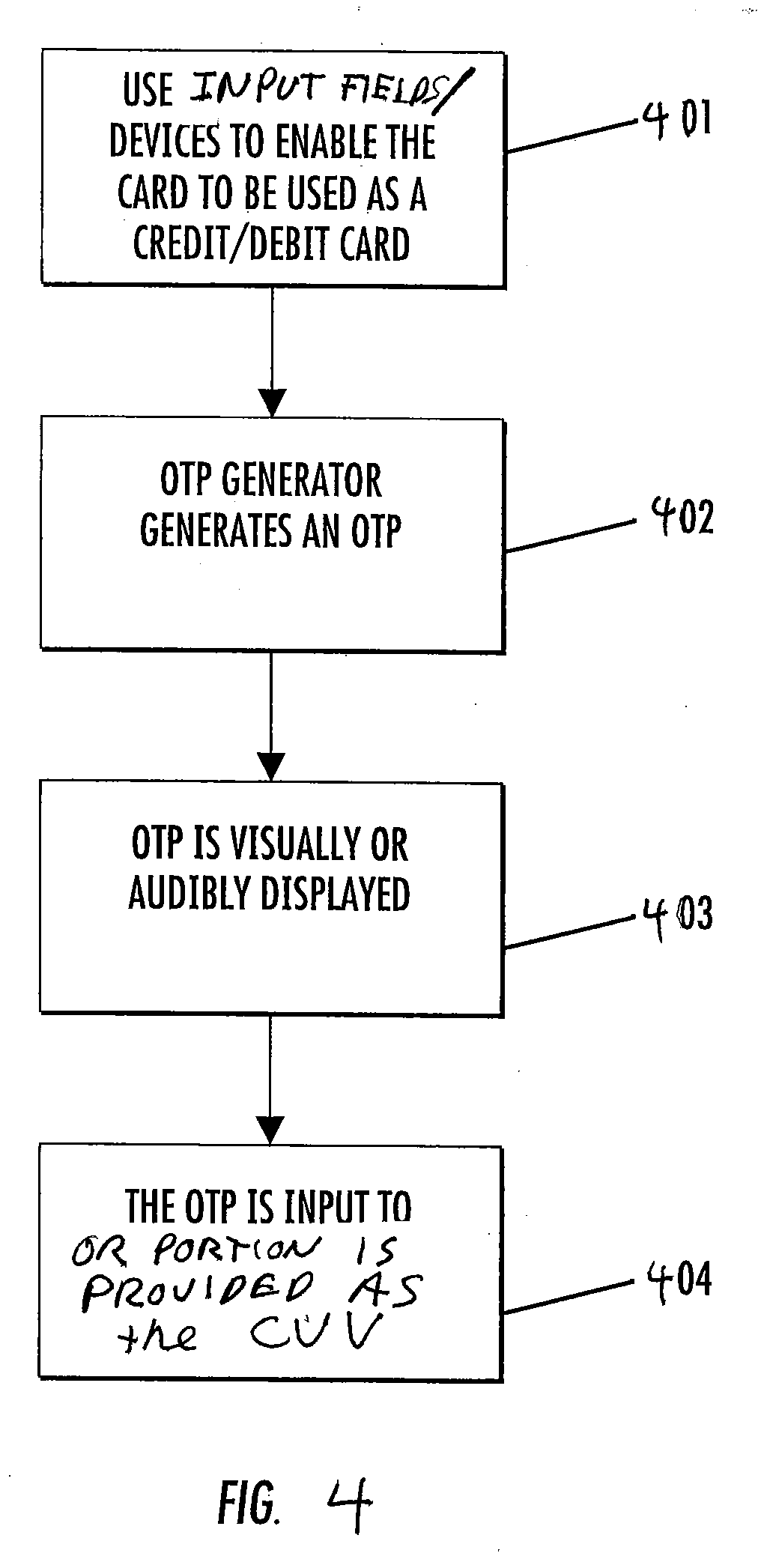
Method and apparatus for using at least a portion of a one-time password as a dynamic card verification value
Method and apparatus for using at least a portion of a one-time password as a dynamic card verification value (CVV) are disclosed. A credit / debit card is able to generate a dynamic card verification value (CVV). Such a card may also include an indication that the dynamic CVV is to be used as a security code for purchasing or other transactions. A card-based financial transaction can be authorized in accordance with the use of a dynamic CVV by receiving a transaction authorization request for a specific credit / debit card, wherein the transaction authorization request includes a dynamic CVV. The dynamic CVV can be compared to at least a portion of a one-time password generated for the specific credit / debit card, and a transaction authorization can be sent to the merchant or vendor when the dynamic CVV matches all or a portion of the one-time password.
Owner:BANK OF AMERICA CORP
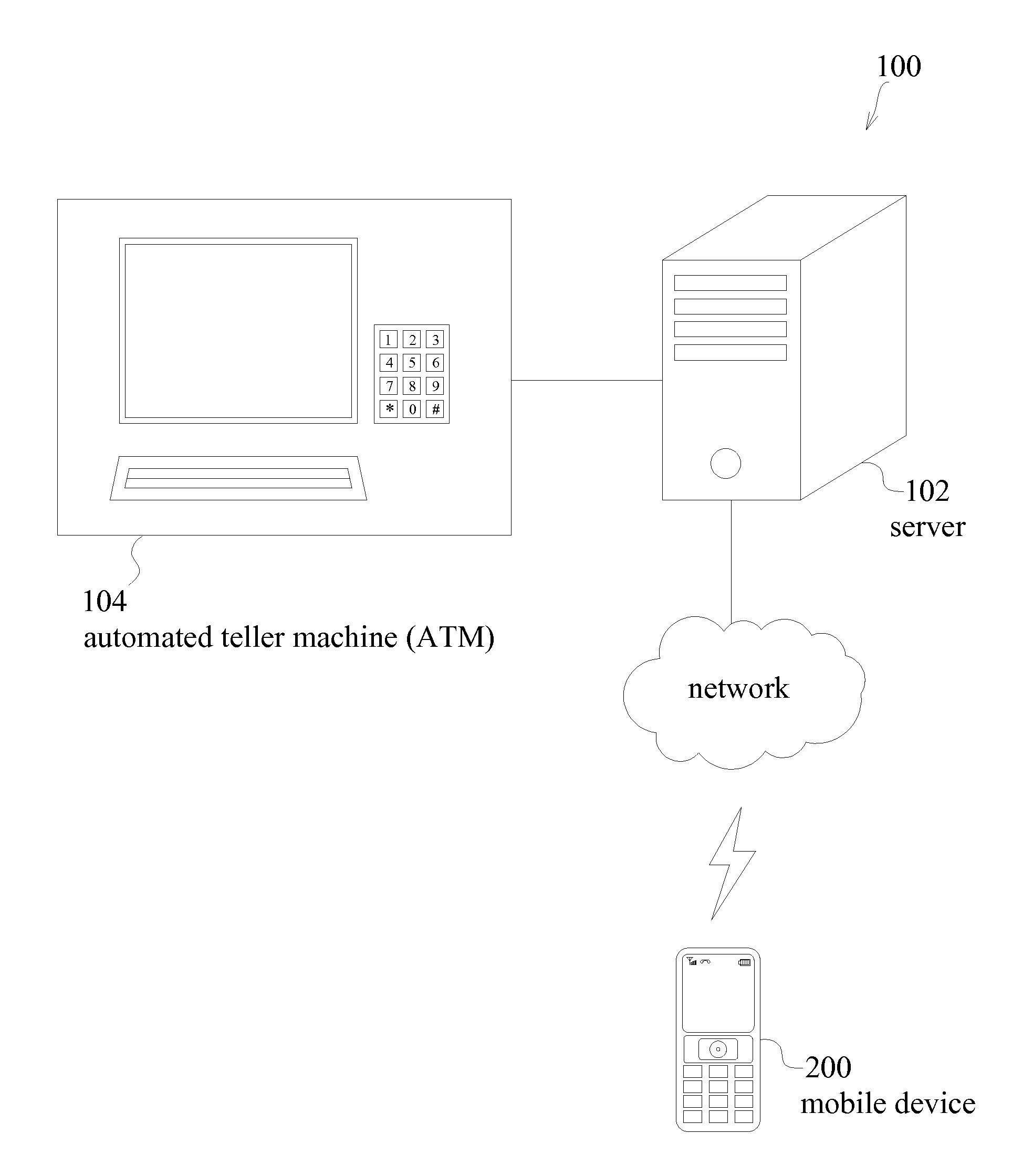
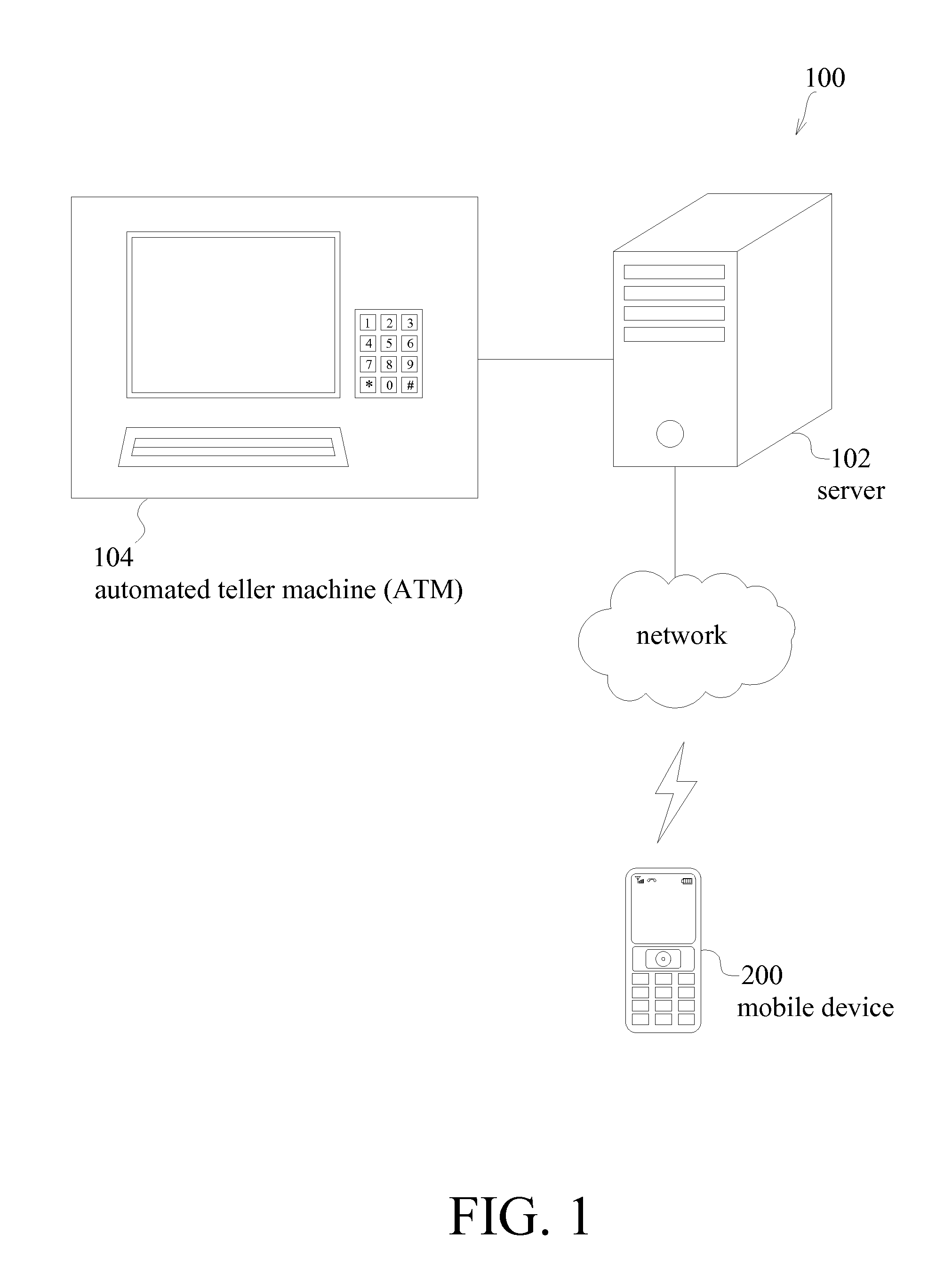
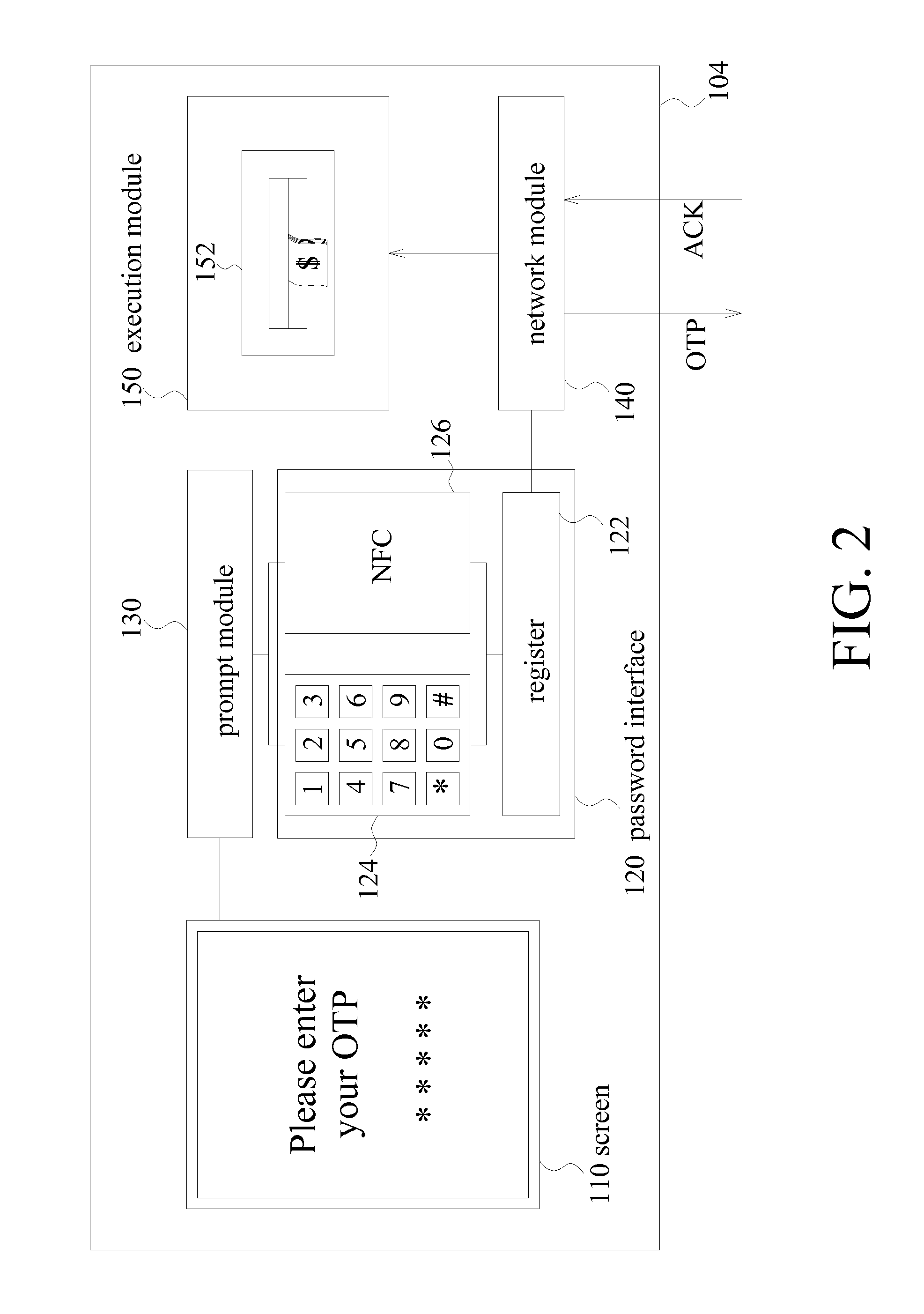
Financial transaction system, automated teller machine (ATM), and method for operating an ATM
InactiveUS20110016047A1Improve transaction securityImprove securityFinanceAutomatic teller machinesFinancial transactionFinancial trading
A financial transaction system is provided. The financial transaction system includes a server and at least one automated teller machine (ATM). In response to a request from a user, the server issues a one-time password (OTP) to the user's mobile device. The ATM receives an OTP from the user and sends the received OTP to the server for verification, in order to perform a financial transaction operation.
Owner:MIXTRAN INC
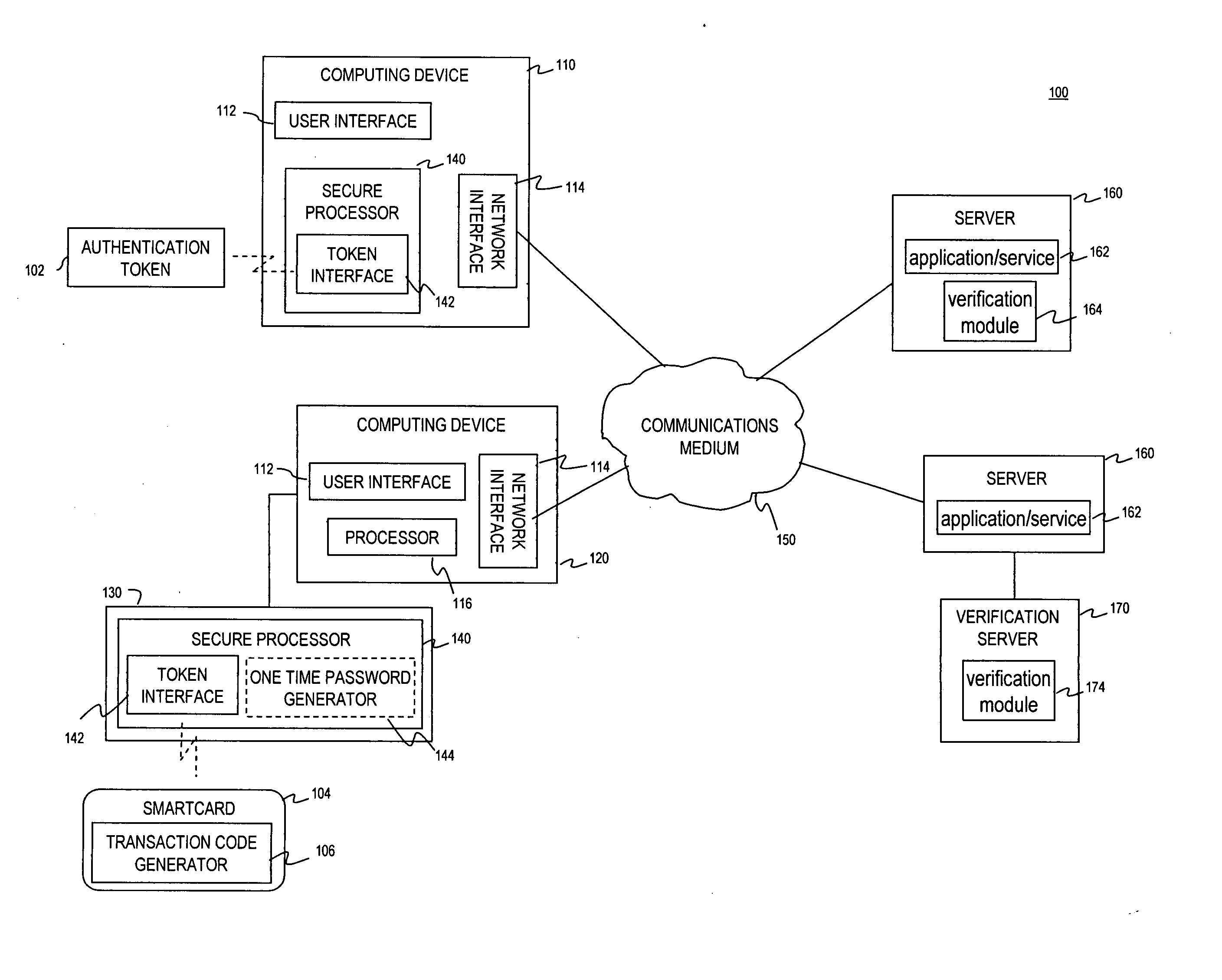
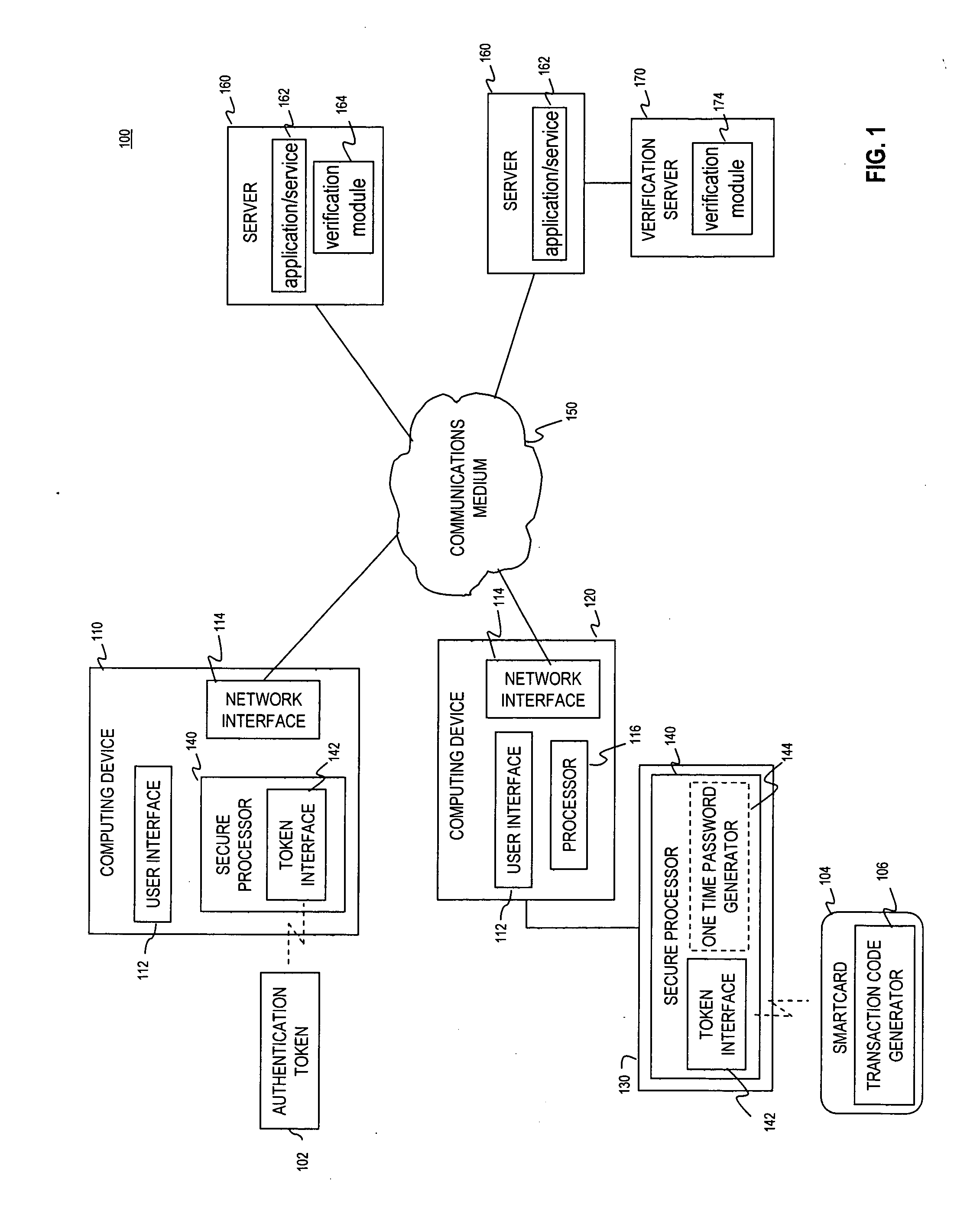
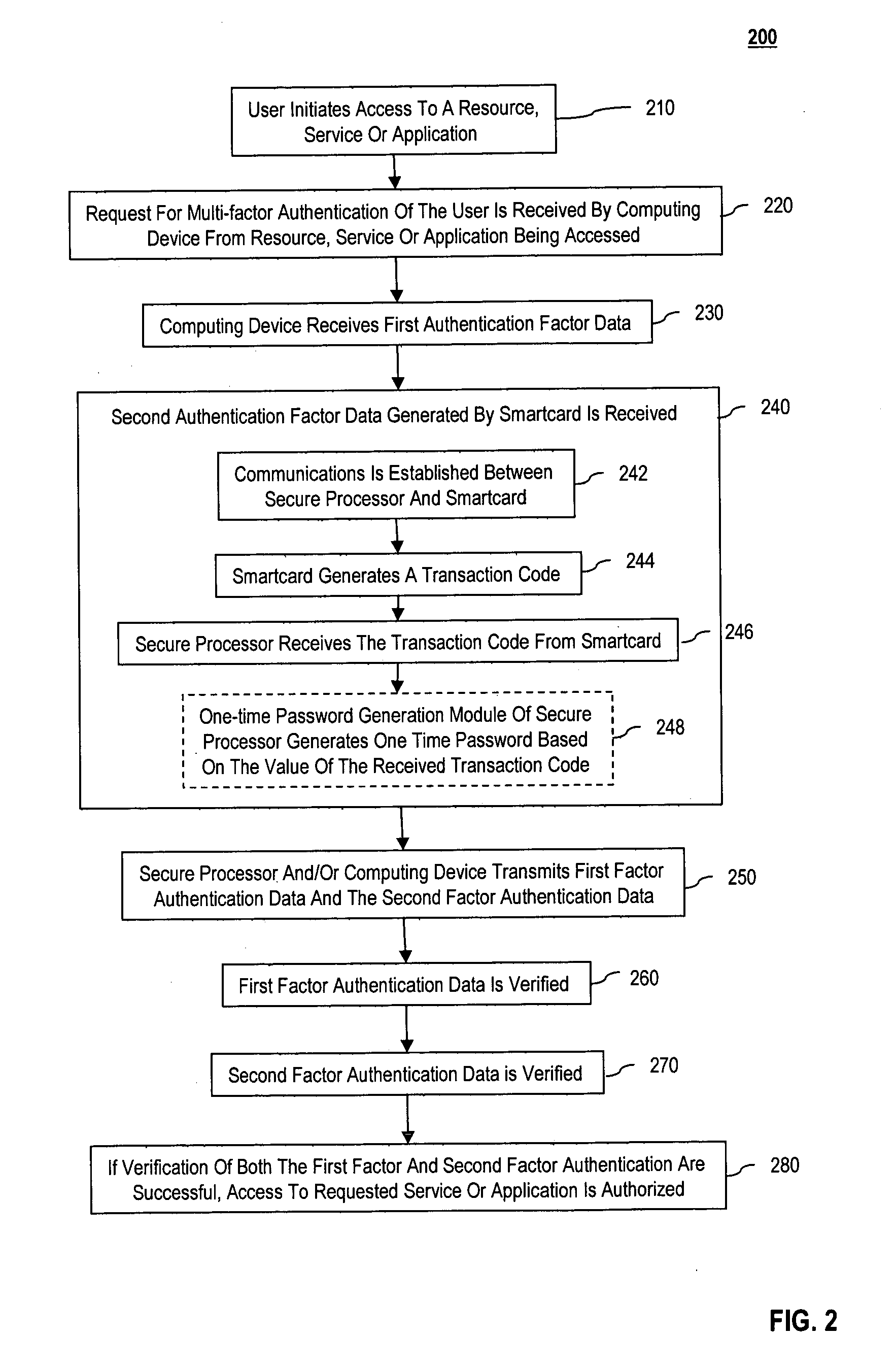
Multi-factor authentication using a smartcard
ActiveUS20070118745A1Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
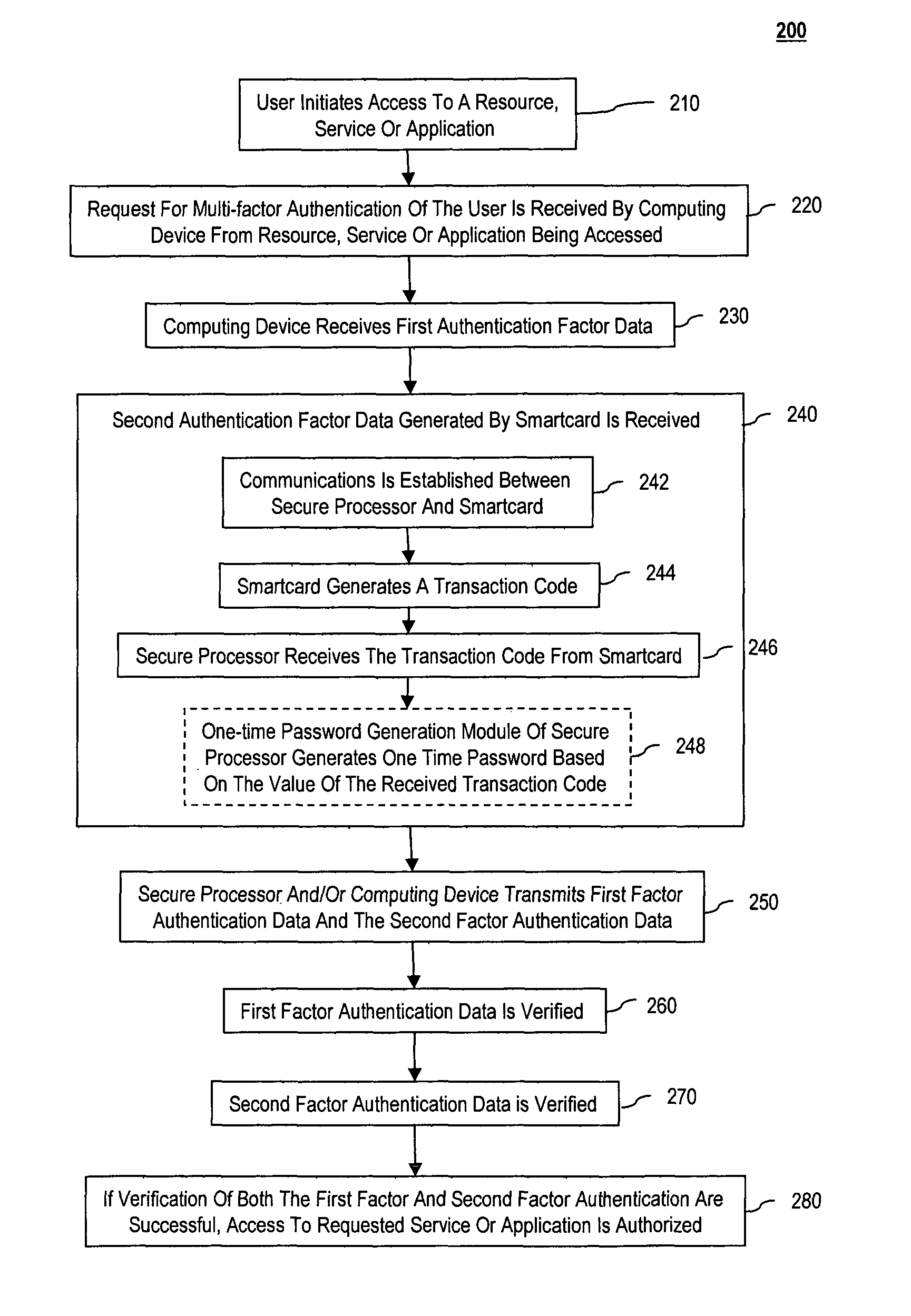
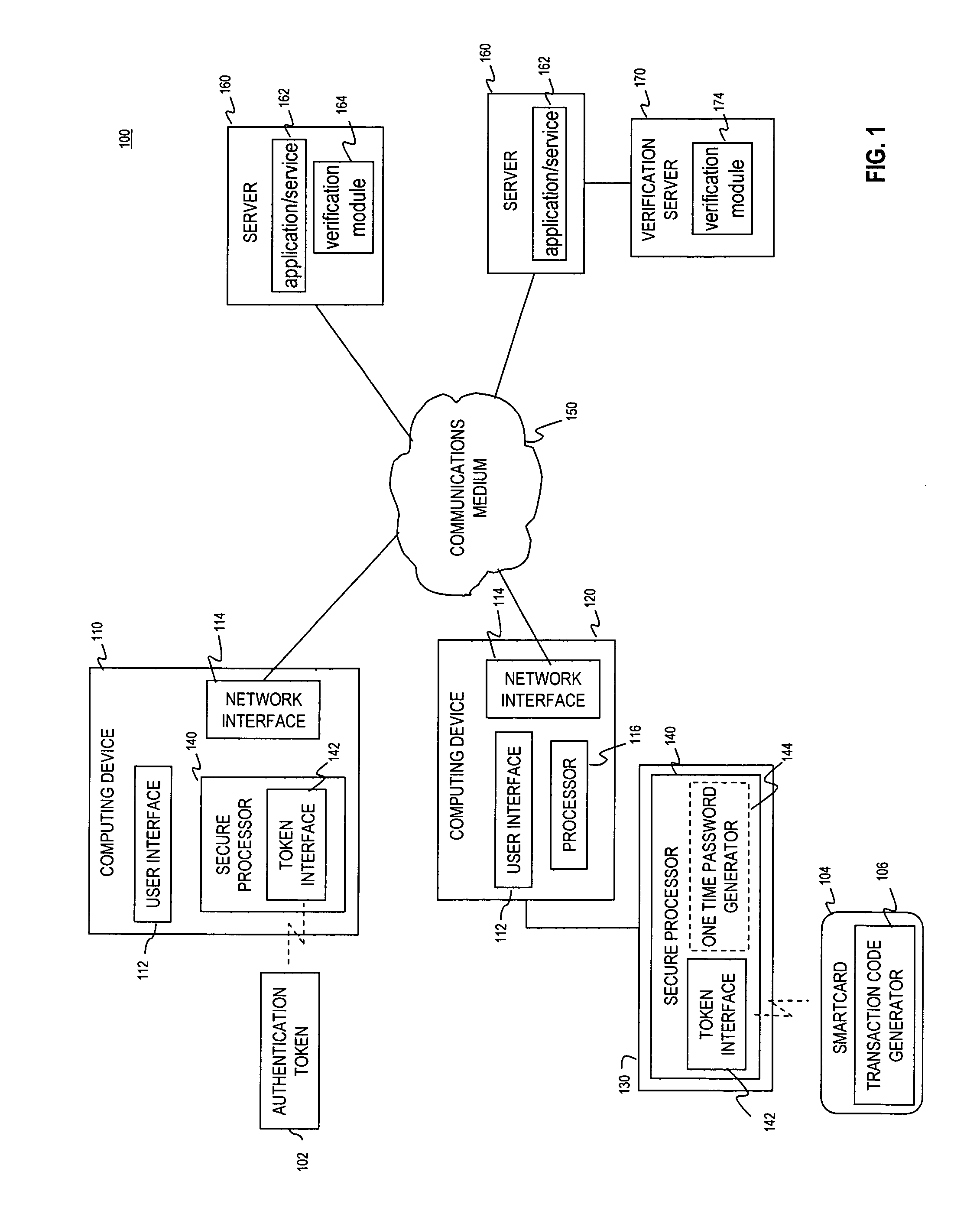
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
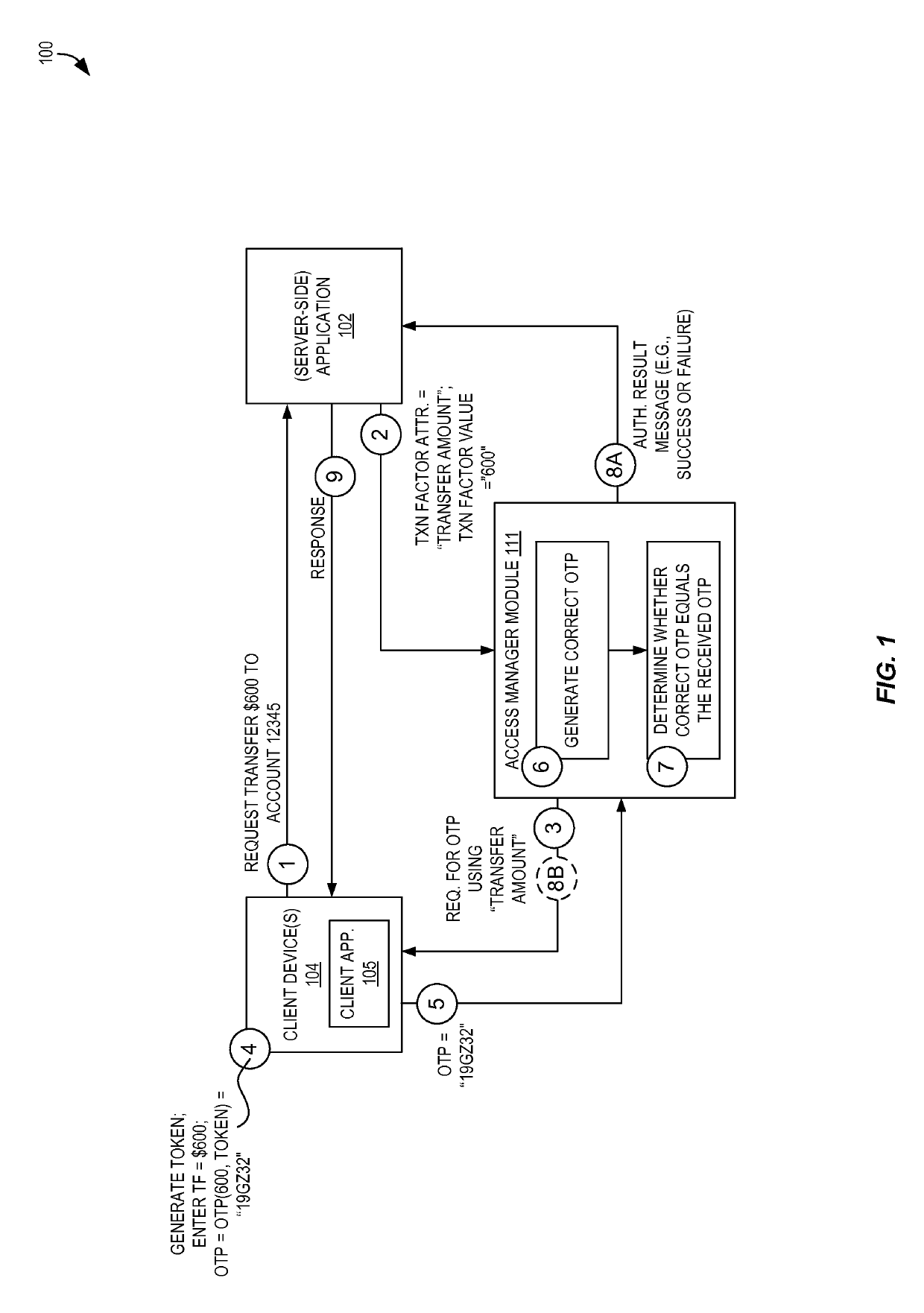
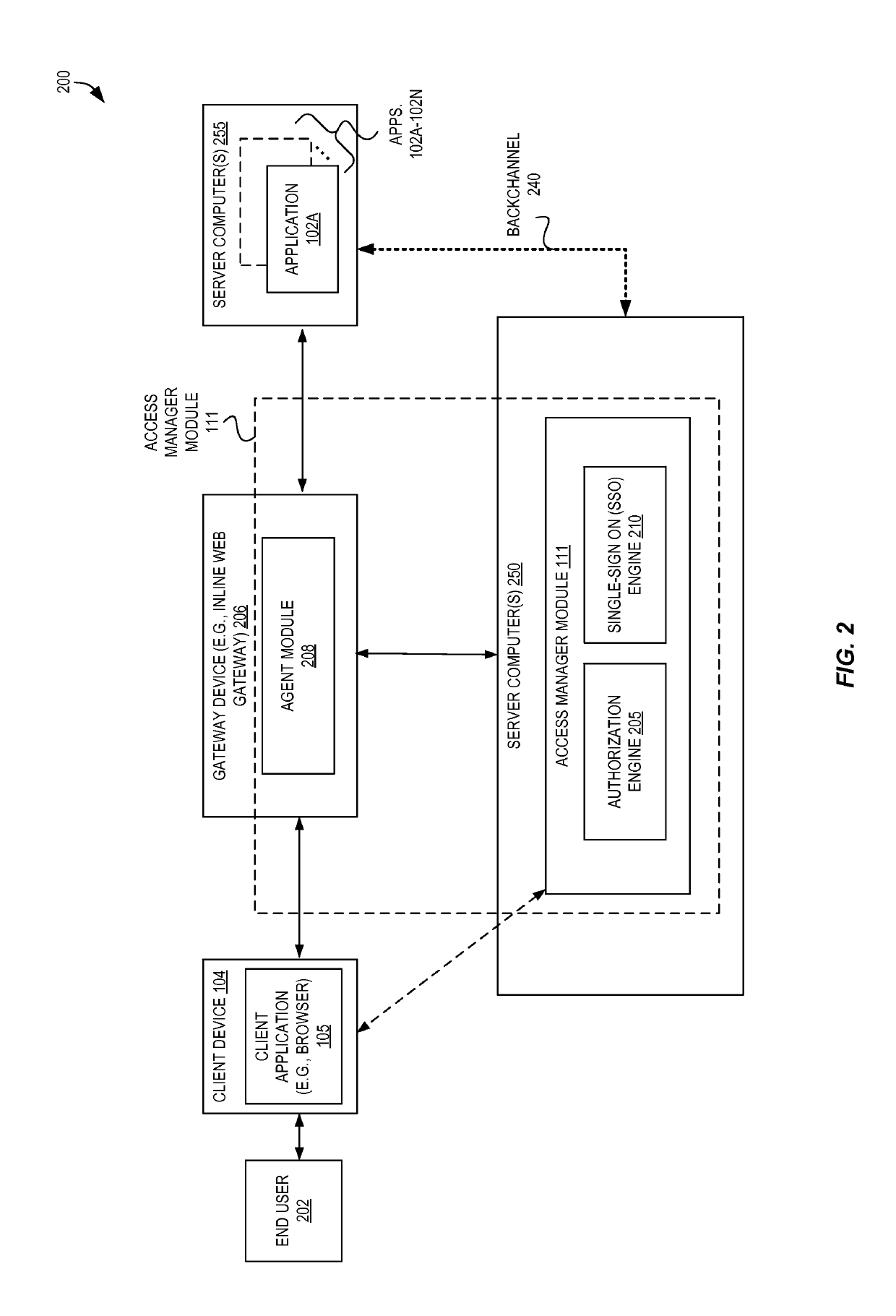
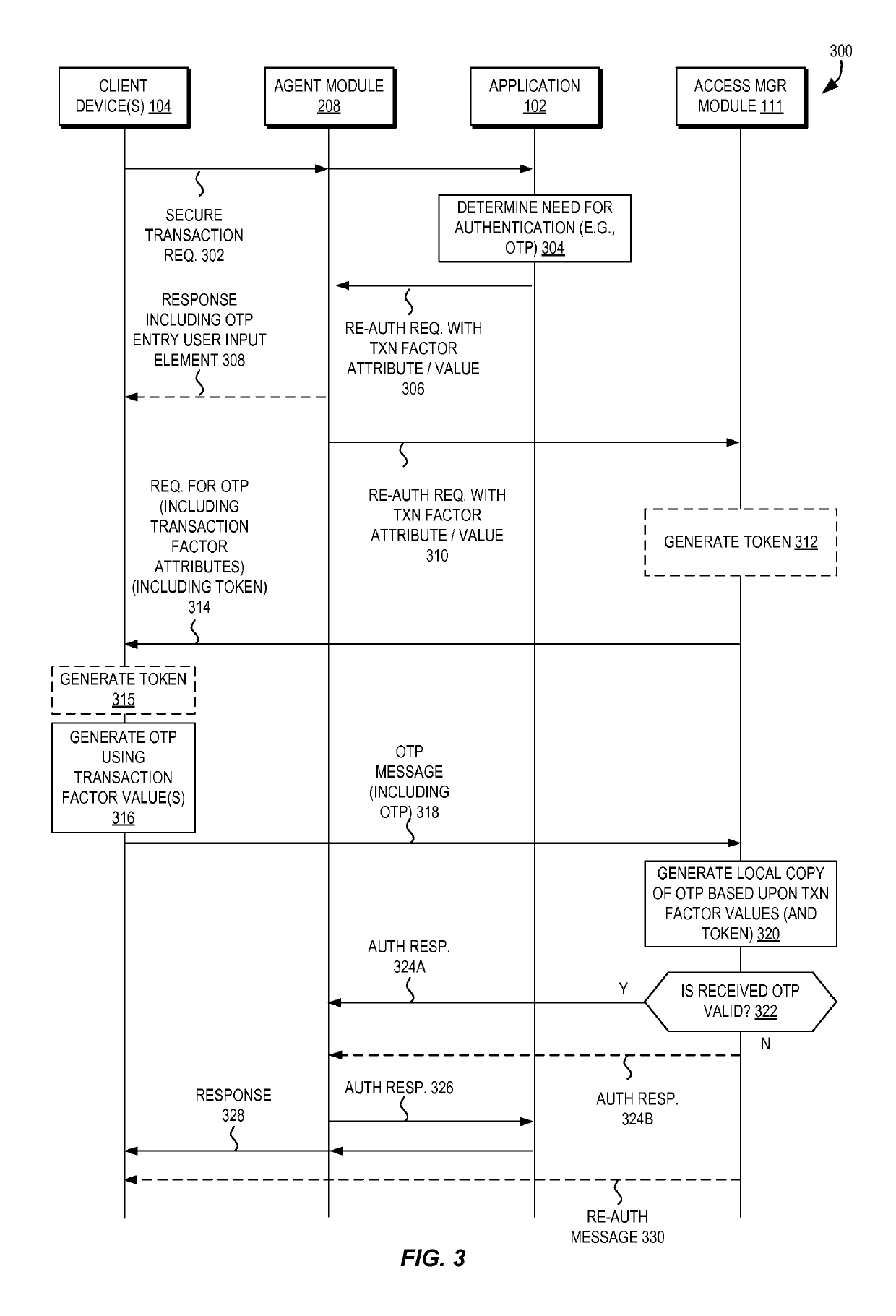
Declarative techniques for transaction-specific authentication
Techniques are disclosed for providing and / or implementing utilizing declarative techniques for transaction-specific authentication. Certain techniques are disclosed herein that enable transaction signing using modular authentication via declarative requests from applications. An application can declaratively specify one or more transaction factor values to be used in an authentication, and the authentication, using a transaction-signed one-time password, can be directed by an access manager module without further involvement of the application. Upon a successful or non-successful authentication, the access manager module can provide the result back to the application. Accordingly, an authentication process specific to (and valid only for) a particular transaction can be performed without direct involvement of the application and without application-centric knowledge required by the access manager module.
Owner:ORACLE INT CORP
Payment card with dynamic account number
ActiveUS8494959B2Avoid processing delaysOvercomes drawbackAcutation objectsFinanceDisplay devicePayment order
A payment card comprises a processor, a trigger source coupled to the processor, and a display for outputting at least a portion of a dynamic account number under control of the processor responsive to the trigger source. The dynamic account number is determined based at least in part on a seed stored in the payment card and an output of the trigger source. In an illustrative embodiment, the dynamic account number is generated utilizing a time-based or event-based one-time password algorithm. For example, in a time-based embodiment, the trigger source may comprise a time of day clock, with the dynamic account number being determined based at least in part on the seed and a current value of the time of day clock. In an event-based embodiment, the trigger source may comprise an event counter, with the dynamic account number being determined based at least in part on the seed and a current value of the event counter.
Owner:EMC IP HLDG CO LLC
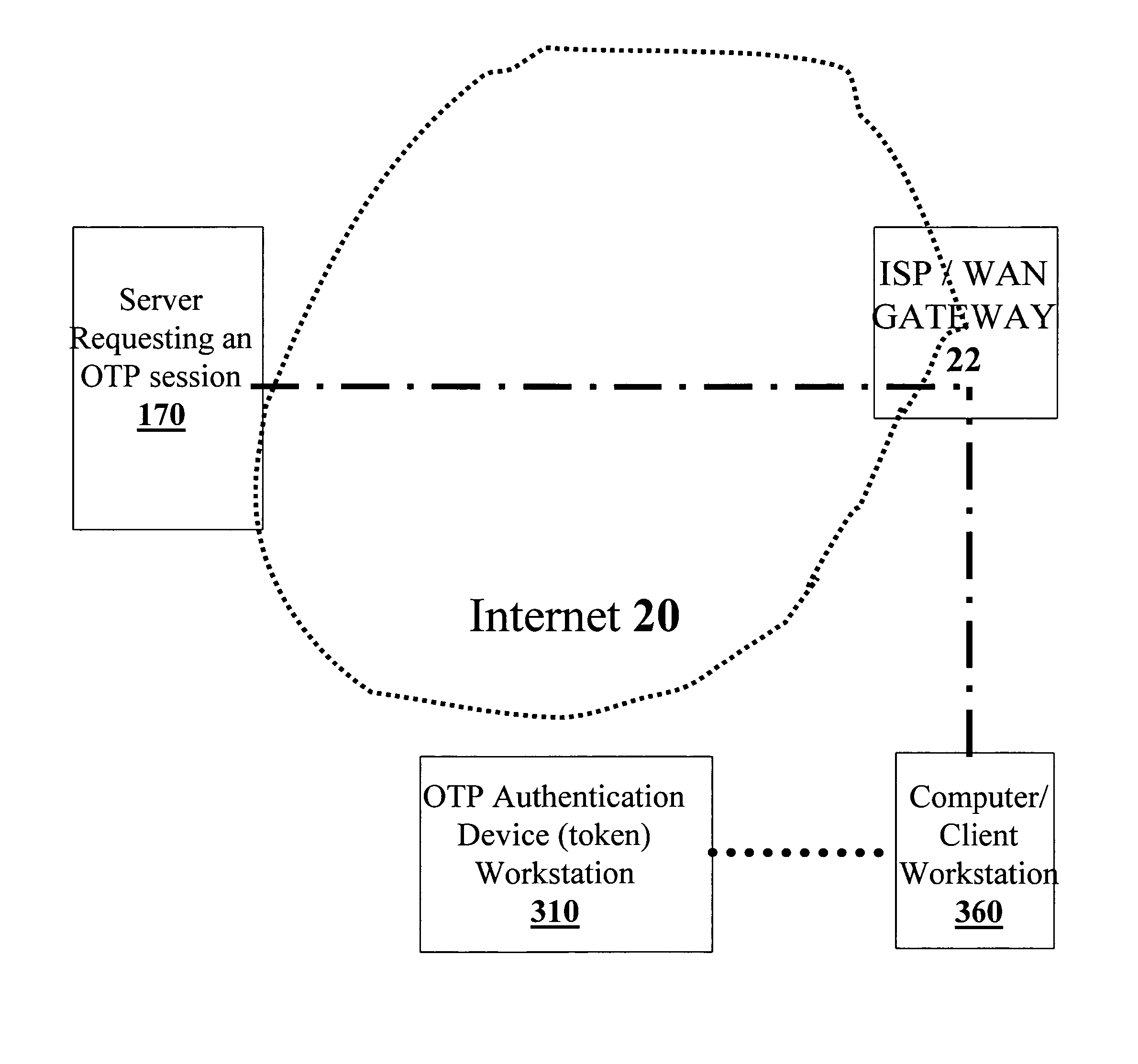
Extended one-time password method and apparatus
ActiveUS20070067828A1Vehicle testingKey distribution for secure communicationThe InternetUser authentication
An OTP token for facilitating the authorizing of a client workstation to conduct a session with a server over the Internet is disclosed. Information at least partially identifying the server is provided to the OTP token and / or the client workstation, and a determination is made, using this identifying information, if the server is a legitimate server. In accordance with this determination, it is decided whether or not to transmit data indicative of a session OTP from the OTP token to the client workstation. In some embodiments, if the identifying information is indicative of a legitimate server, the data indicative of the session OTP is transmitted from the OTP token to the client workstation, and otherwise, the data indicative of the session OTP is withheld from the client workstation. Data indicative of the session OTP may include, in various embodiments, either multi-factor authentication data derived from user authorization data, or session OTP data that is independent of user authentication data.
Owner:WESTERN DIGITAL ISRAEL LTD
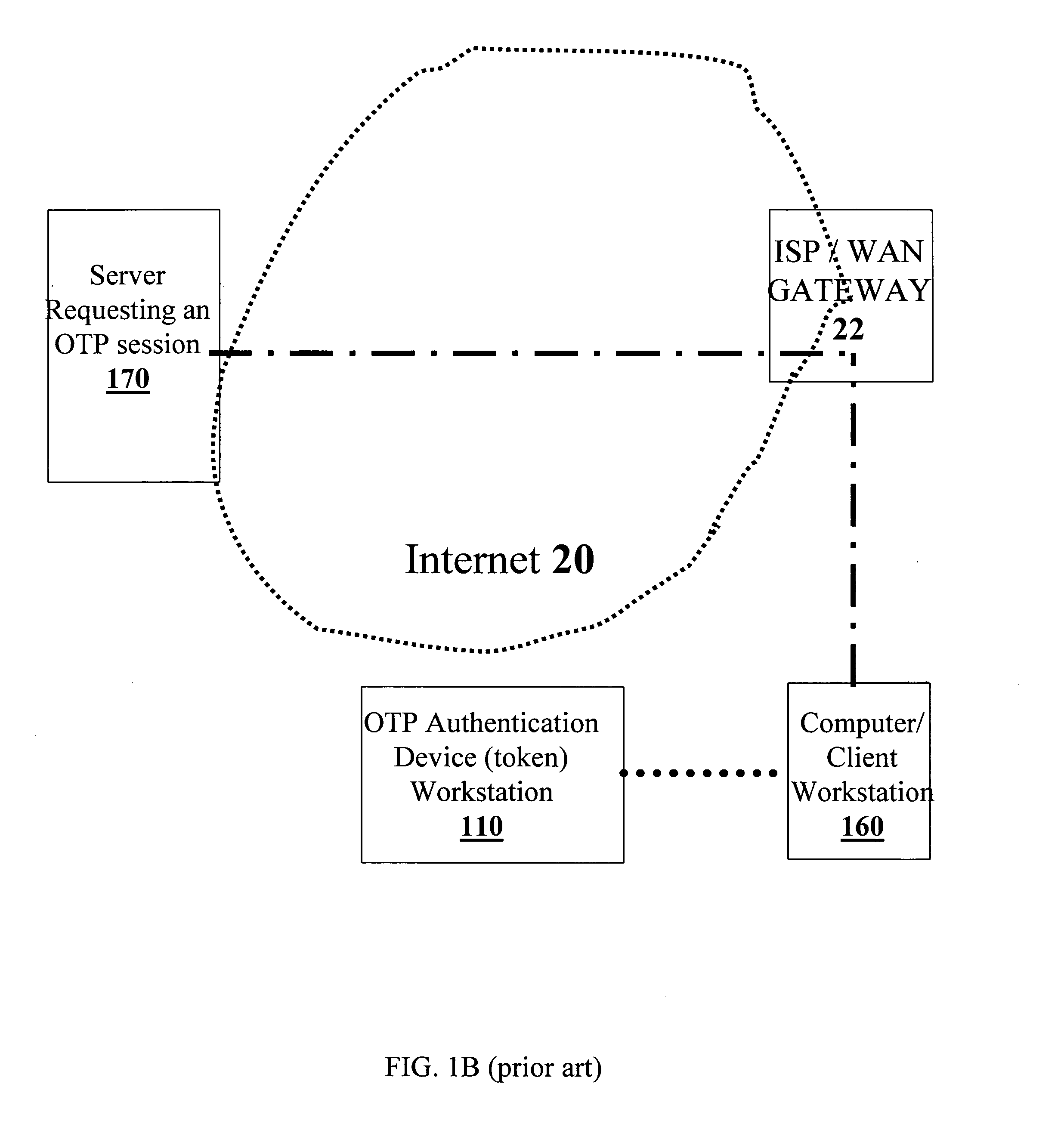
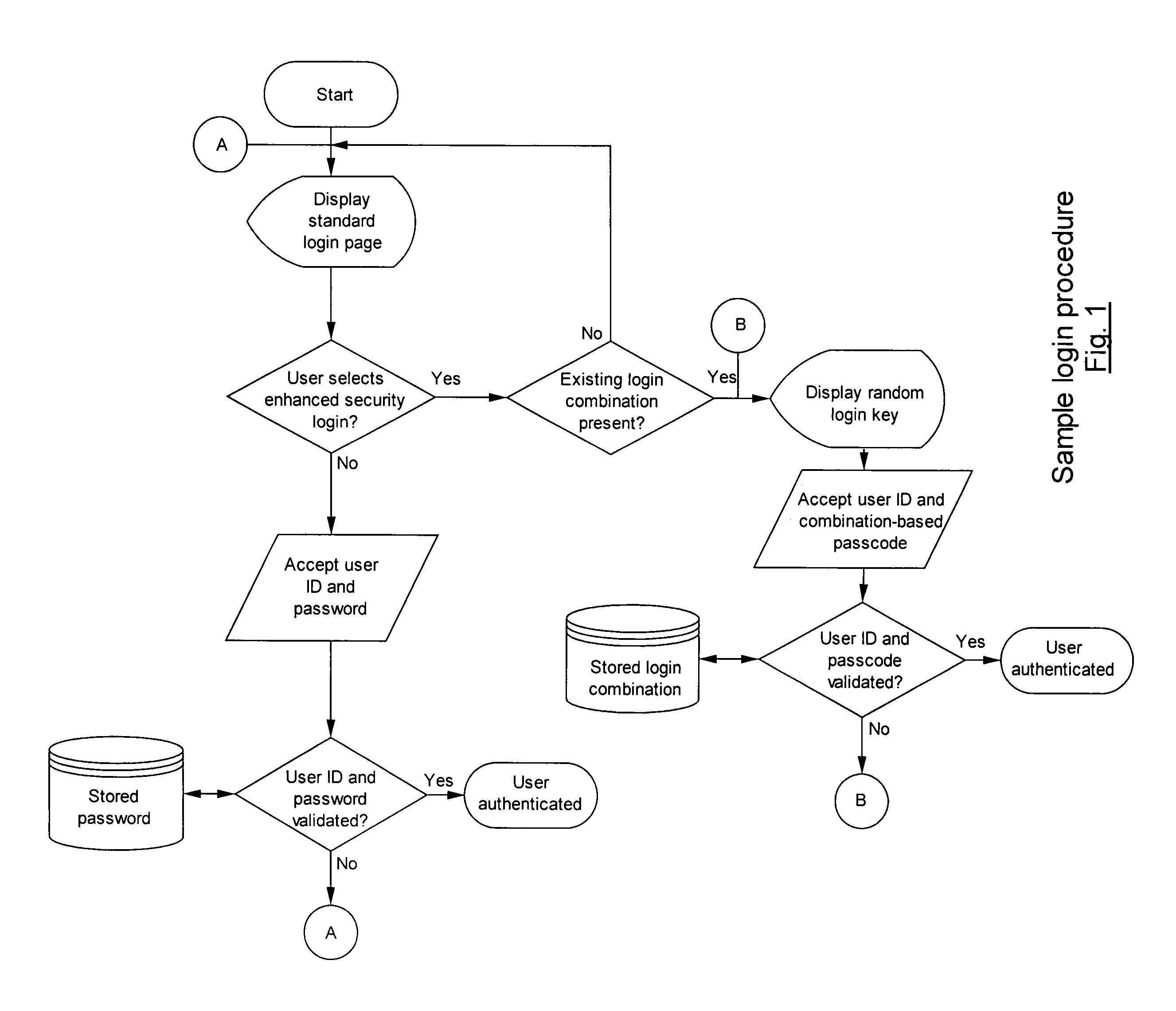
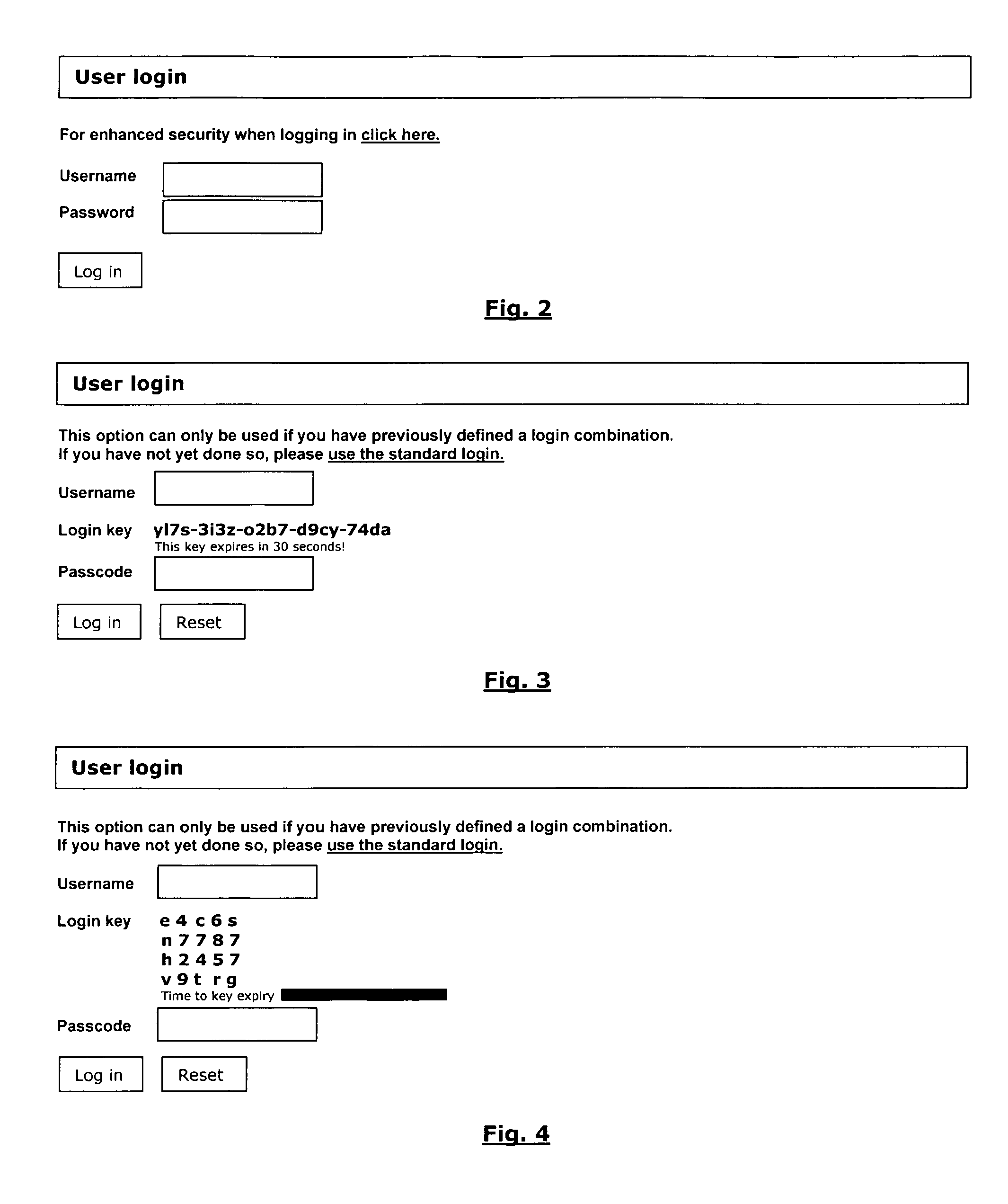
Method and system for providing a secure login solution using one-time passwords
InactiveUS8041954B2Improve securitySimple and elegantDigital data processing detailsUnauthorized memory use protectionComputer hardwareOne-time password
A method and system for a secure login solution for users logging into computers and systems that require authentication is provided incorporating one-time passwords. The method and system allows a user to establish a login key combination in relation to a login key structure. The login key combination is in association with an identification means, such as a username / ID, and allows the user to generate a one-time passcode in response to a random login key. The method and system is directed at situations where the user desires to log into a system from a computer or other electronic device that may not be secure, including for example from computers or devices other than the user's own and / or by using a communications connection that may not be secure, such as a wireless network connection. The method and system is simple and easy to implement and does not require the use of physical devices.
Owner:PLESMAN PAUL
Secure virtual private network
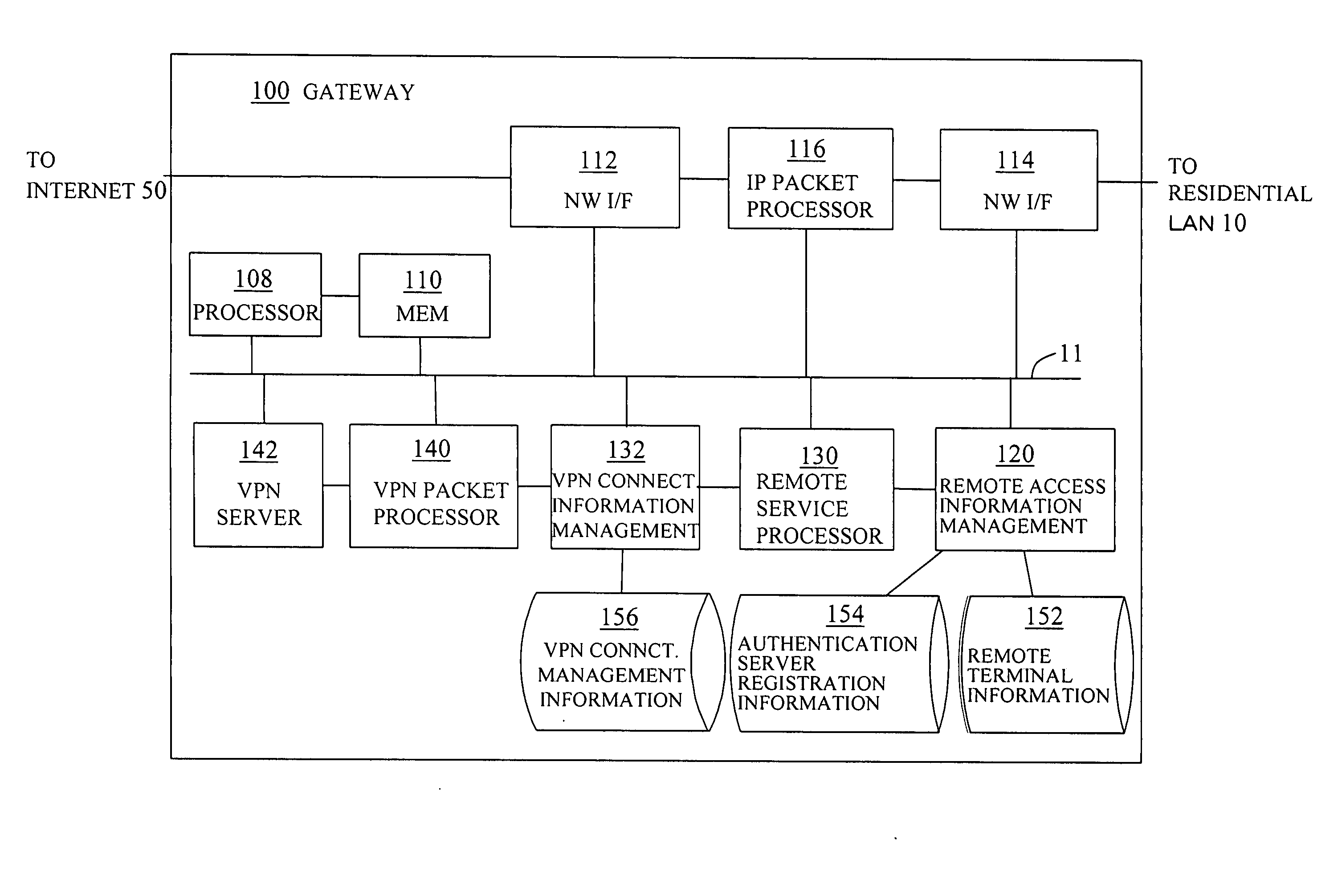
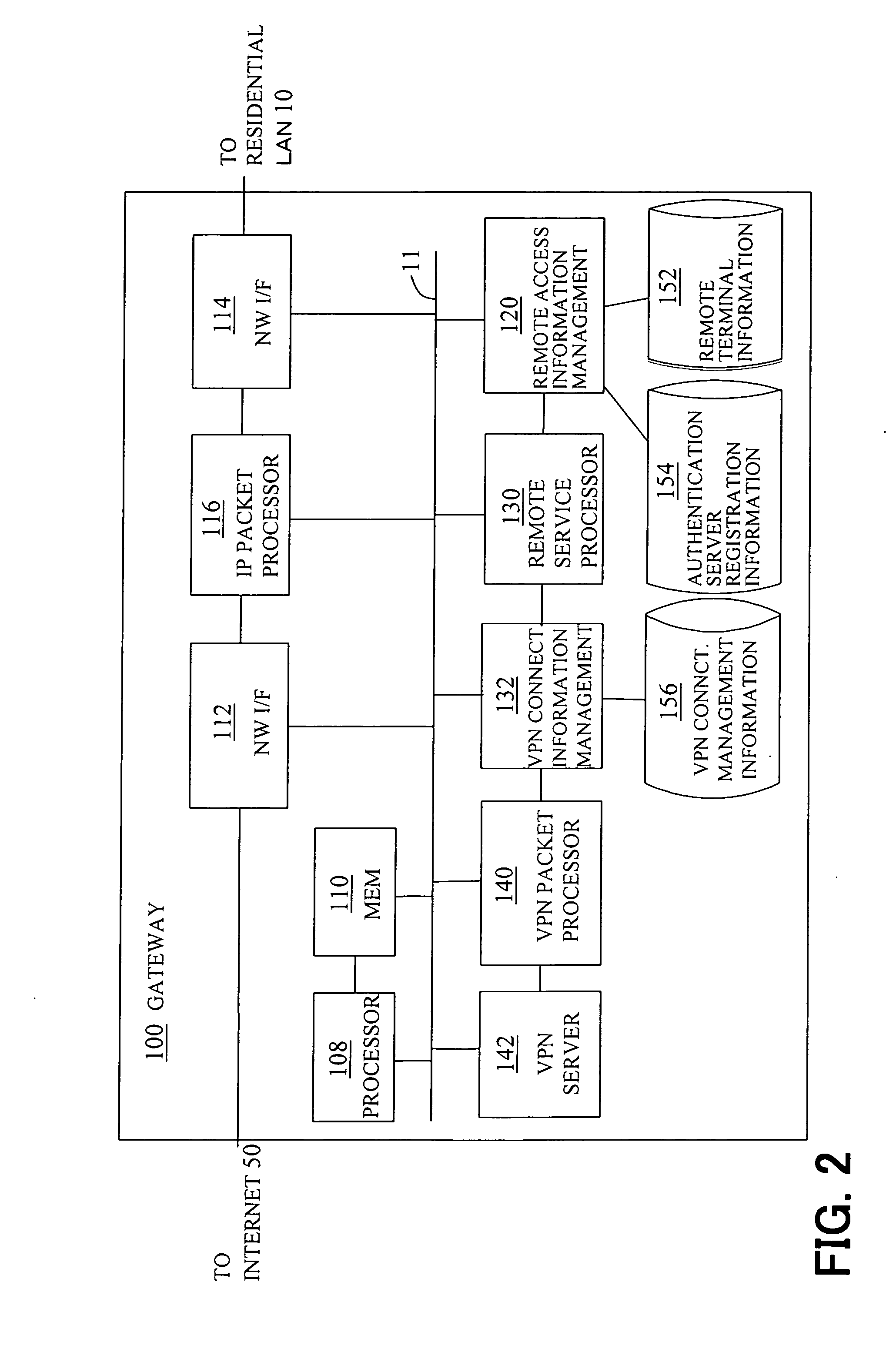
InactiveUS20050169288A1Time-division multiplexData switching by path configurationPrivate networkNetwork connection
A gateway apparatus (100) is capable of connecting to an internal network (10) and an external network (50), and includes an information management unit (120) for managing a global IP address of the gateway apparatus and identification information for a device to be permitted to connect to the internal network. The information management unit transmits the global IP address and the identification information over the external network to an external apparatus. In response to a request received over the external network, the information management unit transmits a one-time password over the external network to the external apparatus. The gateway apparatus further includes: a connector unit (130) permitting the device to connect to the internal network, when it receives a URI containing the global IP address and the one-time password from the device to be permitted to connect over the external network; and an address converter unit (140) for converting between an IP address for the external network into an IP address for the internal network and converting an IP address for the internal network into an IP address for the external network.
Owner:FUJITSU LTD
Protecting one-time-passwords against man-in-the-middle attacks
ActiveUS20070033642A1Key distribution for secure communicationDigital data processing detailsMan-in-the-middle attackKey authentication
To authenticate a user having an associated asymmetric crypto-key having a private / public key pair (D,E) based on a one-time-password, the user partially signs a symmetric session key with the first portion D1 of the private key D. The authenticating entity receives the partially signed symmetric session key via the network and completes the signature with the second private key portion D2 to recover the symmetric session key. The user also encrypts a one-time-password with the symmetric session key. The authenticating entity also receives the encrypted one-time-password via the network, and decrypts the received encrypted one-time-password with the recovered symmetric session key to authenticate the user.
Owner:VMWARE INC
System and method for blocking unauthorized network log in using stolen password
ActiveUS20070266257A1Memory loss protectionDigital data processing detailsInternet privacyOne-time password
The authenticity of a website is determined using a unique string of characters known only to the user and the website on each page of the website that is displayed to the user, with a false site being incapable of displaying this unique string of characters, thereby putting the user on notice that the current site is not the authentic one the user desires to access. Voice methods for conveying one-time pass codes to users and for permitting customer institutions to select authentication rules are also disclosed.
Owner:ANAKAM L L C
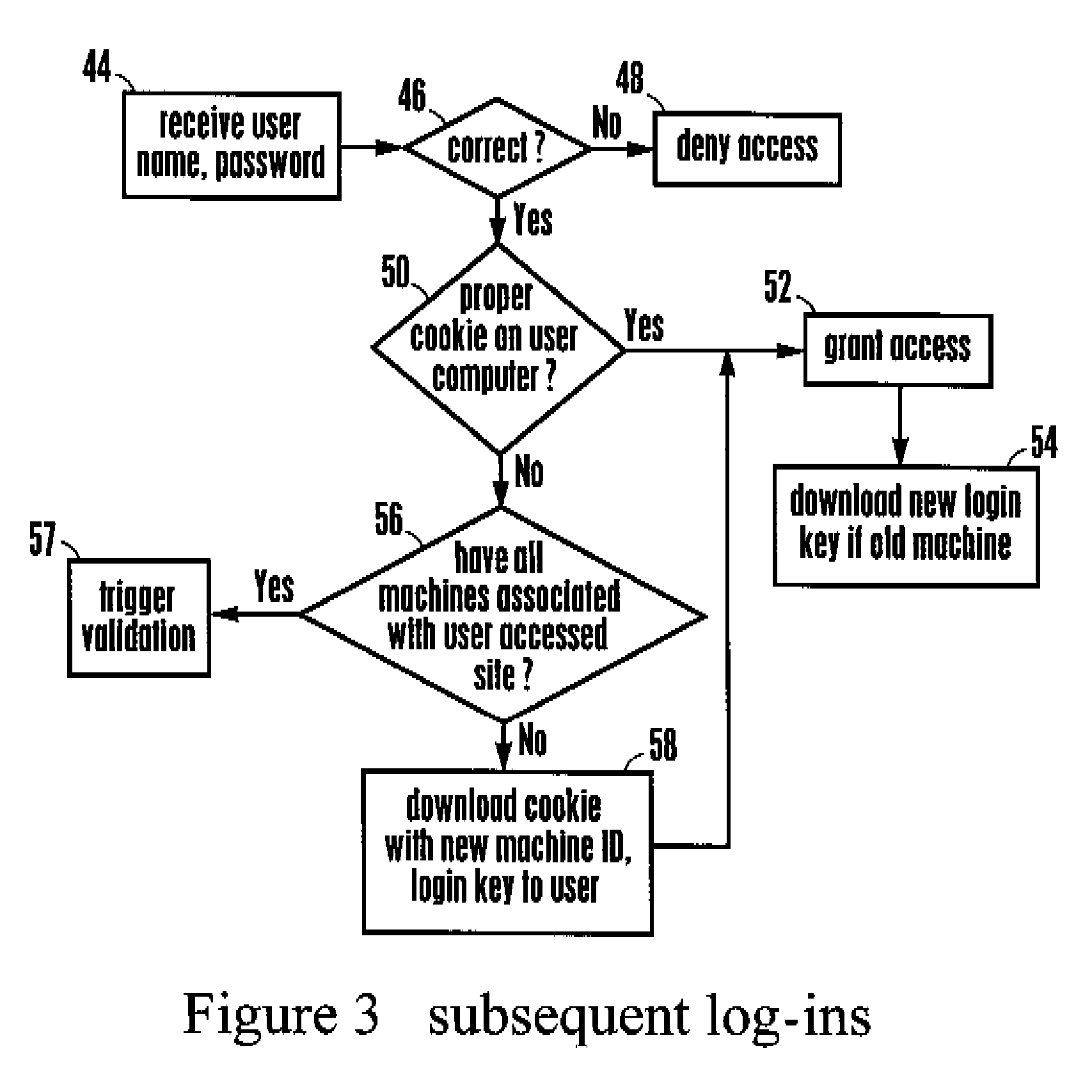
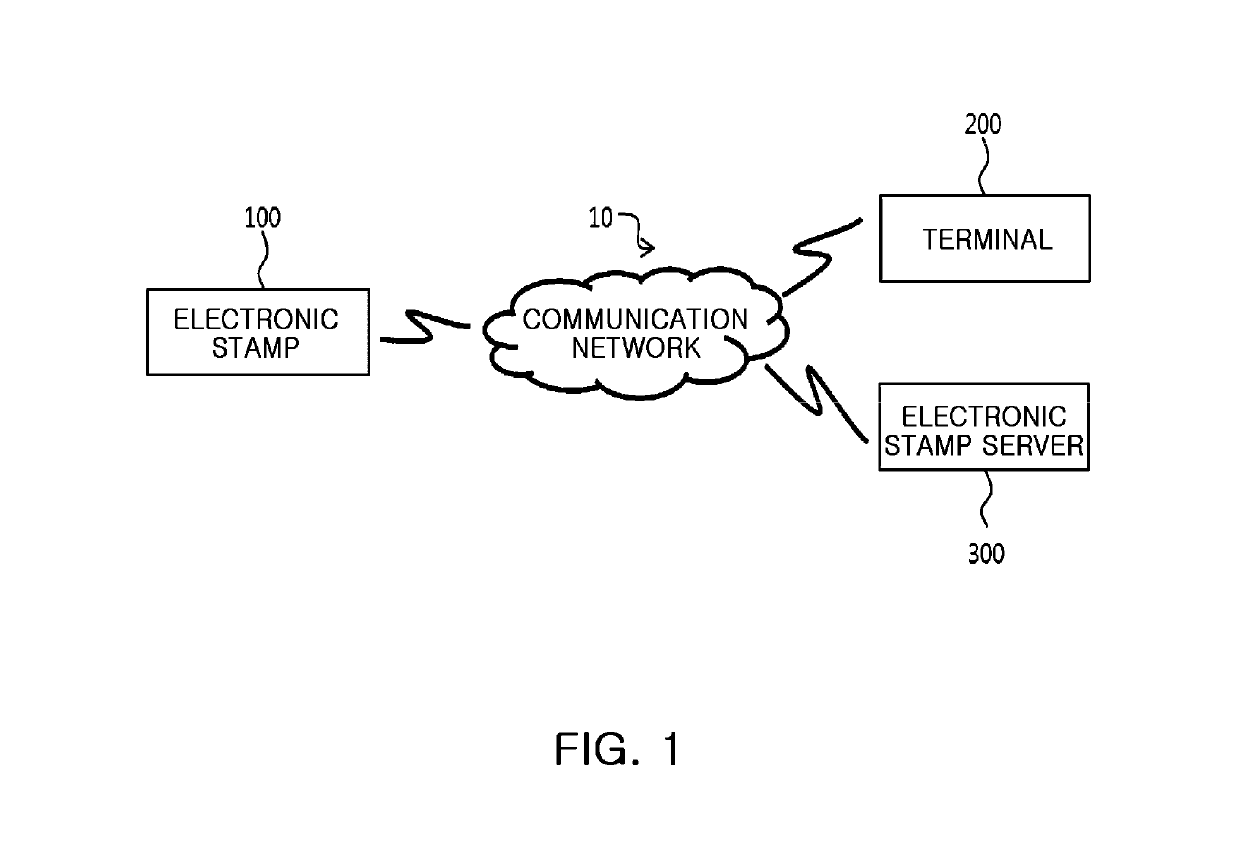
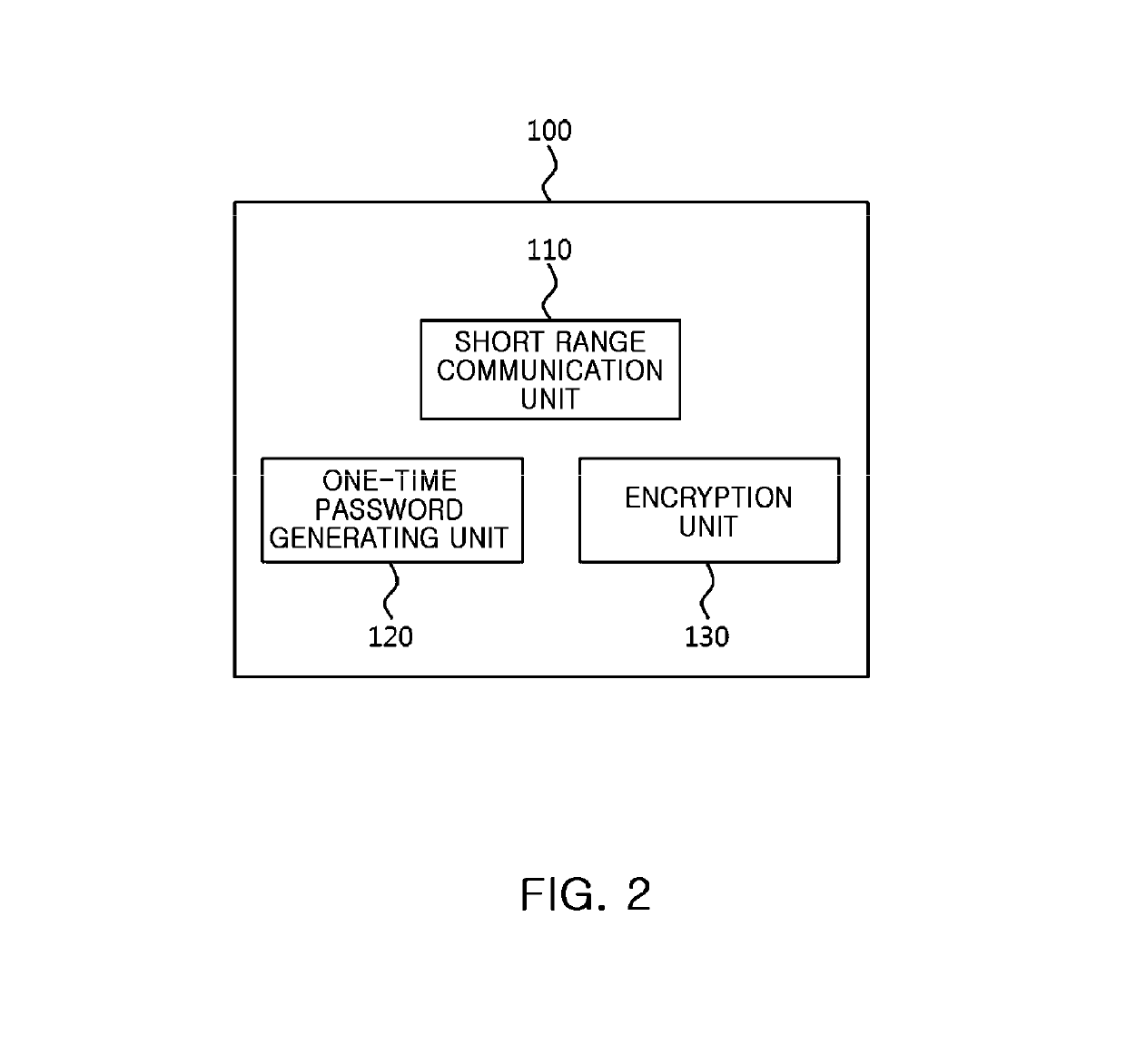
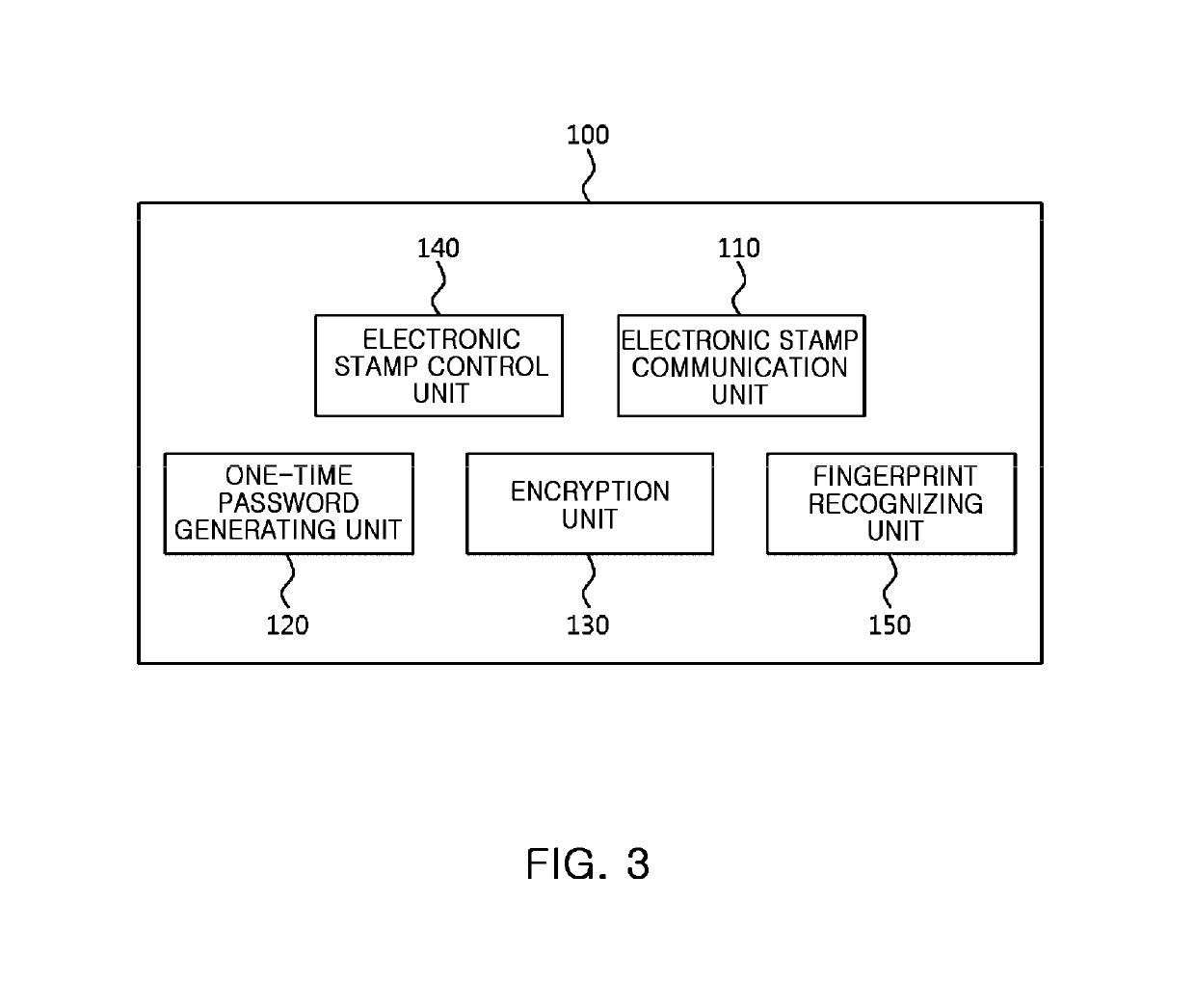
Electronic stamp system for security intensification, control method thereof, and non-transitory computer readable storage medium having computer program recorded thereon
ActiveUS10361857B2Key distribution for secure communicationDiscounts/incentivesComputer hardwareOne-time password
Provided are an electronic stamp system for security intensification, a control method thereof, and a non-transitory computer readable storage medium having a computer program recorded thereon. According to the invention, it is possible to generate an encrypted value based on a membership ID related to a user of a terminal provided from the terminal and an one-time password such as an OTP generated in the electronic stamp and provide the generated encrypted value to the terminal in the electronic stamp, provide the membership ID, electronic stamp information, and the encrypted value to an electronic stamp server from the terminal, and obtain a decryption key based on the electronic stamp ID extracted from the electronic stamp information and then decrypts the encrypted value based on the obtained decryption key, and verify authenticity of the electronic stamp by comparing the decrypted value and the membership ID in the electronic stamp server.
Owner:SK PLANET CO LTD
Method and arrangement for reliably identifying a user in a computer system
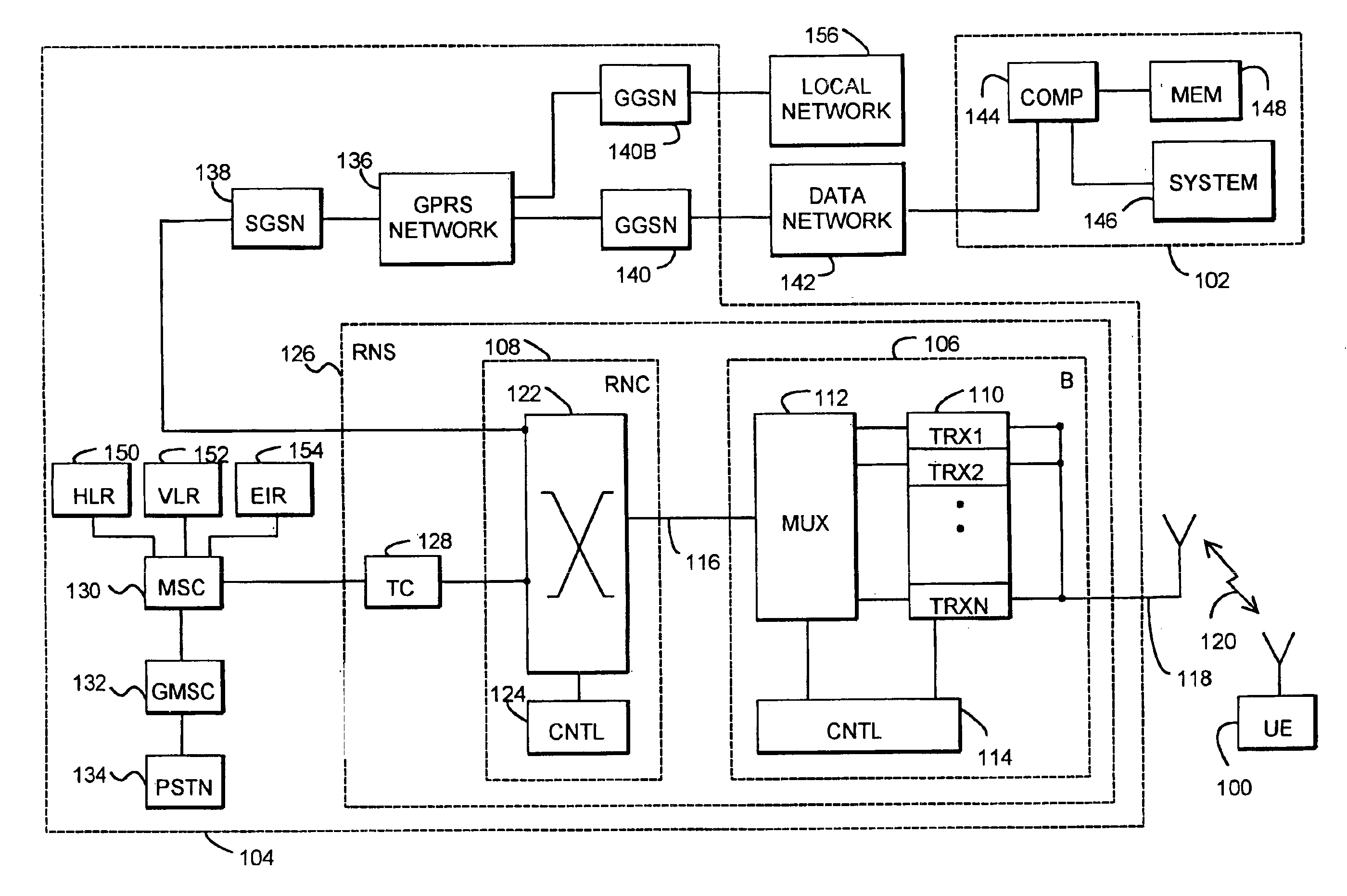
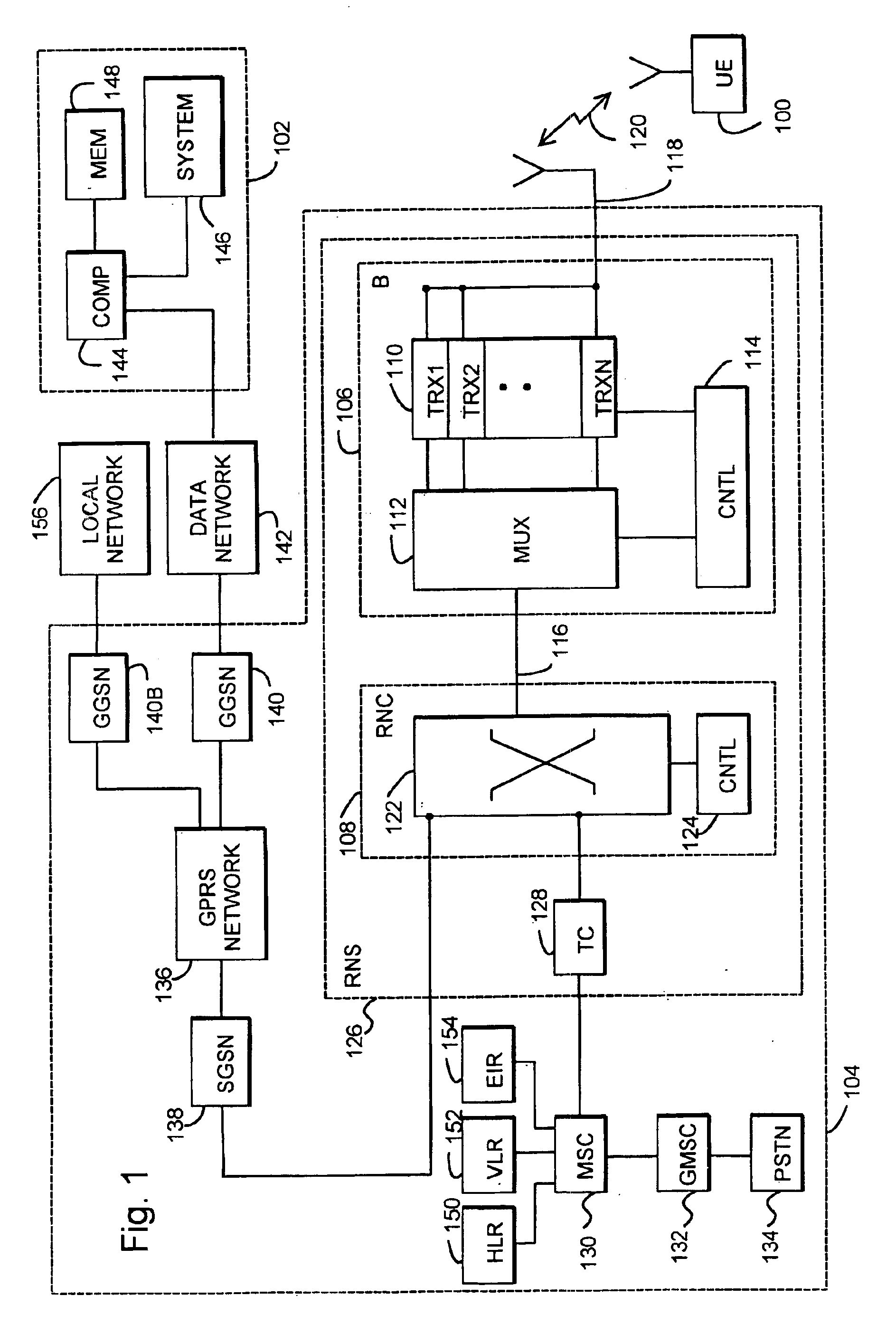
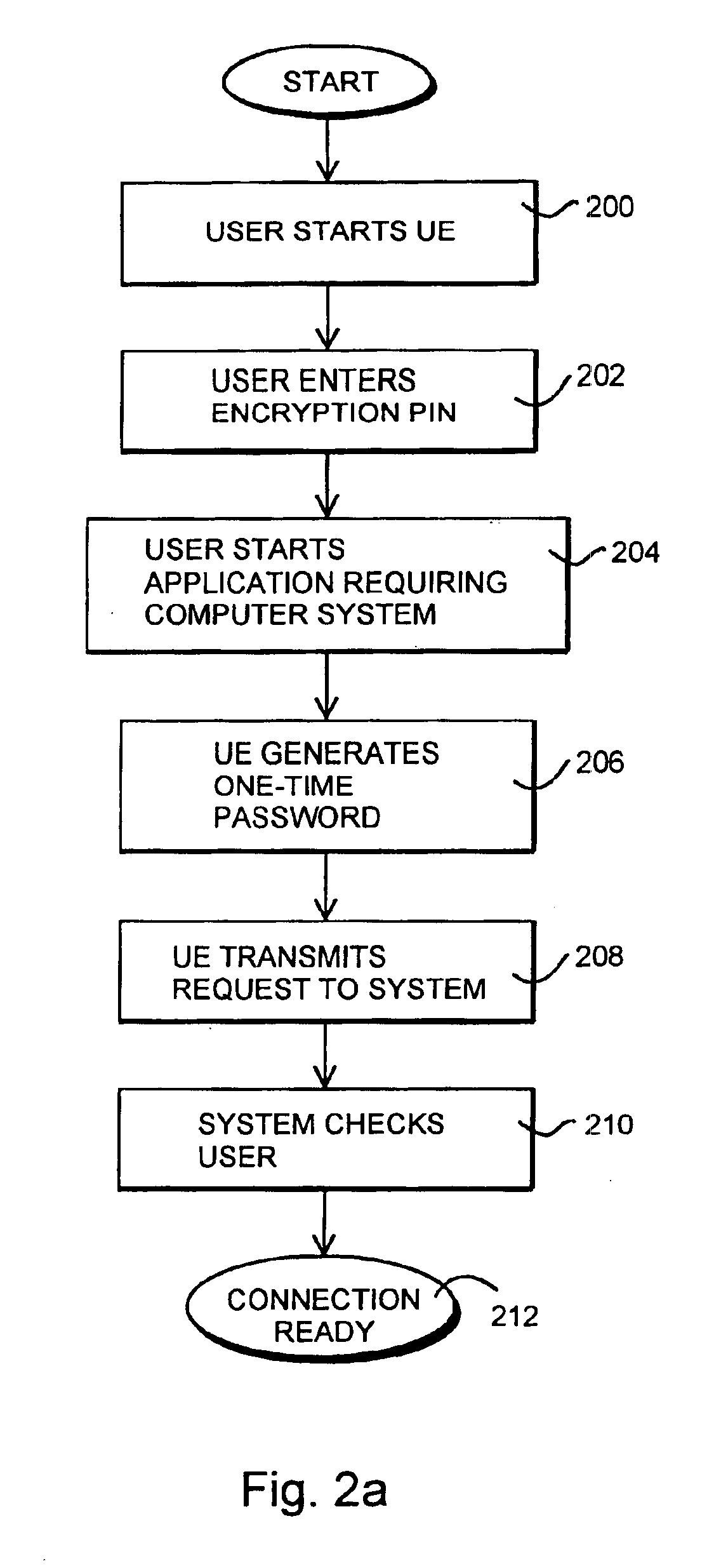
InactiveUS6928558B1Avoid disadvantagesReliable identificationDigital data processing detailsUser identity/authority verificationPersonal identification numberComputerized system
The invention relates to an arrangement and a method for reliably identifying a user in a computer system. The method utilizes a mobile station for communicating with the system. The method comprises generating a first one-time password in the mobile station by utilizing a known algorithm on the basis of the identification number of the user, subscriber-specific identifier, device-specific identifier of the mobile station, and time. The password obtained and the subscriber-specific identifier of the user are encoded and transmitted to an authentication server of the computer system, comprising identifying the user on the basis of the subscriber-specific identifier, searching a database for the personal identifier number of the user and the device-specific identifier of the mobile station associated with the user, generating a second password at the authentication server by utilizing the same predetermined algorithm on the basis of the personal identification number of the user, subscriber-specific identifier, device-specific identifier of the mobile station and time, comparing the first and the second passwords with each other at the authentication server, and if the passwords match, enabling the telecommunication connection between the mobile station and the computer system.
Owner:NOKIA MOBILE PHONES LTD
Methods and systems for authenticating users
ActiveUS20110035788A1Reduce transaction riskReduce riskDigital data processing detailsUser identity/authority verificationWorkstationOne-time password
A method of authenticating users to reduce transaction risks includes indicating a desire to conduct a transaction, inputting information in a workstation, and determining whether the inputted information is known. Moreover, the method includes determining a state of a communications device when the inputted information is known, and transmitting a biometric authentication request from a server to an authentication system when the state of the communications device is enrolled. Additionally, the method includes obtaining biometric authentication data in accordance with a biometric authentication data capture request with the communications device, biometrically authenticating the user, generating a one-time pass-phrase and storing the one-time pass-phrase on the authentication system when the user is authenticated, comparing the transmitted one-time pass-phrase against the stored one-time pass-phrase, and conducting the transaction when the transmitted and stored one-time pass-phrases match.
Owner:DAON TECH
Authentication of card-not-present transactions
ActiveUS20110153496A1Avoid exposureAvoid lossFinanceMultiple digital computer combinationsOne-time passwordDatabase
Methods, systems, and machine-readable media are disclosed for processing a card-not-present transaction. According to one embodiment, processing a card-not-present transaction can comprise receiving a request for a card-not-present transaction involving an enrolled consumer. The request can include information identifying the enrolled consumer. A record of information related to the enrolled consumer can be read and the enrolled consumer can be authenticated based at least in part on the information of the request and the record of information related to the enrolled consumer. In response to authenticating the enrolled consumer, a set of single-use payment information can be generated which can include a one-time password and a dynamic Primary Account Number (PAN) which is valid for a single transaction. The single-use payment information can be provided to the enrolled consumer or the merchant to complete the transaction in place of the true PAN.
Owner:FIRST DATA
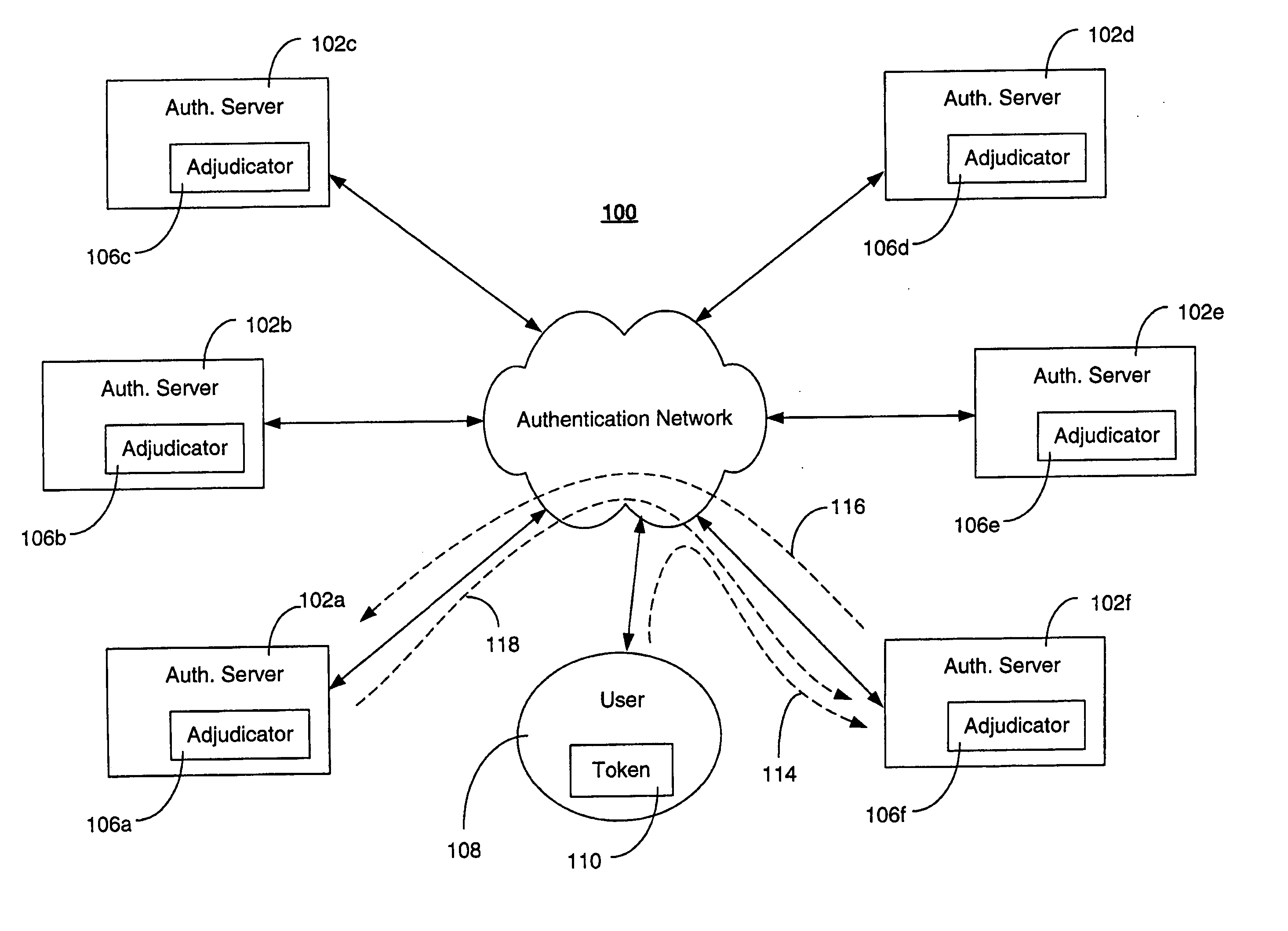
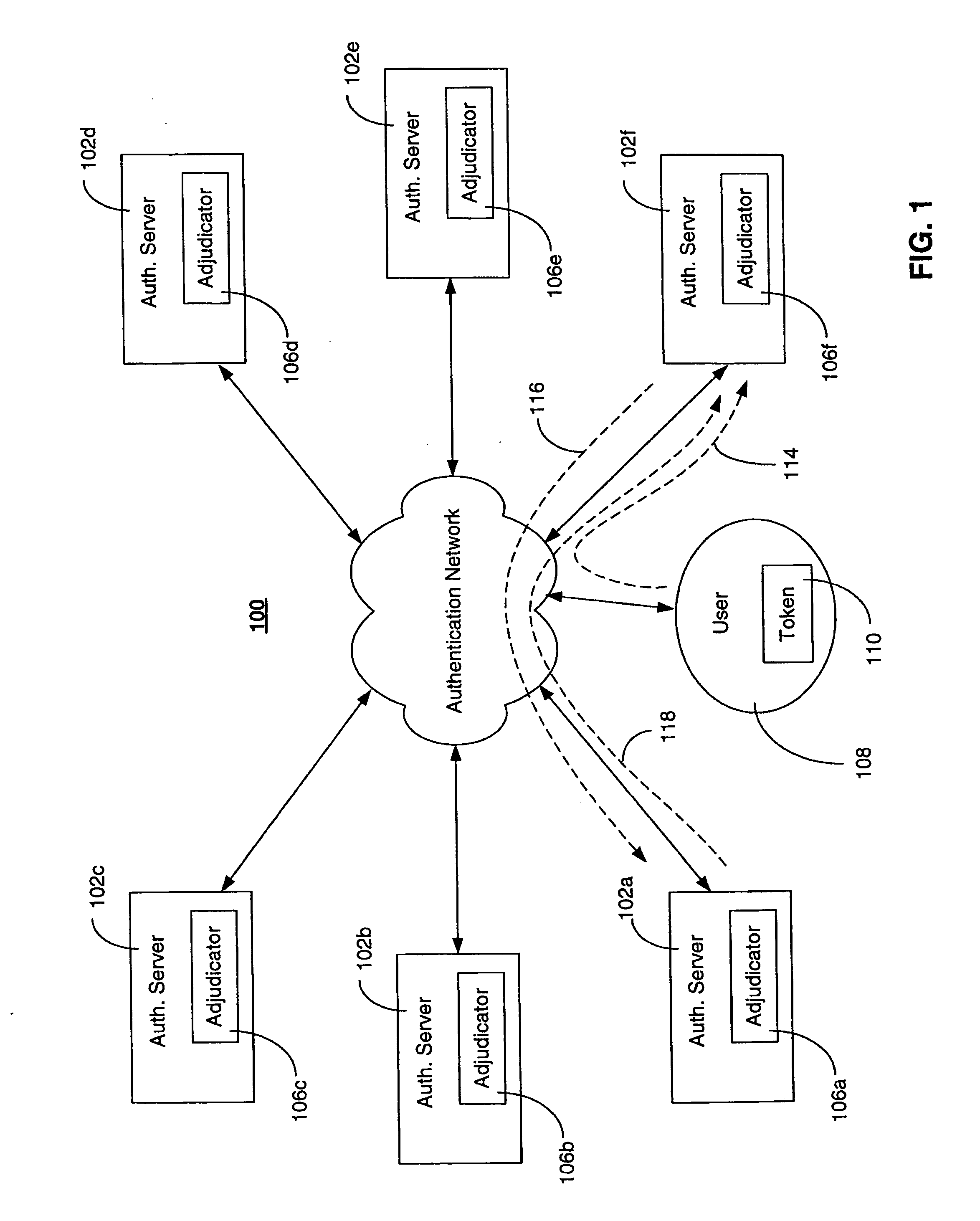
Detecting and preventing replay in authentication systems
ActiveUS20070256123A1Detecting and preventing replay attackAvoid authenticationDigital data processing detailsUser identity/authority verificationAuthentication serverOne-time password
A system for detecting and preventing replay attacks includes a plurality of interconnected authentication servers, and one or more tokens for generating a one-time passcode and providing the one-time passcode to one of the authentication servers for authentication. The system includes an adjudicator function associated with each authentication server. The adjudicator evaluates a high water mark value associated with a token seeking authentication, allows authentication to proceed for the token if the high water mark evaluation indicates that the one-time passcode was not used in a previous authentication, and prevents authentication if the high water mark evaluation indicates that the one-time passcode was used in a previous authentication. The token is associated with a home authentication server that maintains a current high water mark of the token. The home authentication server validates the current high water mark on behalf of the adjudicator function evaluating the token for authentication.
Owner:RSA
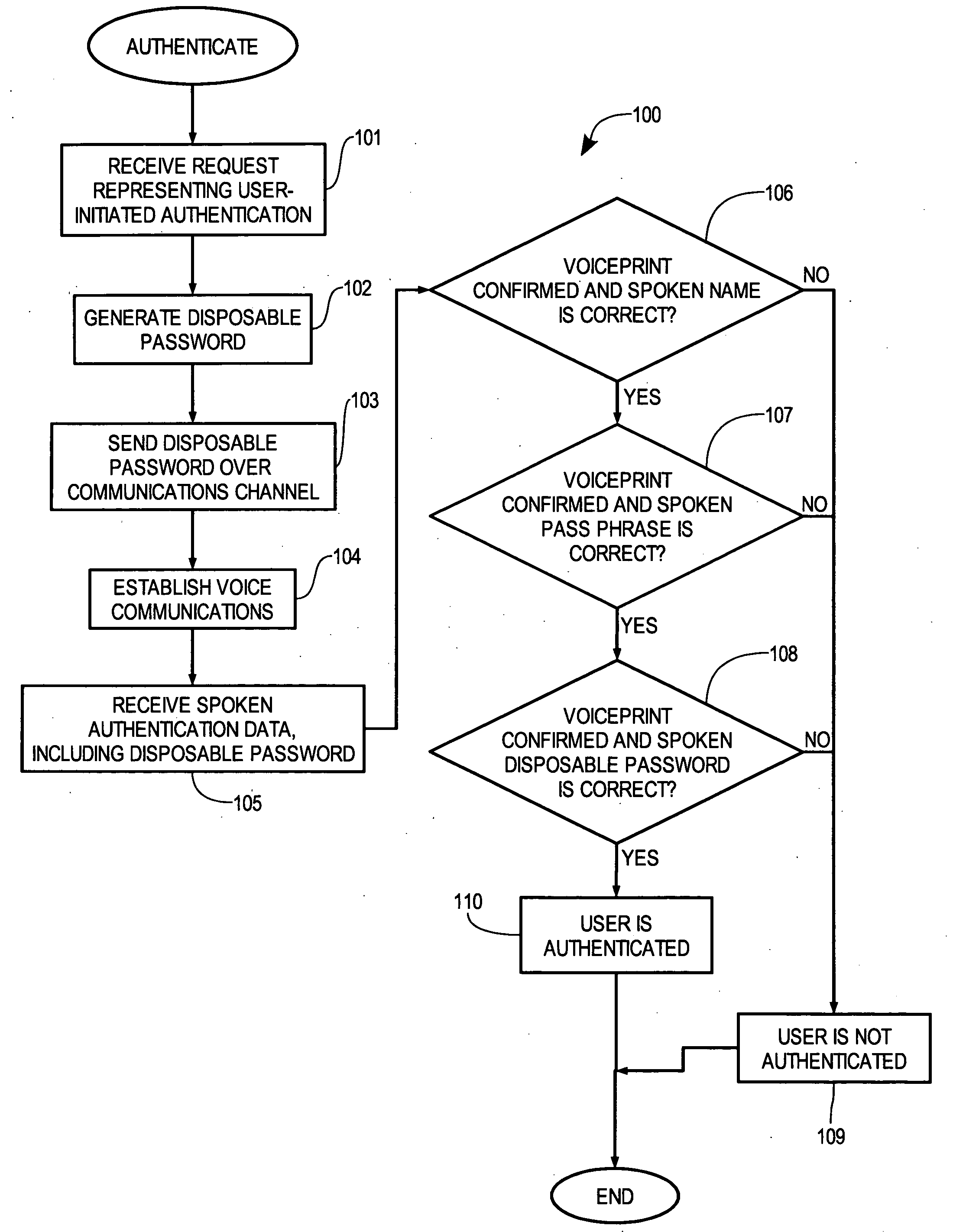
Multi-factor biometric authentication
InactiveUS20070055517A1Digital data authenticationIndividual entry/exit registersSecret codeOne-time password
A method for verifying a person's identity in order to gain access to electronic data, a data network, a physical location, or enable a commercial transaction. A request for identity verification is processed over a data network and the system is initiated which (i) transmits a disposable pass phrase over a data network to the user, (ii) prompts the user to vocalize the disposable pass phrase, a pass phrase, and user id, (iii) compares the recited speech of the user to the stored voiceprint of the user, the stored pass phrase and id of the user, and the generated disposable pass phrase, then (iv) issues a token or signal that represents whether the user was verified or not.
Owner:AUTHENTIVOX
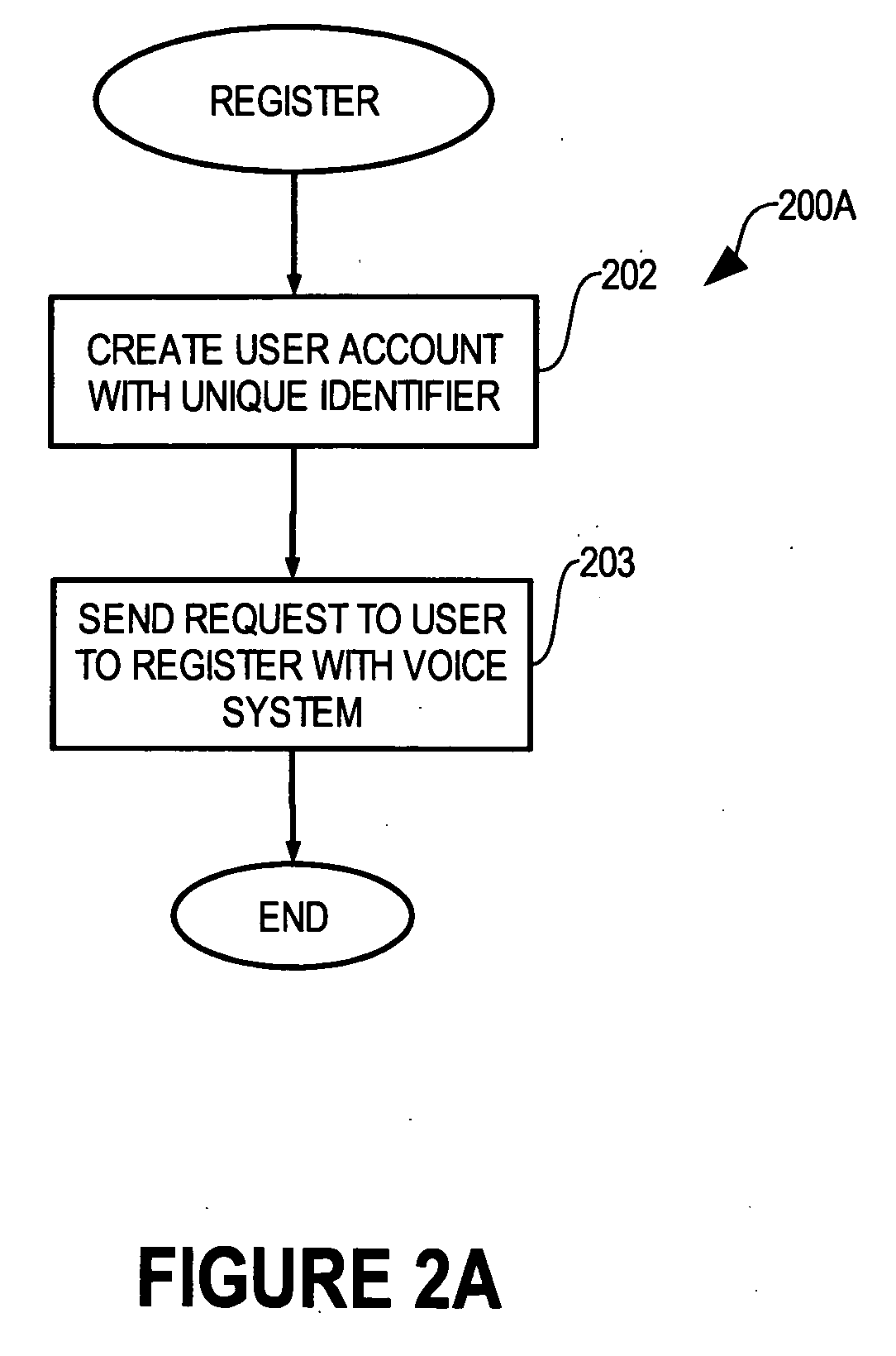
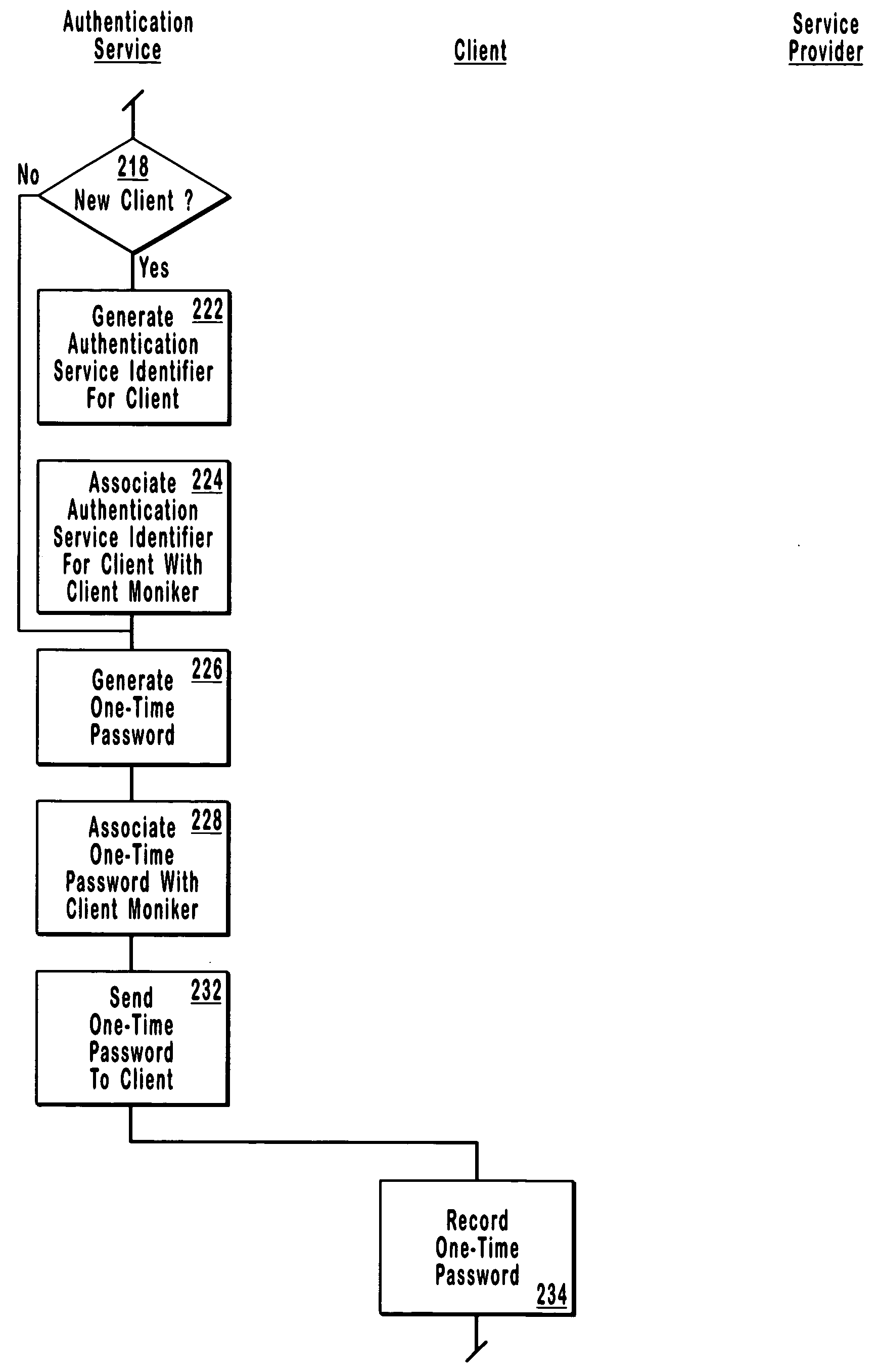
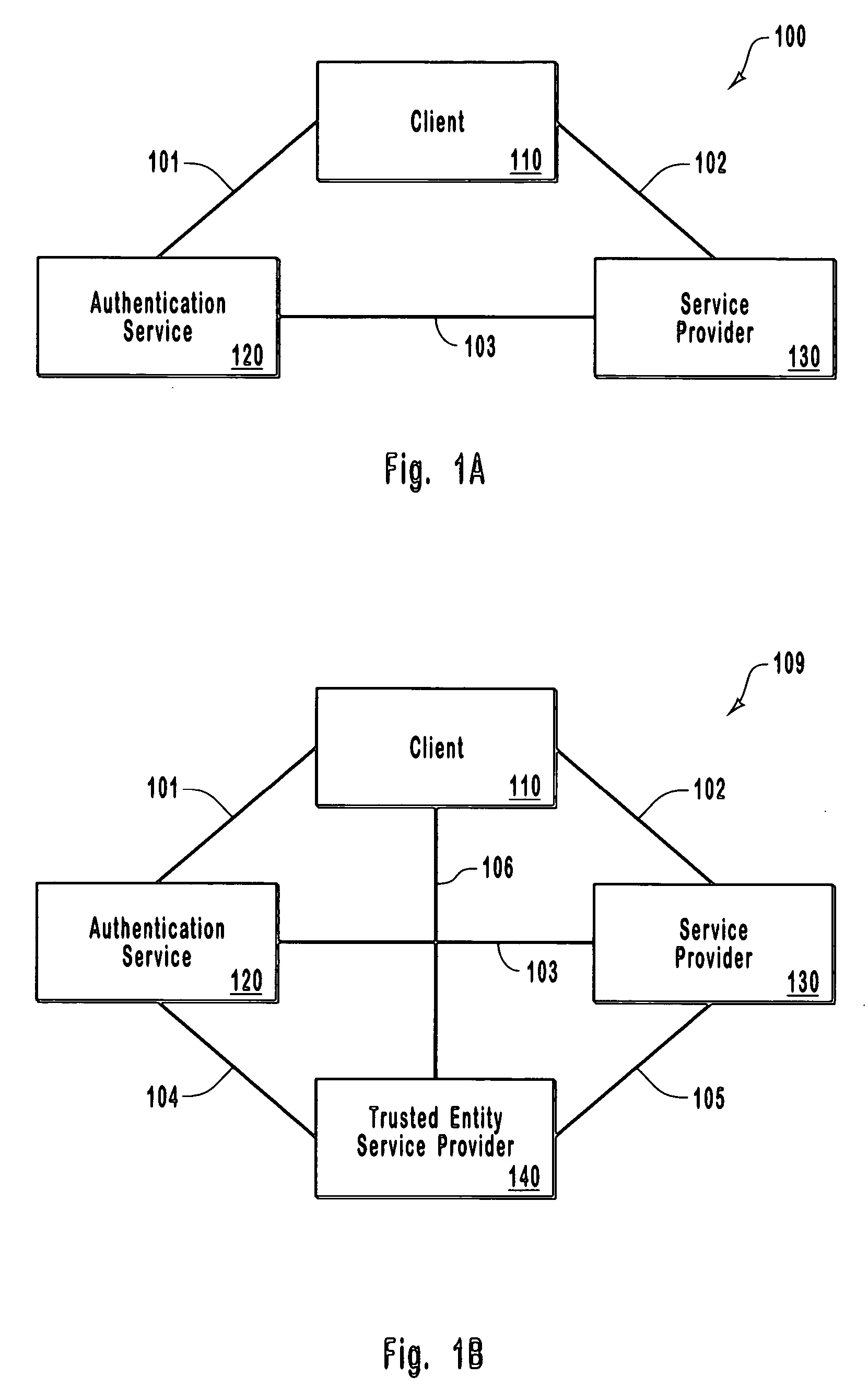
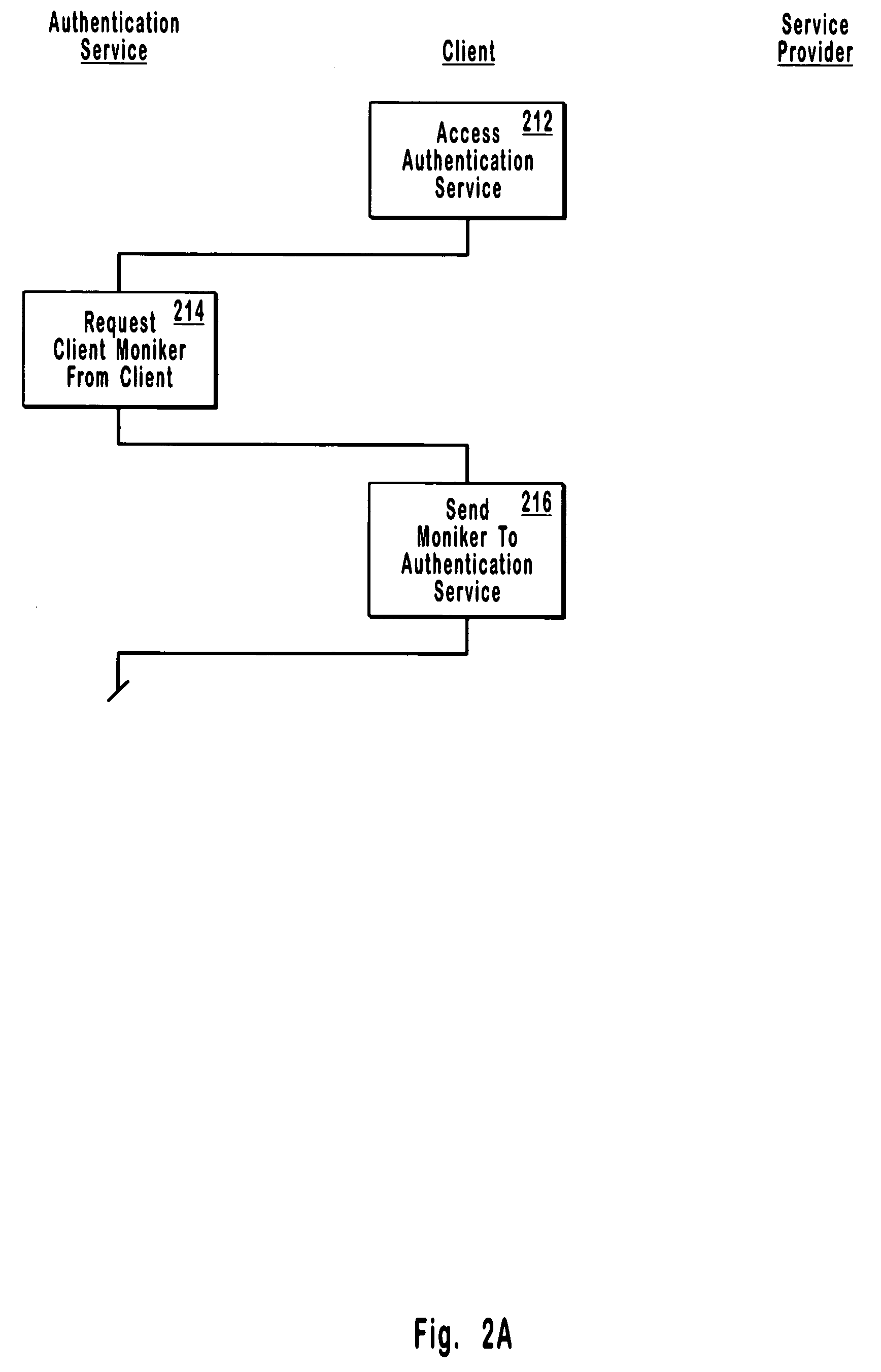
Single-use password authentication
ActiveUS20060080545A1Reduce the possibilityLimited lifetimeDigital data processing detailsMultiple digital computer combinationsClient-sideOne-time password
Systems, computer program products and methods for authentication using a one-time password. In system that includes a client, a service provider, and an authentication service, the authentication service generates an authentication service identifier for the client. Any suitable identifier may be used for the authentication service identifier, which generally takes the form of an arbitrary number of characters. From the client, the authentication service receives a client moniker (e.g., a username) for the client to use when accessing the authentication service. The authentication service sends a one-time password to the client for the client to use in accessing the service provider. When the authentication service receives a one-time password from the service provider, the authentication service sends the authentication service identifier for the client to the service provider to authenticate the client if the one-time password received from the service provider matches the one-time password sent to the client.
Owner:TOKENYM
Multi-factor authentication using a smartcard
ActiveUS8245292B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
Data Replication Across Enterprise Boundaries
ActiveUS20110161289A1Digital data information retrievalDigital data processing detailsData fieldUnique identifier
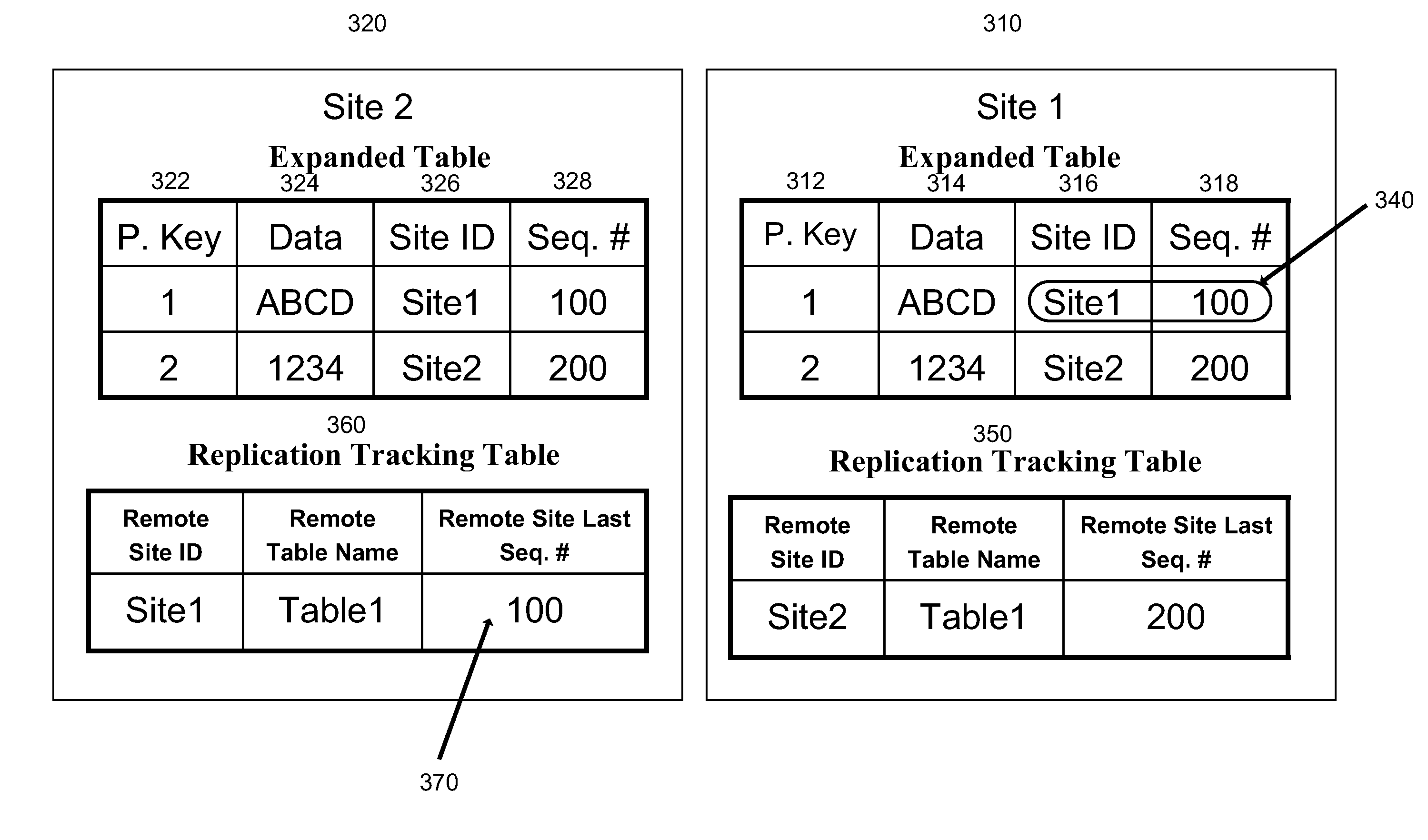
Systems and methods for synchronizing verification data in a distributed database including client and server databases. The server database may exchange verification data regarding one-time passwords to multiple client databases. An update to the server database may be initiated based on information stored in the client database by pushing updated verification information from the client database to the server database via an SSL tunnel. An update to the client database may be initiated based on information stored in the server database by pulling updated verification data from the server database to the client database via an SSL tunnel. The client database and the server database may include a two-dimensional data field including the verification data and an associated key identifier, and a site ID. The site ID may include a unique identifier to identify the respective database in which it is included. The data field may include a sequence number assigned to each row of data that increases every time the row of information is updated. The client database and the server database may also include a replication tracking table including a record of the last known update to a remote database. Data fields that require updating may be determined based on the site ID and a comparison of the sequence numbers from the replication tracking table and the server's database.
Owner:CA TECH INC
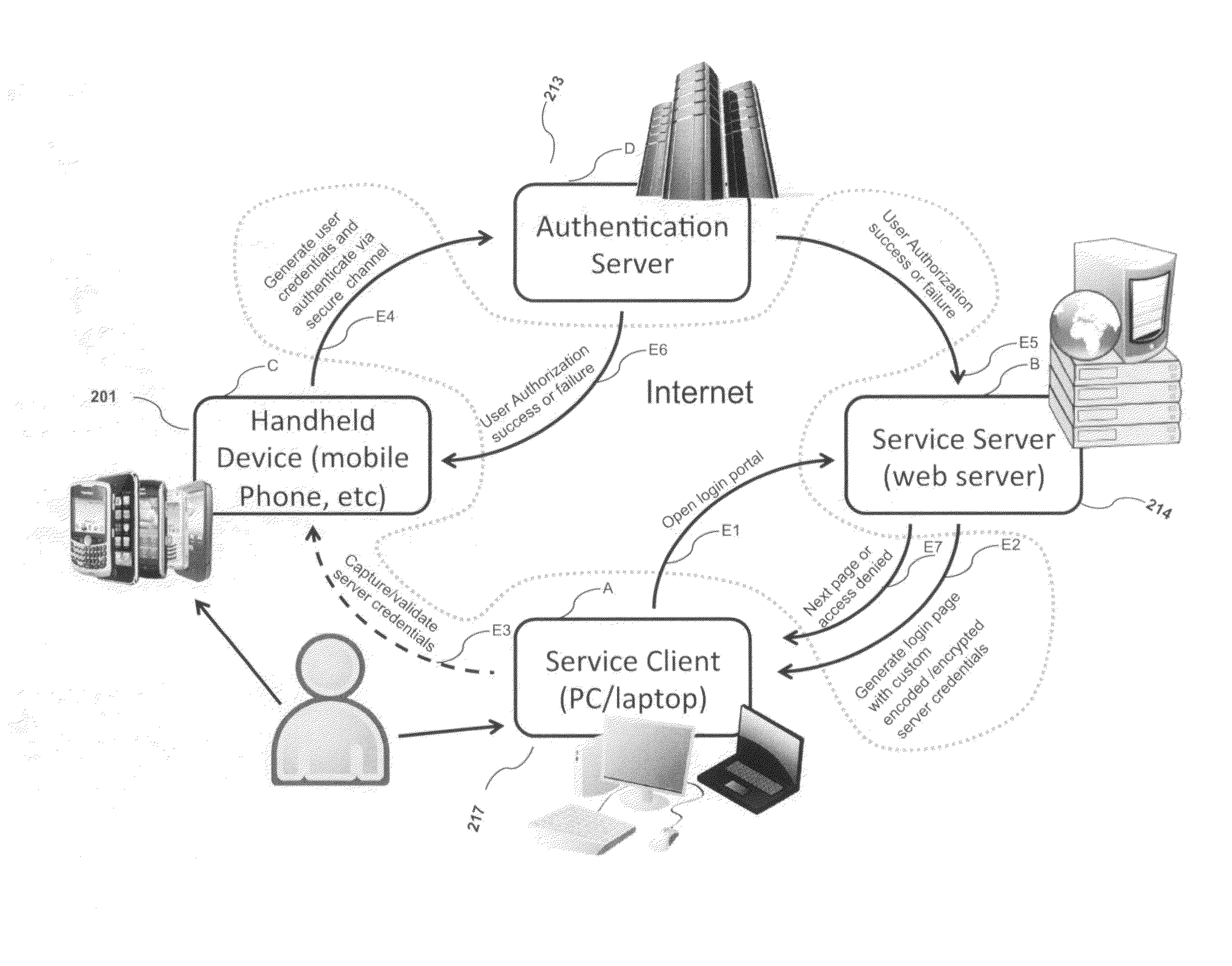
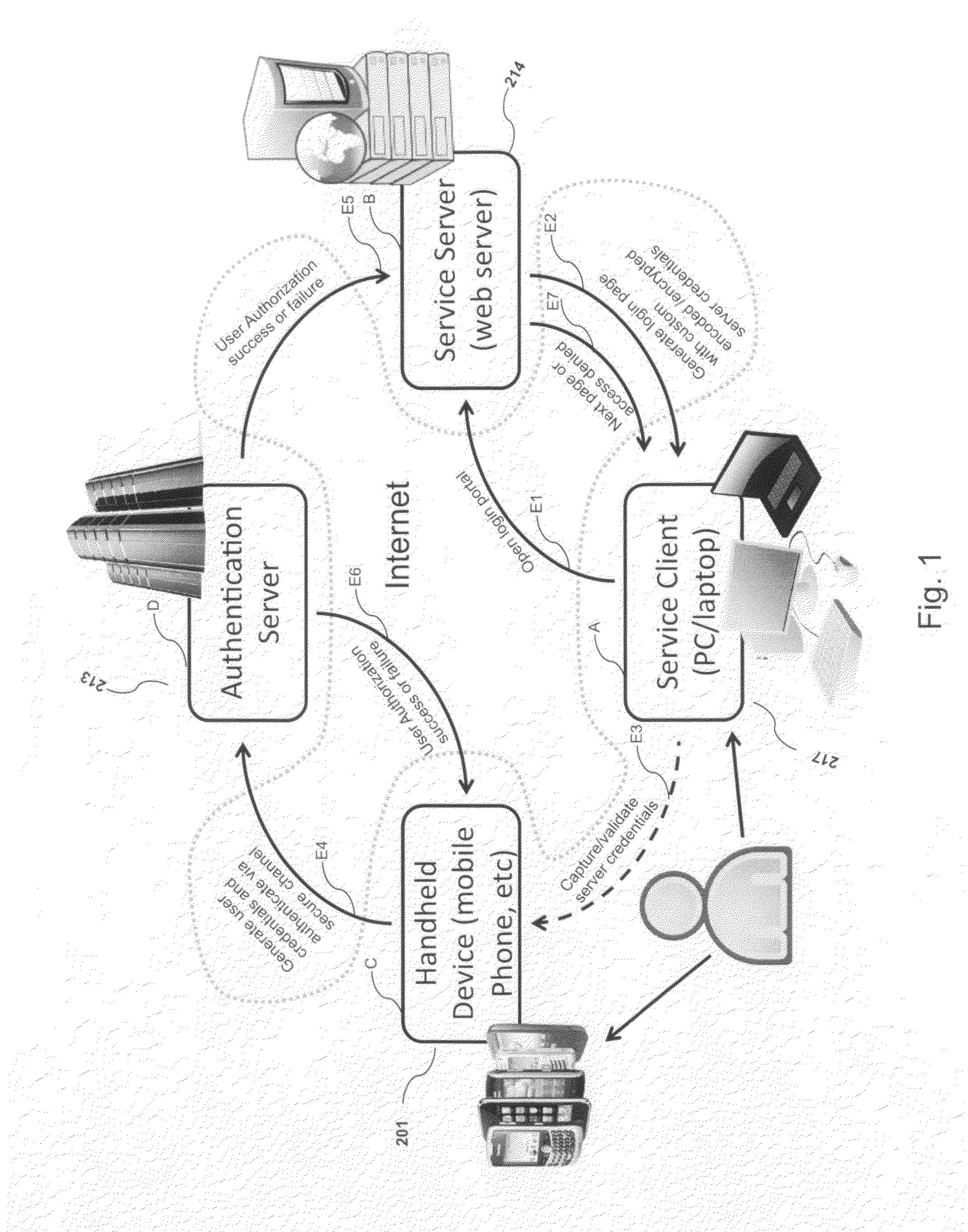
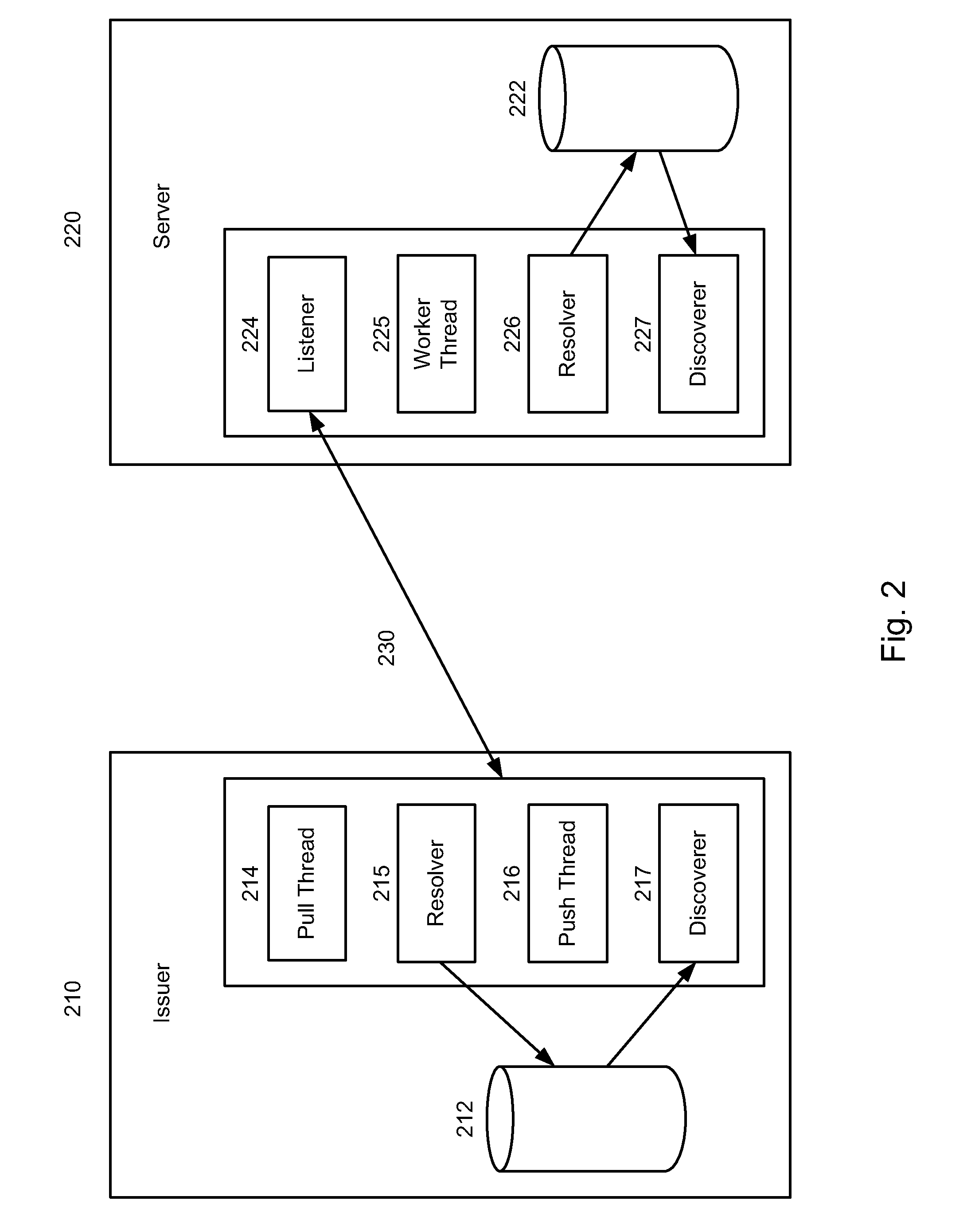
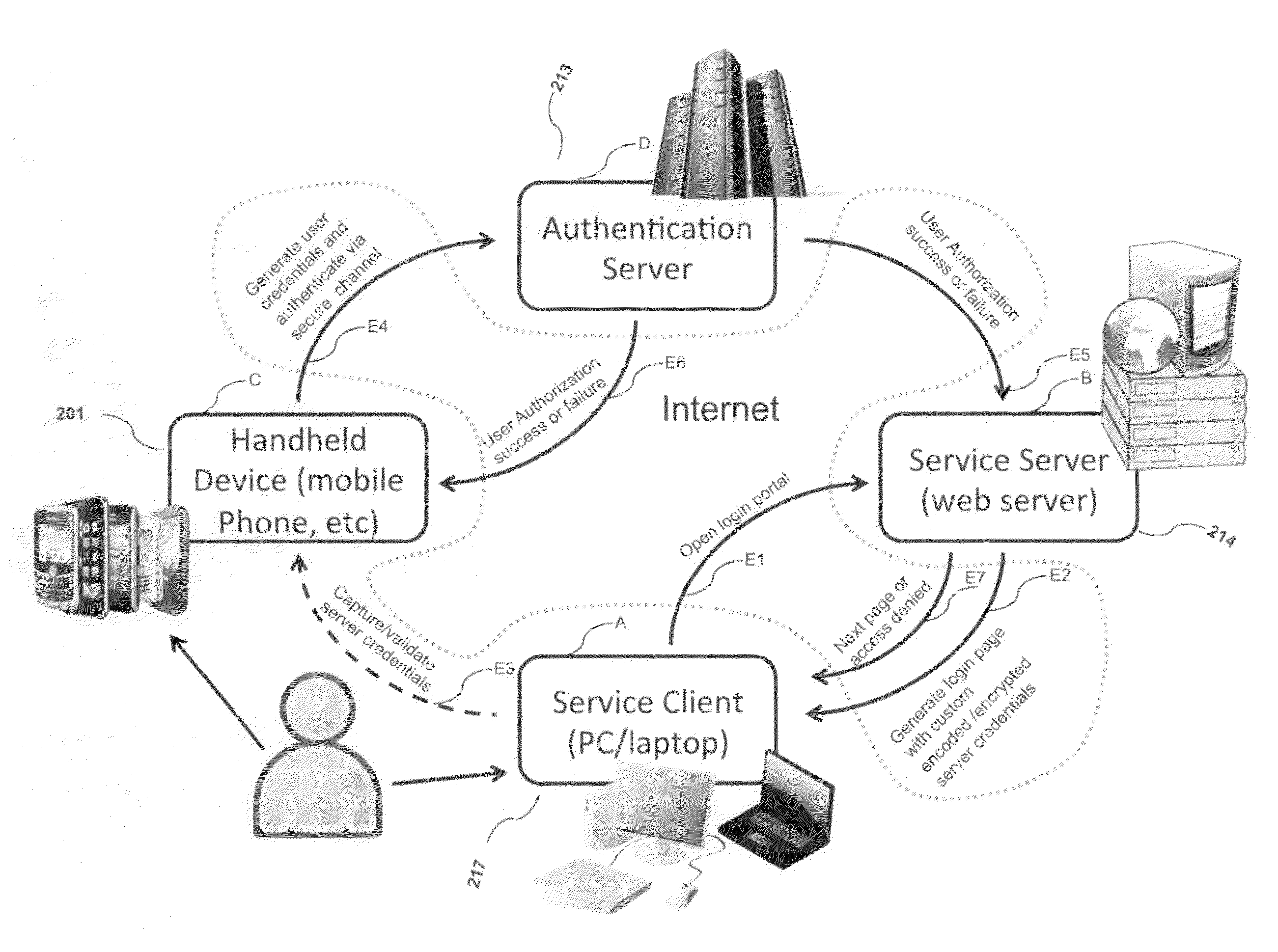
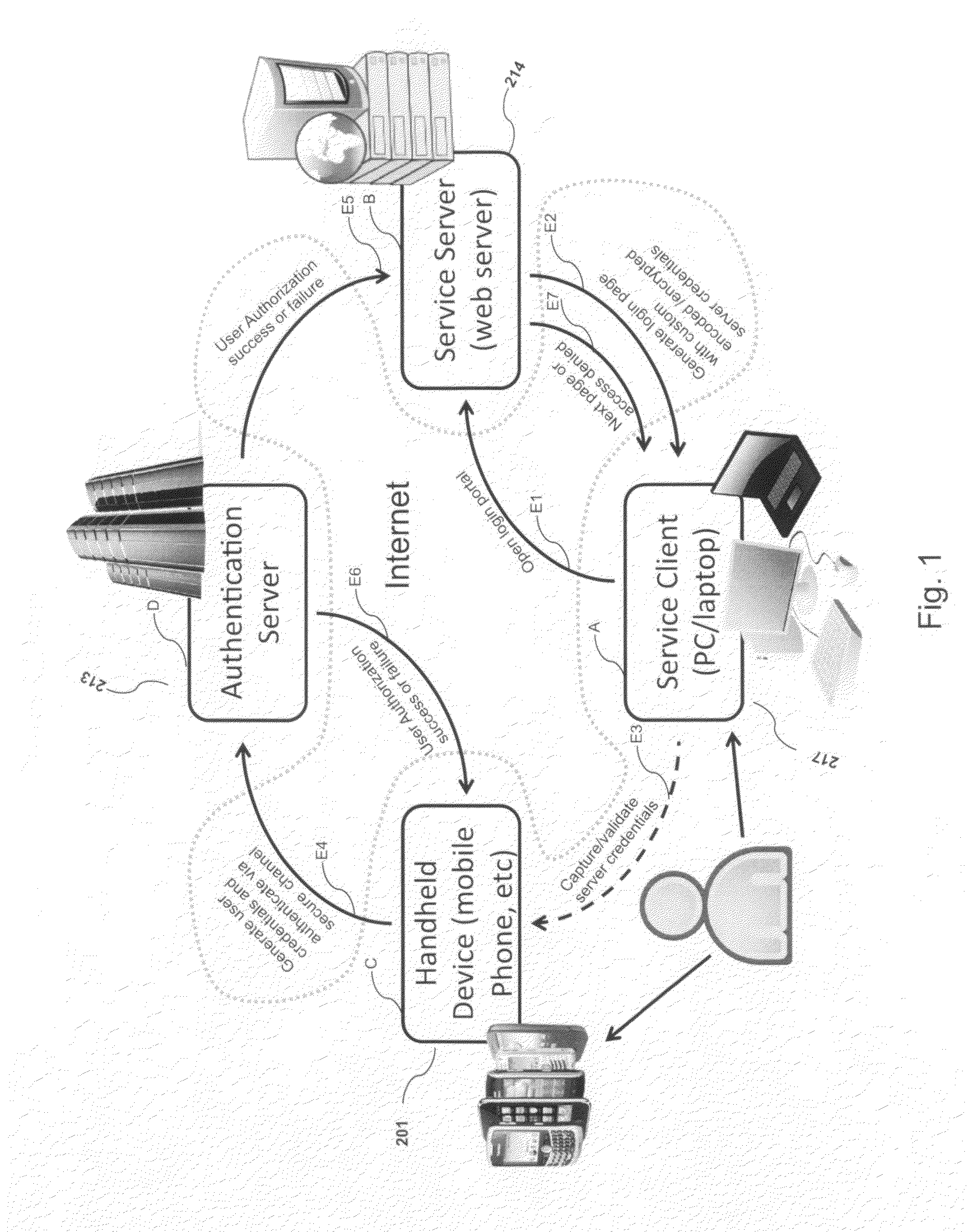
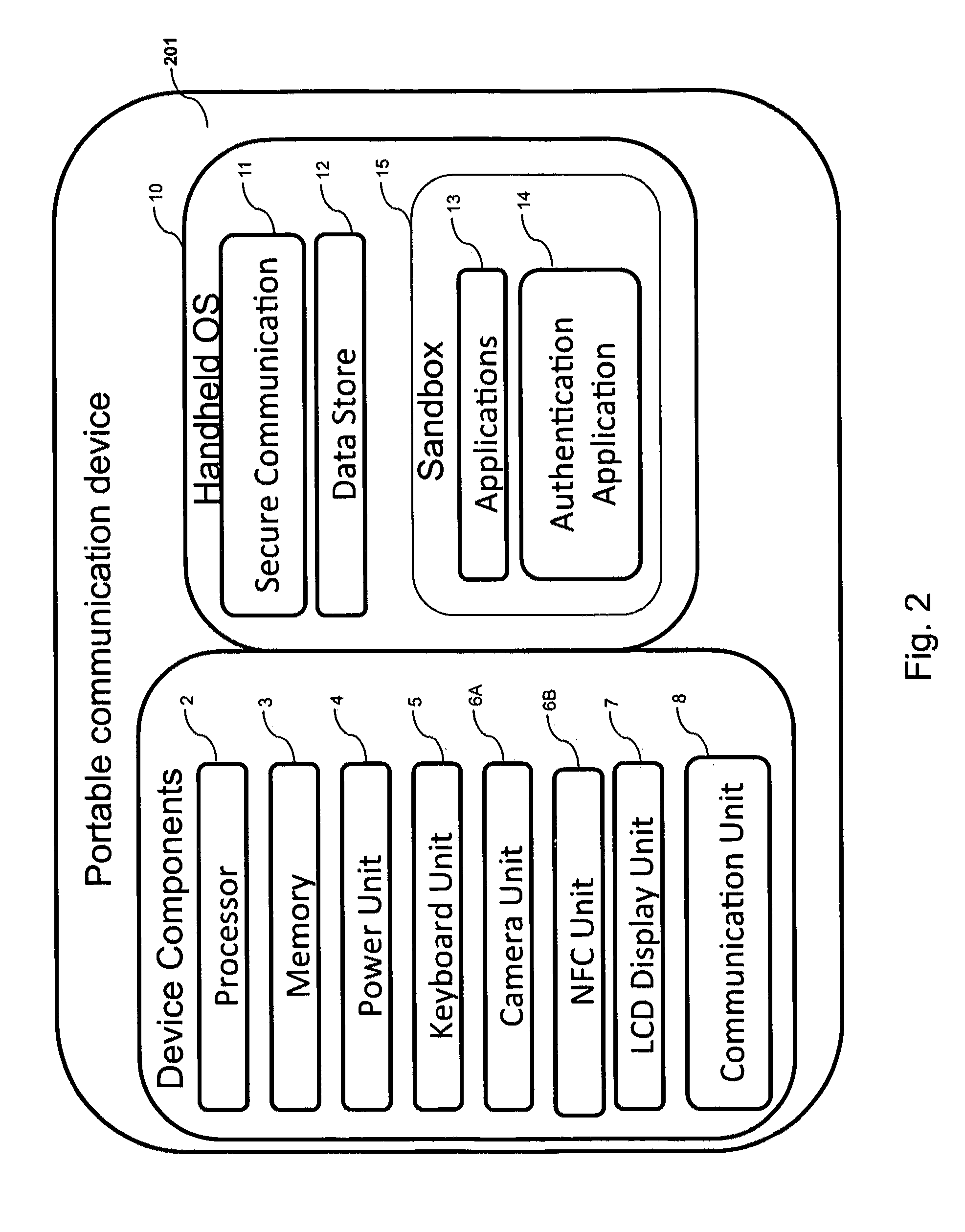
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS20120240204A1Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
Systems and methods of authentication according to the invention are provided comprising a user, a service client, a service server, a portable communications device and an authentication server, wherein the method comprises use of one time passwords and out-of-band outbound communication channels. This system gives access to authentication seekers based on OTP out of band outbound authentication mechanism. The authentication seeker or system user scans a multi-dimensional barcode or another like encoding mechanism and validates the client and triggers the out of band outbound mechanism. The portable mobile device invokes the client server to request authentication. The client server authenticates the user based on a shared secret key and the user is automatically traversed to the next page.
Owner:GCOM IP LLC
Method for secure user and transaction authentication and risk management
ActiveUS8806592B2Compromising usabilityCompromising costDigital data processing detailsUser identity/authority verificationSecret shareOne-time password
To provide a user signature on a network transaction, a security server receives transaction information representing a transaction between a network user and a network site, such as a website, directly from the network site. The security server calculates a one-time-password based on the received transaction information and a secret shared by the security server and the network site, but not by the user. The security server transmits the calculated one-time-password for application as the user's signature on the transaction. The one-time-password is independently calculable by the network site based on the shared secret.
Owner:PAYFONE
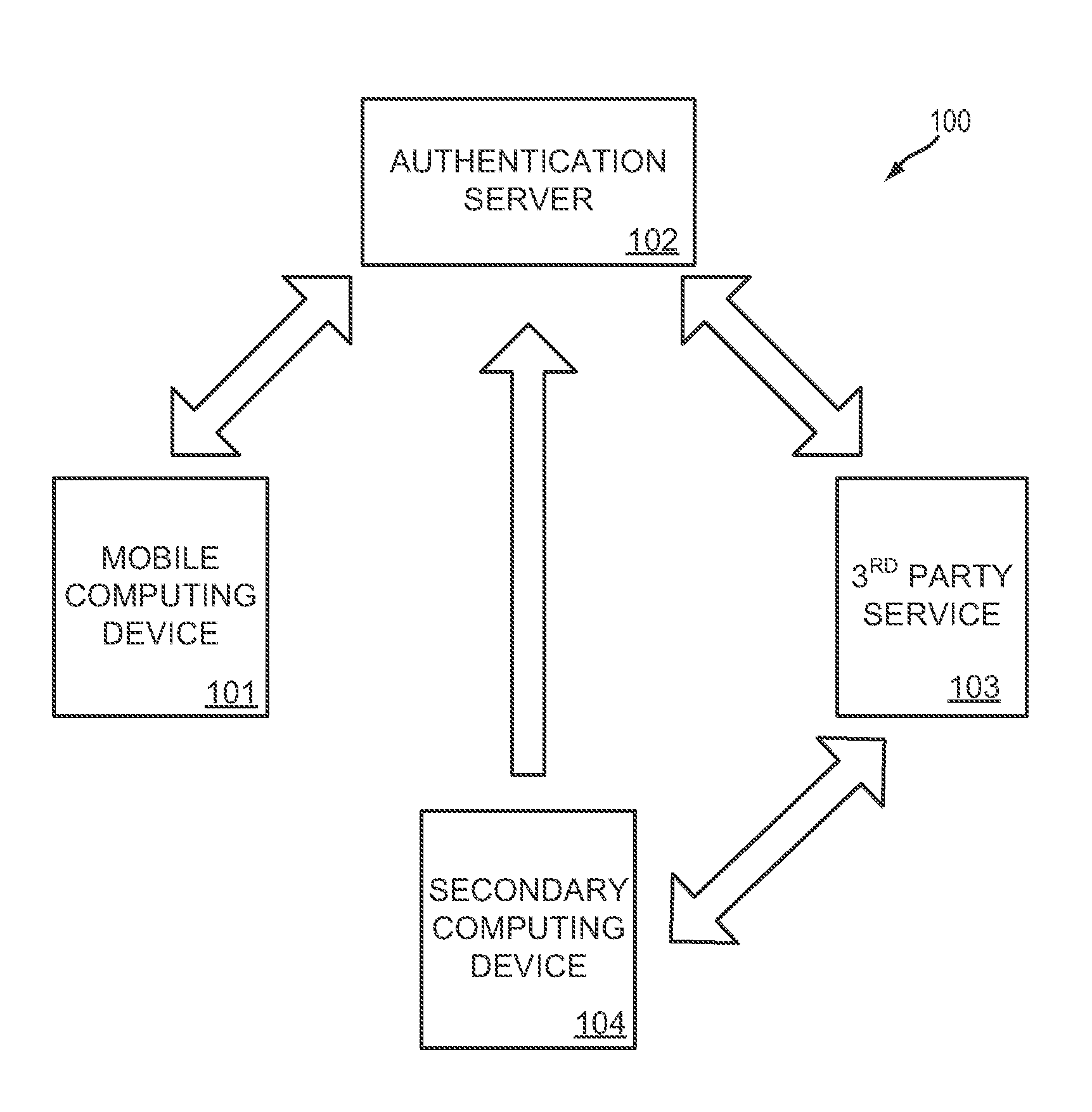
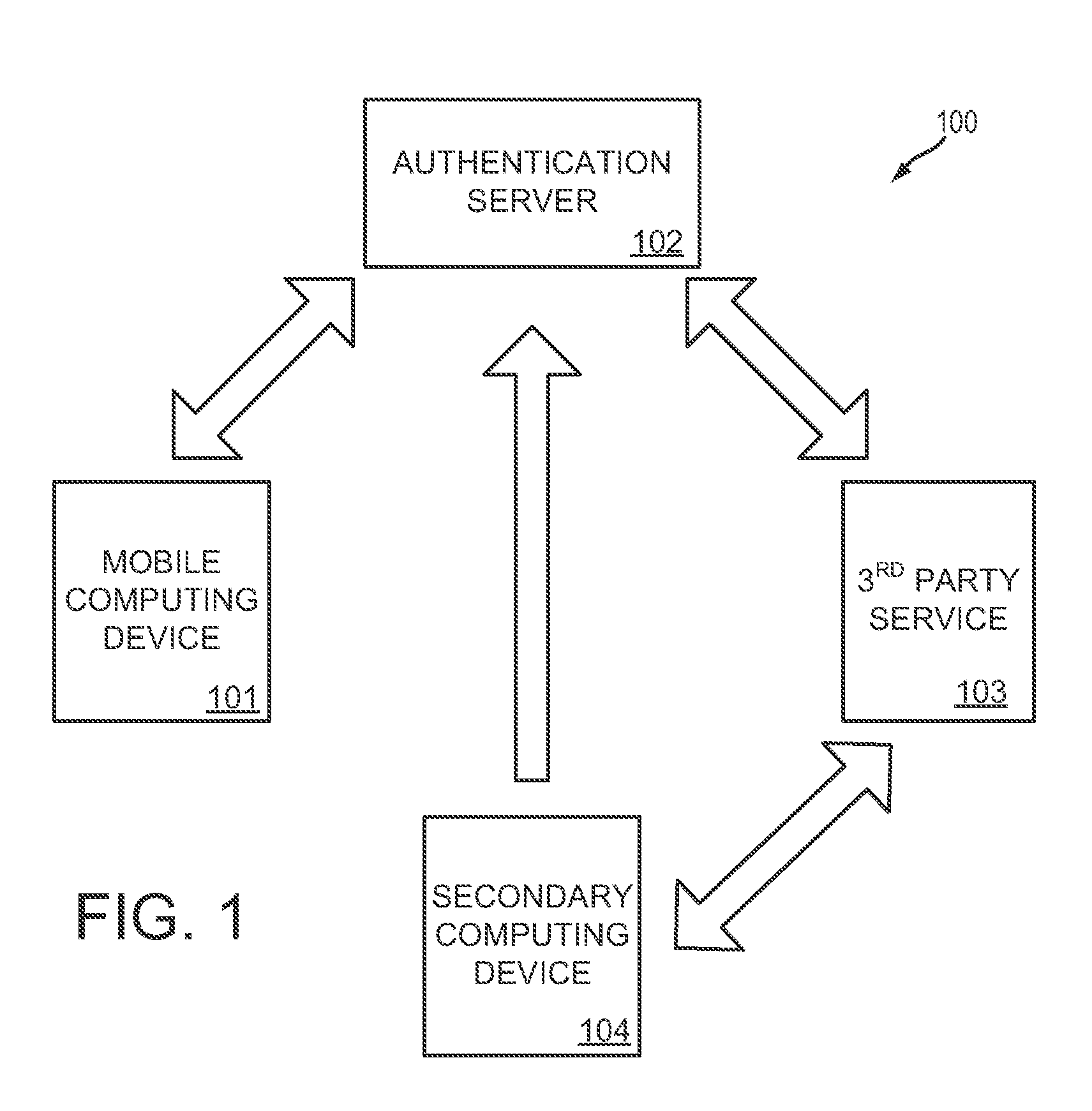
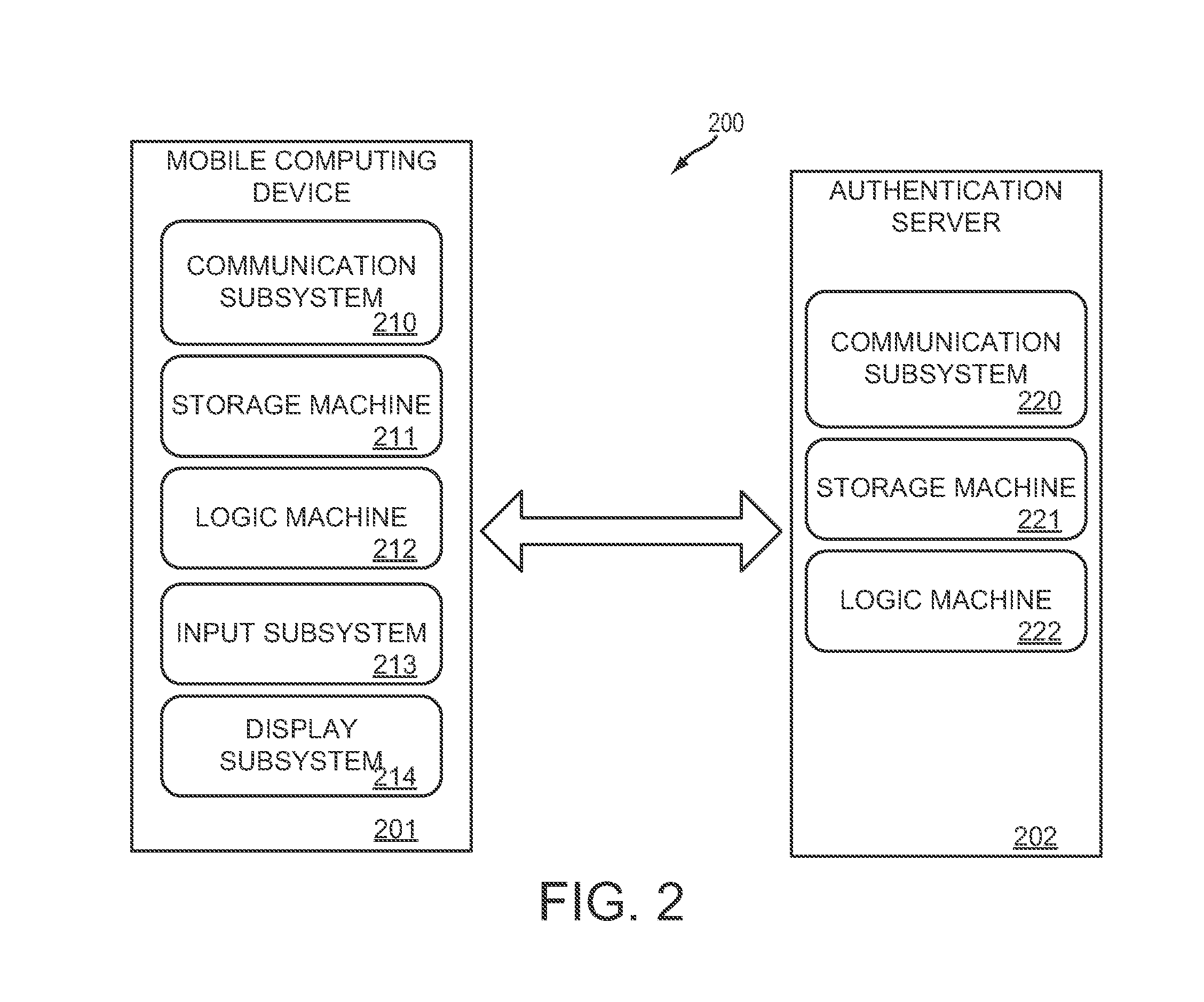
System and methods for one-time password generation on a mobile computing device
InactiveUS20140365780A1Increase the number ofImprove authentication strengthService provisioningDigital data processing detailsAuthentication serverOne-time password
A method for a mobile computing device comprises downloading a one-time password initializer from an authentication server, the one-time password initializer configured to generate a device-specific signature for the mobile computing device; uploading a device-specific signature to the authentication server; and downloading a device-specific configuration and one-time password generator from the authentication server. In this way, both the mobile computing device and authentication server may independently generate equivalent one-time passwords based on unique information associated with the mobile computing device.
Owner:MOVASSAGHI SAFA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com