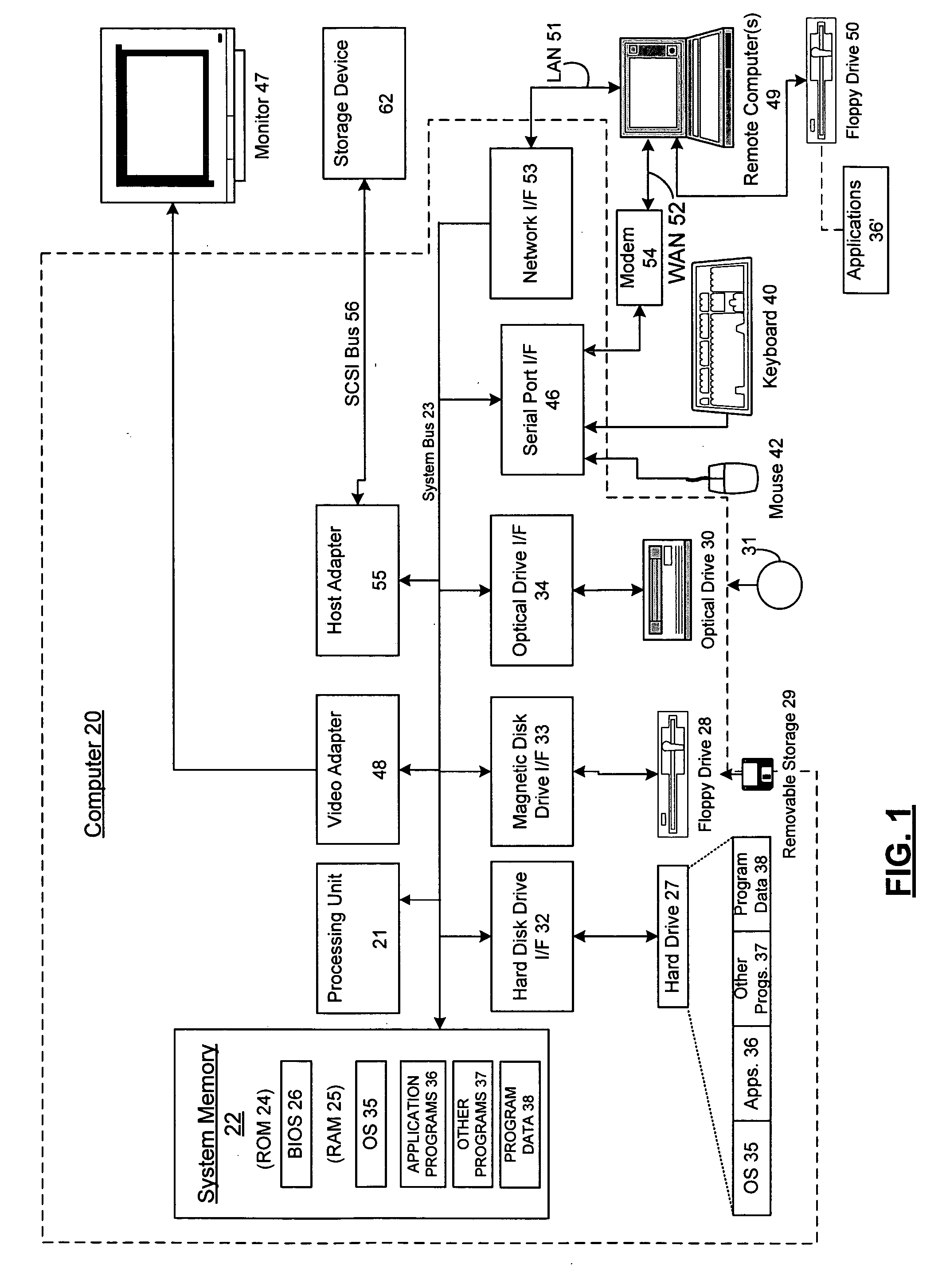
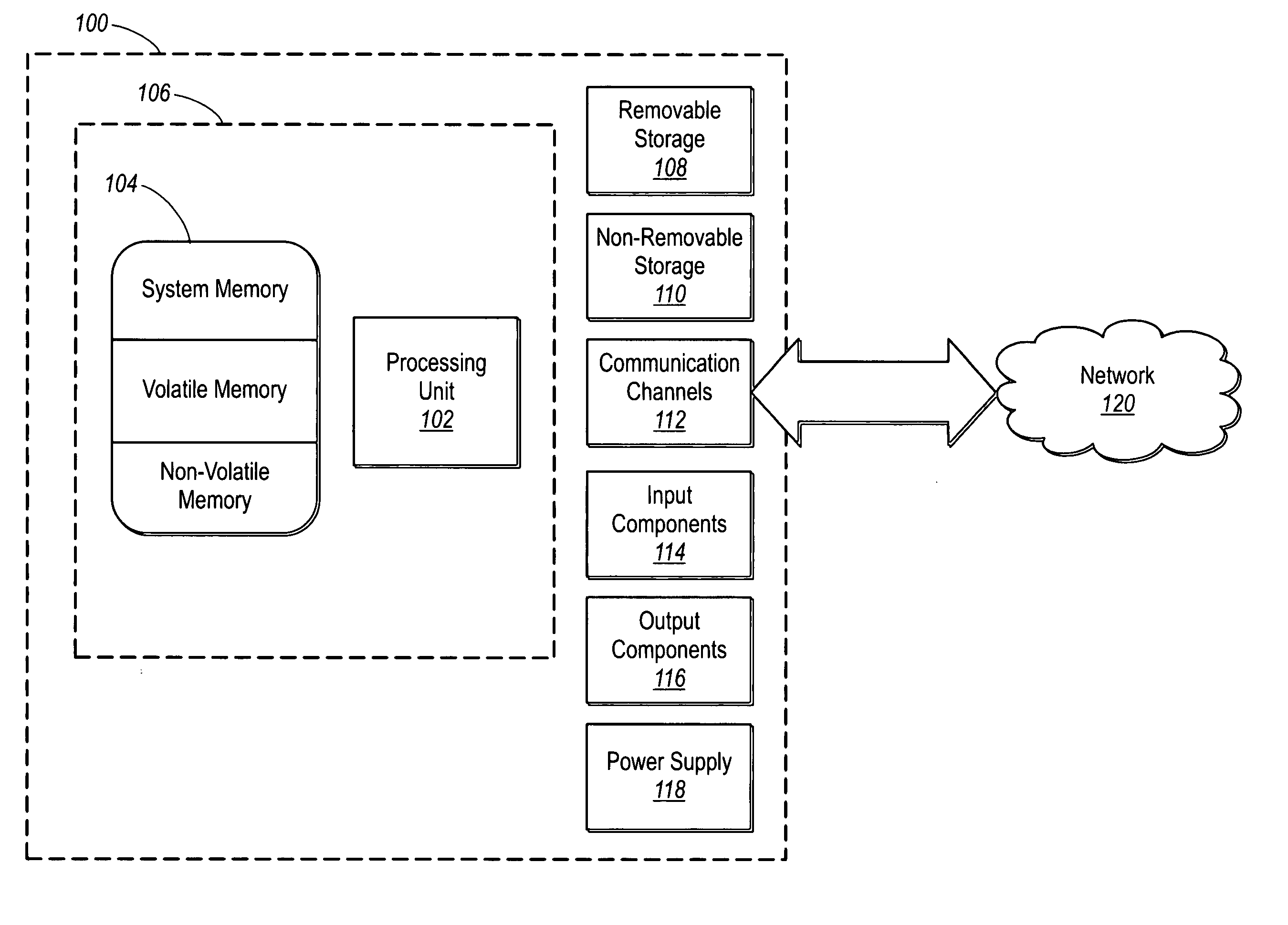
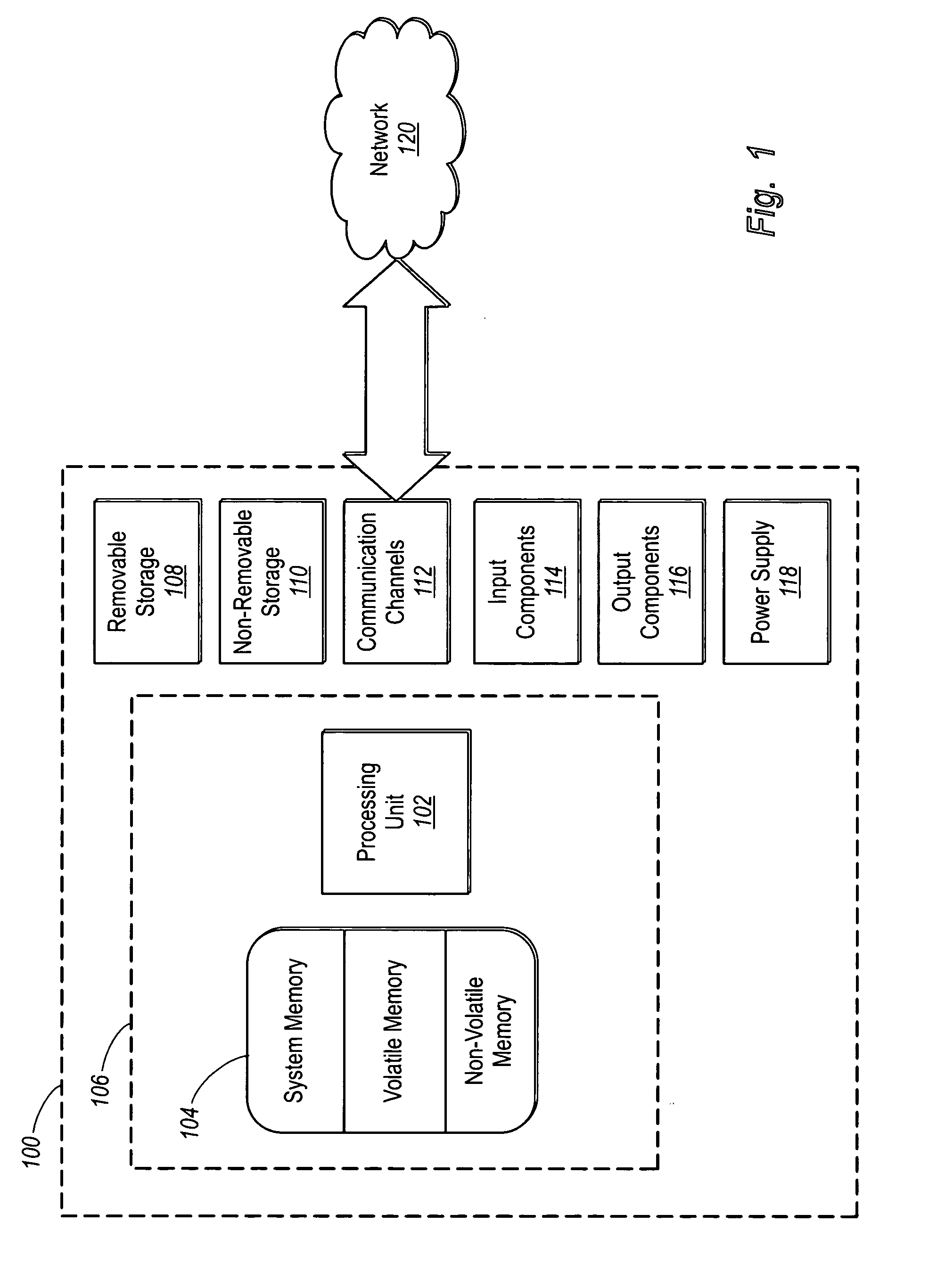
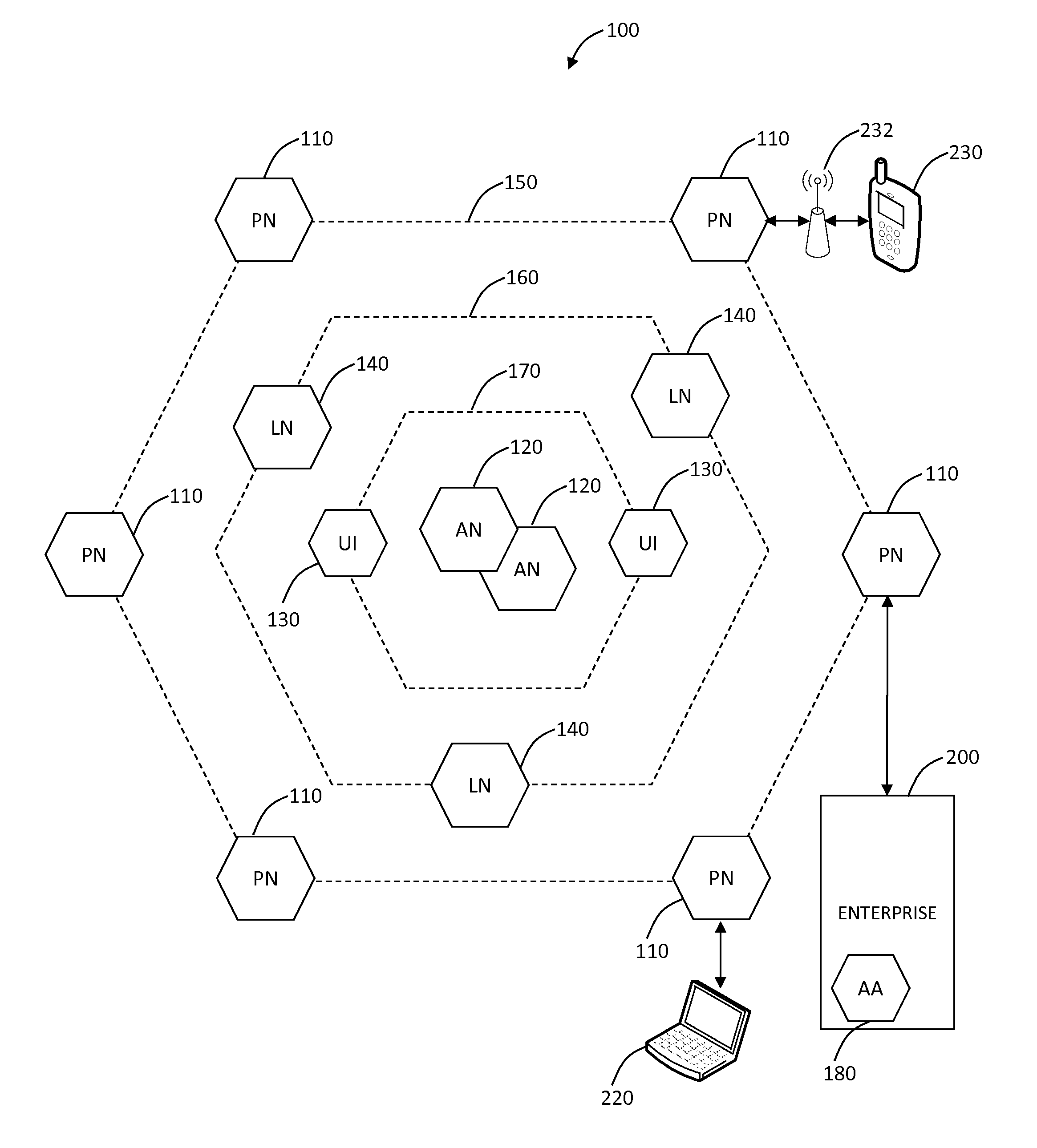
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2312 results about "Logging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Logging is the cutting, skidding, on-site processing, and loading of trees or logs onto trucks or skeleton cars. Logging is the process of cutting trees, processing them, and moving them to a location for transport. It is the beginning of a supply chain that provides raw material for many products societies worldwide use for housing, construction, energy, and consumer paper products. Logging systems are also used to manage forests, reduce the risk of wildfires, and restore ecosystem functions.
Transaction automation and archival system using electronic contract and disclosure units
ActiveUS8228299B1Shorten the timeEliminate mistakesImage analysisFinanceDisplay deviceFinancial transaction
A transaction automation and archival system is provided for controlling, real-time logging, and archiving complex commercial transactions such as the purchase and financing of an automobile. The heart of the system is an electronic contract disclosure unit, or ECDU. The ECDU includes a digitizing display that includes a video display for imaging to participants the various documents involved in the transaction and a digitizer for allowing participants to sign, indicate choices, and otherwise interact directly on documents and images presented on the display. A computer controls the entire progress of the transaction, and thus controls the collaborative space occupied by the participants to the transaction. The computer, for instance, controls the order of presentation of documents to a vehicle purchaser, receives the purchaser's signature on the displayed documents when required, offers choices of various packages that can be accepted or declined by the purchaser, and insures that the entire transaction is carried out properly. The ECDU further logs the transaction for future review and preferably includes a video camera and microphone for logging images and sounds of the participants during the transaction. One or more fingerprint readers are associated with the digitizing display for allowing participants to select between options by pressing their thumb or finger on the reader, which simultaneously verifies the identity of the individual making the selection through the fingerprint.
Owner:REYNOLDS AND REYNOLDS
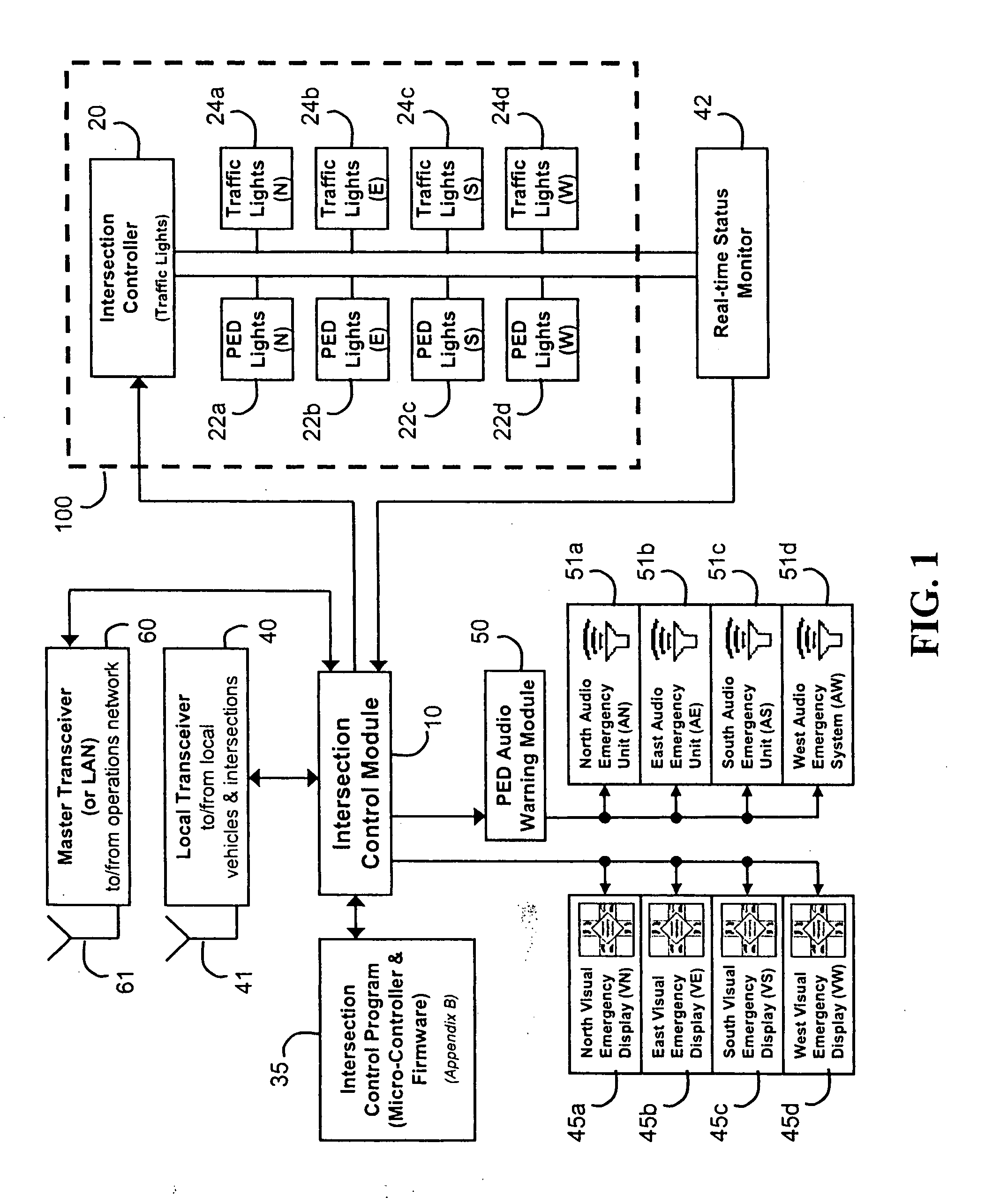
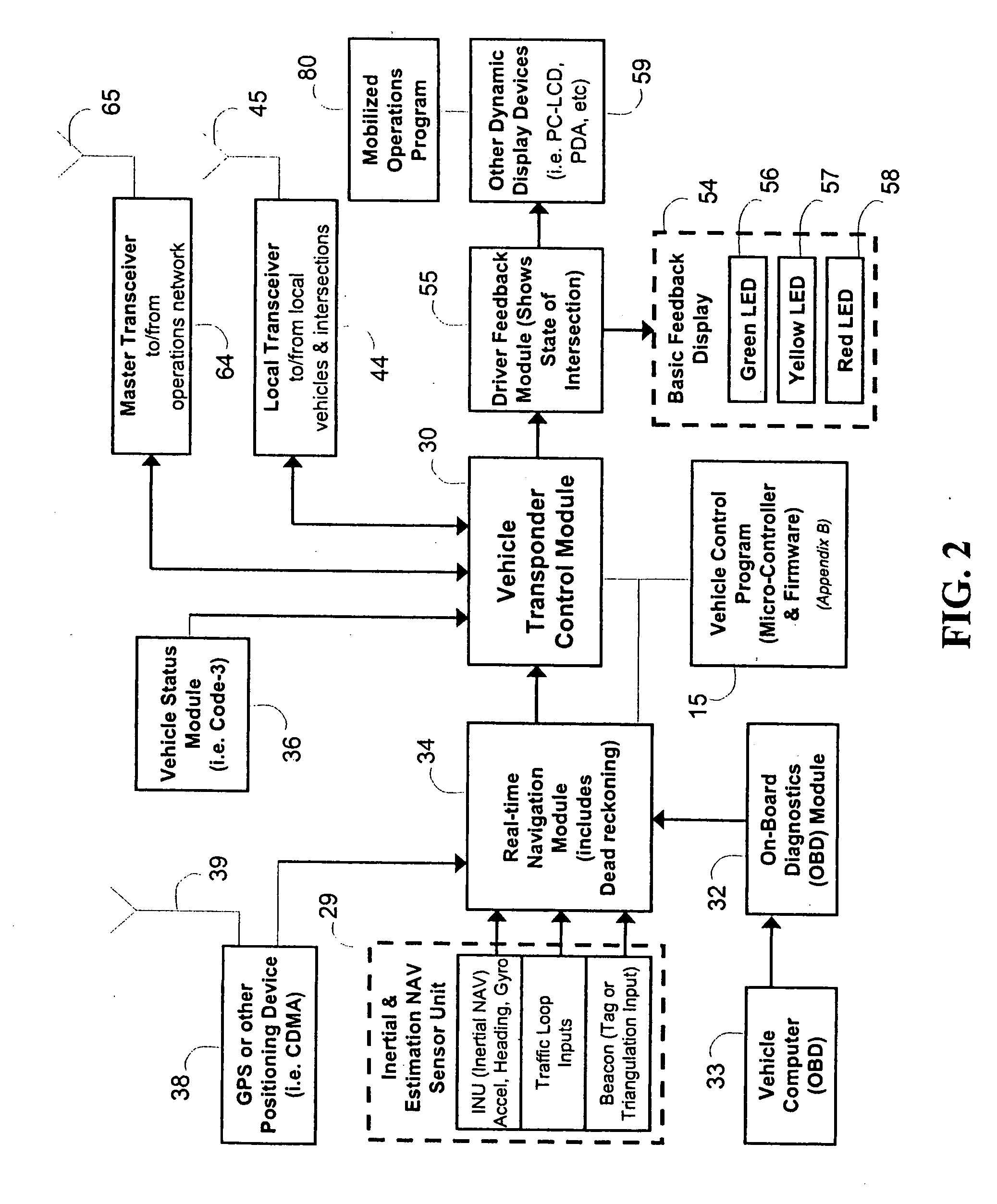
Emergency vehicle traffic signal preemption system
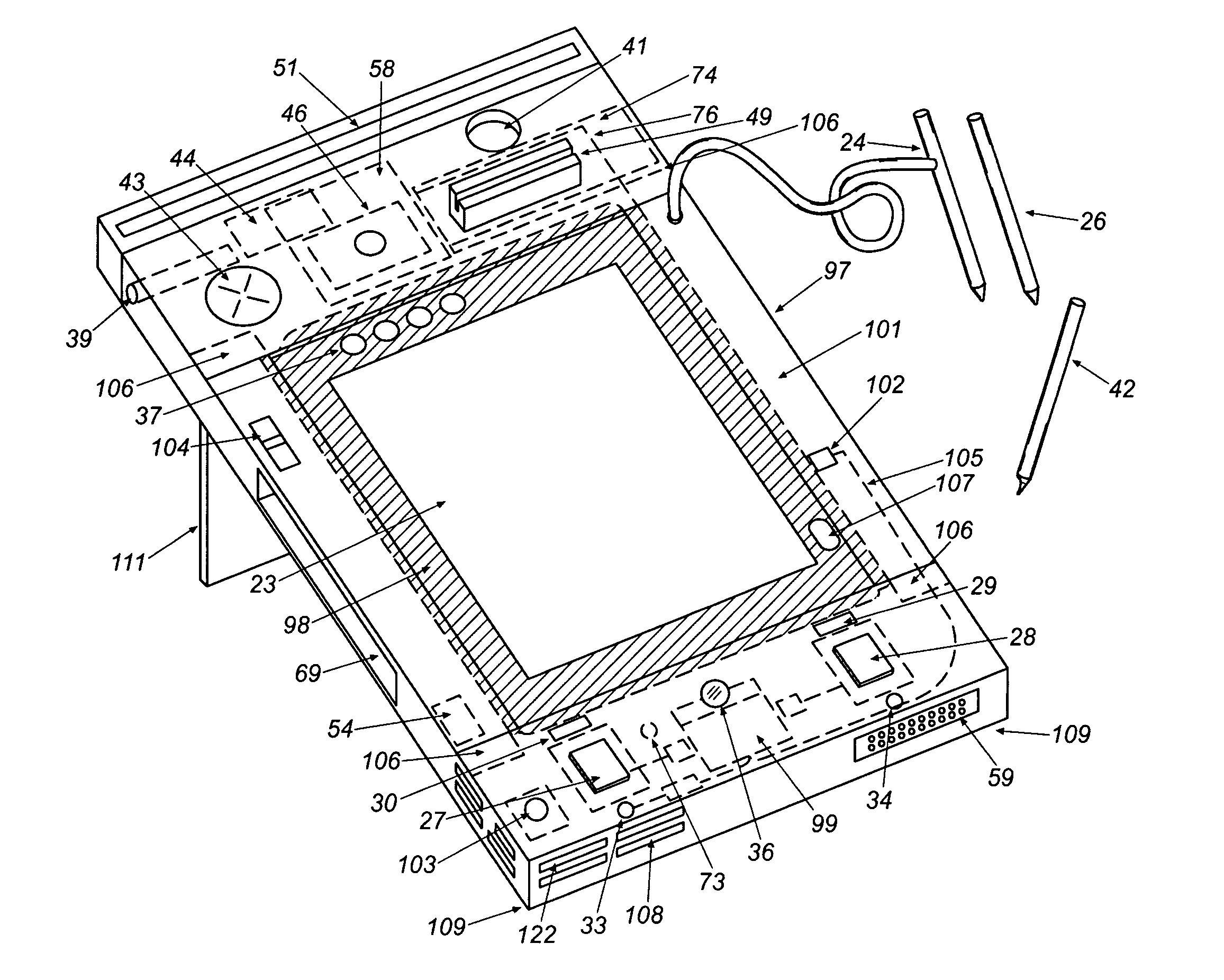
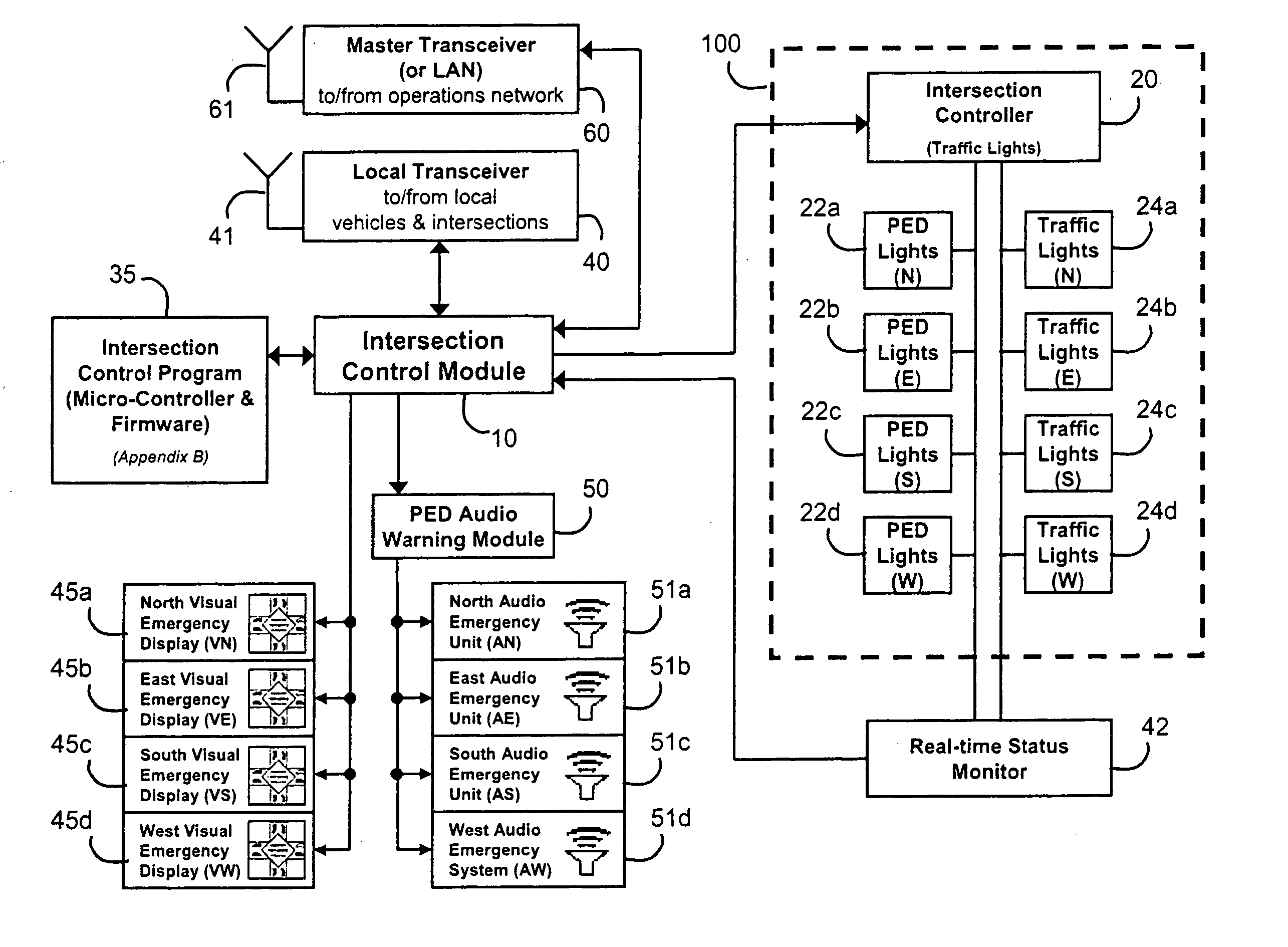
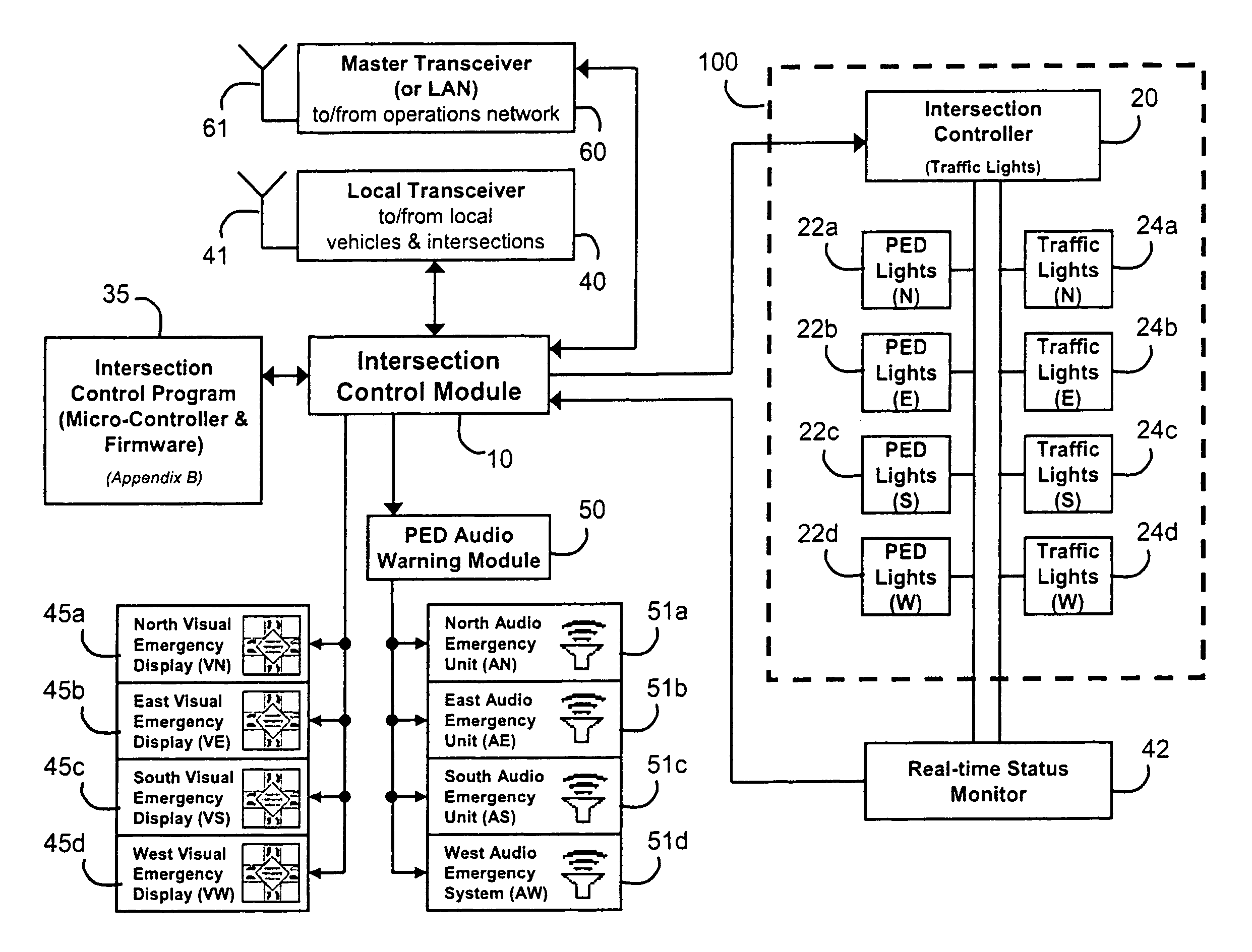
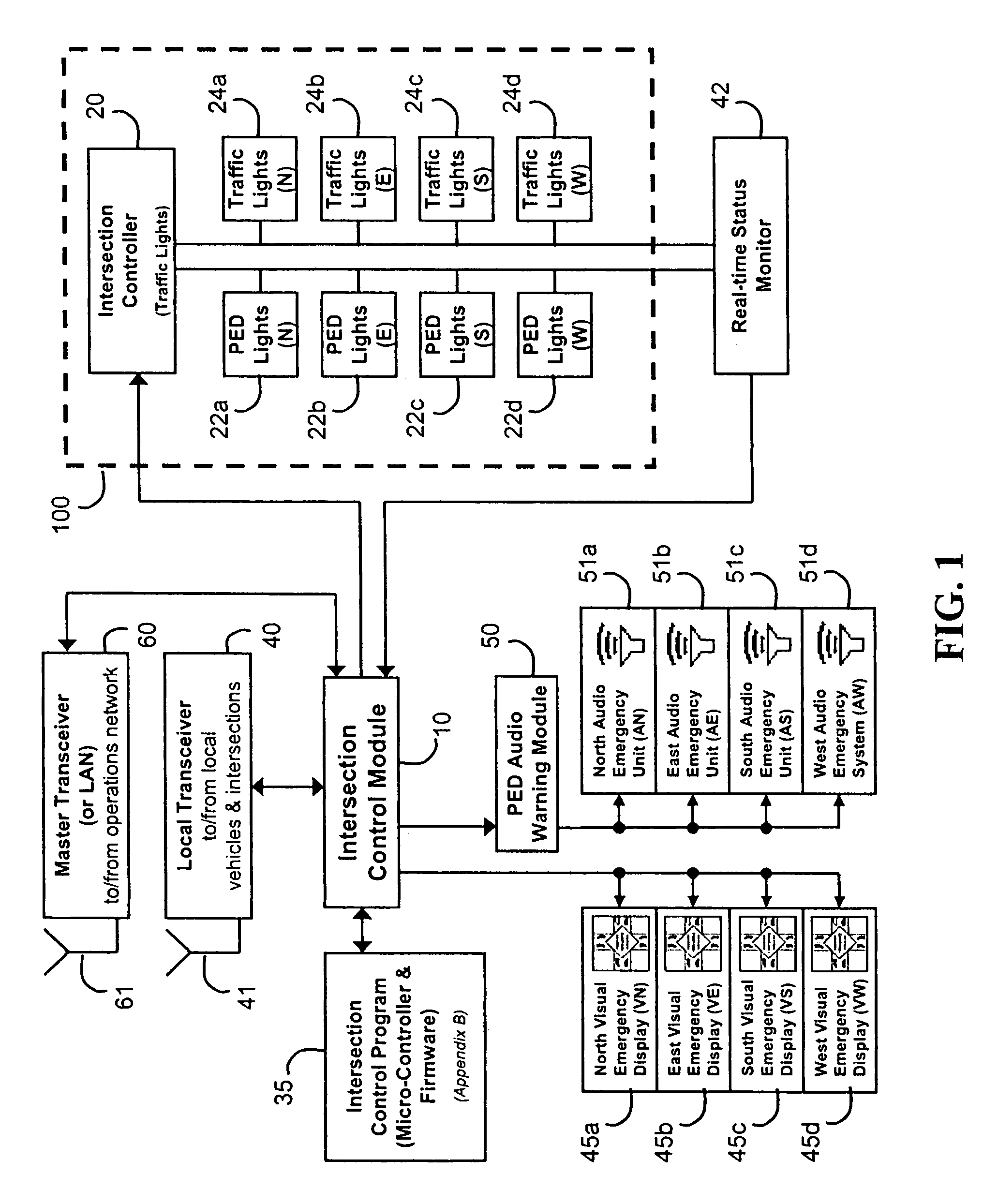
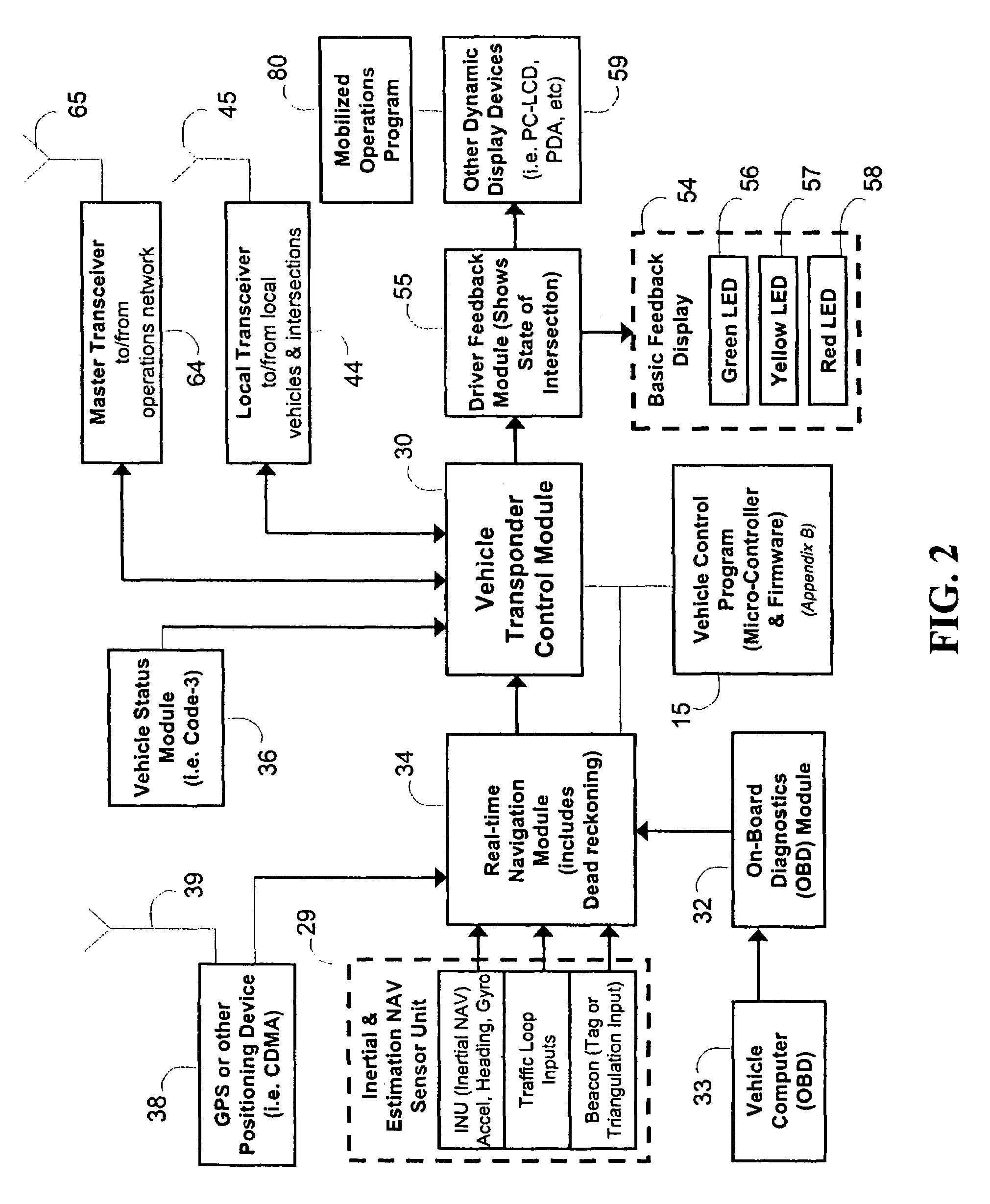
InactiveUS20050104745A1Enough timeSafe passageControlling traffic signalsDetection of traffic movementTraffic signalEngineering
An emergency vehicle traffic light preemption system for preemption of traffic lights at an intersection to allow safe passage of emergency vehicles. The system includes a real-time status monitor of an intersection which is relayed to a control module for transmission to emergency vehicles as well as to a central dispatch office. The system also provides for audio warnings at an intersection to protect pedestrians who may not be in a position to see visual warnings or for various reasons cannot hear the approach of emergency vehicles. A transponder mounted on an emergency vehicle provides autonomous control so the vehicle operator can attend to getting to an emergency and not be concerned with the operation of the system. Activation of a priority-code (i.e. Code-3) situation provides communications with each intersection being approached by an emergency vehicle and indicates whether the intersection is preempted or if there is any conflict with other approaching emergency vehicles. On-board diagnostics handle various information including heading, speed, and acceleration sent to a control module which is transmitted to an intersection and which also simultaneously receives information regarding the status of an intersection. Real-time communications and operations software allow central and remote monitoring, logging, and command of intersections and vehicles.
Owner:CALIFORNIA INST OF TECH
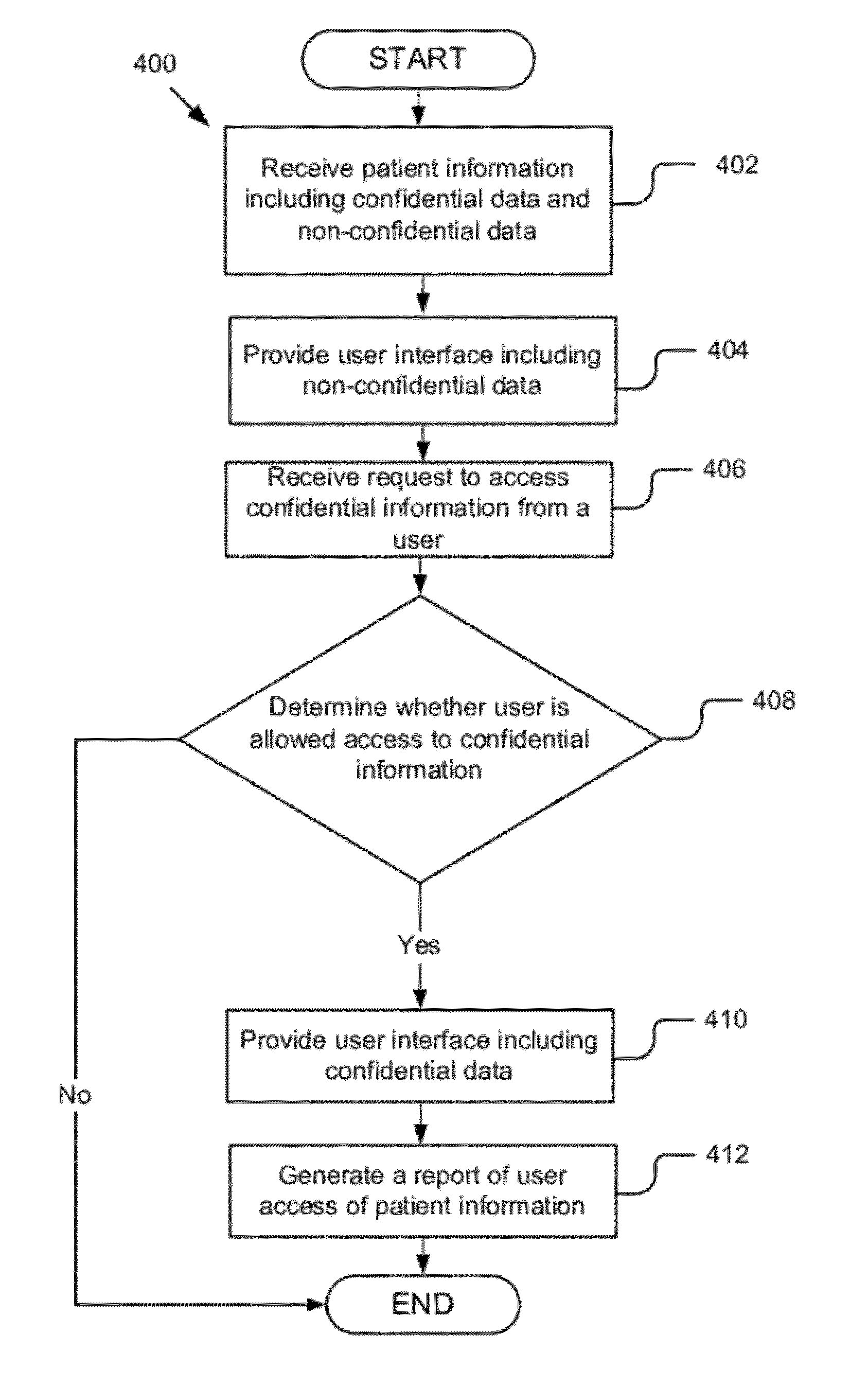
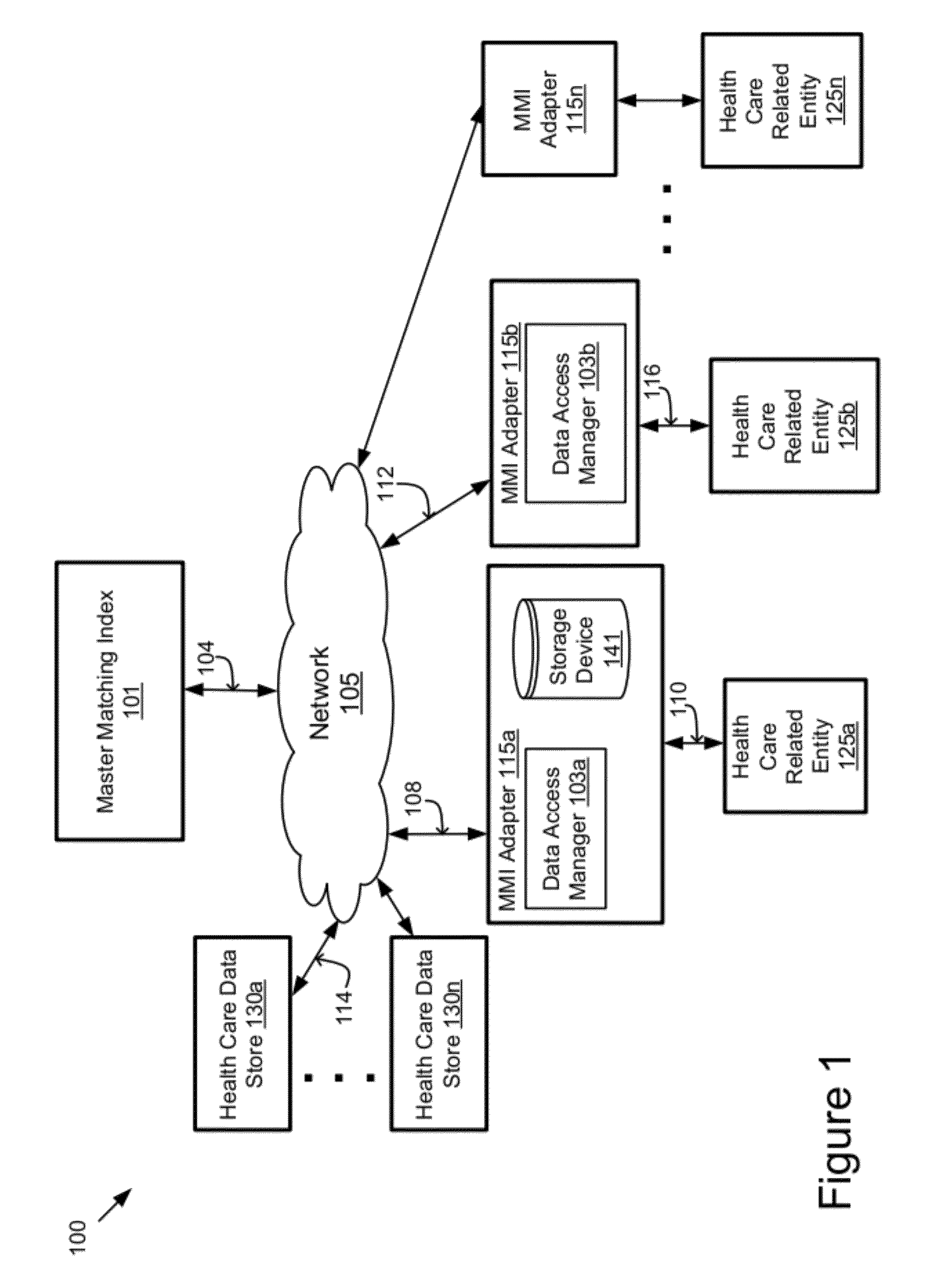
Managing patient consent in a master patient index
ActiveUS8949137B2Digital data processing detailsAnalogue secracy/subscription systemsCore functionData access
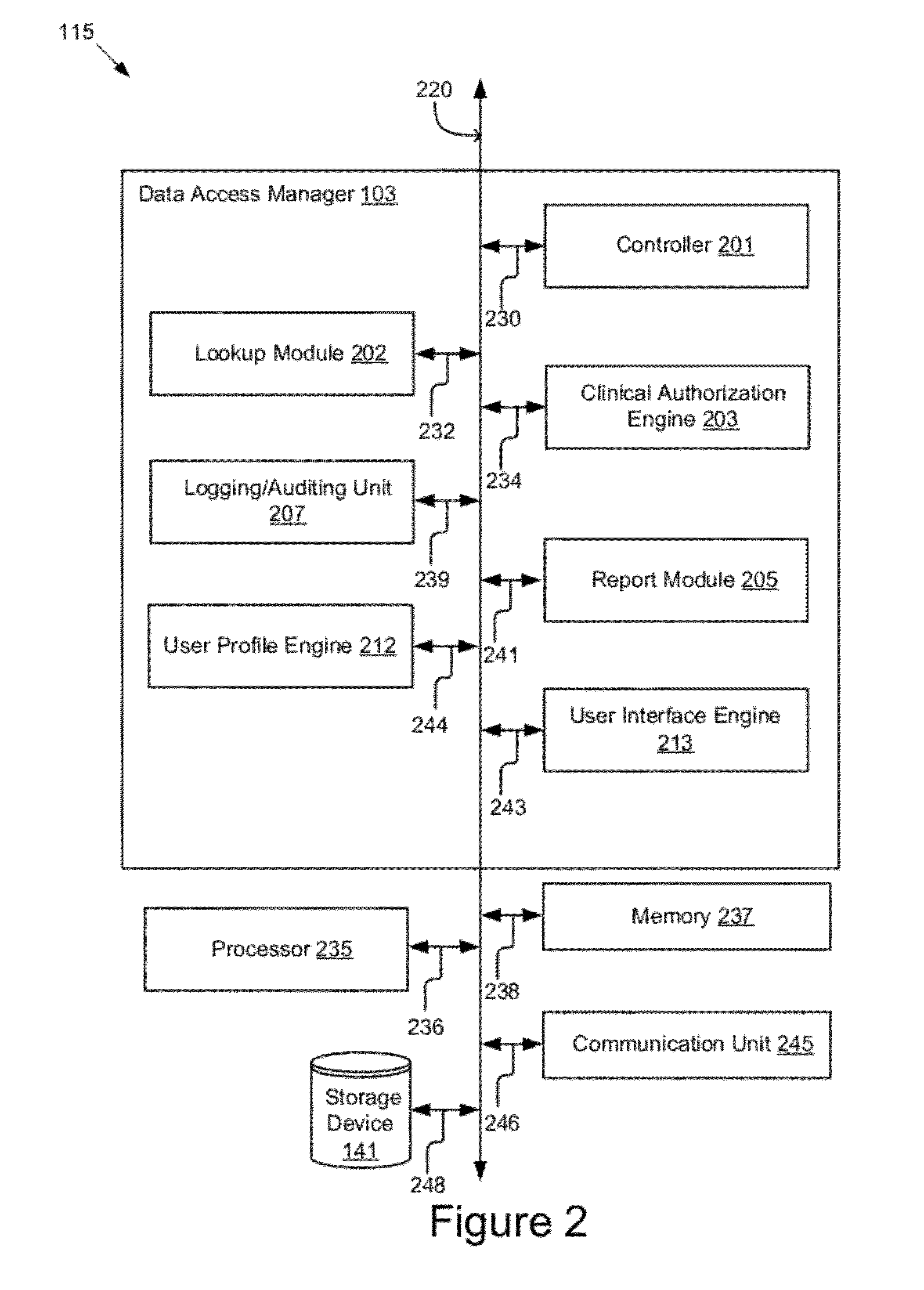
A system and method for managing patient consent. A data access manager includes a controller, a lookup module, a clinical authorization engine, a logging / auditing unit, a user profile engine, a report module and a user interface engine. The controller manages the core functions and the transmission of data between the data access manager components. The lookup module enables a user to query patient data. The clinical authorization engine authorizes access to patient data. The logging / auditing unit logs and monitors user activity. The user profile engine accesses and updates user profile information. The patient profile engine accesses and updates patient profile information. The report module generates reports related to the user activity. The user interface engine generates user interfaces for displaying the user profiles and patient information data.
Owner:HEALTH CATALYST INC
Efficient Logging for Asynchronously Replicating Volume Groups
ActiveUS20110099342A1The process is compact and efficientReduce memoryMemory loss protectionError detection/correctionAuxiliary memoryData store
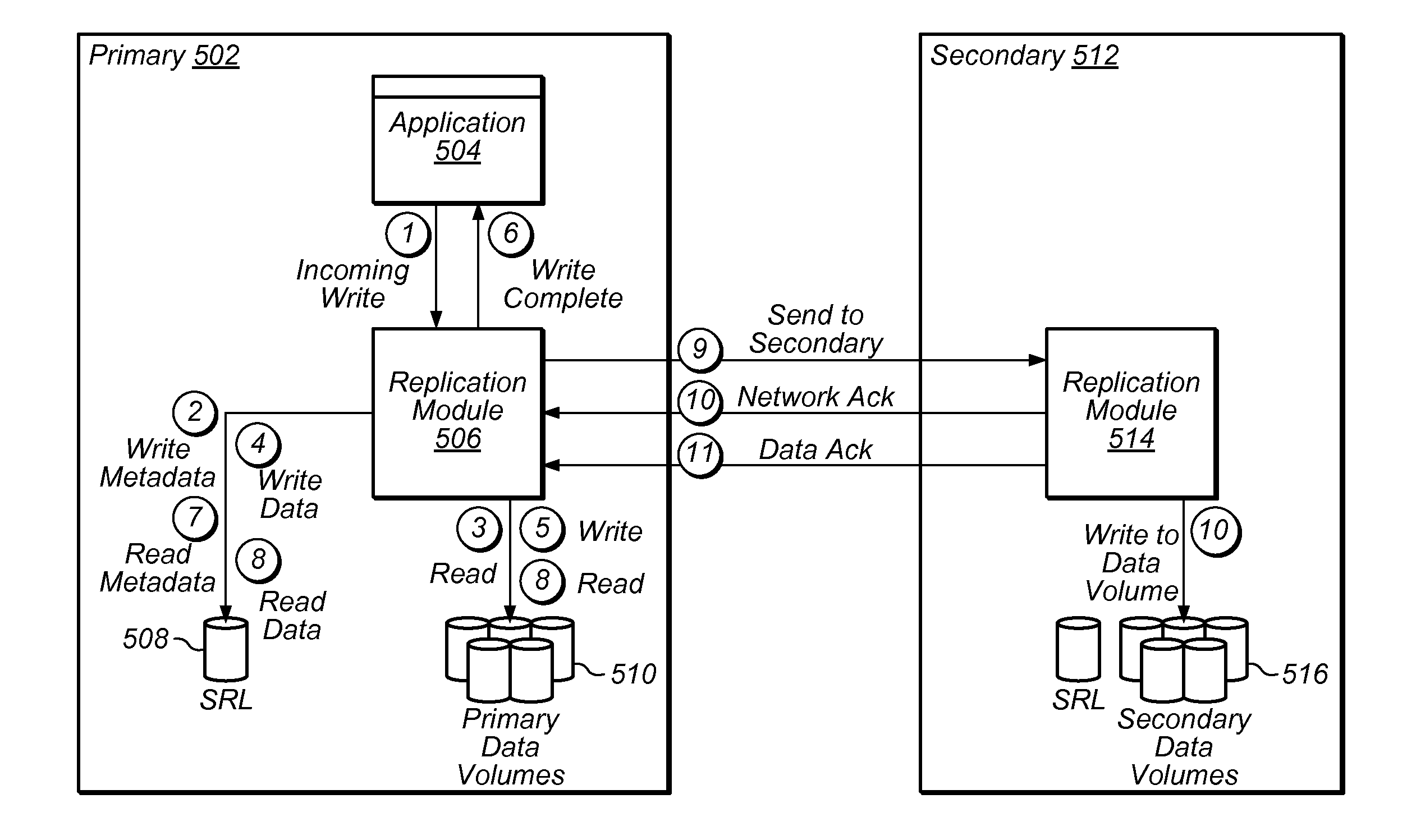
A system and method for logging for asynchronously replicating volume groups. A write request to write data to a location in a volume may be received. Metadata associated with the write request may be stored. It may be determined if the write request possibly overlaps with one or more earlier write requests to the volume that have not yet been replicated to a secondary storage. The data may be stored in a replication log only if the write request possibly overlaps with one or more earlier write requests to the volume. The data may not be stored in the replication log if the write request does not overlap with one or more earlier write requests to the volume. The data may be written to the location in the volume. Changes to the volume may periodically be replicated to the secondary storage using the replication log.
Owner:VERITAS TECH
Electronic-medical-record sharing system based on block chain
InactiveCN107391944AAchieve tamper-proofAchieve rating reviewData processing applicationsSpecial data processing applicationsMedical recordOriginal data
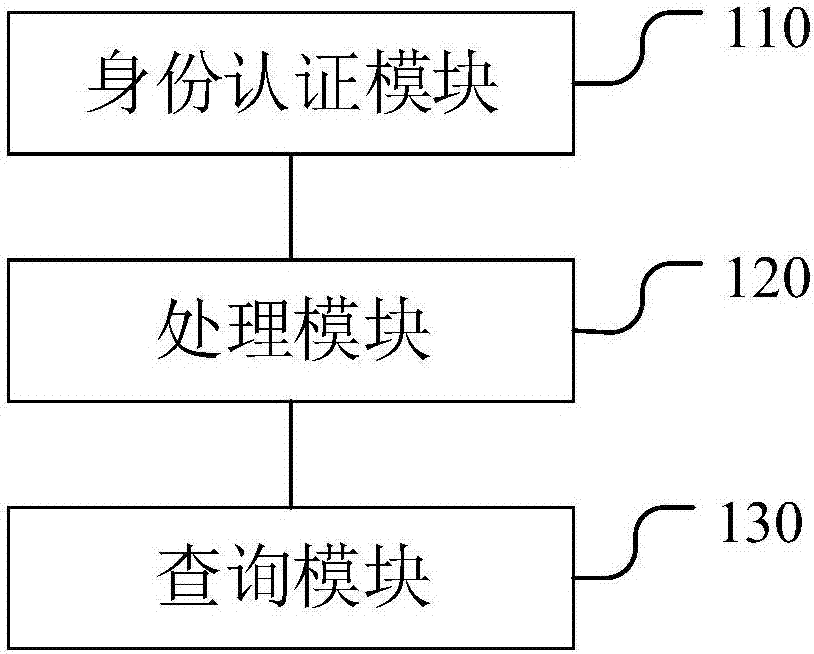
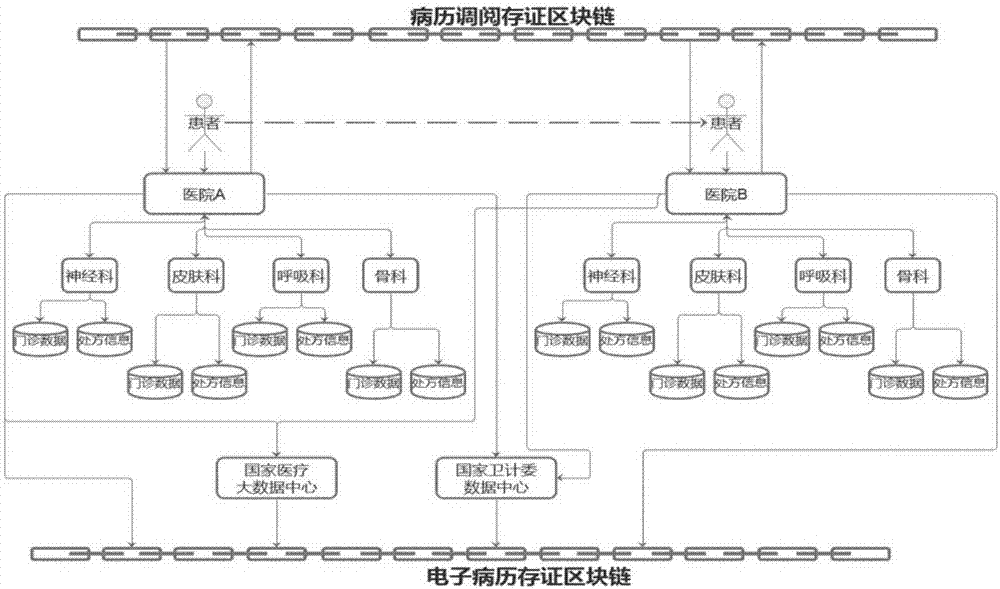
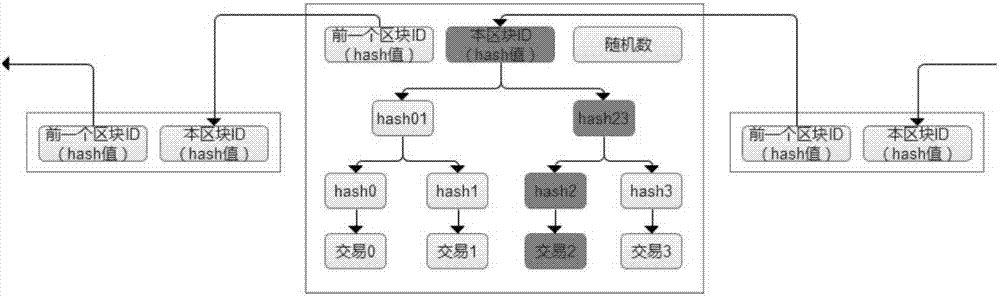
The embodiment of the invention discloses an electronic-medical-record sharing system based on a block chain. The electronic-medical-record sharing system comprises an identity verification module, a processing module and a querying module, wherein the identity verification module is used for receiving a logging-in account input by a user, identifying the logging-in account and configuring corresponding operating authorization for the logging-in account; the processing module is used for being connected with a pre-established block-chain database, wherein the block-chain database comprises a plurality of nodes, and each node corresponds to a hospital database; the querying module is used for receiving a querying order input by the user, obtaining a corresponding electronic medical record from the block-chain database according to the querying order and showing the obtained electronic medical record to the user. The electronic-medical-record sharing system is established based on the block chain technology in the embodiment, all data can be only preserved in a hospital server generated through original data, only data hash values are stored on the block-chain database so that the aims that data cannot be tampered, is looked up in a classified mode and is retrospective in consulting can be achieved, and the electronic-medical-record sharing system has the advantage that the data security is improved.
Owner:BEIJING TAI CLOUD TECH LTD
Systems and methods for providing conflict handling for peer-to-peer synchronization of units of information manageable by a hardware/software interface system
InactiveUS20050044187A1Efficient application developmentFacilitate data sharingDigital data information retrievalData processing applicationsThree stageUsability
Various embodiments of the present invention are directed to conflict handling for conflicts that occur in a peer-to-peer synchronization system, where the ability to correctly and efficiently handle conflicts minimizes data loss while retaining good usability and reduces the need for user intervention during synchronization. Conflict handling in the synchronization service is divided into three stages: (1) conflict detection; (2) automatic conflict resolution and logging; and (3) conflict inspection and resolution. Certain embodiments are directed to a conflict handling schema comprising one or more of the follow conflict handling elements: (a) schematized representation of conflicts; (b) detection of conflicts; (c) logging of conflicts into a durable store; (d) automatic resolution of conflicts according to a flexible and configurable azqsxqxwdconflict resolution policy; (e) composable and extensible conflict handlers to filter and resolve conflicts; (f) automatic detection and removal of obsolete conflicts; and (g) programmatic conflict resolutions.
Owner:MICROSOFT TECH LICENSING LLC
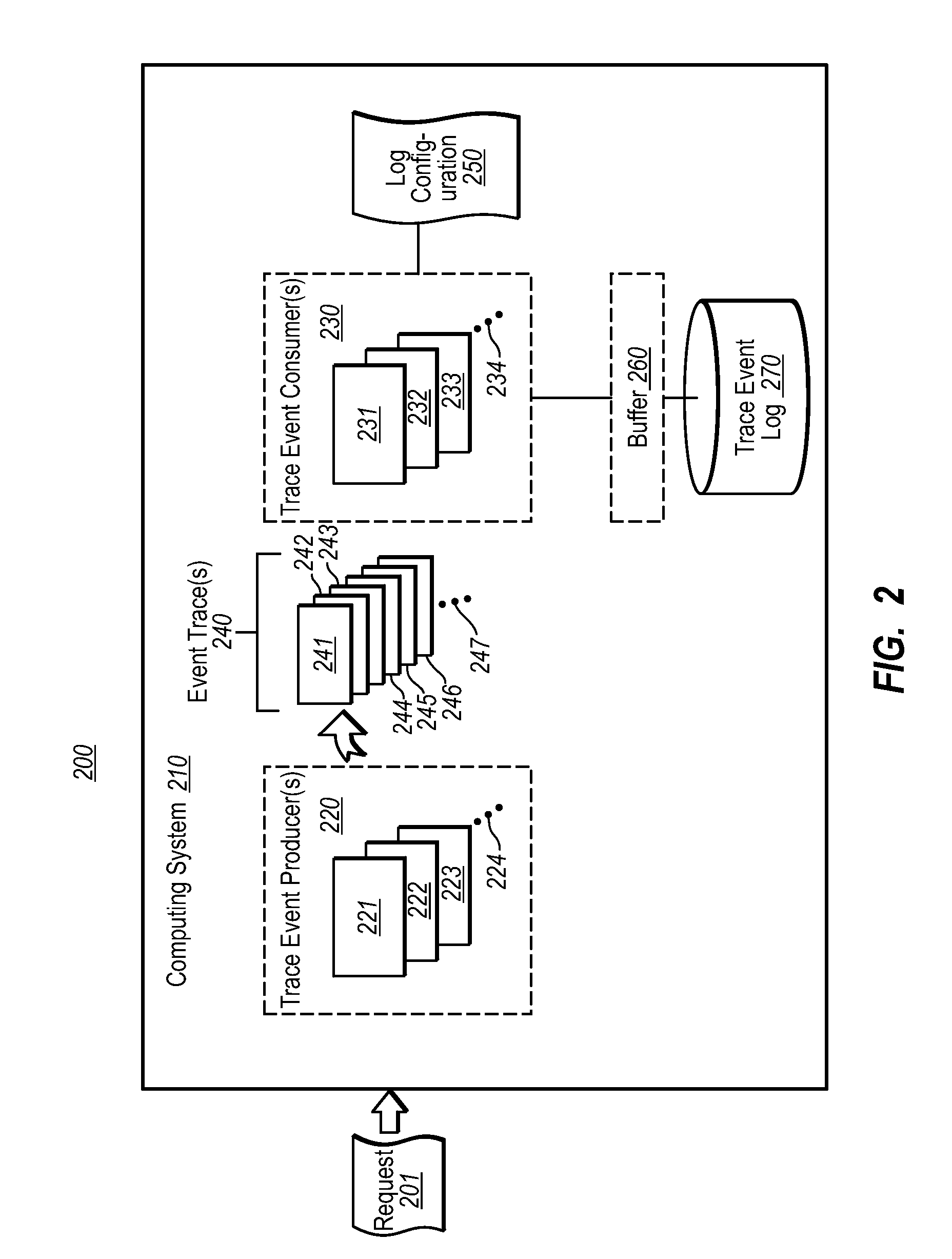
Event trace conditional logging
ActiveUS20070255979A1Reduce in quantityImprove relevanceError detection/correctionEvent trackingOperating system
Owner:MICROSOFT TECH LICENSING LLC
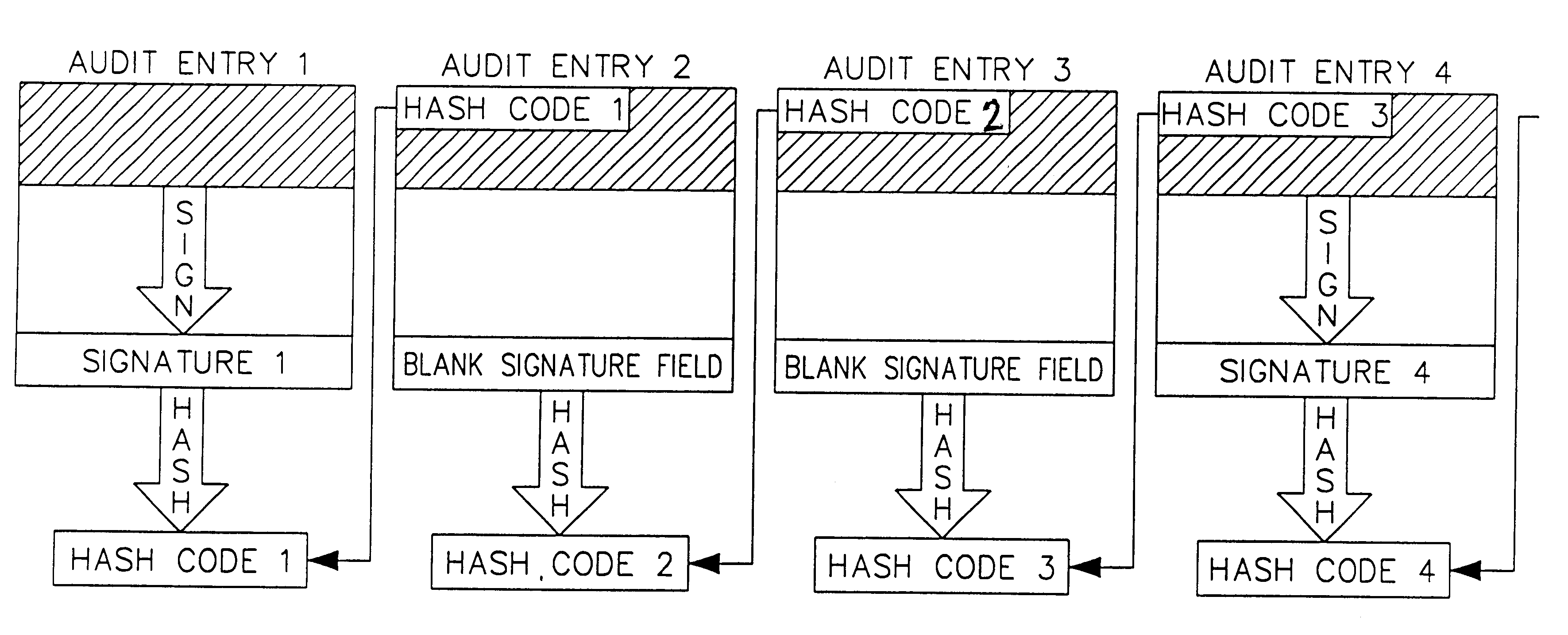
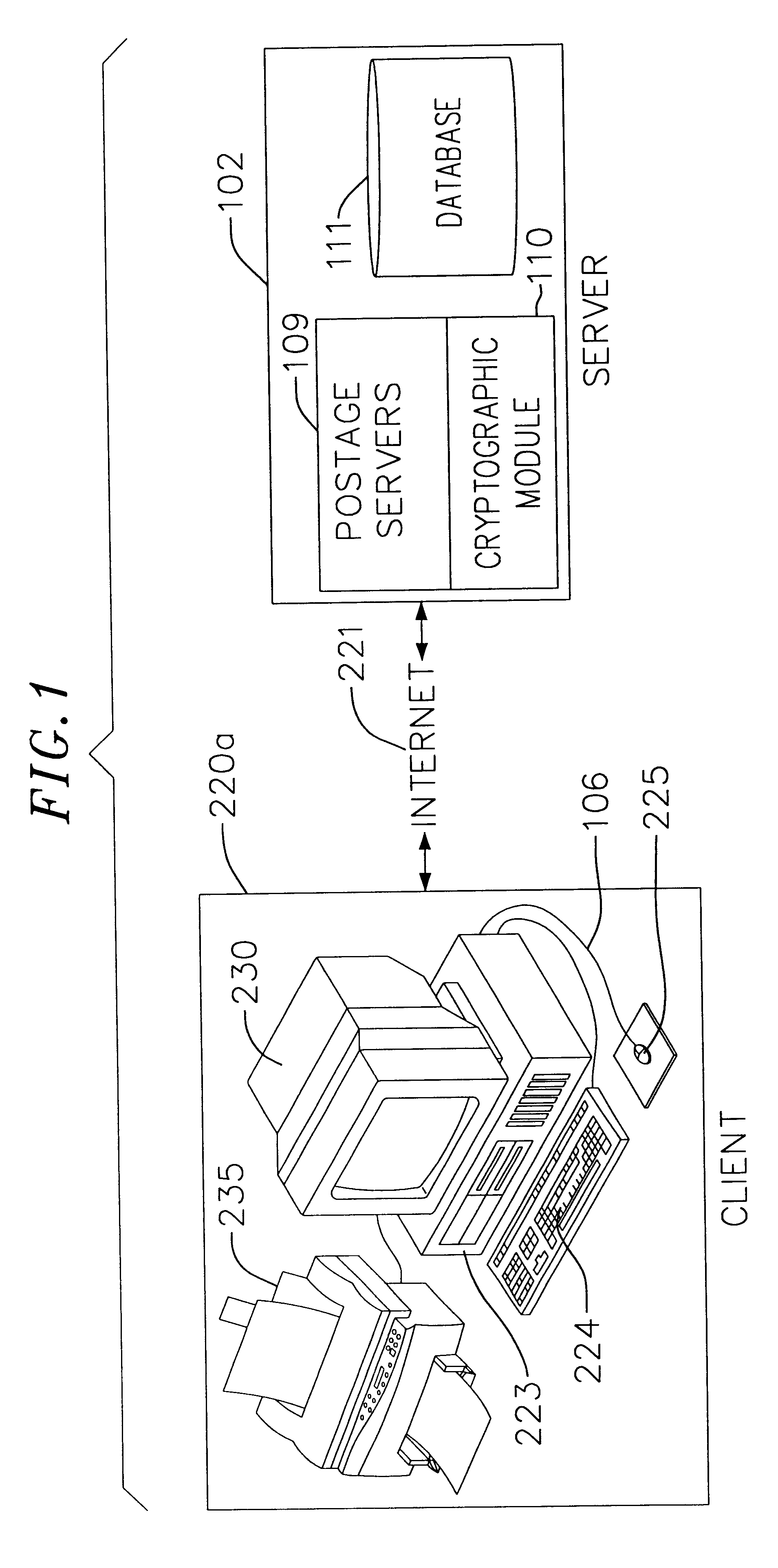
Auditing method and system for an on-line value-bearing item printing system
InactiveUS6868406B1Avoid accessPrevent unauthorized accessPayment architectureFranking apparatusCryptographic nonceCentral database
An on-line value bearing item (VBI) printing system that includes one or more cryptographic modules and a central database is disclosed. The cryptographic modules are capable of implementing the USPS Information Based Indicia Program Postal Security Device Performance Criteria and other required VBI standards. The modules encipher the information stored in the central database for all of the on-line VBI system customers and are capable of preventing access to the database by unauthorized users. Additionally, each cryptographic module is capable of providing audit support functions that enable secure logging of all sensitive actions.
Owner:STAMPS COM
Emergency vehicle traffic signal preemption system
InactiveUS7327280B2Minimized speed reductionAvoid clearingControlling traffic signalsDetection of traffic movementTraffic signalEngineering
An emergency vehicle traffic light preemption system for preemption of traffic lights at an intersection to allow safe passage of emergency vehicles. The system includes a real-time status monitor of an intersection which is relayed to a control module for transmission to emergency vehicles as well as to a central dispatch office. The system also provides for audio warnings at an intersection to protect pedestrians who may not be in a position to see visual warnings or for various reasons cannot hear the approach of emergency vehicles. A transponder mounted on an emergency vehicle provides autonomous control so the vehicle operator can attend to getting to an emergency and not be concerned with the operation of the system. Activation of a priority-code (i.e. Code-3) situation provides communications with each intersection being approached by an emergency vehicle and indicates whether the intersection is preempted or if there is any conflict with other approaching emergency vehicles. On-board diagnostics handle various information including heading, speed, and acceleration sent to a control module which is transmitted to an intersection and which also simultaneously receives information regarding the status of an intersection. Real-time communications and operations software allow central and remote monitoring, logging, and command of intersections and vehicles.
Owner:CALIFORNIA INST OF TECH
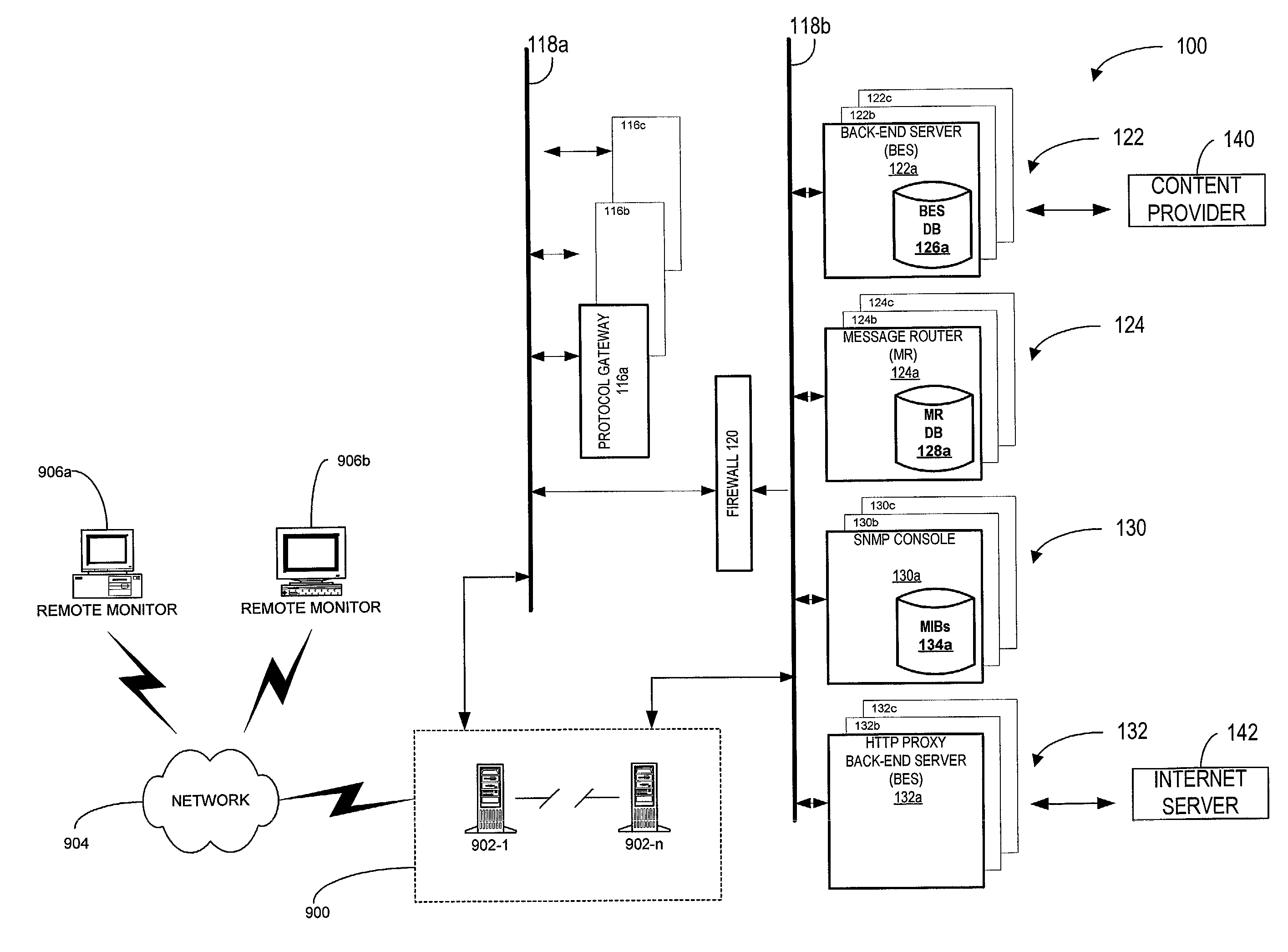
System and method to publish information from servers to remote monitor devices
InactiveUS7024474B2Easy to writeEfficient communicationError prevention/detection by using return channelDigital computer detailsWeb browserApplication software
To assist in monitoring the intelligent messaging network, a system and method for publishing logging and status information from the servers is provided. A list of available servers accessible for monitoring by persons, devices, and applications via a remote monitor device can be provided. The remote monitor device may forward selected servers from the list of available servers in which they are interested. Also, particular information about the selected servers can be requested. Access to certain servers and information may be restricted to those with authorization. Authorization can be verified by the use of digital certificates. The requested information can then be gathered and provided to authorized persons or devices. Typically, the information includes logging and status information from the servers. The information can be provided as an XML page and viewed using, for example, a standard web browser. Further, if the information is provided to the remote monitor device as an XML page, a standard XML parser may be used to extract particular information from the XML page.
Owner:TELECOMM SYST INC
Method and apparatus for securely and dynamically modifying security policy configurations in a distributed system
InactiveUS6920558B2Computer security arrangementsSecret communicationSecure stateApplication software
One embodiment of the present invention provides a system for managing security policies in a distributed computing system. Security policies include, but are not limited to, a firewall policy, a policy for file access, a policy for application access, a policy for an encryption algorithm, a policy for audit trails, and a policy for activity logging. These security policies determine access rights to a computer application. The system operates by creating multiple security policies with individual security policies specifying a differing level of security for the distributed computing system. These security policies are then distributed to each computer in the distributed computing system. Next, a specific security policy is selected for use across the distributed computing system, and each computer in the distributed computing system is directed to use the specified security policy enforcing a selected security posture.
Owner:MCAFEE LLC
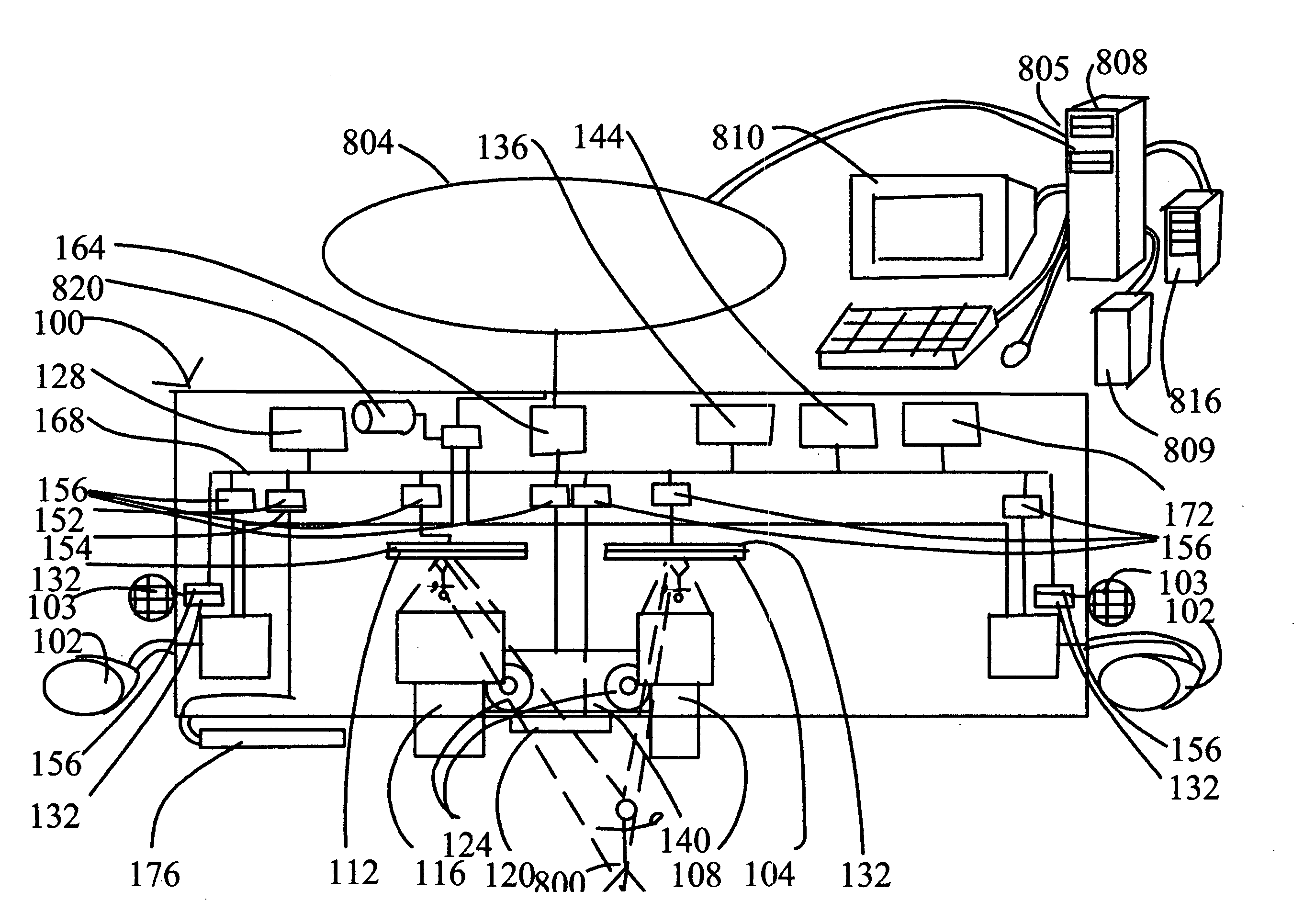
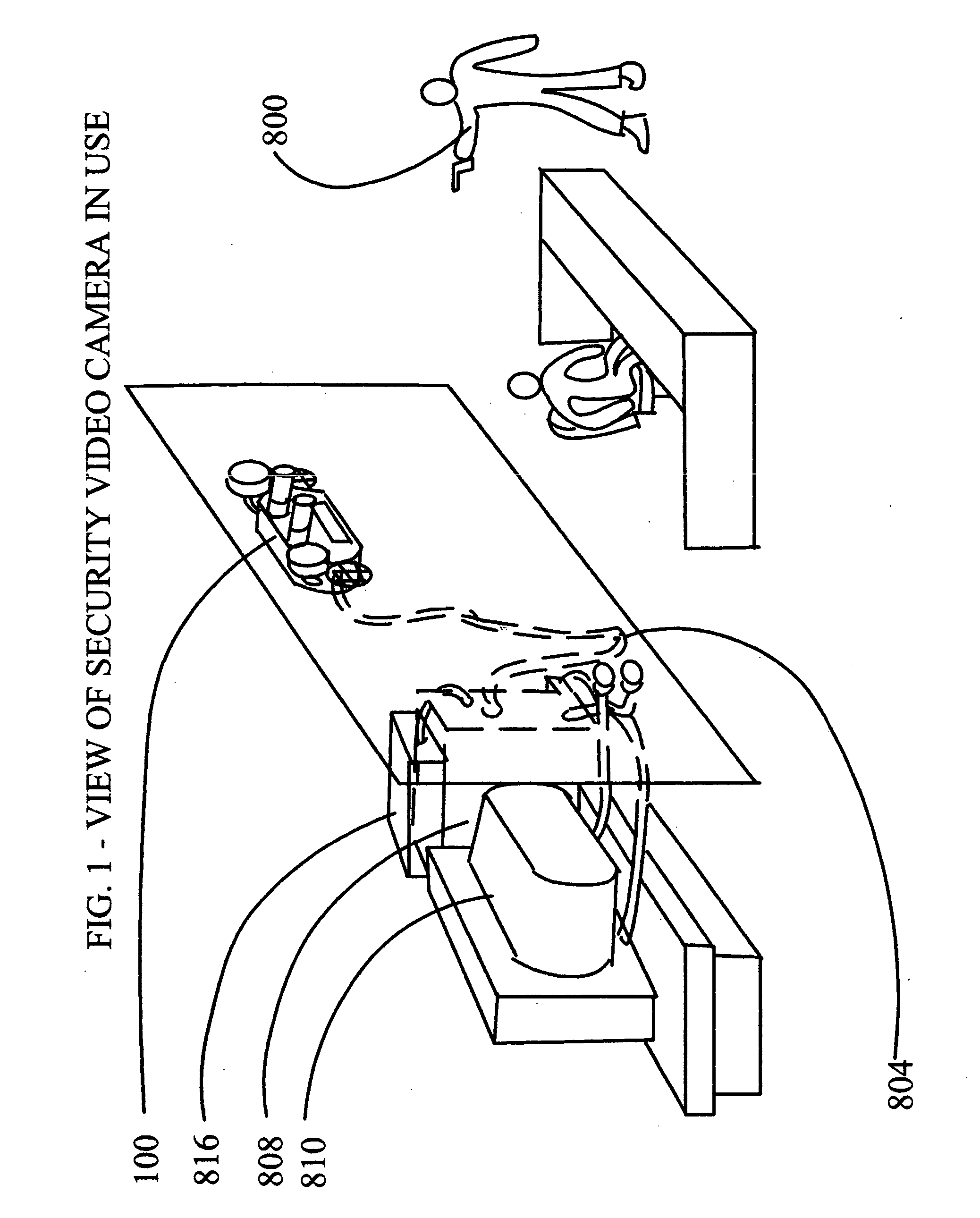
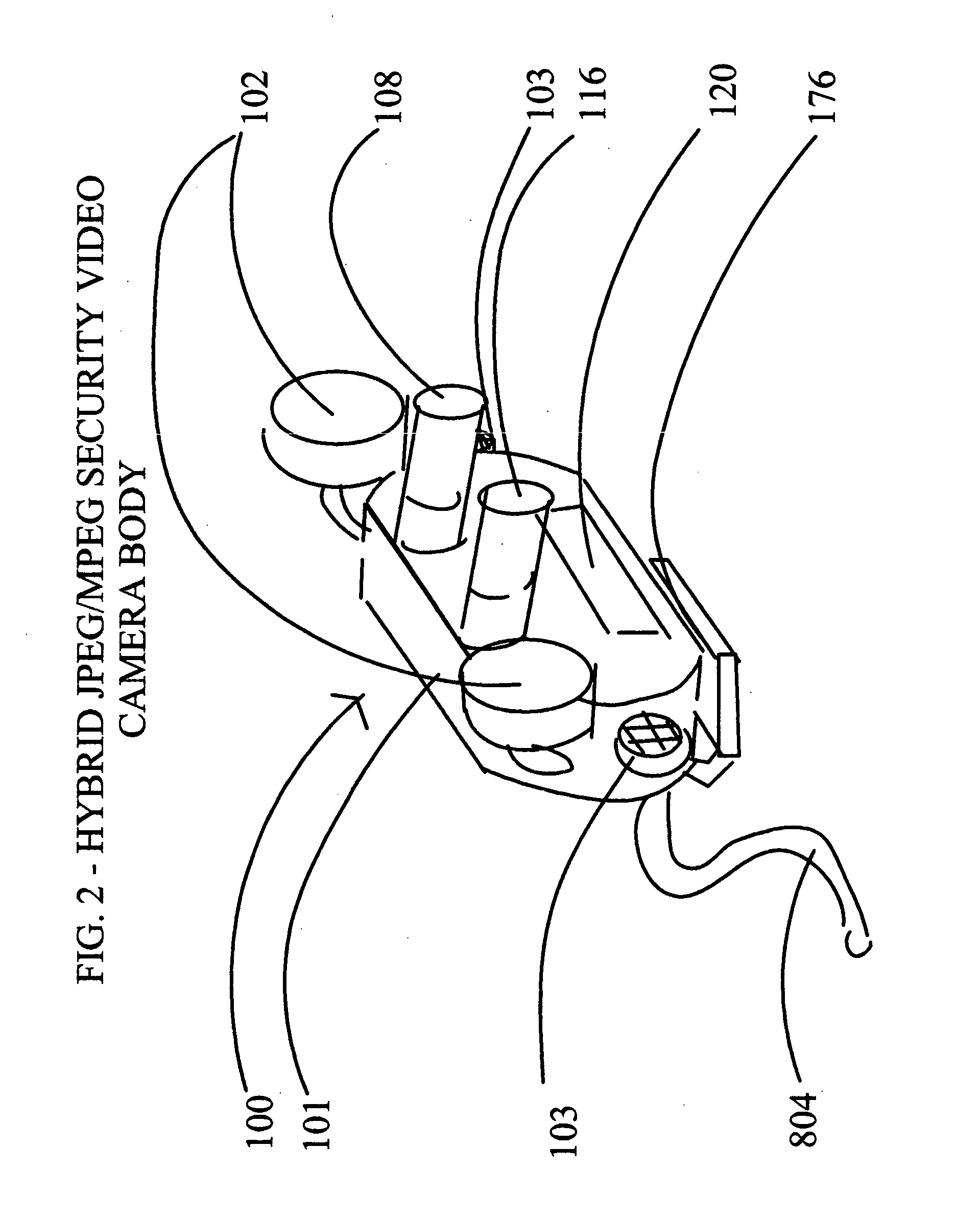
Hybrid joint photographer's experts group (JPEG) /moving picture experts group (MPEG) specialized security video camera
InactiveUS20040109059A1Enhanced eye-mind intuitive orientation and mental coordinationRapid responseColor television detailsClosed circuit television systemsMagnetic tapeJPEG
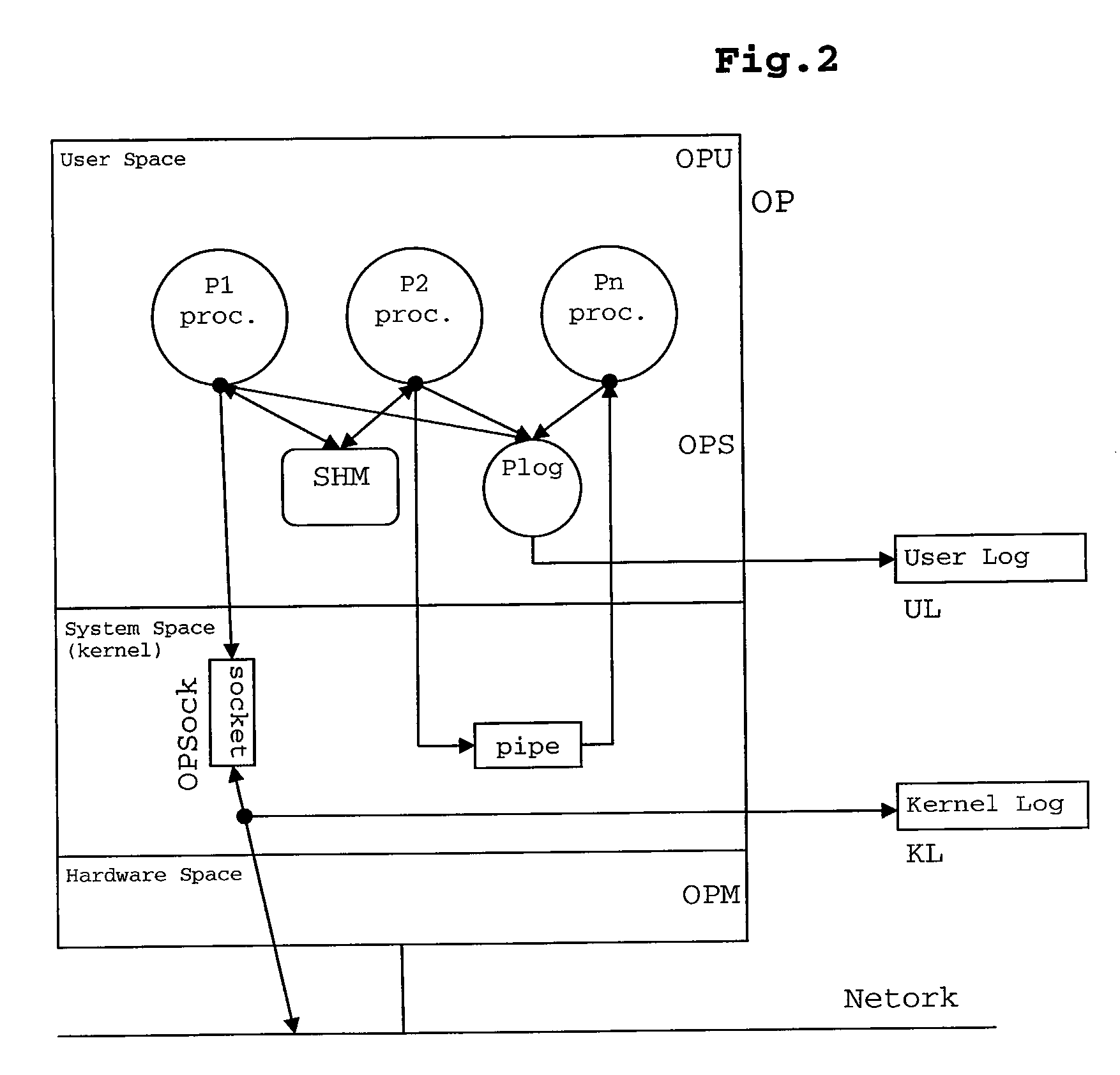
FIG. 1 is a diagram of an unmanned, fully automatic, security installation with electronic pan and tilt functions, the focal plane array based motion sensor (120) of the hybrid simultaneous-mode MPEG X / JPEG X security video camera (100) is positioned to capture moving suspects, the moving suspect (800) is shown, the local area network (LAN) cable (804) is shown leading away from the hybrid MPEG X / JPEG X security video camera (100), a security room personal computer viewing station (808) is shown, lastly a digital computer tape video logging station (816) is shown.
Owner:KAWABOINGO
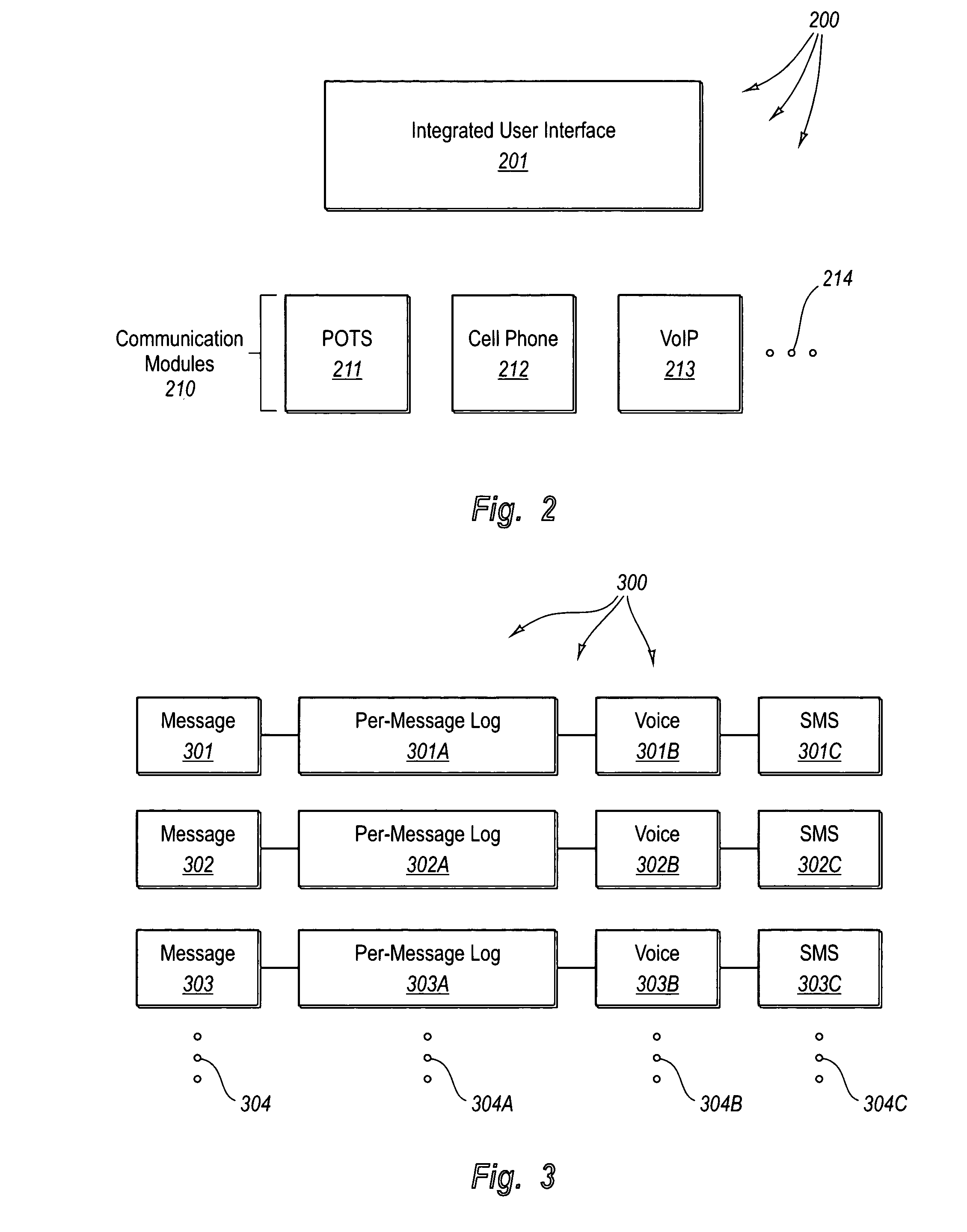
Integrated messaging user interface with message-based logging
ActiveUS20050243979A1Interconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingMessage typeMessage passing
Mechanisms for organizing messages across different message types. This may be accomplished by using a single integrated user interface in which messages across a variety of different message types are represented in a common way. For example, the user experience of placing a telephone call is standardized, regardless of the actual telephone technology (Cell Phone, VoIP, or POTS) used to conduct the telephone conversation. Also, addition to a general log that includes the overall list of messages, each message also has a separate, message-based log, thereby allowing for more flexible querying and organization of the messages regardless of the message type.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic user identification and policy enforcement in cloud-based secure web gateways
ActiveUS20140026179A1Platform integrity maintainanceTransmissionTraffic capacityApplication software
A cloud-based secure Web gateway, a cloud-based secure Web method, and a network deliver a secure Web gateway (SWG) as a cloud-based service to organizations and provide dynamic user identification and policy enforcement therein. As a cloud-based service, the SWG systems and methods provide scalability and capability of accommodating multiple organizations therein with proper isolation therebetween. There are two basic requirements for the cloud-based SWG: (i) Having some means of forwarding traffic from the organization or its users to the SWG nodes, and (ii) Being able to authenticate the organization and users for policy enforcement and access logging. The SWG systems and methods dynamically associate traffic to users regardless of the source (device, location, encryption, application type, etc.), and once traffic is tagged to a user / organization, various polices can be enforced and audit logs of user access can be maintained.
Owner:ZSCALER INC
Predictive Method for Managing Logging or Replaying Non-Deterministic Operations within the Execution of an Application Process
InactiveUS20080086730A1Monitor progressProtection worksElectronic circuit testingError detection/correctionComparative testPredictive methods
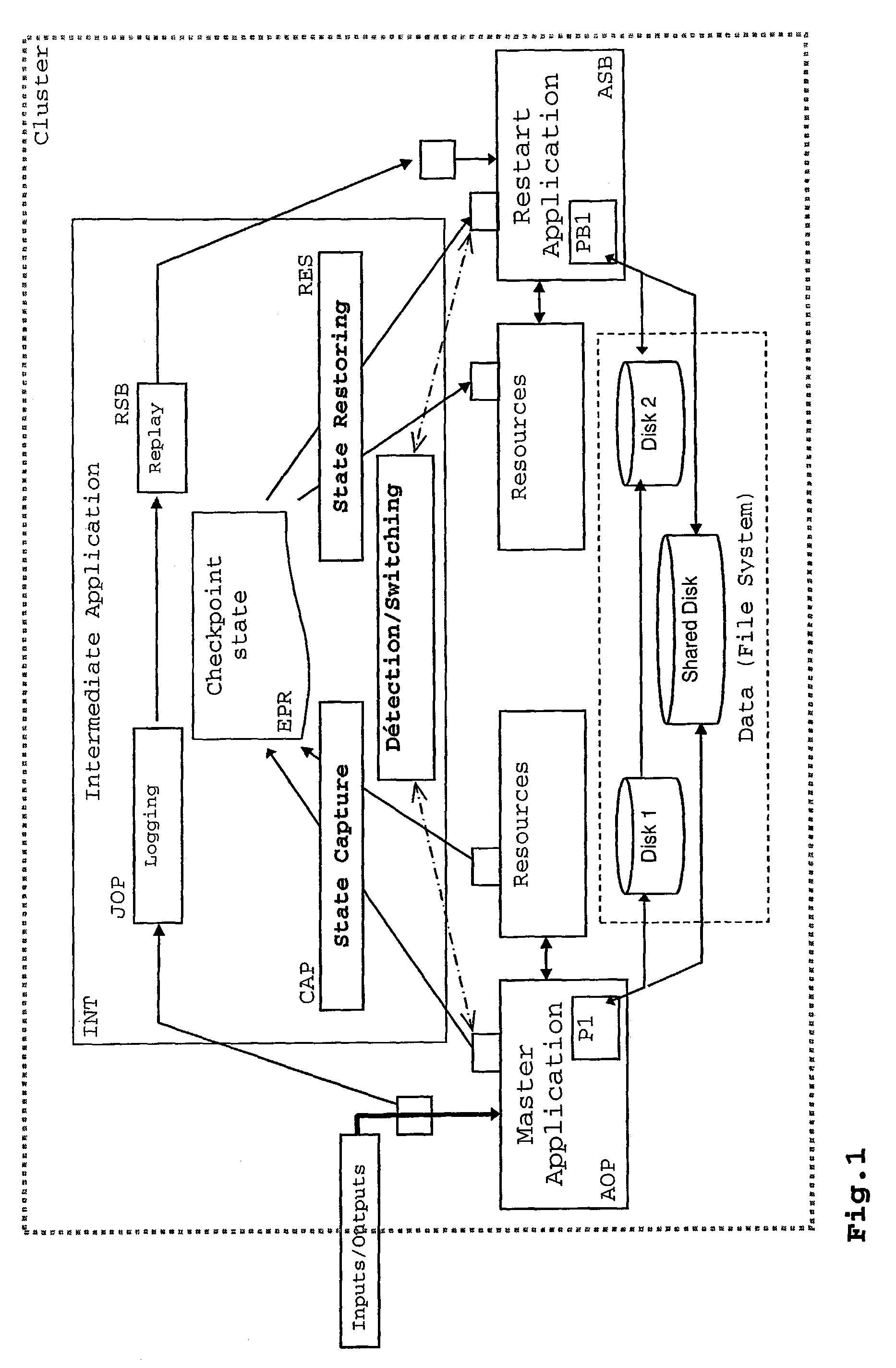
This invention relates to a management method, more particularly by logging and replay, for software operations performed during the execution of an application process executed on a computer. This method applies in particular to internal operations sending a result datum to the managed process, and comprises the following steps: carrying out a deterministic software processing, termed prediction function (FH), based on the state of a managed process or of the application (AOP, ASB), to provide a predicted result (RP) for said operation; comparative test to establish whether the value of the predicted result (RP) corresponds or does not correspond to the value of the actual result (DR, RRJ); performance of a complementary management phase (CH, DH) of said managed operation, this complementary management depending on the result of the preceding test.
Owner:IBM CORP
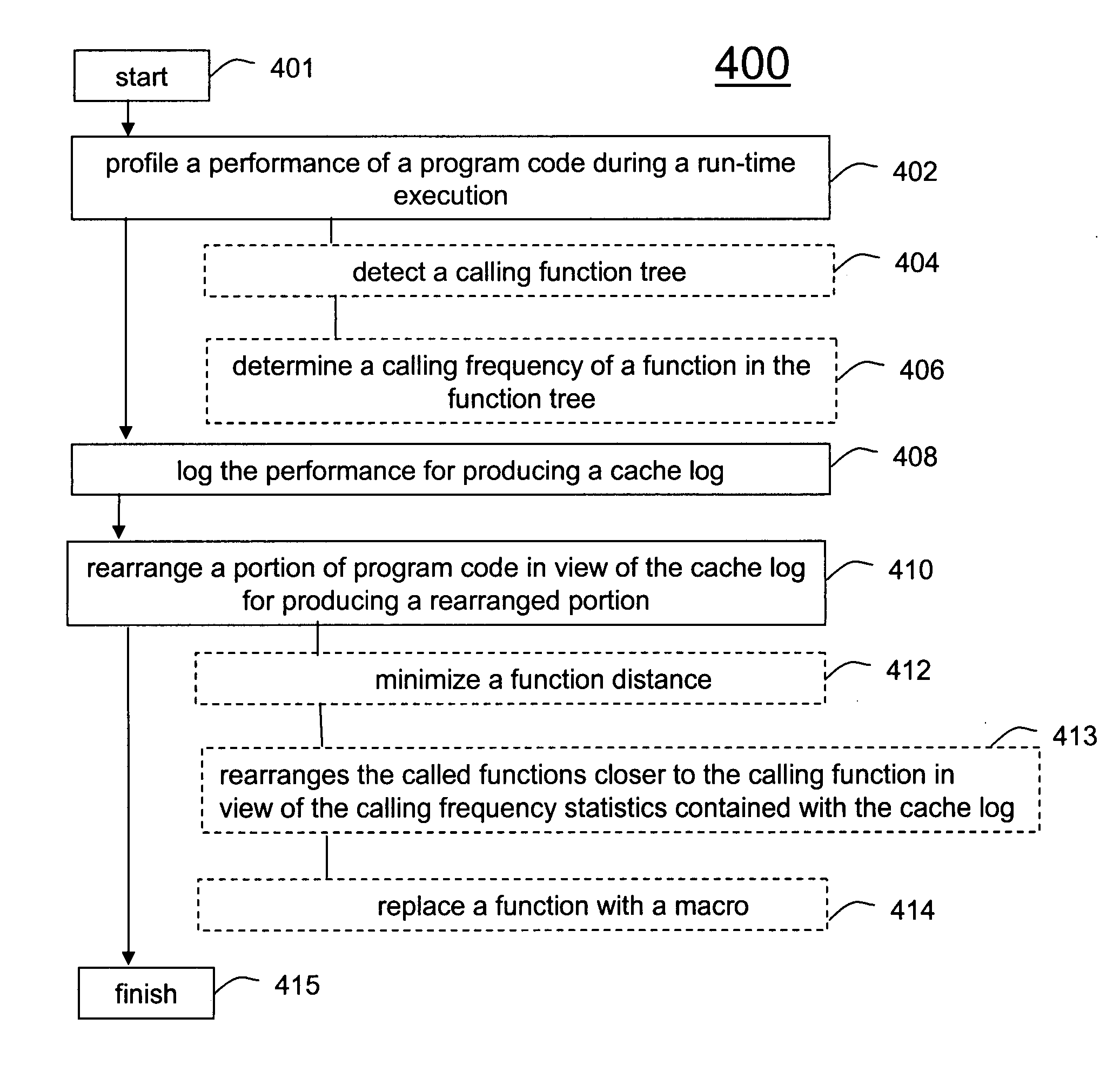
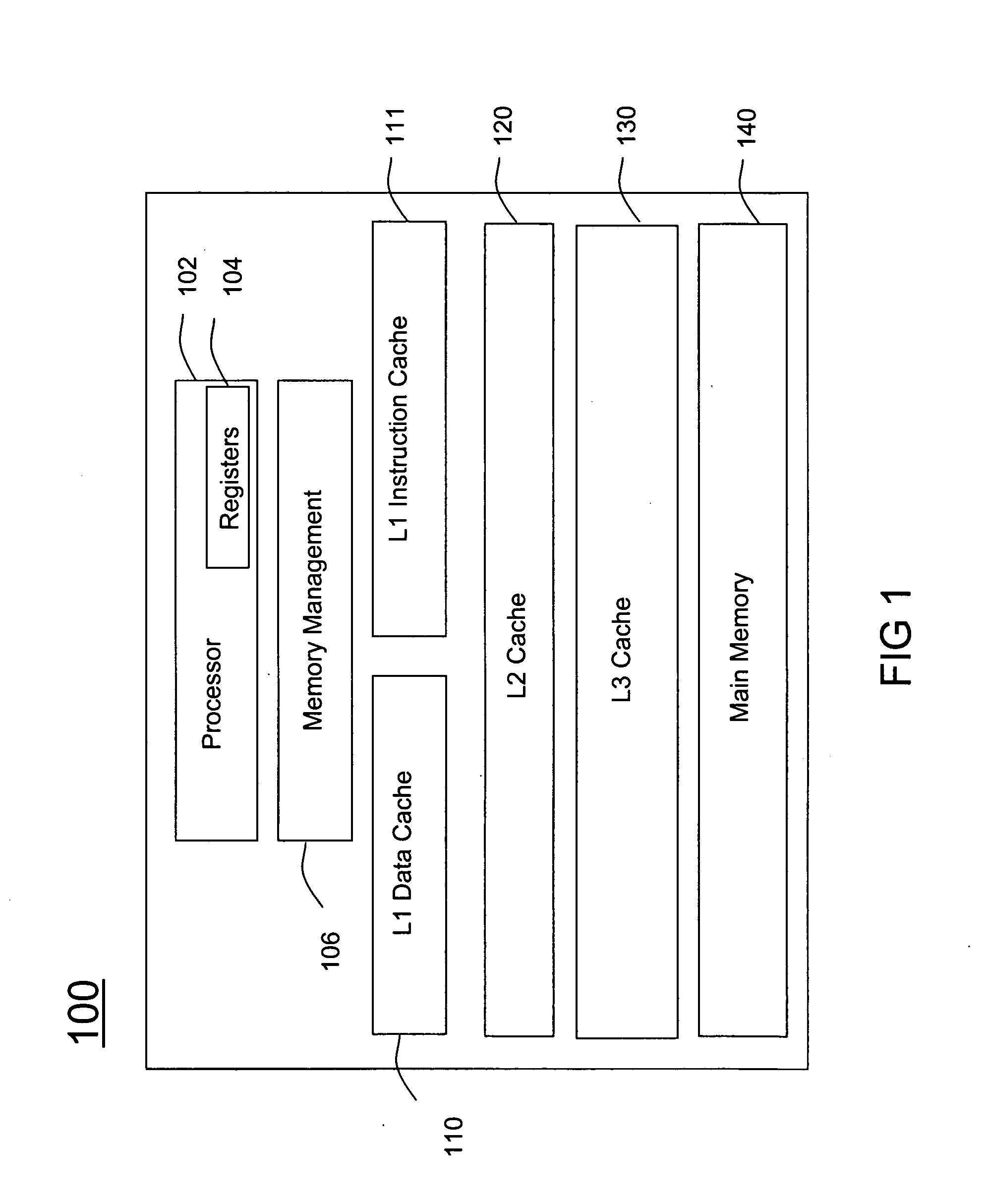
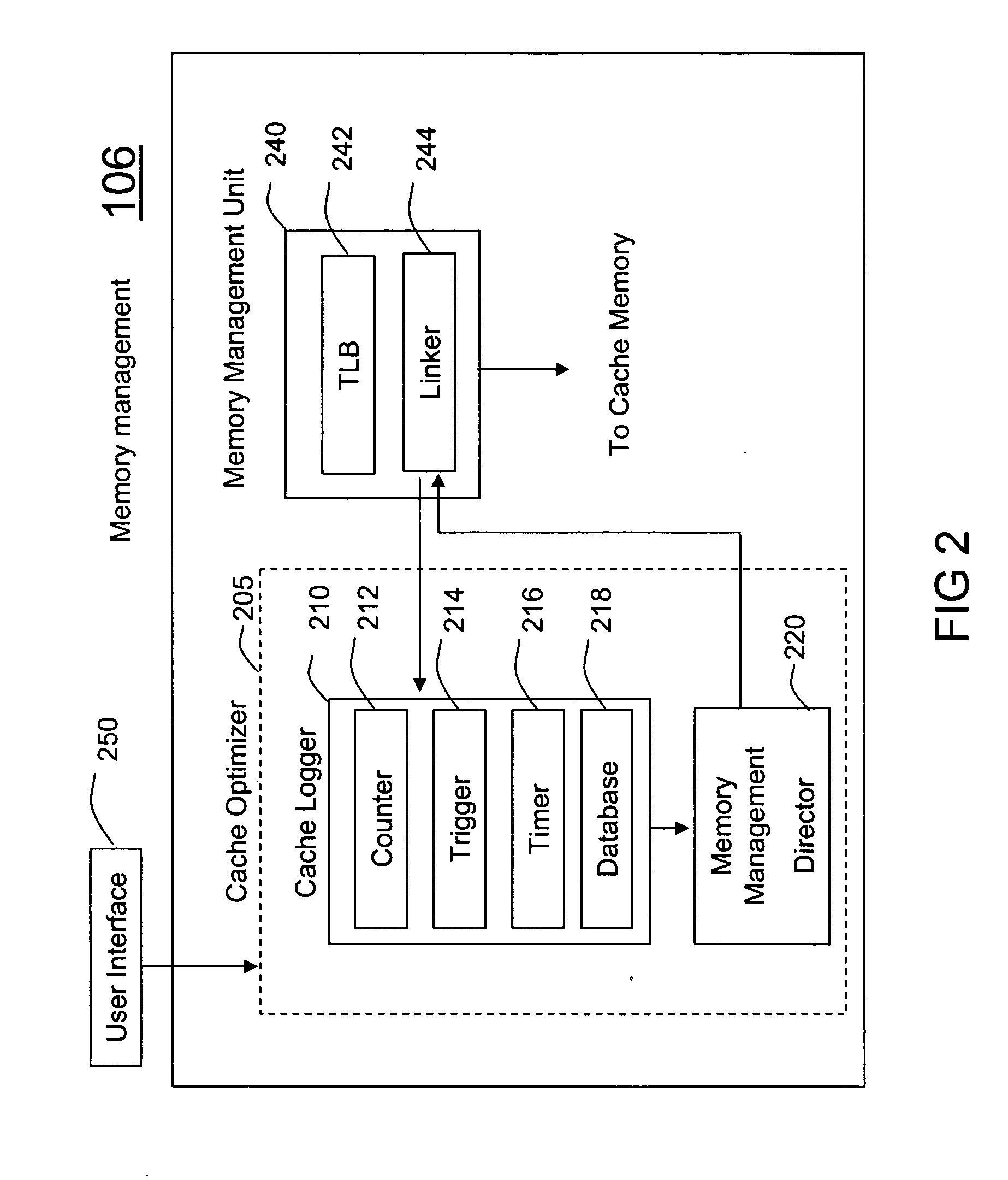
Method and system for run-time cache logging
InactiveUS20070150881A1Increase heightMaximize cache locality compile timeError detection/correctionSpecific program execution arrangementsCache optimizationParallel computing
A method (400) and system (106) is provided for run-time cache optimization. The method includes profiling (402) a performance of a program code during a run-time execution, logging (408) the performance for producing a cache log, and rearranging (410) a portion of program code in view of the cache log for producing a rearranged portion. The rearranged portion is supplied to a memory management unit (240) for managing at least one cache memory (110-140). The cache log can be collected during a real-time operation of a communication device and is fed back to a linking process (244) to maximize a cache locality compile-time. The method further includes loading a saved profile corresponding with a run-time operating mode, and reprogramming a new code image associated with the saved profile.
Owner:MOTOROLA INC
Call recording platform
InactiveUS20060198504A1Quick searchShorten the timeSpecial service for subscribersNetwork connectionsData accessWorkstation
The invention provides a digital voice recording platform that is used for live monitoring of calls, voice logging, incident reconstruction, compliance and liability reduction. The call recording platform is a fully fault tolerant system comprised of industrial grade single board (blade) computers. The call recording platform is provided for digital voice recording, supporting both digital and analog interfaces, all major proprietary PBX systems and providing support for VoIP. The platform makes intelligent use of call triggers, automatically responding to line signaling events to capture all of the associated call data. The platform provides access to a customizable variety of call recording options and modalities, a fast and effective search, and full archiving capabilities and management. At any time, a user can annotate or email a call, create custom search fields, track a case or customer, or burn an archive of recorded calls. As a LAN / WAN based server system, the platform provides seamless call data access from any networked client workstation.
Owner:ACCURATE ALWAYS
Power Management Unit with Sensor Logging
ActiveUS20100295473A1Failure to compensateMaintain lightElectrical apparatusElectric light circuit arrangementSmart lightingDesign improvement
In embodiments of the present invention, a method and system is provided for designing improved intelligent, LED-based lighting systems. The LED based lighting systems may include fixtures with one or more of rotatable LED light bars, integrated sensors, onboard intelligence to receive signals from the LED light bars and control the LED light bars, and a mesh network connectivity to other fixtures.
Owner:OSRAM SYLVANIA INC +1
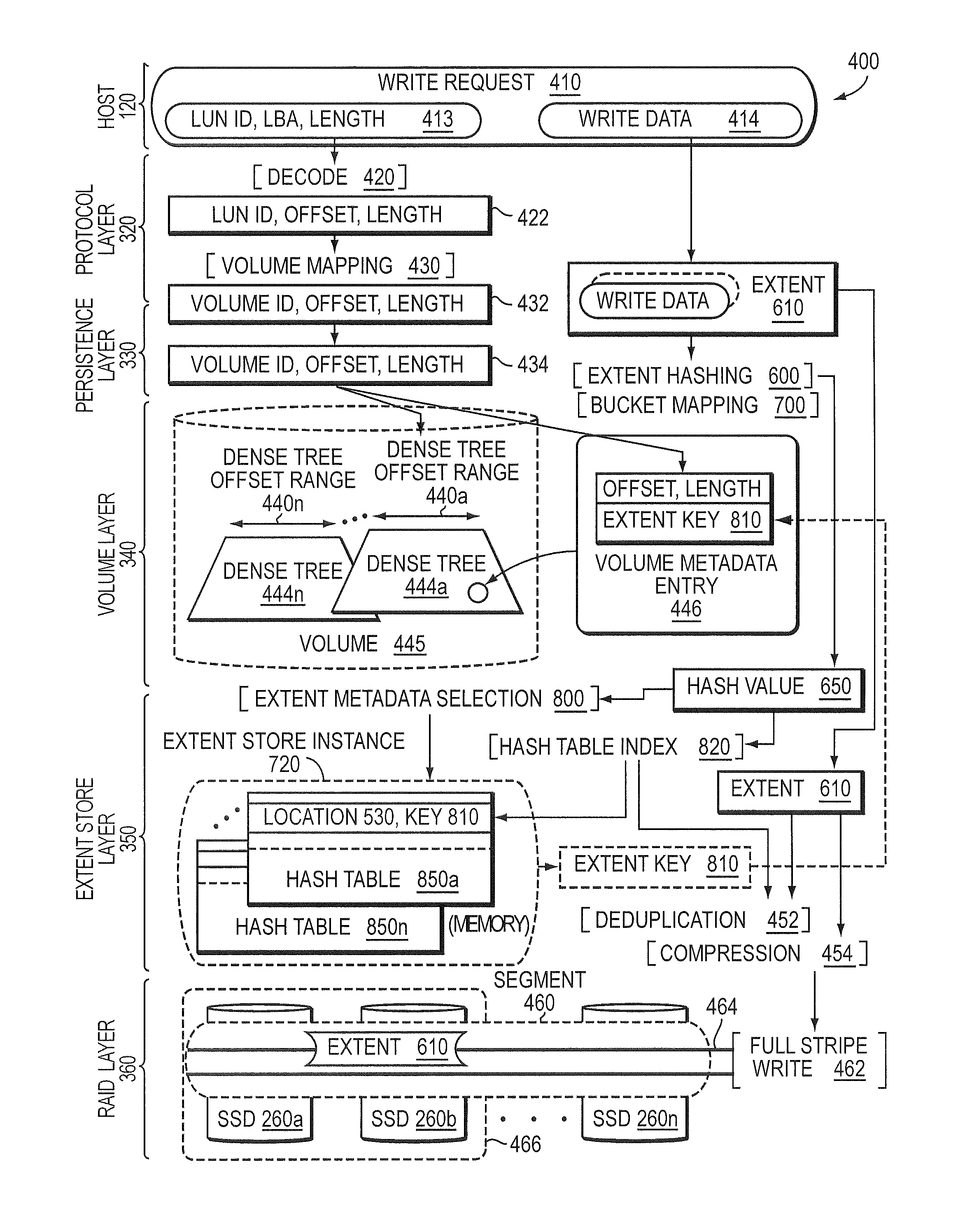
Extent metadata update logging and checkpointing
ActiveUS8880787B1Digital data information retrievalError detection/correctionArray data structureHash table
In one embodiment, an extent store layer of a storage input / output (I / O) stack executing on one or more nodes of a cluster manages efficient logging and checkpointing of metadata. The metadata managed by the extent store layer, i.e., the extent store metadata, resides in a memory (in-core) of each node and is illustratively organized as a key-value extent store embodied as one or more data structures, e.g., a set of hash tables. Changes to the set of hash tables are recorded as a continuous stream of changes to SSD embodied as an extent store layer log. A separate log stream structure (e.g., an in-core buffer) may be associated respectively with each hash table such that changed (i.e., dirtied) slots of the hash table are recorded as entries in the log stream structure. The hash tables are written to SSD using a fuzzy checkpointing technique.
Owner:NETWORK APPLIANCE INC
Design method for distributed hydrological model by using grid as analog unit
InactiveCN102034001AImprove scalabilityImprove execution efficiencyClimate change adaptationSpecial data processing applicationsAridRainfall runoff
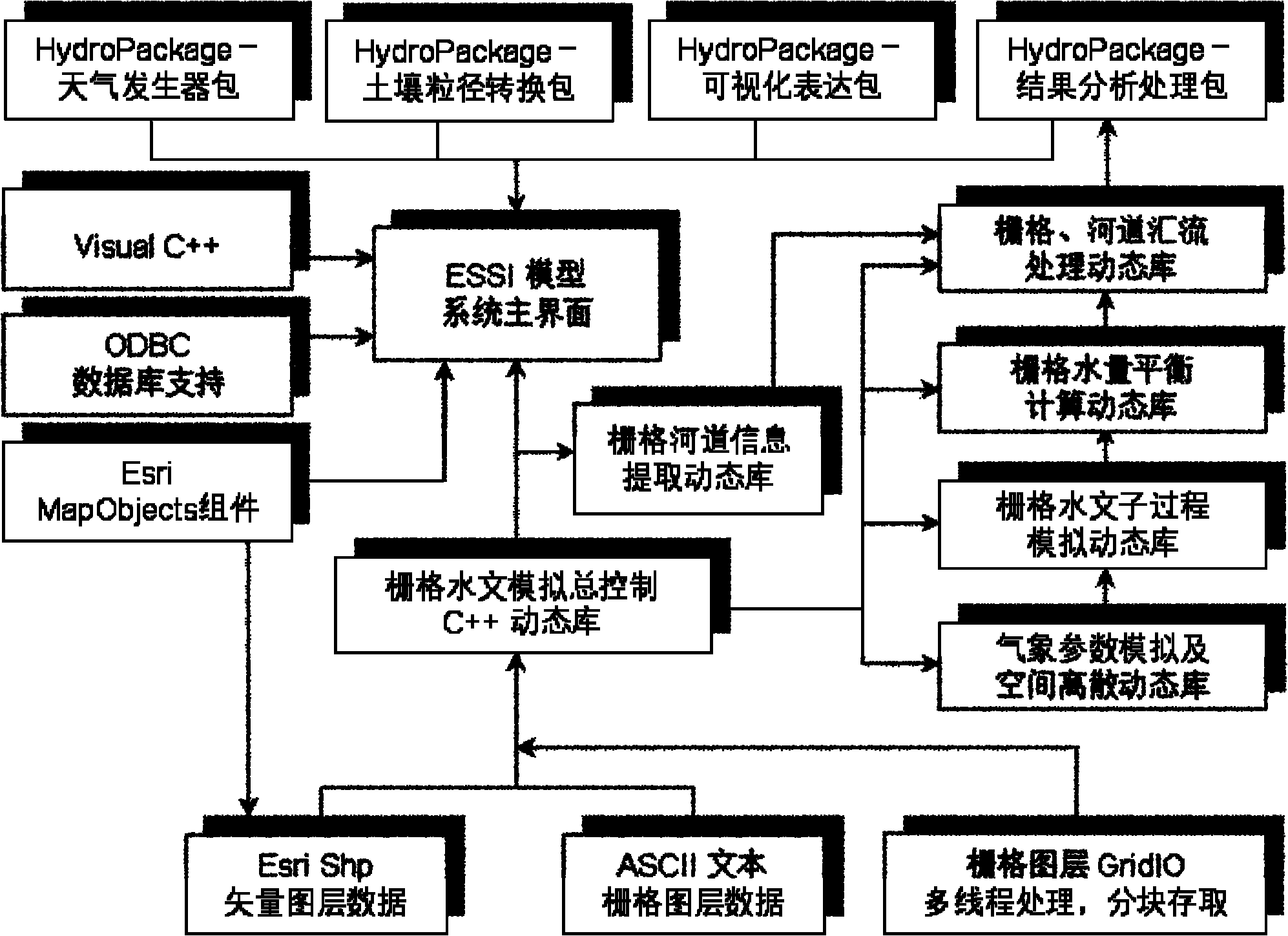
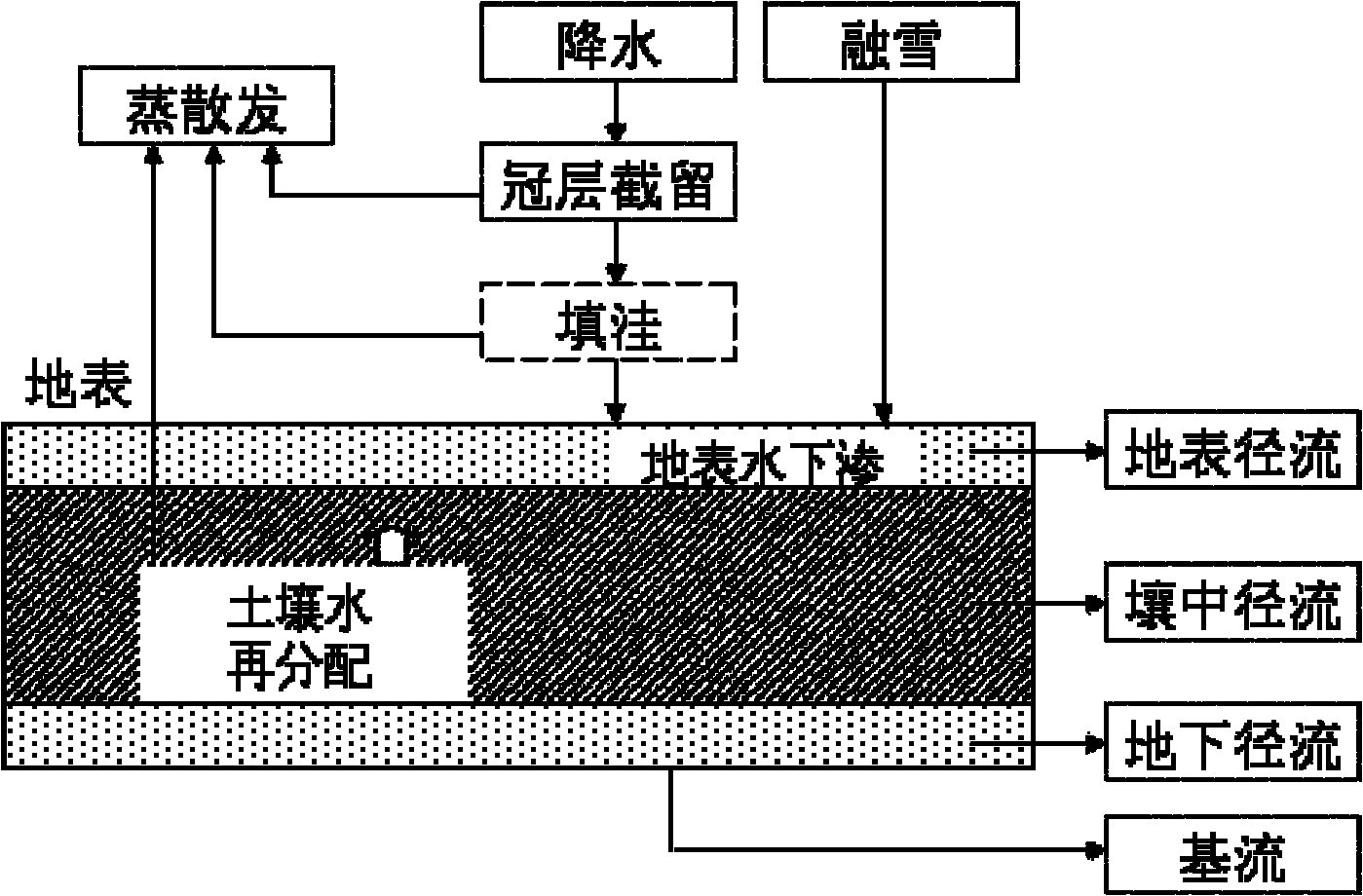
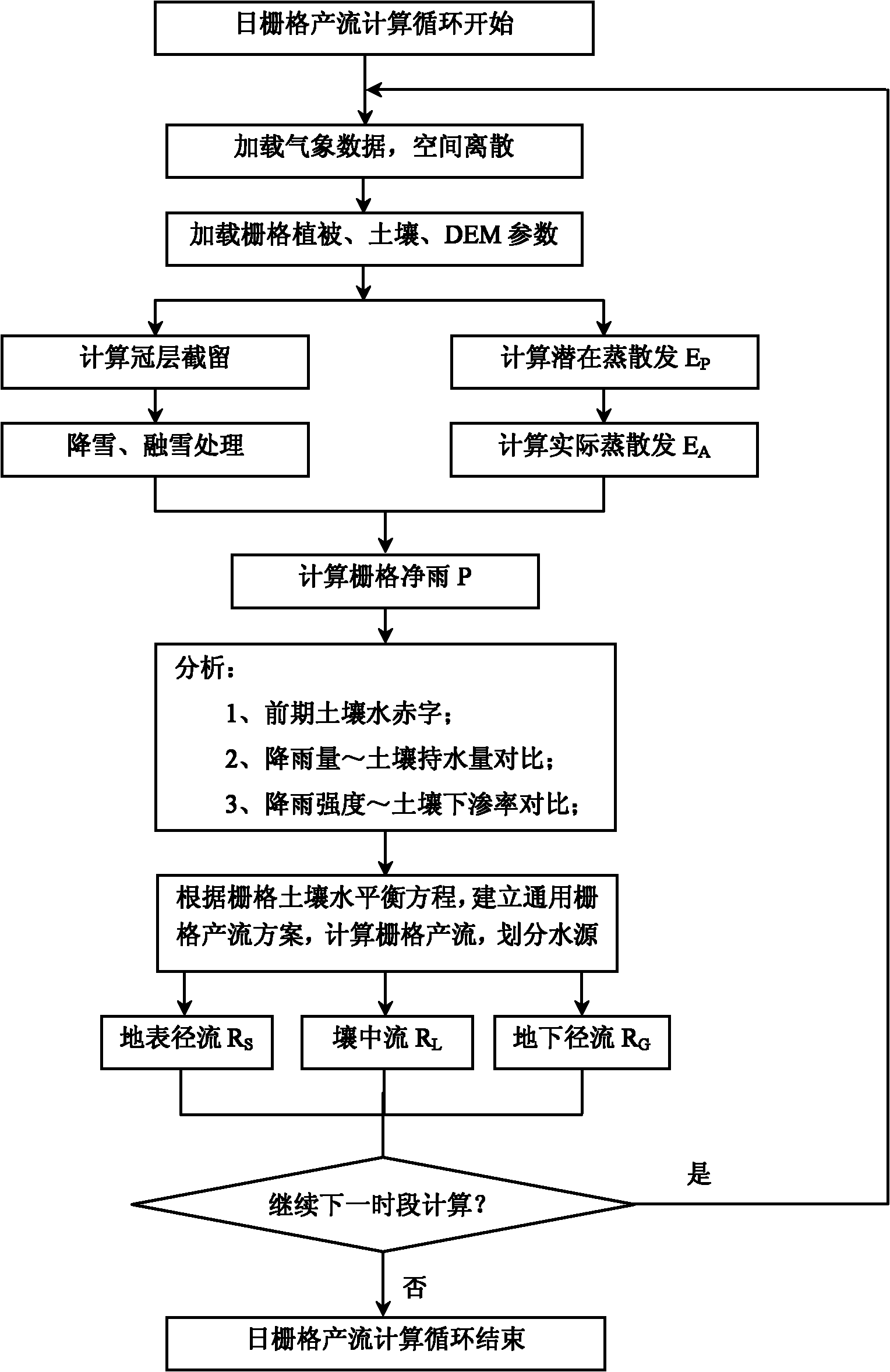
The invention discloses a design method for a distributed hydrological model by using a grid as an analog unit, which is called as ESSI for short. The design method comprises the following steps of: obtainment of a distributed parameter: converting vector data into grid data; generalization of a watershed hydrological process: establishing a universal runoff generating type for the grid; design of a runoff generating process: respectively computing the water-quantity distributing condition of each part according to different prior-period soil water conditions; design of a flow collecting process: respectively designing a Muskingum-Cunge method, a delay algorithm and a riverway segmentation Muskingum method for the flow collecting process computation of the model under different conditions; and model development and integration. The invention not only can finish the watershed hydrological process simulation at an arid region and a humid region, but also can realize the short-term flood forecast and the long-term rainfall-runoff process simulation and prediction of a watershed by using modularization and integration ideas as means, thereby providing scientific reference bases for deeply learning about the physical mechanism of water circulation by people, reducing the drought and water-logging disasters and reasonably developing and utilizing water resources.
Owner:NANJING UNIV
Drive error logging
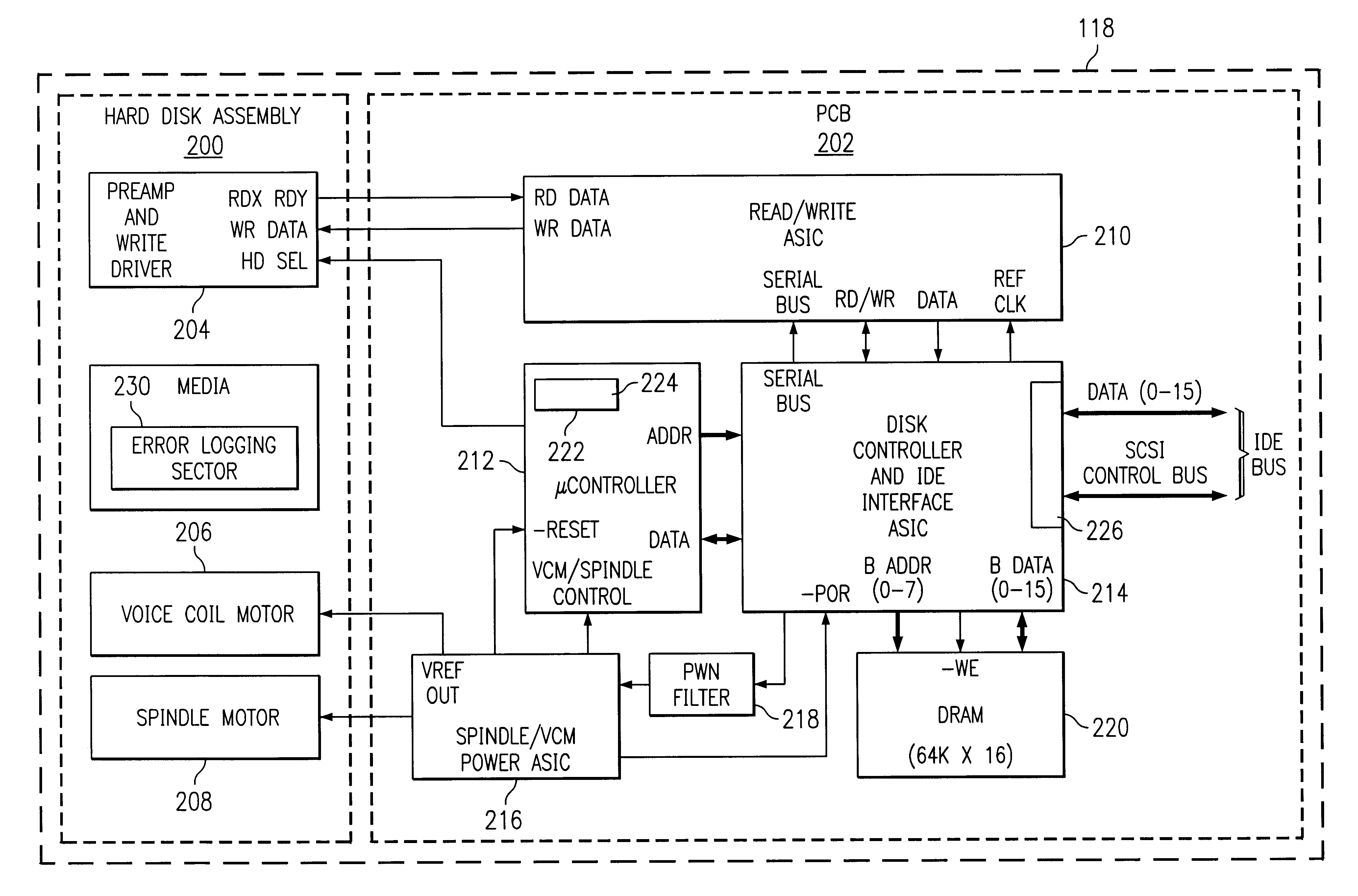
A method and apparatus for logging errors in a storage device. As commands are executed by the storage device a list of previously executed commands is maintained. When an error is detected by the storage device, the previously executed commands and certain error condition codes are stored in an error log in a non-volatile memory of the storage device. The storage device is responsive to a command for reading back the values contained in the error log for diagnostic purposes.
Owner:HEWLETT PACKARD DEV CO LP
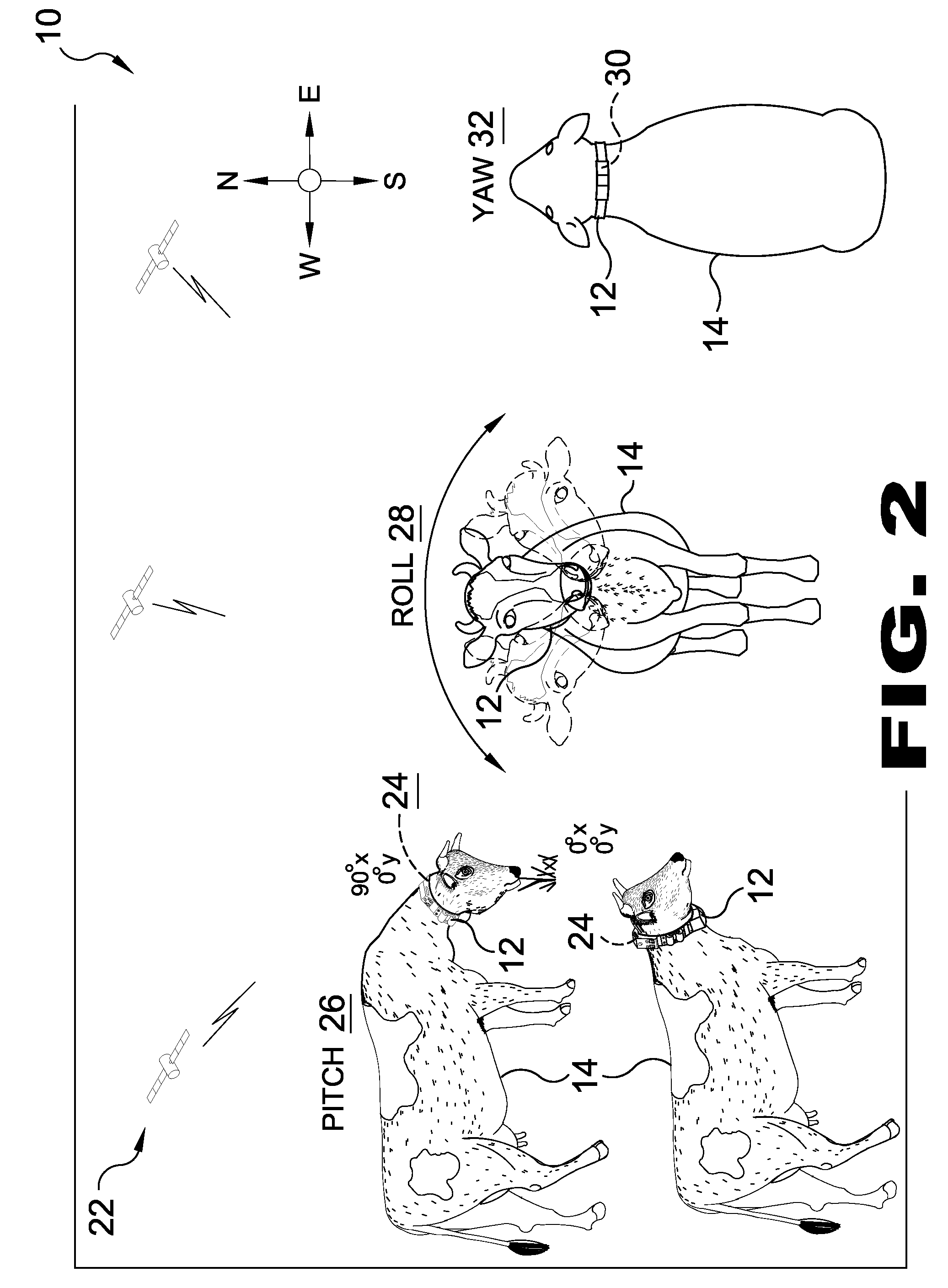
Method and apparatus for data logging of physiological and environmental variables for domestic and feral animals
A GPS data acquisition collar incorporating an individualized rugged watertight collar that monitors factors including GPS location, gazing patterns, elevation, feeding patterns, temperature, movement speed, sleep patterns and signaling or beacon tracking options. Additionally the present invention provides options for visual representation or programming alerting of factors that may affect an animal or herd of animals in a monitored and recorded environment.
Owner:KEDZIORA JOHN
Location Based Vehicle Data Logging and Diagnostic System and Method
A data logging unit configured for installation in a hybrid vehicle communicates with a user device configured to receive data from the data logging unit and to display selected portions of the data to a user for identification of potential vehicle faults associated with vehicle events reported by the vehicle's driver. The data logging unit has a data logger which communicates with hybrid drive system and other vehicle components to receive hybrid drive system data, and with a vehicle position sensor which detects location to receive vehicle location data. A data log processing module correlates location data with the corresponding vehicle data, and creates a correlated log of drive system data and associated vehicle location information, to allow identification of vehicle data within an event window based on vehicle location at the time of a reported event. Accordingly, a user may make a geographical request and the system will report vehicle data corresponding to the geographical request.
Owner:SHEPPARD MULLIN RICHTER & HAMPTON
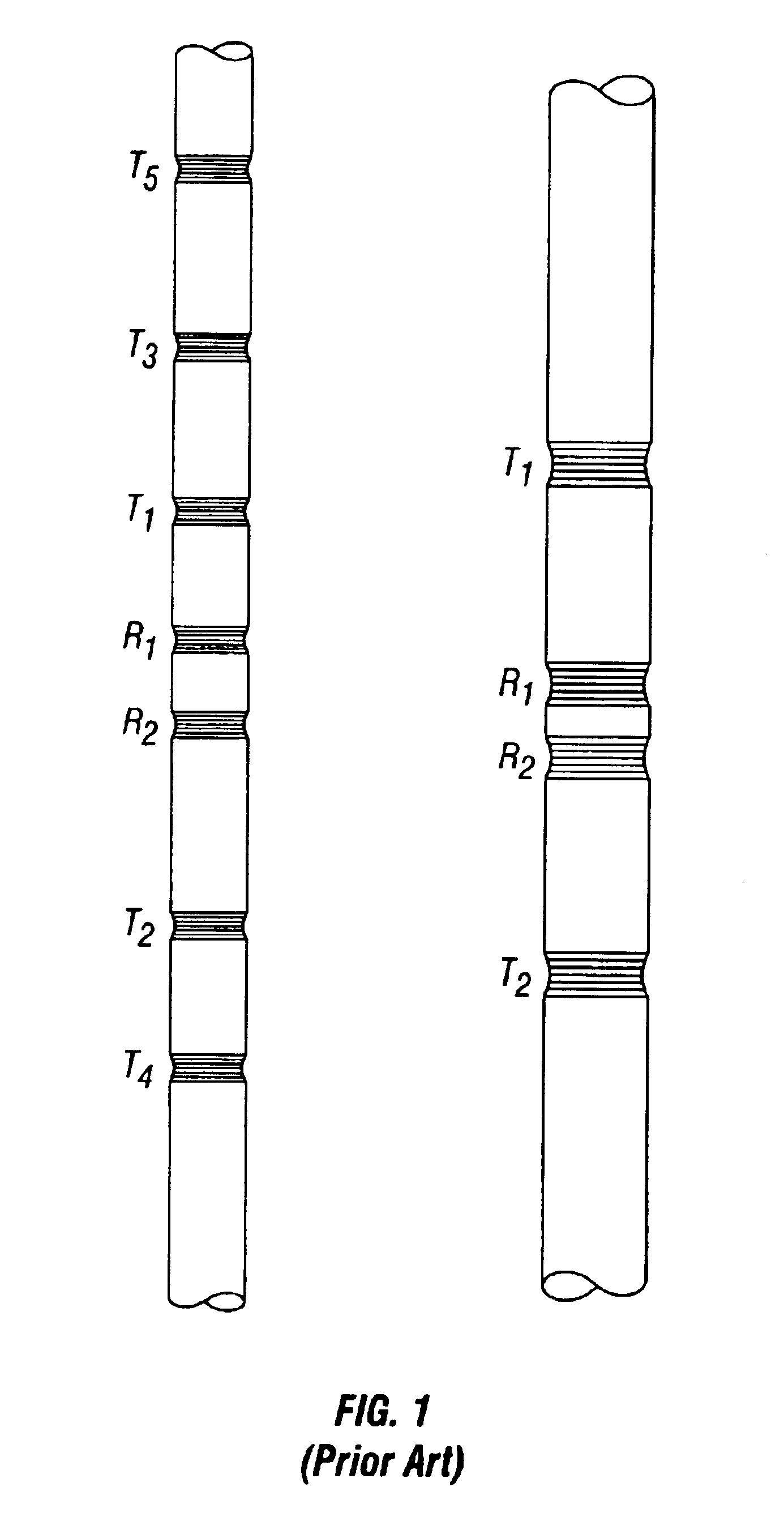
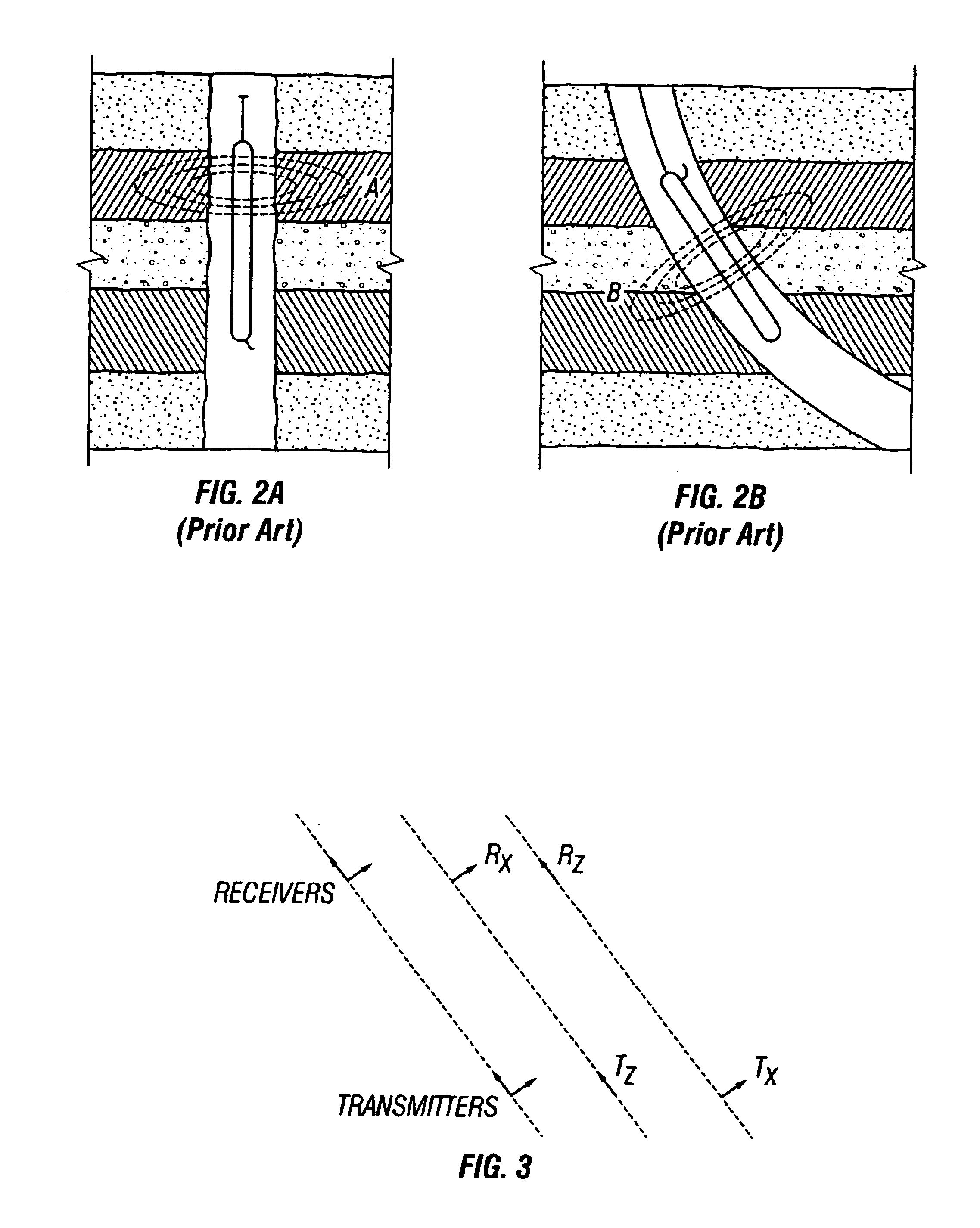
Directional electromagnetic measurements insensitive to dip and anisotropy
InactiveUS6969994B2Electric/magnetic detection for well-loggingAcoustic wave reradiationMagnetic dipoleAnisotropy
Systems and methods are provided for directional propagation-type logging measurements not sensitive to dip and anisotropy over a wide frequency range. Estimates of the distance of the logging tool to a bed boundary are obtained using “up-down” measurements with antenna configurations having tilted magnetic dipoles. These estimates are insensitive to anistropy and dip, undesirable complications of directional measurements.
Owner:SCHLUMBERGER TECH CORP
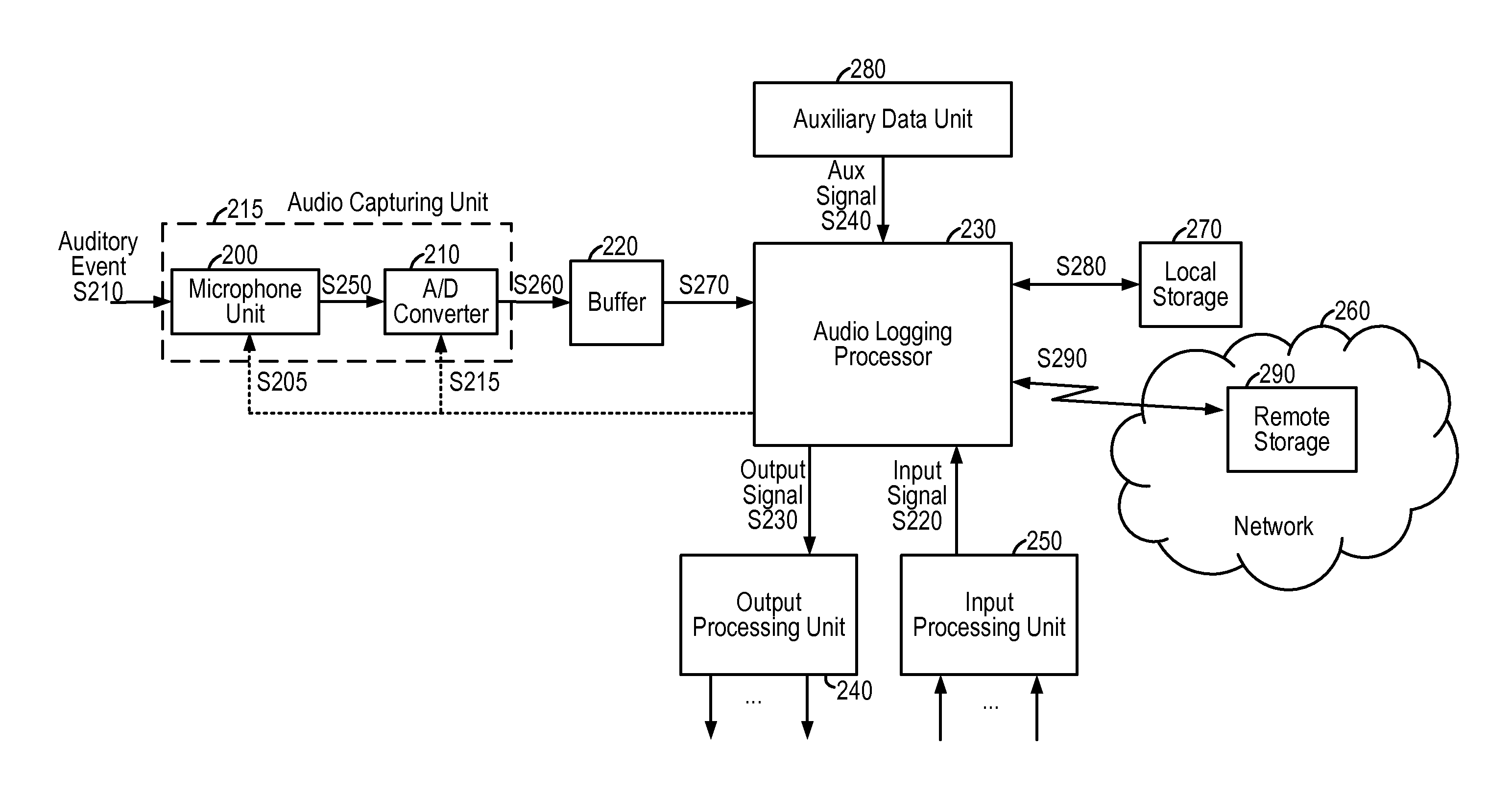
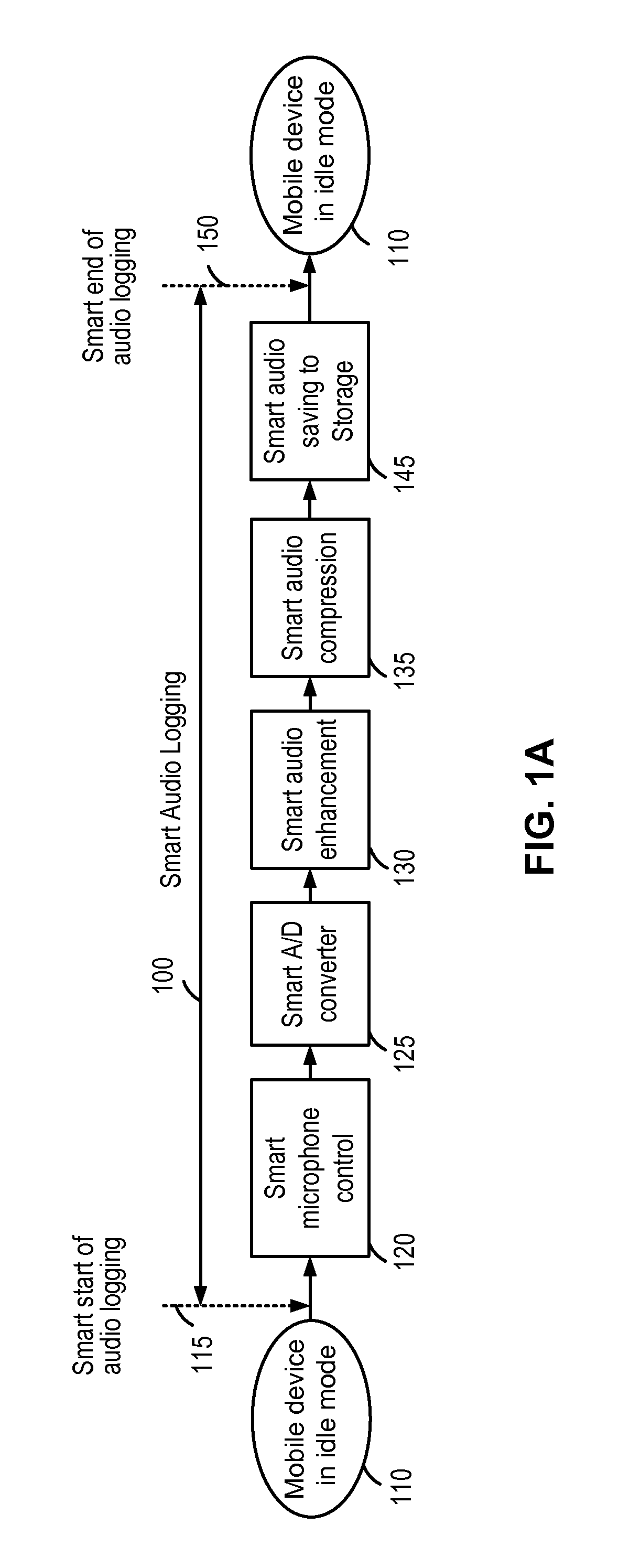
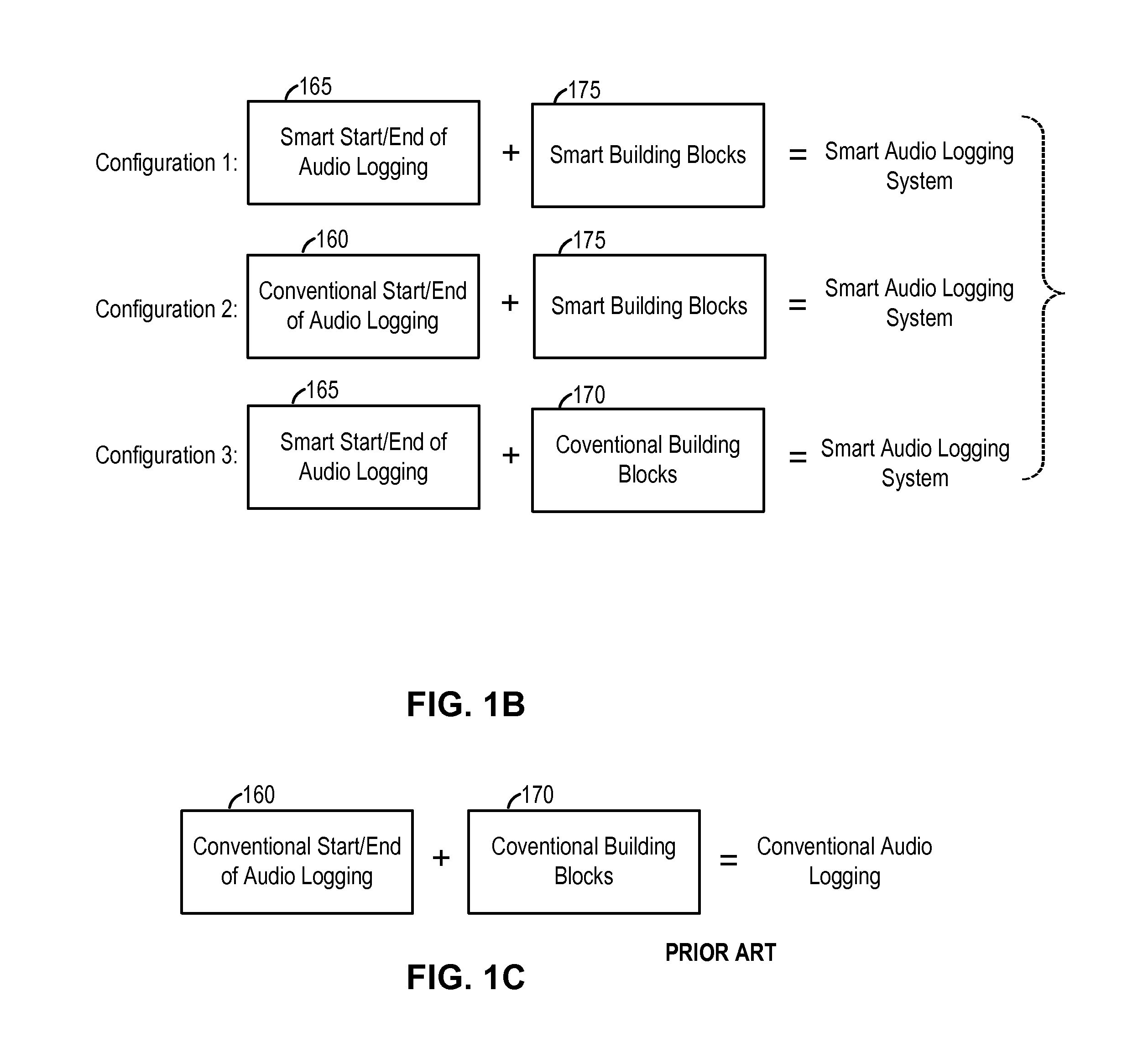
System and method of smart audio logging for mobile devices
InactiveUS20150325267A1Enhanced signalSuppress background noiseRecord information storageSubstation equipmentComputer hardwareMobile device
A mobile device that is capable of automatically starting and ending the recording of an audio signal captured by at least one microphone is presented. The mobile device is capable of adjusting a number of parameters related with audio logging based on the context information of the audio input signal.
Owner:QUALCOMM INC
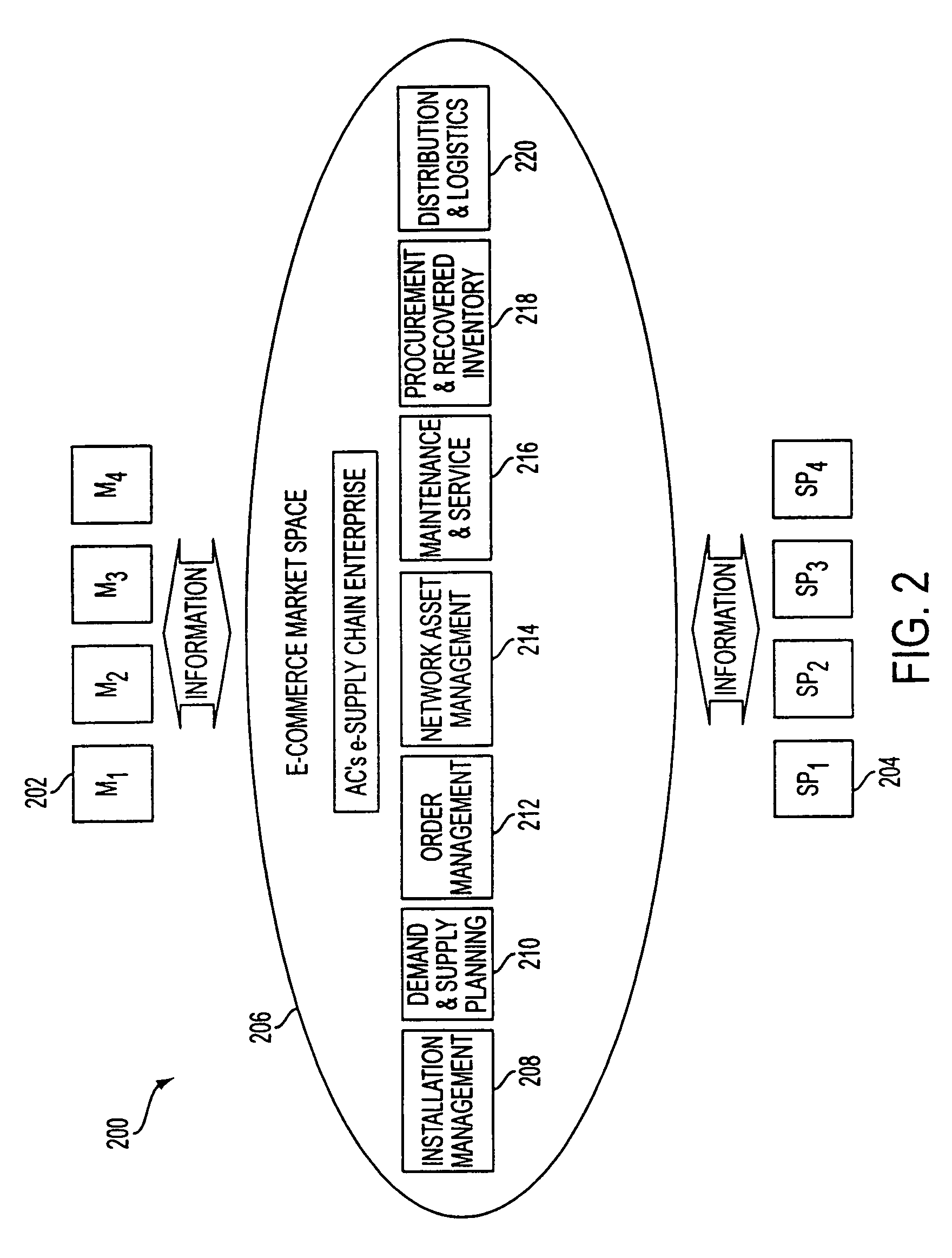
Technology sharing during demand and supply planning in a network-based supply chain environment
A system, method, and article of manufacture are provided for technology sharing during demand and supply planning in a network-based supply chain environment. Steps included are providing locator and mapping capabilities utilizing the network. Technology that includes streaming audio, stereo audio and video data is also shared utilizing the network. Encryption capabilities for the technology are also included. Further, searching capabilities are provided utilizing the network in addition to logging events and passive user profiling. The event logging includes logging network operations. User profile data is automatically received and stored. User profile data includes user identity, state, preferences and interests. User profile data is also automatically exported to an active profile manager which automatically adds additional user profile data. Additional user profile data includes information related to whether the user is a service provider or a manufacturer and the location of user.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for aggregating and extending parental controls auditing in a computer network
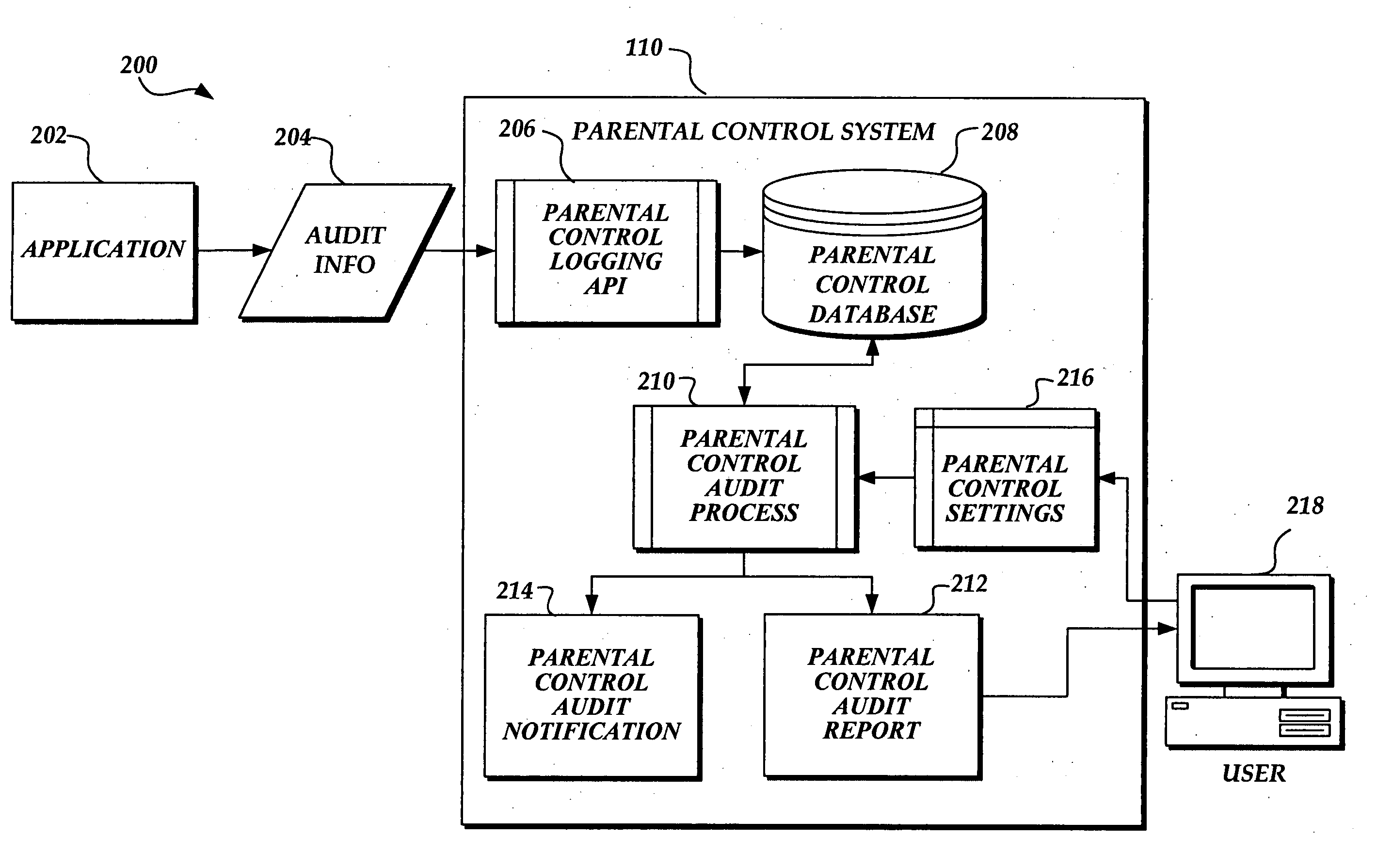
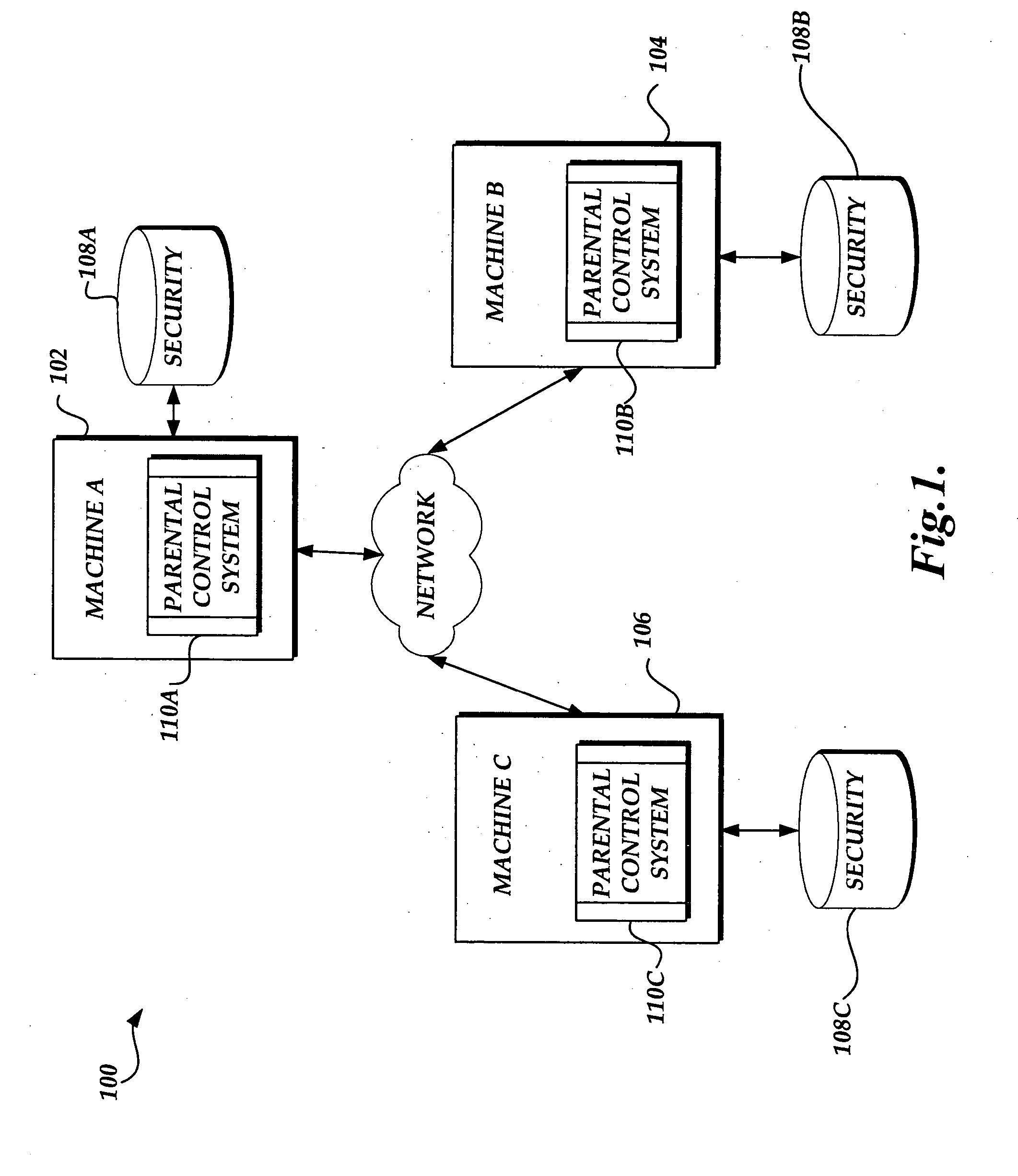
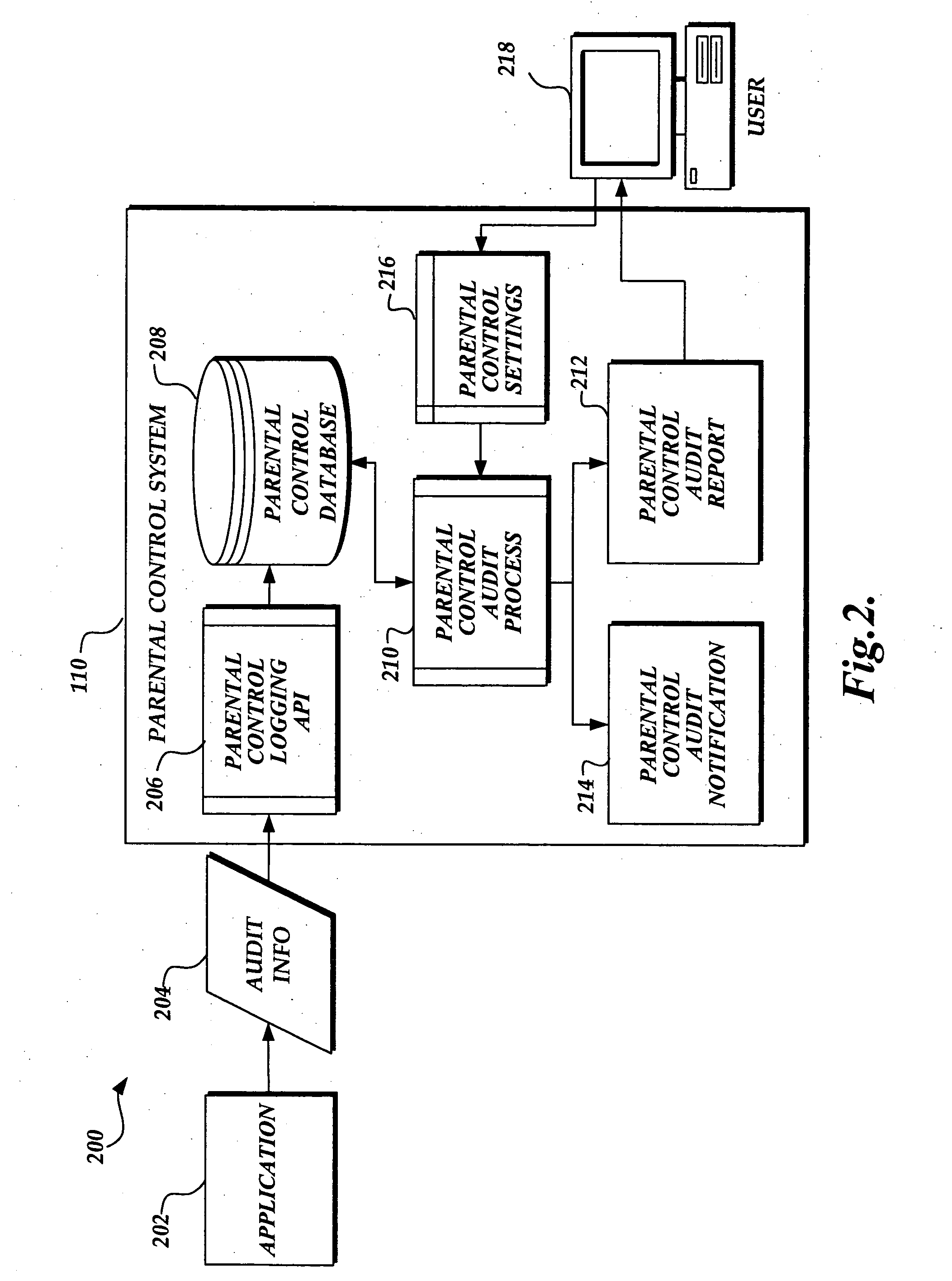
ActiveUS20050228881A1Easy to recordExtending parental controlComputer security arrangementsMultiple digital computer combinationsData synchronizationControl system
A system and method for aggregating and extending parental controls auditing in an unmanaged computing network are provided. A parental control system, including a parental control database, logging interface, and audit process, resides on each host computing device in an unmanaged computing network that is capable of synchronizing data residing on one of the host computing devices with data residing on the other devices in the network. The parental control system facilitates the logging and reporting of parental control audit information in a manner that allows parents to aggregate the audit information to obtain a comprehensive audit report of their children's use of all computers in the home, and is extensible and customizable by the applications from which the parental control audit information originates.
Owner:MICROSOFT TECH LICENSING LLC
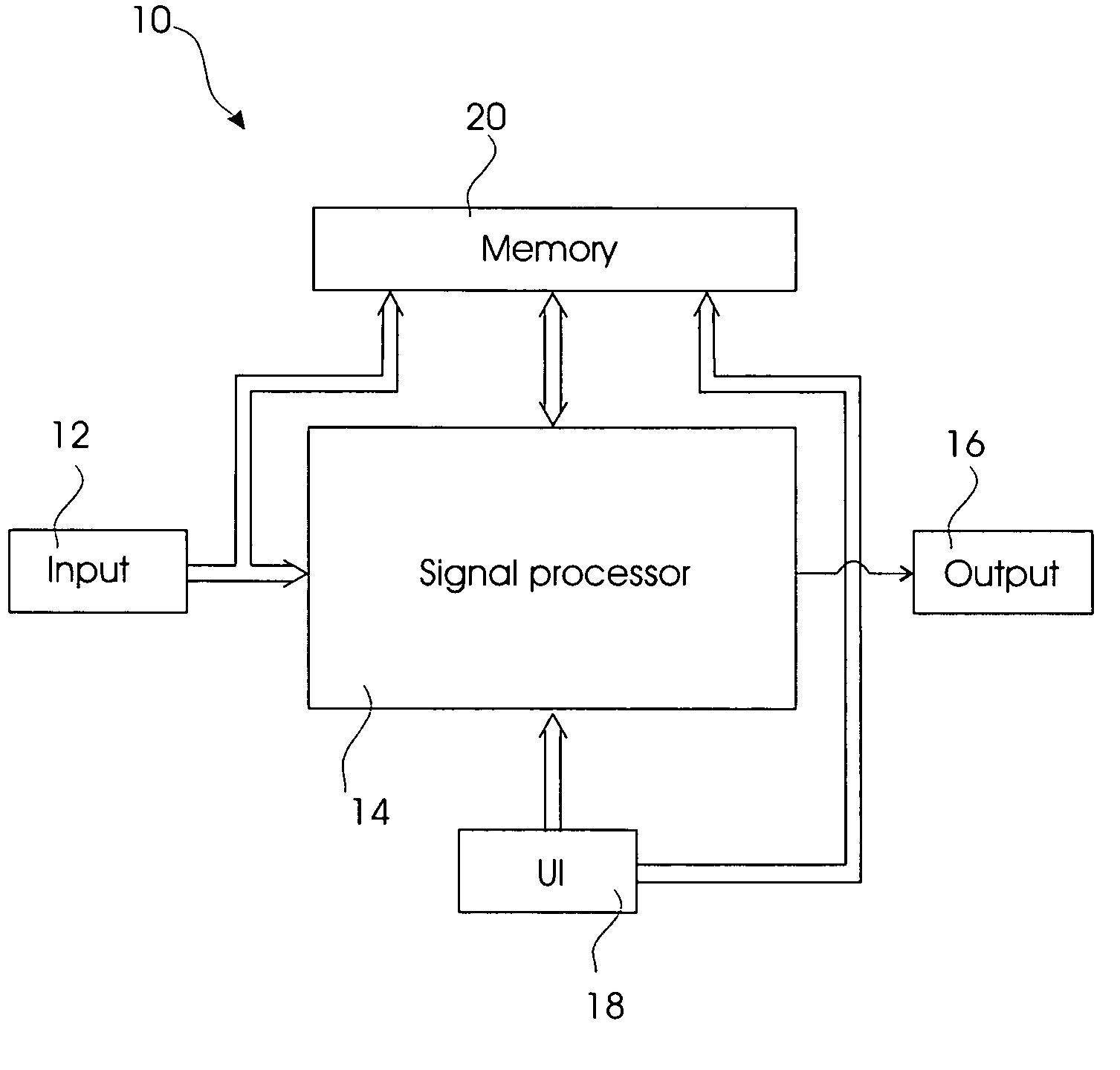
Hearing aid for recording data and learning therefrom
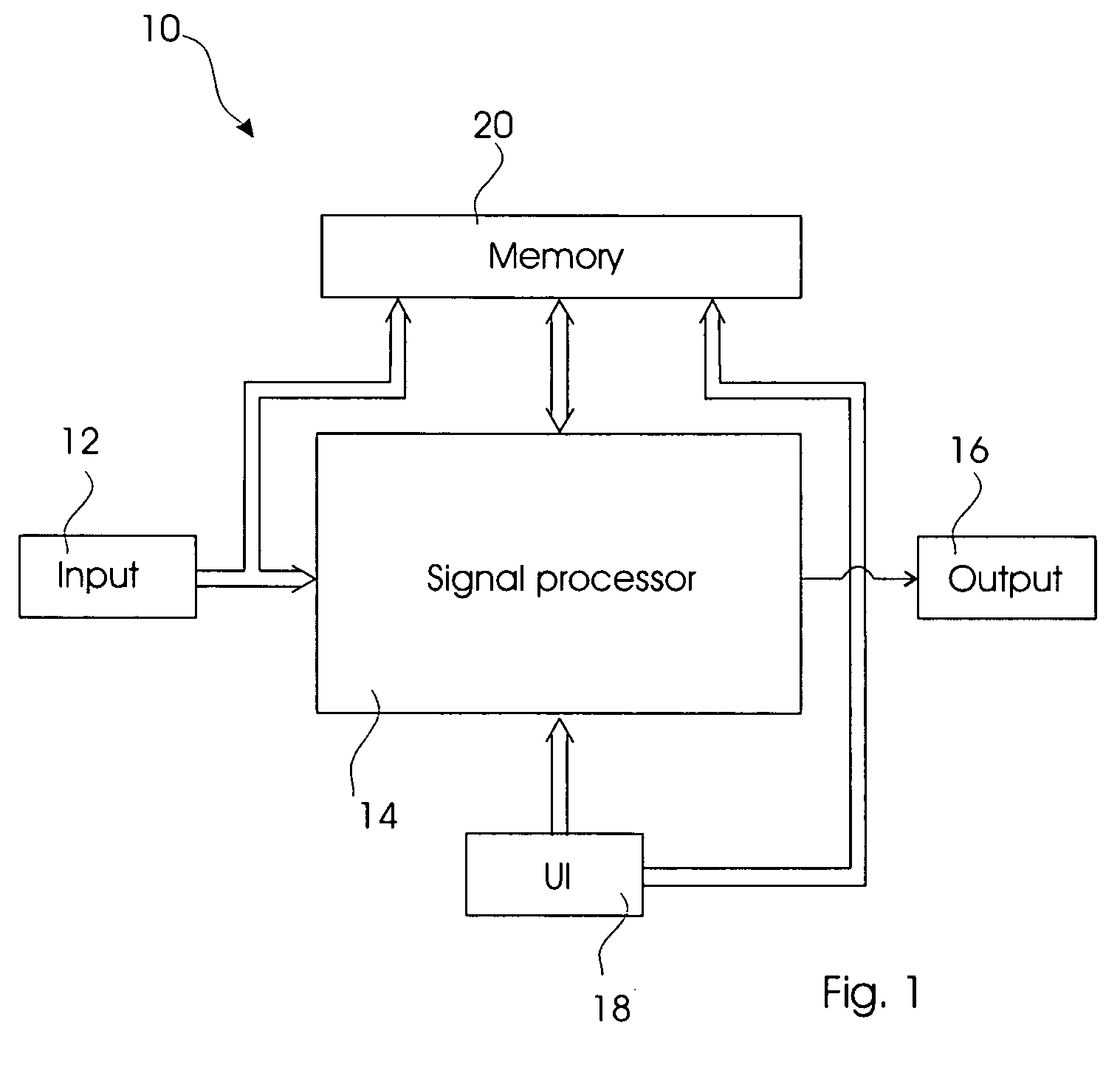
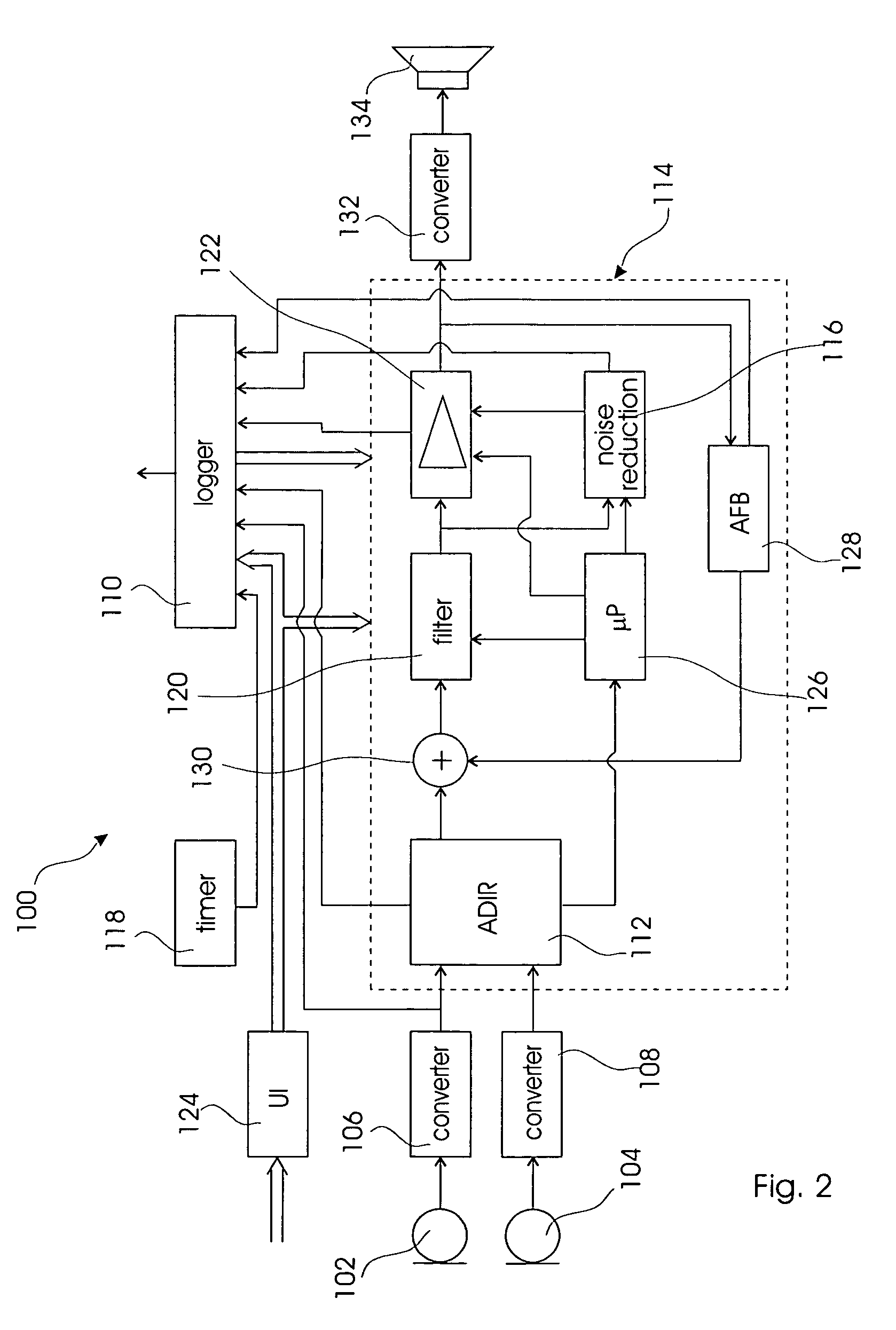
The present invention relates to a hearing aid logging data and learning from these data. The hearing aid (10, 100) comprises an input unit (12) converting an acoustic environment to an electric signal; an output unit (16) converting an processed electric signal to a sound pressure; a signal processing unit (14) interconnecting the input and output unit, and generating the processed electric signal from the electric signal according to a setting; a user interface (18) converting user interaction to a control signal thereby controlling the setting; and finally a memory unit (20) comprising a control section storing a set of control parameters associated with the acoustic environment, and a data logger section receiving data from the input unit (12), the signal processing unit (14), and the user interface (18); and wherein said signal processing unit (14) configures the setting according to the set of control parameters and comprises a learning controller adapted to adjust the set of control parameters according to the data in the data logging section.
Owner:OTICON
Parallelized redo-only logging and recovery for highly available main memory database systems
InactiveUS7305421B2Easy constructionData processing applicationsLight protection screensIn-memory databaseHigh availability
A parallel logging and recovery scheme for highly available main-memory database systems is presented. A preferred embodiment called parallel redo-only logging (“PROL”) combines physical logging and selective replay of redo-only log records. During physical logging, log records are generated with an update sequence number representing the sequence of database update. The log records are replayed selectively during recovery based on the update sequence number. Since the order of replaying log records doesn't matter in physical logging, PROL makes parallel operations possible. Since the physical logging does not depend on the state of the object to which the log records are applied, the present invention also makes it easy to construct a log-based hot standby system.
Owner:TRANSACT & MEMORY
Apparatus and method of object tracking
InactiveUS20090059007A1Low costReduce laborImage enhancementTelevision system detailsSample imageImaging Feature
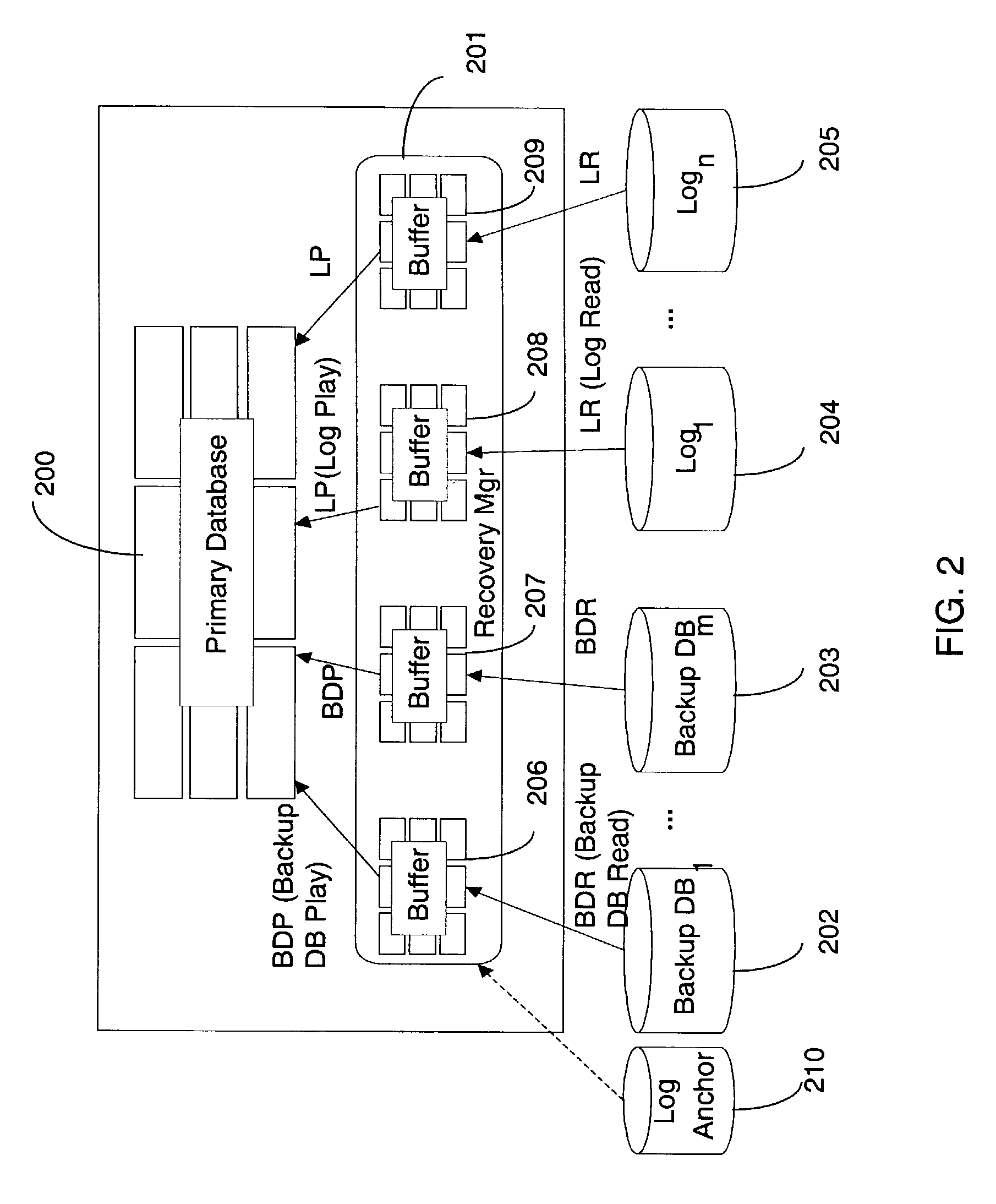
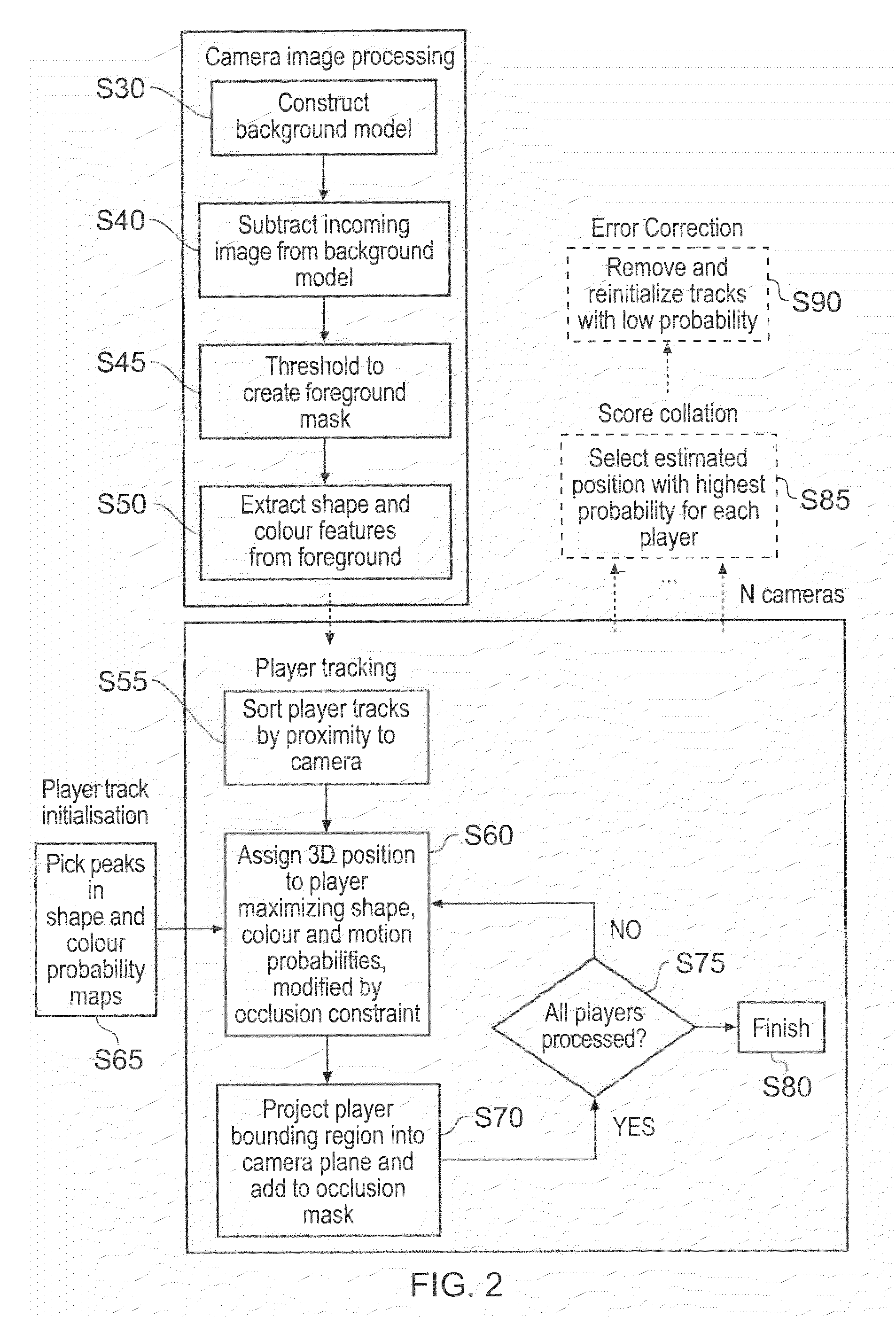
A method of tracking objects on a plane within video images of the objects captured by a video camera. The method includes processing the captured video images so as to extract one or more image features from each object, detecting each of the objects from a relative position of the objects on the plane as viewed from the captured video images by comparing the one or more extracted image features associated with each object with sample image features from a predetermined set of possible example objects which the captured video images may contain; and generating object identification data for each object, from the comparing, which identifies the respective object on the plane. The method further includes generating a three dimensional model of the plane and logging, for each detected object, the object identification data for each object which identifies the respective object on the plane together with object path data. The object path provides a position of the object on the three dimensional model of the plane from the video images with respect to time and relates to the path that each object has taken within the video images. The logging includes detecting an occlusion event in dependence upon whether a first image feature associated with a first of the objects obscures a whole or part of at least a second image feature associated with at least a second of the objects; and, if an occlusion event is detected, associating the object identification data for the first object and the object identification data for the second object with the object path data for both the first object and the second object respectively and logging the associations. The logging further includes identifying at least one of the objects involved in the occlusion event in dependence upon a comparison between the one or more image features associated with that object and the sample image features from the predetermined set of possible example objects, and updating the logged path data after the identification of at least one of the objects so that the respective path data is associated with the respective identified object.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com