Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5382results about How to "Improve execution efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
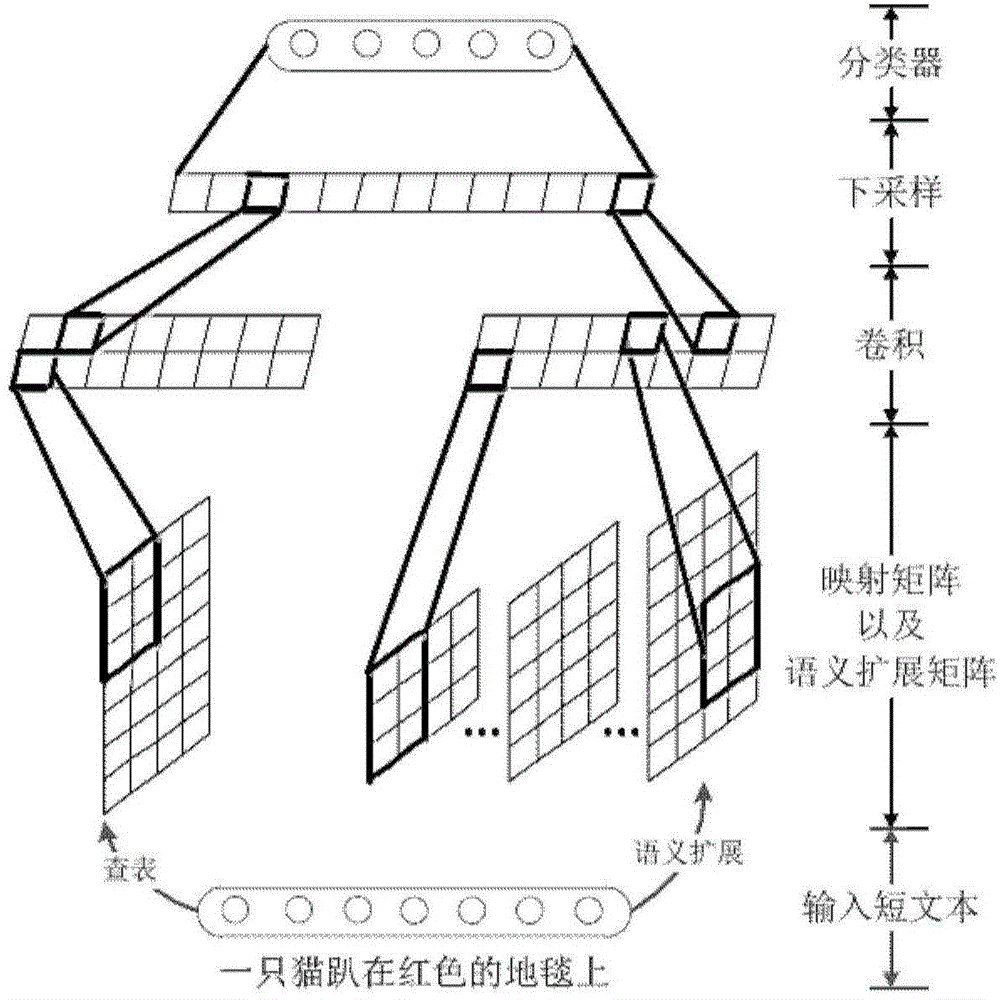
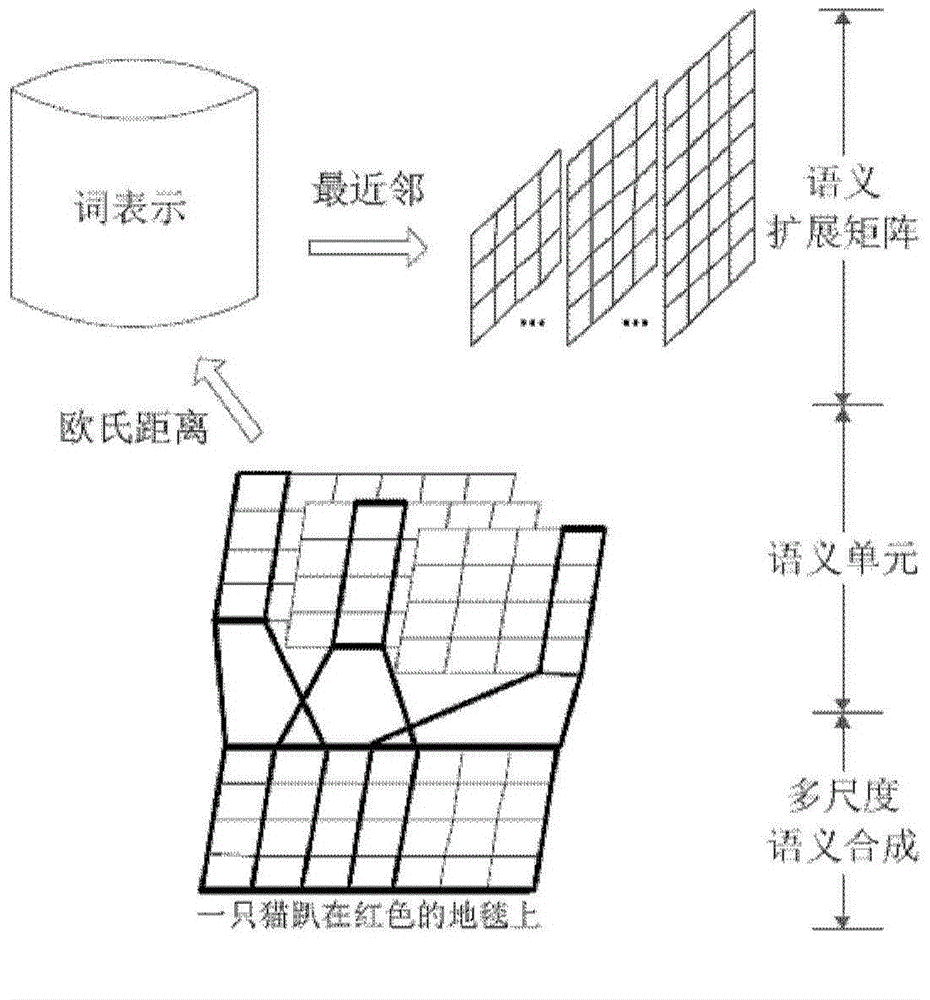
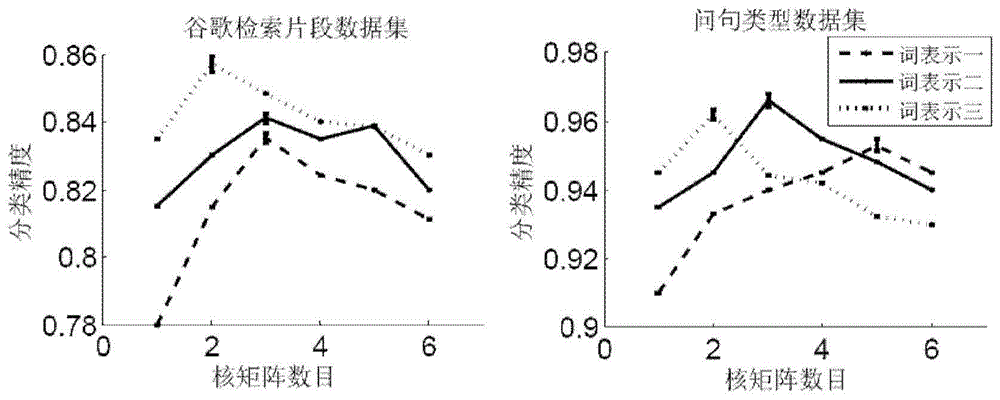
Short text classification method based on convolution neutral network
ActiveCN104834747AImprove semantic sensitivity issuesImprove classification performanceInput/output for user-computer interactionBiological neural network modelsNear neighborClassification methods
The invention discloses a short text classification method based on a convolution neutral network. The convolution neutral network comprises a first layer, a second layer, a third layer, a fourth layer and a fifth layer. On the first layer, multi-scale candidate semantic units in a short text are obtained; on the second layer, Euclidean distances between each candidate semantic unit and all word representation vectors in a vector space are calculated, nearest-neighbor word representations are found, and all the nearest-neighbor word representations meeting a preset Euclidean distance threshold value are selected to construct a semantic expanding matrix; on the third layer, multiple kernel matrixes of different widths and different weight values are used for performing two-dimensional convolution calculation on a mapping matrix and the semantic expanding matrix of the short text, extracting local convolution features and generating a multi-layer local convolution feature matrix; on the fourth layer, down-sampling is performed on the multi-layer local convolution feature matrix to obtain a multi-layer global feature matrix, nonlinear tangent conversion is performed on the global feature matrix, and then the converted global feature matrix is converted into a fixed-length semantic feature vector; on the fifth layer, a classifier is endowed with the semantic feature vector to predict the category of the short text.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
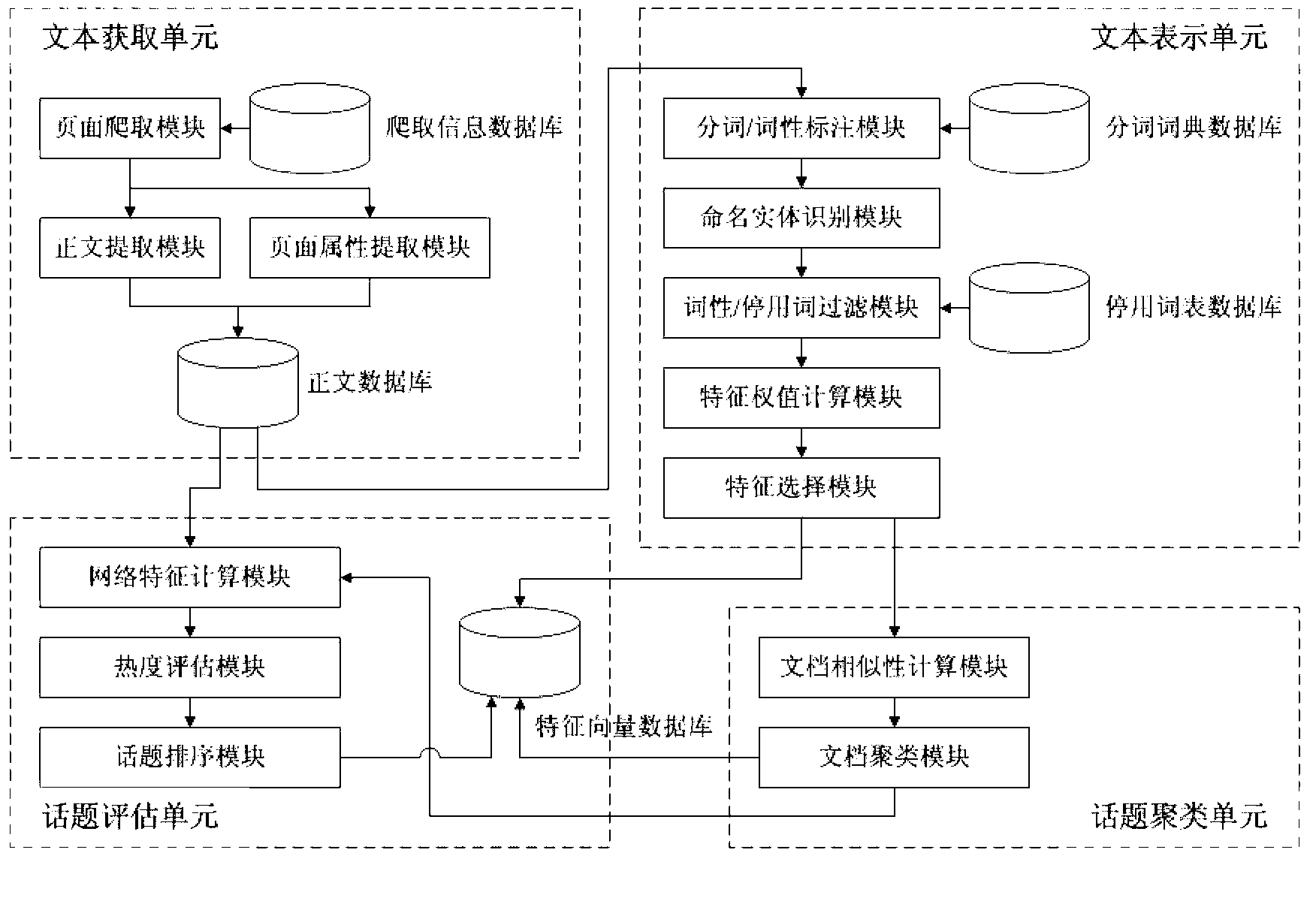
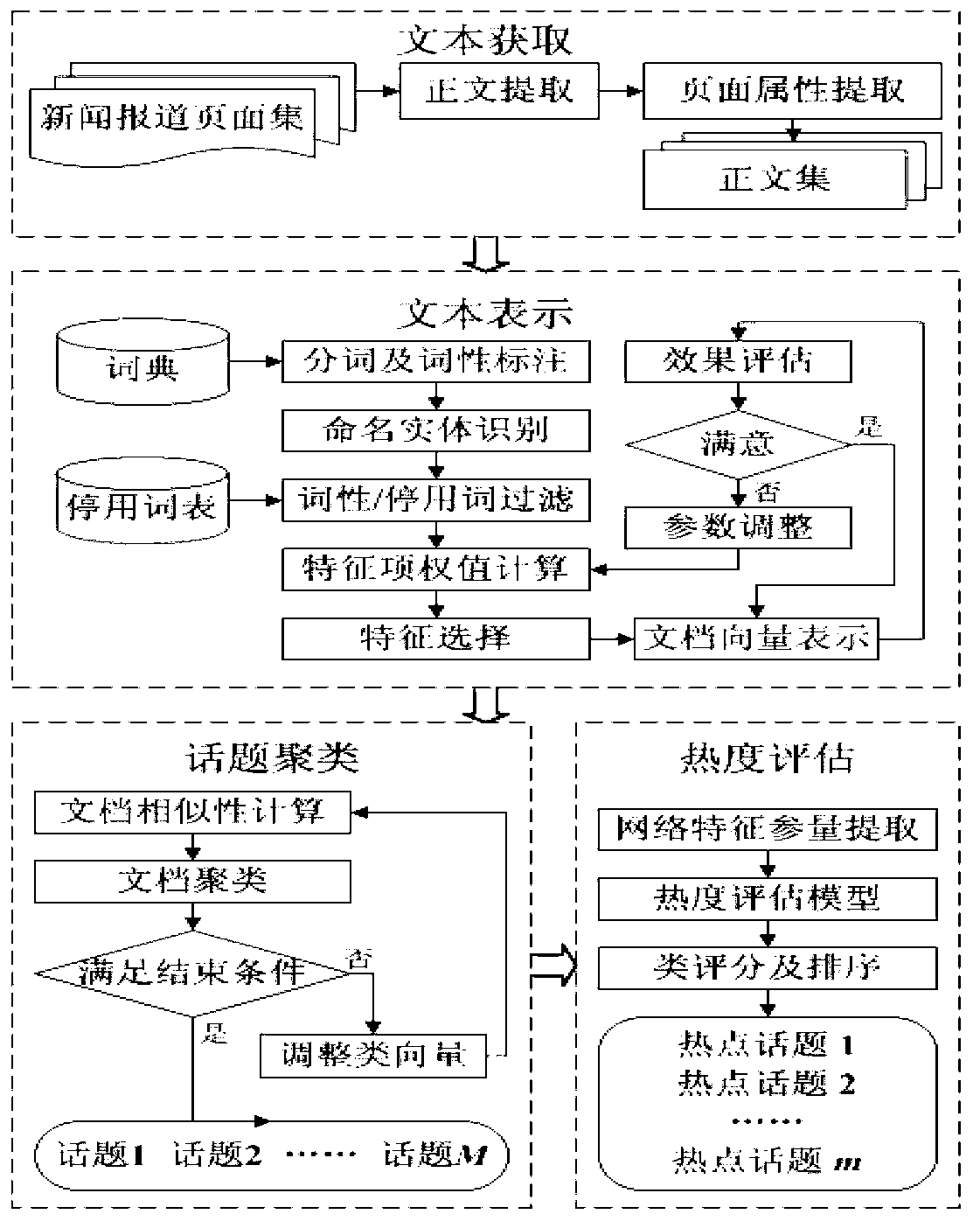
Device and method for identifying and evaluating emergency hot topic
InactiveCN102937960AReduce complexityImprove operational efficiencySpecial data processing applicationsComputation complexityUnexpected events
The invention relates to a device and a method for identifying and evaluating an emergency hot topic. The device is provided with four component parts including a text acquisition unit, a text expression unit, a topic clustering unit and a topic evaluation unit. The device and the method are characterized in that only a title, introduction, relevant features and other information of a text of a news report are extracted and regarded as an effective sample set identified by the hot topic. Compared with the existing full text extraction, the experiment result shows that the result of the existing full text extraction is similar to the result of the partial text extraction, but the operation of the device and the method is greatly simplified. Compared with a classical model, an improved feature weight calculation model is good in execution efficiency and strong in adaptability of text representation capability. The model is used for evaluating the hot value of clustered topics, and the calculated hot topic accords with the expected effect and is adaptive to the features of the emergency news report. In a word, in the process of processing the text of the emergency news report, the device and the method have good performance in aspects of calculation complexity, result accuracy and timeliness.
Owner:BEIJING UNIV OF POSTS & TELECOMM
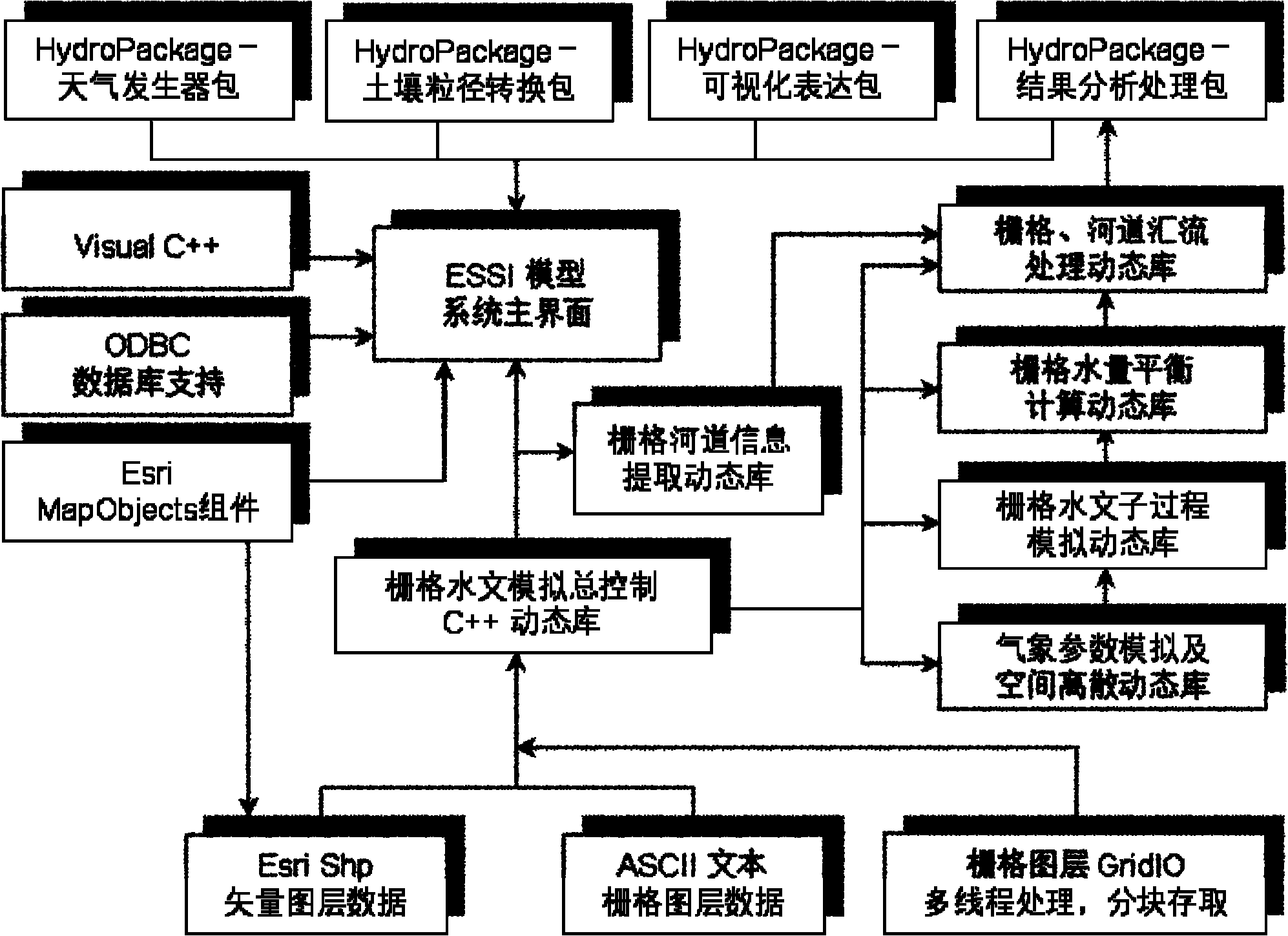
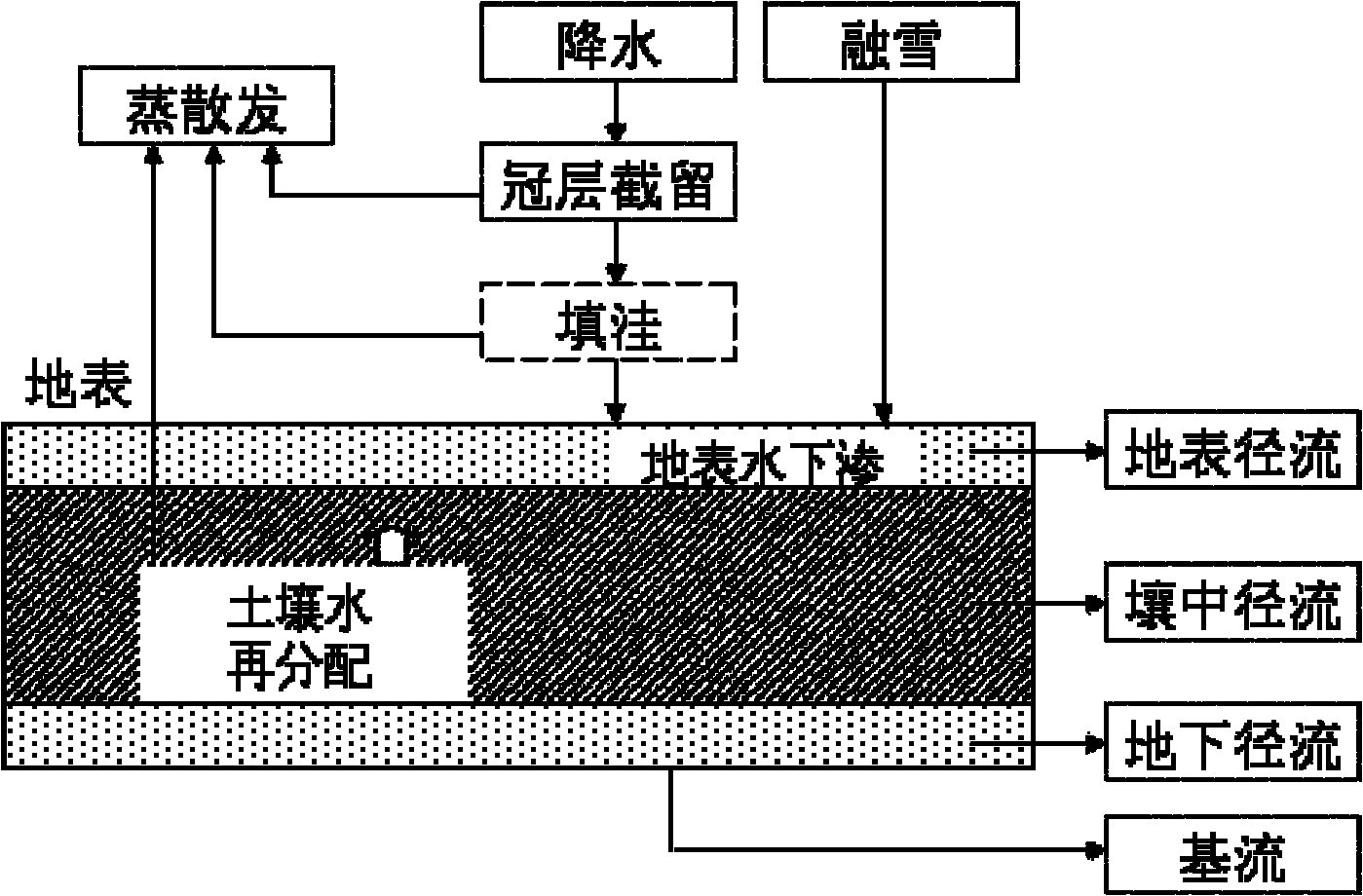
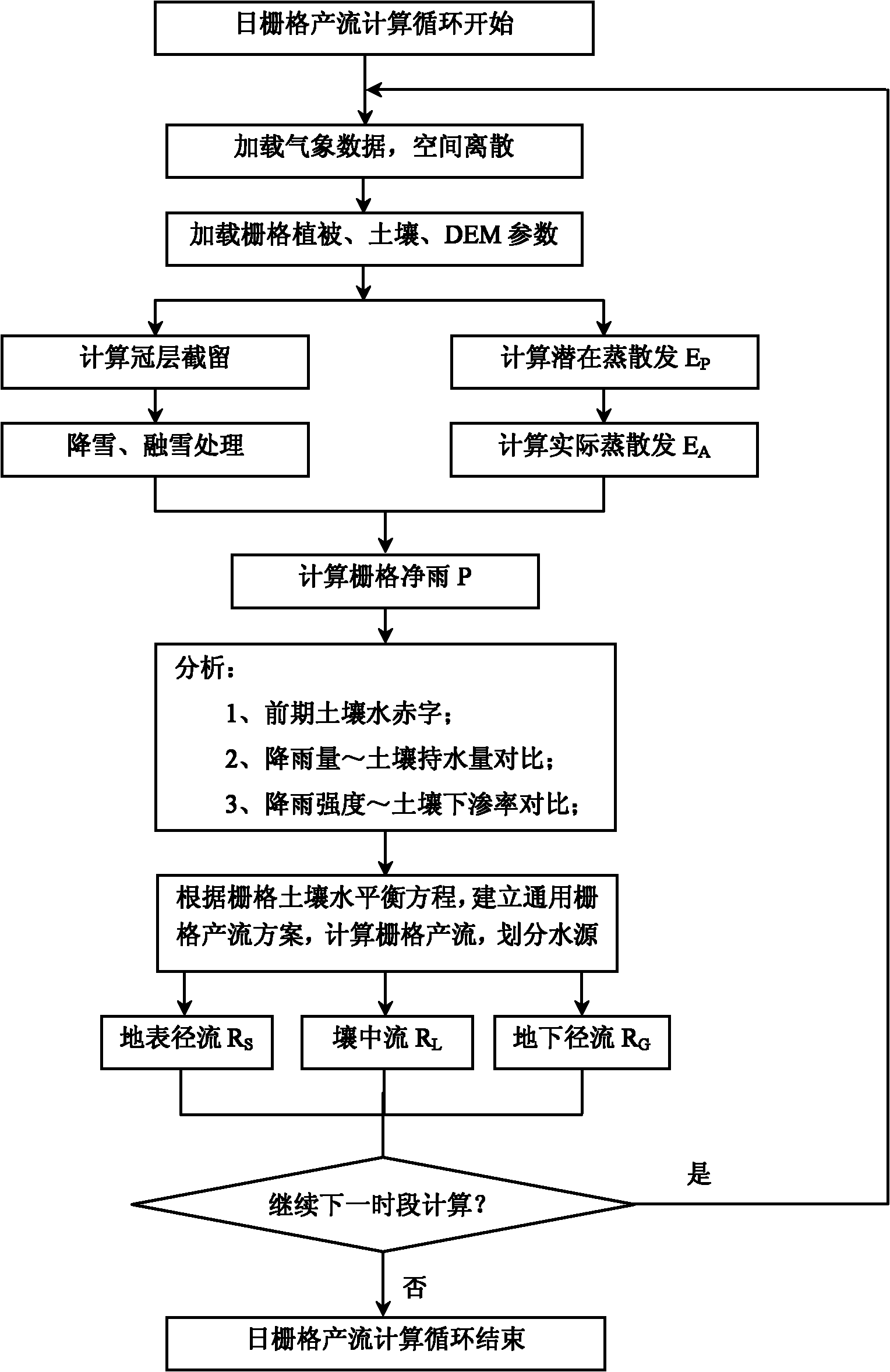
Design method for distributed hydrological model by using grid as analog unit
InactiveCN102034001AImprove scalabilityImprove execution efficiencyClimate change adaptationSpecial data processing applicationsAridRainfall runoff
The invention discloses a design method for a distributed hydrological model by using a grid as an analog unit, which is called as ESSI for short. The design method comprises the following steps of: obtainment of a distributed parameter: converting vector data into grid data; generalization of a watershed hydrological process: establishing a universal runoff generating type for the grid; design of a runoff generating process: respectively computing the water-quantity distributing condition of each part according to different prior-period soil water conditions; design of a flow collecting process: respectively designing a Muskingum-Cunge method, a delay algorithm and a riverway segmentation Muskingum method for the flow collecting process computation of the model under different conditions; and model development and integration. The invention not only can finish the watershed hydrological process simulation at an arid region and a humid region, but also can realize the short-term flood forecast and the long-term rainfall-runoff process simulation and prediction of a watershed by using modularization and integration ideas as means, thereby providing scientific reference bases for deeply learning about the physical mechanism of water circulation by people, reducing the drought and water-logging disasters and reasonably developing and utilizing water resources.
Owner:NANJING UNIV
Multisensory robot used for family intelligent monitoring service
InactiveCN101786272AKeep your family safeAll-round monitoringManipulatorSmart surveillanceLoudspeaker
The invention discloses a multisensory robot used for family intelligent monitoring service. The robot comprises a main control device, wherein the main control device is externally connected with a camera, a sound collector, a cellphone alarm device and a loudspeaker; the main control device is also externally connected with a chassis moving device and a head gesture device; the chassis moving device consists of a chassis controller, a motor driver, an obstacle avoiding sensor and a smoke sensor; the chassis moving device is provided with a lithium battery and wheels required by a mobile platform; the main control device sends a control command to the chassis controller by a serial port to control the corresponding action of a motor and process an obstacle avoiding signal; the head gesture device consists of three steering engines and one relay; and the main control device sends a control command to a head controller by a serial port to control the head and the eyeballs of the robot to rotate and control the mouth of the robot to open and close. The multisensory robot is used for the family intelligent monitoring field, can be used for multisensory fusion and can realize the multifunction family monitoring such as face identification and anomalous event monitoring.
Owner:SHENZHEN INST OF ADVANCED TECH
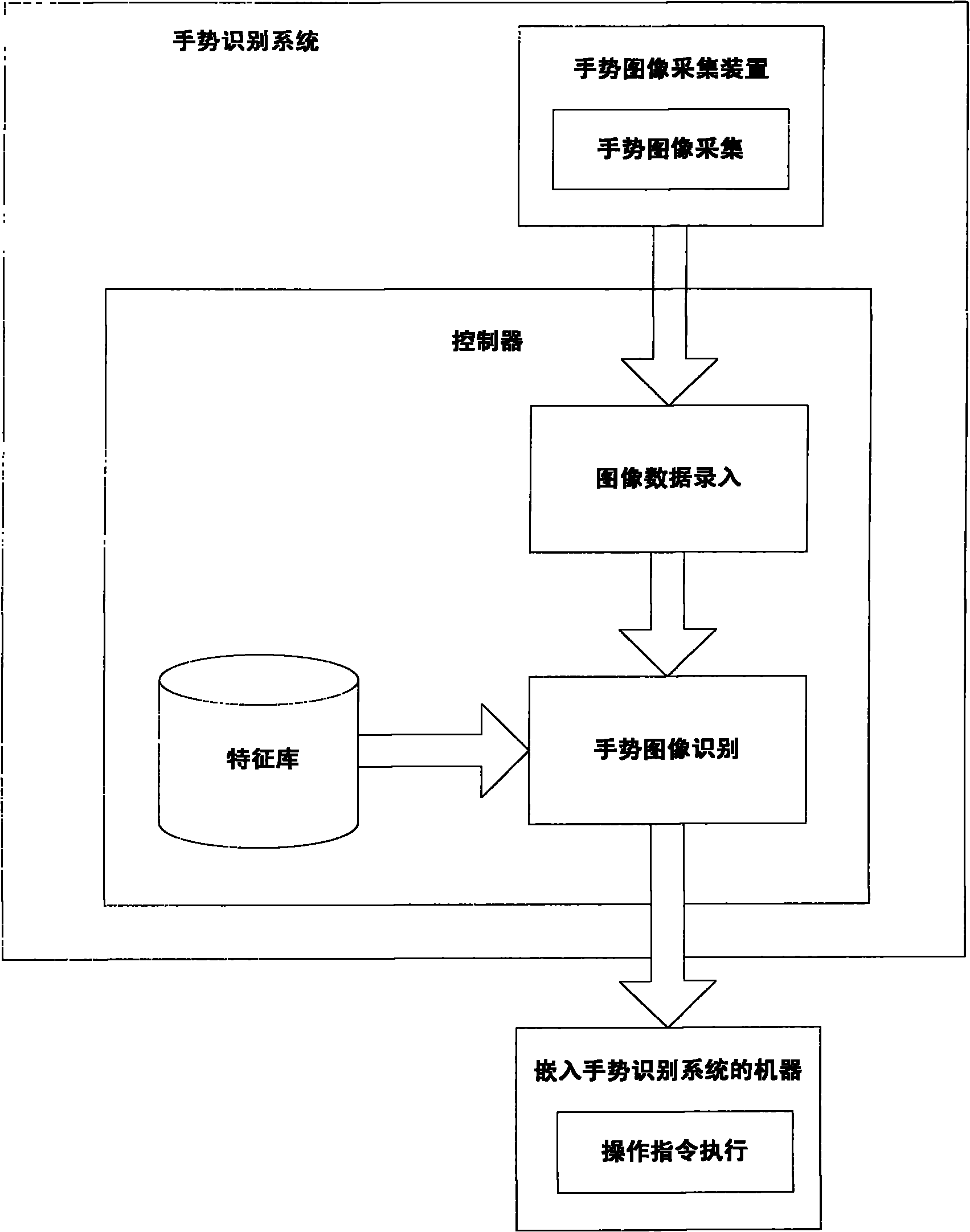
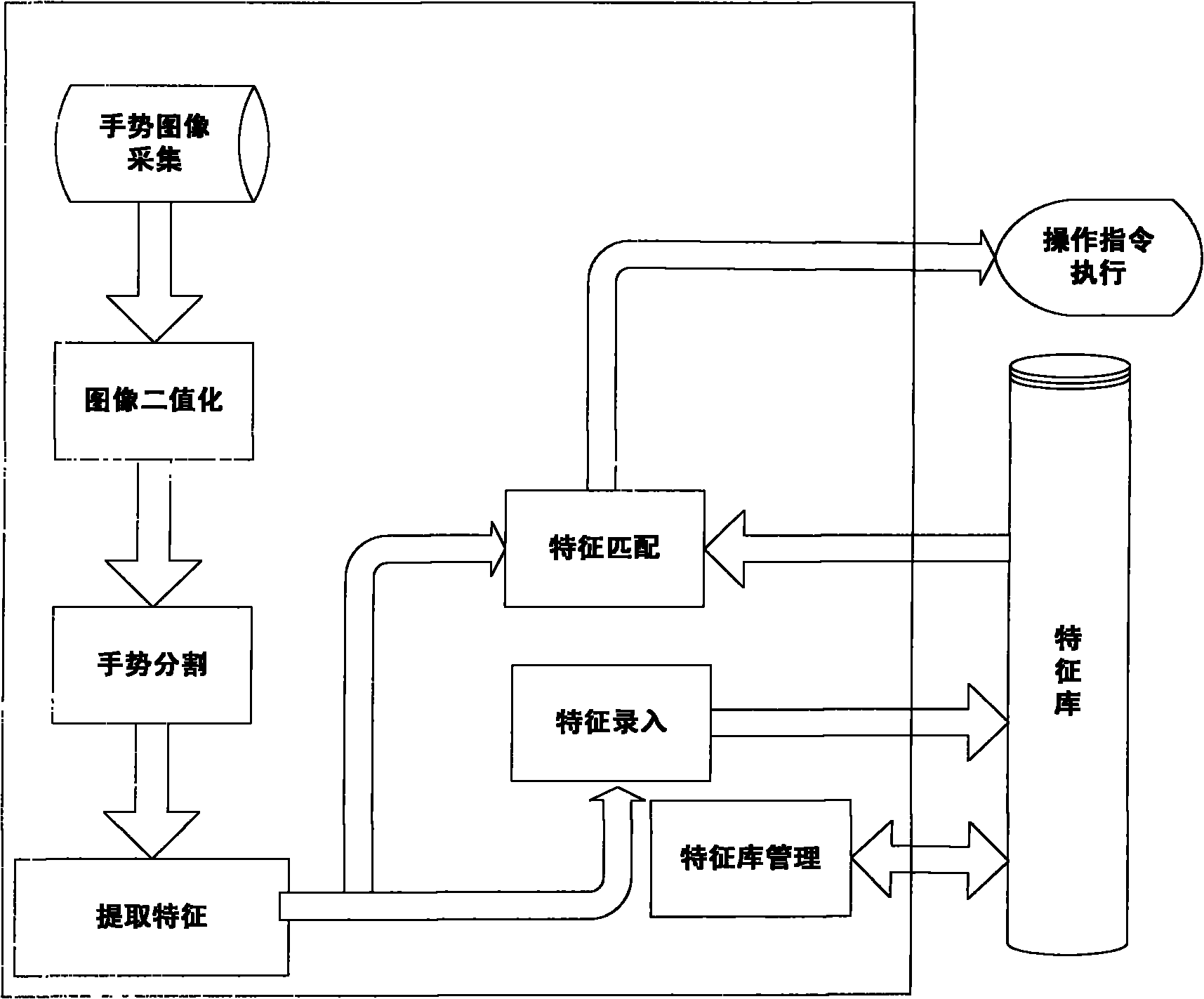
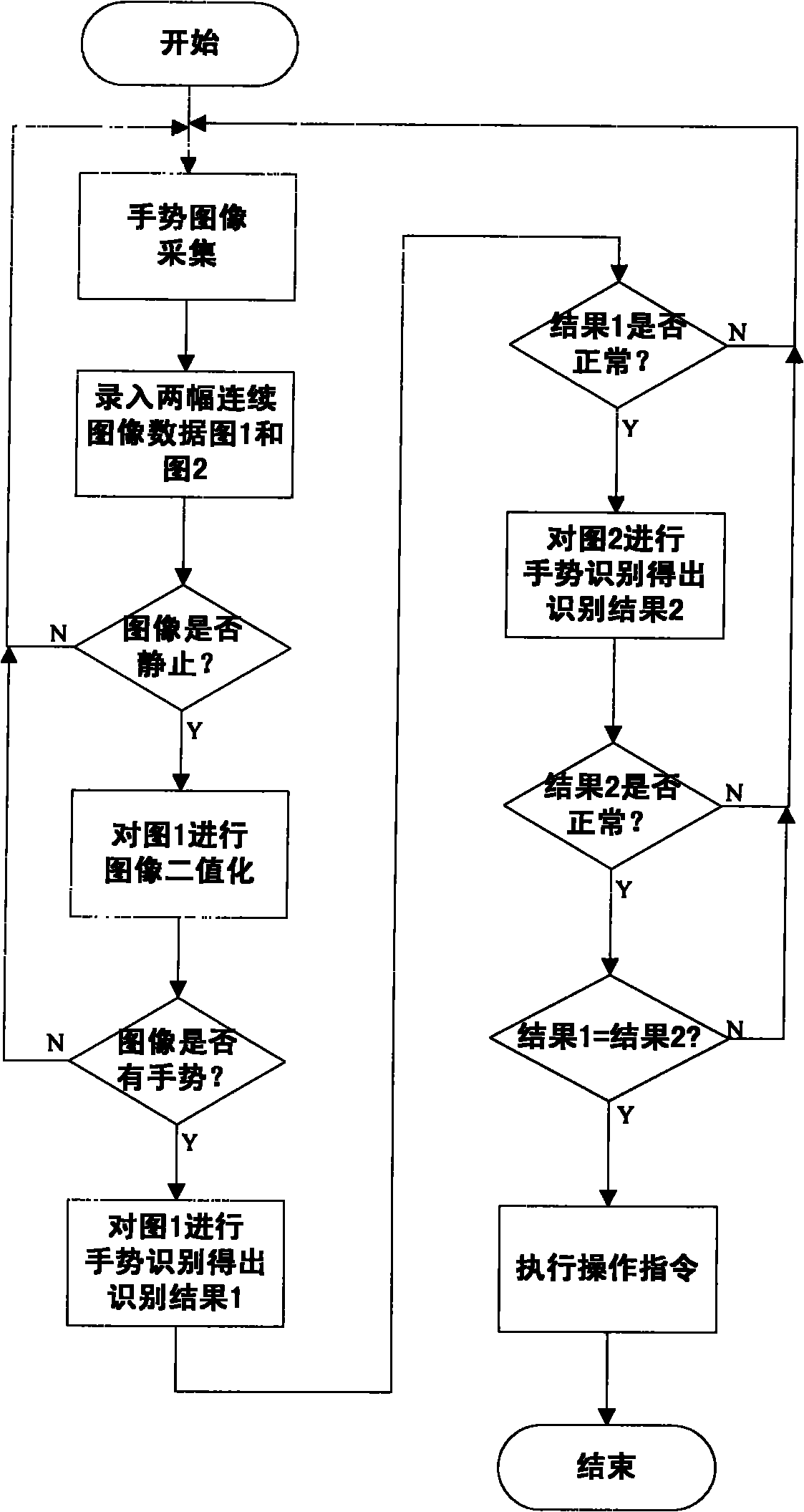
Gesture identification method and system based on visual sense
InactiveCN101853071AImprove usabilityImprove execution efficiencyInput/output for user-computer interactionCharacter and pattern recognitionVision basedUsability
The invention provides gesture identification method and system based on visual sense. The system comprises a gesture image acquisition device and a controller which are mainly used for realizing gesture image acquisition, image data entry, gesture image identification and operation command execution, wherein the gesture image identification comprises image binaryzation, gesture split, feature extraction and feature matching. The invention has real-time performance, obtains identification results by extracting and matching the features of gesture images of a user, and executes corresponding commands according to the identification results. In the invention, hands are used as input devices, only the acquired images need contain complete gestures, and the gestures can be allowed to translate, change in dimension and rotate within a certain angel, thereby greatly improving the use convenience of devices.
Owner:CHONGQING UNIV
Power load forecasting method based on big data technology, and research and application system based on method
InactiveCN105678398AImprove horizontal scalabilityImprove fast data access responsivenessForecastingPower gridDecision-making
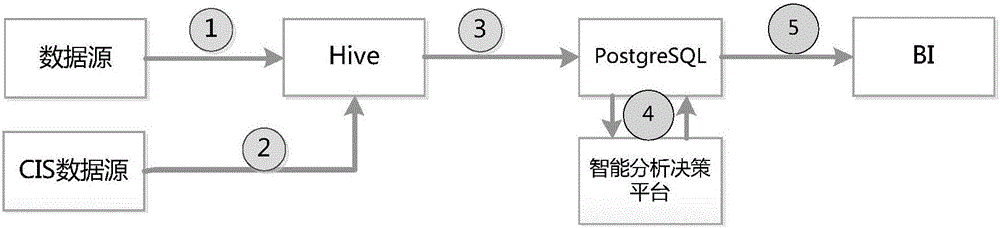
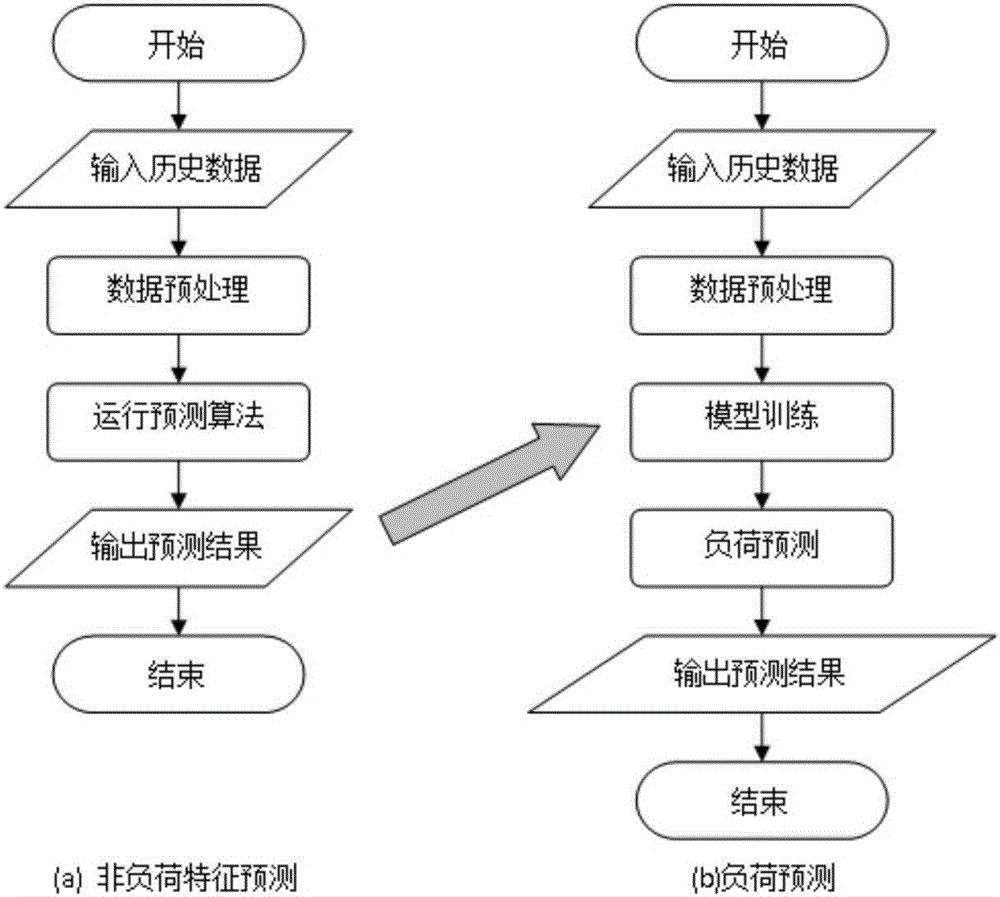
The present invention is a power load forecasting method based on big data technology and a research application system based on the method. With the support of big data technology, a variety of mature open source products are integrated to form a data source, data integration, data storage, Data calculation, data analysis, implementation of electrical load characteristic analysis and electrical load forecast analysis. The invention effectively improves the efficiency of mass data processing, and solves the limitations of traditional statistical analysis assumptions and judgments. It can scientifically and accurately predict the electricity demand of the future power, which is conducive to the peak-shaving and valley-filling and stable operation of the power grid, and provides decision-making support for the company's power grid planning, equipment maintenance, and power deployment.
Owner:STATE GRID CORP OF CHINA +4
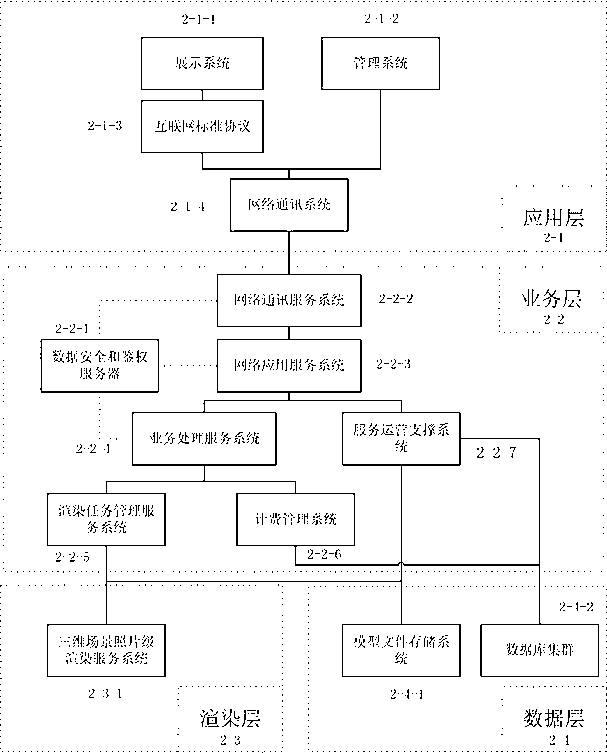
Implementation method for three-dimensional figure render based on cloud computing framework and cloud service system
ActiveCN103106680AIncrease the number ofExtend the display cycleTransmission3D-image renderingTheoretical computer scienceThree dimensional graphics
The invention discloses an implementation method for three-dimensional figure render based on a cloud computing framework. The implementation method includes the steps that existing scene description is uploaded to a scene root explorer of a cloud service system, a model needed by a scene is analyzed by the scene root explorer, and the model is uploaded from a memory system. The belonging model is packaged, a scene object is set, a render instruction supported by a specific renderer is generated, and the render instruction is packed and is sent to a render system. After the render instruction returns to a render picture, the picture is transmitted to an application layer and is displayed. A user interacts with the application layer, the application layer captures action events, and the action events are transmitted to a cloud service layer according to a protocol. After the cloud service layer receives the action events, a scene is automatically adjusted on the background of the cloud service layer according to new action parameters. Format conversion of packaging and render instruction is carried out for a second time, then the action events are transmitted to the render system and are rendered by the render system, and finally the action events are displayed on the application layer anew. Therefore, interactive edit and display of a three-dimensional scene are achieved.
Owner:JIANGSU CUDATEC TECH CO LTD
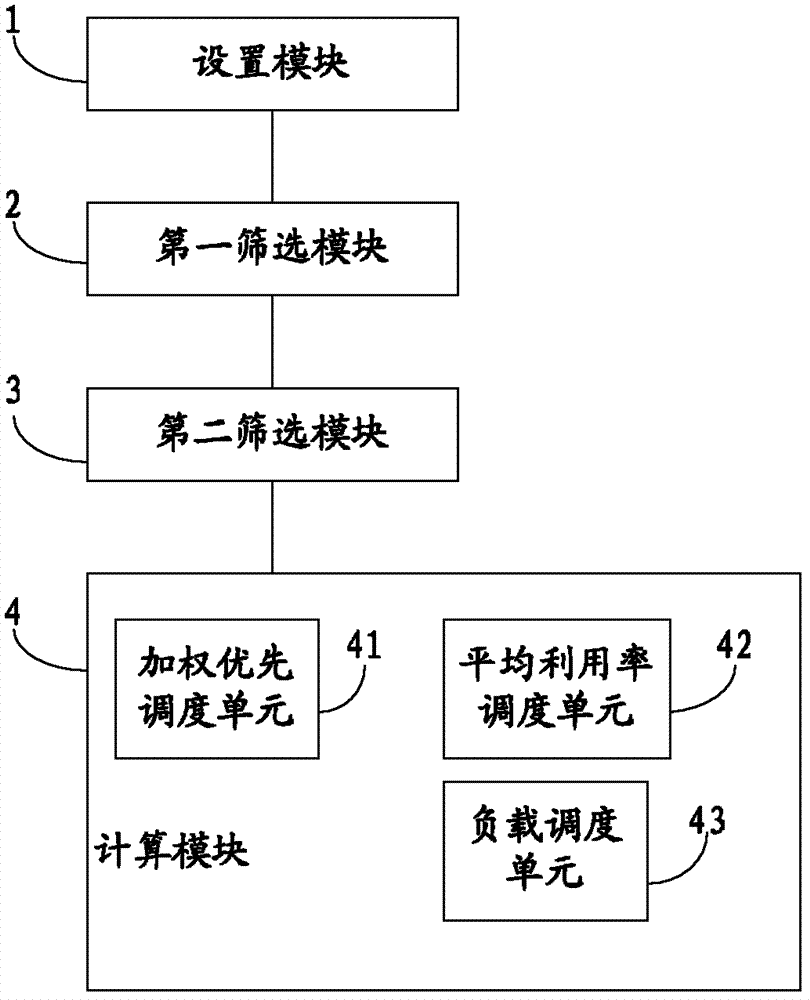
Method and system for dispatching cloud computed resources
The invention provides a method and system for dispatching cloud computed resources. The method comprises the following steps: a resource allocating strategy and a resource dispatching strategy of cloud computing are arranged; the resource allocating strategy is arranged to appoint a resource pool of cloud computed resources used for creating a virtual machine; the arranged resource dispatching strategy is used for sifting a host machine meeting requirements in the resource pool; available host machine information in the resource pool is confirmed and a host machine list is generated according to the resource allocating strategy selected by a user when the virtual machine is created; a host machine conform to the resources for creating the virtual machine is sifted from the host machine list according to the resource dispatching strategy selected by the user, so as to obtain a residual host machine list; and optimized host machines and optimized storage of the residual host machine list are obtained through computing, and are allocated to the virtual machine. The system comprises an arranging module, a first sifting module, a second sifting module and a computing module. The method and system for dispatching cloud computed resources can effectively realize the reasonable dispatch of resources.
Owner:BEIJING TEAMSUN TECH
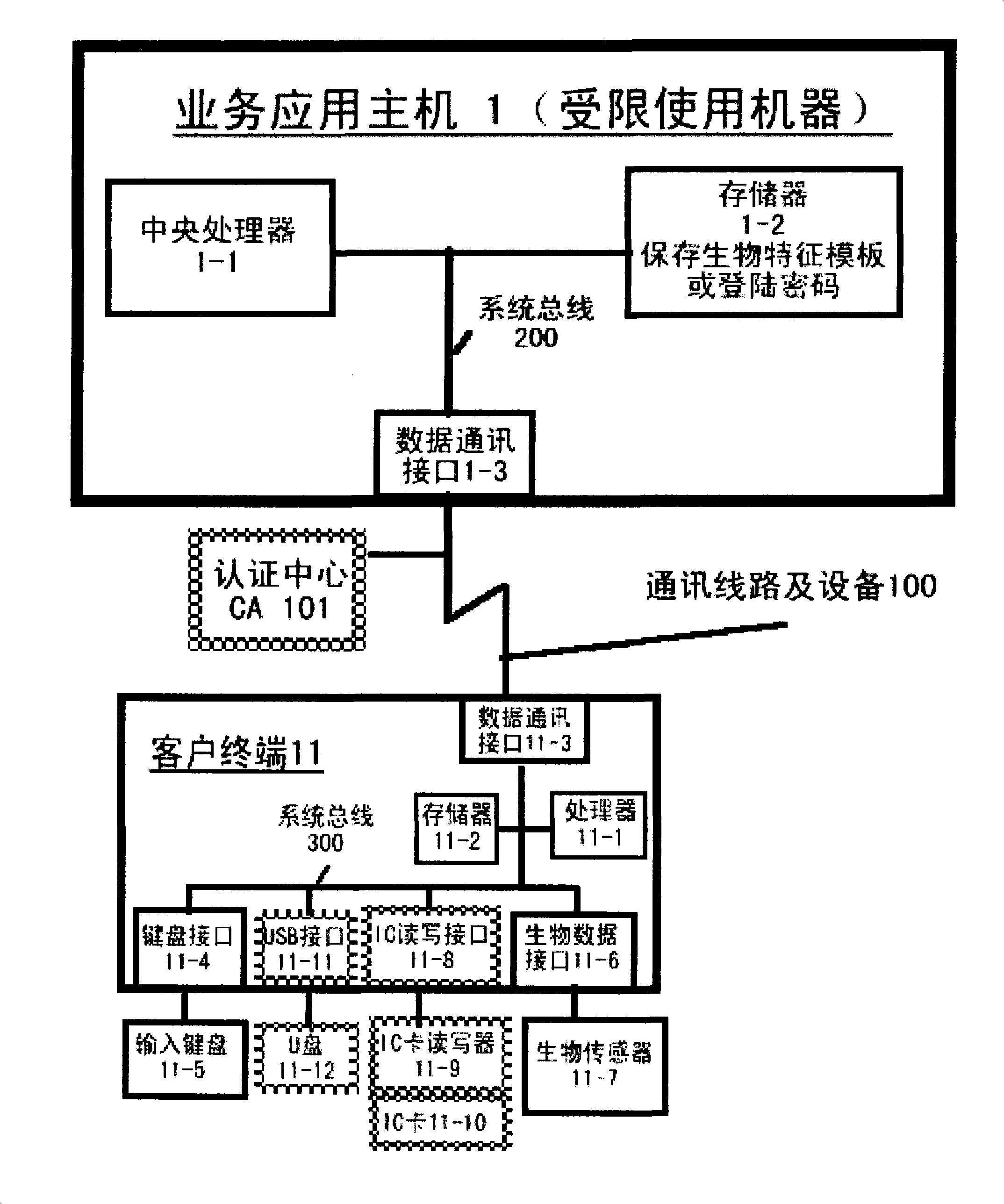
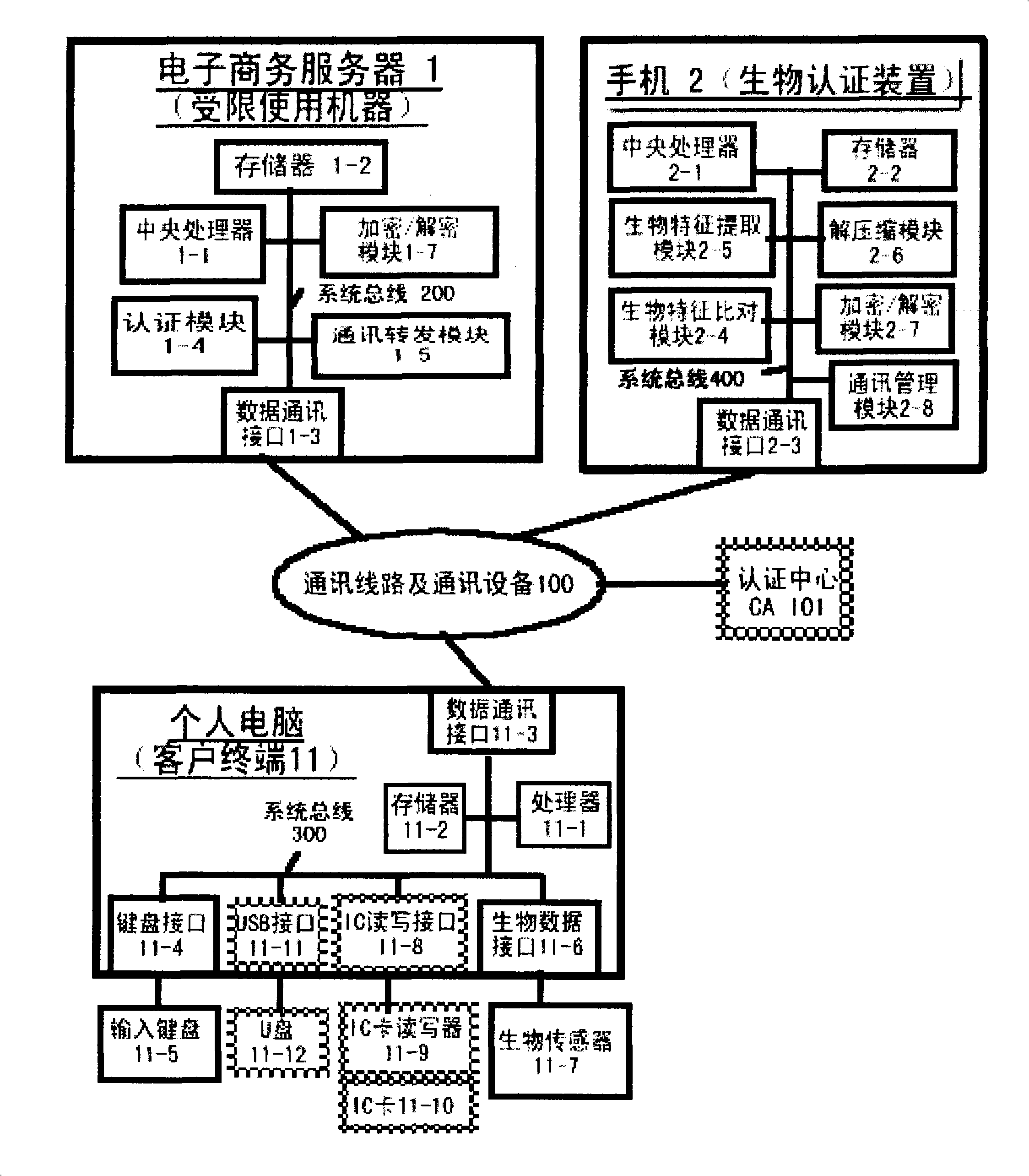
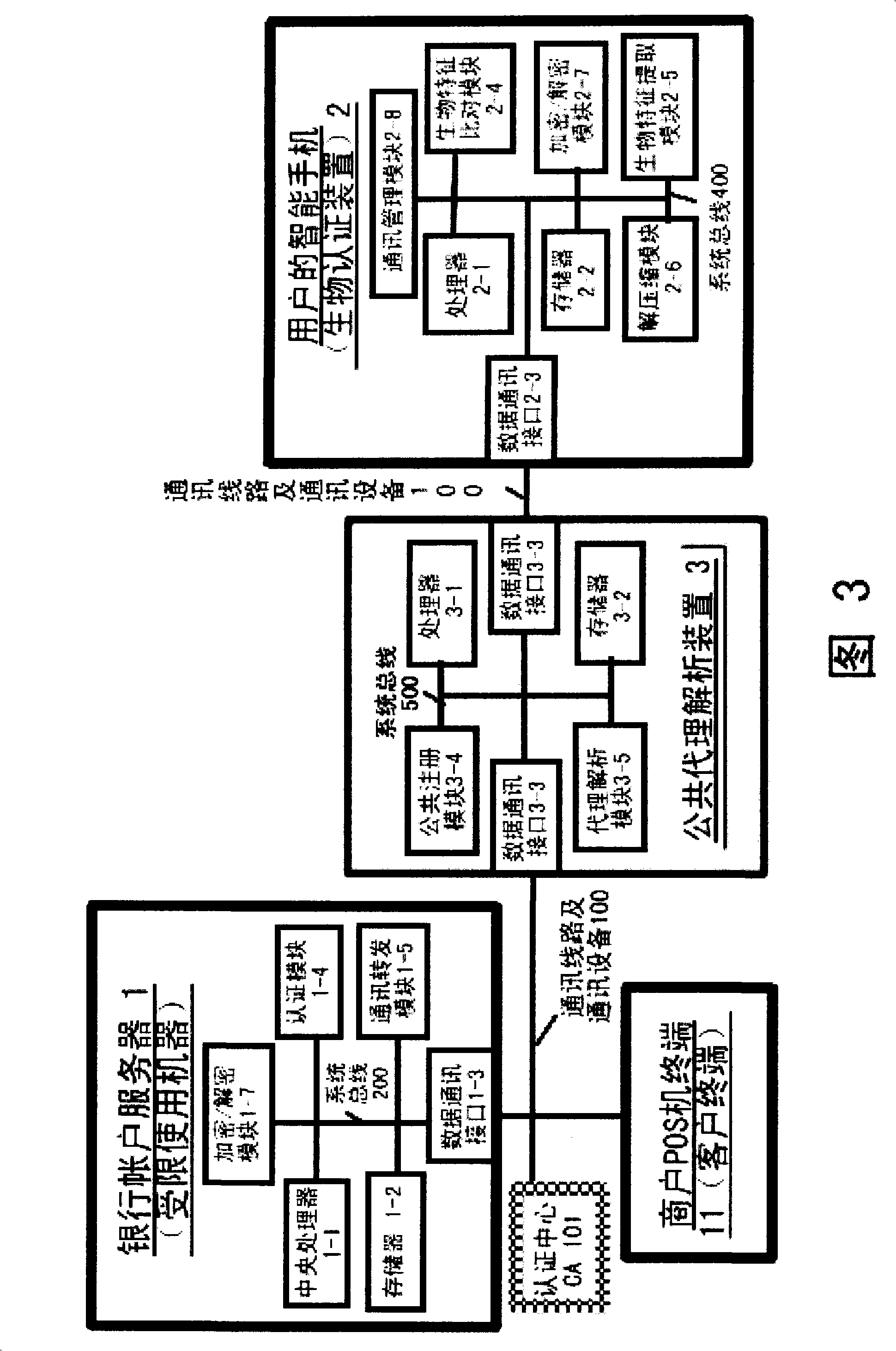
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
Intelligent Chinese request-answering system based on concept
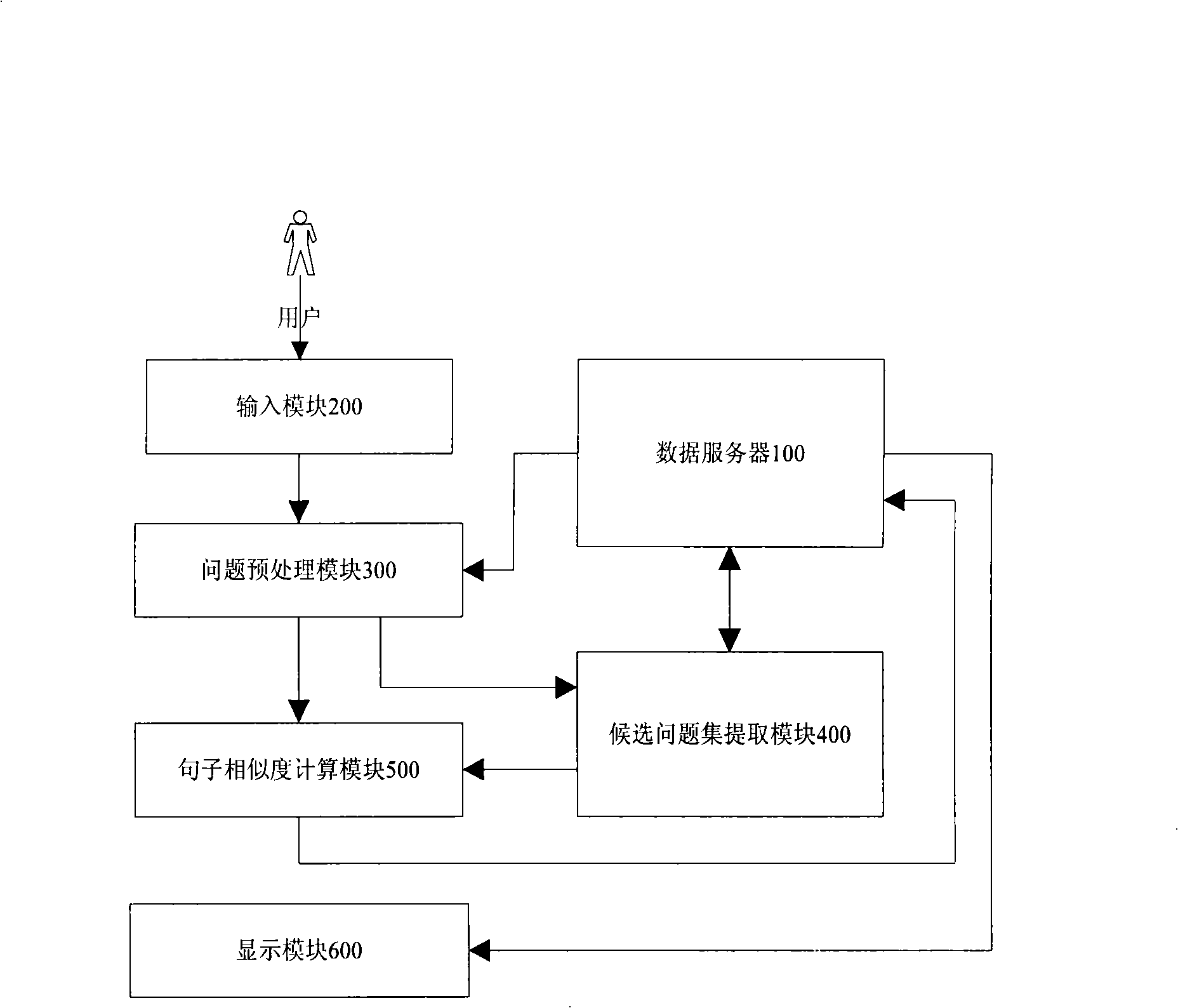
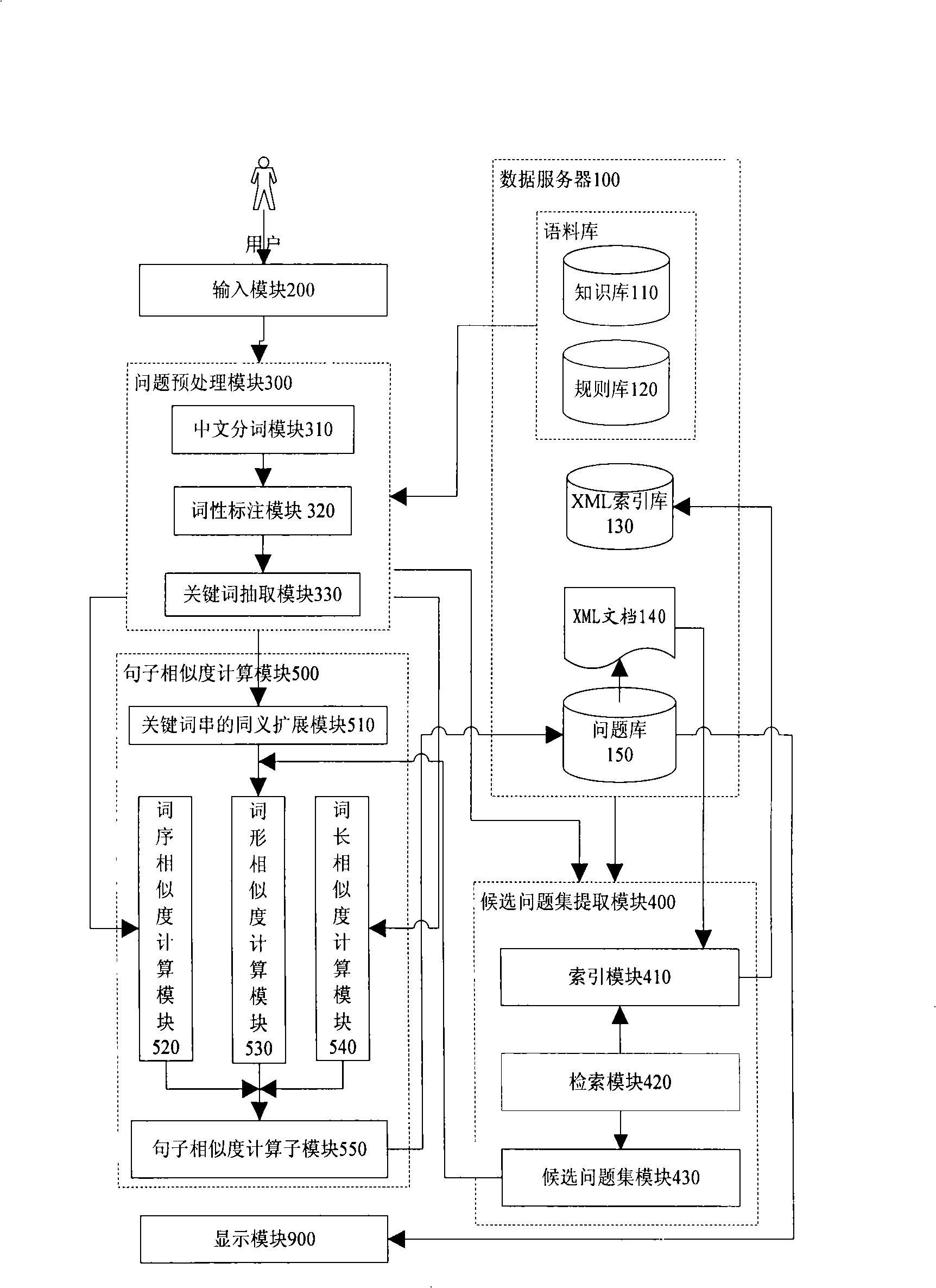
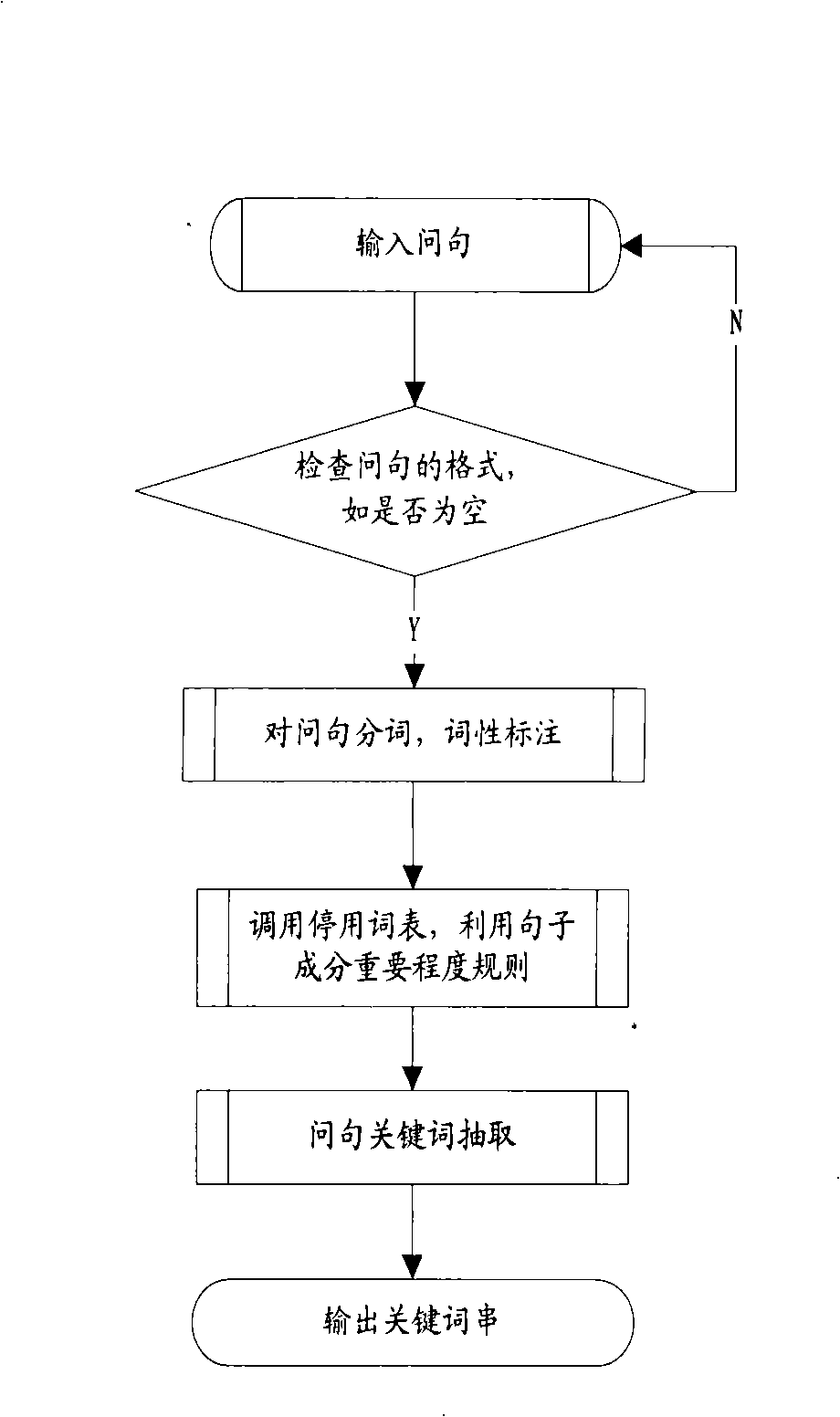
InactiveCN101286161AImprove precisionImprove recallSpecial data processing applicationsUser inputQuestions and answers
The invention discloses a Chinese question answering system based on concept, which mainly comprises a data server, a question pre-treatment module, a candidate question set extracting module and a question sentence similarity calculation module. The invention aims at providing a question answering system which is based on concept, can carry out synonym expansion of keywords which are processed by question sentences which are input by the user, understand question sentences better, carry out searching and improve the recall ratio of the question answering system. Furthermore, the system has a Chinese sentence similarity calculation method based on concept from three aspects: word form, word order and word length, and improves searching precision ratio. Meanwhile, the system adopts a high-efficiency retrieval technology to realize rapid extraction of candidate question set, calculates question sentence similarity, sorts question set quickly and returns the sorted questions and answers to the user. The question answering system of the invention gives more precise understanding in concept to the question sentences input by the user and searches the accurate answers. Experiments show that the question answering system of the invention achieves high recall ratio and precision ratio.
Owner:HUAZHONG UNIV OF SCI & TECH
Vehicle mounted battery management system control method
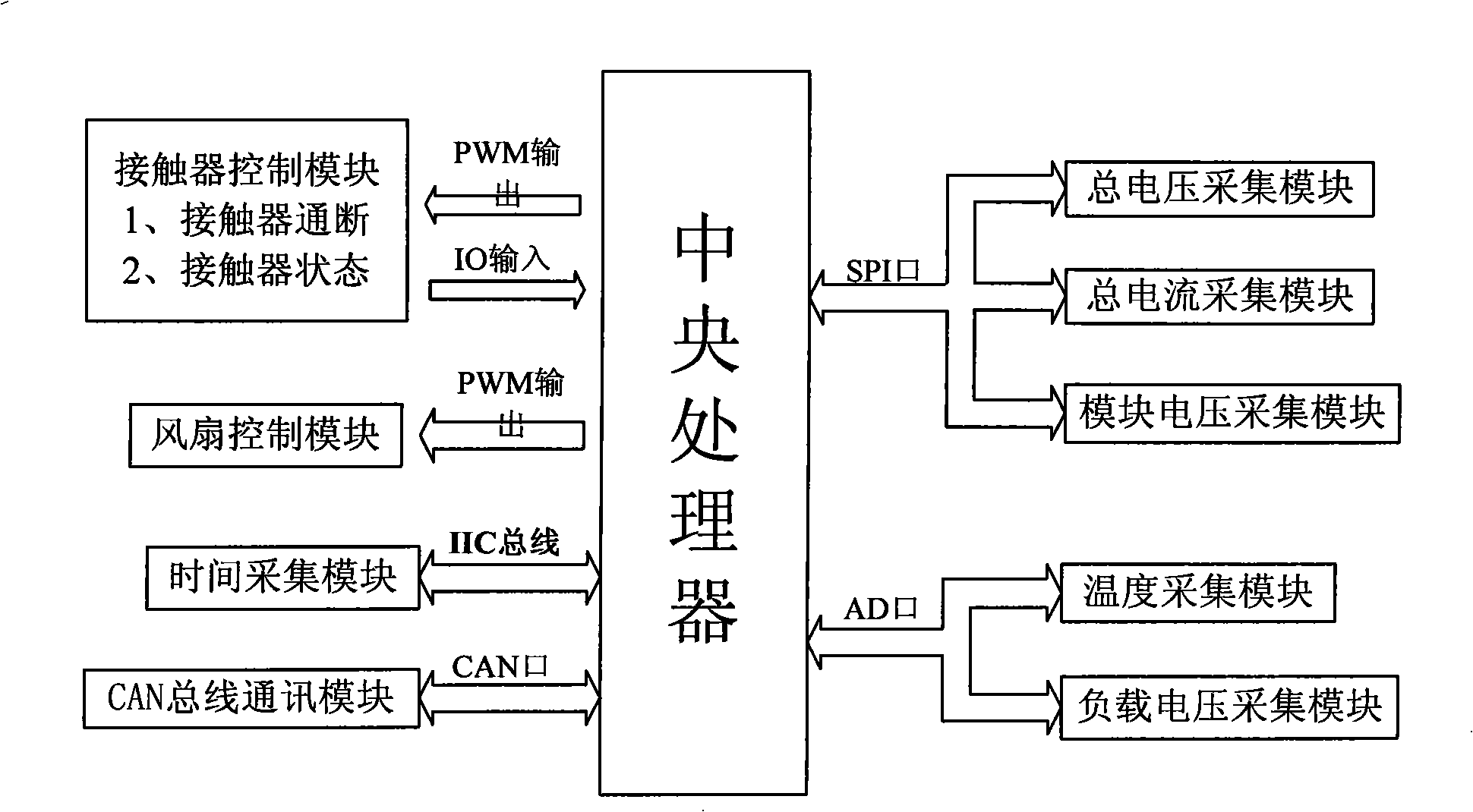
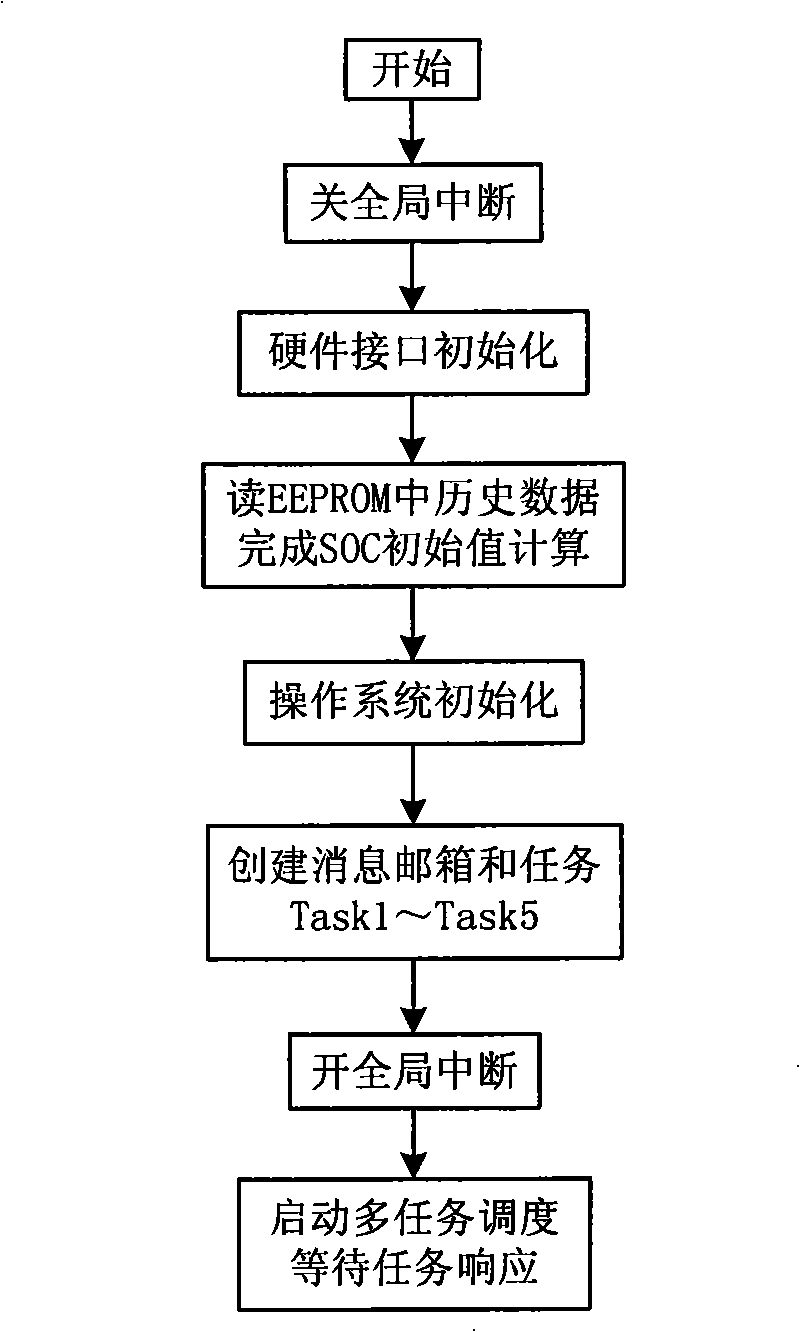
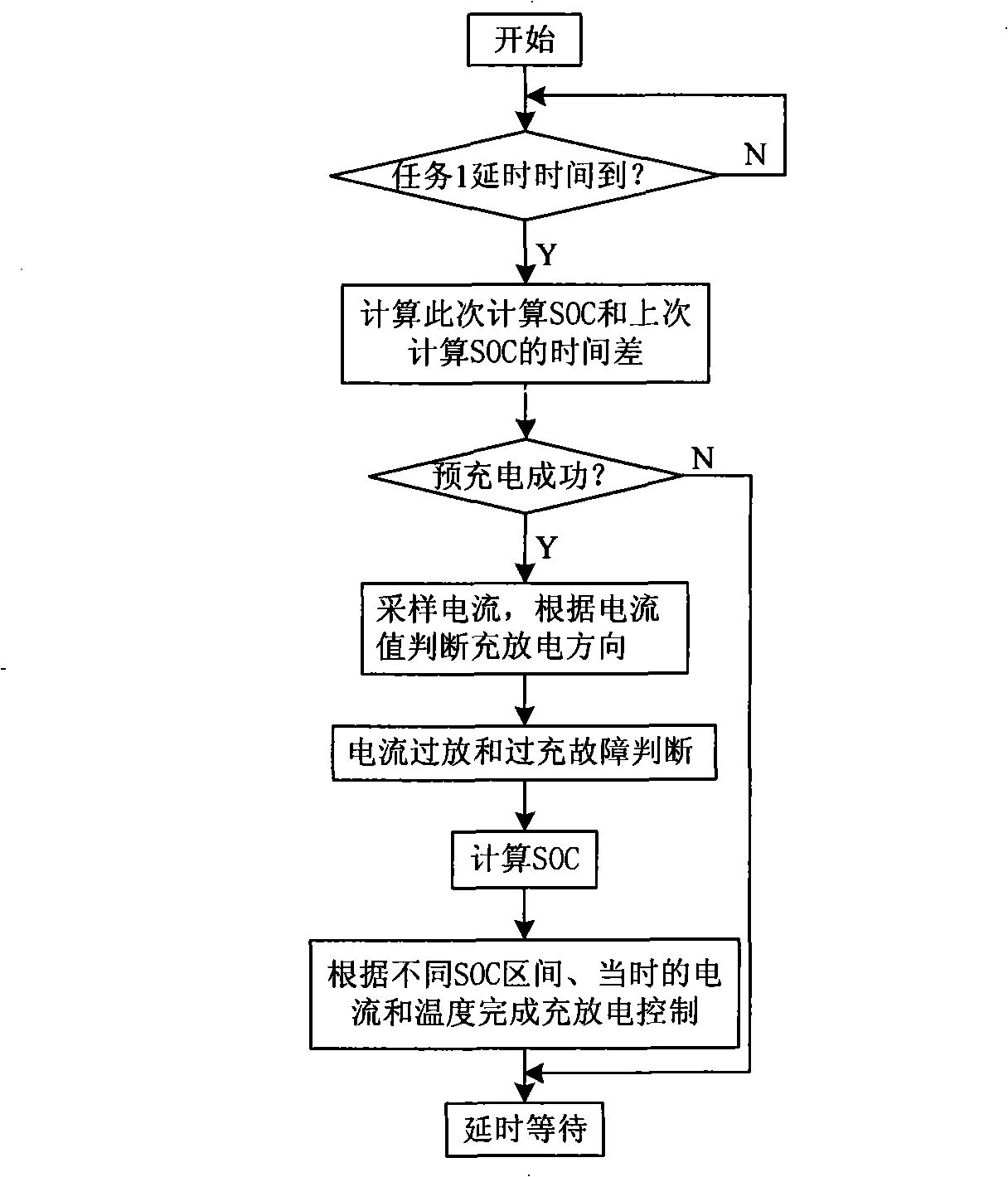
ActiveCN101318489AImprove execution efficiencyEasy to compileSecondary cells servicing/maintenanceElectric vehicle charging technologyOperational systemData acquisition
A battery management system based on a real time operation system which belongs to the technical field of vehicle storage battery management includes a CPU, a load voltage collecting module, a total voltage collecting module, a module voltage collecting module, a current collecting module, a temperature collecting module, a time collecting module, a CAN bus communicating module and a contactor control module. The CPU is respectively connected with a voltage collecting module, the current collecting module, the temperature collecting module, the time collecting module, the CAN bus communicating module and the contactor control module. The battery management system based on a real time operation system transplants a uc / OS-II multi-task real time operation system into the CPU, thus simplifying the software programming of a vehicle storage battery management system under the dispatching of the real time operation system, improving the execution efficiency to manage the system software, ensuring the real time property of data collection and enhancing the working stability of the system.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
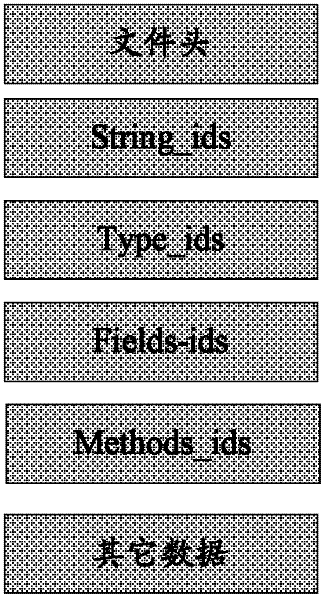
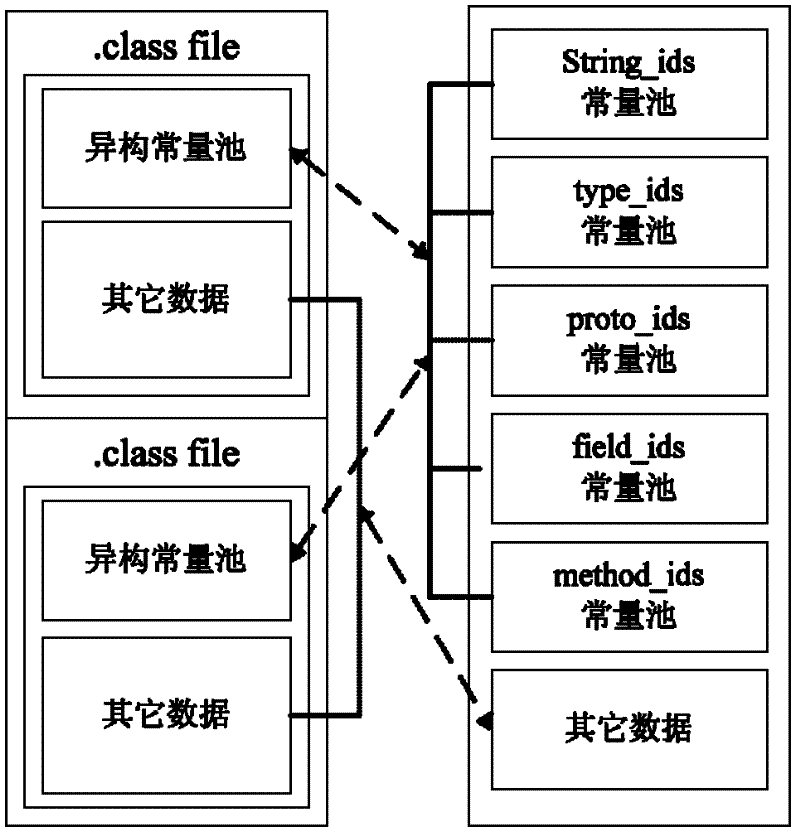
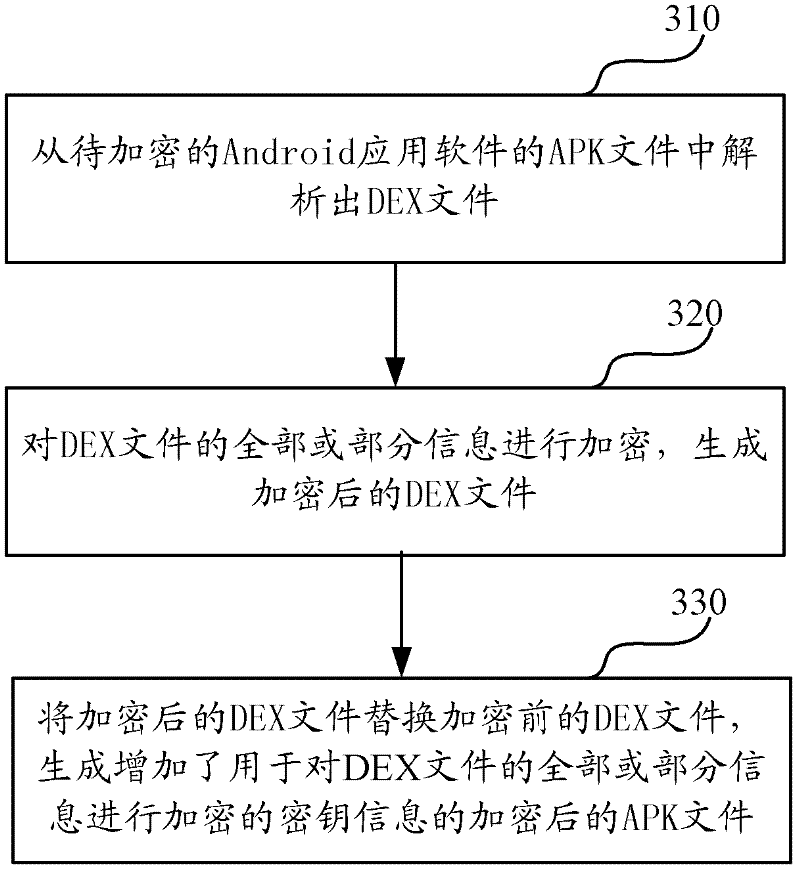
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Industrial robot collision detection method
ActiveCN104985598AWorking conditions without any restrictionsWorking condition limitProgramme-controlled manipulatorProgramme controlCollision detectionEngineering
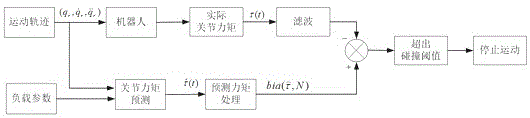
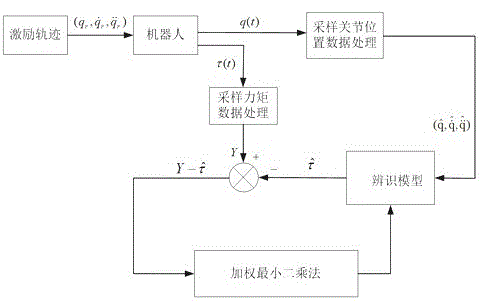
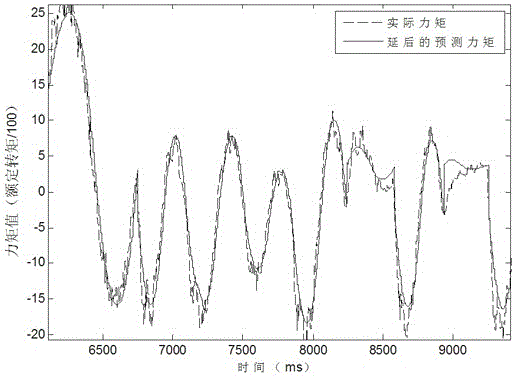
The invention discloses an industrial robot collision detection method. By the adoption of a collision detection method based on torque difference, in a robot operation process, theoretical torque values of joints are predicted in real time according to a movement track, and differences between the theoretical torque values of the joints and actual sampled torque values of the joints are calculated in real time. When the torque differences exceed a collision threshold, it is regarded that collision happens, a motor stops running immediately, and a robot stops moving. According to the method, a sensor does not need to be additionally arranged, the structure of the robot does not need to be changed, the method is suitable for any operation working condition of the robot, and there is no limit on the working conditions. The whole process is carried out off-line, people only need to use prediction results in online programs of collision detection, the programs are simple, and the execution efficiency is high. According to the method, the predicted torque of the joints is delayed by N cycles and processed, the actual torque is filtered through an average value, and then the torque differences are solved so that the collision threshold can be reduced, and sensitivity of the collision detection is improved.
Owner:NANJING ESTUN ROBOTICS CO LTD
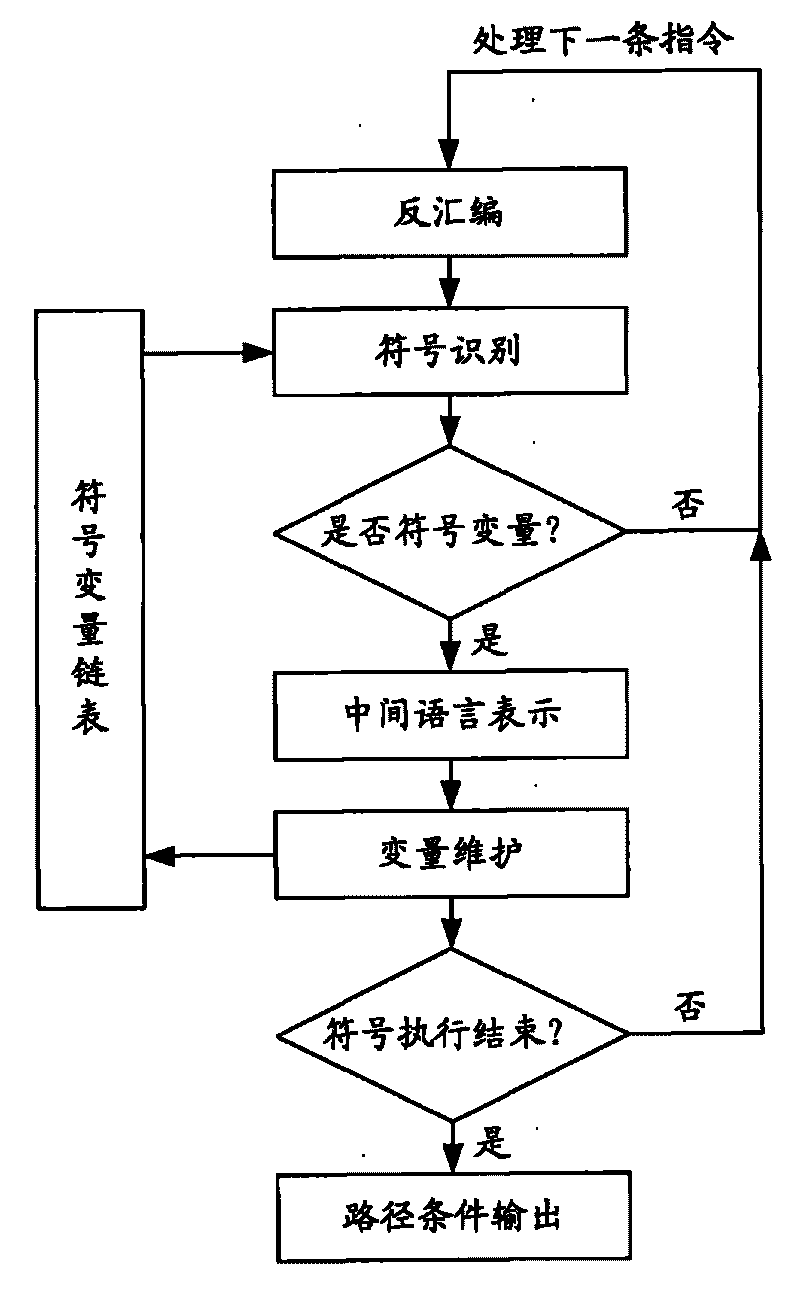
Detector for binary-code buffer-zone overflow bugs, and detection method thereof
InactiveCN101714118AGuaranteed feasibilityGuaranteed accuracyMultiprogramming arrangementsSoftware testing/debuggingBuffer overflowSource code
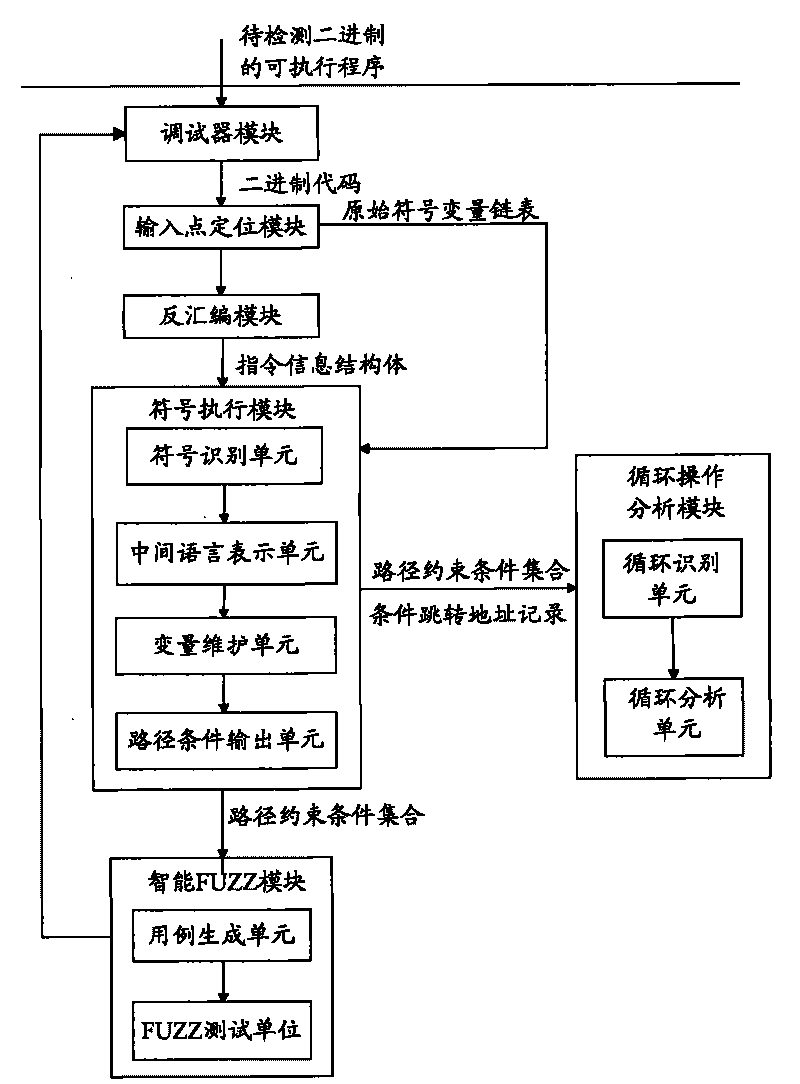
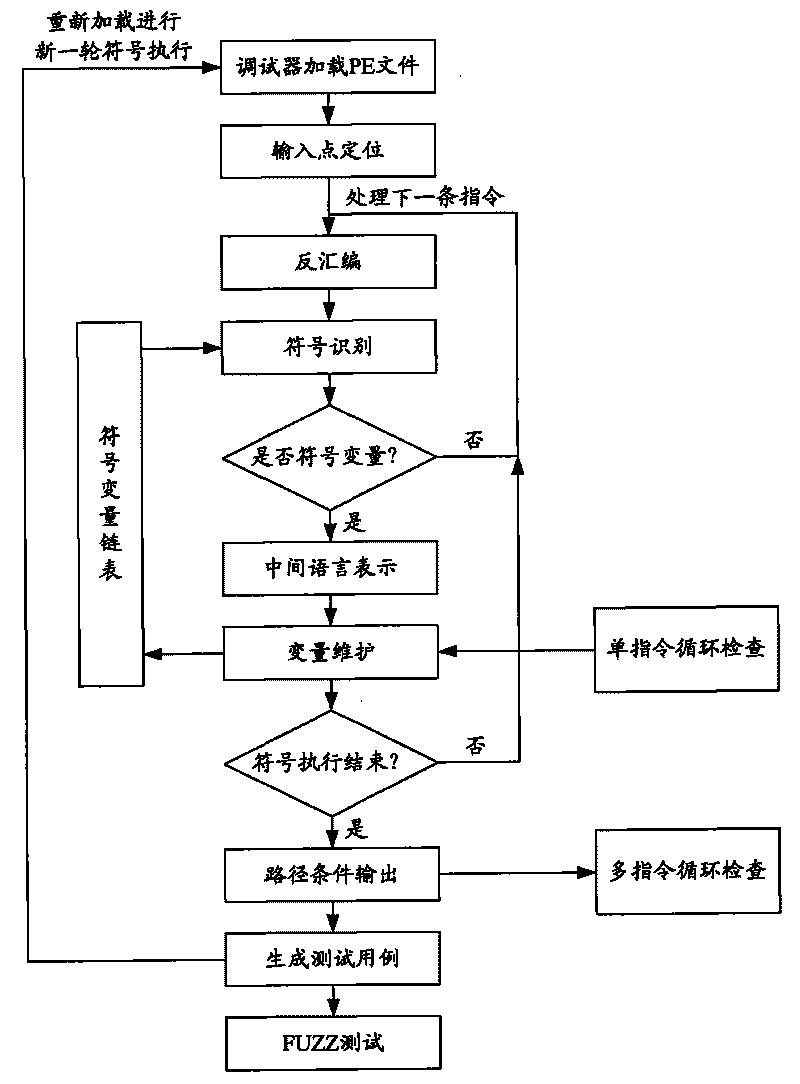
The invention provides a detector for binary-code buffer-zone overflow bugs, and a detection method thereof. The detector comprises six functional modules, namely a debugger module, an input point positioning module, a disassembling module, a symbolic execution module, a loop operation analysis module and an intelligent FUZZ test module. Differing from static symbolic execution, the detection method dynamically loads programs through the self-developed debugger module to synchronously performing symbolic execution and single-step practical execution, and then applies a model to solve each difficulty in binary code analysis so as to test path coverage and detect overflow bugs in accordance with all executable programs of PE format under a Windows platform. The detection can also provide propagation paths of input data and other important information related to bug formation cause while positioning the bugs, only analyzes the selves of the executable programs, needs no source codes, is unrelated to the species of source codes and development tools, and is extensive in applicable occasions, so the detection method has good prospects for popularization and application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
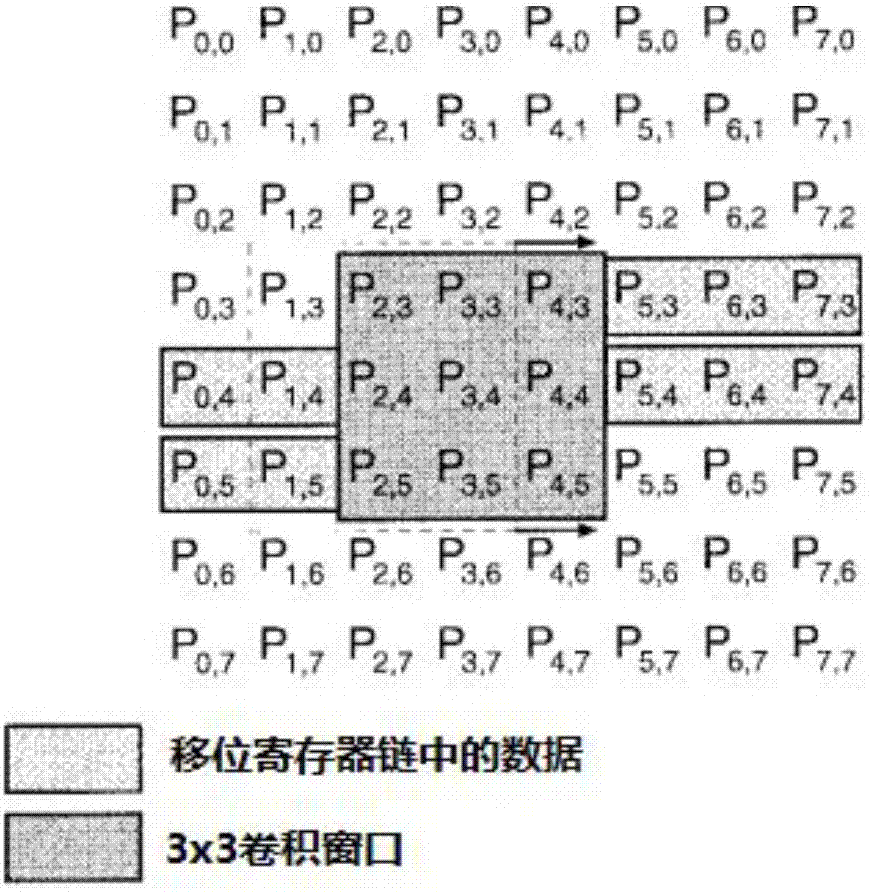
Compressed convolutional neural network-oriented parallel convolution operation method and apparatus
ActiveCN106951395AReduce duplicate readsIncrease profitNeural architecturesComplex mathematical operationsShift registerData stream
The invention provides a compressed convolutional neural network-oriented parallel convolution operation method and apparatus. The method comprises the steps of determining an adopted operation mode according to input control signal convolution data shift chain length selection, accumulated offset enabling and convolution calculation enabling; and by adopting two serial shift register chains, inputting convolution data, convolution parameters and channel offset, and performing 3X3 and 1X1 convolution operation at the same time for a same input convolution data stream. According to the method, a multiplier, an accumulator, a parameter register and an offset register are added only based on original serial shift register chain-based 3X3 convolution operation; the realization method is simple; the executive efficiency is high; and the convolution operation in a compressed neural network algorithm can be effectively accelerated. According to the apparatus, a plurality of characteristic graphs can be output at the same time through simple hardware unit expansion and copying; and the apparatus has the advantages of low power consumption, high function unit utilization rate and high processing speed.
Owner:国交金流供应链科技(上海)有限公司 +1
Human body behavior identification method based on inertial sensor
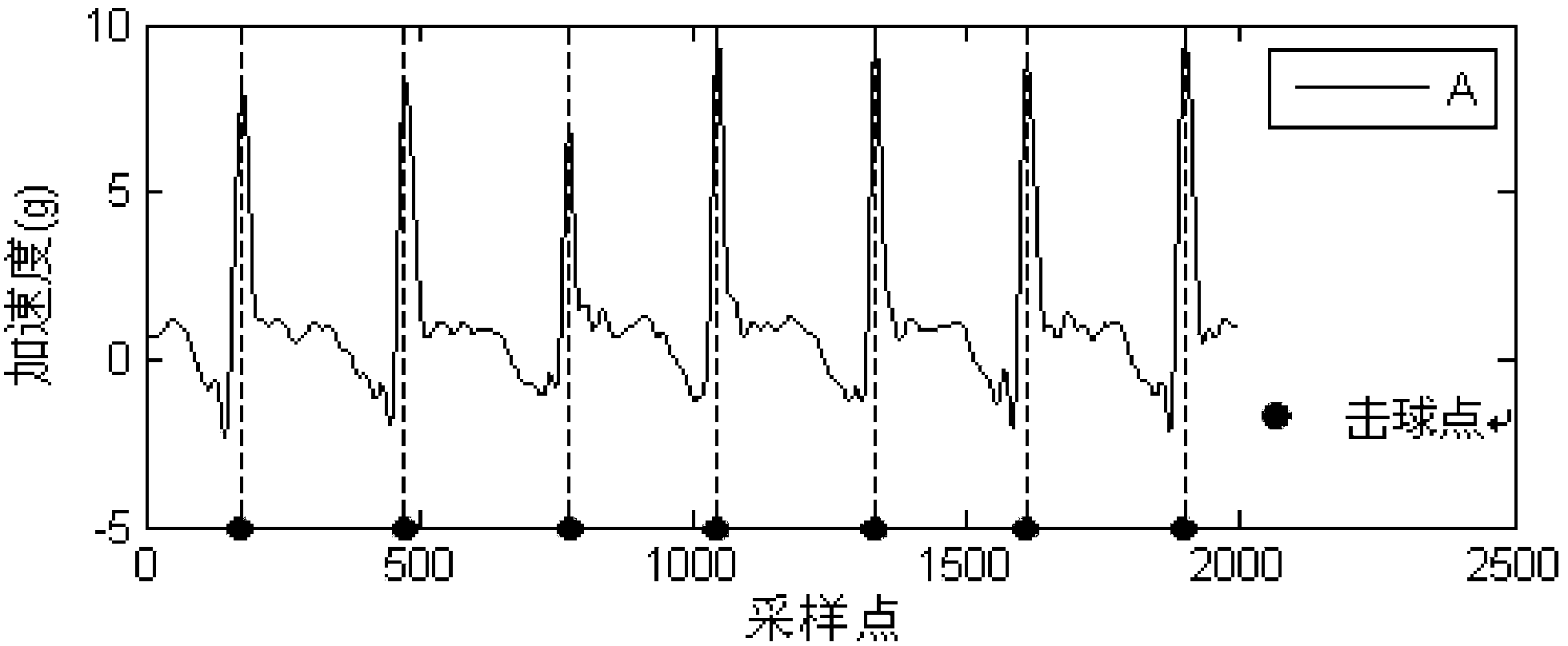
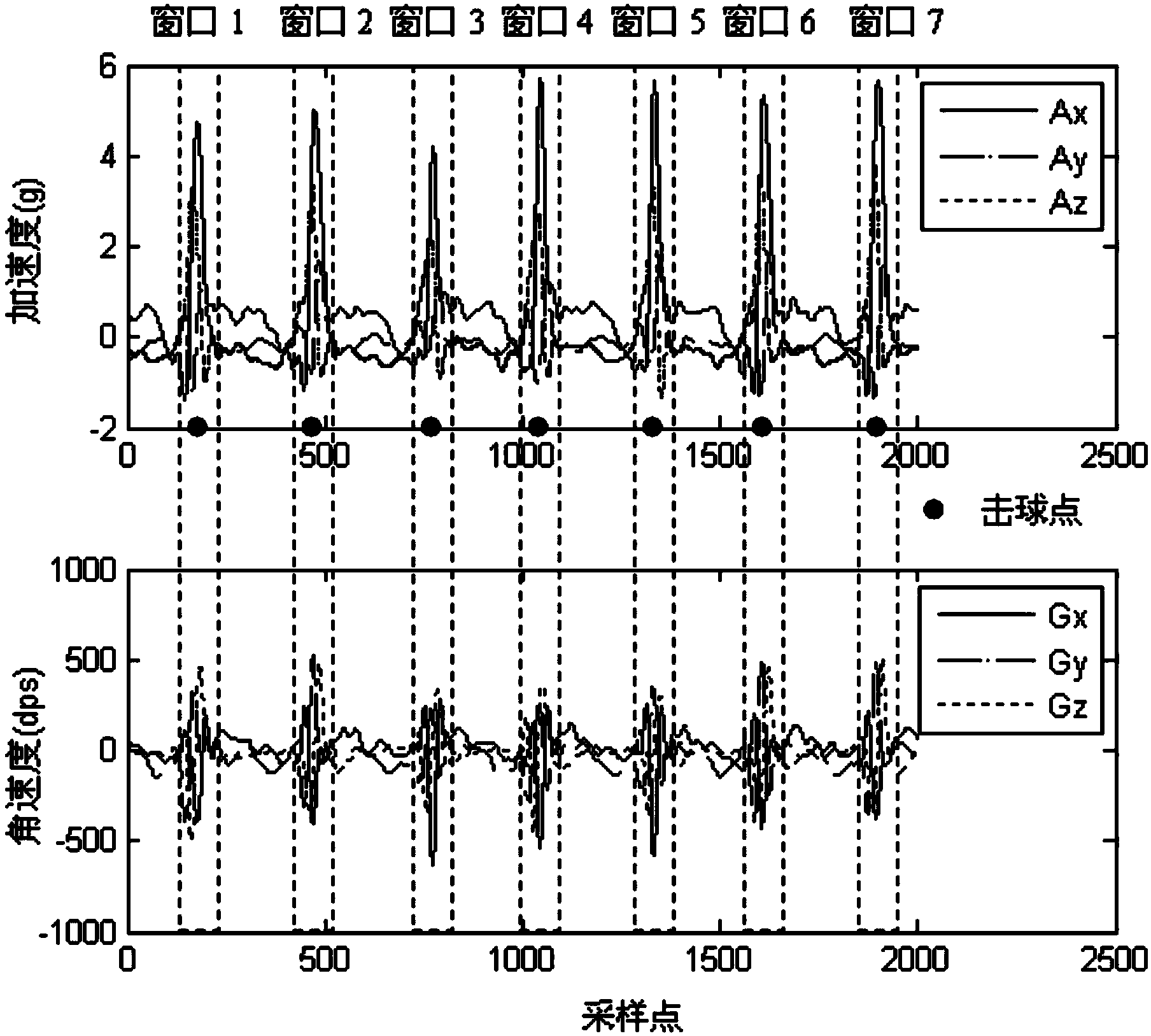
The invention provides a human body behavior identification method based on an inertial sensor. The method comprises the steps of acquiring human body behavior data of testees by means of the inertial sensor, conducting sliding window segmentation on the acquired human body behavior data, conducting feature extraction on a triaxial accelerated speed subsequence and a triaxial angular speed subsequence which are obtained after sliding window segmentation, conducting feature fusion on a feature vector to form a sample set of the human body behaviors of the testees, conducting feature selection on the sample set by means of the least correlated maximum redundant algorithm and the Bayes regularization sparse polynomial logistic regression algorithm, obtaining the classification feature vectors of all human body behaviors of all the testees, obtaining a classifier model of each human body behavior by means of a fuzzy least square support vector machine, and obtaining a human body behavior identification result after the human body behavior data are tested by means of the fuzzy least square support vector machine. By means of the human body behavior identification method, self-adaptation and identification efficiency can be improved.
Owner:DALIAN UNIV OF TECH
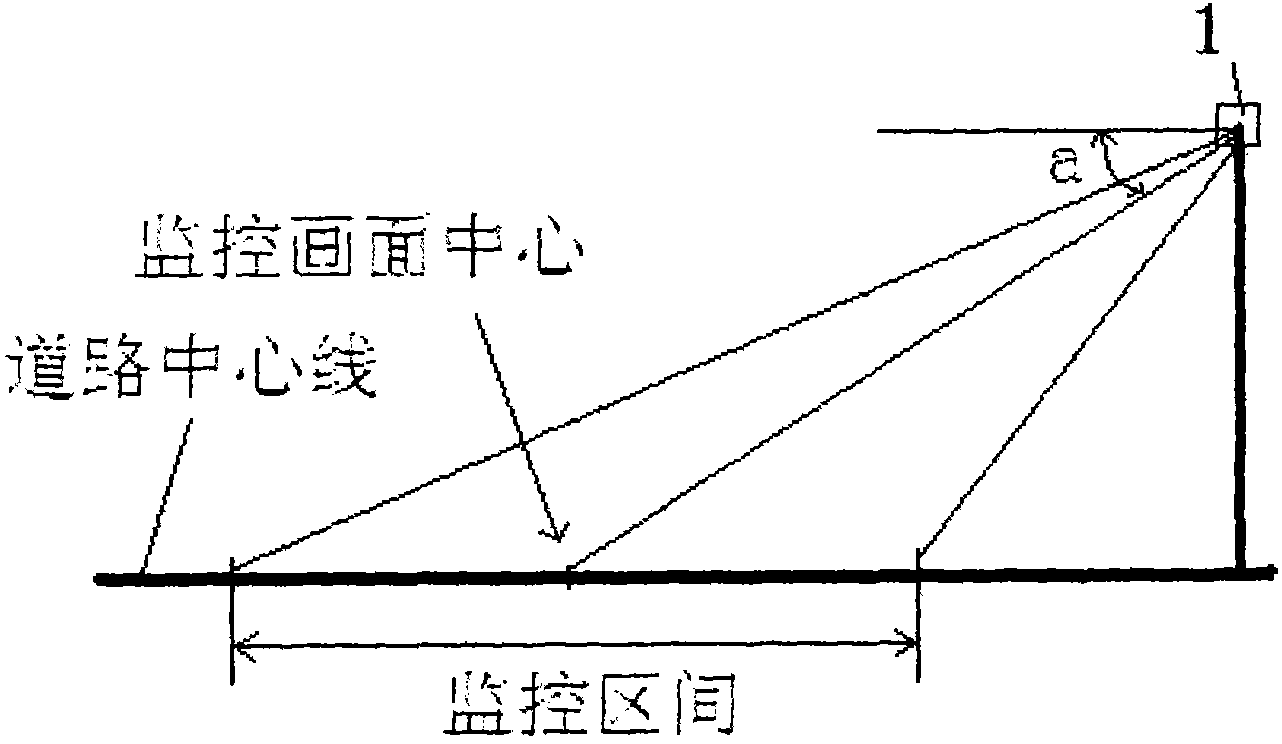
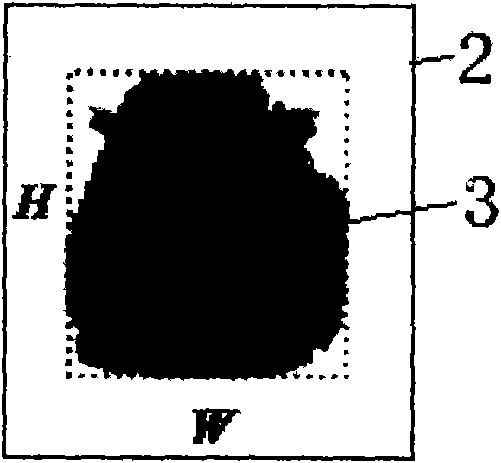
Method for quick vehicle type recognition under video monitoring mode
InactiveCN101783076AAccurate classificationReduce time complexityRoad vehicles traffic controlCharacter and pattern recognitionVideo monitoringComputer vision
The invention discloses a method for quick vehicle type recognition under video monitoring mode, which is implemented according to the following steps: setting up a road monitoring device and classifying the vehicles into cars, taxis marked by special color, microbuses, middle-sized vehicles, public buses and large trucks; step 1, initialization, conducting training to the video monitoring device; step2, extracting the area of the vehicle target area and the length and the width of the boundary rectangle of the area, constructing corresponding characteristics and roughly classifying the vehicles into minitype vehicles, middle-sized vehicles and large vehicles; step 3, extracting the main colors of bodyworks of a plurality of minitype vehicle targets to recognize the taxis, then extracting the characteristic parameter of window position of the minitype vehicles, and furthermore, determining the microbuses or cars; and step 4, extracting the characteristic parameters of roof brightness and roof texture to determine whether the large vehicles are public buses or not. Through the method, a variety of vehicles can be recognized quickly and accurately according to the classification characteristics.
Owner:XIAN UNIV OF TECH
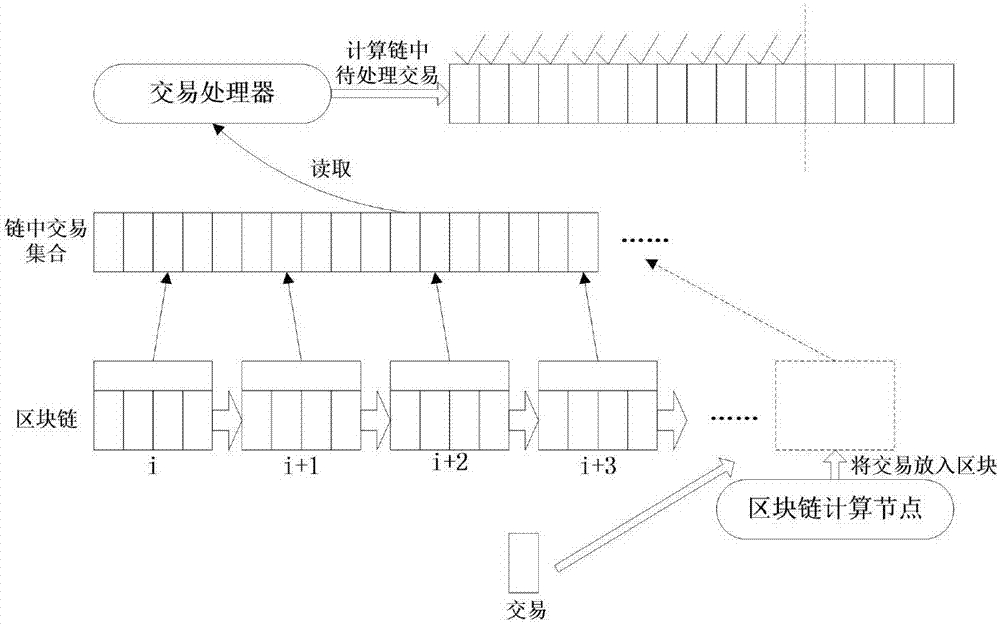
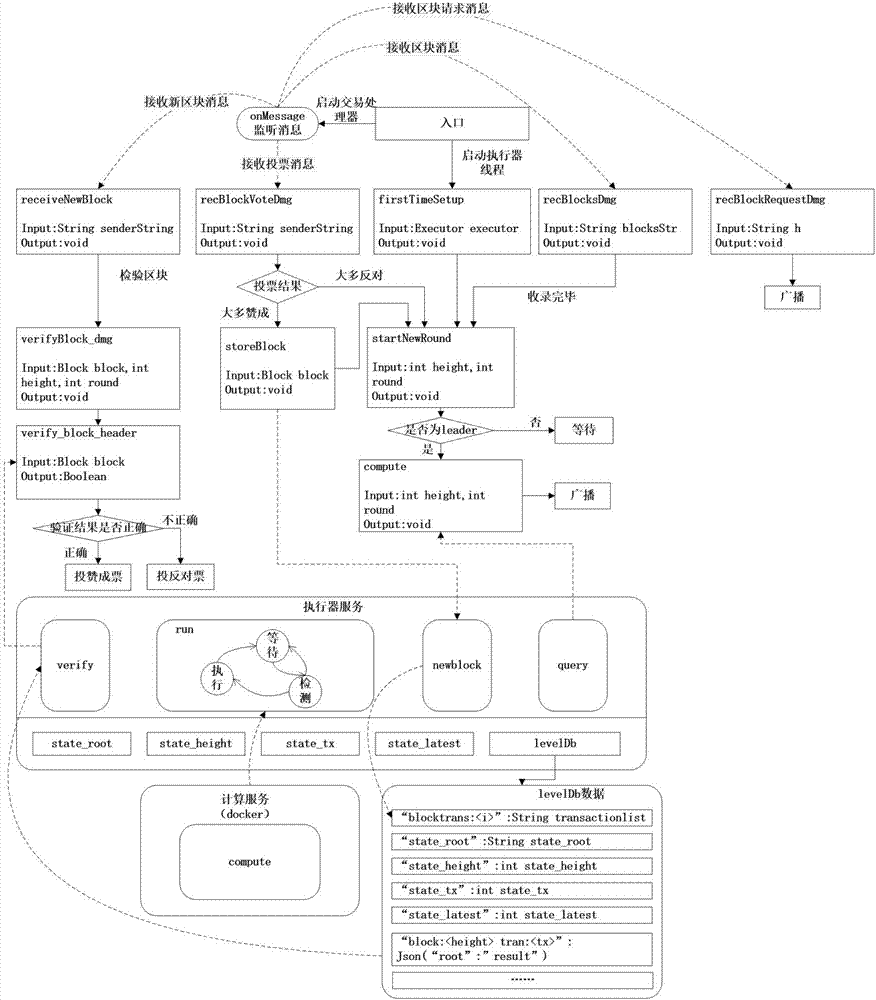
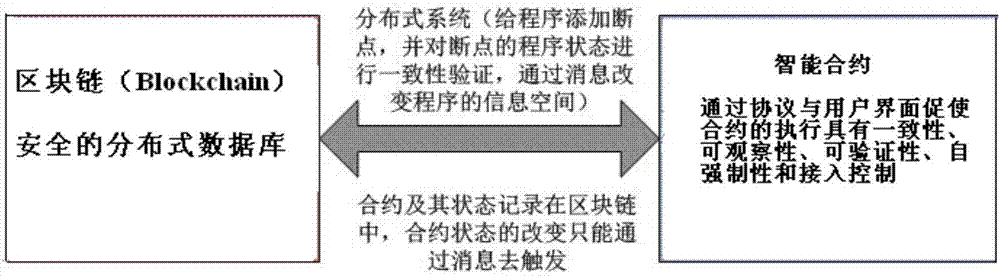
Intelligent contract asynchronous execution storage system of private blockchain and achieving method
ActiveCN107103054AImprove execution efficiencyImprove securityRelational databasesSpecial data processing applicationsSmart contractConsistency problem
The invention provides an intelligent contract asynchronous execution storage system of a private blockchain. The system comprises an execution state machine of the private blockchain, a transaction processor execution state machine and a storage structural module capable of supporting SCAM. The invention further provides an achieving method of the intelligent contract asynchronous execution storage system of the private blockchain. Through the intelligent contract asynchronous execution storage system of the private blockchain and the achieving method thereof, the execution efficiency of an intelligent contract is improved, the safety of the execution with the intelligent contract being a chain code of the blockchain is further improved, and the consistency problem between the intelligent contract code and a text is solved.
Owner:BEIHANG UNIV YUNNAN INNOVATION INST
Method and apparatus for implementing ETL scheduling
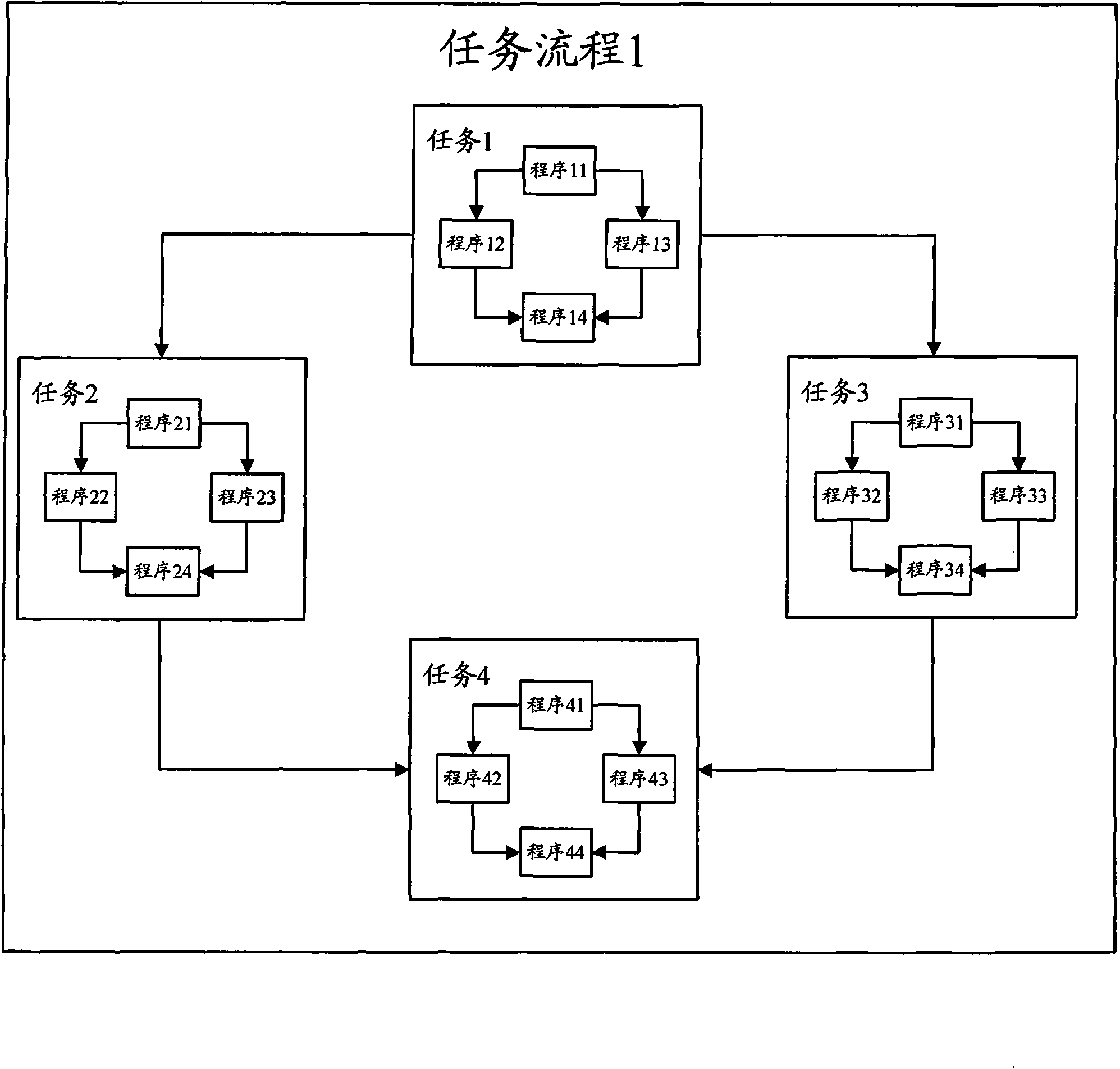
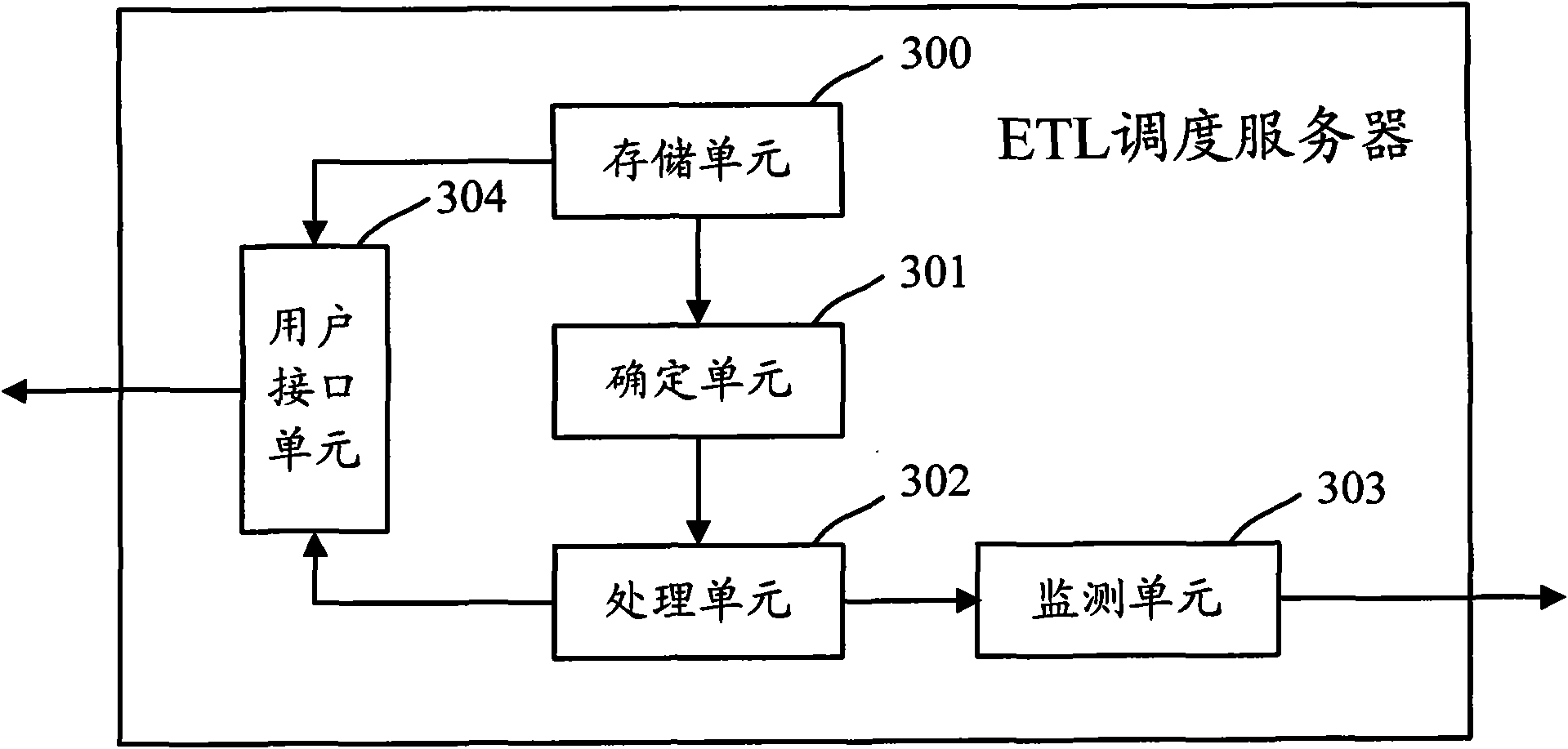
ActiveCN101567013AImprove execution efficiencyClear business logicSpecial data processing applicationsMutual dependencyDistributed computing
The invention discloses a method for scheduling ETL, comprising: determining the triggering mode, operation sequence and mutual dependency relationship of each subtask flow included in the task flow based on preset configuration file aiming at an optional task flow when implementing plural task flows included in the ETL scheduling; triggering corresponding subtask flows in turn according to the set triggering mode and implementing the triggered subtask flow according to set sequence, wherein after determining that at least a subtask flow is implemented, starting to implement other subtask flows depending on at least a subtask flow and other triggered subtasks based on the dependency relationship between subtask flows. Thus, subtask flow in each task flow has clear service logic and service function so as to effectively enhance the implementing efficiency of the ETL scheduling flow. The invention also discloses an apparatus for implementing ETL scheduling.
Owner:ADVANCED NEW TECH CO LTD
Method for generating data processing flow codes
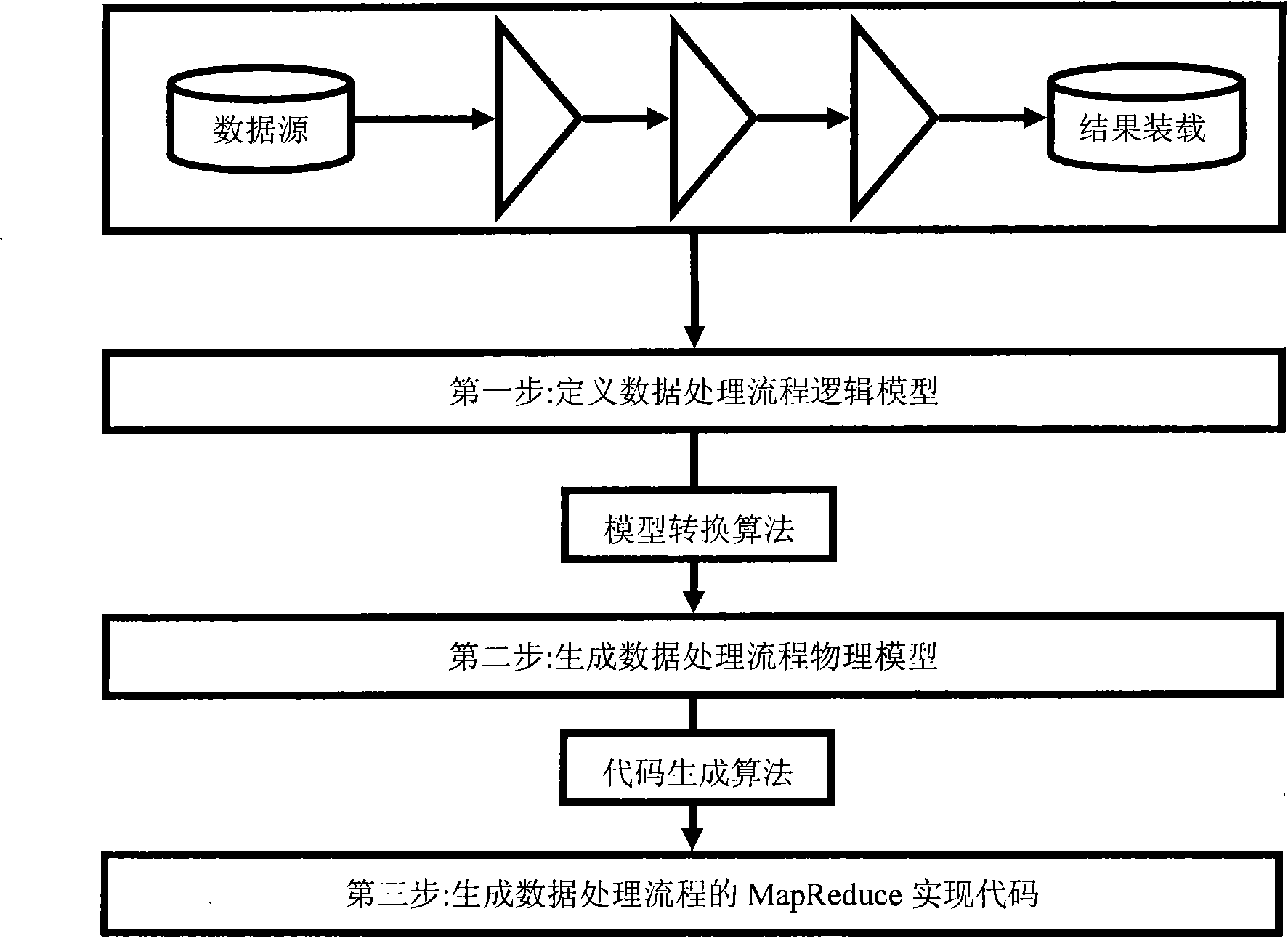
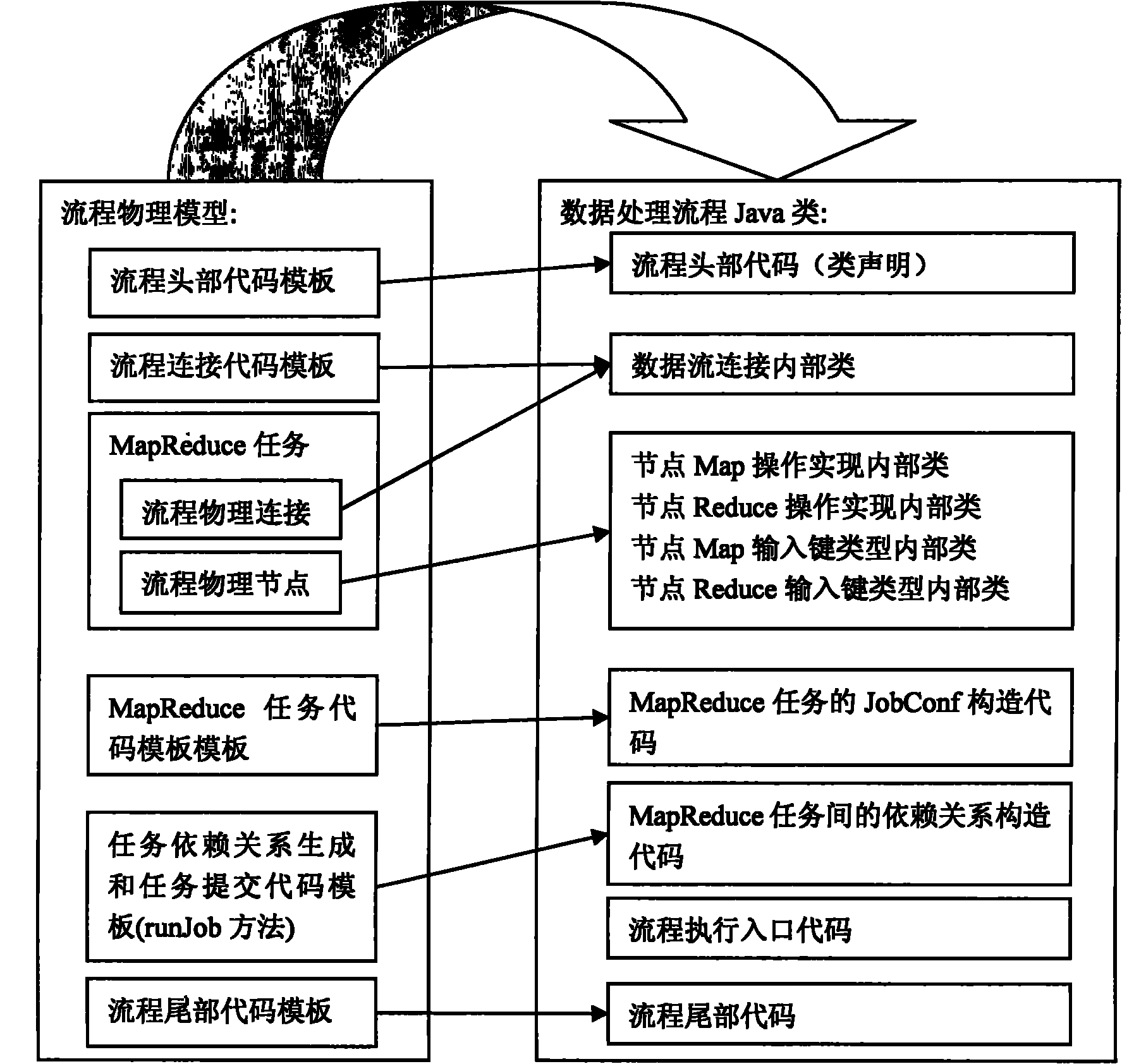
ActiveCN102033748AImprove execution efficiencyReduce difficultySpecific program execution arrangementsPhysical modelProcess logic
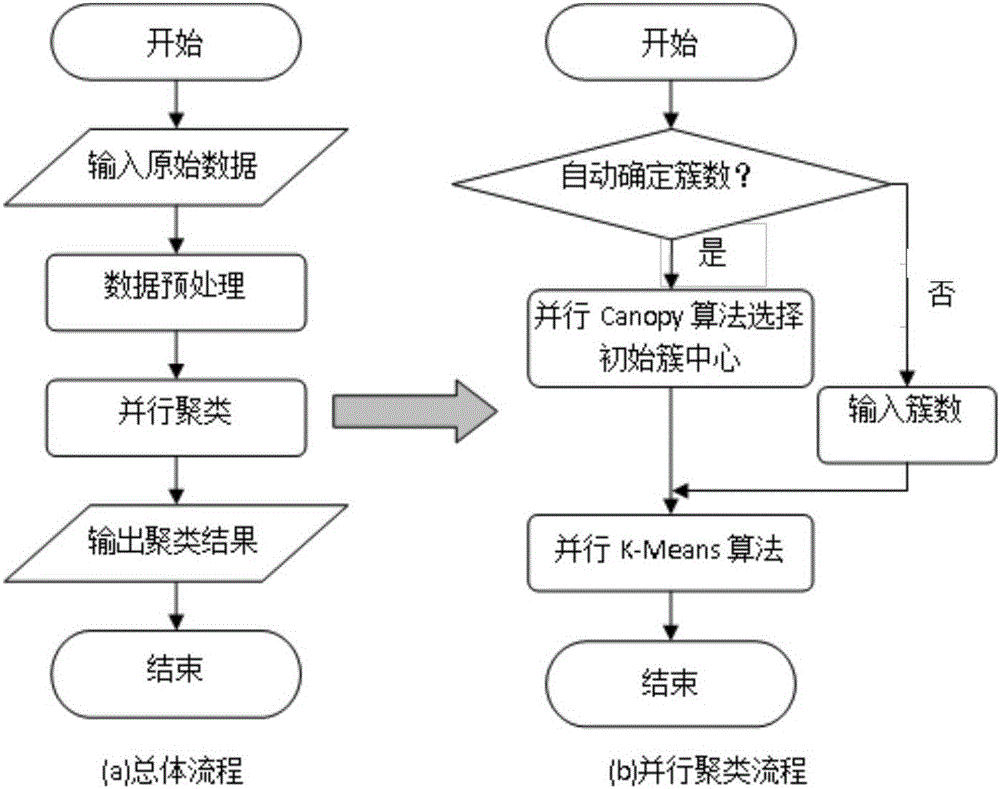
The invention relates to a method for generating data processing flow codes, belonging to the field of data integration of cloud computing. The method comprises the steps of: (1) extracting a visualized data processing flow omega to be used as a logic model embodiment; wherein the data processing flow is a directed acyclic graph flow comprising a flow name, a version, data processing nodes and node connection information; (2) converting the logic model embodiment into a physical model embodiment of the data processing flow, wherein the physical model embodiment is in a directed acyclic graph structure; and (3) generating MapReduce codes of the data processing flow according to the physical model embodiment of the data processing flow. The method is beneficial to the reduction of user development difficulty and the acceleration of data analysis progress; and in addition, by the invention, a user can carry out parameter tuning configuration, code optimization, automatic flow logic optimization and the like on the data processing flow so that the flow execution efficiency is greatly improved.
Owner:WUHAN DAMENG DATABASE
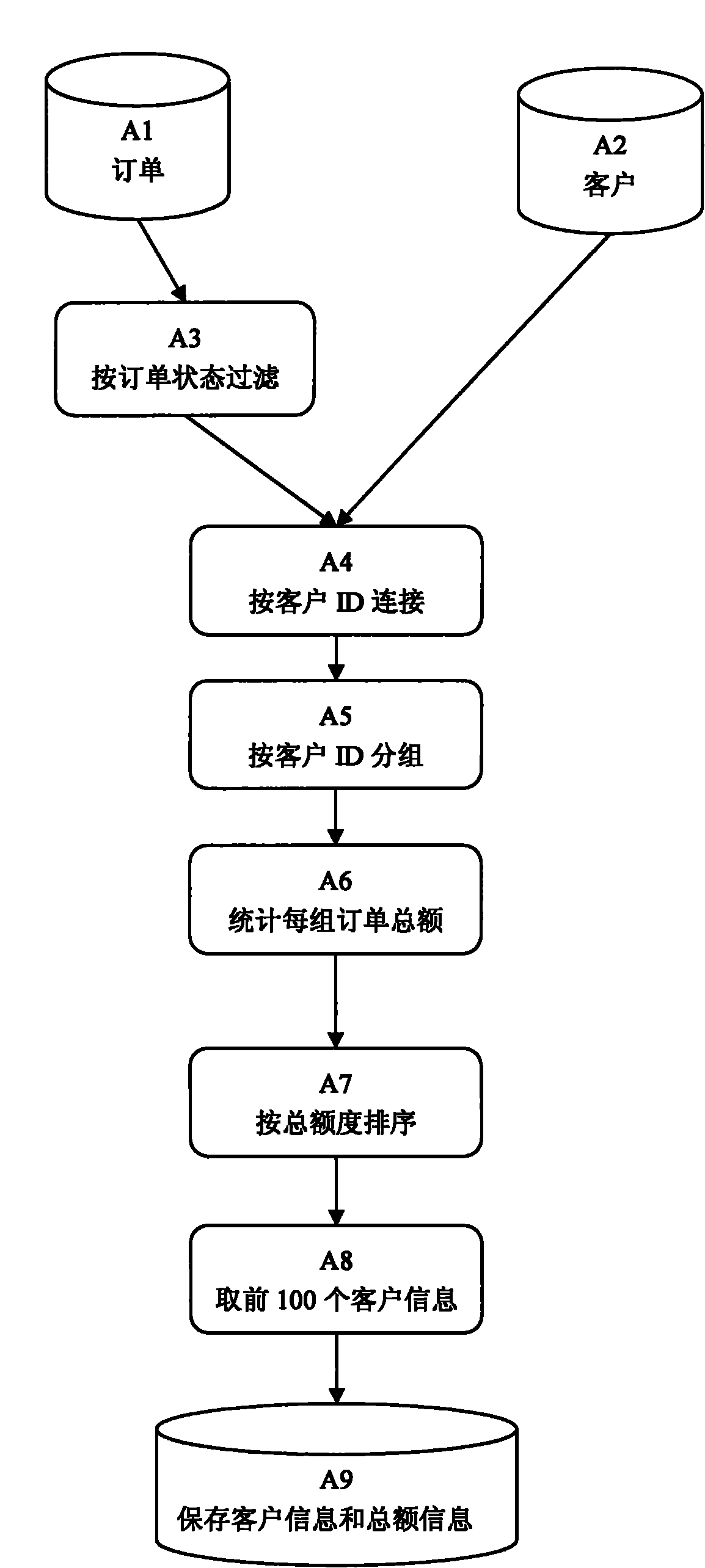
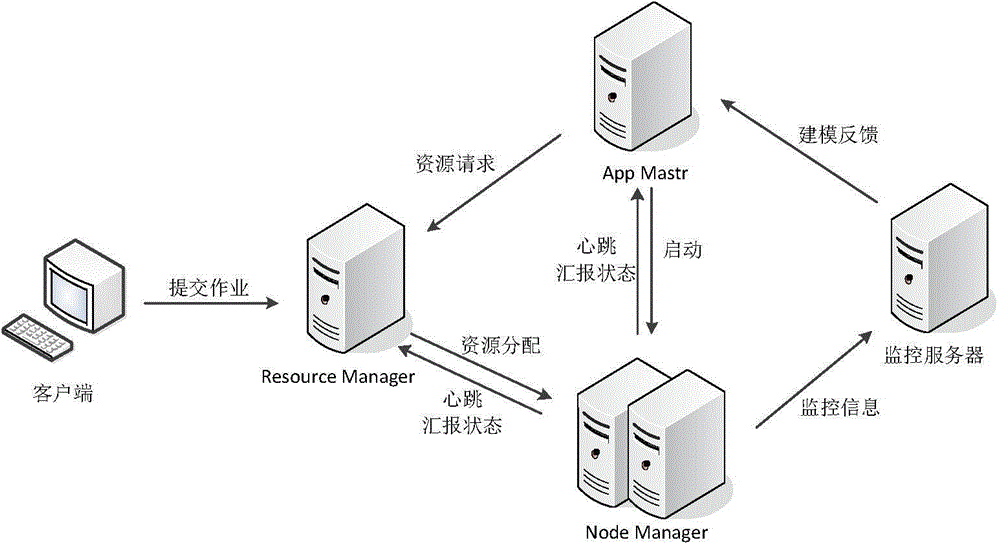
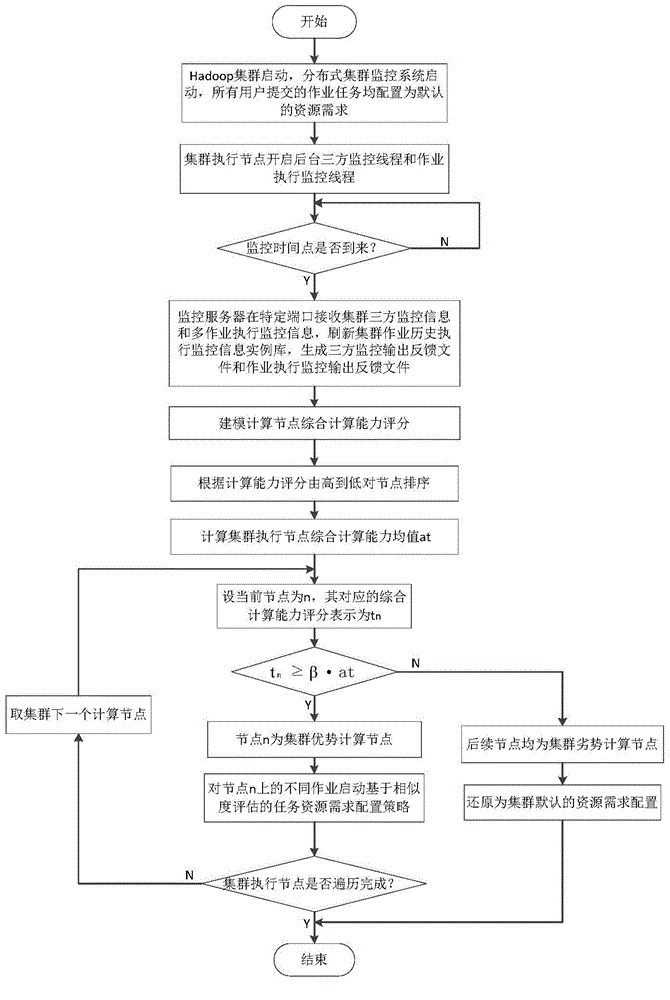
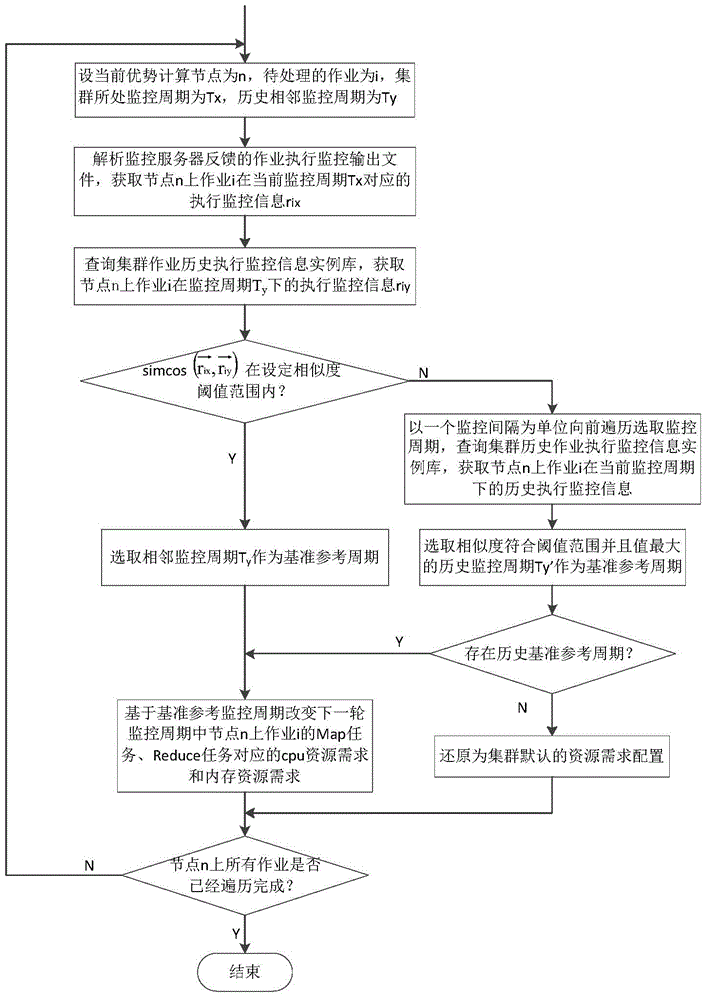
Resource scheduling method under Hadoop-based multi-job environment
ActiveCN104915407AEfficient use ofPromote efficient concurrencyProgram initiation/switchingDatabase distribution/replicationYarnGranularity
The invention discloses a resource scheduling method under a Hadoop-based multi-job environment, which includes: (1) collecting the three-party monitoring information of cluster loads, a Hadoop platform and hardware in real time; (2) collecting the job execution monitoring information of a user on each computing node of a cluster in real time; (3) gathering the three-party monitoring data of the cluster, modeling to evaluate the computing capabilities of the nodes, and dividing the nodes of the cluster into superior computing nodes and inferior computing nodes; (4) if the nodes are the superior computing nodes, then starting a job task resource demand allocation policy based on similarity evaluation; (5) if the nodes are the inferior computing nodes, then returning to a default resource demand allocation policy of the Yarn. The resource scheduling method under the Hadoop-based multi-job environment solves the problem of resource fragments caused by oversize job resource demand division granularity in conventional resource schedulers of the Yarn, can comprehensively take the heterogeneity of cluster nodes and jobs into consideration, and increases the execution concurrency of the cluster by reasonably and effectively allocating the node resources, thus increasing the execution efficiency of the multiple jobs of the Hadoop cluster.
Owner:HUAZHONG UNIV OF SCI & TECH
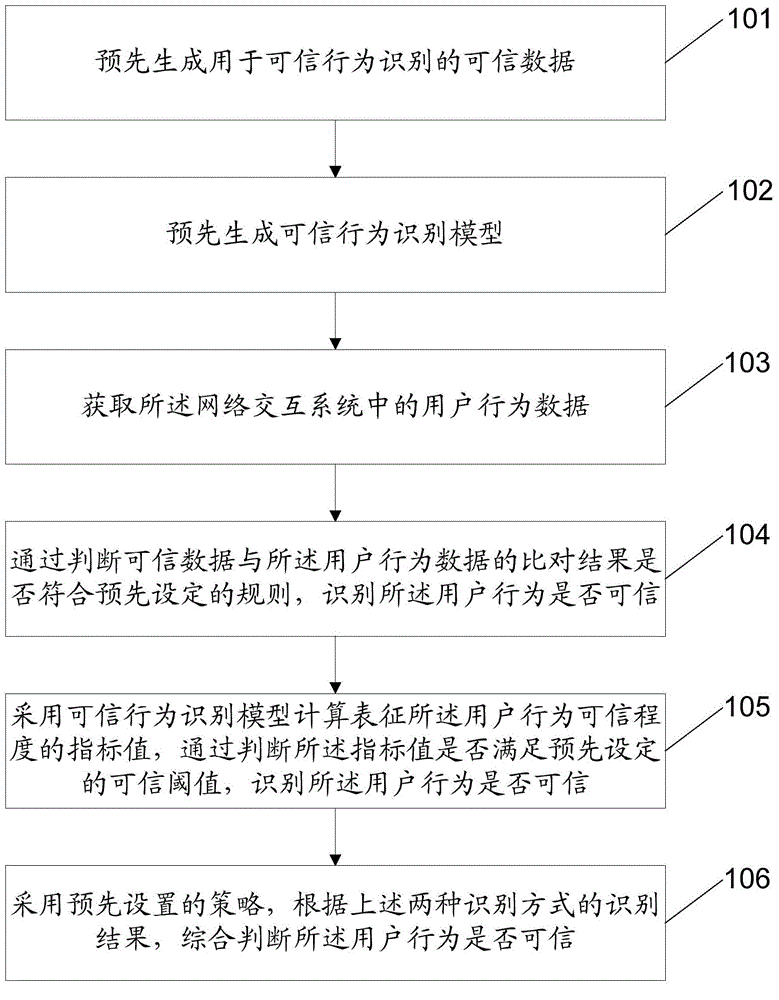
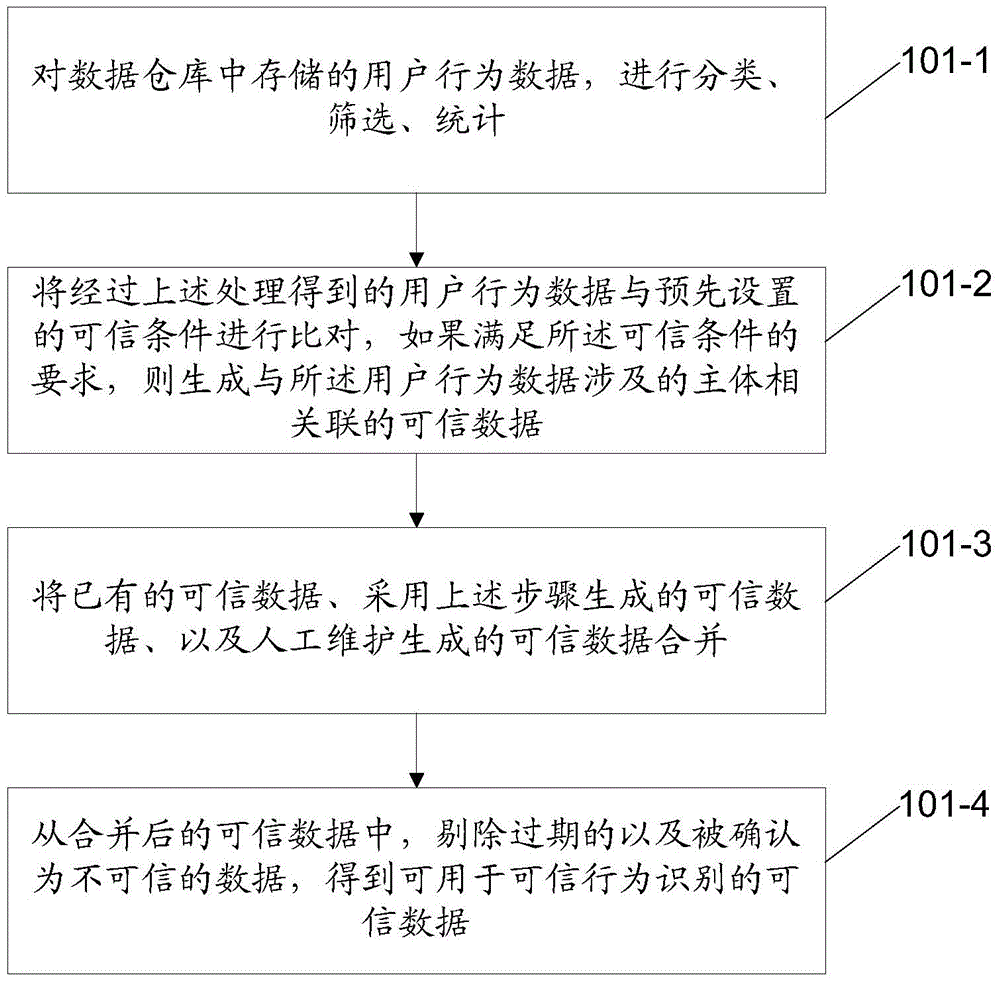
Method and apparatus for identifying trustworthy user behavior in network interaction system
ActiveCN105590055AImprove execution efficiencyImprove recognition accuracyPlatform integrity maintainanceSpecial data processing applicationsBehavior recognitionData mining
The invention discloses a method for identifying a trustworthy user behavior in a network interaction system. The method comprises the steps of obtaining user behavior data in the network interaction system; and identifying whether the user behavior is trustworthy or not in any one of the following modes: identifying whether the user behavior is trustworthy or not by judging whether a comparison result of pre-generated trustworthy data and the user behavior data meets a preset rule or not; or, calculating an index value representing the creditability of the user behavior by adopting a pre-generated trustworthy behavior identification model, and identifying whether the user behavior is trustworthy or not by judging whether the index value is equal to a preset trustworthy threshold or not. At the same time, the invention provides an apparatus for identifying the trustworthy user behavior in the network interaction system. According to the technical scheme provided by the invention, a new thought of identifying the user behavior is provided and most trustworthy behaviors can be accurately and efficiently identified from mass user behaviors only by depending on trustworthy data and original behavior data.
Owner:ADVANCED NEW TECH CO LTD
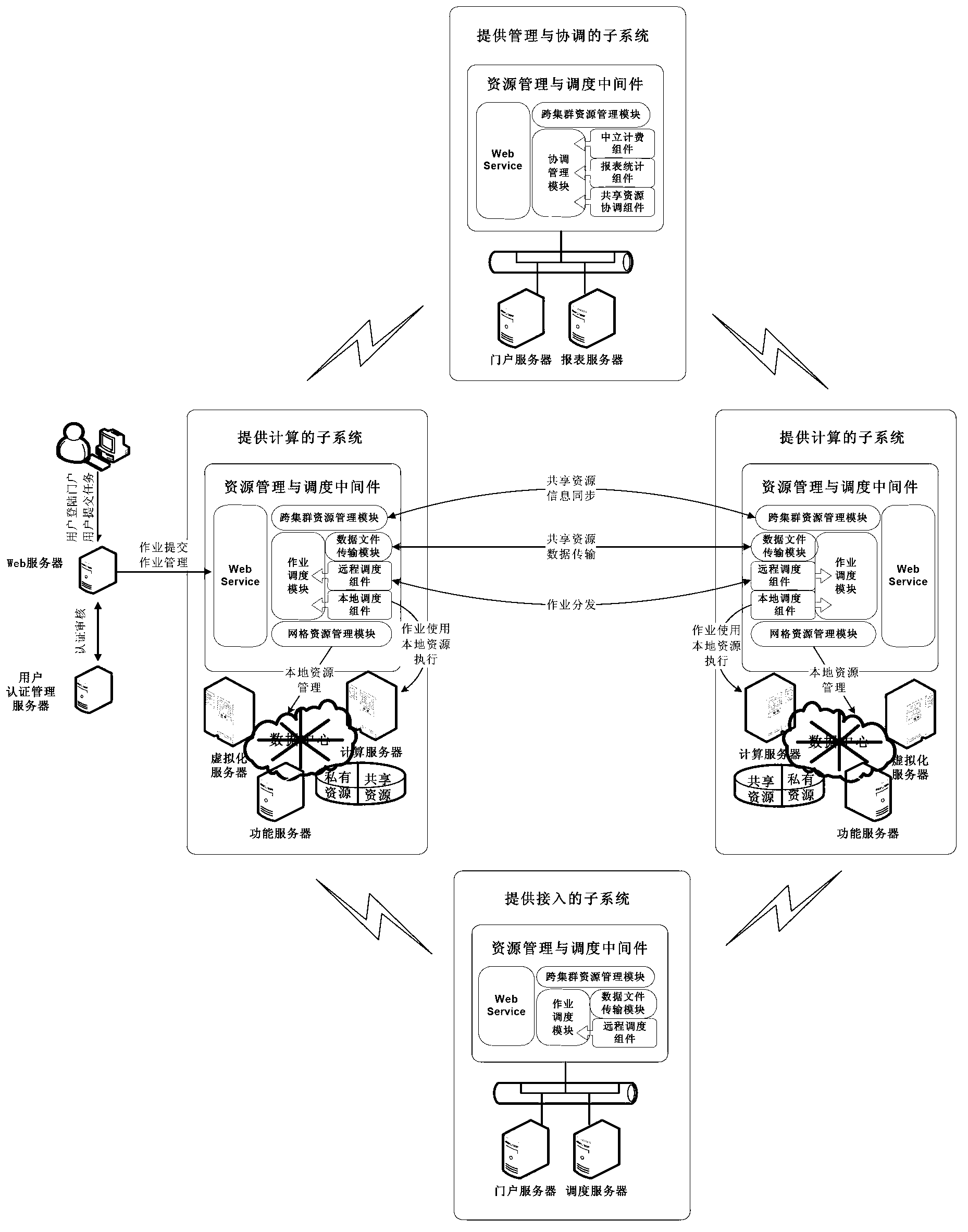
Decentralized cross cluster resource management and task scheduling system and scheduling method
ActiveCN103207814AImprove execution efficiencyImprove experienceResource allocationEnergy efficient computingData centerPerformance computing
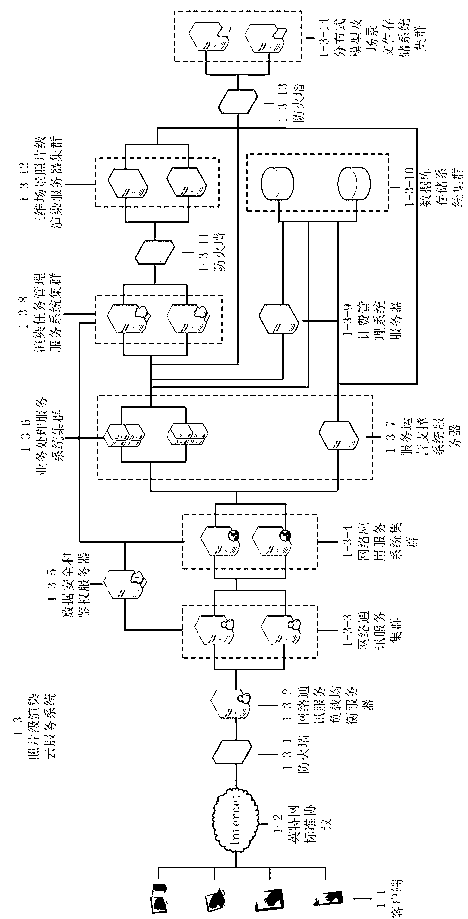
The invention relates to a decentralized cross cluster resource management and task scheduling system and a scheduling method. The scheduling system comprises a subsystem for providing management and coordination service, a subsystem for providing computing service and a subsystem for providing access service, the subsystem for providing the management and coordination service acquires information of other subsystems, provides monitoring, reporting, billing, resource sharing coordination work, and provides decision reference for management and planning of a high-performance computing system. The subsystem for providing the computing service is provided with a data center of a high-performance computing node and collects local and remote resources, so that work scheduling is performed according to the local and remote resources. The subsystem for providing the access service provides localized work submission and access management service for a user. The decentralized cross cluster resource management and task scheduling method integrates single cluster resources, on one hand, work execution efficiency and user experience are improved, on the other hand, existing resources are effectively and maximally used, and the cost for purchasing hardware to expand computing power is saved.
Owner:BEIJING SIMULATION CENT
Method and system for detecting and defending multichannel network intrusion
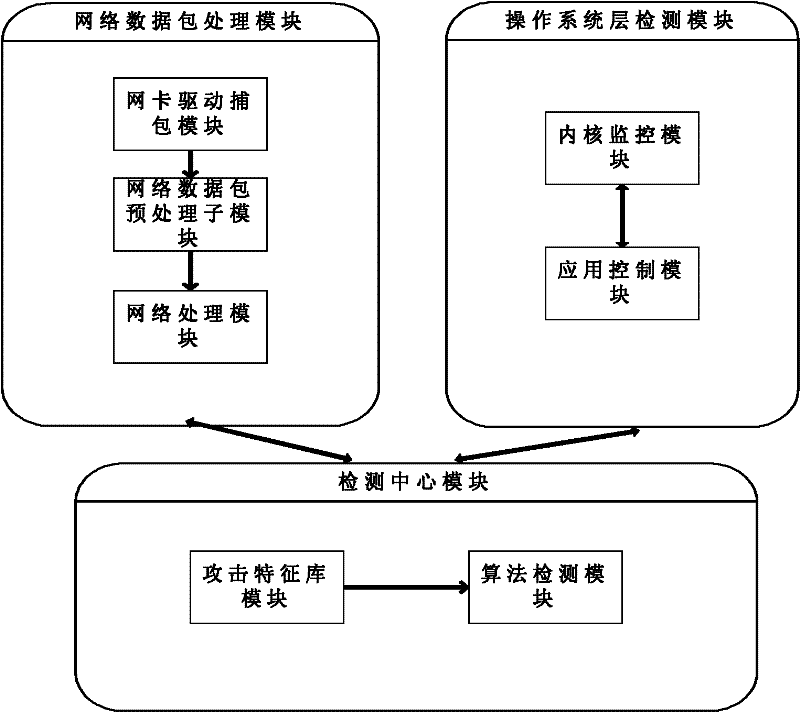
InactiveCN102546624AImprove real-time performanceImprove execution efficiencyData switching networksOperational systemPacket processing
The invention relates to a method and a system for detecting and defending multichannel network intrusion, wherein a half-polling manner is used in a network card driver at a network side to capture a data packet and from a rule for judging abnormal traffic. At an operating system side, secure access control is realized by additionally setting authority control in a Capability module of Linux, meanwhile, monitoring and control treatment is performed on a kernel layer of an operating system, and the monitoring of Trojan and other abnormal operations or virus destruction is realized by carrying out credential privilege arbitration on processes, operating an i-node and carrying out secure control on an application layer. Formed feature data are gathered and sent to a Bayes model for classification, an improved backward propagation neural network (BPNN) is guided in to carry out data training so as to make the produced rule capable of defending corresponding attacks. The system disclosed by the invention comprises three modules and five submodules, wherein the three modules include a network data packet processing module, an operating system layer detecting module ad a detection center module.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Cloud computing task scheduling method based on an improved genetic algorithm
PendingCN109800071AImprove satisfactionImprove execution efficiencyProgram initiation/switchingGenetic modelsAlgorithmCombined method
The invention discloses a cloud computing task scheduling method based on an improved genetic algorithm. A multi-objective-based weighted optimization evaluation method is adopted as a fitness function; Coding is carried out in a real number direct coding mode; Generating an initial population by adopting a static algorithm and random generation combined method; Carrying out selection operation byadopting a hierarchical selection strategy; Performing crossover operation according to the crossover probability and the chromosome difference degree; Performing mutation operation according to thedynamic mutation probability; Judging whether the program is ended or not according to the double-termination condition; And finding an optimal scheme and distributing. Multiple steps of a traditionalgenetic algorithm are optimized and improved, and the user satisfaction degree and the algorithm execution efficiency are improved.
Owner:SOUTH CHINA UNIV OF TECH
Path planning method and apparatus for robot fast collision avoidance
InactiveCN104155974AImprove execution efficiencyGuaranteed stabilityPosition/course control in two dimensionsCollision detectionSimulation
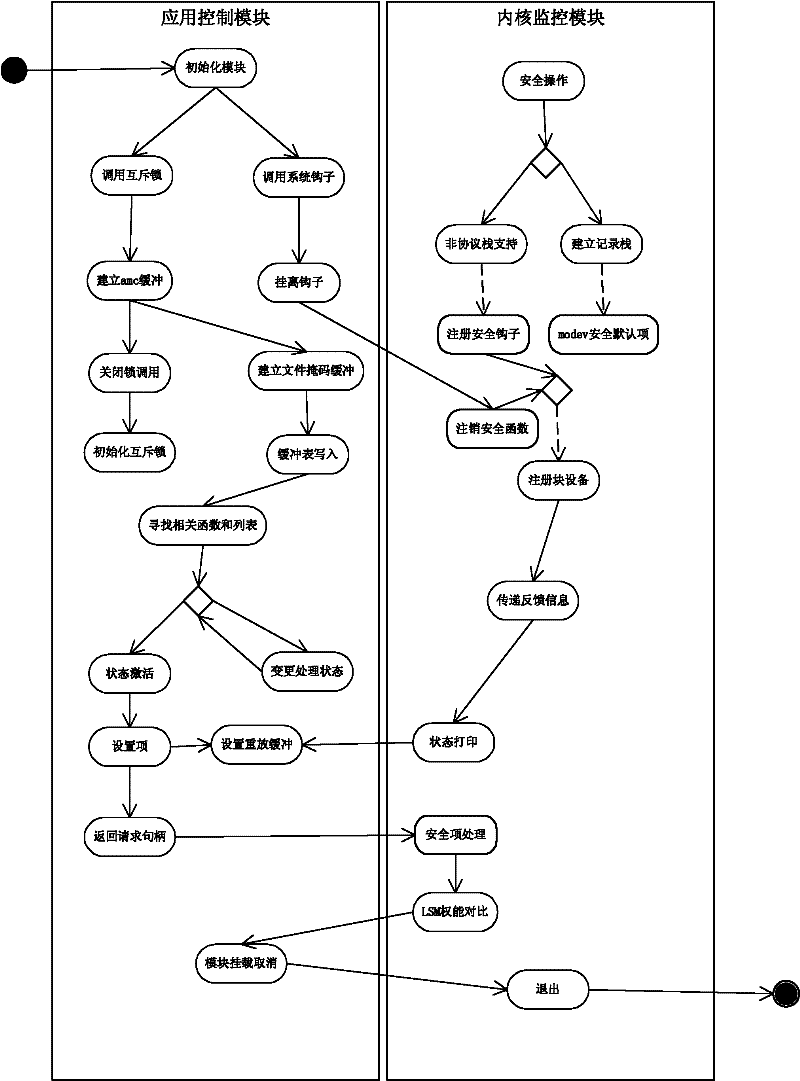
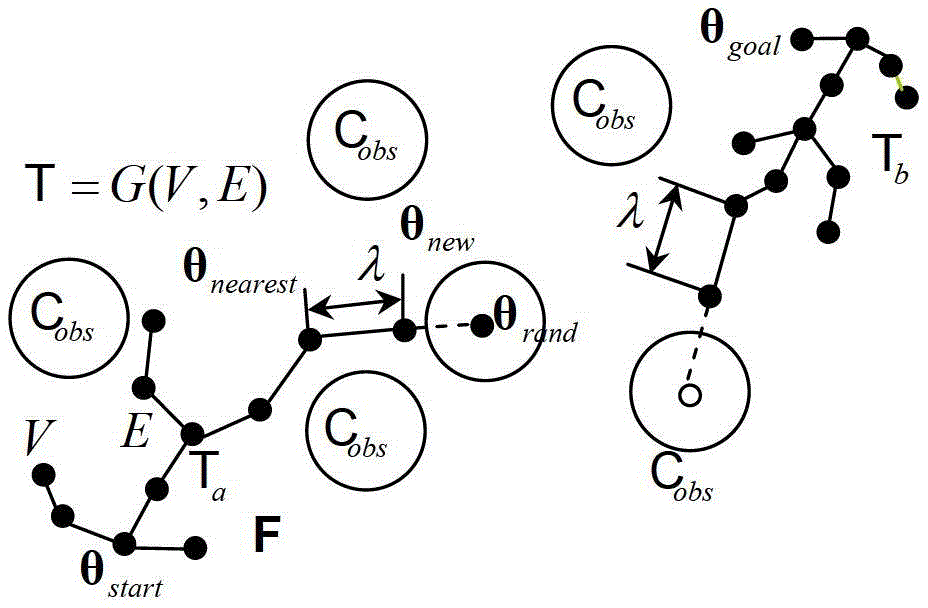
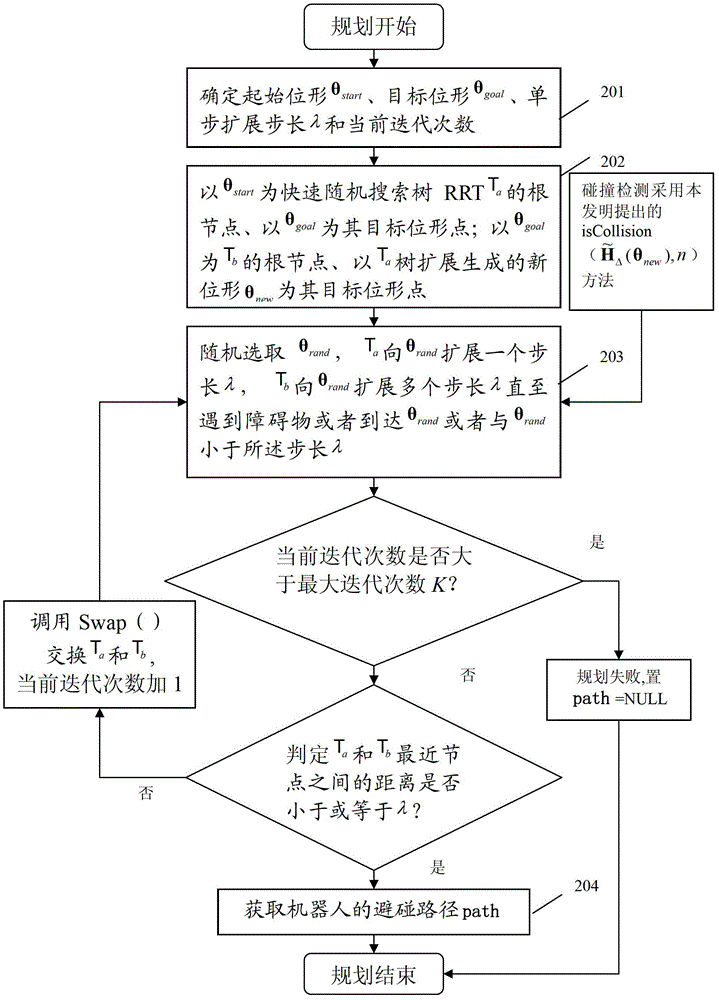
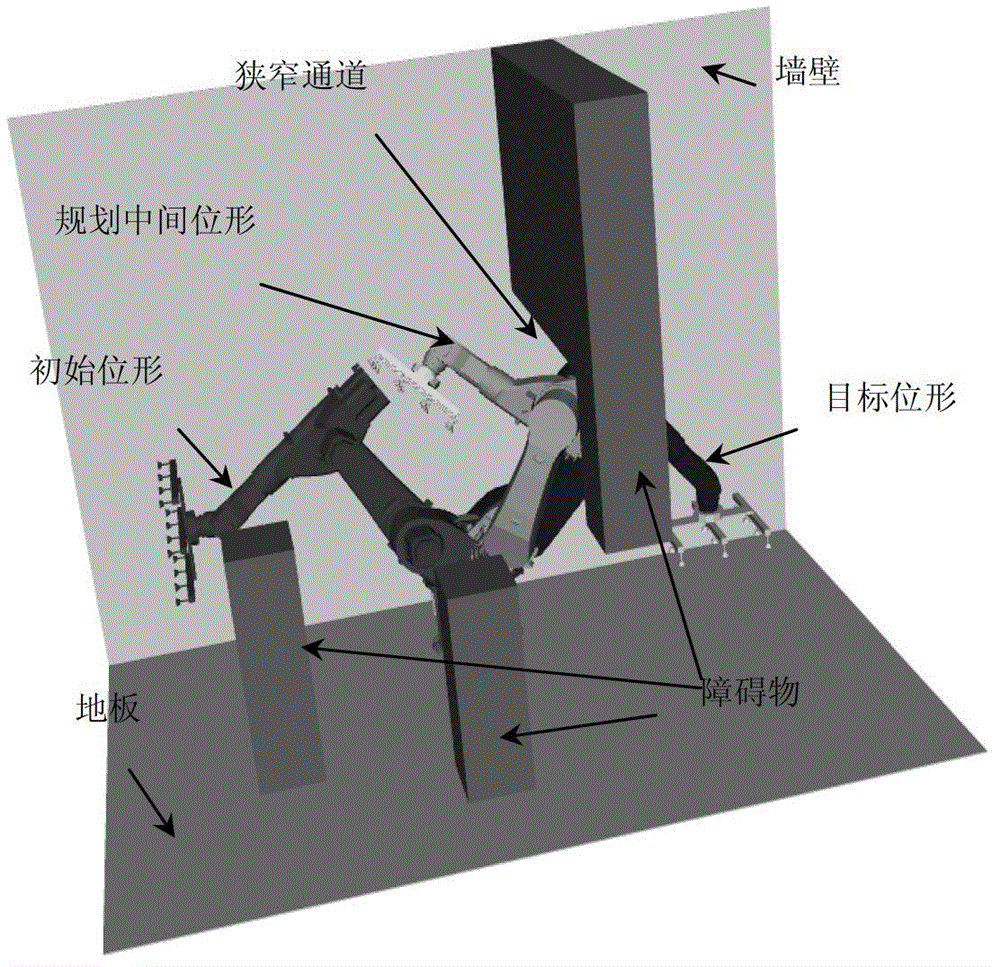
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY
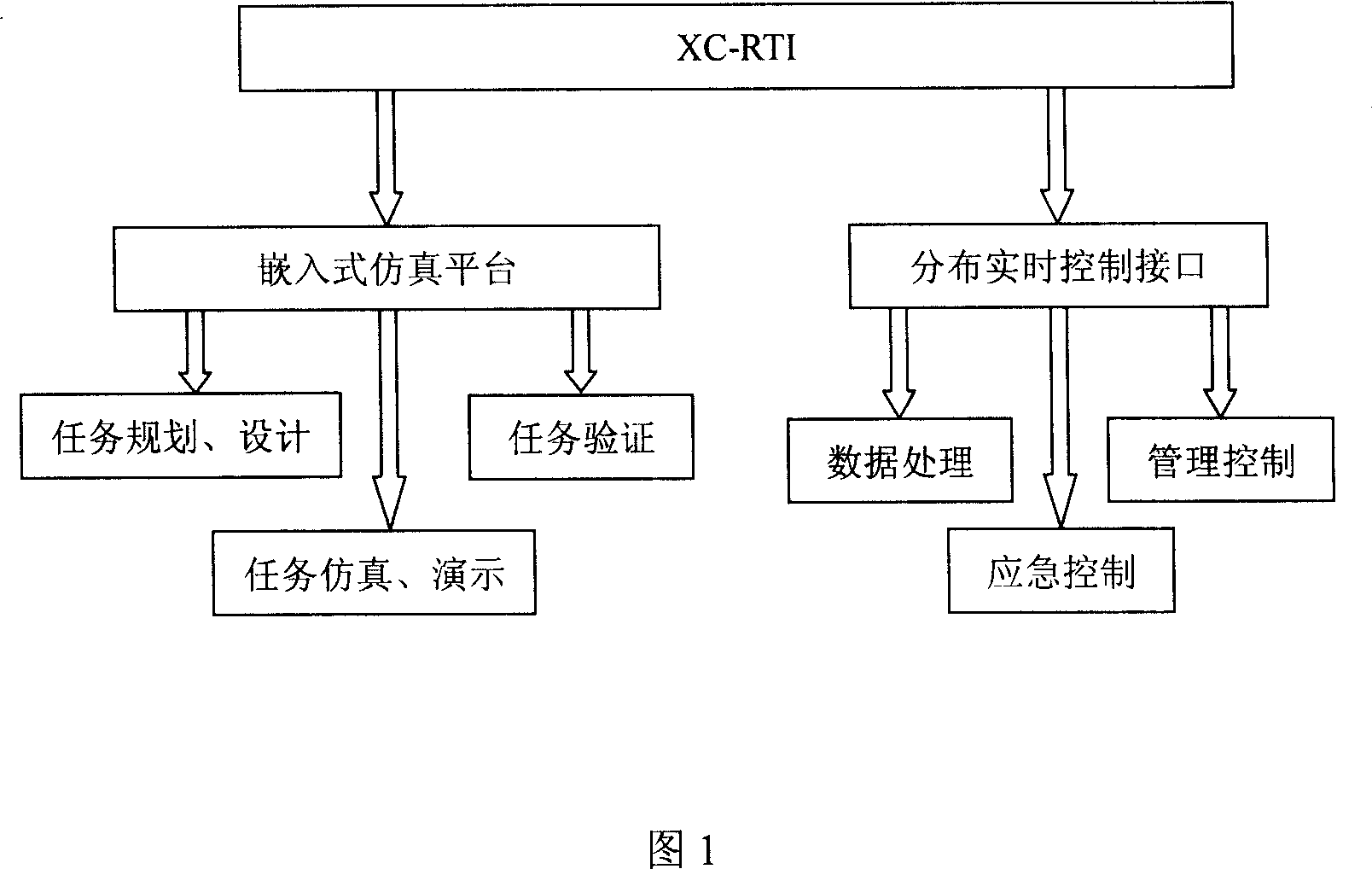
Embedded type distributed simulation platform based on HLA facing to space flight measurement and control and its realization method
InactiveCN101055530AReduce system overheadImprove execution efficiencySoftware simulation/interpretation/emulationControlling environmentPlatform development
The invention relates to an embedded distributing emulation platform basen od HLA faced to space instrumentation and command and a method for carrying out same. The platform supports a distributed interactive simulation and is developped to high application based on HLA / DIS bottom protocol, and carrys out parallel running of multi-emulation platforms, and can record and playback the display and emulation process of two-dimension situation and three-dimension virtual environment for measurement and control environment and measurement and control object during the emulation process. The specific fuction of system includes: carrying out the emulation for measurement and control environment and measurement and control object by the emulation environment platform; adding, replacing or modifying the dynamic model, behavior, sensor and countermeasure of emulation body in the emulation engine by the assemble structure; having expandability; the platform development package having the application interface independently to the protocol; having the functon of route prediction and smoothness in order to display image of situation emulation more fluent and smooth; capable of record in-situ emulation data such that the whole process of virtual emulation training is playbacked, analyzed and evaluated.
Owner:中国人民解放军63791部队
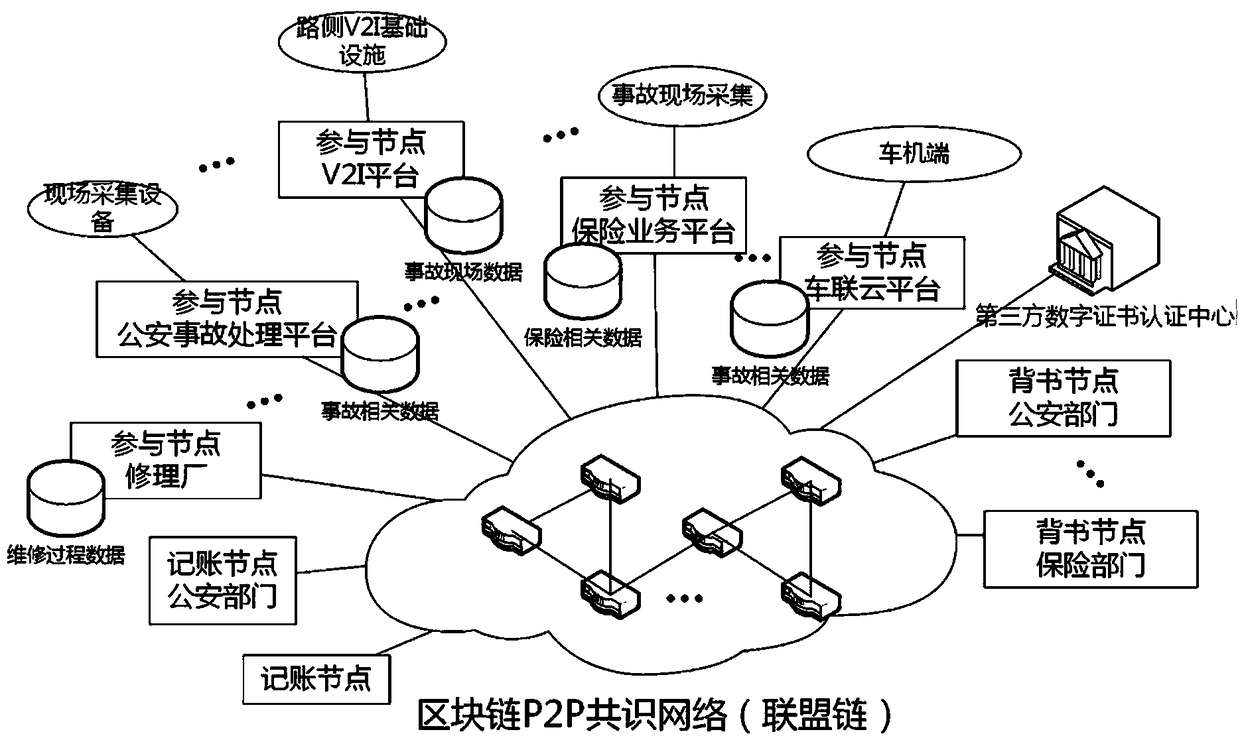
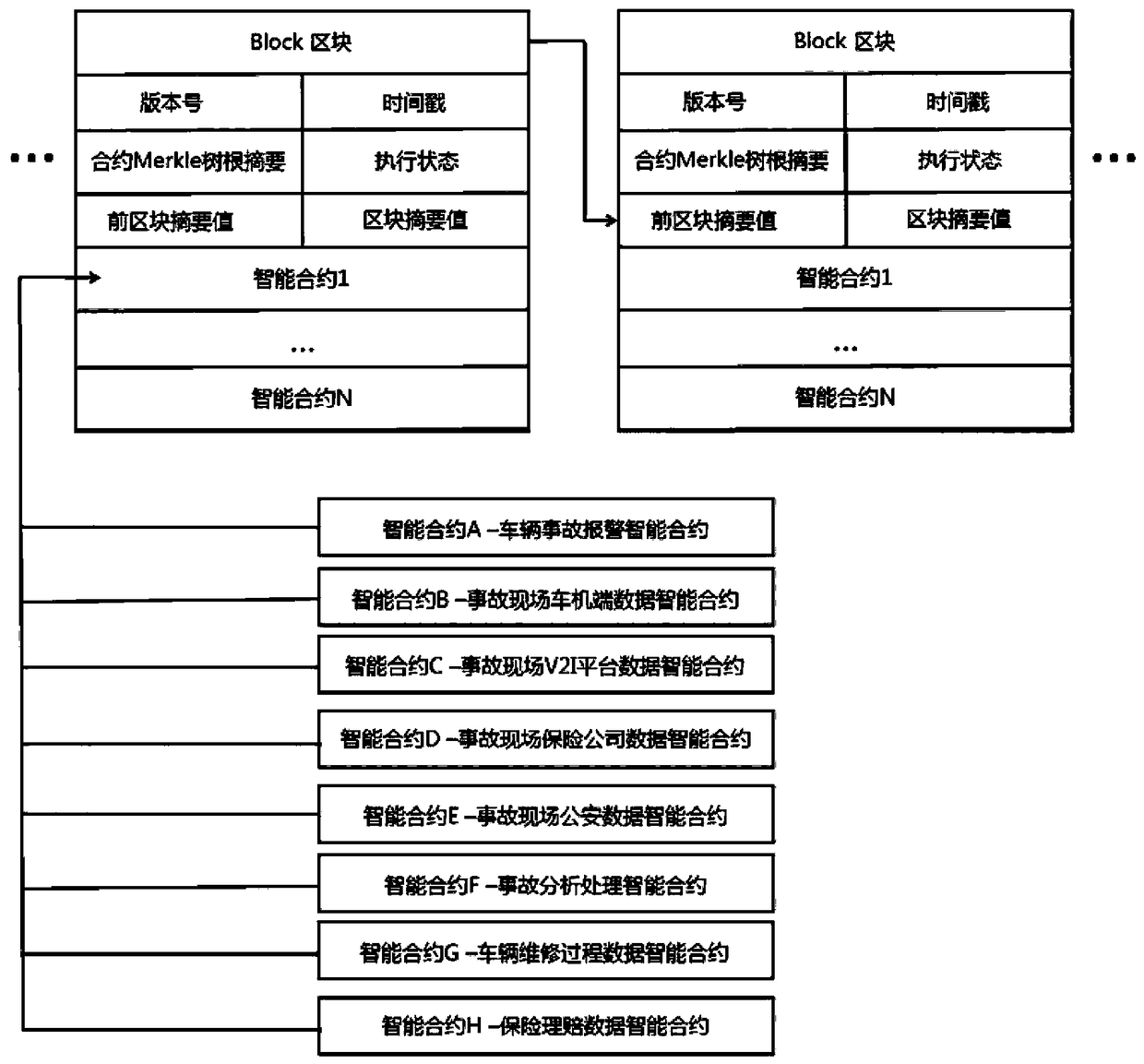
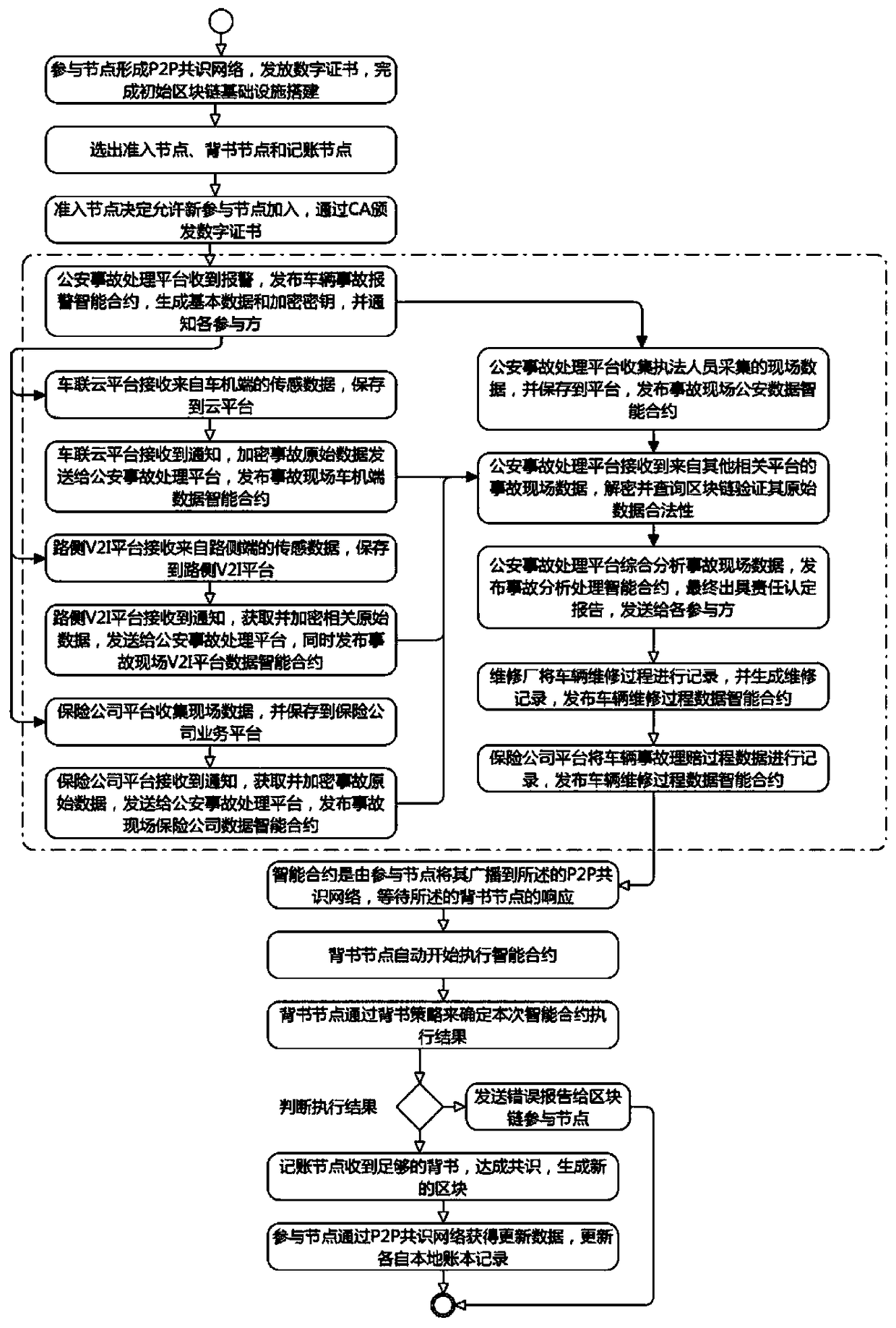
Network connected vehicle accurate accident handling method based on block chain
InactiveCN108446992AImprove accuracyImprove processing speedFinanceUser identity/authority verificationReal-time computingBlockchain
The invention discloses a network connected vehicle accurate accident handling method based on block chain. The implementation process of the method comprises: 1, firstly, through a block chain technology, connecting all participated joints which are associated with accident handling, based on a P2P consensus network, establishing an alliance chain, putting life cycle of accident handling in the block chain to record; through an intelligent terminal on a vehicle accident site, acquiring on-site data and uploading, the participated joints which are associated with accident handling completing accident handling. Compared with the prior art, the network connected vehicle accurate accident handling method based on block chain effectively solves a mutual trust problem of involve parties throughan unified and decentralized method, improves accident responsibility confirmation accuracy rate and handling speed, and provides an accident retroactive function, improves transparency of accident handling process, shortens accident handling time, and saves vehicle accident handling cost.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
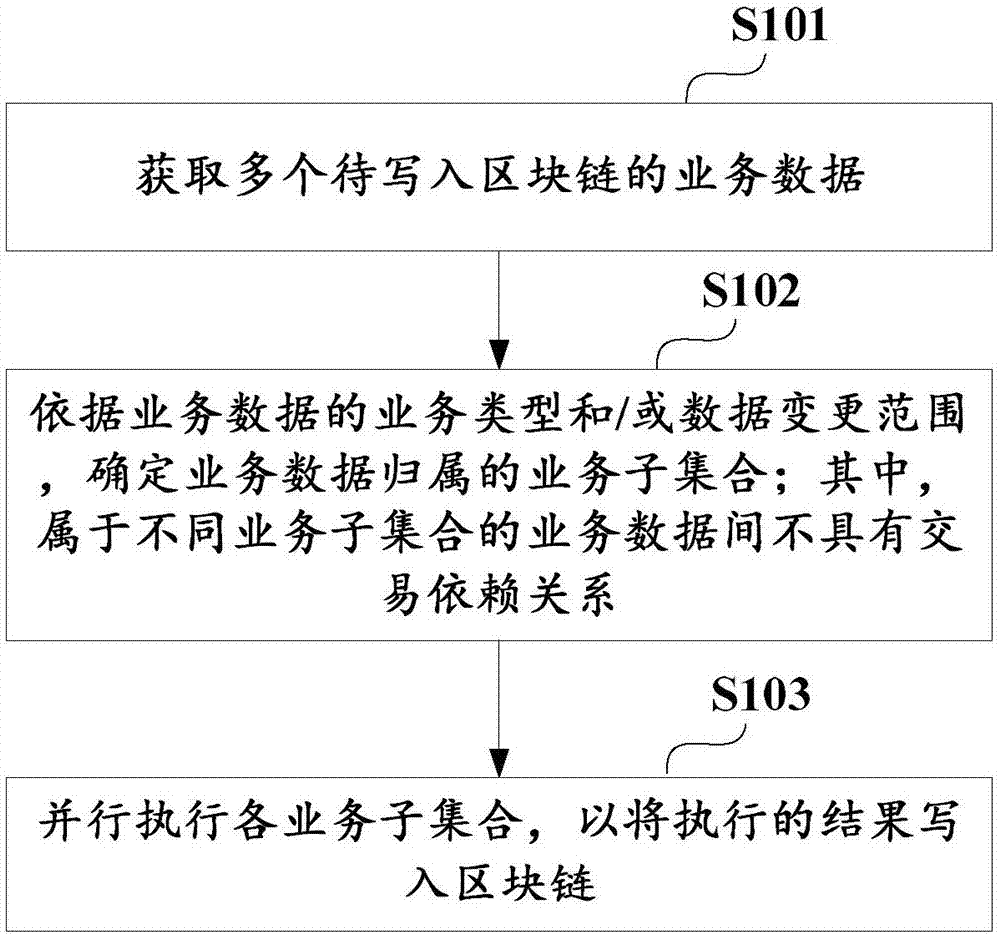
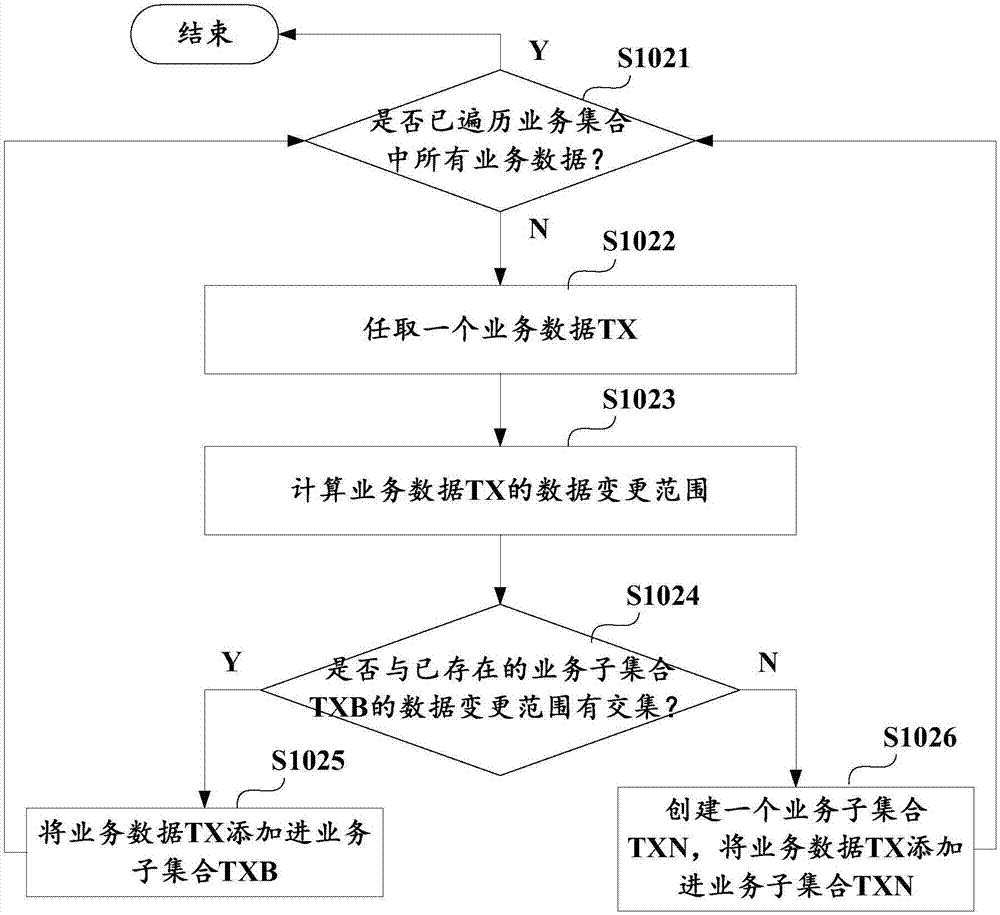
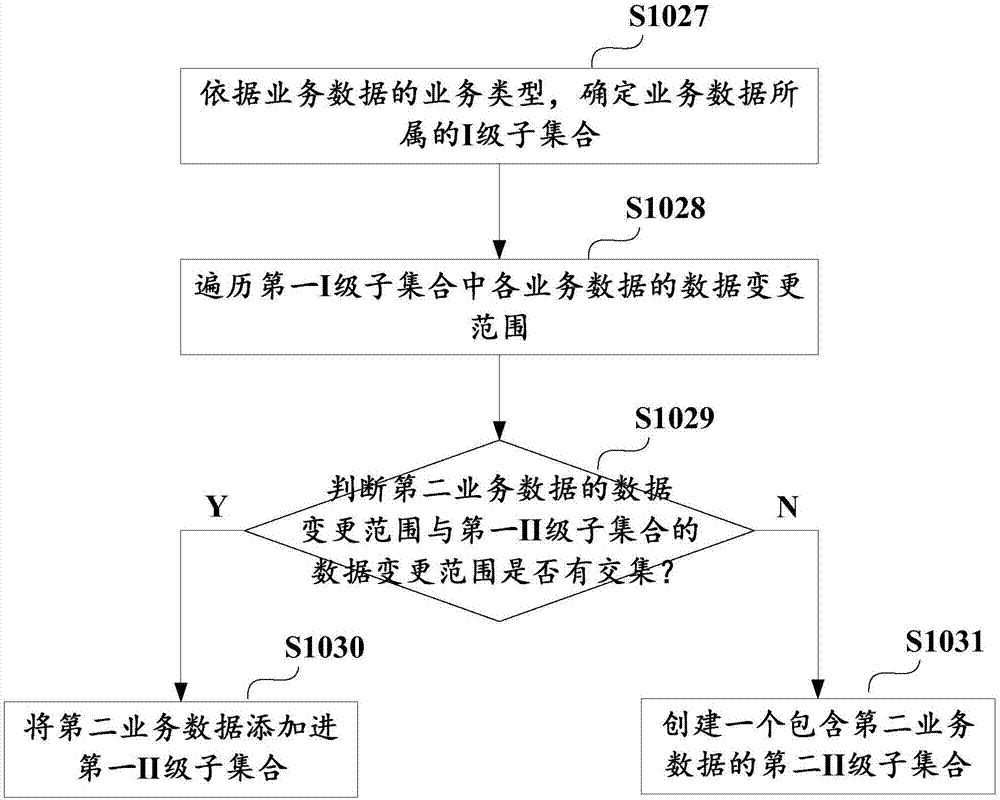
Method and apparatus for writing business data of block chain, and business subset determination method
ActiveCN106980649ADoes not affect consistencyEnsure consistencyOperational speed enhancementDatabase distribution/replicationExtensibilityBusiness data
The invention discloses a method for writing business data of a block chain. The method comprises the steps of obtaining multiple pieces of business data to be written in the block chain; according to business types and / or a data change range of the business data, determining business subsets which the business data belongs to, wherein the business data belonging to different business subsets does not have a transaction dependency relationship; and executing the business subsets in parallel, thereby writing executive results in the block chain. The invention furthermore discloses an apparatus for writing the business data of the block chain, and a business subset determination method. According to the method and the apparatus, parallel execution of the business data free of the transaction dependency relationship can be realized, so that the cost of improving data processing execution efficiency is reduced and the expandability is improved.
Owner:ADVANCED NEW TECH CO LTD
Parallel computation method and system
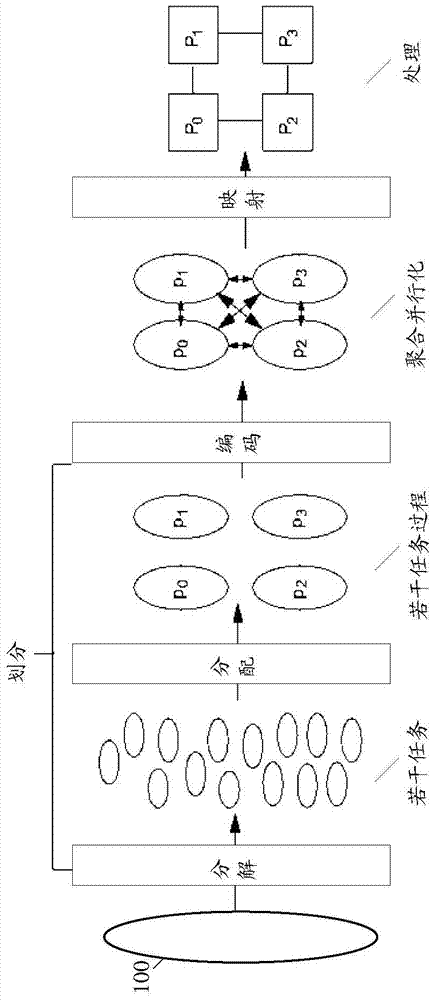
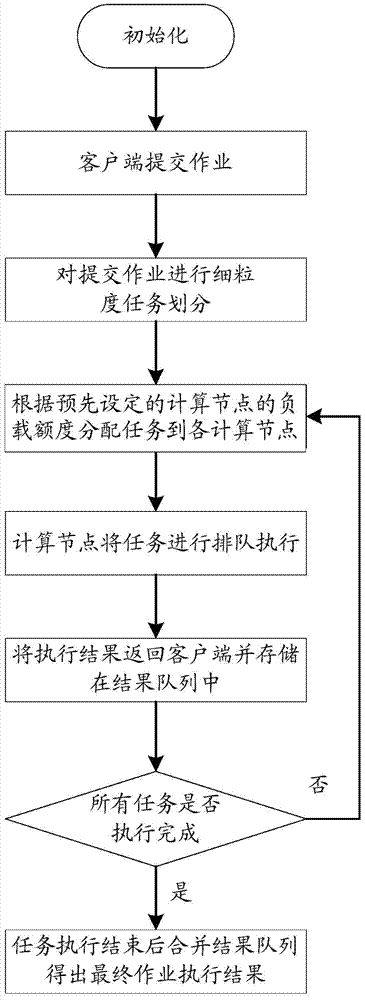
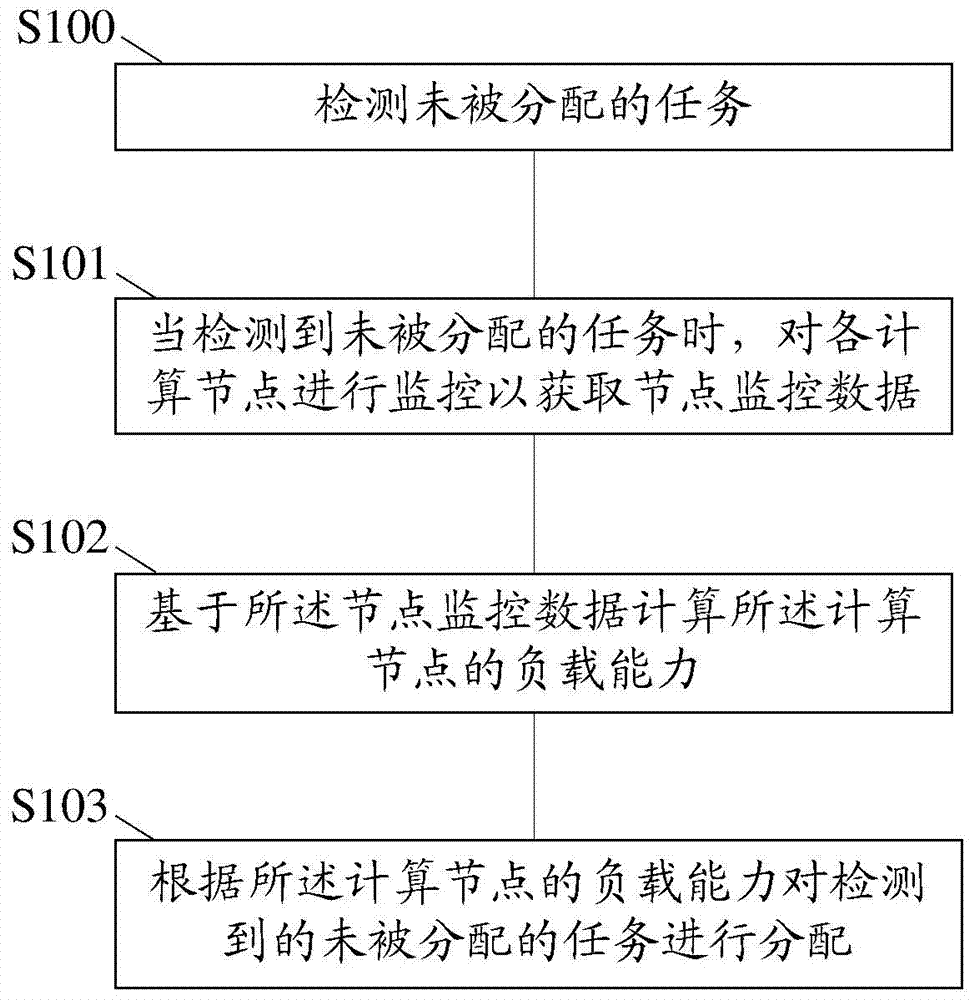
InactiveCN103617086ARealize a reasonable distributionImplement resource monitoringResource allocationParallel computingComputing systems
The invention relates to a parallel computation method and system. The method includes: monitoring each computing node to acquire node monitoring data; calculating load capacity of each computing node according to the node monitoring data; assigning tasks to be assigned according to the load capacities of the computing nodes. Correspondingly, the system comprises a node monitoring unit, a task load management unit and a task scheduling unit. Through the application of the technical scheme, task can be reasonably assigned during parallel computation and parallel computation can be executed more efficiently.
Owner:NEUSOFT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com