Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
20917 results about "Virus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A virus is a small infectious agent that replicates only inside the living cells of an organism. Viruses can infect all types of life forms, from animals and plants to microorganisms, including bacteria and archaea.
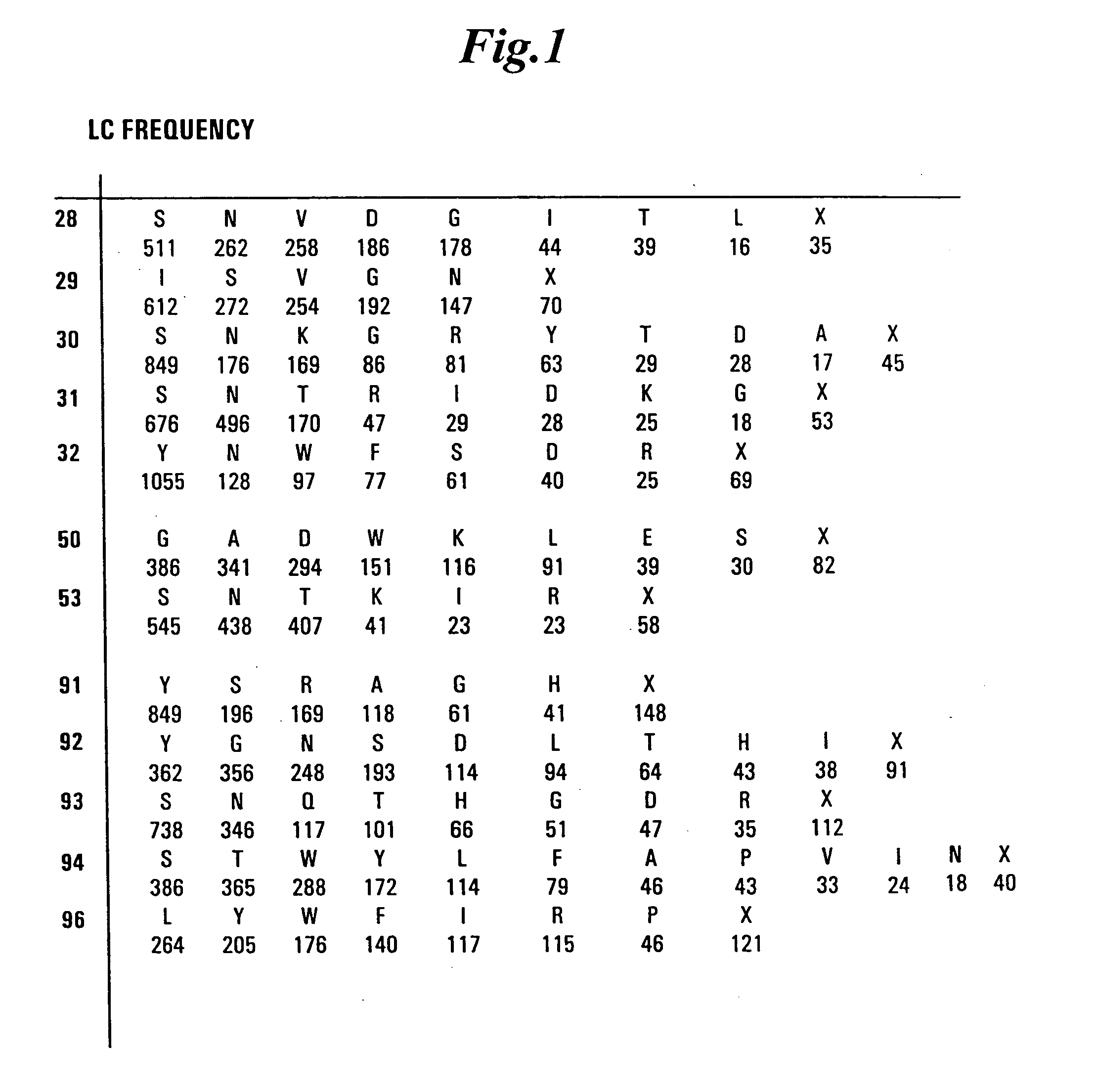
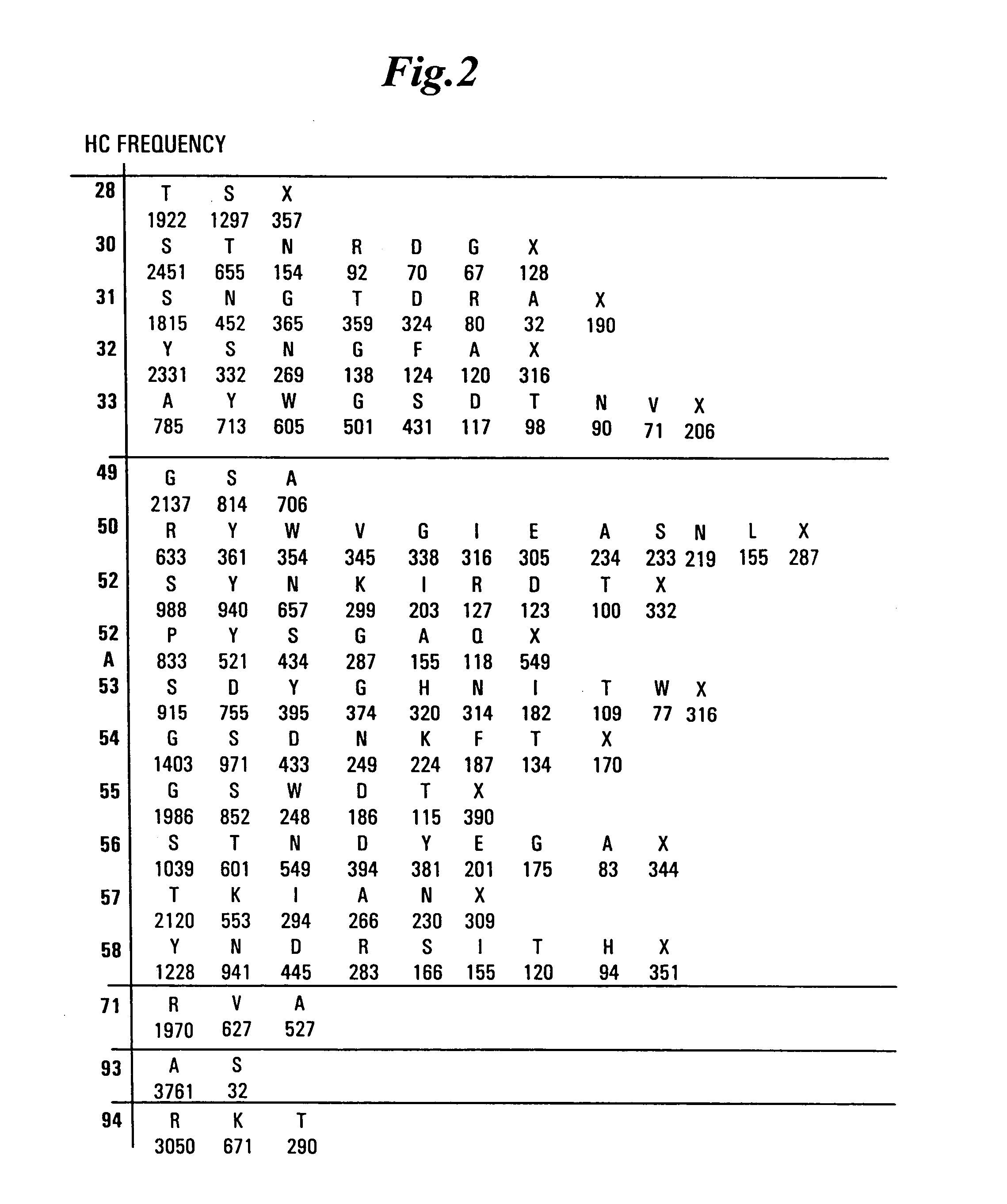
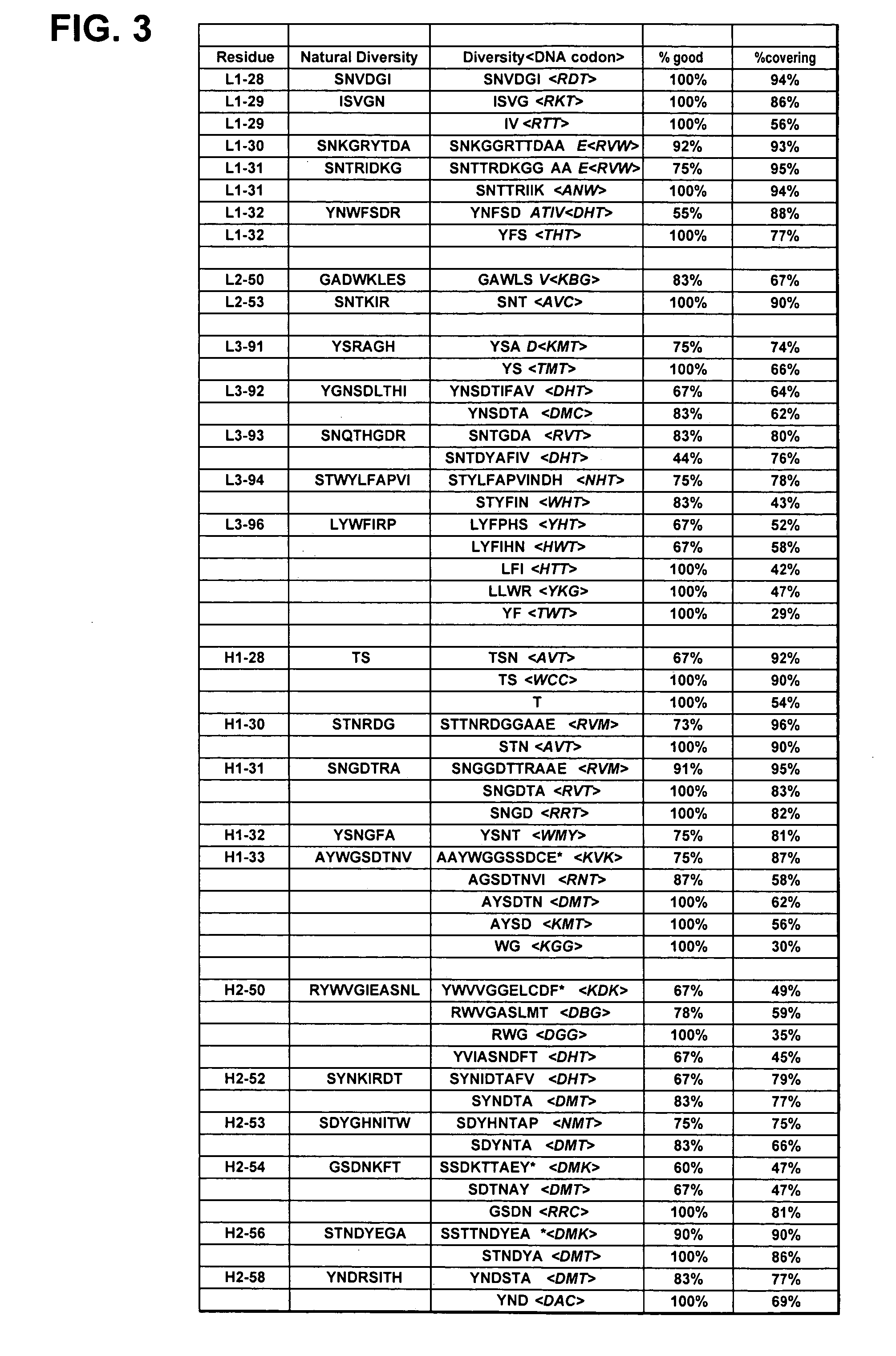
Synthetic antibody phage libraries
InactiveUS20050079574A1High-quality target binding characteristicGenerate efficientlyAntibody mimetics/scaffoldsImmunoglobulins against cell receptors/antigens/surface-determinantsHeterologousIntravenous gammaglobulin
The invention provides immunoglobulin polypeptides comprising variant amino acids in CDRs of antibody variable domains. In one embodiment, the polypeptide is a variable domain of a monobody and has a variant CDRH3 region. These polypeptides provide a source of great sequence diversity that can be used as a source for identifying novel antigen binding polypeptides. The invention also provides these polypeptides as fusion polypeptides to heterologous polypeptides such as at least a portion of phage or viral coat proteins, tags and linkers. Libraries comprising a plurality of these polypeptides are also provided. In addition, methods of and compositions for generating and using these polypeptides and libraries are provided.
Owner:GENENTECH INC
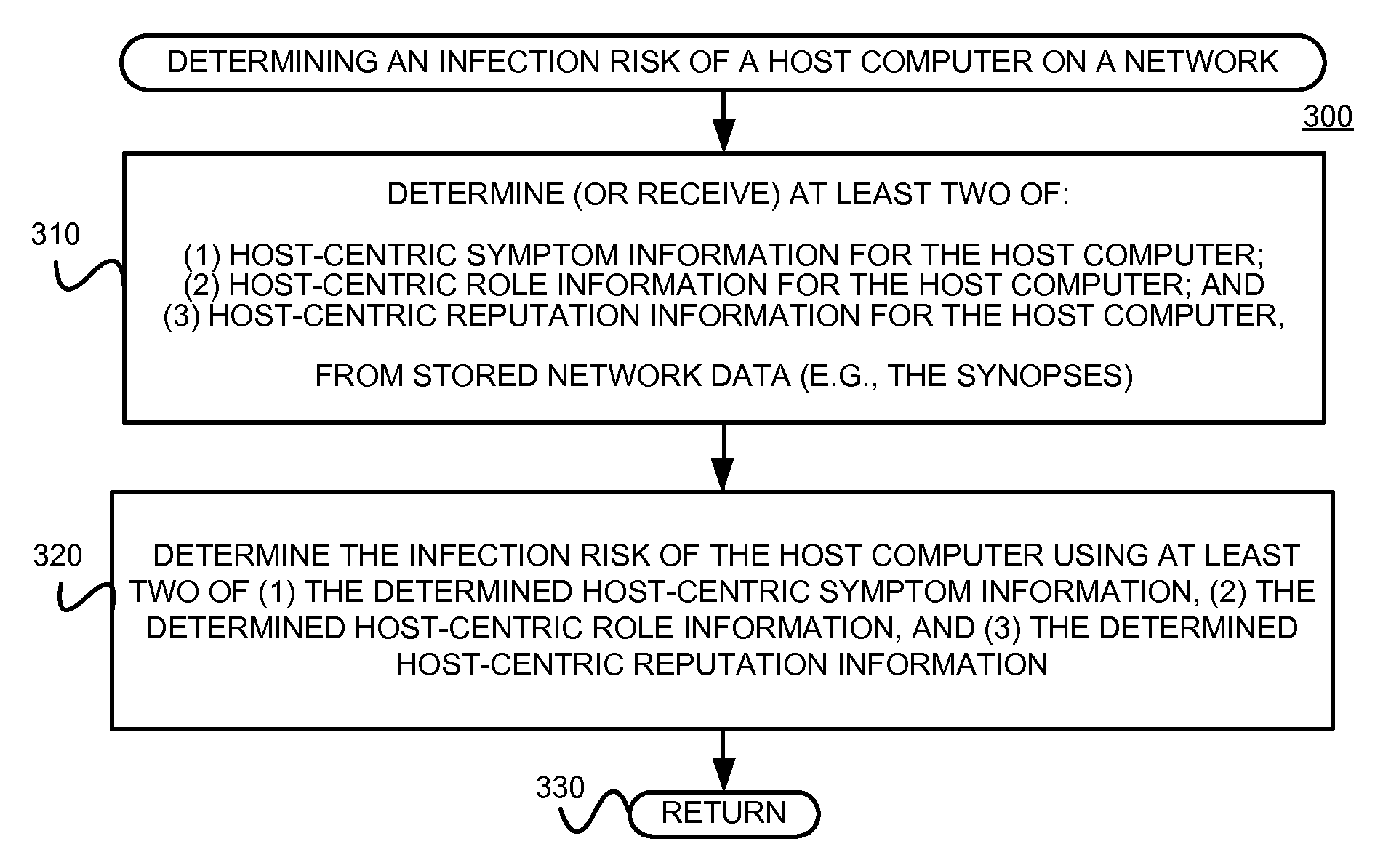
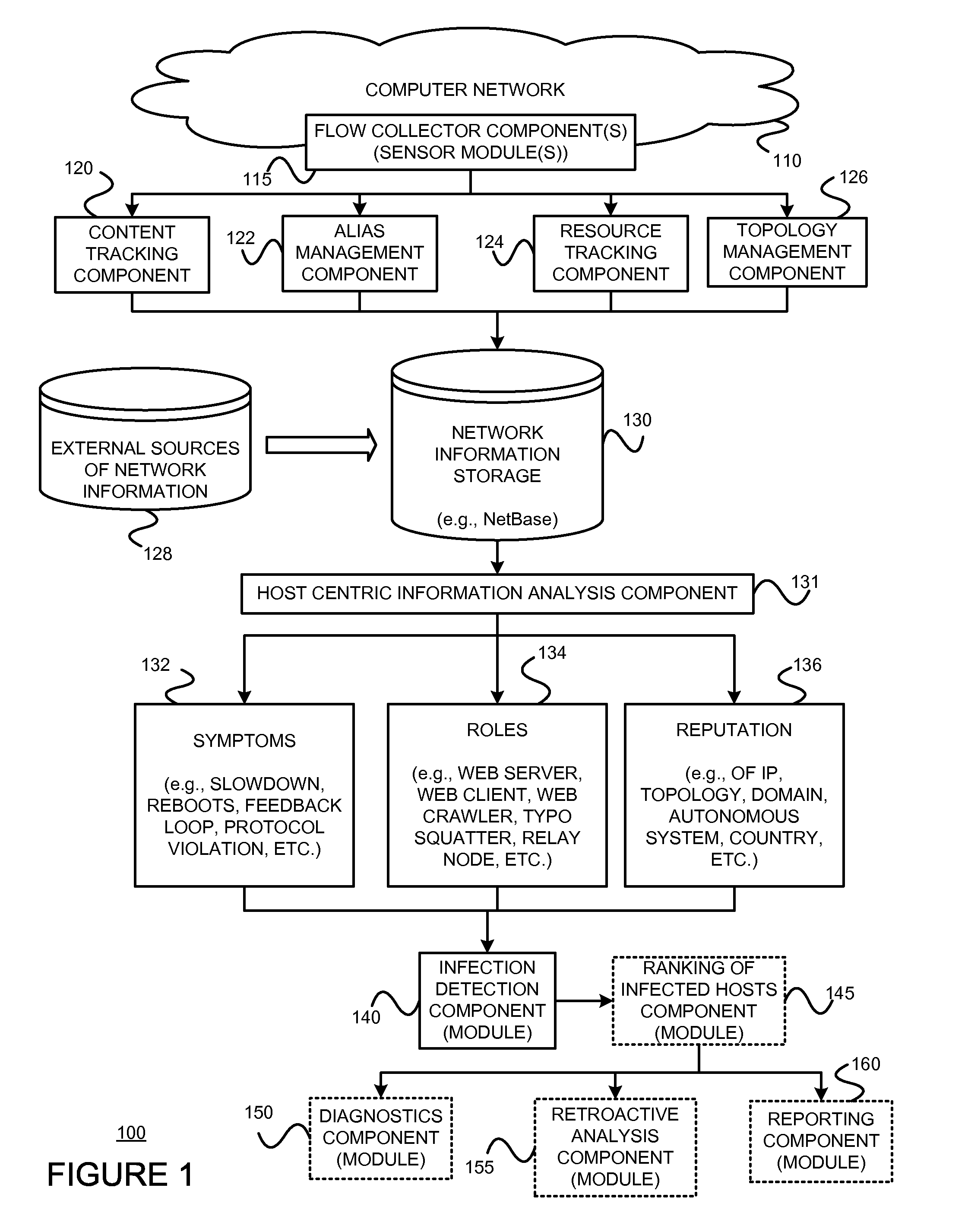
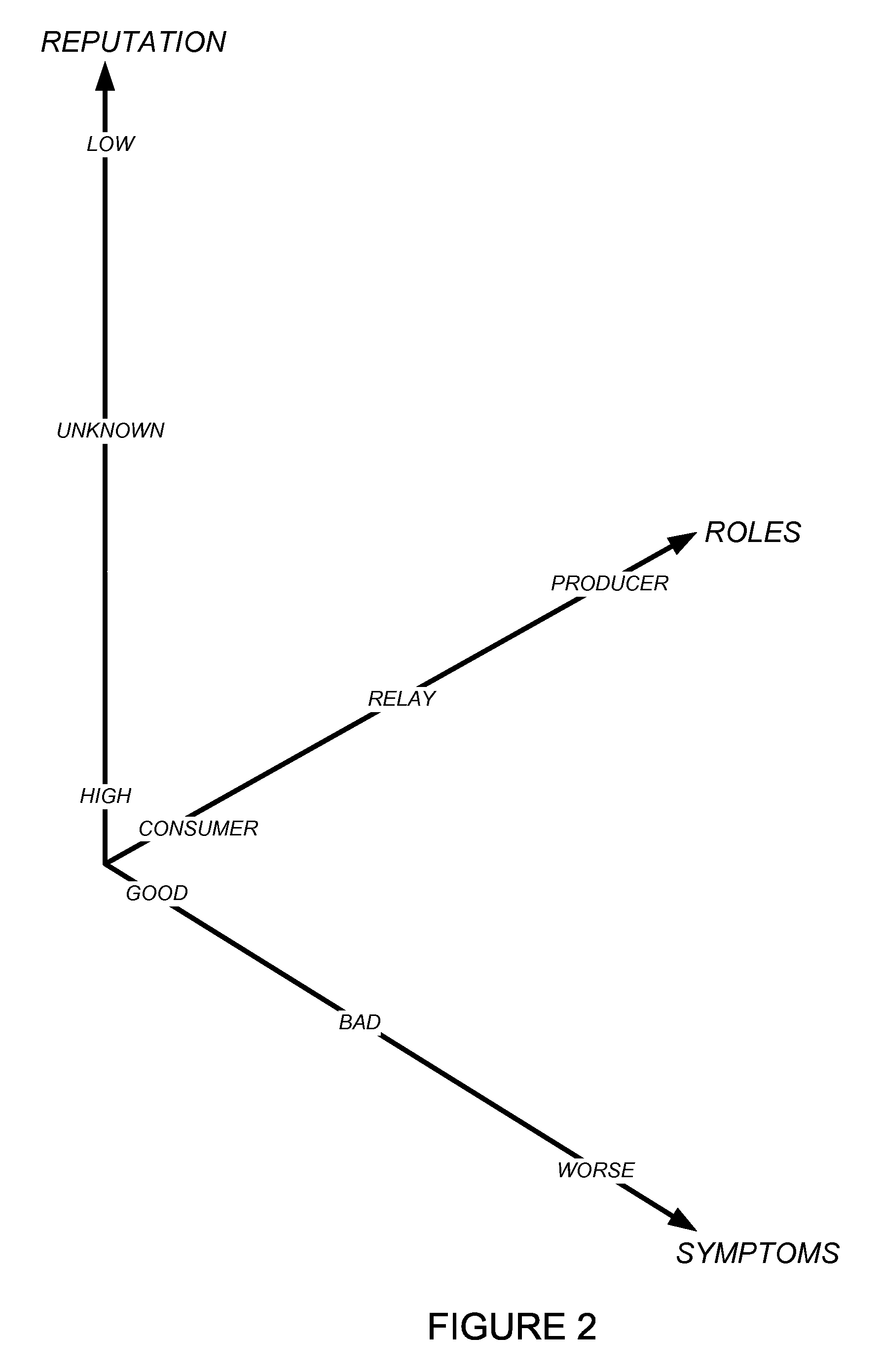
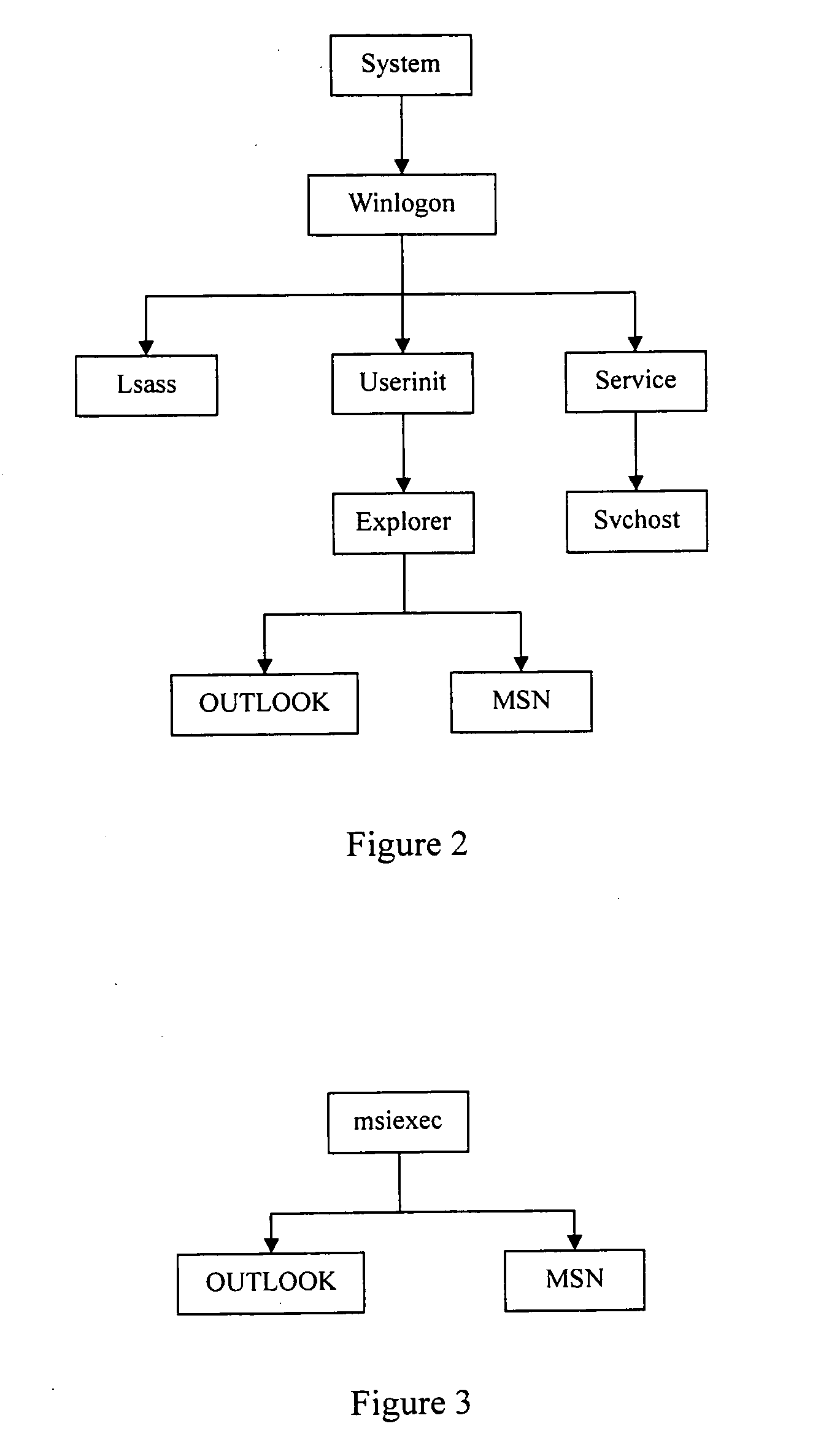
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
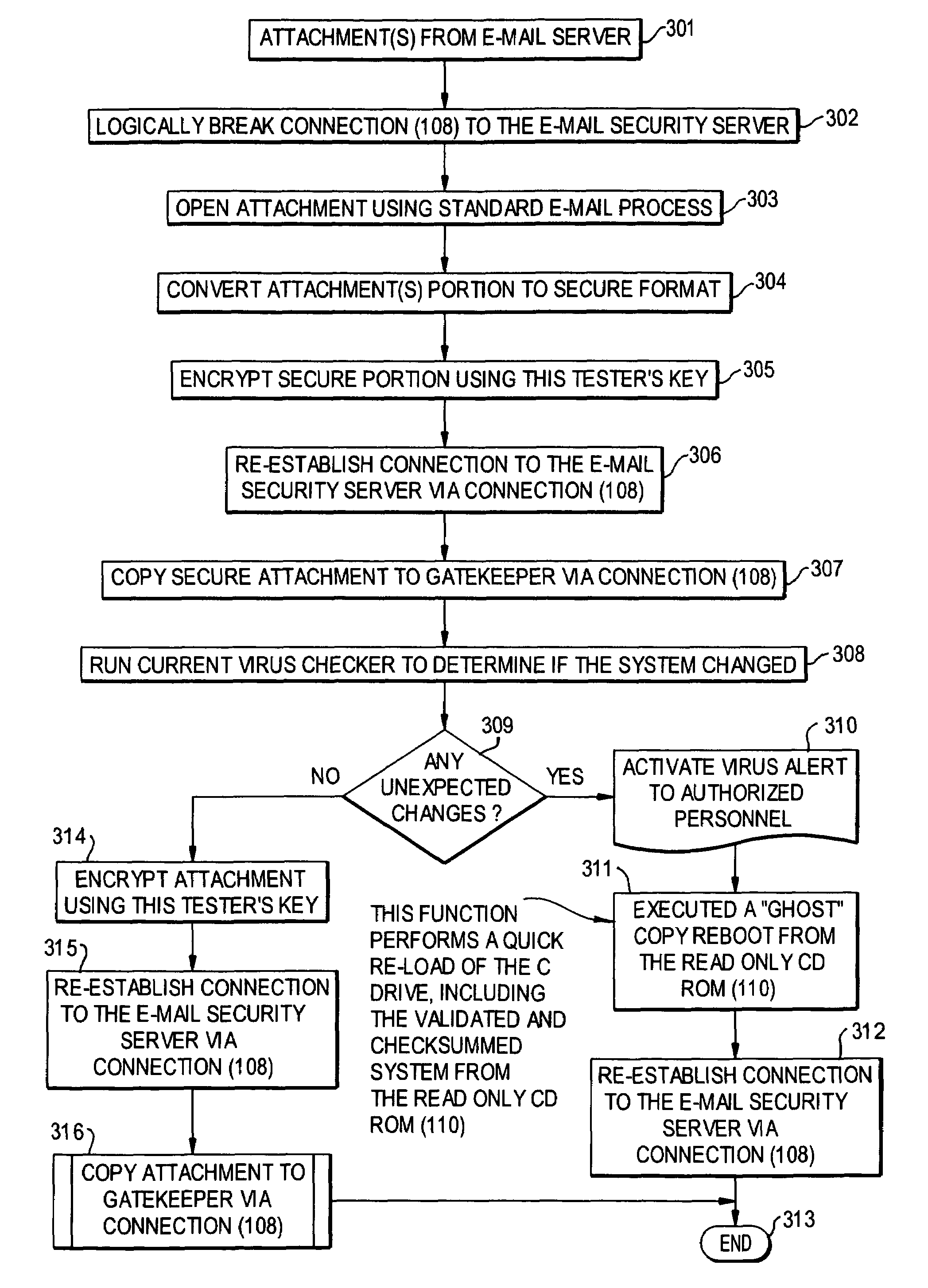
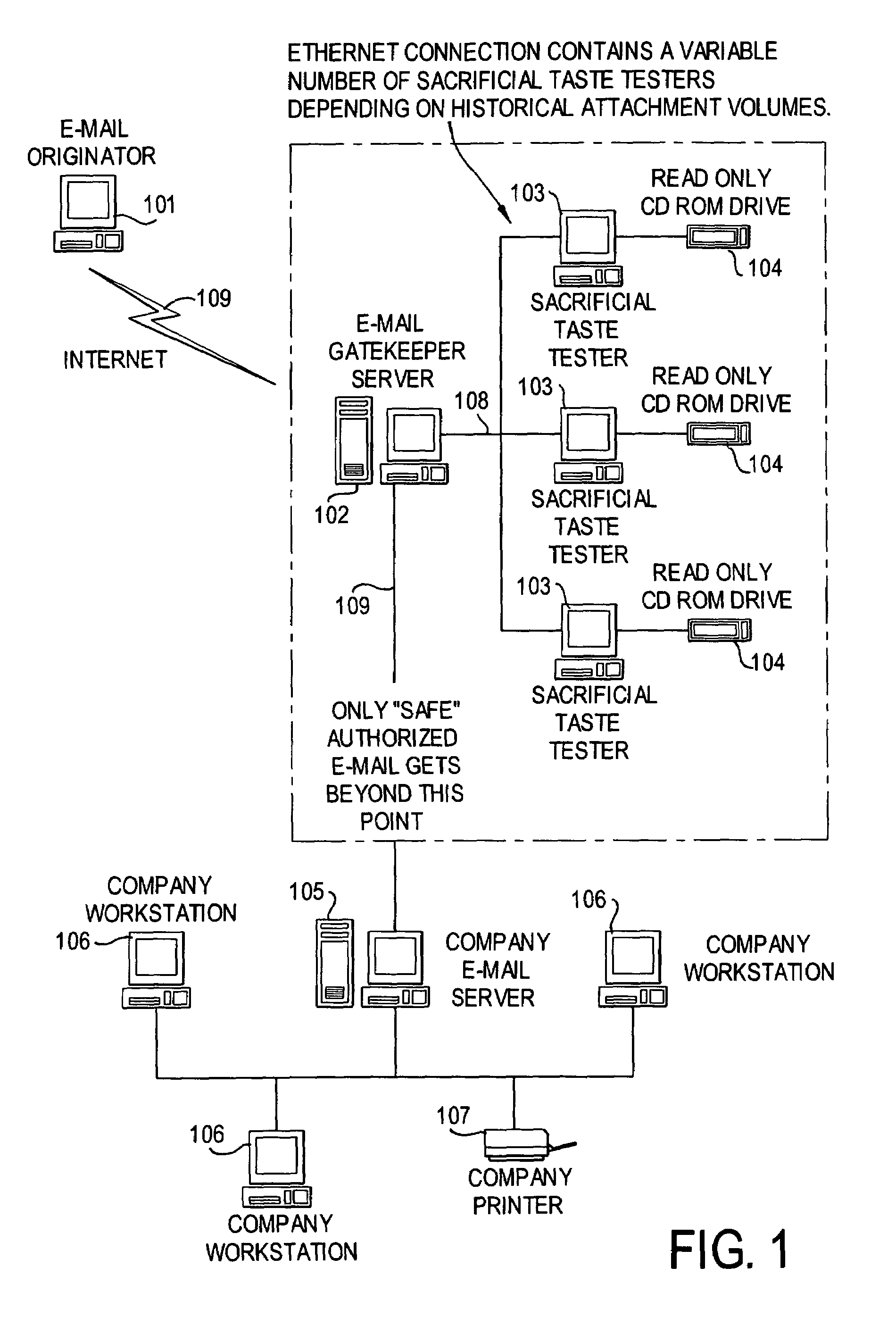
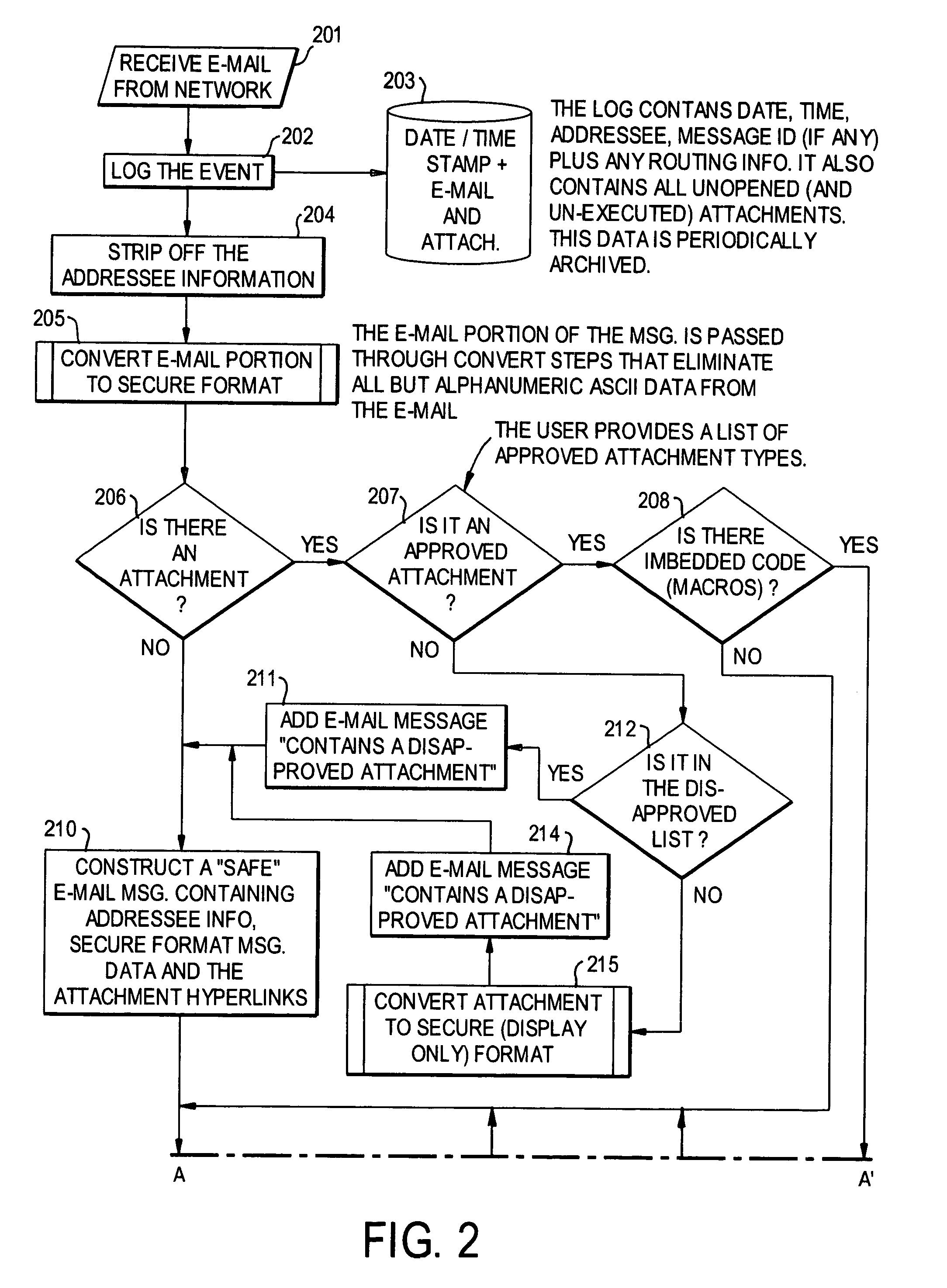
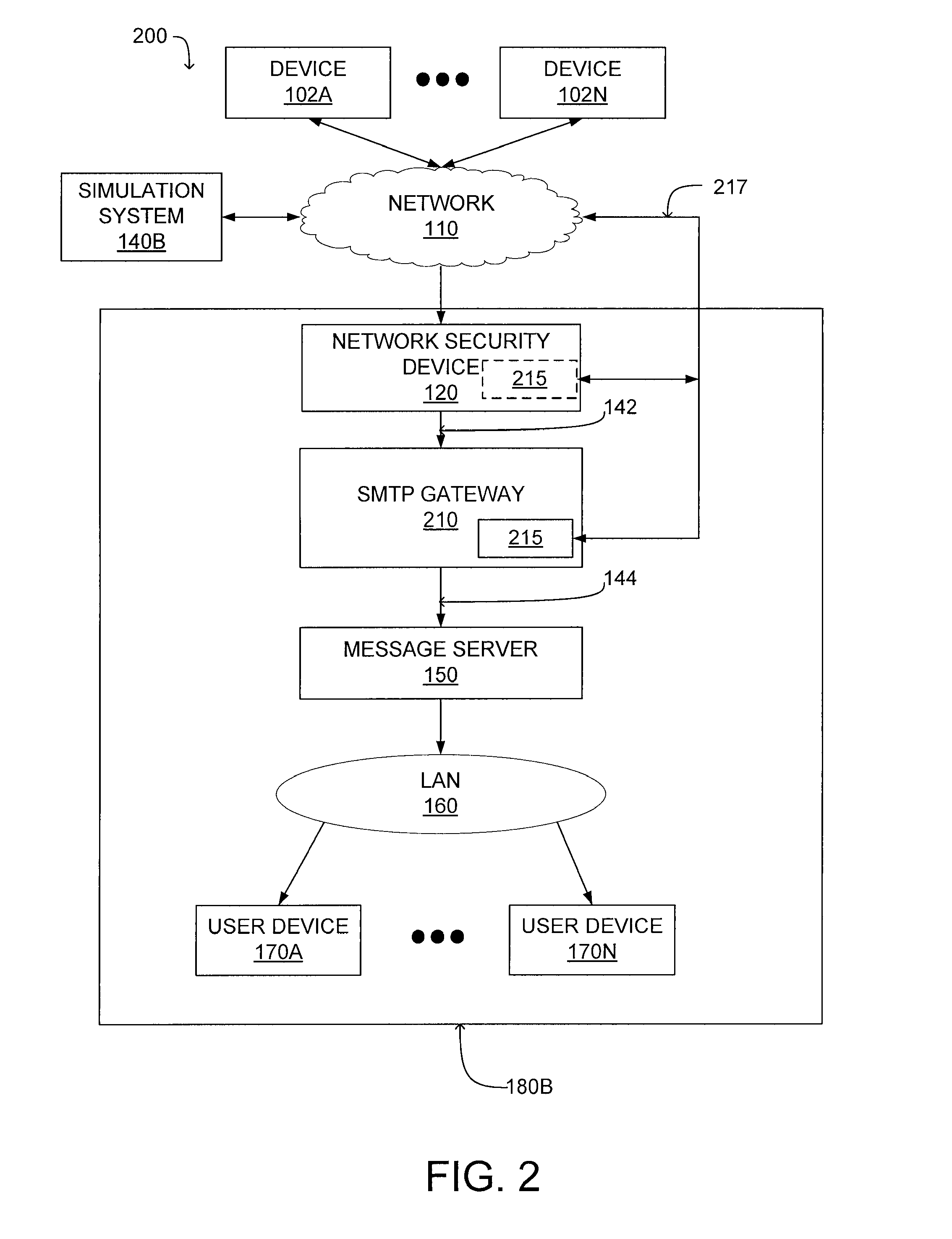
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
Oxazolo, thiazolo and selenazolo [4,5-c]-quinolin-4-amines and analogs thereof
Thiazolo-, oxazolo- and selenazolo[4,5-c]quinolin-4-amines and analogs thereof are described including methods of manufacture and the use of novel intermediates. The compounds are immunomodulators and induce cytokine biosynthesis, including interferon and / or tumor biosynthesis, necrosis factor, and inhibit the T-helper-type 2 immune response. The compounds are further useful in the treatment of viral and neoplastic diseases.
Owner:3M INNOVATIVE PROPERTIES CO
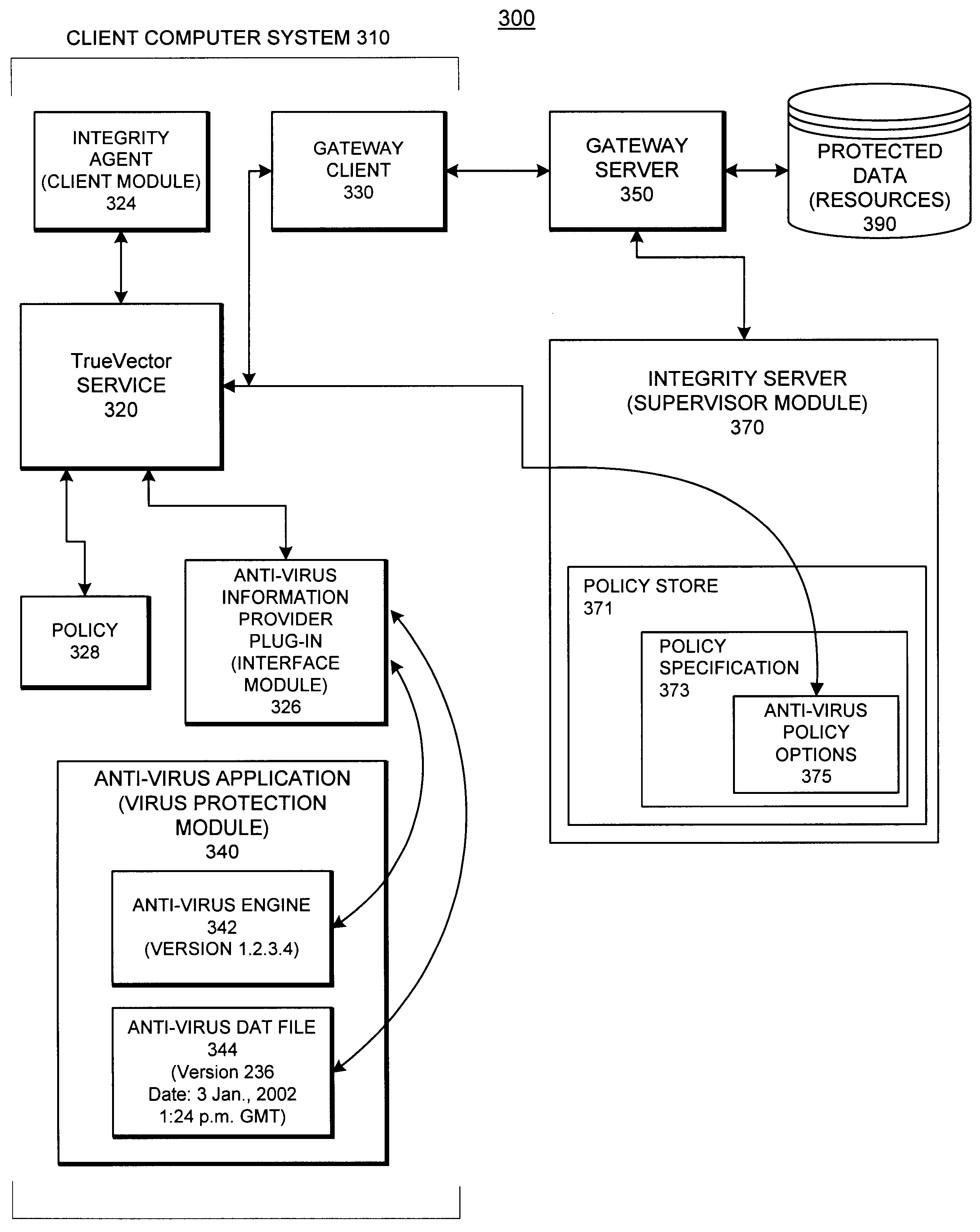
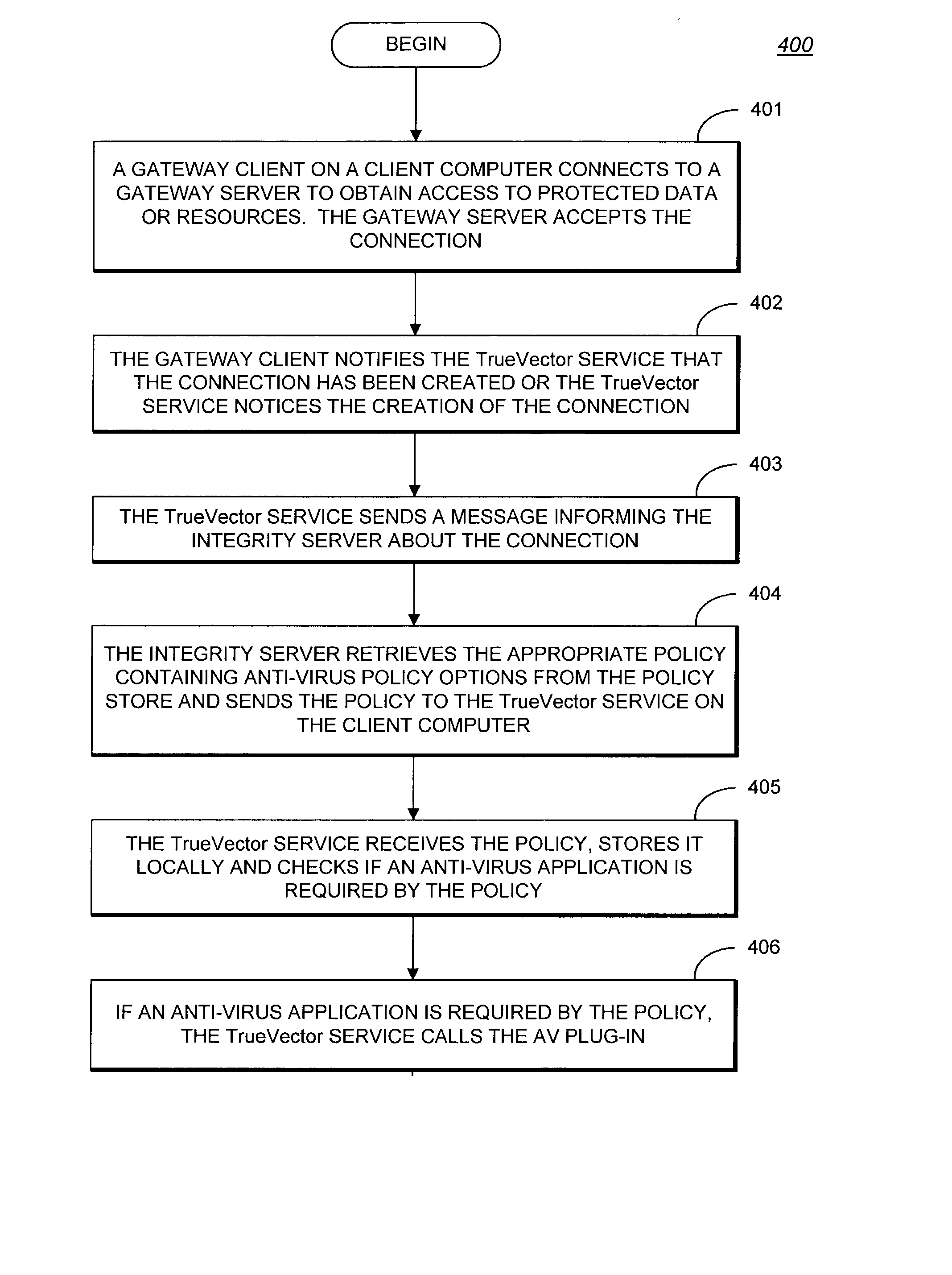
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
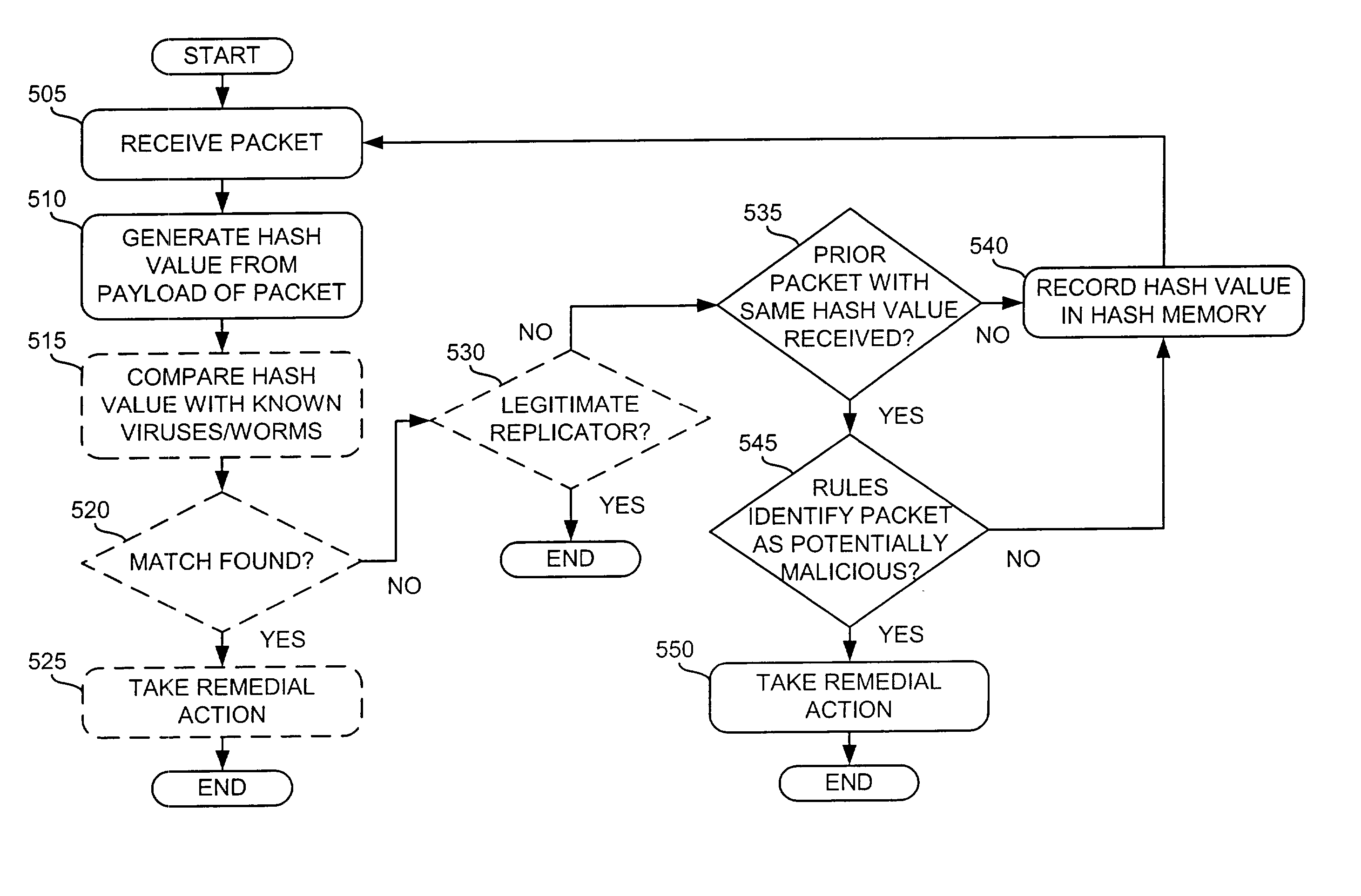
Hash-based systems and methods for detecting, preventing, and tracing network worms and viruses
A system (126-129) detects transmission of potentially malicious packets. The system (126-129) receives packets and generates hash values corresponding to each of the packets. The system (126-129) may then compare the generated hash values to hash values corresponding to prior packets. The system (126-129) determines that one of the packets is a potentially malicious packet when the generated hash value corresponding to the one packet matches one of the hash values corresponding to one of the prior packets and the one prior packet was received within a predetermined amount of time of the one packet. The system (126-129) may also facilitate the tracing of the path taken by a potentially malicious packet. In this case, the system (126-129) may receive a message that identifies a potentially malicious packet, generate hash values from the potentially malicious packet, and determine whether one or more of the generated hash values match hash values corresponding to previously-received packets. The system (126-129) may then identify the potentially malicious packet as one of the previously-received packets when one or more of the generated hash values match the hash value corresponding to the one previously-received packet.
Owner:STRAGENT
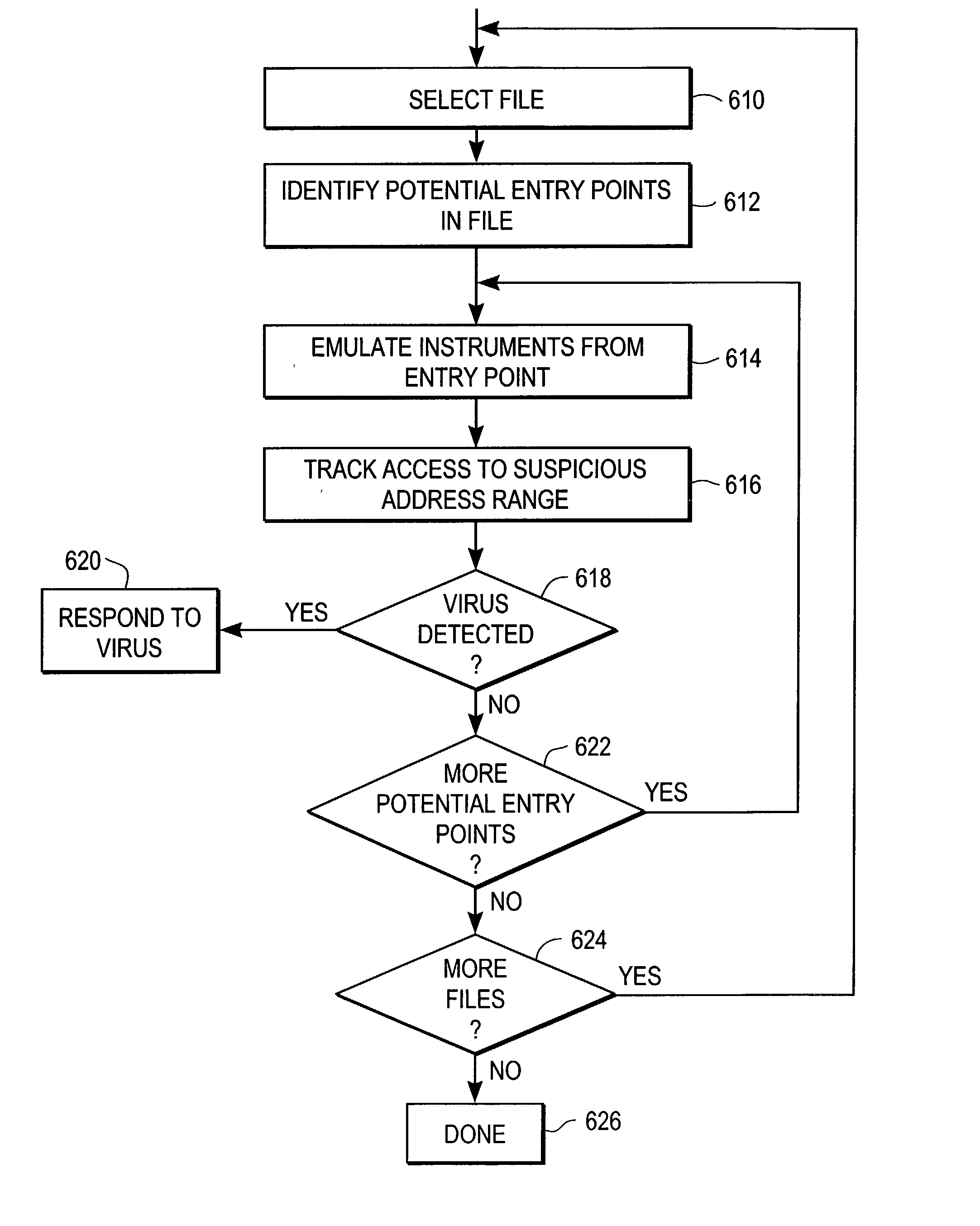
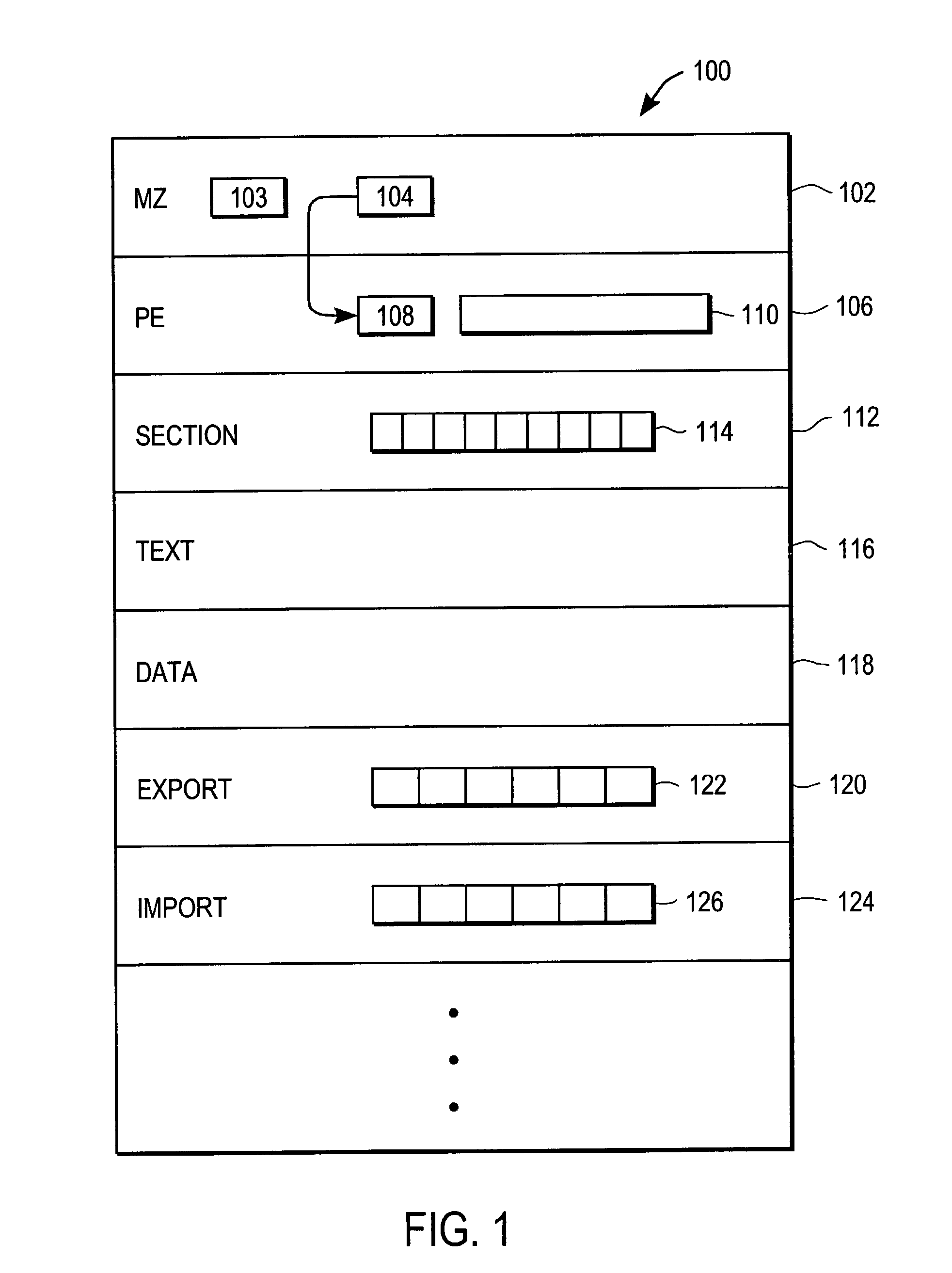
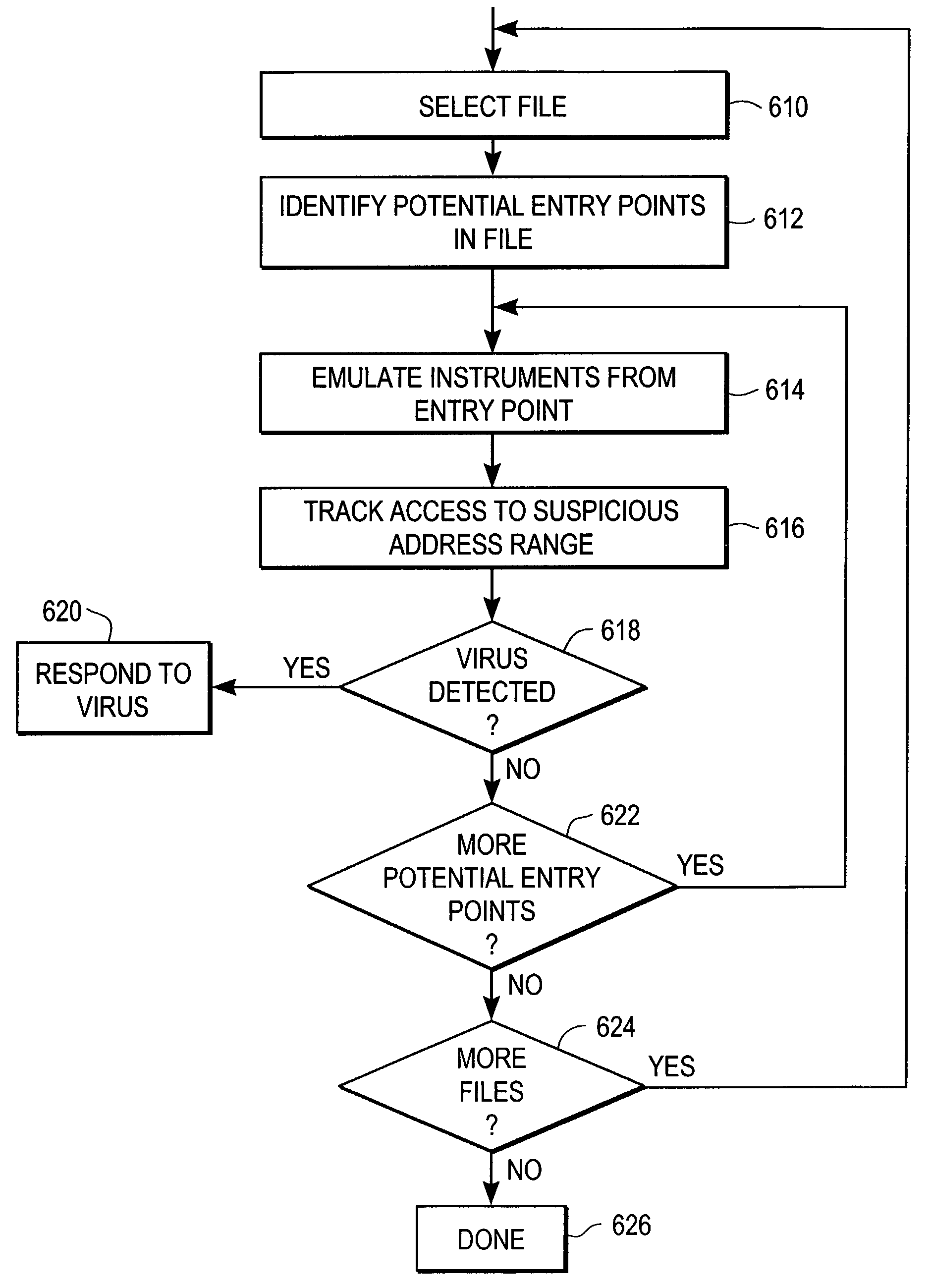
Heuristic detection of malicious computer code by page tracking
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
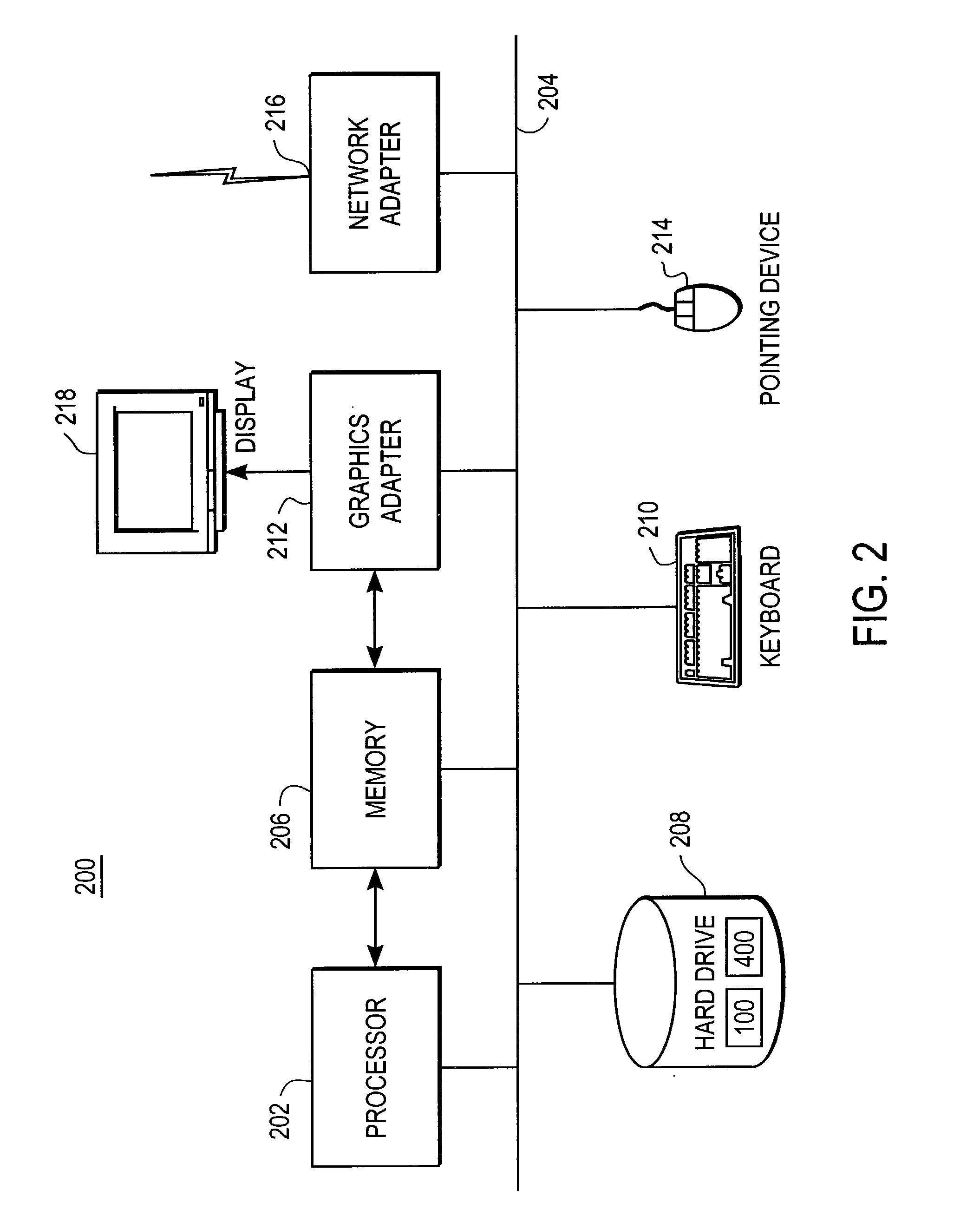
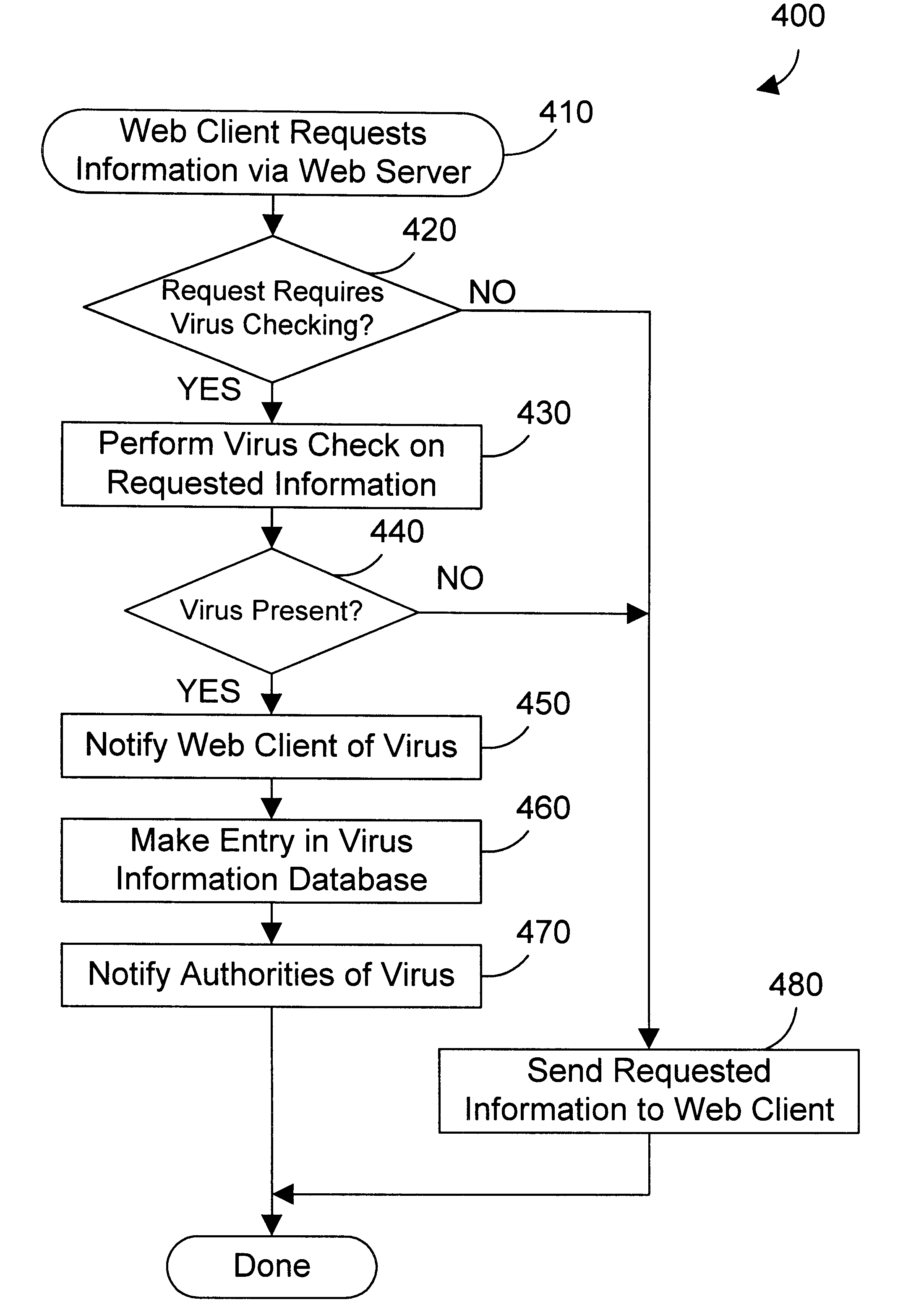
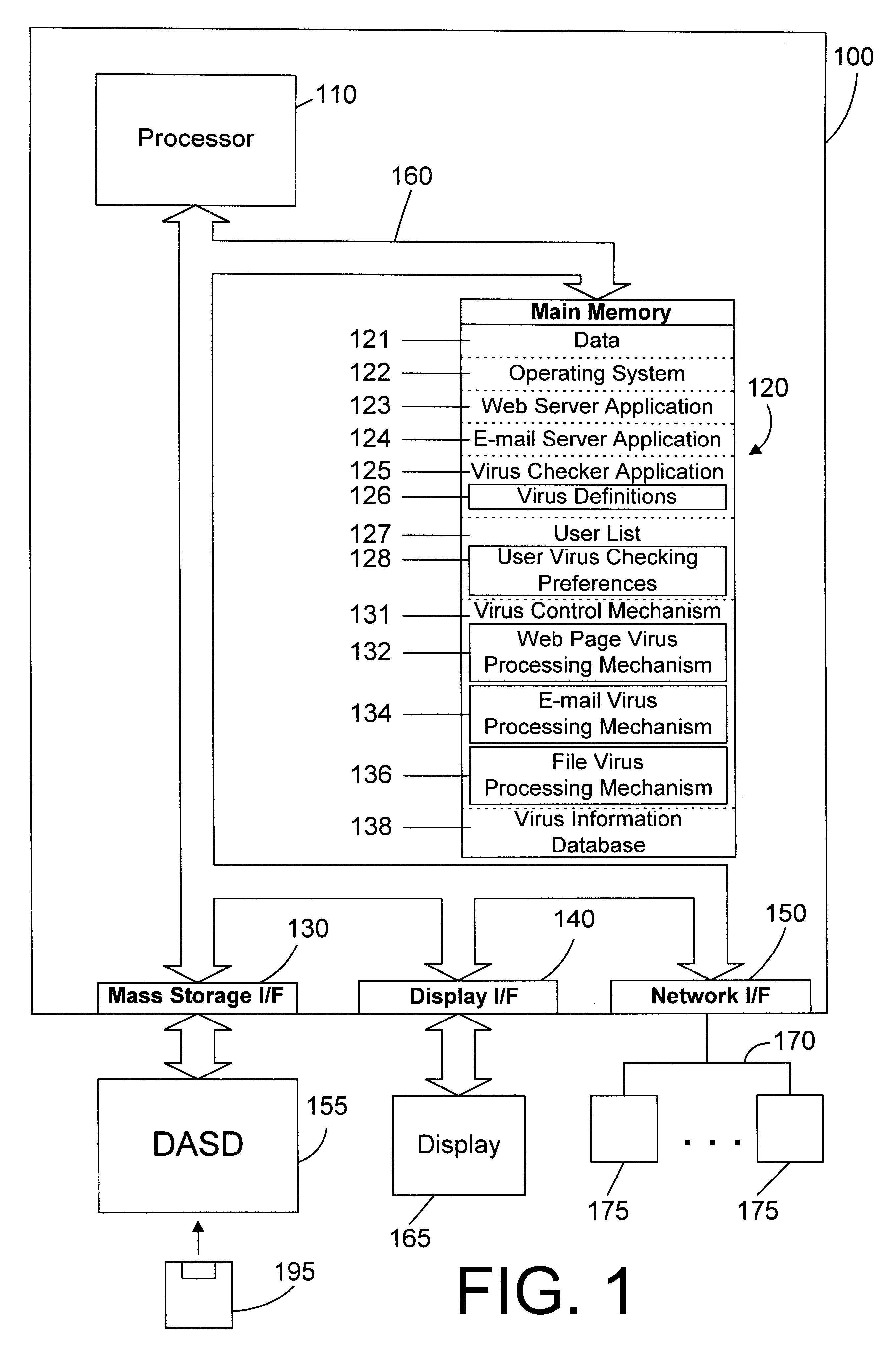
Web server apparatus and method for virus checking
InactiveUS6785732B1Eliminate needPrevent proliferationMemory loss protectionDigital data processing detailsWeb serviceUniform resource locator
A web server computer system includes a virus checker and mechanisms for checking e-mails and their attachments, downloaded files, and web sites for possible viruses. When an e-mail message contains a detected virus, the message is discarded, and both the sender and recipient are informed via e-mail that the message contained a virus. When an e-mail attachment contains a detected virus, the attachment is deleted, and the e-mail message without the attachment is sent to the web client, along with a message explaining that the e-mail message had an attachment that was automatically deleted because it had a virus. When a downloaded file contains a virus, the downloaded file is deleted, and an error message is sent to the web client to inform the web client that the requested file had a virus. When a requested web site (i.e., Uniform Resource Locator (or URL)) has been labeled as a source for a known virus, a message is sent to the web client stating that a virus may have been downloaded from that URL. In addition, if the requested URL has not been labeled as a source for a known virus, but it contains links that have been so labeled, the web page is processed before being sent to the user to identify those potentially dangerous links. In this manner a web server can perform virus checking of different types of information real-time as the information is requested by a web client. In addition, a web client may also request that the server perform virus checking on a particular drive on the web client. If this case, the web server may receive information from the web client drive, scan the information for viruses, and inform the web client whether any viruses were found. In the alternative, the web server may download a client virus checker to the web client and cause the client virus checker to be run on the web client. The preferred embodiments thus allow a virus checker on a web server to dynamically scan incoming data, and to scan web clients coupled to the web server, thereby eliminating the need for virus checking software to be installed on each web client.
Owner:FINJAN BLUE INC
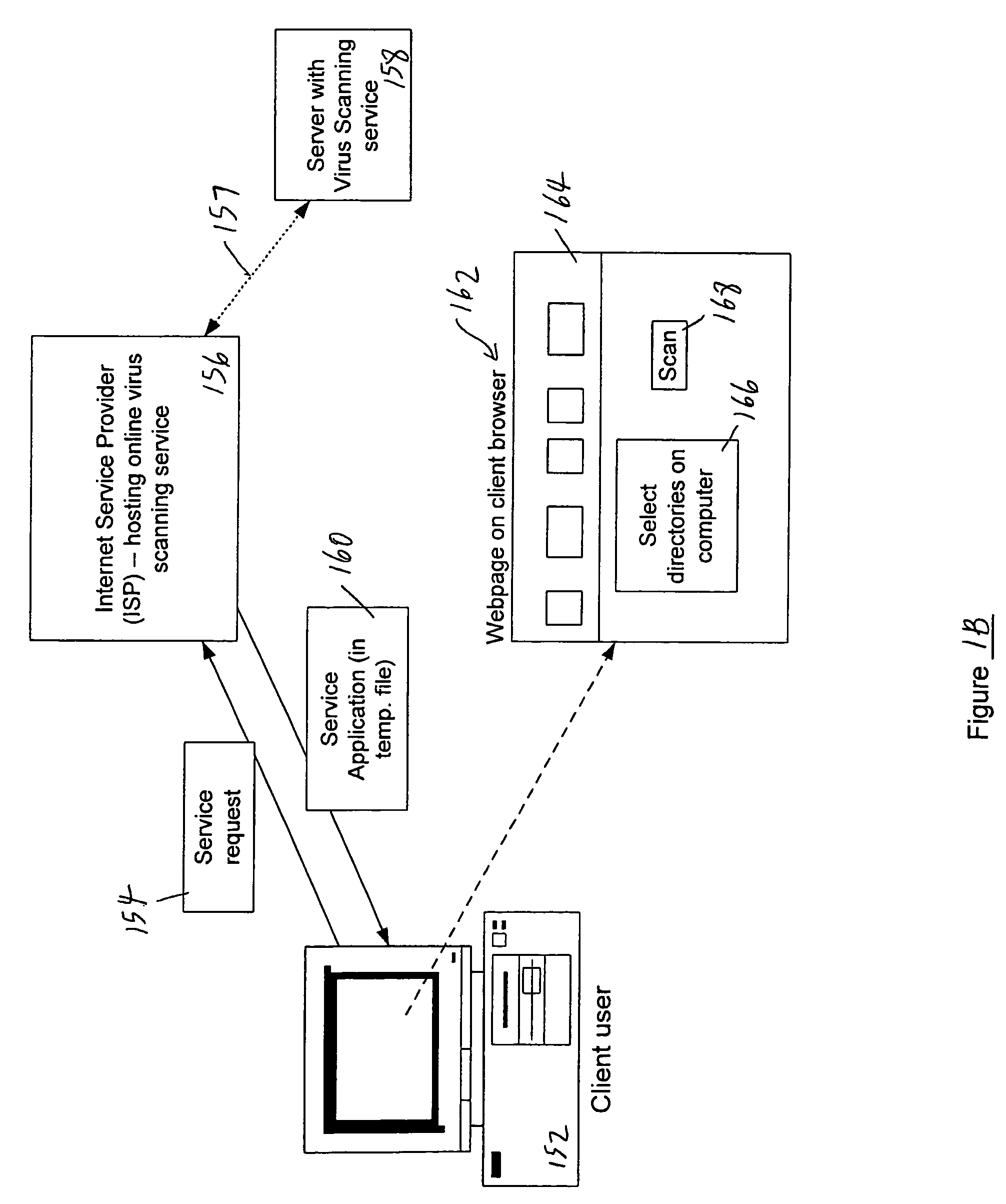
Remote computer virus scanning
InactiveUS20010005889A1Improve network securityLower the volumeMemory loss protectionDigital data processing detailsRemote computerVirus
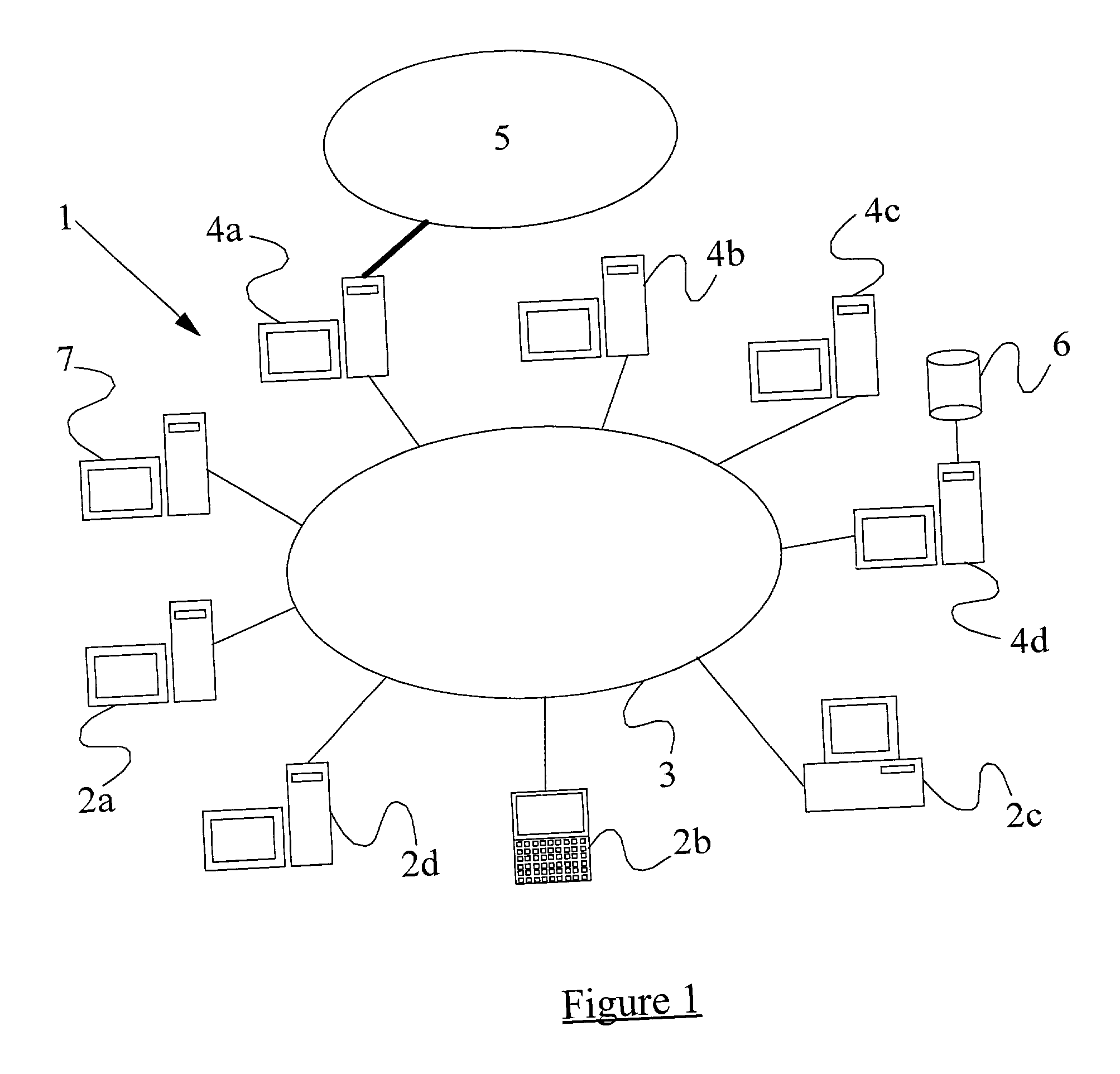
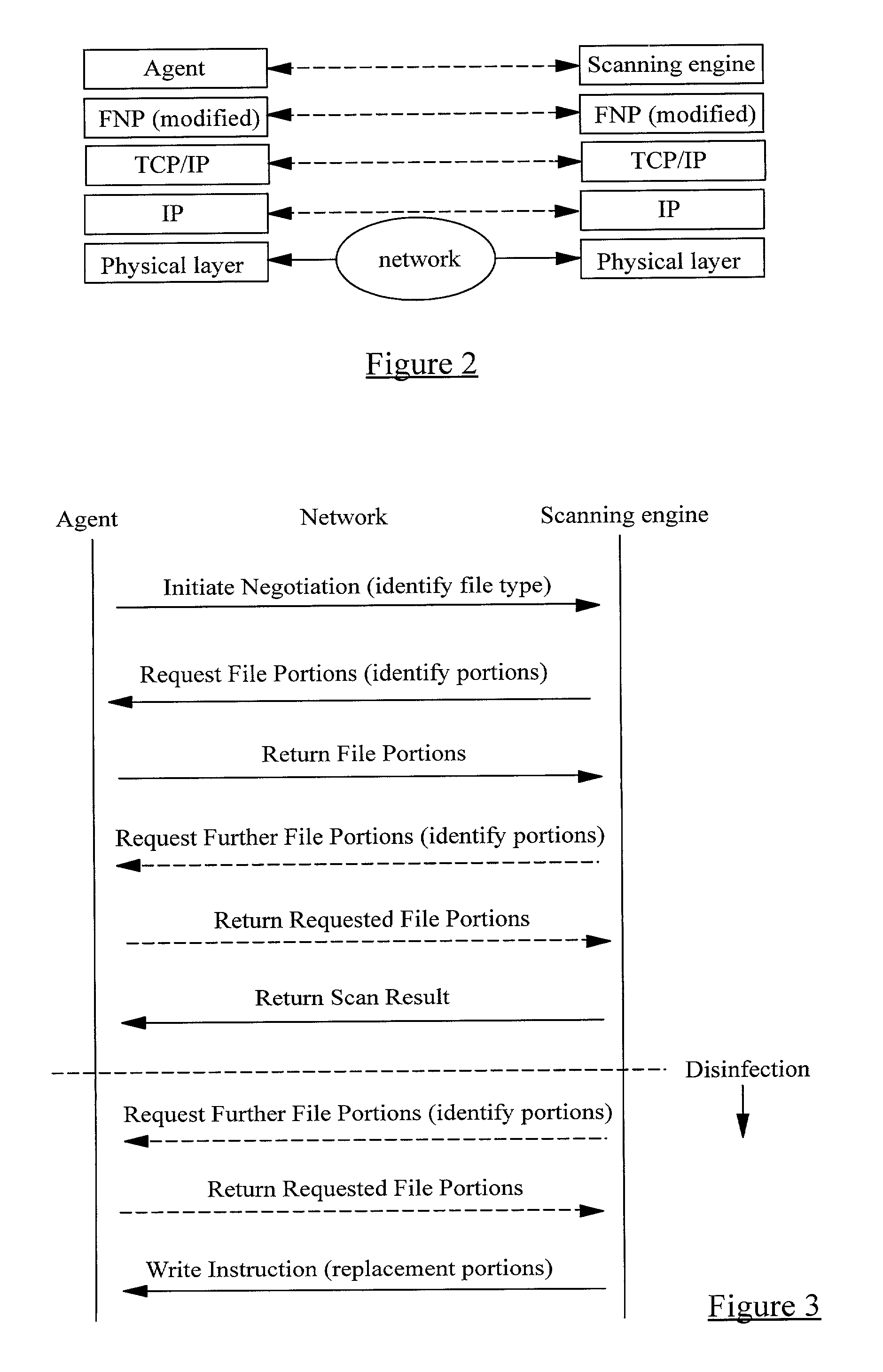
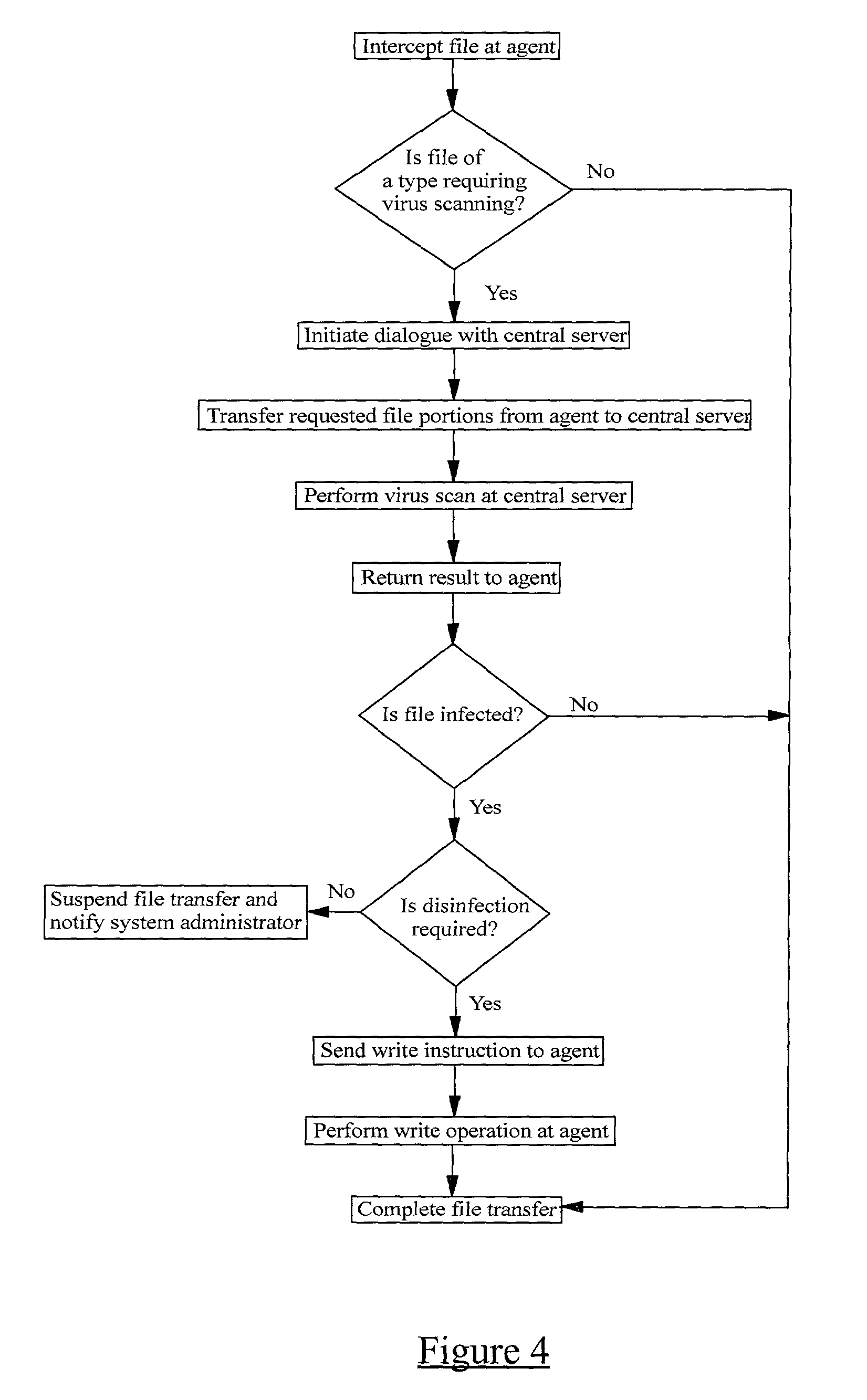
A method of scanning electronic files for computer viruses comprises identifying at a first node 4 of a computer network 1, electronic files which require to be scanned for computer viruses. The first node 4 initiates a dialogue with a second node 7 of the network 1, the second node comprising a virus scanning application. During the dialogue, the second node 7 identifies to the first node 4 one or more portions of the electronic file required by the virus scanning application. The first node 4 transfers the identified portions to the second node 7 which then carries out a virus scanning operation. The result of this operation is then returned to the first node 4.
Owner:F SECURE CORP
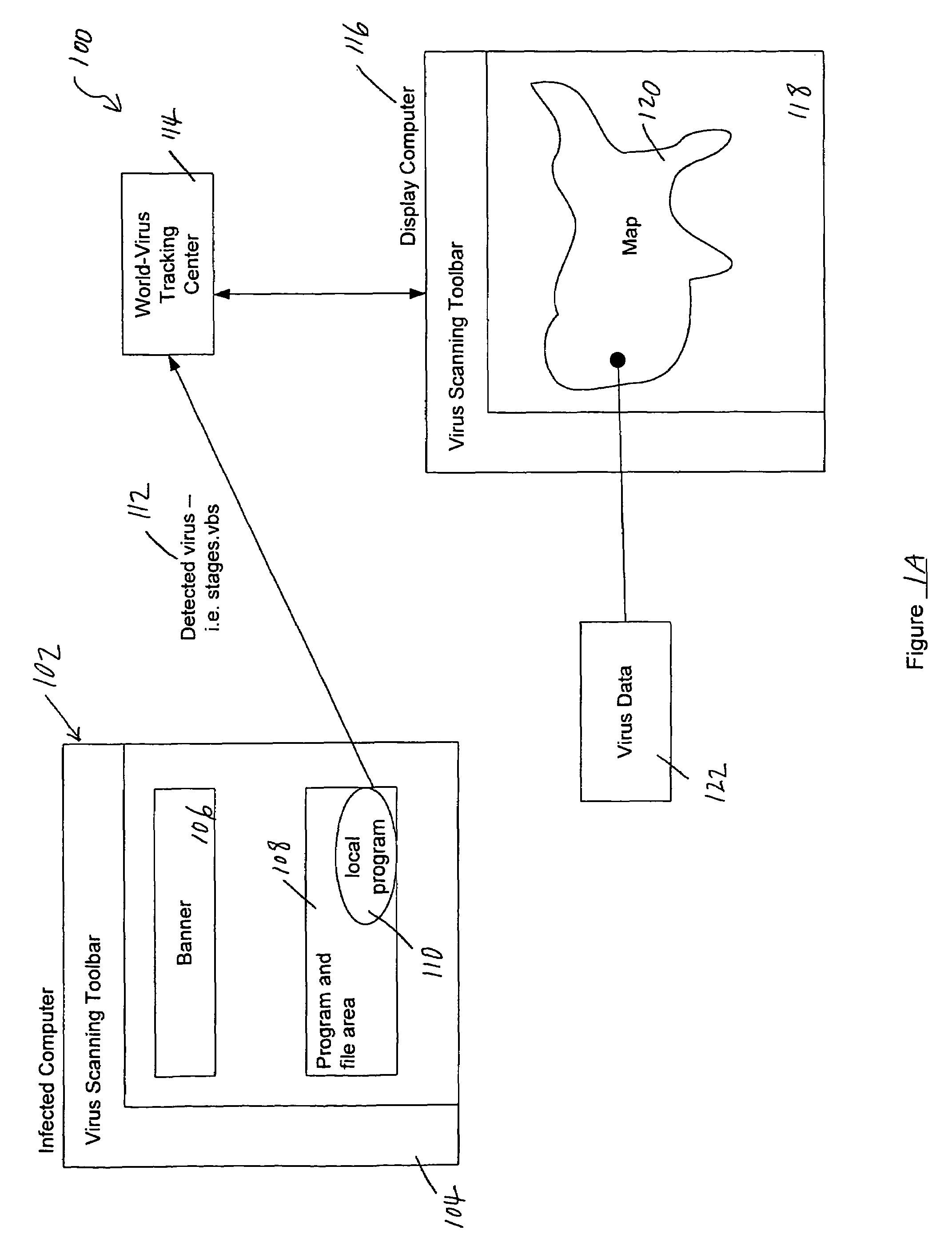
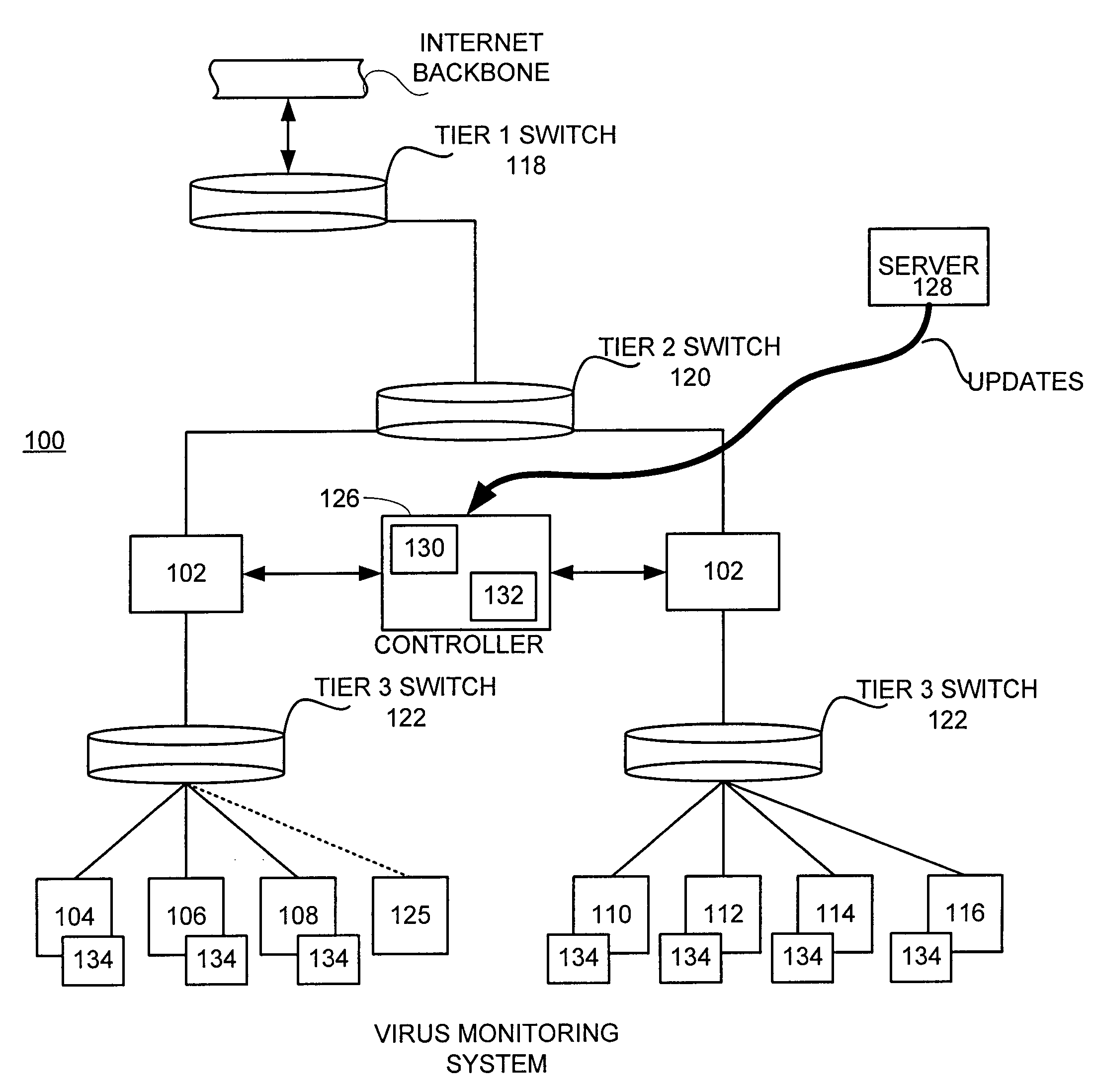
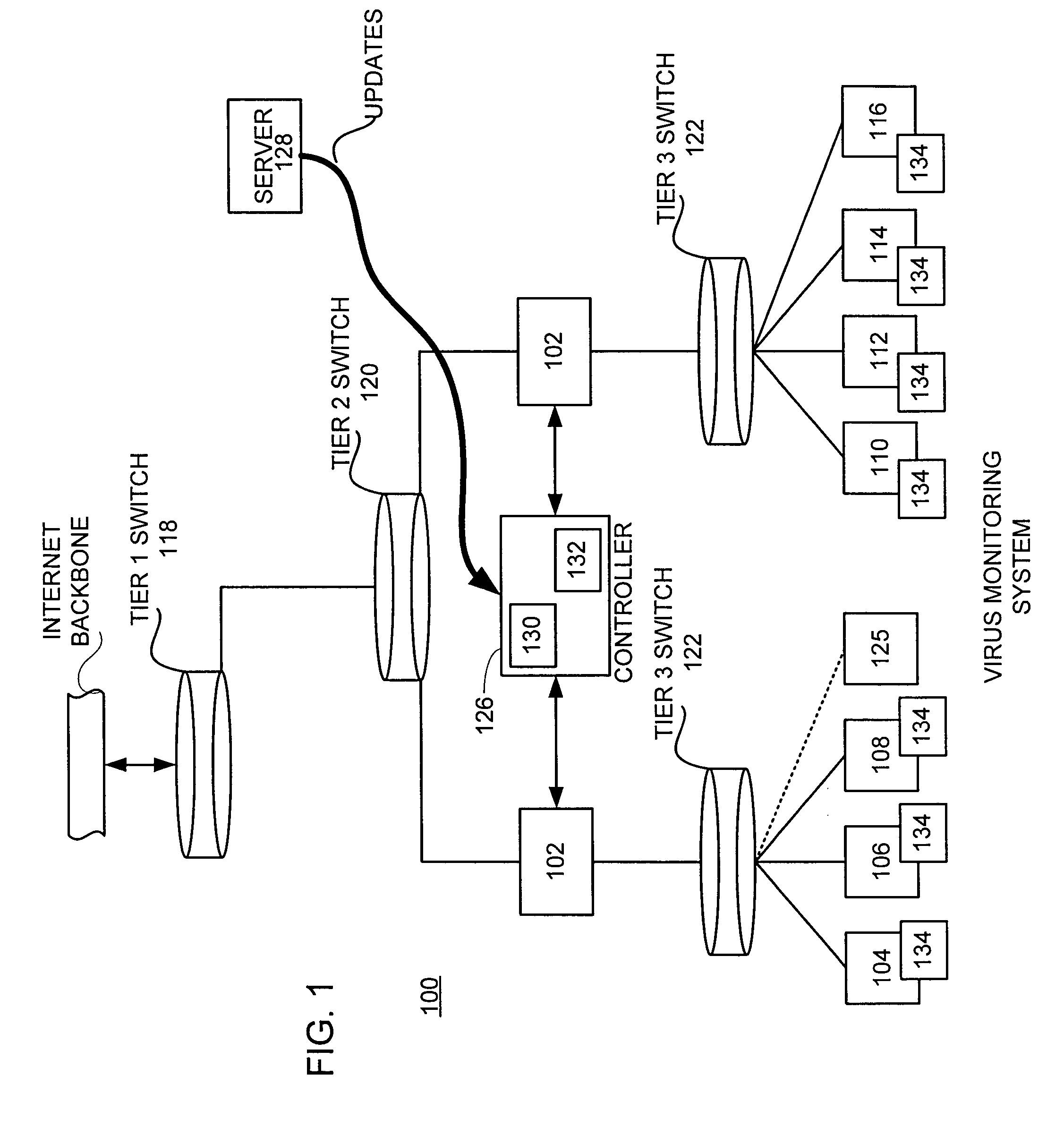
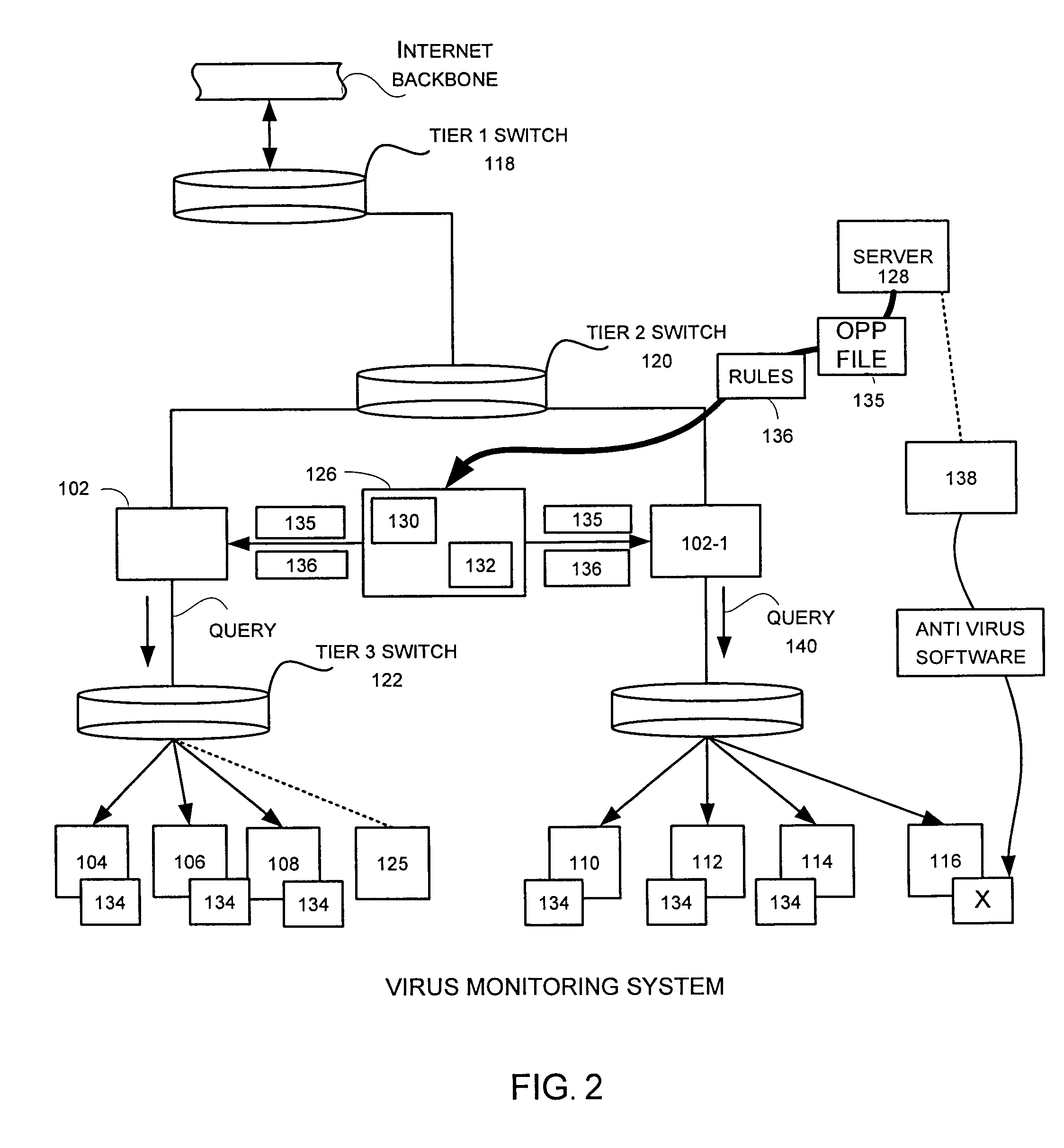
Tracking and reporting of computer virus information
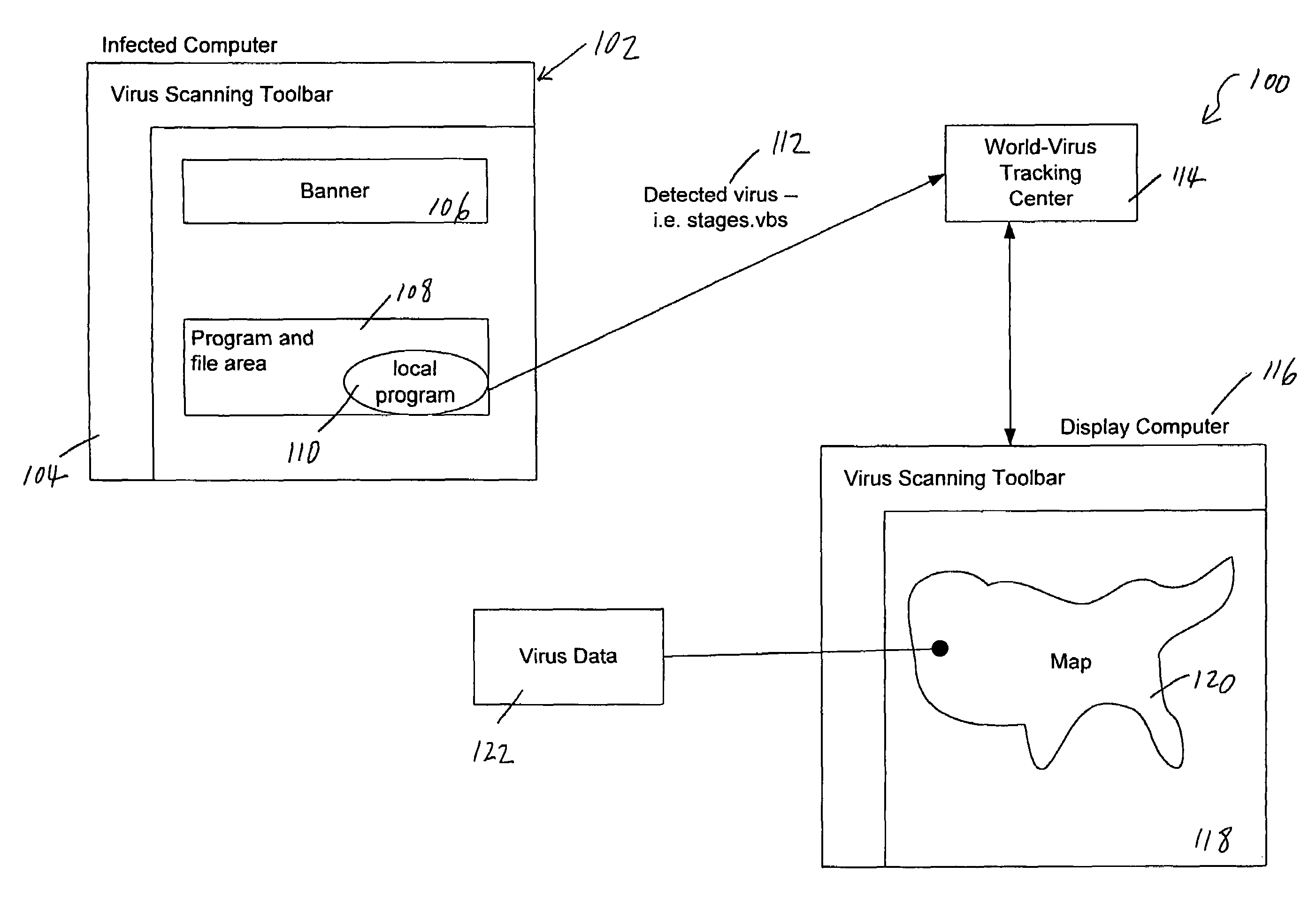
An apparatus and method for providing real-time tracking of virus information as reported from various computers on a distributed computer network. Each client computer on the distributed network contacts an anti-virus scanning site. The site provides a small program or applet that resides in temporary memory of the client computer. The client-user invokes the scan with supplied pattern updates for detecting recent viruses. When the scan has been completed, the user is prompted to supply a country of origin. The name of the virus, its frequency of occurrence, and the country are forwarded as a virus scan log to a virus tracking server, which receives the virus information and thereafter stores it in a database server, which is used to further calculate virus trace display information. A tracking user contacts the virus tracking server and receives map information, which traces the virus activity. The maps show, according to user preference, the names of the viruses encountered in each country, and their frequencies of occurrence.
Owner:TREND MICRO INC
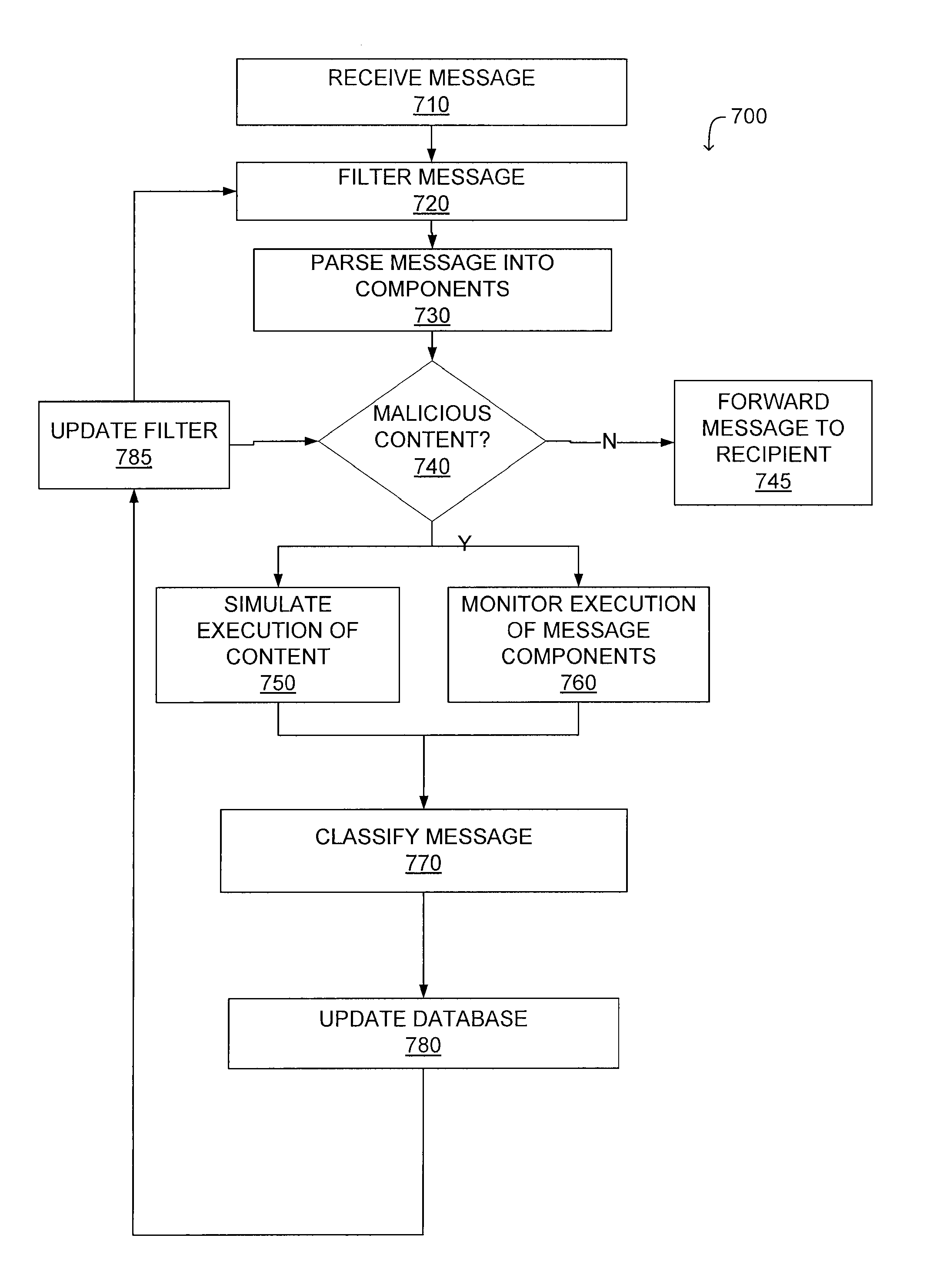
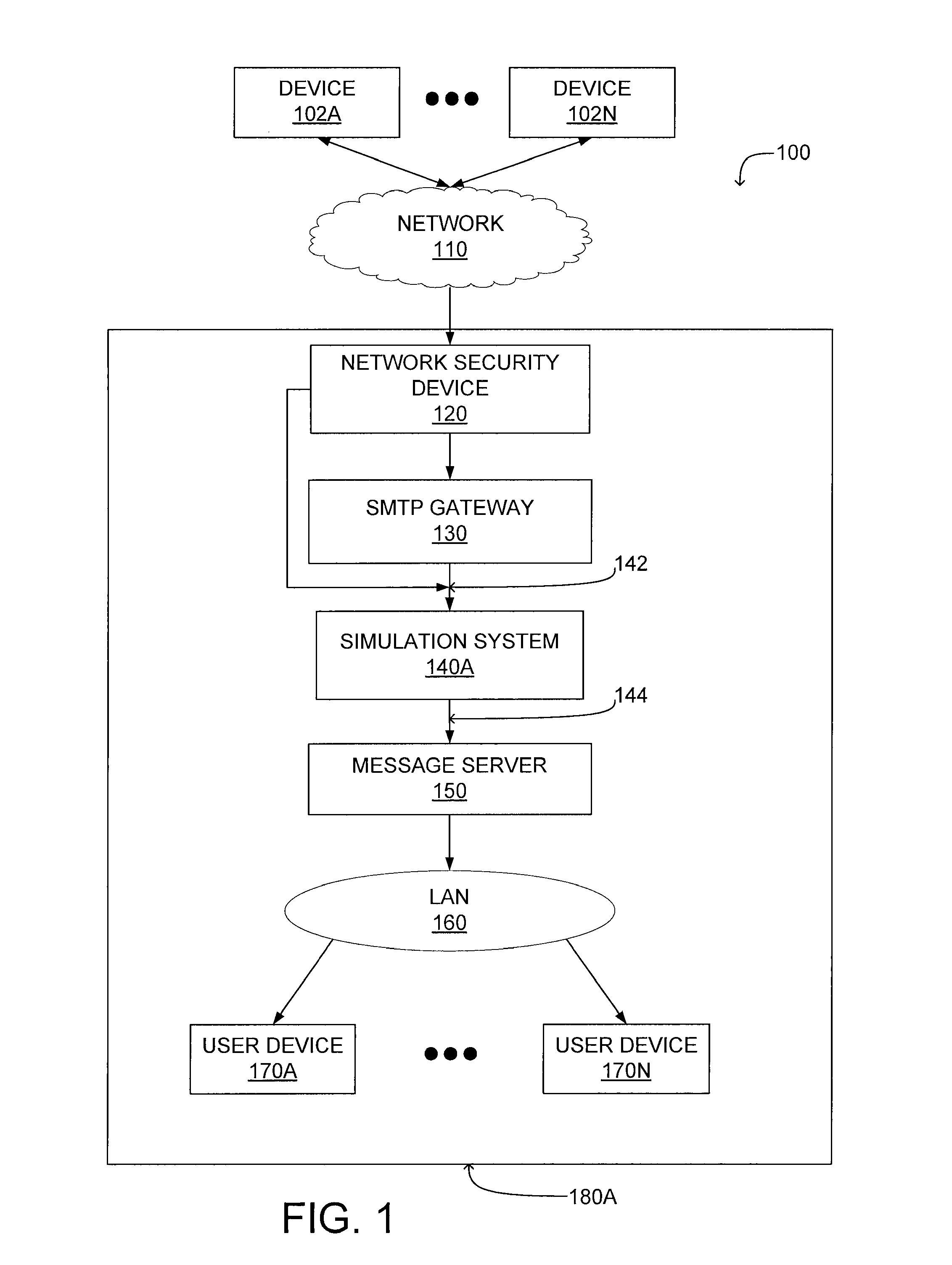
System and method for malicious software detection in multiple protocols
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
Inoculation of computing devices against a selected computer virus
ActiveUS7287278B2Avoid infectionMemory loss protectionUnauthorized memory use protectionComputer scienceVirus
In a distributed network having a number of server computers and associated client devices, method of creating an anti-computer virus agent is described. As a method, the inoculation is carried out by parsing a selected computer virus into a detection module that identifies a selected one of the client devices as a target client device, an infection module that causes the virus to infect those target client devices not infected by the selected virus, and a viral code payload module that infects the targeted client device modifying the infection module to infect those computers already infected by the selected virus; and incorporating inoculation viral code in the payload module that acts to prevent further infection by the selected virus.
Owner:TREND MICRO INC
Microfluidic nucleic acid analysis
ActiveUS20050053952A1Bioreactor/fermenter combinationsBiological substance pretreatmentsCDNA libraryCells isolation
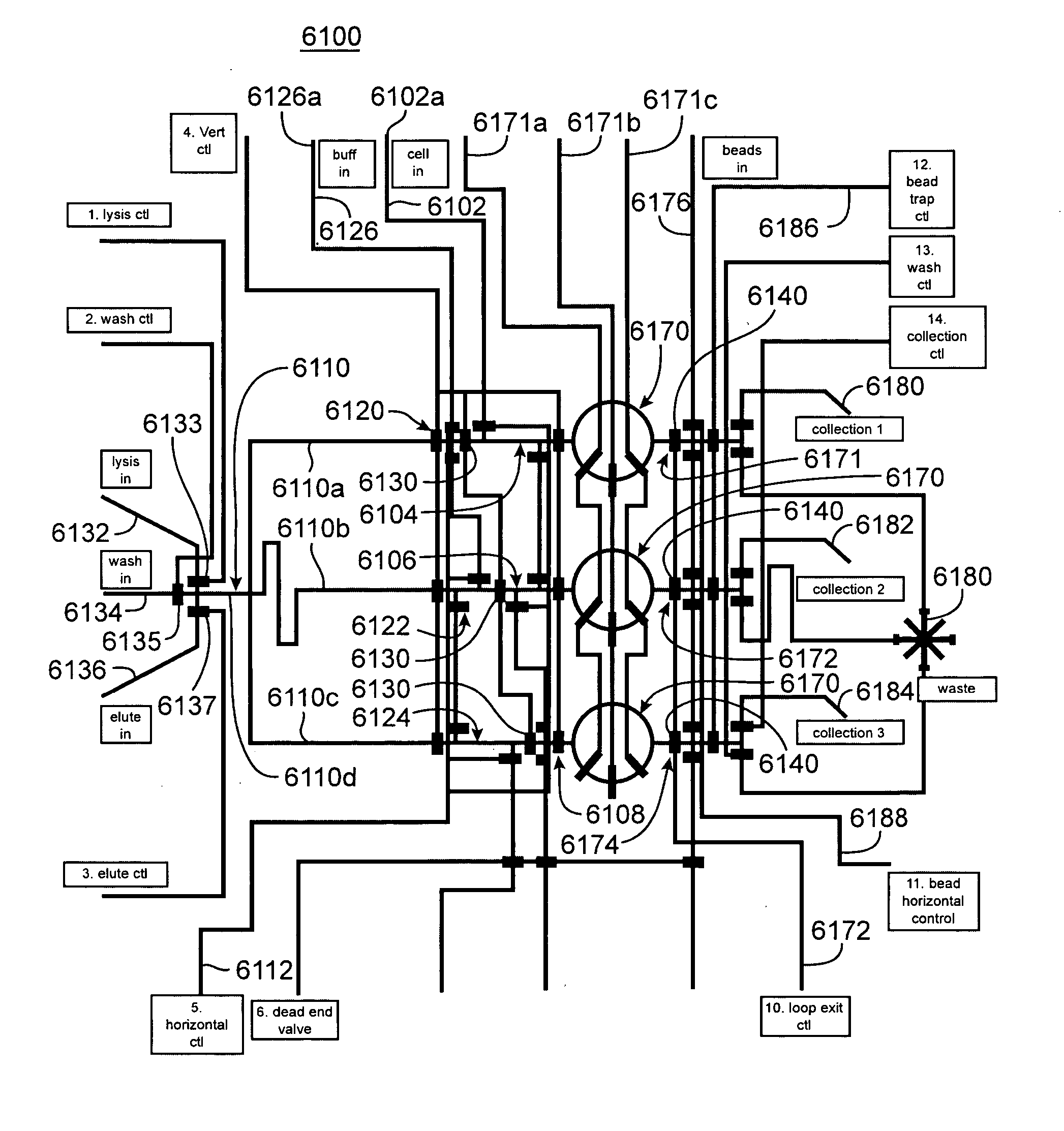
Nucleic acid from cells and viruses sampled from a variety of environments may purified and expressed utilizing microfluidic techniques. In accordance with one embodiment of the present invention, individual or small groups of cells or viruses may be isolated in microfluidic chambers by dilution, sorting, and / or segmentation. The isolated cells or viruses may be lysed directly in the microfluidic chamber, and the resulting nucleic acid purified by exposure to affinity beads. Subsequent elution of the purified nucleic acid may be followed by ligation and cell transformation, all within the same microfluidic chip. In one specific application, cell isolation, lysis, and nucleic acid purification may be performed utilizing a highly parallelized microfluidic architecture to construct gDNA and cDNA libraries.
Owner:CALIFORNIA INST OF TECH
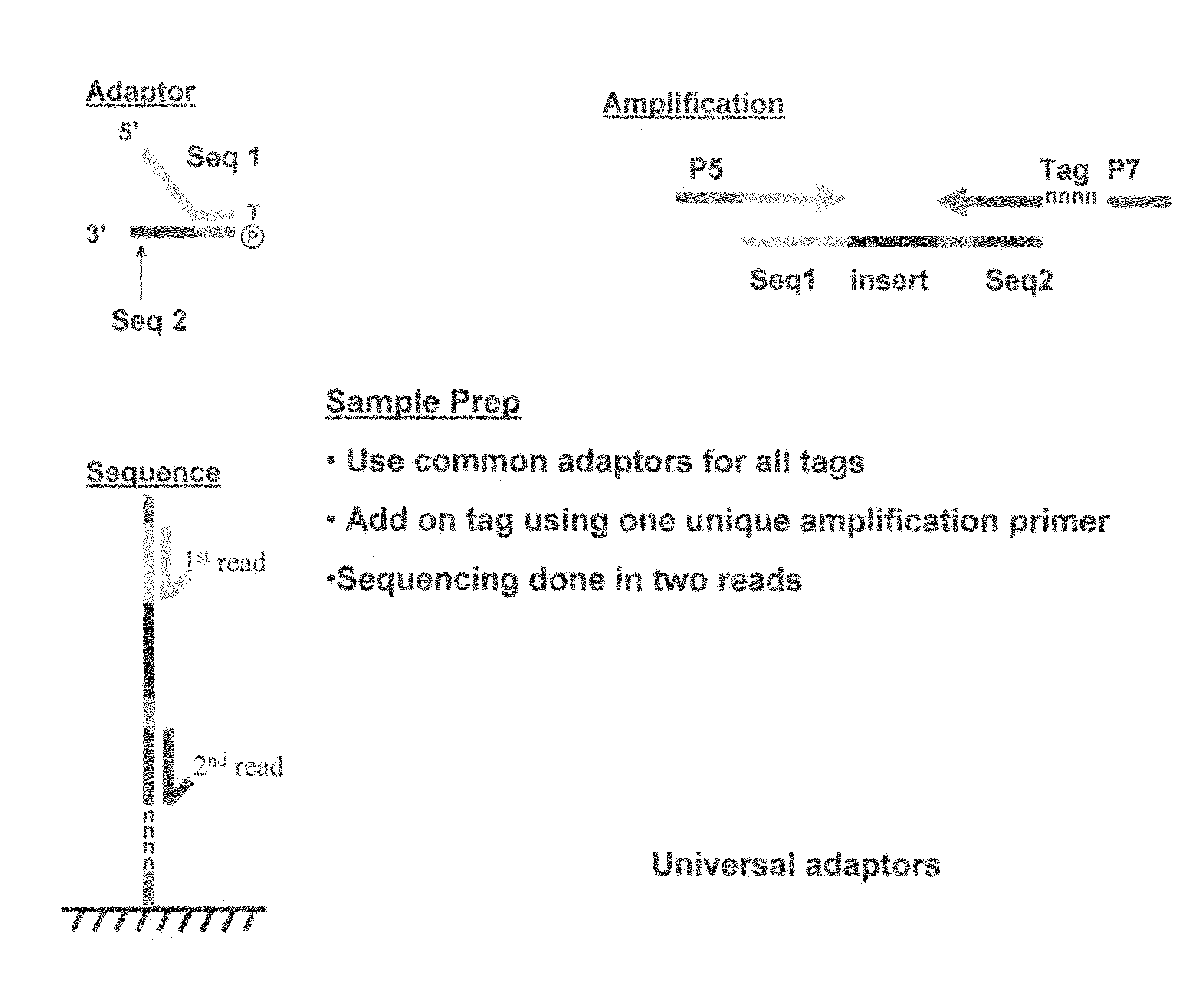
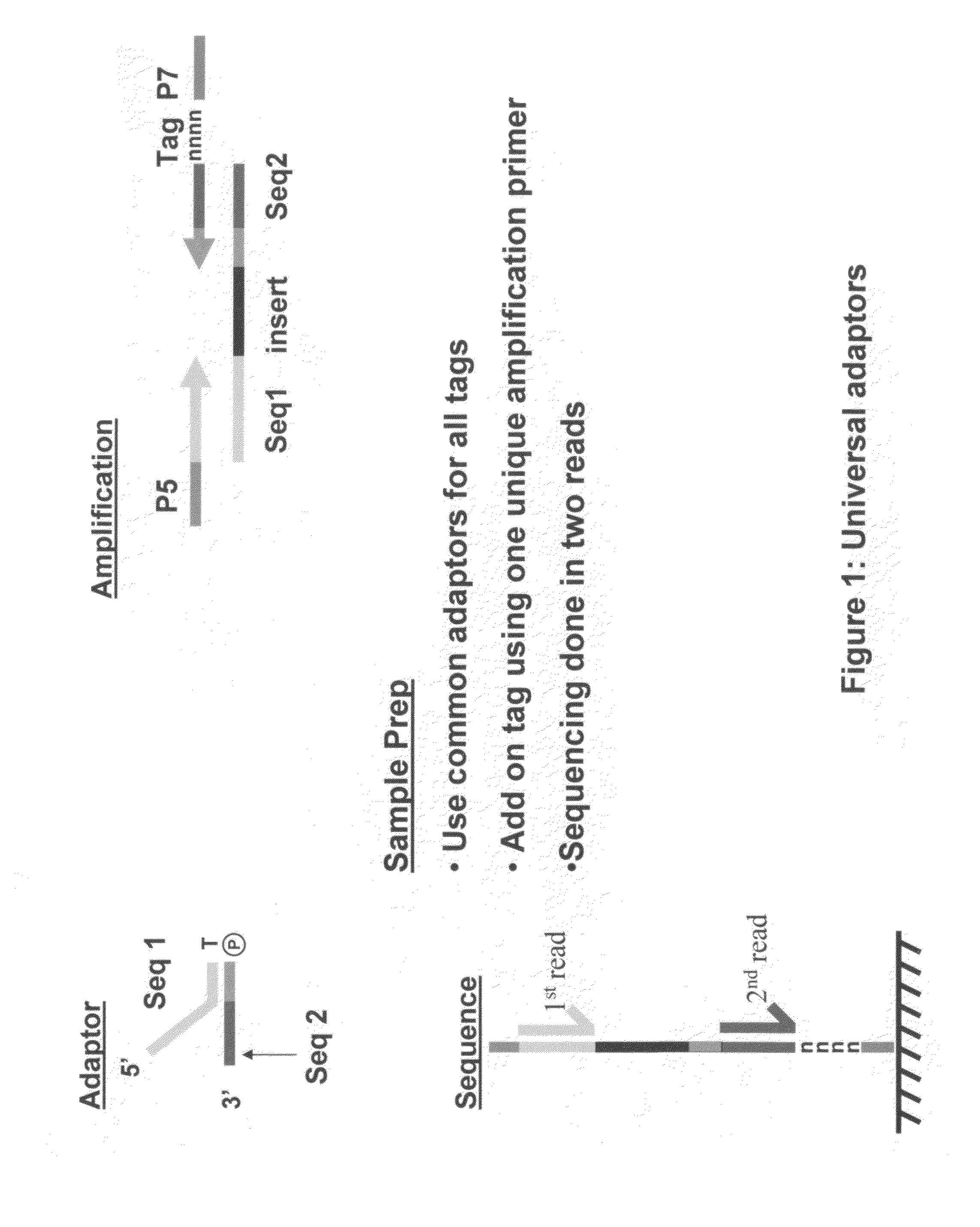
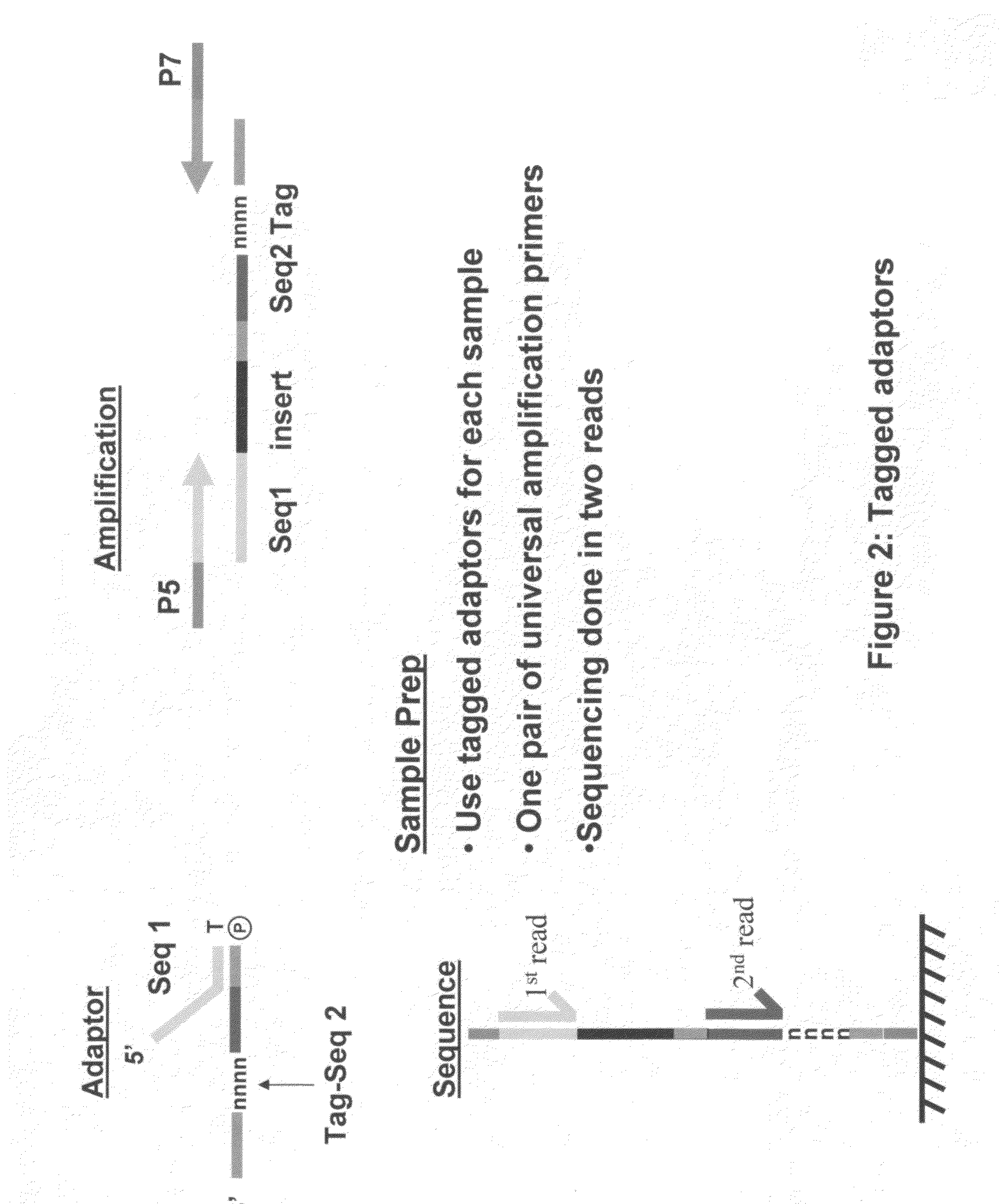
Methods for indexing samples and sequencing multiple polynucleotide templates
The invention relates to methods for indexing samples during the sequencing of polynucleotide templates, resulting in the attachment of tags specific to the source of each nucleic acid sample such that after a sequencing run, both the source and sequence of each polynucleotide can be determined. Thus, the present invention pertains to analysis of complex genomes (e.g., human genomes), as well as multiplexing less complex genomes, such as those of bacteria, viruses, mitochondria, and the like.
Owner:ILLUMINA CAMBRIDGE LTD
Heuristic detection of malicious computer code by page tracking
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
Plant extracts for the preparation of pharmaceutical compositions for the treatment of hepatitis
The use of extracts from the plant Hypericum perforatum in the preparation of pharmaceutical compositions for the treatment of hepatitis C, chronic hepatitis C and related viruses, said pharmaceutical compositions comprising at least one extract of the plant Hypericum perforatum and optionally in addition, one or more pharmaceutically acceptable inactive components, selected from, carriers, coatings, diluents and adjuvants.
Owner:LAVIE DAVID +1
Non-invasive systems and methods for in-situ photobiomodulation
InactiveUS20100016783A1High selectivityAntibacterial agentsPowder deliveryDiseaseBiological regulation
Products, compositions, systems, and methods for modifying a target structure which mediates or is associated with a biological activity, including treatment of conditions, disorders, or diseases mediated by or associated with a target structure, such as a virus, cell, subcellular structure or extracellular structure. The methods may be performed in situ in a non-invasive manner by application of an initiation energy to a subject thus producing an effect on or change to the target structure directly or via a modulation agent. The methods may further be performed by application of an initiation energy to a subject in situ to activate a pharmaceutical agent directly or via an energy modulation agent, optionally in the presence of one or more plasmonics active agents, thus producing an effect on or change to the target structure. Kits containing products or compositions formulated or configured and systems for use in practicing these methods.
Owner:DUKE UNIV +1
Methods for determining sequence variants using ultra-deep sequencing
InactiveUS20060228721A1Reduce effortShorten the timeMicrobiological testing/measurementFermentationUltra deep sequencingDirect sequencing
The claimed invention provides for new sample preparation methods enabling direct sequencing of PCR products using pyrophosphate sequencing techniques. The PCR products may be specific regions of a genome. The techniques provided in this disclosure allows for SNP (single nucleotide polymorphism) detection, classification, and assessment of individual allelic polymorphisms in one individual or a population of individuals. The results may be used for diagnostic and treatment of patients as well as assessment of viral and bacterial population identification.
Owner:454 LIFE SCIENCES CORP
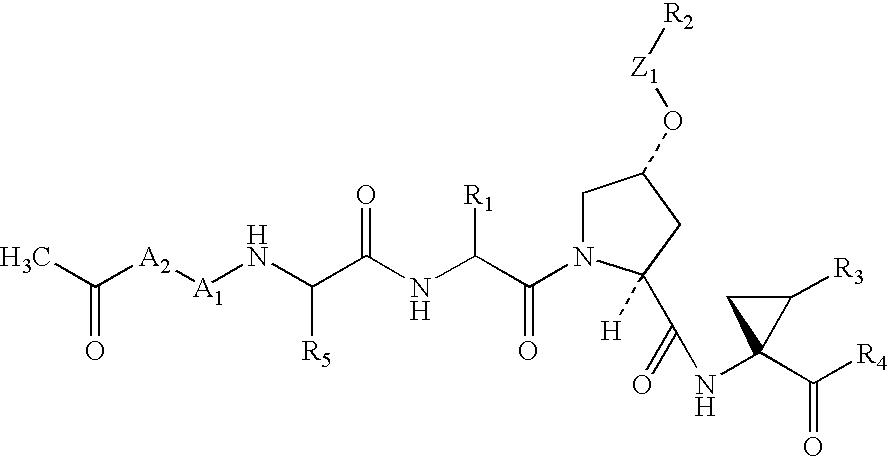
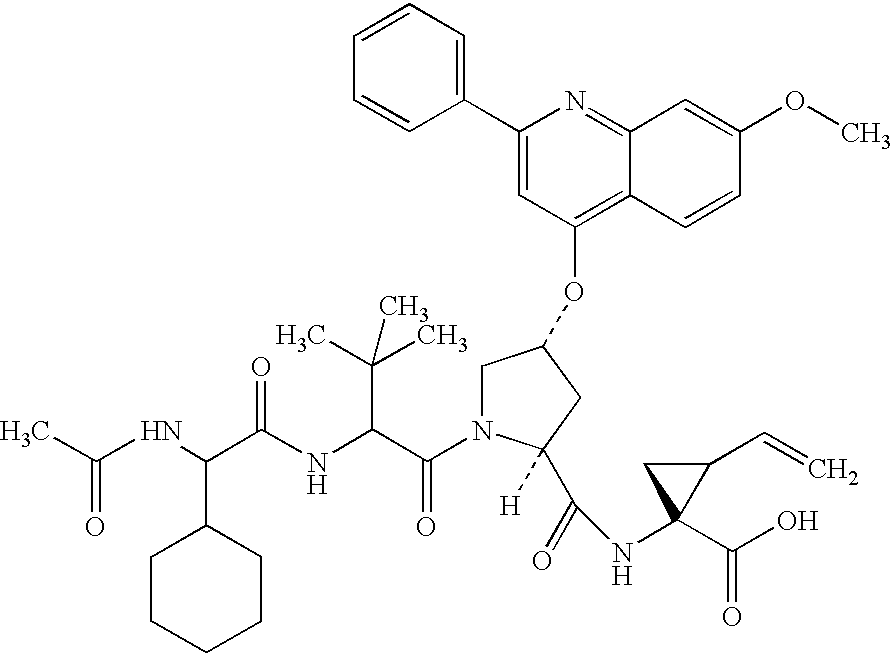
Peptides as NS3-serine protease inhibitors of hepatitis C virus
InactiveUS7012066B2Organic active ingredientsDigestive systemSerine Protease InhibitorsHepatitis C virus
The present invention discloses novel compounds which have HCV protease inhibitory activity as well as methods for preparing such compounds. In another embodiment, the invention discloses pharmaceutical compositions comprising such compounds as well as methods of using them to treat disorders associated with the HCV protease.
Owner:DENDREON PHARMA INC +1
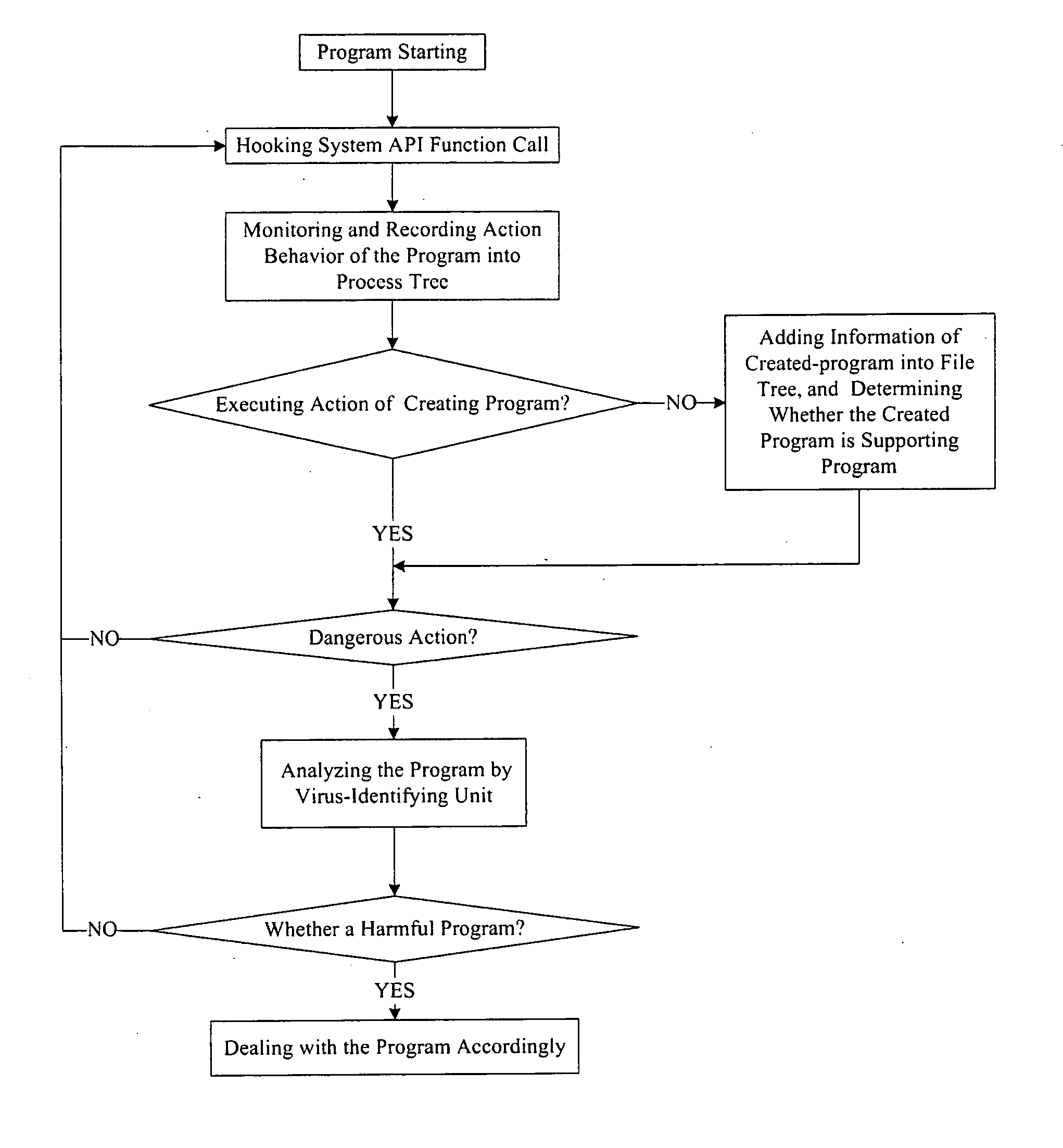
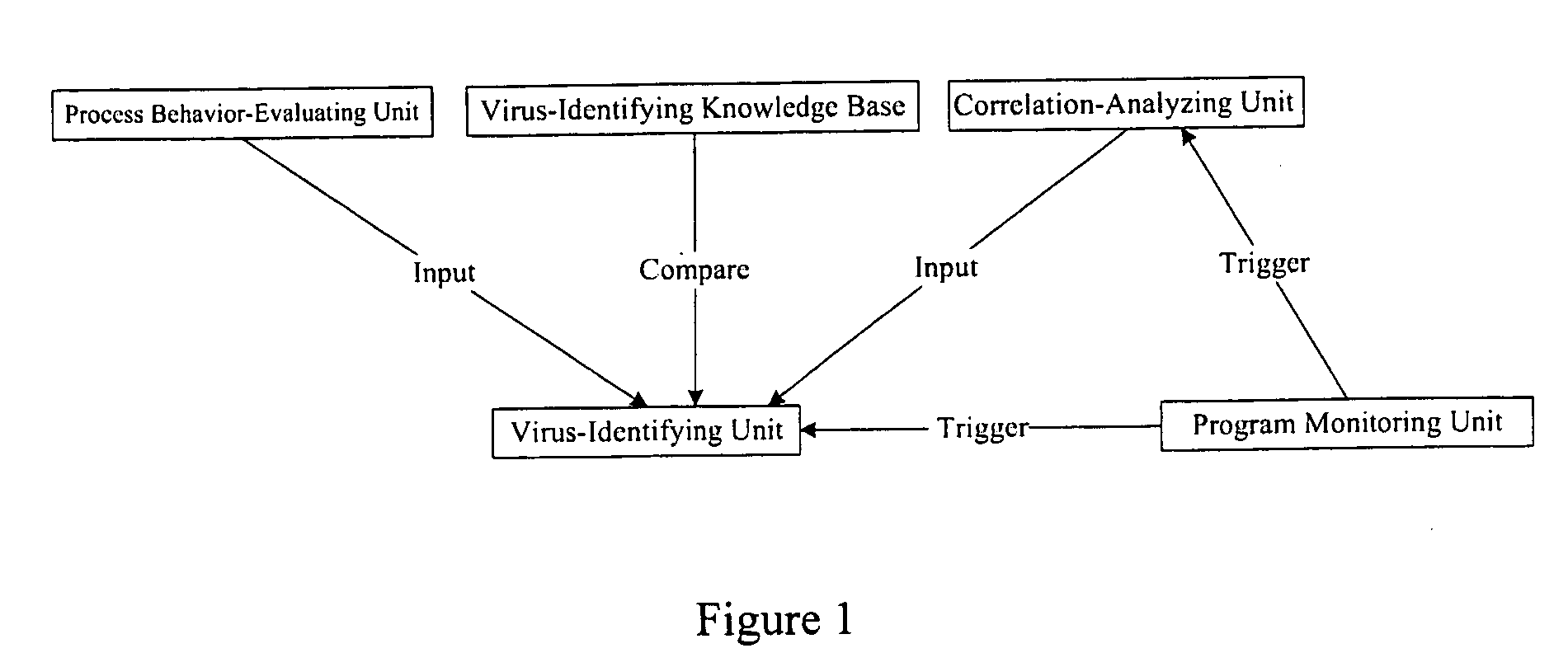
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
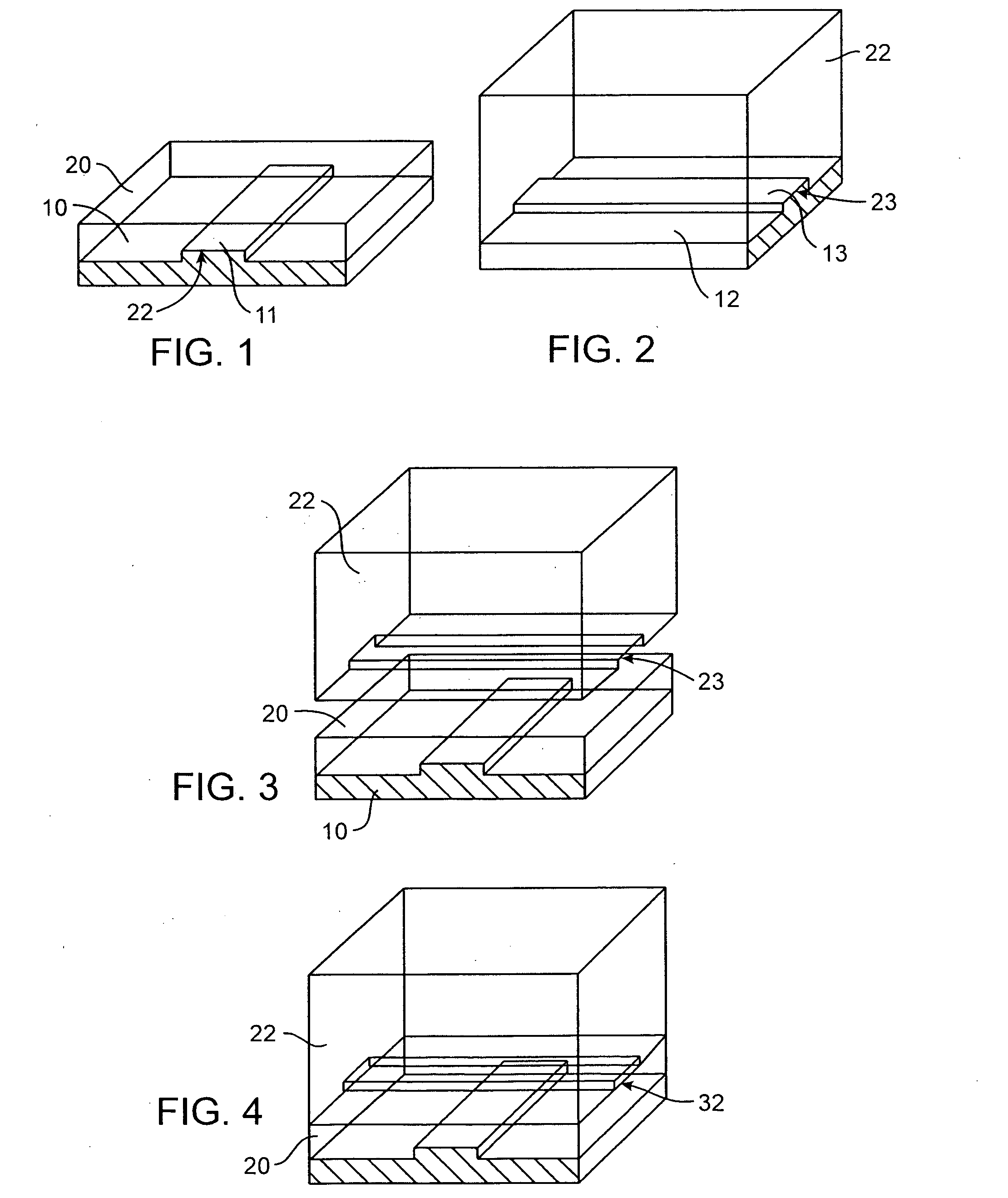
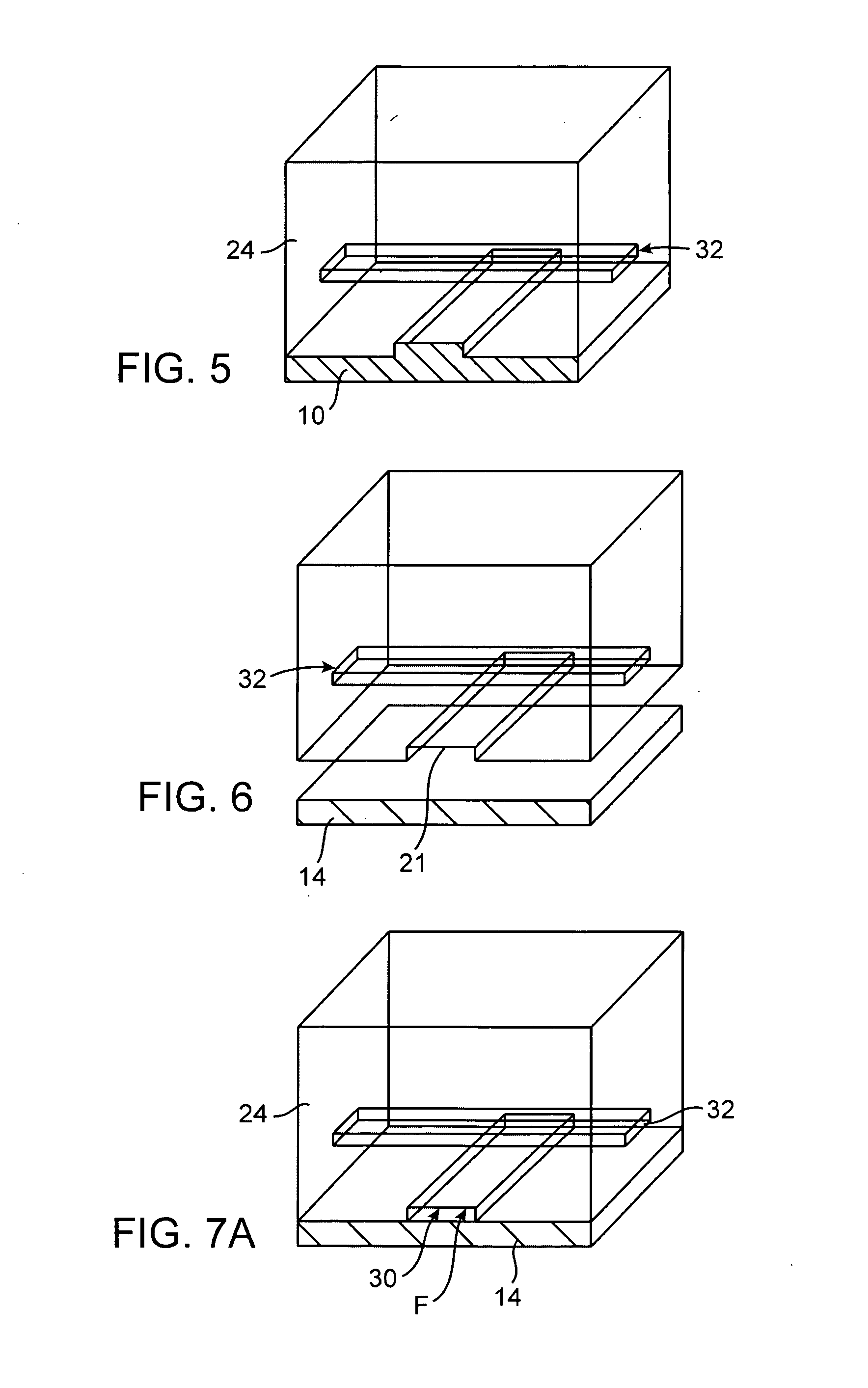
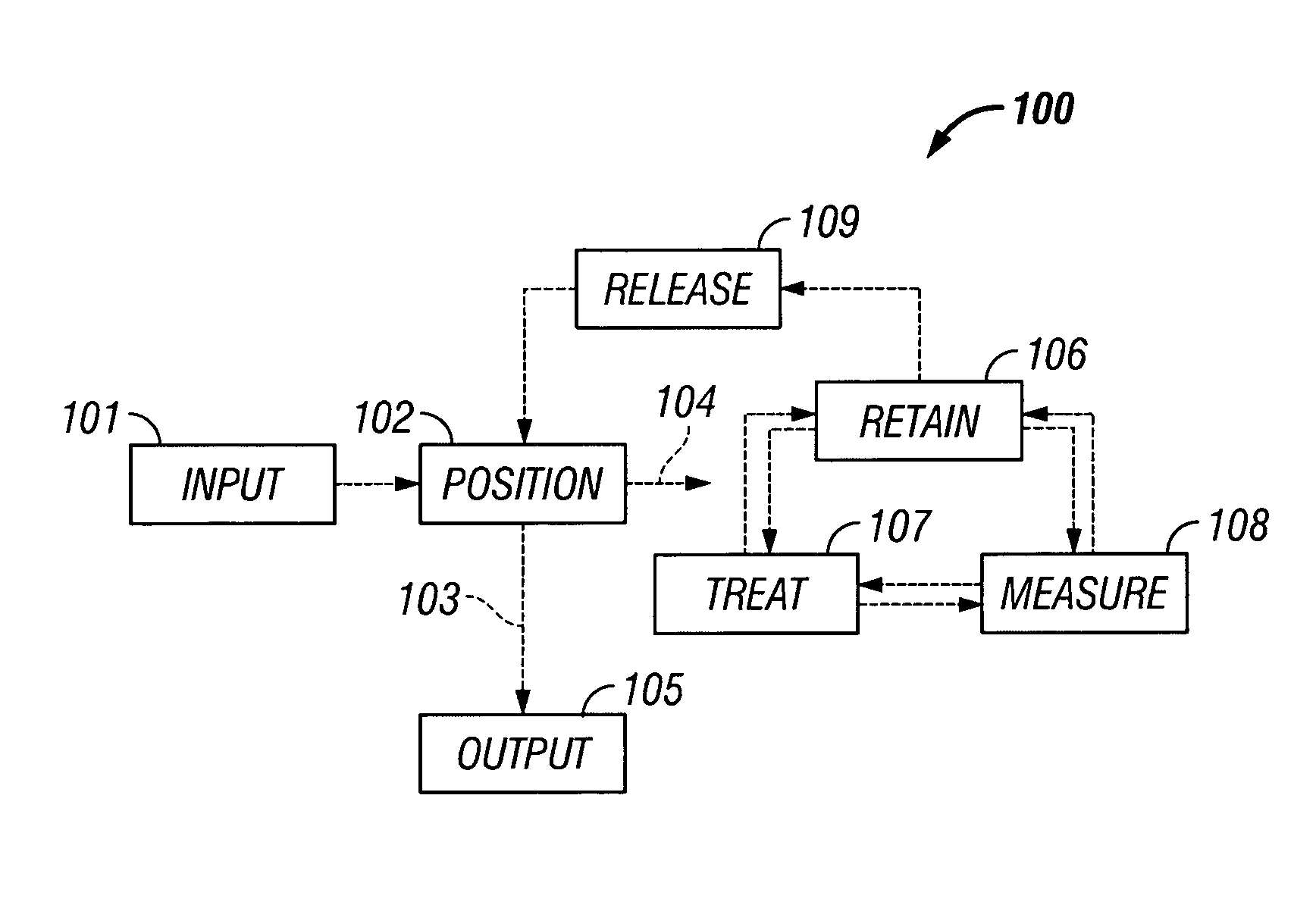
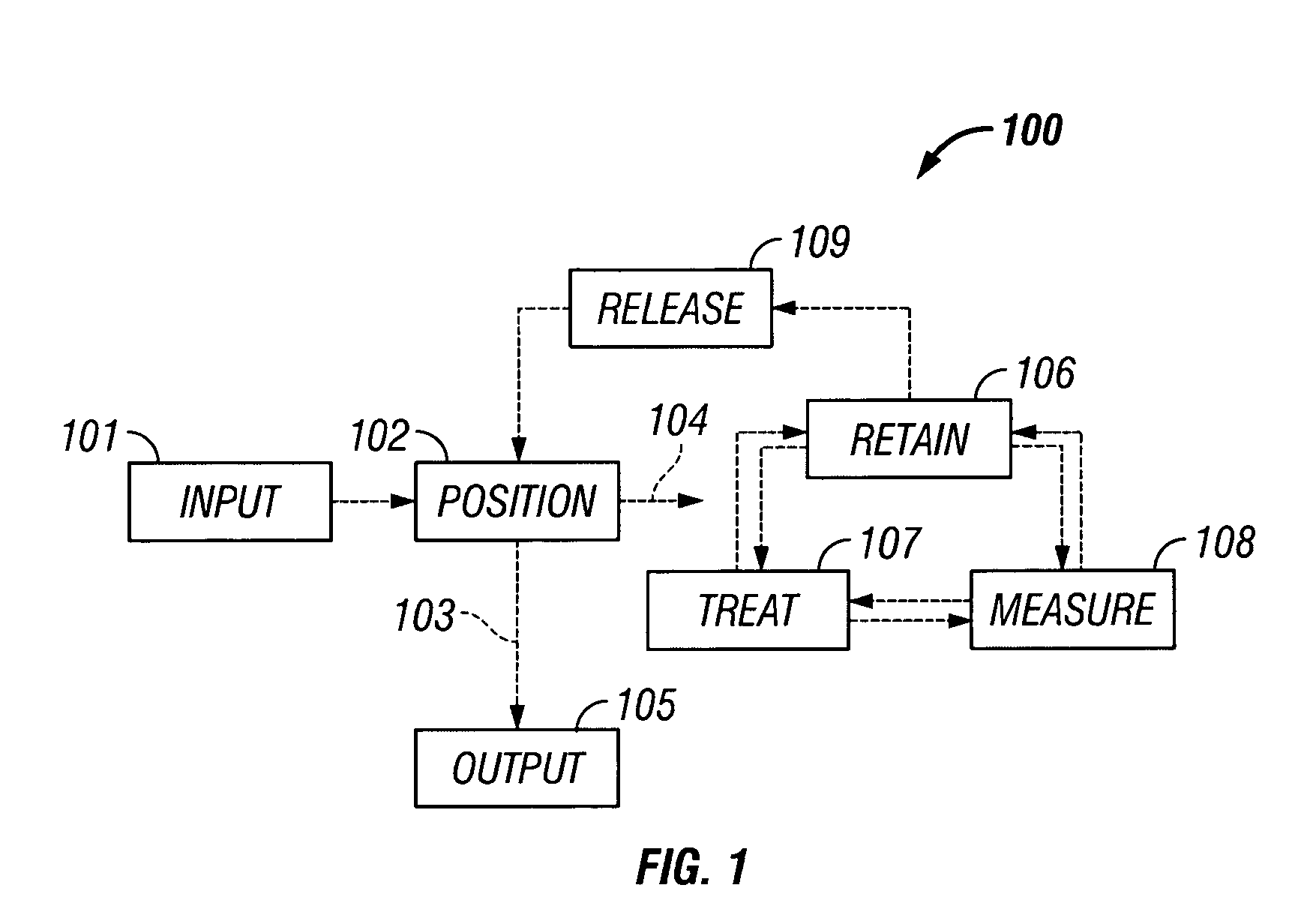
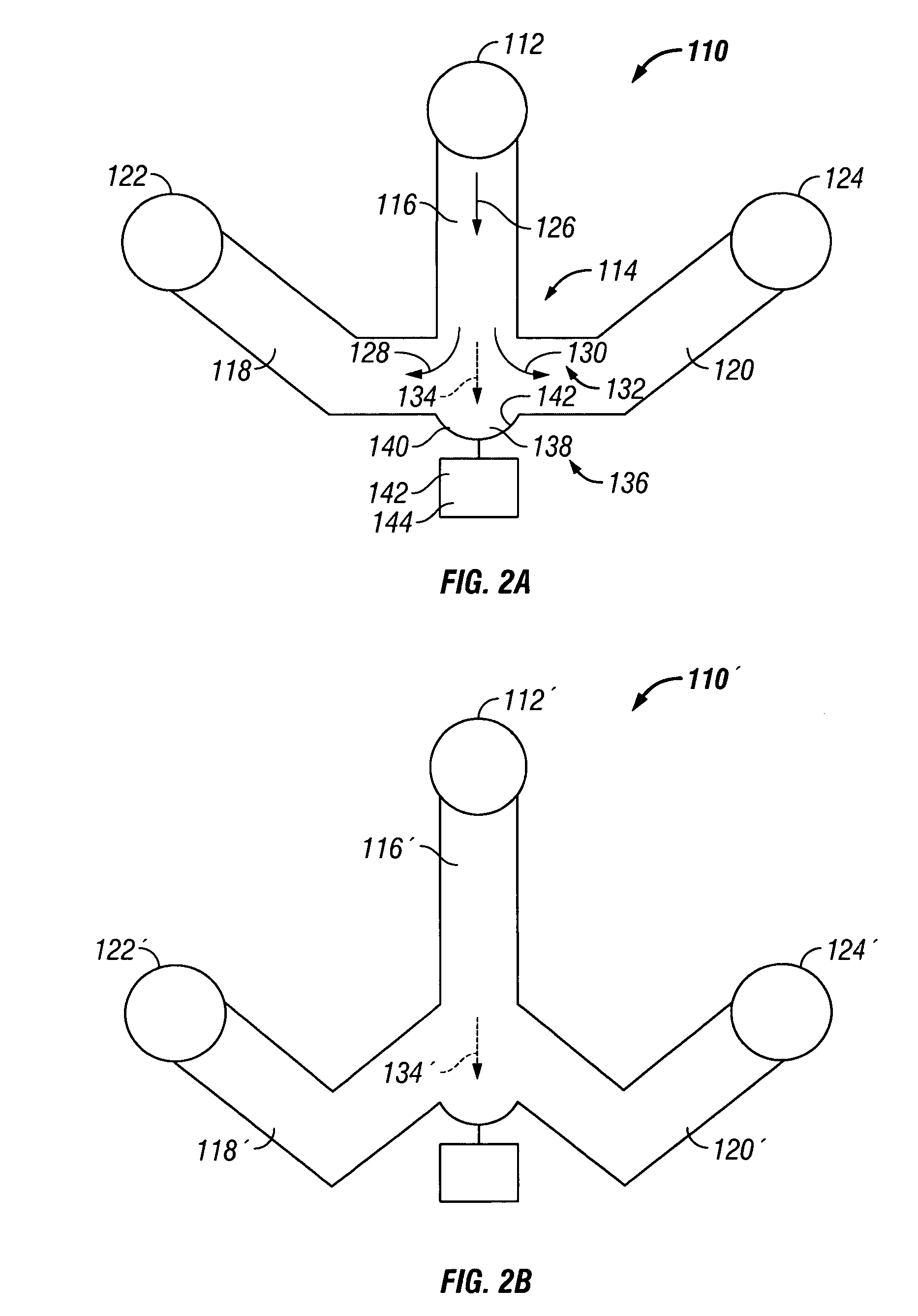
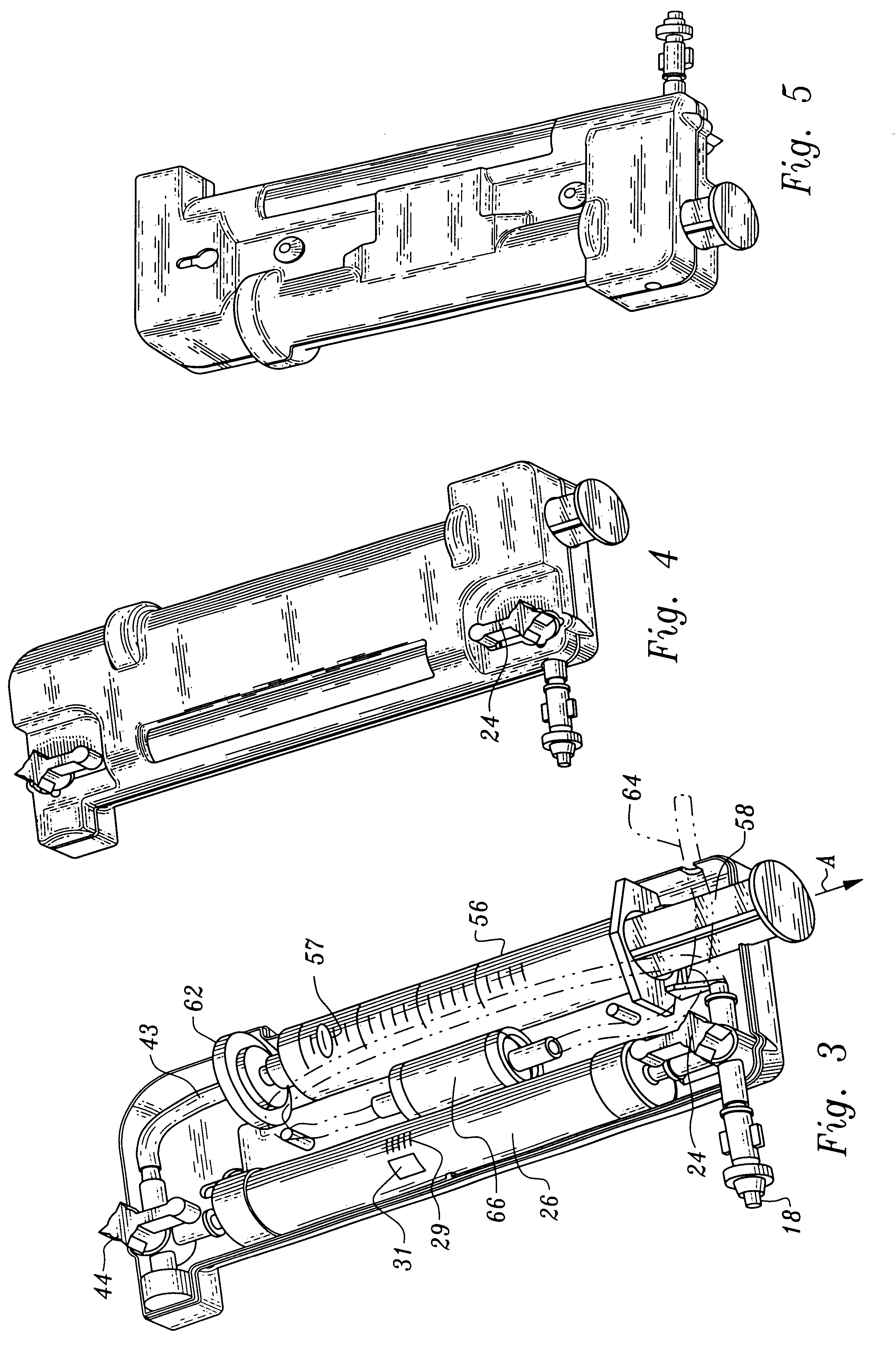
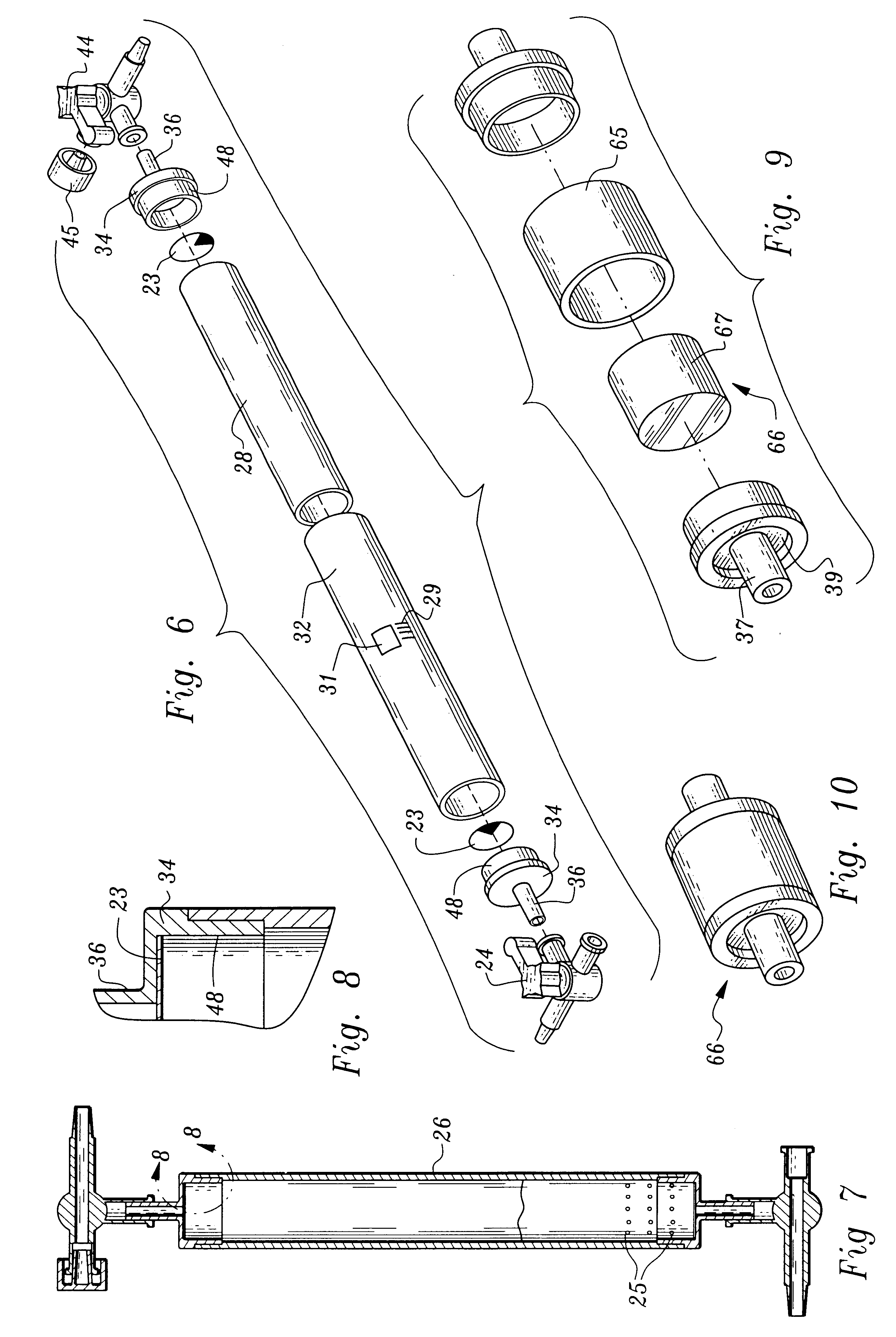
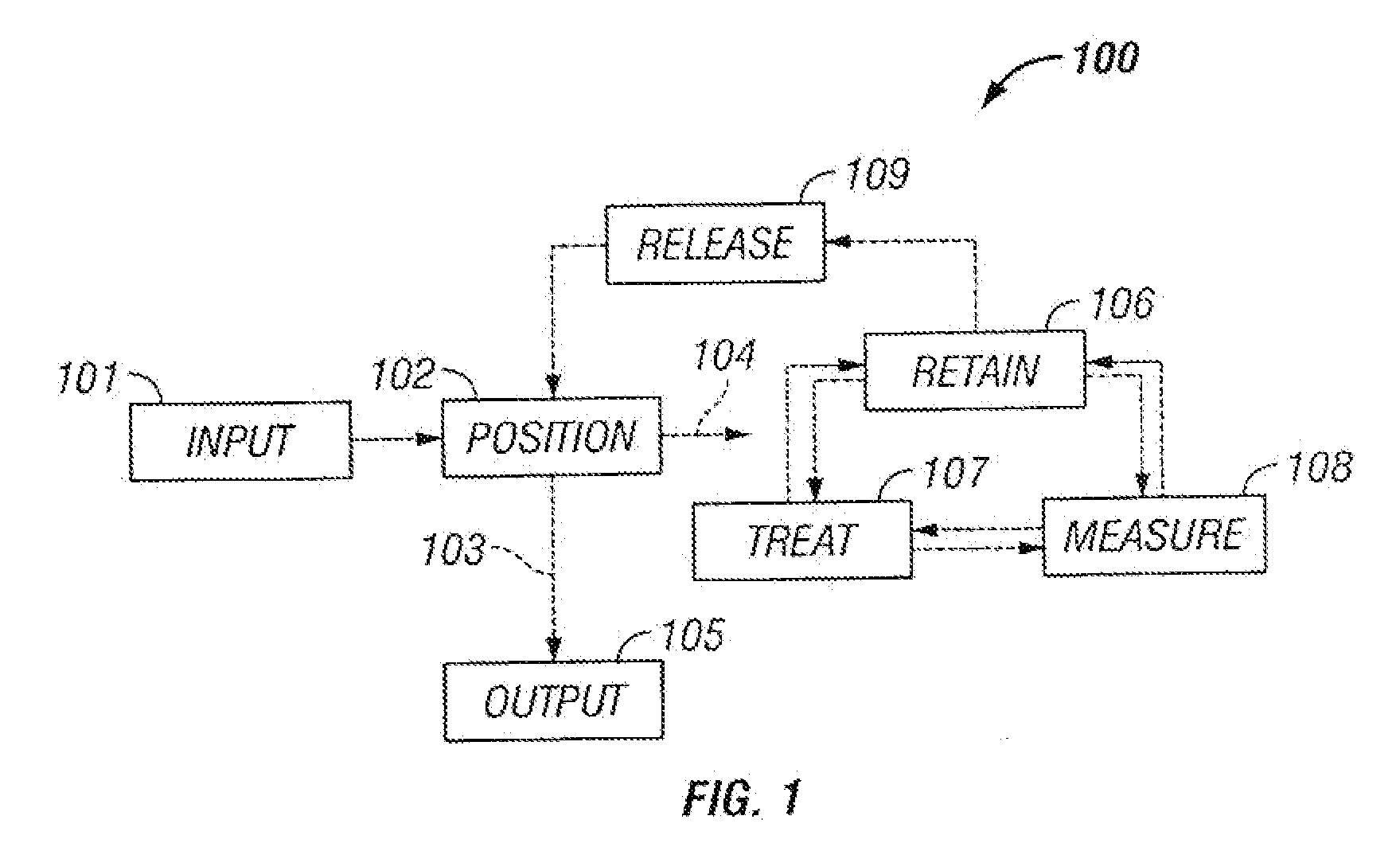
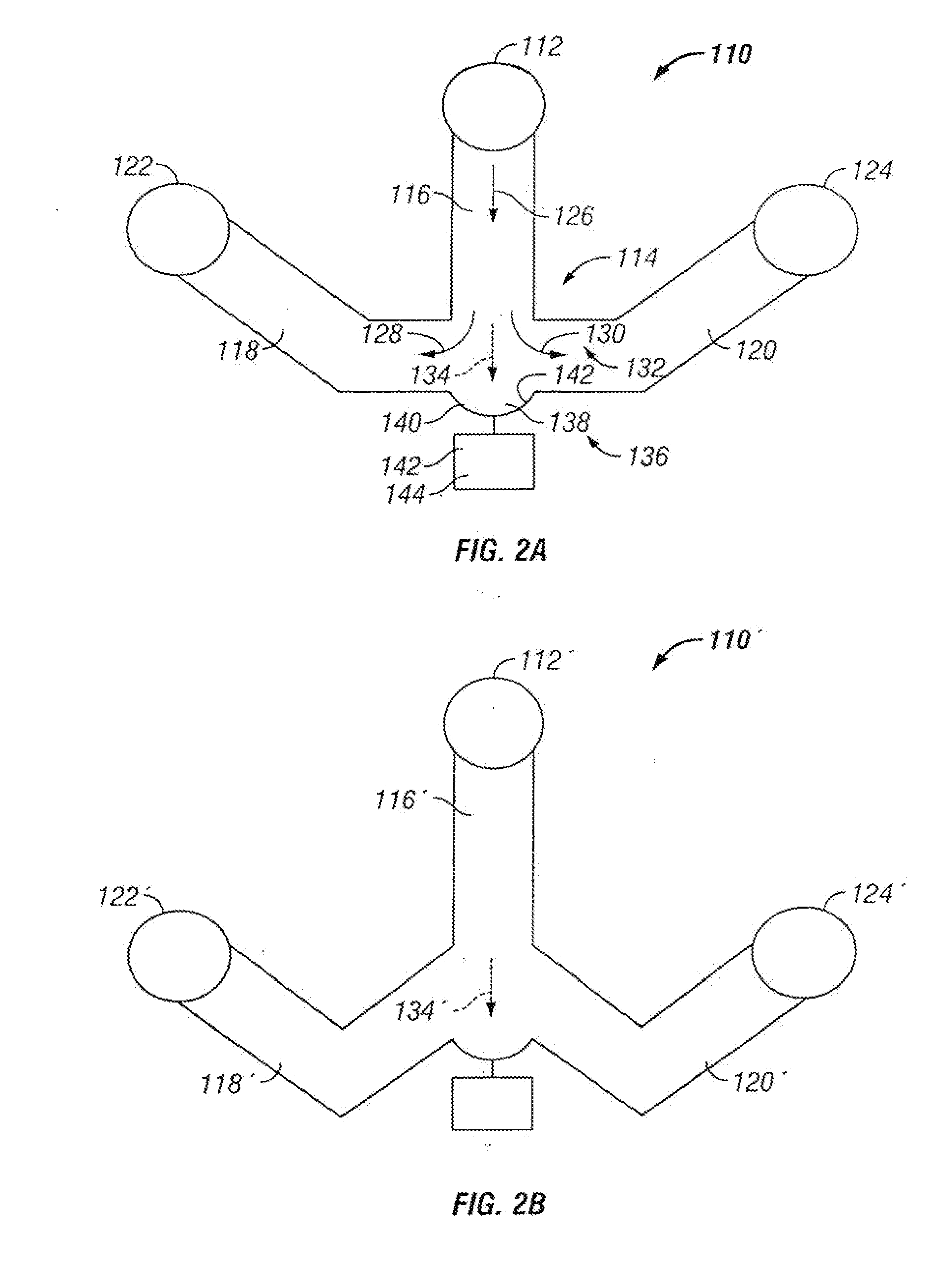
Microfluidic particle-analysis systems
ActiveUS7312085B2Bioreactor/fermenter combinationsBiological substance pretreatmentsReady to useMixed group
The invention provides systems, including apparatus, methods, and kits, for the microfluidic manipulation and / or detection of particles, such as cells and / or beads. The invention provides systems, including apparatus, methods, and kits, for the microfluidic manipulation and / or analysis of particles, such as cells, viruses, organelles, beads, and / or vesicles. The invention also provides microfluidic mechanisms for carrying out these manipulations and analyses. These mechanisms may enable controlled input, movement / positioning, retention / localization, treatment, measurement, release, and / or output of particles. Furthermore, these mechanisms may be combined in any suitable order and / or employed for any suitable number of times within a system. Accordingly, these combinations may allow particles to be sorted, cultured, mixed, treated, and / or assayed, among others, as single particles, mixed groups of particles, arrays of particles, heterogeneous particle sets, and / or homogeneous particle sets, among others, in series and / or in parallel. In addition, these combinations may enable microfluidic systems to be reused. Furthermore, these combinations may allow the response of particles to treatment to be measured on a shorter time scale than was previously possible. Therefore, systems of the invention may allow a broad range of cell and particle assays, such as drug screens, cell characterizations, research studies, and / or clinical analyses, among others, to be scaled down to microfluidic size. Such scaled-down assays may use less sample and reagent, may be less labor intensive, and / or may be more informative than comparable macrofluidic assays.
Owner:STANDARD BIOTOOLS INC
Therapy via targeted delivery of nanoscale particles
InactiveUS20050090732A1Destroying inhibiting vascularityAntibacterial agentsNervous disorderDiseaseProstate cancer
Disclosed are compositions, systems and methods for treating a subject's body, body part, tissue, body fluid cells, pathogens, or other undesirable matter involving the administration of a targeted thermotherapy that comprises a bioprobe (energy susceptive materials that are attached to a target-specific ligand). Such targeted therapy methods can be combined with at least one other therapy technique. Other therapies include hyperthermia, direct antibody therapy, radiation, chemo- or pharmaceutical therapy, photodynamic therapy, surgical or interventional therapy, bone marrow or stem cell transplantation, and medical imaging, such as MRI, PET, SPECT, and bioimpedance. The disclosed therapies may be useful in the treatment of a variety of indications, including but not limited to, cancer of any type, such as bone marrow, lung, vascular, neuro, colon, ovarian, breast and prostate cancer, epitheleoid sarcomas, AIDS, adverse angiogenesis, restenosis, amyloidosis, tuberculosis, cardiovascular plaque, vascular plaque, obesity, malaria, and illnesses due to viruses, such as HIV.
Owner:NANOTX INC
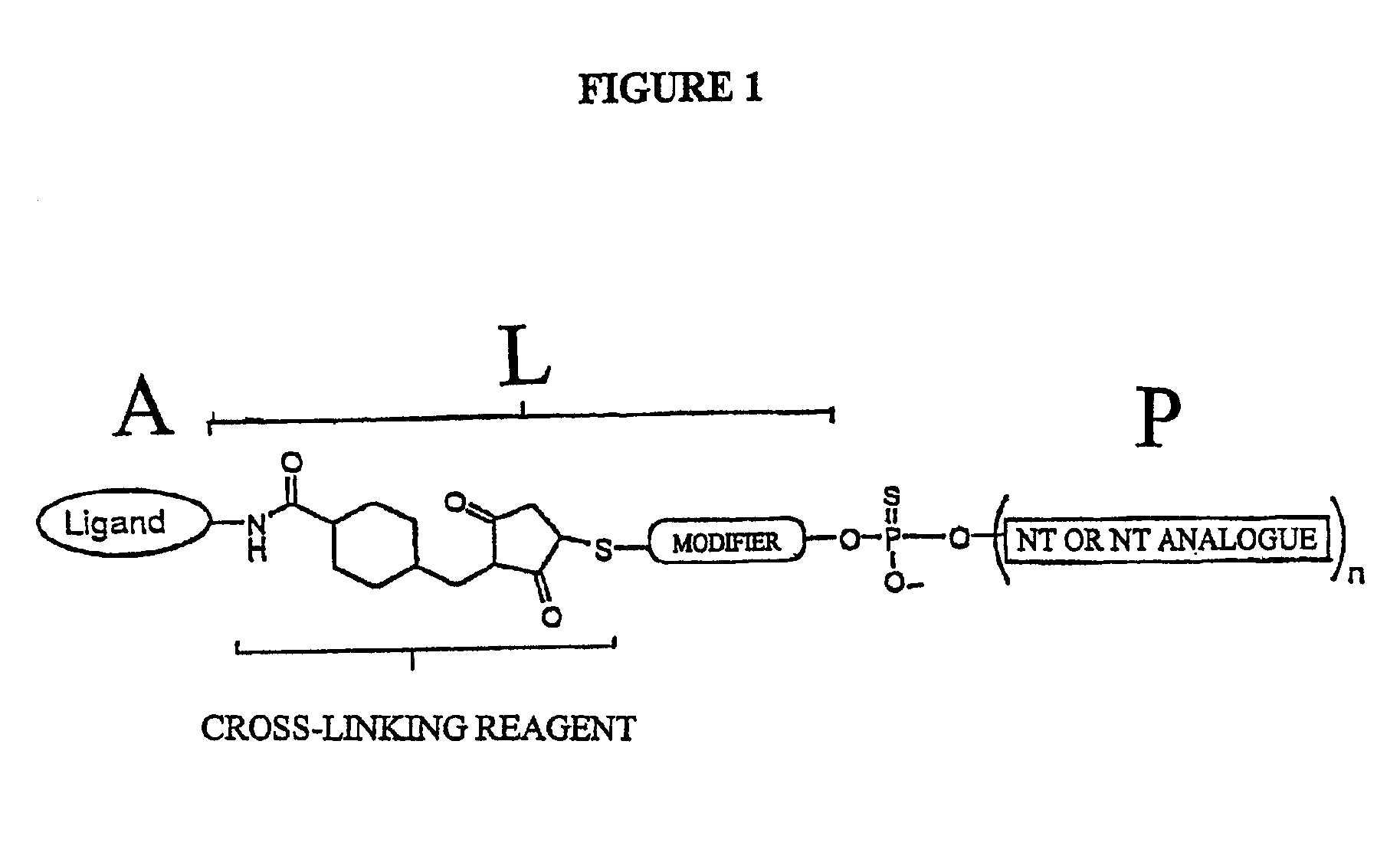
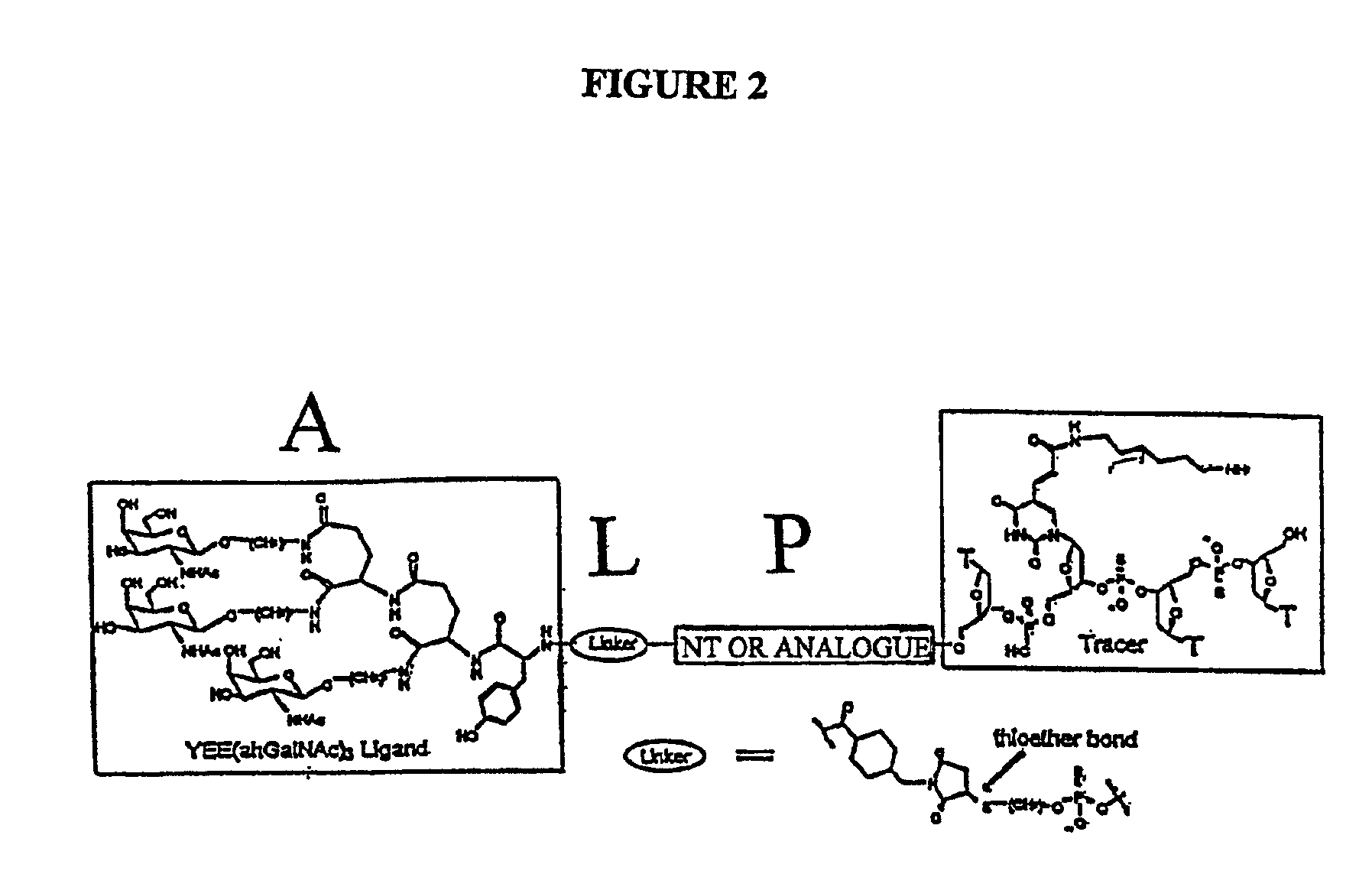
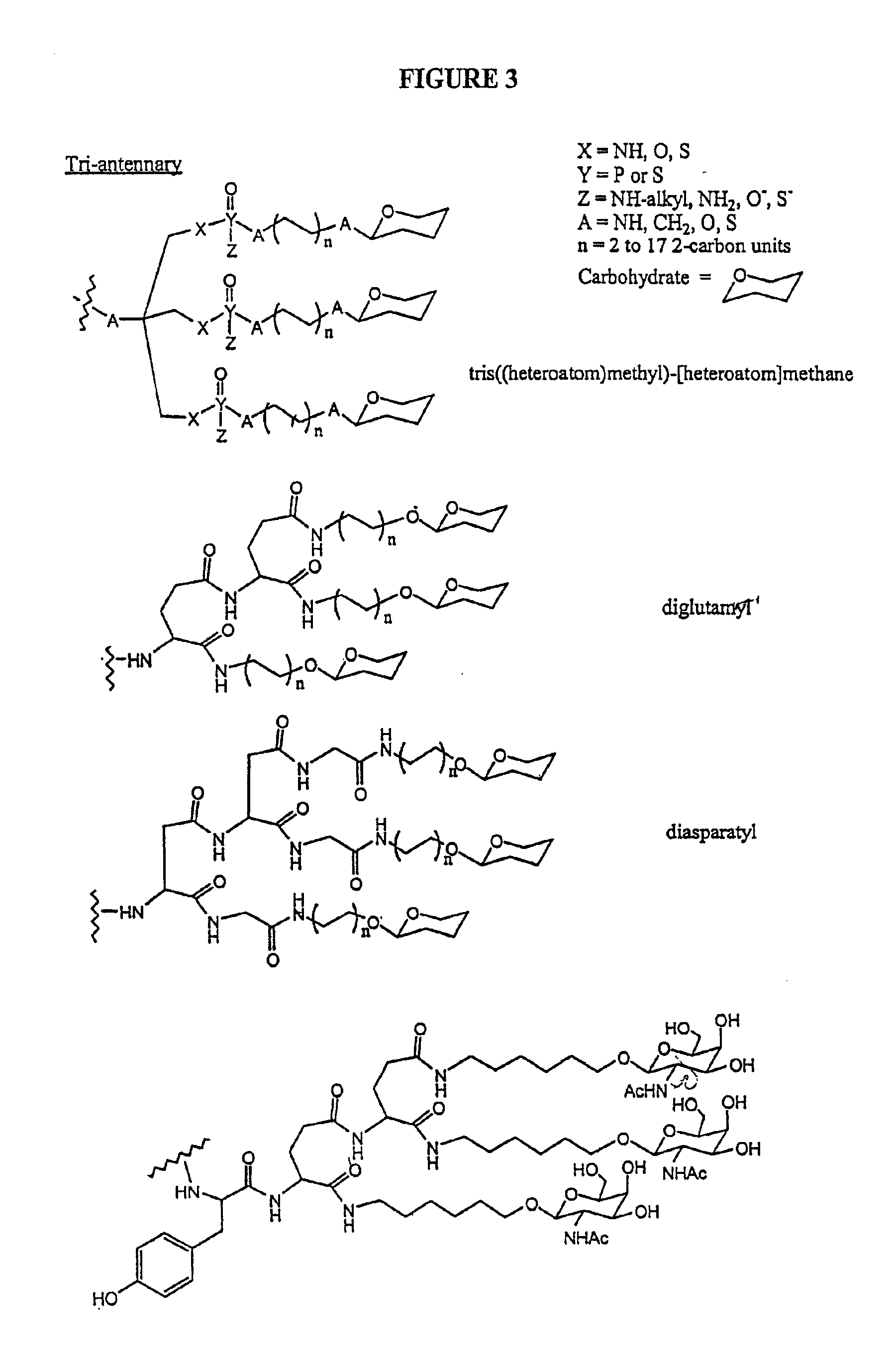
Conjugates of glycosylated/galactosylated peptide, bifunctional linker, and nucleotidic monomers/polymers, and related compositions and method of use
InactiveUS6906182B2Abnormal proliferationInhibition of replicationOrganic active ingredientsBiocideNucleotideEthylene Homopolymers
A conjugate of formula A-L-P, in which:A represents a glycosylated / galactosylated peptide that binds to a cell-surface receptor,L represents a bifunctional linker, which does not comprise a naturally occurring amino acid and is covalently bonded to A and P in a regiospecific manner, andP represents a monomer, homopolymer or heteropolymer comprising at least one nucleotide or an analogue thereof, which inhibits the intracellular biosynthesis of nucleotides or nucleic acids in a sequence-independent manner,wherein either or both of the covalent bond between A and L and the covalent bond between L and P can be cleaved intracellularly; a composition comprising such a conjugate; and a method of inhibiting abnormal cellular proliferation in a mammal; and a method of inhibiting replication of a virus in a mammal.
Owner:CELLECTIVE DX CORP
Computer network intrusion detection
InactiveUS20120297489A1Easily and efficiently identifyingRapid responseMemory loss protectionError detection/correctionBIOSVirus
A method and system of identifying an attacker device attempting an intrusion into a network. At least one managed device of the network detects an incoming TCP / IP connection by the attacker device to the network. It is determined that the incoming TCP / IP connection is a Net BIOS connection that has created an invalid logon by the attacker device, linking the invalid logon with the NetBIOS TCP / IP connection, retrieving event log information from a security event log of the network, and determining (i) that a userid of the invalid logon is a local userid defined on a local device, (ii) that the userid of the invalid logon is a userid in a list of userids used by viruses, or (iii) that the userid of the invalid logon is neither the local userid nor is in the list of userids. The retrieved event log information is stored in a central violation database.
Owner:KYNDRYL INC
Methods for sterilizing biological materials by irradiation over a temperature gradient
InactiveUS6908591B2Effective sterilizationImprove permeabilityDead animal preservationLavatory sanitoryBiological materialsBiology
Methods are disclosed for sterilizing tissue to reduce the level of one or more active biological contaminants or pathogens therein, such as viruses, bacteria, (including inter- and intracellular bacteria, such as mycoplasmas, ureaplasmas, nanobacteria, chlamydia, rickettsias), yeasts, molds, fungi, spores, prions or similar agents responsible, alone or in combination, for TSEs and / or single or multicellular parasites. The methods involve sterilizing one or more tissues with irradiation.
Owner:CLEARANT
Method for preparing thrombin for use in a biological glue
InactiveUS6472162B1Derive fast acting, stable autologous thrombinSimple preparatory procedureBioreactor/fermenter combinationsBiological substance pretreatmentsTissue sealantDonors plasma
A sterile method for preparing stable thrombin component from a single donor's plasma in which the thrombin component and the clotting and adhesive proteins component are harvested simultaneously from the same donor plasma in less than one hour. The combined components provide an improved biological hemostatic agent and tissue sealant by virtue of its freedom from the risk of contaminating viruses or bacteria from allogenic human or bovine blood sources. The thrombin provides polymerization of the clotting and adhesive proteins in less than five seconds, and is sufficiently stable to provide that fast clotting over a six hour period. Further, the clotting times can be predictably lengthened by diluting the thrombin with saline.
Owner:ASAHI KASEI MEDICAL CO LTD
Microfluidic particle-analysis systems
InactiveUS20100120077A1Bioreactor/fermenter combinationsBiological substance pretreatmentsAssayMixed group
The invention provides systems, including apparatus, methods, and kits, for the microfluidic manipulation and / or detection of particles, such as cells and / or beads. The invention provides systems, including apparatus, methods, and kits, for the microfluidic manipulation and / or analysis of particles, such as cells, viruses, organelles, beads, and / or vesicles. The invention also provides microfluidic mechanisms for carrying out these manipulations and analyses. These mechanisms may enable controlled input, movement / positioning, retention / localization, treatment, measurement, release, and / or output of particles. Furthermore, these mechanisms may be combined in any suitable order and / or employed for any suitable number of times within a system. Accordingly, these combinations may allow particles to be sorted, cultured, mixed, treated, and / or assayed, among others, as single particles, mixed groups of particles, arrays of particles, heterogeneous particle sets, and / or homogeneous particle sets, among others, in series and / or in parallel. In addition, these combinations may enable microfluidic systems to be reused. Furthermore, these combinations may allow the response of particles to treatment to be measured on a shorter time scale than was previously possible. Therefore, systems of the invention may allow a broad range of cell and particle assays, such as drug screens, cell characterizations, research studies, and / or clinical analyses, among others, to be scaled down to microfluidic size. Such scaled-down assays may use less sample and reagent, may be less labor intensive, and / or may be more informative than comparable macrofluidic assays.
Owner:STANDARD BIOTOOLS INC
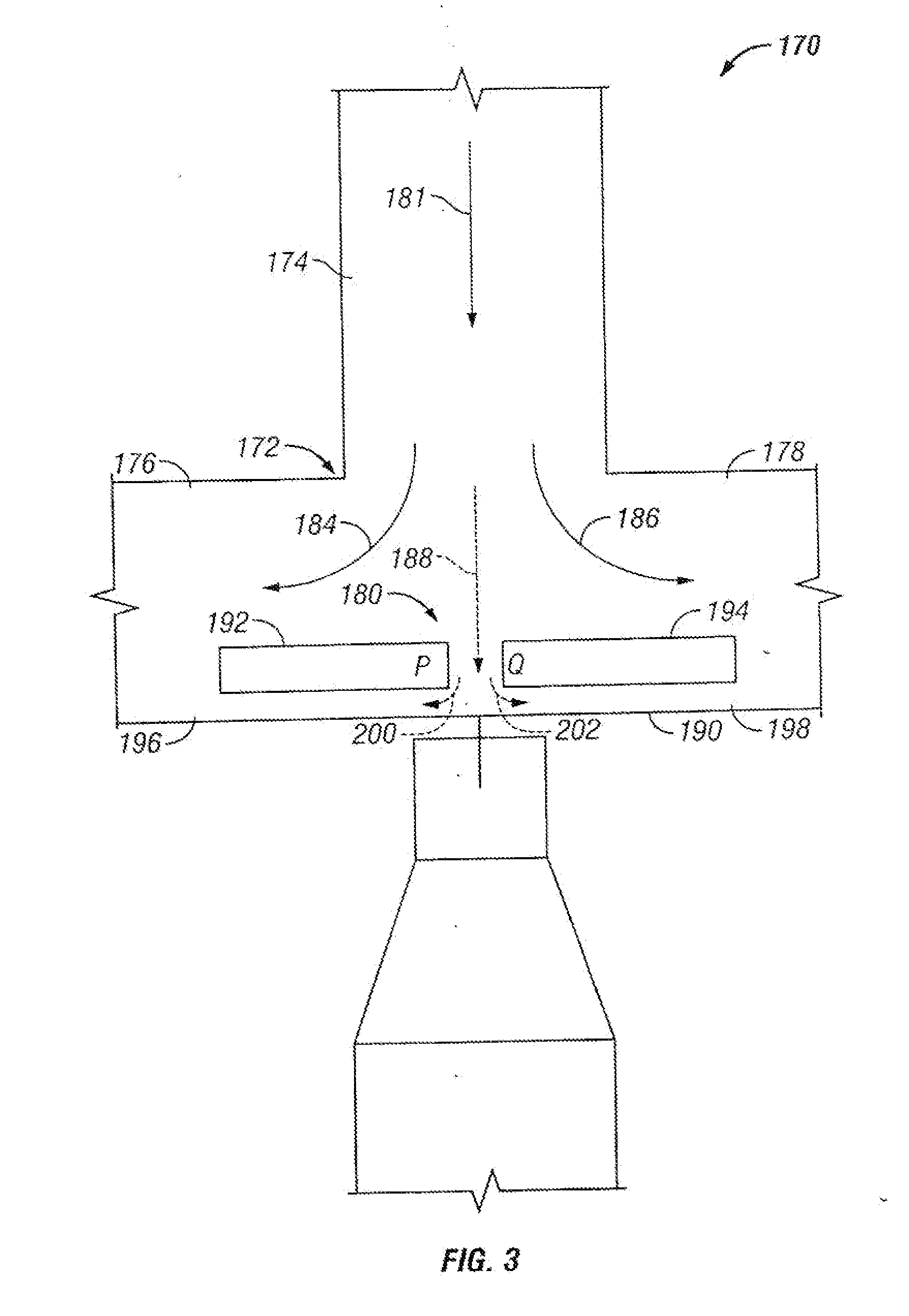
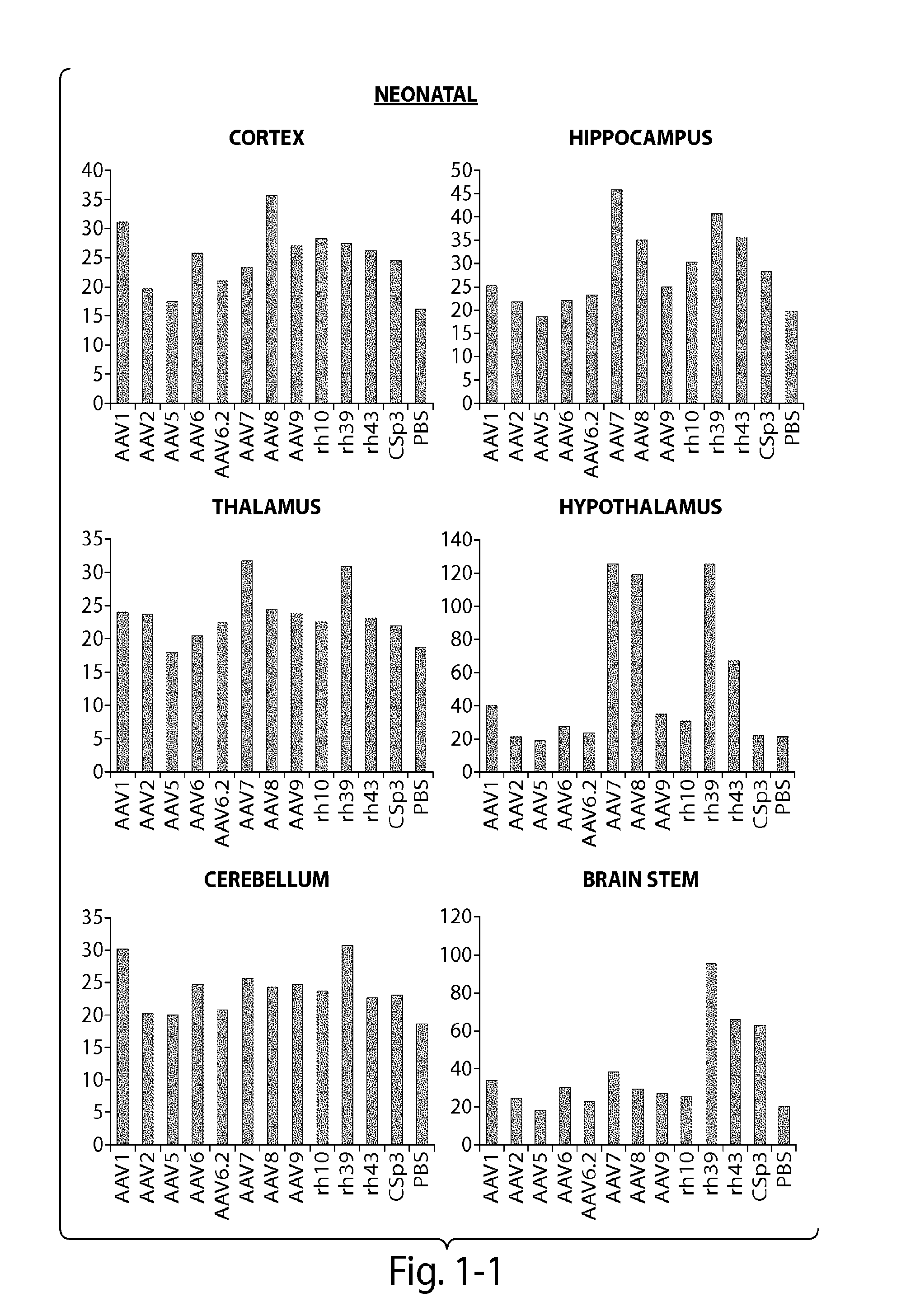
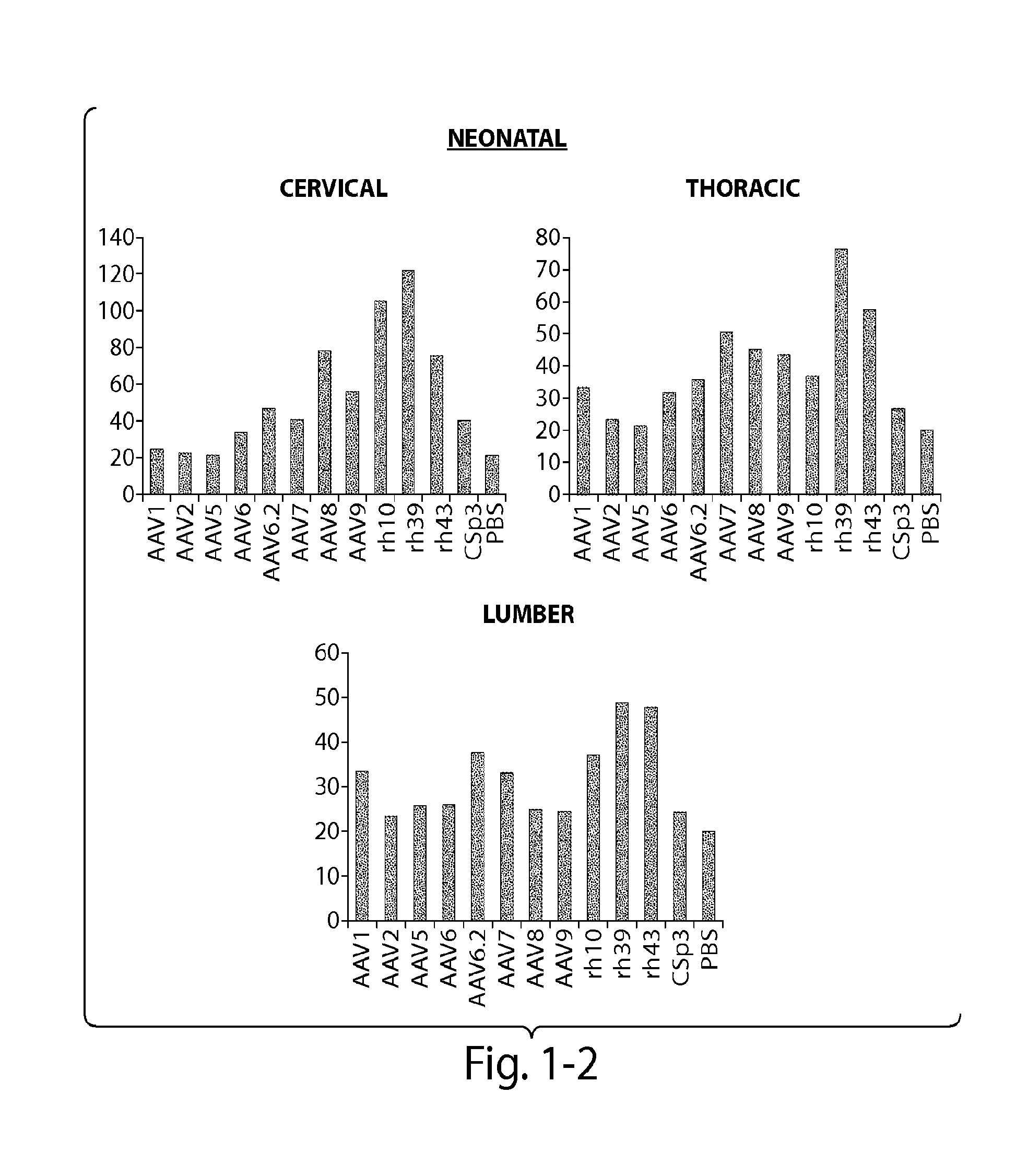
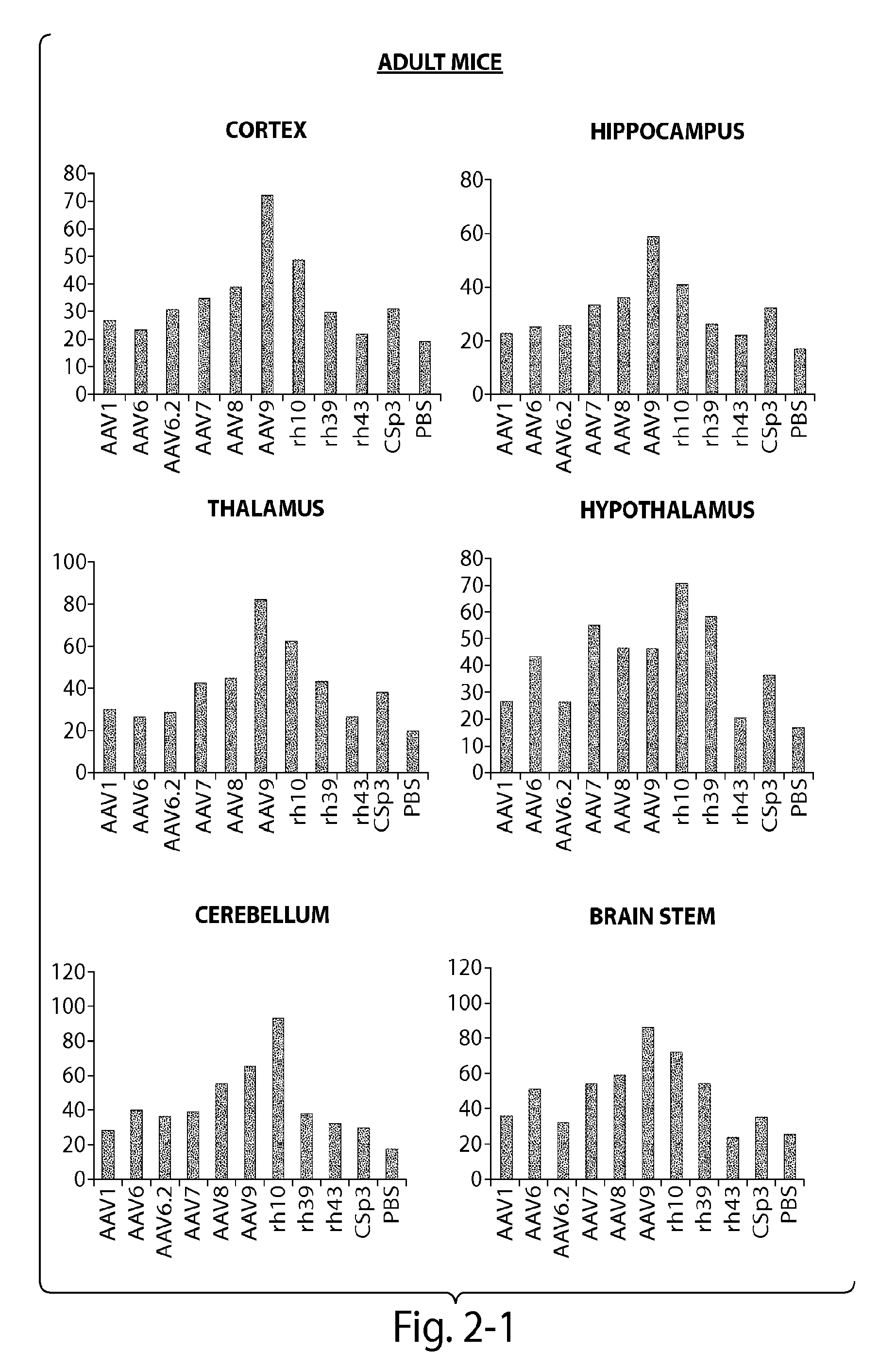
CNS targeting aav vectors and methods of use thereof
ActiveUS20130195801A1Widely distributedStable and nontoxic gene transferOrganic active ingredientsBiocideAdeno associate virusTransgene
Owner:UNIV OF MASSACHUSETTS
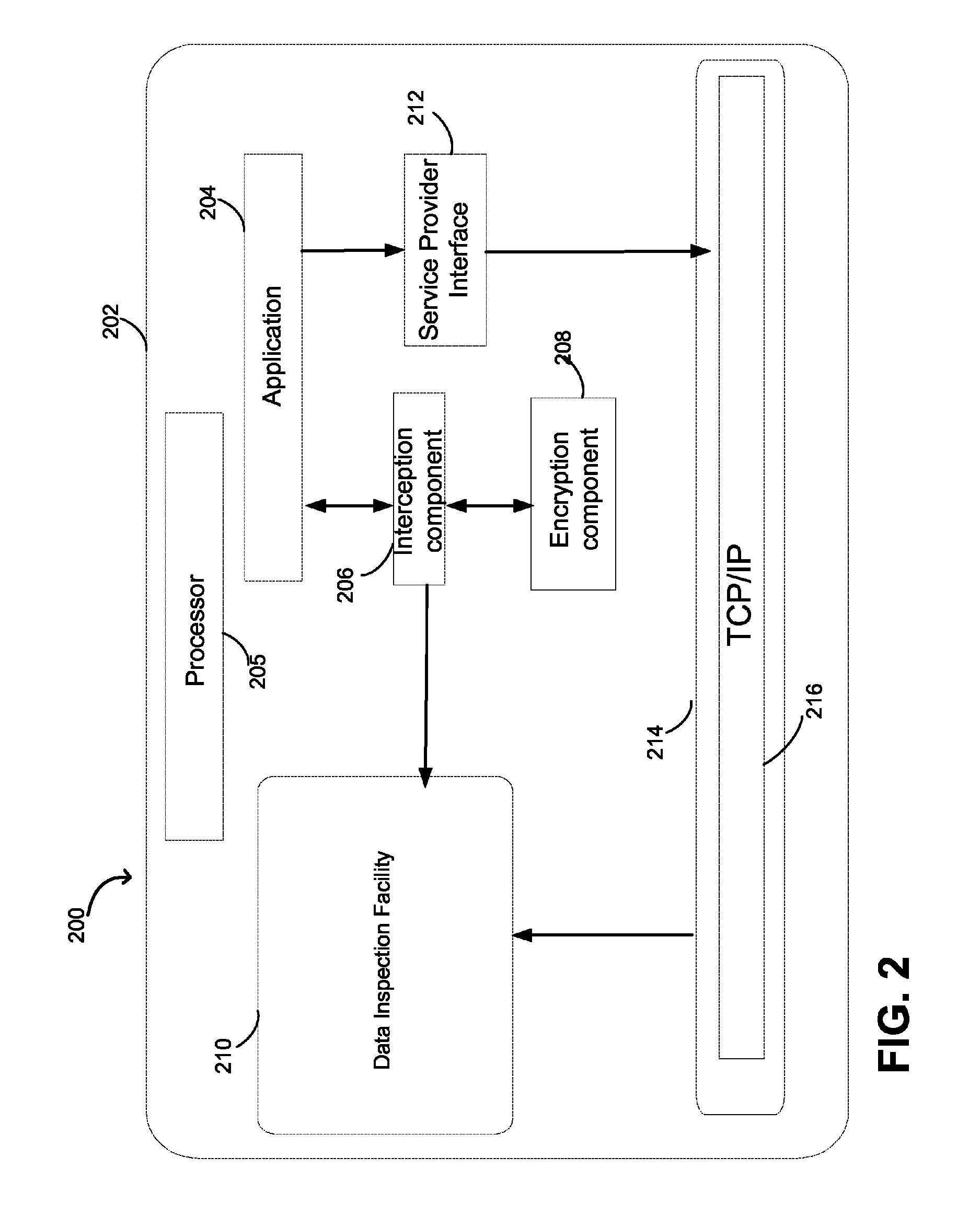
Encrypted network traffic interception and inspection
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com