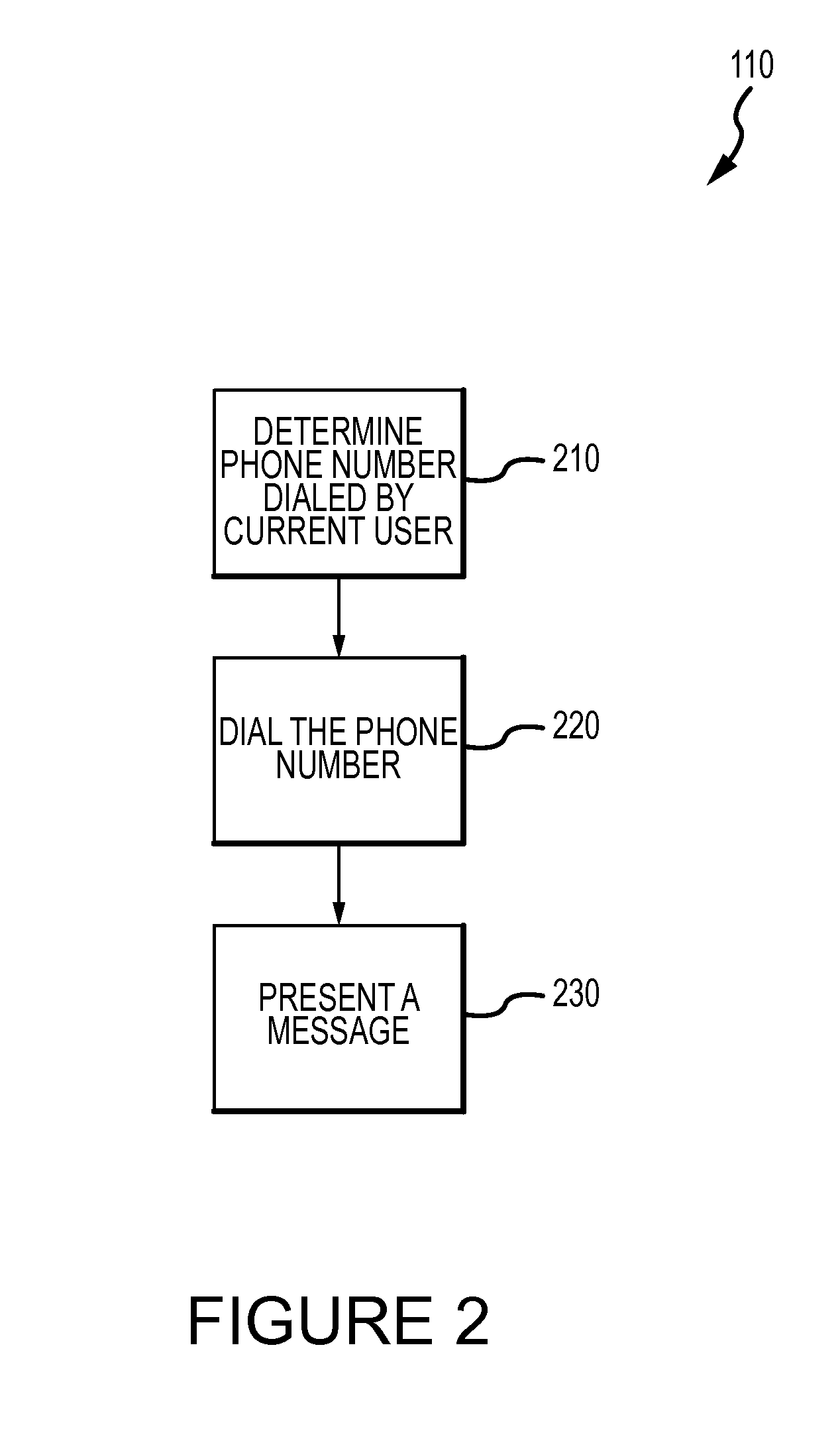
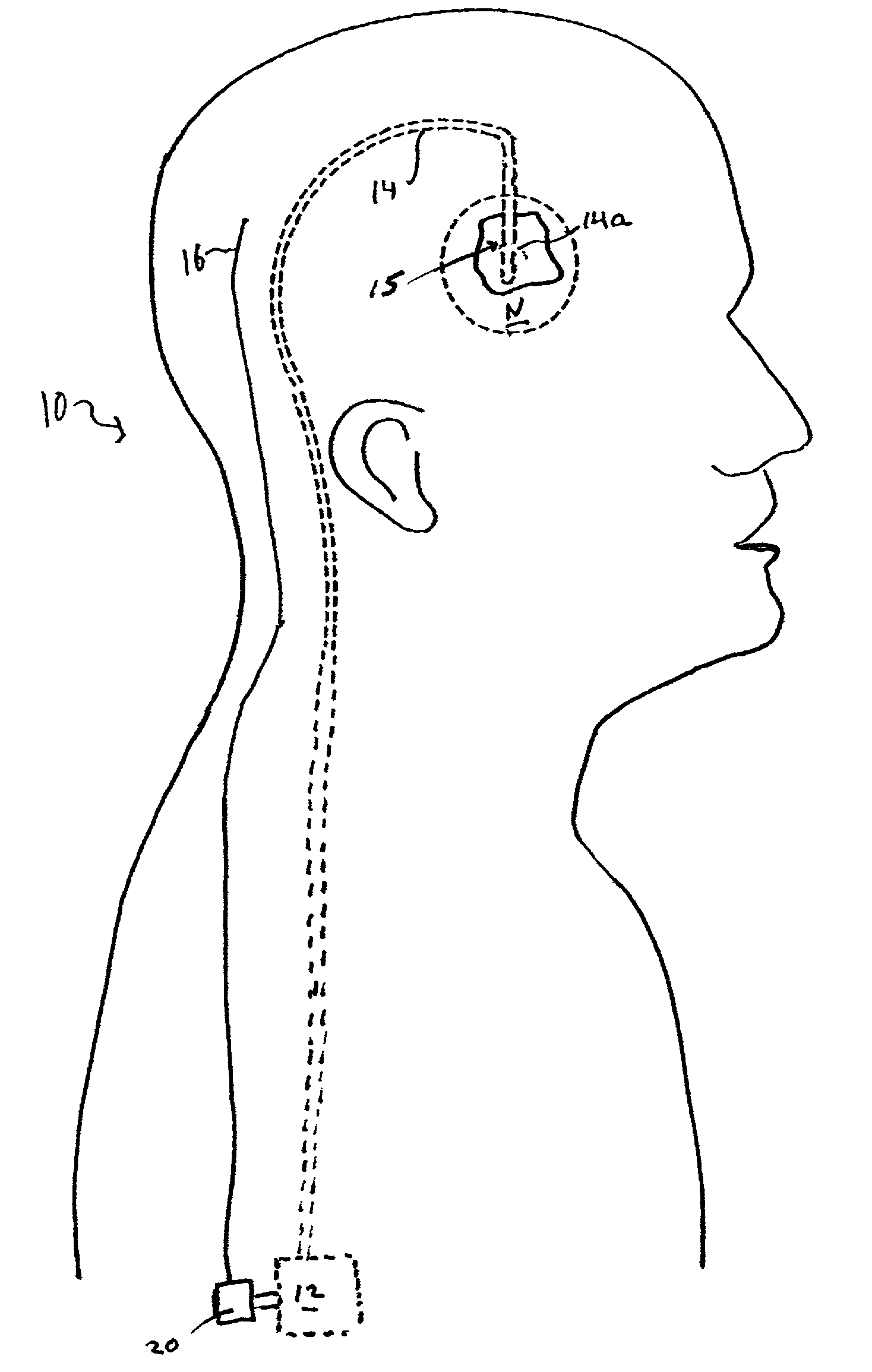
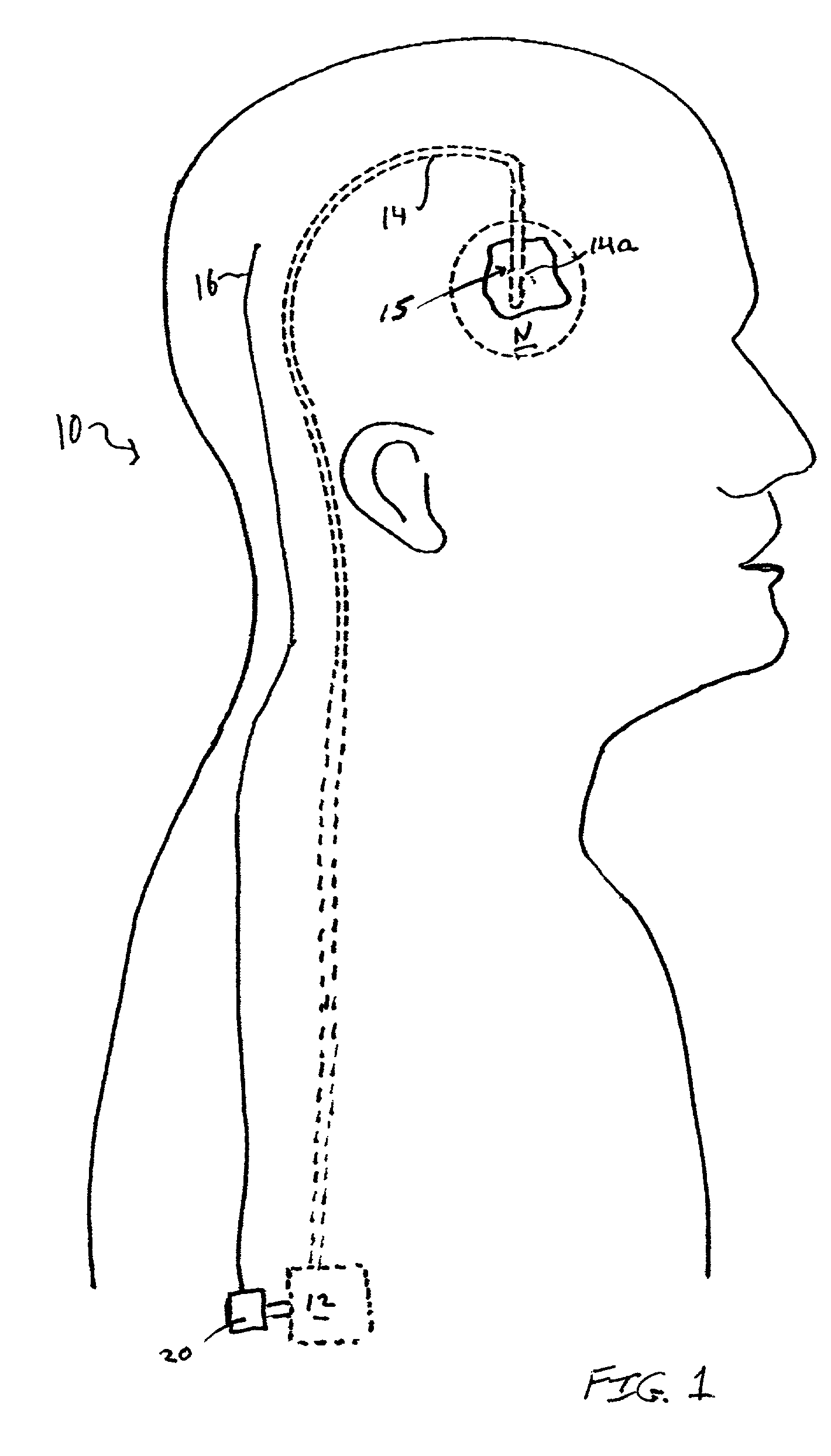
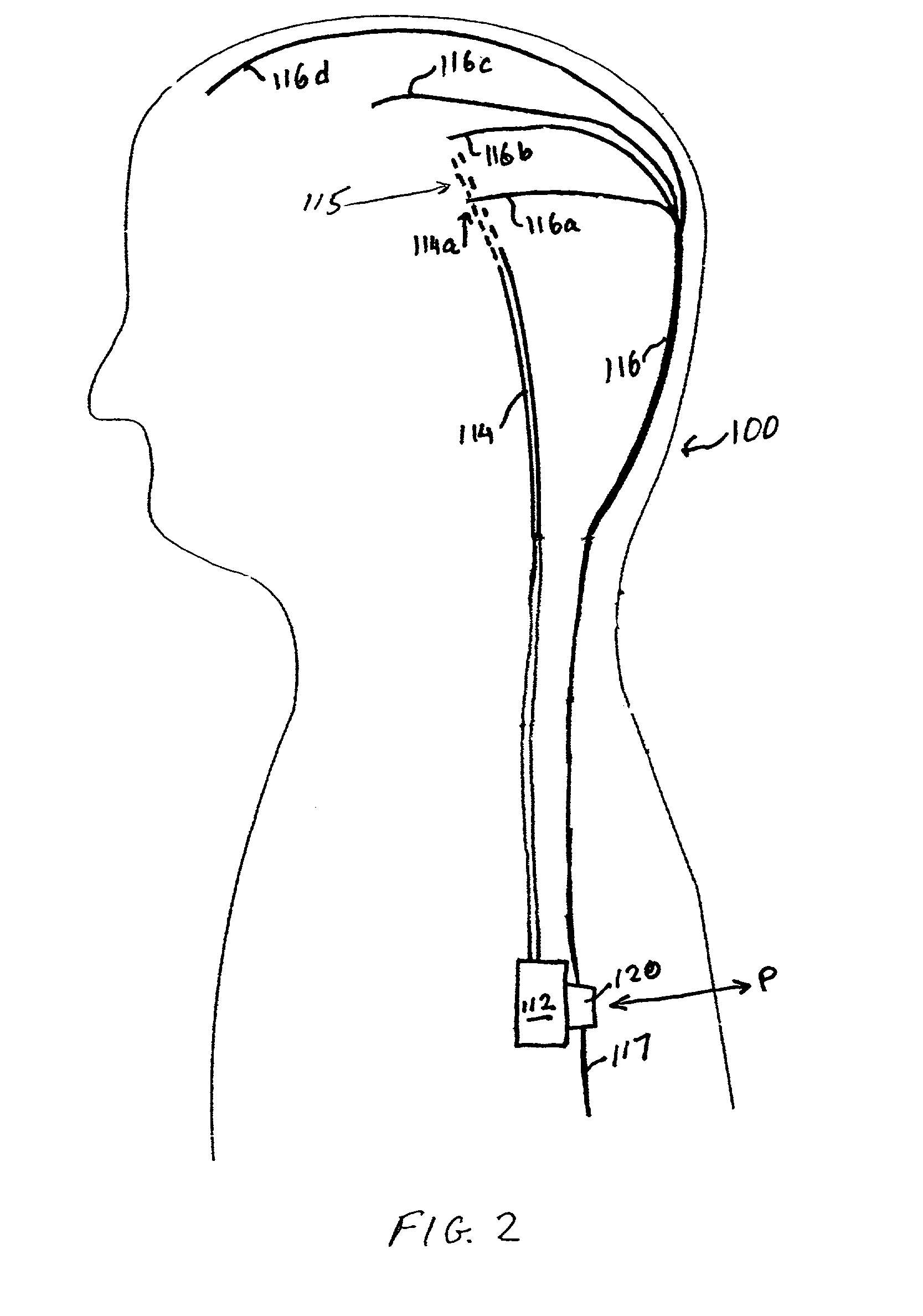
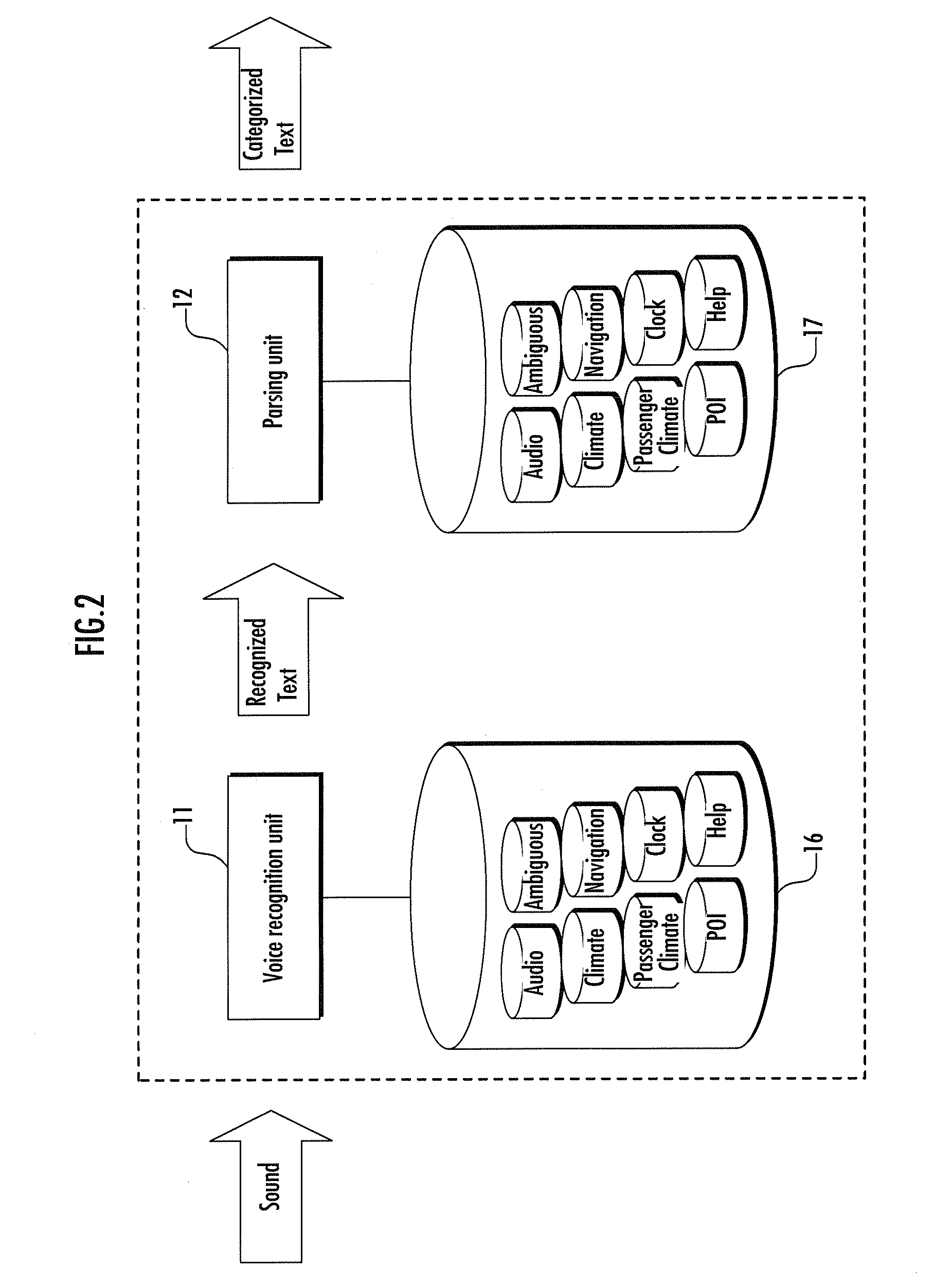
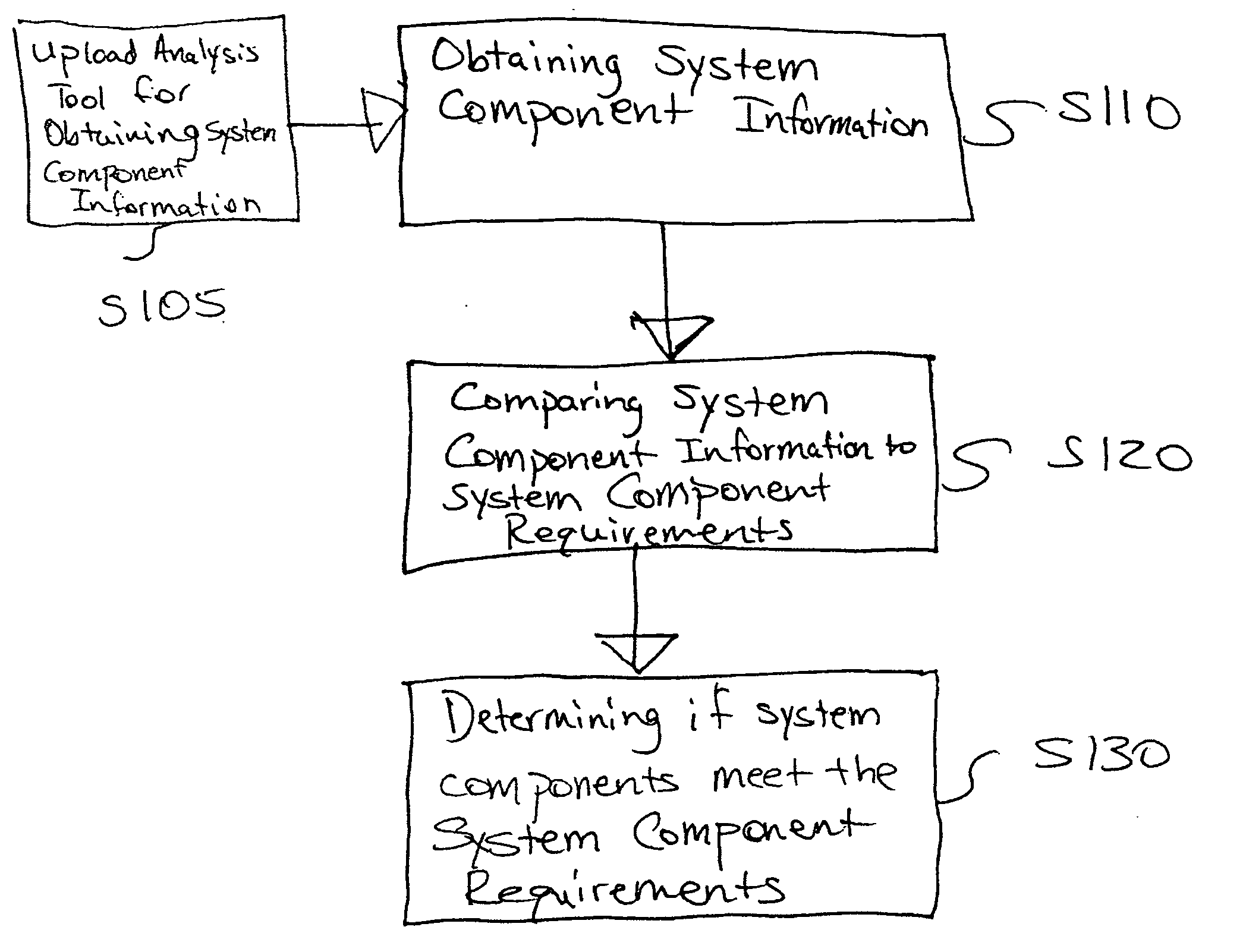
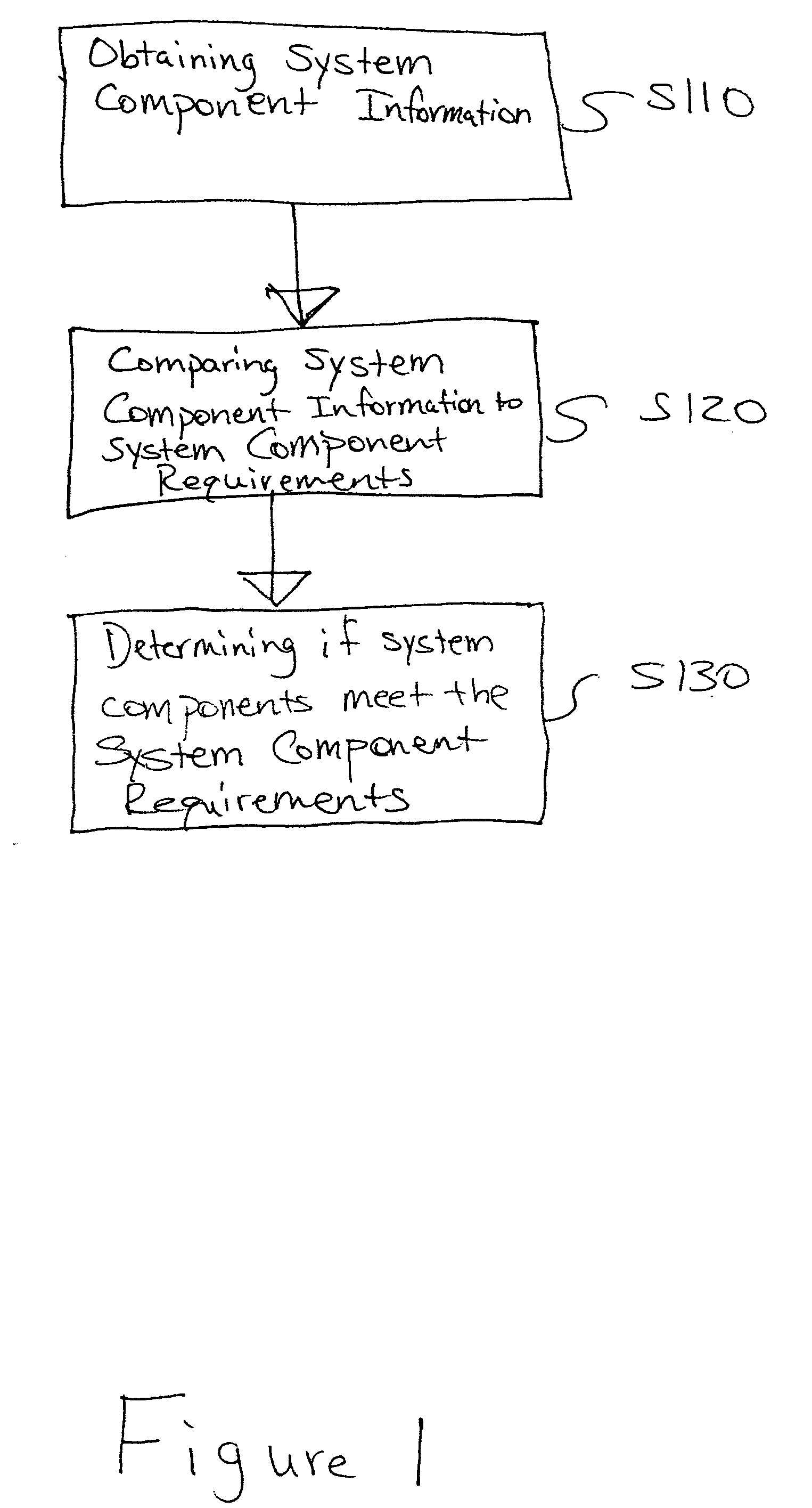
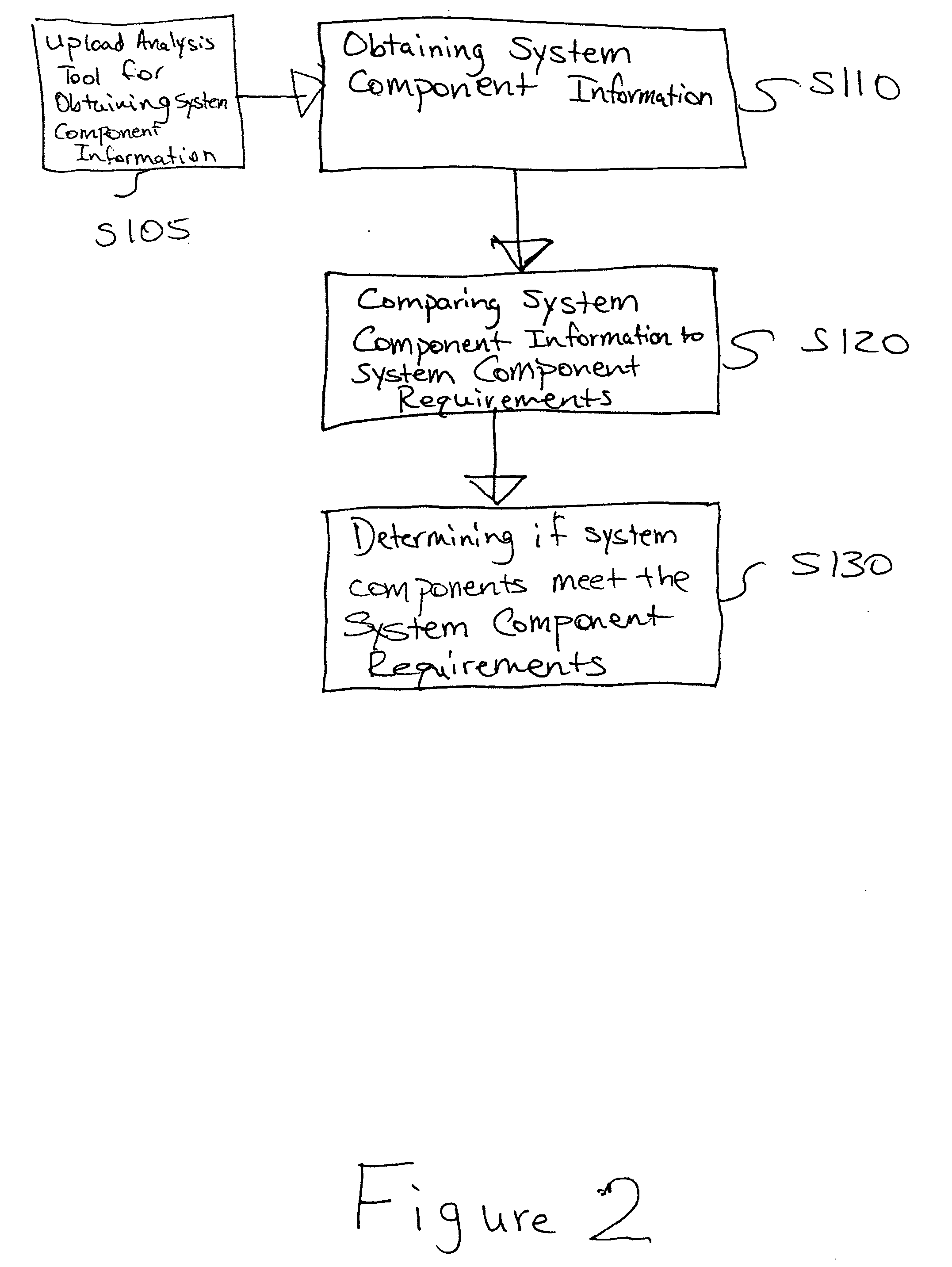
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
16289results about How to "Rapid response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
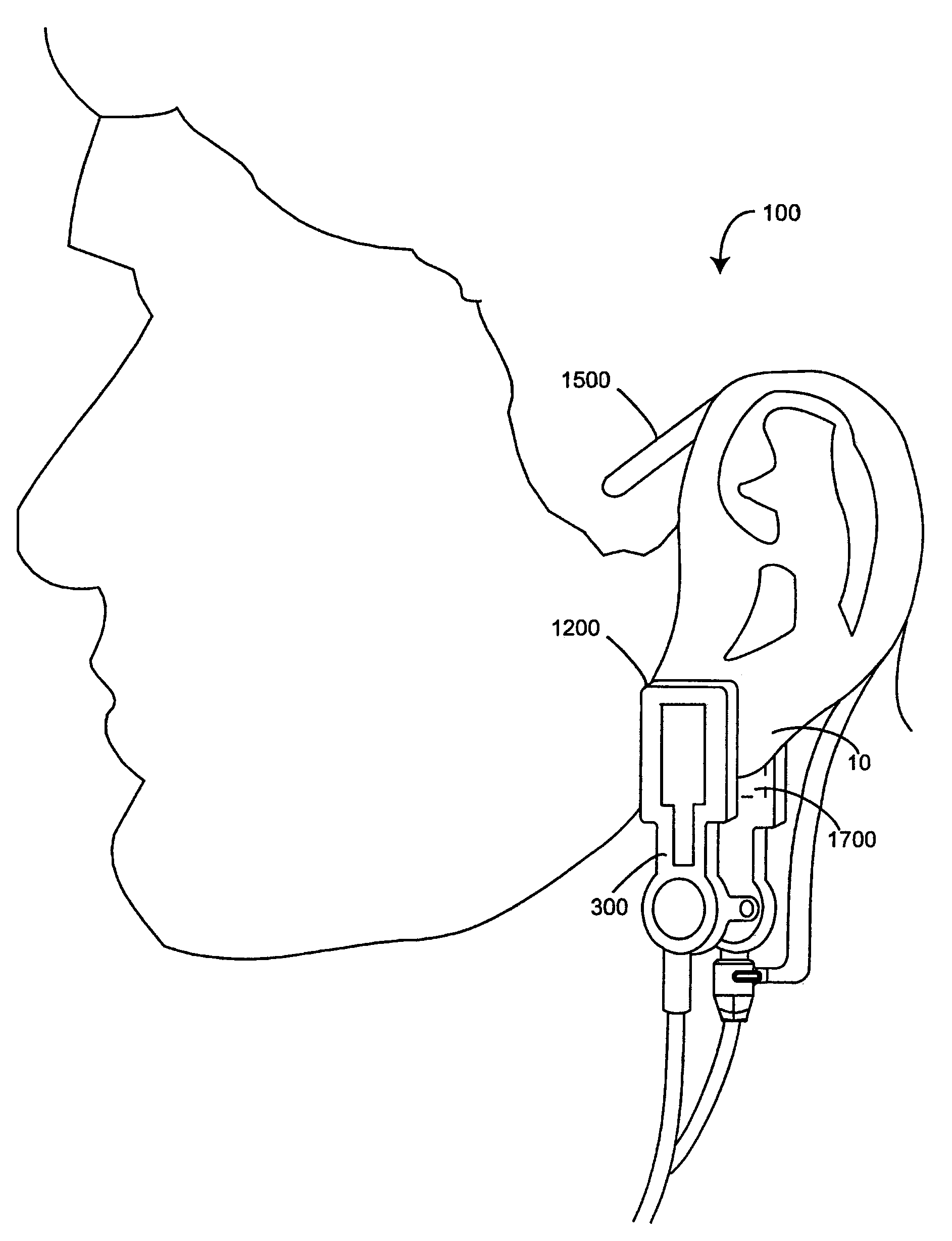
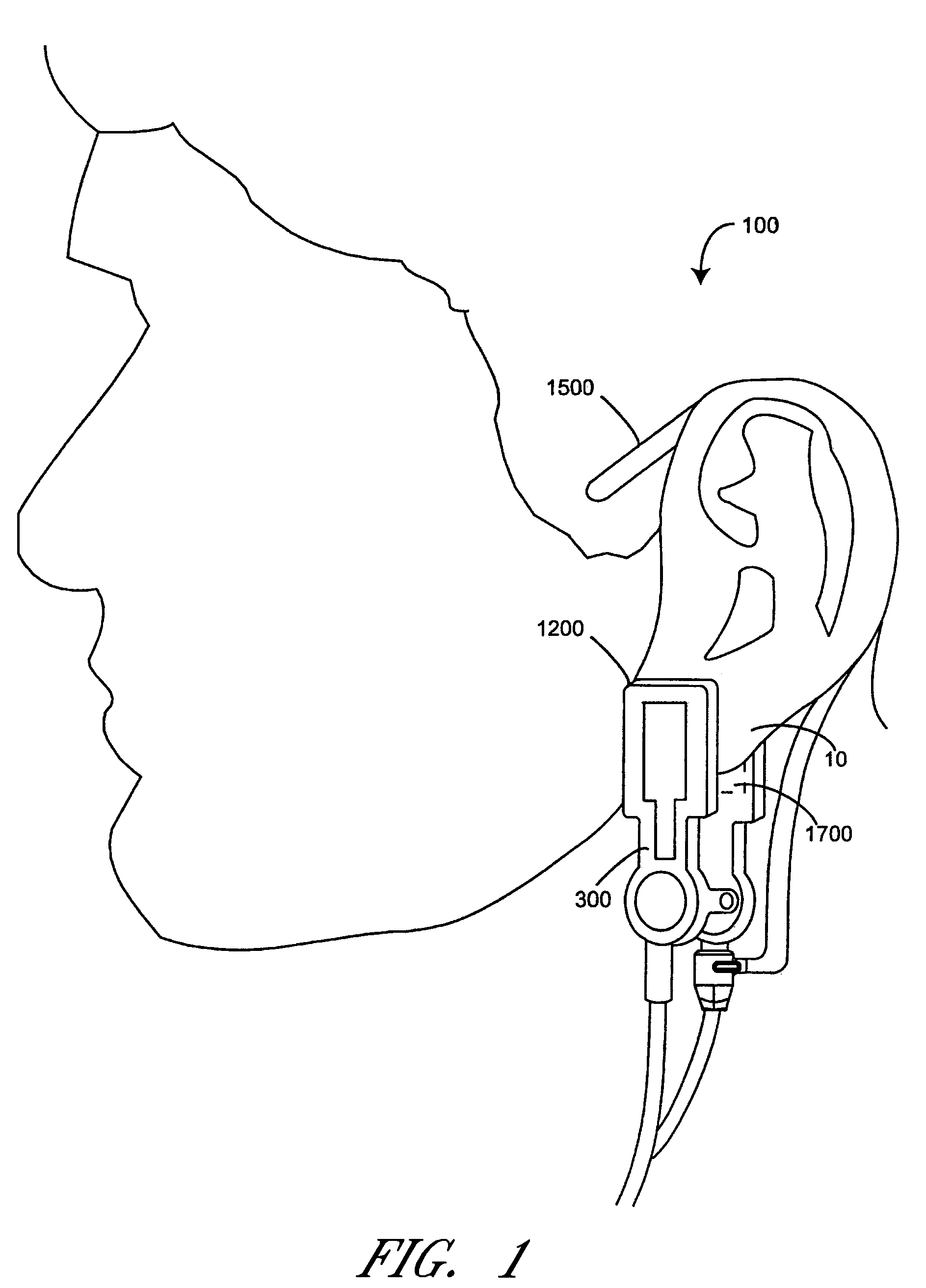
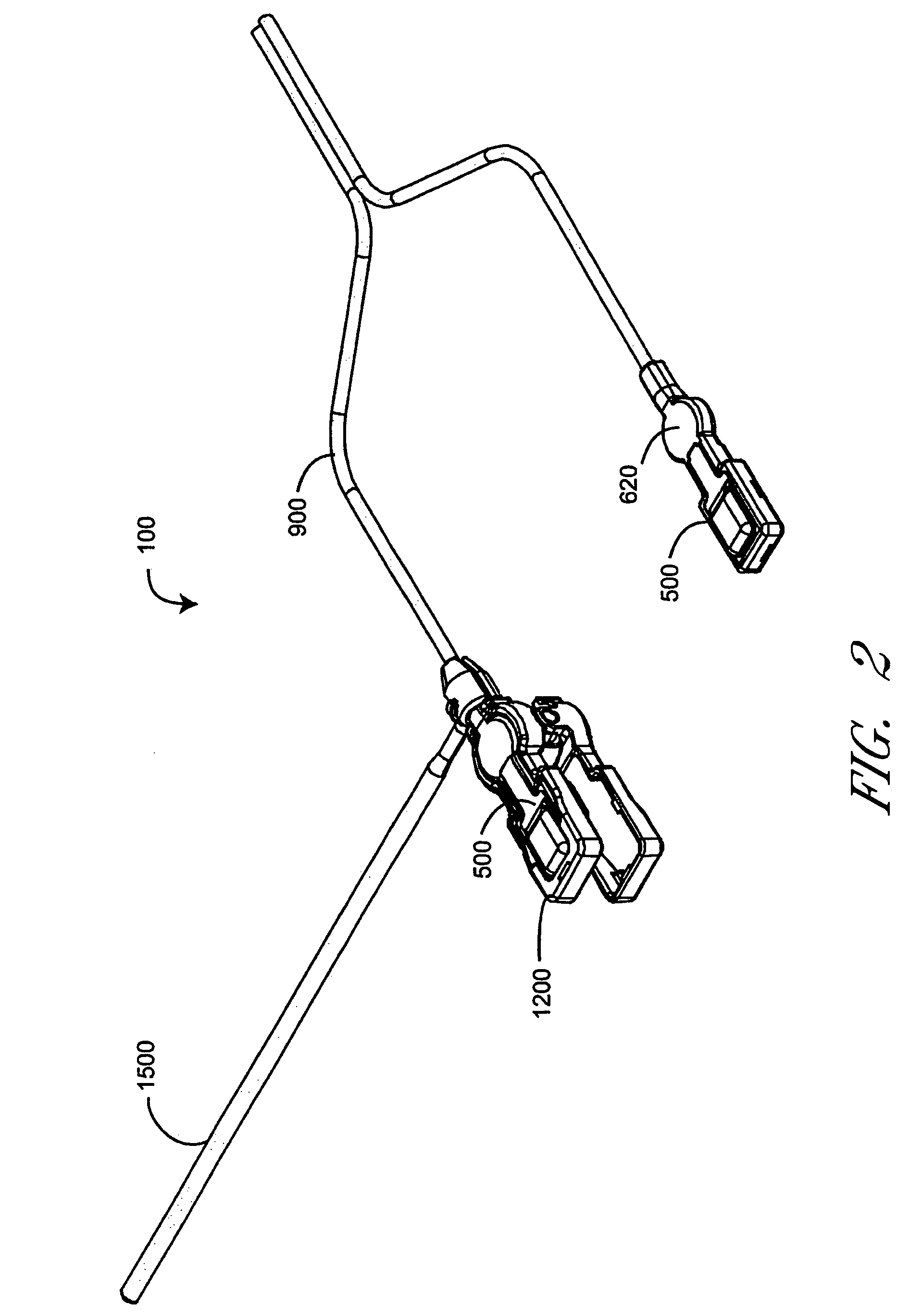
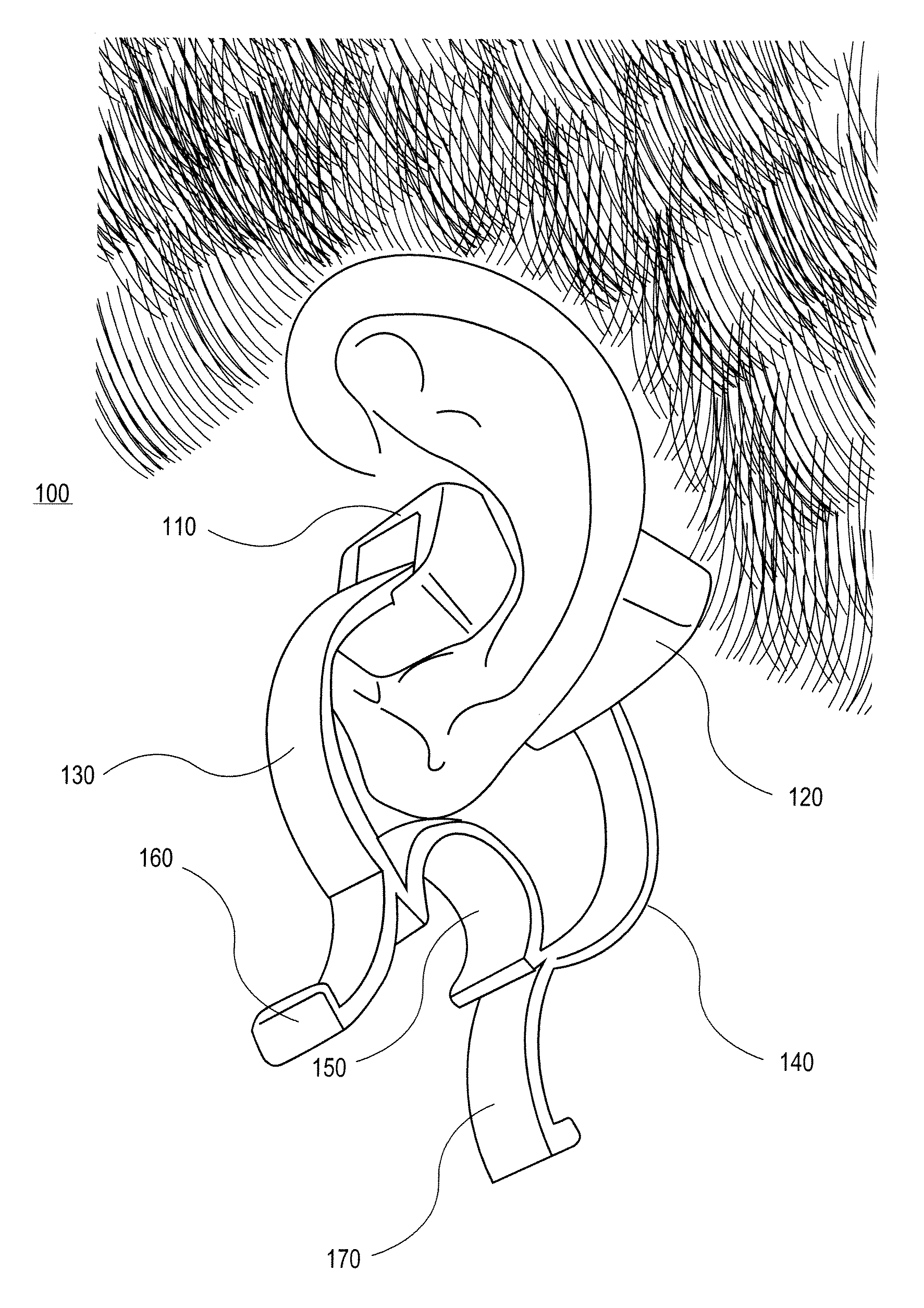
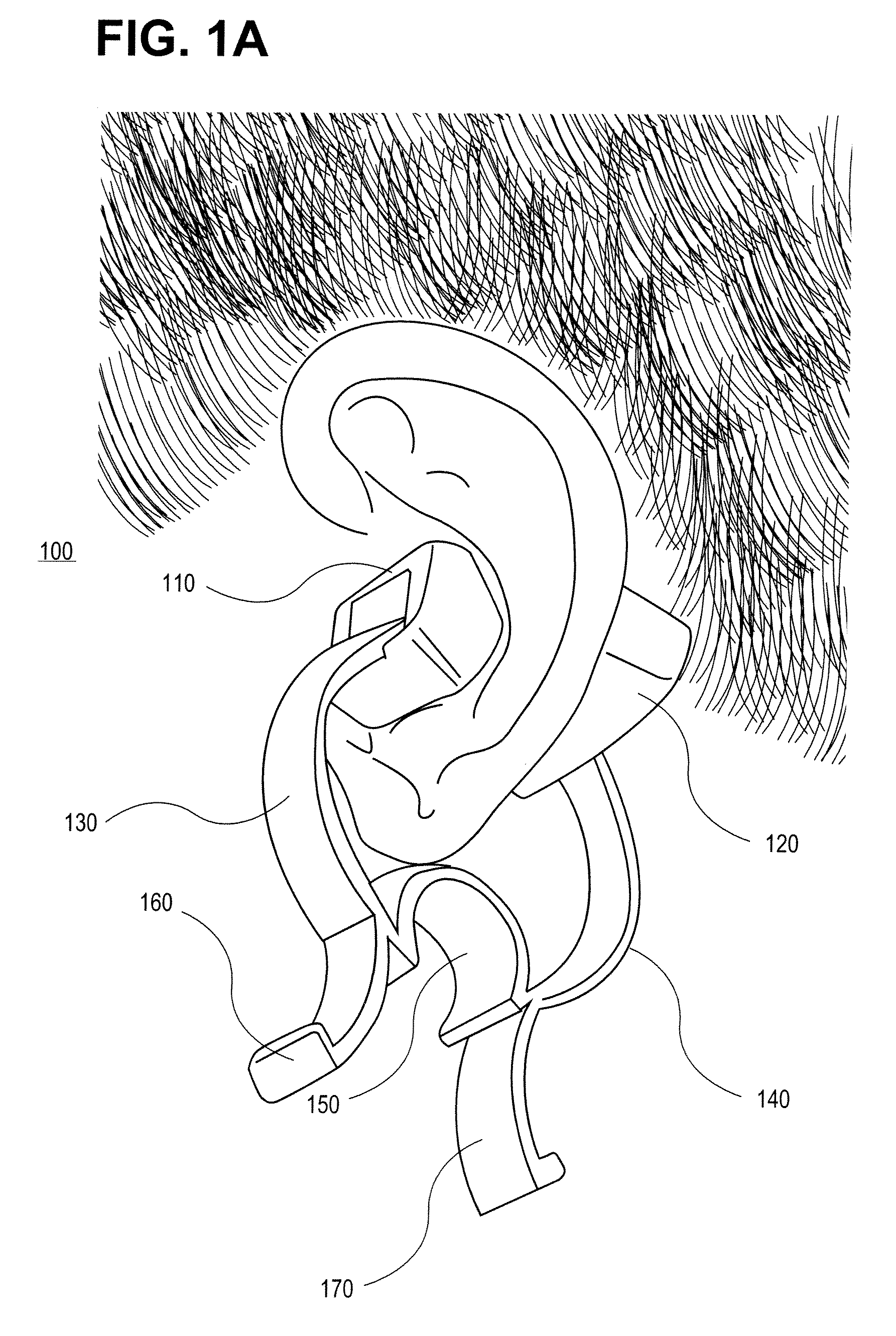
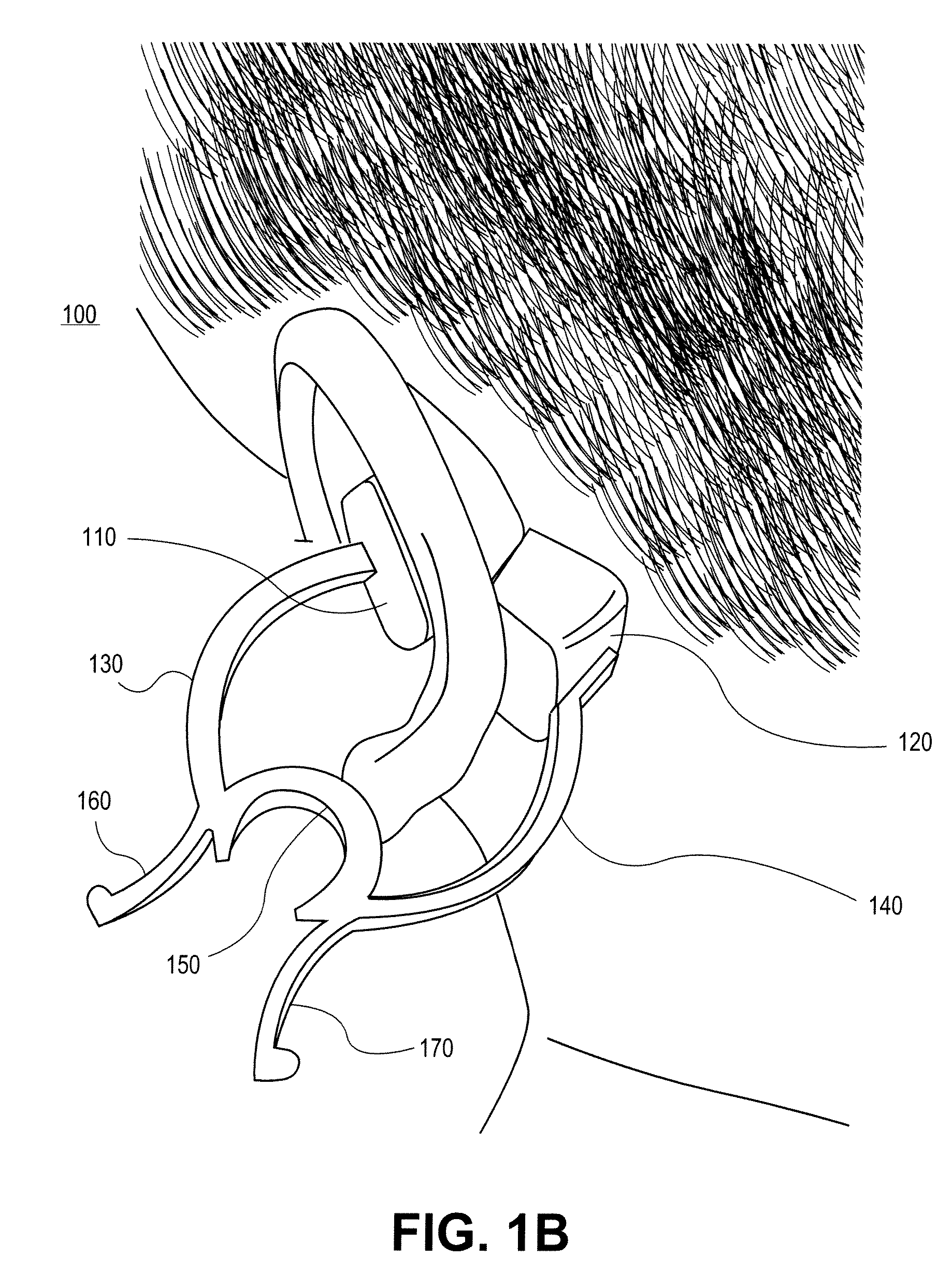
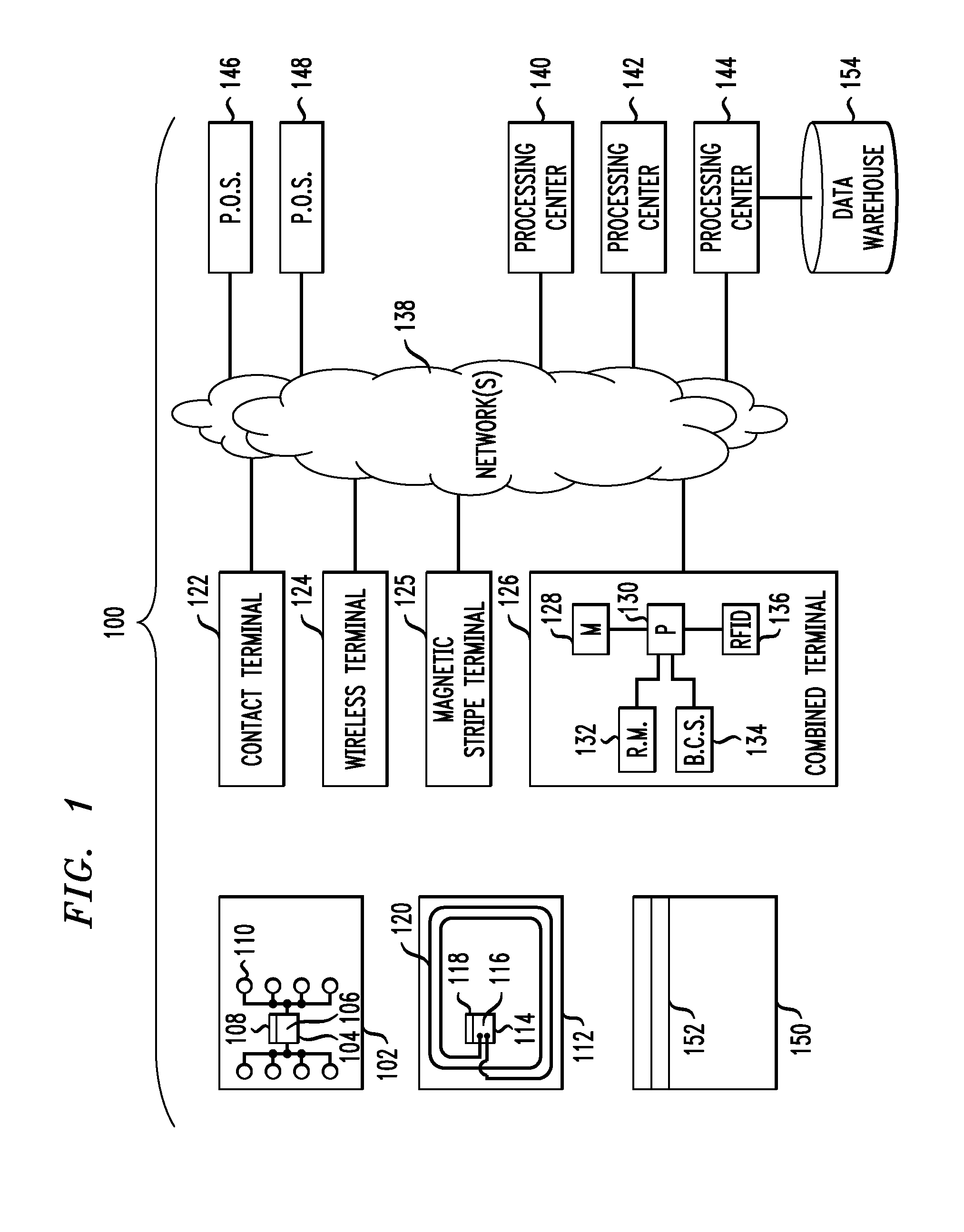
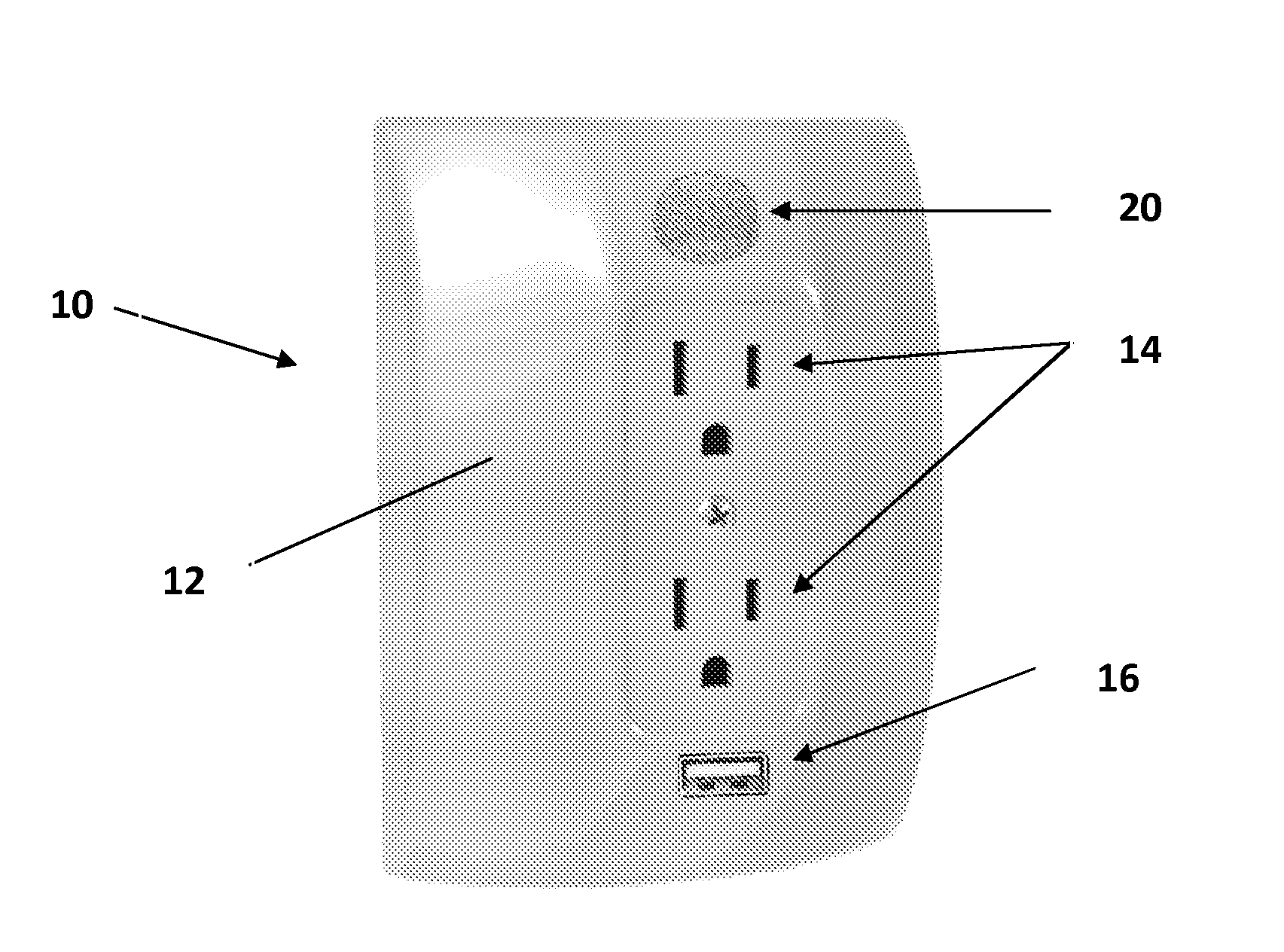
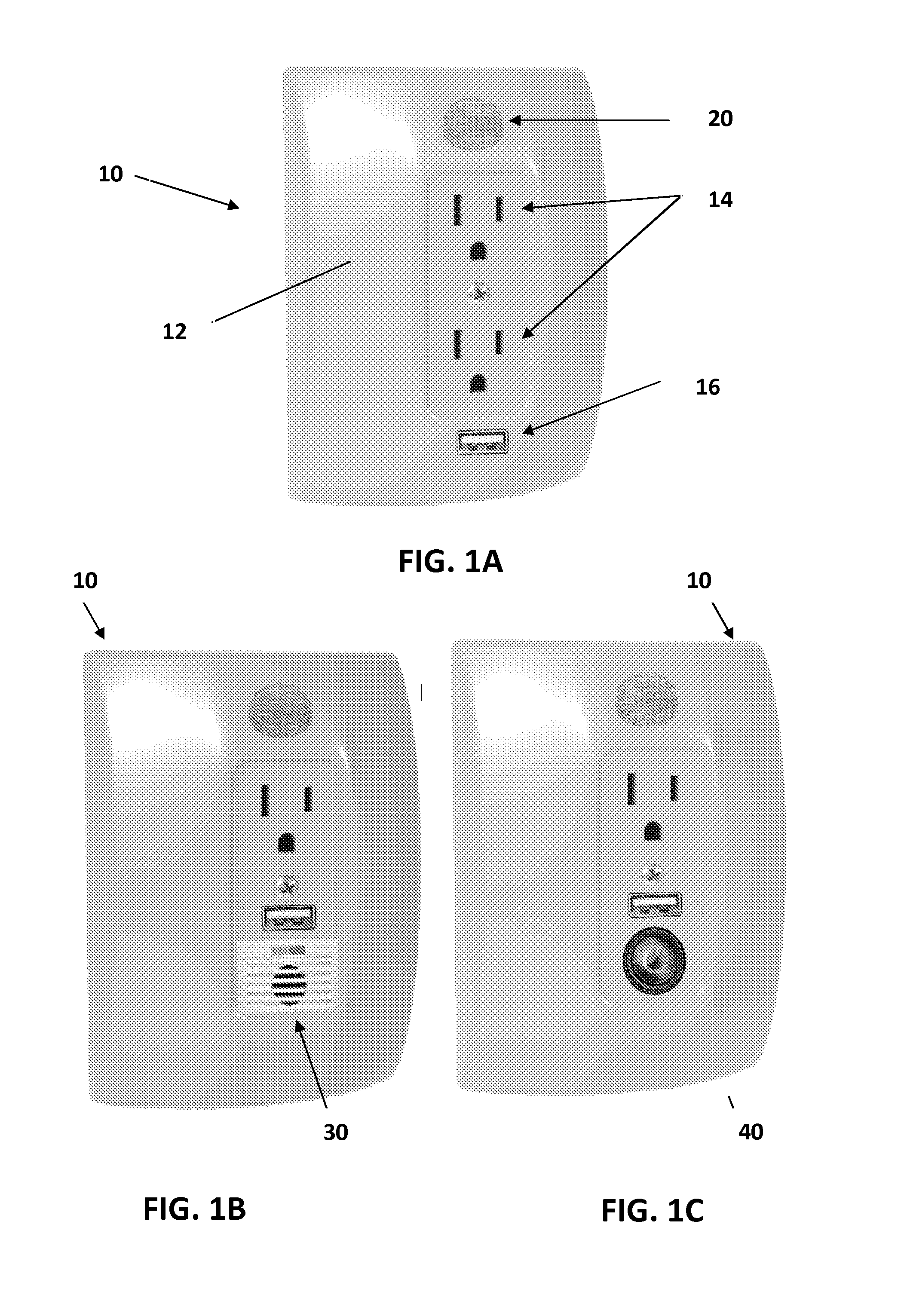
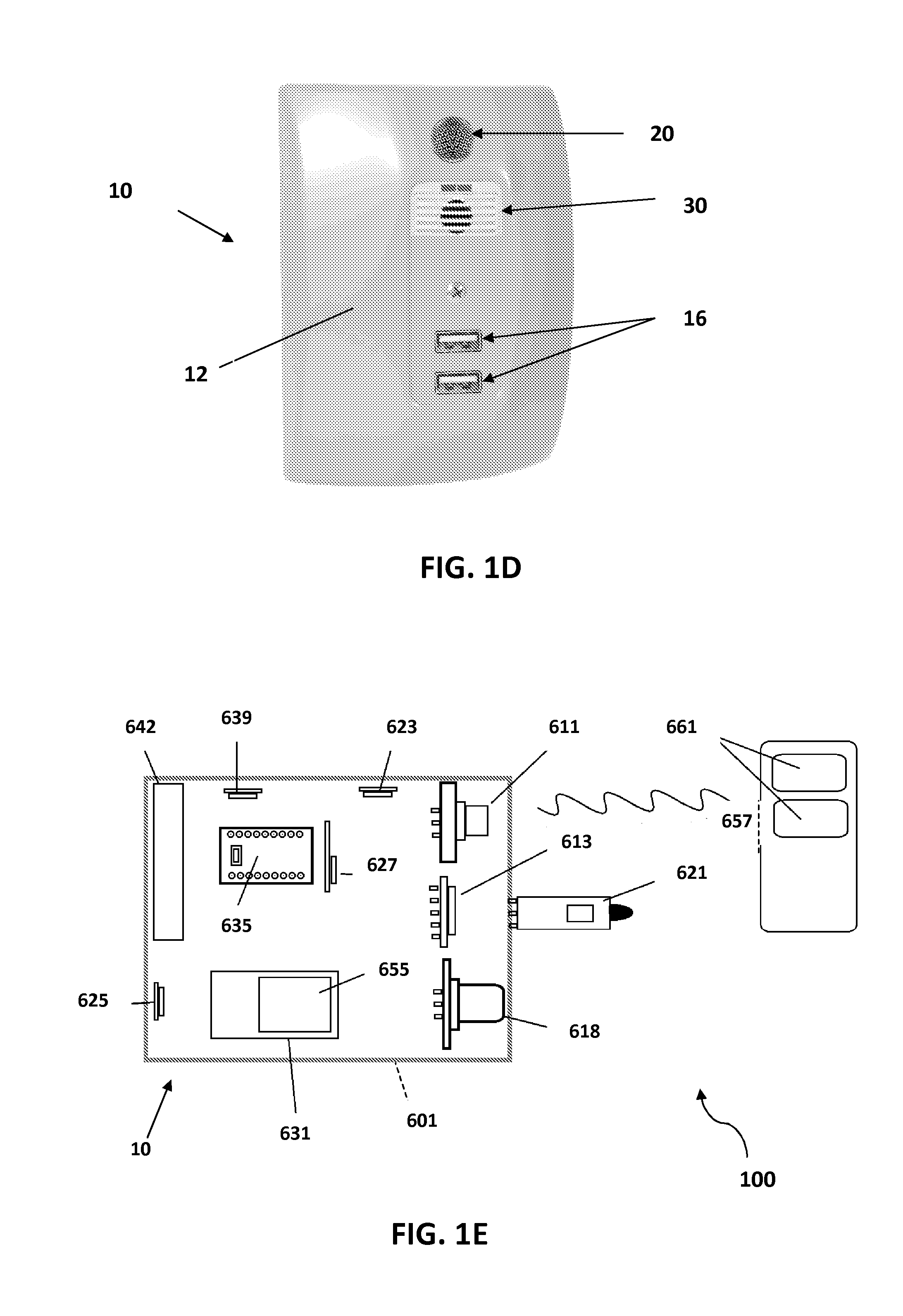
Pulse oximetry ear sensor
ActiveUS7341559B2Rapid responseConstricting ear siteCatheterDiagnostic recording/measuringPulse oximetryBiomedical engineering
An embodiment of an ear sensor assembly comprises an emitter pad and a detector pad. A clip is configured to removably retain each of the pads. The clip has an open position for placement on an ear tissue site and a closed position for securing the pads to opposite sides of the site. The assembly includes a sensor connector adapted to electrically communicate with a host instrument. A sensor cable has a first end terminating at the pads and a second end terminating at the sensor connector and provides electrical communications between the pads and the connector. In one embodiment, one or more silicone lenses or removable adhesive tabs aid in relieving patient discomfort and pressure necrosis.
Owner:JPMORGAN CHASE BANK NA
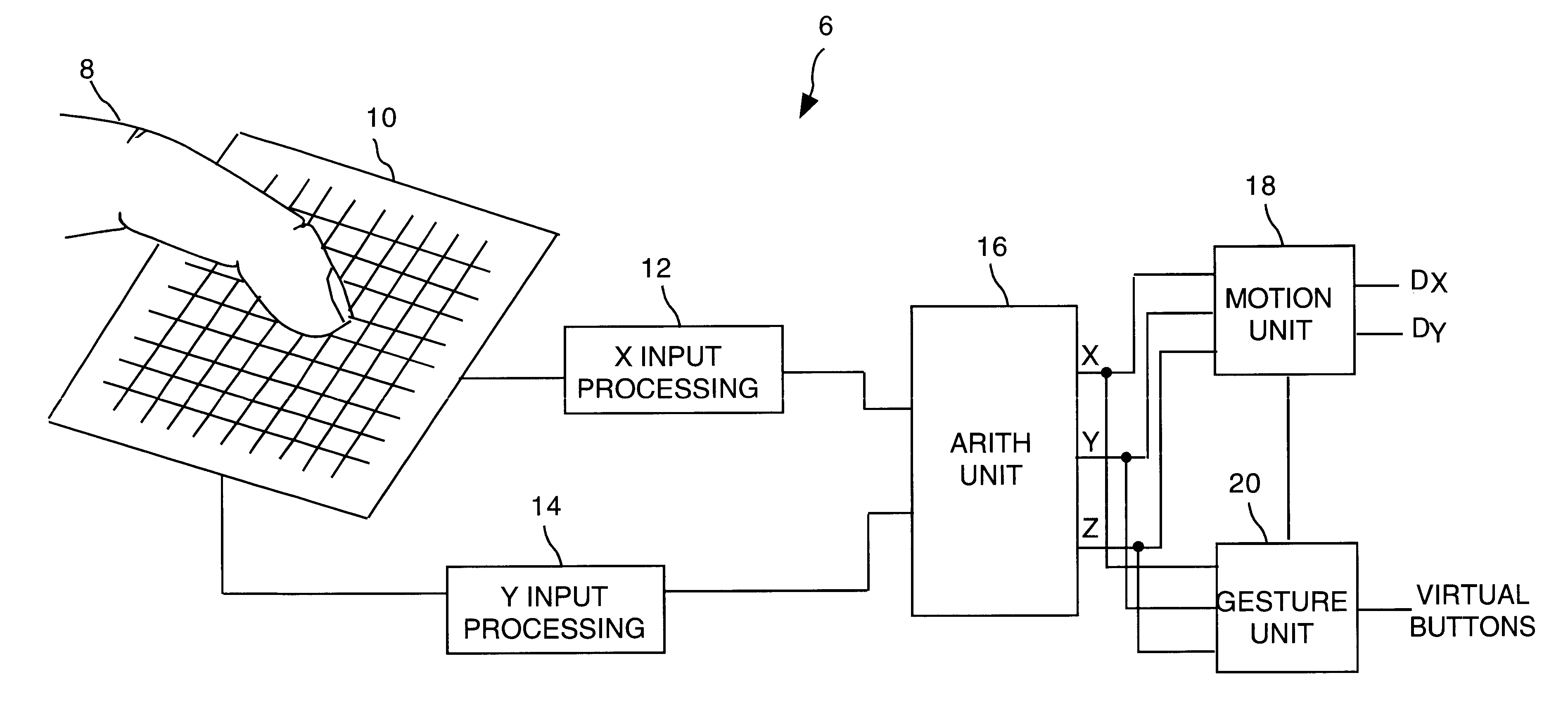
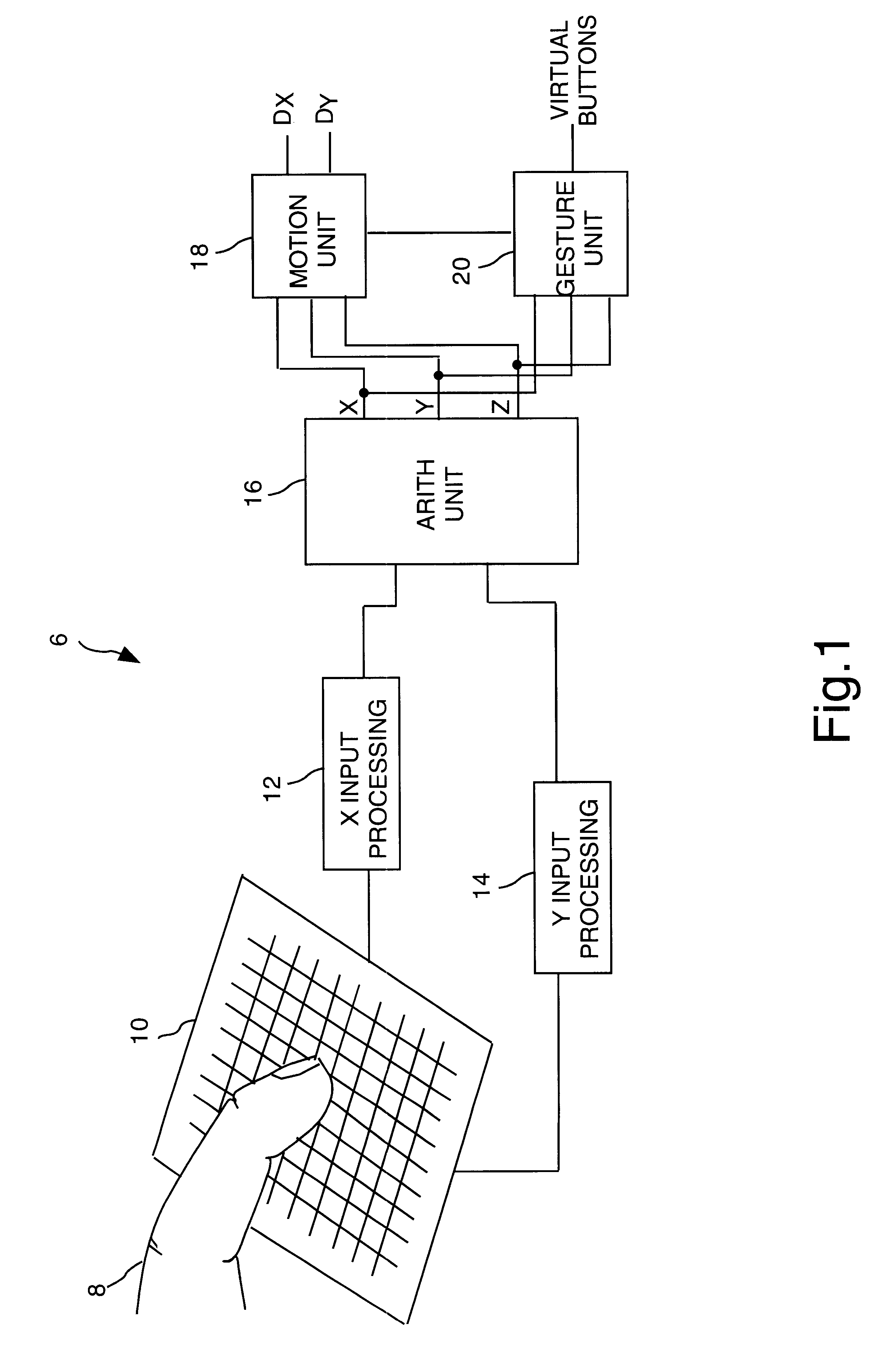
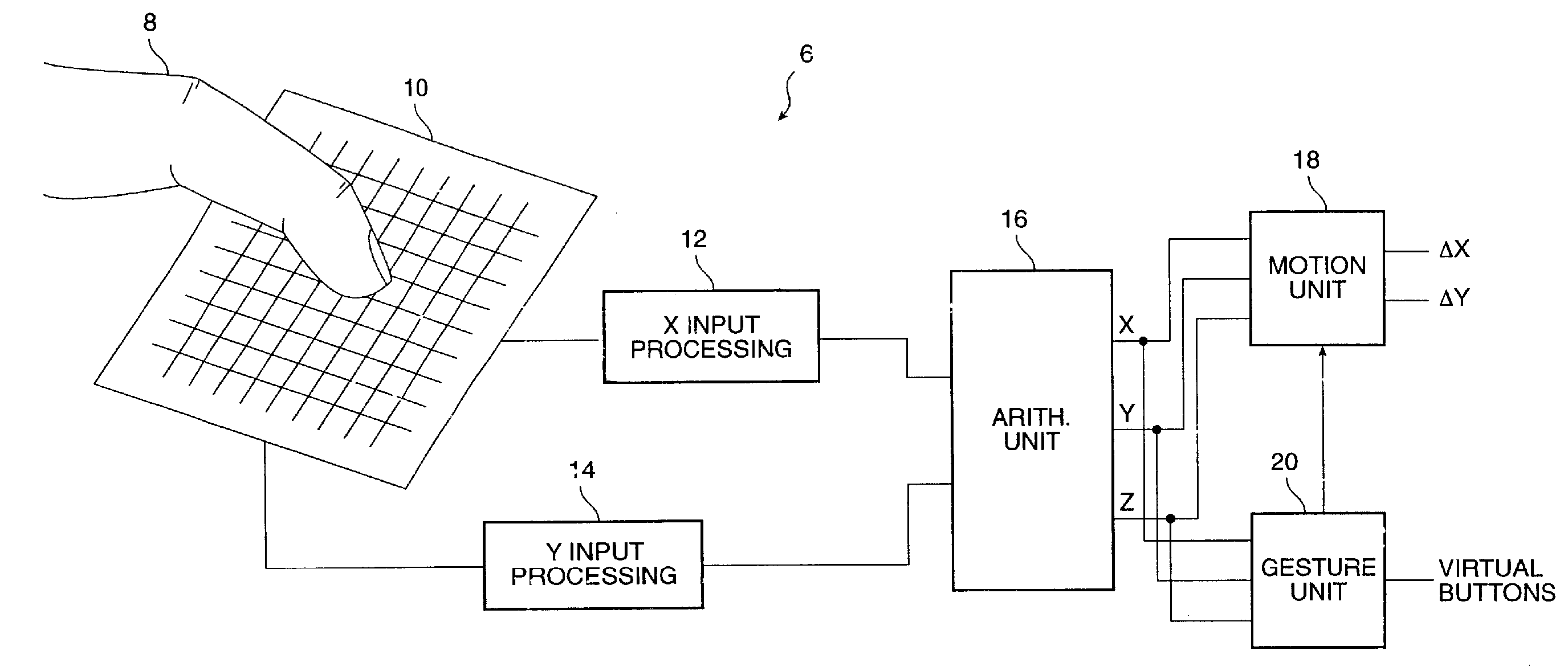
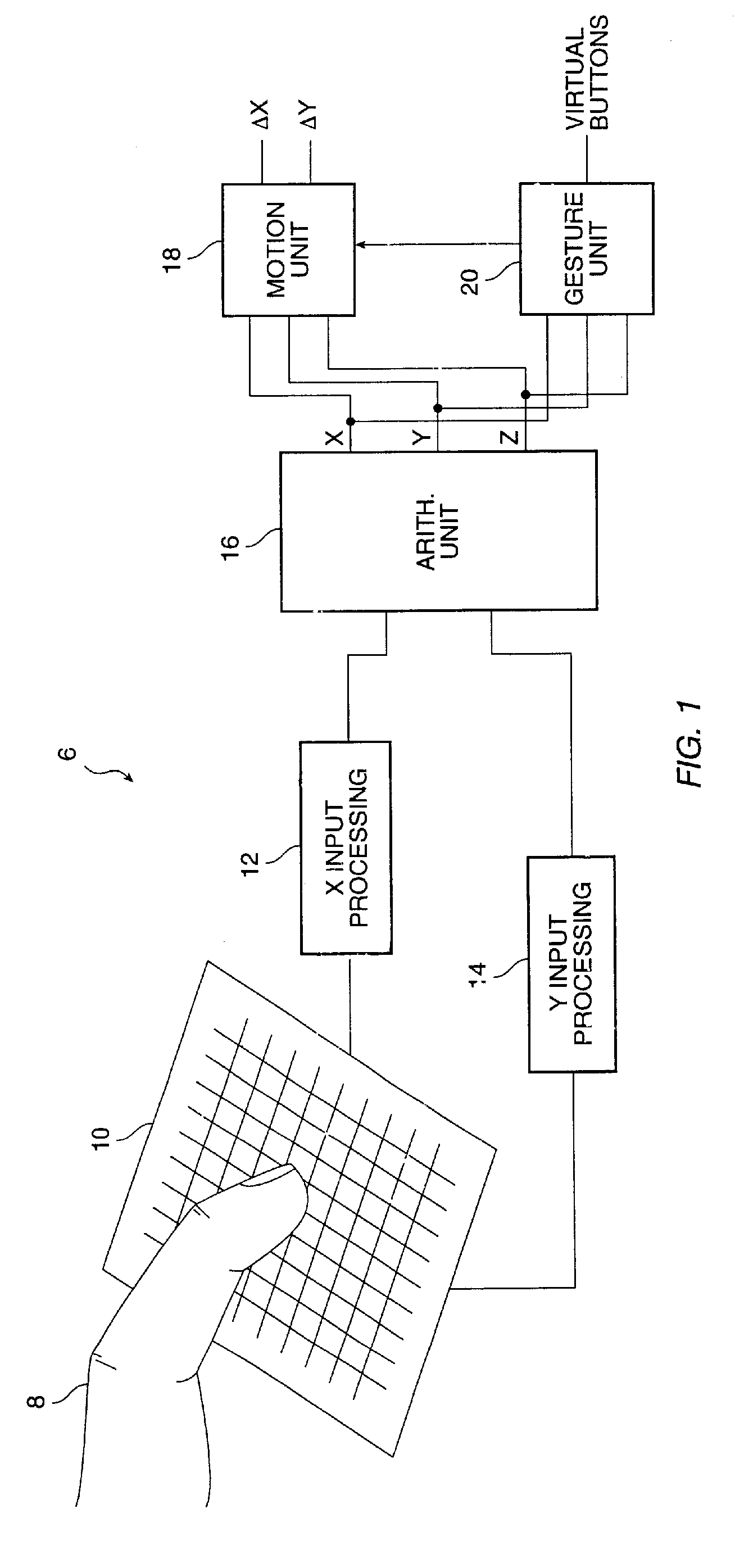
Object position detector with edge motion feature and gesture recognition
InactiveUS6414671B1Highly integratedRapid responseTransmission systemsCharacter and pattern recognitionComputer visionComputer science
Methods for recognizing gestures made by a conductive object on a touch-sensor pad and for cursor motion are disclosed. Tapping, drags, pushes, extended drags and variable drags gestures are recognized by analyzing the position, pressure, and movement of the conductive object on the sensor pad during the time of a suspected gesture, and signals are sent to a host indicating the occurrence of these gestures. Signals indicating the position of a conductive object and distinguishing between the peripheral portion and an inner portion of the touch-sensor pad are also sent to the host.
Owner:SYNAPTICS INC
Image display device and method
InactiveUS7321459B2Inexpensive and stable constructionReduce the driving voltageStatic indicating devicesNon-linear opticsDisplay deviceMaterials science
Owner:BRIDGESTONE CORP
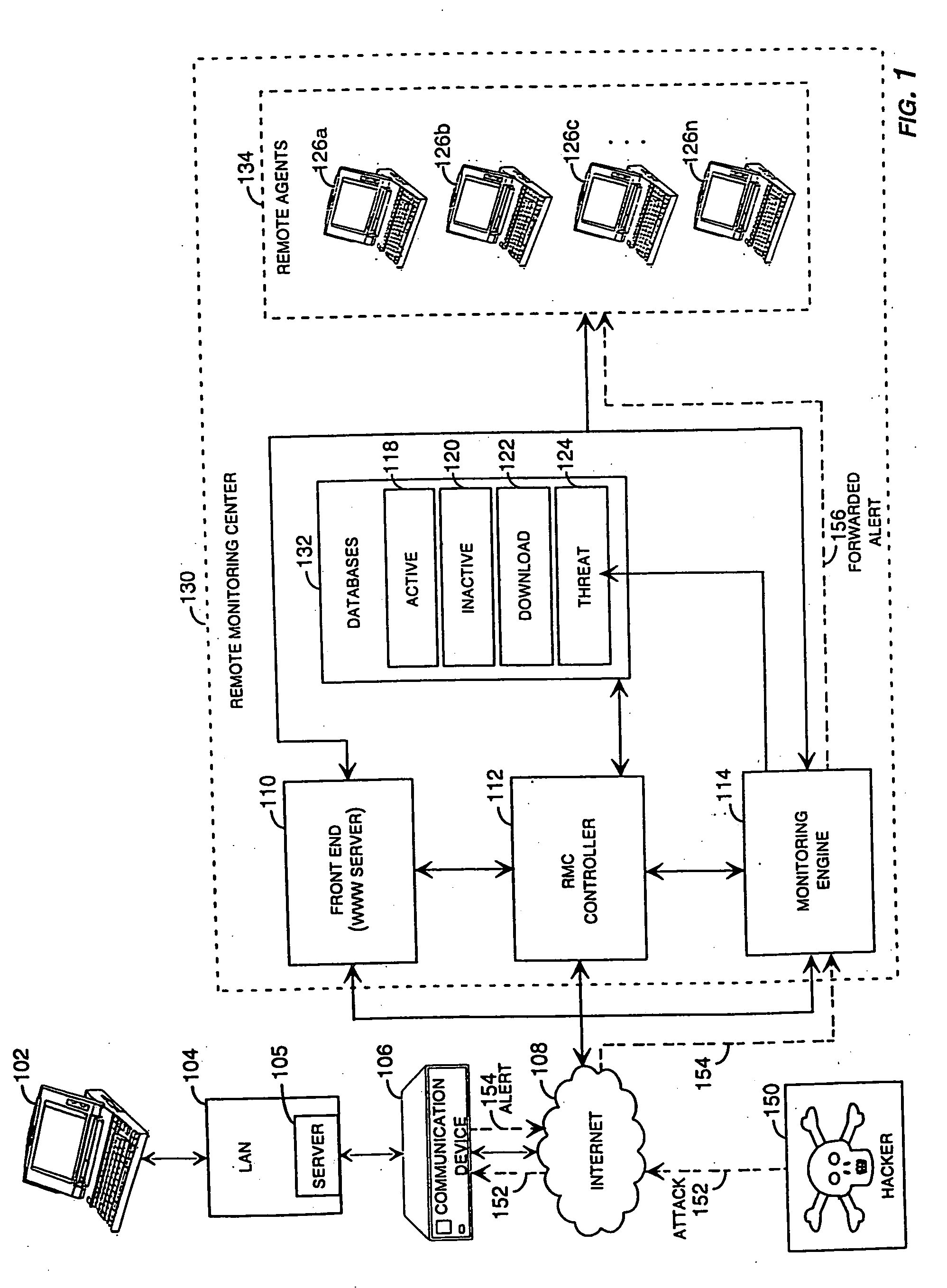
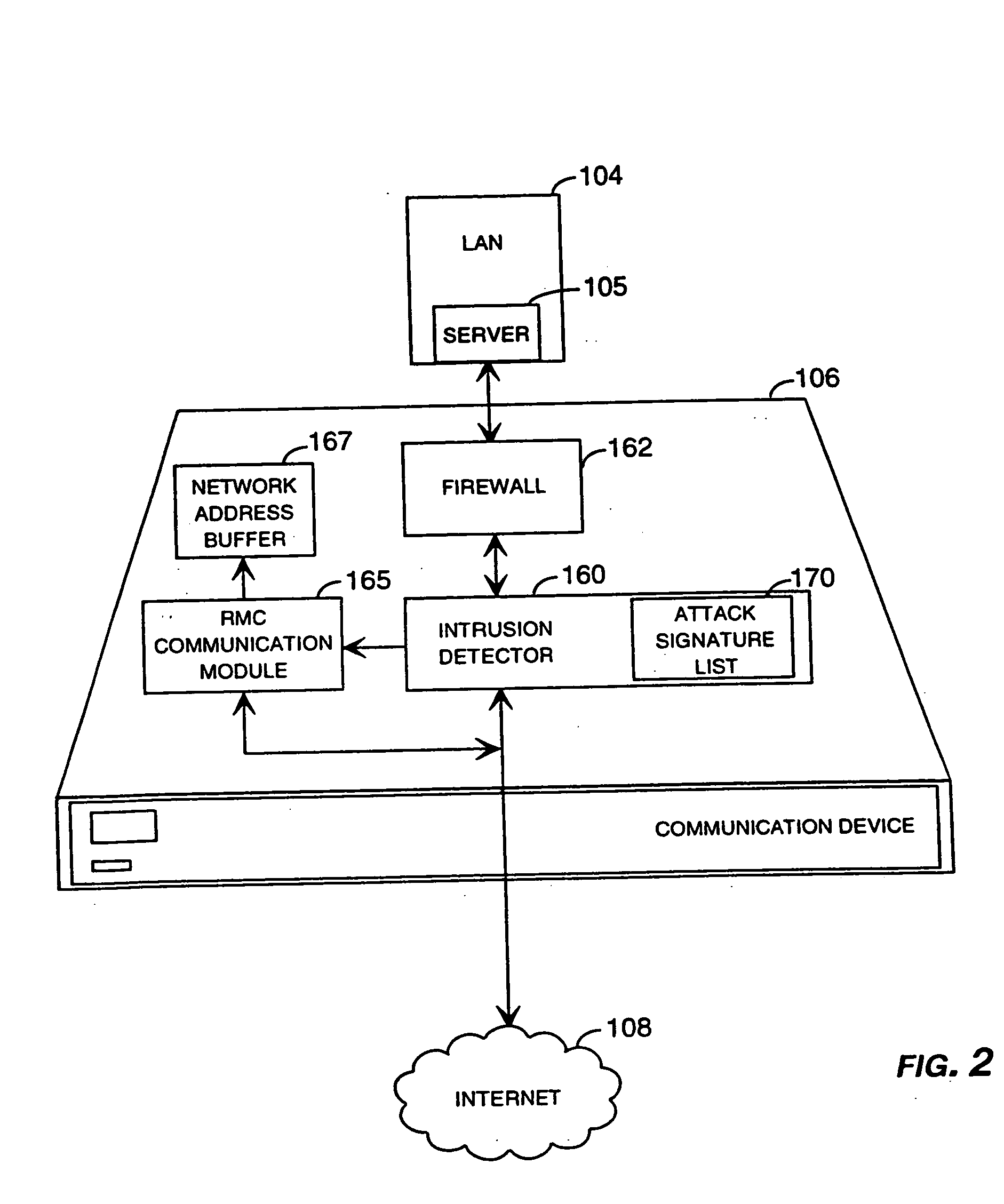
Method and system for remotely configuring and monitoring a communication device
InactiveUS6990591B1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Owner:SECUREWORKS
External ear-placed non-invasive physiological sensor
ActiveUS20090275813A1Lower latencyFast trackDiagnostic recording/measuringSensorsExternal earsMedicine
Owner:RGT UNIV OF CALIFORNIA +1
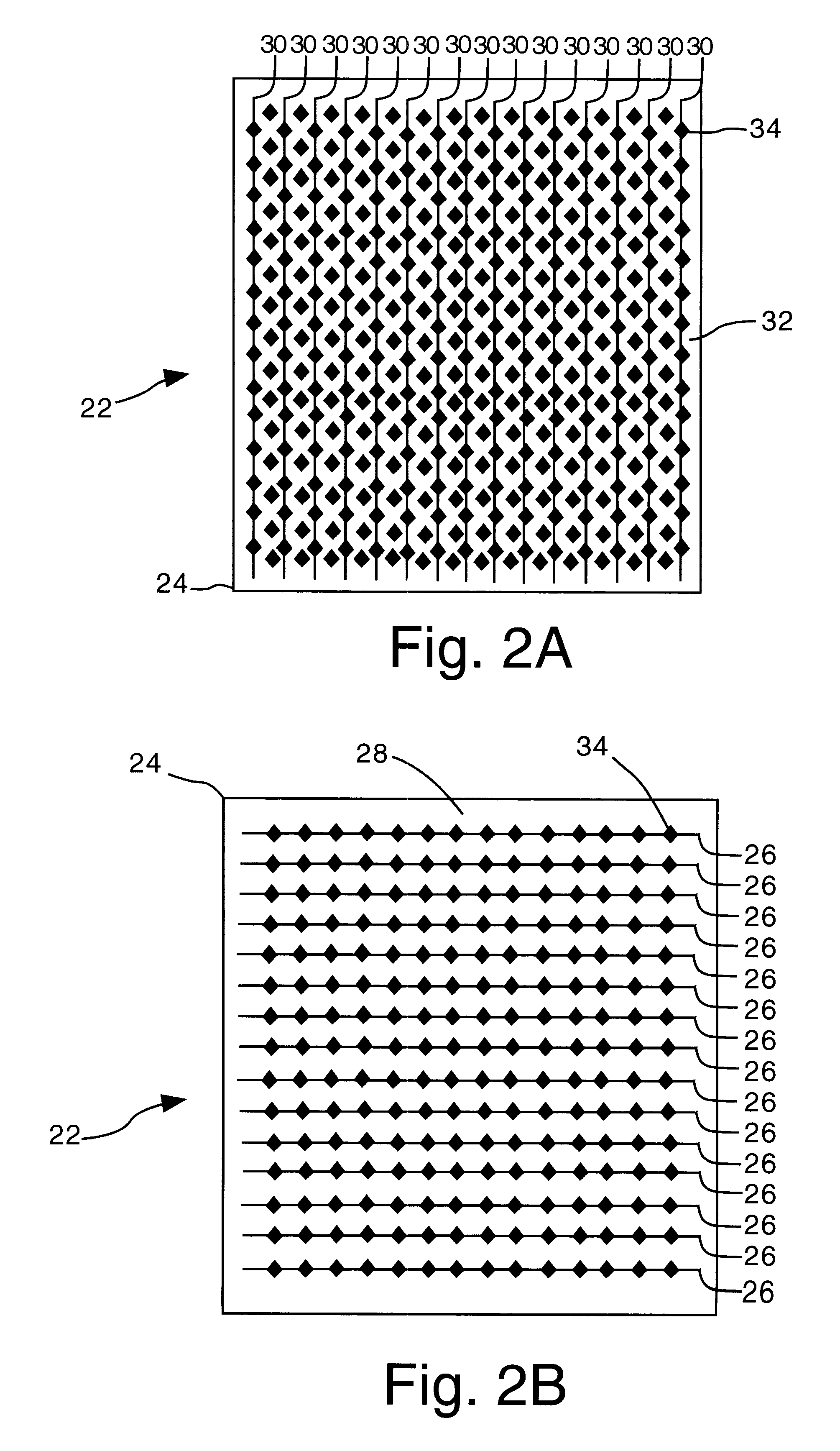
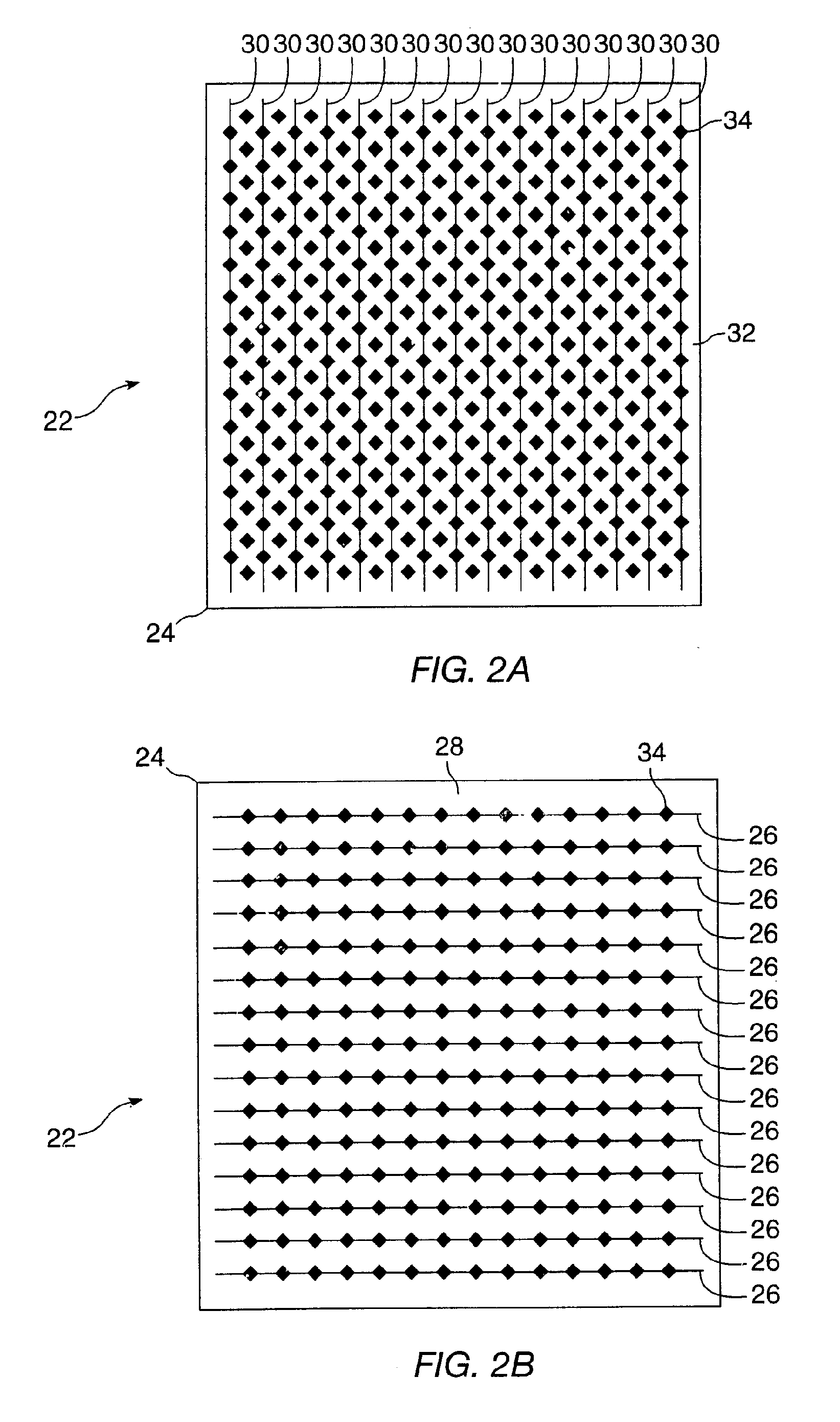
Object position detector with edge motion feature and gesture recognition
InactiveUS20080048997A1Highly integratedRapid responseCharacter and pattern recognitionInput/output processes for data processingCapacitanceElectrical conductor
A method of generating a signal comprising providing a capacitive touch sensor pad including a matrix of X and Y conductors, developing capacitance profiles in one of an X direction and a Y direction from the matrix of X and Y conductors, determining an occurrence of a single gesture through an examination of the capacitance profiles, the single gesture including an application of at least two objects on the capacitive touch sensor pad, and generating a signal indicating the occurrence of the single gesture.
Owner:SYNAPTICS INC
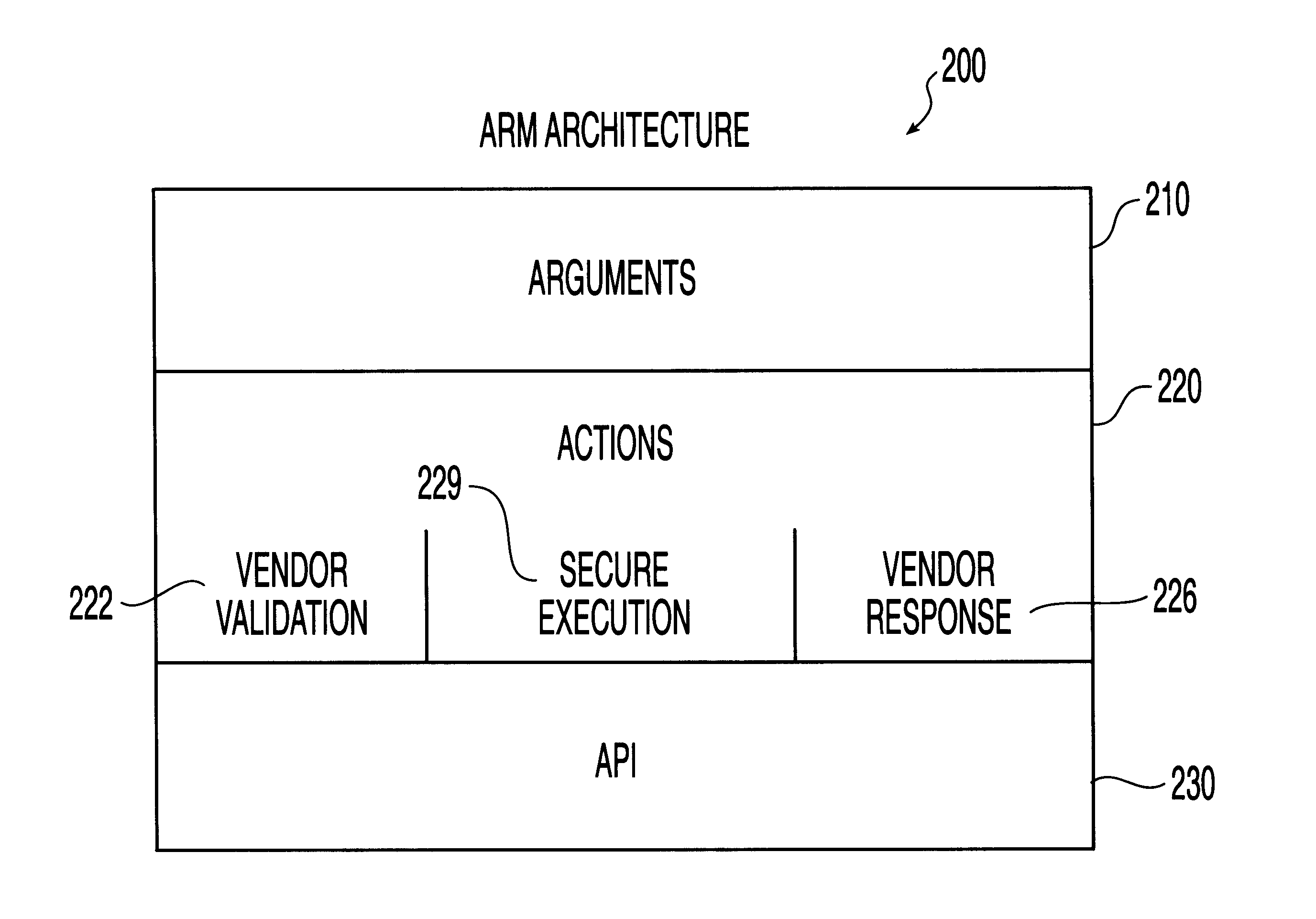
System, method and computer program product for automatic response to computer system misuse using active response modules
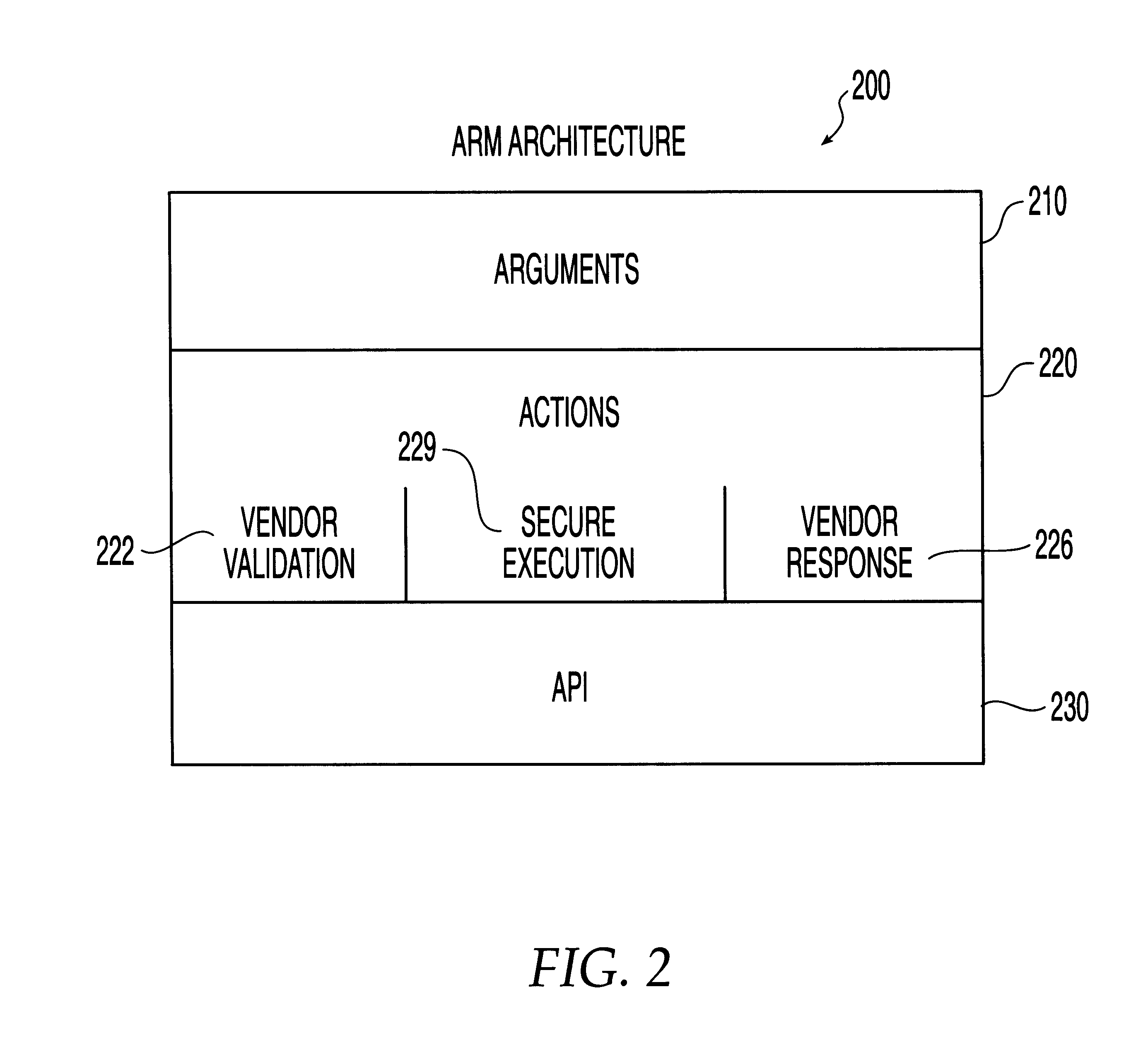
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
Network intrusion prevention
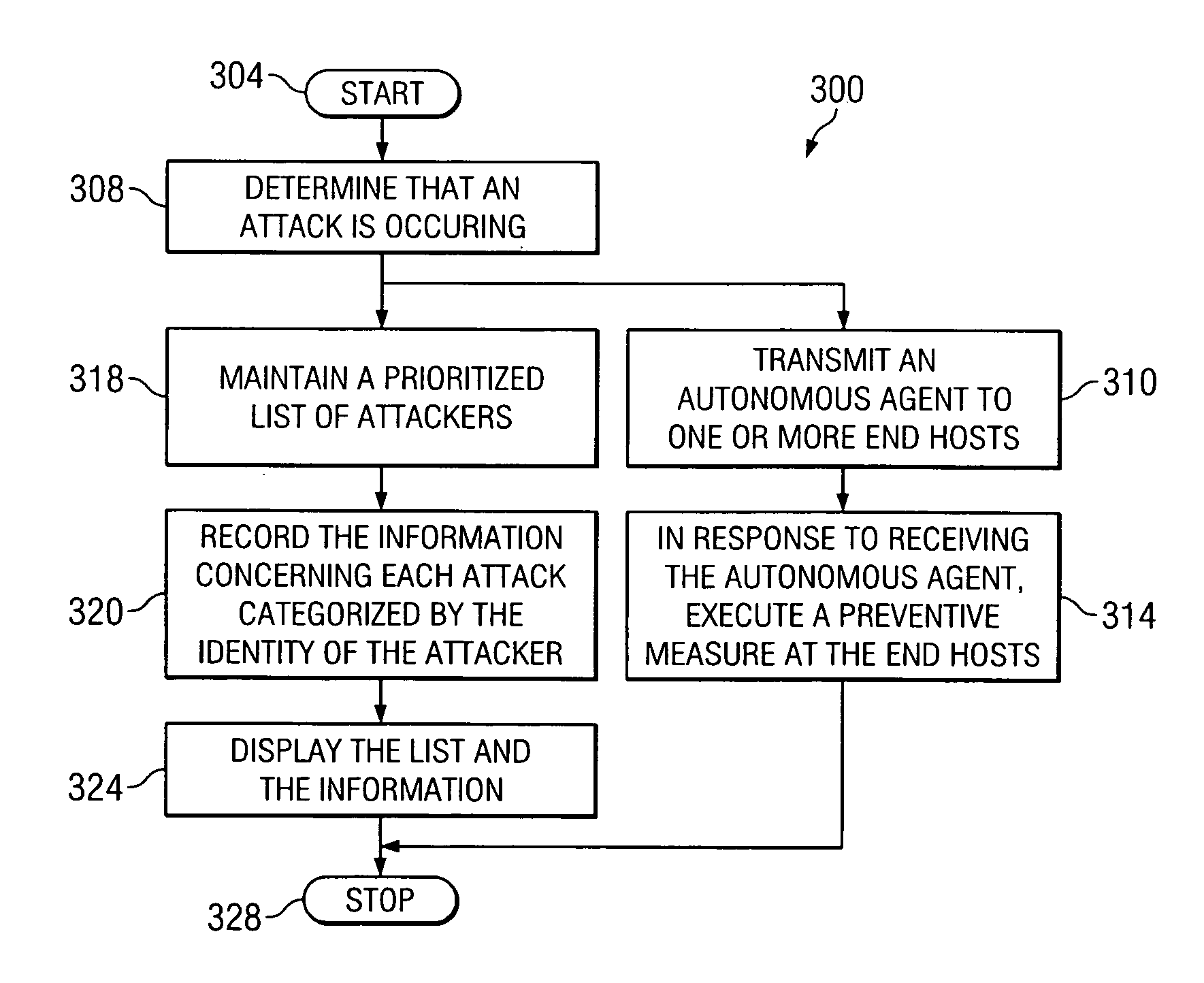
InactiveUS20060143709A1Avoid attackReduce the impactMemory loss protectionError detection/correctionComputer networkNetwork attack
According to one embodiment of the invention, a system for preventing a network attack is provided. The system includes a computer having a processor and a computer-readable medium. The system also includes a shield program stored in the computer-readable medium. The shield program is operable, when executed by the processor, to transmit an agent to each of one or more nodes in a network in response to an attack directed to the network. The agent is operable to initiate a reduction of the effect of the attack on the node.
Owner:RAYTHEON CO
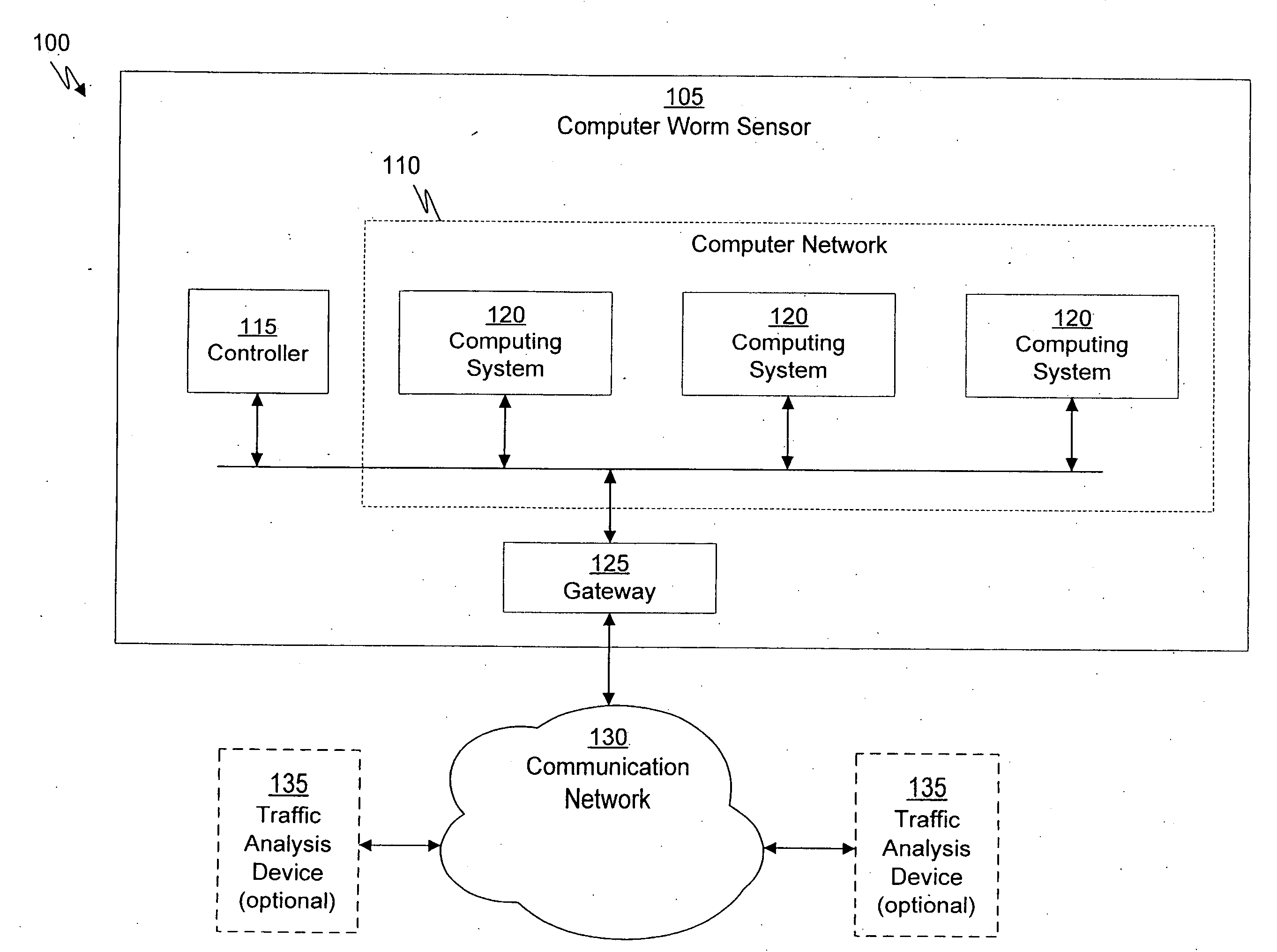
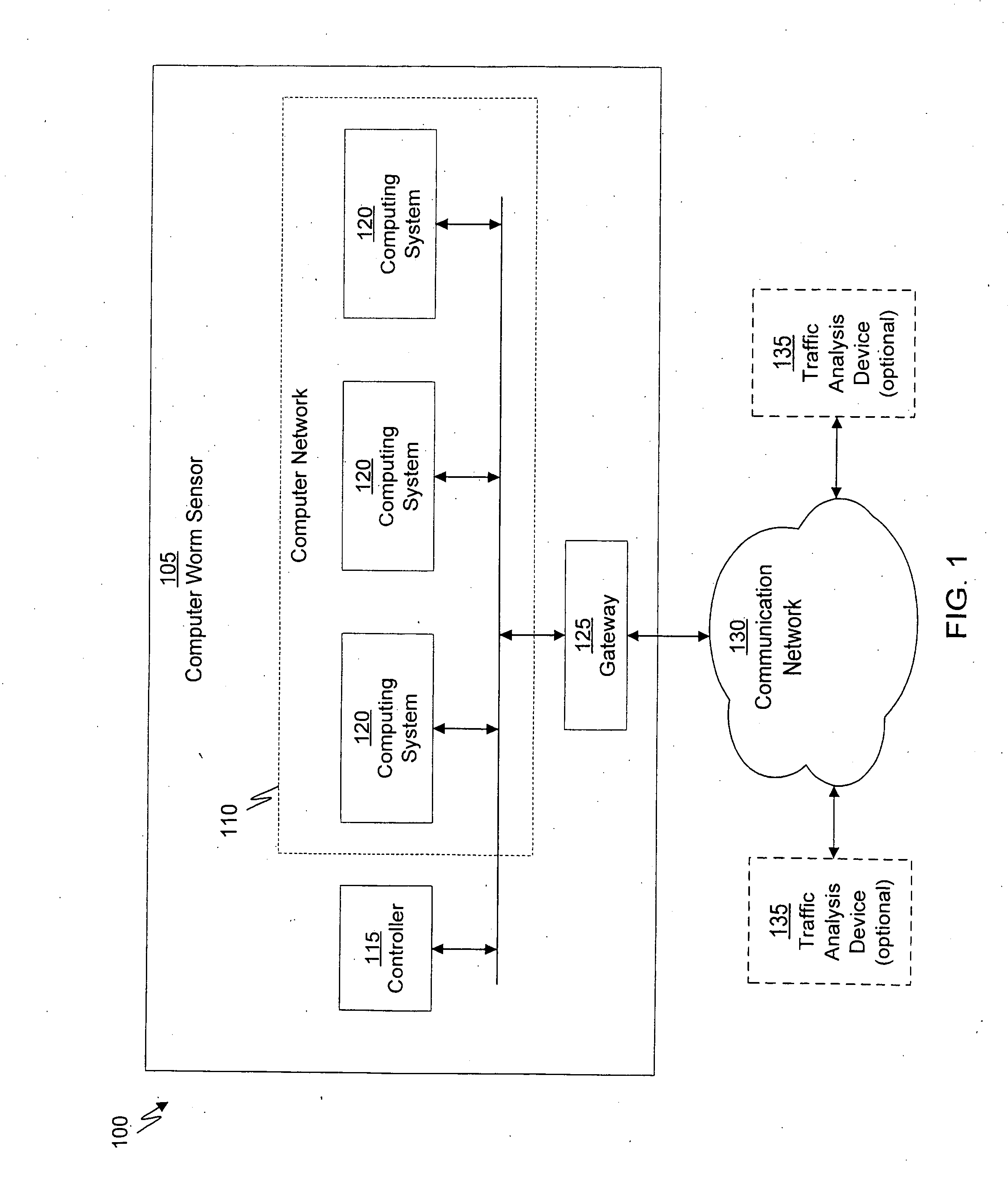
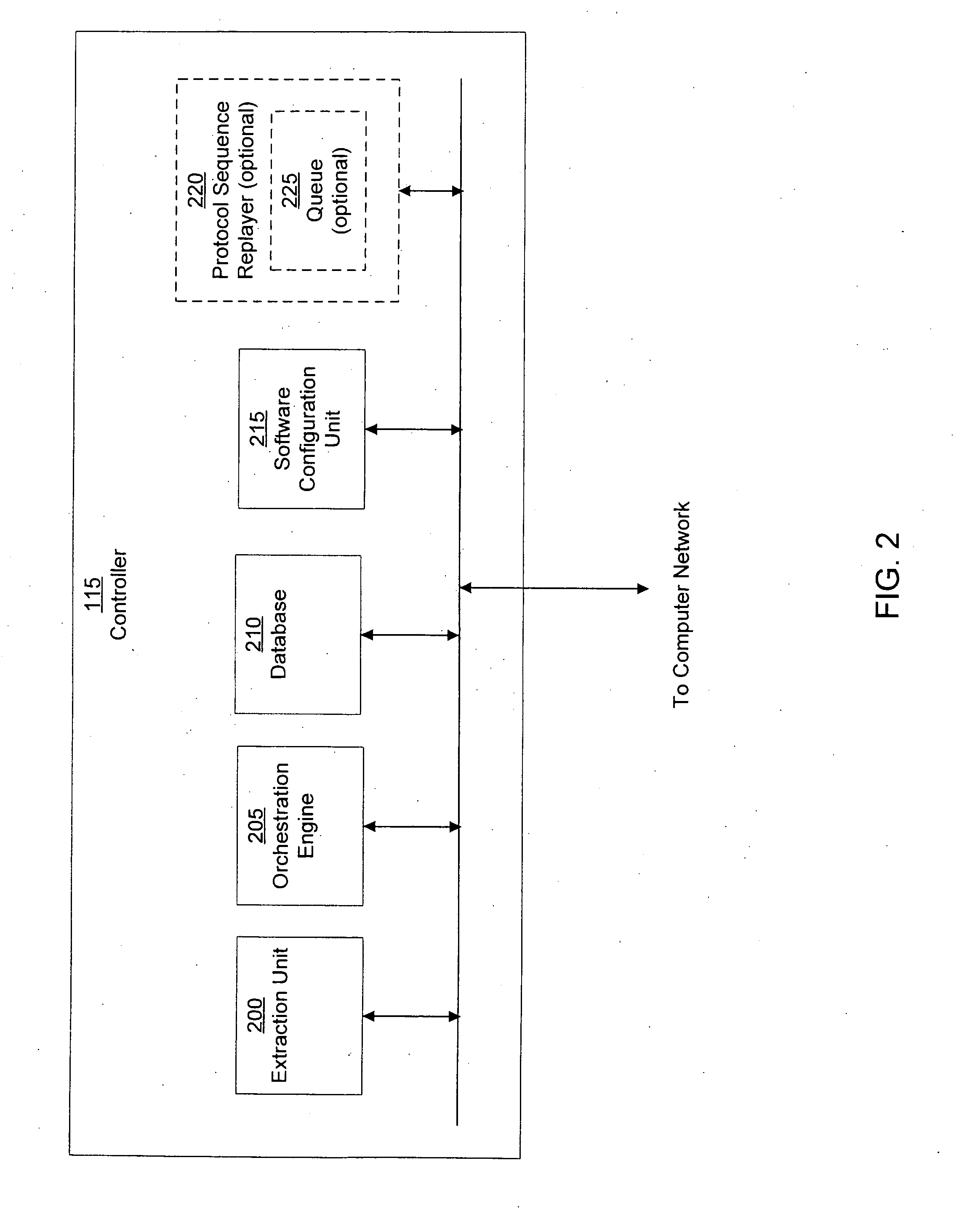
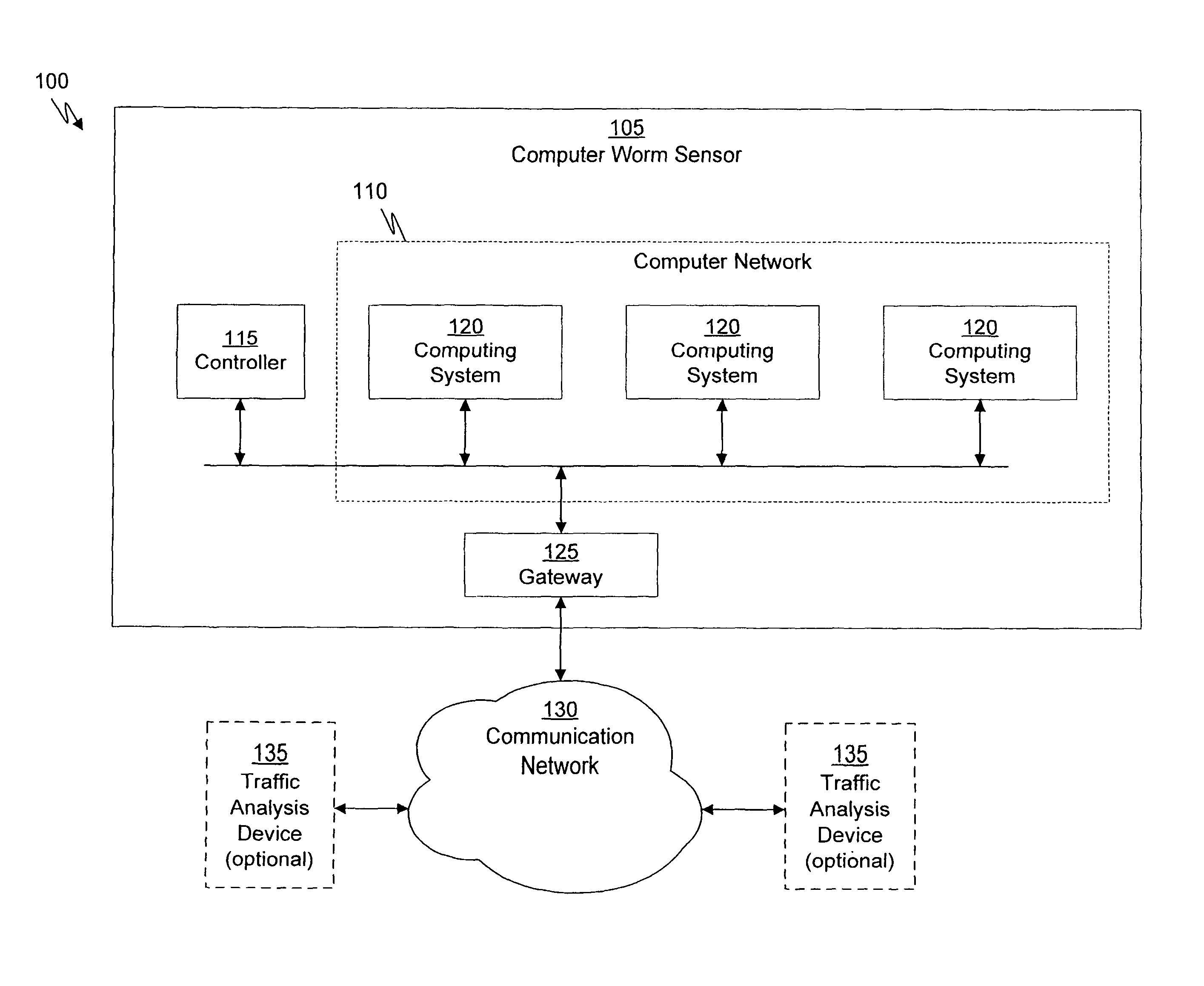
System and method of containing computer worms
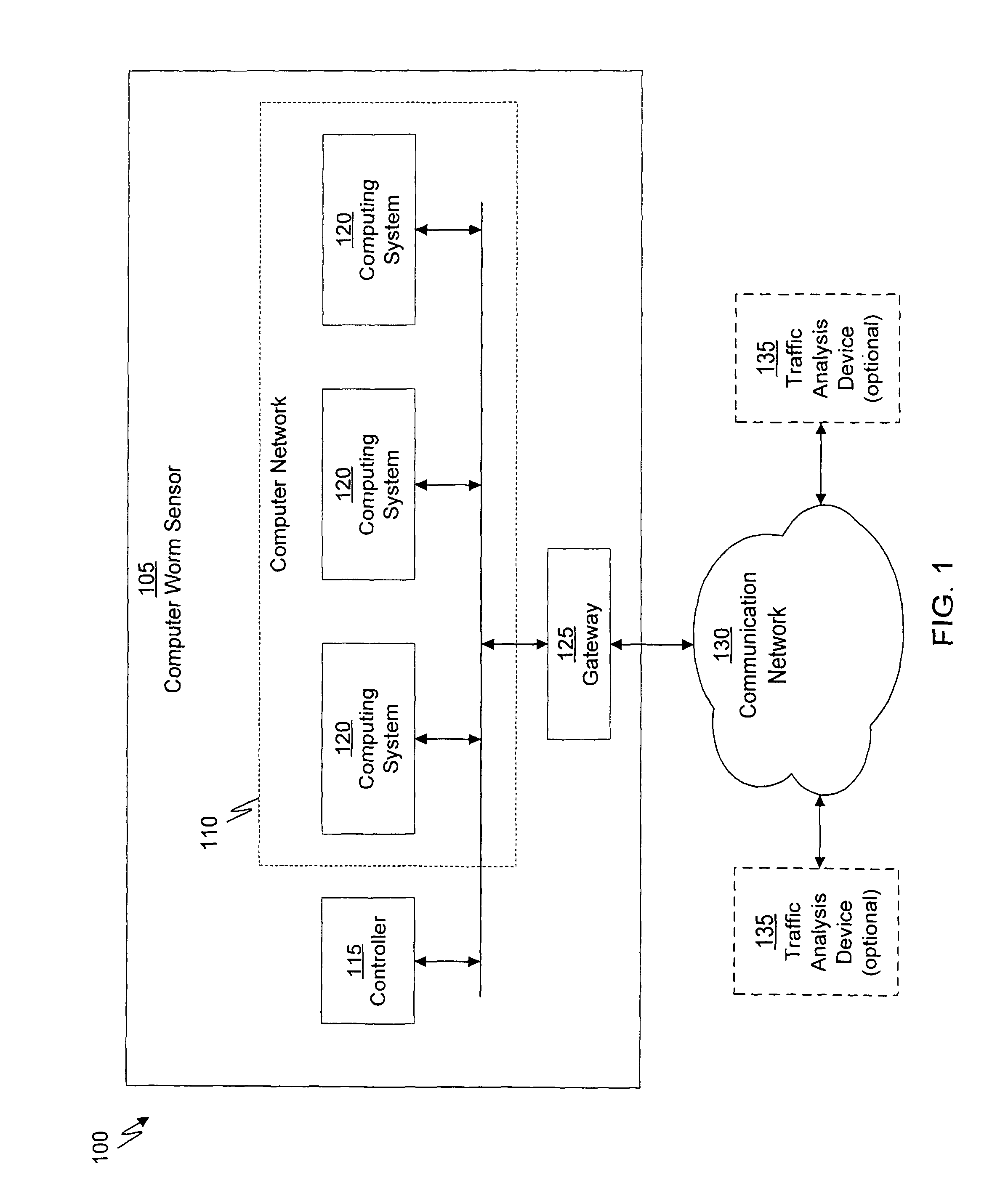
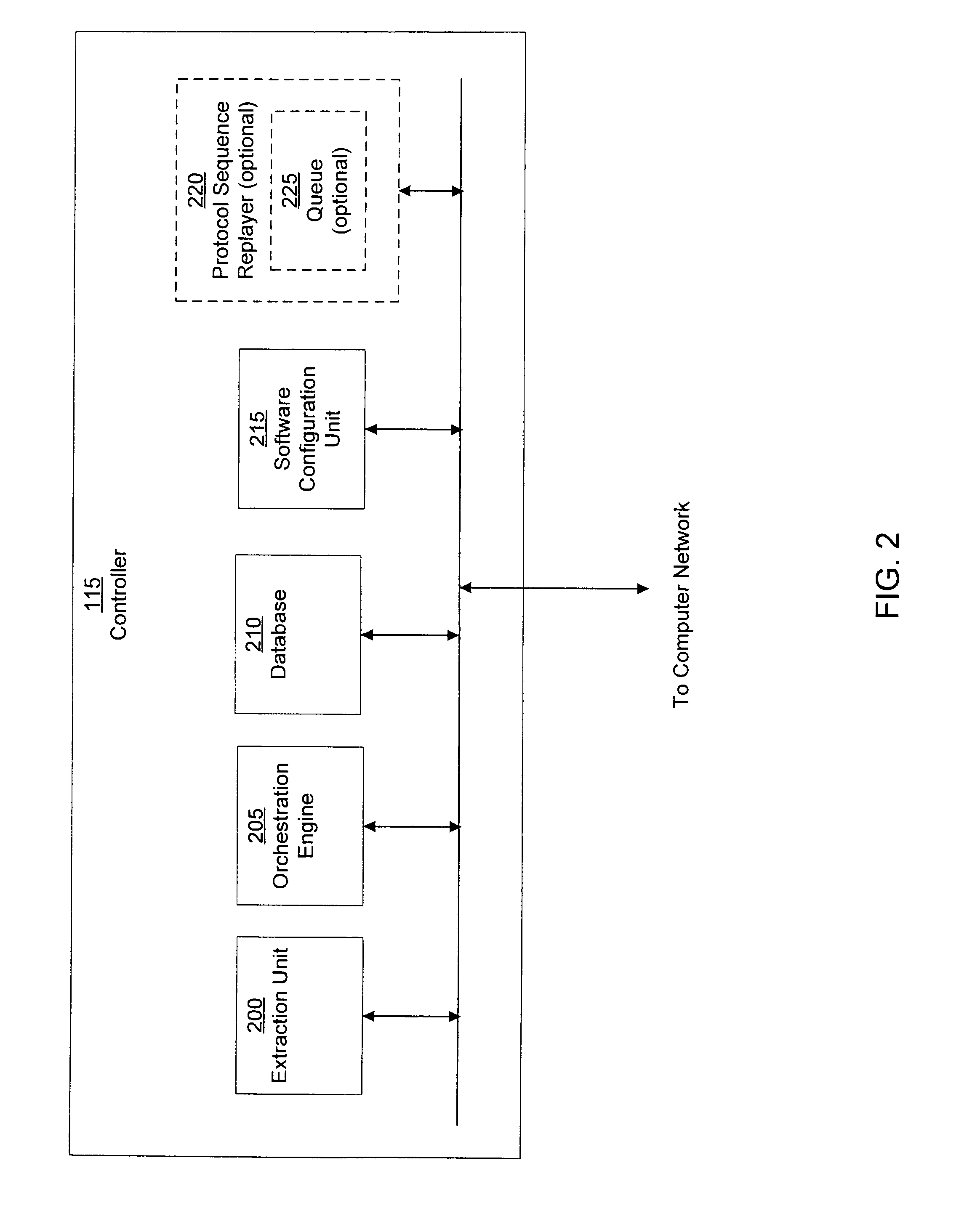
ActiveUS20110099633A1Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of containing computer worms
ActiveUS8549638B2Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
Method for mitigating the unauthorized use of a device
ActiveUS20090253410A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
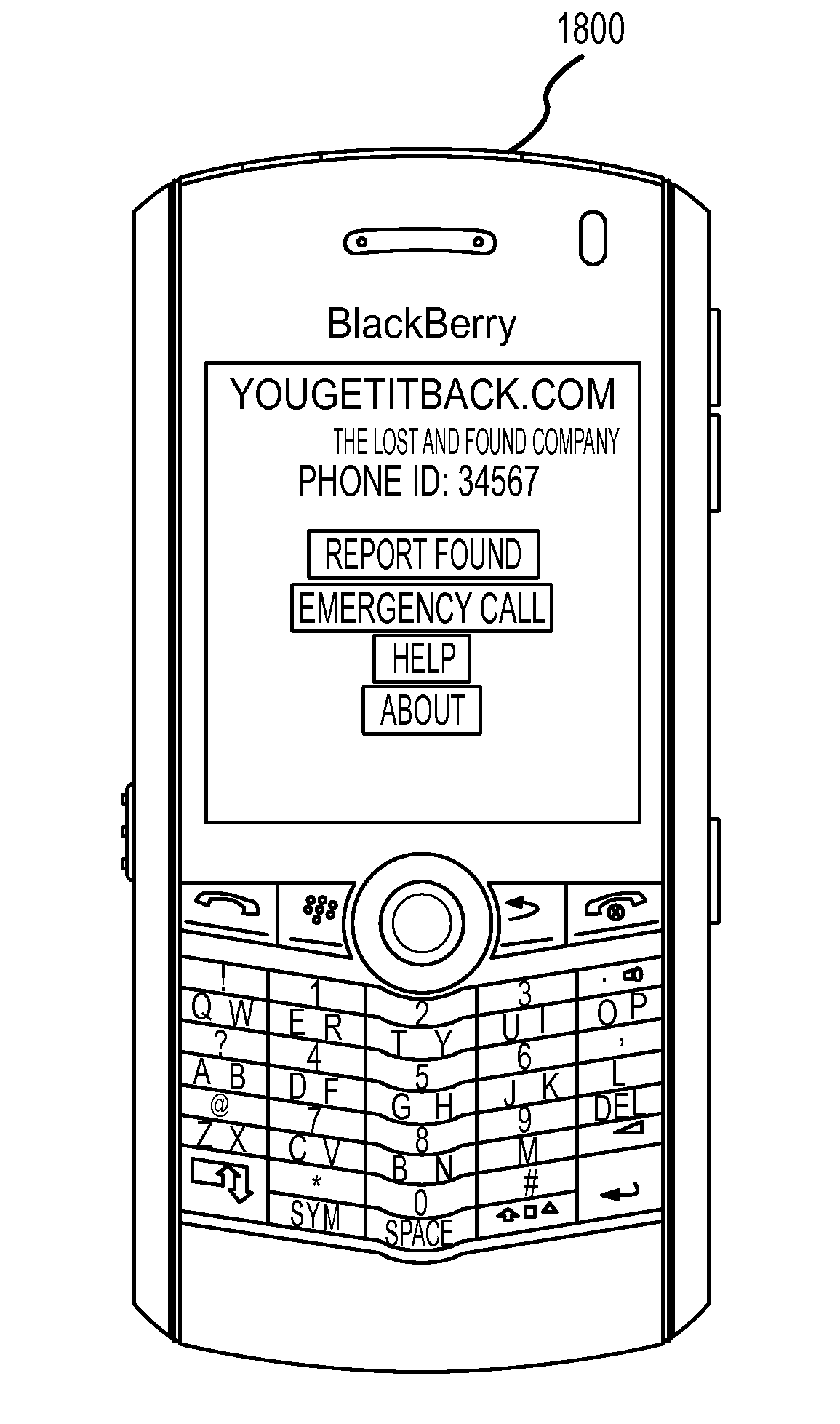
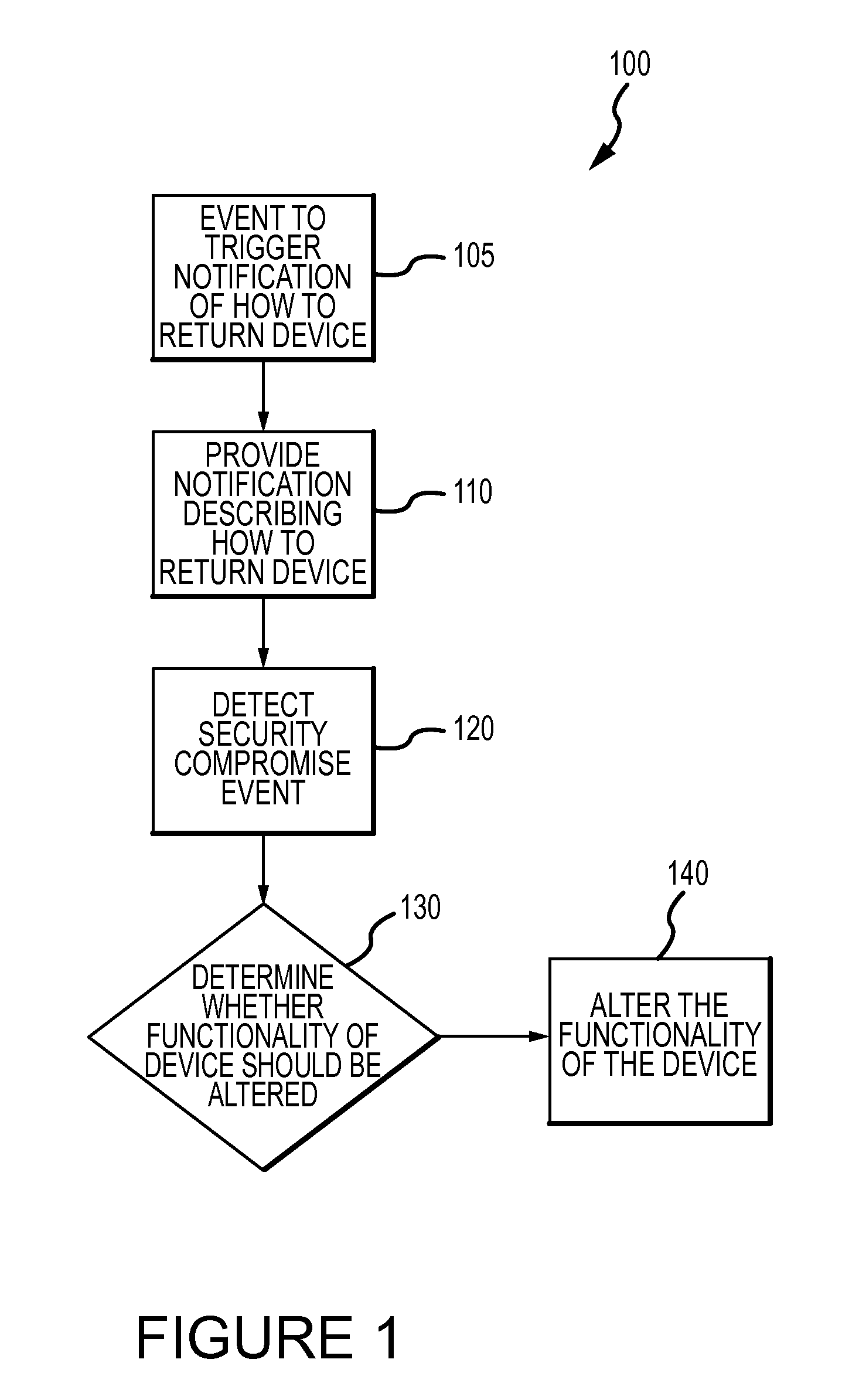
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
Closed-loop drug delivery system
InactiveUS7108680B2Safety and well be enhanceAdvantageousMedical devicesPressure infusionNervous systemImplantable Pump
A delivery system for a drug or bioactive agent includes an implantable pump and a delivery conduit that may be implanted in an organ or other tissue (e.g., the central or the peripheral nervous system) of a subject. A sensor is also implanted, and a controller unit receives the sensor output and directs drug delivery from within the patient pump accordingly. The sensor directly measures a primary biochemical material or state in the tissue or organ system, and the monitoring unit effects closed loop feedback control of the pump to achieve a desired end. The end may be the regulation of metabolism or maintenance of a stable metabolic or other state, or may be treatment regimen, e.g., by delivery of a dosage level or distribution of a drug in specific brain or nervous an system tissue. The sensed material may be the agent itself, a metabolite, or a related native material, tissue state or condition.
Owner:CODMAN & SHURTLEFF INC
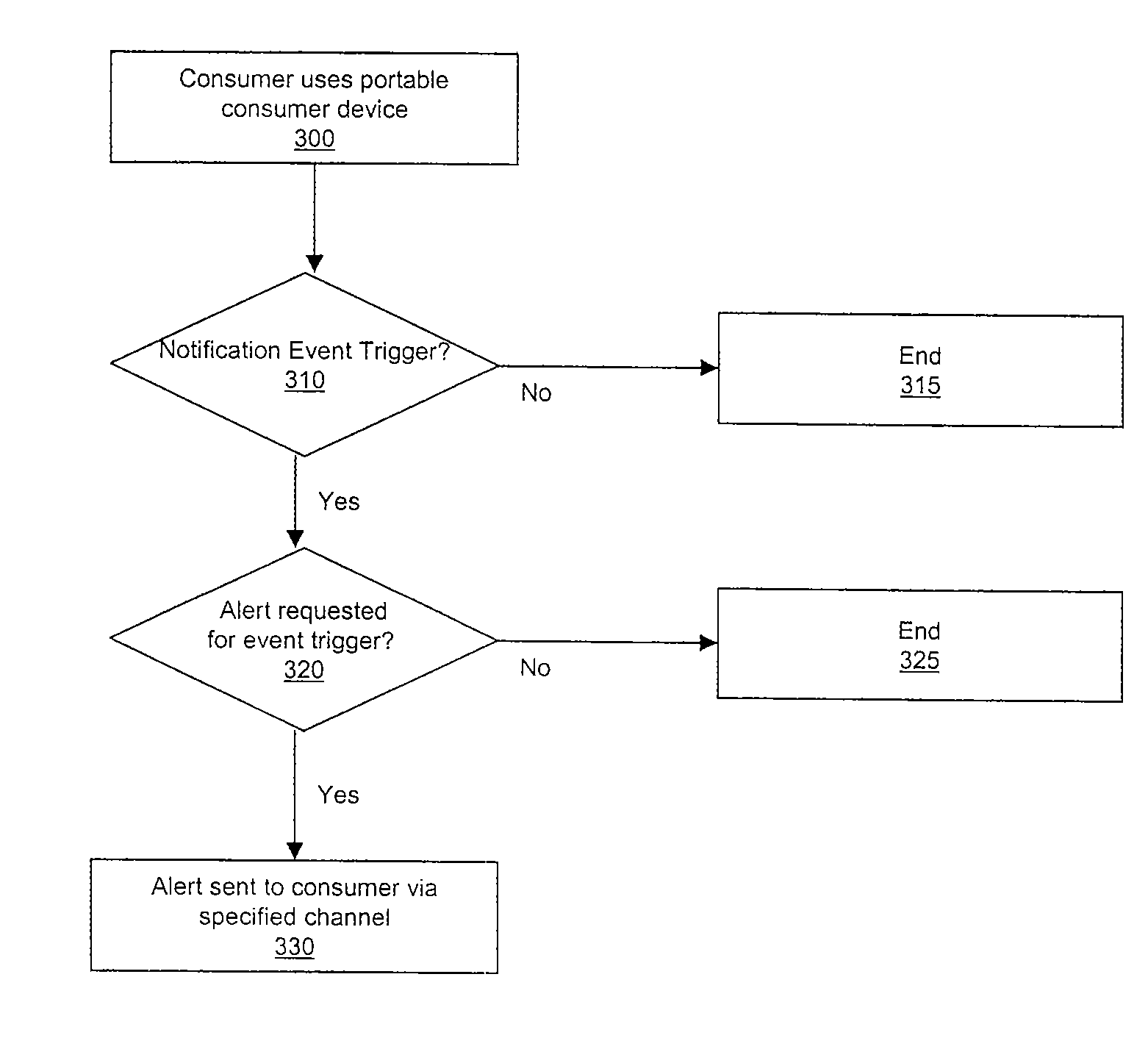
Customized payment transaction notification
InactiveUS20080183480A1Rapid responseAccounting/billing servicesSubstation equipmentPayment transactionReal-time computing
Owner:VISA USA INC (US)
Techniques for authorization of usage of a payment device
ActiveUS20080033880A1High degreeRapid responseComplete banking machinesFinancePaymentInternet privacy
Techniques for authorization of usage of a payment device include facilitating an issuer of the device obtaining an authorization message for an account number associated with the device, based on desired spending limit parameters established by a merchant and / or an issuer of the device; facilitating obtaining an issuer authorization decision; and responsive to the issuer authorization decision, facilitating setting a spending limit for the account number based on at least an appropriate one of the parameters.
Owner:MASTERCARD INT INC
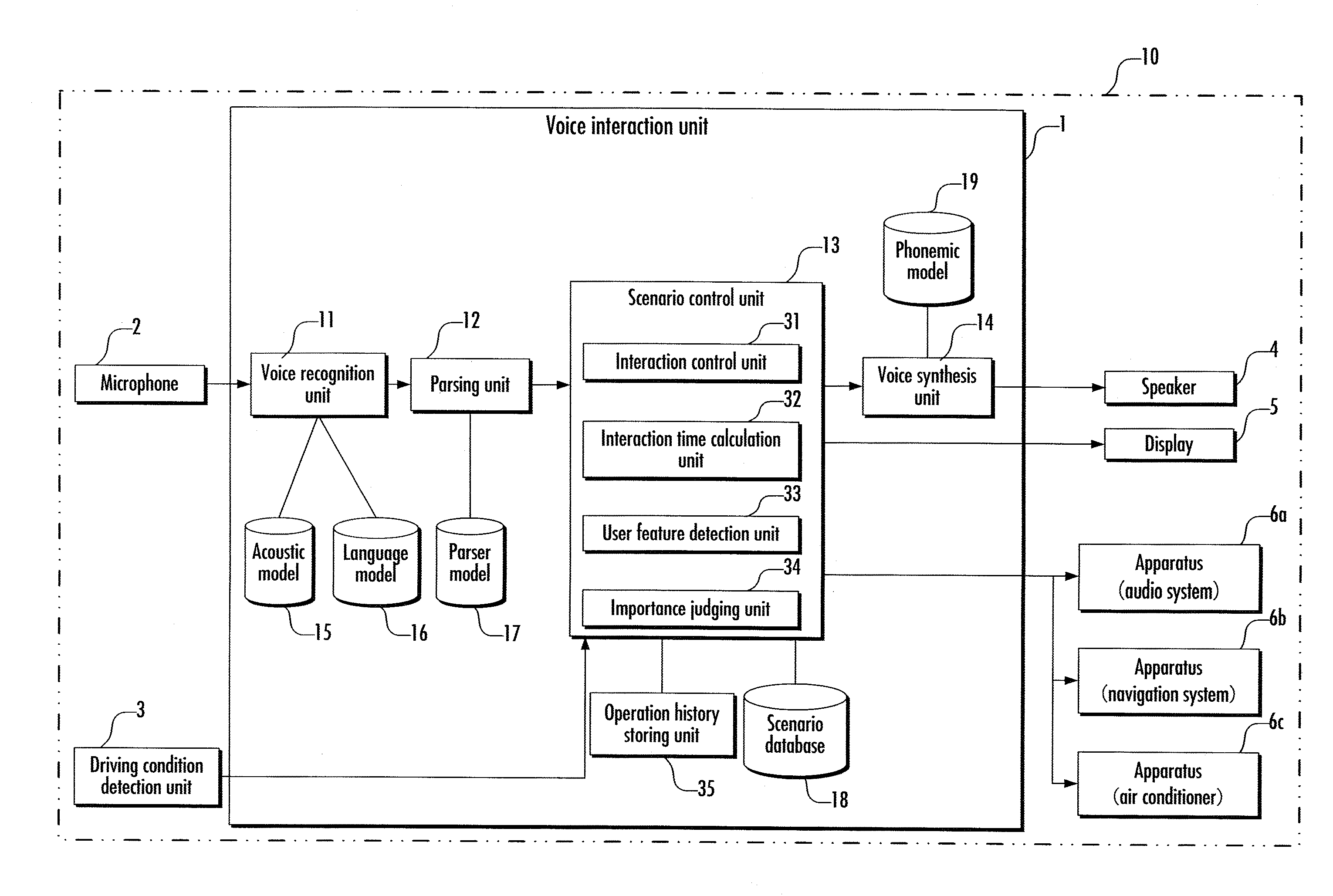
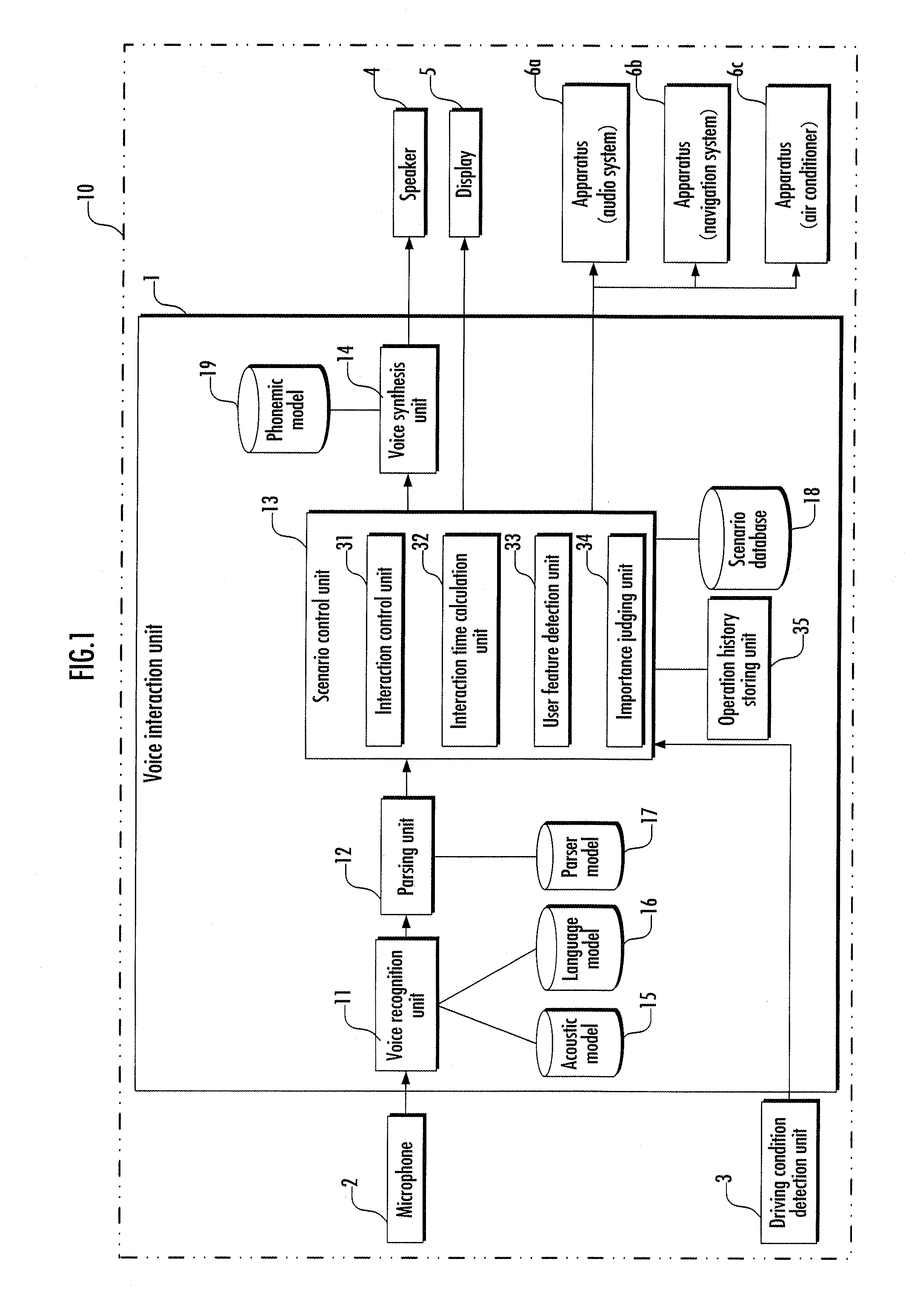
Voice interaction device, voice interaction method, and voice interaction program
The present invention provides a voice interaction device capable of performing an interaction meeting any demand from a user at proper time in flexible response to a circumferential condition of the user, a voice interaction method and a voice interaction program thereof. The voice interaction device controls the interaction with the user in response to an input voice from the user, including an available time calculation unit (32) which calculates an available period of time for interaction with the user based on the circumferential condition of the user, and an interaction control unit (31) which controls the interaction based on at least the available period of time for interaction calculated by the available time calculation unit (32).
Owner:HONDA MOTOR CO LTD
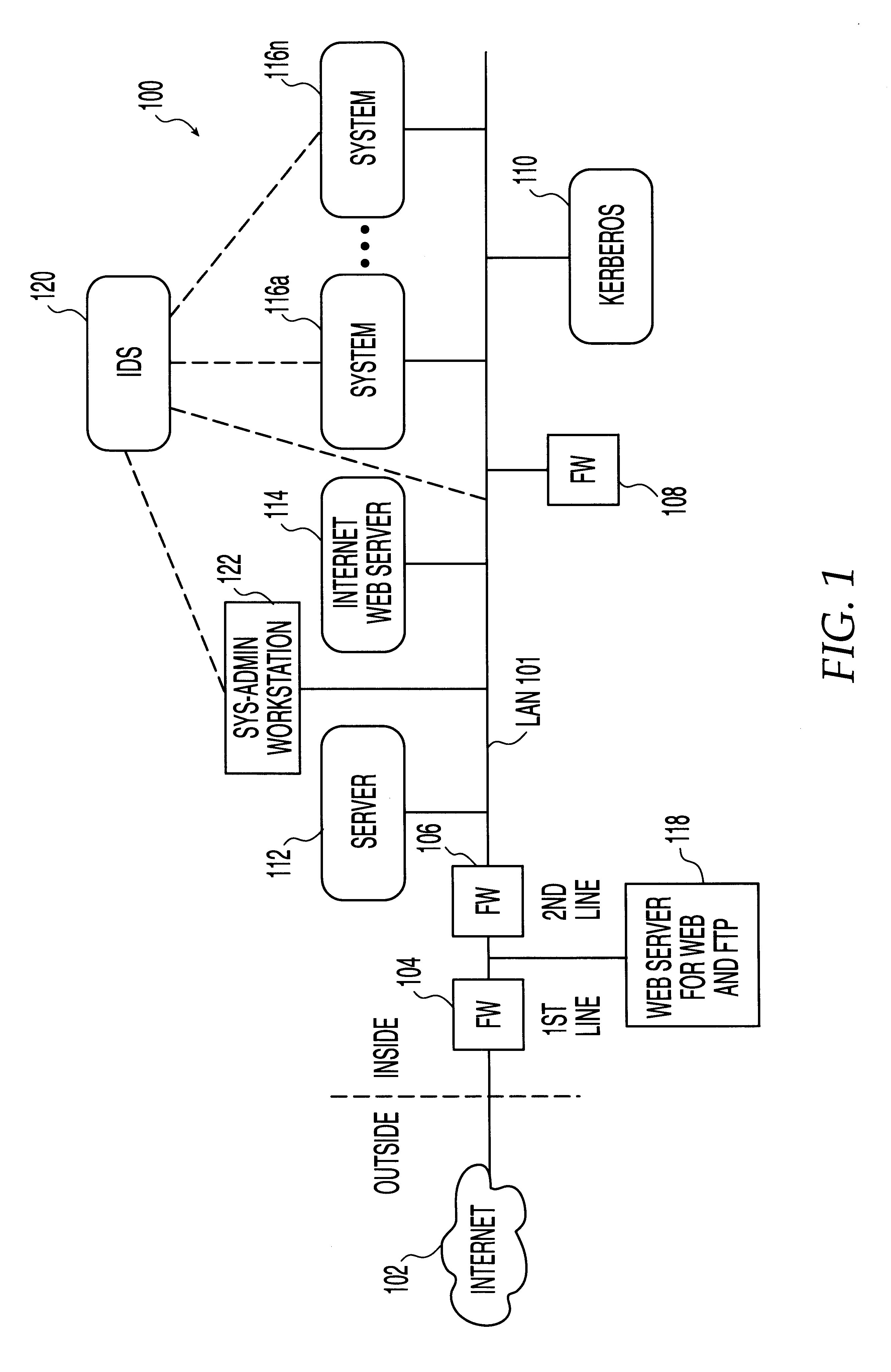
Computer network intrusion detection
InactiveUS20120297489A1Easily and efficiently identifyingRapid responseMemory loss protectionError detection/correctionBIOSVirus
A method and system of identifying an attacker device attempting an intrusion into a network. At least one managed device of the network detects an incoming TCP / IP connection by the attacker device to the network. It is determined that the incoming TCP / IP connection is a Net BIOS connection that has created an invalid logon by the attacker device, linking the invalid logon with the NetBIOS TCP / IP connection, retrieving event log information from a security event log of the network, and determining (i) that a userid of the invalid logon is a local userid defined on a local device, (ii) that the userid of the invalid logon is a userid in a list of userids used by viruses, or (iii) that the userid of the invalid logon is neither the local userid nor is in the list of userids. The retrieved event log information is stored in a central violation database.
Owner:KYNDRYL INC
Tissue interface device
InactiveUS7041057B1Simpler basic array designImprove signal-to-noise ratioDiagnostic recording/measuringSensorsBiological bodyEngineering
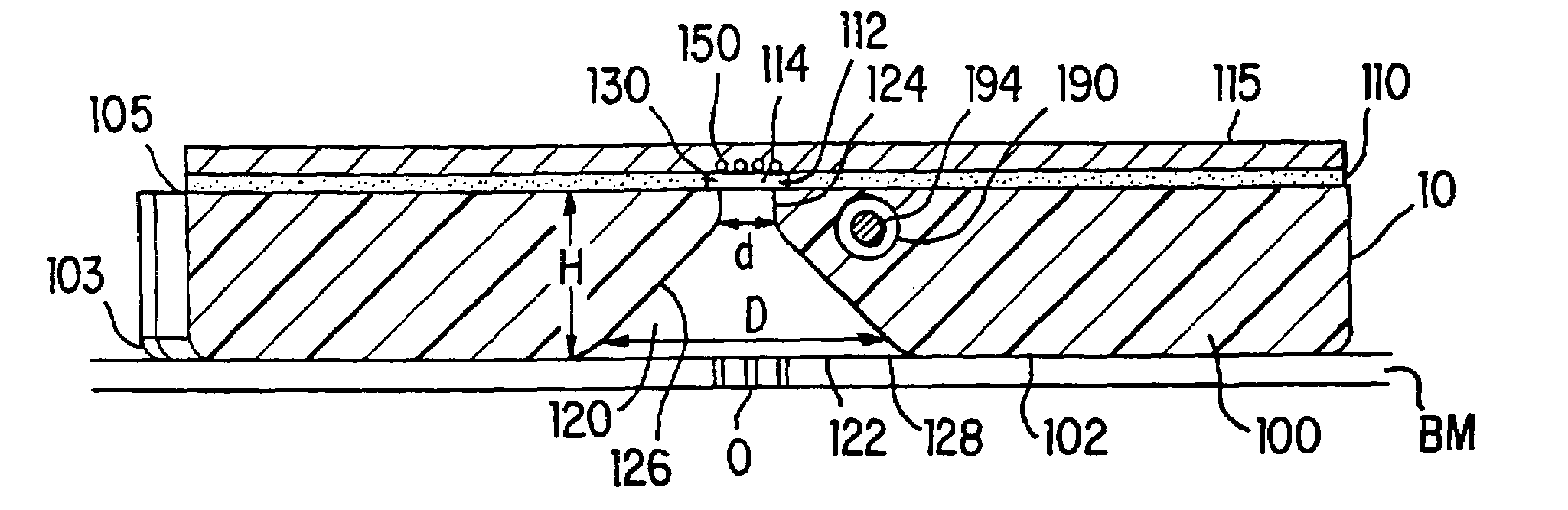
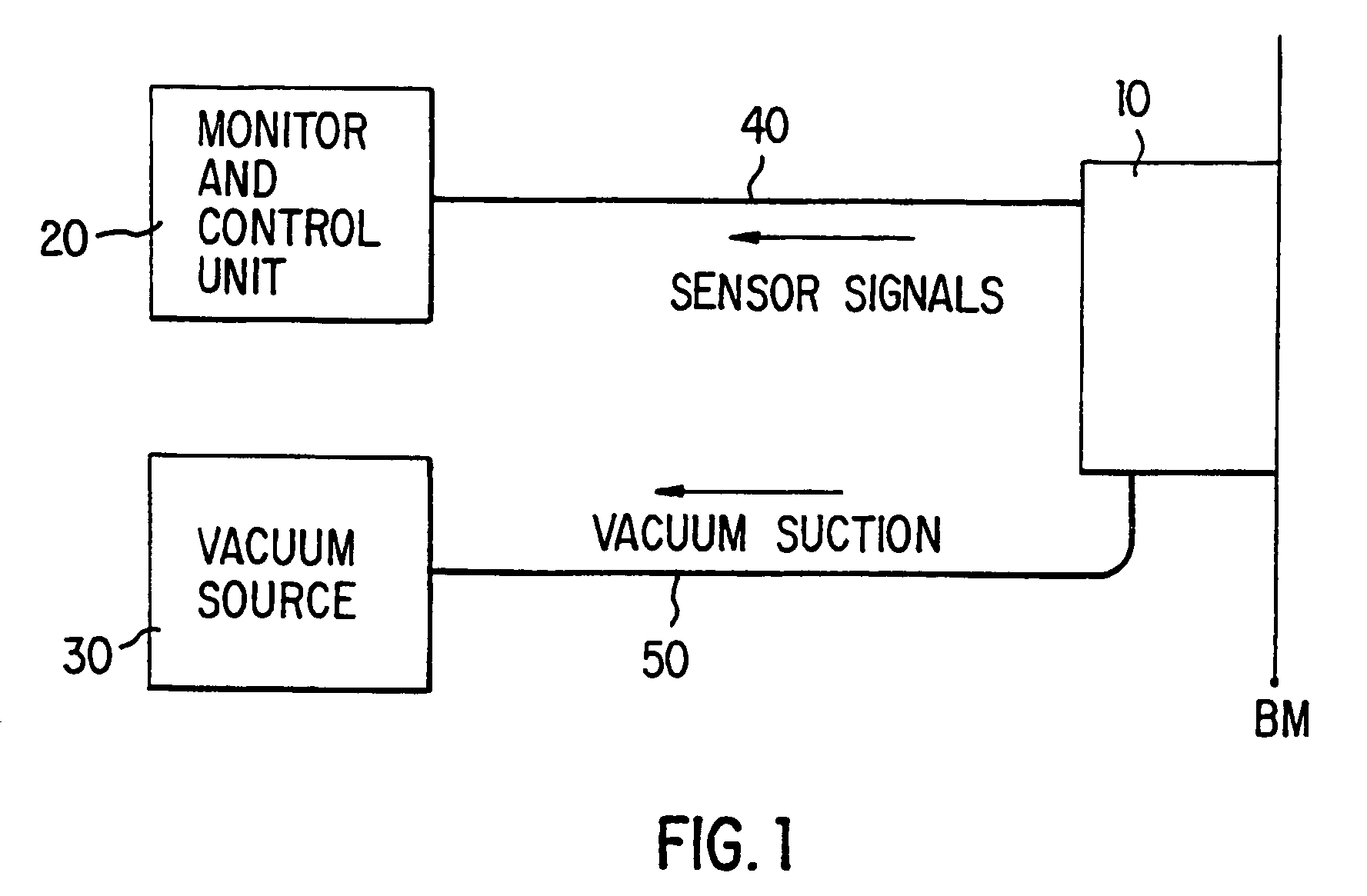
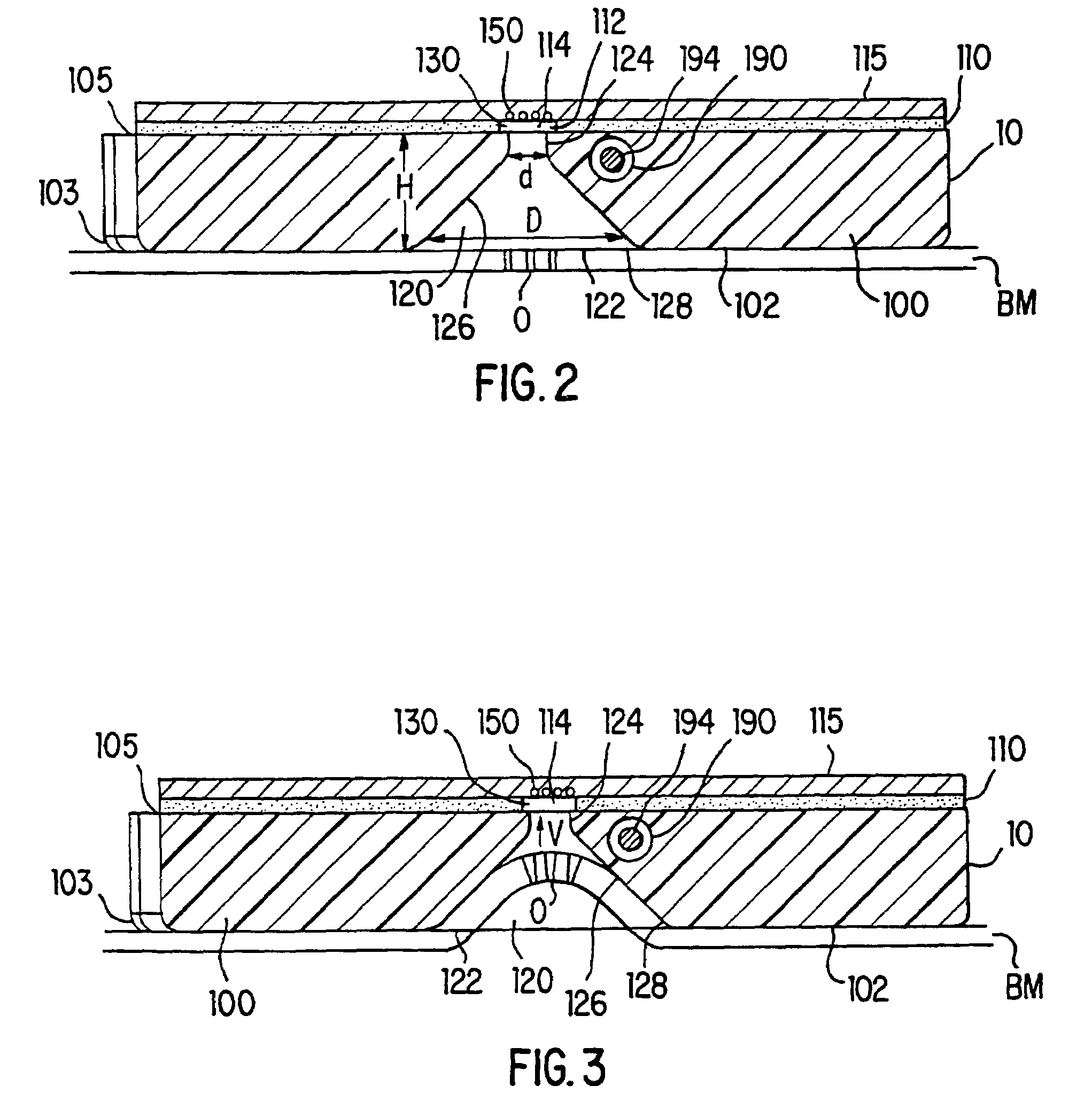
A tissue interface device (10) suitable for positioning on or about one or more artificial openings in a biological membrane of an organism and for coupling to a monitor and control unit and a vacuum source. The tissue interface device (10) comprises a housing (100), a sensor channel (130), and a sensor (150). The housing (100) defines an orifice (120), the orifice (120) having an open inlet port (122) on the bottom end (102) of the housing (100) and a distal end (124) that is in fluid communication with the sensor channel (130). The orifice (120) is in fluid communication with fluid that flows from the artificial opening formed in the biological membranes. The sensor channel (130) is for coupling to, and fluid communication therewith, the vacuum source. The sensor (150) is positioned in the sensor channel (130) in a flow path of the fluid for sensing a characteristic of the fluid as it flows out from the artificial opening. The sensor generates a sensor signal representative thereof.
Owner:ALTEA THERAPEUTIC CORP +1
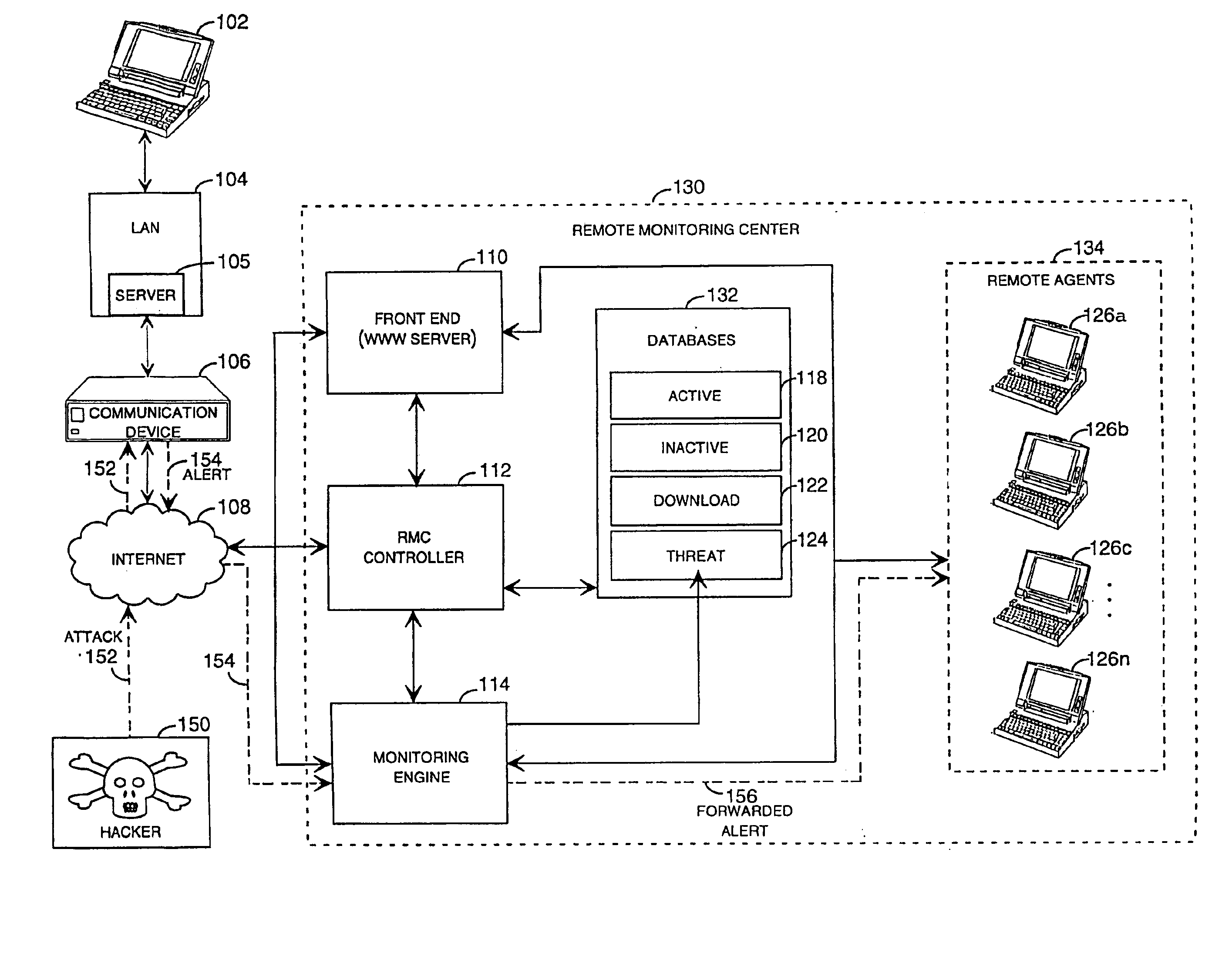
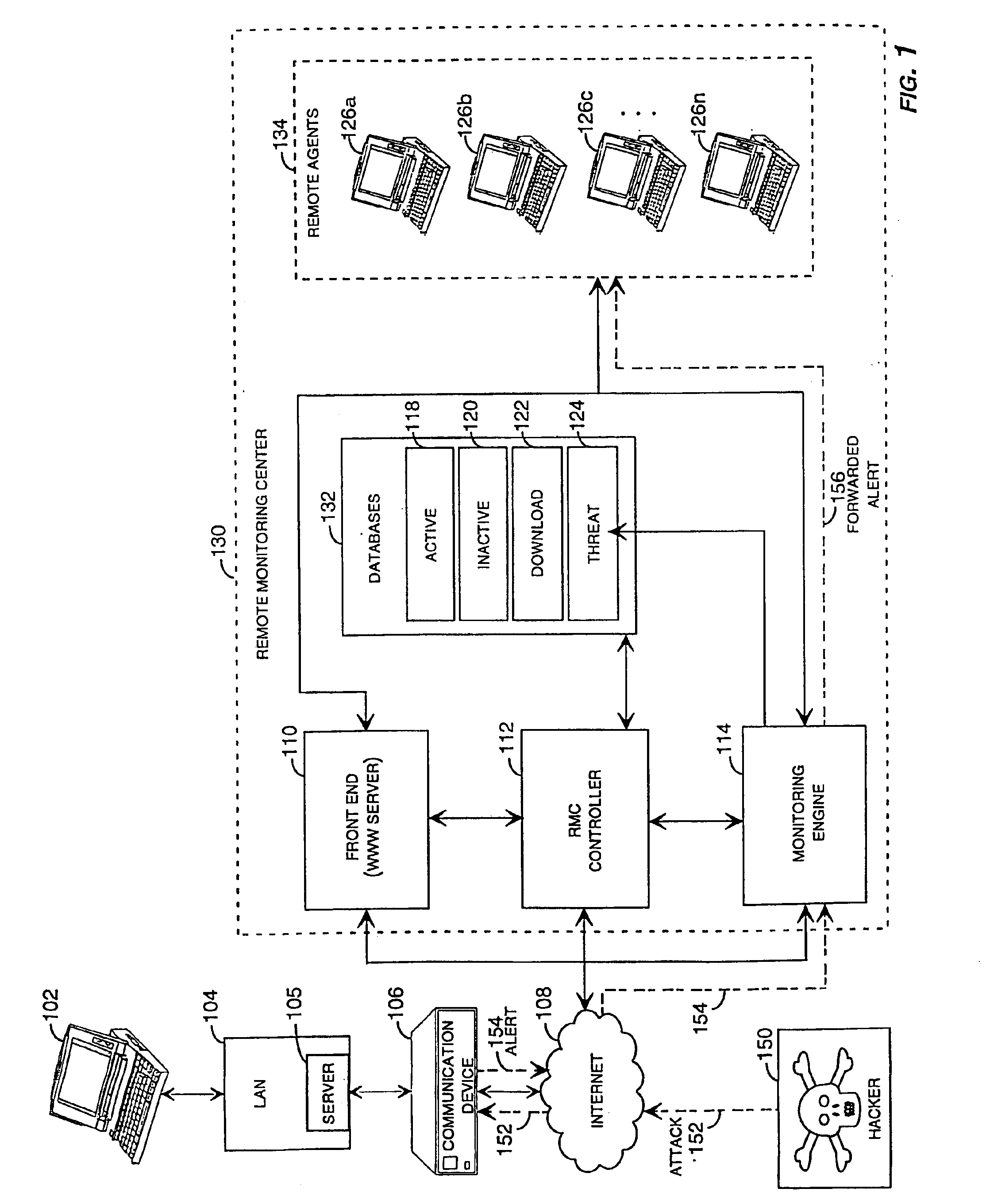
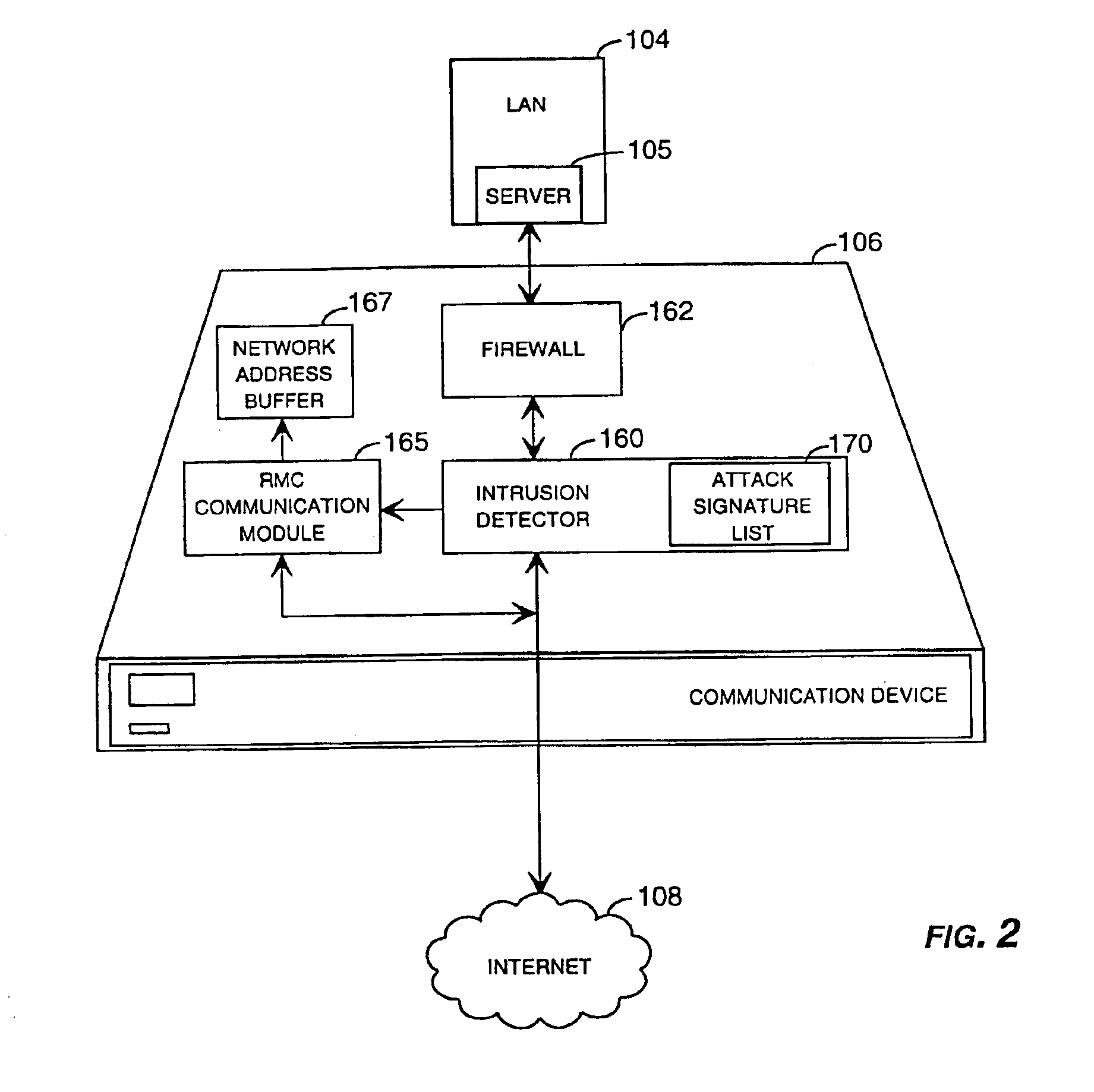
Method and system for remotely configuring and monitoring a communication device
InactiveUS20050235360A1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
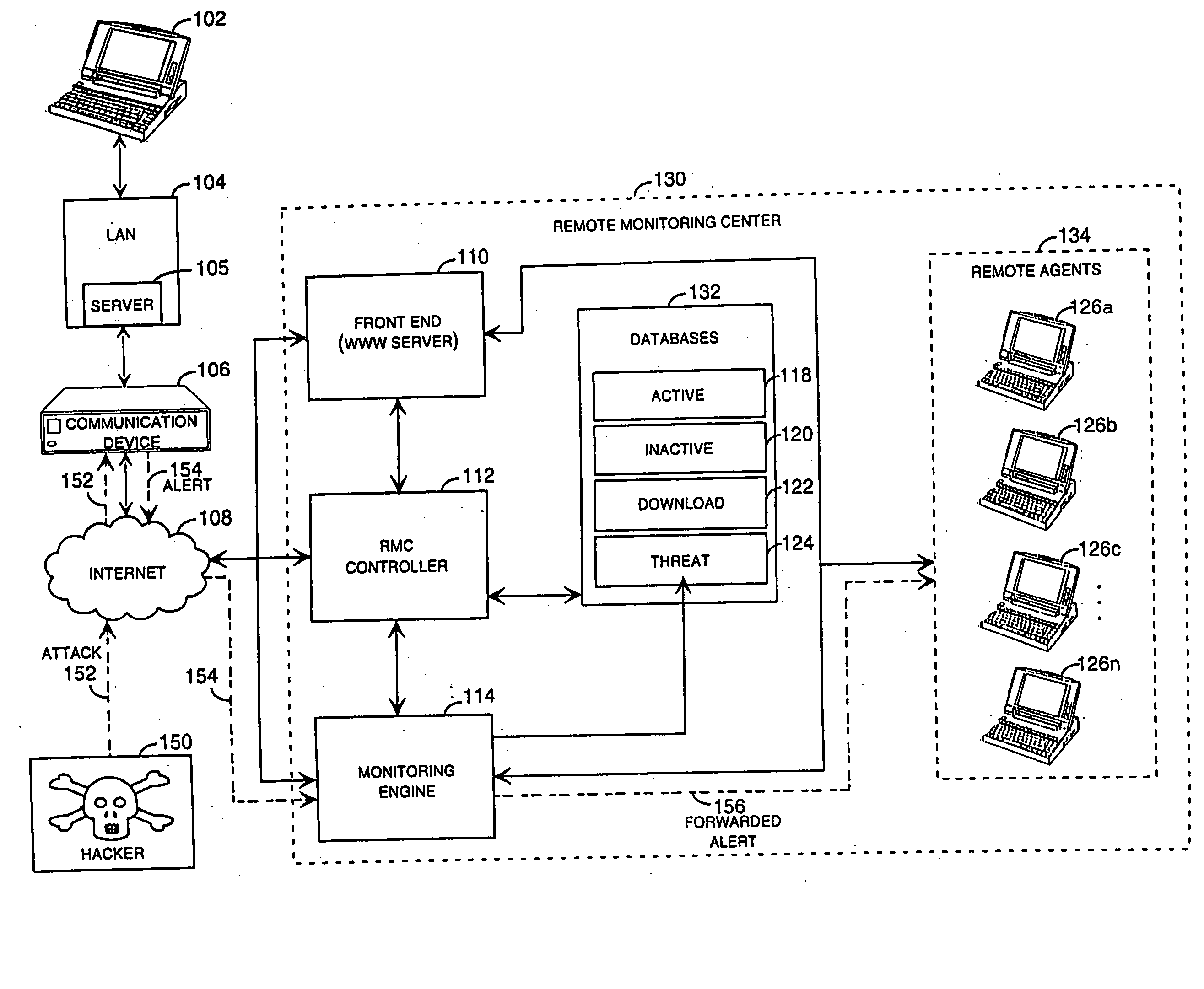
Methods and systems for remotely configuring and monitoring a communication device are provided, especially useful in a computer network environment such as the Internet. A communication device or network appliance compares communications entering the communication device to a list of communication types established as known security risks, for example hacker attacks, unauthorized attempted access to network resources, or similar network security threats. If the received communication corresponds to a known security risk, the communication is classified as either a high security risk or low security risk, and an alert signal is transmitted to a remote monitoring center. Upon receiving the alert signal, the remote monitoring center assigns a priority to the alert signal based upon the type of the communication that triggered the transmission of the alert signal. Based on the assigned priority, the prioritized alert signal is then forwarded to a remote monitoring agent for resolution. The remote monitoring agent may then analyze the communication, contact the end user of the communication device with an appropriate resolution, or take other appropriate action in response to the received communication. The communication device may also be remotely configured.
Owner:SECUREWORKS
Jettable compositions
ActiveUS20050171237A1Prevent long-term corrosionReaction is slowAdditive manufacturing apparatusLiquid surface applicatorsMeth-Oligomer
A fully curable jettable composition having a viscosity less than 30 cps at a temperature within the range of 15-180° C., more preferably at a temperature of 15-100° C., e.g. 60-80° C. the composition comprising: (A) at least one low viscosity reactive resin selected from the group consisting of compounds containing an oxetane ring, cycloaliphatic epoxy resins, tetrahydrofurans, hexahydropyrans and mono-functional (meth)acrylates, said resin having a molecular weight of not greater than 300 Daltons, e.g. 250 Daltons or less, and a viscosity at a temperature in the said range of less than 30 cps, e.g. 5 to 15 cps; (B) at least one higher viscosity resin selected from the group consisting of epoxy resins, compounds containing an oxetane ring and acrylates, which resin acts to thicken the low viscosity resin and strengthen a jetted deposit of the composition, the higher viscosity resin having: a viscosity greater than twice that of the low viscosity resin at the said temperature in the range stated above, and a functionality of greater than or equal to 2; (C) at least one curable toughener, preferably having a functionality of at least 2, such as hydroxy, epoxy, acrylic or other reactive functionalised polymer / oligomer (e.g. derived by functionalising poly(tetrahydrofuran), polycaprolactone, polycarbonate diol, or a dendrimeric polyol; (D) at least one initiator for the polymerisation of the resins, and (E) at least one stabiliser for delaying the curing of the resins of the composition; wherein the low viscosity resin is slower to react than the higher viscosity resin and acts to solvate the higher viscosity resin prior to curing and at least partly during curing and wherein at least 30% of the components A and B are cationically curable resins. The composition can be jetted from piezo electric printing heads under the control of a computer program to form a multi-layered article, e.g. a three dimensional article, in which the adjacent droplets merge and are cured homogeneously together.
Owner:3D SYST INC +1
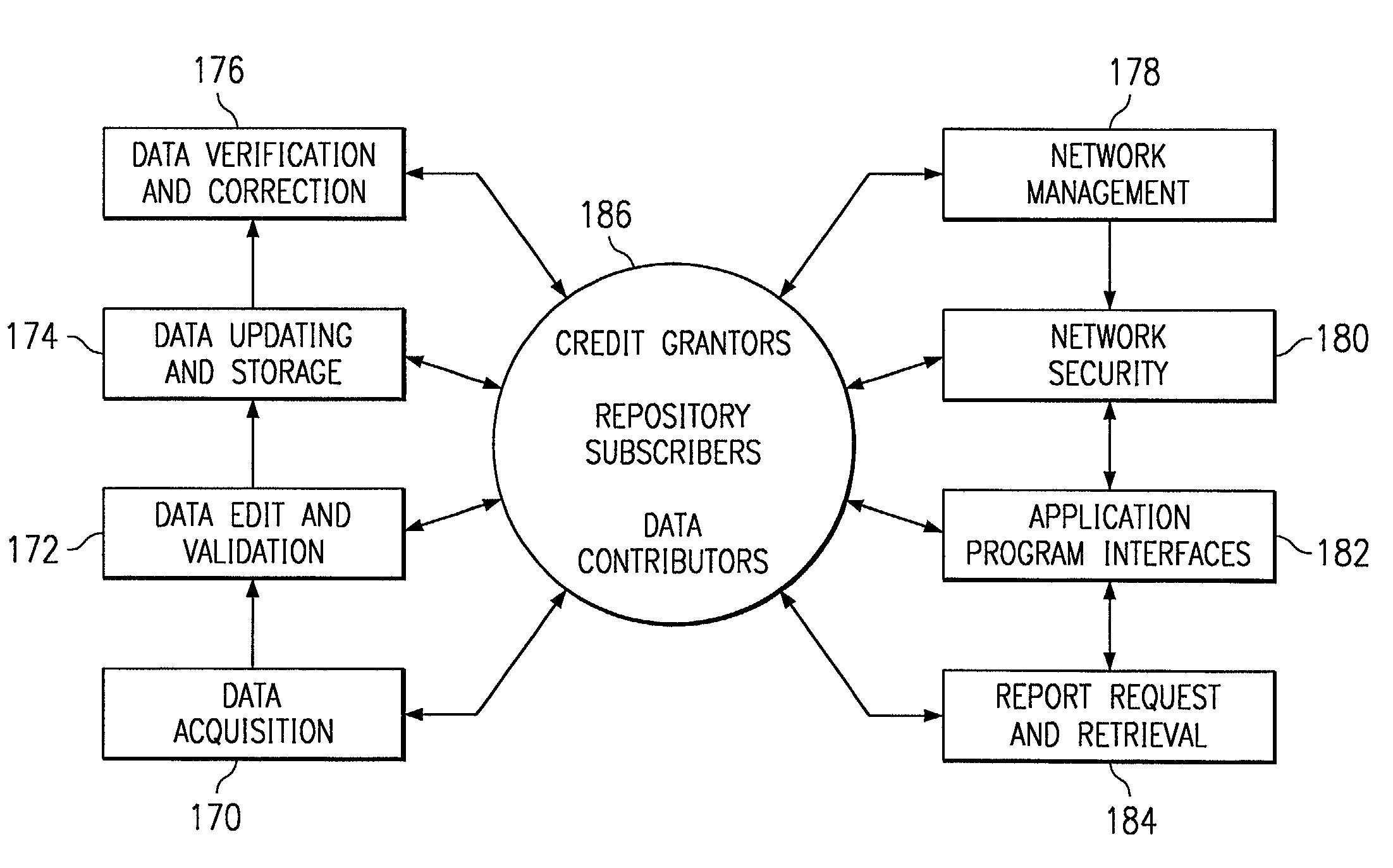
Consumer credit data storage system
InactiveUS7584146B1Rapid responseEasy to analyzeFinancePayment circuitsData informationComputerized system
A consumer credit information data base for storing current consumer credit information, as well as historical credit data information. On-line computerized systems can access the data base and present current and historical credit data information to users so that better assessments can be made as to the credit worthiness of a consumer.
Owner:INNOVIS DATA SOLUTIONS
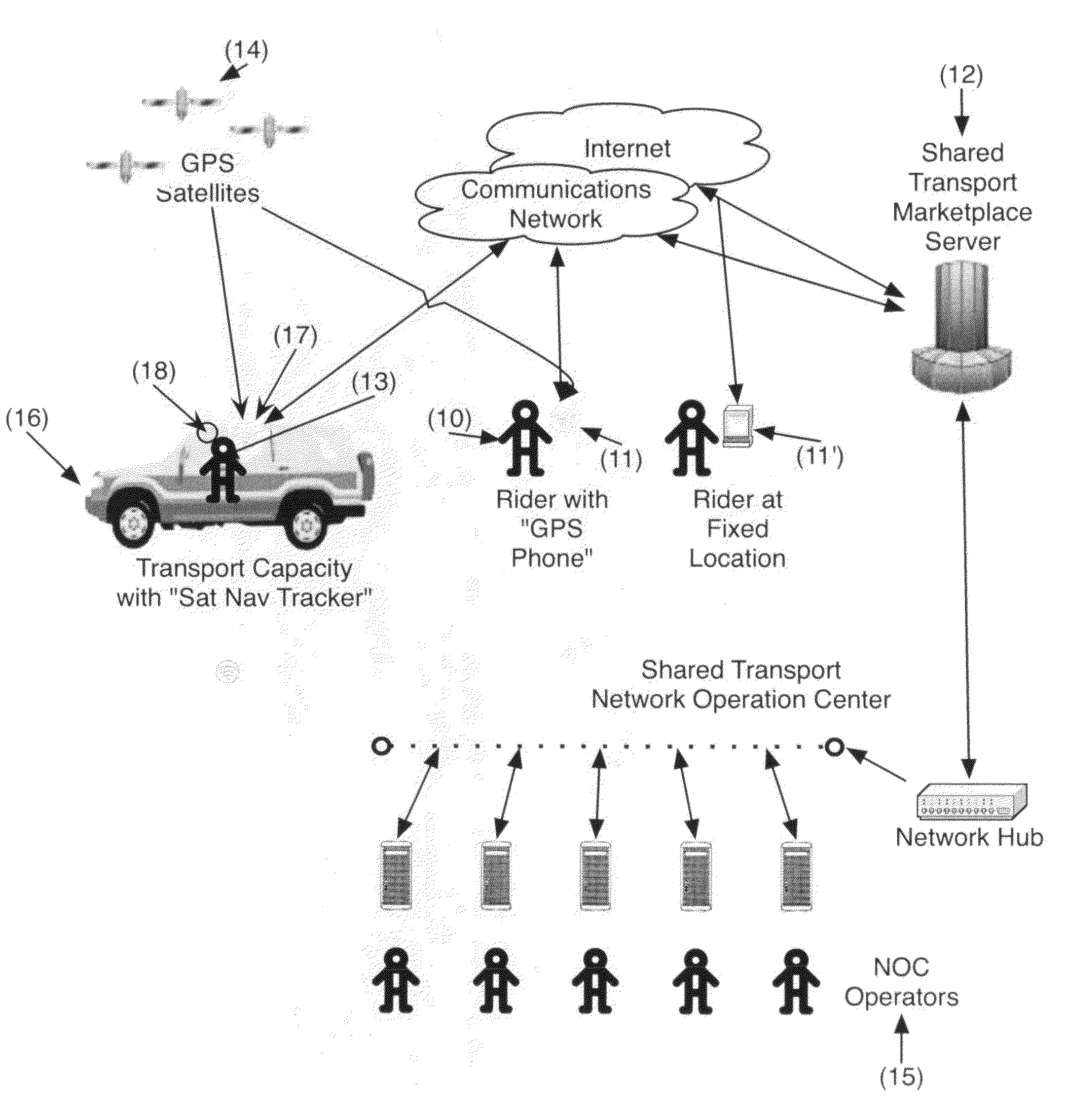
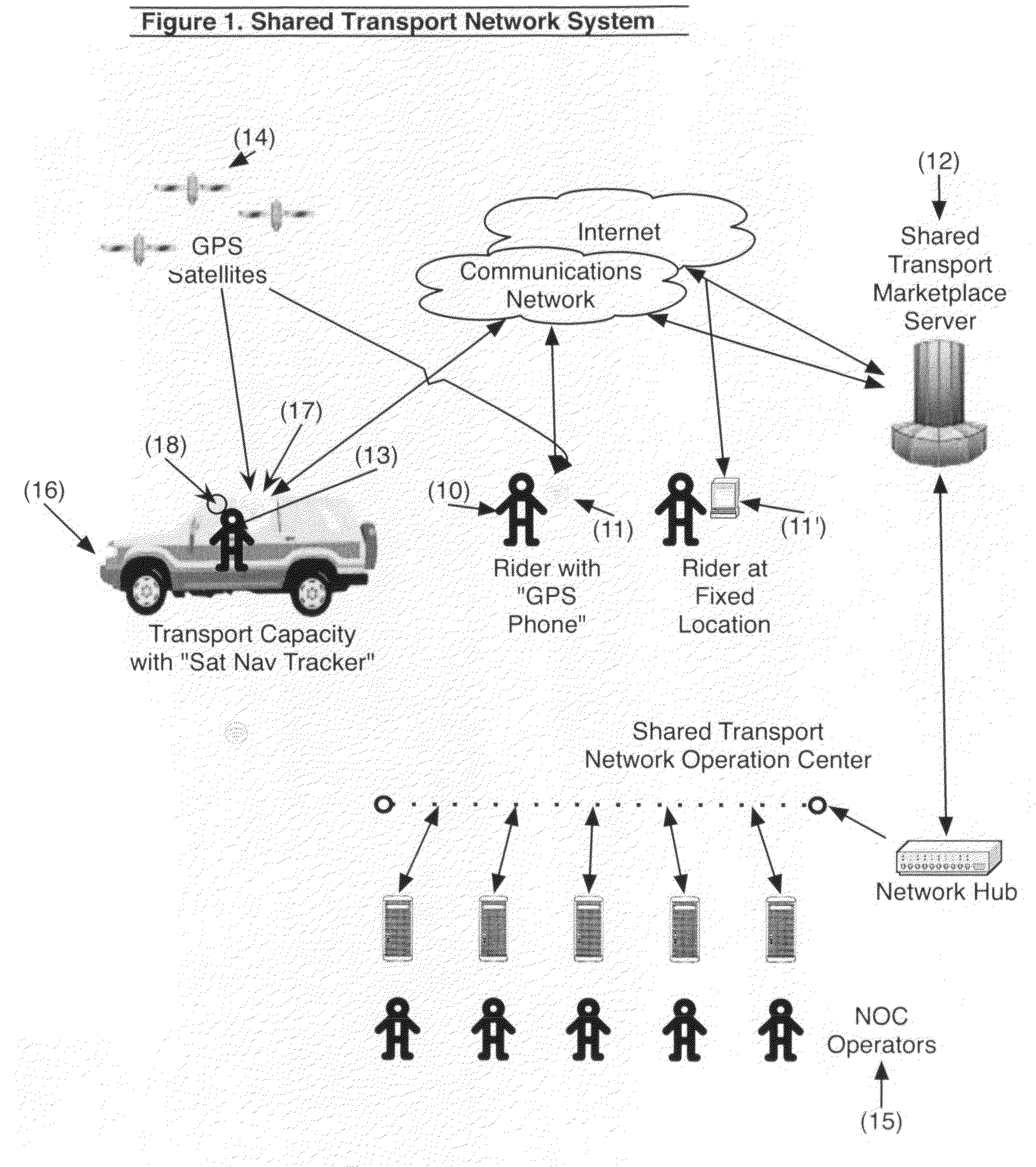
Shared transport system and service network
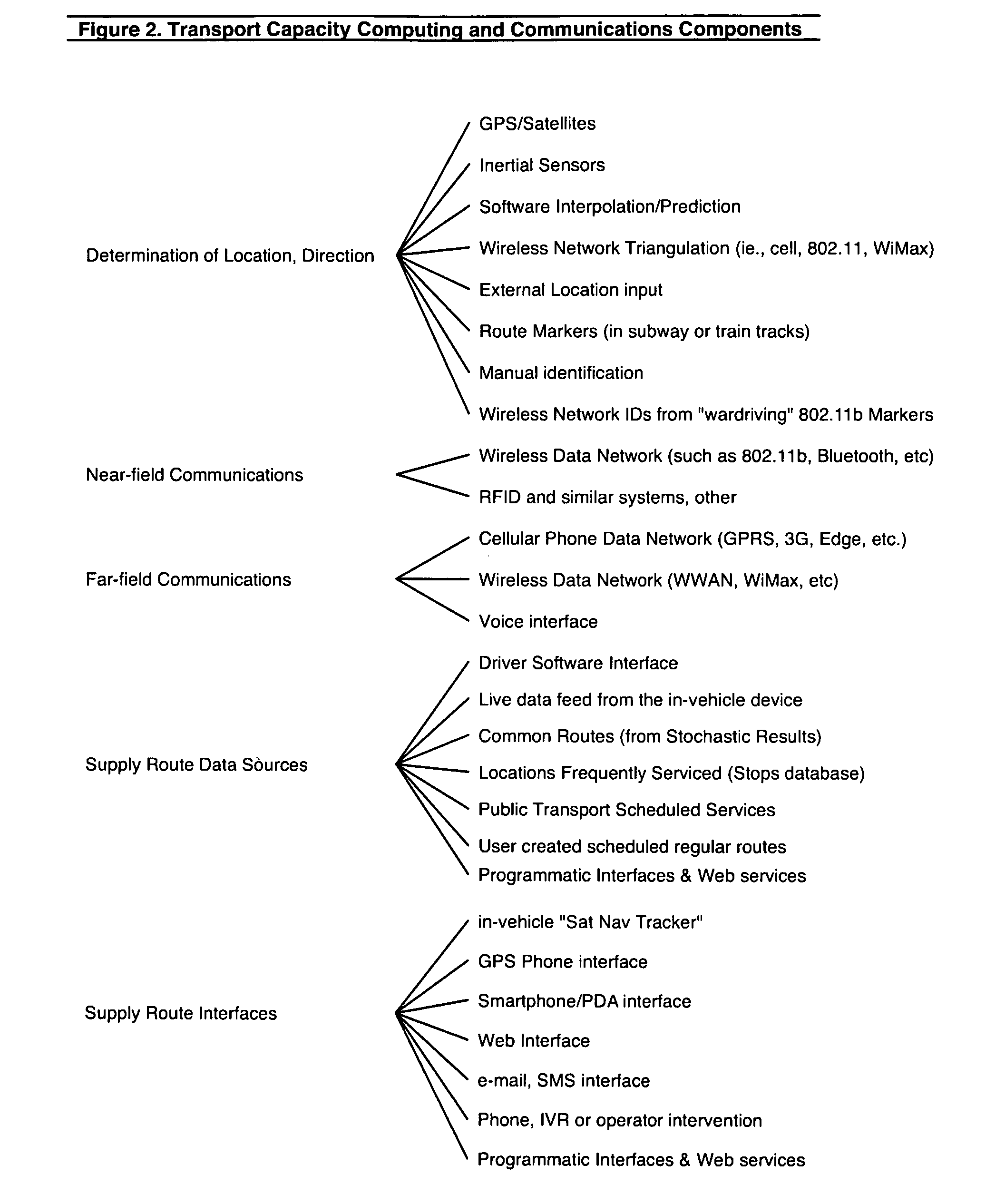
ActiveUS7840427B2Increase the number ofRapid responseInstruments for road network navigationRoad vehicles traffic controlTransport systemTransportation capacity
The network system matches the supply and demand of transportation services by incorporating unused transportation capacity (i.e., empty seats) with a real-time allocation and matching service that enables individuals and goods to conveniently hire that capacity with attractive pricing, rapid responsiveness, better information availability and trusted security. The network system provides an electronic registry of capacity containing an indication of the spare transport capacity and location of a plurality of transport vehicles, an electronic registry of demand containing an indication of the demand for transportation needs of a plurality of individuals and a central processing capability to effect a match of the transport capacity of at least one transport vehicle with the transport demand of at least one individual.
Owner:CARMA TECH LTD
Signal quality metrics design for qualifying data for a physiological monitor
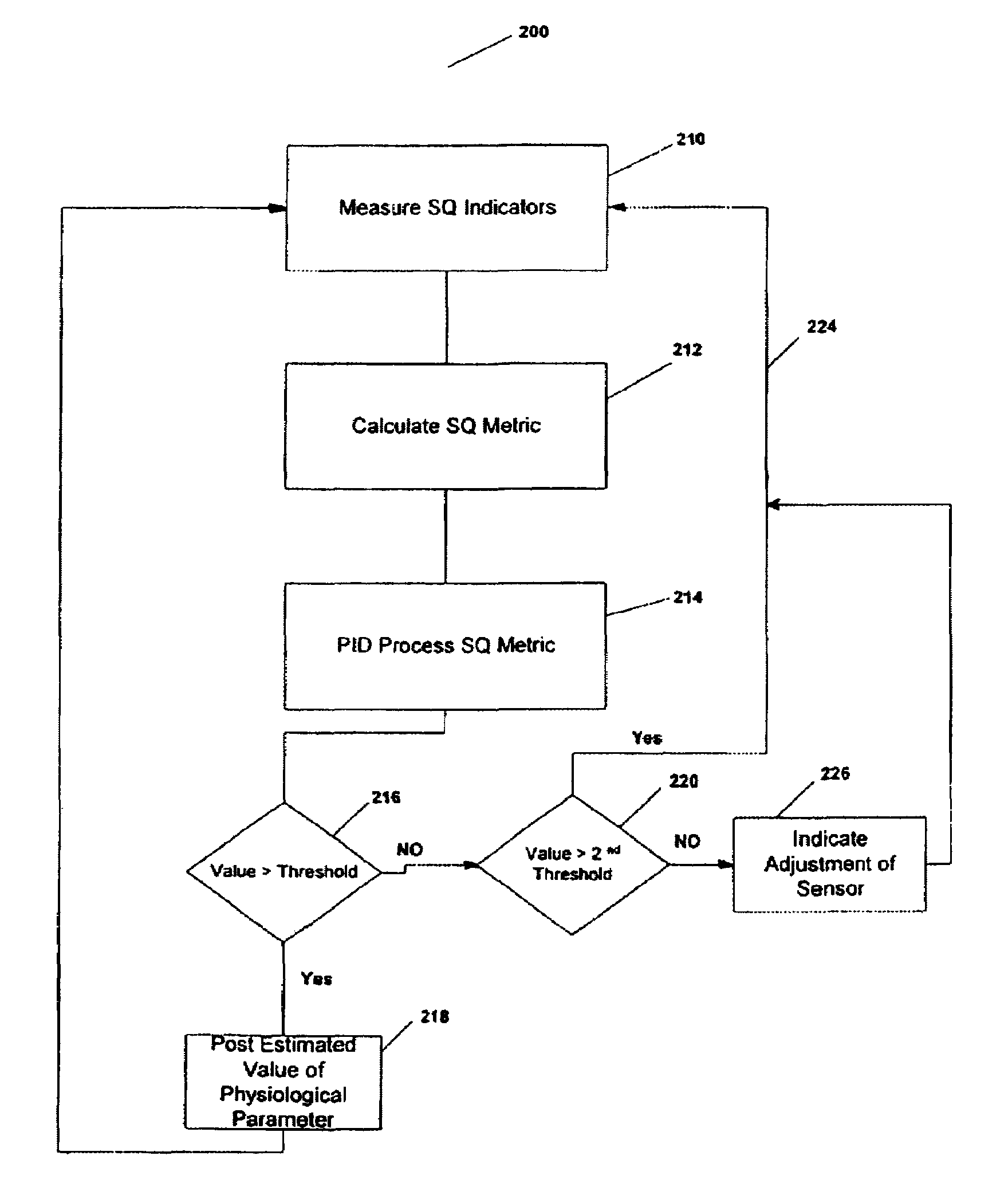
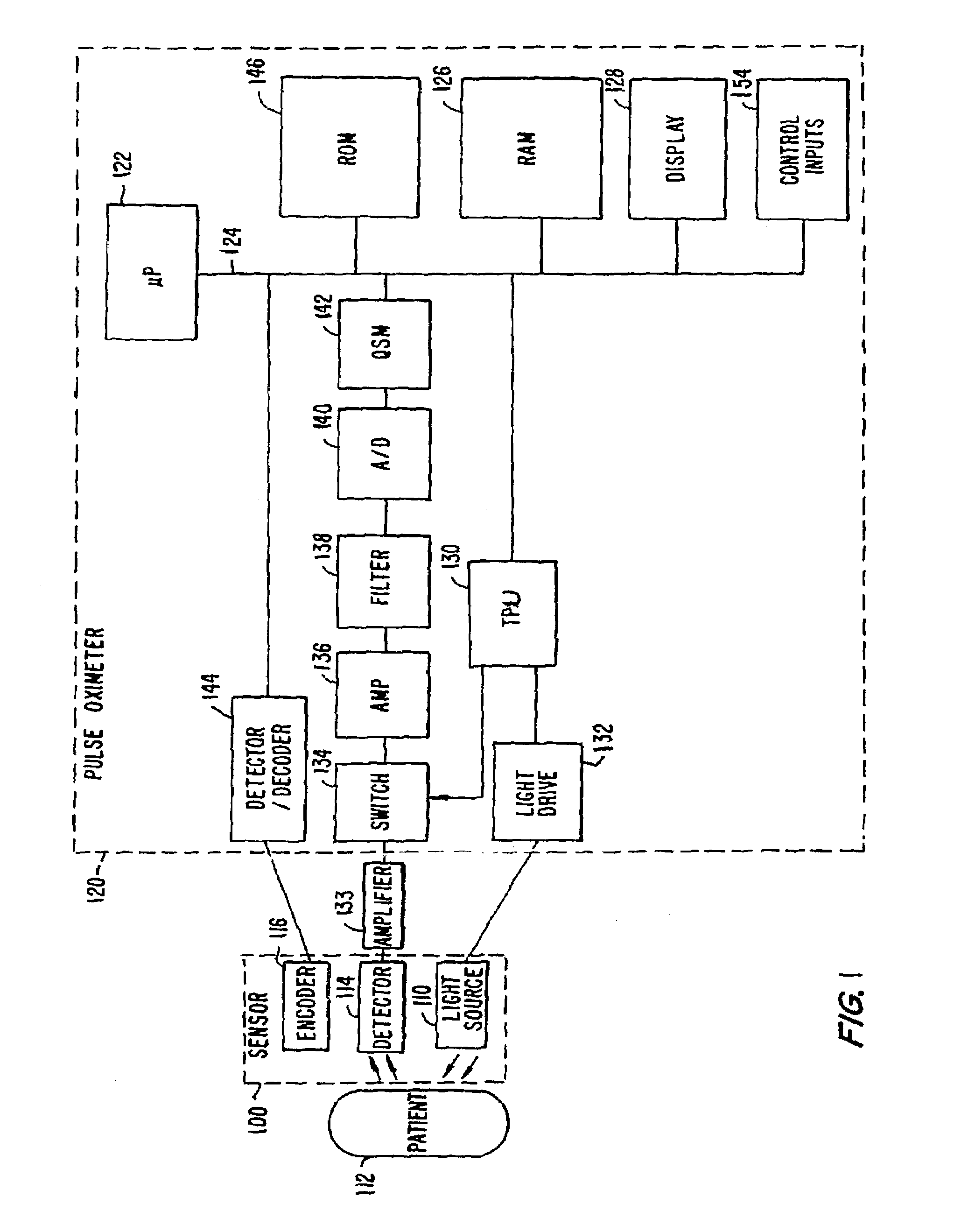
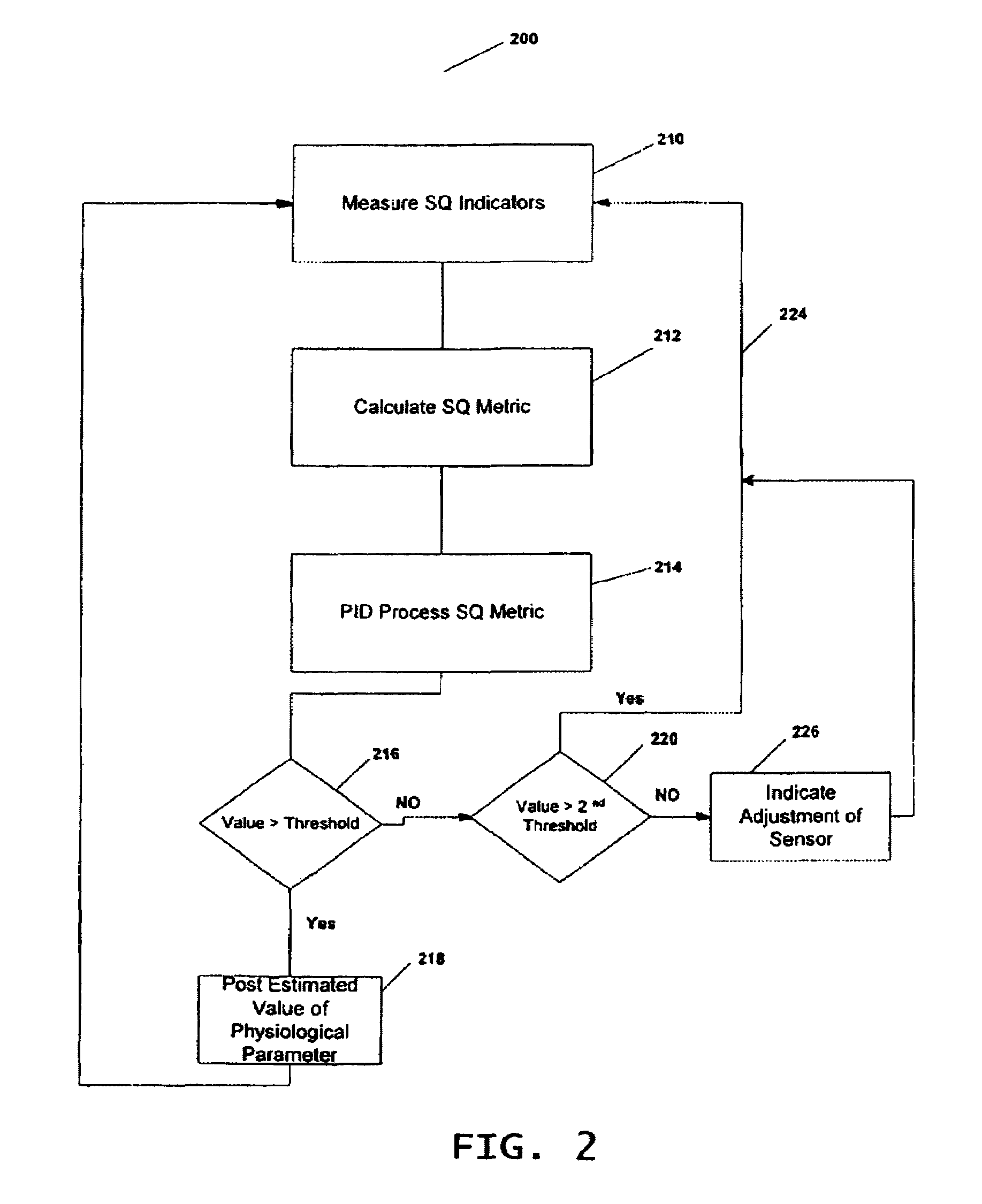
ActiveUS7006856B2Small magnitudePrevent spurious responseSensorsMeasuring/recording heart/pulse rateEngineeringSignal quality
A method and a device for determining the quality of signal used for measuring a physiological parameter. One embodiment of the present invention is directed towards a pulse oximeter, where the measured physiological parameter includes a patient's pulse rate and blood oxygen saturation. The signal quality, which is indicative of the accuracy and reliability of the measured physiological parameter, is calculated by combining a plurality of signal quality indicators, each of which is an indicator of a quality of the measured signal. The value of the signal quality metric is compared to a threshold and based on this comparison various decisions are made by the medical device. One decision is directed towards deciding whether or not to display the measured physiological parameter, to ensure that only accurate measured values are displayed. Another decision is directed towards providing feedback to guide the clinician to adjust the location of the sensor to a more suitable tissue location.
Owner:TYCO HEALTHCARE GRP LP
Software and hardware analysis test
InactiveUS20060217823A1Easy pairingEasy to operateComputer controlError detection/correctionComputer softwareRapid response
Embodiments described herein relate to techniques, tools and processes for analyzing a computer system and determining the type and capabilities of hardware and software components resident on the computer system. This information can then be used for multiple different purposes. For example, the information may be used for (1) communicating an individual computer's ability to effectively operate a specific computer software and / or computer hardware product, (2) relaying the information to a technical support operation to allow a more rapid response, or (3) making a simple evaluation of the stand alone performance of a computer. These processes can be used for analyzing an individual computer's system inventory (computer hardware components and system software components) against a static set of manufacturer validated requirements for a hardware or software product.
Owner:HUSDAWG
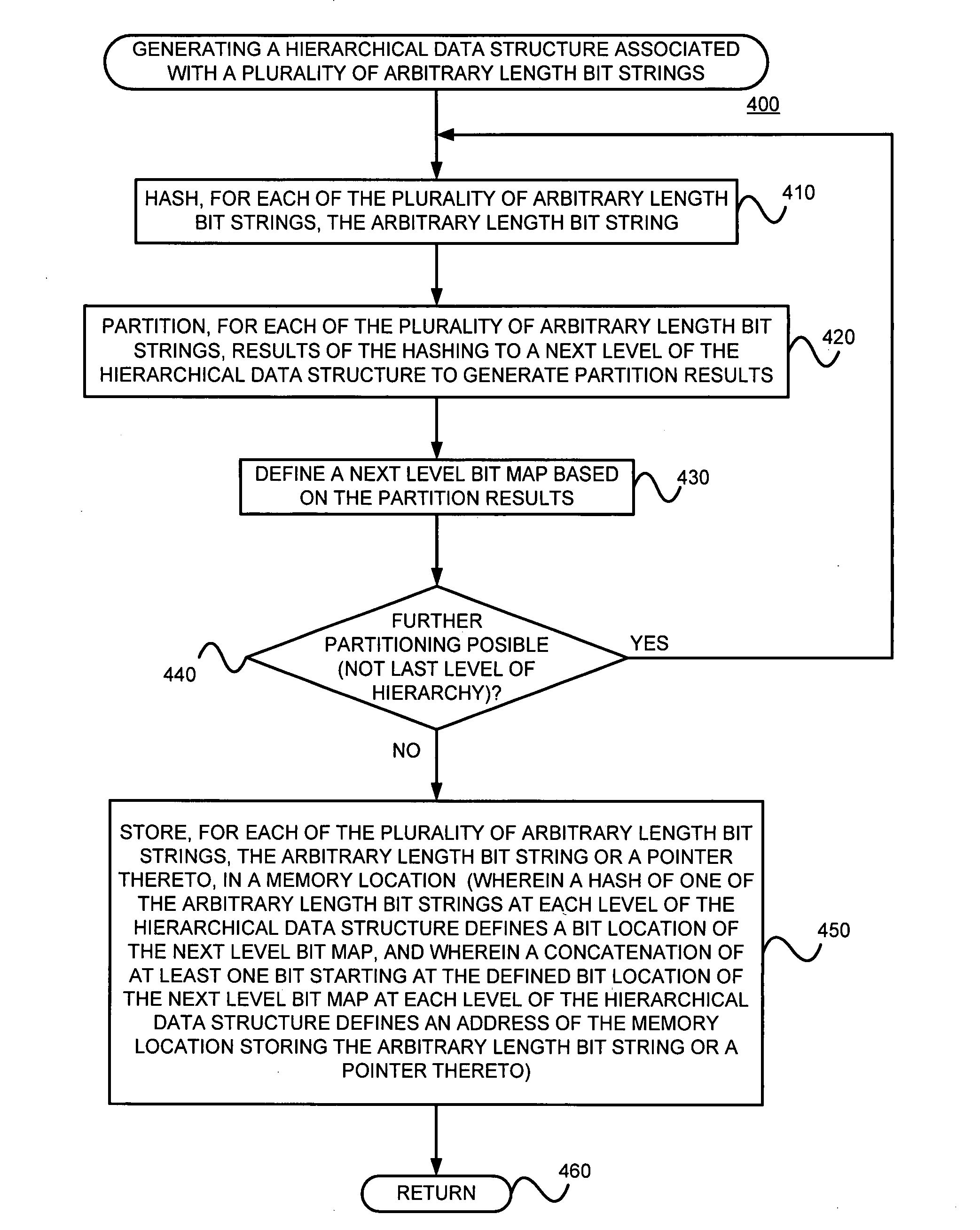
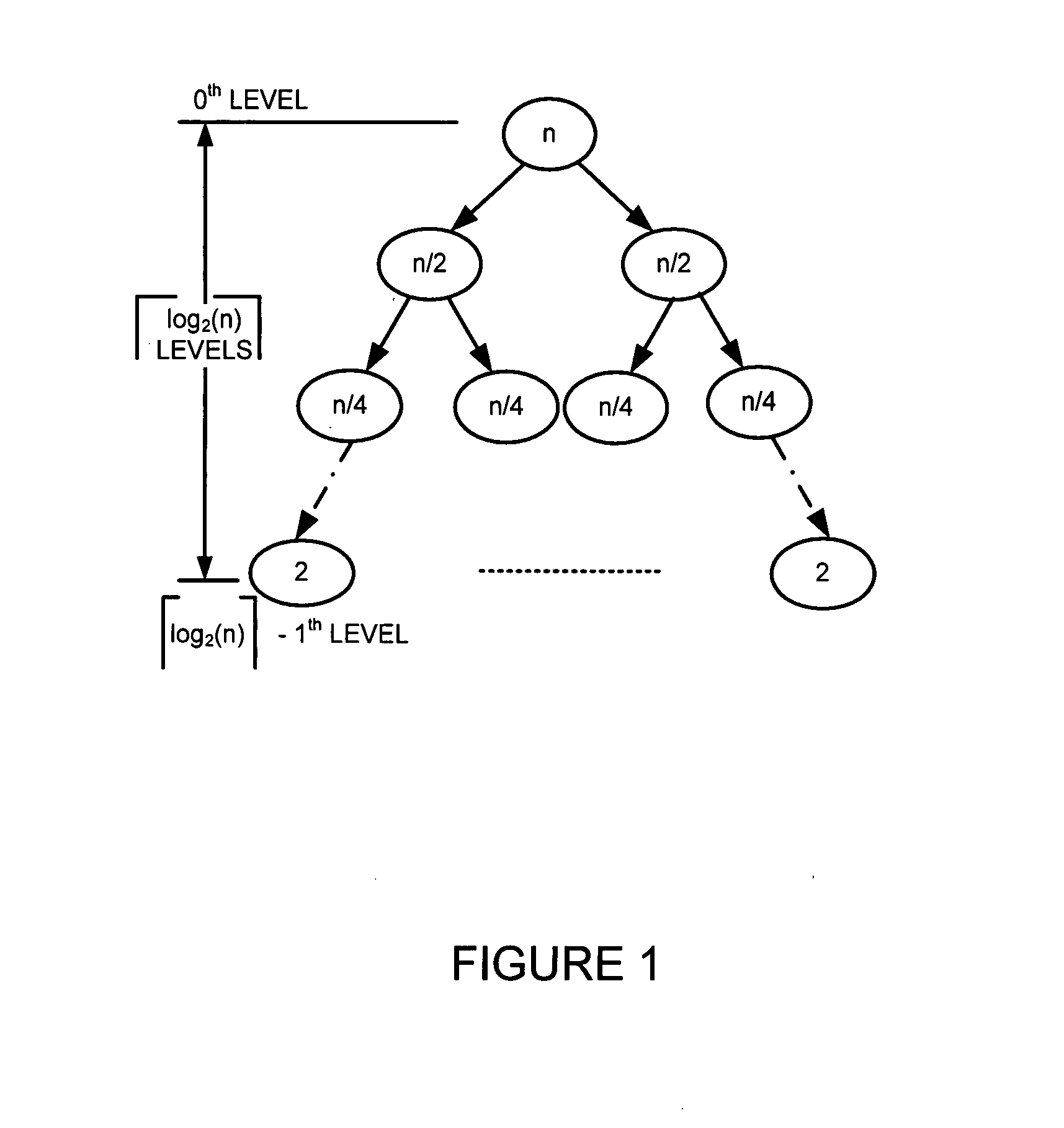
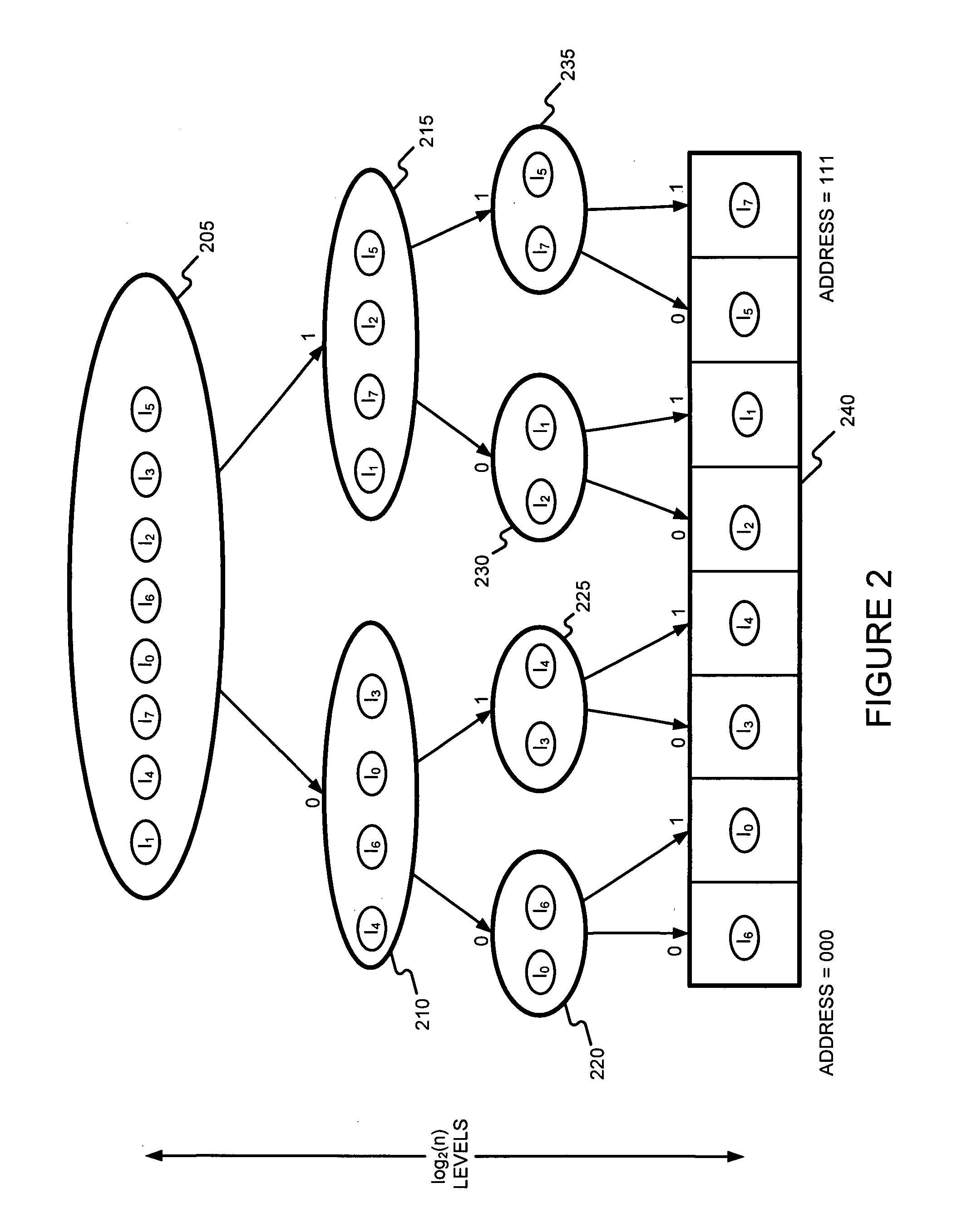
Generating a hierarchical data structure associated with a plurality of known arbitrary-length bit strings used for detecting whether an arbitrary-length bit string input matches one of a plurality of known arbitrary-length bit string
ActiveUS20080133583A1Easy to updateImprove search rateDigital data processing detailsComputer security arrangementsTheoretical computer sciencePerfect hash function
Generating and using a high-speed, scalable, and easily updateable data structure are described. The proposed data structure provides minimal perfect hashing functionality while intrinsically supporting low-cost set-membership queries. In other words, in some embodiments, it provides at most one match candidate in a set of known arbitrary-length bit strings that is used to match the query.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
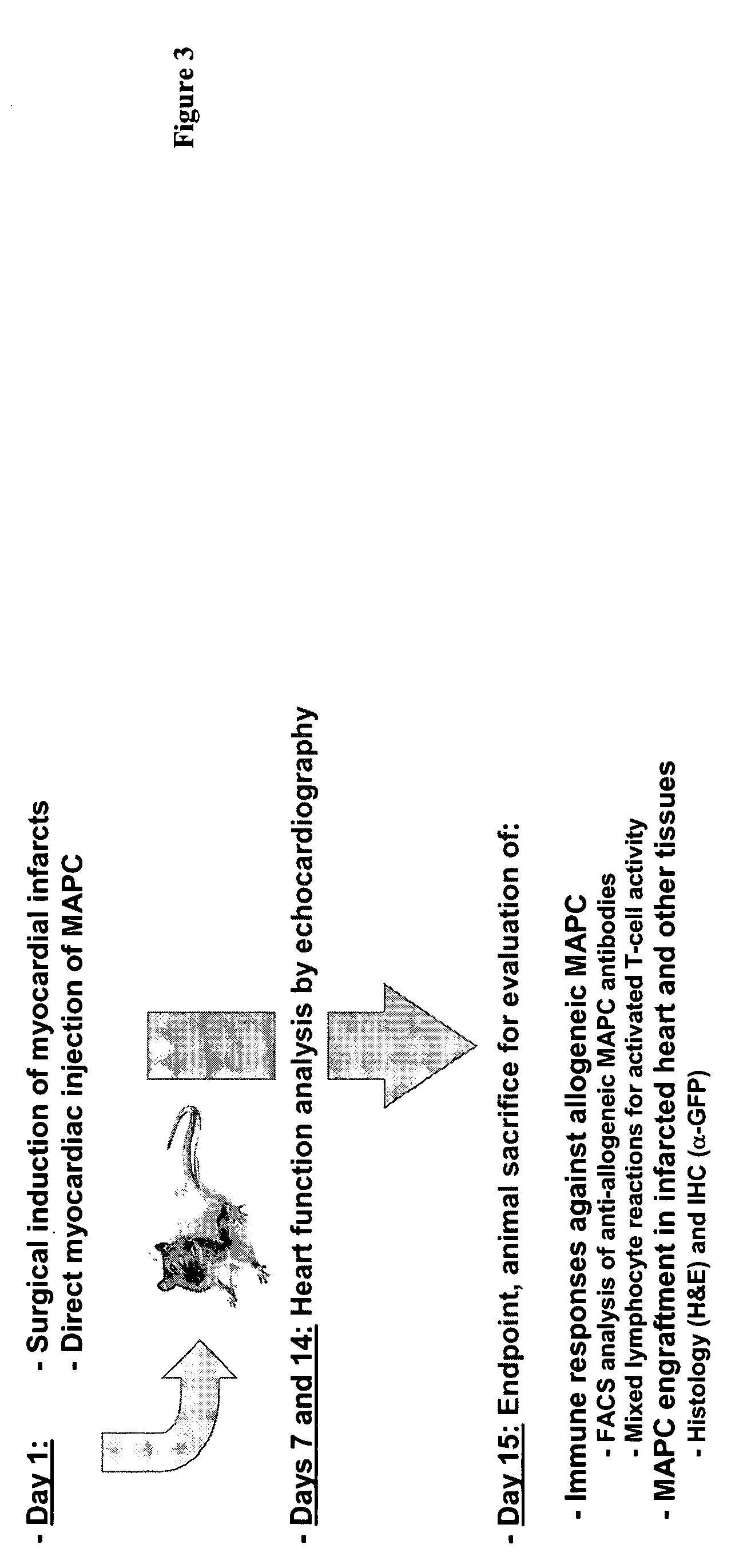
Use of multipotent adult stem cells in treatment of myocardial infarction and congestive heart failure
ActiveUS20060008450A1Restore and enhance cardiac muscle functionRapid responseBiocideGenetic material ingredientsTissues typesEmbryo
Owner:RGT UNIV OF MINNESOTA
Method to provide information in an internet telecommunication network
InactiveUS6862607B1Reduce the number of connectionsRapid responseError preventionFrequency-division multiplex detailsTelecommunications networkThe Internet
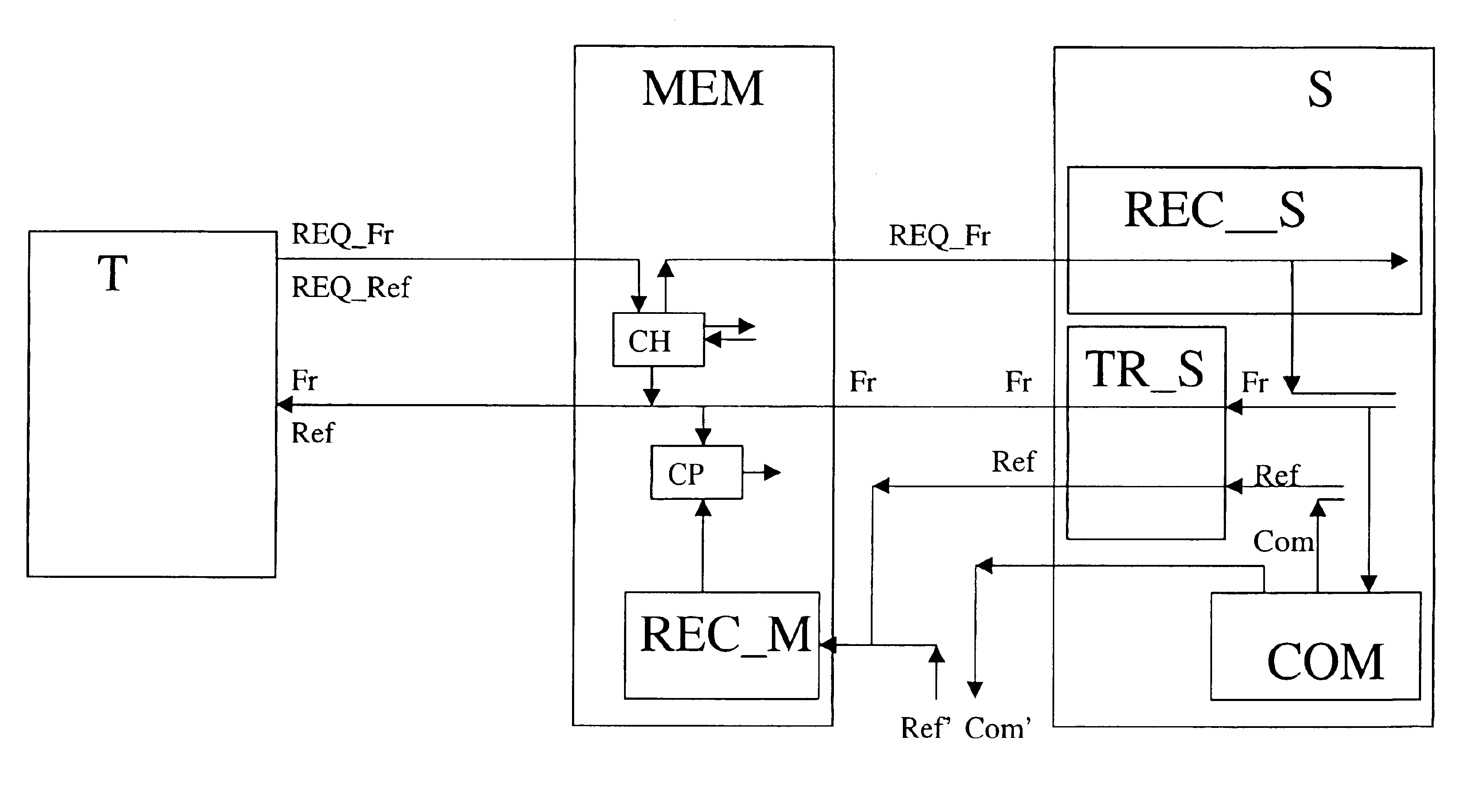
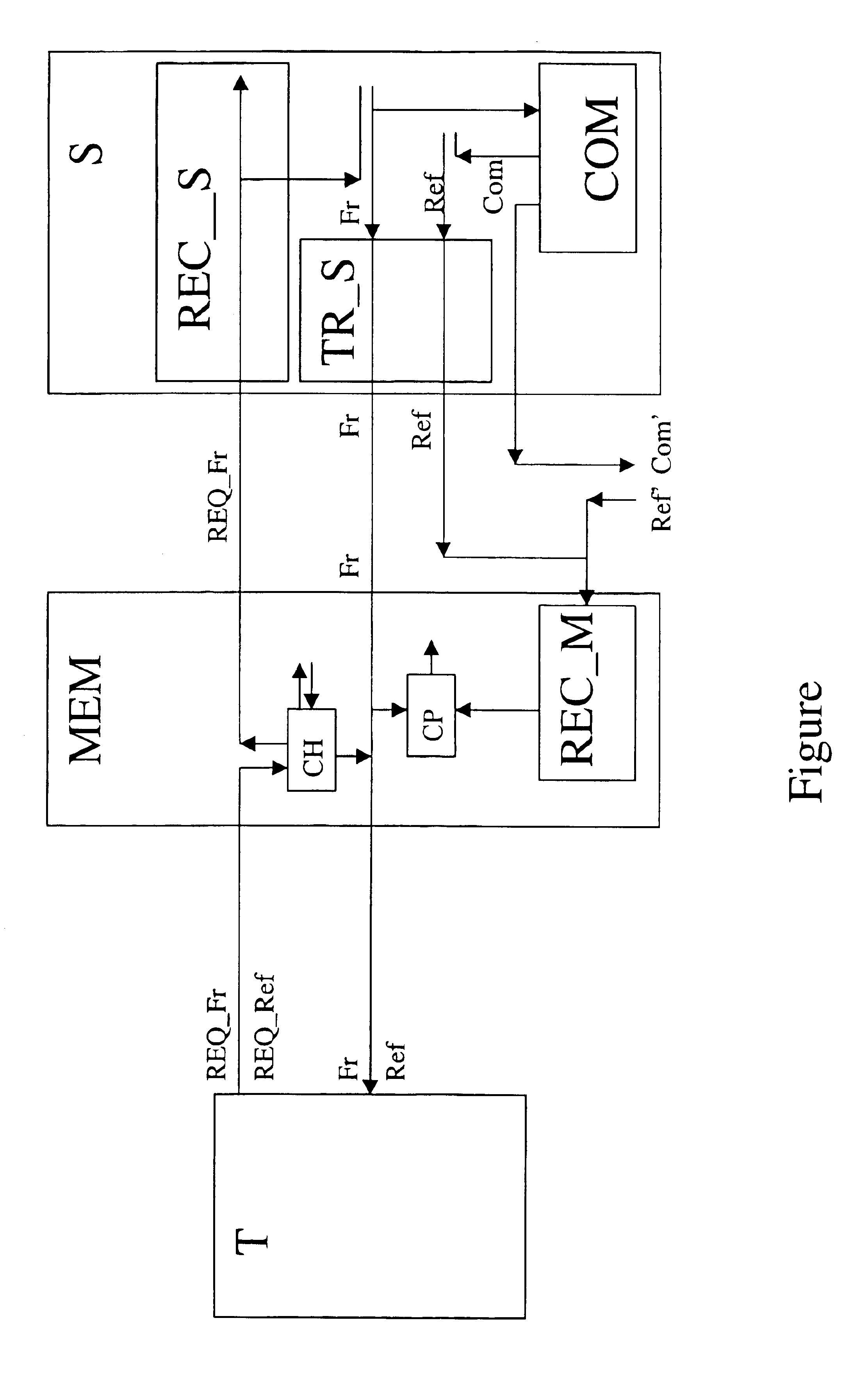
The invention concerns a method to provide information (INF) in an Internet telecommunication network from a server (S) to a terminal (T) of a user. The method comprises the steps of requesting with a frame information request (REQ_Fr) by the terminal (T) to the server (S) for transmission of frame information (Fr). The frame information (Fr) is in the information (INF) and comprises itself least one reference to referred information (Ref) of the information (INF). Upon reception of said the information request (REQ_Fr) the step of transmitting the frame information (Fr) to the terminal (T) is executed. The method further comprises reacting upon reception of the frame information request (REQ_Fr) also by commanding transmission of at least the referred information (Ref) according to the reference. This referred information (Ref) is commanded to be transmitted to a memory means (MEM) via a channel that is different from the one that is used for transmission of the frame information (Fr). A further step of the method is receiving the referred information (Ref) by the memory means (MEM) via the other channel. Hereby, in the event when the terminal (T) received at least part of the frame information, the terminal (T), which is associated to the memory means (MEM), is enabled to find the referred information (Ref) according to the reference in the frame information, at the location of the memory means (MEM) when requesting for it.
Owner:WSOU INVESTMENTS LLC
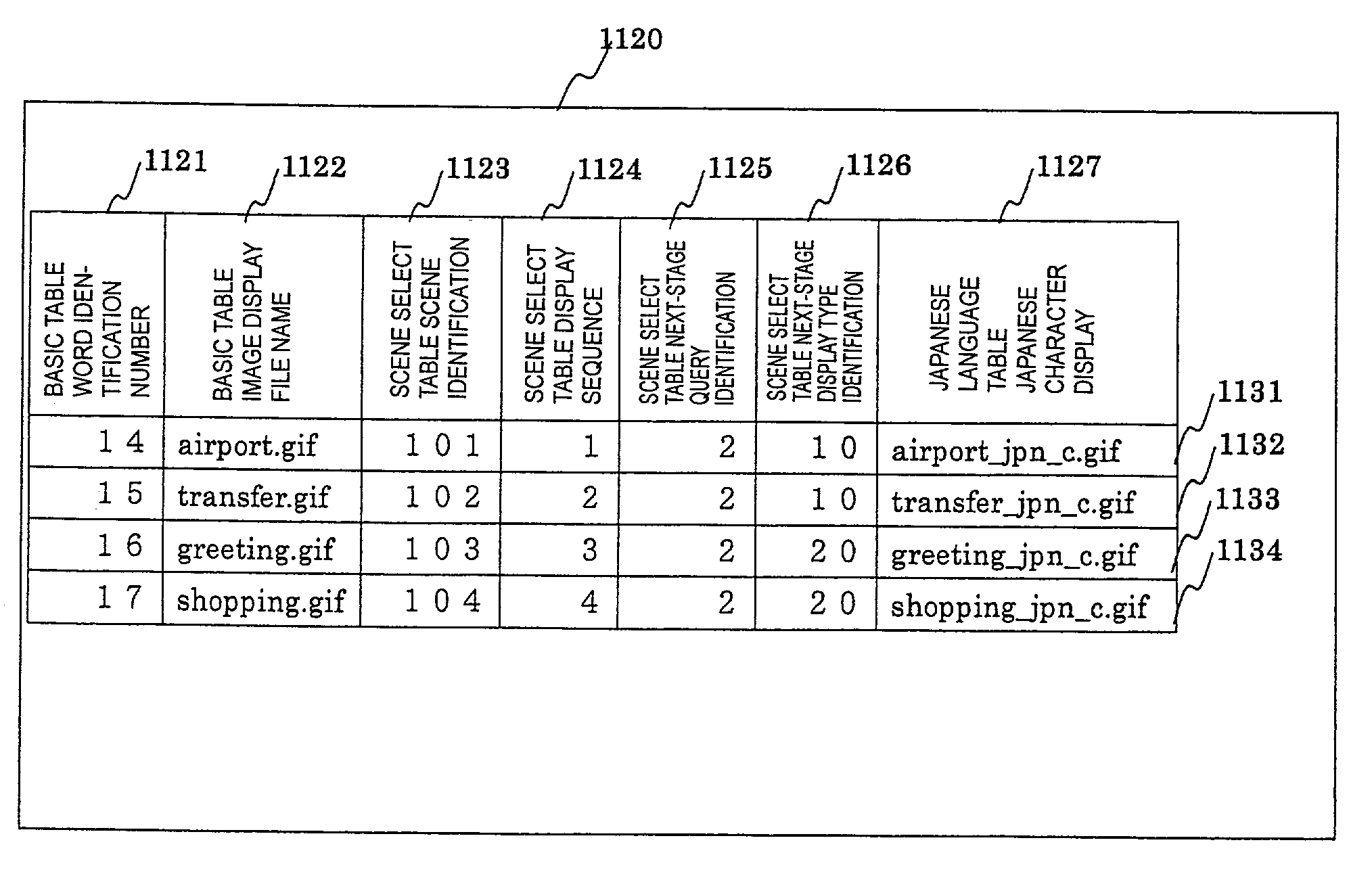
Multilingual conversation assist system
InactiveUS7162412B2Rapid responseNatural language translationSpecial data processing applicationsKnowledge managementAuxiliary system
A multilingual conversation database has subdatabases set according to a combination of languages different from each other for use in a conversation. Each of the subdatabases has a first area for setting a conversational situation and a second area for storing units of languages likely to be used for respective situations; if the situation in the first area is selected, a language unit in the second area corresponding to the situation is displayed. A multilingual conversation system comprises the multilingual conversation database and a communication facility into which the database is downloaded.
Owner:EVIDENCE CORP
System and method to provide interactivity for a networked video server
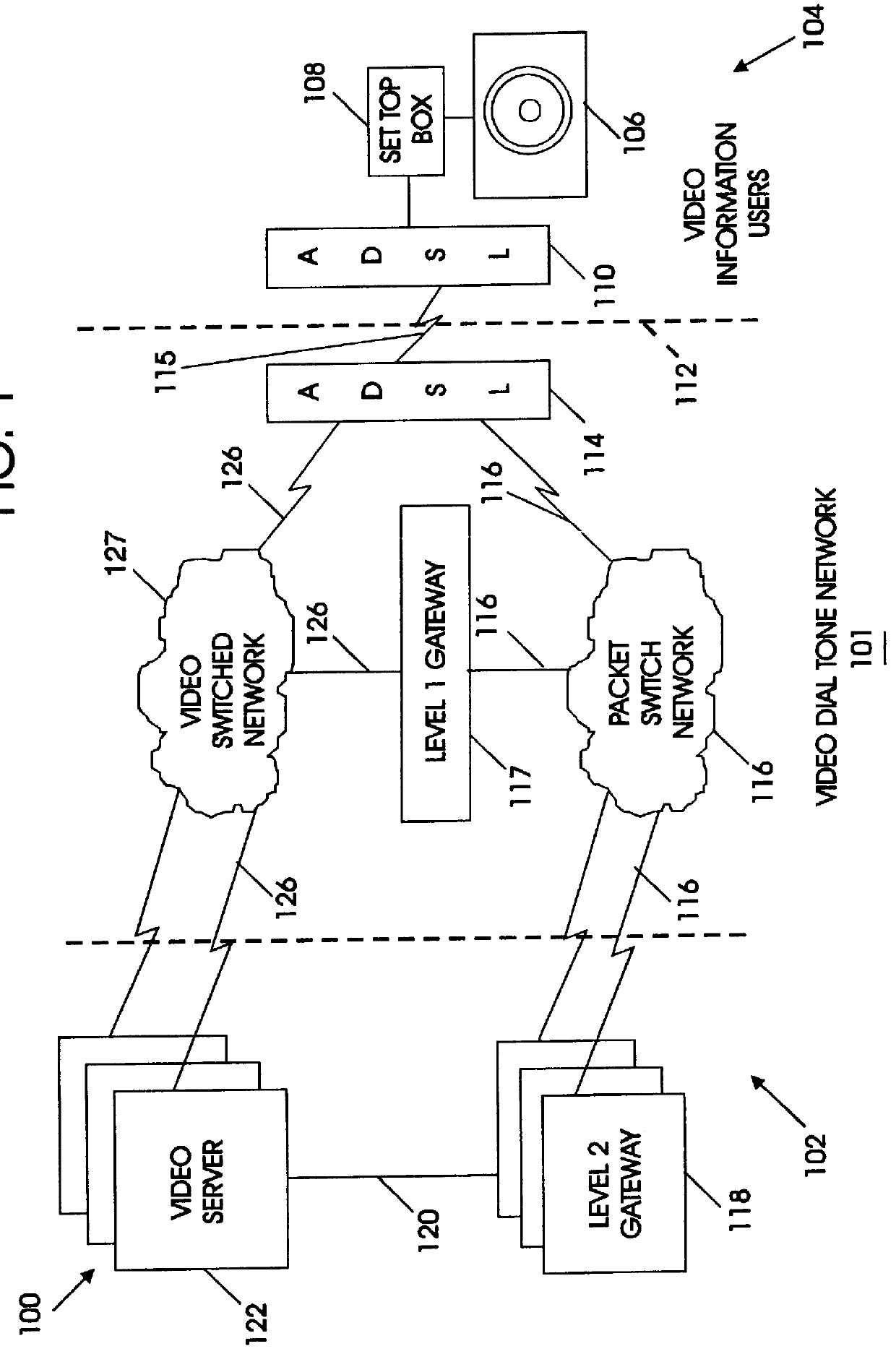
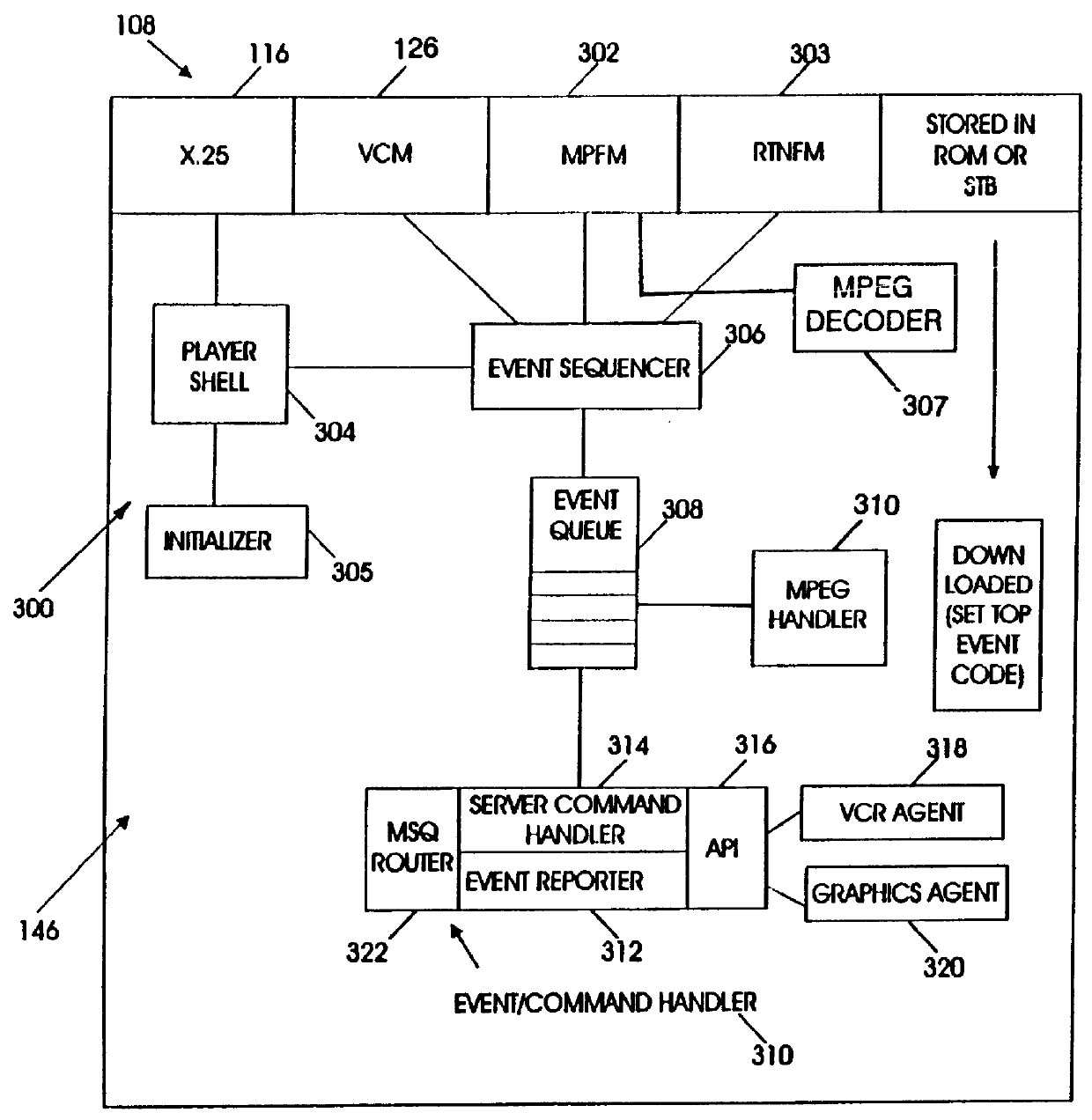
InactiveUS6055560AMinimizes burden and hence costRapid responseTelevision system detailsAnalogue secracy/subscription systemsVideo serverData channel
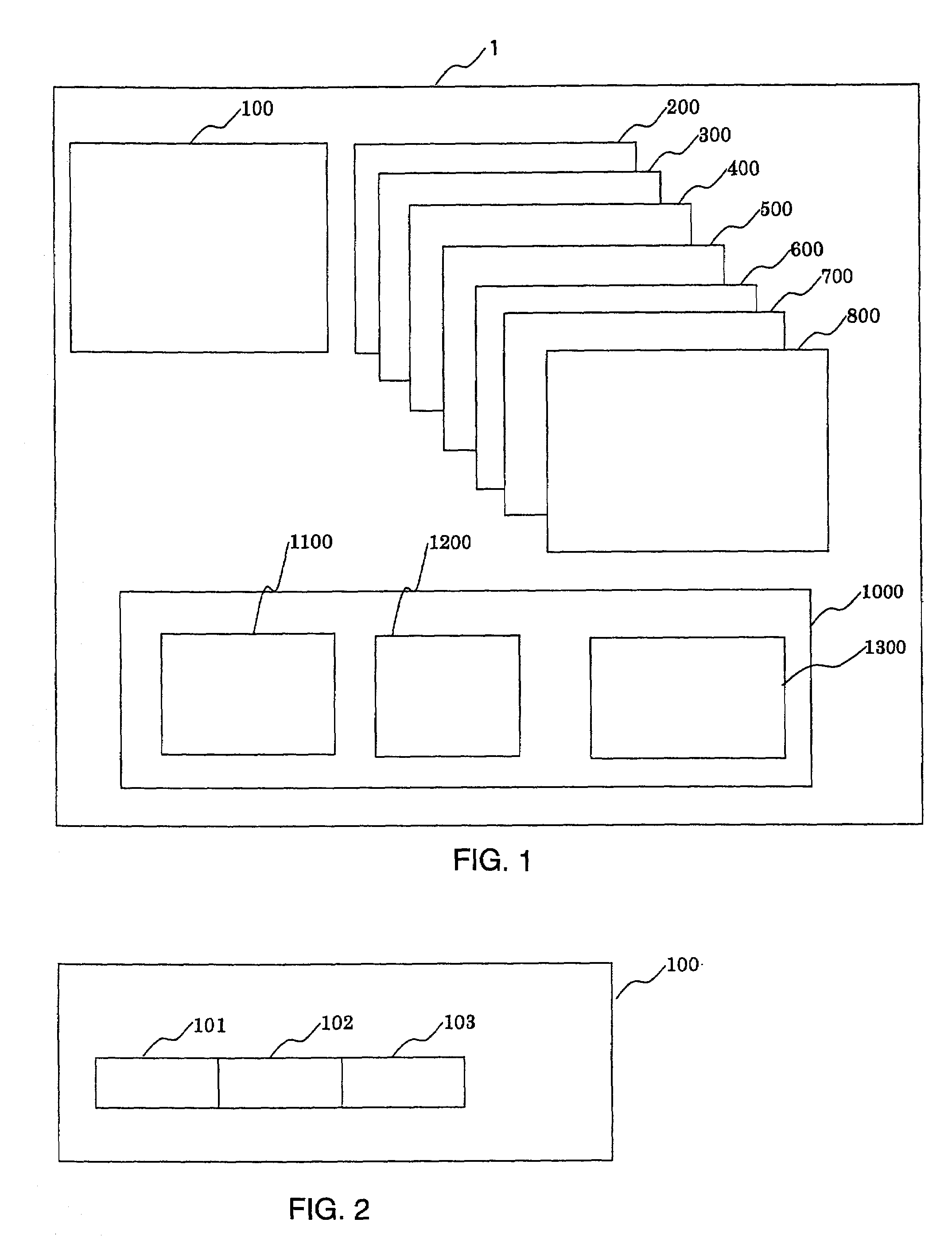
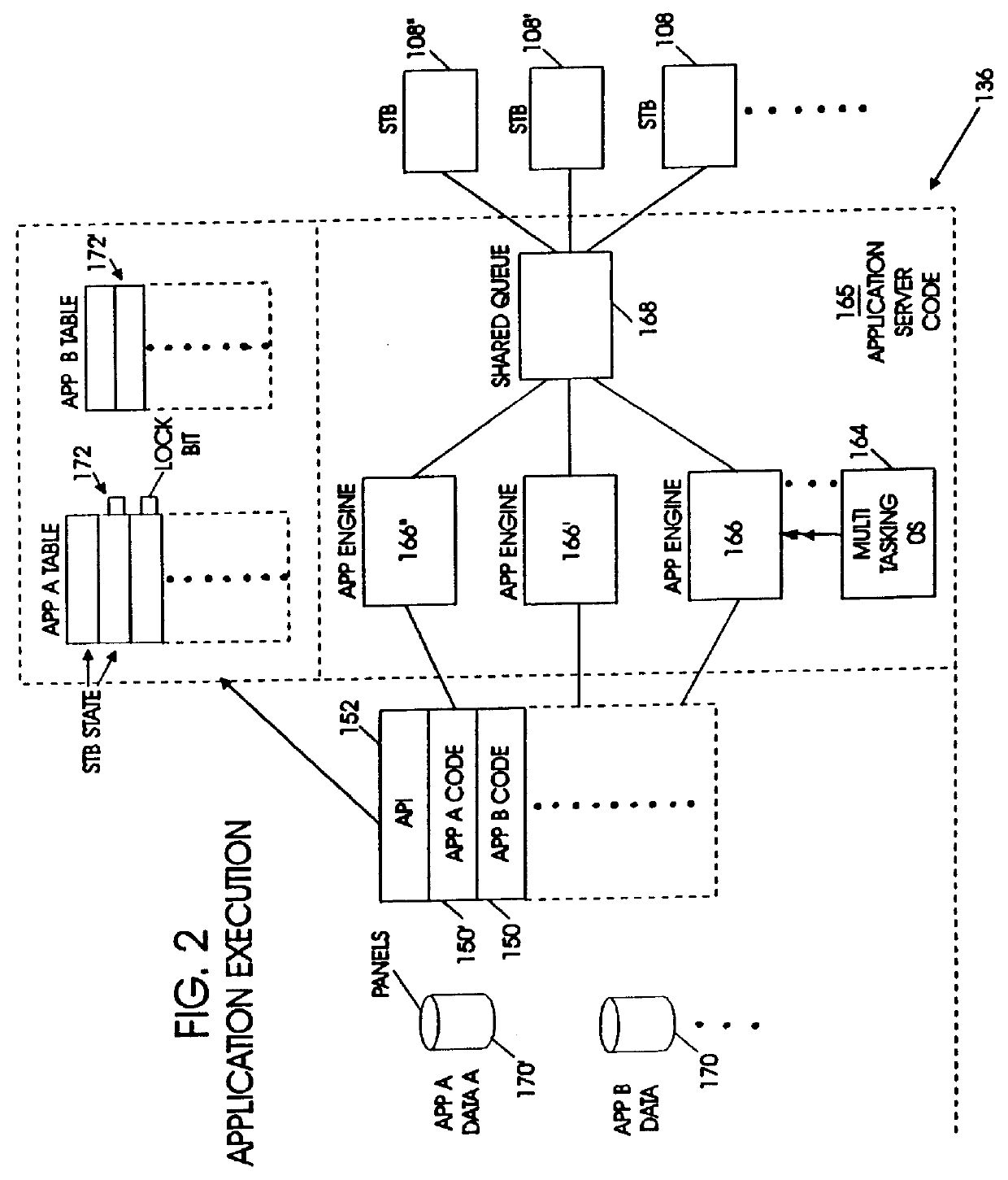
An interactive video system supports functions typically expected with a VCR such as play, pause, fast forward and rewind. A set top box is coupled to a display terminal and a first interface. The set top box includes a memory for storing an operating system in set top enabling codes. A video dial tone network includes a control channel and a data channel coupled to a second interface linked to the first interface. A first gateway controls establishment of a video session between a video server and the display terminal. A second gateway establishes connection between the video server and the set top box over a data channel in response to an input from the first gateway. An application server coupled to the first gateway and the video server contains executable code for transferring video data, video and audio information from the video server to the display terminal. The application server includes a shared queue coupled to a plurality of application engines and set top boxes and includes program code for multi-tasking operation. The code operates the application engines in response to application tables to provide video transmission as a panel object indicative of the state of set top boxes in a video session.
Owner:IBM CORP
Electric control and supply system
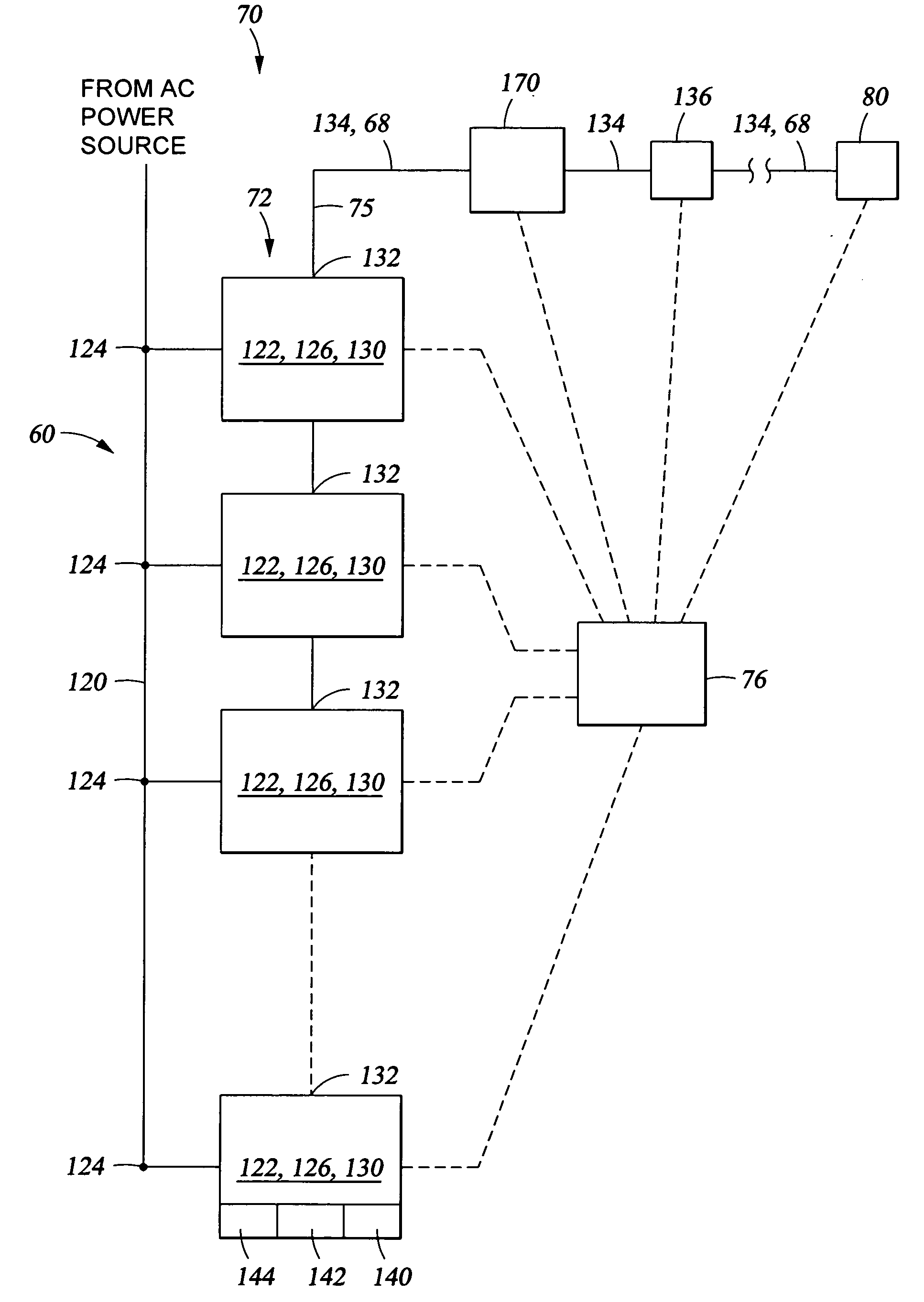
InactiveUS20050029476A1Rapid responseEliminate the problemOperating means/releasing devices for valvesAc-dc conversion without reversalVoltage converterElectricity
A system supplies electrical power to a remote electrical device. The system includes an AC / DC voltage converter coupled to the AC voltage source for converting an AC voltage from the AC voltage source to a high DC voltage output at a first location. The AC / DC voltage converter comprises a plurality of AC / DC voltage converter components which, on the input side thereof, are connected in parallel with the AC voltage source and which, on the output side thereof, are connected serially to an electric conductor. The electric conductor extends to a plurality of voltage converters at a remote location having inputs connected serially to the electrical conductor and having outputs providing an appropriate voltage to the electrical device, the plurality of voltage converters converting the high DC voltage to either a lower DC voltage or an alternating voyage without a cooling mechanism that would otherwise be needed when less than the plurality of voltage converters are implemented to convert the high DC voltage to the lower DC voltage or alternating voltage.
Owner:ONESUBSEA IP UK LTD
System and method of automated gunshot emergency response system
InactiveUS20160232774A1Reduce the impactAvoiding obtrusiveCharacter and pattern recognitionBurglar alarmMessage passingCommunication device
A threat sensing system is provided including, in some aspects, a plurality of threat sensing devices distributed throughout a school or facility, with each of the threat sensing devices comprising one or more acoustic sensors, one or more gas sensors, and a communication circuit or communication device configured to output sensor data to a system gateway. The system gateway is configured to receive and process the sensor data output from the threat sensing devices and determine whether the processed sensor data corresponds to one of a predetermined plurality of known threats (e.g., a gunshot) and, if so, to communicate the existence of the threat, the processed sensor information, and / or predetermined messaging information to one or more recipient devices (e.g., first responders, dispatchers).
Owner:ONALERT GUARDIAN SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com