Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
427 results about "Anomalous behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
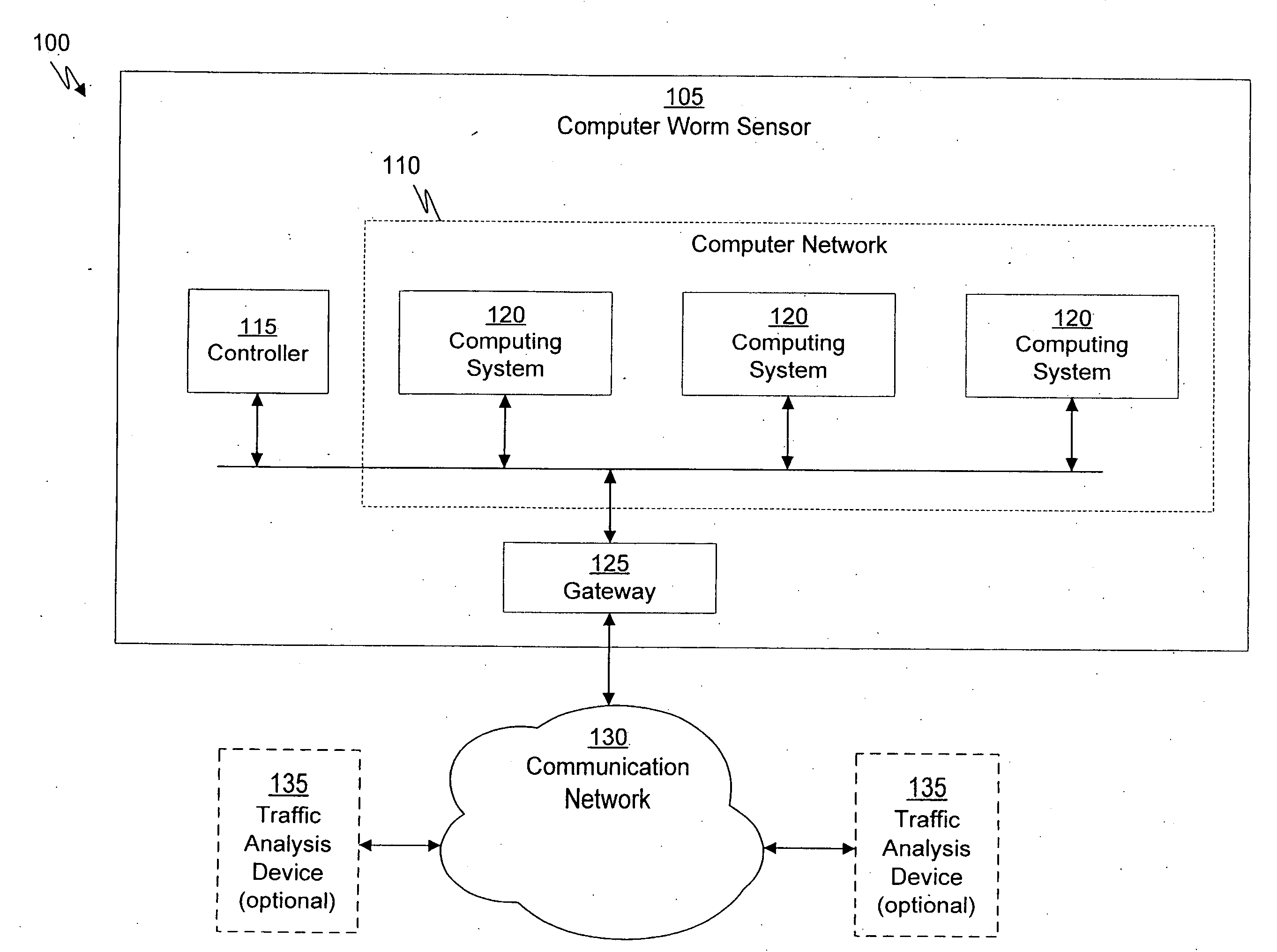
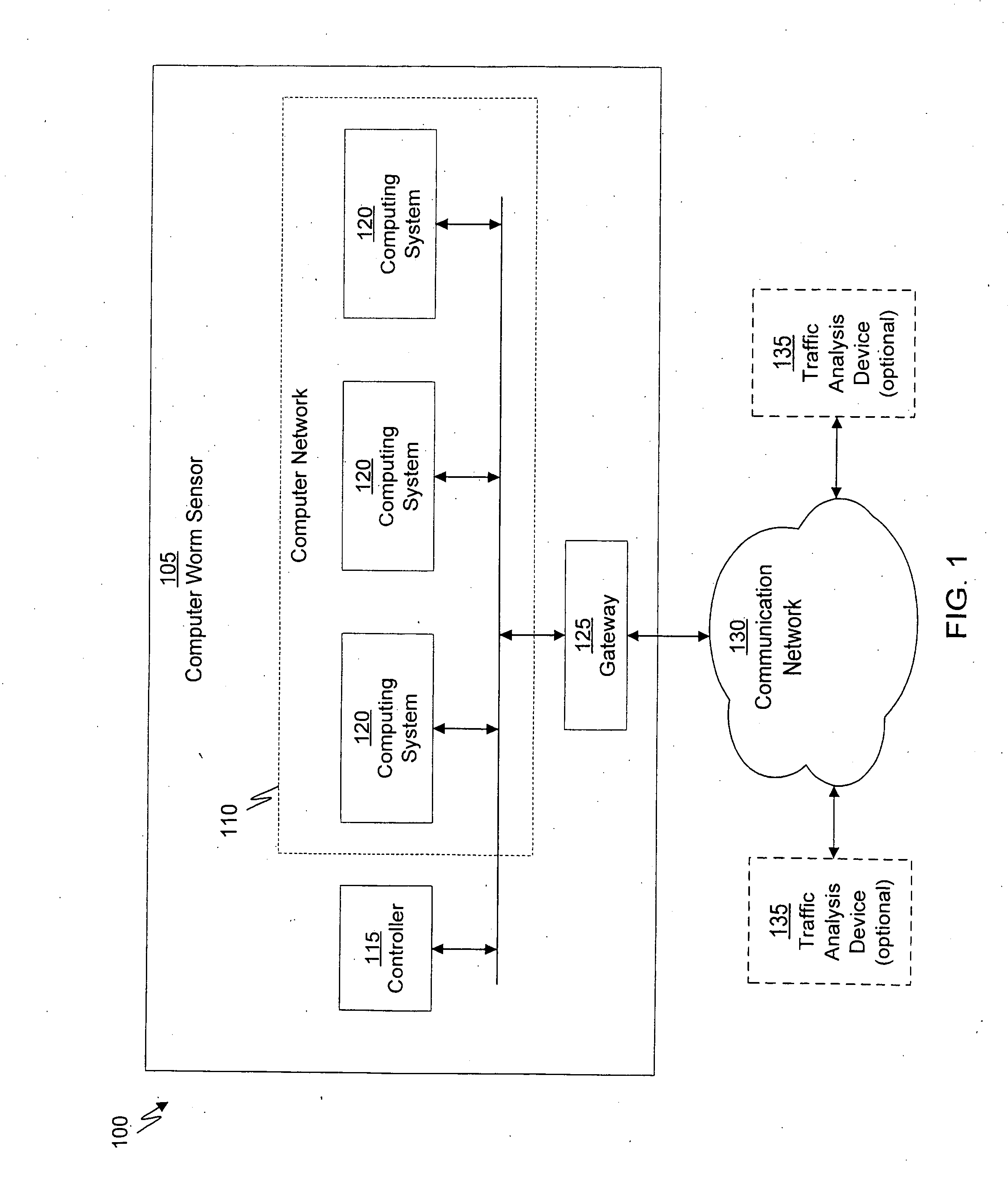
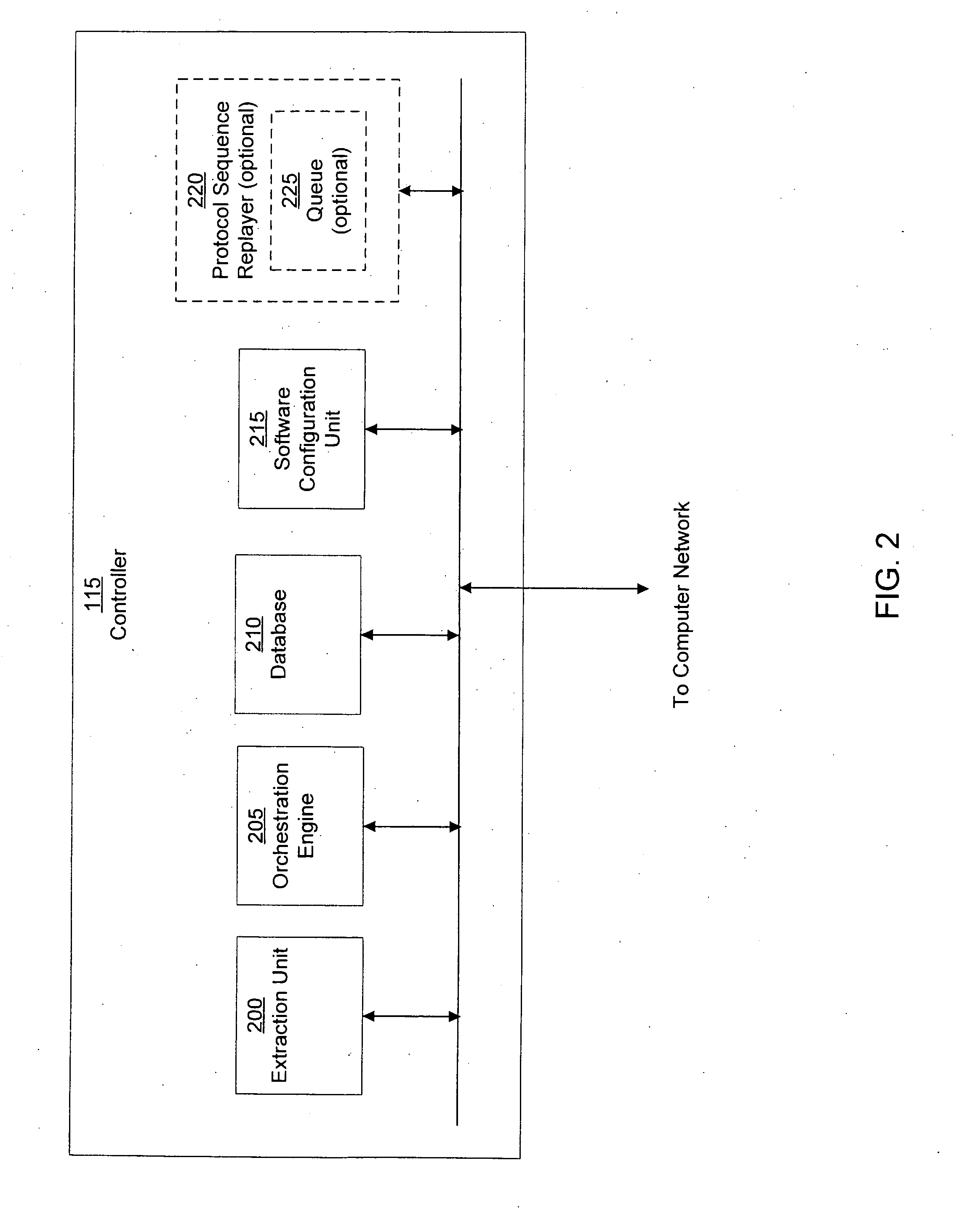
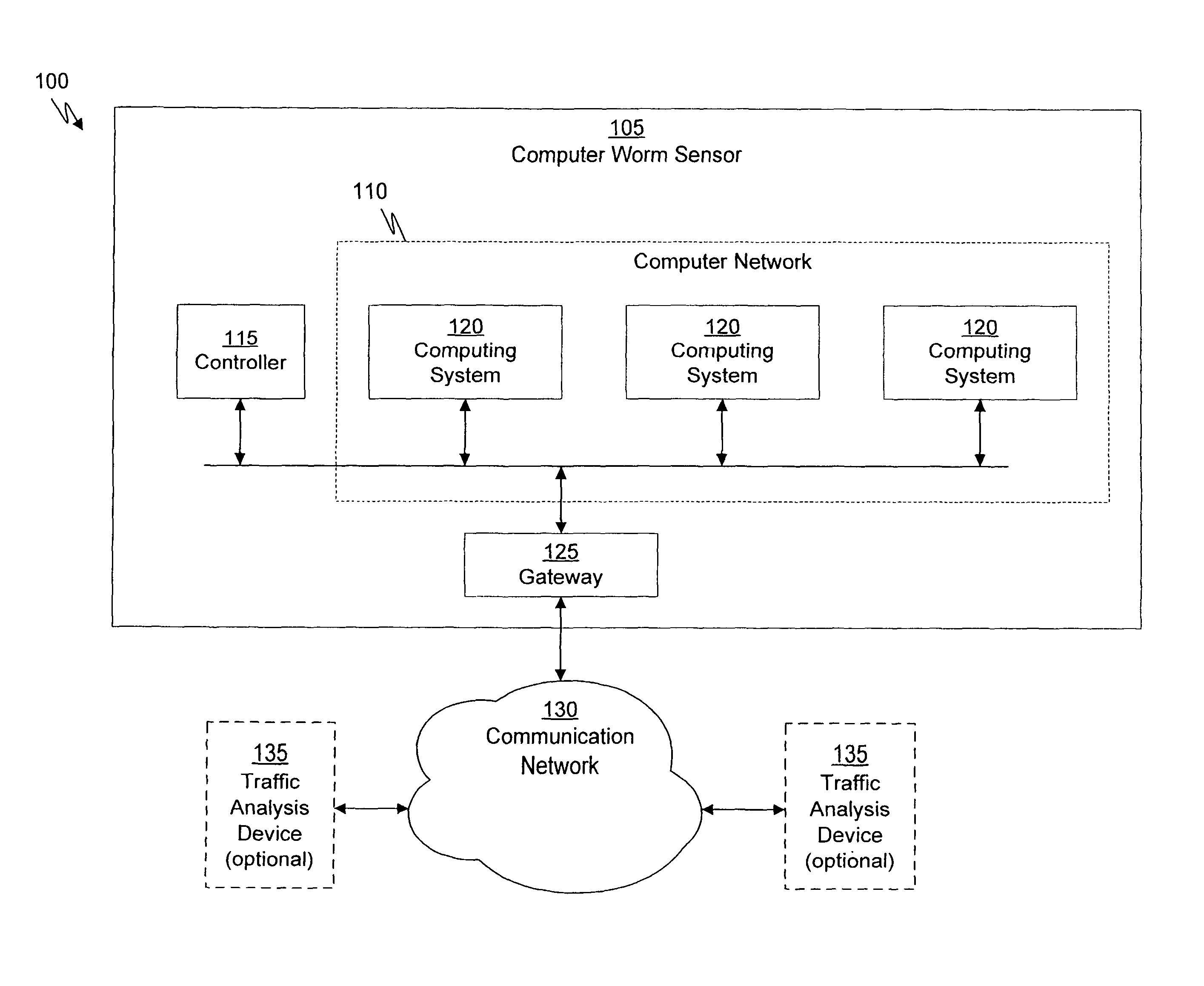
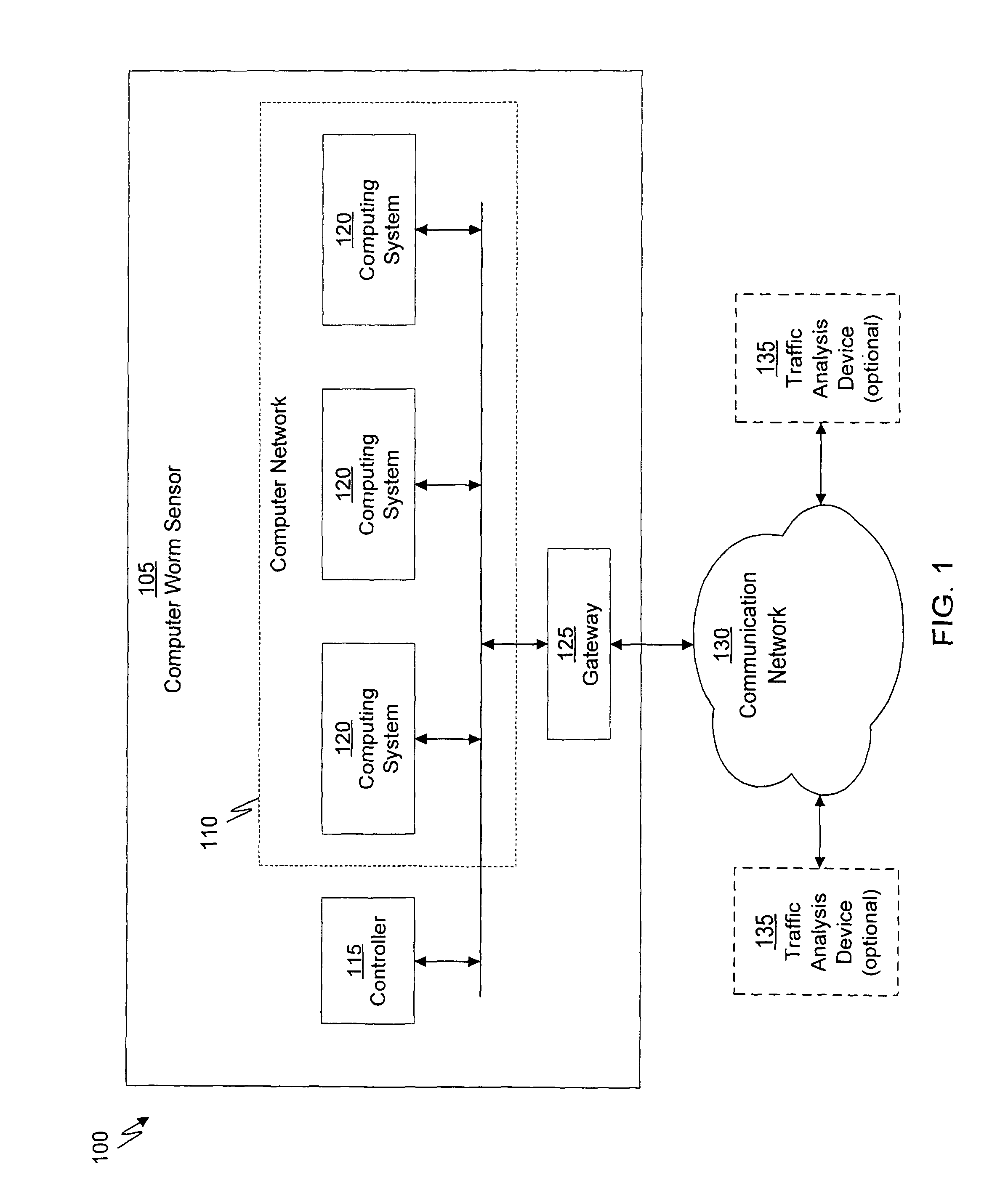
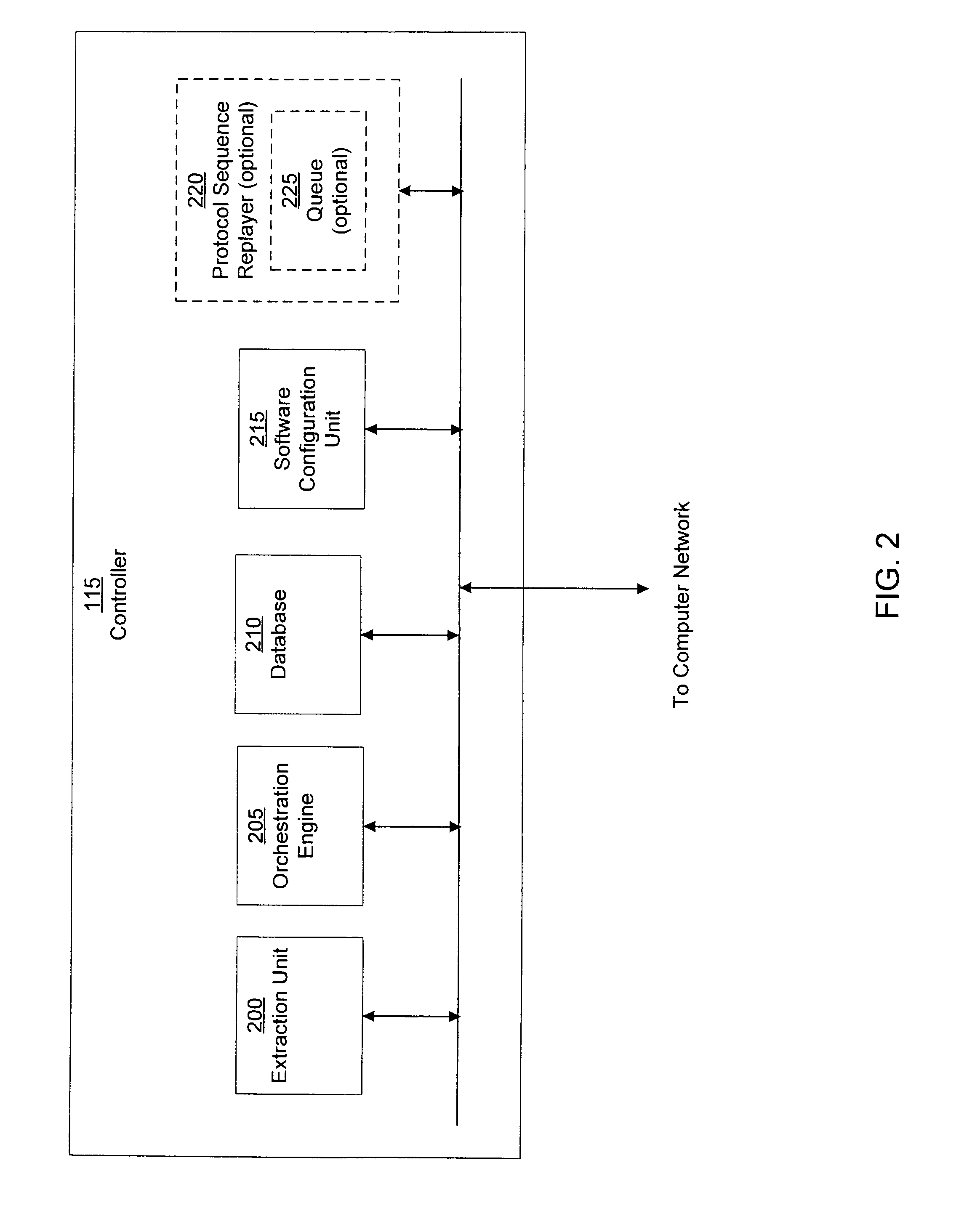
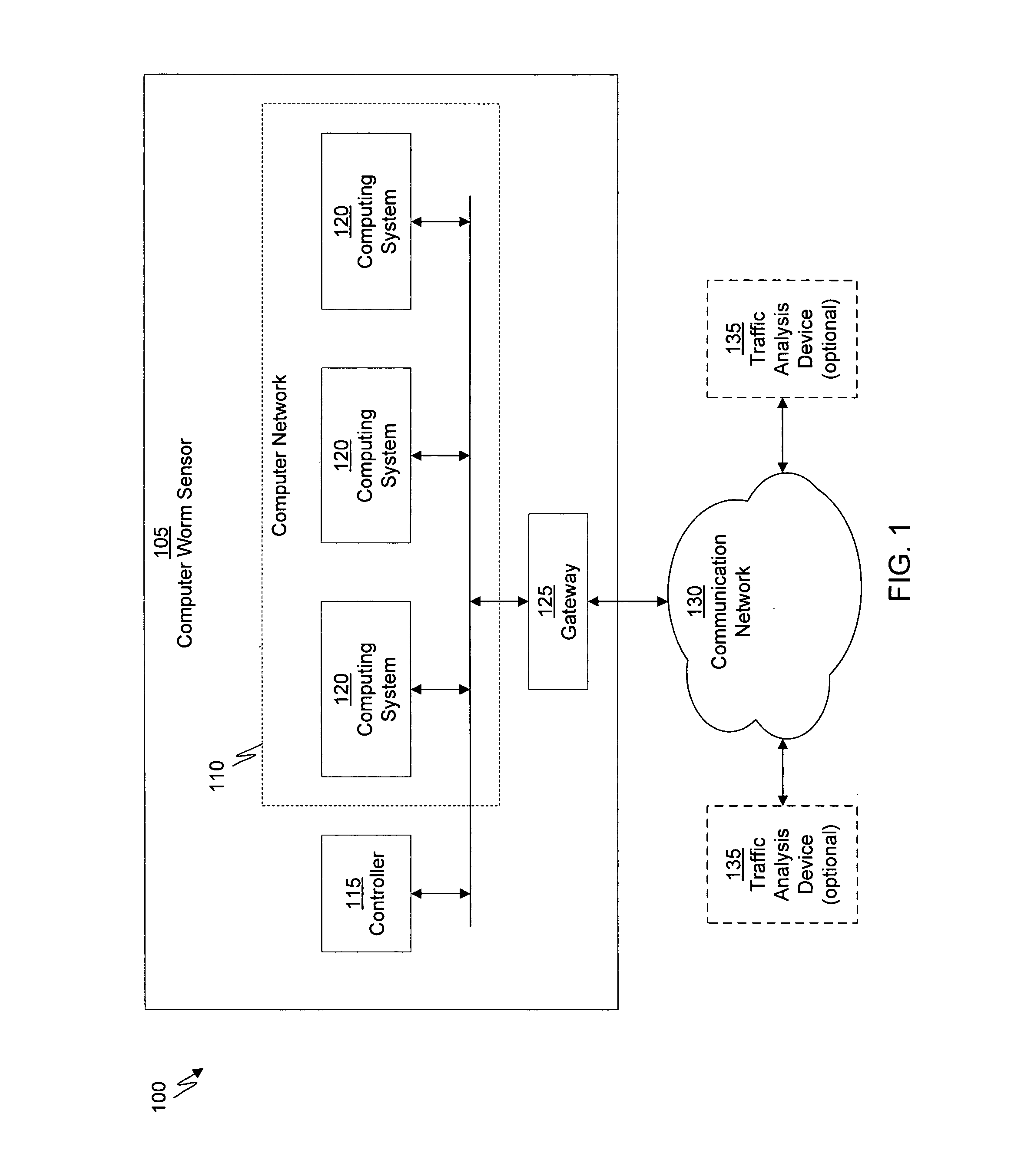
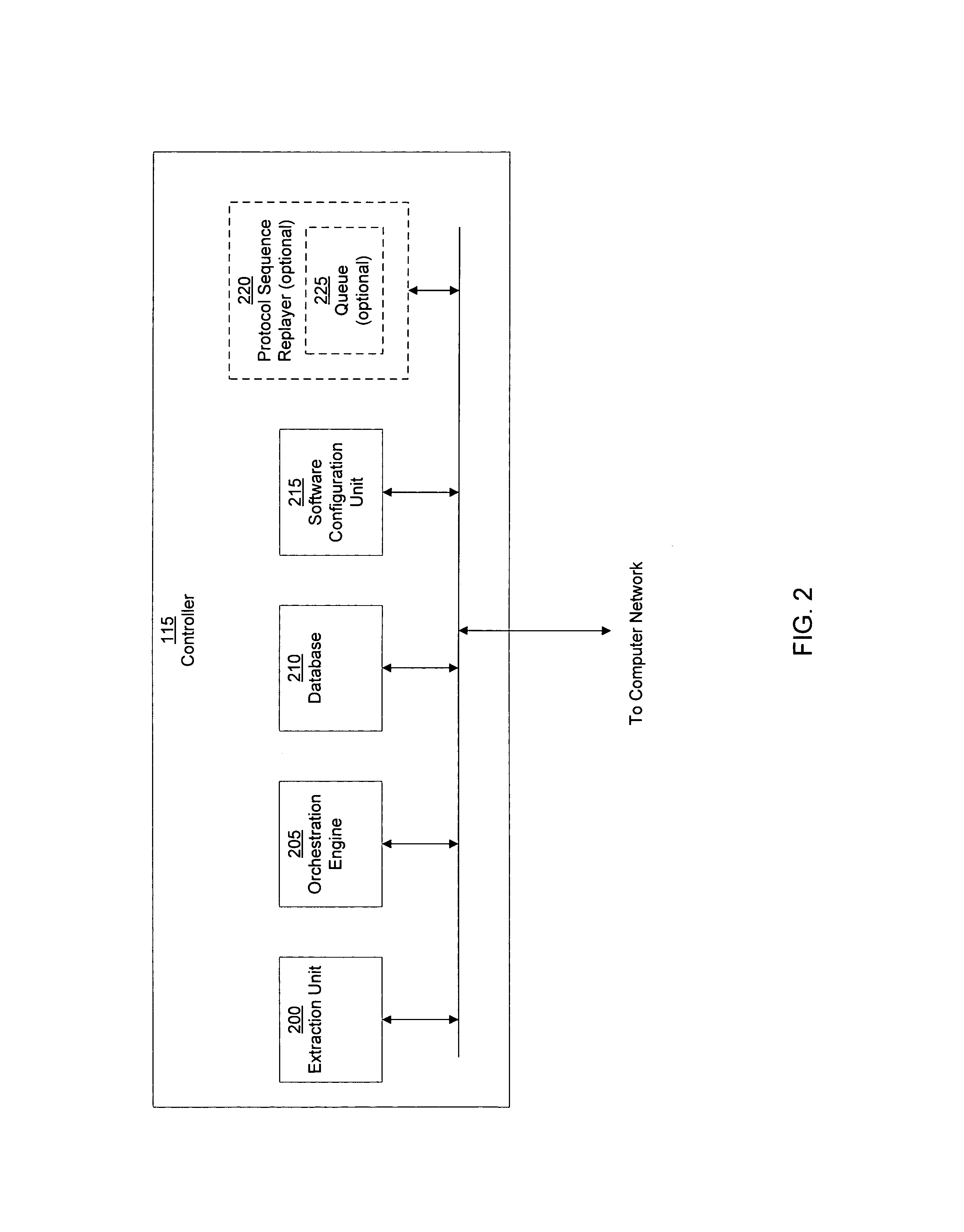
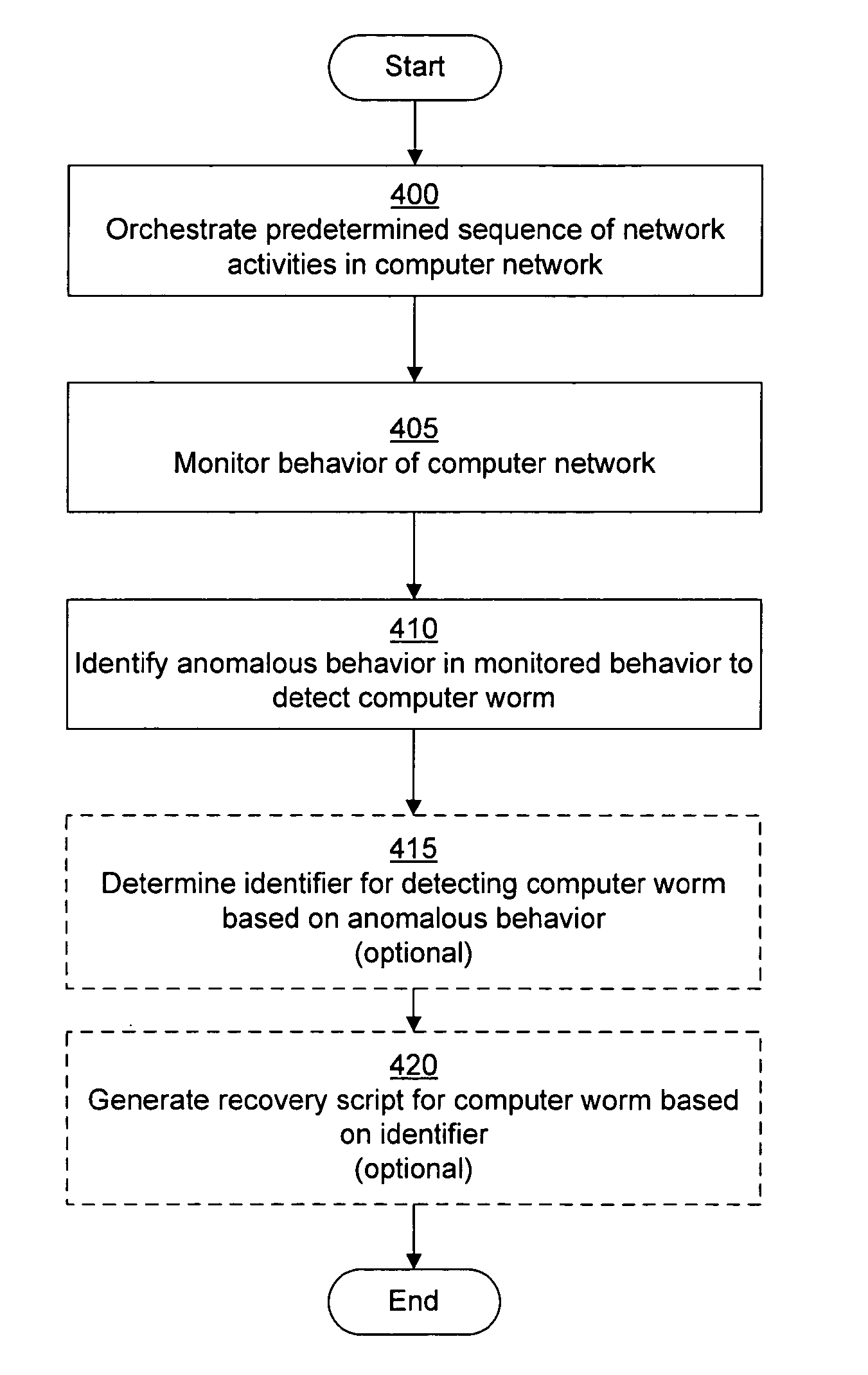
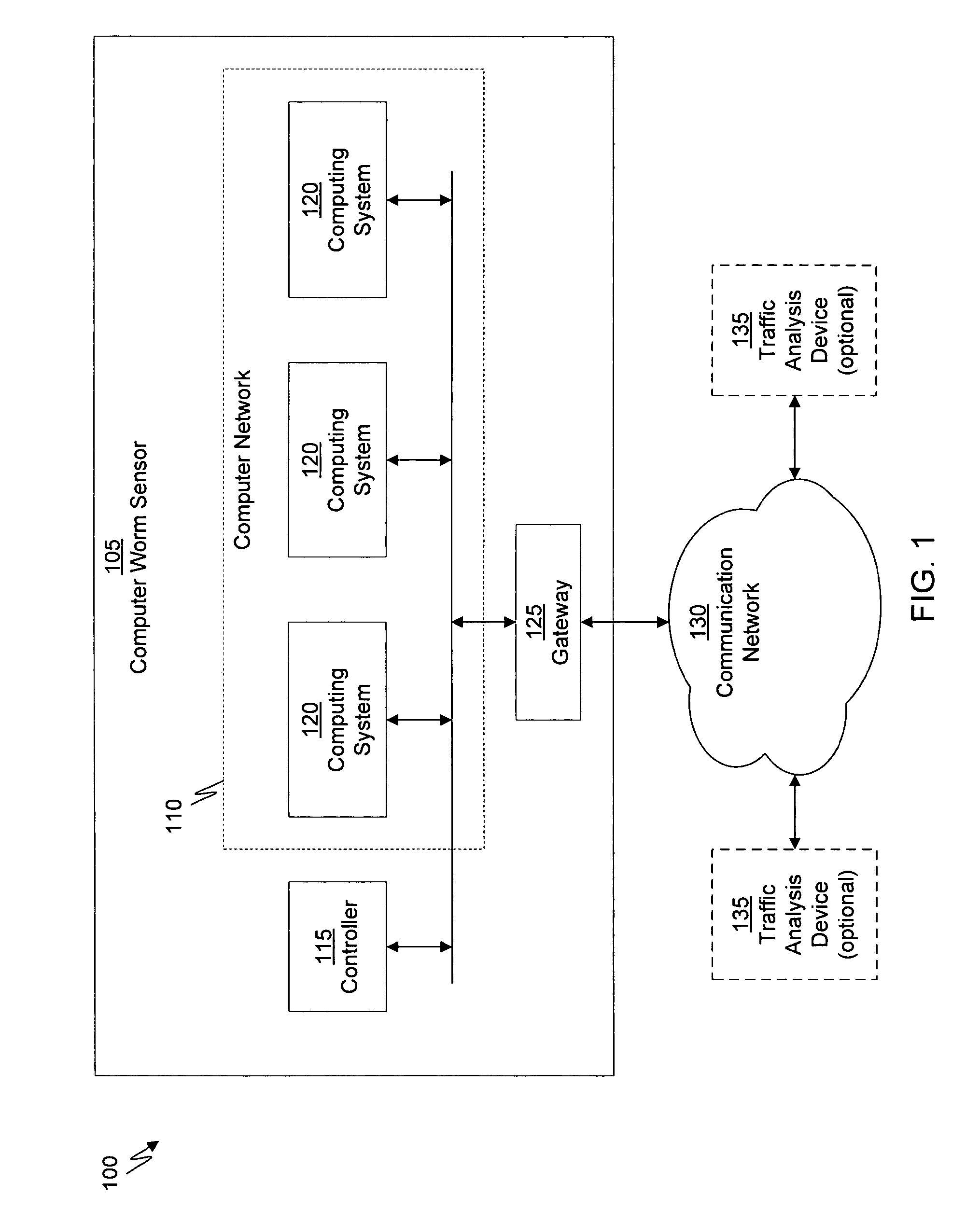
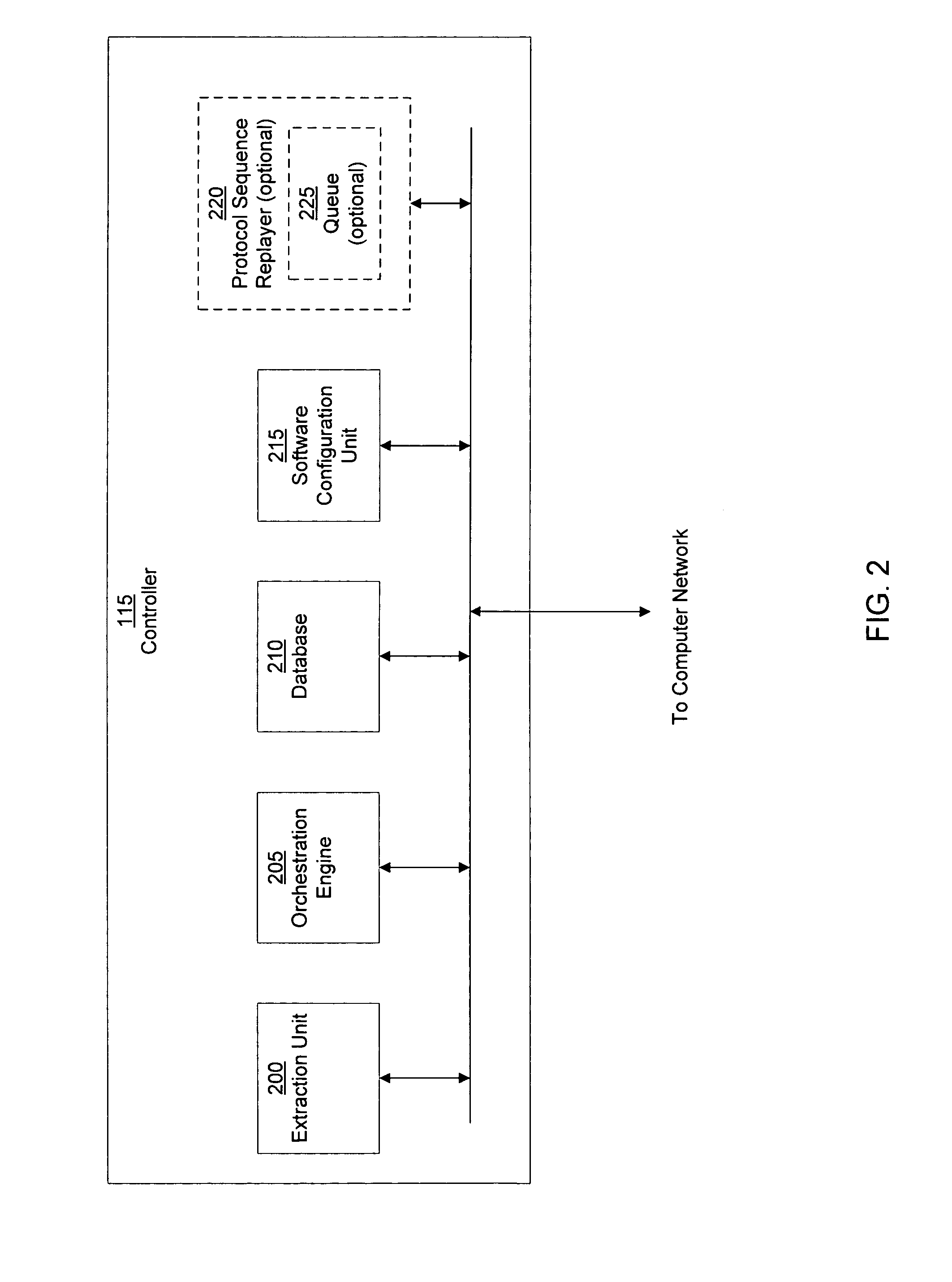
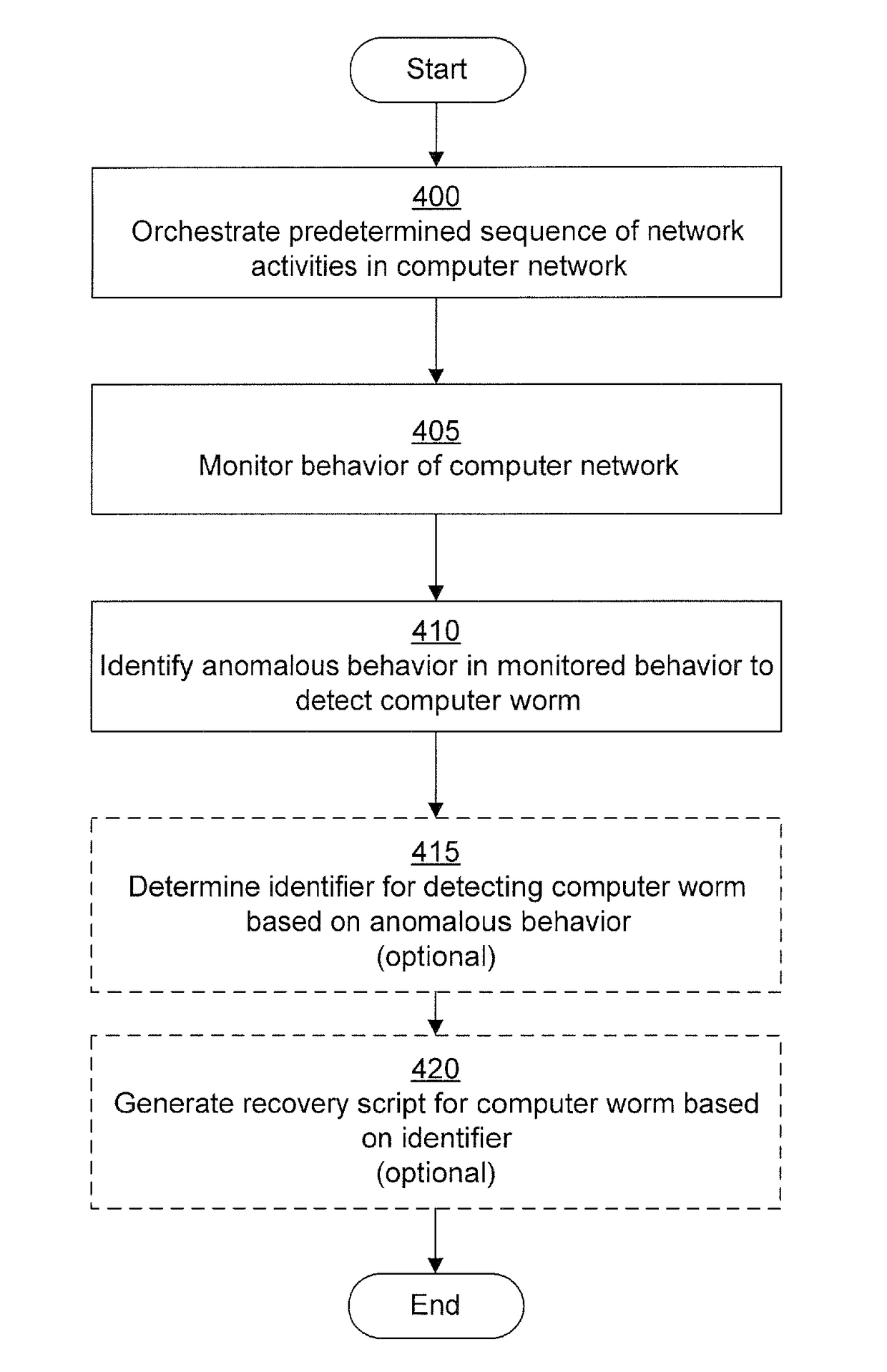
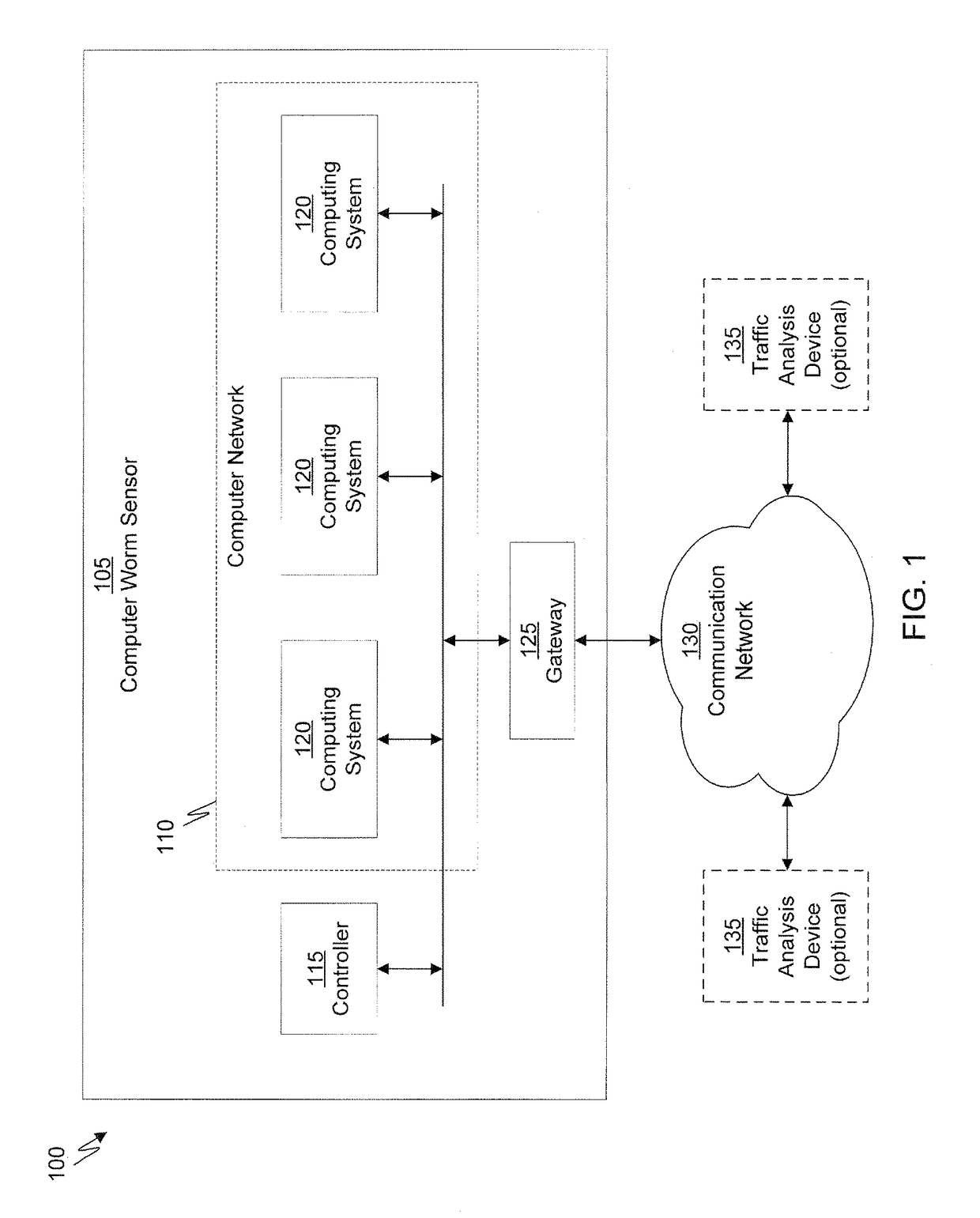
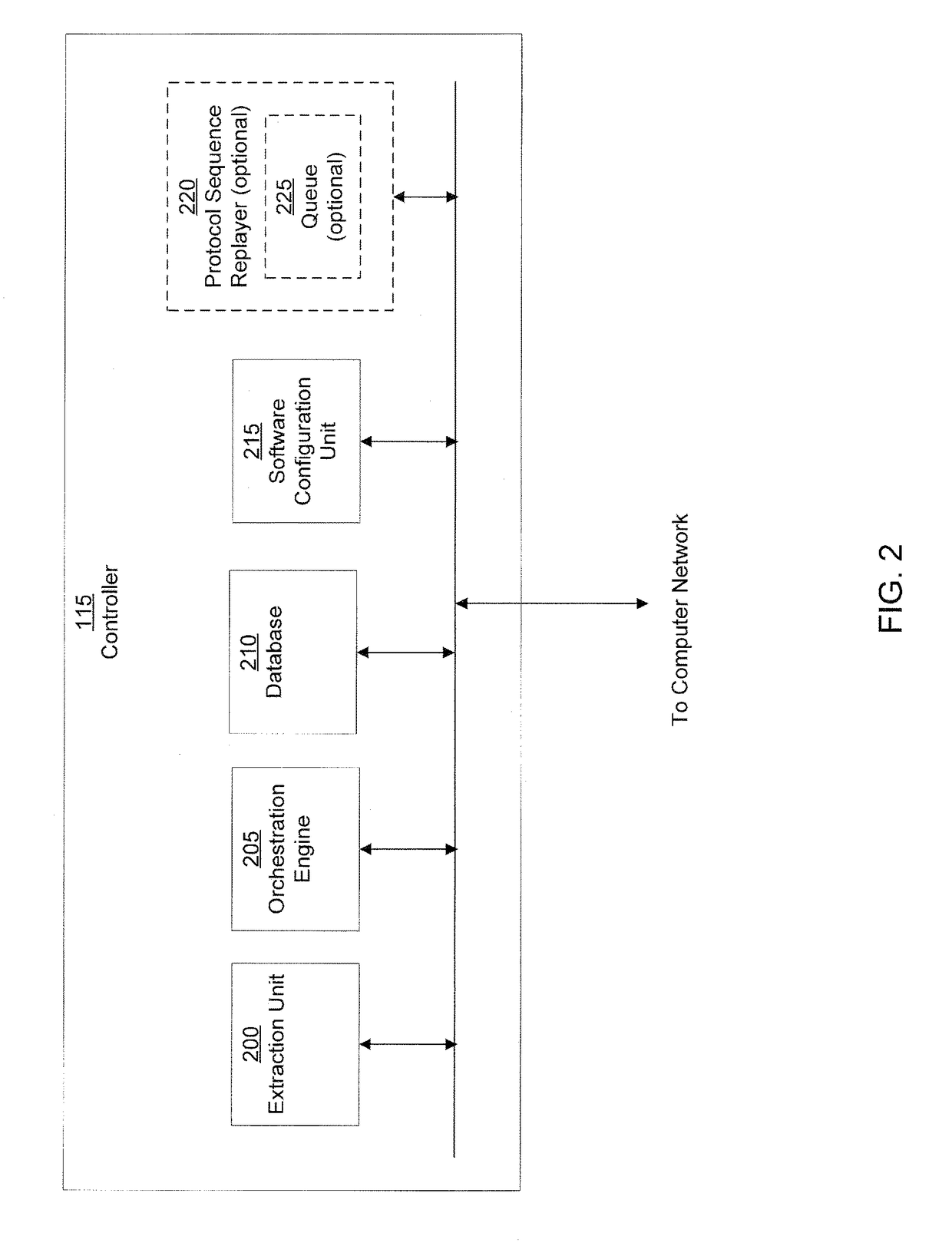
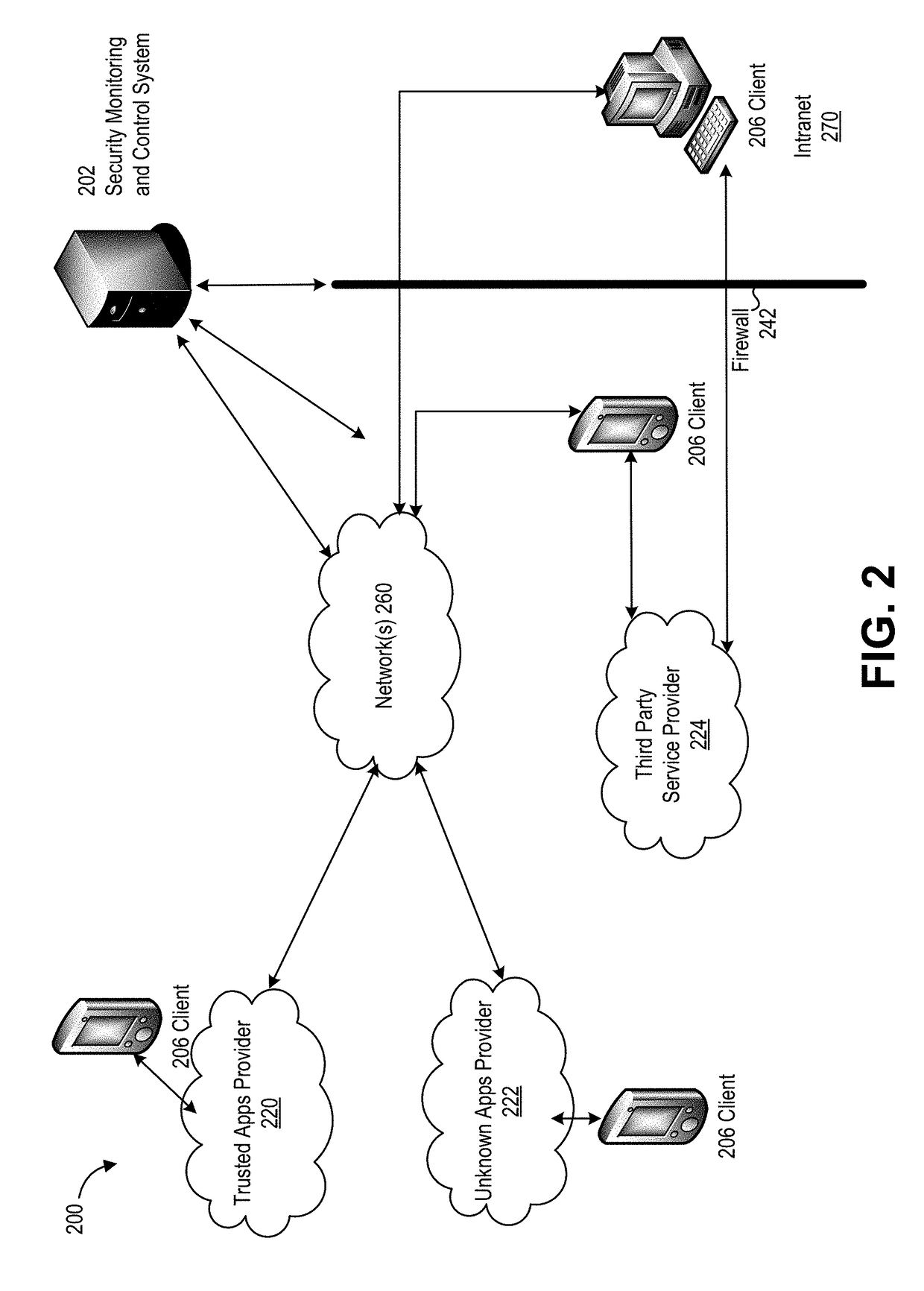
System and method of containing computer worms
ActiveUS20110099633A1Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of containing computer worms
ActiveUS8549638B2Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
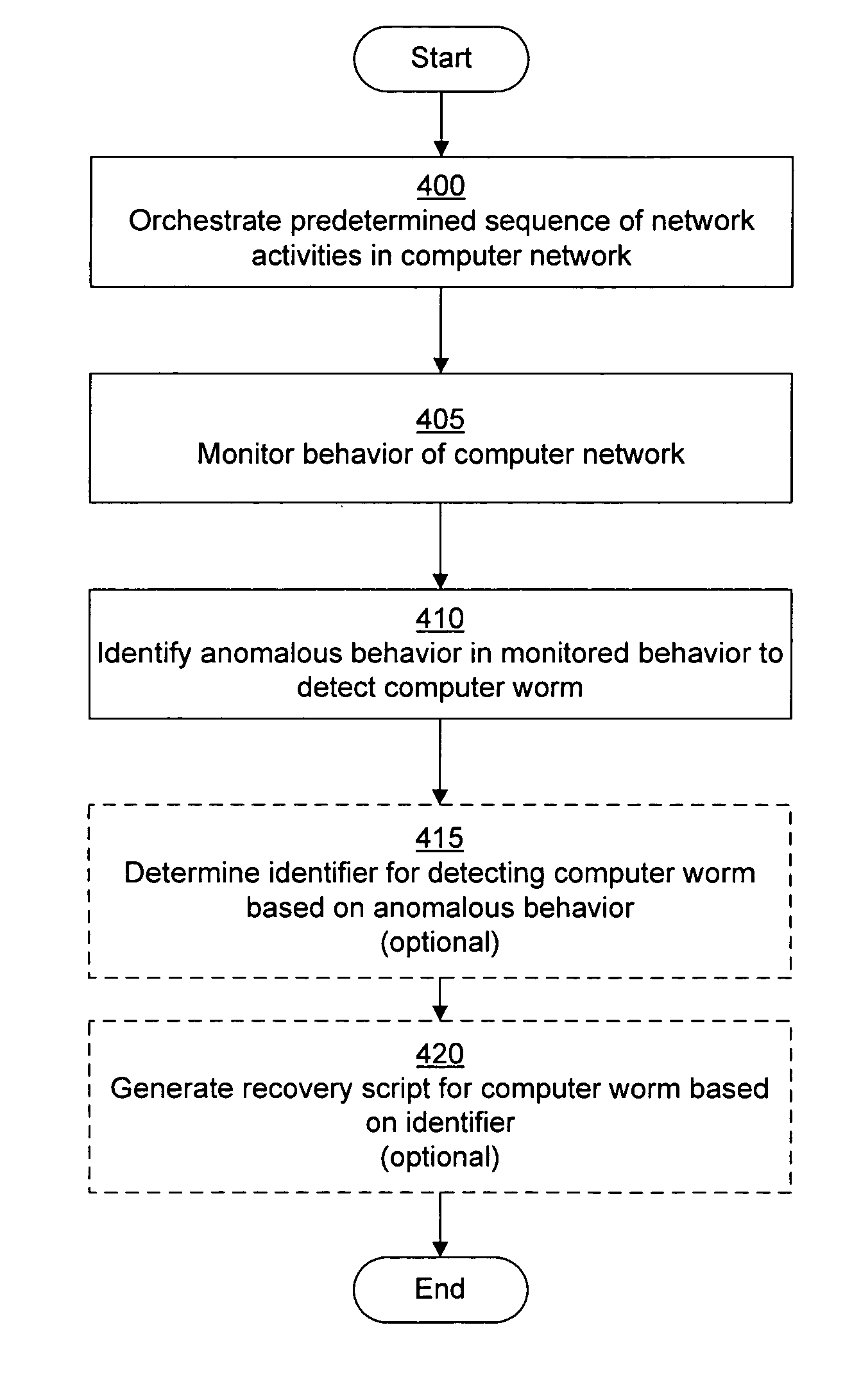
System and method of detecting computer worms
A computer worm detection system orchestrates a sequence of network activities in a computer network and monitors the computer network to identify an anomalous behavior of the computer network. The computer worm detection system then determines whether the anomalous behavior is caused by the computer worm and can determine an identifier for detecting the computer worm based on the anomalous behavior. The computer worm detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of detecting time-delayed malicious traffic
A system for detecting a computer worm comprises a traffic analysis device in communication with a network device. The traffic analysis device can analyze network traffic received over a communication network and duplicate at least select network communications within the network traffic having characteristics associated with one or more computer worms. The network device comprises a controller in communication with one or more virtual machines that are configured to receive the duplicated network communications from the traffic analysis device. The network device may (i) monitor a behavior of a first virtual machine of the one or more virtual machines in response to processing of the duplicated network communications within the first virtual machine, (ii) identify an anomalous behavior as an unexpected occurrence in the monitored behavior, and (iii) determine, based on the identified anomalous behavior, the presence of the one or more computer worms in the duplicated network communications.
Owner:FIREEYE SECURITY HLDG US LLC
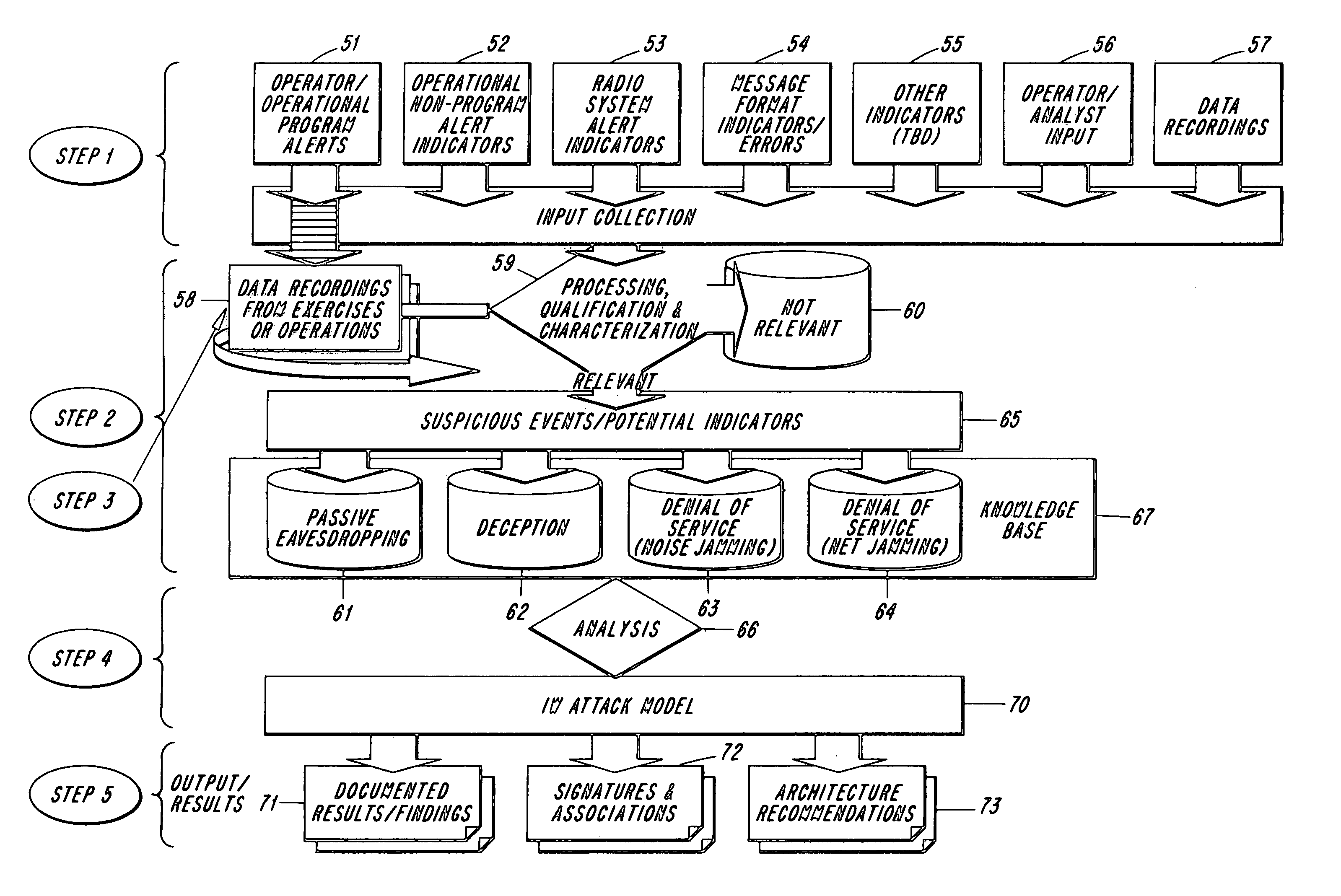
Methodology for the detection of intrusion into radio frequency (RF) based networks including tactical data links and the tactical internet
InactiveUS7068998B2Solid comprehensionEnhance information resiliencyUnauthorised/fraudulent call preventionMemory loss protectionInformation analysisAttack model
The present invention provides strategies for detecting intrusions in wireless environments, and the strategies are based on innovative applications of information analysis as well as other information correlating techniques. The key to detecting intrusions in a RF based environment is to understand the normal spectrum of behavior so that deviations can be detected and analyzed. For a wireless communications grid, this process requires empirical knowledge about how the radios work together as components of the information grid, and how this grid network is managed. Once normal behavior has been characterized, anomalous behavior can be identified. Potential intrusions into the wireless network can be analyzed and an attack model can be created. The attack model can be utilized as the basis for initiating appropriate adaptive responses.
Owner:NORTHROP GRUMMAN SYST CORP
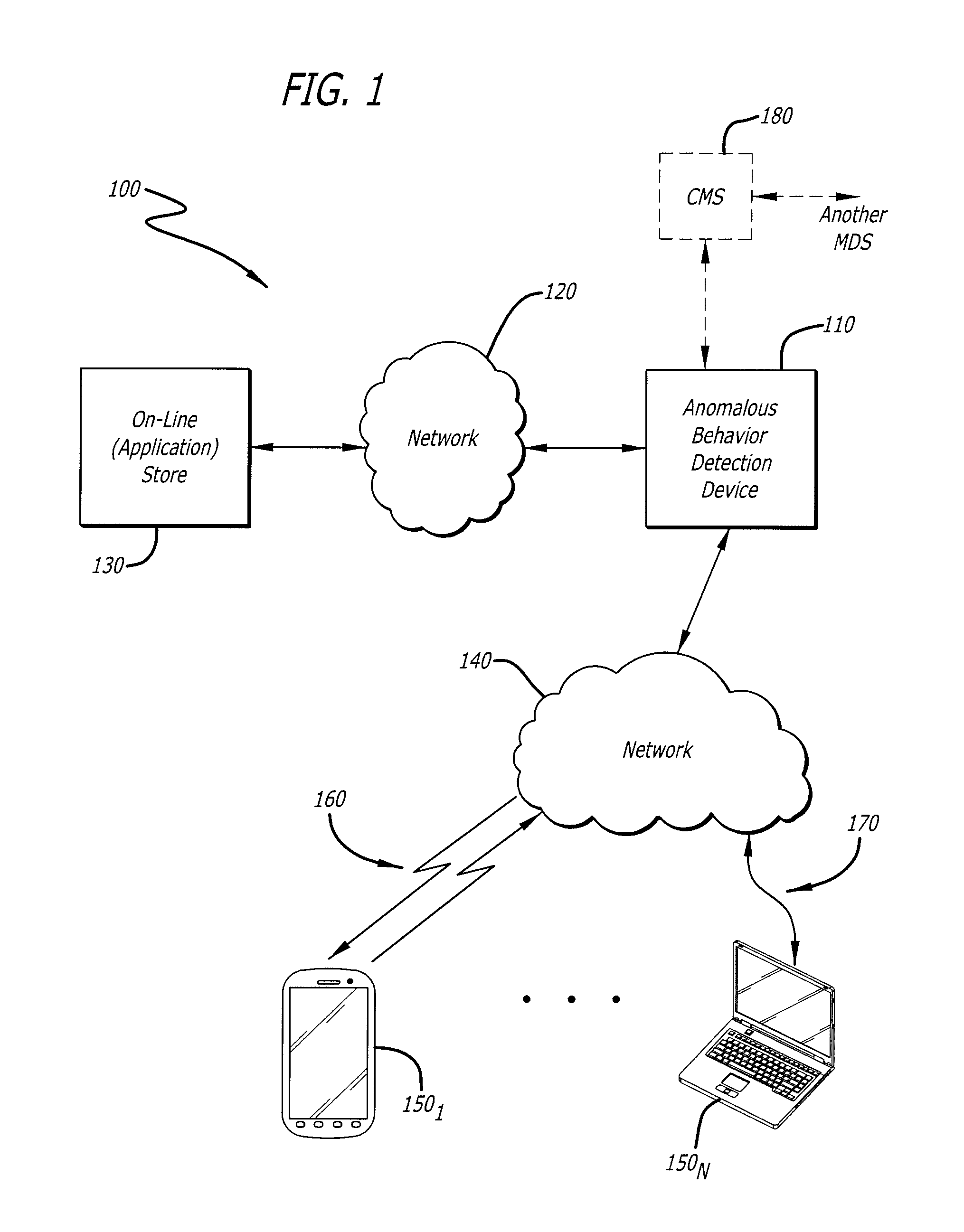
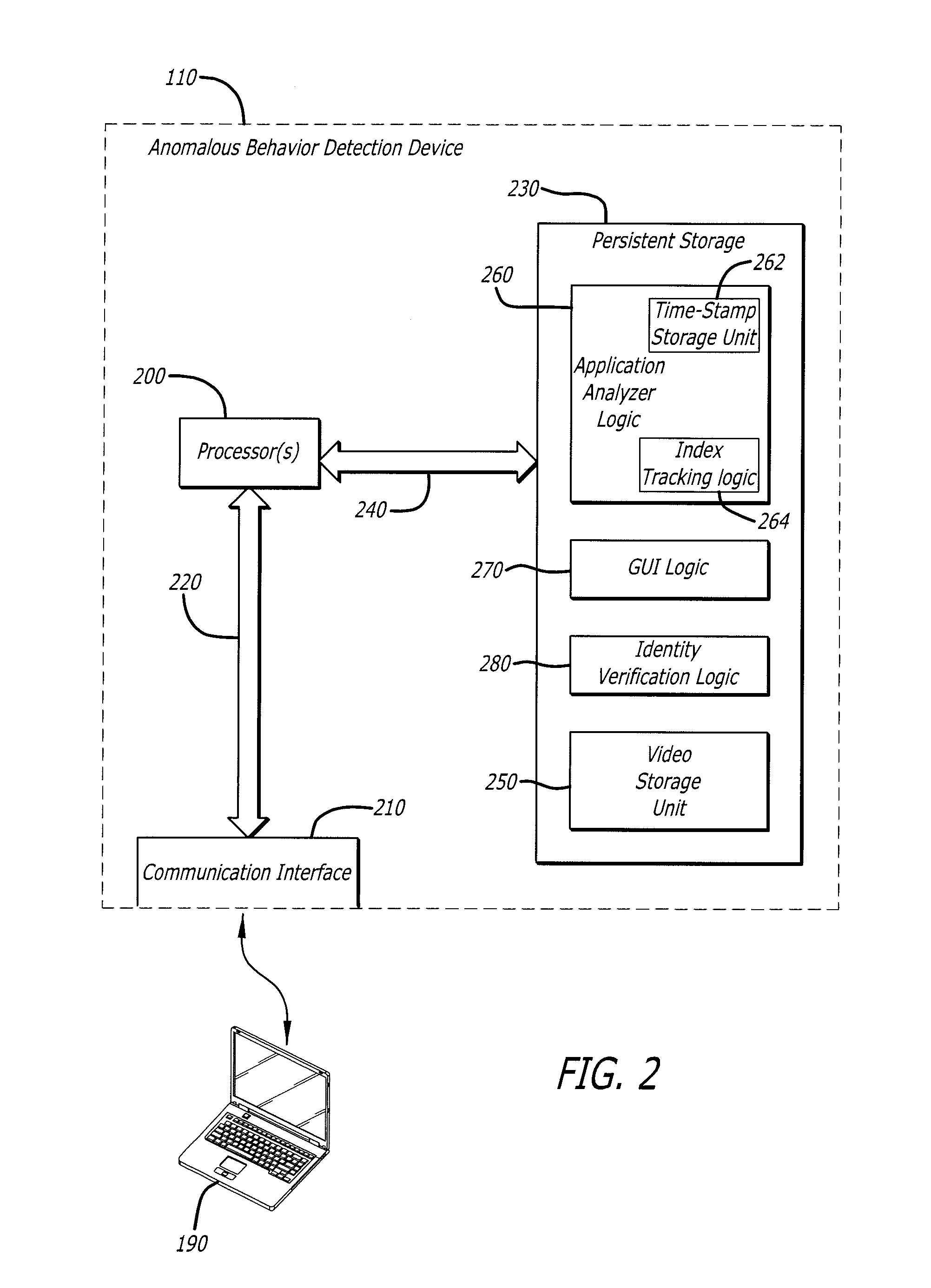
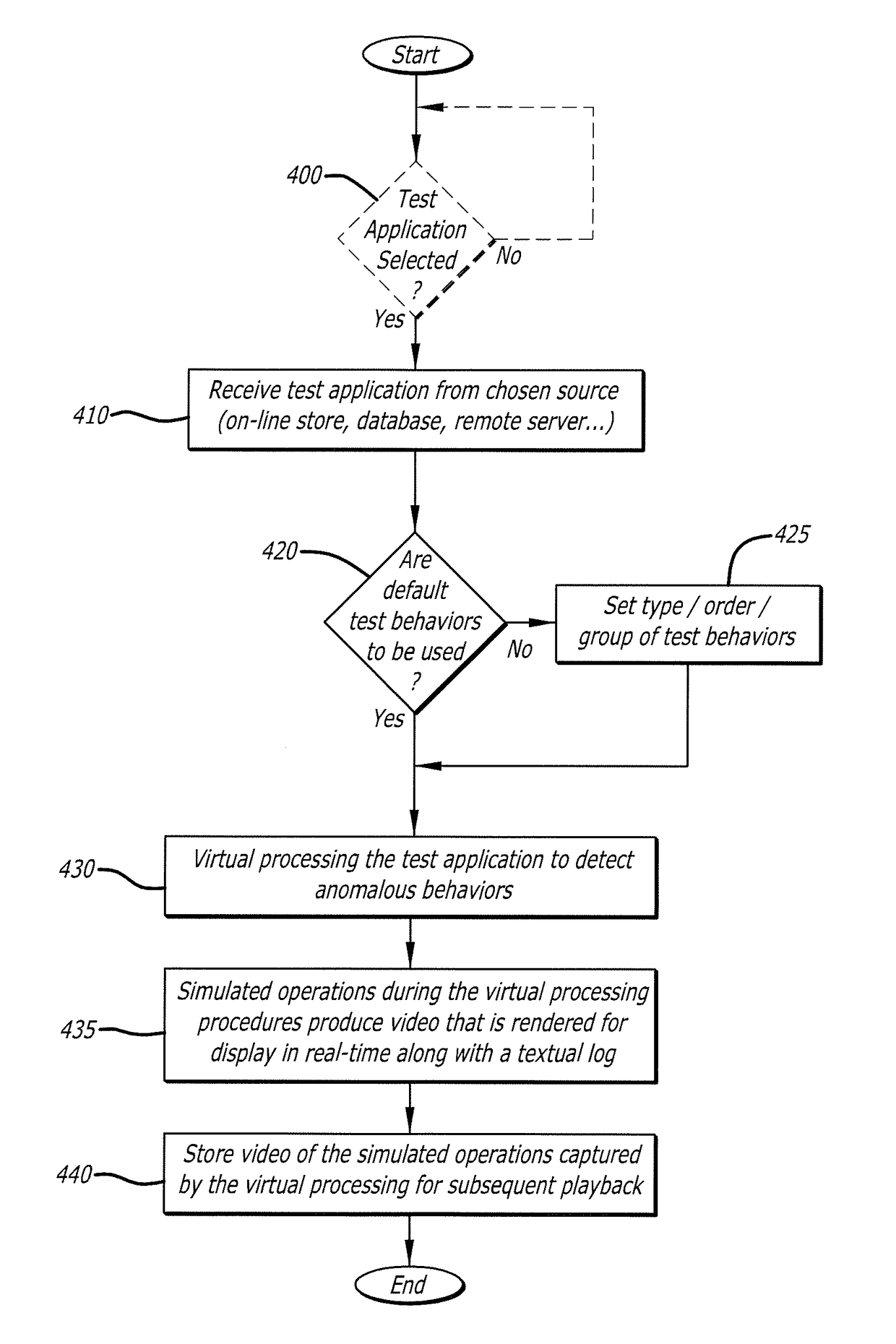
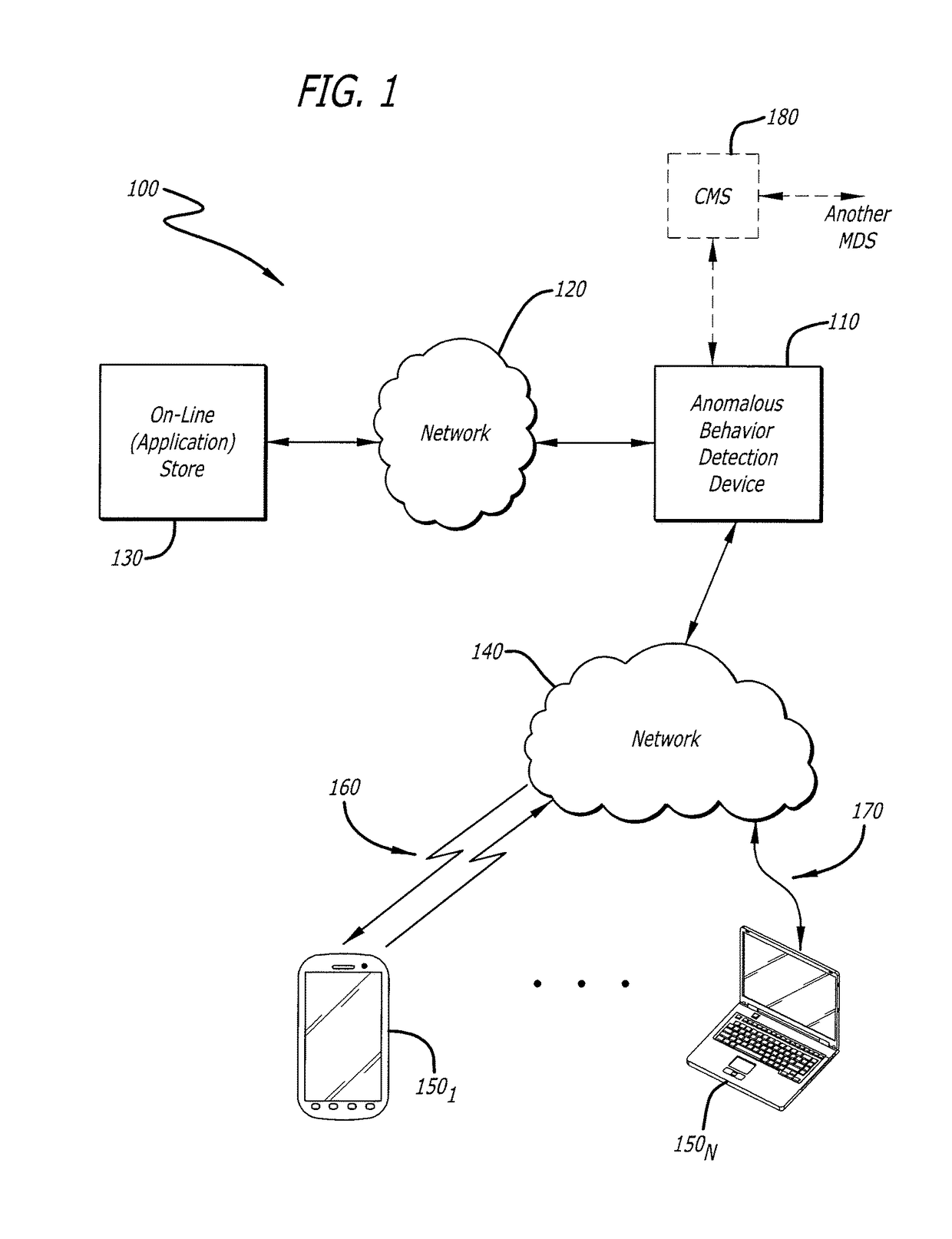
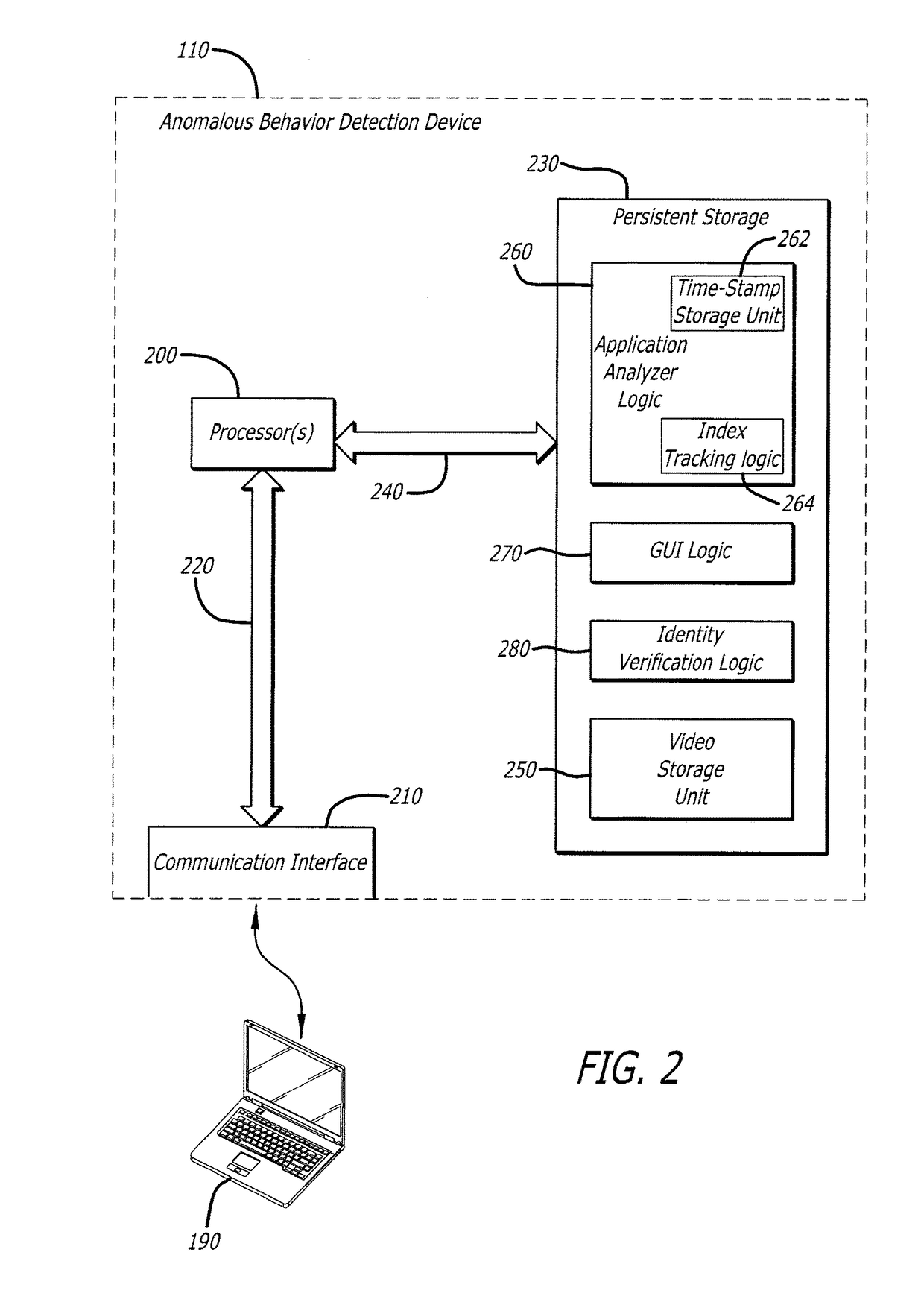
User interface with real-time visual playback along with synchronous textual analysis log display and event/time index for anomalous behavior detection in applications
ActiveUS9195829B1Television system detailsColor signal processing circuitsAnomalous behaviorApplication software
According to one embodiment, a method comprises conducting an analysis for anomalous behavior on application software and generating a video of a display output produced by the application software. The video is to be displayed on an electronic device contemporaneously with display of one or more events detected by the analysis being performed on the application software.
Owner:FIREEYE SECURITY HLDG US LLC
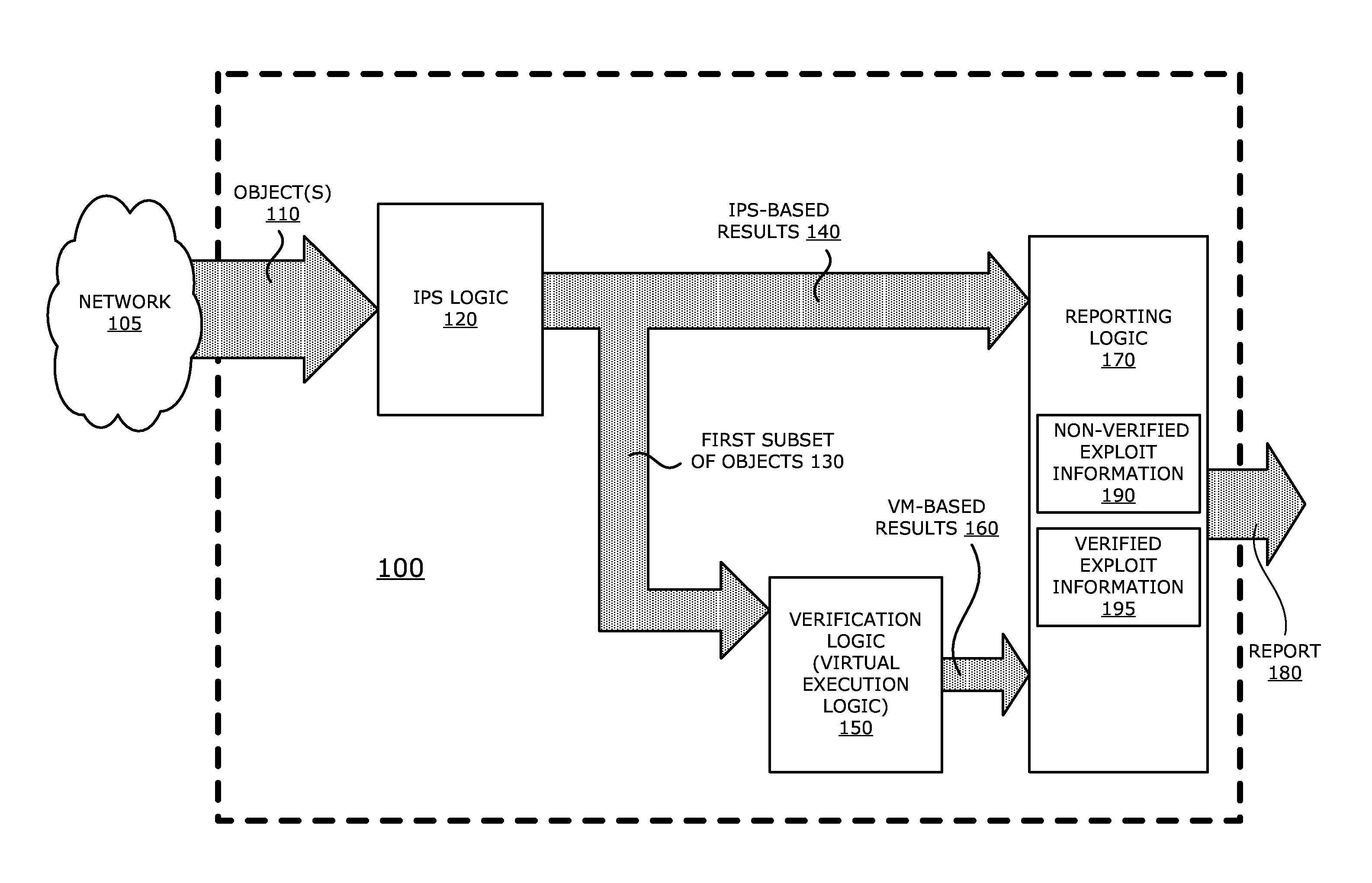
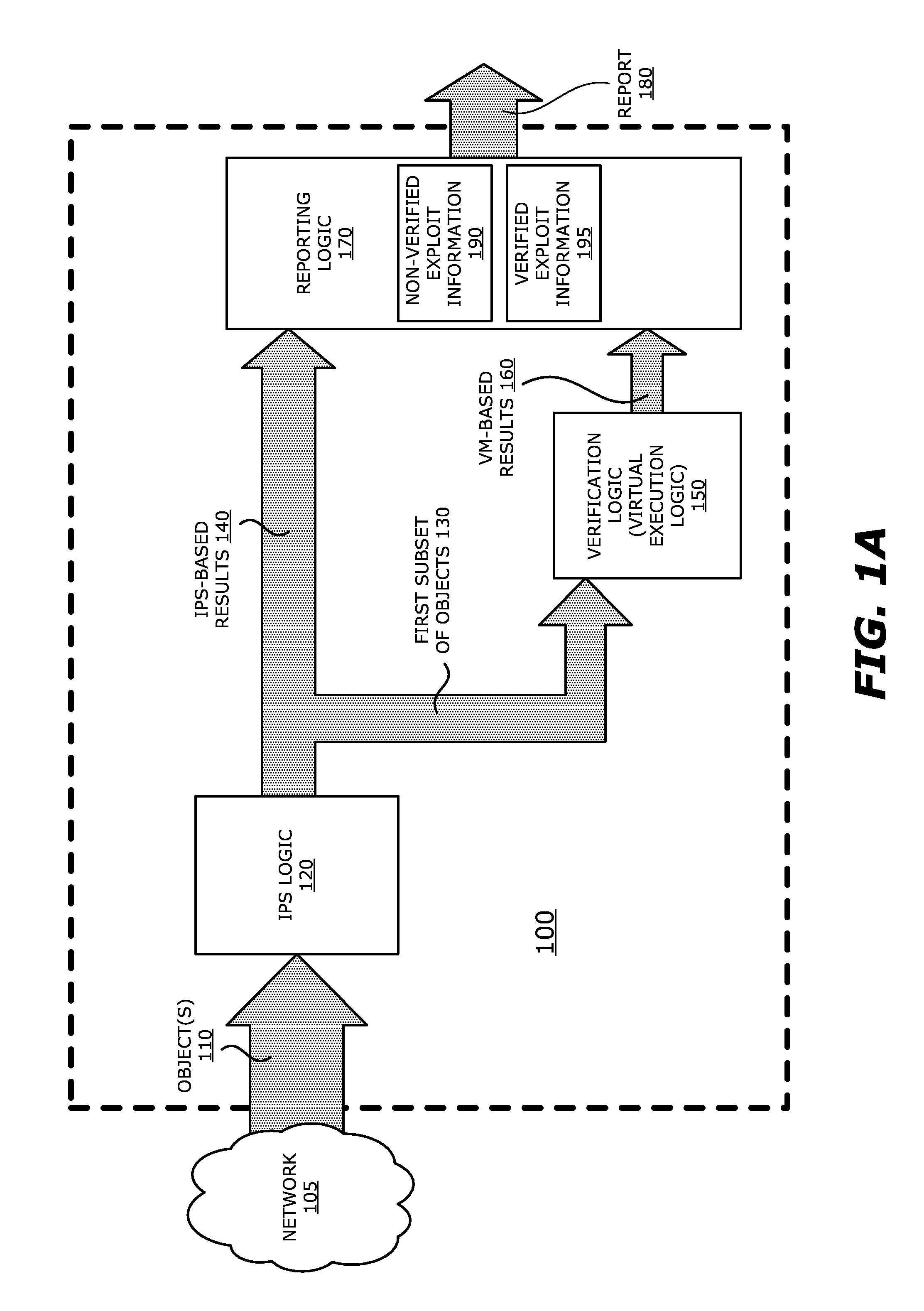
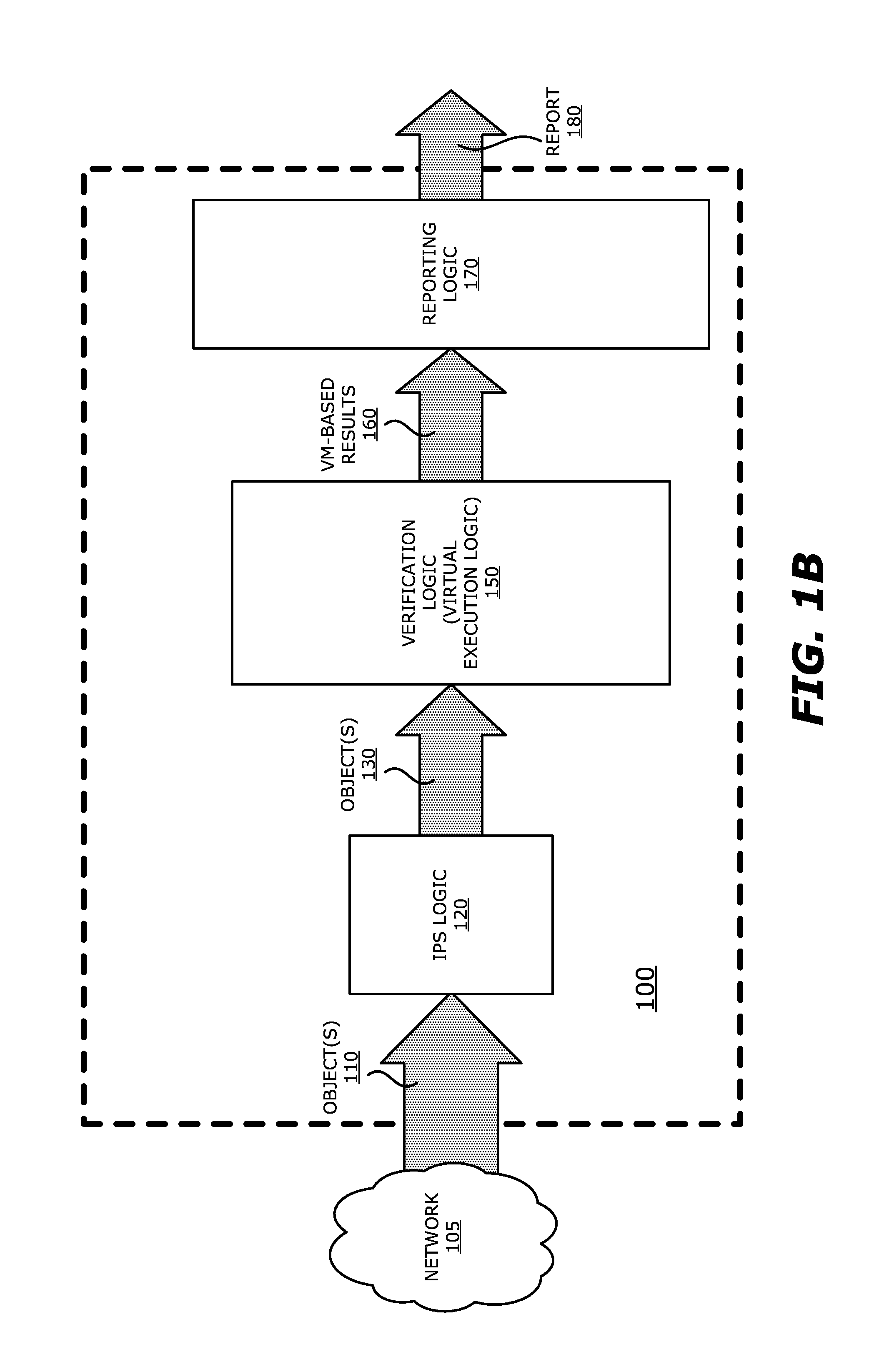
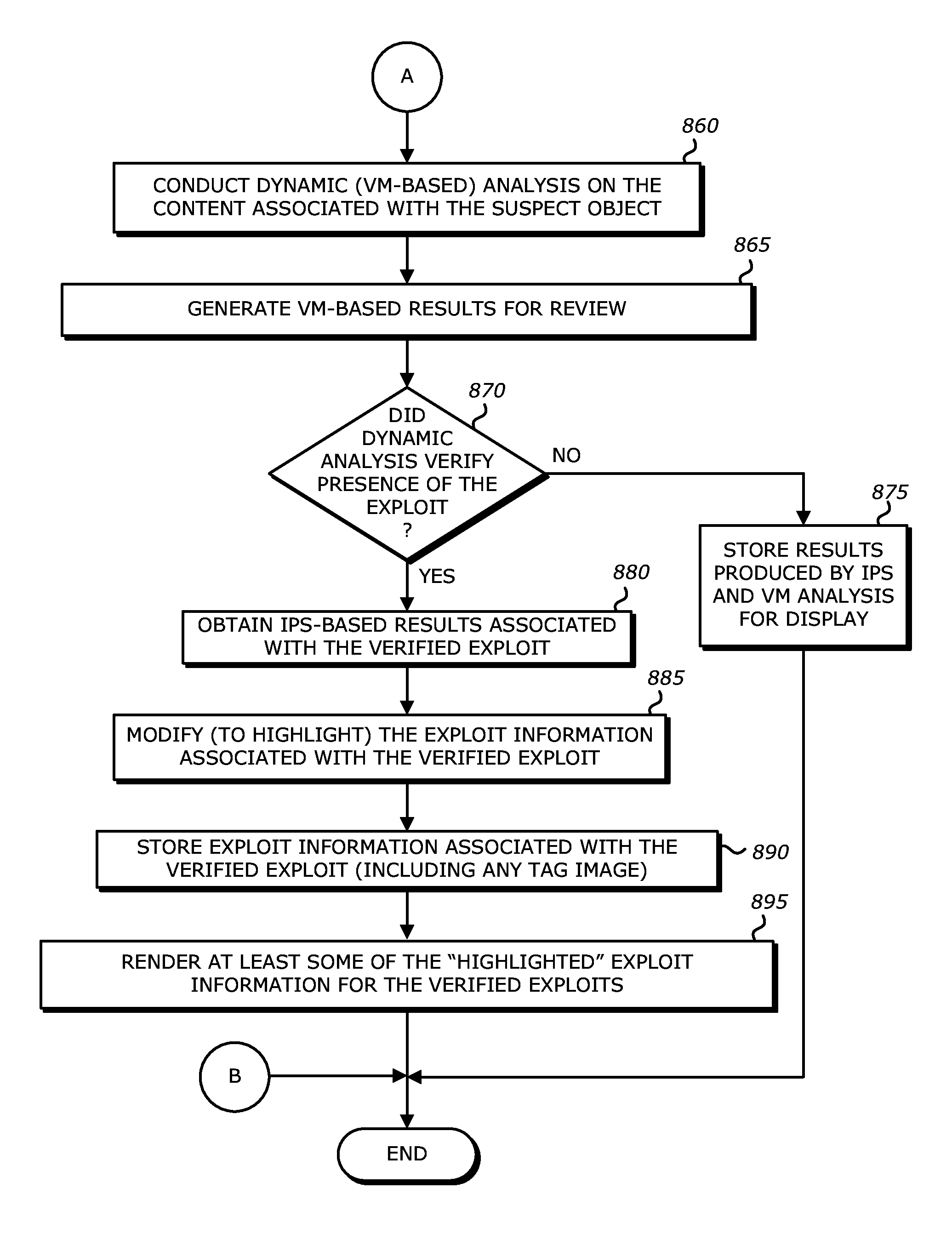
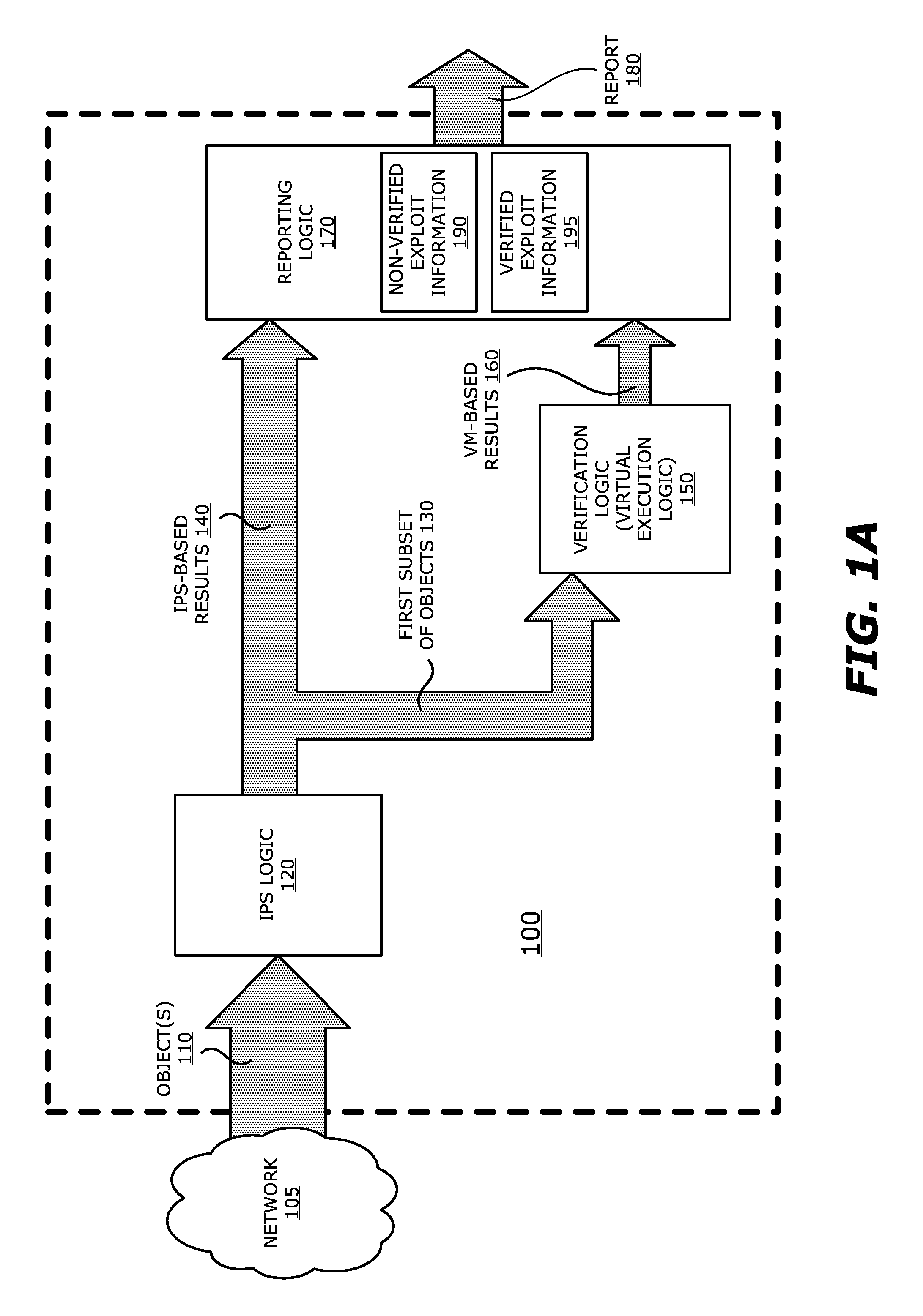
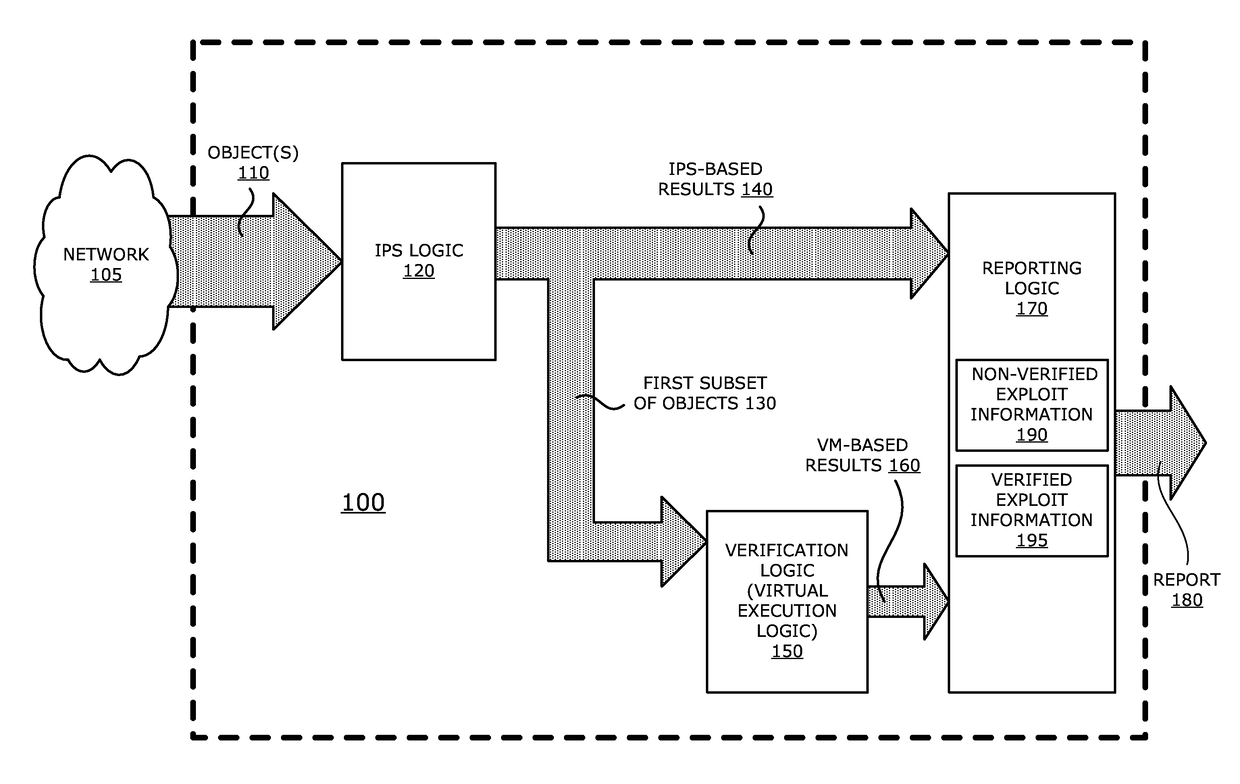
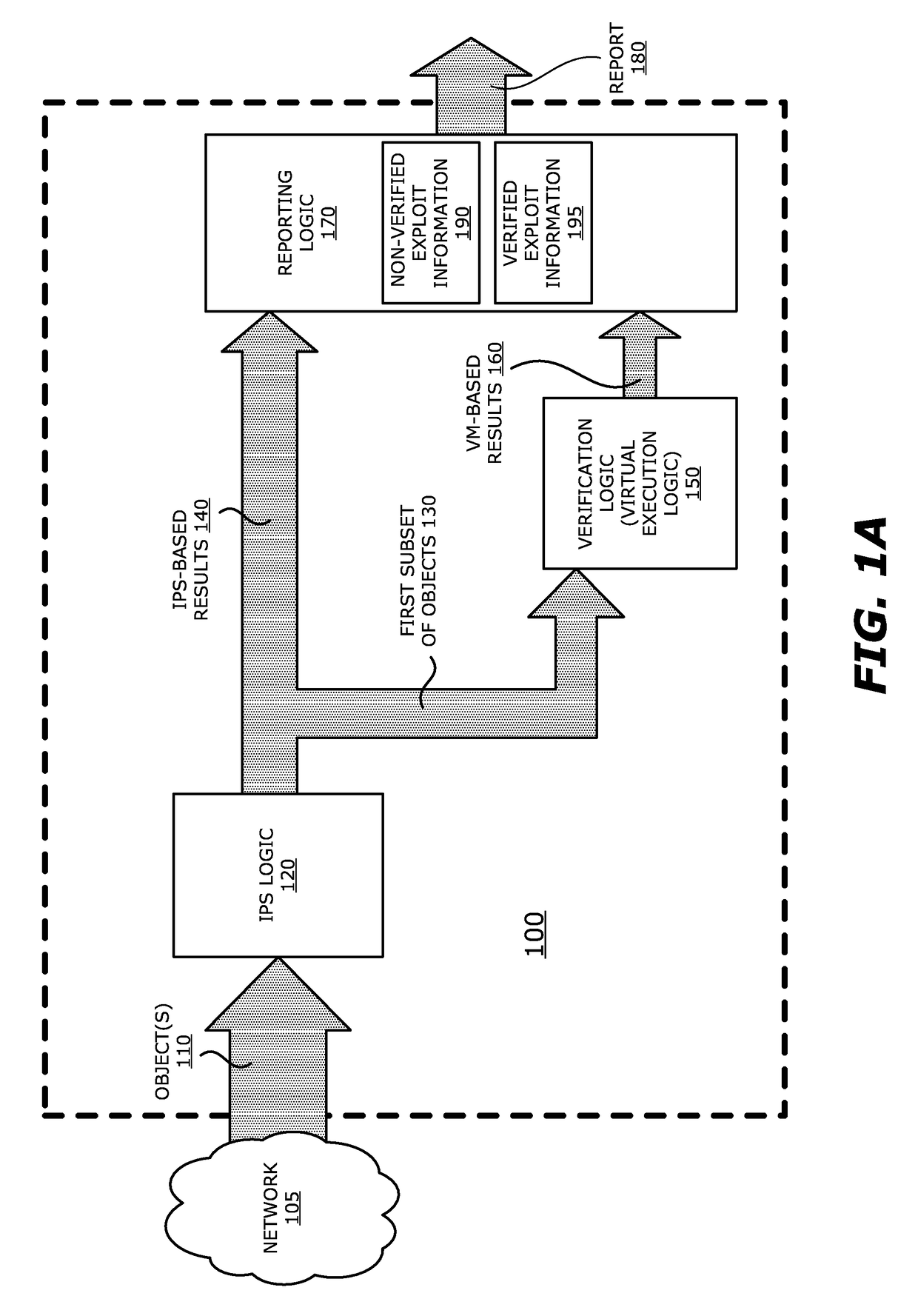
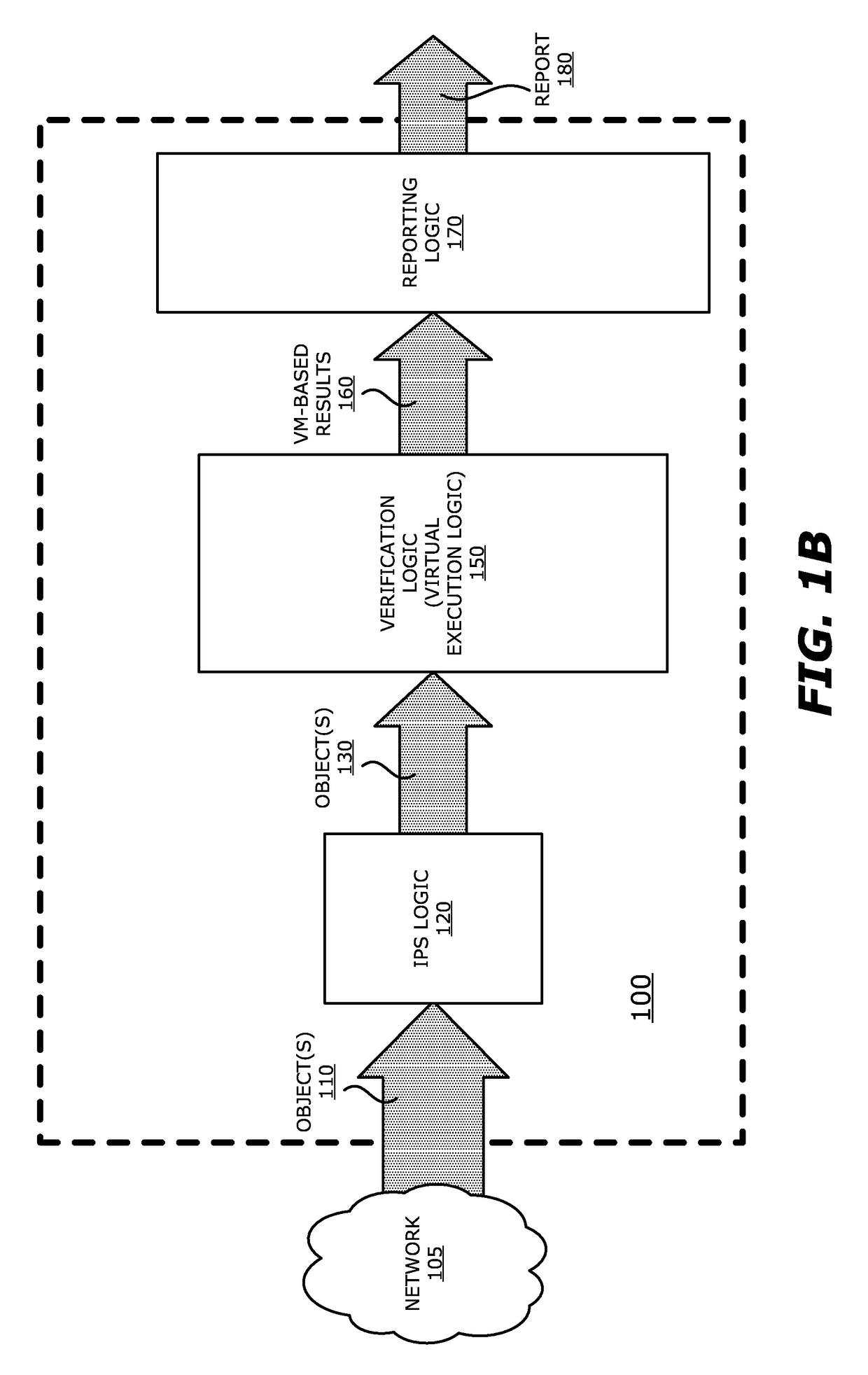
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS20150186645A1Quickly and easily determineReduce disadvantagesMemory loss protectionError detection/correctionAnomalous behaviorProtection system
According to one embodiment, a threat detection system is integrated with intrusion protection system (IPS) logic and virtual execution logic. The IPS logic is configured to receive a first plurality of objects and filter the first plurality of objects by identifying a second plurality of objects as suspicious objects. The second plurality of objects is a subset of the first plurality of objects and is lesser or equal in number to the first plurality of objects. The virtual execution logic is configured to automatically verify whether any of the suspicious objects is an exploit. The virtual execution logic comprises at least one virtual machine configured to virtually process content within the suspicious objects and monitor for anomalous behaviors during the virtual processing that are indicative of exploits.
Owner:FIREEYE SECURITY HLDG US LLC
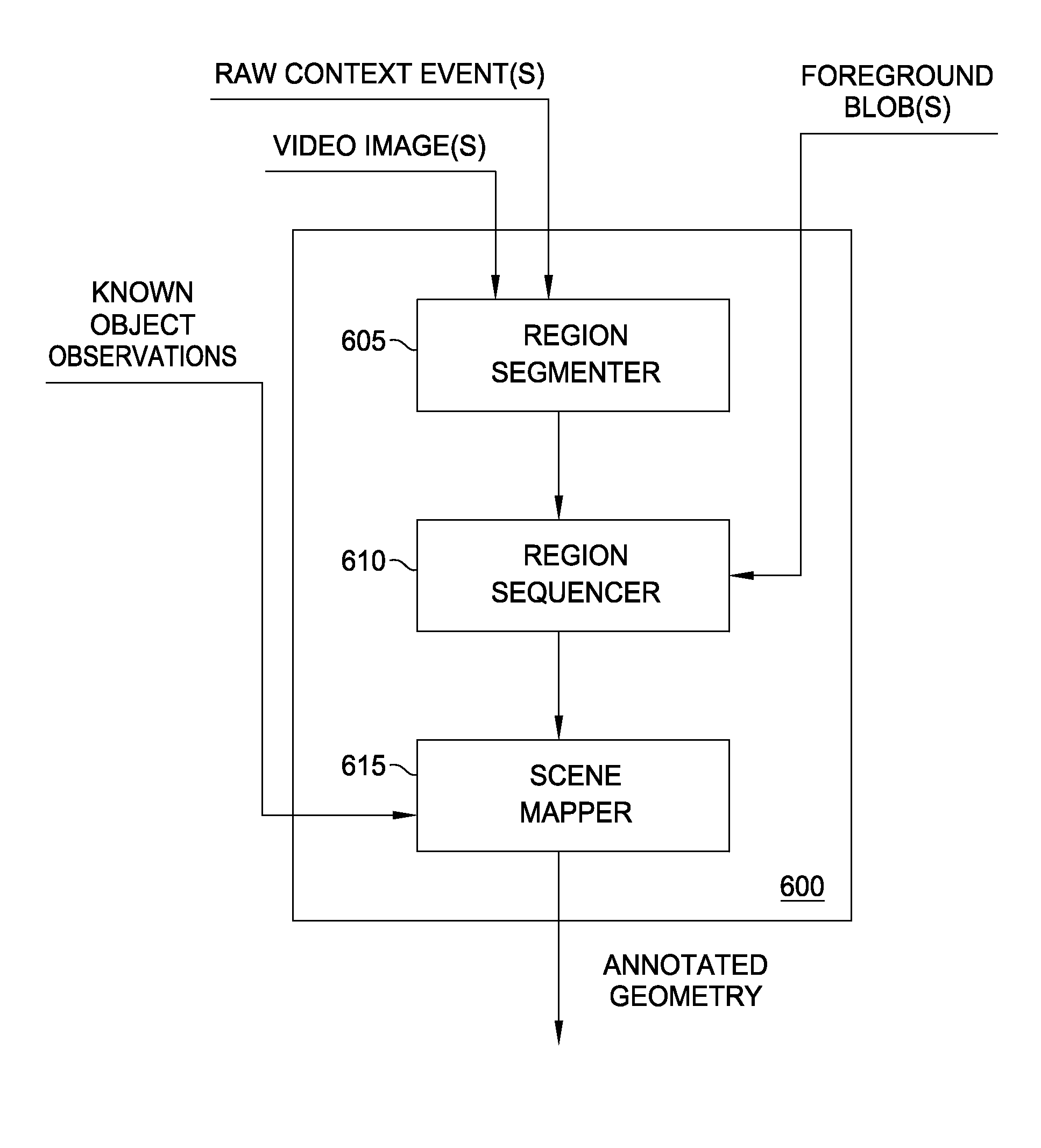
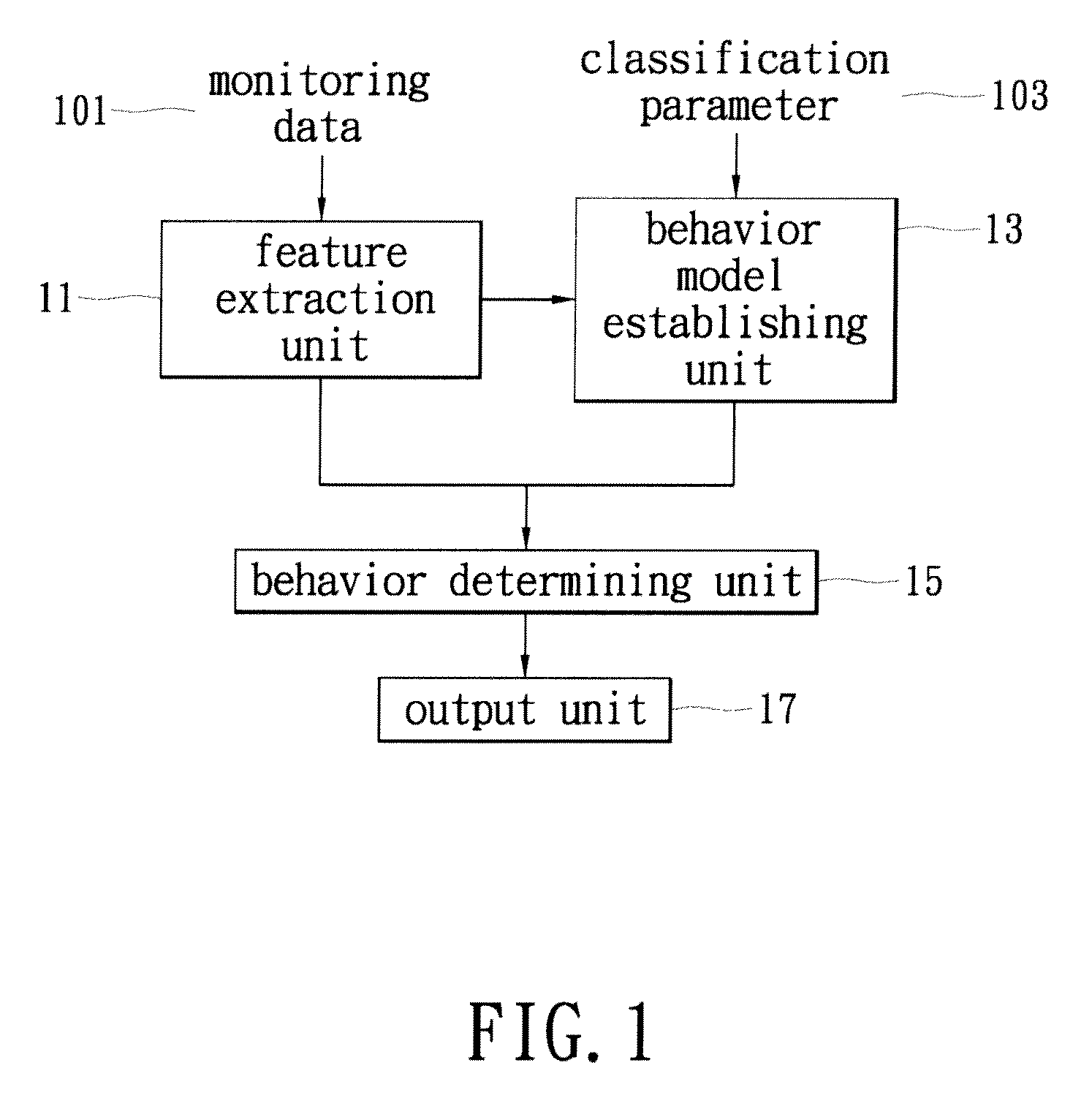
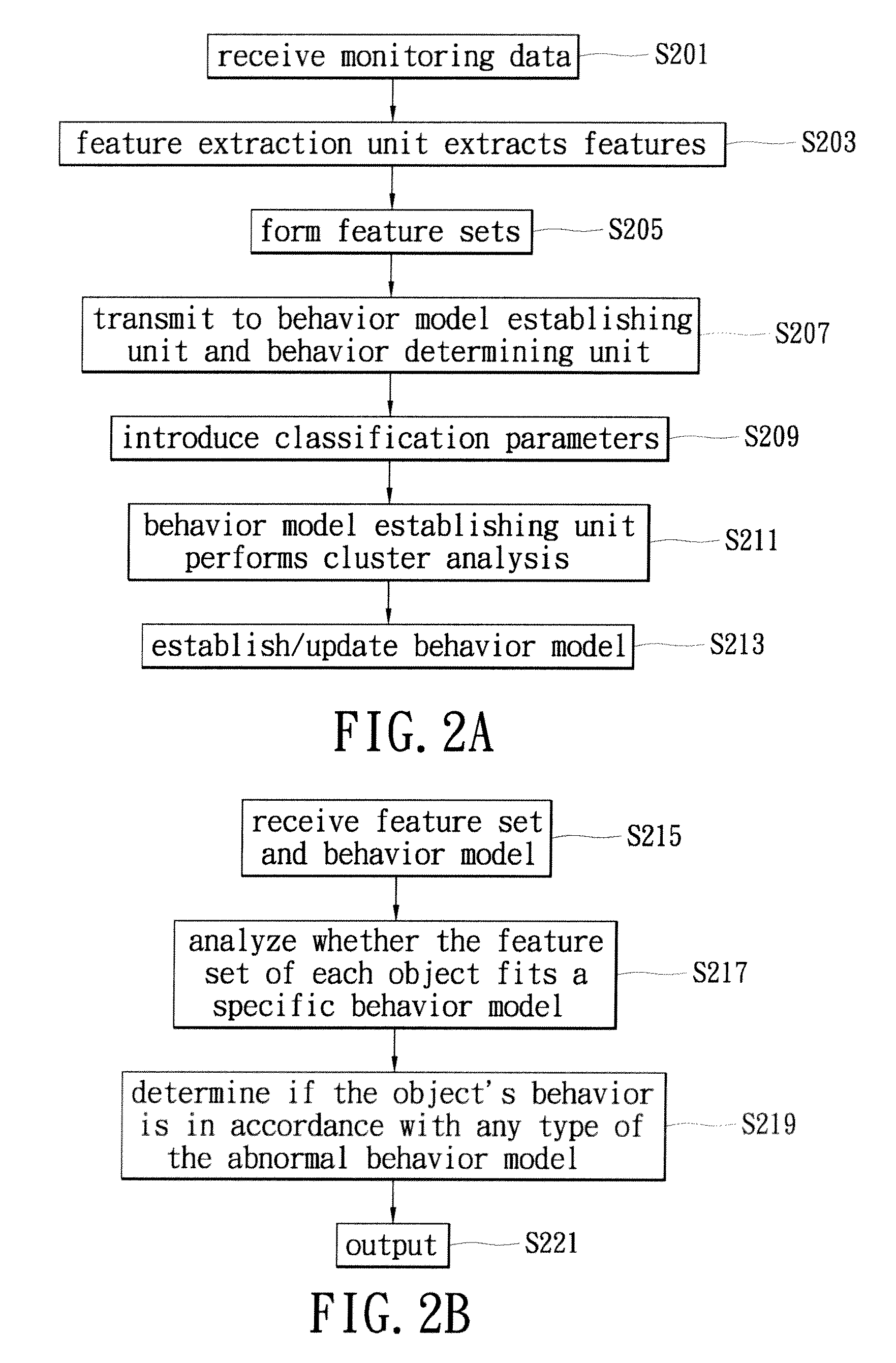
Behavioral recognition system
ActiveUS20080193010A1Digital computer detailsCharacter and pattern recognitionSemantic representationAnomalous behavior
Embodiments of the present invention provide a method and a system for analyzing and learning behavior based on an acquired stream of video frames. Objects depicted in the stream are determined based on an analysis of the video frames. Each object may have a corresponding search model used to track an object's motion frame-to-frame. Classes of the objects are determined and semantic representations of the objects are generated. The semantic representations are used to determine objects' behaviors and to learn about behaviors occurring in an environment depicted by the acquired video streams. This way, the system learns rapidly and in real-time normal and abnormal behaviors for any environment by analyzing movements or activities or absence of such in the environment and identifies and predicts abnormal and suspicious behavior based on what has been learned.
Owner:MOTOROLA SOLUTIONS INC
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS9306974B1Quickly and easily determineReduce disadvantagesPlatform integrity maintainanceAlarmsAnomalous behaviorProtection system
Owner:FIREEYE SECURITY HLDG US LLC
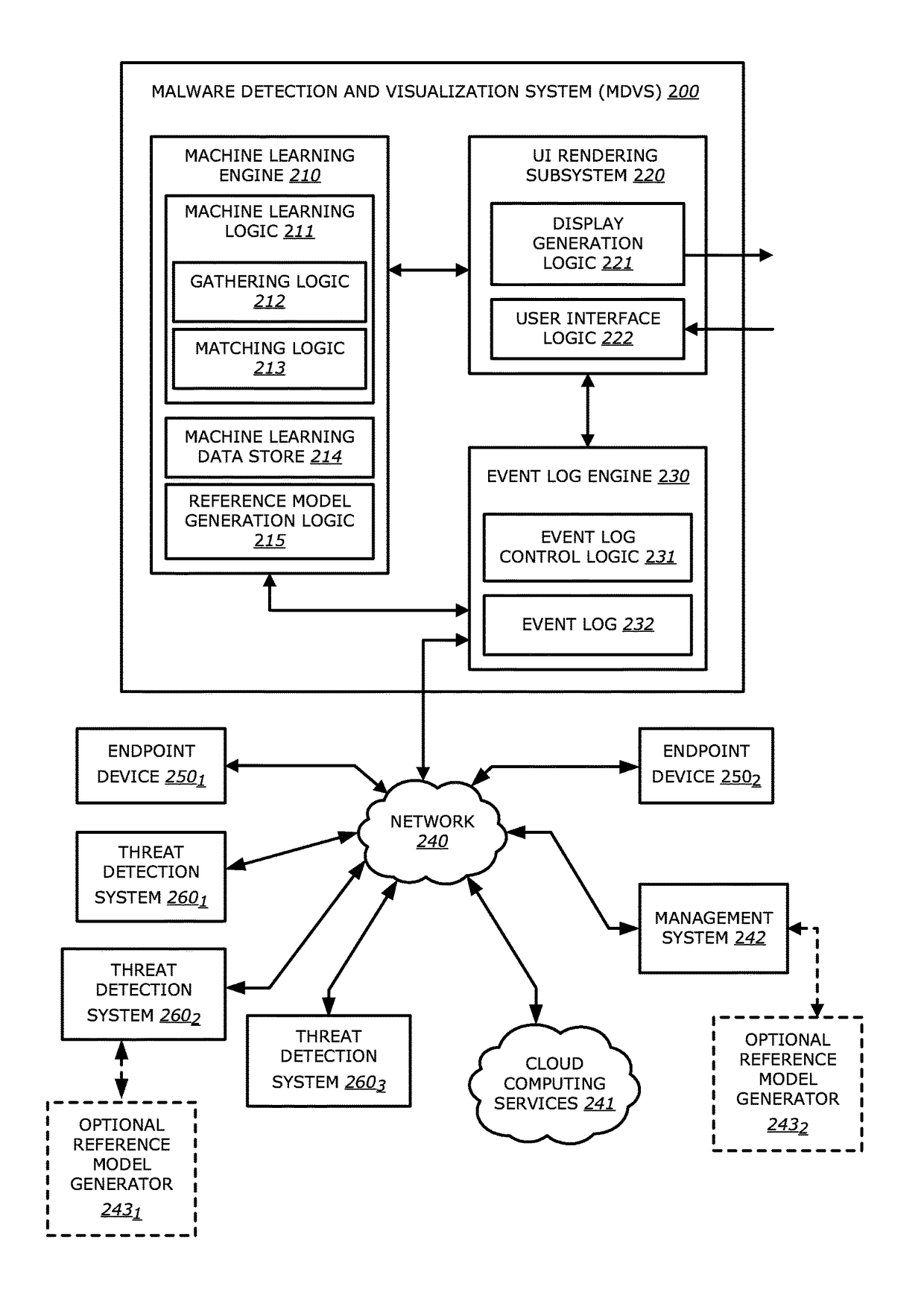
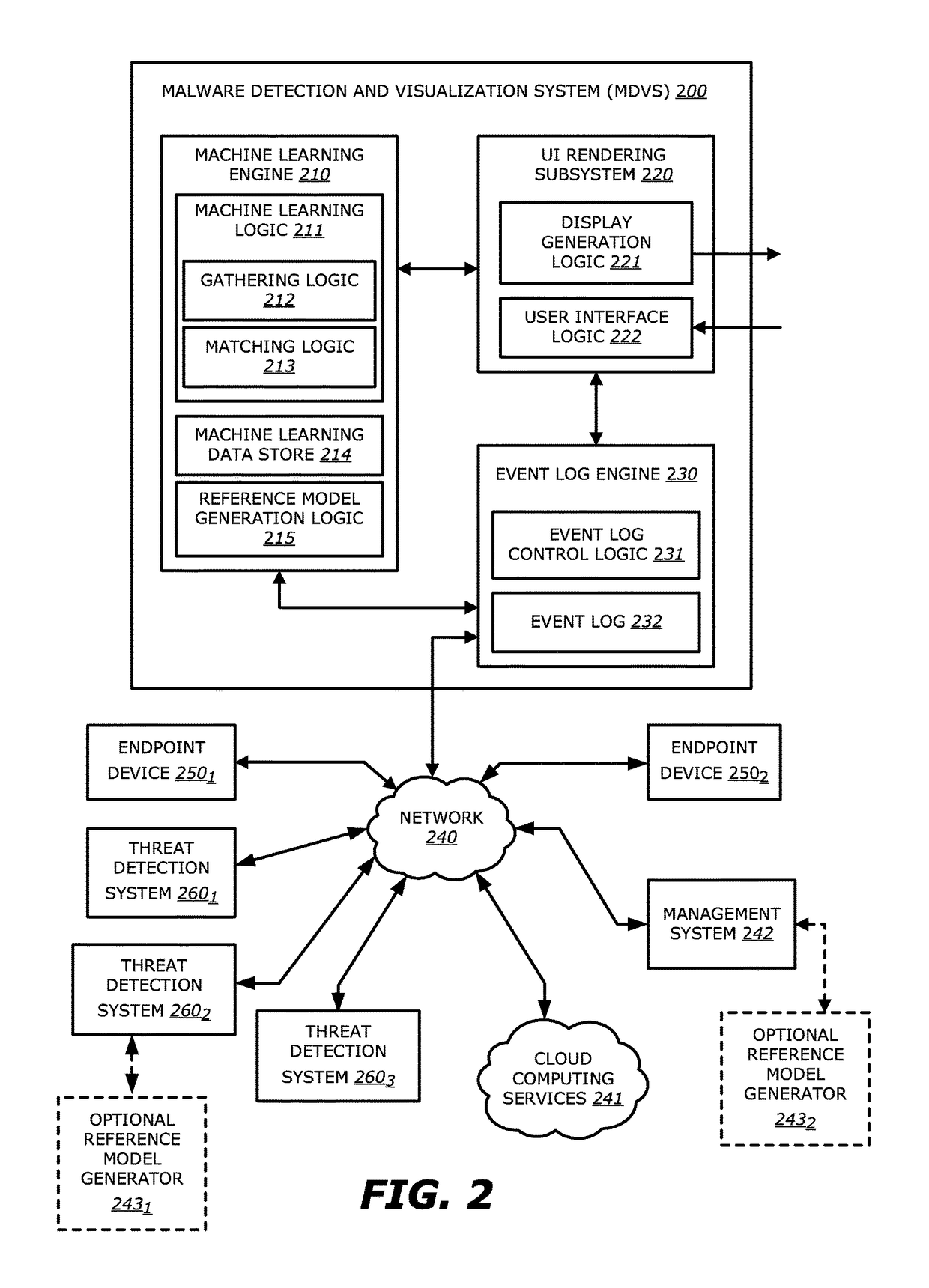
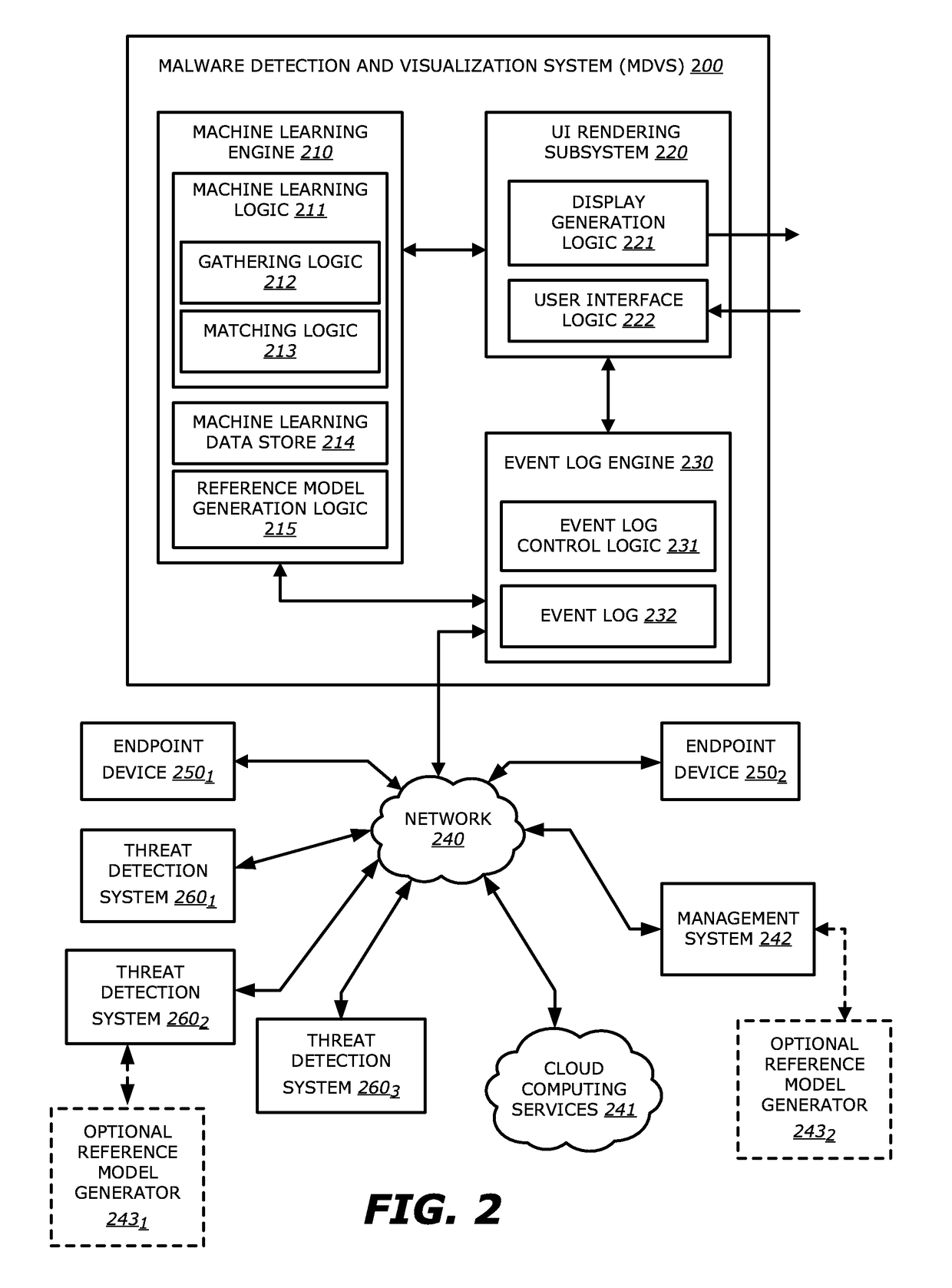
Interactive infection visualization for improved exploit detection and signature generation for malware and malware families
According to one embodiment, a malware detection and visualization system comprises one or more processors; and a storage module communicatively coupled to the one or more processors, the storage module comprises logic, upon execution by the one or more processors, that accesses a first set of information that comprises (i) information directed to a plurality of observed events and (ii) information directed to one or more relationships that identify an association between different observed events of the plurality of observed events; and generates a reference model based on the first set of information, the reference model comprises at least a first event of the plurality of observed events, a second event of the plurality of observed events, and a first relationship that identifies that the second event is based on the first event, wherein at least one of (i) the plurality of observed events or (ii) the one or more relationships constitutes an anomalous behavior is provided.
Owner:FIREEYE SECURITY HLDG US LLC
Exploit detection of malware and malware families
According to one embodiment, a computerized method comprises, accessing information associated with one or more observed events, wherein one or more of the observed events constitutes an anomalous behavior; accessing a reference model based on a first plurality of events, the reference model comprises a first event of the first plurality of events, a second event of the first plurality of events and a relationship that identifies that the second event of the first plurality of events is based on the first event of the first plurality of events, wherein at least one of the first event and the second event constitutes an anomalous behavior; and comparing the information associated with the one or more observed events with the reference model to determine whether at least one observed event of the one or more observed events matches at least one of the first event of the first plurality of events or the second event of the first plurality of events that constitutes the anomalous behavior is provided.
Owner:FIREEYE SECURITY HLDG US LLC
System, device and method for detecting a malicious attack based on communcations between remotely hosted virtual machines and malicious web servers
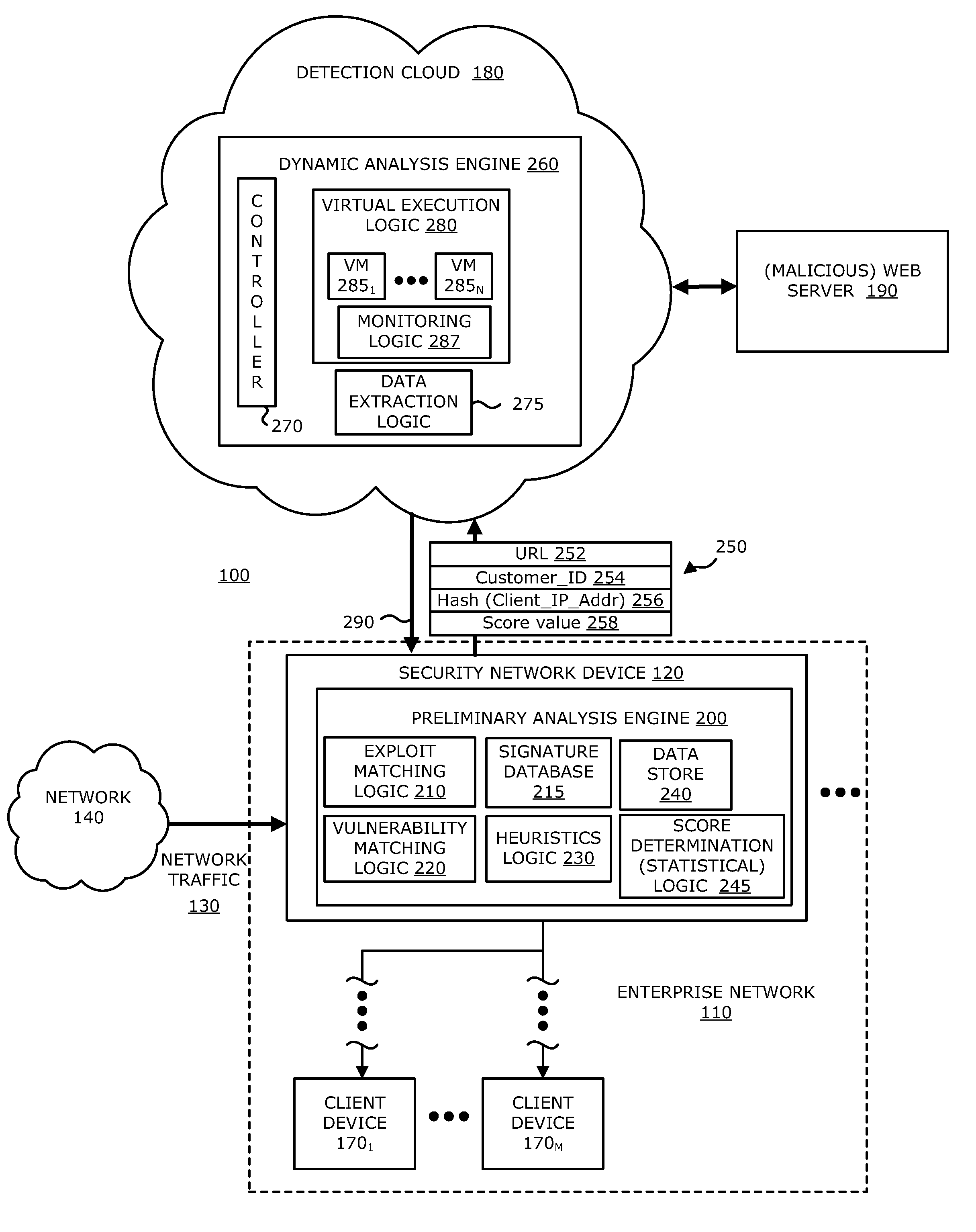
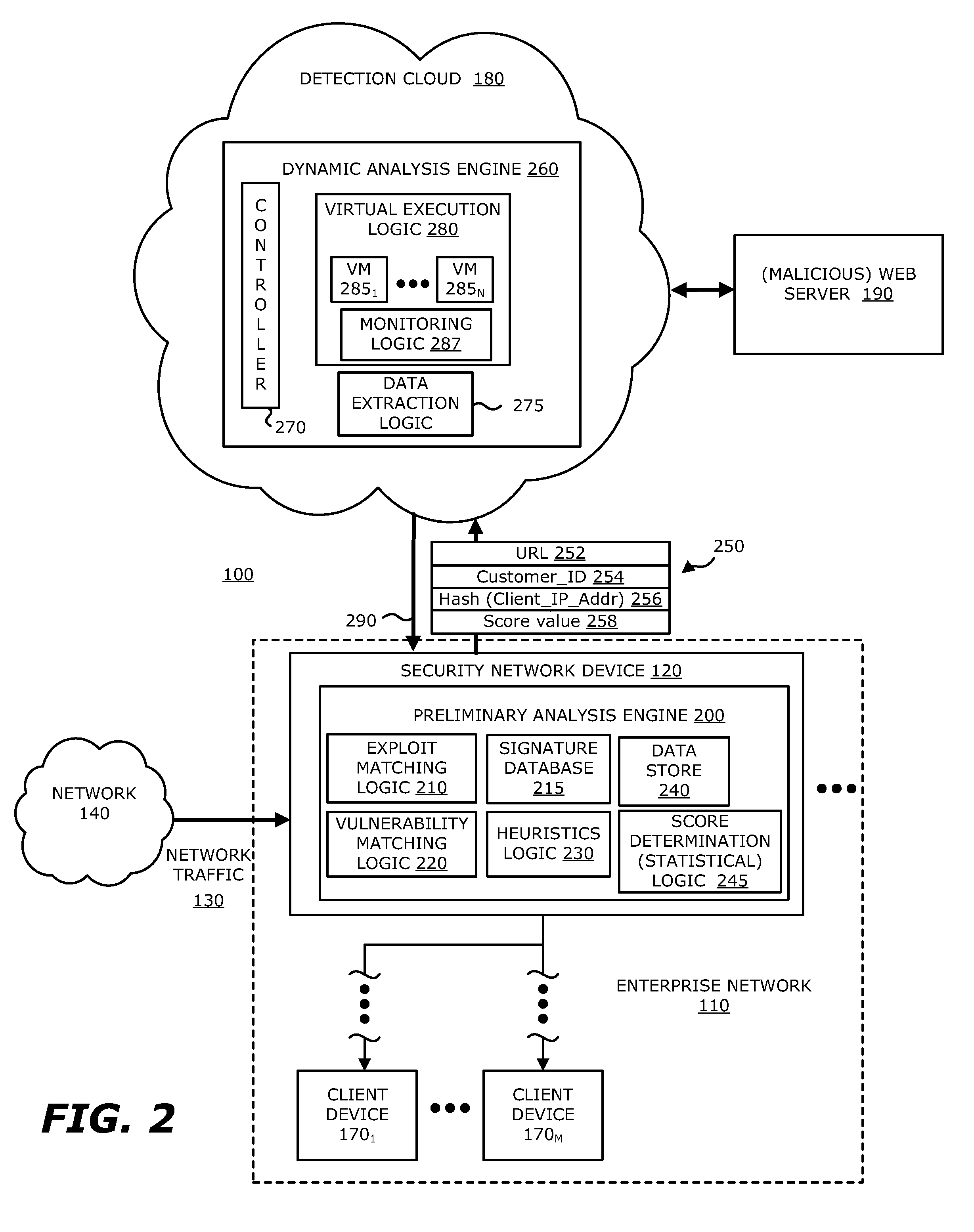
In an embodiment, a dynamic analysis engine is configured to receive an identifier associated with a source for network traffic including at least one object having at least a prescribed probability of being associated with an exploit. Deployed within a detection cloud, the dynamic analysis engine comprises one or more virtual machines and monitoring logic. The virtual machines are adapted to virtually process the identifier by establishing a communication session with a server hosting a website accessible by the identifier. In communication with the virtual machines, the monitoring logic is adapted to detect anomalous behaviors by the virtual machines during the communication session with the server.
Owner:FIREEYE SECURITY HLDG US LLC +1
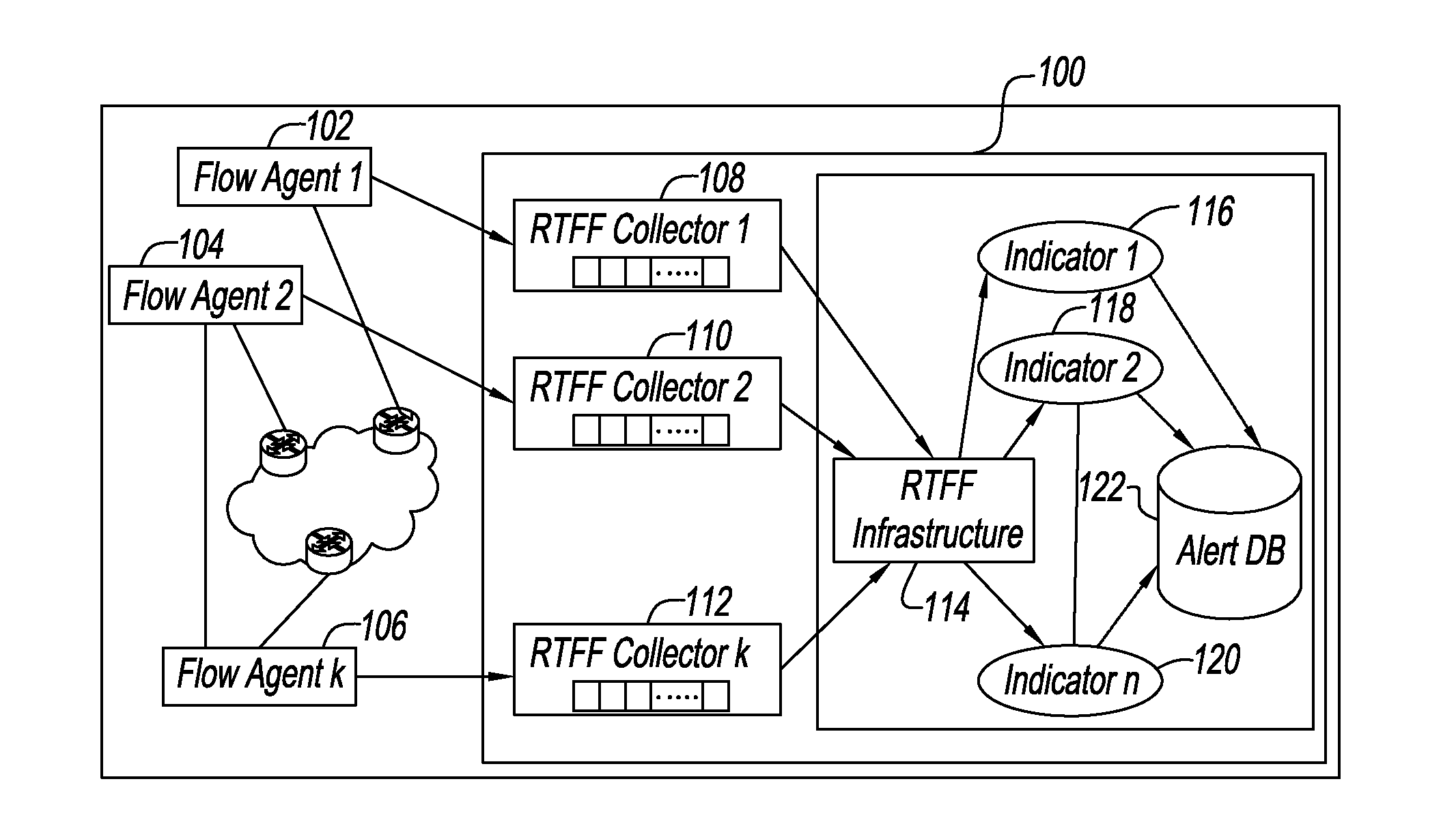
System and method for correlating historical attacks with diverse indicators to generate indicator profiles for detecting and predicting future network attacks
InactiveUS20140082730A1Reduce detectionAccurately detect and predictMemory loss protectionError detection/correctionTraffic characteristicAnomalous behavior
An apparatus and method predict and detect network attacks by using a diverse set of indicators to measure aspects of the traffic and by encoding traffic characteristics using these indicators of potential attacks or anomalous behavior. The set of indicators is analyzed by supervised learning to automatically learn a decision rule which examines the temporal patterns in the coded values of the set of indicators to accurately detect and predict network attacks. The rules automatically evolve in response to new attacks as the system updates its rules periodically by analyzing new data and feedback signals about attacks associated with that data. To assist human operators, the system also provides human interpretable explanations of detection and prediction rules by pointing to indicators whose values contribute to a decision that there is an existing network attack or an imminent network attack. When such indictors are detected, an operator can take remediation actions.
Owner:PERSPECTA LABS INC +1
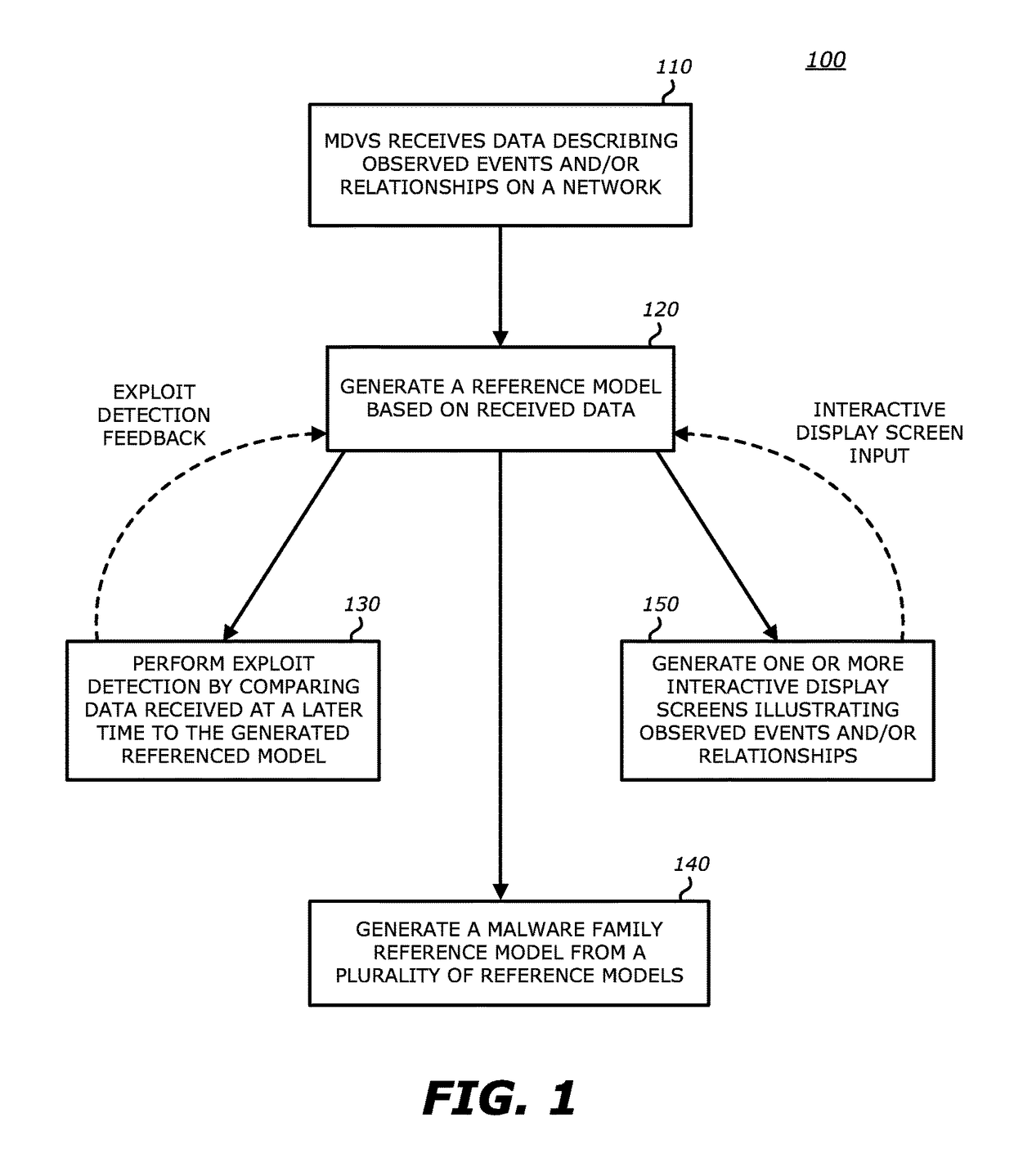
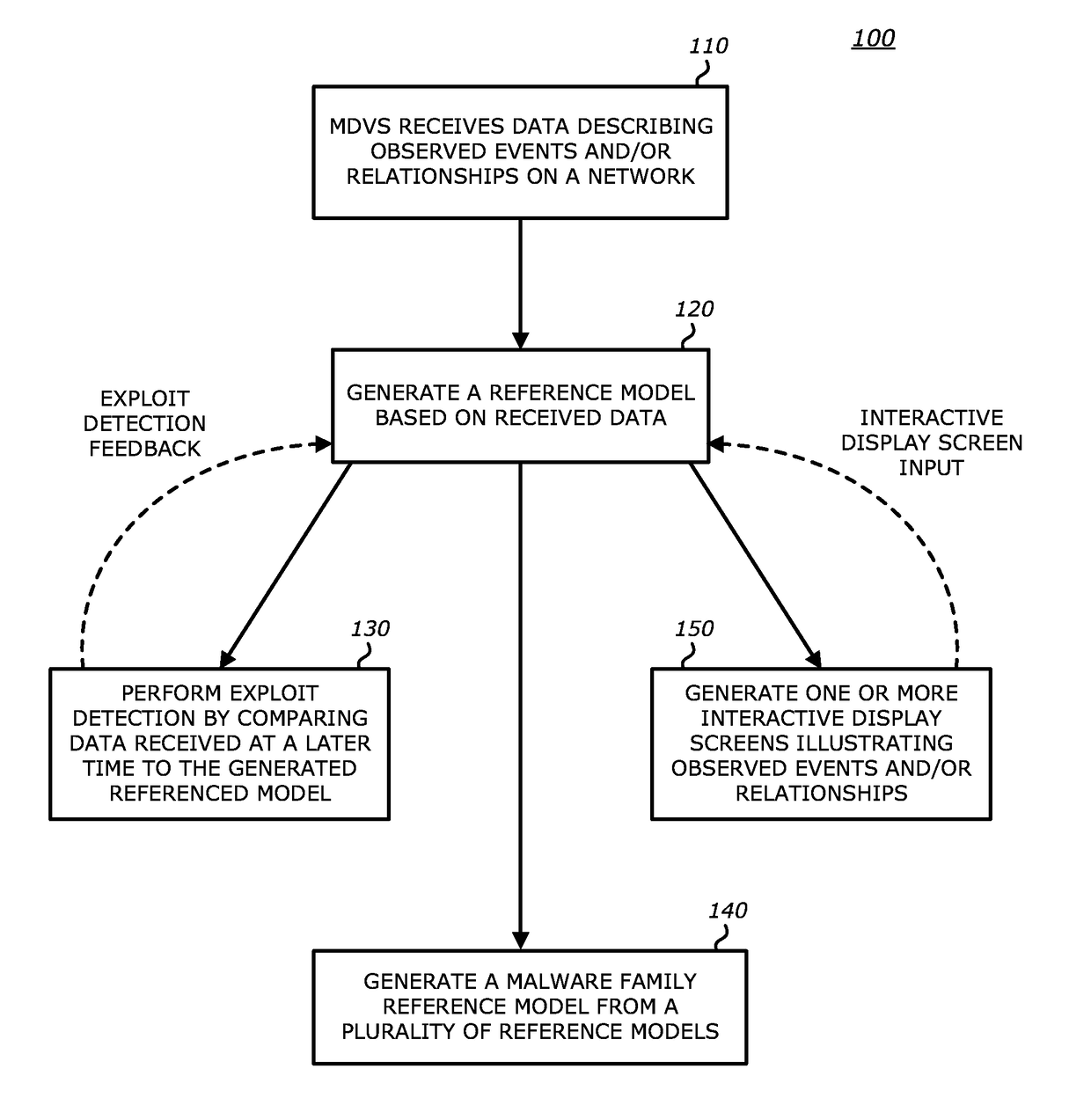
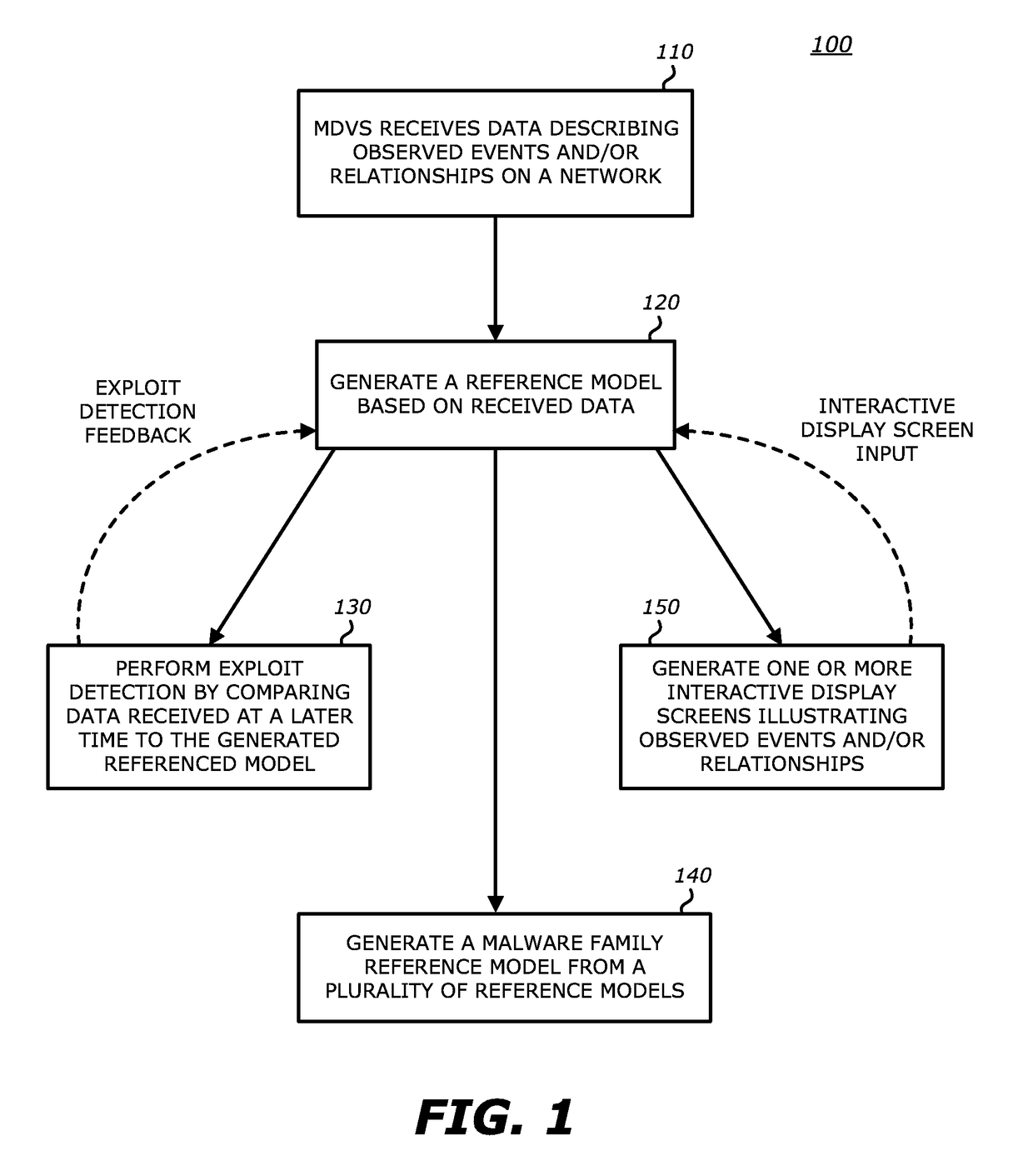
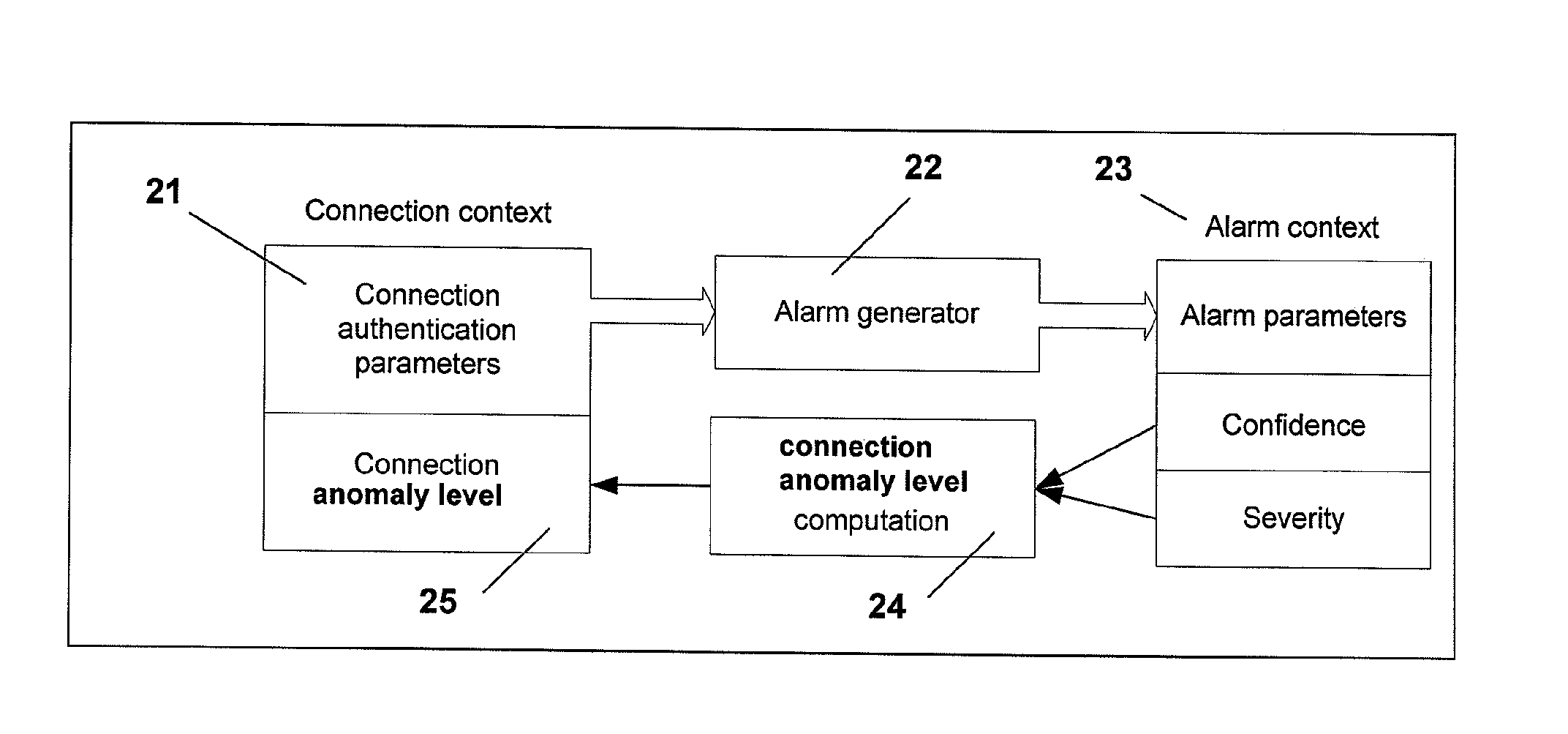
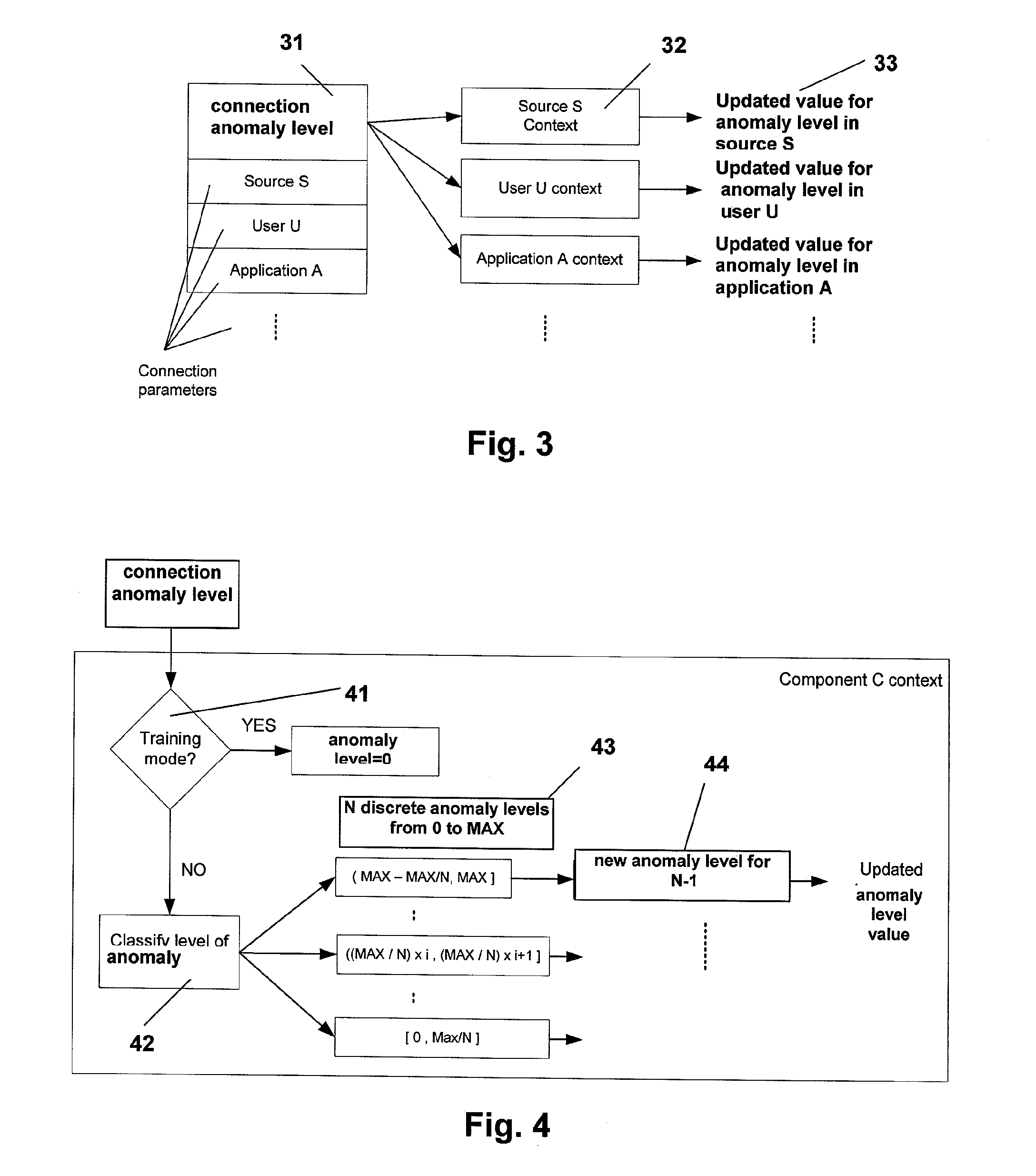
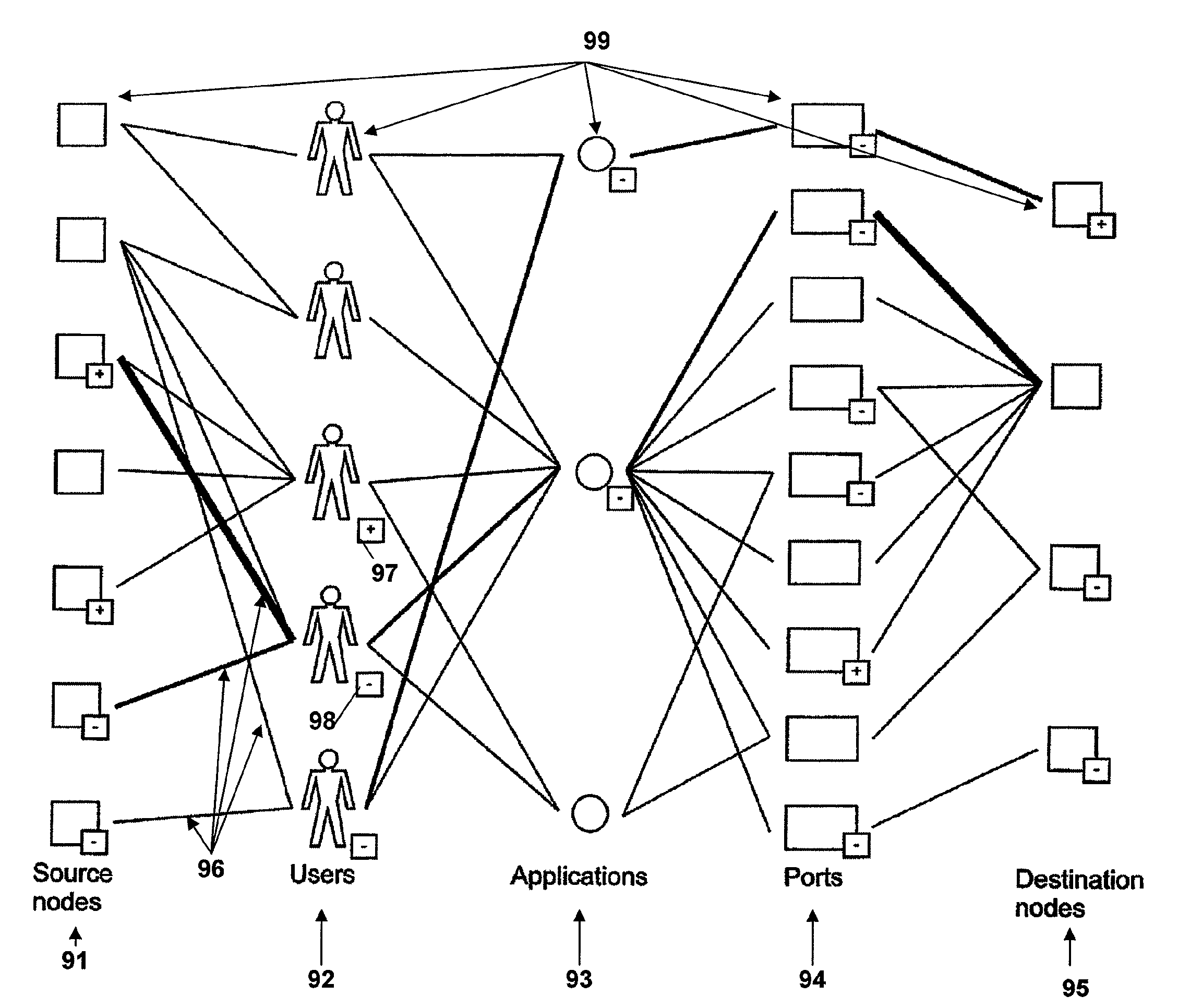
Method for the detection and visualization of anomalous behaviors in a computer network
ActiveUS20070118909A1Anomalous behaviorMemory loss protectionError detection/correctionAnomalous behaviorDistributed computing
A method for the detection of anomalous behaviors in a computer network, comprising the steps of: collecting data relating to connections in a plurality of nodes in a network, sending the data from said nodes to an ADS platform, computing from said data at least one value representative of the anomaly level of the connections of each said node and / or of applications initiating said connections and / or of users, computing a multidimensional chart for visualizing the behavior of a plurality of nodes, applications and / or users in said network, wherein said value representative of the anomaly level is used as a dimension in said chart.
Owner:NEXTHINK
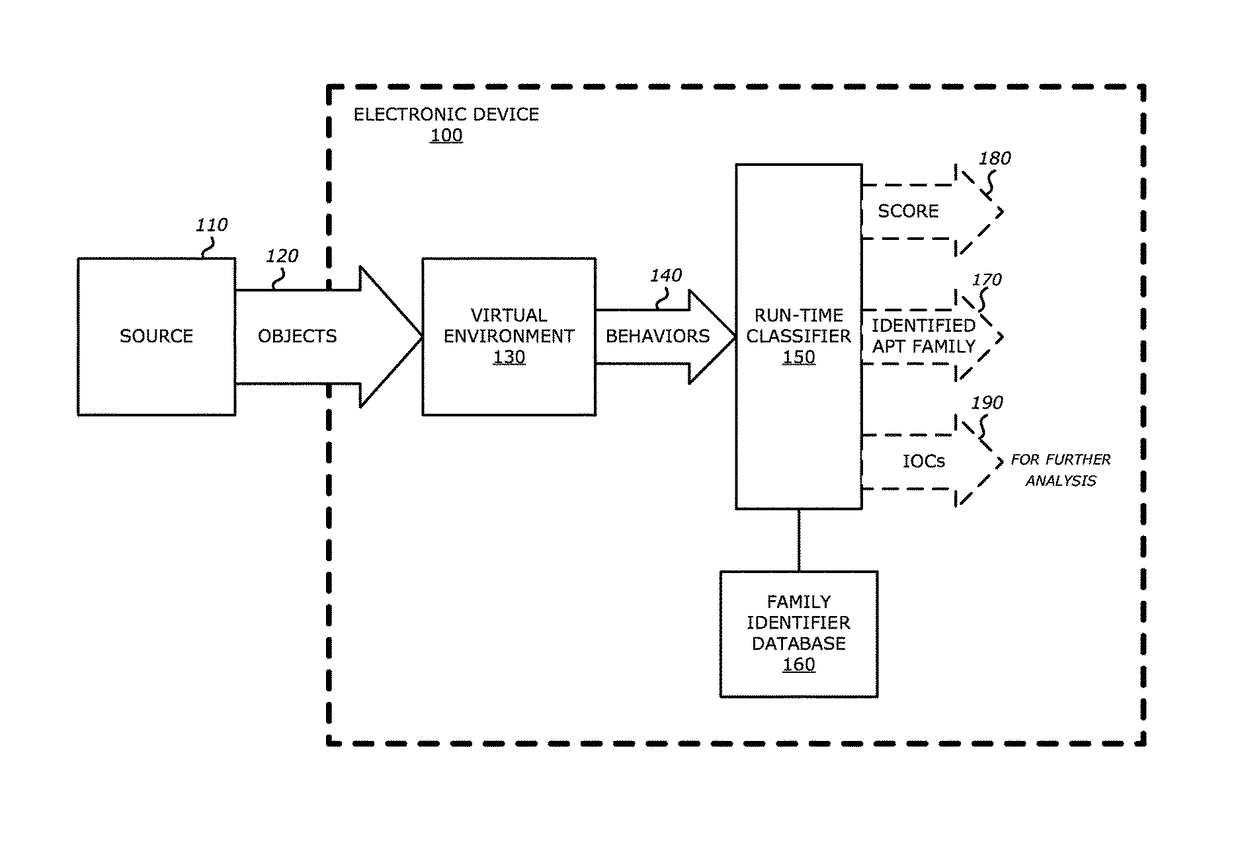
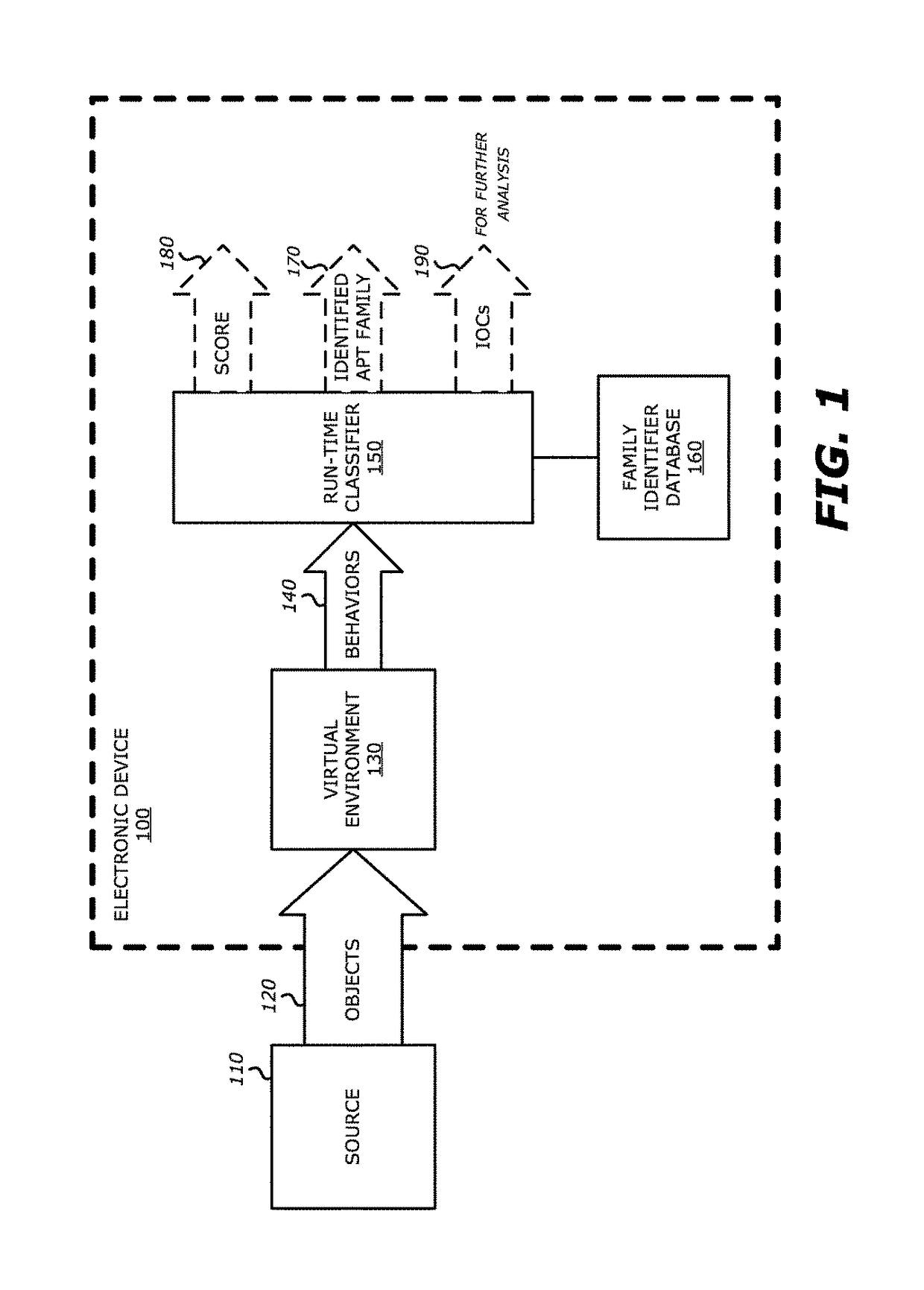
System and method for run-time object classification
One embodiment of an electronic device comprises a processor and a memory accessible by the processor. The memory comprises virtual execution logic and run-time classifier logic. The virtual execution logic includes at least one virtual machine that is configured to virtually process content within an object under analysis and monitor for anomalous behaviors during the virtual processing that are indicative of malware. The run-time classifier logic performs, during run-time, a first analysis on the monitored anomalous behaviors and a pre-stored identifier to determine if the monitored anomalous behaviors indicate that the object is malware belonging to a classified malware family. The pre-stored identifier is a collection of data associated with anomalous behaviors that uniquely identify the malware family.
Owner:FIREEYE SECURITY HLDG US LLC +1
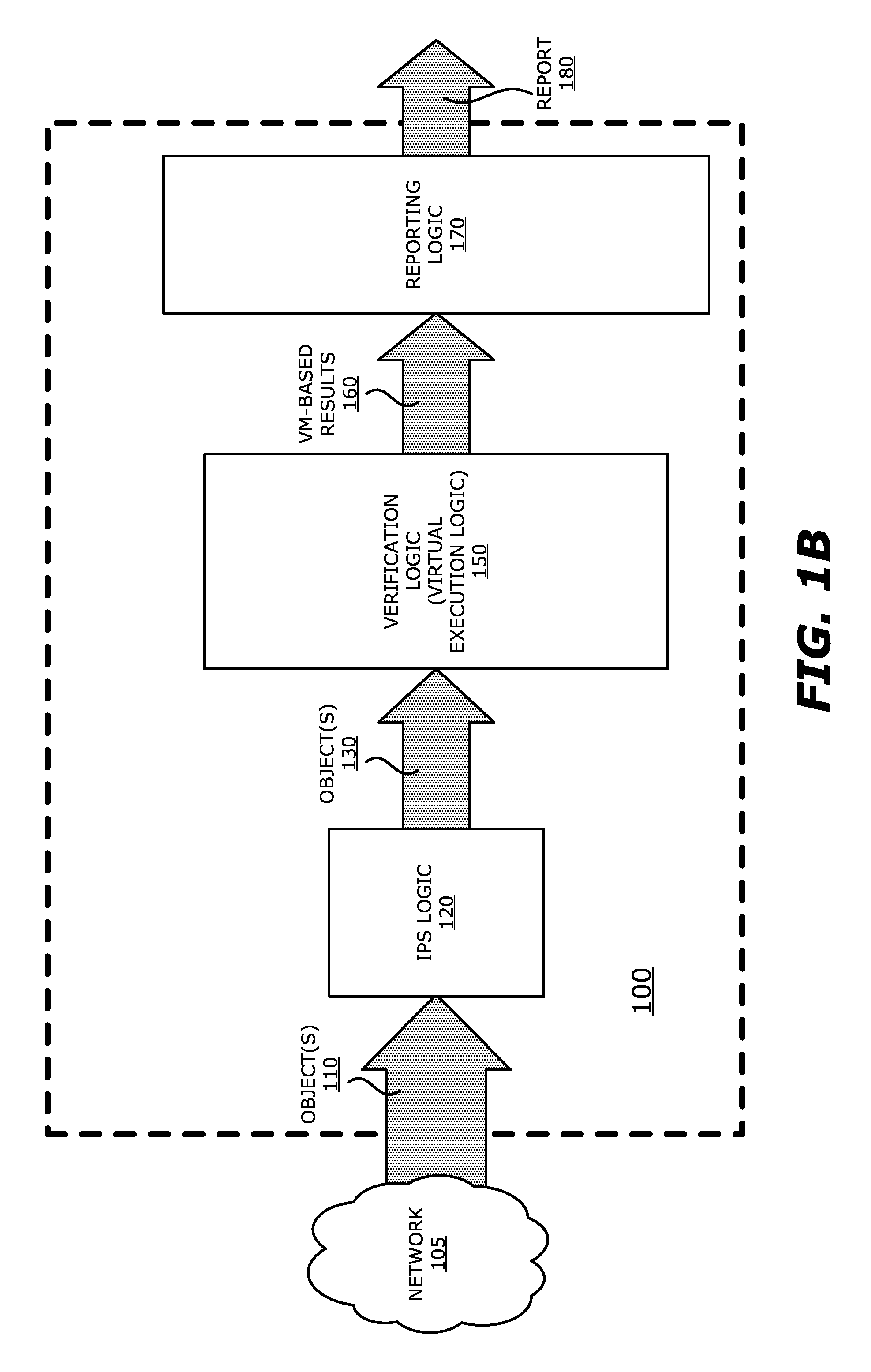
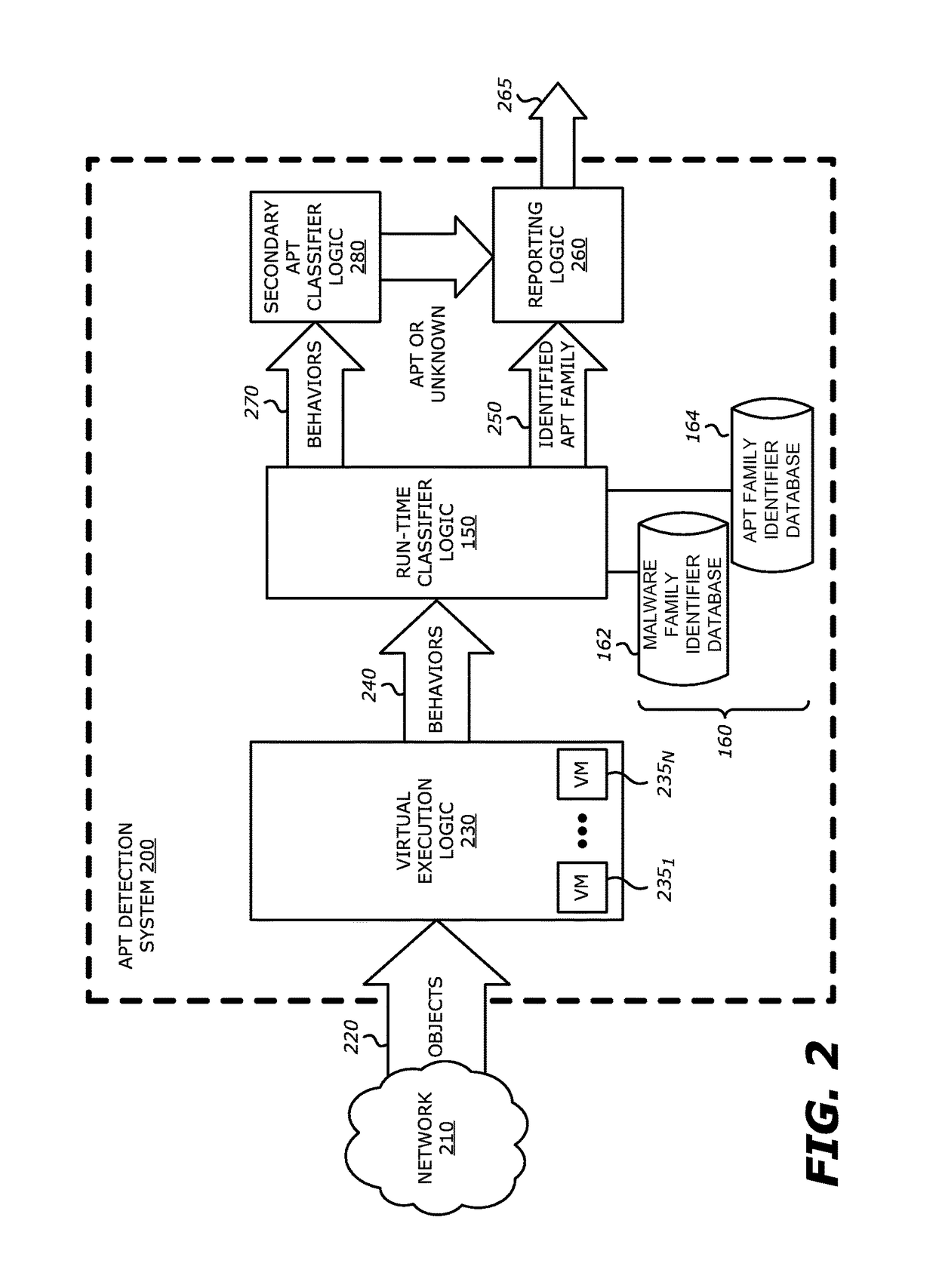
System and method for IPS and VM-based detection of suspicious objects
ActiveUS9756074B2Quickly and easily determineReduce disadvantagesPlatform integrity maintainanceTransmissionPattern recognitionAnomalous behavior
A threat detection system is integrated with intrusion protection system (IPS) logic and virtual execution logic is shown. The IPS logic is configured to receive a first plurality of objects and filter the first plurality of objects by identifying a second plurality of objects as suspicious objects. The second plurality of objects is a subset of the first plurality of objects and is lesser or equal in number to the first plurality of objects. The virtual execution logic is configured to automatically verify whether any of the suspicious objects is an exploit. The virtual execution logic comprises at least one virtual machine configured to virtually process content within the suspicious objects and monitor for anomalous behaviors during the virtual processing that are indicative of exploits.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of detecting malicious content
ActiveUS9838416B1Rapid responsePlatform integrity maintainanceTransmissionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
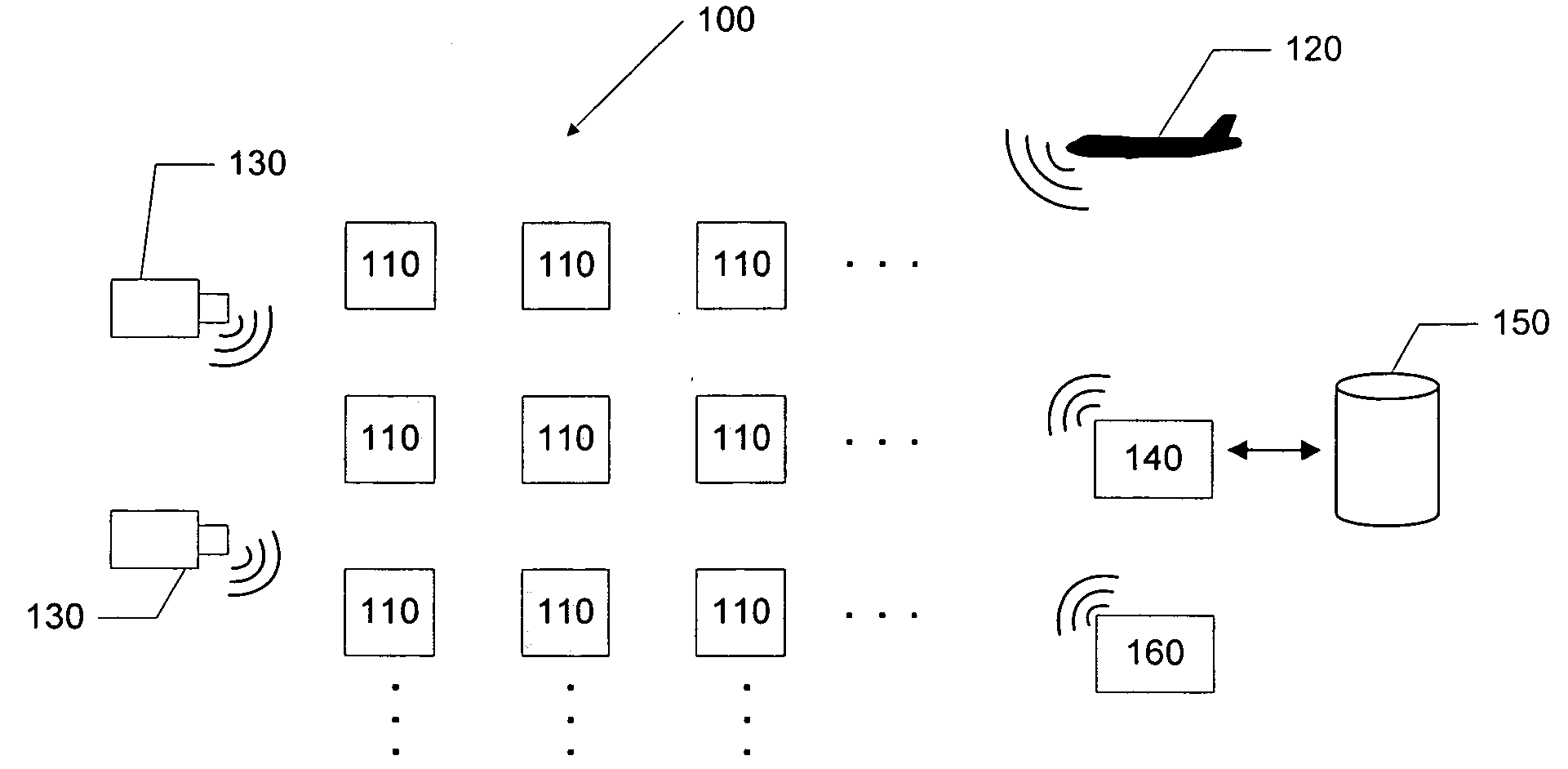
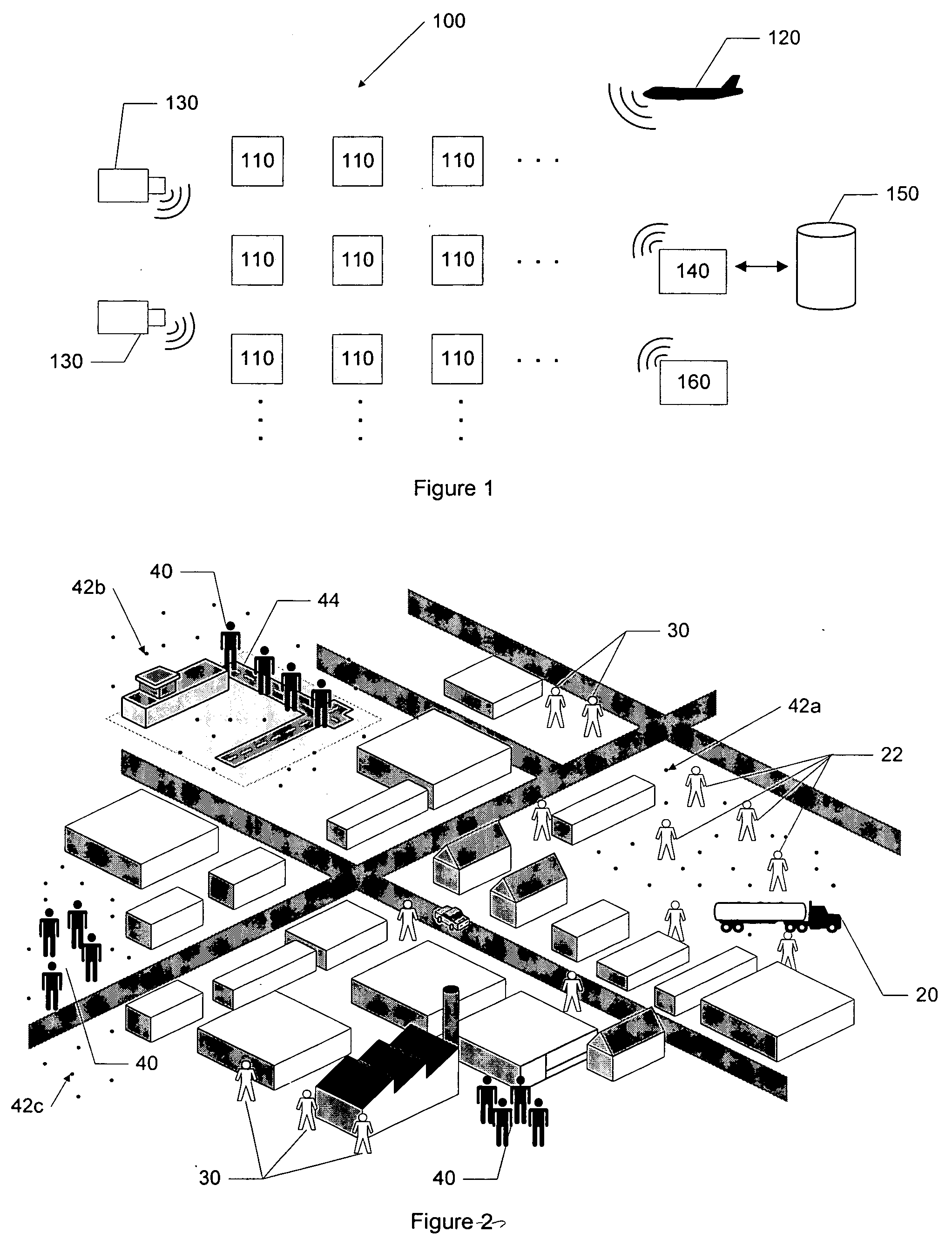
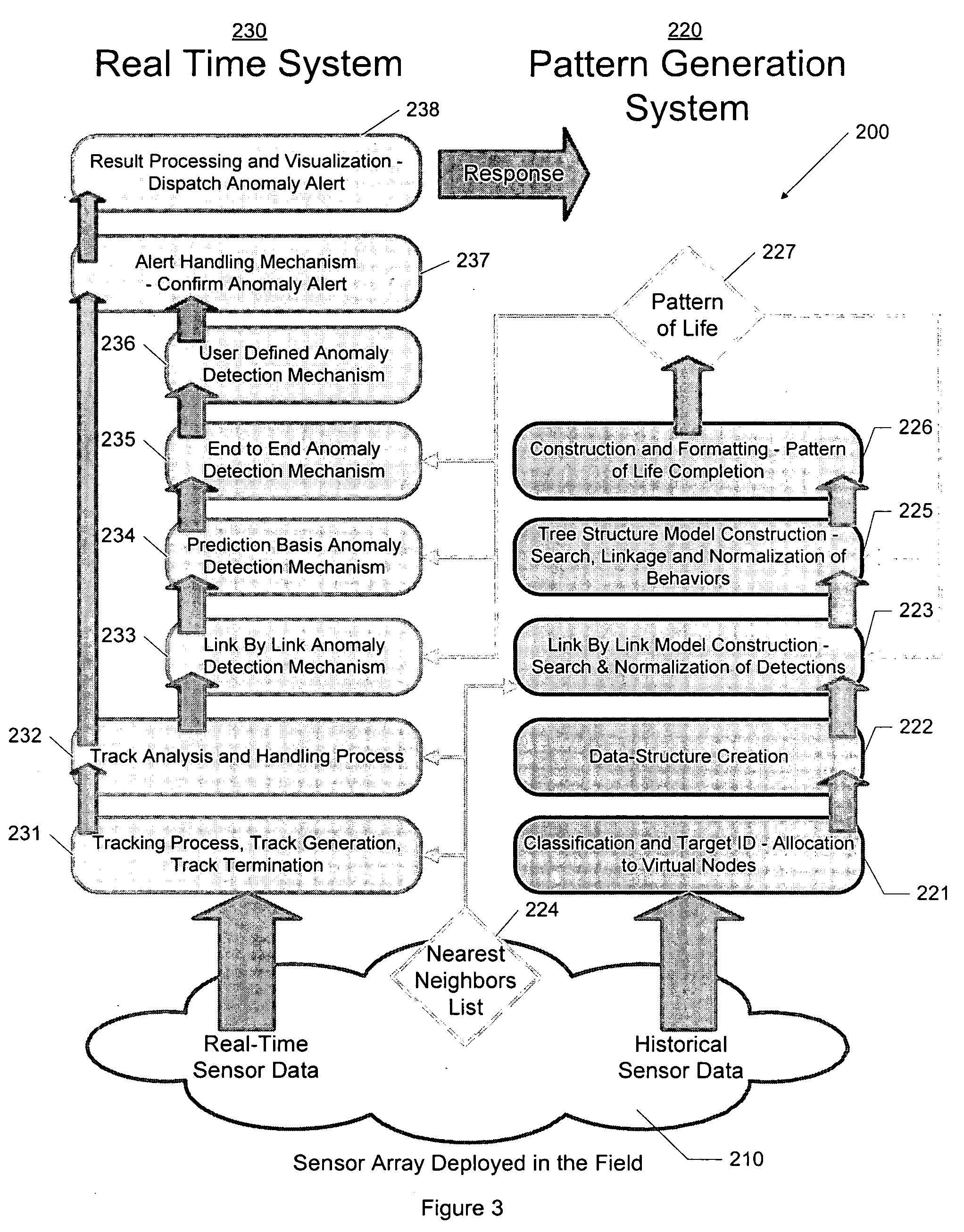
Apparatus and method for surveillance system using sensor arrays
InactiveUS20090195401A1Easy to processGreat communication rangeCharacter and pattern recognitionAlarmsSensor arrayMonitoring system
Embodiments of the invention may include a sensor system and a method used to track the behaviors of targets in an area under surveillance. The invention may include a sensor array located in the area that is capable of sending messages to a user when behavior of a tracked target is determined to be anomalous. In making the determination of anomalous behavior, the sensor system and method may generate and continuously refine a pattern of life model that may examine, for example, the paths a target may take within the sensor array and the end points of the paths taken. The sensor system and method may also incorporate any user defined conditions for anomalous behavior.
Owner:GENERAL DYNAMICS UK
User interface with real-time visual playback along with synchronous textual analysis log display and event/time index for anomalous behavior detection in applications
Owner:FIREEYE SECURITY HLDG US LLC
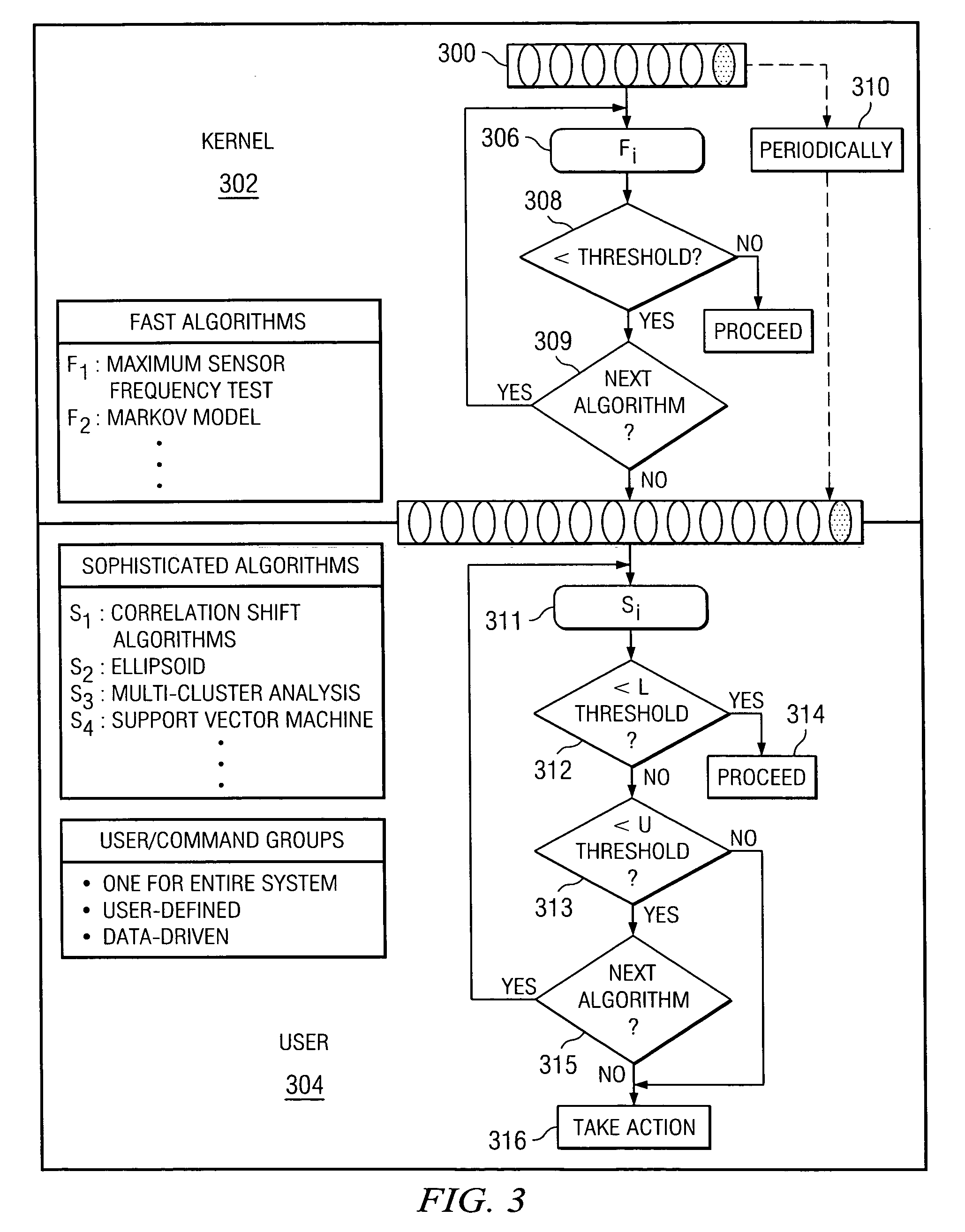
Method and system for detecting intrusive anomalous use of a software system using multiple detection algorithms
InactiveUS20060085854A1Improve detection accuracyAccurate detectionMemory loss protectionDetecting faulty computer hardwareCountermeasureSoftware system
A method of detecting an intrusion into (or an anomaly in a behavior of) a target software system begins by instrumenting the target software system to generate behavior data representing a current observation or observation aggregate. The method then determines whether the current observation or observation aggregate warrants a second level examination; preferably, this determination is made by processing the current observation or observation aggregate through a first level detection algorithm that provides a first, provisional indication of a possible intrusion. If a result of executing the first level detection algorithm indicates that the current observation or observation aggregate warrants a second level examination, the method continues by processing the current observation or observation aggregate through at least one or more second level detection algorithms to provide a second, more definite, fine grain indication of a possible intrusion. The observation aggregates used by the first and second level detection algorithms may be the same or different. The first and second level detection algorithms may be executed in the same or different systems, machines or processors. The target software system operation may be suspended as the current observation or observation aggregate is processed through the one or more second level detection algorithms. A given action (e.g., sending an alert, logging the event, activating a countermeasure, or the like) may be taken if the result of the second level examination indicates a possible intrusion. Multiple algorithms may be executed together within a single examination level, with the individual results then analyzed to obtain a composite result or output indicative of intrusive or anomalous behavior.
Owner:STRATACLOUD
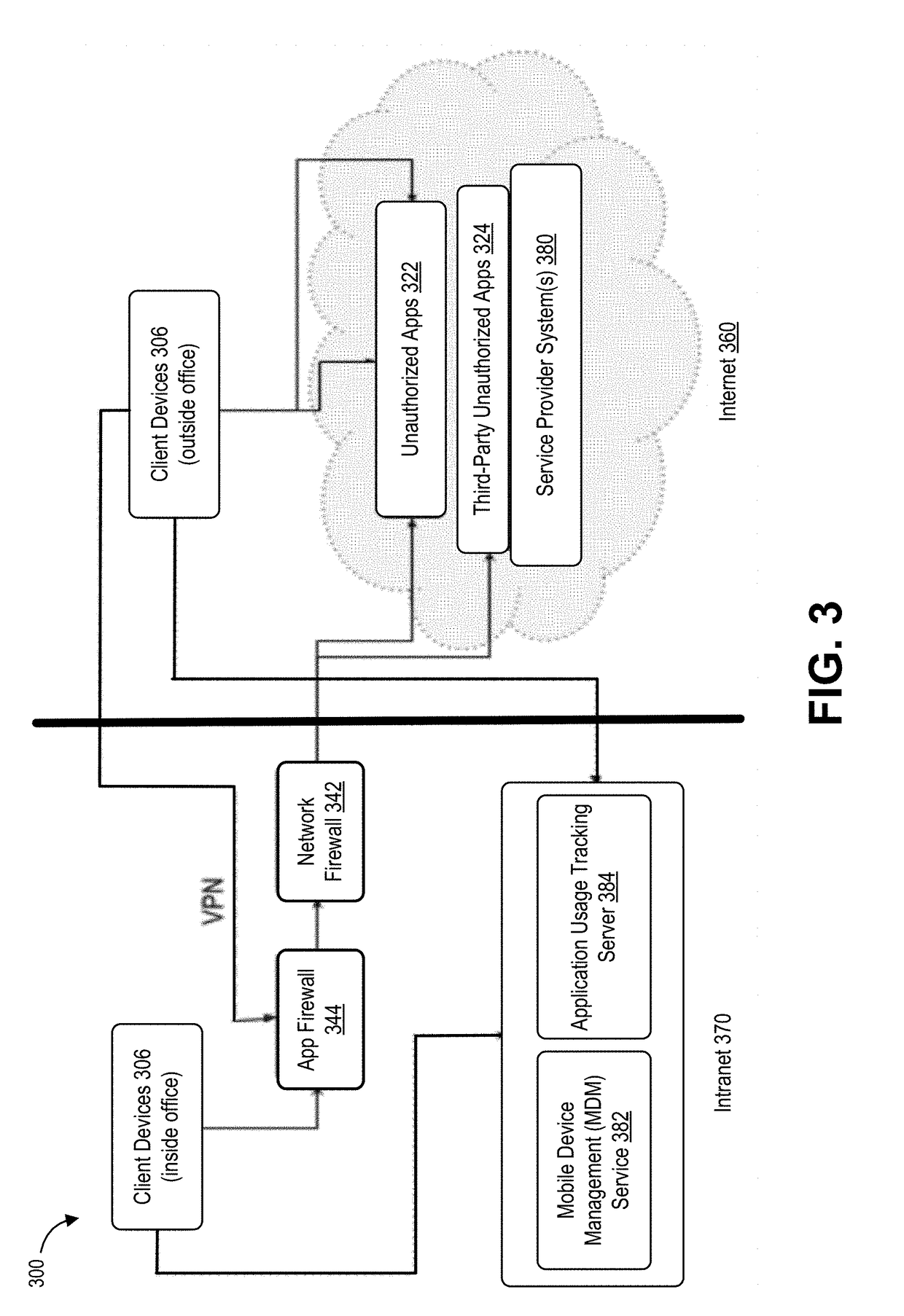
Dynamic guest image creation and rollback
According to one embodiment, a computerized method comprises three operations. First, an incoming object is analyzed to determine if the incoming object is suspicious by having characteristics that suggest the object is an exploit. Next, a virtual machine is dynamically configured with a software image representing a current operating state of a targeted client device. The software image represents content and structure of a storage volume for the targeted client device at a time of configuring the virtual machine. Lastly, the object is processed by the virtual machine in order to detect any anomalous behaviors that may cause the object to be classified as an exploit.
Owner:FIREEYE SECURITY HLDG US LLC
Automatic root cause analysis of performance problems using auto-baselining on aggregated performance metrics
InactiveUS20080235365A1Multiple digital computer combinationsTransmissionDrill downAnomalous behavior
Anomalous behavior in a distributed system is automatically detected. Metrics are gathered for transactions, subsystems and / or components of the subsystems. The metrics can identify response times, error counts and / or CPU loads, for instance. Baseline metrics and associated deviation ranges are automatically determined and can be periodically updated. Metrics from specific transactions are compared to the baseline metrics to determine if an anomaly has occurred. A drill down approach can be used so that metrics for a subsystem are not examined unless the metrics for an associated transaction indicate an anomaly. Further, metrics for a component, application which includes one or more components, or process which includes one or more applications, are not examined unless the metrics for an associated subsystem indicate an anomaly. Multiple subsystems can report the metrics to a central manager, which can correlate the metrics to transactions using transaction identifiers or other transaction context data.
Owner:CA TECH INC
Cloud based security monitoring using unsupervised pattern recognition and deep learning
Provided are systems and methods for a cloud security system that learns patterns of user behavior and uses the patterns to detect anomalous behavior in a network. Techniques discussed herein include obtaining activity data from a service provider system. The activity data describes actions performed during use of a cloud service over a period of time. A pattern corresponding to a series of actions performed over a subset of time can be identified. The pattern can be added a model associated with the cloud service. The model represents usage of the cloud service by the one or more users. Additional activity data can be obtained from the service provider system. Using the model, a set of actions can be identified in the additional activity data that do not correspond to the model. The set of actions and an indicator that identifies the set of actions as anomalous can be output.
Owner:ORACLE INT CORP
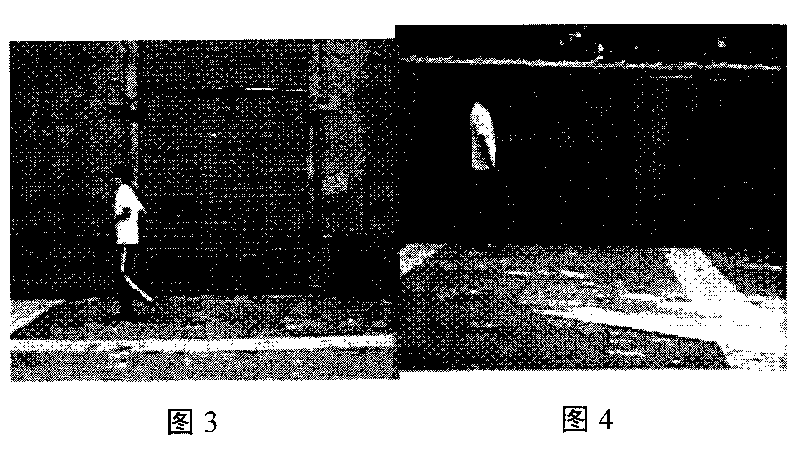
Movement human abnormal behavior identification method based on template matching
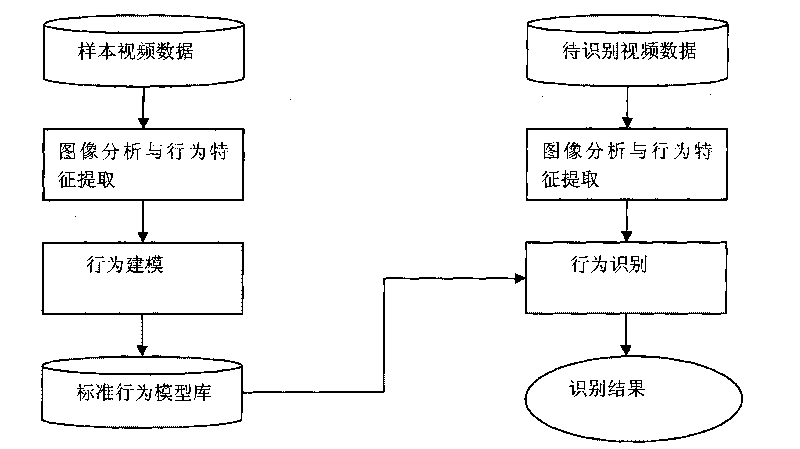
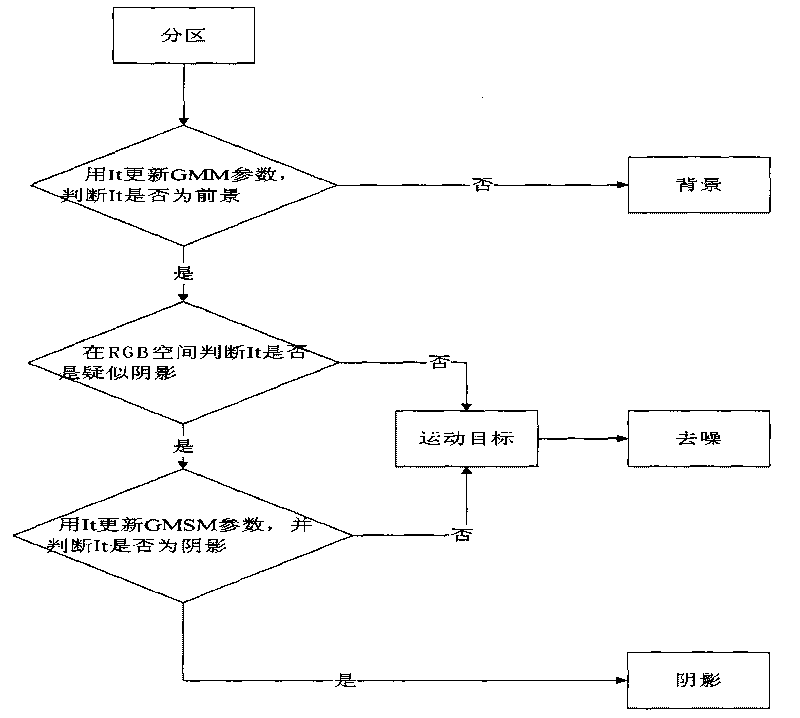
InactiveCN101719216AGood effectThe effect is accurateCharacter and pattern recognitionVisual technologyAnomalous behavior
The invention relates to a movement human abnormal behavior identification method based on template matching, which mainly comprises the steps of: video image acquisition and behavior characteristic extraction. The movement human abnormal behavior identification method is a mode identification technology based on statistical learning of samples. The movement of a human is analyzed and comprehended by using a computer vision technology, the behavior identification is directly carried out based on geometric calculation of a movement region and recording and alarming are carried out; the Gaussian filtering denoising and the neighborhood denoising are combined for realizing the denoising, thereby improving the independent analysis property and the intelligent monitoring capacity of an intelligent monitoring system, achieving higher identification accuracy for abnormal behaviors, effectively removing the complex background and the noise of a vision acquired image, and improving the efficiency and the robustness of the detection algorithm. The invention has simple modeling, simple algorithm and accurate detection, can be widely applied to occasions of banks, museums and the like, and is also helpful to improve the safety monitoring level of public occasions.
Owner:XIDIAN UNIV
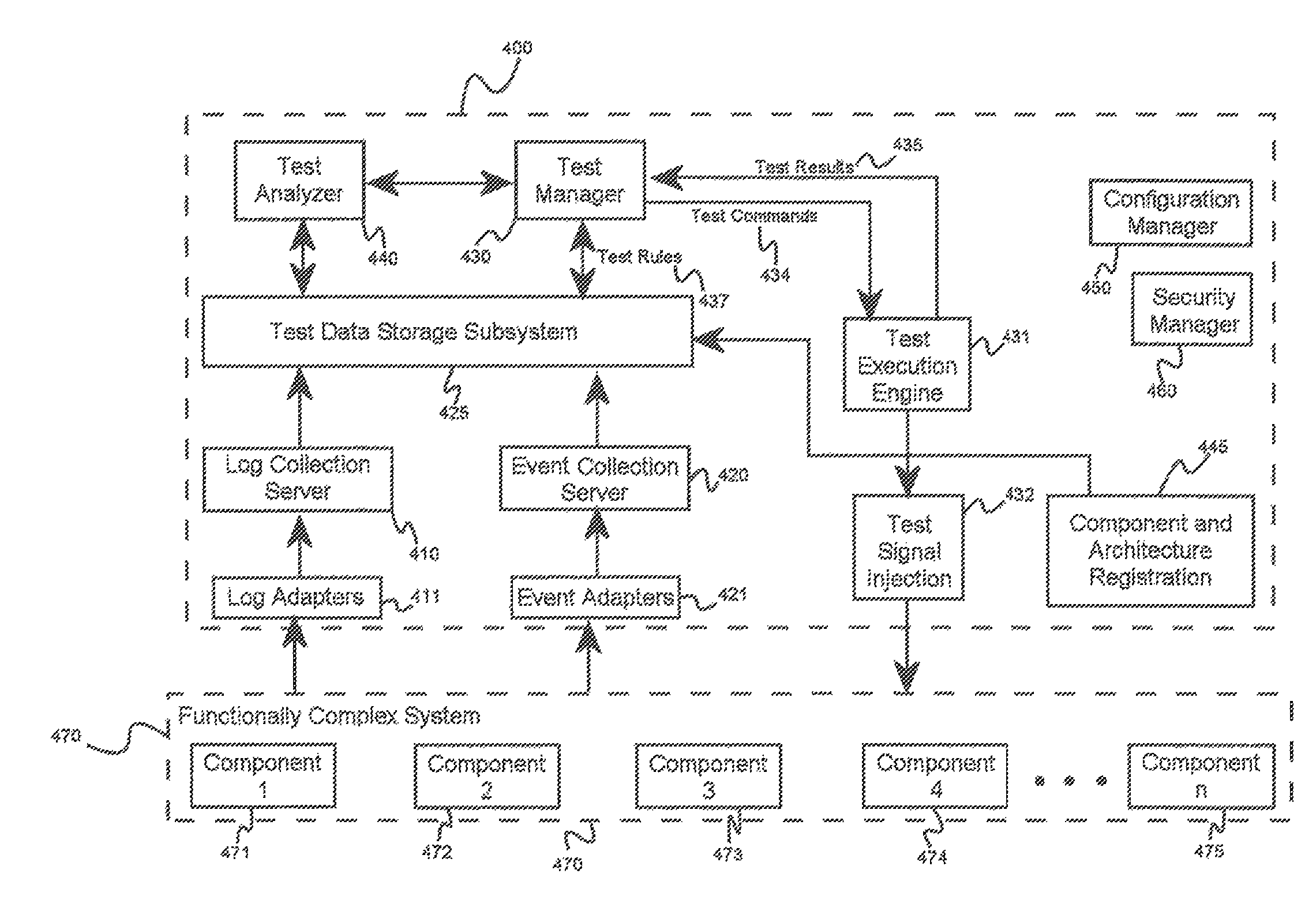
System and methods for automated testing of functionally complex systems
ActiveUS8418000B1Avoid mistakesNon-redundant fault processingTransmissionComputer hardwareAnomalous behavior
A system for automated testing of functionally complex systems, comprising a test manager module operating on a server computer, a test data storage subsystem coupled to the test manager module and adapted to store at least test results, a test execution module operating on a server computer, and a test analysis module operating on a server computer and adapted to receive test data from the test data storage subsystem. The test manager module causes tests to be executed by the test execution engine, and on detection of an anomalous test result, the test manager module at least causes additional testing to be performed and causes the test analysis module to analyze the results of at least some of the additional testing in order to isolate at least one component exhibiting anomalous behavior.
Owner:BFACTOR LLC
Method for the detection and visualization of anomalous behaviors in a computer network
Owner:NEXTHINK
Systems and methods to detect abnormal behavior in networks
Systems and methods implemented by a computer to detect abnormal behavior in a network include obtaining Performance Monitoring (PM) data including one or more of production PM data, lab PM data, and simulated PM data; determining a model based on machine learning training with the PM data; receiving live PM data from the network; utilizing the live PM data with the model to detect an anomaly in the network; and causing an action to address the anomaly.
Owner:CIENA
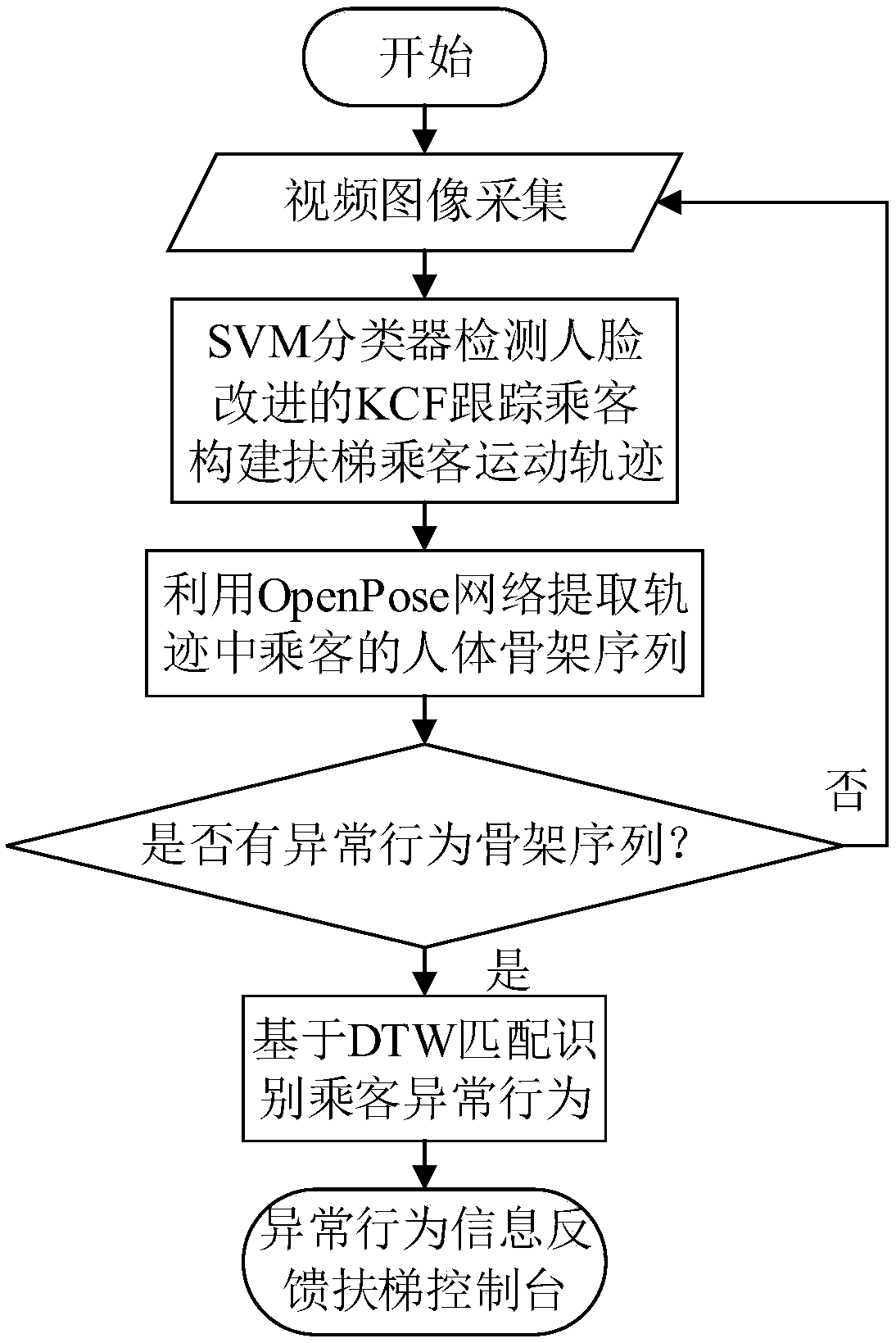
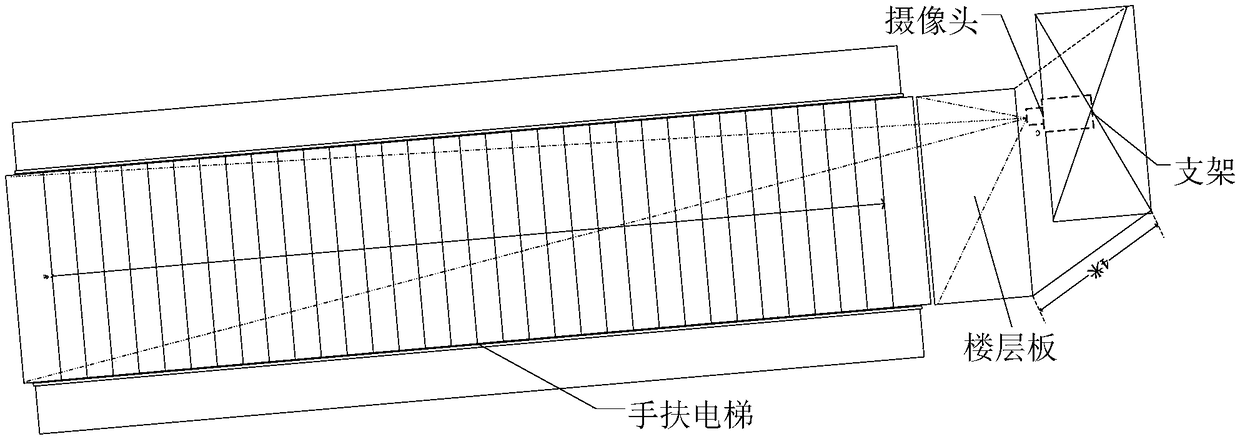
Passenger abnormal behavior recognition method based on human skeleton sequence
ActiveCN109460702AAccurate and stable buildAccurate and stable trajectoryImage enhancementImage analysisTemplate matchingAnomalous behavior
The invention discloses a passenger abnormal behavior identification method based on a human skeleton sequence, which comprises the following steps: 1) shooting an escalator area monitoring video image by a camera; 2) detecting that passenger face through the SVM and trac the passenger face with the KCF to obtain the passenger motion trajectory in the escalator; 3) extracting that human skeleton from the image by using the OpenPose depth learn network; 4) matching that human skeleton to the corresponding passenger trajectory to construct the human skeleton sequence of the passenger; 5) detecting that abnormal behavior skeleton sequence from the passenger human skeleton sequence through template match; 6) using DTW to match it with various abnormal behavior skeleton sequence template to identify abnormal behavior. That invention can accurately and real-time identify a plurality of abnormal behavior of passengers in the escalator base on human skeleton sequence, according to the abnormalbehavior type to control the operation situation of the escalator, and avoid the occurrence of safety accident.
Owner:SOUTH CHINA UNIV OF TECH +1
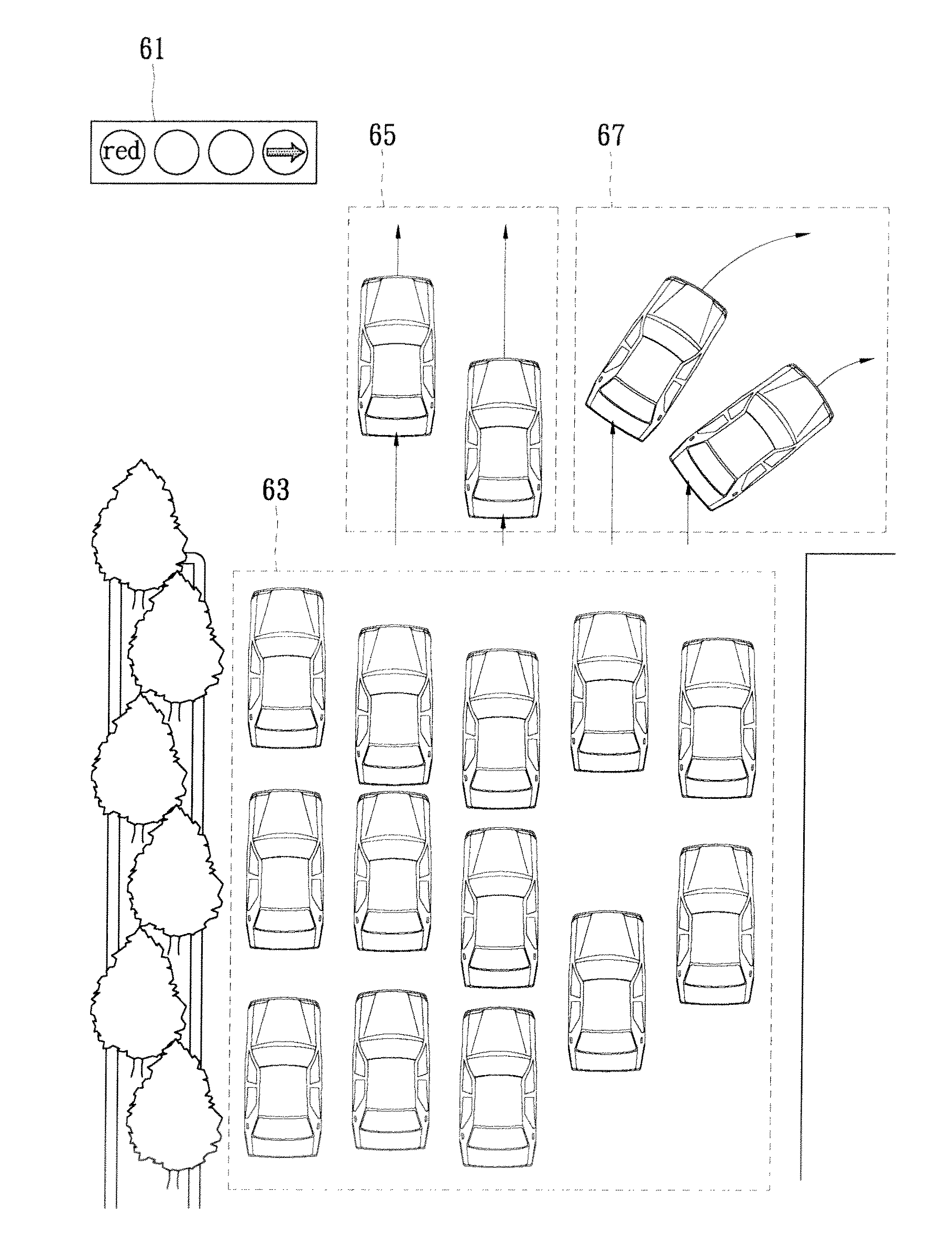
Abnormal behavior detection system and method using automatic classification of multiple features
ActiveUS20120134532A1Reduce construction costsEnhances practicabilityRoad vehicles traffic controlCharacter and pattern recognitionPattern recognitionAnomalous behavior
Described herein are a system and a method for abnormal behavior detection using automatic classification of multiple features. Features from various sources, including those extracted from camera input through digital image analysis, are used as input to machine learning algorithms. These algorithms group the features and produce models of normal and abnormal behaviors. Outlying behaviors, such as those identified by their lower frequency, are deemed abnormal. Human supervision may optionally be employed to ensure the accuracy of the models. Once created, these models can be used to automatically classify features as normal or abnormal. This invention is suitable for use in the automatic detection of abnormal traffic behavior such as running of red lights, driving in the wrong lane, or driving against traffic regulations.
Owner:GORILLA TECH UK LTD
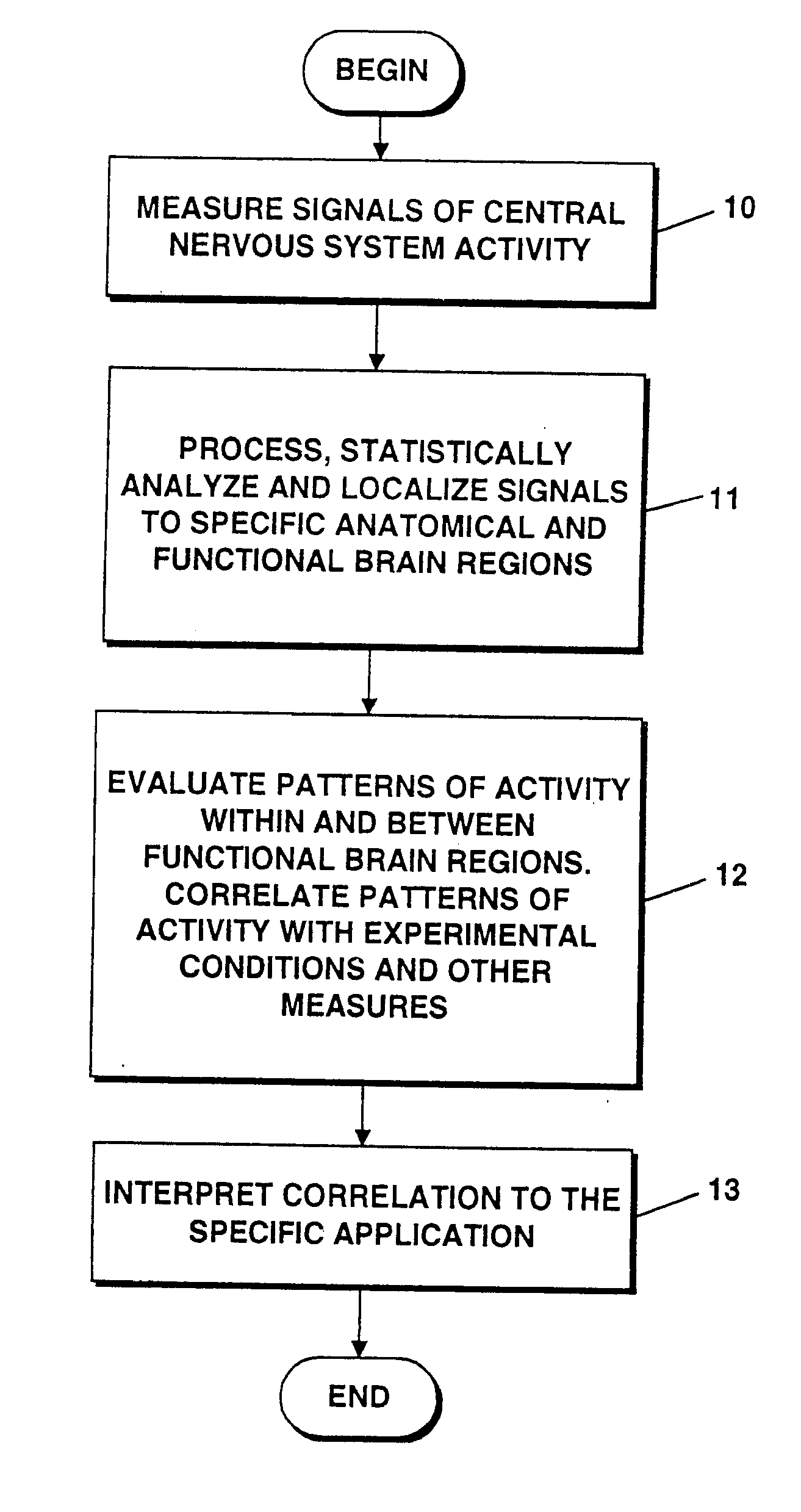
Method and apparatus for measuring indices of brain activity during motivational and emotional function
Owner:THE GENERAL HOSPITAL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com