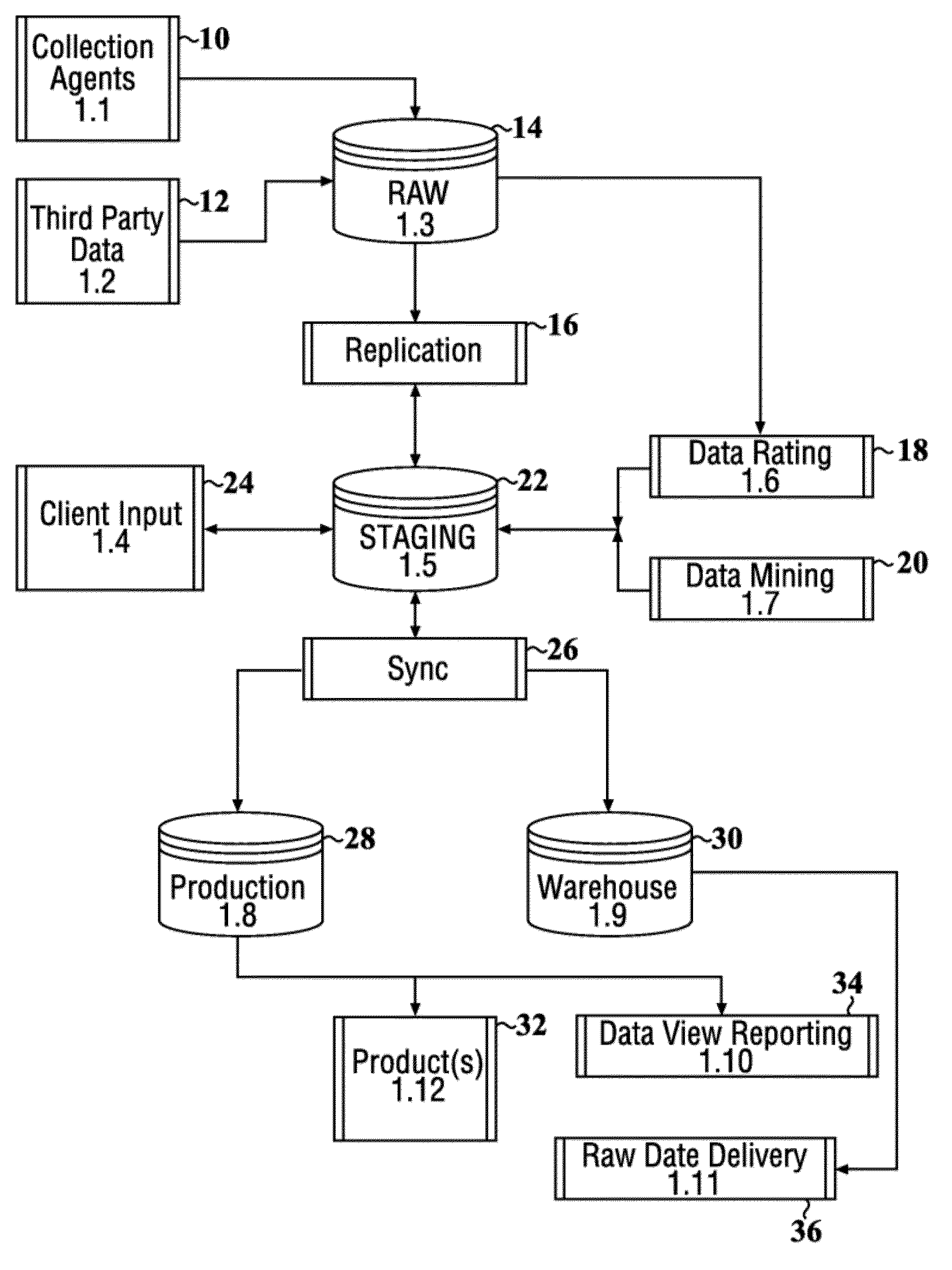
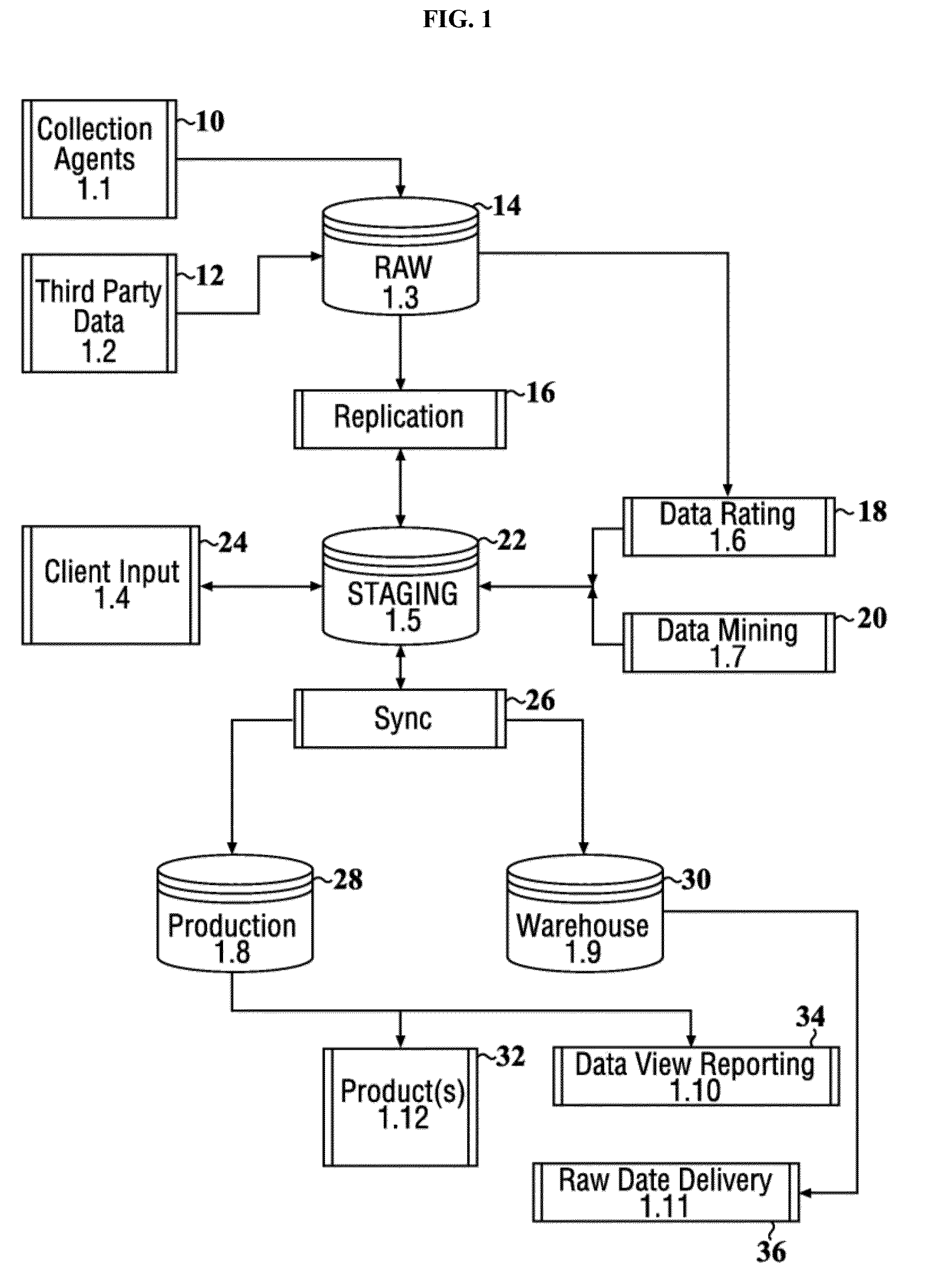
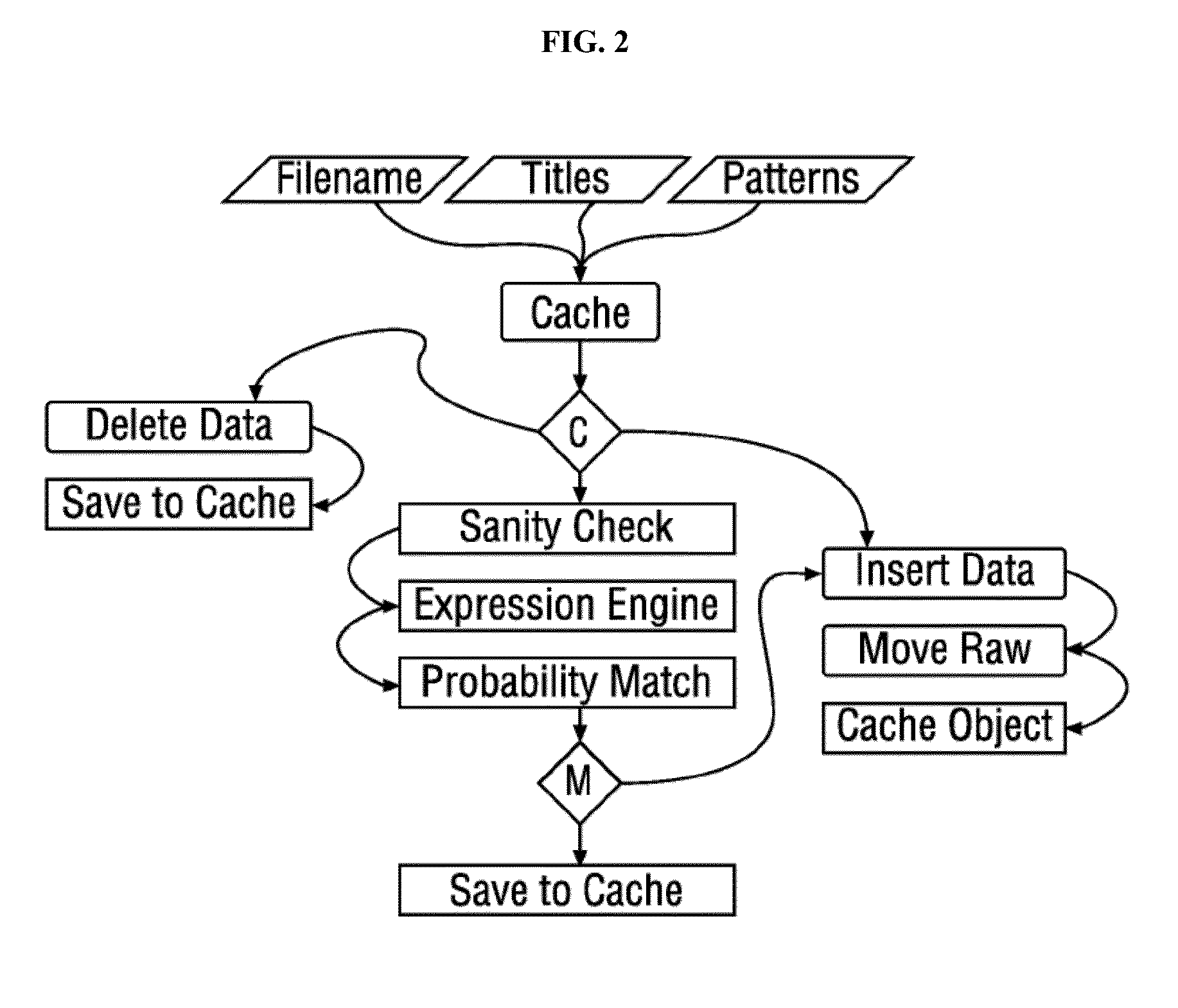
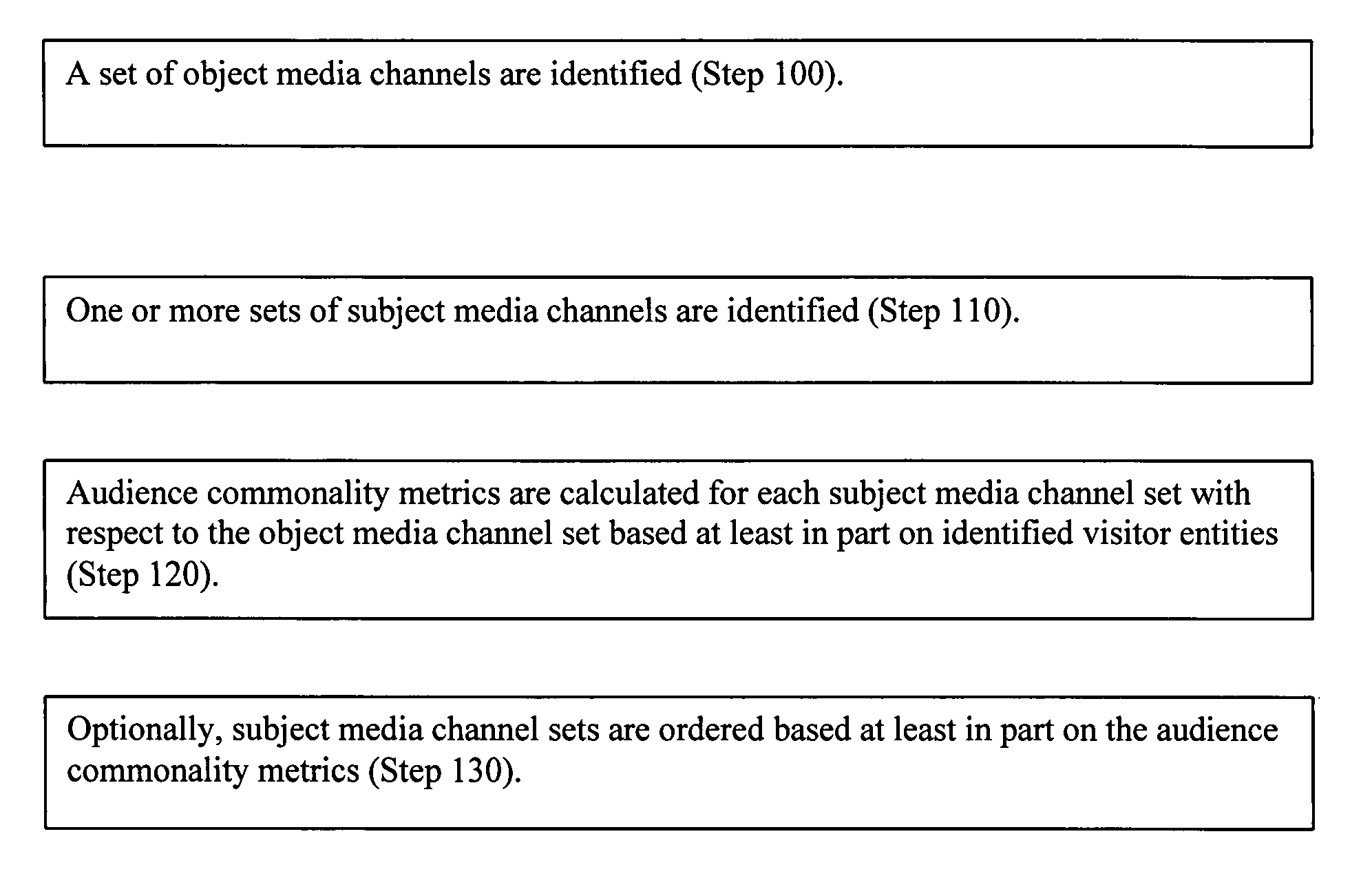
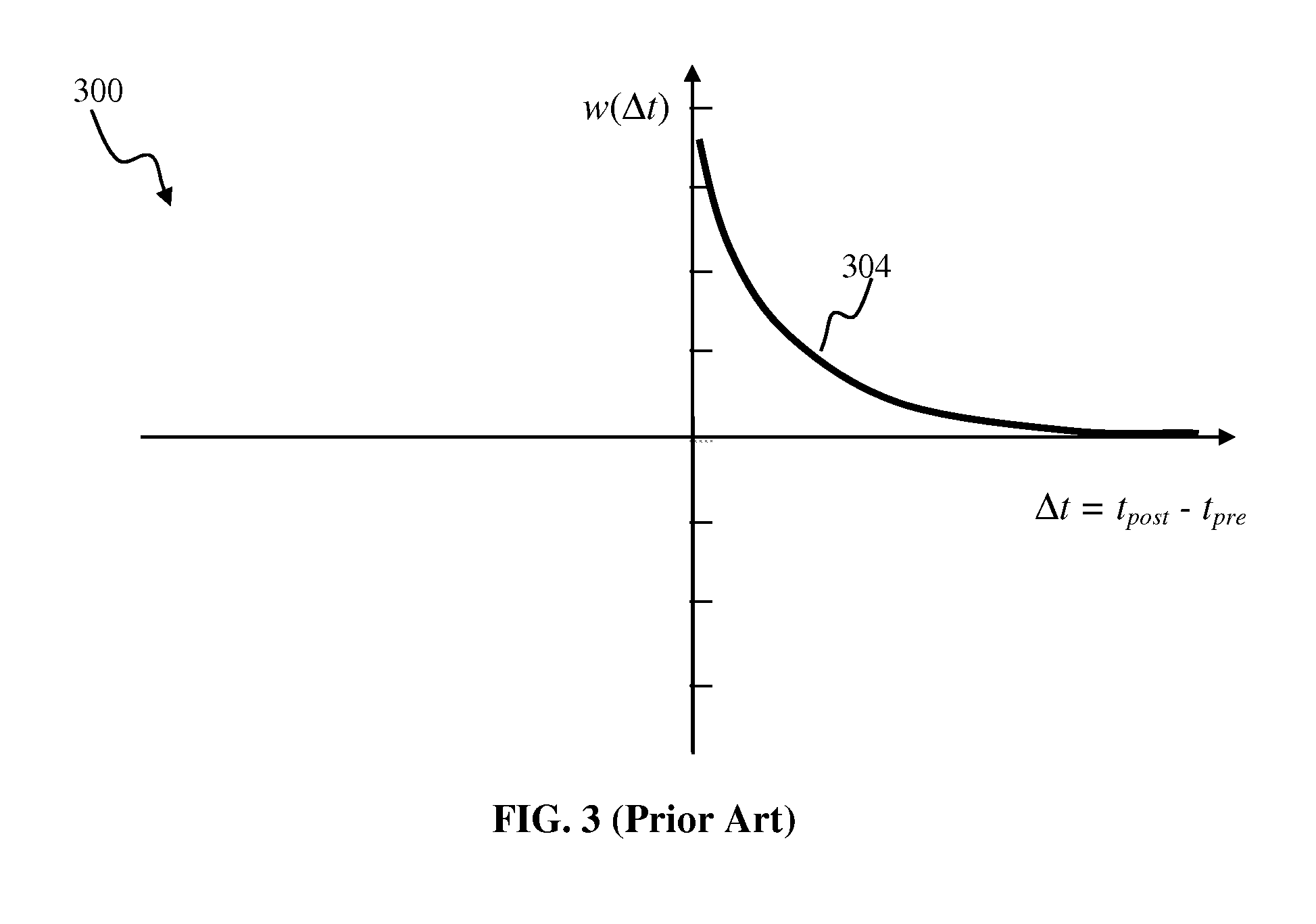
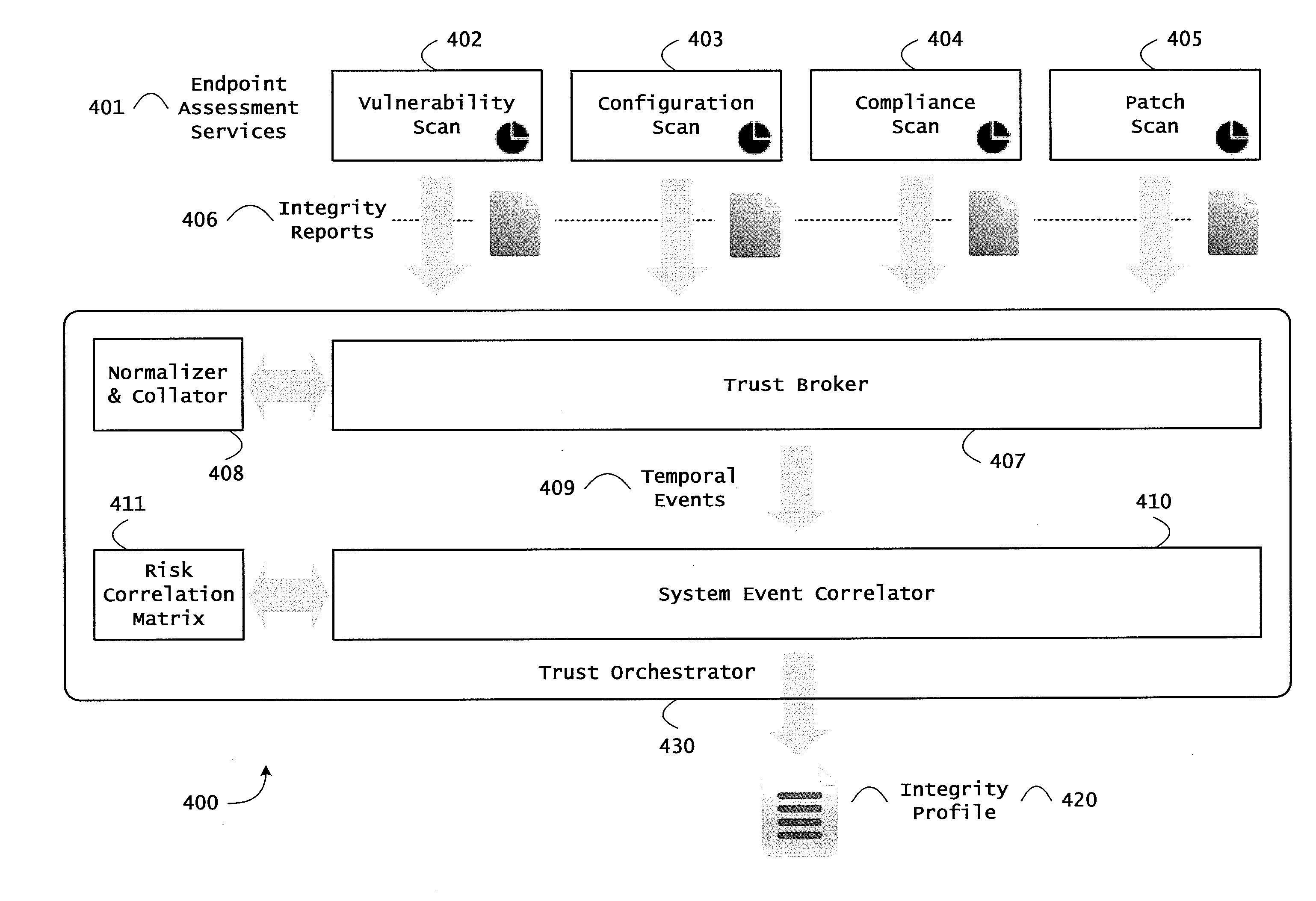
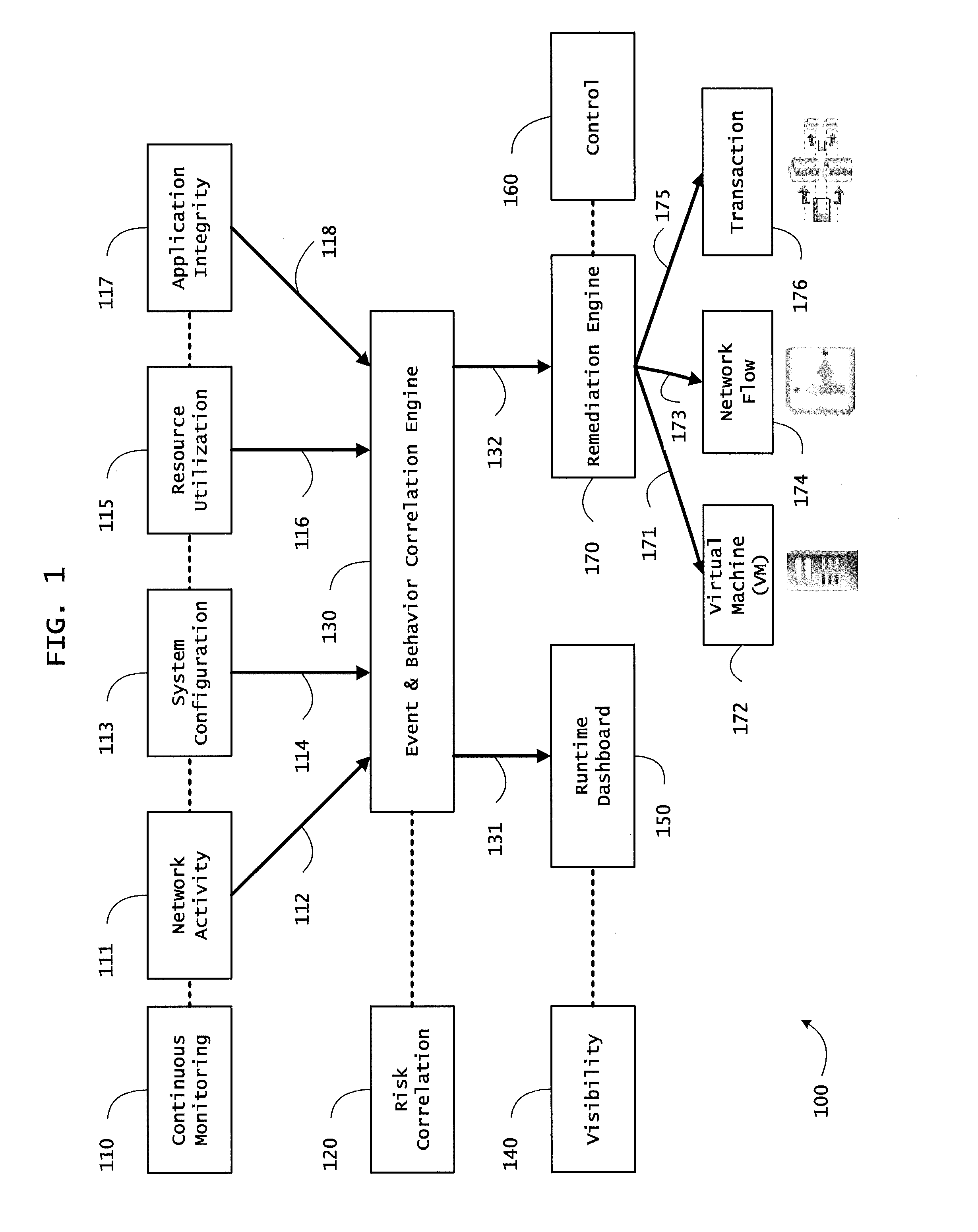
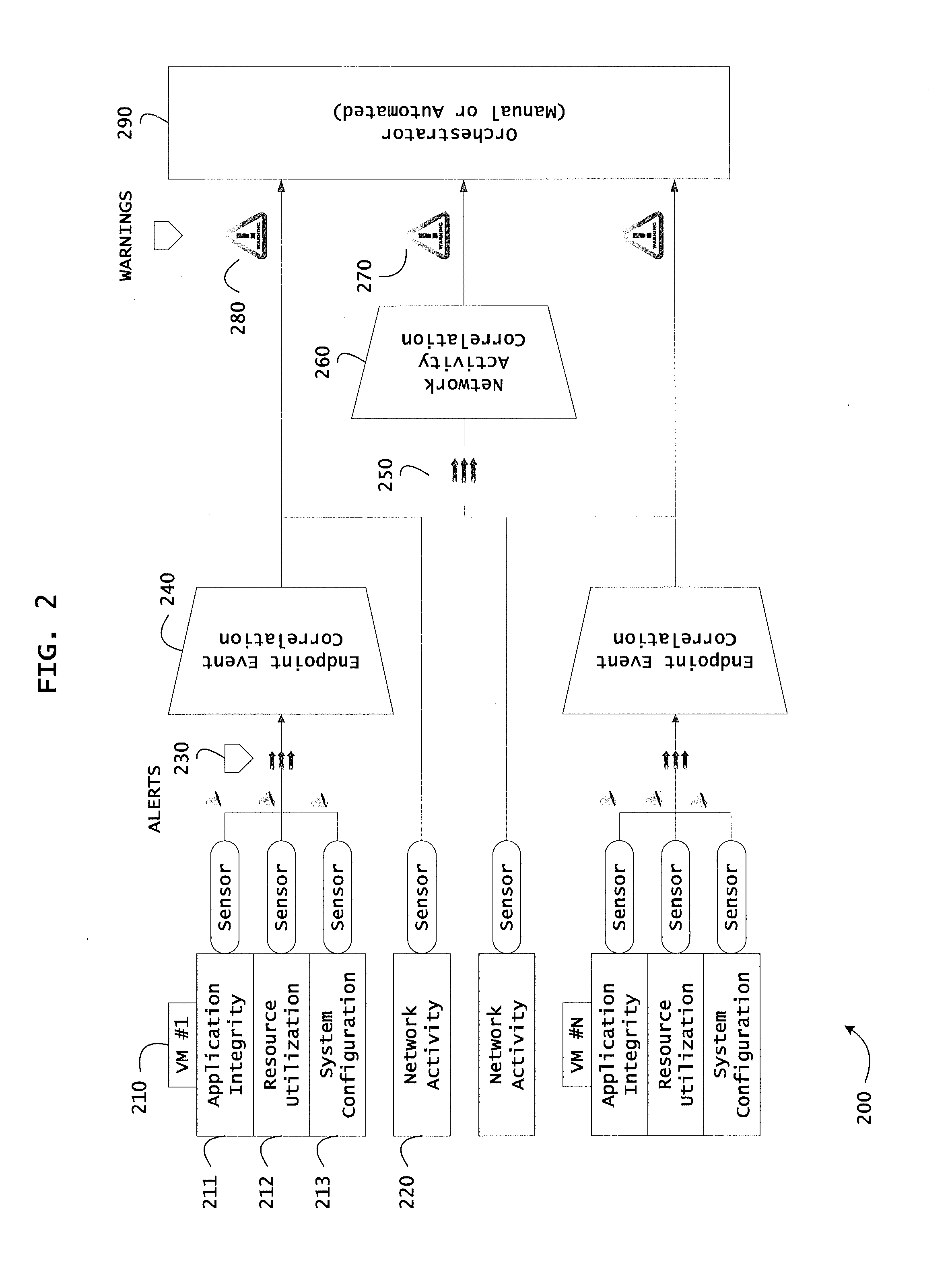
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
456 results about "Network activity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
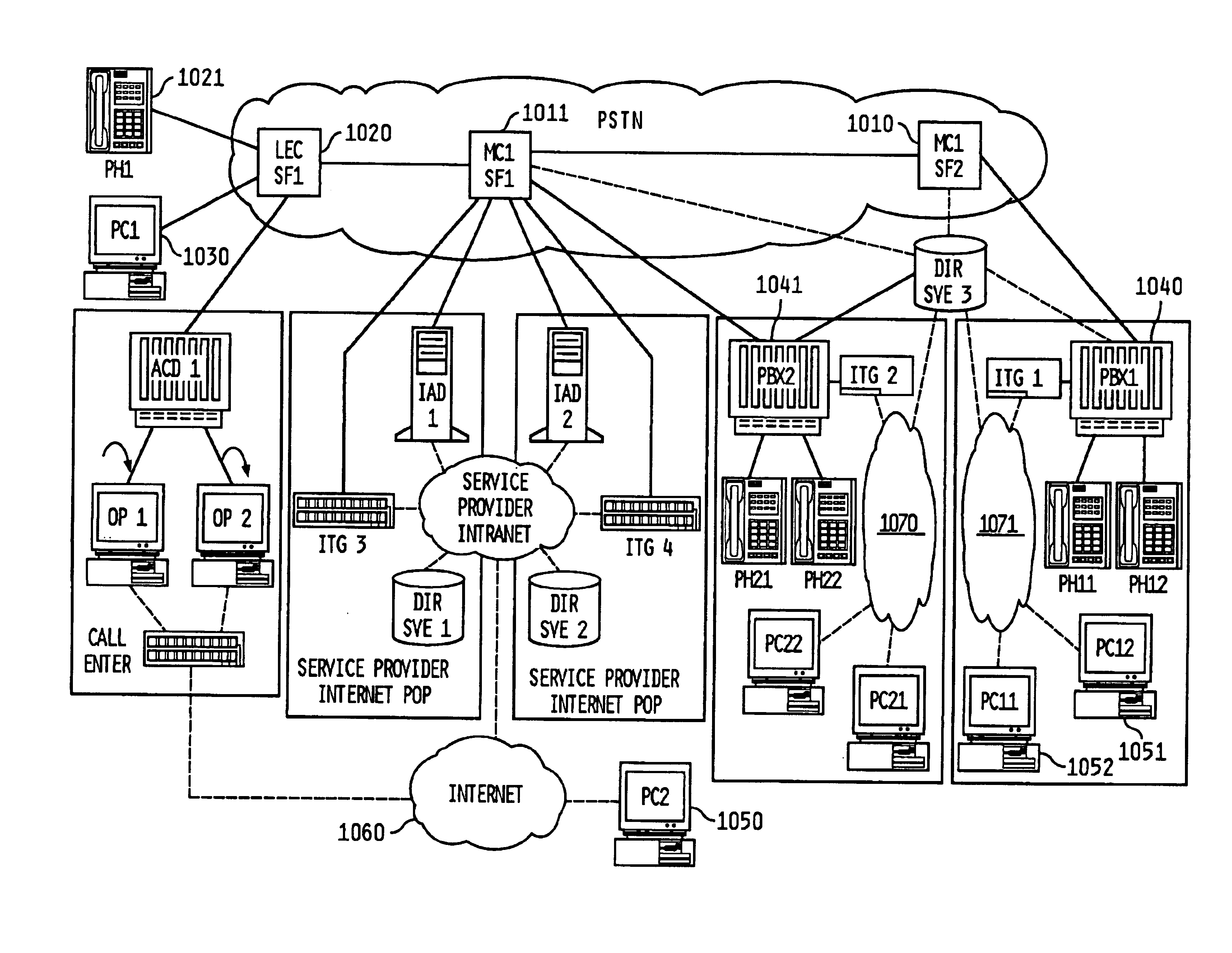
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
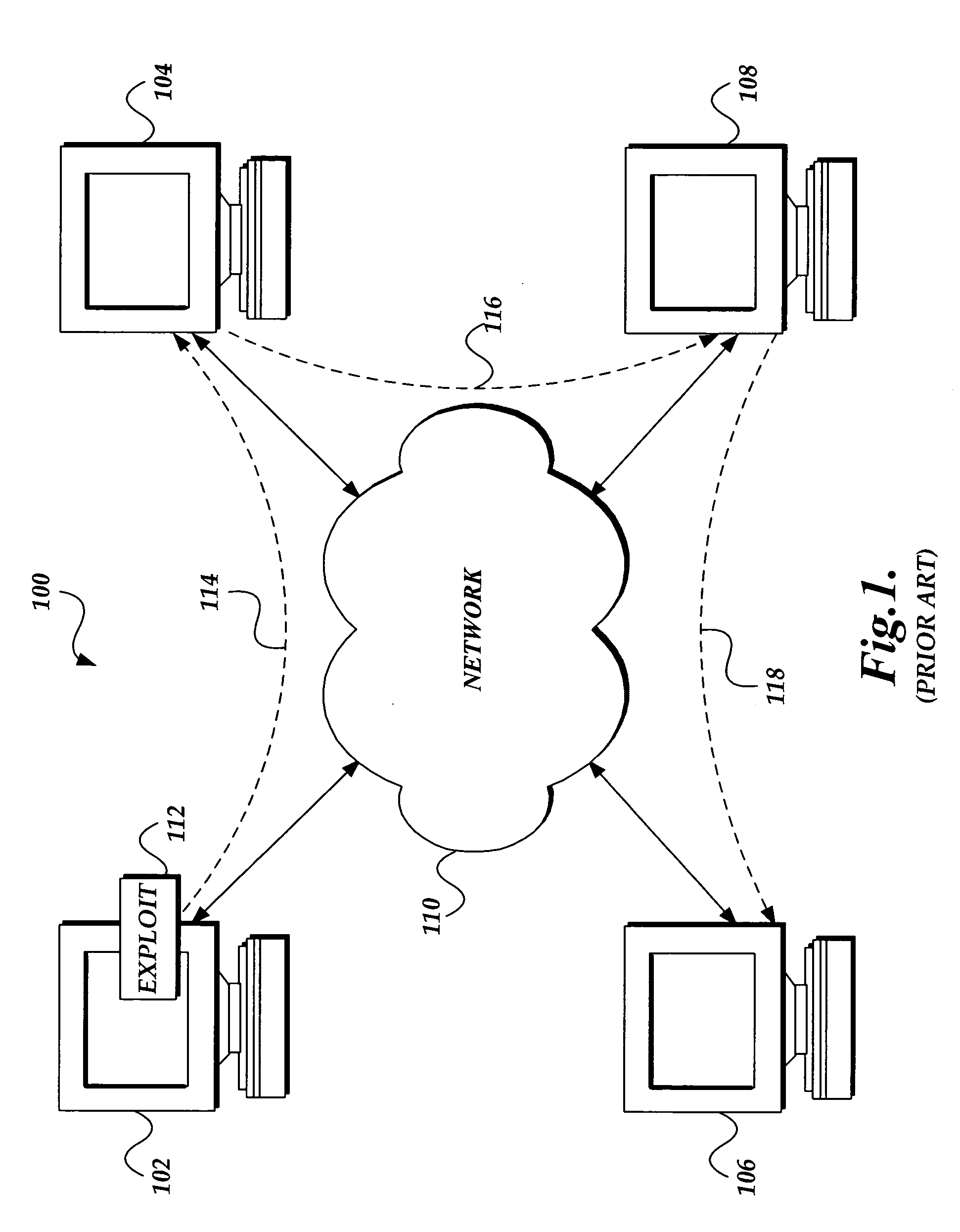
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
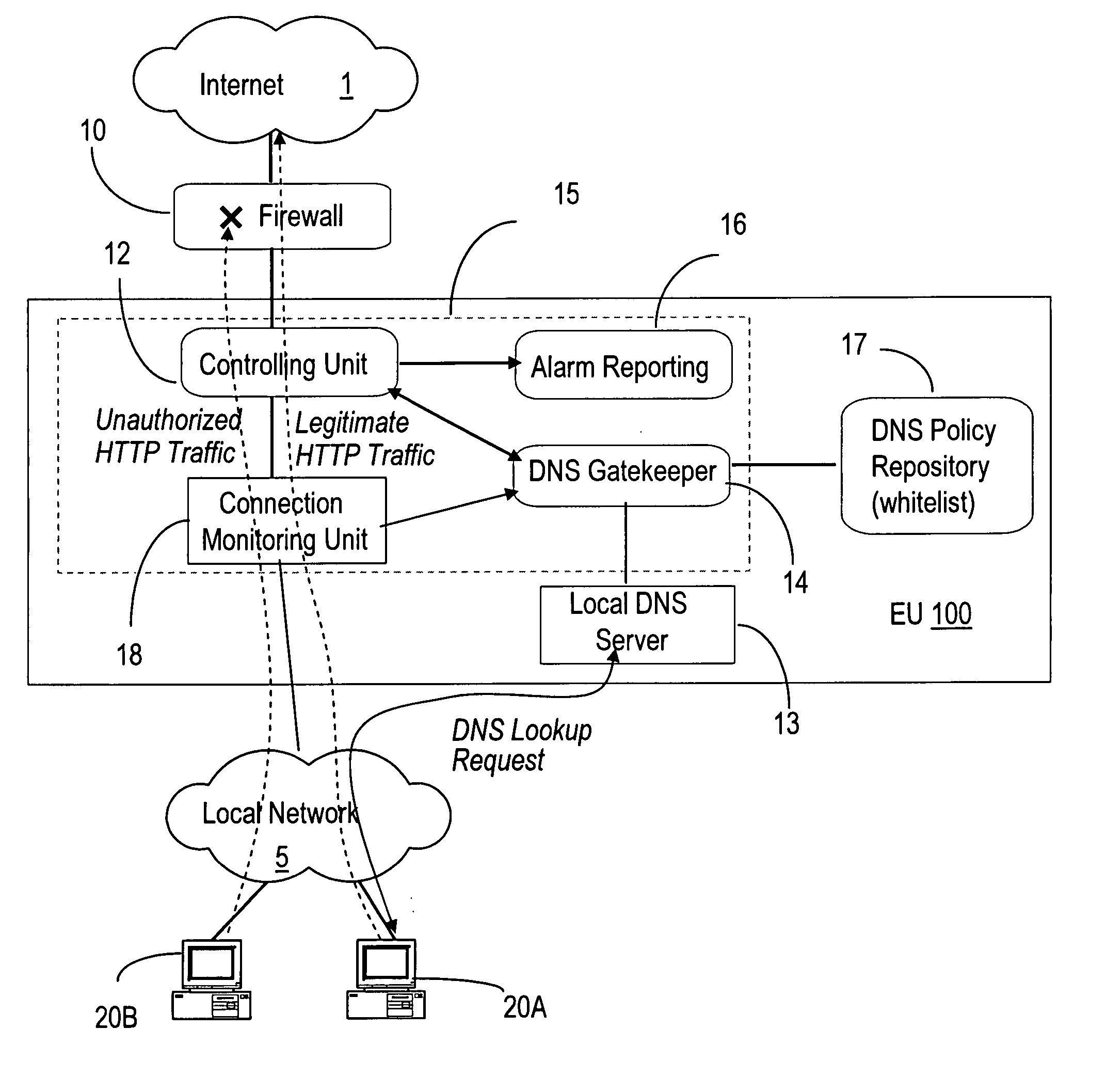
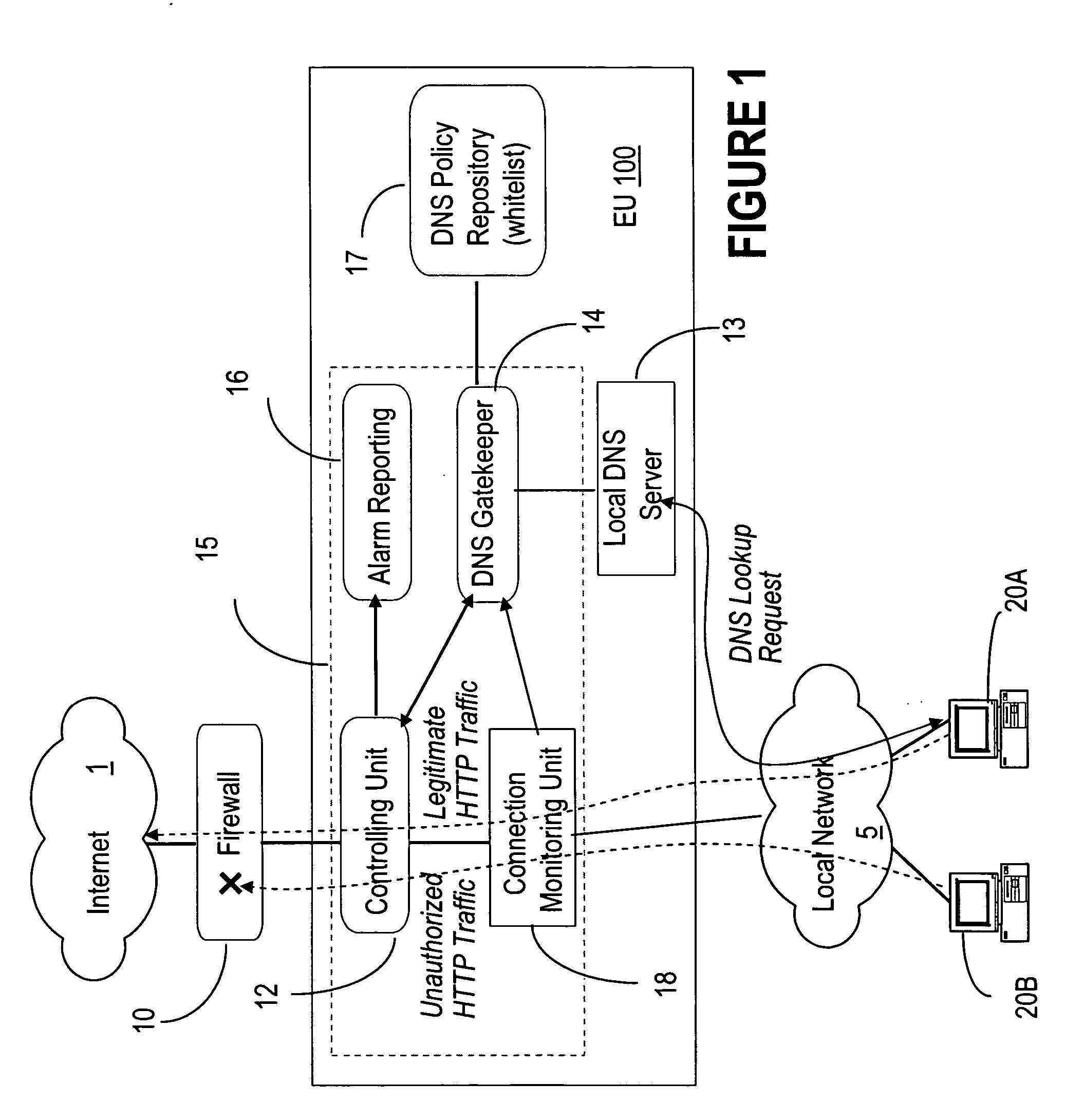
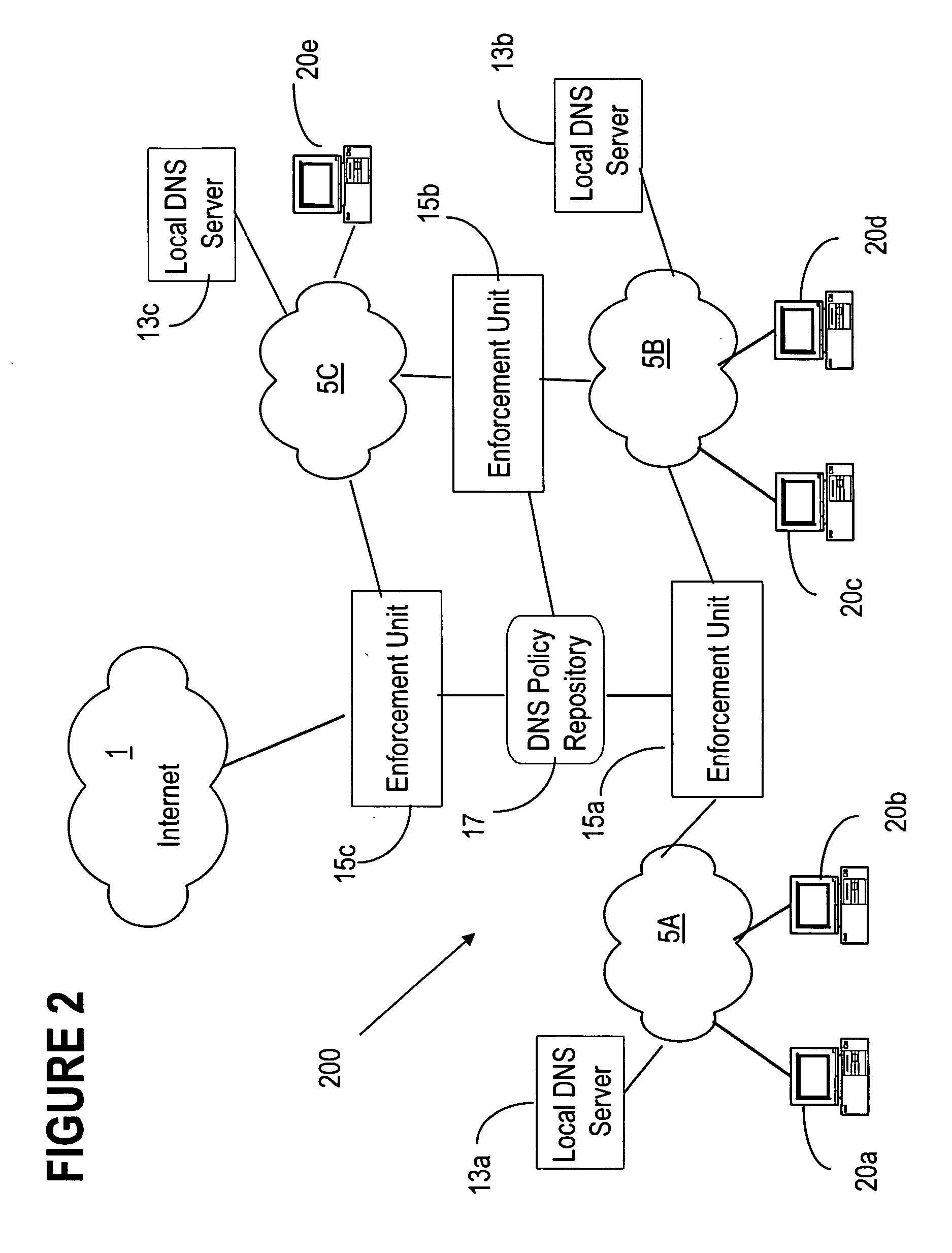
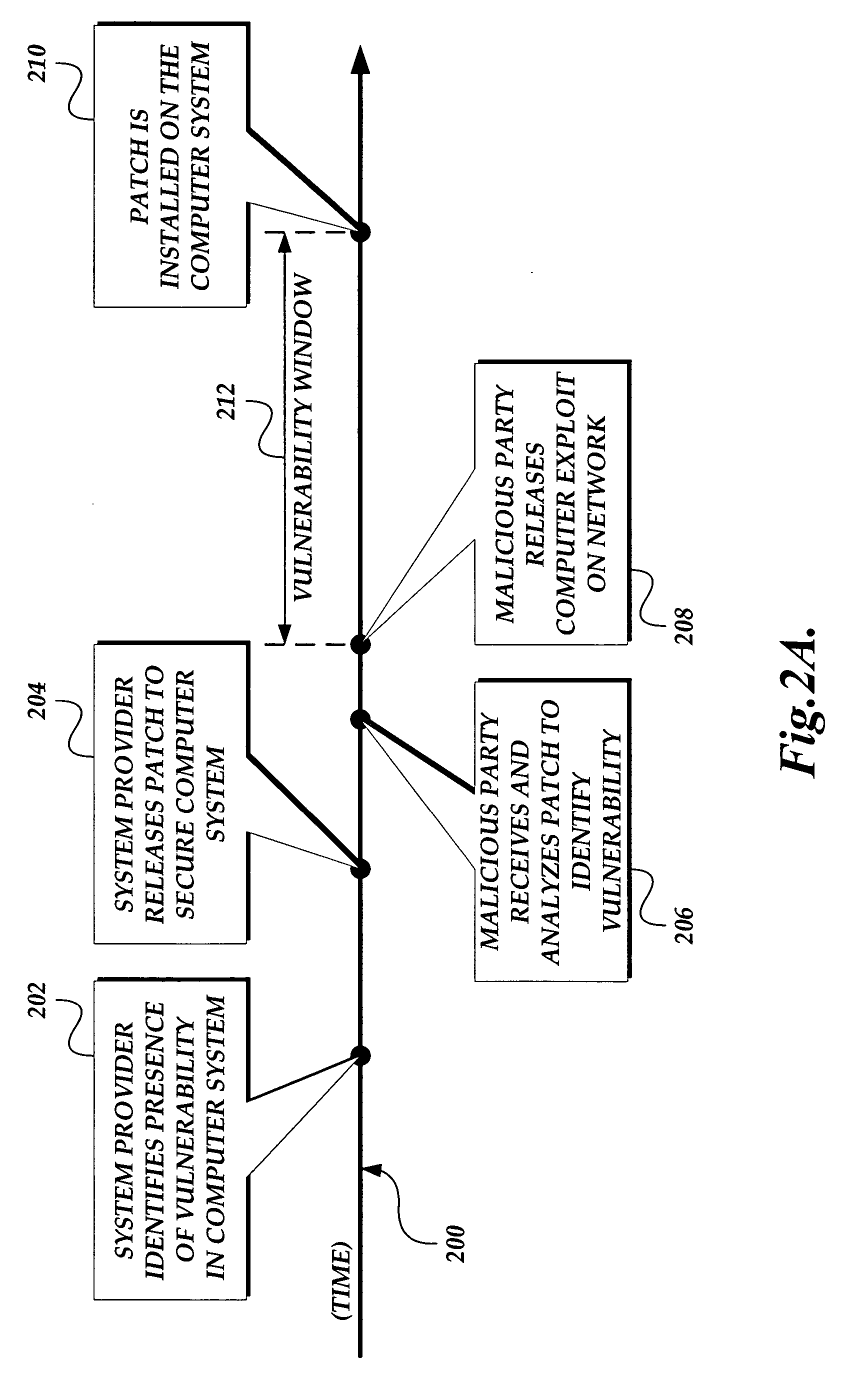
DNS based enforcement for confinement and detection of network malicious activities
InactiveUS20070033645A1Avoid detectionAvoid spreadingDigital data processing detailsUnauthorized memory use protectionDomain nameNetwork activity
Malicious network activities do not make use of the Domain Name System (DNS) protocol to reach remote targets outside a local network. This DNS-based enforcement system for confinement and detection of network malicious activities requires that every connection toward a resource located outside the local network is blocked by default by the local enforcement box, e.g. a firewall or a proxy. Outbound connections are allowed to leave the local network only when authorized directly by an entity called the DNS Gatekeeper.
Owner:RPX CORP
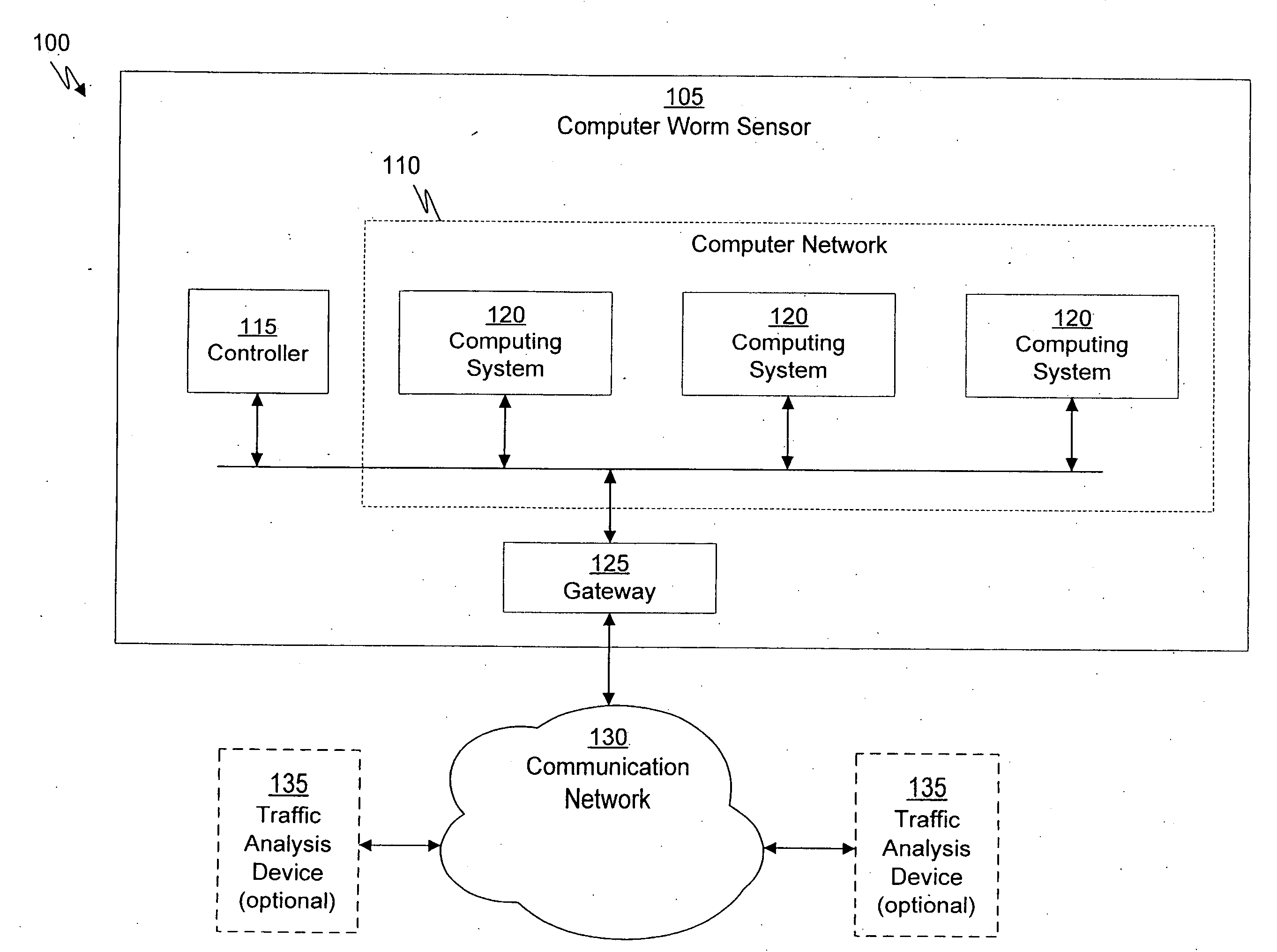
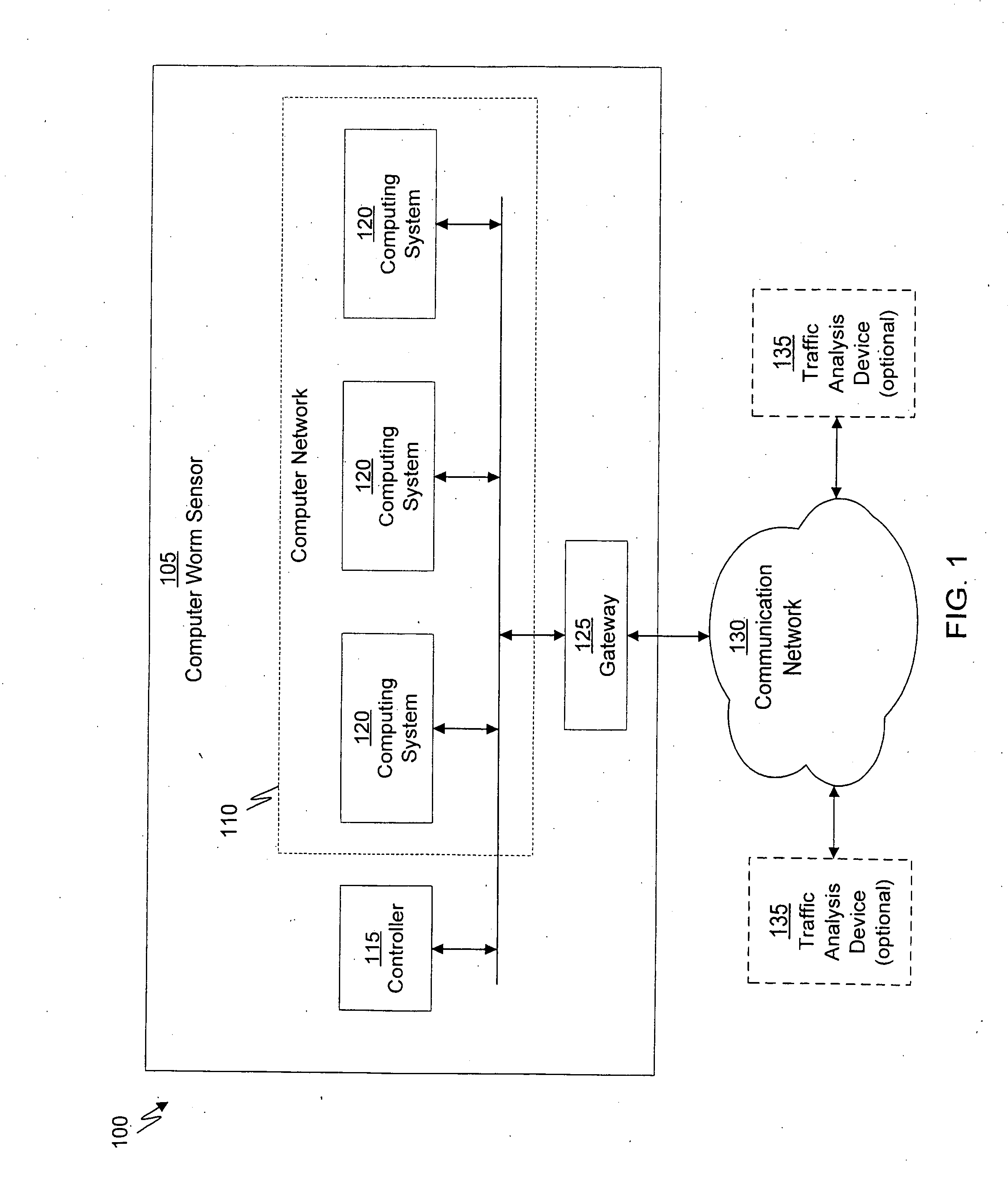
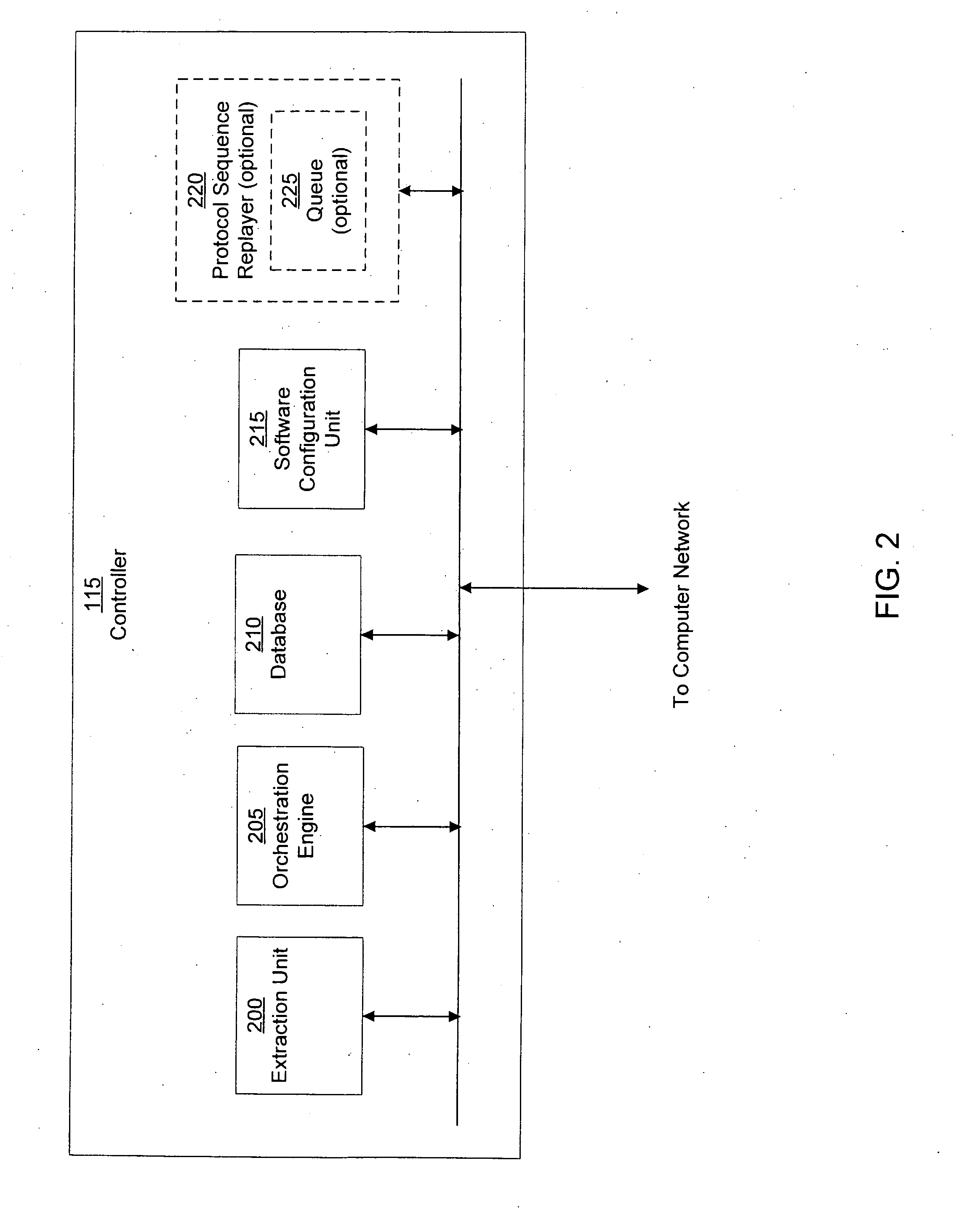
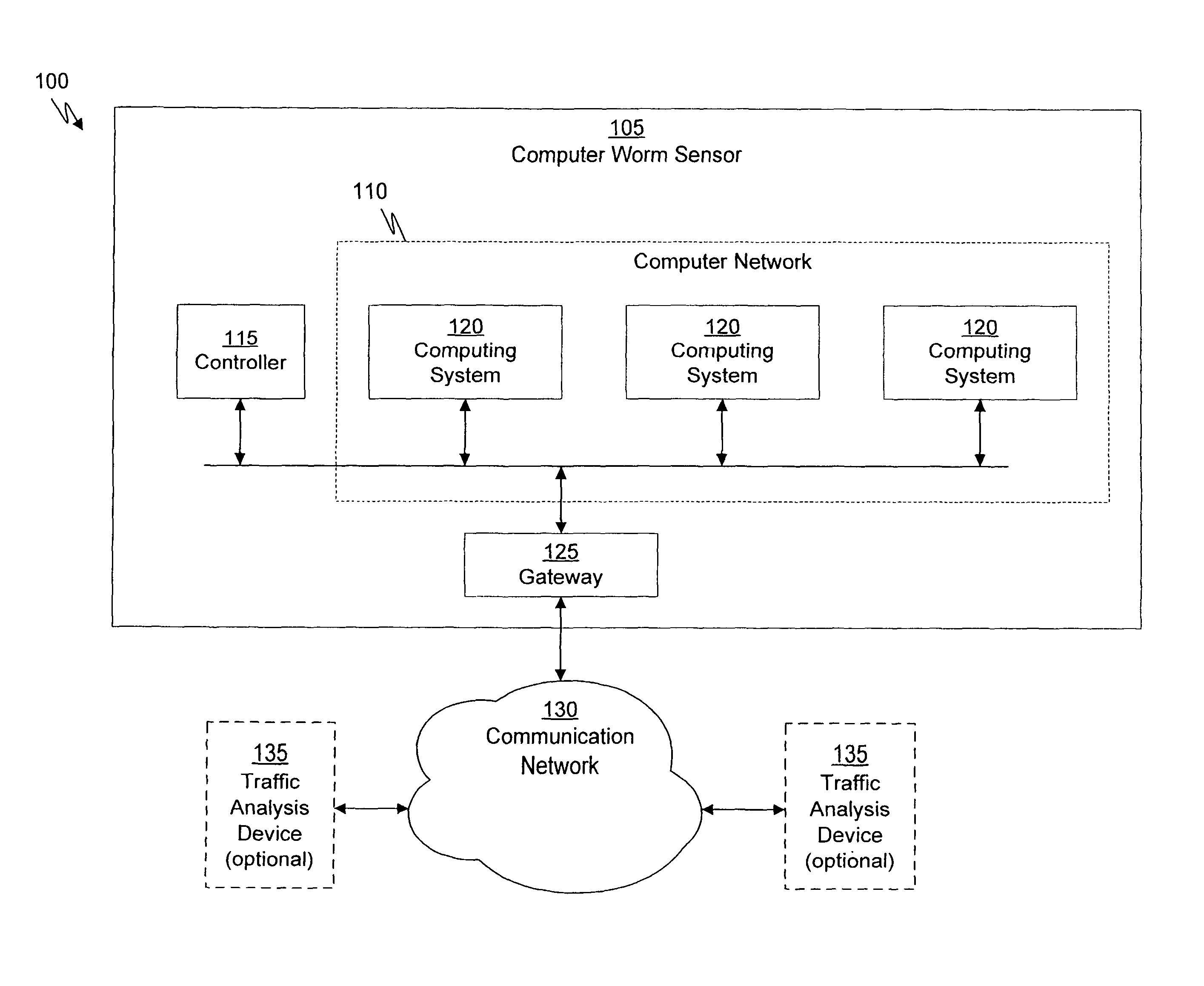
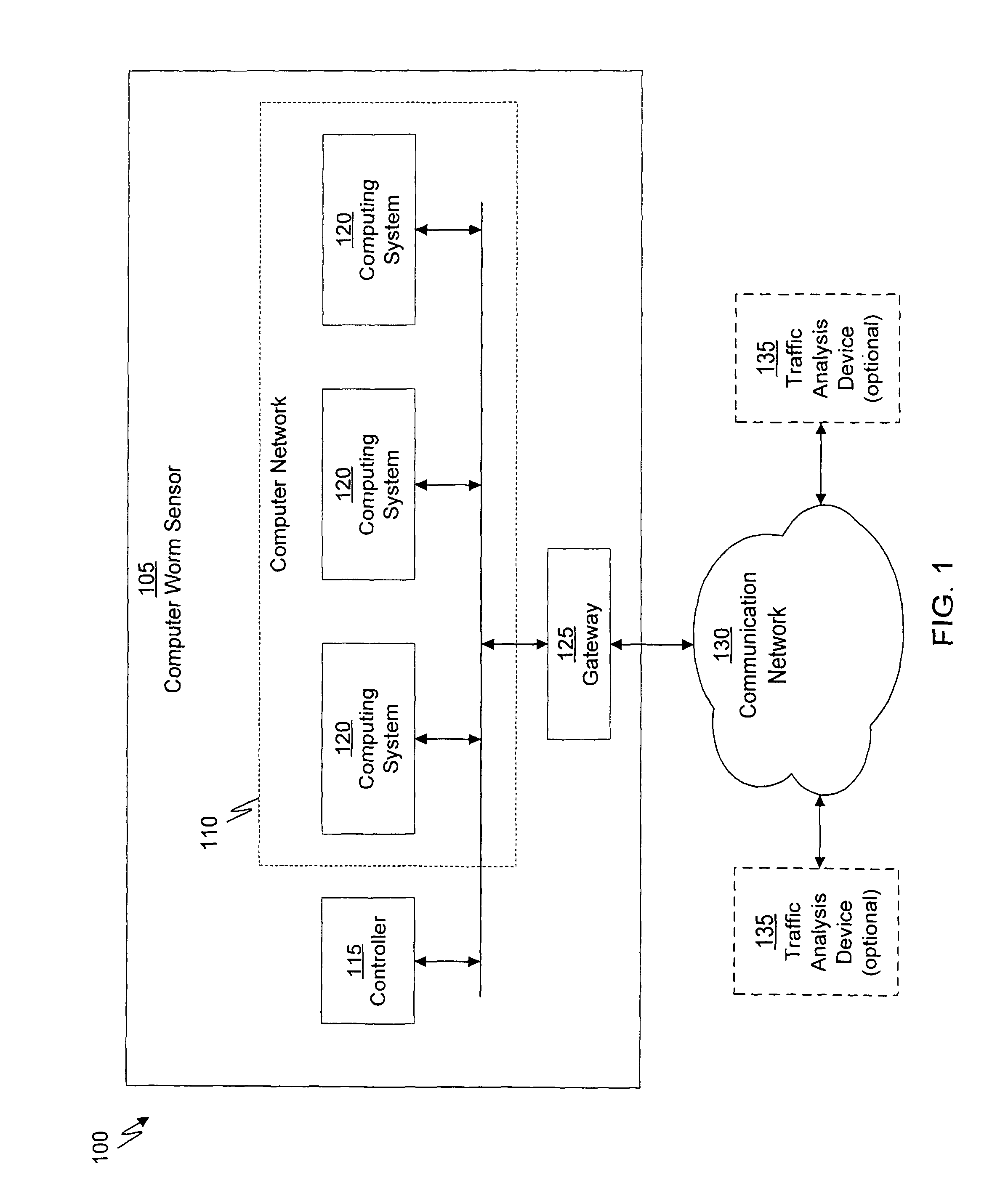
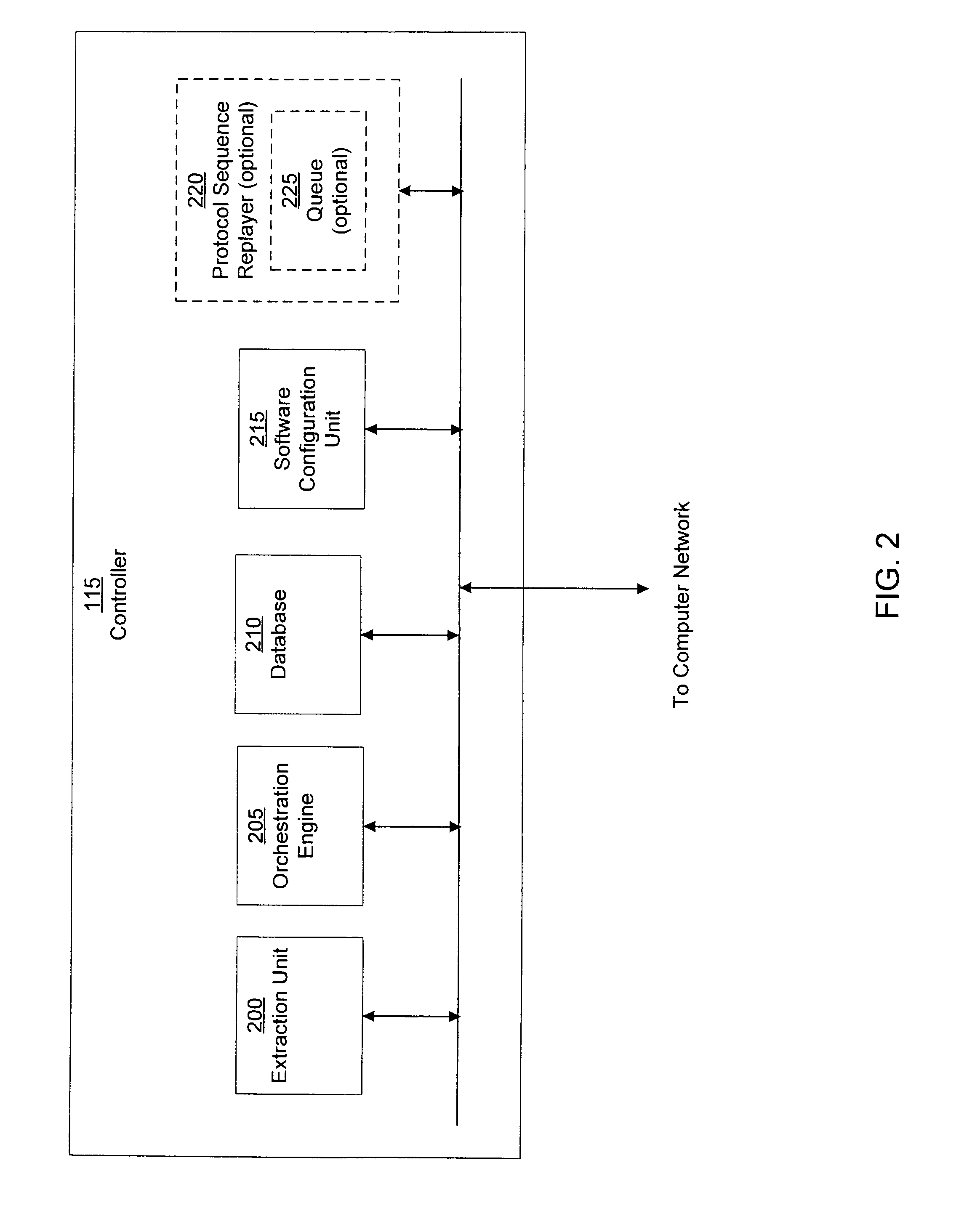
System and method of containing computer worms
ActiveUS20110099633A1Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
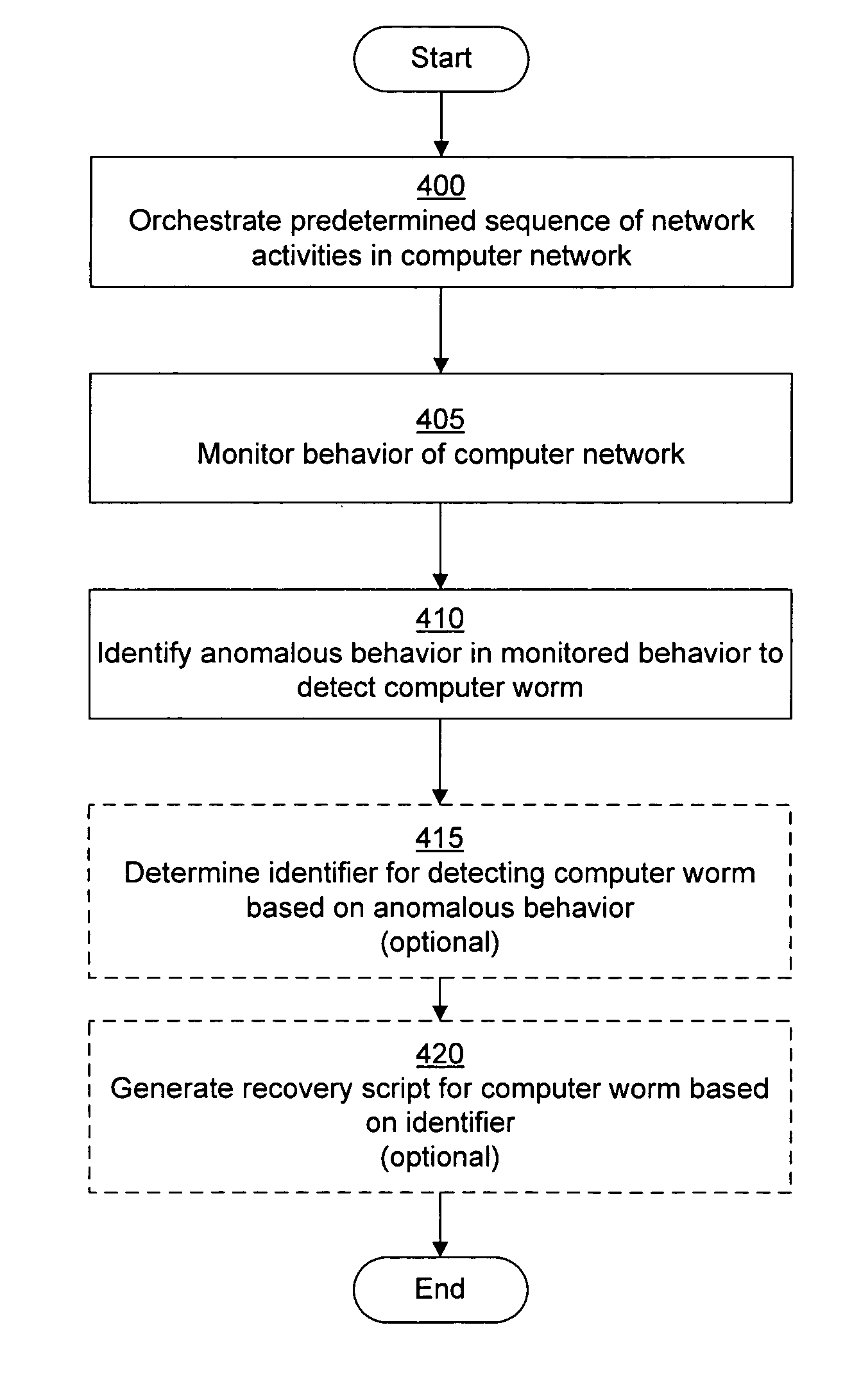
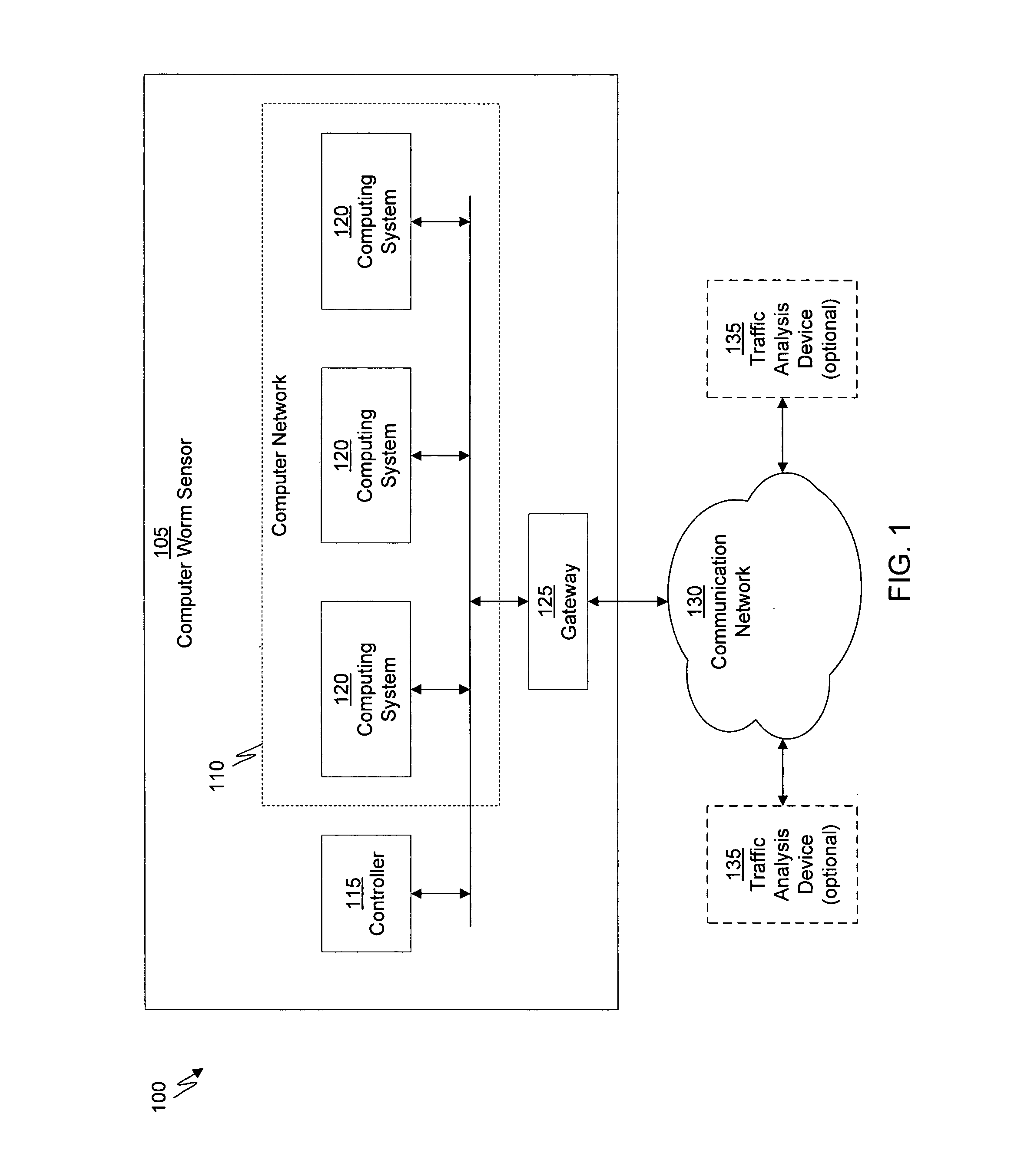
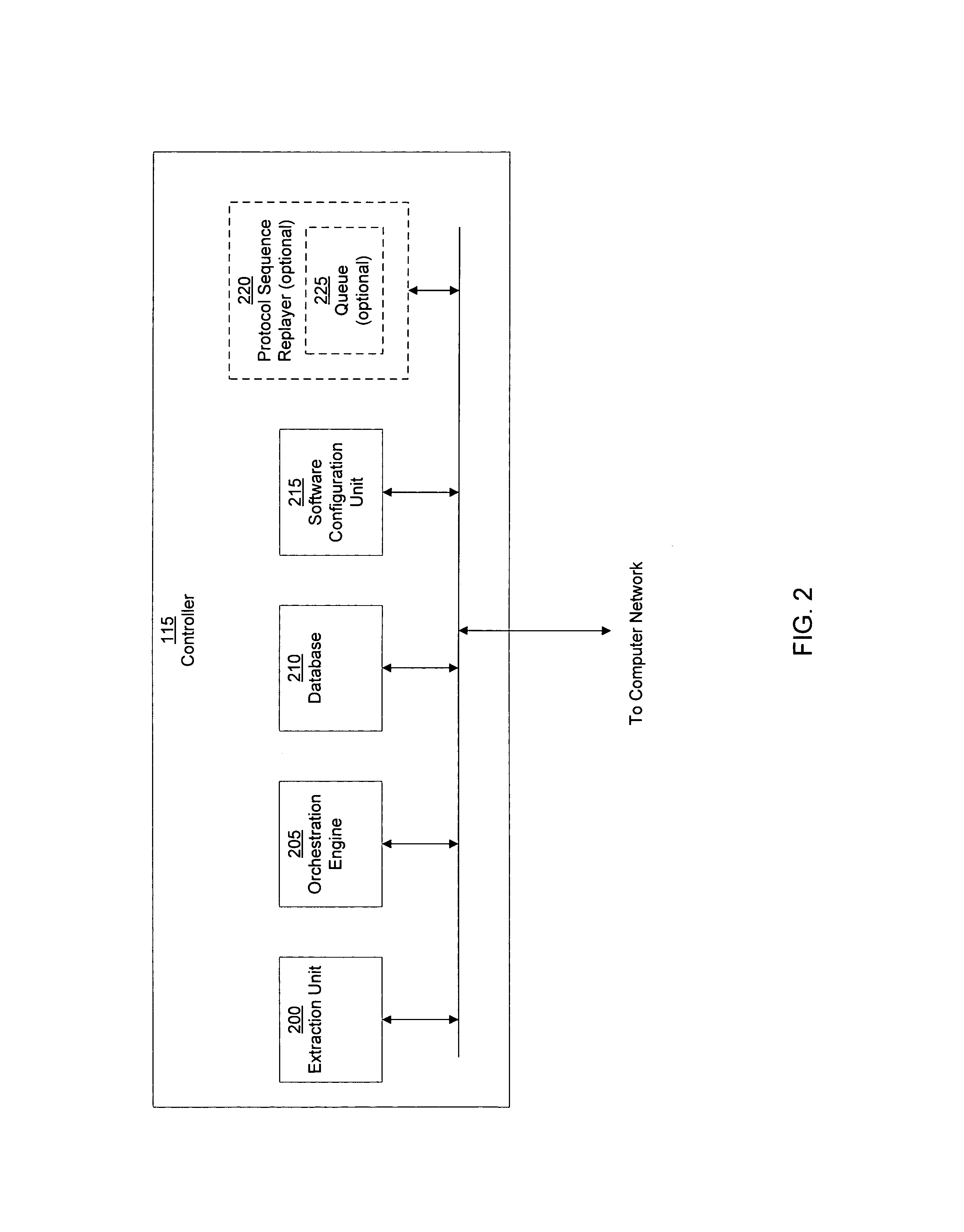
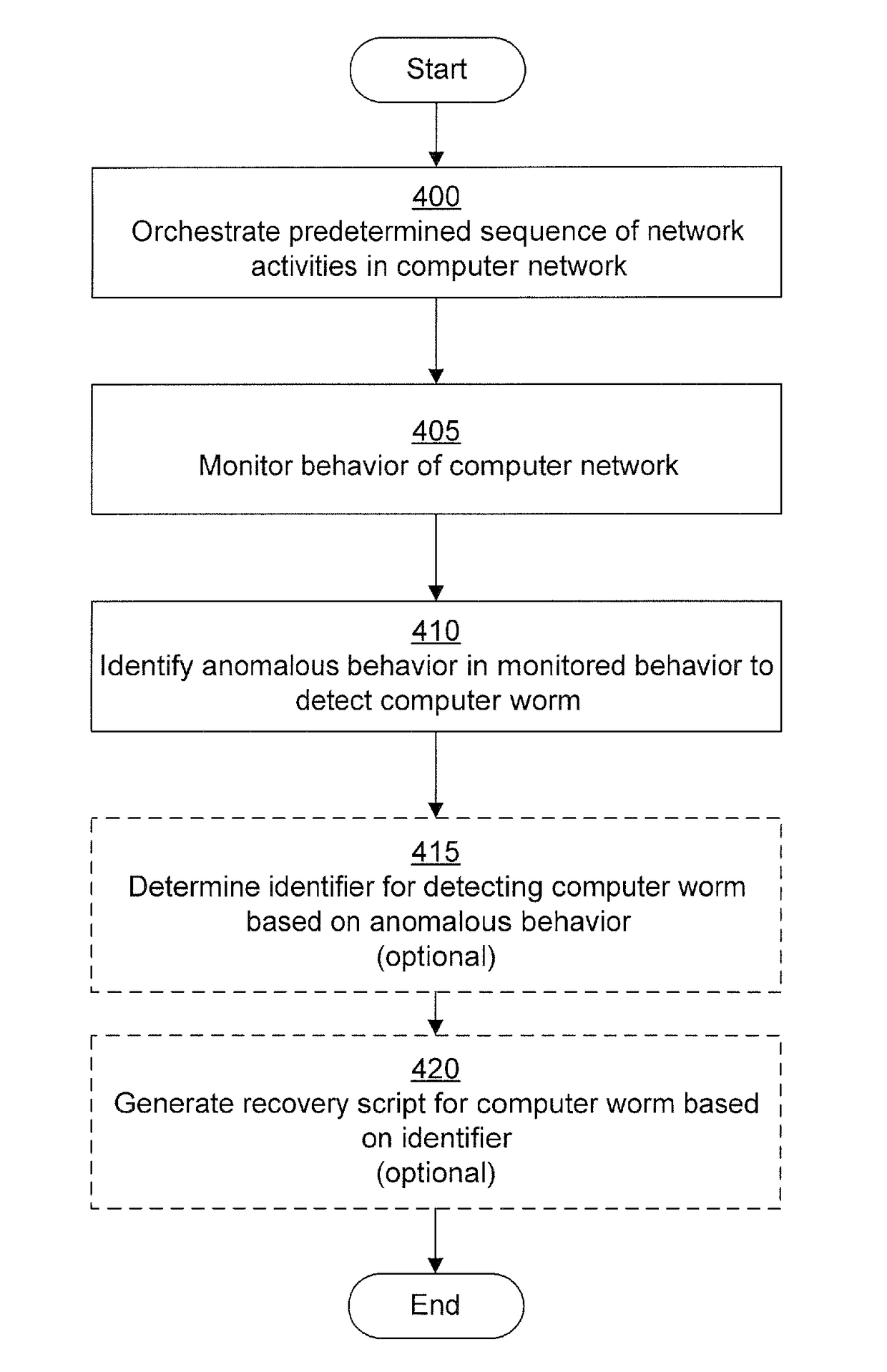
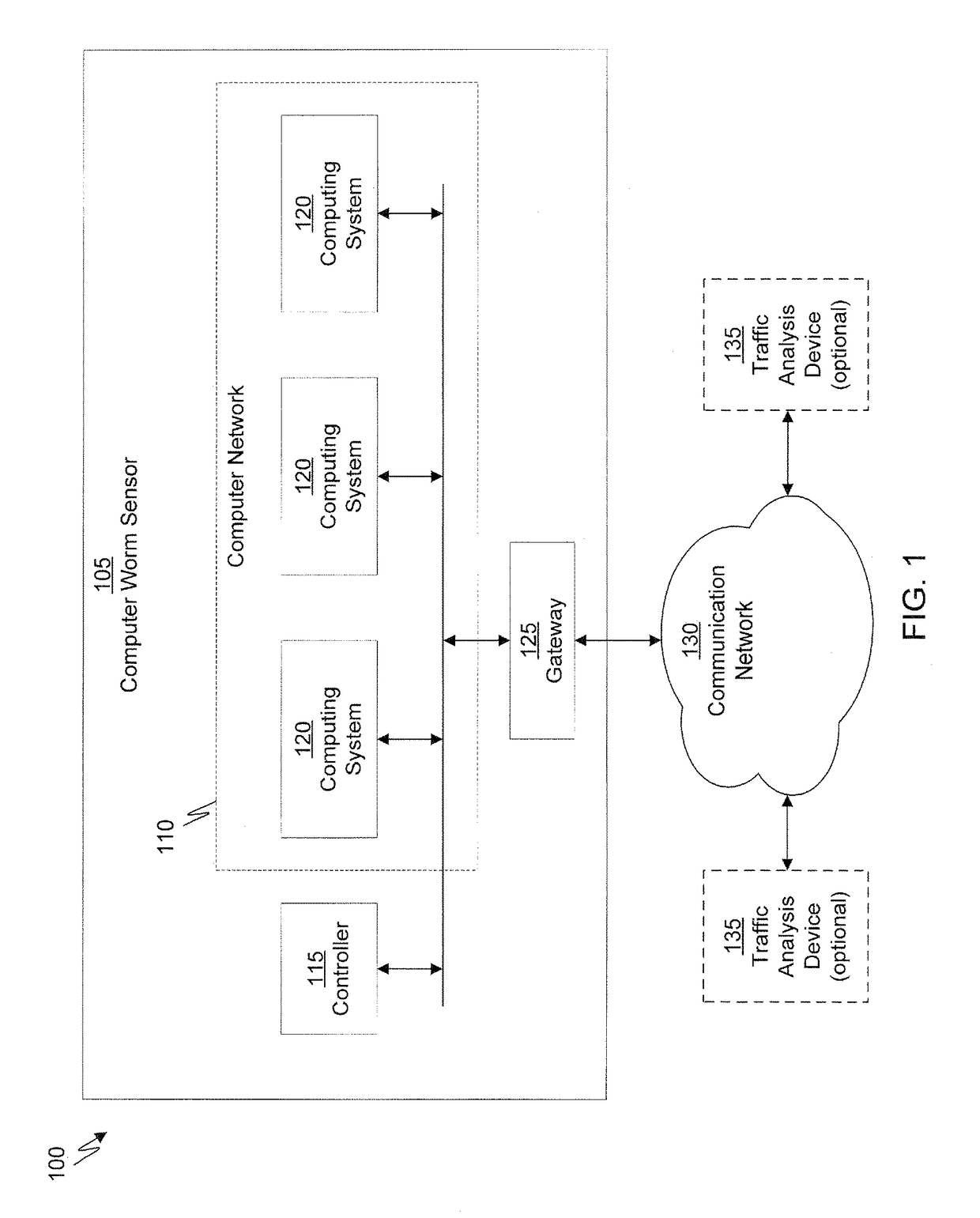
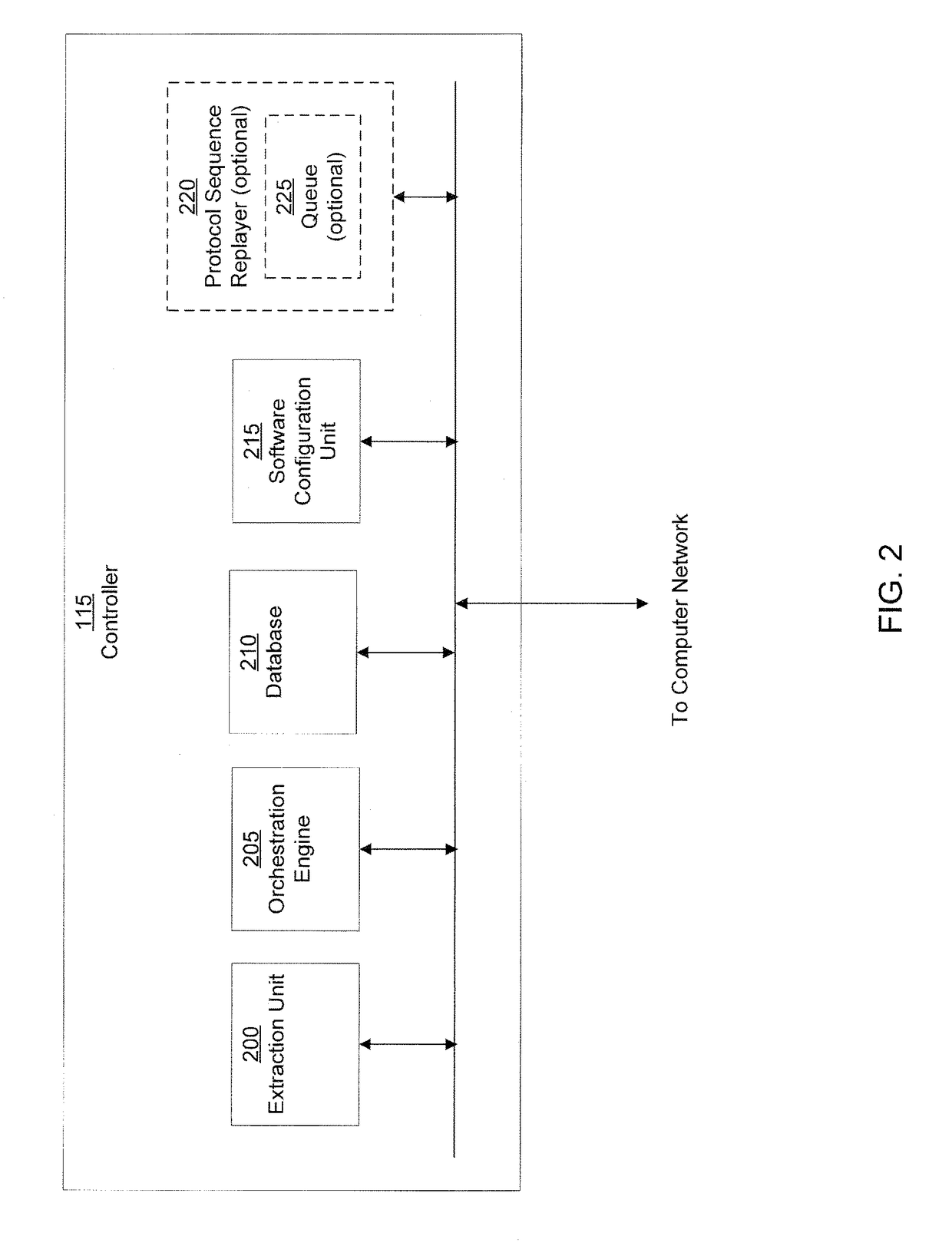
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of containing computer worms
ActiveUS8549638B2Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of detecting computer worms
A computer worm detection system orchestrates a sequence of network activities in a computer network and monitors the computer network to identify an anomalous behavior of the computer network. The computer worm detection system then determines whether the anomalous behavior is caused by the computer worm and can determine an identifier for detecting the computer worm based on the anomalous behavior. The computer worm detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm.
Owner:FIREEYE SECURITY HLDG US LLC
Insider threat detection
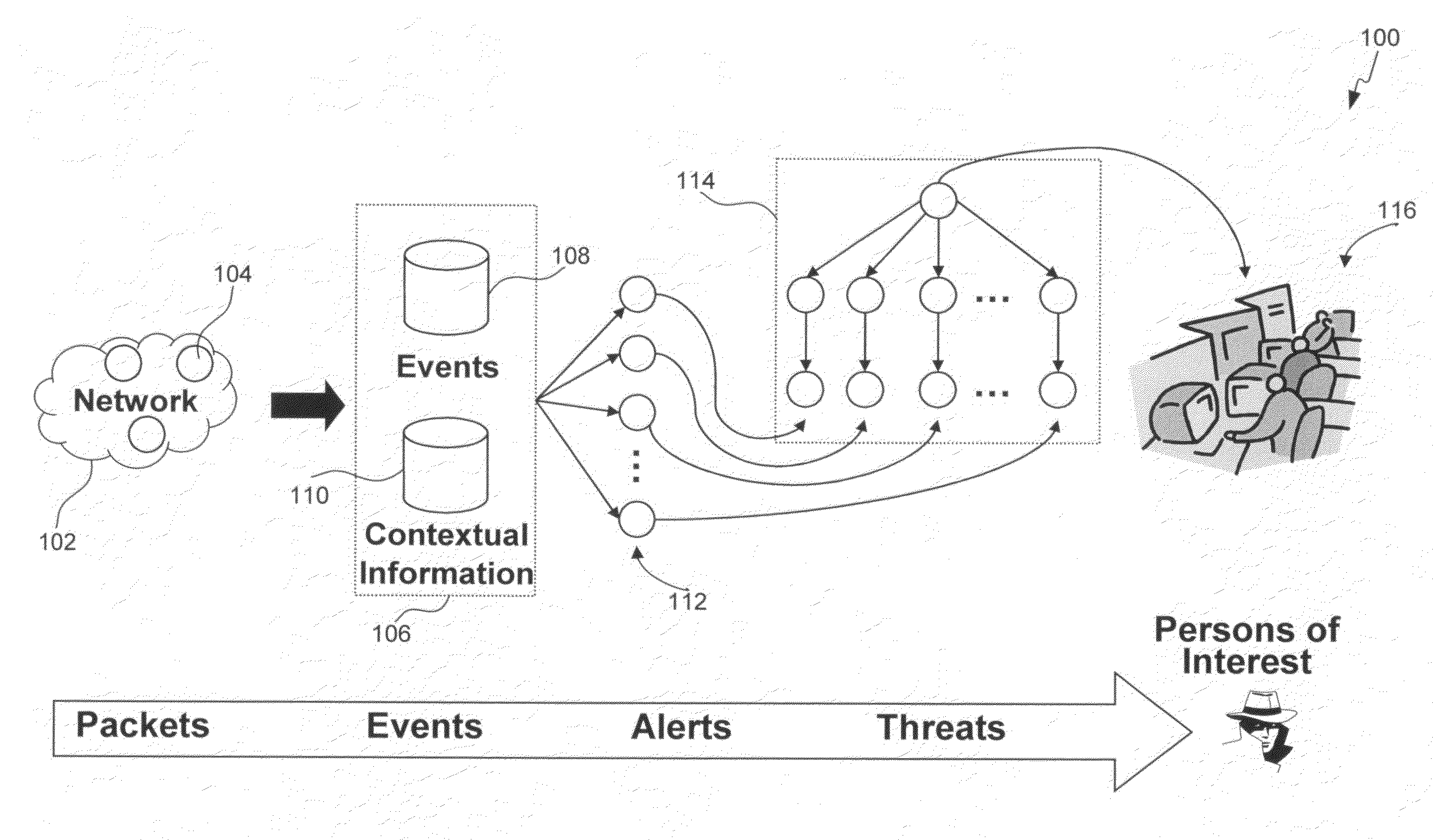
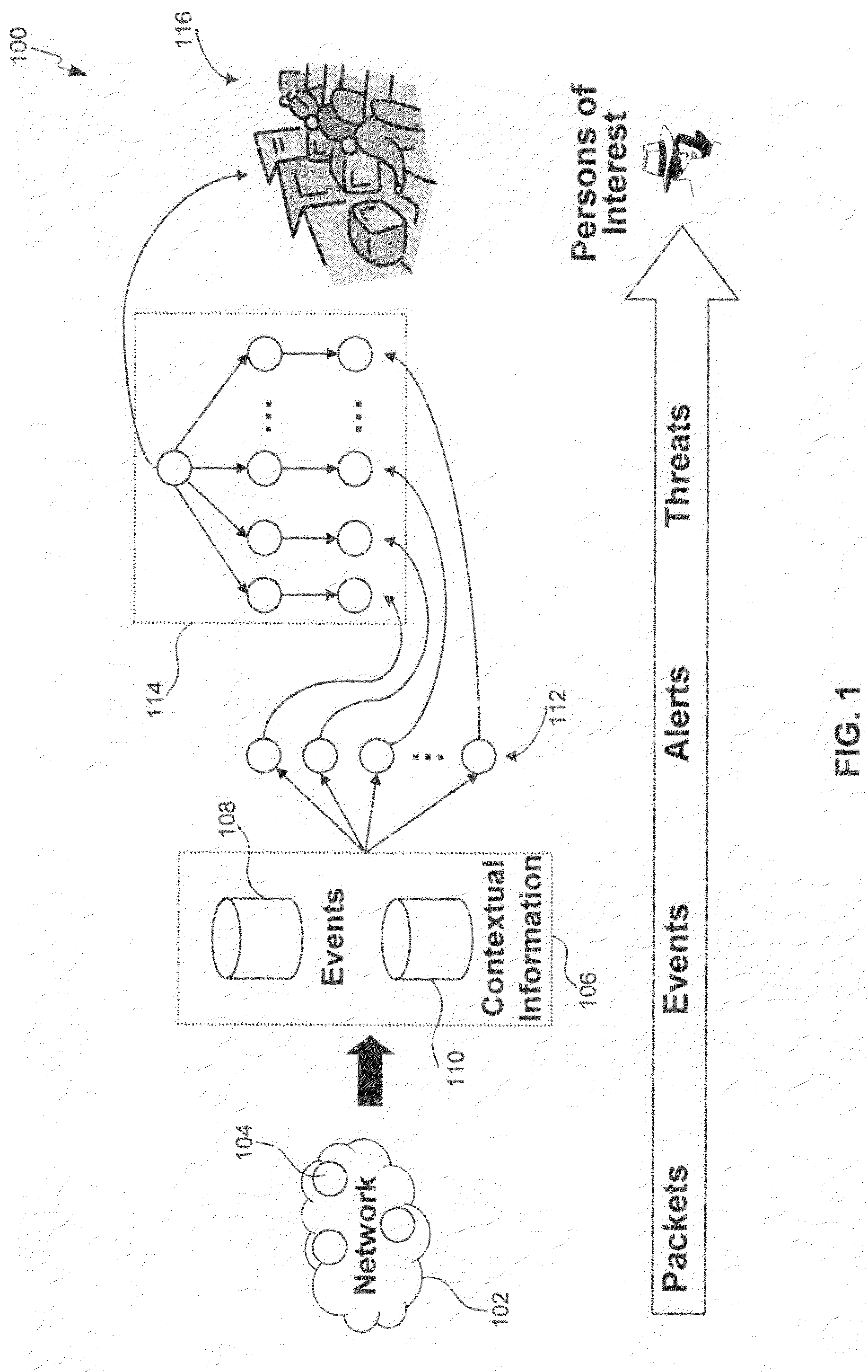
Methods, systems, and computer program products for insider threat detection are provided. Embodiments detect insiders who act on documents and / or files to which they have access but whose activity is inappropriate or uncharacteristic of them based on their identity, past activity, and / or organizational context. Embodiments work by monitoring the network to detect network activity associated with a set of network protocols; processing the detected activity to generate information-use events; generating contextual information associated with users of the network; and processing the information-use events based on the generated contextual information to generate alerts and threat scores for users of the network. Embodiments provide several information-misuse detectors that are used to examine generated information-use events in view of collected contextual information to detect volumetric anomalies, suspicious and / or evasive behavior. Embodiments provide a user threat ranking system and a user interface to examine user threat scores and analyze user activity.
Owner:MITRE SPORTS INT LTD
Network activity anomaly detection
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
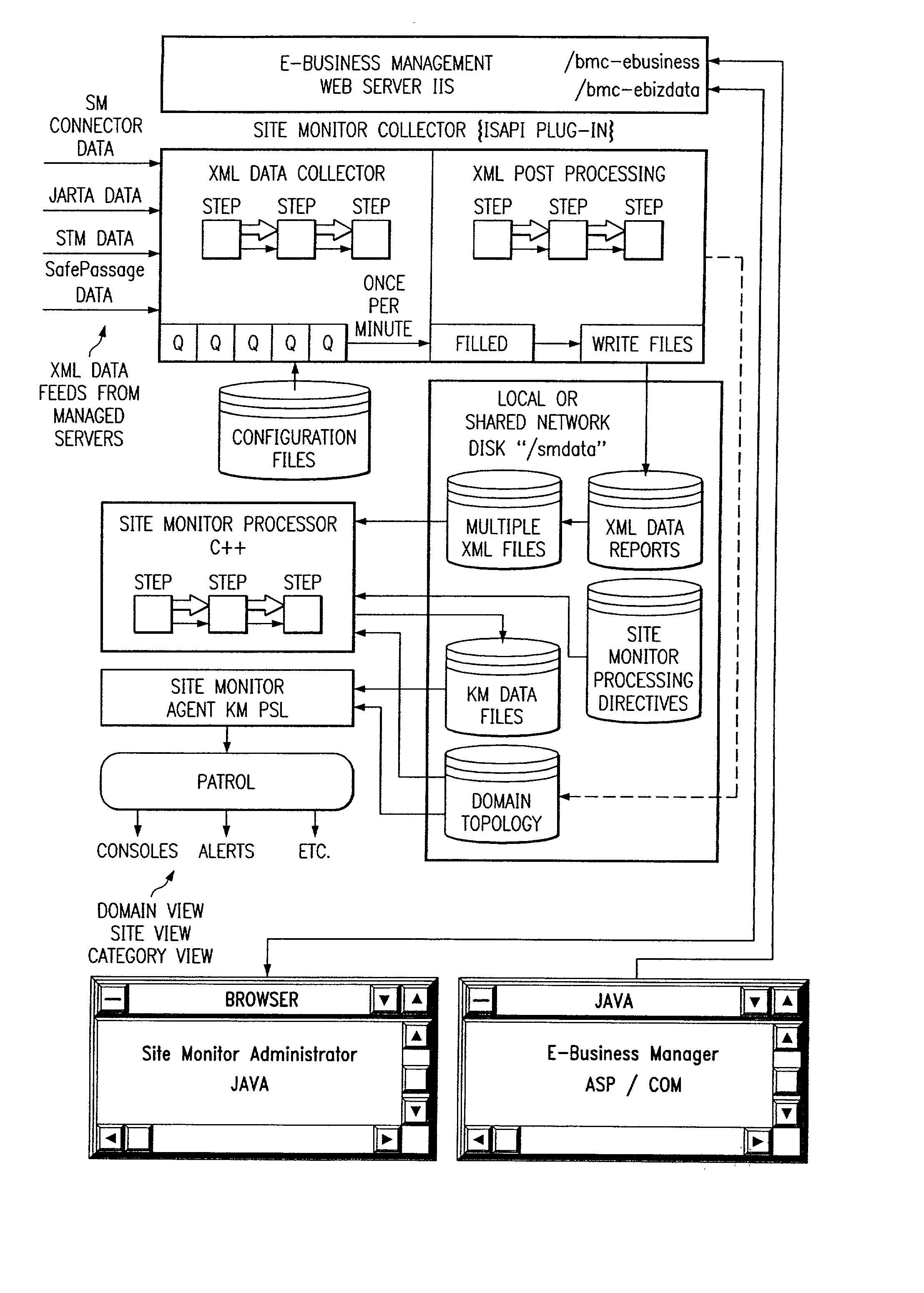
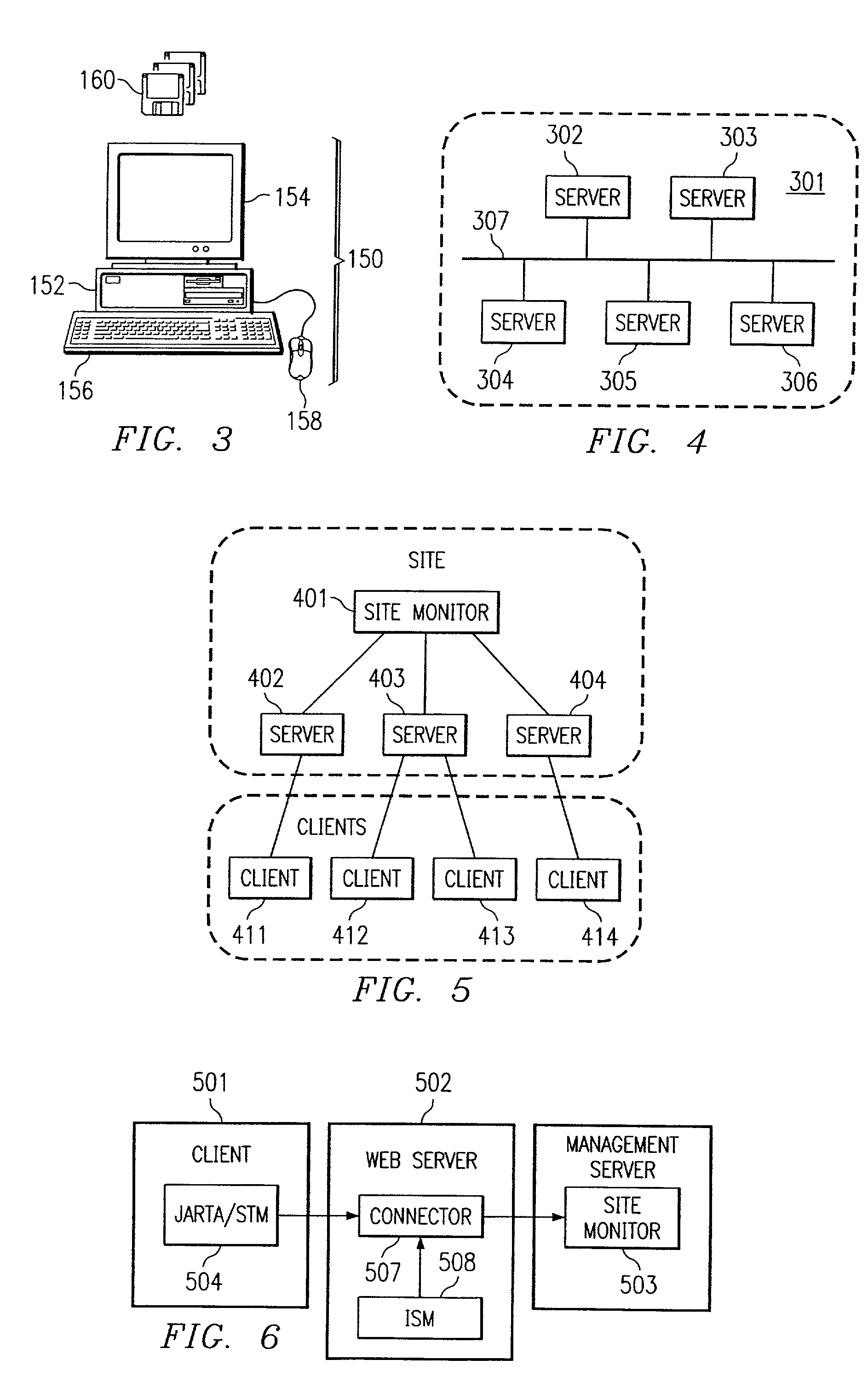
Site monitor
Systems and methods for network service management, wherein the internet service management system includes one or more components which collectively enable an administrator to obtain a site-wide view of network activities on servers such as web servers, FTP servers, e-mail servers, domain name servers, etc. In addition to collecting information relating to web server latency and processing time, the internet service management system may collect actual user transaction information and system information from end users on client computers. The internet service management system may provide domain summary information for a domain, or it may provide management information organized by "categories" according to how a site manager wants to view and manage his business; e.g., byline of business (books, auctions, music, etc.), by site function (searches, shopping cart, support, quotes, sales automation), or most any other categorization customers may choose.
Owner:BMC SOFTWARE
Network appliance for dynamic protection from risky network activities
InactiveUS20160044054A1Efficient solutionLighten the taskMemory loss protectionError detection/correctionNetwork activityDistributed computing
Electronic appliances, computer-implemented systems, non-transitory media, and methods are provided to identify risky network activities using intelligent algorithms. The appliances, systems, media, and methods enable rapid detection of risky activities.
Owner:NORSE NETWORKS INC
System for making personalized offers for business facilitation of an entity and methods thereof
Systems and methods for leveraging social data by entities to acquire new customers through social channels are disclosed. Offers are personalized as these are transmitted based on the desire of the prospect, which may be expressed through network activities. The interest profile of members of social network communities is determined and offers are propagated through conduits having a high influence score. Implementation of these engines is disclosed. If there are multiple people connected to a conduit, the prospect whose degree of social interaction is high may be considered for making the offer available to the prospect.
Owner:INFOSYS LTD
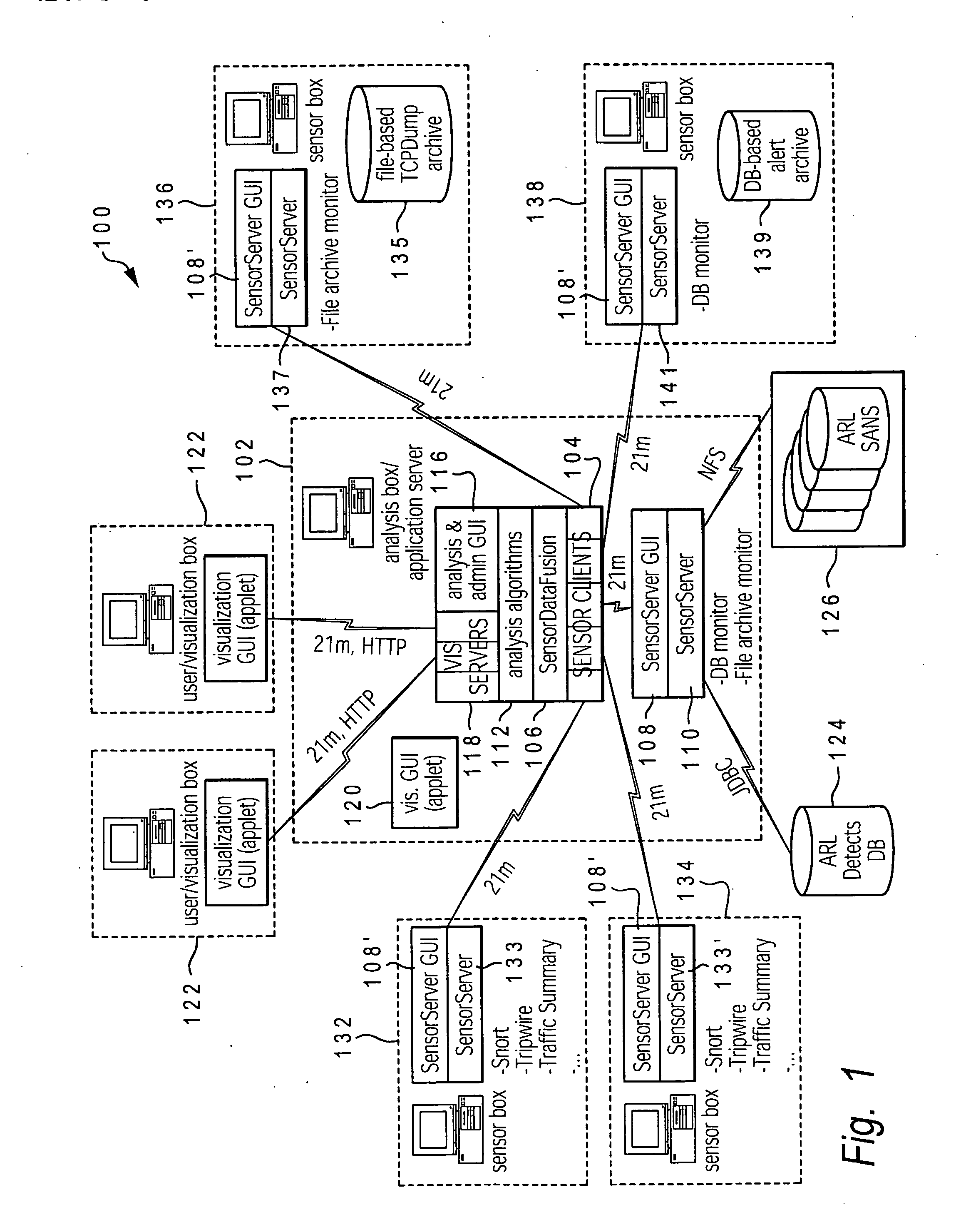
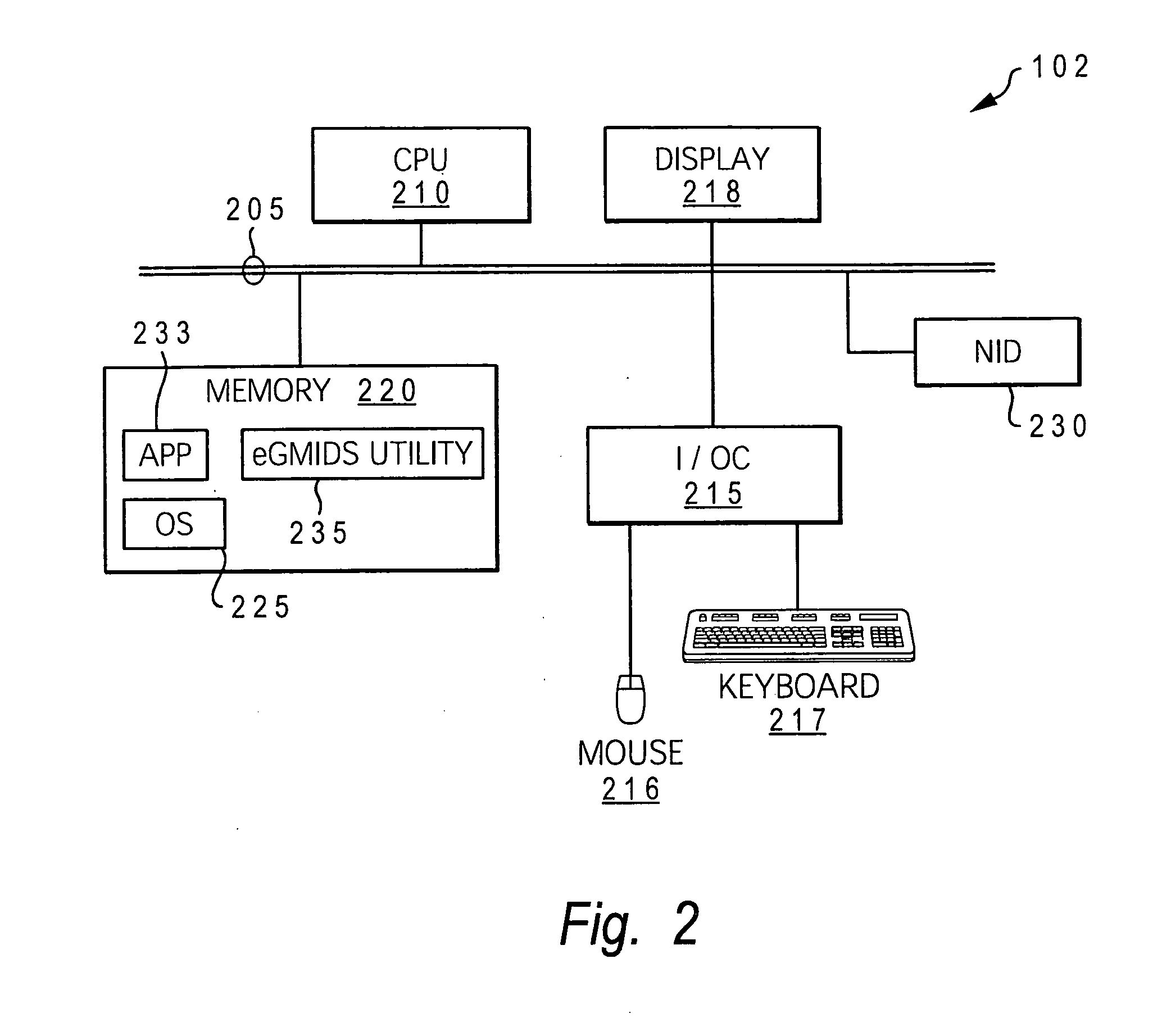
Intelligent intrusion detection system utilizing enhanced graph-matching of network activity with context data
ActiveUS20070209074A1Reduce in quantitySmall sizeMemory loss protectionError detection/correctionNetwork activityGraphics
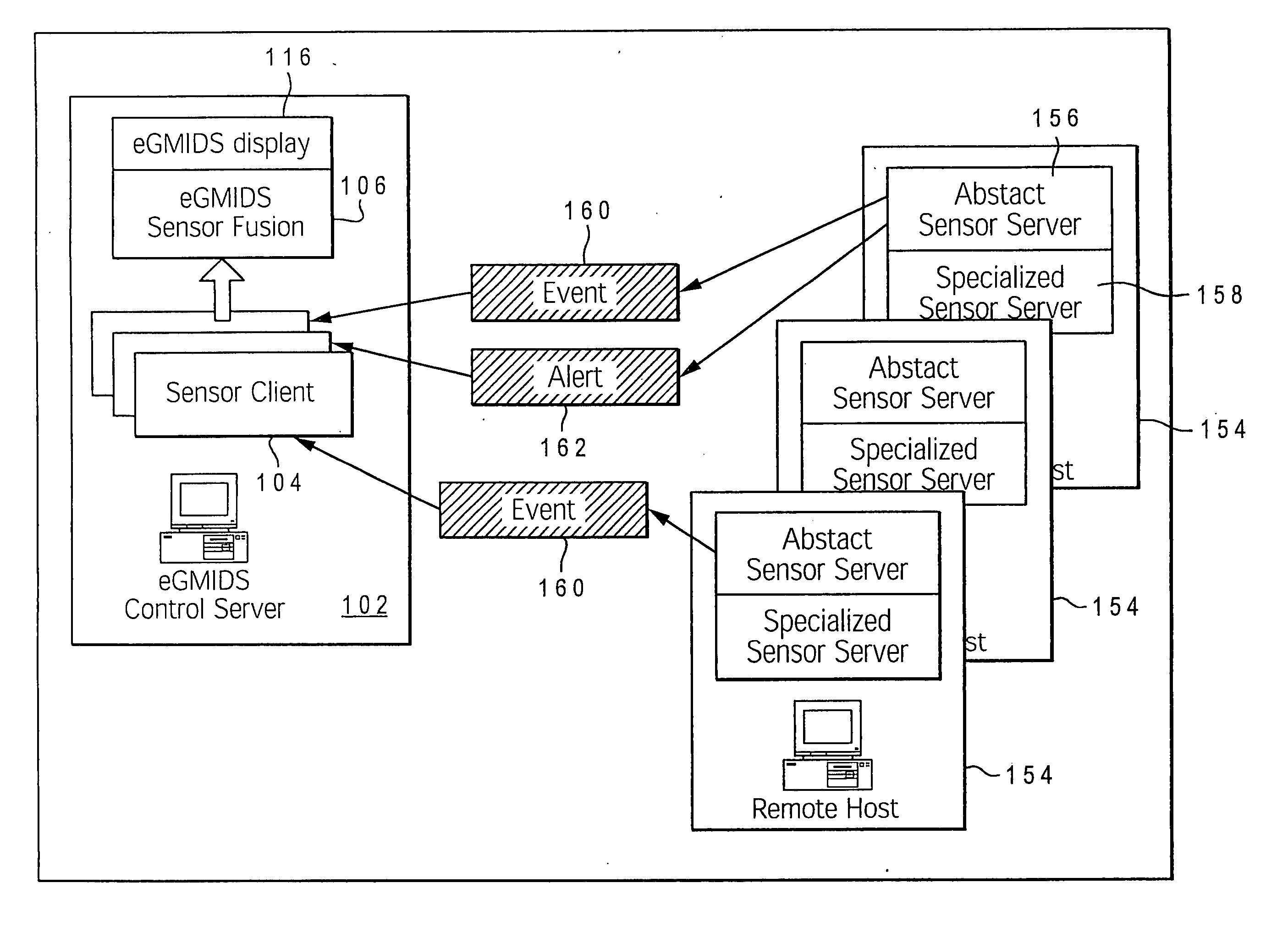
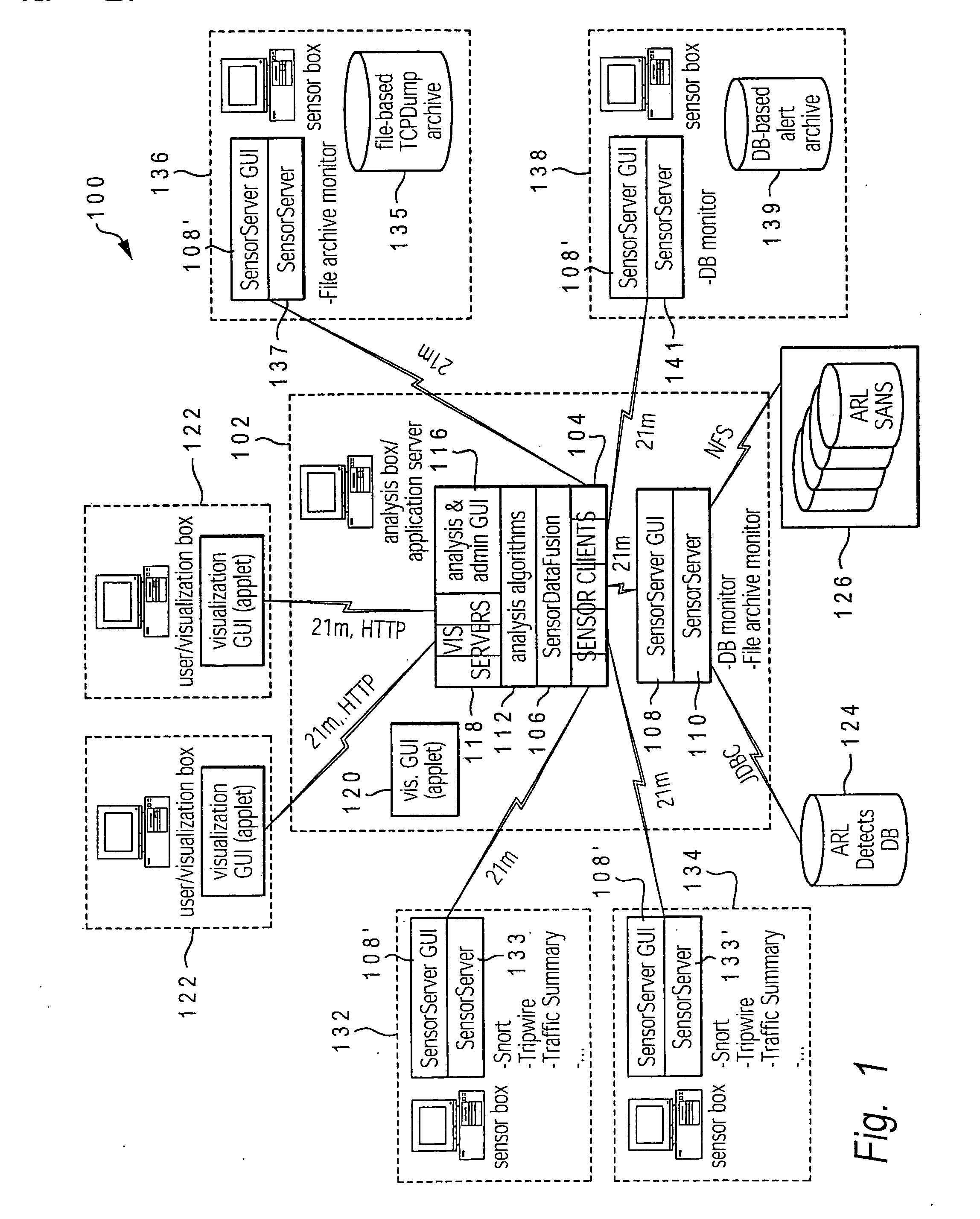
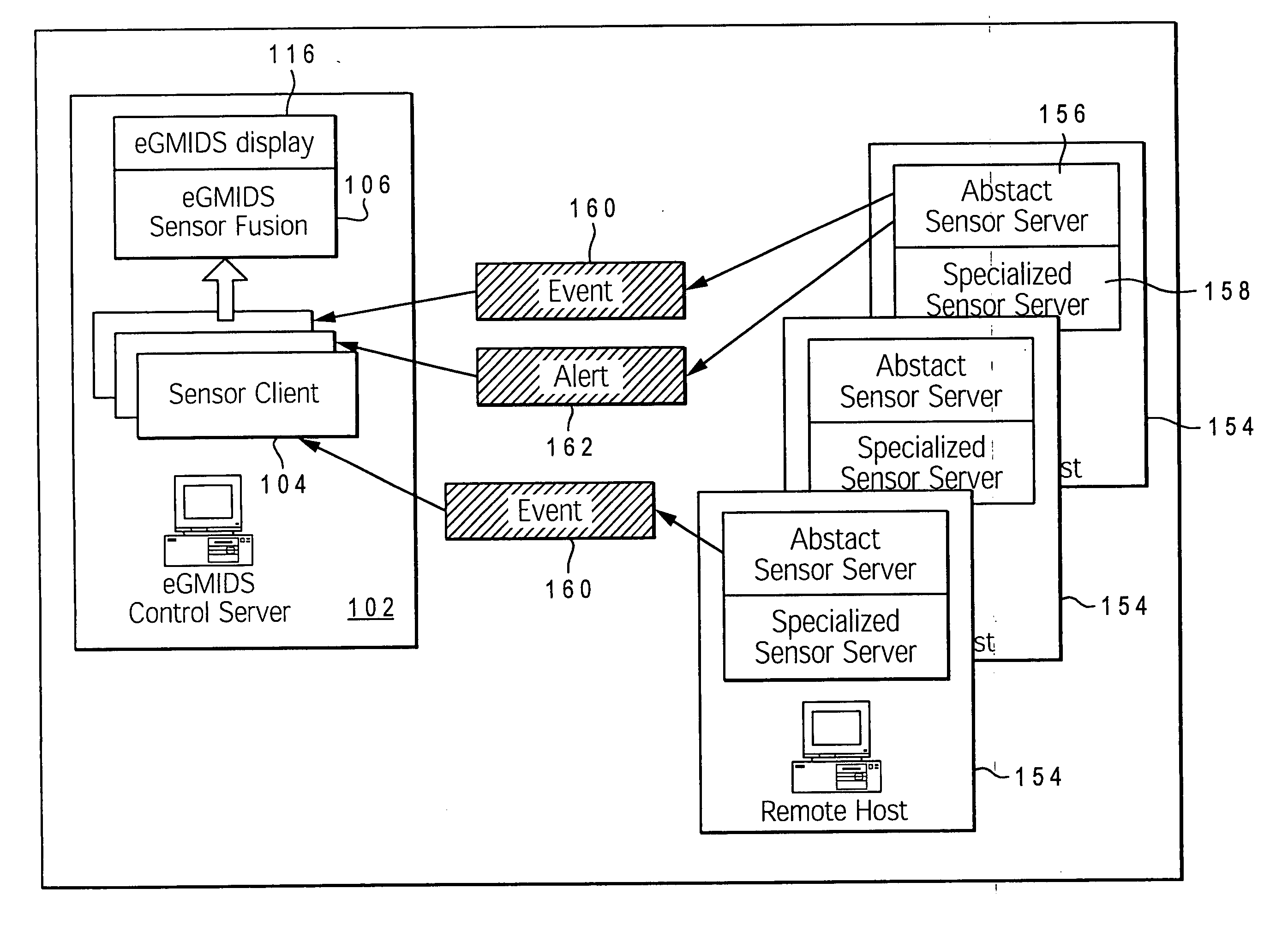
A method, system, and computer program product for utilizing a mapping of activity occurring at and between devices on a computer network to detect and prevent network intrusions. An enhanced graph matching intrusion detection system (eGMIDS) is provided that provides data collection functions, data fusion techniques, graph matching algorithms, and secondary and other search mechanisms. Threats are modeled as a set of entities and interrelations between the entities and sample threat patterns are stored within a database. The eGMIDS utility initiates a graph matching algorithm by which the threat patterns are compared within the generated activity graph via subgraph isomorphism. A multi-layered approach including a targeted secondary layer search following a match during a primary layer search is provided. Searches are tempered by attributes and constraints and the eGMIDS reduces the number of threat patterns searched by utilizing ontological generalization.
Owner:NORTHROP GRUMMAN SYST CORP
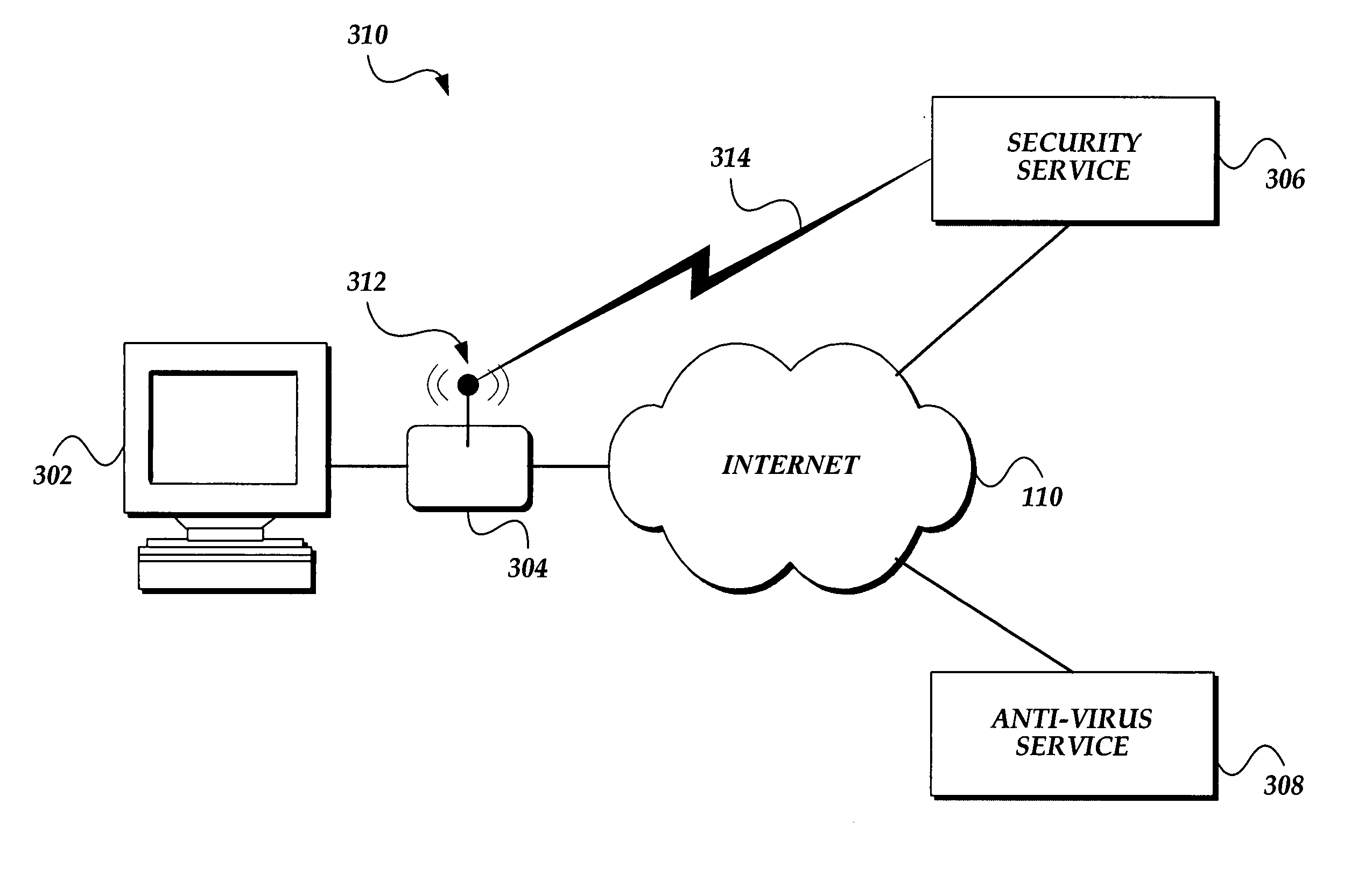
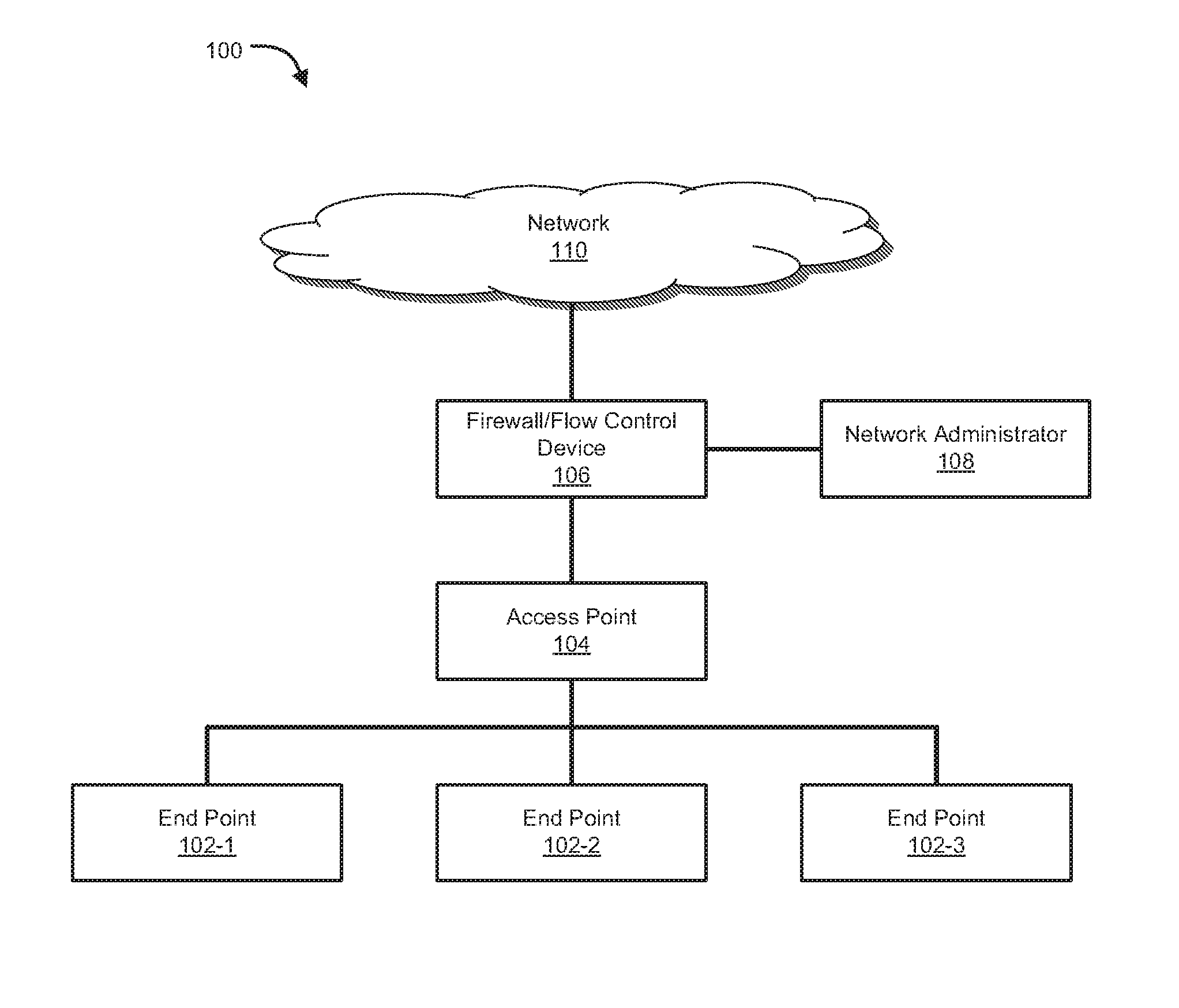
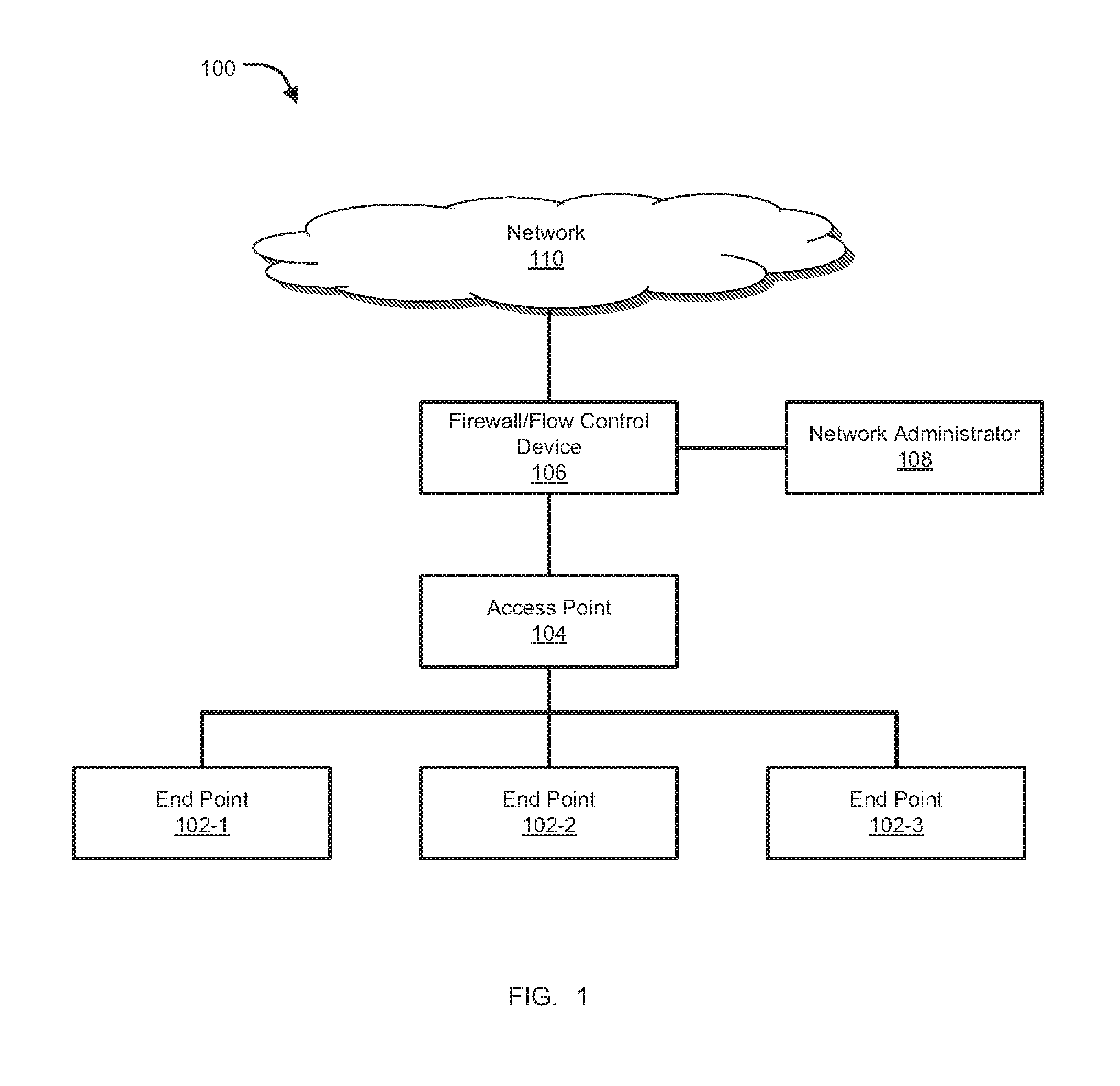
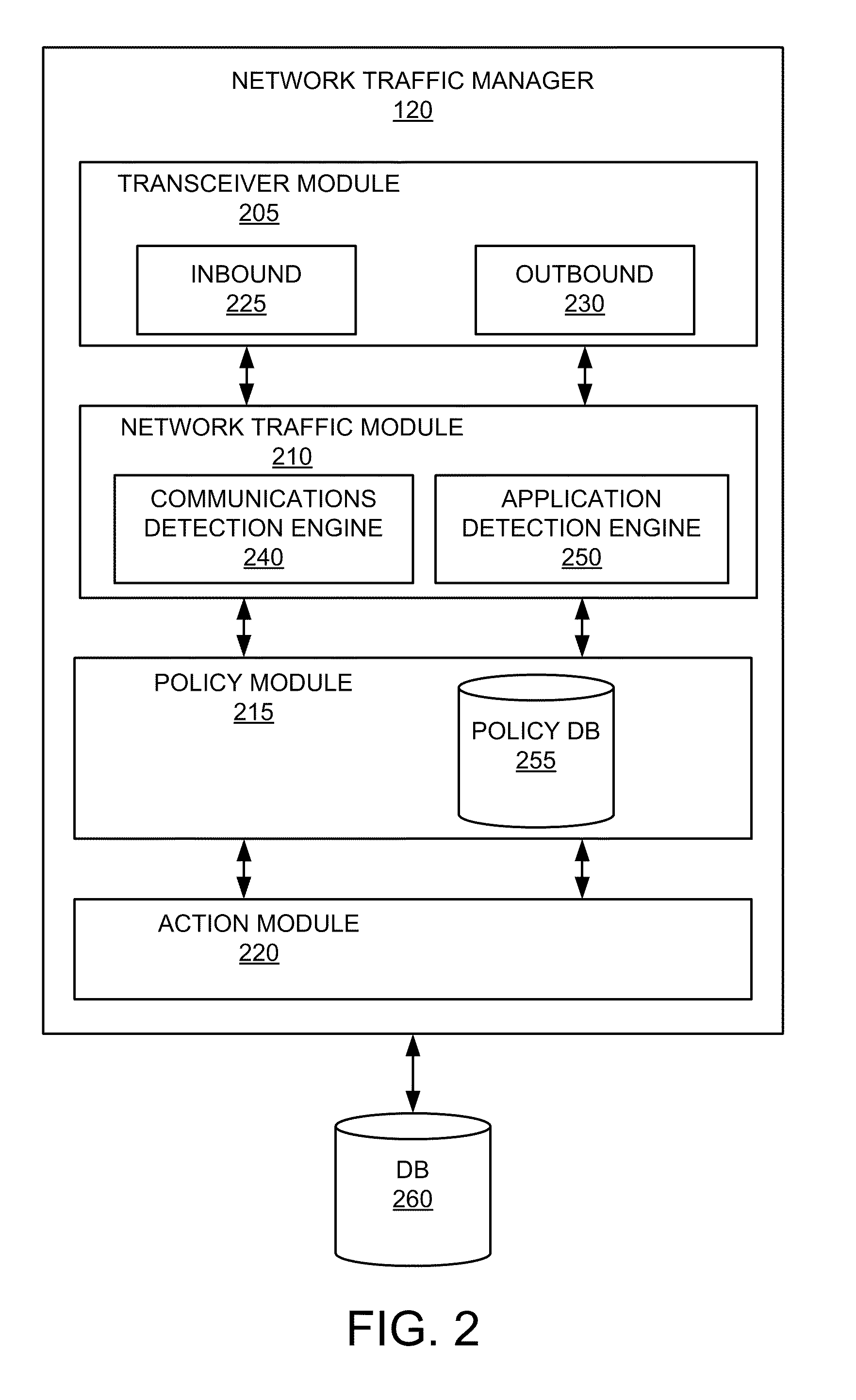
Network security device and method for protecting a computing device in a networked environment
ActiveUS20060095965A1Memory loss protectionDetecting faulty computer hardwareNetwork activitySecurity Measure
A network security module for protecting computing devices connected to a communication network from security threats is presented. The network security module is interposed, either logically or physically, between the protected computer and the communication network. The network security module receives security information from a security service. The security information comprises security measures which, when enforced by the network security module, protect the computer from a security threat to the computer. The network security module implements the security measures by controlling the network activities between the protected computer and the network. The network security module also temporarily implements security patches until corresponding patches are installed onto the protected computer.
Owner:MICROSOFT TECH LICENSING LLC
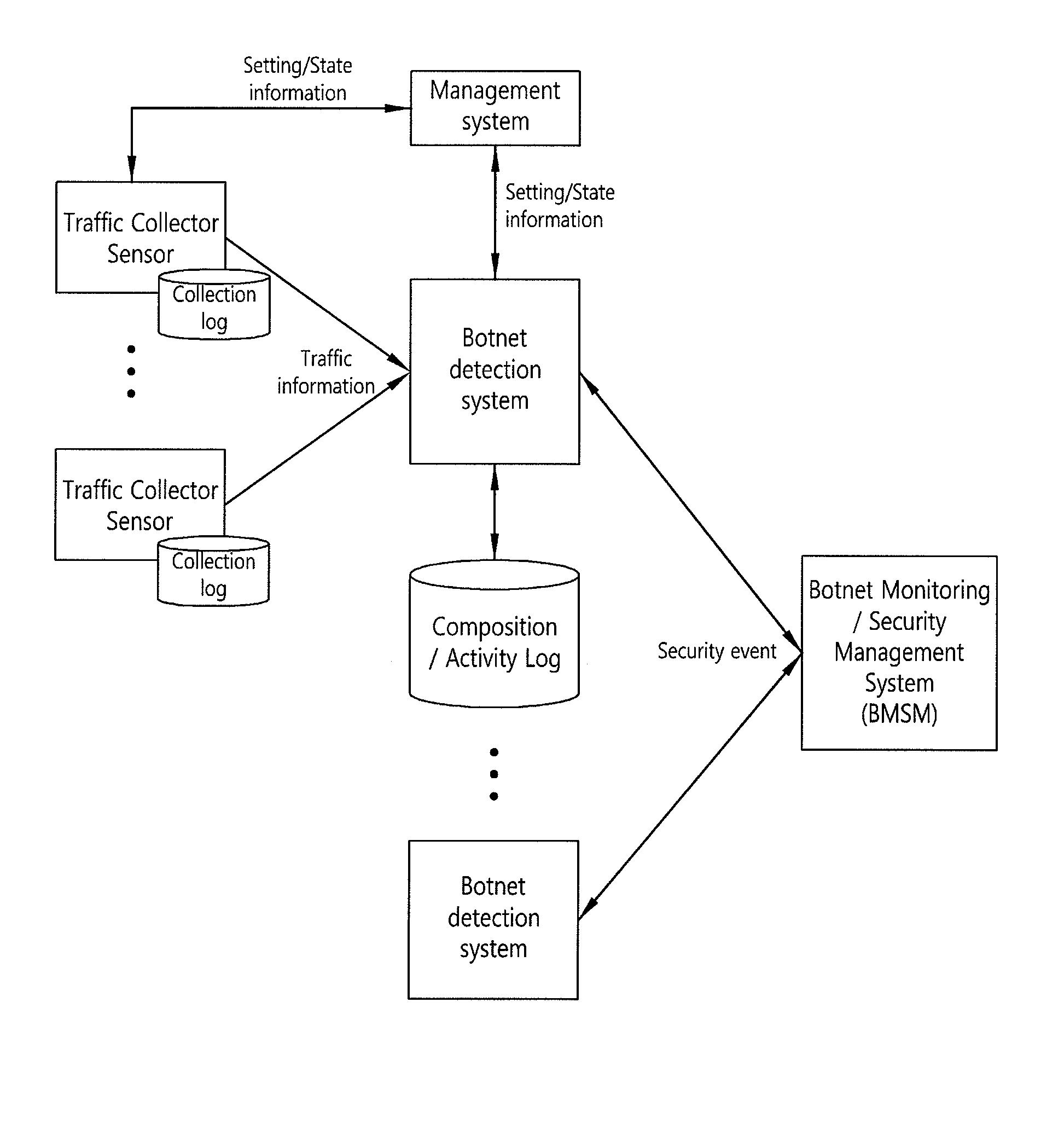
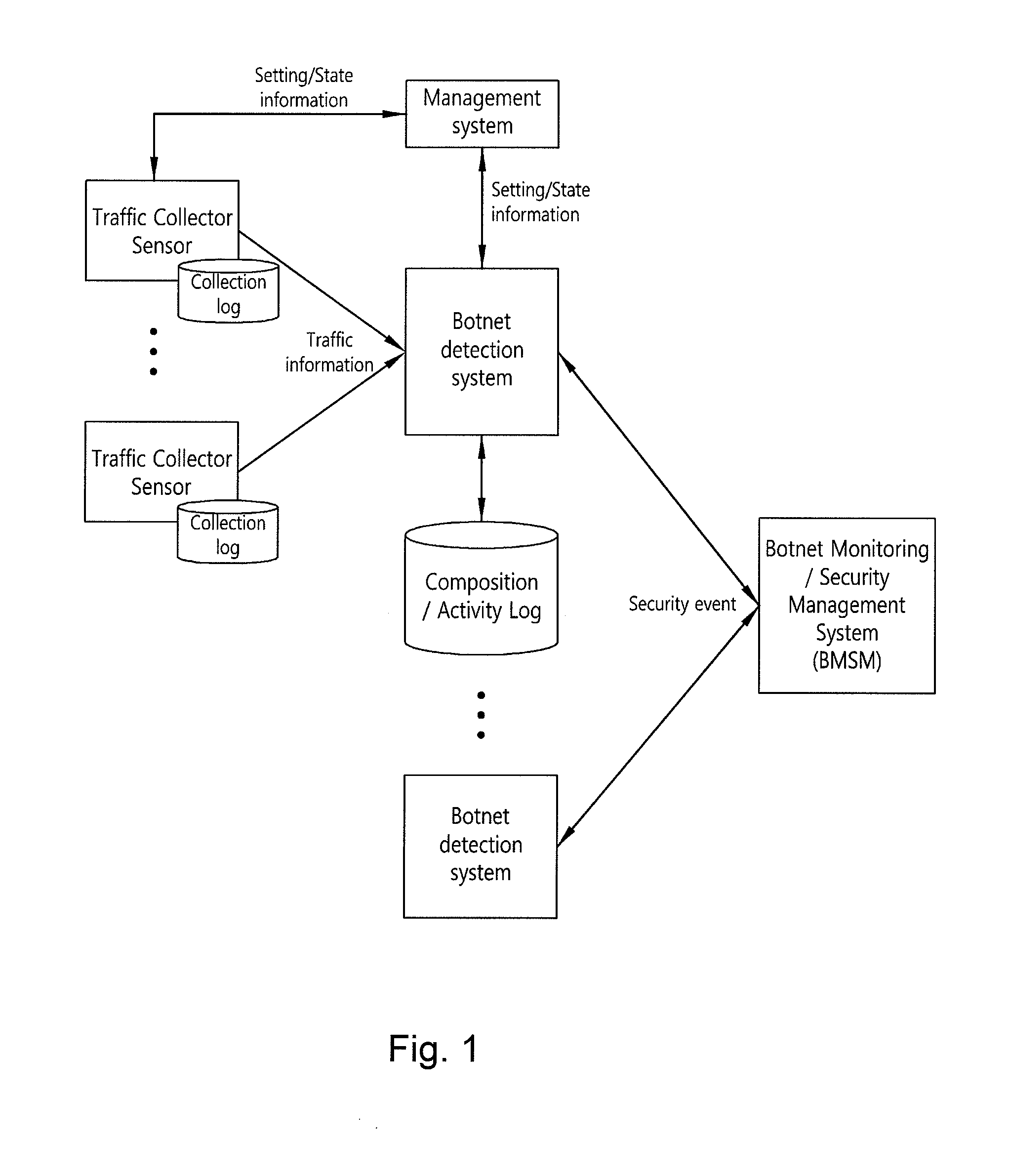
System and method for modeling activity patterns of network traffic to detect botnets
InactiveUS20110153811A1Efficient detectionDigital computer detailsTransmissionNetwork activityActivity classification
The invention relates to a system and method that can detect botnets by classifying the communication activities for each client according to destination or based on similarity between the groups of collected traffic. According to certain aspects of the invention, the communication activities for each client can be classified to model network activity by differentiating the protocols of the collected network traffic based on destination and patterning the subgroups for the respective protocols. Those servers that are estimated to be C&C servers can be classified into download and upload, spam servers and command control servers, within a botnet group detected by modeling network activity, i.e. analyzing network-based activity patterns. Also, botnet groups can be detected by way of a group information management function, for generating an activity pattern-based group matrix based on group data, and a mutual similarity analysis, performed on groups suspected to be botnets from the group information.
Owner:KOREA INTERNET & SECURITY AGENCY
Computer Implemented Techniques for Detecting, Investigating and Remediating Security Violations to IT Infrastructure
A method includes collecting system calls and call parameters invoked by monitored applications for target computer systems. The system calls and call parameters are received from operating system kernels on the plurality of target computer systems. Sequences of systems calls and call parameters of the monitored applications are correlated among different target computer systems to deduce malicious activities. Remedial action(s) are performed in response to malicious activities being deduced as being malicious by the correlating. Another method includes determining that network activity at a specific time is deemed to be suspicious. Using IP addresses involved in the suspicious network activity, computer system(s) are determined that are sources of the suspicious network activity. Based on the specific time and the determined computer system(s), application(s) are determined that are executing on the determined computer system(s) that are causing the suspicious network activity. Remedial action(s) are performed for the determined computer system(s).
Owner:IBM CORP
System and method of detecting malicious content
ActiveUS9838416B1Rapid responsePlatform integrity maintainanceTransmissionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
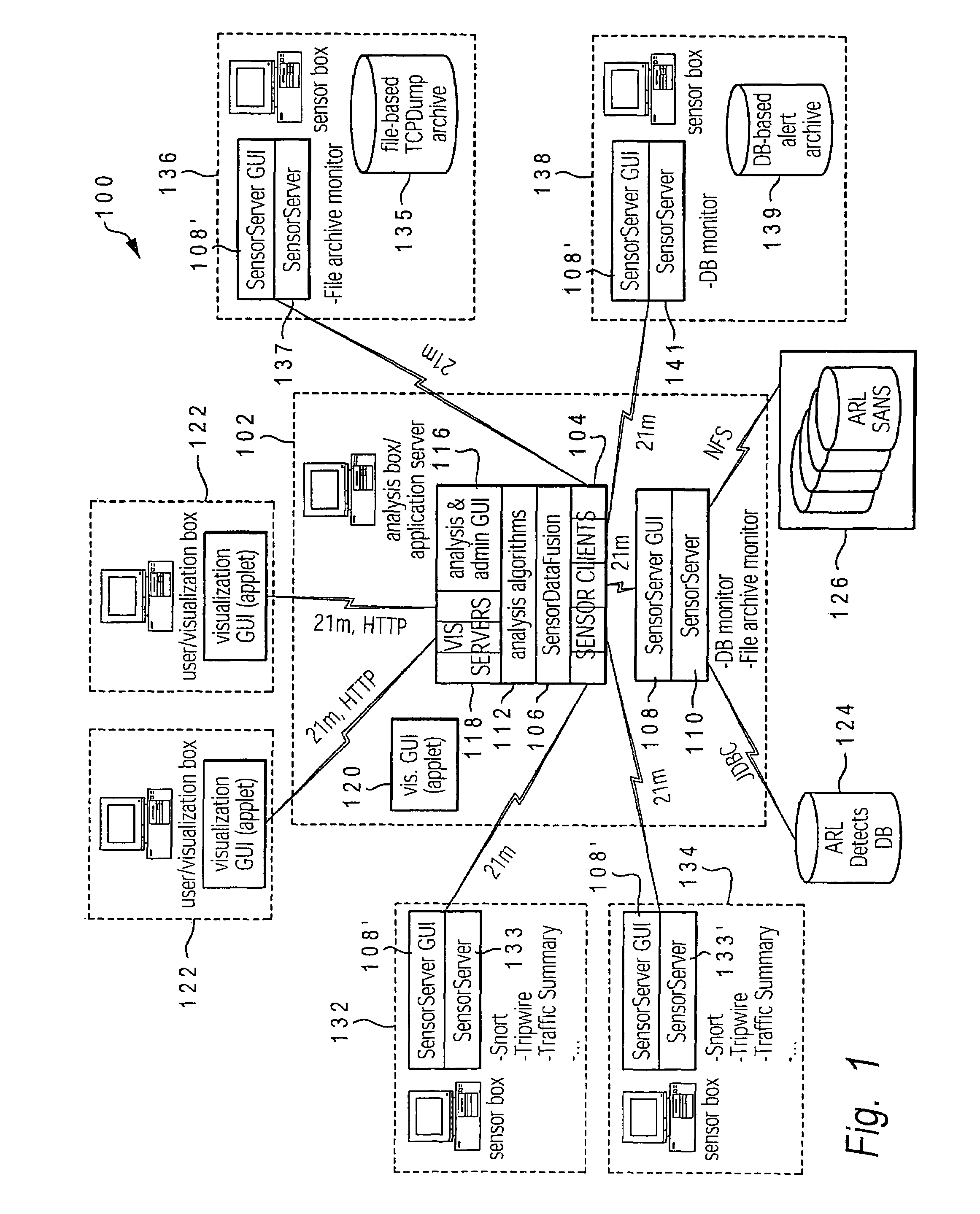
Enabling network intrusion detection by representing network activity in graphical form utilizing distributed data sensors to detect and transmit activity data
ActiveUS20070209075A1Reduce in quantitySmall sizeMemory loss protectionError detection/correctionData packNetwork activity
A method, system, and computer program product for detecting and mapping activity occurring at and between devices on a computer network for utilization within an intrusion detection mechanism. An enhanced graph matching intrusion detection system (eGMIDS) utility executing on a control server provides data collection functions and data fusion techniques. The eGMIDS comprises multiple sensors and associated unique adaptors that are located at different remote devices of the network and utilized to detect specific types of activity occurring at the respective devices relevant to eGMIDS processing. The sensors convert the data into eGMIDS format and encapsulate the data in a special transmission packet that is transmitted to the control server. The eGMIDS utility converts the activity data within these packets into eGMIDS-usable format and then processes the converted data via a data fusion technique to generate a graphical representation of the network (devices) and the activity occurring at / amongst the various devices.
Owner:NORTHROP GRUMMAN SYST CORP
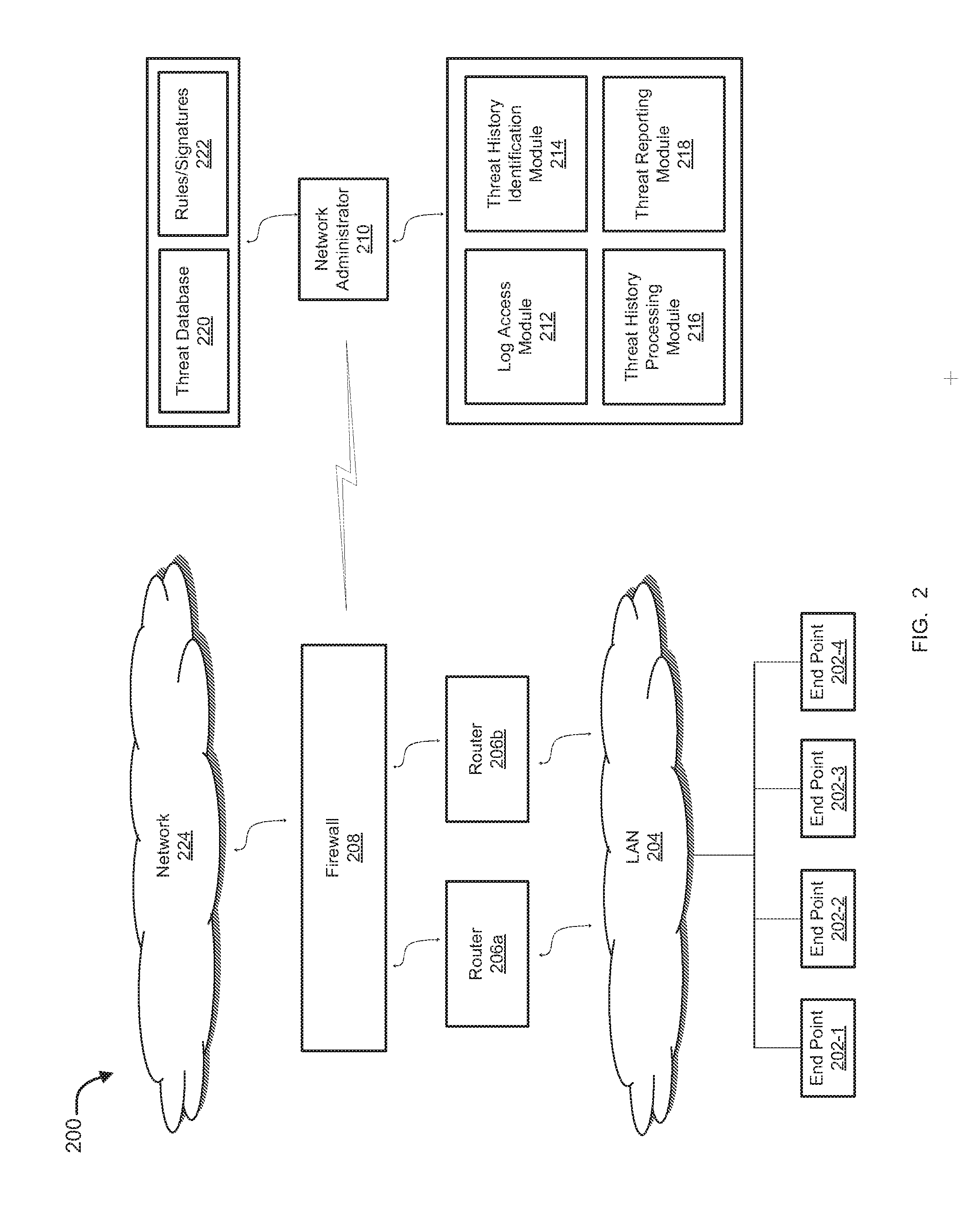
Presentation of threat history associated with network activity
ActiveUS20160173446A1Multiple digital computer combinationsProgram controlNetwork activityInternet privacy
Methods and systems for extracting, processing, displaying, and analyzing events that are associated with one or more threats are provided. According to one embodiment, threat information, including information from one or more of firewall logs and historical threat logs, is maintained in a database. Information regarding threat filtering parameters, including one or more of types of threats to be extracted from the database, parameters of the threats, network-level details of the threats, a time interval of detection of the threats and source-destination details of the threats, is received. Information regarding threats matching the threat filtering parameters are extracted from the database and is presented in a form of an interactive historical graph. Responsive to receiving from a user an indication regarding a selected subset of time in which to zoom into for further details, a list of threats within the selected subset is presented in tabular form.
Owner:FORTINET
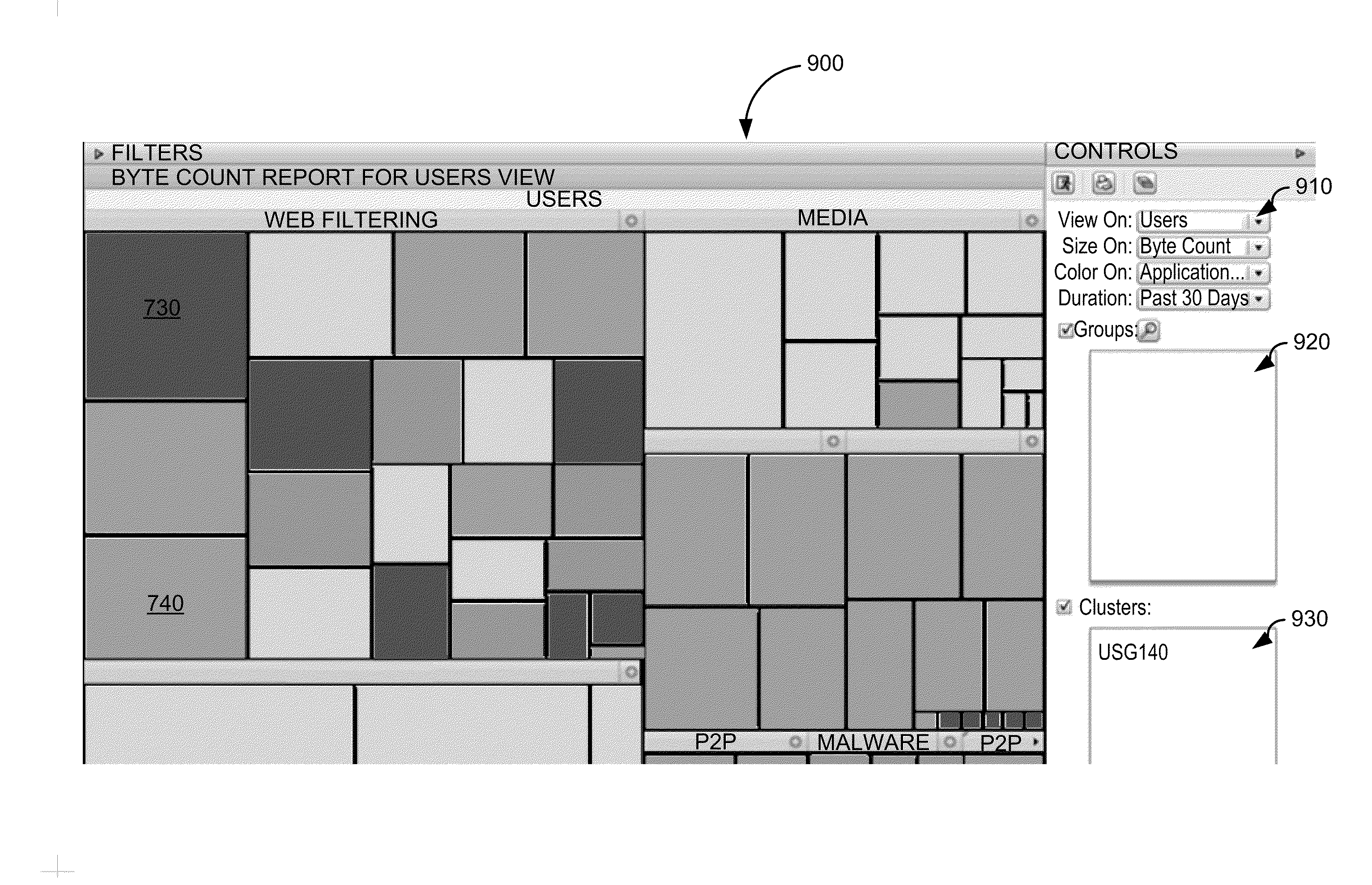
Method and apparatus for correlating network activity through visualizing network data
Correlating network activity through visualizing network data and with identifying entities associated with targeted activities and correlating therewith other activities from those entities. Network traffic is classified into a number of conceptual views of network traffic, each instantiating view objects that are a representation of network traffic that satisfies a set of conditions. Configuration files define a hierarchy, the structure of the hierarchy, and its makeup. Any point on the hierarchy can be accessed using its Graphical Request Language (GRL) designation. Further GRL designations are used to label views associated with a point. A plurality of view objects are linked to corresponding view object databases. Define new view objects using one or more GRL does correlation and combining using logical operators. Generate a new list of addresses from the GRL address lists and place all current and subsequent traffic for those machines in the new view object.
Owner:IBM CORP
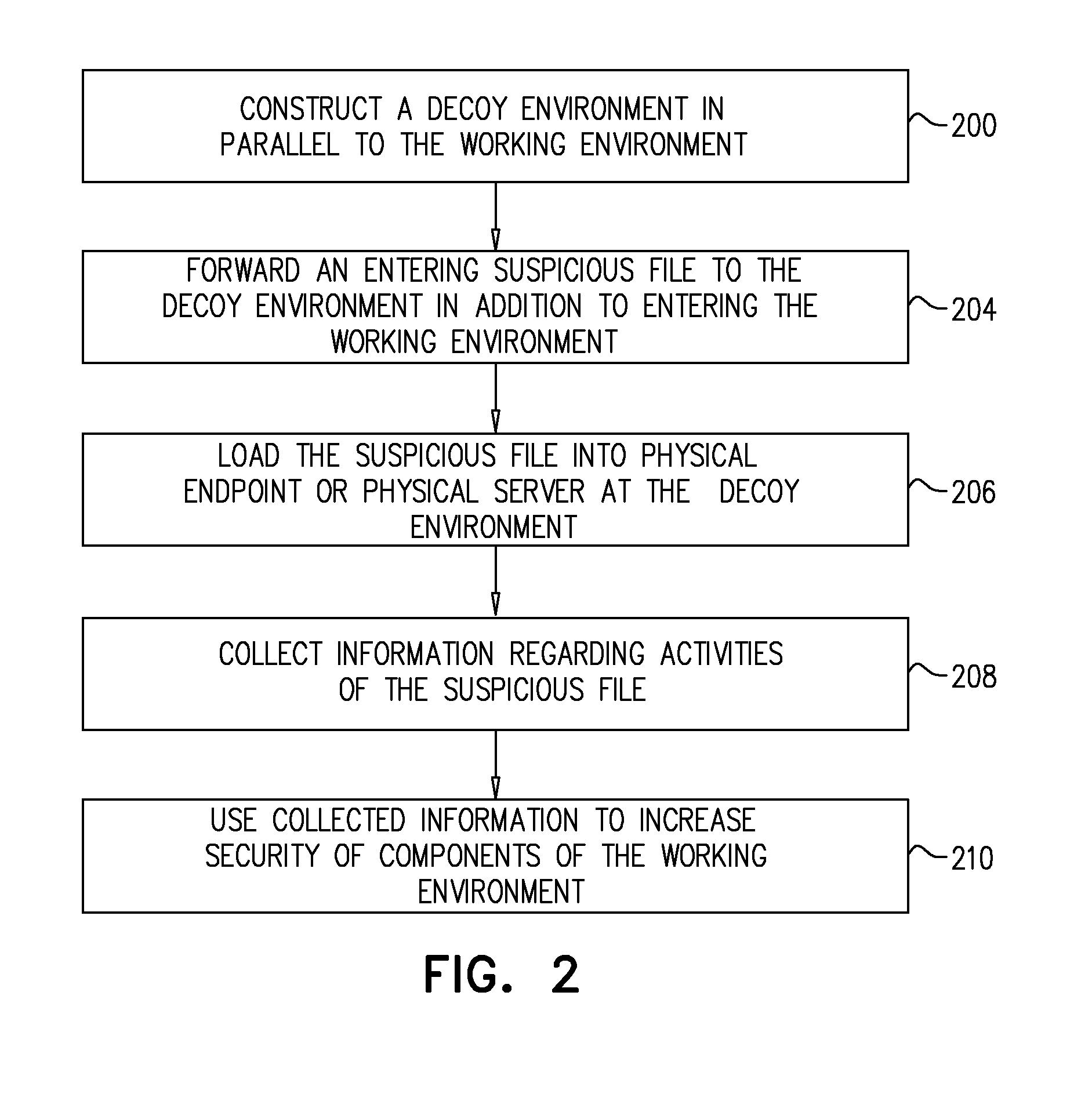
System and a Method for Identifying Malware Network Activity Using a Decoy Environment
A system for gathering information about malware and a method of use therefor, the system comprising a working environment including physical working environment servers, physical working environment endpoints, a working environment network, a switch, and a router directing traffic between said working environment network and an external network, a decoy environment including at least one physical machine, a decoy environment server, a decoy environment endpoint, a decoy environment network and a decoy environment router, a file directing mechanism directing at least some files to the decoy environment, and a threat tracking mechanism tracking and observing actions triggered by the files in the decoy environment.
Owner:FIDELIS SECURITY SYSTEMS
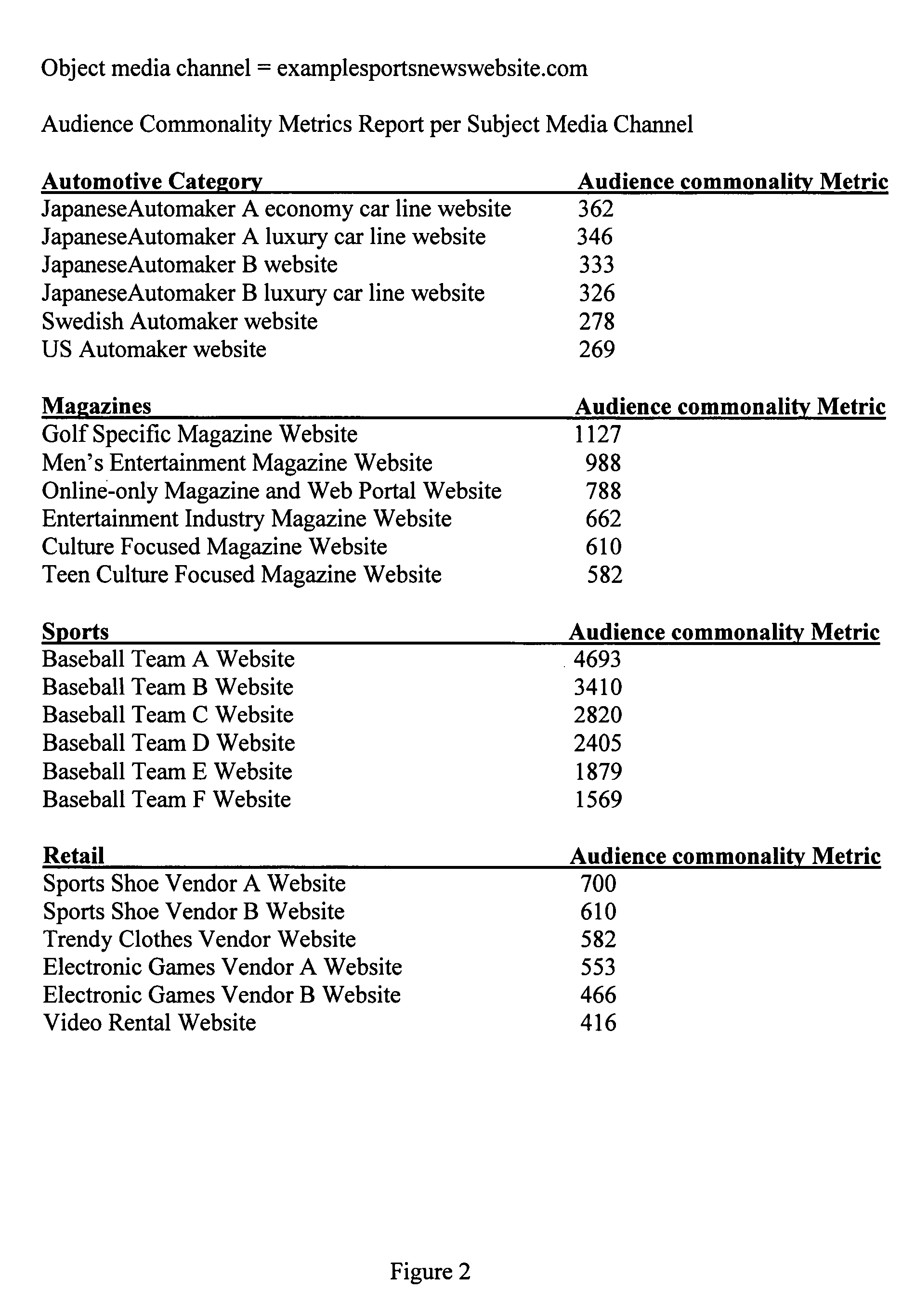
Audience commonality and measurement
InactiveUS20080086741A1Analogue secracy/subscription systemsBroadcast information monitoringNetwork activityClient agent
Audience commonality metrics for characterizing the relationship between networked media channels based on audience overlap of identified visitor entities and their related media consumption histories. Audience commonality metrics may be scalars or multi-dimensional metrics and may take into account and / or be used in conjunction with data related to on- or off-network media channels, on- or off-network activities, sociographics and / or demographics. The current invention may be used in the design of networked advertising campaigns, identification of new or unusual market segments and / or valuation of media buys. A system according to the current invention comprises access to a configuration, an input for receiving audience commonality data, an audience commonality metrics engine and an output for providing calculated audience commonality metrics. Data related to identified visitor entities may be received, determined and / or inferred from resources such as a cookie, log file, sniffer, firewall, proxy server, client agent, tracking pixel and / or tool
Owner:QUANTCAST CORP
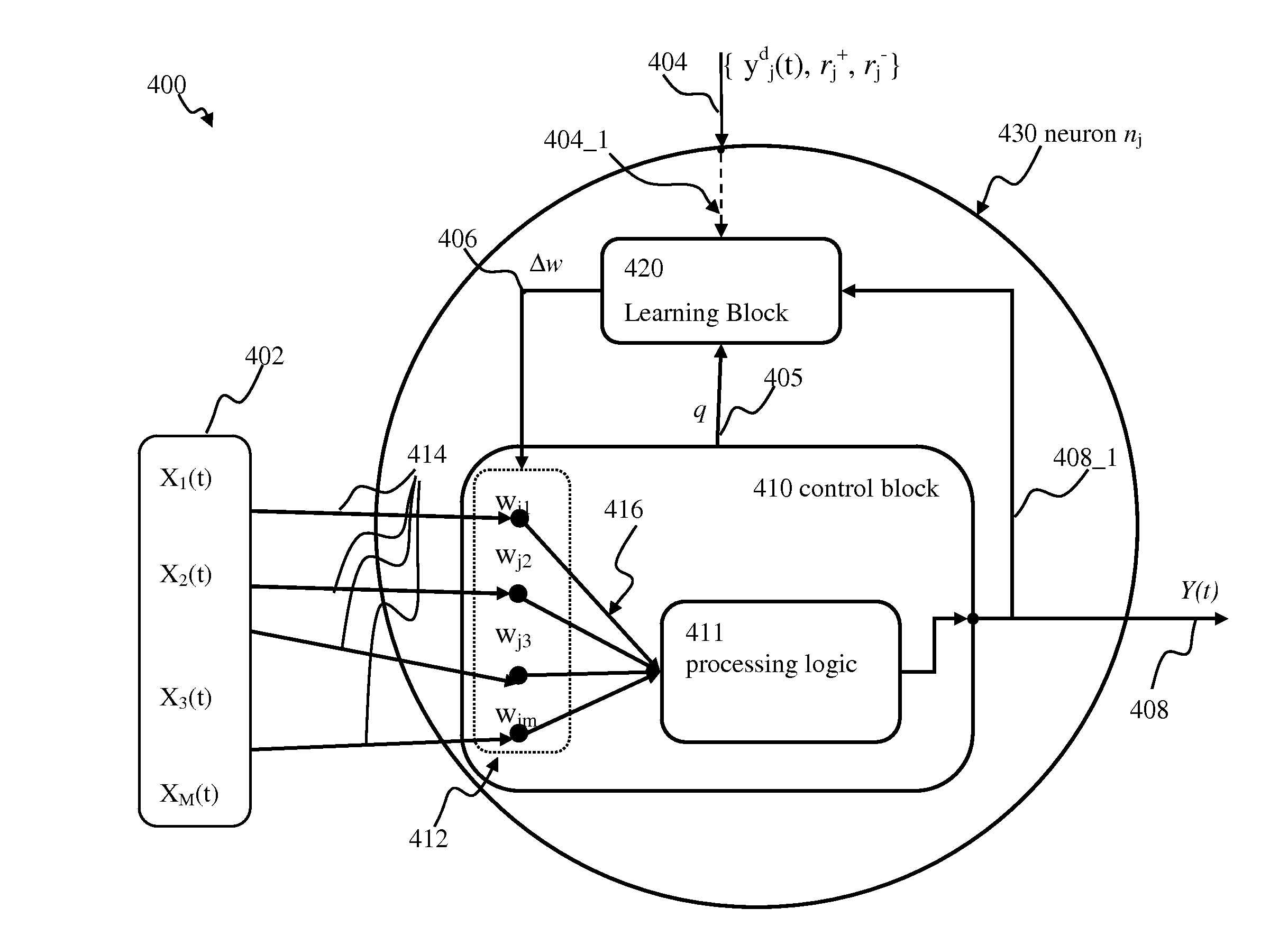
Apparatus and methods for efficient updates in spiking neuron network
Efficient updates of connections in artificial neuron networks may be implemented. A framework may be used to describe the connections using a linear synaptic dynamic process, characterized by stable equilibrium. The state of neurons and synapses within the network may be updated, based on inputs and outputs to / from neurons. In some implementations, the updates may be implemented at regular time intervals. In one or more implementations, the updates may be implemented on-demand, based on the network activity (e.g., neuron output and / or input) so as to further reduce computational load associated with the synaptic updates. The connection updates may be decomposed into multiple event-dependent connection change components that may be used to describe connection plasticity change due to neuron input. Using event-dependent connection change components, connection updates may be executed on per neuron basis, as opposed to per-connection basis.
Owner:QUALCOMM INC
Enabling network intrusion detection by representing network activity in graphical form utilizing distributed data sensors to detect and transmit activity data
ActiveUS8266697B2Increase speedImprove accuracyMemory loss protectionError detection/correctionGraphicsNetwork activity
A method, system, and computer program product for detecting and mapping activity occurring at and between devices on a computer network for utilization within an intrusion detection mechanism. An enhanced graph matching intrusion detection system (eGMIDS) utility executing on a control server provides data collection functions and data fusion techniques. The eGMIDS comprises multiple sensors and associated unique adaptors that are located at different remote devices of the network and utilized to detect specific types of activity occurring at the respective devices relevant to eGMIDS processing. The sensors convert the data into eGMIDS format and encapsulate the data in a special transmission packet that is transmitted to the control server. The eGMIDS utility converts the activity data within these packets into eGMIDS-usable format and then processes the converted data via a data fusion technique to generate a graphical representation of the network (devices) and the activity occurring at / amongst the various devices.
Owner:NORTHROP GRUMMAN SYST CORP
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
Systems and Methods to Automate Social Networking Activities
Systems and methods are provided to automate certain social networking activities in response to payments processed via mobile communications. In one aspect, a system includes a data storage facility to store social networking preferences with a phone number of the user and an interchange coupled with the data storage facility. The interchange includes a common format processor and a plurality of converters to interface with a plurality of different controllers of mobile communications. The converters are configured to communicate with the controllers in different formats; and the converters are configured to communicate with the common format processor in a common format. The common format processor is configured to communicate with a third party social networking site in accordance with the social networking preferences on behalf of the user, during processing of the payment, such as posting a message about a purchase, checking the user in at a location of the merchant, etc.
Owner:BOKU
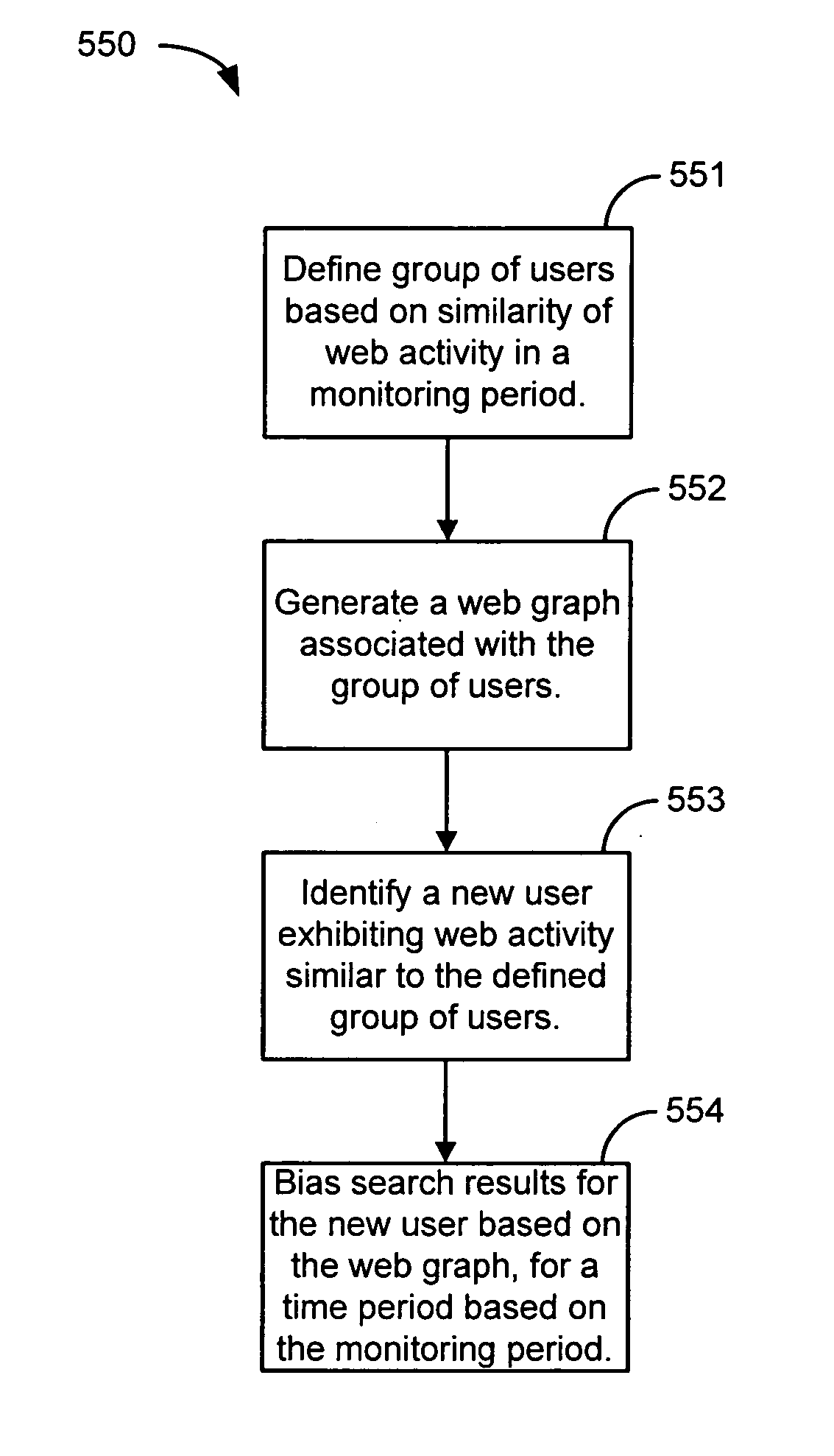
Sampling Internet user traffic to improve search results
ActiveUS20070112730A1Improve freshnessWeb data indexingDigital data processing detailsTraffic capacityNetwork activity
Methods, systems and apparatus for improving Internet search results include monitoring network activity on a communications network, generating a near real-time map of the network activity, and integrating the near real-time map with a search engine.
Owner:IAC SEARCH & MEDIA
Methods, systems, and user interfaces for graphical summaries of network activities
InactiveUS20110252327A1Hardware monitoringMultiple digital computer combinationsGraphicsNetwork activity
Owner:ACTIANCE
Intelligent intrusion detection system utilizing enhanced graph-matching of network activity with context data
ActiveUS7624448B2Increase speedImprove accuracyMemory loss protectionError detection/correctionGraphicsNetwork activity
Owner:NORTHROP GRUMMAN SYST CORP
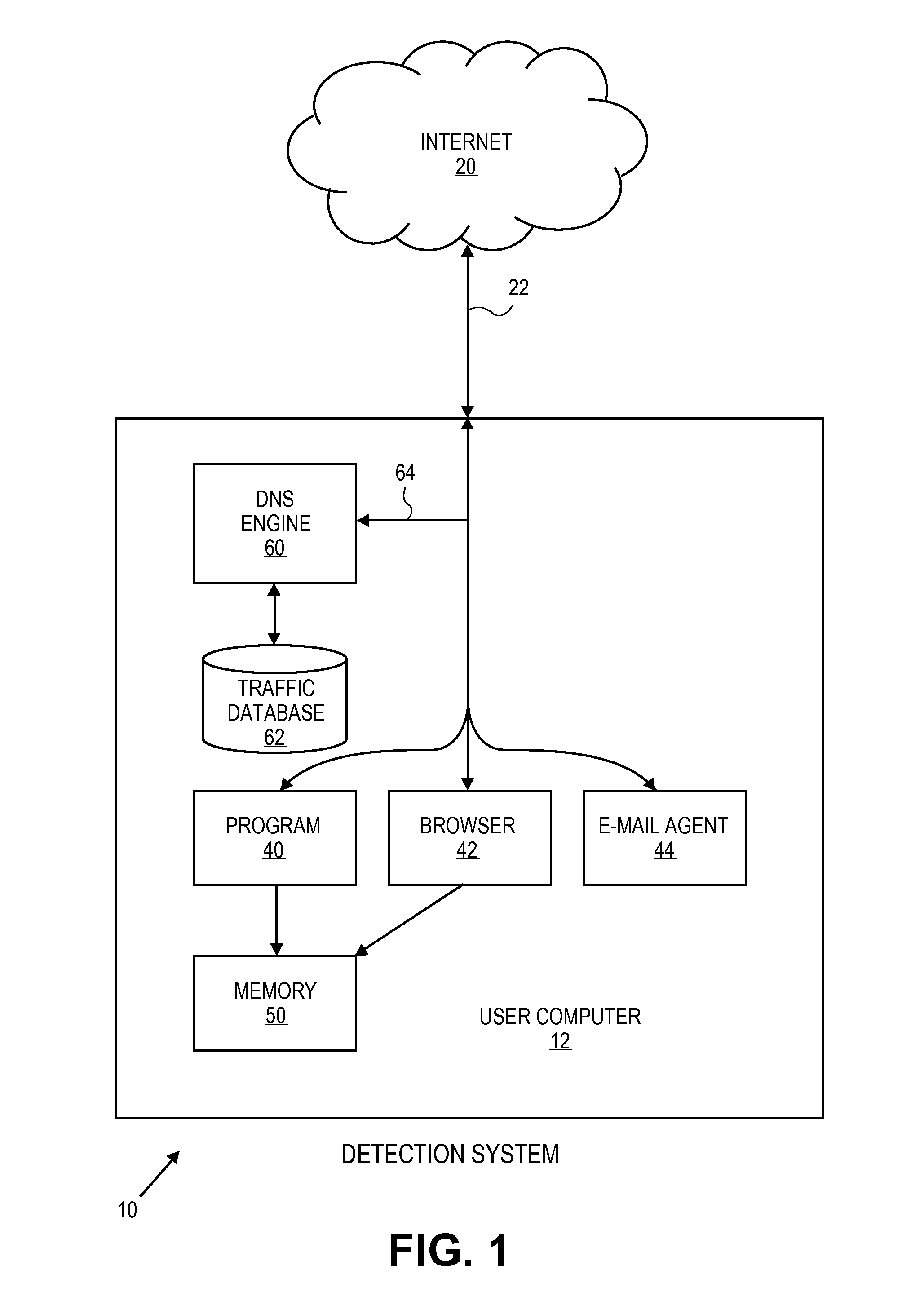
Detection of downloaded malware using DNS information
ActiveUS8347394B1Low costPushes the cost to a client or host computerMemory loss protectionError detection/correctionDomain nameNetwork activity
A DNS engine monitors domain name system (DNS) network activity occurring between a user computer and a remote computer server. The engine collects DNS traffic information during a specified time window at the user computer using the monitored DNS network activity. The engine generates a local DNS reputation for the user computer and stores the local DNS reputation on the user computer. When a triggering event is received at the user computer the engine determines that the triggering event is abnormal in comparison to the stored local DNS reputation. An alert is issued to a software product on the user computer. The engine takes an action using a software product upon the alert. The reputation may be a frequency distribution for each accessed domain name and IP address. A triggering event may be an abnormal access to a domain name or IP address, or a mismatch between DNS queries and DNS responses of the user computer.
Owner:TREND MICRO INC
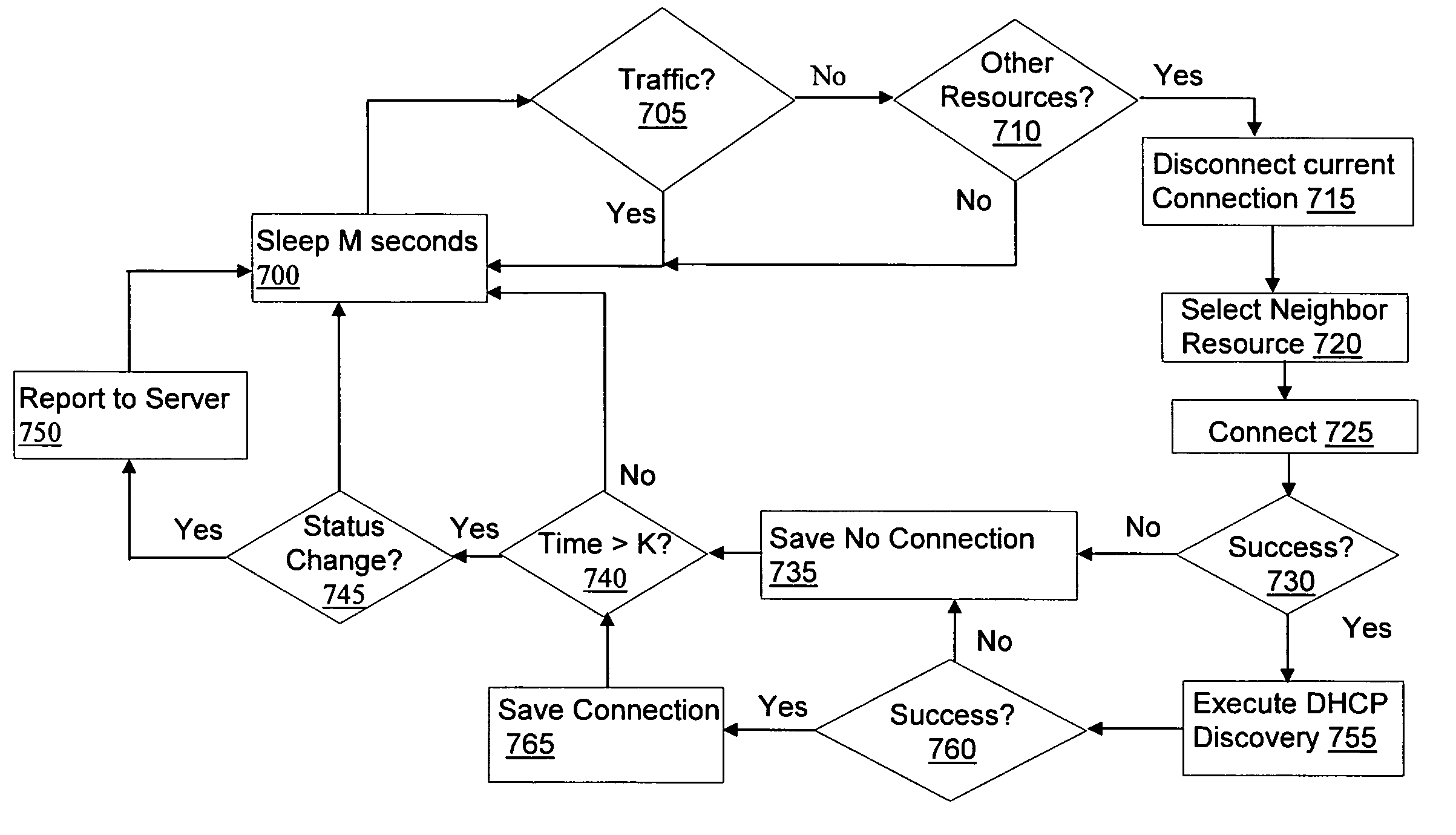
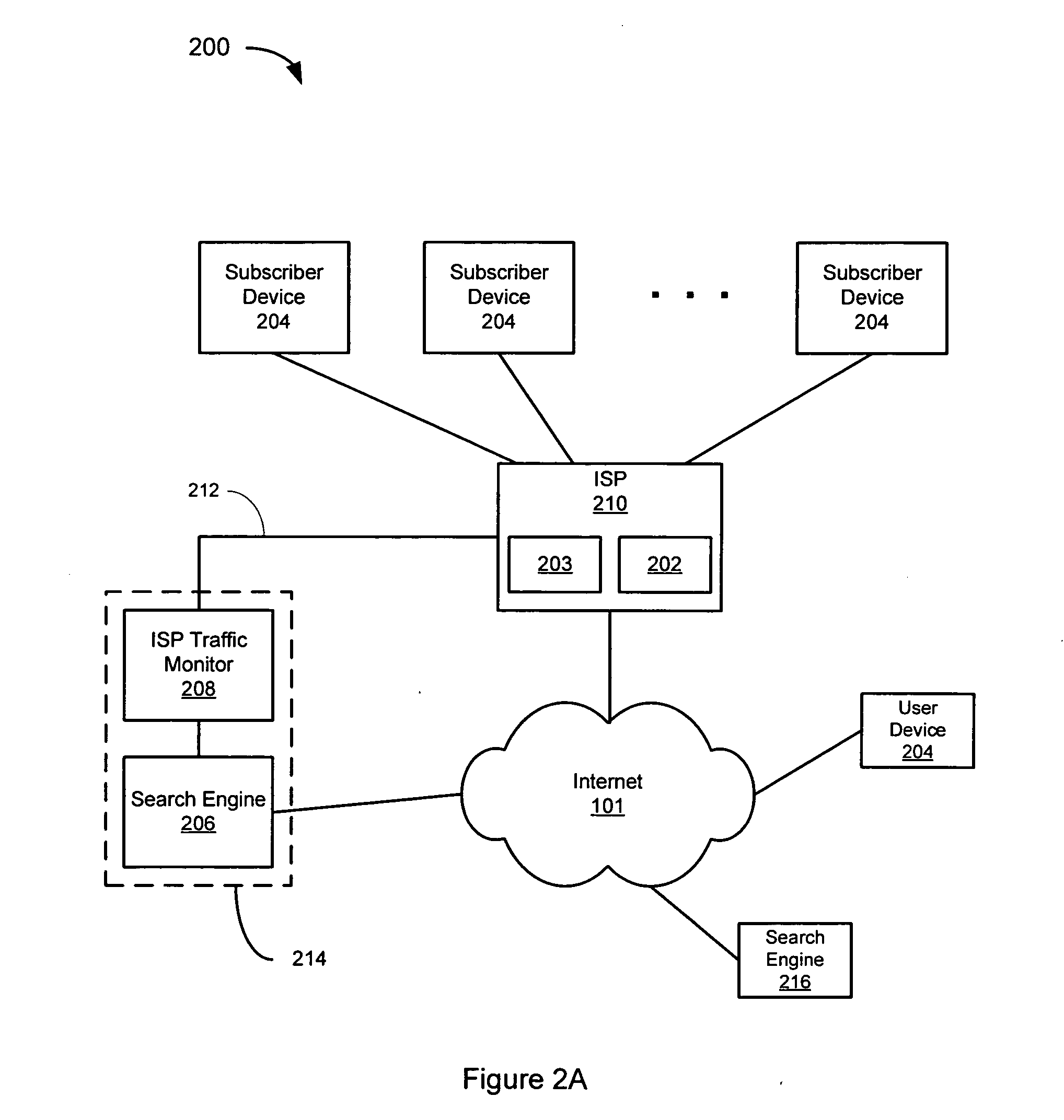
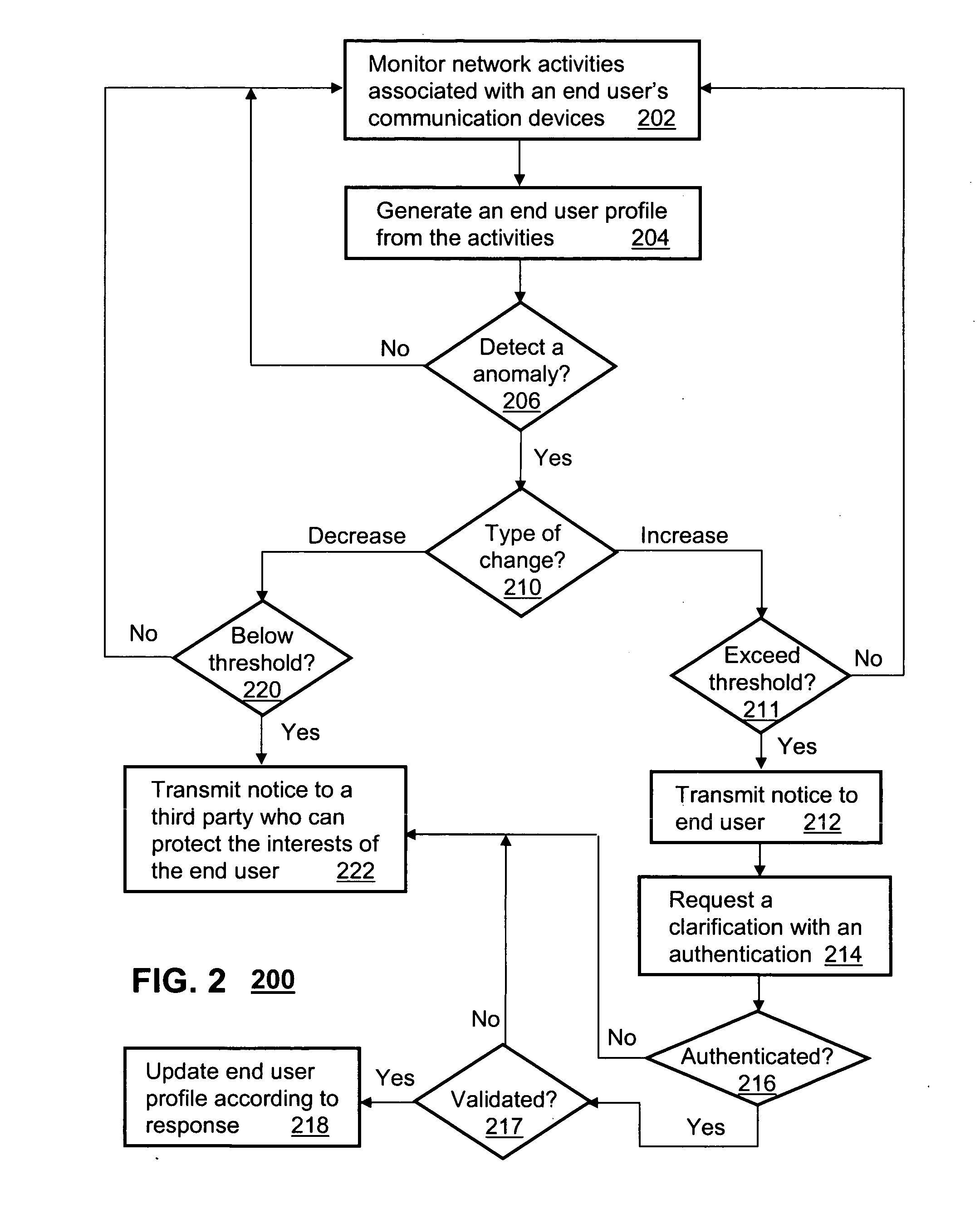
Method and apparatus for monitoring network activity
InactiveUS20070206741A1Emergency connection handlingConnection managementCommunication interfaceNetwork activity
A method (200) and apparatus (102, 108) are disclosed for monitoring network activity. An apparatus that incorporates teachings of the present disclosure may include, for example, an activity notification system (ANS) (102) having a controller (104) that manages operations of a communications interface (110) for communicating with network elements (101) in a communication system. The controller can be programmed to monitor (202) network activities associated with a plurality of communication devices of an end user, generate (204) from the monitored activities an end user profile that predicts a behavior of the end user, and transmit (212, 222) a notice when a change in the monitored activities differs from a behavior predicted by the end user profile. Additional embodiments are disclosed.
Owner:SBC KNOWLEDGE VENTURES LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com