Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3152 results about "Network monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network monitoring is the use of a system that constantly monitors a computer network for slow or failing components and that notifies the network administrator (via email, SMS or other alarms) in case of outages or other trouble. Network monitoring is part of network management.
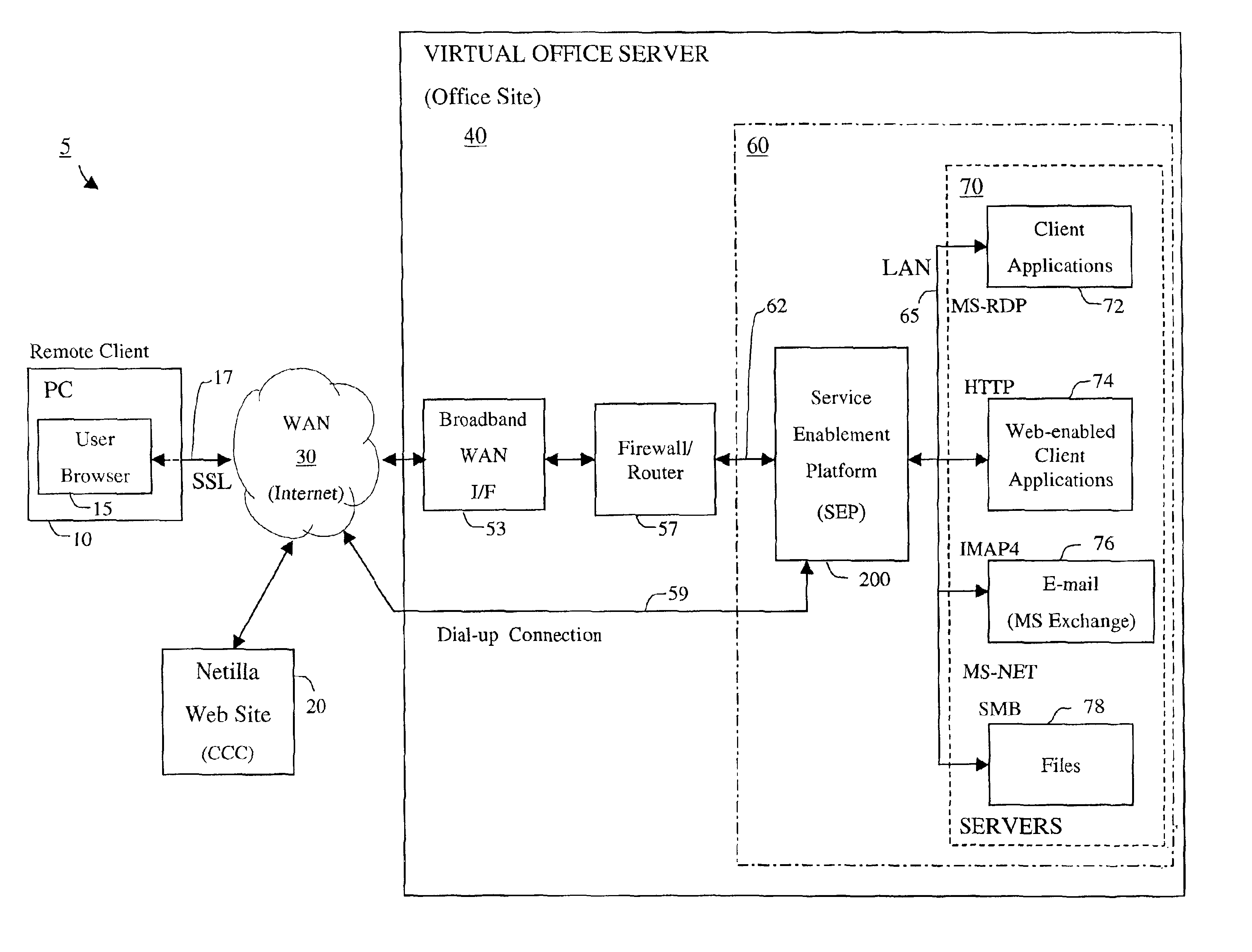
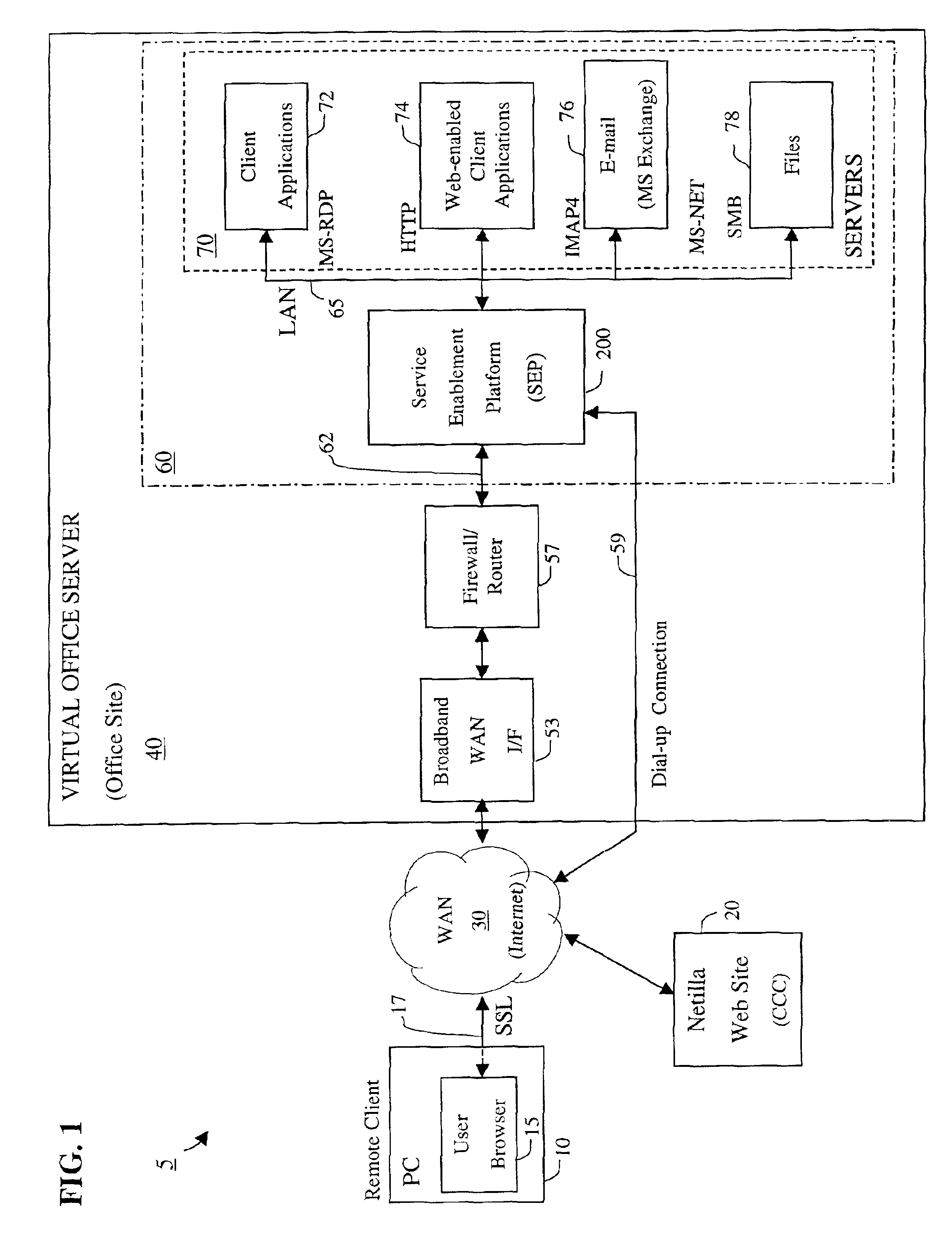
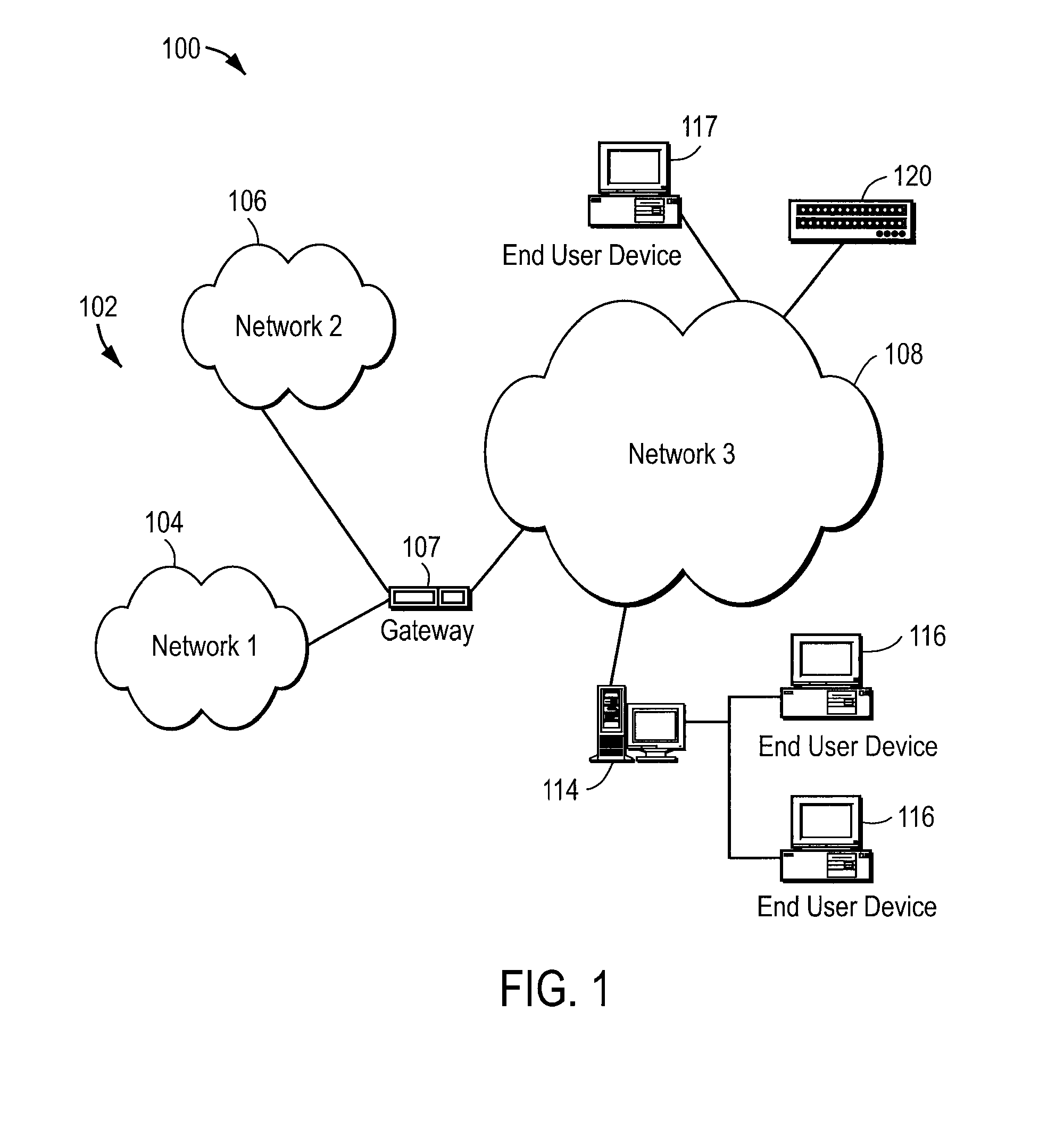
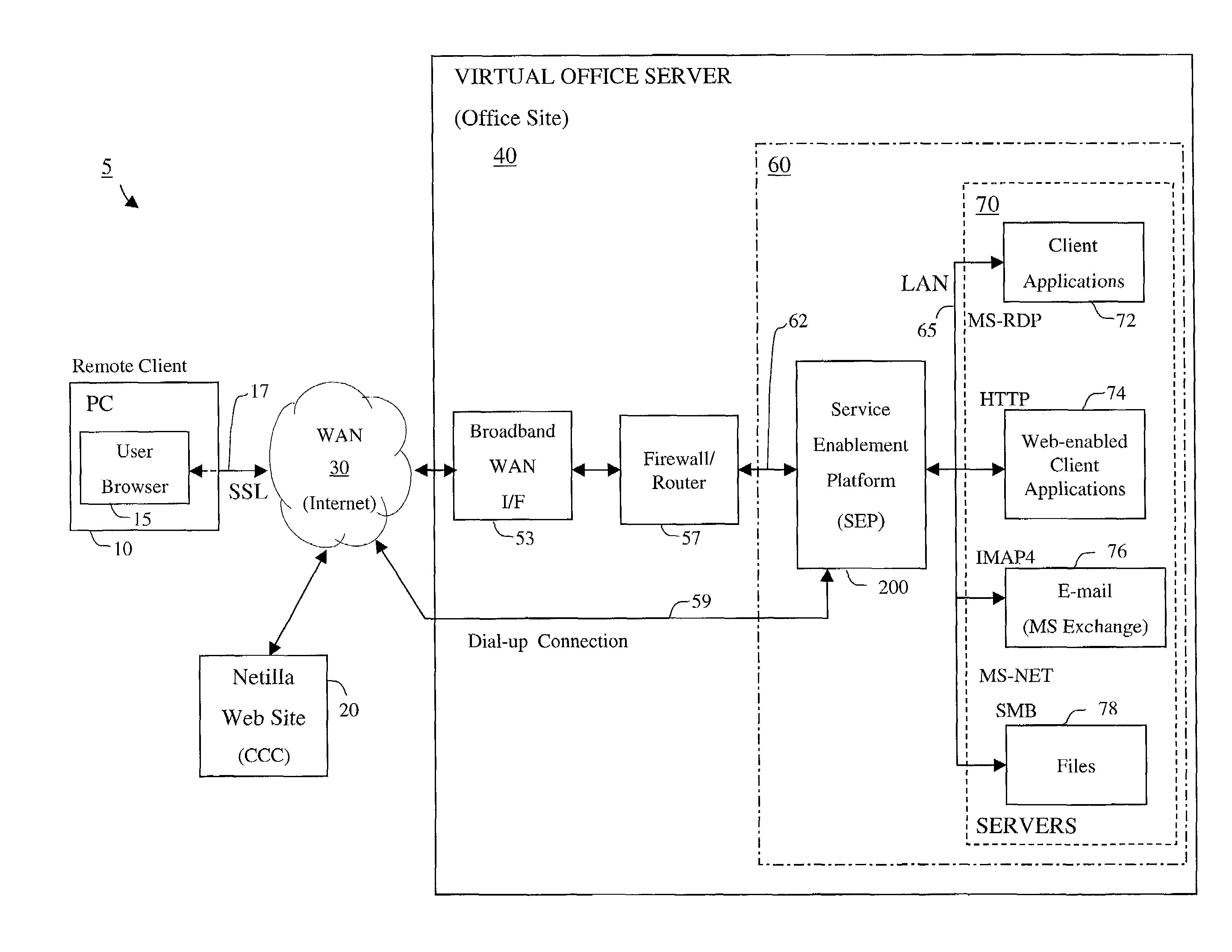
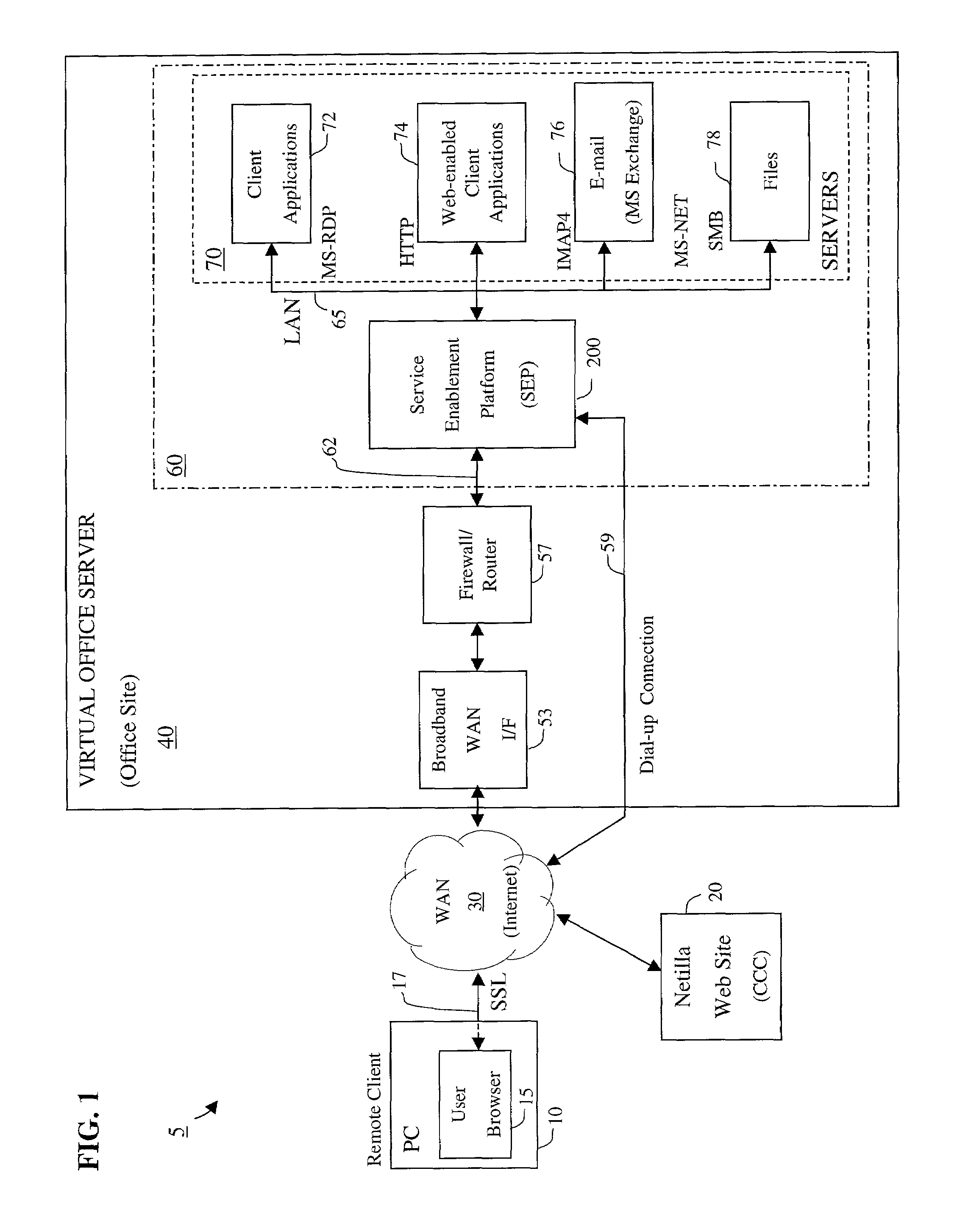
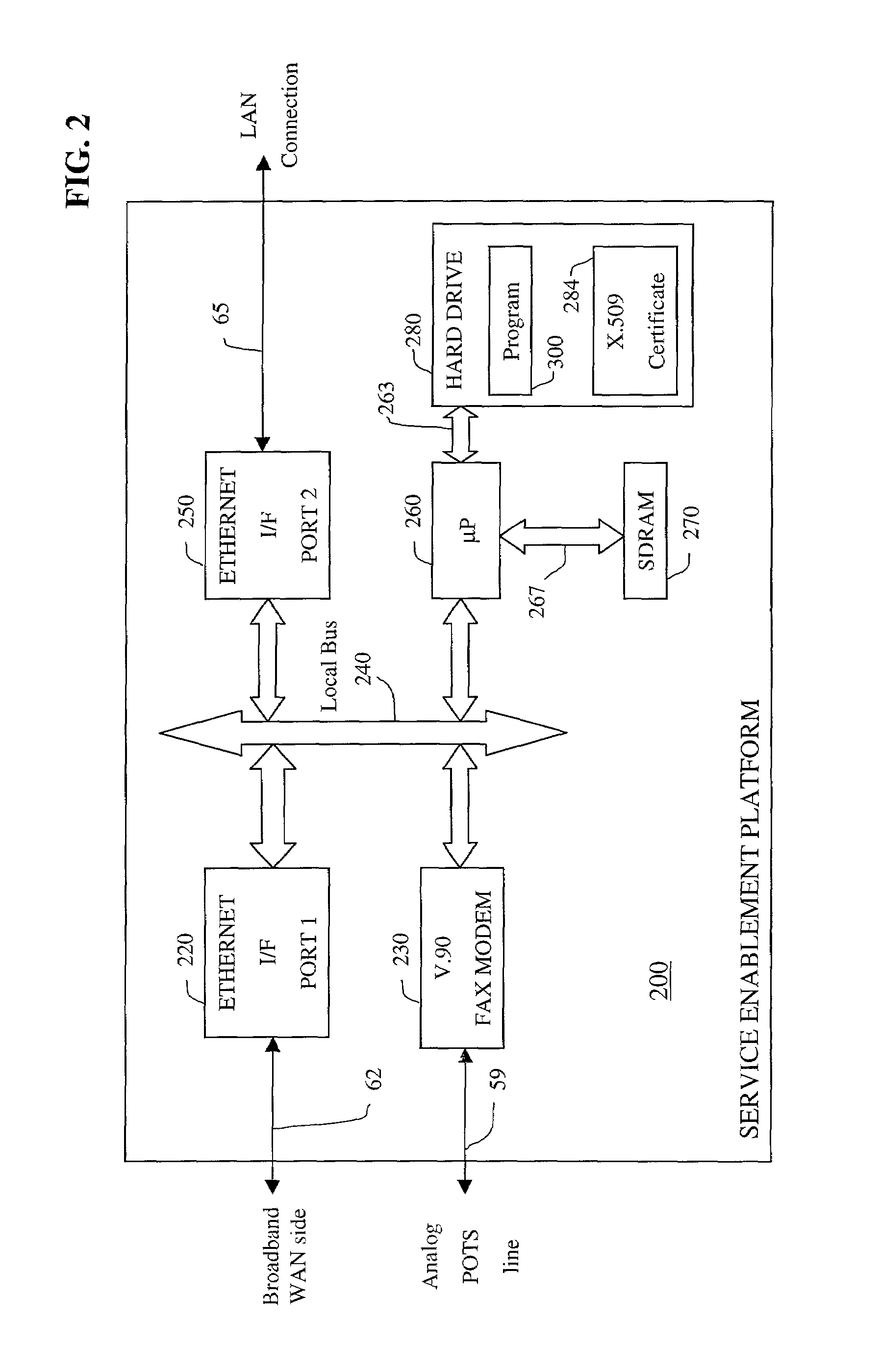
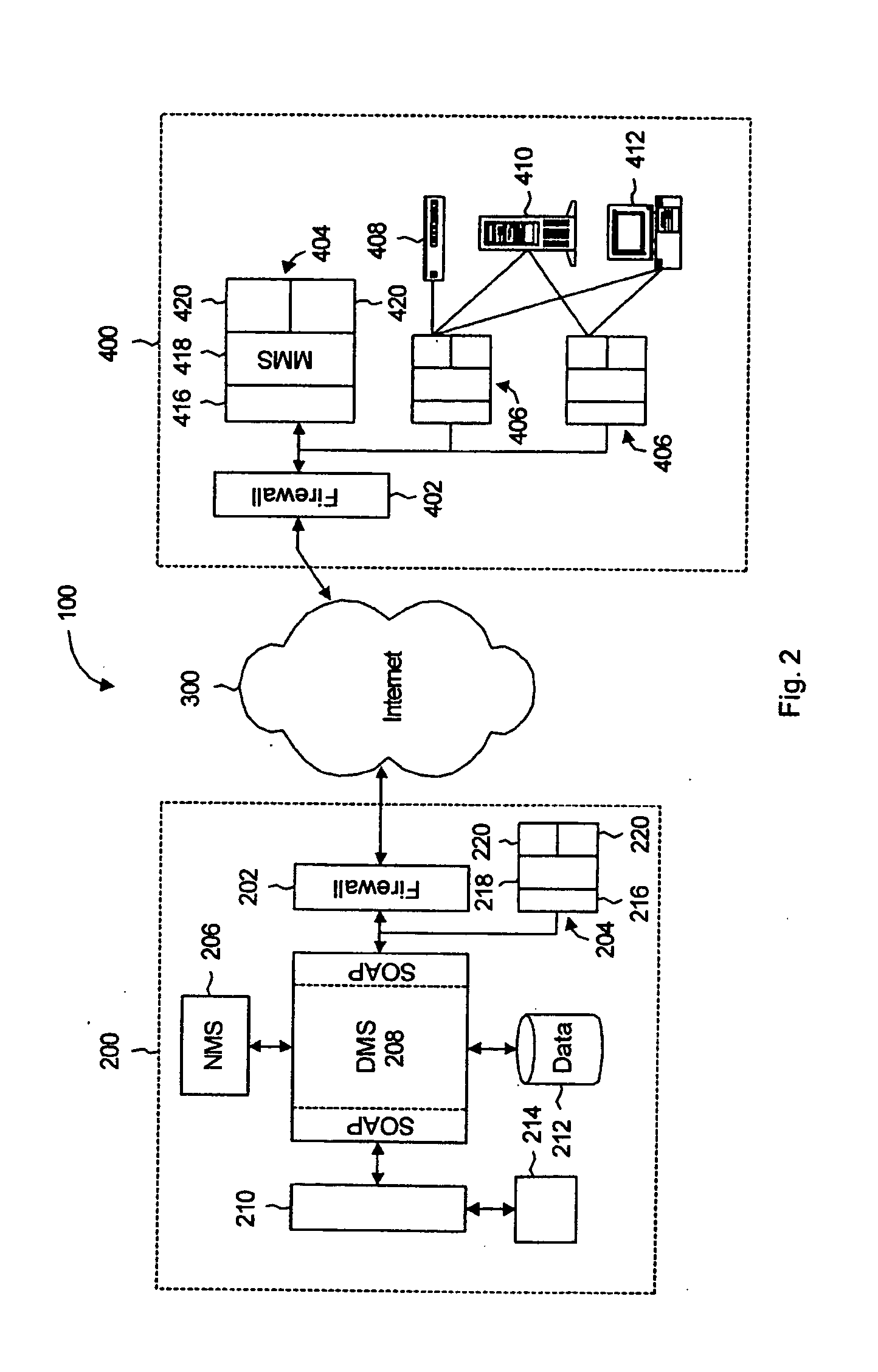
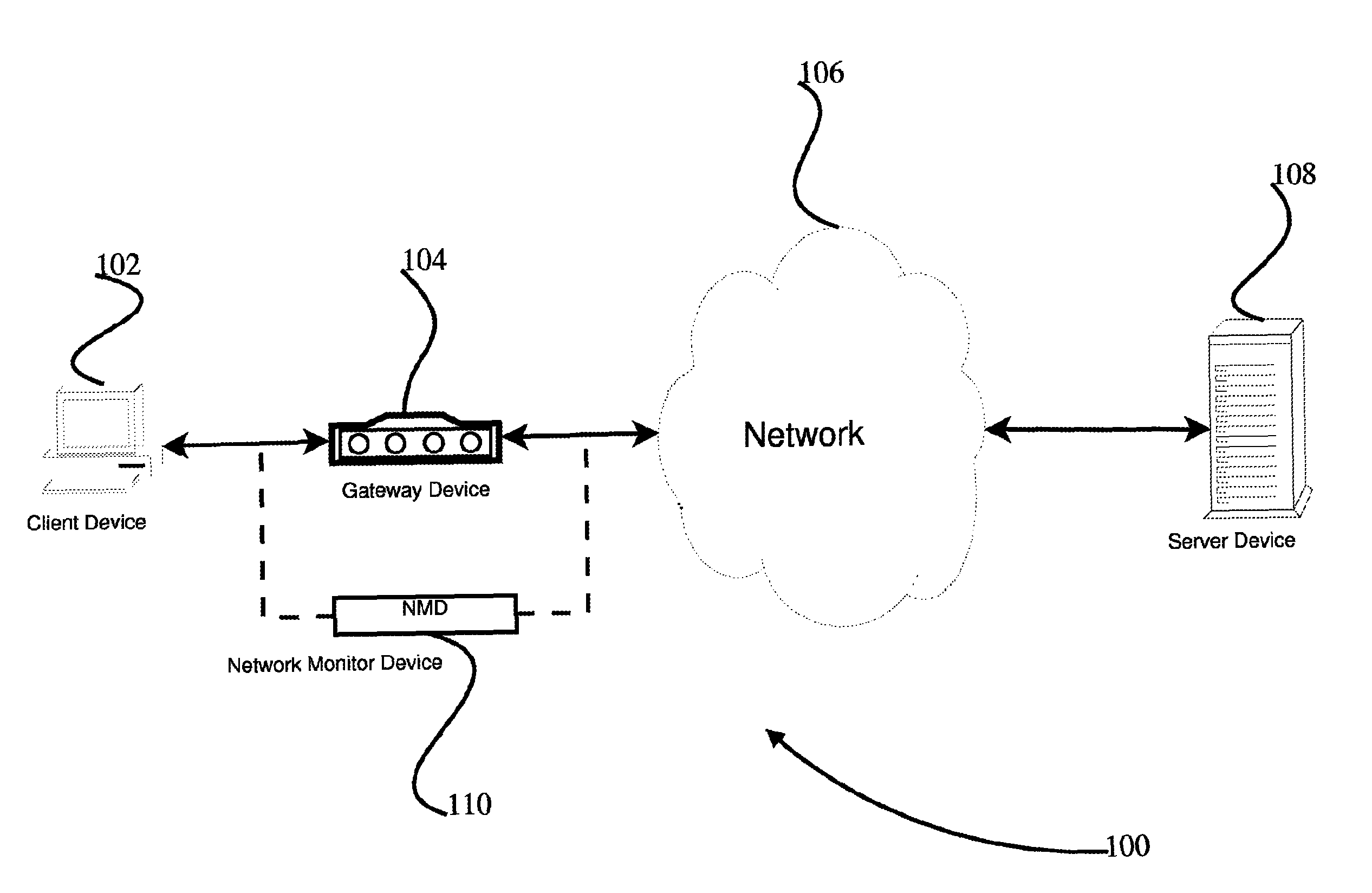
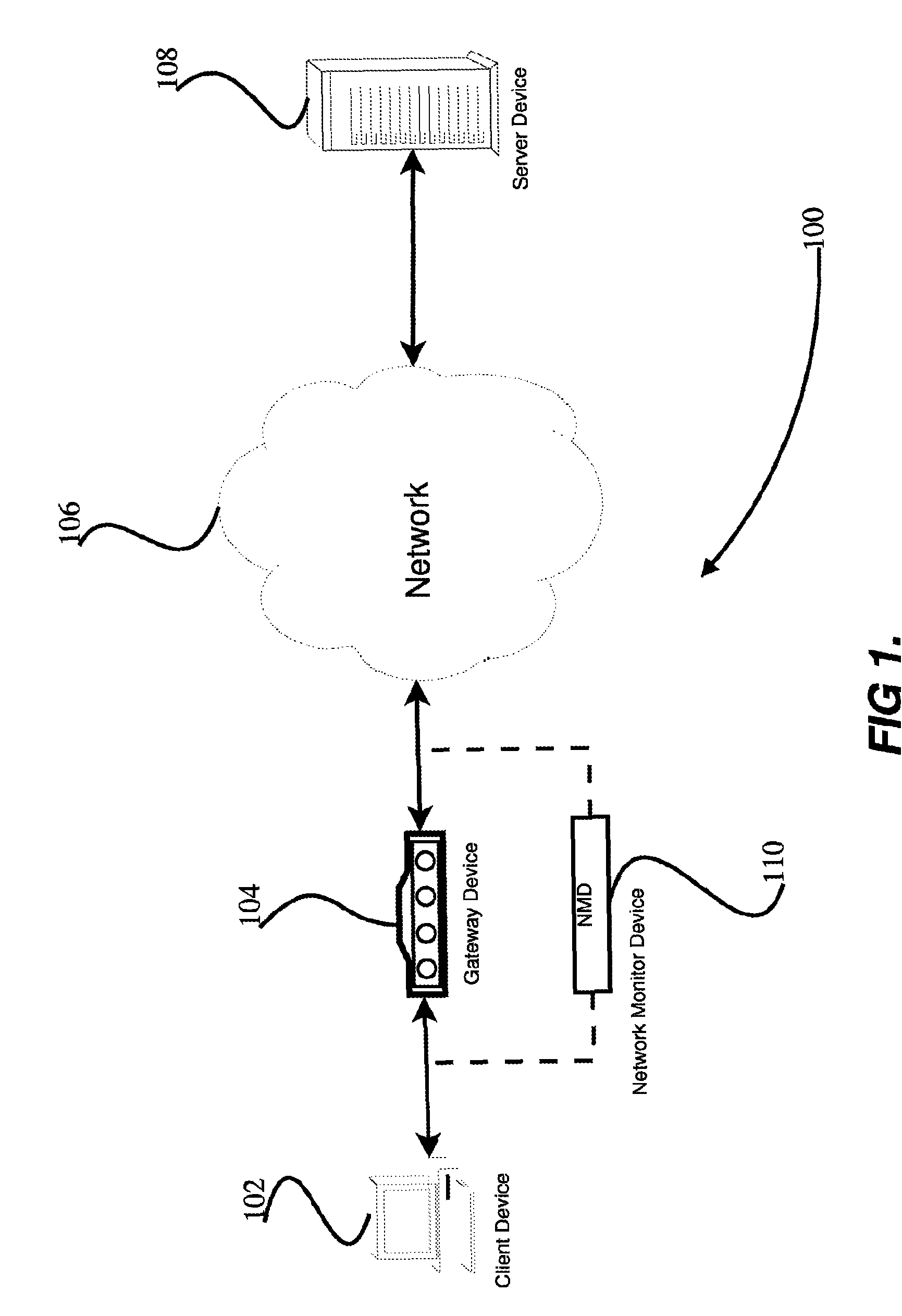
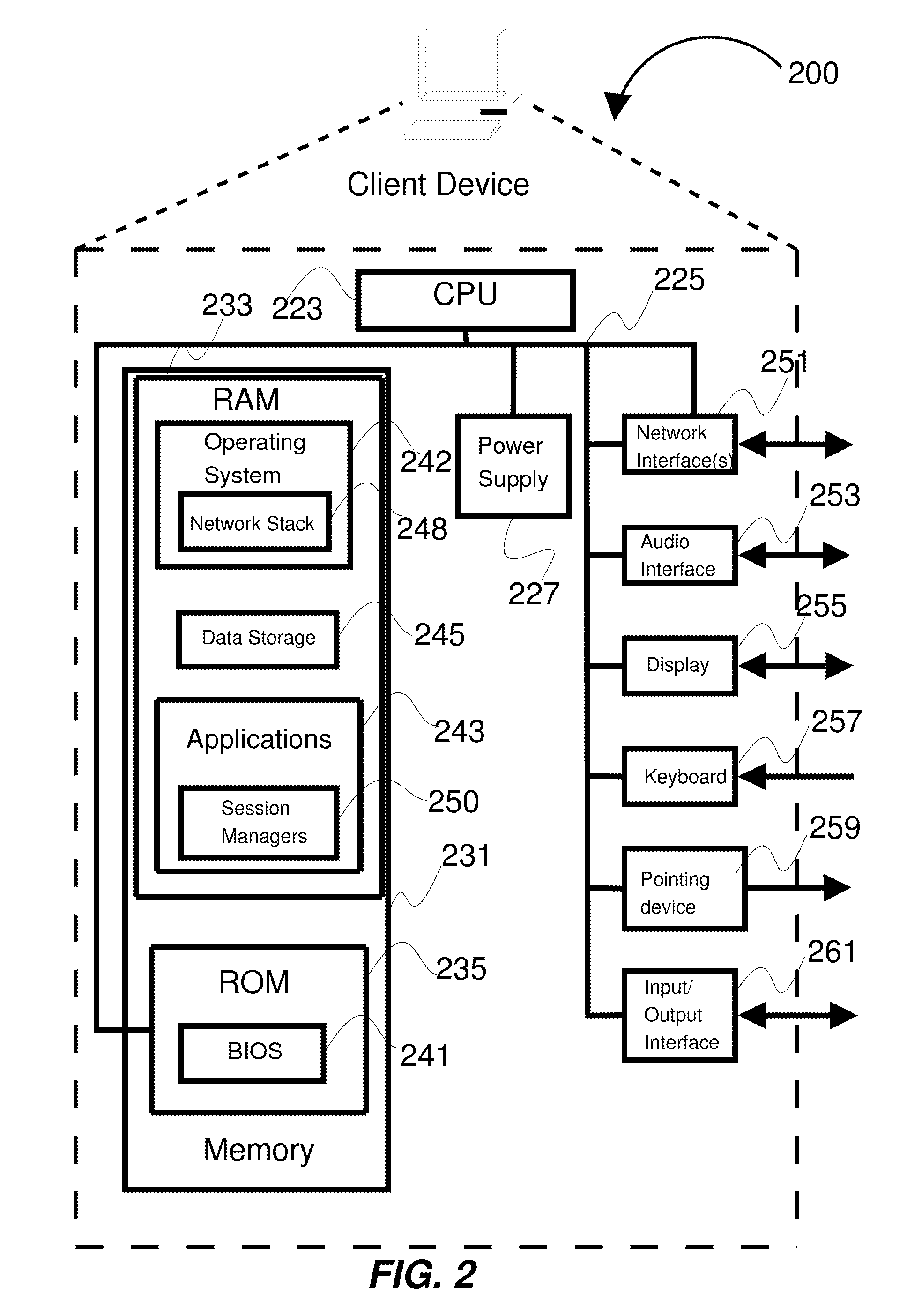
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6920502B2Readily and easily accommodateExpanding processing and storage capacityMultiple digital computer combinationsProgram controlCA protocolNetwork connection
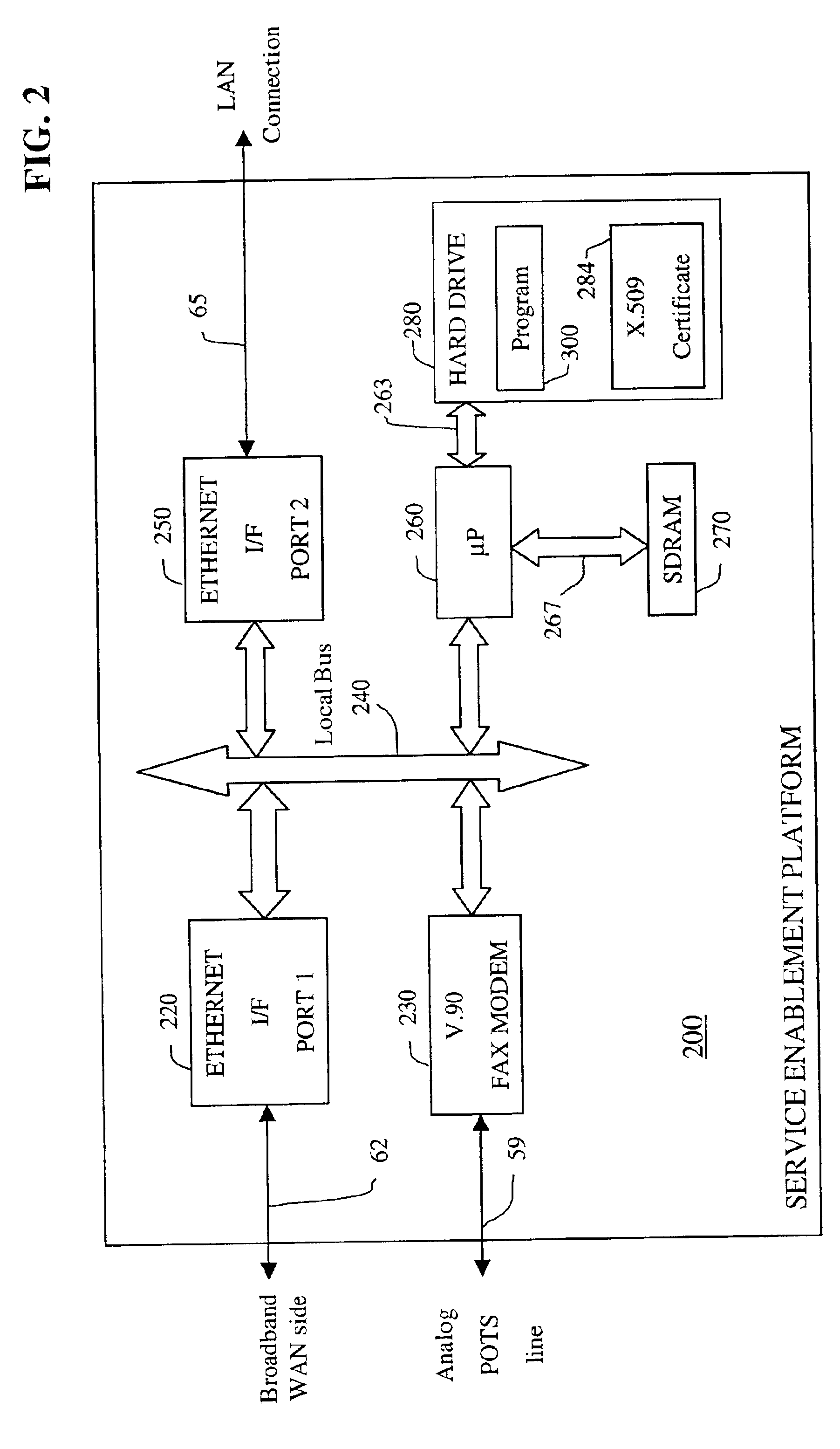
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Media module apparatus and method for use in a network monitoring environment
InactiveUS7299277B1Avoid data lossReduce probabilityError preventionTransmission systemsApplication softwareMaster processor
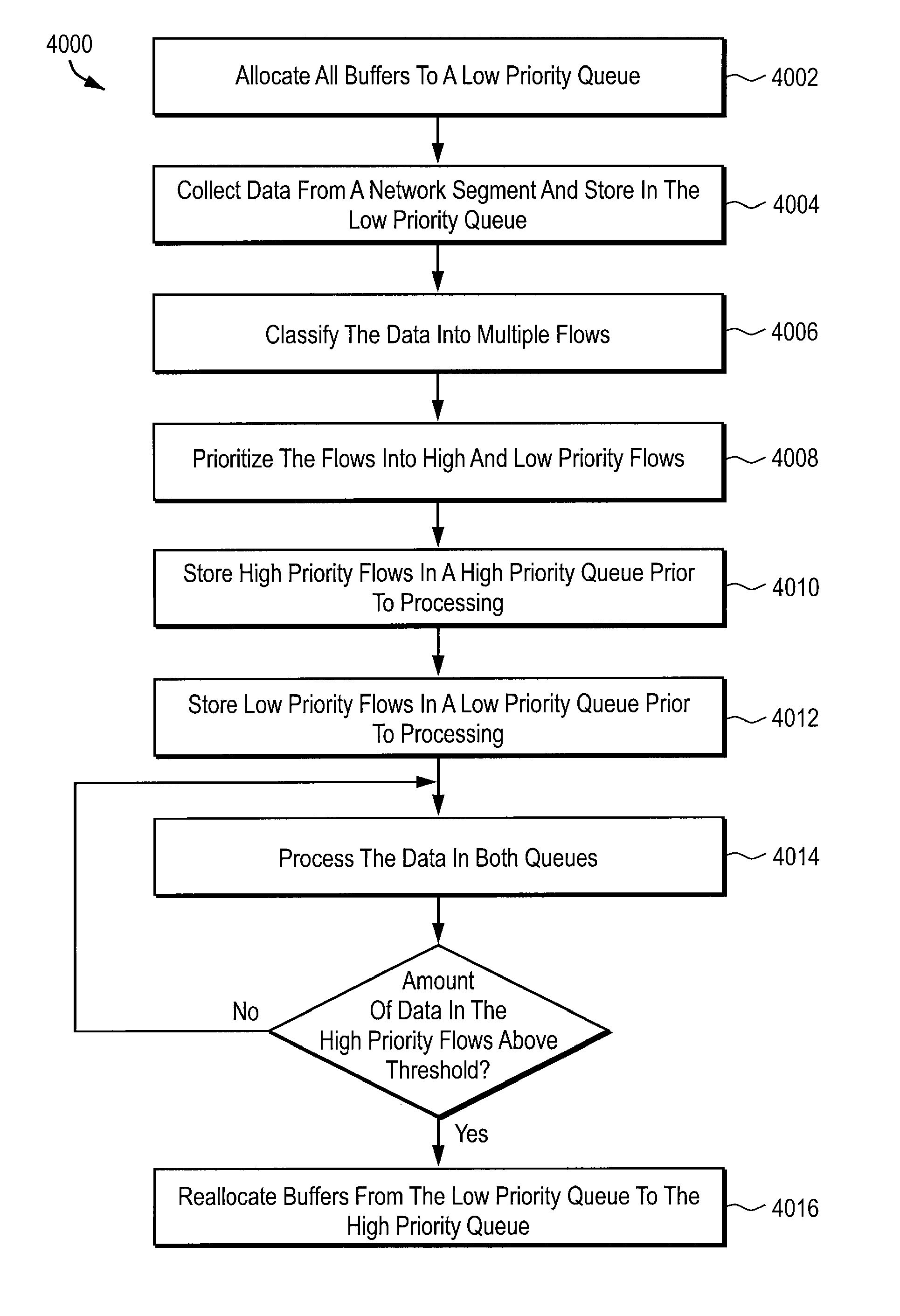
A probe apparatus, method and computer program product for application monitoring are provided. A data collection module collects data from a network segment. A flow processor coupled to the data collection module classifies the collected data into a plurality of flows. A capture system coupled to the flow processor filters and buffers the collected data. A main processor processes the filtered data.
Owner:NETWORK GENERAL TECH
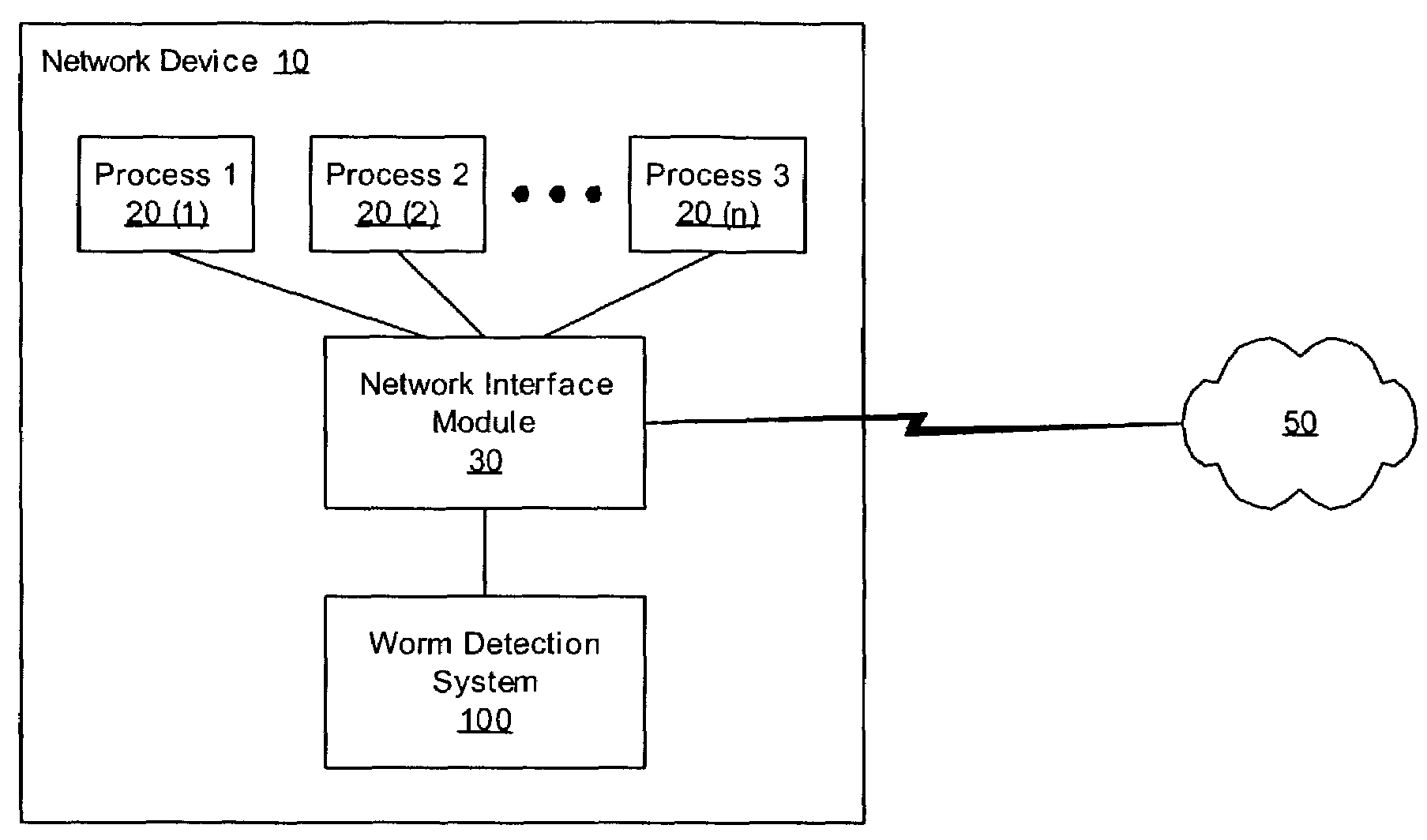
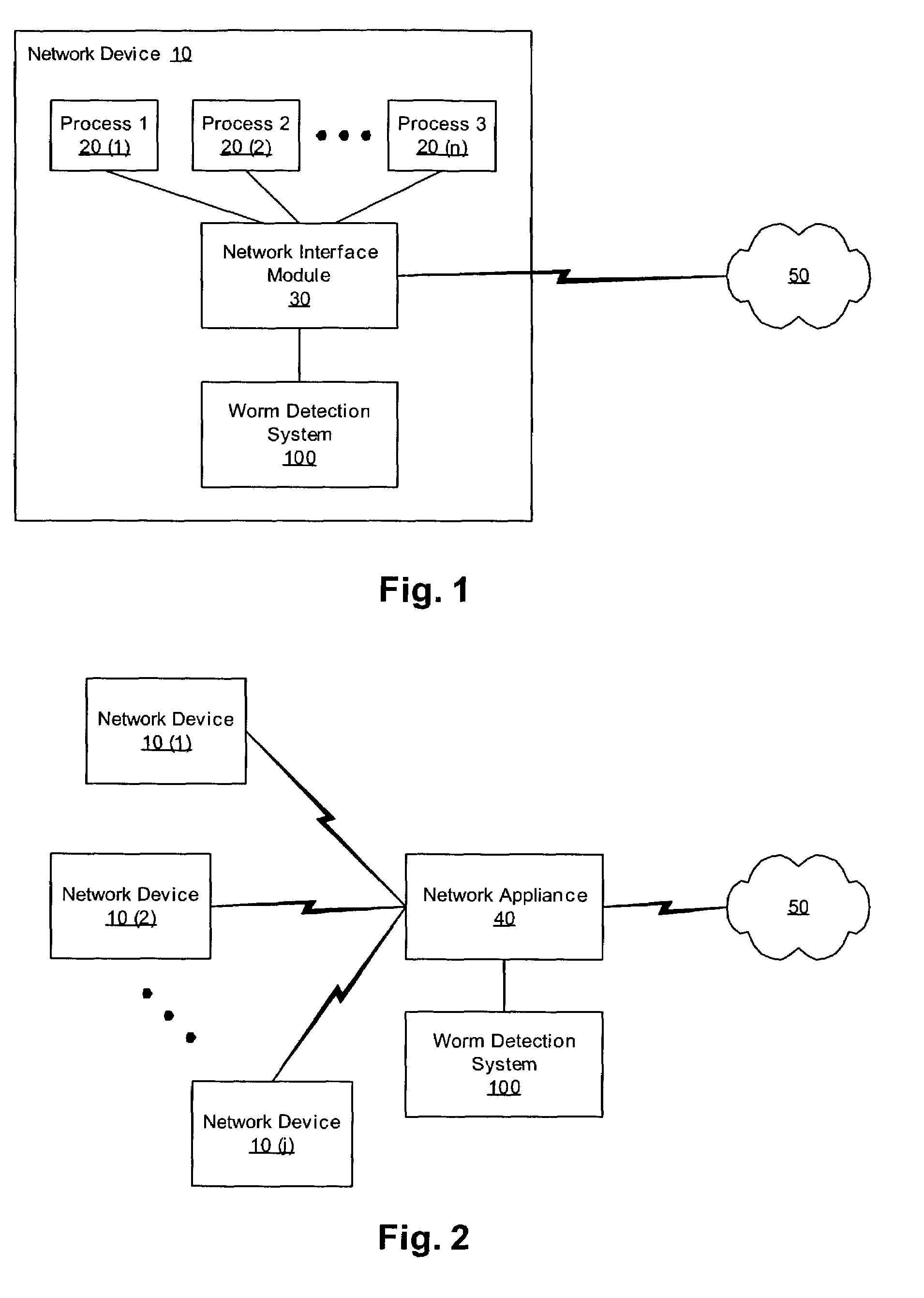
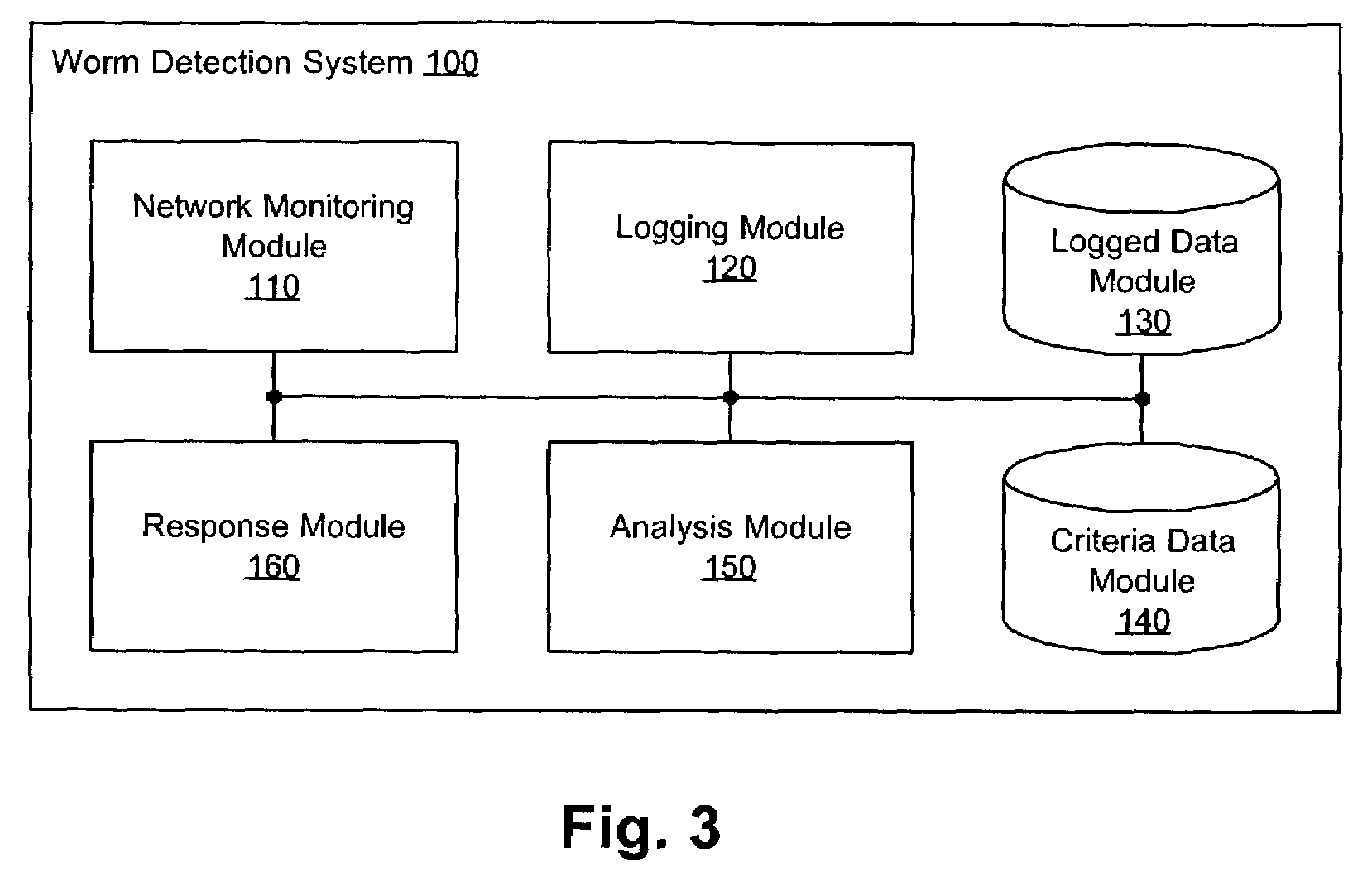
Heuristic detection and termination of fast spreading network worm attacks
Methods, apparati, and computer program products for detecting and responding to fast-spreading network worm attacks include a network monitoring module (110), which observes (205) failed network connection attempts from multiple sources. A logging module (120) logs (220) the failed connection attempts. An analysis module (150) uses the logged data on the failed connection attempts to determine (225) whether a sources is infected with a worm using a set of threshold criteria. The threshold criteria indicate whether a source's failed connection attempts are non-normal. In one embodiment, a response module (160) responds (240) to the computer worm by, e.g., alerting a user or system administrator, terminating an infected process (20), or terminating the infected source's network access.
Owner:CA TECH INC
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6981041B2Expanding processing and storage capacityEasy to scaleMultiple digital computer combinationsData switching networksCA protocolNetwork connection
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Methods, apparatuses and systems facilitating classification of web services network traffic
InactiveUS7774456B1Easy to classifyImprove networkingMultiple digital computer combinationsTransmissionTraffic capacityWeb service
Methods, apparatuses and systems that facilitate the classification of web services network traffic. In one implementation, the present invention processes interface definitions corresponding to a given Web service to construct a traffic classification configuration for the Web service, including one or more traffic classes and corresponding matching rules or attributes for each traffic class. In one implementation, the present invention automatically creates traffic classes and matching rules that allow for differentiation between the operations supported by a Web service. Implementations of the present invention provide a mechanism allowing for classification of Web services network traffic on a granular basis to enhance network monitoring and analysis tasks, as well as network control functions, such as bandwidth management, security and other functions.
Owner:CA TECH INC
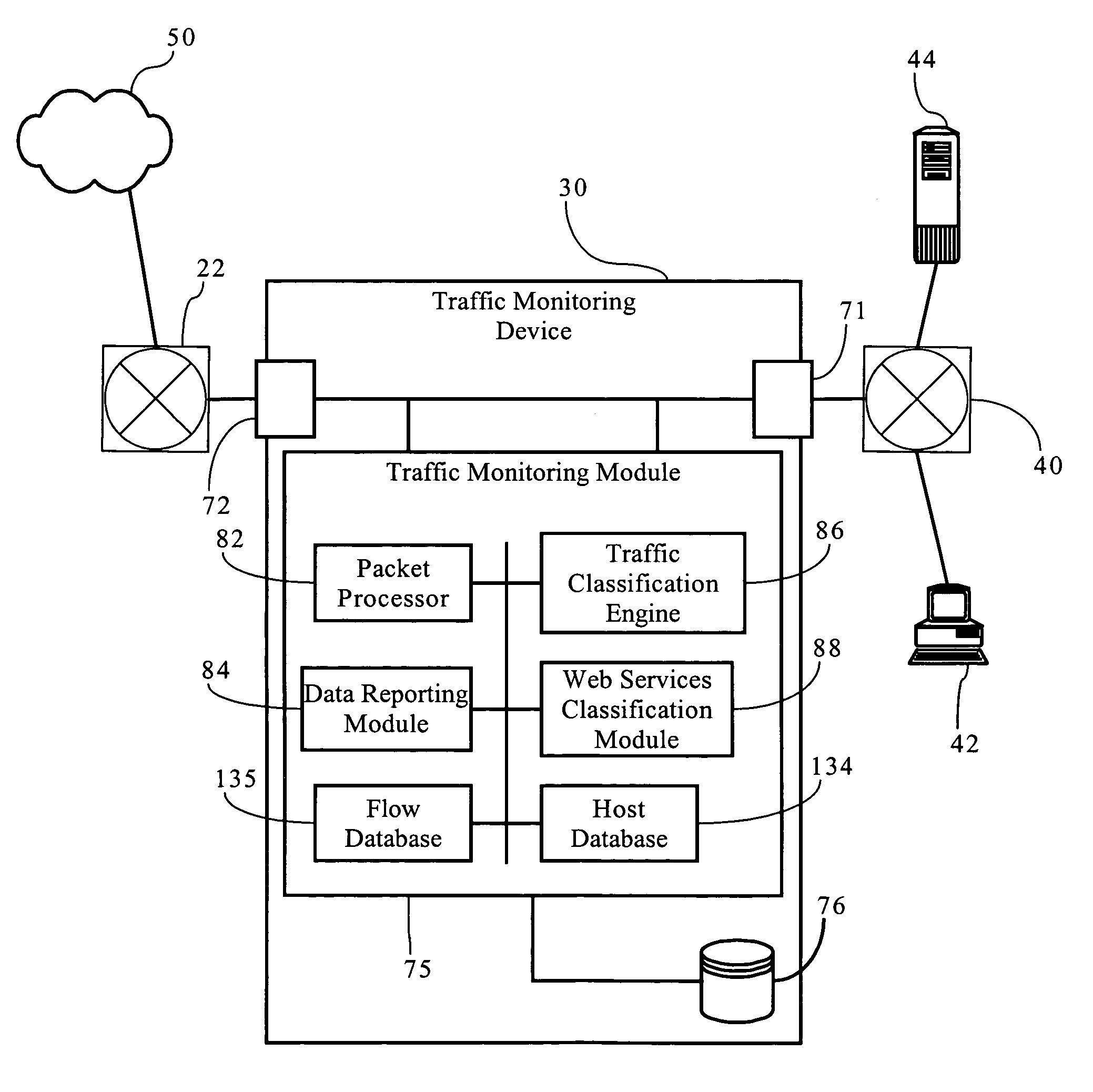
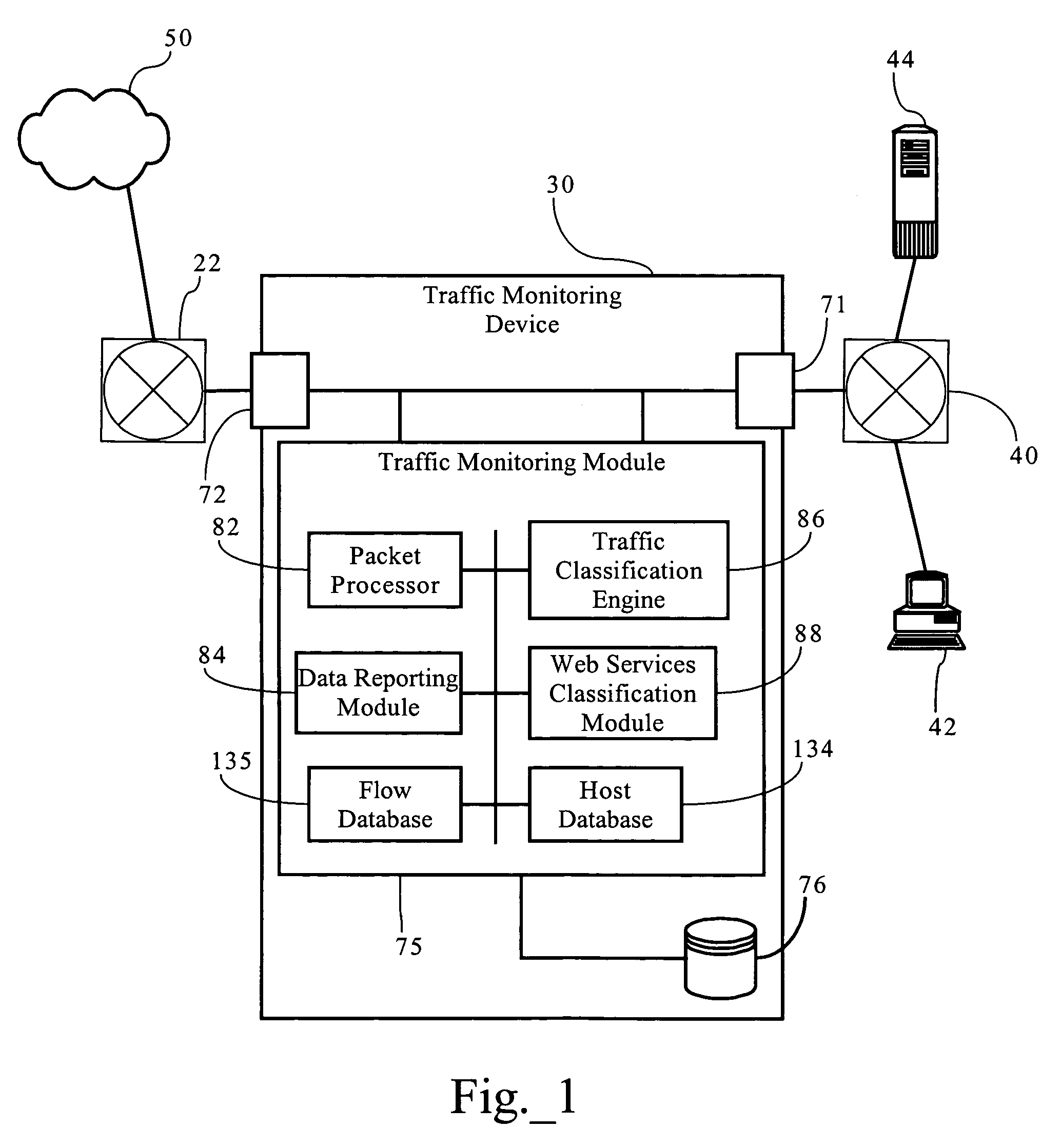
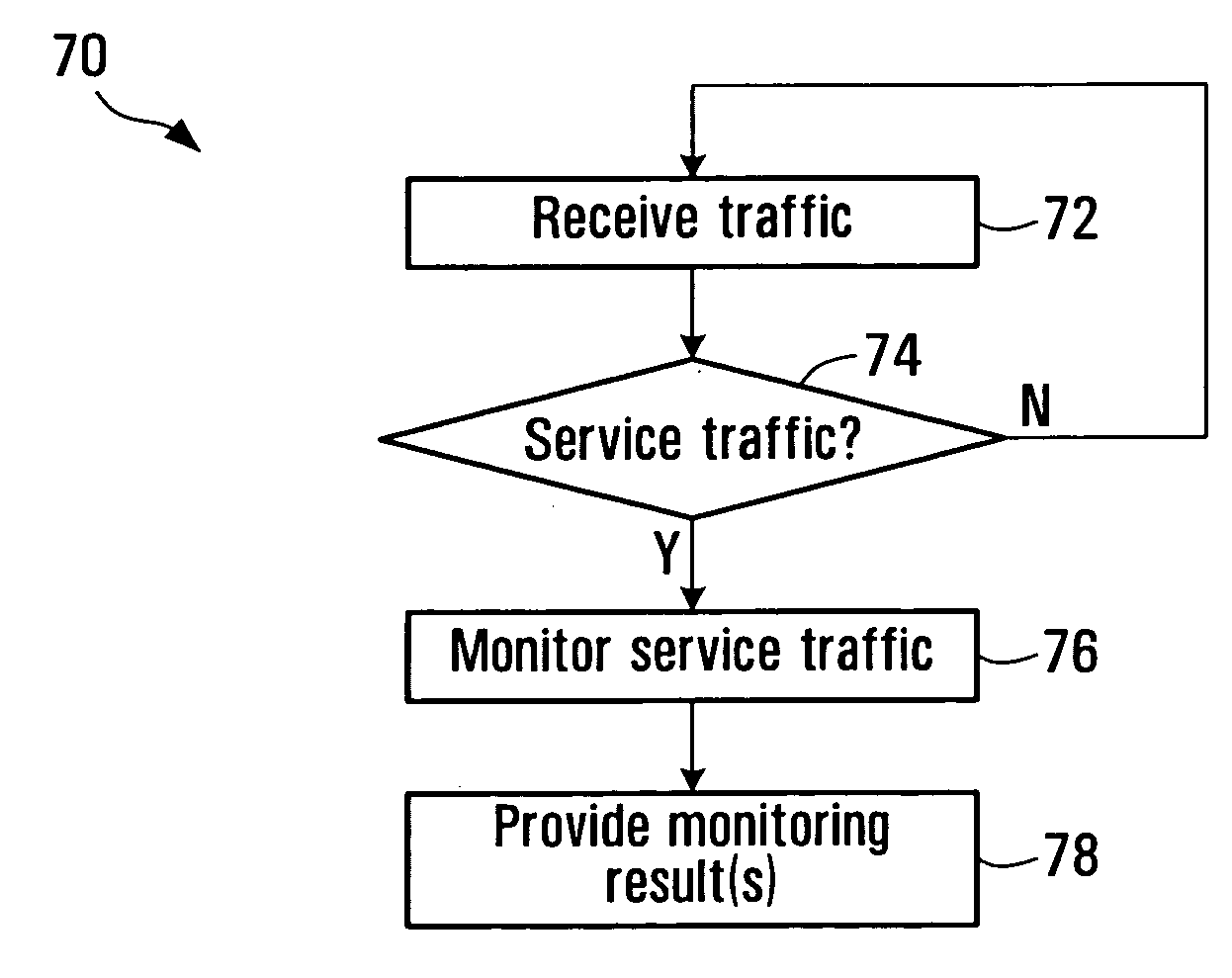
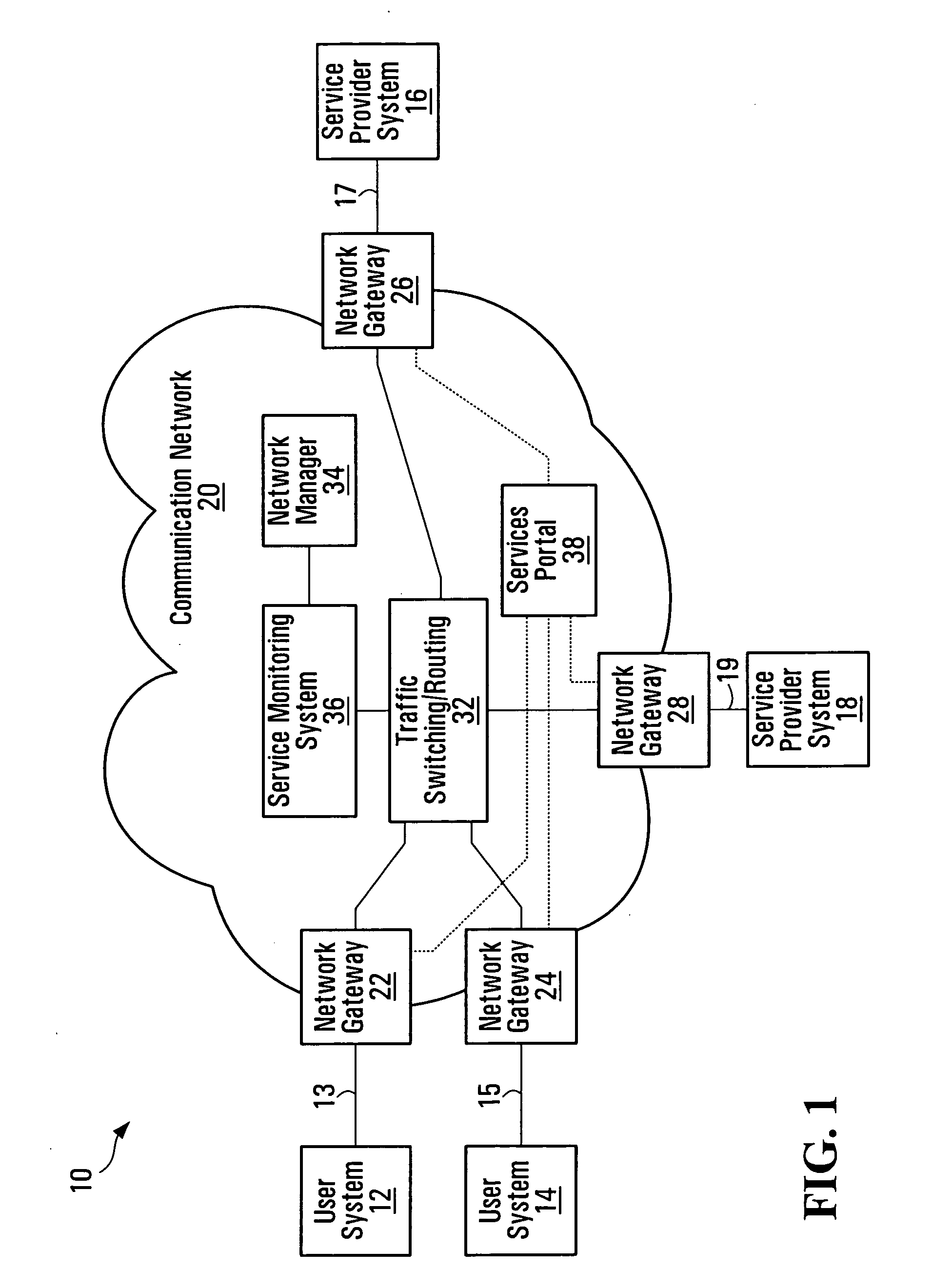
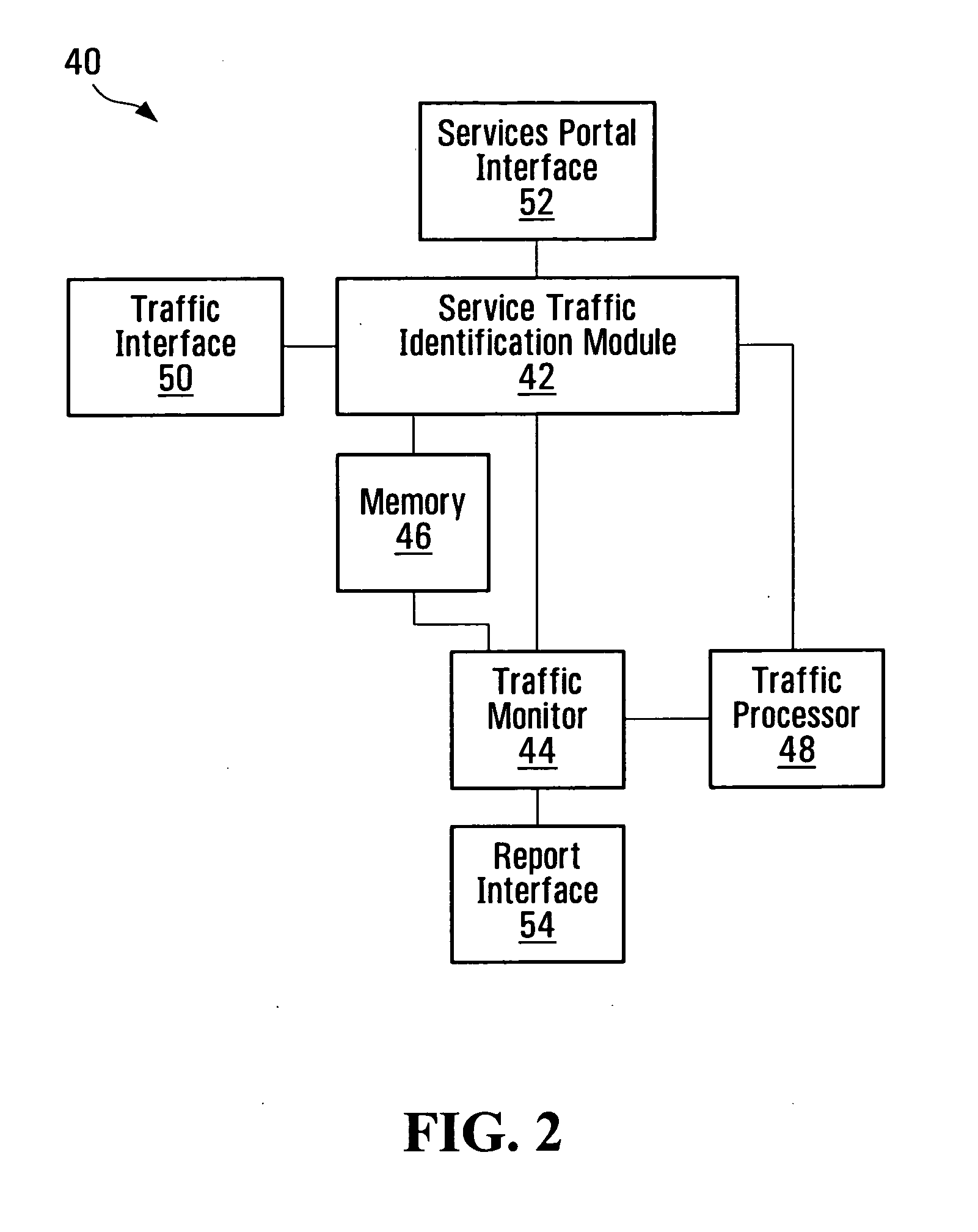
Service-centric communication network monitoring
Service-centric communication network monitoring apparatus and methods are provided. Service traffic, associated with a third-party service provided by an external service provider that is controlled independently of a communication network, is identified in communication traffic that is being transferred through that communication network. The identified service traffic is monitored, for example, to compile service usage statistics, to police usage of the service, to generate billing records for usage of the service, and / or to mirror the identified service traffic. A registry in which the service is registered may interact with a monitoring system of the communication network so as to establish monitoring for the service traffic.
Owner:ALCATEL LUCENT SAS
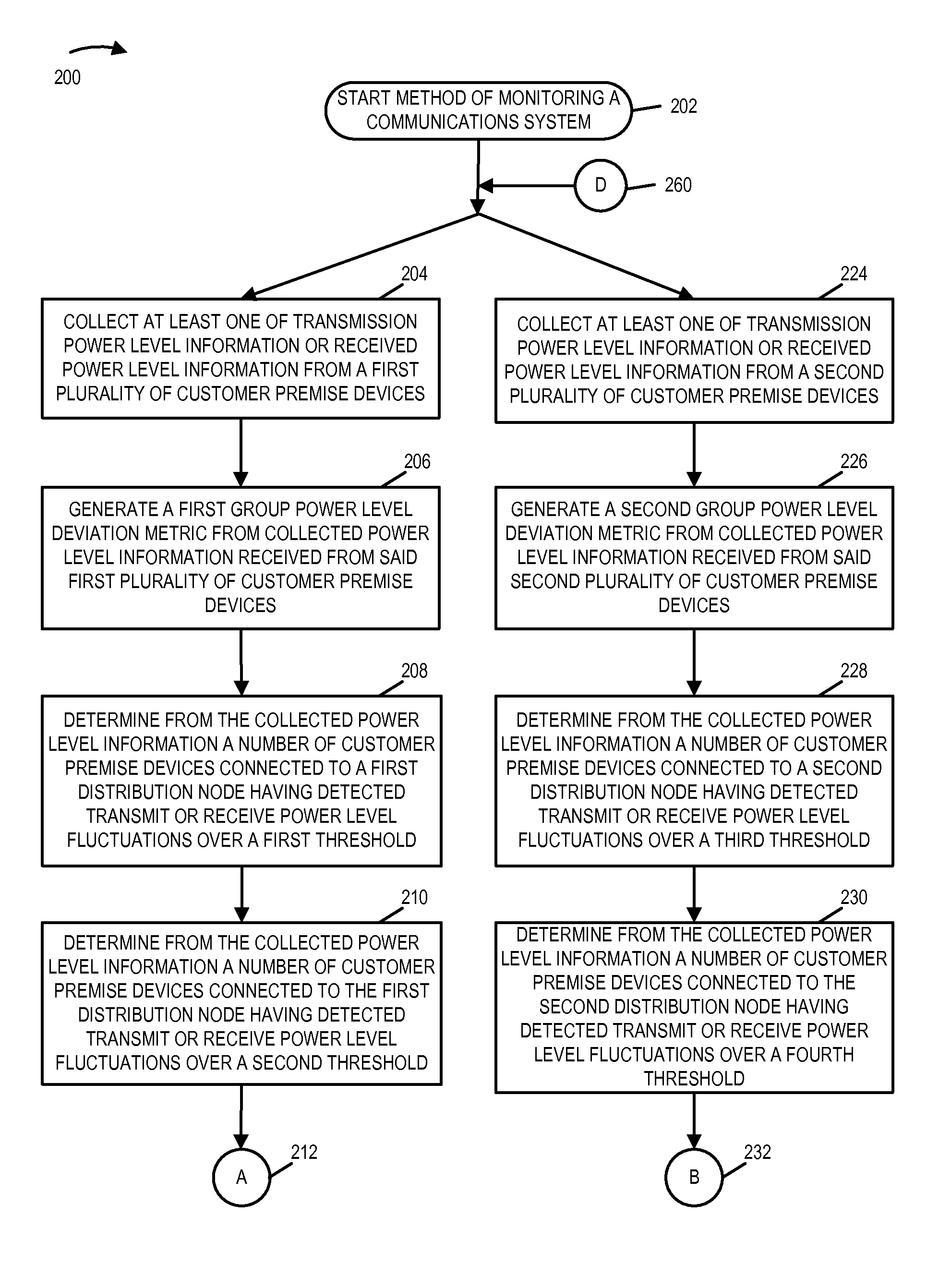
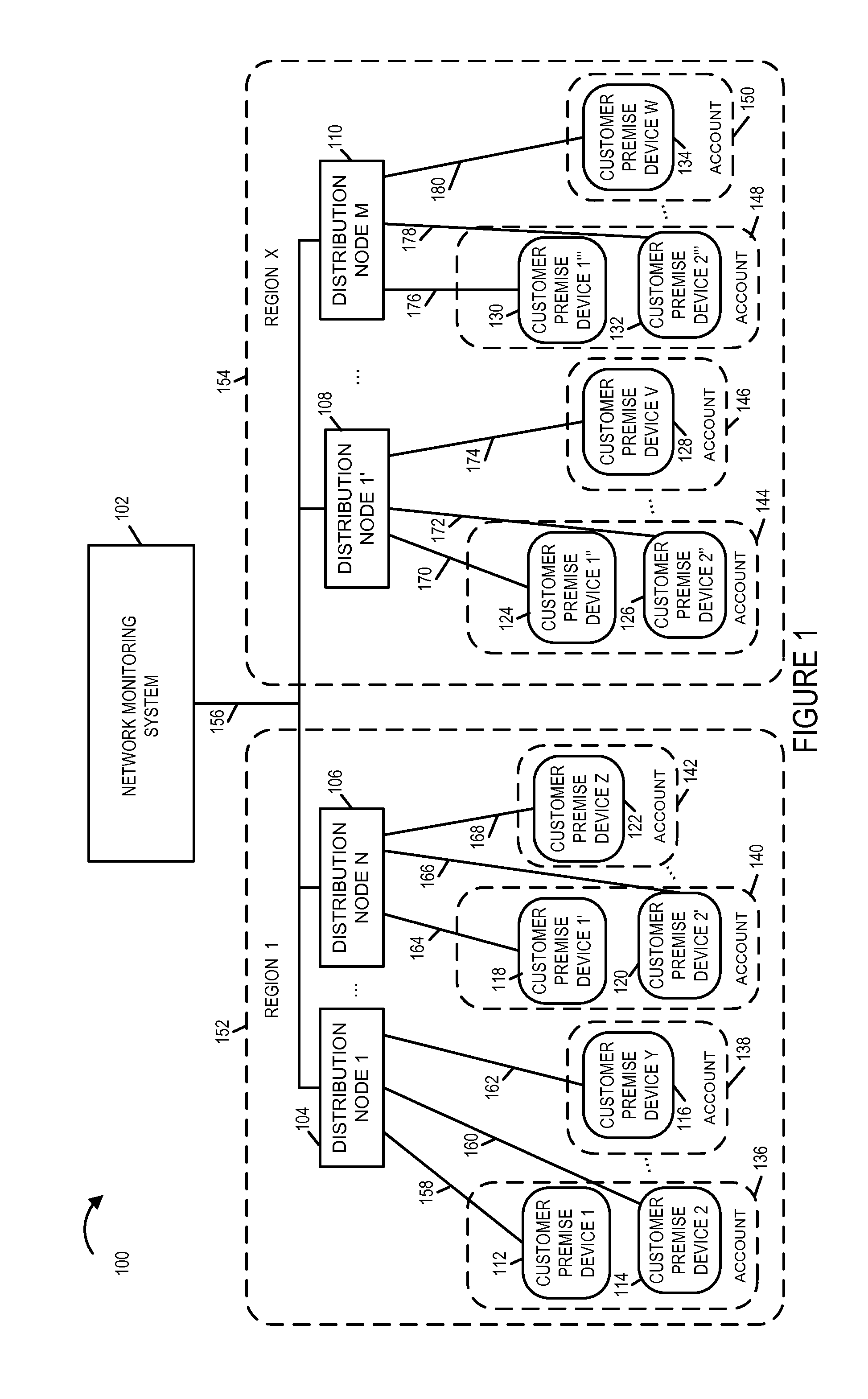
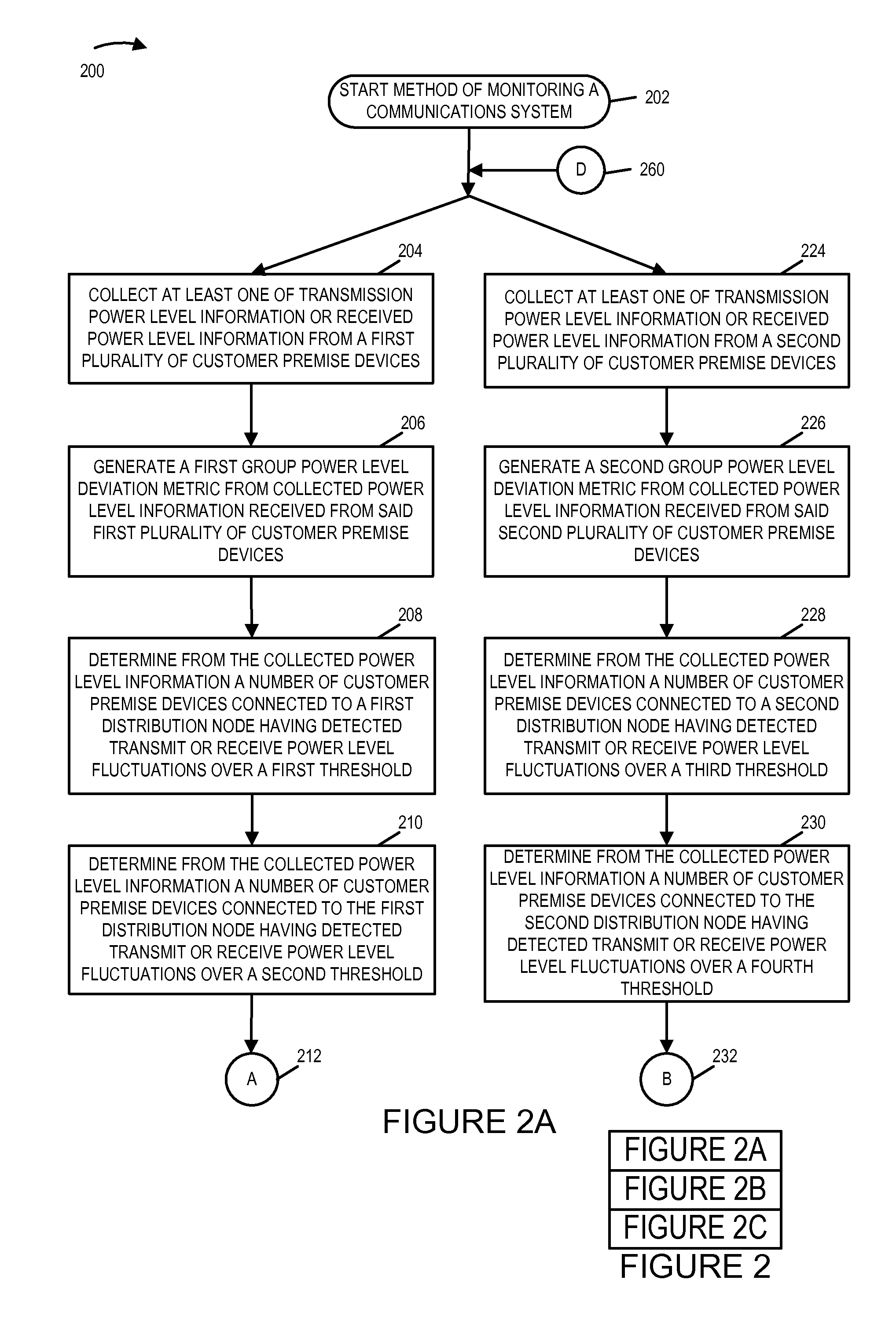
Power fluctuation detection and analysis
ActiveUS20150358222A1Easy to identifyEasy to detectError preventionTransmission systemsEngineeringClient-side
The network monitoring system collects transmission and / or receive power level information from a plurality of customer premise devices connected to the same distribution node for each of a plurality of network distribution nodes. For an individual network distribution node, the network monitoring system calculates a set of fluctuation parameters including a group power level deviation metric, e.g., a modified standard deviation ratio. The network monitoring system evaluates the generated fluctuation parameters and responds, e.g., outputting a fluctuations report, modifying a data collection profile being used by a set of customer premise devices corresponding to a distribution node, commanding diagnostics to be performed on a portion of the network and / or directing a service technician. The network monitoring system compares generated fluctuation parameters corresponding to different distribution nodes, and uses the results of the comparison to assign priority with regard to the assignment of limited available troubleshooting and repair resources.
Owner:TIME WARNER CABLE ENTERPRISES LLC
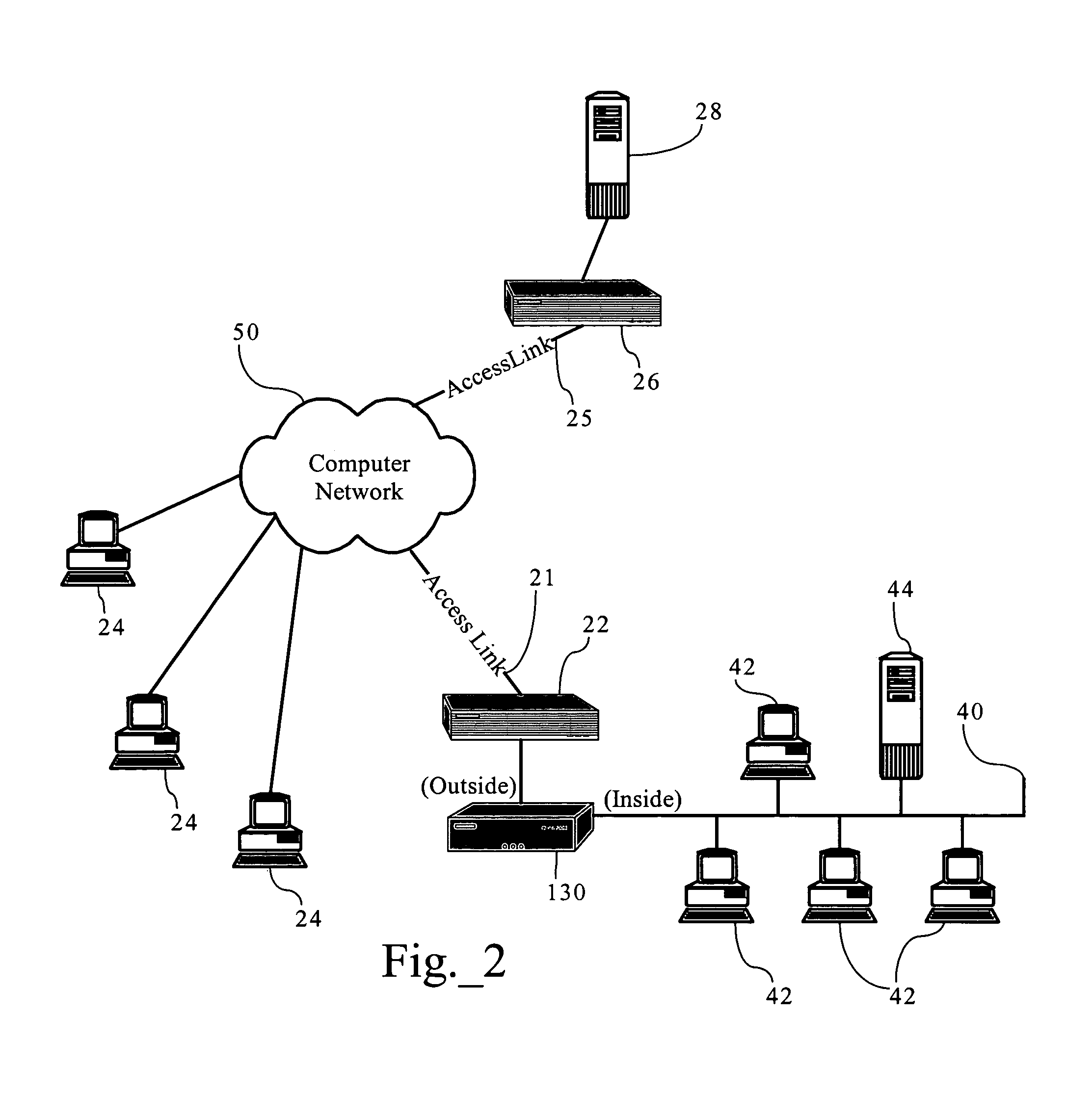
Network system, traffic balancing method, network monitoring device and host
ActiveUS8194553B2Traffic balance in the networksControl balanceError preventionFrequency-division multiplex detailsTraffic capacityIp address
A traffic balancing system, traffic balancing device and traffic balancing method that converts IP packets by switching IP address of the destination host between the dual stack hosts communicating with each other, in order to control traffic balancing in the networks.
Owner:INT BUSINESS MASCH CORP
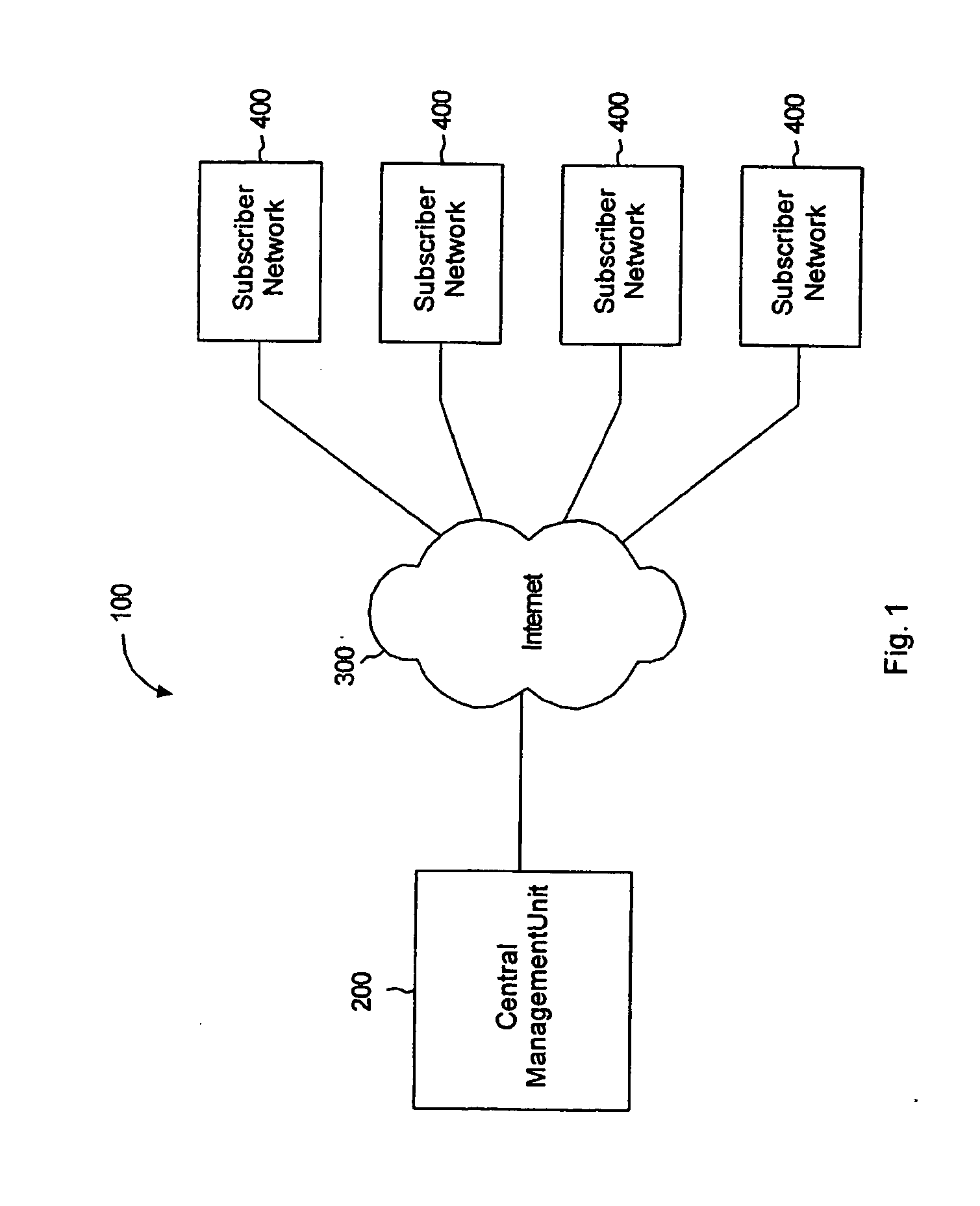
Multi-network monitoring architecture
InactiveUS20050235058A1Error detection/correctionDigital computer detailsManagement unitThe Internet
A network monitoring architecture for multiple computer network systems is disclosed. In particular, the network monitoring architecture includes an agent system installed within each computer network and a remote central management unit in communication with the agent system of each computer network. The agent systems collect data from key network devices that reside on the corresponding computer network, and send the collected data to the remote central management unit as a message through the Internet. The data from the computer networks are processed at the remote central management unit to determine imminent or actual failure of the monitored network devices. The appropriate technicians can be immediately notified by the central management unit through automatically generated messages.
Owner:N ABLE TECH INT
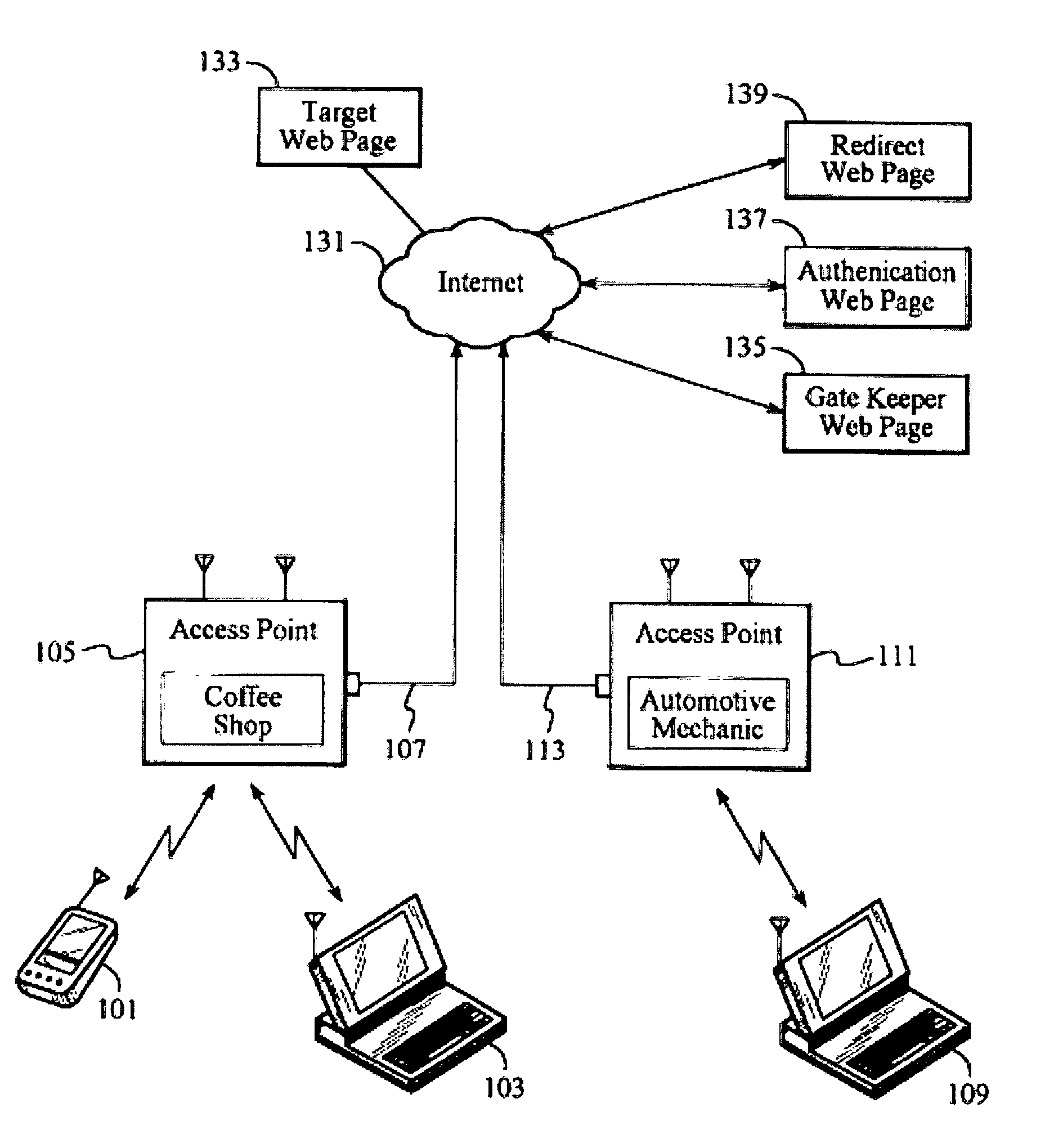
System for distributed network authentication and access control
InactiveUS7185360B1Facilitate wireless accessEasy accessError preventionFrequency-division multiplex detailsWeb authenticationGate-keeper
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
Network monitoring using virtual packets
ActiveUS8451731B1Attendant limitationIncrease the number ofEnergy efficient ICTError preventionTraffic capacityProcessing element
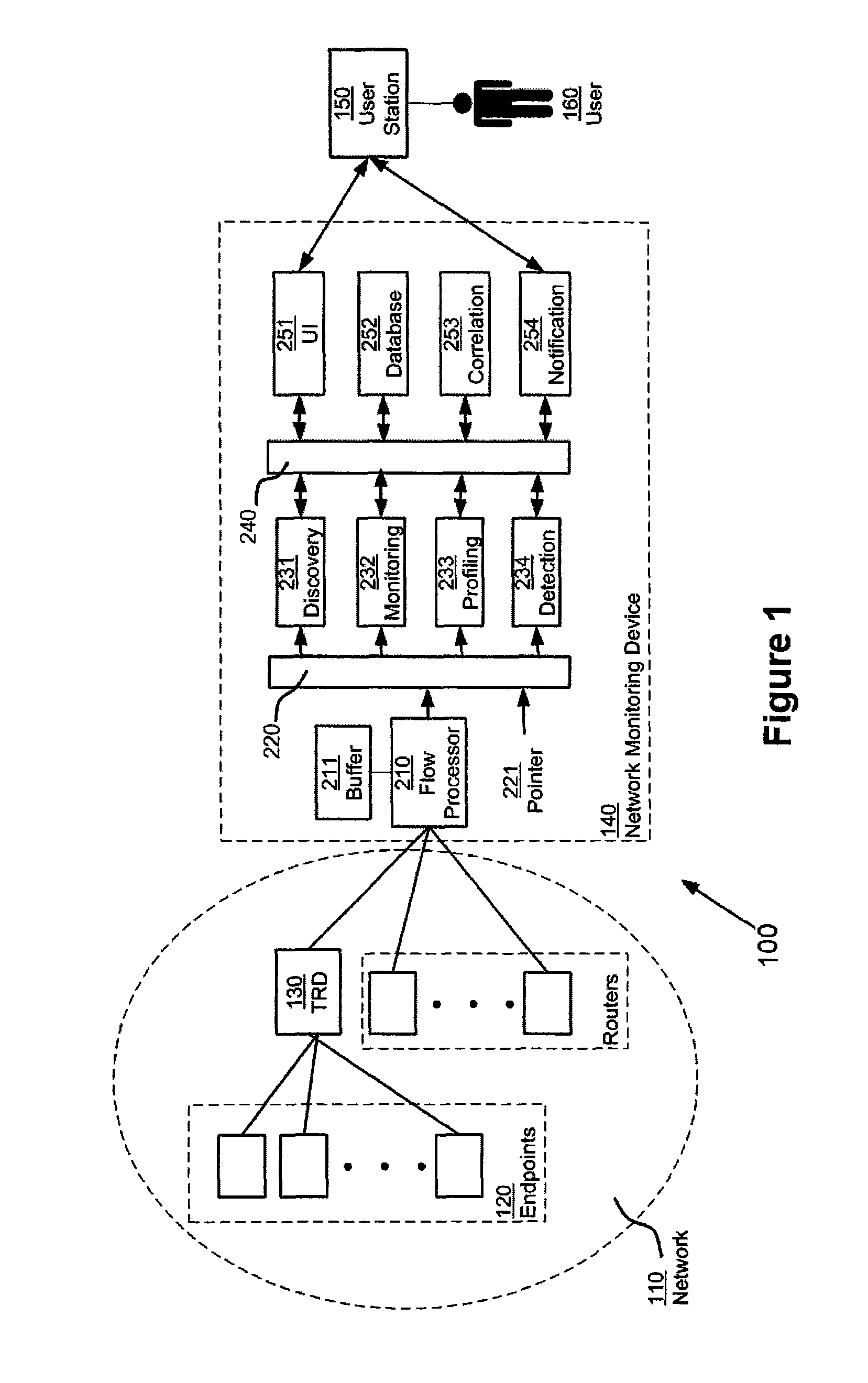
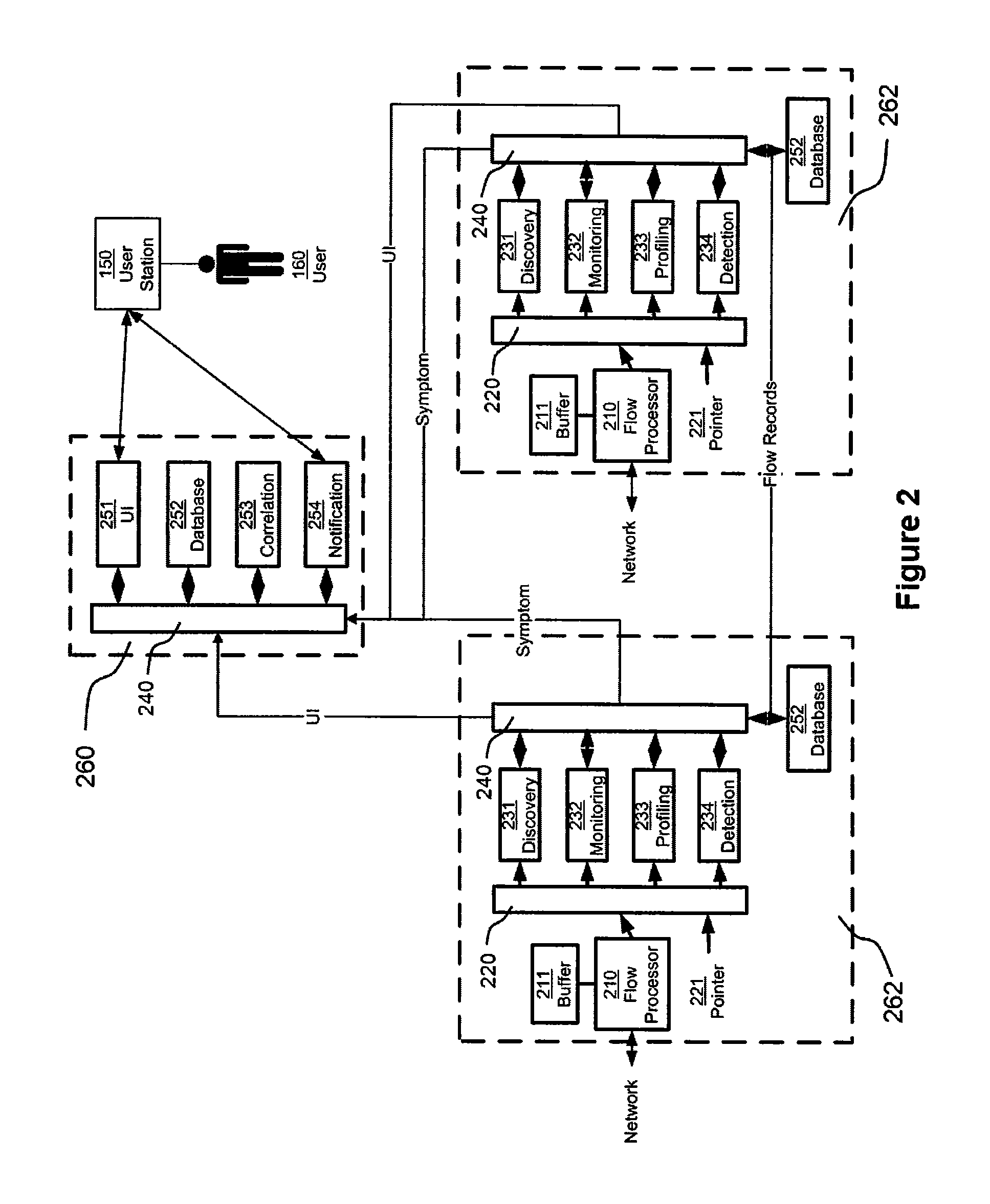
A network monitoring device includes a flow processing element, disposed to receive flow information relating to network flows, and to generate a set of virtual packets, each representing a portion of a network flow. The virtual packets are maintained in a time-sequential order, and read by elements of the network monitoring device to generate information relating to network traffic, such as symptoms affecting the communication network, problems affecting the communication network, and otherwise. The network monitoring device randomly samples virtual packets, with at least one of two effects: (1) flow information from traffic reporting devices that are themselves sampling at differing rates can be equalized, with the effect of standardizing information from all of them; (2) the network monitoring device itself can restrict its attention to a fraction of all virtual packets, with the effect of keeping up with a relatively large number of virtual packets.
Owner:VIRTUAL INSTR CORP
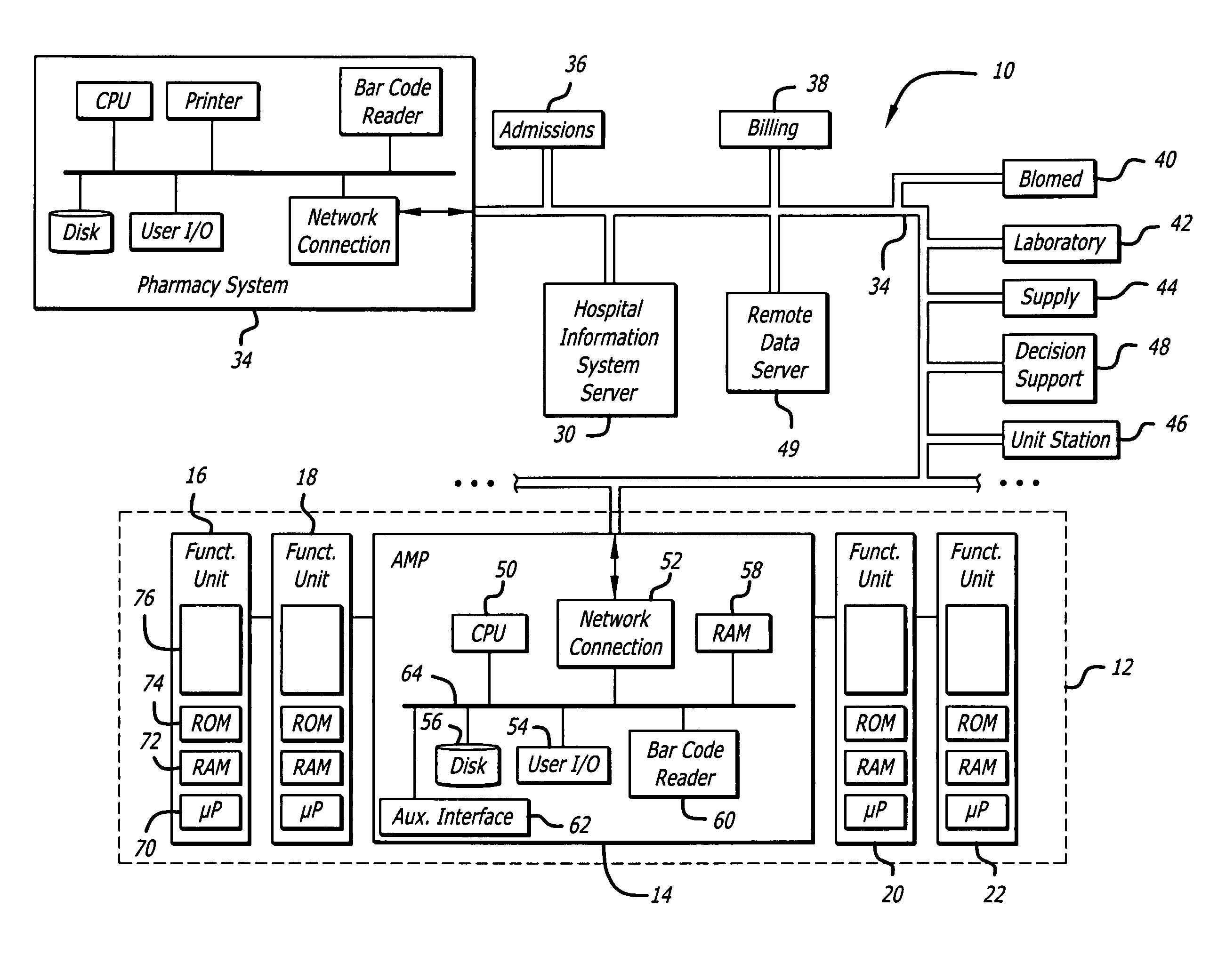
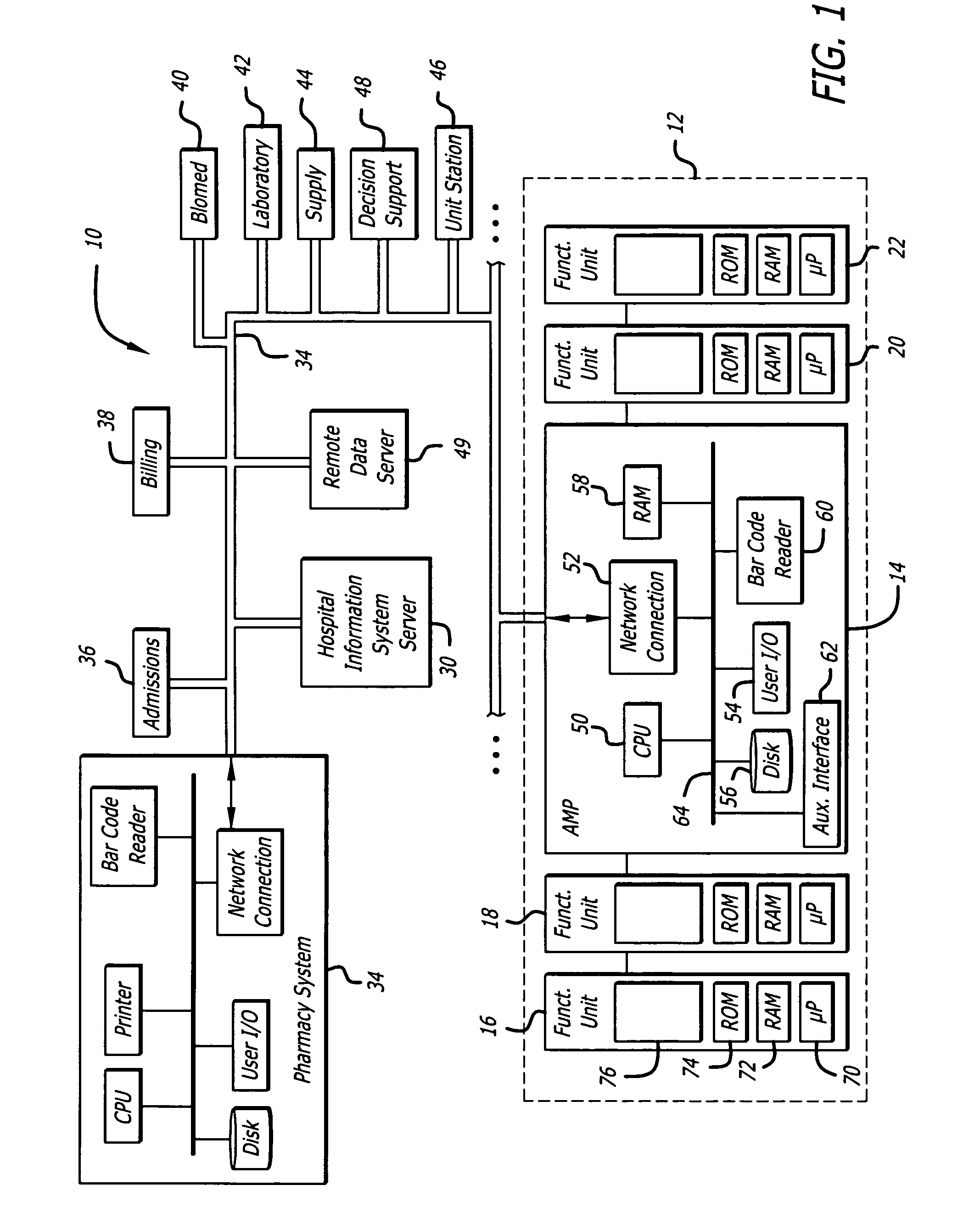
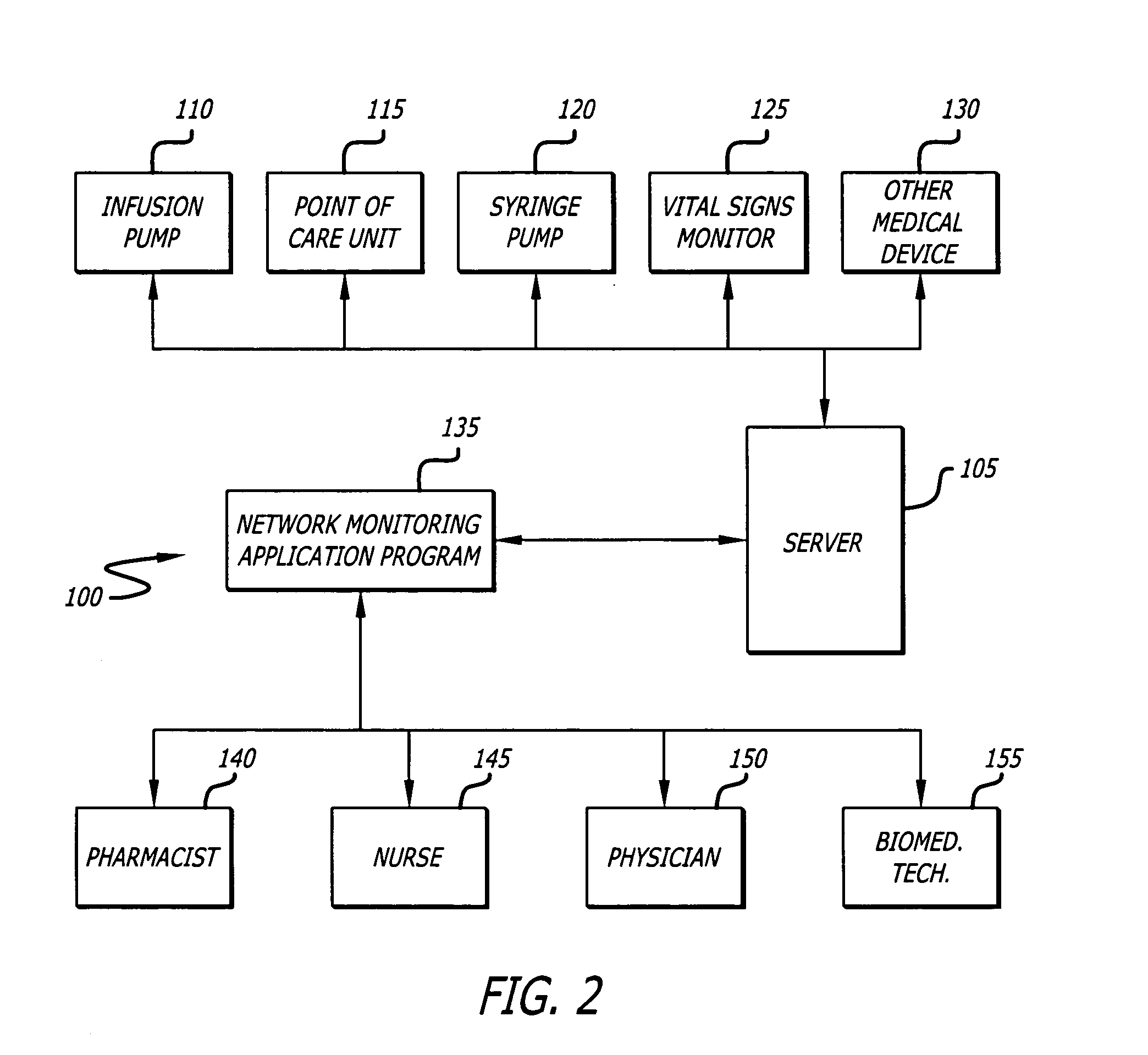
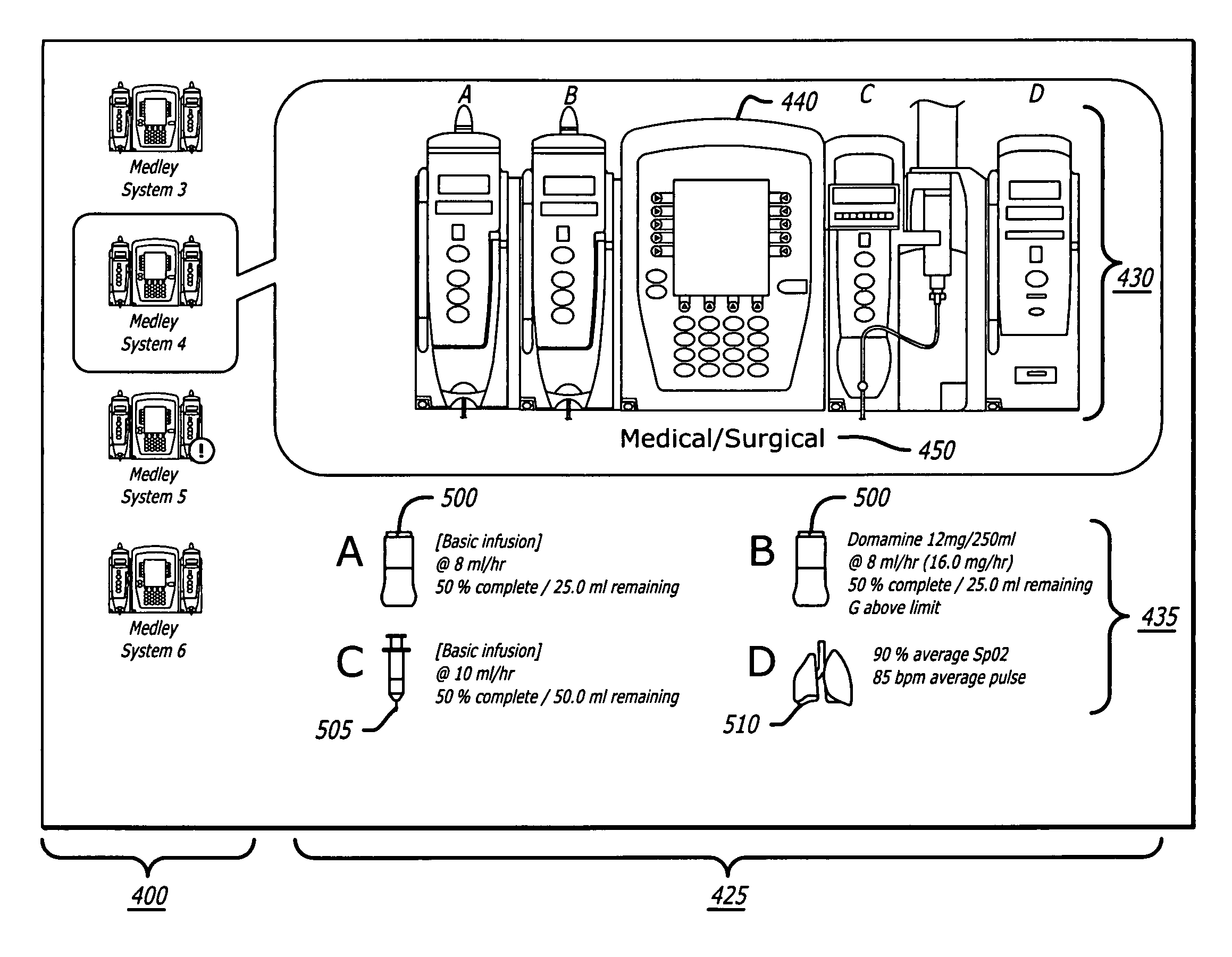
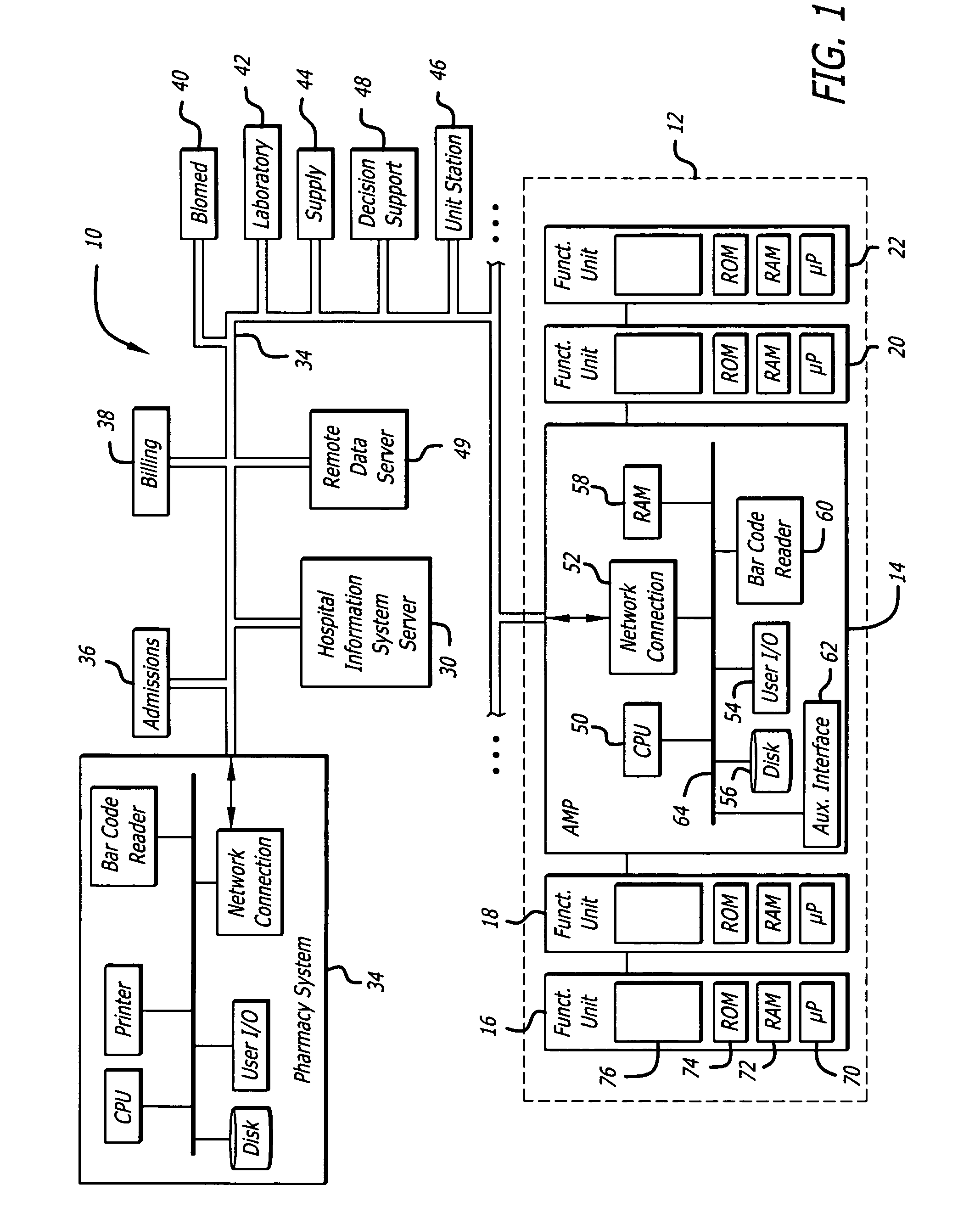
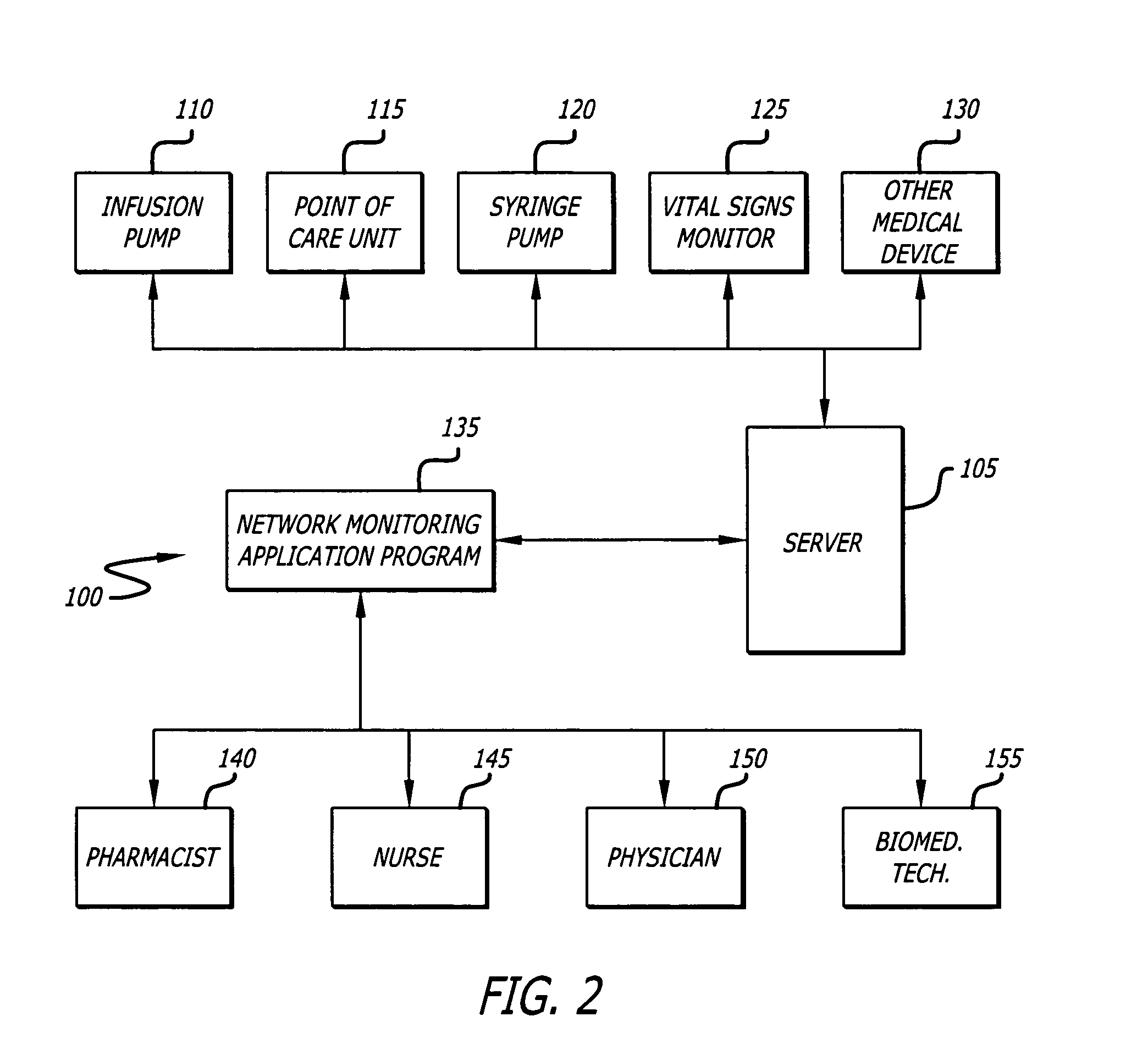
System and method for network monitoring of multiple medical devices
The present invention provides for a system an method of monitoring the status of a plurality of medical devices connected to a central computer or server using a wired or wireless network, and displaying information representative of the status of the medical devices to a user on a display screen using both graphics and text. The system is also capable of determining when a condition or alarm warranting notification of the care giver to correct the condition exists, and displaying information about the condition or alarm on the display, including associating a warning graphic or icon representative of the condition or alarm with an icon representing a specific medical device or portion of a medical device. The system includes a rules data base and decision engine that may be used to determine the existence of conditions that require notification to the care giver.
Owner:CAREFUSION 303 INC
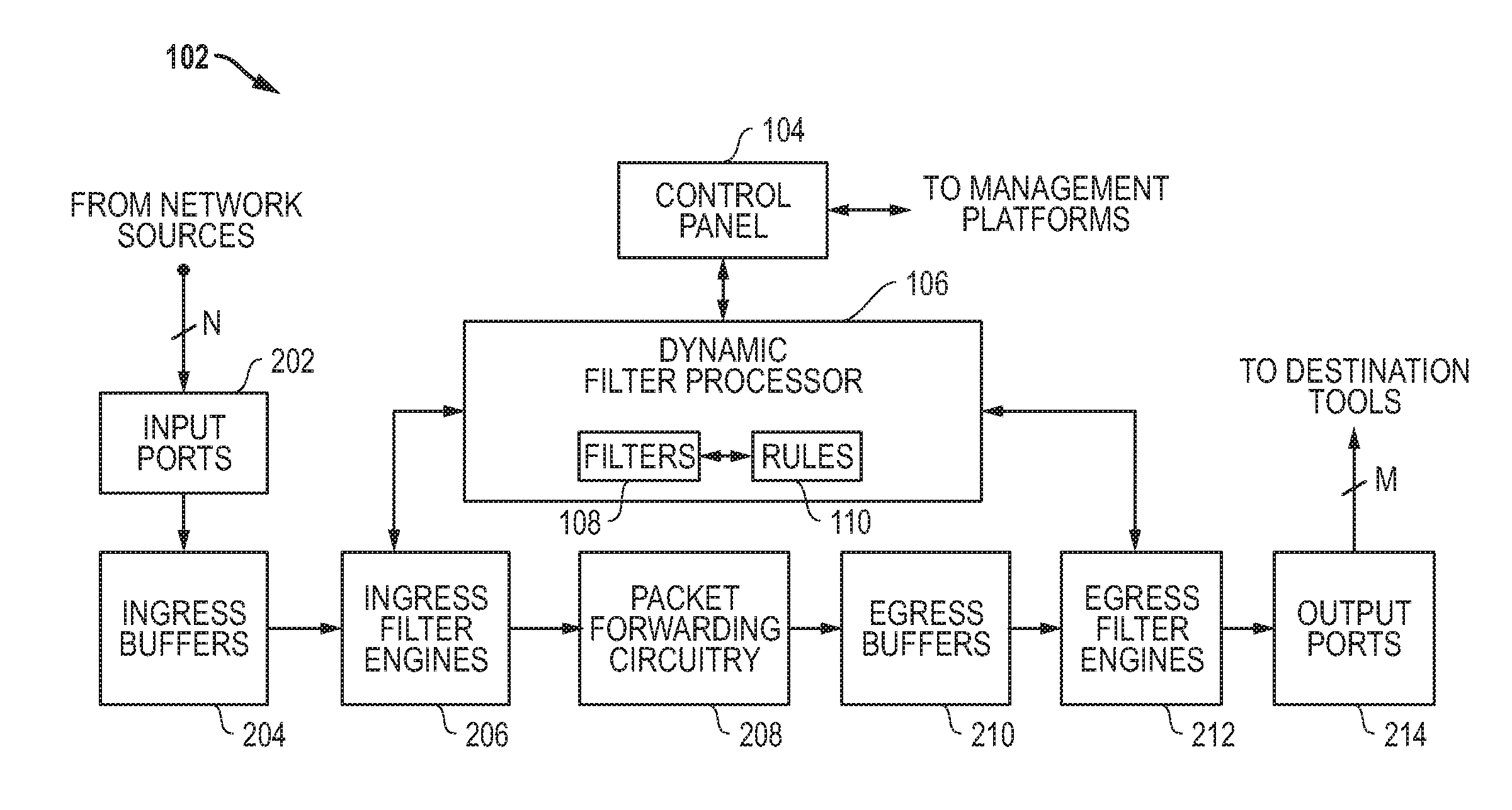
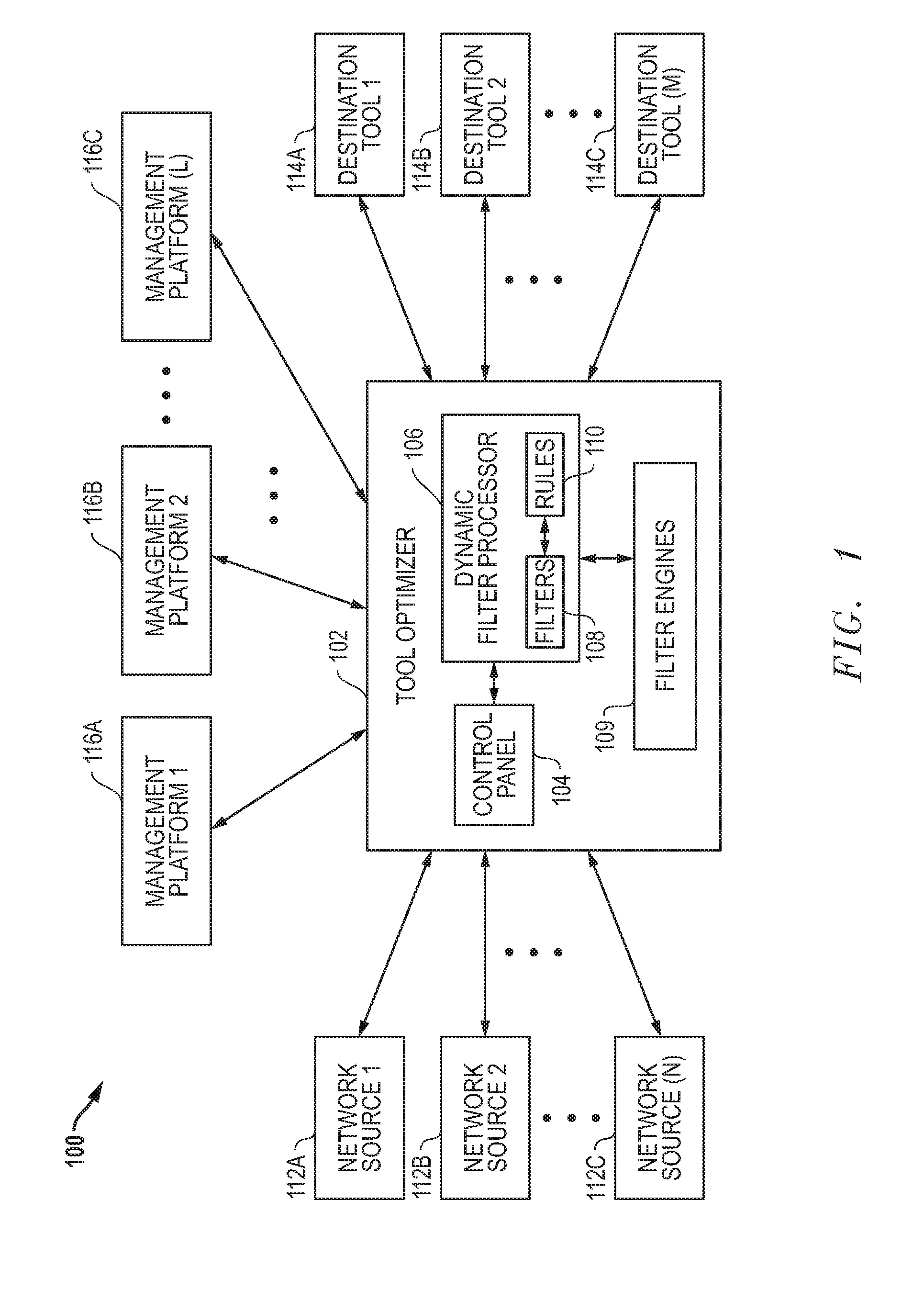
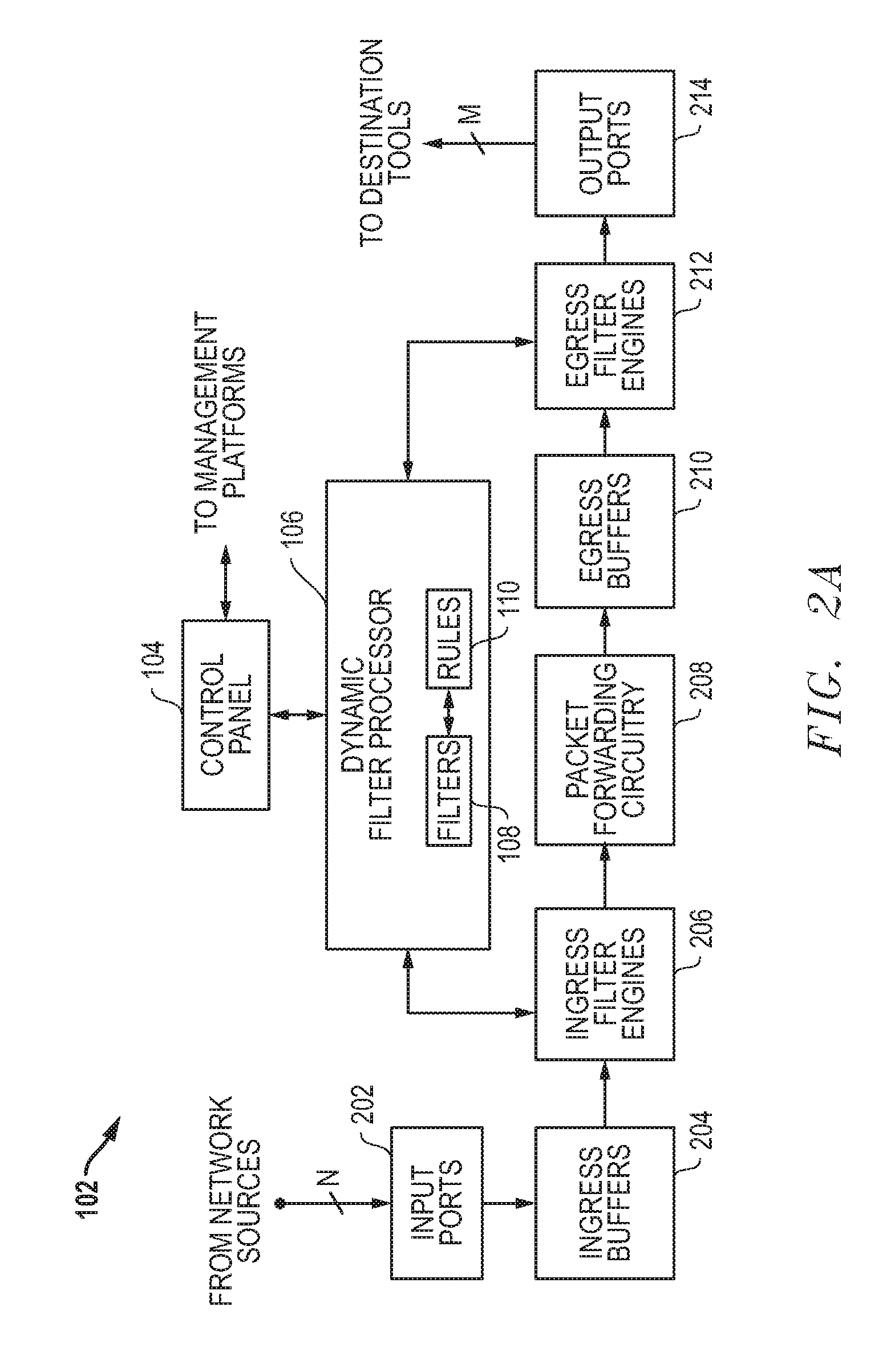
Superset packet forwarding for overlapping filters and related systems and methods
ActiveUS20120106354A1Improved management and controlImproved packet forwardingError preventionTransmission systemsNetwork monitoringIngress filtering
Systems and methods are disclosed that allow for improved management and control of packet forwarding in network systems. Network devices and tool optimizers and a related systems and methods are disclosed for improved packet forwarding between input ports and output ports. The input ports and output ports are configured to be connected to source devices and destination devices, for example, network sources and destination tools in a network monitoring environment. The network devices and tool optimizers disclosed can use superset packet forwarding, such that ingress filter engines are configured with ingress filter rules so as to forward a superset of packets to output ports associated with overlapping filters. Egress filter engines are configured with egress filter rules to then determine which of the superset packets are actually sent out the output ports.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
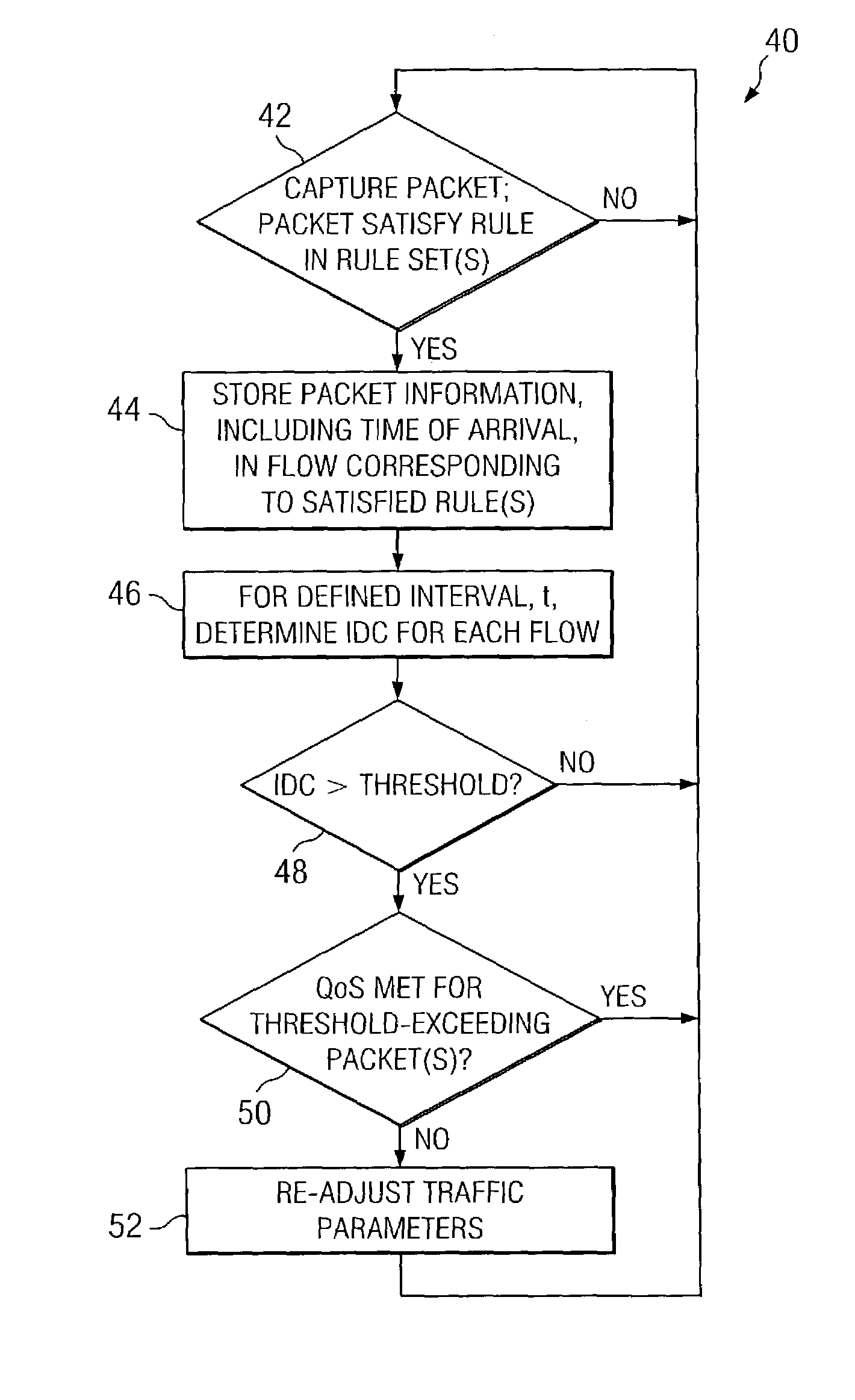
Network monitoring system responsive to changes in packet arrival variance and mean
InactiveUS7242668B2Error preventionFrequency-division multiplex detailsPacket arrivalMonitoring system
A network monitoring system (10) for monitoring a network along which network traffic flows in a form of packets. The system comprises circuitry (36, 42) for receiving a packet communicated along the network and for determining whether the received packet satisfies a set of conditions. The system further comprises circuitry (36 / 30, 46), responsive to a determination that the received packet satisfies the set, for determining a measure, wherein the measure is determined over a defined time interval and comprises a ratio of packet arrival variance and a mean of packets arriving during the time interval and for comparing the measure to a threshold. Lastly, the system comprises circuitry (36, 52), responsive to the measure exceeding the threshold, for adjusting network resources.
Owner:WSOU INVESTMENTS LLC
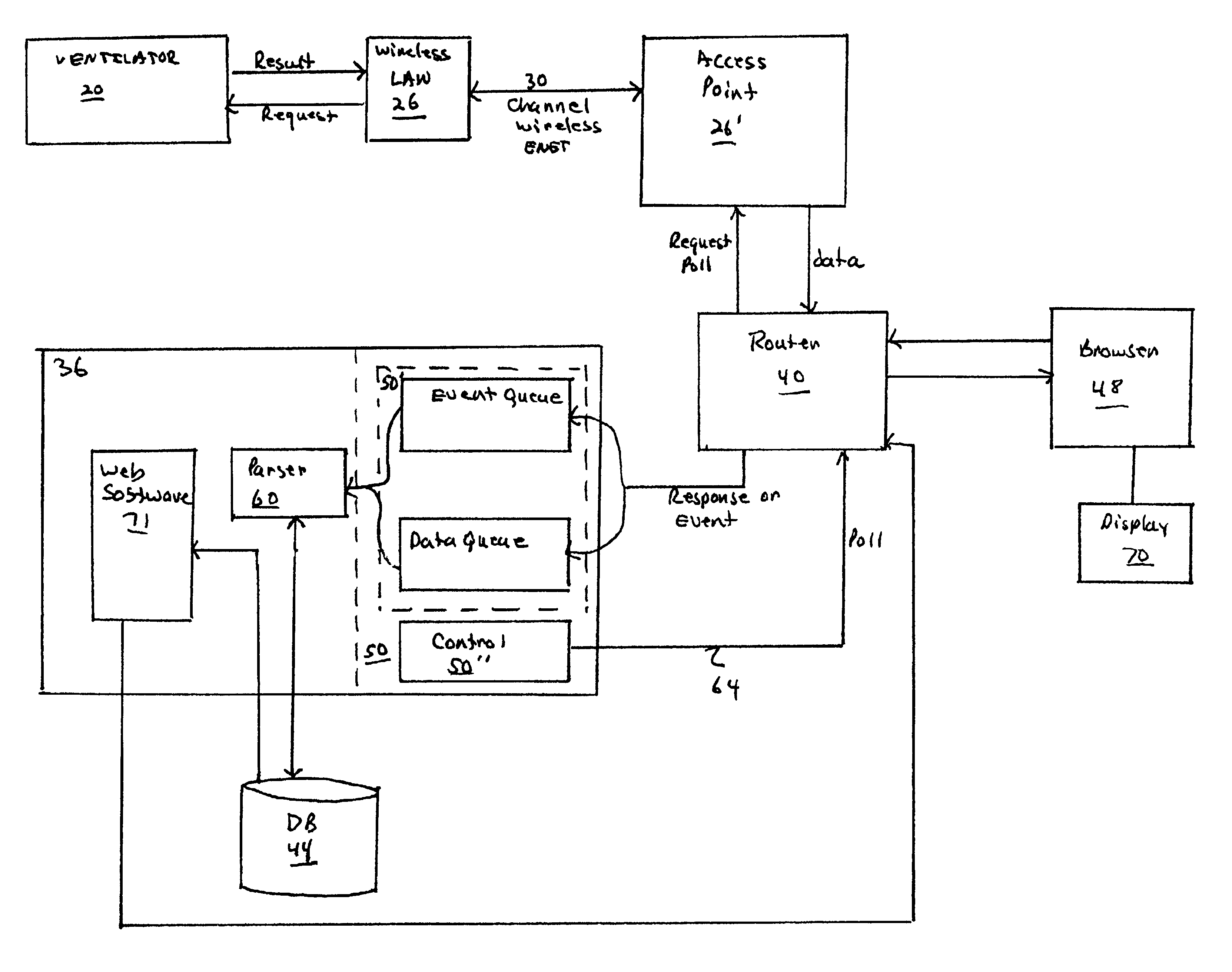
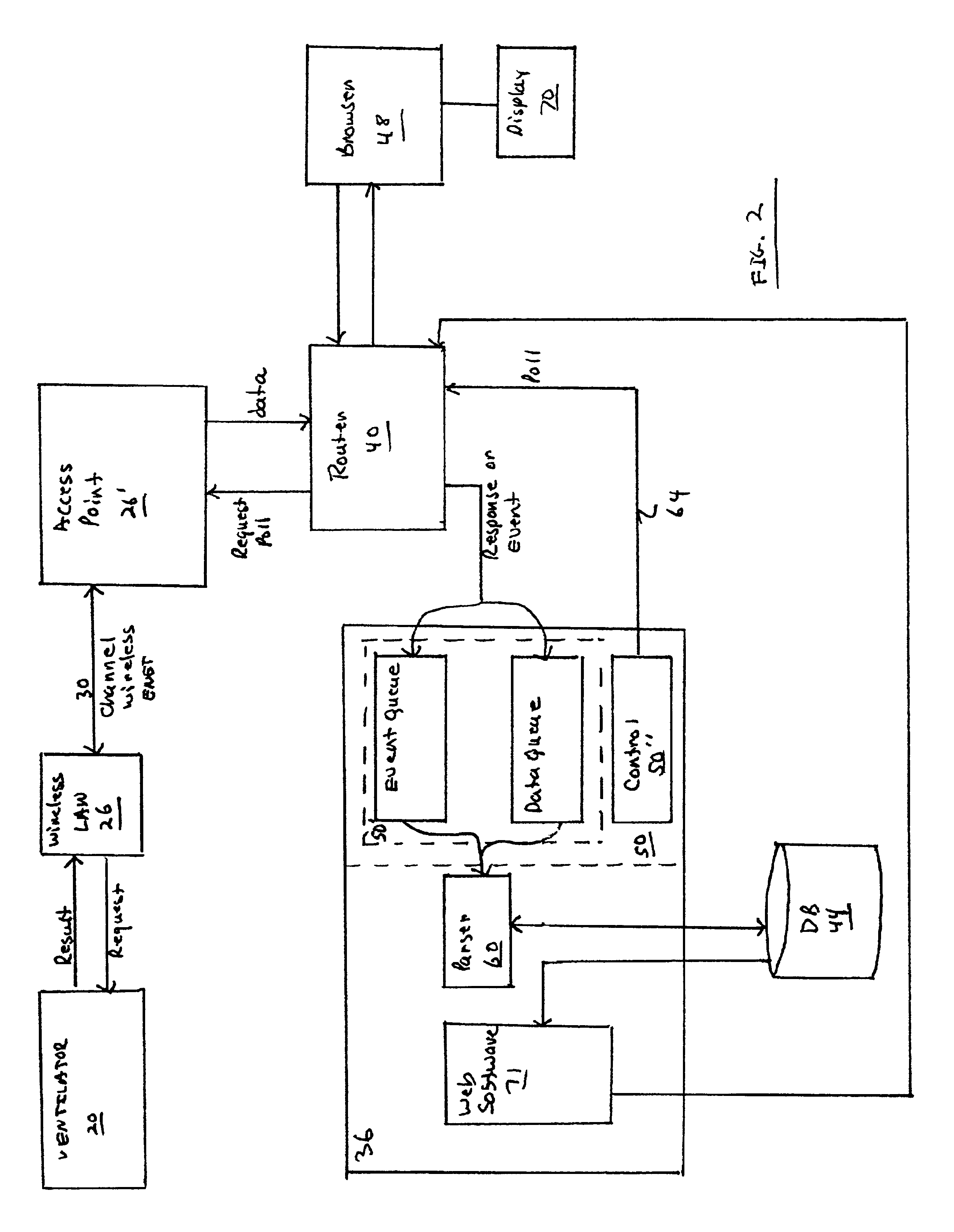
Network monitoring systems for medical devices
A ventilator monitoring system is described for monitoring a plurality of ventilators. In one embodiment, a server including a dedicated ventilator application program for each type of ventilator, monitors a plurality of heterogeneous ventilators over a wireless network.
Owner:PHILIPS CAPSULE CORP
Detecting anomalous network application behavior
ActiveUS8185953B2Memory loss protectionError detection/correctionInformation analysisInternet traffic
System and Method for detecting anomalous network application behavior. Network traffic between at least one client and one or more servers may be monitored. The client and the one or more servers may communicate using one or more application protocols. The network traffic may be analyzed at the application-protocol level to determine anomalous network application behavior. Analyzing the network traffic may include determining, for one or more communications involving the client, if the client has previously stored or received an identifier corresponding to the one or more communications. If no such identifier has been observed in a previous communication, then the one or more communications involving the client may be determined to be anomalous. A network monitoring device may perform one or more of the network monitoring, the information extraction, or the information analysis.
Owner:EXTRAHOP NETWORKS
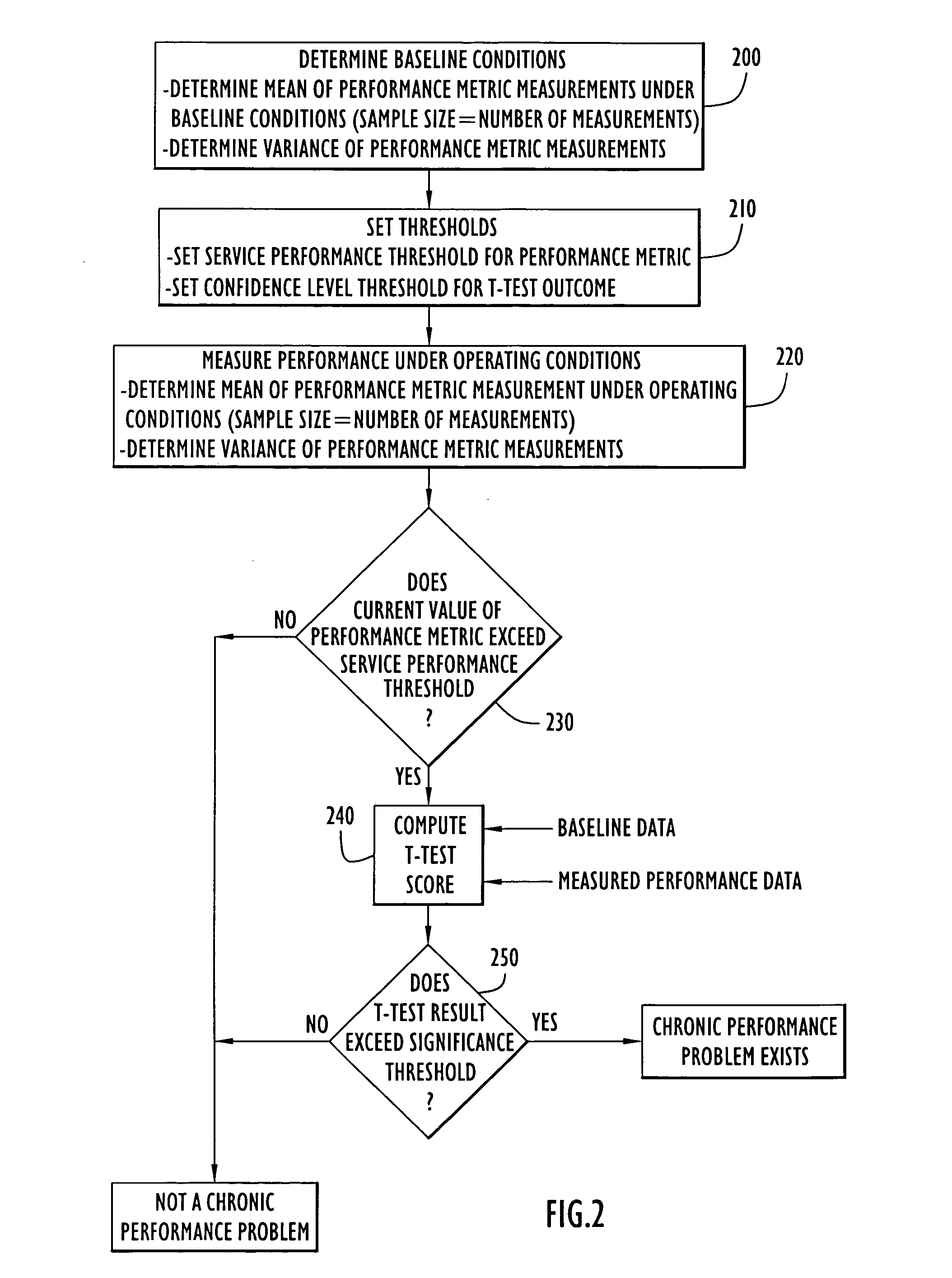
Methods and apparatus for identifying chronic performance problems on data networks
ActiveUS20060176824A1Reliable and accurate measurementError preventionFrequency-division multiplex detailsNetwork behaviorHandling system
A system for identifying chronic performance problems on data networks includes network monitoring devices that provide measurements of performance metrics such as latency, jitter, and throughput, and a processing system for analyzing measurement data to identify the onset of chronic performance problems. Network behavior is analyzed to develop a baseline performance level (e.g., computing a mean and variance of a baseline sample of performance metric measurements). An operating performance level is measured during operation of the network (e.g., computing a mean and variance of an operating sample of performance metric measurements). A chronic performance problem is identified if the operating performance level exceeds a performance threshold and a difference between the baseline performance level and the operating performance level is determined to be statistically significant. A t-test based on the baseline mean and variance and the operating mean and variance can be used to determine if this difference is significant.
Owner:NETSCOUT SYSTEMS
System and method for network monitoring of multiple medical devices
Owner:CAREFUSION 303 INC
Re-using information from data transactions for maintaining statistics in network monitoring
InactiveUS6839751B1Multiple digital computer combinationsData switching networksQuality of serviceTraffic capacity
A method of and monitor apparatus for analyzing a flow of packets passing through a connection point on a computer network. The method includes receiving a packet from a packet acquisition device, and looking up a flow-entry database containing flow-entries for previously encountered conversational flows. The looking up to determine if the received packet is of an existing flow. Each and every packet is processed. If the packet is of an existing flow, the method updates the flow-entry of the existing flow, including storing one or more statistical measures kept in the flow-entry. If the packet is of a new flow, the method stores a new flow-entry for the new flow in the flow-entry database, including storing one or more statistical measures kept in the flow-entry. The statistical measures are used to determine metrics related to the flow. The metrics may be base metrics from which quality of service metrics are determined, or may be the quality of service metrics.
Owner:PACKET INTELLIGENCE
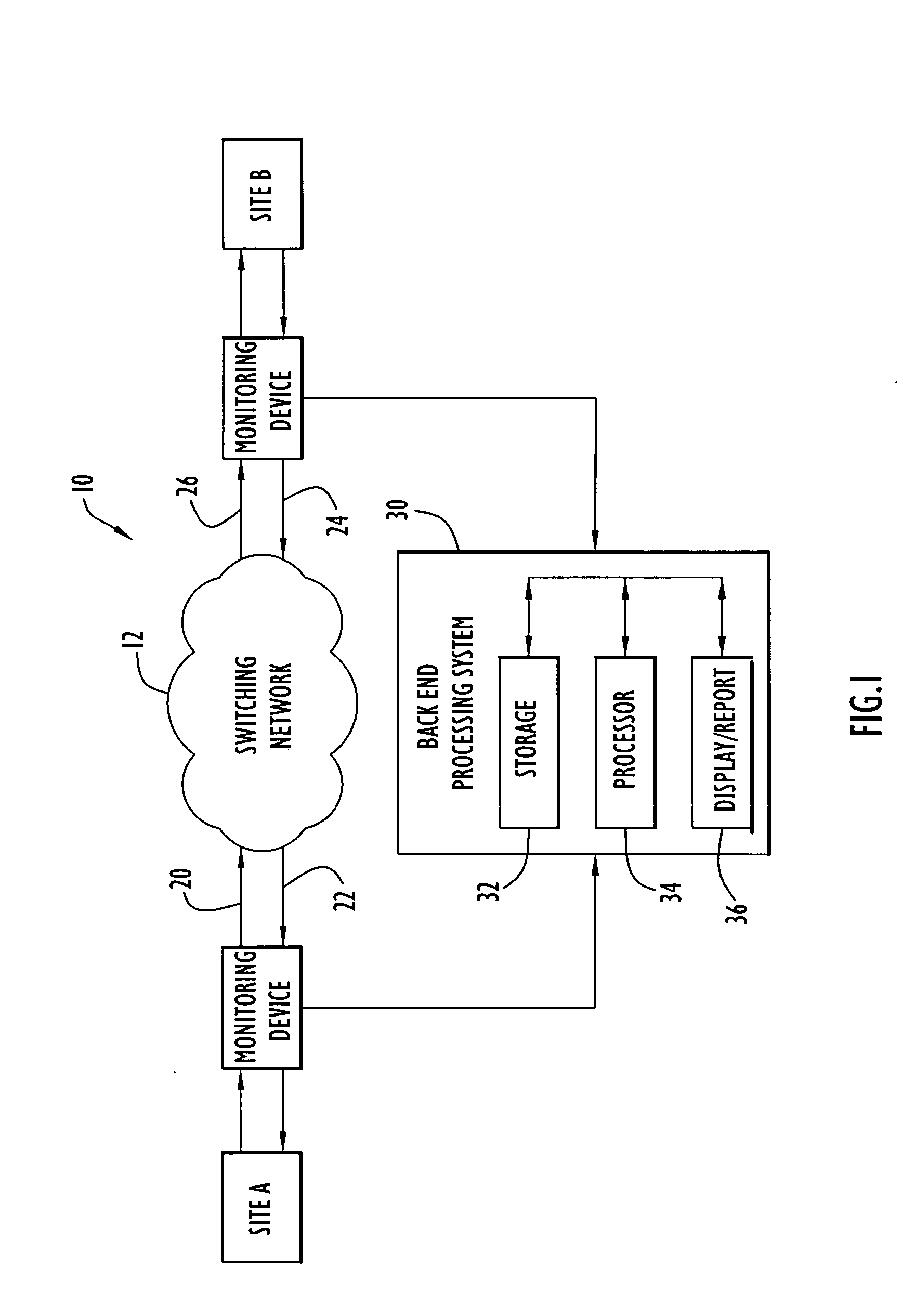
Network resource monitoring and measurement system and method
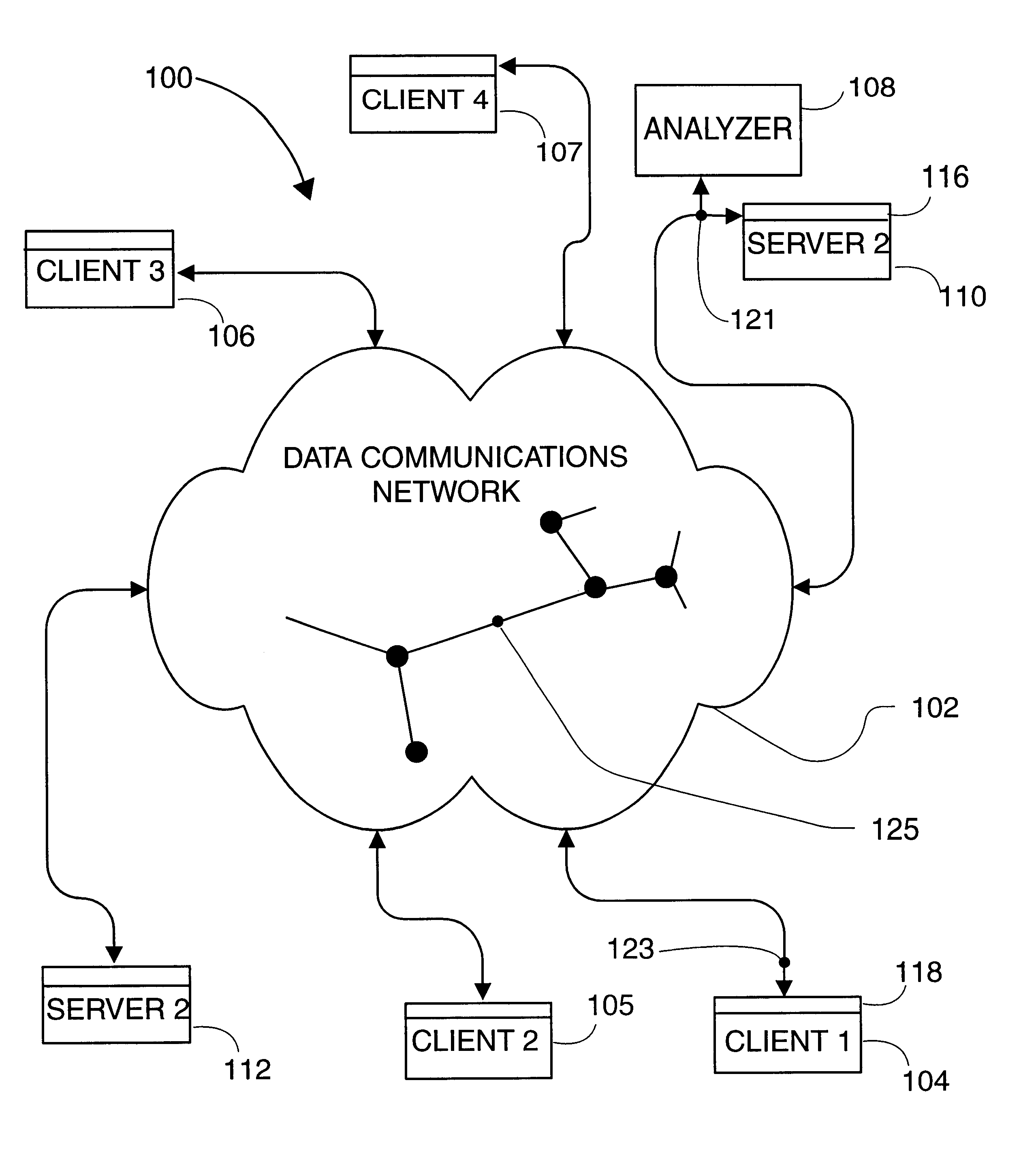
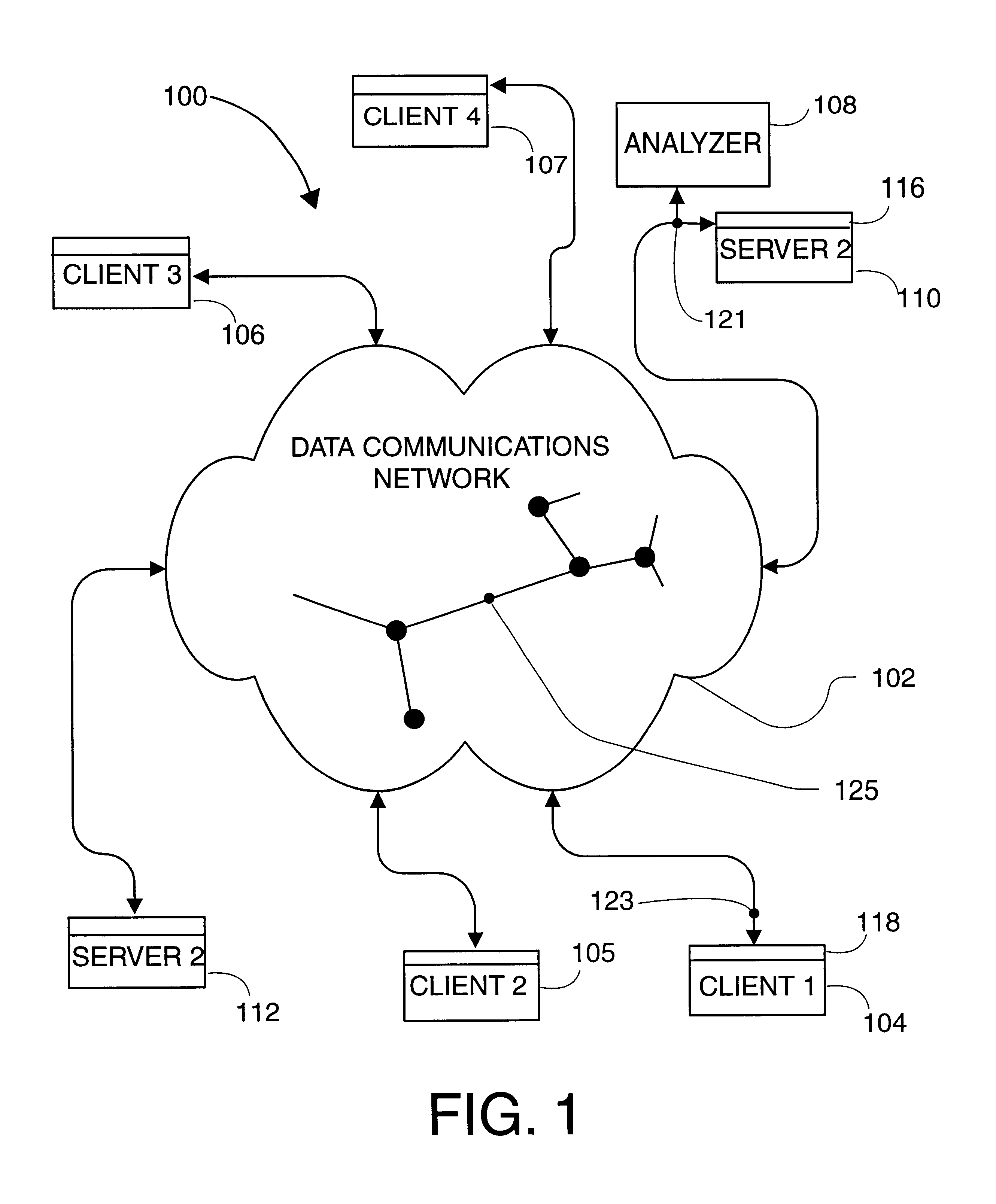
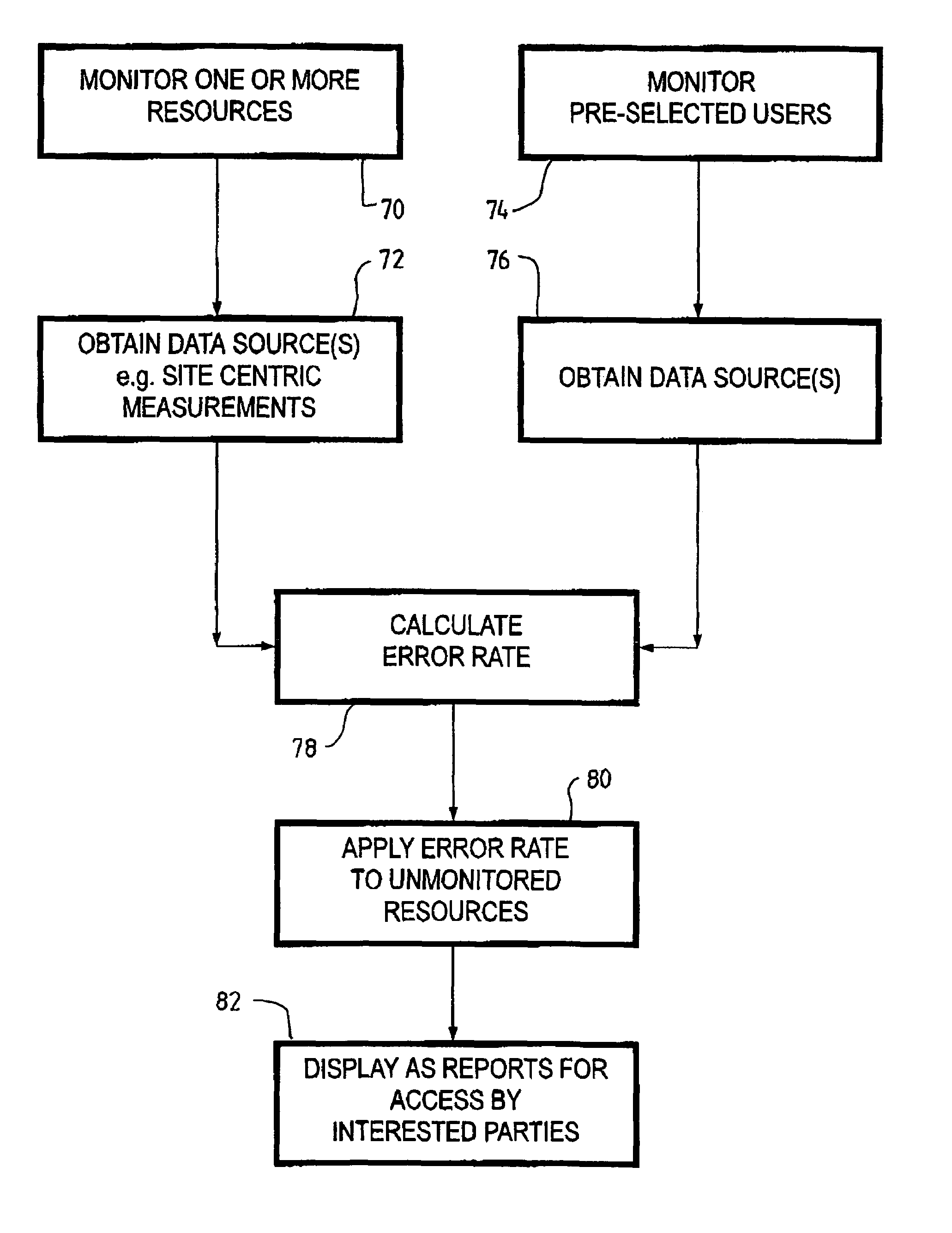
ActiveUS7376722B1Impacting on user timeDivert attentionDigital data information retrievalDigital computer detailsData sourceNetwork monitoring
A method and system for analysing and measuring multiple sources of data over a communication network (18) so as to ascertain information or usage of one or more resources, such as resource servers (2). A data collection and processing means (20) collects and processes the data sources which are forwarded to a reporting server (34) as a combined data source made available to interested parties.
Owner:NETRATINGS LLC
System and Method for Distributed Network Authentication and Access Control
InactiveUS20070124802A1Easy accessReduce difficultyRandom number generatorsUser identity/authority verificationWeb siteWeb authentication
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
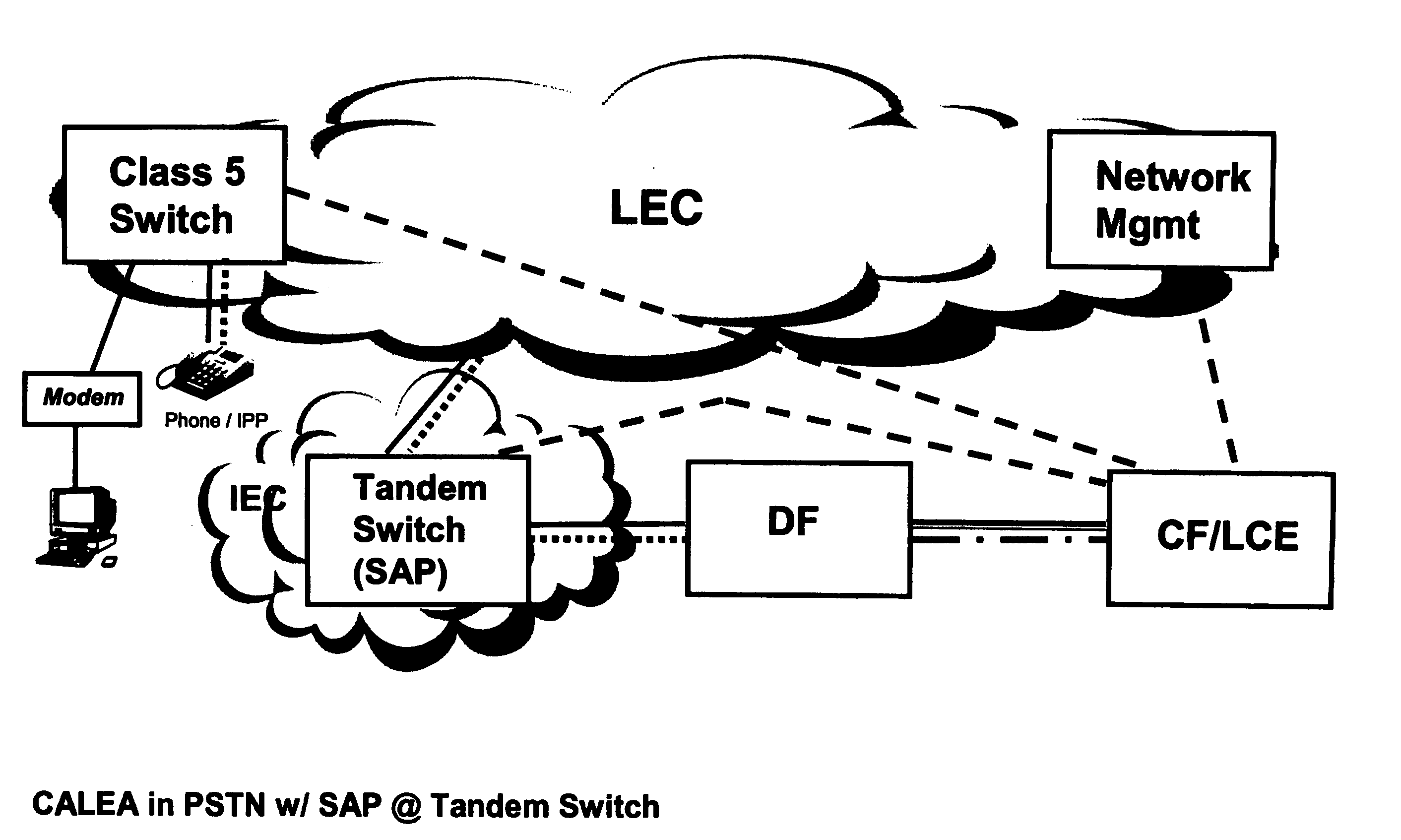
Surveillance implementation in managed VOP networks
A procedure for accomplishing surveillance within a managed VoP network when end-user encryption / decryption and NAT are in place. The procedure comprises first analyzing the network from call signaling and message standpoints, leading to the identification of suitable surveillance access points (SAPs) for packet interception. A Delivery Function (DF) facilitated by the network service provider provides the means to intercept (without alteration) and replicate packets transmitted across the SAPs. The packets are then transmitted via the DF for collection within a Collection Function (CF), which is managed by a Law Enforcement Agency (LEA), for analysis by the LEA. This analysis provides, among other benefits, the opportunity to decrypt the intercepted packets and to identify additional suitable SAPs. In demonstrating the procedure, several embodiments of network surveillance models are described. Each one identifies the location of SAPs for that model. In each model, different information is collected and different processes are followed.
Owner:TELOGY NETWORKS
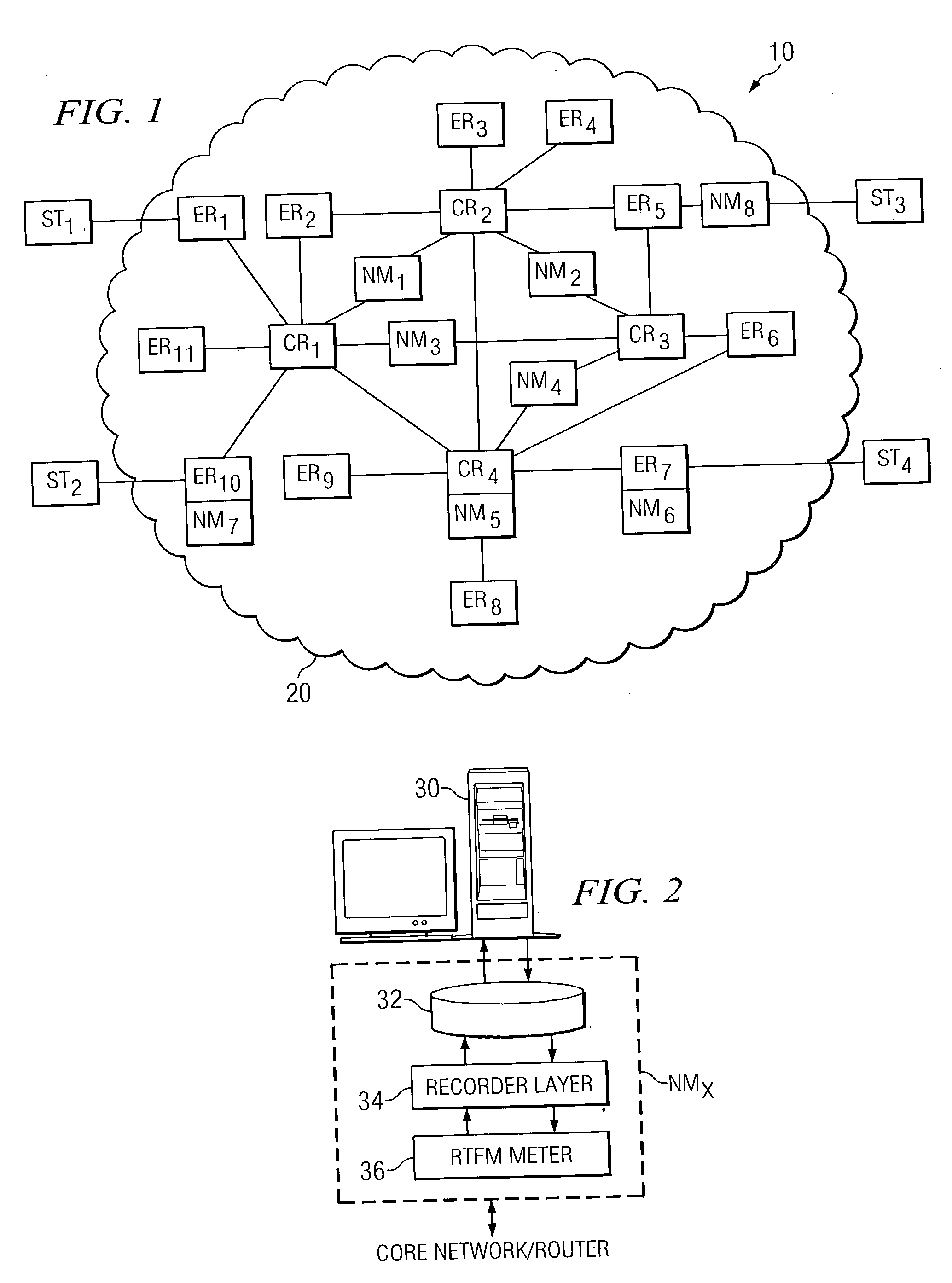
HyperLock technique for high-speed network data monitoring
In one embodiment, a network architecture includes a plurality of application monitoring modules for monitoring network traffic data in a plurality of network segments. Network monitoring modules include a staging area that receives network traffic data from a packet capture and analysis engine and an indexing area that stores the data in meta-flow tuples with associated measures divided into time interval buckets. Index tables store dimension-based sorted pointers to the storage locations in the data buckets. HyperLock queries collect time aggregated results for measure based operators with respect to a queried dimension. For each value of the queried dimension, the time interval buckets are traversed compiling a partial result that is finally stored in a stack as the time aggregated value. The stored sorted pointers are used to determine the starting location in each bucket with respect to the next value of the queried dimension.
Owner:NETSCOUT SYSTEMS
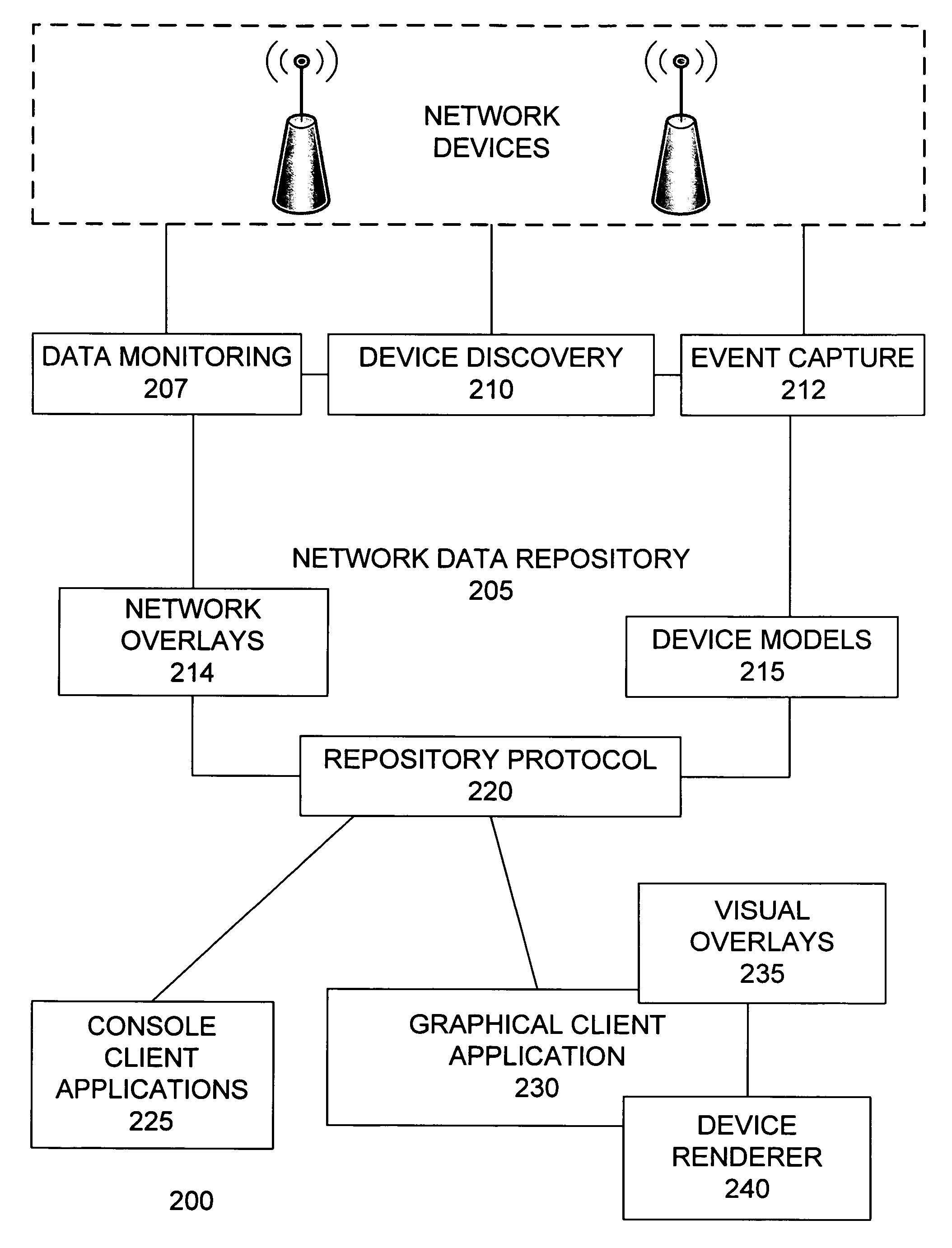
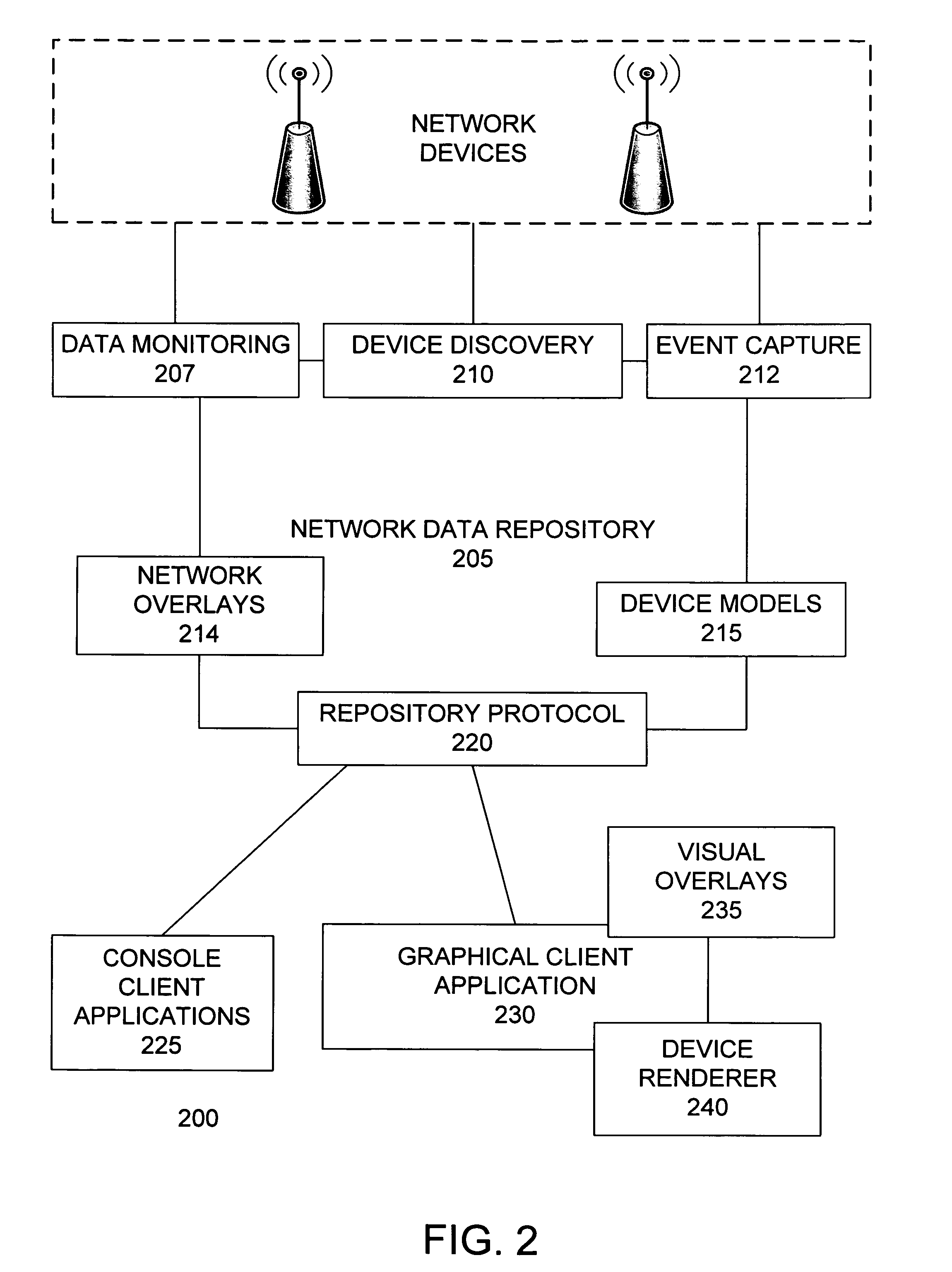
Network monitoring device
ActiveUS20070014248A1CommunicationData switching by path configurationMonitoring systemSystem maintenance
A network monitoring system monitors a data network and enables observation of the data network state in the present or any arbitrary previous time. The system maintains an object-oriented network model that mirrors the state of network devices. A network data repository stores and maintains the network model. The network model retains a history of network events, enabling the system to reconstruct the state of all or a portion of the devices in the network at any previous time. The network data repository detects network devices on the data network to be monitored, communicates with network devices, monitors the state of network devices, receives and records network events, provides device and network state information to client applications, and manages data storage. Client applications can rewind and replay the history of the network model, allowing the observation of network devices and all of their state data at any prior time.
Owner:CHANNEL IP BV
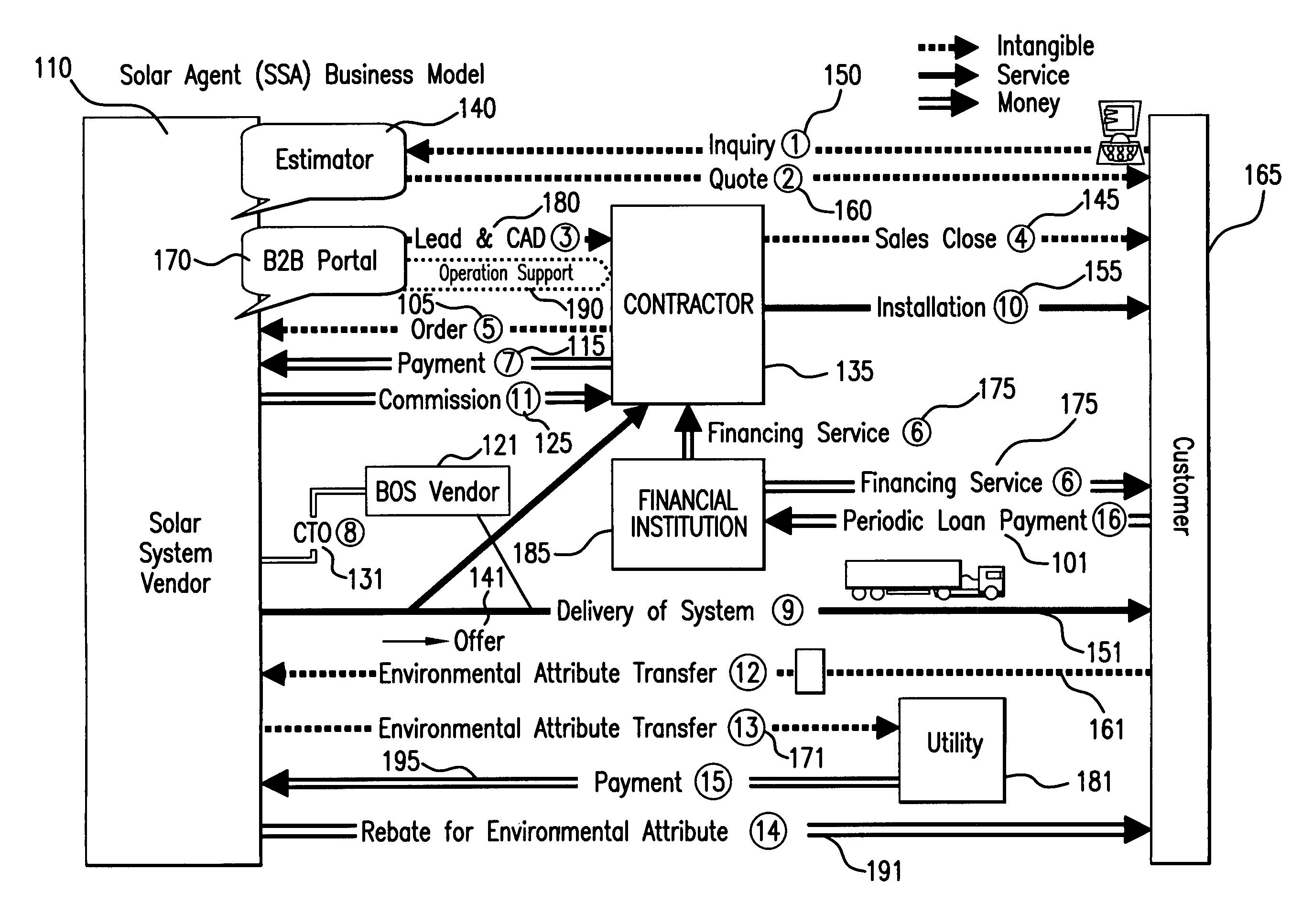
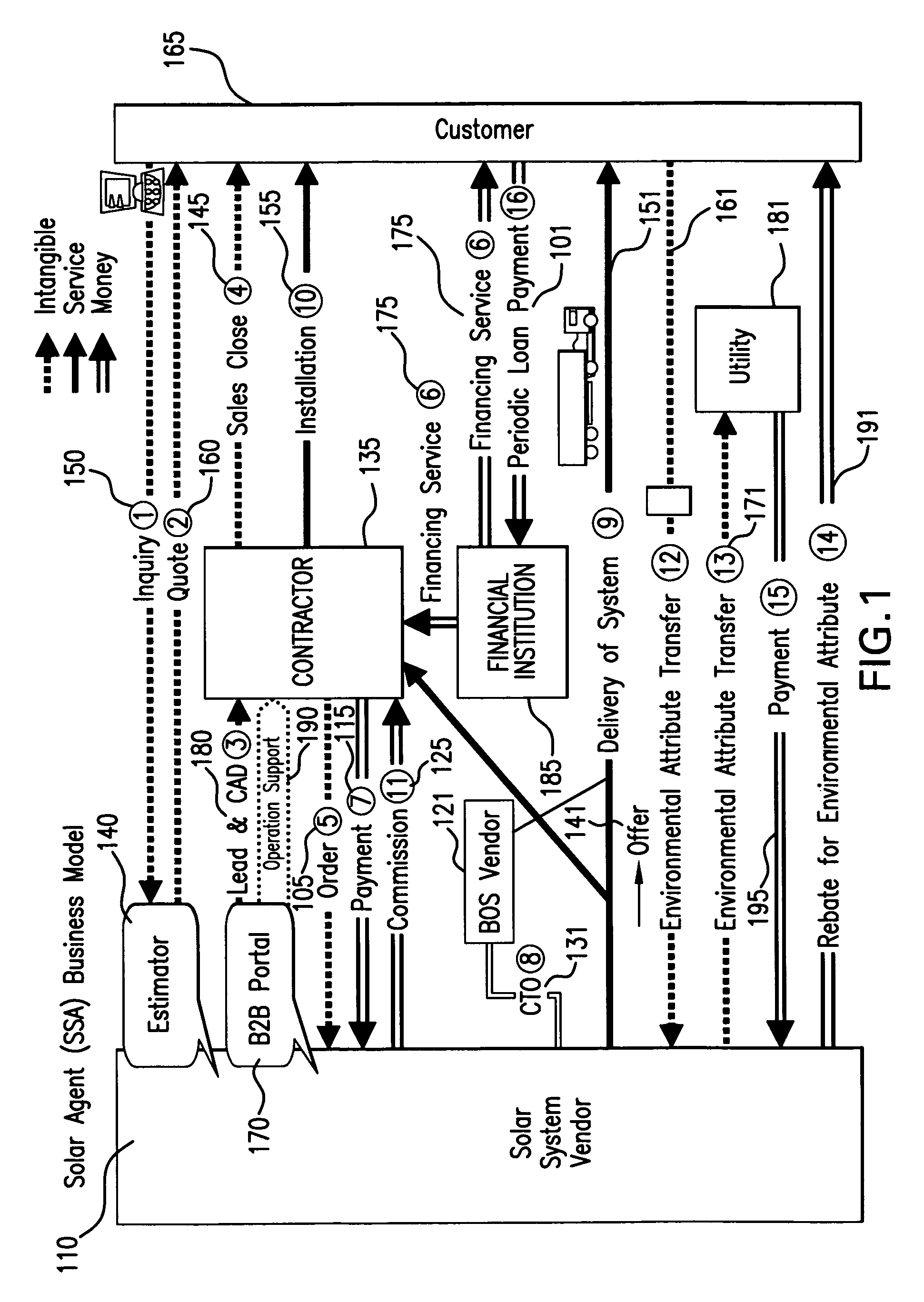
Integrated solar agent business model
Owner:SHARP ELECTRONICS
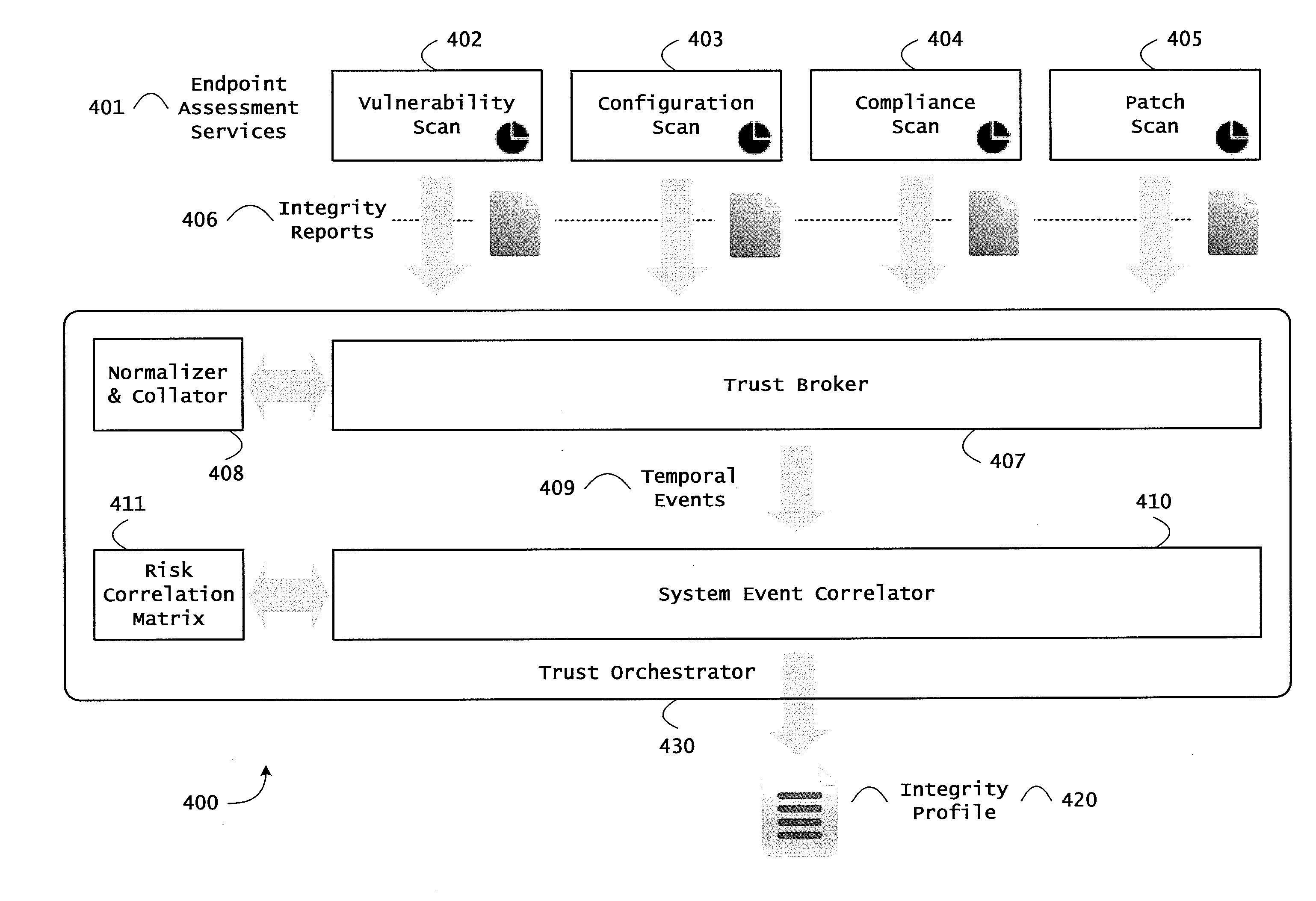
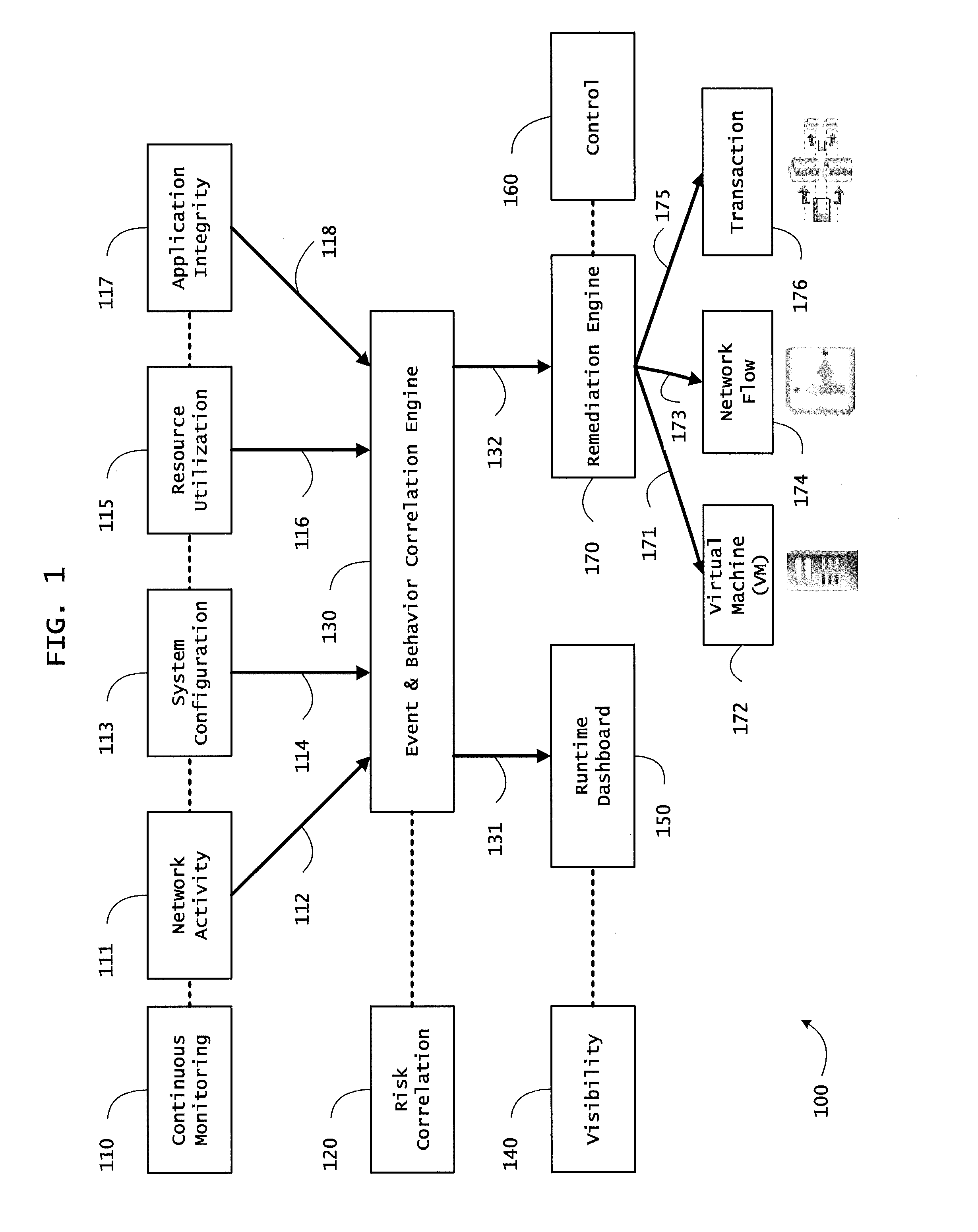
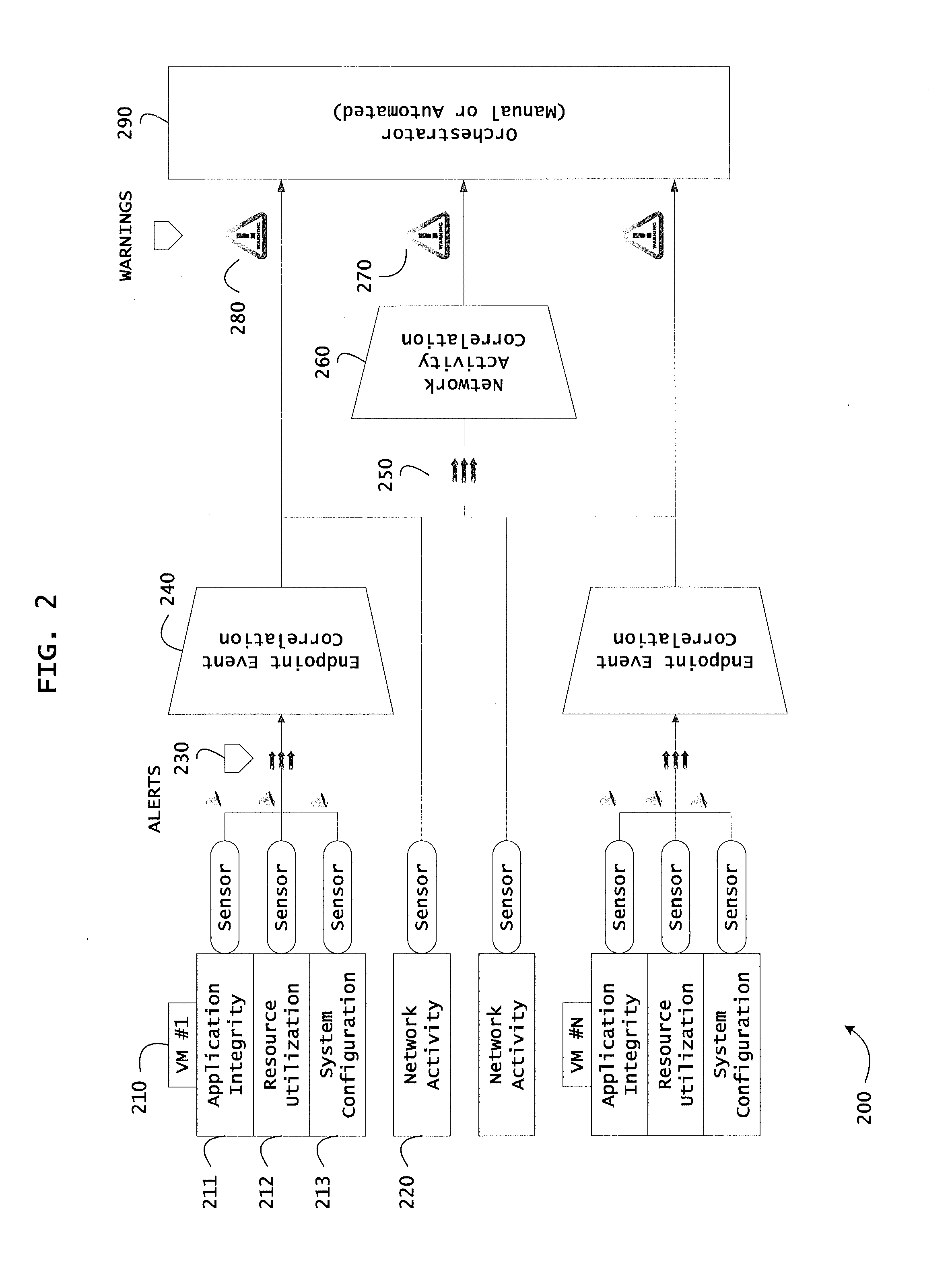
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
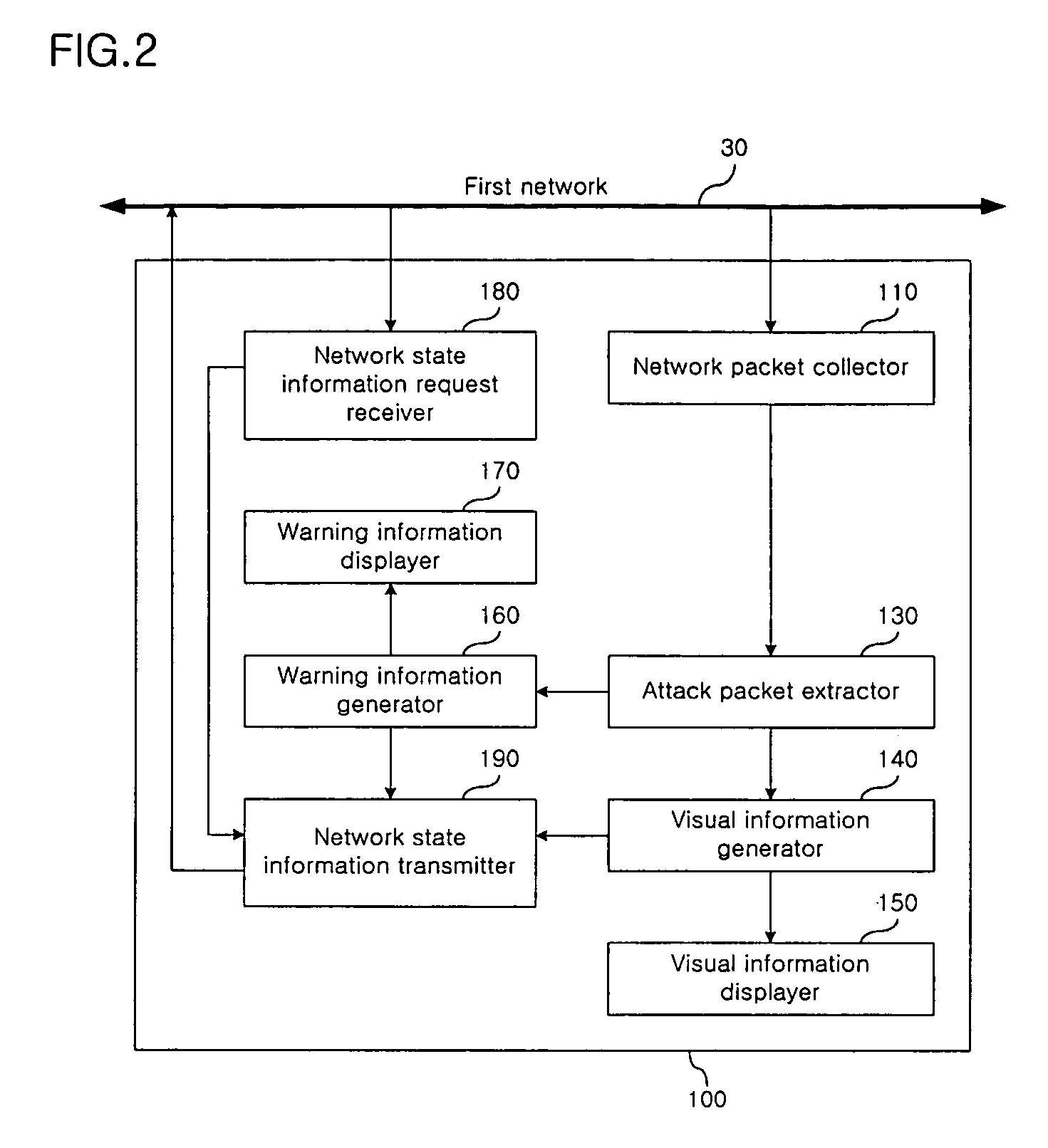
Apparatus and method for monitoring network using the parallel coordinate system
InactiveUS20070044147A1Data switching by path configurationMultiple digital computer combinationsData packNetwork attack
A network monitoring apparatus collects packets of a first network, and generates visual information by displaying the packets on a parallel coordinate system which has one or more parallel axis for parameters of the packets. The network monitoring apparatus may extract attack packets from the packet, and the network monitoring apparatus may transmit the visual information to a remote server. Through the network monitoring apparatus, the network manager can visually grasp the state of the network or the existence of a network attack.
Owner:KOREA UNIV IND & ACAD COLLABORATION FOUNDATION
Network monitoring using a proxy
A method and apparatus for network monitoring using a proxy are disclosed. In one embodiment, a method generally comprises receiving at a proxy, path information for a label switched path (LSP) from a forwarding device located in the LSP, generating a connectivity verification message based on the path information, adding a proxy label to the connectivity verification message, and transmitting the connectivity verification message to the forwarding device. The proxy label is configured to inject the connectivity verification message into a forwarding plane at the forwarding device and the connectivity verification message is configured for transmittal from the forwarding device over the LSP to a destination node to verify a forwarding path associated with the path information received from the forwarding device.
Owner:CISCO TECH INC
Detecting Anomalous Network Application Behavior
ActiveUS20080222717A1Memory loss protectionError detection/correctionTraffic capacityInformation analysis
System and Method for detecting anomalous network application behavior. Network traffic between at least one client and one or more servers may be monitored. The client and the one or more servers may communicate using one or more application protocols. The network traffic may be analyzed at the application-protocol level to determine anomalous network application behavior. Analyzing the network traffic may include determining, for one or more communications involving the client, if the client has previously stored or received an identifier corresponding to the one or more communications. If no such identifier has been observed in a previous communication, then the one or more communications involving the client may be determined to be anomalous. A network monitoring device may perform one or more of the network monitoring, the information extraction, or the information analysis.
Owner:EXTRAHOP NETWORKS
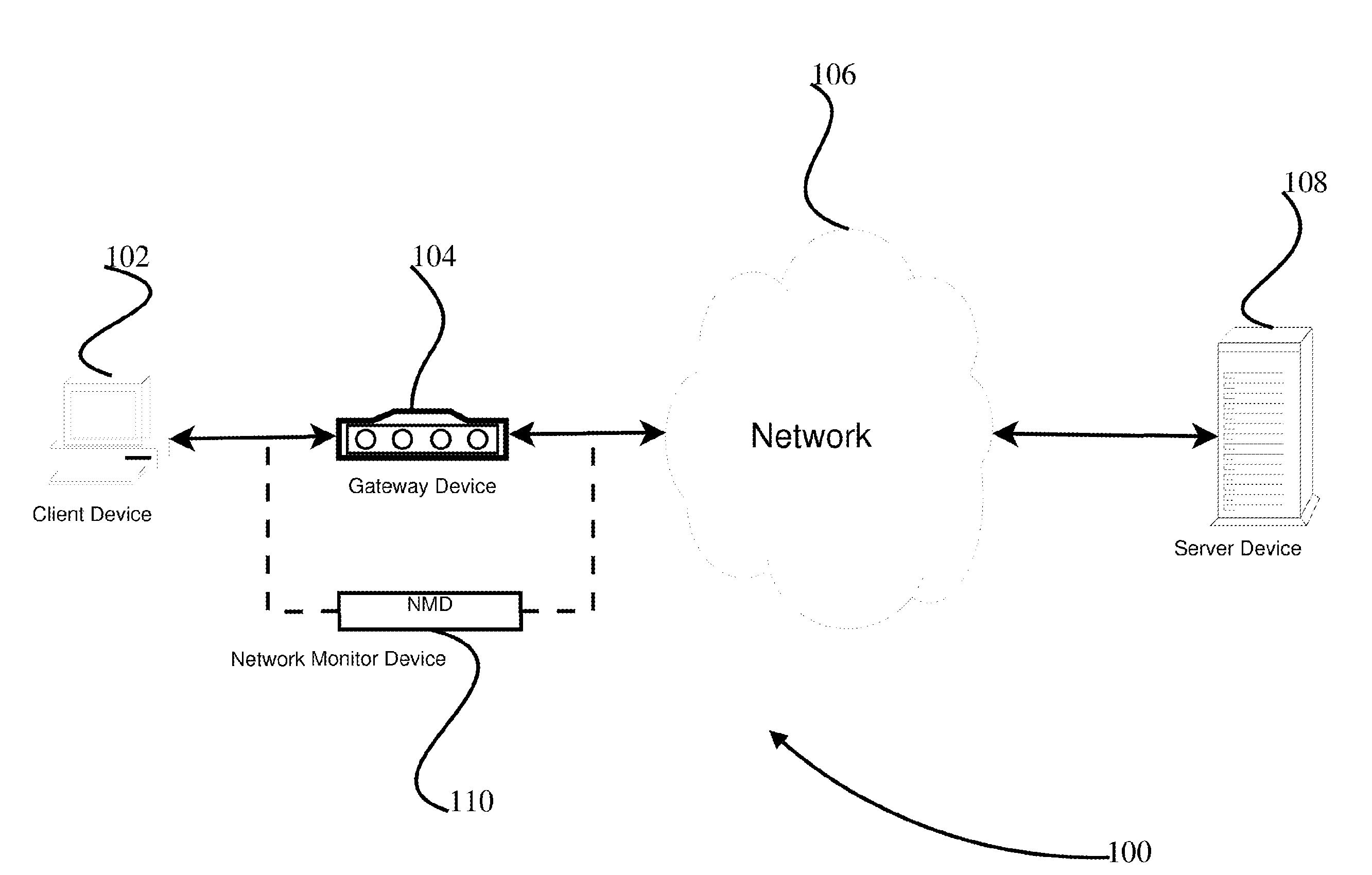
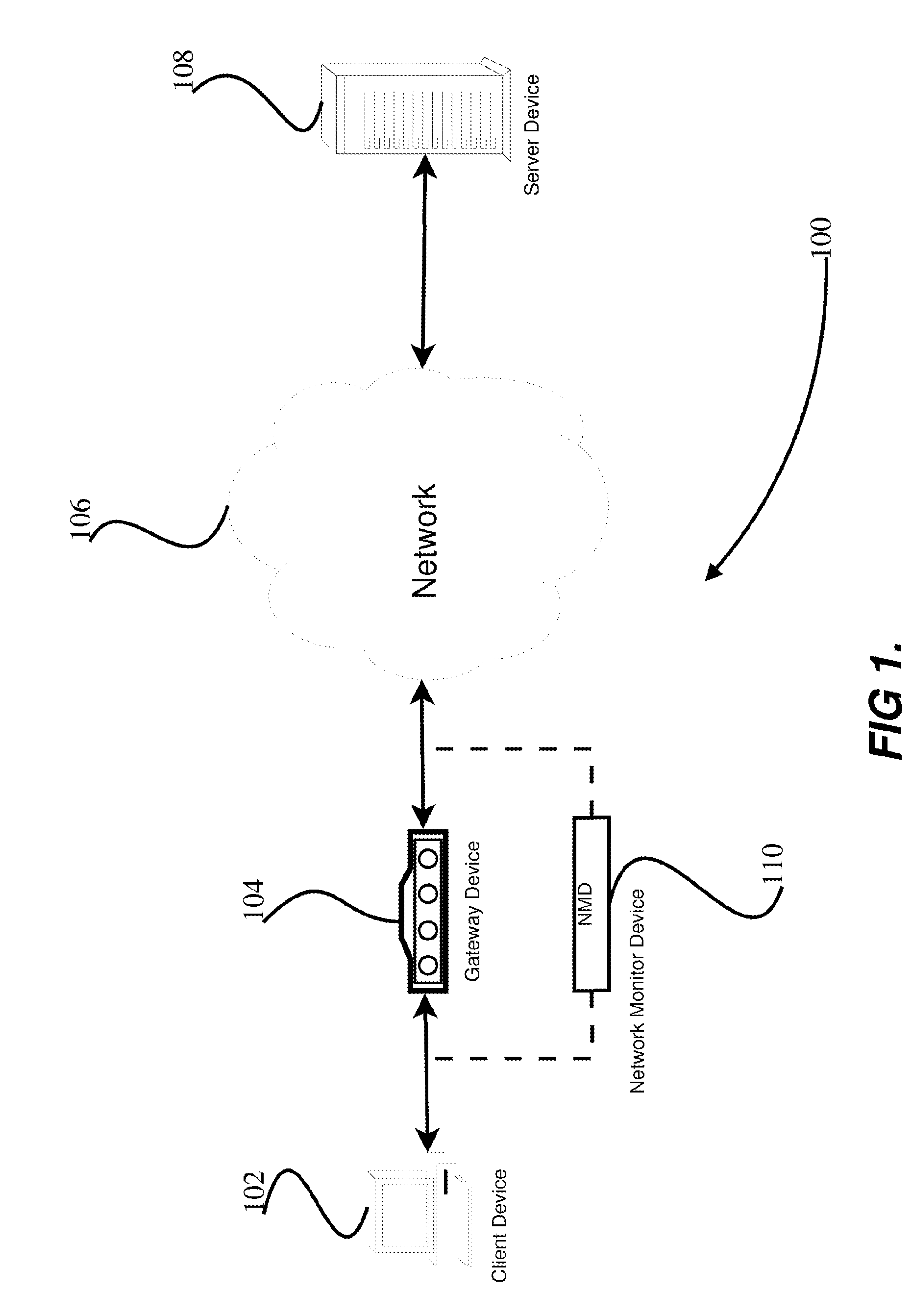
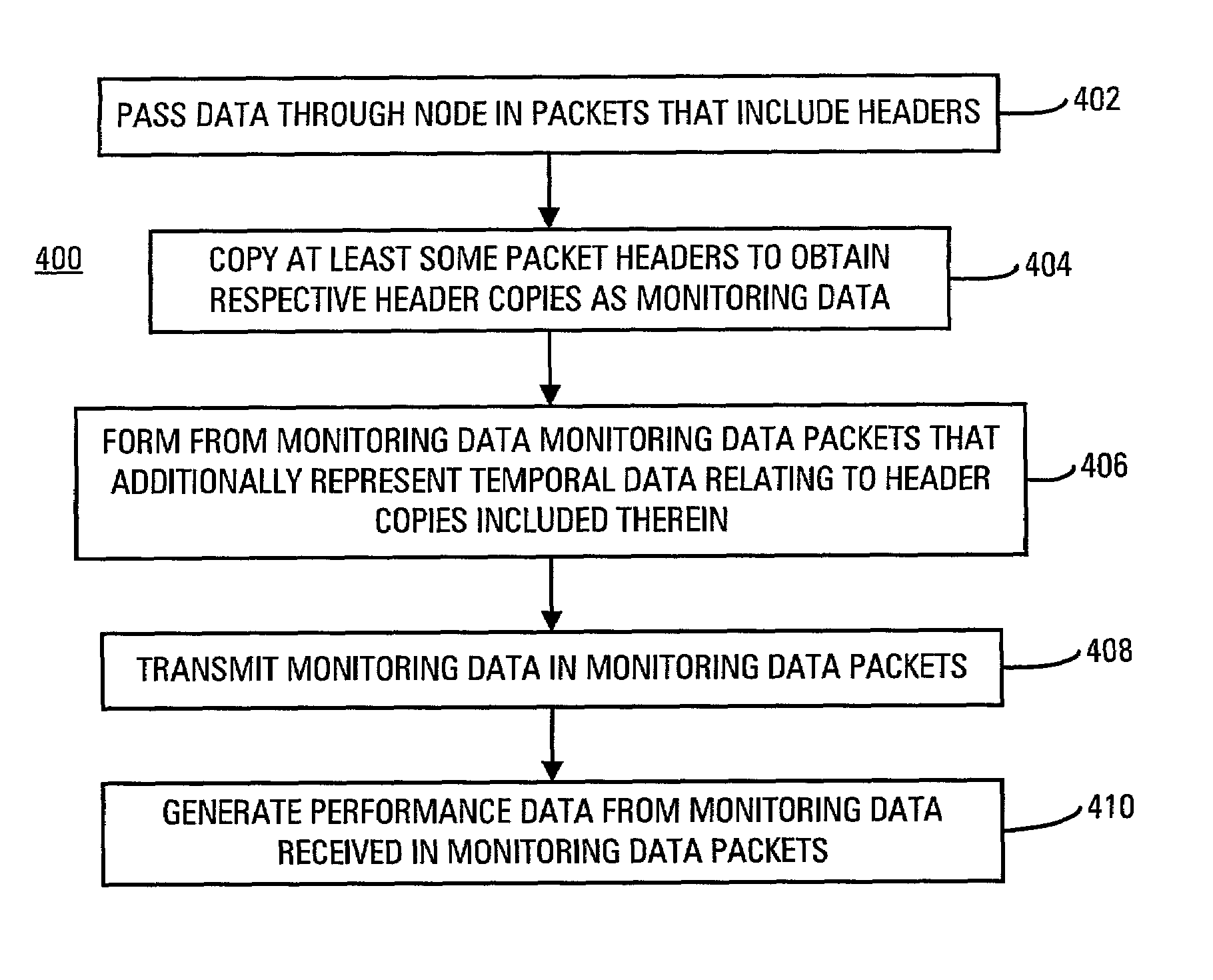
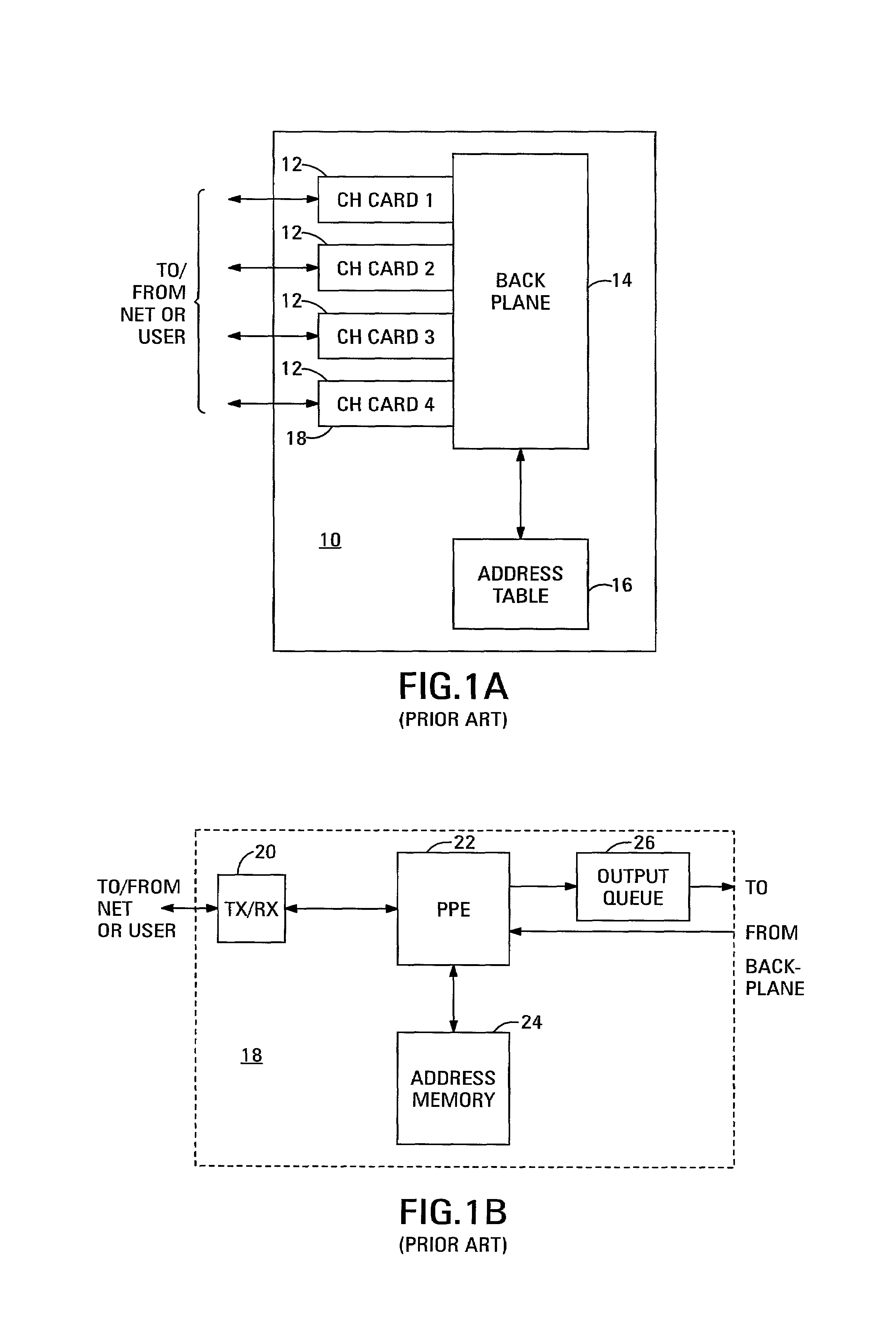
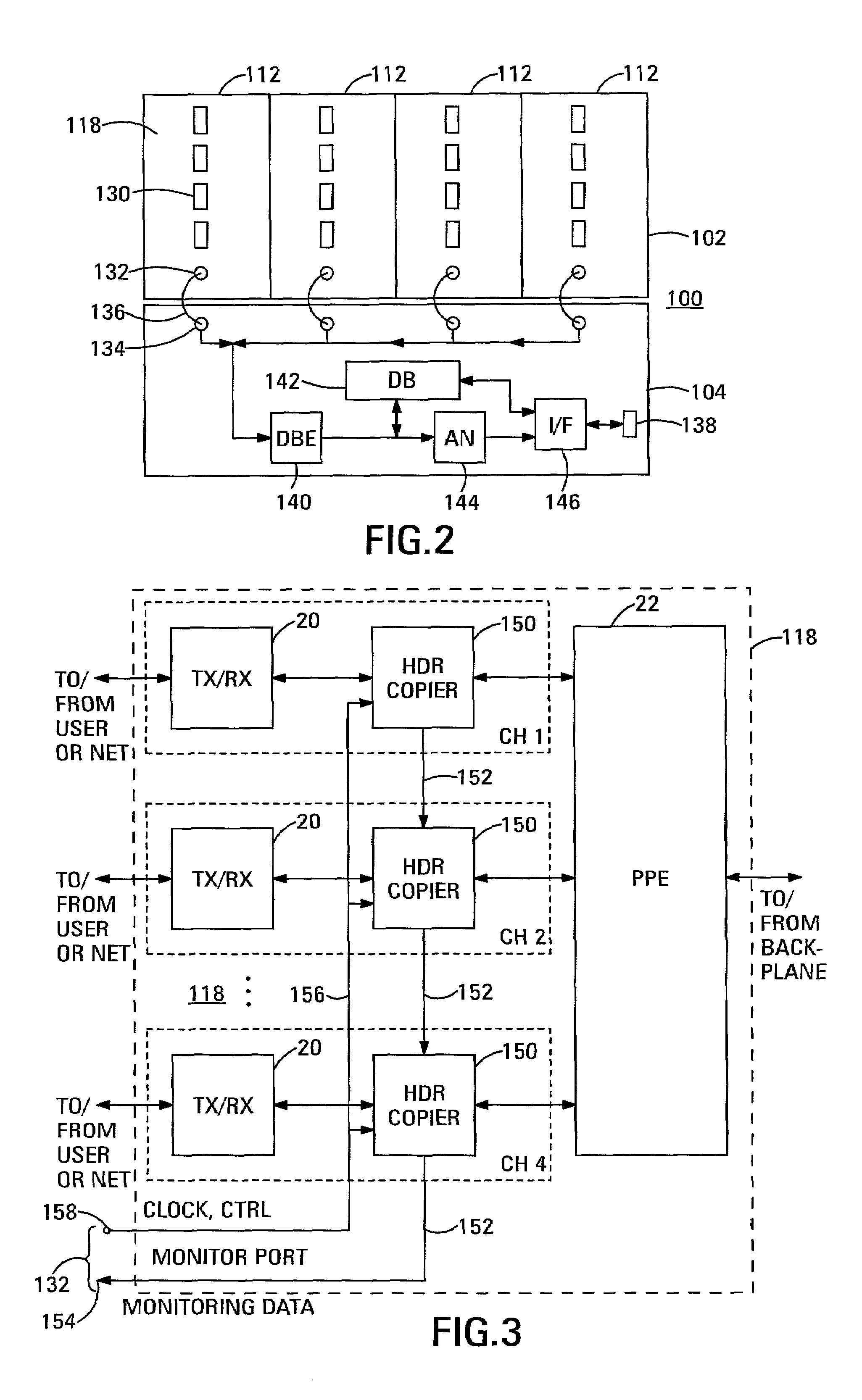
Network monitoring system with built-in monitoring data gathering
The network monitoring system comprises a network router with built-in monitoring data gathering. The network router includes channels through which data pass in packets. Each of the packets includes a packet header. The network router additionally includes a header copier and a packet generator. The header copier generates a header copy from the packet header of at least some of the packets. The packet generator receives the header copies and forms monitoring data packets from them. Each monitoring data packet additionally represents temporal data relating to the header copies included in it. A method of obtaining performance data relating to a data transmission network that includes a node passes data through the node in packets. Each of the packets includes a packet header. At least some of the packet headers are copied to obtain respective header copies as monitoring data from which monitoring data packets are formed. The monitoring data packets additionally represent temporal data relating to the header copies included in them. The monitoring data packets are transmitted and the performance data are generated from the monitoring data contained in the monitoring data packets.
Owner:AGILENT TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com