Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
21139 results about "Monitoring data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
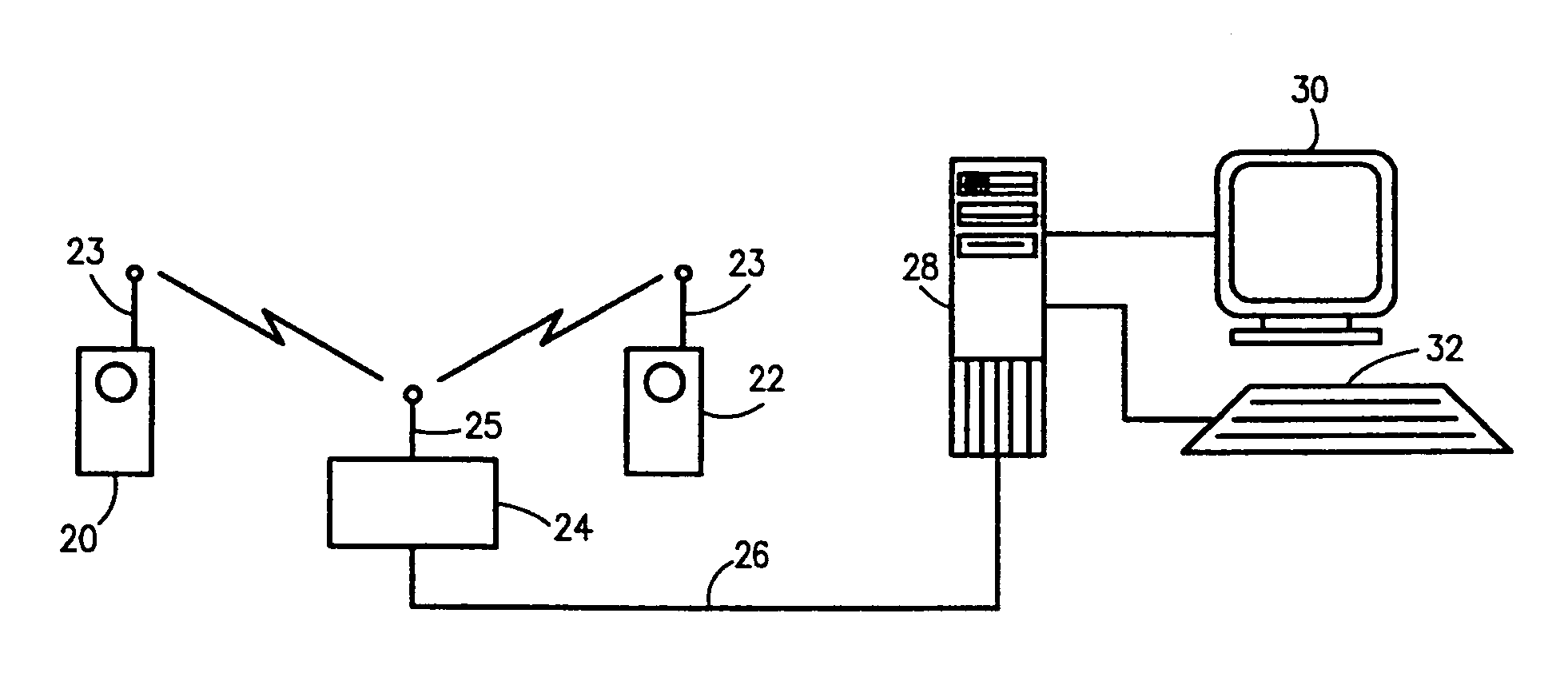
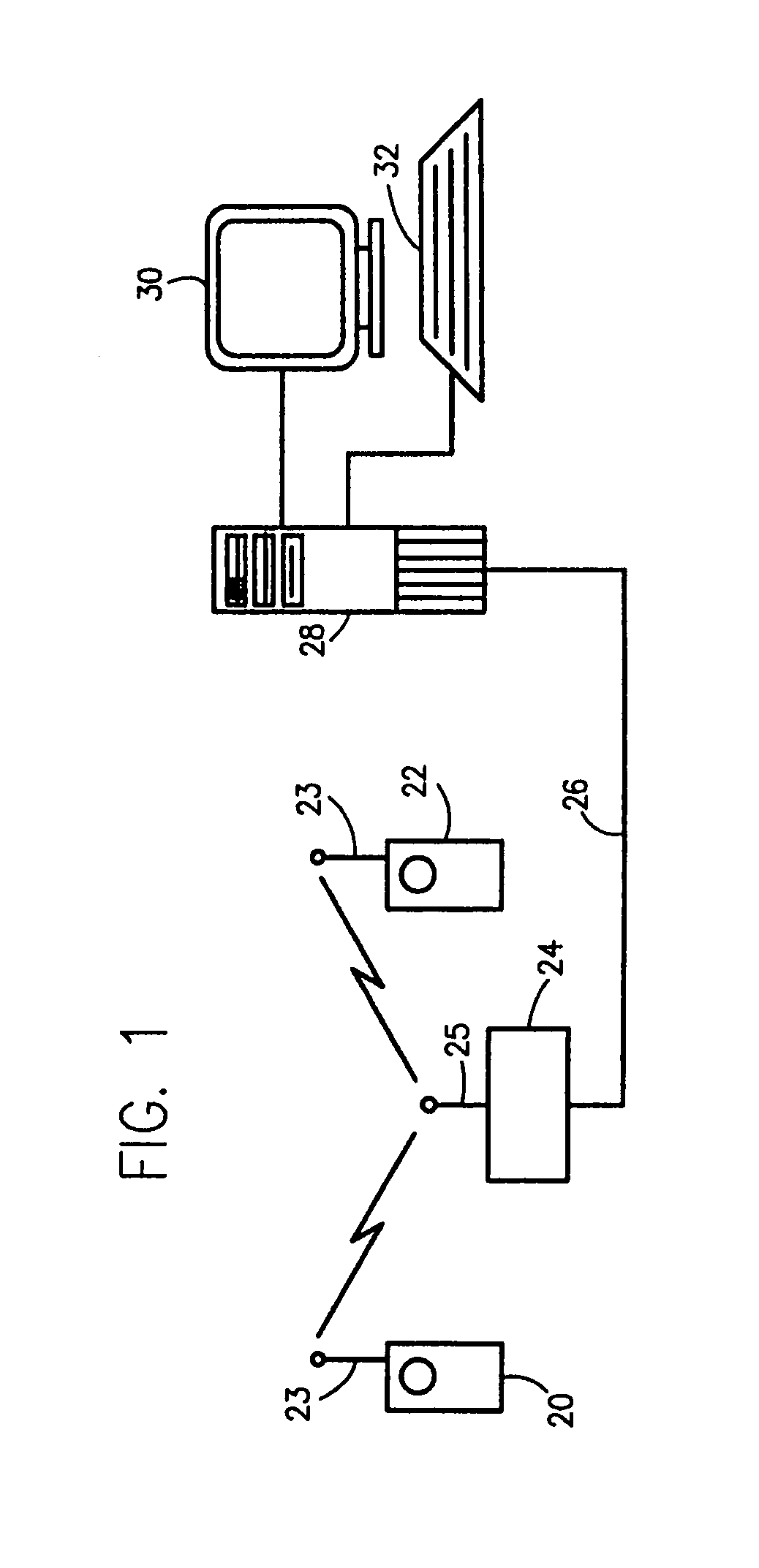
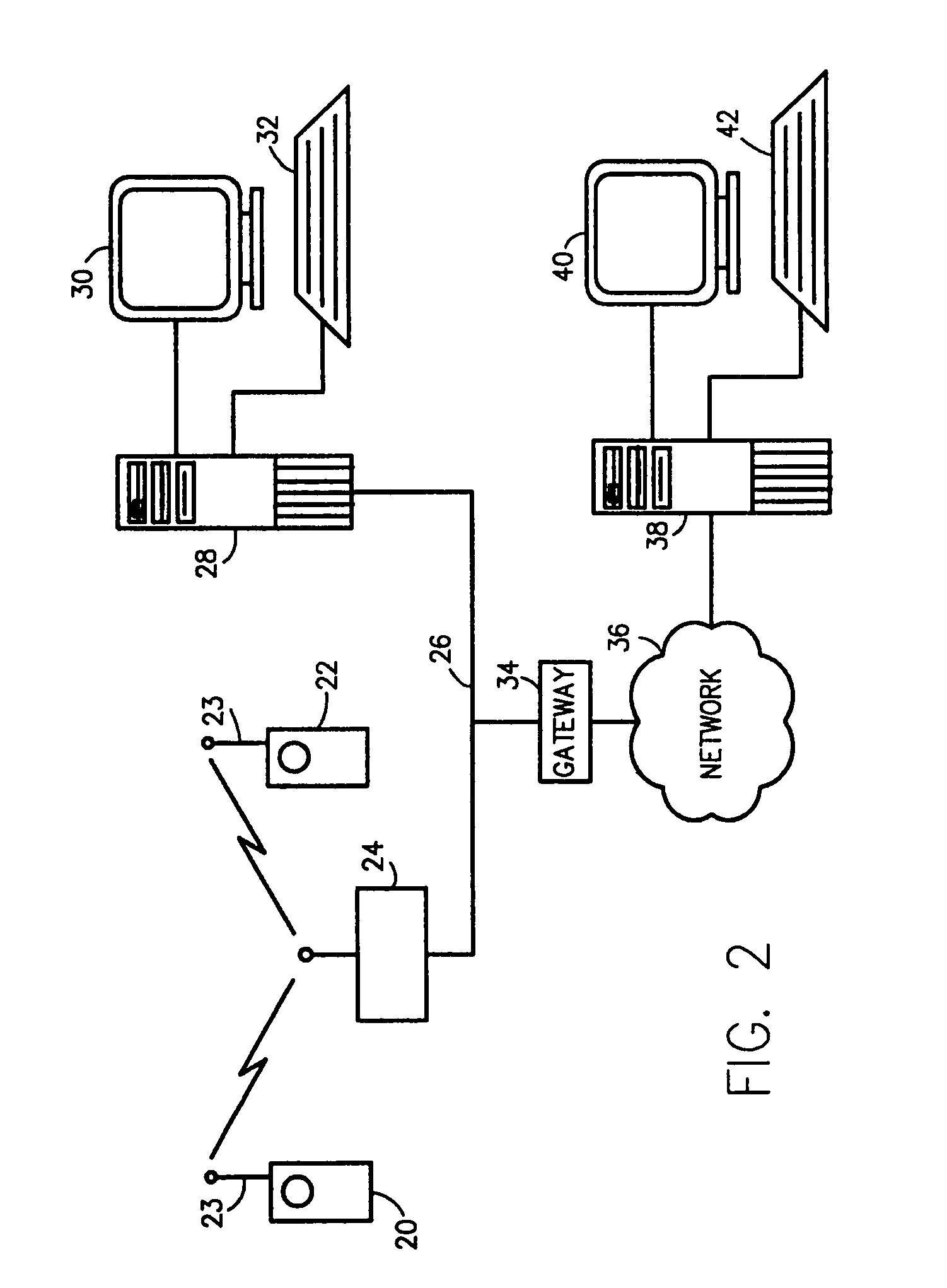
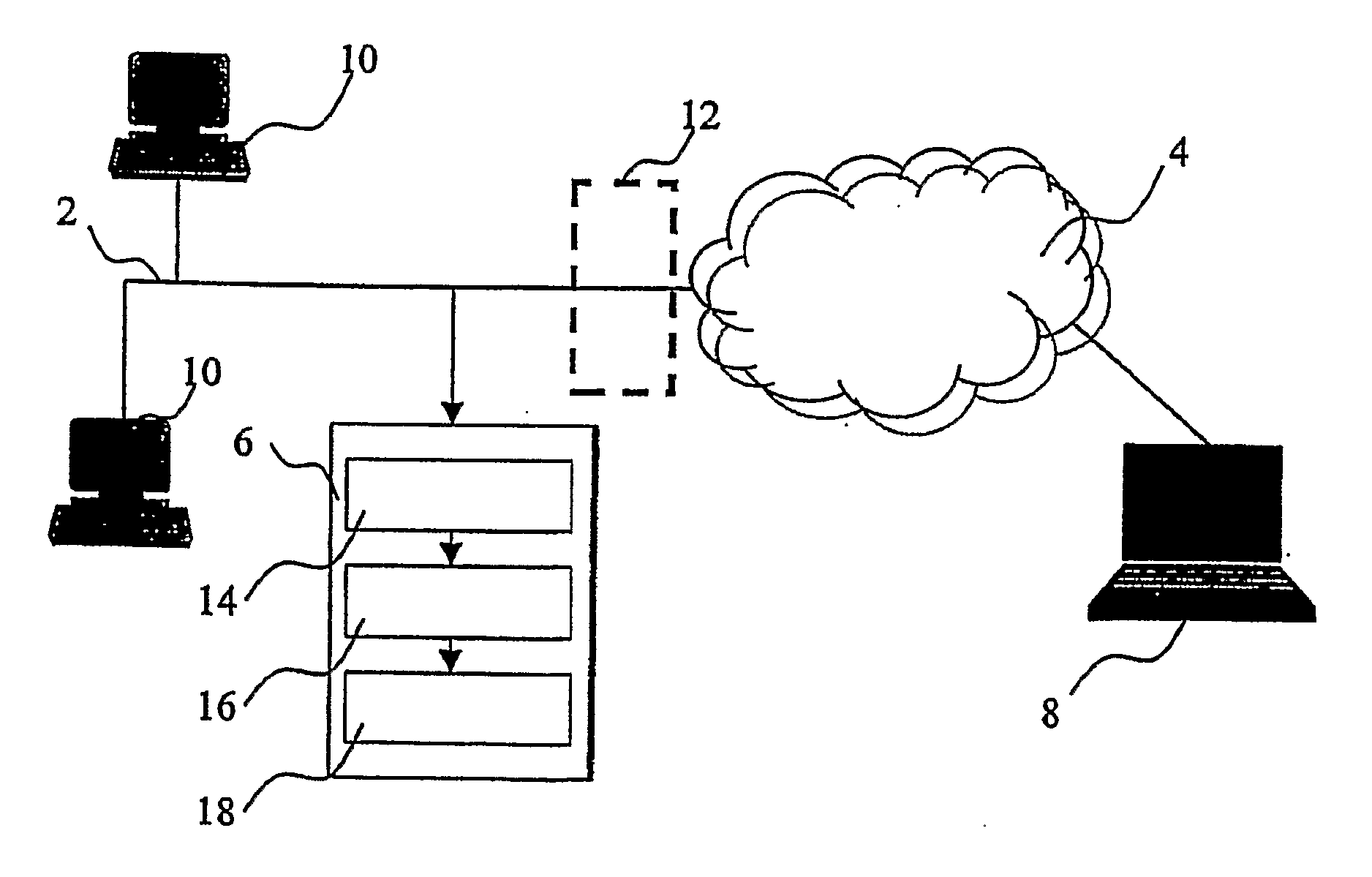
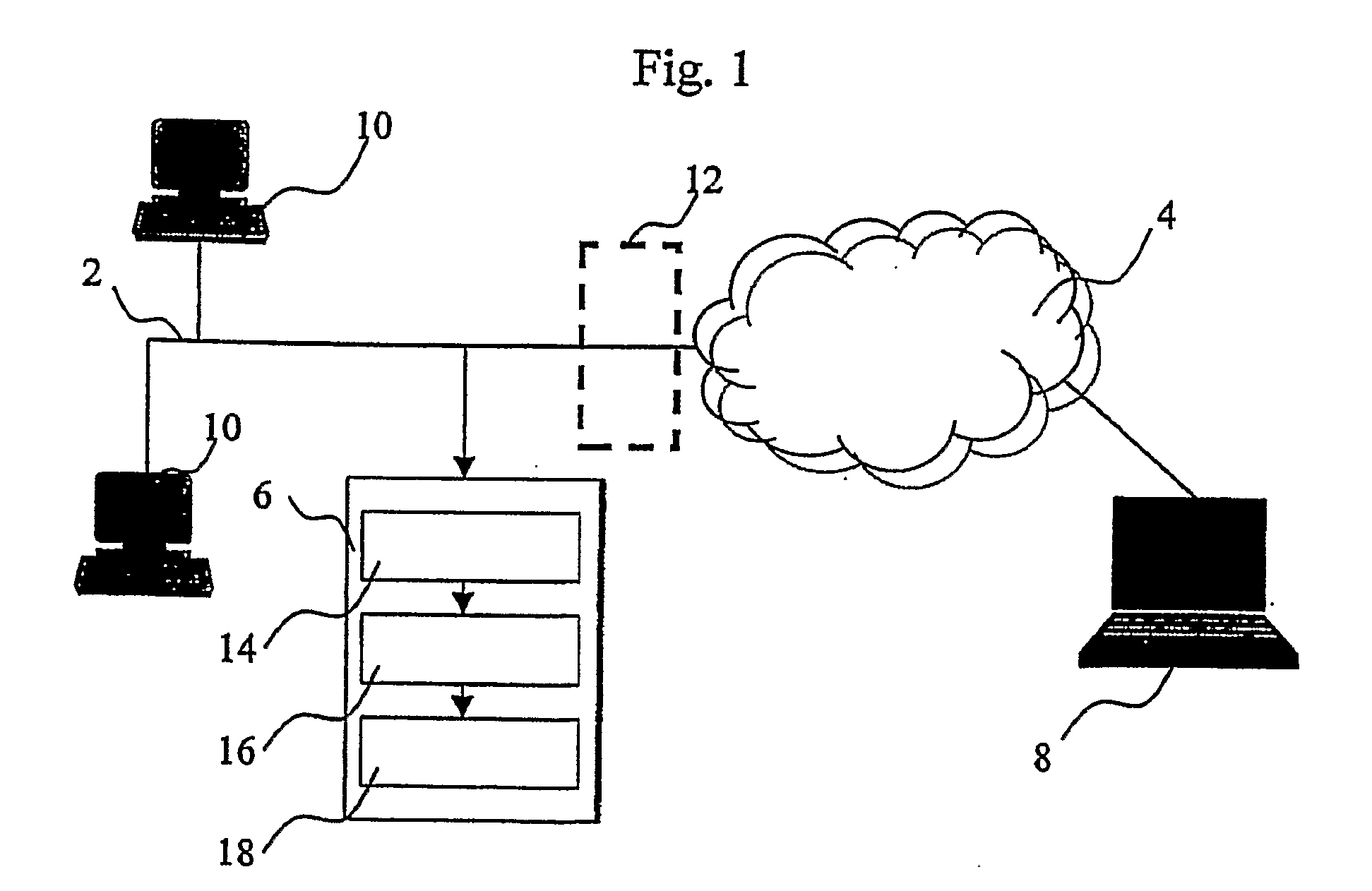
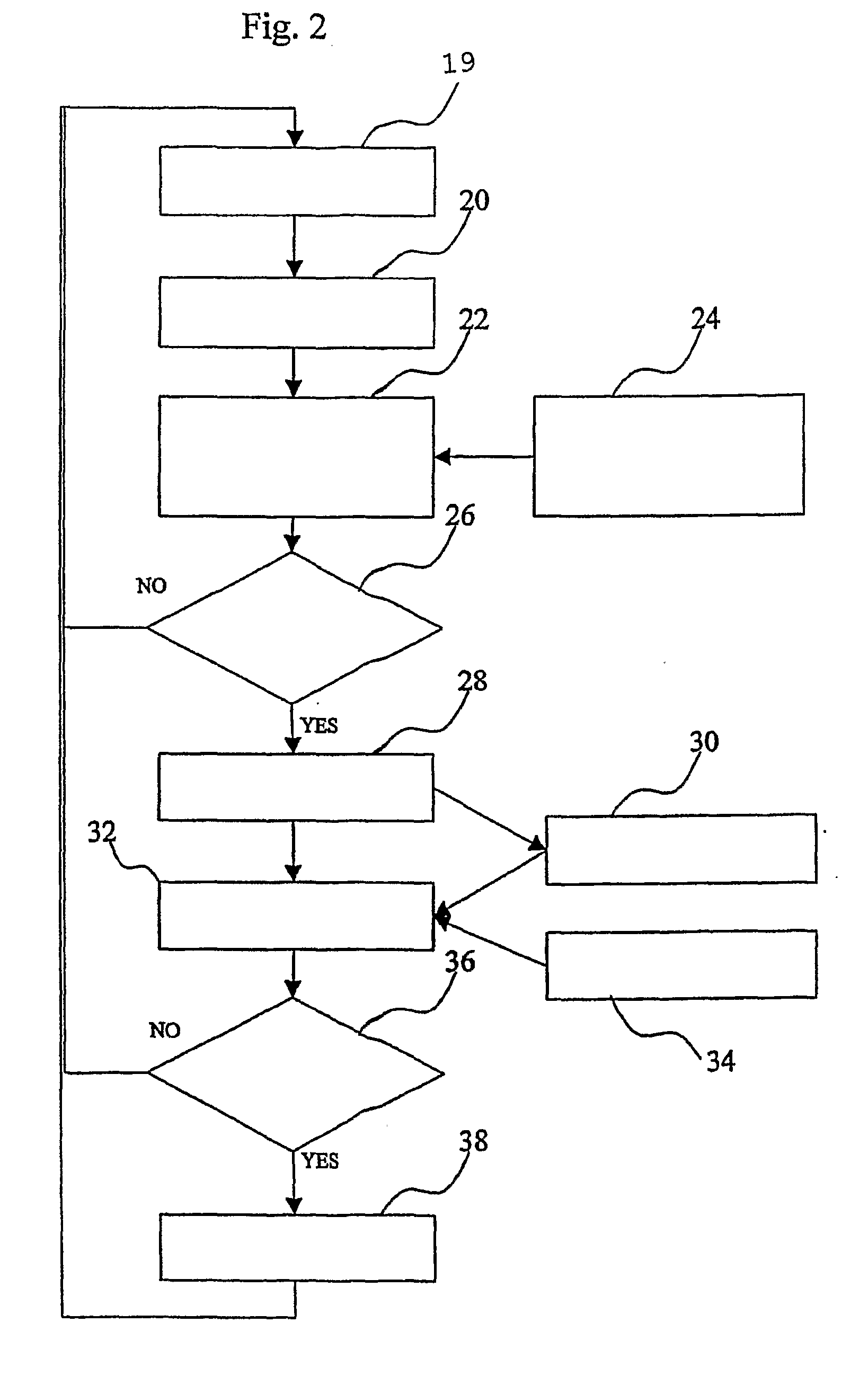
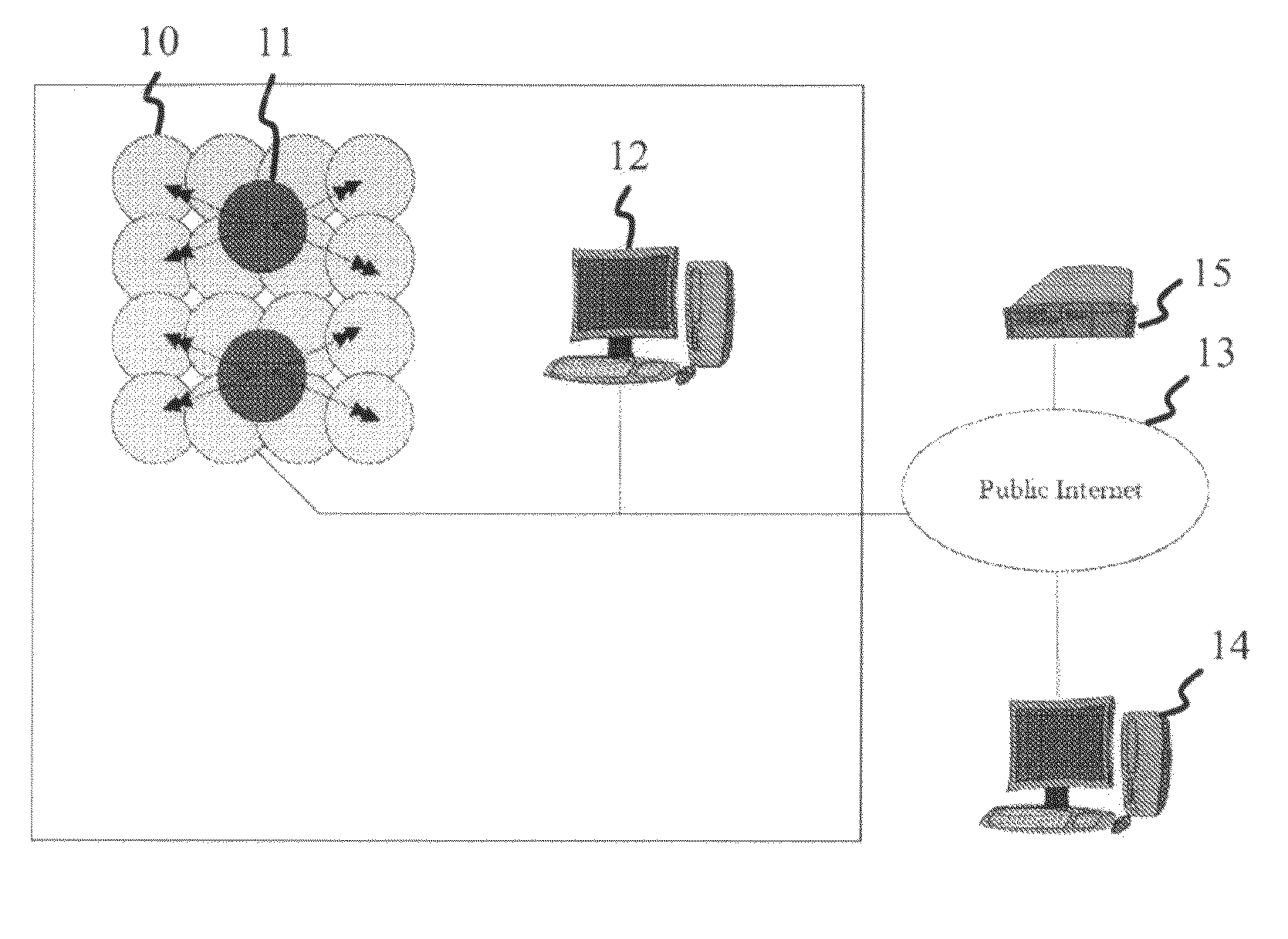
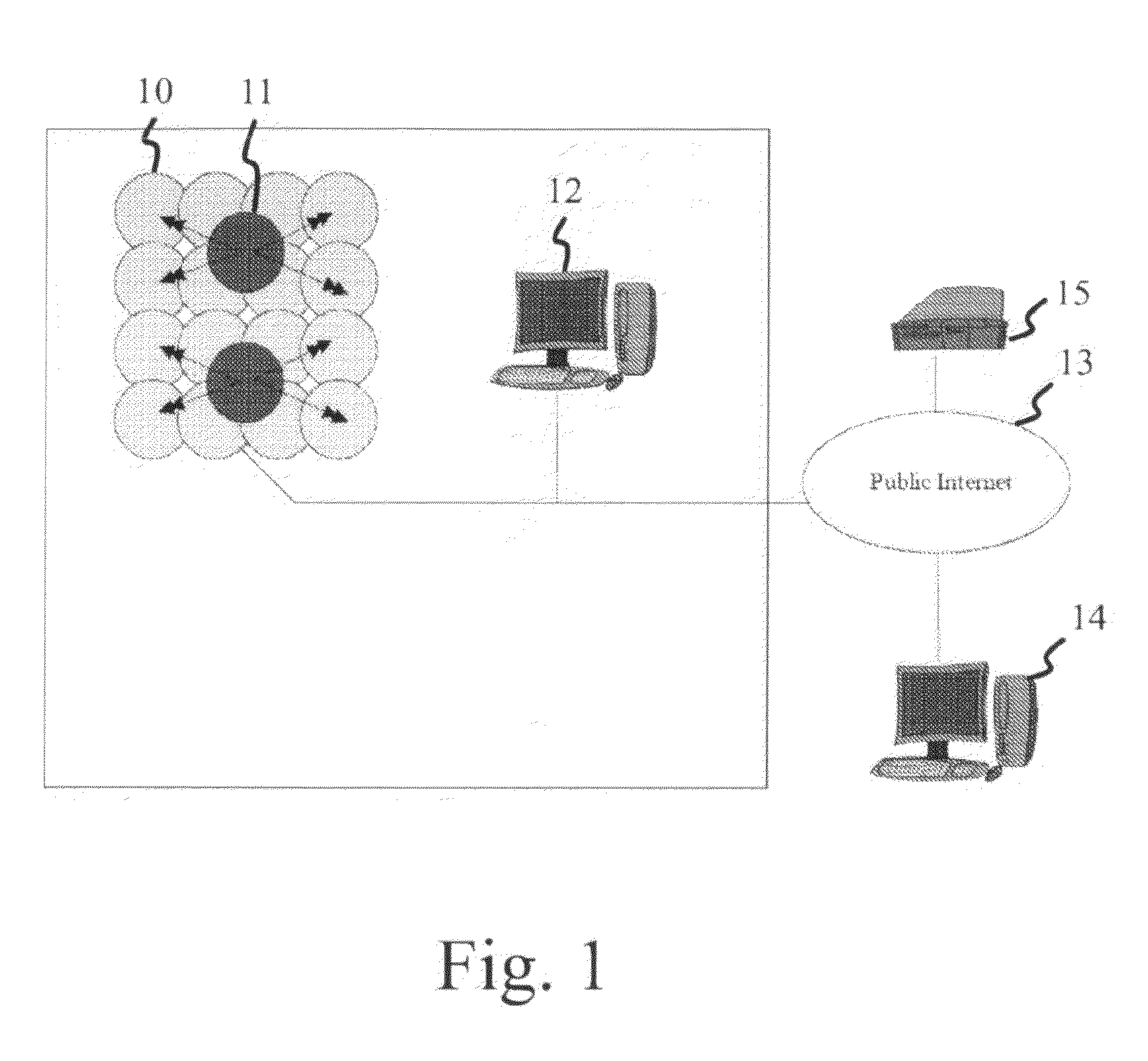
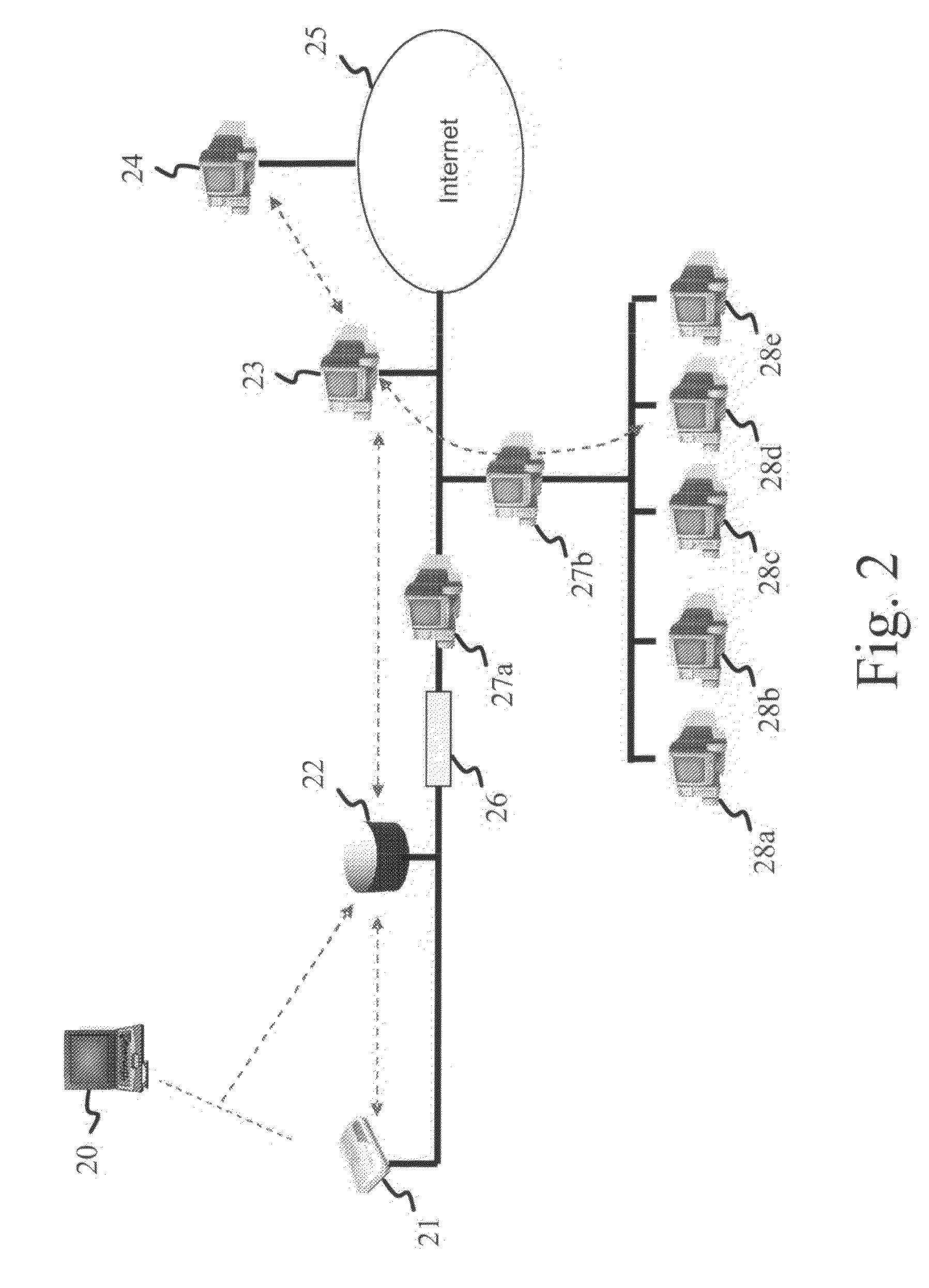
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
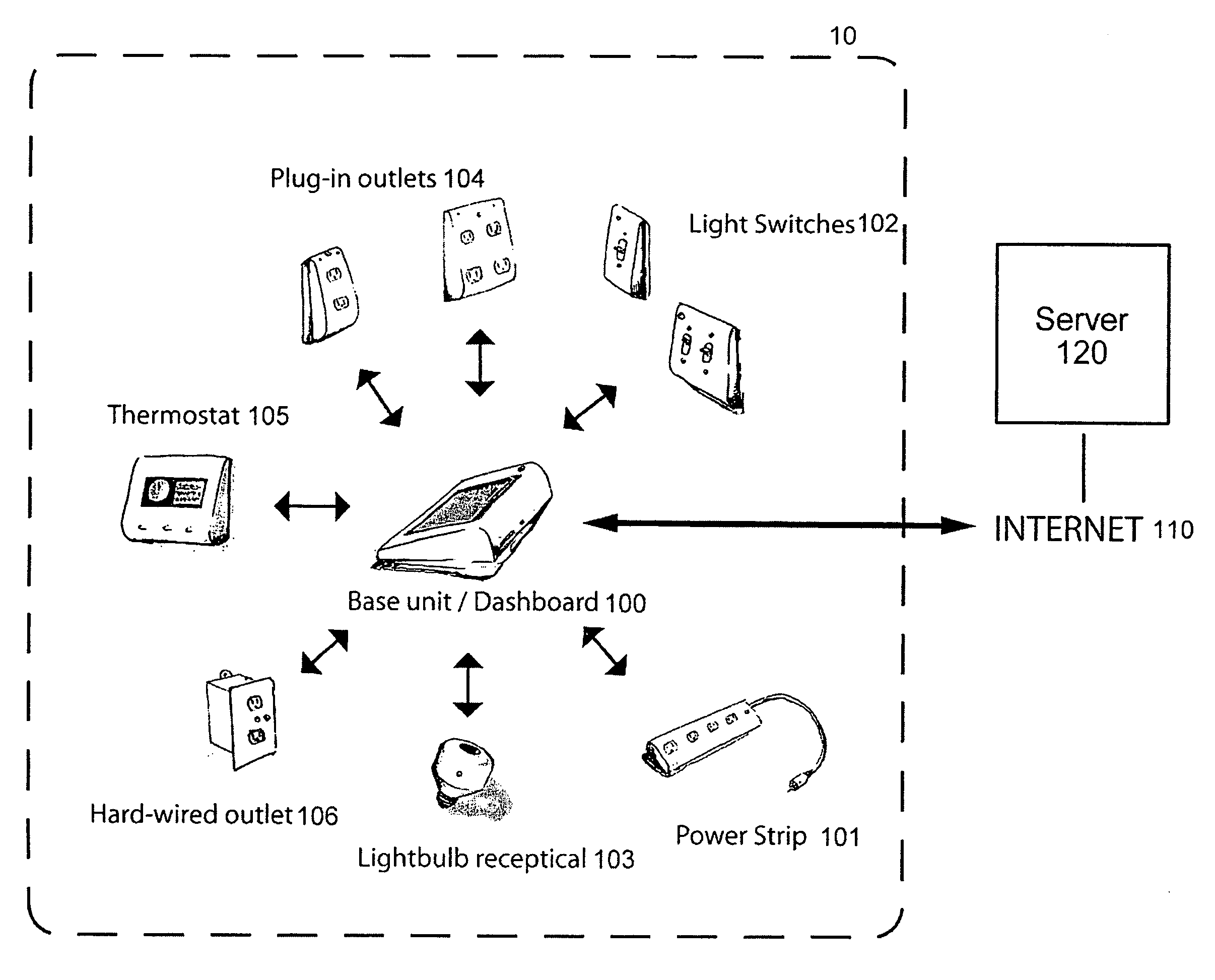
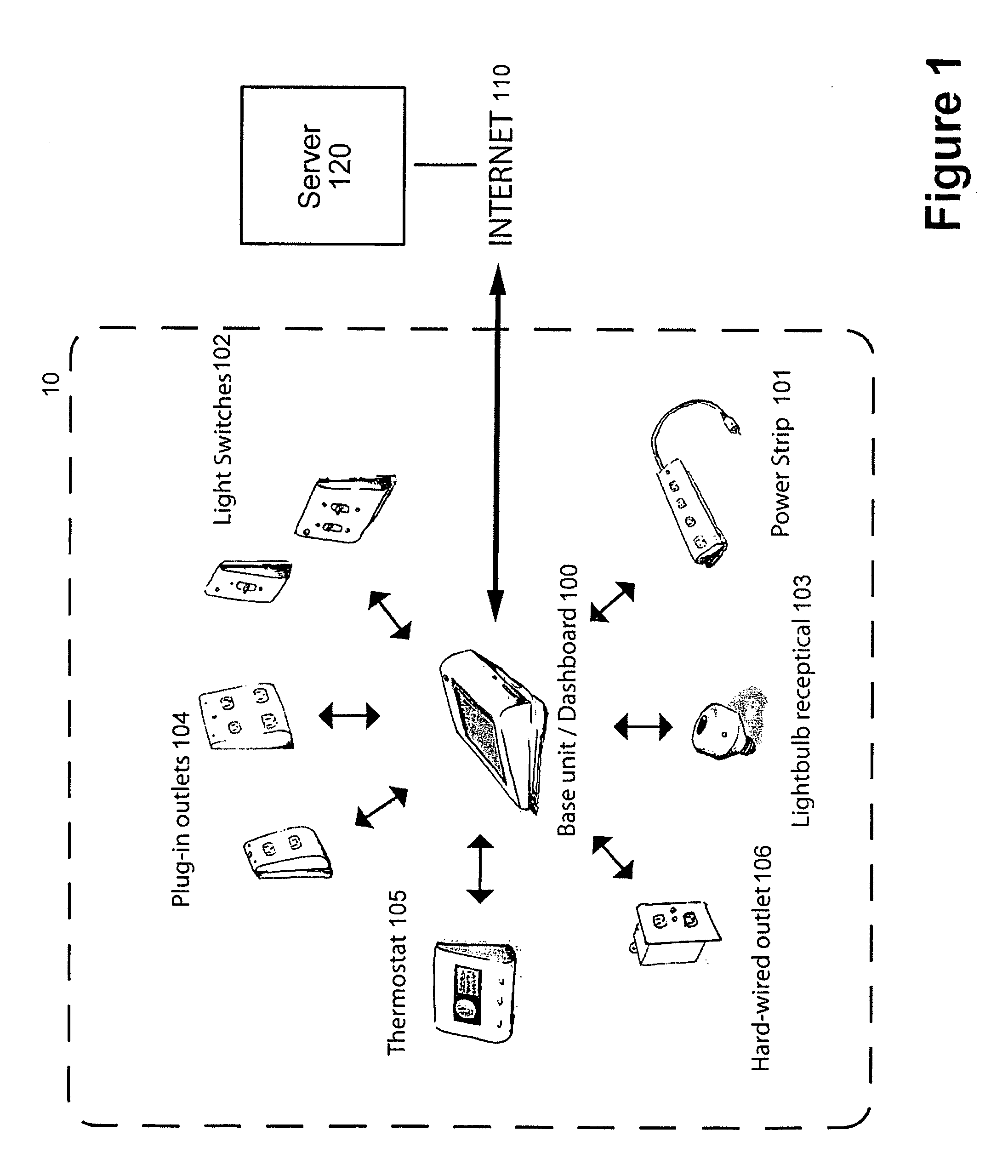
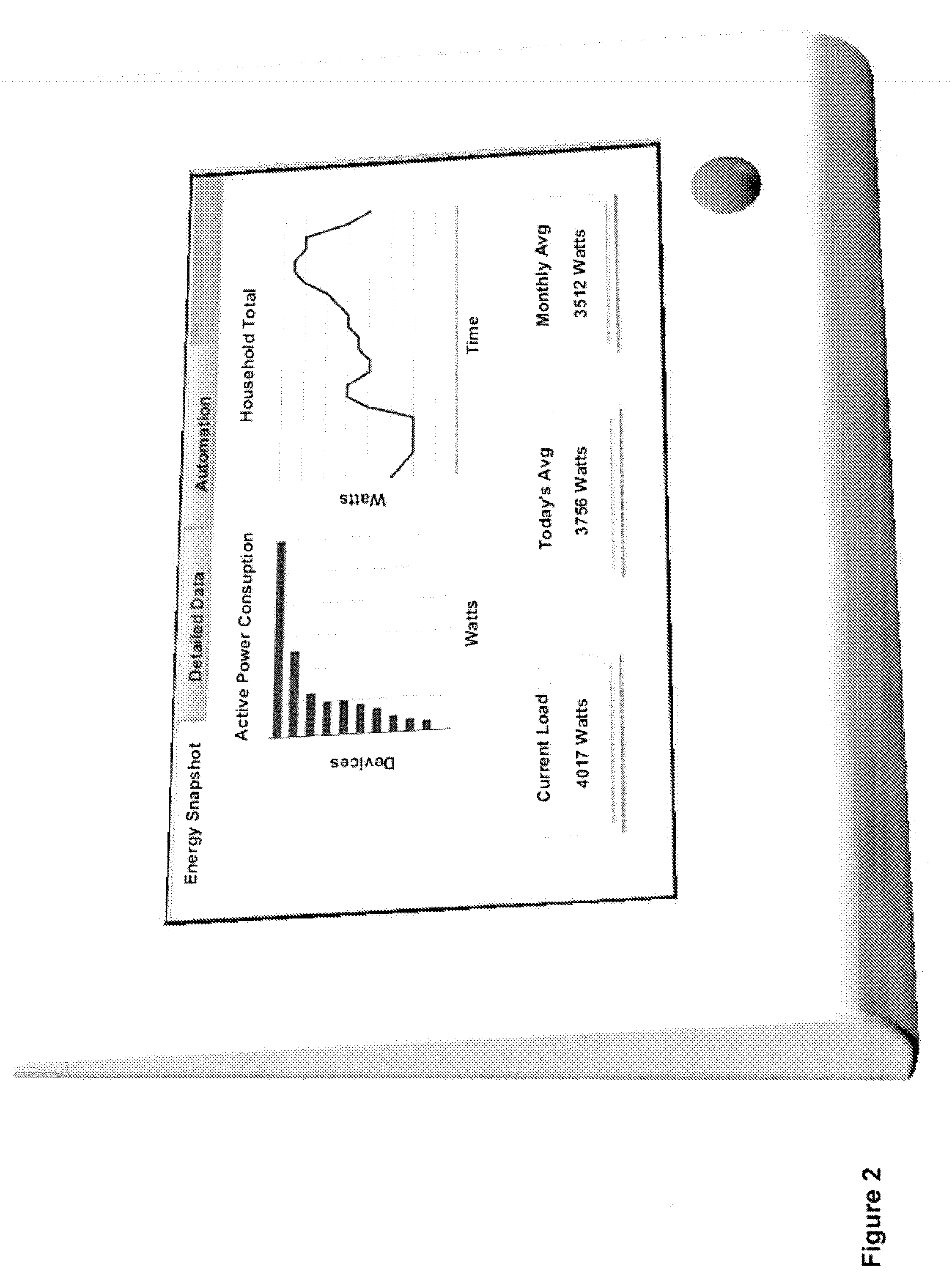
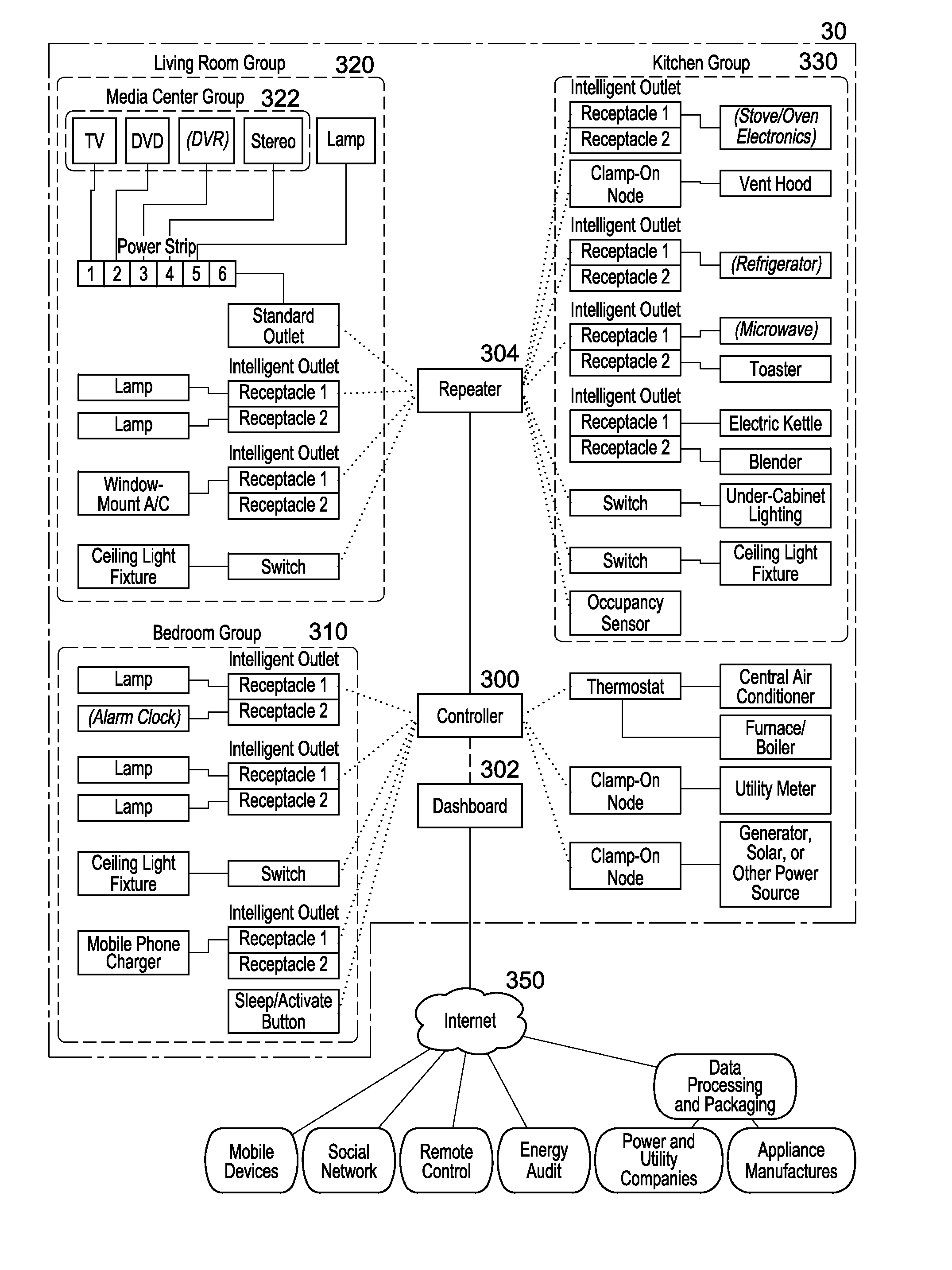
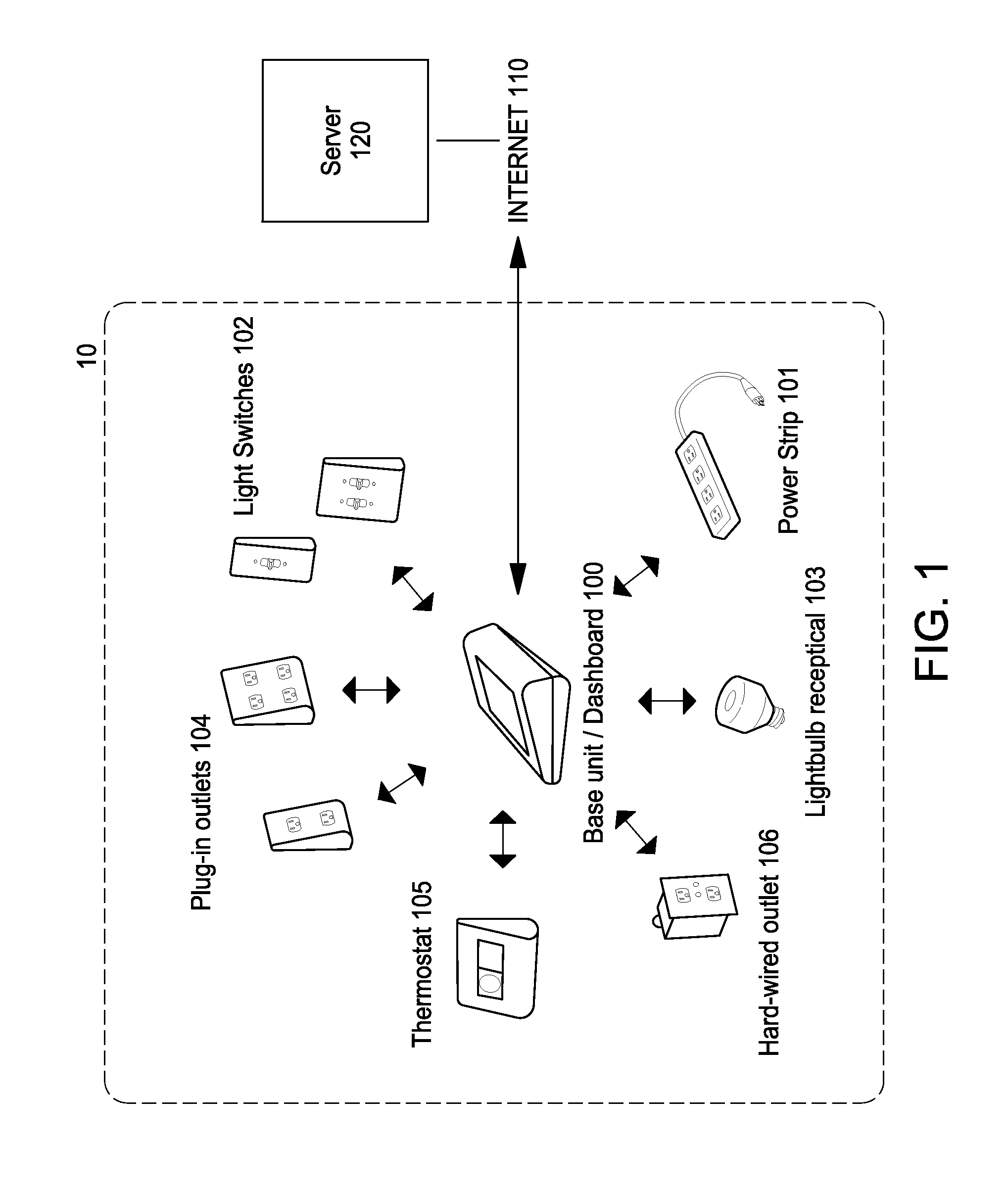
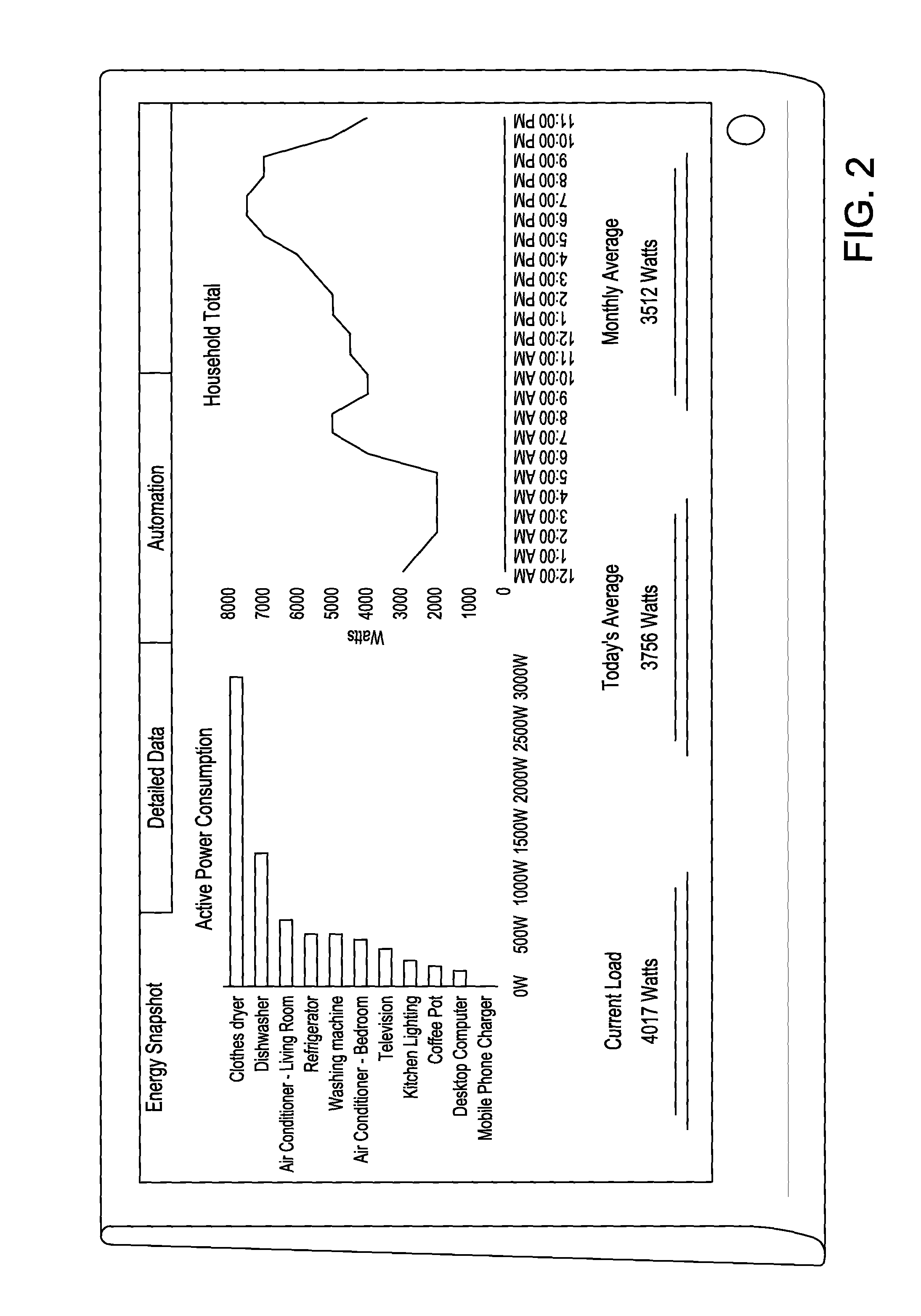
System and method for home energy monitor and control
ActiveUS20090195349A1Increase powerEfficient managementLevel controlPayment architectureCommunity basedMonitoring system
The invention generally concerns systems and methods for monitoring and controlling the power consumption of a power-consuming device. The system and method may connect to a power source and a power-consuming device, connecting the power-consuming device to the power source. The power usage of the power-consuming device may then be measured and monitored. This monitoring data may then be stored and optionally sent to a controlling device on a data network. The location of the power-consuming device may also be determined, recorded, and sent to a controlling device. The system may also control the power usage of the power-consuming device. In some cases, a remote server may connect multiple energy monitoring systems in order to gain additional efficiencies and foster a community-based social network.
Owner:ENERGYHUB
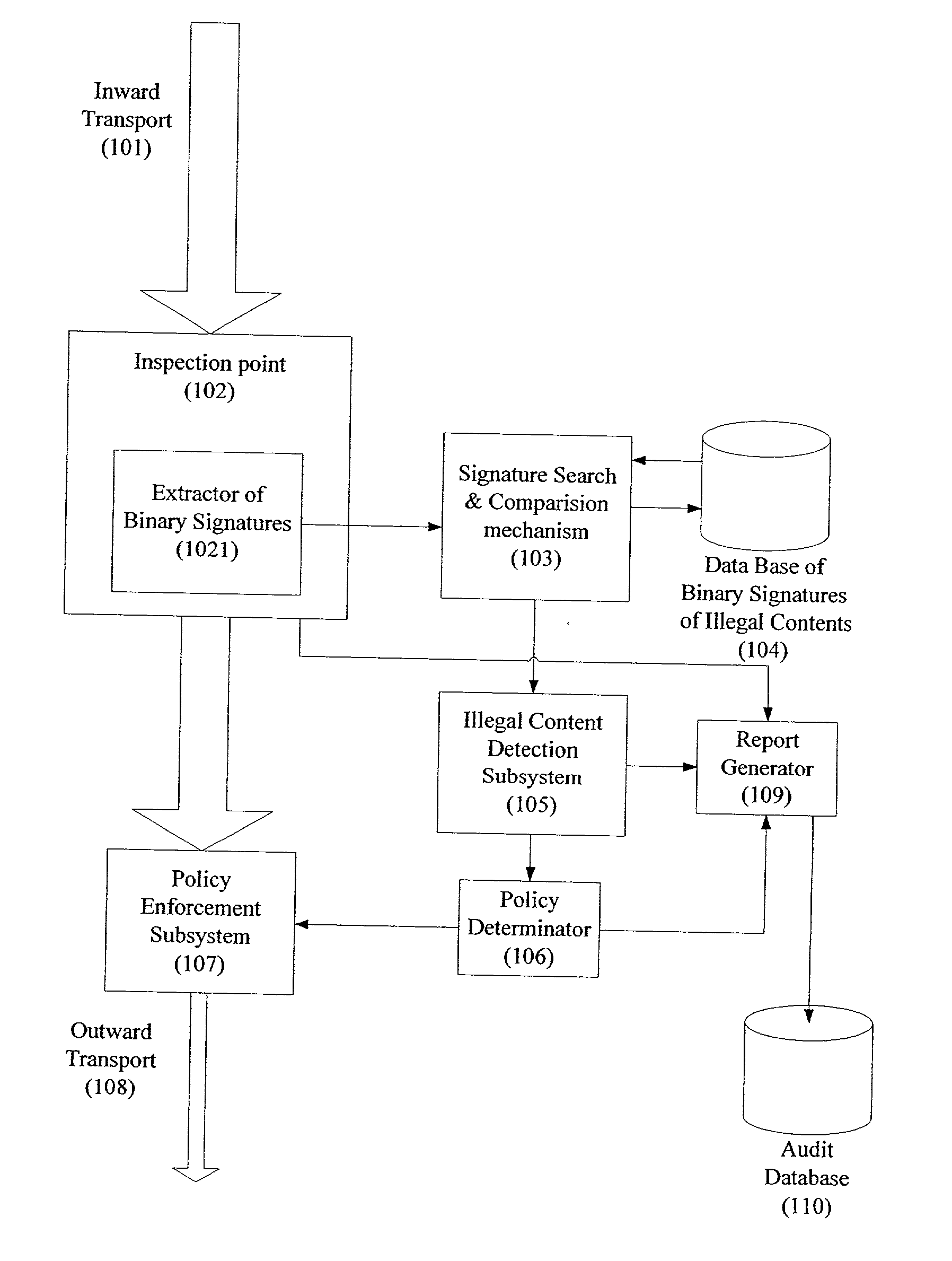
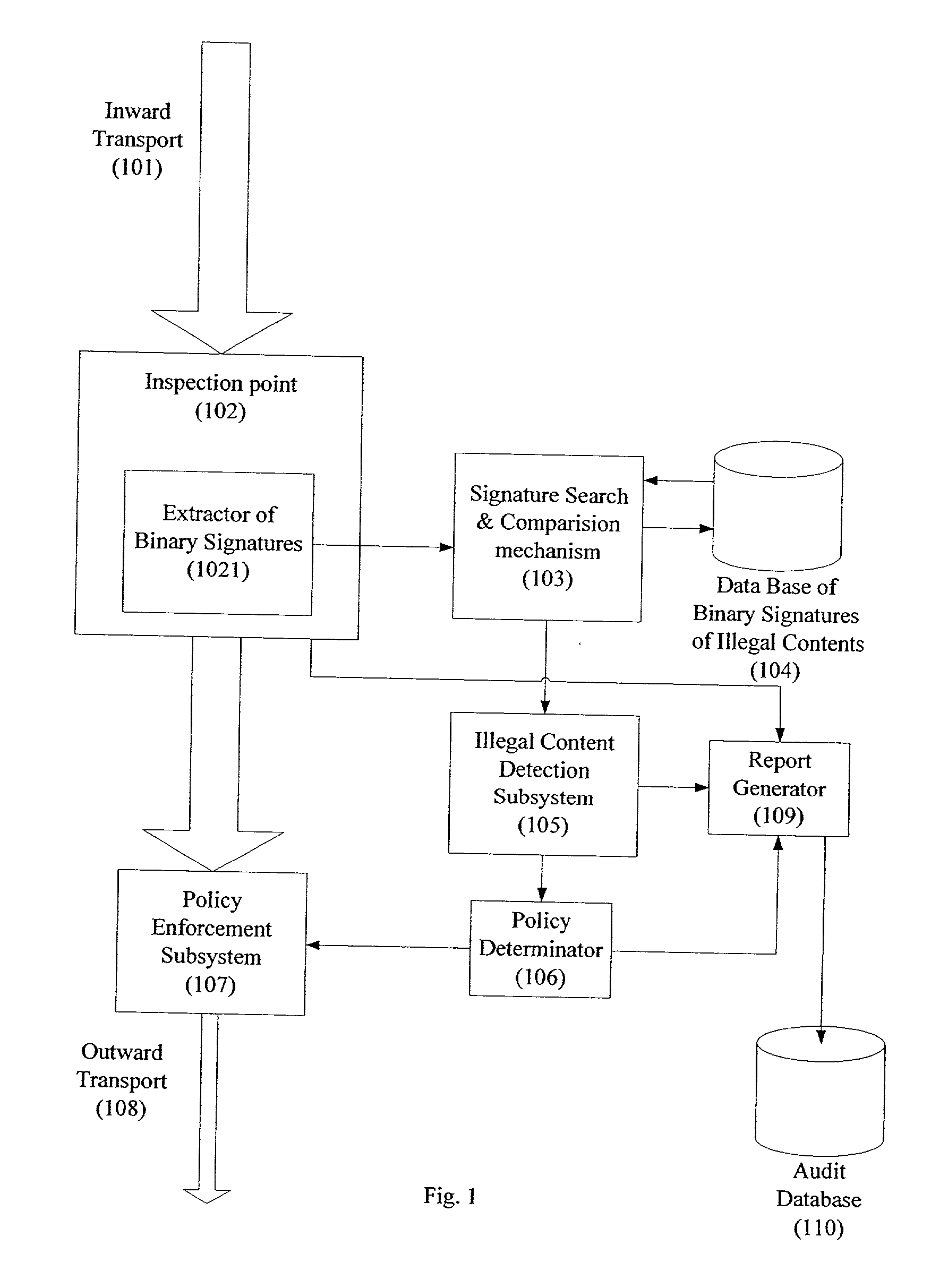
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
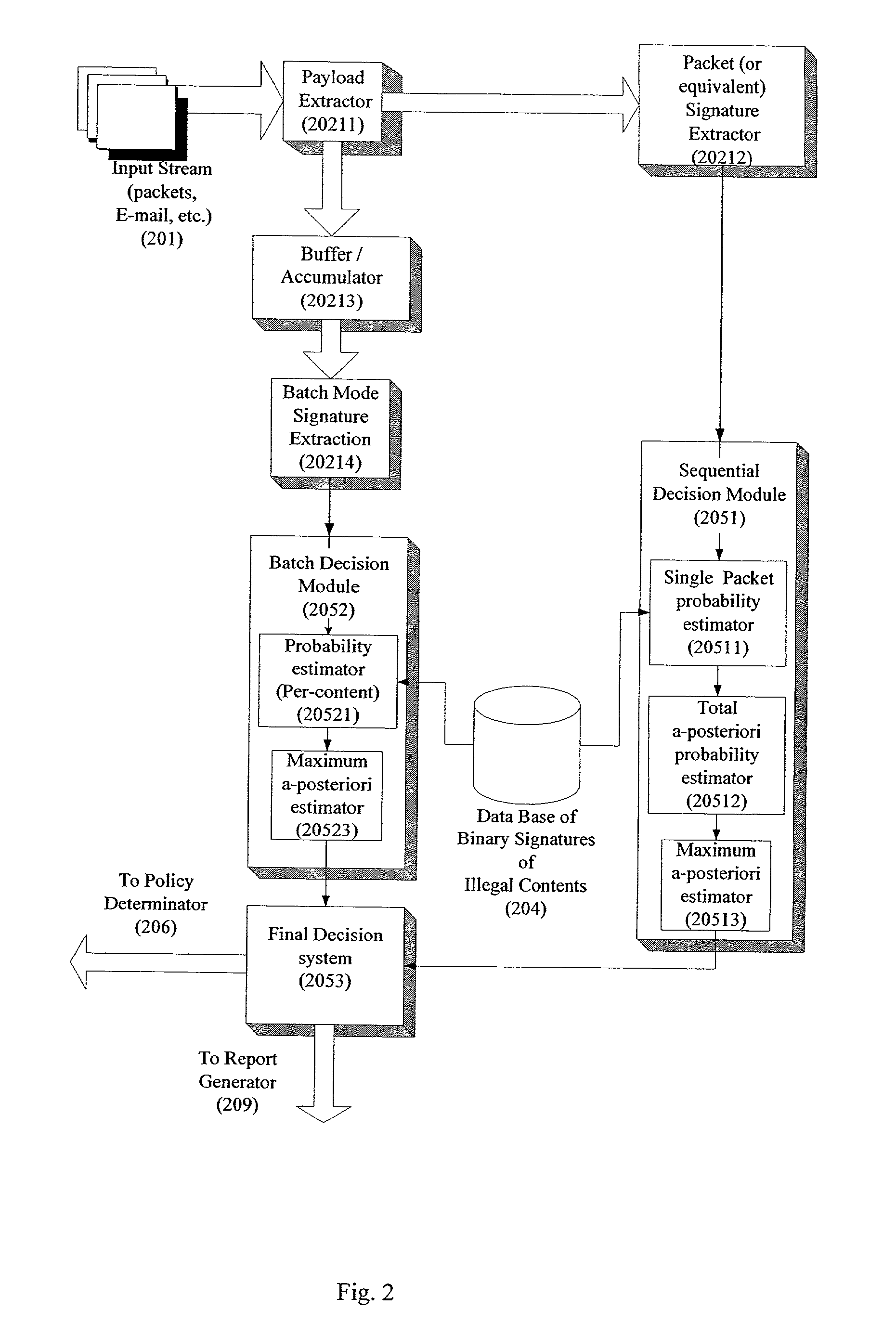
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
Method, system, and computer program product for the evaluation of glycemic control in diabetes from self-monitoring data
InactiveUS7025425B2Easy to monitorContinuous informationMedical simulationTelemedicineMonitors blood glucoseSmart data
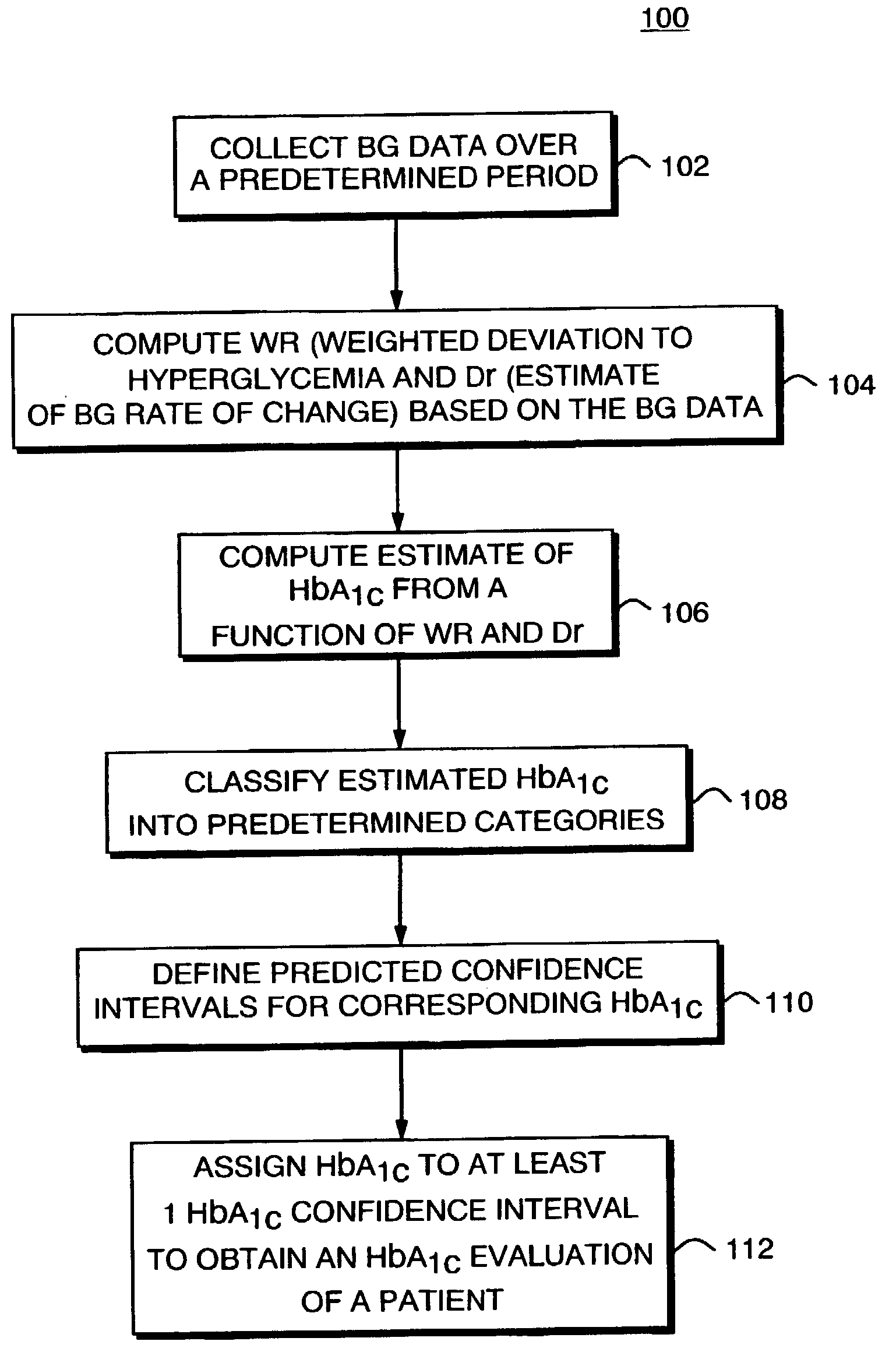
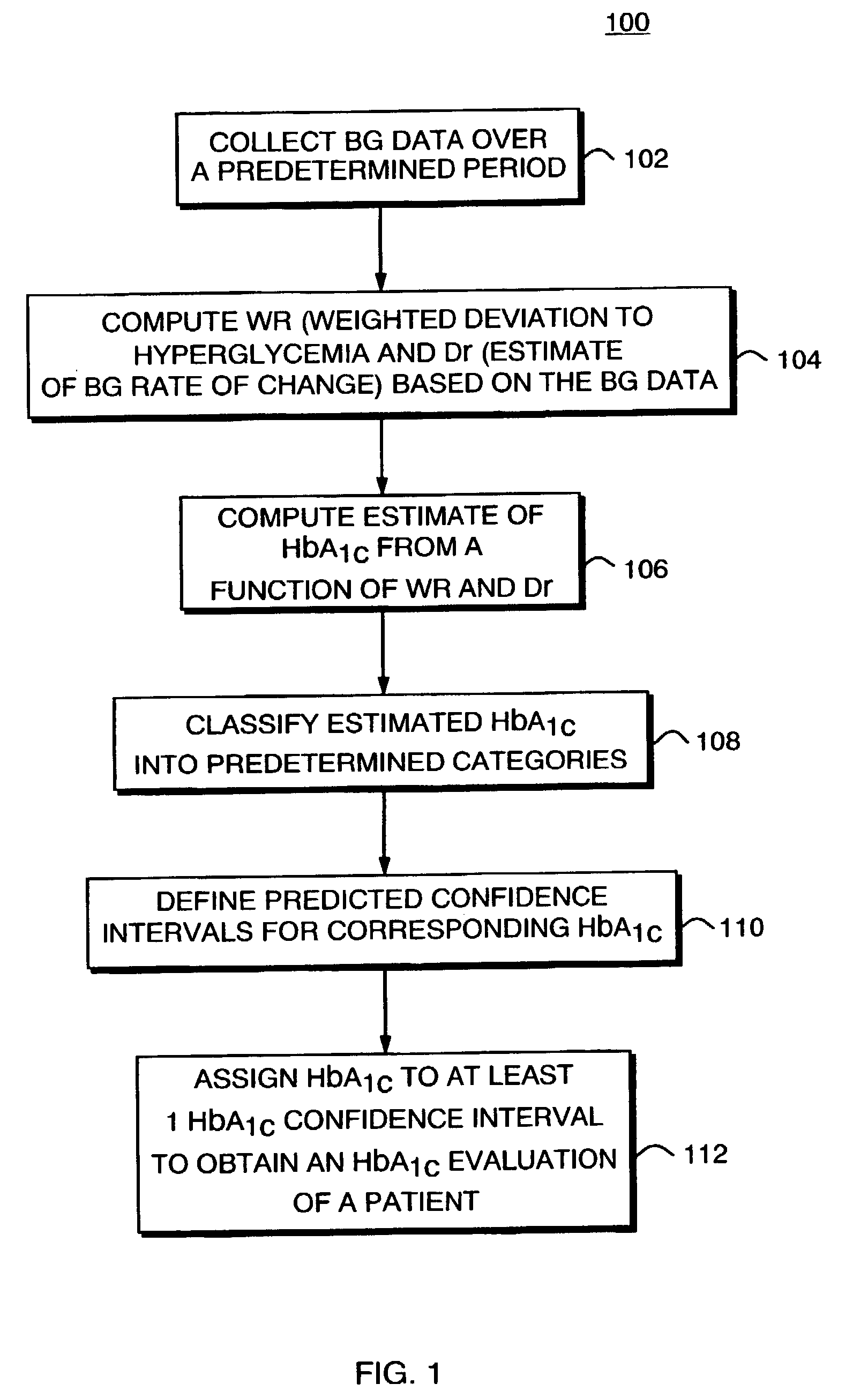
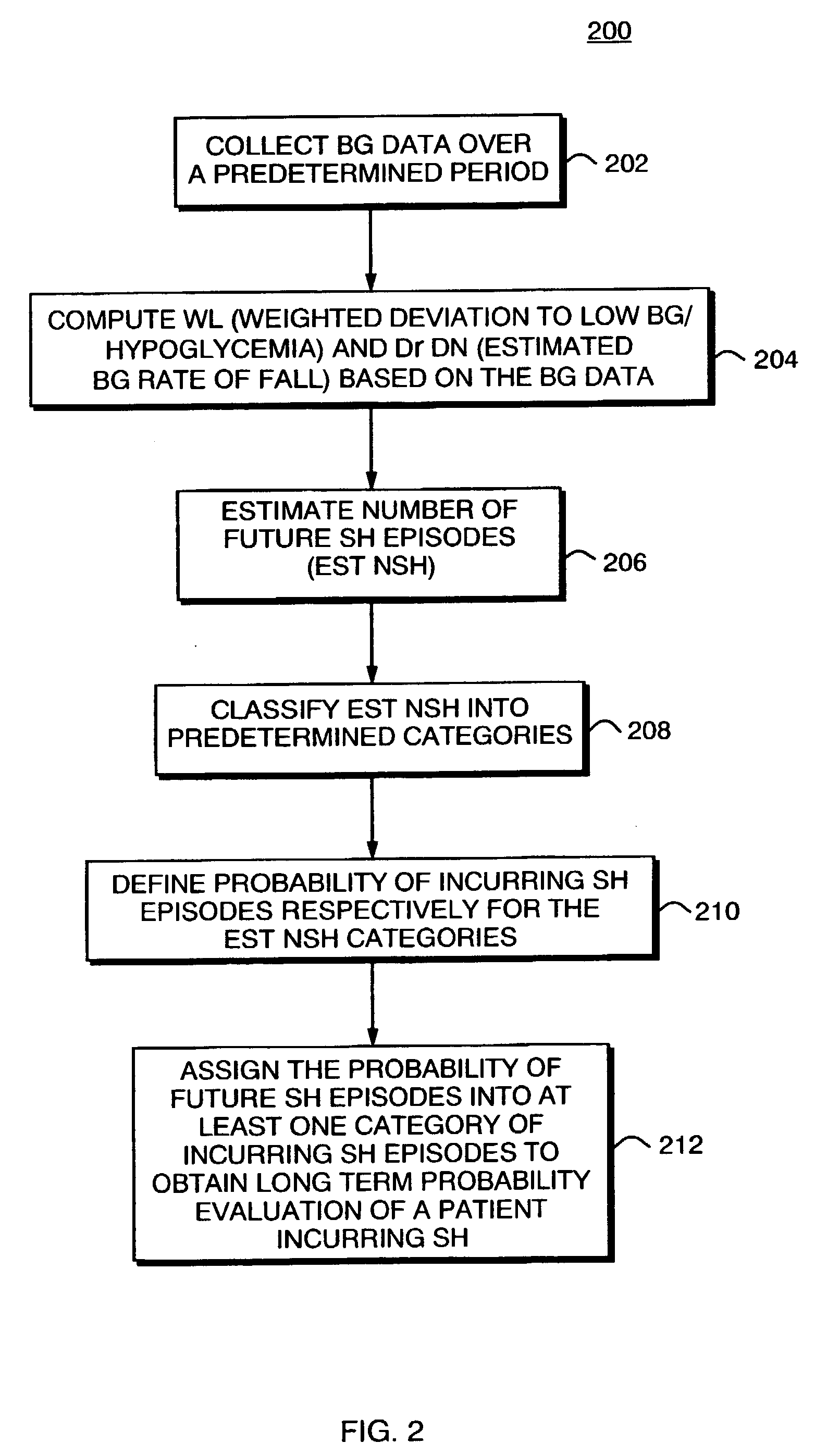
A method, system, and computer program product related to the diagnosis of diabetes, and is directed to predicting the long-term risk of hyperglycemia, and the long-term and short-term risks of severe hypoglycemia in diabetics, based on blood glucose readings collected by a self-monitoring blood glucose device. The method, system, and computer program product pertain directly to the enhancement of existing home blood glucose monitoring devices, by introducing an intelligent data interpretation component capable of predicting both HbA1c and periods of increased risk of hypoglycemia, and to the enhancement of emerging continuous monitoring devices by the same features. With these predictions the diabetic can take steps to prevent the adverse consequences associated with hyperglycemia and hypoglycemia.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND +1
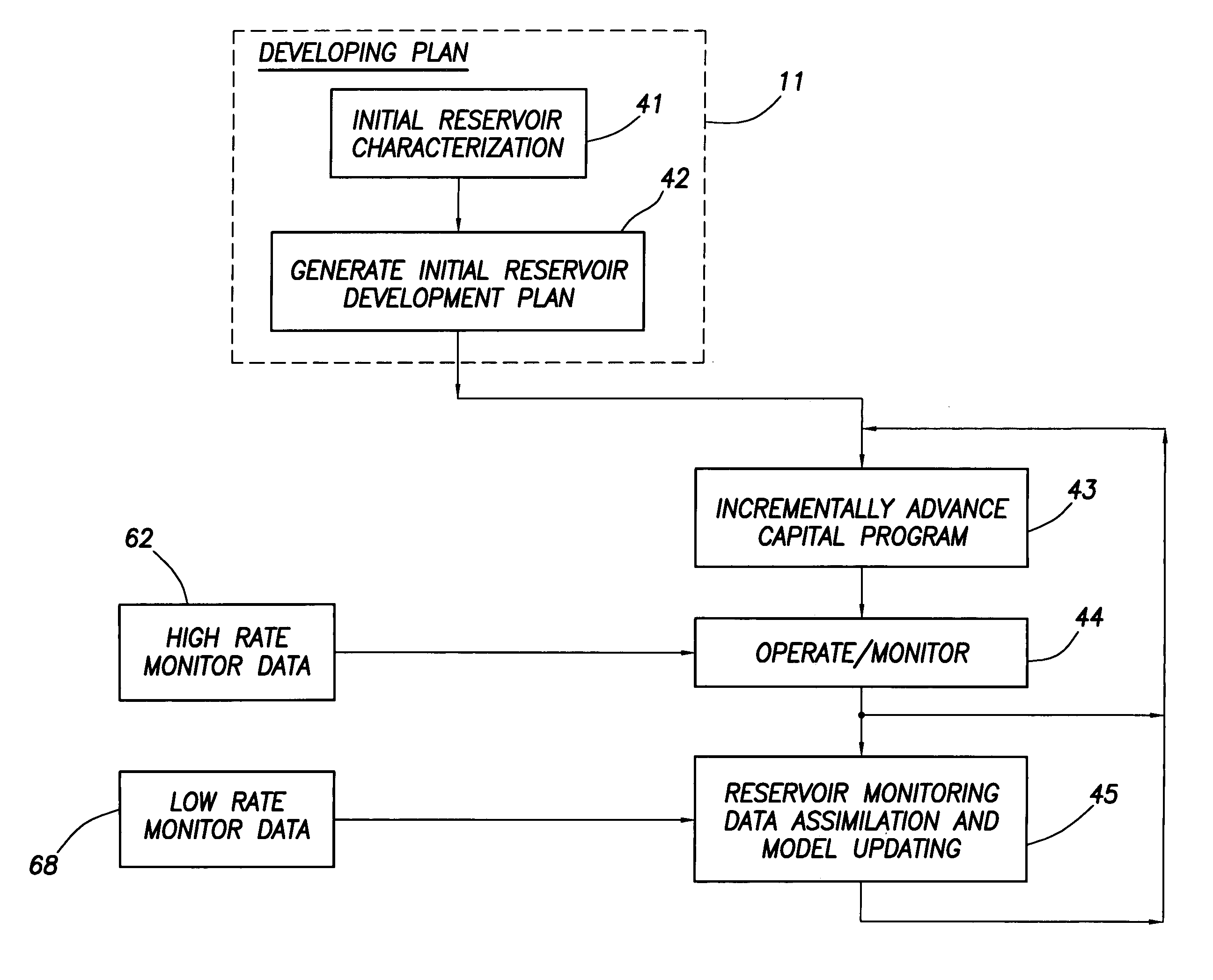
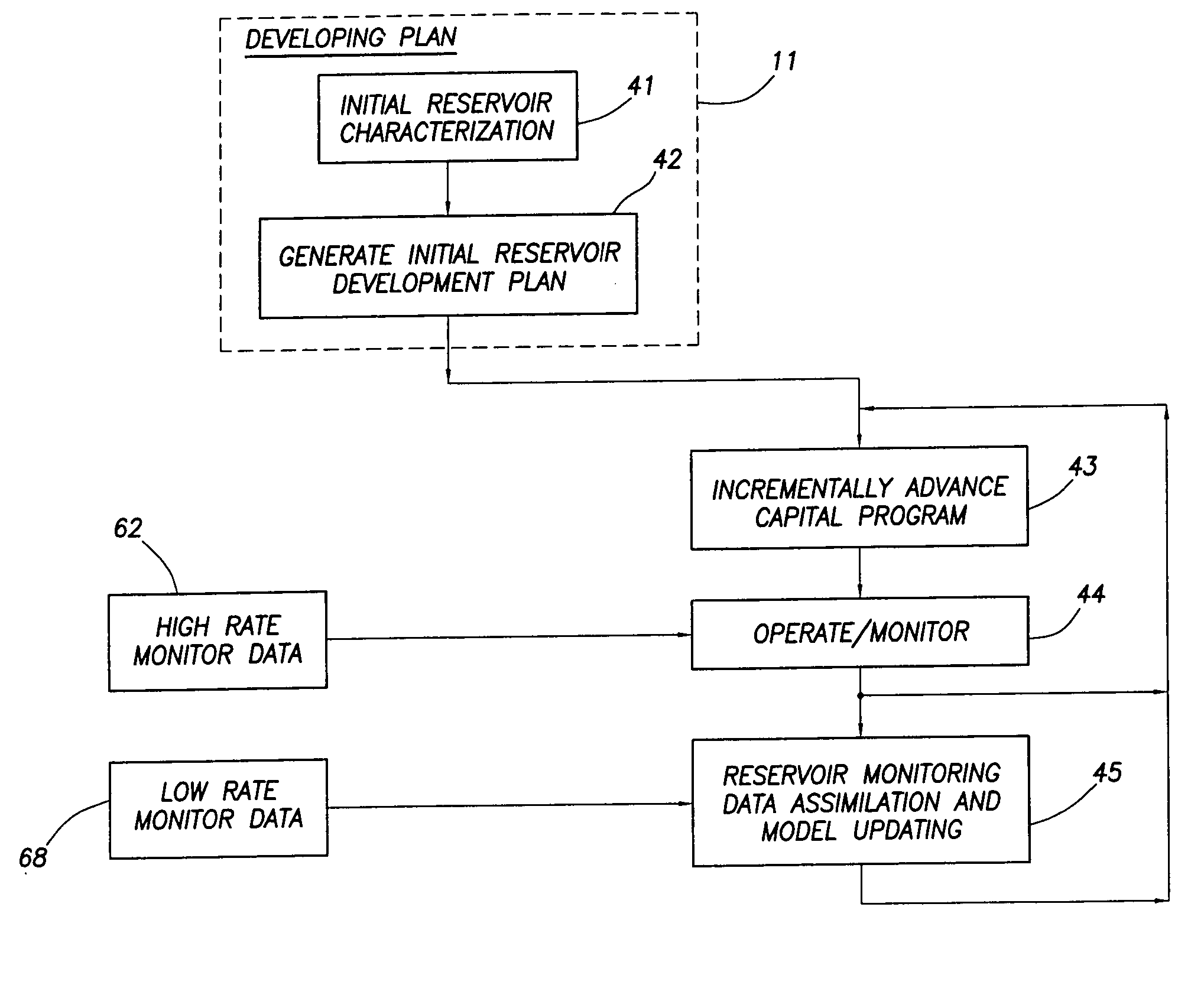
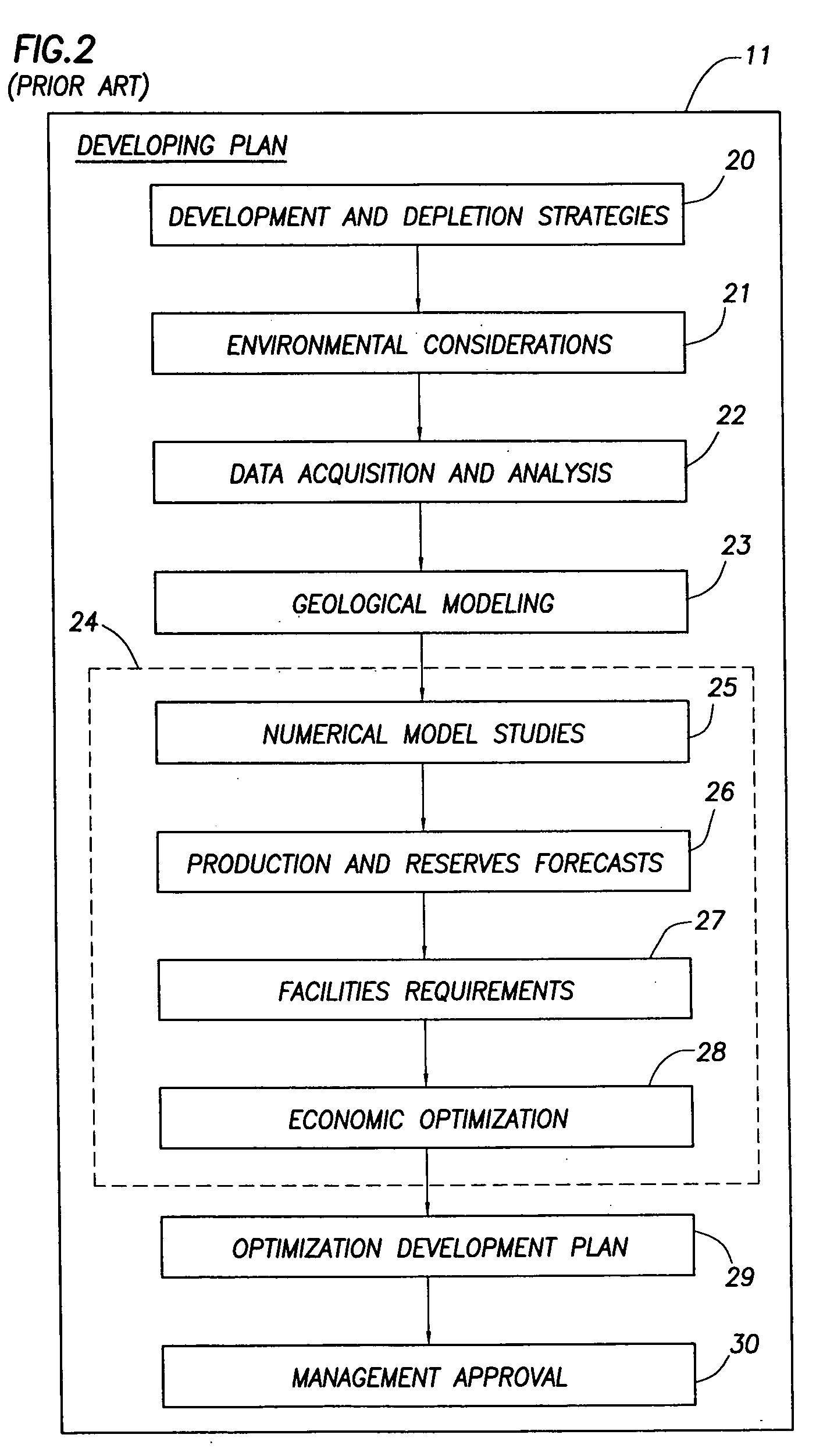
Intergrated reservoir optimization
A method of managing a fluid or gas reservoir is disclosed which assimilates diverse data having different acquisition time scales and spatial scales of coverage for iteratively producing a reservoir development plan that is used for optimizing an overall performance of a reservoir. The method includes: (a) generating an initial reservoir characterization, (b) from the initial reservoir characterization, generating an initial reservoir development plan, (c) when the reservoir development plan is generated, incrementally advancing and generating a capital spending program, (d) when the capital spending program is generated, monitoring a performance of the reservoir by acquiring high rate monitor data from a first set of data measurements taken in the reservoir and using the high rate monitor data to perform well-regional and field-reservoir evaluations, (e) further monitoring the performance of the reservoir by acquiring low rate monitor data from a second set of data measurements taken in the reservoir, (f) assimilating together the high rate monitor data and the low rate monitor data, (g) from the high rate monitor data and the low rate monitor data, determining when it is necessary to update the initial reservoir development plan to produce a newly updated reservoir development plan, (h) when necessary, updating the initial reservoir development plan to produce the newly updated reservoir development plan, and (i) when the newly updated reservoir development plan is produced, repeating steps (c) through (h). A detailed disclosure is provided herein relating to the step (a) for generating the initial reservoir characterization and the step (b) for generating the initial reservoir development plan.
Owner:SCHLUMBERGER TECH CORP
Health monitoring system
A health monitoring system which tracks the state of health of a patient and compiles a chronological health history of the patient uses a multiparametric monitor which periodically and automatically measures and records a plurality of physiological data from sensors in contact with the patient's body. The data collected is not specifically related to a particular medical condition but, instead, provides the information necessary to derive patterns which are characteristic of healthy patients as well as those who are ill. The data collected is periodically uploaded to a database in which it is stored along with similar health histories for other patients. The monitor is preferably self-contained in a chest strap which is located on the patient's torso, and makes use of a controller which controls sampling of the desired data and storage of the data to a local memory device pending uploading to the database. The more voluminous data collected is reduced and compressed prior to storage in the local memory device. Preferably, much of the monitor circuitry is run intermittently to conserve power. The monitor data is supplemented with subjective data (such as psychological and environmental conditions) collected from the patient using a handheld data input device which runs a program to solicit information from the patient. The subjective data collected is chronologically aligned with the monitor data in the database such that the health history of a patient includes both objective and subjective medical data.
Owner:THE BRIGHAM & WOMEN S HOSPITAL INC
Computer interfaces including physiologically guided avatars
This invention provides user interfaces that more intuitively display physiological data obtained from physiological monitoring of one or more subjects. Specifically, the user interfaces of this invention create and display one or more avatars having behaviors guided by physiological monitoring data. The monitoring data is preferably obtained when the subject is performing normal tasks without substantial restraint. This invention provides a range of implementations that accommodate user having varying processing and graphics capabilities, e.g., from handheld electronic devices to ordinary PC-type computers and to systems with enhanced graphics capabilities.
Owner:ADIDAS
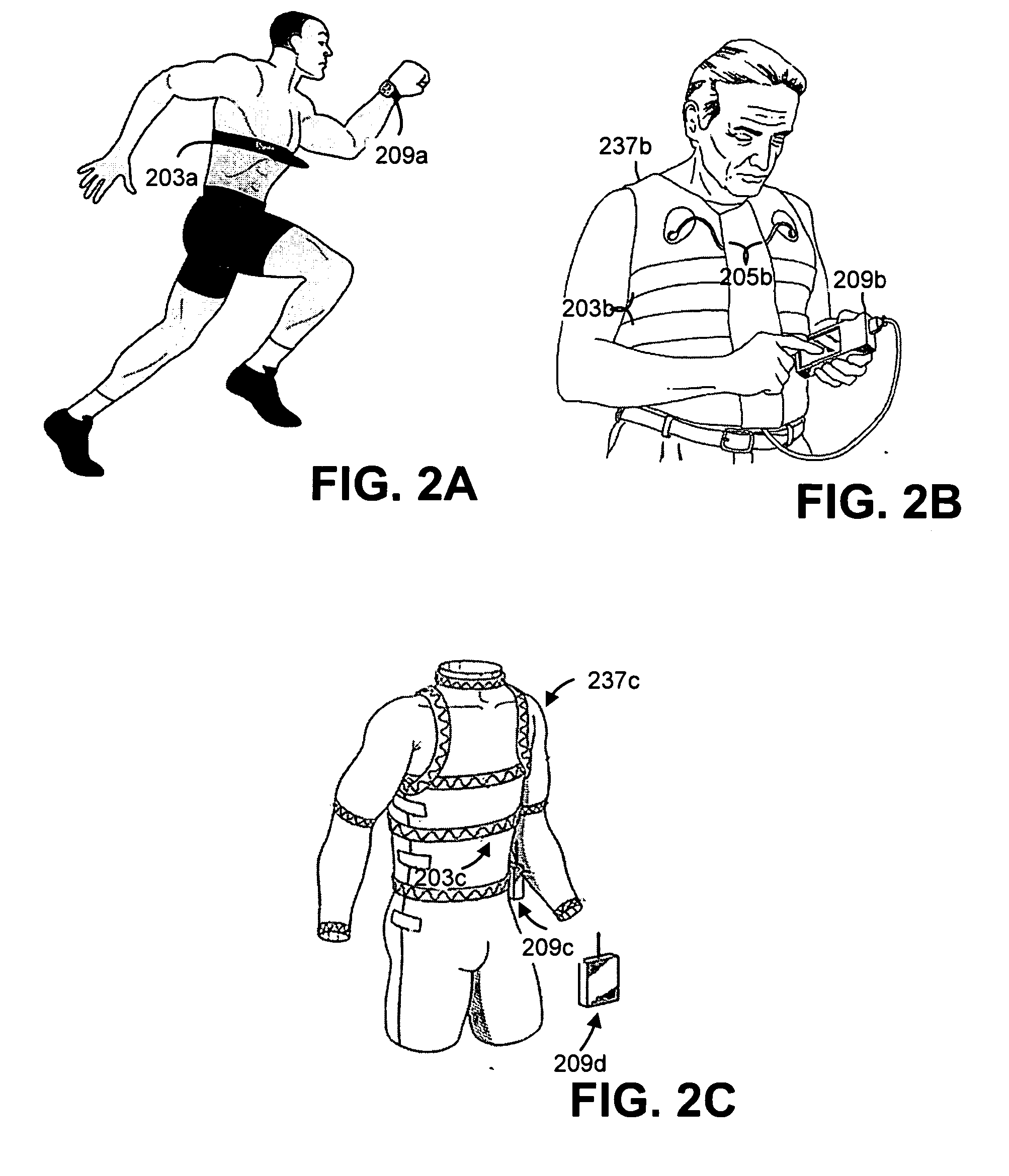
Continuous analyte monitor data recording device operable in a blinded mode
A system is provided including a continuous analyte sensor that produces a data stream indicative of a host's analyte concentration and a device that receives and records data from the data stream from the continuous analyte sensor. The data received from the continuous analyte sensor may be used to provide alarms to the user when the analyte concentration and / or the rate of change of analyte concentration, as measured by the continuous analyte sensor, is above or below a predetermined range. Data received from the continuous analyte sensor may also be used to prompt the diabetic or caregiver to take certain actions, such as to perform another single point blood glucose measurement. The device may provide for toggling between modes that allow or prevent the display of glucose concentration values associated with the continuous glucose sensor.
Owner:DEXCOM
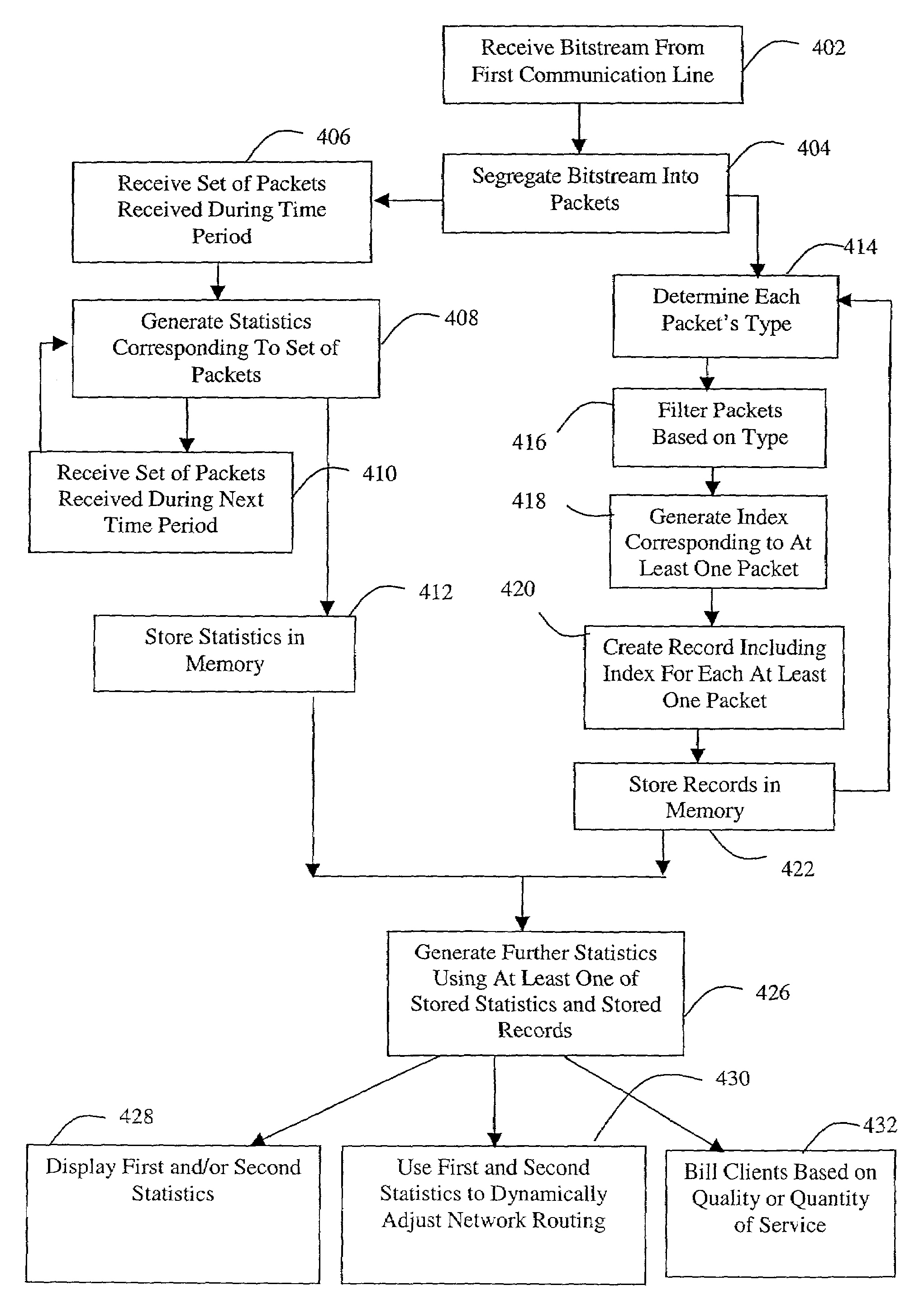
Apparatus and method for collecting and analyzing communications data
InactiveUS7492720B2Error preventionFrequency-division multiplex detailsMonitoring dataReal-time computing
A method for monitoring data on a first communication line. Data is received from the first communication line and a plurality of packets are extracted from the data. Statistics are then recursively generated, the statistics corresponding to the plurality of packets.
Owner:NIKSUN
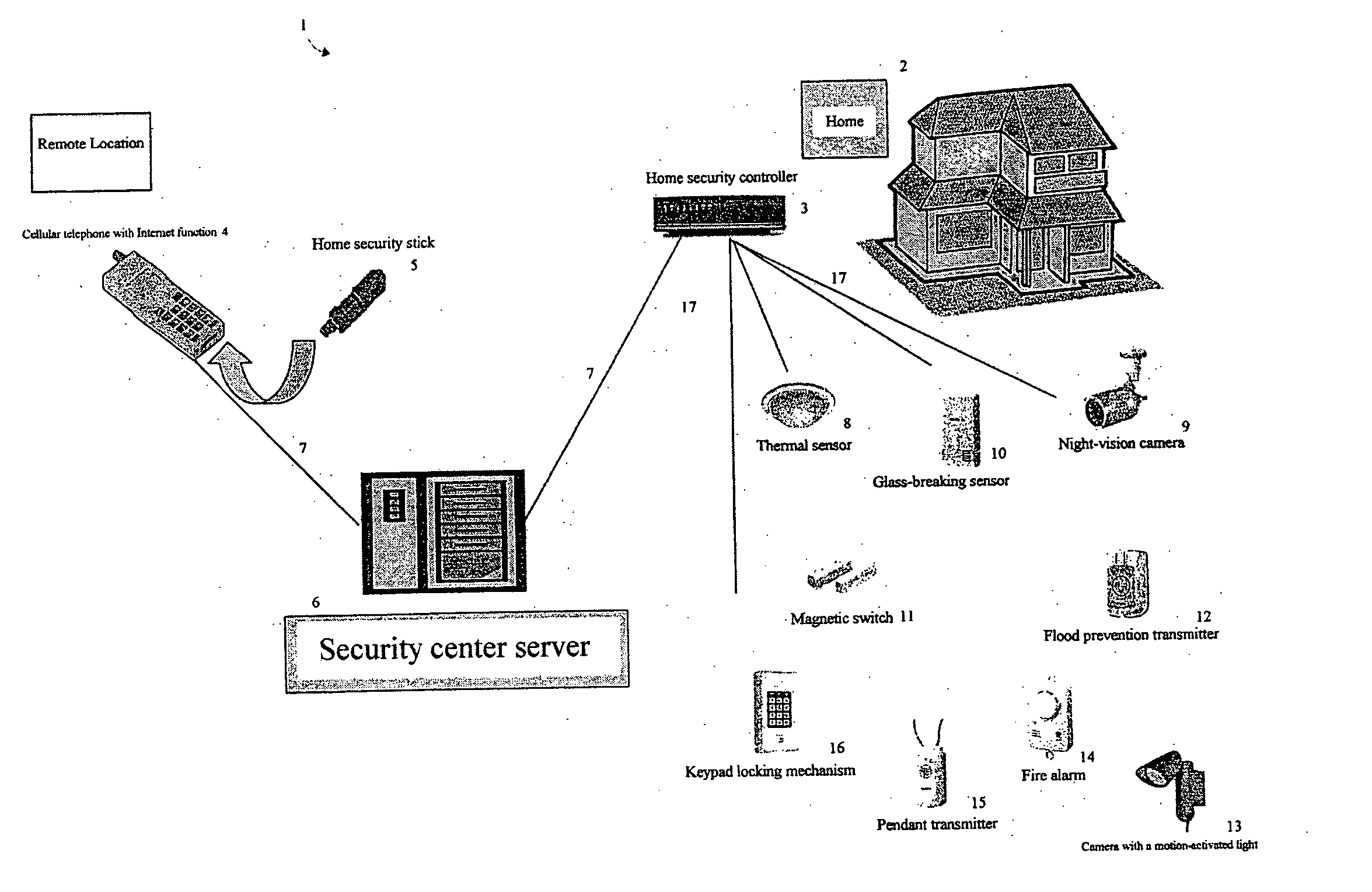
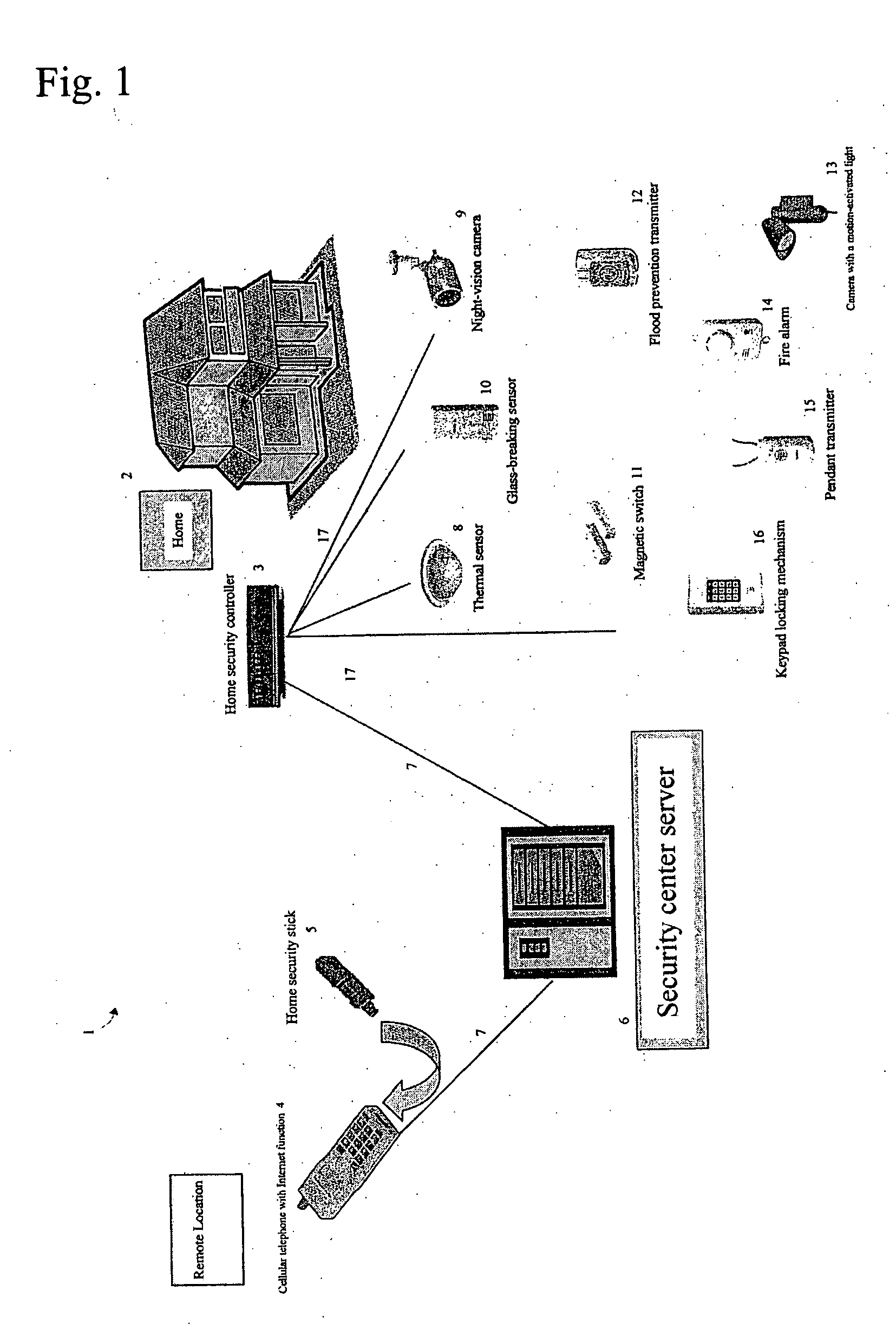
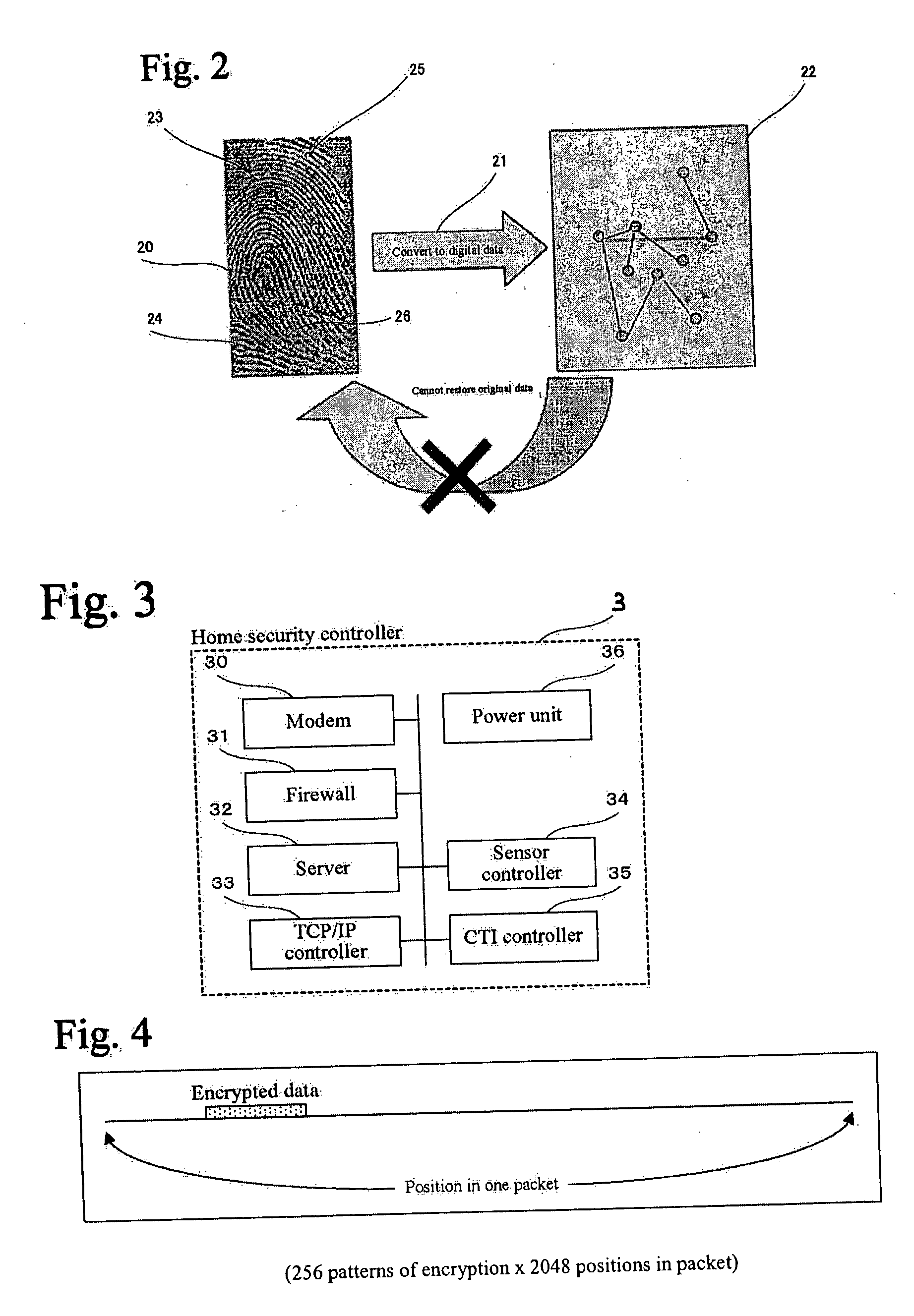
Home security system
InactiveUS20060022816A1Prevent intrusionEasy to operateElectric signal transmission systemsImage analysisRemote controlEngineering
The present invention provides a home security system that includes a home security controller for collecting monitor data from various crime prevention and disaster prevention sensors installed in a home via a home network and notifying the portable terminal when a state of emergency occurs. The home security controller also enables devices in the home to be operated through remote control signals via an external network. The home security system further includes a portable terminal capable of connecting to the external network and having fingerprint data inputting means mounted on the body of the portable terminal for inputting fingerprints used for authentication. The fingerprint data inputting means has an assigned ID number. The home security system further includes a security center server having fingerprint authenticating means for receiving fingerprint data from the portable terminal via the external network and authenticating the fingerprint data through comparisons with registered fingerprint data. The fingerprint authenticating means completes authentication by checking the assigned ID number of the fingerprint data inputting means and matching the received fingerprint data with fingerprint data registered in association with the ID number. The security center server allows a connection between the portable terminal and the home security controller and controls bi-directional communications between the two after the security center server has completed authentication, enabling the portable terminal to receive monitor data from and transmit remote control signals to the home security controller via the external network.
Owner:AMERICAN TECH GRP JAPAN
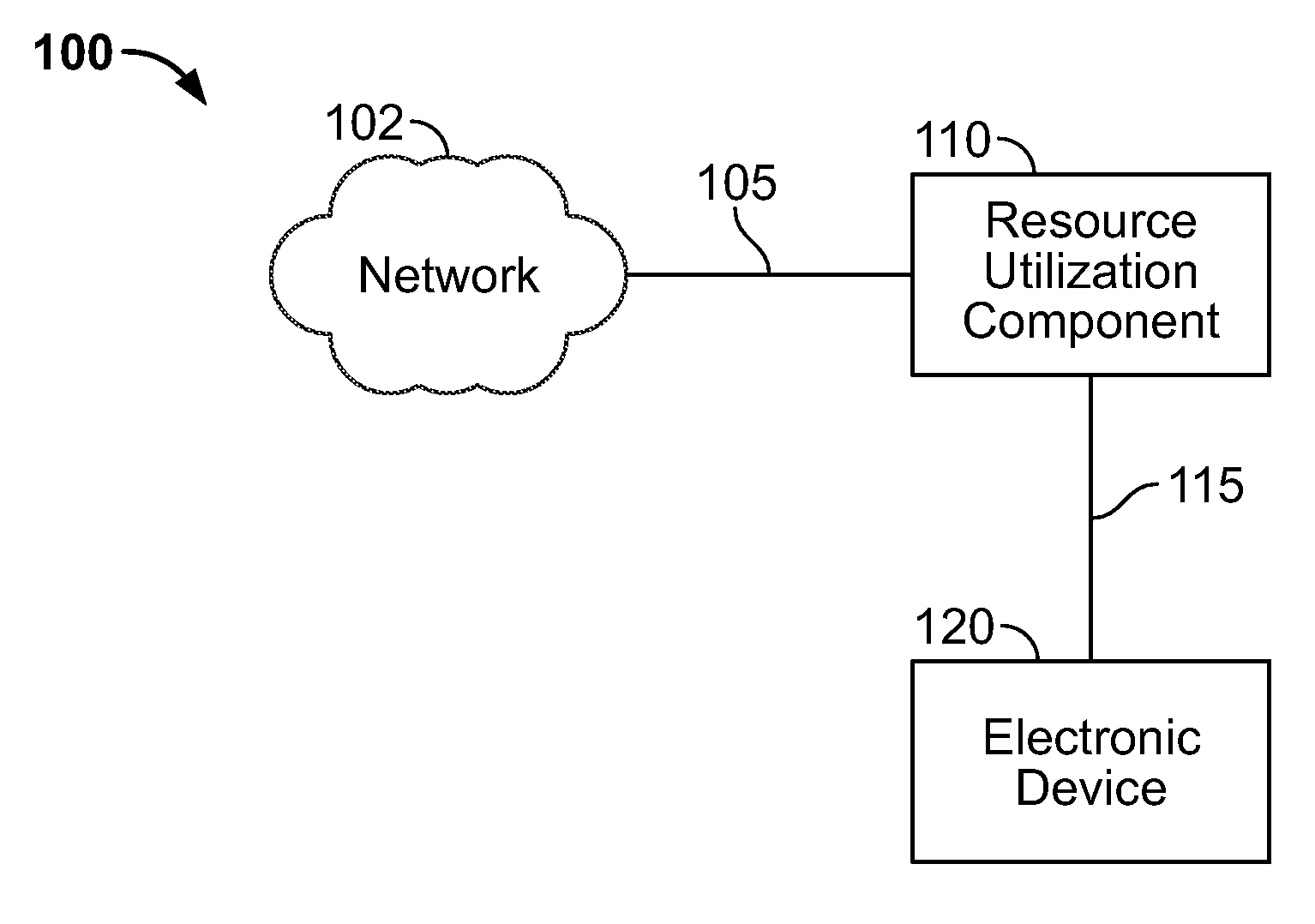
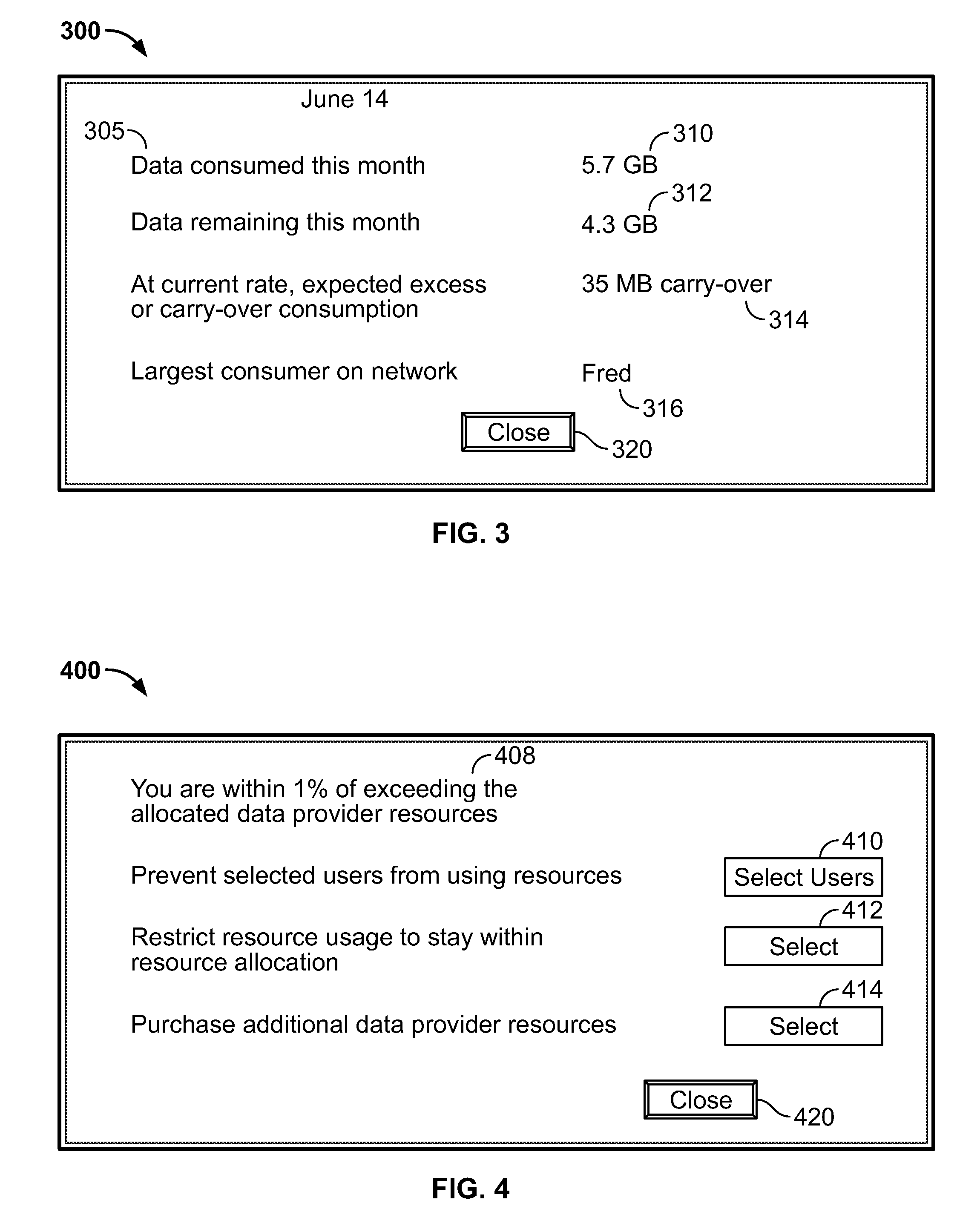
Systems and methods for monitoring data and bandwidth usage
ActiveUS20100017506A1Assess restrictionMultiple digital computer combinationsResource consumptionResource utilization
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
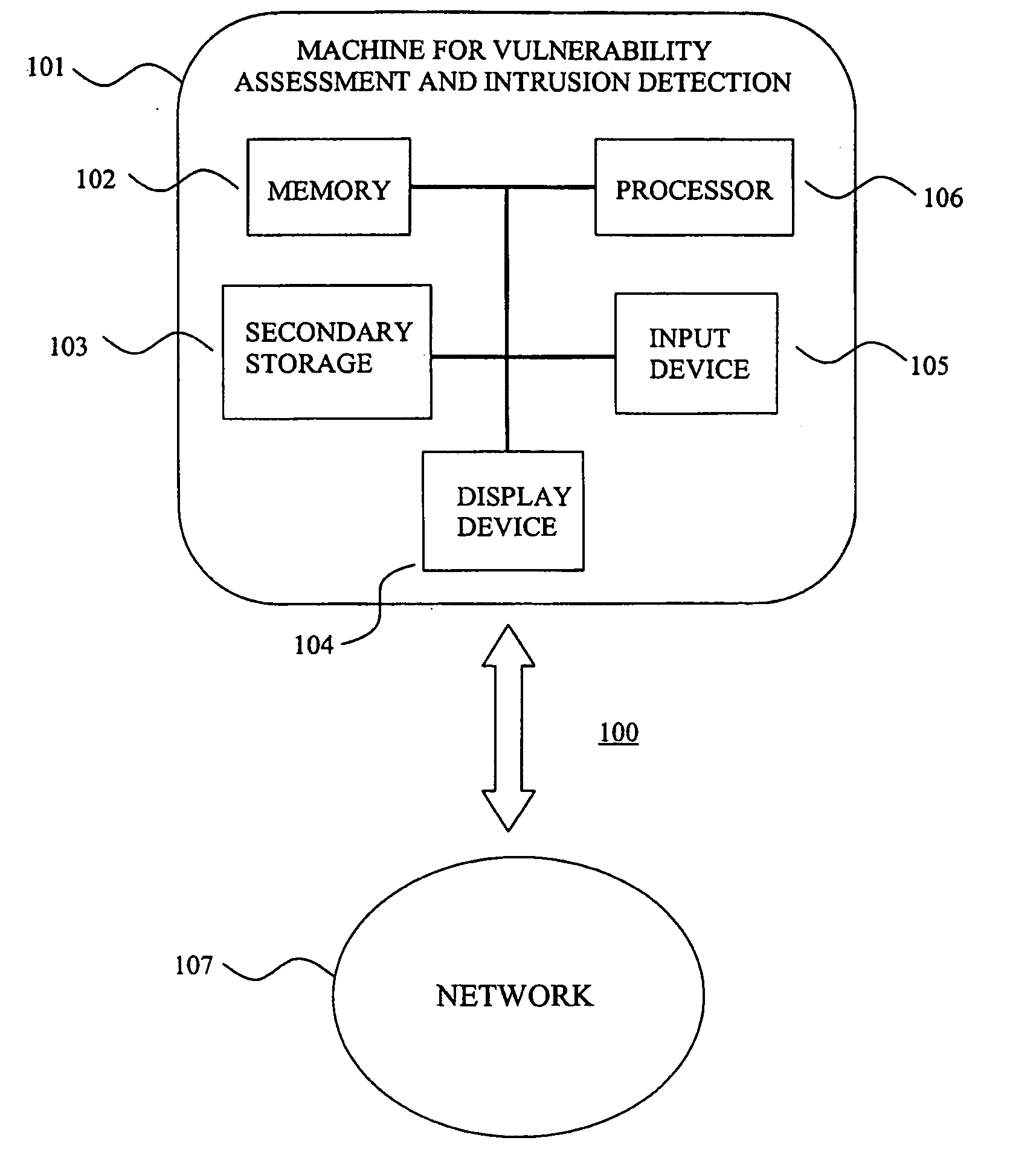
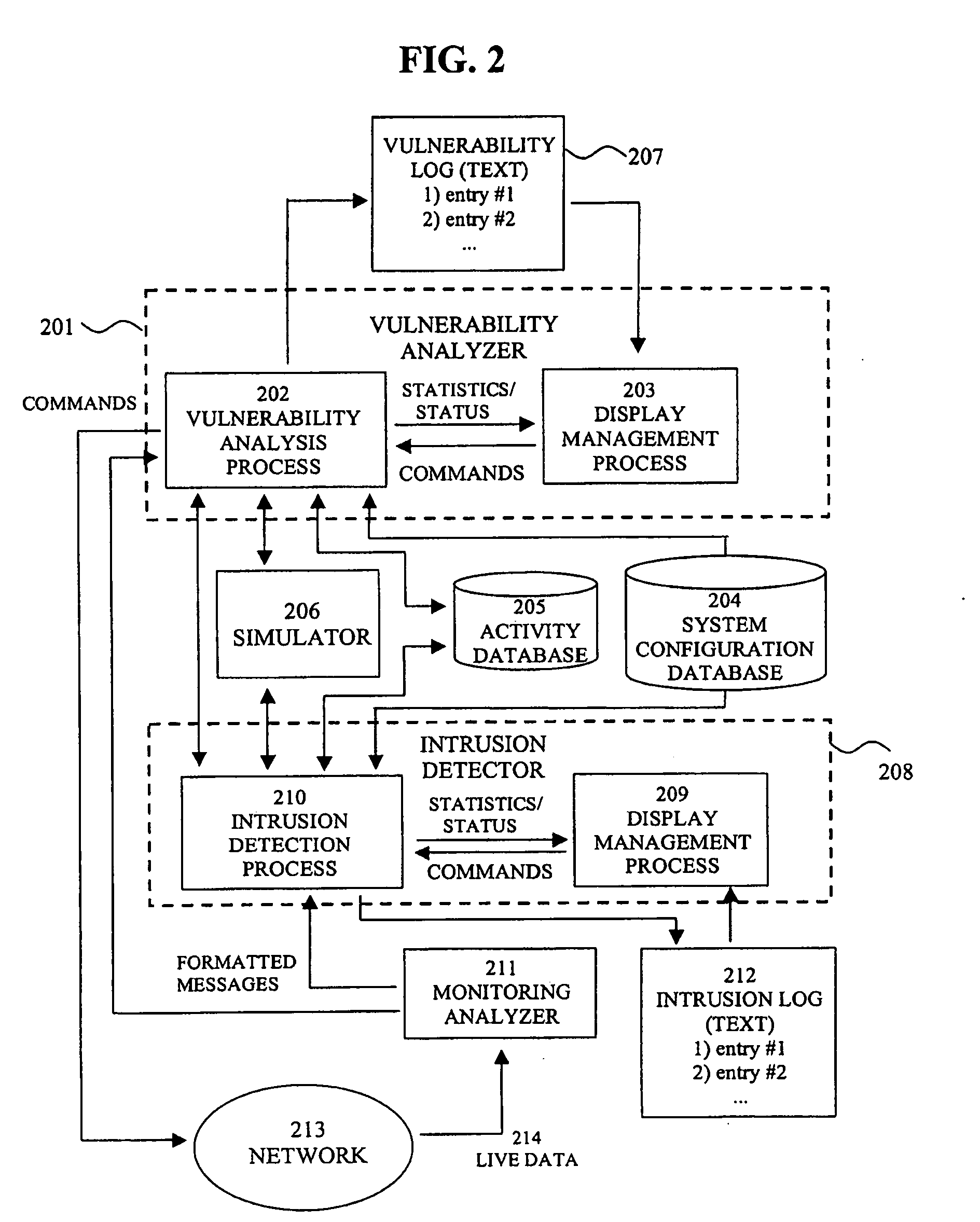
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
Performance monitoring based dynamic voltage and frequency scaling
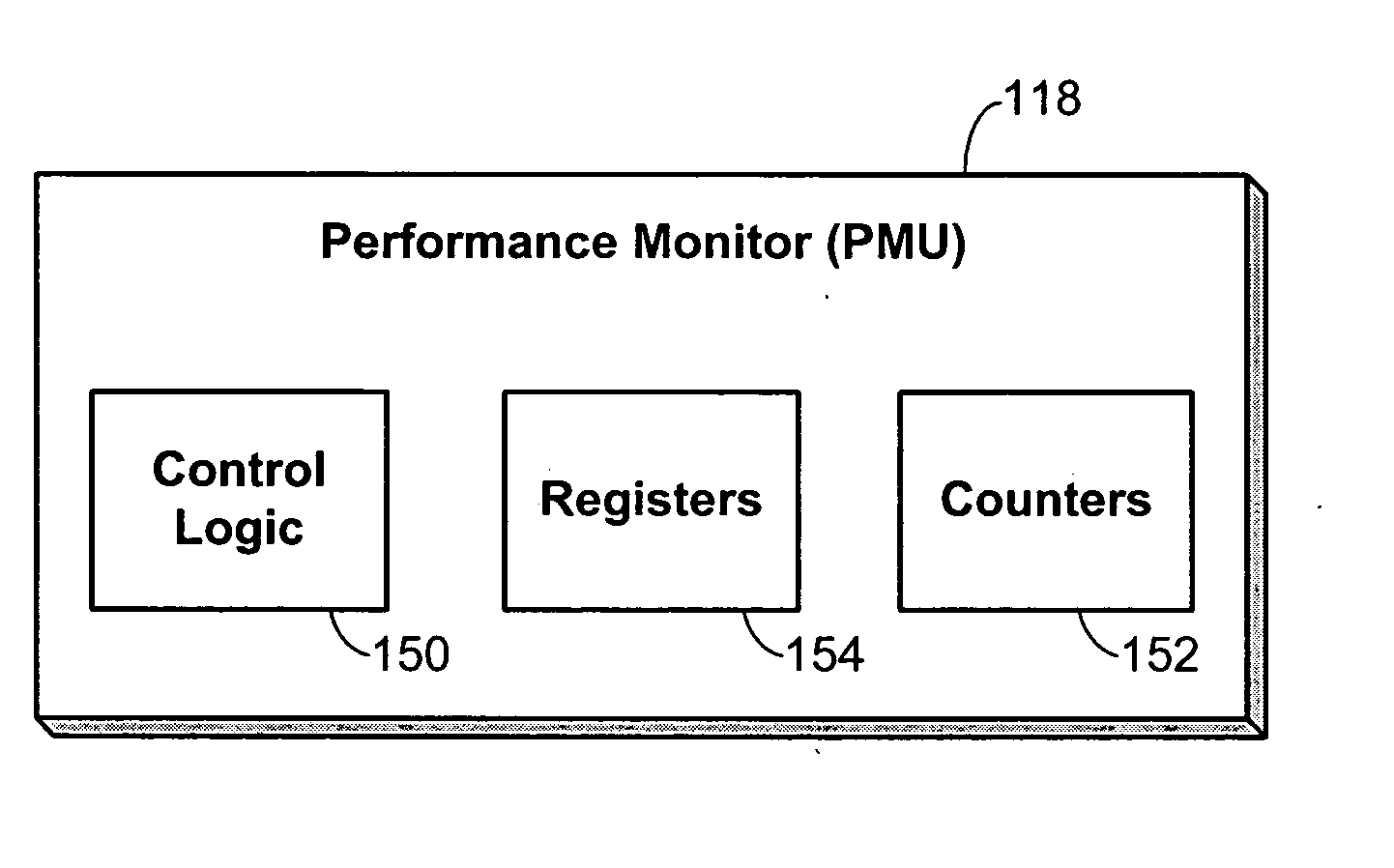
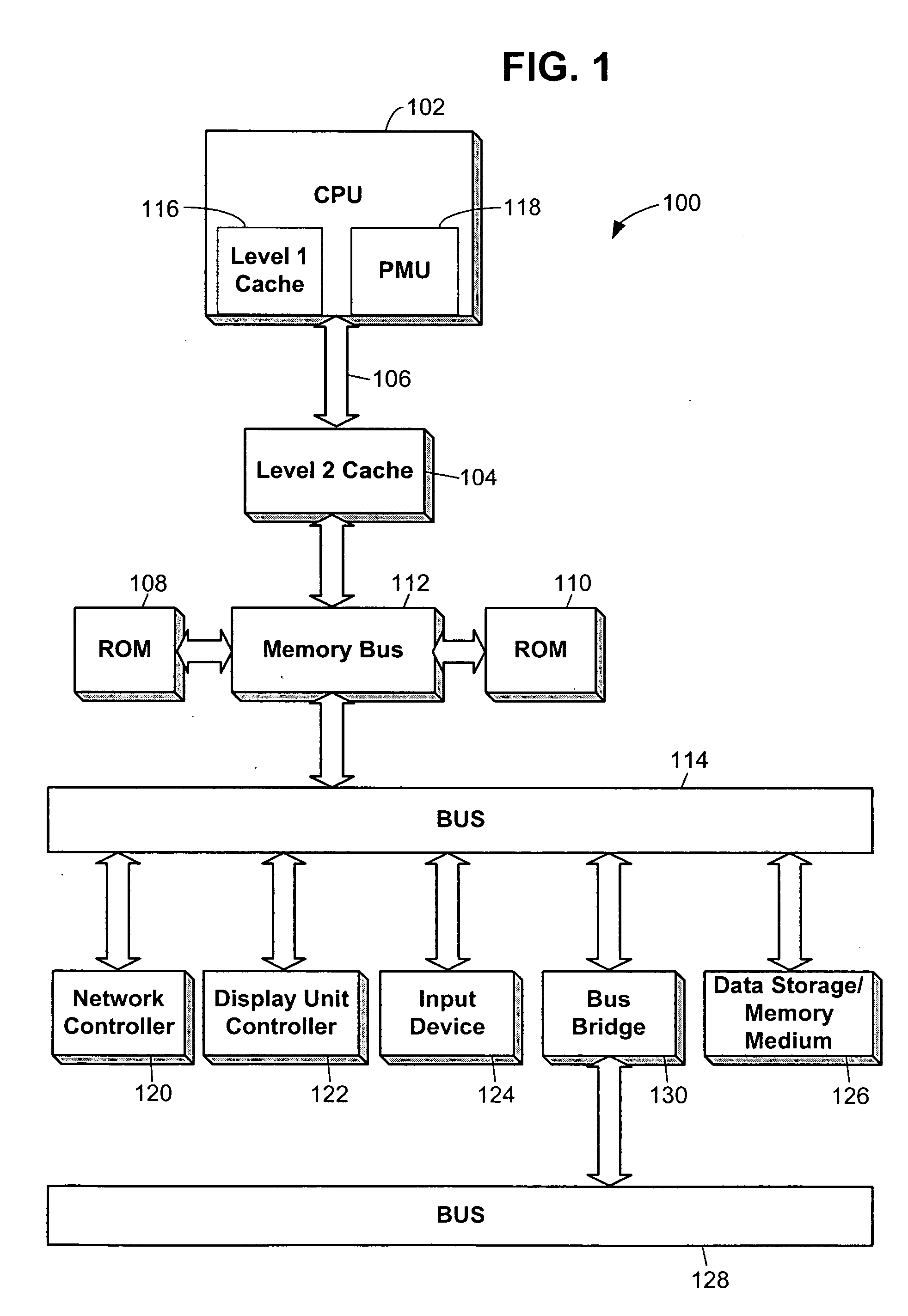
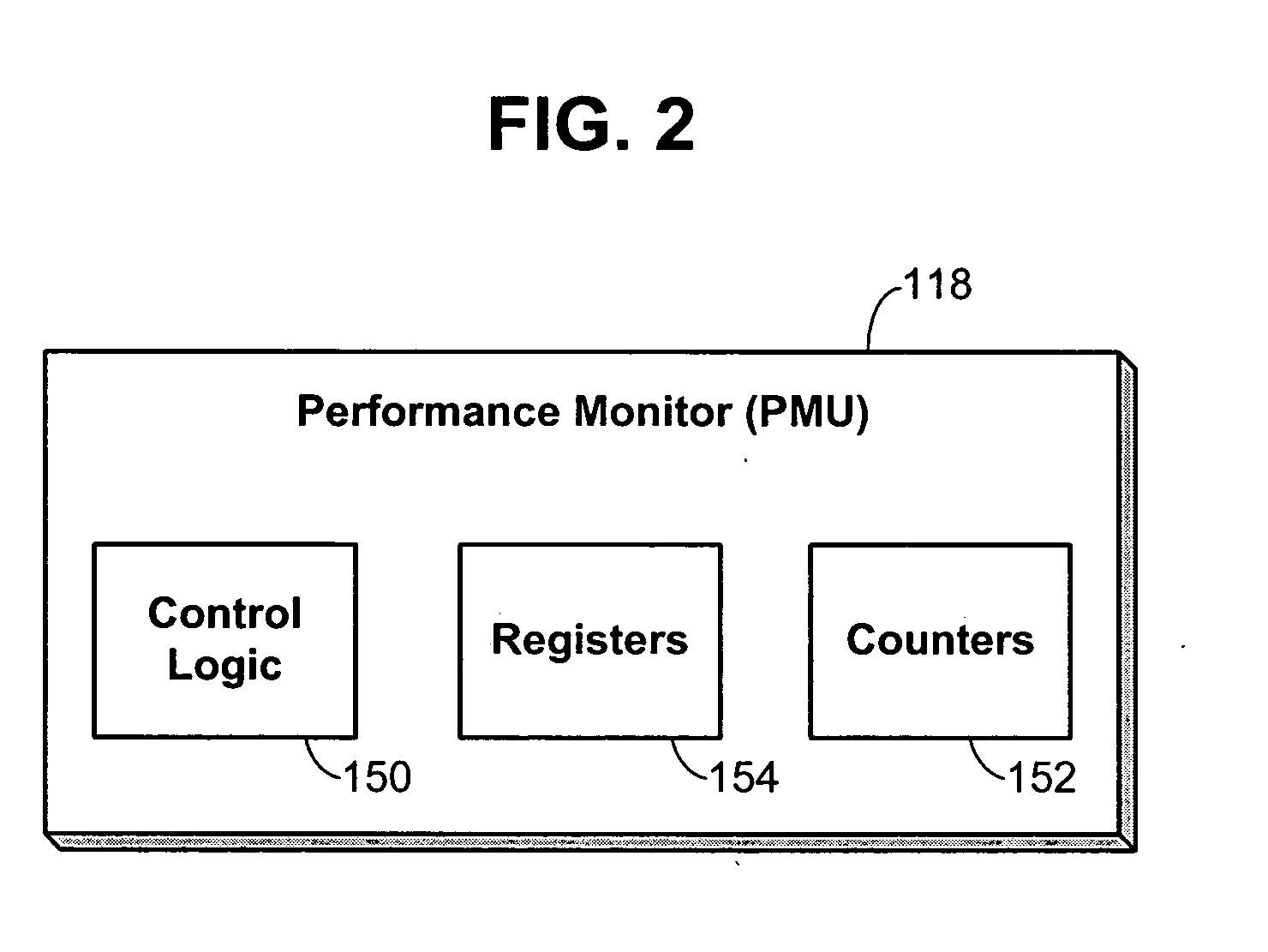
Voltage and frequency scaling techniques that are based upon monitored data are provided. The techniques may be used to better manage the power and energy consumption of a processor in an embedded system, such as a cellular telephone, personal data assistant, smart device, or the like. The techniques may be used with processors that offer a performance monitoring capability. The performance monitor may monitor thread-level utilization at runtime. Instructions per cycle and memory references per cycle are example metrics that may be monitored by the performance monitor. The voltage and frequency scaling techniques may adjust the operating voltage and operating frequency of the processor based on the values of these two metrics. For example, the techniques may include accessing a voltage and frequency scheduler lookup table. The techniques may be employed with non-embedded systems, as well, embedded systems.
Owner:TAHOE RES LTD
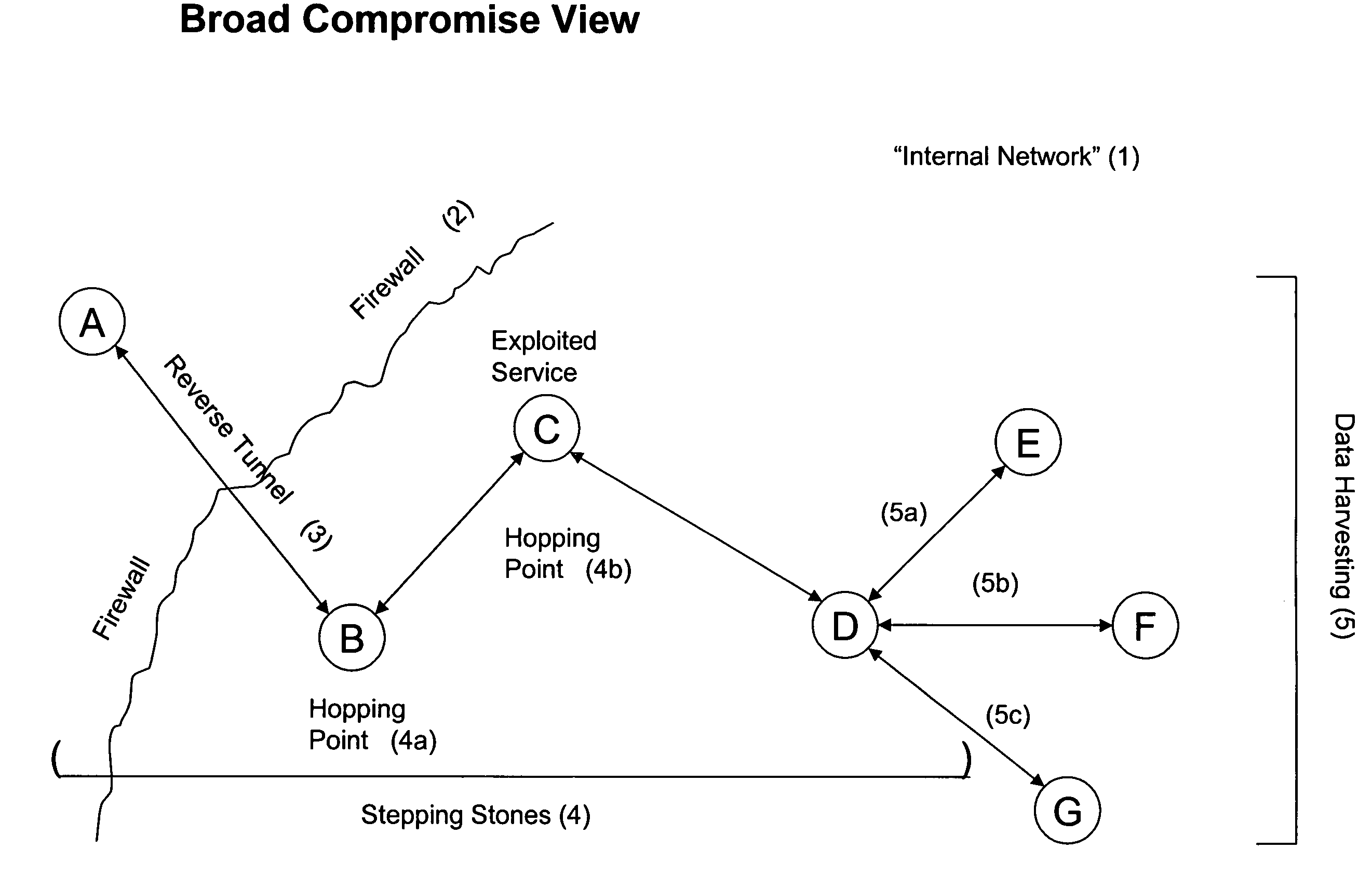
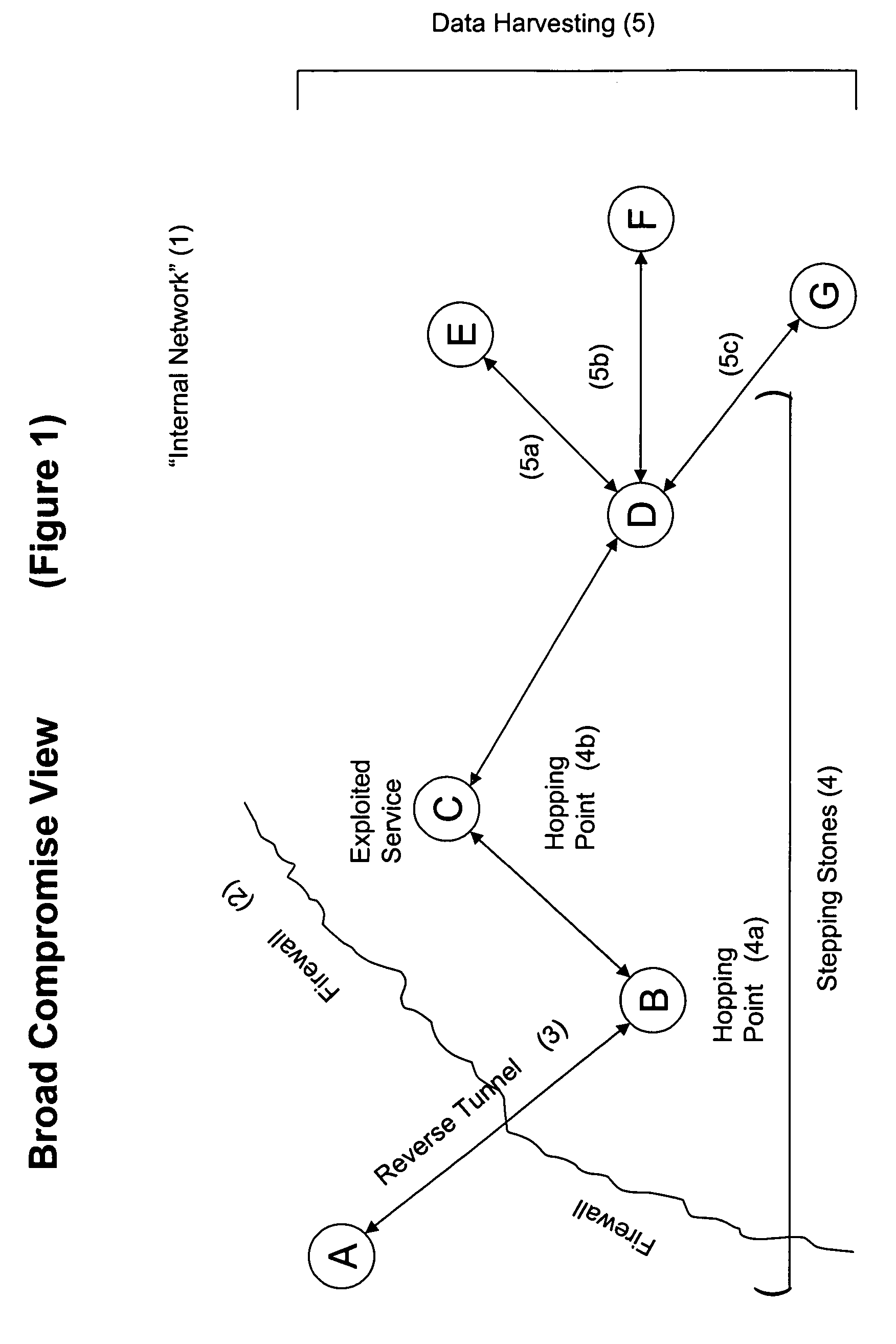
Systems and methods for detecting a compromised network
InactiveUS20050157662A1Reduce false positive resultsDigital data processing detailsComputer security arrangementsAnalysis dataData transmission
Systems and methods are disclosed for monitoring data transmissions on a network and detecting compromised networks. The systems and methods monitor communications involving network hosts and analyze the communications in view of the business function of the hosts. In certain embodiments the analysis is performed by associating a set of rules of operation for the sessions, hosts, and / or environment, and analyzing data packet transmissions to ascertain violations of the rules.
Owner:INTRUSIC
System and method for home energy monitor and control
ActiveUS8255090B2Increase powerEfficient managementLevel controlPayment architectureCommunity basedMonitoring system
The invention generally concerns systems and methods for monitoring and controlling the power consumption of a power-consuming device. The system and method may connect to a power source and a power-consuming device, connecting the power-consuming device to the power source. The power usage of the power-consuming device may then be measured and monitored. This monitoring data may then be stored and optionally sent to a controlling device on a data network. The location of the power-consuming device may also be determined, recorded, and sent to a controlling device. The system may also control the power usage of the power-consuming device. In some cases, a remote server may connect multiple energy monitoring systems in order to gain additional efficiencies and foster a community-based social network.
Owner:ENERGYHUB
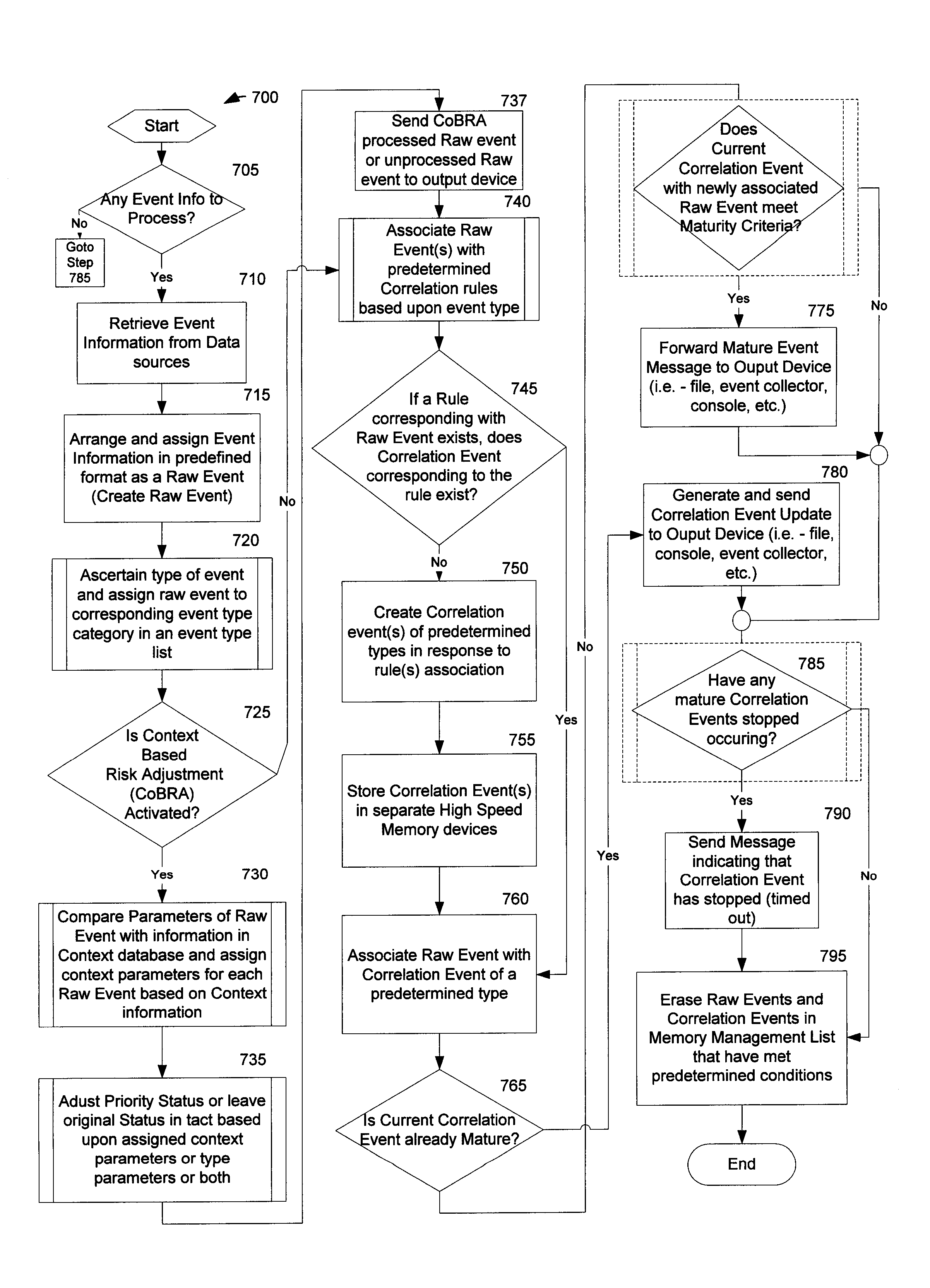
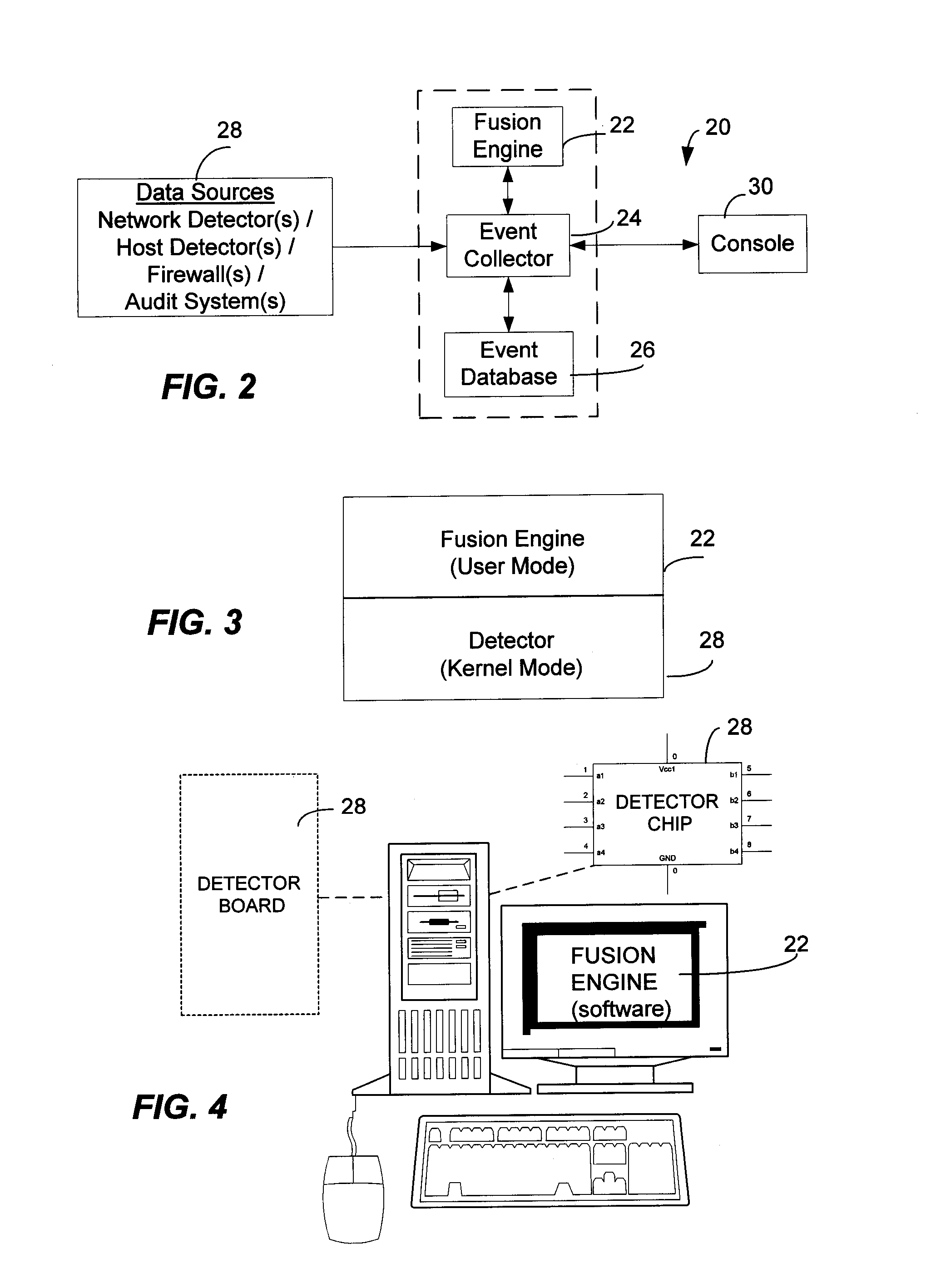
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
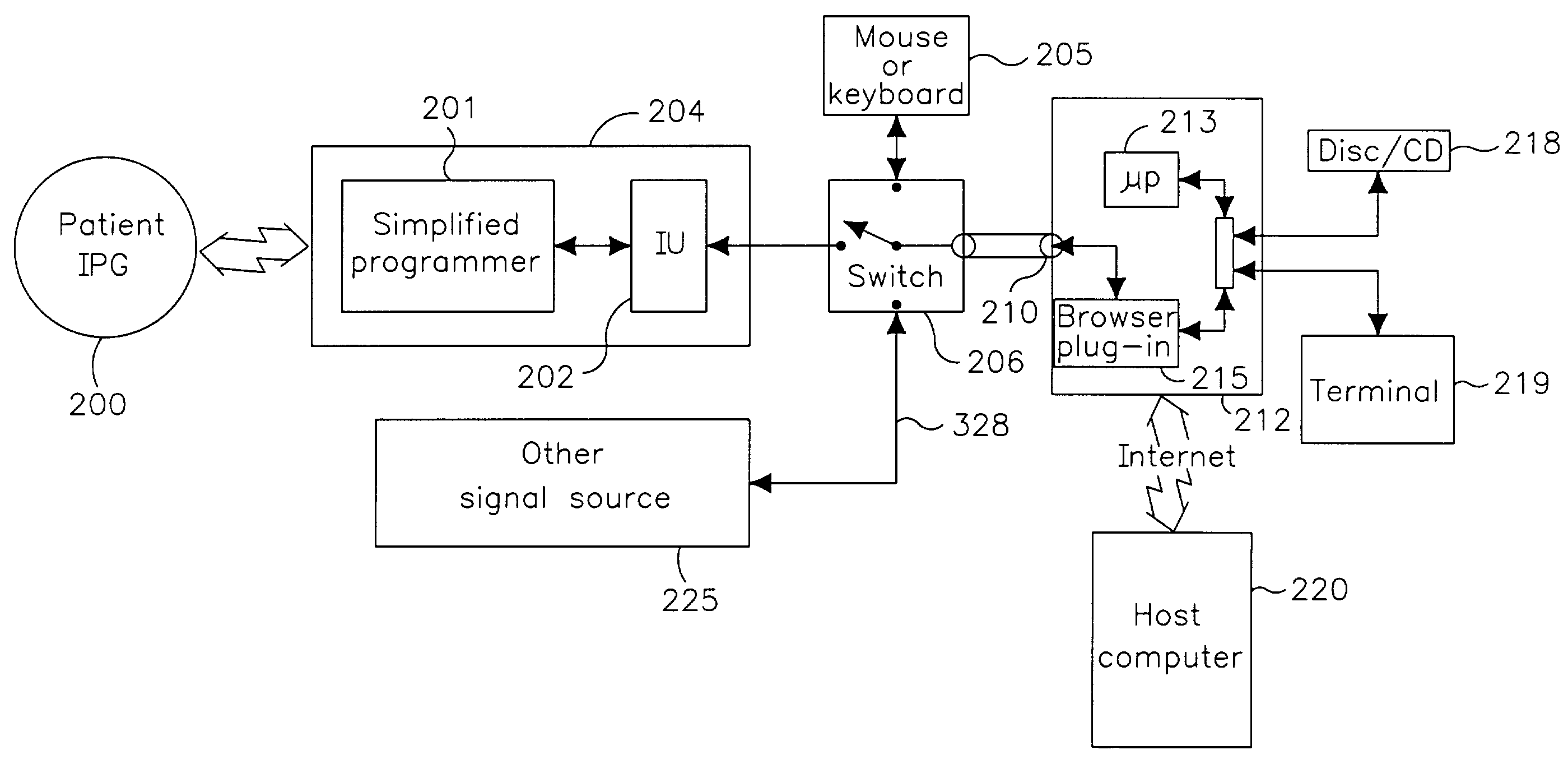
System and method for transmission of medical and like data from a patient to a dedicated internet website
InactiveUS7082334B2Improve mobilitySafe interconnectionElectrotherapyArtificial respirationWeb siteImplanted pacemaker
The invention provides a system and method for easy and reliable connection of patient-originated medical data through a simple port of a computer to a dedicated web site. A device originating medical data, such as an implanted pacemaker, downloads data into a transmit / receive device, and the data is then transformed in an interface unit to be accepted by a simple port of a computer, e.g. a keyboard port or a mouse port. The patient logs on to a dedicated web site, and transfers the data along with typed input to the web site for analysis. Following analysis, a reply message is sent back to the patient, which may include a control instruction for modifying or reprogramming the operation of the device that is used to originate the medical data. For a pacemaker application, the data transformation is done at a simple interface unit that is portable and easily manipulated by the patient. For other applications such as monitoring data from a diabetic, the data is transformed by the interface unit, and may be stored daily in the PC and transmitted to the web site after collection of a predetermined number of days of data.
Owner:MEDTRONIC INC
Integrated reservoir optimization
InactiveUS20050149307A1Maximize productionMaximizing value of propertyElectric/magnetic detection for well-loggingSurveyHigh rateAcquisition time
A method of managing a fluid or gas reservoir is disclosed which assimilates diverse data having different acquisition time scales and spatial scales of coverage for iteratively producing a reservoir development plan that is used for optimizing an overall performance of a reservoir. The method includes: (a) generating an initial reservoir characterization, (b) from the initial reservoir characterization, generating an initial reservoir development plan, (c) when the reservoir development plan is generated, incrementally advancing and generating a capital spending program, (d) when the capital spending program is generated, monitoring a performance of the reservoir by acquiring high rate monitor data from a first set of data measurements taken in the reservoir and using the high rate monitor data to perform well-regional and field-reservoir evaluations, (e) further monitoring the performance of the reservoir by acquiring low rate monitor data from a second set of data measurements taken in the reservoir, (f) assimilating together the high rate monitor data and the low rate monitor data, (g) from the high rate monitor data and the low rate monitor data, determining when it is necessary to update the initial reservoir development plan to produce a newly updated reservoir development plan, (h) when necessary, updating the initial reservoir development plan to produce the newly updated reservoir development plan, and (i) when the newly updated reservoir development plan is produced, repeating steps (c) through (h). A detailed disclosure is provided herein relating to the step (a) for generating the initial reservoir characterization and the step (b) for generating the initial reservoir development plan.
Owner:SCHLUMBERGER TECH CORP
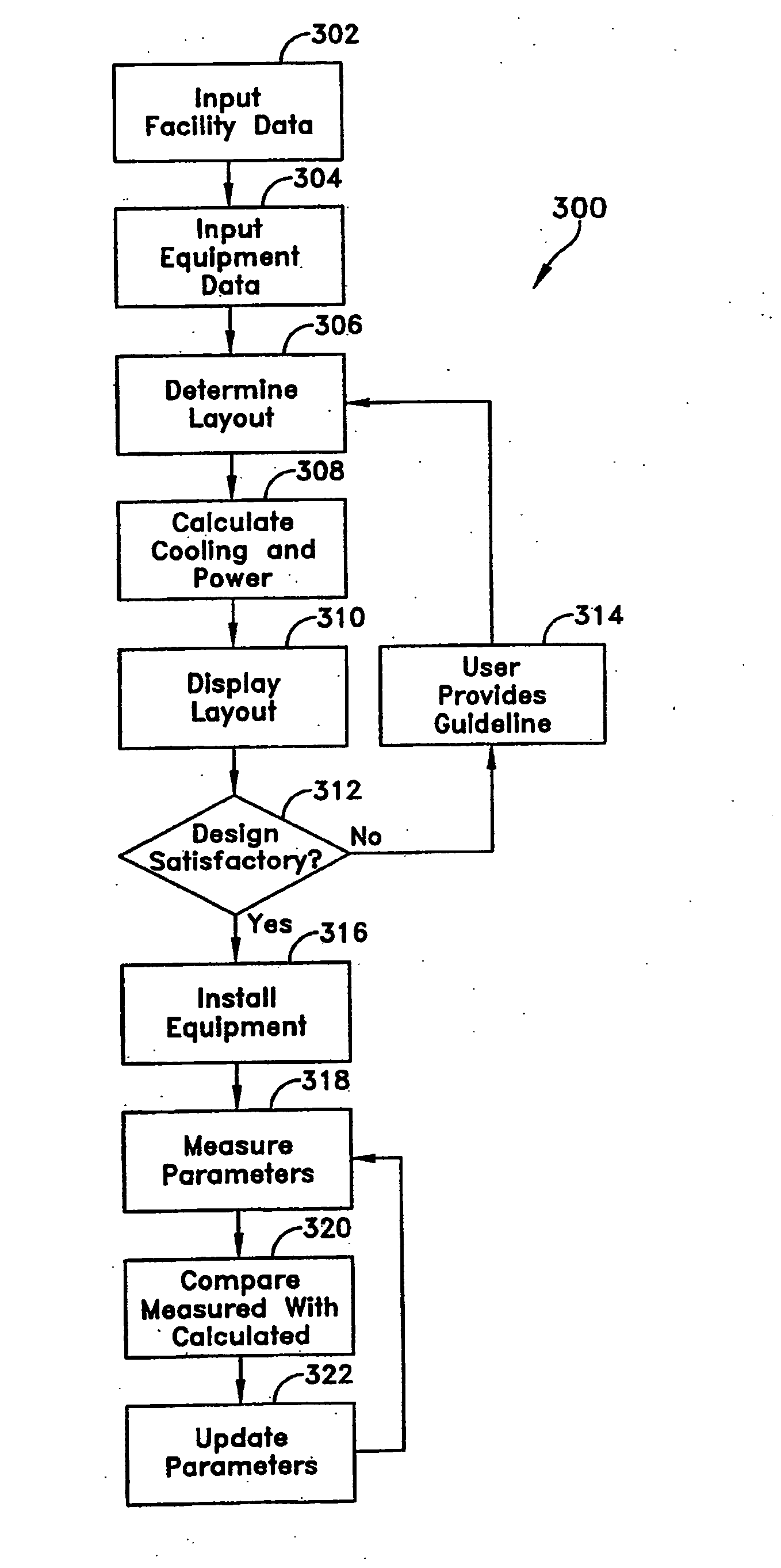
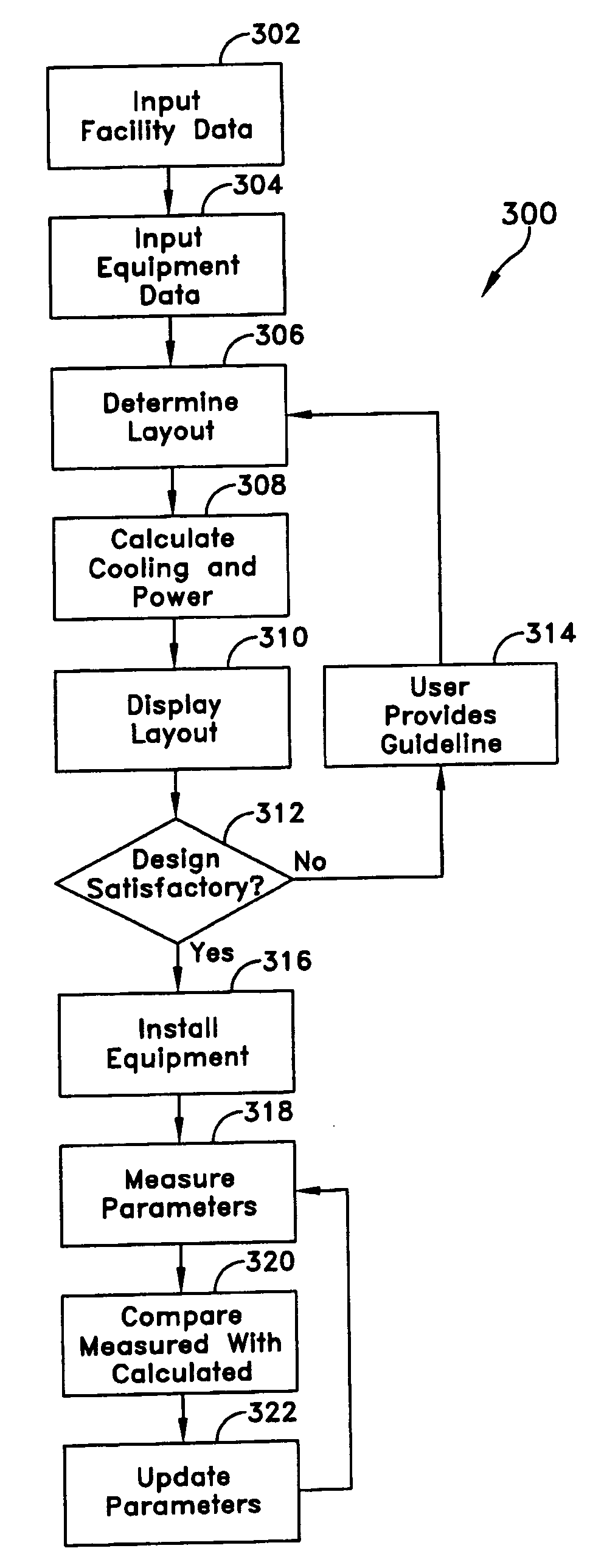
Methods and systems for managing facility power and cooling
Systems and methods are provided for determining data center cooling and power requirements and for monitoring performance of cooling and power systems in data centers. At least one aspect provides a system and method that enables a data center operator to determine available power and cooling at specific areas and enclosures in a data center to assist in locating new equipment in the data center.
Owner:SCHNEIDER ELECTRIC IT CORP
Method for controlling cyclic plasma-assisted process
ActiveUS8790743B1Deterioration of film qualityMinimize the numberElectric discharge tubesVacuum evaporation coatingEngineeringMonitoring data
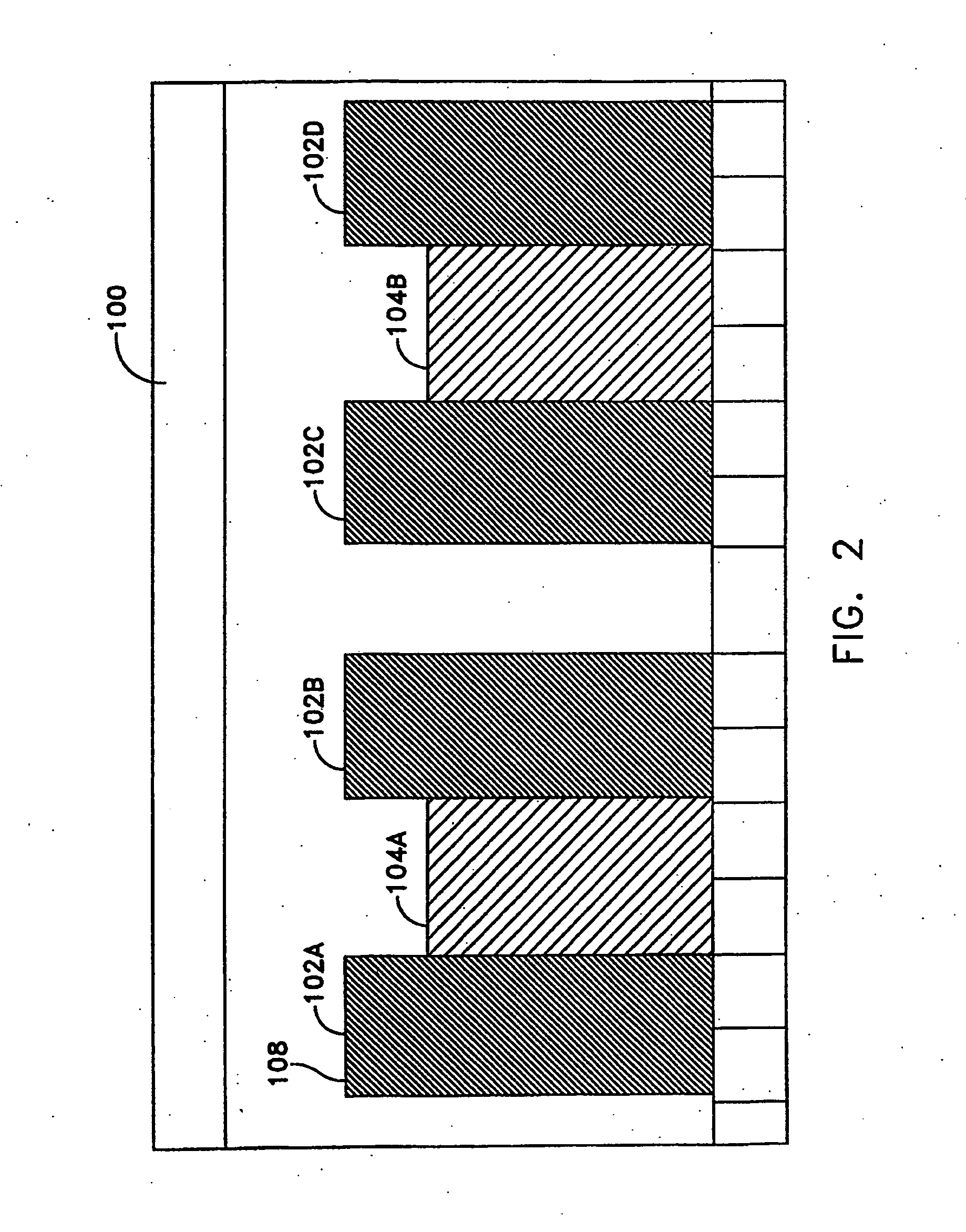
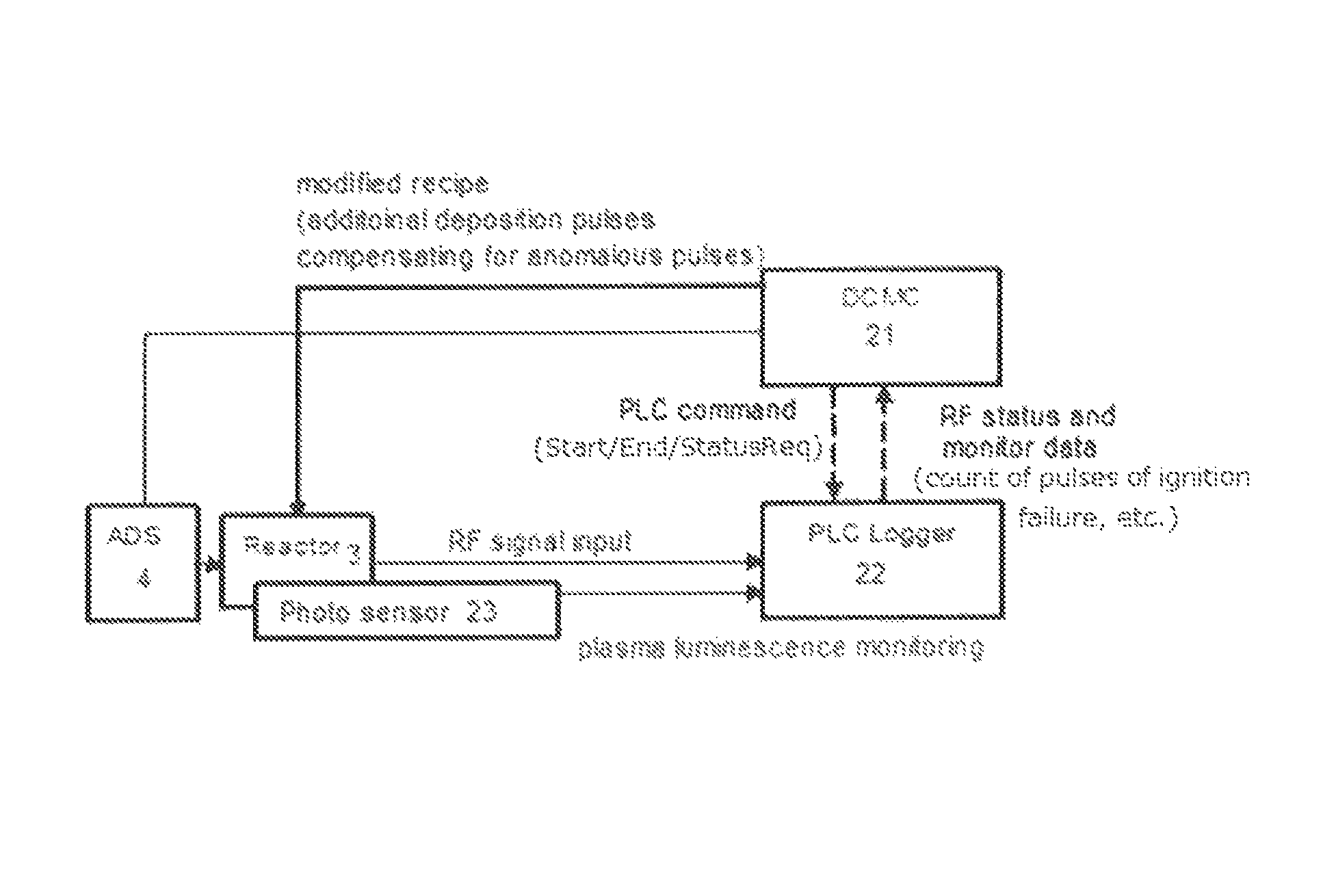
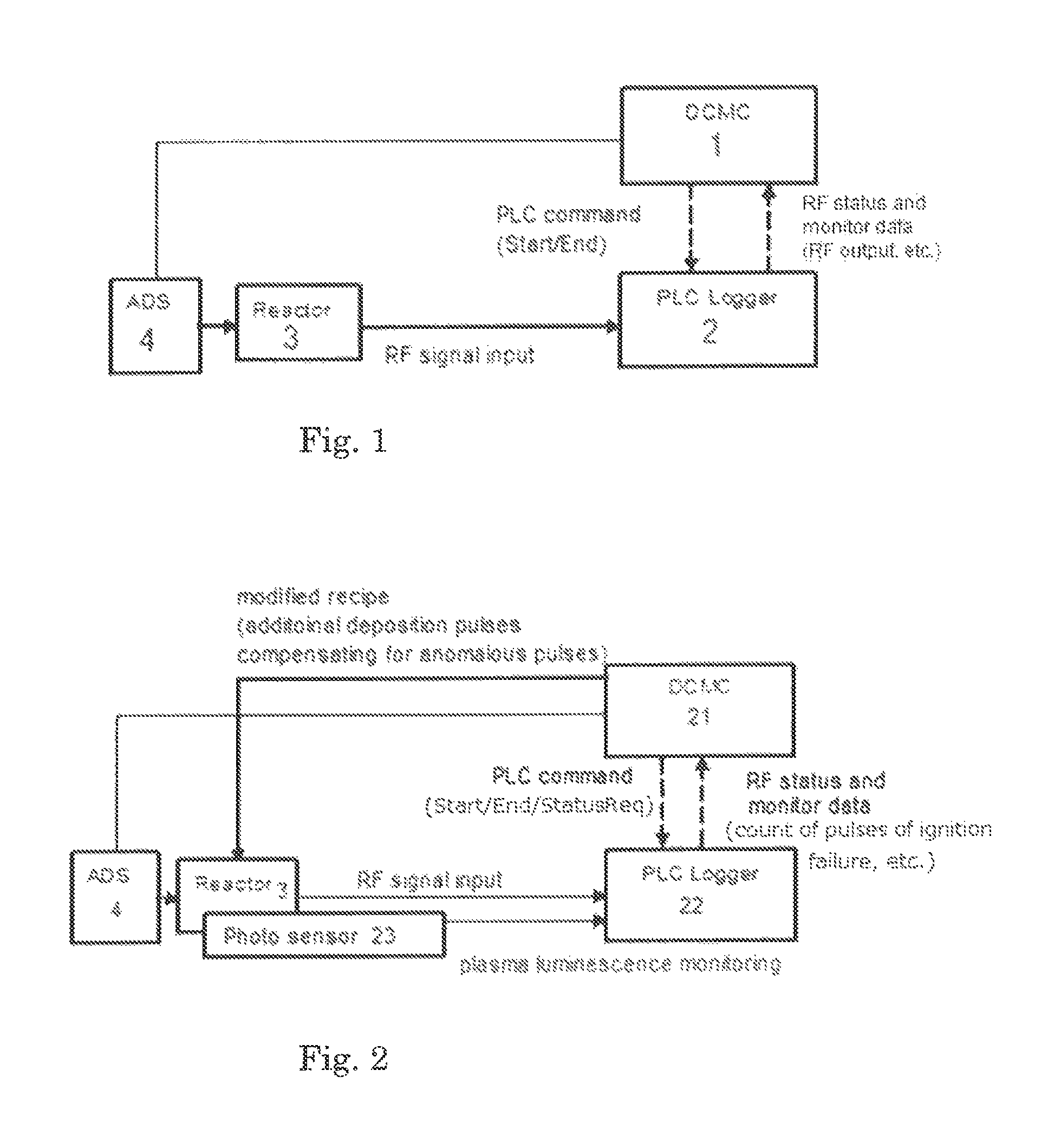
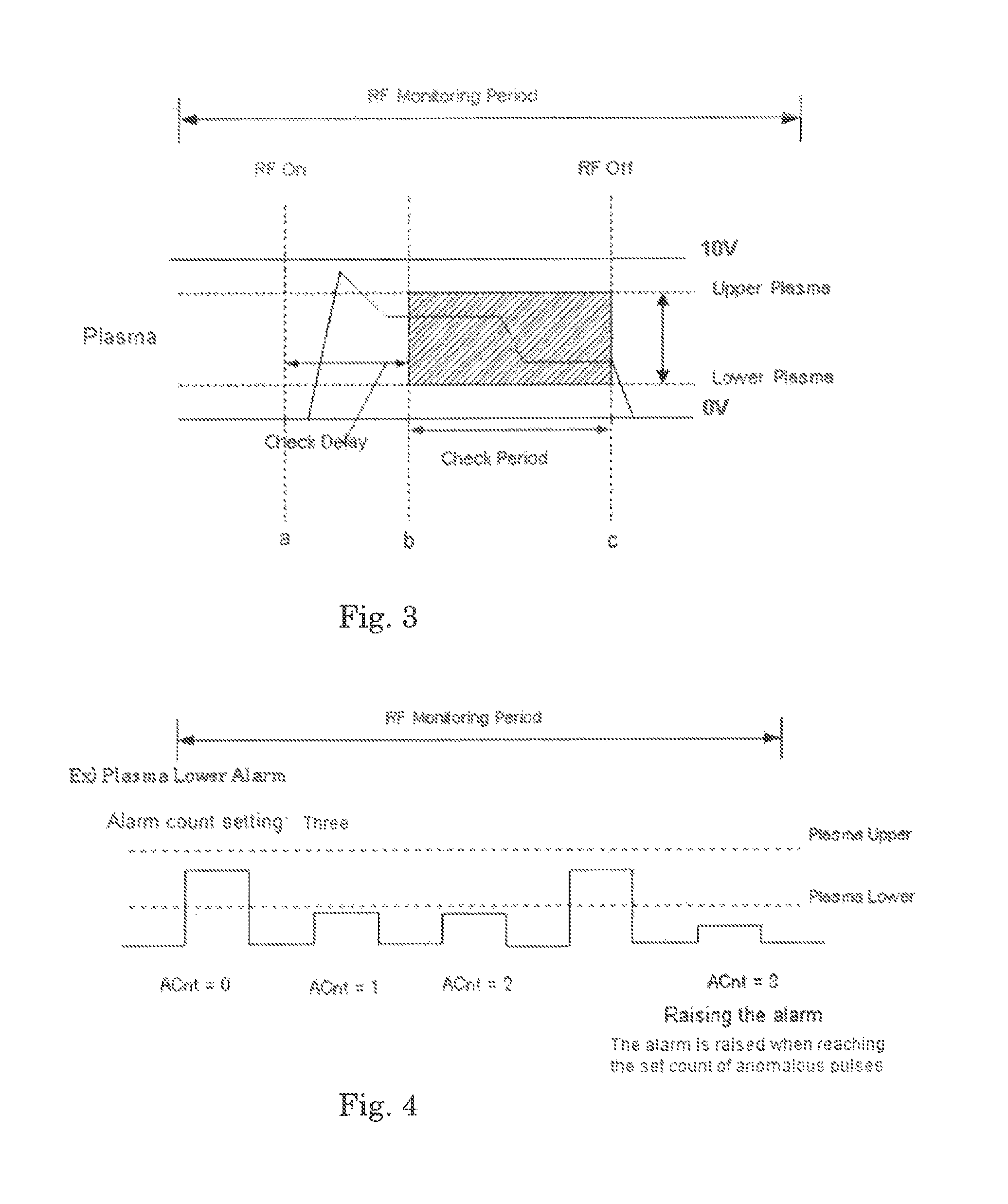
A method for processing a substrate in a reactor by pulsing RF power, includes: applying RF power in pulses in the reactor to process the substrate; monitoring data from the reactor indicative of anomalous pulses of RF power, including data from a photo sensor equipped in the reactor; counting the number of anomalous pulses of RF power in the monitored data; determining whether or not the number of anomalous pulses of RF power is acceptable; and initiating a pre-designated sequence if the number of anomalous pulses of RF power is determined to be unacceptable.
Owner:ASM IP HLDG BV
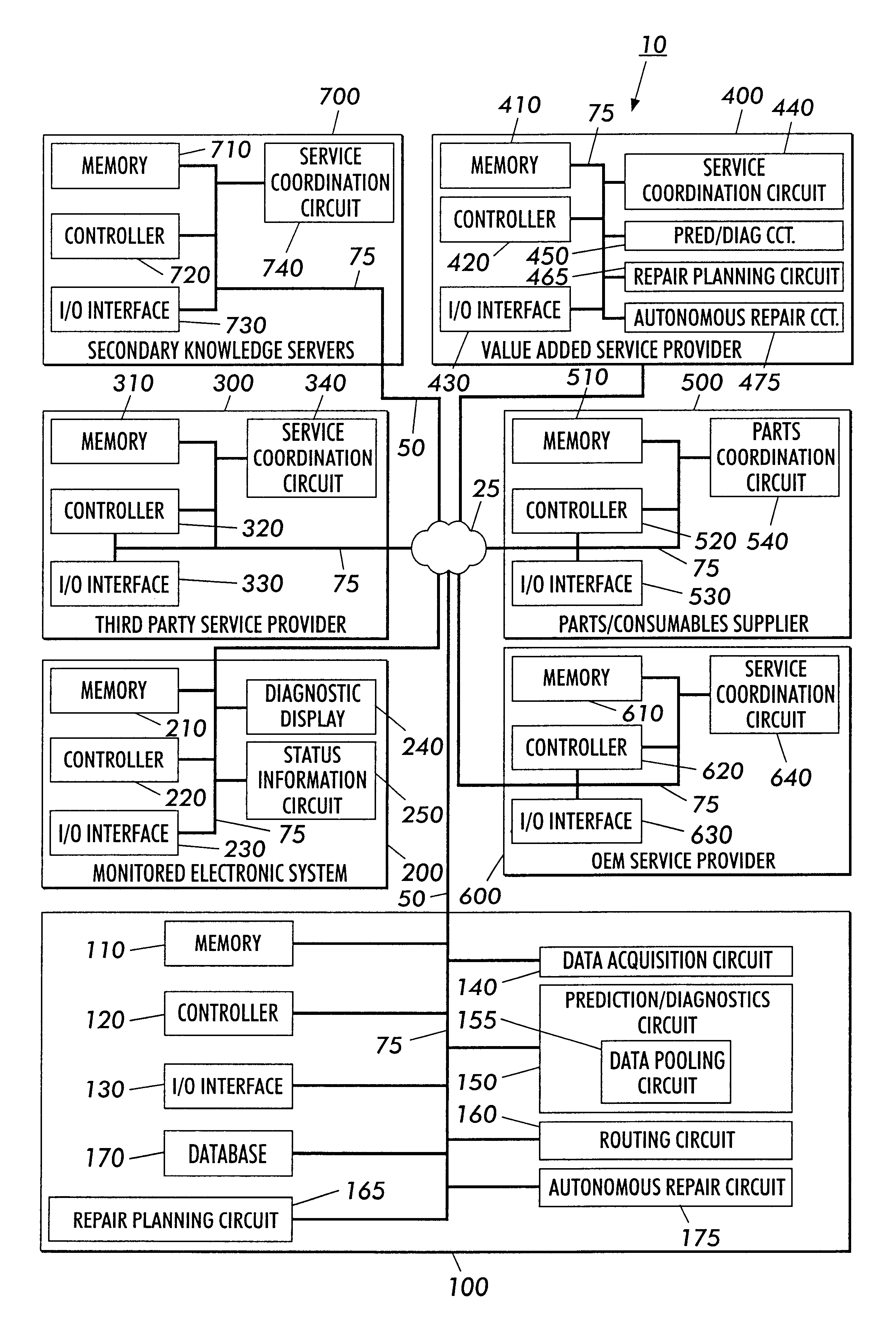
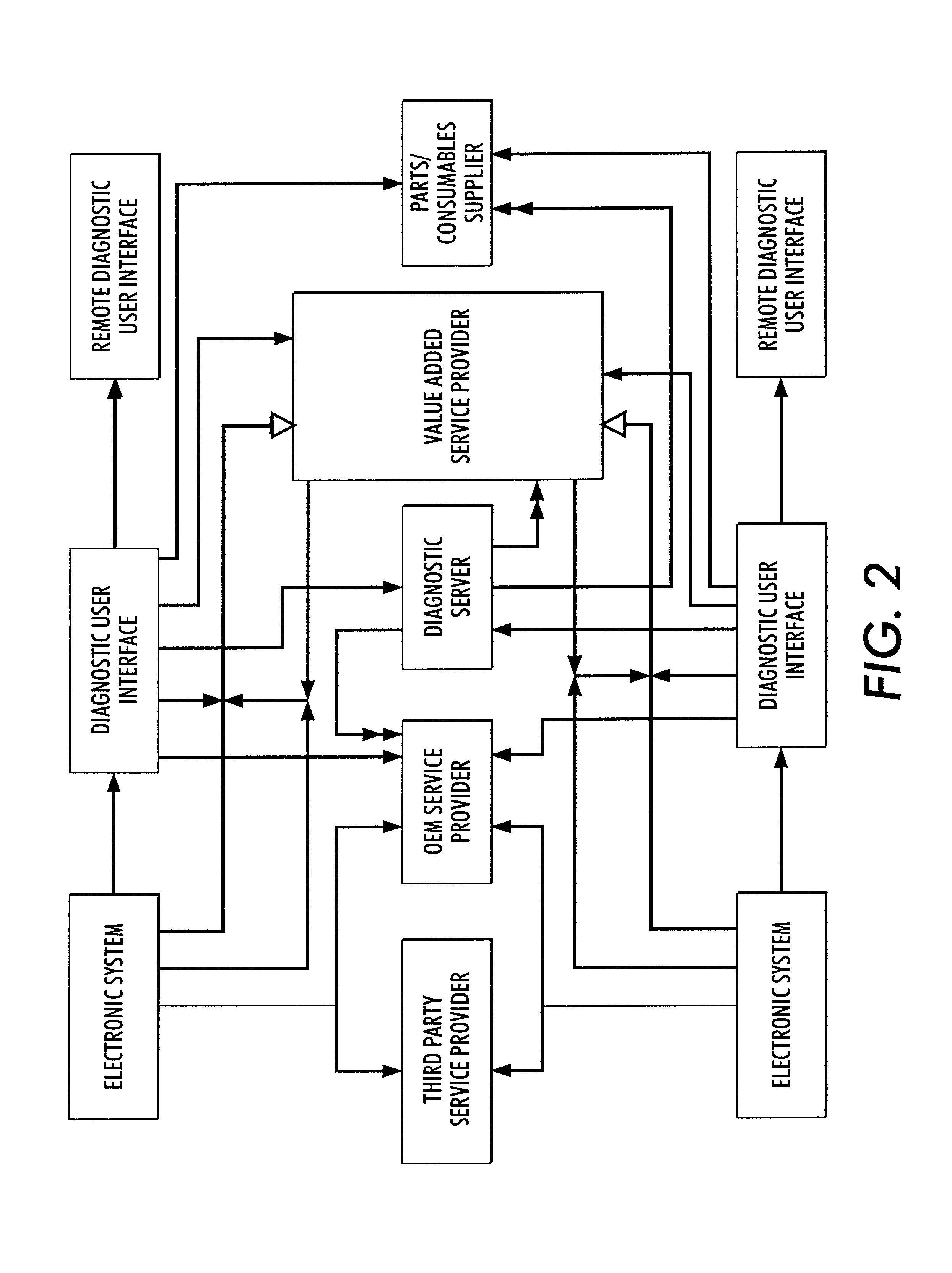
Systems and methods for failure prediction, diagnosis and remediation using data acquisition and feedback for a distributed electronic system
InactiveUS6892317B1Highly reliable actionHighly reliable responseData processing applicationsLogical operation testingPredictive systemsElectronic systems
By using monitoring data, feedback data, and pooling of failure data from a plurality of electronic devices, real-time failure prediction and diagnoses of electronic systems operating in a network environment can be achieved. First, the diagnostic system requests data on the state of a machine and / or its components and collections thereof as part of the machine's normal operation. Secondly, real-time processing of the data either at the machine site or elsewhere in the distributed network allows for predicting or diagnosing system failures. Having determined and / or predicted a system failure, a communication to one or more remote observers in the network allows the remote observers to view the diagnostic information and / or required action to repair the failure. Furthermore, interrogation of either the particular electronic system, or a database containing data on similar electronic systems by the diagnostic server allows the diagnostic server to refine original diagnoses based on this population data to achieve a comprehensive failure predication / diagnosing system.
Owner:LONGHORN HD LLC
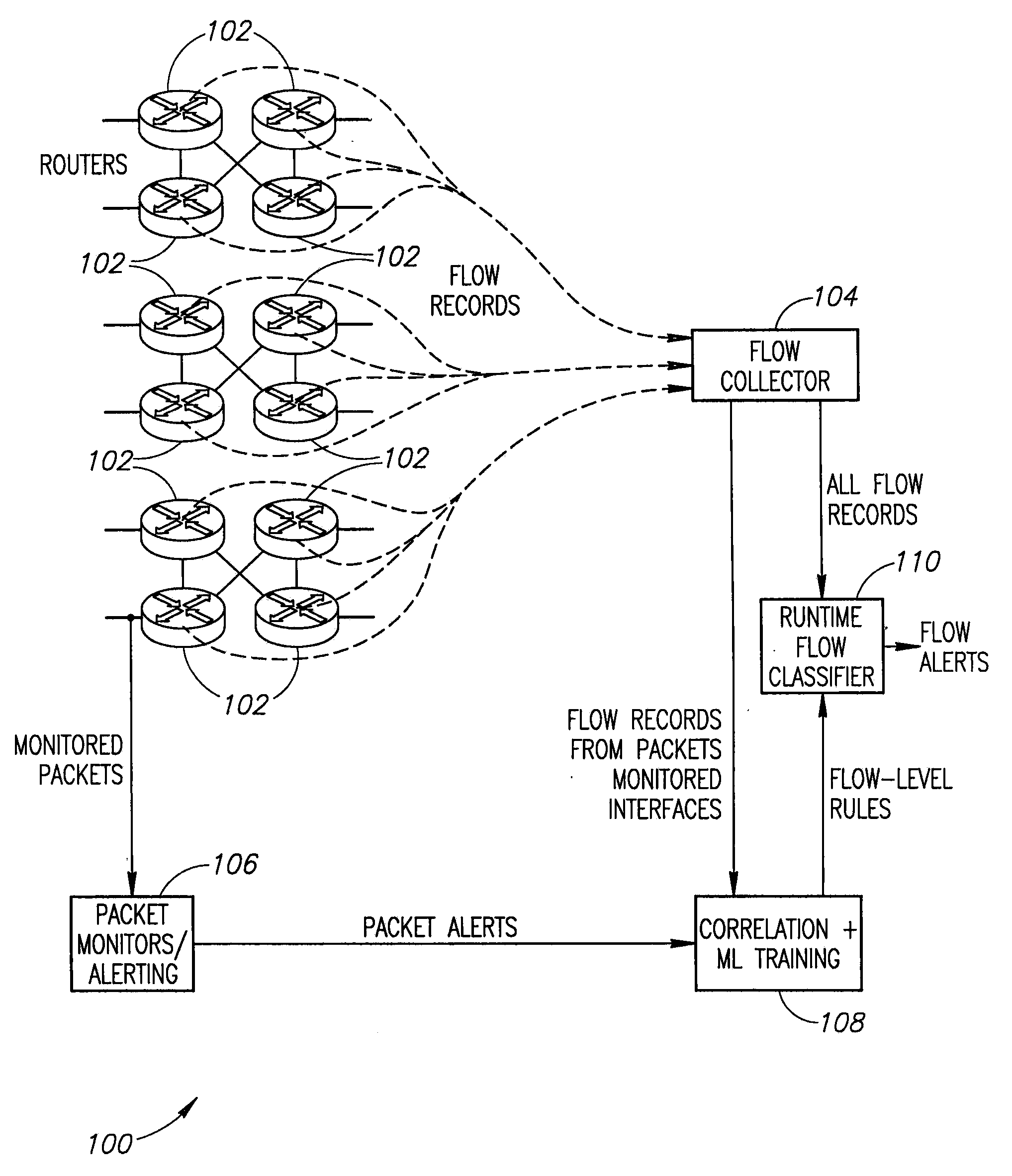
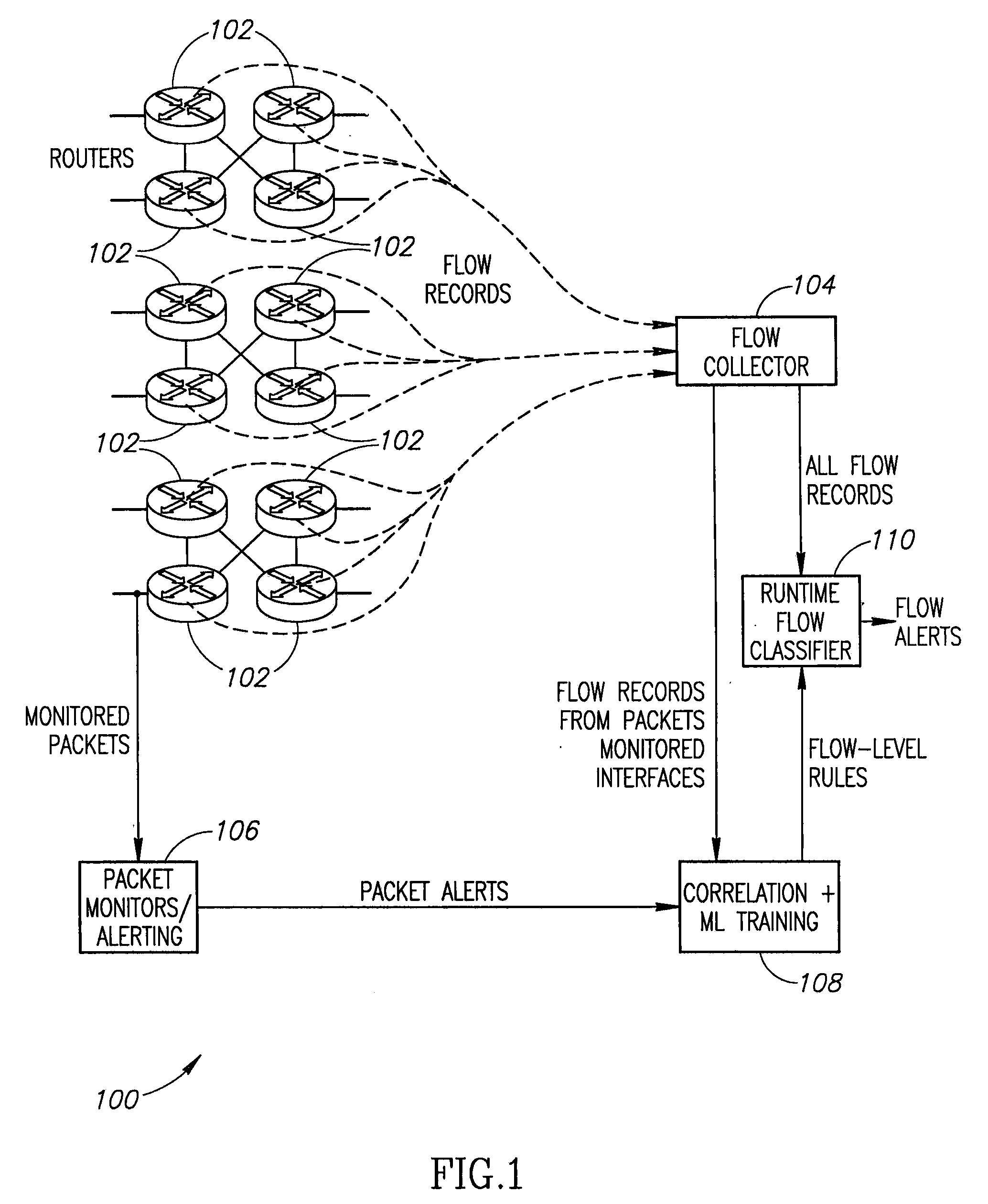
Systems and methods for rule-based anomaly detection on IP network flow
A system to detect anomalies in internet protocol (IP) flows uses a set of machine-learning (ML) rules that can be applied in real time at the IP flow level. A communication network has a large number of routers that can be equipped with flow monitoring capability. A flow collector collects flow data from the routers throughout the communication network and provides them to a flow classifier. At the same time, a limited number of locations in the network monitor data packets and generate alerts based on packet data properties. The packet alerts and the flow data are provided to a machine learning system that detects correlations between the packet-based alerts and the flow data to thereby generate a series of flow-level alerts. These rules are provided to the flow time classifier. Over time, the new packet alerts and flow data are used to provide updated rules generated by the machine learning system.
Owner:AT&T INTPROP I L P
Methods and systems for managing facility power and cooling
Systems and methods are provided for determining data center cooling and power requirements and for monitoring performance of cooling and power systems in data centers. At least one aspect provides a system and method that enables a data center operator to determine available power and cooling at specific areas and enclosures in a data center to assist in locating new equipment in the data center.
Owner:SCHNEIDER ELECTRIC IT CORP
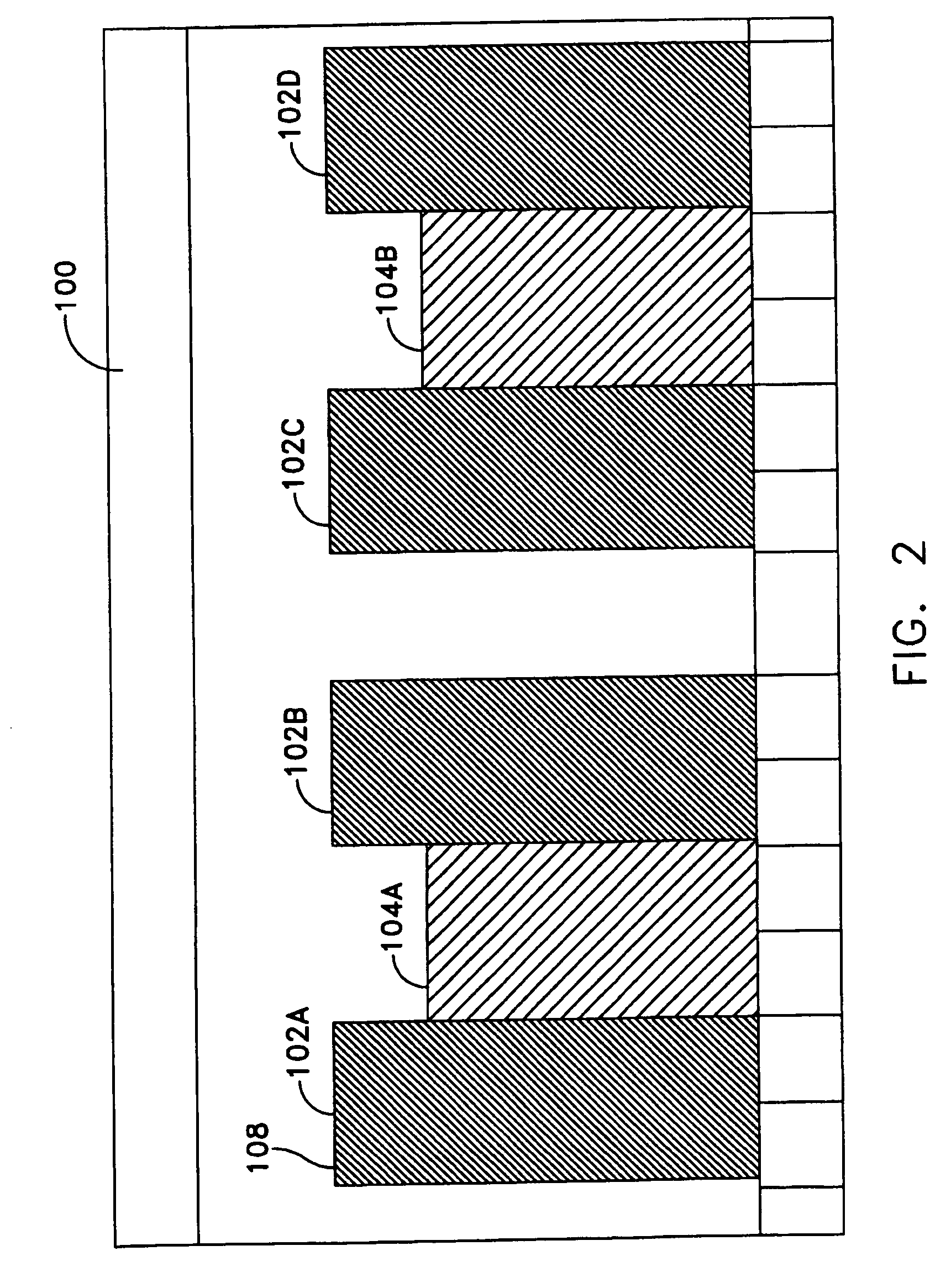
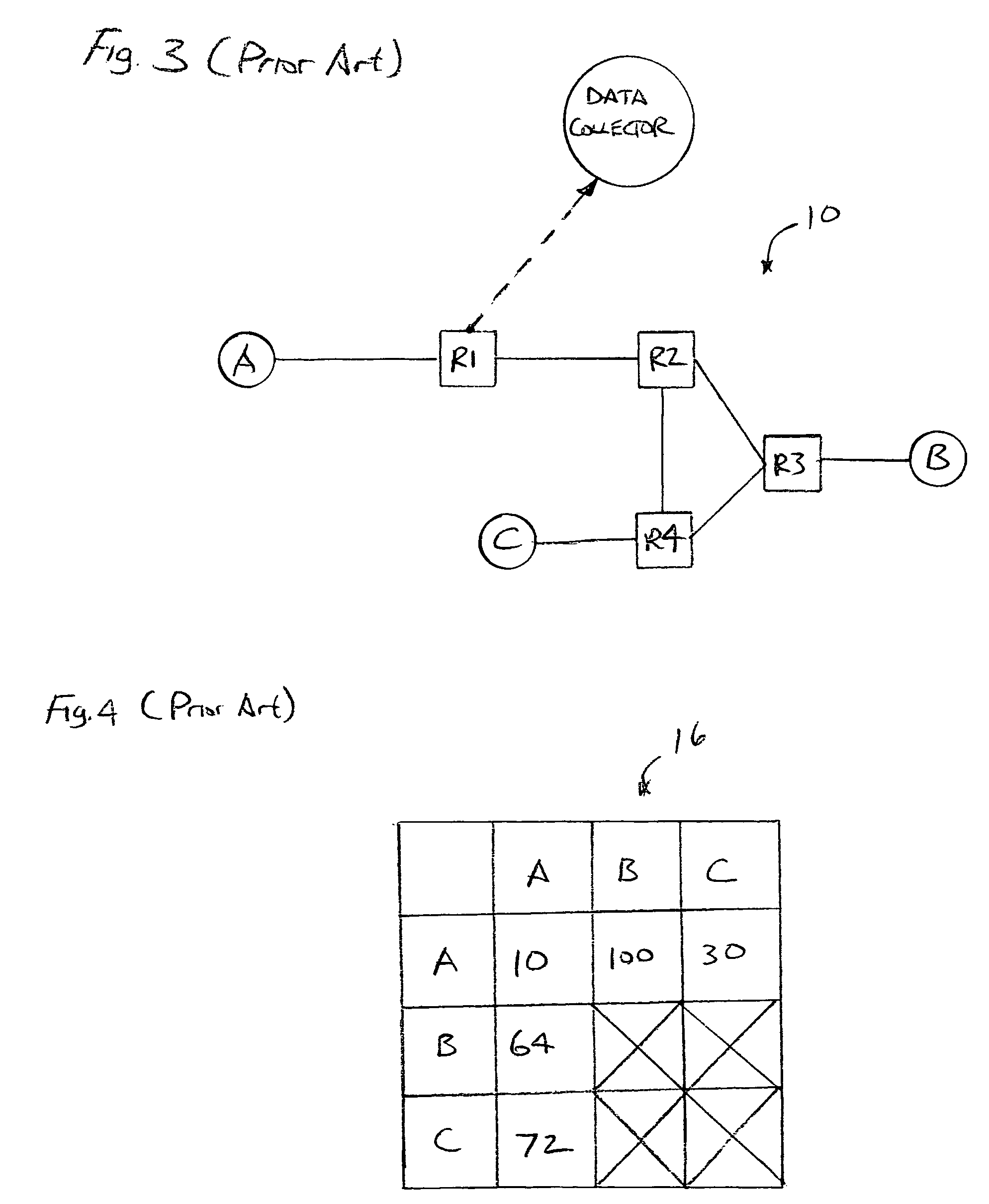
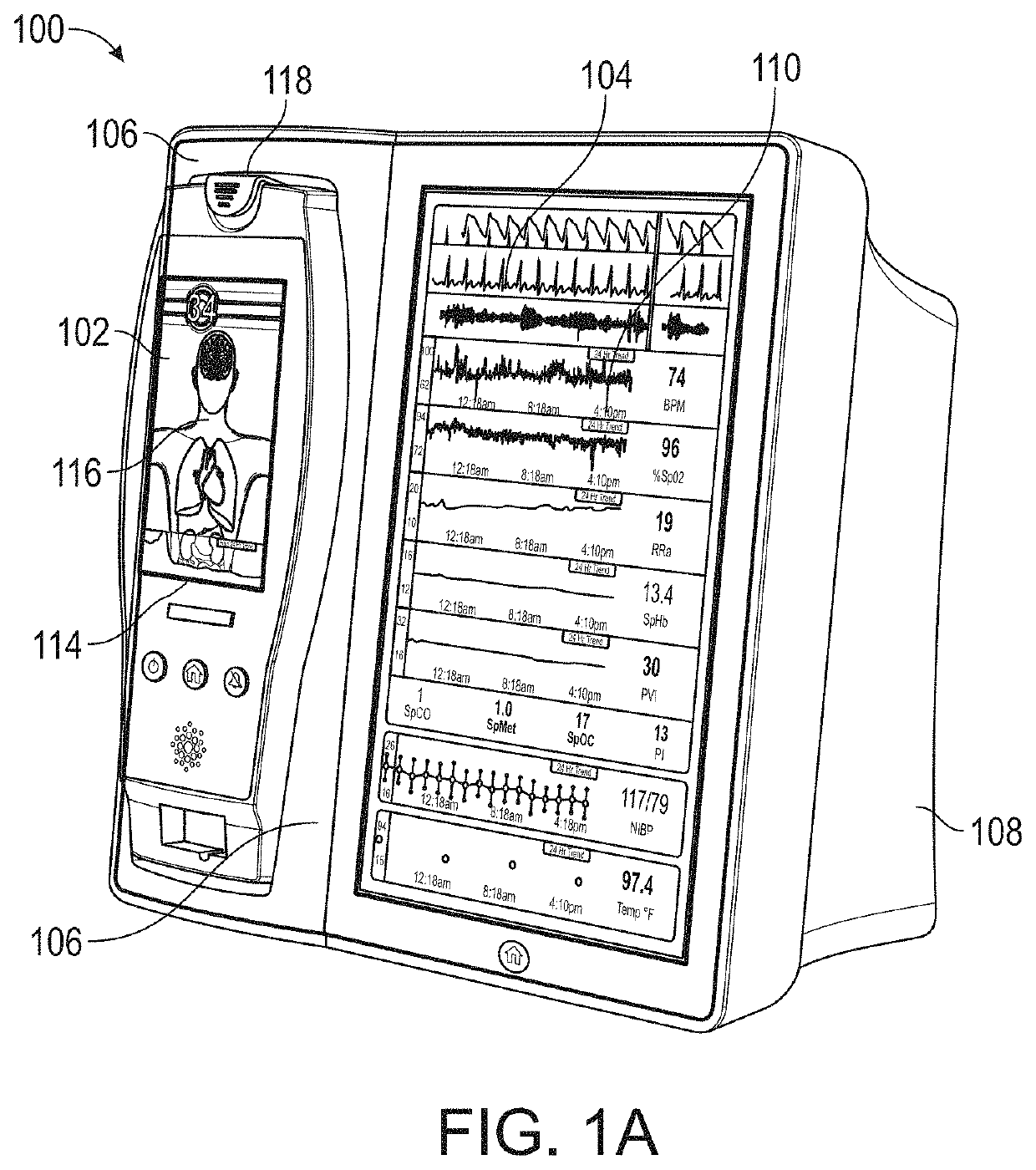
System for displaying medical monitoring data
A first medical device can receive a physiological parameter value from a second medical device. The second physiological parameter value may be formatted according to a protocol not used by the first medical device such that the first medical device is not able to process the second physiological parameter value to produce a displayable output value. The first medical device can pass the physiological parameter data from the first medical device to a separate translation module and receive translated parameter data from the translation module at the first medical device. The translated parameter data can be processed for display by the first medical device. The first medical device can output a value from the translated parameter data for display on the first medical device or an auxiliary device.
Owner:MASIMO CORP
Method and apparatus for web caching
InactiveUS6990526B1Reduced activityAvoid delayDigital data information retrievalMultiple digital computer combinationsHash functionData access
A method and apparatus for web caching is disclosed. The method and apparatus may be implemented in hardware, software or firmware. Complementary cache management modules, a coherency module and a cache module(s) are installed complementary gateways for data and for clients respectively. The coherency management module monitors data access requests and or response and determines for each: the uniform resource locator (URL) of the requested web page, the URL of the requestor and a signature. The signature is computed using cryptographic techniques and in particular a hash function for which the input is the corresponding web page for which a signature is to be generated. The coherency management module caches these signatures and the corresponding URL and uses the signatures to determine when a page has been updated. When, on the basis of signature comparisons it is determined that a page has been updated the coherency management module sends a notification to all complementary cache modules. Each cache module caches web pages requested by the associated client(s) to which it is coupled. The notification from the cache management module results in the cache module(s) which are the recipient of a given notice updating their tag table with a stale bit for the associated web page. The cache module(s) use this information in the associated tag tables to determine which pages they need to update. The cache modules initiate this update during intervals of reduced activity in the servers, gateways, routers, or switches of which they are a part. All clients requesting data through the system of which each cache module is a part are provided by the associated cache module with cached copies of requested web pages.
Owner:POINTRED TECH
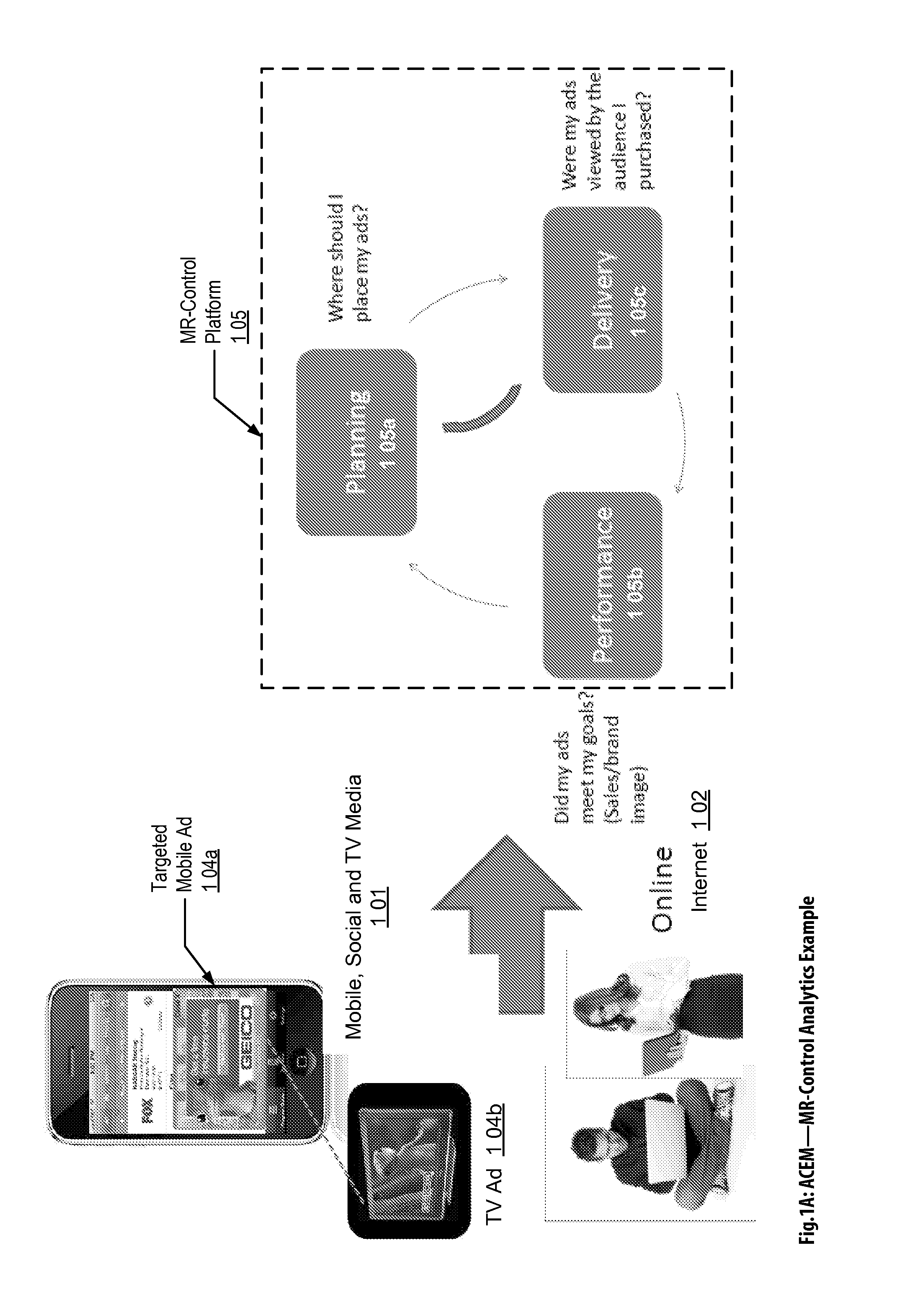
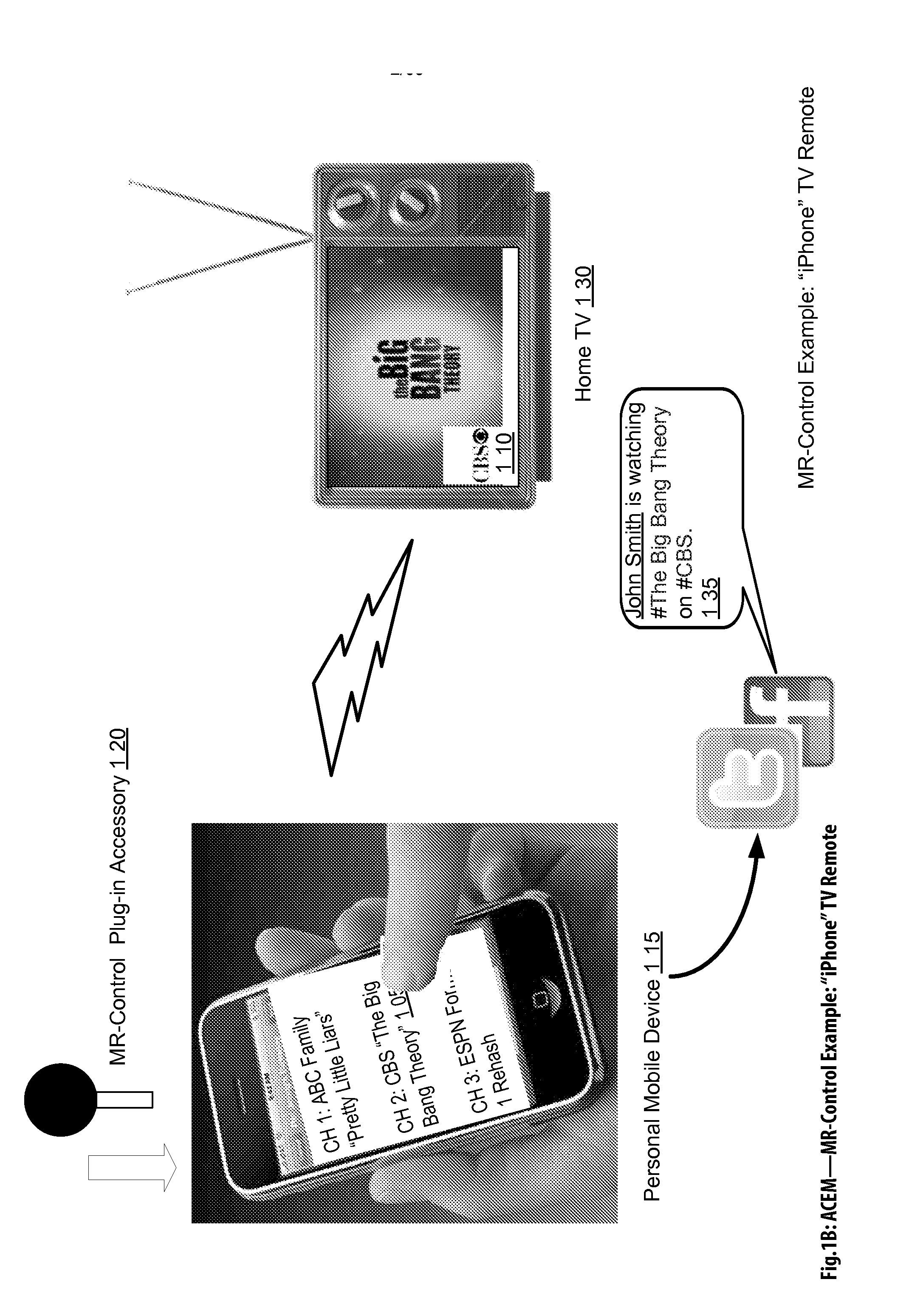
Audience Content Exposure Monitoring Apparatuses, Methods and Systems
ActiveUS20160007083A1Analogue secracy/subscription systemsBroadcast information monitoringSocial mediaMobile device
The Audience Content Exposure Monitoring Apparatuses, Methods and Systems (“ACEM”) transforms pulsing request (e.g., 1107), viewing status, purchase request, channel selection, survey request, sentiment request, atmospherics, social media posts, response events, data request and access token, app / device input monitoring, check-in, URL access, etc. inputs via ACEM components into atmospherics sampling record (e.g., 1106), ad contents (e.g., 1115), RT data / records, ad tags, media program, full page content outputs. In some embodiments, the ACEM provides a mobile metering system that configures the data collection of audience environment atmospherics to evaluate audience media exposure. In one implementation, the ACEM may employ media data collection technology using a combination of mobile device metering app and cloud hosted server side technology to determine when and how often a user mobile device should record and / or generate monitoring atmospherics of audience environment; and to determine what content the audience has been exposed to based on the collected monitoring data.
Owner:SYMPHONY ADVANCED MEDIA
Methods and computer programs for generating data traffic matrices
ActiveUS8005009B2High accuracy of resultsIncrease the number ofError preventionTransmission systemsTraffic capacityData traffic
A method and system for monitoring traffic flow includes assigning a subset of sampling points to a node or unique pair of nodes. The sampling points are determined to be the most likely to monitor data traffic, and preferably all data traffic, associated with the node or node pair. The sampling point subset may automatically be determined and assigned to the node or node pair, based, for example, on historical traffic within the network. The method further includes collecting diagnostic network traffic data from the sampling points, and obtaining sampled traffic flow counts for a flow associated with a node pair from the diagnostic traffic data collected from the sampling points assigned to the source and destination nodes of the node pair. The method further includes performing a function on the sampled traffic flow counts to obtain an estimated traffic flow count for the respective flow.
Owner:INMON
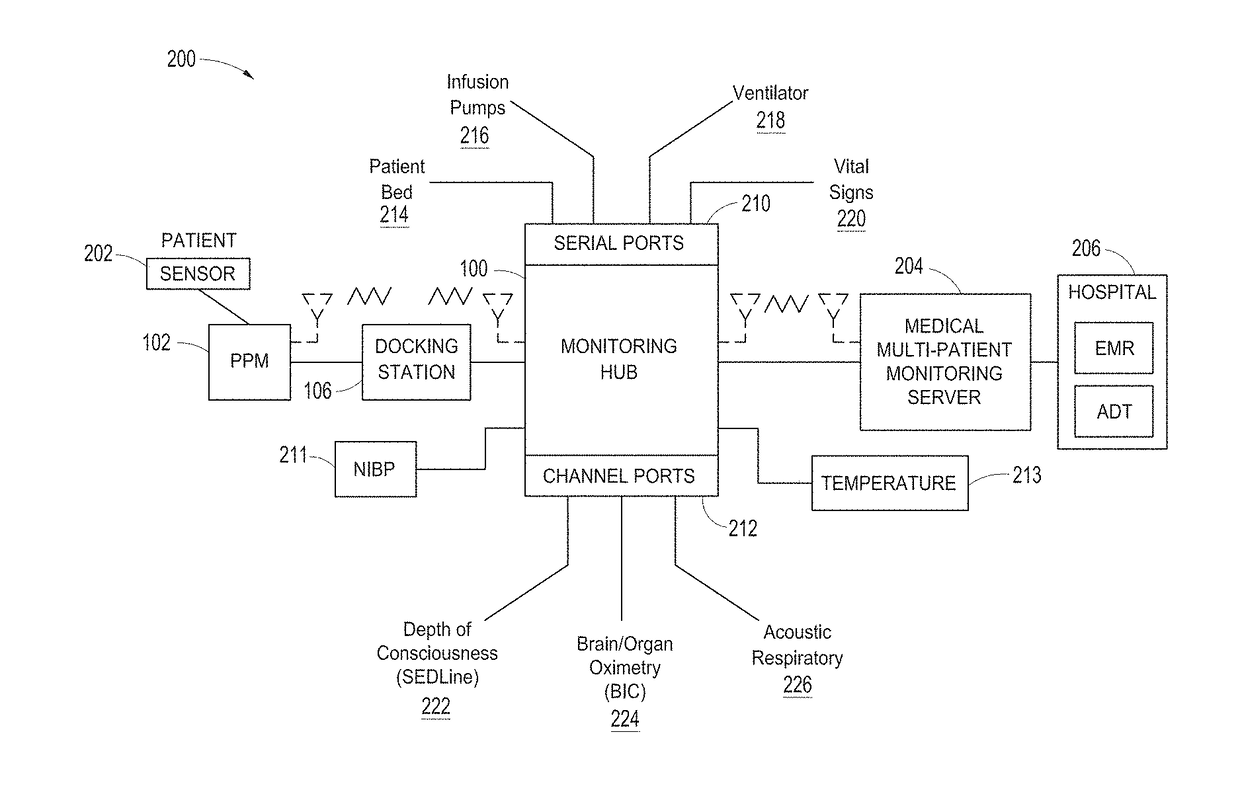
System for displaying and controlling medical monitoring data
A first medical device can acquire a physiological parameter value from a patient and communicate the physiological parameter value to a medical network interface. The medical network interface can link a patient ID associated with the physiological parameter and a device ID associated with the first medical device with the medical network interface's device ID. The medical network interface can pass the physiological parameter value to a second medical device for further processing or routing to another medical device.
Owner:MASIMO CORP
Method And System For Network Intrusion Detection, Related Network And Computer Program Product
ActiveUS20070214504A1Easy to detectMemory loss protectionError detection/correctionData streamProtocol Application
A system for providing intrusion detection in a network wherein data flows are exchanged using associated network ports and application layer protocols. The system includes a monitoring module configured for monitoring data flows in the network, a protocol identification engine configured for detecting information on the application layer protocols involved in the monitored data flows, and an intrusion detection module configured for operating based on the information on application layer protocols detected. Intrusion detection is thus provided independently of any predefined association between the network ports and the application layer protocols.
Owner:III HLDG 1
End-to-end service quality monitoring method and system in a radio network
ActiveUS20110096678A1Prevent data security threatGuaranteed continuous availabilityError preventionTransmission systemsQuality of serviceRadio networks
The present invention discloses a method and a system for service quality monitoring in a network comprising radio interfaces. The measurements are end-to-end measurements between the end user and chosen network element. The measurements are implemented using monitoring stations which can monitor the traffic passively or actively by transmitting test signals. The antenna beam directions of the monitoring stations can be controlled. The performance server works as a counterpart of the active tests. A reporting suite may define the performed measurements and it also collects the measurement data from different monitoring stations. Monitoring data from several corporate intranets can also be collected to an external server through internet connection.
Owner:7SIGNAL OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com