Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4062 results about "Vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
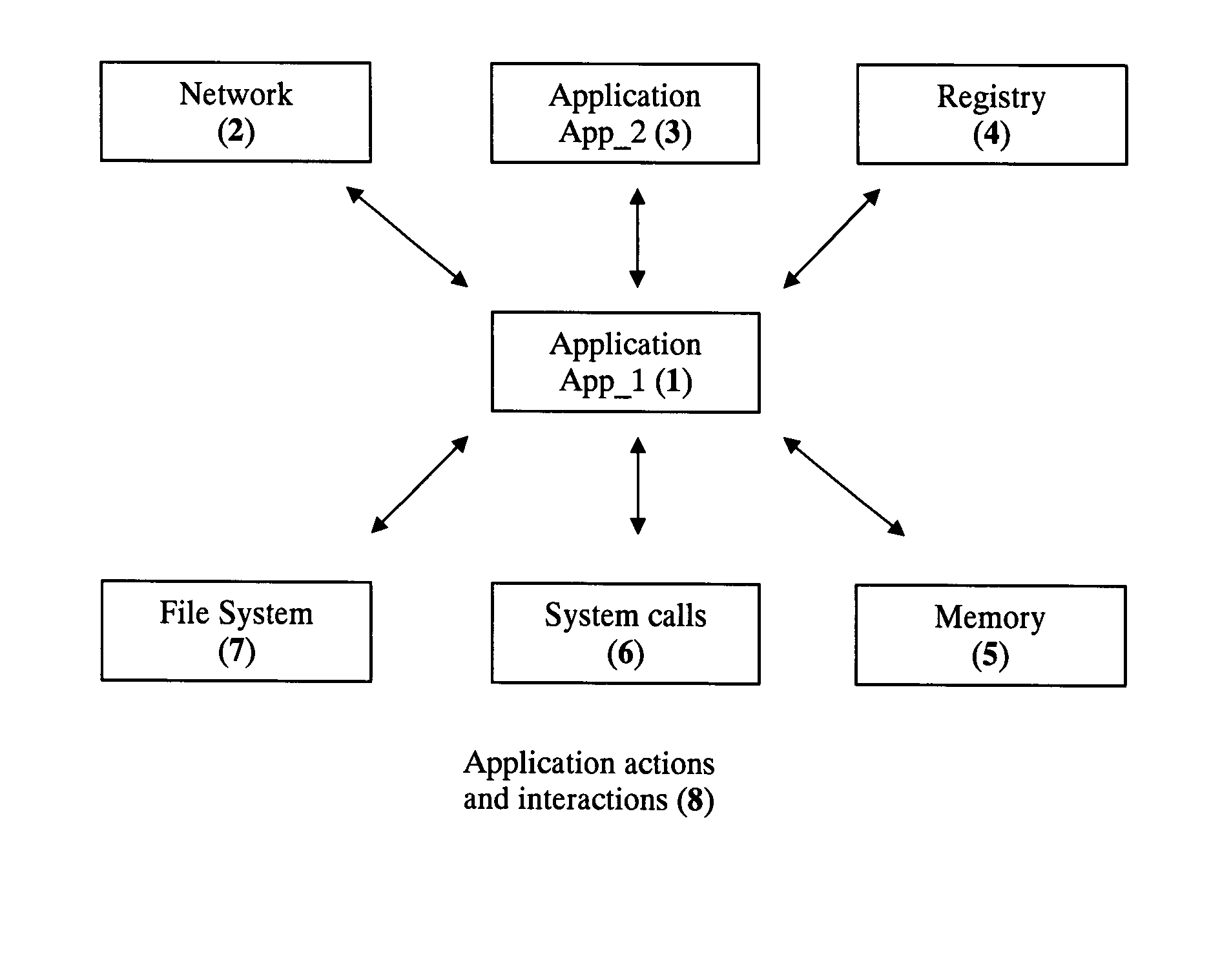
Vulnerability refers to the inability (of a system or a unit) to withstand the effects of a hostile environment. A window of vulnerability (WOV) is a time frame within which defensive measures are diminished, compromised or lacking.
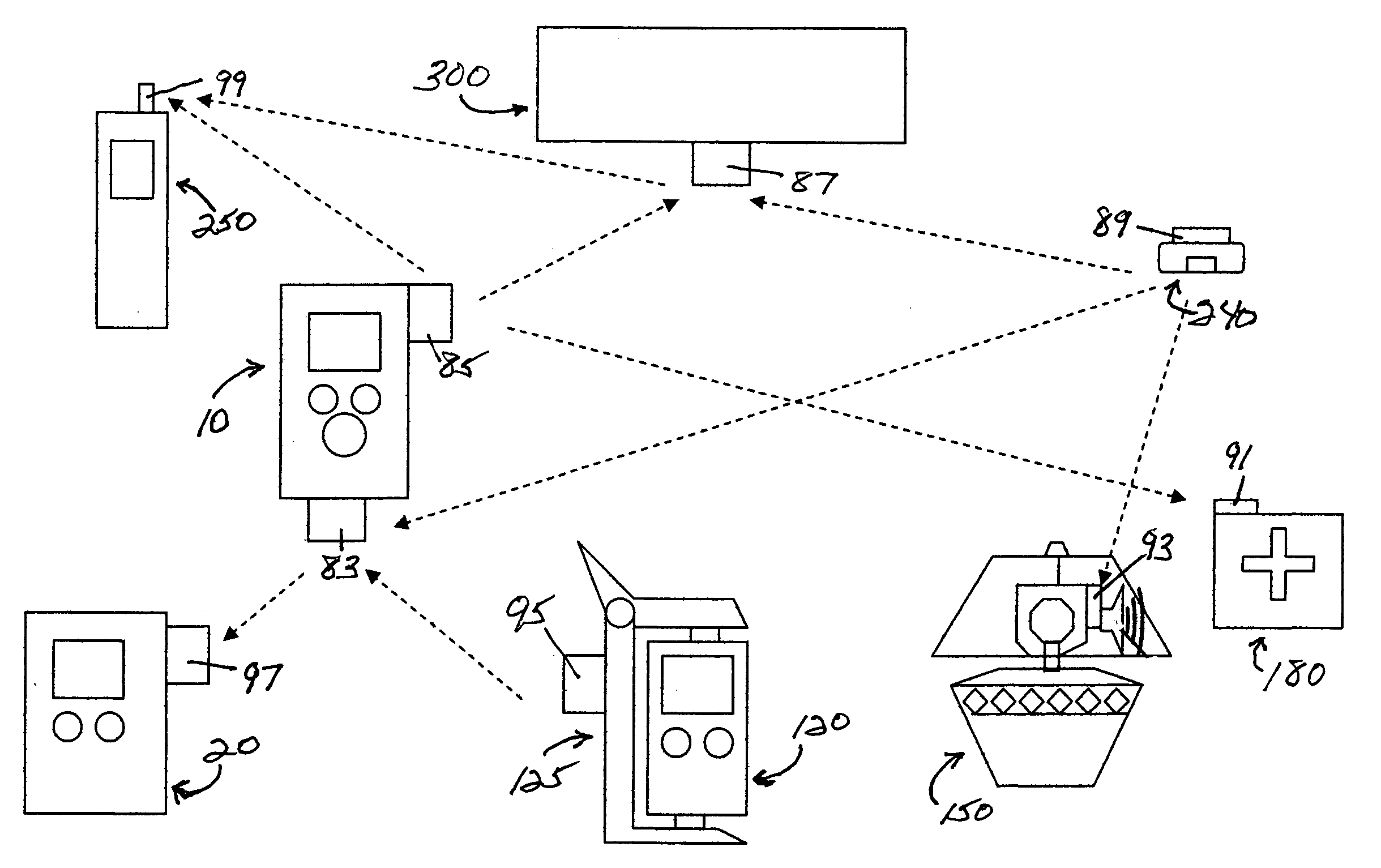
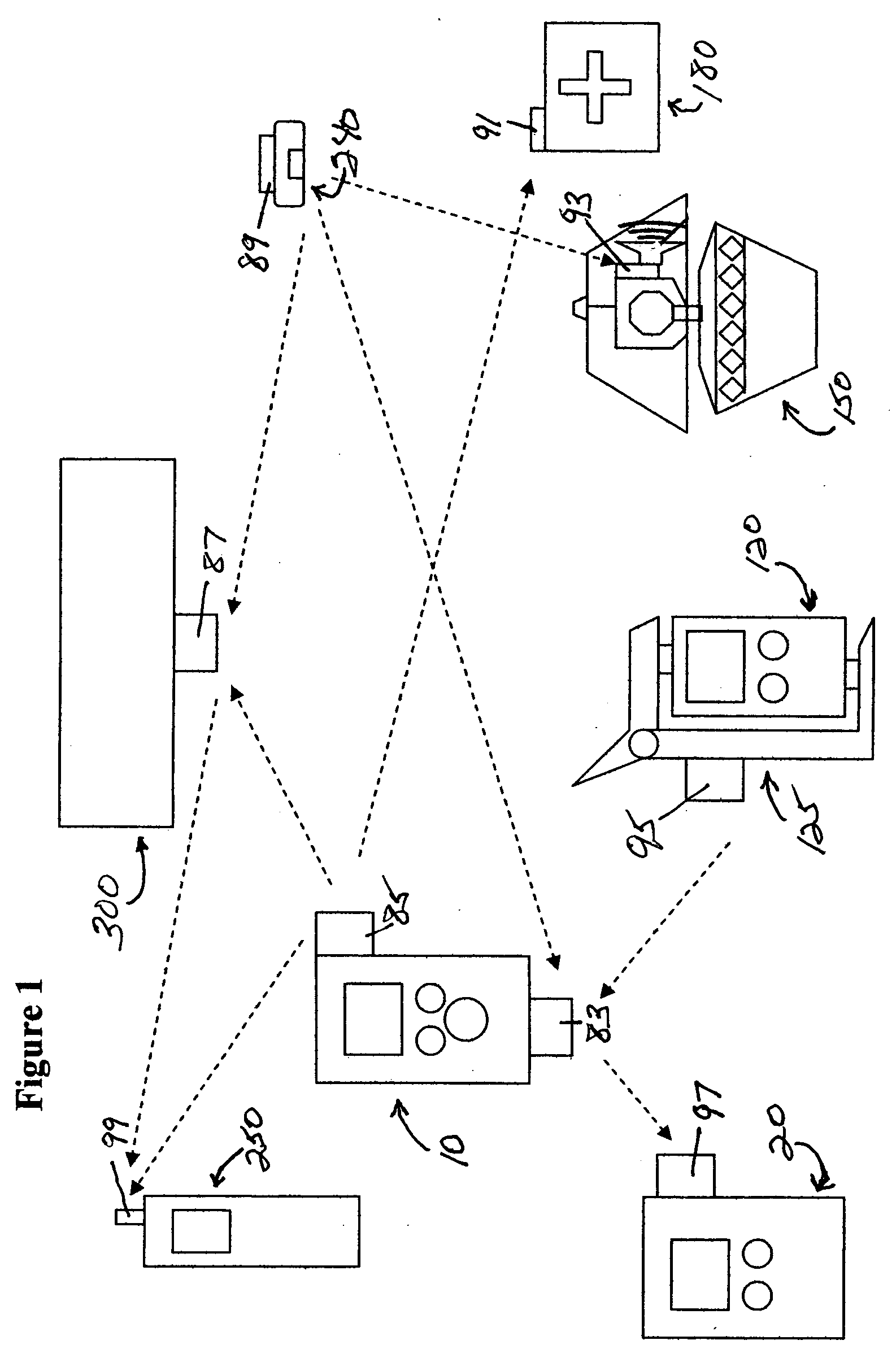
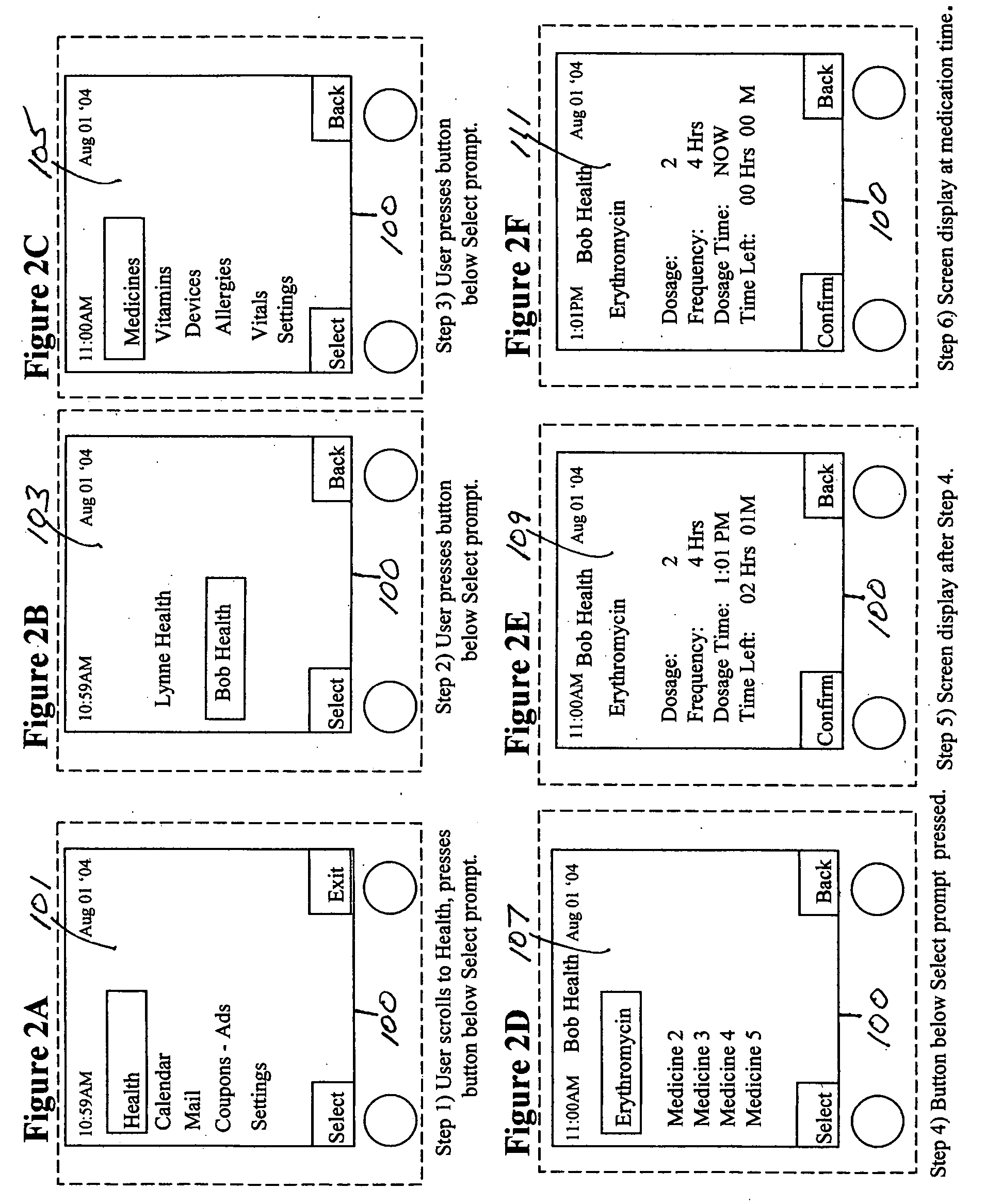
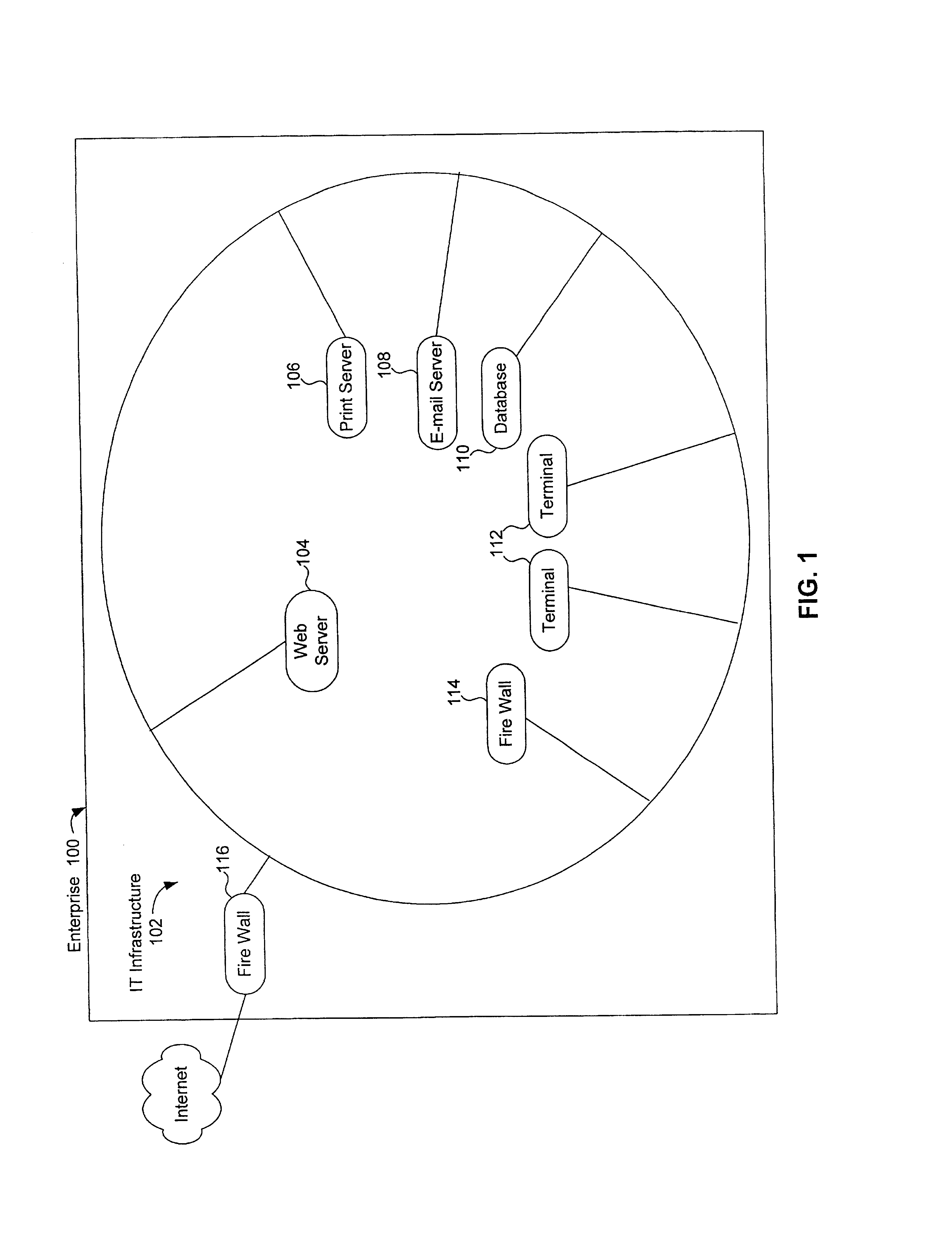
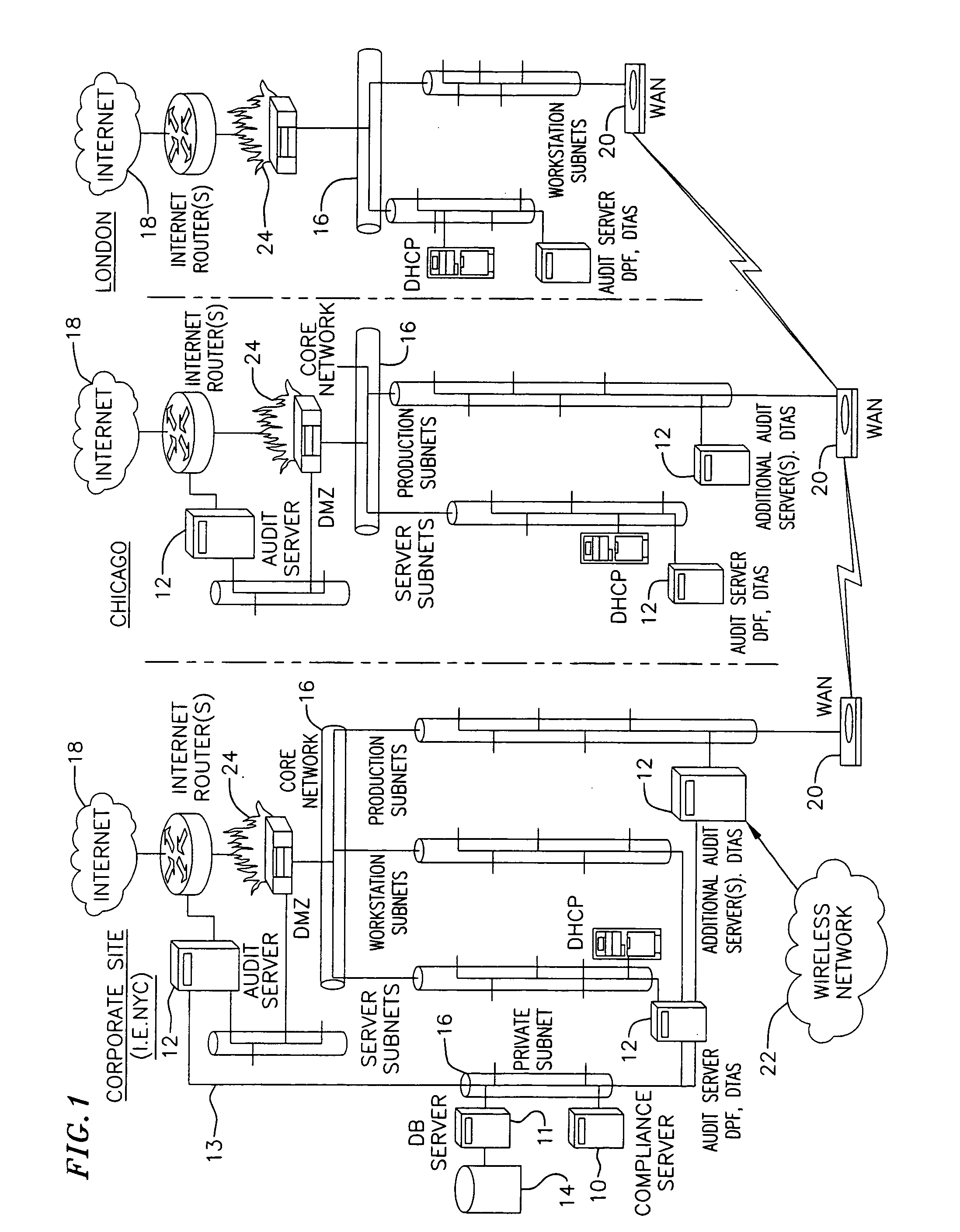
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
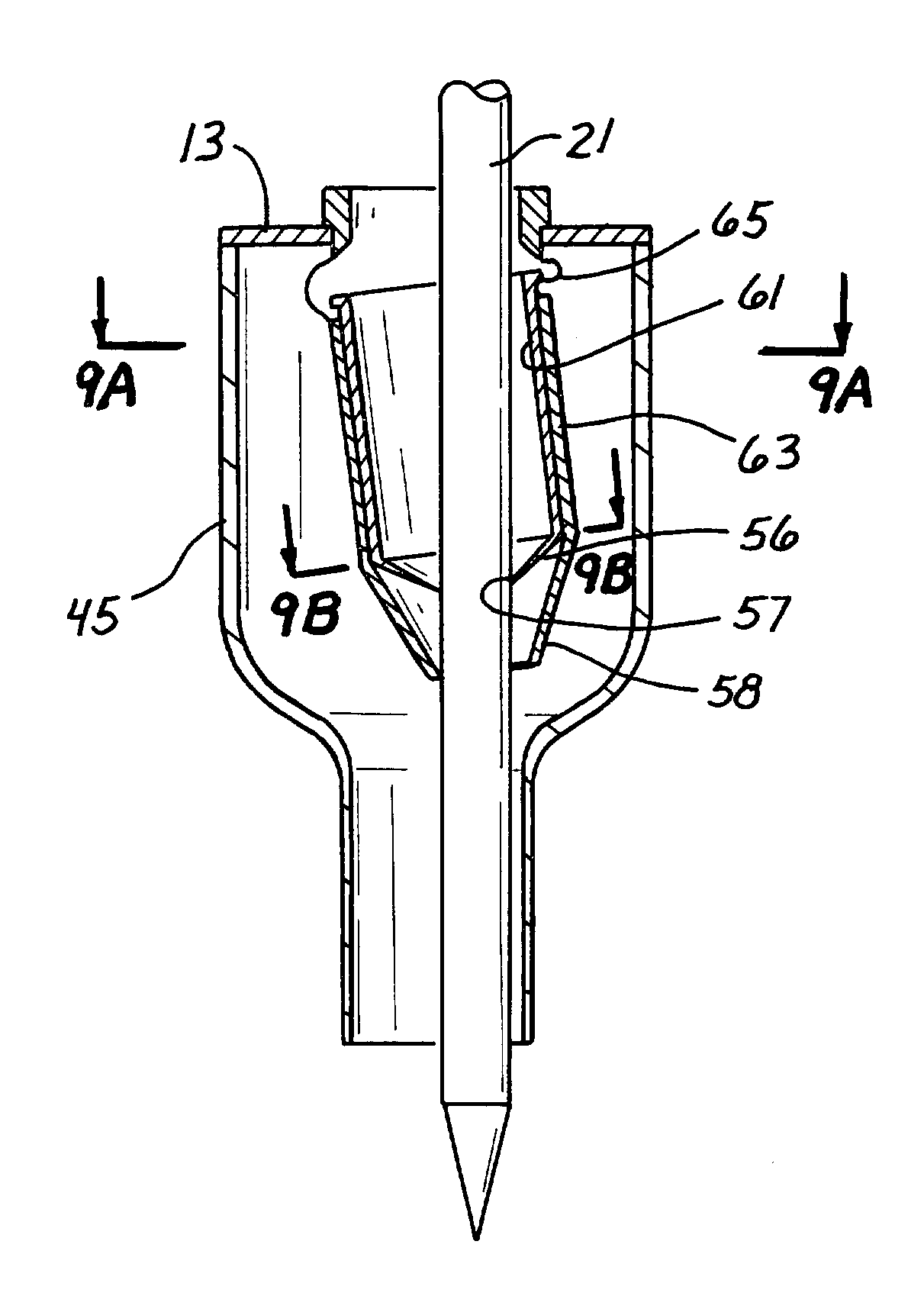
Surgical access device with pendent valve
InactiveUS7083626B2Precise positioningMaximize ease and safetyEar treatmentCannulasSurgical departmentVALVE PORT
A surgical access device, such as a trocar, includes a pendent valve having an elongate structure extending from a proximal end to a septum valve disposed at a distal end. In operation, the elongate structure follows the angle of the instrument to pre-position the septum valve into the path of the instrument where it is not significantly challenged during instrument insertion or manipulation. The pendant valve can be made to float at both the proximal end and the distal end of the elongate structure, to further reduce the vulnerability of the septum valve. Since the valve is less vulnerable to instrument insertion, it can be formed to minimize friction and maximize the functional range of the access device.
Owner:APPL MEDICAL RESOURCES CORP
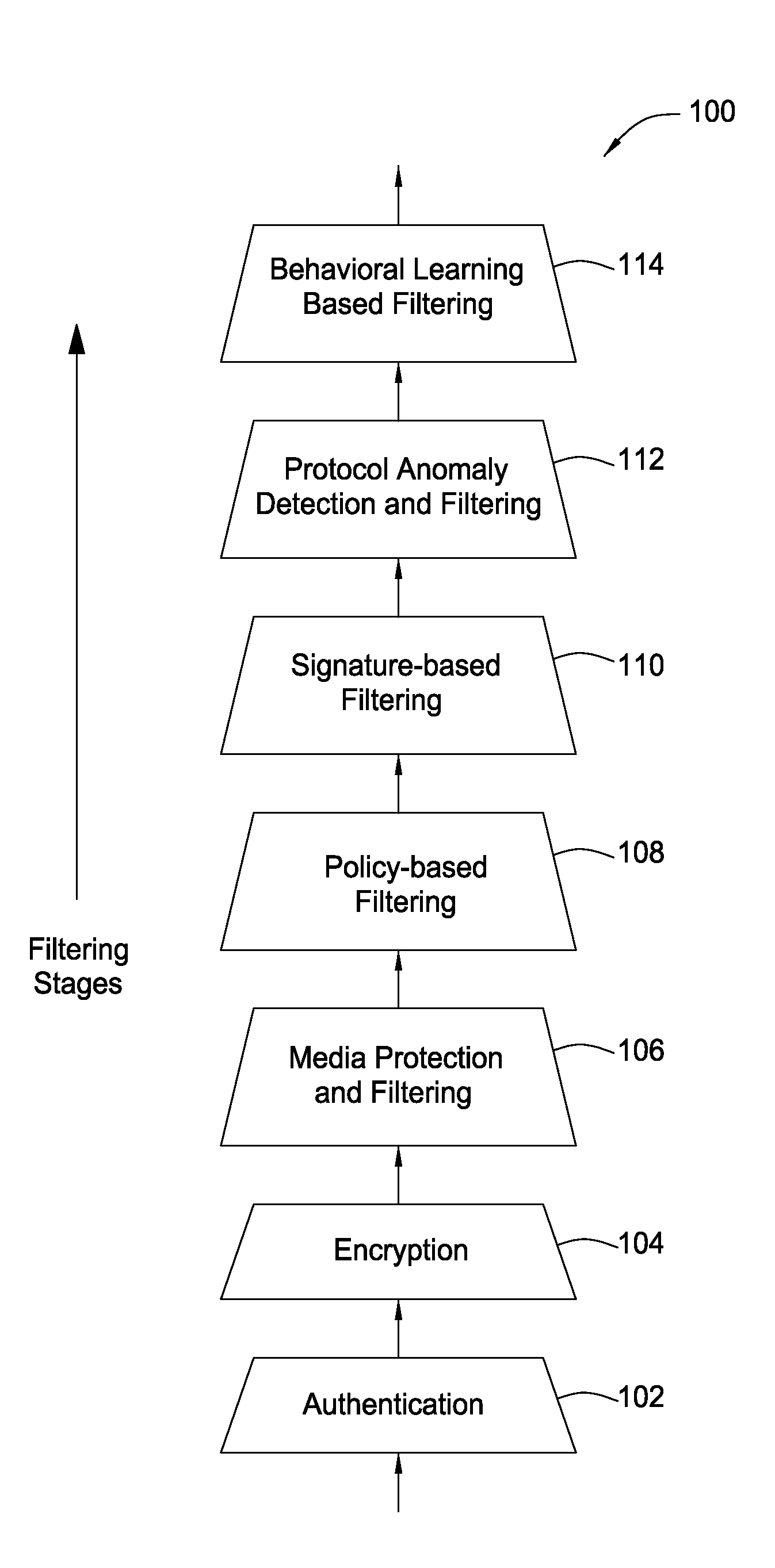
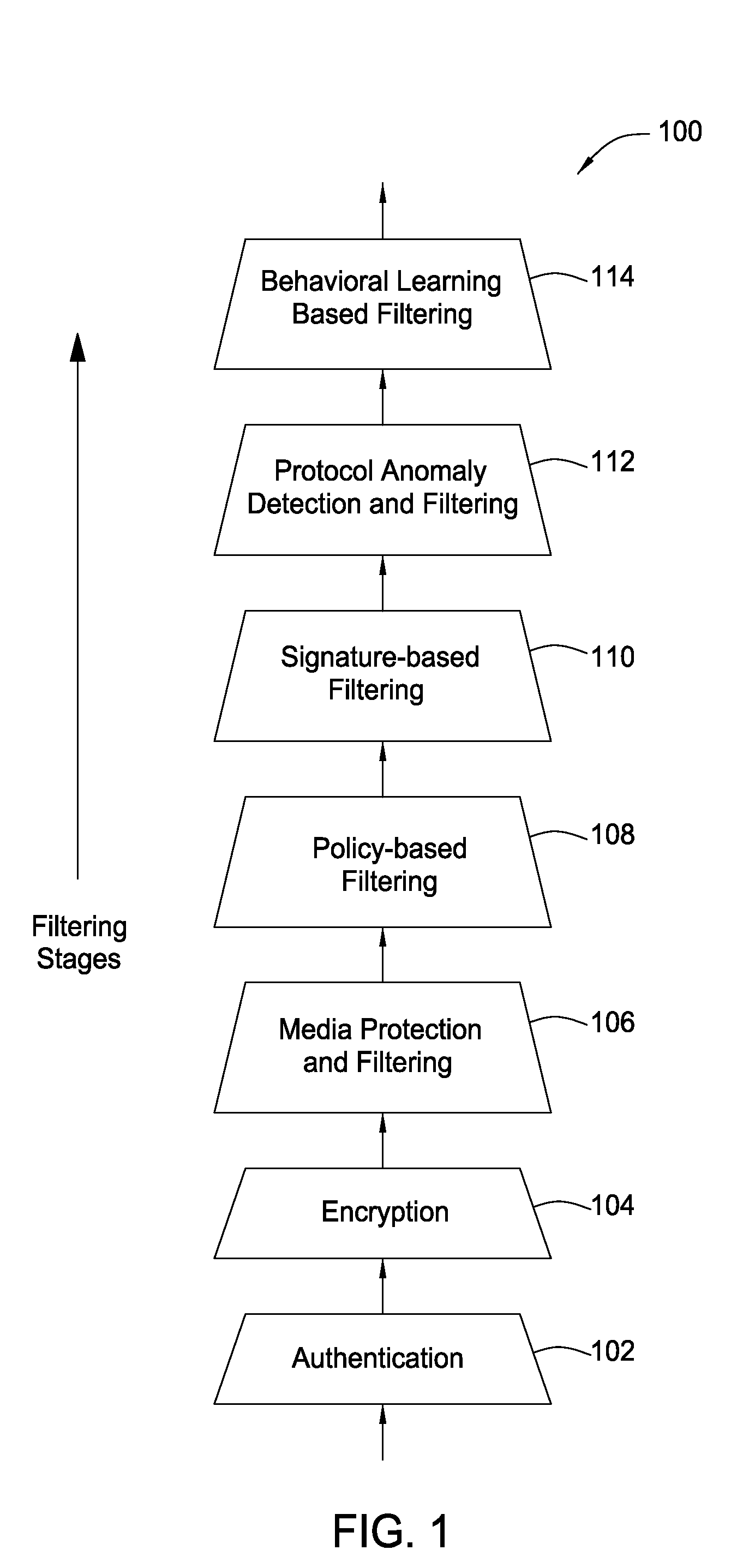
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
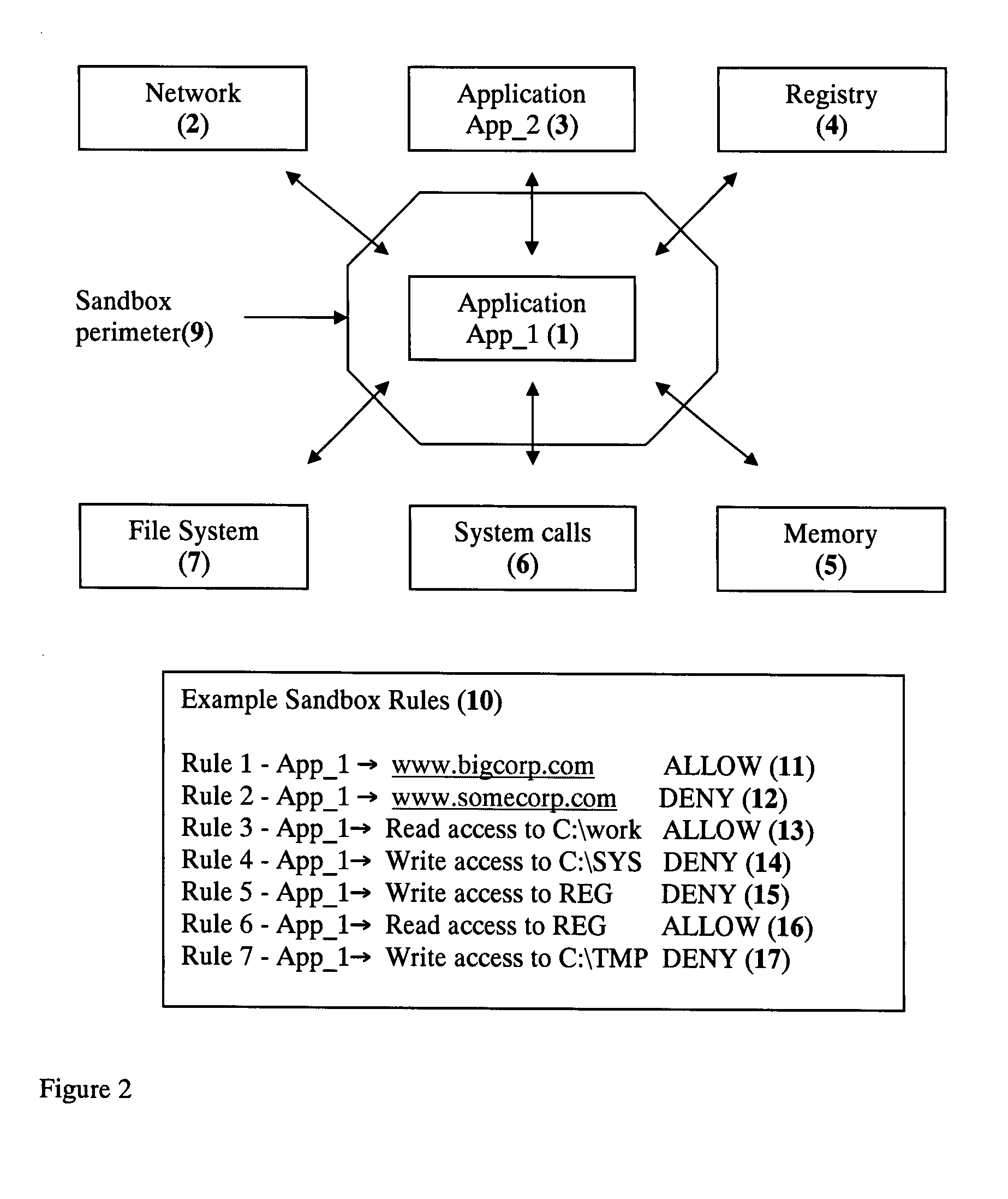
Application Sandbox to Detect, Remove, and Prevent Malware
InactiveUS20080016339A1Limit and eliminate attackRemove or neutralized malware on disk and in memoryPlatform integrity maintainanceSecuring communicationNetwork attackMalware
The disclosed invention is a new method and apparatus for protecting applications from local and network attacks. This method also detects and removes malware and is based on creating a sandbox at application and kernel layer. By monitoring and controlling the behavior and access privileges of the application and only selectively granting access, any attacks that try to take advantage of the application vulnerabilities are thwarted.
Owner:SHUKLA JAYANT
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
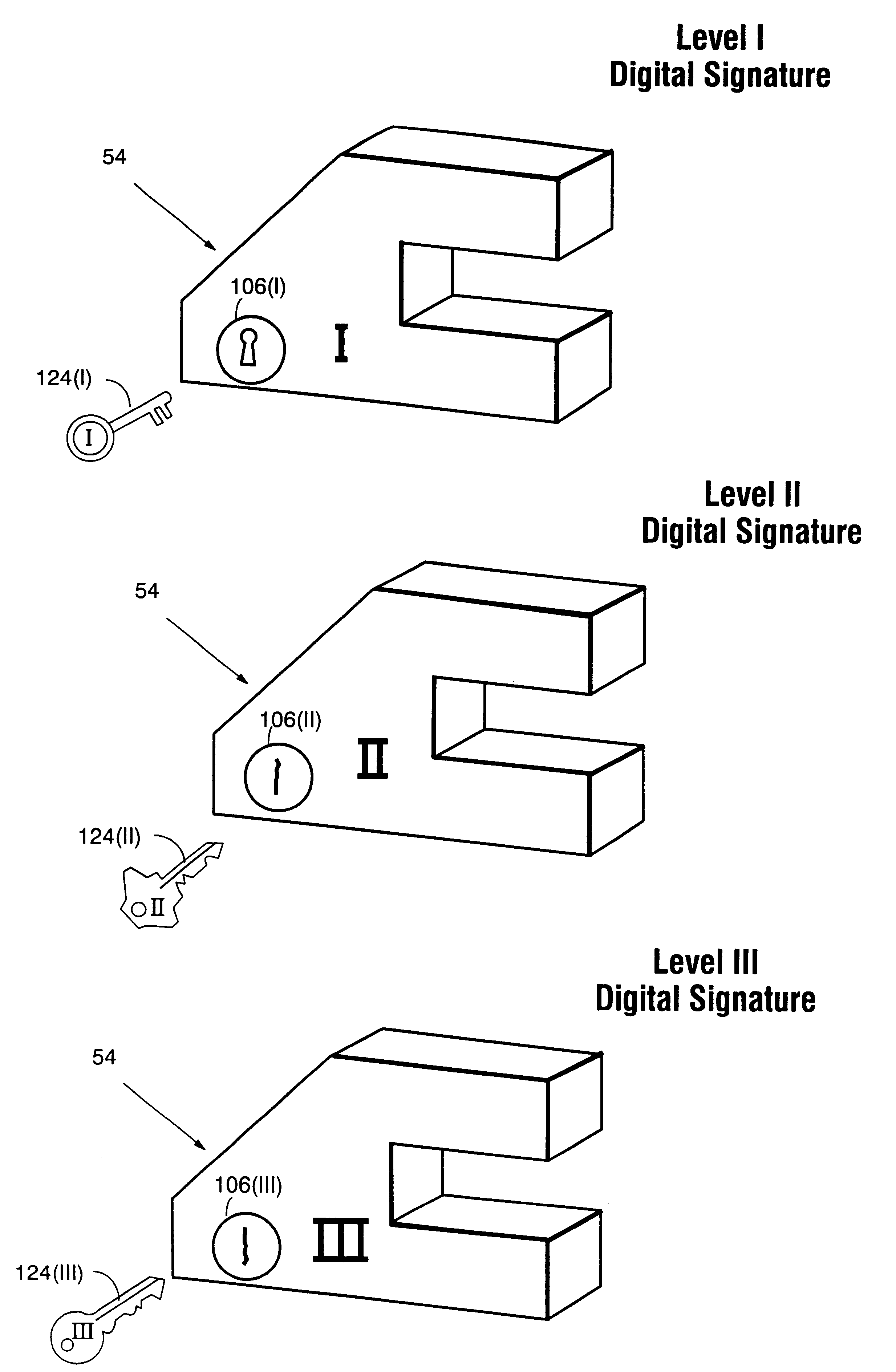
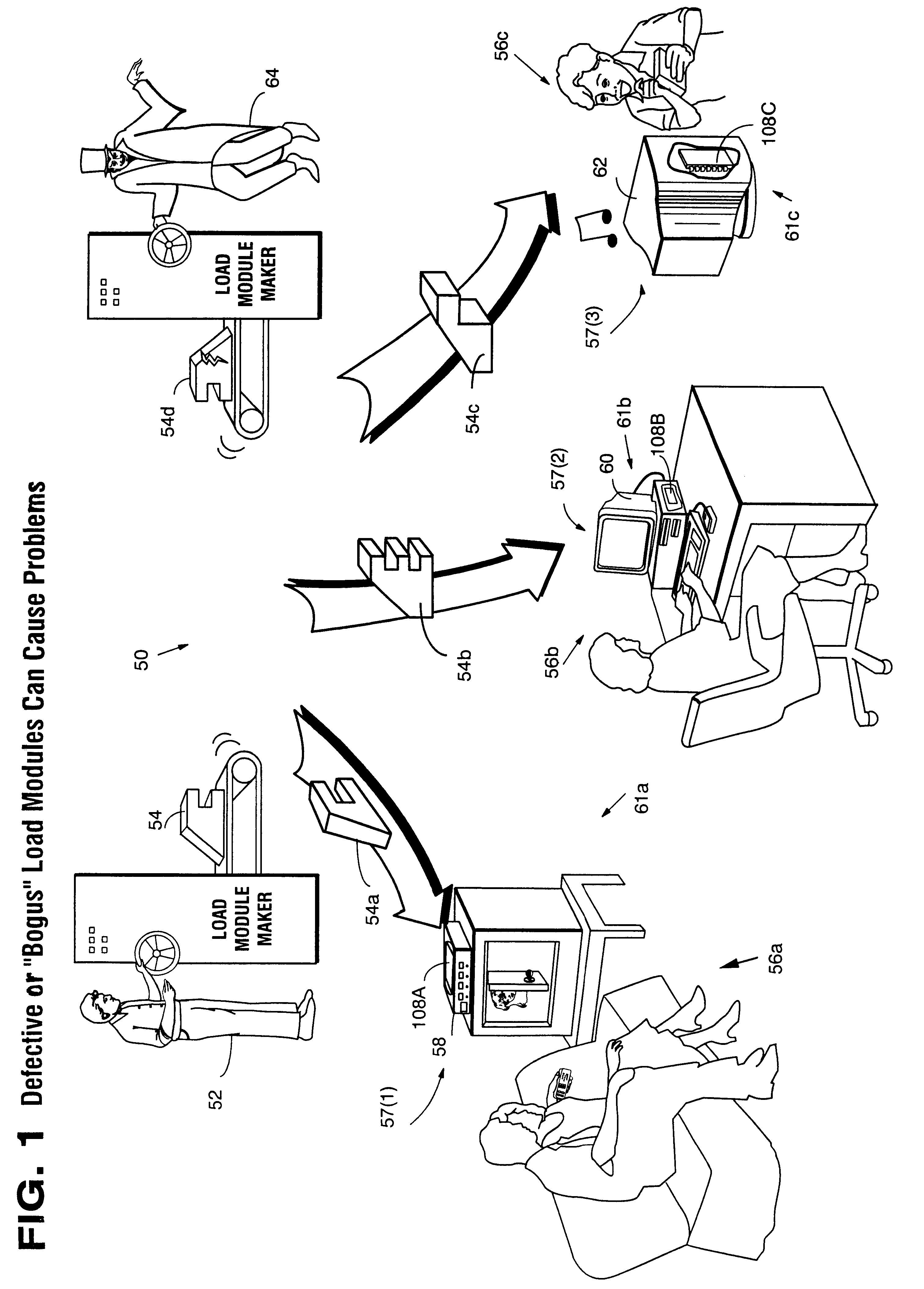
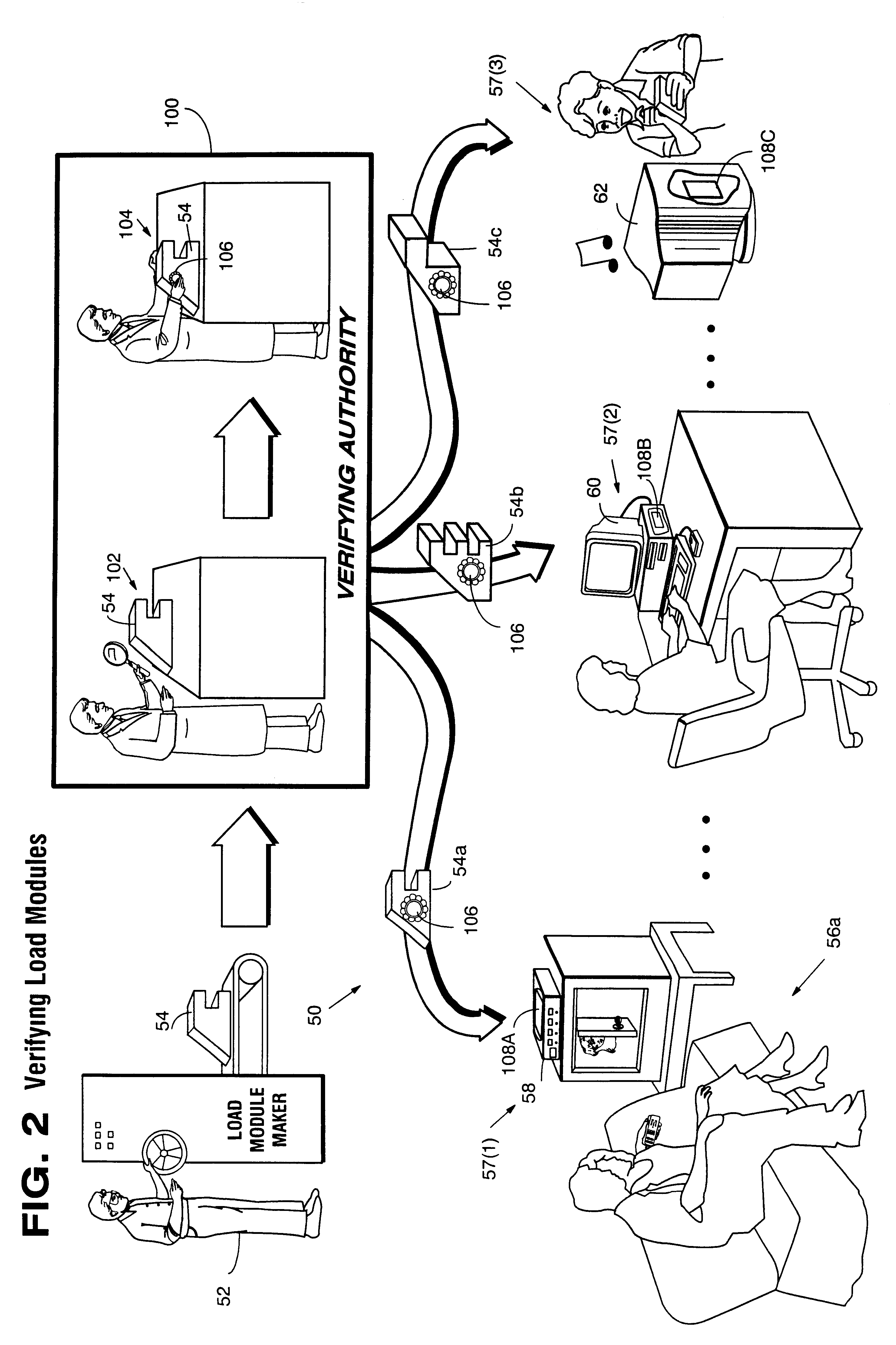
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
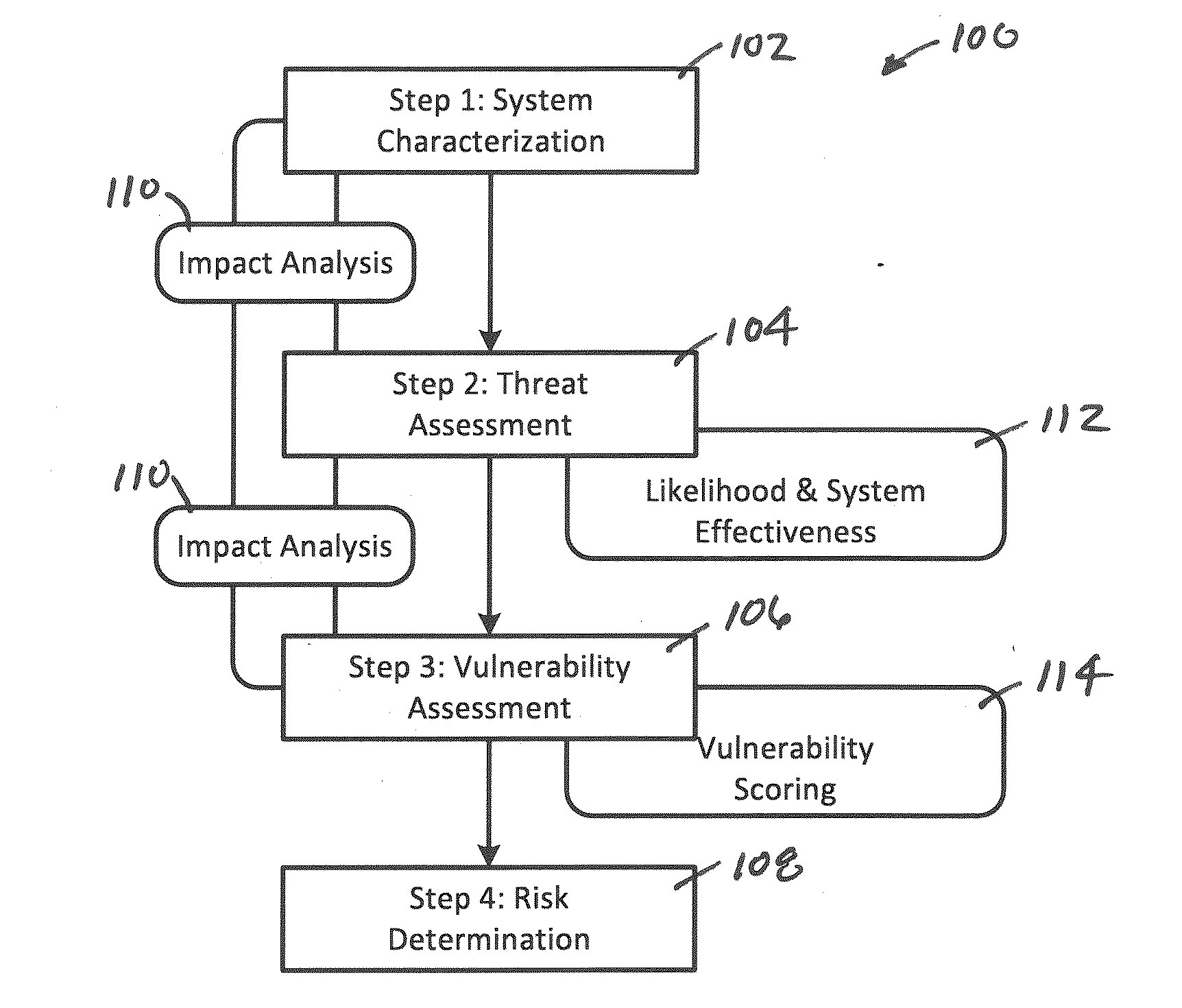
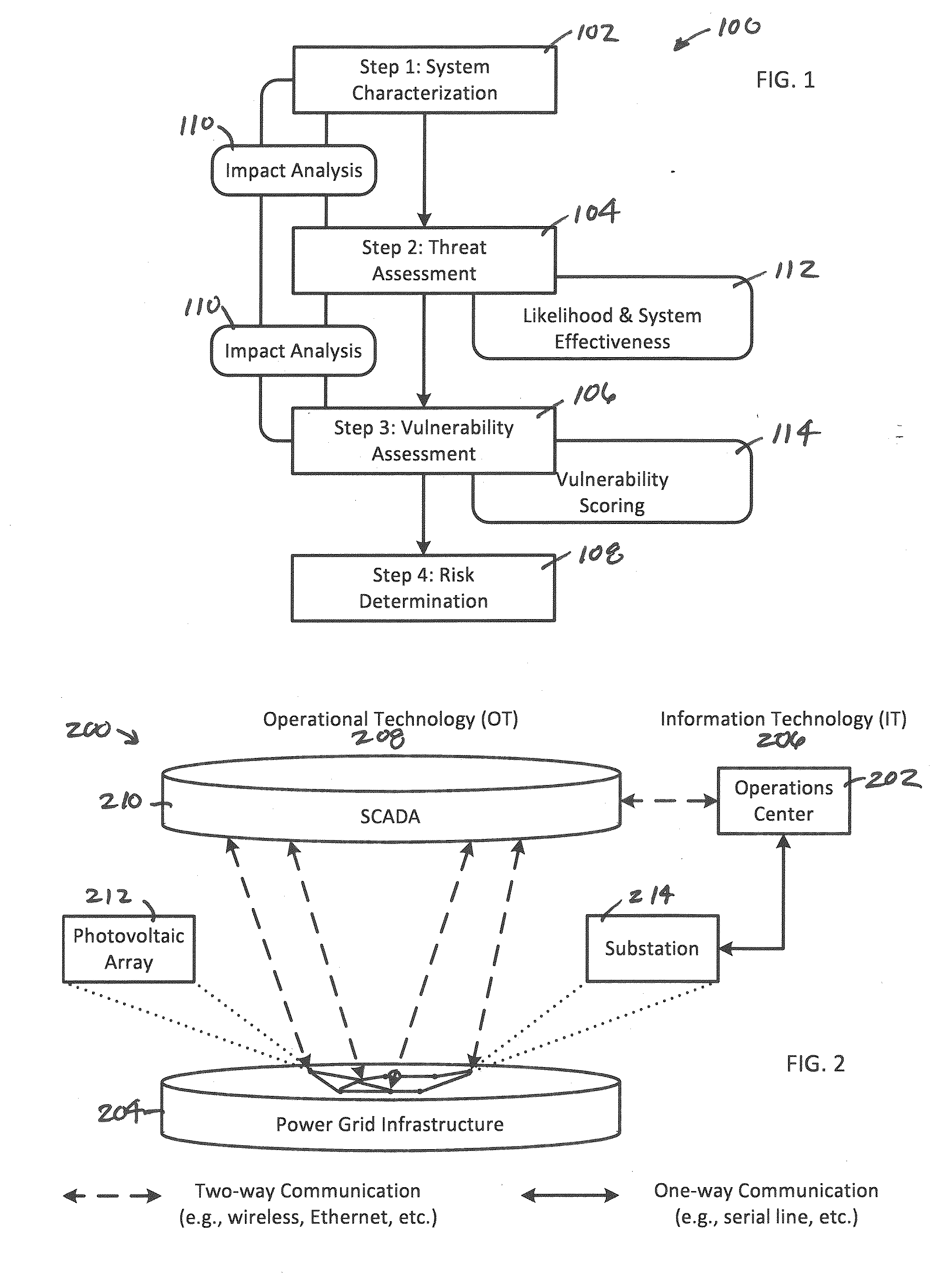
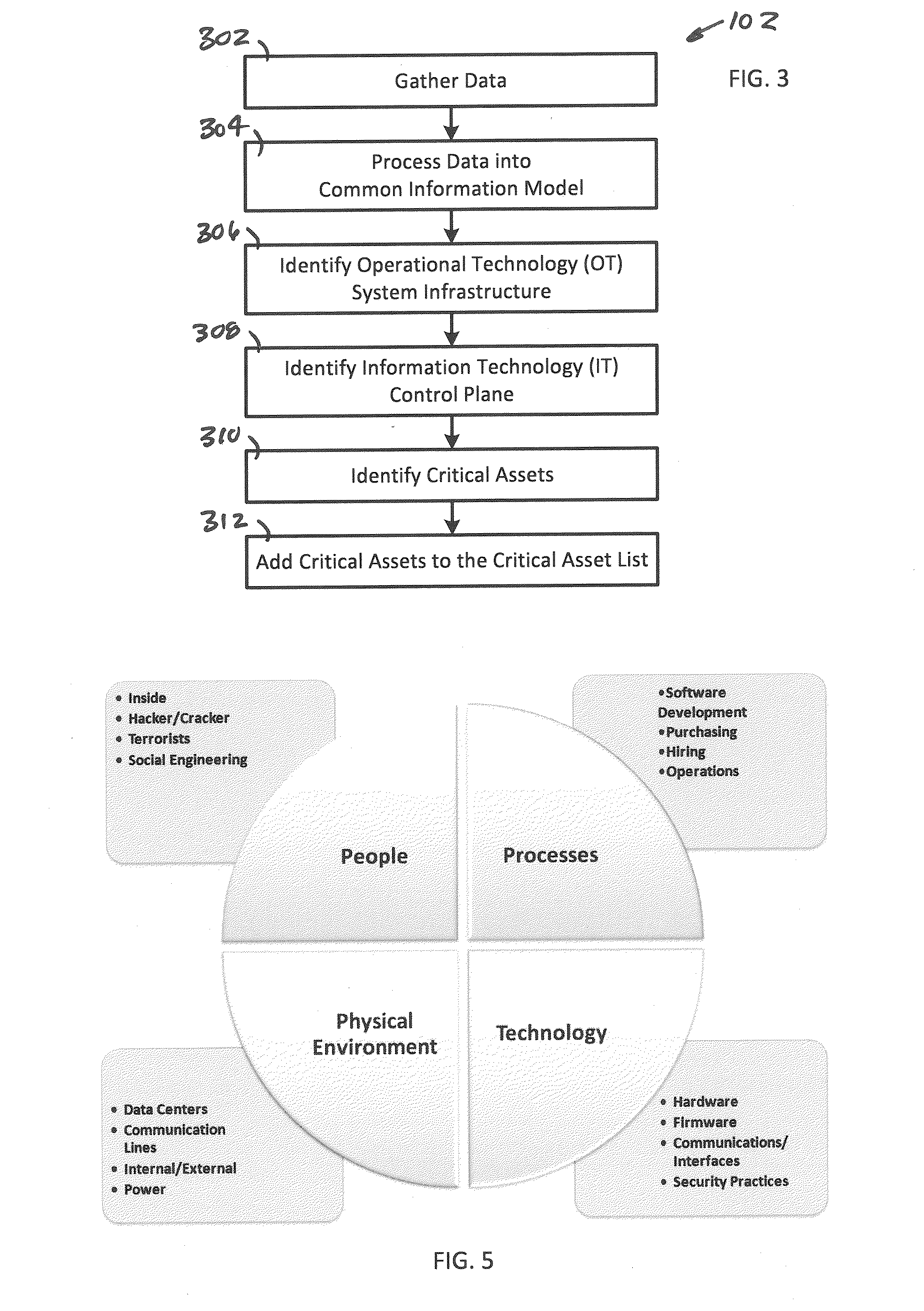
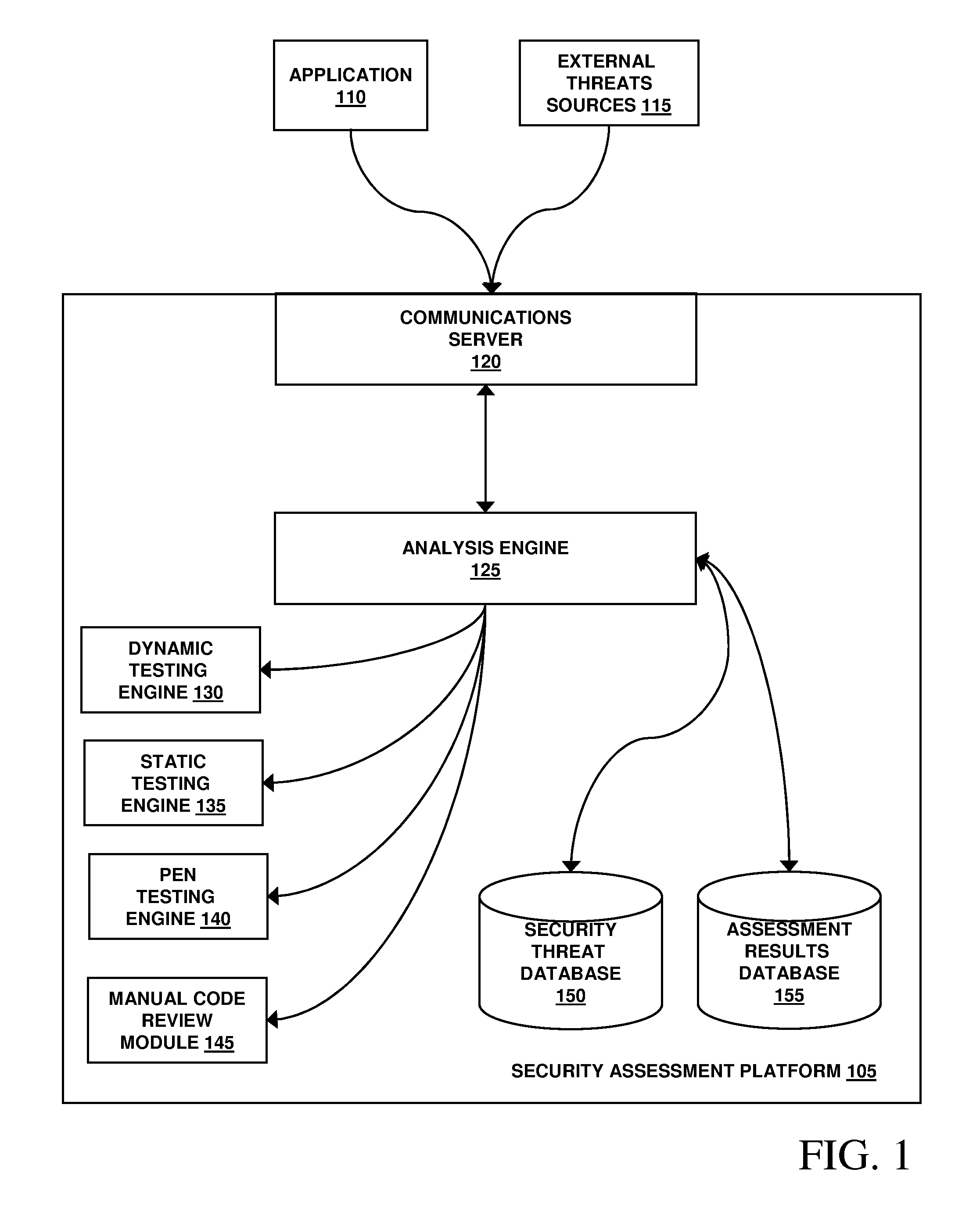
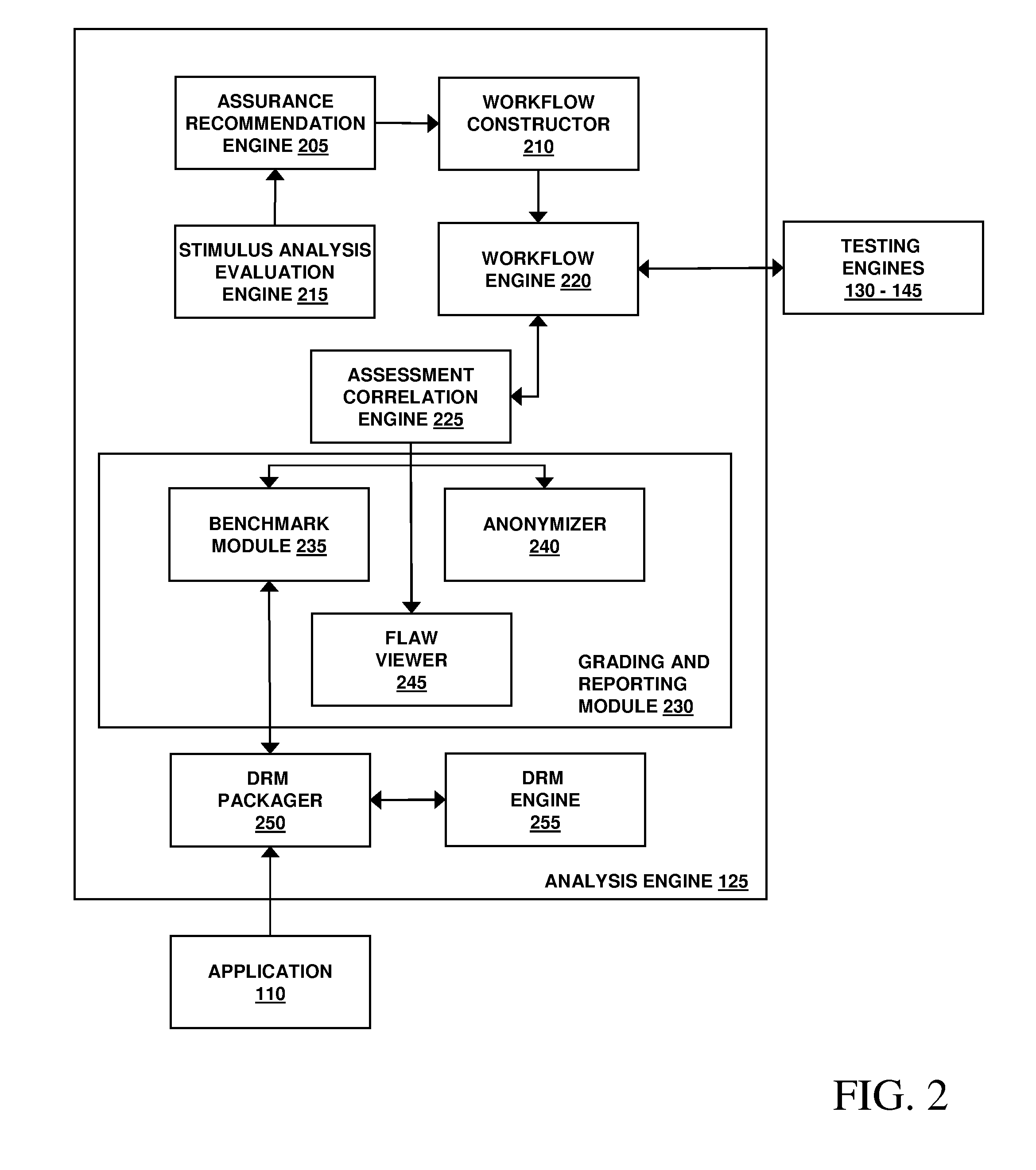
System, Method and Apparatus for Assessing a Risk of One or More Assets Within an Operational Technology Infrastructure
A system, method and apparatus assesses a risk of one or more assets within an operational technology infrastructure by providing a database containing data relating to the one or more assets, calculating a threat score for the one or more assets using one or more processors communicably coupled to the database, calculating a vulnerability score for the one or more assets using the one or more processors, calculating an impact score for the one or more assets using the one or more processors, and determining the risk of the one or more assets based on the threat score, the vulnerability score and the impact score using the one or more processors.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
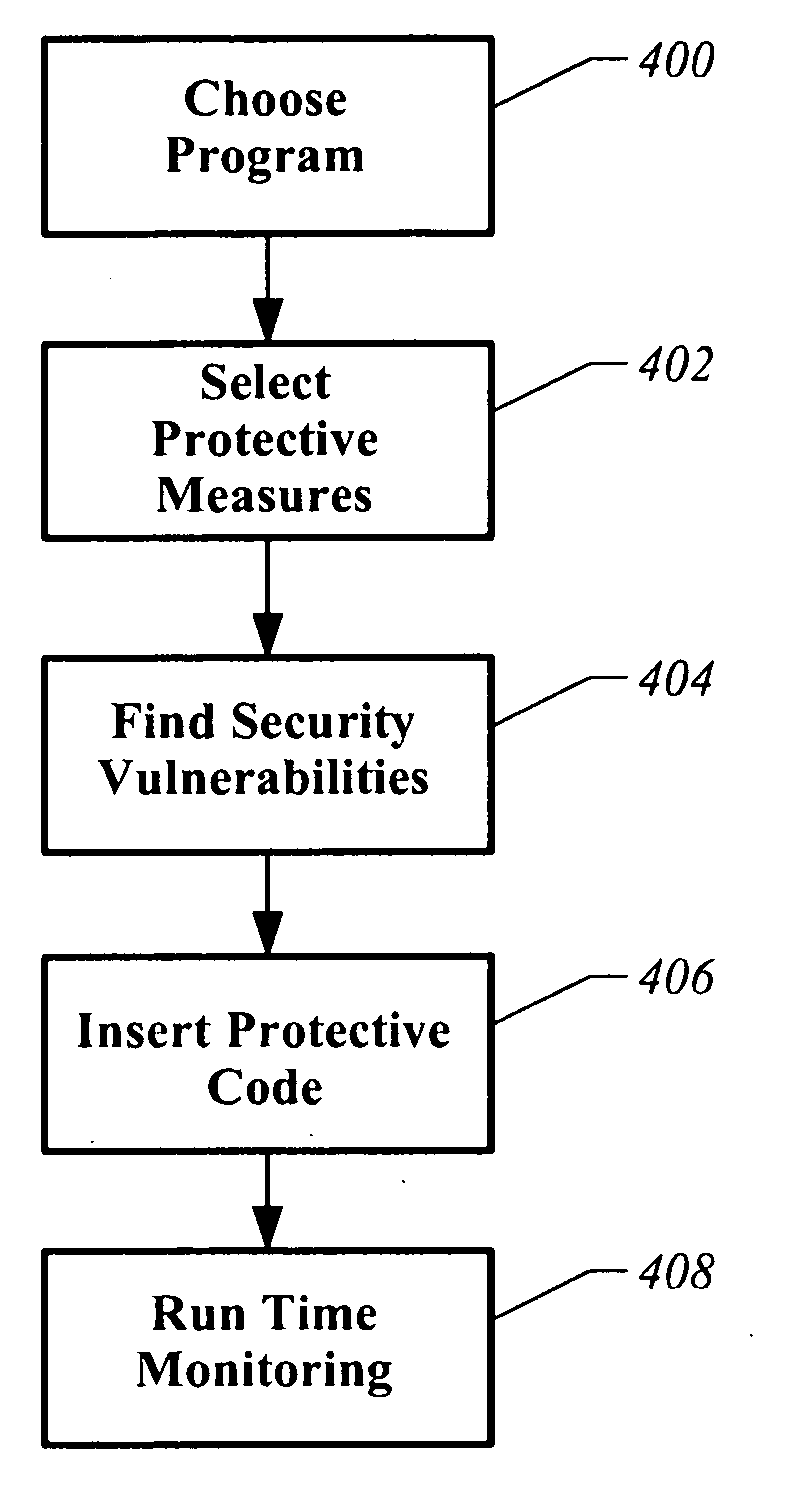
Apparatus and method for analyzing and supplementing a program to provide security
ActiveUS20070074169A1Memory loss protectionError detection/correctionProgramming languageProgram instruction
A computer readable storage medium has executable instructions to perform an automated analysis of program instructions. The automated analysis includes at least two analyses selected from an automated analysis of injection vulnerabilities, an automated analysis of potential repetitive attacks, an automated analysis of sensitive information, and an automated analysis of specific HTTP attributes. Protective instructions are inserted into the program instructions. The protective instructions are utilized to detect and respond to attacks during execution of the program instructions.
Owner:MICRO FOCUS LLC
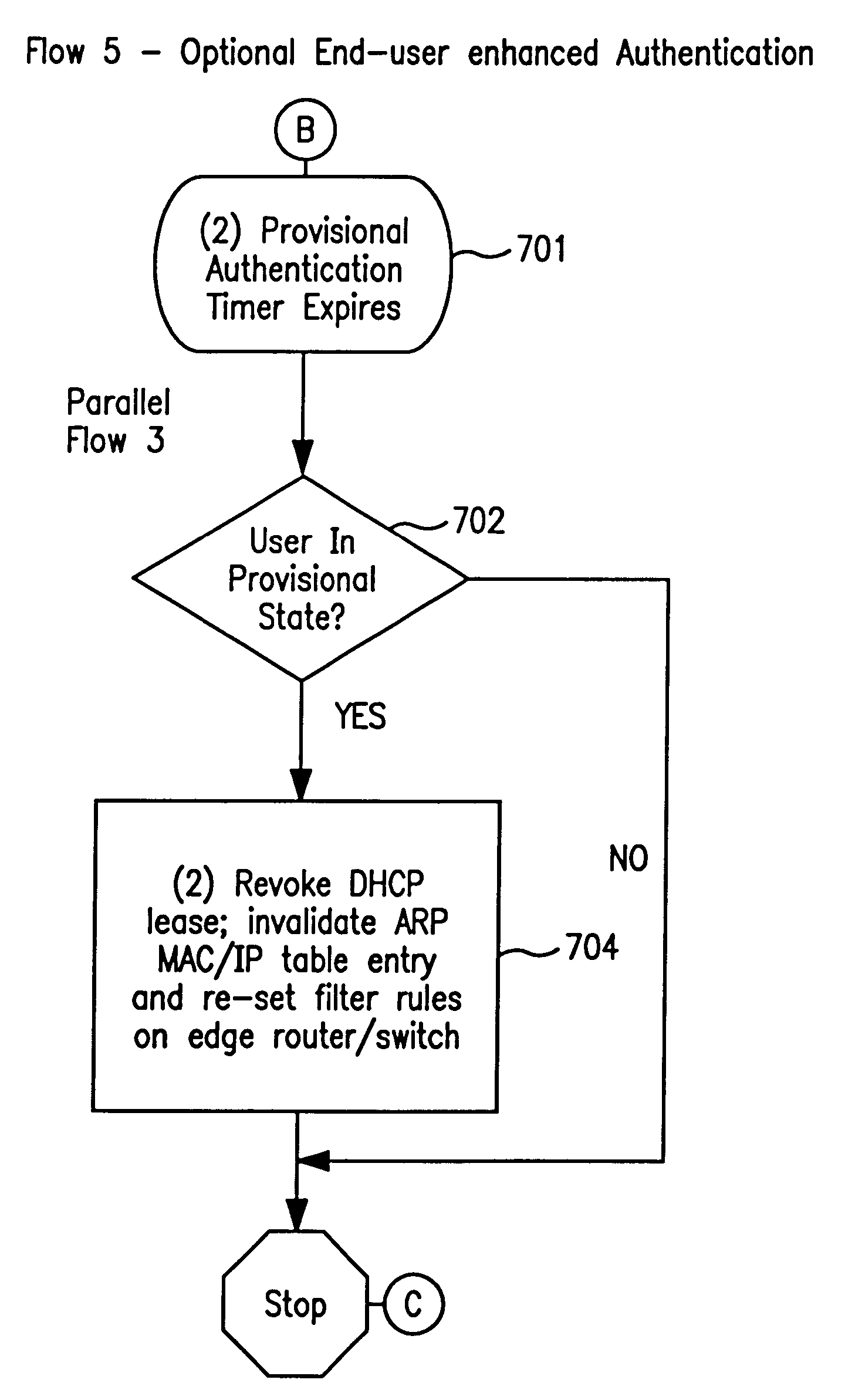
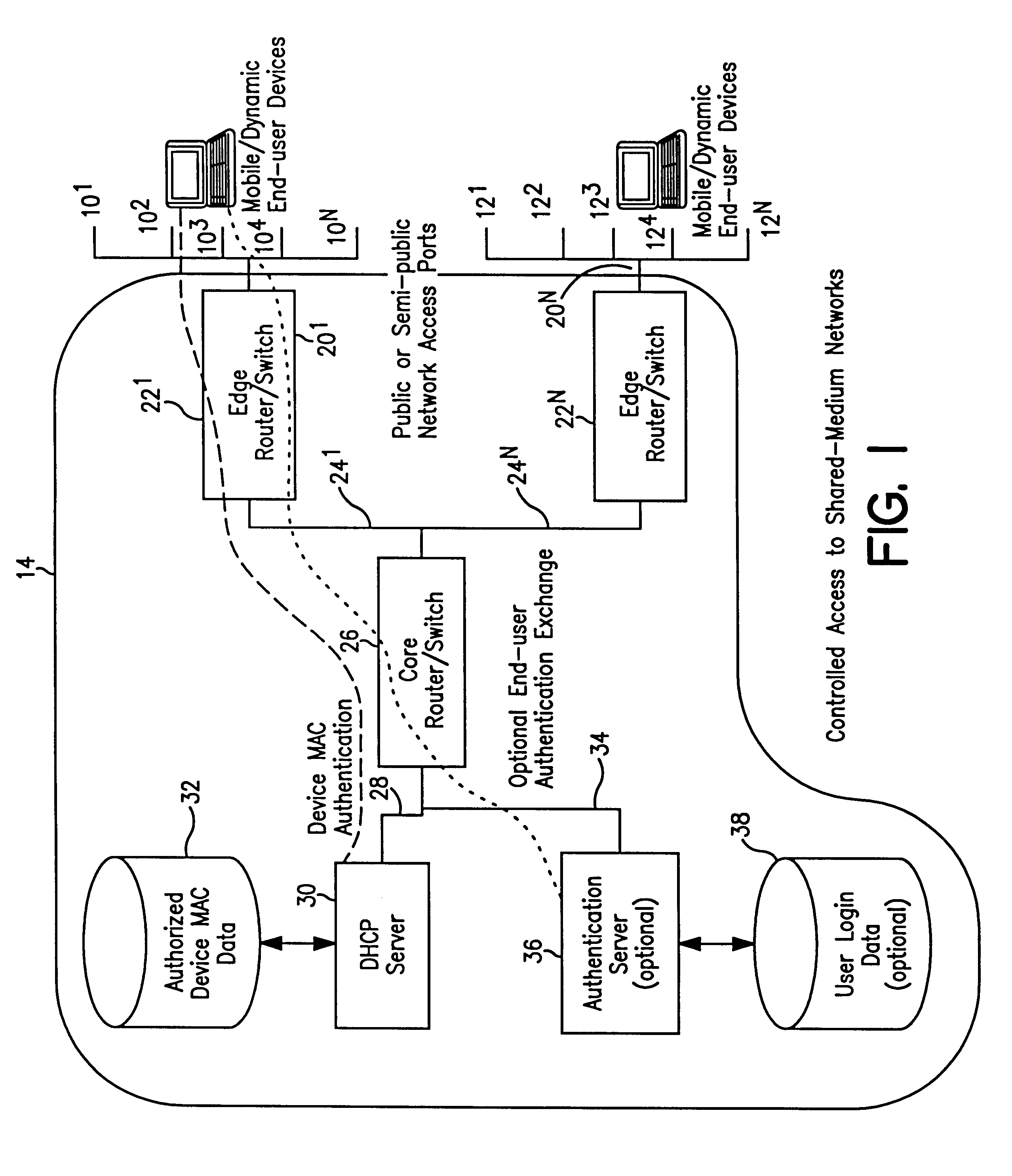
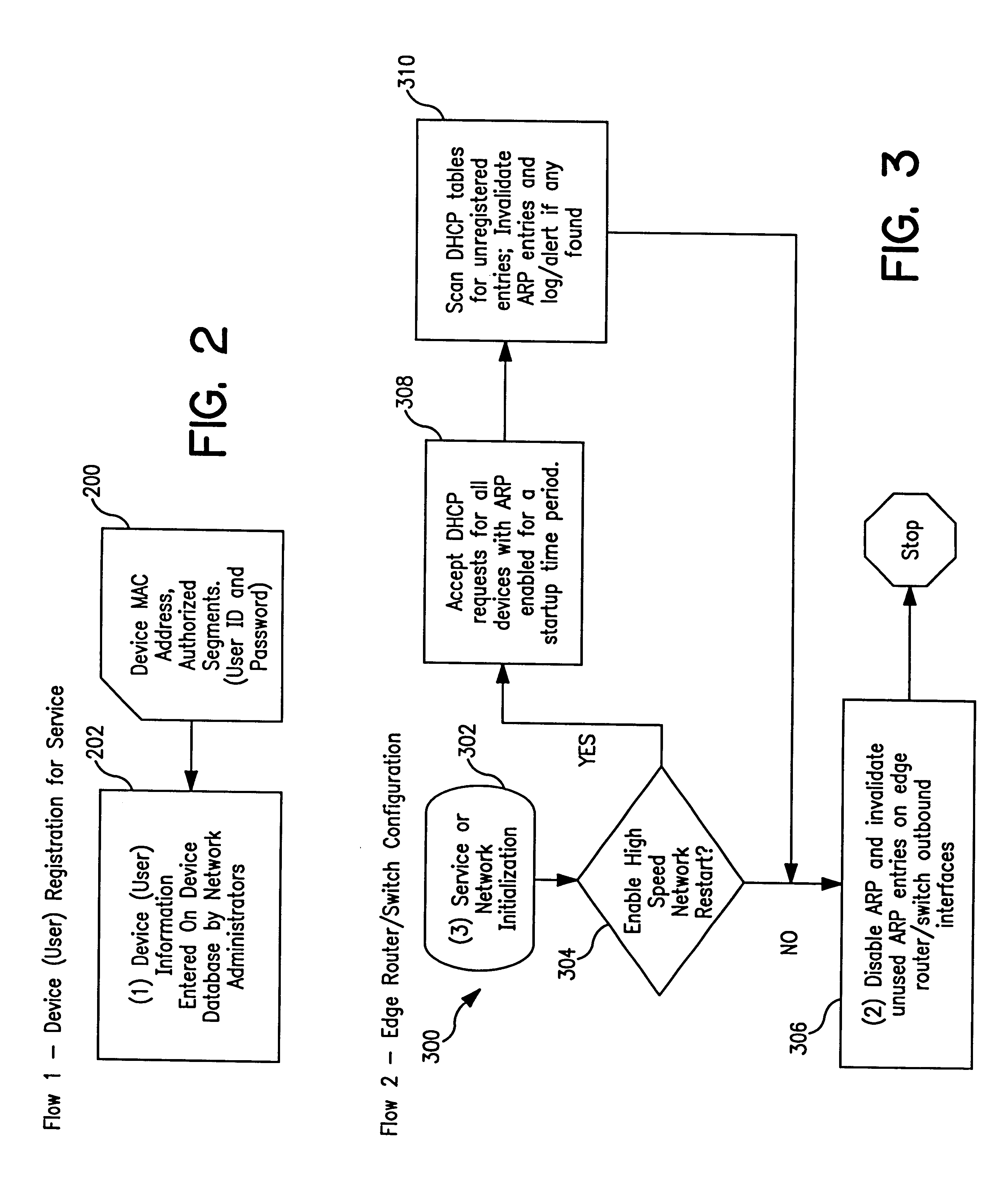
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
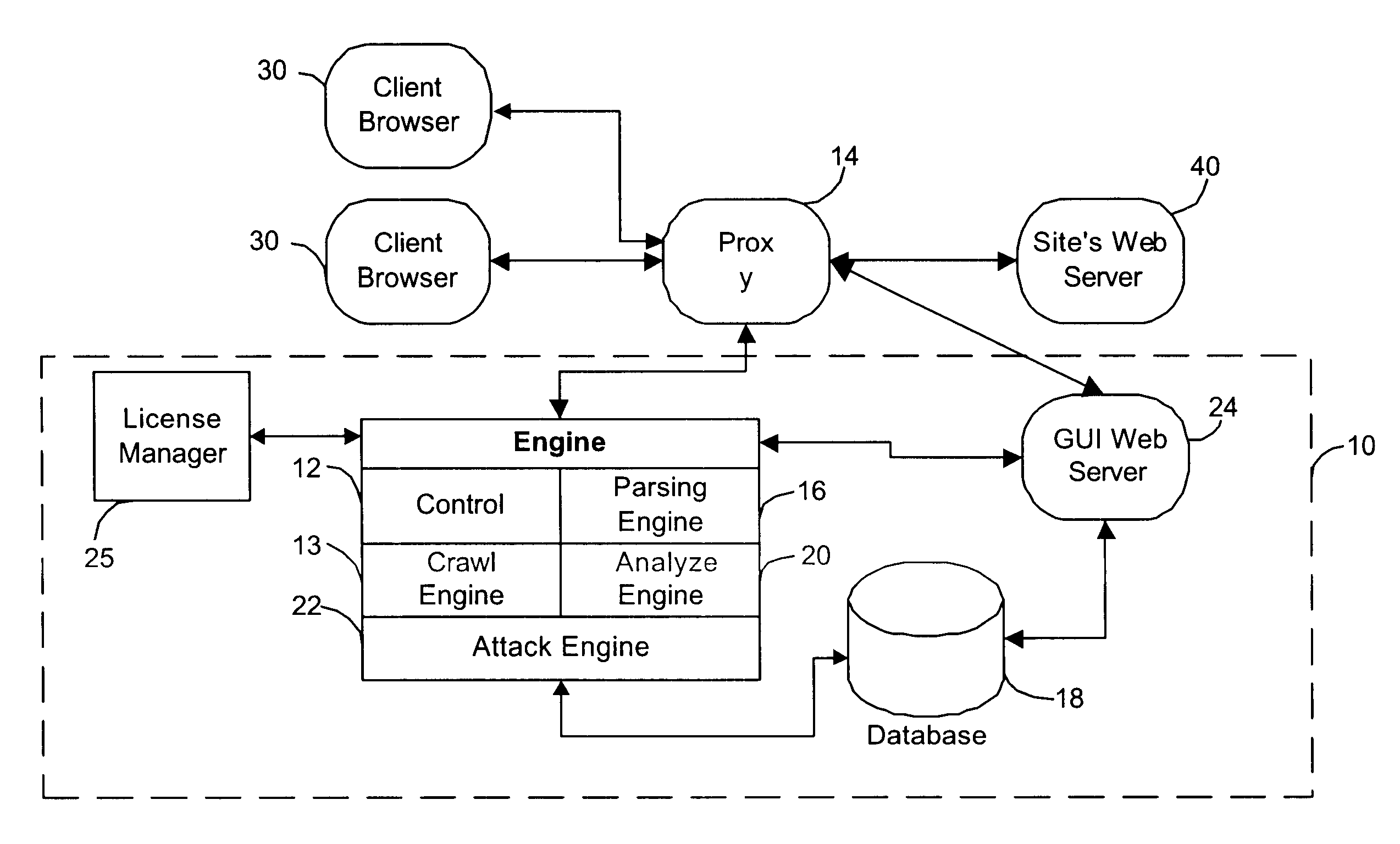
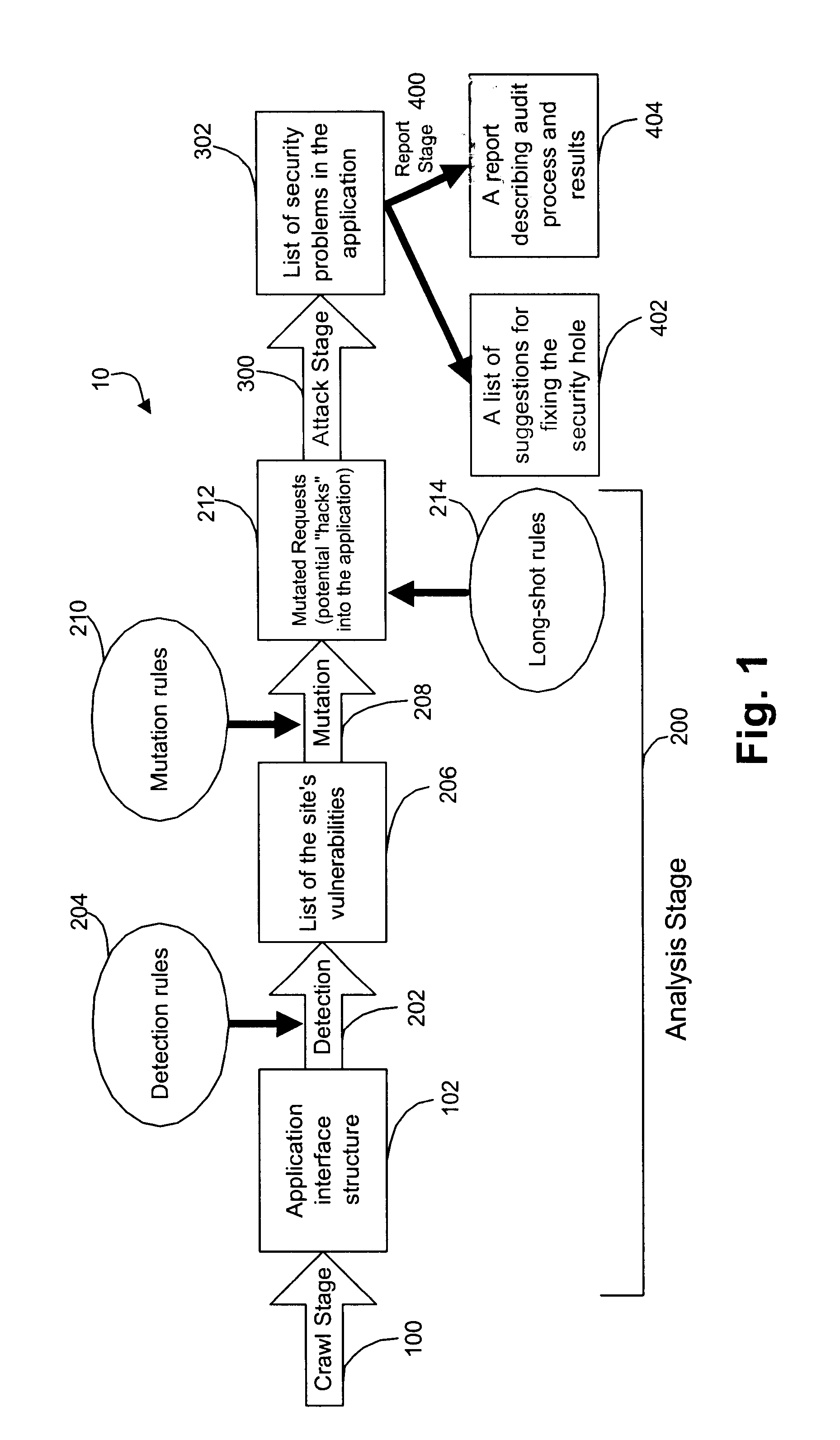
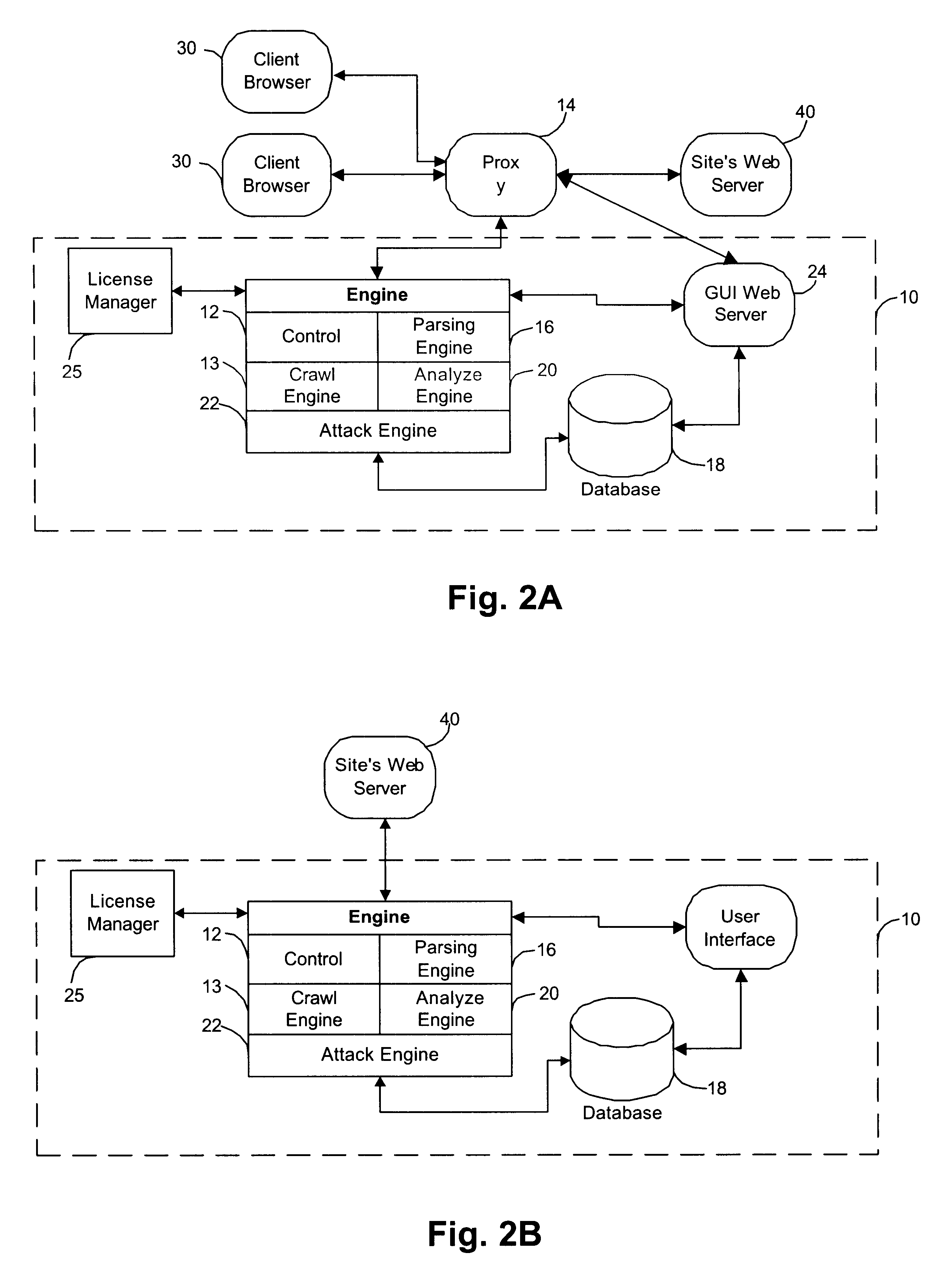
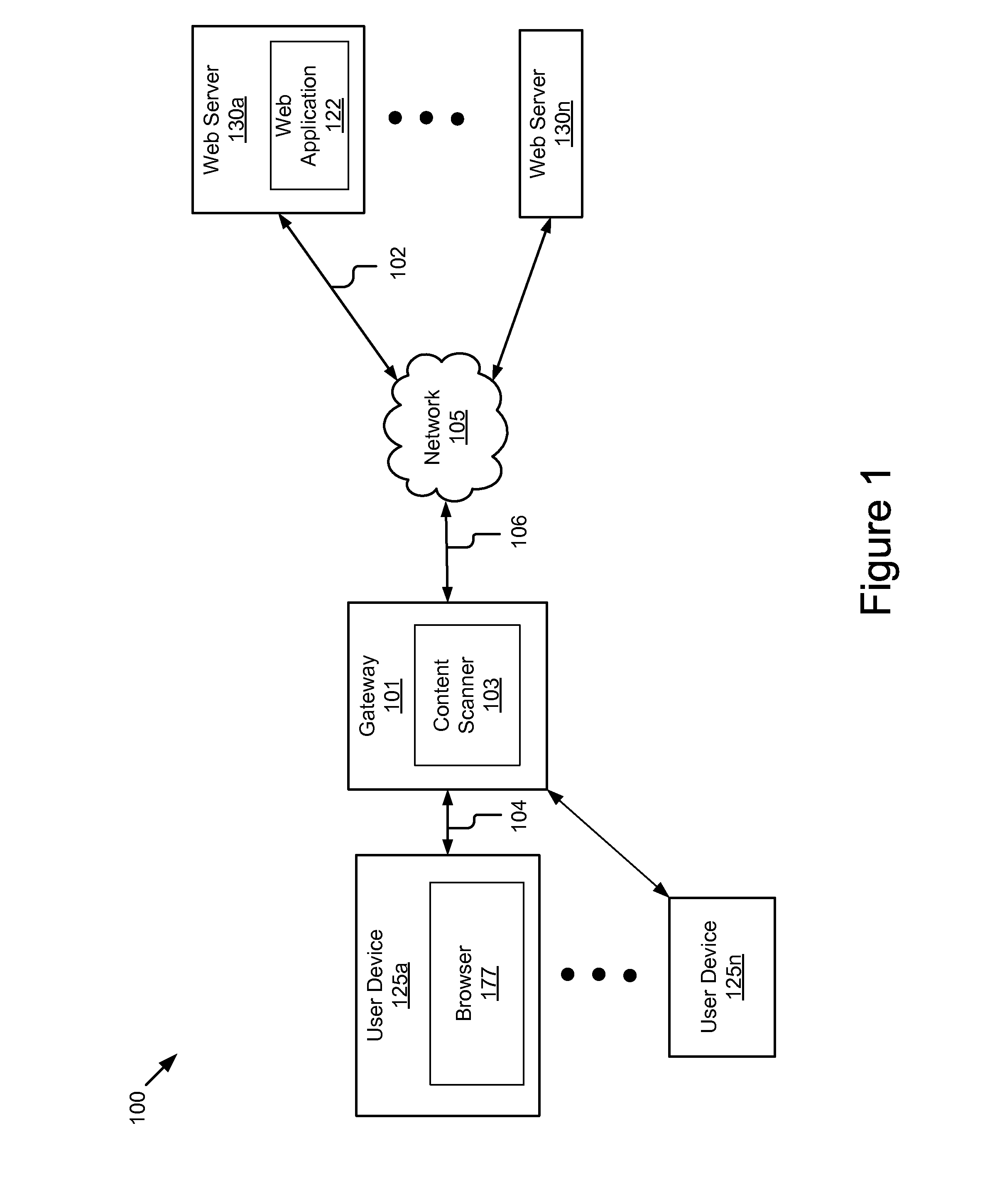
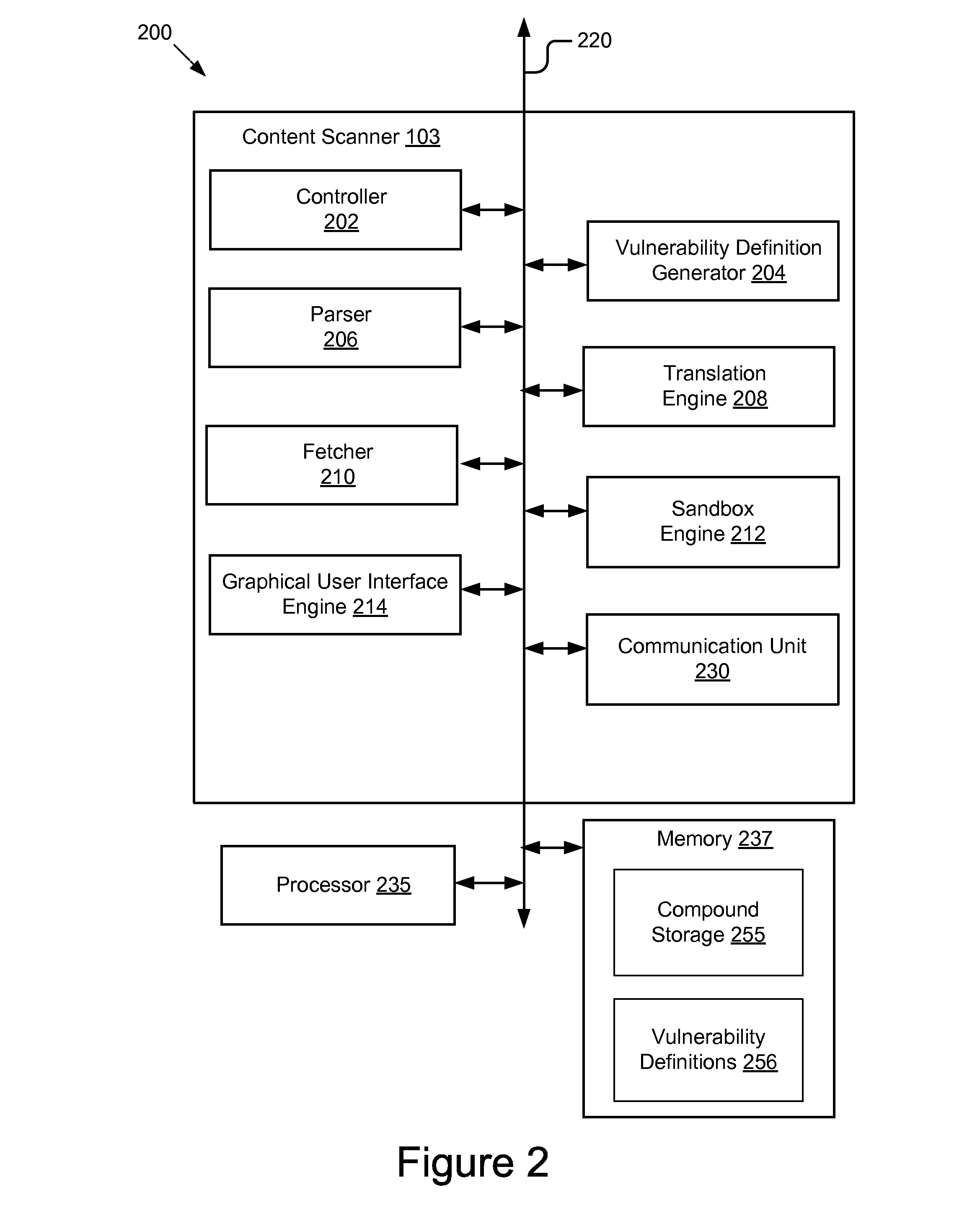
System for determining web application vulnerabilities
InactiveUS6584569B2Memory loss protectionUnauthorized memory use protectionWeb applicationApplication procedure
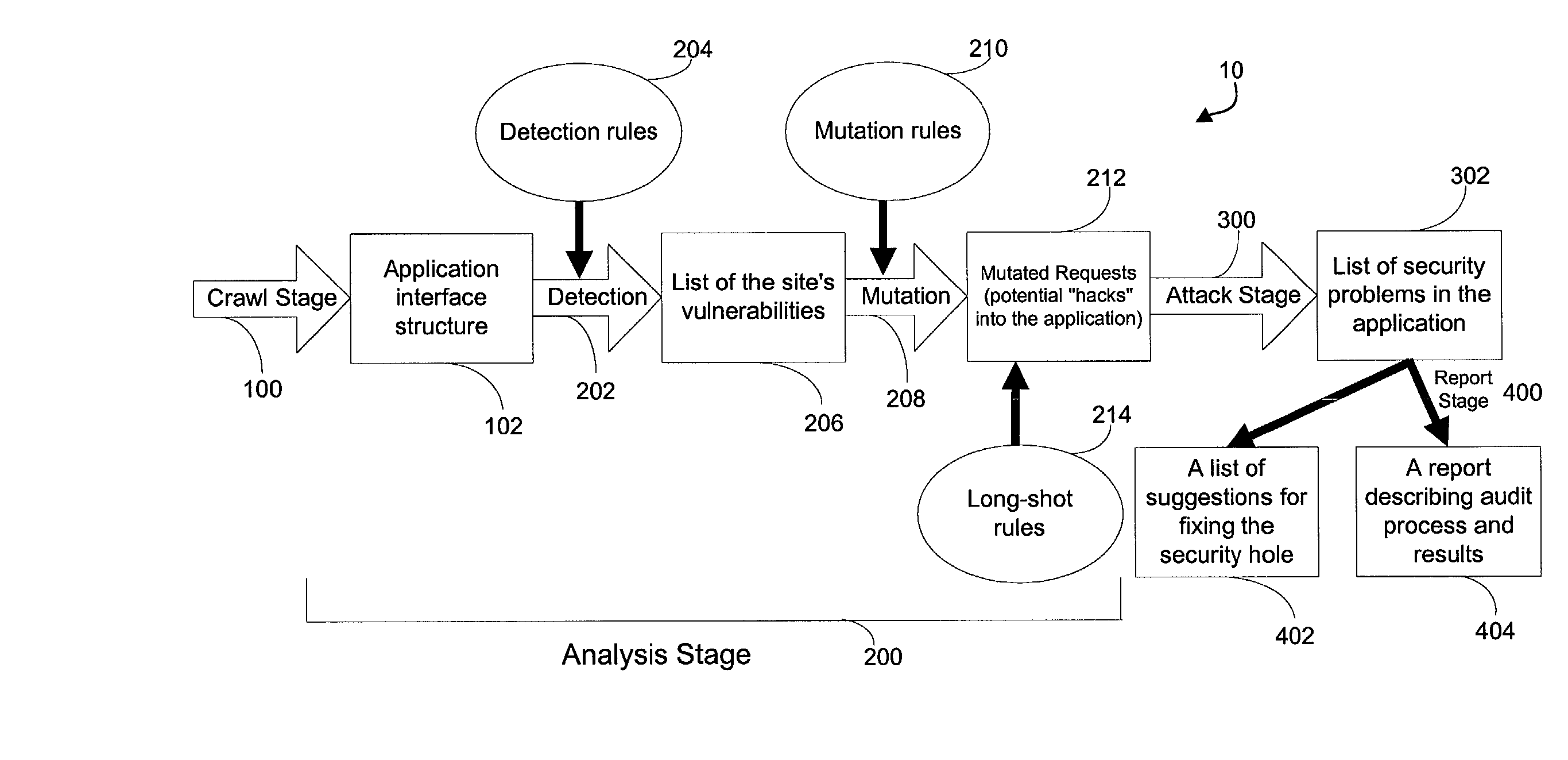
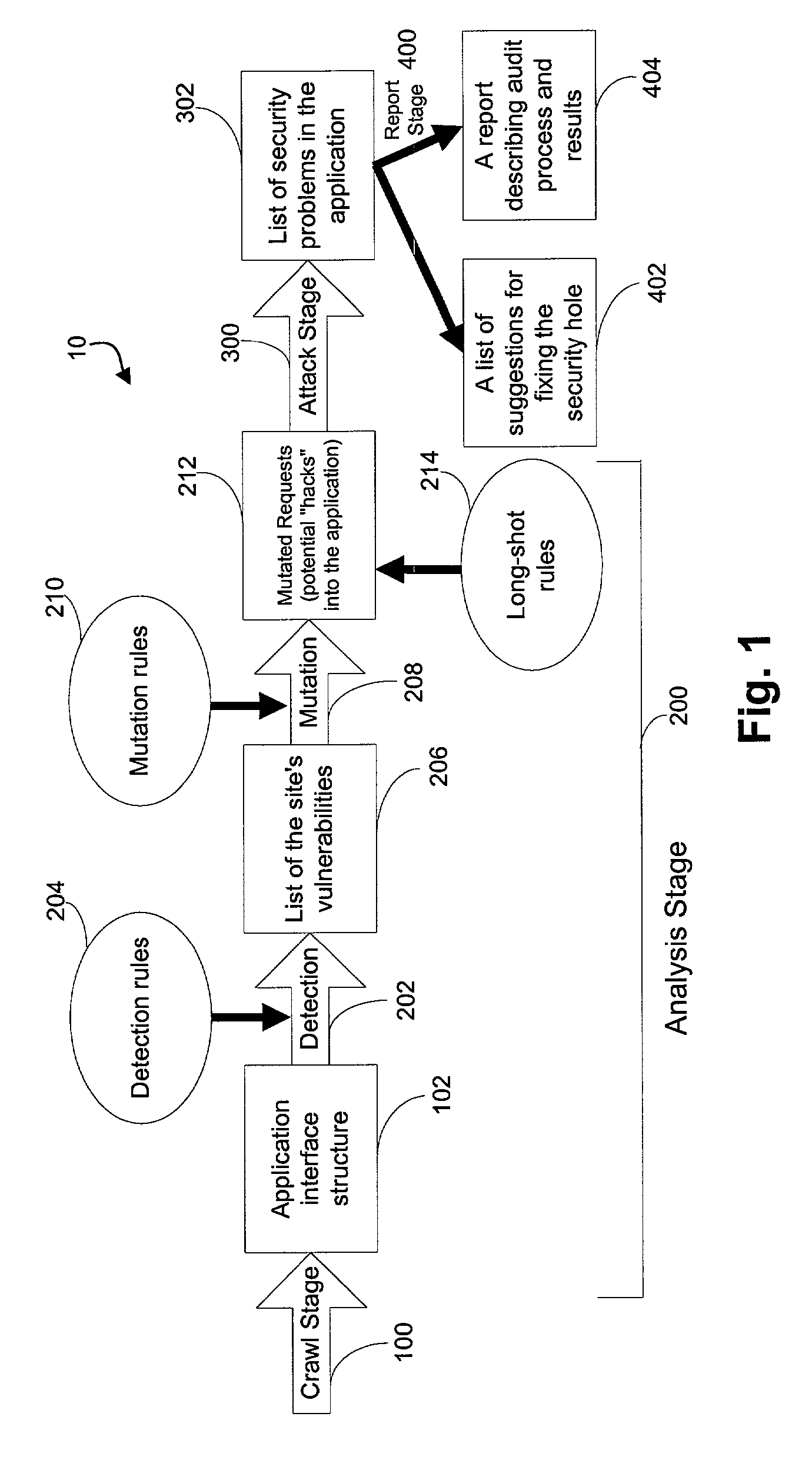
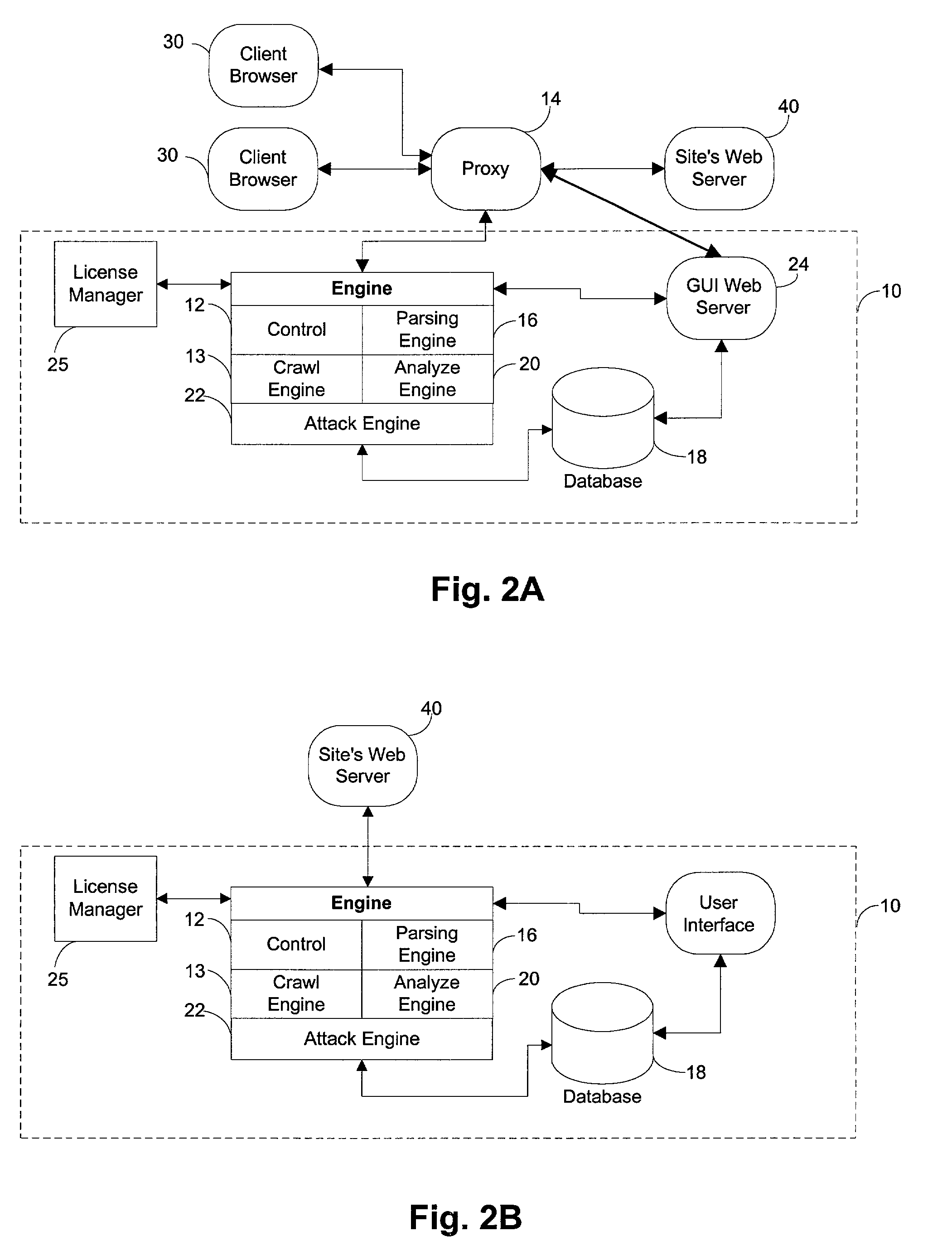
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
Method, system and computer program product for assessing information security
A method, system and computer program product for assessing information security interviews users regarding technical and non-technical issues. In an embodiment, users are interviewed based on areas of expertise. In an embodiment, information security assessments are performed on domains within an enterprise, the results of which are rolled-up to perform an information security assessment across the enterprise. The invention optionally includes application specific questions and vulnerabilities and / or industry specific questions and vulnerabilities. The invention optionally permits users to query a repository of expert knowledge. The invention optionally provides users with working aids. The invention optionally permits users to execute third party testing / diagnostic applications. The invention, optionally combines results of executed third party testing / diagnostic applications with user responses to interview questions, to assess information security. A system in accordance with the invention includes an inference engine, which may include a logic based inference engine, a knowledge based inference engine, and / or an artificial intelligence inference engine. In an embodiment, the invention includes an application specific tailoring tool that allows a user to tailor the system to assess security of information handled by a third party application program.
Owner:SAFEOPERATIONS
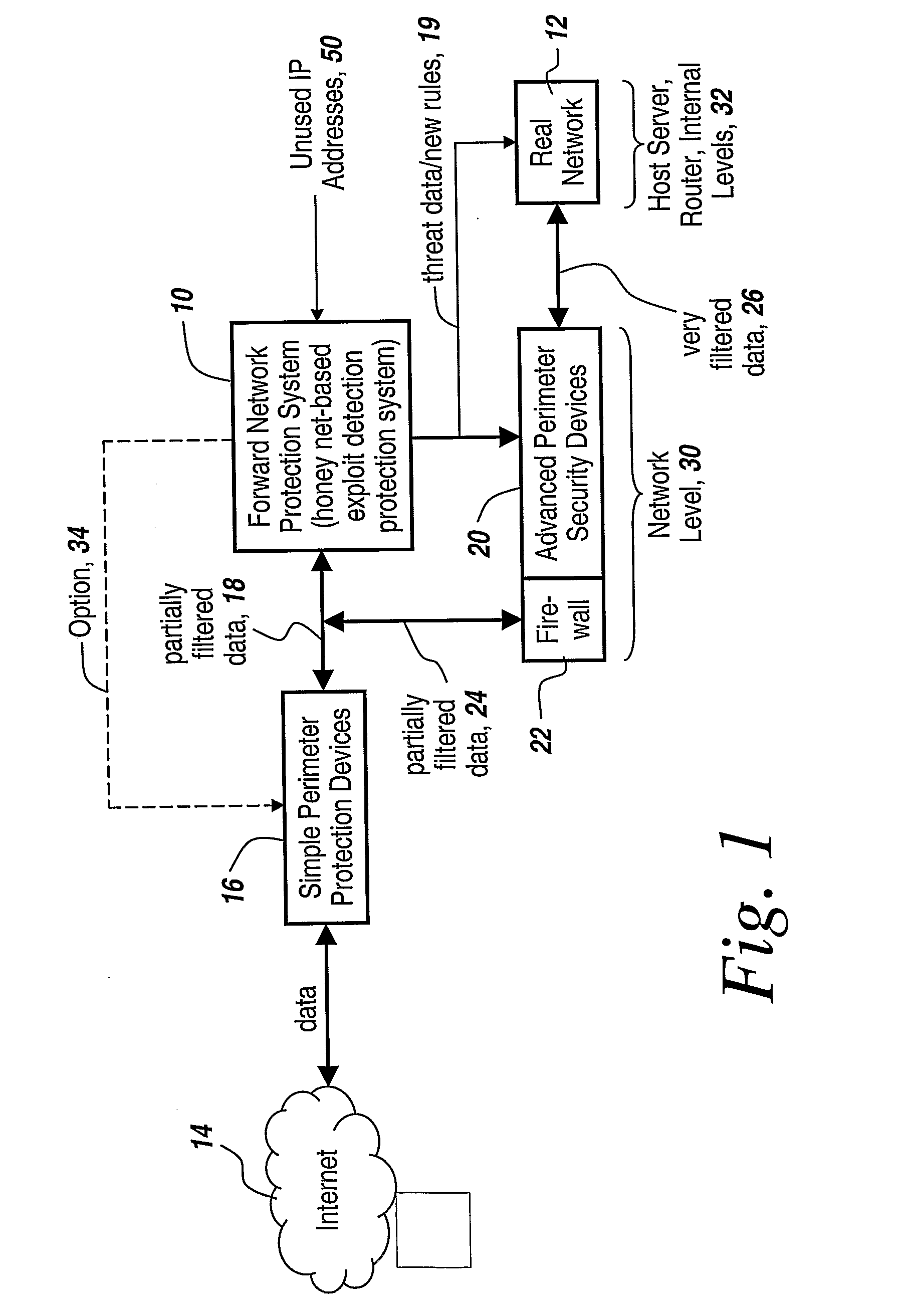
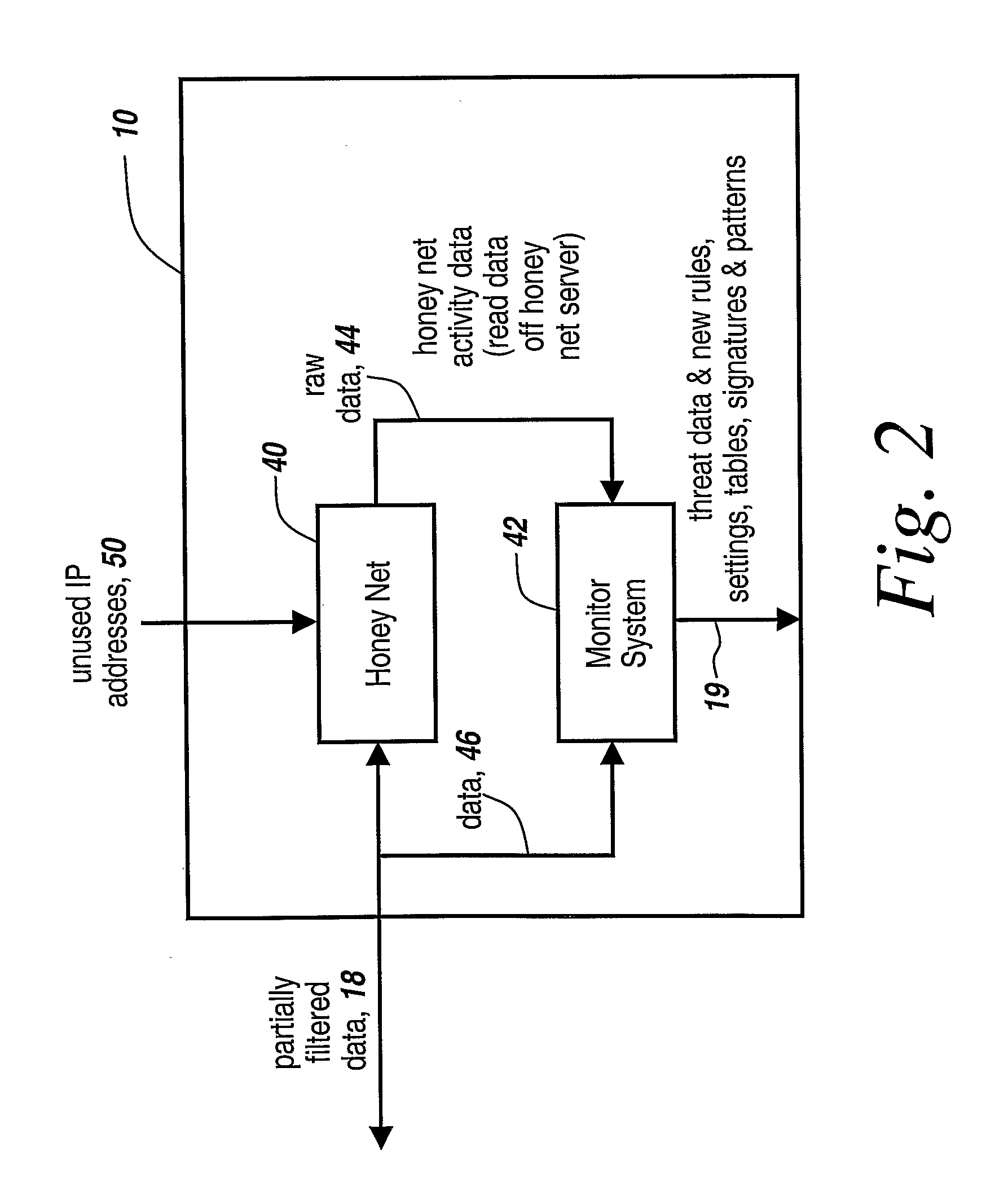
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
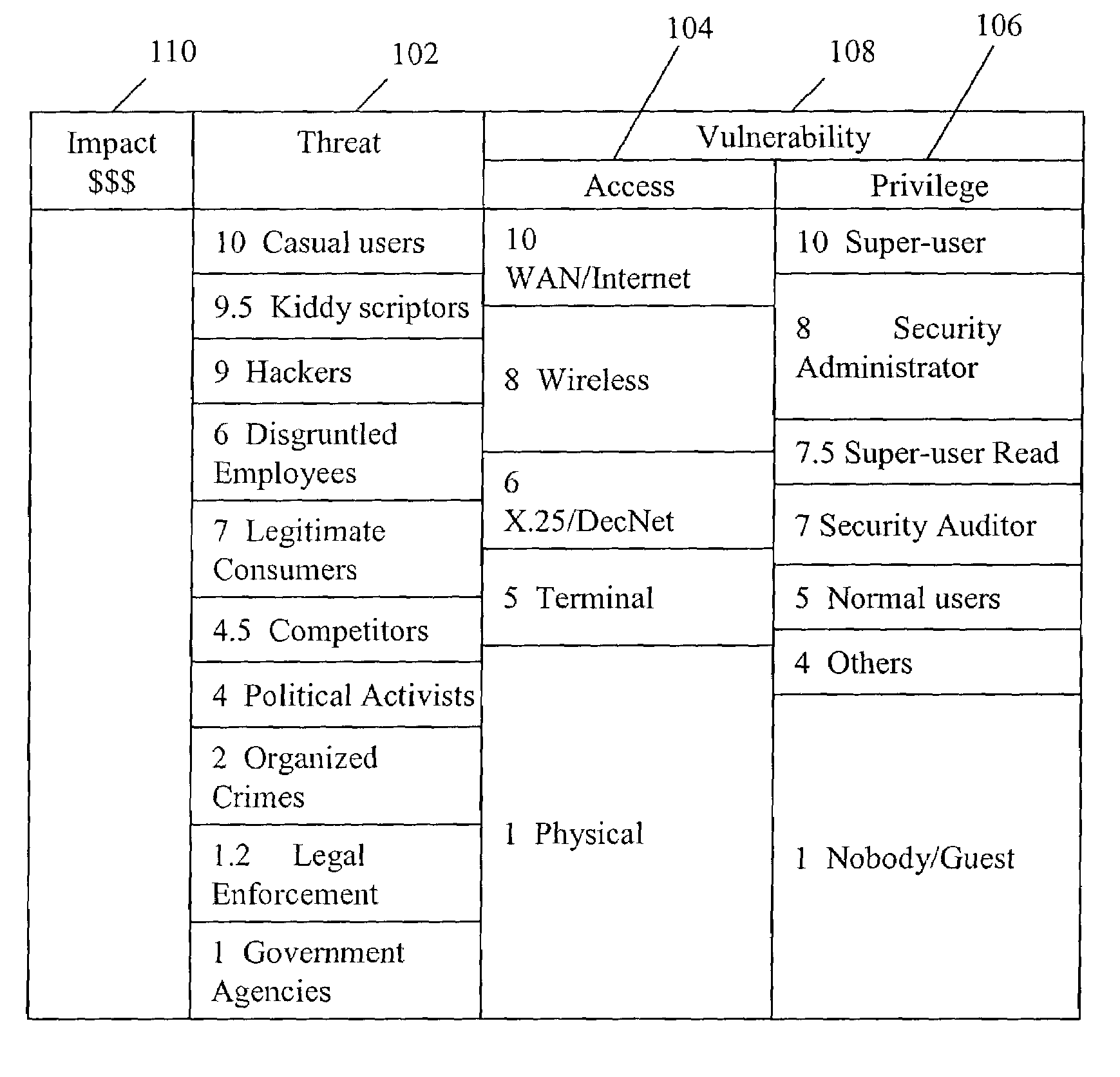
Method and system of assessing risk using a one-dimensional risk assessment model
A quantitative model combines a one-dimensional risk-assessment approach with expert knowledge to enable calculation of a probability or likelihood of exploitation of a threat to an information system asset without referring to actuarial information. A numerical value is established for one or more threats of attack on the information system asset based on expert knowledge without reference to actuarial data, and likewise, based on expert knowledge without reference to actuarial data, a numerical value is established for each of one or more access and privilege components of one or more vulnerabilities to attack on the information system asset. A security risk level for the information system asset is computed based upon the numerical values for threat and the access and privilege components for vulnerability so established.
Owner:CITIBANK
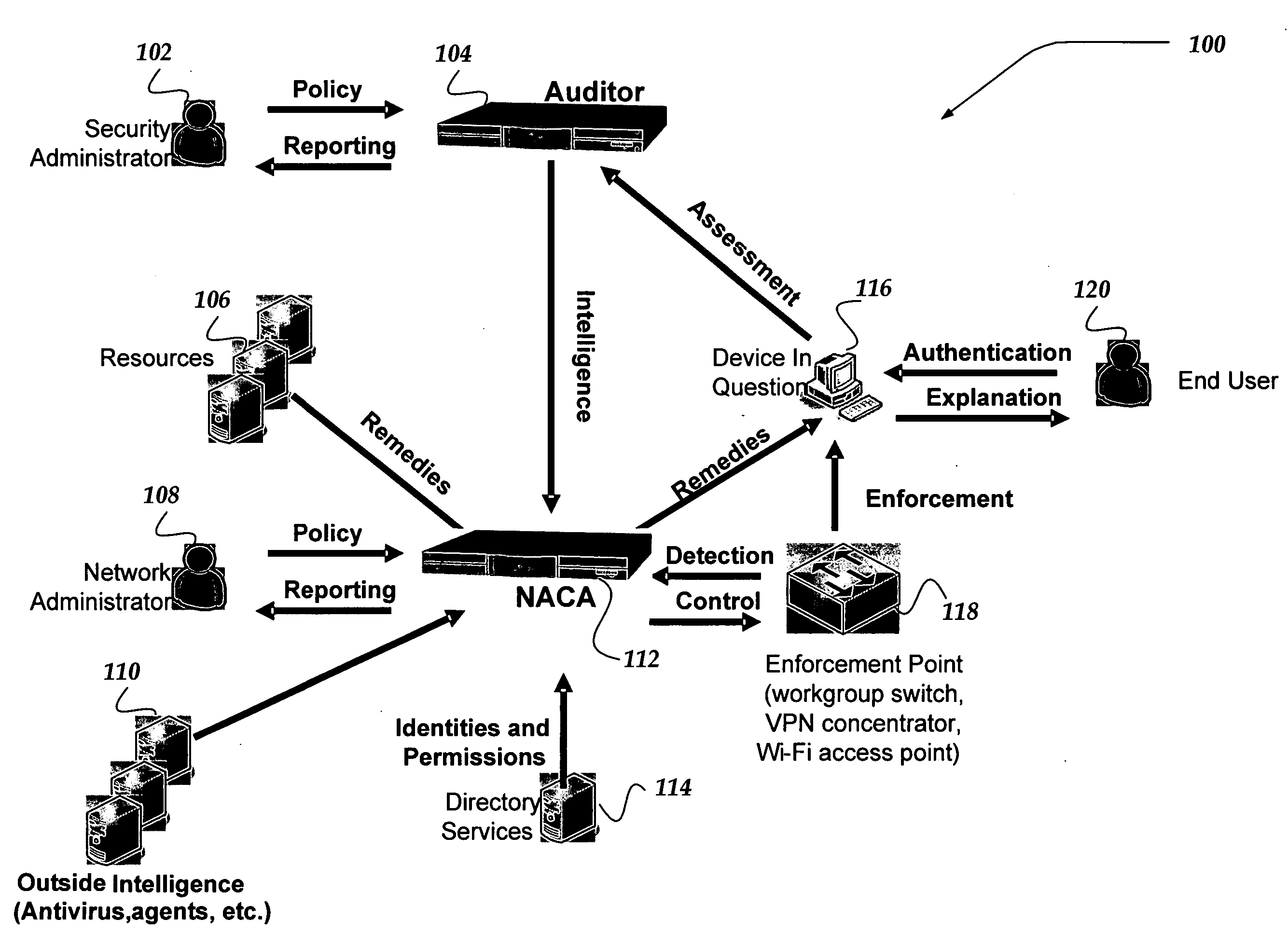
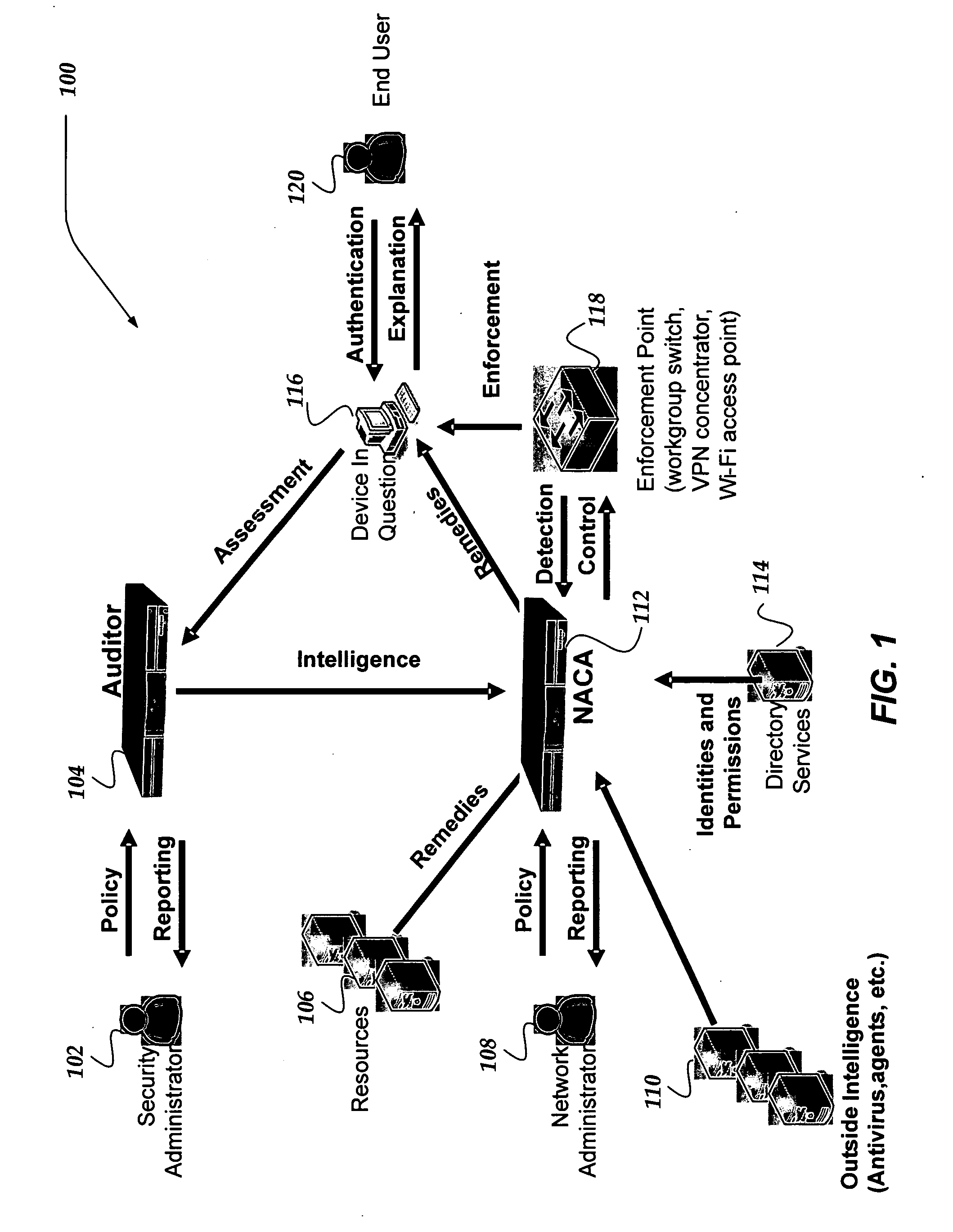
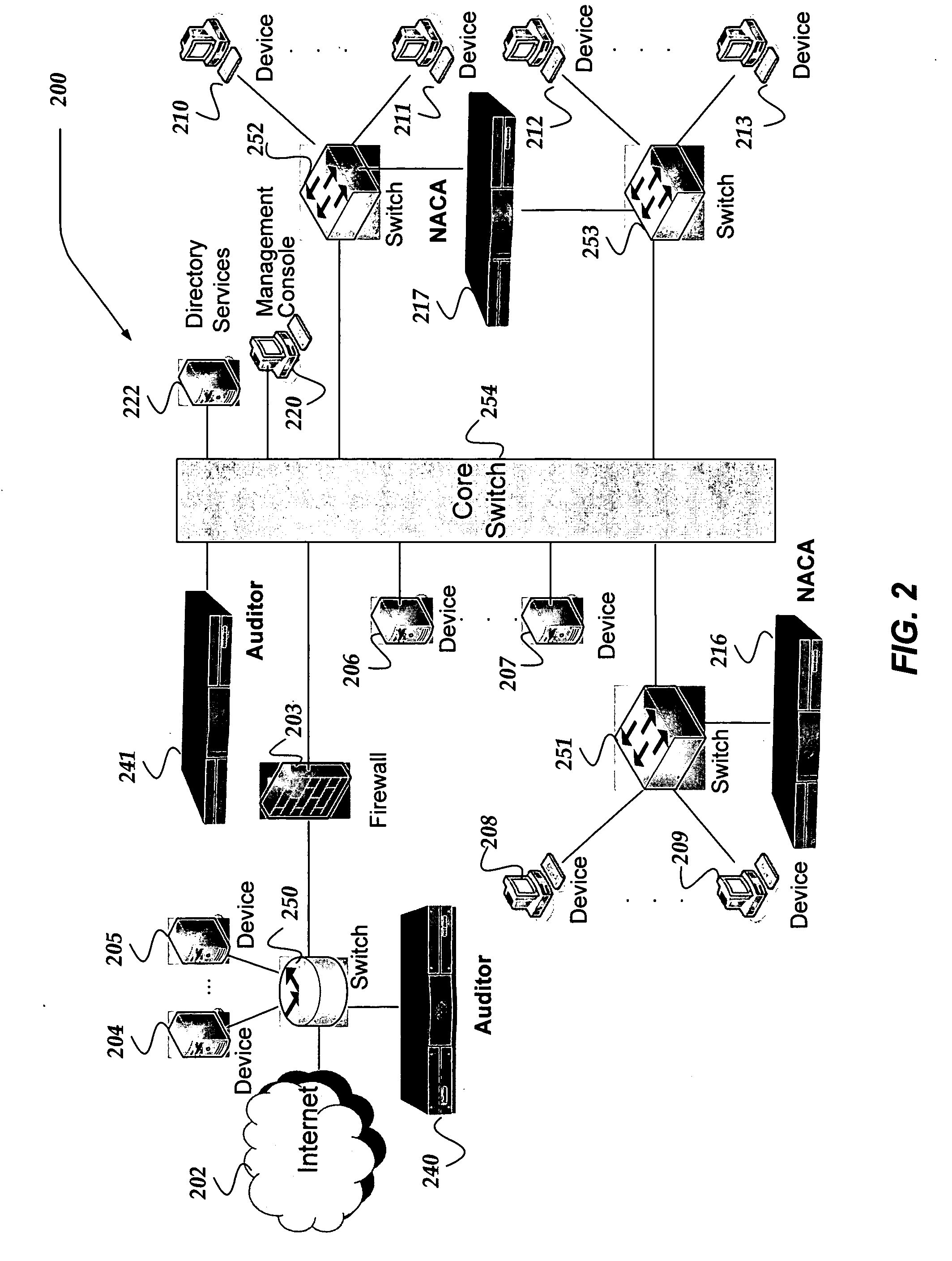
Network appliance for securely quarantining a node on a network
InactiveUS20060164199A1Transformers/inductances magnetic coresData switching networksNetwork Access ControlSecurity policy
An apparatus, system, and method for managing dynamic network access control. The invention provides services and controlled network access that includes quarantining nodes so that they may be identified, audited, and provided an opportunity to be brought into compliance with a security policy. The invention is configured to detect a device seeking to join the network, and determine if the device is allowed to join the network. If the invention determines that the device is not to be allowed, the device may be quarantined using a VLAN. The suspect device may then be audited for vulnerabilities. If vulnerabilities are identified, remediation may be employed to guide the suspect device, a user, and / or administrator of the suspect device towards a resolution of the vulnerabilities, such that the device may be reconfigured for acceptance onto the network.
Owner:MCAFEE INC
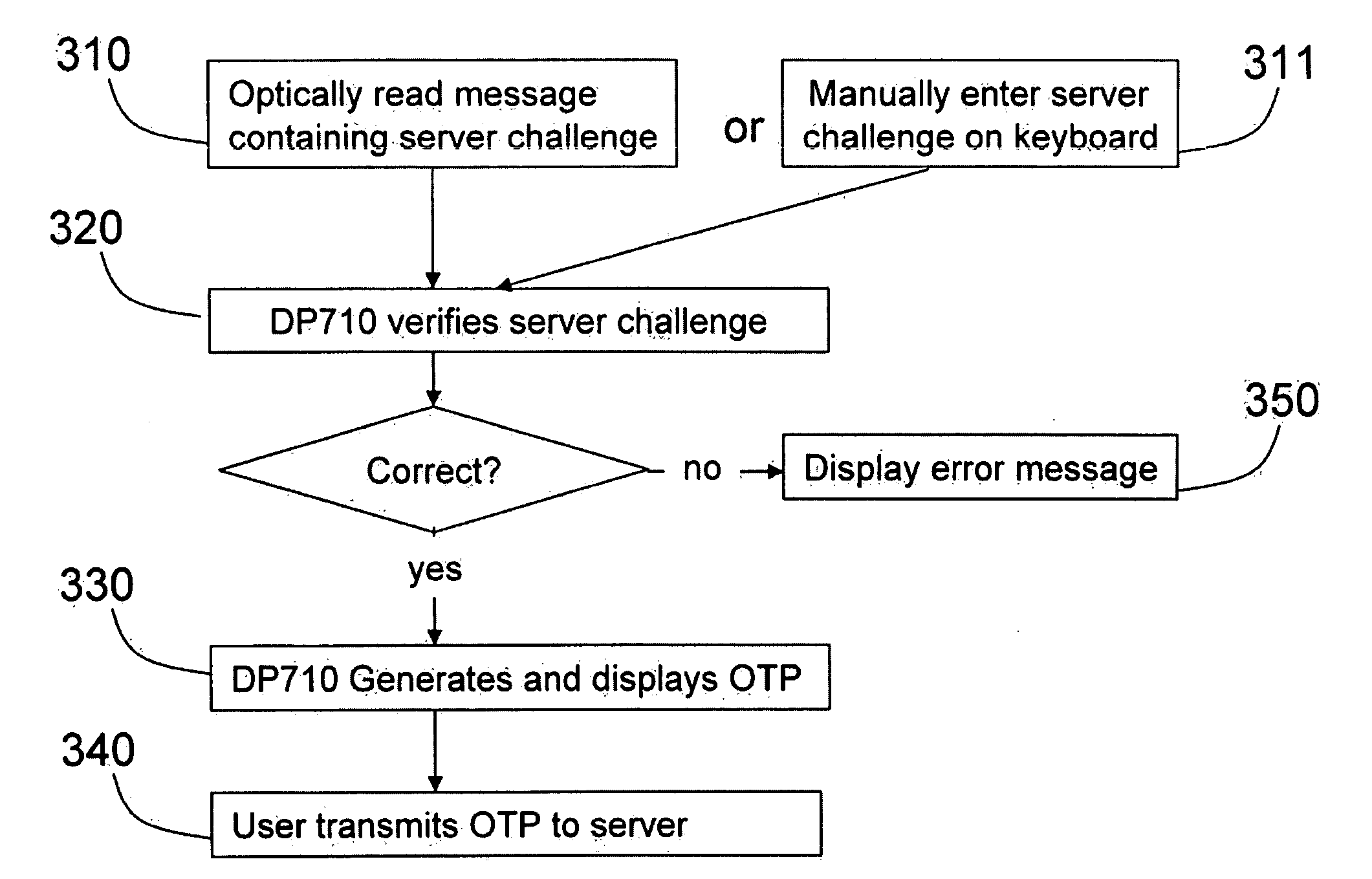
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
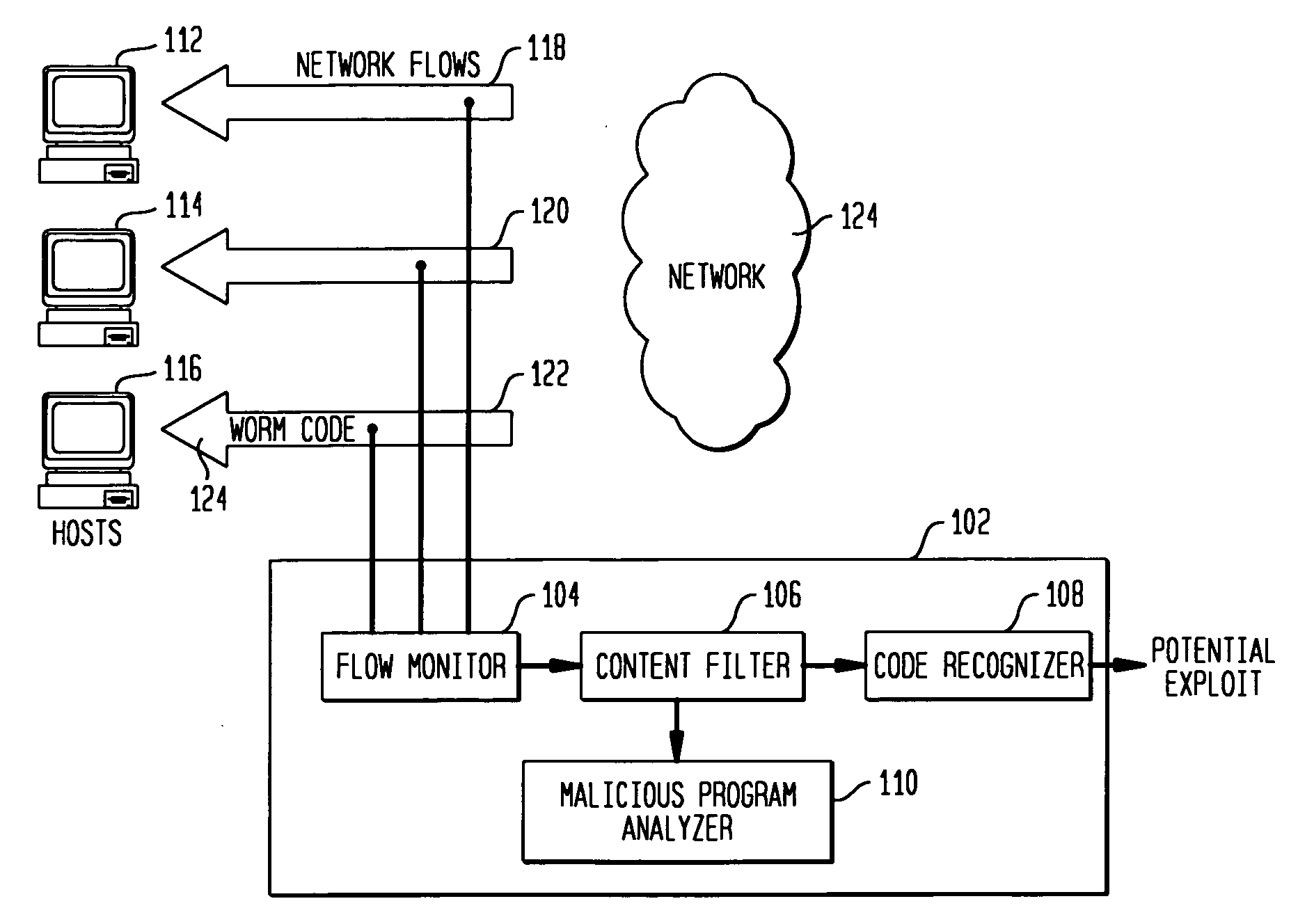
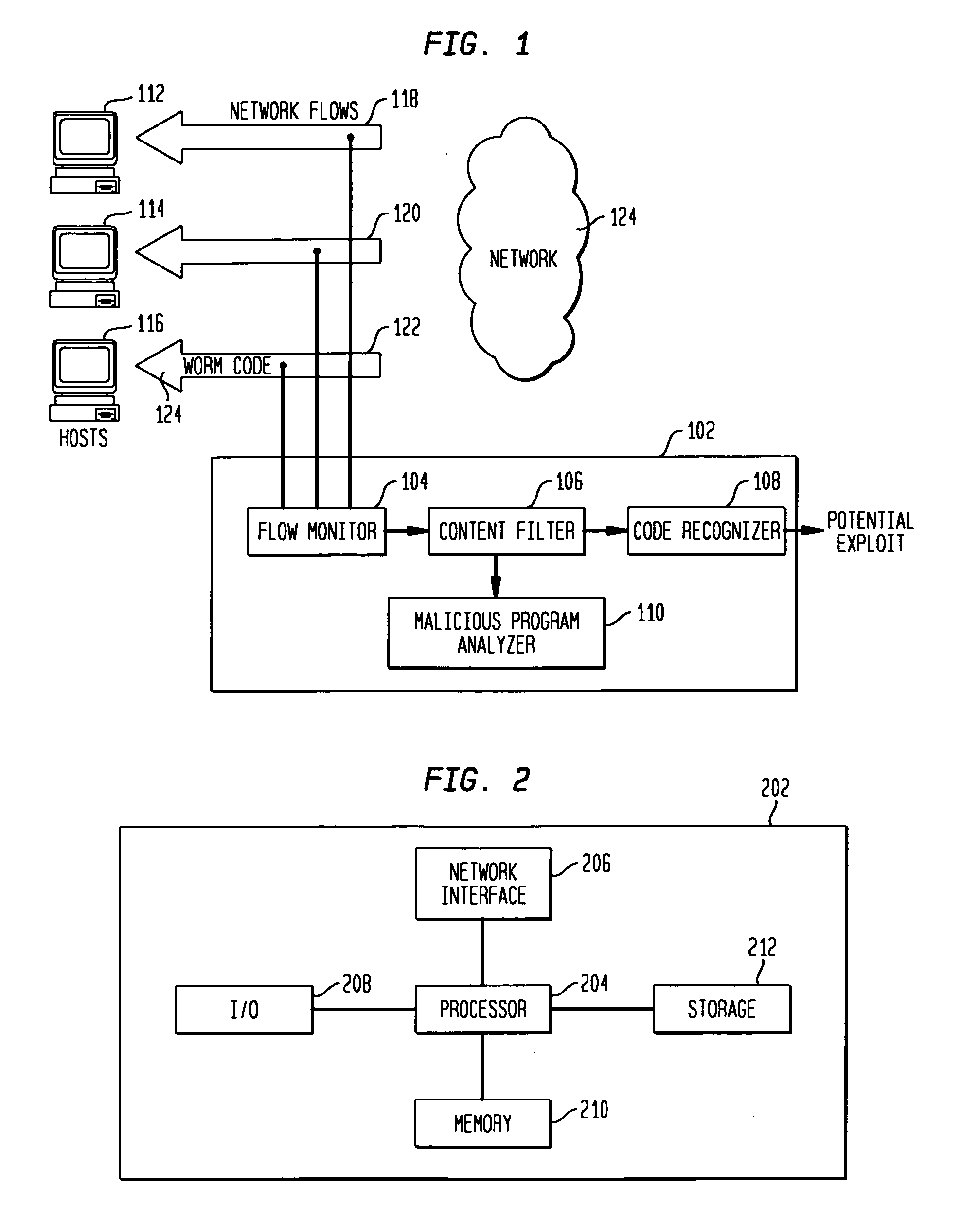
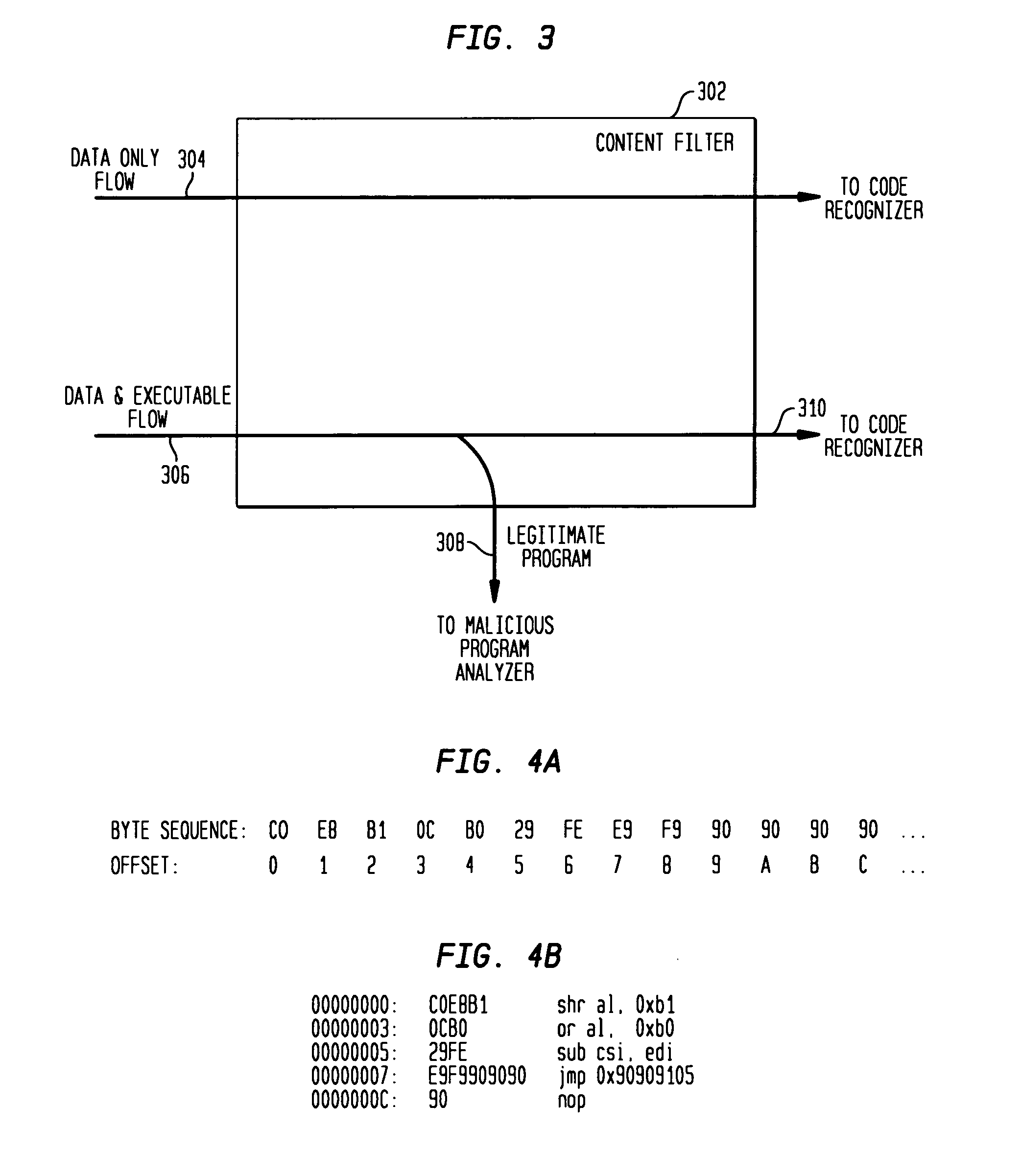
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
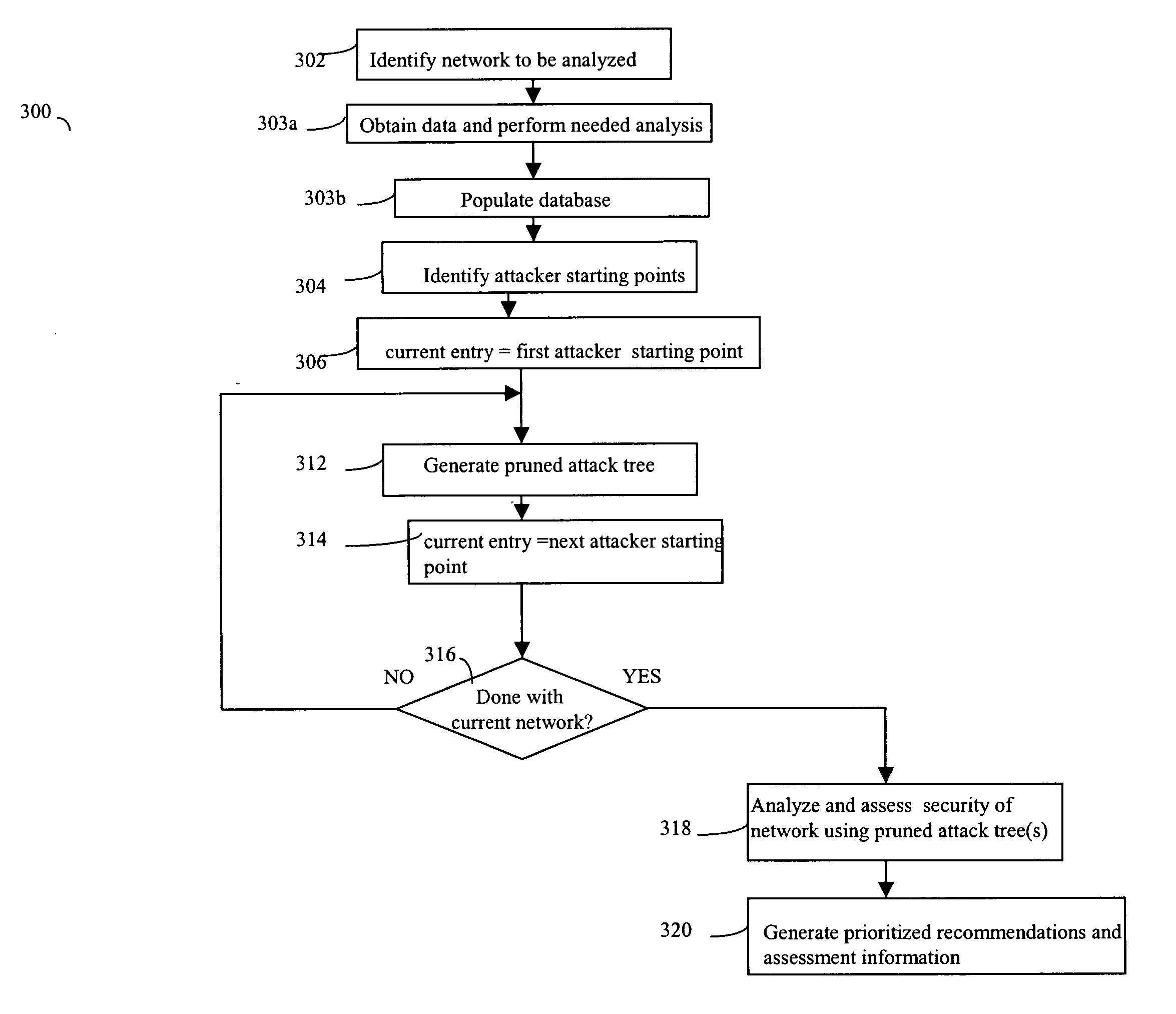
Network security planning architecture
ActiveUS20050138413A1Expand accessBroaden their knowledgeMemory loss protectionDigital data processing detailsForward chainingAttack tree
Described are techniques used for assessing the security of a network. Pruned attack trees are generated using a forward chaining, breadth-first technique representing the attack paths of a possible attacker in the network. A vulnerability score is determined for each network and attacker starting point using attack loss values assigned to each host and information extracted from the attack tree(s) concerning compromised hosts. Different hypothetical alternatives may be evaluated to improve security of the network and each alternative may be evaluated by recomputing the network vulnerability score and comparing the recomputed score to the original network vulnerability score. Also disclosed is a method for determining end-to-end connectivity of a network. The resulting end-to-end connectivity information is used in generating the pruned attack tree.
Owner:MASSACHUSETTS INST OF TECH
System and method for detecting malicious content
ActiveUS20110307955A1Easy to detectMemory loss protectionError detection/correctionApplication programming interfaceApplication software
Owner:TRUSTWAVE HOLDINGS
Systems and methods for wireless vulnerability analysis
ActiveUS20070142030A1Memory loss protectionUnauthorised/fraudulent call preventionComputer networkVulnerability
Security vulnerability assessment for wireless networks is provided. Systems and methods for security vulnerability assessment simulate an attack upon the wireless network, capture the response from the wireless network, and identify a vulnerability associated with the wireless network after analyzing the response from the wireless network.
Owner:EXTREME NETWORKS INC
Systems, program product and methods for performing a risk assessment workflow process for plant networks and systems
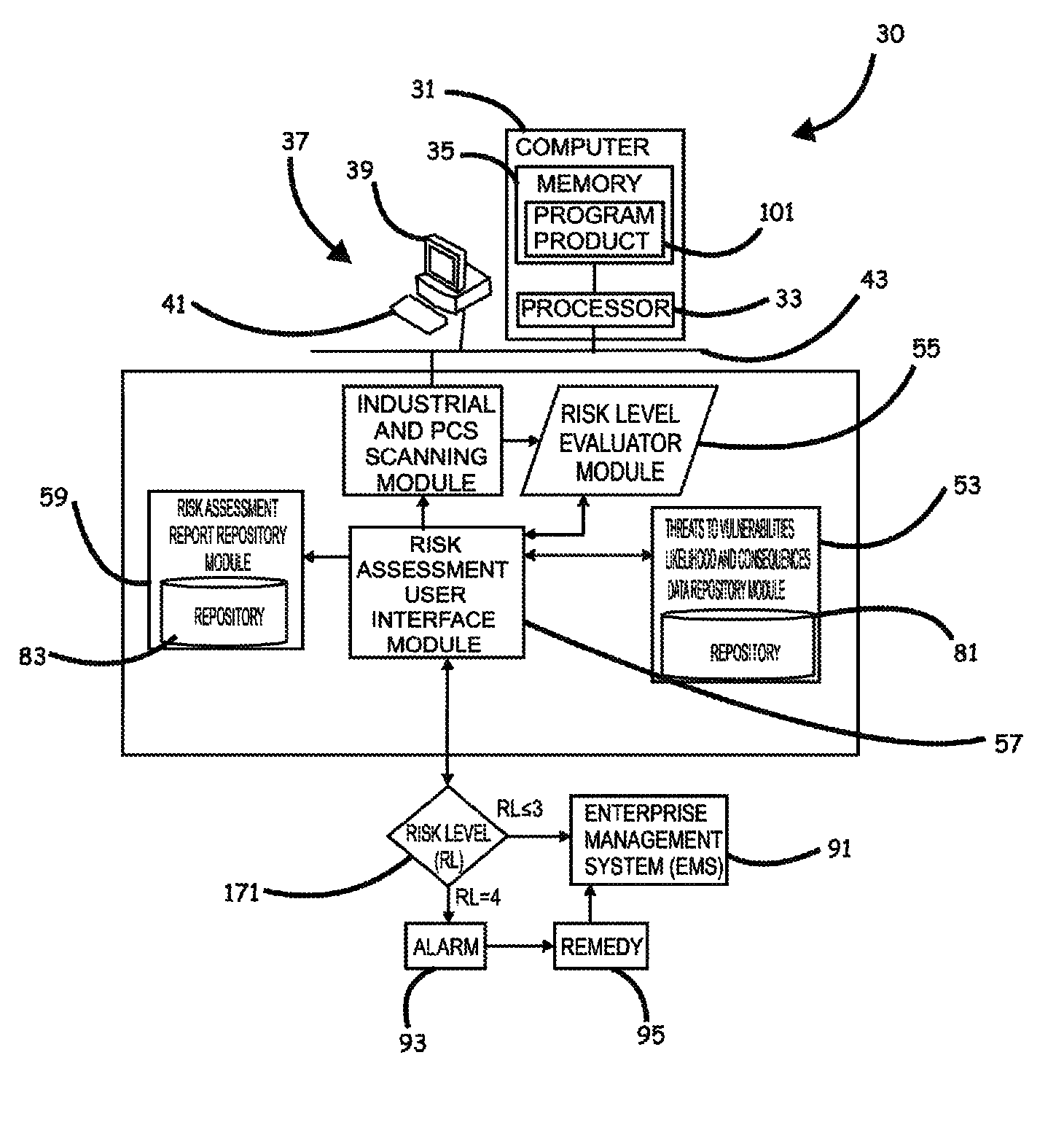
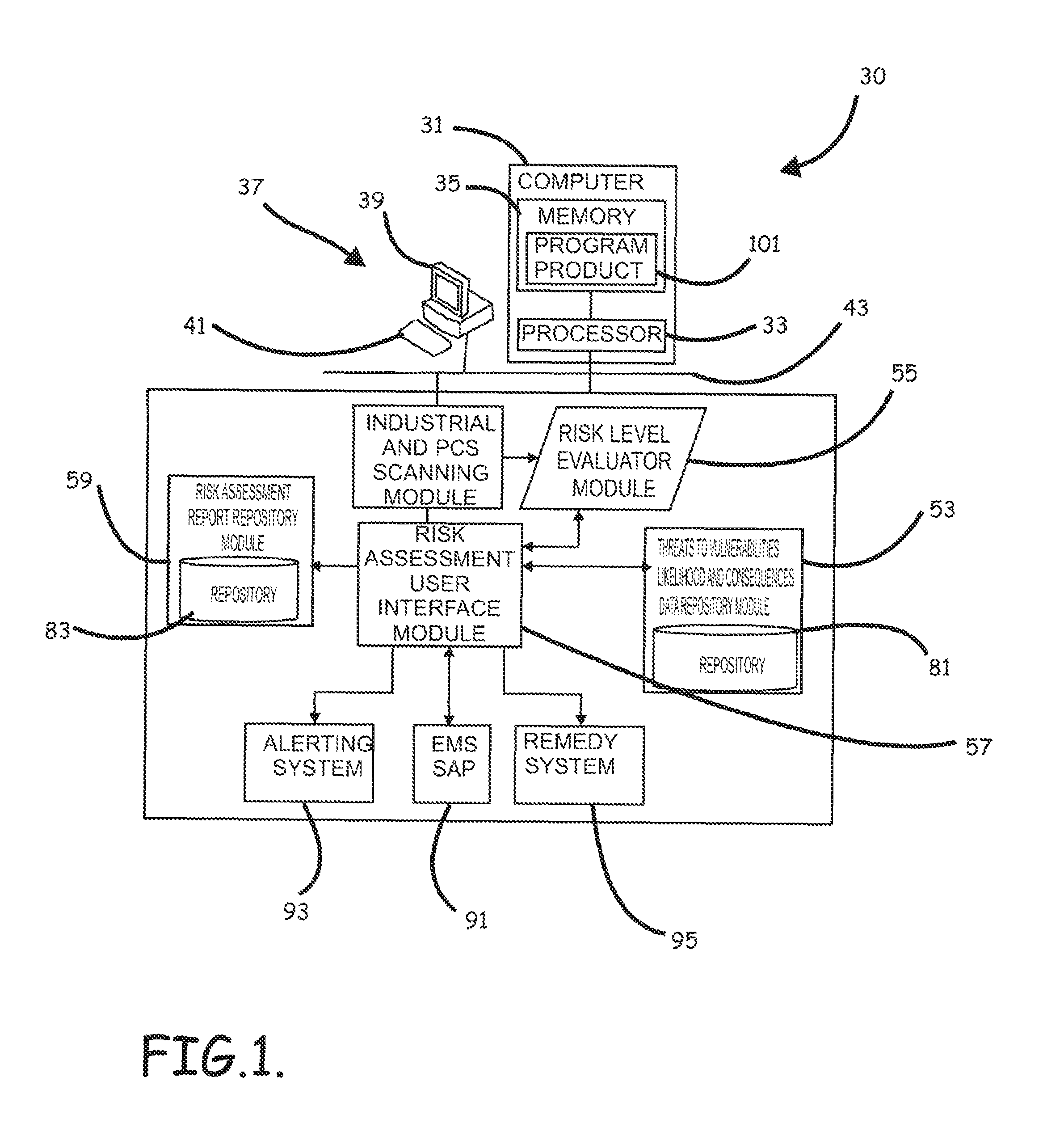
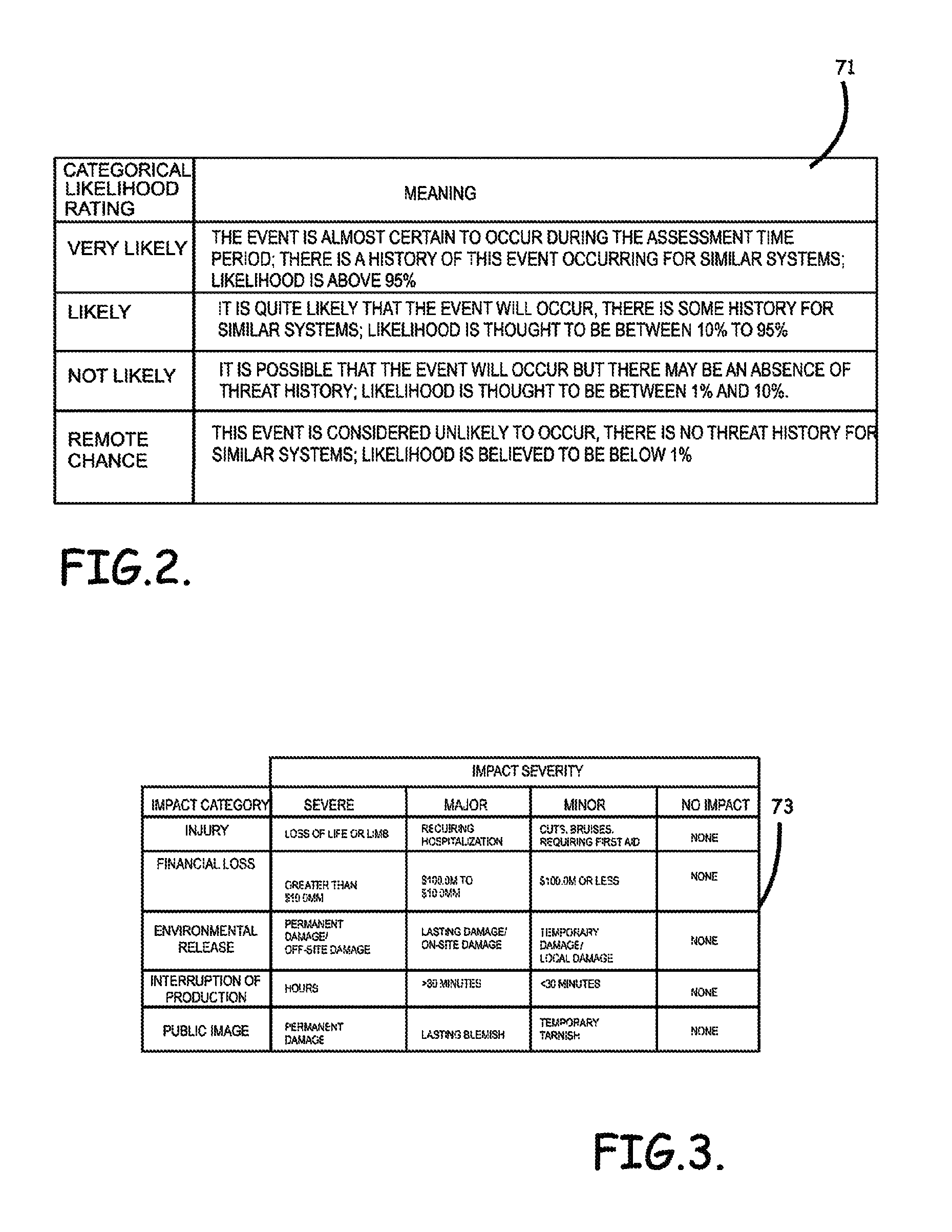
ActiveUS8621637B2Minimizing human interactionEasy to implementProgramme controlMemory loss protectionRisk levelProcess control network
Systems, methods, and program product to perform a cyber security risk assessment on a plurality of process control networks and systems comprising a plurality of primary network assets at an industrial process facility, are provided. An example of a system and program product can include an industrial and process control systems scanning module configured to identify networks and systems topology and to execute system and network security, vulnerability, virus, link congestion, node congestion analysis to thereby detect susceptibility to know threats to define potential vulnerabilities; a threats to vulnerabilities likelihood and consequences data repository module configured to determine a likelihood of each of a plurality of known threats exploiting identified vulnerabilities and to identify consequences of the exploitation to individual impacted systems and to overall plant operation; and a risk level evaluator module configured to determine a risk level rating for any identified vulnerabilities and provide recommended corrective actions.
Owner:SAUDI ARABIAN OIL CO
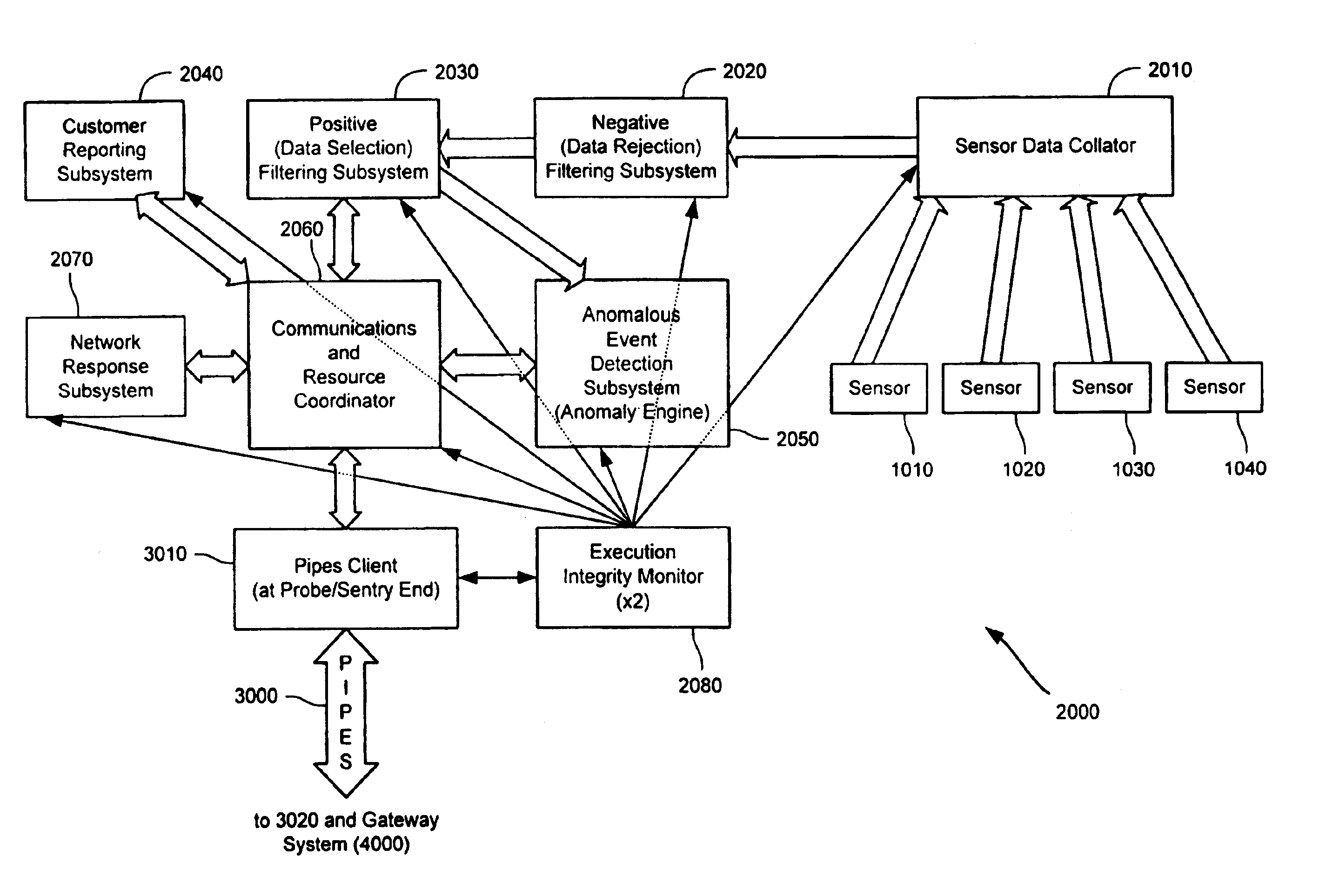
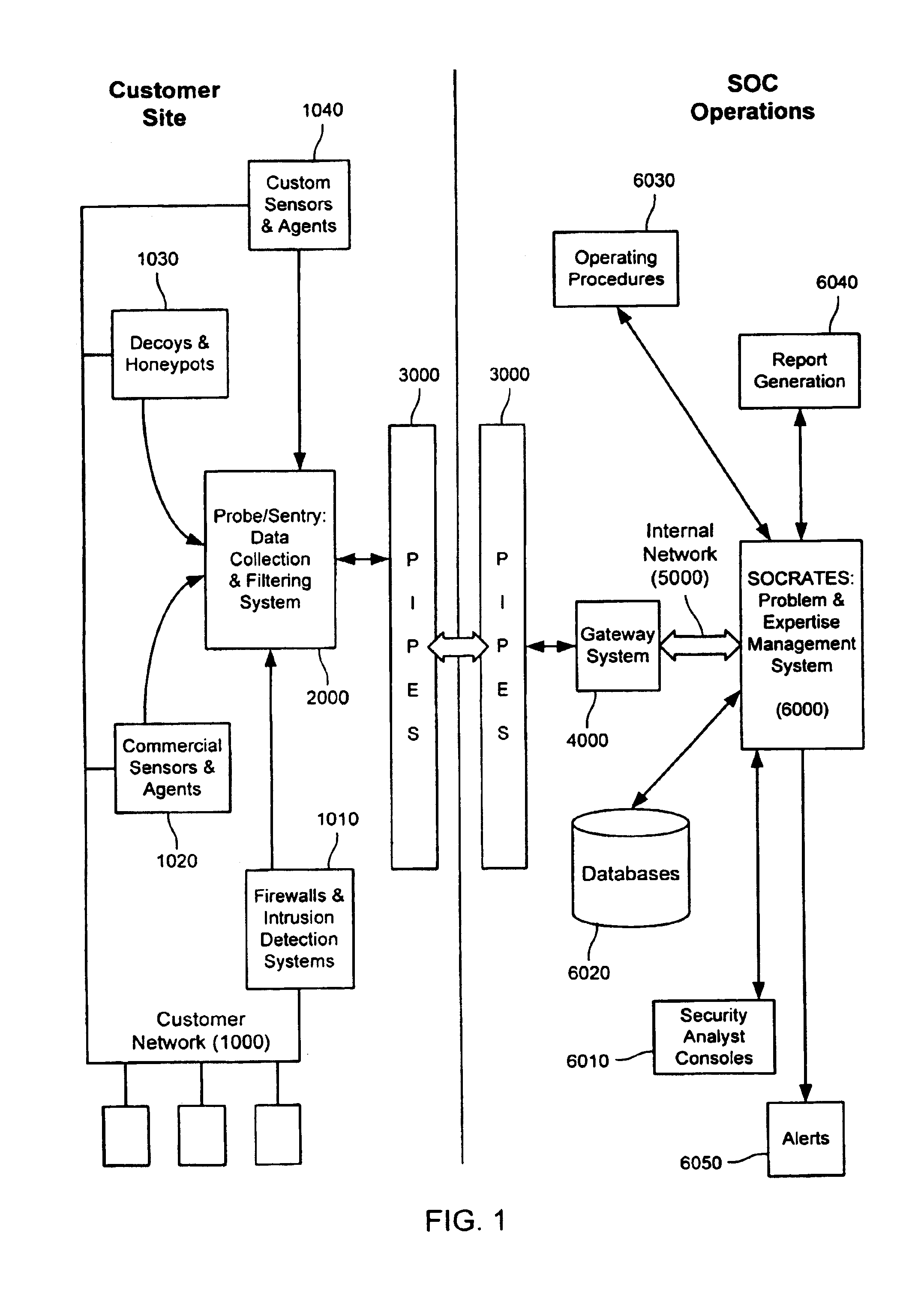
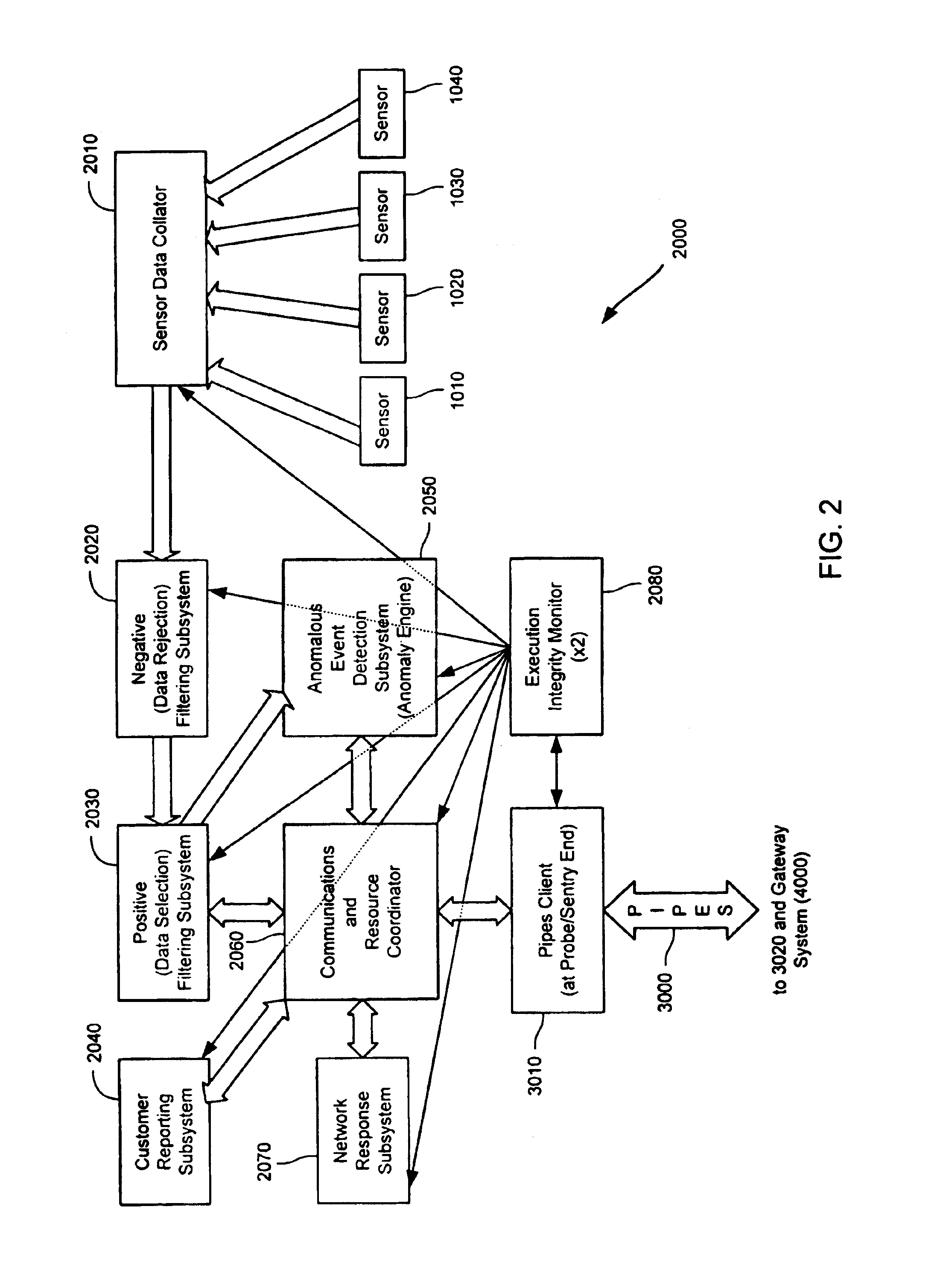
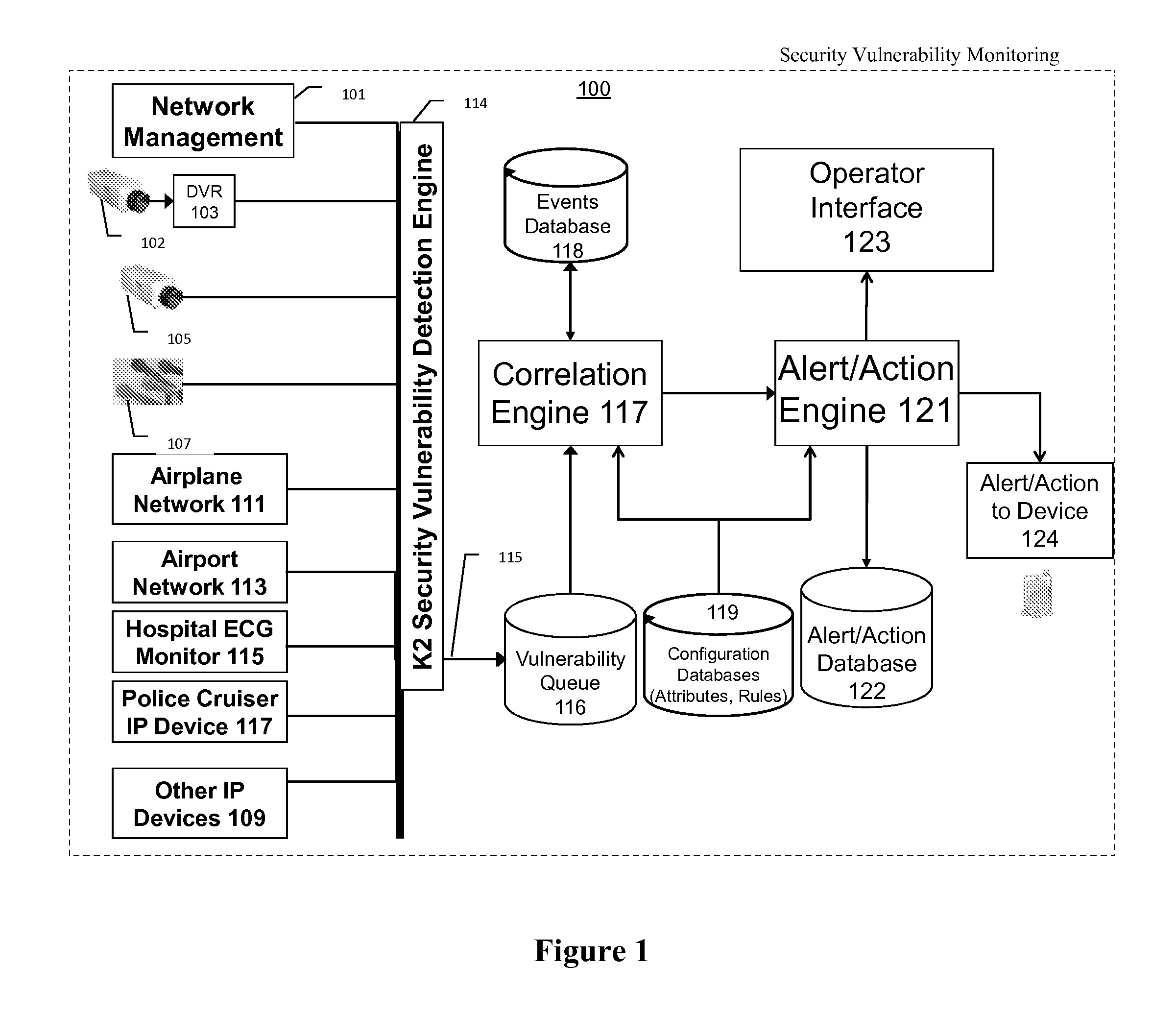
Method and system for dynamic network intrusion monitoring, detection and response
InactiveUS7159237B2Eliminate false positivesIncrease in sizeMemory loss protectionDigital data processing detailsProblem resolutionVulnerability
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
Network audit and policy assurance system
ActiveUS20050257267A1Reduce riskMemory loss protectionError detection/correctionGraphicsGraphical user interface
A prevention-based network auditing system includes a central compliance server generating network policies and configuring audits of the data communications network. The compliance server presents a graphical user interface (GUI) to describe the specific data gathering parameters, policies to be analyzed, and the schedule of analysis. One or more audit servers strategically deployed around the network employ heterogeneous data-gathering tools to gather information about the network in response to the configured audits, and transmit the gathered information to the compliance server. An audit repository stores the gathered information for use by the compliance server for security and regulatory policy assessment, network vulnerability analysis, report generation, and security improvement recommendations.
Owner:MCAFEE LLC
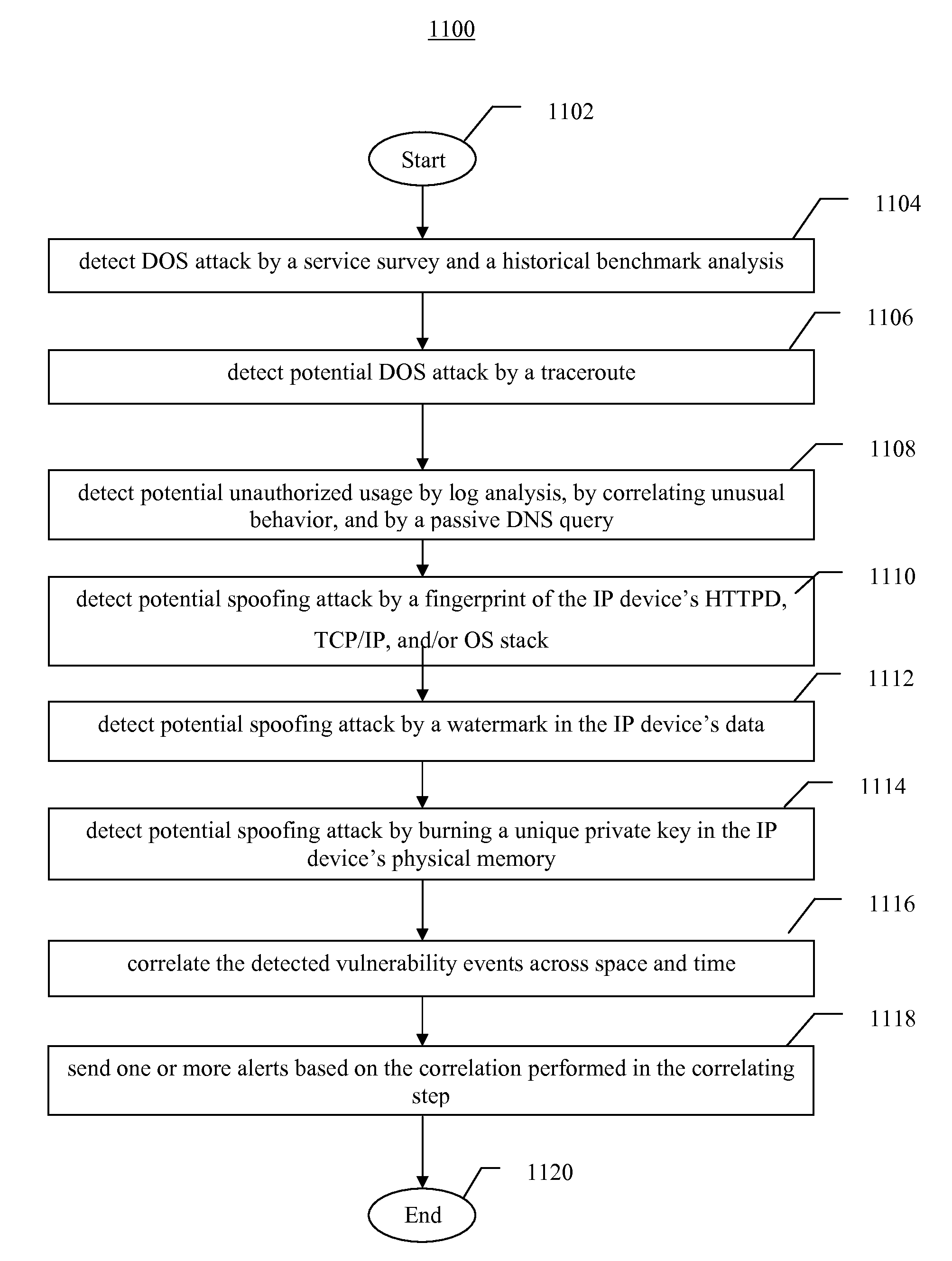
Systems, methods, and devices for detecting security vulnerabilities in IP networks
InactiveUS20100262688A1Detect and prevent spoofingEasy to addMemory loss protectionDigital data processing detailsBaseline dataData stream
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack; and (3) Spoofing Attack. A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint of the IP device or its configuration settings, a watermark inserted in the data-stream, and a private key burned into the IP devices' physical memory may be used to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:HUSSAIN DANIAR +1
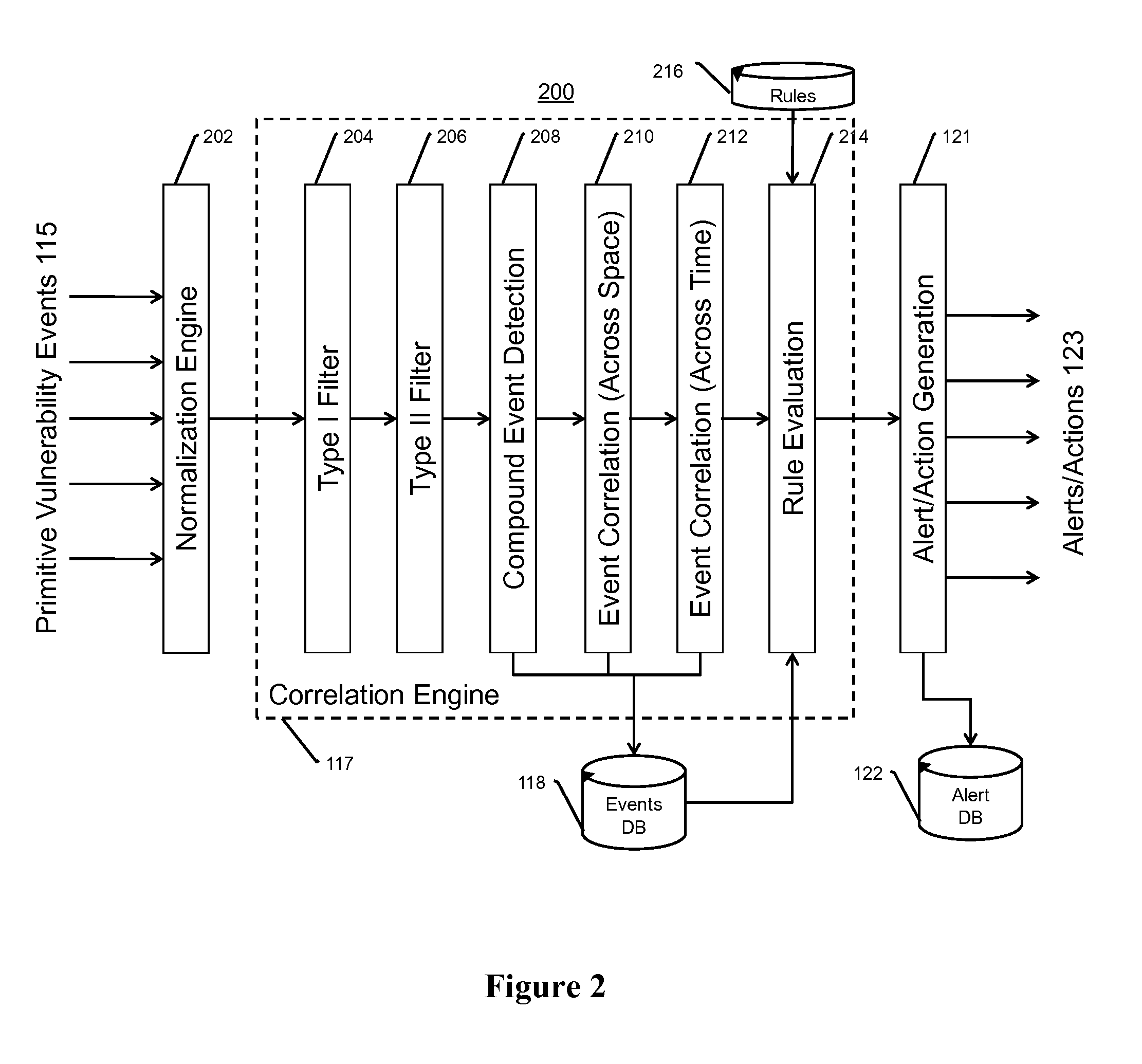
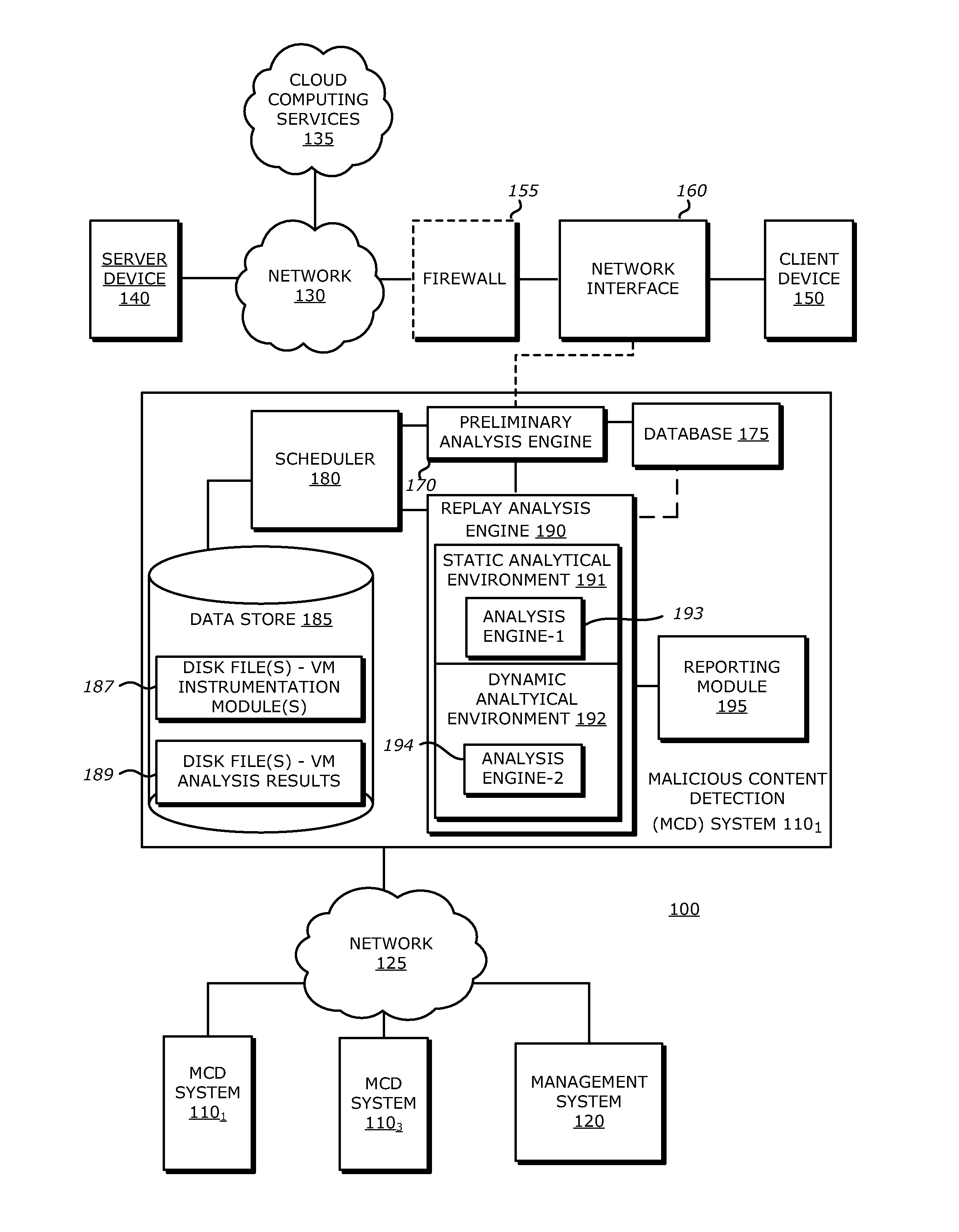
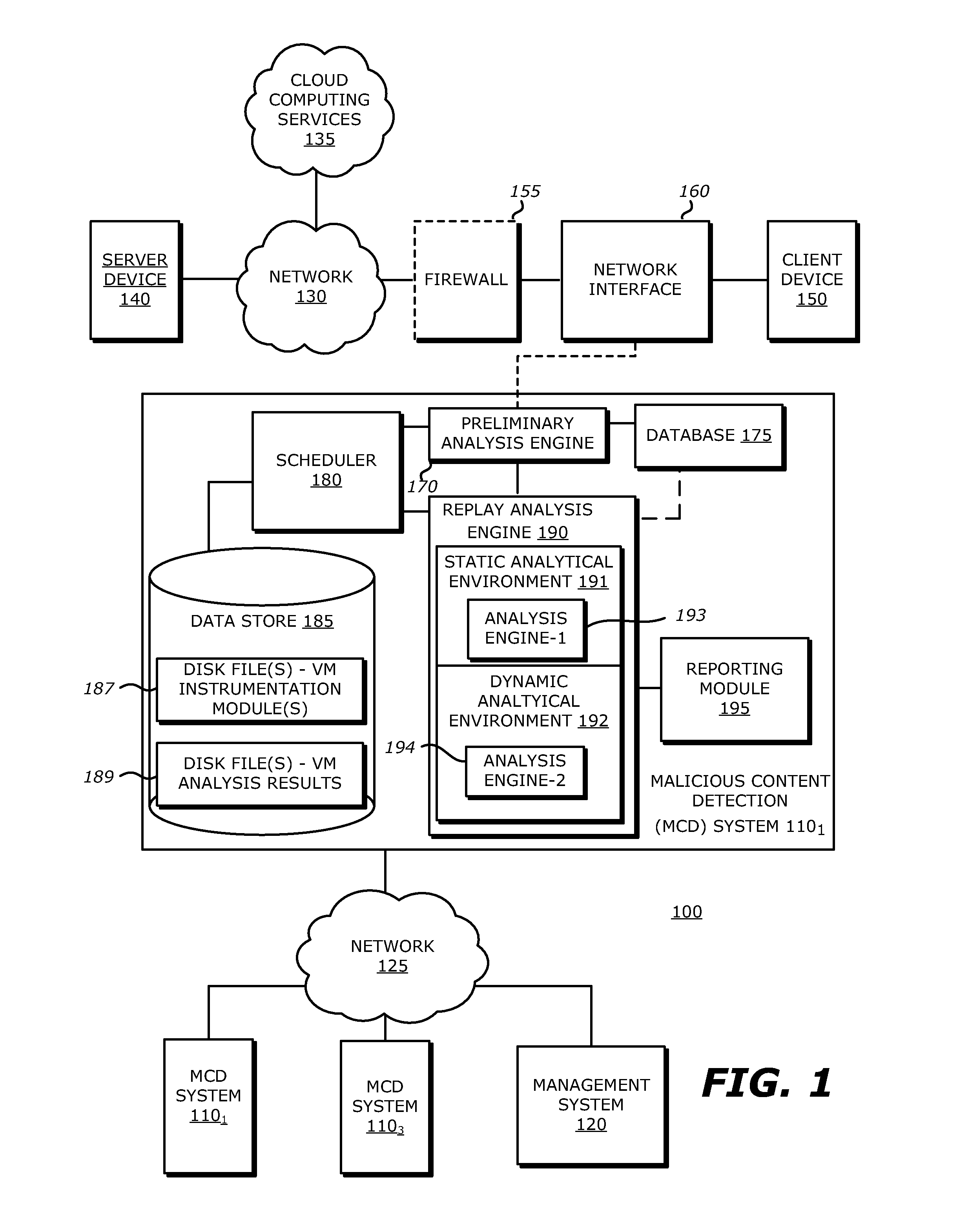
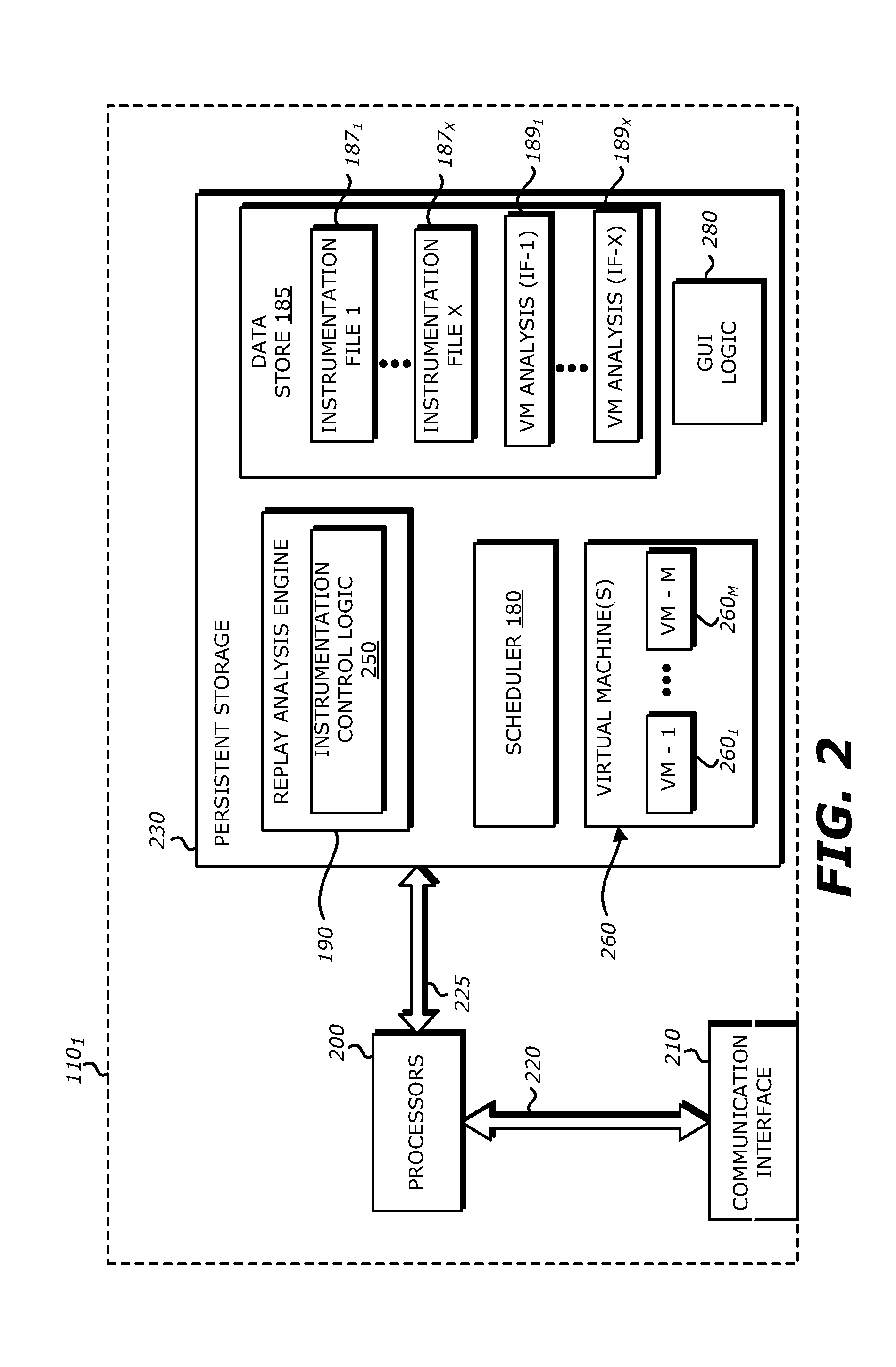
System, Apparatus and Method for Using Malware Analysis Results to Drive Adaptive Instrumentation of Virtual Machines to Improve Exploit Detection
According to one embodiment, an electronic device comprises a memory to store information and a processor. The processor is adapted to receive information associated with content such as network traffic, to process the stored information and to conduct operations on the content. These operations may comprise determining, by a virtual machine processed by the processor, an occurrence of an event during malware analysis of an object associated with the content, and dynamically altering a virtual machine instrumentation of the virtual machine based on information associated with the event.
Owner:FIREEYE SECURITY HLDG US LLC
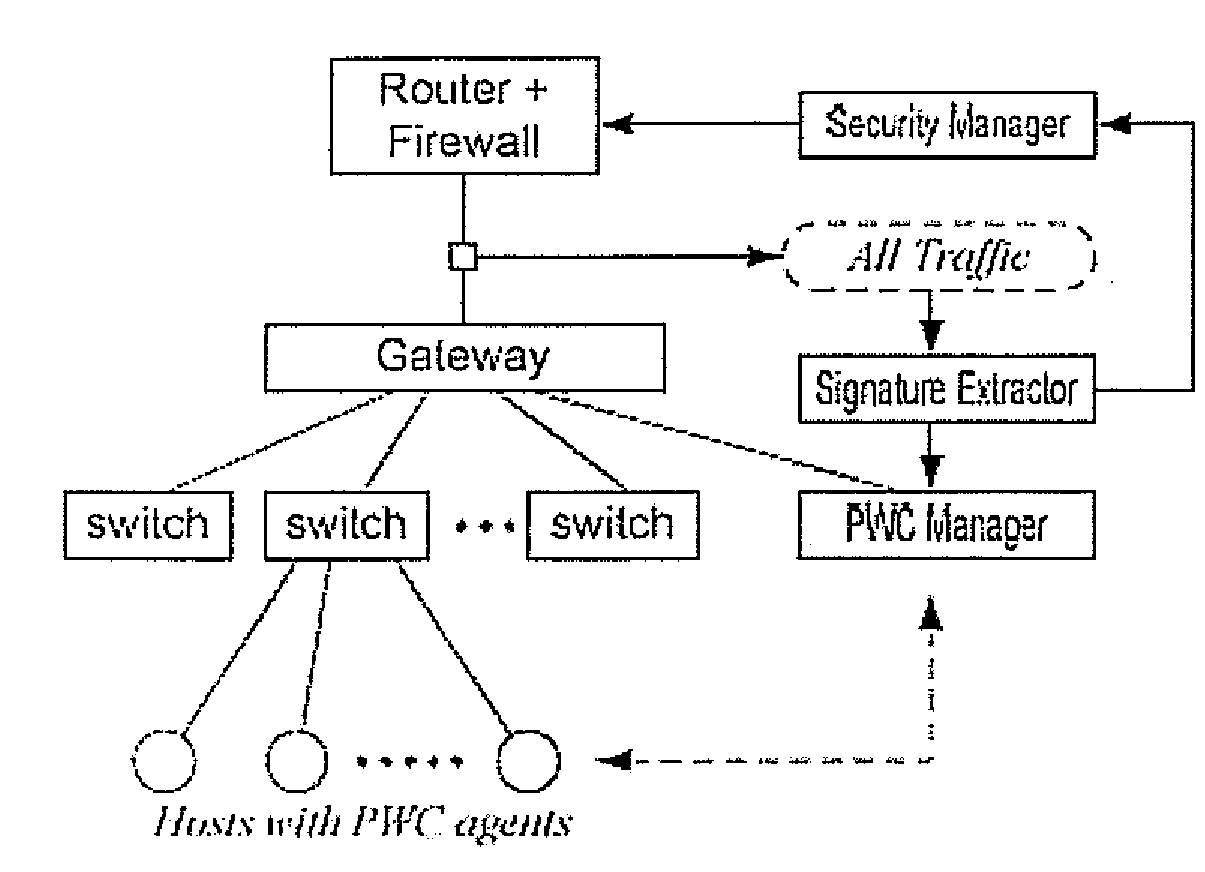
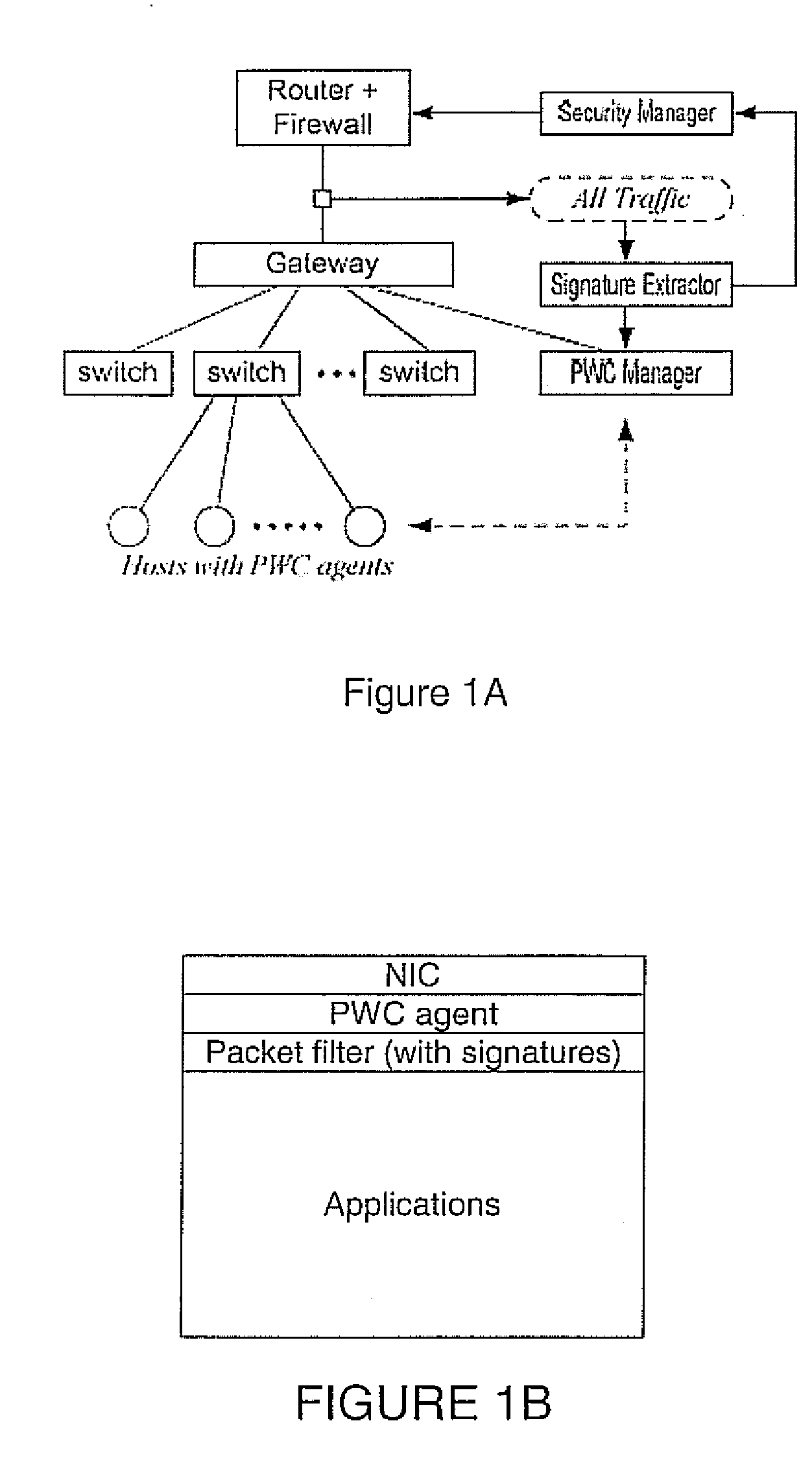
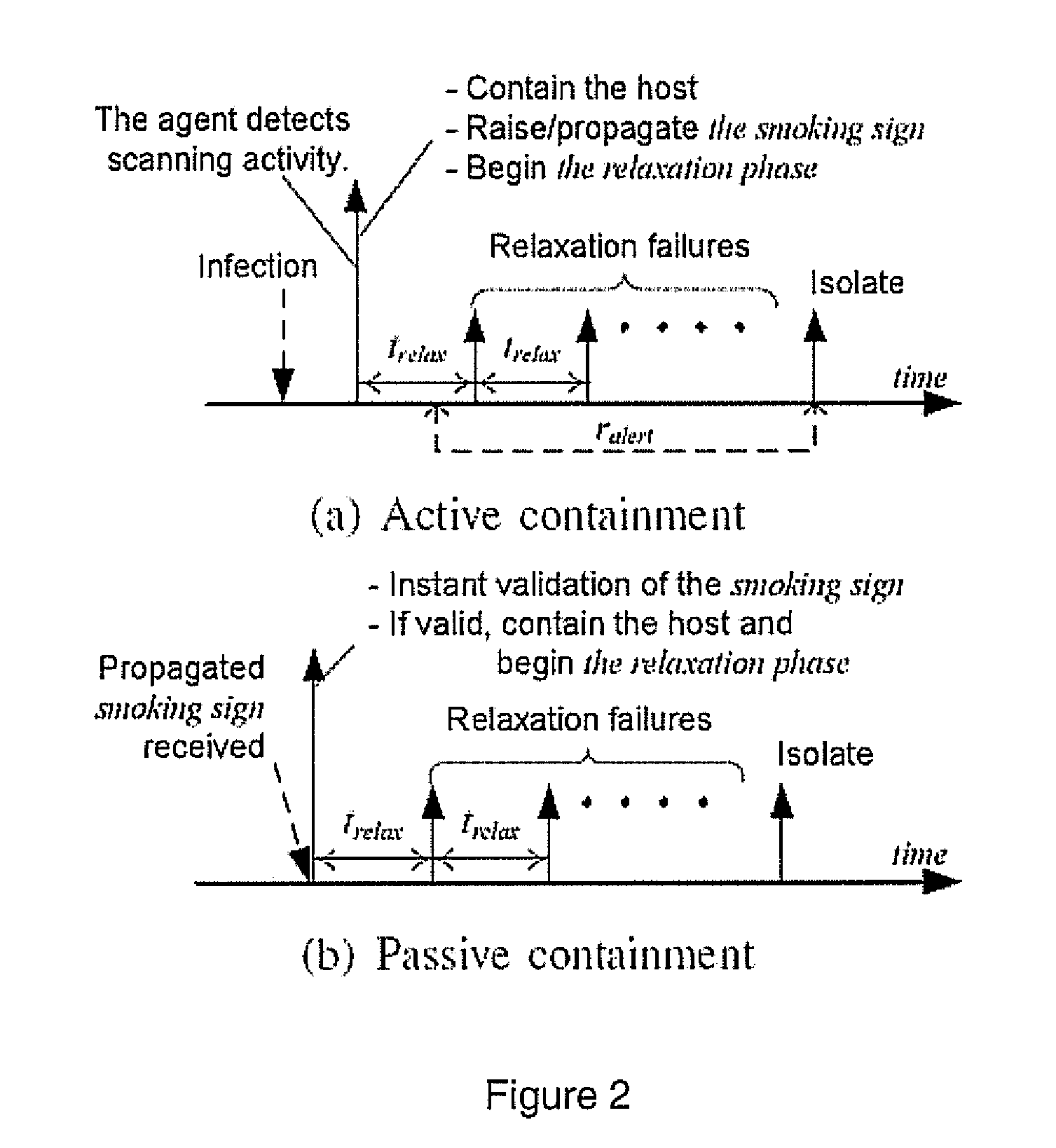
Proactive worm containment (PWC) for enterprise networks
ActiveUS20090031423A1Quick and proactive containmentAvoid false initial containmentMemory loss protectionError detection/correctionOperational systemNetwork level
A proactive worm containment (PWC) solution for enterprises uses a sustained faster-than-normal outgoing connection rate to determine if a host is infected. Two novel white detection techniques are used to reduce false positives, including a vulnerability time window lemma to avoid false initial containment, and a relaxation analysis to uncontain (or unblock) those mistakenly contained (or blocked) hosts, if there are any. The system integrates seamlessly with existing signature-based or filter-based worm scan filtering solutions. Nevertheless, the invention is signature free and does not rely on worm signatures. Nor is it protocol specific, as the approach performs containment consistently over a large range of worm scan rates. It is not sensitive to worm scan rate and, being a network-level approach deployed on a host, the system requires no changes to the host's OS, applications, or hardware.
Owner:PENN STATE RES FOUND
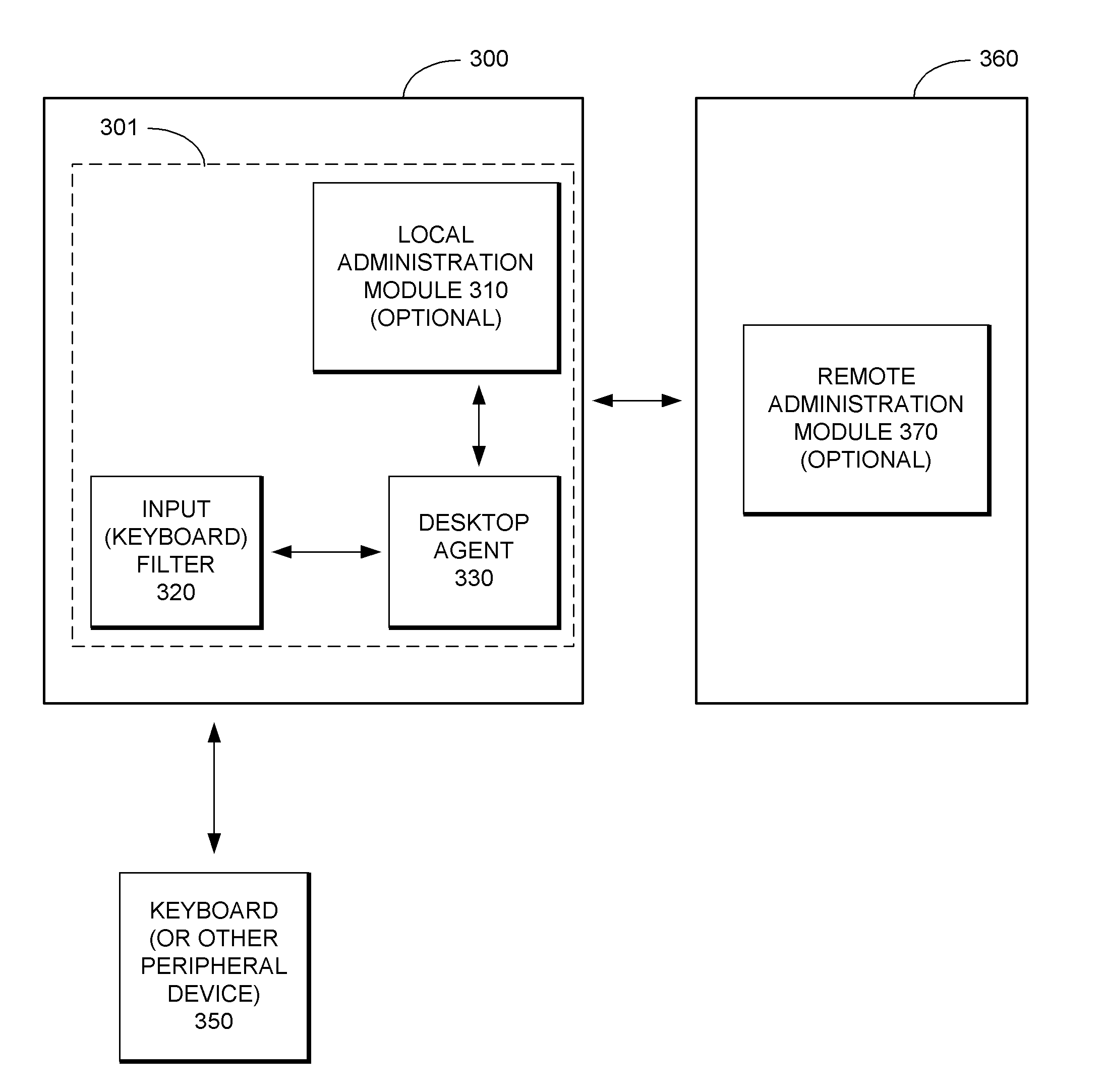
Security System with Methodology for Defending Against Security Breaches of Peripheral Devices
ActiveUS20050138433A1Digital data processing detailsAnalogue secracy/subscription systemsAuthorizationSecurity system
A security system with methodology for defending against security breaches of peripheral devices is described. In one embodiment, for example, a method is described for protecting a computer from security breaches involving devices that may be attached to the computer, the method comprises steps of: when a device is first attached to the computer, specifying authorization information indicating that the device is allowed to communicate with the computer; detecting detachment of the device from the computer; updating the authorization information to indicate that the device is no longer authorized to communicate with the computer; and upon reattachment of the device, blocking communication with the device while the device remains unauthorized, thereby preventing a security breach involving the device.
Owner:CHECK POINT SOFTWARE TECH INC
System and method for risk detection and analysis in a computer network
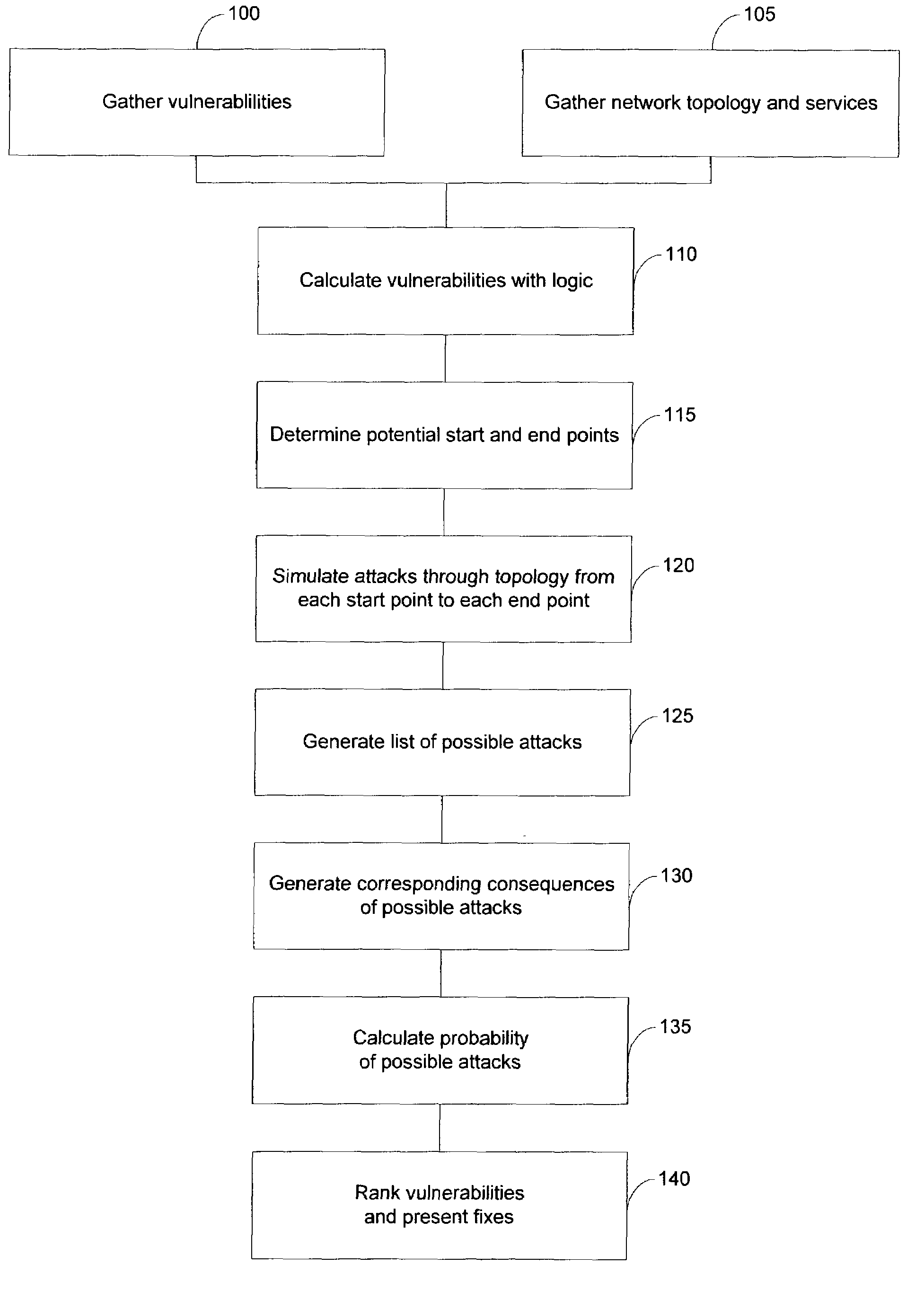
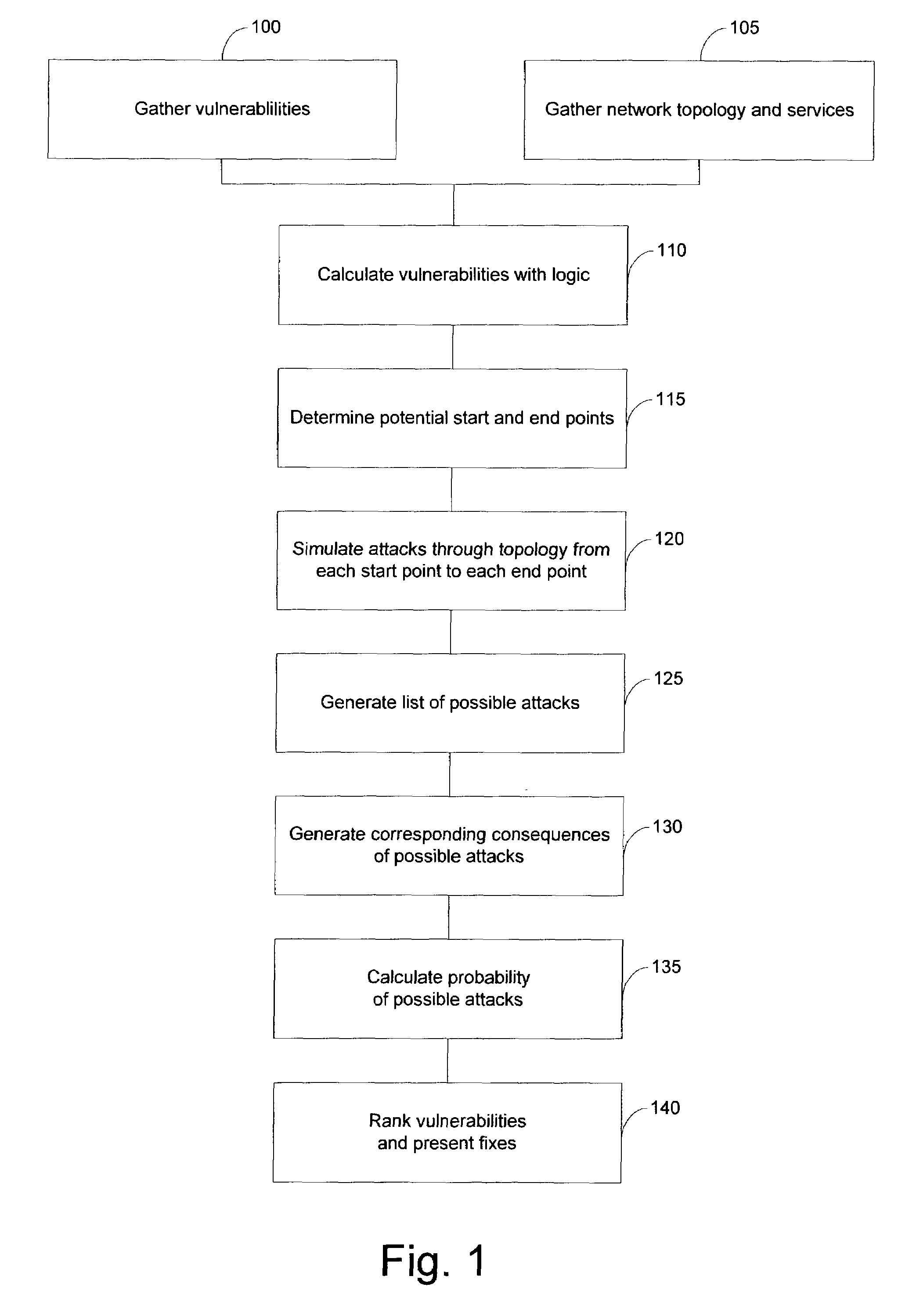
The present invention provides systems and methods for risk detection and analysis in a computer network. Computerized, automated systems and methods can be provided. Raw vulnerability information and network information can be utilized in determining actual vulnerability information associated with network nodes. Methods are provided in which computer networks are modeled, and the models utilized in performing attack simulations and determining risks associated with vulnerabilities. Risks can be evaluated and prioritized, and fix information can be provided.
Owner:SKYBOX SECURITY
System for determining web application vulnerabilities
InactiveUS20020010855A1Memory loss protectionError detection/correctionWeb applicationApplication procedure
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
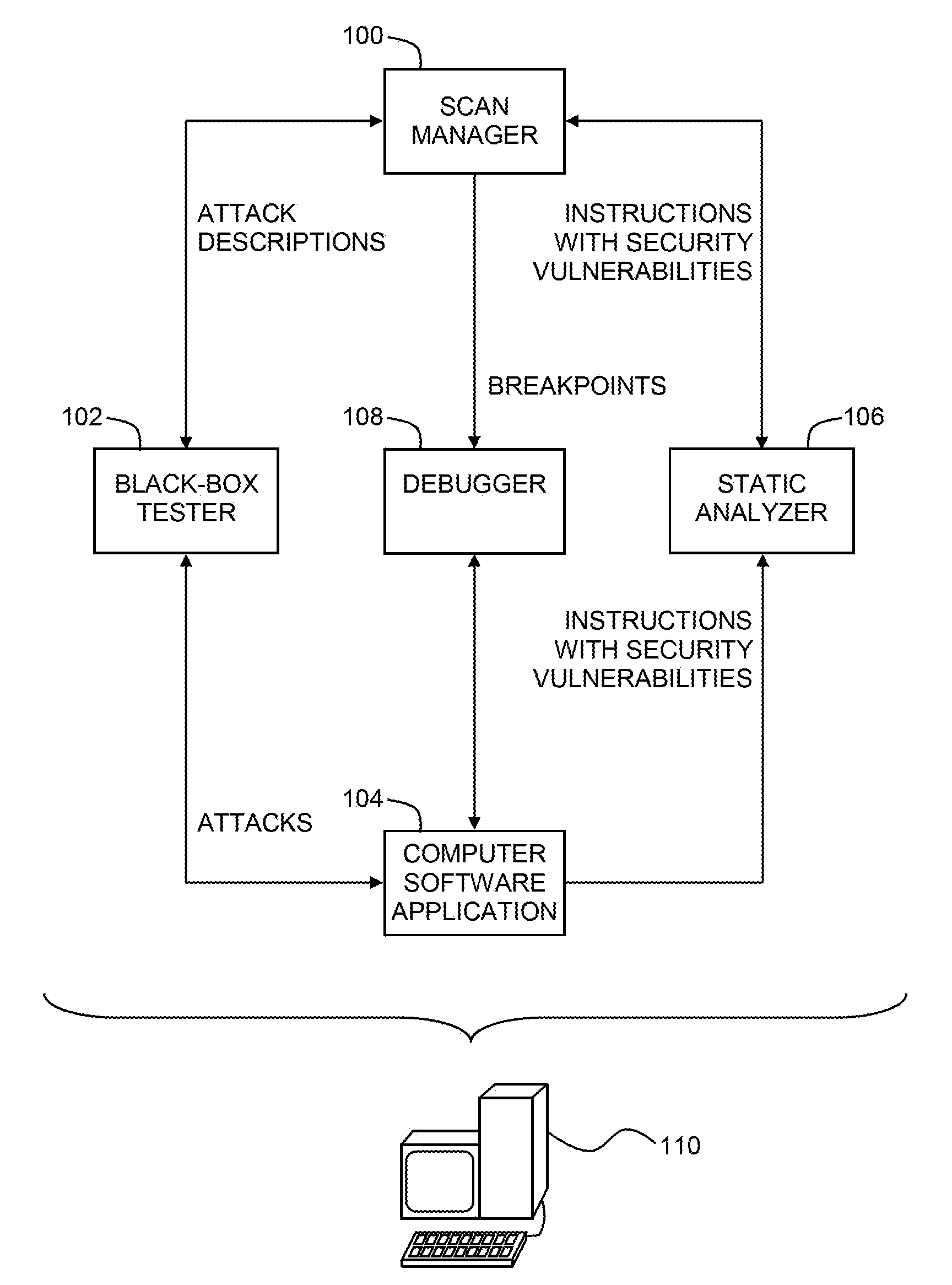
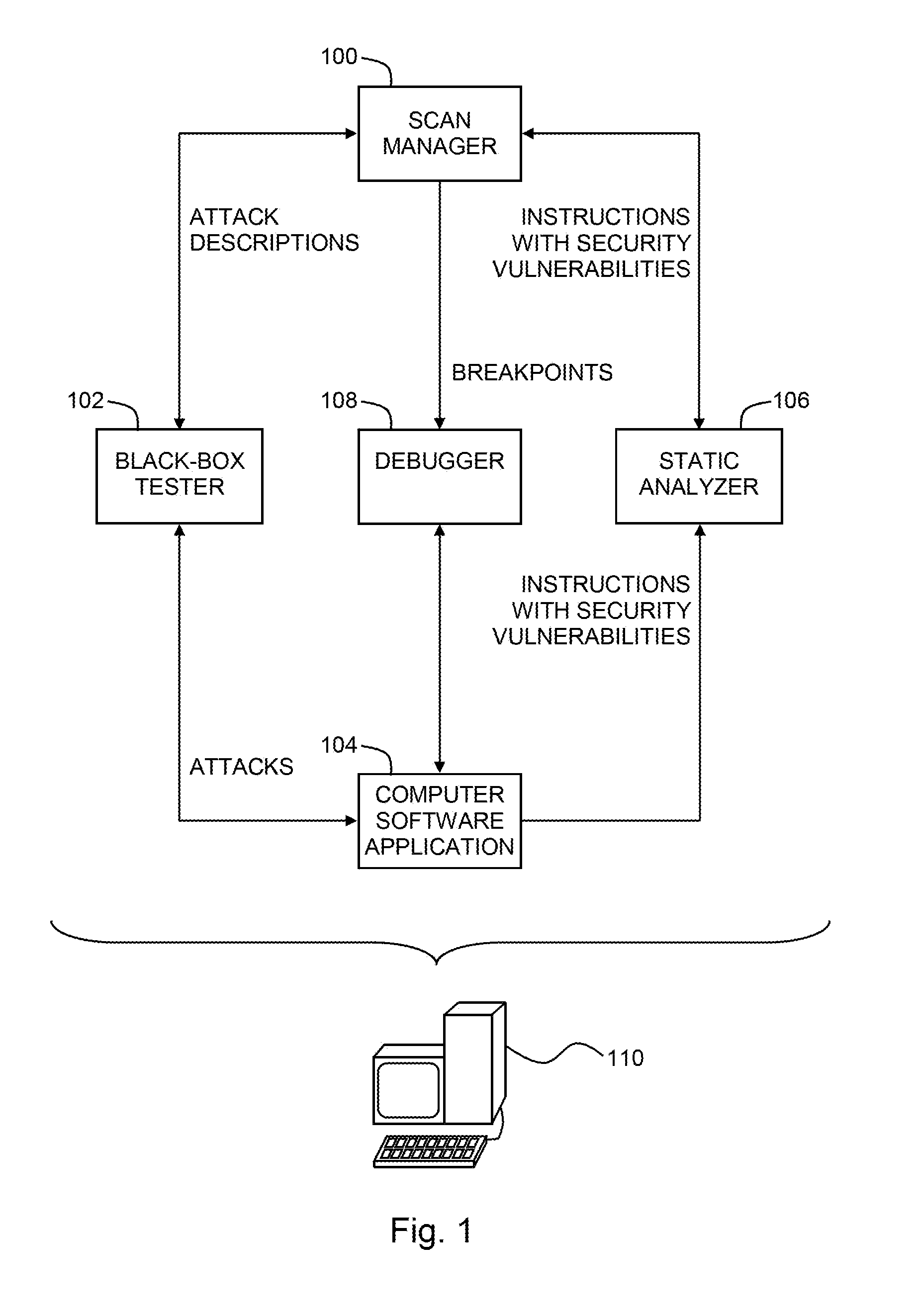
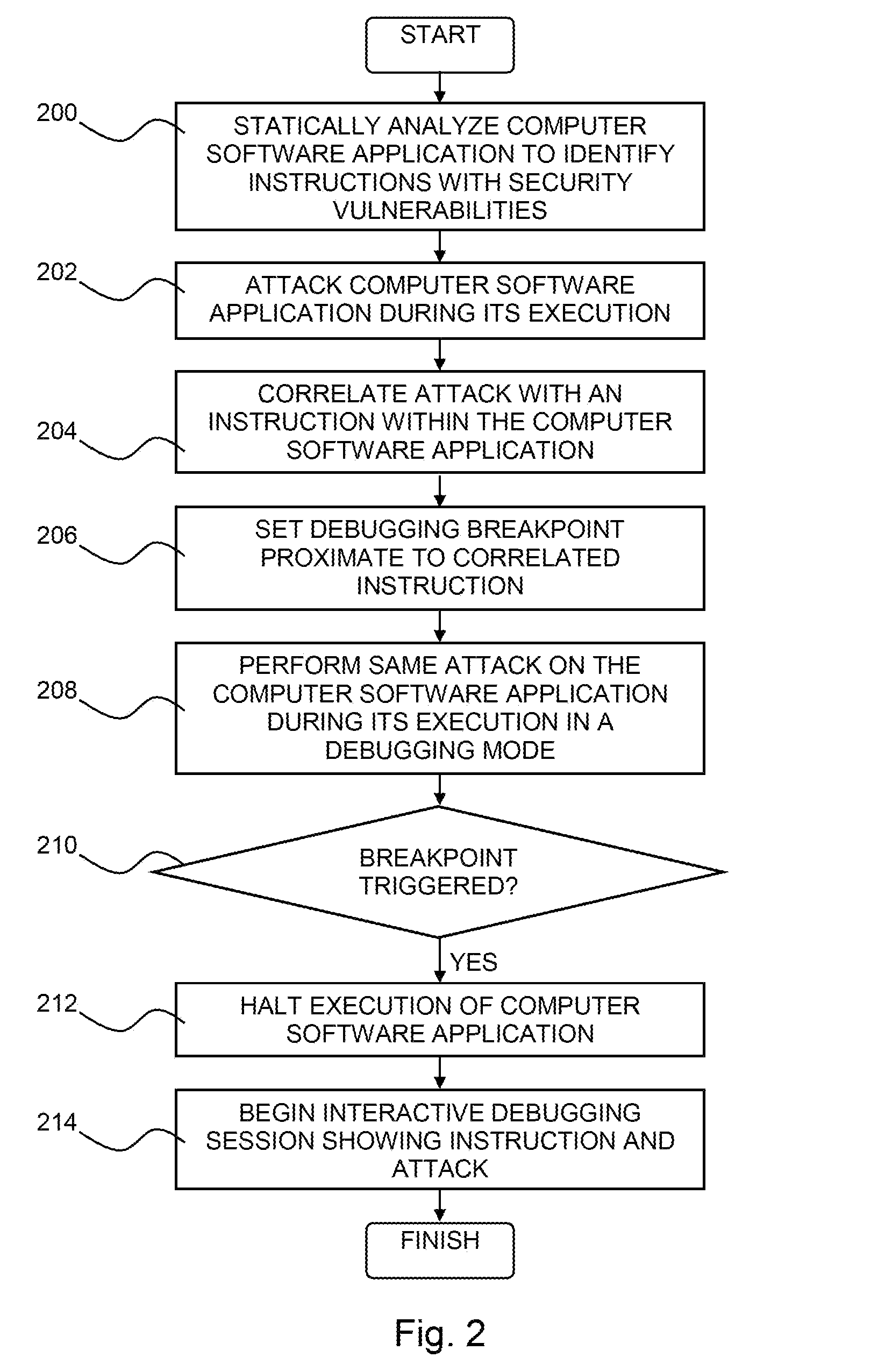
Pinpointing security vulnerabilities in computer software applications
ActiveUS8510842B2Memory loss protectionUnauthorized memory use protectionSoftware engineeringApplication software
Owner:FINJAN BLUE INC
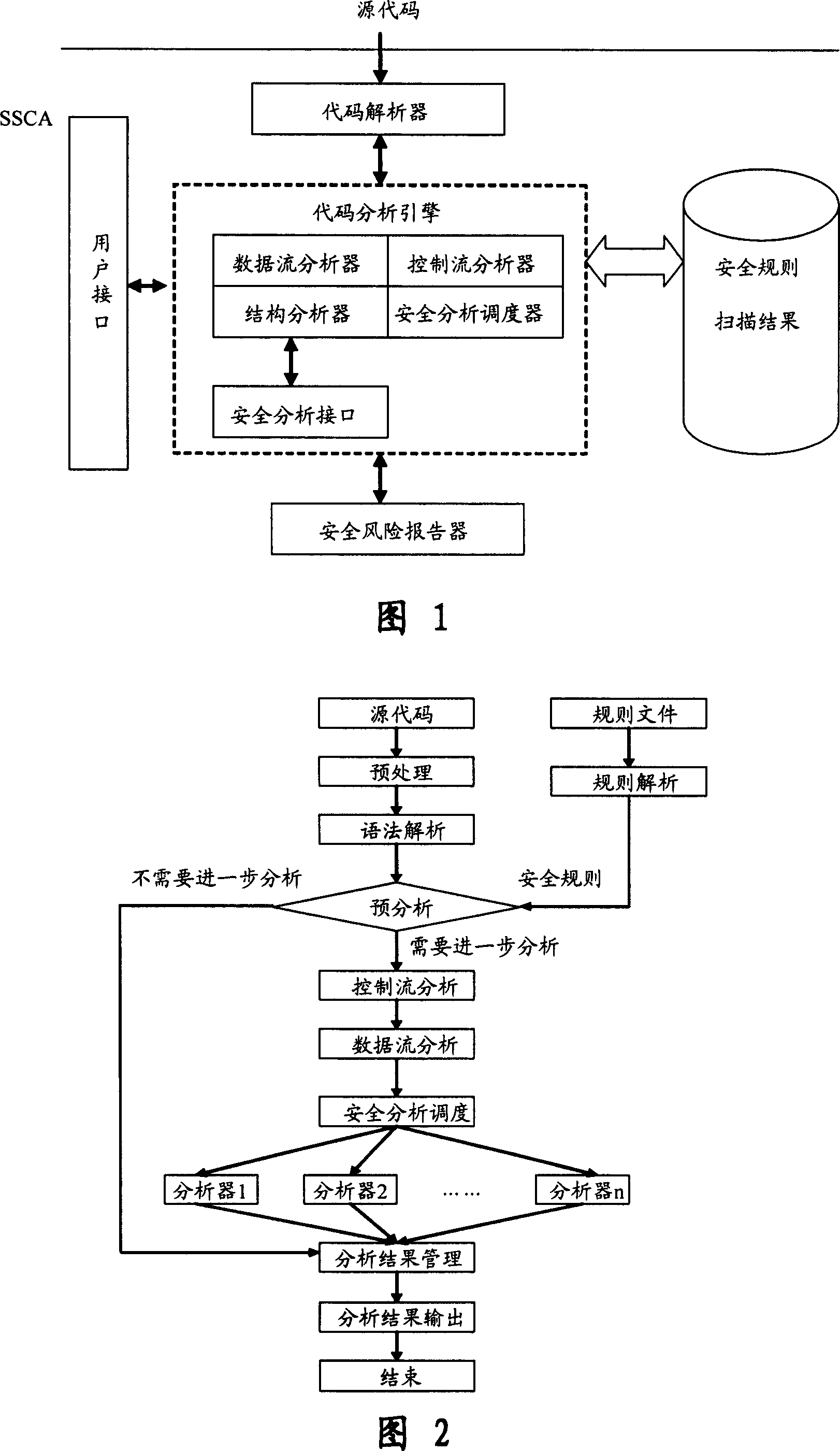
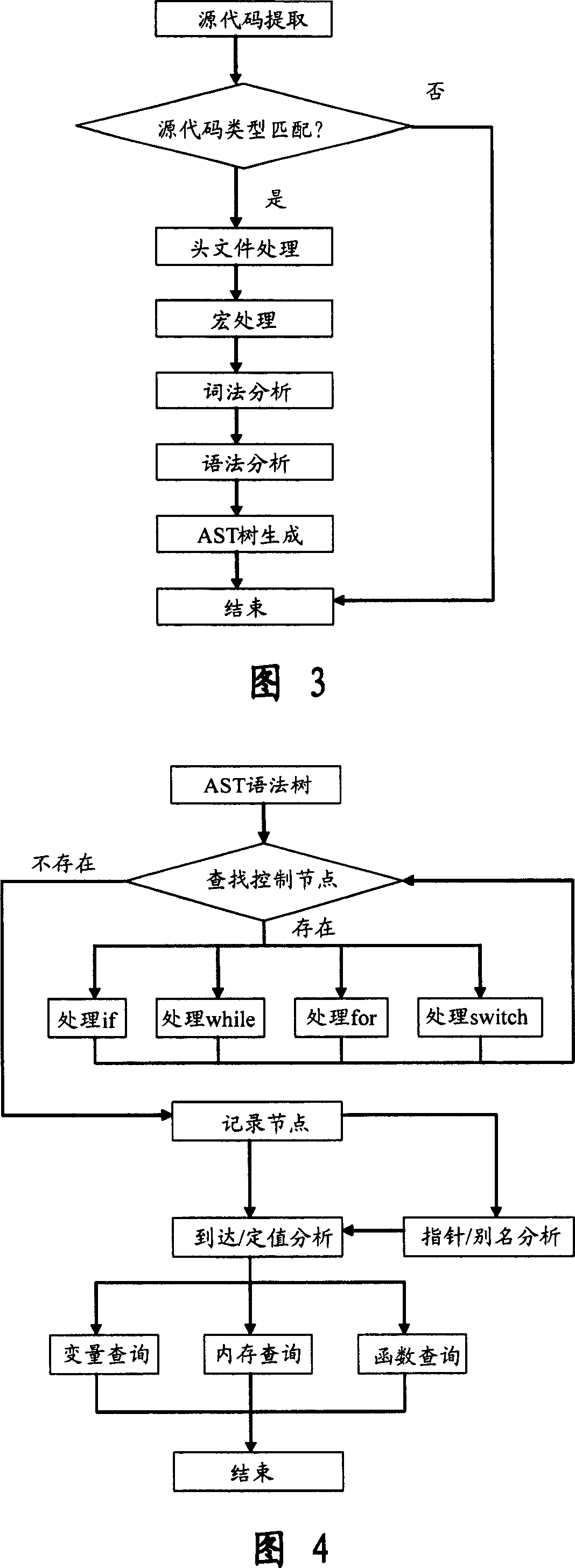
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
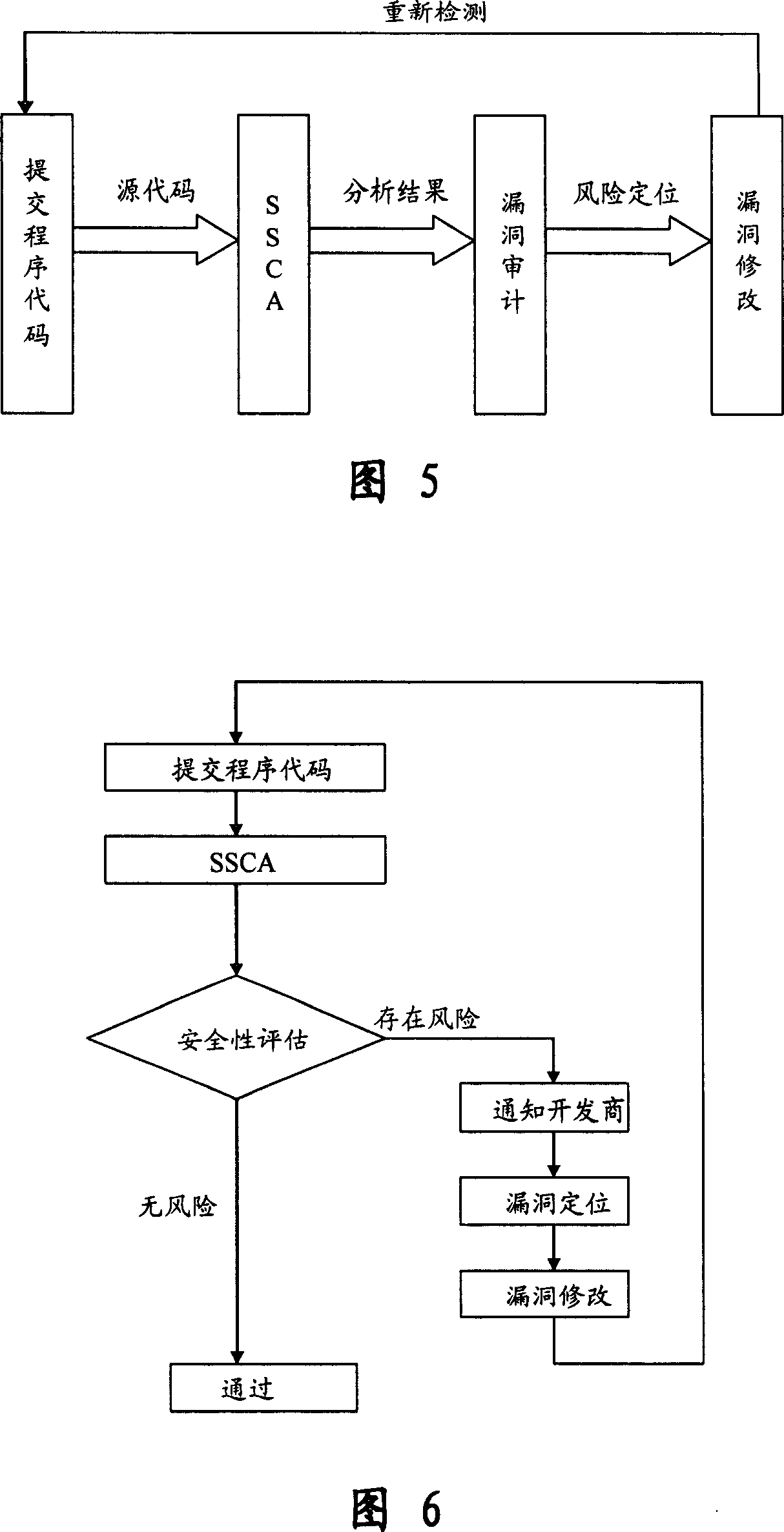
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
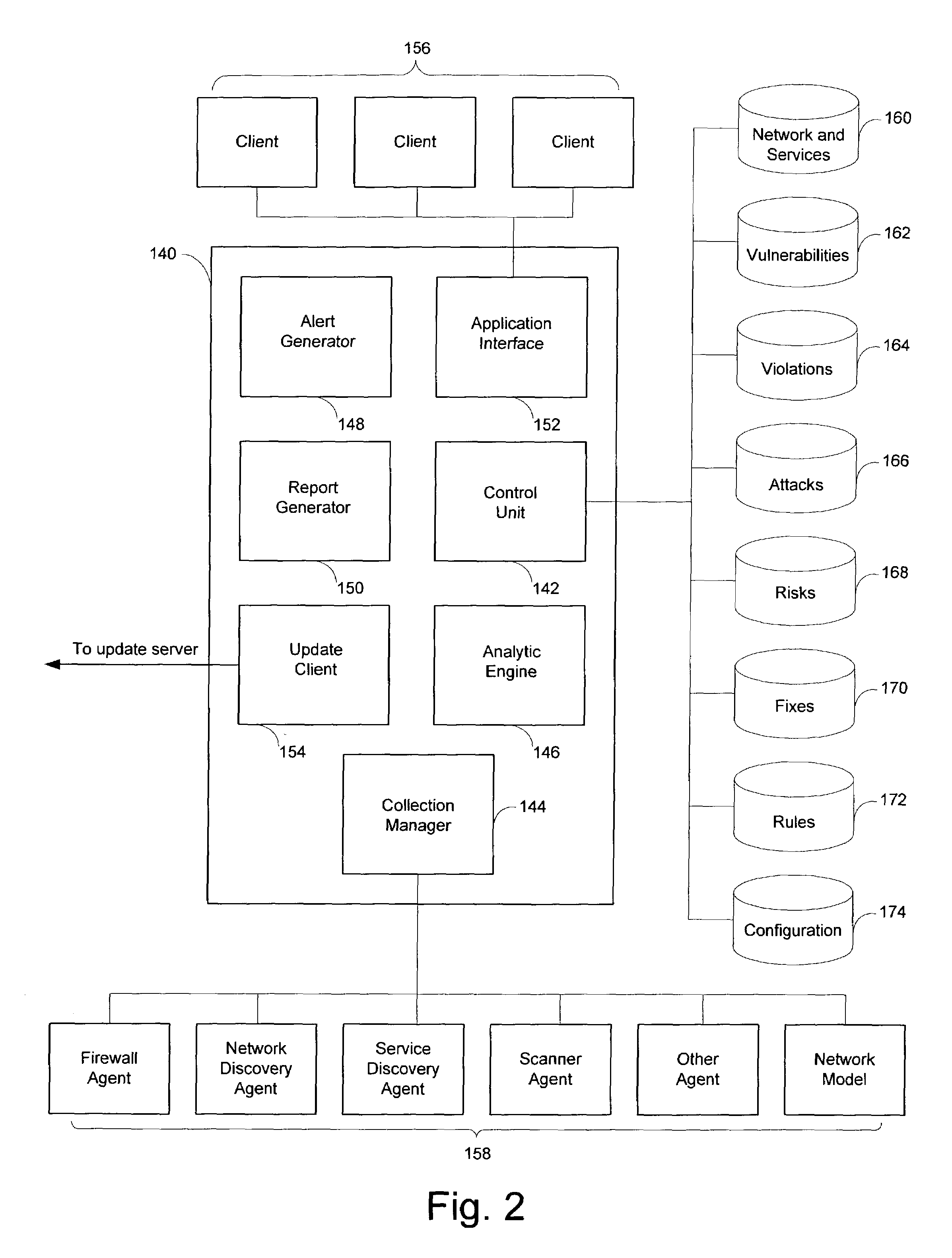
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com