Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
643 results about "Network access point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
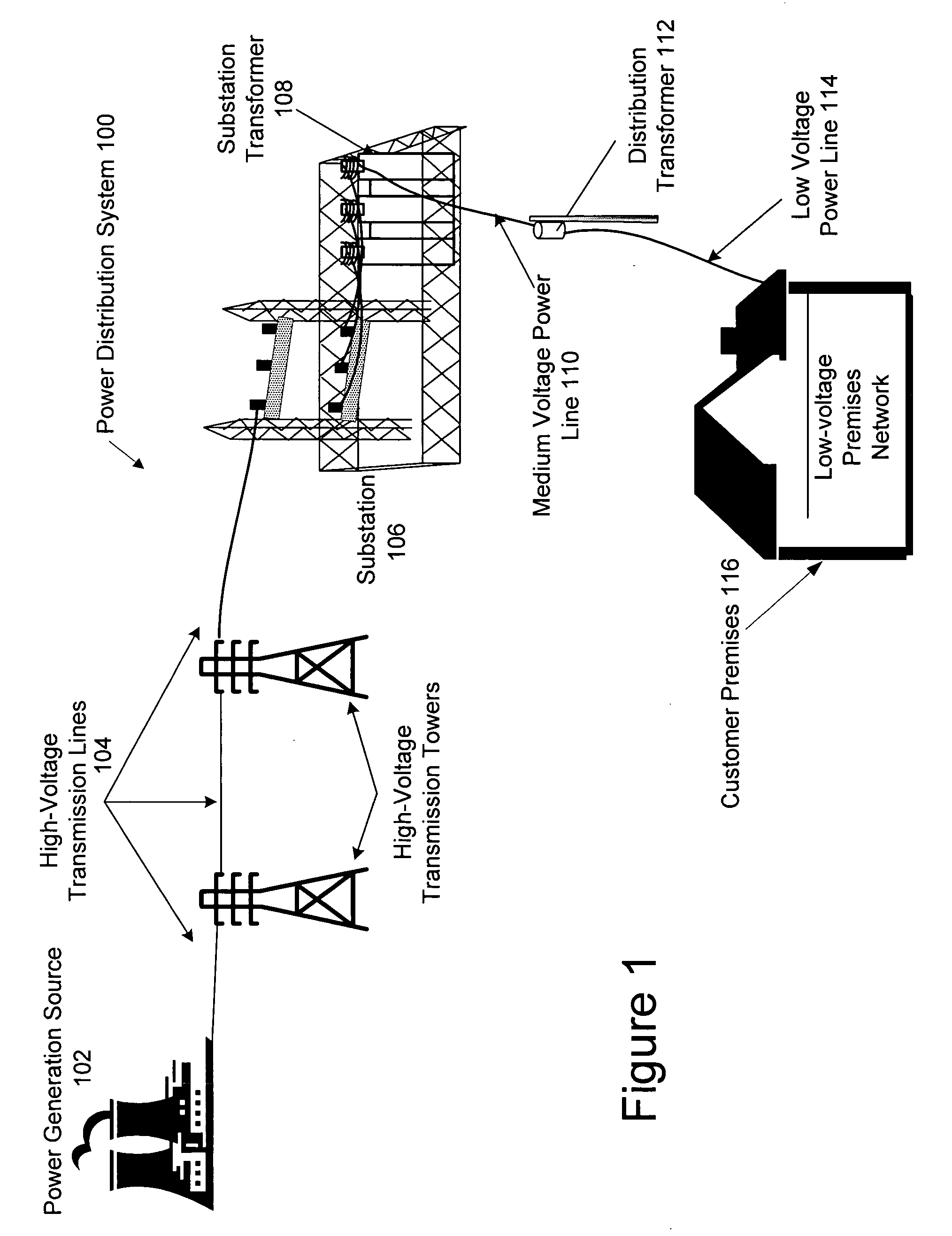
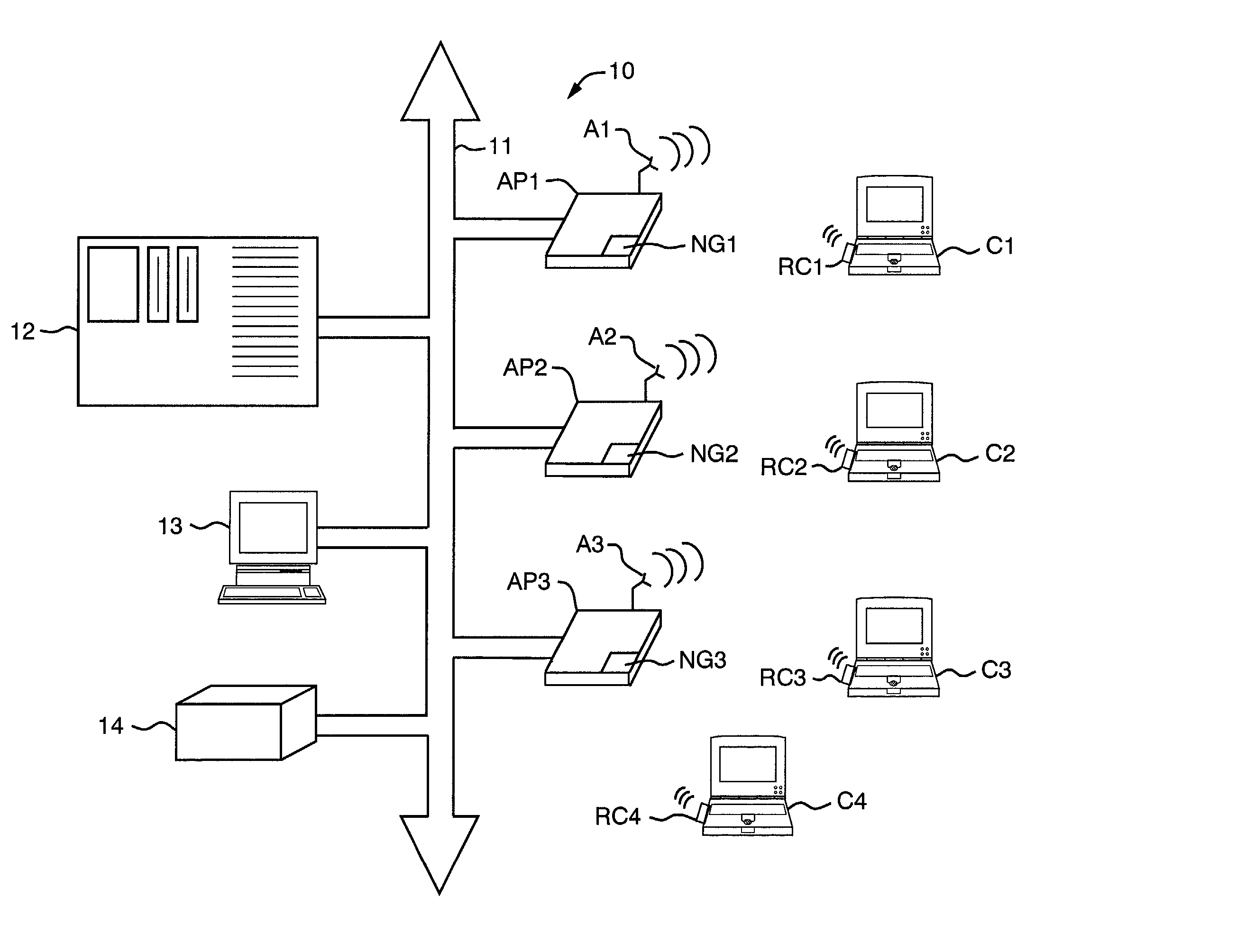
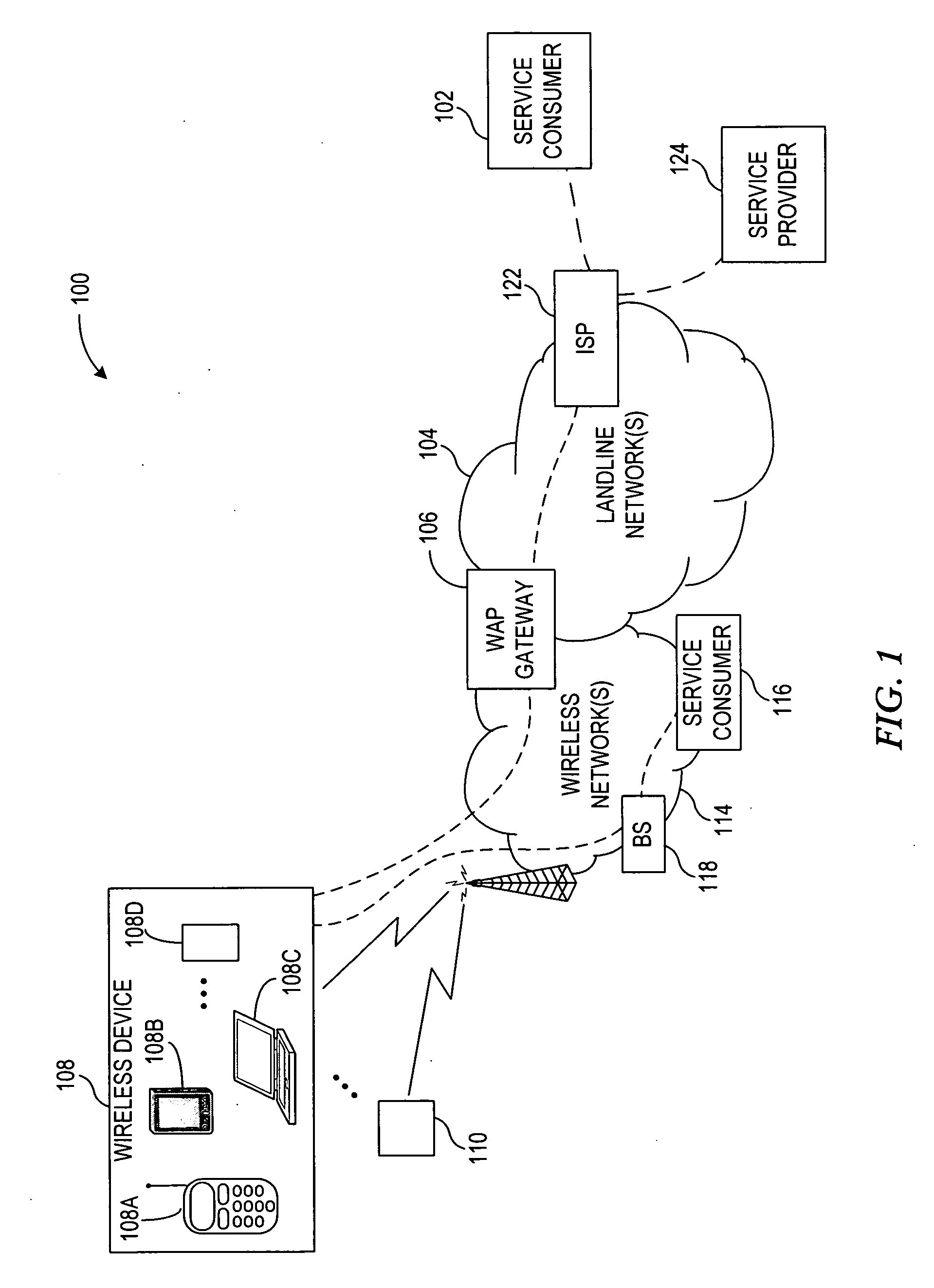
A Network Access Point (NAP) was a public network exchange facility where Internet service providers (ISPs) connected with one another in peering arrangements. The NAPs were a key component in the transition from the 1990s NSFNET era (when many networks were government sponsored and commercial traffic was prohibited) to the commercial Internet providers of today. They were often points of considerable Internet congestion.
Industrial design for consumer device based scanning and mobility
ActiveUS20150028104A1Easy to holdLine/current collector detailsCharacter and pattern recognitionDisplay deviceTouchscreen
A data entry and scanning apparatus that includes a commercially available mobile device wherein said commercially available mobile device with a touch screen display, a processor, and a wireless communications network access point, a scanning device, an interface, and a power source that external to the commercially available mobile device and connected to the interface, and a casing that does not cover the touch screen display.
Owner:HONEYWELL INT INC
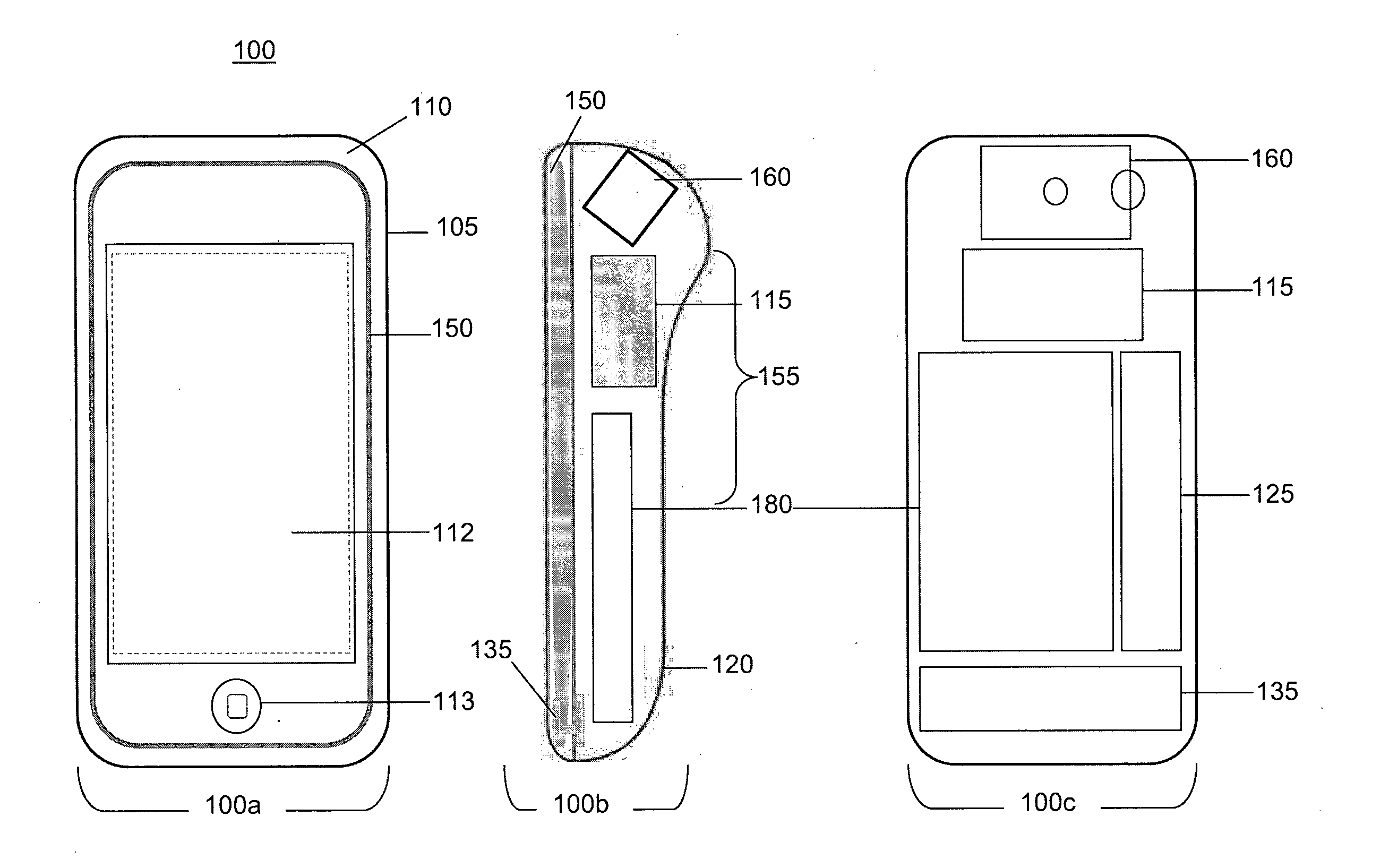
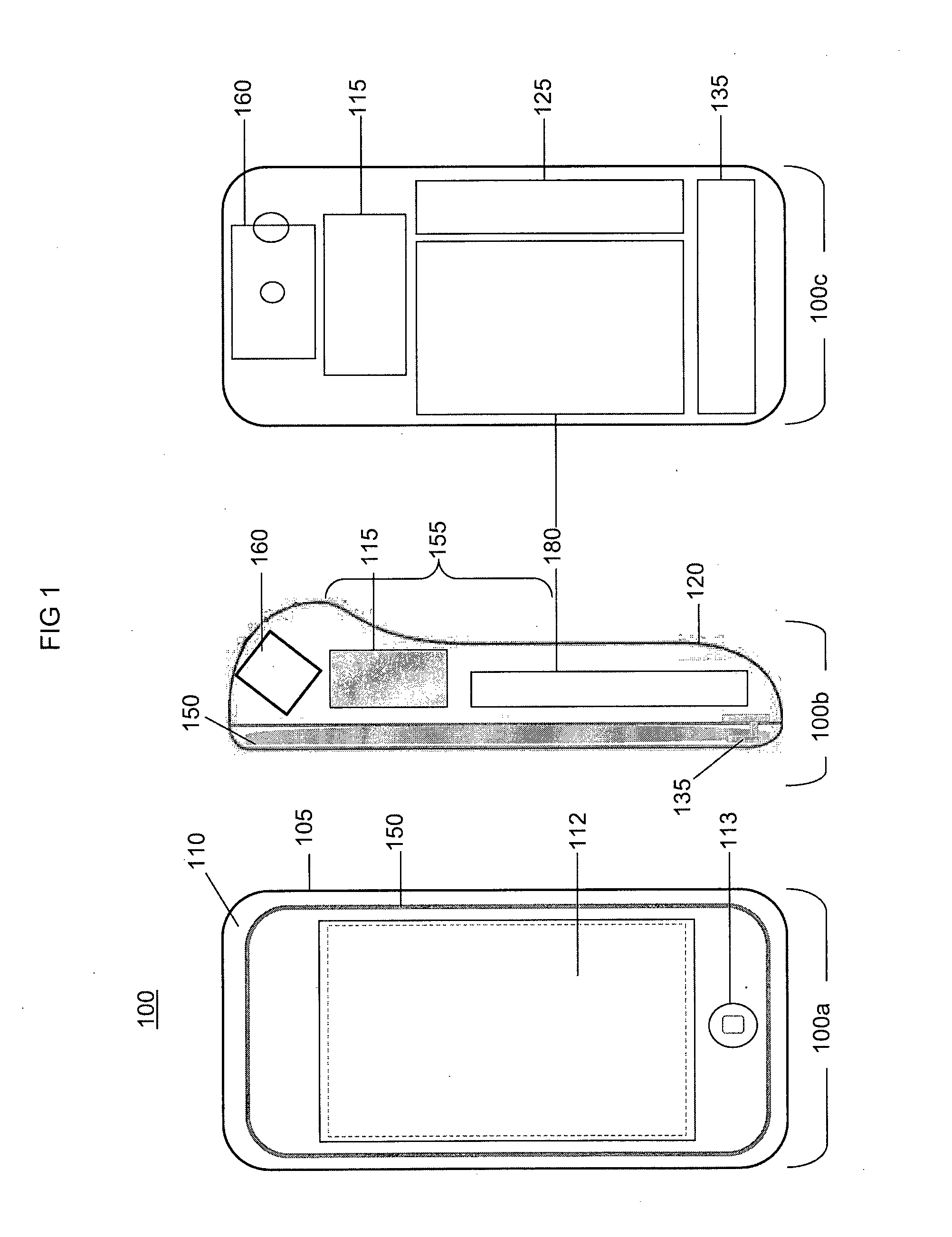
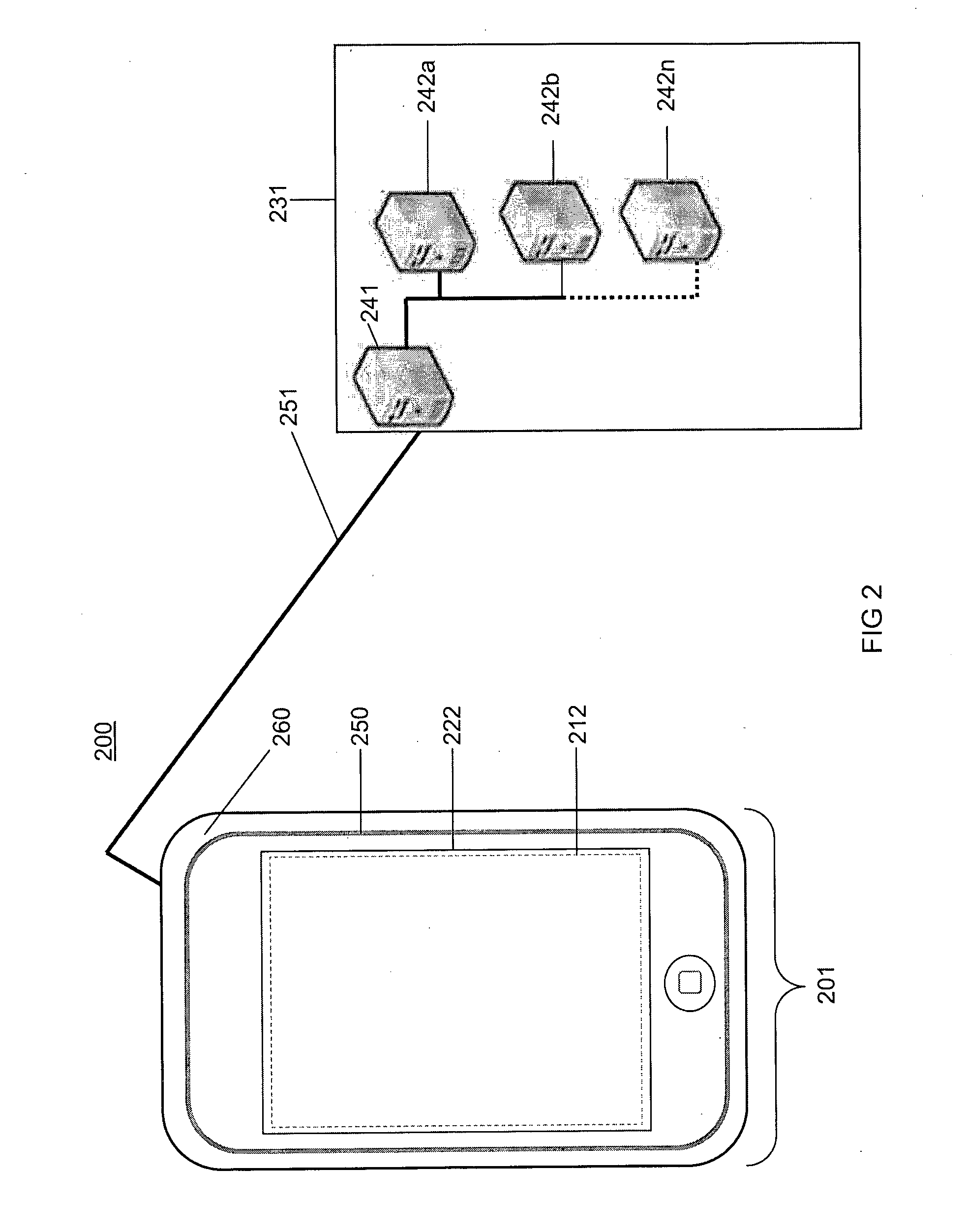
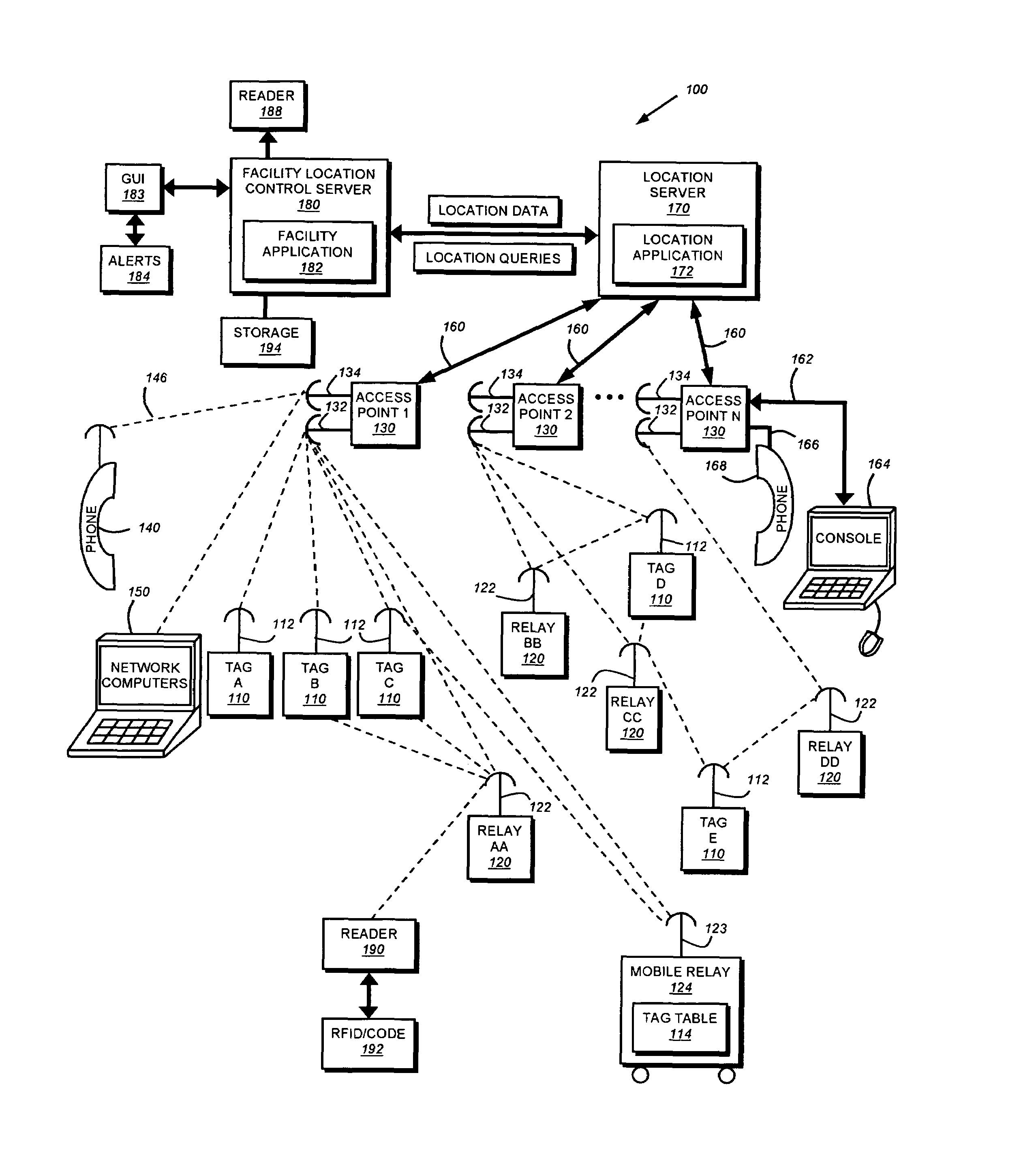
System and method for locating and communicating with personnel and equipment in a facility
InactiveUS7323991B1Increase redundancyQuickly and frequently and continuously updatedElectric signal transmission systemsTicket-issuing apparatusTransceiverWireless data
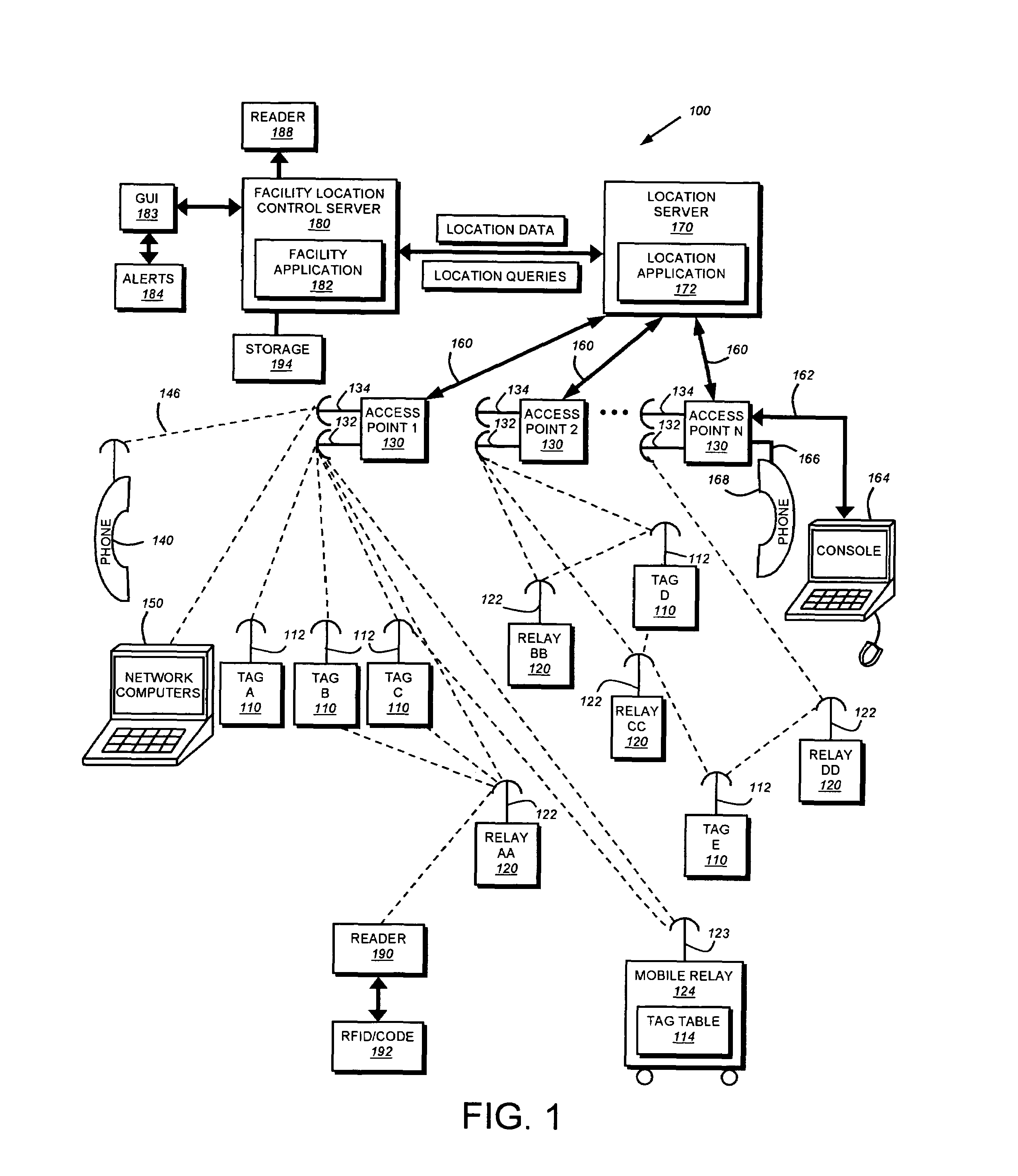
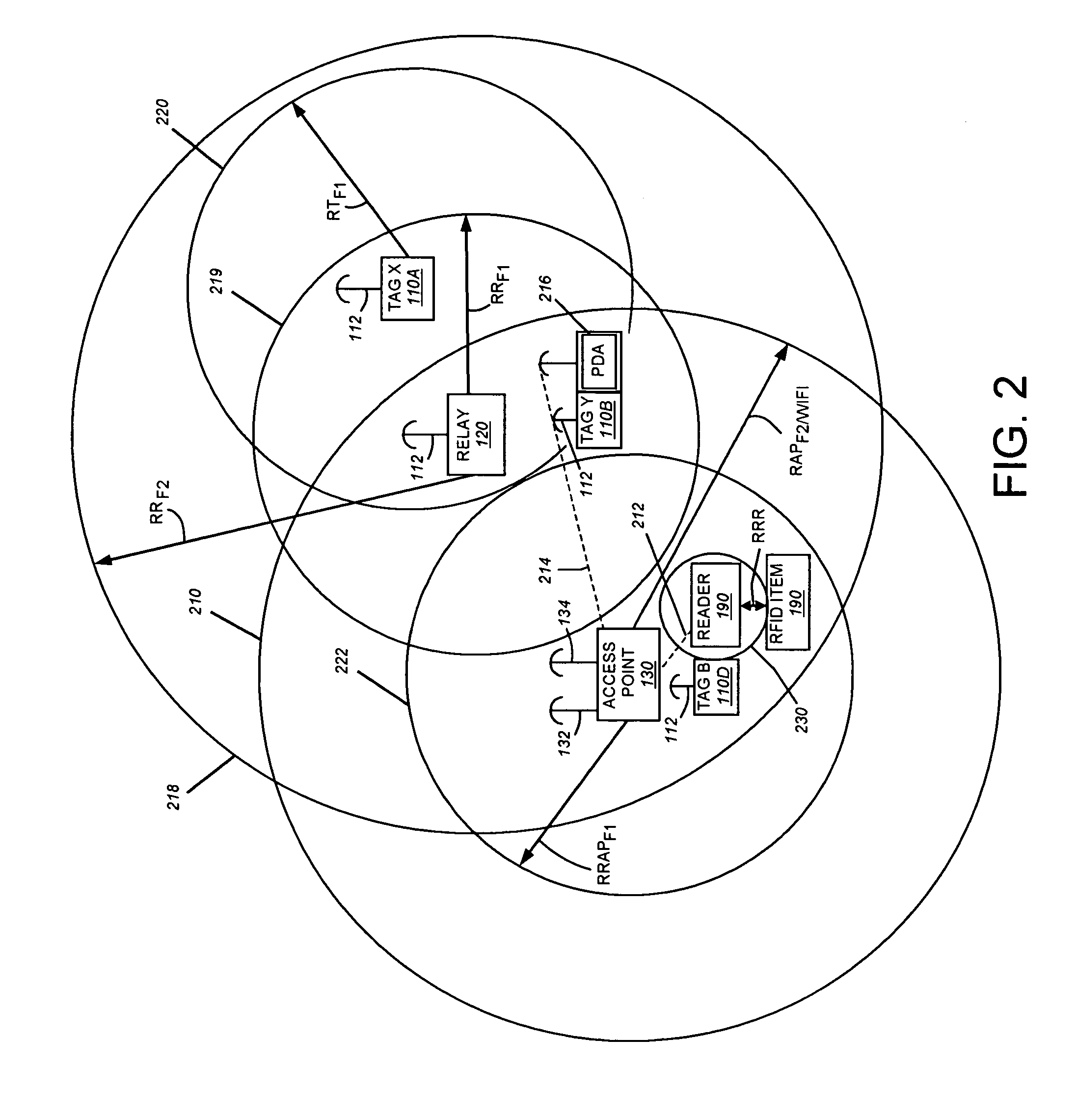
This invention provides a system and method for identifying, locating, authorizing by proximity and communicating with equipment and personnel in a facility that generally employs a series of limited range transceivers for location determination and a distributed wireless data network for data transfer. The system employs unique RF transceiver tags on personnel and equipment that are each uniquely identified and registered with a facility control application that oversees activities in the facility. The tags are tracked by RF communication based upon their proximity to one or more fixed-base networked access points and relays (which transfer location data by RF back to access points) within four range zones. Location data on all tags is uploaded periodically to a location server that interfaces with the facility control server. Tag data is monitored by the facility control server to track, authorize and deauthorize certain data transfers, movements and activities in accordance with rules established for each tag (or type of tag) within the facility control server's application. Wireless networking (WiFi, for example), in combination with the RF-derived location information, allows the facility control server to correlate and transmit data to staff in conjunction with location and proximity. WiFi can transmit authorizations, deauthorizations and general data based upon triggers established by proximity and location. Likewise, data can be transmitted over WiFi from readers etc. from personnel and equipment located and identified by the system.
Owner:TIDEWATER HLDG
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
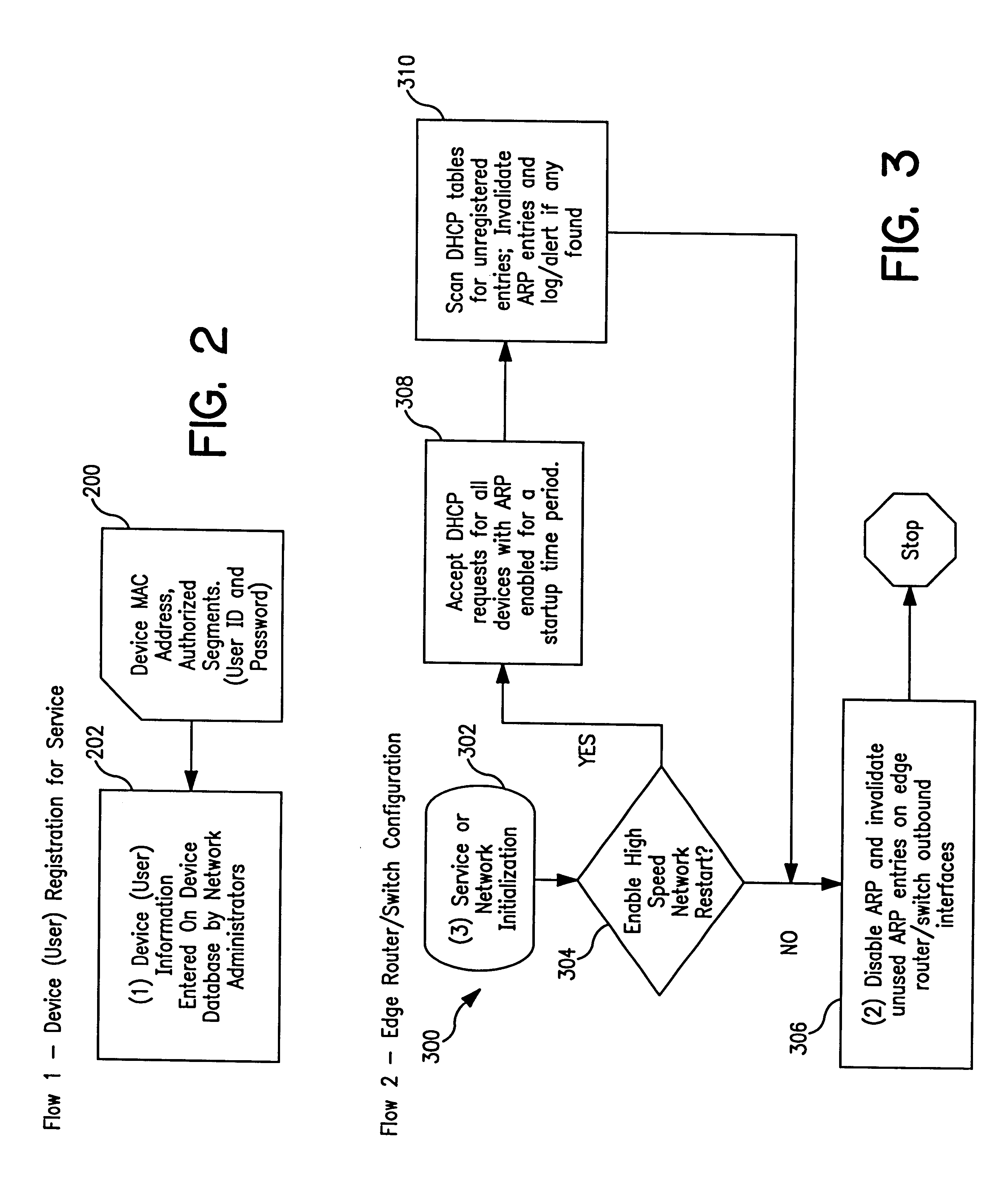
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
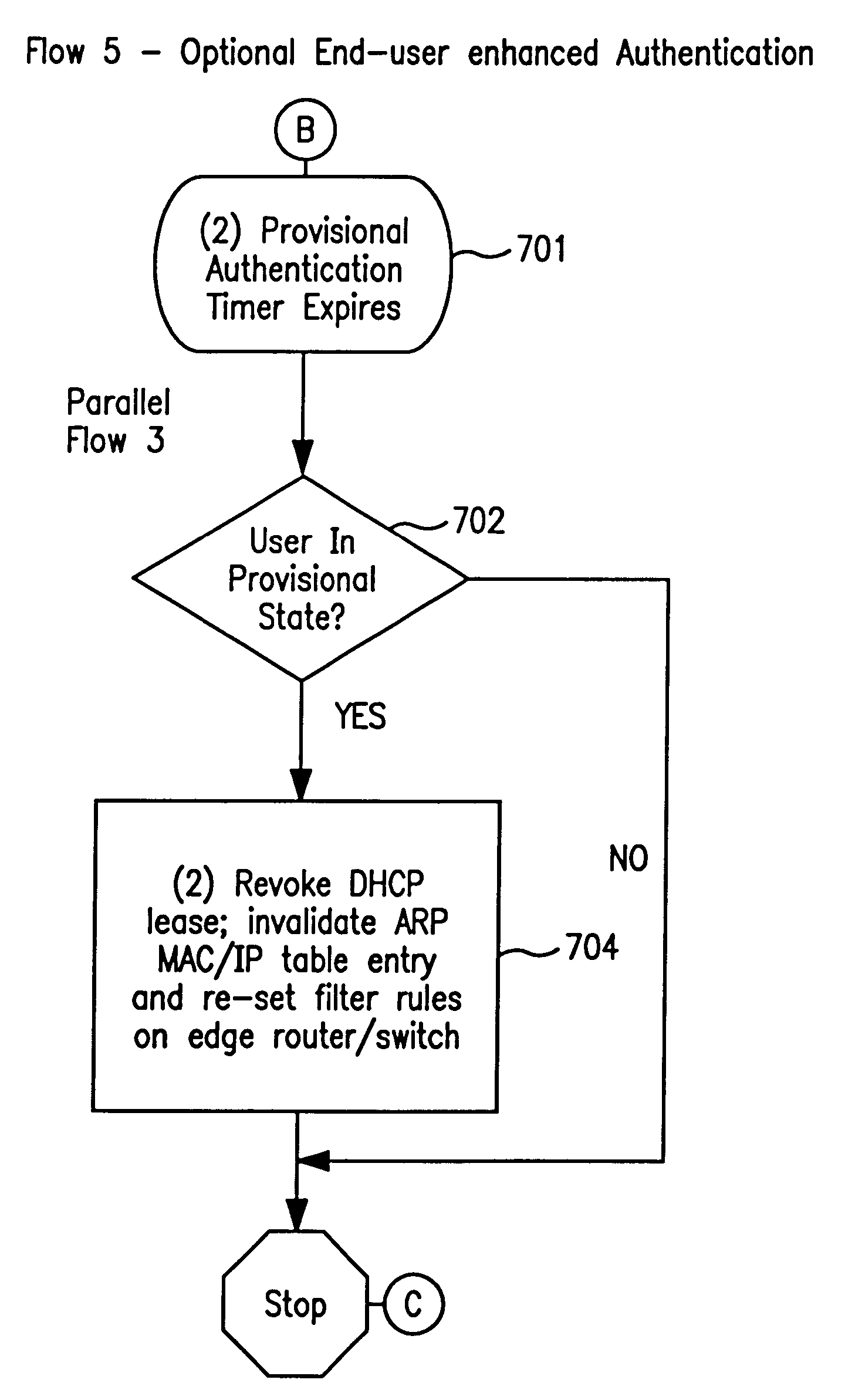
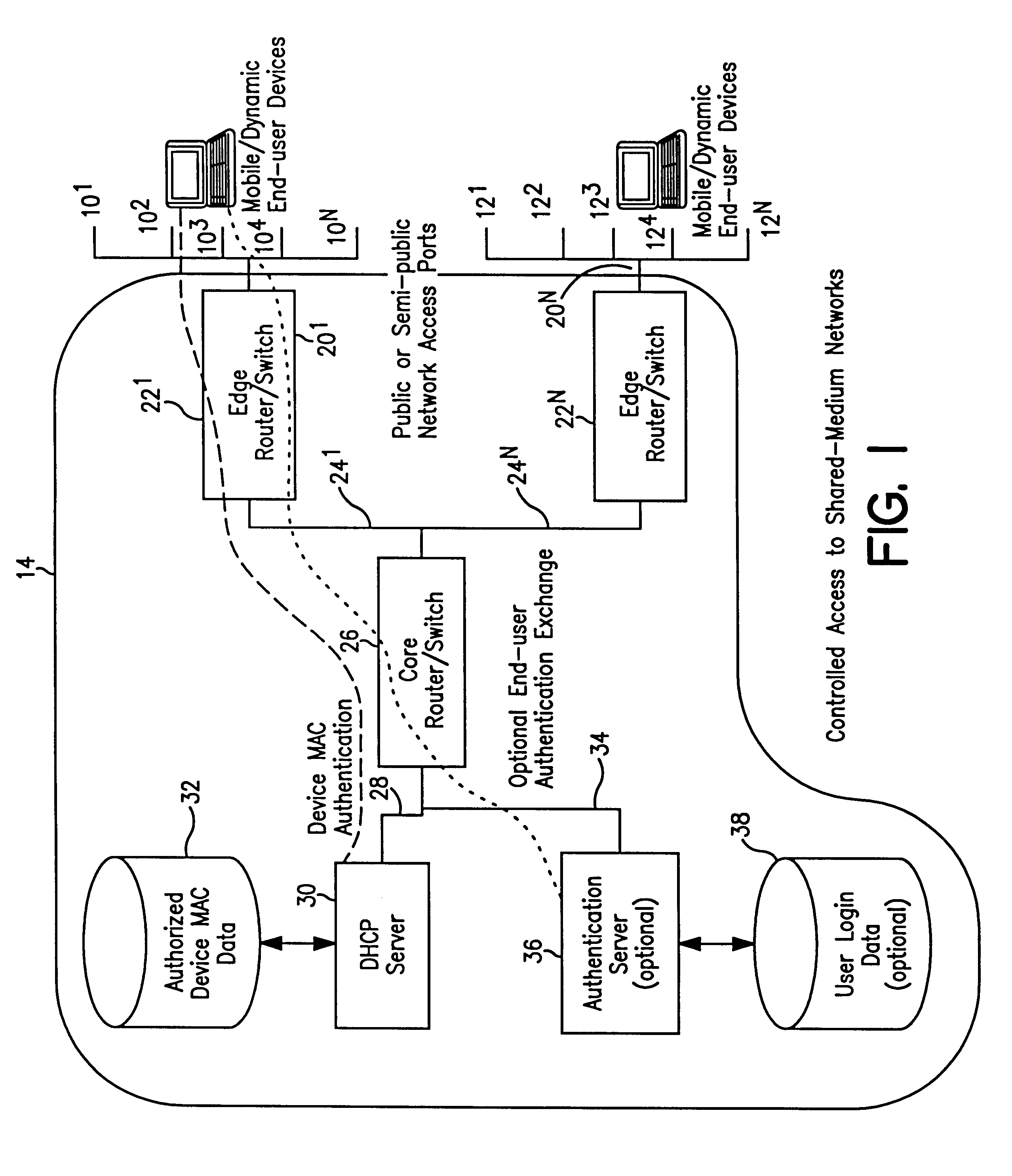
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
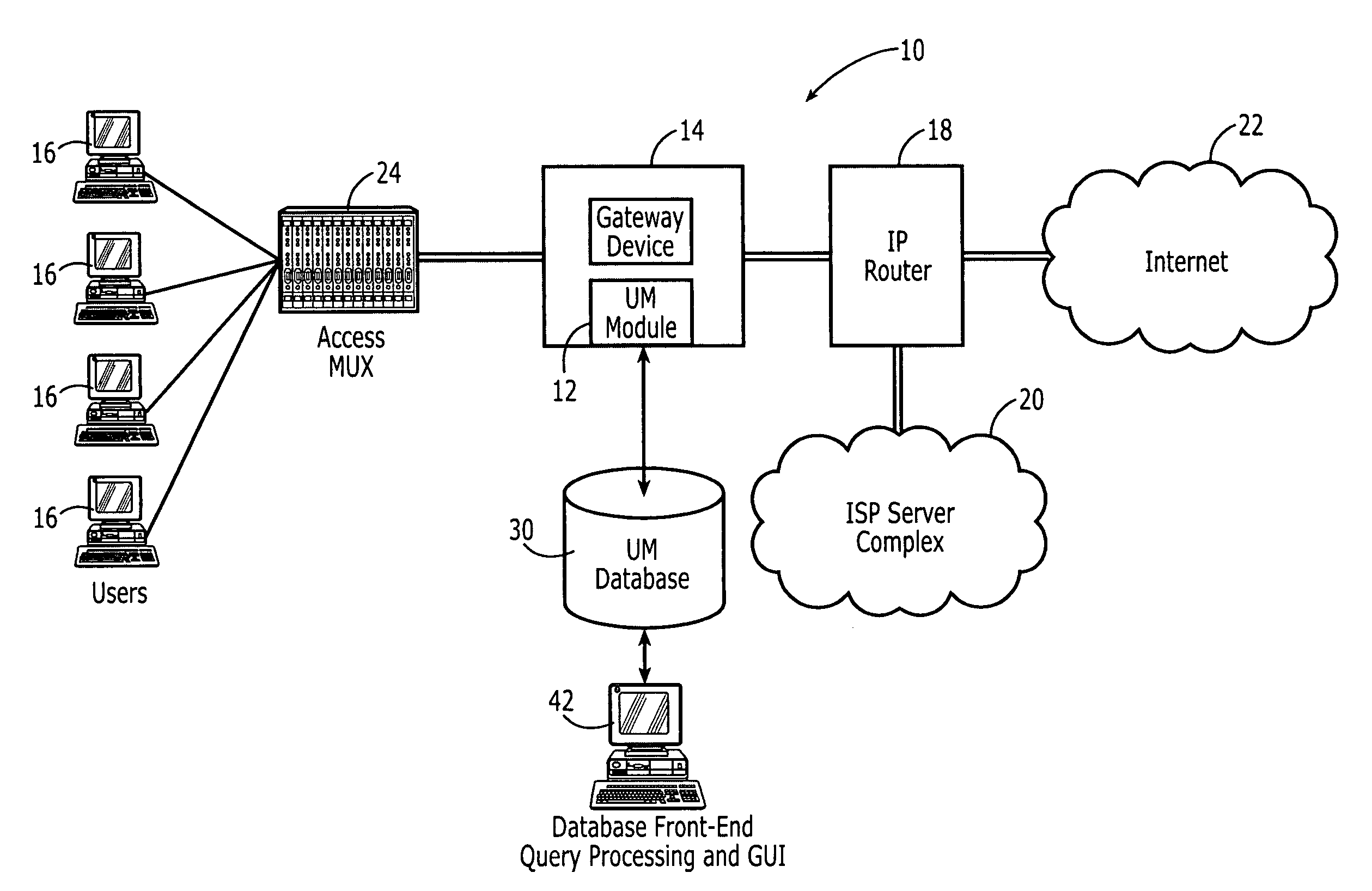
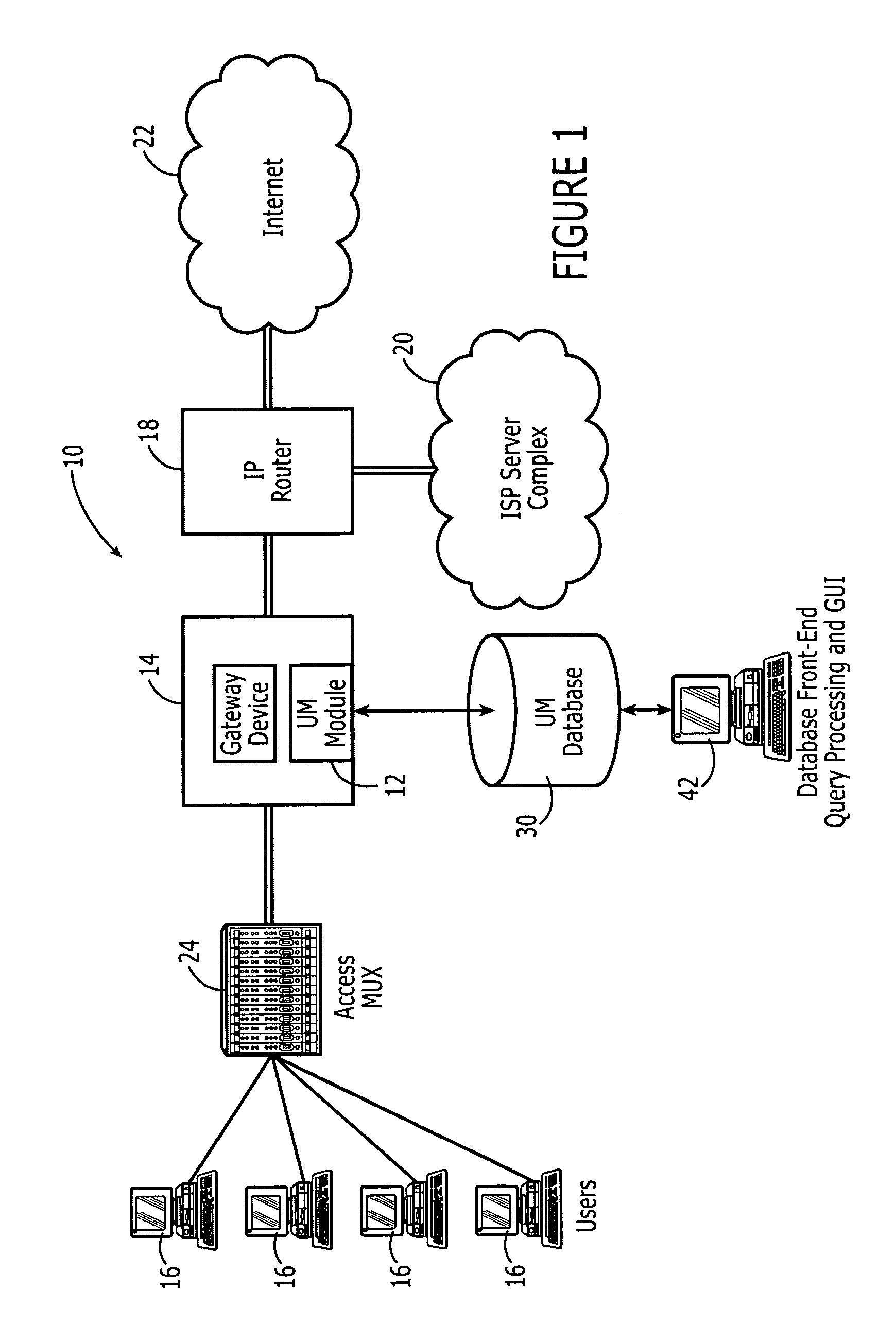
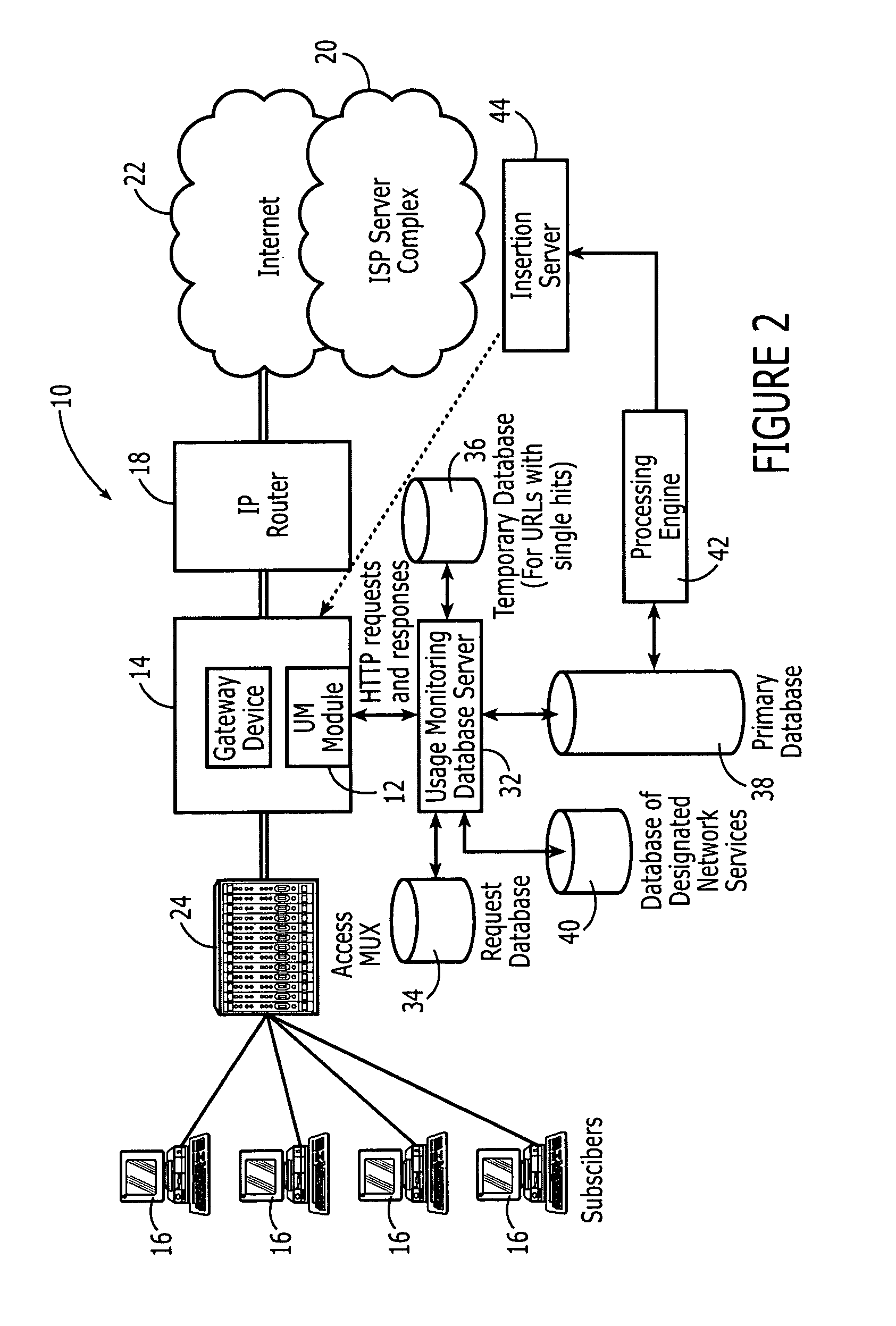
Network usage monitoring device and associated method
InactiveUS7020082B2Information can be usedIncrease valueError preventionFrequency-division multiplex detailsTraffic capacityNetwork interface device
A network usage monitoring module is provided for monitoring network usage at a network access point, i.e. network traffic aggregation point, typically at a gateway device or a similar network interface device. As such, the network usage monitoring module can monitor the usage of a number of network users who are attempting to access various network services provided via the gateway device. Thus, the usage information collected by the usage monitoring module is considerably more robust than that offered by conventional monitoring techniques. As such, the information is considerably more valuable to network service providers, network users, network beneficiaries and the like. In addition, the usage monitoring method and apparatus offers a number of particular features to improve the monitoring process as well as the value of the usage information that is collected.
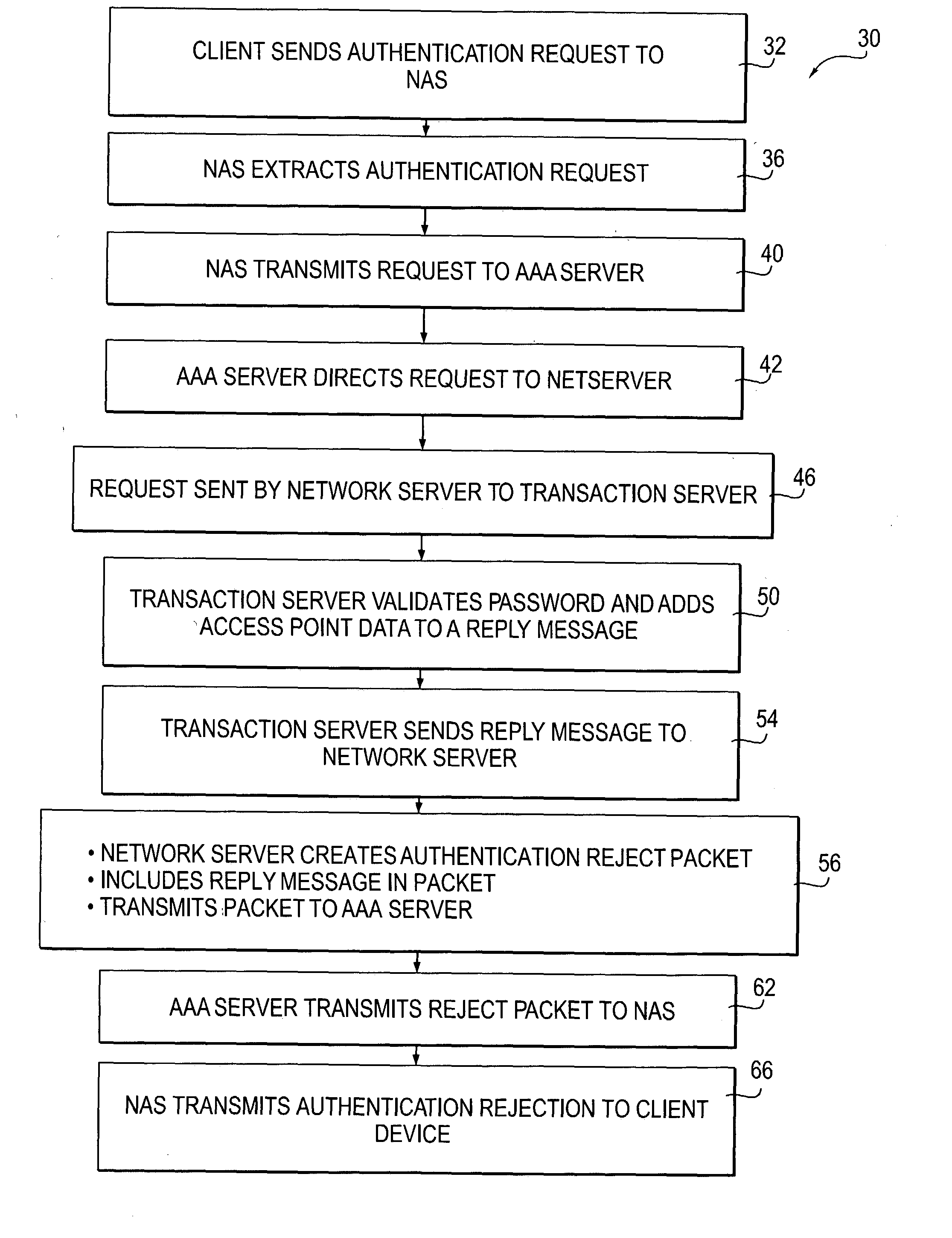
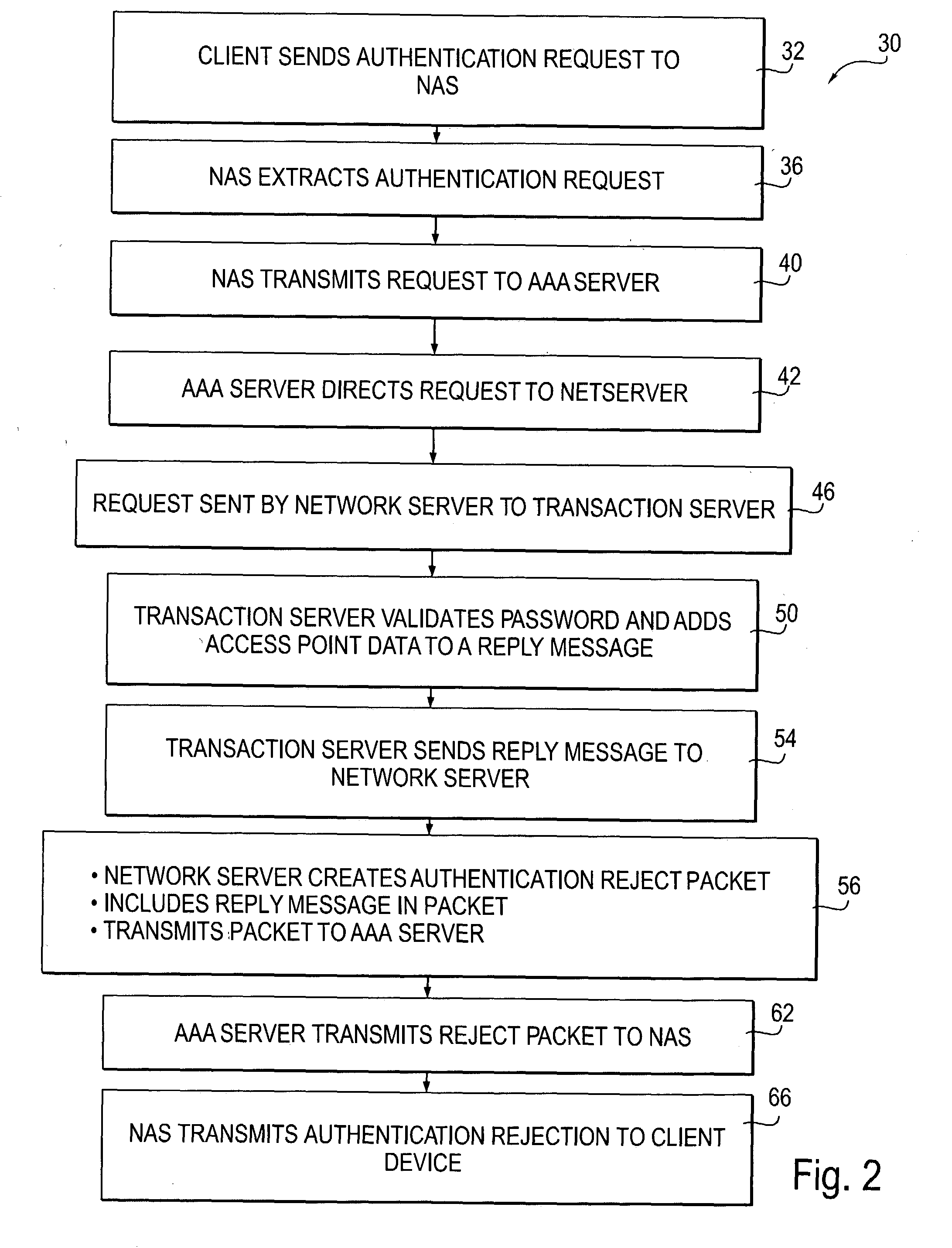
Owner:NOMADIX INC
Automated updating of access points in a distributed network
InactiveUS20020157090A1Data switching by path configurationProgram loading/initiatingProgrammable read-only memoryRandom access memory
A method and system for maintaining network access point equipment including installing and upgrading software. The system includes a network server, and access point equipment including one or more access point devices, with each device equipped with a CPU including a random access memory (RAM) and a programmable read only memory (PROM). The server is configured for receiving software for maintaining the programming of access point devices. Both the access point devices and the server are programmed with authentication software for identifying each other prior to transmission of maintenance data. The access point devices are further programmed to periodically do a software check with the server. If the current software version in the device is the same as that stored in the server, no action is taken. If the version in the server is different, then the server and device automatically load the current software version into the device.
Owner:HEREUARE COMMUNICATIOINS
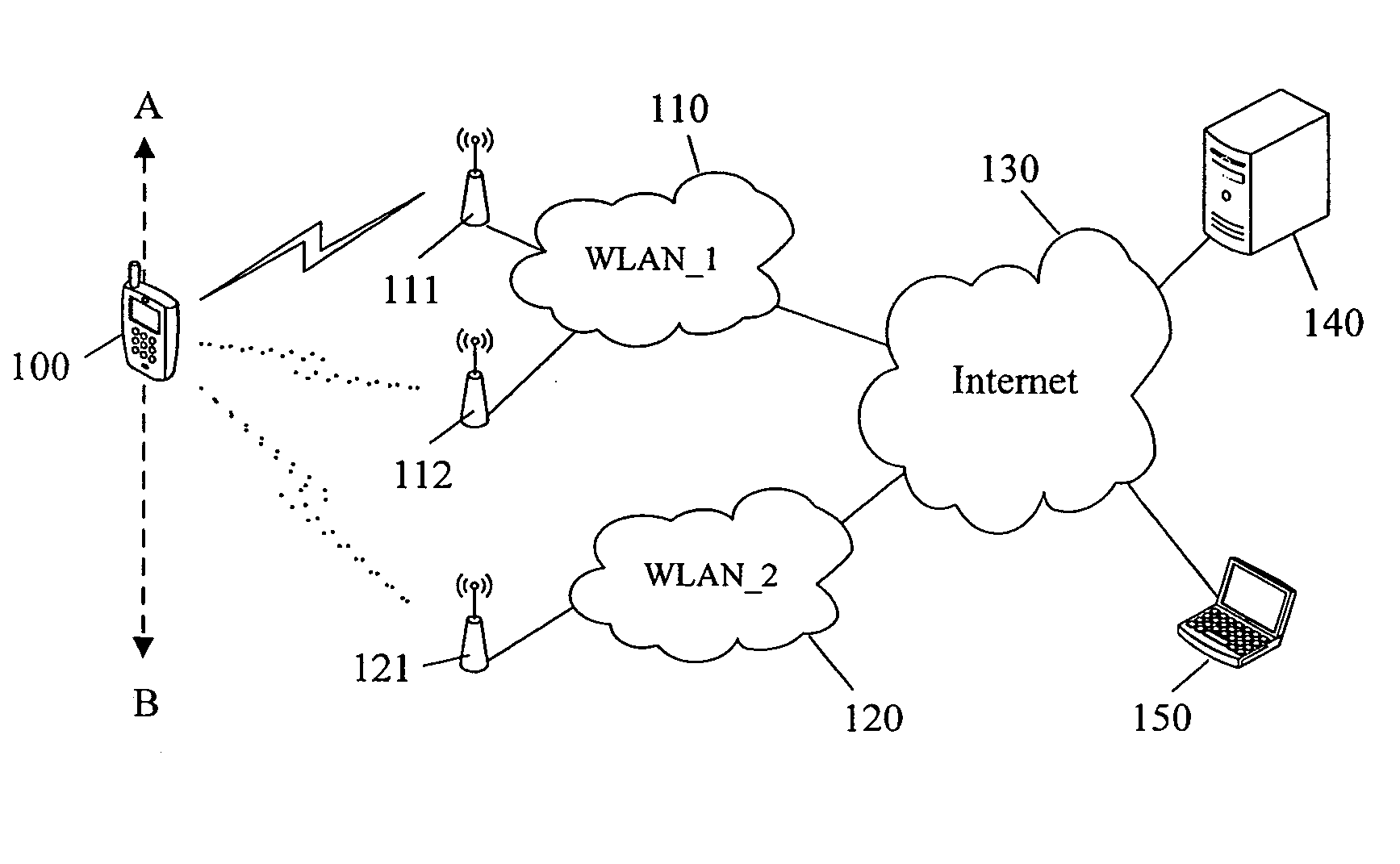
System and Method of Automatically Connecting A Mobile Communication Device to A Network using A Communications Resource Database
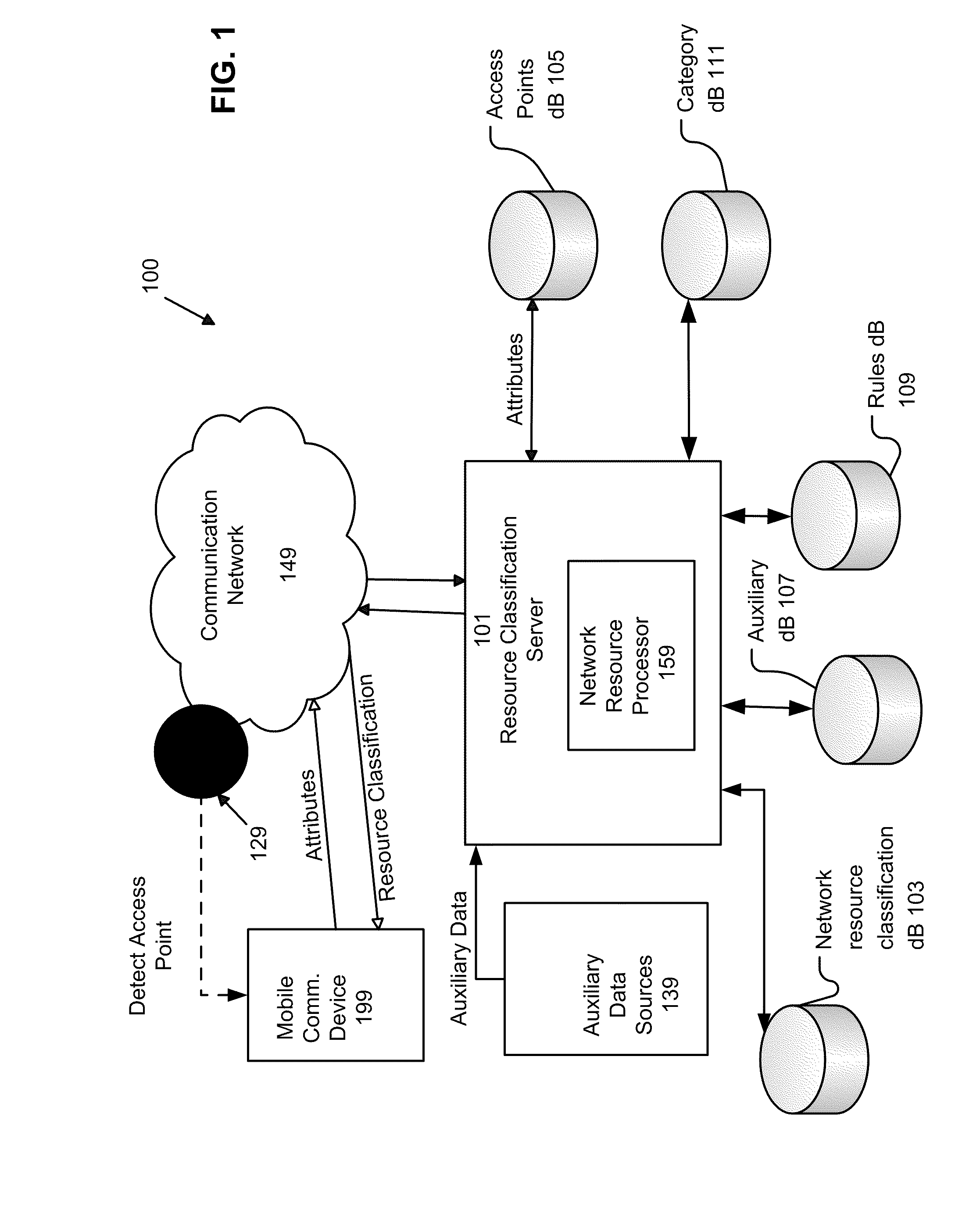
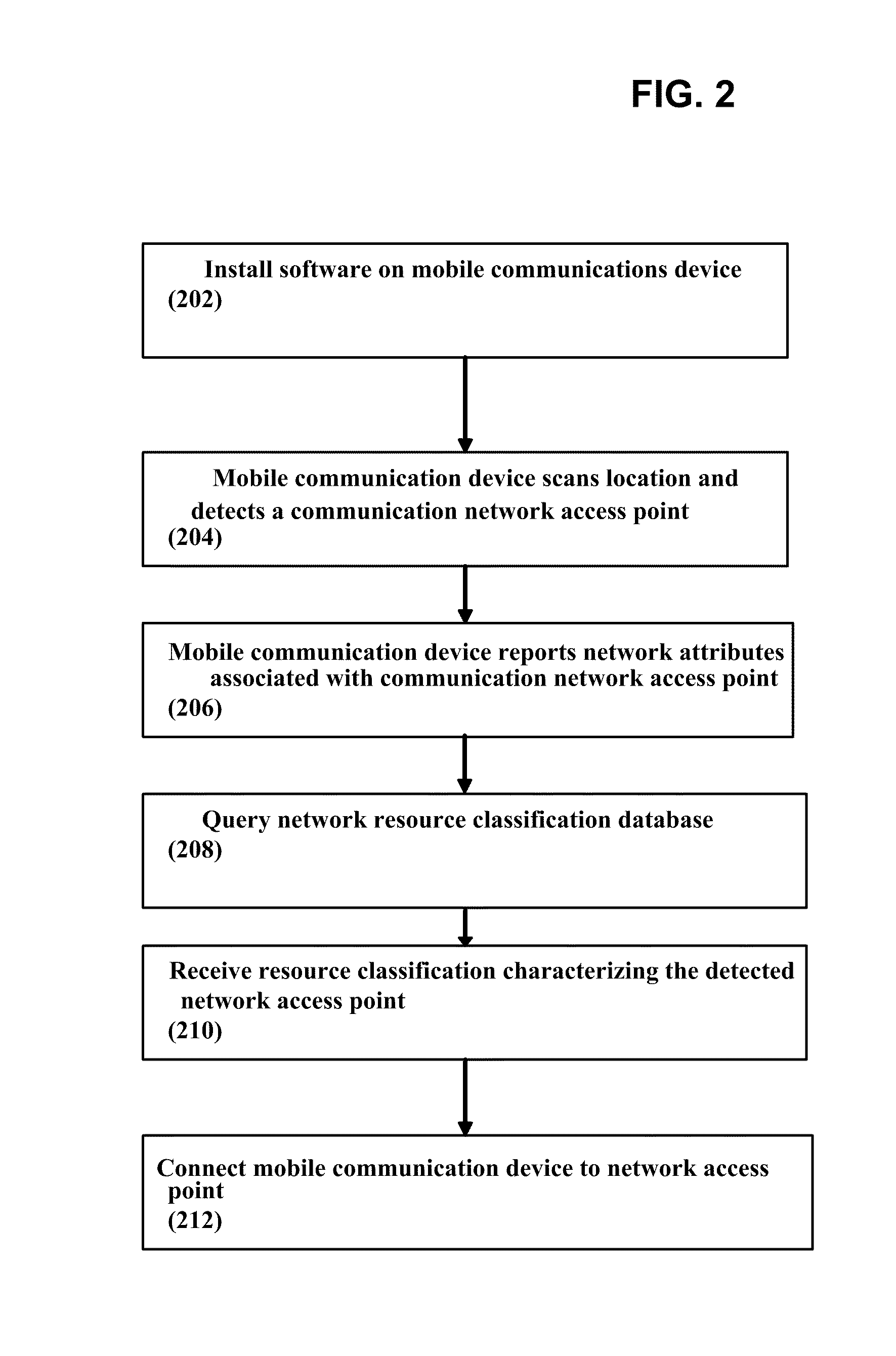
ActiveUS20110013569A1Bridging the gapEasy to useDigital data processing detailsAssess restrictionNetwork access pointCommunication device
A system, method, and computer program product of automatically connecting a mobile communication device to a communication network using a network resource classification database includes detecting a communication network access point using the mobile communication device and reporting network attributes associated with the access point to a resource classification server. The server analyzes and stores the network attributes, determines auxiliary data related to the access point, and uses a rules database to determine a category identifier associated with the access point. The server creates a resource classification characterizing the access point based upon the network attributes, auxiliary data, and category identifier. The mobile communication device queries the server, receives a resource classification, and connects to an access point based upon the received resource classification.
Owner:WEFI
Hybrid power line wireless communication system
InactiveUS20070054622A1Increase system capacityLower latencyModulated-carrier systemsTransmission path divisionCommunication interfaceTelecommunications link
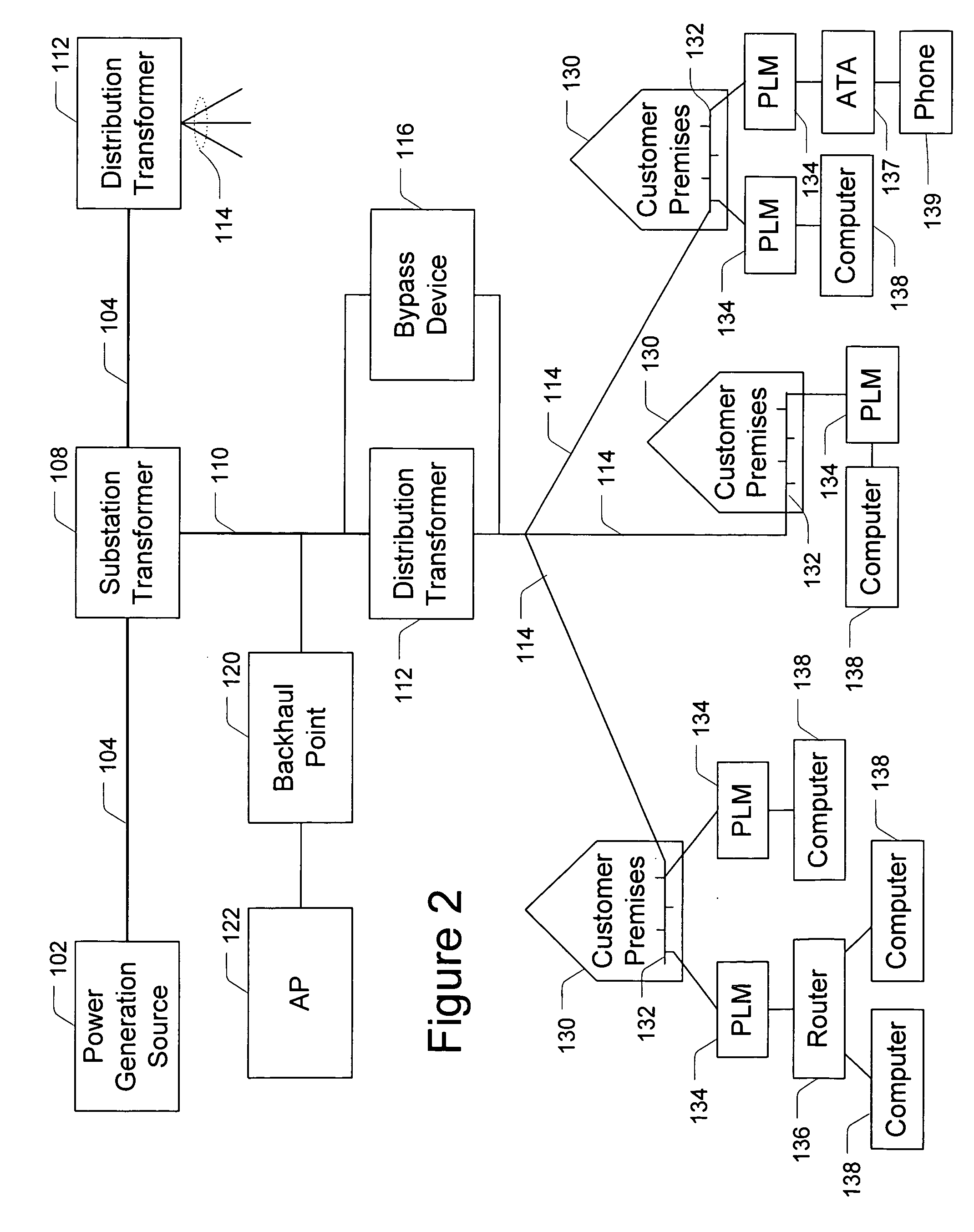
In a hybrid communication system a wireless communication link is maintained between a power line communication medium and a non-power line communication medium. Wireless communication is established within an unlicensed frequency band and monitored for quality. If the quality falls below a threshold, a wireless communication link is established within a licensed frequency band. The wireless link may be maintained between a power line communication system (PLCS) backhaul point and an internet protocol (IP) network access point, and / or between a PLCS endpoint communication interface and a premises communication device.
Owner:CURRENT TECH
System and Method of Automatically Connecting a Mobile Communication Device to A Network Using a Communications Resource Database
ActiveUS20110159818A1Easy to useBridging the gapError preventionFrequency-division multiplex detailsNetwork access pointCommunication device
A system, method, and computer program product of automatically connecting a mobile communication device to a communication network using a network resource classification database includes detecting a communication network access point using the mobile communication device and reporting network attributes associated with the access point to a resource classification server. The server analyzes and stores the network attributes, determines auxiliary data related to the access point, and uses a rules database to determine a category identifier associated with the access point. The server creates a resource classification characterizing the access point based upon the network attributes, auxiliary data, and category identifier and the network attributes, auxiliary data, and / or category identifier data of other access points. The mobile communication device queries the server, receives a resource classification, and connects to an access point based upon the received resource classification.
Owner:WEFI
System and method for delivering high-performance online multimedia services
InactiveUS6370571B1Easy to scaleIncrease speedSpecial service provision for substationResource allocationFiberCoaxial cable
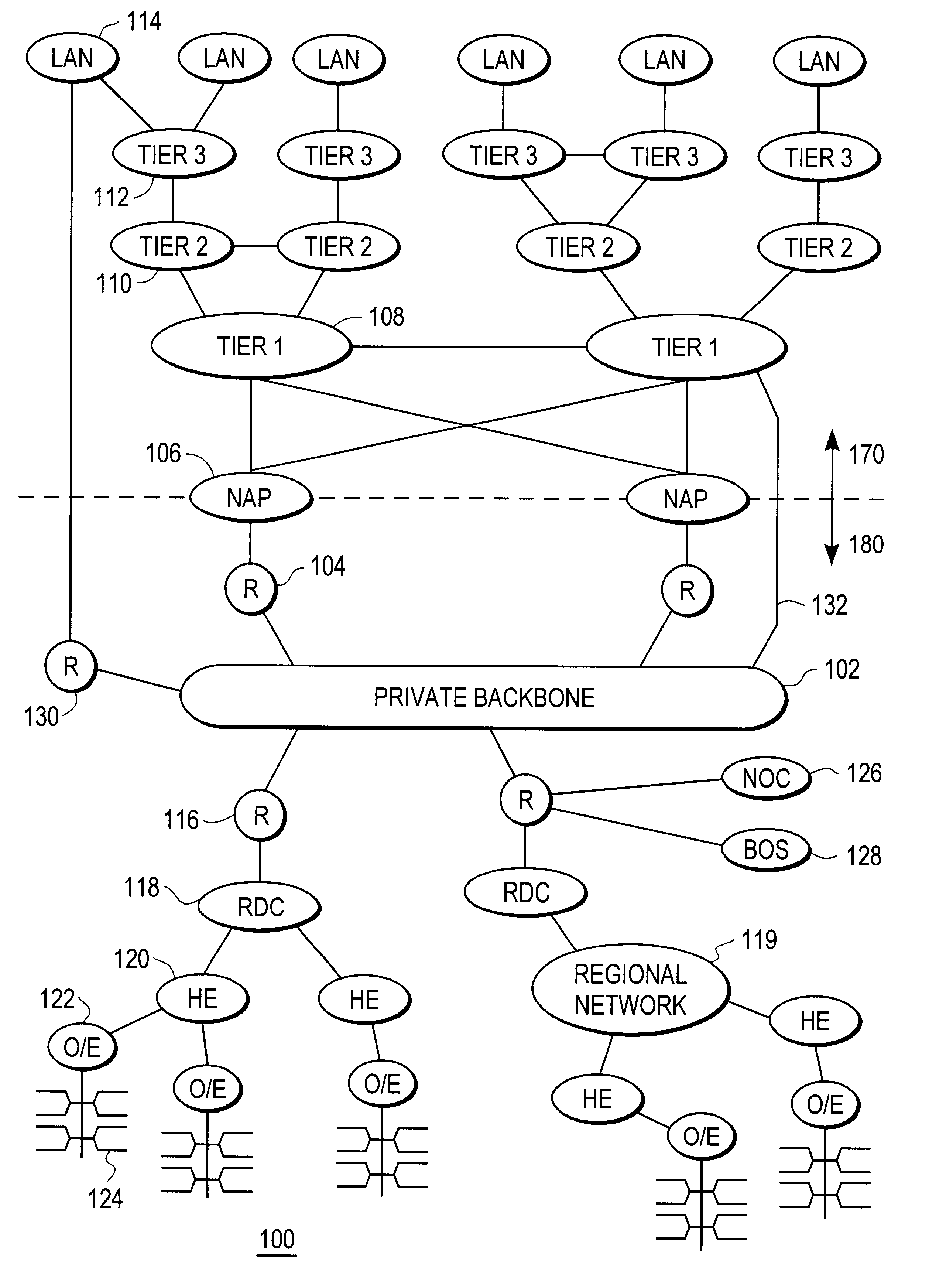
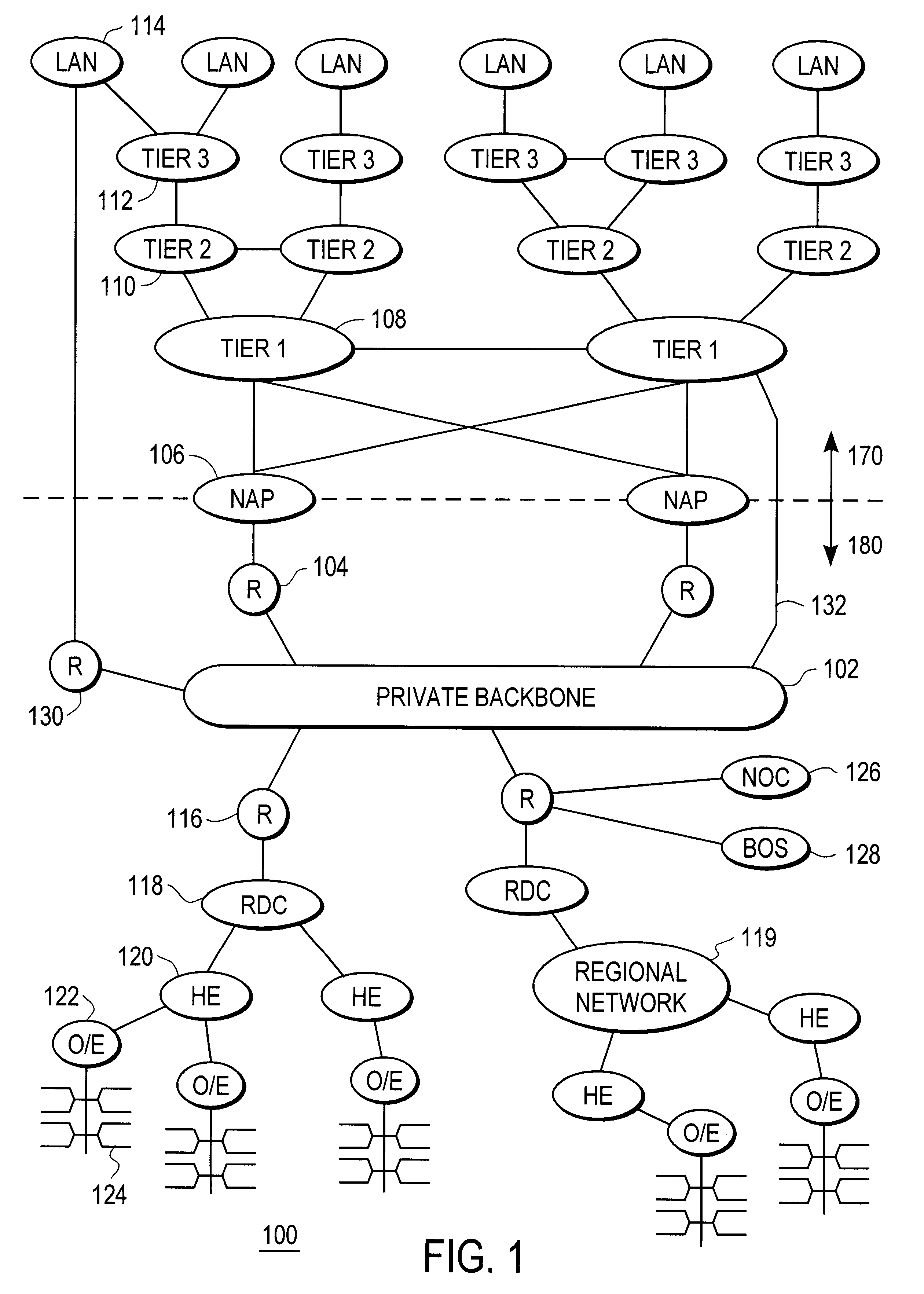
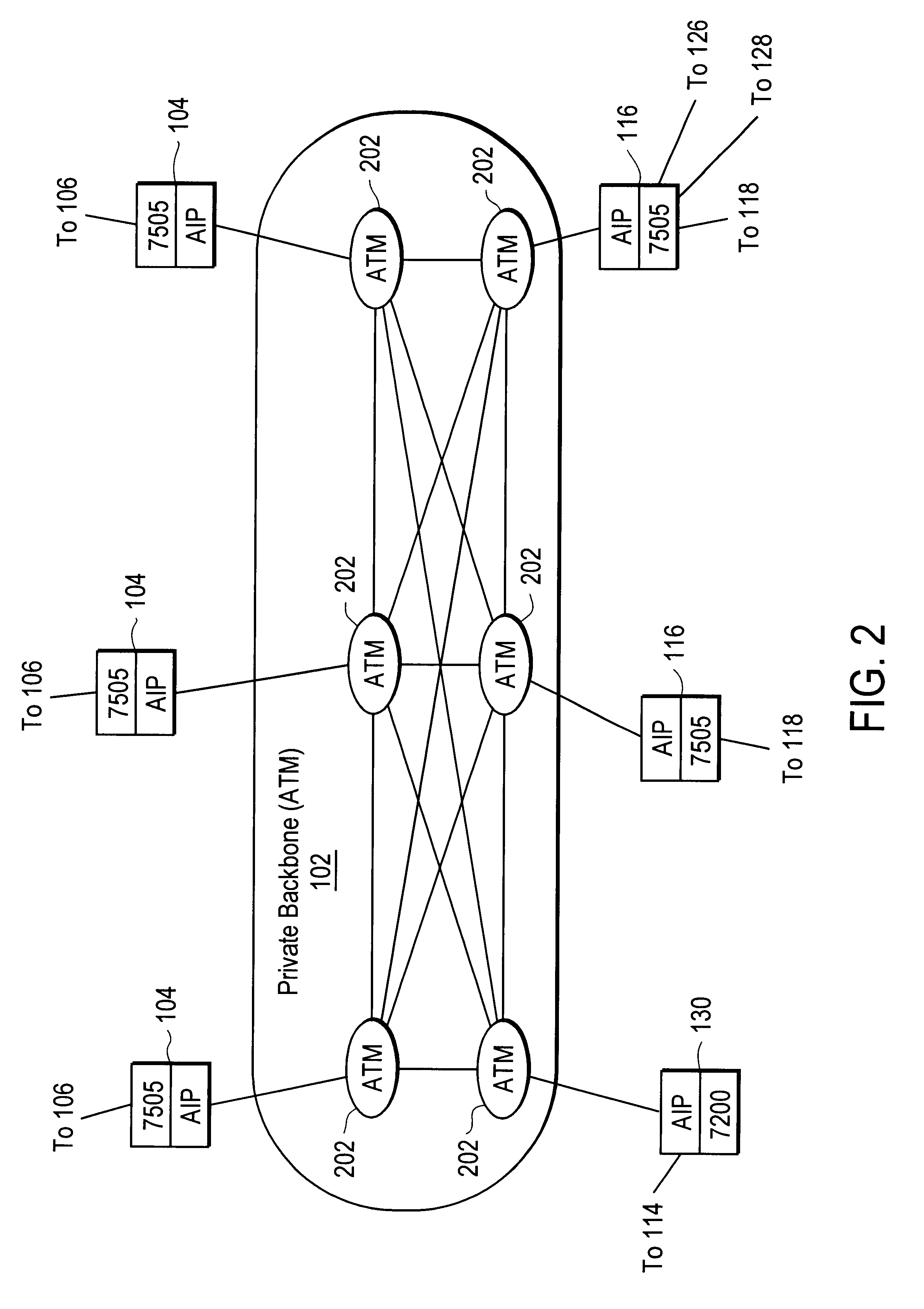
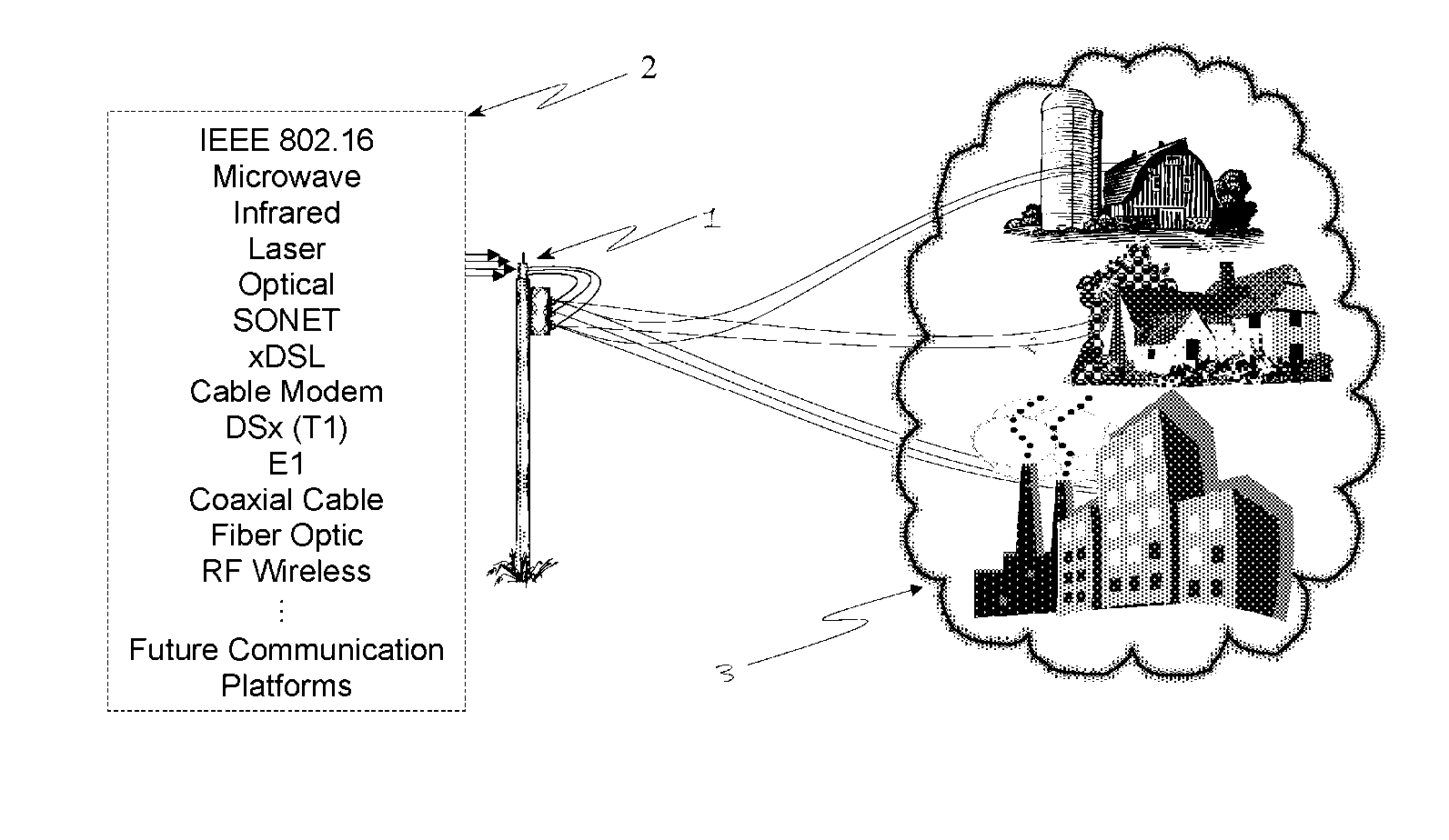
Disclosed is a scalable, hierarchical, distributed network architecture and processes for the delivery of high-performance, end-to-end online multimedia services, including Internet services such as World Wide Web access. The network architecture connects a high-speed private backbone to multiple network access points of the Internet, to a network operation center, to a back office system, and to multiple regional servers in regional data centers. Each of the regional servers connects to several caching servers in modified head-ends, which in turn connect via fiber optics to many neighborhood nodes. Finally, each node connects via coaxial cable to multiple end-user systems. The processes include those for replicating and caching frequently-accessed content, and multicasting content customized per region or locality.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST +1
Rogue AP detection
InactiveUS7181530B1Quick launchReduce complexityMultiple digital computer combinationsTransmissionRogue access pointNetwork access point
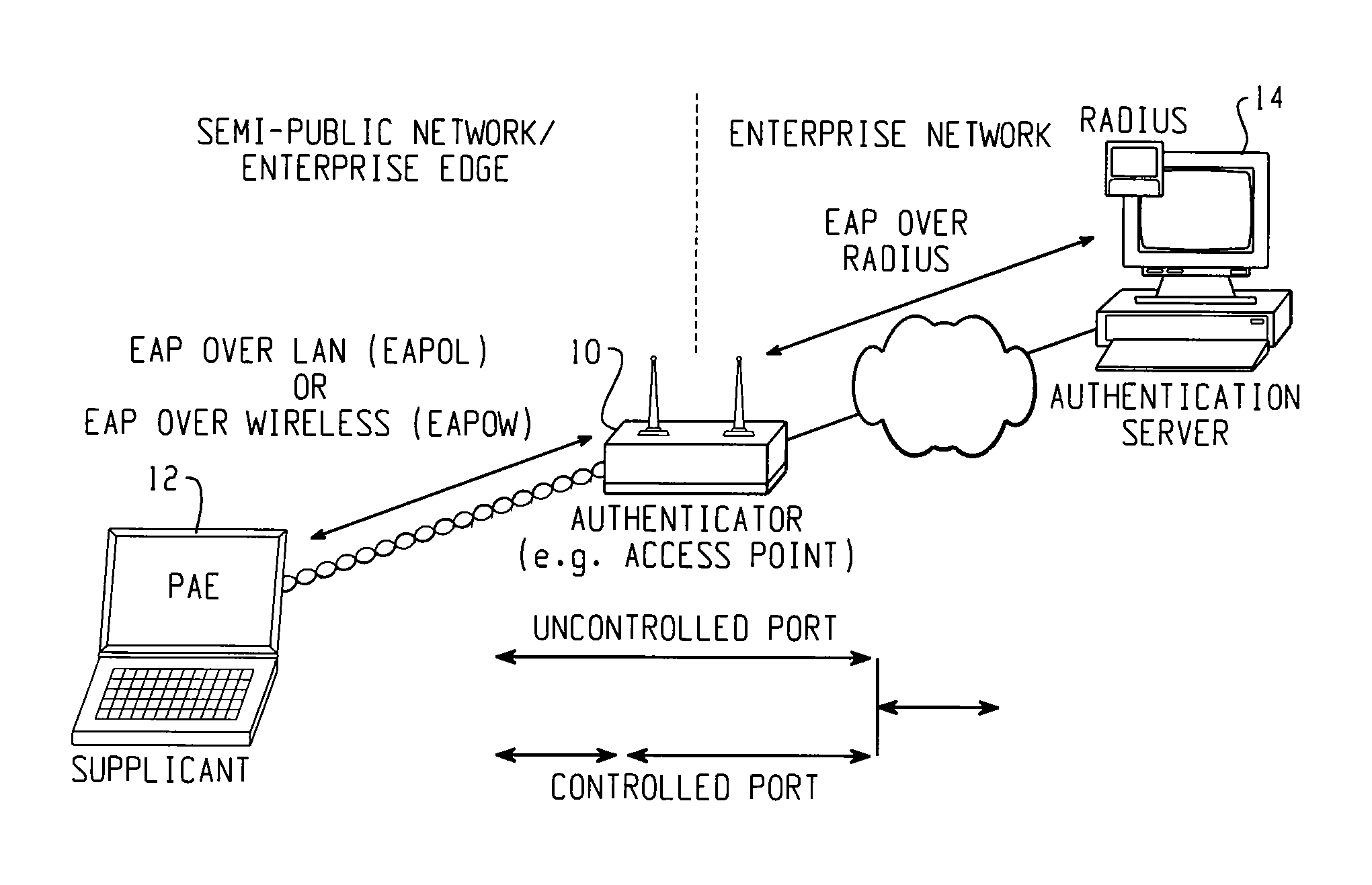
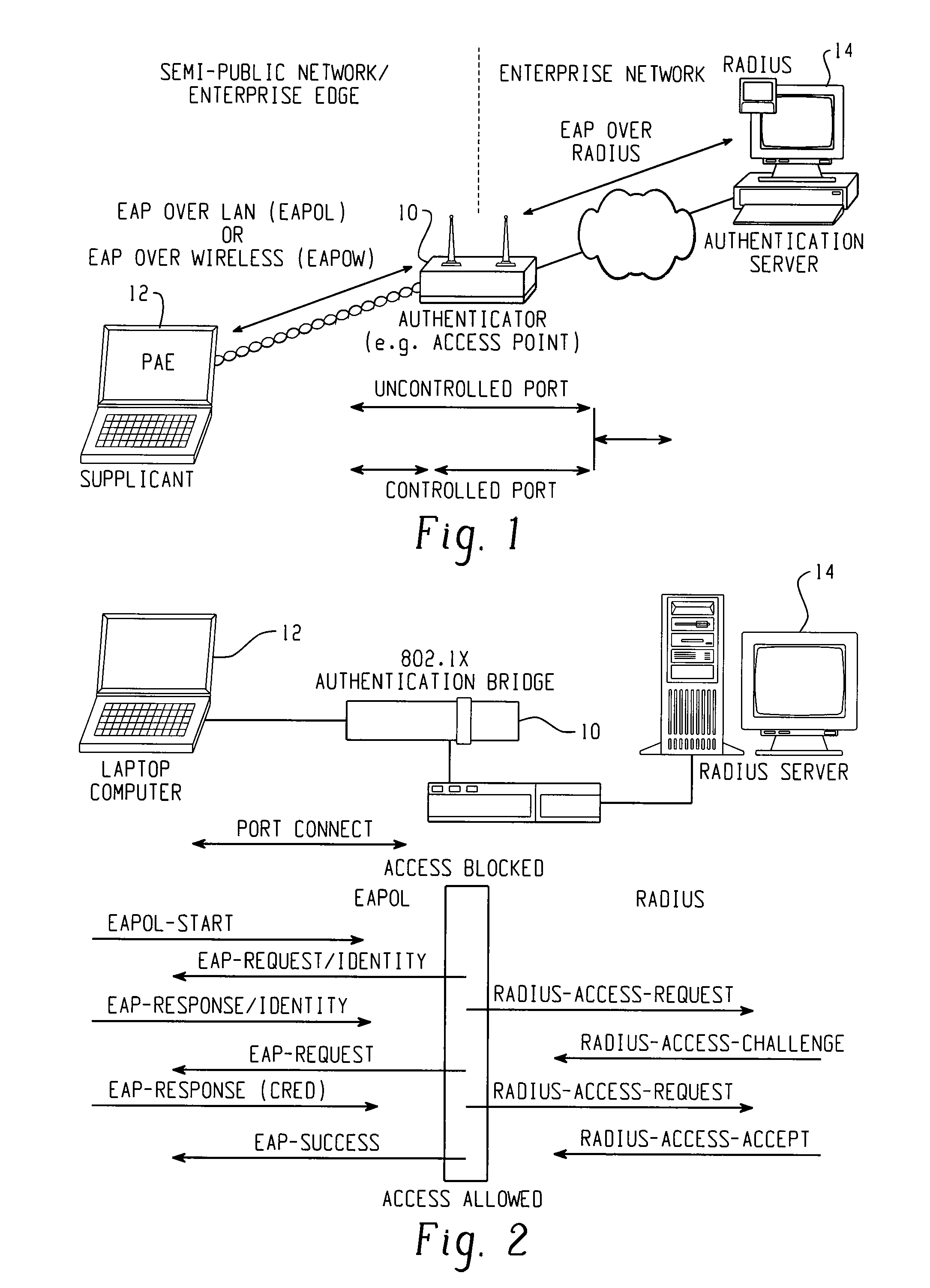
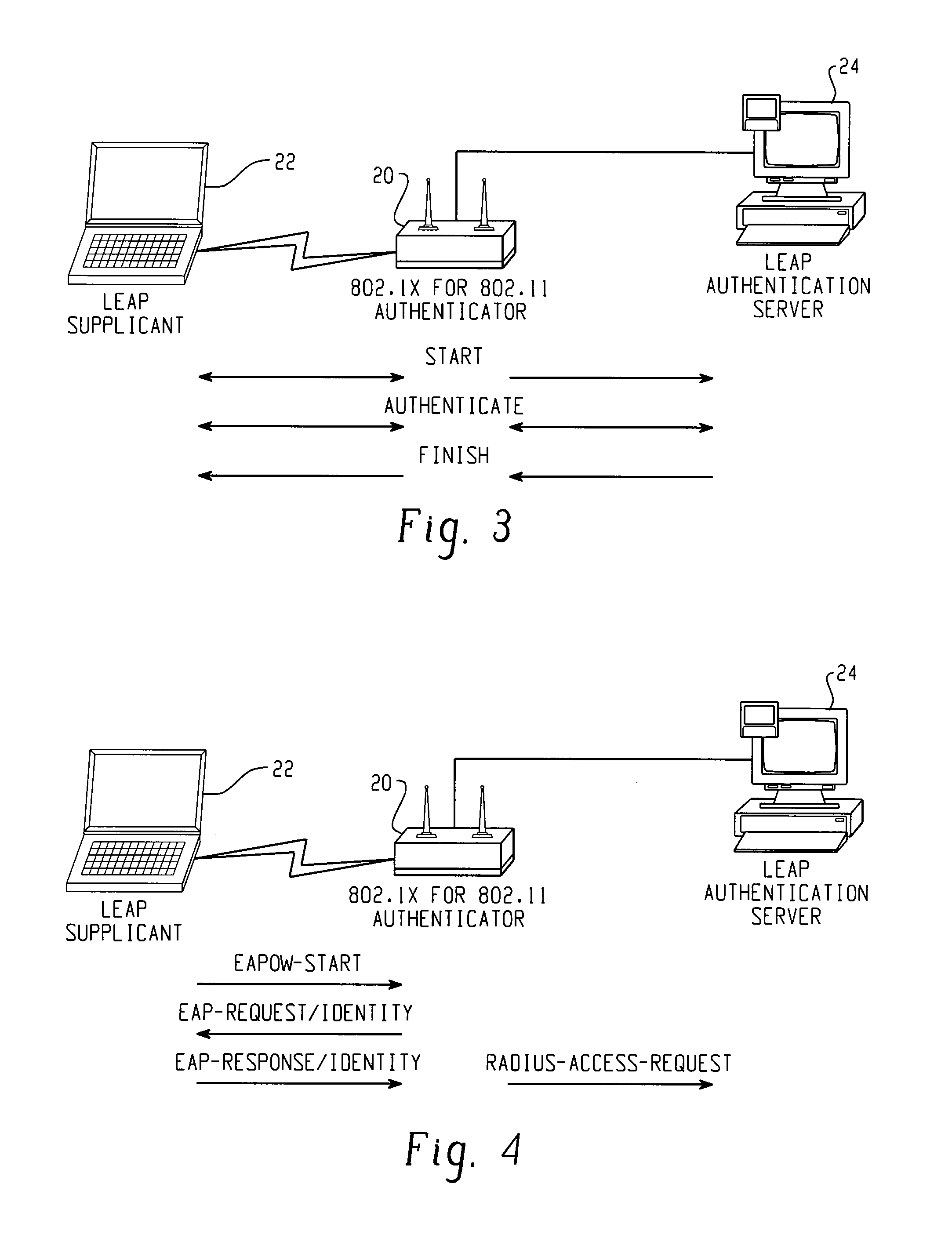
A method of detecting a rogue access point is disclosed. A message is directed from a supplicant to a network through an access point. A network response message is received by the supplicant from the access point. A step of determining whether the access point is one of a valid network access point and a rogue access point is performed based on whether the received network response message is respectively in conformity or nonconformity with predetermined expectations. If the access point is determined to be a rogue access point, it is reported to the network. If the access point is determined to be a valid network access point, the supplicant is authenticated to the network.
Owner:CISCO TECH INC
Autonomous Infrastructure Wireless Networks
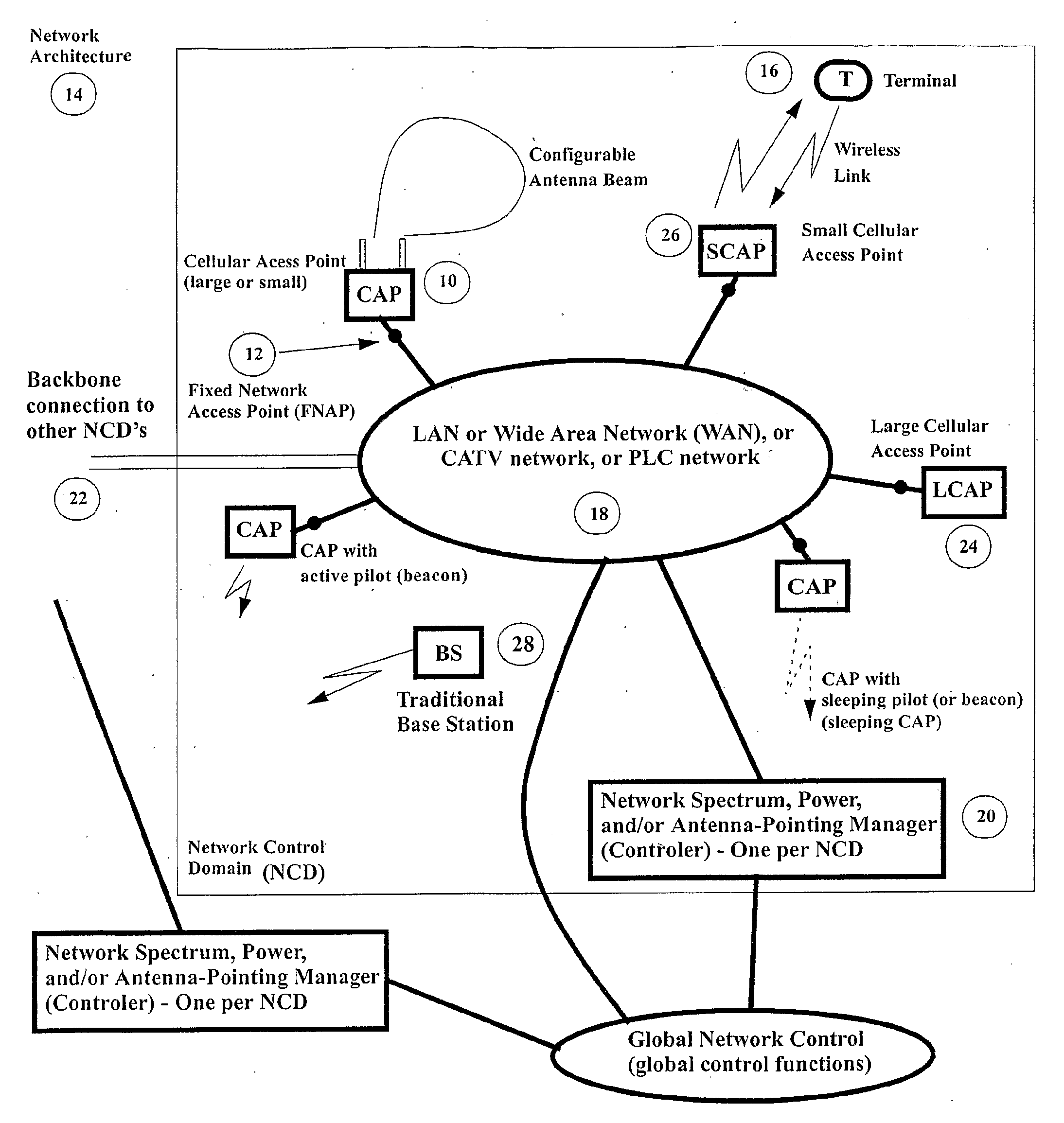
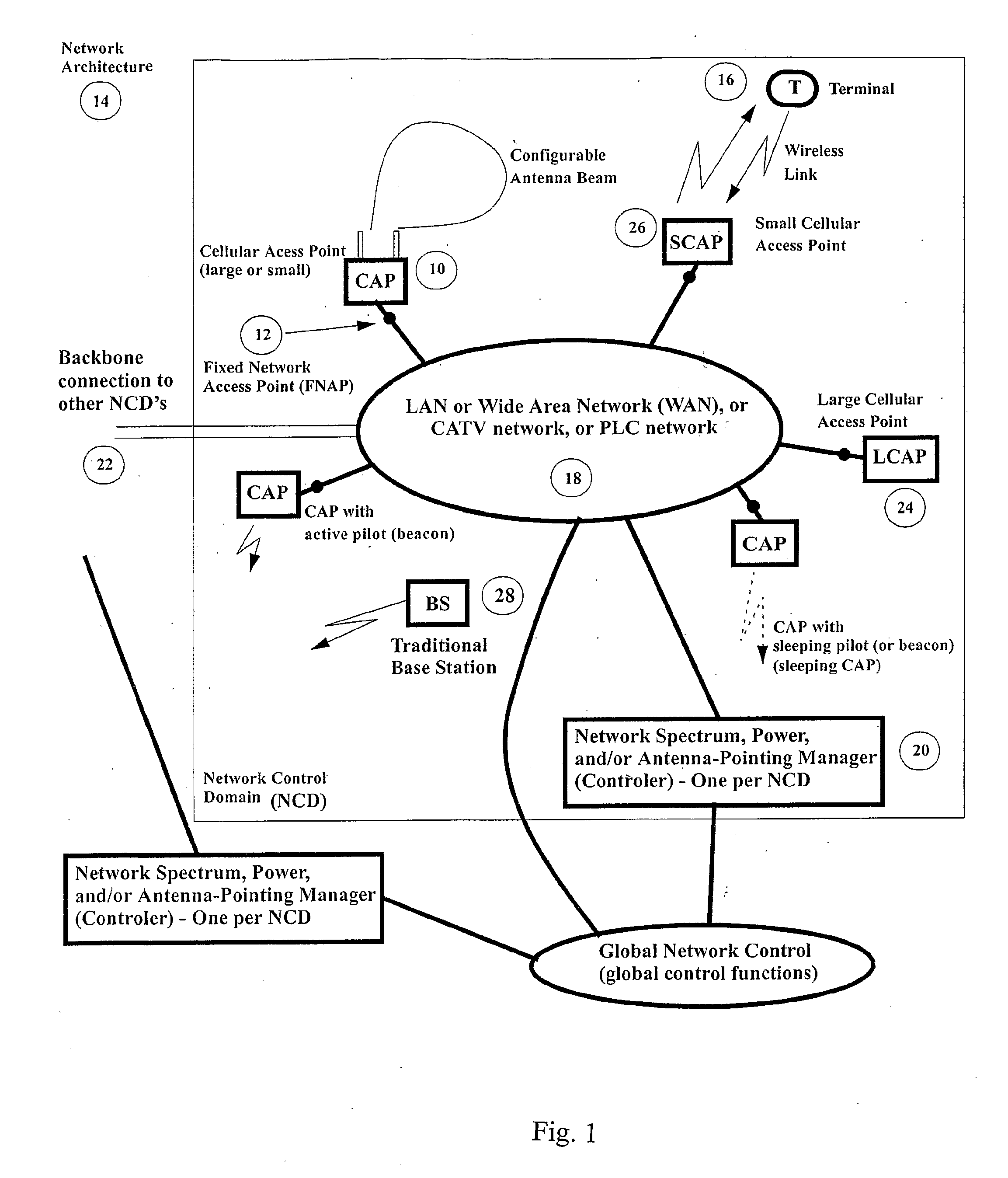
InactiveUS20080298275A1Large network capacityLow costNetwork topologiesData switching by path configurationWireless mesh networkData transmission
A method for deploying a cellular wireless communication network is provided. The method consists of: providing one or more micro base stations; autonomously deploying the micro base stations using a network access point linked to a cellular wireless communication network; and enabling configuration of the micro base stations to execute network operation commands from a network controller associated with the wireless communication network. Another aspect consists of enabling cooperation and network connectivity between micro base stations and other base stations, including micro base stations and large network base stations. Network connectivity to one or more cellular communication terminals associated with individuals or businesses subscribing to the cellular wireless communication network is enabled. A wireless network is also provided which is configurable to link a cellular wireless network through a high data transmission connection so as to define at least one access point between the micro base station and the wireless network. The network includes a wireless interface and receives operation commands from a network controller for configuration of micro base stations, to support the linking of cellular wireless terminals to the wireless network via the wireless interface by operation of the micro base station, as an intermediary. A corresponding system and computer readable medium is also provided
Owner:DE SOUSA ELVINO SILVEIRA MEDINA
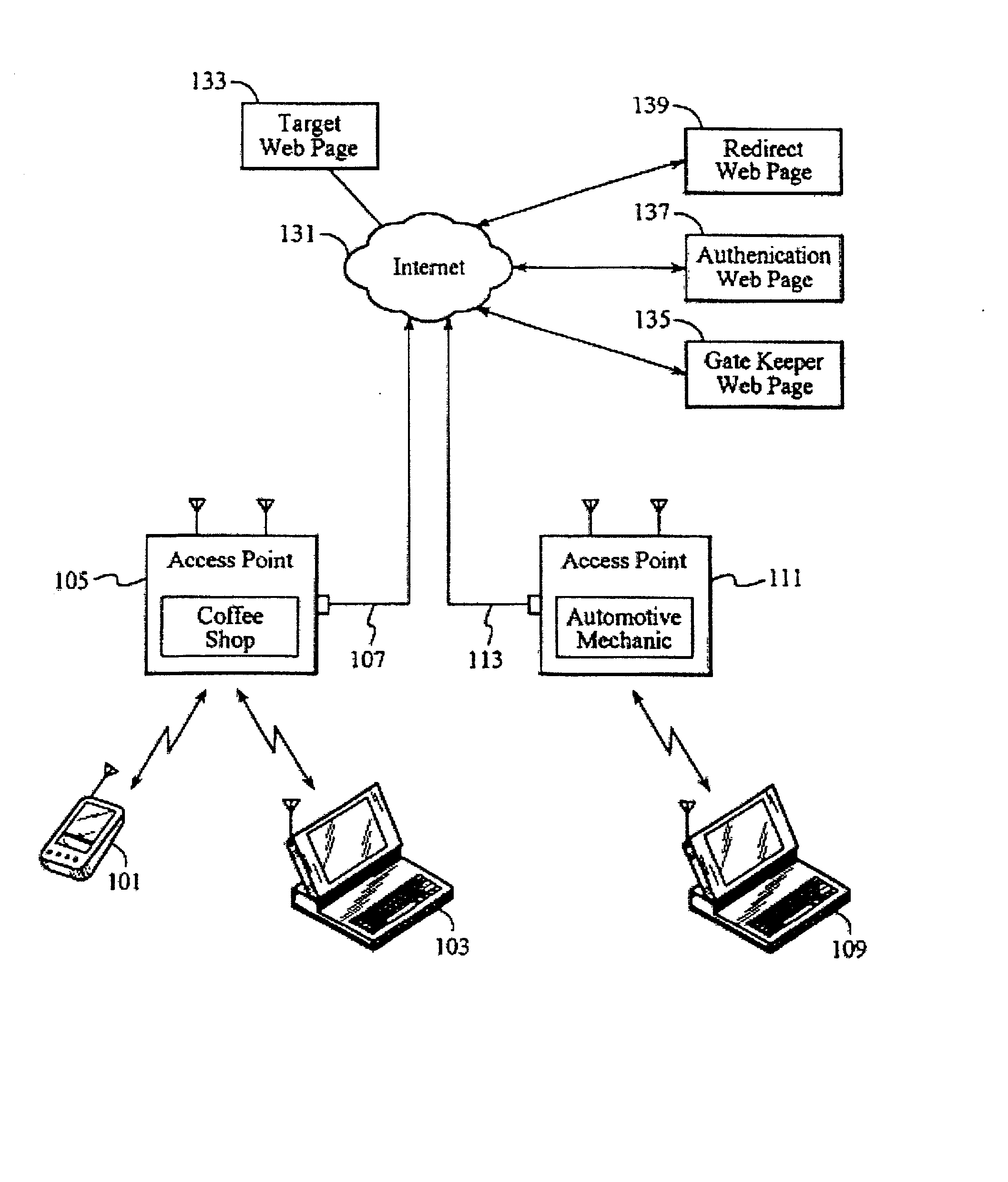
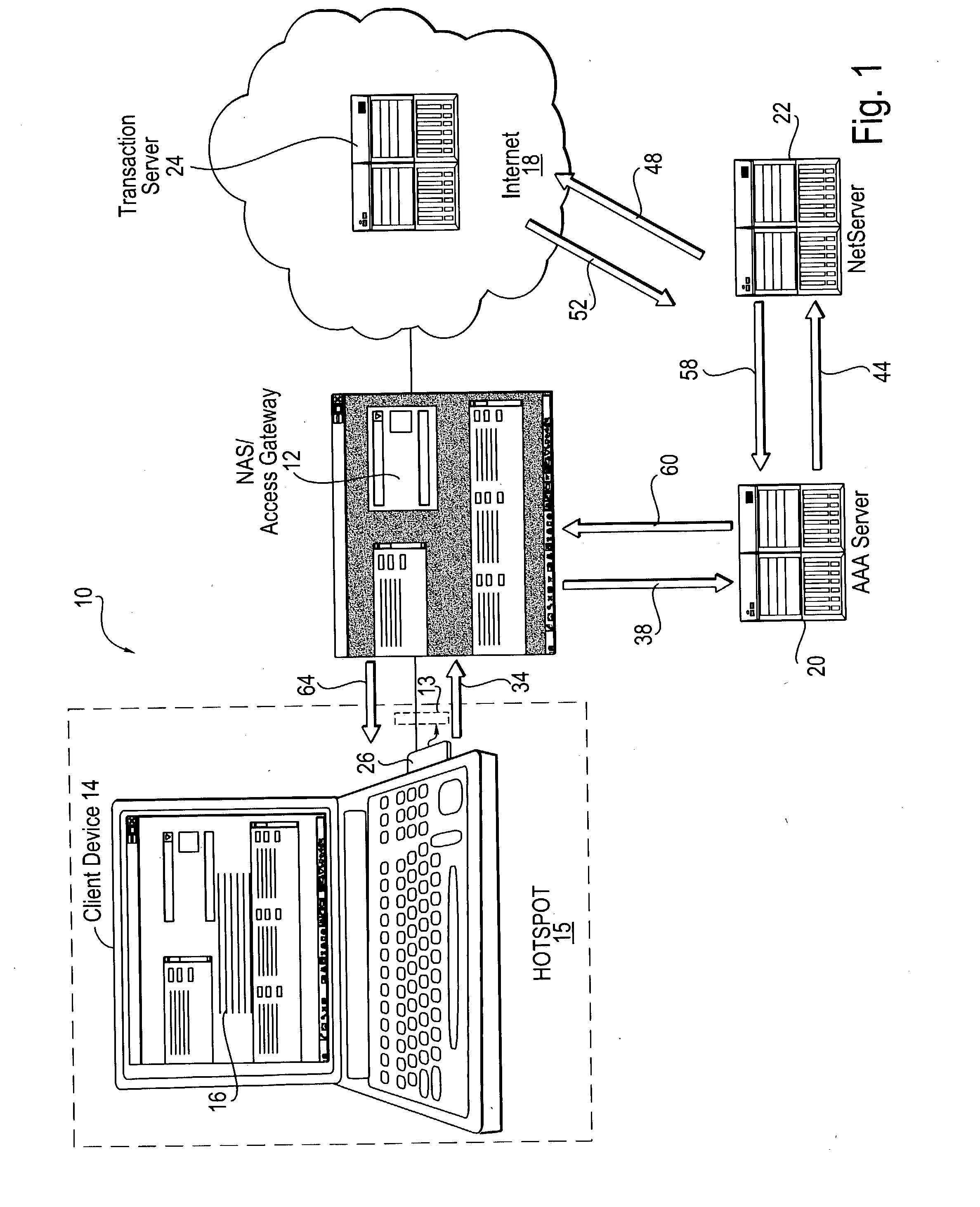
Method and system of providing access point data associated with a network access point
ActiveUS20050021781A1Digital data processing detailsNetwork topologiesAuthentication serverClient-side
A method of, and system for, communicating data via a network access point is provided. The method includes receiving an authentication request from a client device at the access point wherein the access request includes identification credentials. The authentication request is then communicated to an authentication server and data associated with the authentication request is retrieved. A reply message is communicated to the access point that includes the data and that rejects the authentication request. The access point may service a wireless hotspot and, thus, a client device in the hotspot may identify the particular hotspot with which it is communicating.
Owner:CHANNEL IP BV
Distributed infrastructure for wireless data communications
InactiveUS6215779B1Wireless network protocolsRadio/inductive link selection arrangementsForeign agentWireless data
A mobile user terminal 402 accesses a packet data network 450 through one or more of several network access points 404-412. One or more control points 432-440 determines which network access point or points the user terminal is to access. Control may be retained in the current control point, or transferred to another control point, whenever it is convenient. There are preferably several routers, each having an associated home agent 418-420 which determines which foreign agents need to be accessed on behalf of each user terminal. There are several foreign agents 422-430, which forward packets received from a user terminal's home agent to the control point currently controlling communications with the user terminal.
Owner:QUALCOMM INC
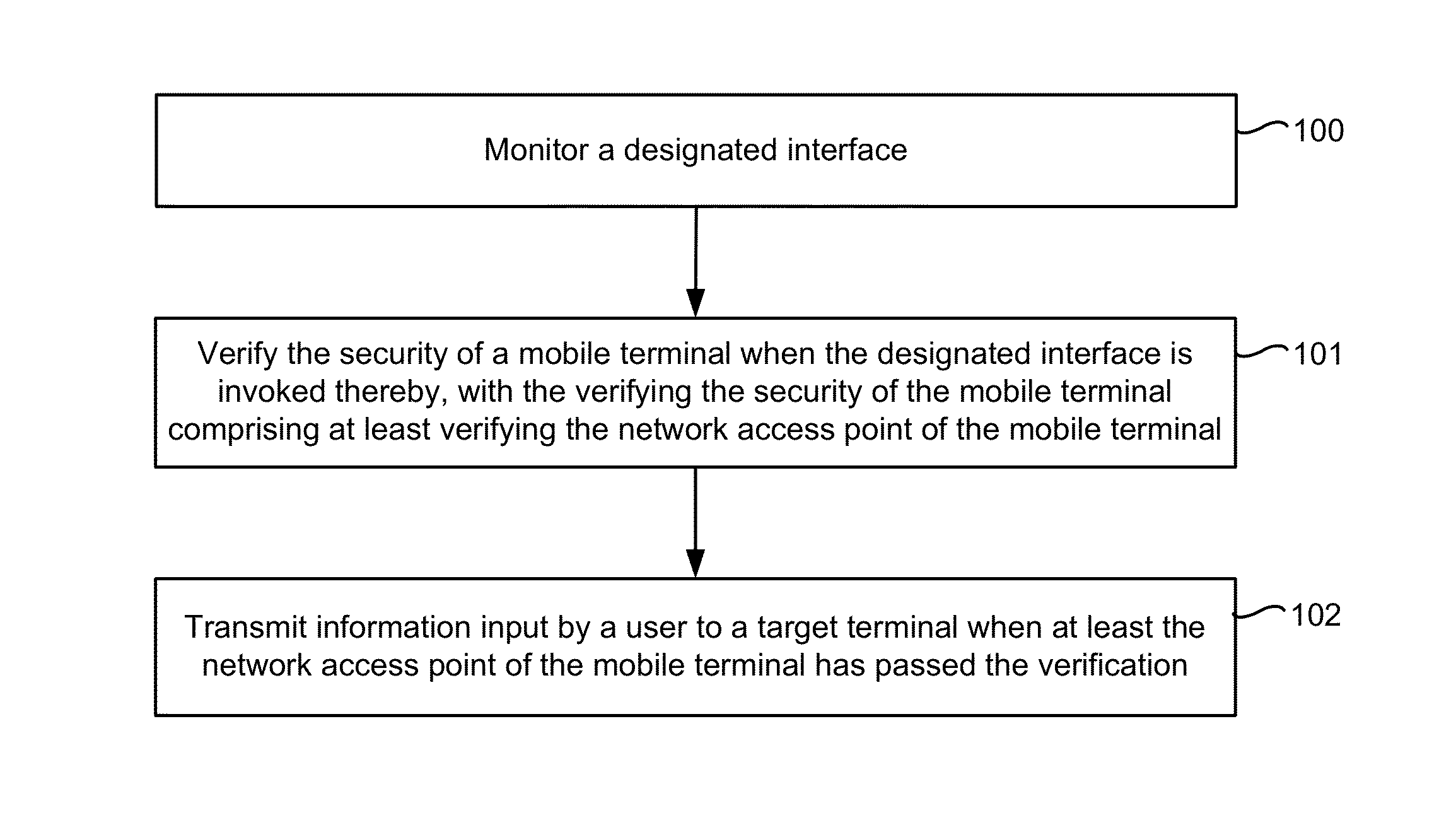
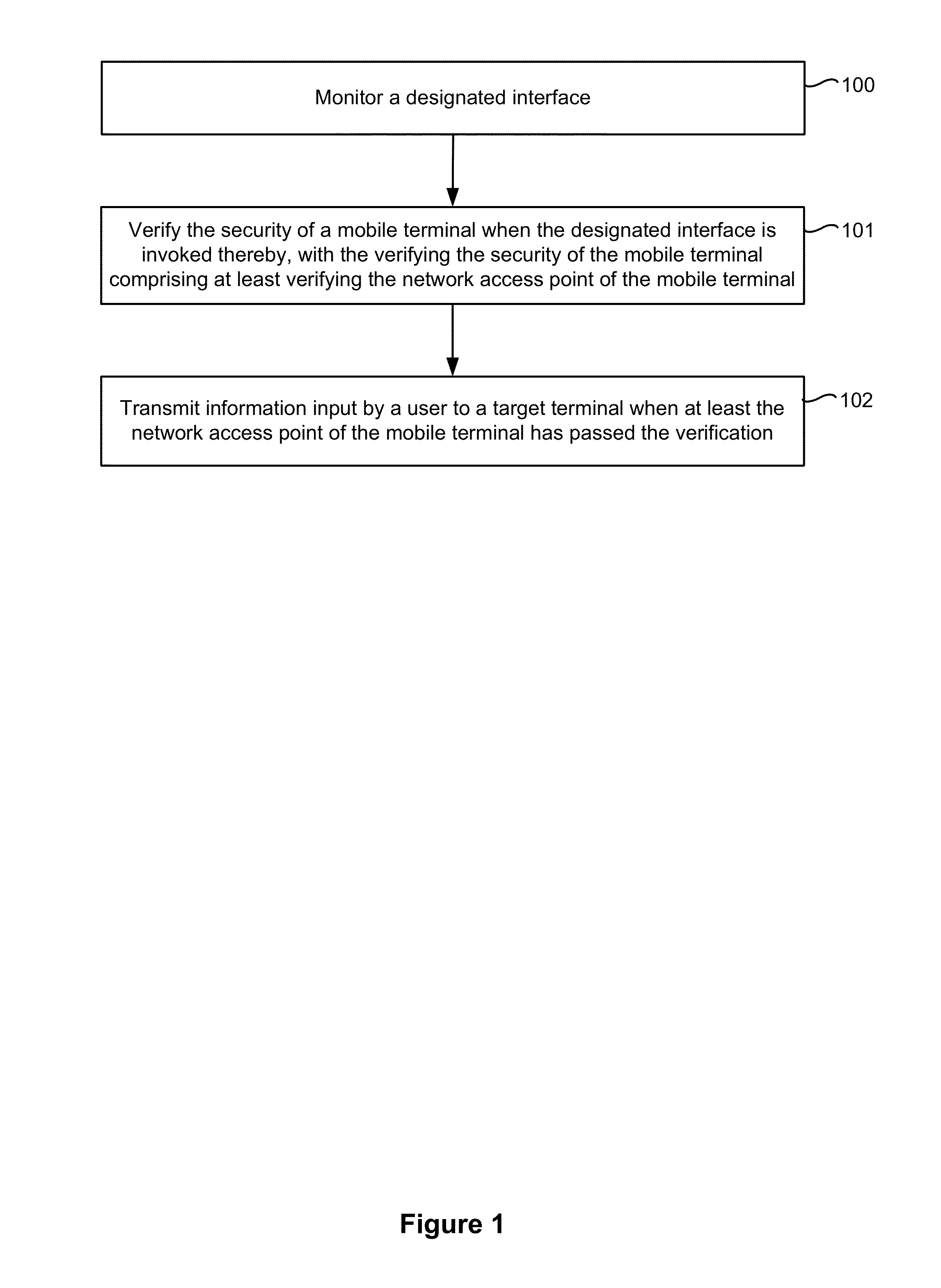
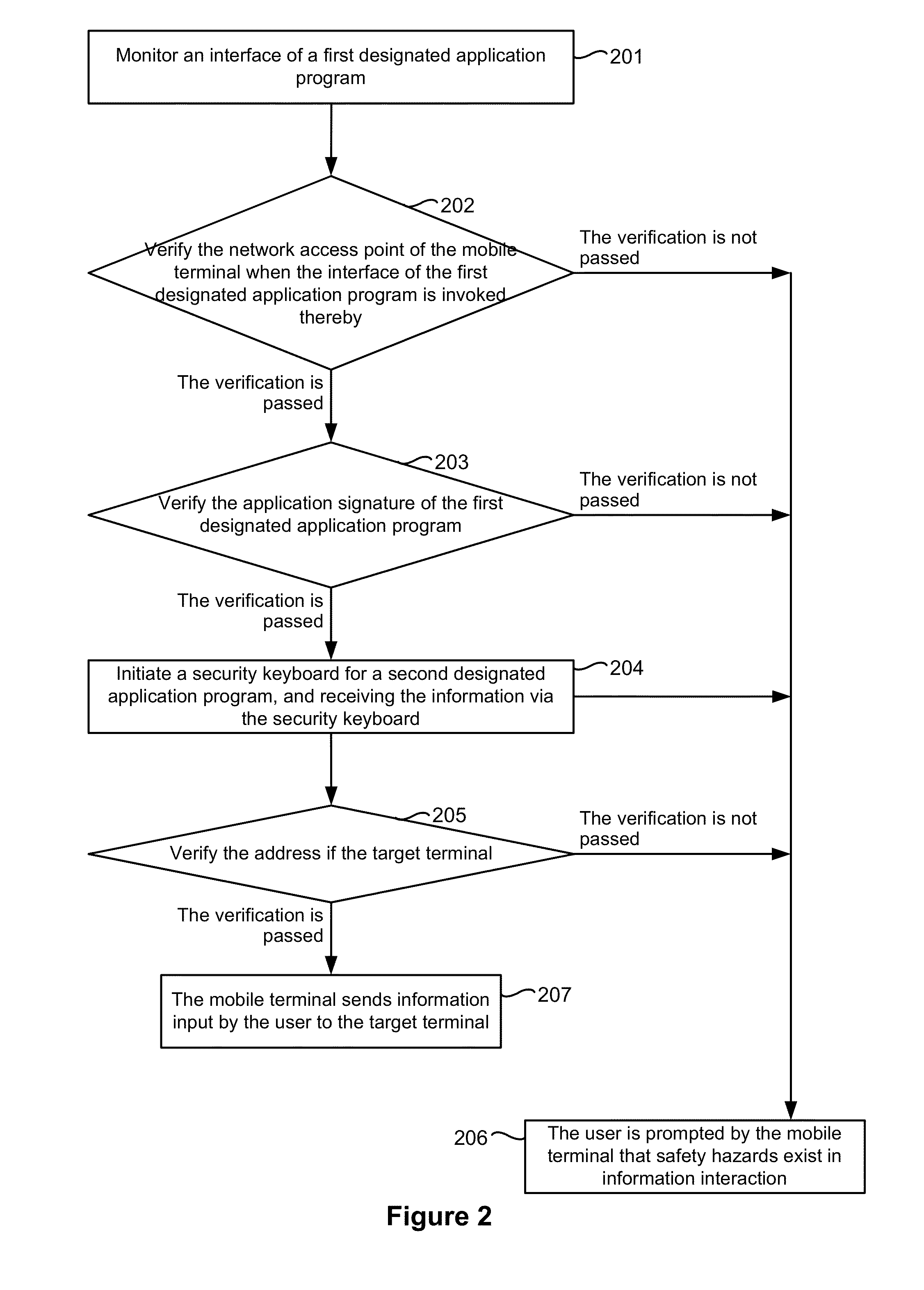
Method and device for securing an information interaction process
ActiveUS20140074716A1Improve securityAvoid security issuesFinanceComputer security arrangementsDisplay deviceComputer terminal
An electronic device with one or more processors, memory, and a display detects a user interaction with a user interface of a first application and, in response to detecting the user interaction with the user interface of the first application, determines whether one or more security parameters are satisfied, where a first security parameter is satisfied when a network access point being used by the electronic device satisfies predefined criteria. In accordance with a determination that the one or more security parameters are satisfied, the device: displays a security keyboard on the display corresponding to a second application different from the first application; and receives user information input via the security keyboard by a user of the electronic device. The device transmits the user information to a target terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
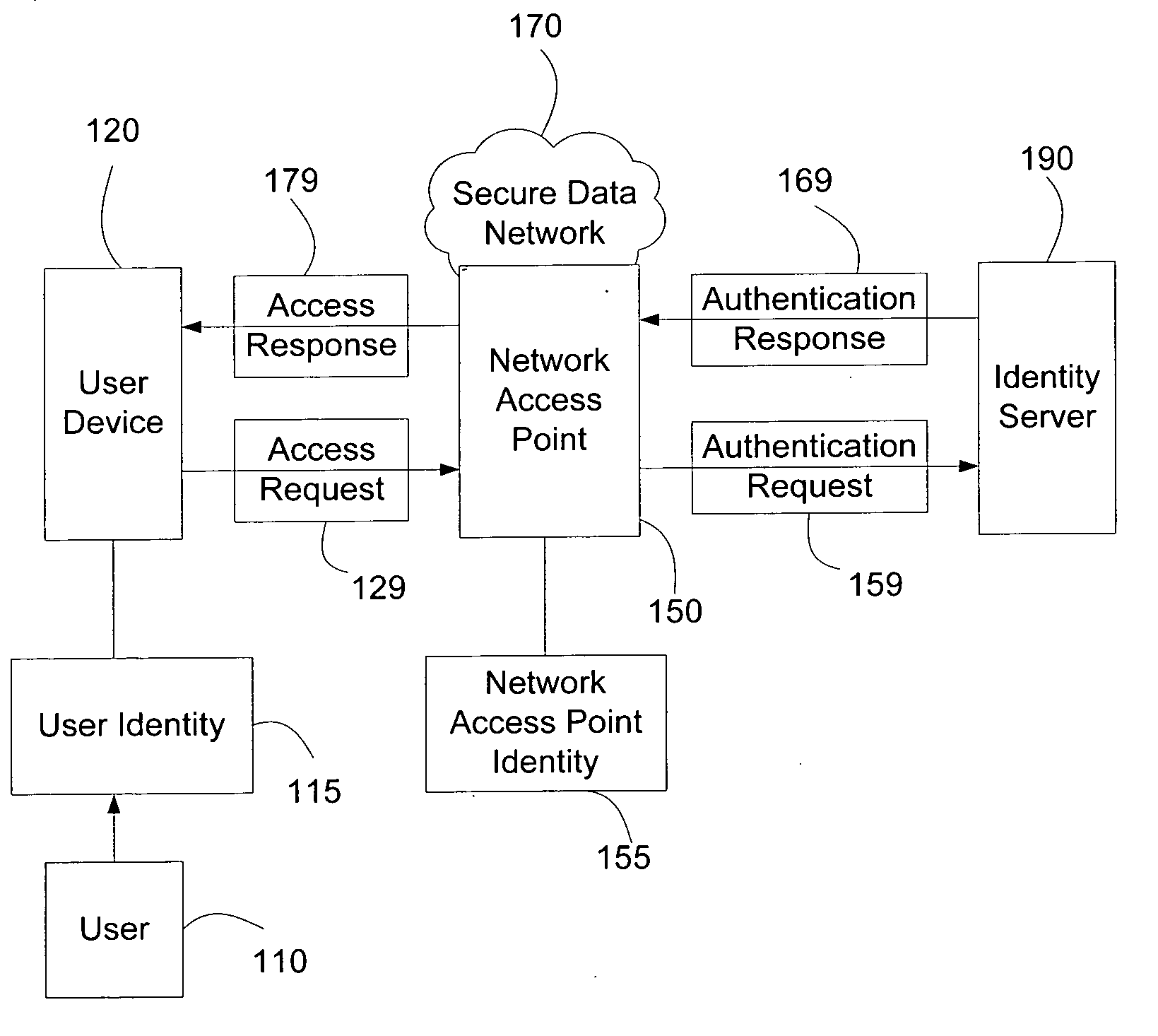
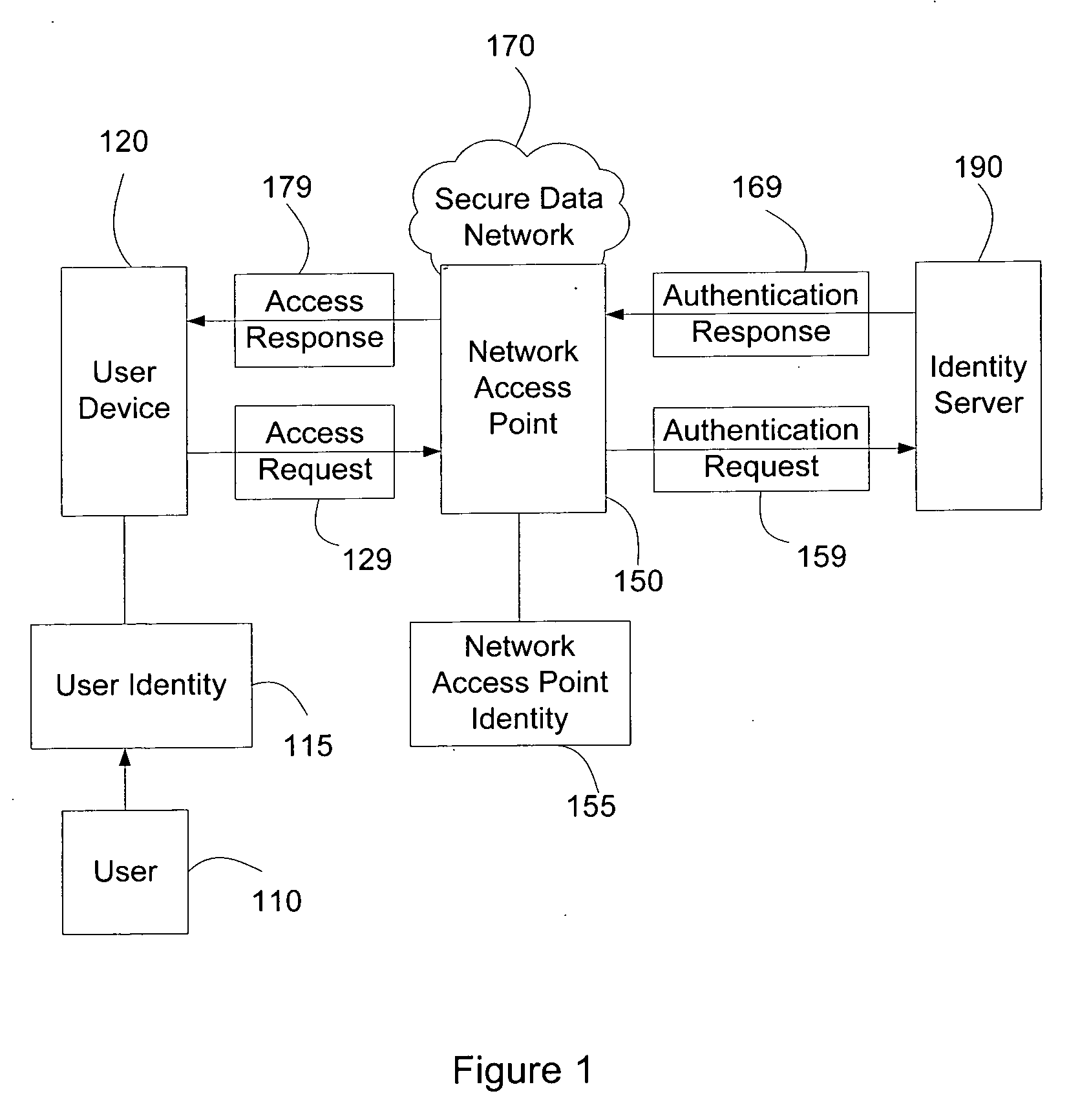
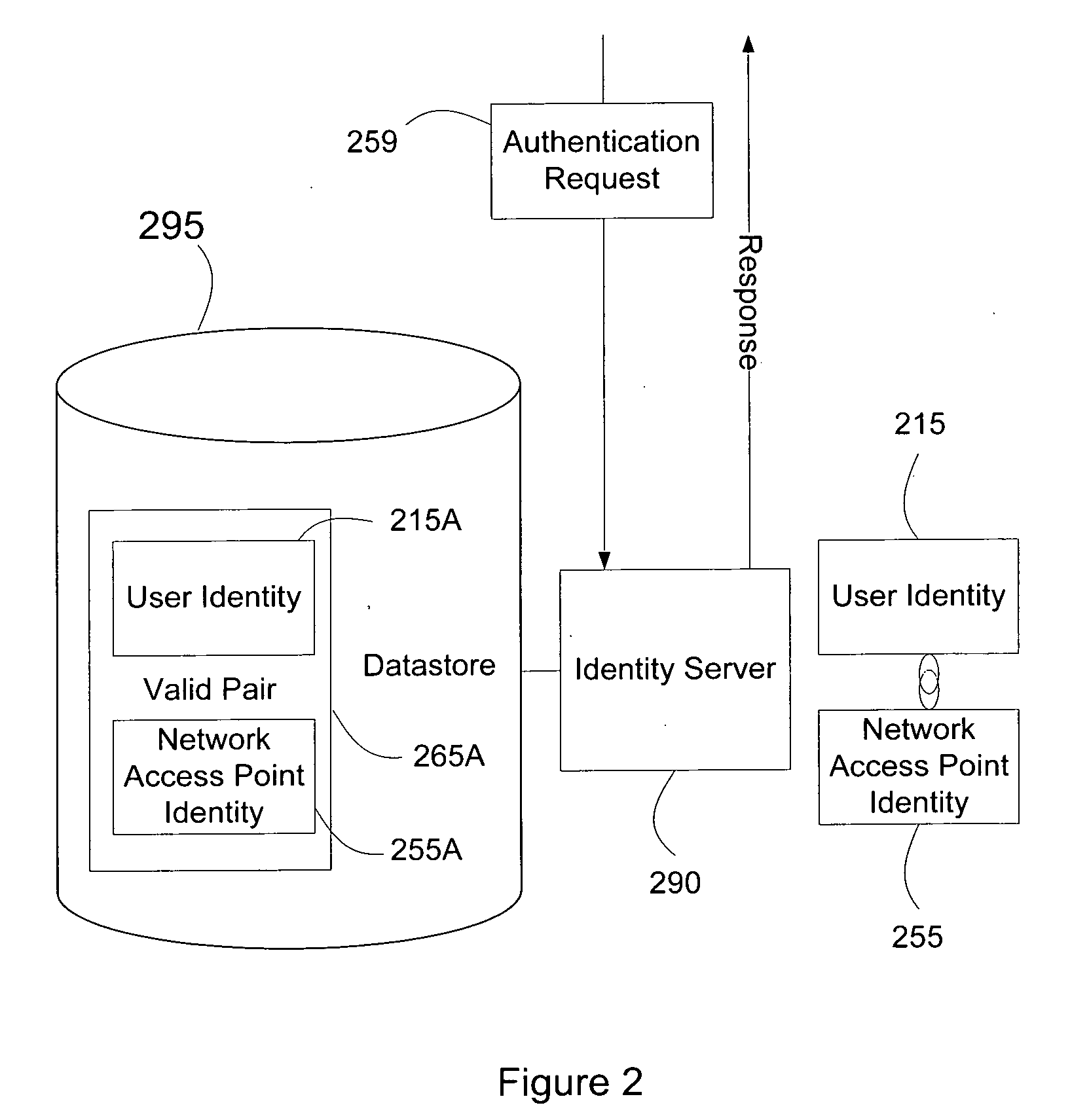
Systems and methods for user access authentication based on network access point
ActiveUS20070271598A1Random number generatorsUser identity/authority verificationTime informationAuthentication system
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
Method of seamlessly roaming between multiple wireless networks using a single wireless network adaptor
InactiveUS20080069065A1Reduce in quantityConnection managementRadio/inductive link selection arrangementsTelecommunicationsRogue access point
A method of roaming between access points on the same or different wireless networks using a single wireless network interface adaptor. A device will establish a connection with a second wireless network access point while still connected with a first wireless network access point such that the device can concurrently communicate with both wireless access points. During and after connection with the second wireless network access point real-time IP data transfer is maintained with another network device by switching between the first and second access points for concurrently sending and receiving data packets via both access points using a switching strategy based at least in part on a number of the data packets to be send to each network access point. The method also determines when to roam, scans for candidate wireless network access points to connect to and selects the best access point for roaming based on selection criteria.
Owner:HONG KONG APPLIED SCI & TECH RES INST
Seamless user mobility in a short-range wireless networking environment
InactiveUS6975864B2Enable connectivityNear-field transmissionDigital computer detailsUser authenticationHand held devices
The present invention provides methods, systems, and computer program instructions for enabling a variety of devices, particularly low-power hand-held devices, to travel seamlessly through a networking environment such as that encountered within a building by establishing connectivity to a plurality of network access points. The illusion of seamless network connectivity is provided by having these access points coordinate with a core server to perform user authentication, device address assignment, and handoff services.
Owner:REEFEDGE
System and method to provide enhanced security in a wireless local area network system
InactiveUS20030095663A1User identity/authority verificationNetwork topologiesClient-sideNetwork access point
A system and method for enhancing Wireless Local Area Network (WLAN) security. The system and method include the generation of a pair of WEP-based encryption keys by a network access point. The key pair is transmitted to one or more clients associated with the access point after the client has been authenticated for access to the network. Each key is preferably randomly generated and the pair is further changed periodically. The timing of the changing of the keys is dependent upon the existing crypto analysis attack capabilities. Individual clients may have unique key pairs or a plurality of clients associated with an access point may share the key pair.
Owner:ENTERASYS NETWORKS
Methods, systems, and computer program products for providing multimedia information services over a communication network
ActiveUS7509124B2Save network resourcesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkMobile device
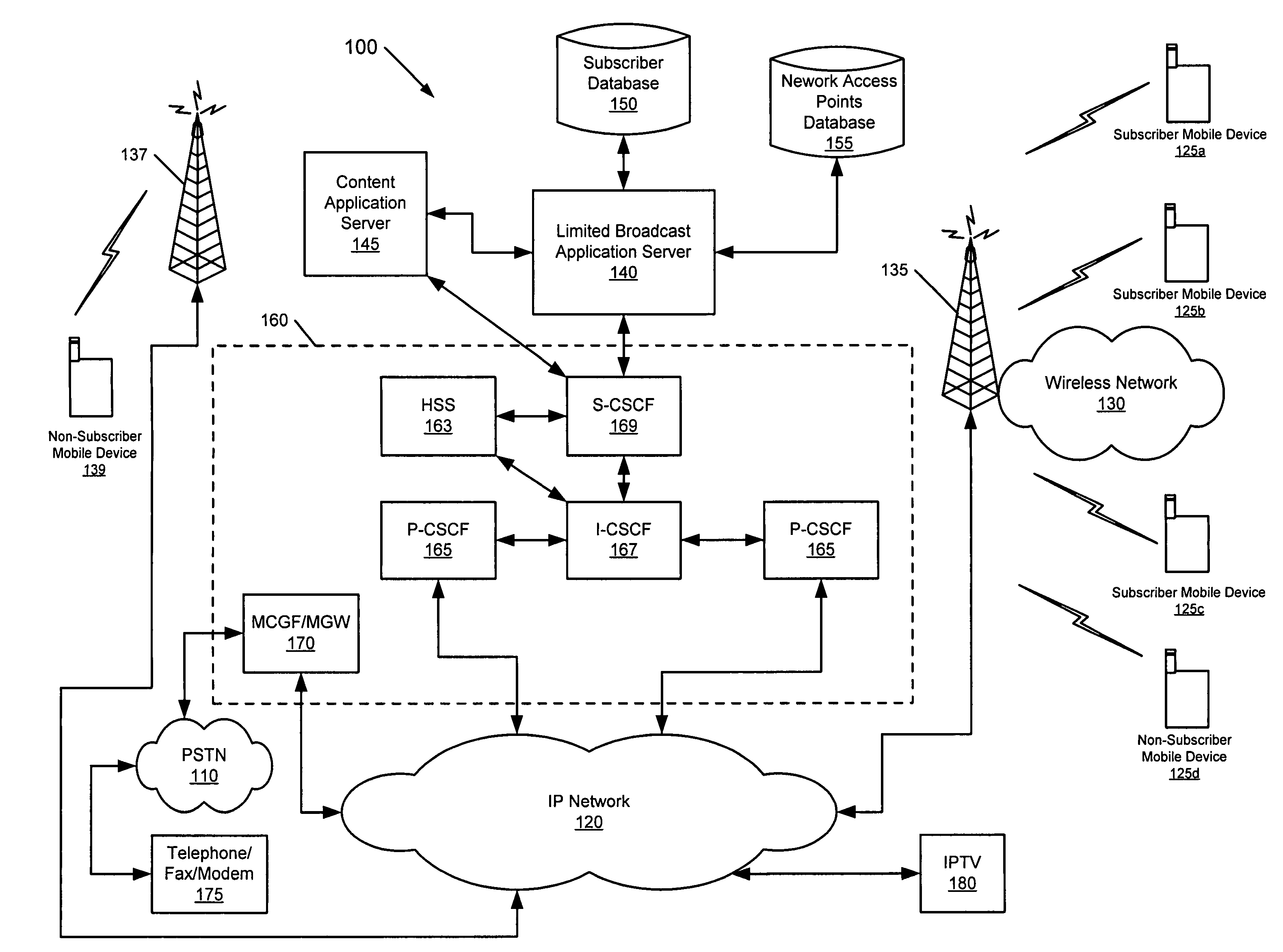
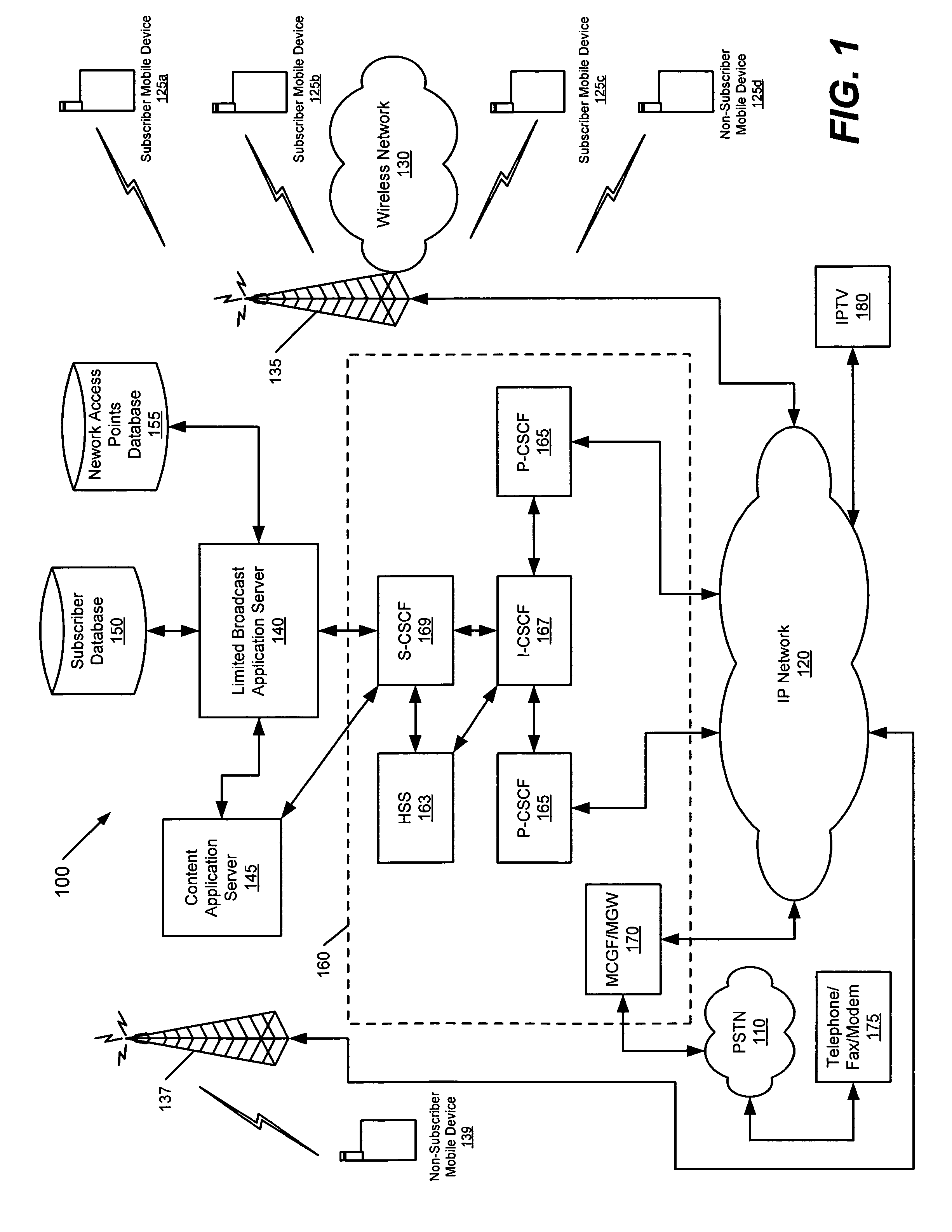
In a communications network, a network access point address is determined that is currently associated with at least one of a plurality of subscriber mobile devices associated with a subscription to an information service. Content associated with the information service is formatted to provide subscriber content that is configured to be used by the plurality of subscriber mobile devices. The subscriber content is broadcast from a transmitter at the determined network access point address to the at least one subscriber mobile device over a wireless network.
Owner:BELLSOUTH INTPROP COR
Applications for geographically coded access points
Applications and uses for geographic coded of network access points includes a method for generating a geographic code and an associated graphical user-interface; a method for rejecting or filtering out geographic codes of inaccurately labeled access points; a method for using geographic codes as part of network service discovery; a method for using geographic codes as part of resource discovery and display; a method for using geographic codes for asset tracking; a method for using geographic codes for file transfer and an associated user interface; a method for using geographic codes for location tracking; a method for using geographic codes as part of a domain name registry; and a method for sending geographic codes automatically.
Owner:RICOH KK
Flexible optical fiber tape and distribution cable assembly using same
InactiveUS20080187276A1Reduce curvatureEasy to separateFibre mechanical structuresEngineeringOptical communication
A flexible optical fiber tape is formed from a substrate in the form of a strip adapted to maintain at least one optical fiber. The substrate may include an adhesive layer on at least one side for securing the tape to an external surface such as an interior floor, wall or ceiling. The tape may also have a flame-retardant characteristic. The optical fiber can run substantially longitudinally along the substrate, or can have one or more curved sections that allow for bending the tape without a substantially bending the at least one optical fiber. The tape may also include one or more network access points (NAPs) adapted to allow for optical communication between at least one external optical fiber and the at least one optical fiber maintained by the substrate. A distribution cable based on the optical-fiber-based tape is also described.
Owner:CORNING CABLE SYST LLC
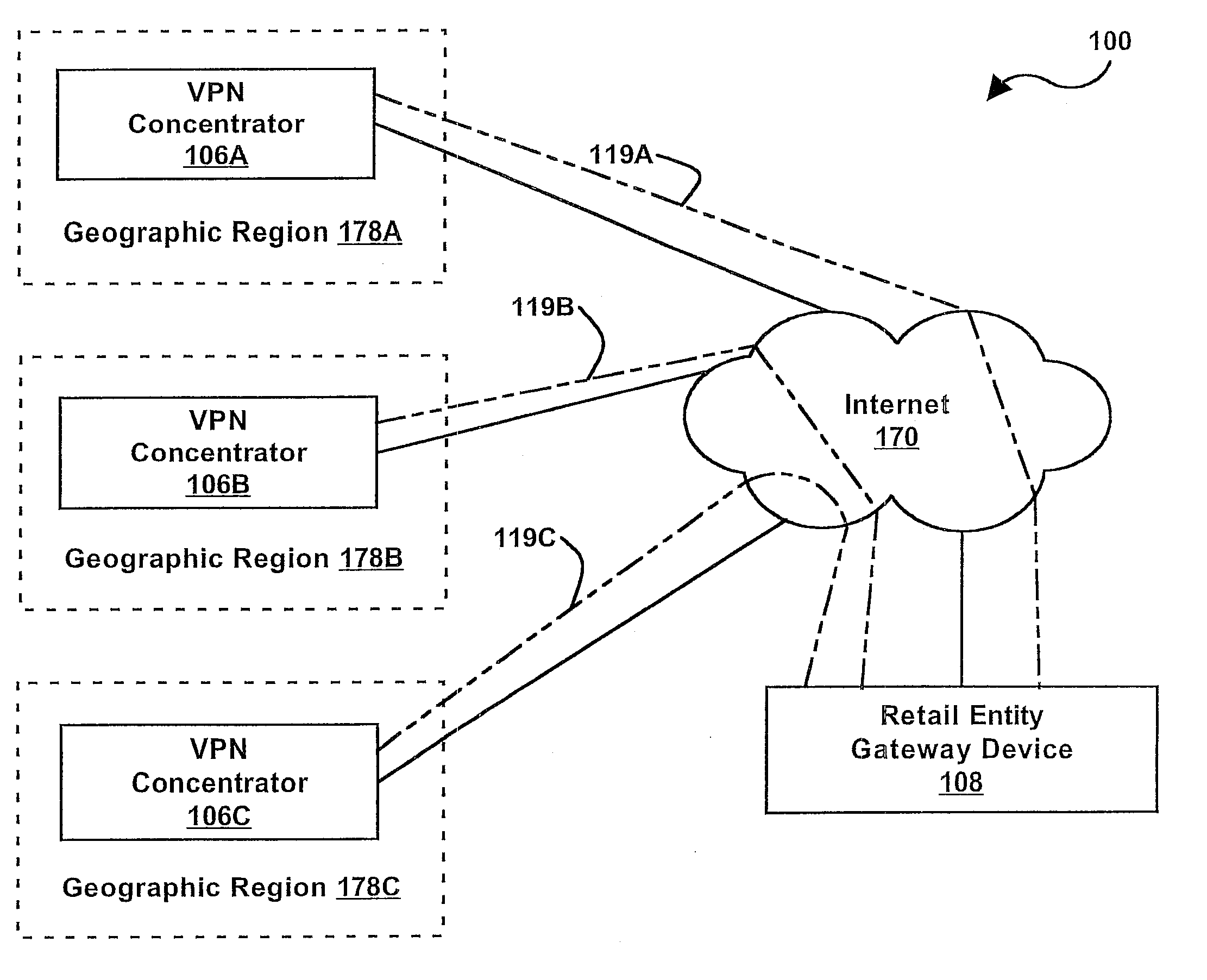
System and method for integration of wireless computer network in position determining technology
ActiveUS20050064877A1Position fixationRadio/inductive link selection arrangementsCommunications systemGeographic regions
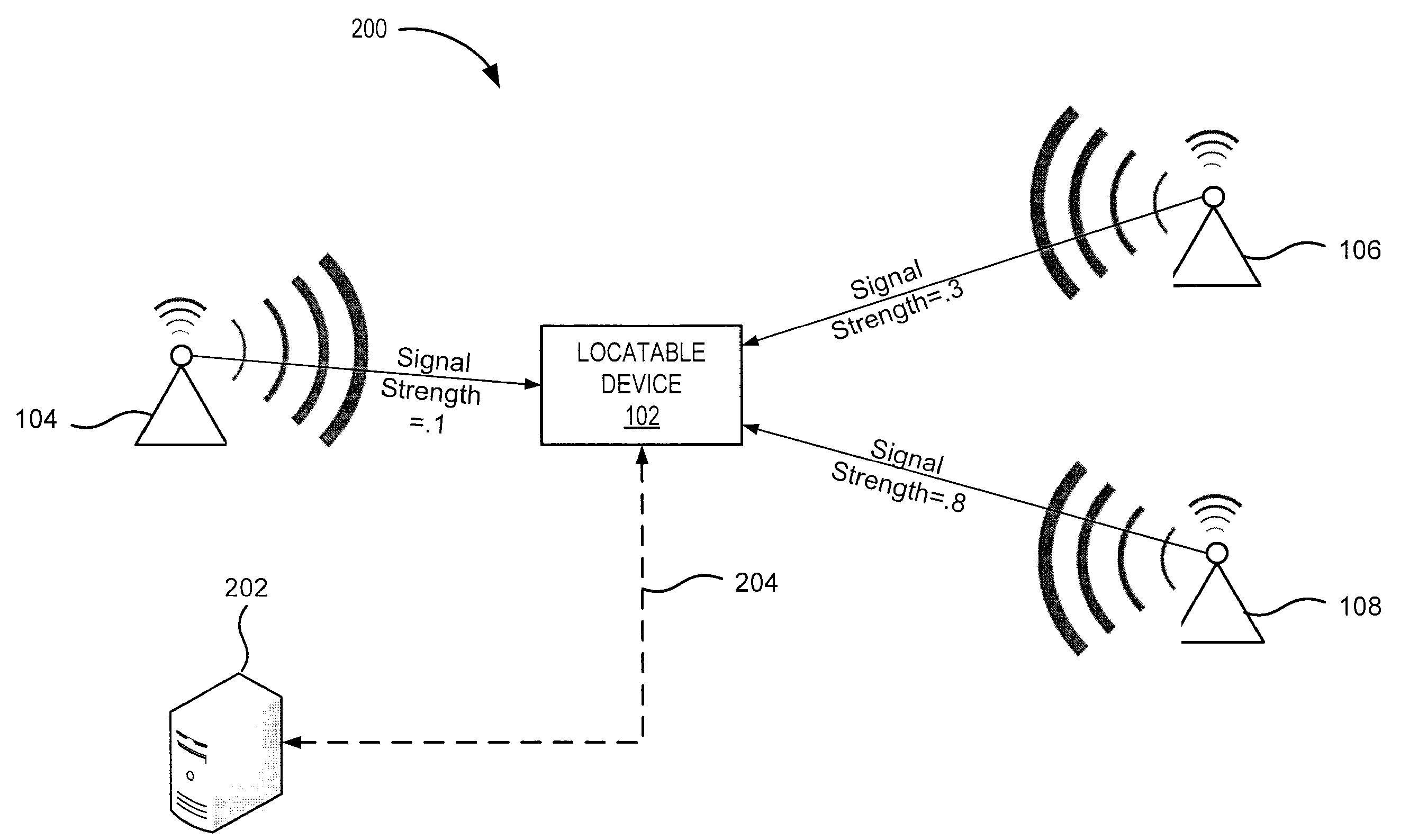
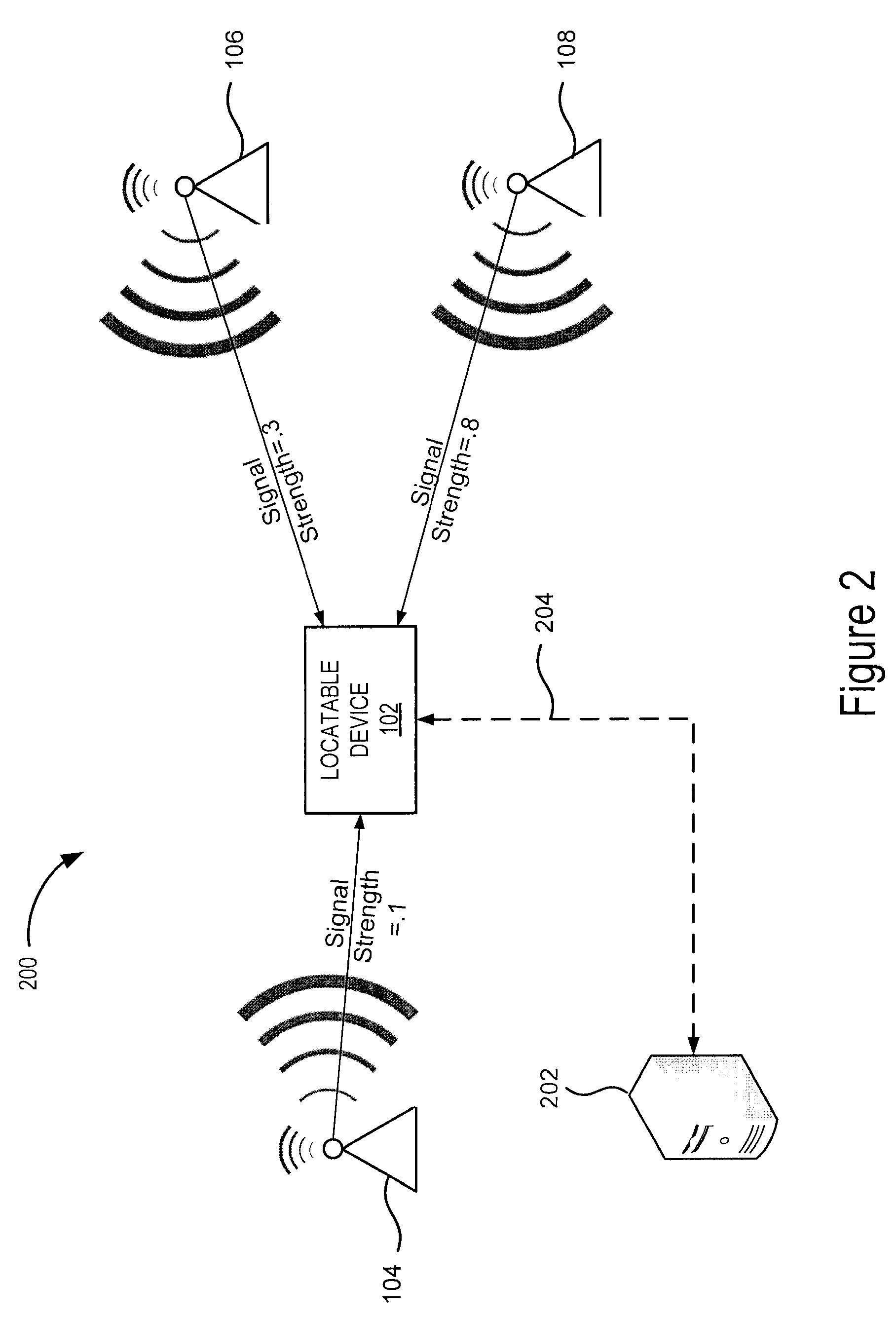
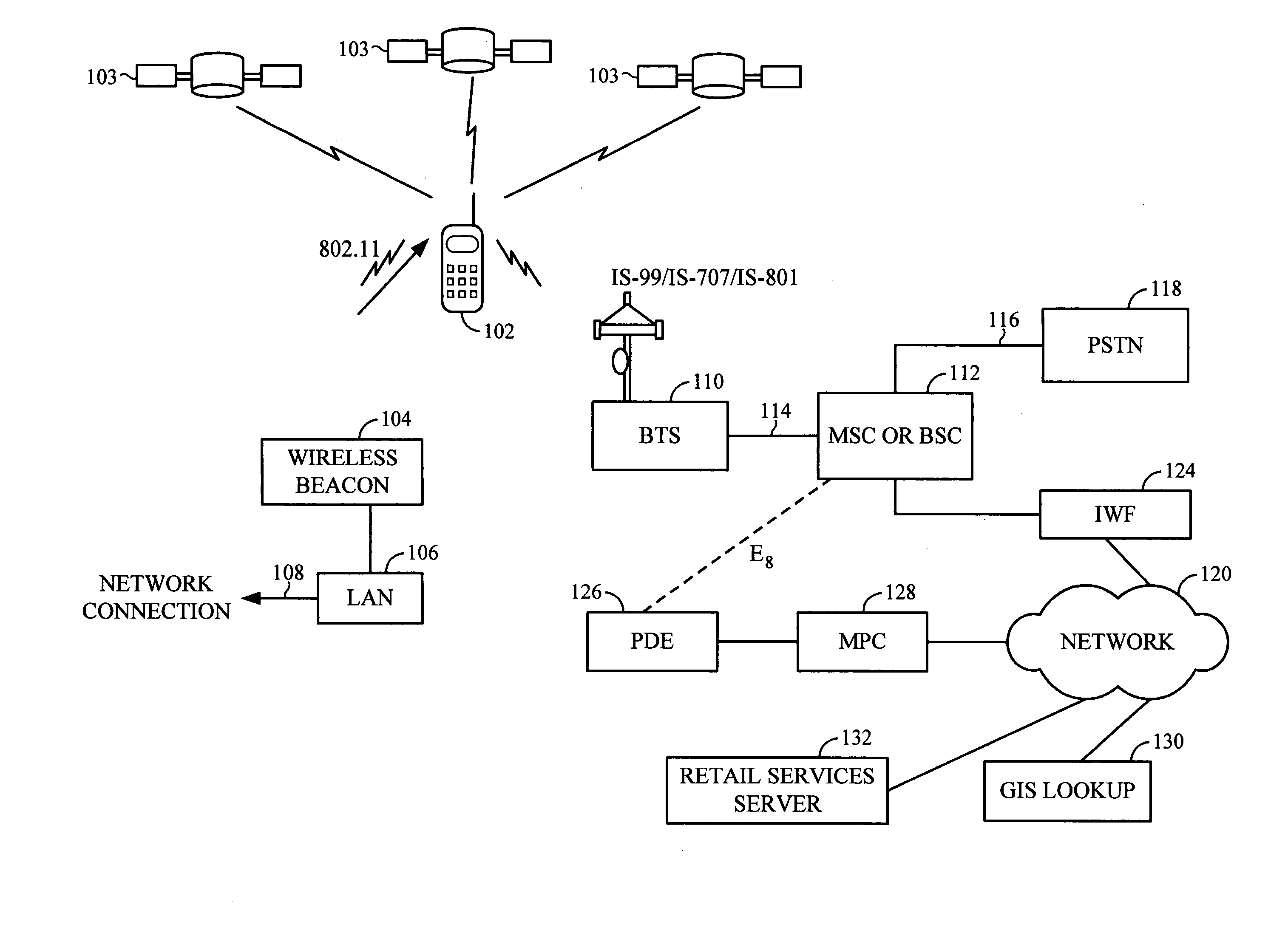
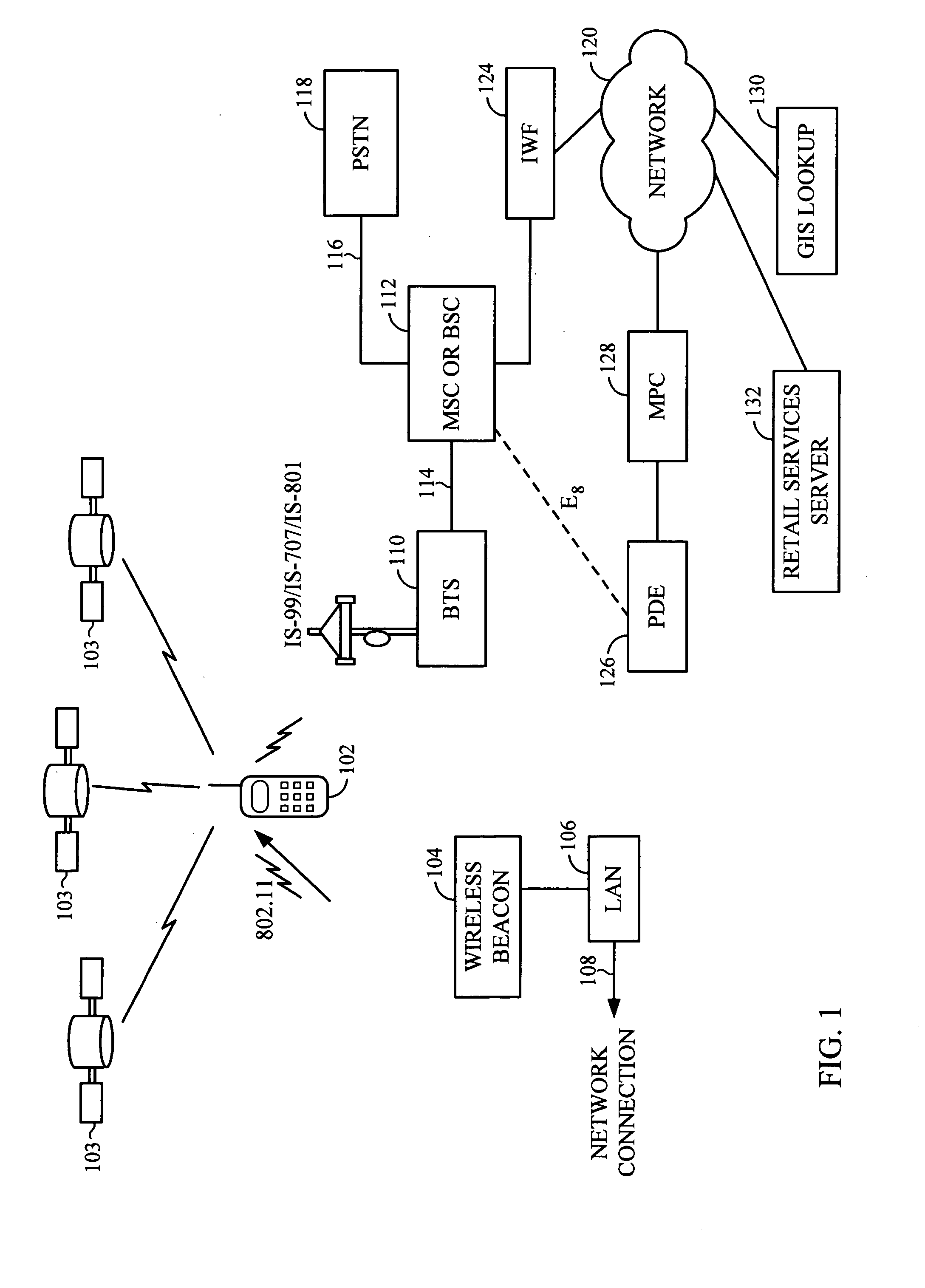
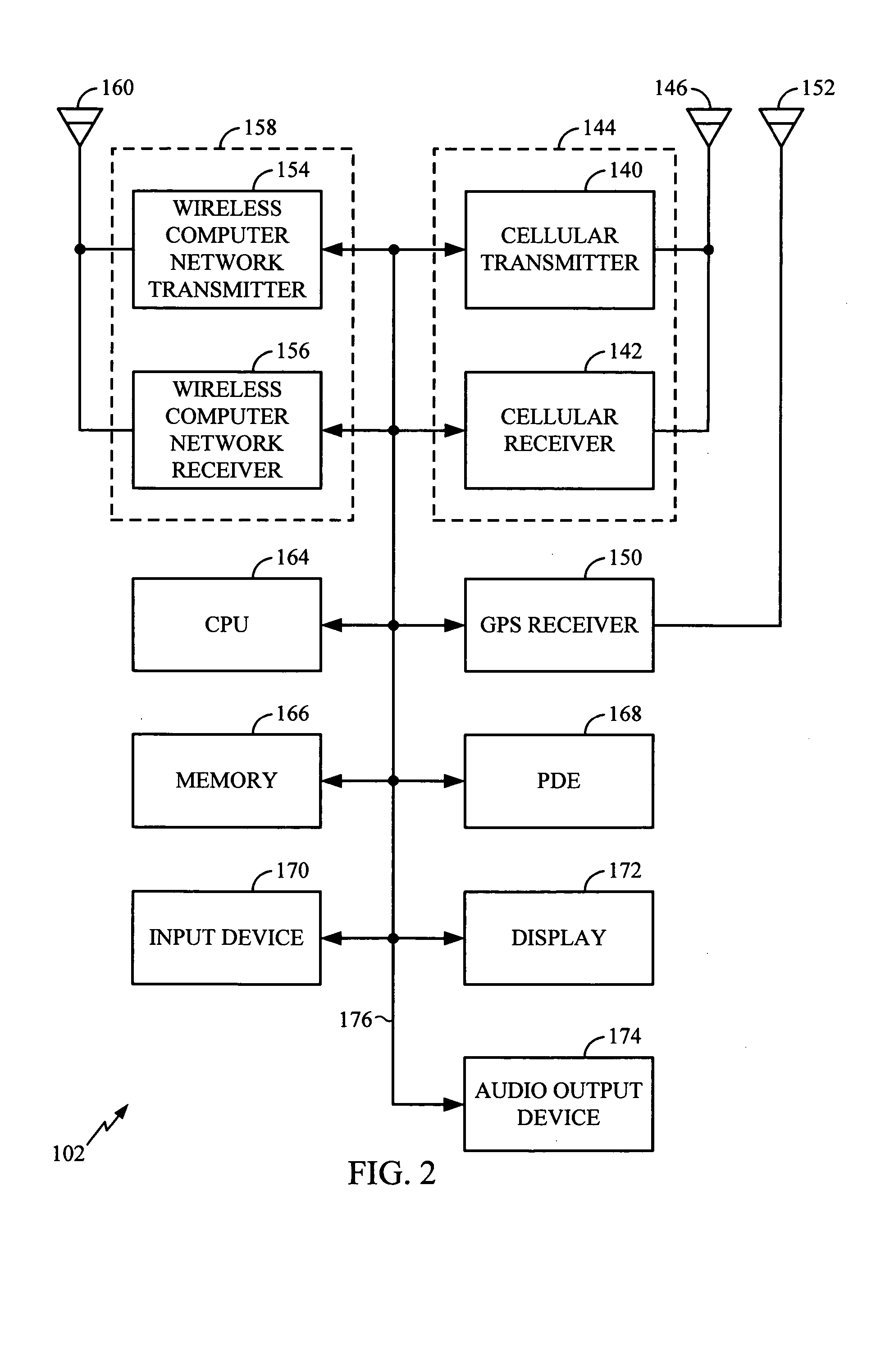
A wireless communication device, known as a mobile station (MS), contains a conventional wireless communication system and further comprises a wireless computer network communication subsystem and may also include GPS capability. The operator of the MS may utilize any or all of these subsystems to determine the current position of the MS. Based on the current position of the MS, location-based services are provided to the MS as sales information, schedules, prices, maps, and the like. In a typical implementation a plurality of computer network access points, or beacons, are distributed throughout a geographic region and used to determine the position of the MS with a reasonably high degree of accuracy. Based on the current position of the MS, the beacons can provide location-based services.
Owner:QUALCOMM INC
Bridging between a Bluetooth scatternet and an Ethernet LAN
InactiveUS20040167988A1Multiple digital computer combinationsNetworks interconnectionNetwork packetAdministrative domain
System and method are disclosed for bridging a point-to-point network such as a Bluetooth scatternet with a shared medium network such as an Ethernet LAN. The scatternet is connected to the LAN via a network access point (NAP). Data packets sent from the LAN to the scatternet are filtered at the NAP to eliminate unnecessary data packets from being sent to the scatternet. Only certain ones of the data packets are forwarded between the LAN and the scatternet. An inter-NAP protocol is used to exchange messages where two or more NAPs are connected to the LAN. Broadcast loops are prevented from occurring in the scatternet and the LAN by defining Administrative domains and NAP service areas (NAPSAs), and controlling the borders thereof according to a broadcast type of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
Decentrallizing Core Network Functionalities
ActiveUS20110158171A1Low production costEasy to operateNetwork traffic/resource managementAssess restrictionNetwork access pointCore network
The present invention relates to methods and apparatuses for providing network access, wherein a connection to a core network is established via a wireless access device and a gateway device. Connectivity of the wireless access device is restricted to a pre-defined group of core network address of a pool of gateway devices with multi-node connectivity to the core network, and a single address is selected to establish the connection to a one of the gateway devices. The gateway device is provided with a relay function for mapping a single input address to a plurality of core network addresses based on a location information of the wireless access device and with at least one co-located decentralized core network functionality.
Owner:NOKIA SOLUTIONS & NETWORKS OY
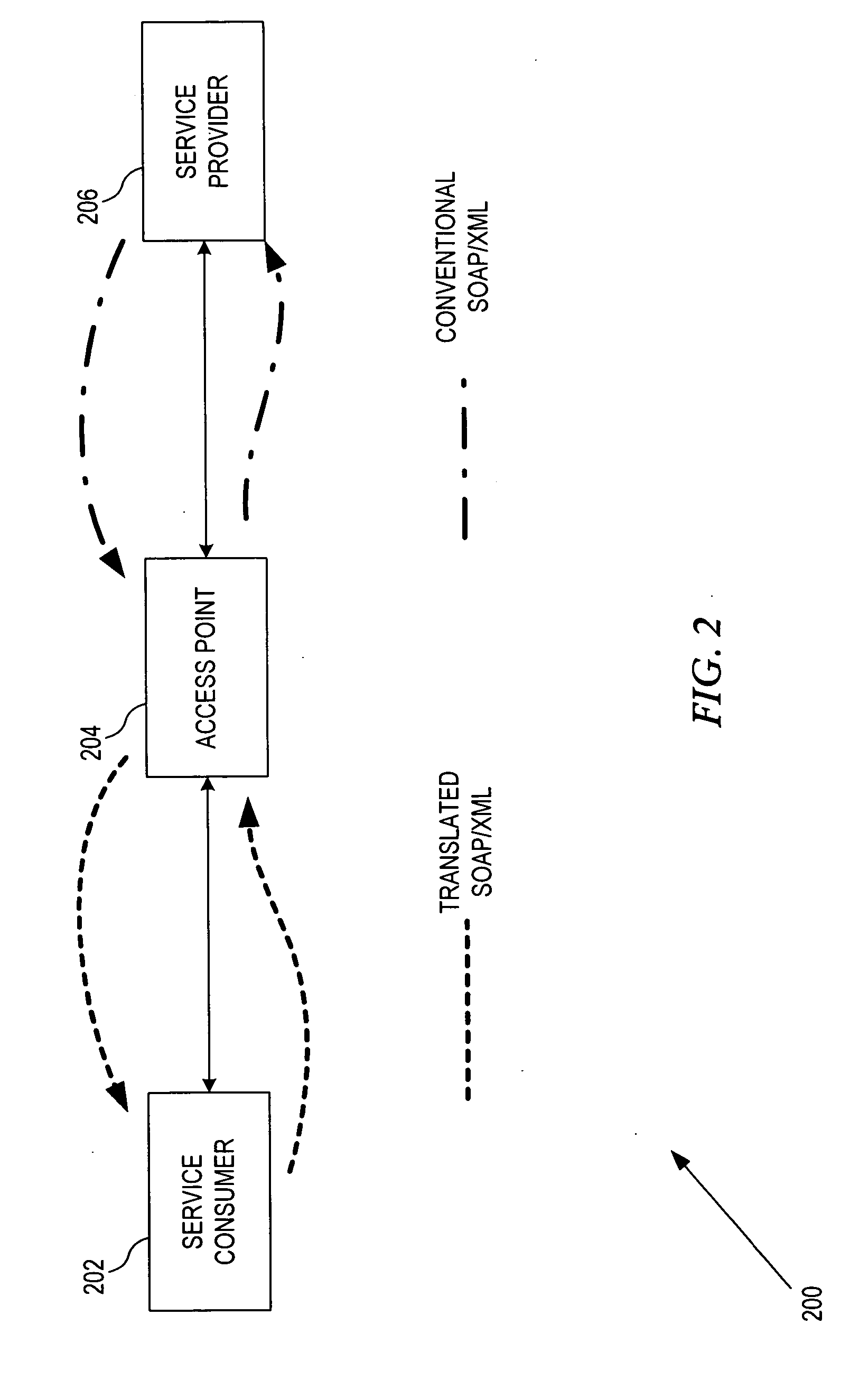
System and method for access point translation of web service content
InactiveUS20050198304A1Multiple digital computer combinationsTransmissionWeb serviceNetwork access point
A system and method for using a network access point to implement transparent Web Service functionality between processing deficient terminals and Web Service providers by allowing the terminals to access Web Services using abbreviated Web Service requests. The abbreviated Web Service requests are then translated into conventional Web Service requests by the network access point and subsequently forwarded onto the Web Service provider. The conventional Web Service response is then optionally translated into an abbreviated response to accommodate the processing deficiencies of the Web Service requester.
Owner:NOKIA CORP
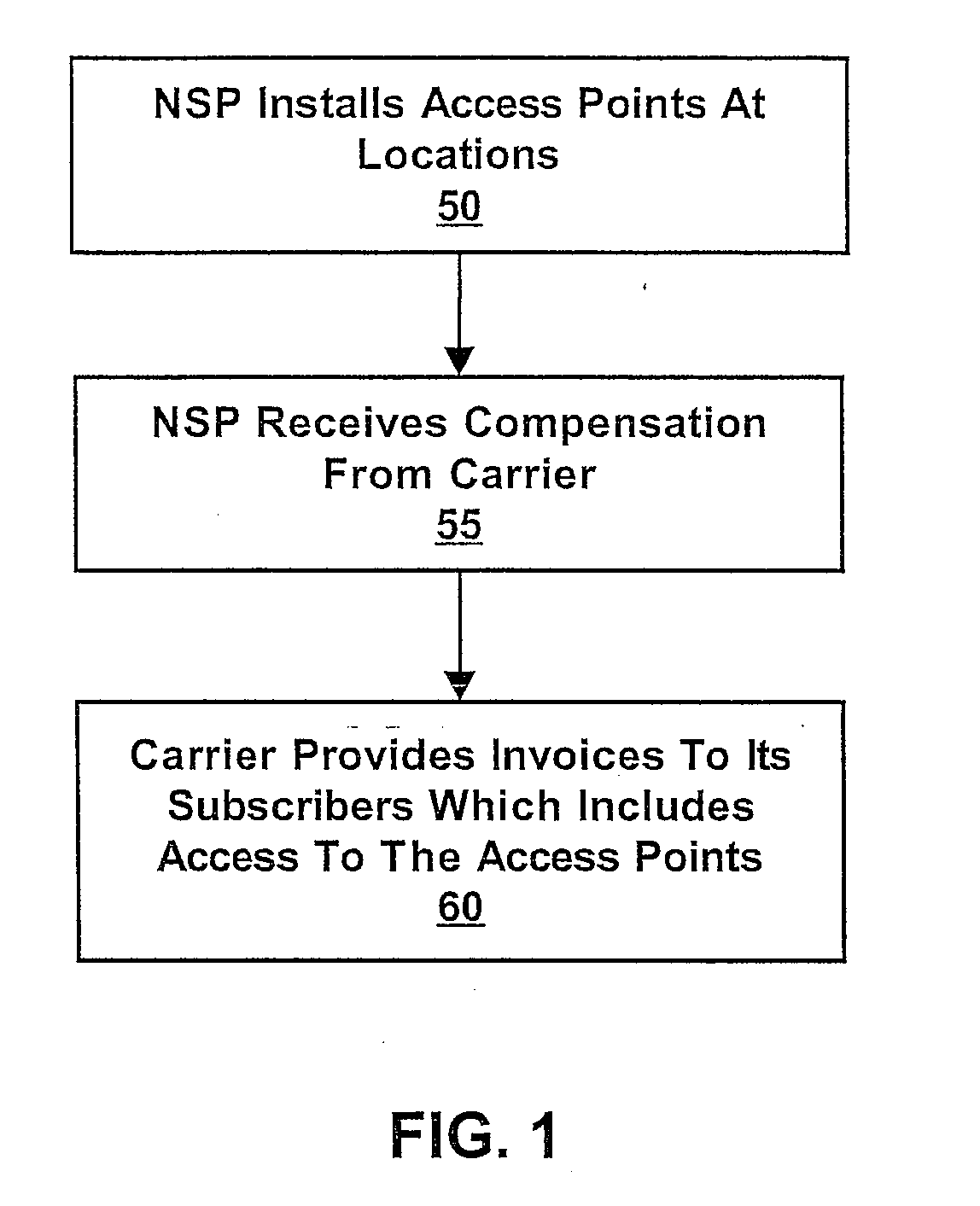
System, method and program product for delivery of digital content offerings at a retail establishment
ActiveUS20080097858A1Recover installationRecover maintenanceMetering/charging/biilling arrangementsDiscounts/incentivesGraphicsDigital content
A method and system for providing distributed network access point installation and management. A network provider installs and / or operates a plurality of access points at locations of a retail entity. Each access point may provide services such as Internet access, and / or content such as audio, video, text, and / or graphics, among other types of services. A carrier, such as a telephone or cable company, may compensate the network service provider for installation and operation of the access points. The carrier may in turn charge its subscribers for network access at the retail entity locations. A plurality of different carriers may provide compensation and allow respective subscriber access. The network access points may be configured to allow each carrier to present a point of presence to its subscribers at the retail entity locations. The installed network may also provide service for retail entity back office functions.
Owner:WAYPORT
Network access point having interchangeable cartridges
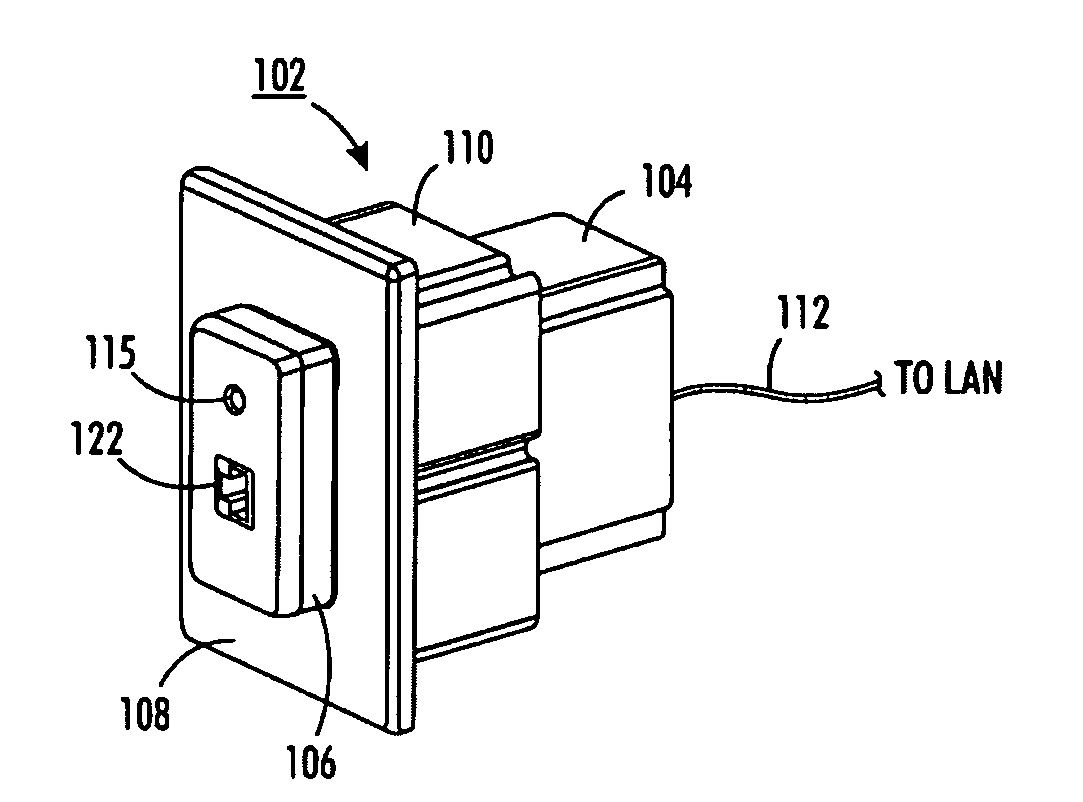
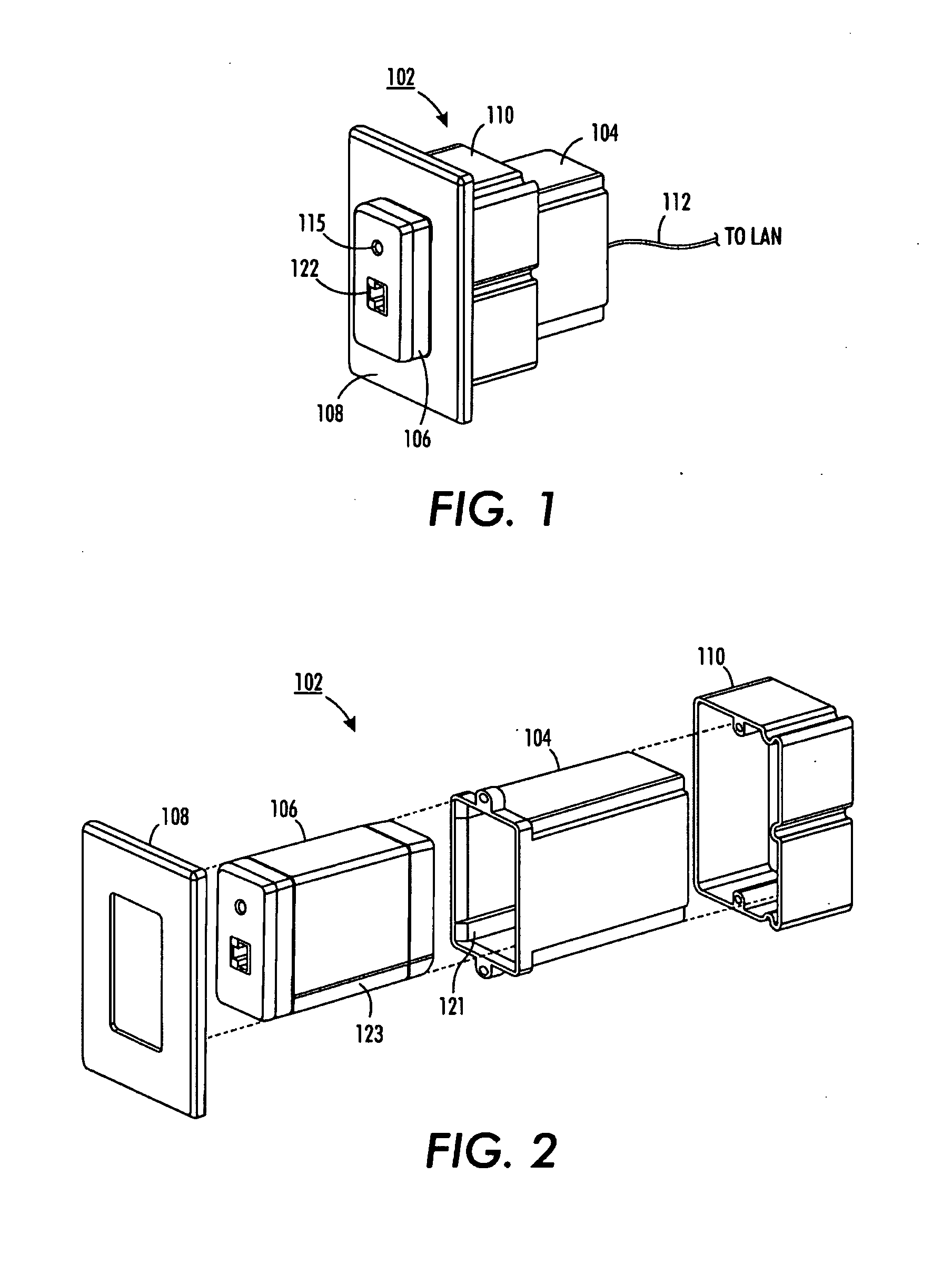
InactiveUS20090247006A1Easy to transportEasy to disassembleCoupling device detailsNetwork connectorsComputer networkMagnetic tape
Disclosed is multimedia system having at least one network access point comprising two discrete, but interrelated, components, a communications module and a device interface cartridge whereby in combination implement a network access point to accommodate via a medium. The interface cartridge is interchangeable to permit the access point to be customized to a desired application.
Owner:WI3
A Power Line Communication System that Enables Low-Cost Last Mile Access to any Legacy or Emerging Network Infrastructure
InactiveUS20050226200A1Eliminate needBroadband local area networksPower distribution line transmissionPower line networkTransformer
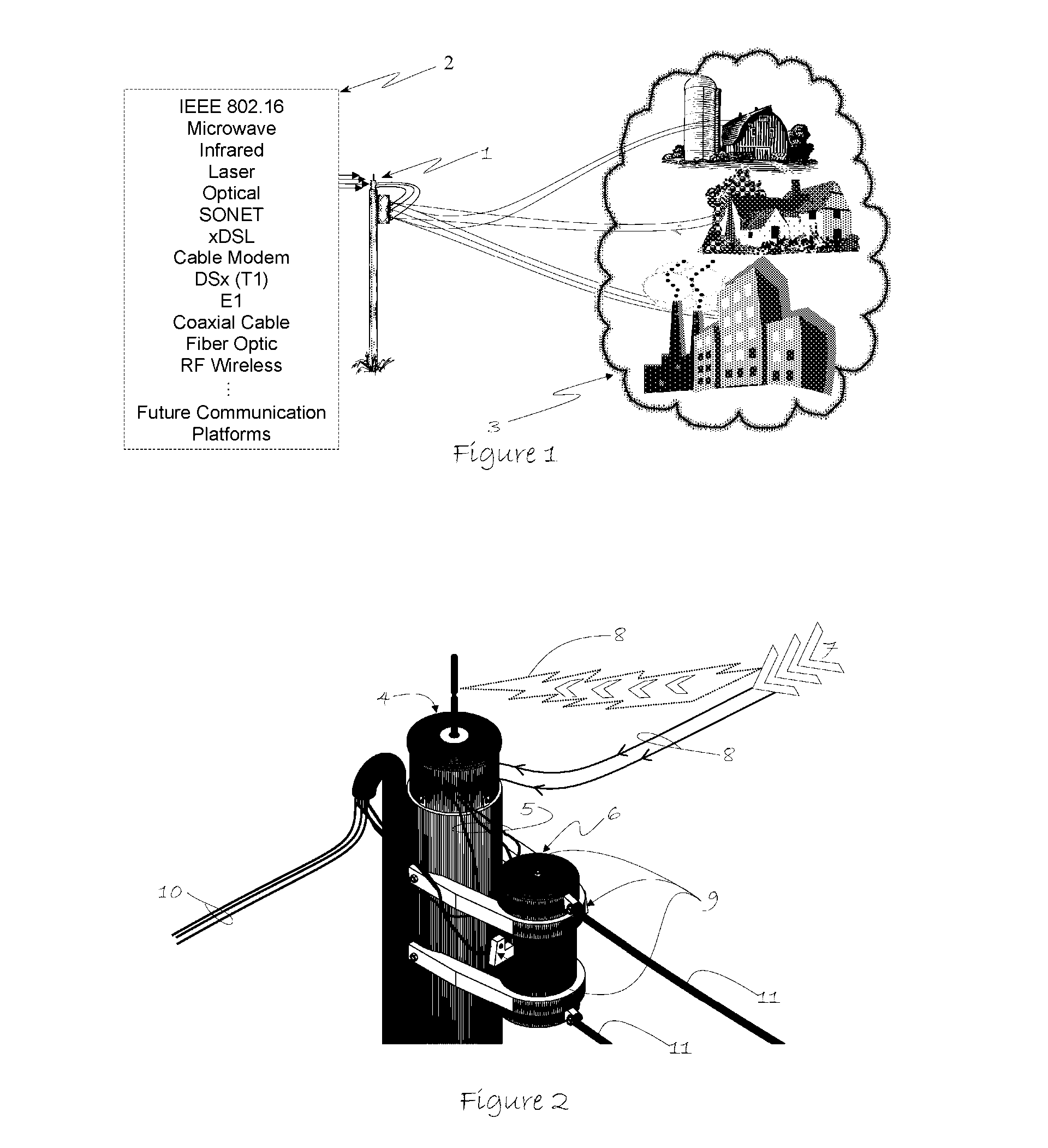
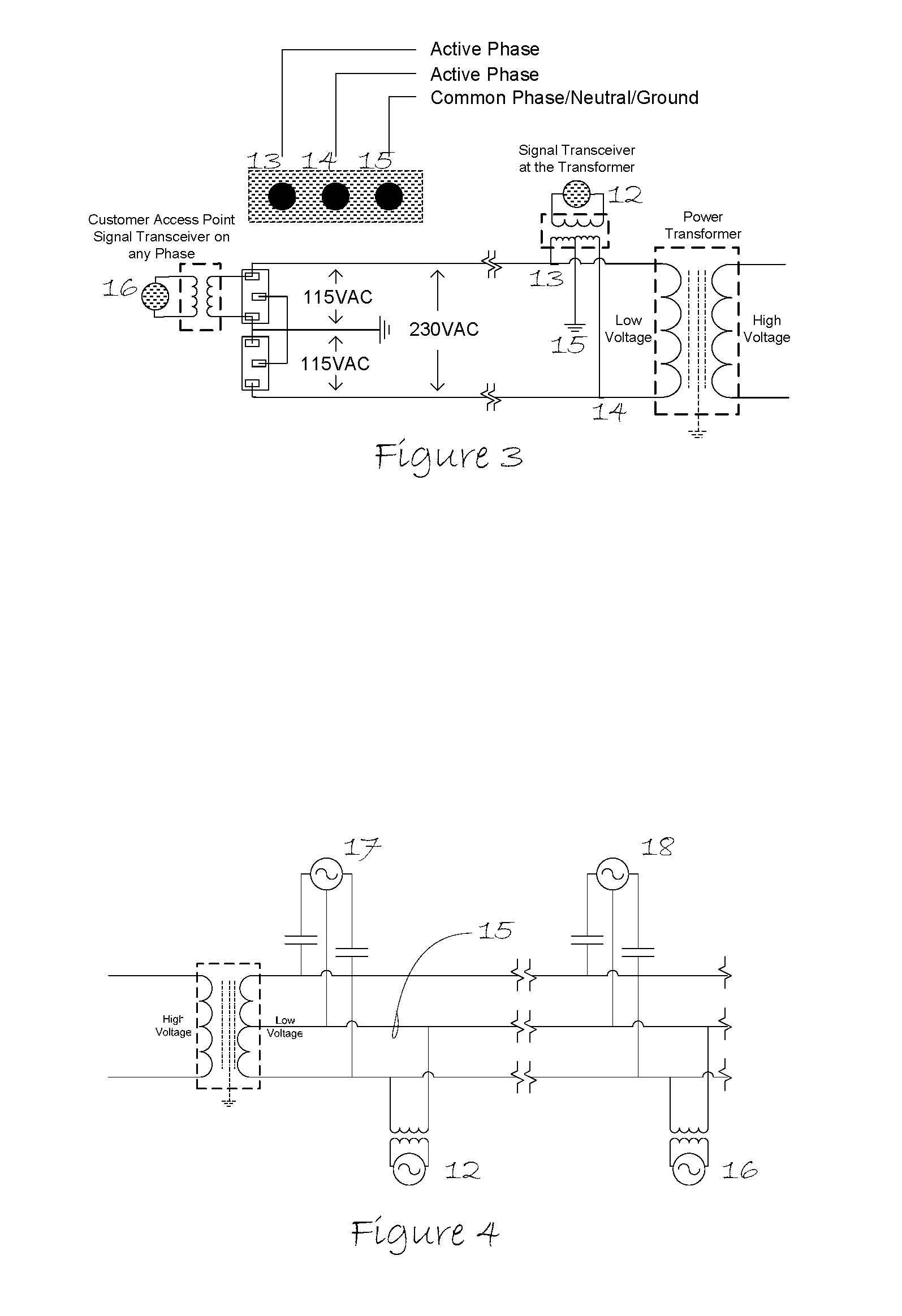
An economically attractive method to provide multiuse broadband connectivity to the edge of legacy telecommunication and emerging networks is disclosed. The invention utilizes a multi-phase common signal return coupling scheme that passes signals onto the step-down side of power transformers. This invention enables the transformer to serve as an economically attractive distribution point that transfers external payload signals from service providers to customer network access points on the load side of the transformer. The resulting power line network will permit remote control of utilization and access to any legacy or emerging network payload such as ITU and IETF that is present at any type of electric power transformer.
Owner:EDGECOM
Method and apparatus for controlling the allocation of bandwidth of a network access point to an application having a message transmitted on the network
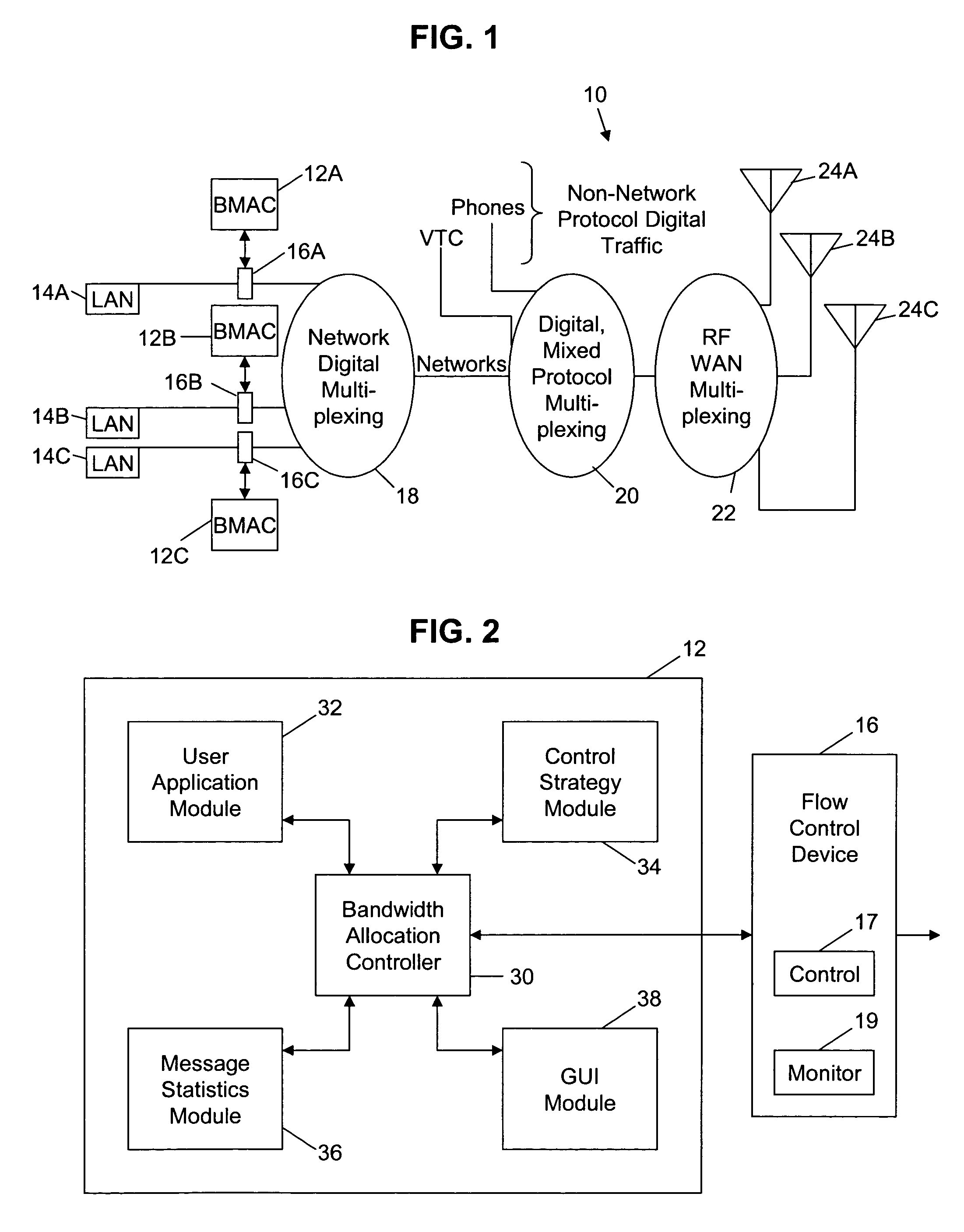
InactiveUS7493407B2Multiple digital computer combinationsData switching networksGraphicsGraphical user interface
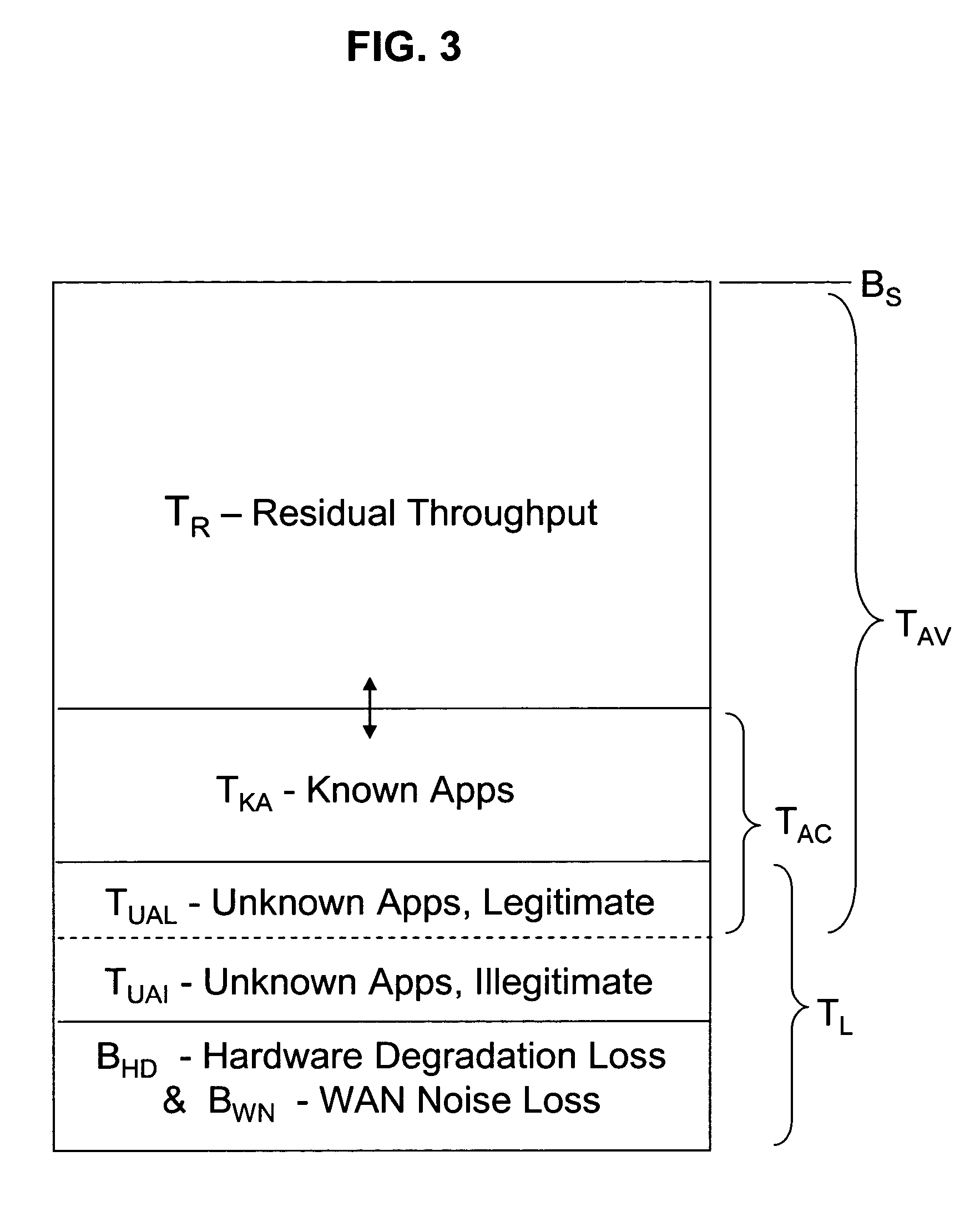
An automated bandwidth monitoring and control method and system provides for real time, dynamic control of the allocation of bandwidth to selected applications in a communications network based on the selected operational context and the fixed bandwidth available at a network access point. A graphical user interface, using operational terms common to the overall enterprise in which and for which the network is implemented and understandable by an operator, displays the bandwidth allocation strategy, and in substantially real time displays statistics representative of actual bandwidth use at the access point, input functions for modifying the bandwidth allocation strategy in substantially real time and estimated message delay distributions for the applications of the strategy determined based on the actual bandwidth use statistics.
Owner:DRS TECHN SERVICES
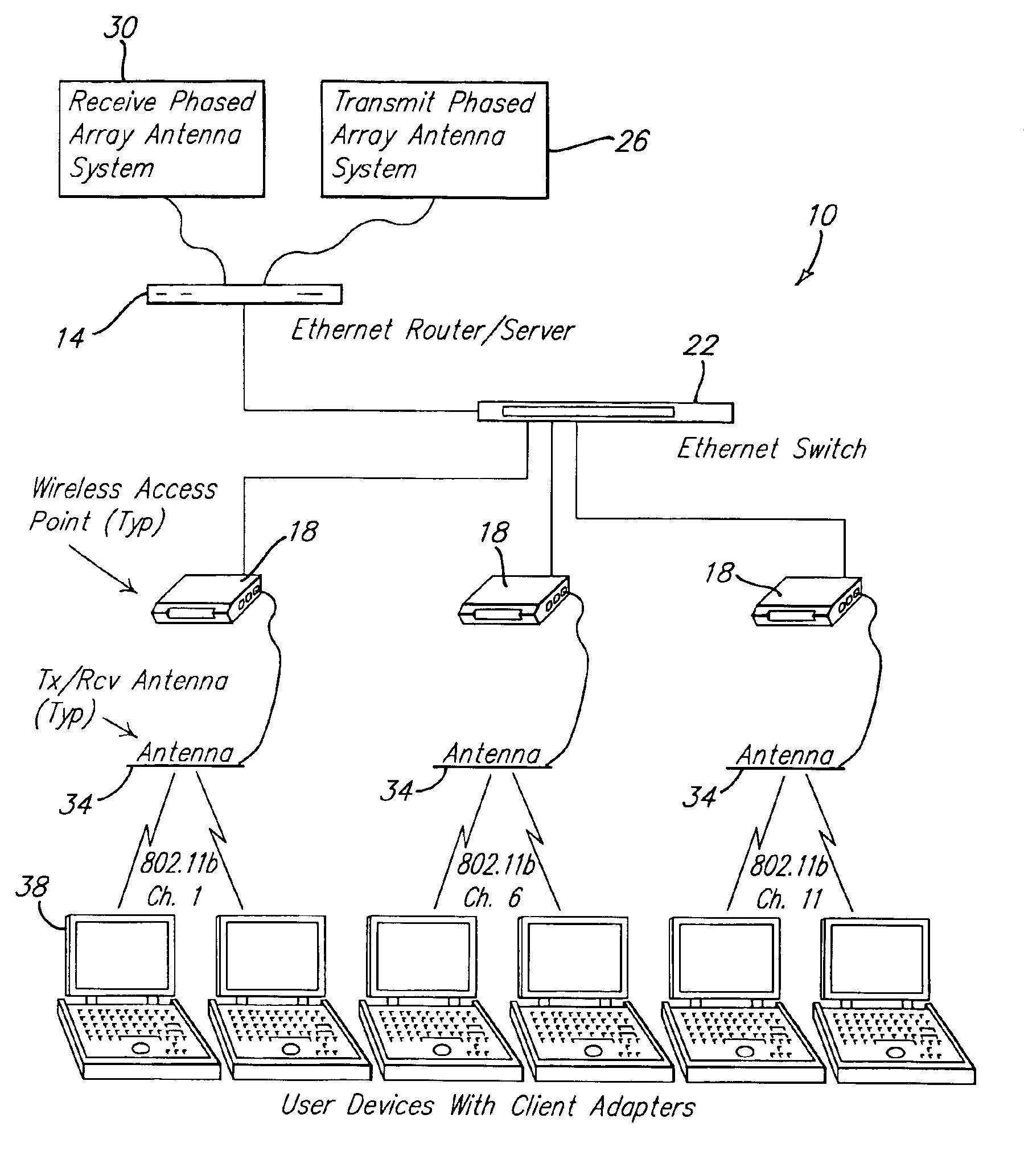
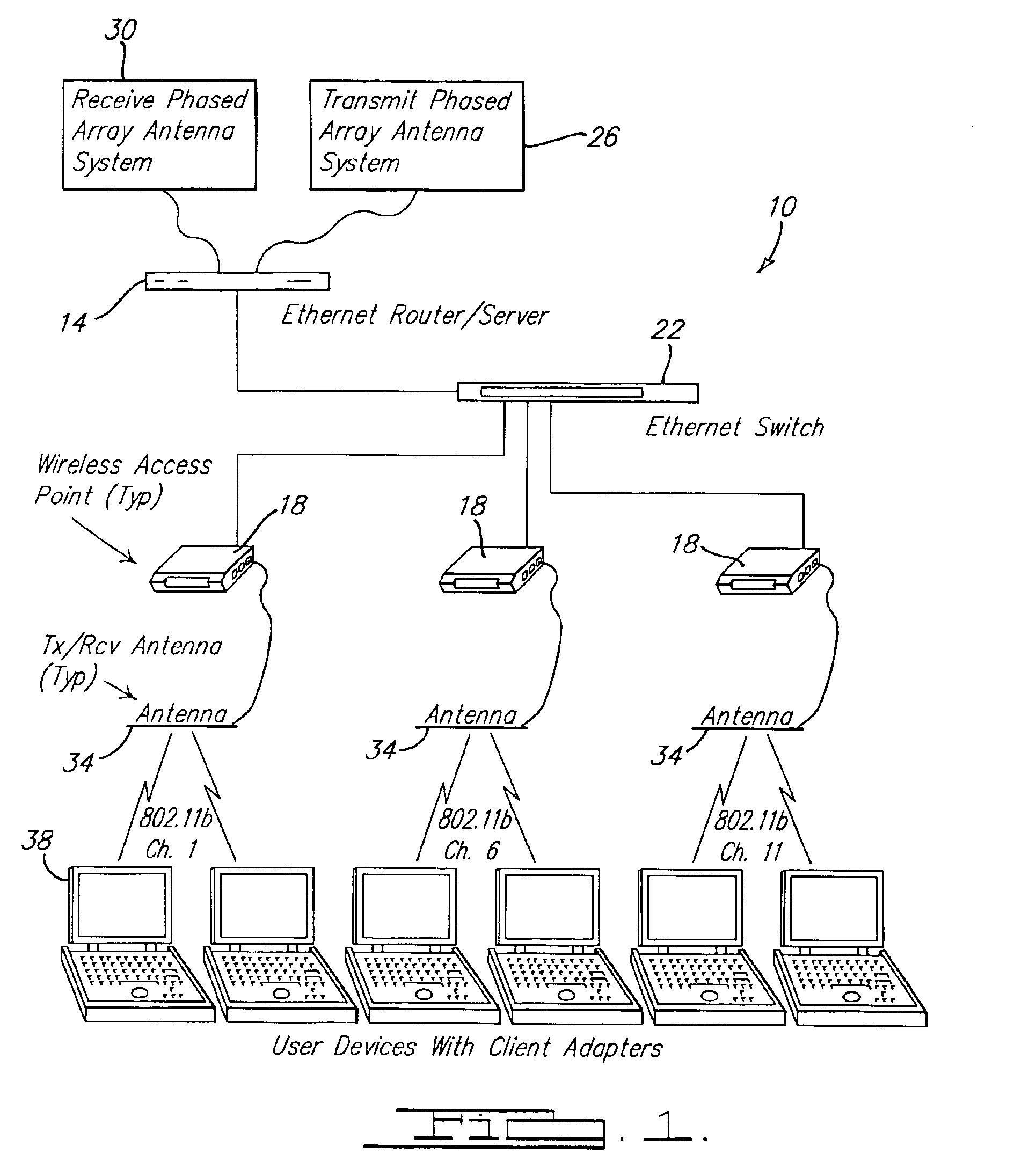
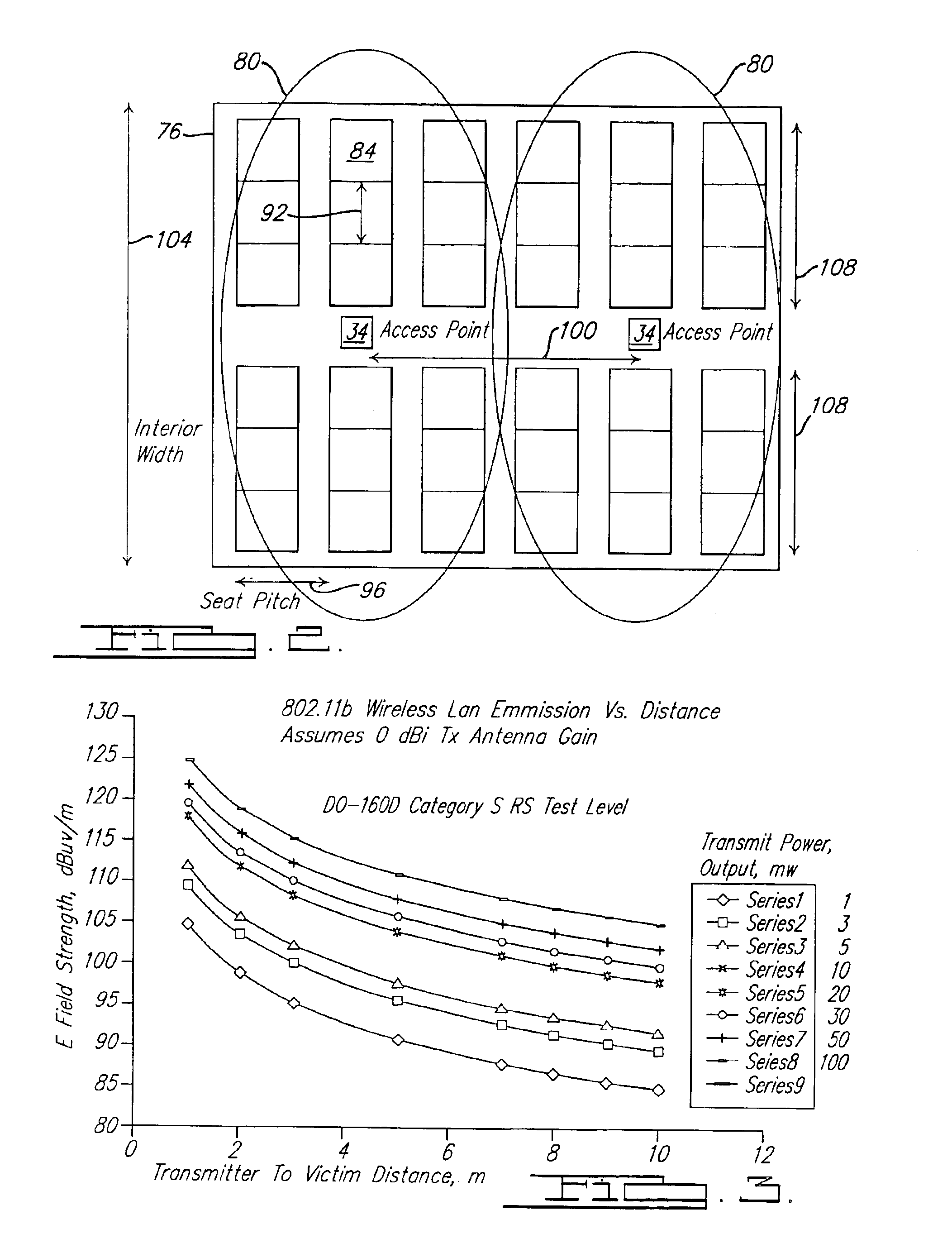
Mobile wireless local area network and related methods
InactiveUS6990338B2Data switching by path configurationClosed circuit television systemsRf exposureNetwork service
A wireless local area network adapted for use by users traveling on a mobile platform such as an aircraft. The network includes a network server located on the mobile platform, and at least one network access point connected to the server and accessible wirelessly by at least one user portable electronic device over one of a plurality of non-overlapping network frequency channels. The RF characteristics of this wireless network are specifically tailored to meet applicable standards for electromagnetic compatibility with aircraft systems and RF exposure levels for passengers and flight crews.
Owner:THE BOEING CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com