Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1299 results about "Network usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
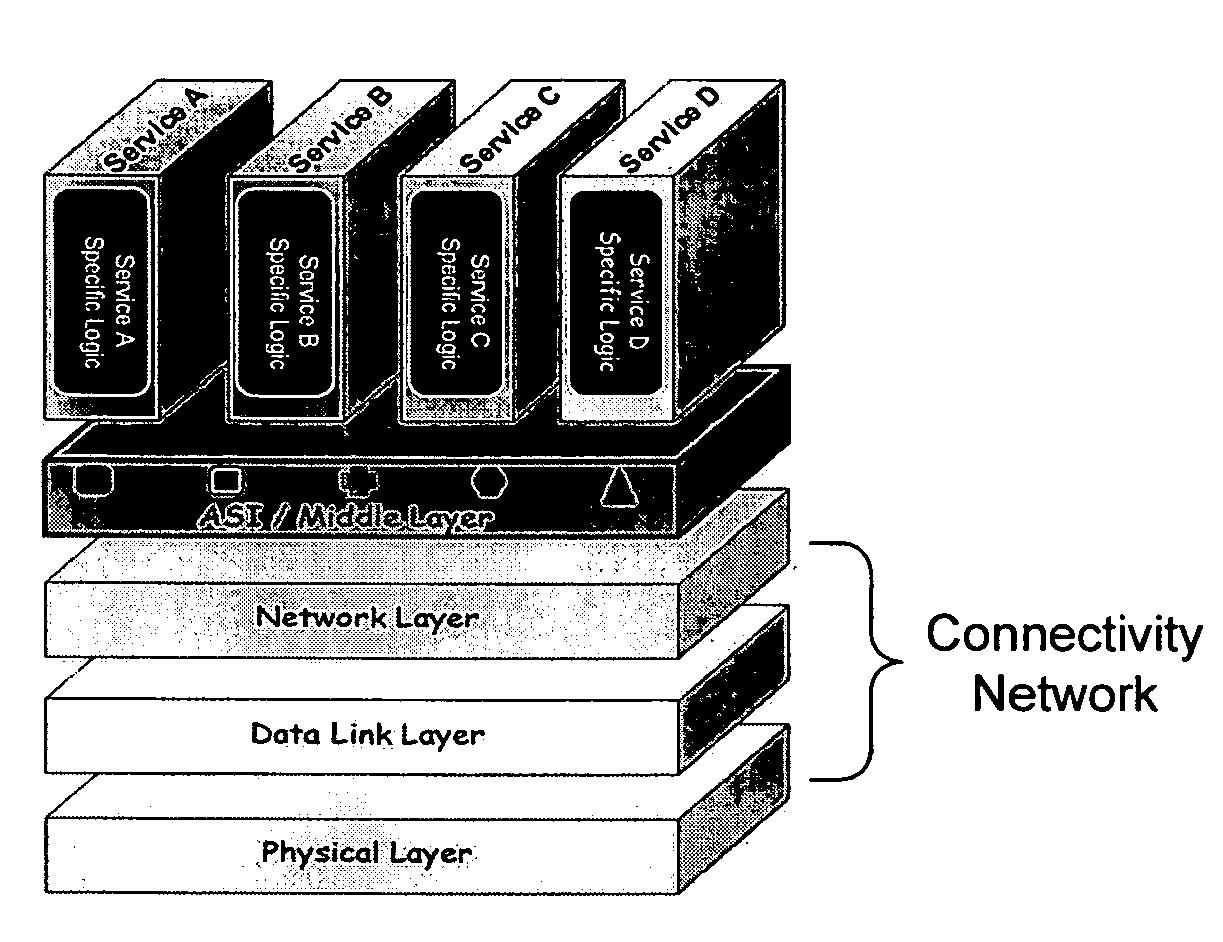
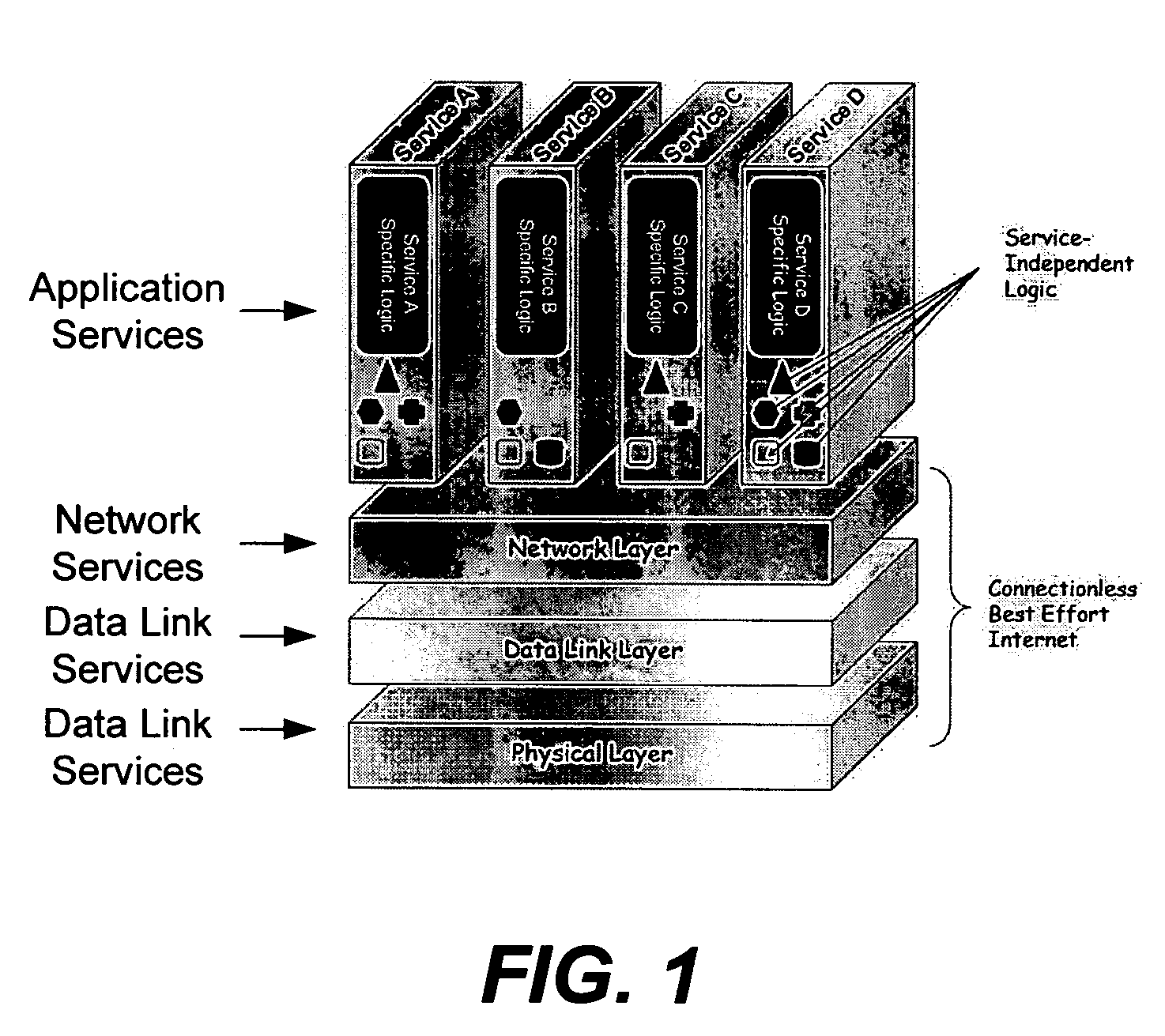
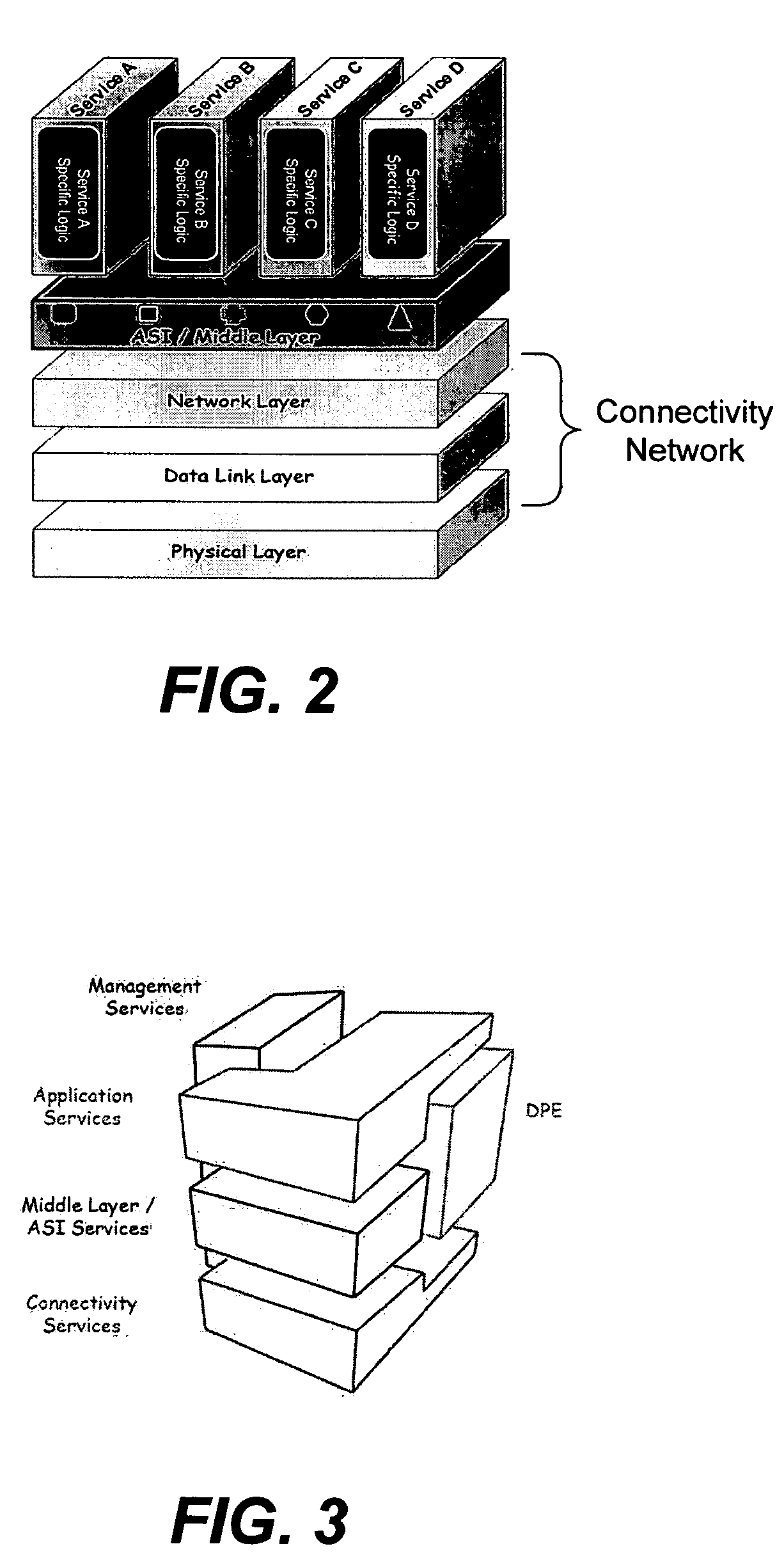
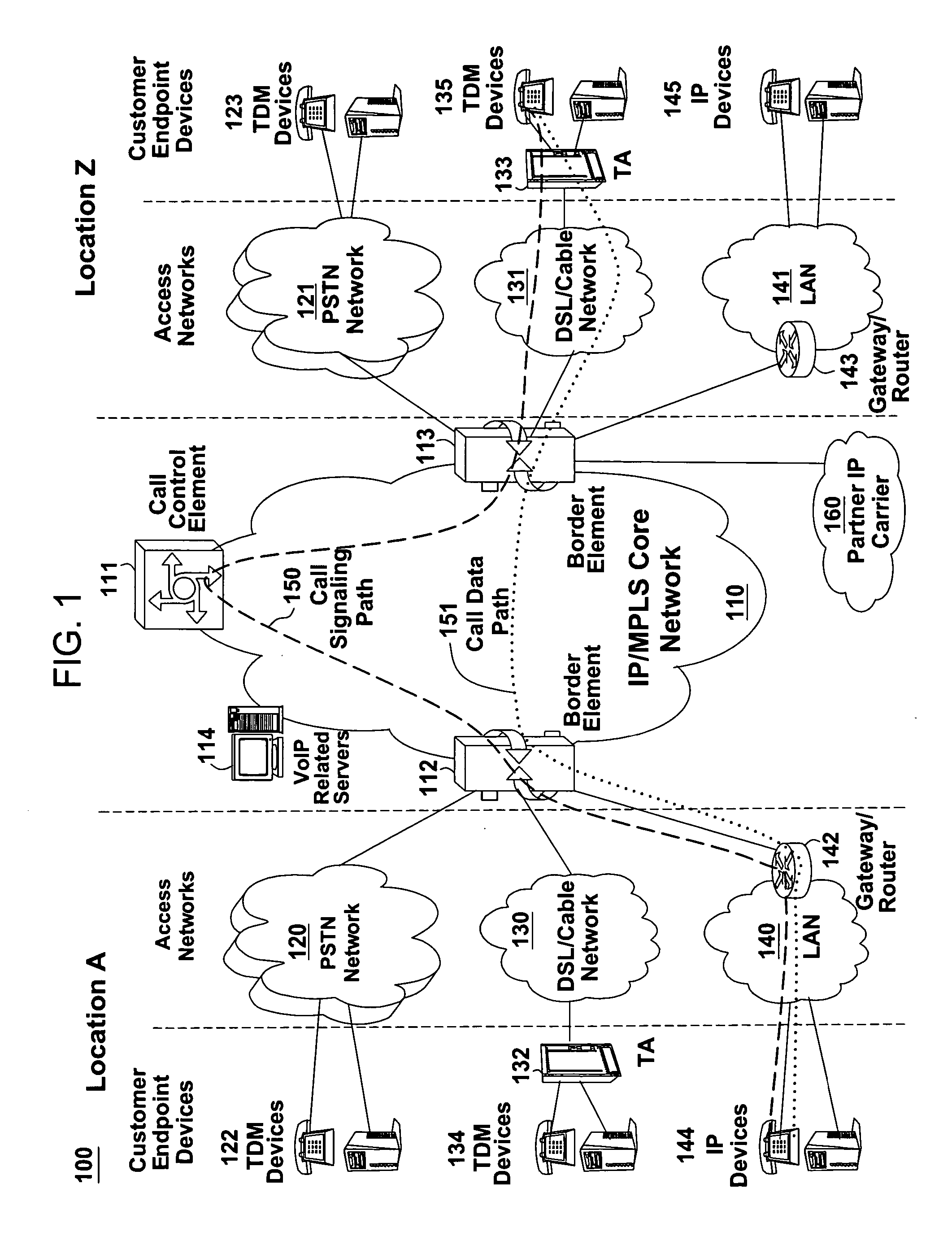
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
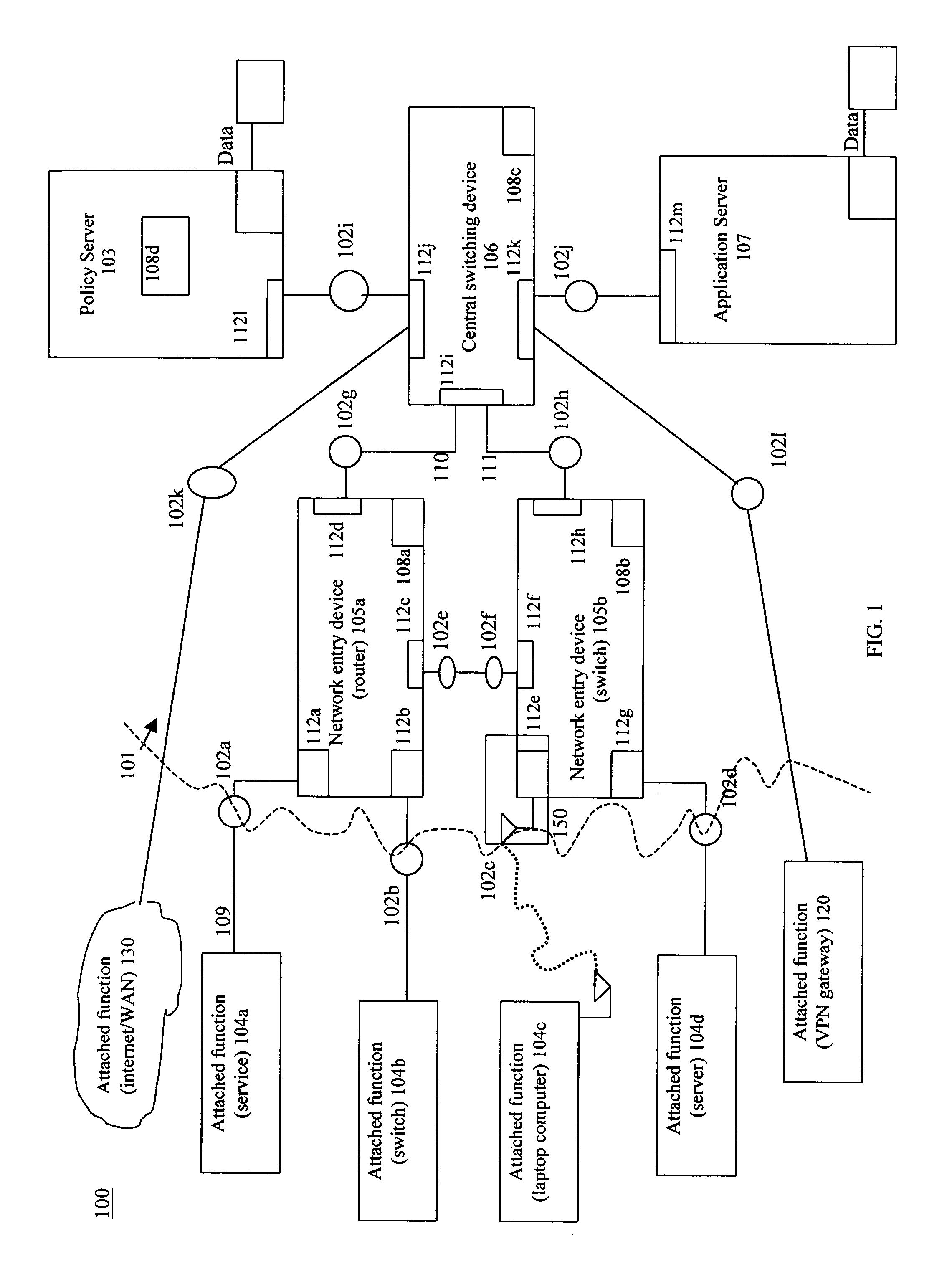
System and method for configuring computer applications and devices using inheritance
InactiveUS20020091819A1Multiple digital computer combinationsData switching networksStructure of Management InformationNetwork topology
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises determining a hierarchical tree structure based upon locations of devices in a network topology, each device being a node in the hierarchical tree structure, determining policies for each node in the hierarchical tree structure to be enforced by an agent corresponding to each node, the agent being in communication with the device and the resources corresponding to the device, and communicating the policy to the corresponding agent, wherein the policies corresponding to the resources of each device are selectively inherited along the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
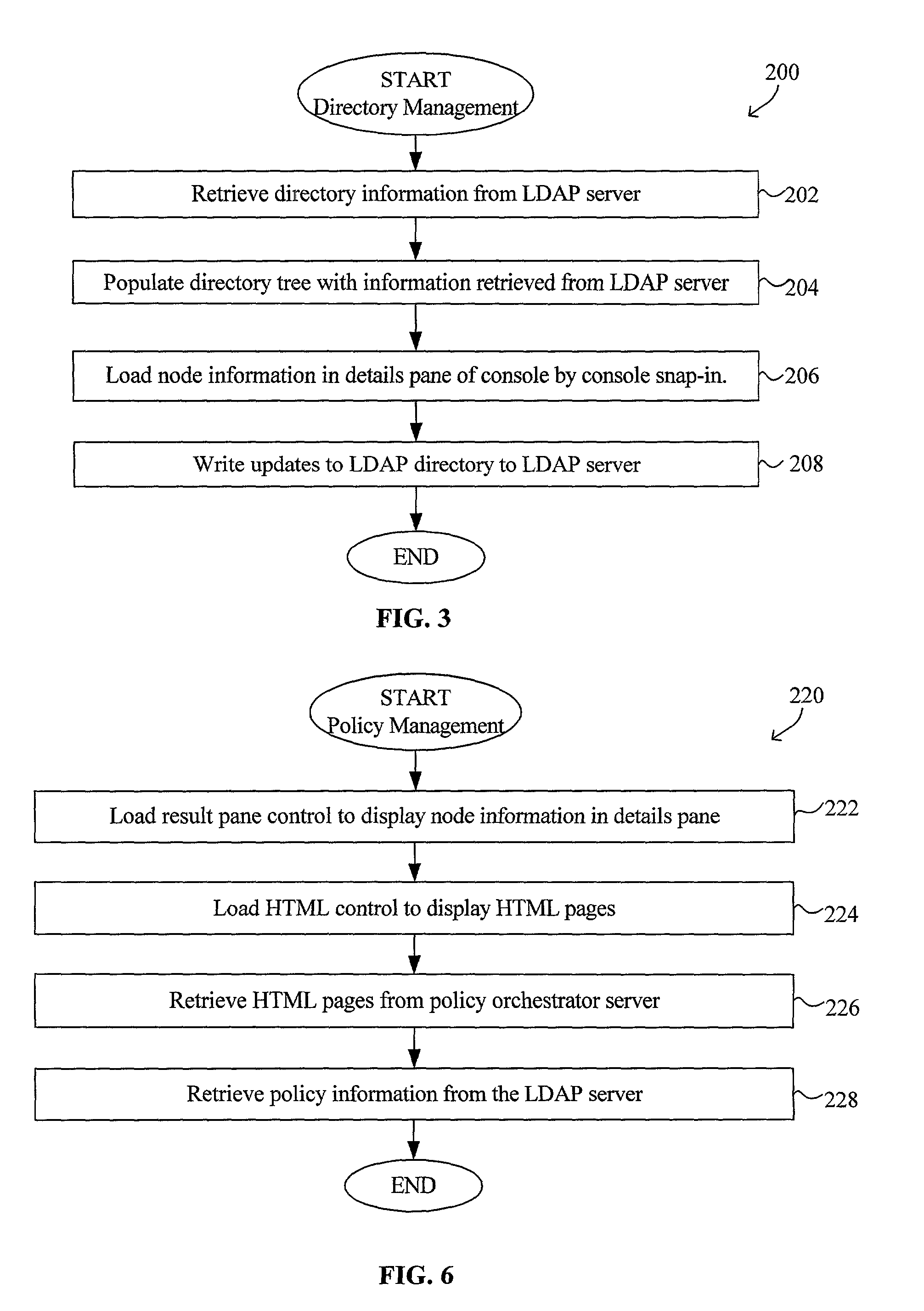
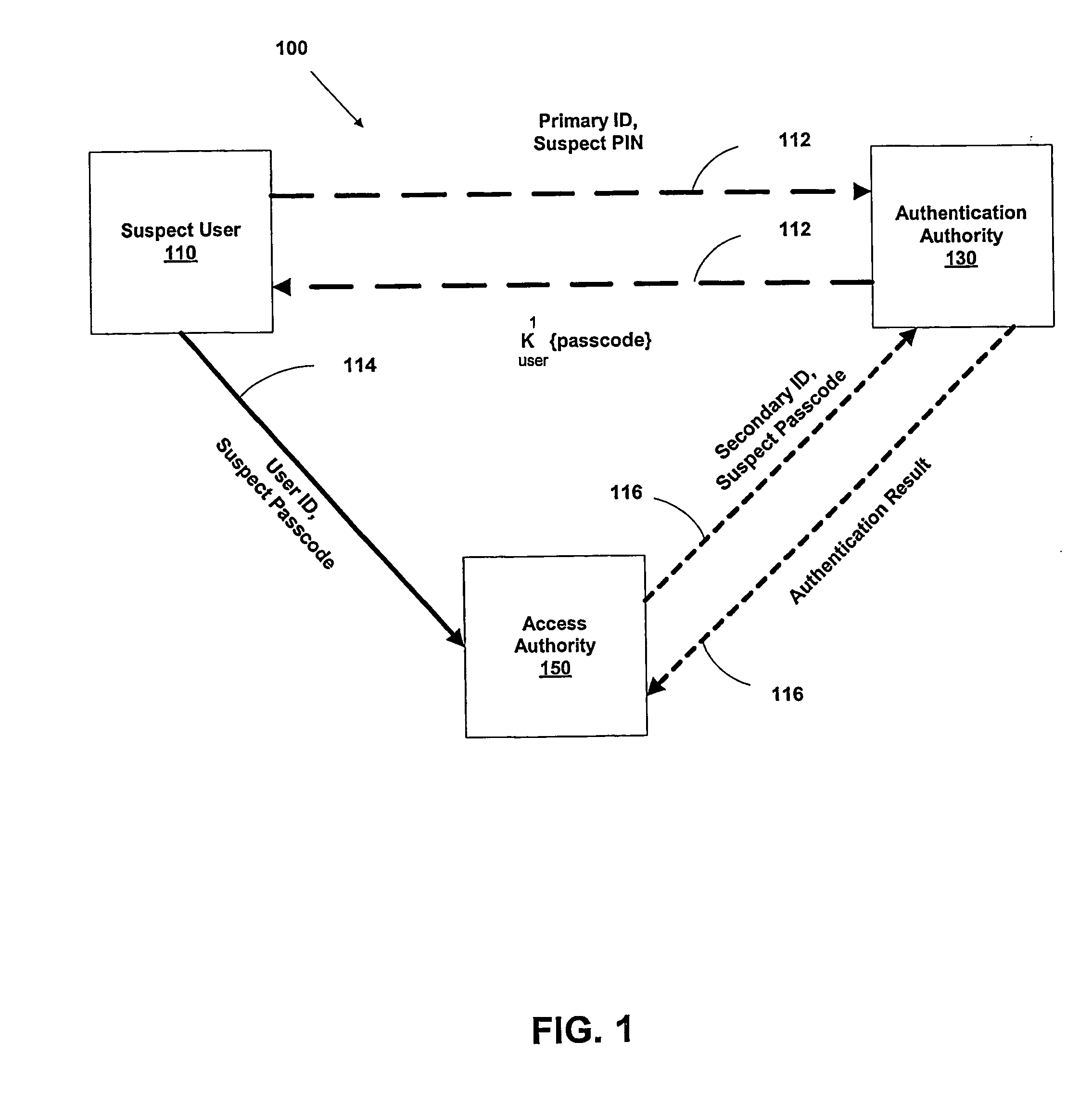
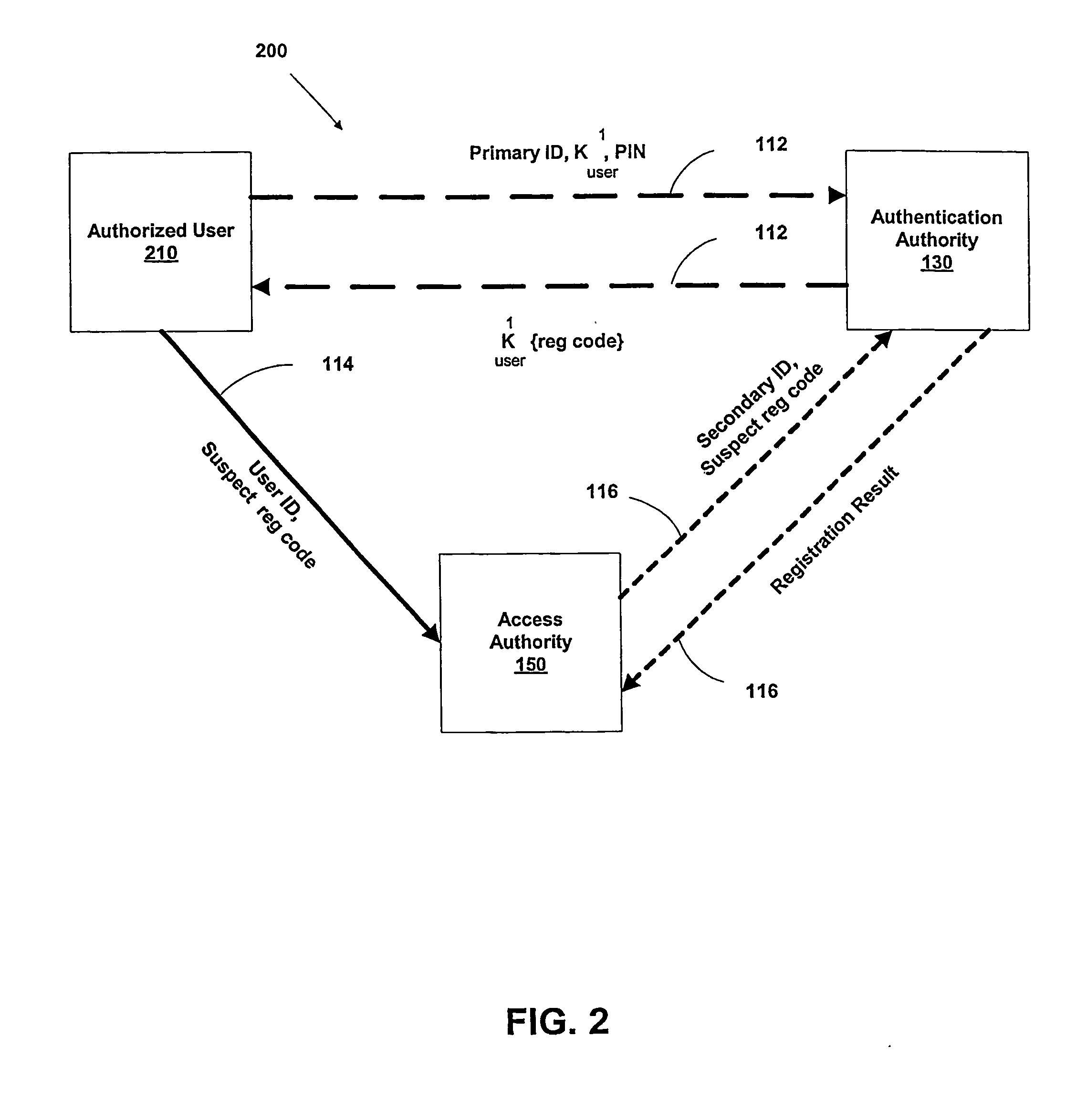
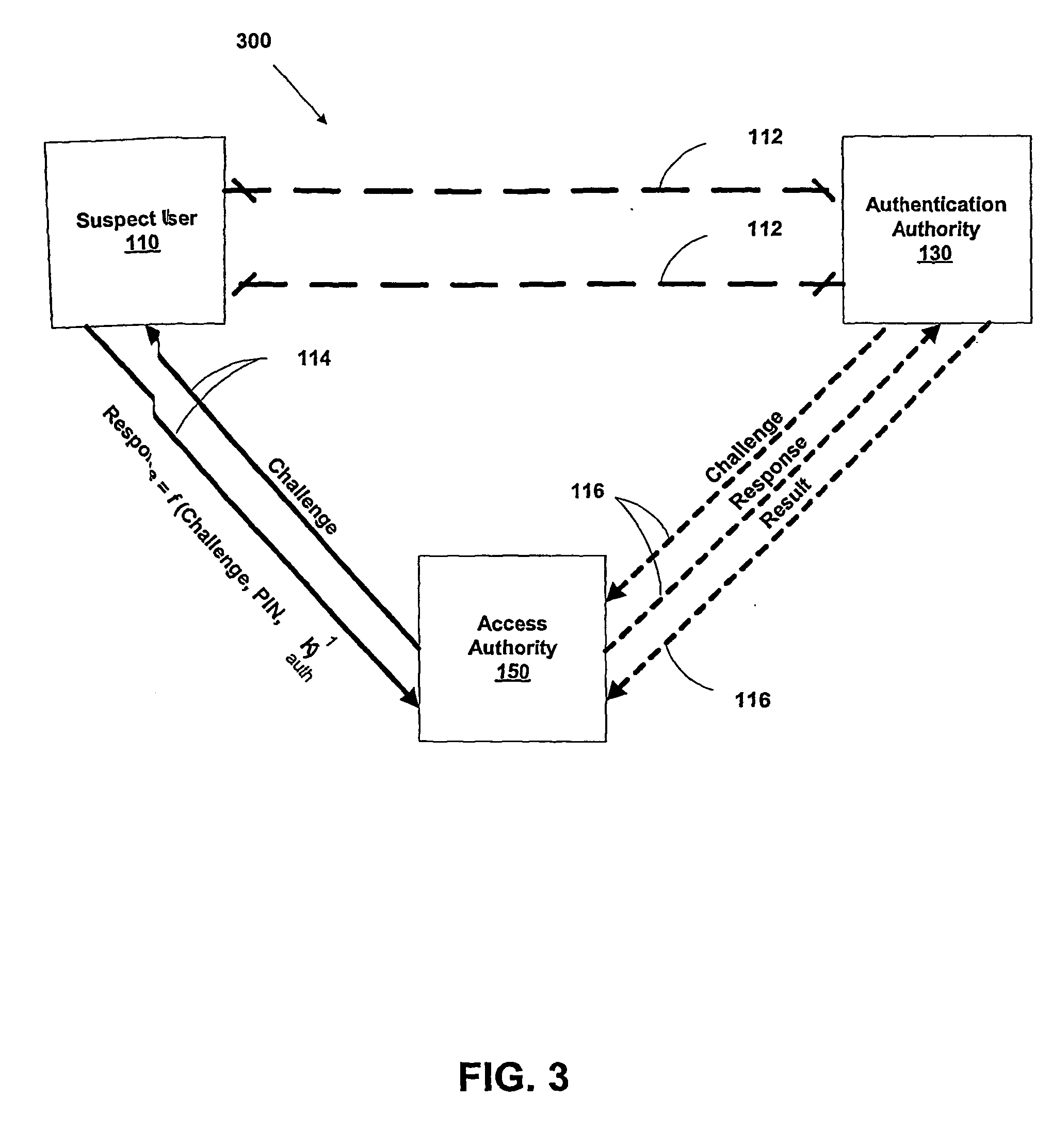
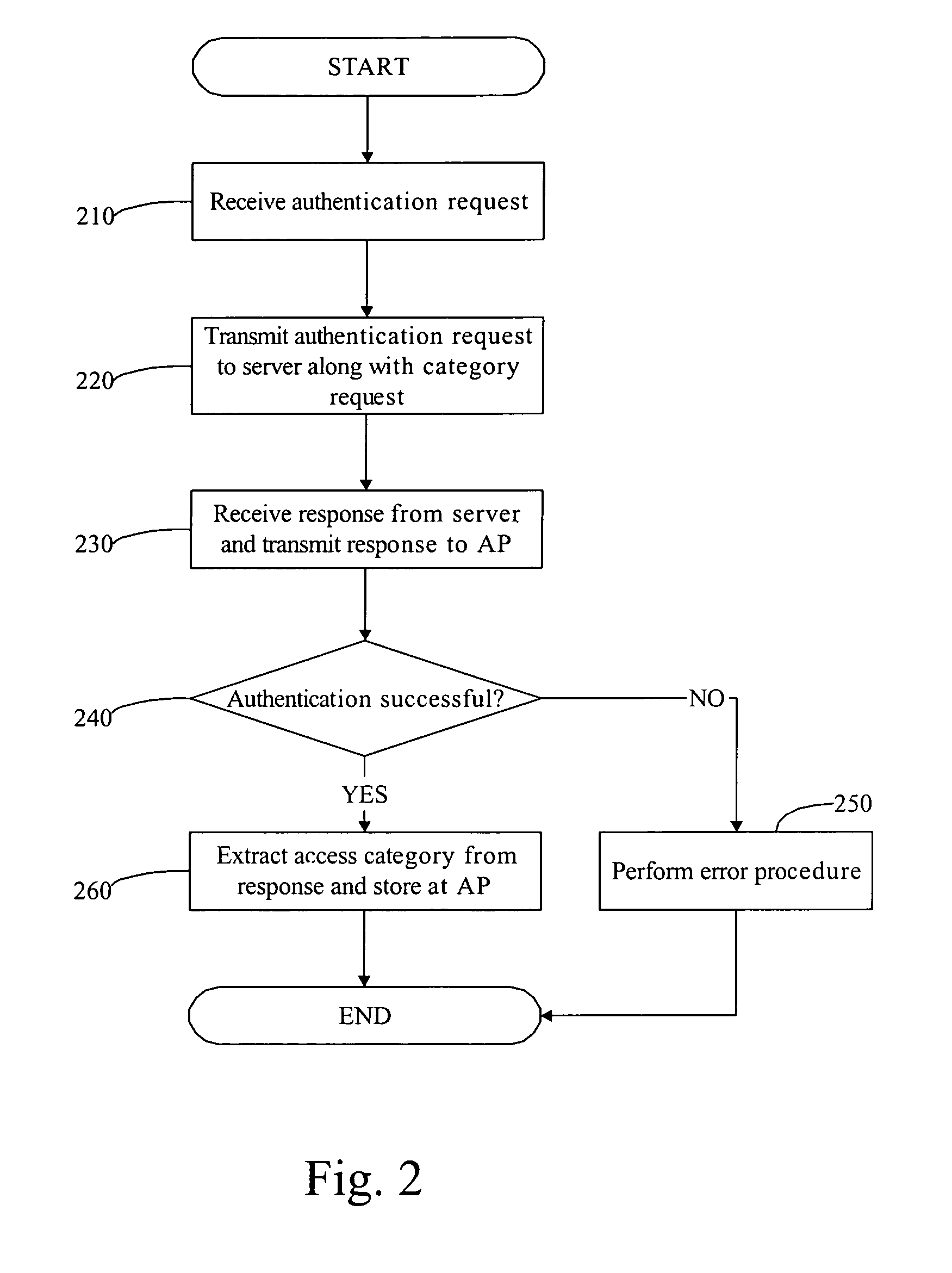
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
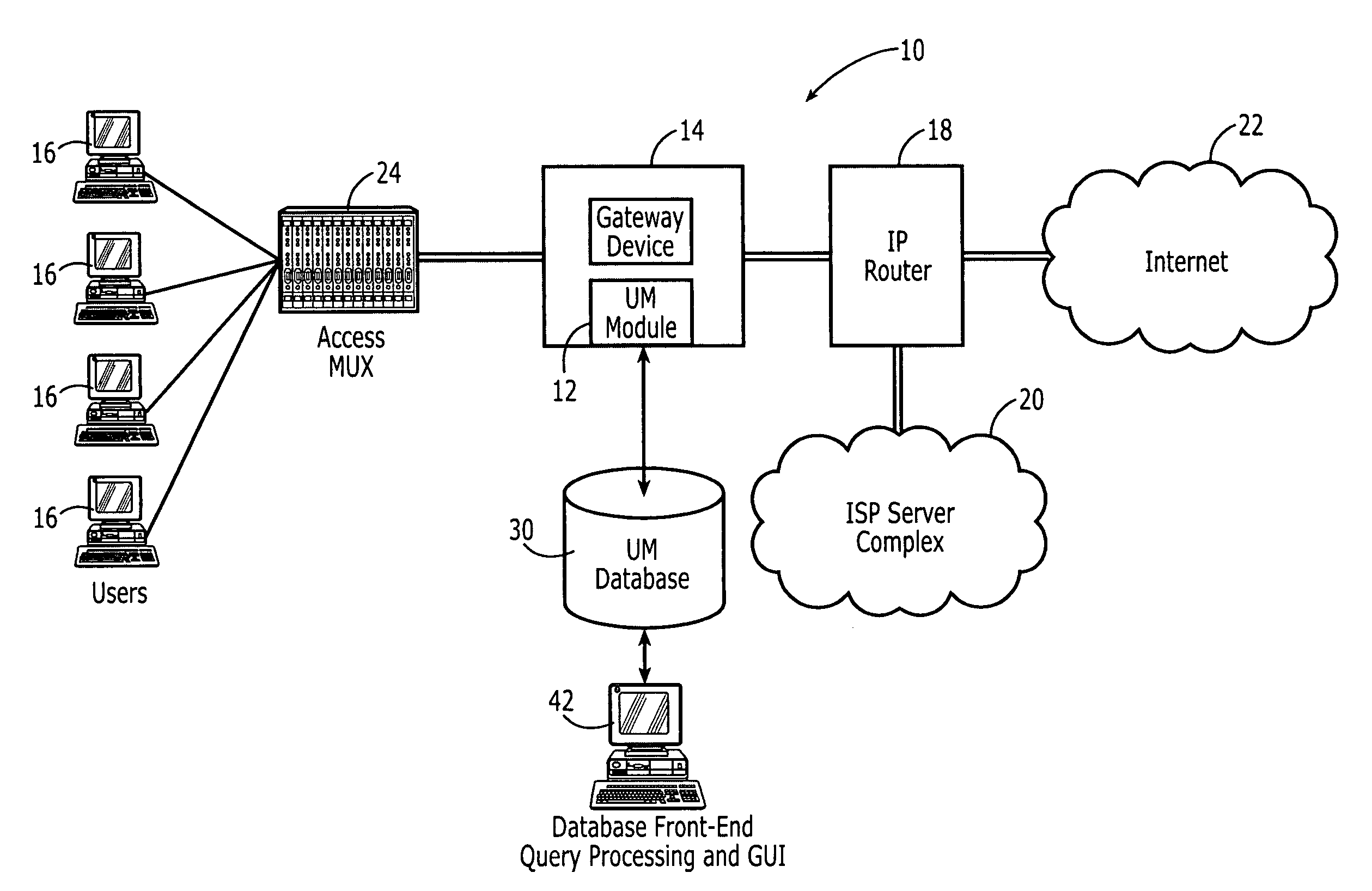
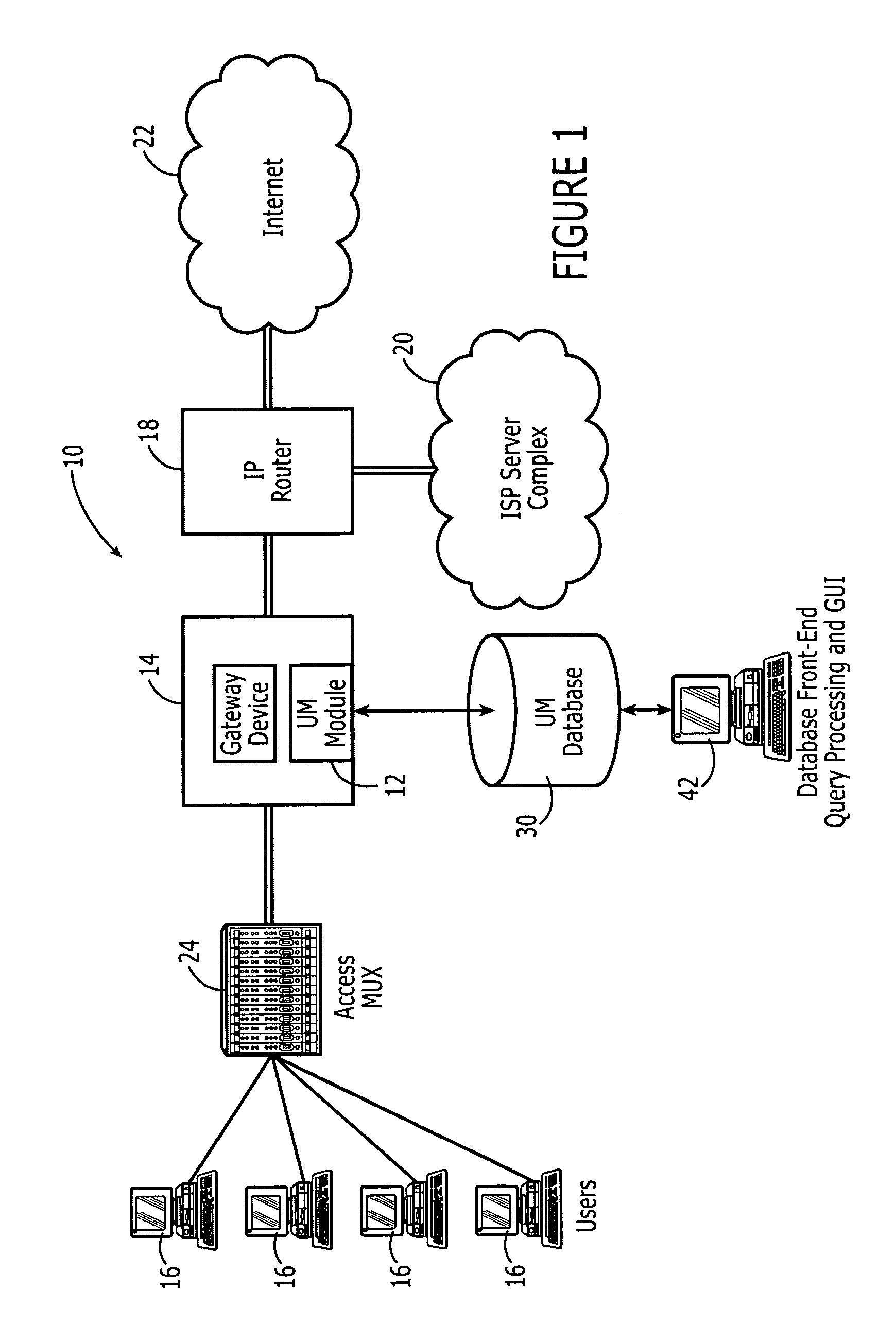
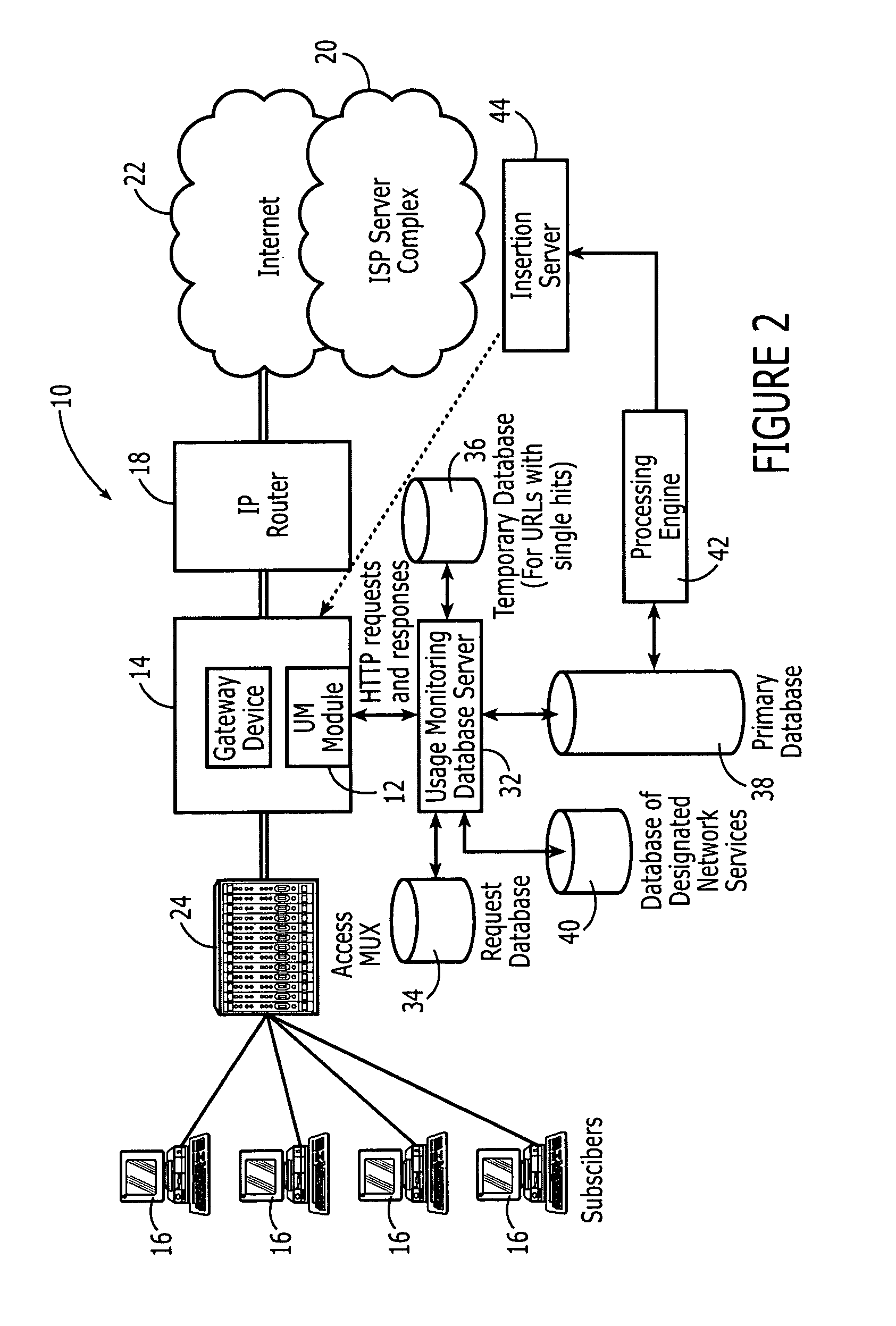
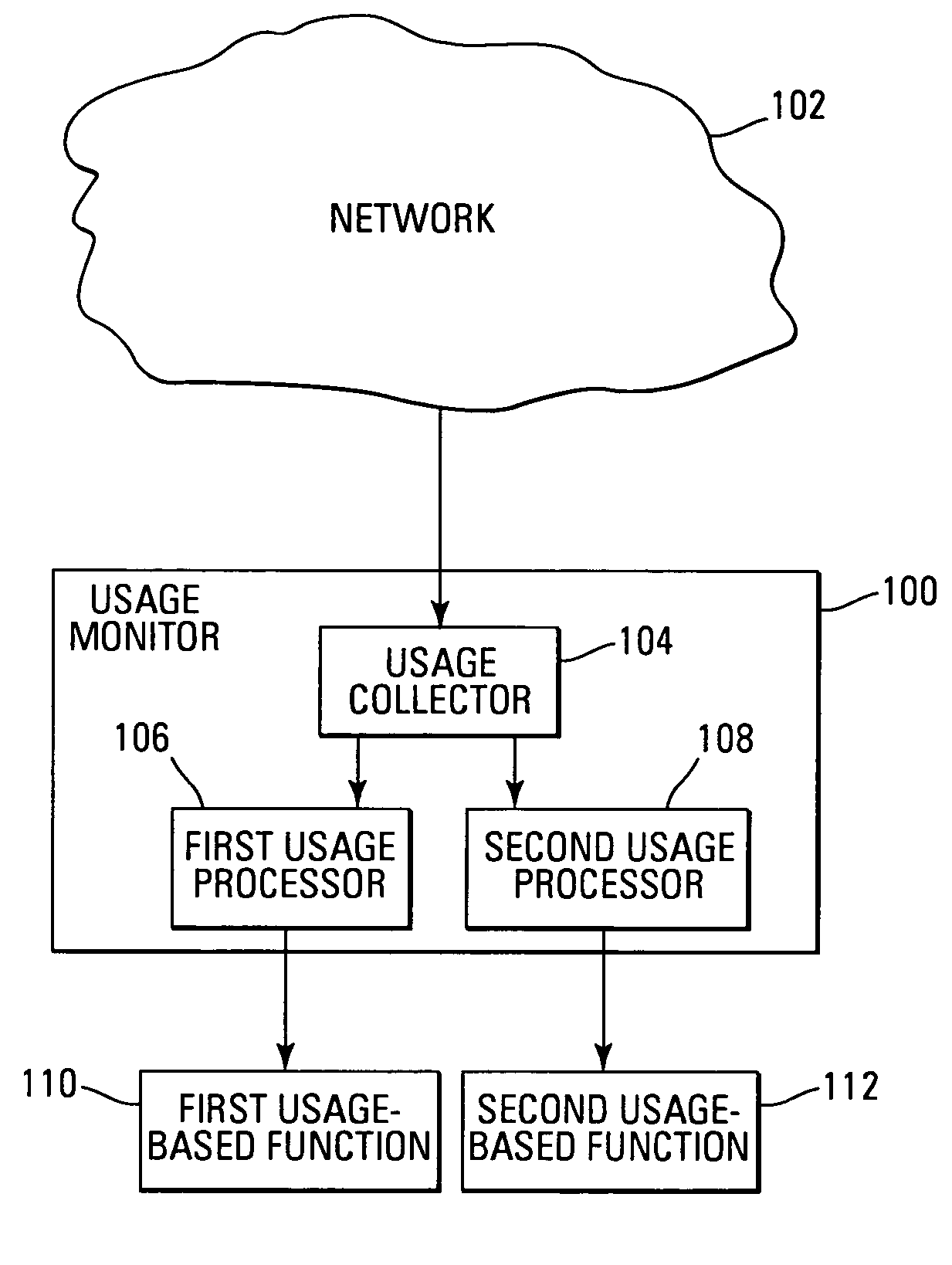
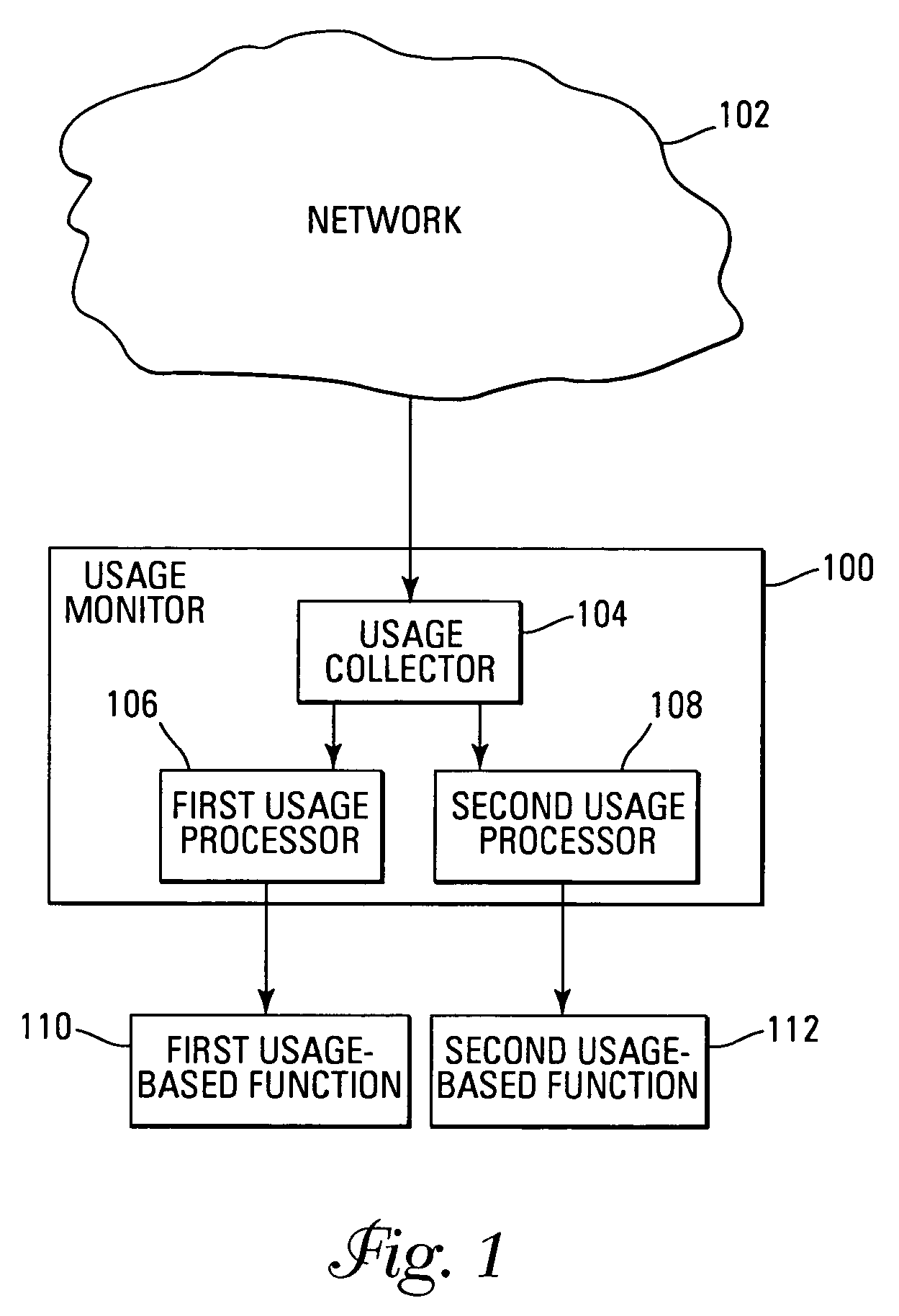
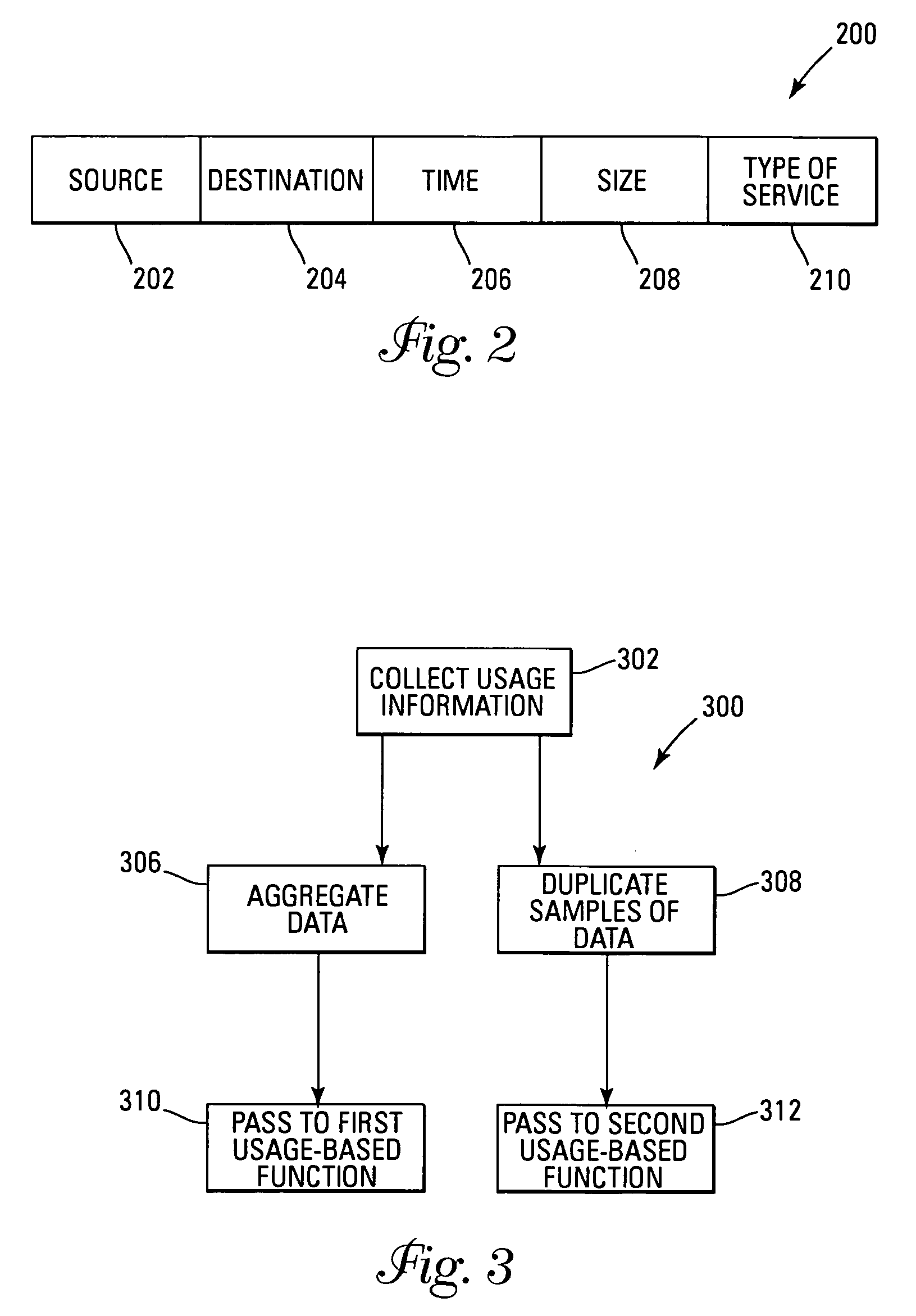
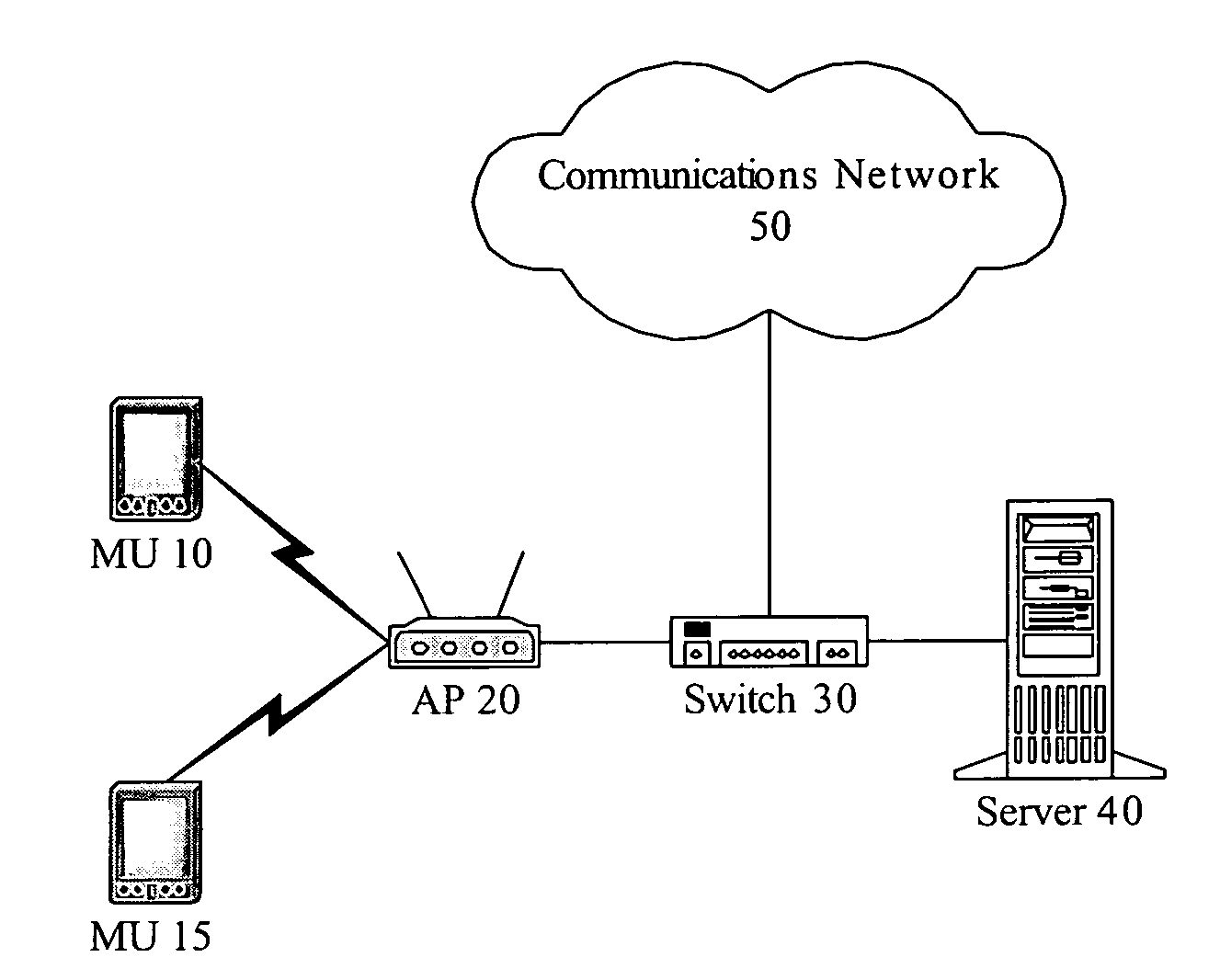
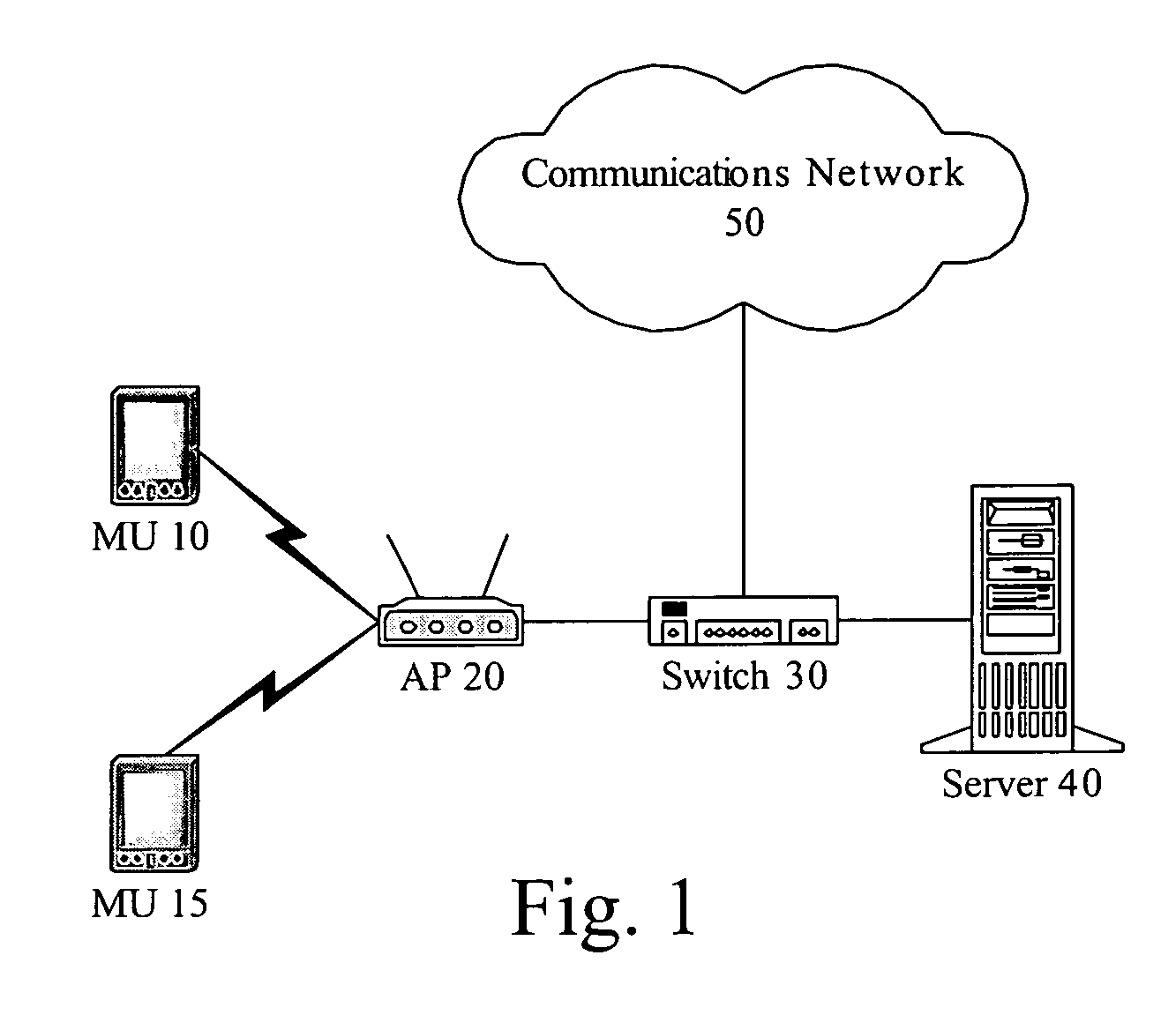
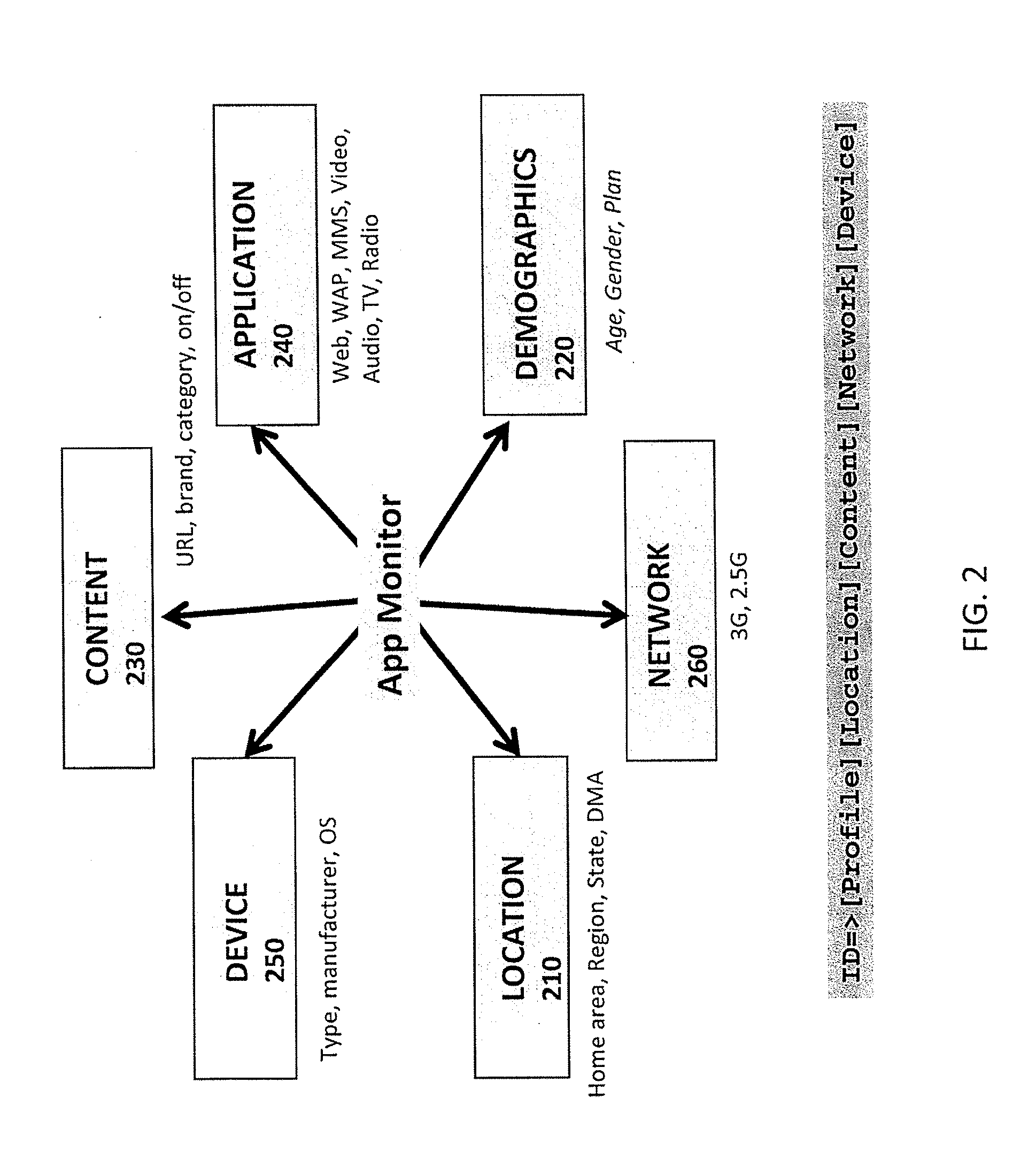
Network usage monitoring device and associated method
InactiveUS7020082B2Information can be usedIncrease valueError preventionFrequency-division multiplex detailsTraffic capacityNetwork interface device
A network usage monitoring module is provided for monitoring network usage at a network access point, i.e. network traffic aggregation point, typically at a gateway device or a similar network interface device. As such, the network usage monitoring module can monitor the usage of a number of network users who are attempting to access various network services provided via the gateway device. Thus, the usage information collected by the usage monitoring module is considerably more robust than that offered by conventional monitoring techniques. As such, the information is considerably more valuable to network service providers, network users, network beneficiaries and the like. In addition, the usage monitoring method and apparatus offers a number of particular features to improve the monitoring process as well as the value of the usage information that is collected.
Owner:NOMADIX INC
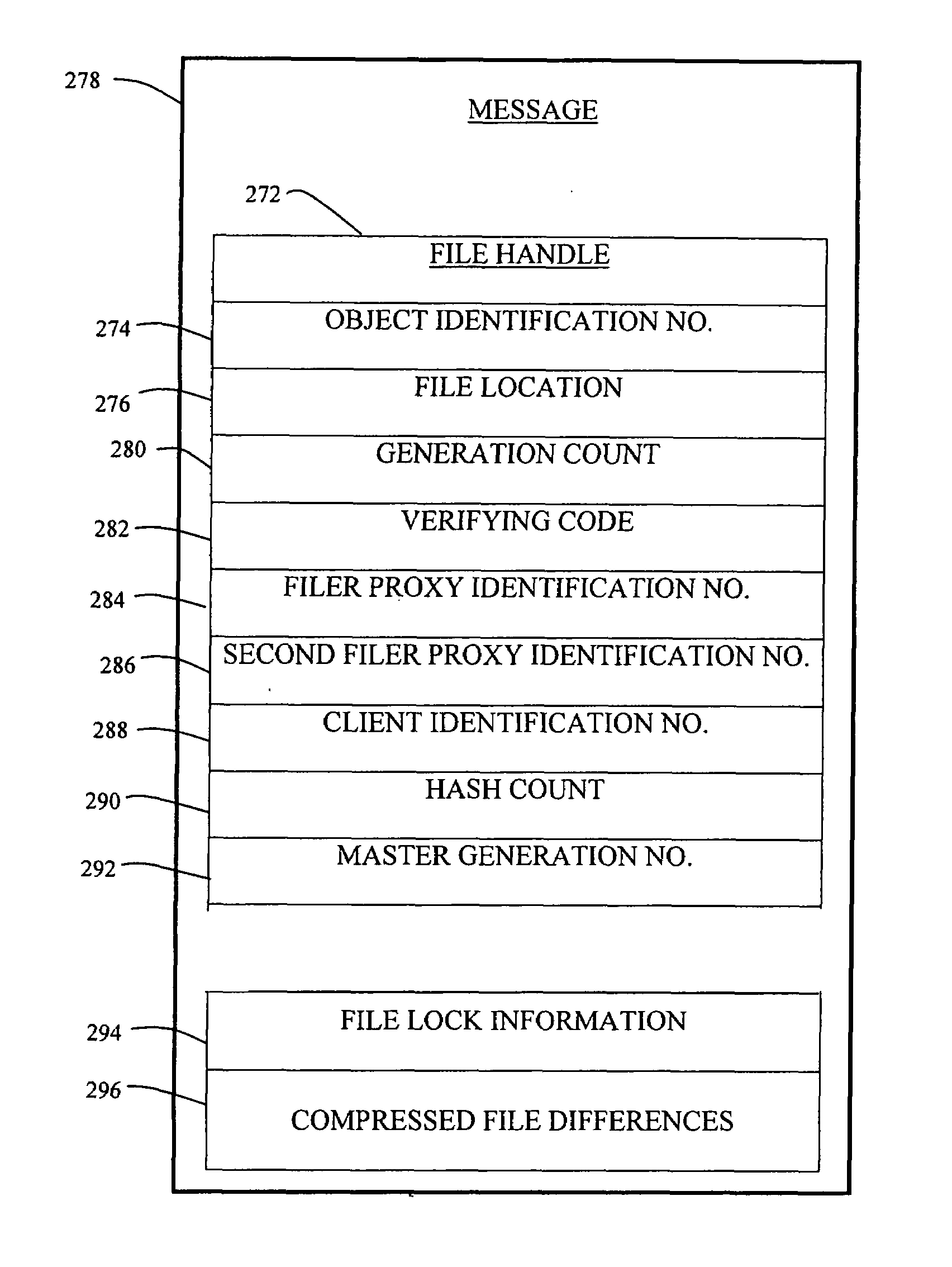
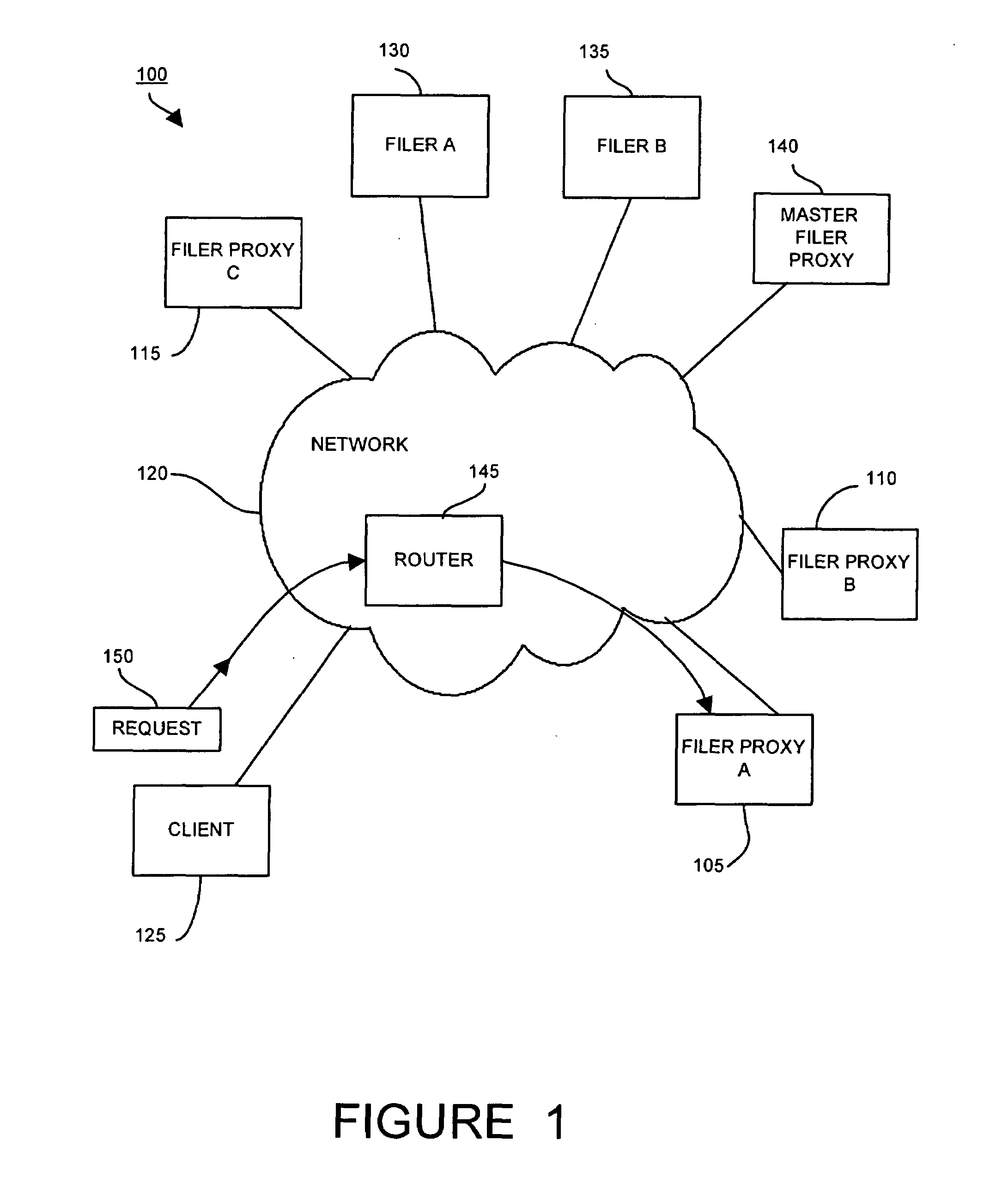
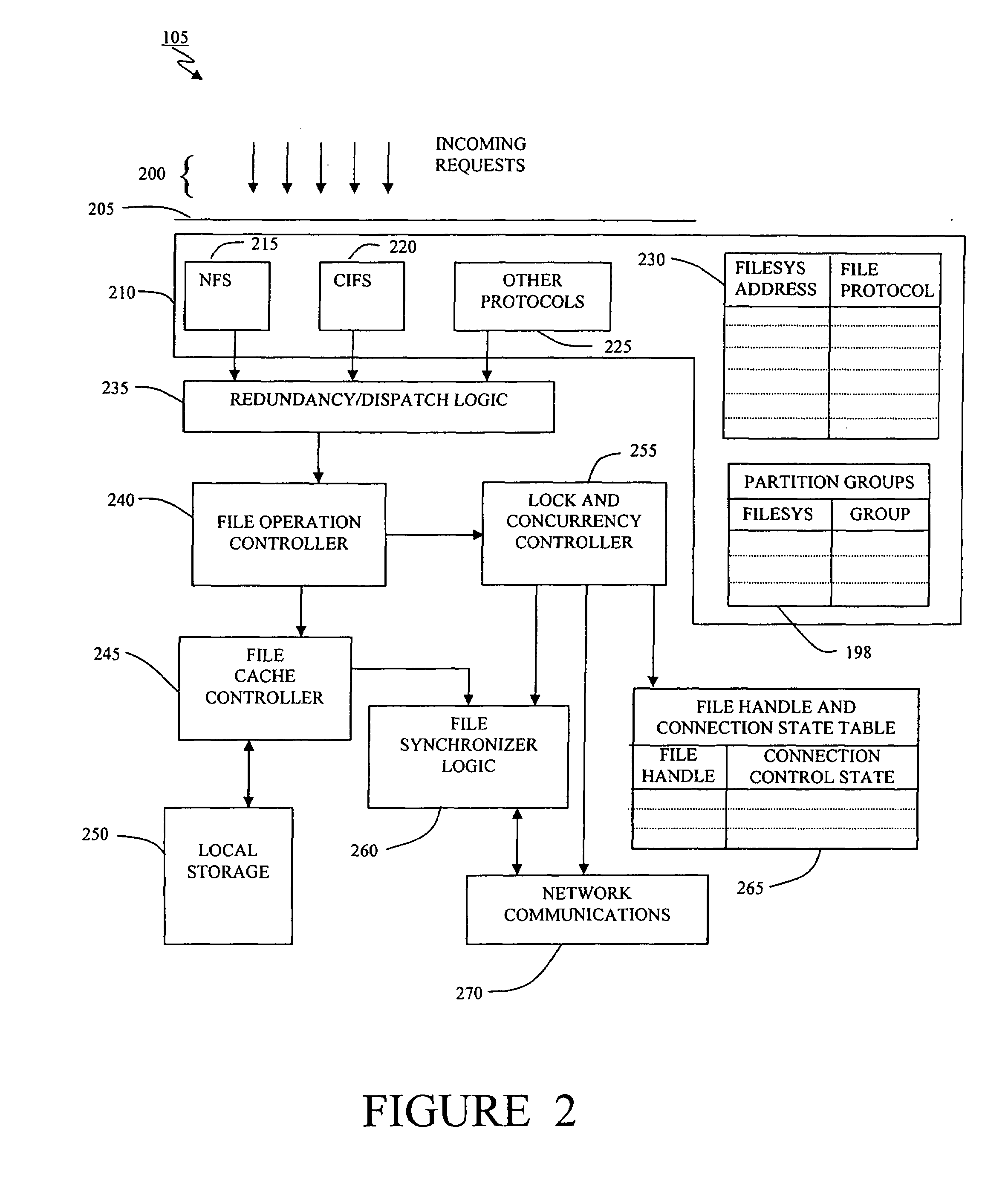
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
Fair use management method and system
InactiveUS20100103820A1Reduce in quantityMinimize the numberError preventionFrequency-division multiplex detailsService flowTelecommunications
A method of managing a plurality of subscribers using a communication network involving: obtaining network usage data for a plurality of service flows associated with the plurality of subscribers using the network; from the network usage data, determining which of the plurality of subscribers has been using an excess amount of bandwidth; determining that at least some part of the network is currently in a congested state; and in response to determining that at least some part of the network is currently in the congested state, sending a policy decision to a gateway device that controls bandwidth resources currently being provided to the identified subscriber, said policy decision instructing the gateway device to reduce network bandwidth that is currently being provided to support existing service flows for the identified subscriber.
Owner:CAMIANT INC
Self-managed network access using localized access management
ActiveUS7574731B2Provide usageAvoid modificationRandom number generatorsUser identity/authority verificationProgram planningBack end server
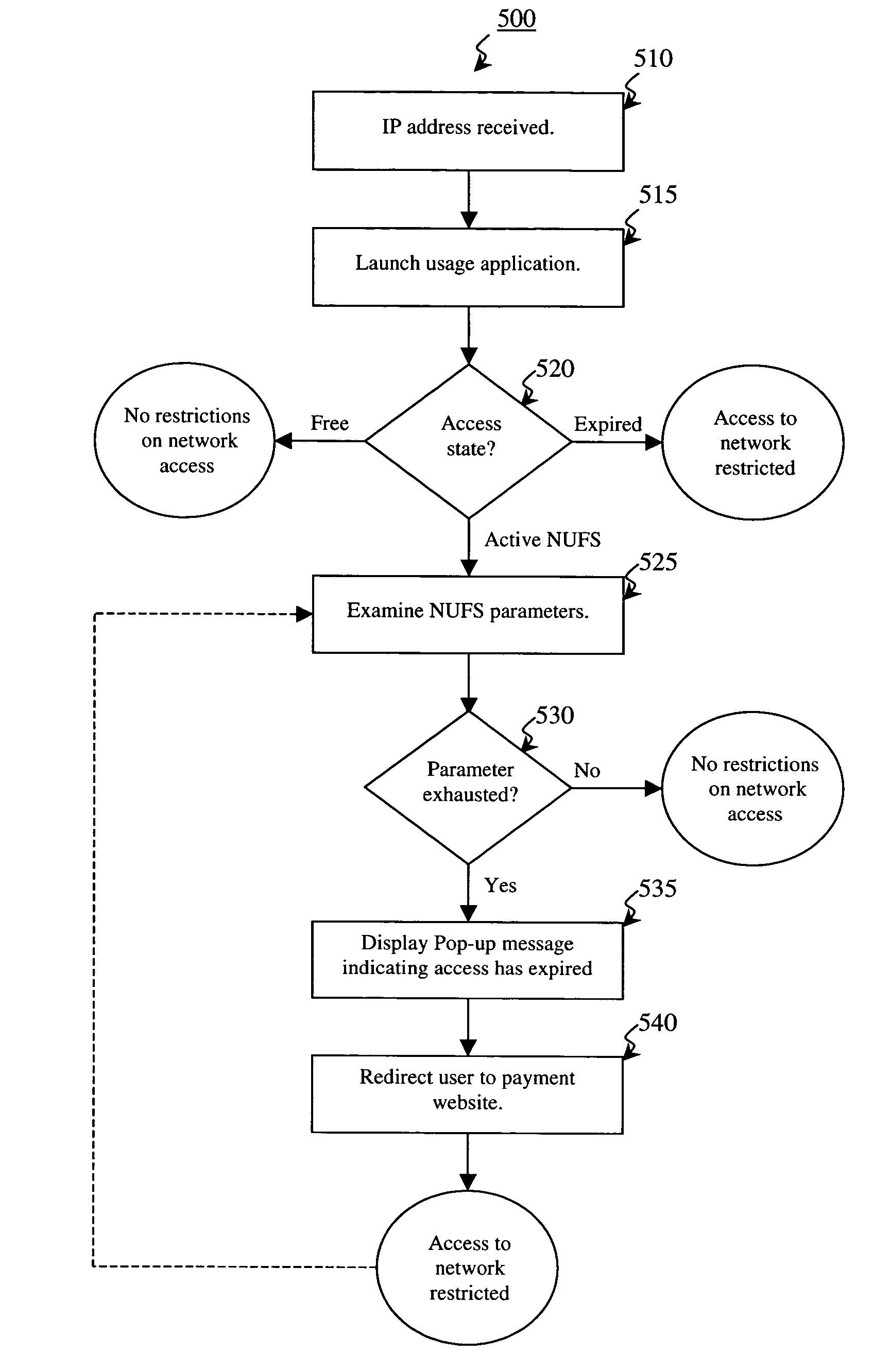
The invention provides a method and system for locally tracking network usage and enforcing usage plans at a client device. In an embodiment of the invention, a unique physical key, or token, is installed at a client device of one or more networks. The key comprises a usage application and one or more access parameters designated the conditions and / or limits of a particular network usage plan. Upon initial connection to the network, the usage application grants or denies access to the network based on an analysis of the current values of the access parameters. Therefore, network usage tracking and enforcement is made simple and automatic without requiring any back-end servers on the network while still providing ultimate flexibility in changing billing plans for any number of users at any time.
Owner:KOOLSPAN
Method and apparatus for accessing networks by a mobile device
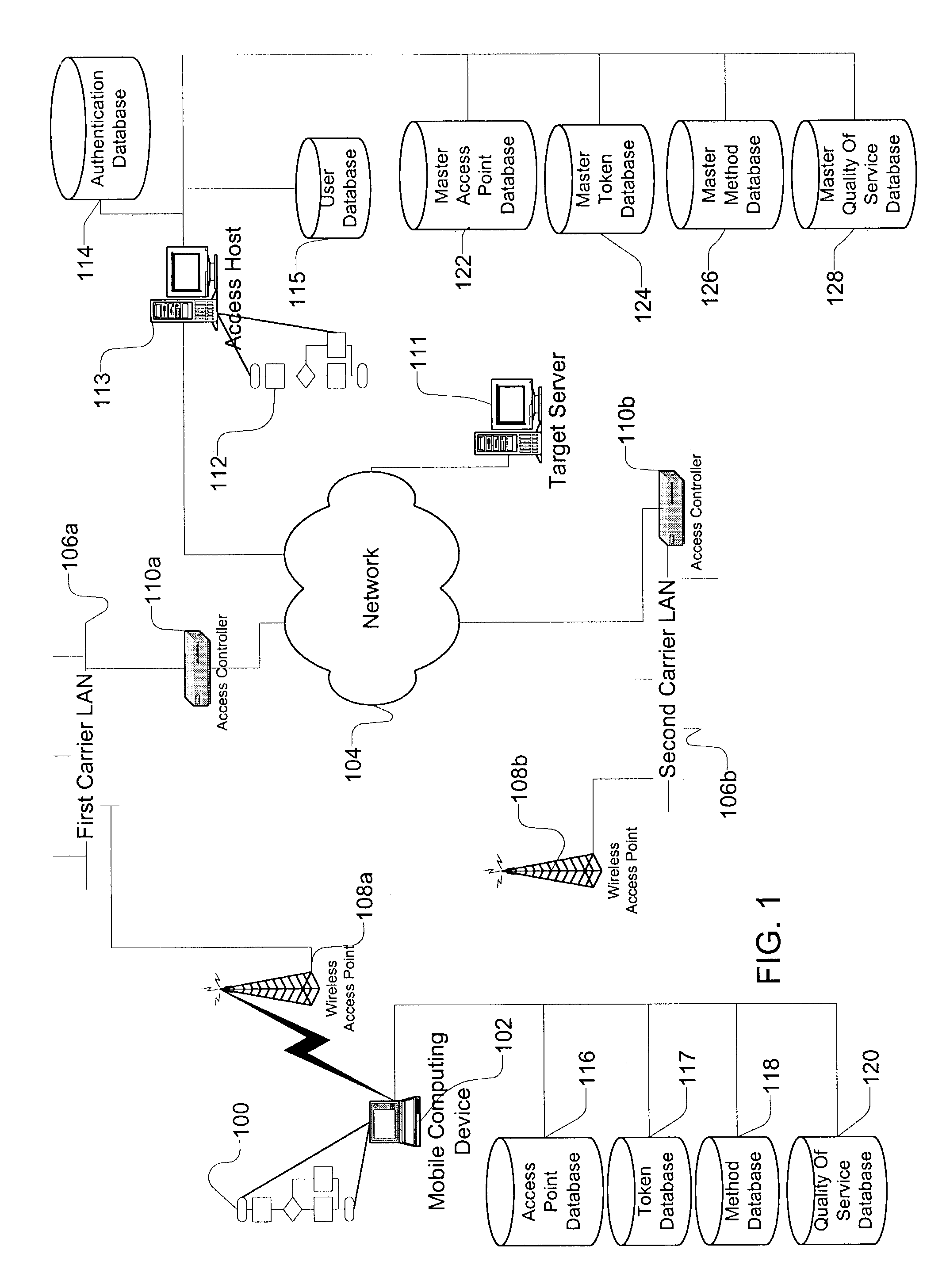
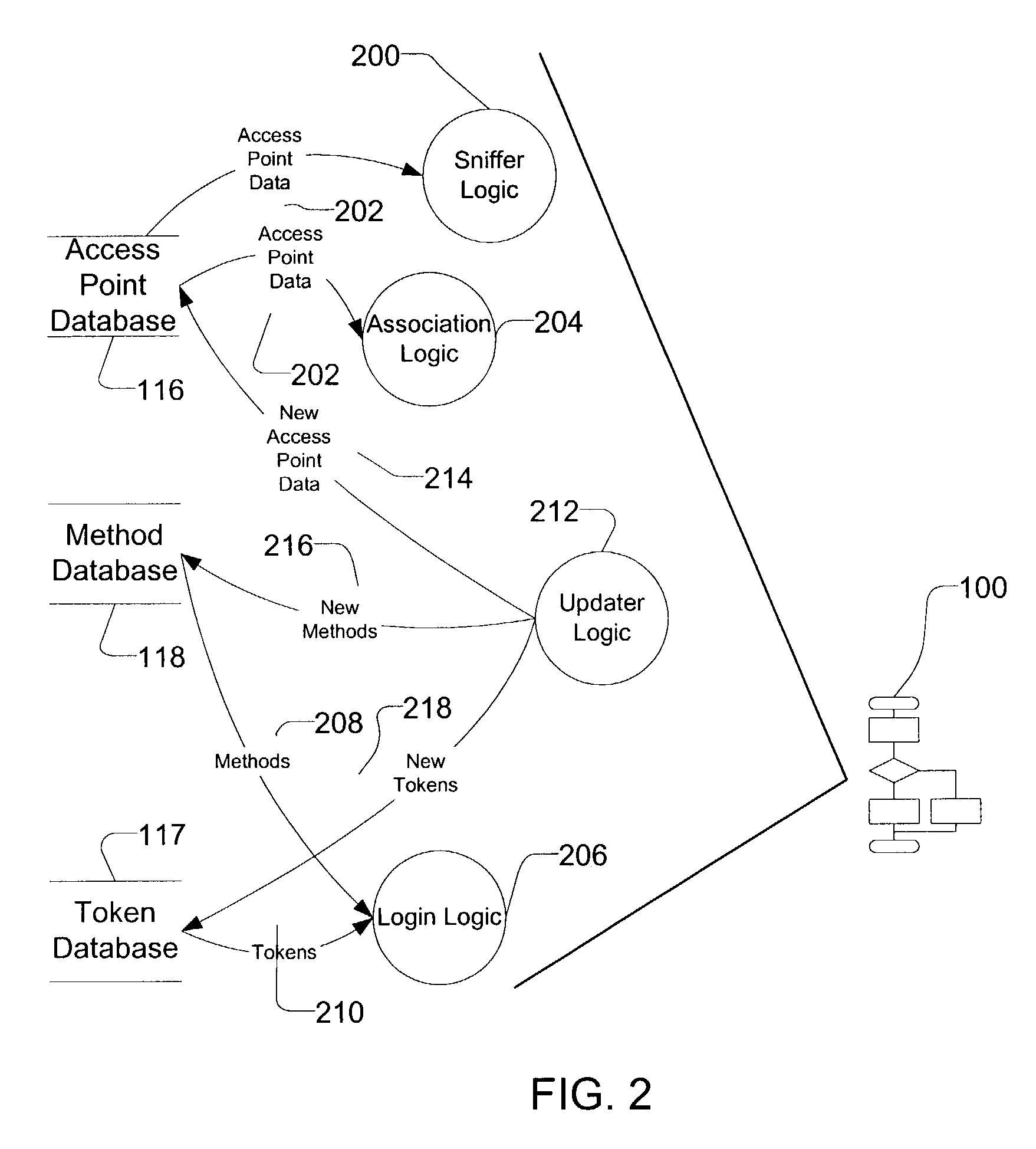
InactiveUS7483984B1Assess restrictionMultiple digital computer combinationsAccess networkNetwork generation
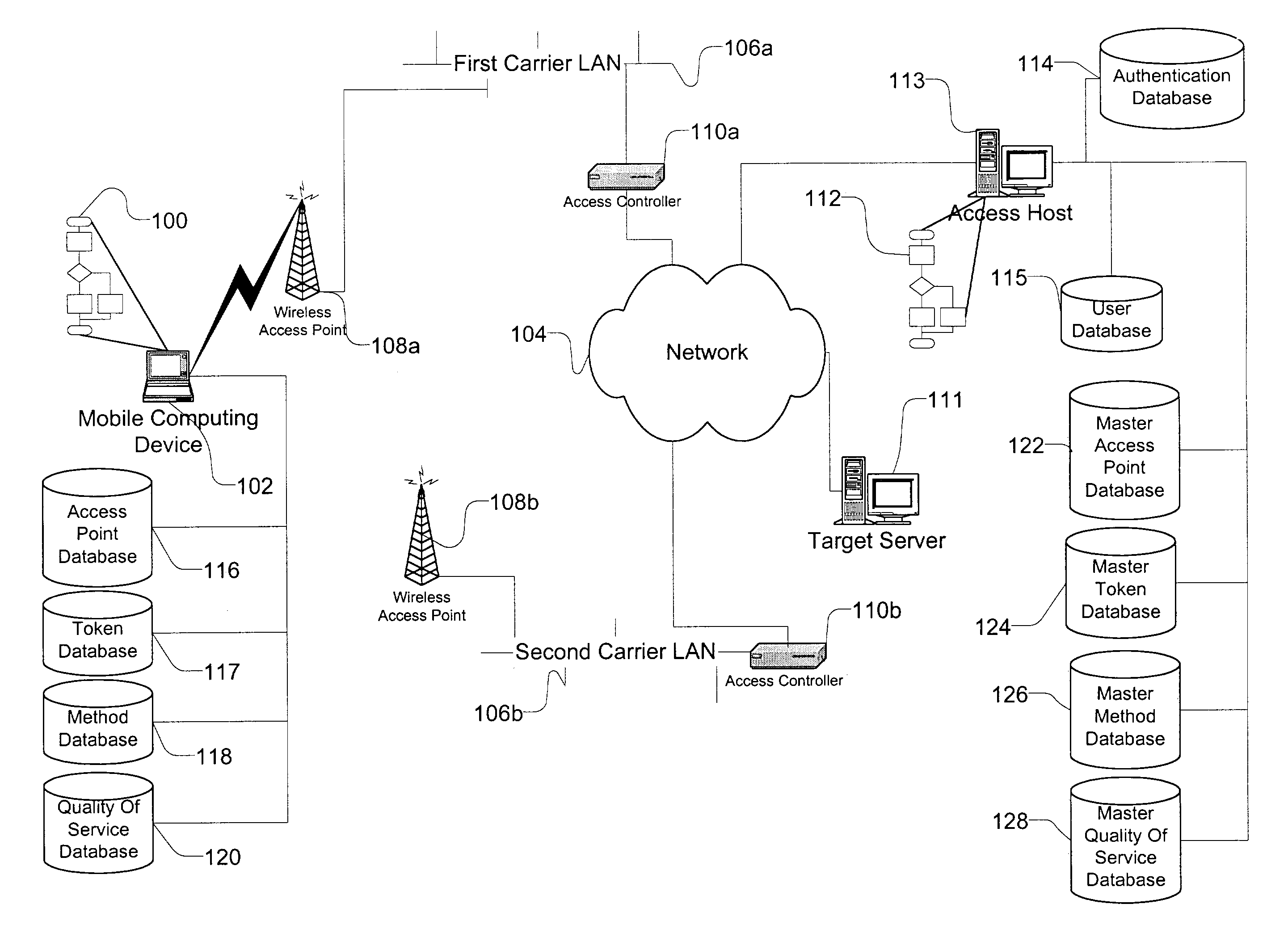
A method and apparatus for accessing wireless carrier networks by mobile computing devices. An access client hosted by a mobile computing device accesses carrier networks using wireless access points. The access client uses an access point database to identify access points and carrier networks. The access client uses a methods database and a tokens database to access the carrier networks. The access client updates the access point database, the methods database, and the token database using an access server when the access client is operably coupled to a carrier network. The access client transmits user information to the carrier network. The carrier network uses the user information to authenticate the user and to generate session data while the user is accessing the carrier network. The carrier network transmits the session data to the access server. The access server uses the session data to generate billing information for the user. The access client also collects network performance data for individual access points and carrier networks. The access client transmits the network performance data to the access server. The access server aggregates network performance data from a plurality of access clients to generate quality of server reports for both individual access points and carrier networks. The access client further includes access point detection and evaluation features for use by a user in selecting access points available at a single location.
Owner:BOINGO WIRELESS
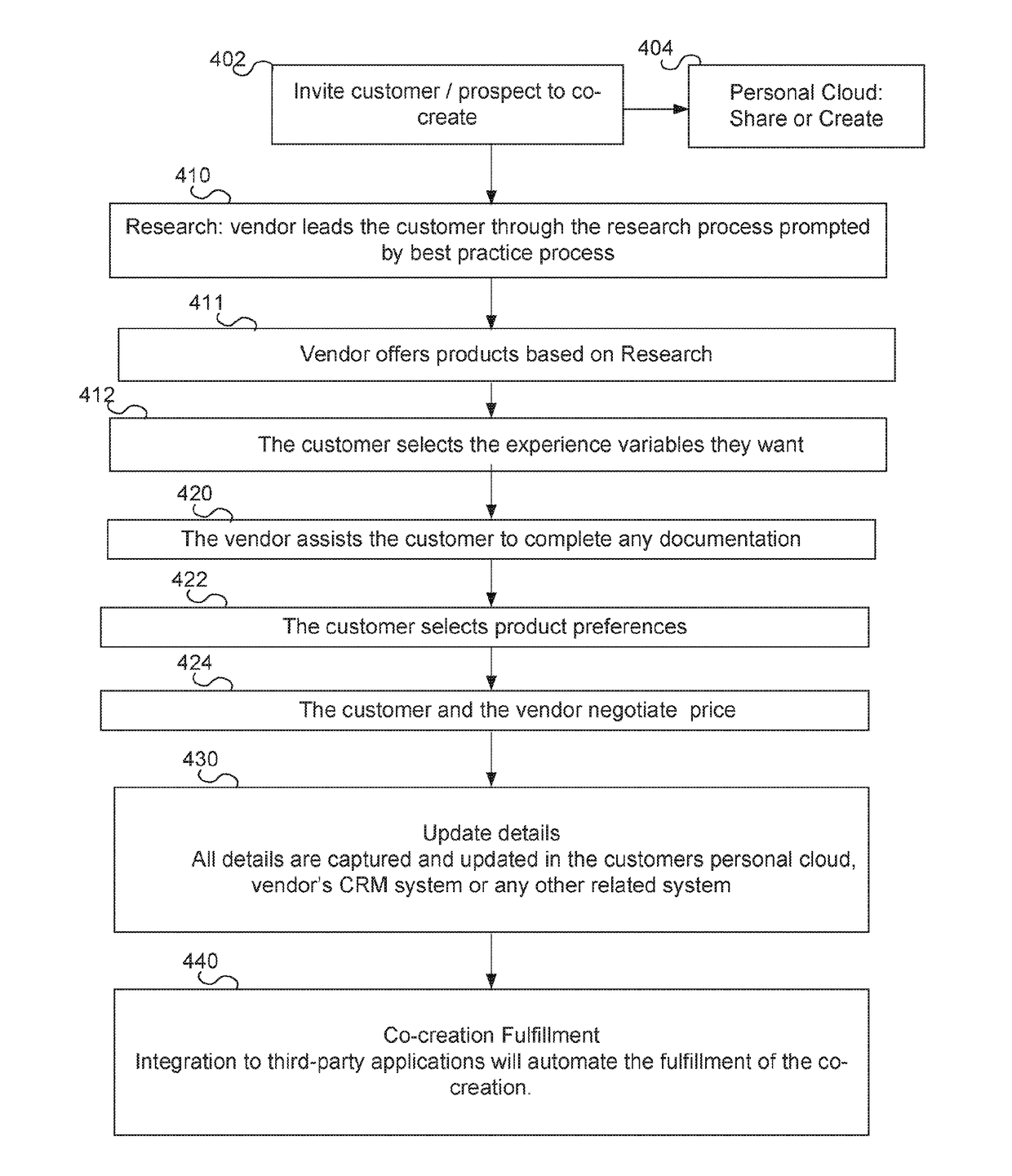
Customer experience personalisation management platform
InactiveUS20170278117A1Easy to understandMarket predictionsAdvertisementsPersonalizationHuman–computer interaction
Methods and systems for allowing multiple parties to coordinate, including a computer server in communication with a network and a database, the computer server configured to run the platform and allow a vendor user to, and invite a customer user to use the platform via the network. Also, research the customer user by sending questions to the customer user and receive responses to the questions from the customer user, wherein the questions include stored platform questions, and prompt the customer user to upload personal information from a personal networked storage. In addition, send the customer user a product preferences template, receive answers to the product preferences template from the customer user via the network, and offer products to the customer user based on the received responses.
Owner:FLAMINGO VENTURES
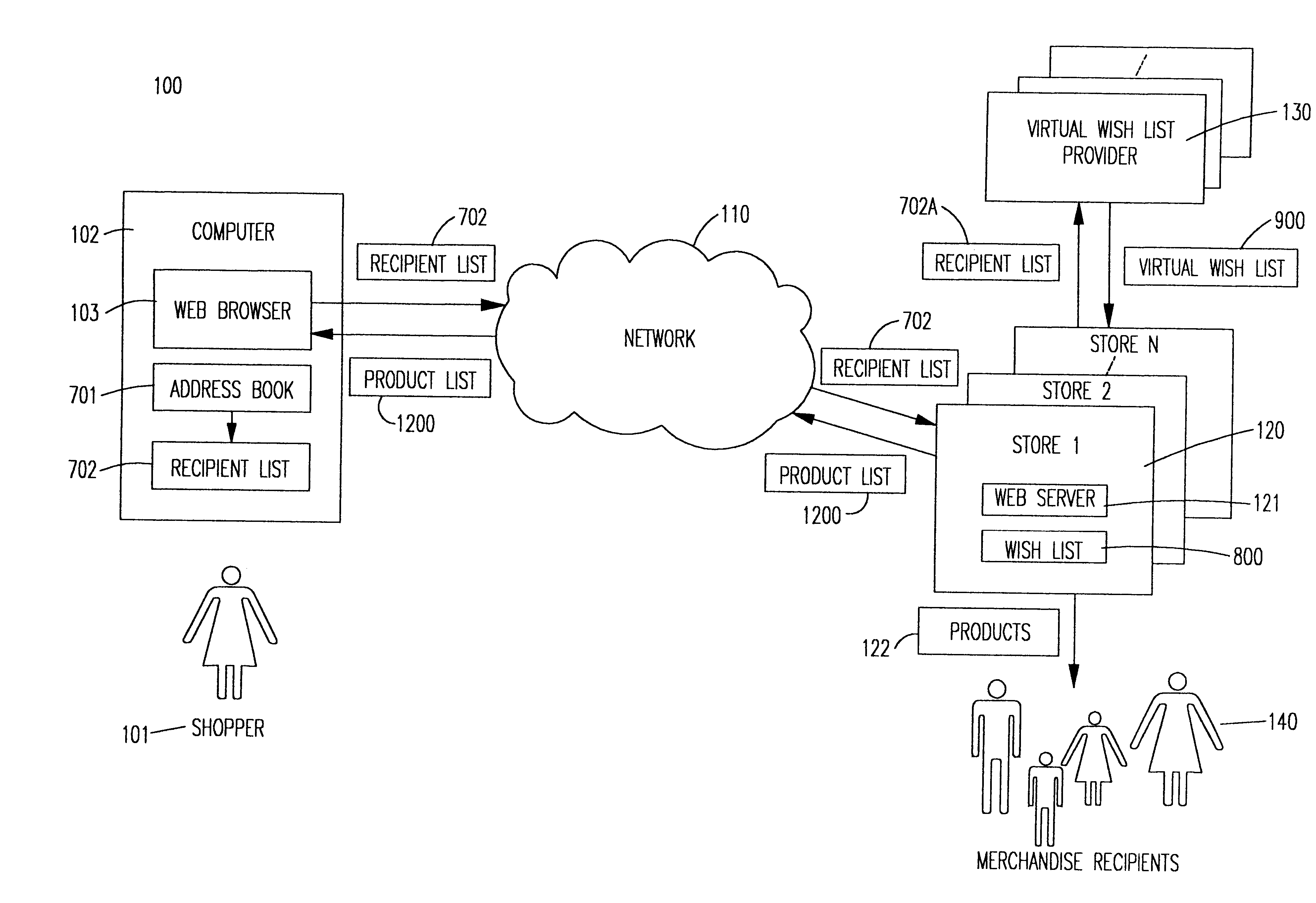
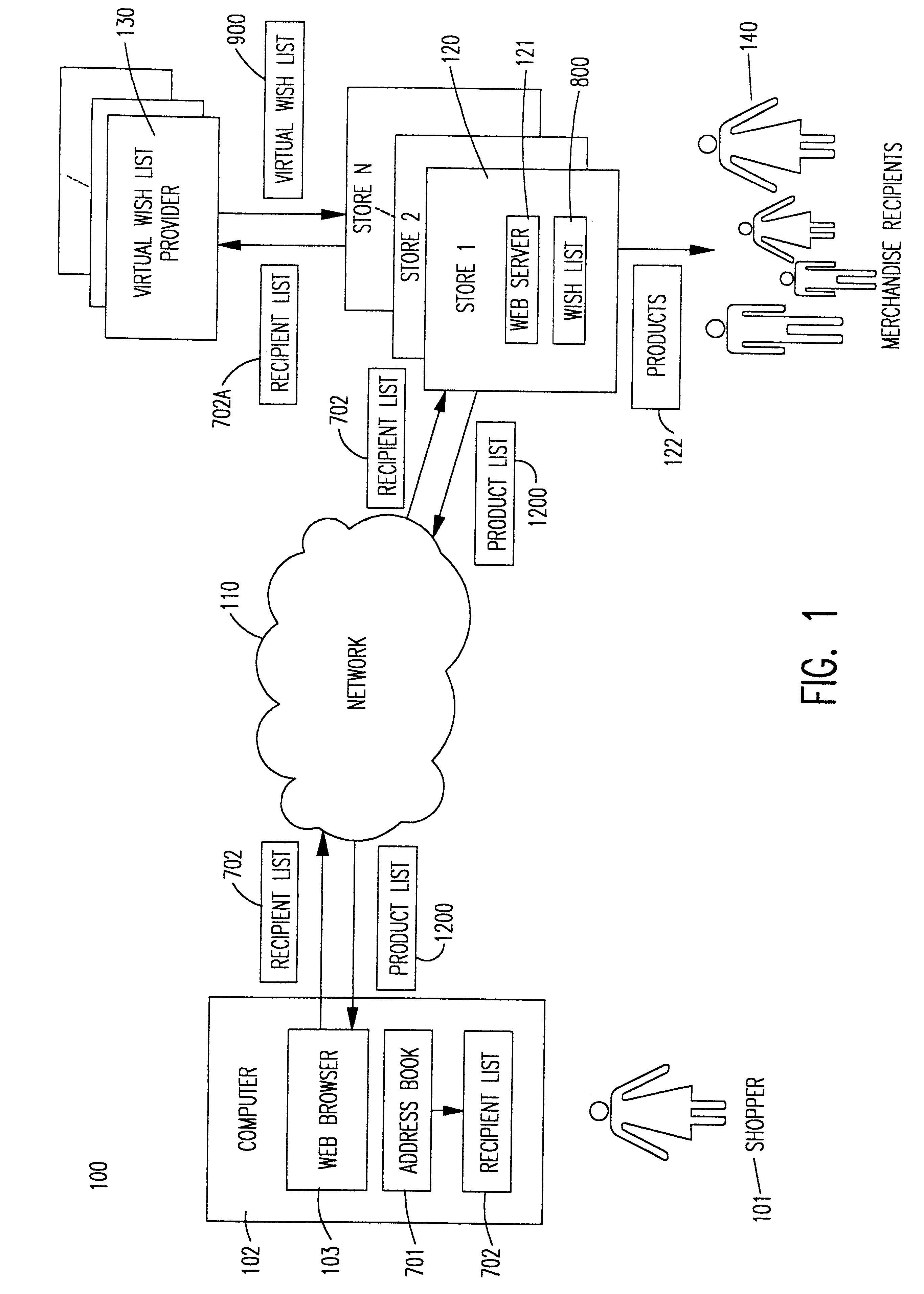
System and method for using virtual wish lists for assisting shopping over computer networks
InactiveUS6611814B1Convenient shoppingBuying/selling/leasing transactionsSpecial data processing applicationsWeb siteAddress book
A computer system and method uses one or more virtual wish lists of one or more shoppers over a computer network. One process extracts information from online address books or other personal databases, and creates lists of recipients for whom a shopper wants to purchase products. A second process obtains virtual wish lists of recipients by observing their visits to online stores, and other online behavior. Recipients are asked for permission to make this data available to other shoppers, online stores, and other Web sites. Recipients can modify their virtual wish lists, and selectively approve of their use by other shoppers, etc. A third process creates shopping lists for the recipients, and generates lists of recommended products for shoppers to buy for intended recipients.
Owner:PAYPAL INC +1
Method and apparatus for dynamically calculating the capacity of a packet network
InactiveUS20060291477A1Interconnection arrangementsData switching by path configurationUsage dataDistributed computing
A method and apparatus for calculating the engineered capacity of a packet network is described. In one example, subscriber usage data is collected from the packet network. The engineered capacity is then updated using the usage data on a periodic basis. In another example, the engineered capacity is subsequently compared with the actual network usage. Afterwards, an alarm is triggered if the actual network usage reaches a predefined threshold of the engineered capacity.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
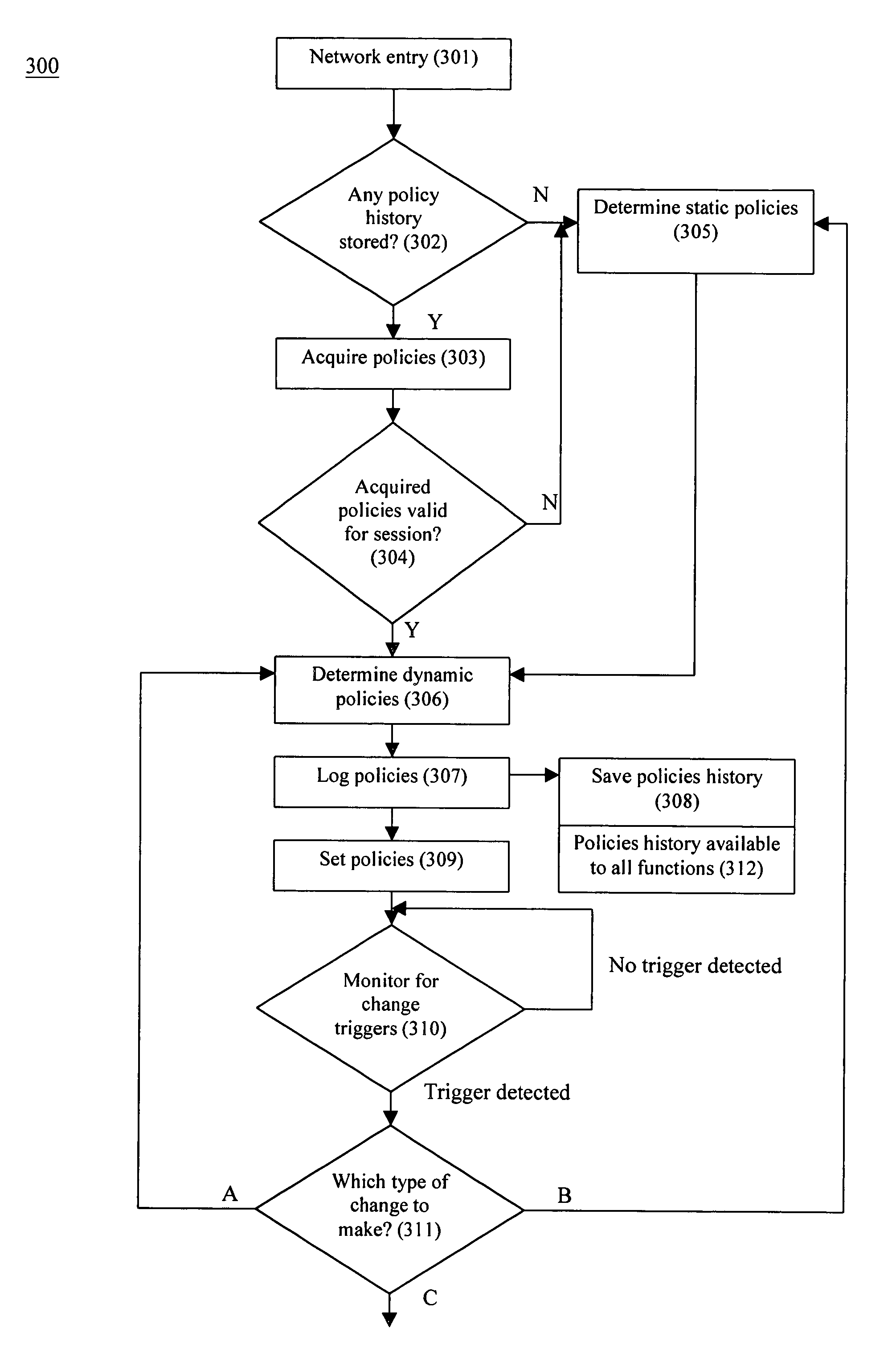
System and method for dynamic network policy management
InactiveUS7526541B2Improve accuracyImprove allocationDigital data protectionMultiple digital computer combinationsNetwork serviceNetwork administrator
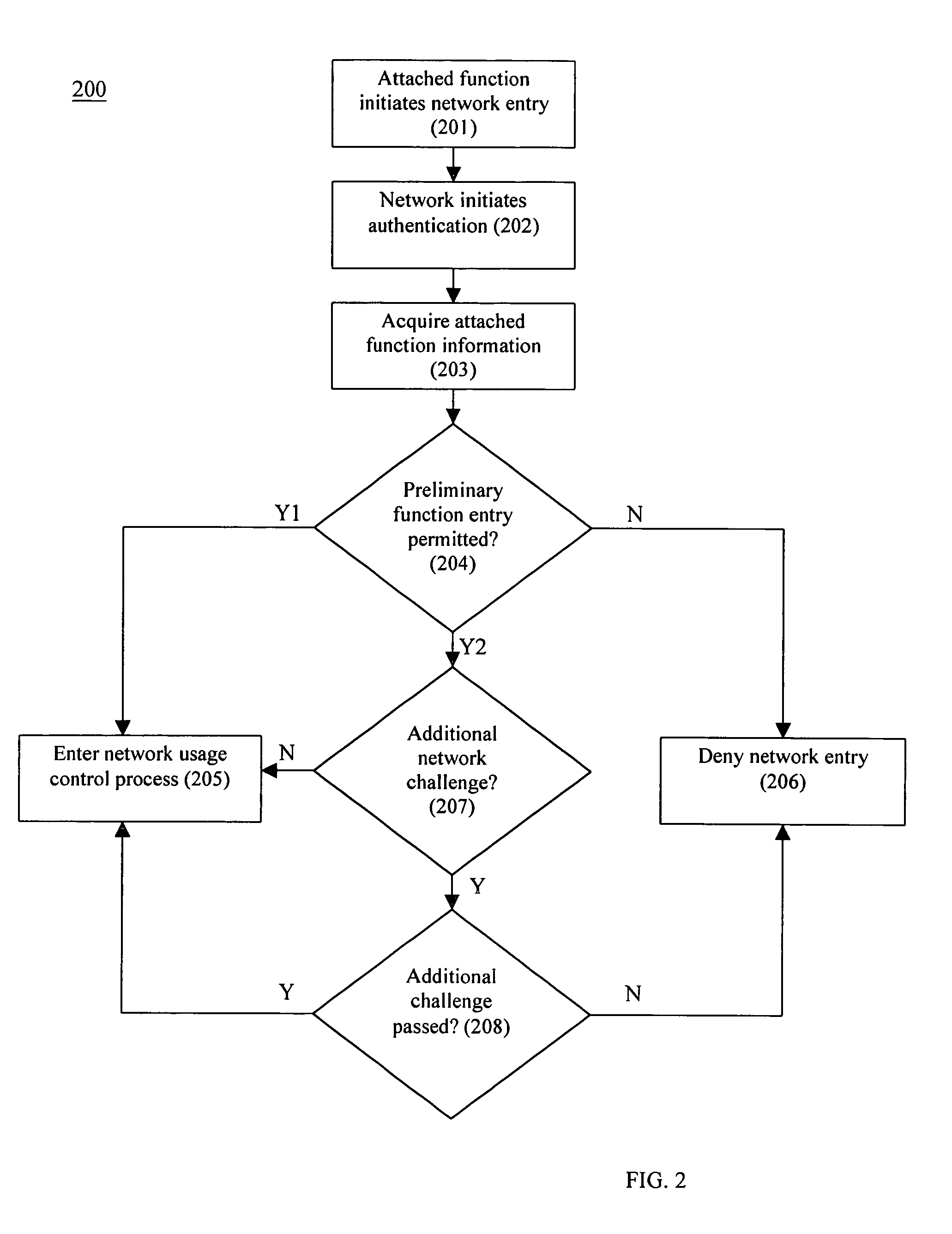
A system and method that provides dynamic network policy management. The system enables a network administrator to regulate usage of network services upon initiation of and throughout network sessions. The system employs a method of identifying selectable characteristics of attached functions to establish static and dynamic policies, which policies may be amended before, during and after any session throughout the network based on the monitored detection of any of a number of specified triggering events or activities. Particular policies associated with a particular identified attached function in prior sessions may be cached or saved and employed in subsequent sessions to provide network usage permissions more rapidly in such subsequent sessions. The cached or saved policy information may also be used to identify network usage, control, and security. The system and method of the present invention provides static and dynamic policy allocation for network usage provisioning.
Owner:EXTREME NETWORKS INC
Wireless telecommunications system and method of operation providing users' carrier selection in overlapping hetergenous networks
InactiveUS6591103B1Improve securityAssess restrictionNetwork topologiesProcessor registerCarrier signal
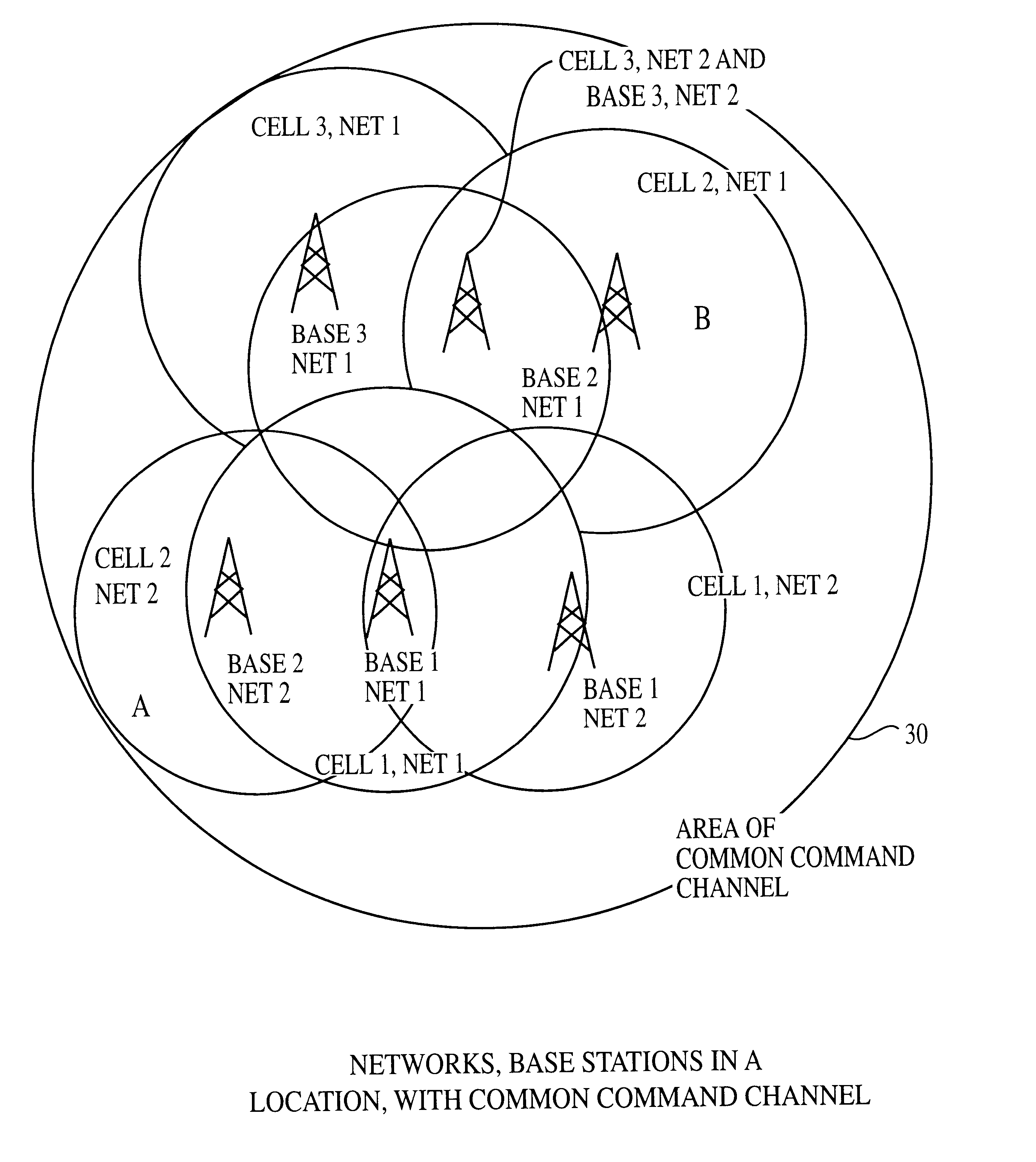
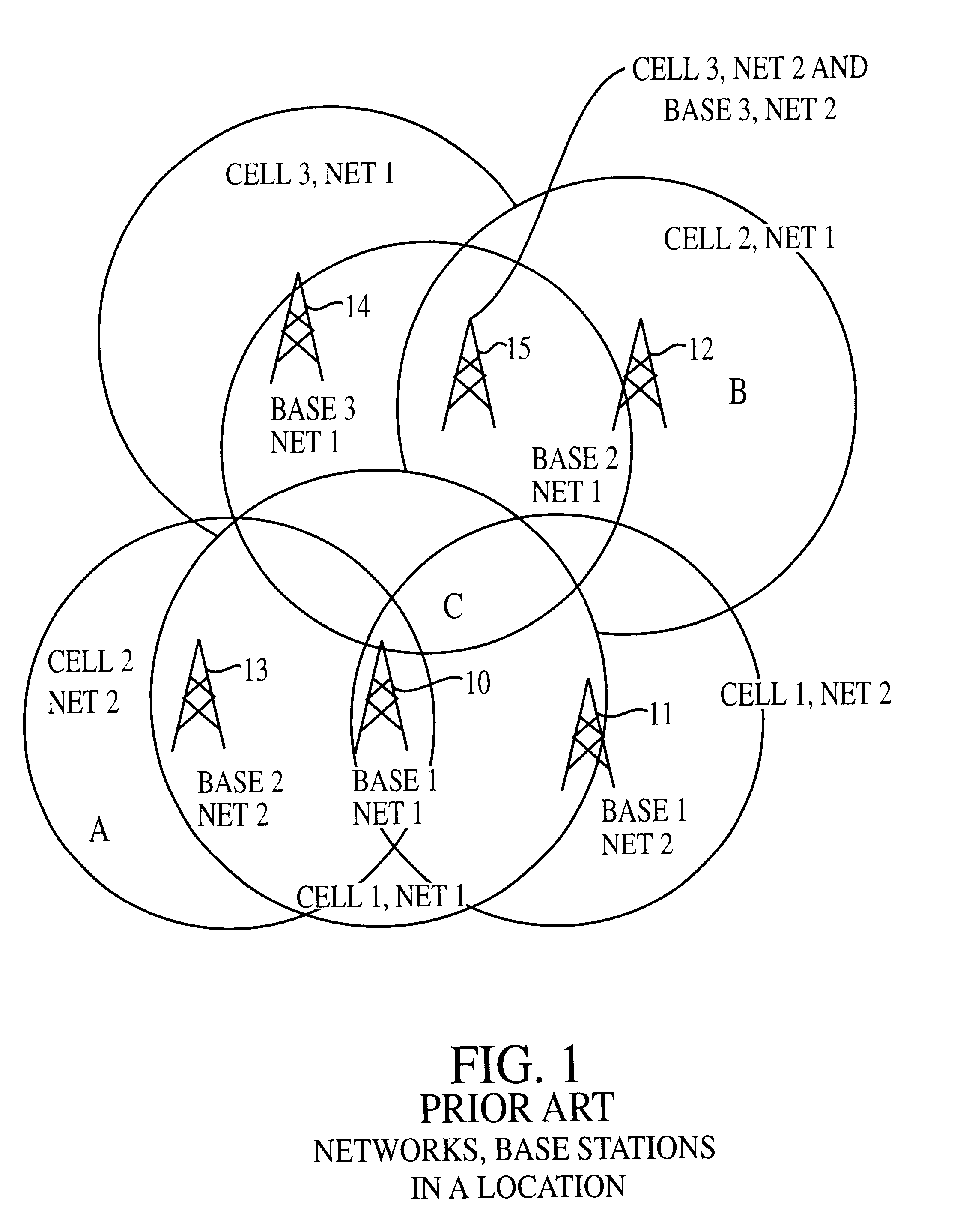
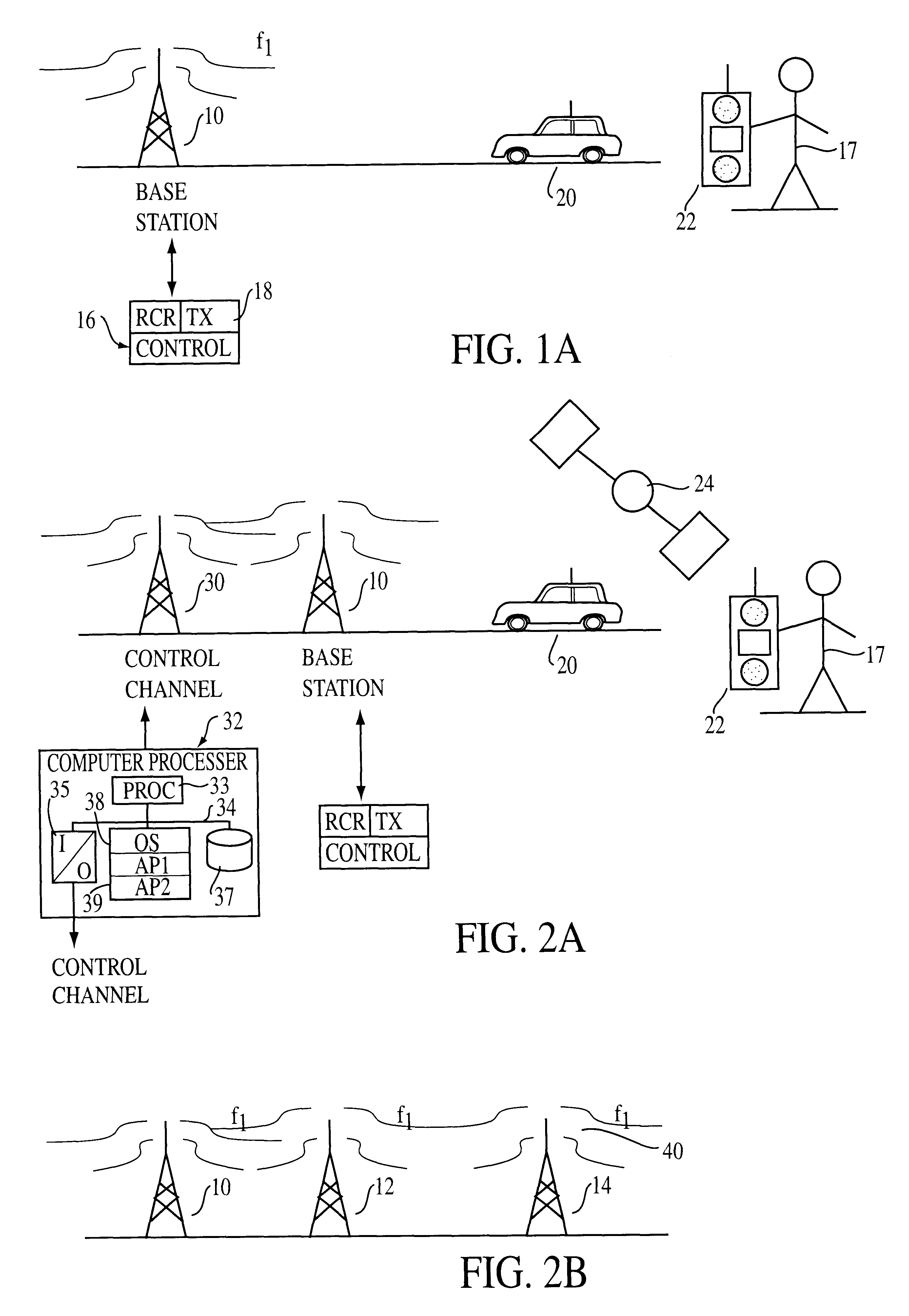
An improved wireless telecommunication system enables a user to obtain communication services in overlapping wireless heterogeneous or homogeneous cellular networks at the most economical cost and bandwidth. A plurality of overlapping cellular networks includes a common command channel, a Central Selection Agency (CSA), a home location register, a visitor location register, and a user device positional location mechanism. In one embodiment the user device is equipped with a Global Positioning System (GPS) to determine its location. In placing a call, the user device broadcasts its ID, location and connection capability requirements on the common command channel. When a base station for the command channel bears the request, the CSA and the home location register for the user are informed. The CSA capability / requirements determine which network and base station selections are potential carriers for the call. Based on user preferences established by a profile stored in an accessible database, the CSA assigns a network and base station to handle the connection. The user device is informed and tunes to the appropriate network and protocols. For incoming calls, the calling party checks the home location register to determine the last known location. The user device is informed that a called is waiting. The user device selects the network and base station to receive the call in a fashion similar to that of placing the call. A call may be transferred from one network to a different network, the networks using different protocol. The user device may be programmed to change networks at random times to provide enhanced security for a call.
Owner:IBM CORP
Processing of usage data for first and second types of usage-based functions
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
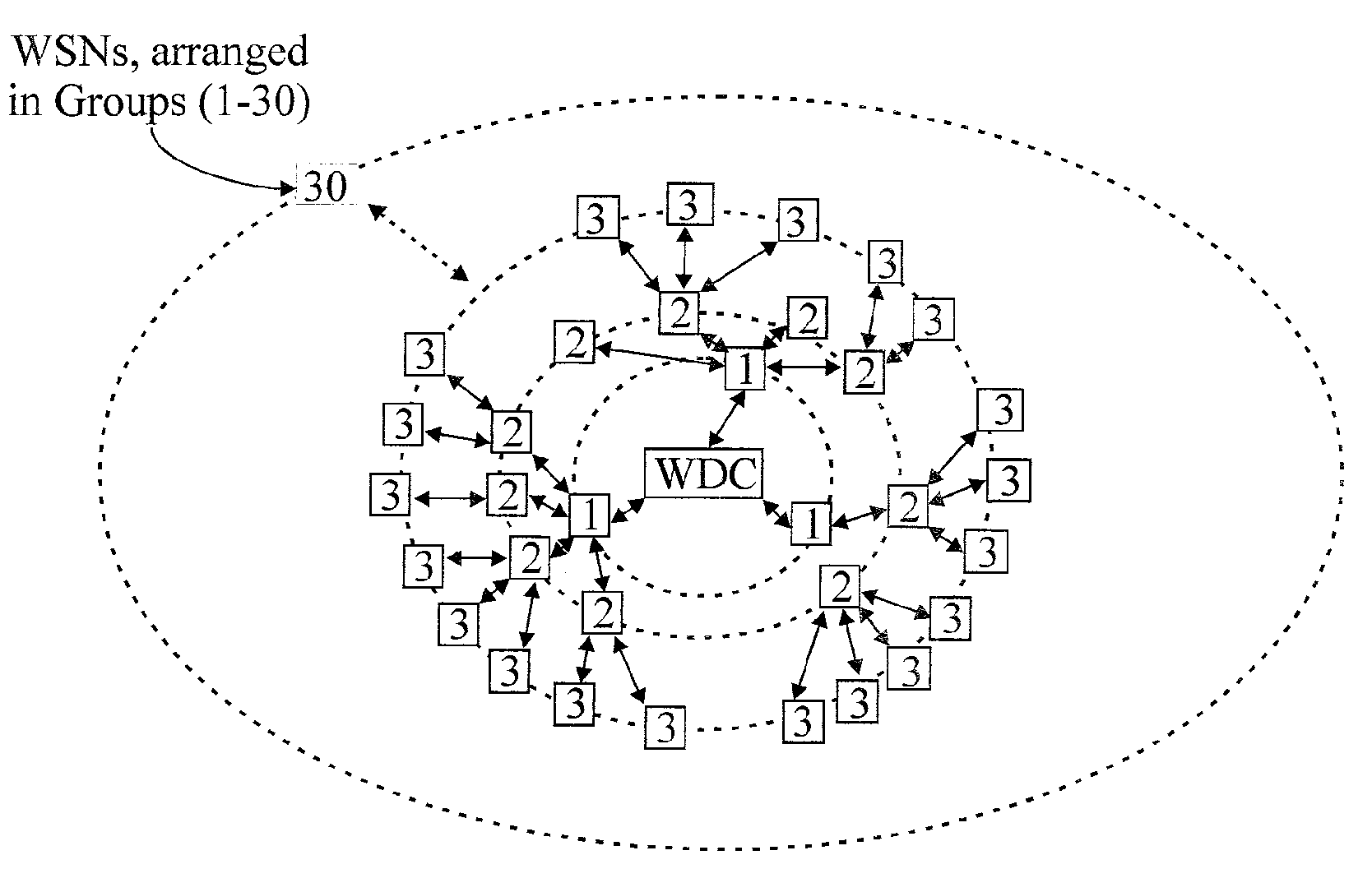
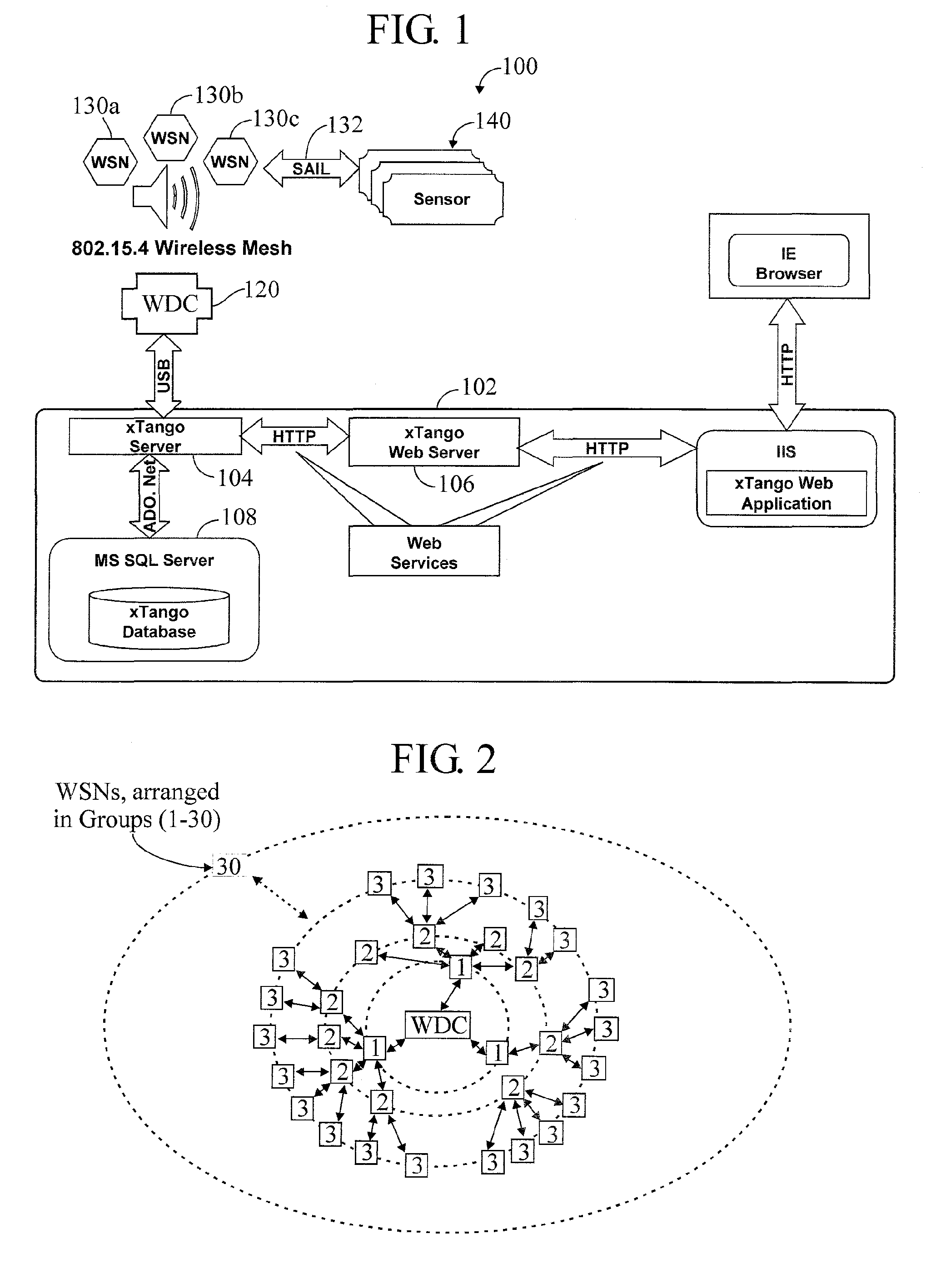
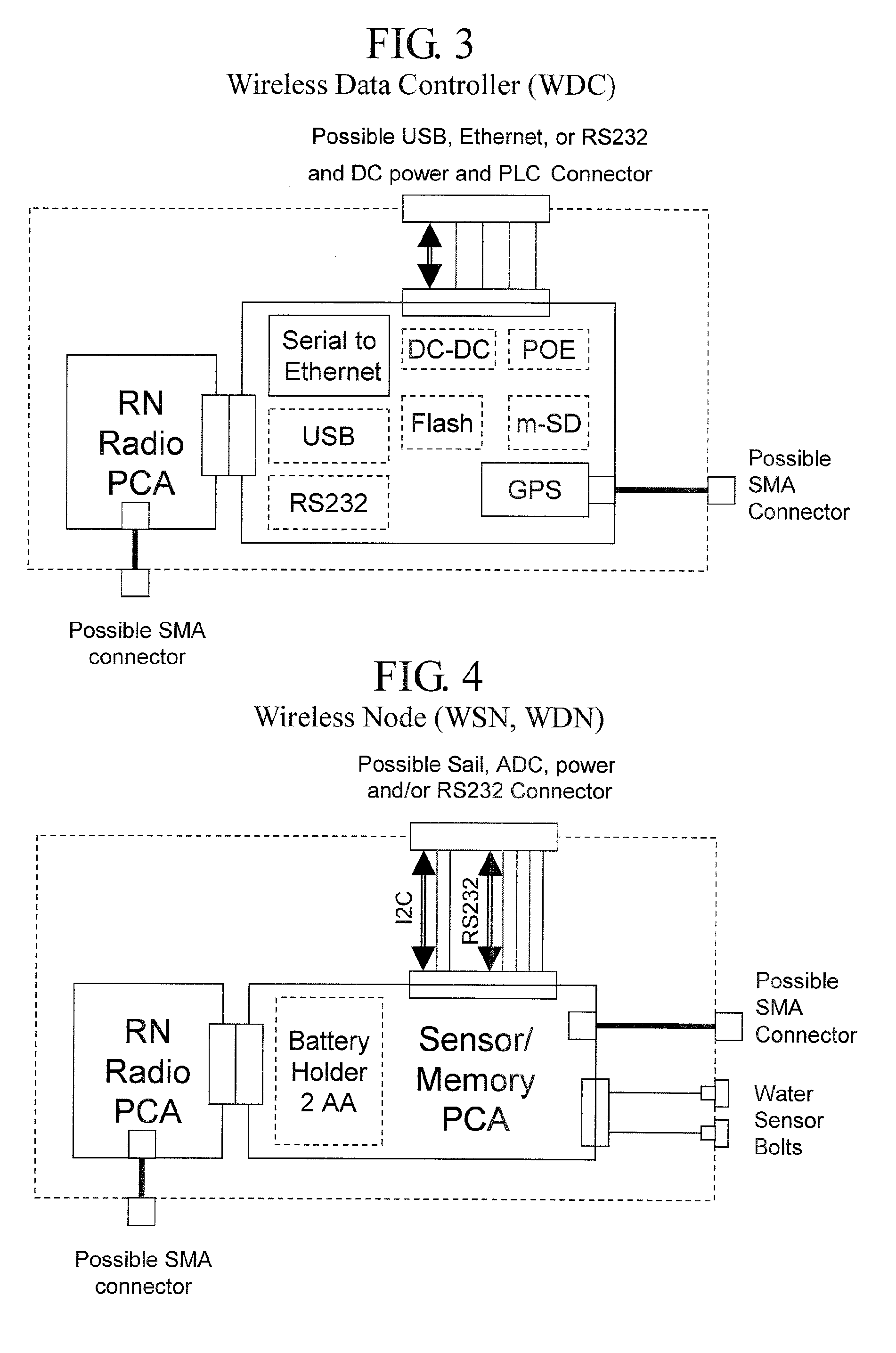
Wireless Data Networking
ActiveUS20080291855A1Low powerBetter read rateEnergy efficient ICTPower managementWireless dataNetwork mapping
A meshing network comprising one full function controller (WDC) and a plurality of nodes (WDN, WSN), that is RF quiet capable with very low power consumption and the ability to quickly heal itself and create new network paths. The network uses an addressing scheme that allows for each node to not have a network map but still be able to route messages. A piping scheme allows a mesh to become a high throughput network. A sensor rail protocol definition allows sensor devices to connect to nodes and route messages through the network.
Owner:RAYTHEON CO
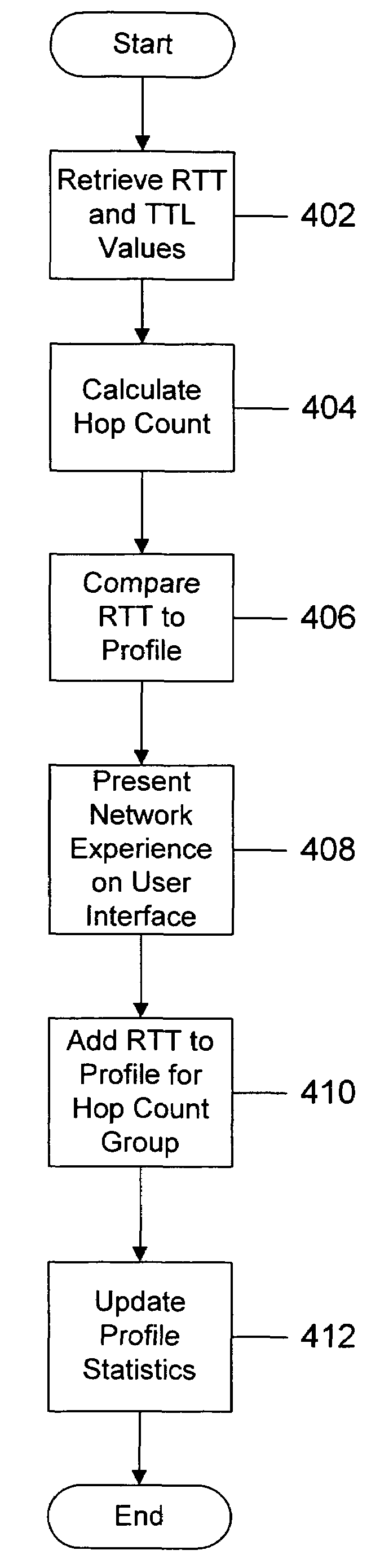
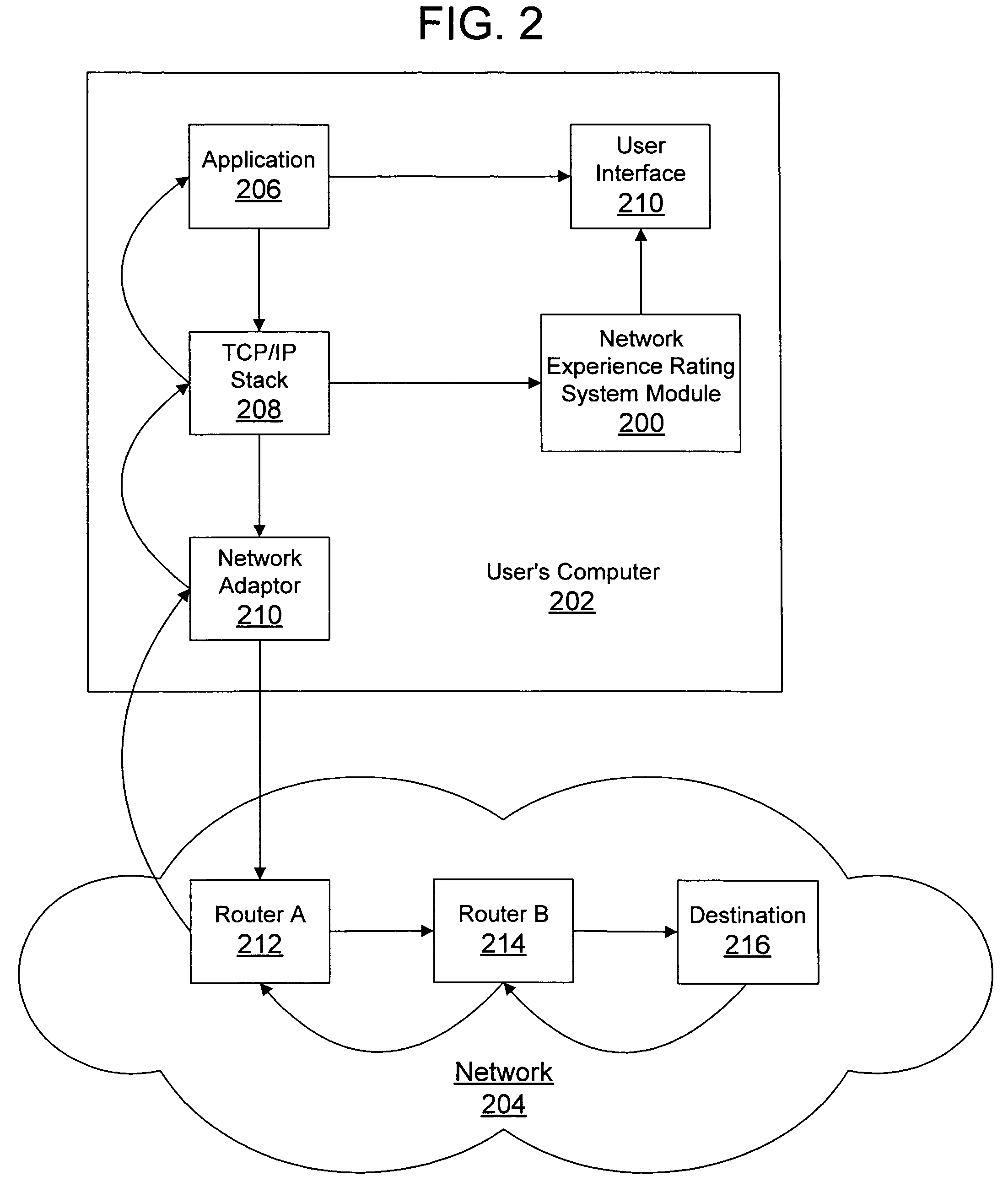
Network experience rating system and method
InactiveUS7506052B2Reliably perceiveMultiple digital computer combinationsTransmissionRating systemPersonalization
A network experience rating system and method determines a network connection quality for a computer by monitoring characteristics of data traffic through a connection with another computer on the network. The network experience rating system statistically analyzes the characteristic data and compares the statistically analyzed data to historical data gathered for the computer. The network experience rating system thus provides a rating that is individualized for a particular computer based on the computer's network usage.
Owner:MICROSOFT TECH LICENSING LLC
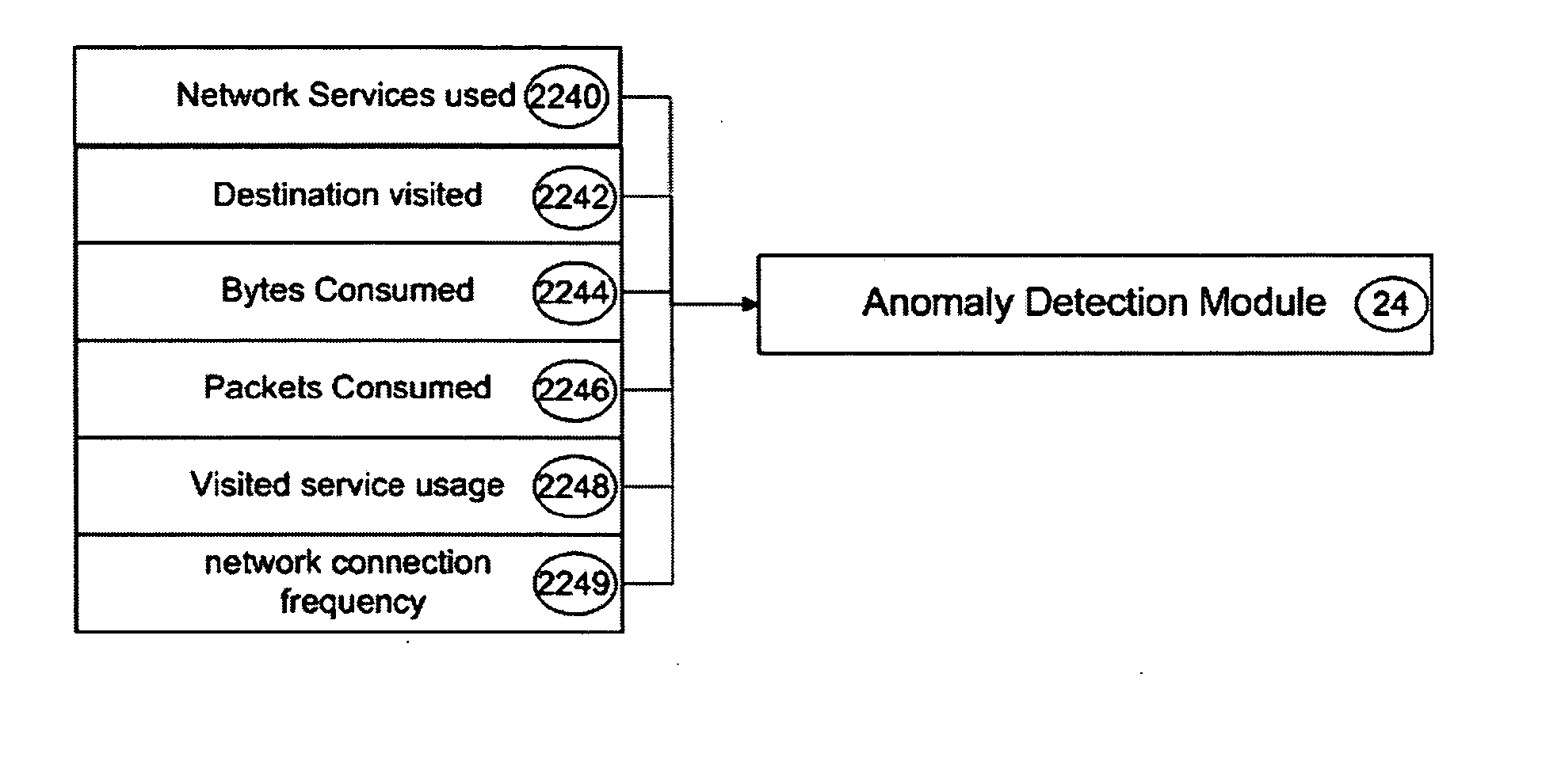
Method and system for user network behavioural based anomaly detection
InactiveUS20070245420A1Memory loss protectionError detection/correctionApplication softwareBehavioural analysis
A baseline can be defined using specific attributes of the network traffic. Using the established baseline, deviation can then be measured to detect anomaly on the network. The accuracy of the baseline is the most important criterion of any effective network anomaly detection technique. In a local area network (LAN) environment, the attributes change very frequently by many change agents; for example, new entities, such as users, application, and network-enabled devices, added to and removed from the LAN environment. The invention provides an improved method of establishing a baseline for network anomaly detection based on user's behaviour profiling. A user behaviour profiling is a distinct network usage pattern pertaining to a specific individual user operating on the LAN environment. No two users profiling would be the same. A group of users that have similar network usage attributes can be extrapolated using data mining technique to establish a group profiling baseline to detect network usage anomaly. By combining user and group profiling, a network anomaly detection system can measure subtle shift in network usage and as a result separate good user's network usage behaviour from the bad one. Using the said technique, a lower rate of false positives of network anomaly can be created that is suitable to operate in a highly dynamic LAN environment.
Owner:YONG YUH MING +1
Method and apparatus for using multicarrier interferometry to enhance optical fiber communications
InactiveUS7076168B1Increase diversityImprove efficiencyEnergy efficient ICTModulated-carrier systemsSignal qualityFrequency reuse
A redundently modulated multicarrier protocol known as Carrier Interference Multiple Access (CIMA) is used in an optical-fiber network having wireless links at network nodes. CIMA is a protocol that can be used to create wireless protocols (such as TDMA and CDMA) having enhanced capacity and reduced system complexity. A CIMA optical-fiber network uses dispersion to enhance signal quality and facilitate switching. CIMA achieves both diversity benefits and capacity enhancements by providing redundancy in at least one diversity parameter while providing orthogonality in another diversity parameter. This basic operating principle of CIMA may be combined with multi-user detection to achieve frequency reuse and improved power efficiency. In the wireless link, diversity may be used to reduce the effects of small-scale fading on interferometry multiplexing.
Owner:DEPARTMENT 13 INC
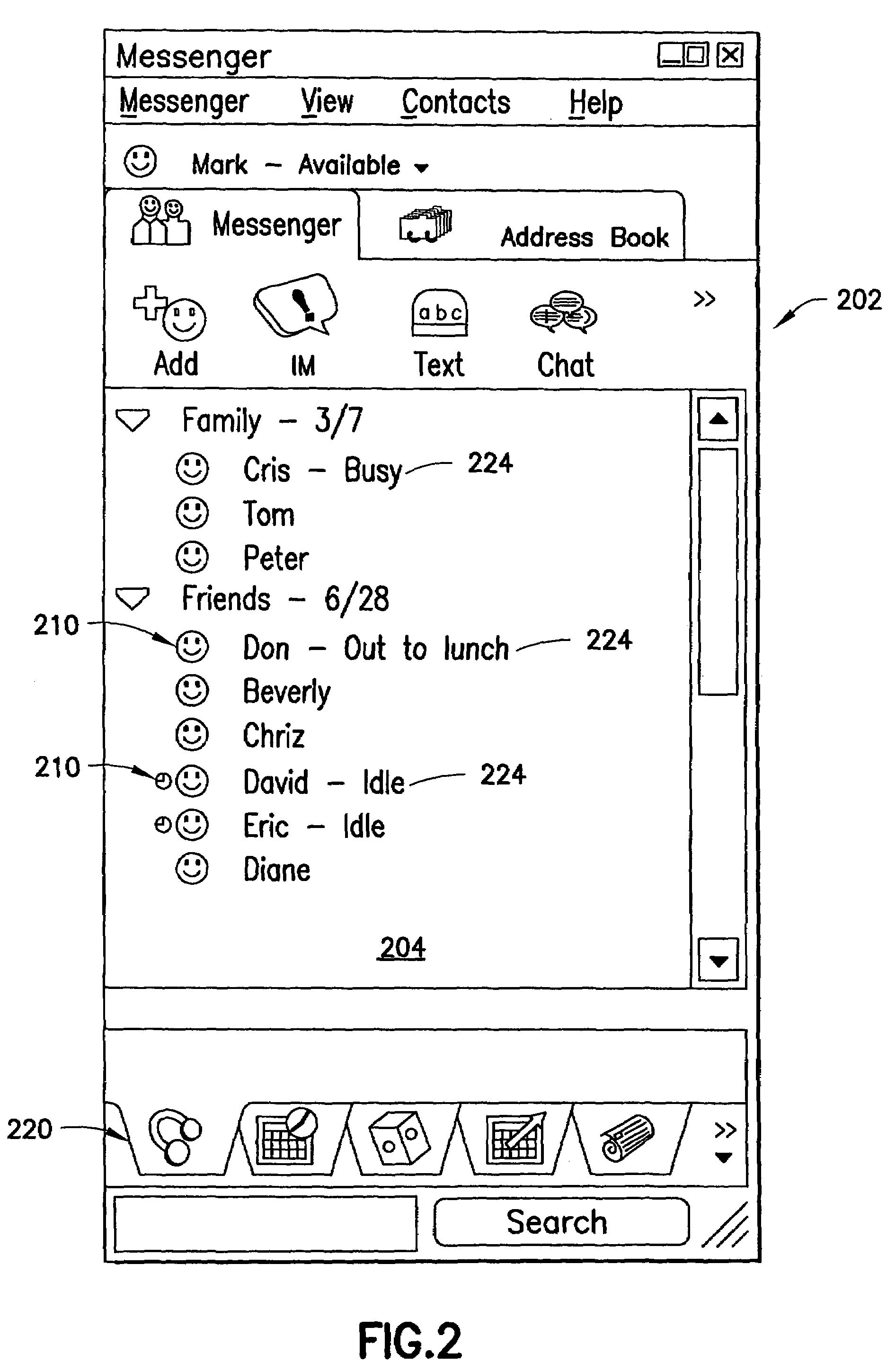
System and method facilitating a shared content experience using enhanced messaging including a displayable status indicator
ActiveUS7496633B2Easy to shareFacilitate communicationMultiple digital computer combinationsBuying/selling/leasing transactionsThe InternetMetadata
A system and method for enhancing the experience of a user using a communication program over the Internet or other network. The system and method according to one embodiment utilizes a user's status indicator in a communication program to share content such as music or videos among users. One system and method according to the present invention allows a user to display an indicator and to set an actionable status message which indicates to other users the media content that the first user is experiencing. In another embodiment, a user is given the ability to access content that other users are listening to or viewing at that time. The system and method in an alternate embodiment broadcast metadata about the user's content to other users and the other users are able to utilize that metadata to receive and experience the same or similar content that the first user is experiencing.
Owner:ENERGETIC POWER INVESTMENT
System and method for providing differentiated service levels to wireless devices in a wireless network
ActiveUS7720464B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDifferentiated servicesTelecommunications
Owner:EXTREME NETWORKS INC
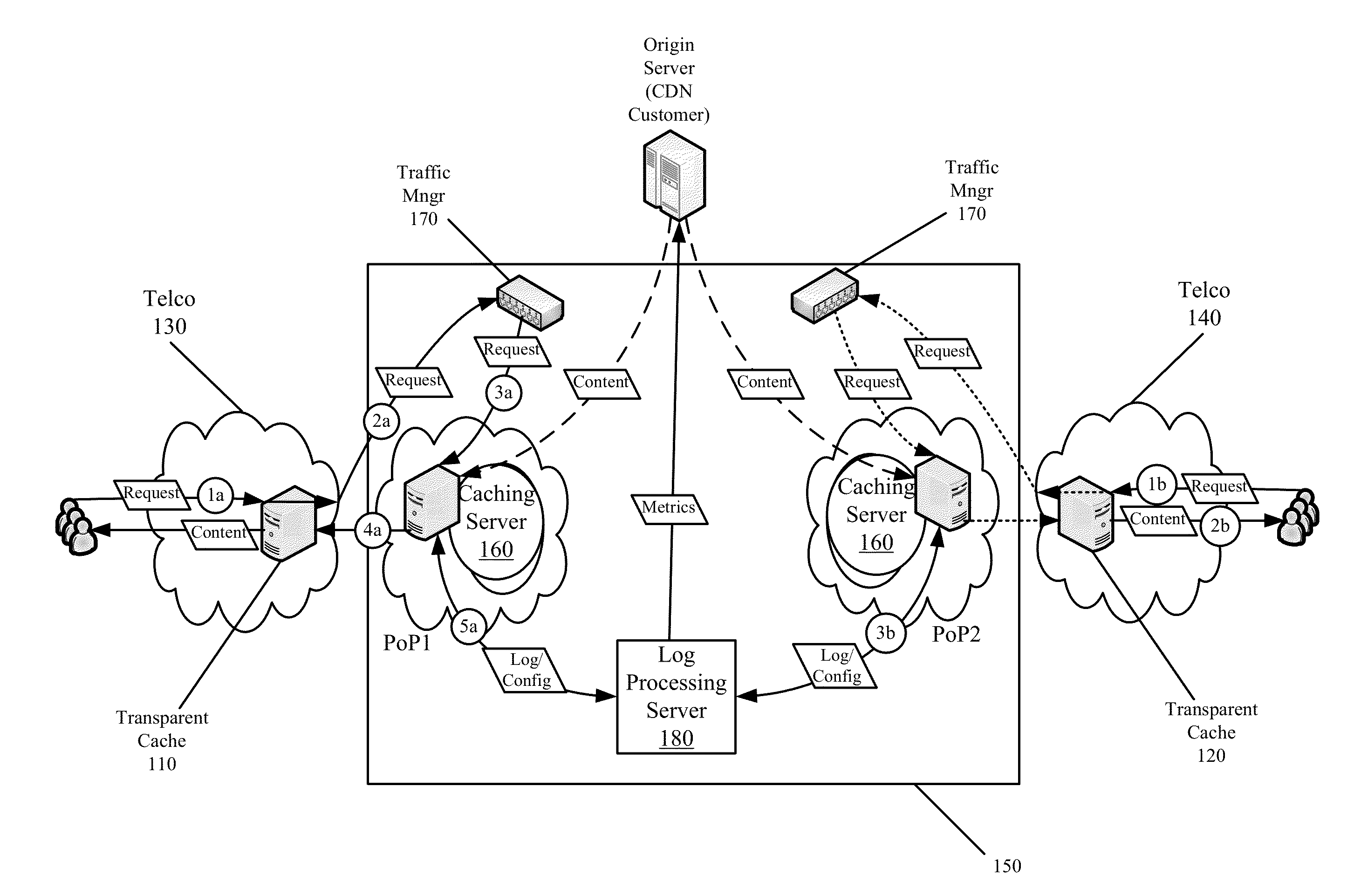
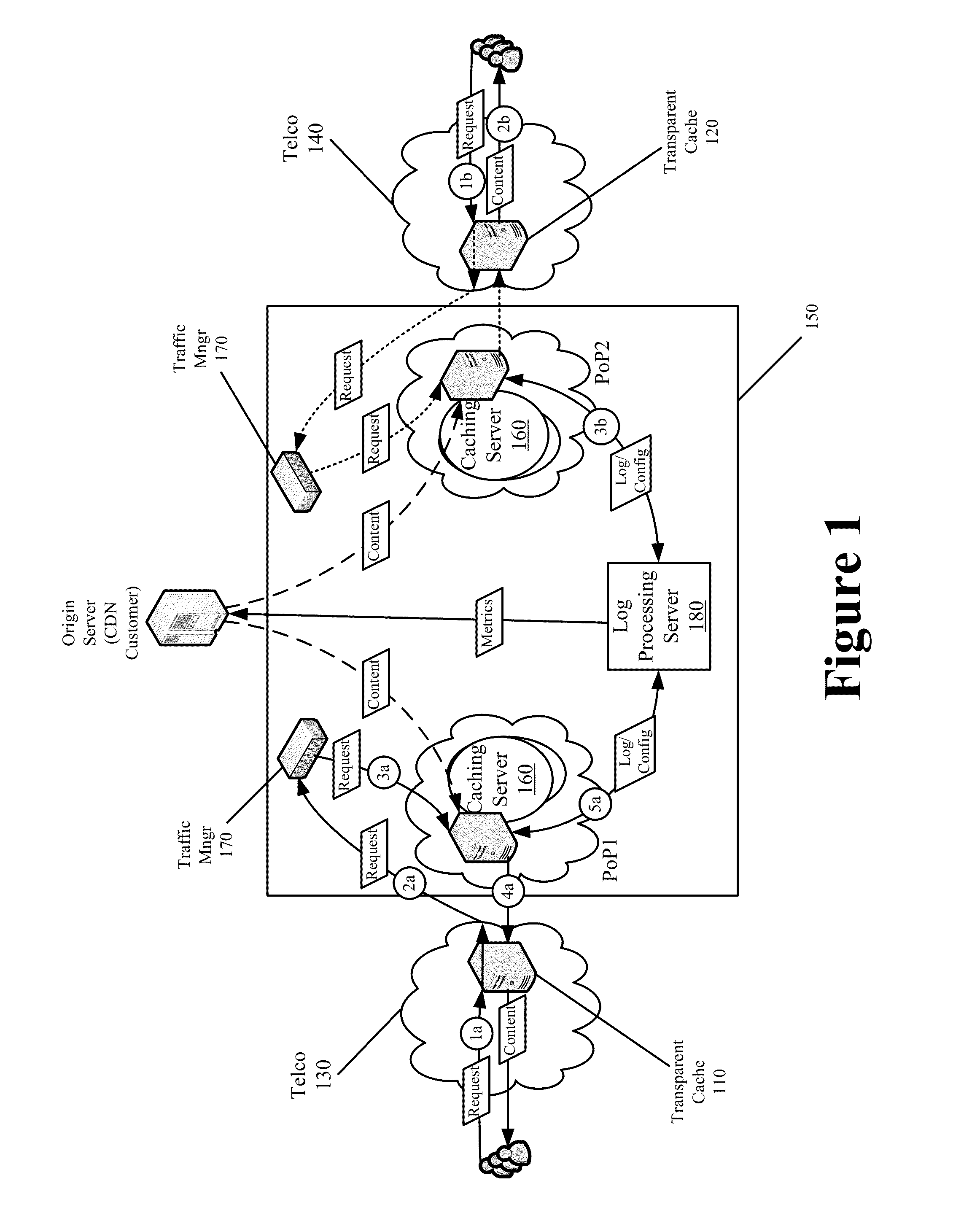
End-to-End Content Delivery Network Incorporating Independently Operated Transparent Caches and Proxy Caches
ActiveUS20130046883A1Accurately and comprehensively track and report metricImproves content deliveryDigital data information retrievalDigital computer detailsServer logCache server
Some embodiments provide an end-to-end federated CDN solution that assimilates a transparent caching server that is operated by a transparent caching server operator into a CDN that independently operates CDN caching servers. Specifically, the logs from the transparent caching server are assimilated into the CDN by aggregating the logs from the transparent caching server and processing the transparent caching server logs to identify network usage for content of a CDN content provider customer that is delivered by the transparent caching server. The network usage is then combined with the network usage that tracked by the CDN caching servers in order to provide comprehensive report metrics for the content provider customer and to bill the content provider customer for all network usage related to delivering the content provider customer's content irrespective of whether the content was delivered by a transparent caching server or a CDN caching server.
Owner:EDGIO INC
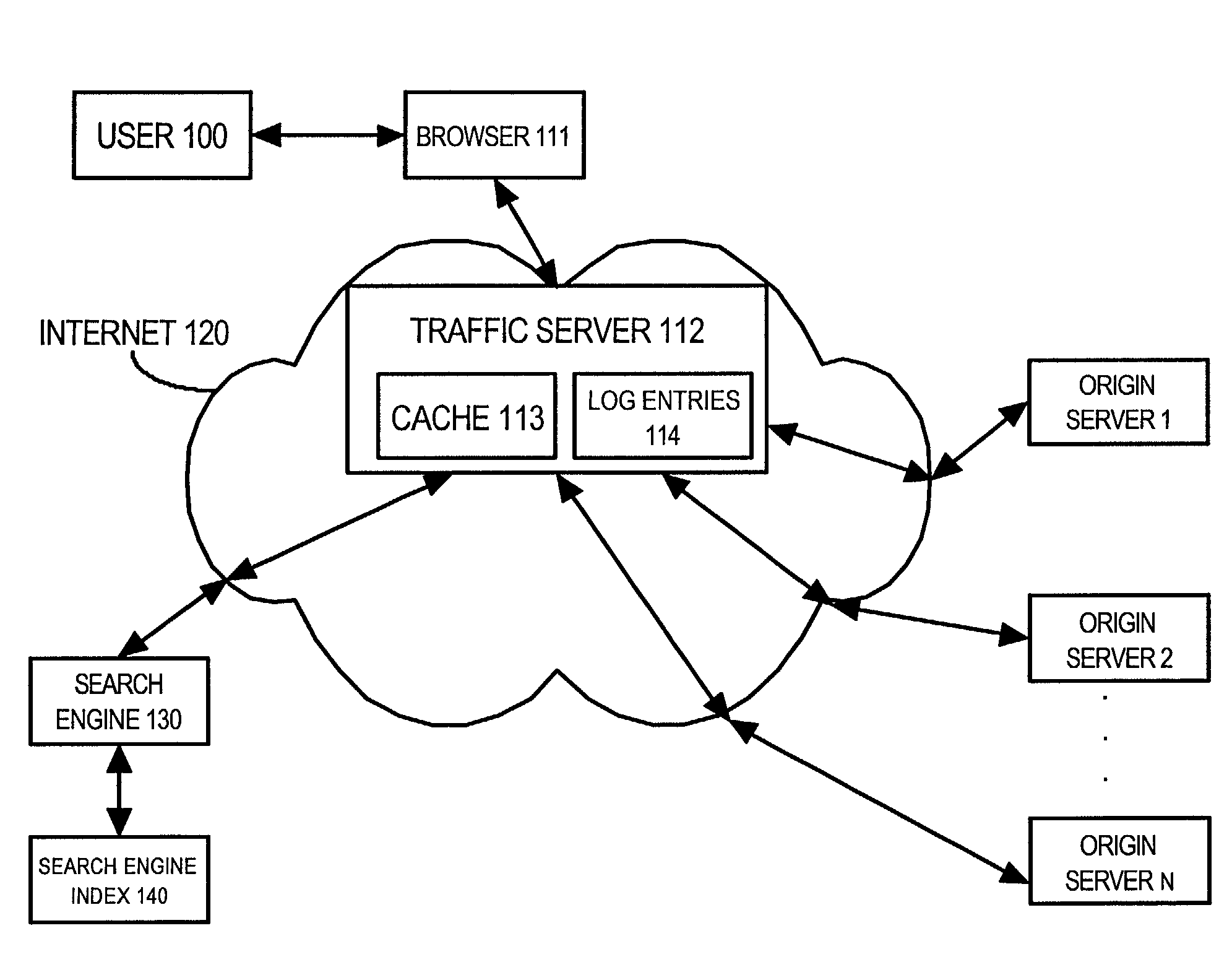
Using network traffic logs for search enhancement
ActiveUS7398271B1Handy search resultsImprove the level ofData processing applicationsWeb data indexingTraffic capacityLink weight
A method and apparatus for using network traffic logs for search enhancement is disclosed. According to one embodiment, network usage is tracked by generating log files. These log files among other things indicate the frequency web pages are referenced and modified. These log files or information from these log files can then be used to improve document ranking, improve web crawling, determine tiers in a multi-tiered index, determine where to insert a document in a multi-tiered index, determine link weights, and update a search engine index.
Owner:R2 SOLUTIONS
Method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about user of a mobile data network
A method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about a user of a mobile data network. A data manager receives information about application-level activity from a mobile data network and stores the information to provide dynamic real-time reporting on network usage. The data manager comprises a database, data processing module, and analytics module. The database stores the application-level data for a predetermined period of time. The data processing module monitors the data to determine if it corresponds to a set of defined reports. If the data is relevant, the processing module updates the defined reports. The analytics module accesses the database to retrieve information satisfying operator queries about network usage. If the operator chooses to convert the query into a defined report, the analytics module creates a newly defined report and populates it accordingly.
Owner:RIBBON COMM SECURITIES CORP
System and Method for Sharing Anonymous User Profiles with a Third Party
The invention provides a system and method for sharing anonymous user profiles with a third party. In one aspect of the invention, the system shares user profiles with content servers on a mobile data network so that they may select content responsive to the user's profile. The system provides a store of user profiles for associating profile information with either a source IP address or mobile phone number, where the profile includes information on the user and the user's network usage. The system detects a user's transaction request and inspects it for either an IP address or phone number, which it uses to retrieve the appropriate profile. The system subsequently applies predetermined opt-out policies to determine how much of the user profile may be provided in response to the profile request. The system then returns the profile information such that the user's identity is masked.
Owner:RIBBON COMM SECURITIES CORP
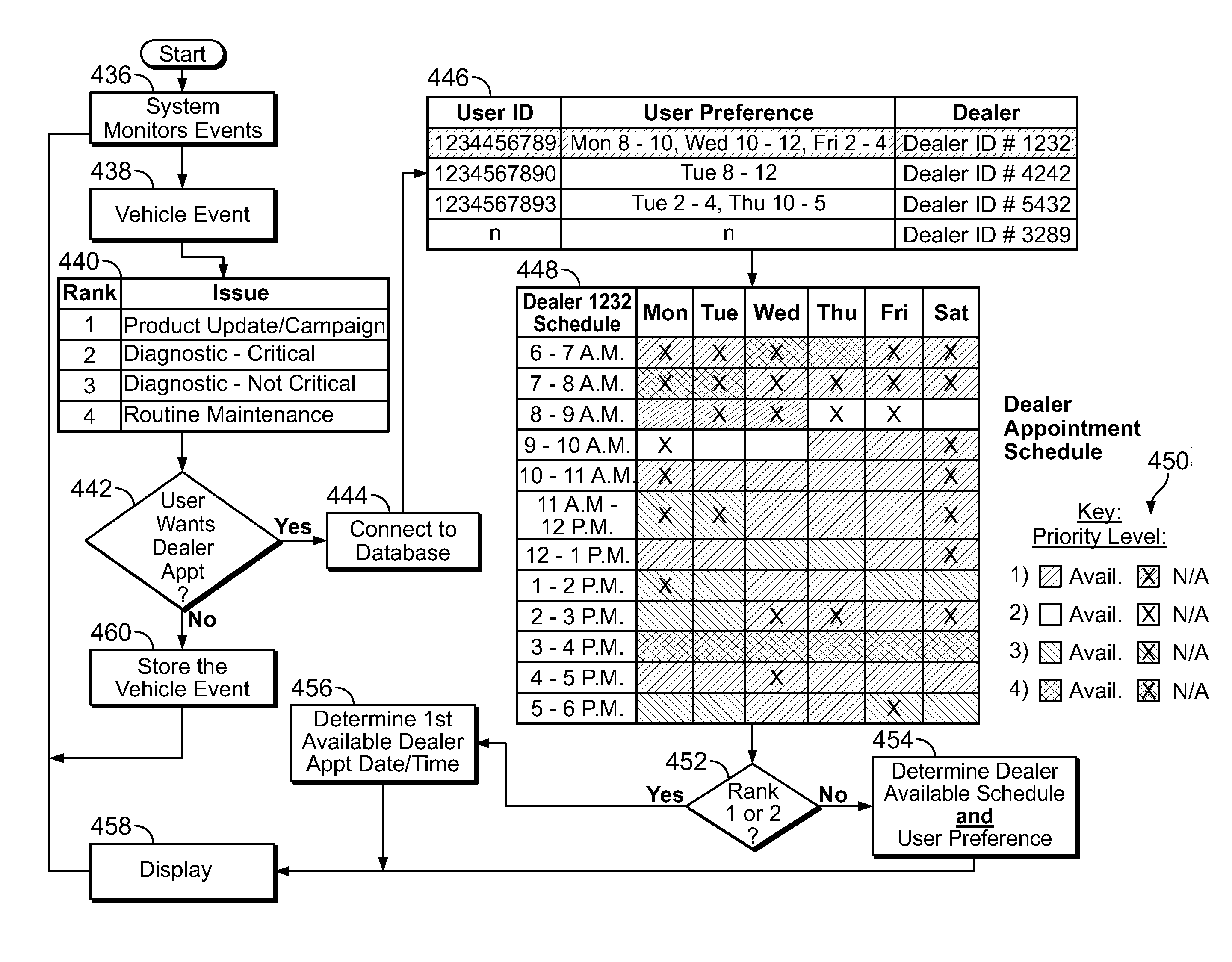
Method and system for making automated appointments
InactiveUS20090106036A1Maximizes schedulingAbility to provideData processing applicationsTime scheduleCellular data
Methods and systems for scheduling vehicle service appointments from a remote site via an onboard system are provided. For example, there is provided a method for broadcasting vehicle event information to a plurality of vehicles that can include product update information and vehicle maintenance reminders. The user is able to respond to the vehicle event by requesting a service appointment from a desired dealer using the onboard system to communicate with a remote site using a cellular data line over a wireless communication network. In one embodiment, a proposed service appointment date and time is presented to the user. The proposed appointment date and time is based on the vehicle user's preference setting and a dealer's schedule corresponding to the dealer selected by the user. Proposed service appointment dates and times are released to other users when the user has not confirmed the appointment during a predetermined response time.
Owner:HONDA MOTOR CO LTD
Systems and methods for providing and installing software
ActiveUS7707573B1Limited bandwidthSufficient processor shareDigital computer detailsProgram loading/initiatingComputer usersNetwork connection
The present invention comprises systems and methods, and computer readable media comprising the methods, for installing software components. A user's need for a software component may be determined prior to installation. The systems and methods of the present invention provide automation and flexibility to the installation process. In an embodiment, processor usage and network usage are monitored and software installation are initiated and / or continued during periods where processor and / or network usage are low. The installation process may be halted when the processor and / or network connection are called upon for other uses. Processor and / or network usage may also be throttled, for example limiting the bandwidth available for the installation to maintain sufficient processor share and / or bandwidth for other tasks. Adverse impact on a computer user is minimized.
Owner:GOOGLE LLC
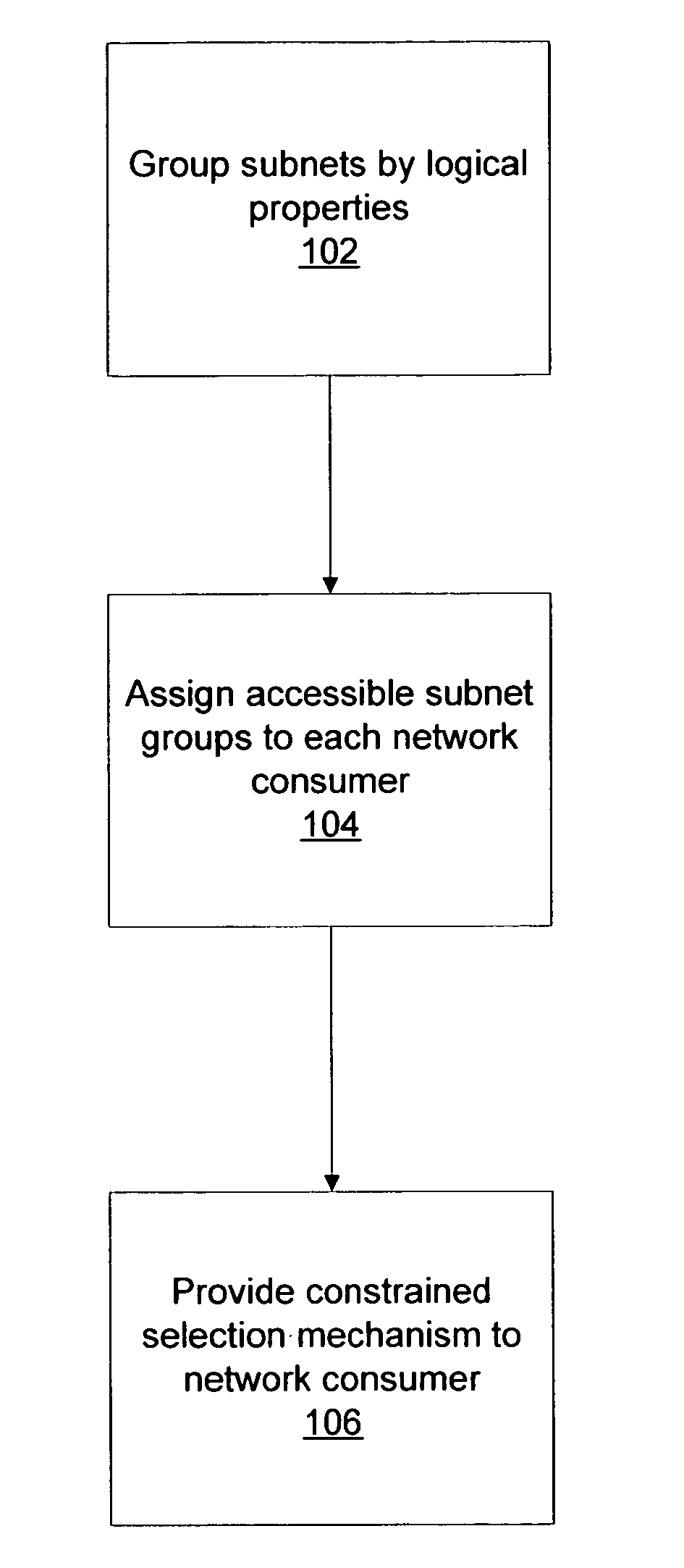
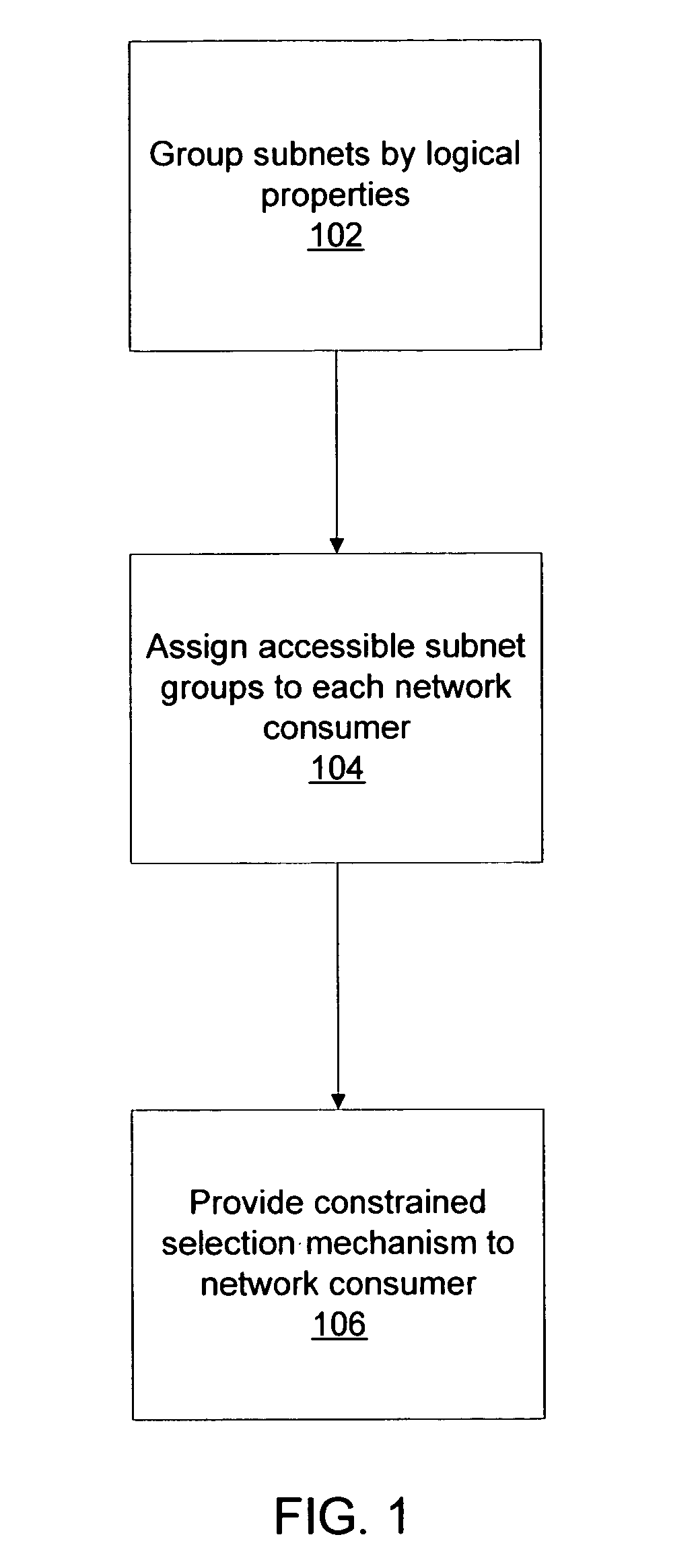
System and method for subnet configuration and selection
One embodiment disclosed relates to a method for provisioning subnets. The subnets are grouped into subnet groups based on logical properties of the subnets. Each network consumer is assigned those subnet groups that are accessible to that network consumer. The network consumer is then provided with an interface for constrained selection of a particular subnet.
Owner:REGIONAL RESOURCES LTD
Systems with user selectable data attributes for automated electronic search, identification and publication of relevant data from electronic data records at multiple data sources
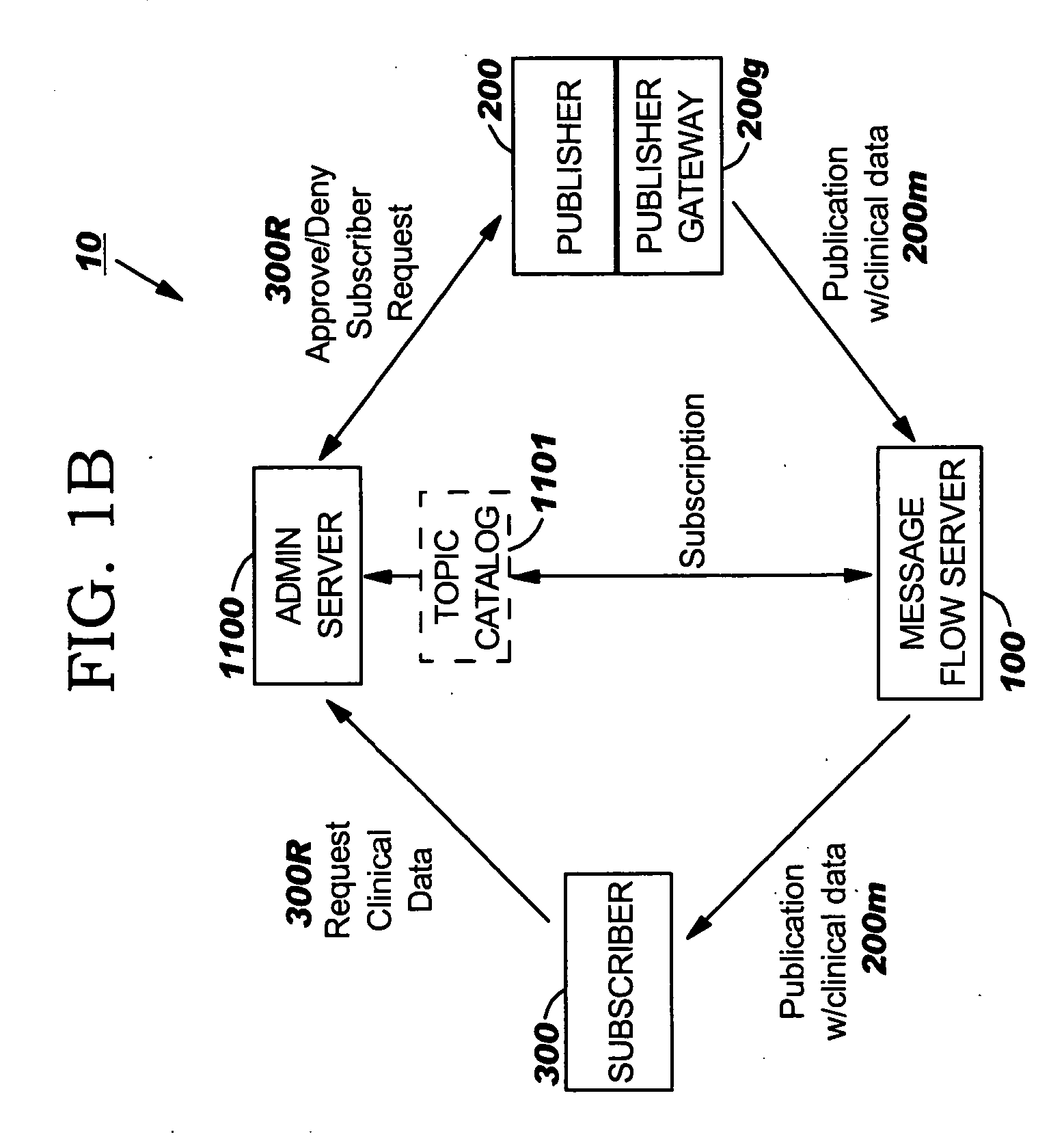
Systems, methods and computer program products that allow Subscribers to electronically obtain data of interest from participating Publishers using a computer network which employ an Administrative Server configured to allow Subscribers to electronically define, select and / or request an electronic topic data request with data elements of interest from a plurality of Publishers having non-public respective electronic repositories of source data using a web portal and a computer network.
Owner:IBM CORP
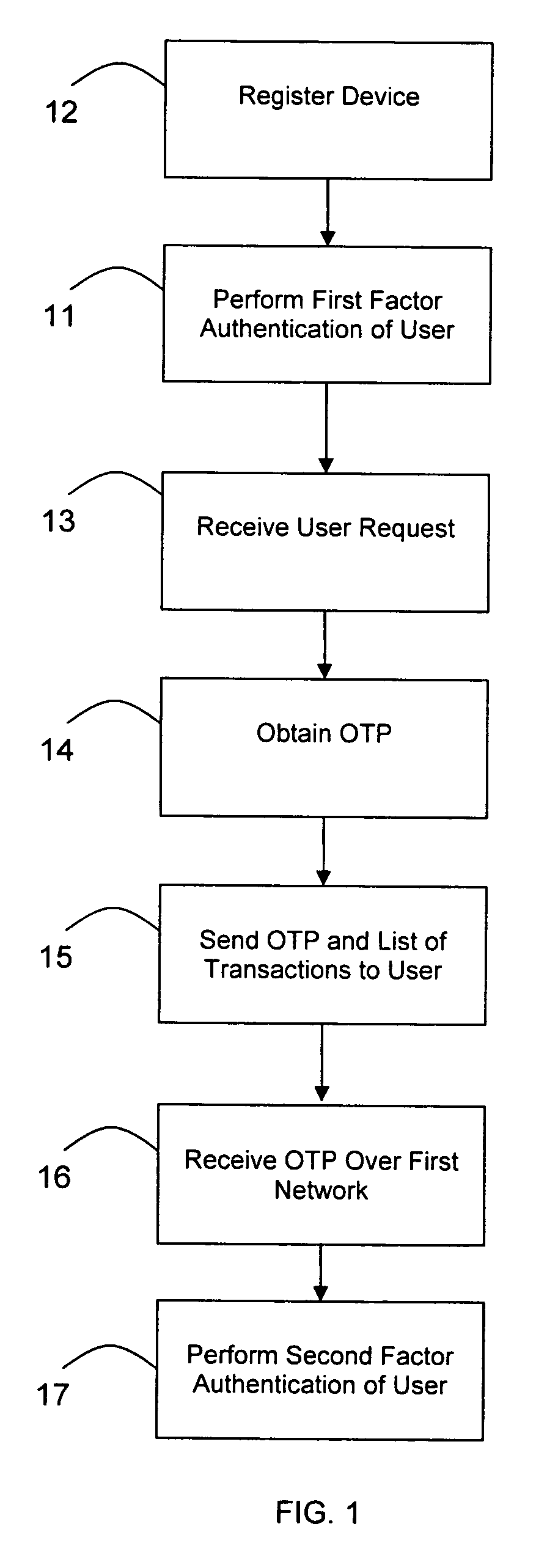
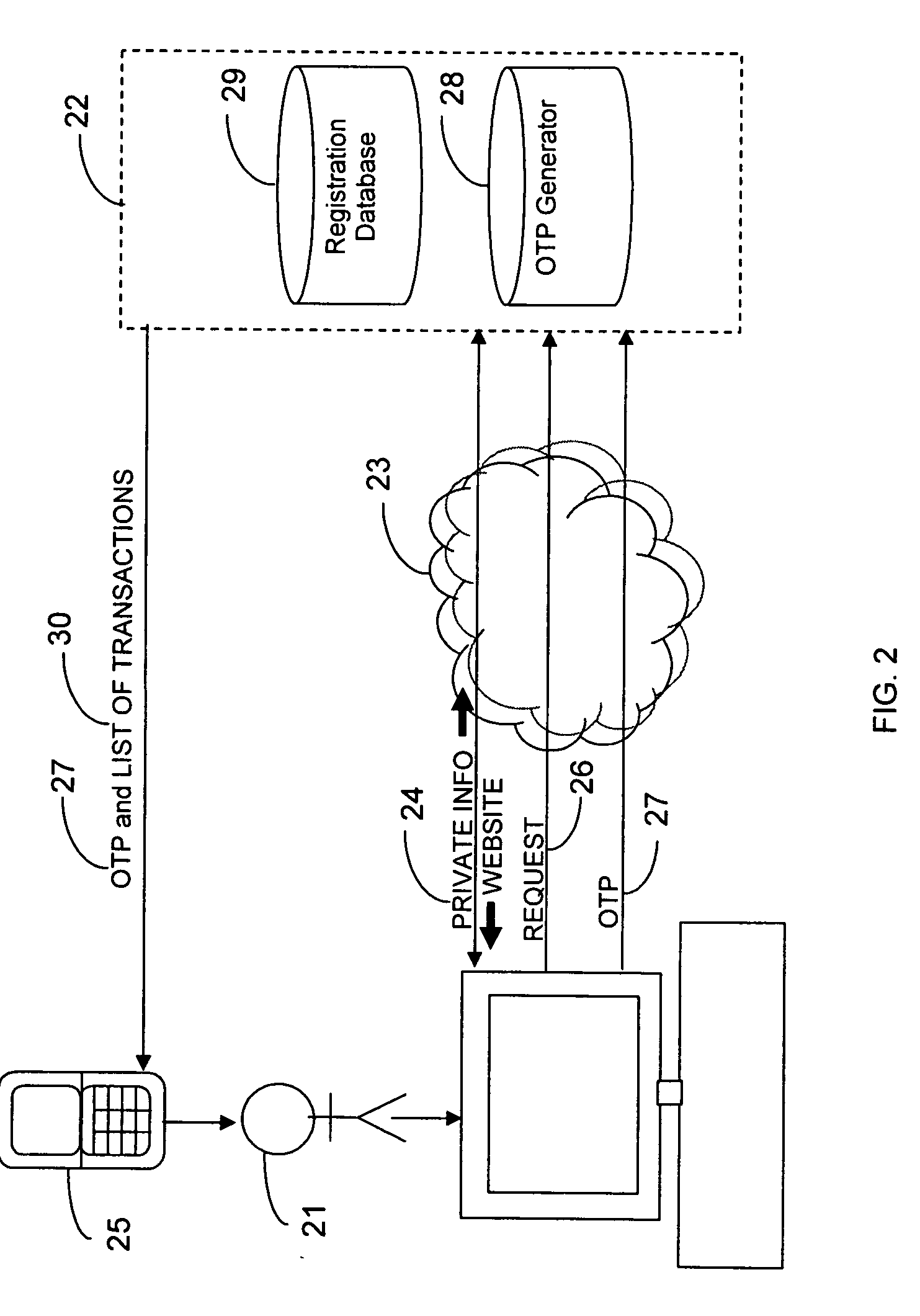
Transaction authentication over independent network
InactiveUS20090106138A1Accelerating transactionFinanceProtocol authorisationOne-time passwordCommunication device
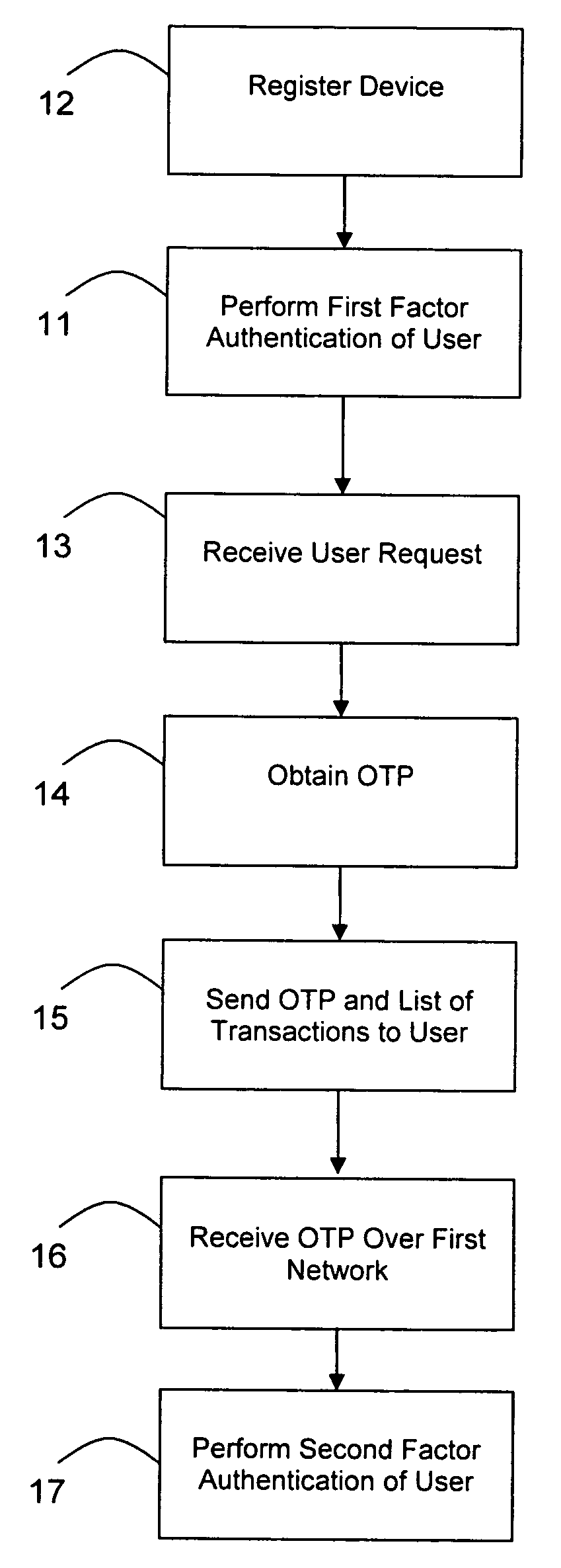
A method of authenticating an online transaction over a first network uses 2-factor authentication of the user to defeat hacker attacks. A communication device is registered for use with the method. The communication device is configured to receive messages over a second network independent of the first network. The user is authenticated over the first network using a first factor, such as a username and password, and then initiates the transaction. A request to execute the transaction is received and a one-time password is obtained to be used as a second factor of authentication. The one-time password and details describing the transaction are sent to the communication device over the second network. The one-time password is received from the user over the first network to complete the second factor of authentication.
Owner:CLAREITY VENTURES INC
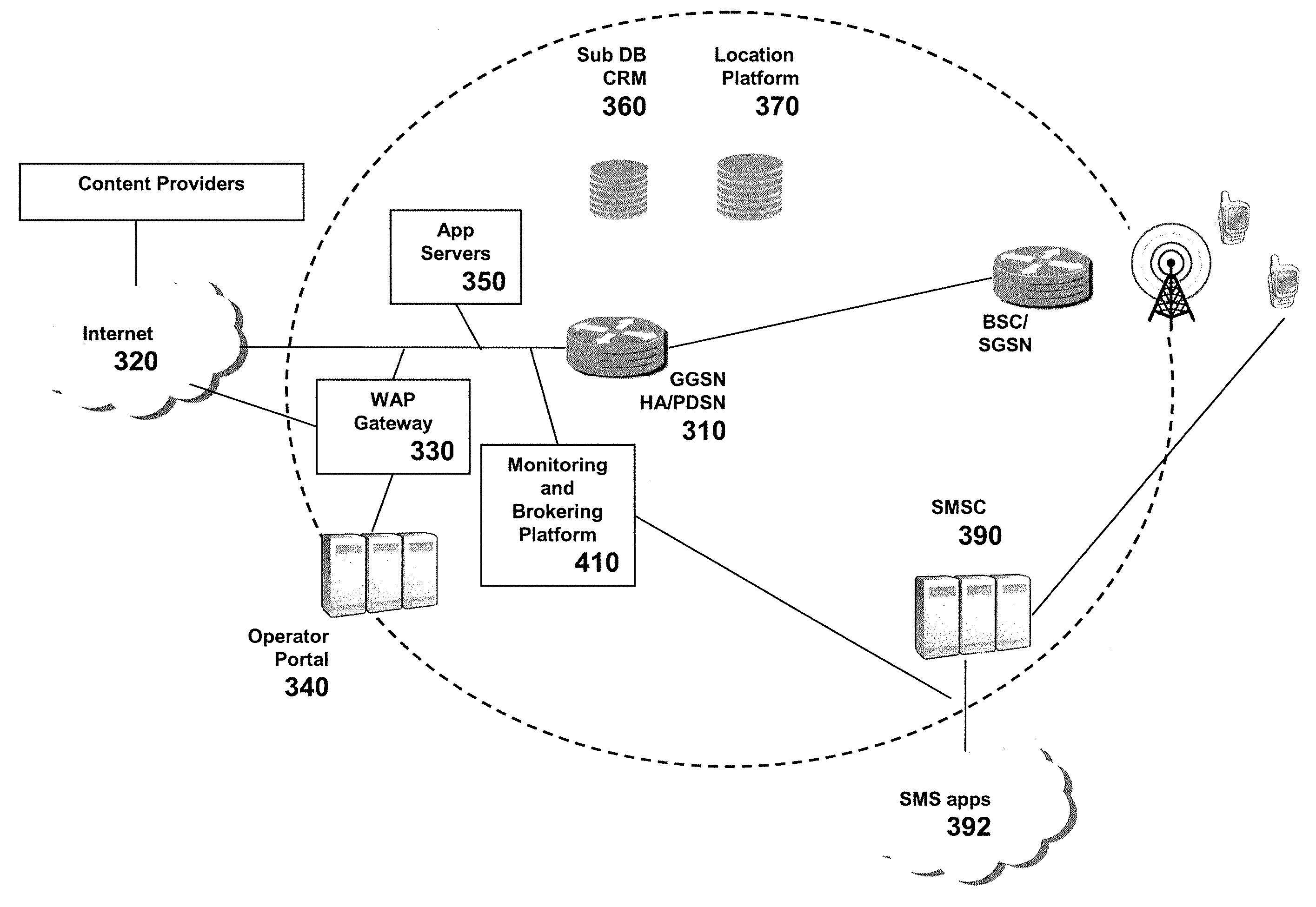
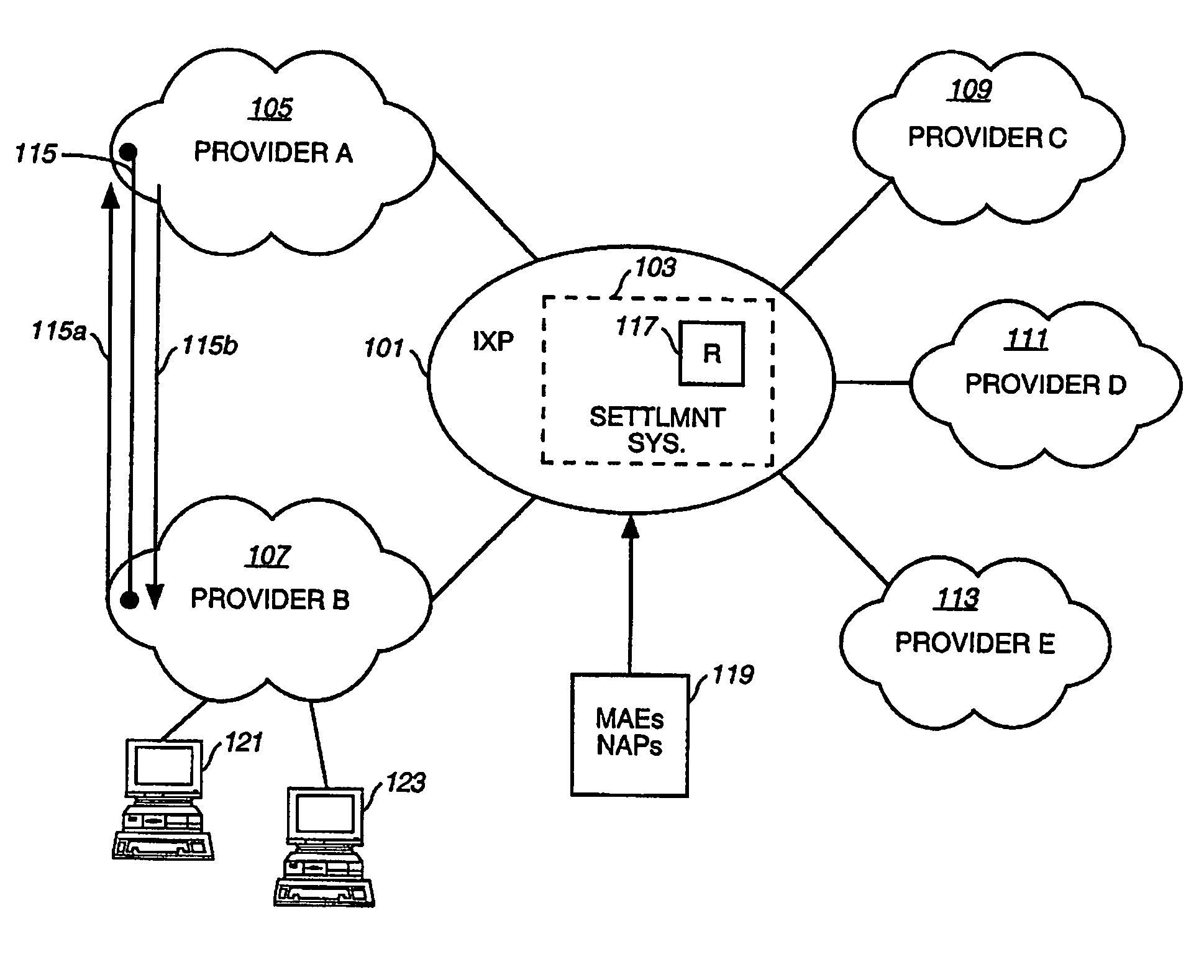
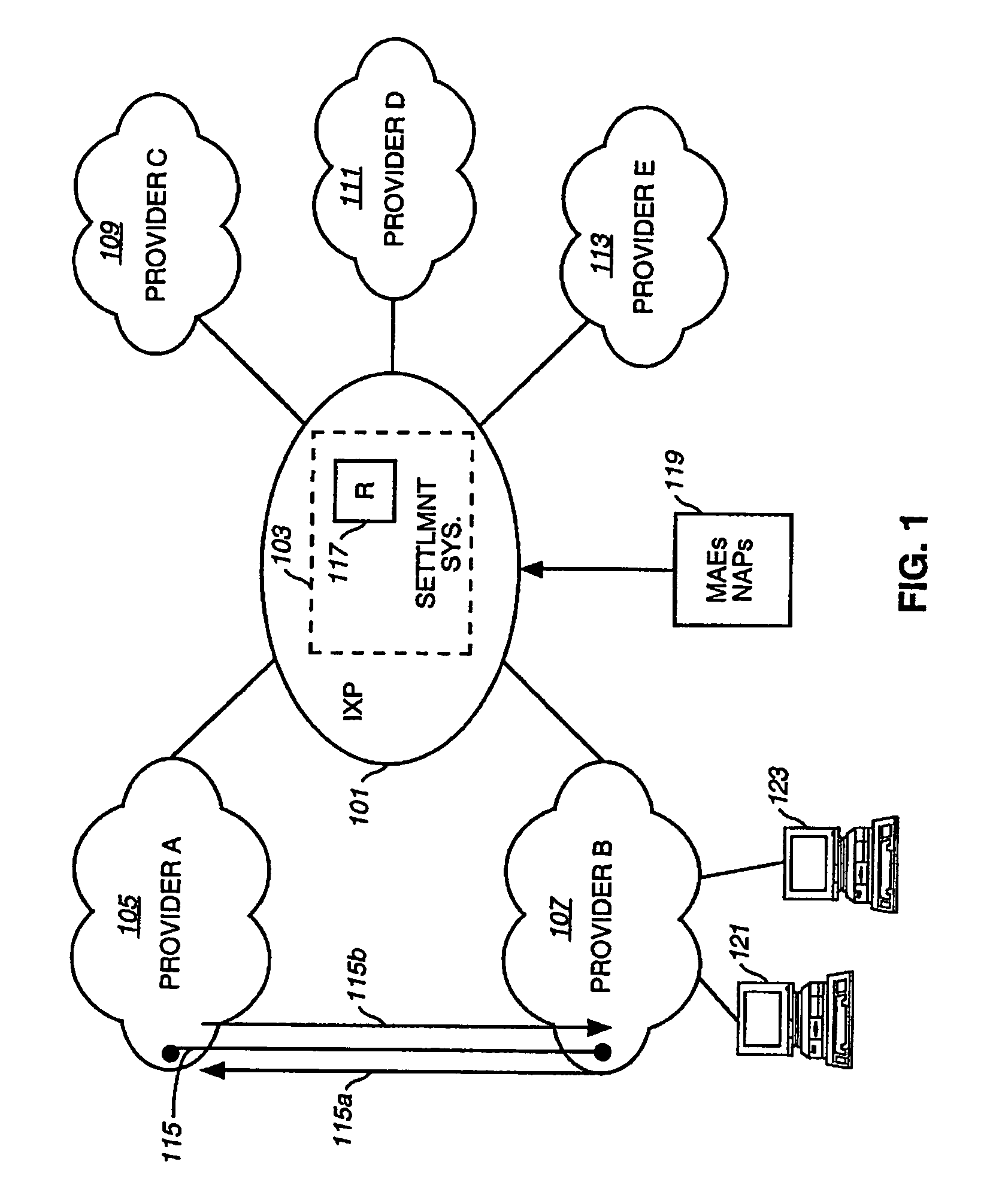
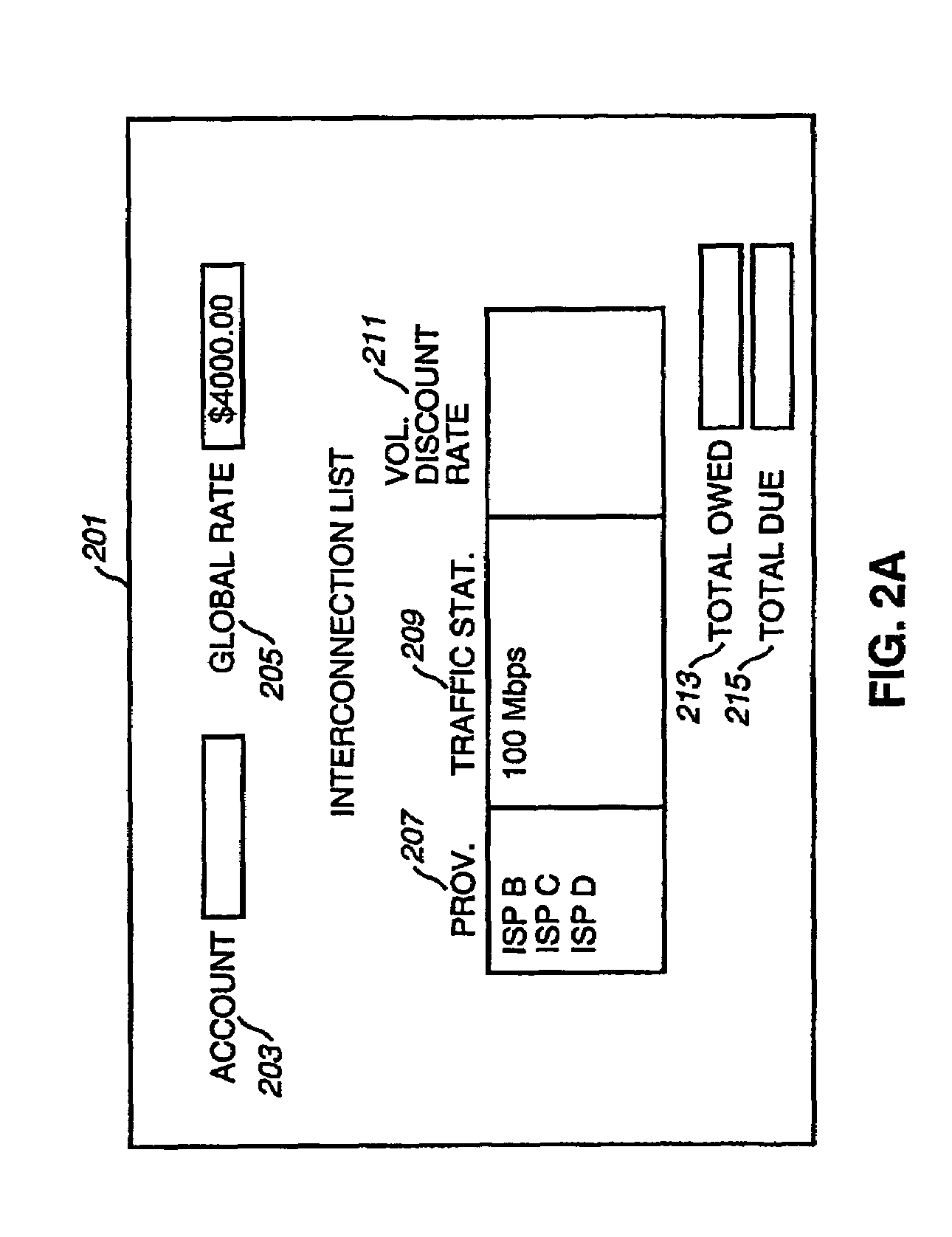
Method and system for providing settlement of interconnected packet-switched networks
InactiveUS6950407B1Interconnection arrangementsMetering/charging/biilling arrangementsTraffic capacityNetwork service
An approach for supporting settlement of network usage associated with multiple network service providers is disclosed. A settlement system includes a processor that determines a settlement agreement among the network service providers. The settlement agreement specifies rate information associated with traffic exchange among the corresponding networks of the network service providers. A traffic monitor measures source traffic statistics, which is stored in a settlement database. Additionally, the settlement database stores the settlement agreement. The processor computes settlement information based upon the stored traffic statistics; the settlement information includes usage cost differential information for reconciliation of network usage among the various networks.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com