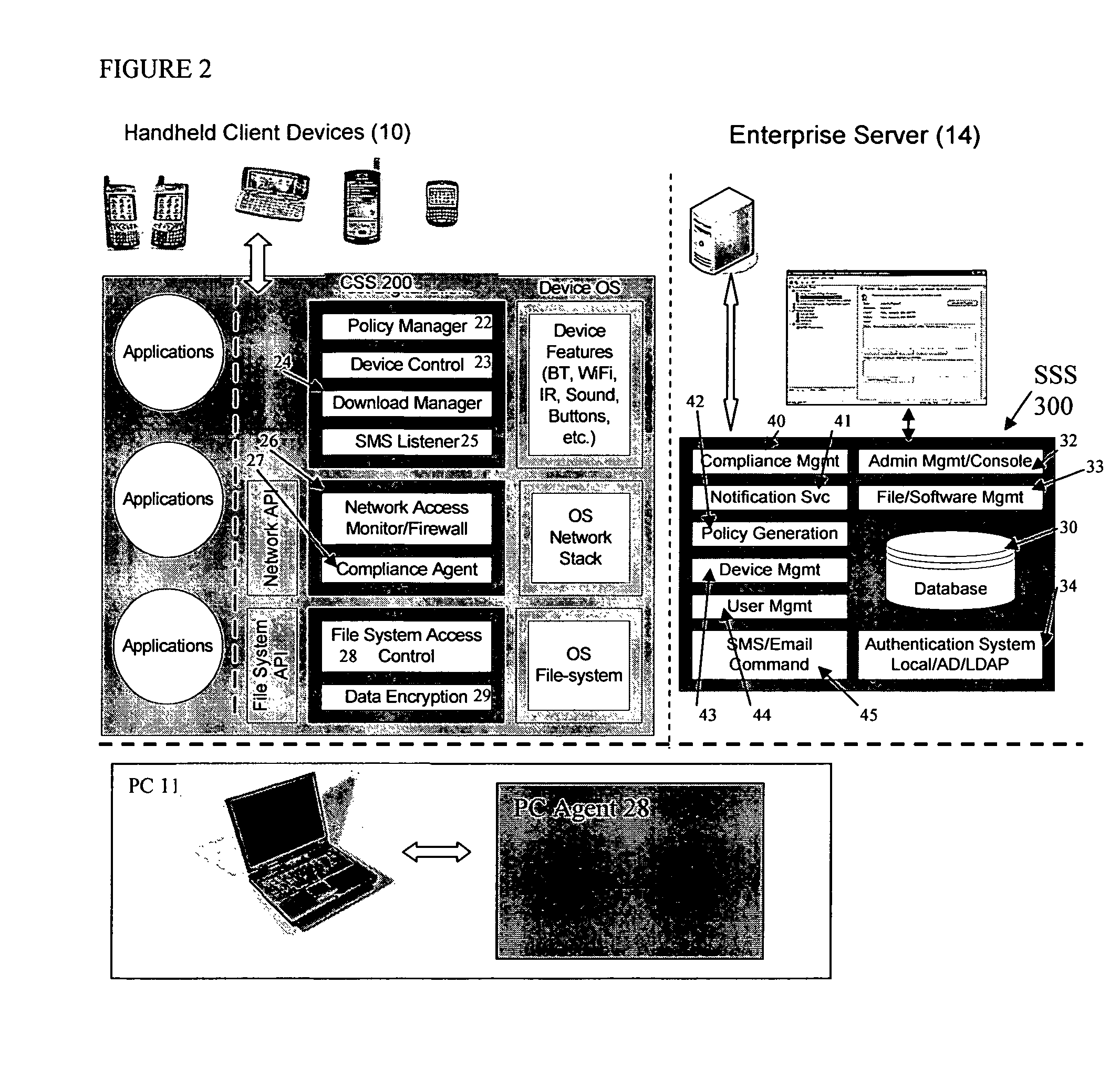
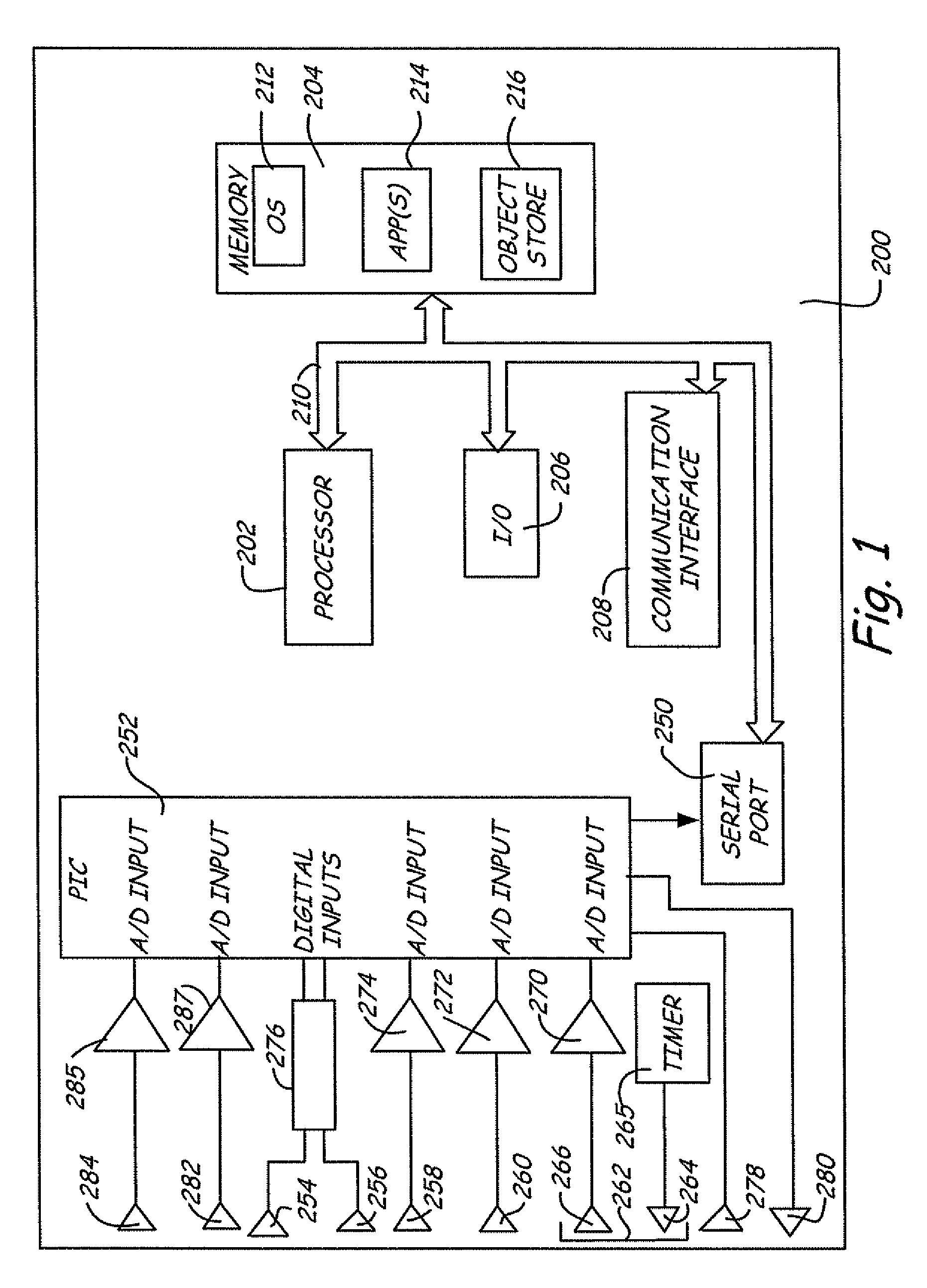
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2889 results about "Mobile computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
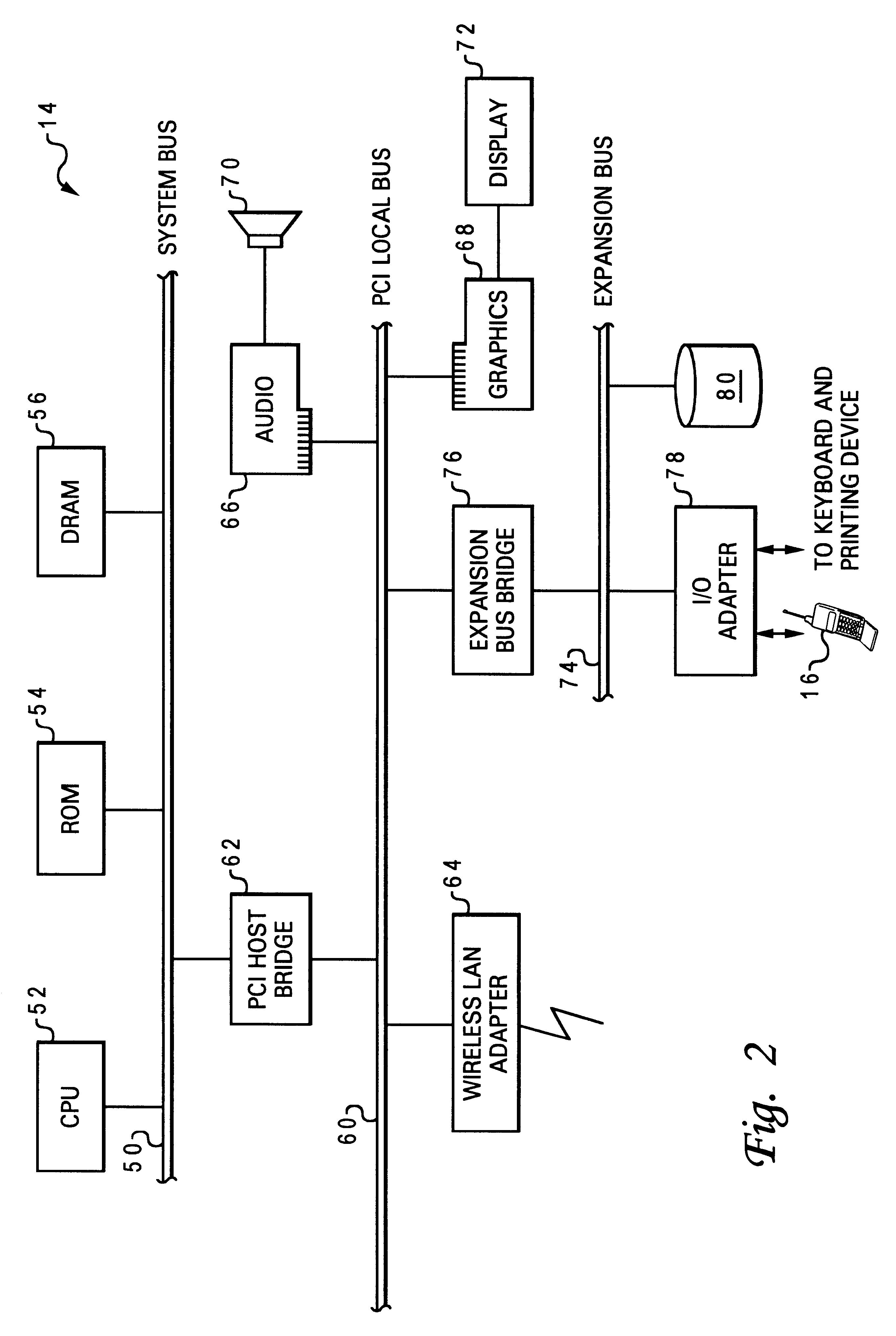
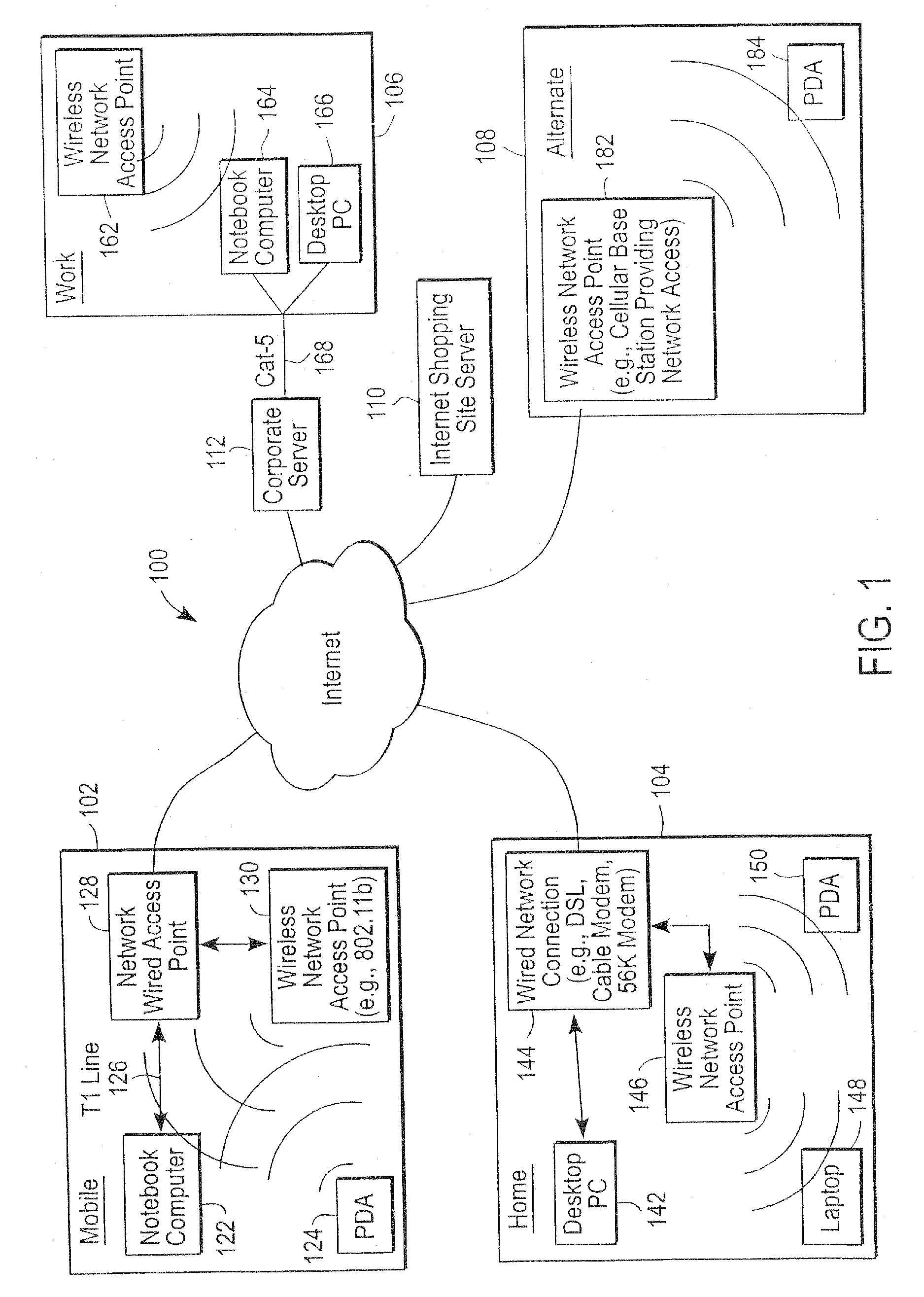
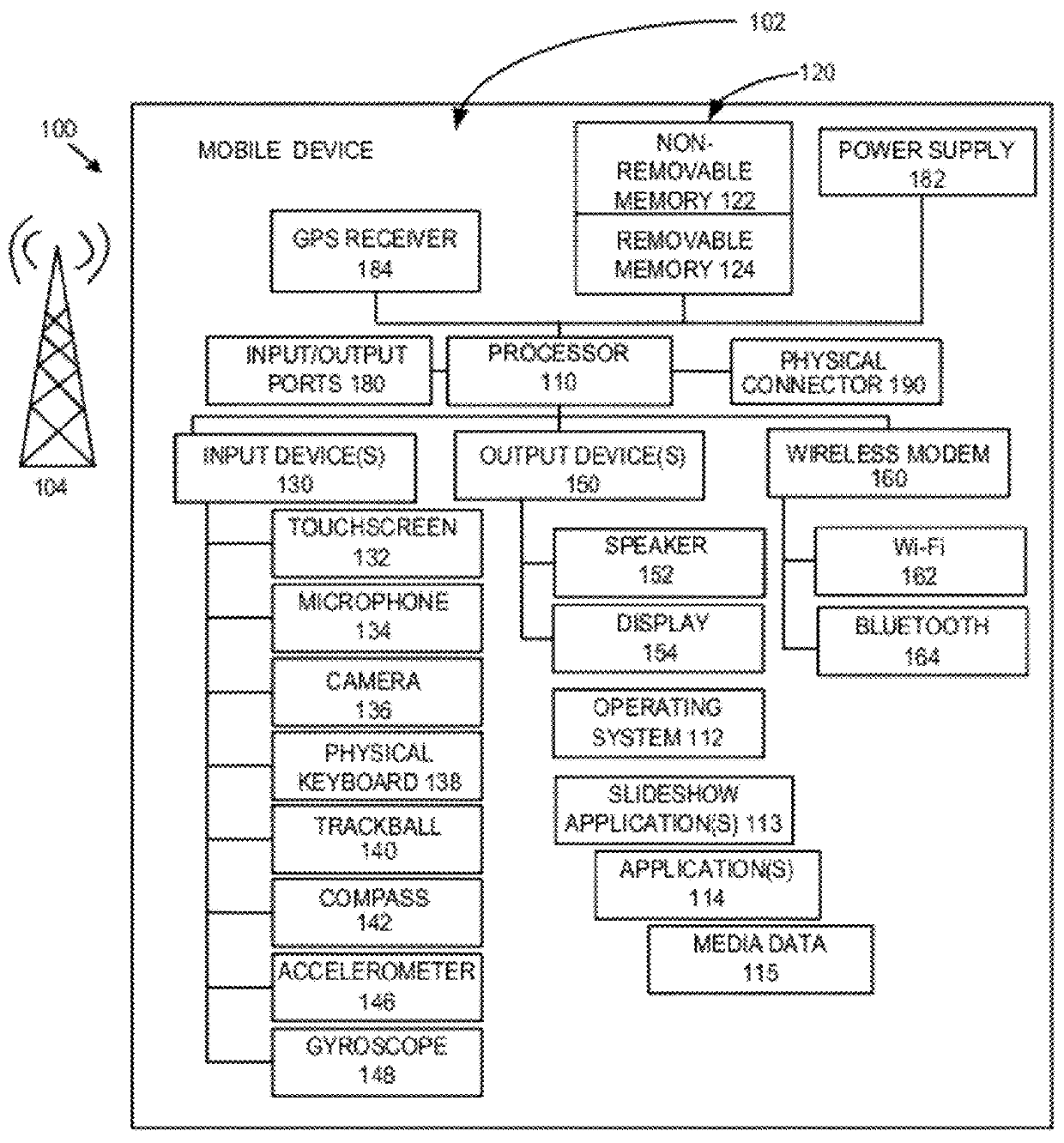
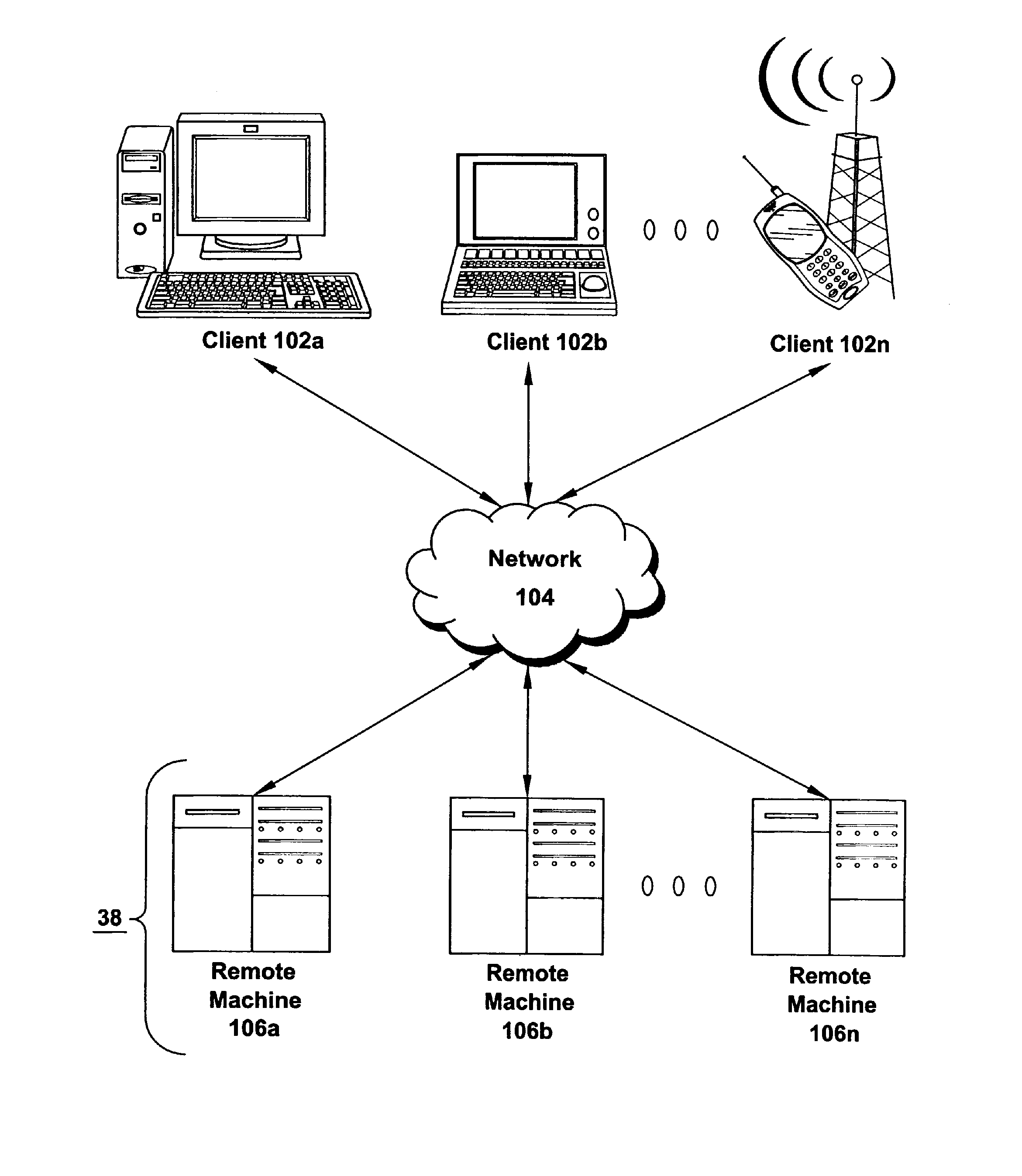
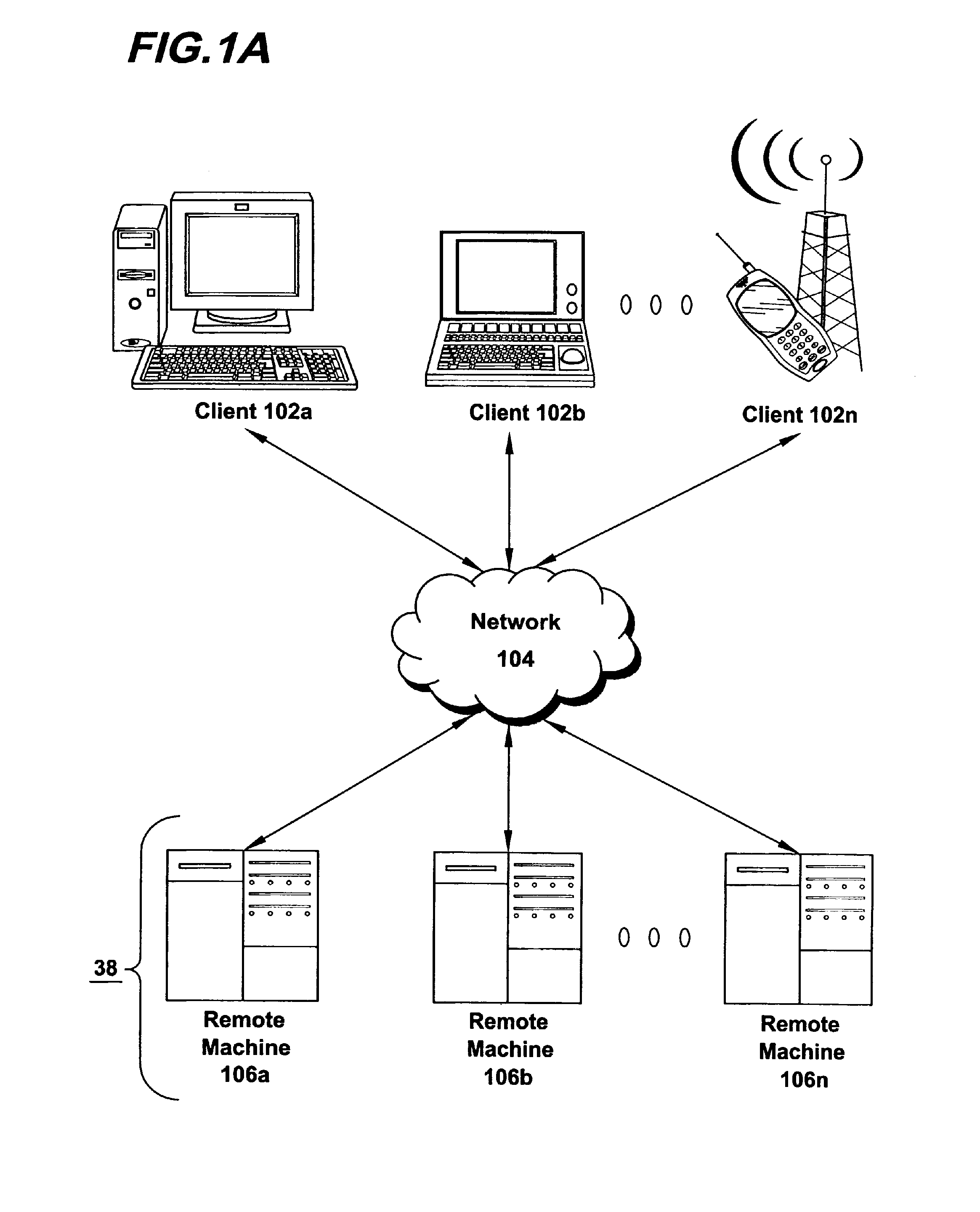
Mobile computing is human–computer interaction in which a computer is expected to be transported during normal usage, which allows for transmission of data, voice and video. Mobile computing involves mobile communication, mobile hardware, and mobile software. Communication issues include ad hoc networks and infrastructure networks as well as communication properties, protocols, data formats and concrete technologies. Hardware includes mobile devices or device components. Mobile software deals with the characteristics and requirements of mobile applications.
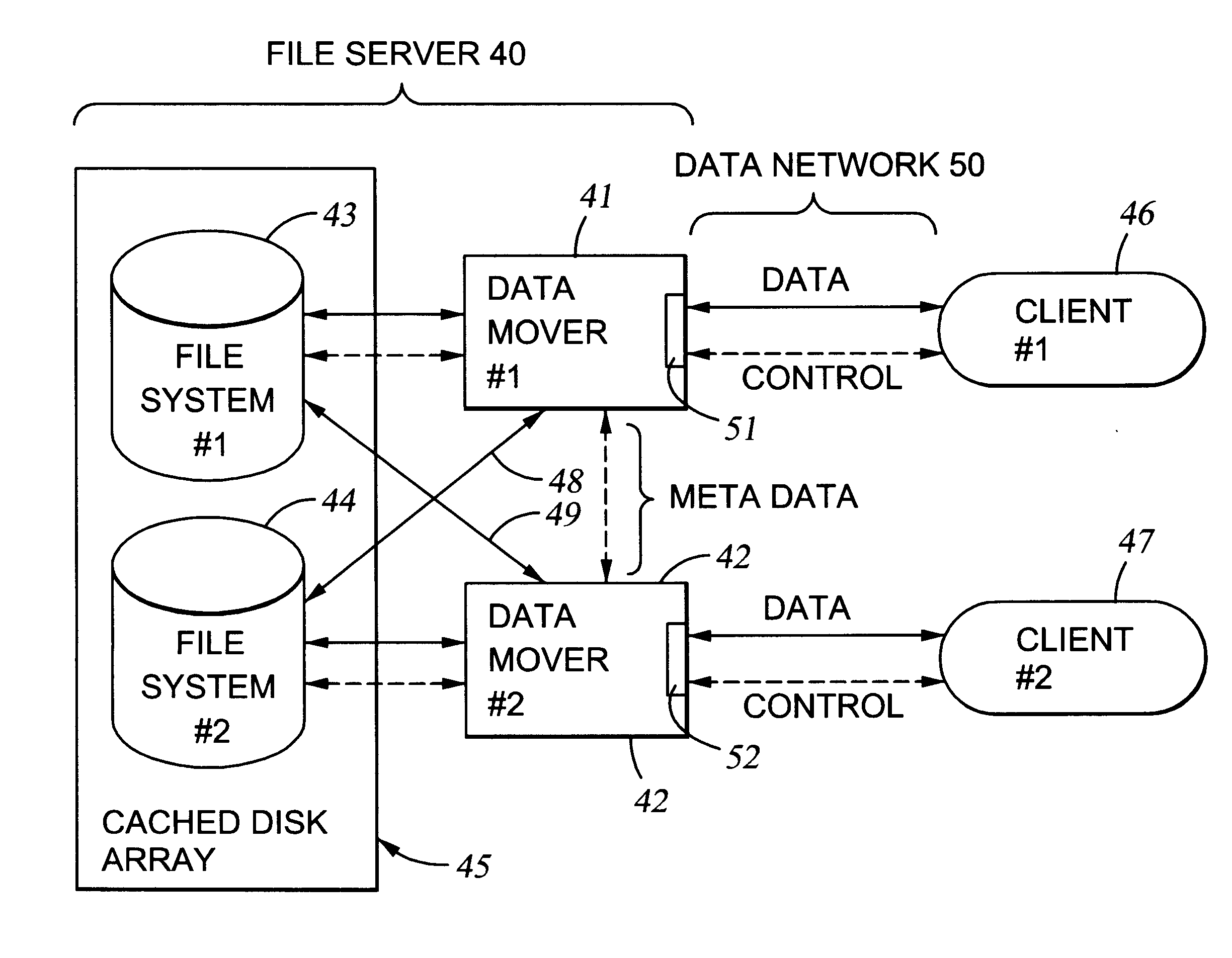
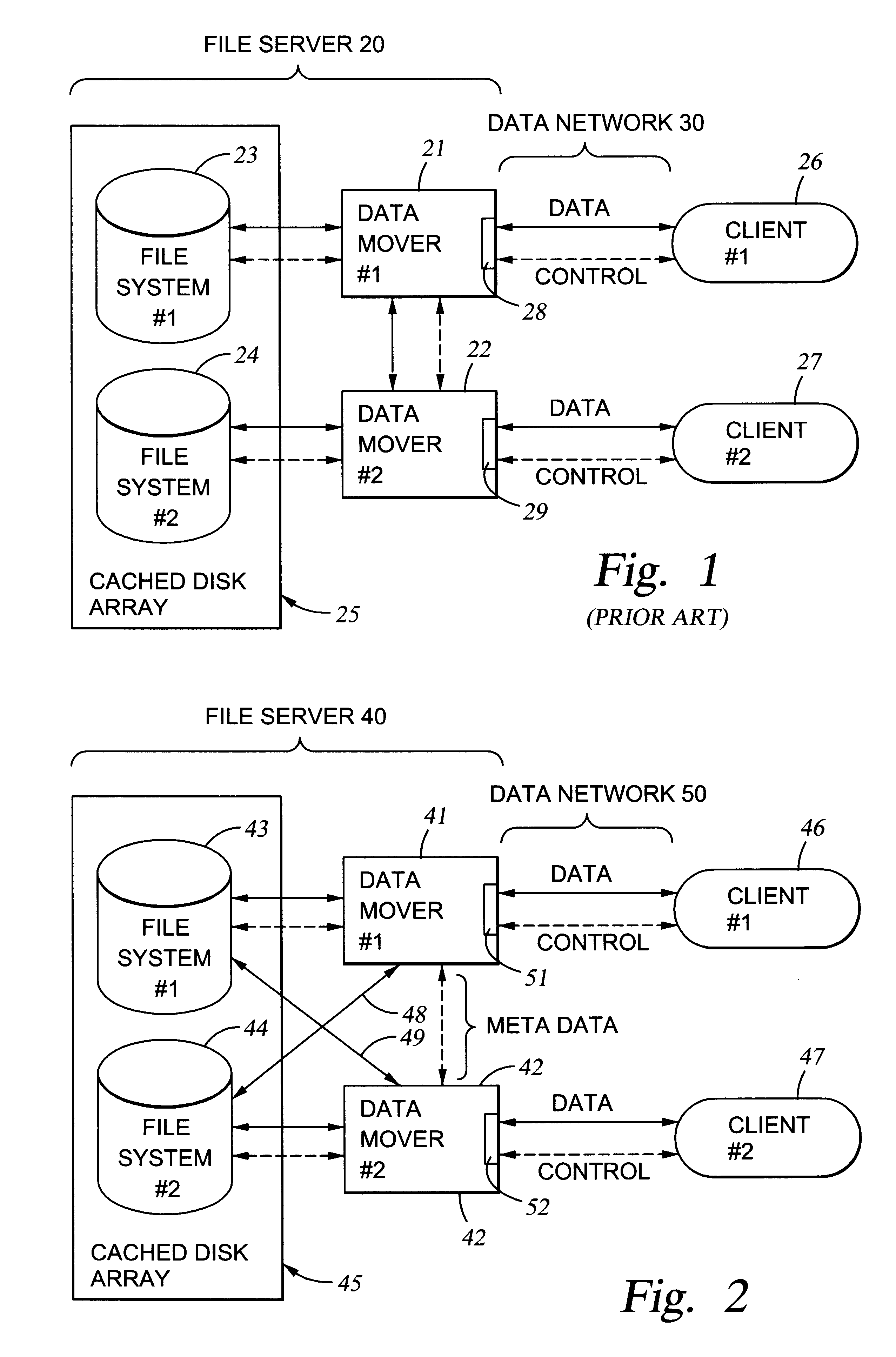
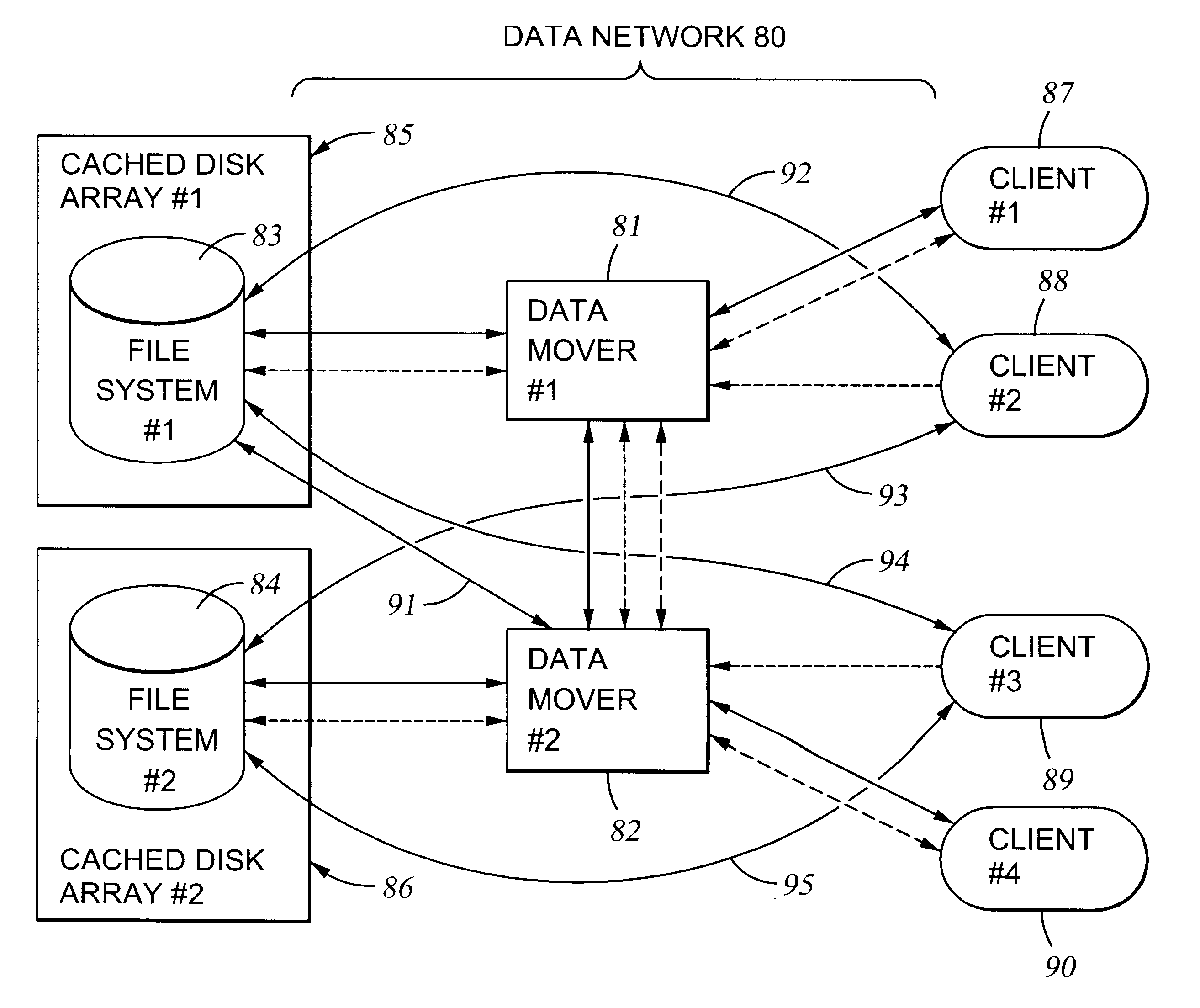
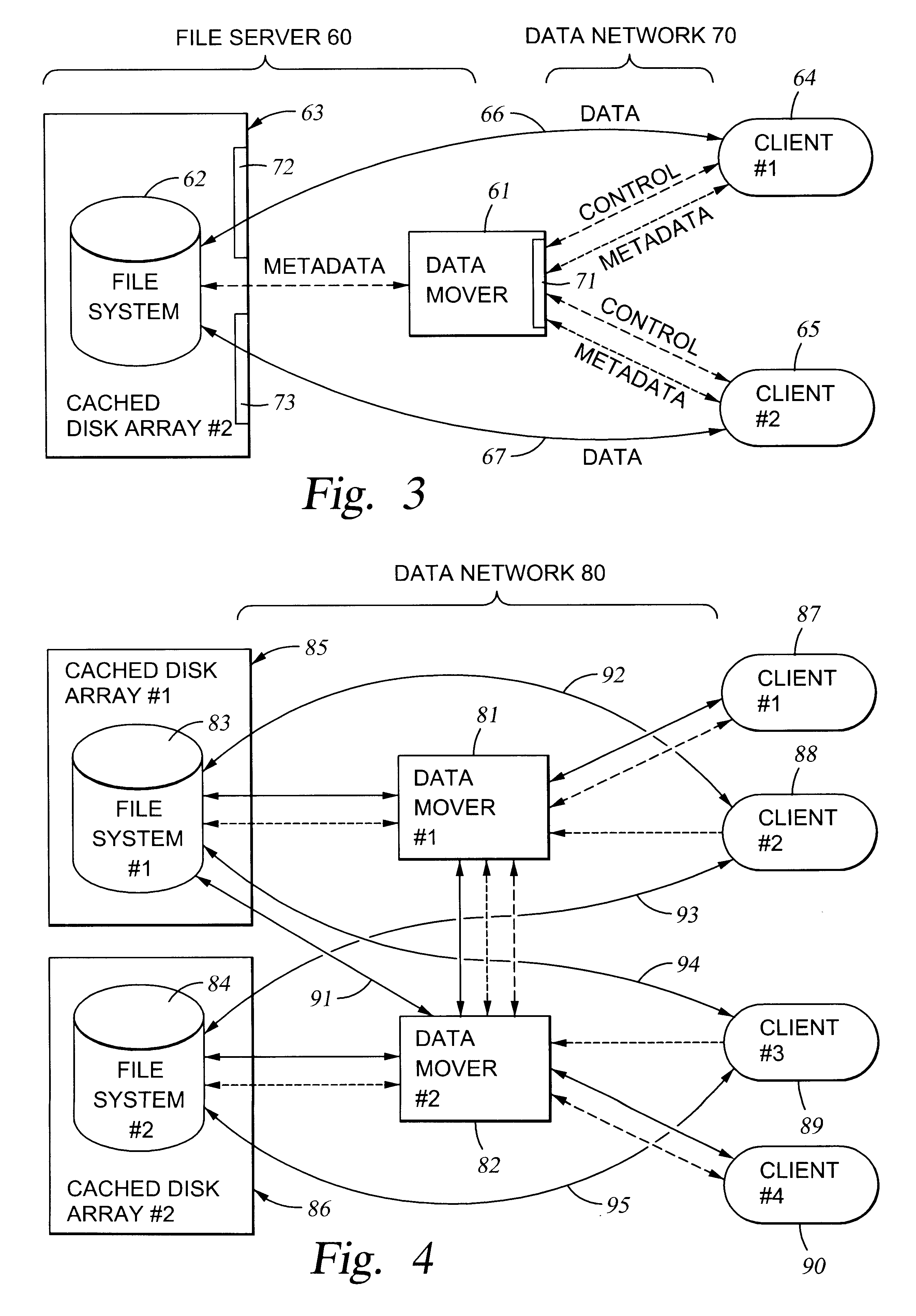
File server system using file system storage, data movers, and an exchange of meta data among data movers for file locking and direct access to shared file systems
InactiveUS6324581B1Digital data information retrievalMultiple digital computer combinationsFile systemData access
A plurality of data mover computers control access to respective file systems in data storage. A network client serviced by any of the data movers can access each of the file systems. If a data mover receives a client request for access to a file in a file system to which access is controlled by another data mover, then the data mover that received the client request sends a metadata request to the data mover that controls access to the file system. The data mover that controls access to the file system responds by placing a lock on the file and returning metadata of the file. The data mover that received the client request uses the metadata to formulate a data access command that is used to access the file data in the file system over a bypass data path that bypasses the data mover computer that controls access to the file system.
Owner:EMC IP HLDG CO LLC
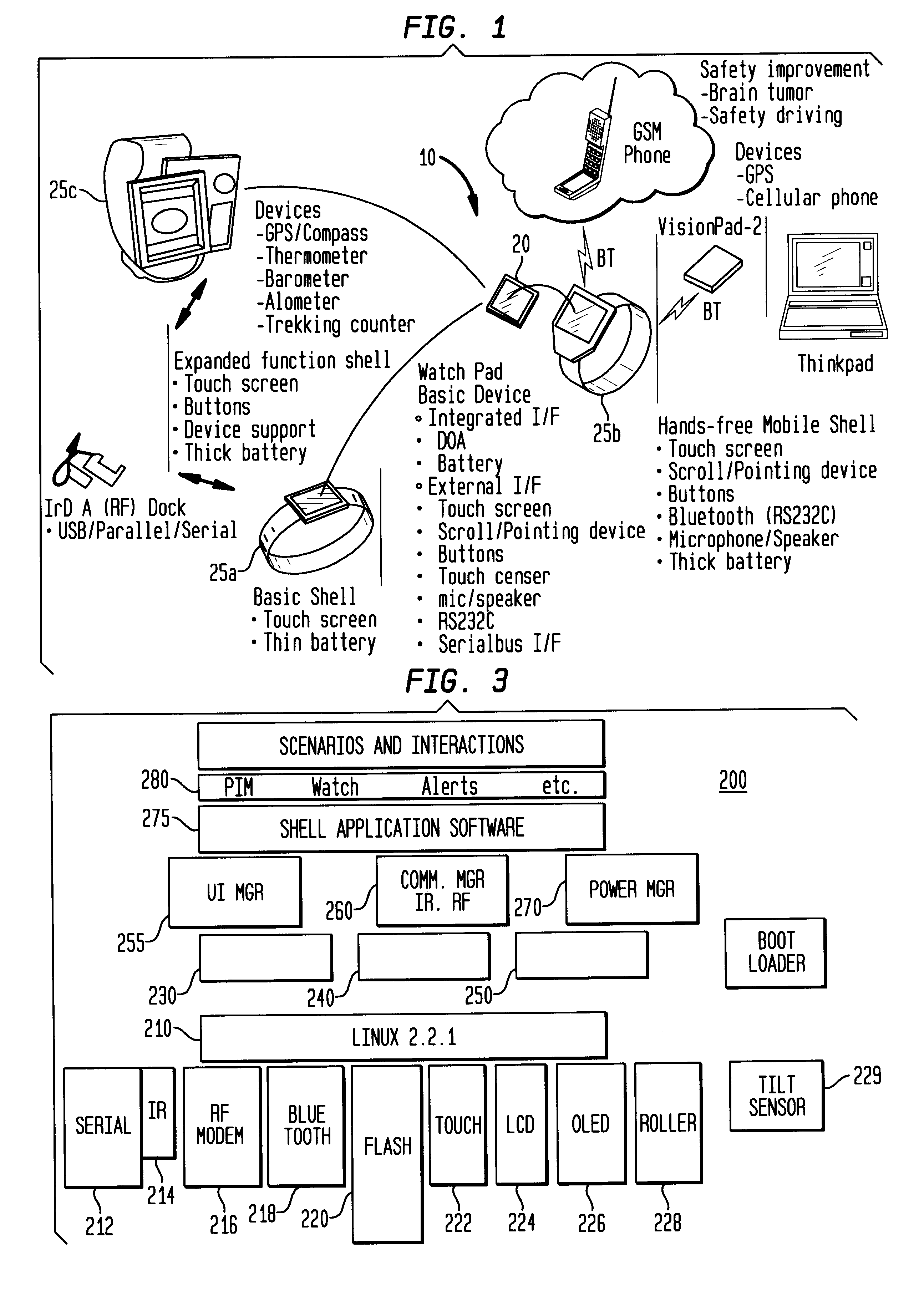
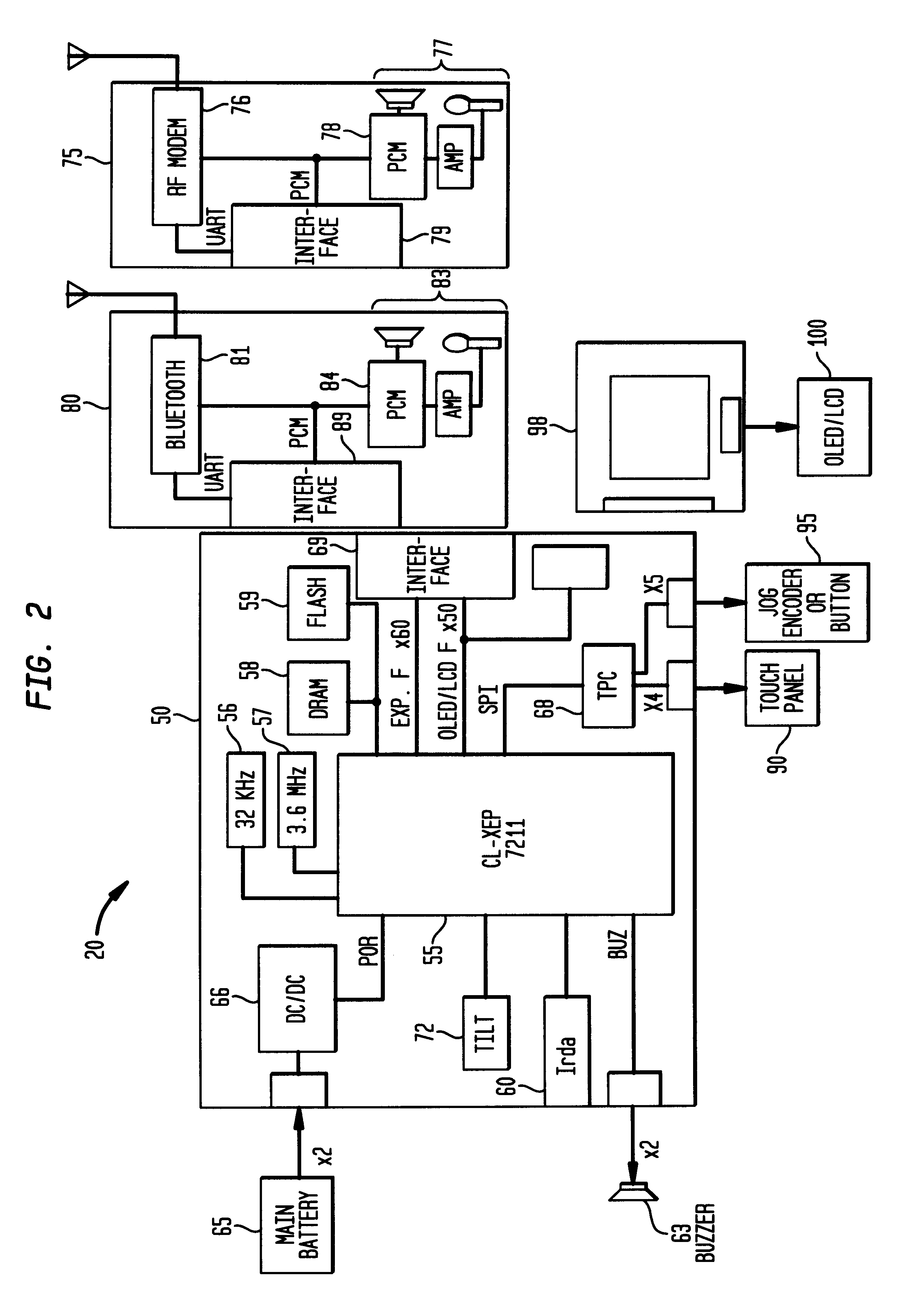
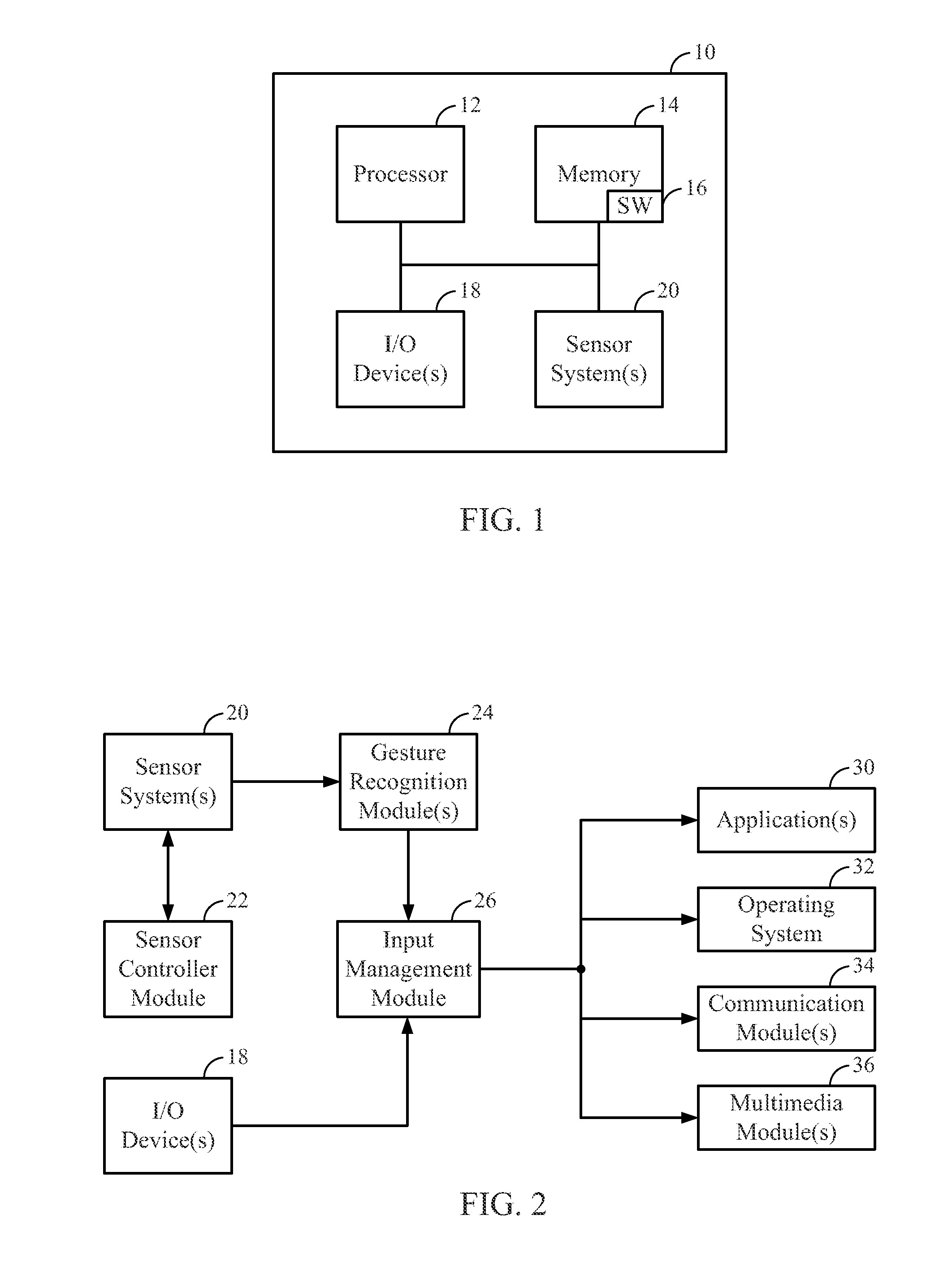
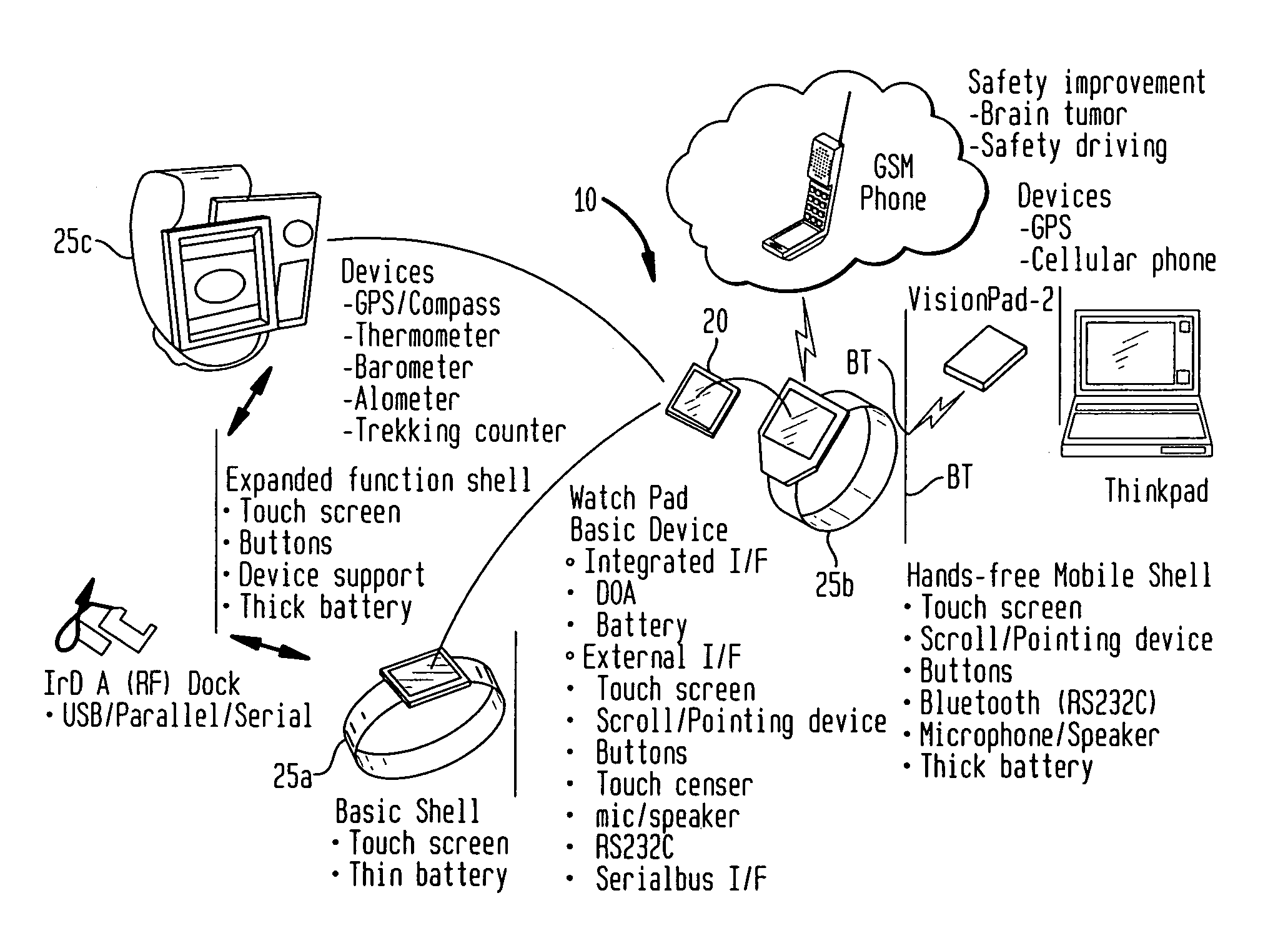
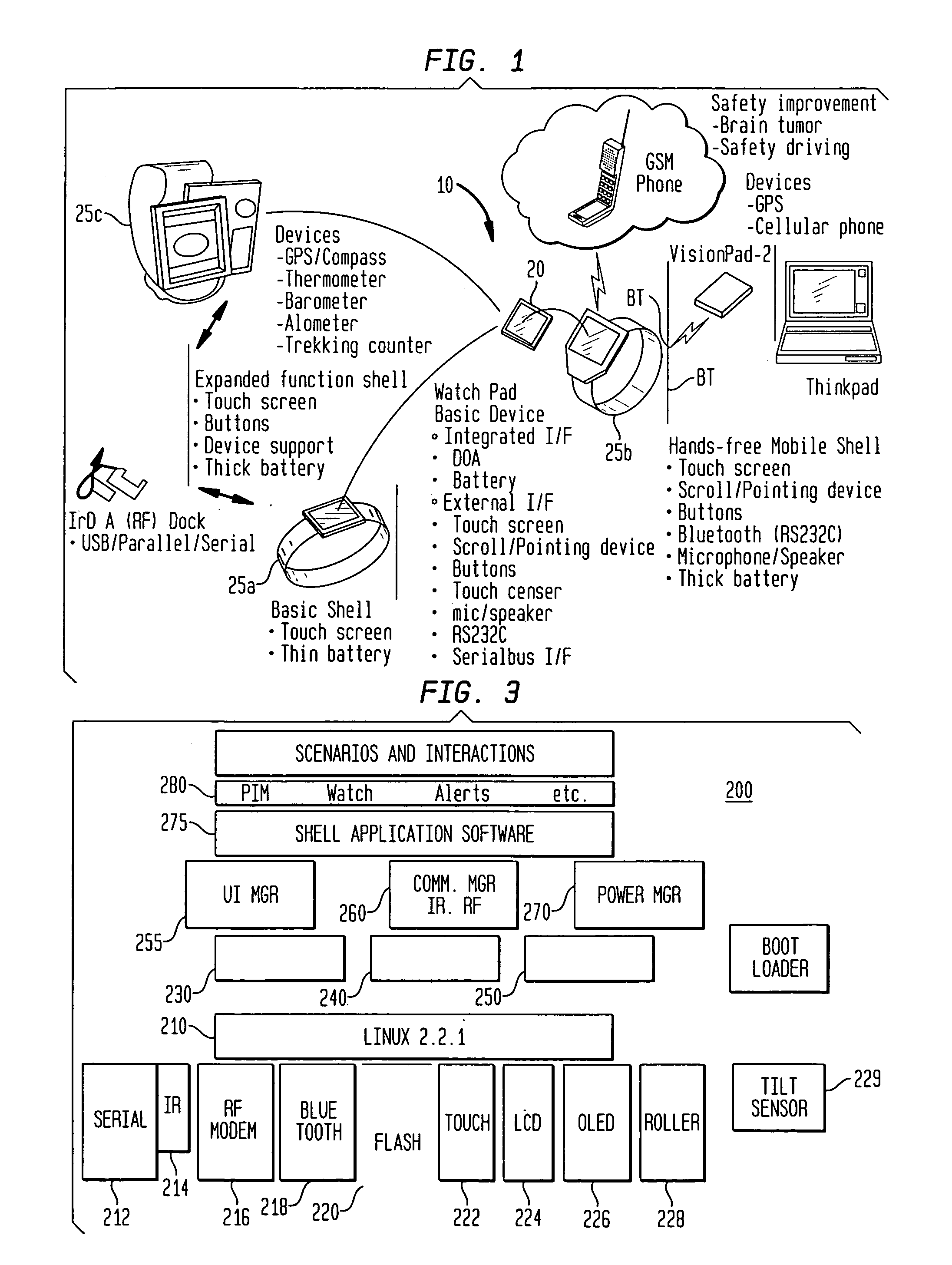
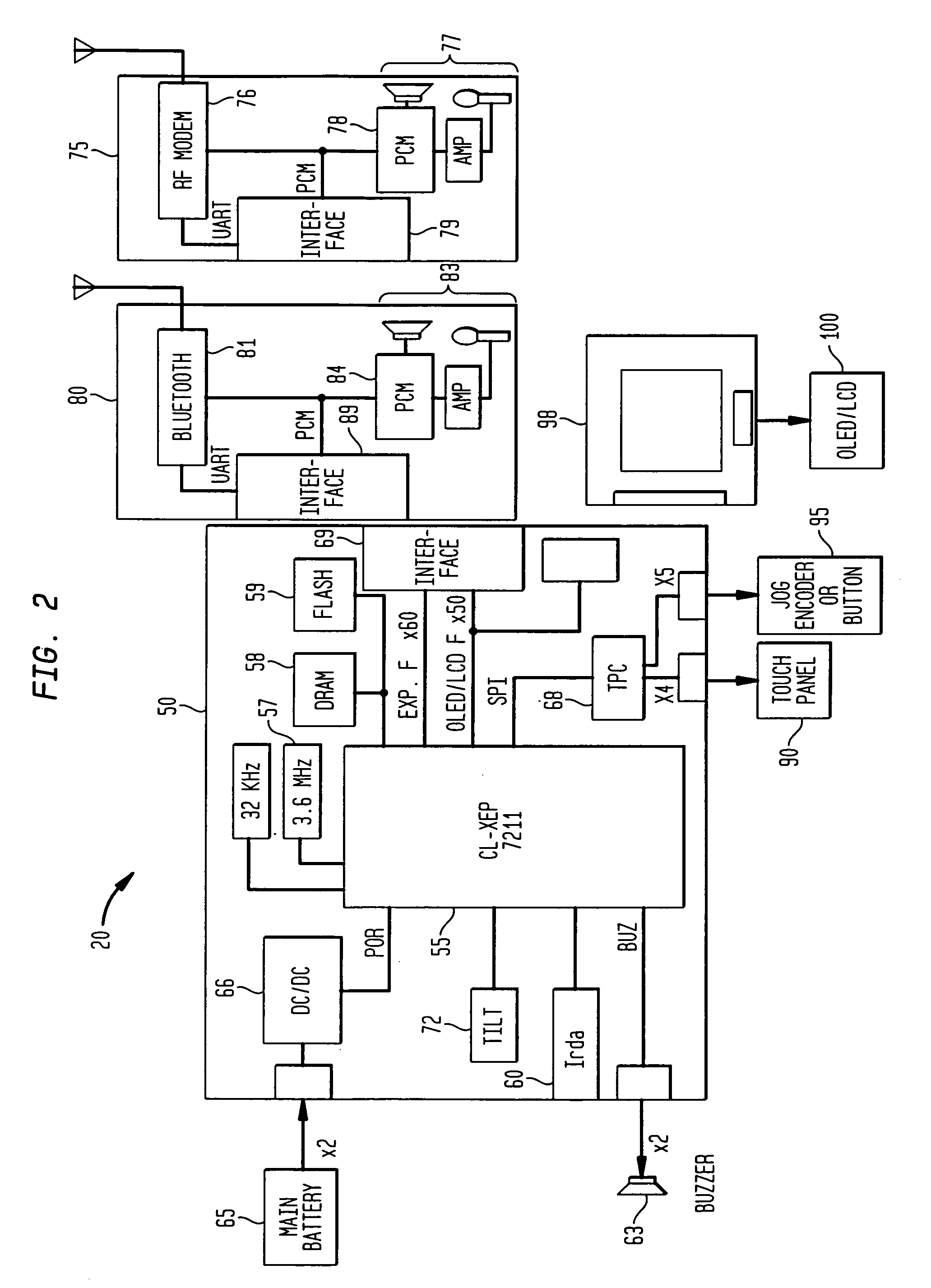
Alarm interface for a smart watch
InactiveUS6477117B1Minimal effort and concentrationVisual indicationAcoustic time signalsDisplay deviceHuman–computer interaction
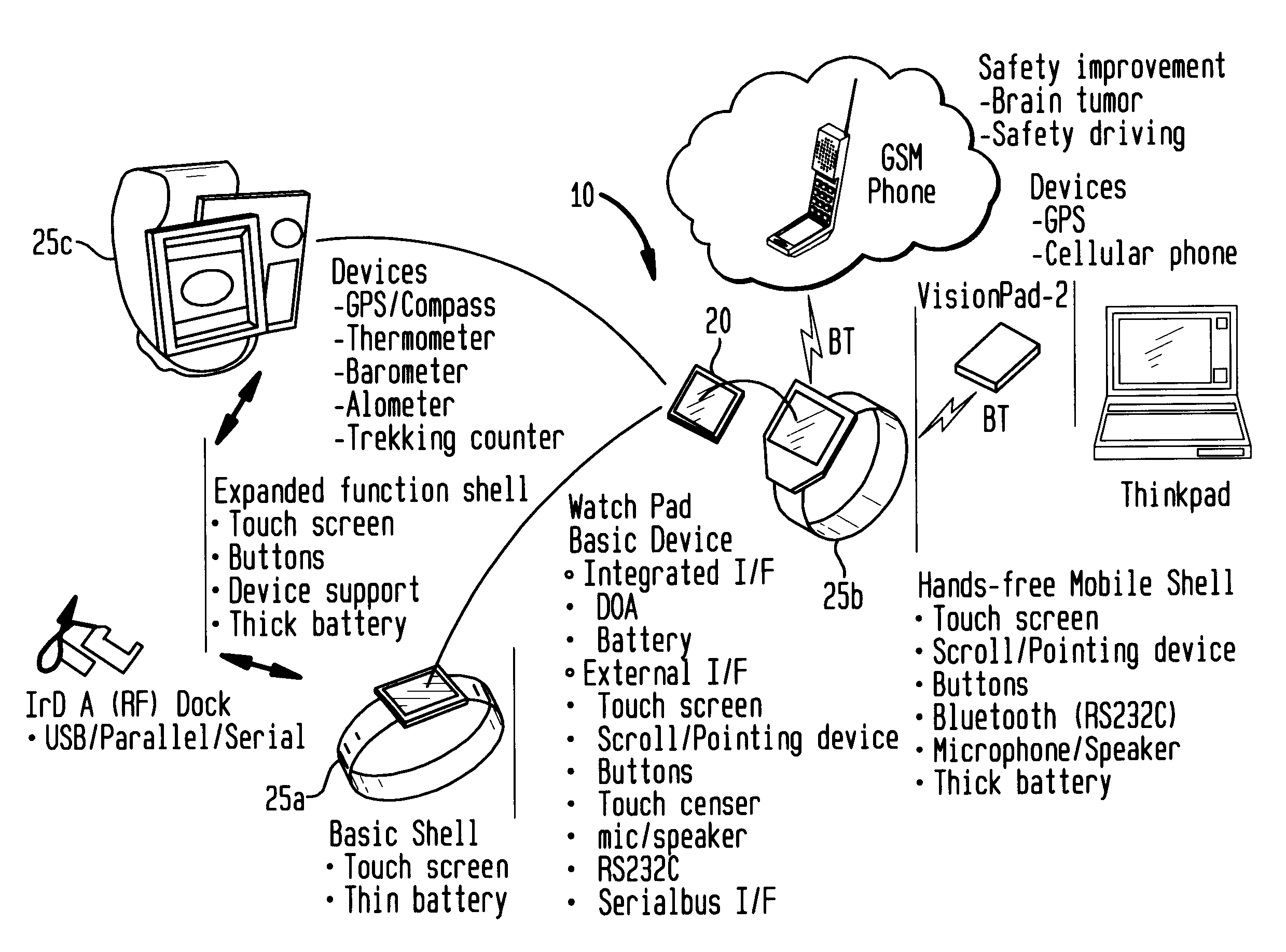
A wearable mobile computing device / appliance (a wrist watch) with a high resolution display that is capable of wirelessly accessing information from a network and a variety of other devices. The mobile computing device / appliance includes a user interface that is used to efficiently interact with alarms and notifications on the watch.
Owner:IBM CORP
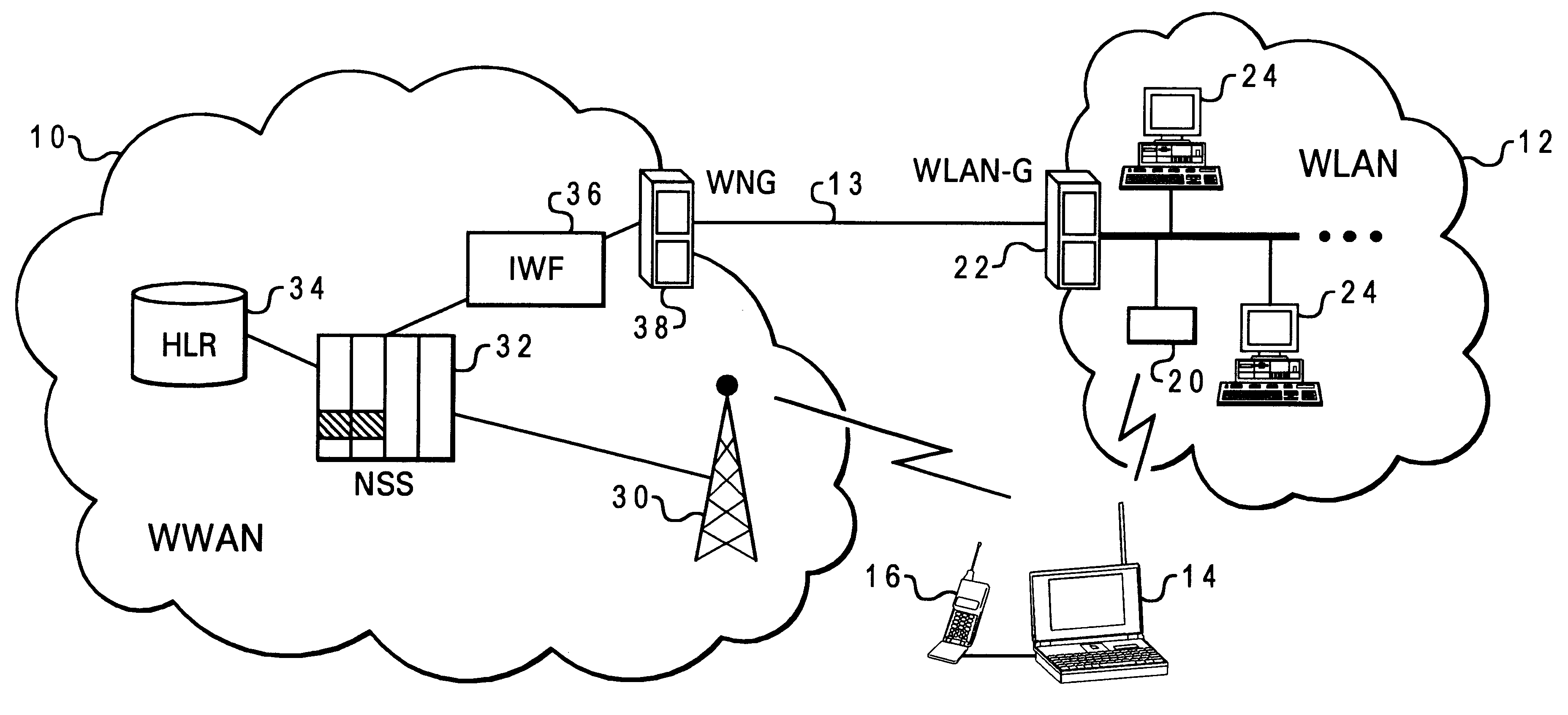
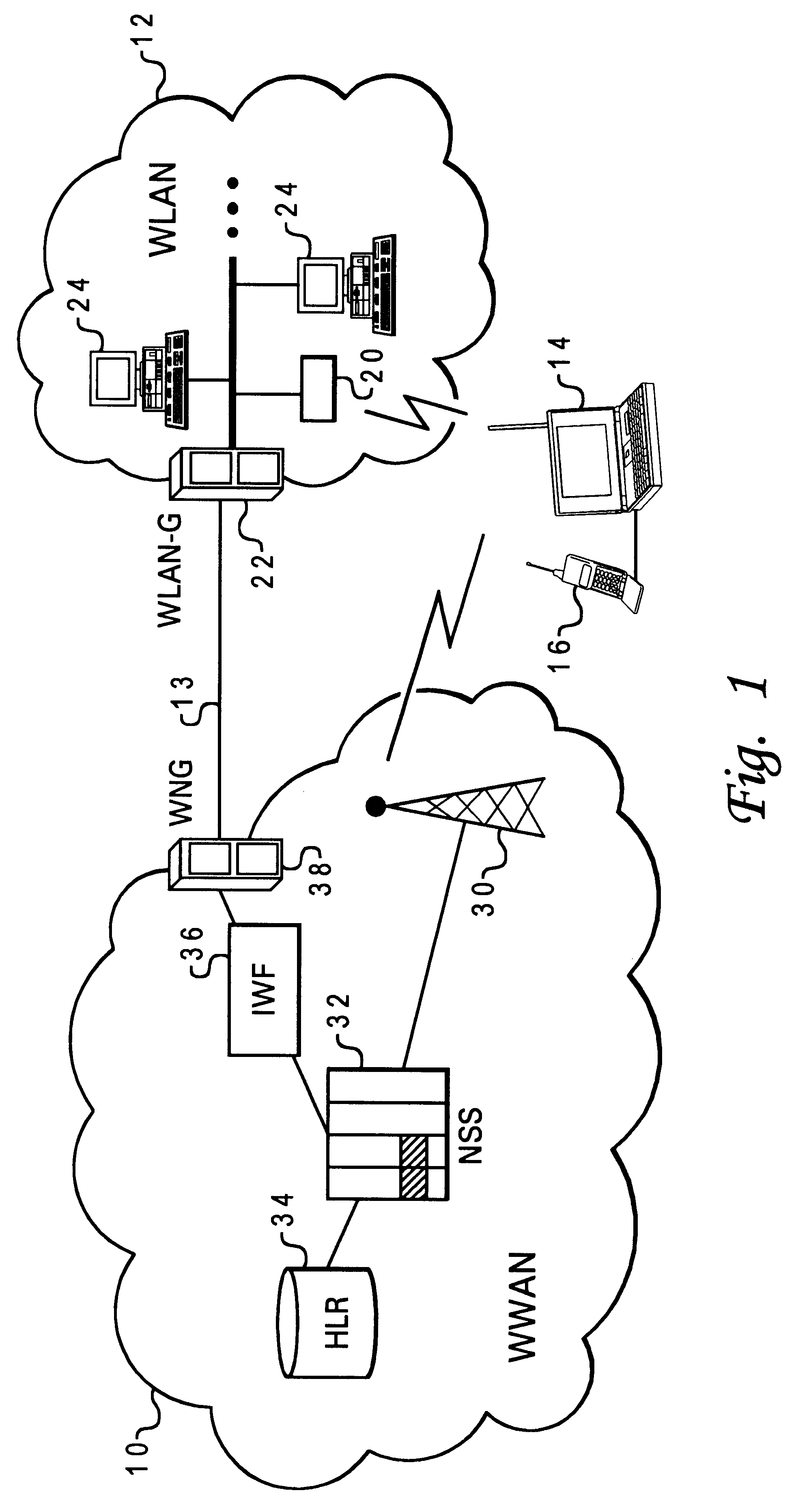
Method and system for seamless roaming between wireless communication networks with a mobile terminal
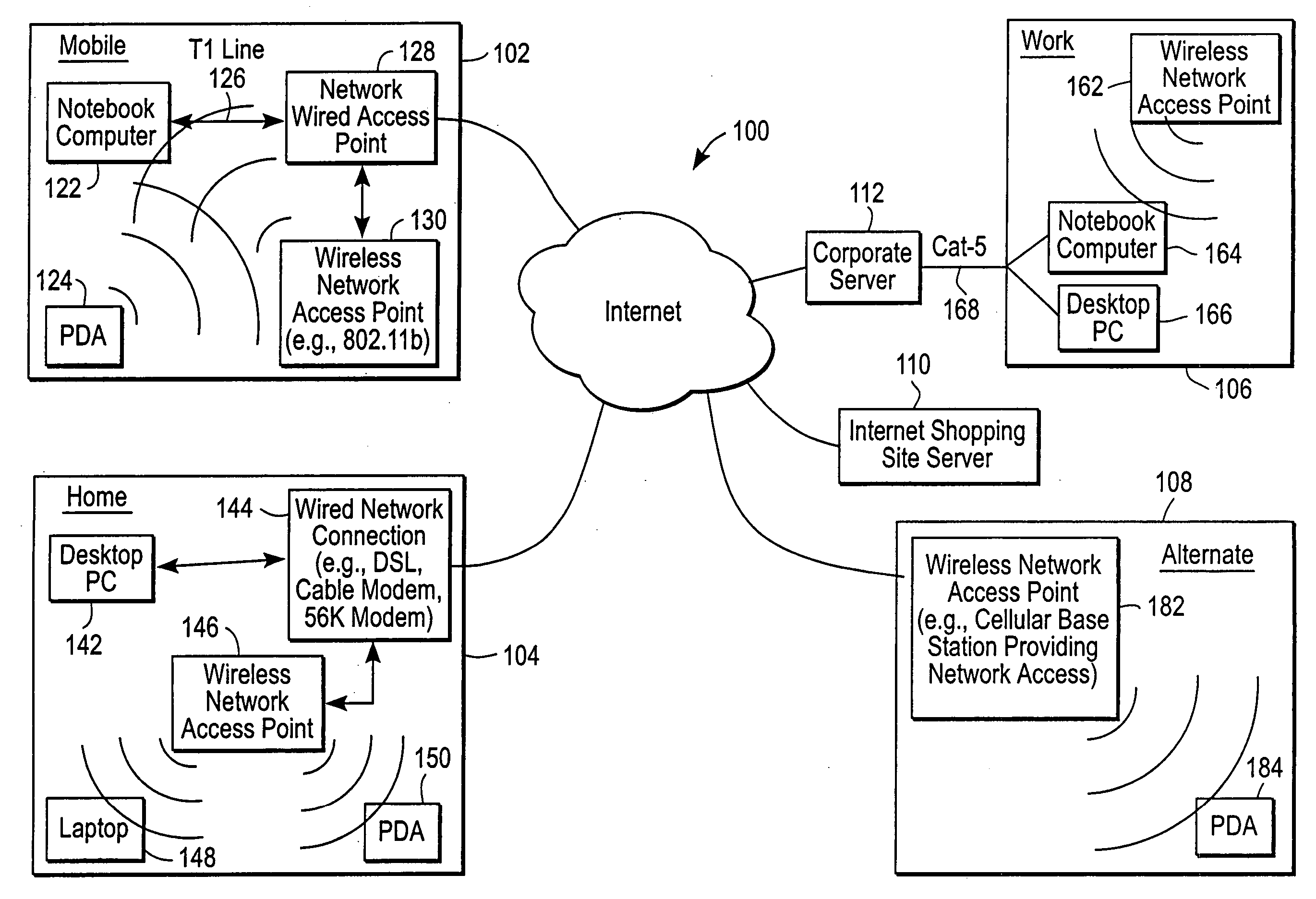
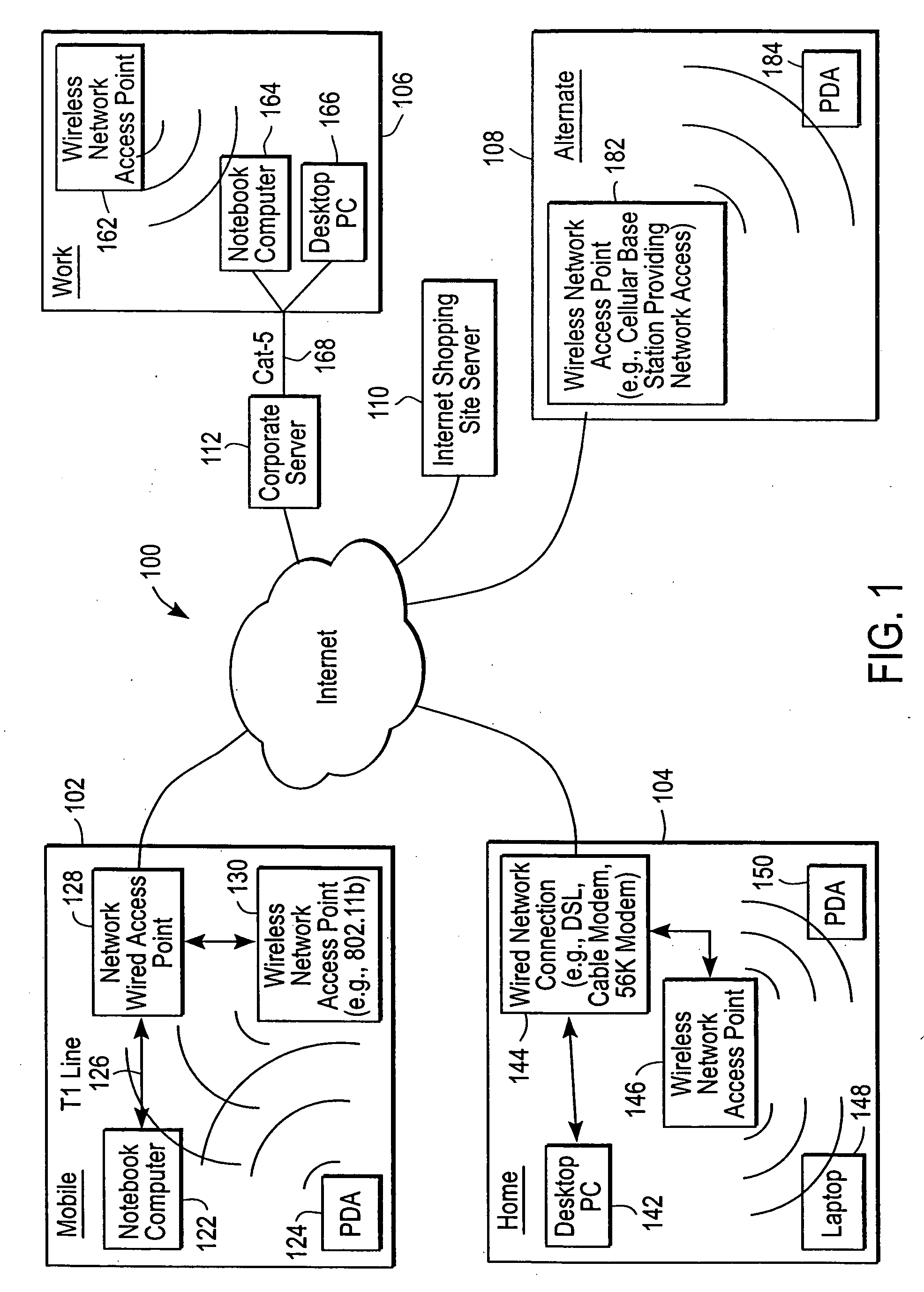
A mobile computer system capable of seamless roaming between wireless communication networks includes data processing resources for executing software, a plurality of wireless interfaces that supports simultaneous wireless connections with first and second wireless communication networks, and a network access arbitrator that routes data communicated between the software executed by the data processing resources and the first and second wireless communication networks. To permit seamless roaming, the network access arbitrator routes the data to the first wireless communication network via a first wireless interface and then seamlessly reroutes the data to a second wireless communication network via a second wireless interface. According to one embodiment, the network access arbitrator reroutes the data in response to the data bandwidths of the connections with the first and second wireless communication networks.
Owner:NORTEL NETWORKS LTD
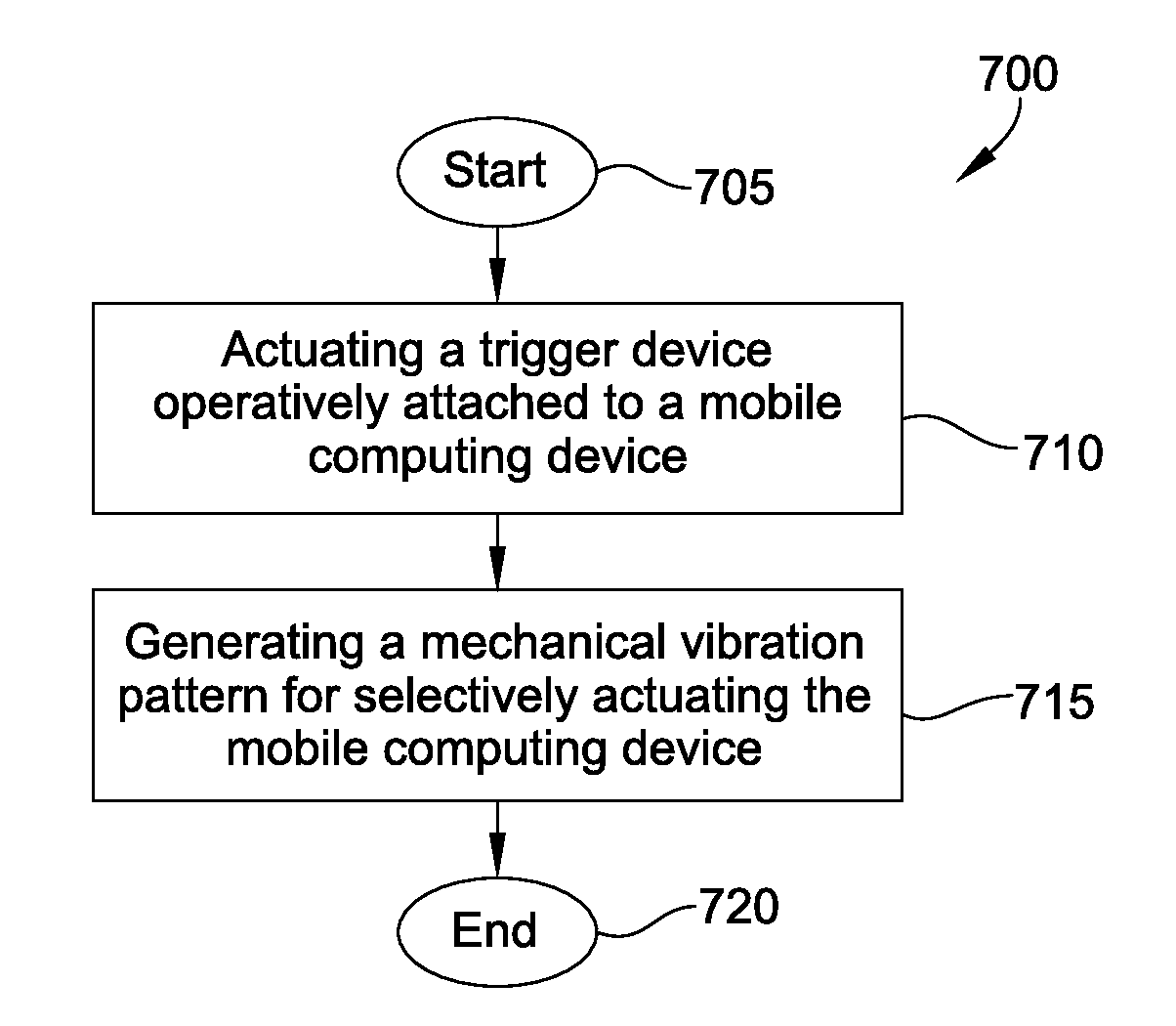
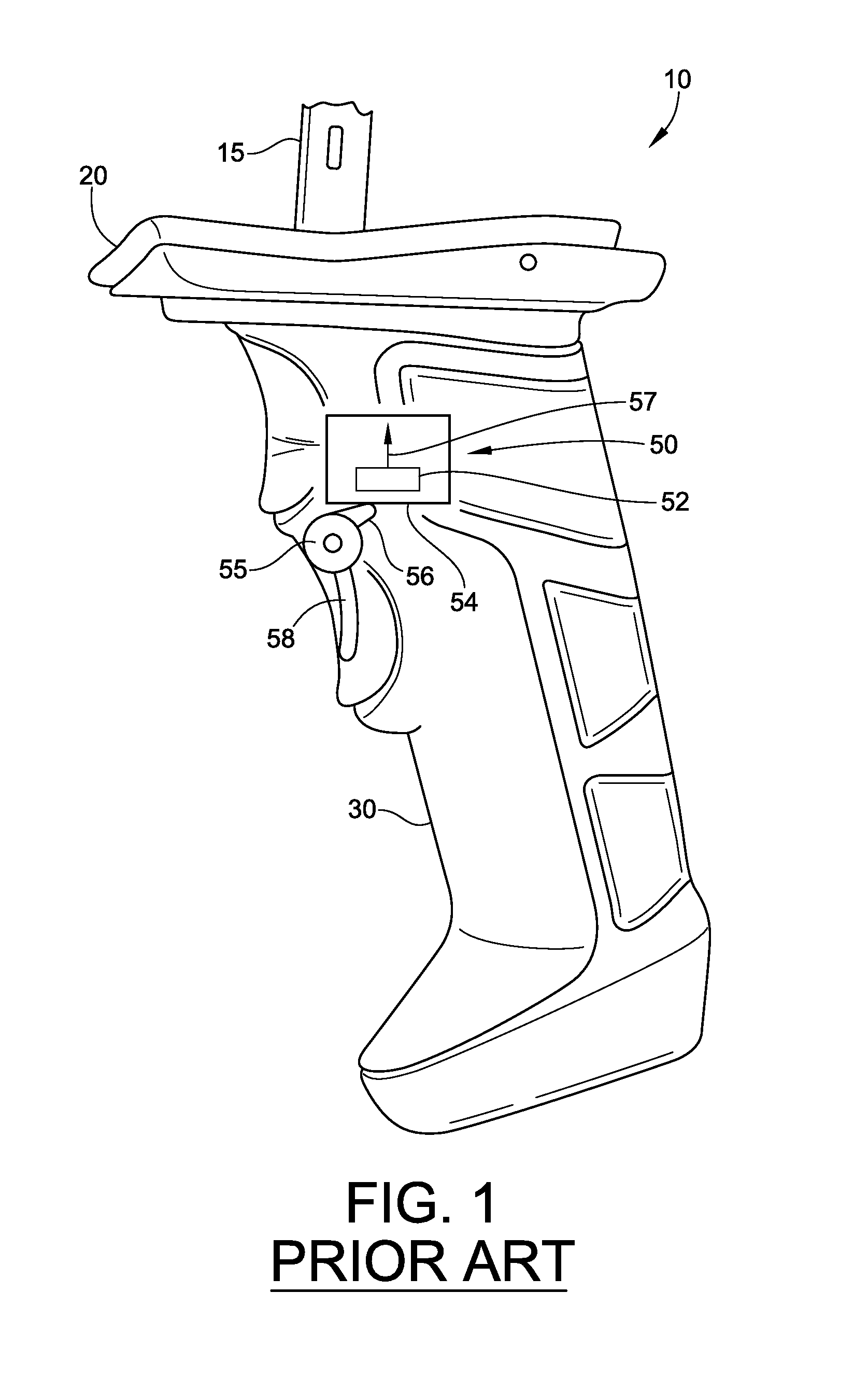
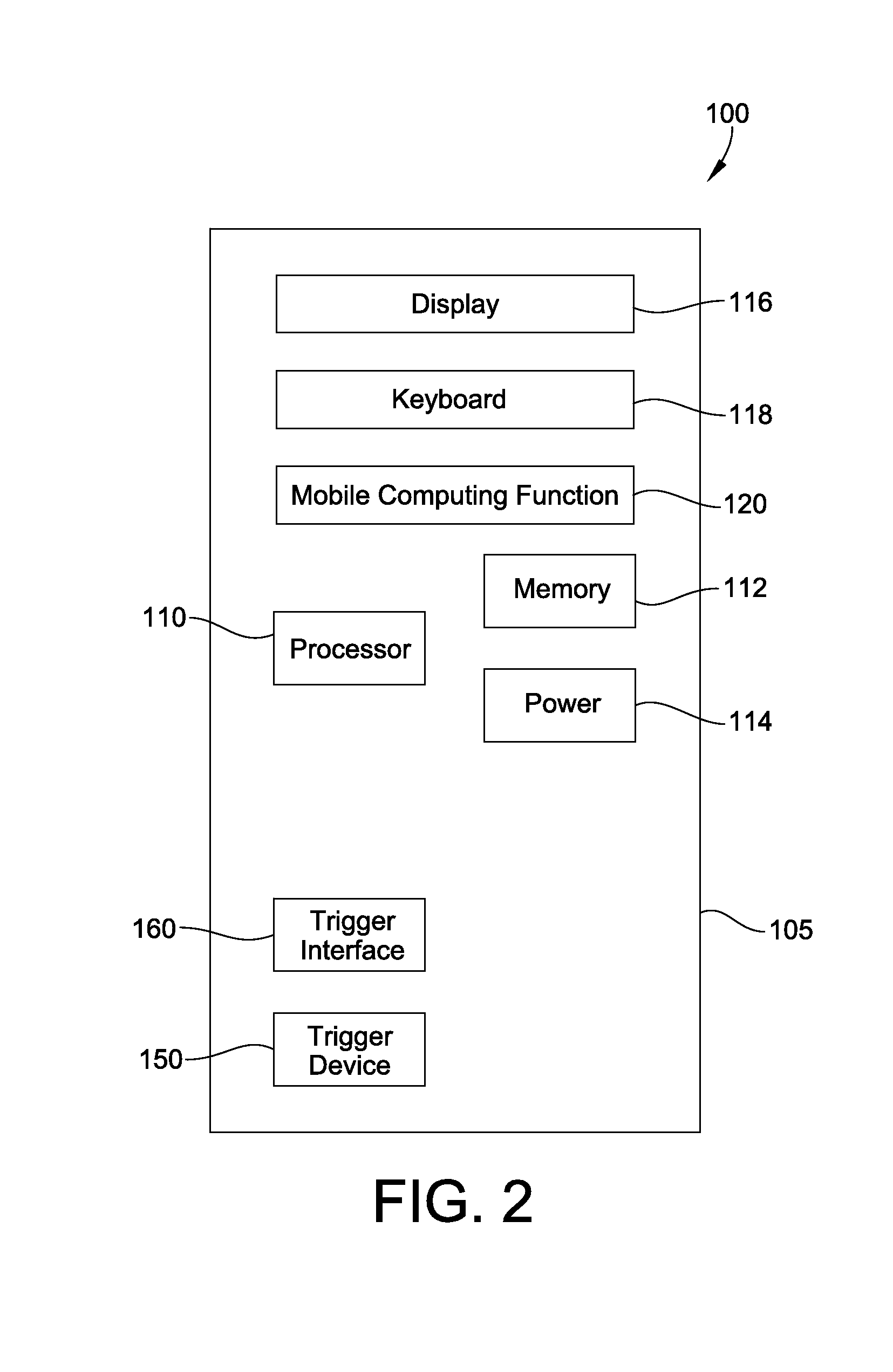
Trigger device for mobile computing device
InactiveUS20140049120A1Controlling membersManual control with multiple controlled membersAccelerometerComputer science
A mobile computing device includes a processor and a trigger device operatively attached to the mobile computing device and configured to generate a mechanical vibration pattern for selectively actuating the mobile computing device. A trigger interface, illustratively an accelerometer, is configured to convert the mechanical vibration pattern into an electrical signal pattern. The processor is configured to actuate a mobile computing function depending on the mechanical vibration pattern generated by the trigger device. A table of properties stored in memory correlates the mechanical vibration generated by the trigger device with a specific mobile computing function. The trigger device may include a plurality of trigger parts; and the mechanical vibration pattern generated by the trigger device may include multiple bits of data generated by the plurality of trigger parts. The mobile computing device may be in a candy bar, clam shell, or other form factor and may include a removable handle.
Owner:INTERMEC IP
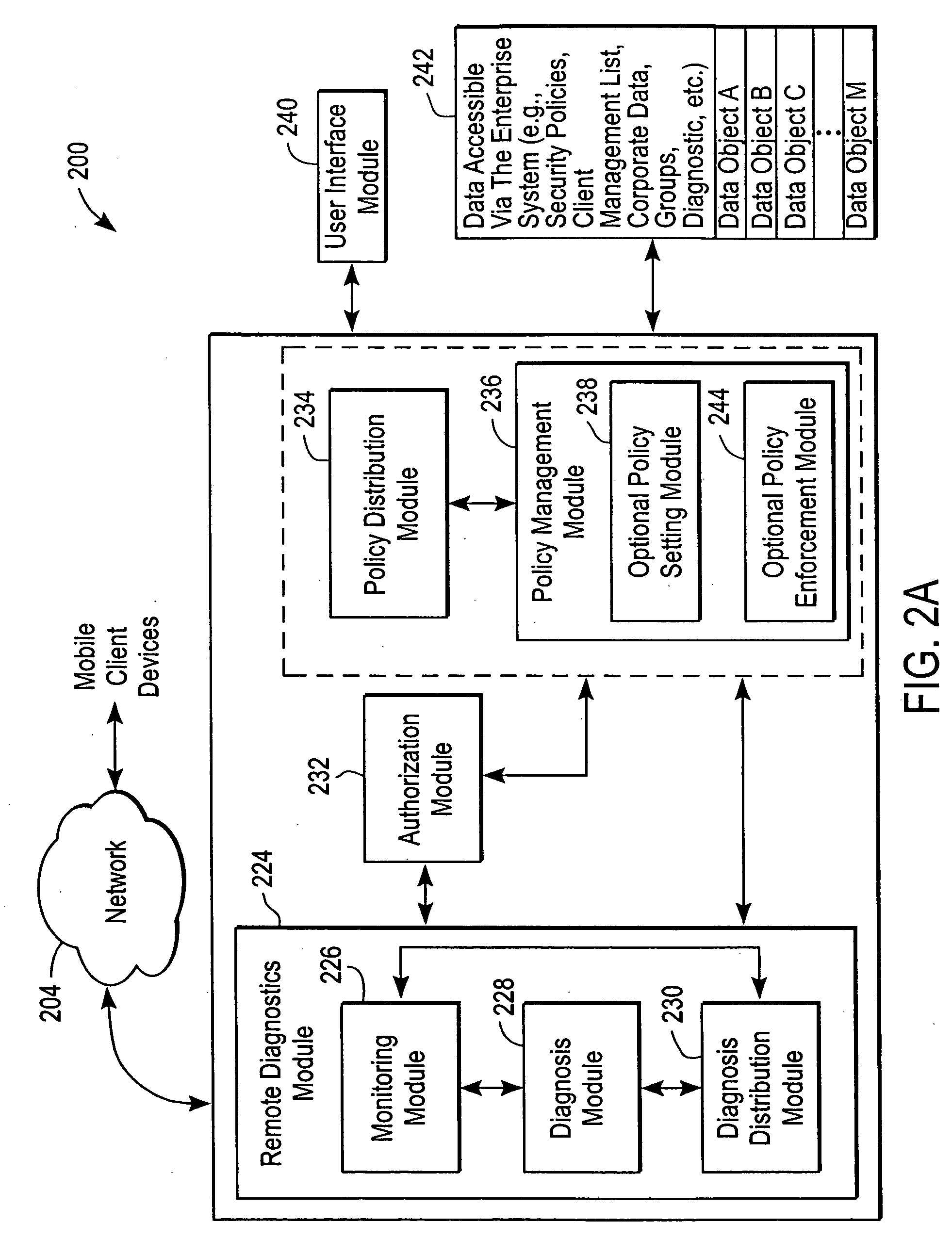
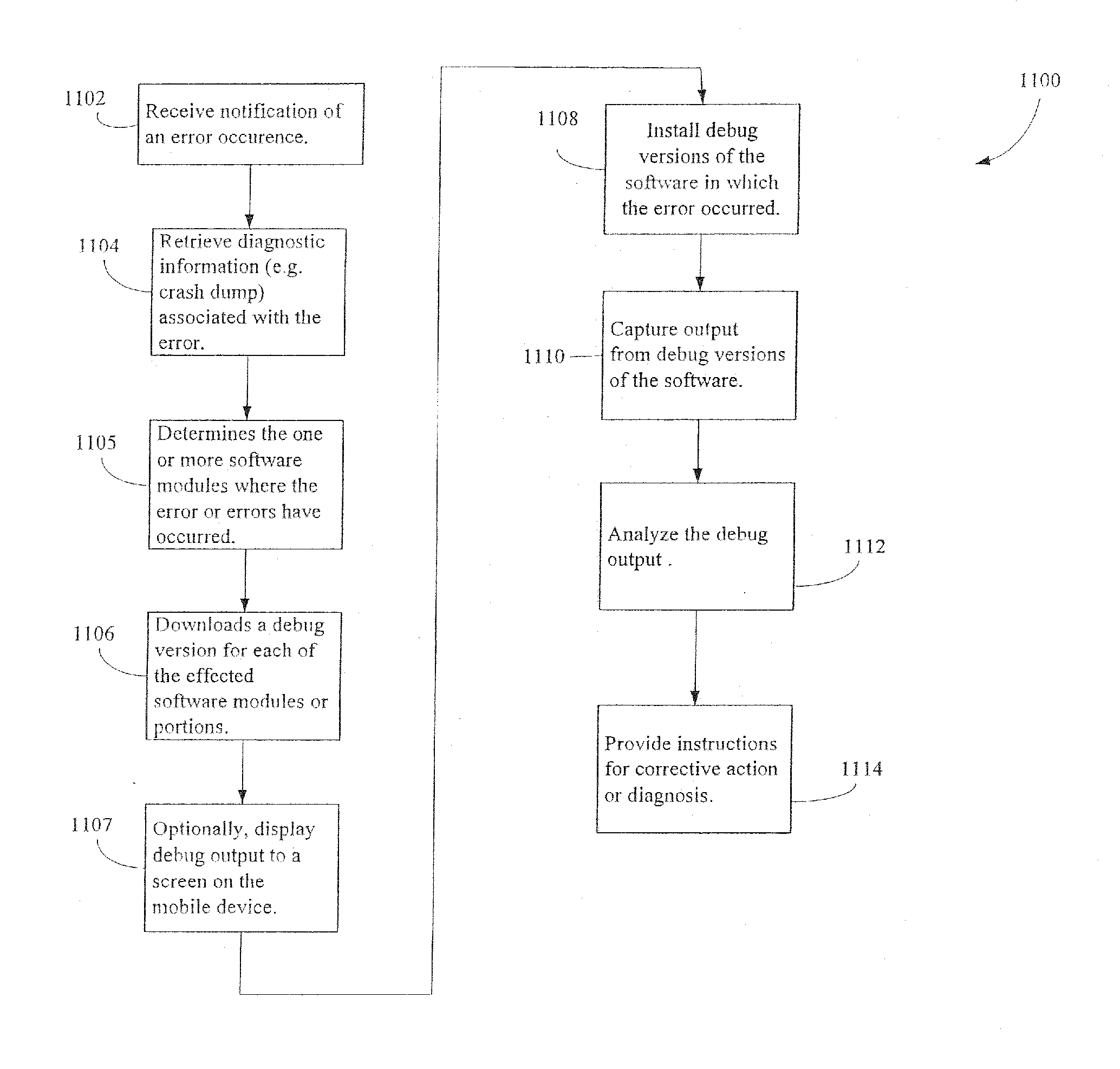
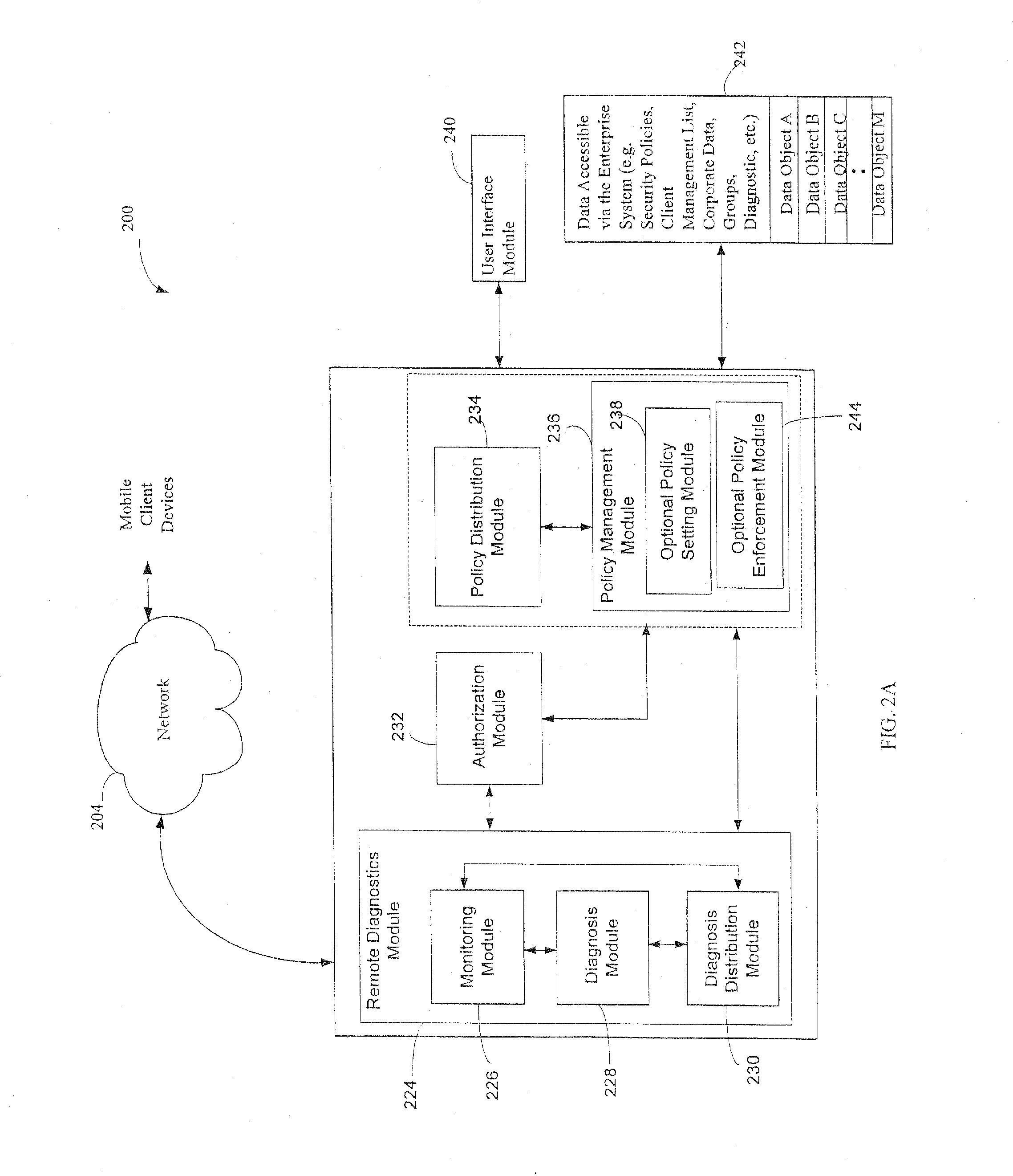
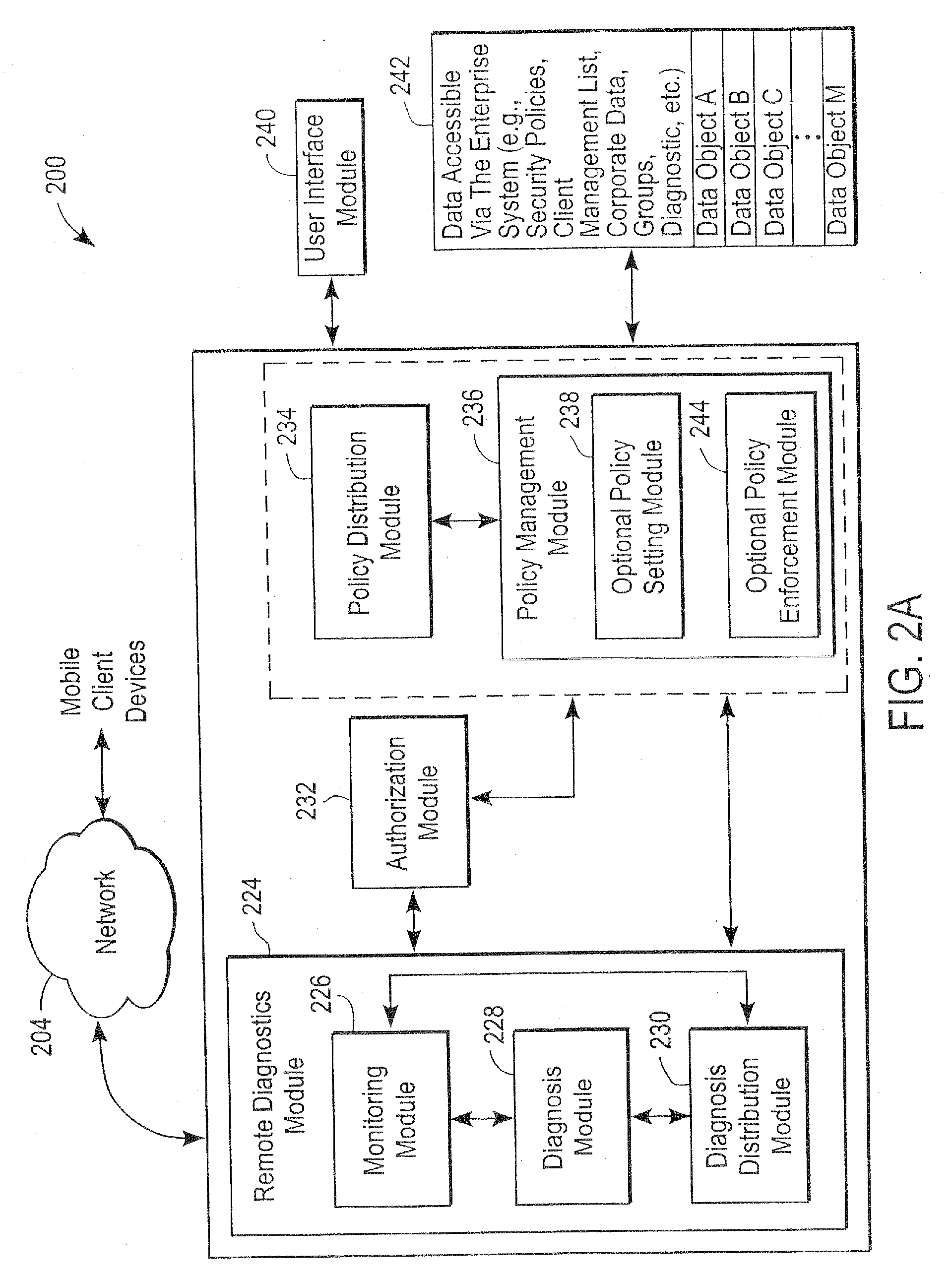
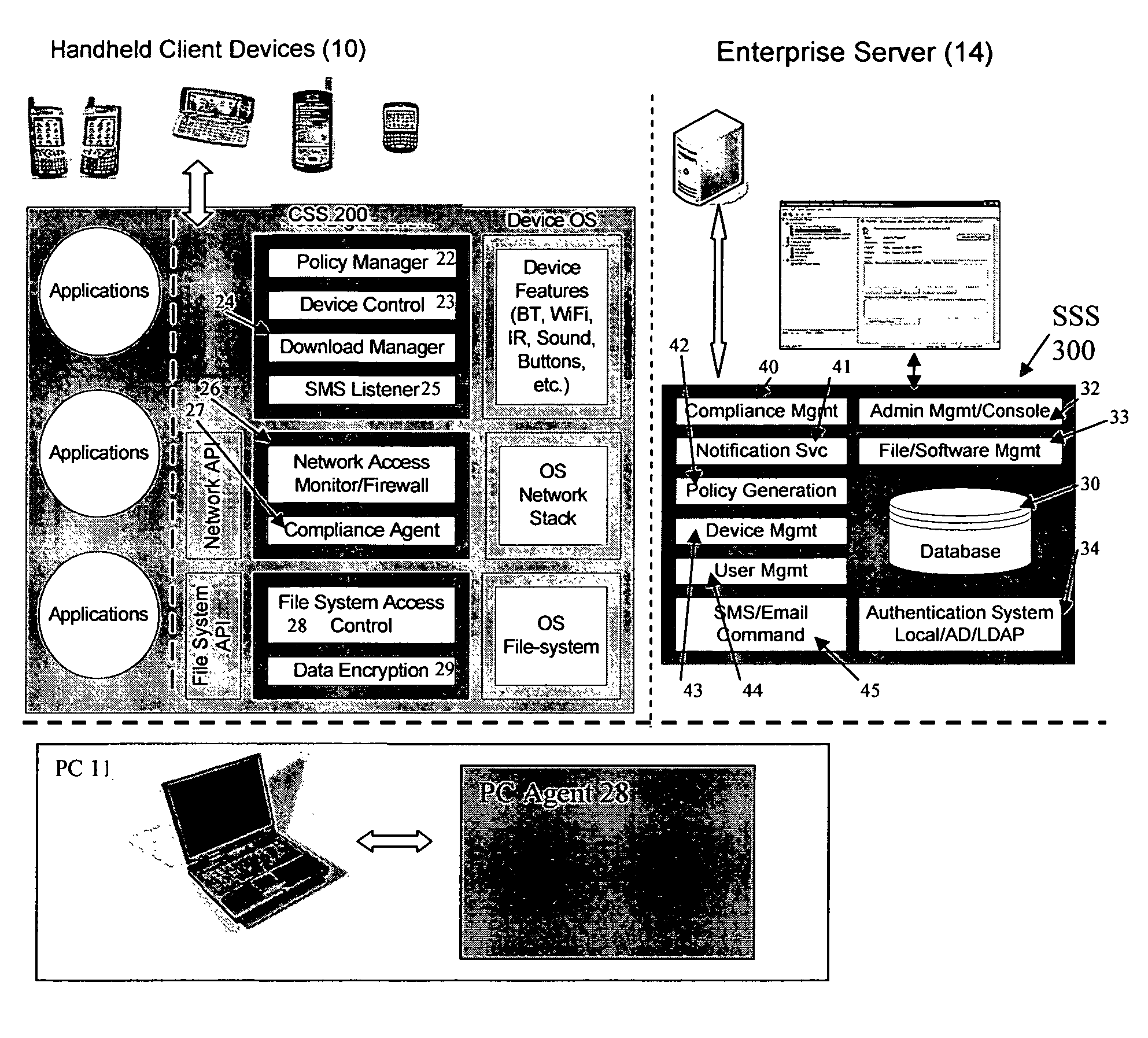
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Distributed sensing techniques for mobile devices
ActiveUS20050093868A1Input/output for user-computer interactionServices signallingHuman–computer interactionMobile device
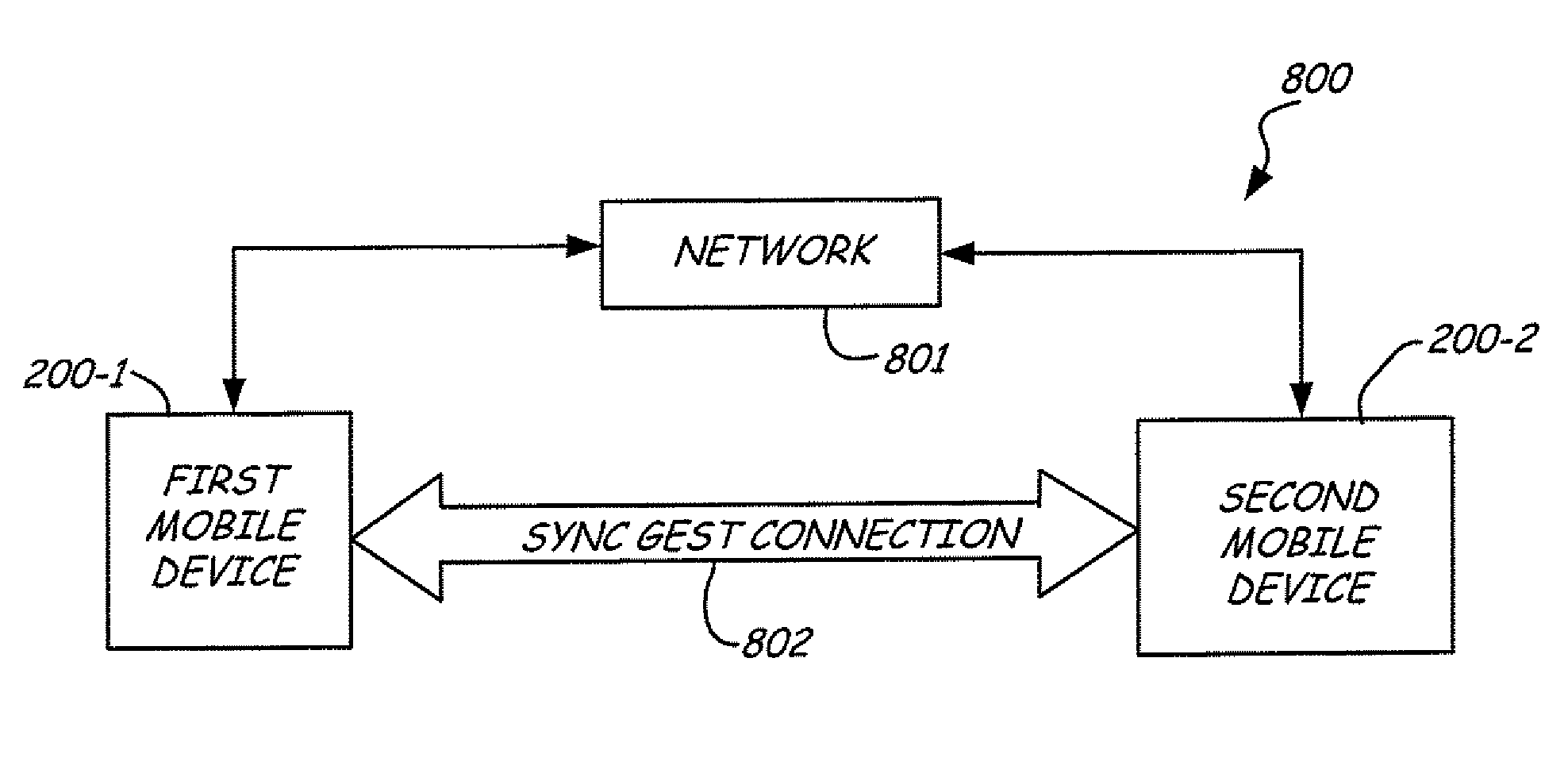
Methods and apparatus of the invention allow the coordination of resources of mobile computing devices to jointly execute tasks. In the method, a first gesture input is received at a first mobile computing device. A second gesture input is received at a second mobile computing device. In response, a determination is made as to whether the first and second gesture inputs form one of a plurality of different synchronous gesture types. If it is determined that the first and second gesture inputs form the one of the plurality of different synchronous gesture types, then resources of the first and second mobile computing devices are combined to jointly execute a particular task associated with the one of the plurality of different synchronous gesture types.
Owner:MICROSOFT TECH LICENSING LLC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
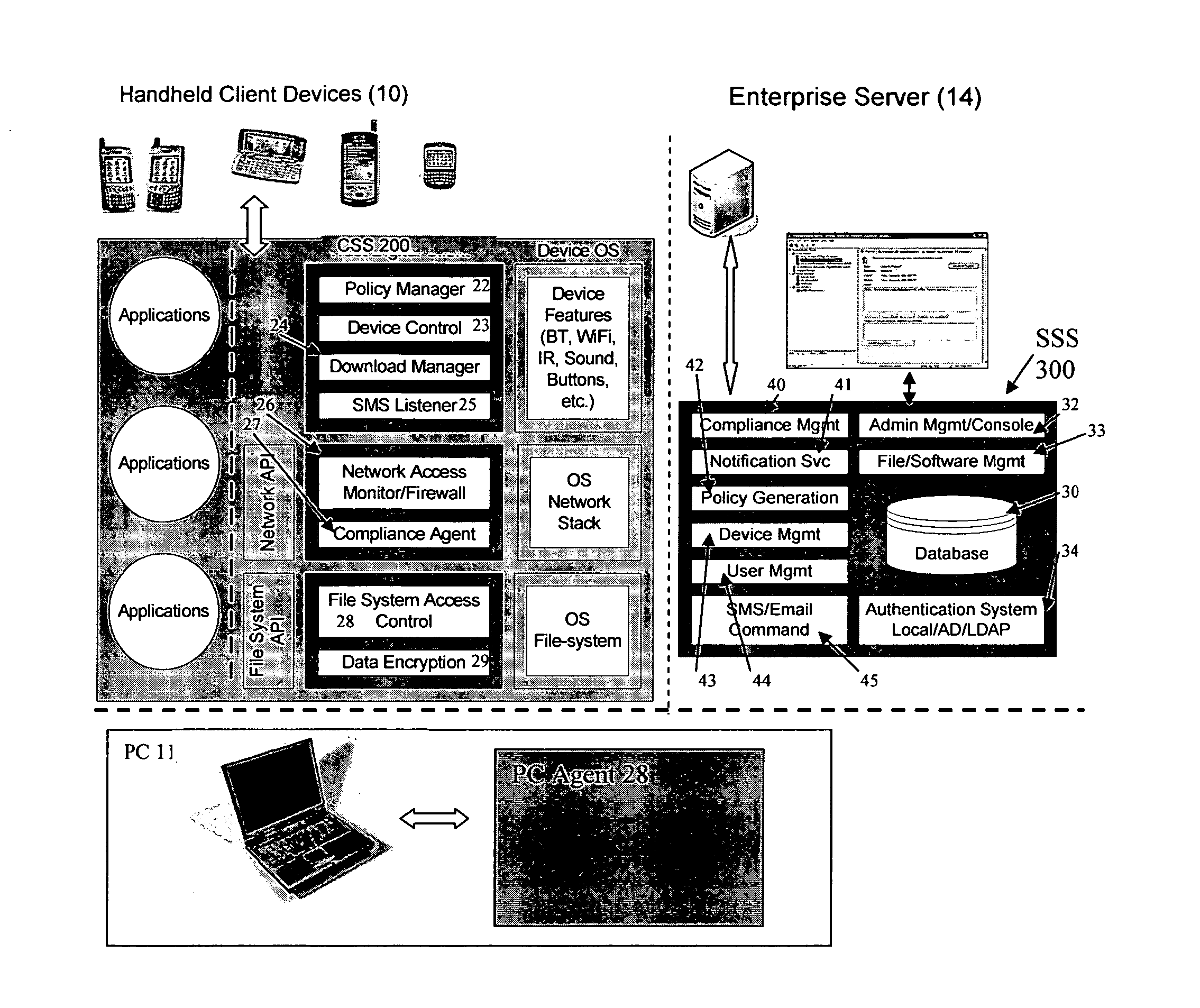
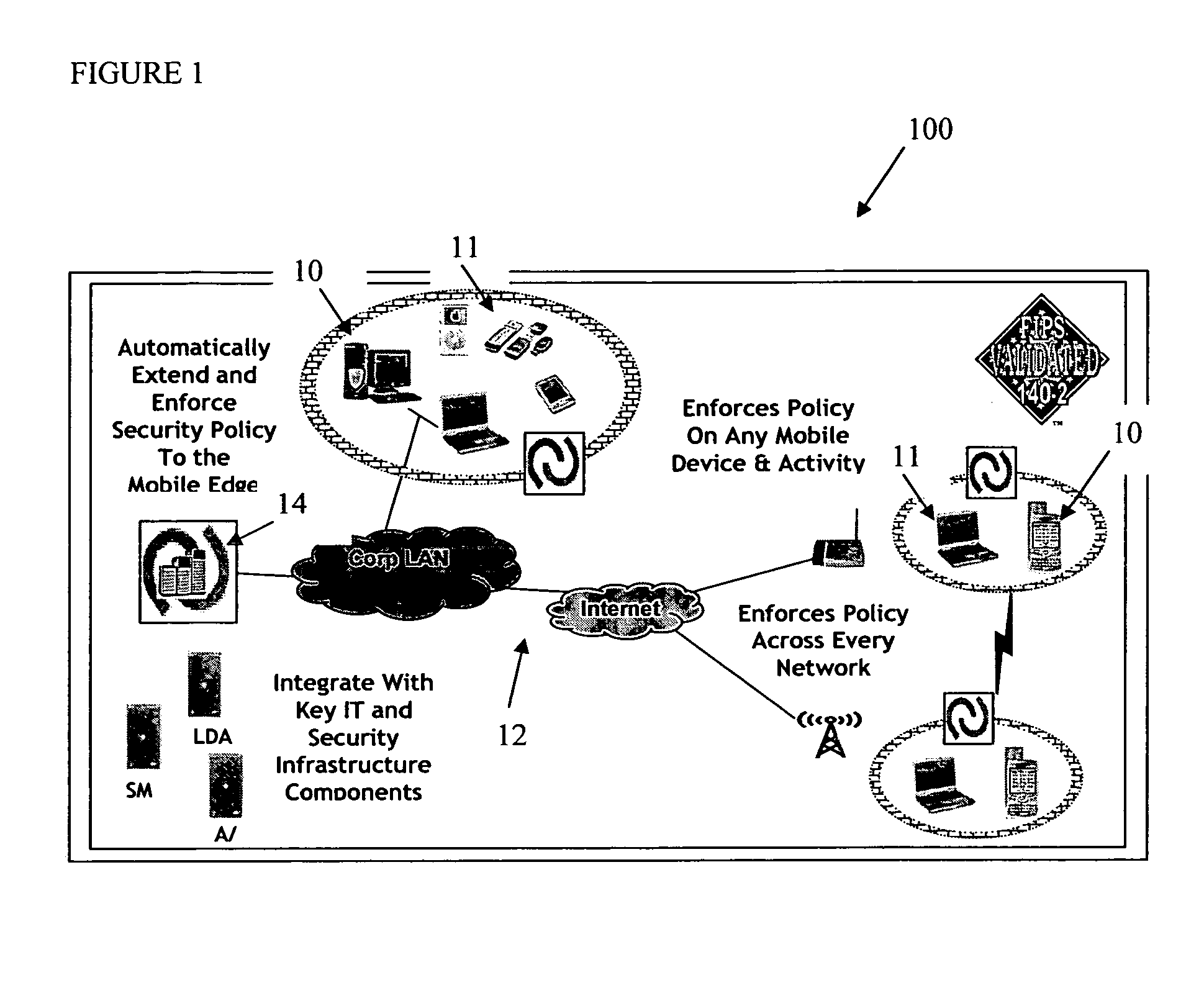
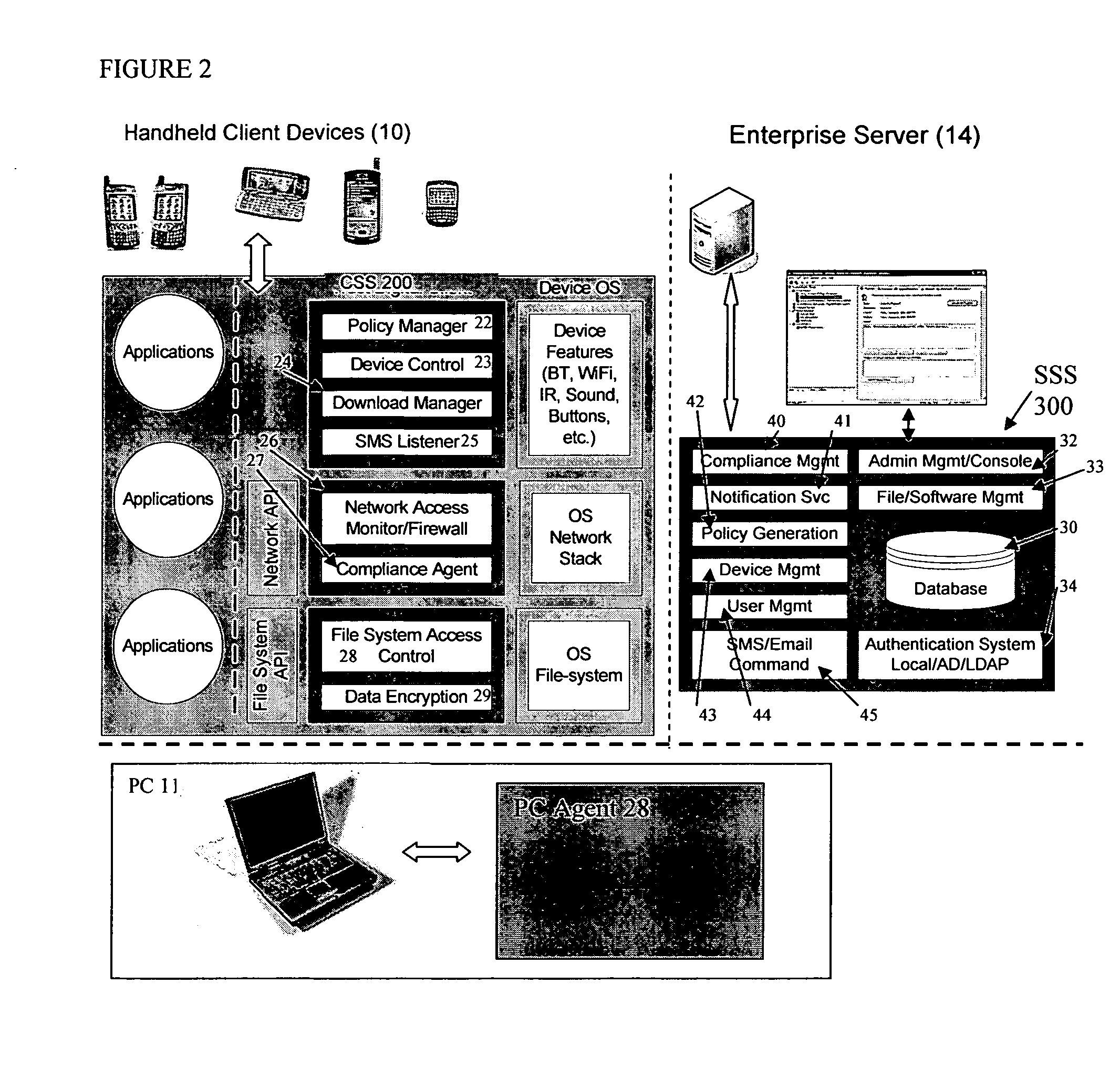
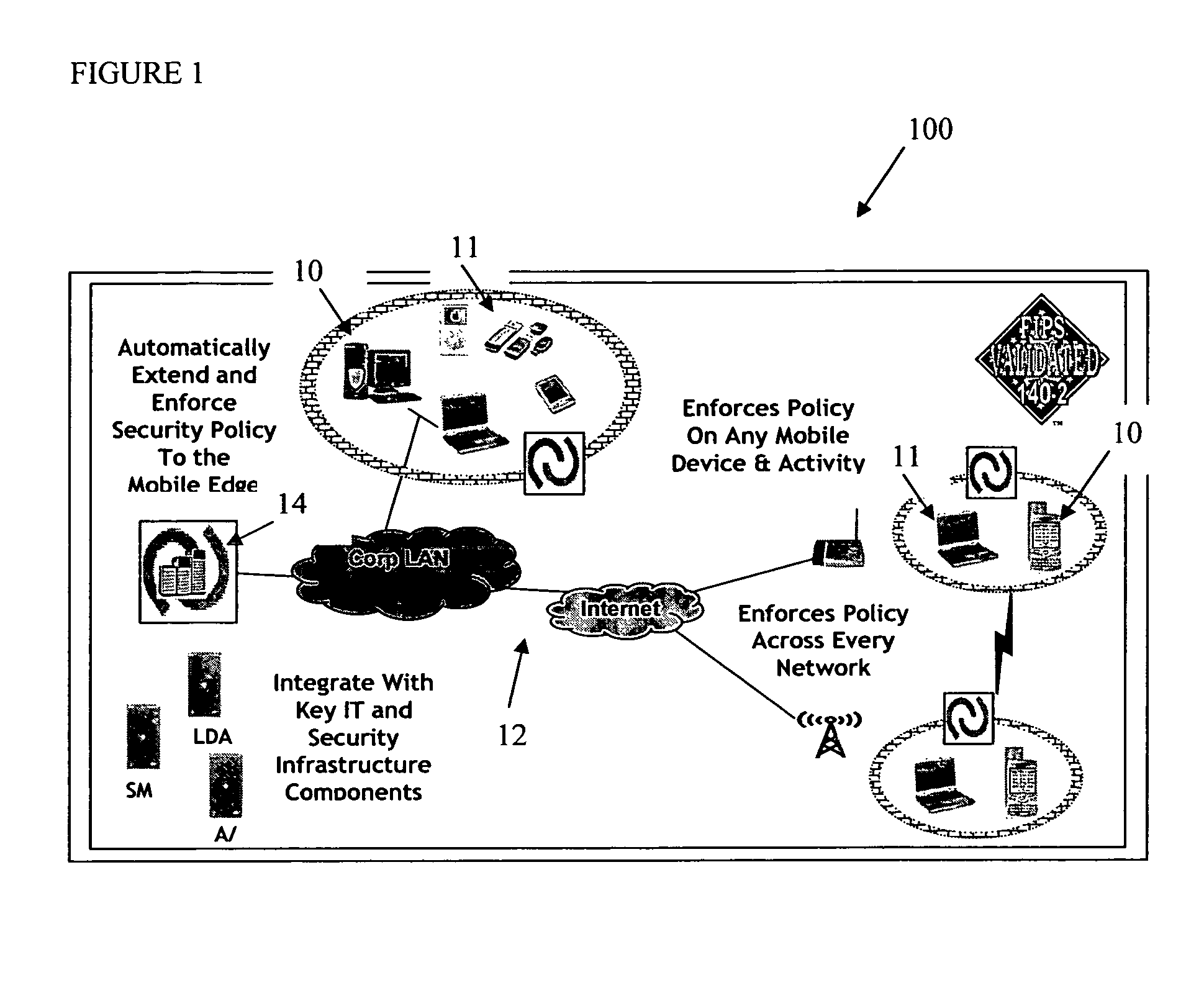
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
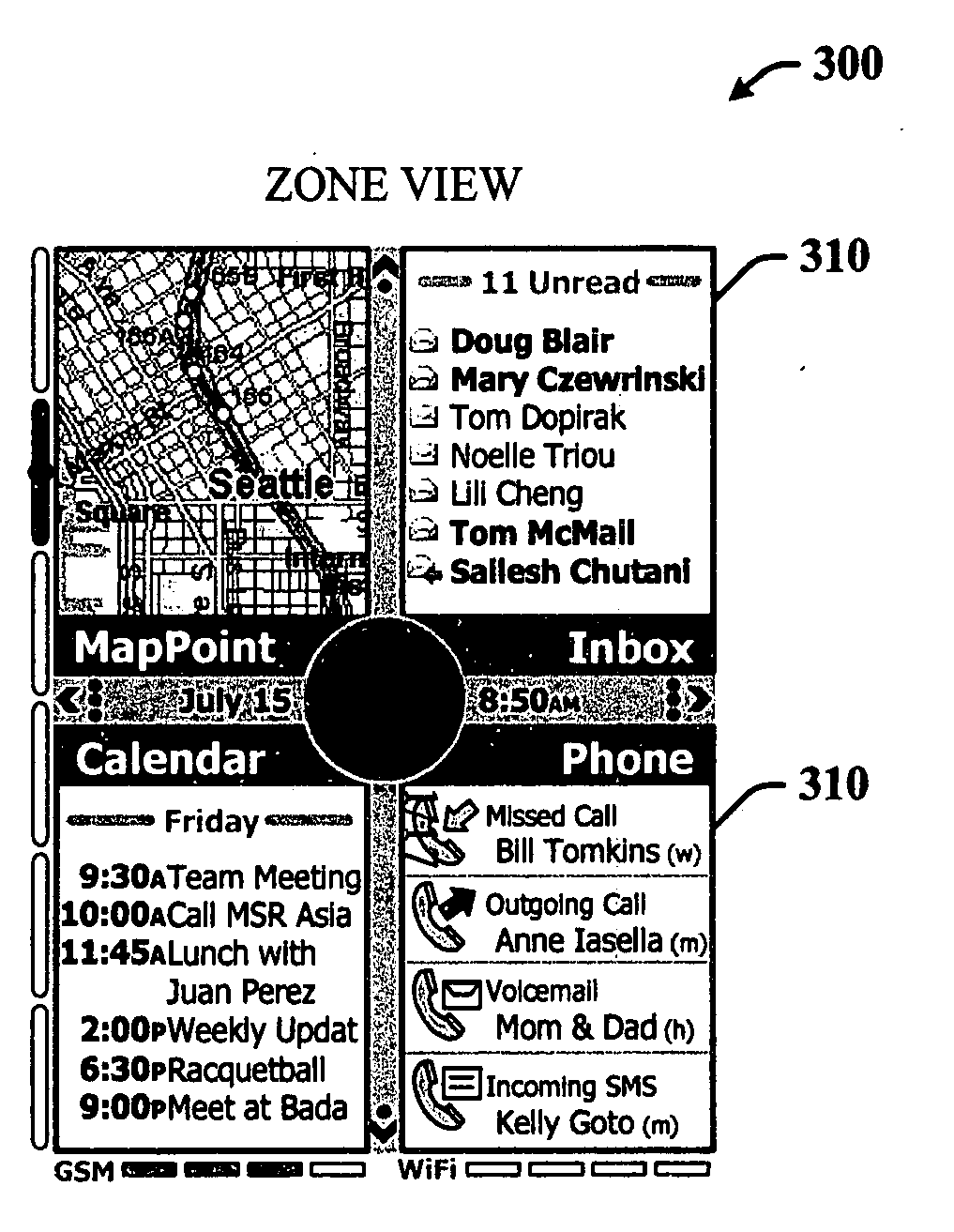
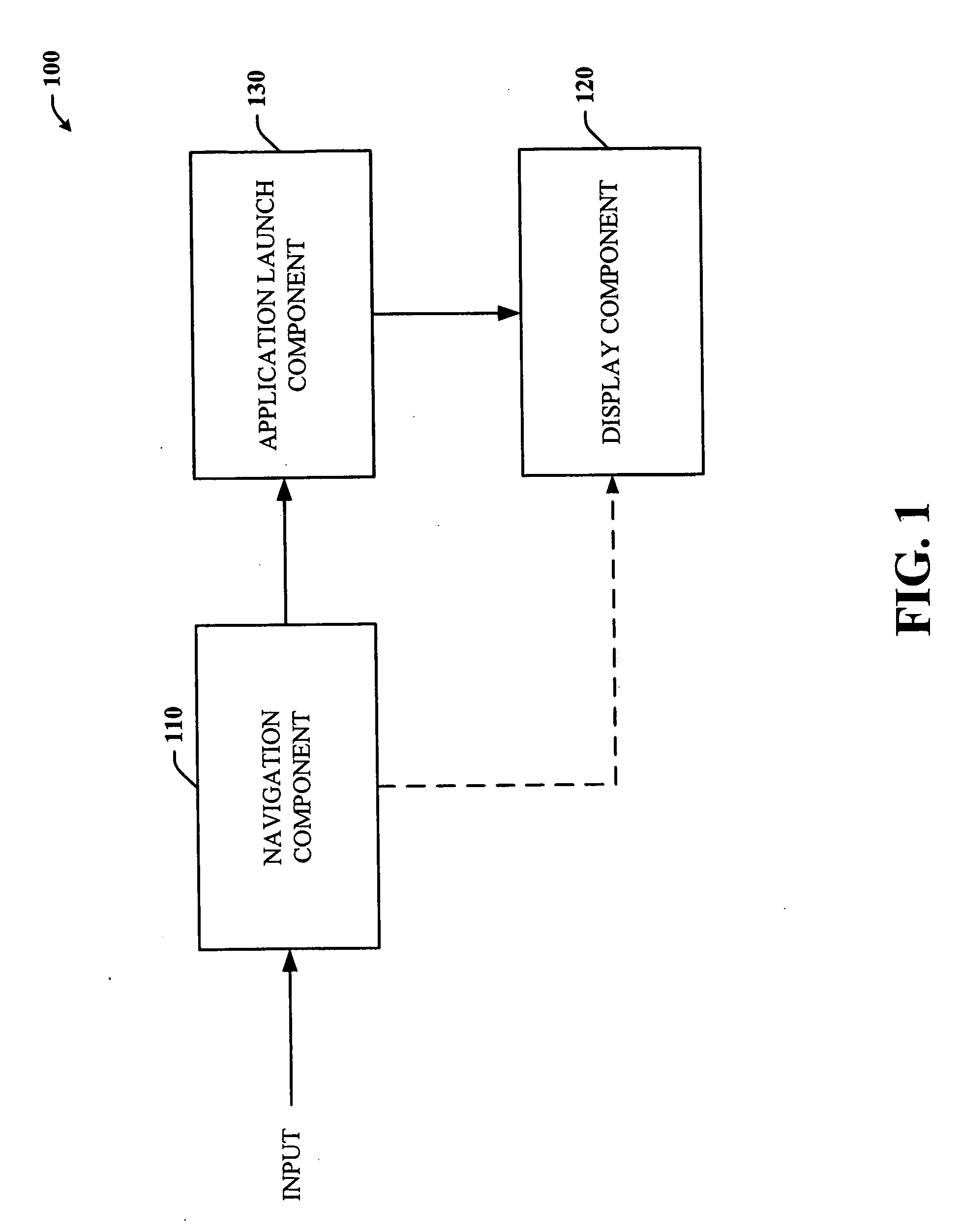
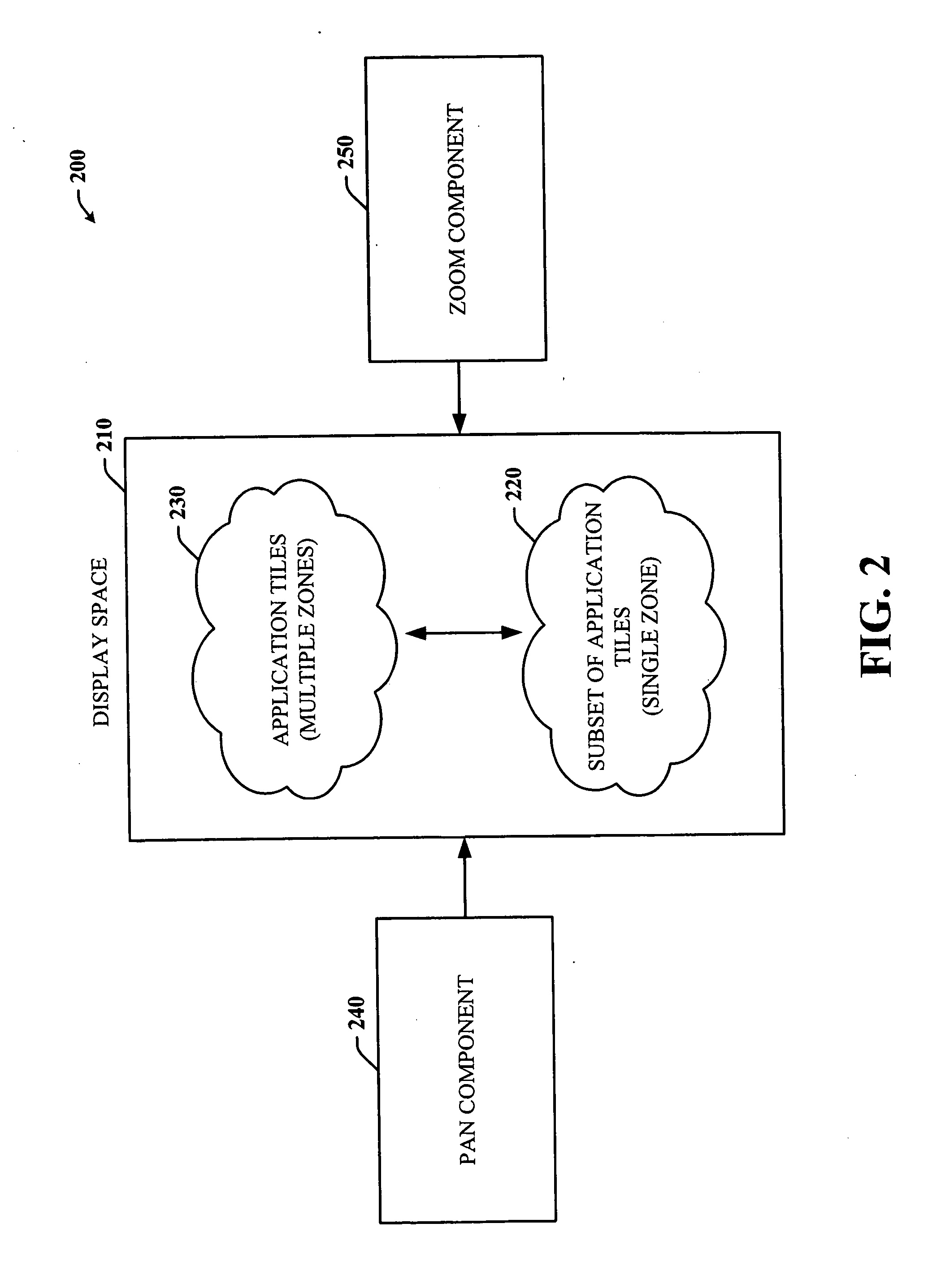
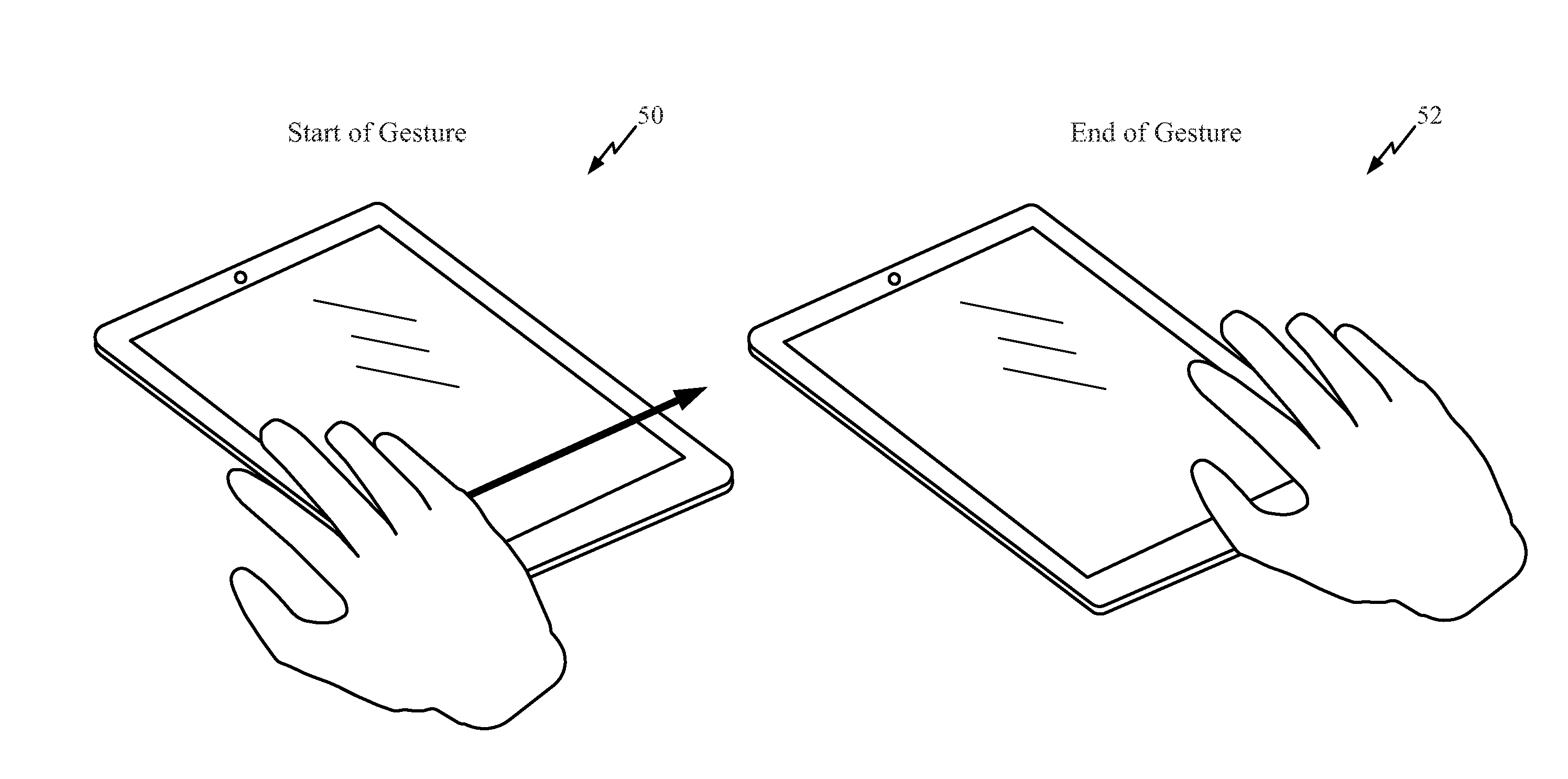
Single-handed approach for navigation of application tiles using panning and zooming
ActiveUS20060190833A1Maintain positionEnhanced interactionAnimationCommerceMarine navigationMobile computing
The subject invention provides a unique interactive system and method that facilitate single-handed navigation and interaction with applications within a display space on any type of mobile computing device. The system and method include or employ scalable application tiles corresponding to applications, whereby the application tiles can provide or indicate the current state of the corresponding application. The state information provided in each tile can vary as well depending on the current size of the tile. The tiles can be arranged into a plurality of zones such that a user can view one particular zone at a time and obtain more context and information from the application tiles in that zone rather than working with all tiles and all zones at the same time. The view of the display space can be of the world or all application tiles, zone, or application. Panning and zooming among the zones, application tiles and / or views can be performed single-handedly using designated on or off screen controls.
Owner:APPLE INC
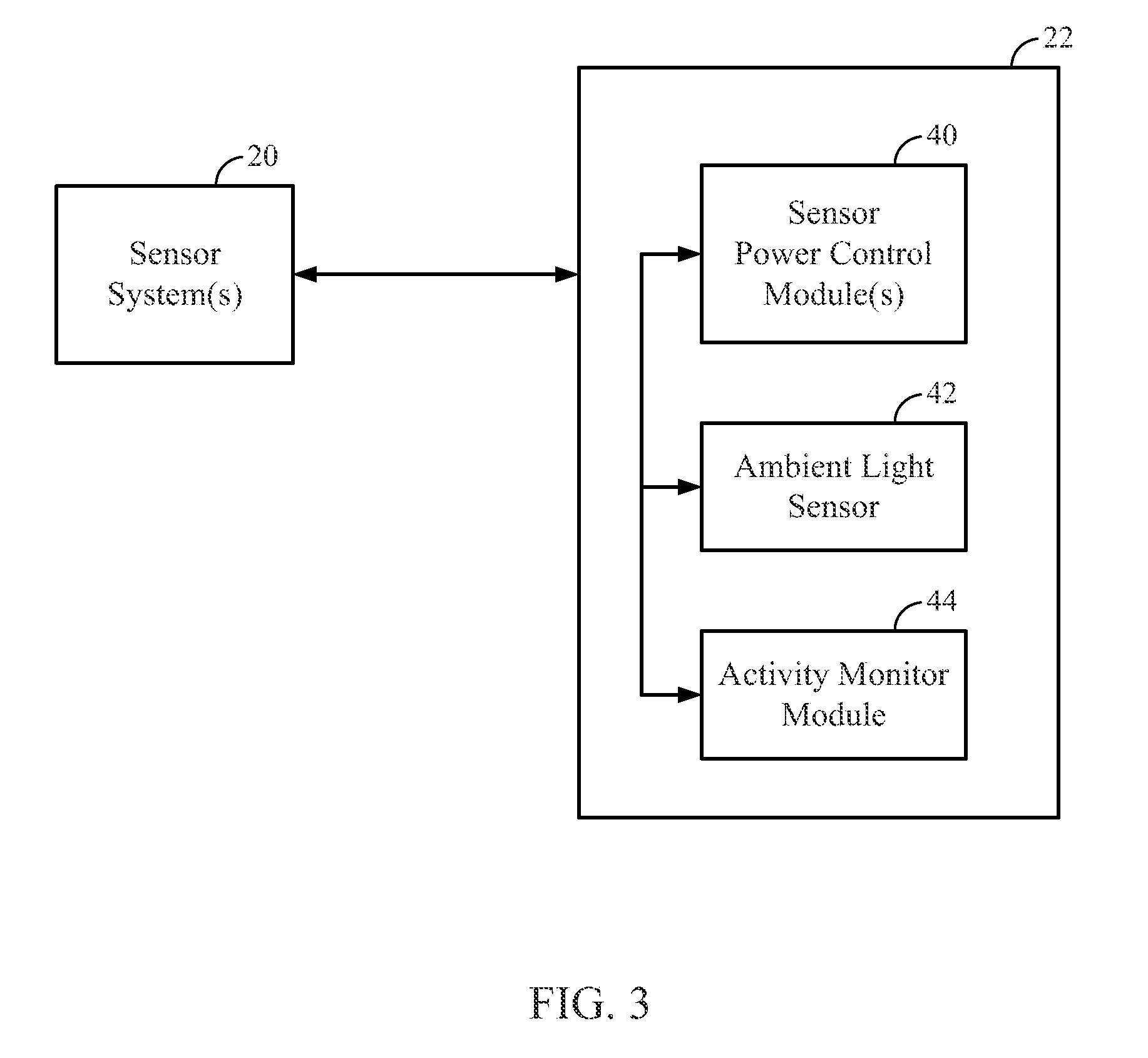
Methods and apparatus for contactless gesture recognition
InactiveUS20110310005A1Reduce wearImprove aestheticsInput/output for user-computer interactionEnergy efficient ICTProximity sensorHuman–computer interaction
Systems and methods are described for performing contactless gesture recognition for a computing device, such as a mobile computing device. An example technique for managing a gesture-based input mechanism for a computing device described herein includes identifying parameters of the computing device relating to accuracy of gesture classification performed by the gesture-based input mechanism and managing a power consumption level of at least an infrared (IR) light emitting diode (LED) or an IR proximity sensor of the gesture-based input mechanism based on the parameters of the computing device.
Owner:QUALCOMM INC
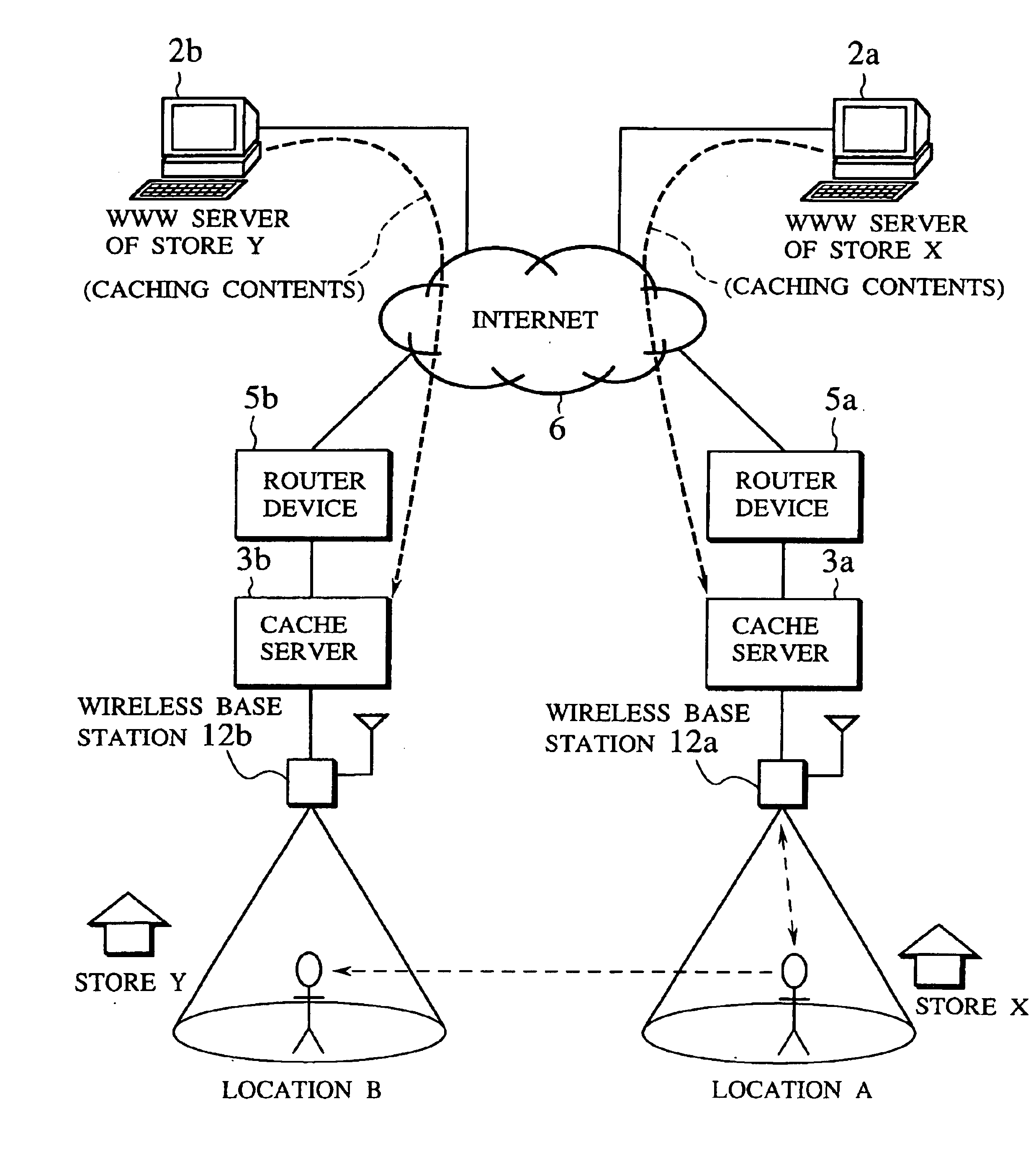
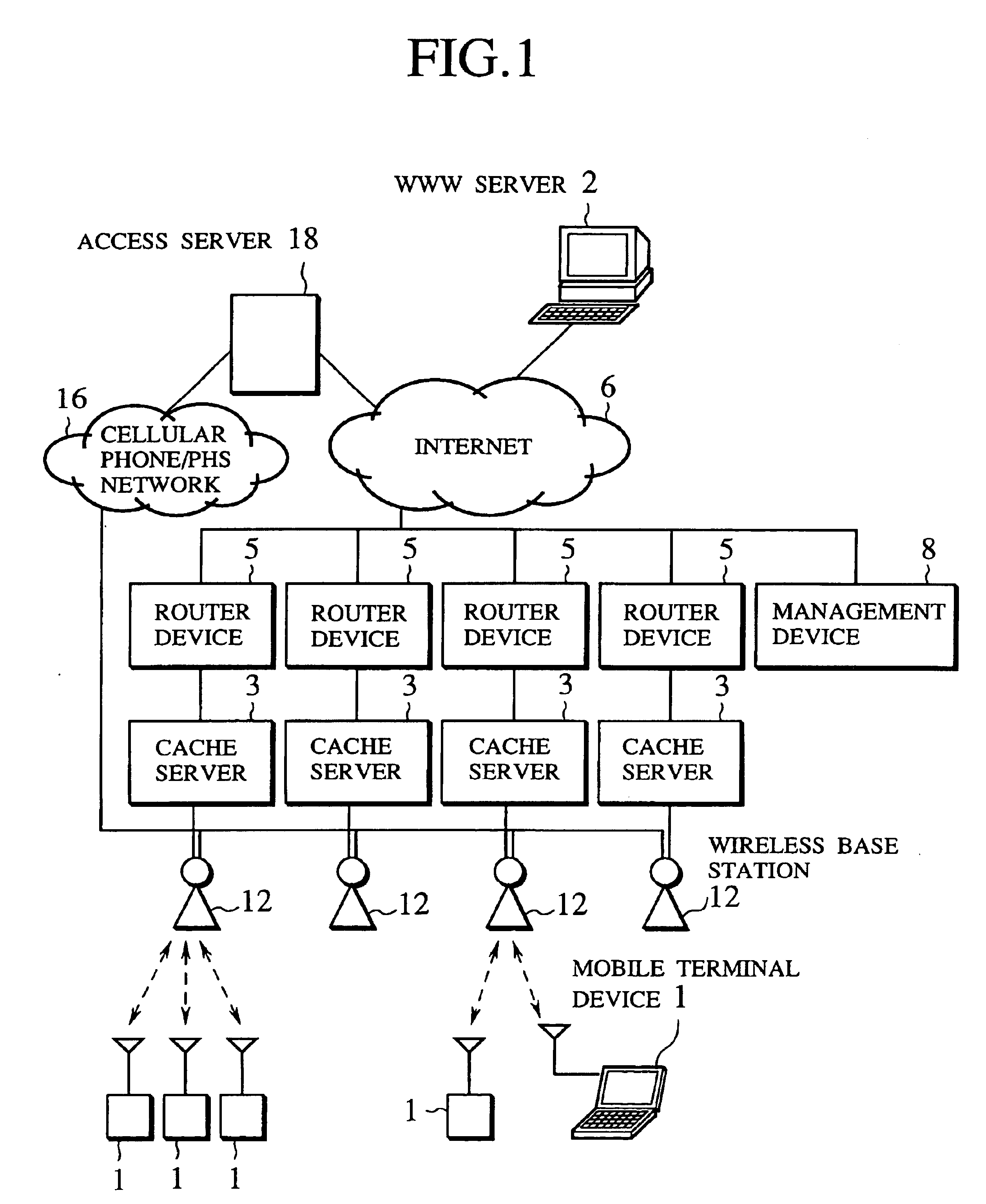
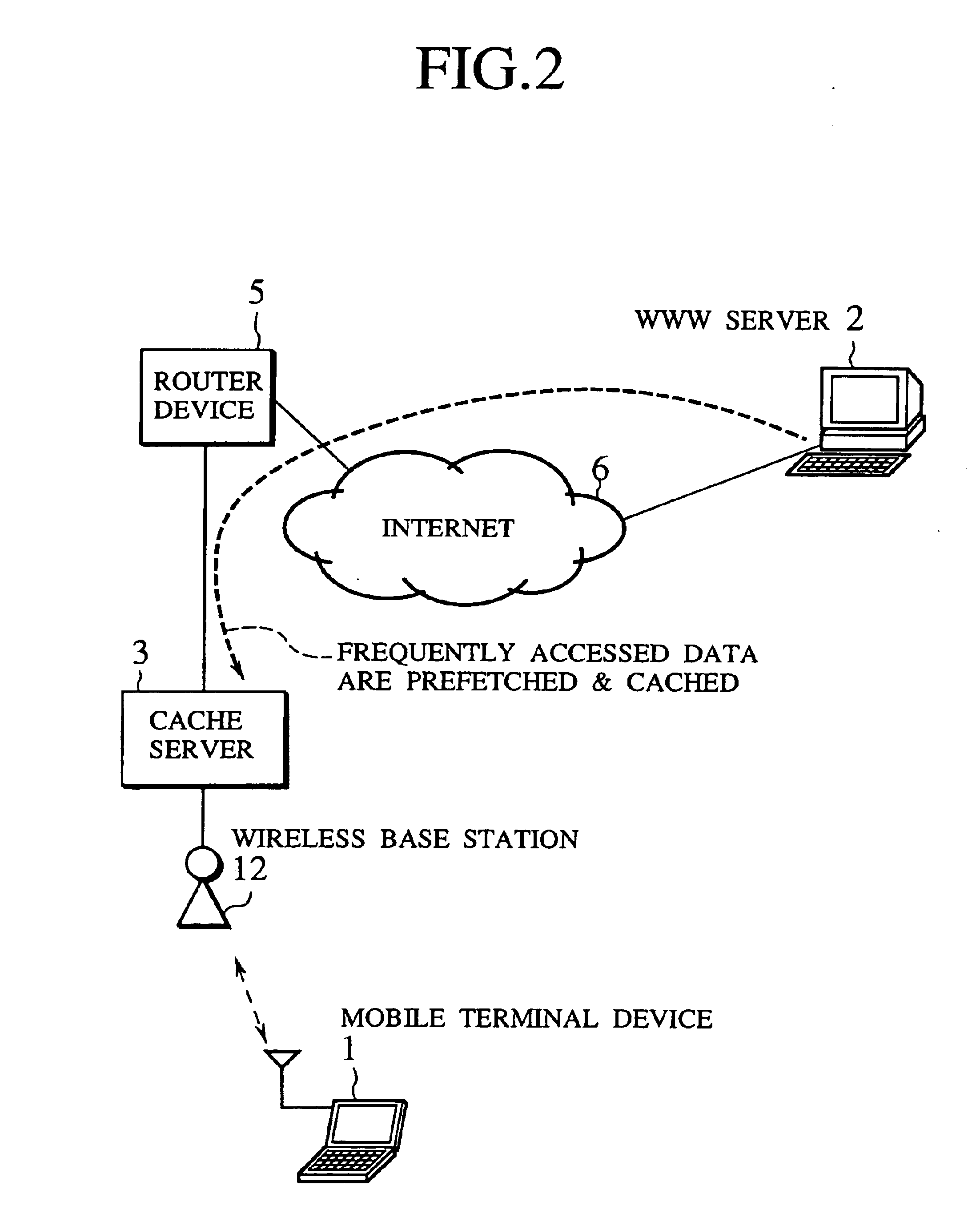
Scheme for information delivery to mobile computers using cache servers
InactiveUS6874017B1Effective cachingEasy accessSpecial service provision for substationDigital data information retrievalCache serverThe Internet
In the disclosed information delivery scheme for delivering WWW information provided by information servers on the Internet to mobile computers connected to the Internet through a wireless network, a plurality of cache servers capable of caching WWW information provided by the information servers are provided in association with the wireless network. The cache servers can be managed by receiving a message indicating at least a connected location of a mobile computer in the wireless network from the mobile computer, selecting one or more cache servers located nearby the mobile computer according to the message, and controlling these one or more cache servers to cache selected WWW information selected for the mobile computer, so as to enable faster accesses to the selected WWW information by the mobile computer. Also, the cache servers can be managed by selecting one or more cache servers located within a geographic range defined for an information provider who provides WWW information from an information server, and controlling these one or more cache servers to cache selected WWW information selected for the information provider, so as to enable faster accesses to the selected WWW information by the mobile computer.
Owner:KK TOSHIBA
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Cloud based mobile device security and policy enforcement
ActiveUS20120240183A1Computer security arrangementsMobile application execution environmentsTablet computerOperational system
The present disclosure relates to cloud based mobile device security and policy systems and methods to use the “cloud” to pervasively enforce security and policy on mobile devices. The cloud based mobile device security and policy systems and methods provide uniformity in securing mobile devices for small to large organizations. The cloud based mobile device security and policy systems and methods may enforce one or more policies for users wherever and whenever the users are connected across a plurality of different devices including mobile devices. This solution ensures protection across different types, brands, operating systems, etc. for smartphones, tablets, netbooks, mobile computers, and the like.
Owner:ZSCALER INC
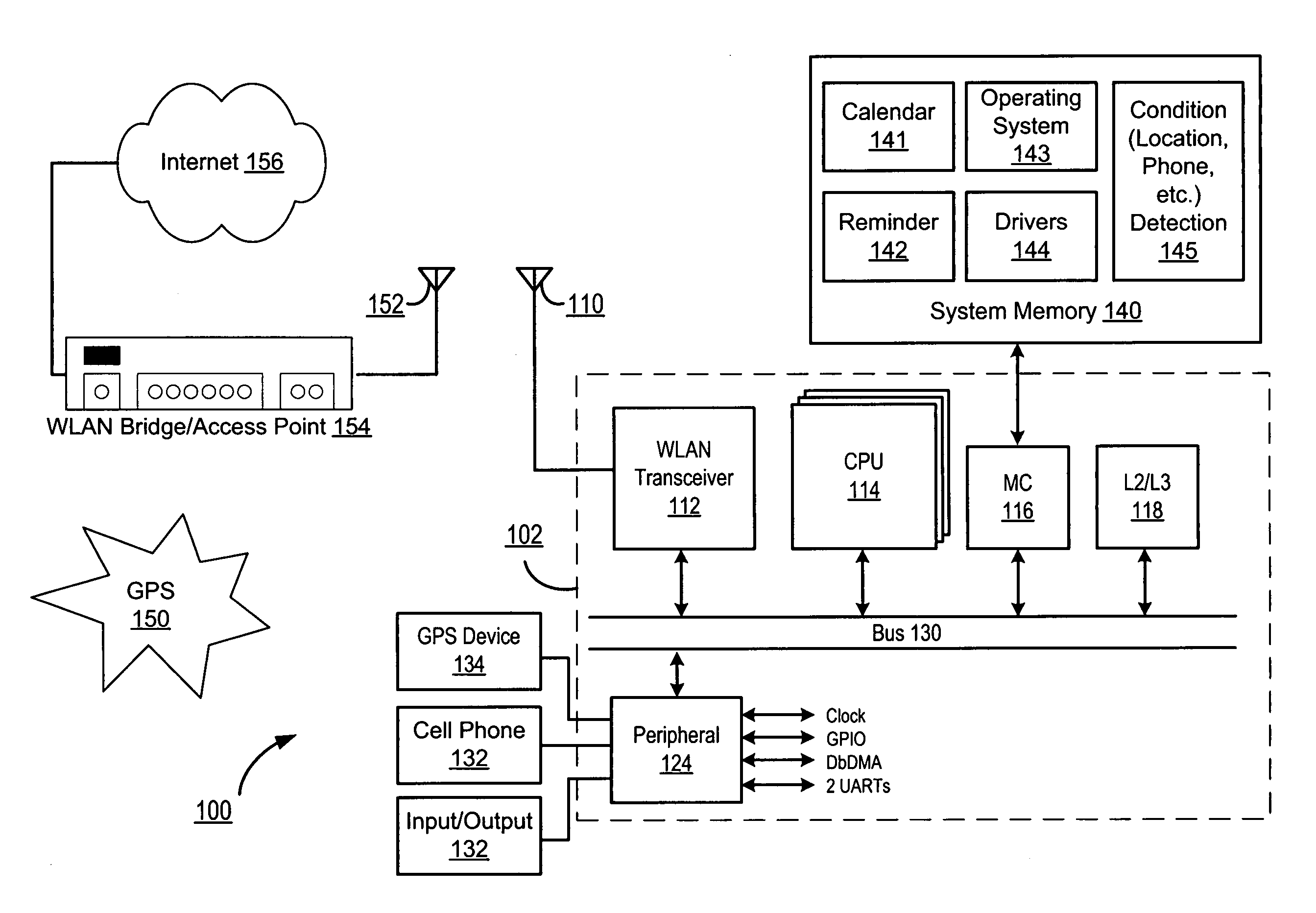
Location-based reminders
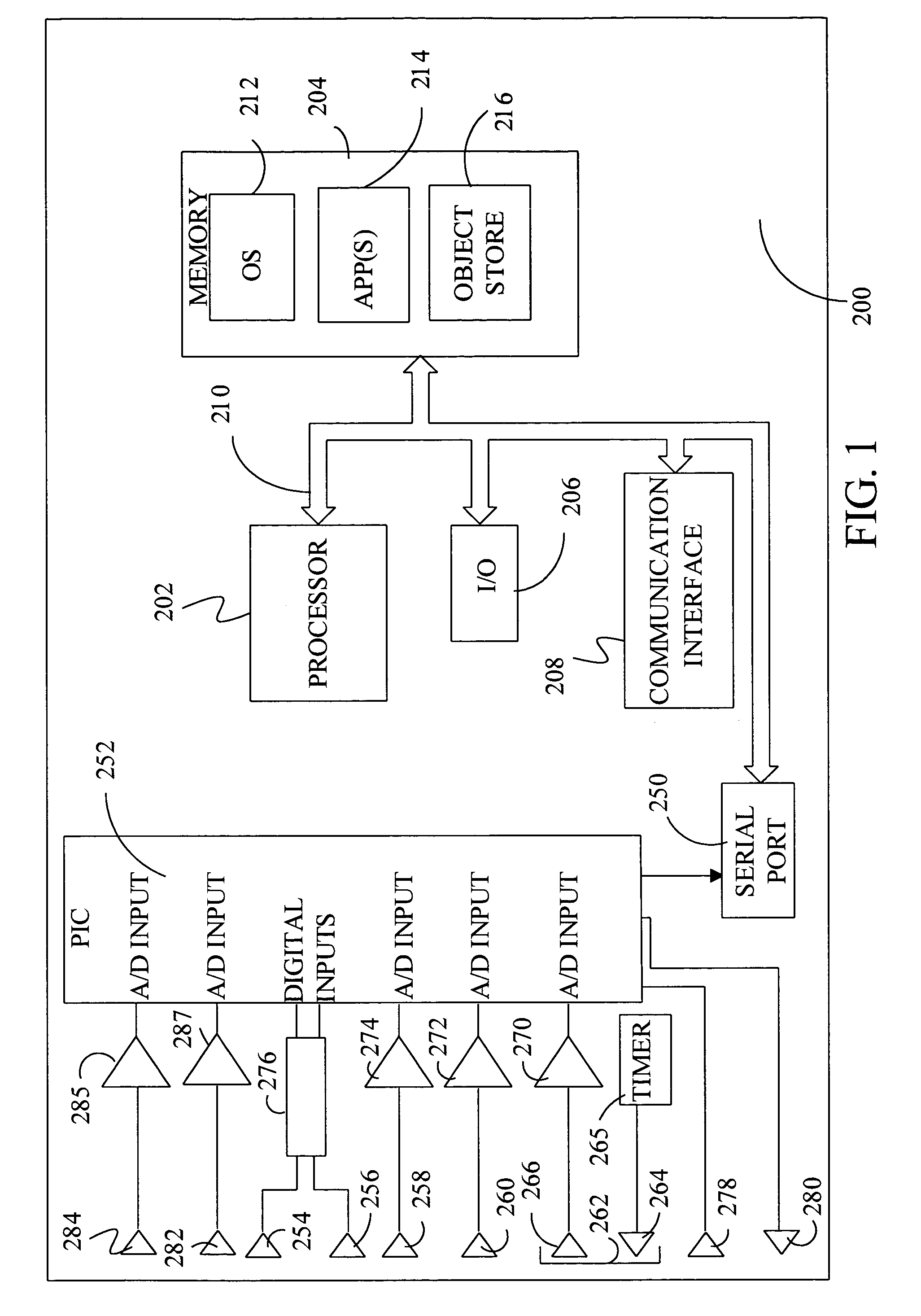
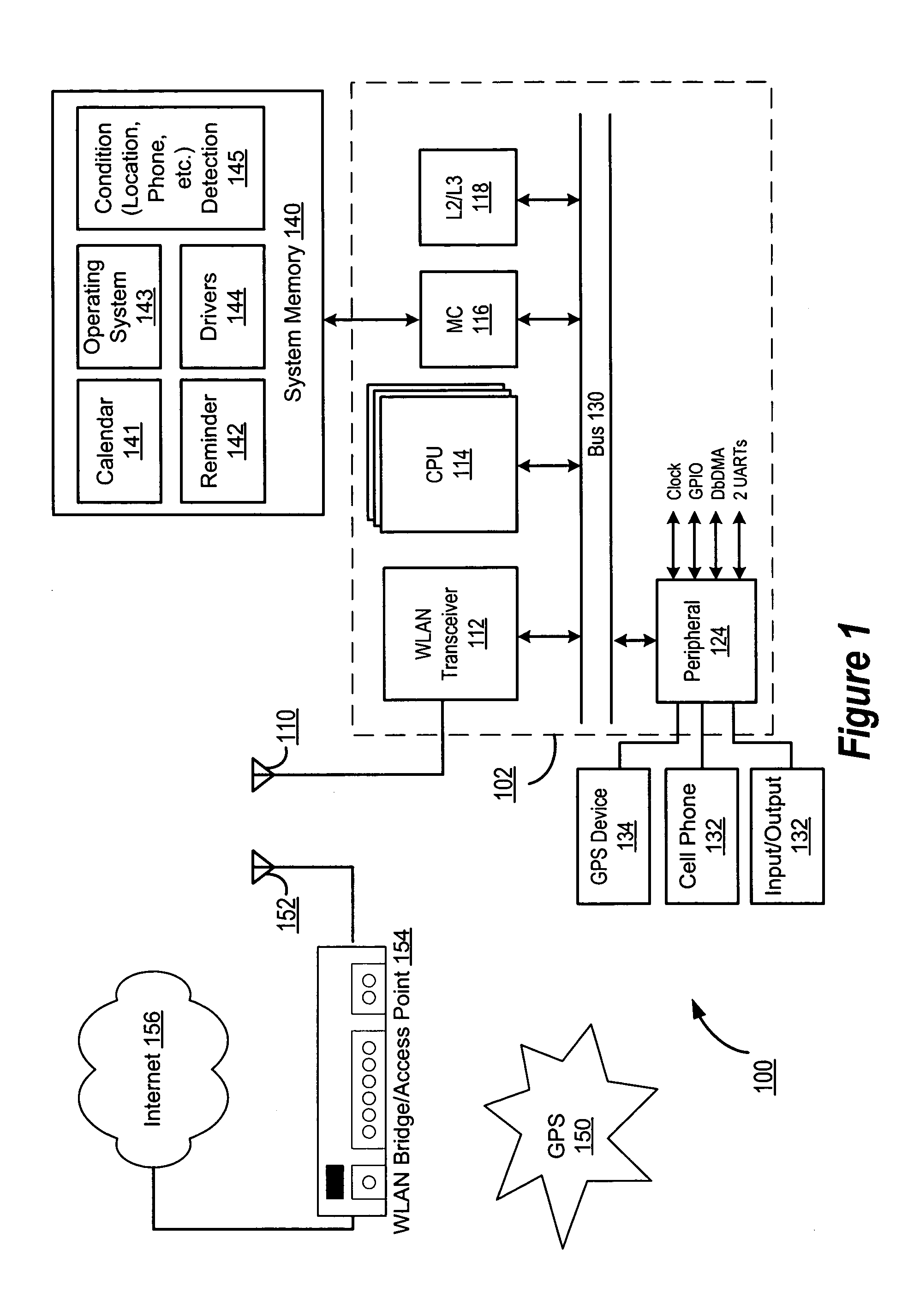
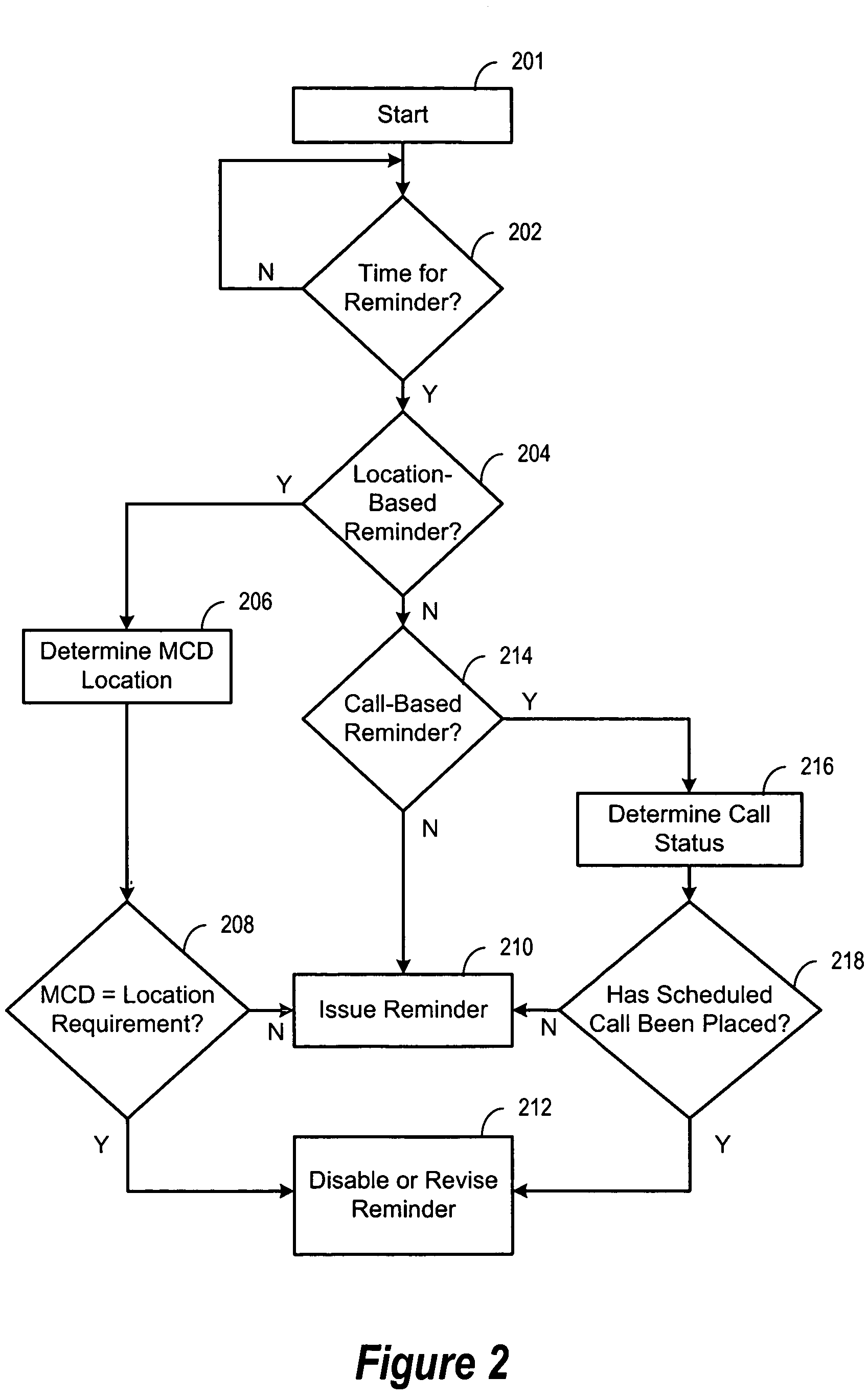
ActiveUS7084758B1Devices with GPS signal receiverSubstation equipmentTransceiverGlobal Positioning System
A mobile computing device, such as a personal digital assistant (PDA) or smart phone (102), is equipped with a location detector, such as a WLAN transceiver (112) or global positioning system (GPS) receiver (134), and is programmed with a condition detection program (145) by the user to suppress or modify reminder alerts (212) for an event scheduled in the calendar program (141) if a condition or status associated with scheduled event is detected by the condition detection program (145). The condition detection program (145) is further programmed to issue a reminder alert (210) if the condition or status is not detected.
Owner:GLOBALFOUNDRIES US INC
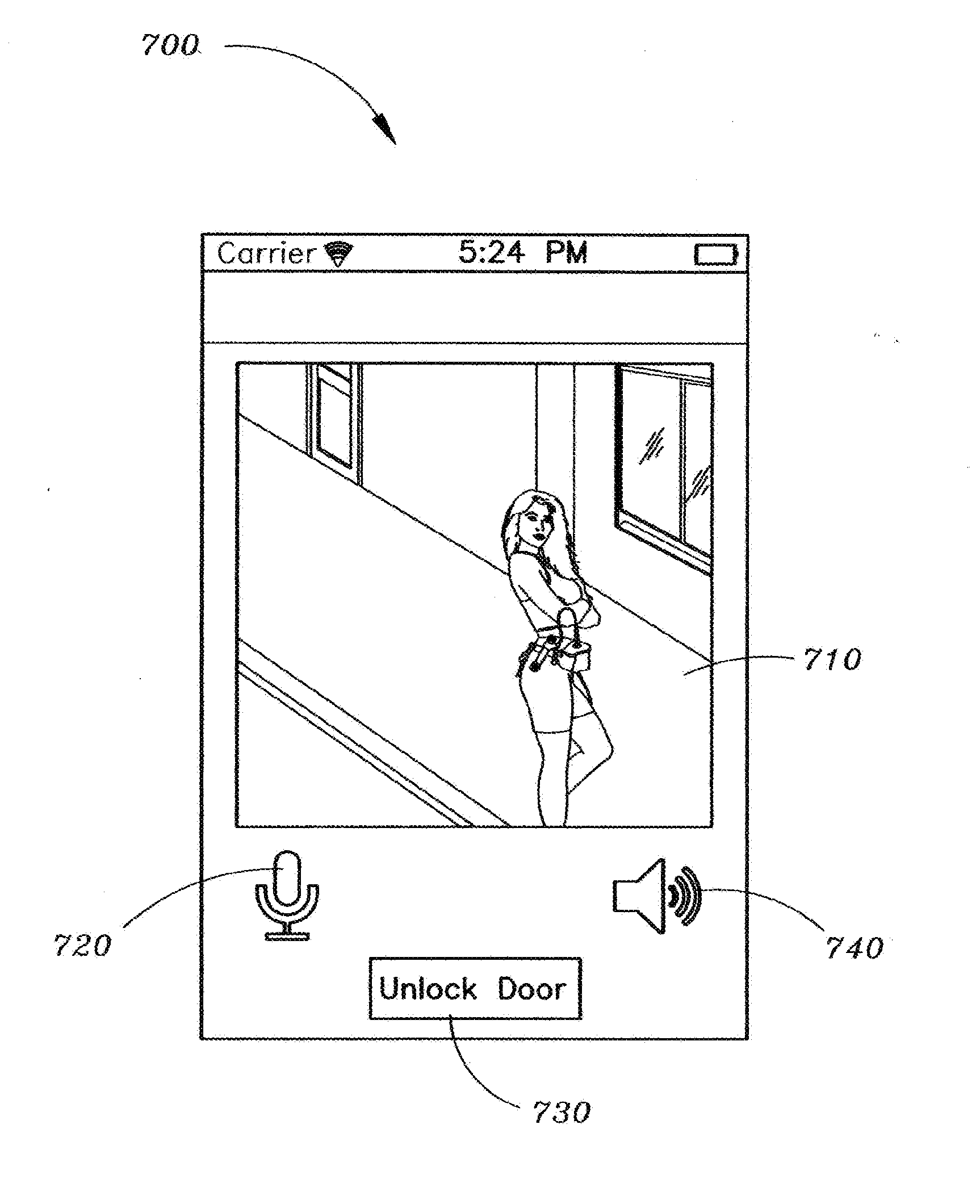
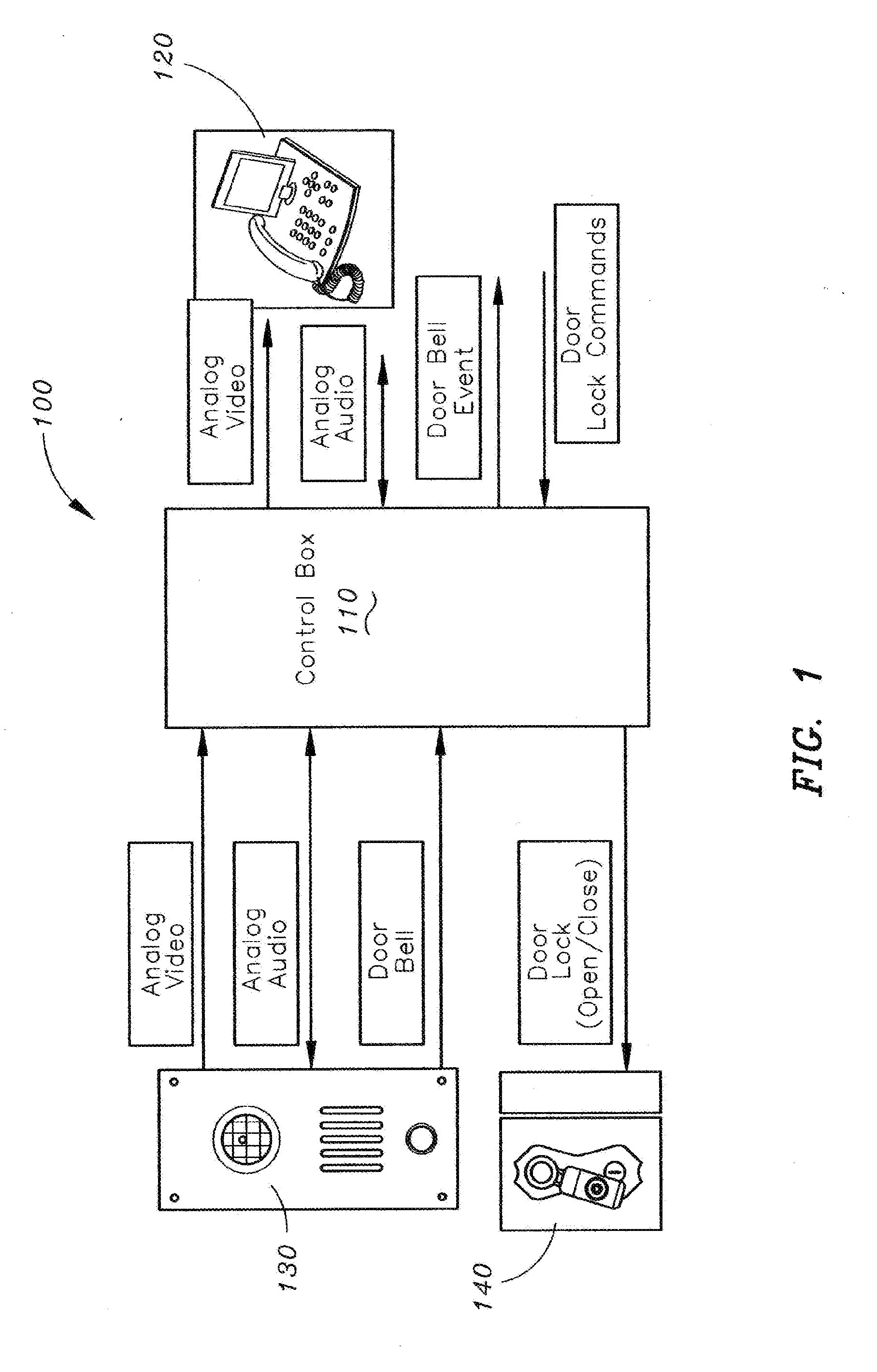
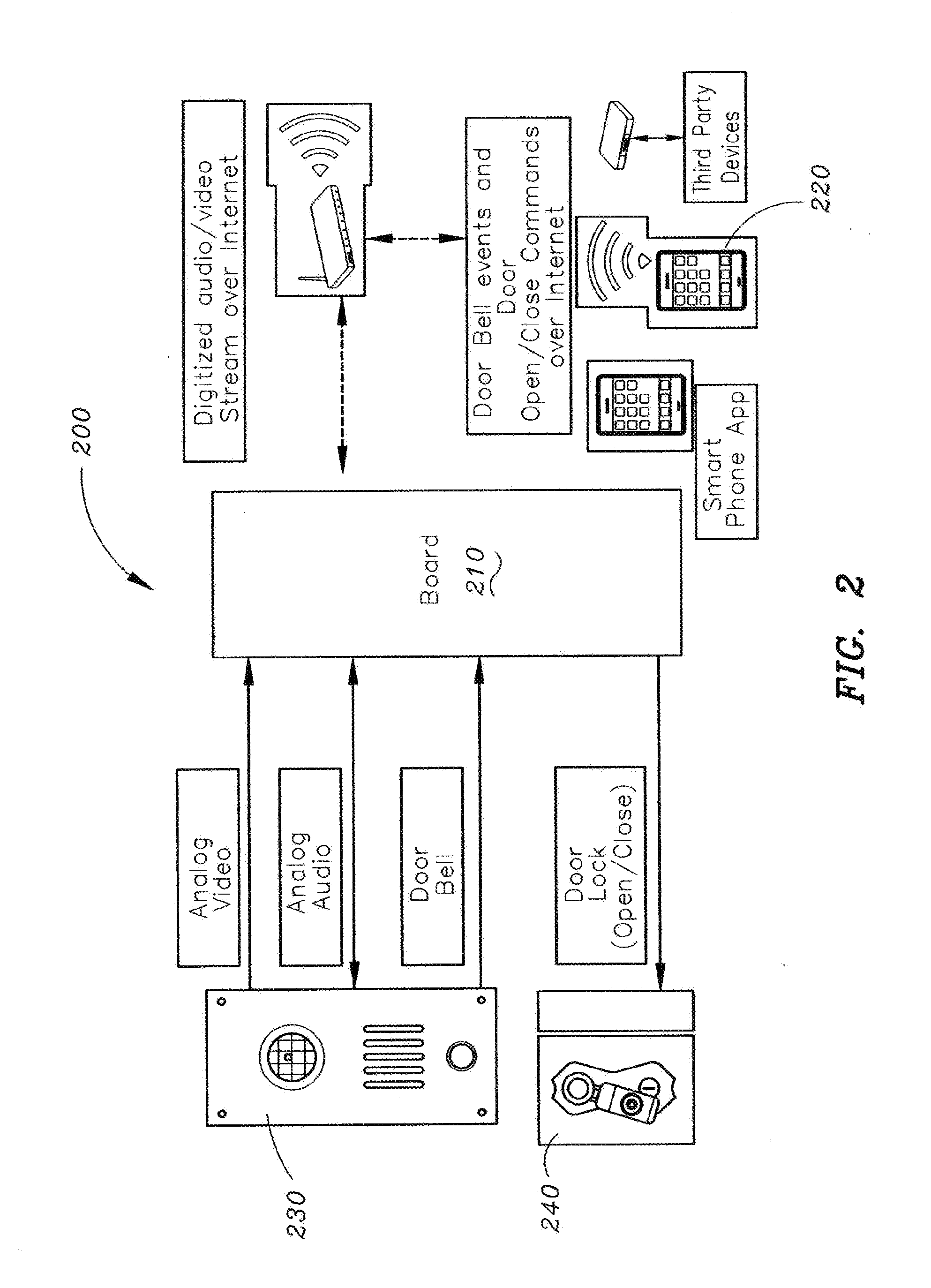
Method and apparatus for unlocking/locking a door and enabling two-way communications with a door security system via a smart phone
A method for operating a doorbell security system. The method may include receiving a doorbell press event signal and sending a doorbell press event notification to at least one mobile computing device. The method may further include receiving an acceptance response from a particular mobile computing device, wherein the acceptance response. The method may include receiving audio from a microphone and video from a camera located in proximity to a doorbell. The method may also include sending the audio from the microphone and the video from the camera to the particular mobile computing device. The method may additionally include receiving a command from the mobile computing device and unlocking, locking, opening, or closing a door.
Owner:HUISKING TIMOTHY J
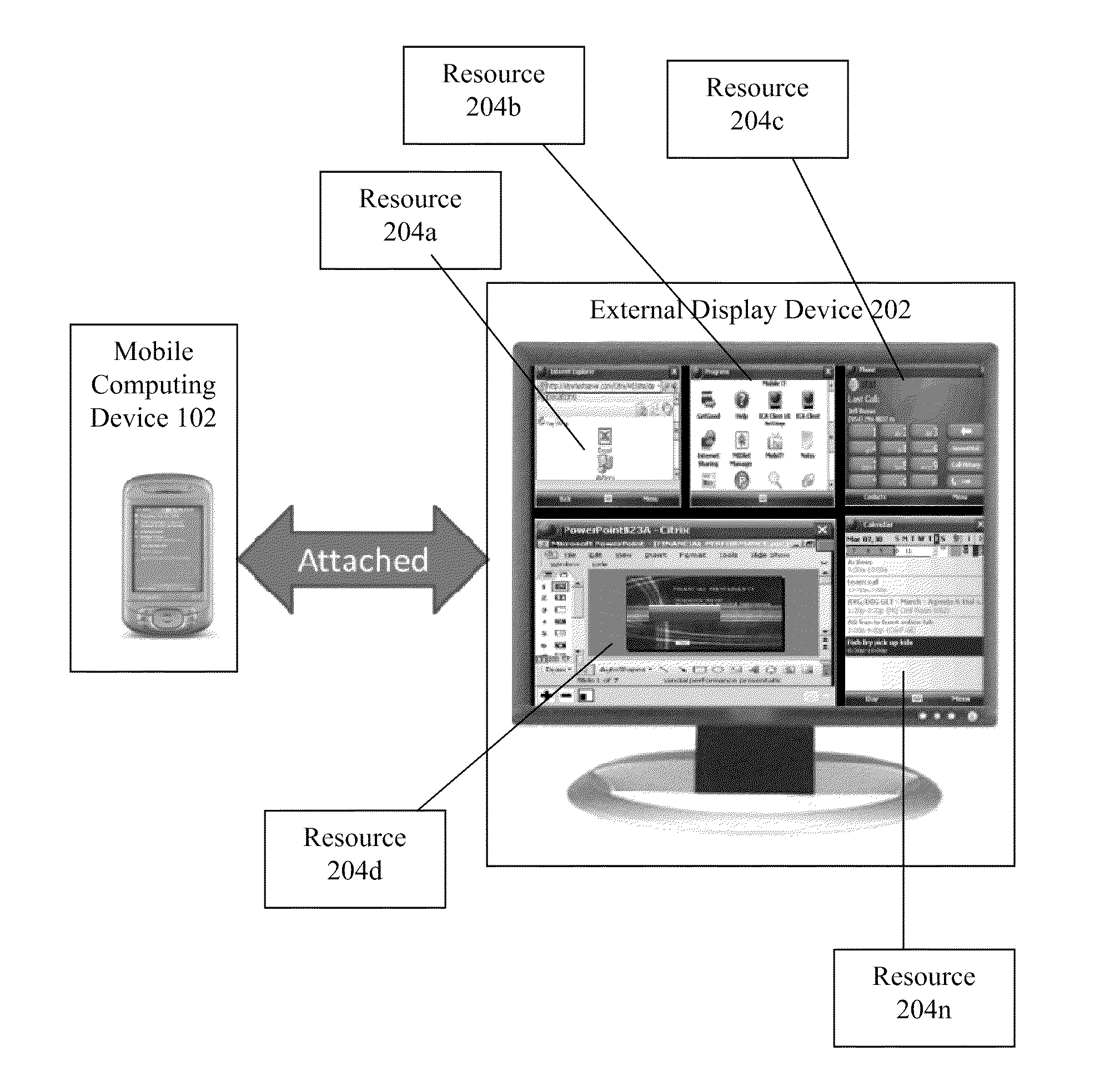
Methods and systems for using external display devices with a mobile computing device
InactiveUS20100138780A1Sacrificing of capabilitySacrificing qualityDigital computer detailsCathode-ray tube indicatorsDisplay deviceHuman–computer interaction
The present disclosure relates to methods and systems for using external display devices with a mobile computing device. When an external display device is connected or attached to a mobile computing device, output data associated with a resource executing on the mobile computing device may be displayed on the external display device. The output data may include a user interface appropriate for the display of the external display device. Execution of the resource may be transferred from the mobile computing device to the external display device.
Owner:CITRIX SYST INC
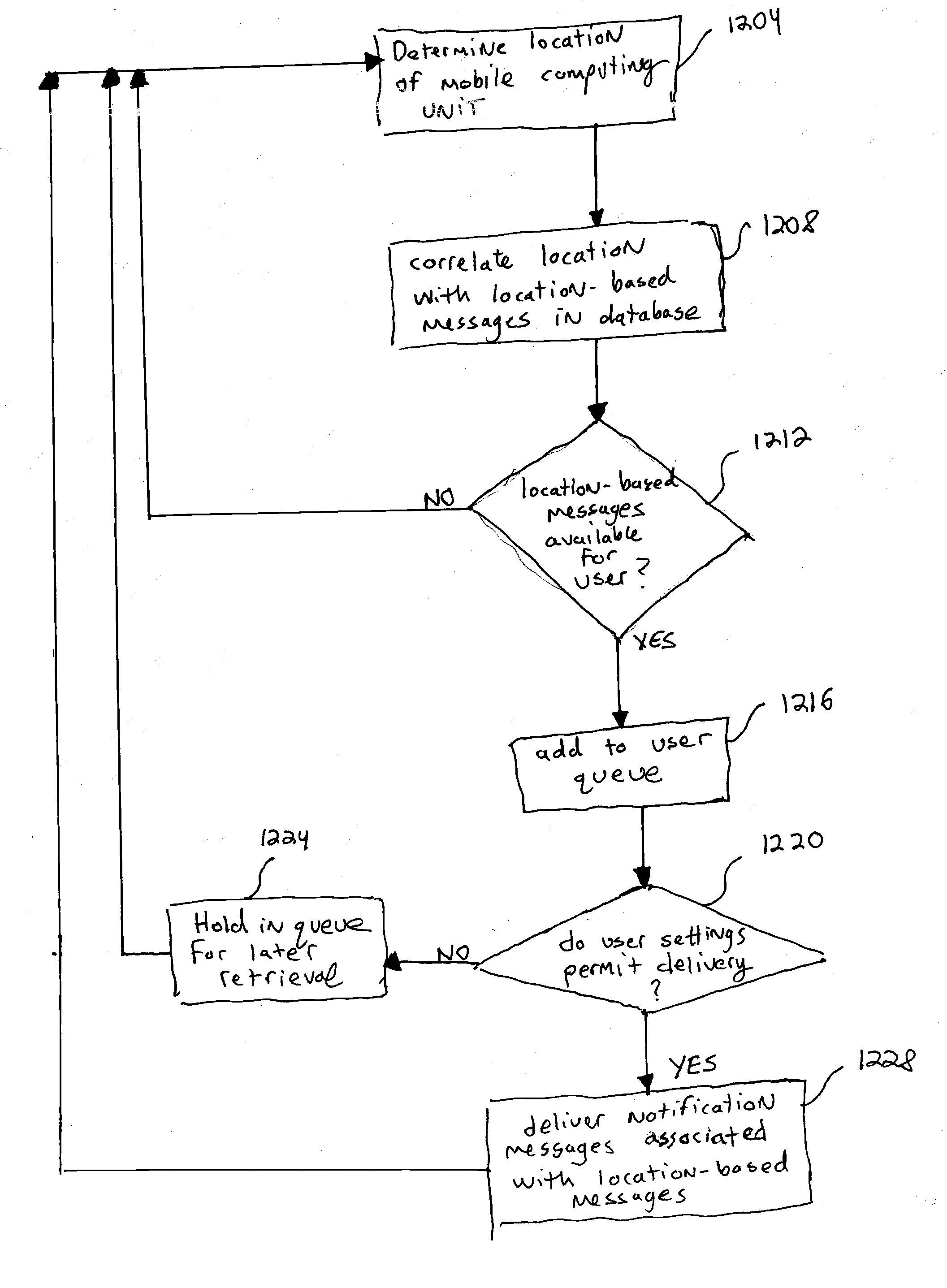
System and method including asynchronous location-based messaging
InactiveUS20070161382A1Efficient consumptionProvide feedbackMultiple digital computer combinationsRadio/inductive link selection arrangementsGeographic siteMessage passing
A system and method including asynchronous location-based messaging is provided. Multimedia content may be created and associated with a specific geographic location. Notification messages associated with location-based content may be designated for receipt by particular users, for example, when the users are located within a predetermined distance of the geographic location. The notification messages, which may be transmitted to users' mobile computing devices, may include information about, as well as a pointer to, the location-based content to enable the content to be accessed immediately or at a later time through any number of interfaces.
Owner:KAMIDA
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Location-Based Searching
ActiveUS20110137881A1Web data indexingDigital data processing detailsSubject matterLocation based information
In general, the subject matter described in this specification can be embodied in methods, systems, and programs for providing location-based information. A geographical location of a mobile computing device is received at a server system. A request for content is received at the server system and from the mobile computing device. A search area that corresponds to the geographical location is selected by the sever system. The search area is selected from among a collection of search areas that correspond to the geographical location. At least one of the search areas in the collection is geographically nested within at least one other of the search areas. A search result that is most-relevantly ranked for the selected search area is determined by the server system. Content that represents the determined search result is provided by the server system and for receipt by the mobile computing device.
Owner:GOOGLE LLC
File server system using connection-oriented protocol and sharing data sets among data movers
InactiveUS6453354B1Digital data information retrievalMultiple digital computer combinationsMultiplexingData set
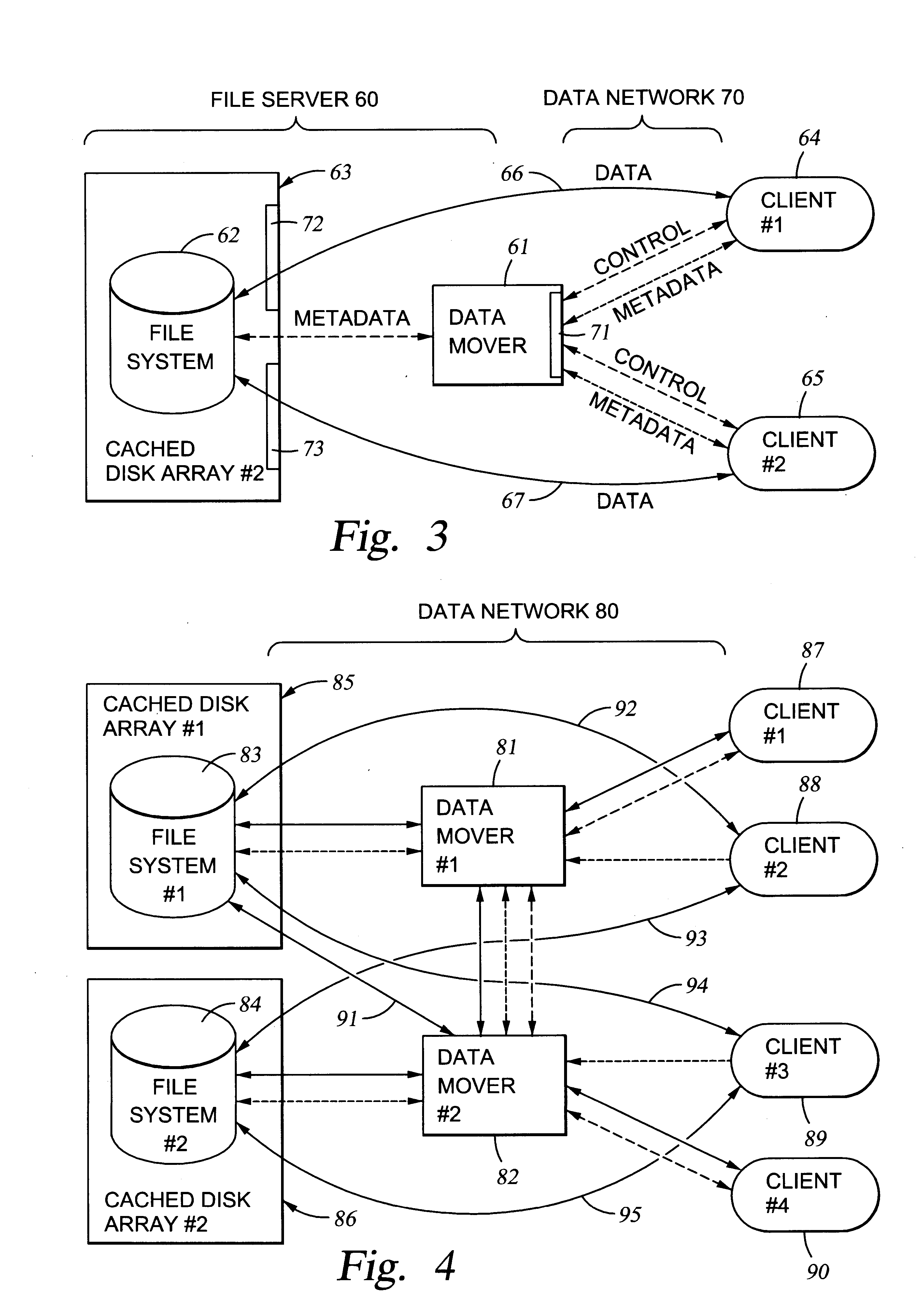
A first data mover computer services data access requests from a network client, and a second data mover computer is coupled to the first data mover computer for servicing data access requests from the first data mover computer. The first data mover computer uses a connection-oriented protocol to obtain client context information and to respond to a session setup request from the client by authenticating the client. Then the first data mover computer responds to a file system connection request from the client by forwarding the client context information and the file system connection request to the second data mover computer. Then the first data mover computer maintains a connection between the first data mover computer and the second data mover computer when the client accesses the file system and the first data mover computer passes file access requests from the client to the second data mover computer and returns responses to the file access requests from the second data mover computer to the client. In a preferred embodiment, the connection-oriented protocol is the Common Internet File System (CIFS) Protocol, and multiple clients share a Transmission Control Protocol (TCP) connection between the first data mover computer and the second data mover computer by allocation of virtual channels within the shared TCP connection and multiplexing of data packets of the virtual channels over the shared TCP connection.
Owner:EMC IP HLDG CO LLC
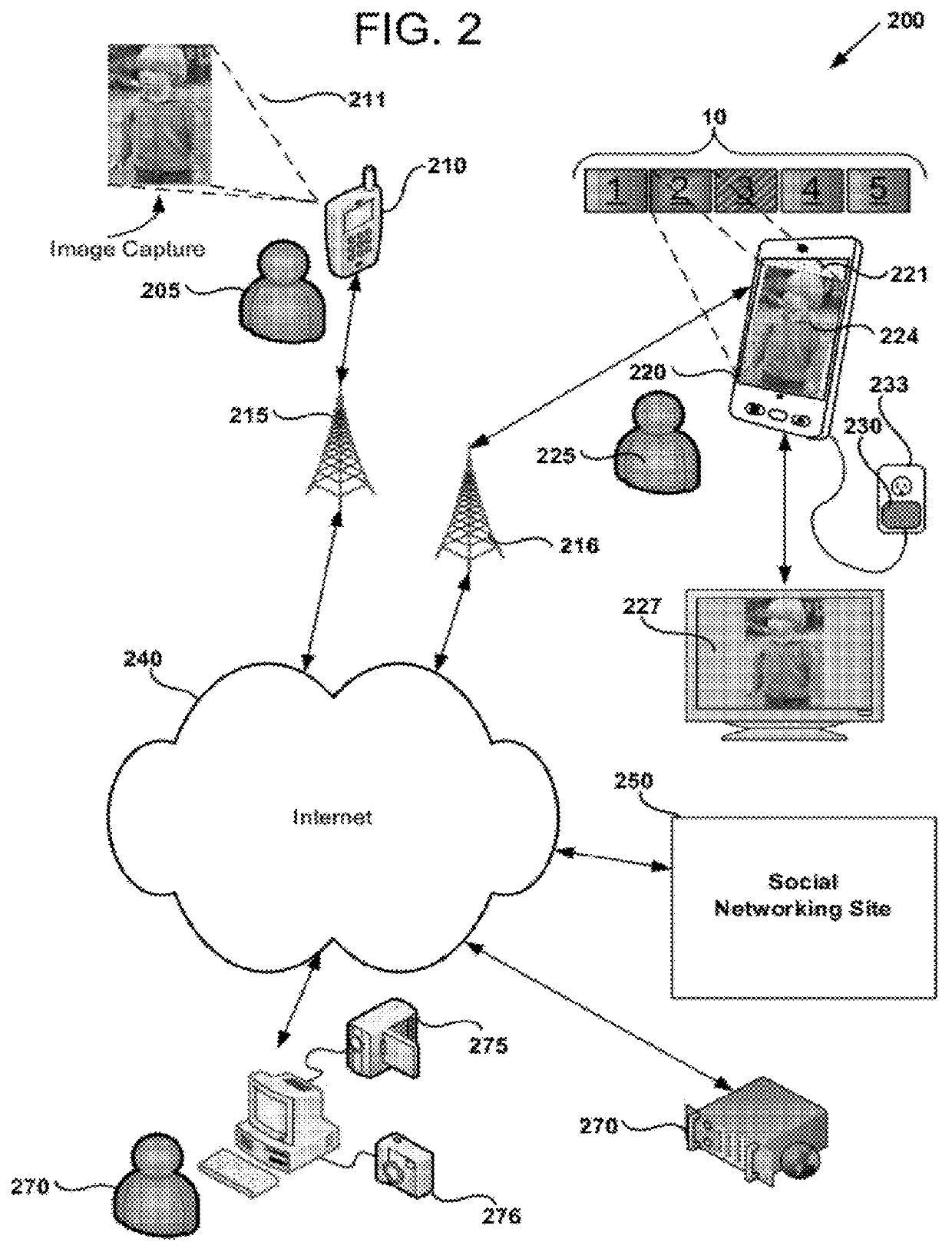
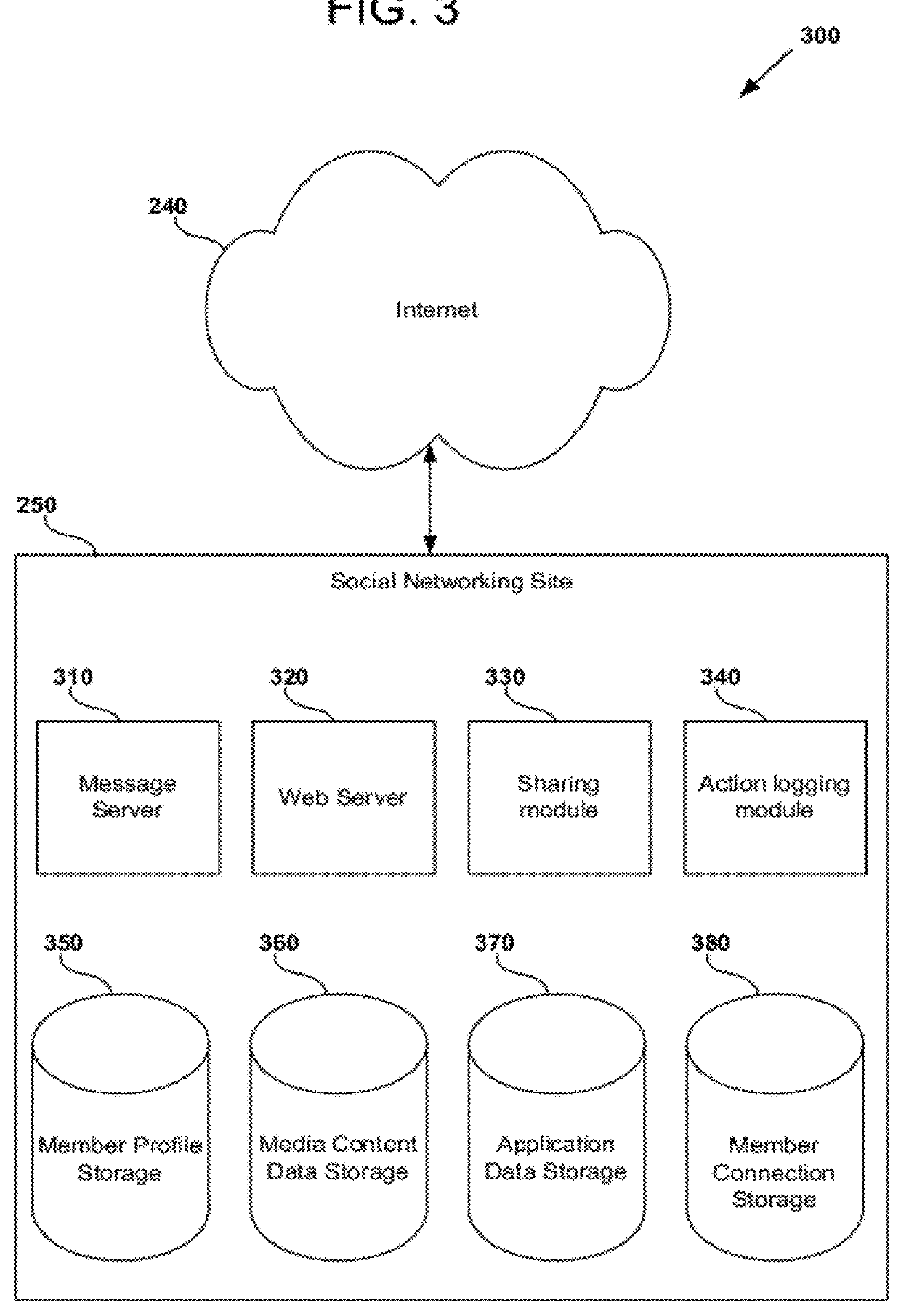
Automatic multimedia slideshows for social media-enabled mobile devices
Apparatus, computer-readable storage media, and methods are disclosed for allowing wireless communication device users to retrieve and view photographs, videos, and other media content using mobile computing platforms for display using a slideshow application. According to one disclosed embodiment, a method of performing a client-side slideshow application on a wireless communication device comprises, based on detecting that that wireless communication device is connected to a charging device, automatically invoking a slideshow application operable to display a series of images using the wireless communication device. The method further comprises transmitting a request for images via the Internet and receiving a series of images selected based at least in part on the request, adding at least one image from the series of images to an image playlist, and displaying at least a portion of the image playlist sequentially using the slideshow application on the wireless communication device.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for dynamically controlling scroller speed employed for a user interface of a wearable appliance
InactiveUS7081905B1Amount of user manipulation of the scroller to get to a particular positionElectric indicationFrequency stabilisation mechanismDisplay deviceHuman–computer interaction
A wearable mobile computing device / appliance (e.g., a wrist watch) with a high resolution display that is capable of wirelessly accessing information from the network and a variety of other devices. The Wrist Watch device / appliance includes a user interface that is used to efficiently interact with alarms, time keeping functions and notifications on the watch via use of a scroll device implementing dynamic scroll speed controller capability which enables seamless fine-grain and coarse-grain scroll and / or cursor movement through displayed content without notice to the user of the scroll device.
Owner:IBM CORP
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
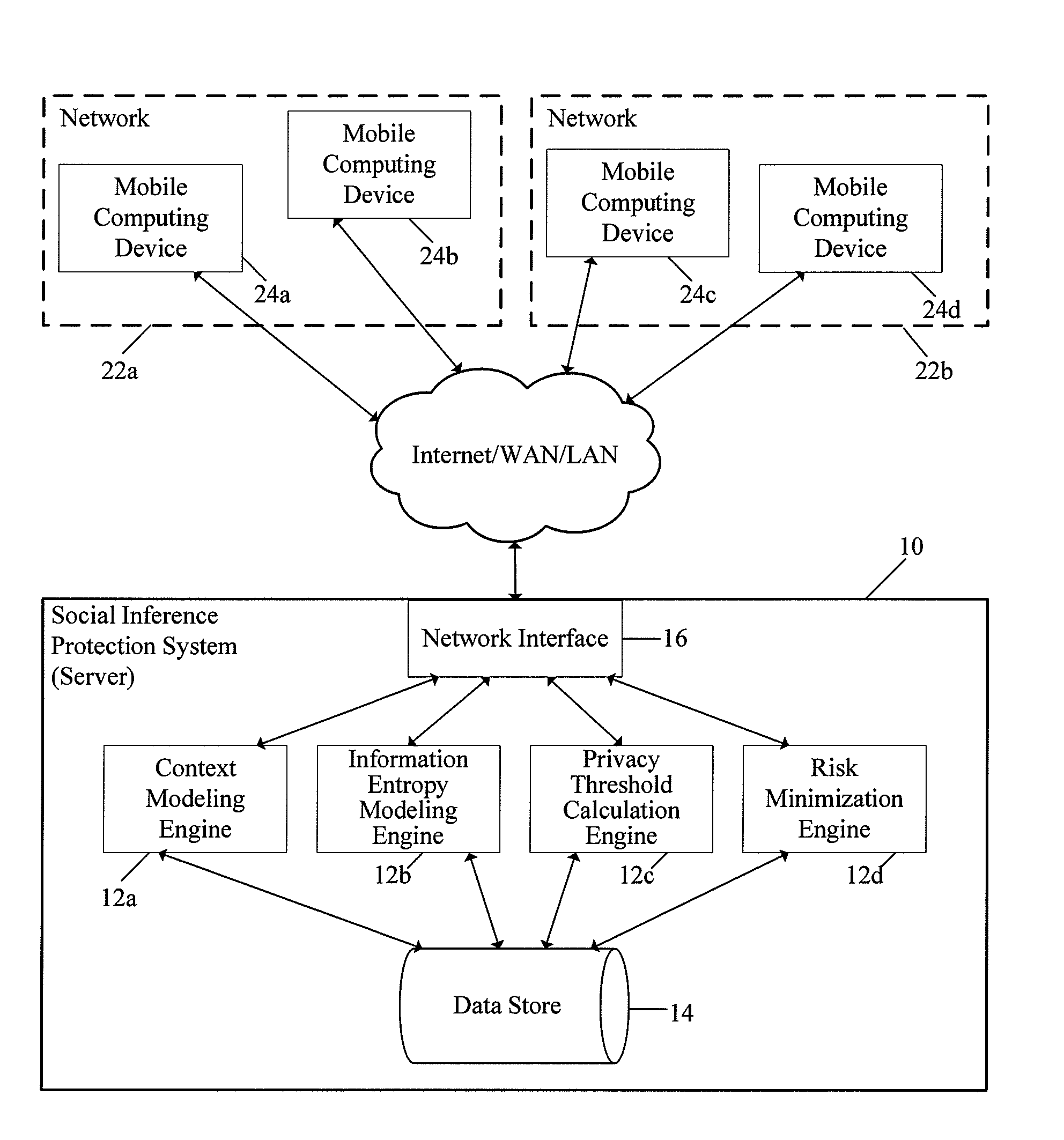
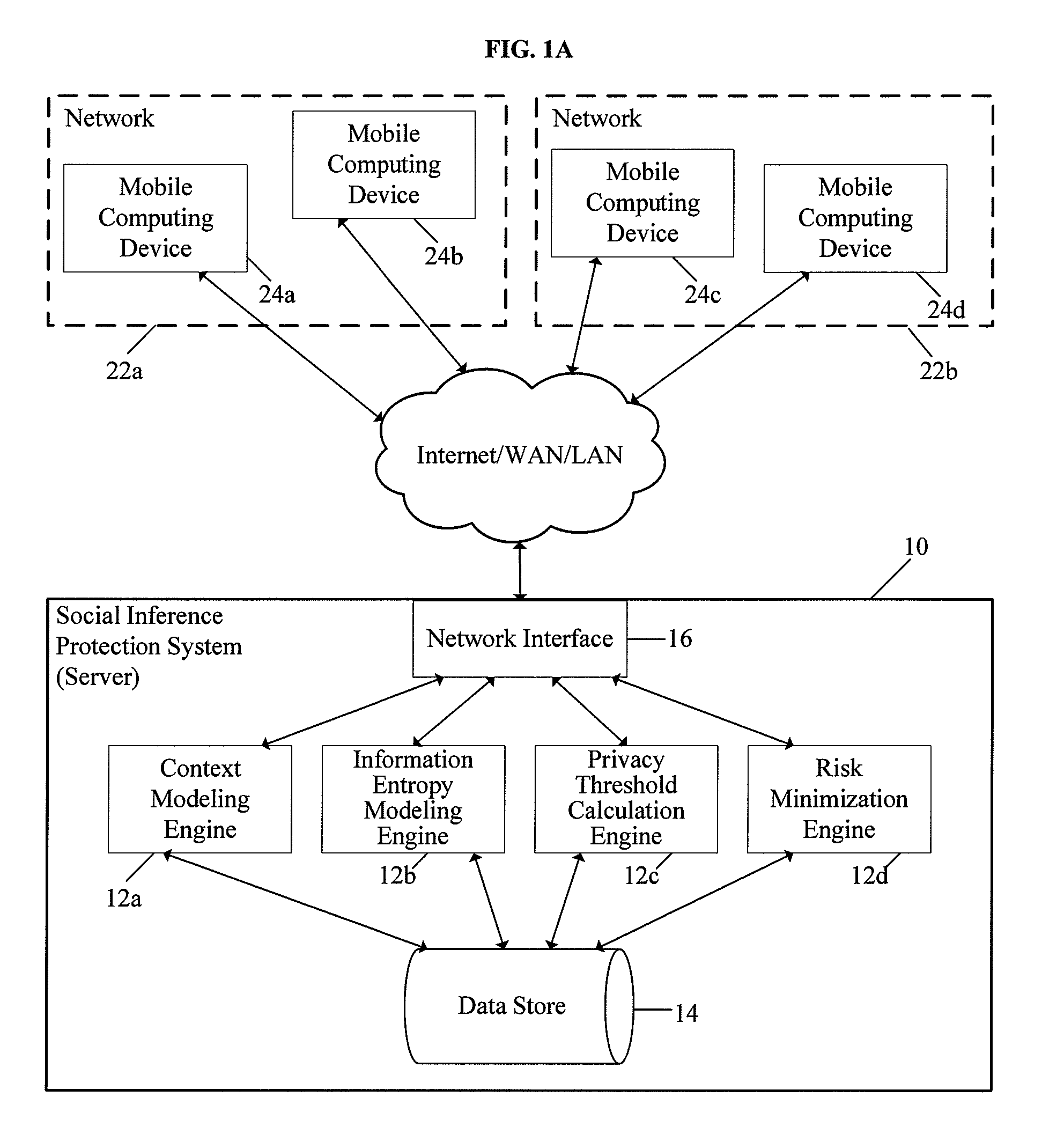
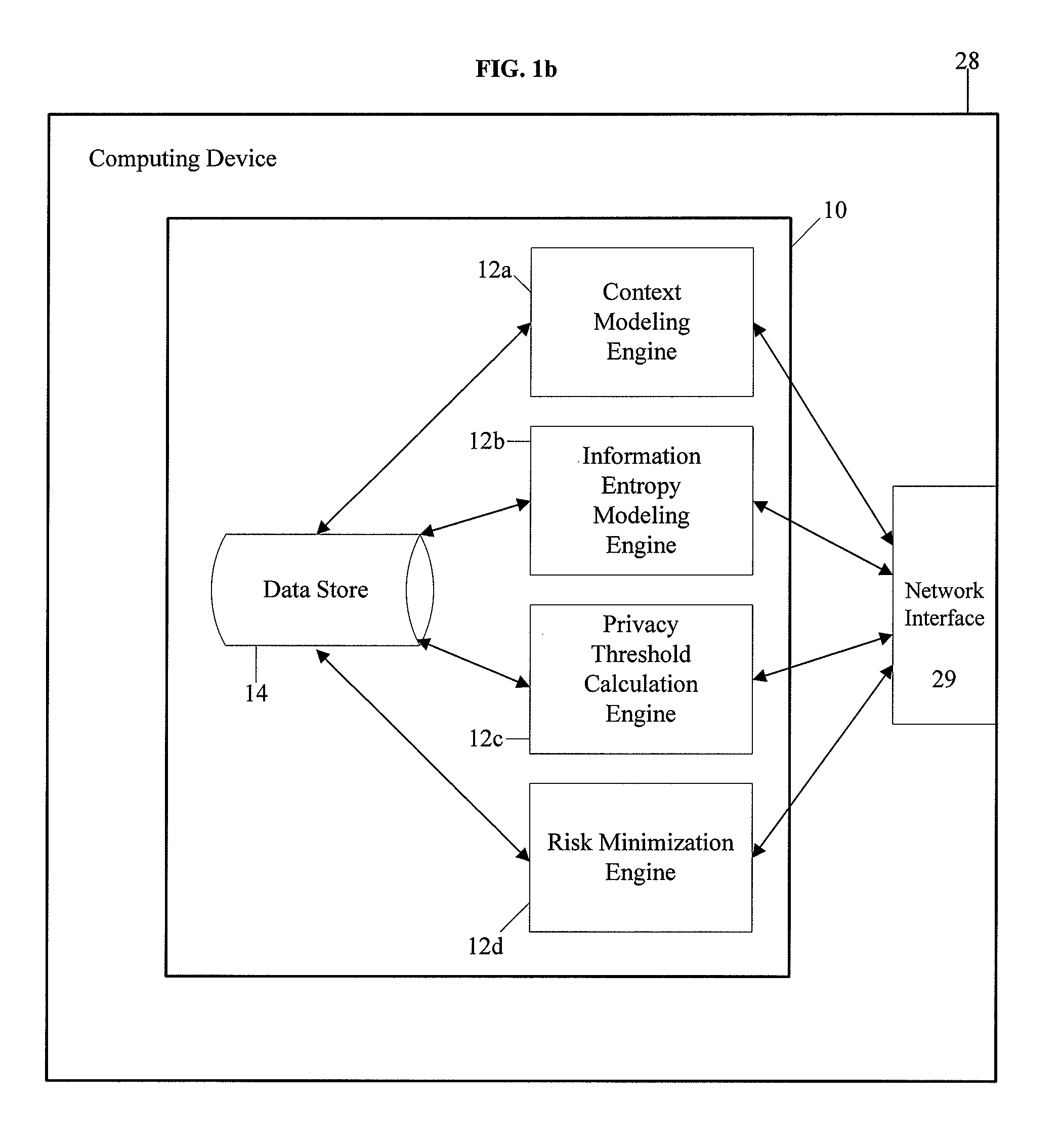
System and method for protecting user privacy using social inference protection techniques
InactiveUS8504481B2Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
Methods and Systems for Using External Display Devices With a Mobile Computing Device
ActiveUS20100299436A1Sacrificing of capabilitySacrificing quality of displayDevices with multiple display unitsDigital data processing detailsData displayDisplay device
The present disclosure relates to methods and systems for using external display devices with a mobile computing device. The mobile computing device may be repurposed to display a virtual input device for interacting with a resource with output data being displayed on an external display device.
Owner:CITRIX SYST INC
Distributed sensing techniques for mobile devices
ActiveUS7532196B2Input/output for user-computer interactionServices signallingHuman–computer interactionMobile device
Methods and apparatus of the invention allow the coordination of resources of mobile computing devices to jointly execute tasks. In the method, a first gesture input is received at a first mobile computing device. A second gesture input is received at a second mobile computing device. In response, a determination is made as to whether the first and second gesture inputs form one of a plurality of different synchronous gesture types. If it is determined that the first and second gesture inputs form the one of the plurality of different synchronous gesture types, then resources of the first and second mobile computing devices are combined to jointly execute a particular task associated with the one of the plurality of different synchronous gesture types.
Owner:MICROSOFT TECH LICENSING LLC
Techniques to manage vehicle communications
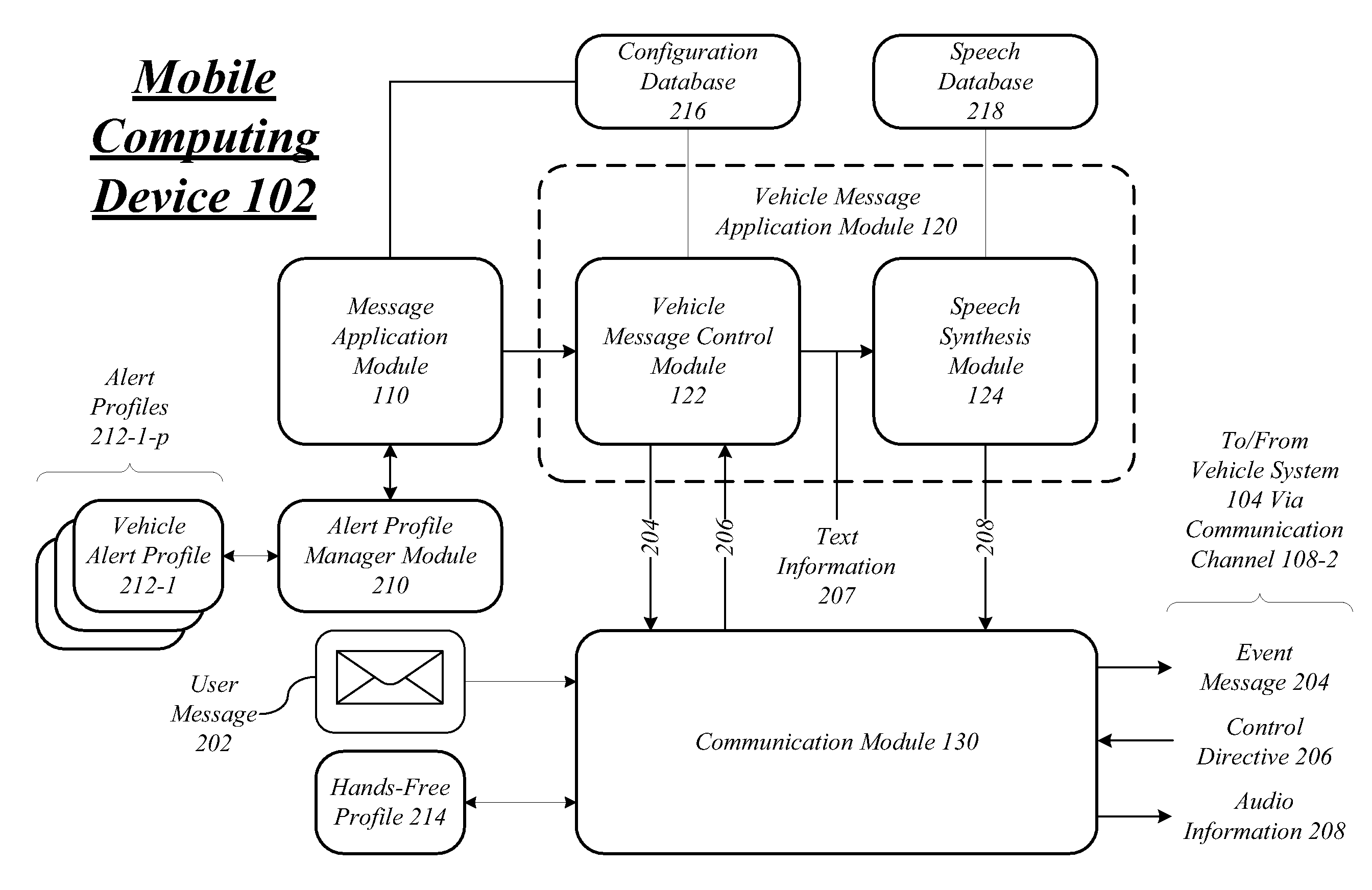
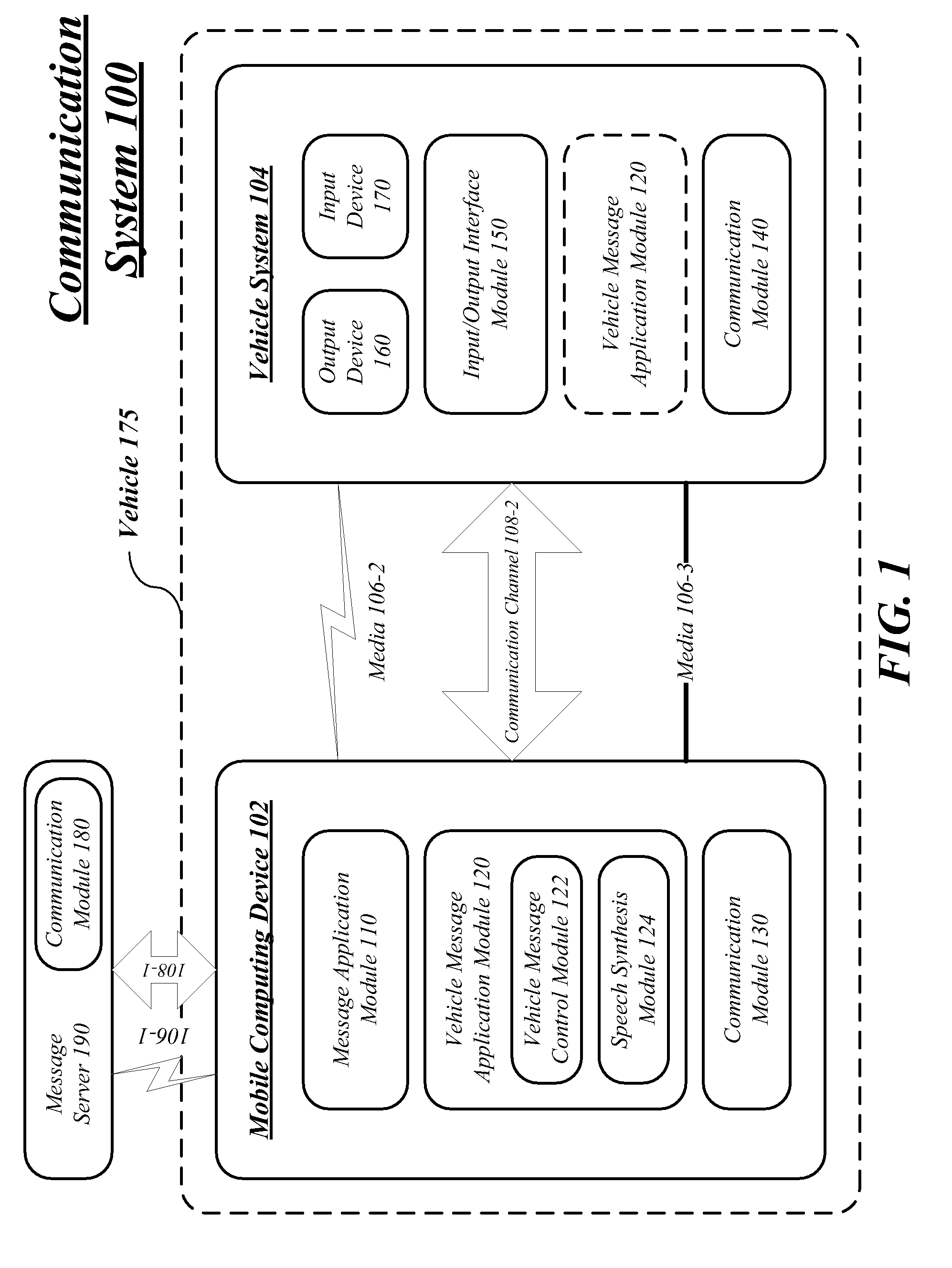
InactiveUS20090298474A1Special service for subscribersMultiple digital computer combinationsApplication moduleReal-time computing
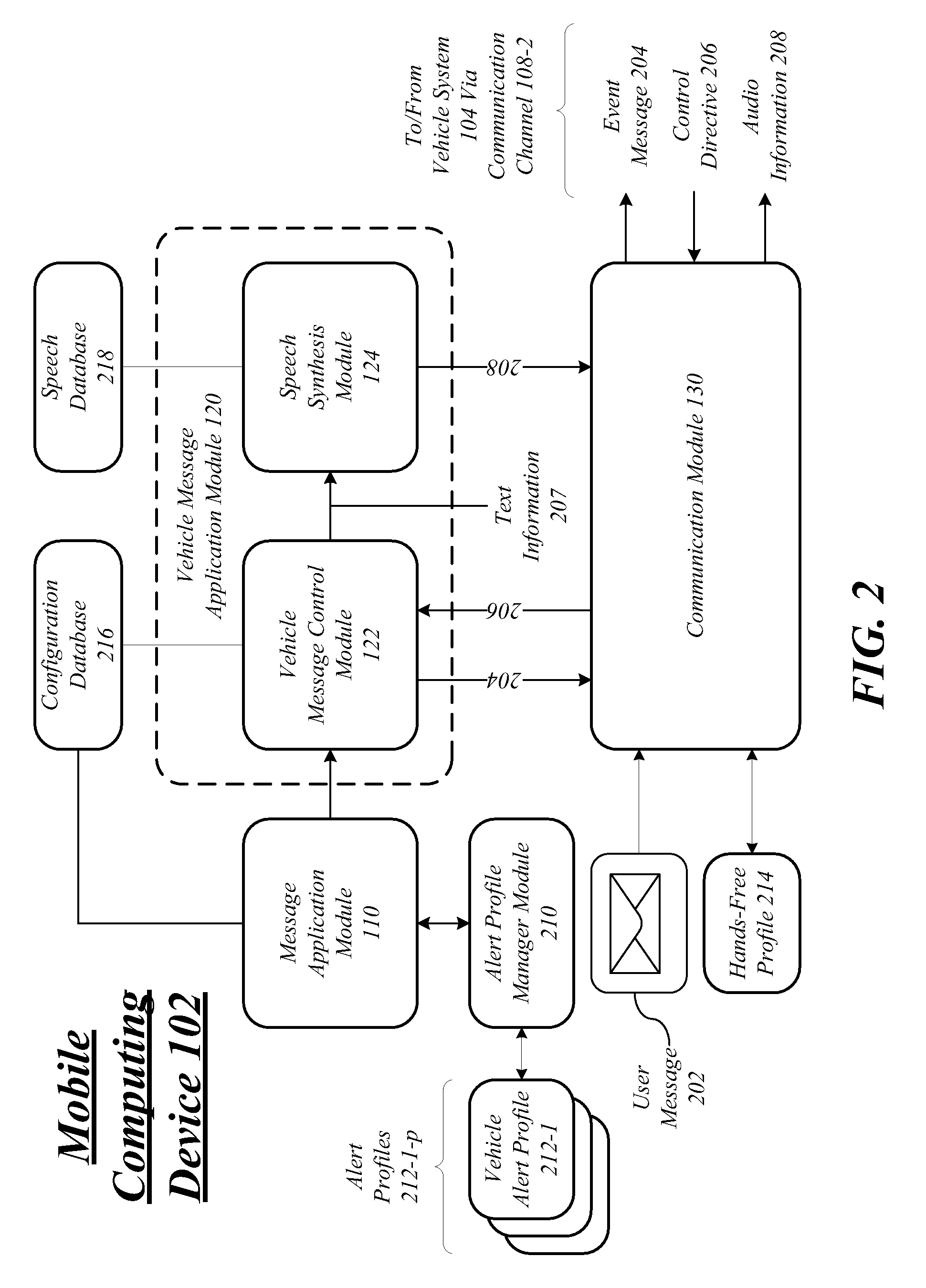
Techniques to manage vehicle communications are described. A mobile computing device may include a communication module operative to establish a first communication channel with a message server, and a second communication channel with a vehicle system, a message application module communicatively coupled to the communication module, the message application module operative to receive a user message over the first communication channel, and send an event message over the second communication channel, and a vehicle message application module communicatively coupled to the message application module, the vehicle message application module operative to receive a read control directive over the second communication channel, convert text information from the user message to mail audio information, and send the mail audio information over the second communication channel. Other embodiments are described and claimed.
Owner:QUALCOMM INC
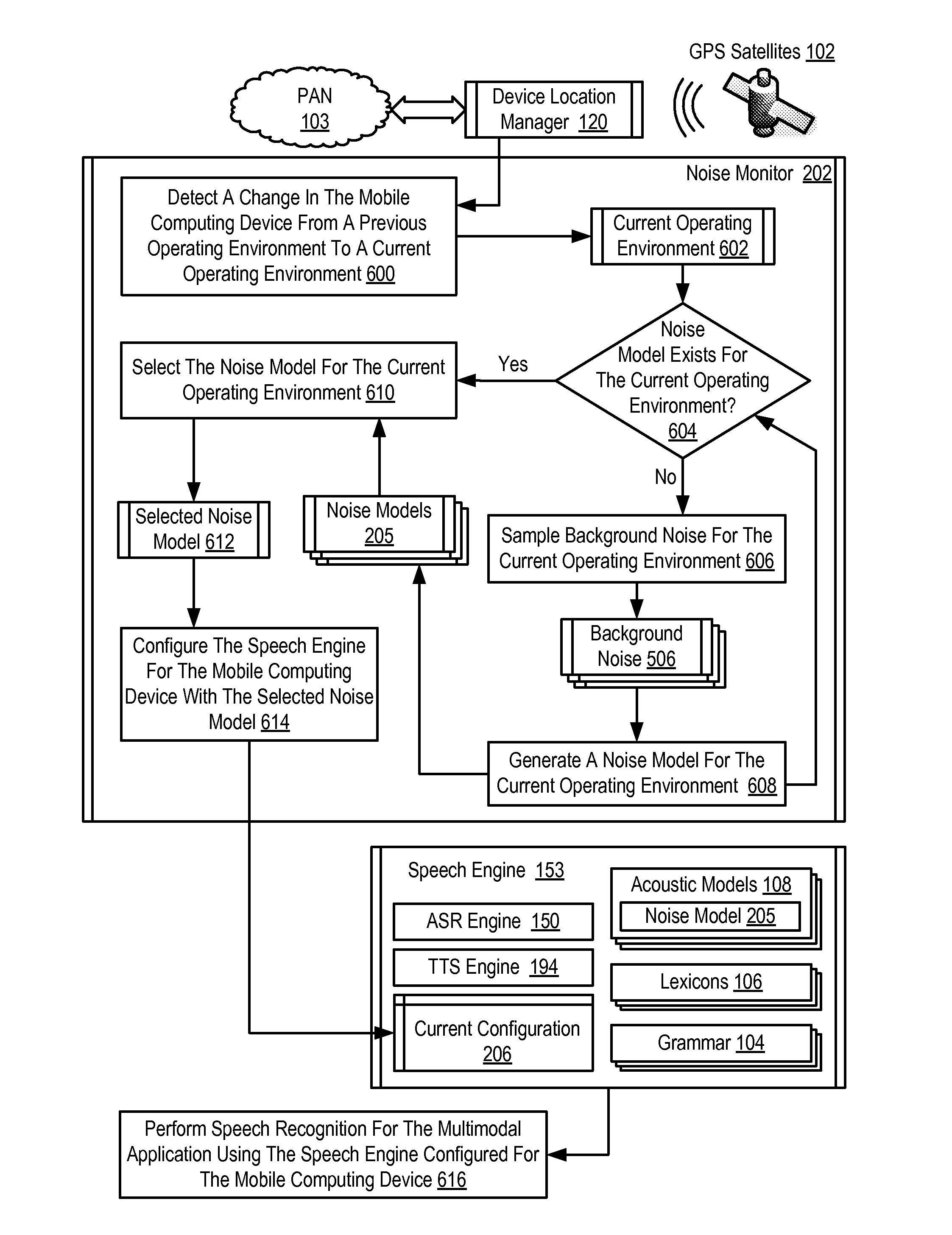
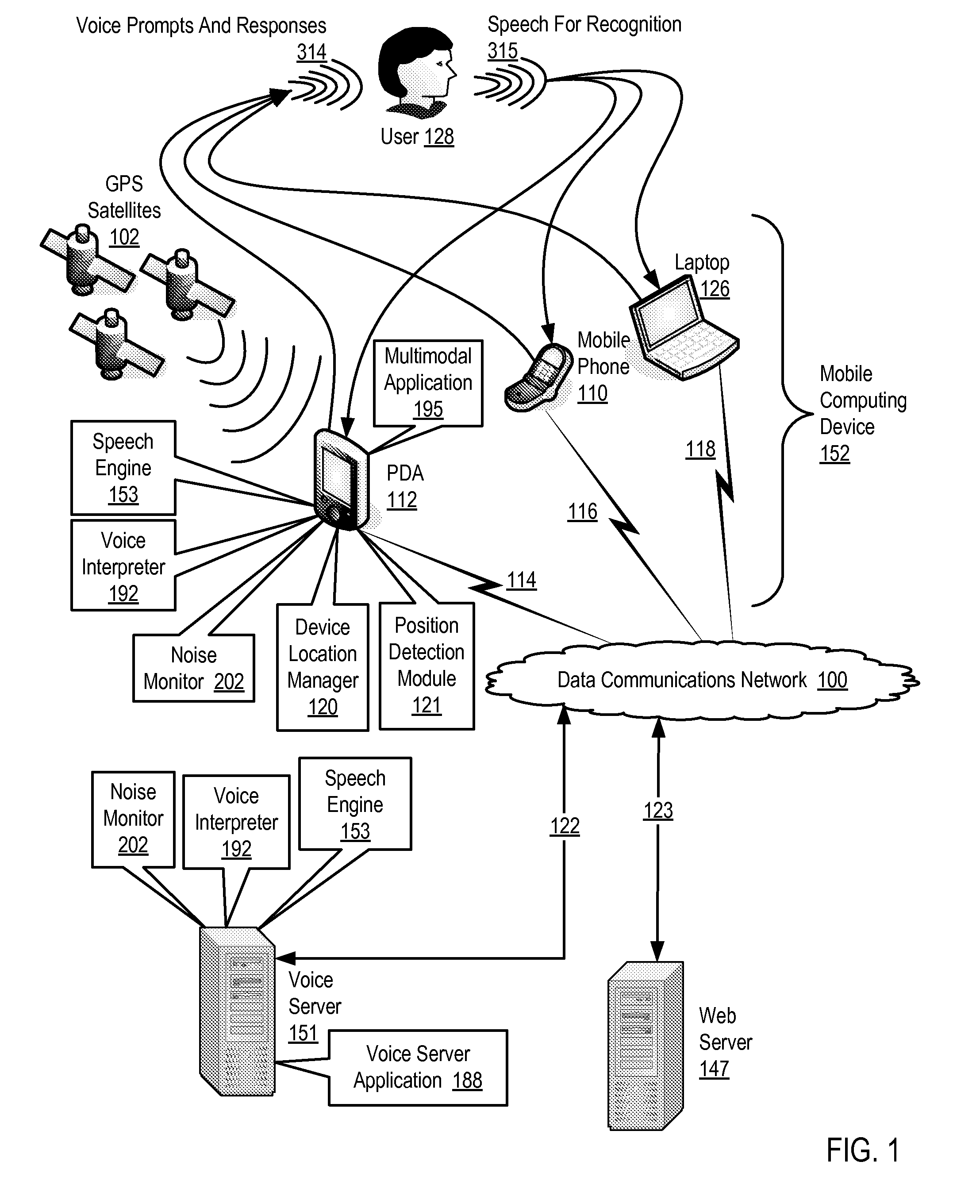
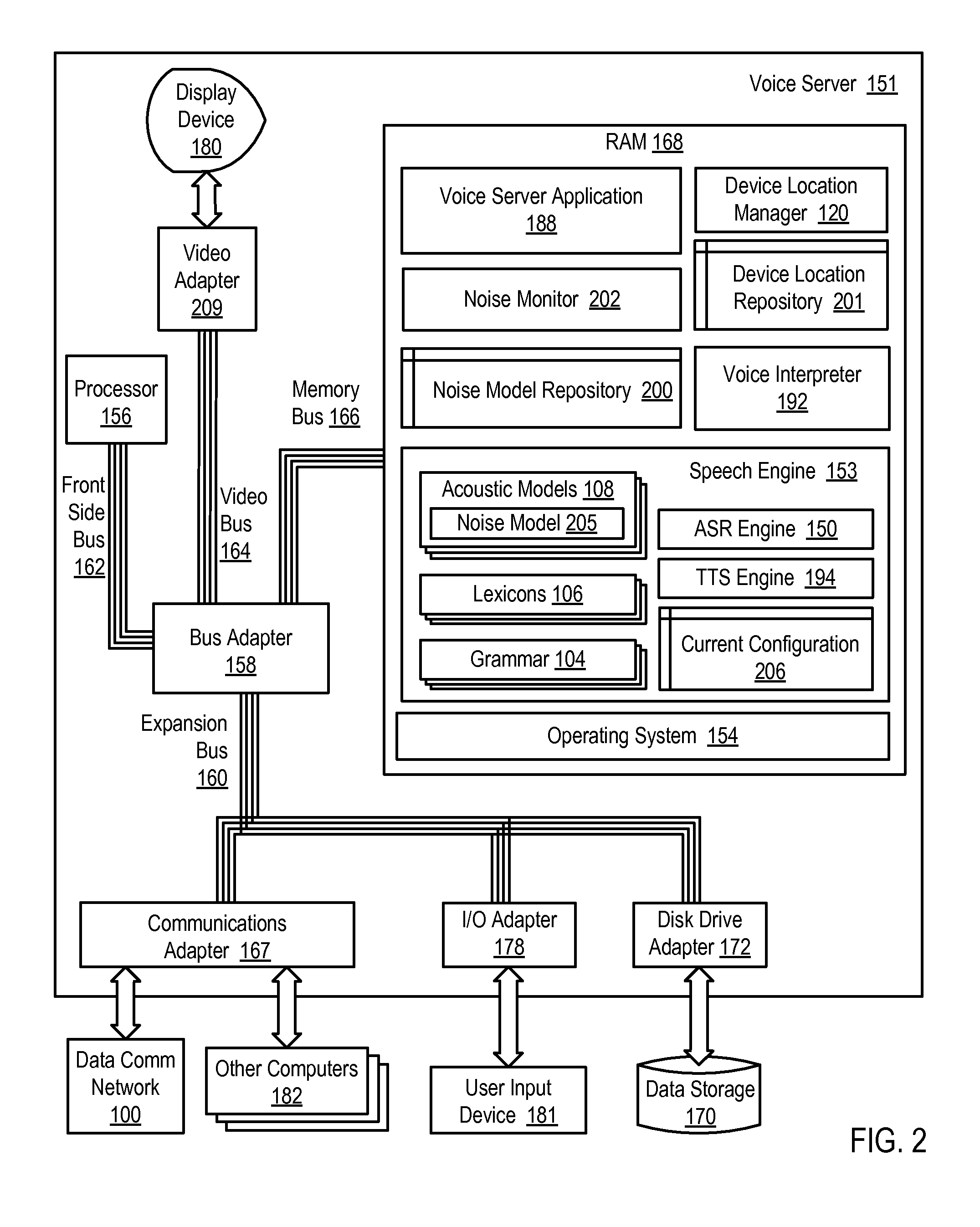
Adjusting a speech engine for a mobile computing device based on background noise
Owner:CERENCE OPERATING CO
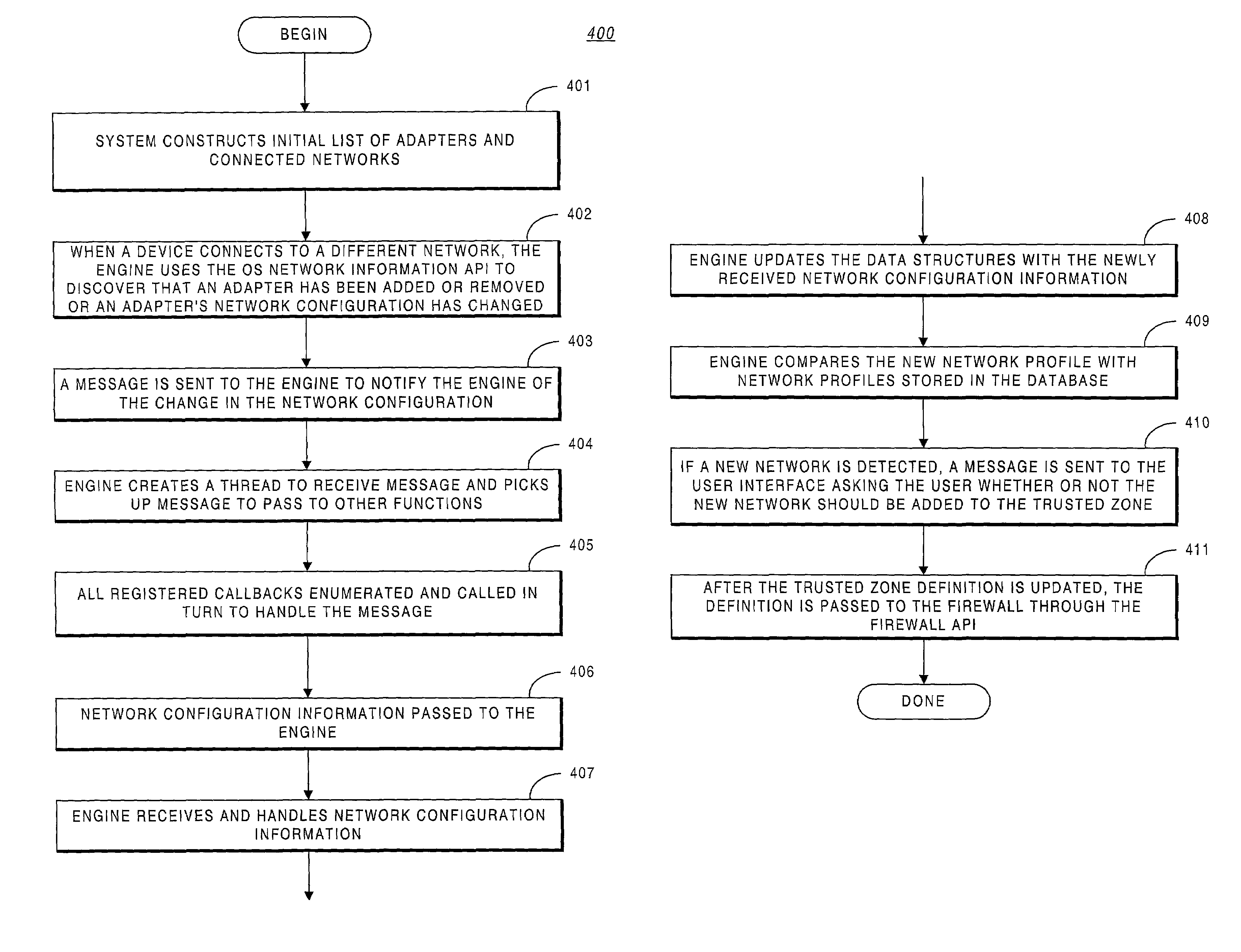
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
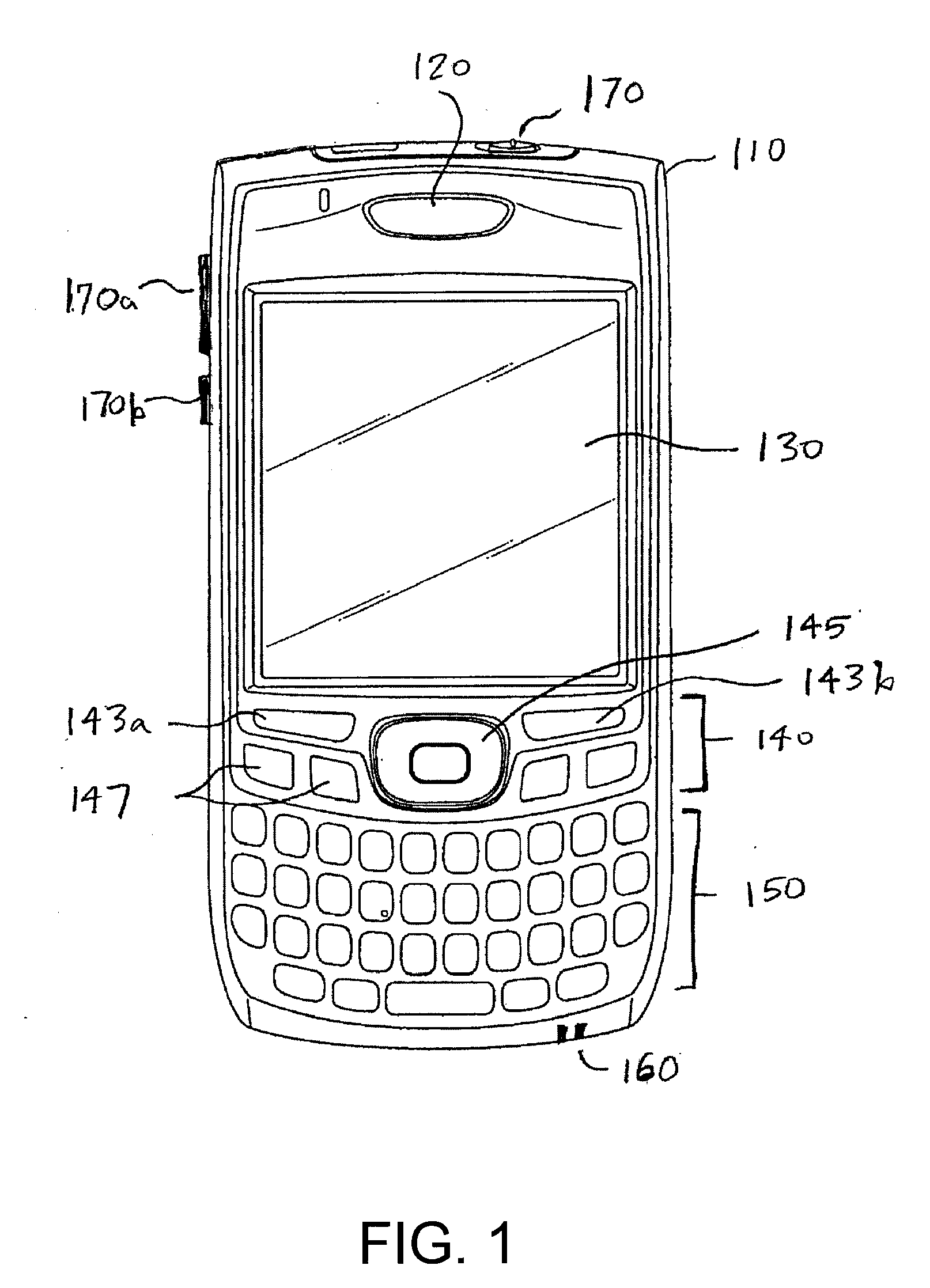
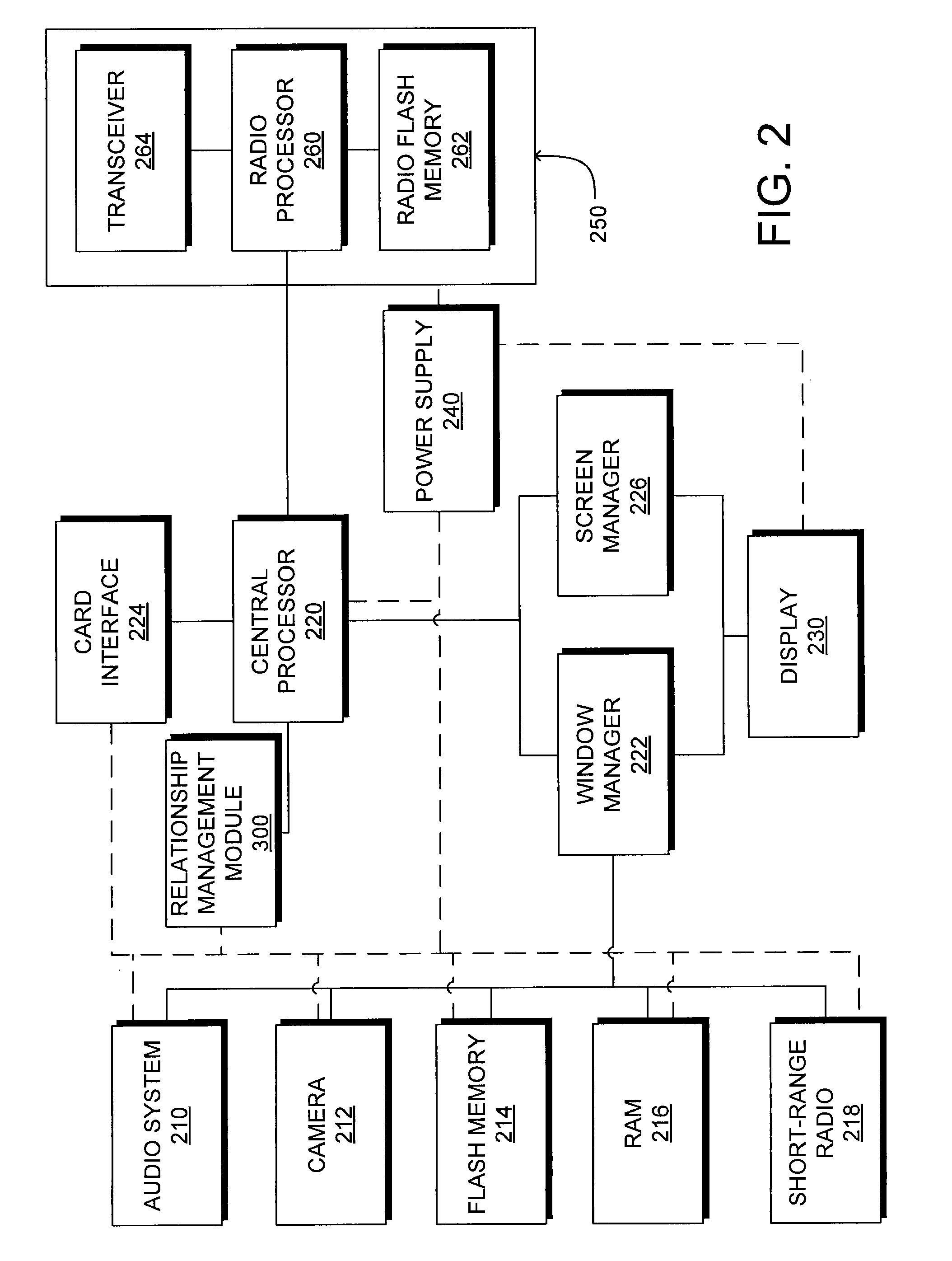
Relationship management on a mobile computing device
InactiveUS20100057643A1Accurate descriptionQuickly access and viewDigital data processing detailsSubstation equipmentValue creationCommunication device
A system and a method are disclosed for implementing managing relationships between data on a mobile computing based on user creation and definition of the relationships. A mobile computing device user generates asymmetric relationships between stored entities, events, tasks and communications. These asymmetric relationships are custom-generated by the user to reflect the user's classification and evaluation of the relationships. The user also assigns a score to each relationship and stored entity, event, task and communication to represent the user's classification of the relationship, entity, event, task or communication. Hence, the user assigns a value to the relationships between data as well as the stored data to indicate which relationship or stored data is most valuable to the user. The user-defined relationships between data can be automatically displayed when the mobile communication device is used to interact with a stored entity.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com