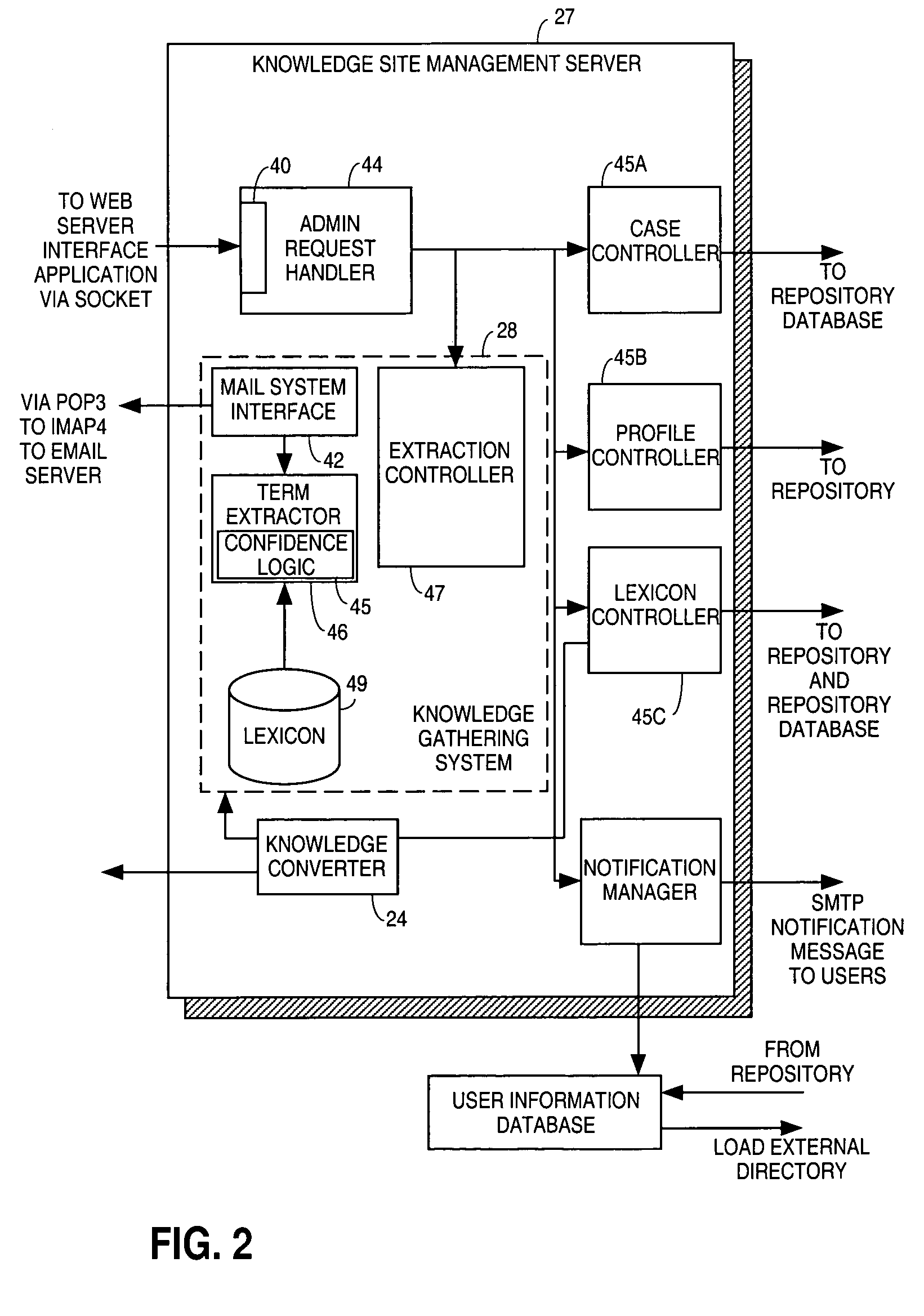
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1517 results about "System administrator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
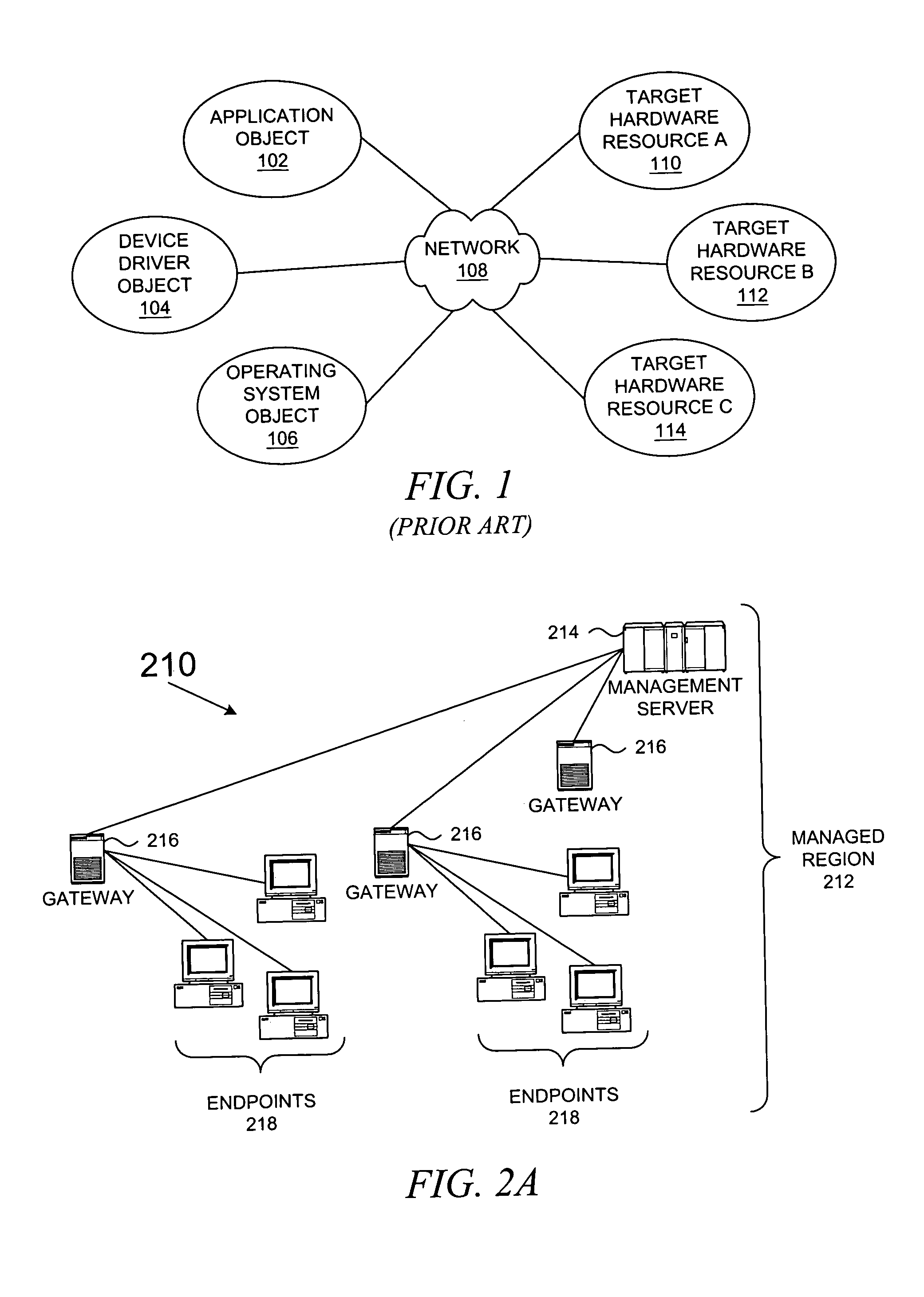
A system administrator, or sysadmin, is a person who is responsible for the upkeep, configuration, and reliable operation of computer systems; especially multi-user computers, such as servers. The system administrator seeks to ensure that the uptime, performance, resources, and security of the computers they manage meet the needs of the users, without exceeding a set budget when doing so.
Open Web Services-Based Indoor Climate Control System
InactiveUS20080281472A1Improve productivityCost of sameProgramme controlSampled-variable control systemsReal-time Control SystemWeb service
The present invention relates generally to a building automation system, and, more particularly, to an Internet-centric, open, extensible software and hardware framework supporting all aspects of control and monitoring of a smart building ecosphere. The present invention further relates to an “intelligent,” real-time control system capable of both autonomous process control and interaction with system users and system administrators, which is configured to accommodate functional extensions and a broad array of sensors and control devices. The system allows individuals to communicate, monitor and adjust their personal environmental preferences (temperature, light, humidity, white noise, etc.) much like they would in an automobile, via the Internet. The system is equipped with an occupancy sensor that recognizes the presence and identity of the individual. A built-in expert system can make decisions based on data from multiple sources so that the system can alter its activity to conserve energy while maintaining users' comfort.
Owner:SYRACUSE UNIVERSITY
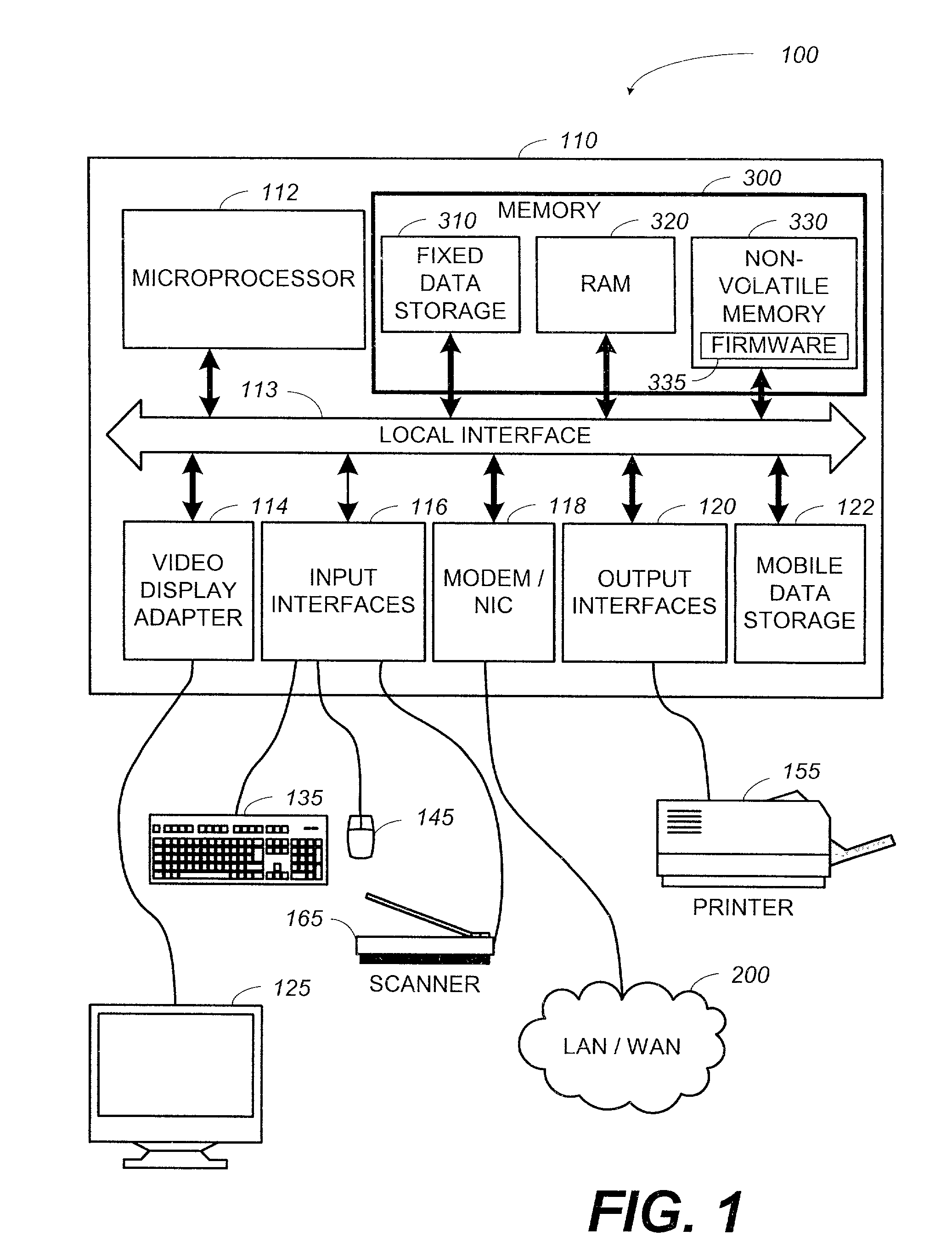
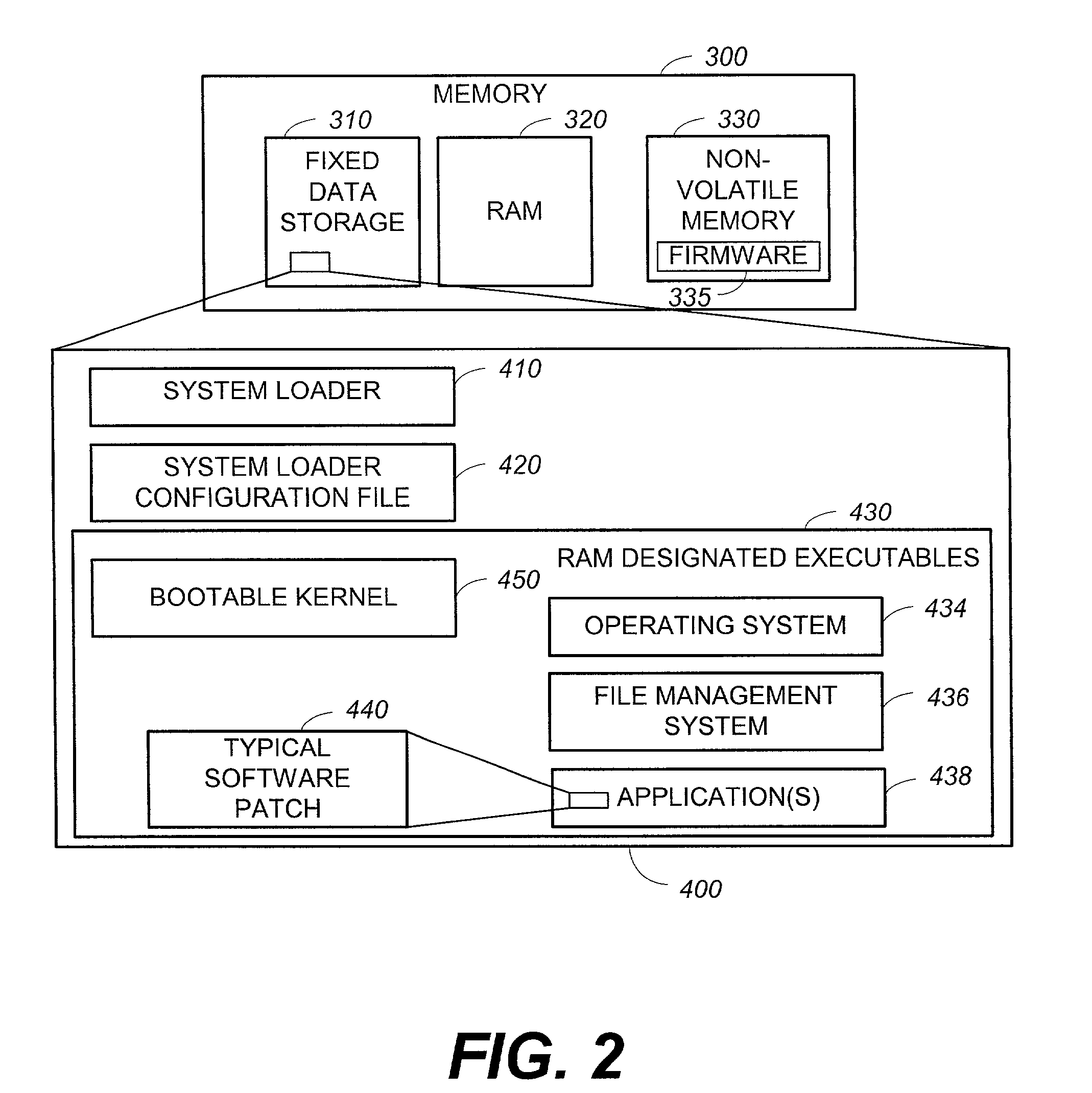
System and method for updating firmware
InactiveUS7055148B2Avoid manual interventionDigital computer detailsProgram loading/initiatingOperational systemFirmware version
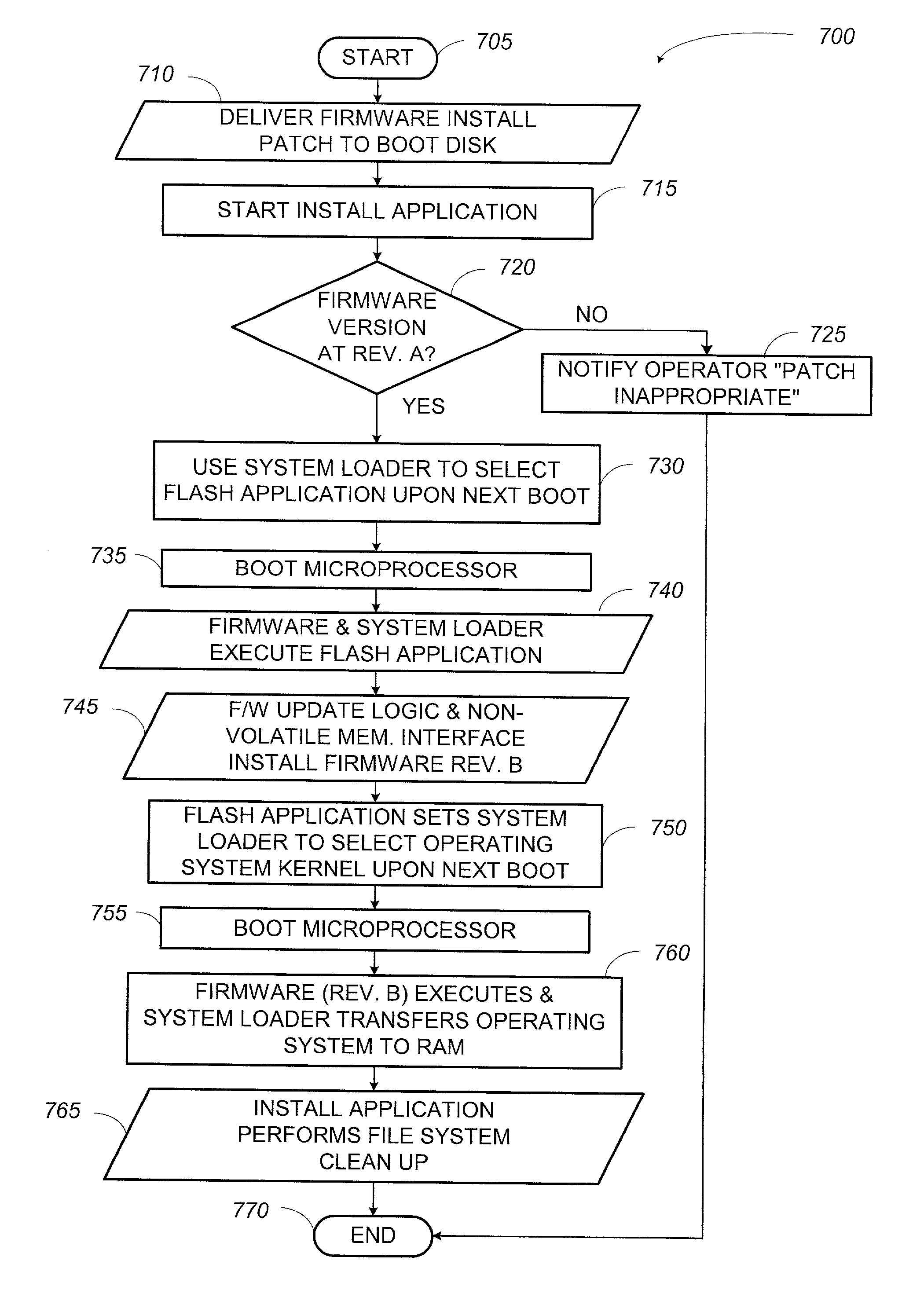
A system and a method that uses a software application operable under a current firmware / operating system configuration to install a new firmware version without “compromising” the operating system are presented. The software application may configure a computer system to install a plurality of software fixes configured to enhance functionality under a new firmware / operating system environment after the firmware has been successfully upgraded. Such functionality enhancements may be associated with external peripherals, as well as, input / output circuit cards, processors, and the like. In addition, the software application may configure the computing device to “boot” under the new firmware / operating system environment upon subsequent system initializations. Furthermore, the software application permits the distribution of firmware upgrades via a network. The capability to install firmware remotely permits a system administrator to “push” the new firmware to a plurality of network coupled computing devices, thus avoiding manual intervention at each device.
Owner:HEWLETT PACKARD DEV CO LP
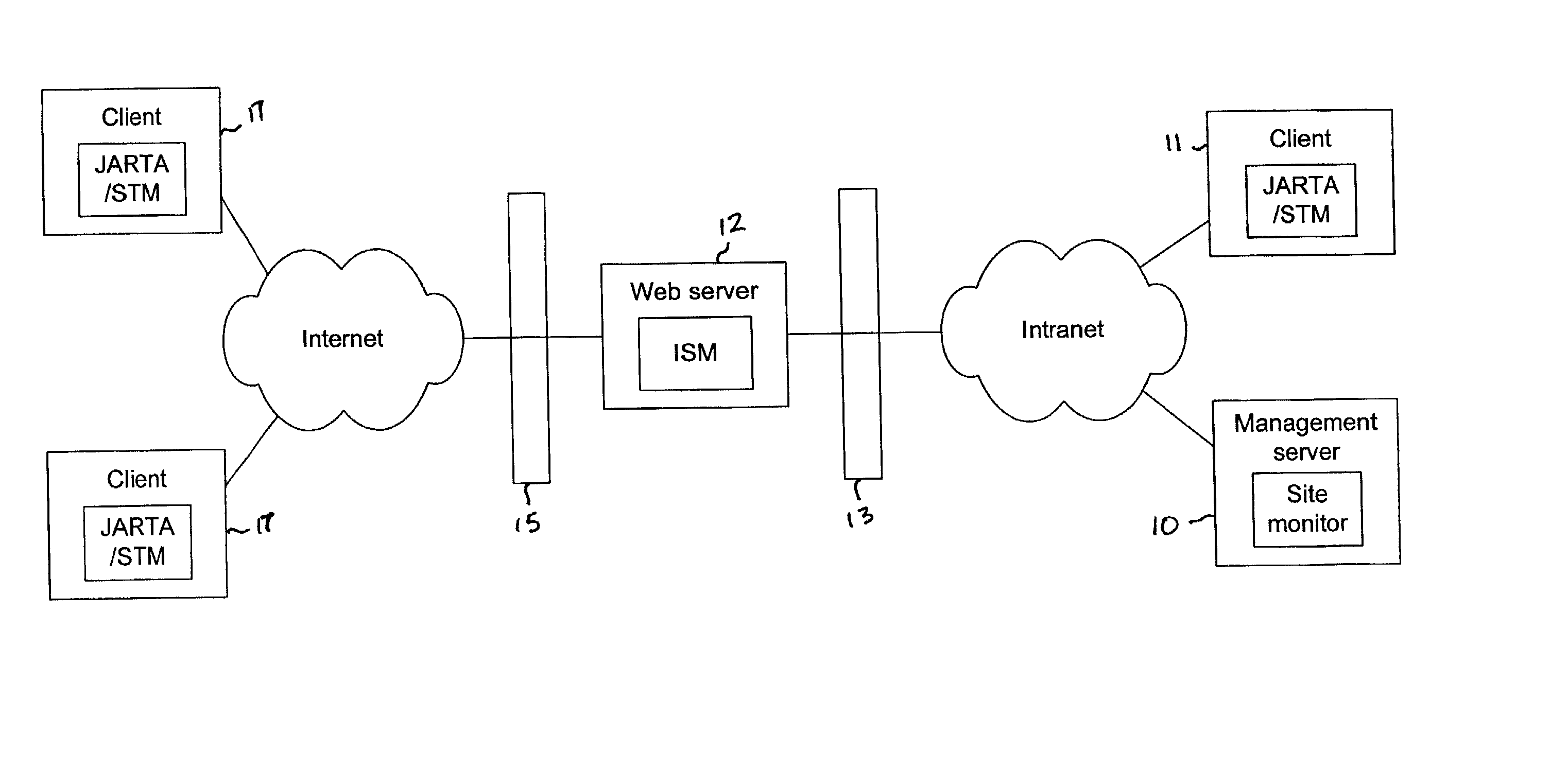
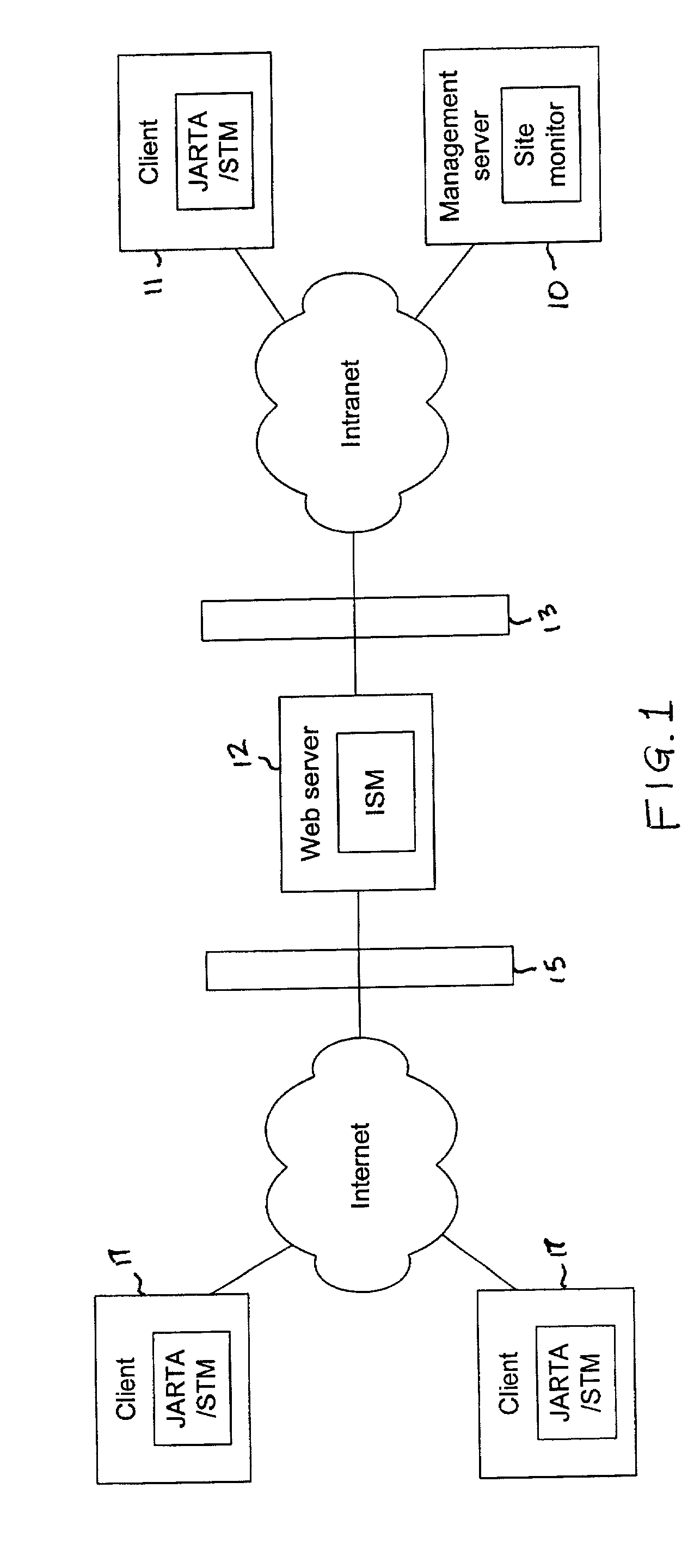
Synthetic transaction monitor
ActiveUS20030055883A1Data processing applicationsHardware monitoringFinancial transactionClient server systems
Systems and methods for recording and replaying client-server transactions on selected clients in order to gauge the performance of the client-server system from the perspective of the client. In one embodiment, a method comprises playing back a set of recorded transactions on a client, monitoring selected performance-related parameters at the client, and transmitting monitored data to the server for analysis or for viewing by a system administrator. The set of transactions is recorded on a first client by replacing a standard Internet transaction driver (e.g., WinInet.DLL) with a modified driver that is configured to intercept function calls. The function calls and corresponding parameters are recorded in a file which is later transmitted to a client, where the recorded transaction information is used to reproduce the transactions on the client. As the transactions are played back, performance data may be monitored and forwarded to a management server for analysis, display, etc.
Owner:BMC SOFTWARE
Heuristic detection and termination of fast spreading network worm attacks
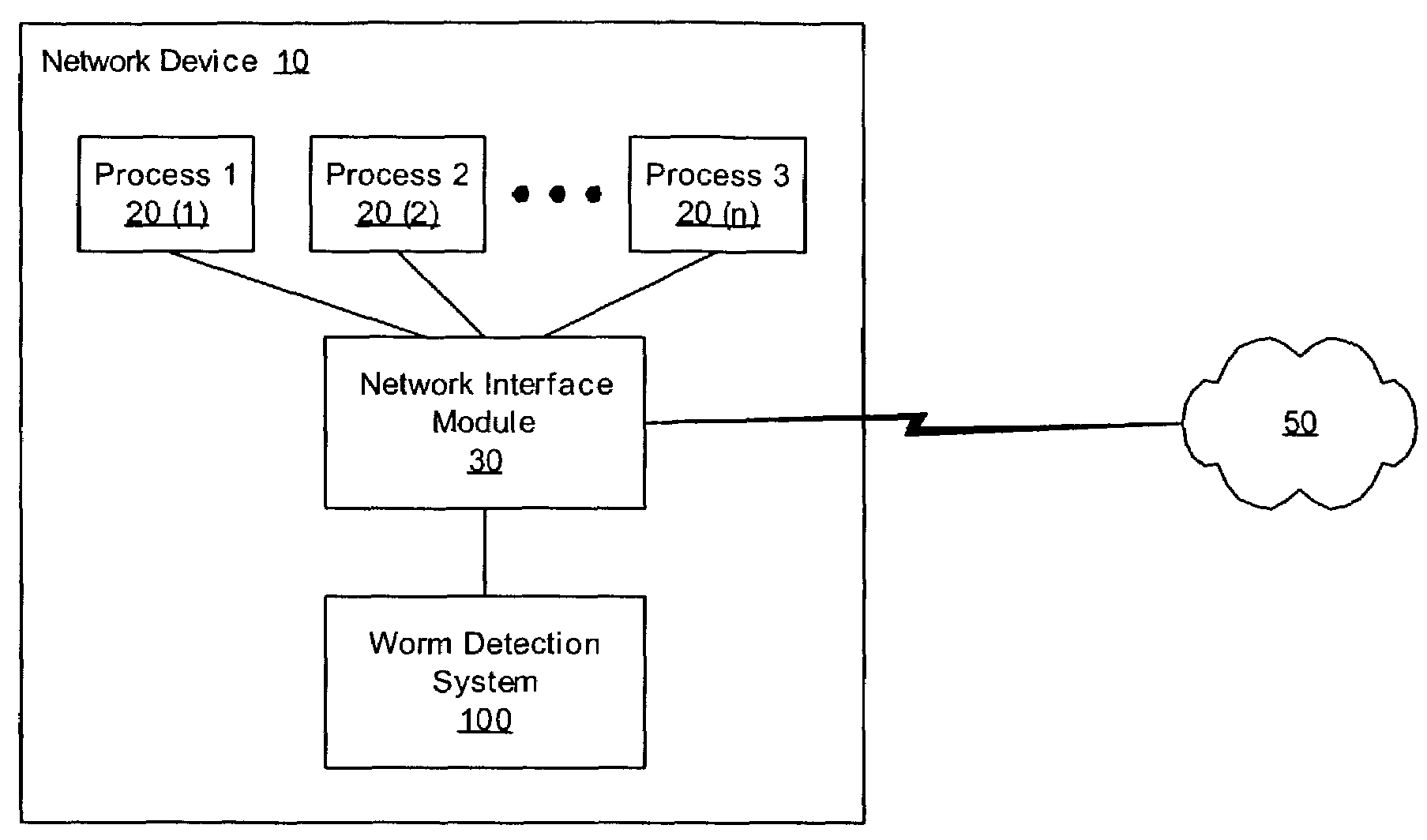
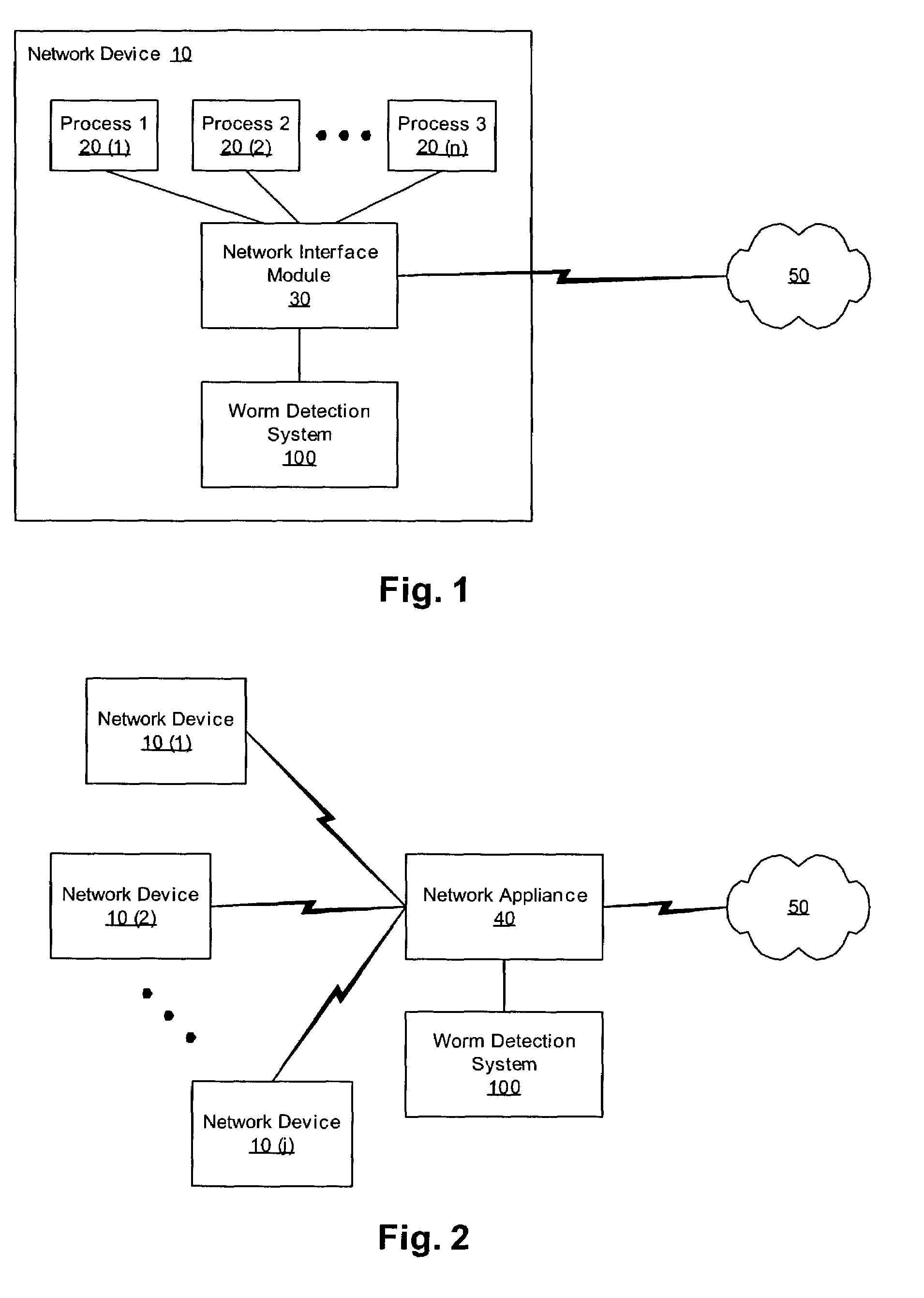
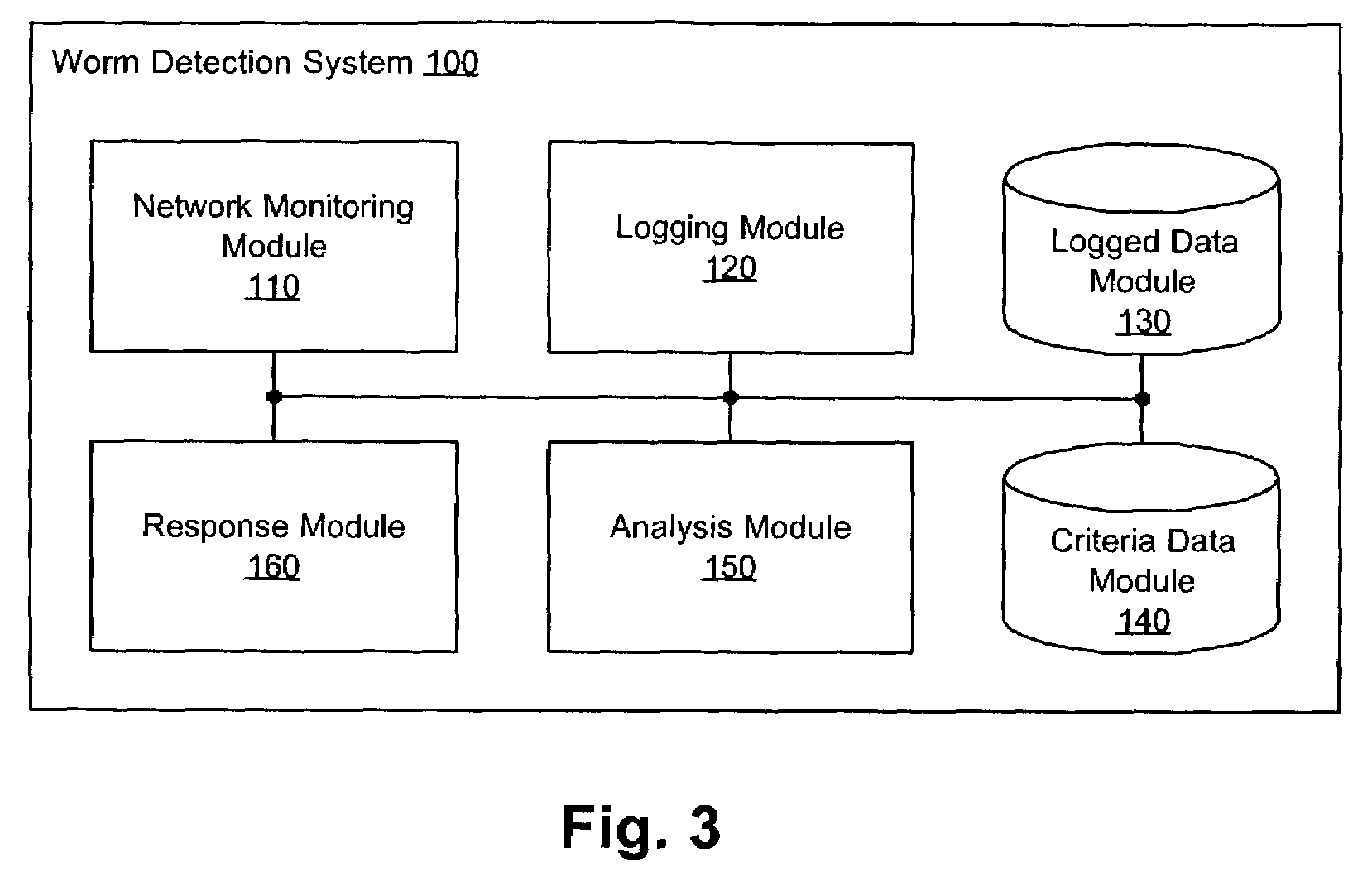
Methods, apparati, and computer program products for detecting and responding to fast-spreading network worm attacks include a network monitoring module (110), which observes (205) failed network connection attempts from multiple sources. A logging module (120) logs (220) the failed connection attempts. An analysis module (150) uses the logged data on the failed connection attempts to determine (225) whether a sources is infected with a worm using a set of threshold criteria. The threshold criteria indicate whether a source's failed connection attempts are non-normal. In one embodiment, a response module (160) responds (240) to the computer worm by, e.g., alerting a user or system administrator, terminating an infected process (20), or terminating the infected source's network access.
Owner:CA TECH INC
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
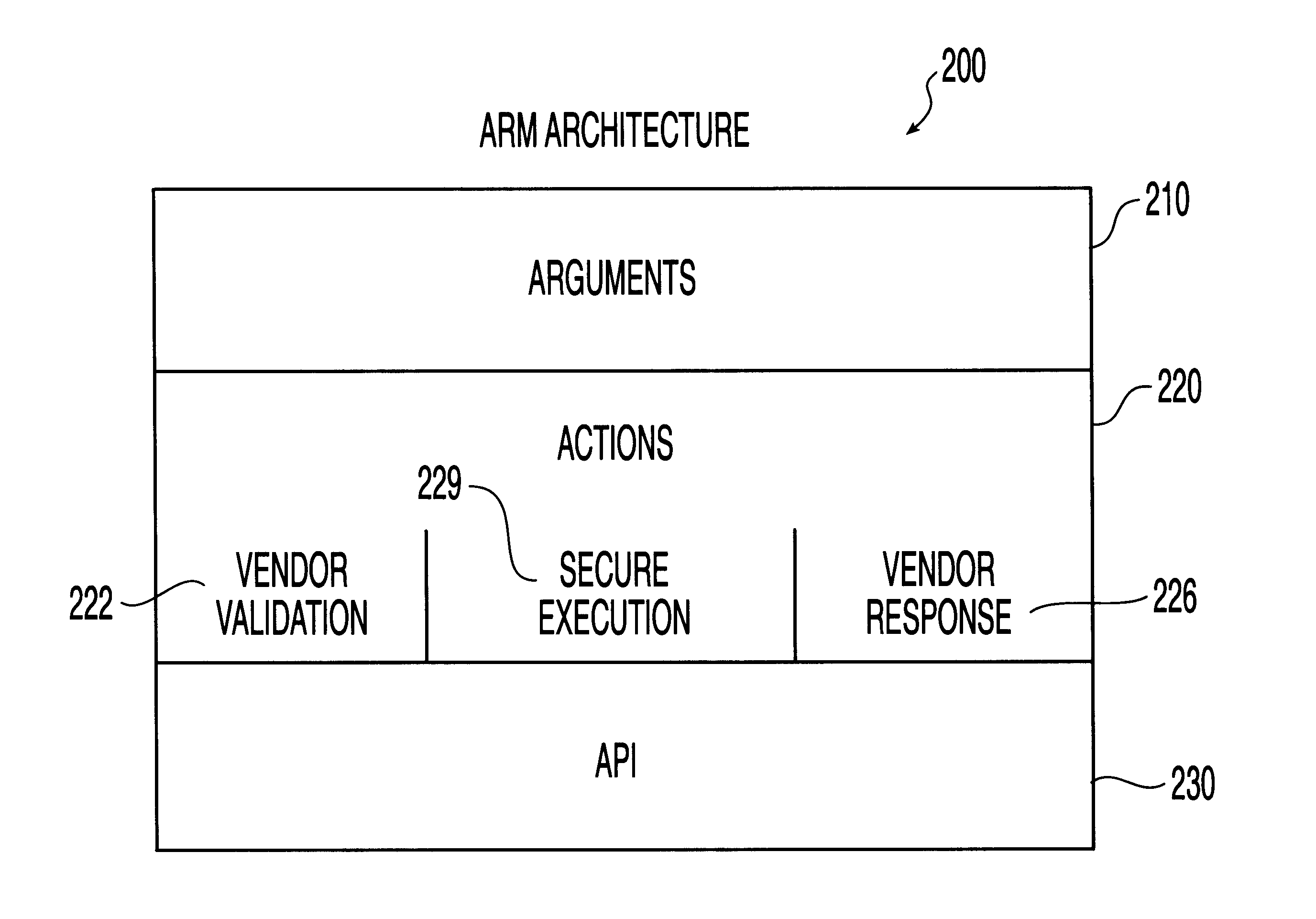
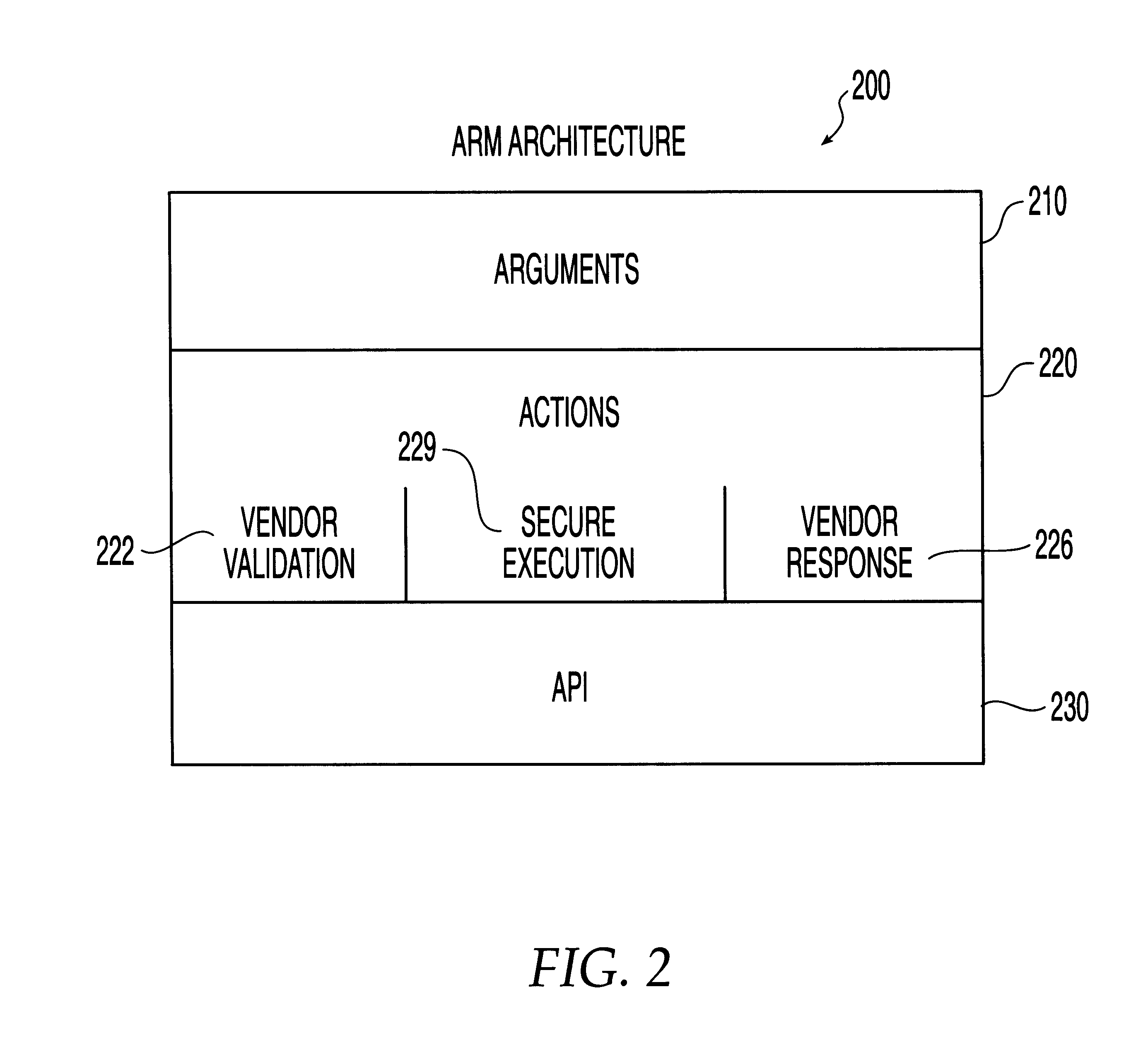
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
Open web services-based indoor climate control system
InactiveUS7904209B2Improve productivityCost of sameProgramme controlSampled-variable control systemsReal-time Control SystemWeb service
The present invention relates generally to a building automation system, and, more particularly, to an Internet-centric, open, extensible software and hardware framework supporting all aspects of control and monitoring of a smart building ecosphere. The present invention further relates to an “intelligent,” real-time control system capable of both autonomous process control and interaction with system users and system administrators, which is configured to accommodate functional extensions and a broad array of sensors and control devices. The system allows individuals to communicate, monitor and adjust their personal environmental preferences (temperature, light, humidity, white noise, etc.) much like they would in an automobile, via the Internet. The system is equipped with an occupancy sensor that recognizes the presence and identity of the individual. A built-in expert system can make decisions based on data from multiple sources so that the system can alter its activity to conserve energy while maintaining users' comfort.
Owner:SYRACUSE UNIVERSITY
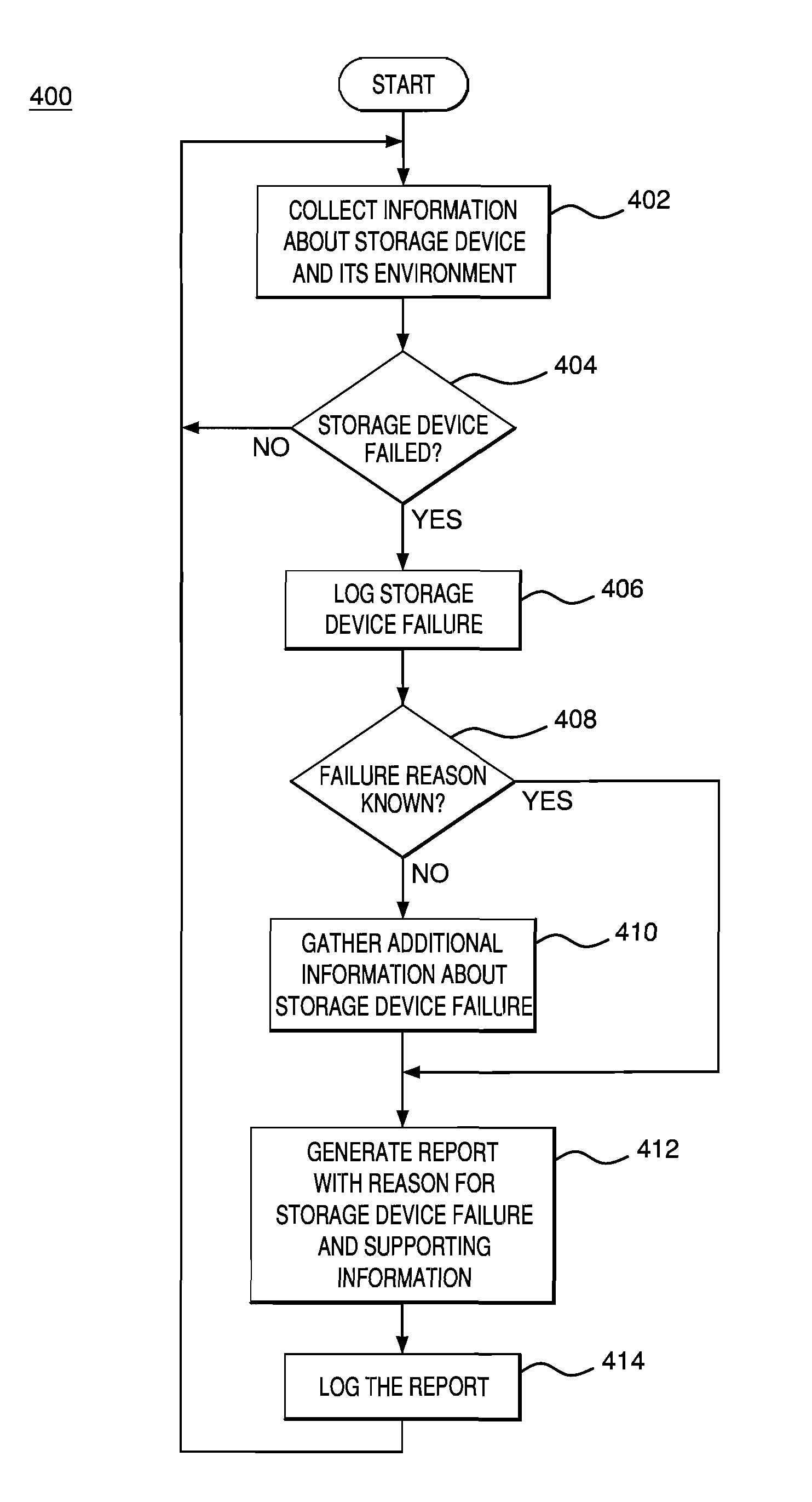
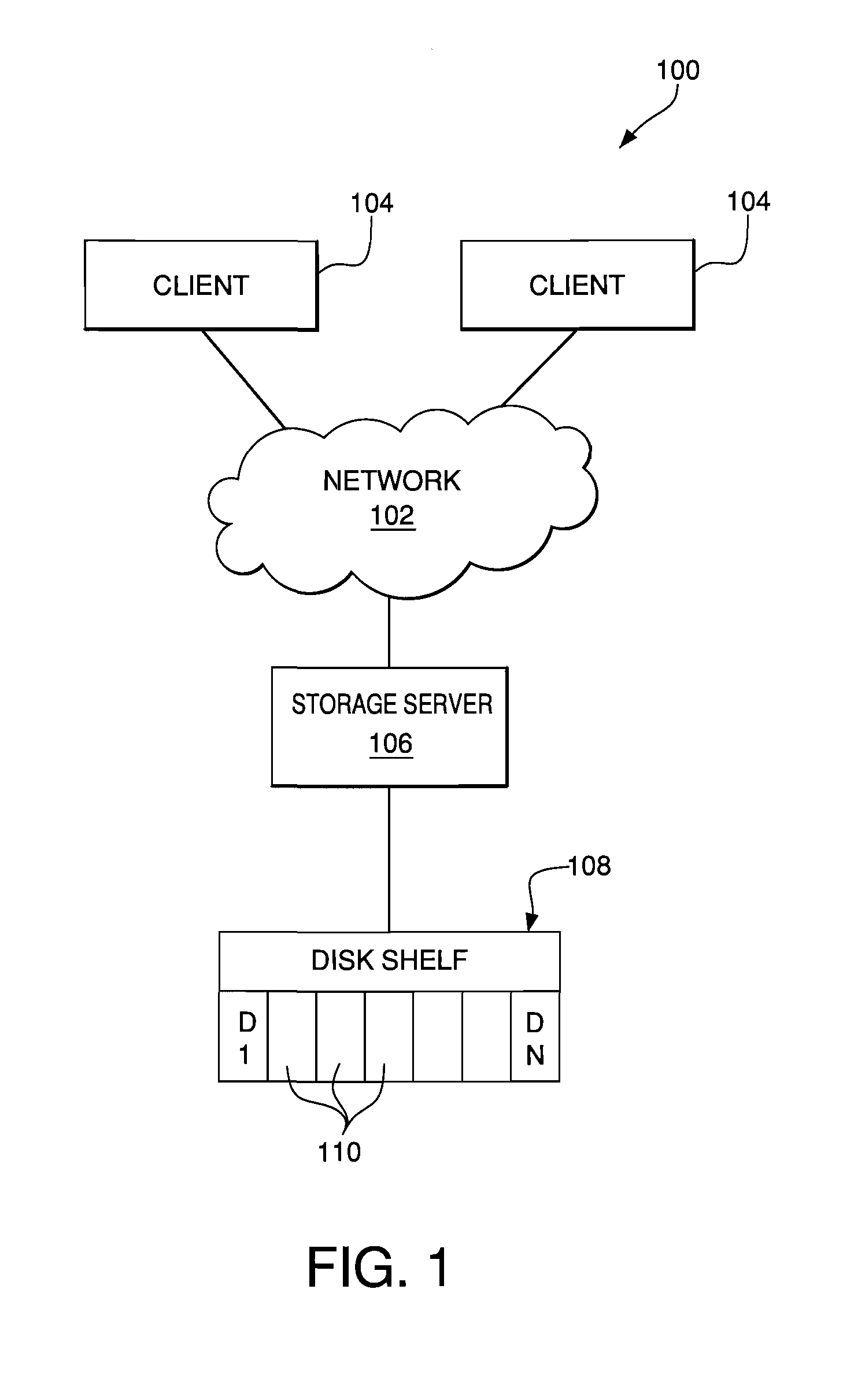
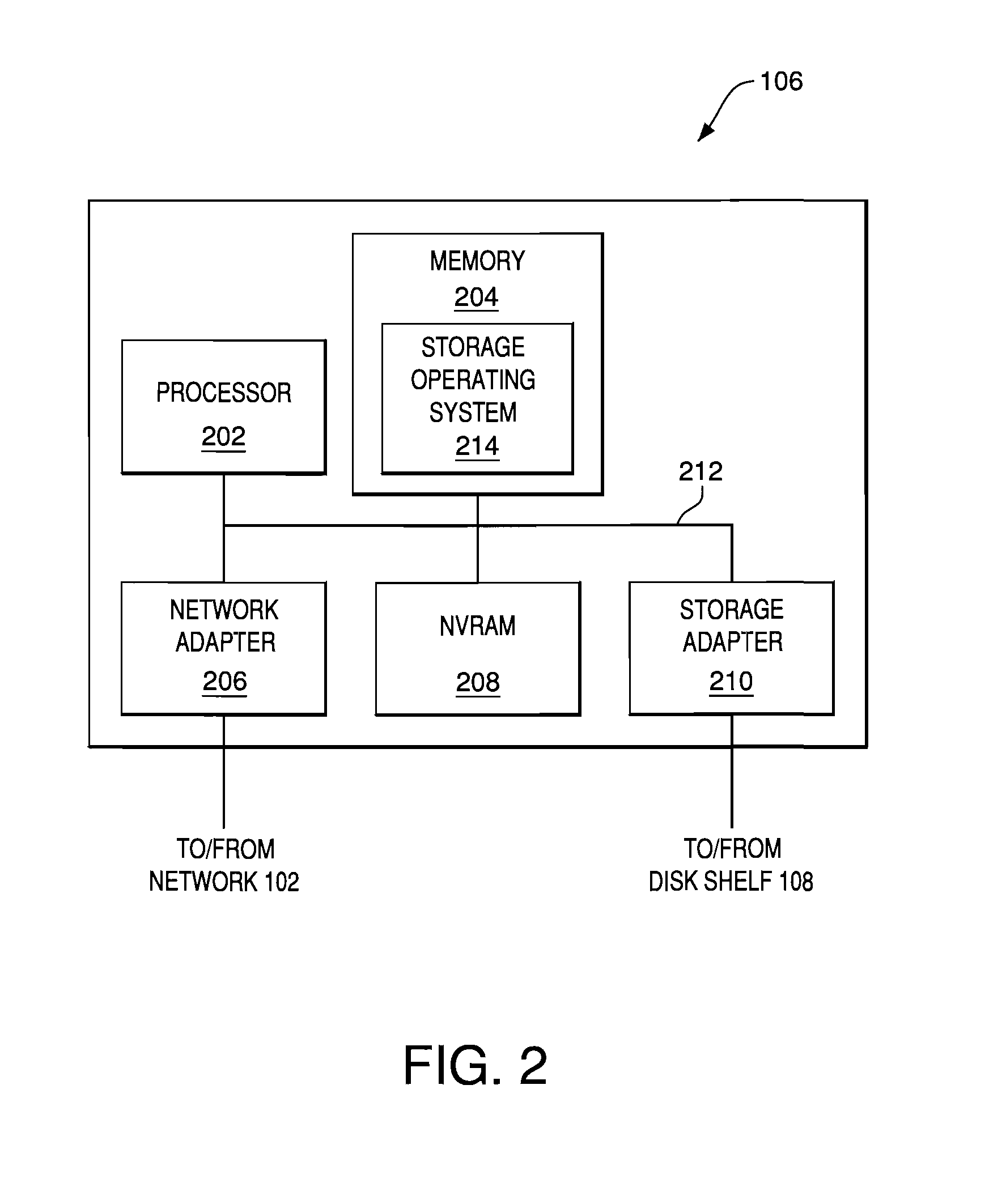
Creating environmental snapshots of storage device failure events
InactiveUS8949863B1Interprogram communicationNon-redundant fault processingRelevant informationDevice failure
A storage device failure in a computer storage system can be analyzed by the storage system by examining relevant information about the storage device and its environment. Information about the storage device is collected in real-time and stored; this is an on-going process such that some information is continuously available. The information can include information relating to the storage device, such as input / output related information, and information relating to a storage shelf where the storage device is located, such as a status of adjacent storage devices on the shelf. All of the relevant information is analyzed to determine a reason for the storage device failure. Optionally, additional information may be collected and analyzed by the storage system to help determine the reason for the storage device failure. The analysis and supporting information can be stored in a log and / or presented to a storage system administrator to view.
Owner:NETWORK APPLIANCE INC
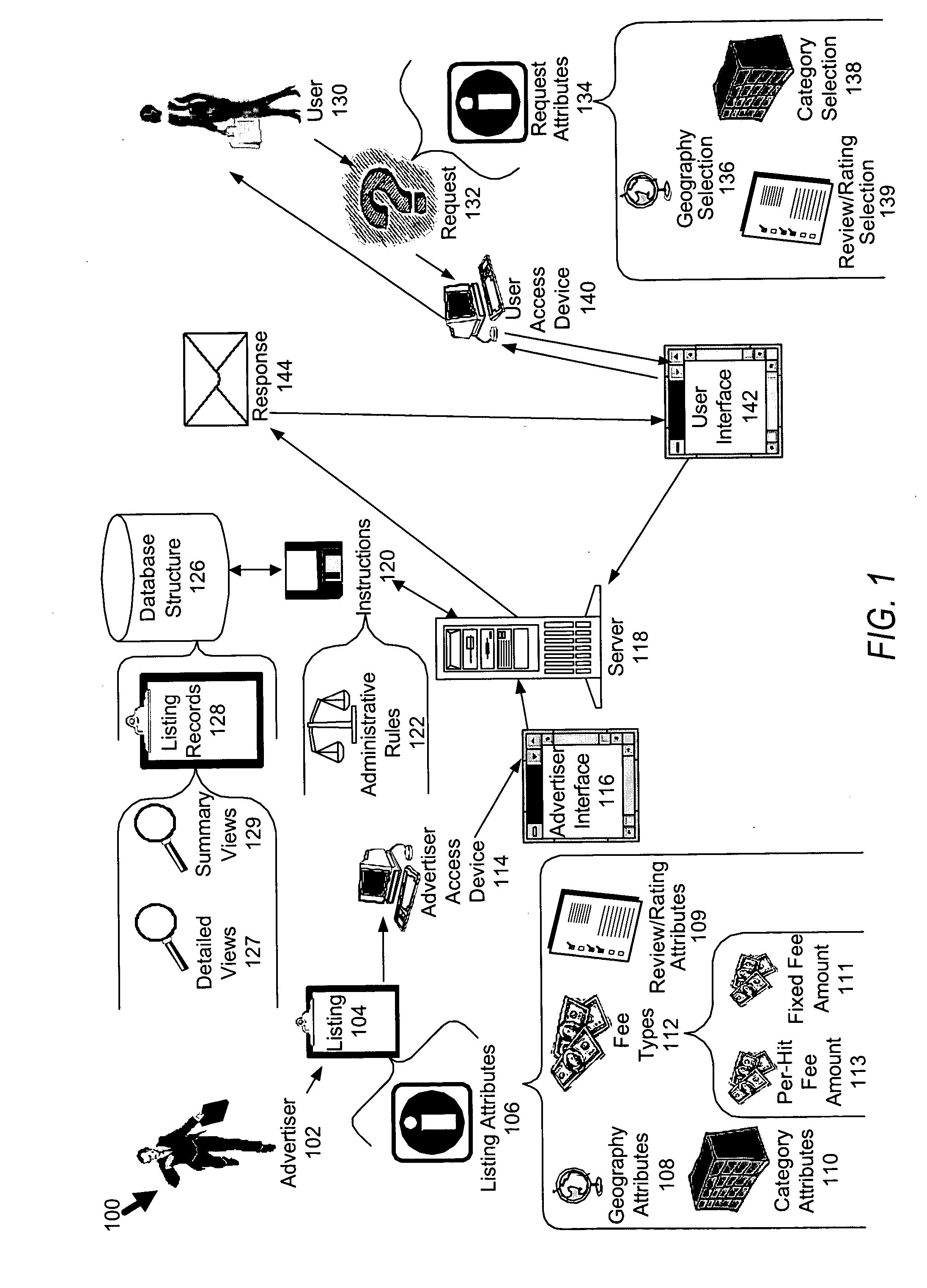
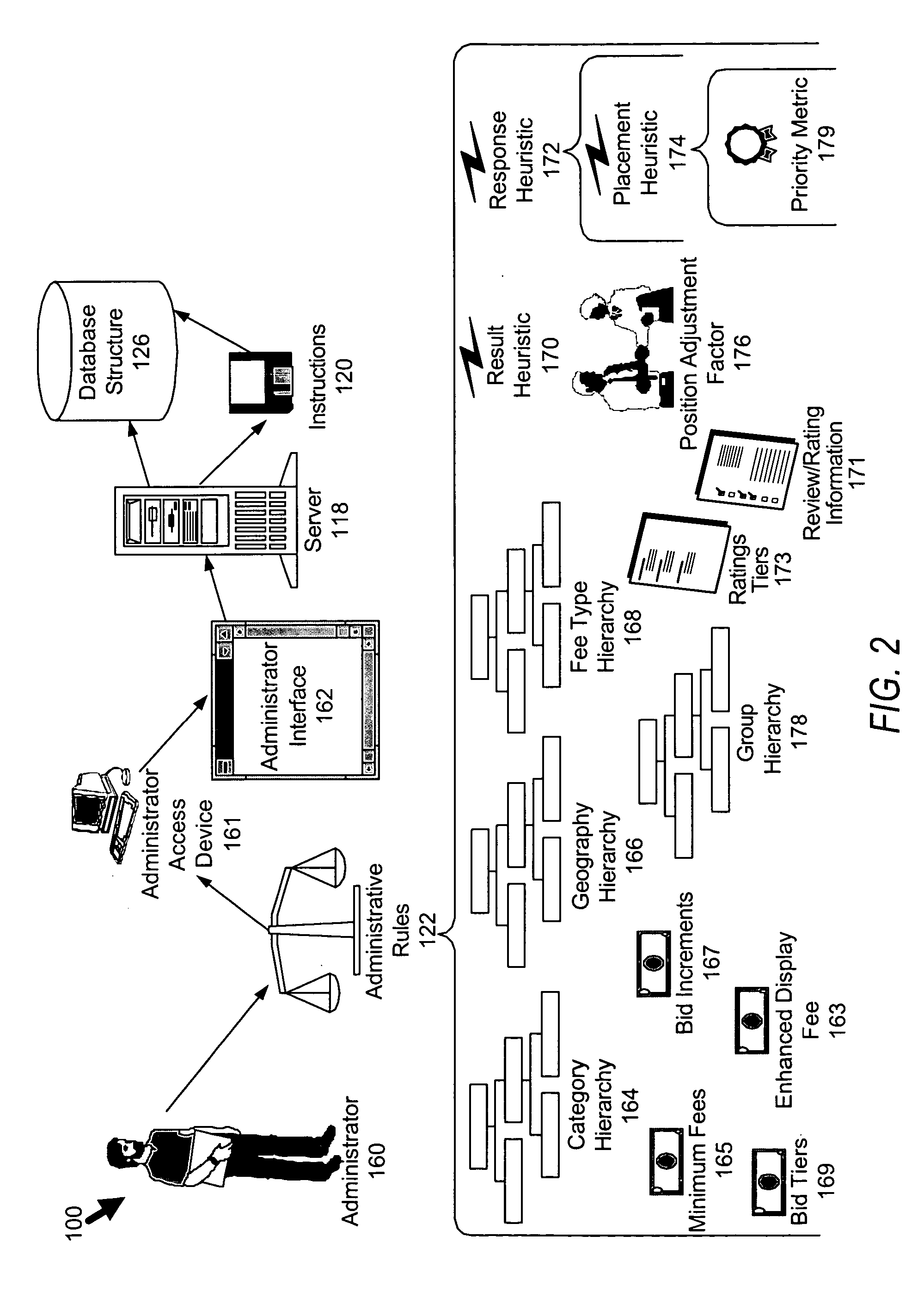
Business rating placement heuristic
ActiveUS20050065811A1Enhance priority metricImprove abilitiesFinanceAdvertisementsData miningSystem administrator
A system and method for distributing information (collectively the “system”) is disclosed. The system includes category-based, geography-based, and ratings-based attributes to better “focus” the information distributed by the system. In the processing of listing-based attributes (e.g. attributes limited to a particular listing), the system can also be influenced by relationship-based attributes (e.g. attributes between the administrator of the system and the advertisers, and even potentially users).
Owner:THRYV INC
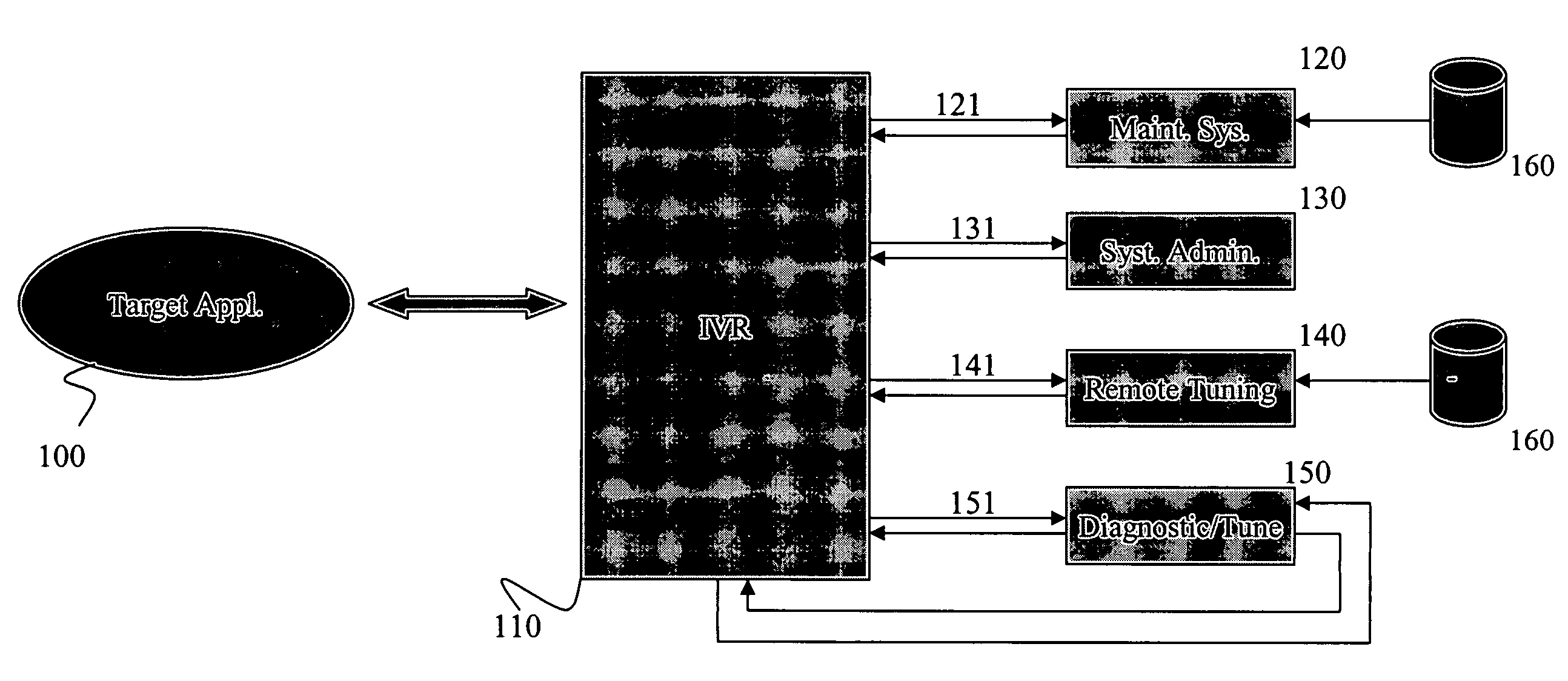
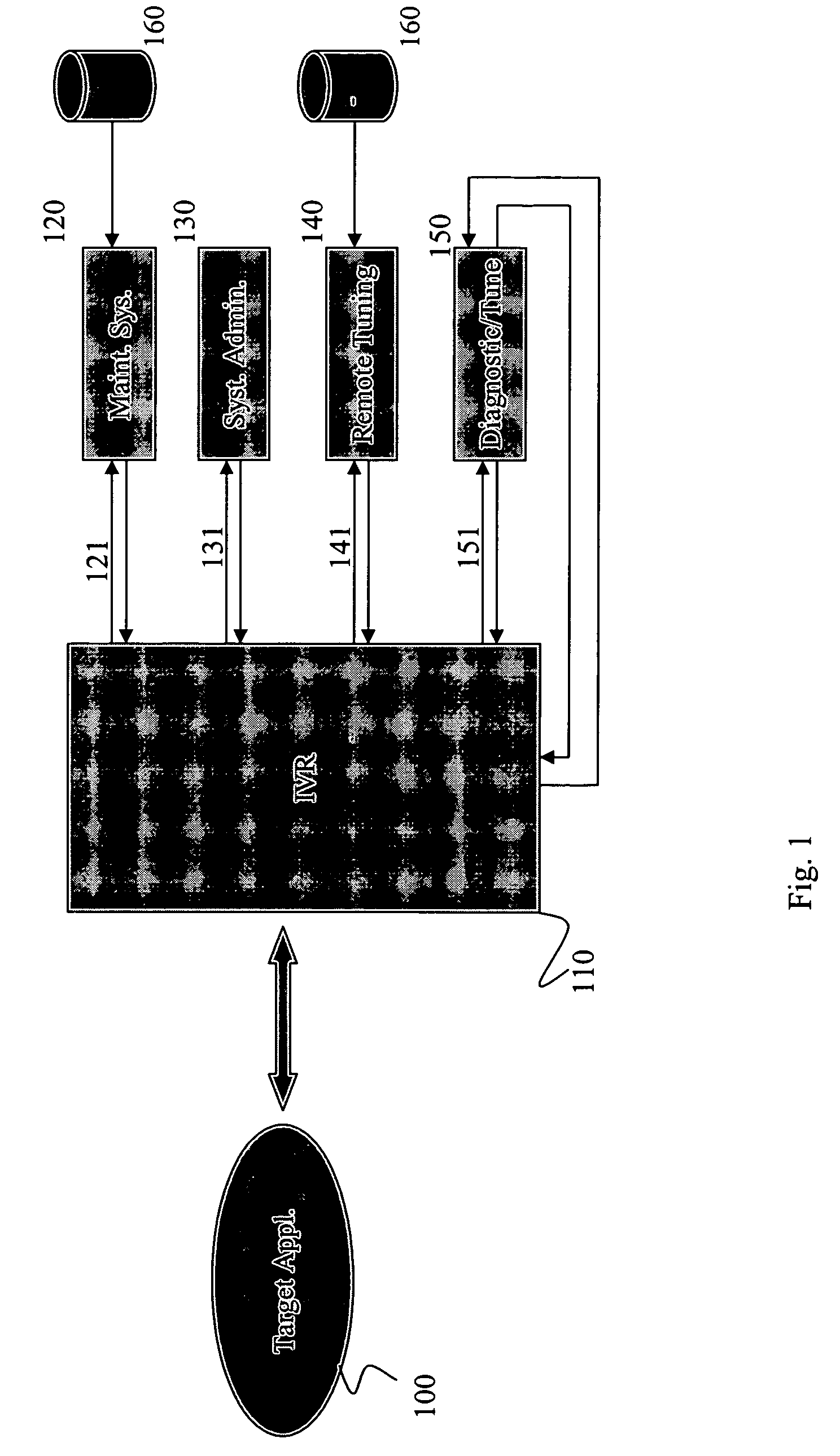
Method and apparatus for remote command, control and diagnostics of systems using conversational or audio interface
ActiveUS8224649B2Limited abilityEffectively diagnose and maintainSpeech recognitionInteractive voice response systemApplication software
A method and apparatus for remote access to a target application is disclosed where a system administrator may establish telephonic contact with an interactive voice response system and obtain access to the target application by speech communication. The interactive response system may authenticate the system administrator by implementing various measures including biometric measures. Once access is granted, the interactive response system may broker a communication between the target application using text / data and the system administrator using natural language.
Owner:GENERAC POWER SYST INC
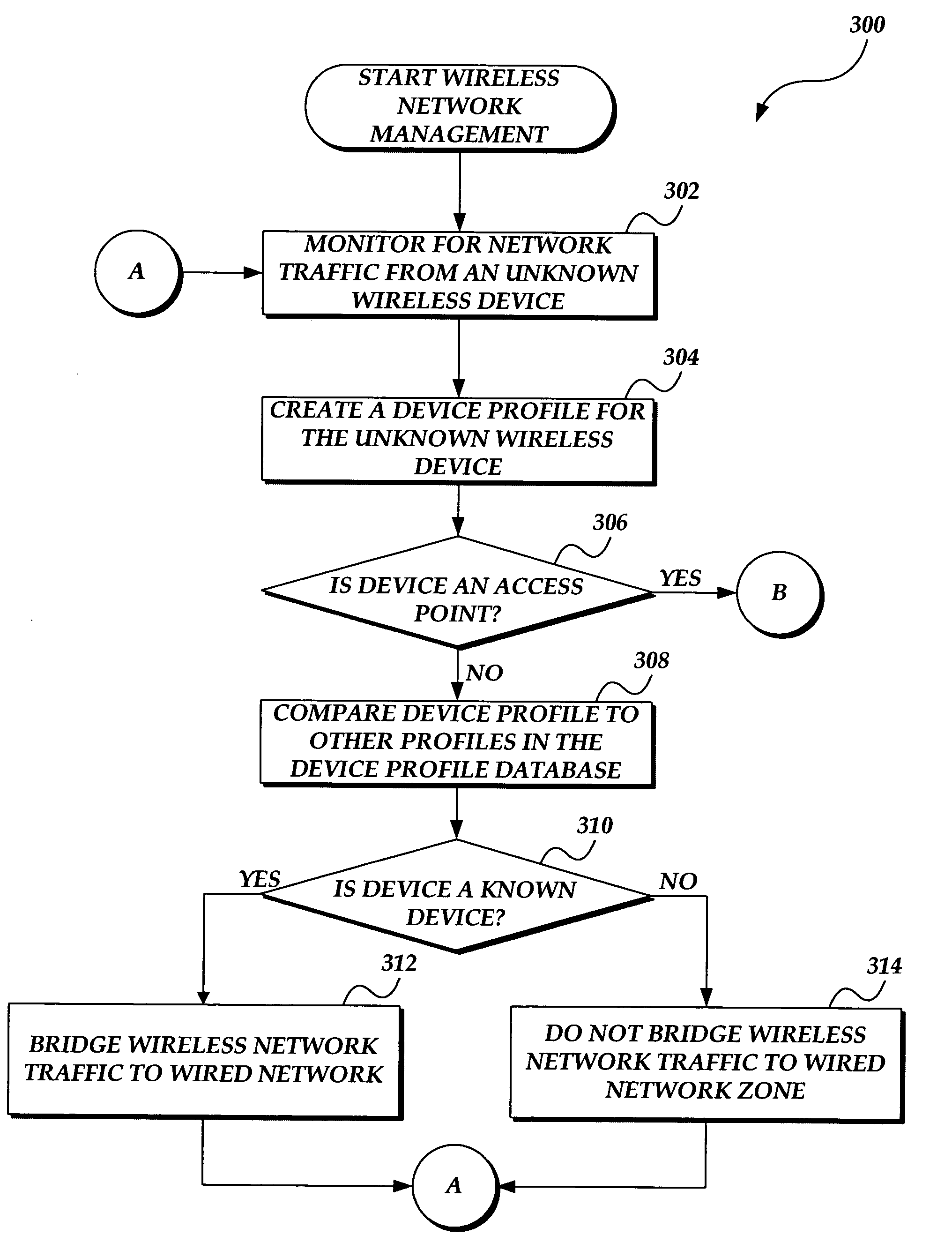
System and method for wireless local area network monitoring and intrusion detection
InactiveUS7340768B2Memory loss protectionDigital data processing detailsThreat levelNotification system
The present invention provides a system and method for providing real-time wireless network monitoring and intrusion detection. The present invention profiles wireless devices and maintains a database of known / authorized wireless device profiles. Wireless devices are analyzed to determine the threat level they pose to the network, and if the threat level exceeds a predetermined threshold, the invention refuses to bridge the network traffic from the wireless devices to the wired network. The present invention provides reporting of the wireless network activity, the known and unknown wireless devices, and the threat levels posed by the wireless devices. If an unknown wireless device is determined to be, or may be, a wireless access point, an alert is generated, such as notifying a system administrator to take appropriate action.
Owner:WIMETRICS CORP
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
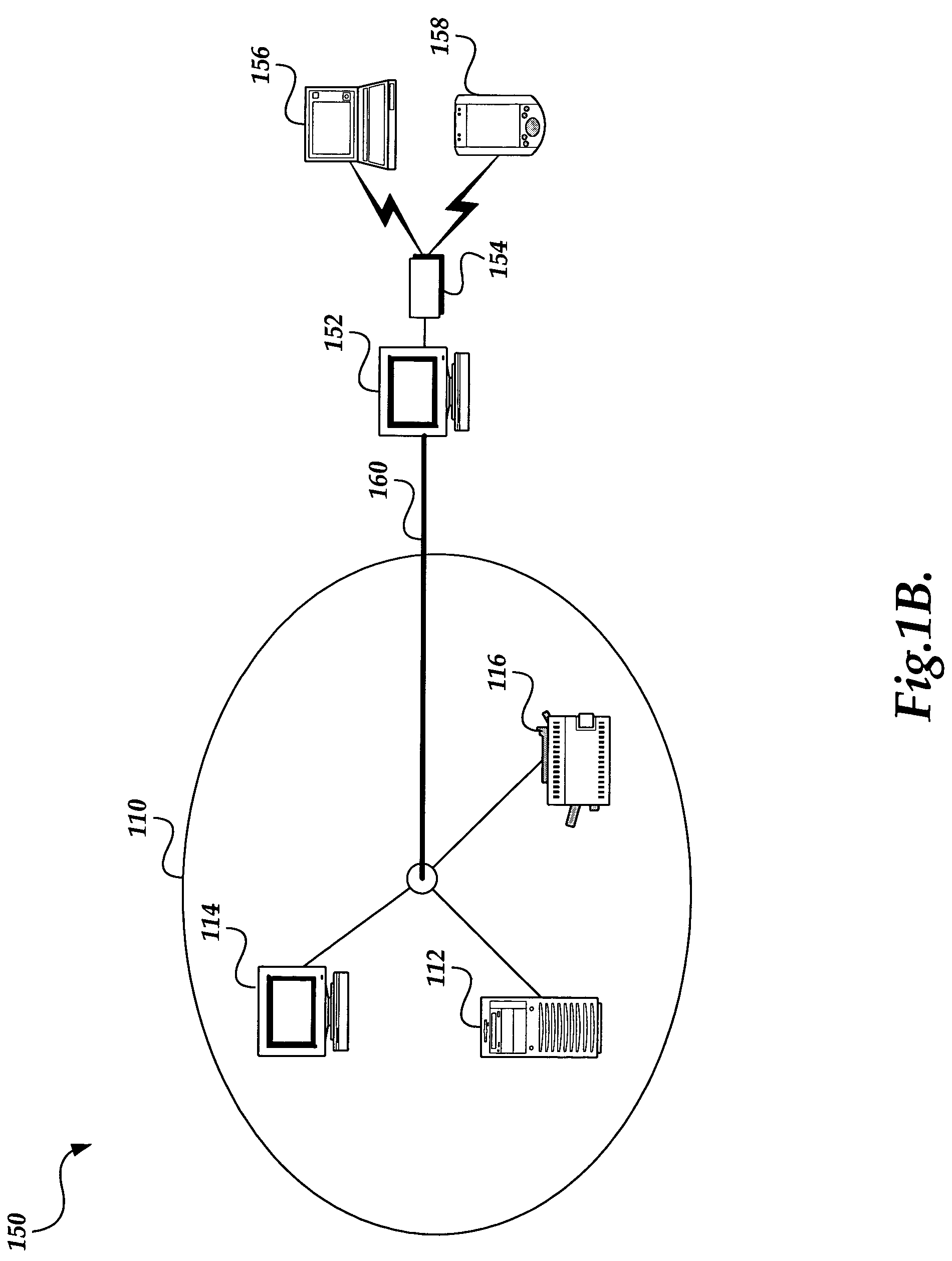
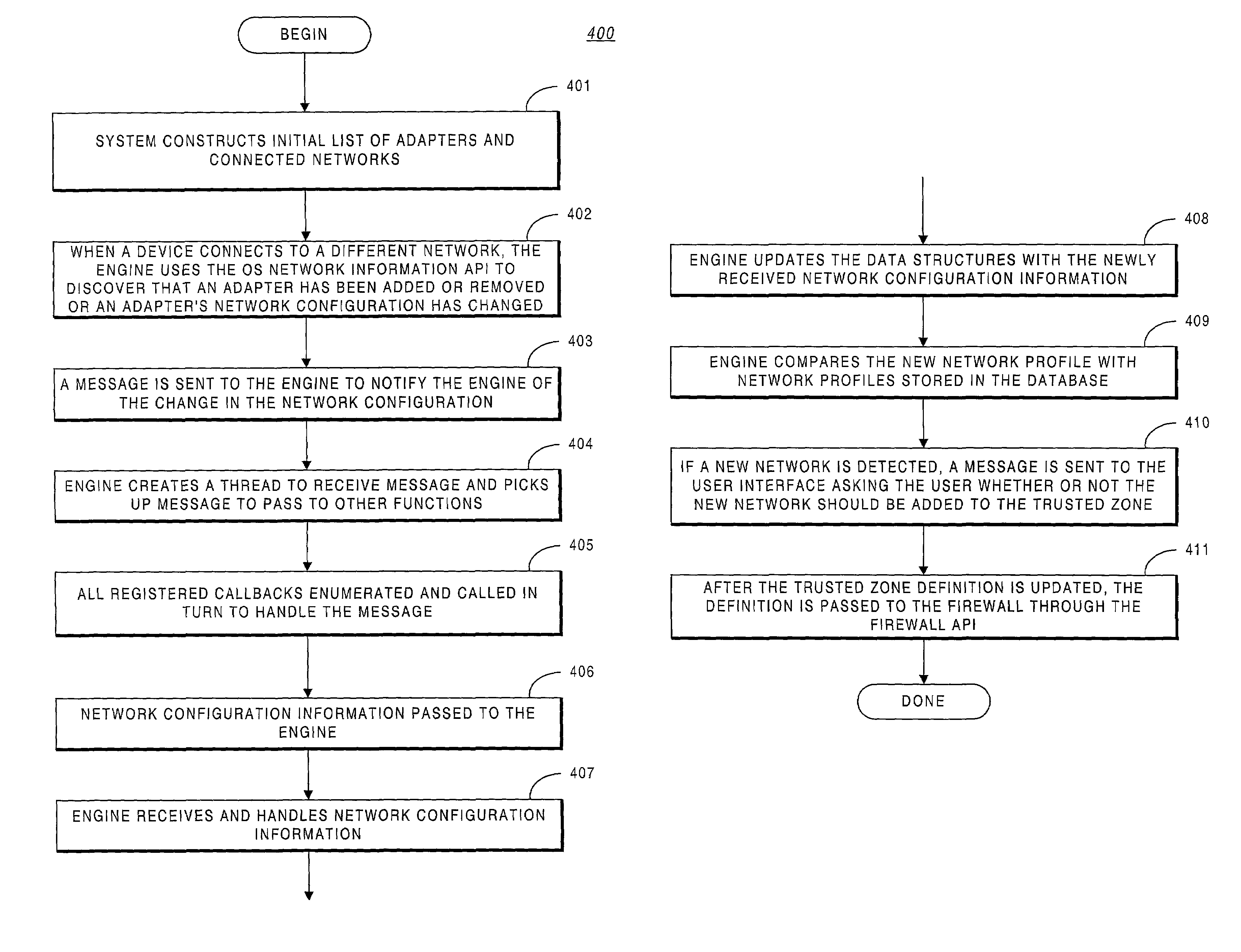
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
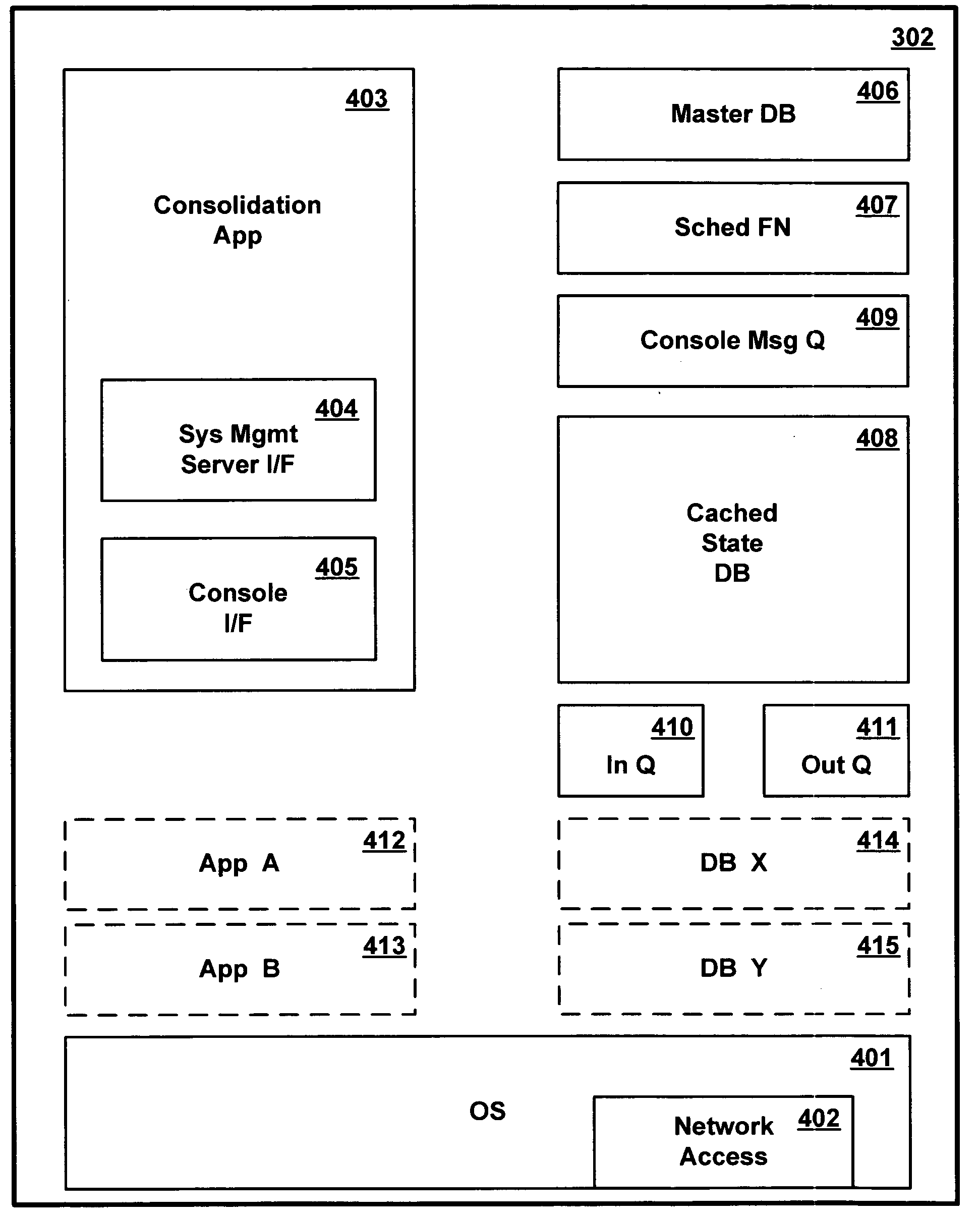
Method and apparatus for managing multiple data processing systems using existing heterogeneous systems management software
InactiveUS20050102683A1Less expensiveMultiprogramming arrangementsMultiple digital computer combinationsPublic interfaceData processing system
A common consolidation management application provides an interface to the multiple different system management software applications and at least one user input console. An adapter in each of the system management software applications supports communication with the consolidation application. A system administrator issues requests to different system management software applications using a common interface provided by the consolidation application. The consolidation application can be installed over an existing complex of computer systems managed by different management applications, without modifying the managed systems or replacing the management applications.
Owner:IBM CORP
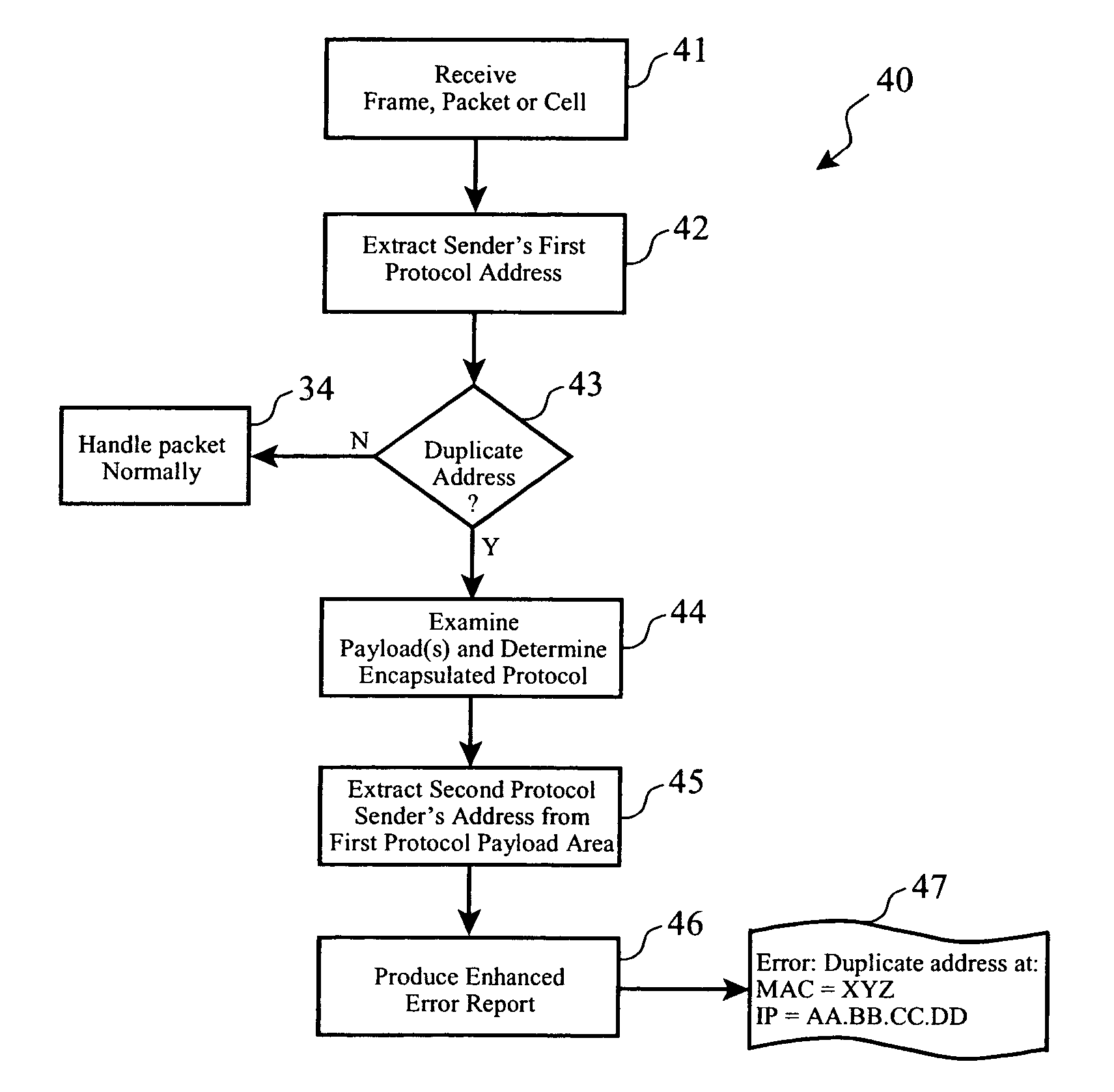
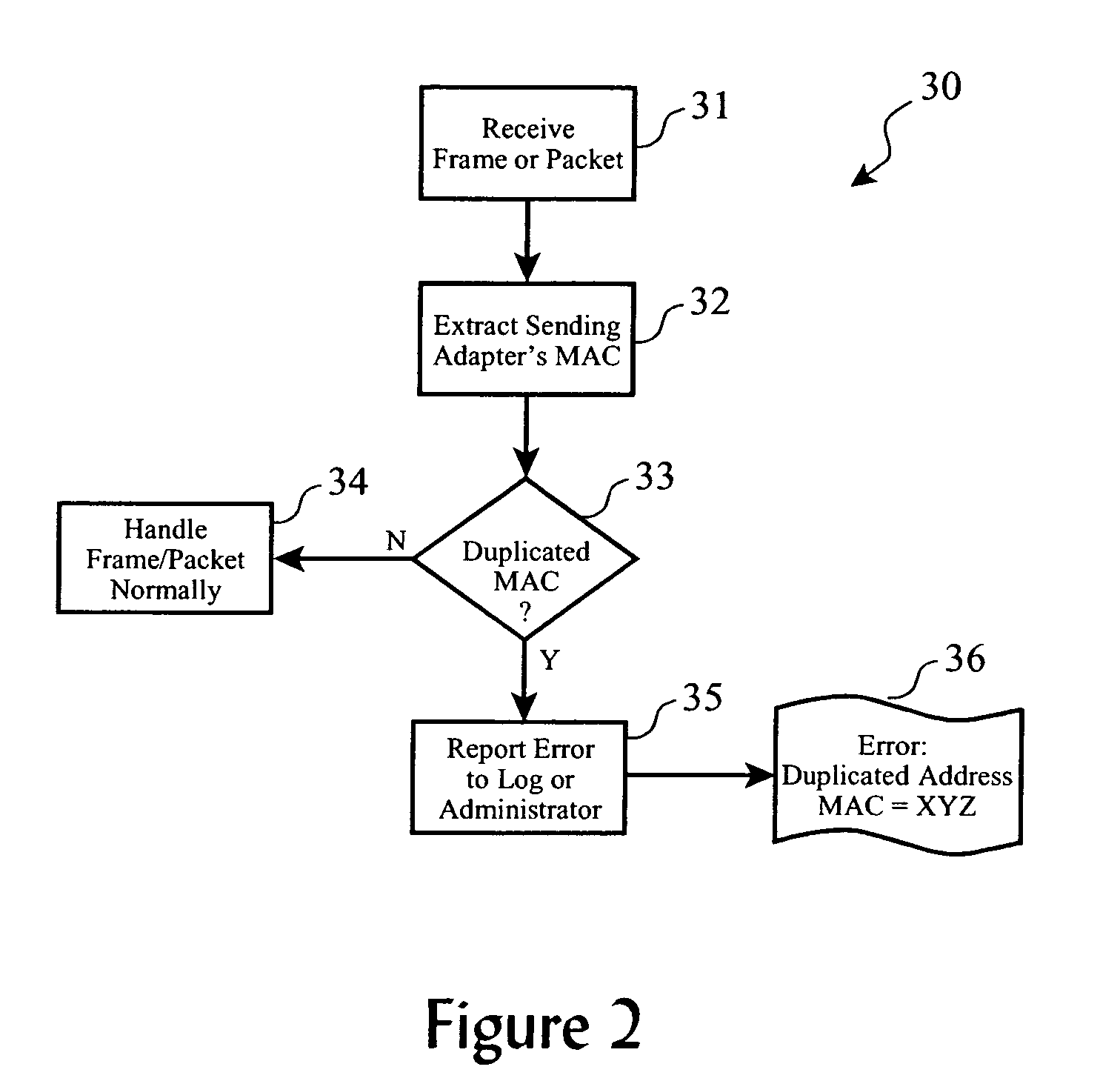
Duplicate network address detection
ActiveUS7246272B2Easy to detectError detection/correctionData switching by path configurationEncapsulated dataNetwork addressing
A plurality of data packets encoded according to a first protocol are received which encapsulate data encoded according to a second protocol. A first source address is extracted from the packets according to the first protocol, it is determined whether or not the first source address is a substantial duplicate of a known assigned address. If it is a duplicate, a second source address is extracted from the encapsulated data according to the second protocol, and the first source address and said second source address are provided in an enhanced error log so that a system administrator may correct the duplicate assigned address. Enhanced embodiments of the invention included analysis of data encapsulated by a third, fourth and subsequent protocols, and automatic determination of each protocol encoding format.
Owner:GOOGLE LLC
Method and System for Maintaining and Distributing Wireless Applications
InactiveUS20080301231A1Greater assurance of their ability to successfully executeRaise the possibilityAccounting/billing servicesNetwork traffic/resource managementSupply managementApplication computers
Computer- and network-based methods and systems for maintaining and provisioning wireless applications are provided. Example embodiments provide a Mobile Application System (MAS), which is a collection of interoperating server components that work individually and together in a secure fashion to provide applications and resources to mobile subscriber devices, such as wireless devices. Embodiments of the present invention can also be used to deploy applications and resources for wired subscriber devices. Application, resources, and other content is provisioned and verified by the MAS for authorized access by the subscriber, compatibility with a requesting subscriber device, and the security and billing policies of the carrier and system administrators of the MAS. In this manner, applications, resources, and other content can be downloaded to devices, such as wireless devices, with greater assurance of their ability to successfully execute. In one embodiment, content is provisioned by one or more of the steps of inspecting the content for malicious or banned code, optimizing the content for smaller size and greater speed, instrumentation of code that implements security, billing, and other carrier policies, and packaging of code for the intended subscriber device. Additional security is provided through application filters that are used to prevent applications that contain designated API from being downloaded to a subscriber's device. In one embodiment, the MAS includes a Protocol Manager, Provisioning Manager, Cache, Deployment Manager, Billing Manager, Logging Manager, Administrator, and Heartbeat Monitor, which interoperate to provide the provisioning functions.
Owner:MEHTA SAMIR NARENDRA +2
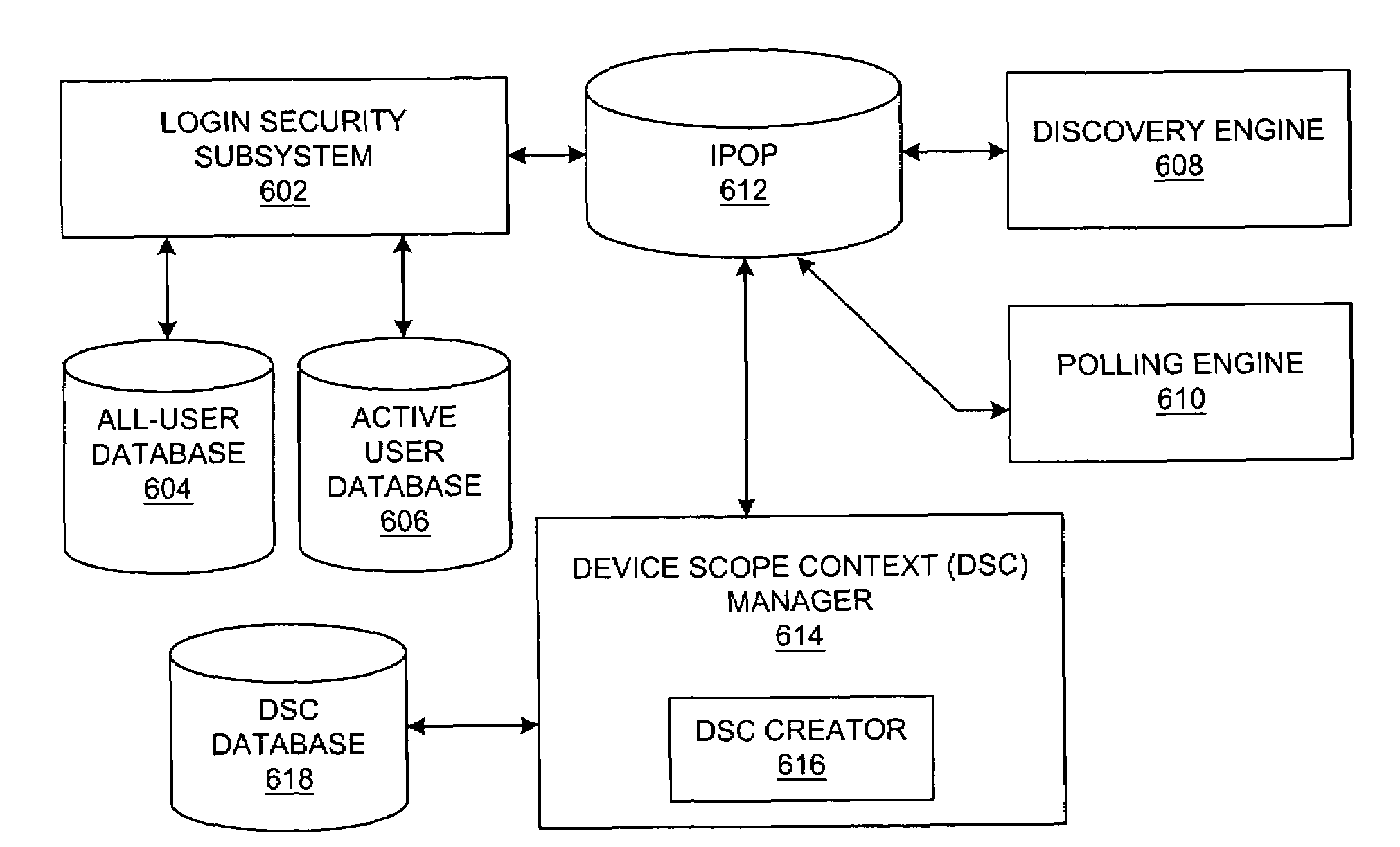
Method and system for network management with adaptive monitoring and discovery of computer systems based on user login
InactiveUS7337473B2Digital data processing detailsUser identity/authority verificationNetwork resource managementData processing system
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. A network management framework allows system administrators to configure user-associated monitoring parameters and device-associated monitoring parameters for users and devices within the distributed data processing system. Resources within the distributed data processing system are dynamically discovered, and the discovered resources are adaptively monitored using the network management framework.
Owner:GOOGLE LLC
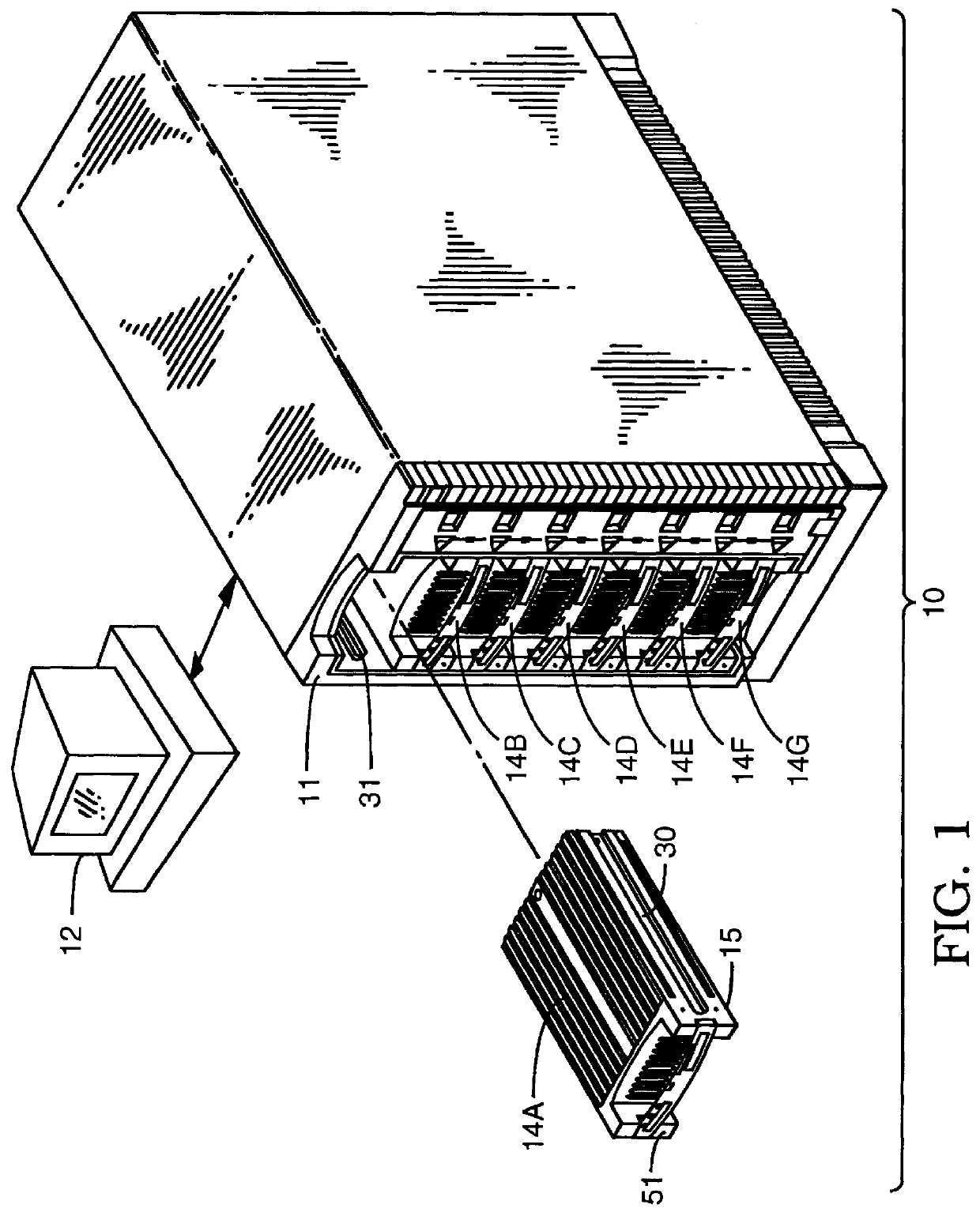
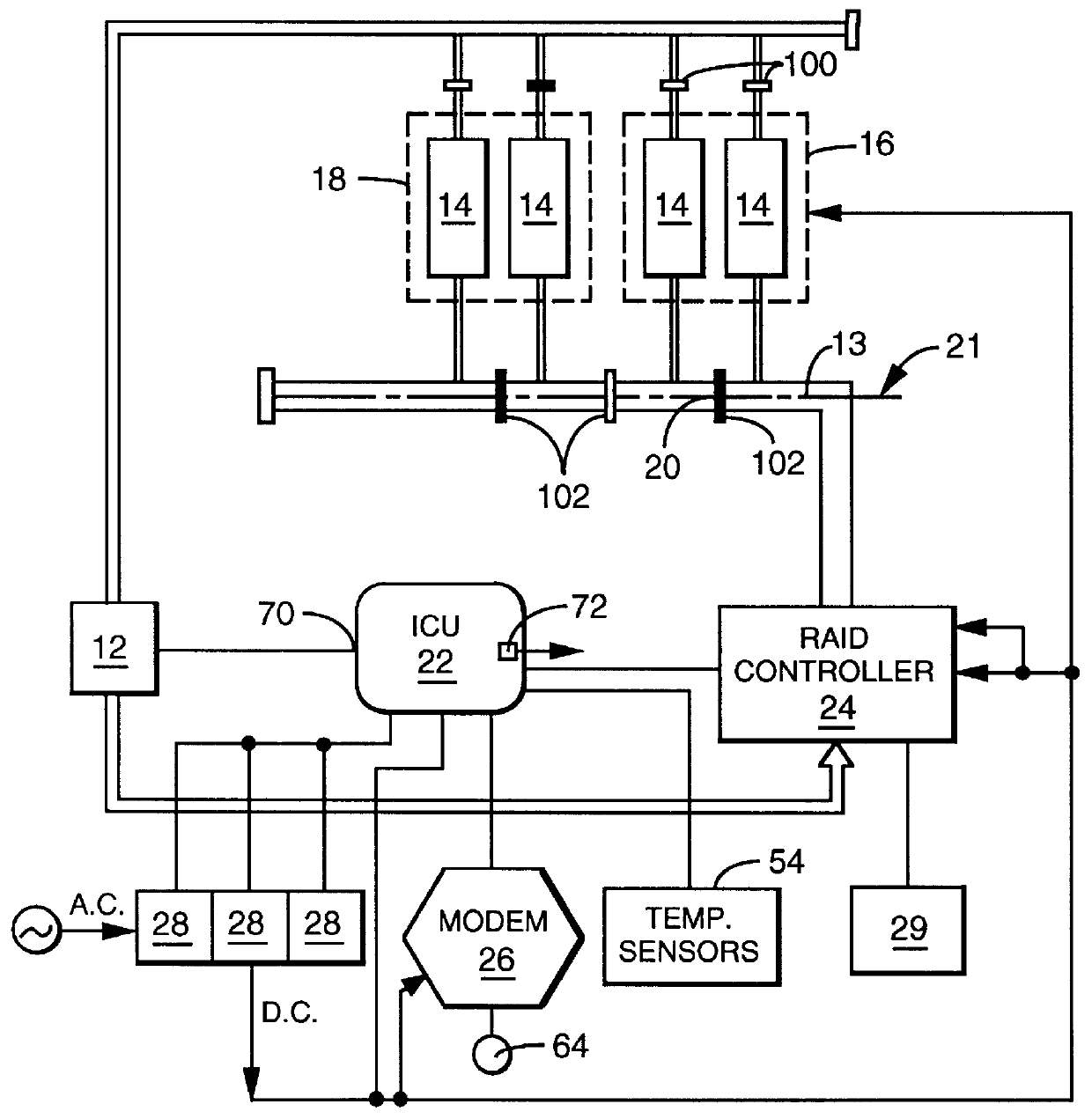
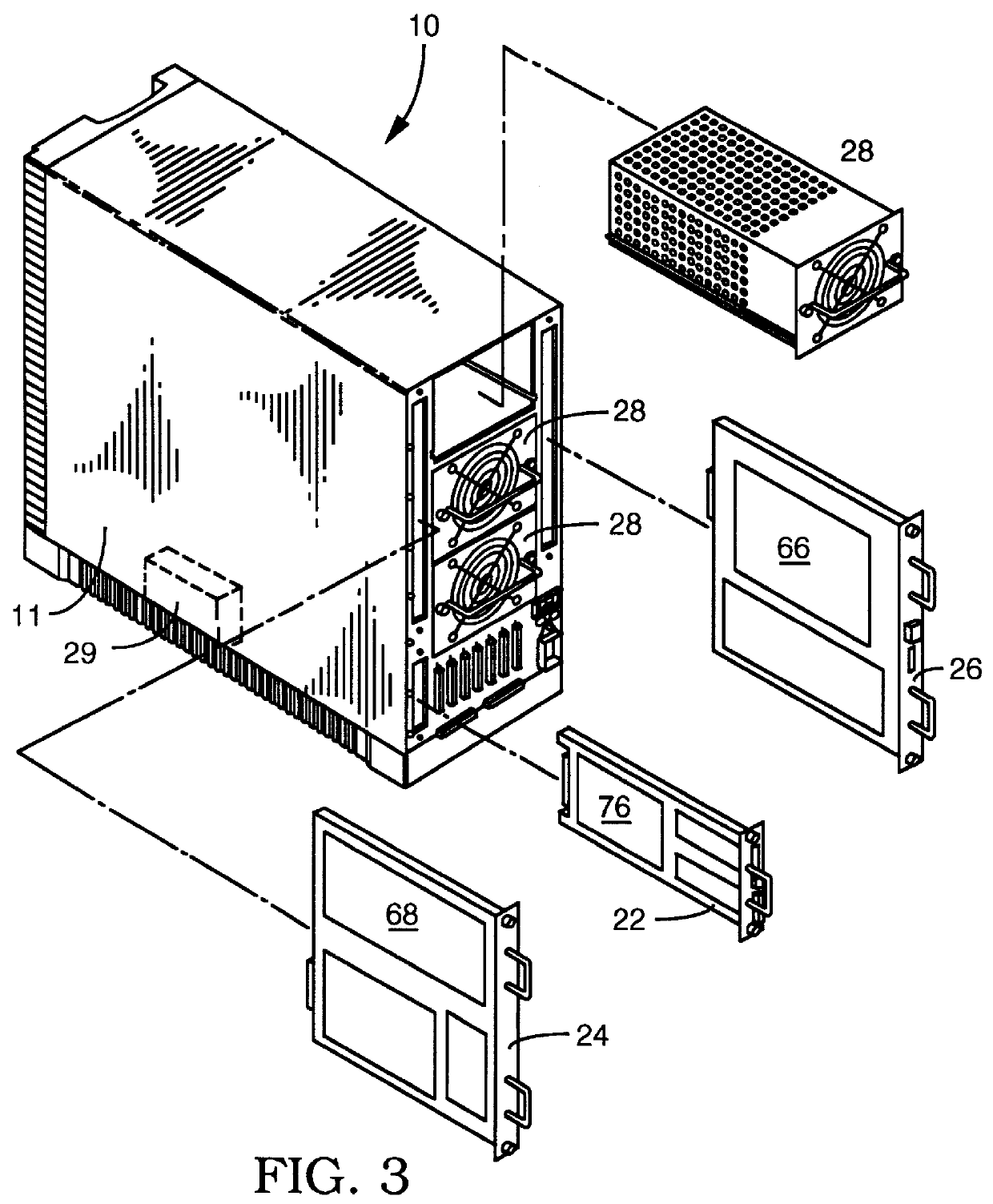
User configurable raid system with multiple data bus segments and removable electrical bridges
InactiveUS6076142ACarrier constructional parts dispositionError detection/correctionMass storageModem device
A user configurable RAID system designed to provide RAID functions as well as mass storage functions in a non-RAID mode. Flexibility is built into the system to allow the user to configure the SCSI bus to which removable drive modules are connected into one or more channels to define some of the drive modules in a RAID set and others as stand-alone drives which are independently operated or logically grouped and operated in a non-RAID mode. Removable internal SCSI bridges allow the SCSI bus to be configured into one or more channels. In the RAID mode, the system is configured to prevent a wrong drive from being removed from the system in the event of a drive failure. The system automatically unlatches only the failed drive. The RAID system includes an intelligent control unit ("ICU"), a RAID controller and a modem. The ICU allows the system administrator to access the RAID system Monitor Utility so that the status of the system may be monitored and its configuration changed. The ICU also monitors the failure status of the various components of the system. The ICU has a built-in pager feature that can be configured with the Monitor Utility to page the system administrator via the modem when a component or system failure is encountered. The RAID controller controls the functions of the RAID set as programmed and configured using the Monitor Utility. The Monitor Utility may be remotely accessed using a computer via the modem. Redundant removable power supply and fan units are provided to improve system integrity. The removable power supply and fan units are configured such when the unit is plugged into the system housing, the fan is first turned on and the power through the unit is allowed to stabilize before turning on the power supply to begin providing DC power to the components in the system. A set of manual release buttons are provided for manually unlatching the drive modules from the system housing. A locking mechanism is provided for simultaneously locking all the manual release buttons.
Owner:MICRONET TECH
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS20030167405A1Easy to detectDigital data processing detailsHardware monitoringNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
Method and system for network management with backup status gathering
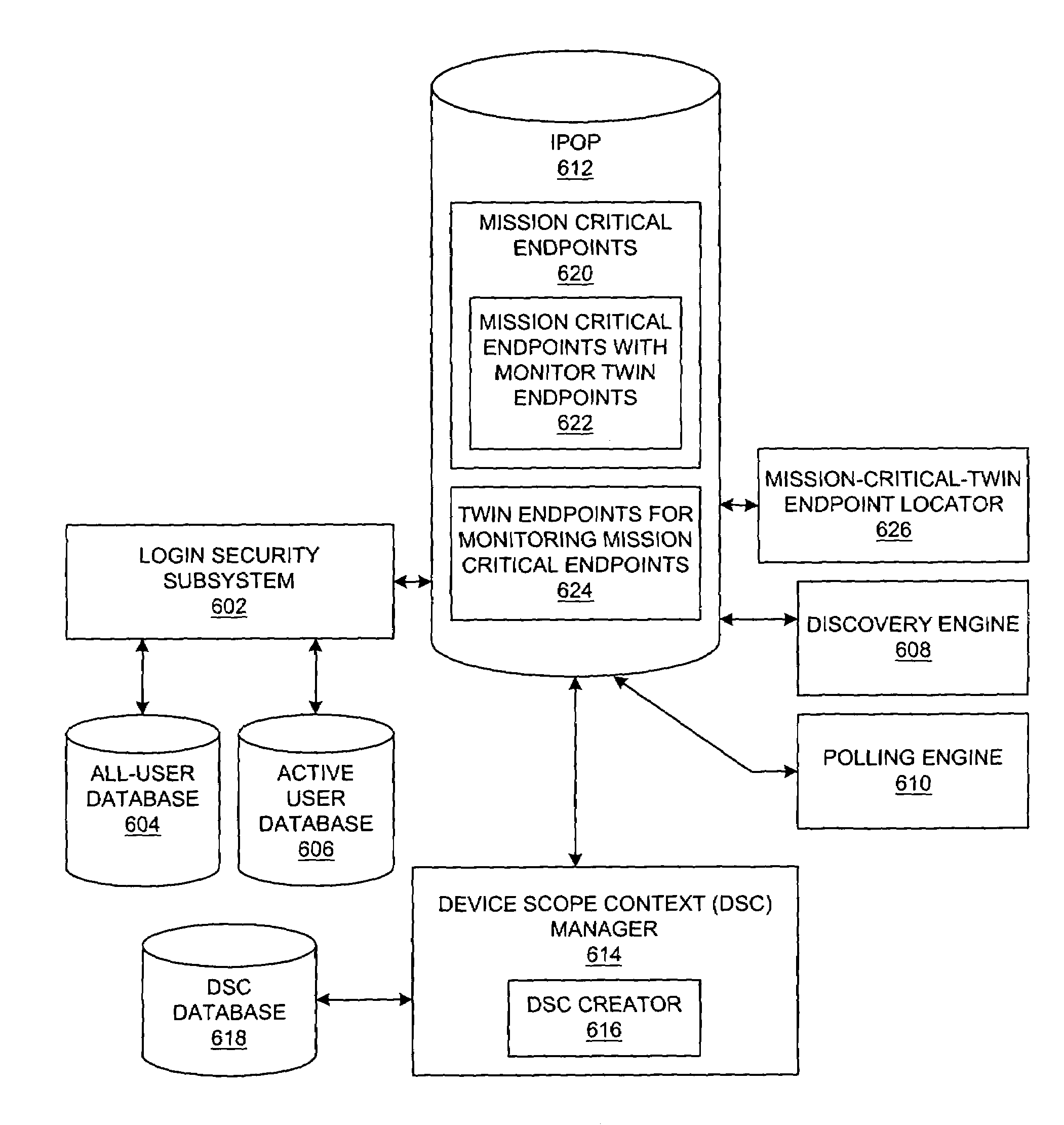
A method, system, apparatus, and computer program product are presented for management of a distributed data processing system. Resources within the distributed data processing system are dynamically discovered, and the discovered resources are adaptively monitored using the network management framework. A network or system administrator configures some mission critical endpoints with multiple network interface cards (NICs) and specifies mission critical endpoints, non-mission critical actions, etc. During status collection activities associated with network or system management activities, the categorization of an endpoint as a mission-critical or non-mission critical endpoint affects the manner in which the status collection activity is performed. Applications can request the performance of actions at endpoints without regard to the categorization of the endpoint or without regard to the categorization of the requested action, and the network management system routes the action based on whether or not the specified endpoint is a mission critical endpoint. A non-mission-critical endpoint is associated with a mission-critical endpoint based on the non-mission-critical endpoint's communication history with the mission critical endpoint. The management system may use the status of a non-mission-critical endpoint as a reflection of the status of a mission-critical endpoint.
Owner:GOOGLE LLC
Storage network management system and method
InactiveUS20050044199A1OptimizationDigital data information retrievalDigital computer detailsVirtual LANCountermeasure
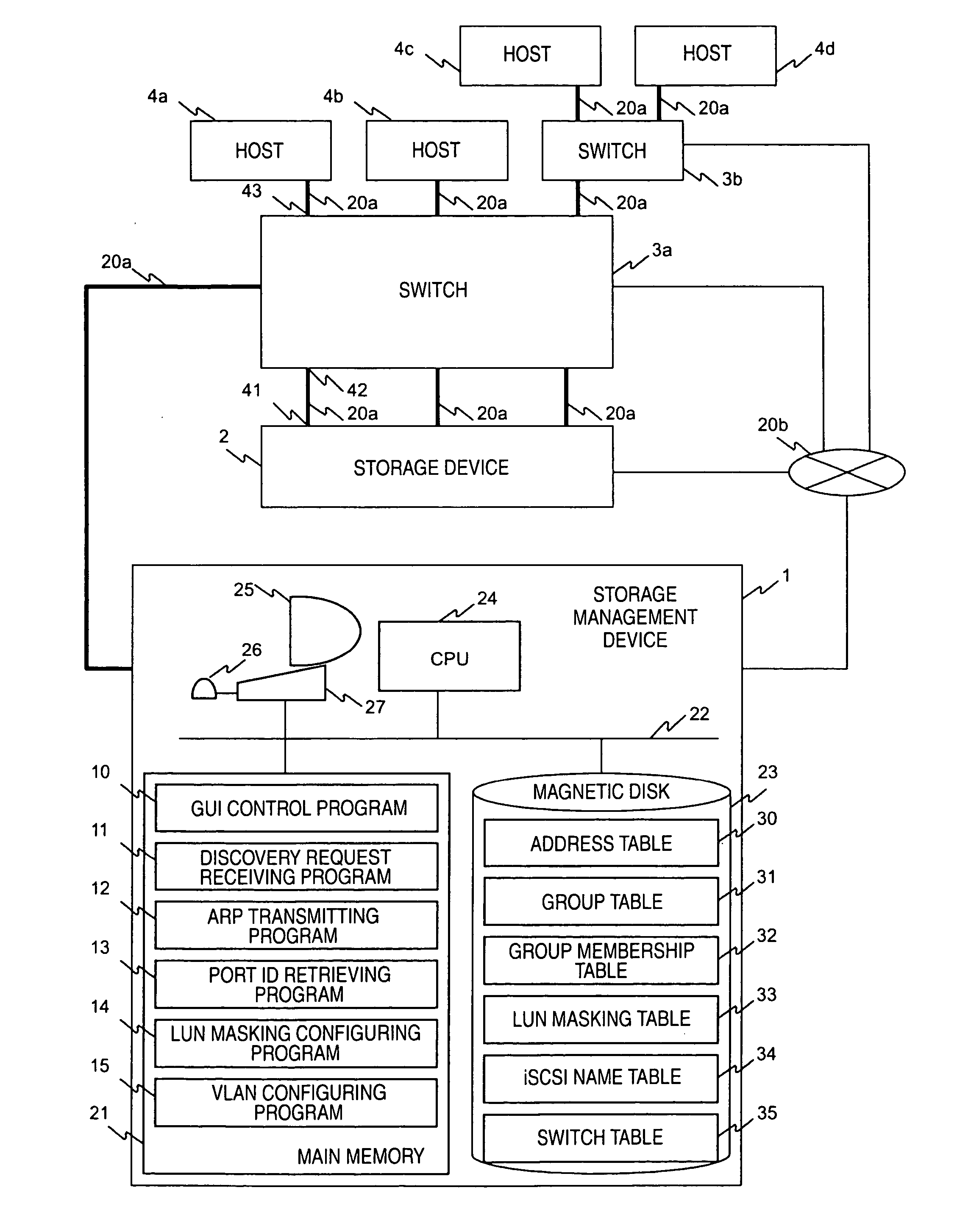
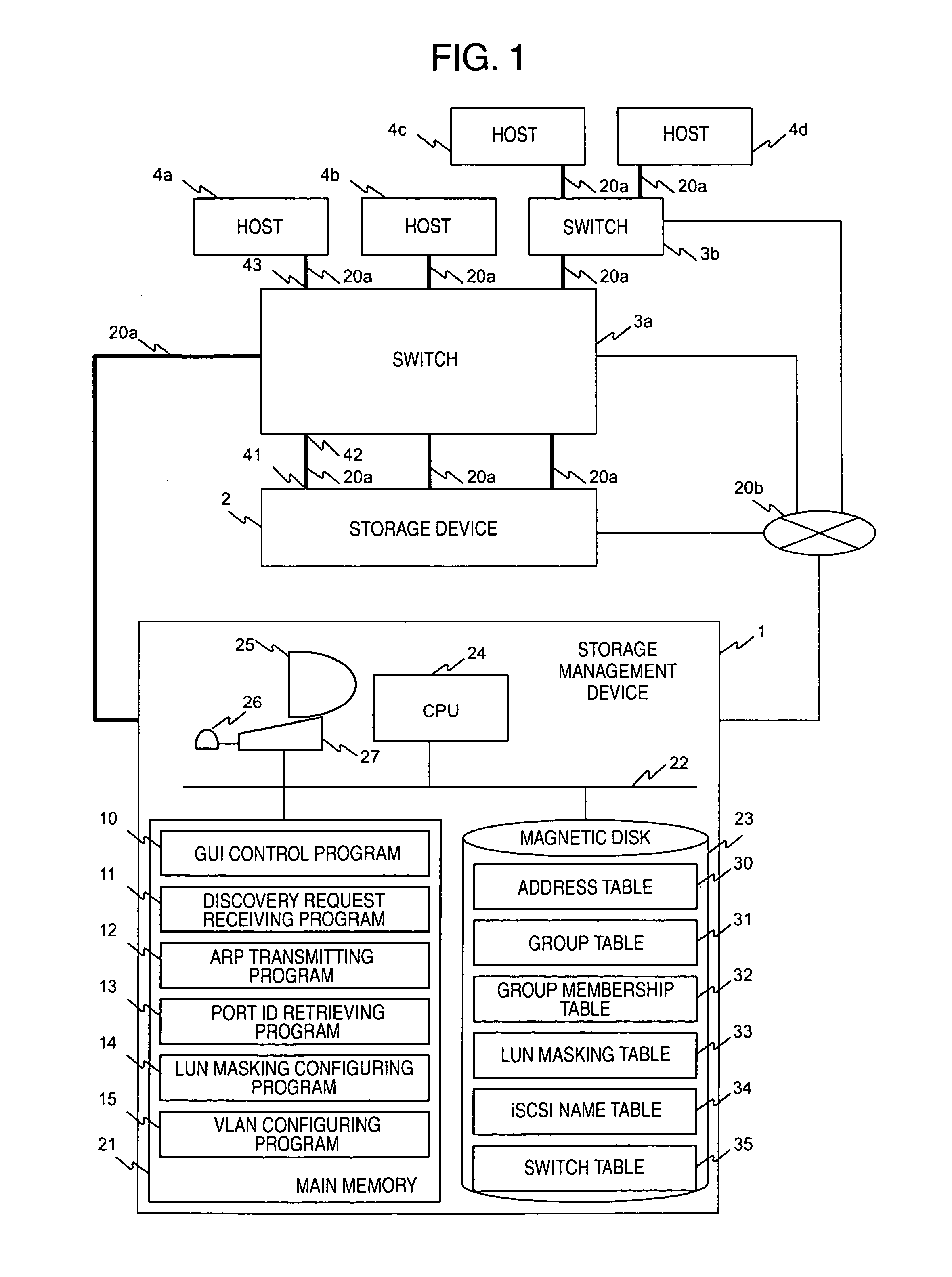
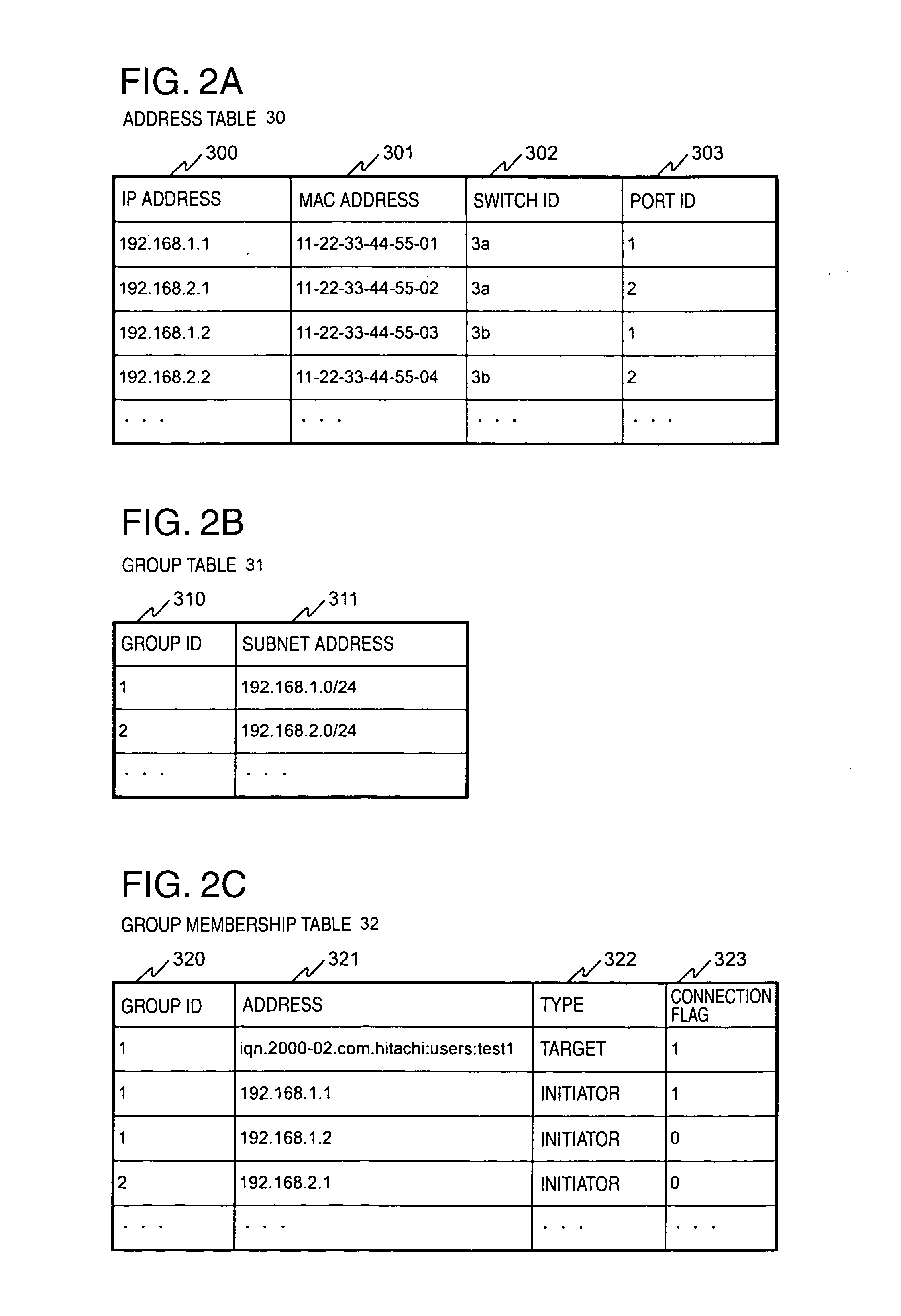
In a computer system having a storage device, switches and hosts respectively connected by a network, in accordance with an ID of a logical volume of the storage device and an IP address of a host, access control configuration of the logical volume is performed relative to the storage device, the IP address of the host is converted into a MAC address, the MAC address of the host is converted into a port ID of the switch connected to the host, and addition of the port to virtual local area network (VLAN) is performed for the switch. Logical unit number (LUN) masking and VLAN configuration essential for security countermeasure of IP-SAN (Internet protocol-storage area network) can be managed collectively by a system administrator so that the running cost of IP-SAN can be lowered.
Owner:HITACHI LTD
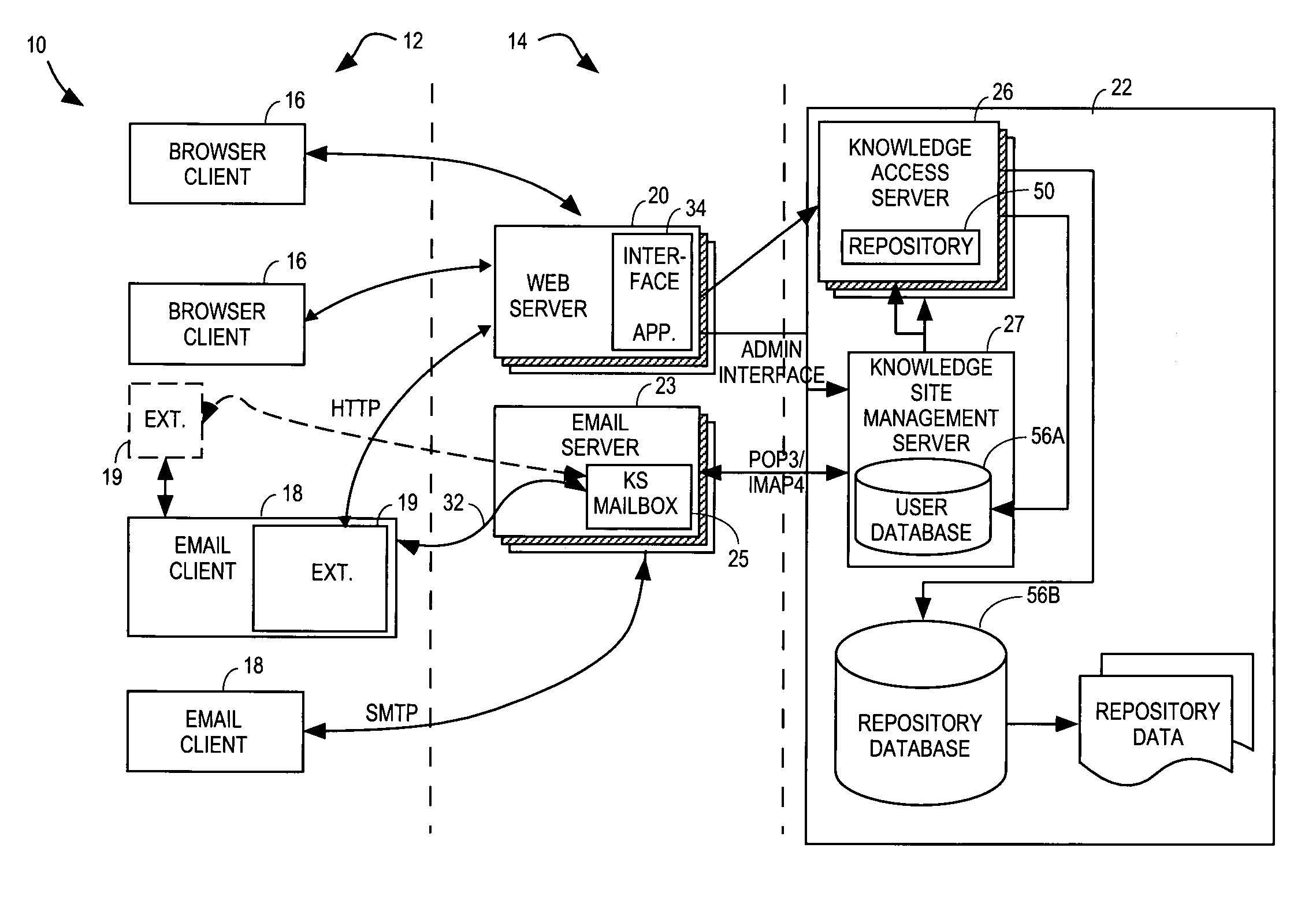
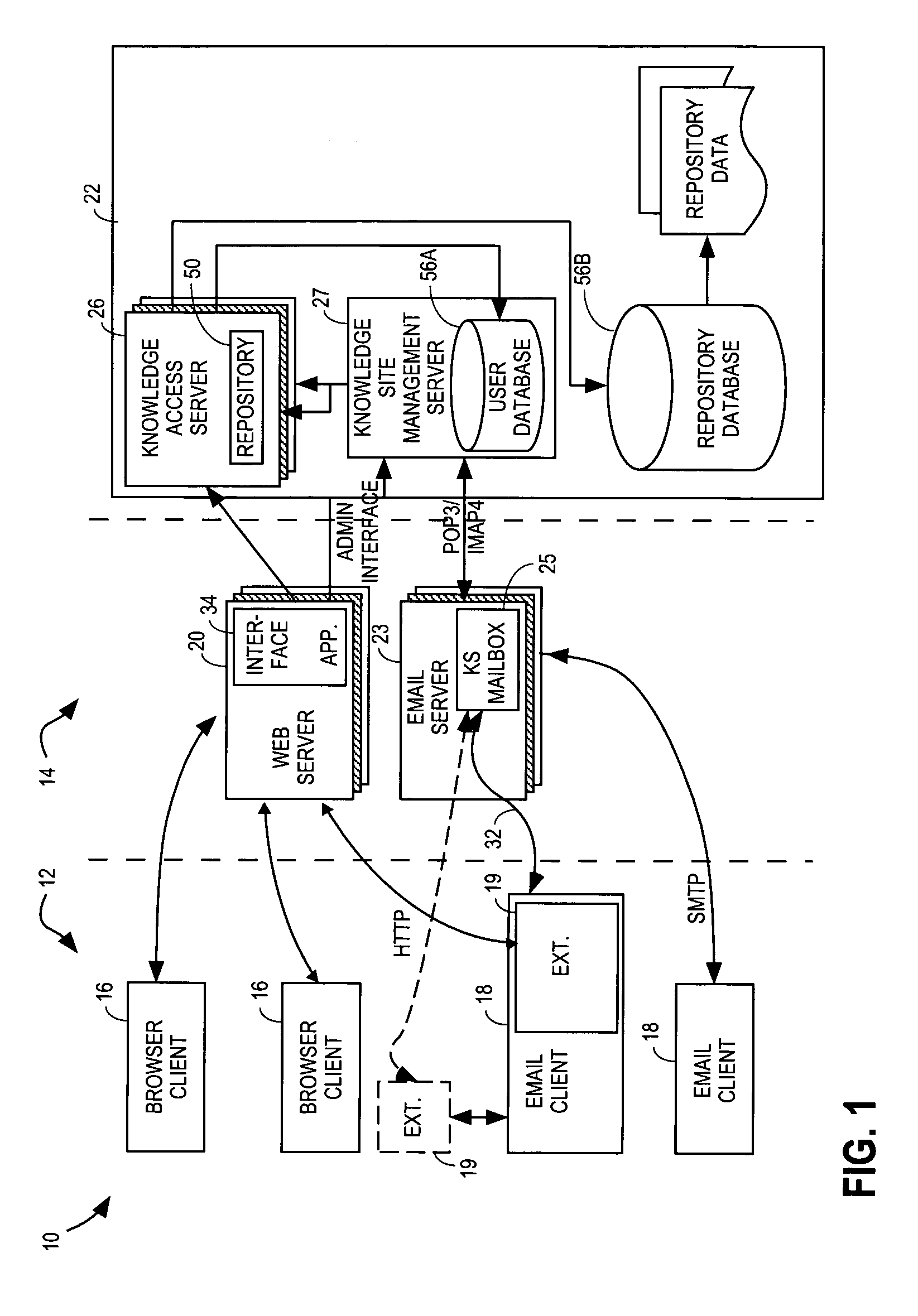
Method and system for enhanced knowledge management
InactiveUS6901394B2Raise the possibilityLarge knowledge baseKnowledge representationInference methodsTacit knowledgeSession management
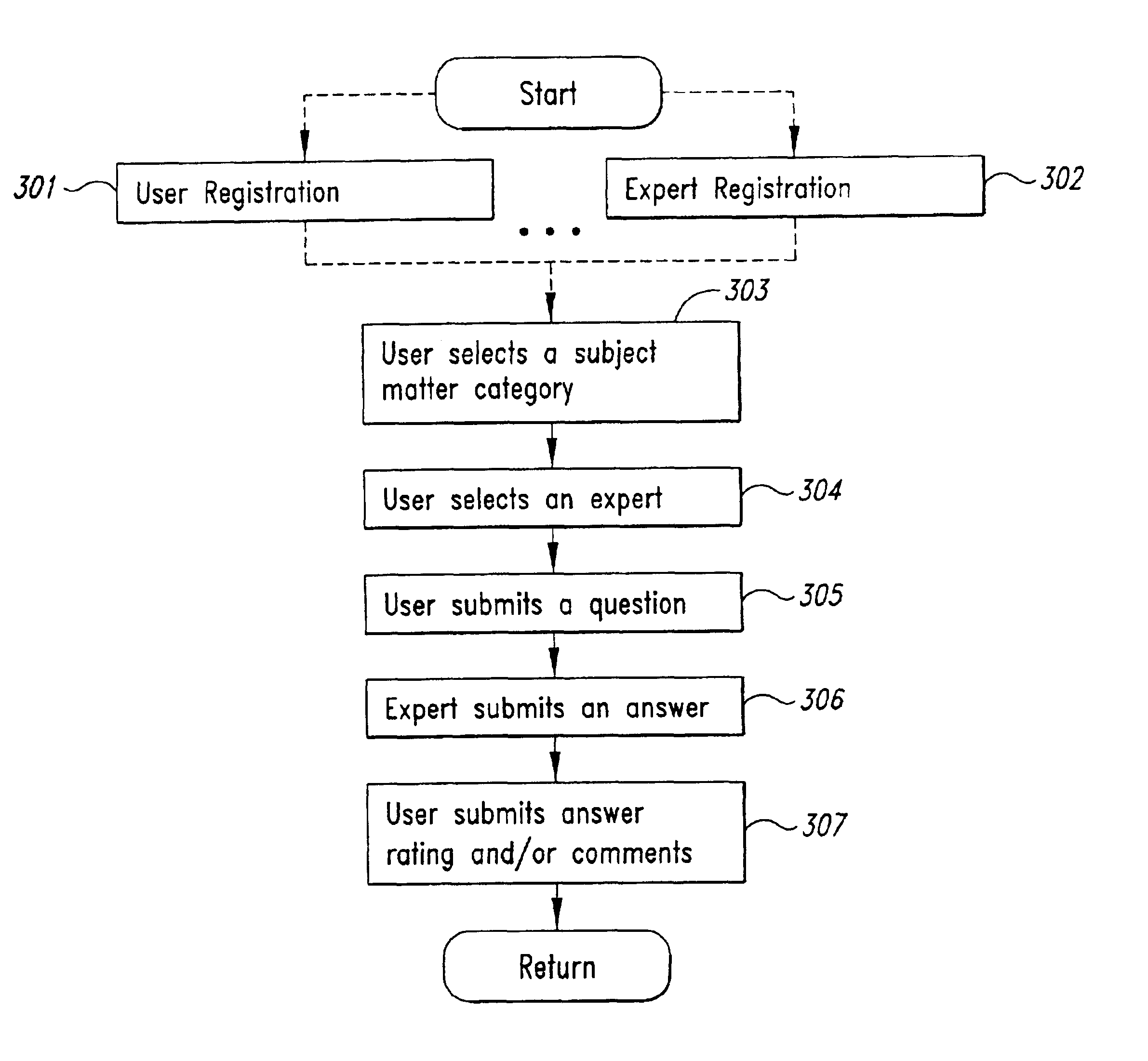
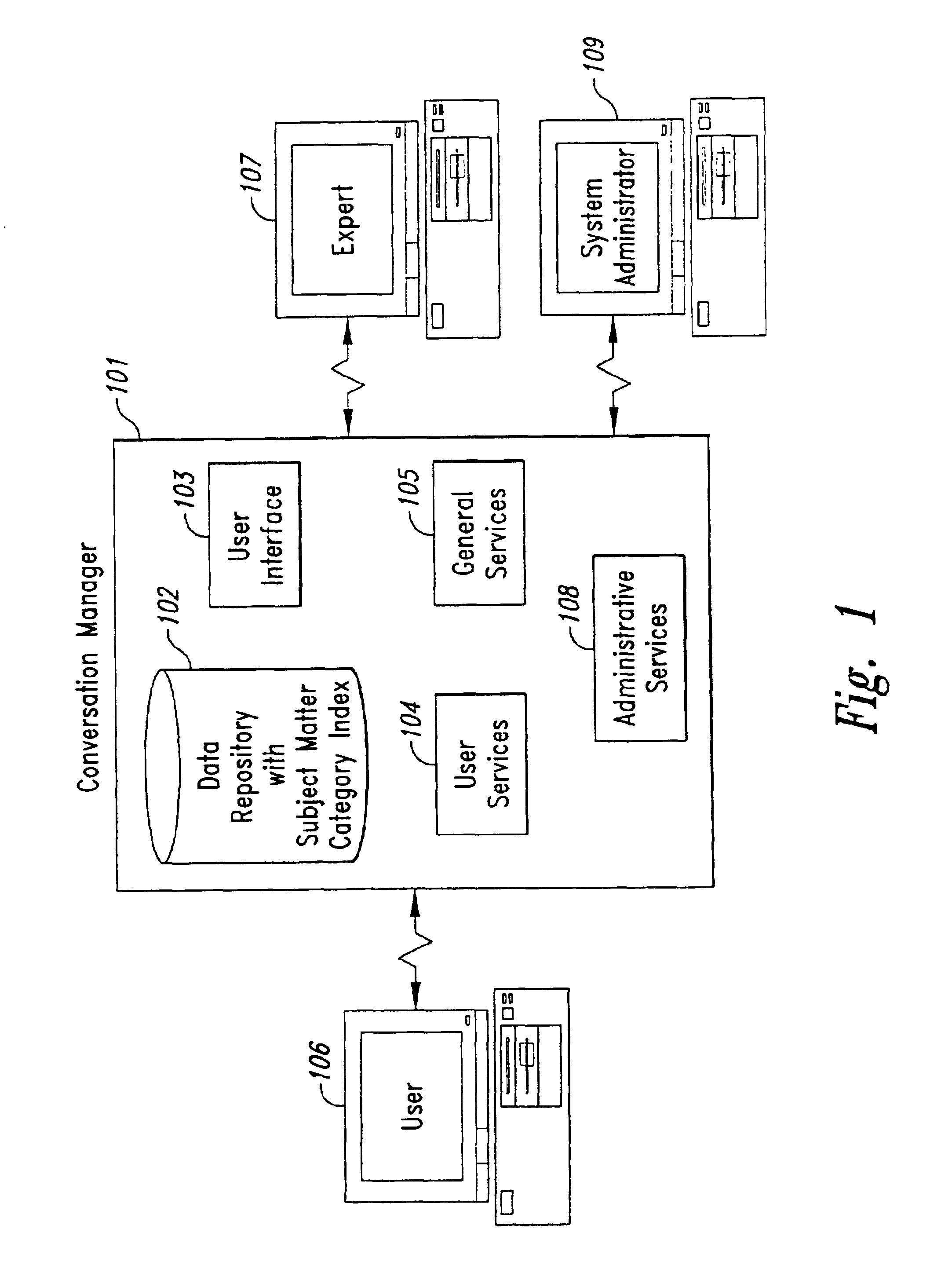
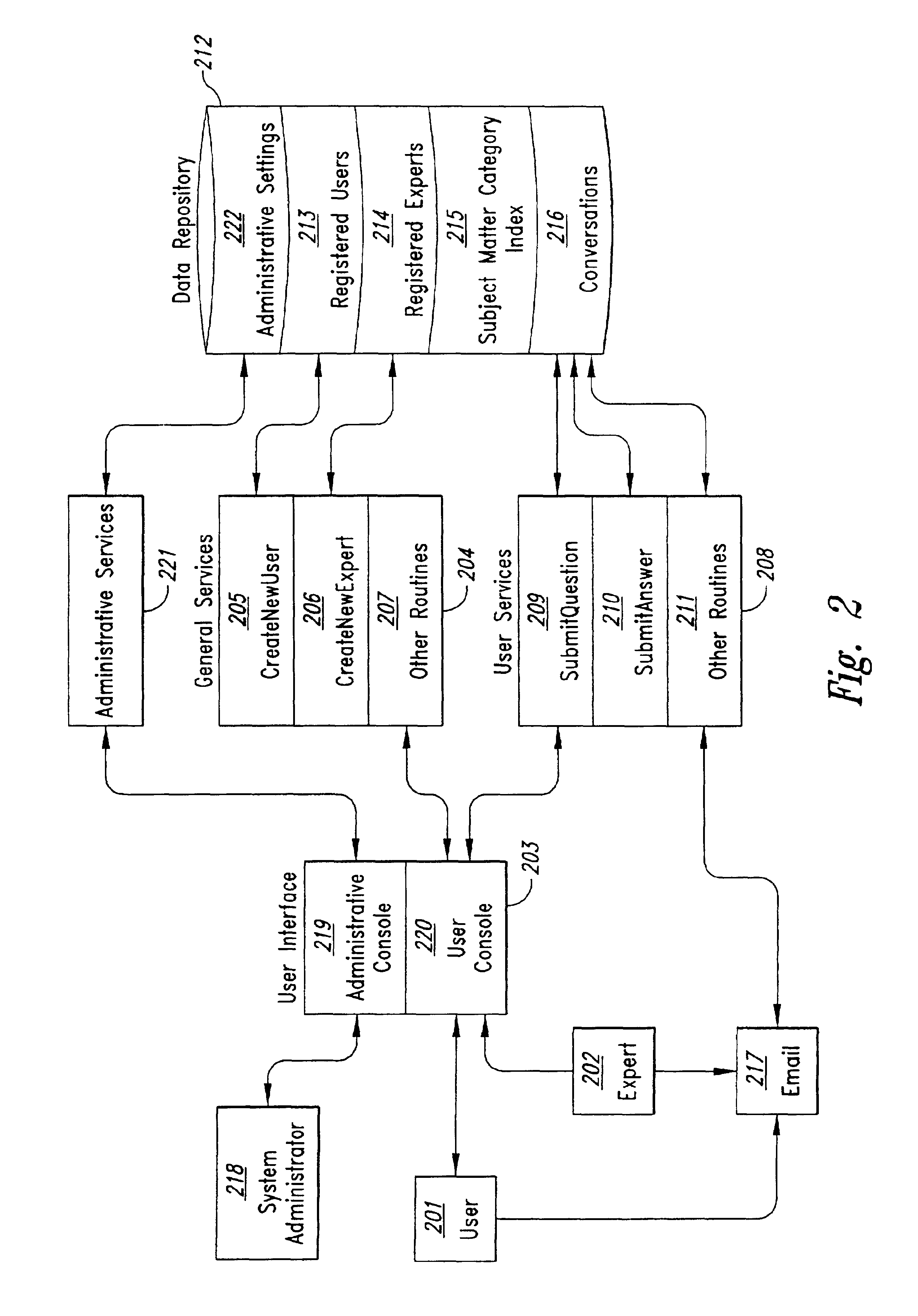
An enhanced knowledge management system (“KMS”) is provided. The enhanced KMS provides a customizable, person-to-person, knowledge sharing portal that manages concurrent one-on-one conversations between requesters and expert resources. Through the knowledge sharing portal, the KMS provides the automatic capture, organization, and reuse of tacit knowledge, as well as integration with existing systems that manage already documented (explicit) knowledge. Example embodiments provide a Conversation Manager, which manages communication in the form of conversations (question and answer sequences) between users (requesters) and experts (expert resources), and allows system administrators to customize the system. Conversations are organized by subject matter categories and experts are ranked preferably by the system and by users, thereby increasing the likelihood of the KMS providing answers to users' questions. The Conversation Manager, in conjunction with managing these conversations, produces a dynamic knowledge base of knowledge that is searchable by other users. In this manner, the KMS enhances the ability in a multitude of environments to capture previously untapped knowledge and to integrate such knowledge with existing data.
Owner:REALCOM U S INC
Storage area network (SAN) security
ActiveUS7437753B2Digital data processing detailsUser identity/authority verificationStorage area networkSystem administrator
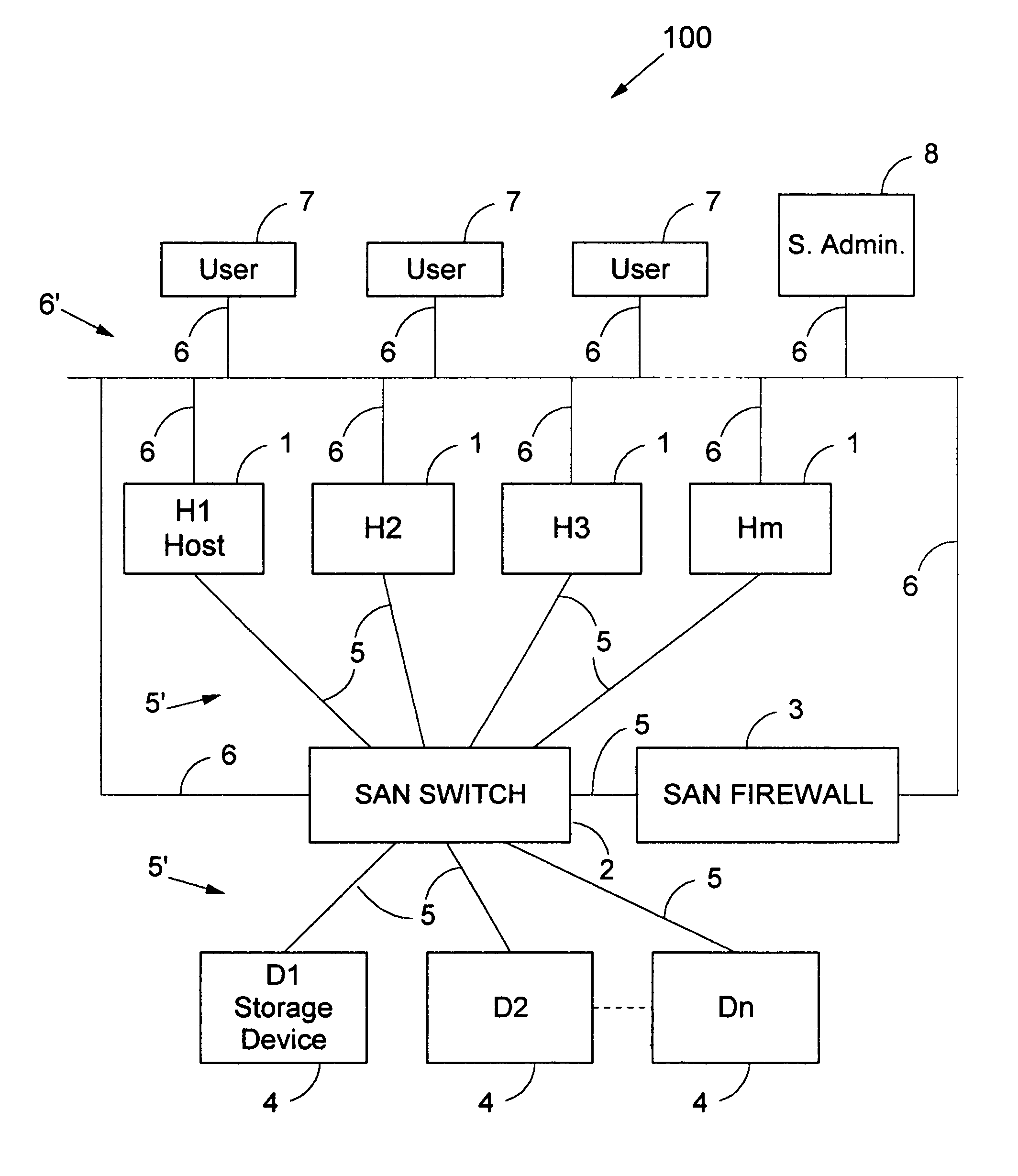
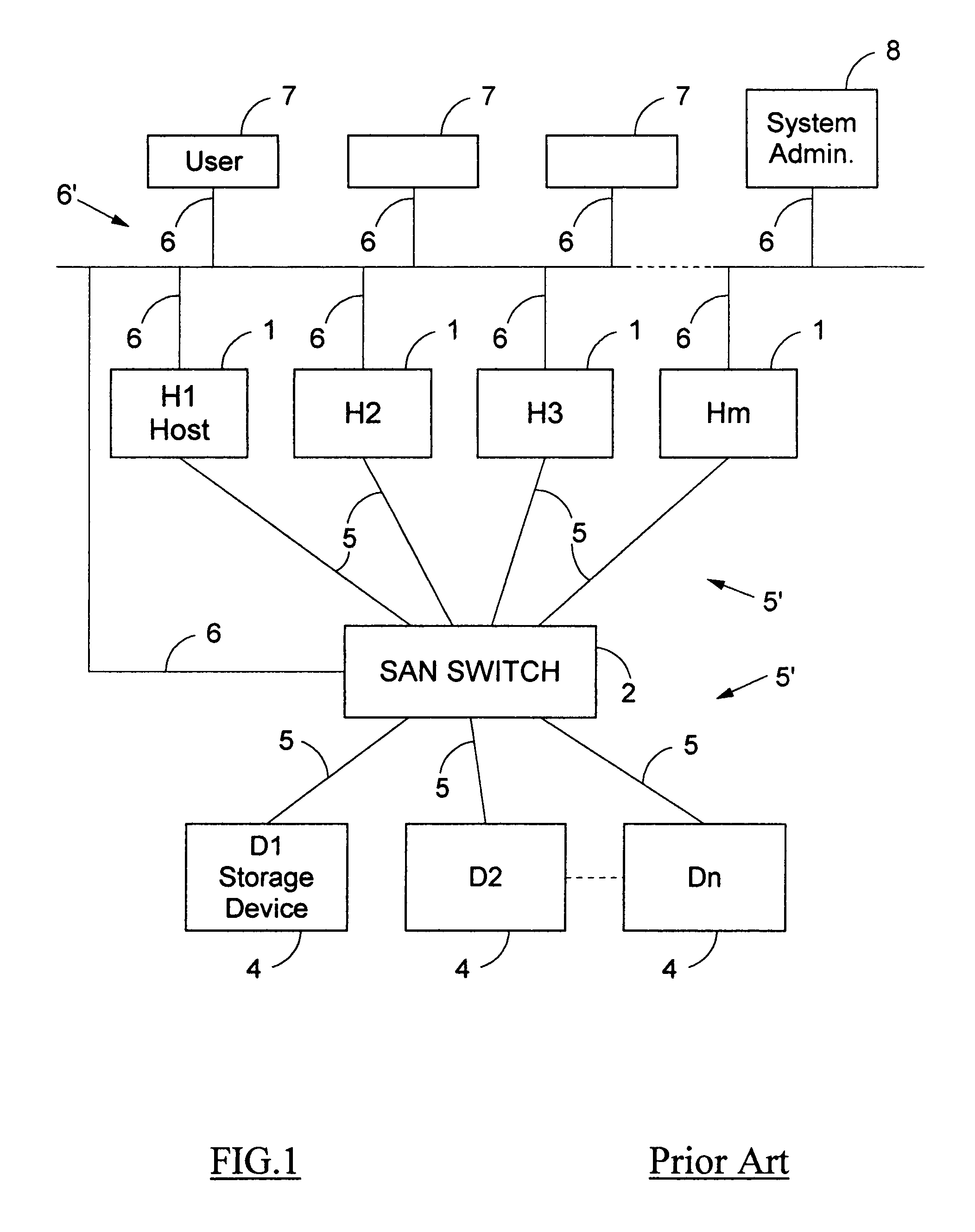
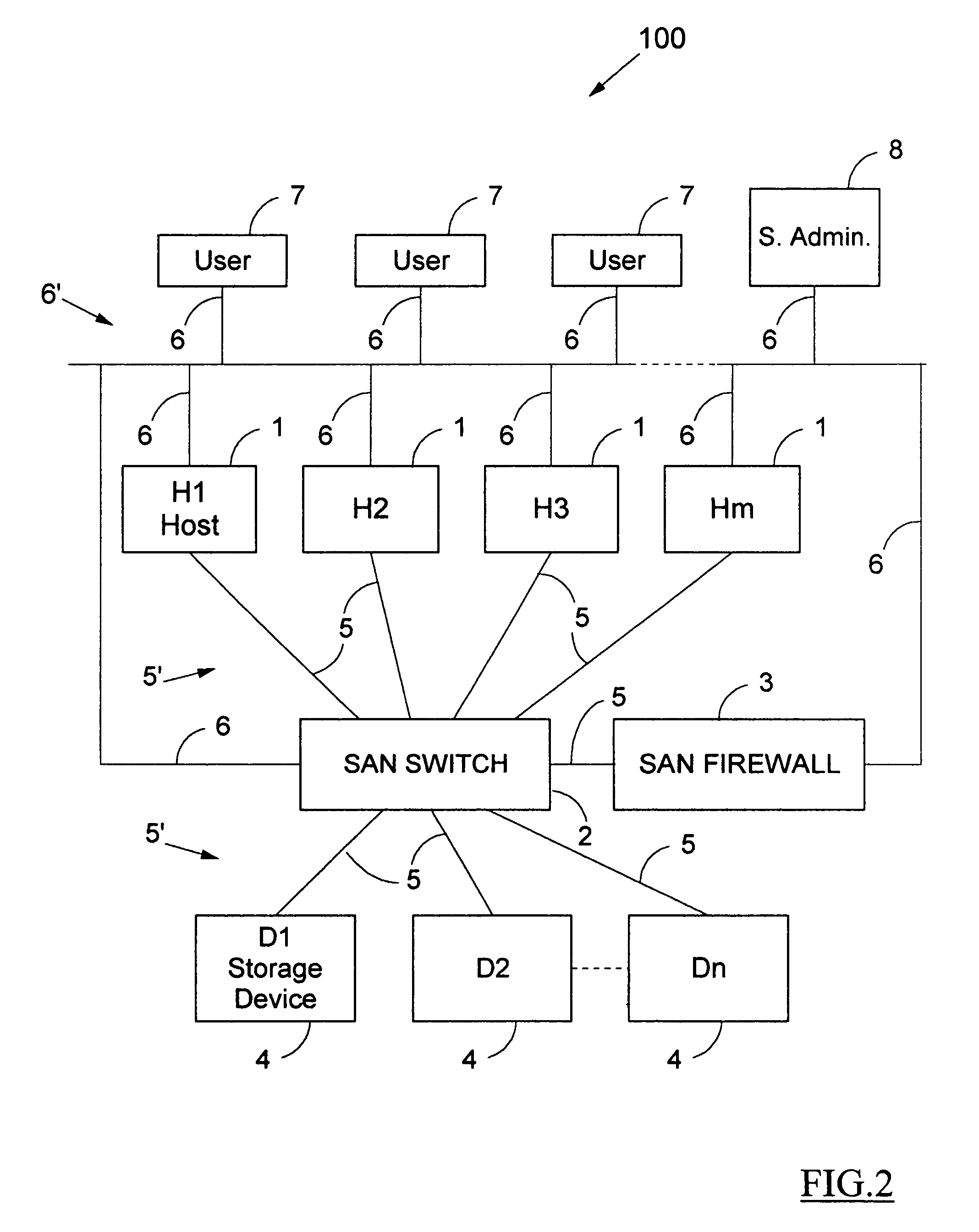
A method for the binary zoning of a Storage Area Network (SAN) for security is disclosed, for a SAN with physical devices consisting of a first array of hosts (1) and a second array of storage devices (4), and a SAN Switch (2, 2A) coupled intermediate the hosts and the storage devices. The SAN Switch routes I / O commands and accepts zoning commands. The method is based on starting operation of the SAN with mutually isolated physical devices and accepting zoning commands only after running security verification procedures requiring that hosts be authenticated and that storage devices be identified. Zoning is dynamically controlled from a workstation (8) operated by a System Administrator entering meta-zoning instructions which are used to automatically program the zoning of the SAN Switch for legitimate physical devices. The method is implemented for security and booting of a SAN.
Owner:NETWORK APPLIANCE INC
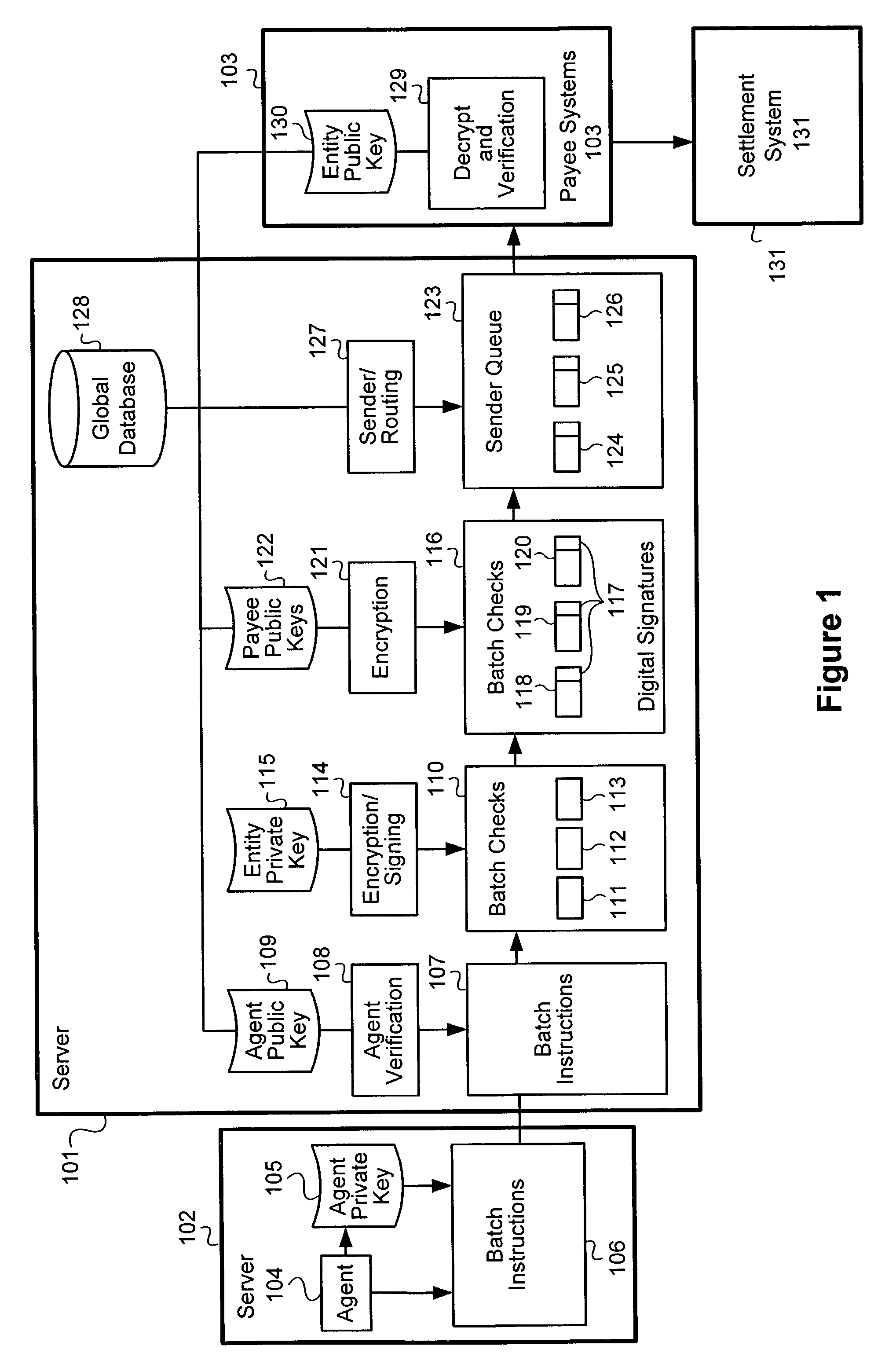
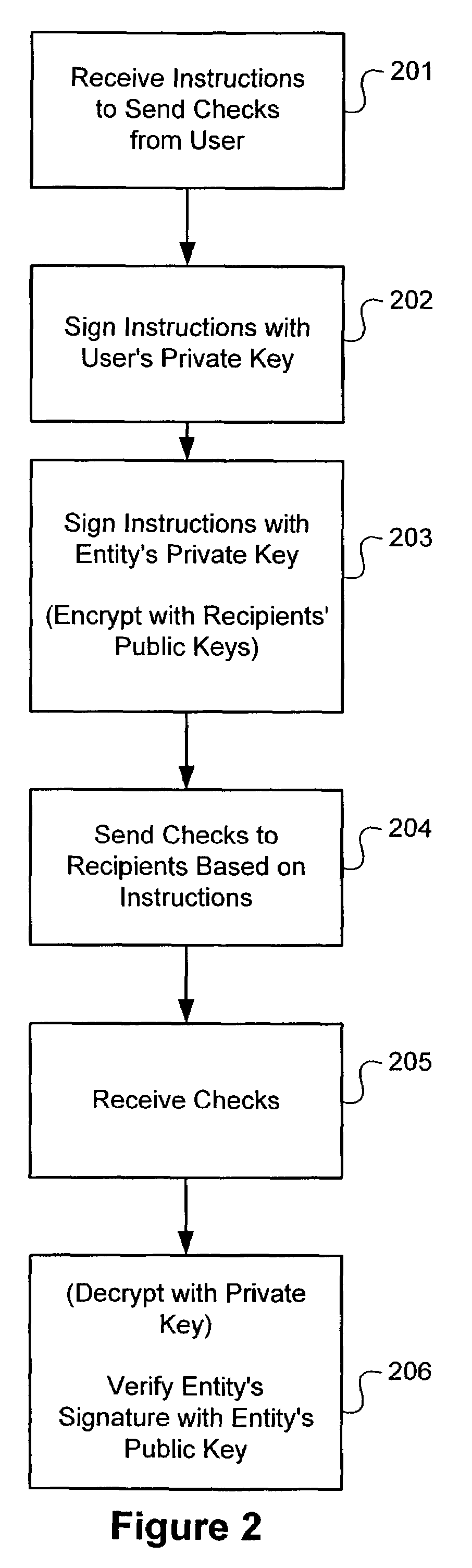
System and method for electronic authorization of batch checks
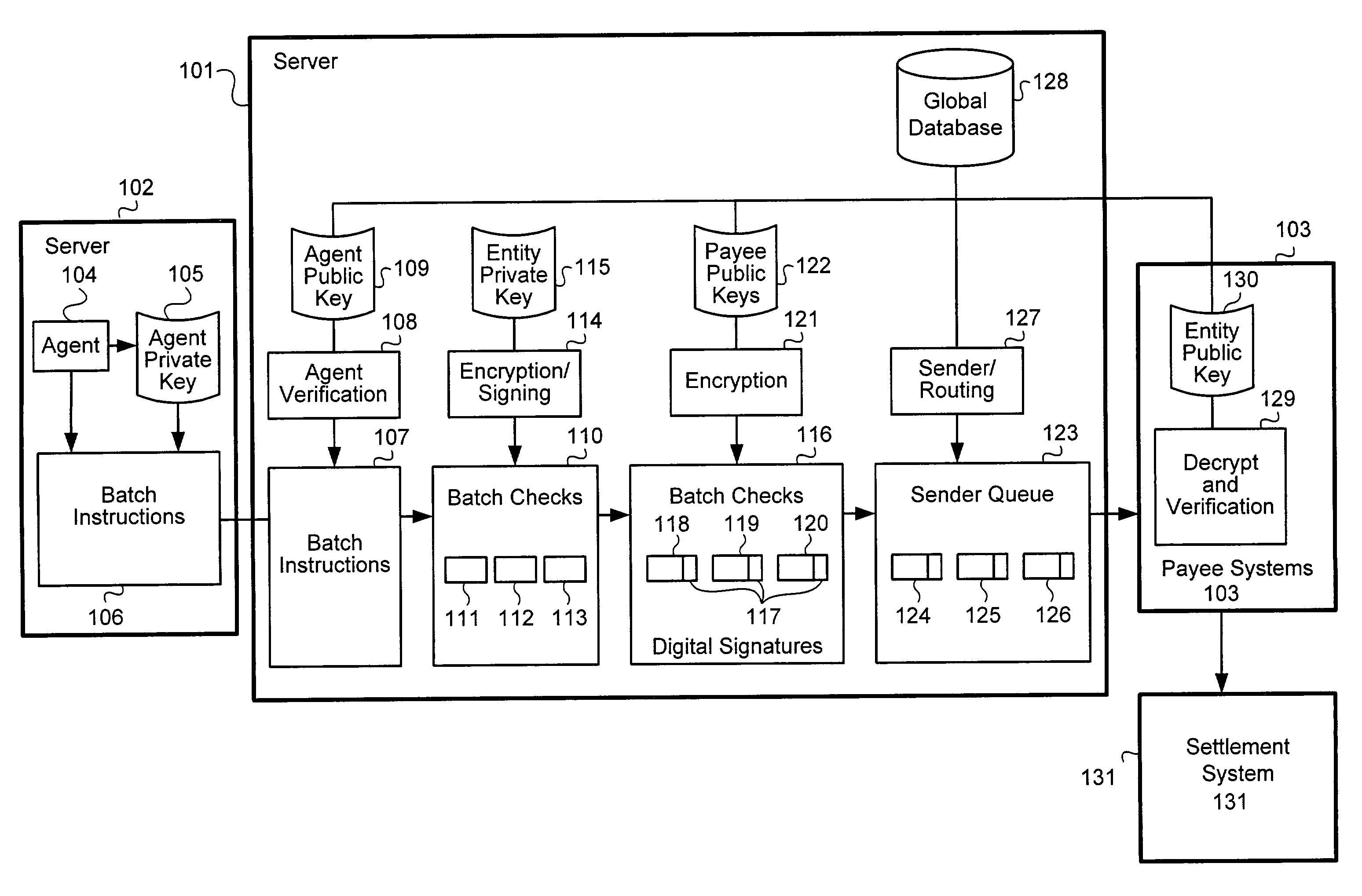
A method of effecting payment. A system for effecting payment. Instructions to send a set of financial instruments to a set of recipients are received at a first system from an agent. A digital signature of the agent is created using a private key associated with the agent is added to the instructions. The agent is associated with a first entity. The instructions are transmitted to a second system. The second system in the instructions are verified using a public key corresponding to a private key associated with the agent. A set of financial instructions is created electronically and digital signatures created using a second private key are added to the financial instruments. The financial instruments from among the set of financial instruments are sent to respective recipients according to the instruments. According to one embodiment of the invention, the financial instruments are encrypted using public keys of respective recipients. According to another embodiment of the invention, terms are presented to the system administrator indicating that the entity shall be responsible for transactions effected by the agent before authorization is provided to the agent to effect creation of the checks with the digital signatures using the private key of the entity.
Owner:JPMORGAN CHASE BANK NA
Method of constructing and displaying an entity profile constructed utilizing input from entities other than the owner
A method of constructing a profile comprising terms indicative of a characteristic of an entity commences when first electronic mail address, associated with a first entity, is created within a knowledge management system. The electronic mail address may be created automatically upon submission of an electronic mail document, or may be created manually by a systems administrator. A first electronic document is received via an electronic communications network at the first electronic mail address from a second entity, typically a user of the knowledge management system who is a registered and interactive user. The first electronic document is then parsed to identify profile terms therein. These profile terms are included within a first profile for the first entity. In this way, users of a knowledge management system may construct a profile of an entity (e.g., a customer) that is not a user of or participant within the knowledge management system.
Owner:ORACLE INT CORP
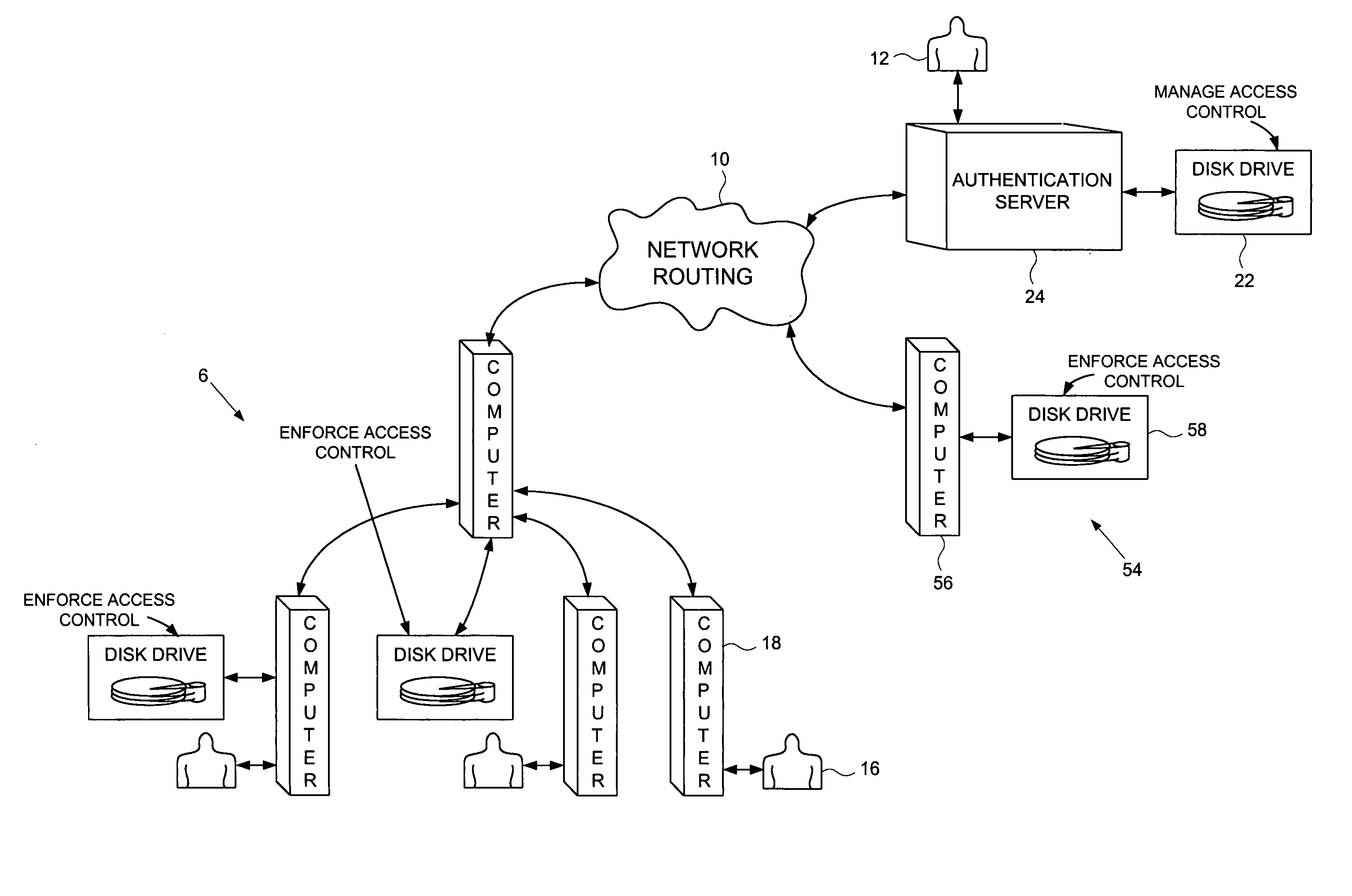
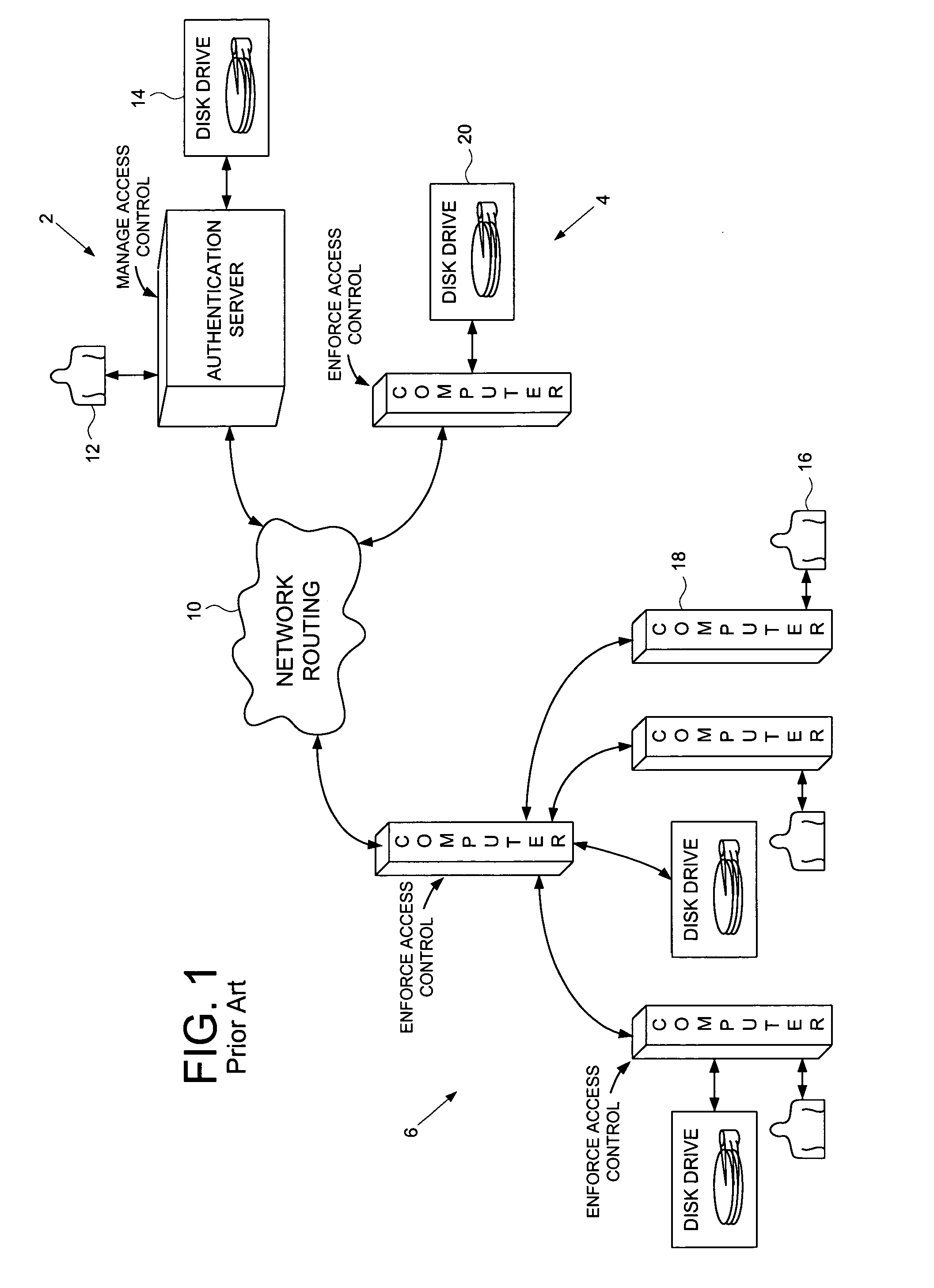
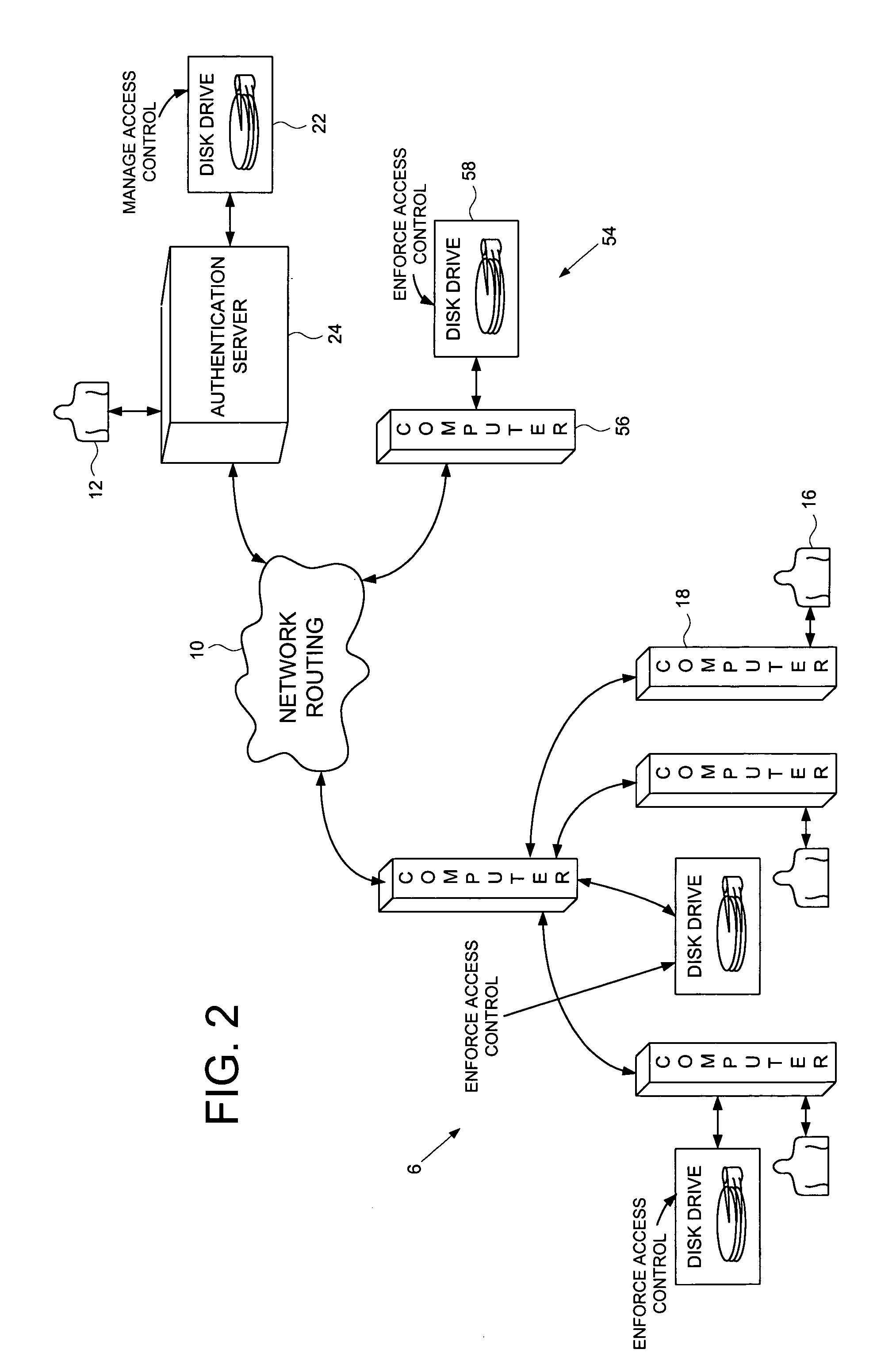
Computer network comprising network authentication facilities implemented in a disk drive
InactiveUS7155616B1Digital data processing detailsUser identity/authority verificationDisk controllerAuthentication server
A computer network is disclosed comprising a plurality of interconnected network devices including a plurality of client computers, an authentication server computer operated by a system administrator, and a disk drive connected to the authentication server computer. The disk drive comprises an interface for receiving the personal authentication data and user access data from the system administrator, a disk for storing data, and a disk controller for controlling access to the disk. An authenticator within the disk drive, responsive to the personal authentication data, enables the disk controller, and cryptographic circuitry encrypts the user access data received from the system administrator into encrypted data stored on the disk.
Owner:WESTERN DIGITAL TECH INC
Limit access to program function
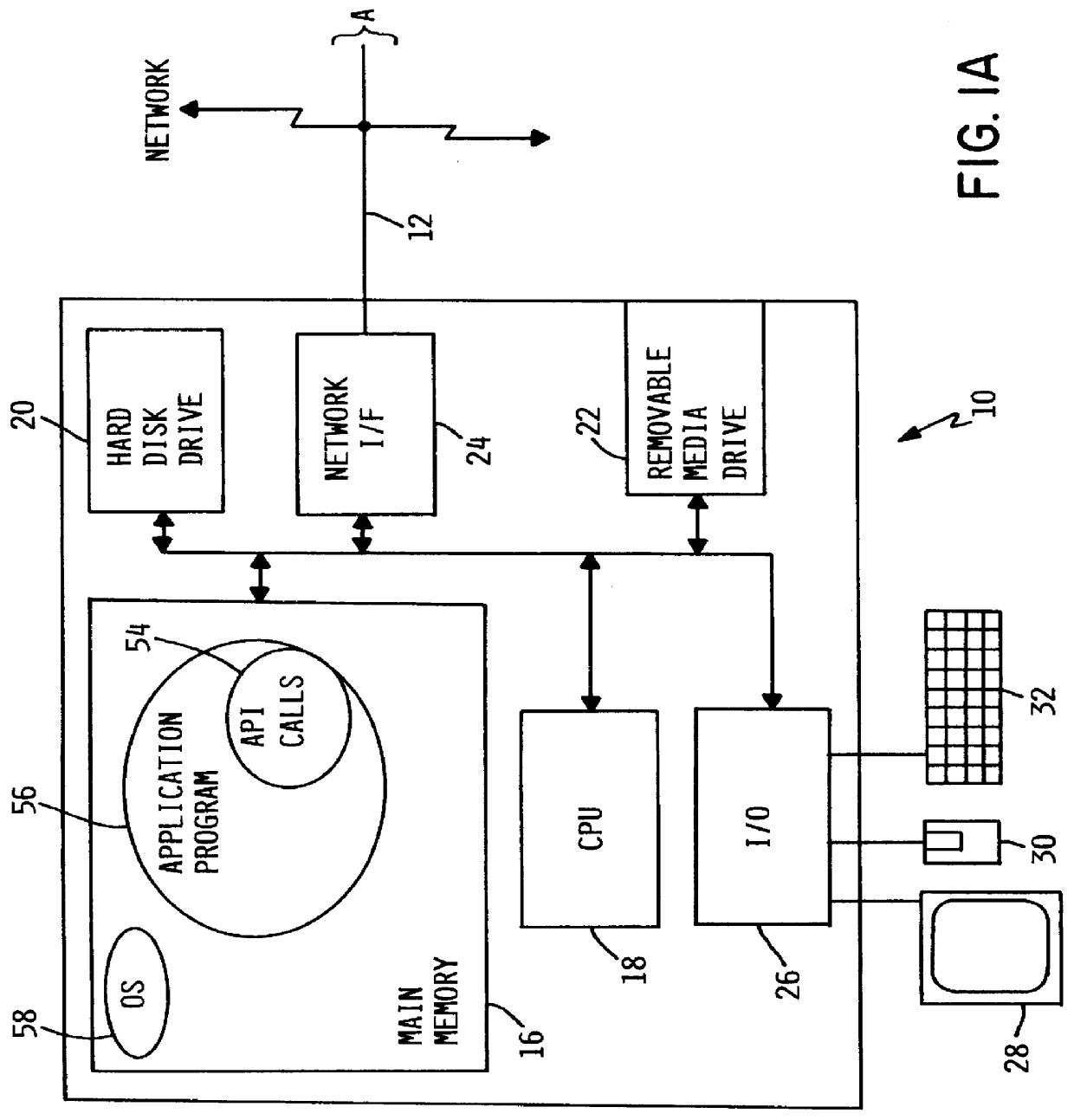
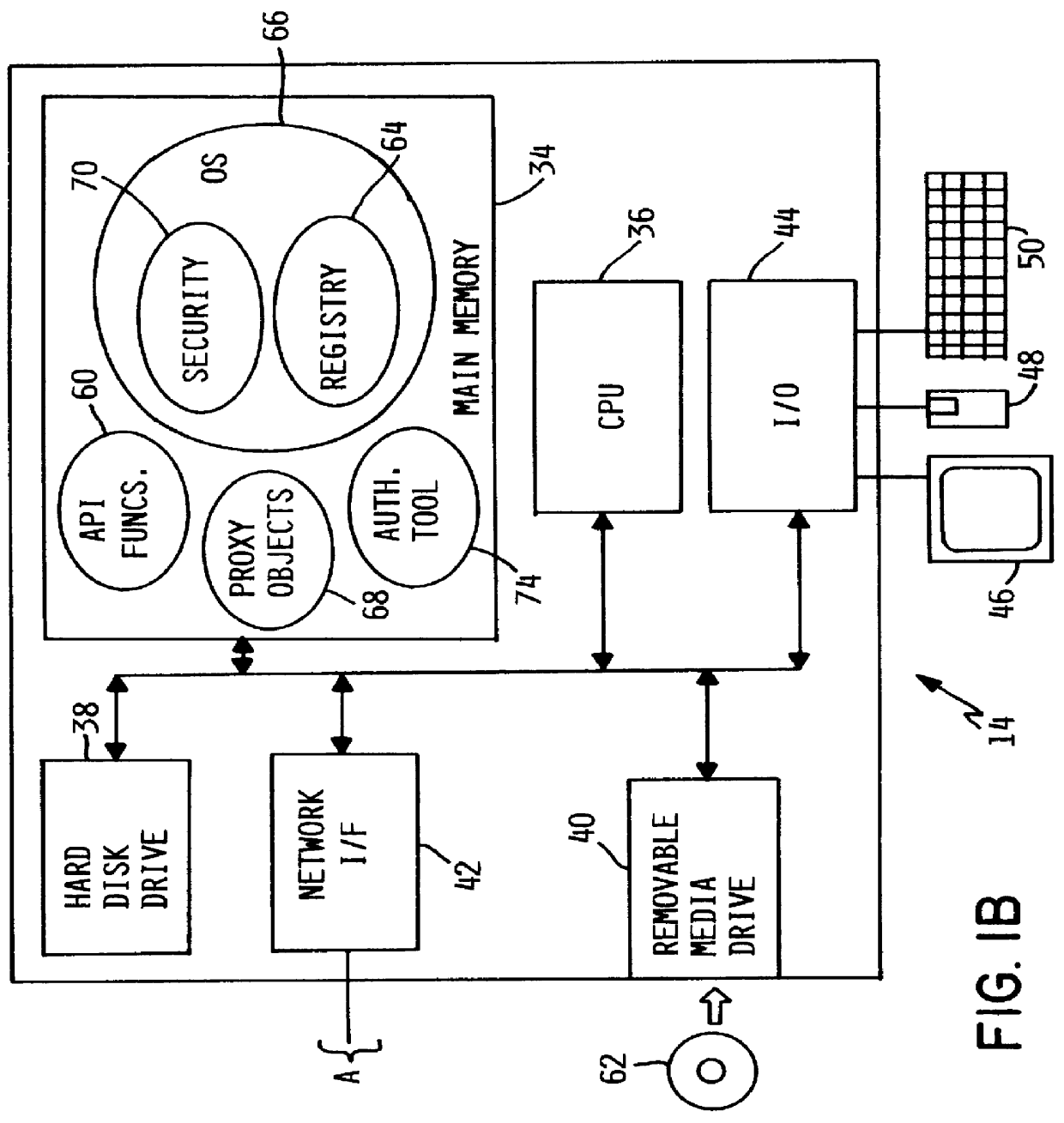
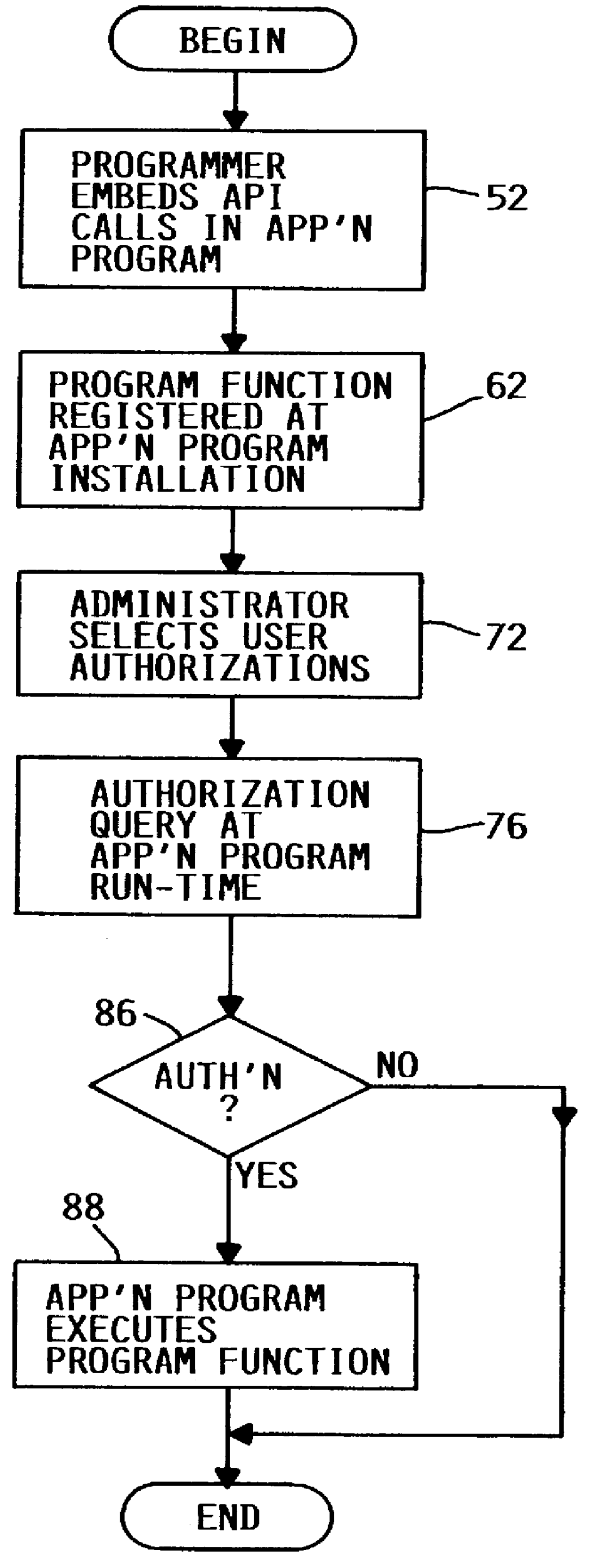
InactiveUS6101607ASpecific access rightsDigital data processing detailsOperational systemApplication programming interface
A method, system and computer program product for selectively restricting access to a program function in a computer system having an operating system security mechanism operates via an application programming interface (API) that includes a program function registration API function, an authorization selection API function, and an authorization query API function. In response to a call to the API registration function, the program function is registered in a repository in the computer system. After the program function has been registered, a system administrator can select user authorizations using a software tool that includes calls to the authorization selection API function. The system administrator may select whether a particular user or group of users is authorized to access each registered program function. A programmer can embed a call to the authorization query API function in an application program, which includes or calls the program function. When the application program reaches the call to the authorization query API function, the function is executed and returns an indicator or value indicating whether or not that user is allowed to access the program function.
Owner:IBM CORP
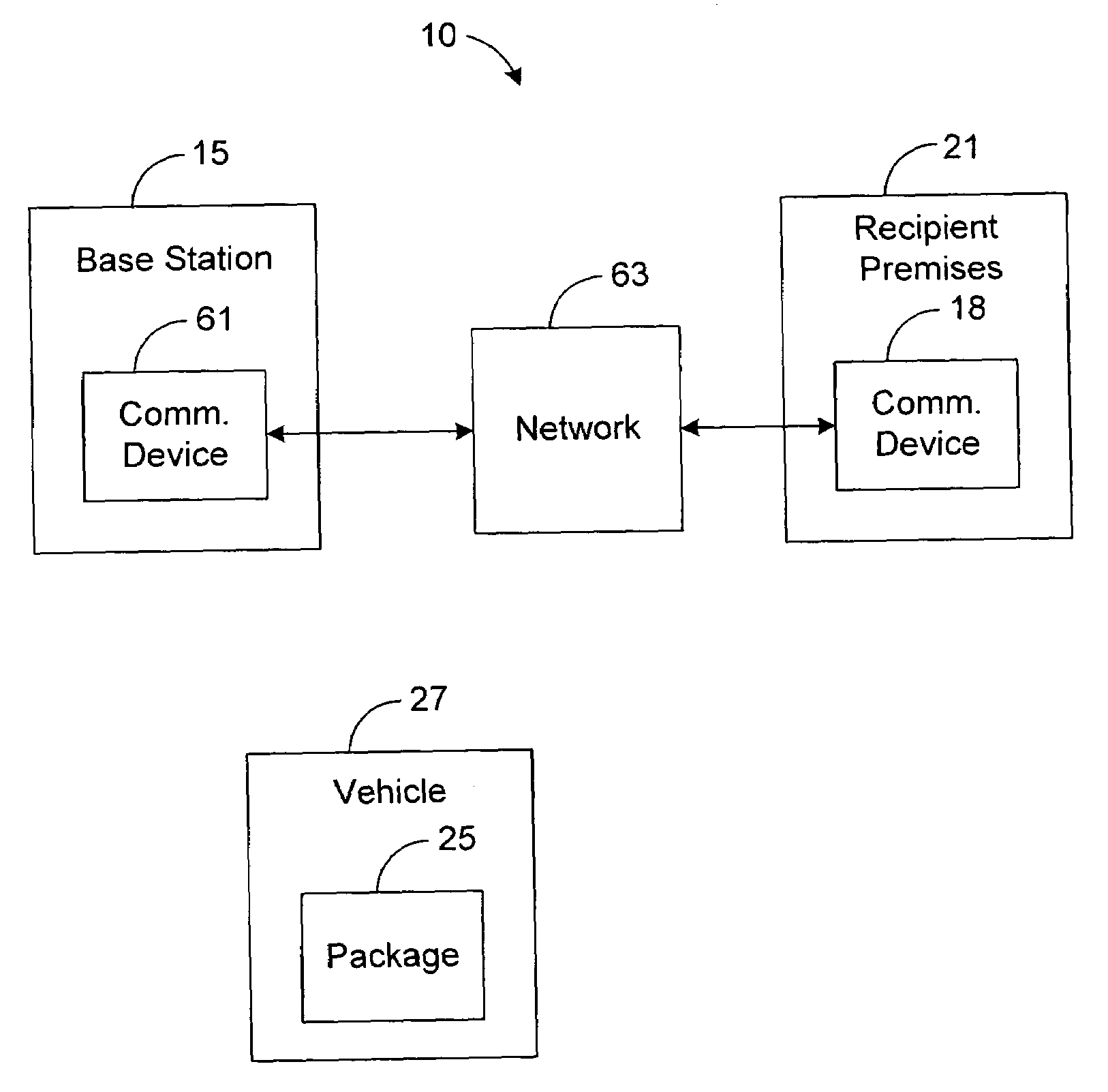
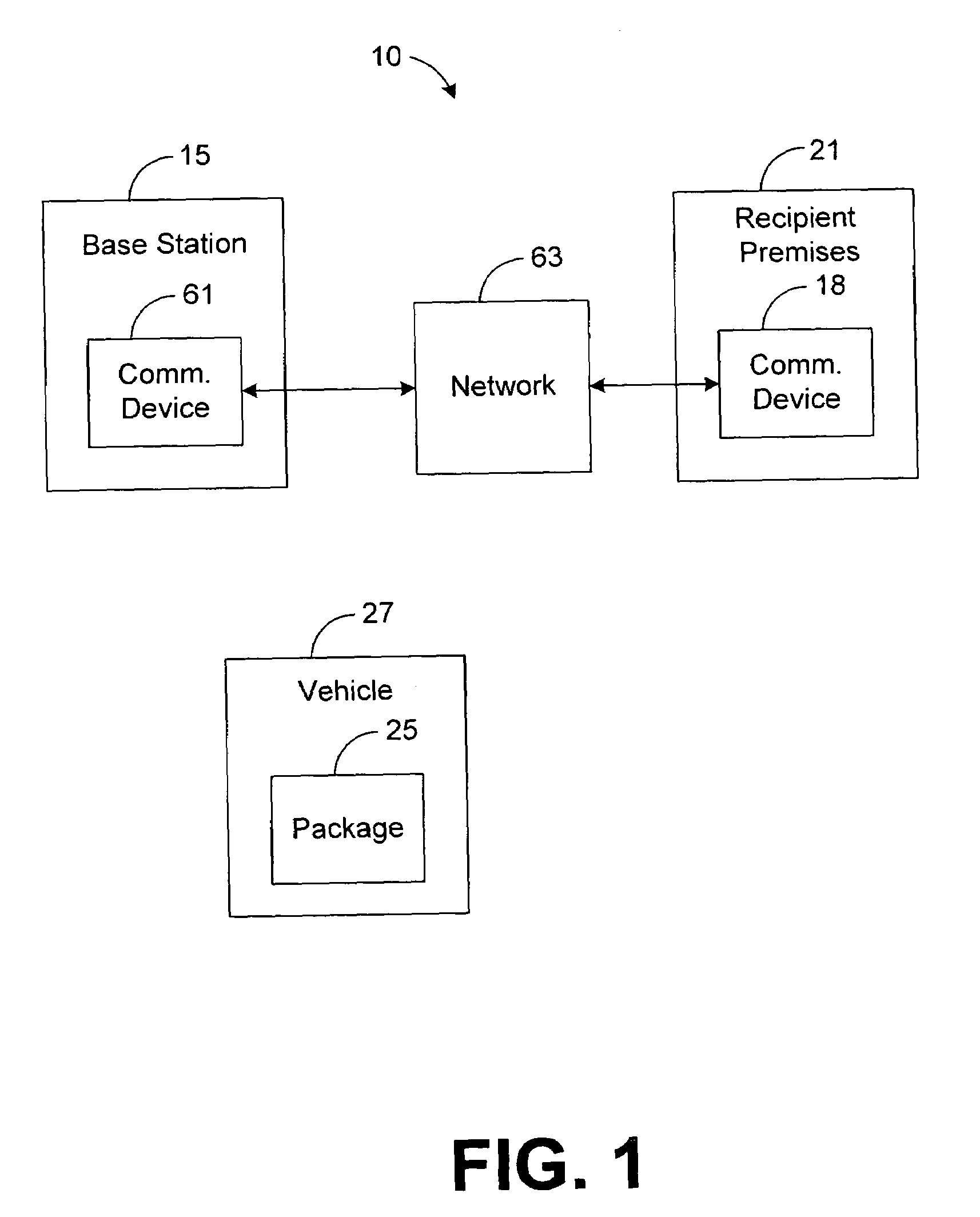
Package delivery notification system and method
InactiveUS6975998B1Accurately notifiedOvercomes inadequacy and deficiencyInstruments for road network navigationWrappersNotification ReceiverSystems management
A package delivery notification system reports impending package deliveries and precisely notifies recipients of when to expect the deliveries. The package delivery notification system utilizes memory, a communications device, and a system manager. Package data identifying a package that is to be delivered to a recipient is stored in the memory. The package data indicates that the recipient is to receive the package and indicates the expected time that the package is to be delivered. When the package is assigned to a vehicle that will deliver the package to a premises of the recipient, the system manager transmits, via the communications device, a notification message to the recipient. The notification message preferably indicates the approximate time that the package is expected to arrive.
Owner:INNOVATION LICENSING SERVICE LLC
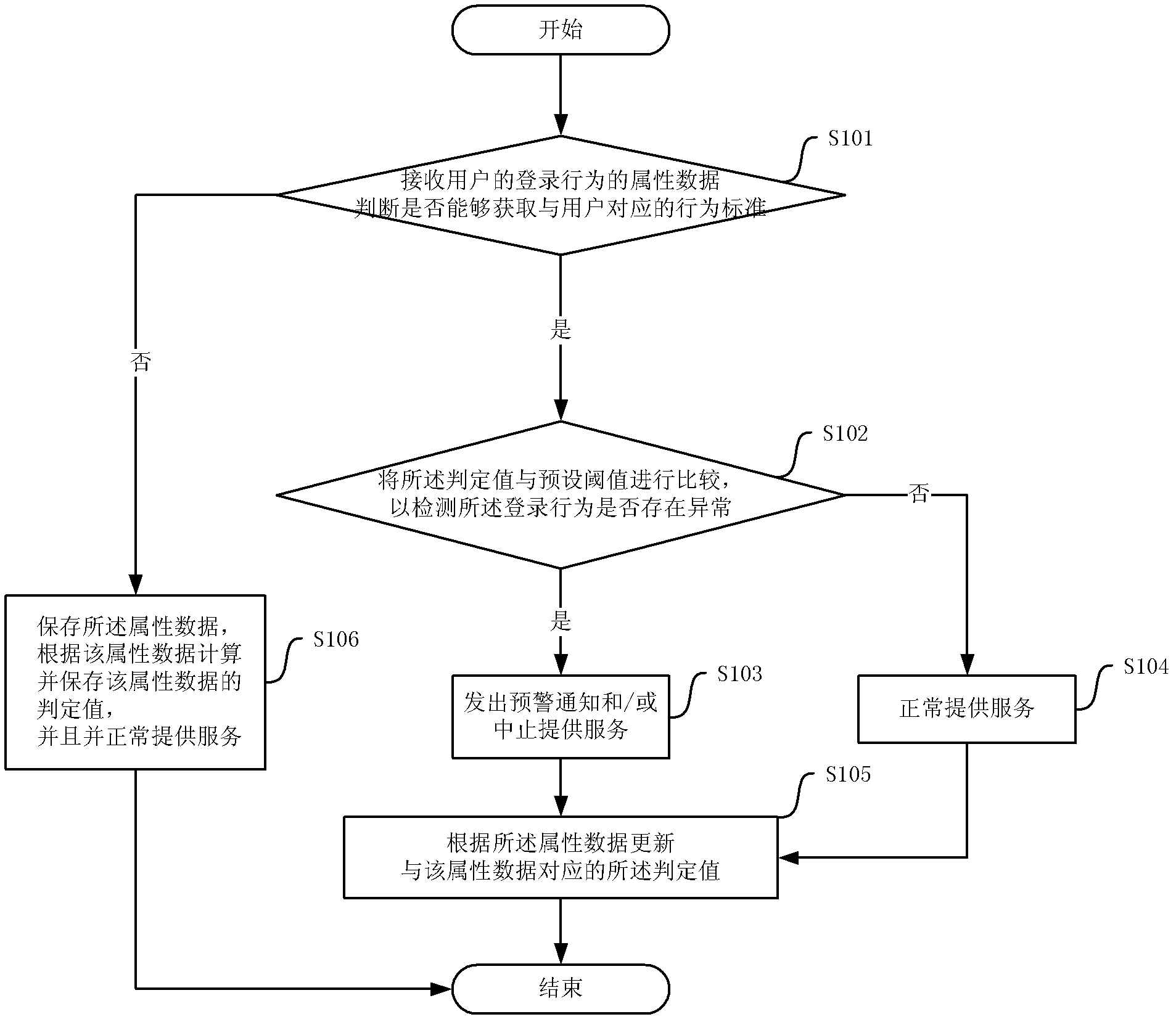
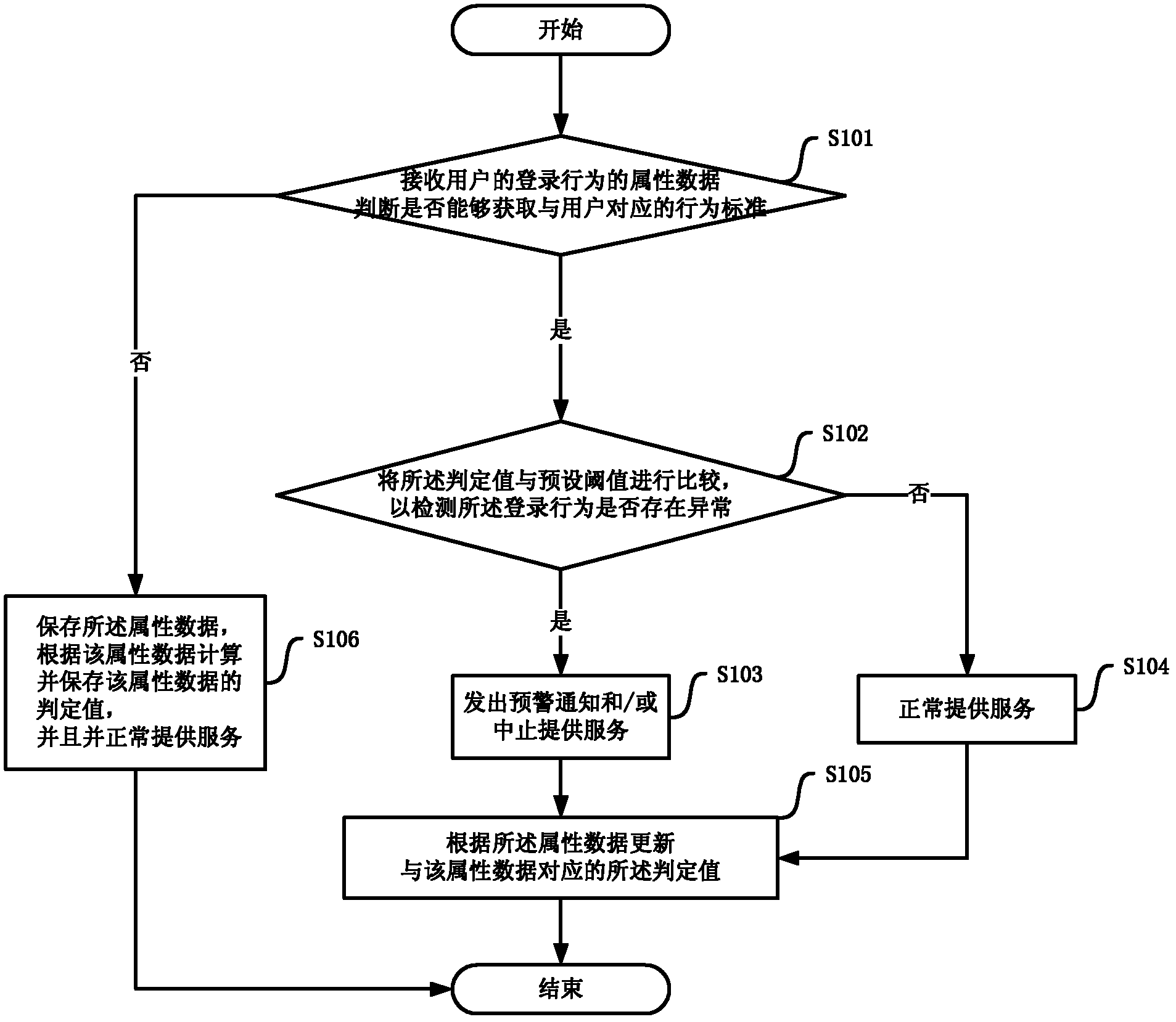
Abnormal login detecting method and device
The invention provides an abnormal login detecting method. The method comprises the following steps of: receiving the attribute data of a login behavior of a user; obtaining a behavior standard corresponding to the user, wherein the behavior standard records at least one group of history attribute data of the login behavior and records a decision value generated according to a calculating result of the at least one group of history login behavior data; comparing the decision value with a preset threshold value and detecting whether the login behavior data are abnormal or not; if the login behavior is not abnormal, normally providing service; and if the login behavior is abnormal, sending a prewarning notice or stopping providing service. Correspondingly, the invention provides an abnormal login detecting device. By applying the invention, the safety of a service providing system is improved, the workload of a service providing system administrator is reduced, and the working efficiency is increased.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD
Method and system for simplifying distributed server management
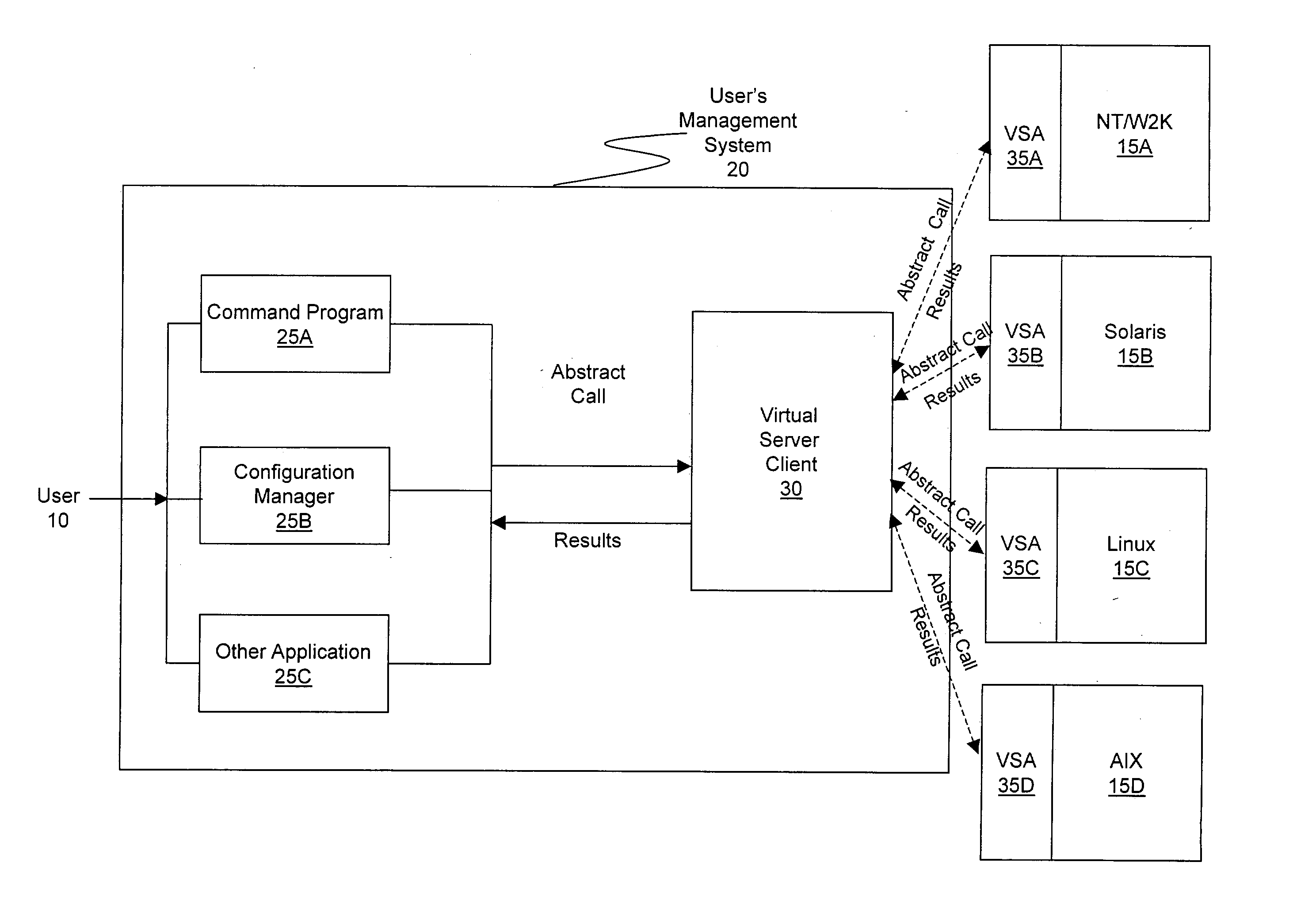
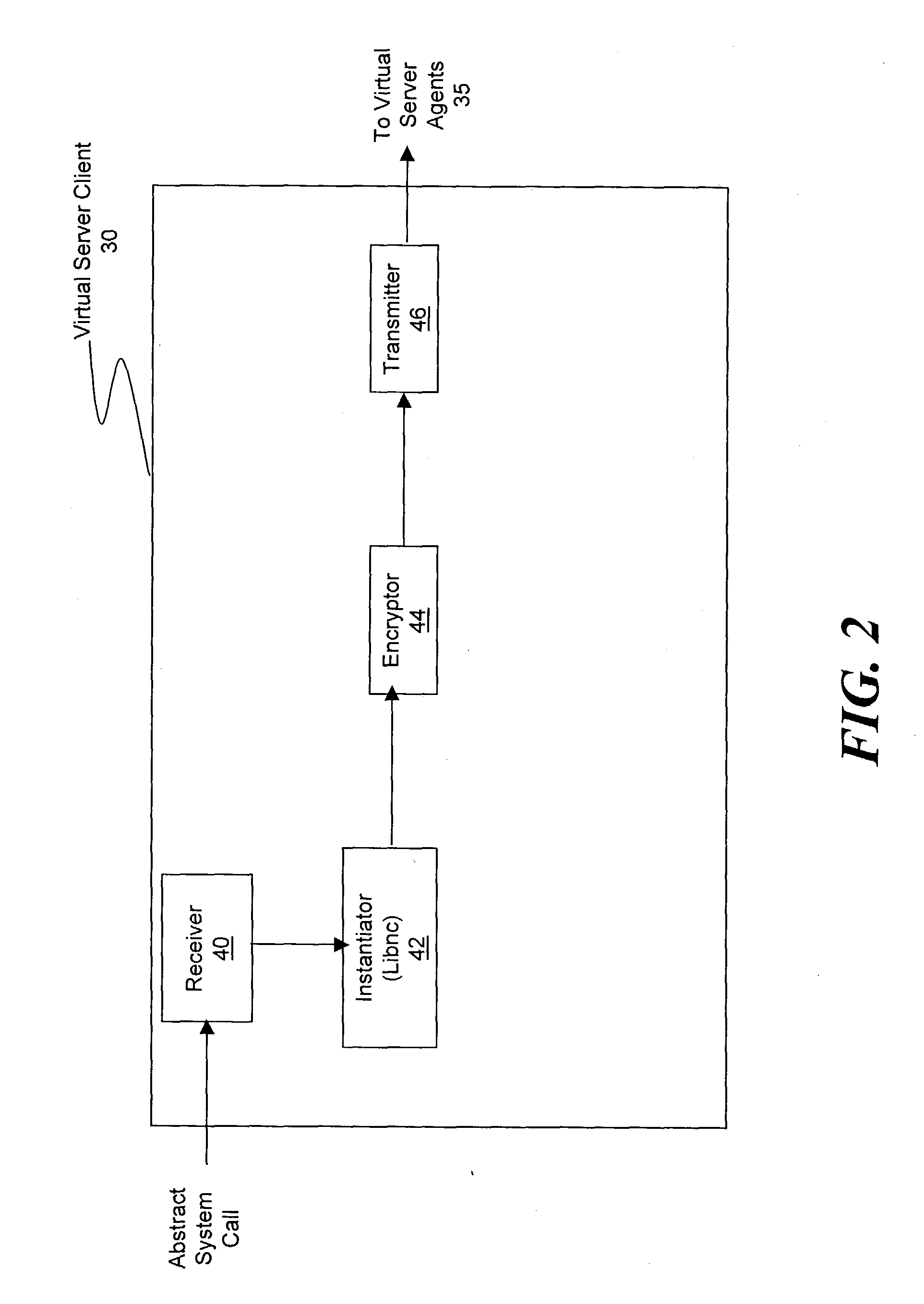
ActiveUS20030233571A1Error detection/correctionInterprogram communicationOperational systemSystem call
A method and system for managing a large number of servers and their server components distributed throughout a heterogeneous computing environment is provided. In one embodiment, an authenticated user, such as a IT system administrator, can securely and simultaneously control and configure multiple servers, supporting different operating systems, through a "virtual server." A virtual server is an abstract model representing a collection of actual target servers. To represent multiple physical servers as one virtual server, abstract system calls that extend execution of operating-system-specific system calls to multiple servers, regardless of their supported operating systems, are used. A virtual server is implemented by a virtual server client and a collection of virtual server agents associated with a collection of actual servers.
Owner:BLADELOGIC
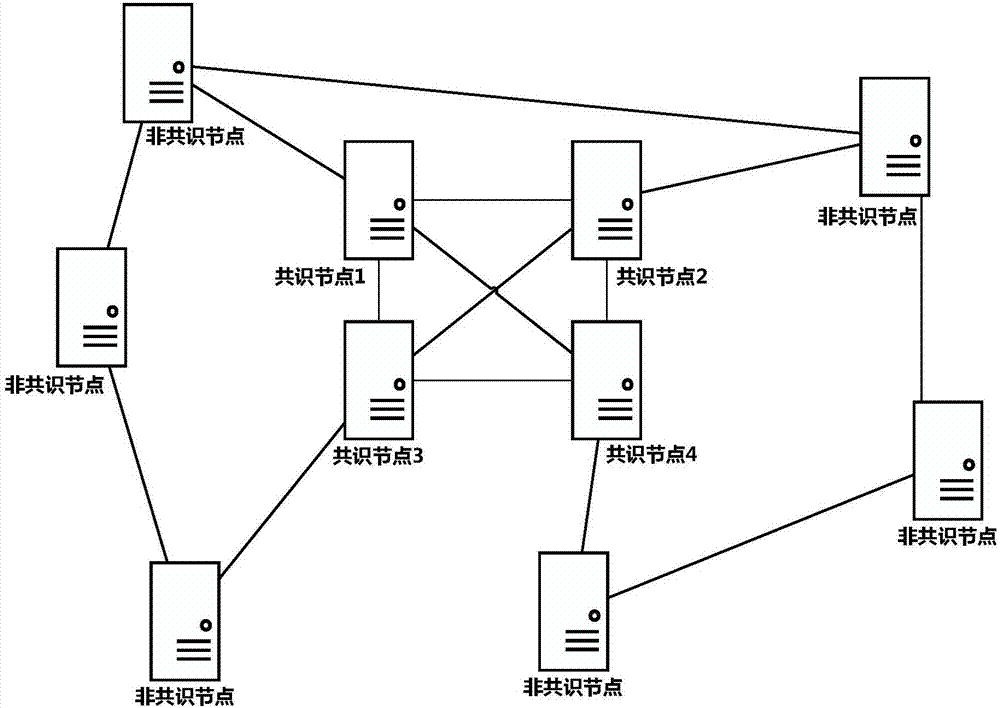
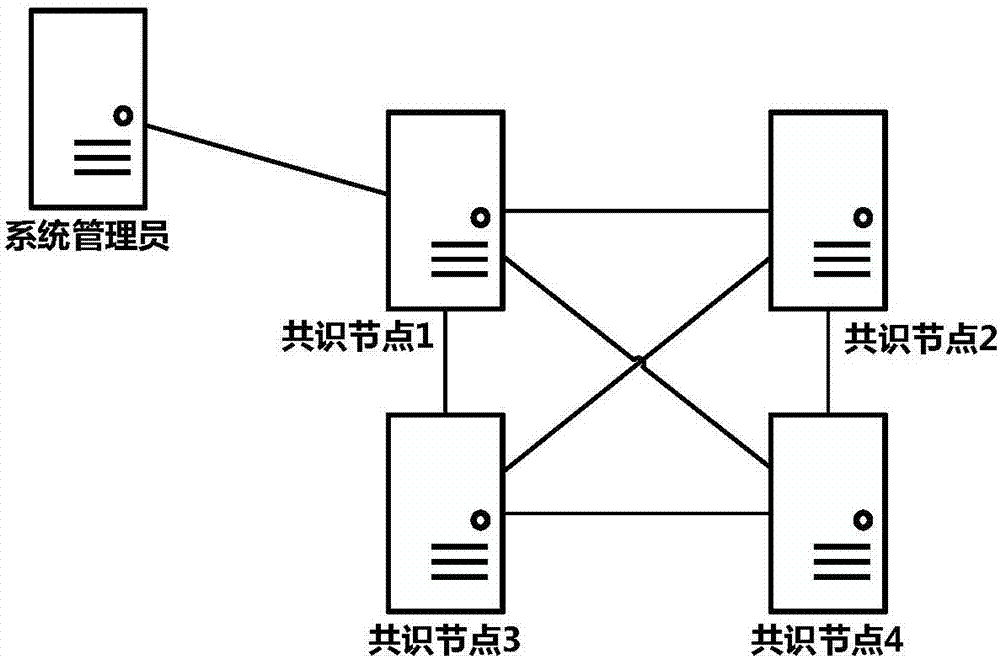
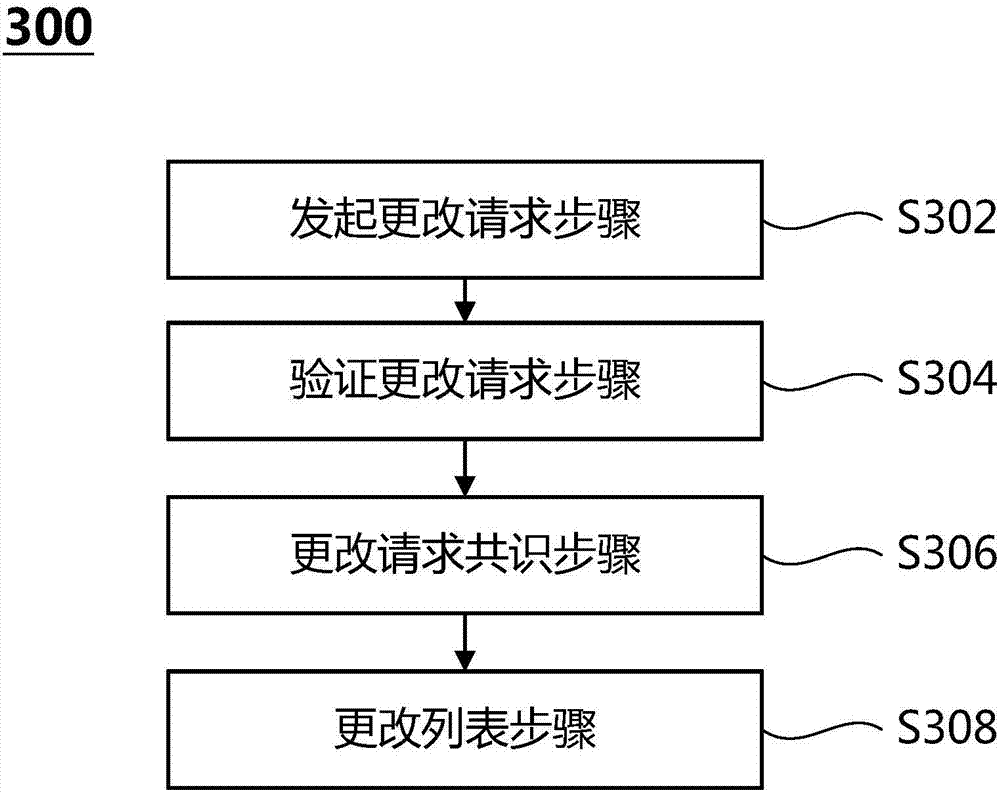
Method for dynamically changing consensus node in practical Byzantine fault tolerant consensus mechanism
ActiveCN107579848ASafe and reliable dynamic changesDynamically change the implementationFault responseData switching networksByzantine fault toleranceSmart contract
The invention provides a method for dynamically changing a consensus node in a practical Byzantine fault tolerant consensus mechanism. The method comprises the following steps: a system administratorinitiates a change request of increasing or decreasing the consensus node to the consensus node as a system-level transaction, and the change request is signed by using a private key of the system administrator; the consensus node verifies the change request, if the verification is successful, a special system transaction head is added to the change request, the change request is broadcast, and each consensus node puts the change request into a priority transaction queue; a new round of consensus operation is performed, a selected proposal node proposes a proposal block including the change request and broadcasts the proposal block to all consensus nodes, all the consensus nodes verify transactions in the proposal block, firstly verify the transaction heads of the transactions, and enter system transaction operation logic rather than smart contracts when a special system transaction head is verified; and after reaching a consensus, the node executes the change request and updates a consensus node set list, and the updated consensus node set list is stored to a local file of the nodes.
Owner:上海保险交易所股份有限公司
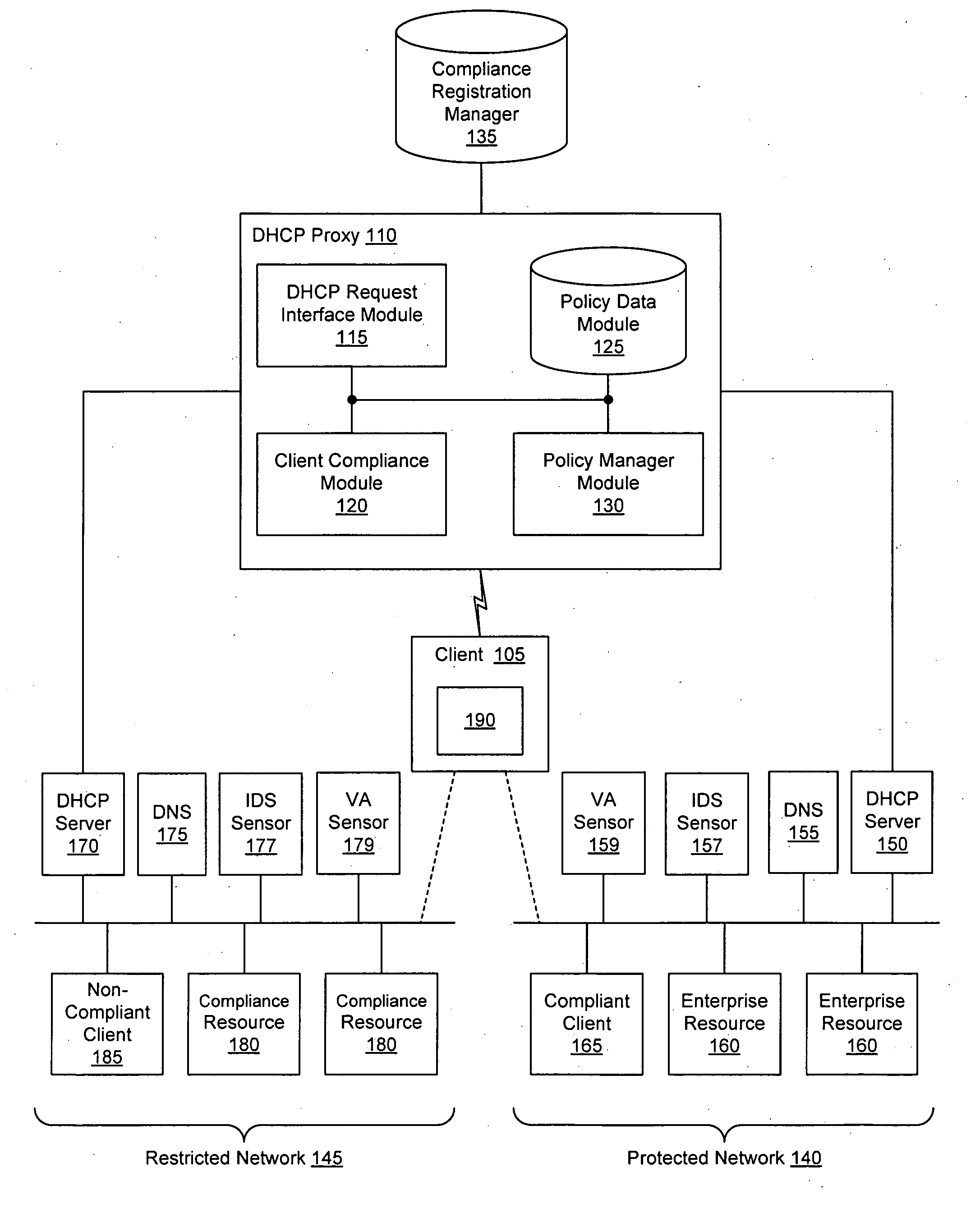
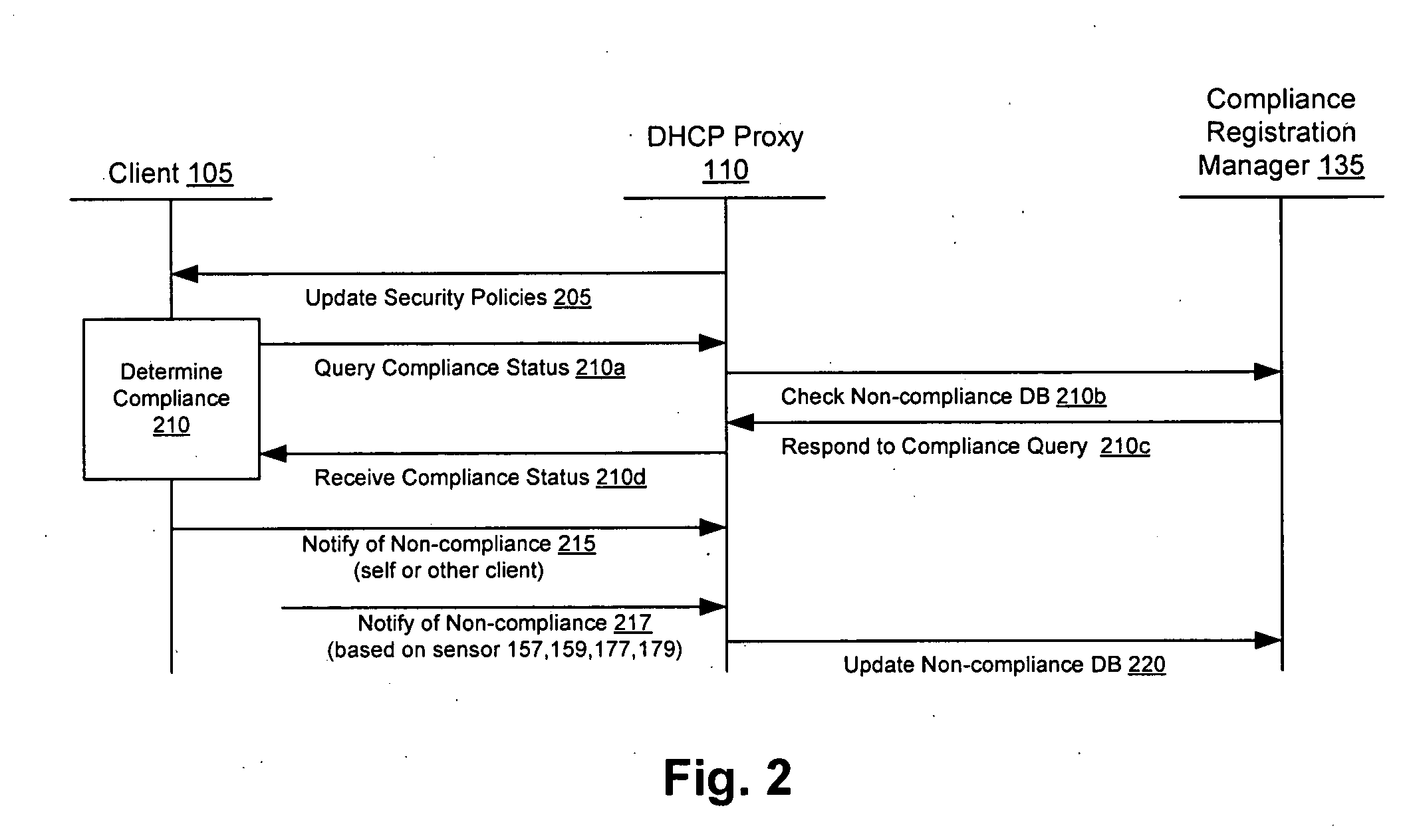
Client compliancy with self-policing clients
InactiveUS20060130139A1Memory loss protectionDigital data processing detailsNon complianceClient compliance
Security sensor data from intrusion detection system (IDS) sensors, vulnerability assessment (VA) sensors, and / or other security sensors is used to enhance the compliancy determination in a client compliancy system. A database is used to store the security sensor data. In one particular embodiment, a list of device compliance statuses indexed by corresponding identifiers (e.g., IP / MAC addresses) combined from IDS, VA, and / or other security sensing technologies is made available as a non-compliance database for query, so that clients and other compliancy authentication elements can tell that a particular client appears to be out of compliance. A client-side self-policing compliance system is enabled, and can be used in conjunction with automated endpoint compliance policy configuration to reduce system administrator burden.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com