Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1533 results about "Virtual LAN" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
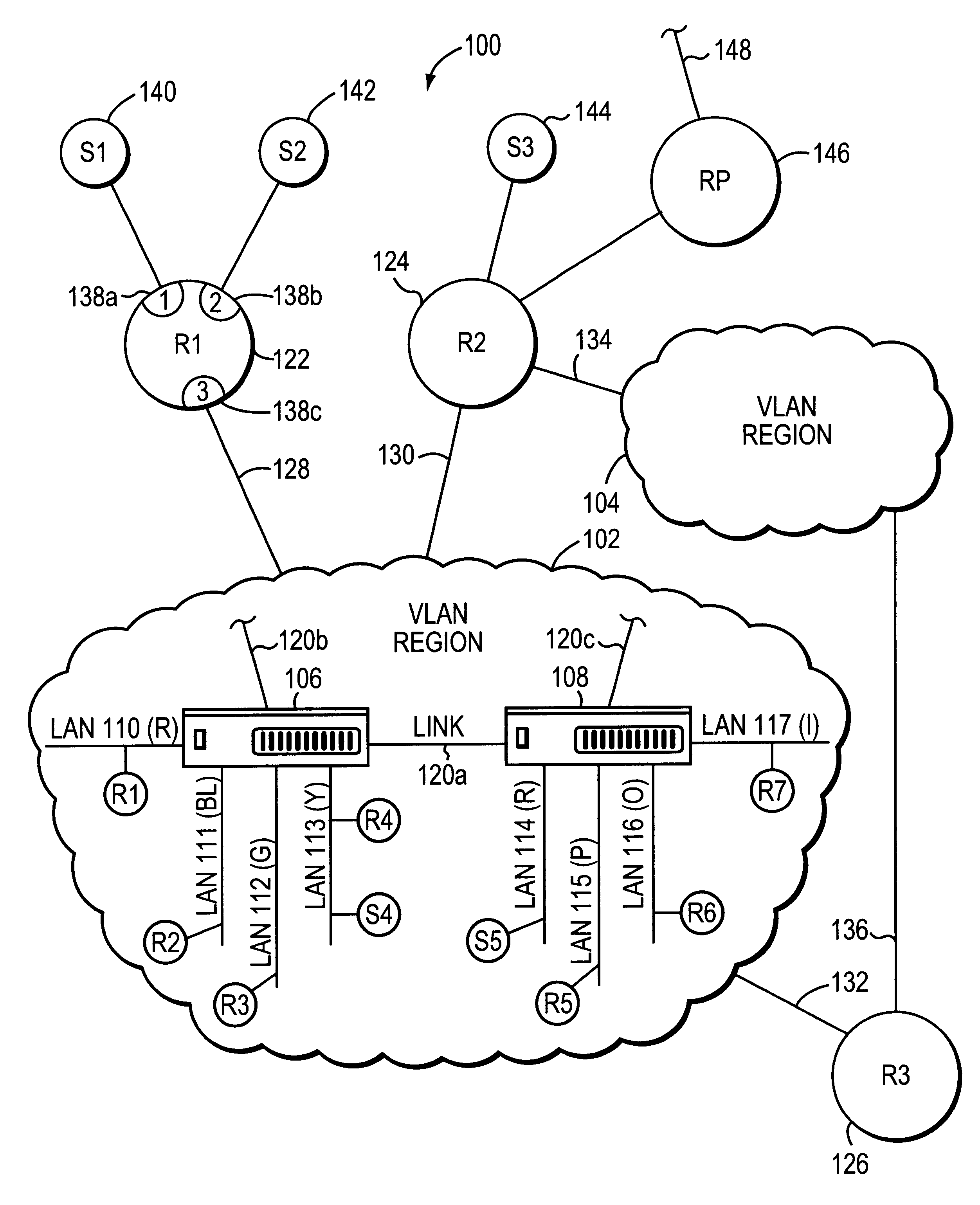
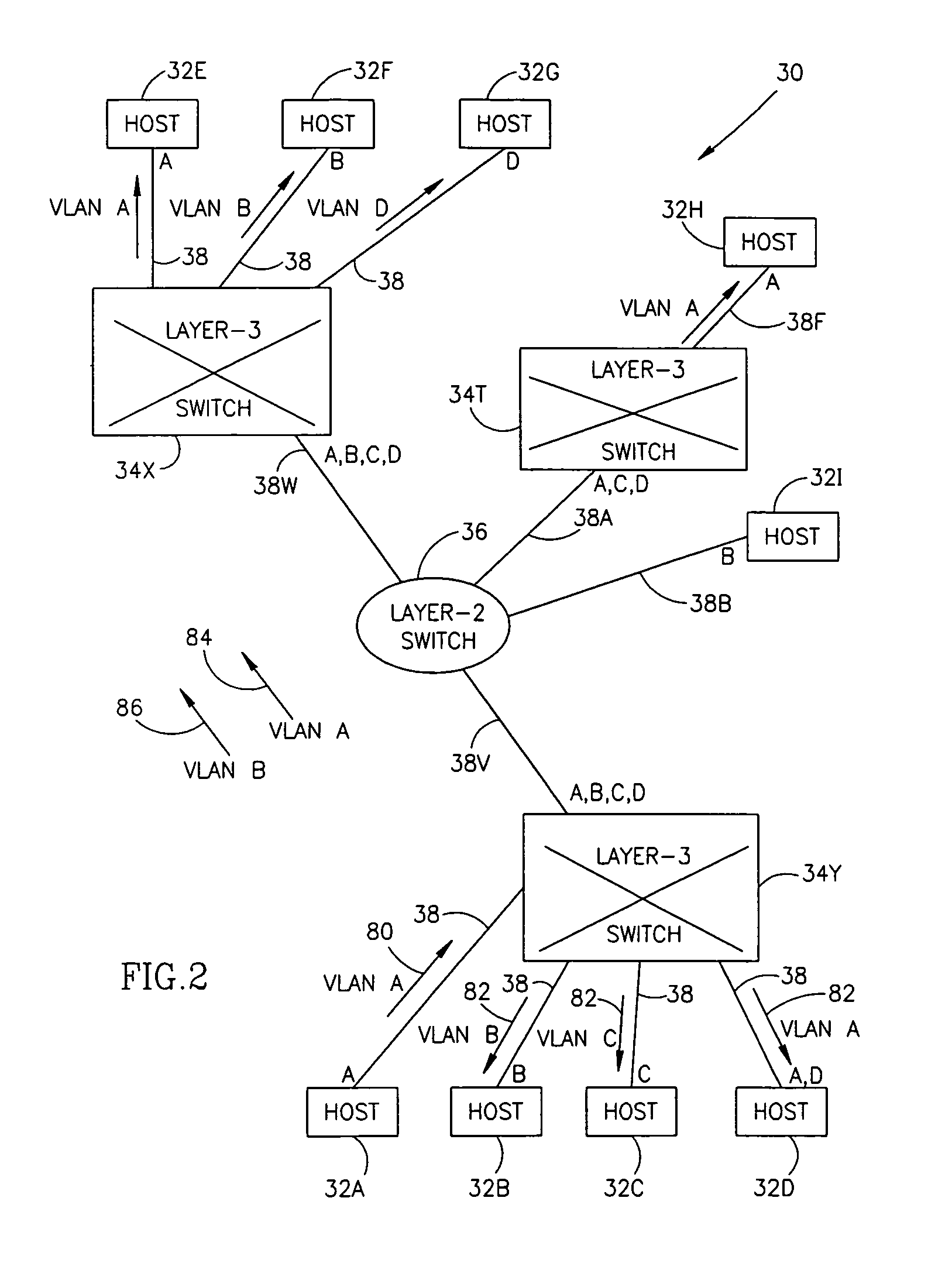
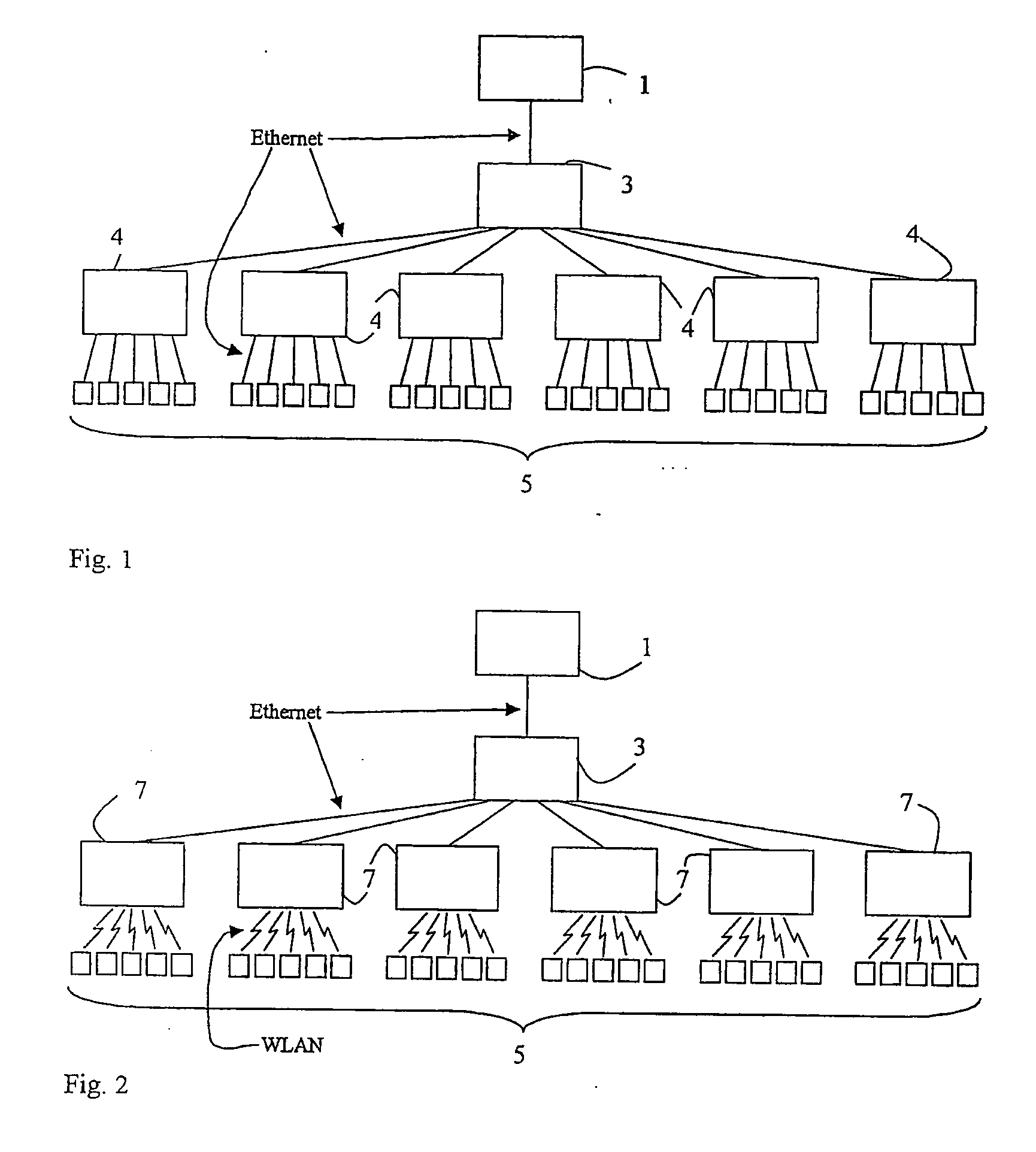
A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer (OSI layer 2). LAN is the abbreviation for local area network and in this context virtual refers to a physical object recreated and altered by additional logic. VLANs work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed.
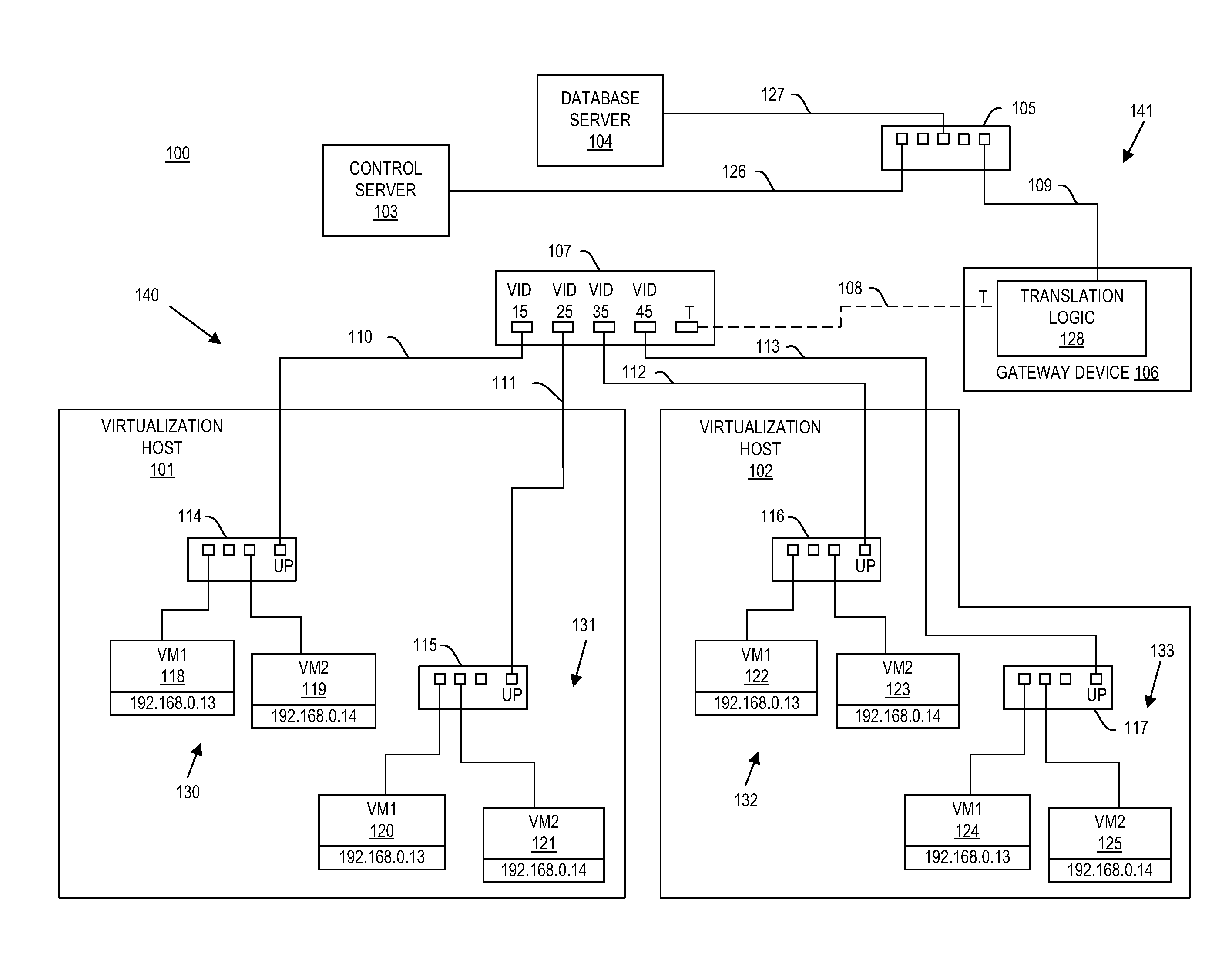
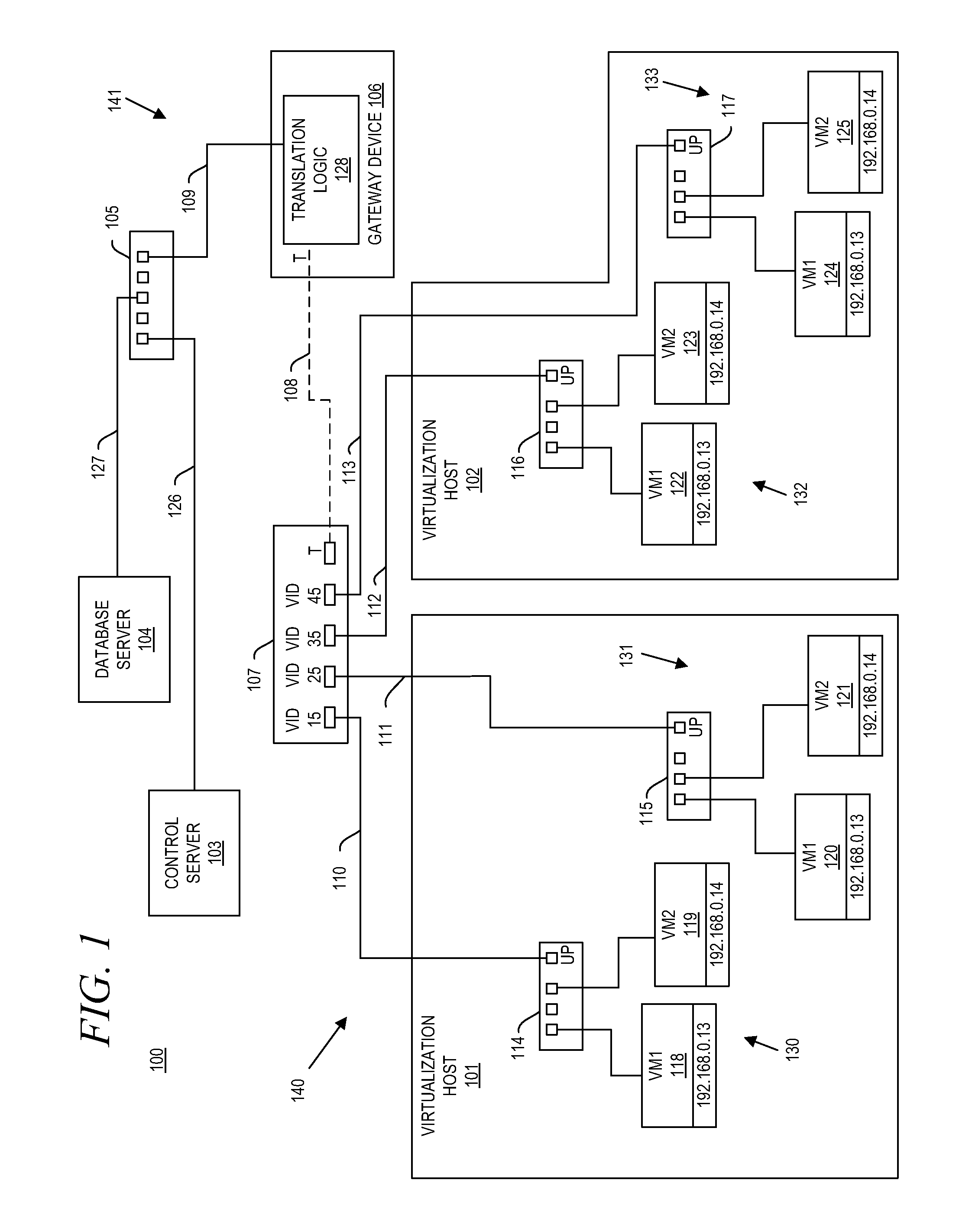
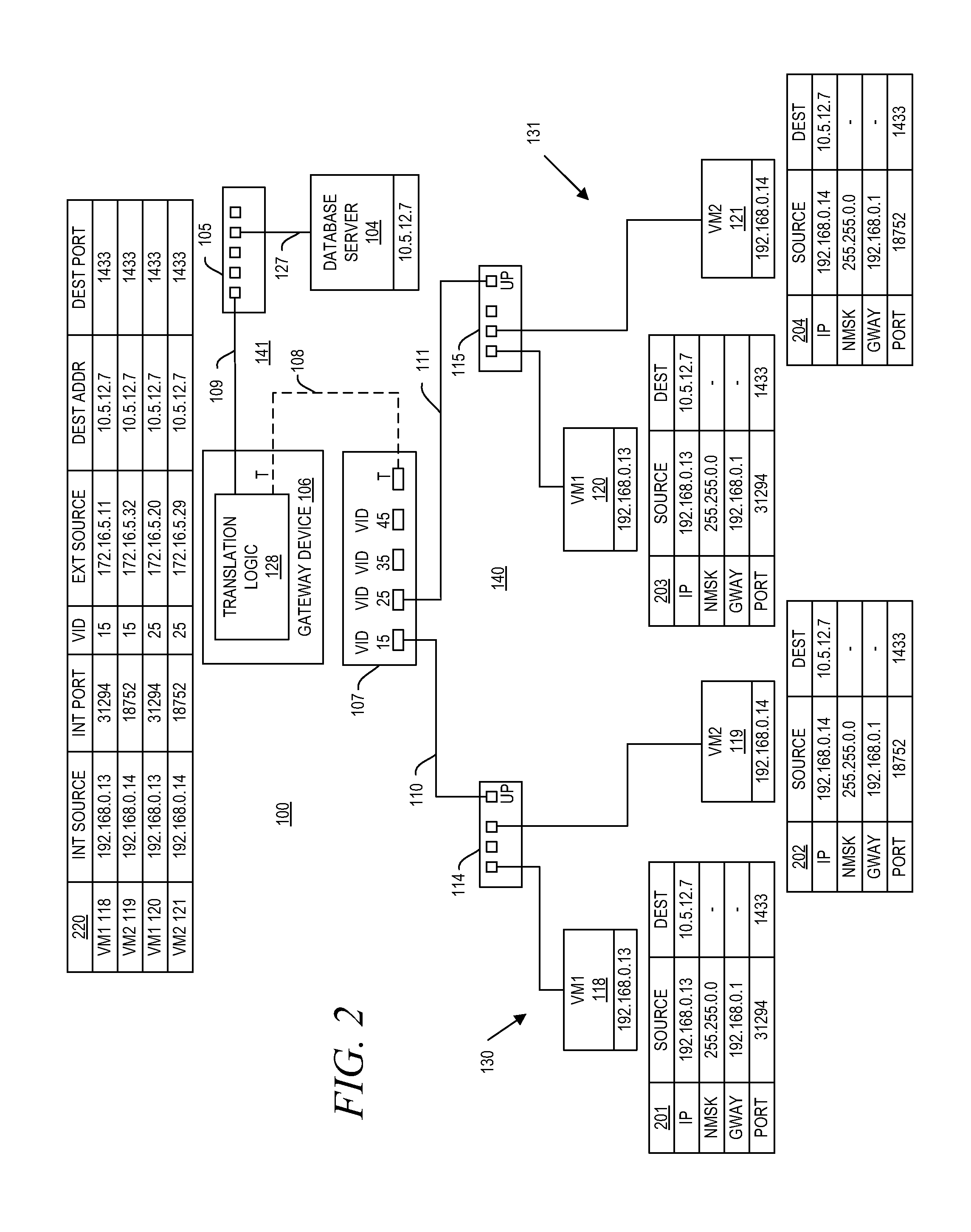
System and method for aggregating communications and for translating between overlapping internal network addresses and unique external network addresses
A gateway device including an access interface to an external network, a trunked interface, and translation logic. The access interface is associated with multiple external source addresses. The trunked interface is interfaced with multiple different virtual local area networks (VLANs), where each VLAN is associated with a corresponding VLAN tag and at least one of potentially overlapping internal source addresses. The translation logic translates between each external source address and each unique combination of internal source address and VLAN tag. A method of network address translation including assigning one of first network addresses to each first device of a first network, dividing the first network into a plurality of VLANs, separating the first devices with the same first network address into different VLANs, and assigning first devices with the same first address to different second network addresses.
Owner:QUEST SOFTWARE INC
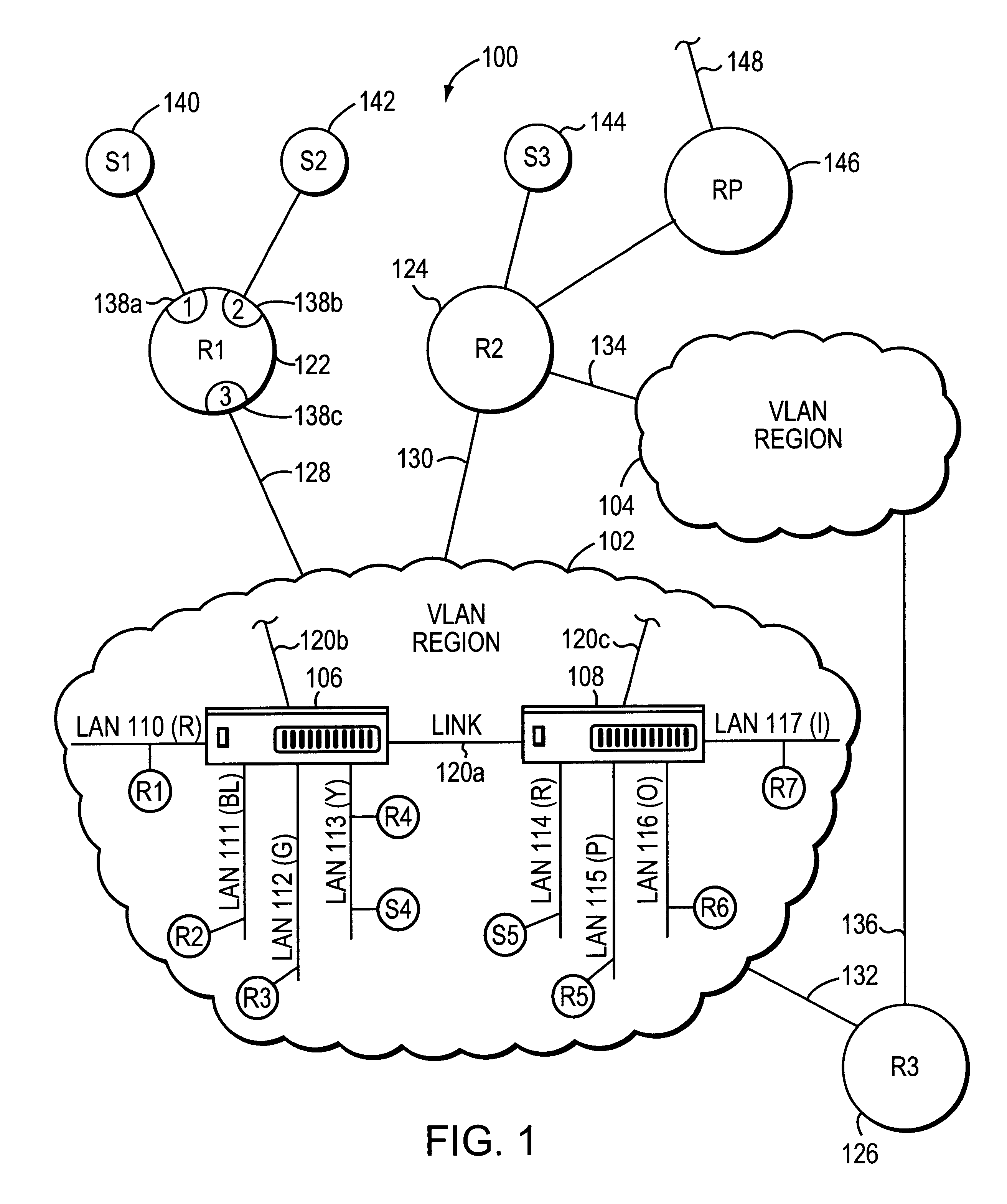
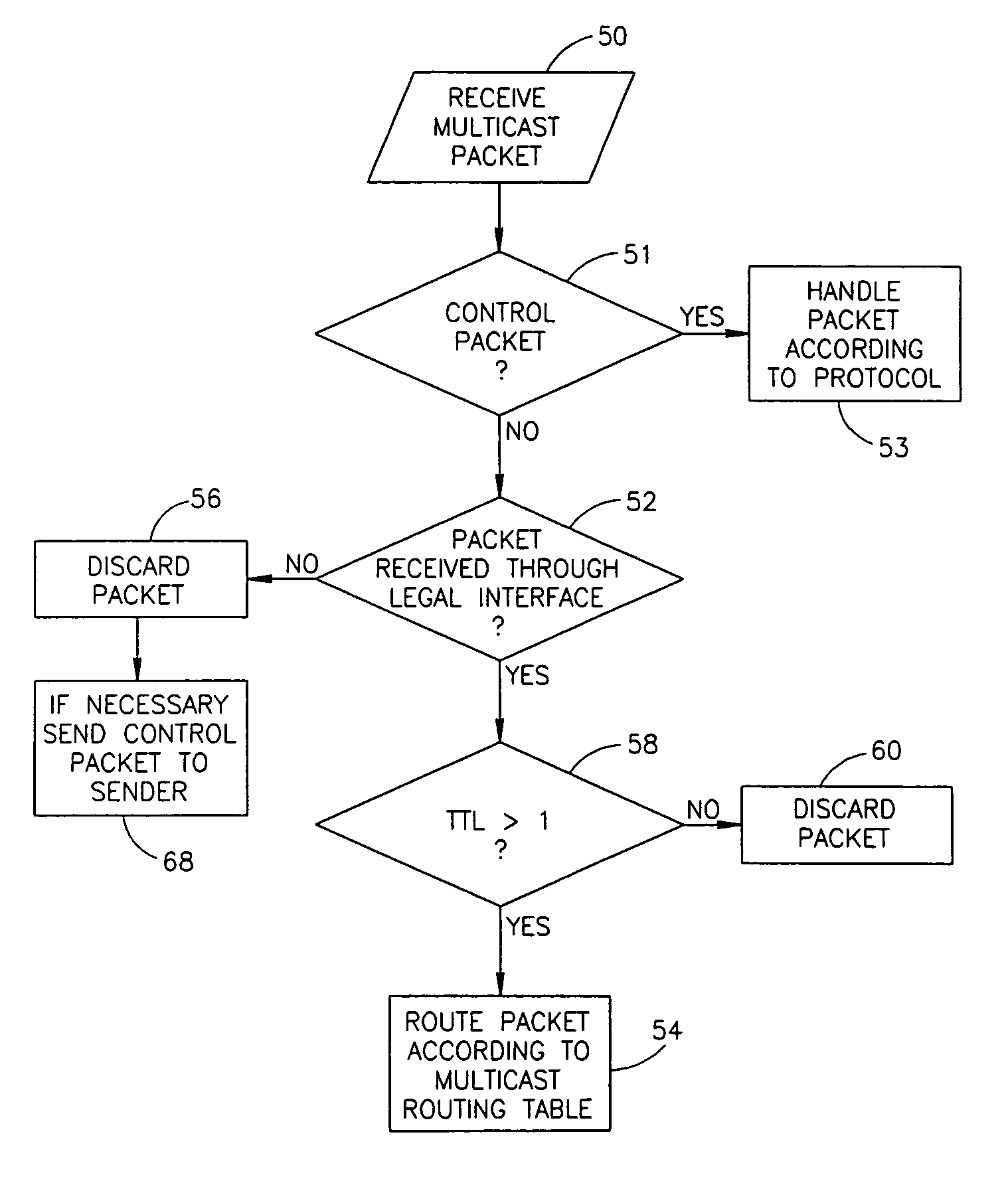
System and method for distributing multicasts in virtual local area networks
InactiveUS6839348B2Effective distributionEfficiently distributedSpecial service provision for substationTime-division multiplexVirtual LANIP multicast
The invention relates to a system and method for efficiently distributing multicast messages within computer networks configured to have one or more virtual local area network (VLAN) domains. A multicast network device (MND), having a plurality of interfaces, includes a multicast controller for efficiently distributing multicast messages among subscribing entities associated with various VLAN domains. The multicast controller, which is in communicating relationship with the interfaces, includes a VLAN assignment engine for assigning responsibility for the VLAN domains to the extent there are multiple MNDs. The multicast controller also accesses a multicast tag source to establish a plurality of novel VLAN tags for efficiently distributing multicast messages, including a sub-regional Multicast VLAN Identifier (MVLAN-ID) that encompasses all of the VLAN domains for which the respective MND is responsible, and one or more color-limited MVLAN-IDs that encompass all of the VLAN domains for which the MND is responsible except for one. The multicast controller then tags multicast messages with its sub-regional or a color-limited MVLAN-ID depending on whether the message is considered internal or external by the respective MND. The tagged messages are then forwarded for distribution to the subscribers associated with the various VLAN domains.
Owner:CISCO TECH INC
IP multicast in VLAN environment
ActiveUS7924837B1Avoid layeringEasy to implementError preventionTransmission systemsRouting tableVirtual LAN
A method of determining local multicast information of a local area network (LAN), comprising dividing the LAN to a number of segments larger than the number of virtual LANs (VLANs) in the network and creating a layer-3 multicast routing table, which relates to each of the segments separately.
Owner:AVAYA TECH CORP +1
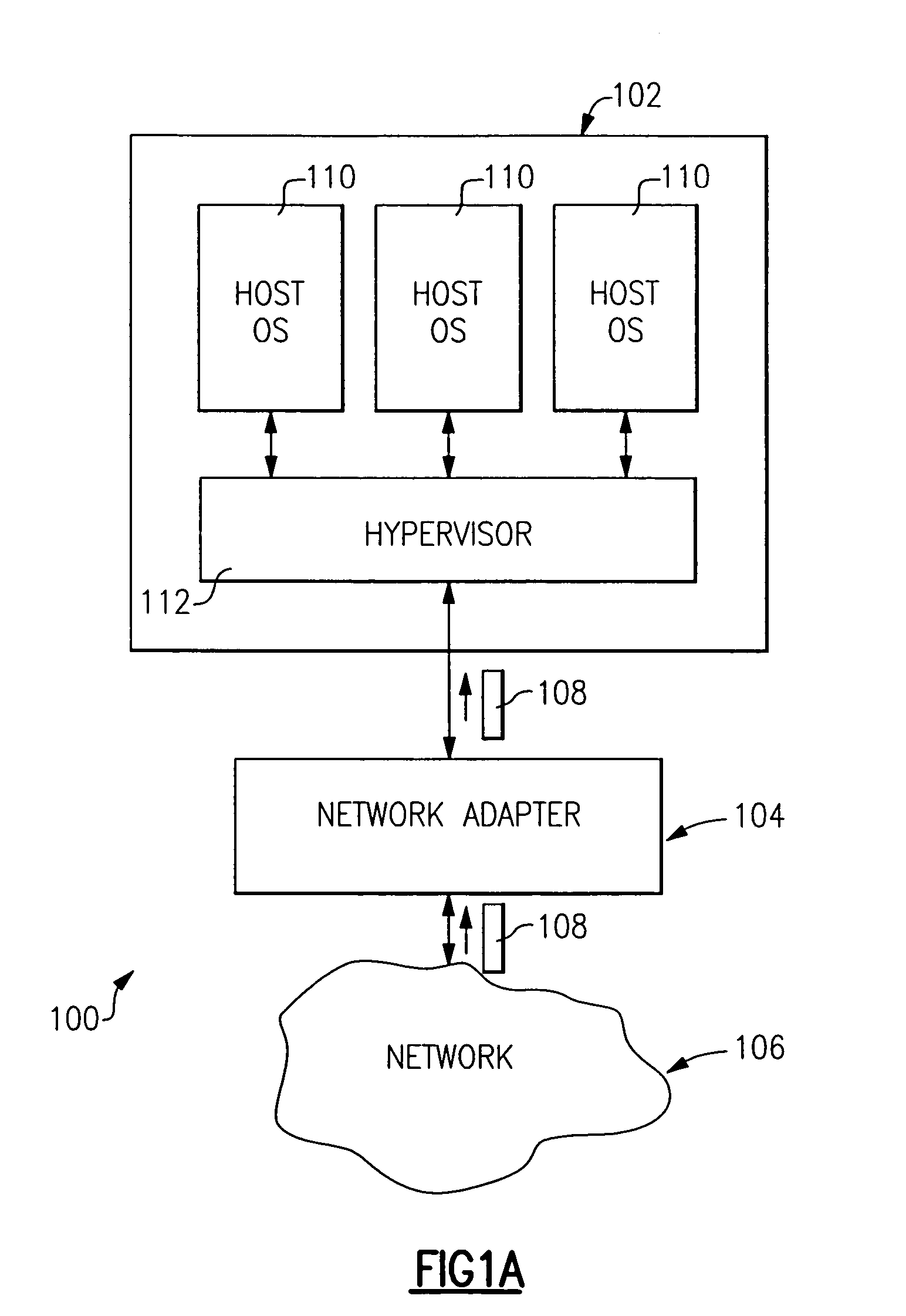
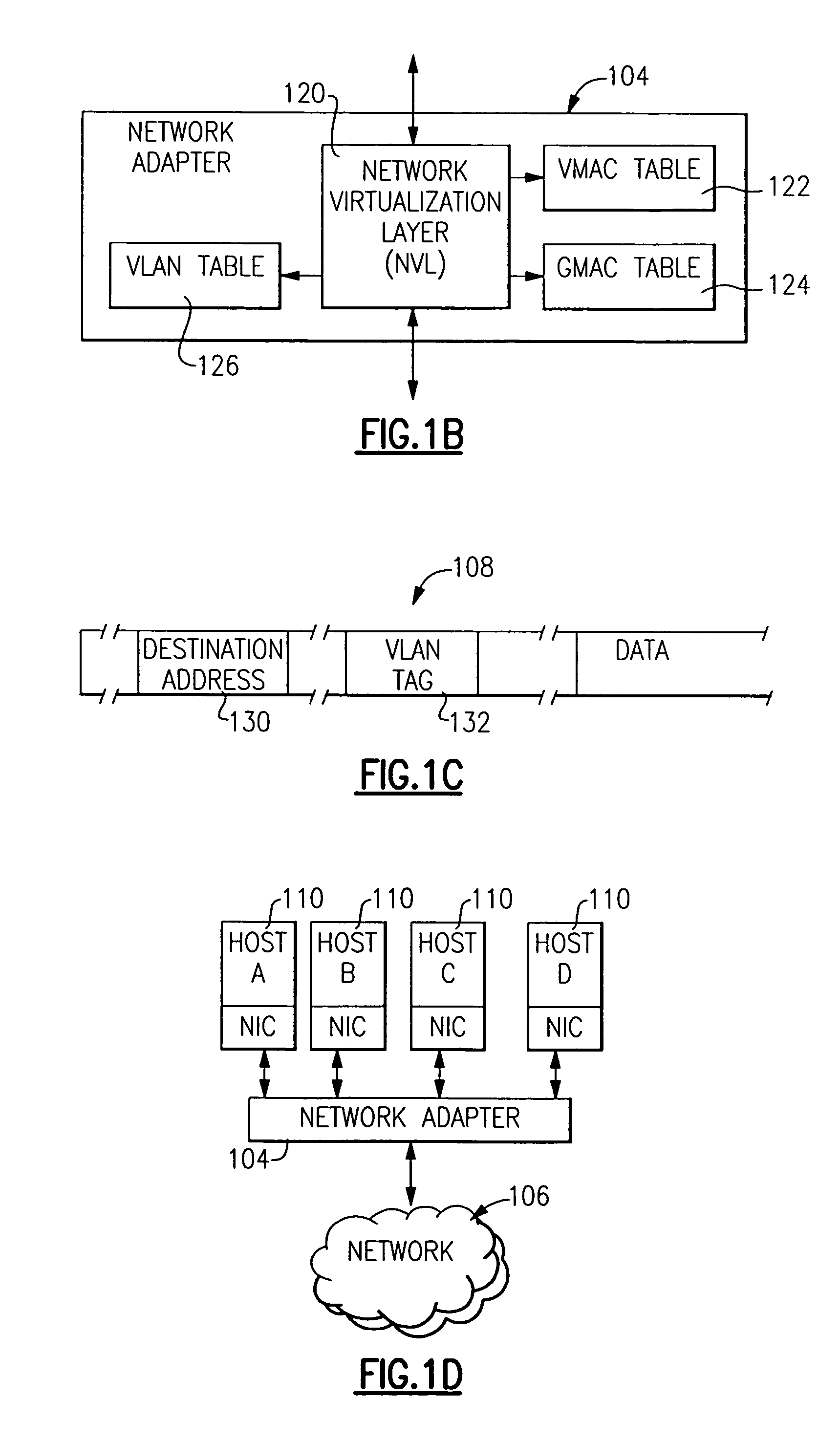
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
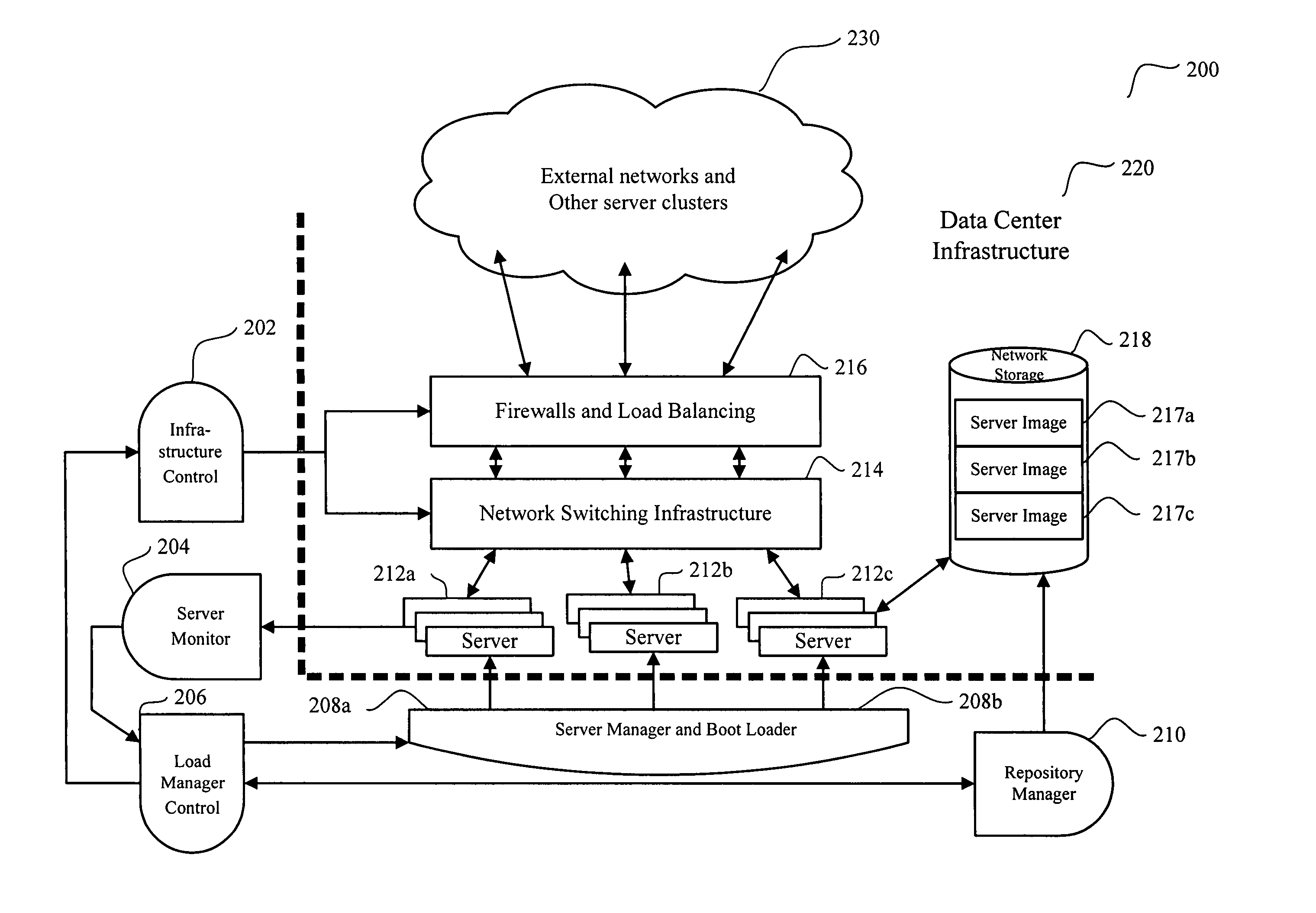
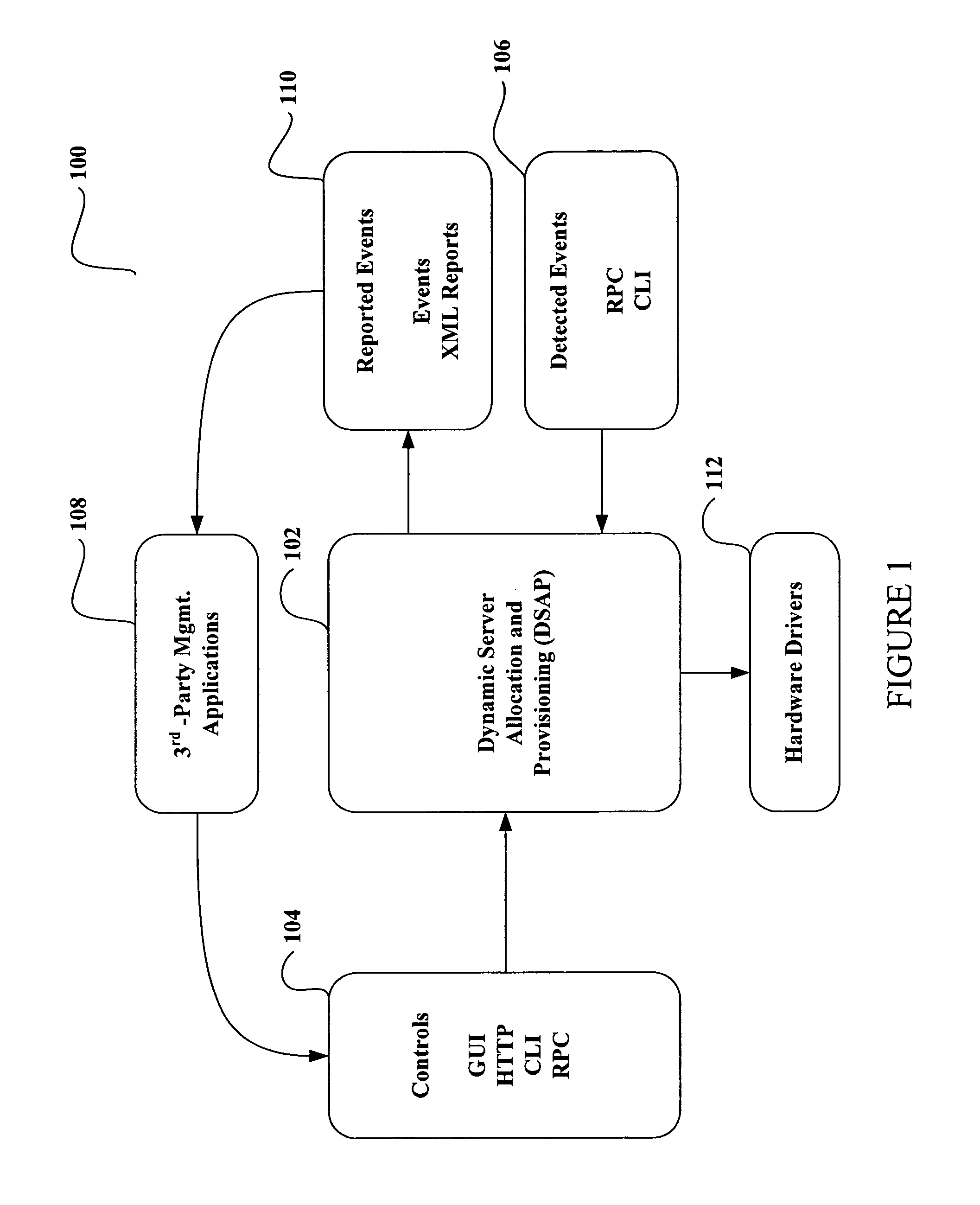
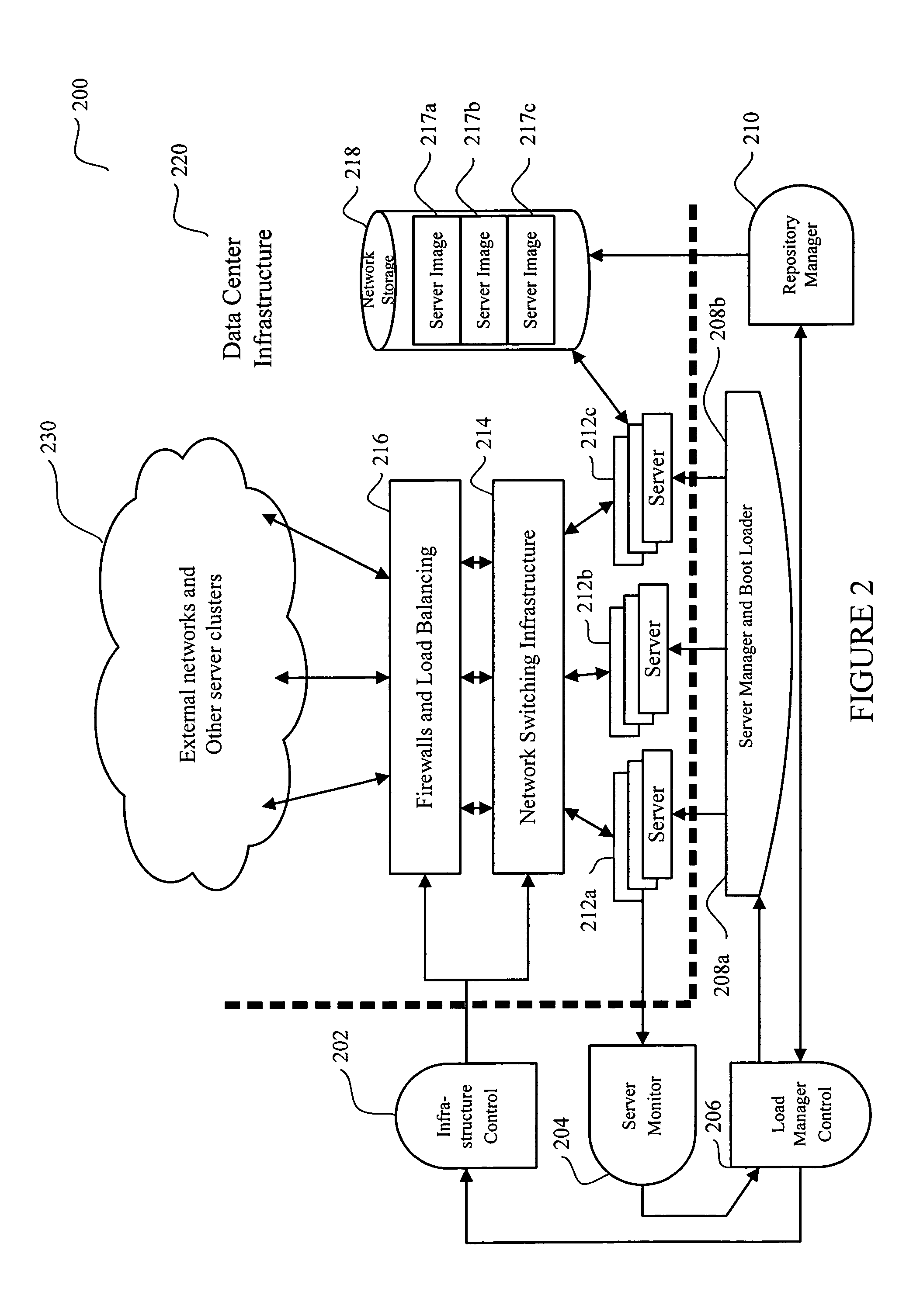
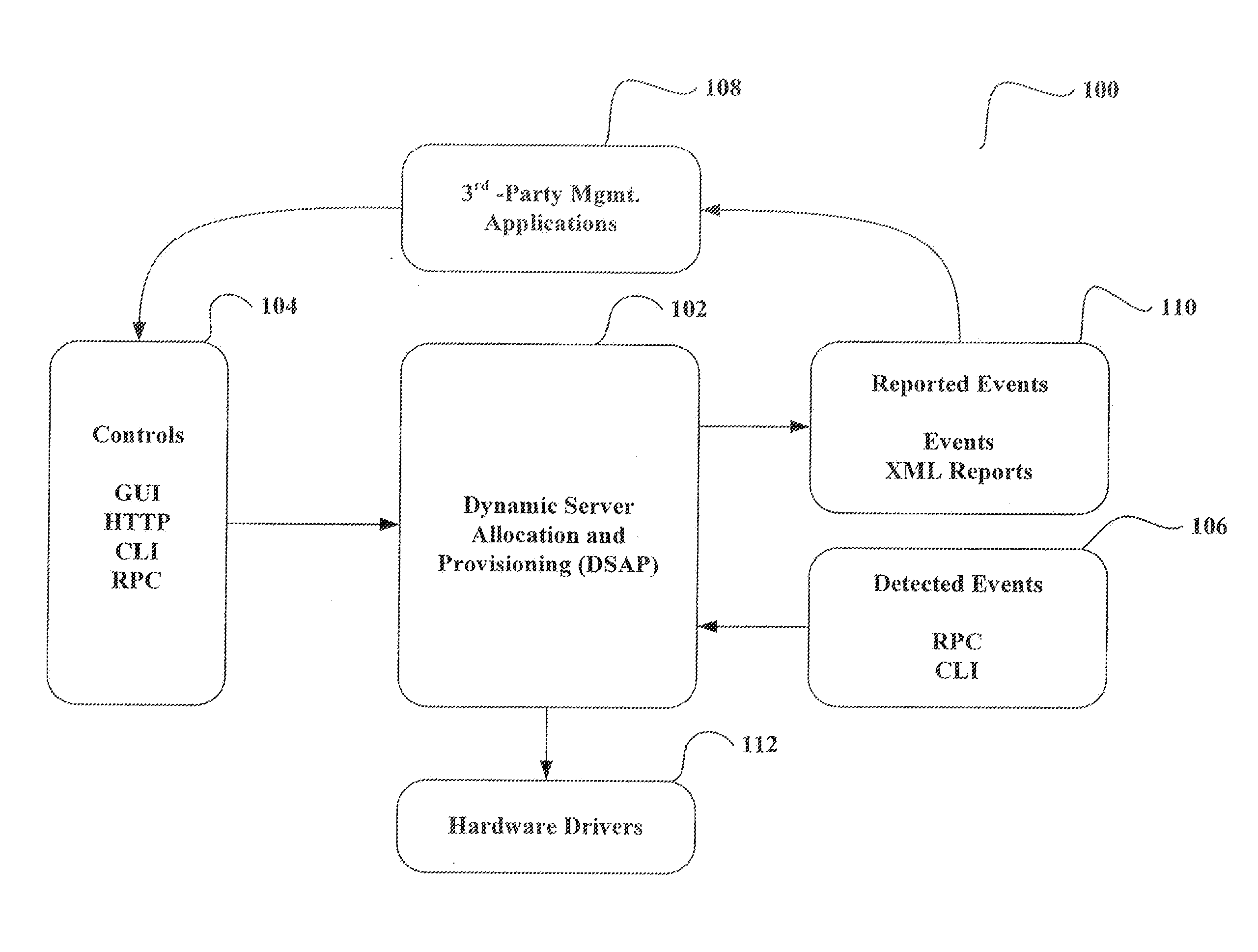
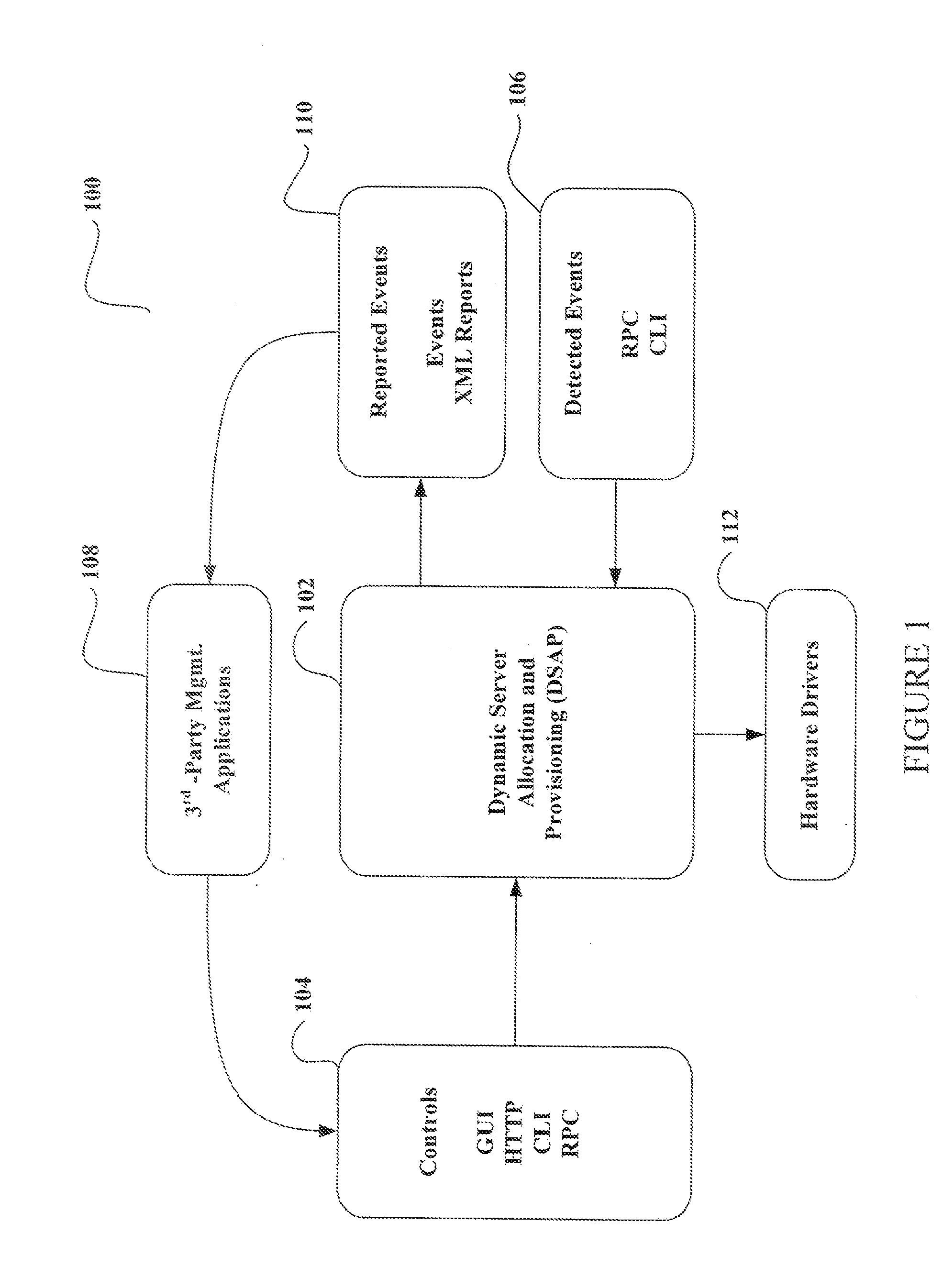
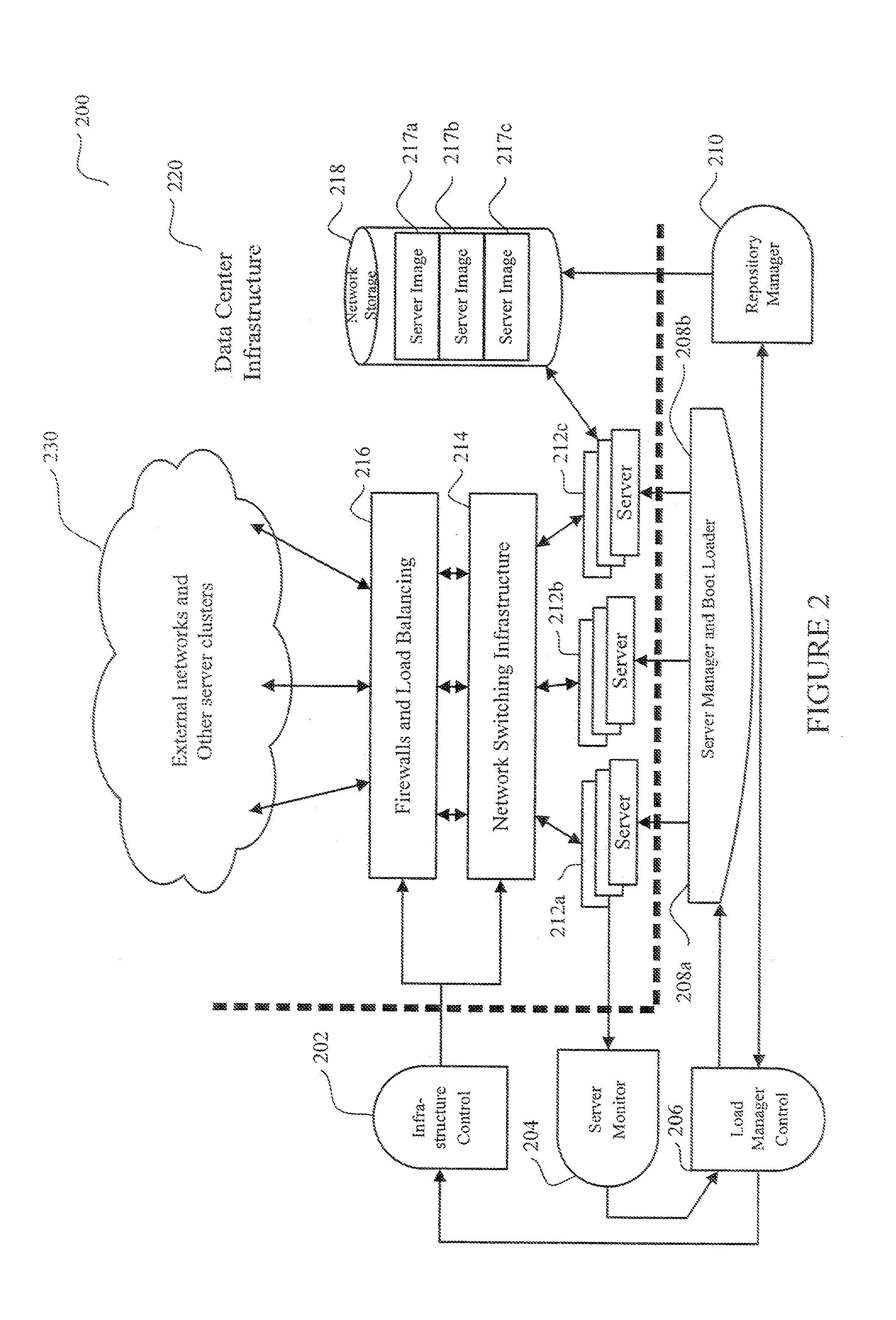
System and method for dynamic server allocation and provisioning
ActiveUS7213065B2Lower cost of capitalQuality improvementResource allocationDigital computer detailsManagement toolVirtual LAN
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
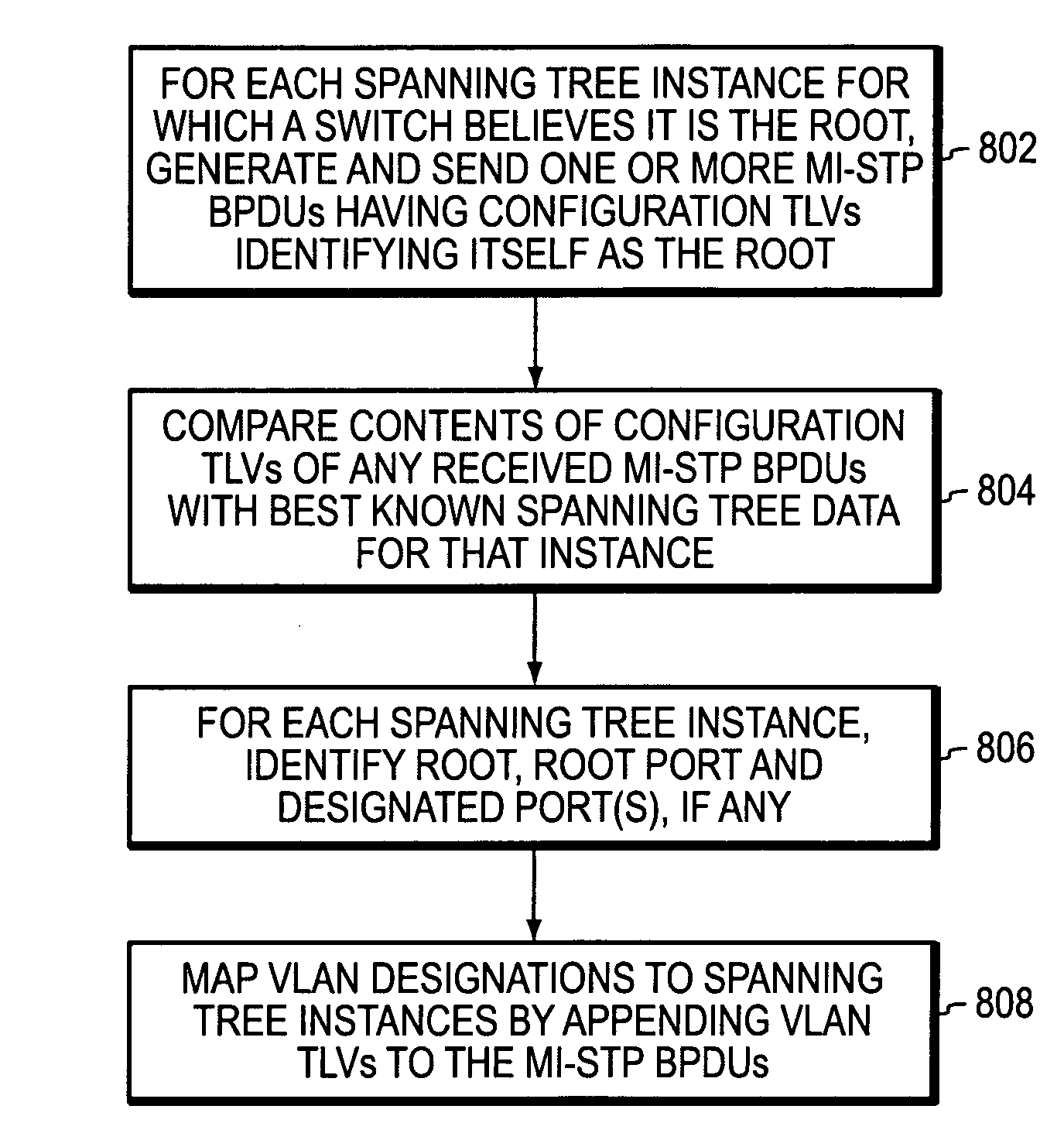
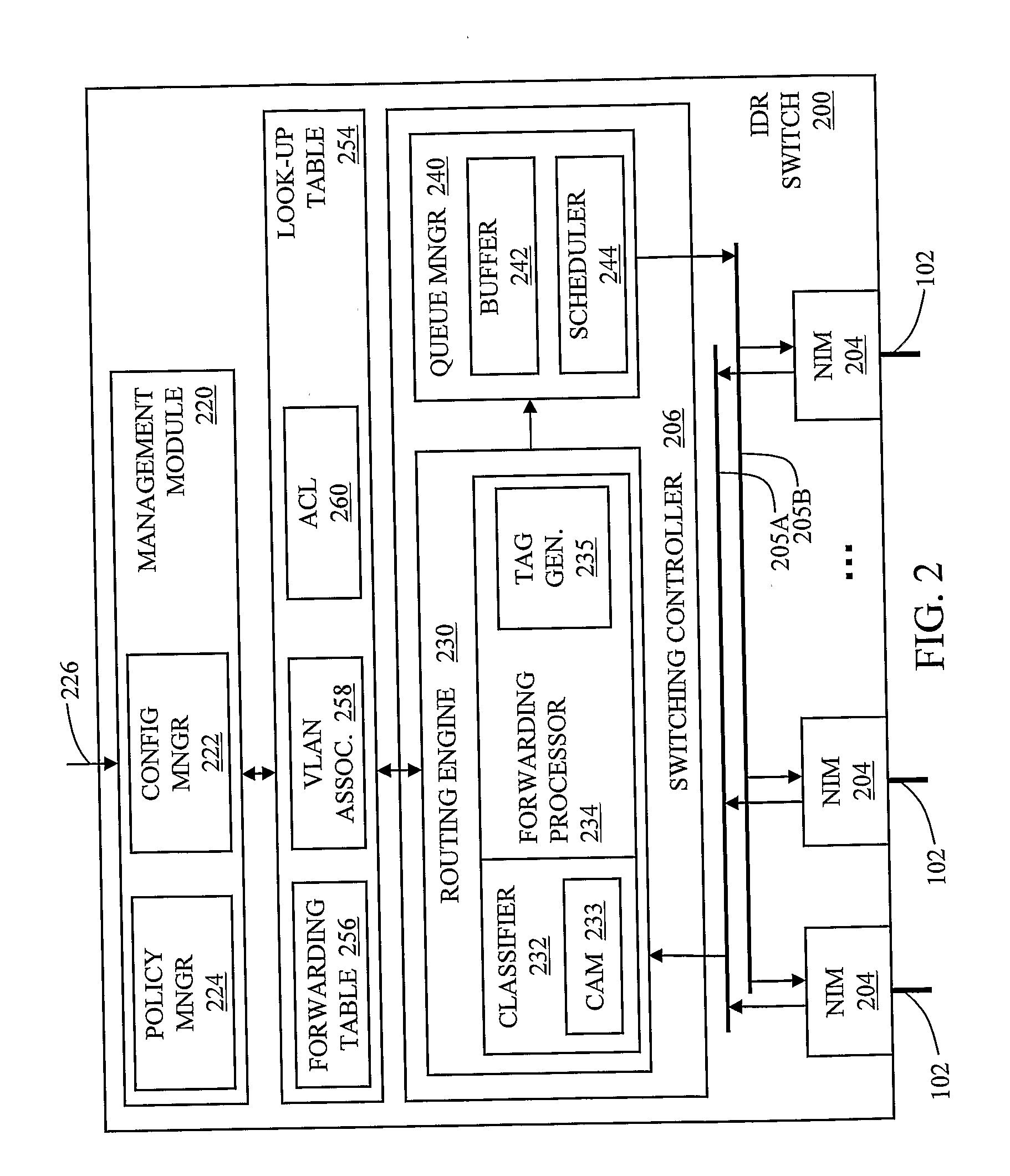
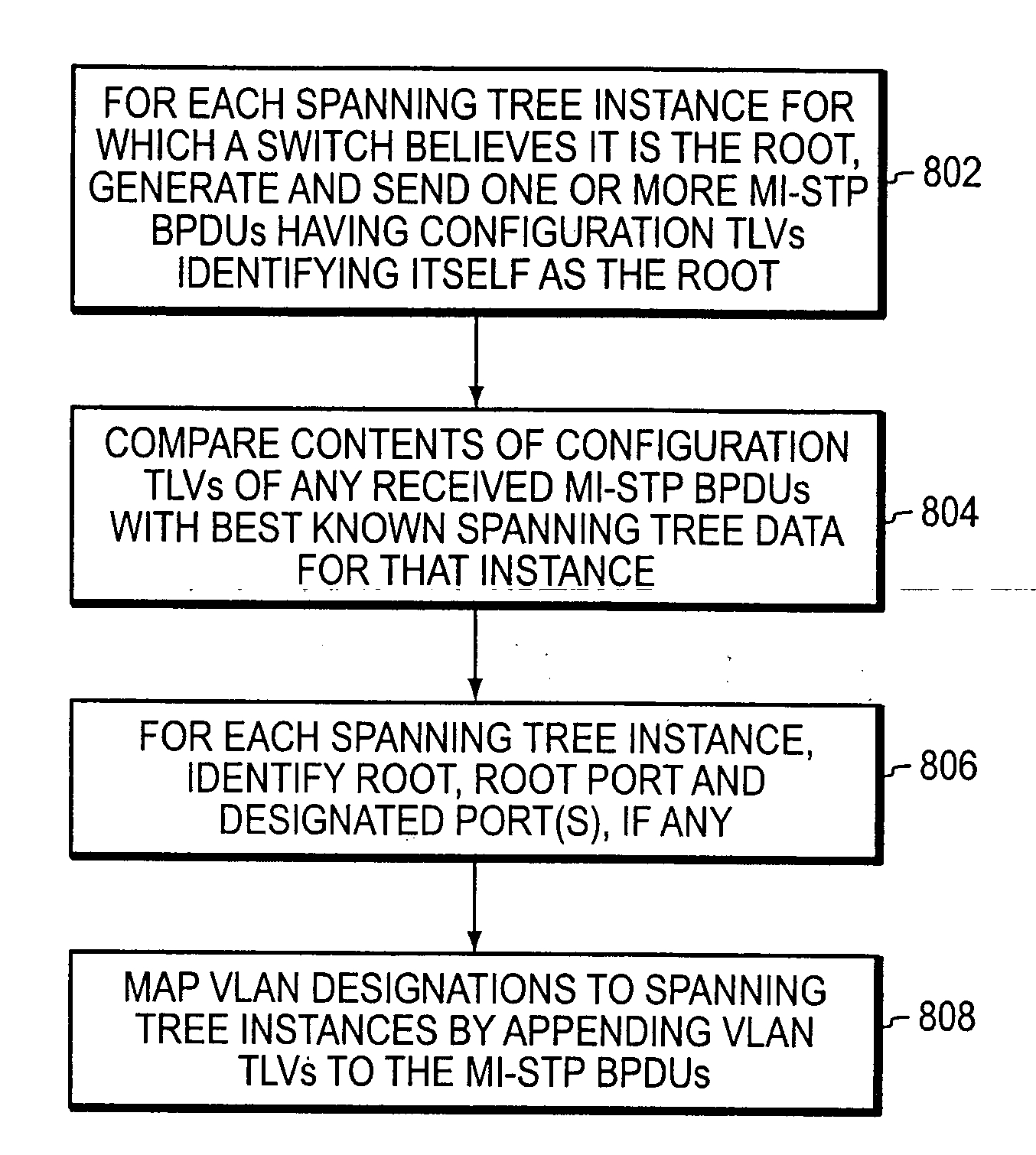
Multiple instance spanning tree protocol
A multiple instance spanning tree protocol (MI-STP) creates a plurality of active topologies (i.e., loop-free paths) within a computer network. These active topologies may be established through the exchange and processing of multiple instance spanning tree bridge protocol data unit messages (MI-STP BPDUs) by the intermediate network devices within the network. The active topologies are preferably created independently of any virtual local area network (VLAN) designations defined within the network. Once the active topologies are defined, each VLAN designation is then mapped to a single active topology, although multiple VLAN designations are preferably mapped to the same active topology to provide load balancing.
Owner:CISCO TECH INC
Mobile virtual LAN
InactiveUS6847620B1Not burdened with associated computational overheadNetwork topologiesWireless network protocolsCommunications systemVirtual LAN
A communication system in which multiple protocols and proxy services are executed by an access point. In one embodiment of the invention, GVRP and GMRP registrations are combined in a single packet when a wireless device roams to a different VLAN. In addition, outbound GVRP and GMRP multicast messages are handled by an access point (also referred to as a GVRP and GMRP “gateway”) such that the wireless device is not burdened with the associated computational overhead. In a further embodiment, a wireless device may dynamically switch between a VLAN-aware state and a VLAN-unaware state depending on the nature of a detected access point. For example, if a relevant access point supports GVRP, the wireless device may operate as a VLAN terminal. If a wireless device is not attached to an access point with a matching VLAN ID, the wireless device sends and receives VLAN tagged frames. If a wireless device configured with a VLAN ID is attached to an access point with a matching VLAN ID, or if the wireless device is attached to a non-VLAN access point, then the wireless device may send and receive raw / untagged frames. In addition to the gateways described below, the ability of a wireless device to detect when it can send untagged frames is considered novel. In another embodiment of the invention, a special ID that is different than the native VLAN ID for a switch port is used for VLAN-unaware devices. This allows such devices that do not issue tagged frames to belong to a single VLAN ID.
Owner:AVAGO TECH INT SALES PTE LTD
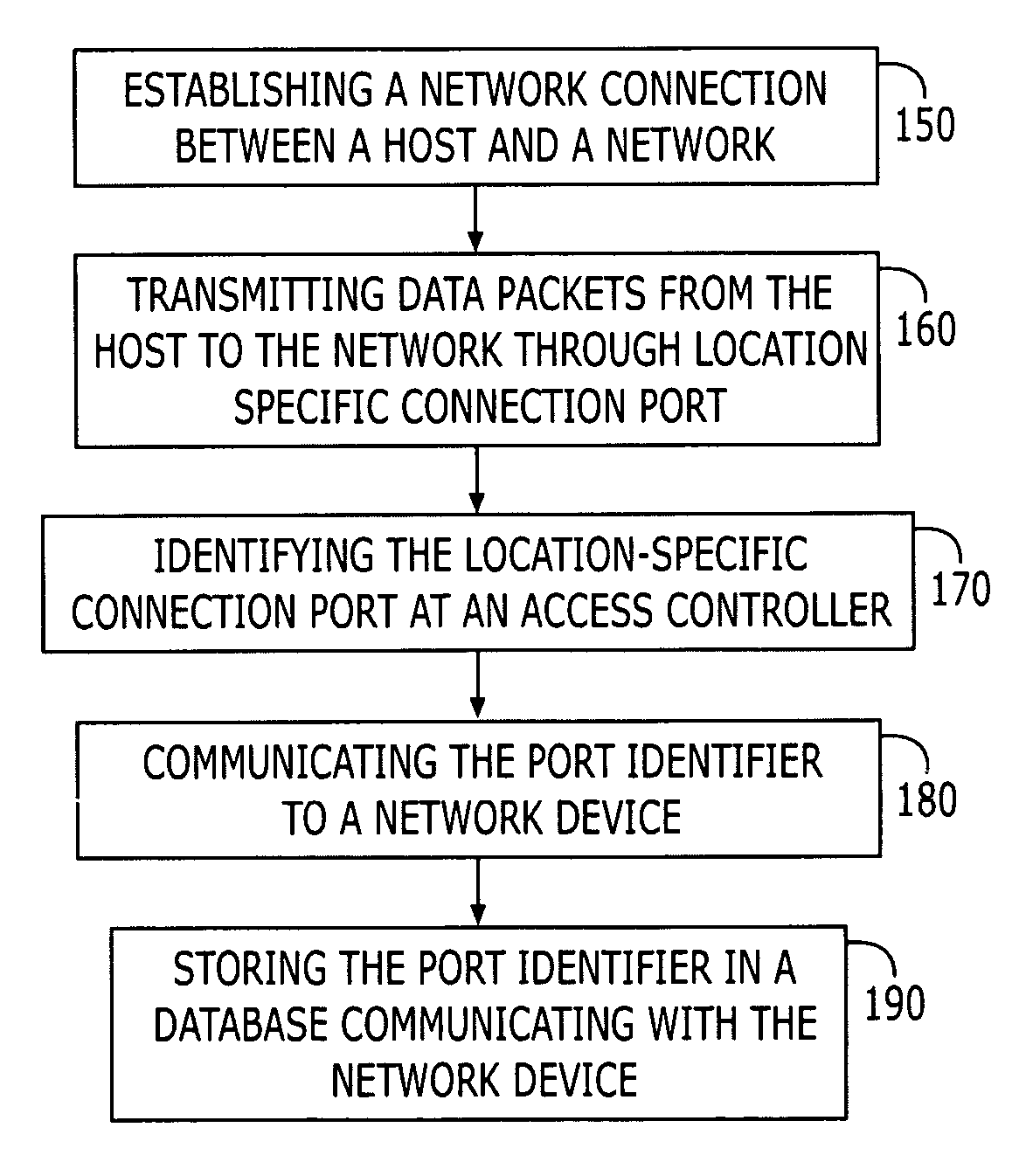
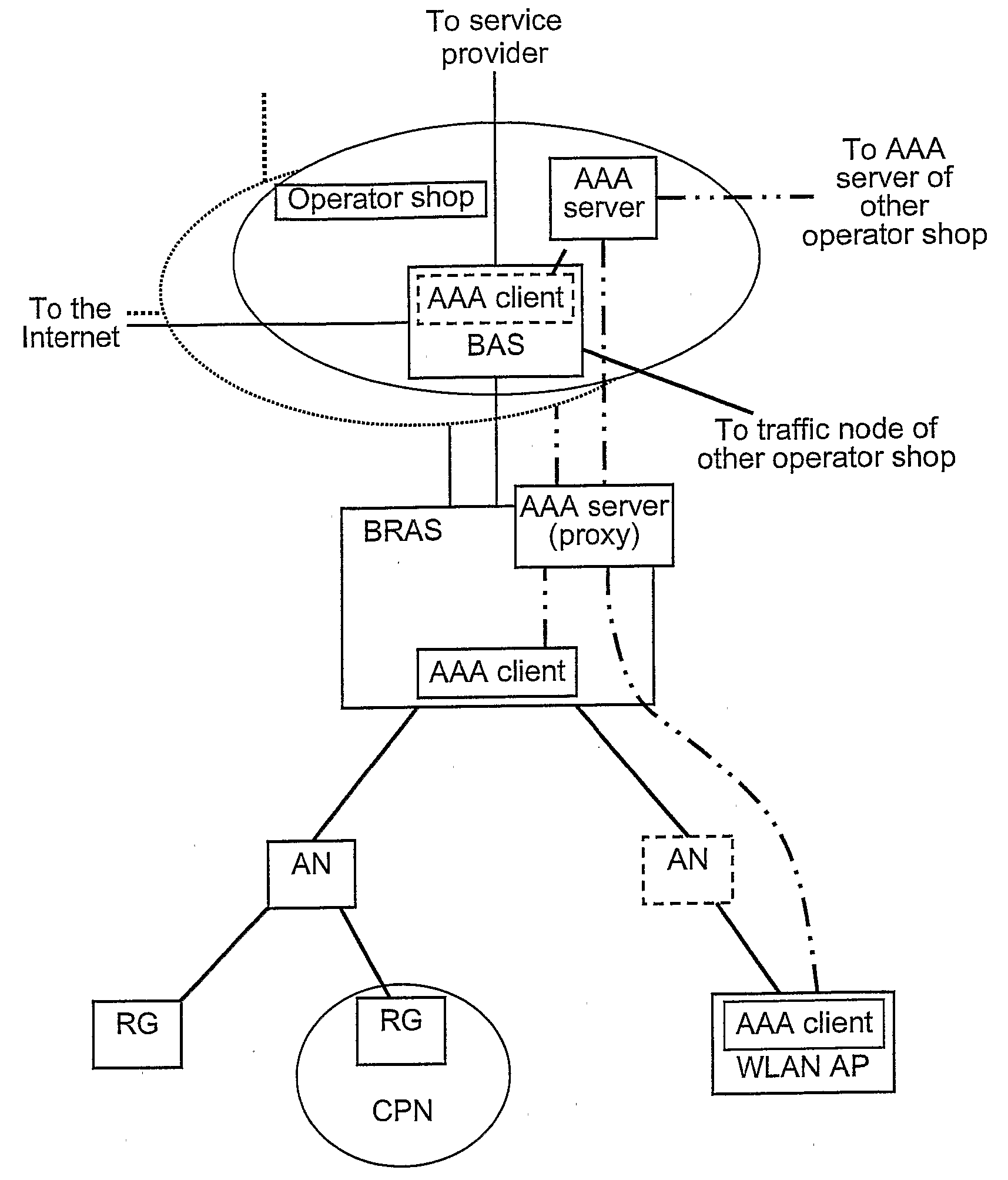
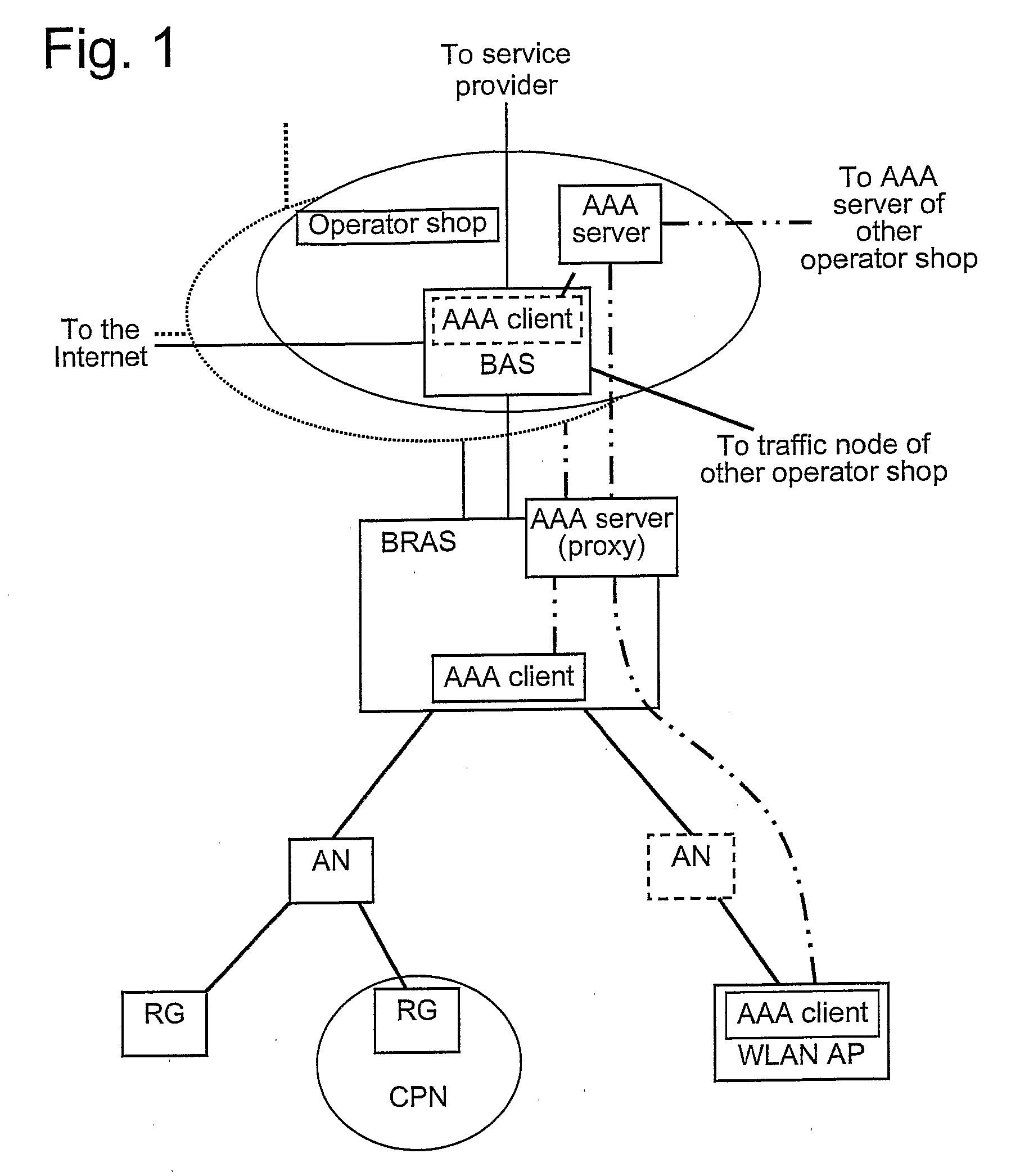
Location-based identification for use in a communications network
A method and apparatus for implementing location-based identification in a communication network. The method comprises establishing a network connection between a host and a network, transmitting network data packets from the host through a connection port, transmitting data packets from the host through a location-specific connection port and identifying the port at an access concentrator in the form of a port identifier. The port identifier is then communicated to a network device, typically a gateway device, and stored in a database in communication with the network device. The method may include tagging the network packets at the access concentrator with a port identifier that corresponds to a media access control (MAC) address. The access concentrator and the network device will tag and communicate port numbers by assigning VLAN (Virtual Local Area Network) identifiers to the ports.
Owner:NOMADIX INC
Isolation of hosts connected to an access network
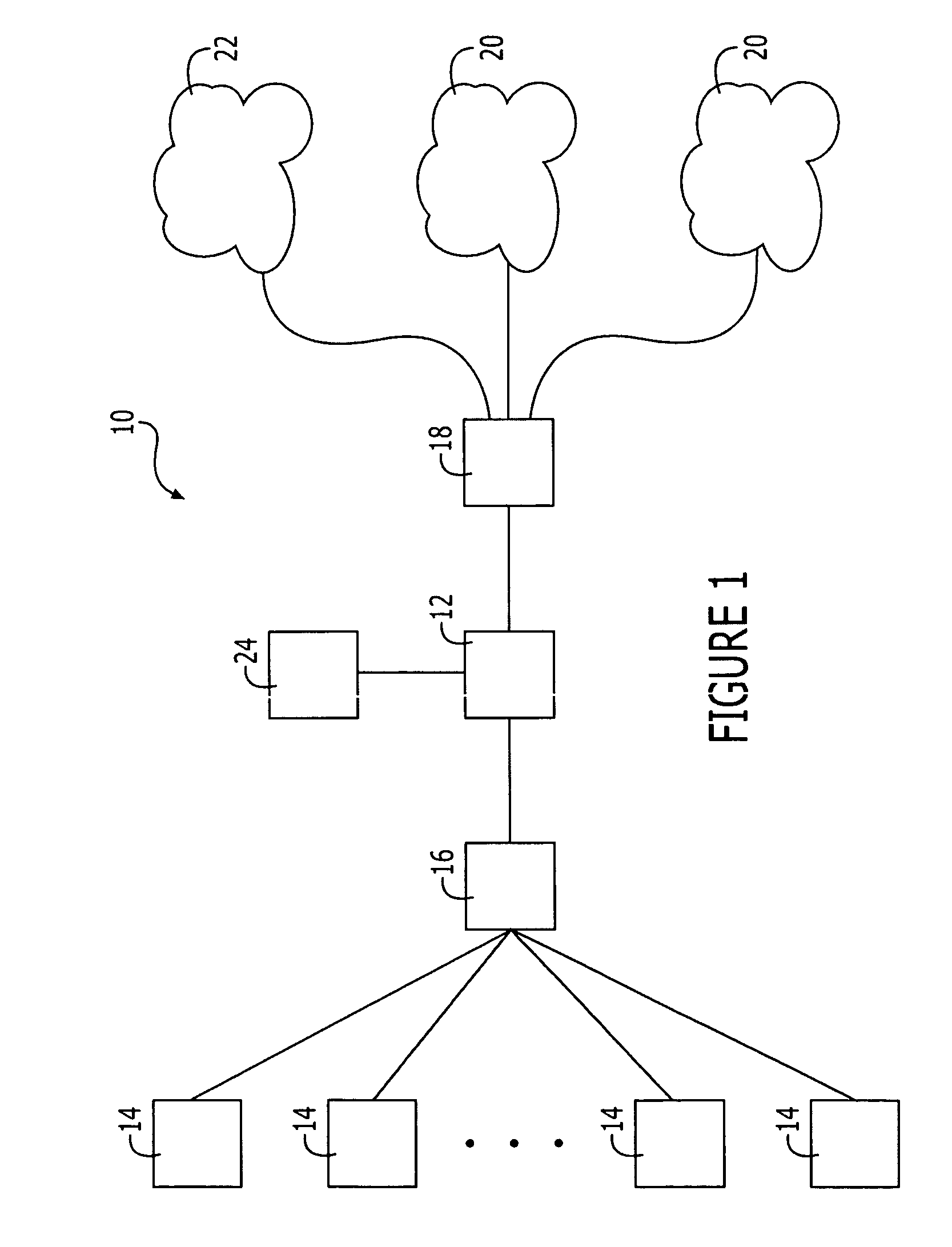
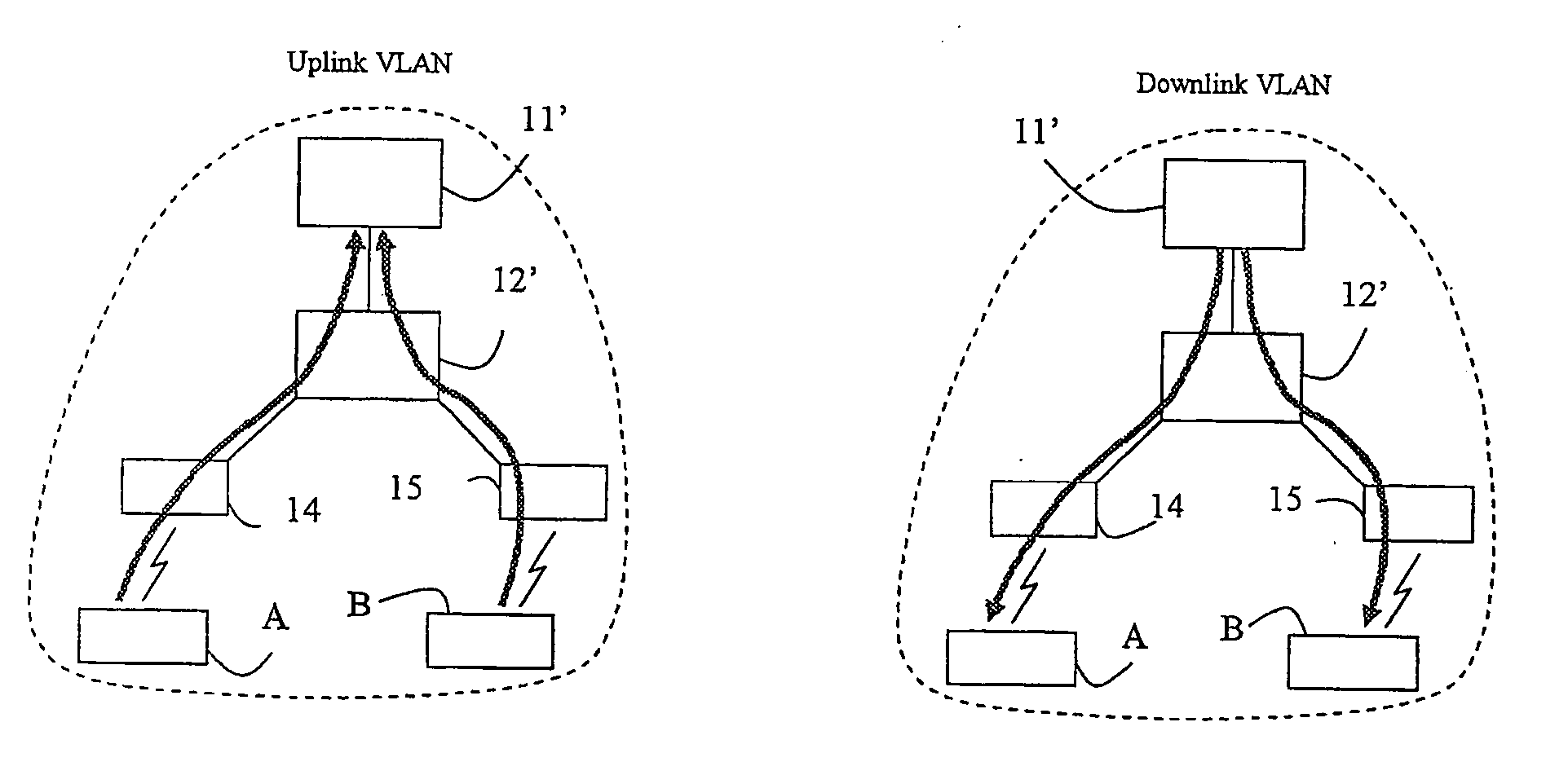
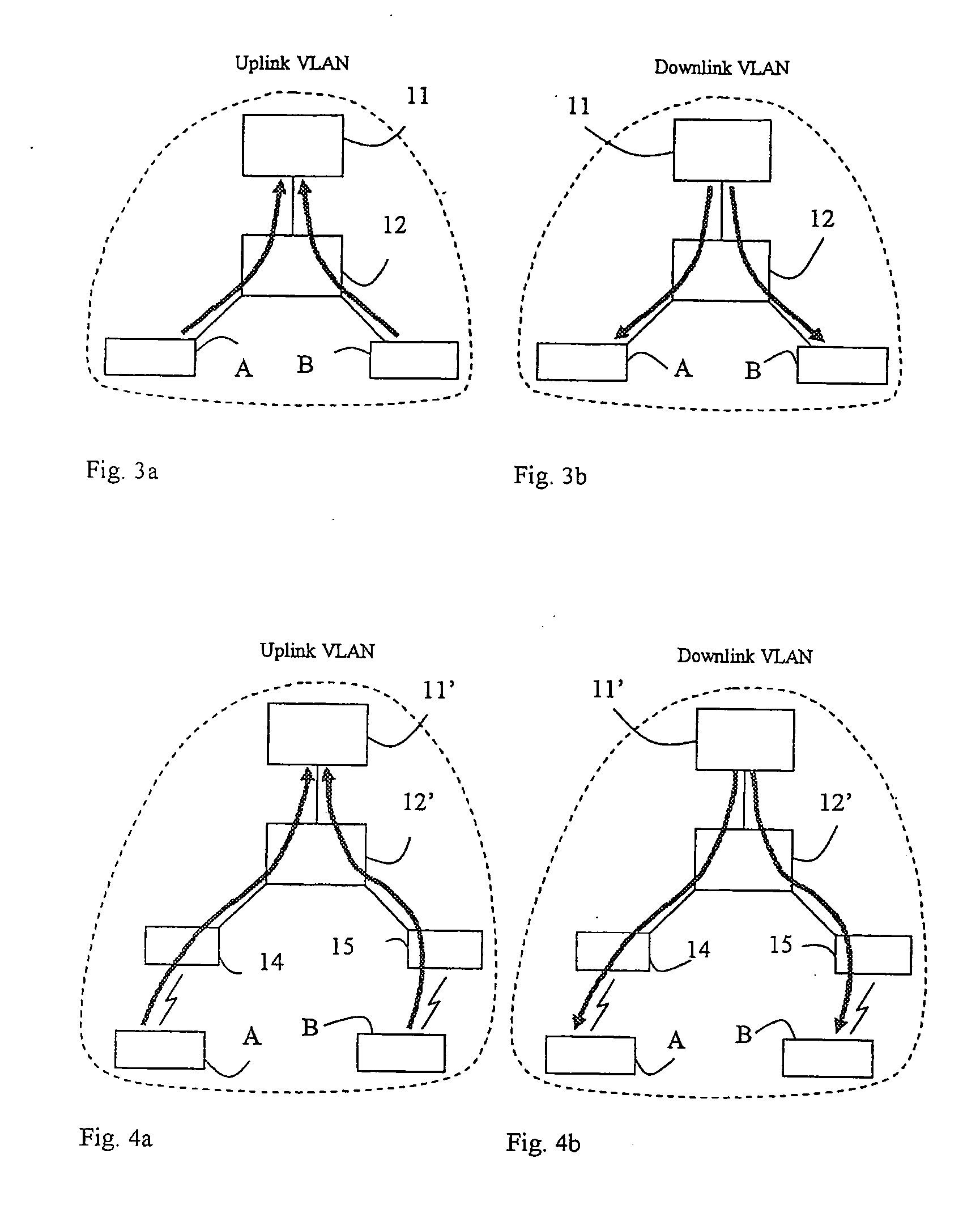
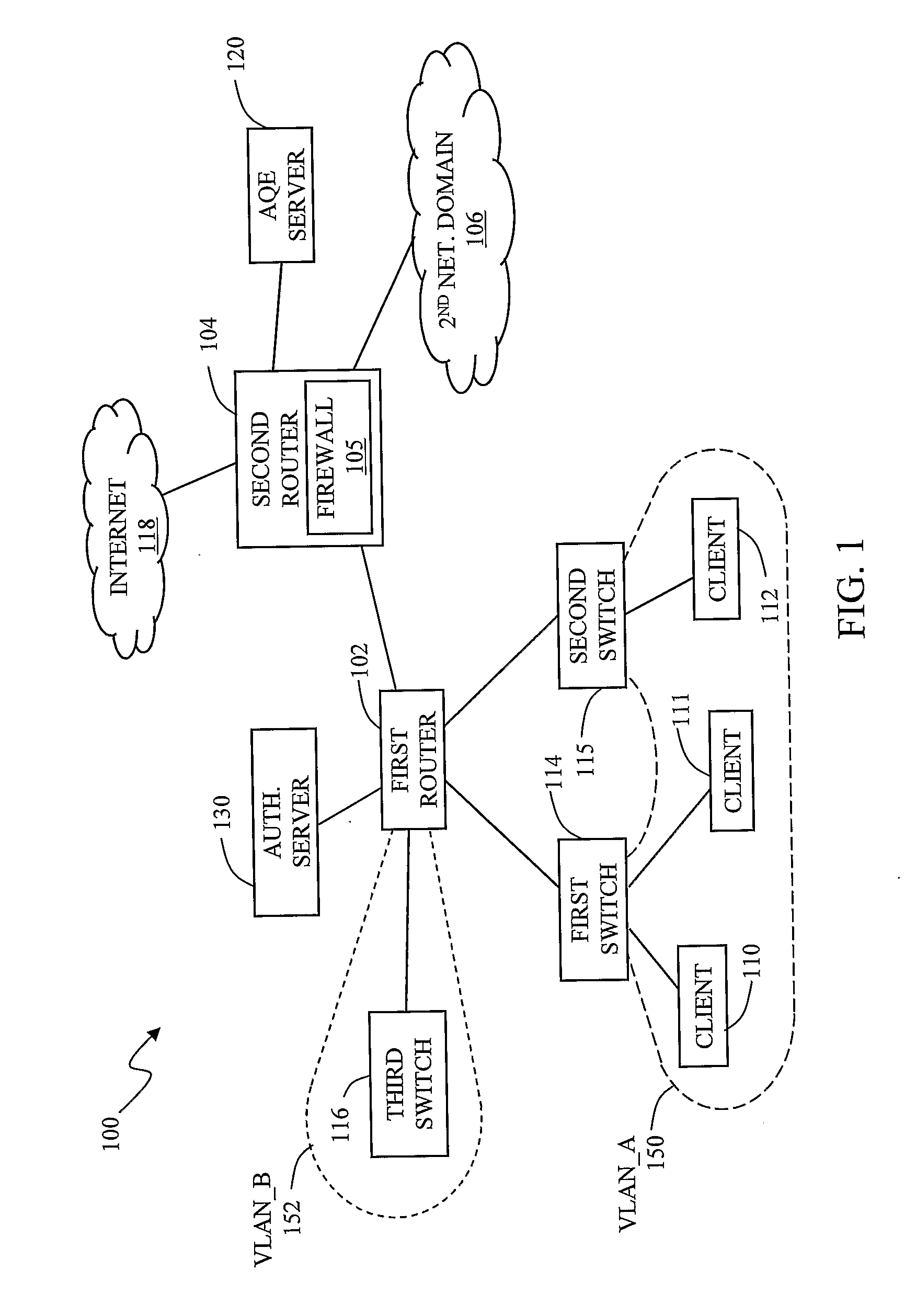
InactiveUS20060062187A1Effective trafficEfficiently broadcastedRadio/inductive link selection arrangementsWireless commuication servicesAccess networkAddress Resolution Protocol
A method and an arrangement in an access network for preventing hosts (5;A,B) connected to the access network from communicating directly with each other. Said method comprises the steps of defining Virtual Local Area Networks, VLANs, in switches (3;12;12′;35,36,37;83) such that traffic arriving in the switches from said hosts is forced to an access router (1;11;11′;11″;81) and defining in the switches one asymmetrical downlink VLAN for downlink traffic from the access router to the hosts, said downlink VLAN being common to said hosts. According to the invention the method comprises the further steps of configuring the VLANs such that said hosts connected to the access network belong to the same IP subnet and configuring the access router to perform intra-subnet routing and to be an Address Resolution Protocol proxy.
Owner:TELEFON AB LM ERICSSON (PUBL)
Automated containment of network intruder
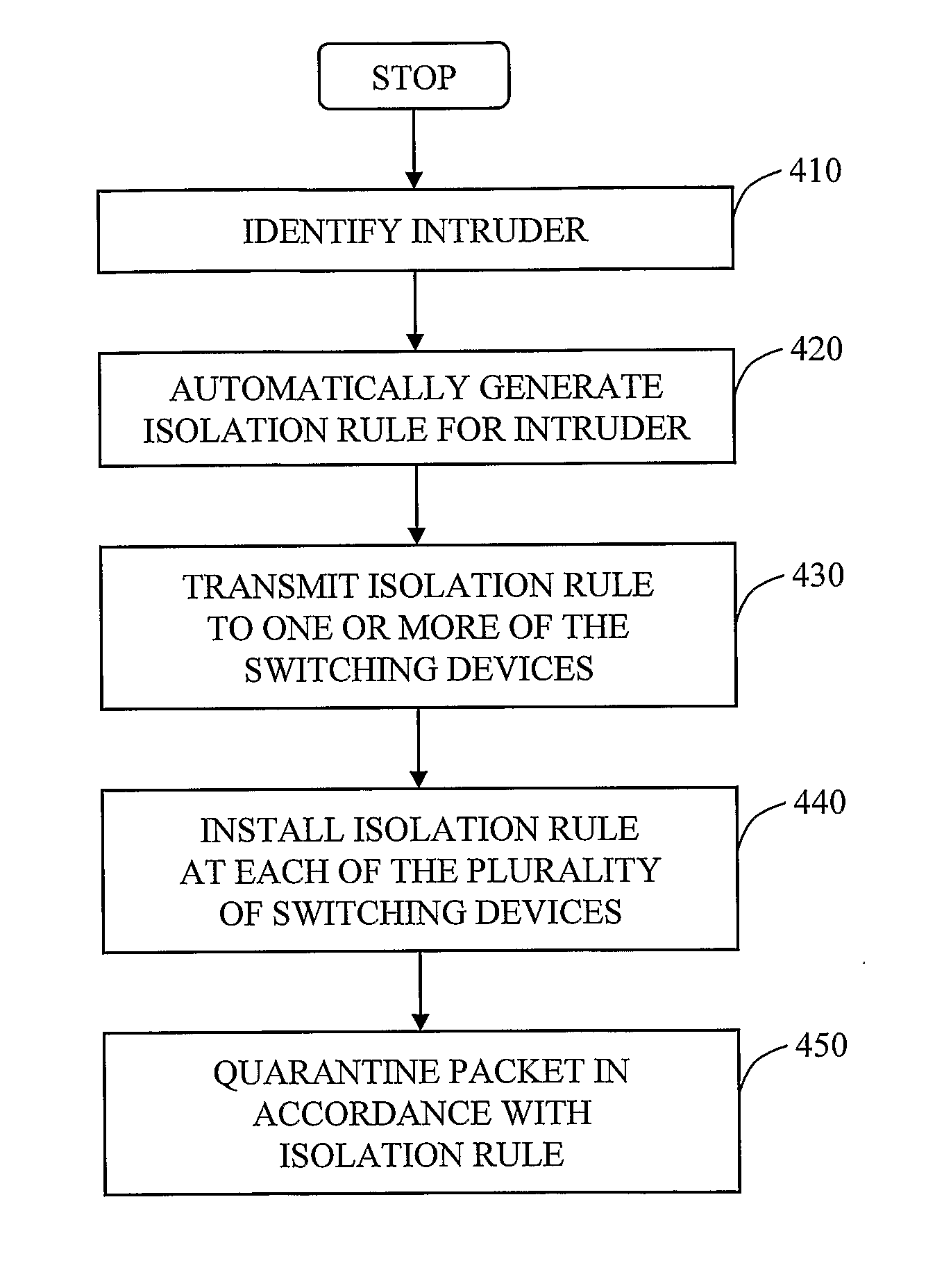
InactiveUS20070192862A1Network degradationLow costMemory loss protectionError detection/correctionAutomatic controlVirtual LAN
The invention in the preferred embodiment features a system (200) and method for automatically segregating harmful traffic from other traffic at a plurality of network nodes including switches and routers. In the preferred embodiment, the system (200) comprises an intrusion detection system (105) to determine the identity of an intruder and a server (130) adapted to automatically install an isolation rule on the one or more network nodes (114, 115, 116) to quarantine packets from the intruder. The isolation rule in the preferred embodiment is a virtual local area network (VLAN) rule or access control list (ACL) rule that causes the network node to route any packets from the intruder into a quarantine VLAN or otherwise isolate the traffic from other network traffic. In large networks, the isolation rule may be installed on a select plurality of network nodes under the gateway router (104) associated with the node at which the intruder first entered the network (100).
Owner:VERMEULEN VINCENT +1
Forwarding frames in a computer network using shortest path bridging
Methods, apparatus, and products are disclosed for forwarding frames in a computer network using shortest path bridging (‘SPB’). The network includes multiple bridges, and each edge bridge is assigned a unique service virtual local area network (‘VLAN’) identifier. One of the bridges receives a frame for transmission to a destination node. The received frame includes a service VLAN identifier for the ingress bridge through which the frame entered the network and a customer VLAN identifier. The one bridge identifies an SPB forwarding tree in dependence upon the service VLAN identifier. The SPB forwarding tree specifies a shortest route in the network from the ingress bridge through the one bridge to the other bridges in the network. The one bridge then forwards the received frame to the egress bridge without MAC-in-MAC encapsulation in dependence upon the SPB forwarding tree and the customer VLAN identifier.
Owner:JUMIPER NETWORKS INC
Multiple instance spanning tree protocol
A multiple instance spanning tree protocol (MI-STP) creates a plurality of active topologies (i.e., loop-free paths) within a computer network. These active topologies may be established through the exchange and processing of multiple instance spanning tree bridge protocol data unit messages (MI-STP BPDUs) by the intermediate network devices within the network. The active topologies are preferably created independently of any virtual local area network (VLAN) designations defined within the network. Once the active topologies are defined, each VLAN designation is then mapped to a single active topology, although multiple VLAN designations are preferably mapped to the same active topology to provide load balancing.
Owner:CISCO TECH INC
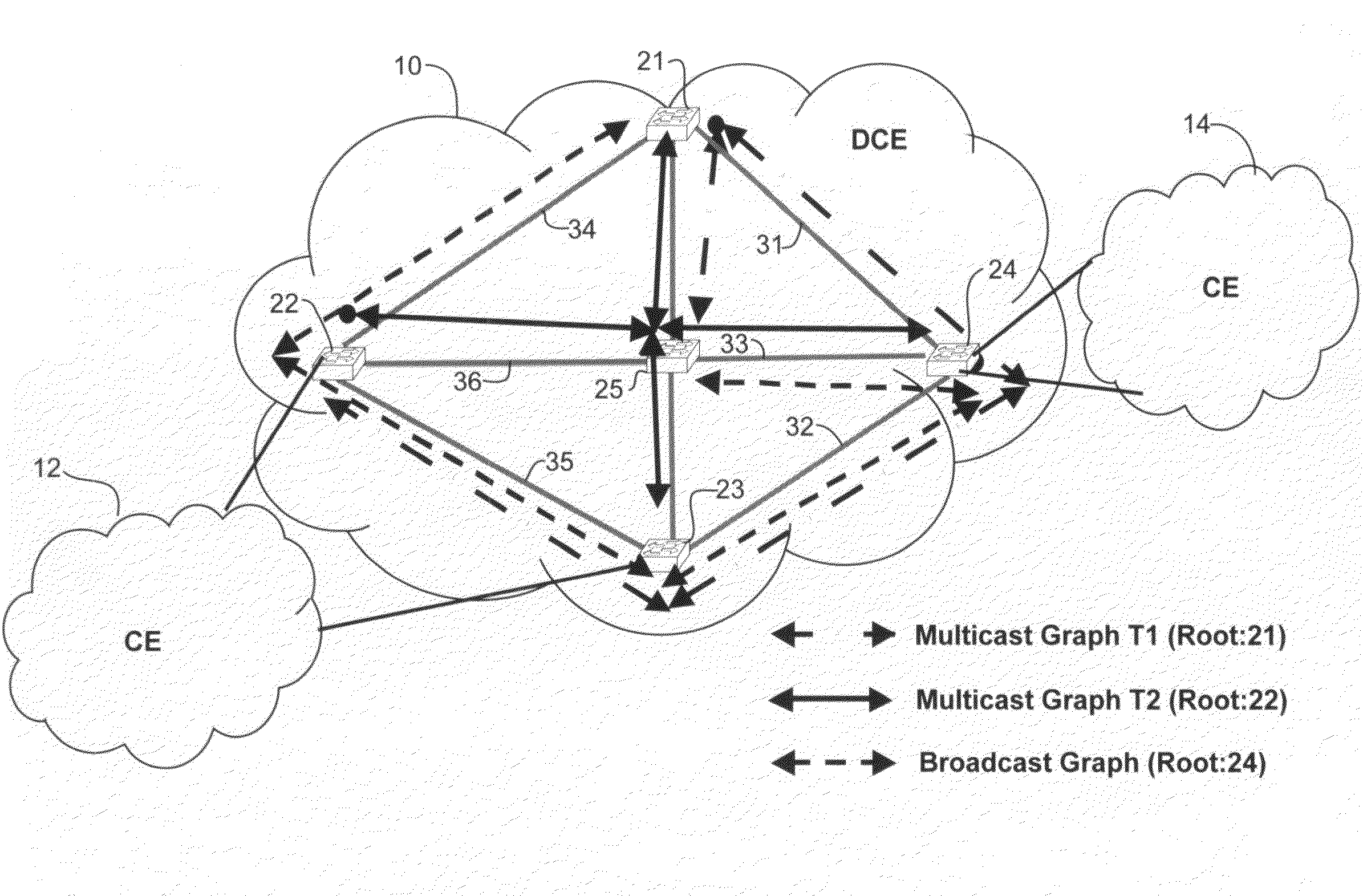
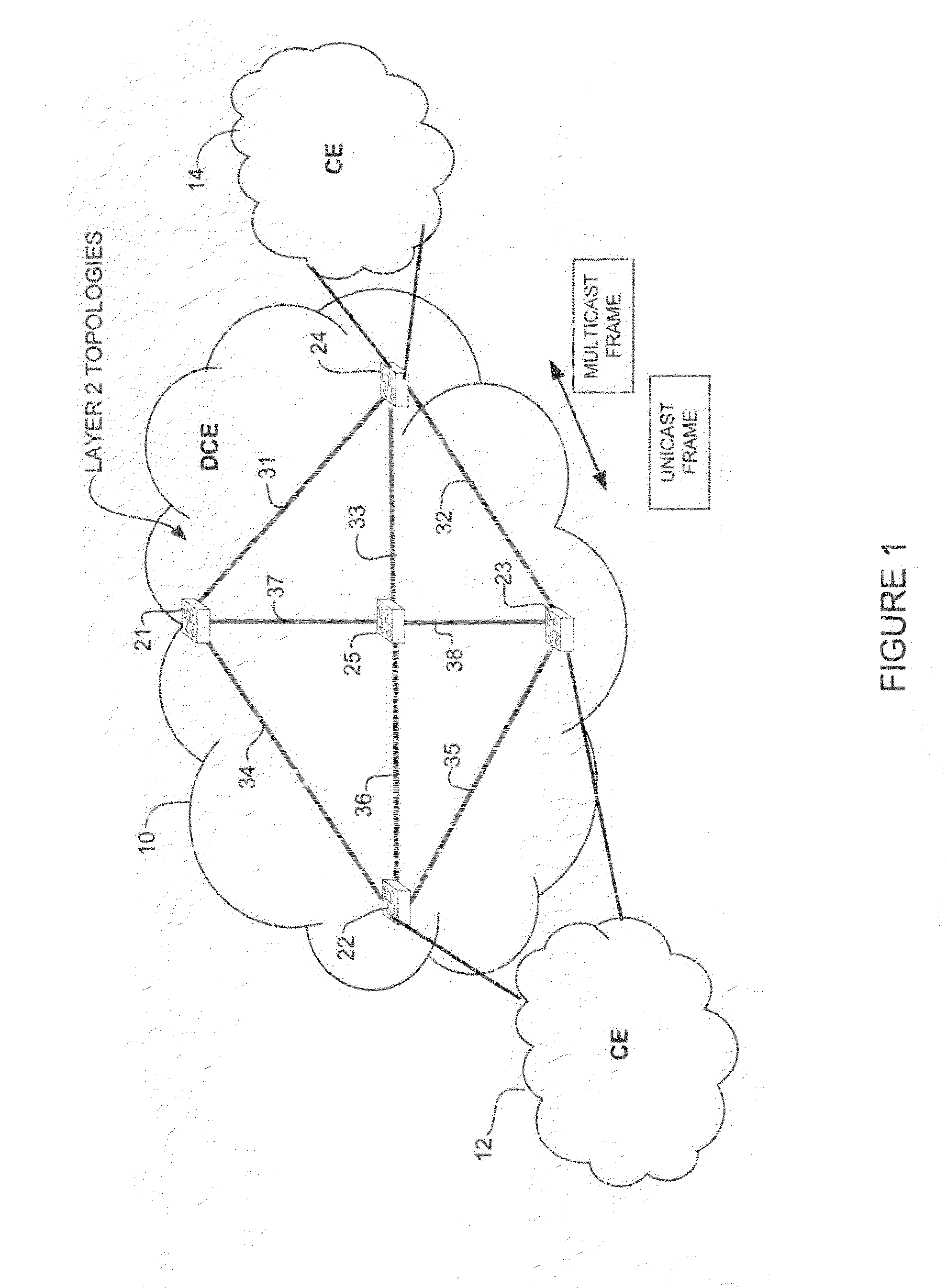
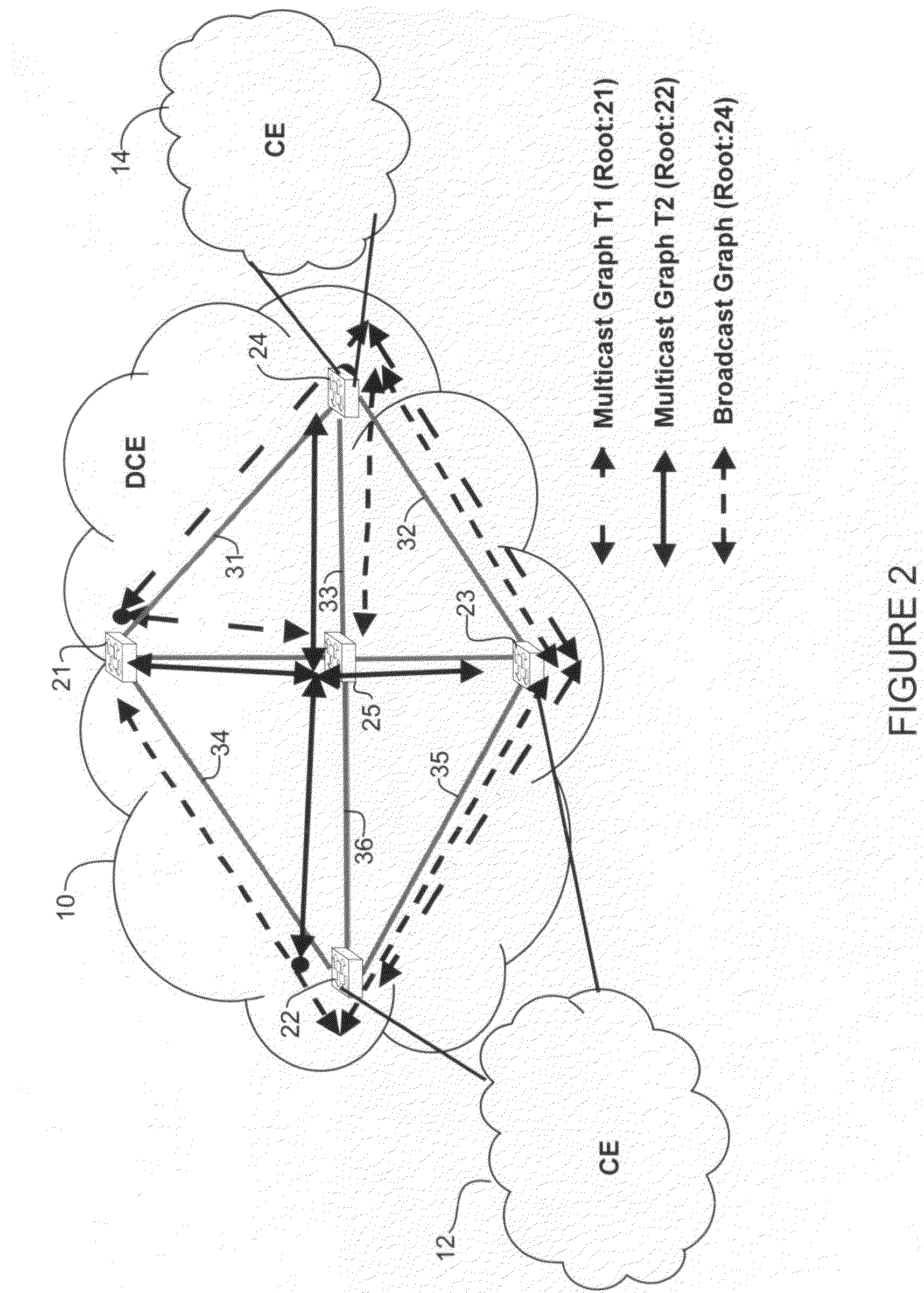
Differentiated services for unicast and multicast frames in layer 2 topologies
In one embodiment, a method includes receiving information on layer 2 topologies at a network device in a core network, mapping one or more Virtual Local Area Networks (VLANs) to the layer 2 topologies to provide differentiated services in said layer 2 topologies, defining multiple paths for each of the layer 2 topologies, and forwarding a packet received at the network device on one of the multiple paths. An apparatus for providing differentiated services in layer 2 topologies is also disclosed.
Owner:CISCO TECH INC
System and method for dynamic server allocation and provisioning
InactiveUS20070250608A1Lower cost of capitalQuality improvementResource allocationDigital computer detailsLoad SheddingManagement tool
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
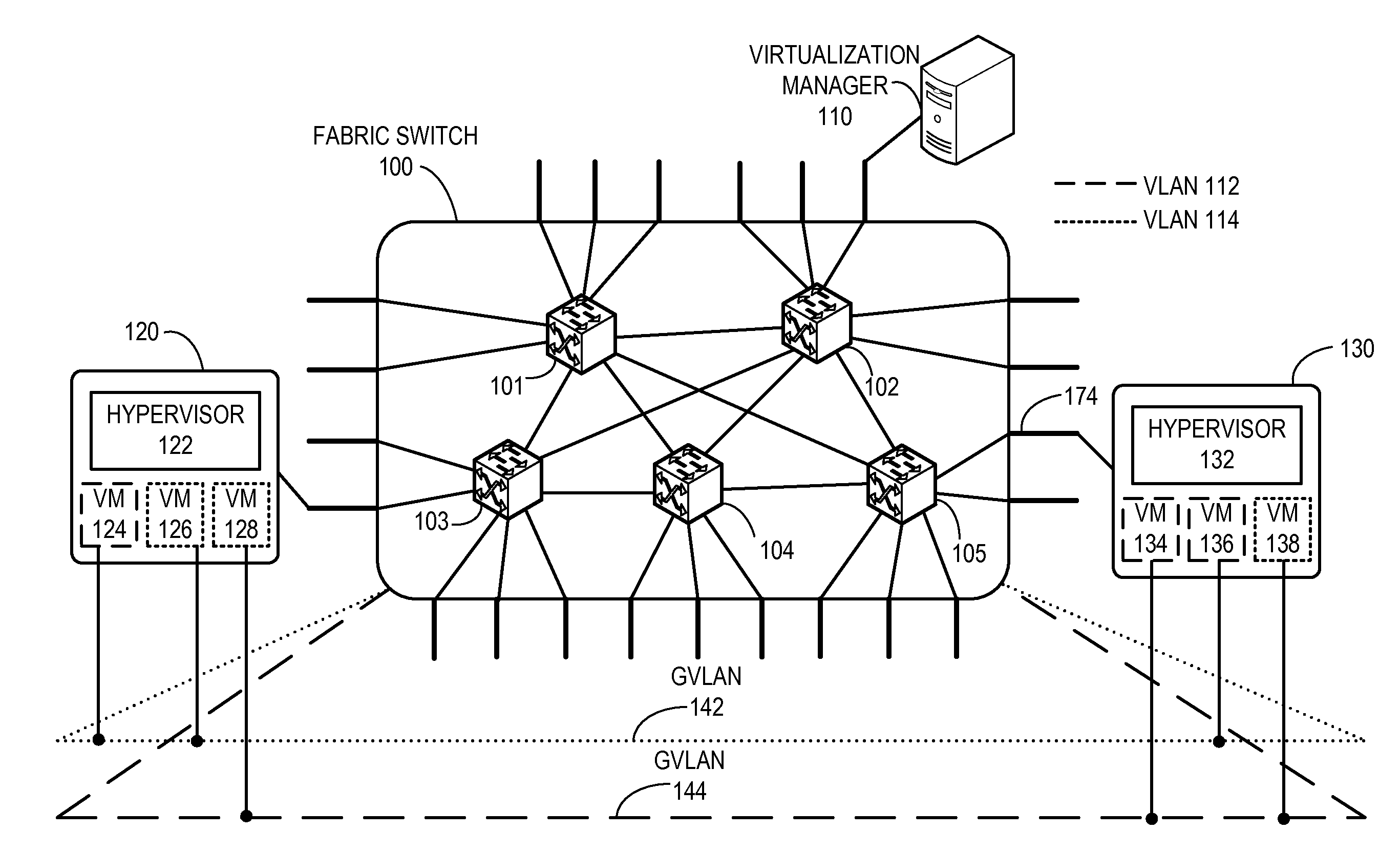
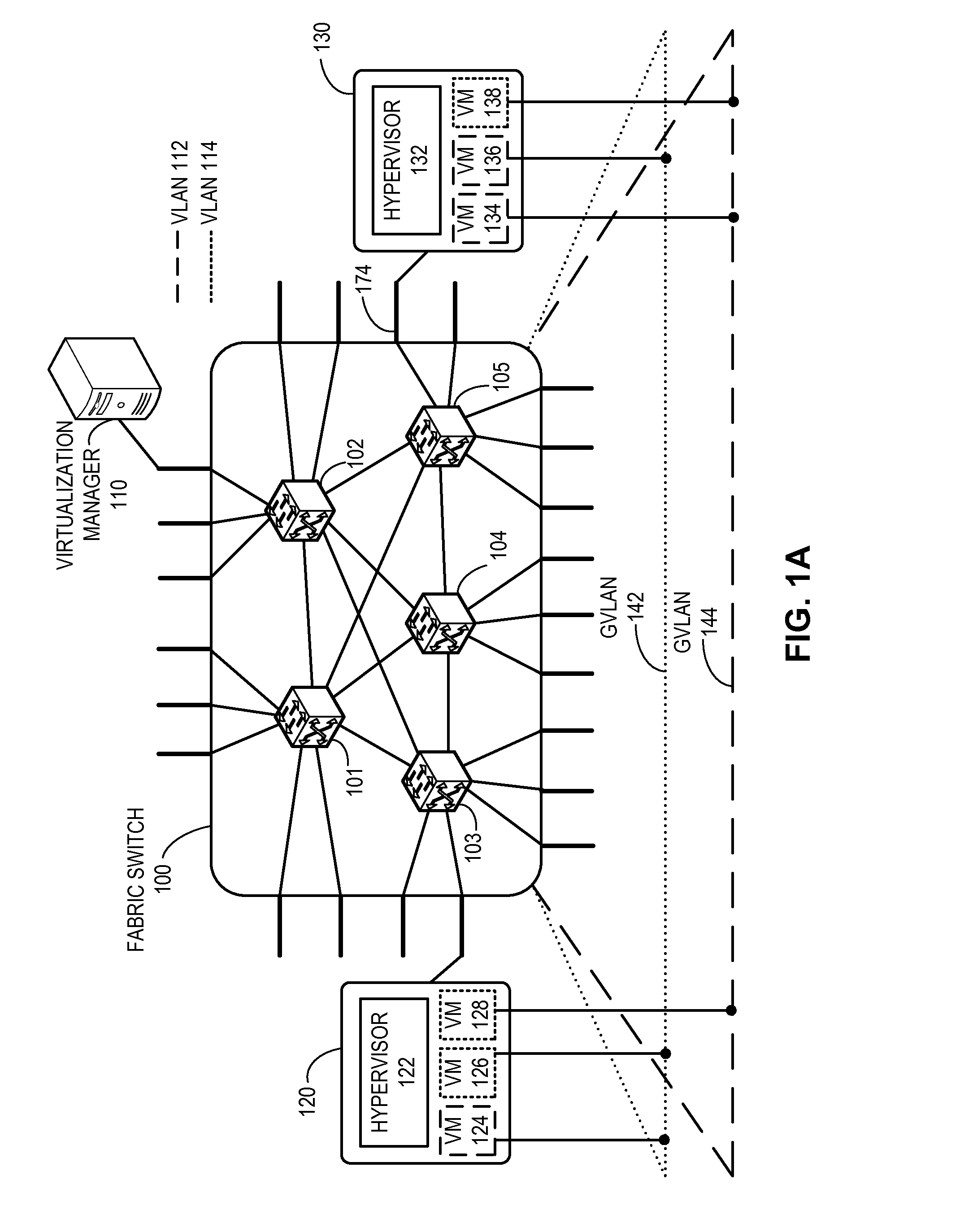
Global vlans for fabric switches
One embodiment of the present invention provides a switch. The switch includes a virtual local area network (VLAN) configuration module. During operation, the VLAN configuration module maps local resources of the switch and / or locally coupled end device information to a global VLAN identifier, wherein the global VLAN is persistent across a fabric switch. The fabric switch is operable to accommodate a plurality of switches and operates as a single logical switch.
Owner:AVAGO TECH INT SALES PTE LTD
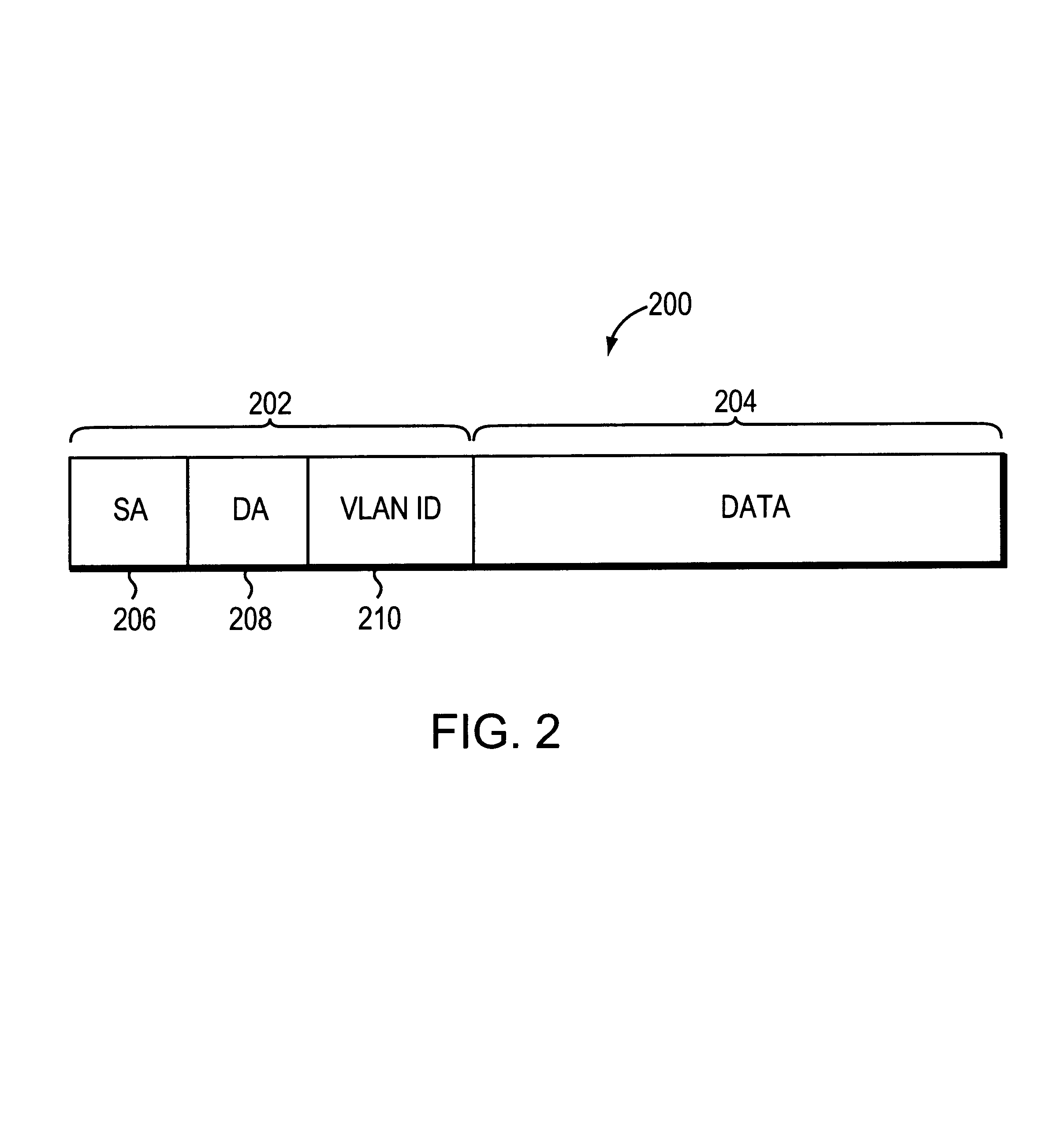
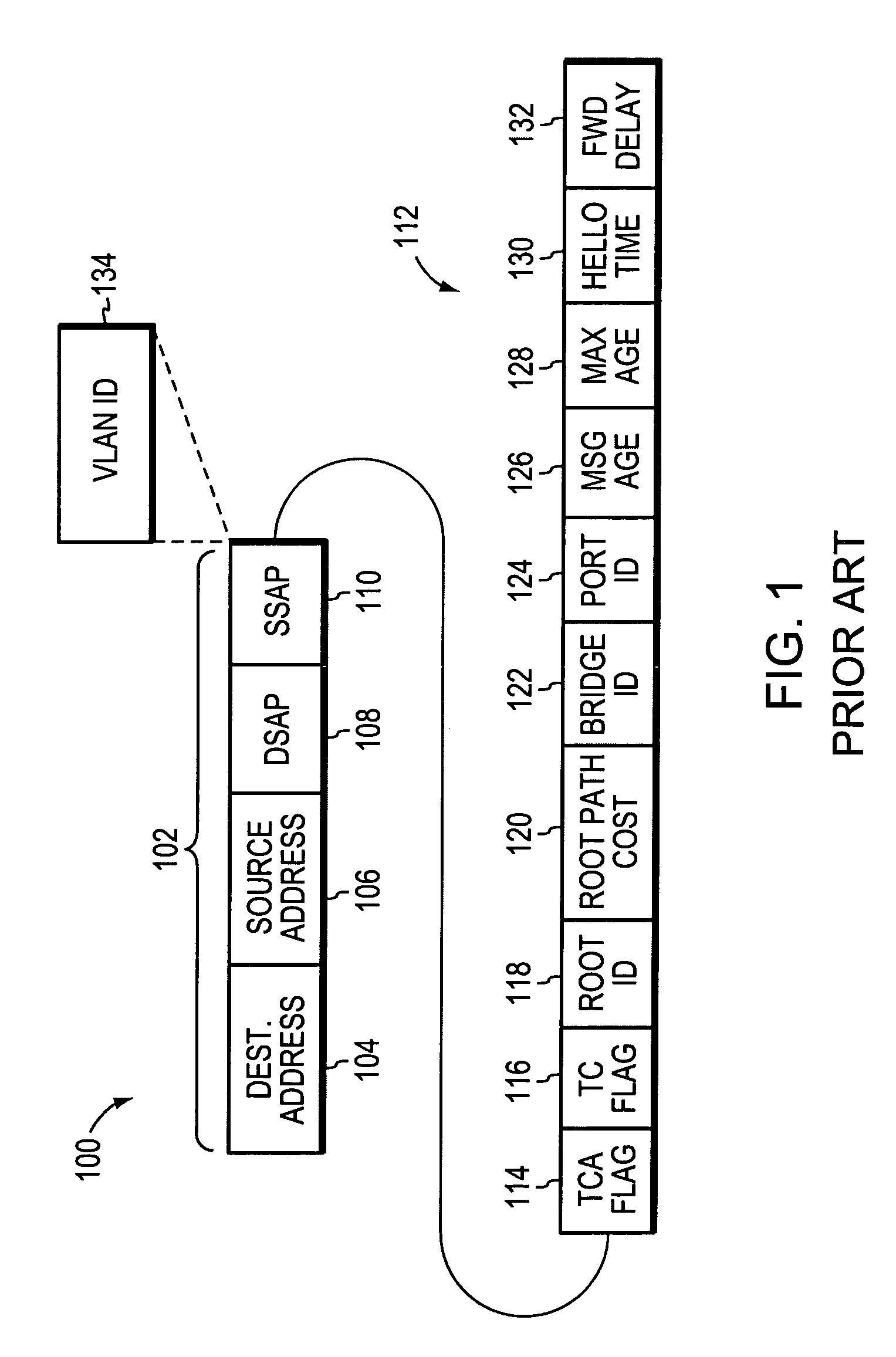
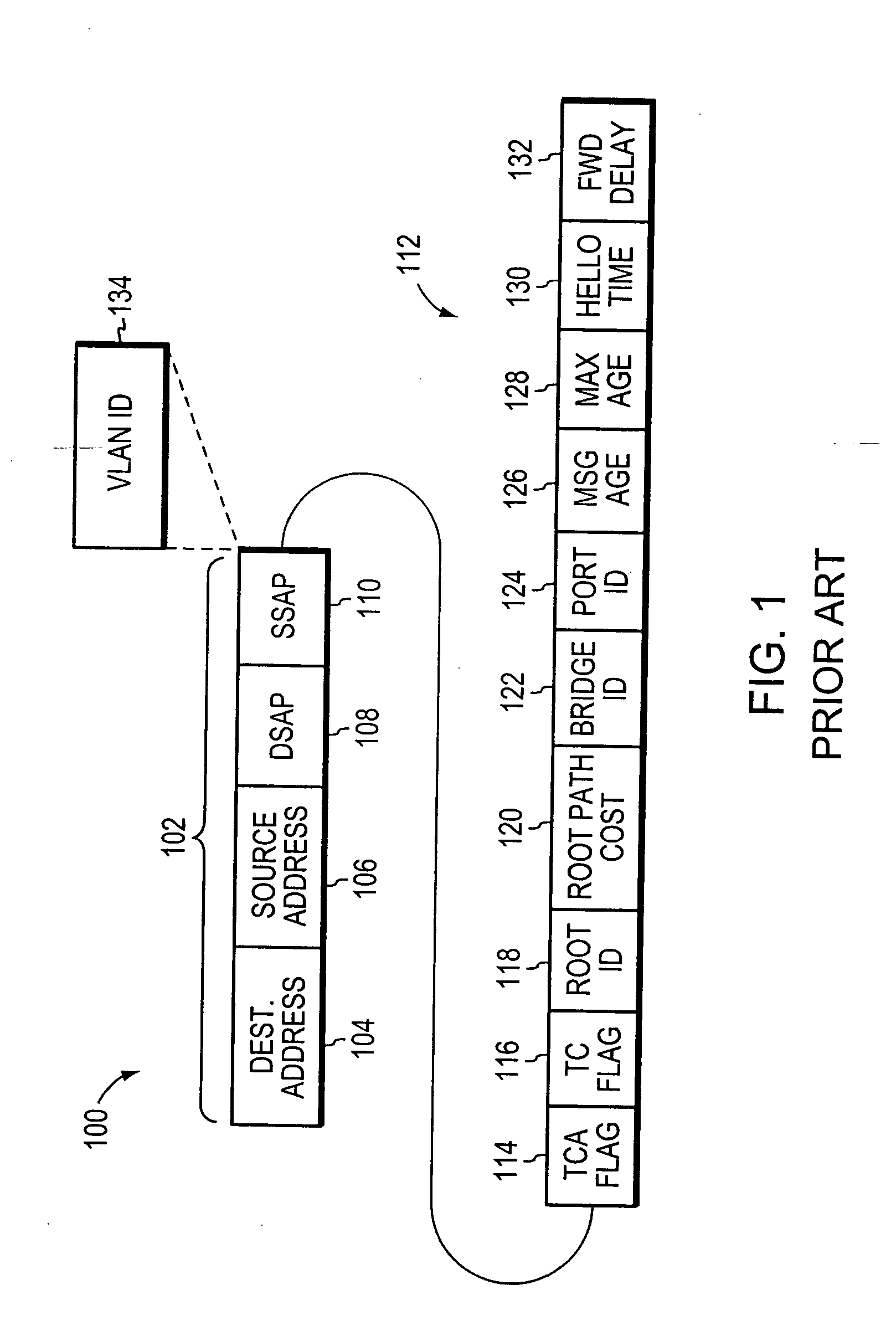
VLAN frame format
InactiveUS6111876AReduce decreaseAvoid ambiguityNetwork topologiesTime-division multiplexVirtual LANNetwork switch
In a network device such as a network switch having a port coupled to a communications medium dedicated to a single virtual local area network and another port coupled to a communications medium shared among multiple virtual local area networks for transmitting data frames between the dedicated communications medium and the shared communications medium, a method of identifying the virtual network associated with each data frame received by the network switch when transmitting the data frames over the shared communications medium. The method comprises receiving data frames from the dedicated communications medium coupled to one port, and, with respect to each data frame so received, inserting a new type field and a virtual network identifier field. The contents of the new type field indicate the data frame comprises a virtual network identifier field. The method further includes placing a value in the virtual network identifier field identifying the virtual network associated with the data frame and transmitting the data frame over the shared communications medium. Upon receipt of the data frames from over the shared communications medium, another network device can discern from the virtual network identifier field in each data frame the virtual network from which the data frames were received and determine whether to forward the data frames accordingly.
Owner:INT LICENSE EXCHANGE OF AMERICA LLC
Storage network management system and method
InactiveUS20050044199A1OptimizationDigital data information retrievalDigital computer detailsVirtual LANCountermeasure
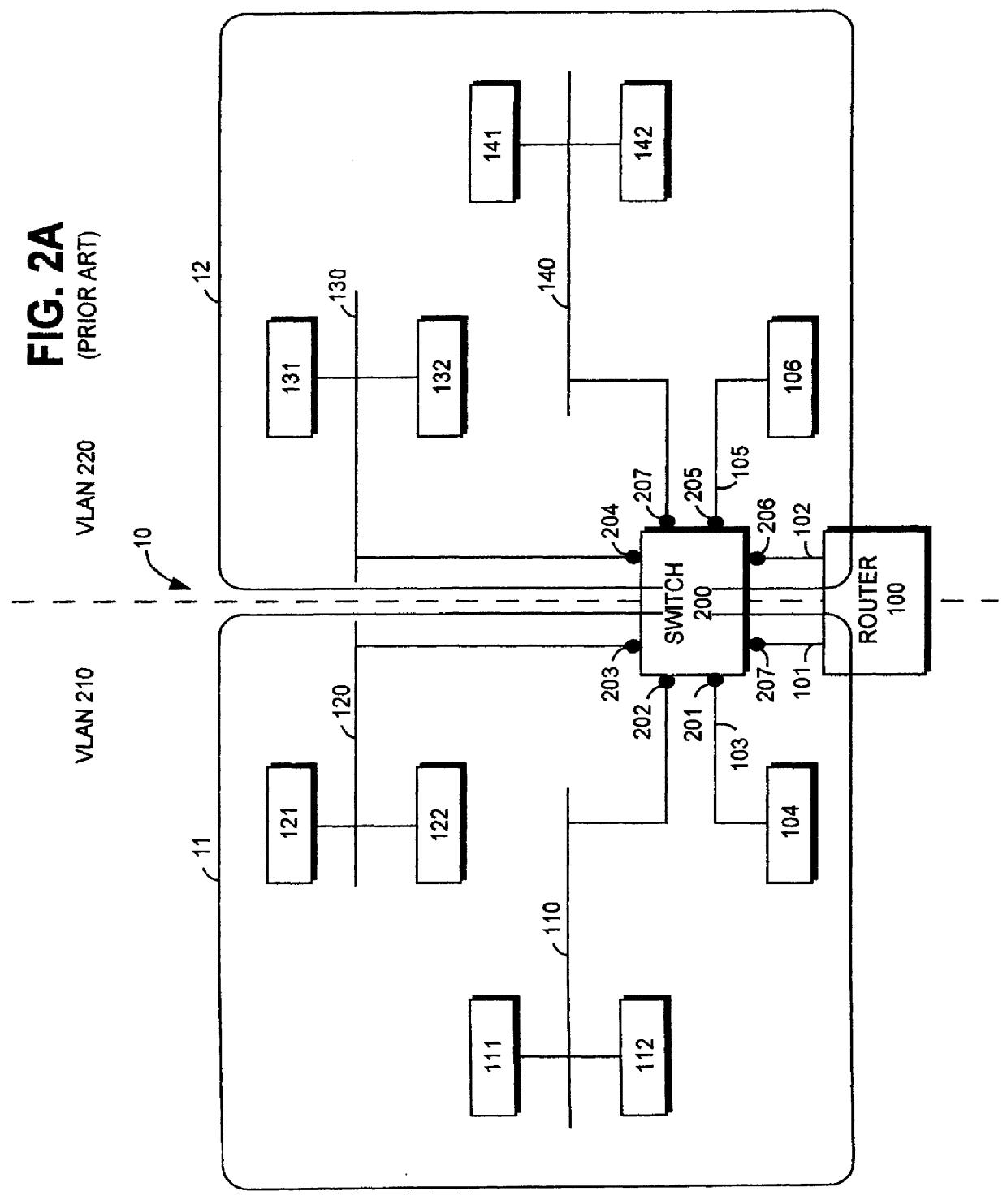
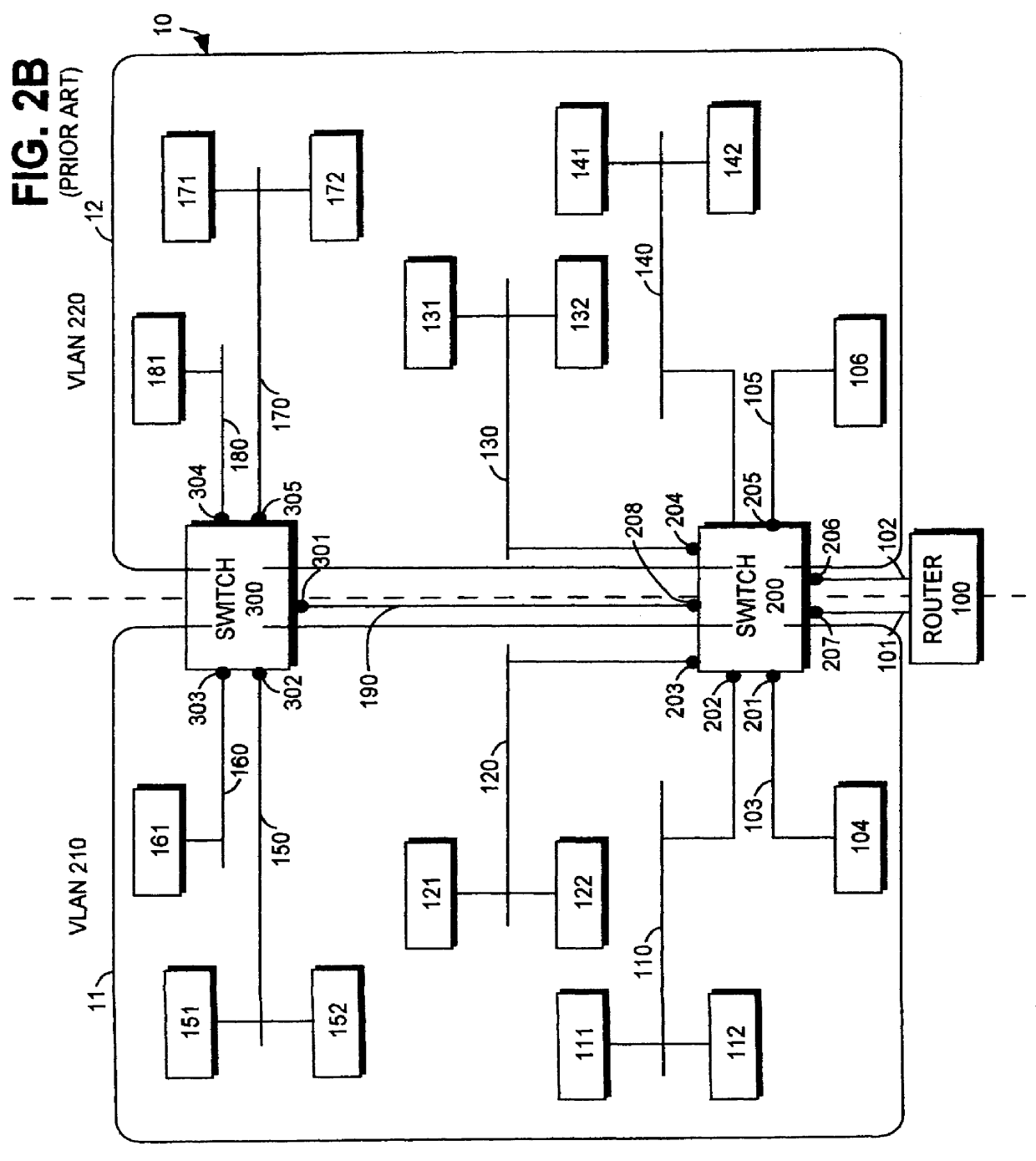
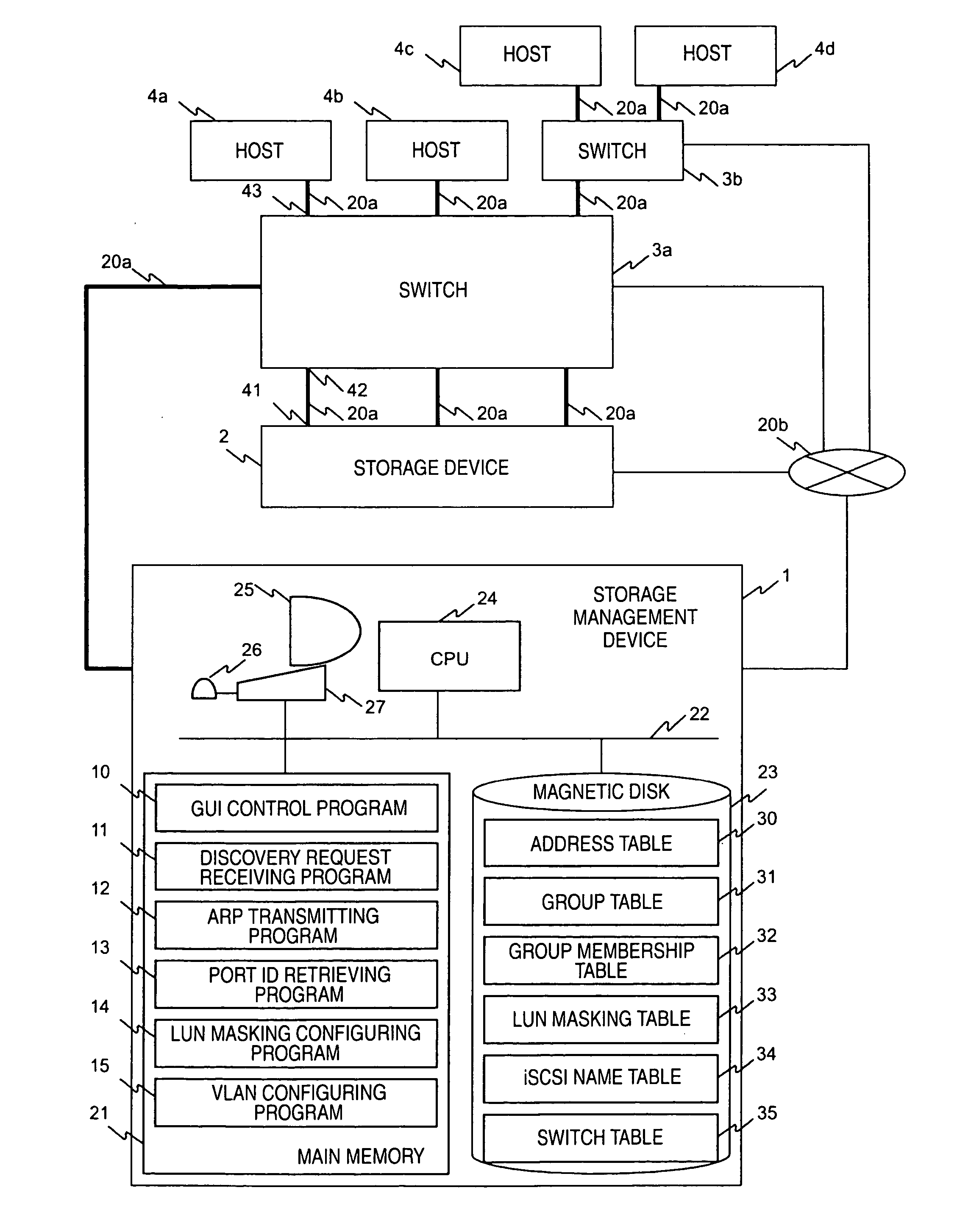
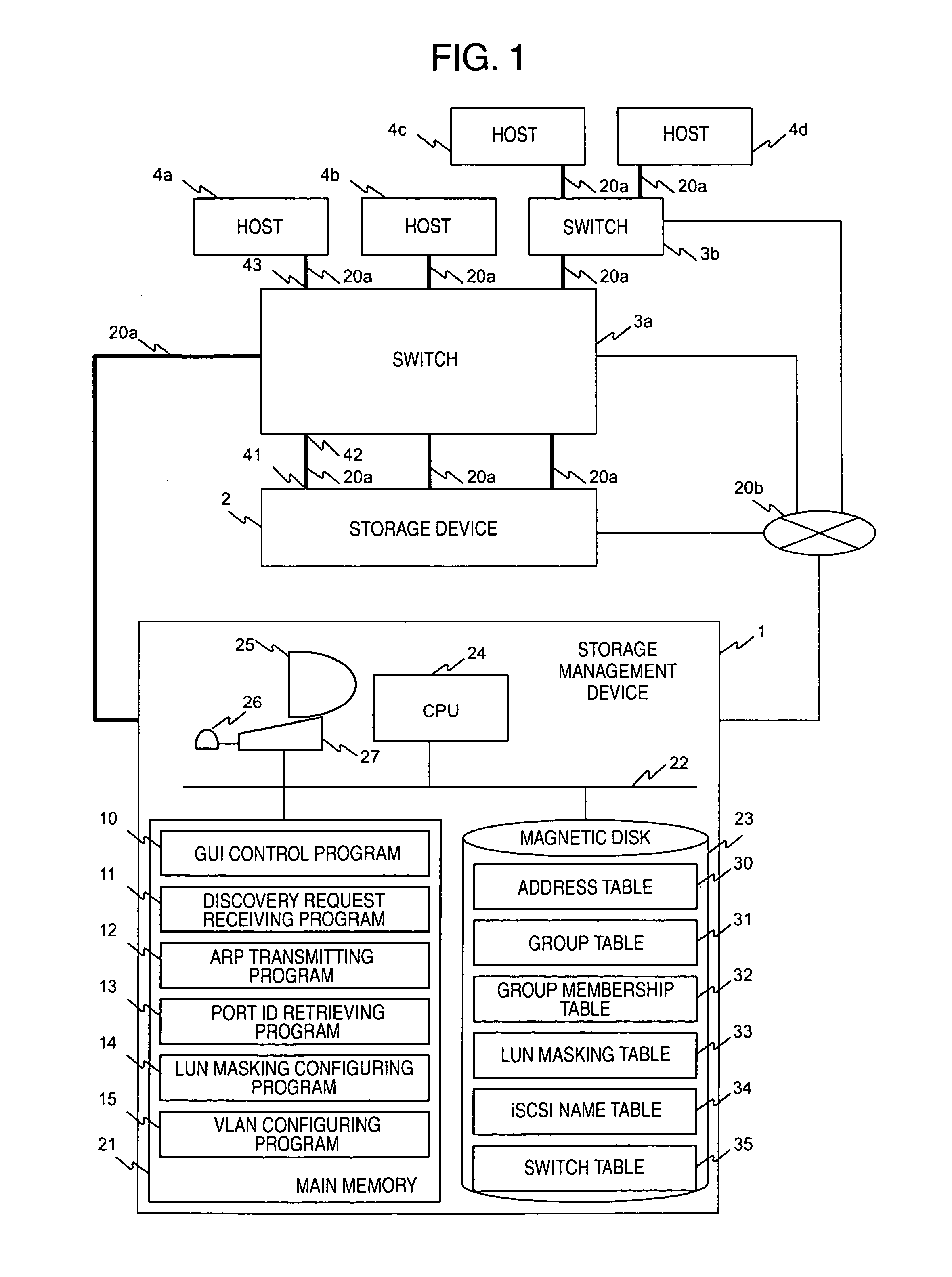
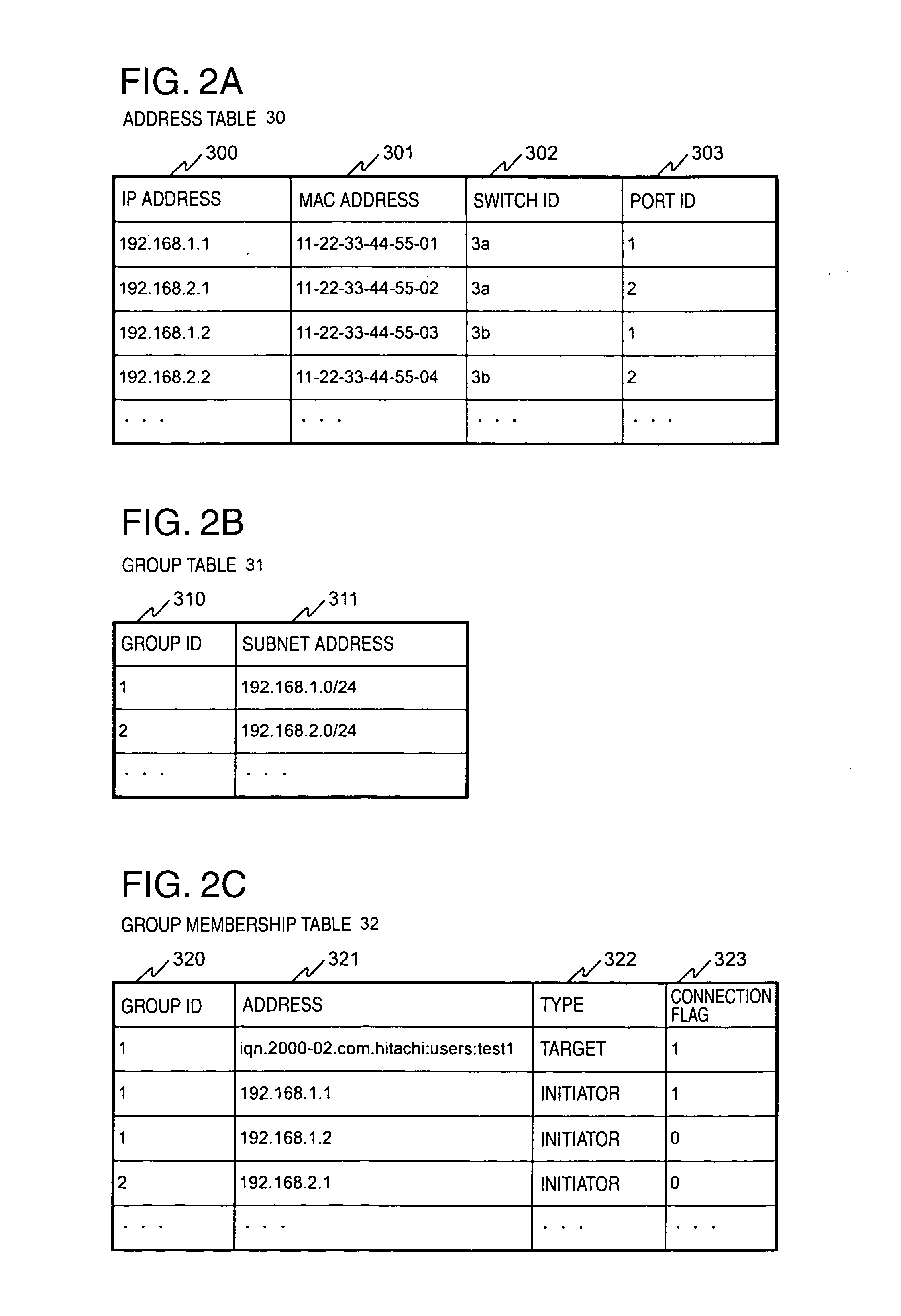
In a computer system having a storage device, switches and hosts respectively connected by a network, in accordance with an ID of a logical volume of the storage device and an IP address of a host, access control configuration of the logical volume is performed relative to the storage device, the IP address of the host is converted into a MAC address, the MAC address of the host is converted into a port ID of the switch connected to the host, and addition of the port to virtual local area network (VLAN) is performed for the switch. Logical unit number (LUN) masking and VLAN configuration essential for security countermeasure of IP-SAN (Internet protocol-storage area network) can be managed collectively by a system administrator so that the running cost of IP-SAN can be lowered.
Owner:HITACHI LTD
Fast connection protection in a virtual local area network based stack environment
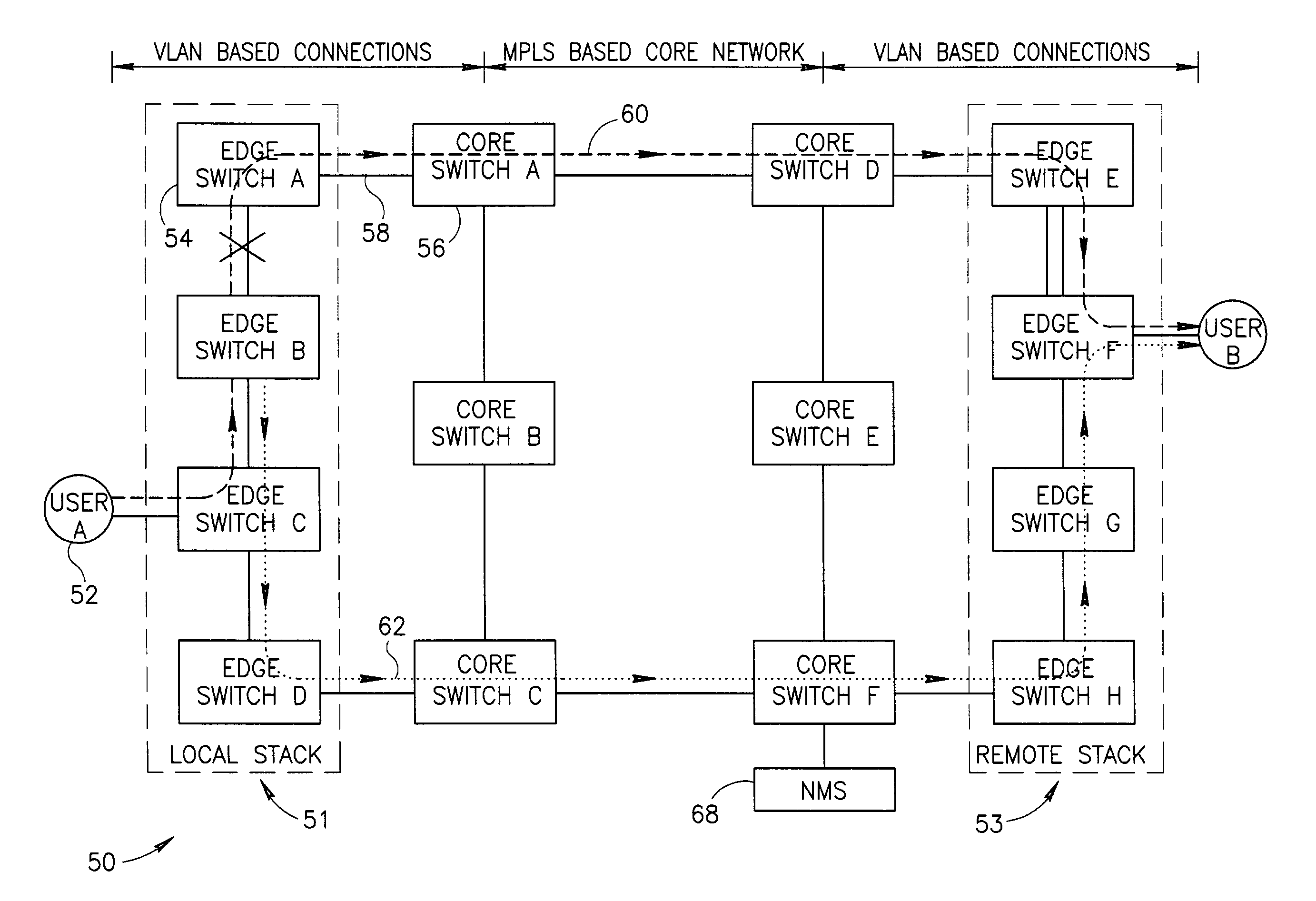
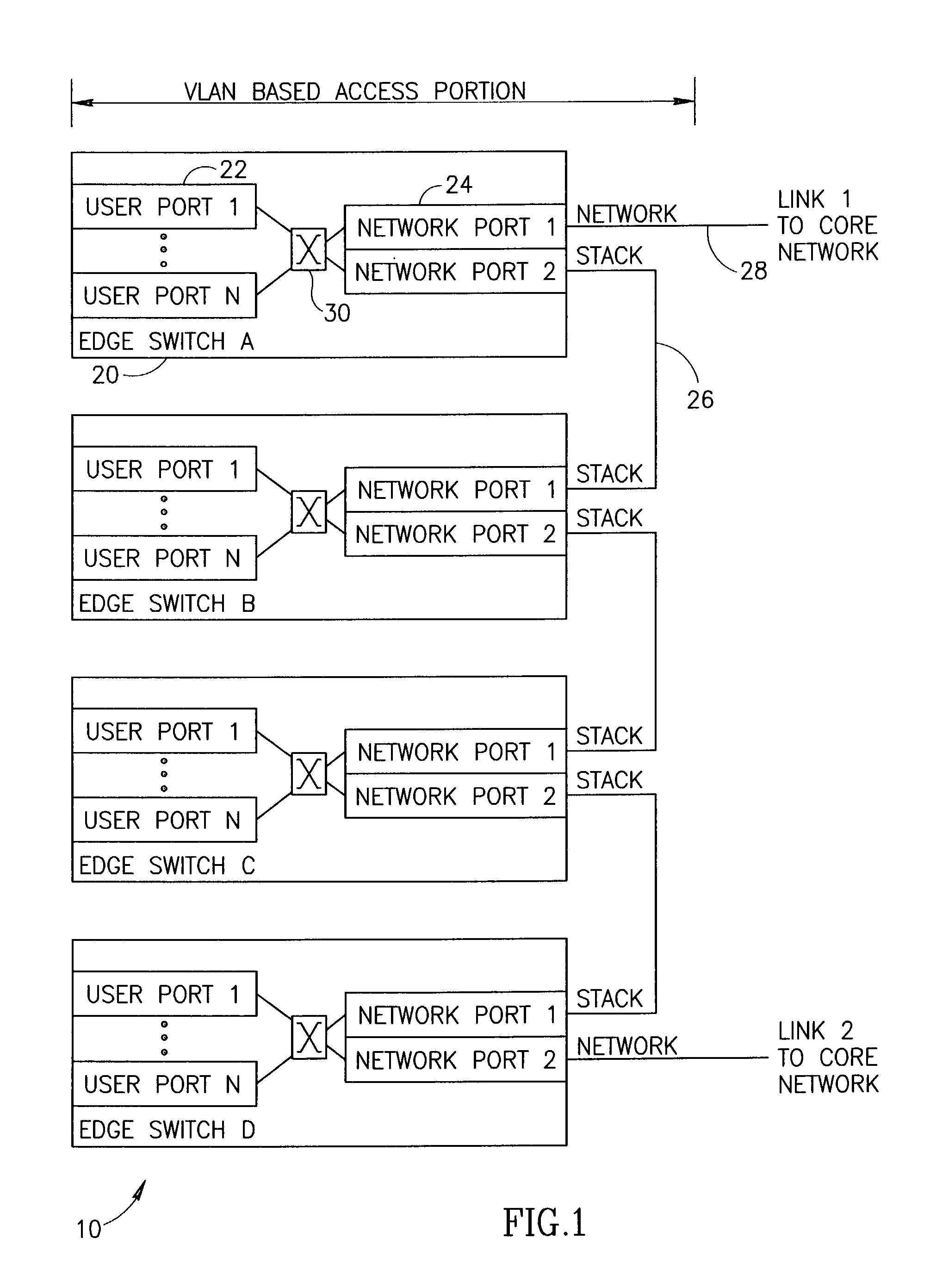
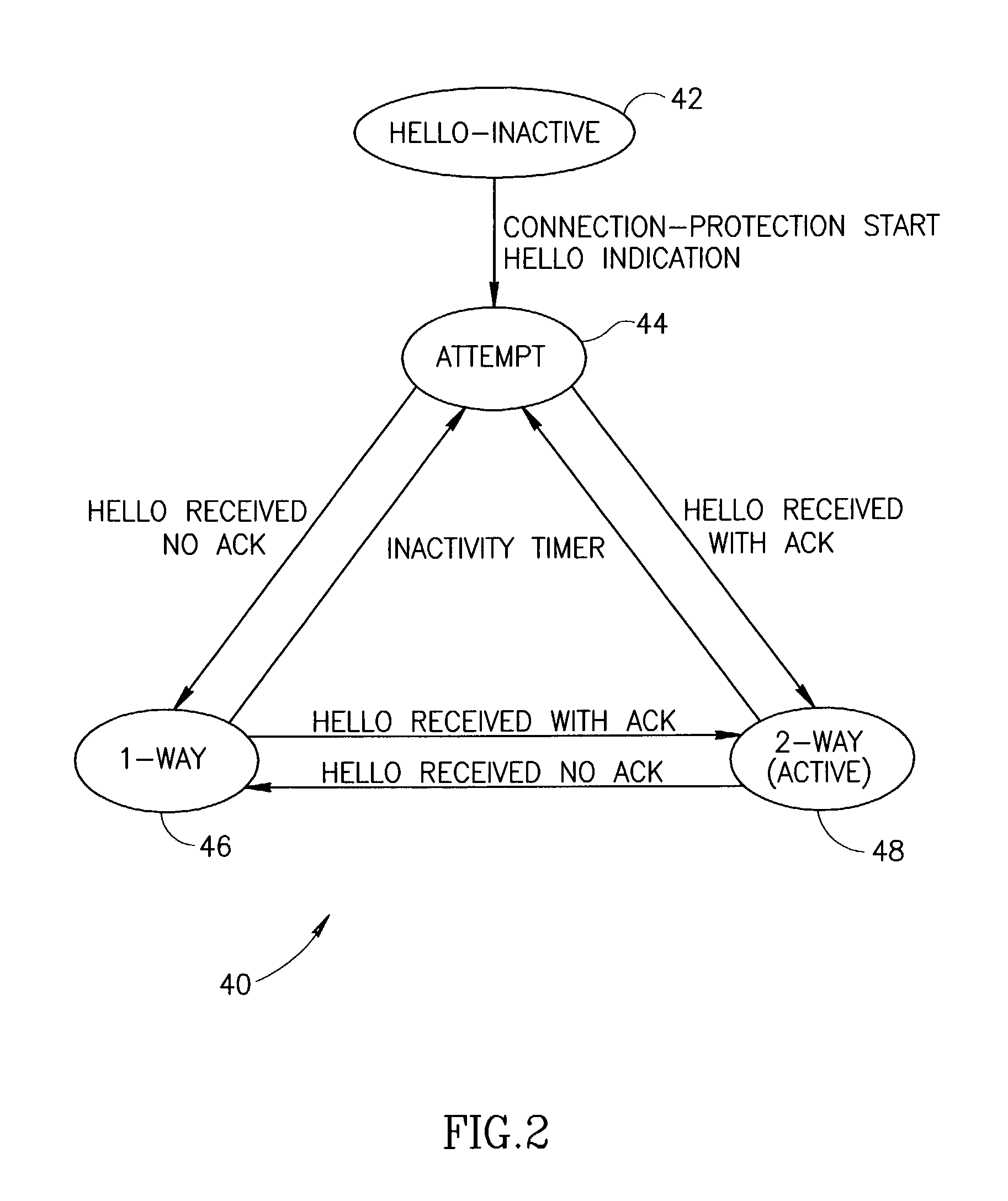
A fast protection mechanism capable of maintaining end-to-end and fast local protection on the order of sub 50 ms for both VLAN only based connections and for connections that are based partially on VLAN technology and partially on MPLS technology. The present invention is suitable for use edge switches configured in a stack or ring topology. The NMS provisions both the main and alternative VLANs in each edge switch in the stack portions of the network. When a link failure occurs, the edge switches on either end of the failed link immediately switch all protected traffic going through that link to the alternative VLAN. The packets are then returned on the links over which they were received. Hello messages are used to signal the remote end that a link failure has occurred and that protected traffic must be switched to the main or alternative VLAN in accordance with the VLAN the Hello message was received on.
Owner:VENTURE LENDING & LEASING III +1
Wireless local area network with clients having extended freedom of movement
A wireless virtual local area network (VLAN) and a device selectively connecting to the wireless VLAN over a second wireless network that may be independent of the wireless VLAN. The device is capable of connecting to at least the wireless VLAN and to the second wireless network. Wireless VLAN access points are each connected to an Ethernet aggregation switch, which is VLAN aware and matches client traffic from connected access points with access VLANs. A wireless VLAN switch maintains an association table between access VLANs and core VLANs. The second wireless network may be remotely connected over the Internet or a private network to a tunnel endpoint. The tunnel endpoint is connected to the VLAN switch, which uses the association table to manage free-form client traffic between connected devices and other mobile stations at access VLANs and appropriate core VLANs.
Owner:SIEMENS CANADA LTD
Virtual LAN override in a multiple BSSID mode of operation
ActiveUS20070081477A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsVirtual LAN
Methods, apparatuses and systems directed to the integration of VLANs and wireless access points operating in a Multiple BSSID mode of operation. According to one implementation of the present invention, a wireless access point dynamically maps an SSID provided by a mobile station to a BSSID based on a VLAN assignment corresponding to the mobile station. In one implementation, the wireless access point learns the correct VLAN / BSSID for a given mobile station, while proxying an authentication session between the mobile station and an authentication server.
Owner:CISCO TECH INC
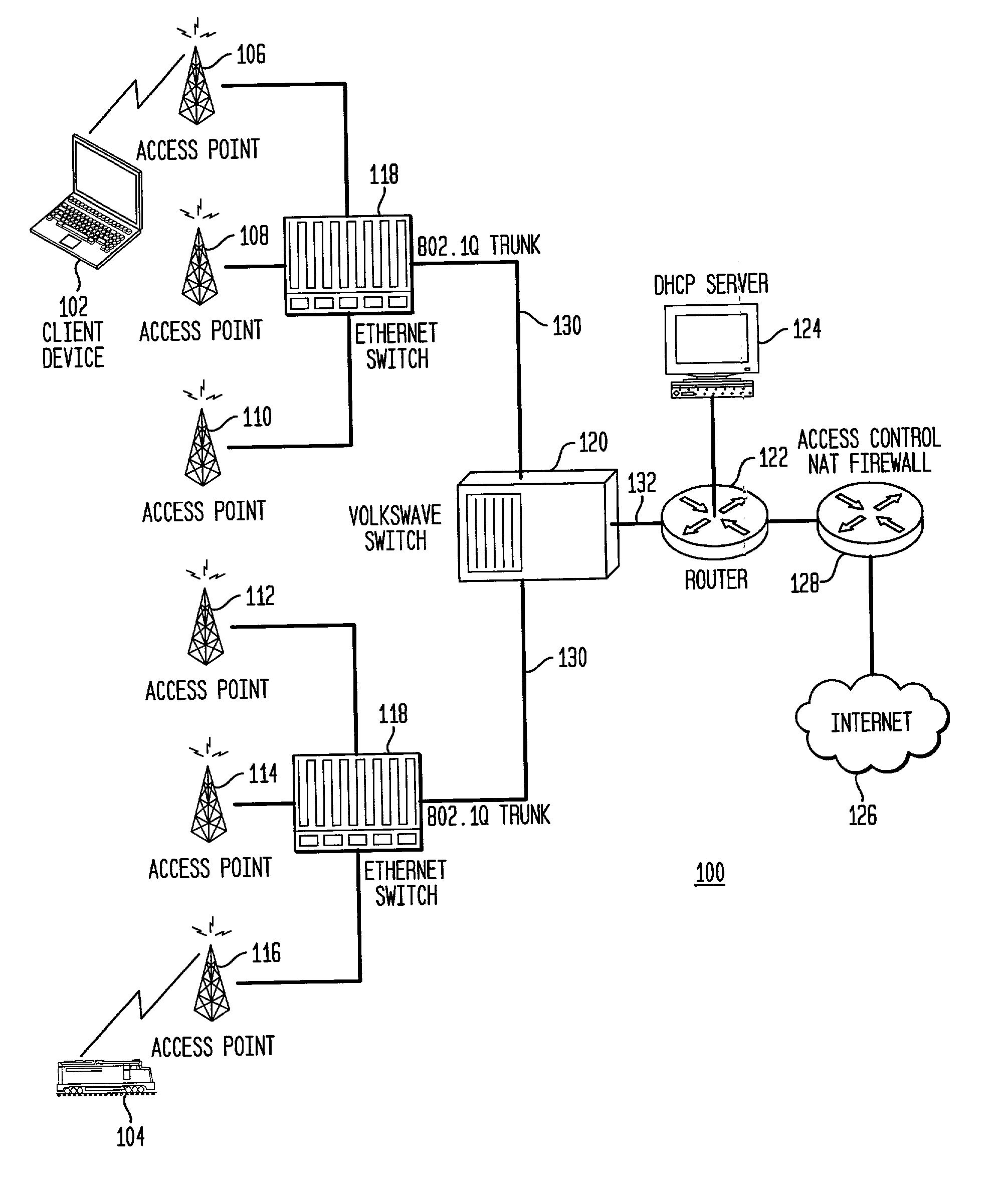
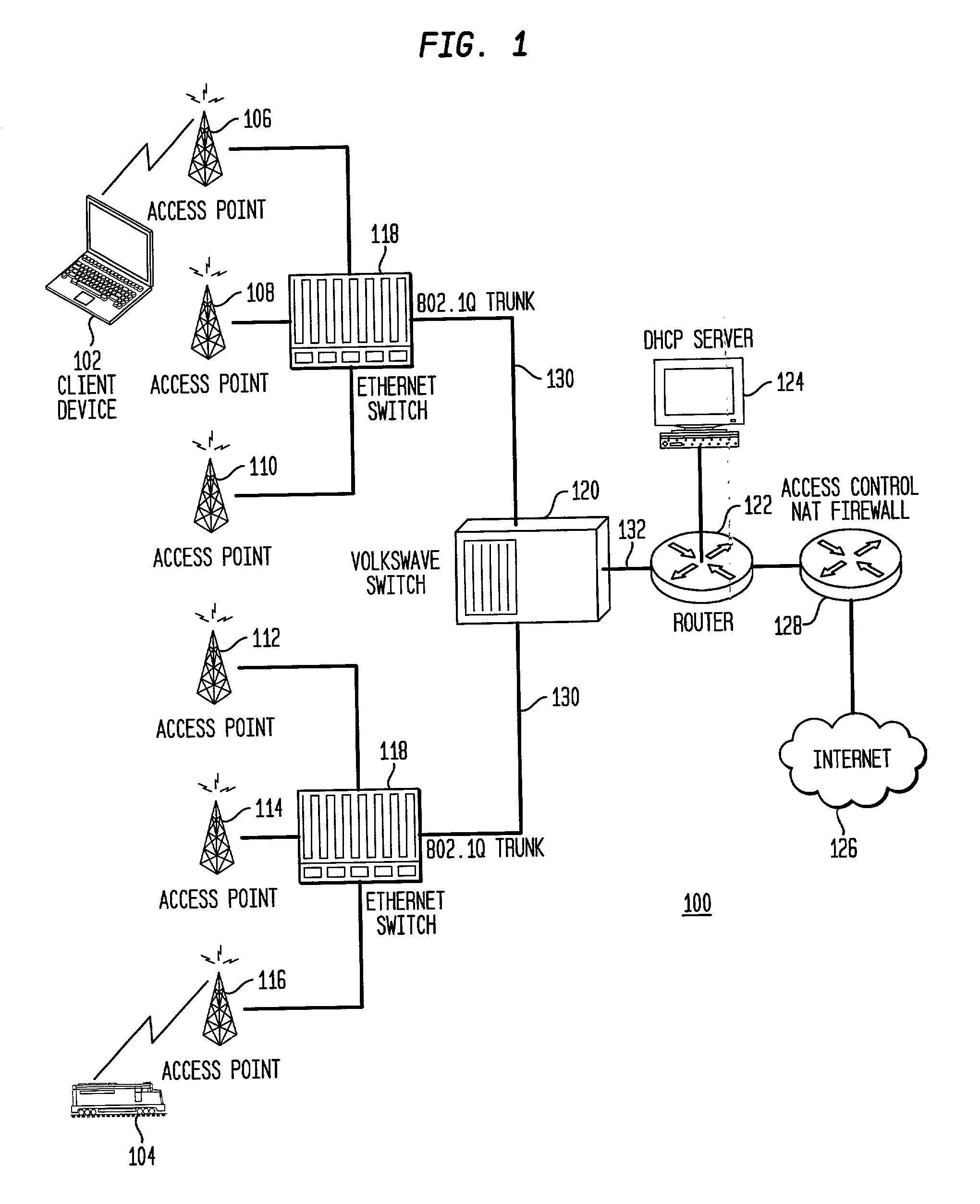
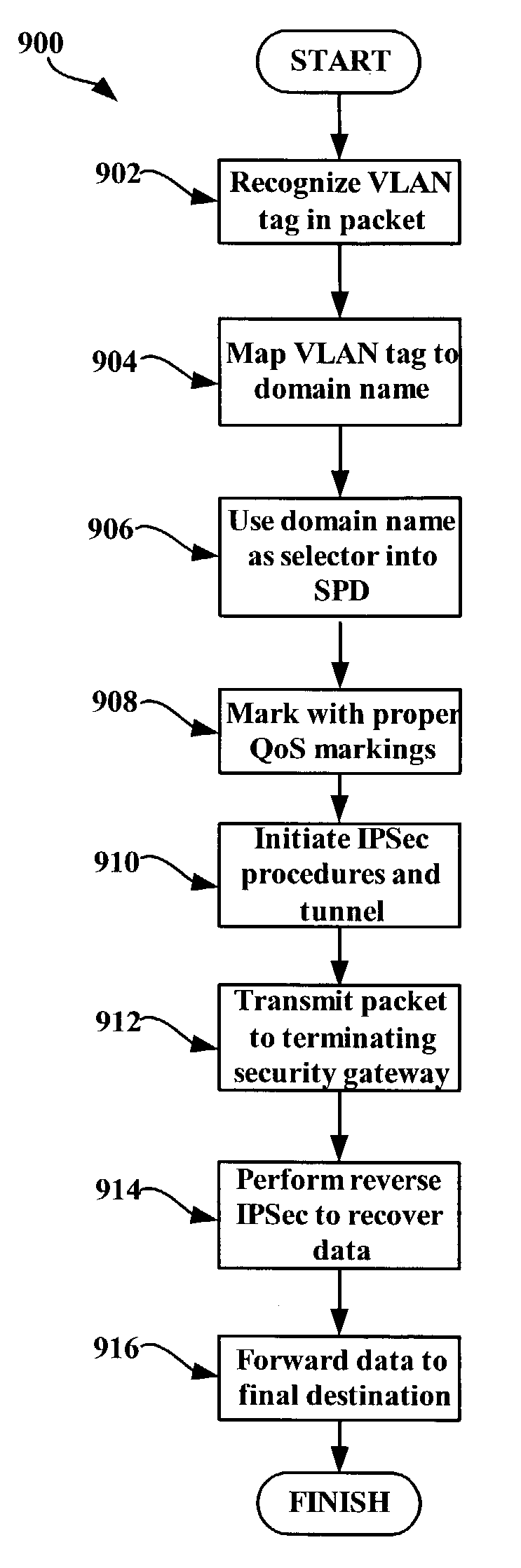
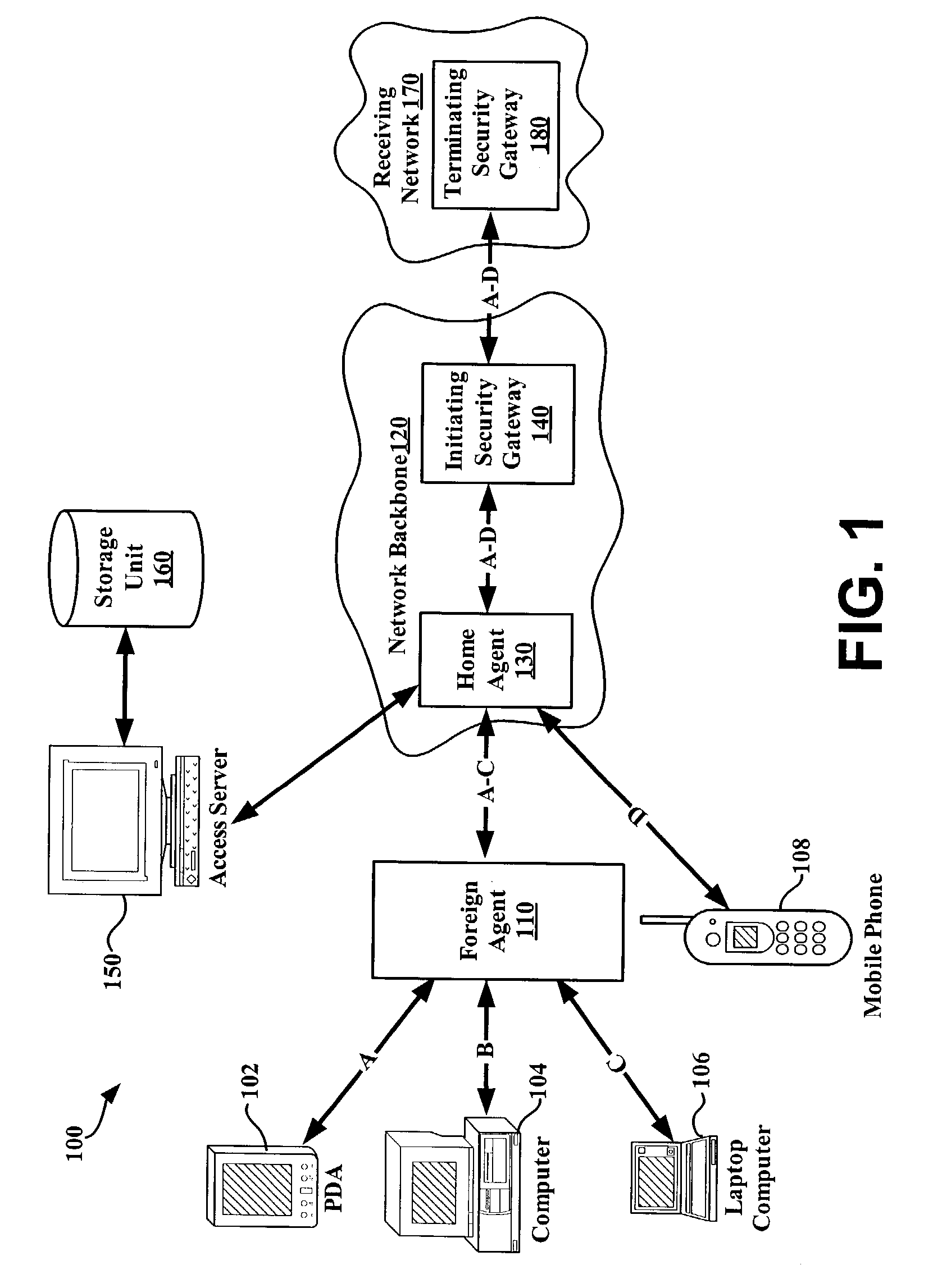
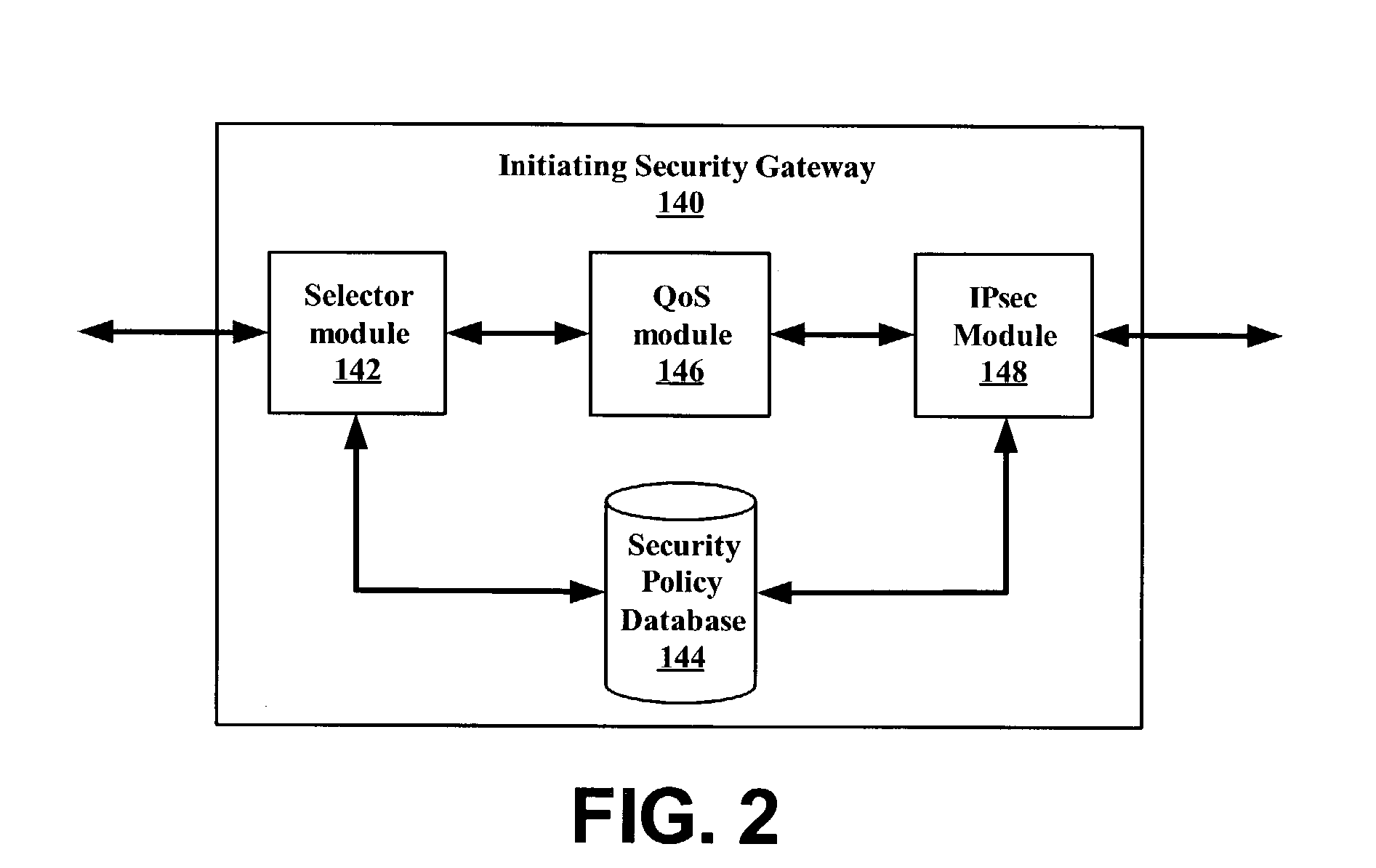
System and method for using virtual local area network tags with a virtual private network
An exemplary system and method for using a network access system, such as a virtual private network (VPN), are provided. A user device may have a user session with a home agent. Additionally, an initiating security gateway may be in communication with the home agent, and a terminating security gateway may be in communication with the initiating security gateway via a tunnel (e.g., Internet Protocol in Internet Protocol (IP-in-IP) or Internet Protocol security (IPsec) tunnel). Further, a virtual local area network (VLAN) tag associated with the user session may map to a selector operable in a security policy database. The selector may be used to find a security policy defining an IPsec procedure, and the security policy may be applied to the tunnel. Also, the initiating security gateway may also include a Quality of Service (QoS) module that determines QoS markings for a packet traveling along the tunnel.
Owner:VALTRUS INNOVATIONS LTD
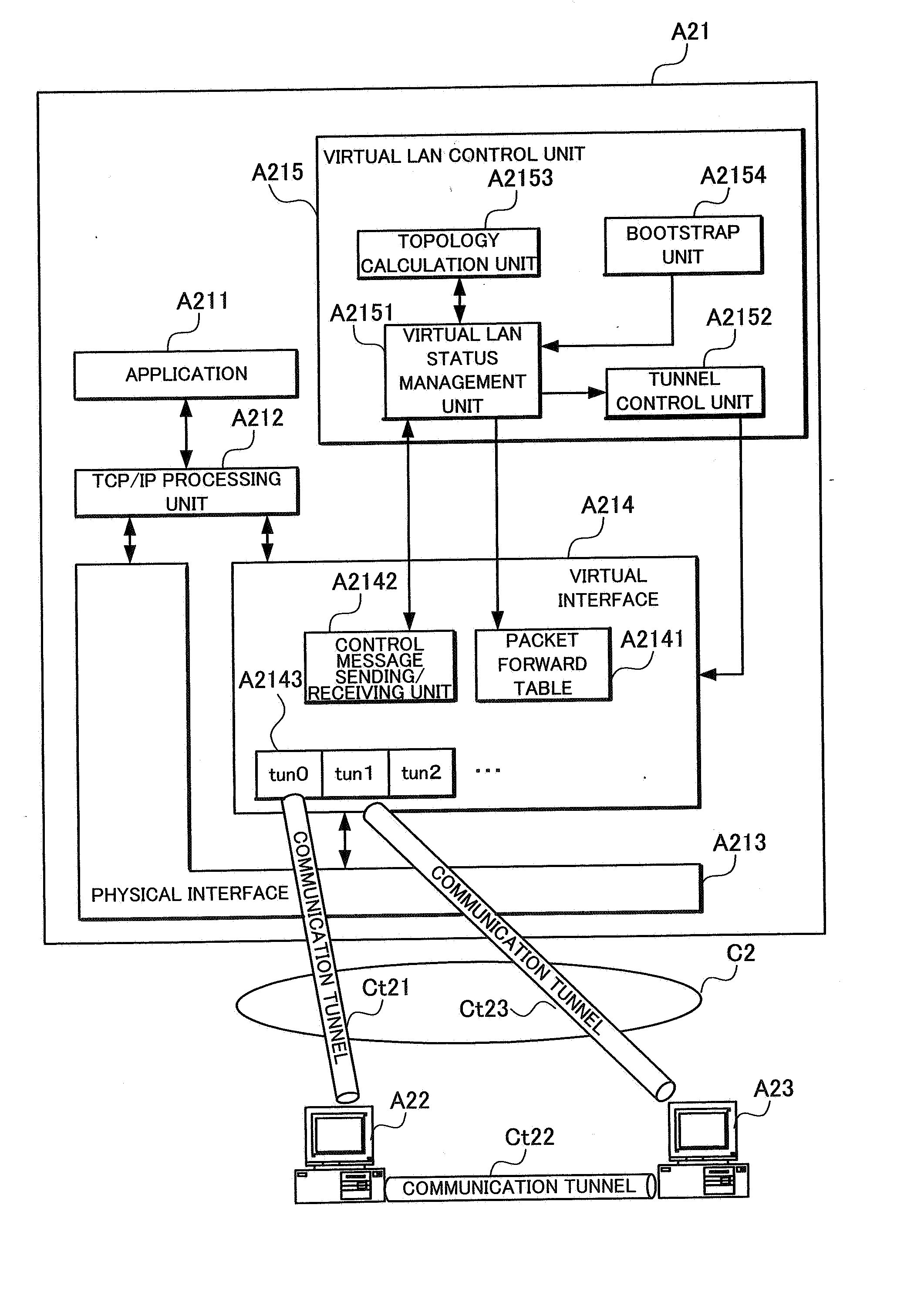
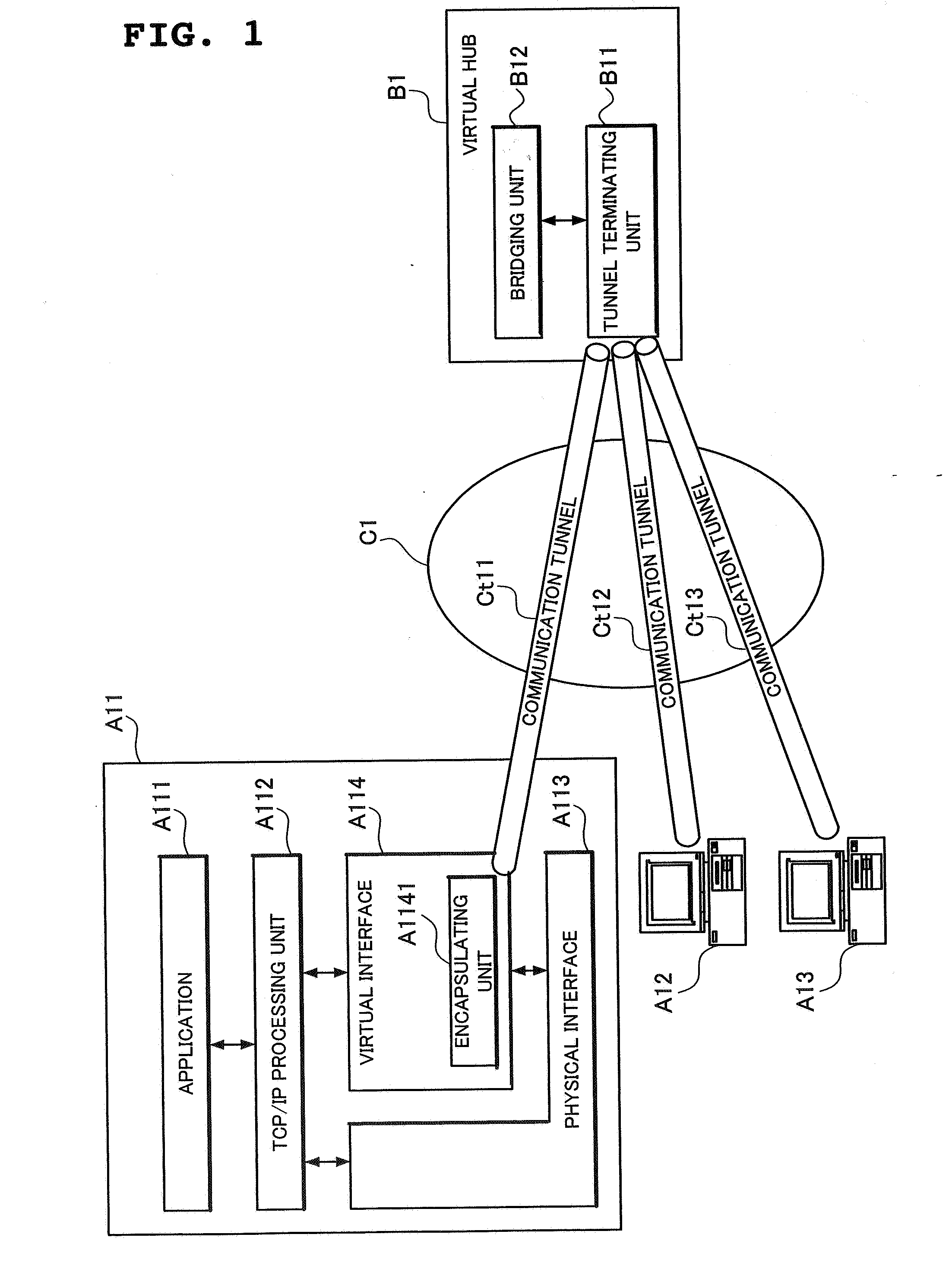
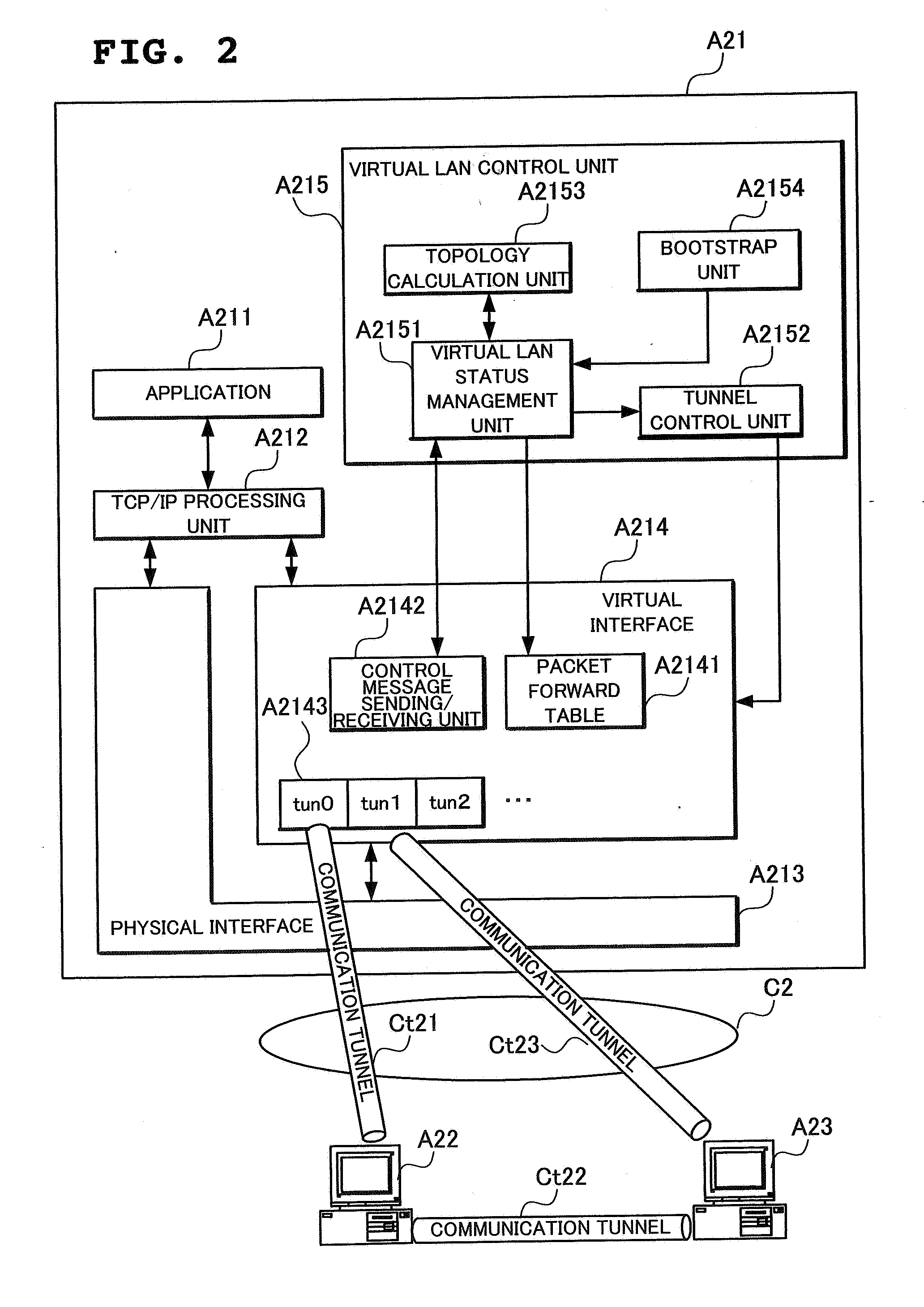
Virtual lan system and node device
A node A21 sets a communication tunnel for encapsulating a data link packet with other nodes joining in a virtual LAN to a peer-to-peer type, and comprises a packet forward table A2141 for forwarding the data link layer packet received from a communication tunnel to another communication tunnel. In addition, the node A21 reconfigures the topology of the virtual LAN using a topology calculation unit A2153 when another node withdrew from the virtual LAN, and opens or removes communication tunnels according to the reconfigured topology using a tunnel control unit A2152.
Owner:NEC CORP
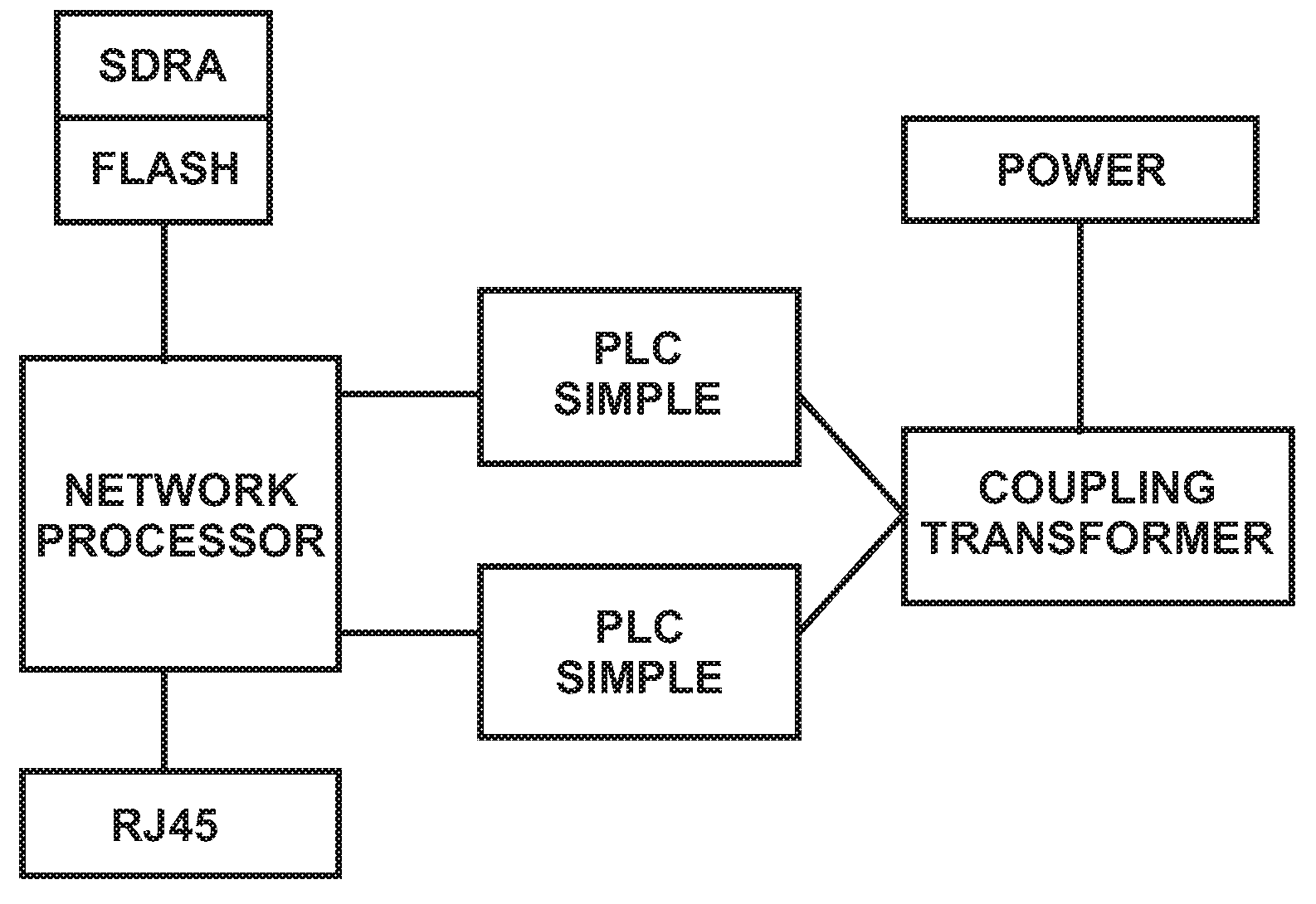
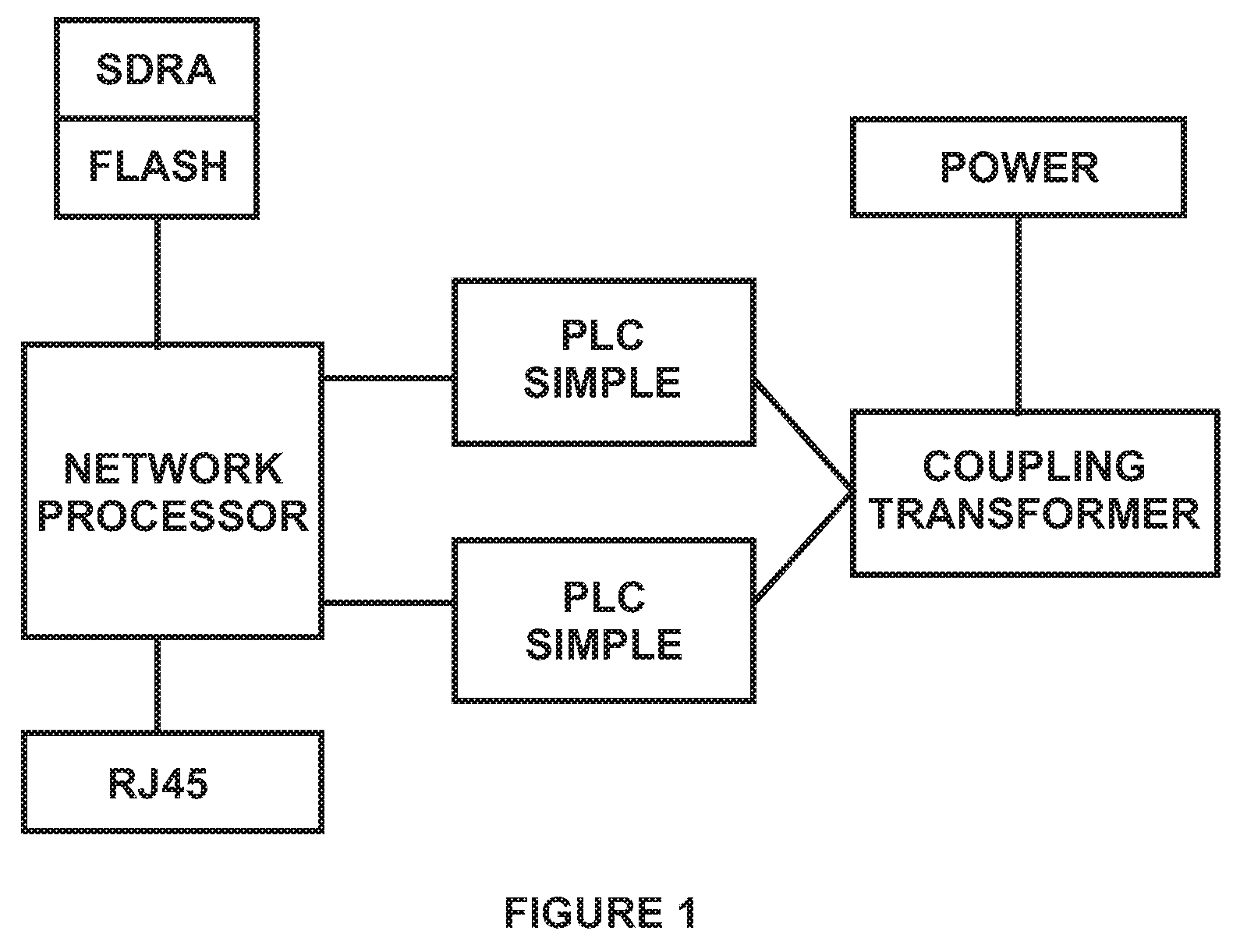
System and Method for Repeater in a Power Line Network
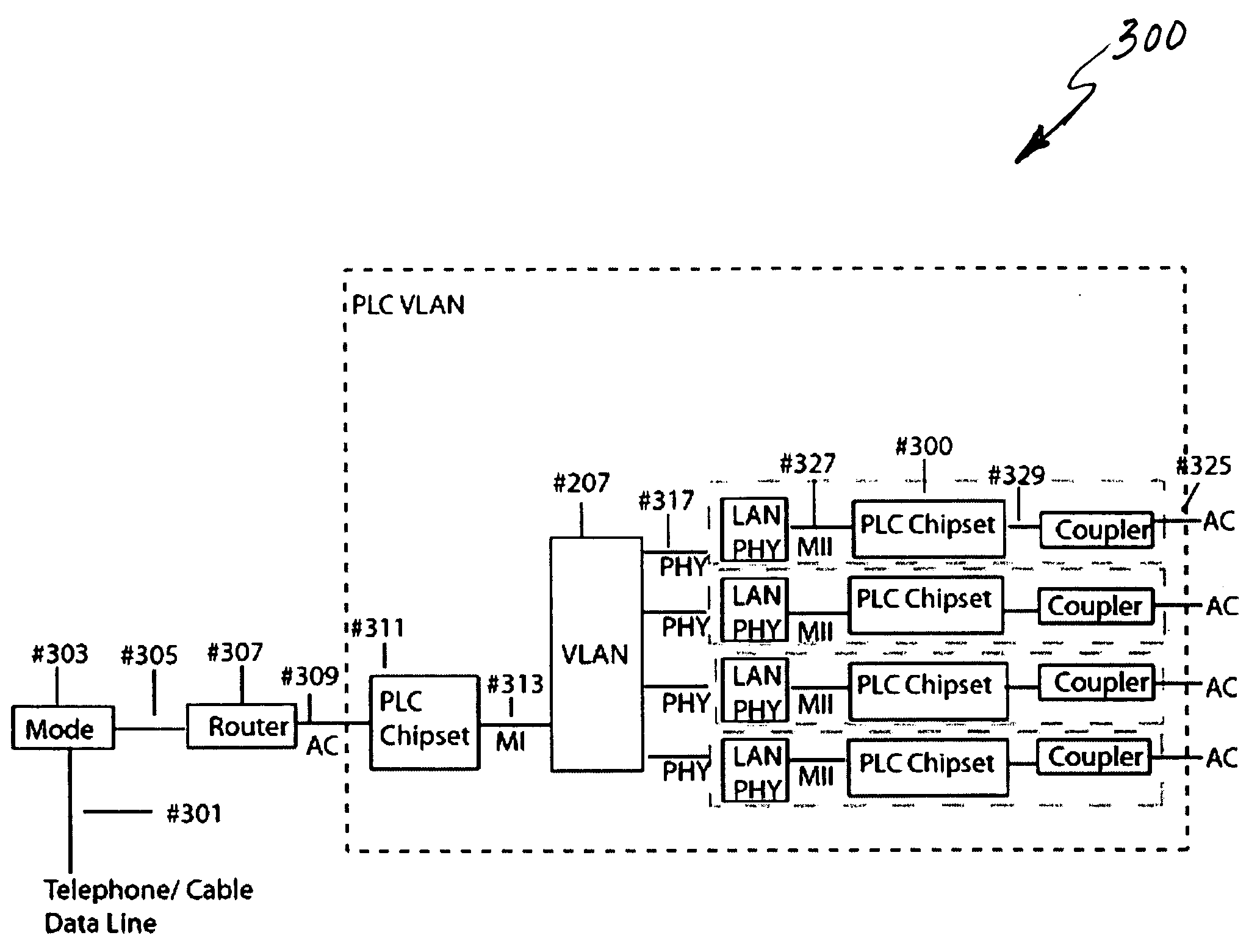
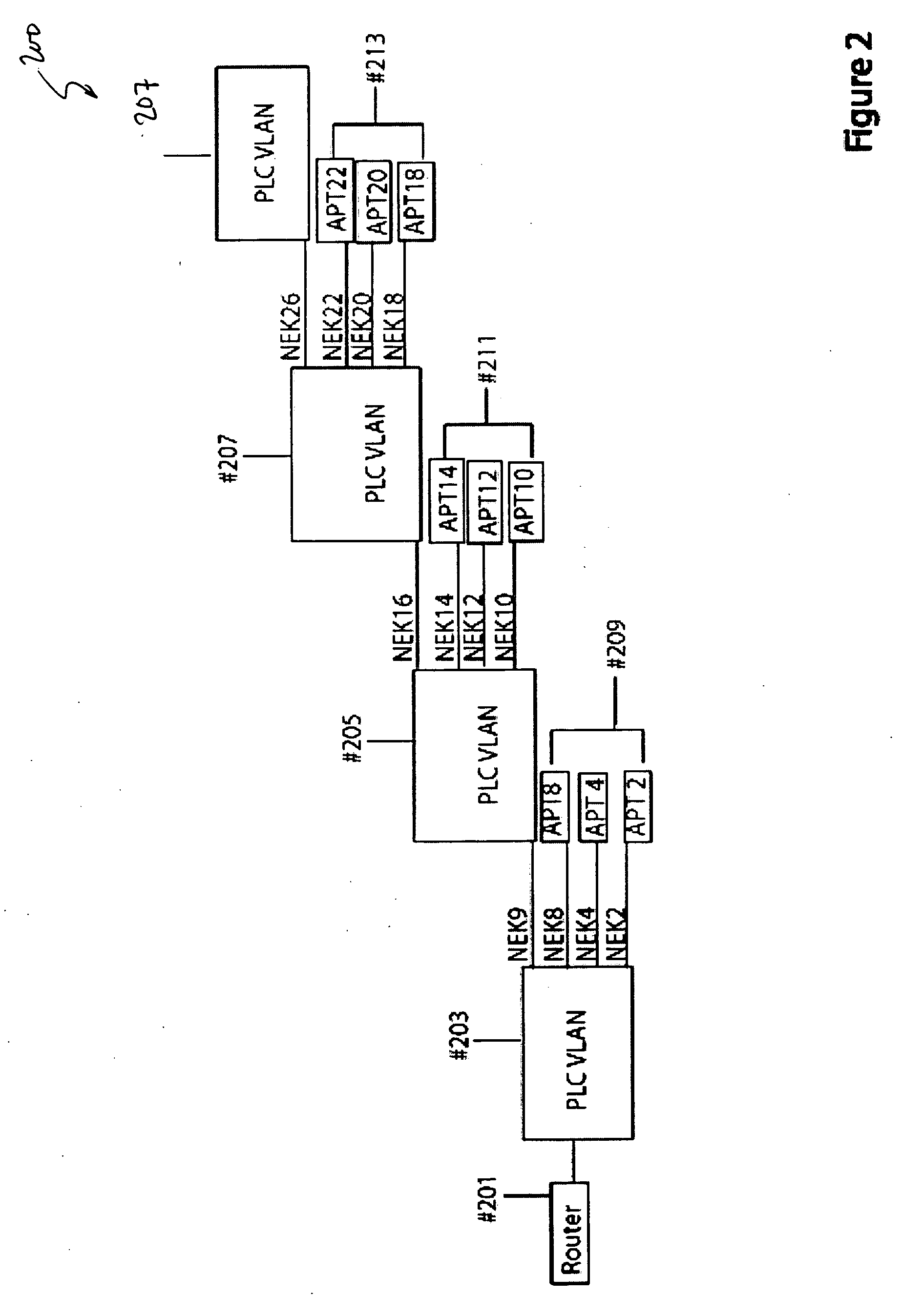
InactiveUS20090135848A1Low costSmall sizeModulated-carrier systemsPower distribution line transmissionVirtual LANPower line network
System and method for repeater in a power line network. According to an embodiment, the present invention provides a method for power line communication network. The method includes providing a virtual local area network (VLAN), which VLAN includes at least a repeater, a client, and a gateway. The VLAN is associated with a network encryption key. The repeater is associated with a first identification. The client is associated with a second identification. The gateway is associated with a third identification. The first identification and the third identification are a service identification type. The second identification is a client identification type. The method also includes providing a power line network that is configured to transmit data through OFDM signaling. The method includes sending a first data packet in first format from the client through the power line network. The method additionally includes receiving the first data packet by the repeater through the power line network at through a first network interface.
Owner:ASOKA USA CORP
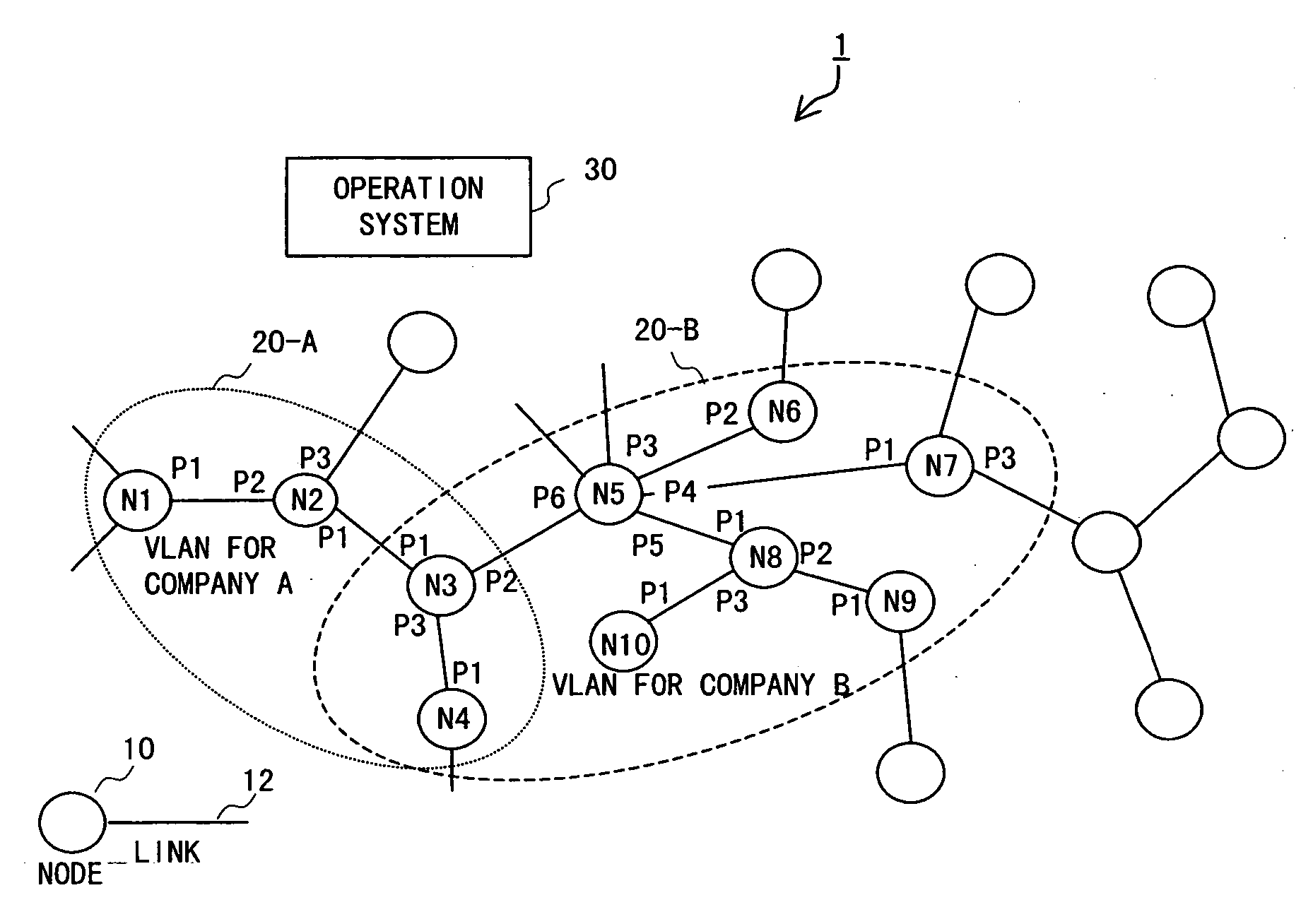
Method and apparatus for keeping track of virtual LAN topology in network of nodes
An arbitrary node that belongs to a virtual LAN sends a request packet including a count value indicating the number of communication hops across nodes to each of its adjacent nodes that belong to the virtual LAN and are adjacent. Upon receiving the request packet, each of the adjacent nodes sends the request packet in which the count value is incremented or decremented, as predetermined, to each of its adjacent nodes that belong to the virtual LAN and are adjacent to the node, excluding a sender of the request packet received, and sends a reply packet including the sender's address (sender address), an address of the node that is a replying node (replying node address), and the count value to a given return destination. The return destination collects reply packets sent thereto and keeps track of the topology of the nodes constituting the virtual LAN from information contained in the reply packets.
Owner:FUJITSU LTD
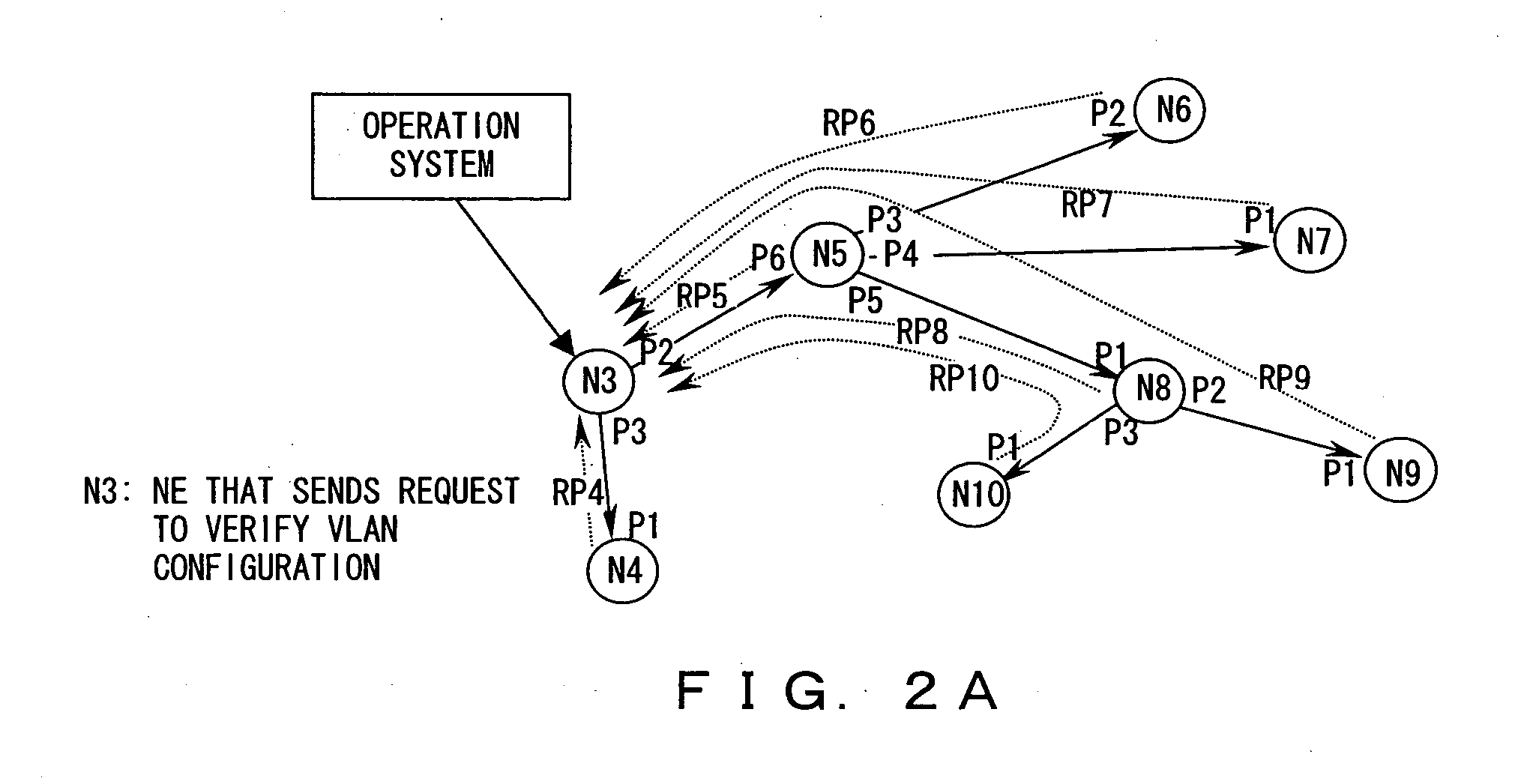
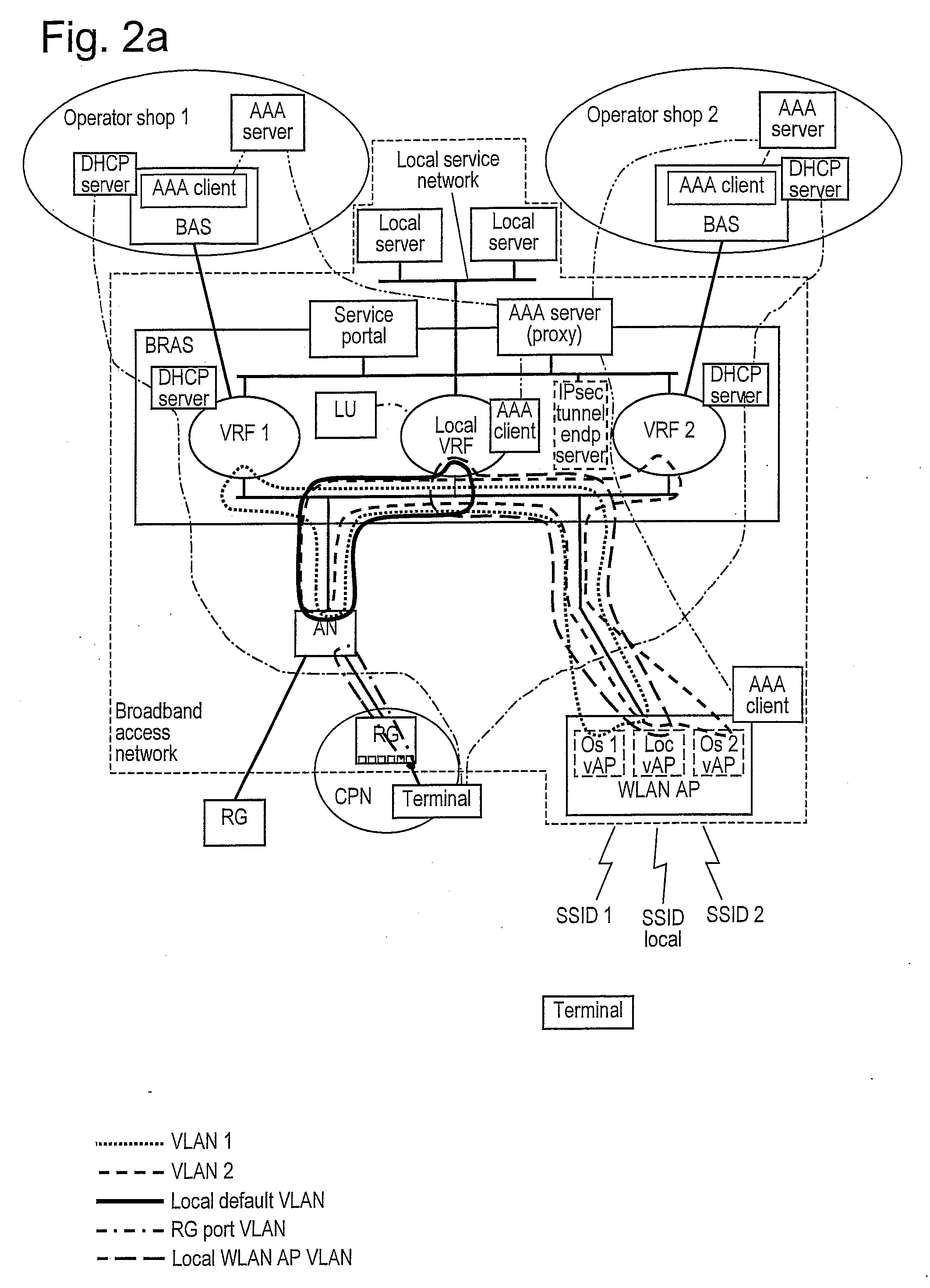
Operator Shop Selection
An access node for an Ethernet network is connected between an access point of user devices and a broadband remote access server for access to a plurality of service providing networks. It includes a VLAN handling unit having a memory for storing identifications of Ethernet frames transmitted in a first VLAN including the access node and a local virtual router function unit of the access server in a second VLANs. Each of the second VLANs including the access node, the local virtual router function unit and one of the virtual router function units of the access server for each of the virtual router function units. A control unit commands the handling unit to transmit frames from a new user device that has connected itself to the access point into the first virtual local area network. The control unit also receives information from the access server in respect of routing frames and its commands to the handling unit to transmit frames from user device which is connected to the access point and the frames from which are transmitted into the first VLAN to be instead transmitted into one of the second VLAN as given by the information received from the broadband remote access server, the frames thereby being transmitted to the server of the respective service providing network.
Owner:TELEFON AB LM ERICSSON (PUBL)
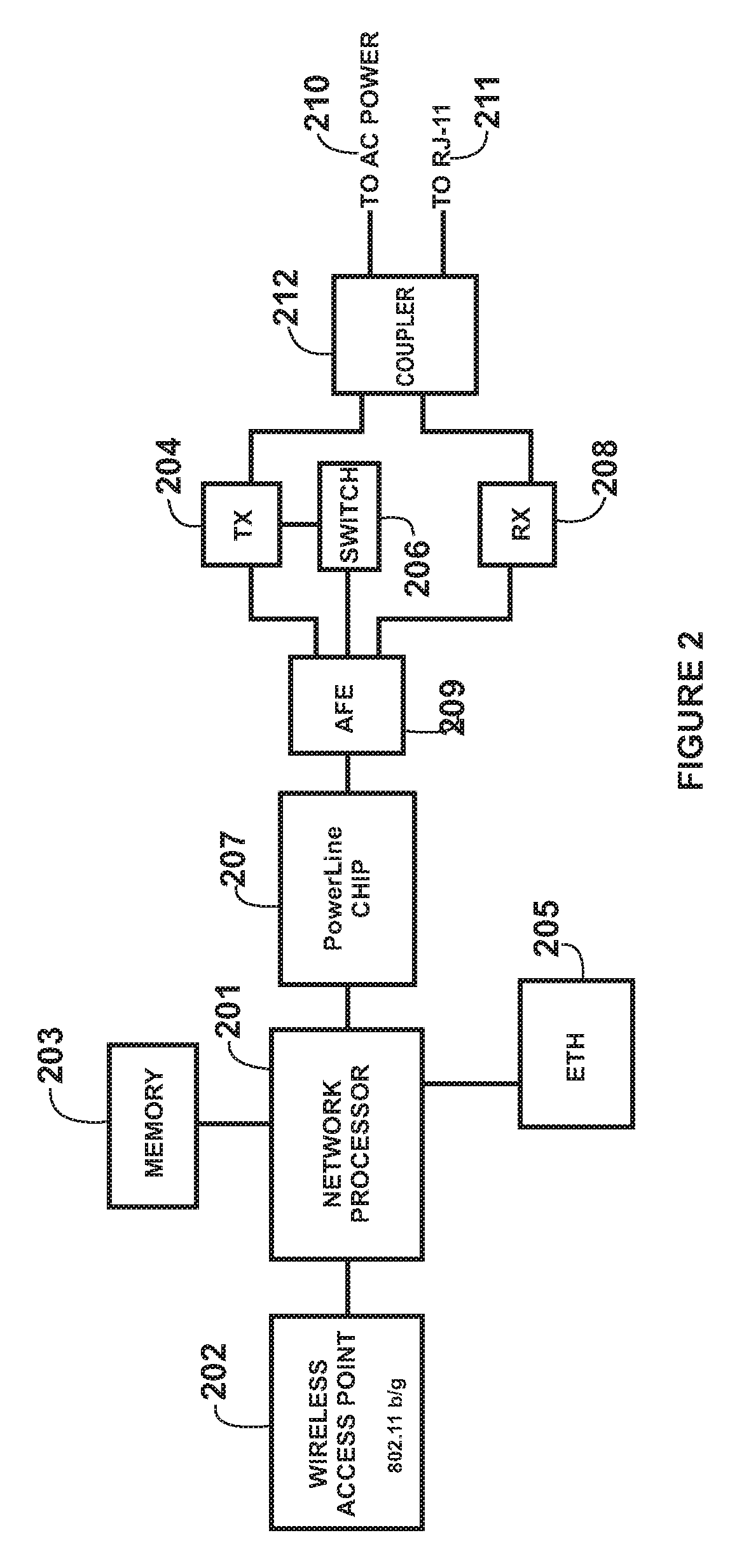
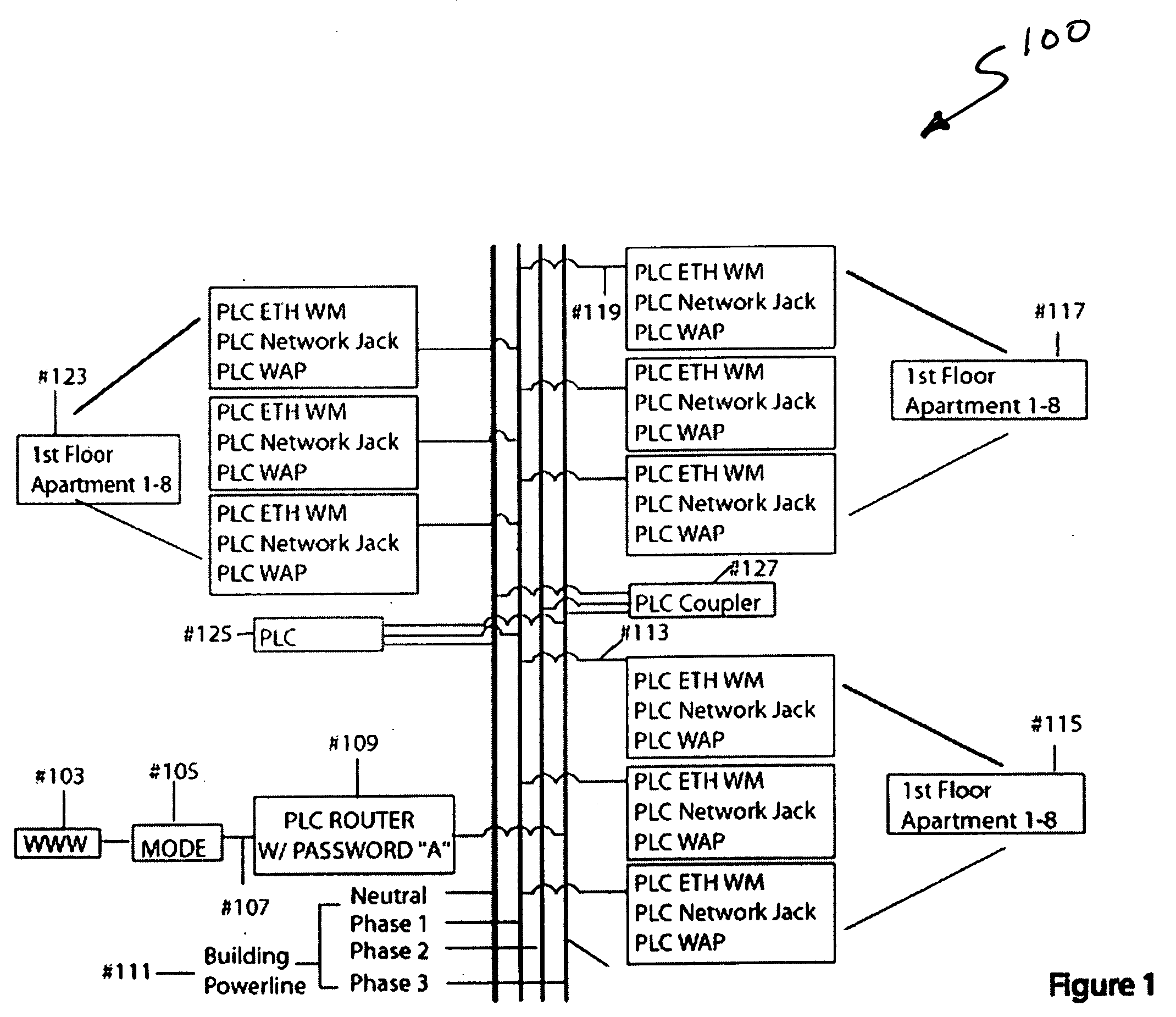
Method and system for virtual powerline local area networks
InactiveUS20050076148A1Easy to implementSelective connectionSystems using filtering and bypassingPower distribution line transmissionVirtual LANModem device
A system for powerline networking. The system has an external data source, which is derived from a world wide networks of computers. A router is coupled to the external data source and coupled to a first datasource connection. A powerline network switch apparatus is coupled to the first datasource connection. The apparatus has a second datasource connection, which is coupled to the first data source connection. The apparatus also has a powerline device coupled to the second datasource connection. Preferably, the powerline device is adapted to receive and transmit information in a first format from the second data source connection and adapted to receive and transmit information in a second format. The apparatus also has a virtual local area network device including a first input / output port and a plurality of second input / output ports. Each of the second input / output ports is numbered from 1 through N, where N is an integer greater than 1. A plurality of modem devices are coupled to the virtual local area network device. The plurality of modem devices are numbered from 1 through N, where each of the plurality of modem devices being coupled respectively to one of the plurality of second input / output ports and where each of the plurality of modem devices also being coupled to one of a plurality of power lines numbered from 1 through N, each of the power lines being capable of communicating information to and from the second data source connection.
Owner:ASOKA USA CORP
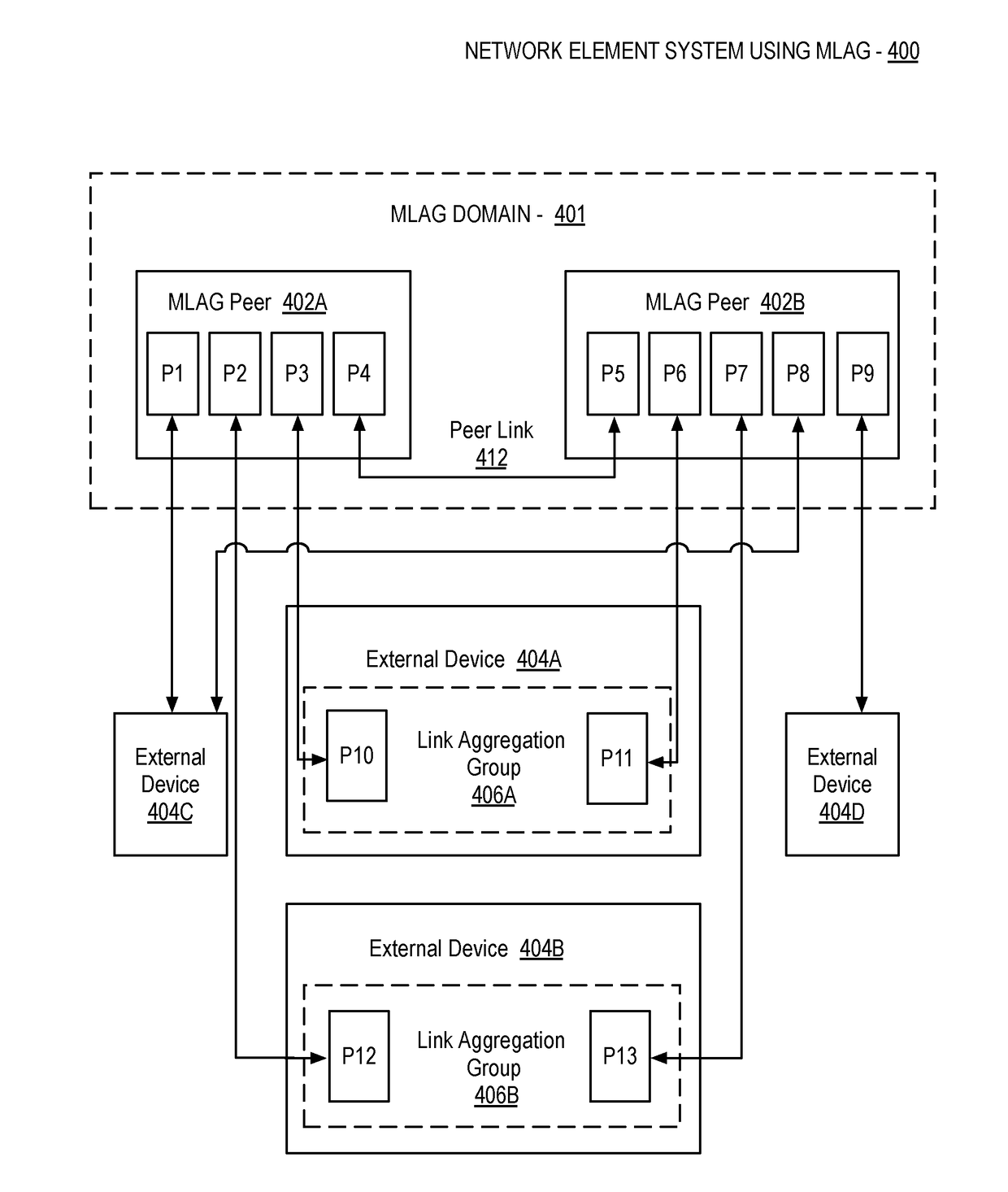
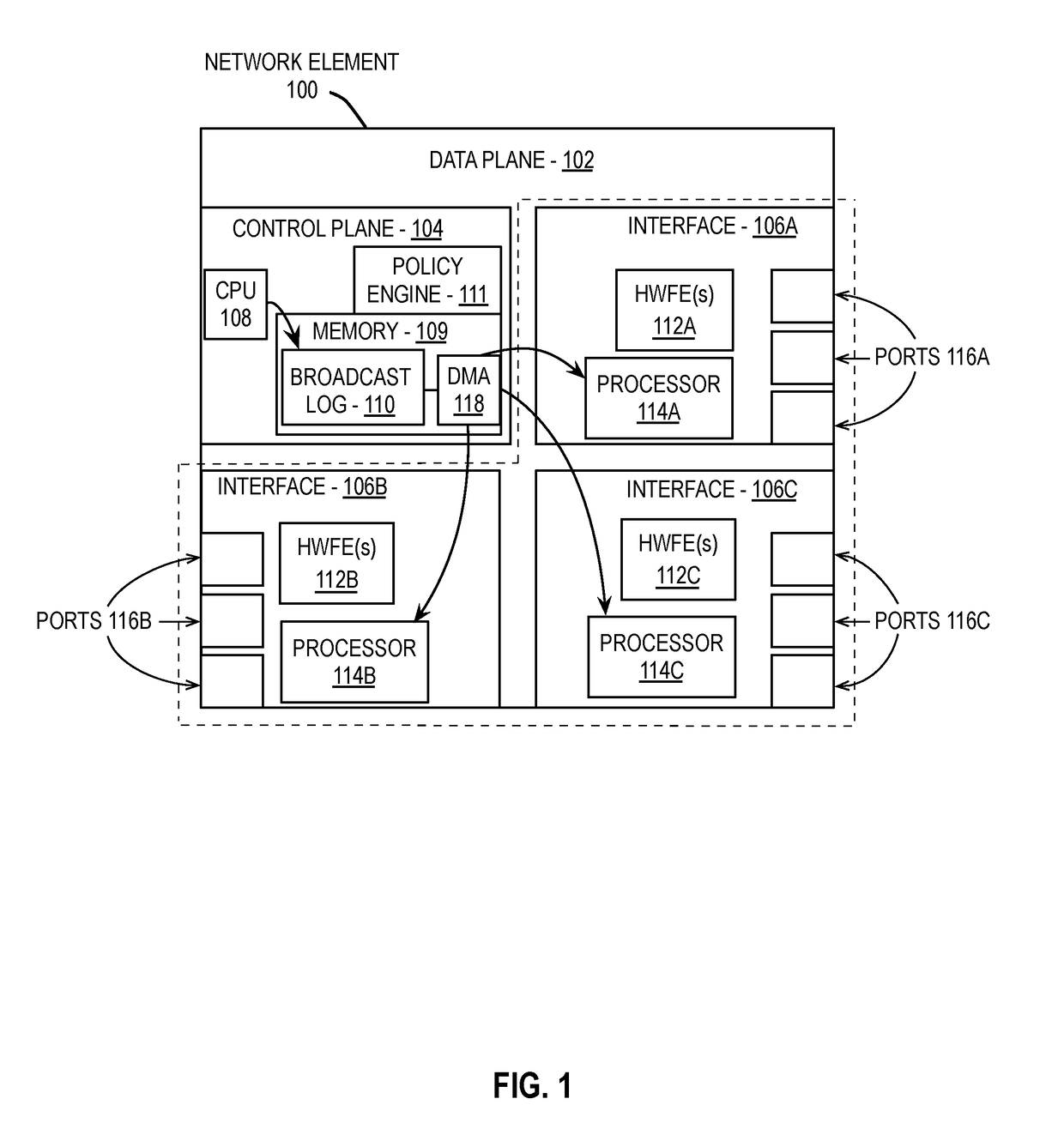
Network management system control service for vxlan on an mlag domain
Various embodiments are described herein that provide a network system comprising a first network element coupled to a network and a second network element directly coupled to the first network element. The first network element and the second network element are to connect to form a link aggregation group. The system additionally includes a network management device including a control agent, where the control agent is configured to configure the link aggregation group as a logical virtual tunnel end point (VTEP) of a virtual local area network (VLAN).
Owner:ARISTA NETWORKS
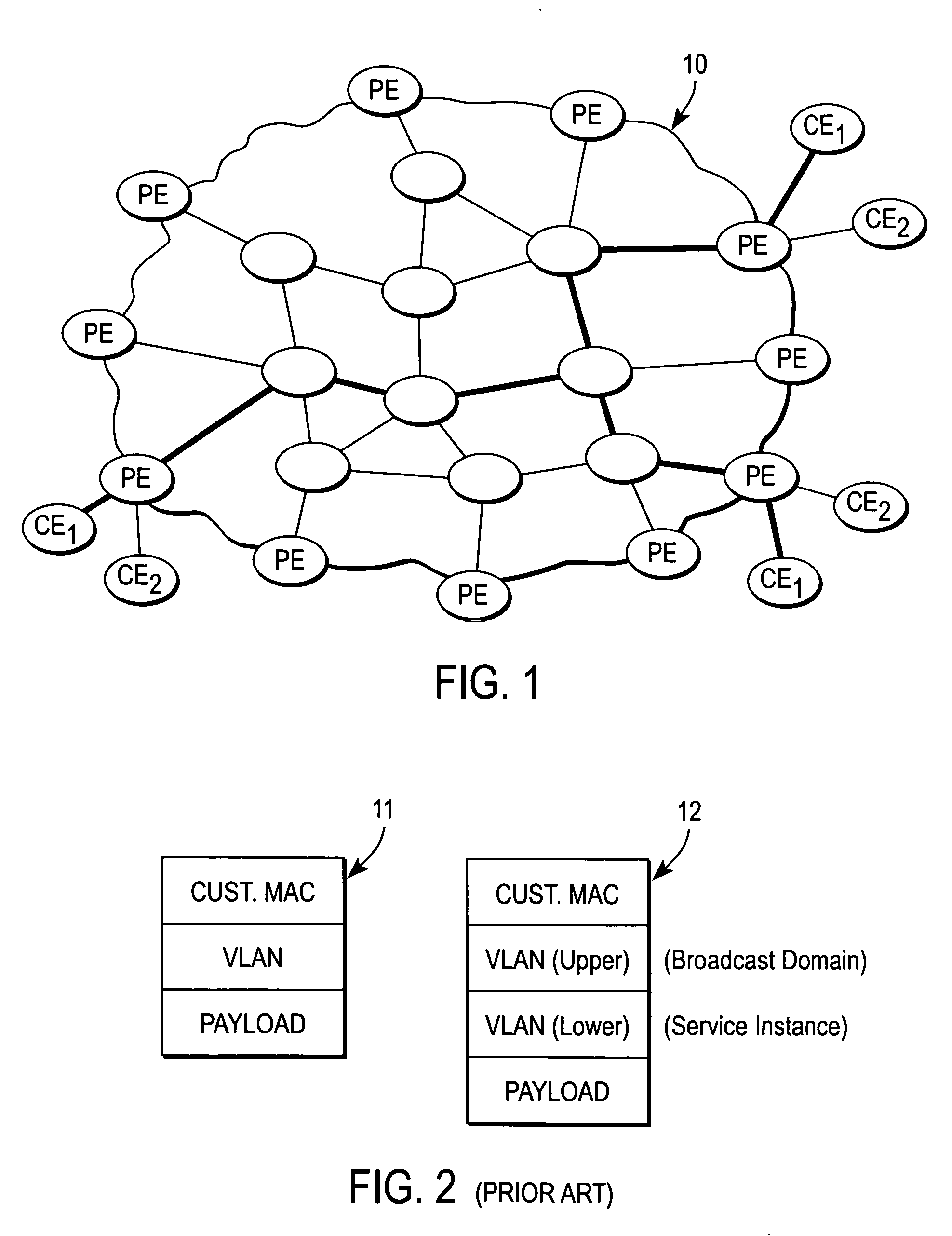
Metro ethernet network with scaled broadcast and service instance domains
ActiveUS20060245438A1Special service provision for substationMetropolitian area networksAccess networkVirtual LAN
A method of operation for a provider edge device of a core network includes receiving a customer frame from an access network; the customer frame having a first Virtual Local Area Network (VLAN) tag of a first predetermined bit length. The first VLAN tag including a service instance identifier. The service instance identifier of the first VLAN tag is then mapped into a second VLAN tag of a second predetermined bit length greater than the first predetermined bit length. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
System and method for initializing and maintaining a series of virtual local area networks contained in a clustered computer system
InactiveUS20090106405A1Multiple digital computer combinationsProgram controlVirtual LANNetwork connection
A system and method for sharing network resources; the system comprising: (1) at least one network switch; (2) a plurality of computing devices, where the computing device comprises (i) at least one network connection; (ii) a plurality of processing nodes; and (iii) at least one storage device containing software for (a) initializing and maintaining a plurality of top-layer virtual local area networks (VLANs), (b) initializing and maintaining a plurality of client VLANs; and (c) using an empty VLAN as a virtual wire between the client VLAN and a shared network resource.
Owner:VIRTUDATACENT HLDG
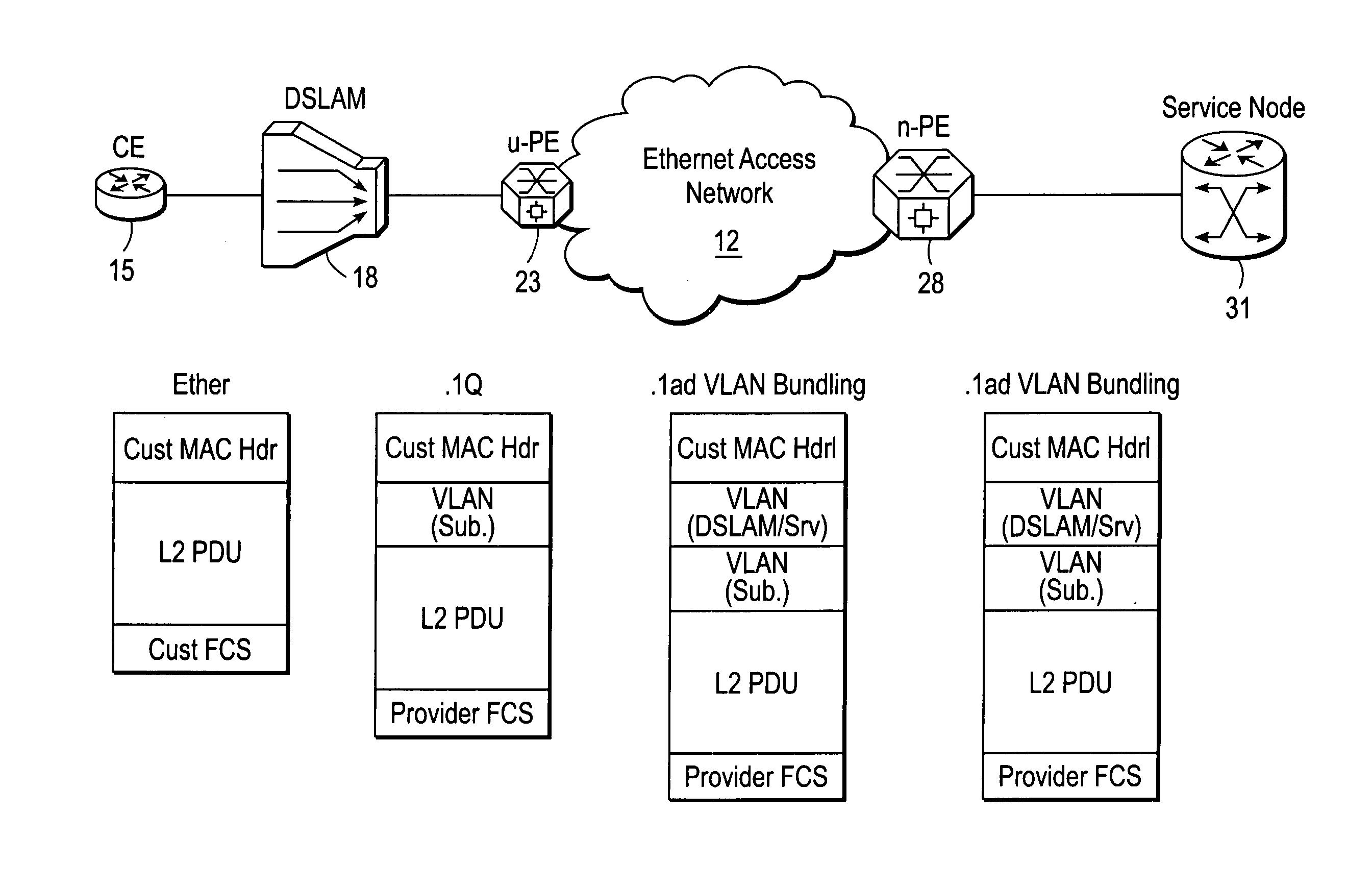
System and method for DSL subscriber identification over ethernet network
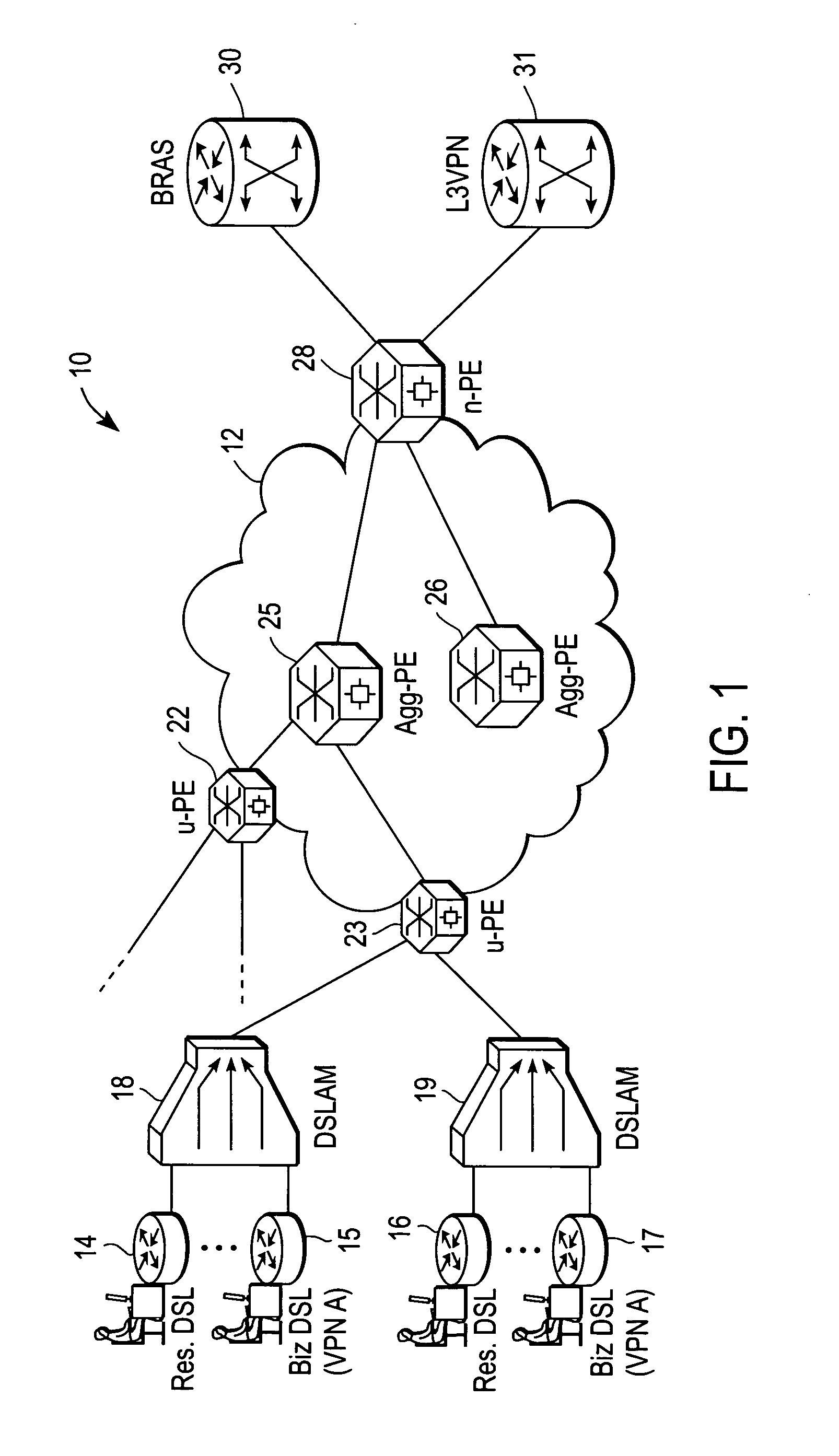
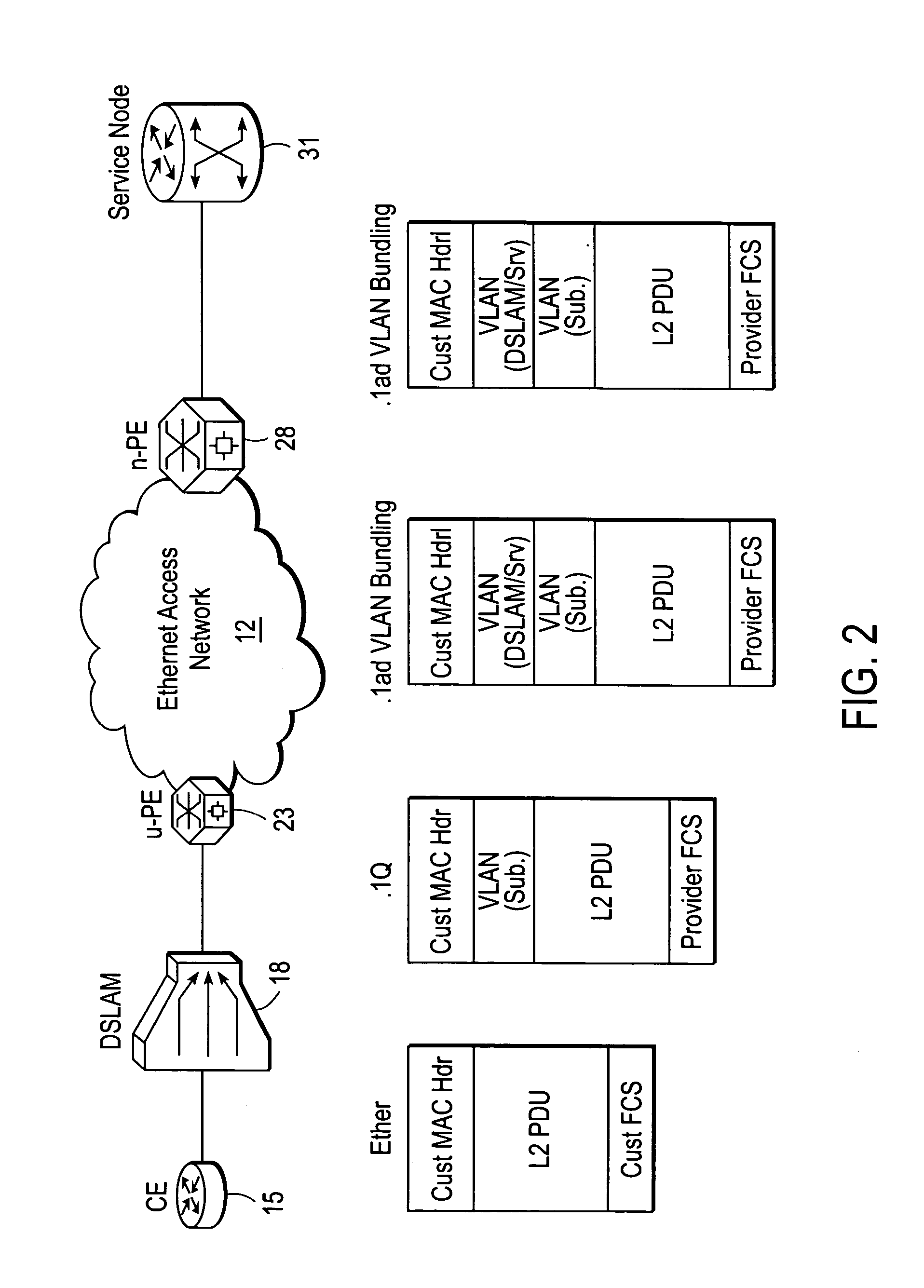
ActiveUS20060245439A1Data switching by path configurationNetwork connectionsDigital subscriber lineAccess network
A DSLAM aggregation topology VLAN bundling mechanism includes an edge device port that receives a packet from a Digital Subscriber Line Access Multiplexer (DSLAM) device, the packet including an inner Virtual Local Area Network (VLAN) tag that identifies a Digital Subscriber Line (DSL) subscriber. A processor of the edge device adds an outer VLAN tag to the packet, the outer VLAN tag identifying the DSLAM and a destination server coupled to an Ethernet access network. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com