Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
468 results about "Provider Edge" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
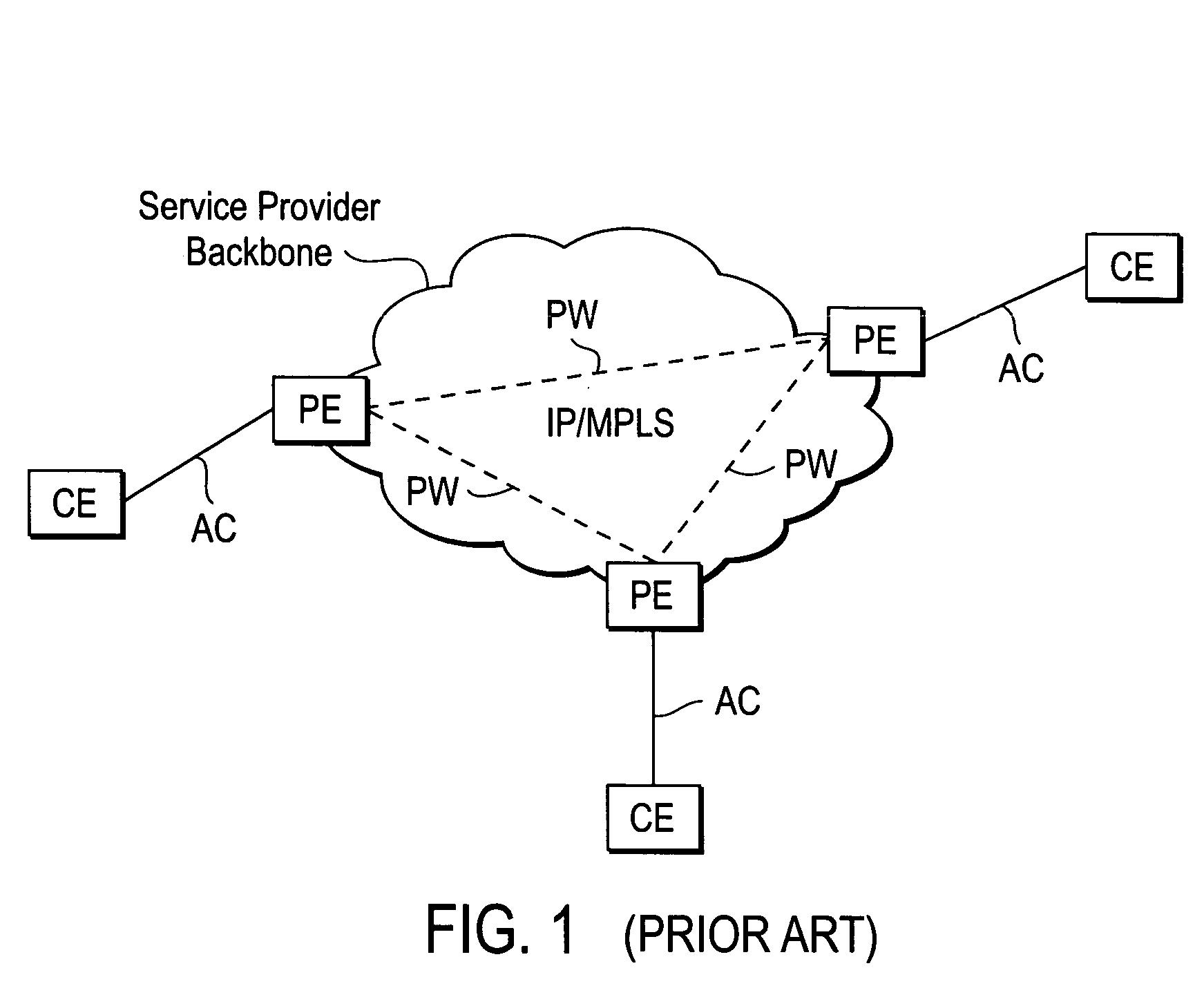
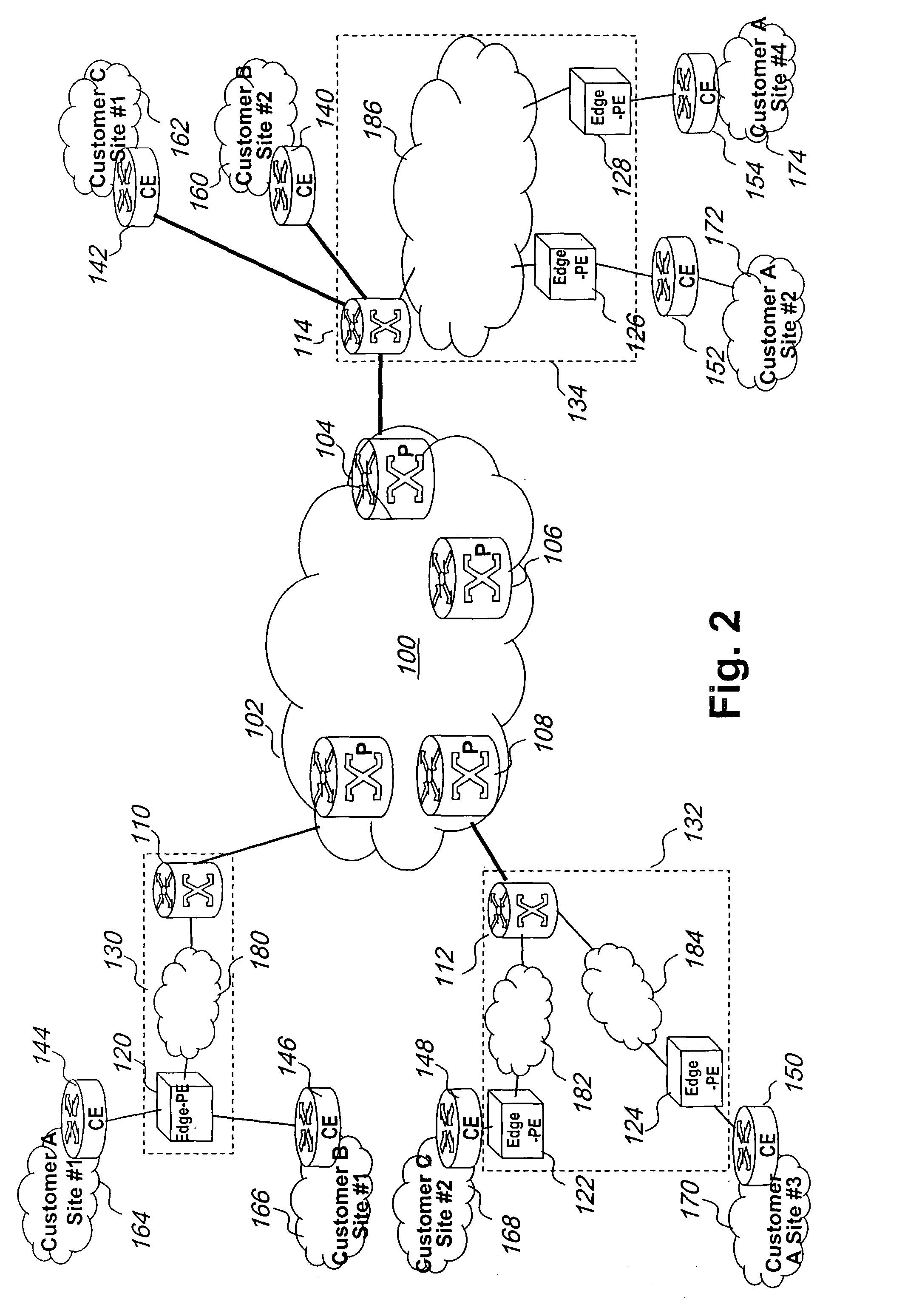
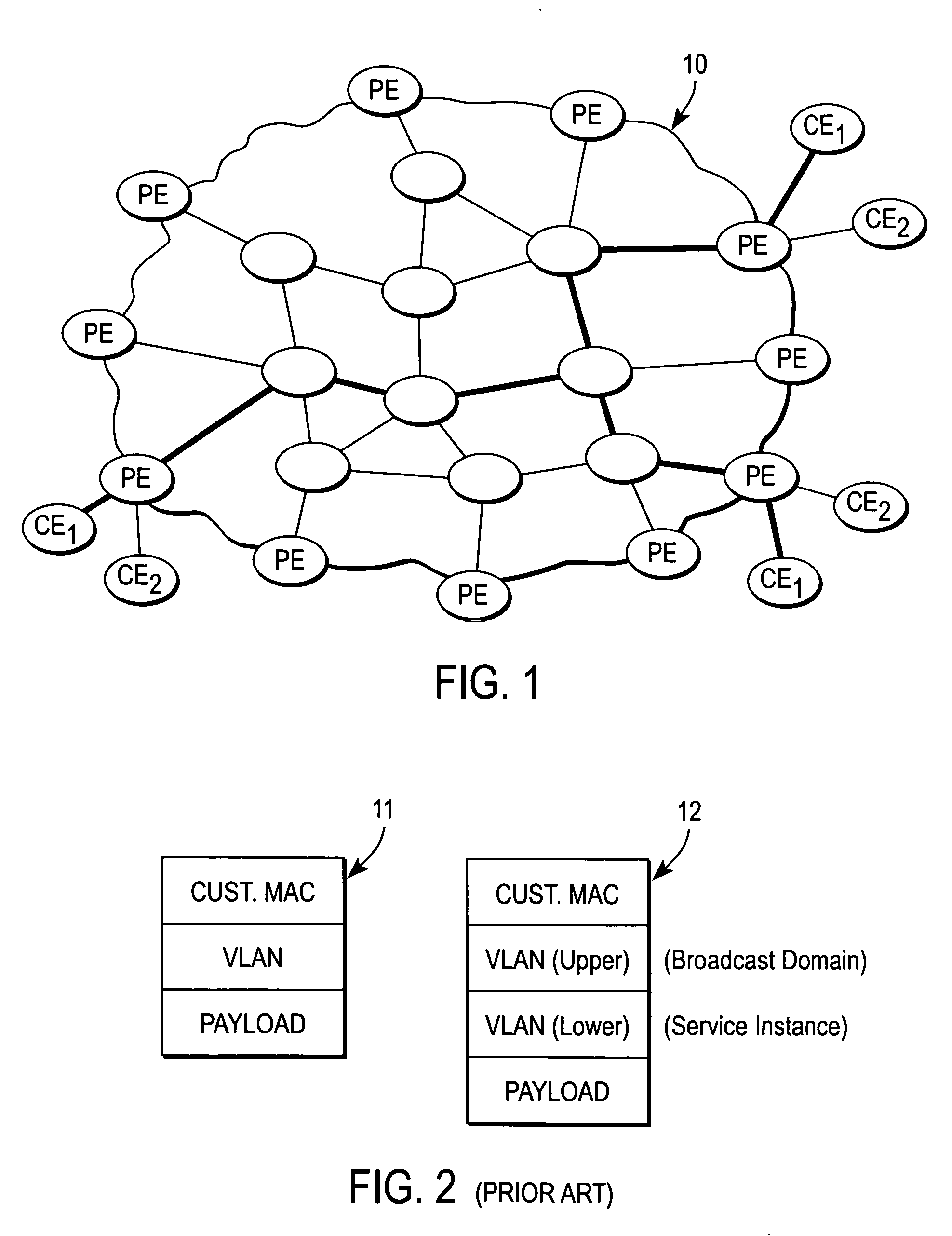
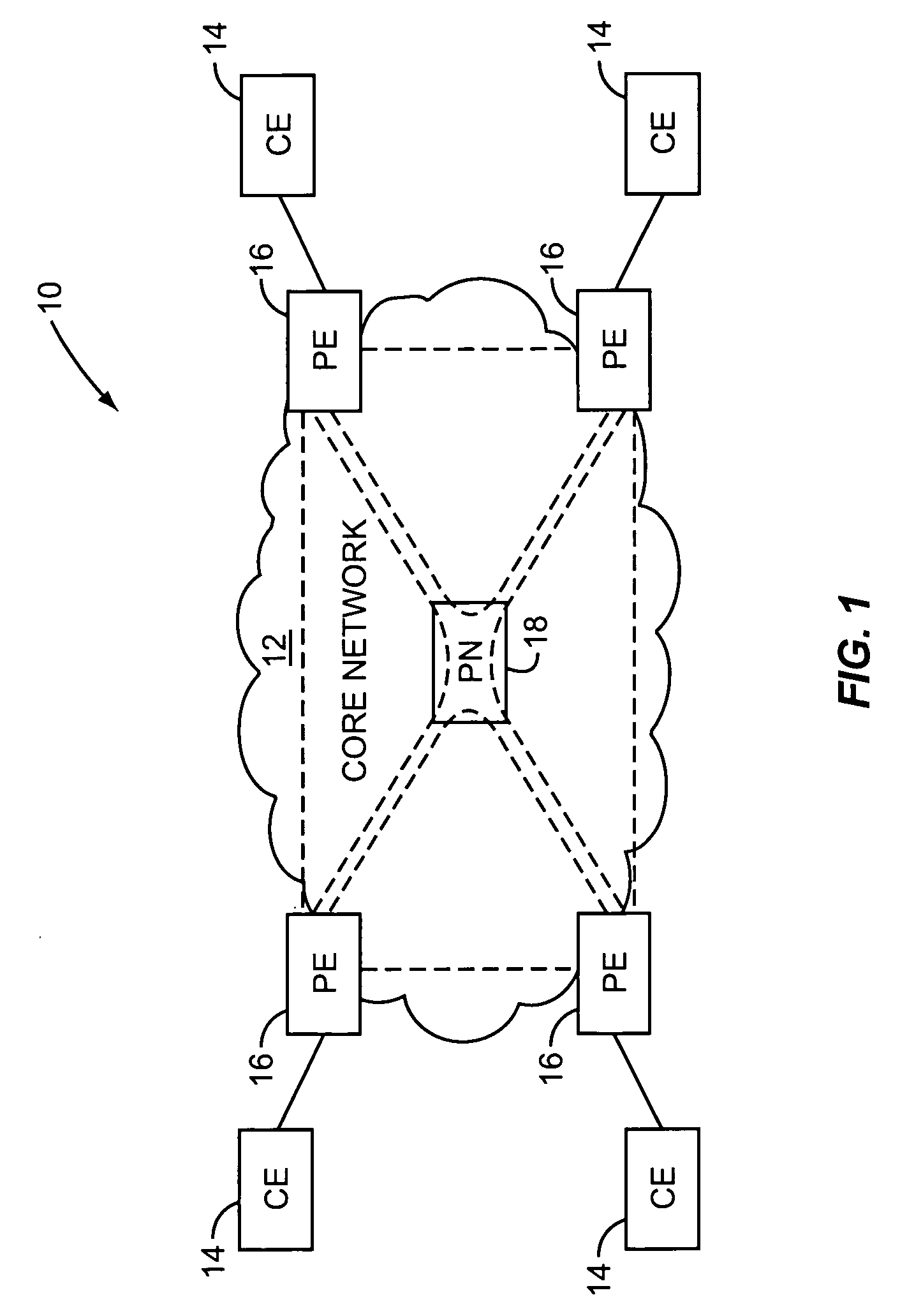
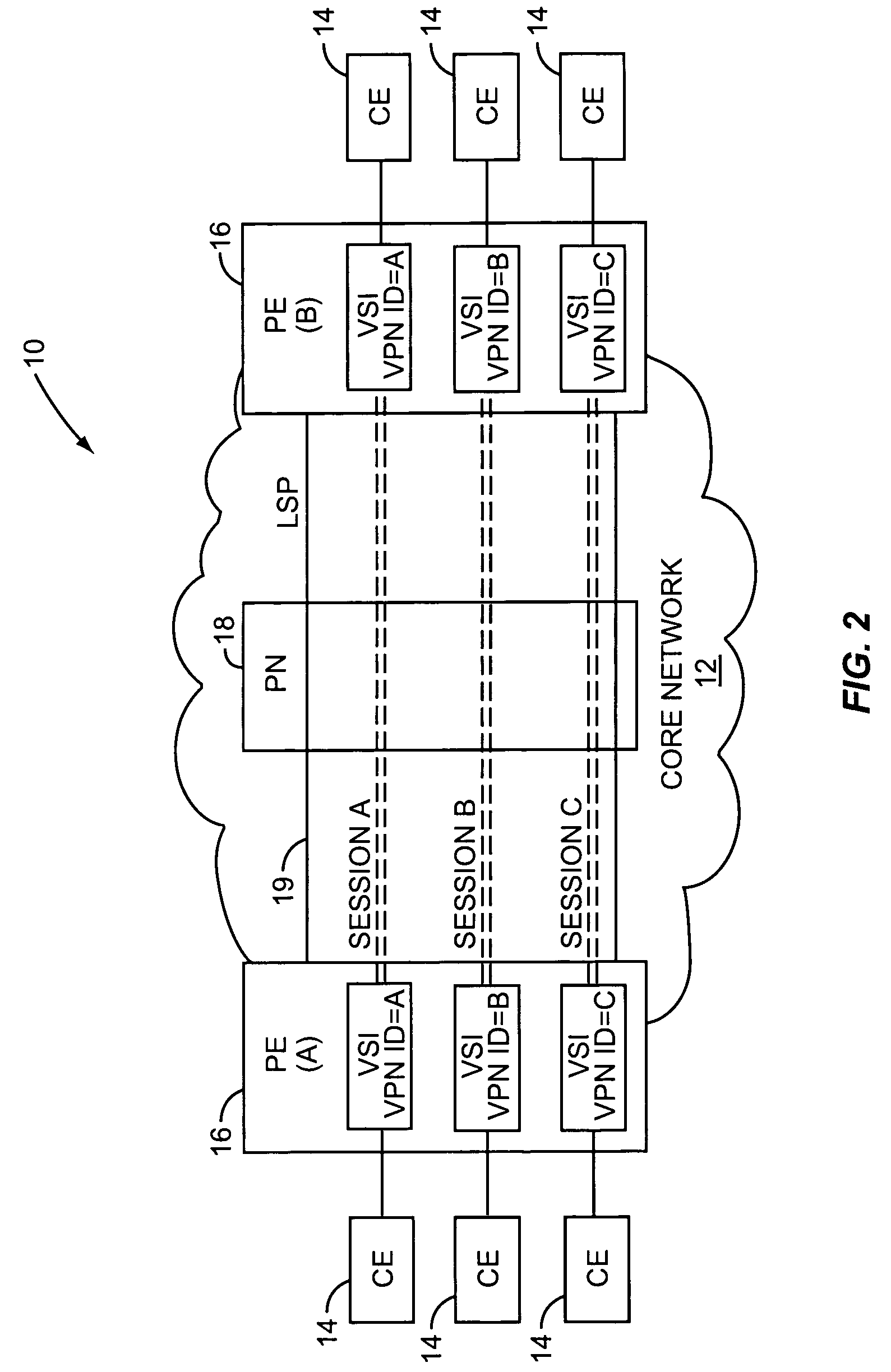
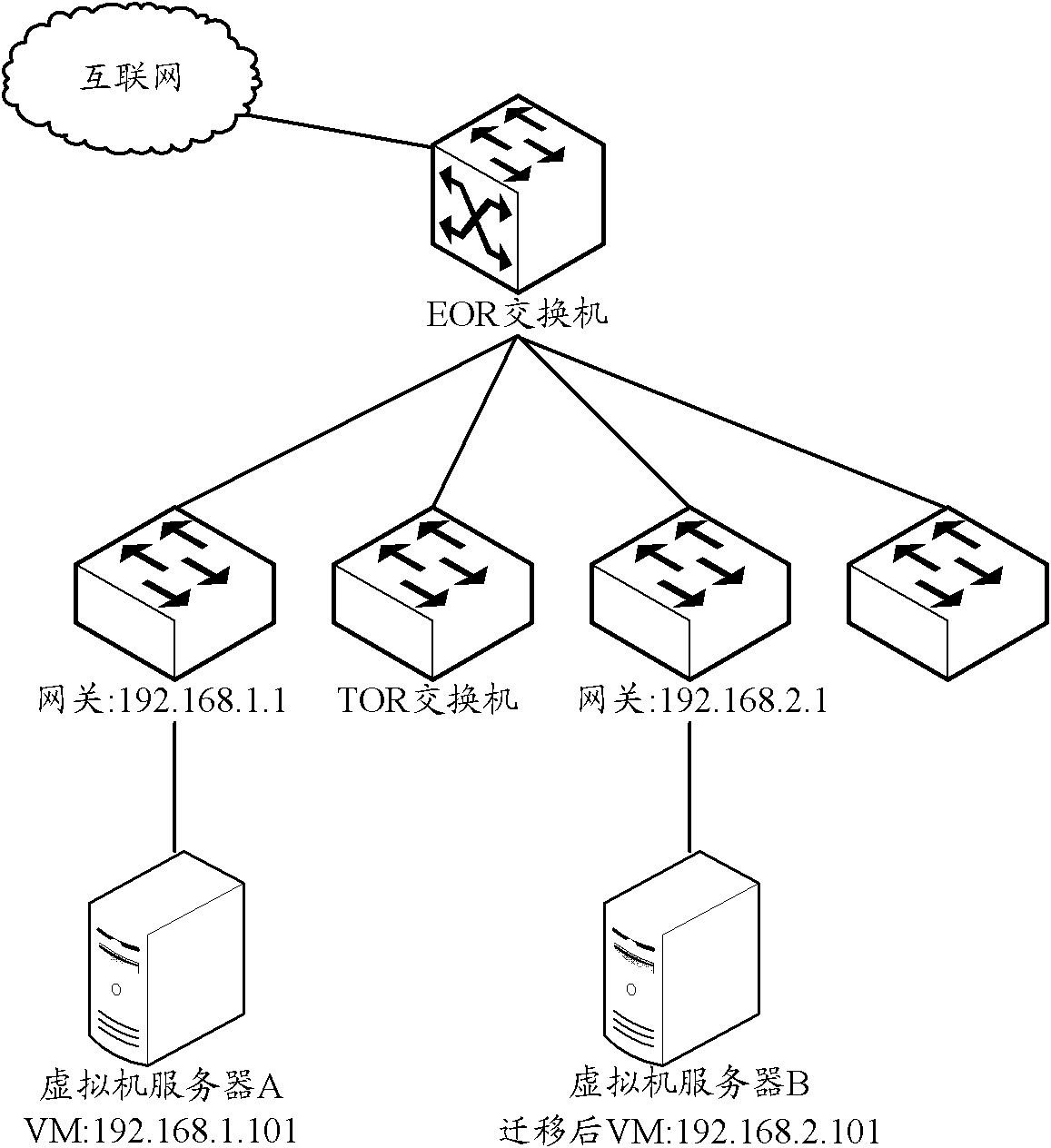
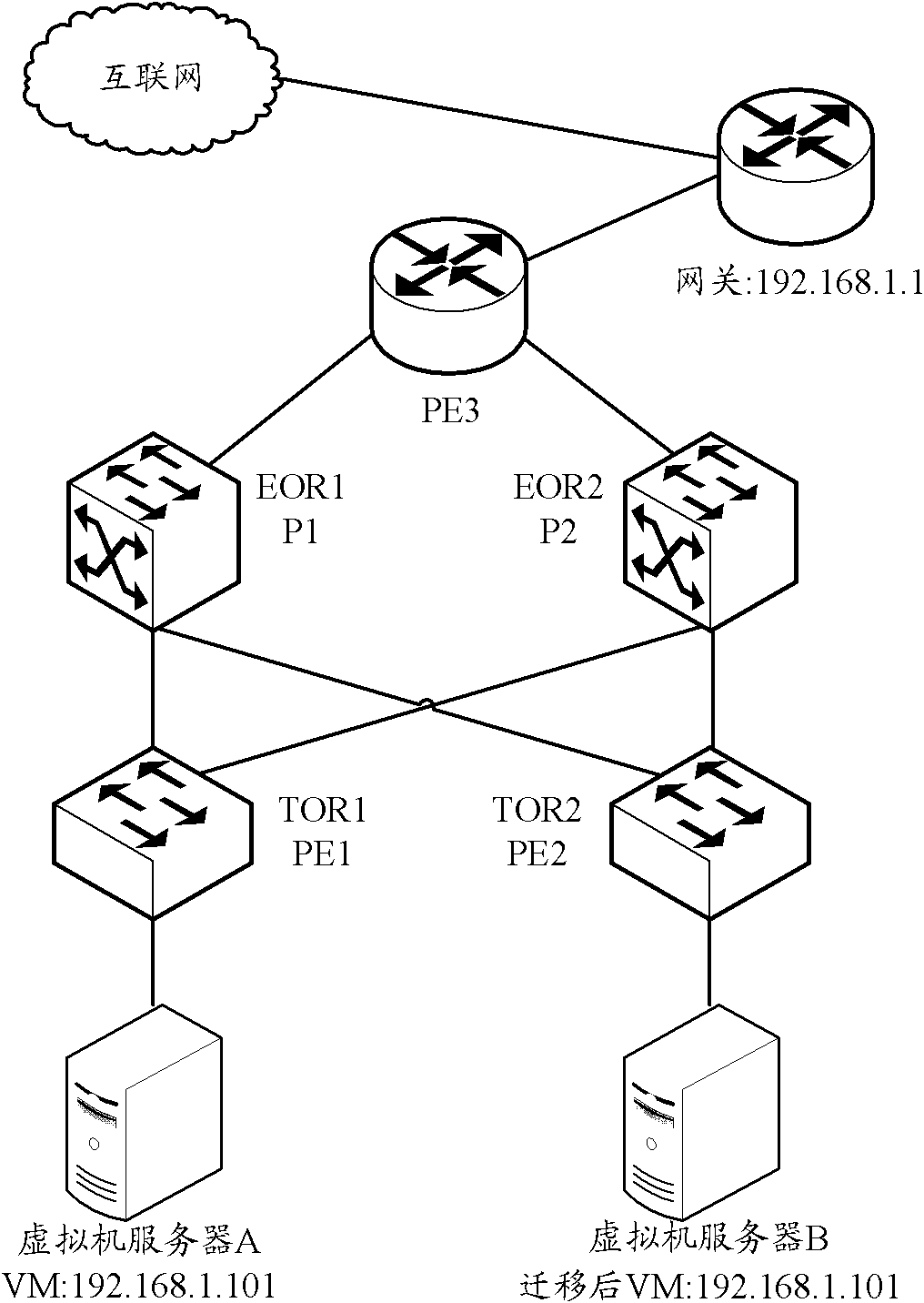
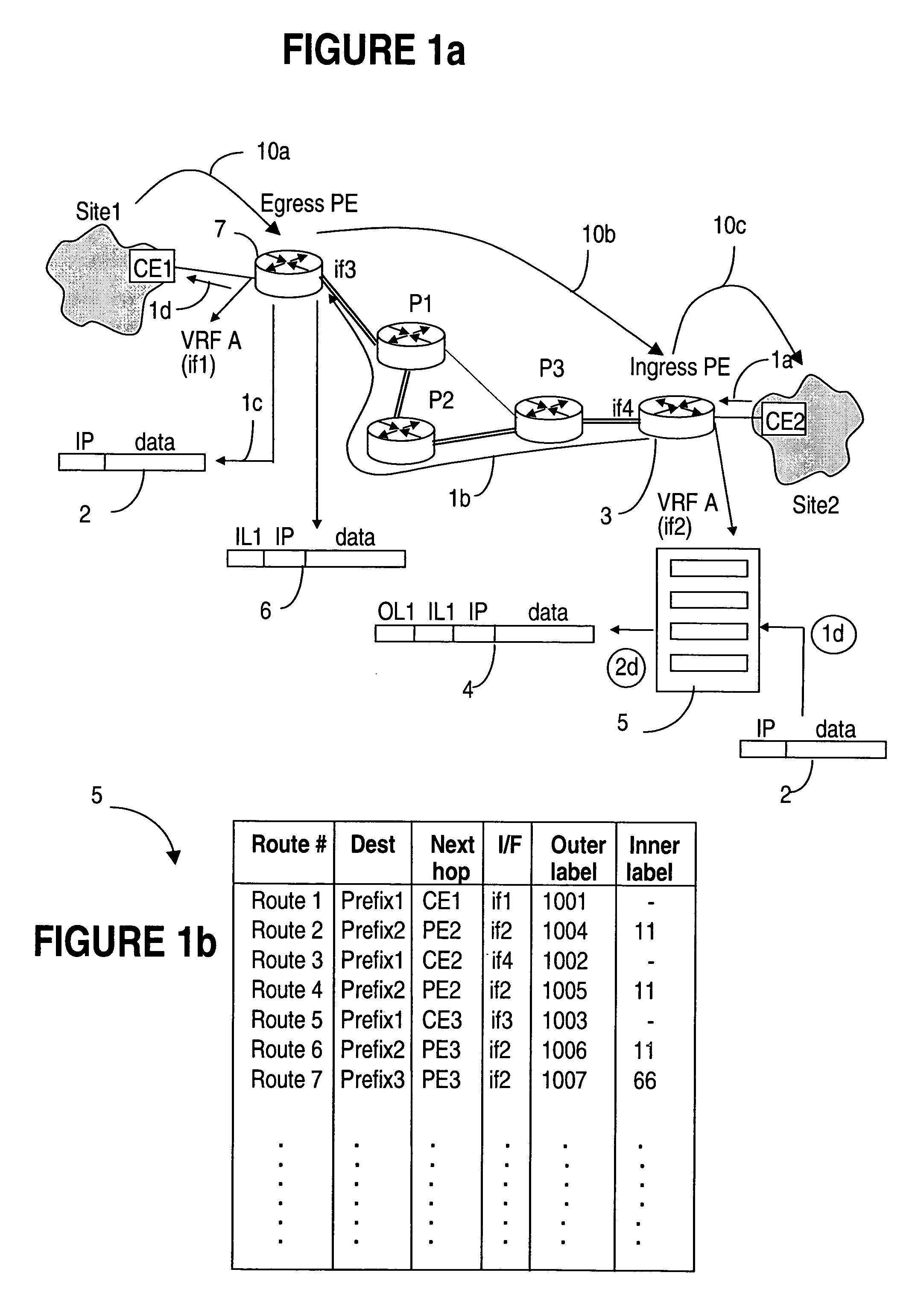
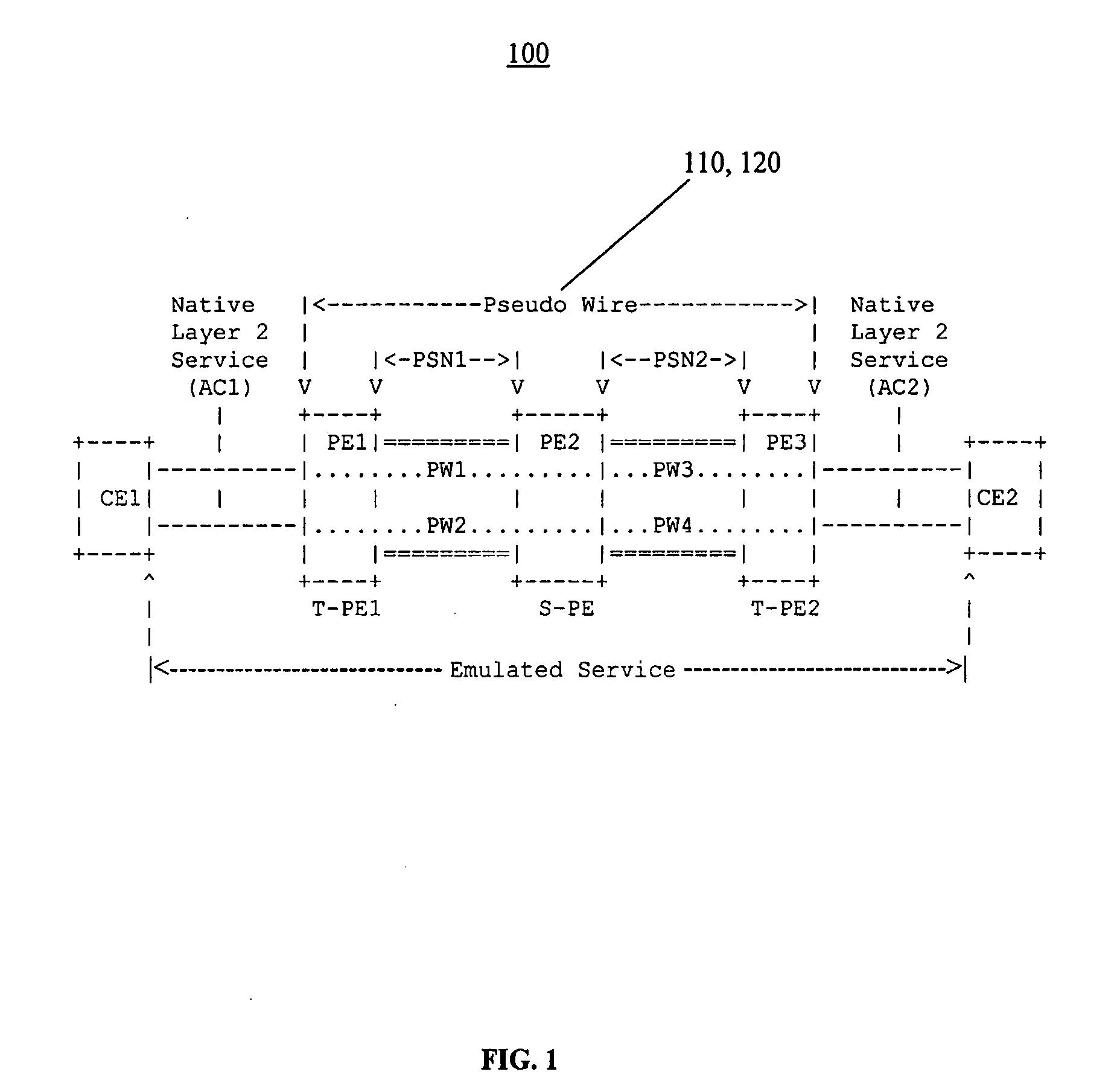
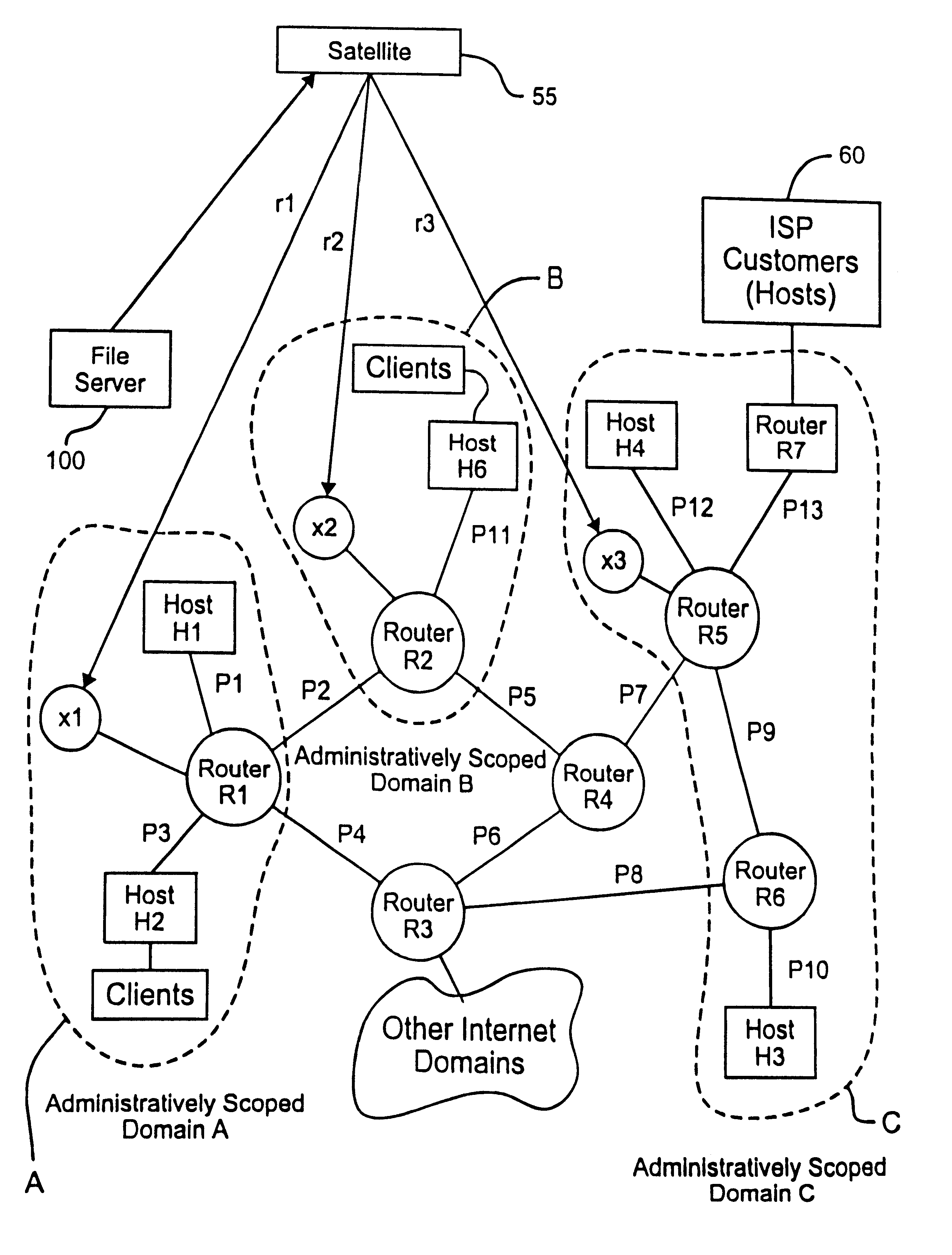
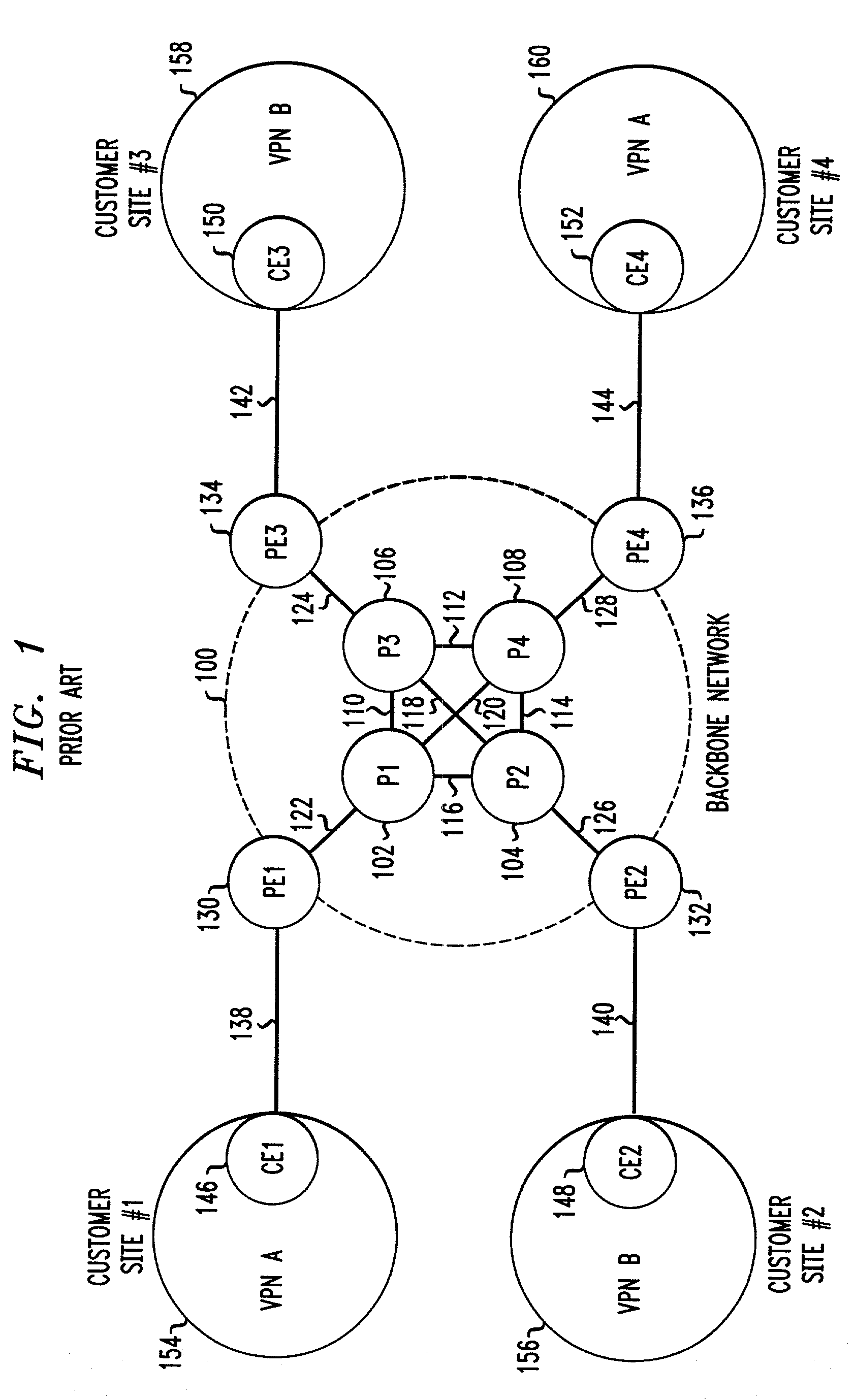
A Provider Edge router (PE router) is a router between one network service provider's area and areas administered by other network providers. A network provider is usually an Internet service provider as well (or only that).
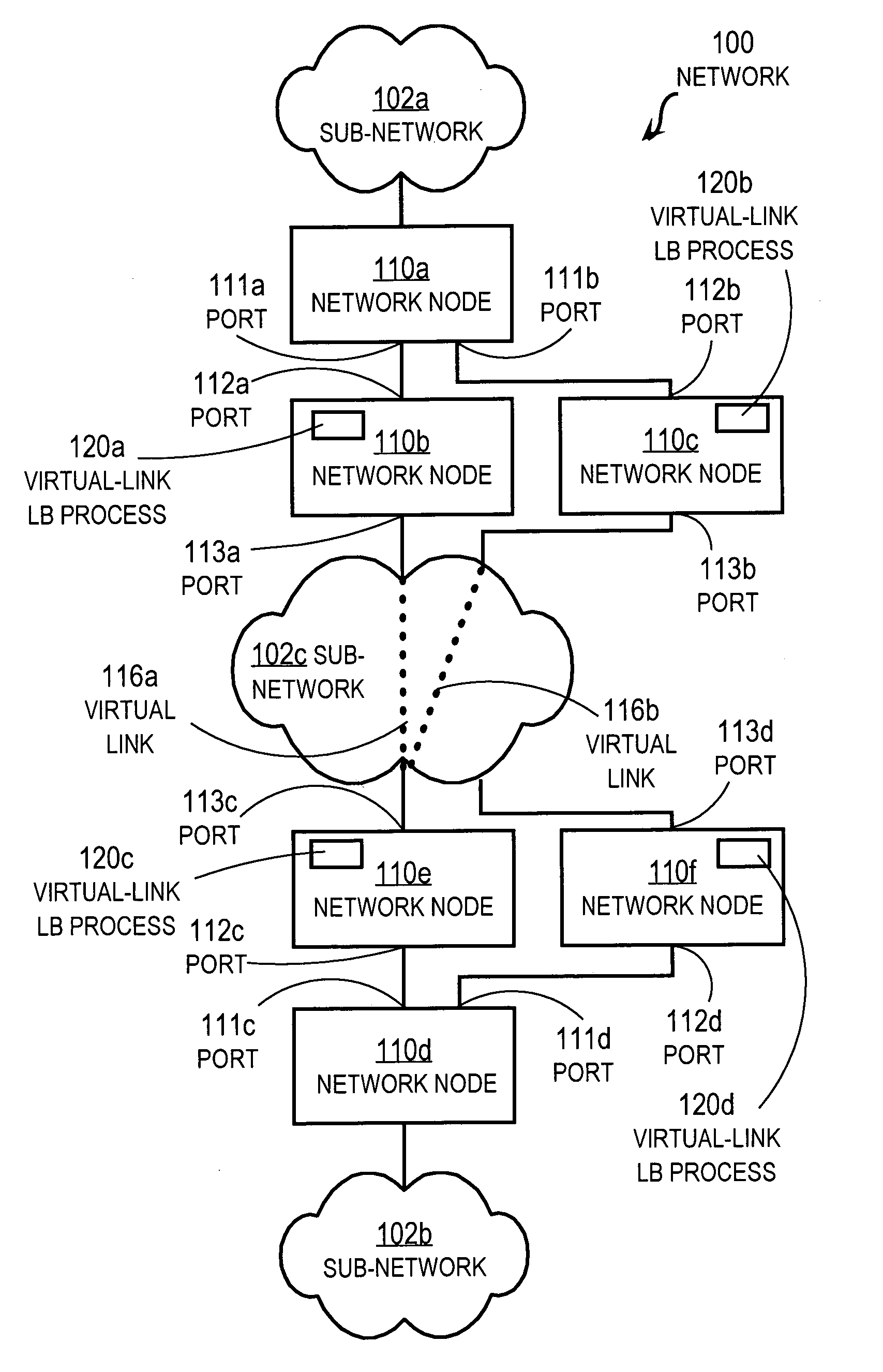
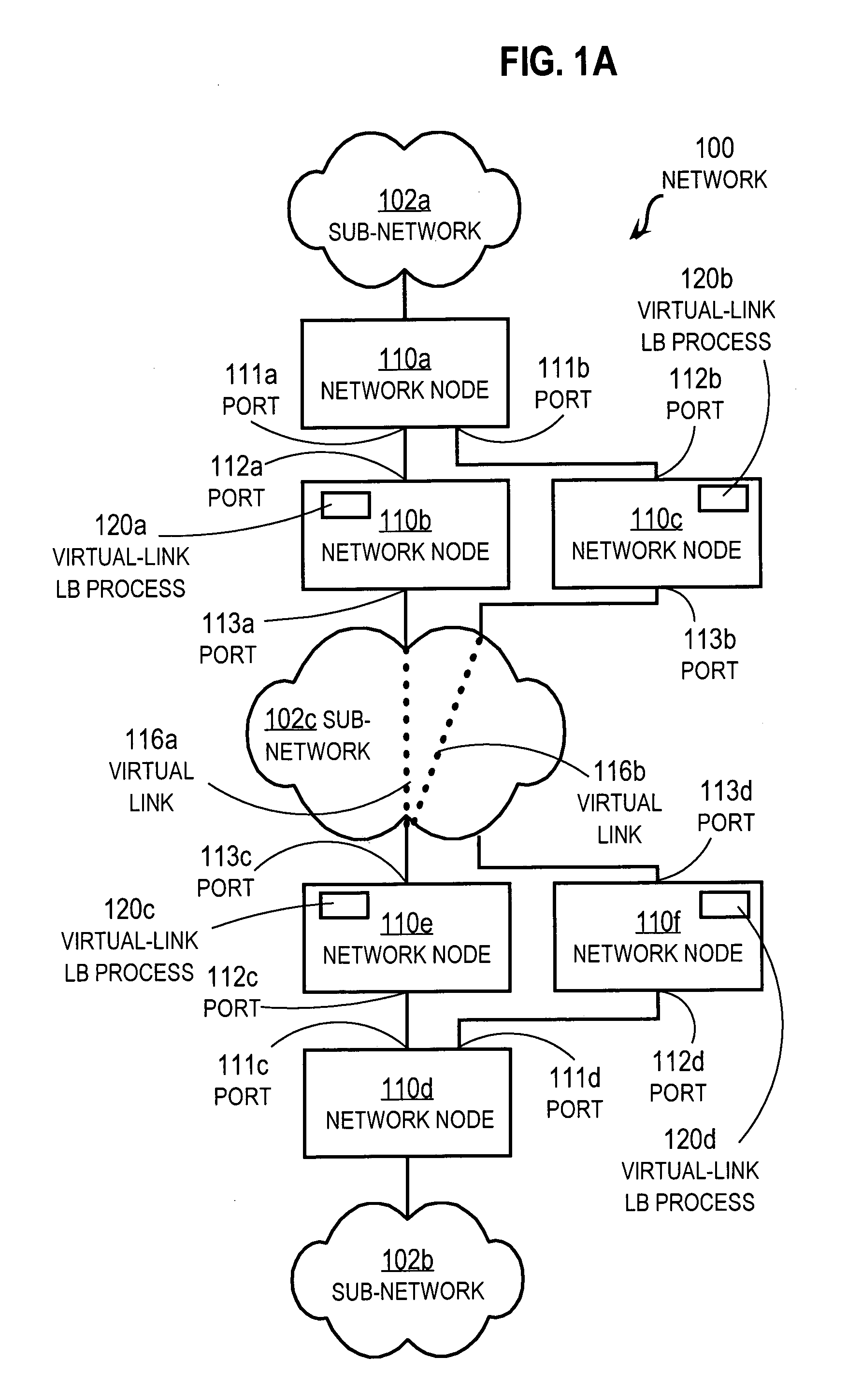
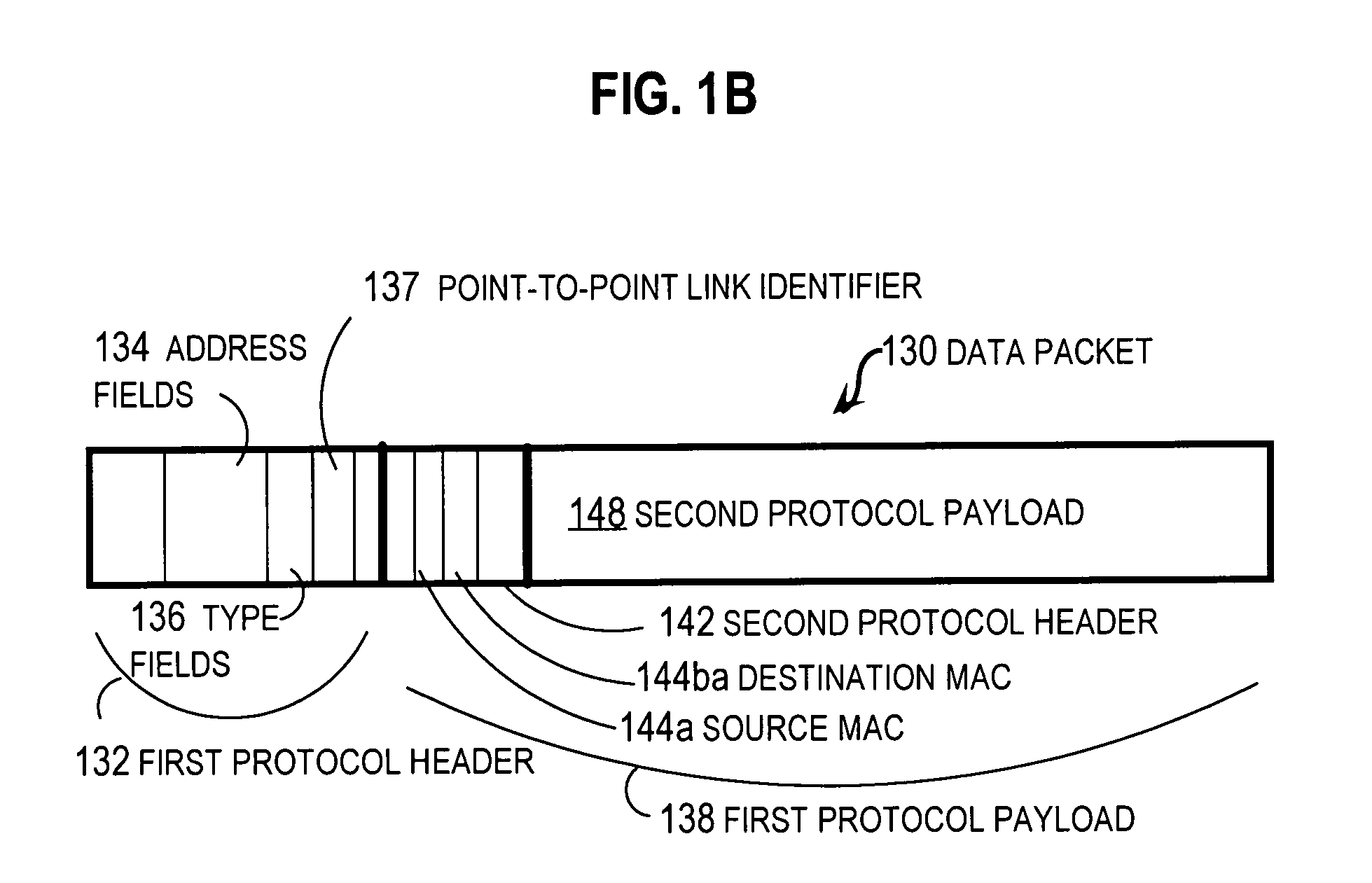
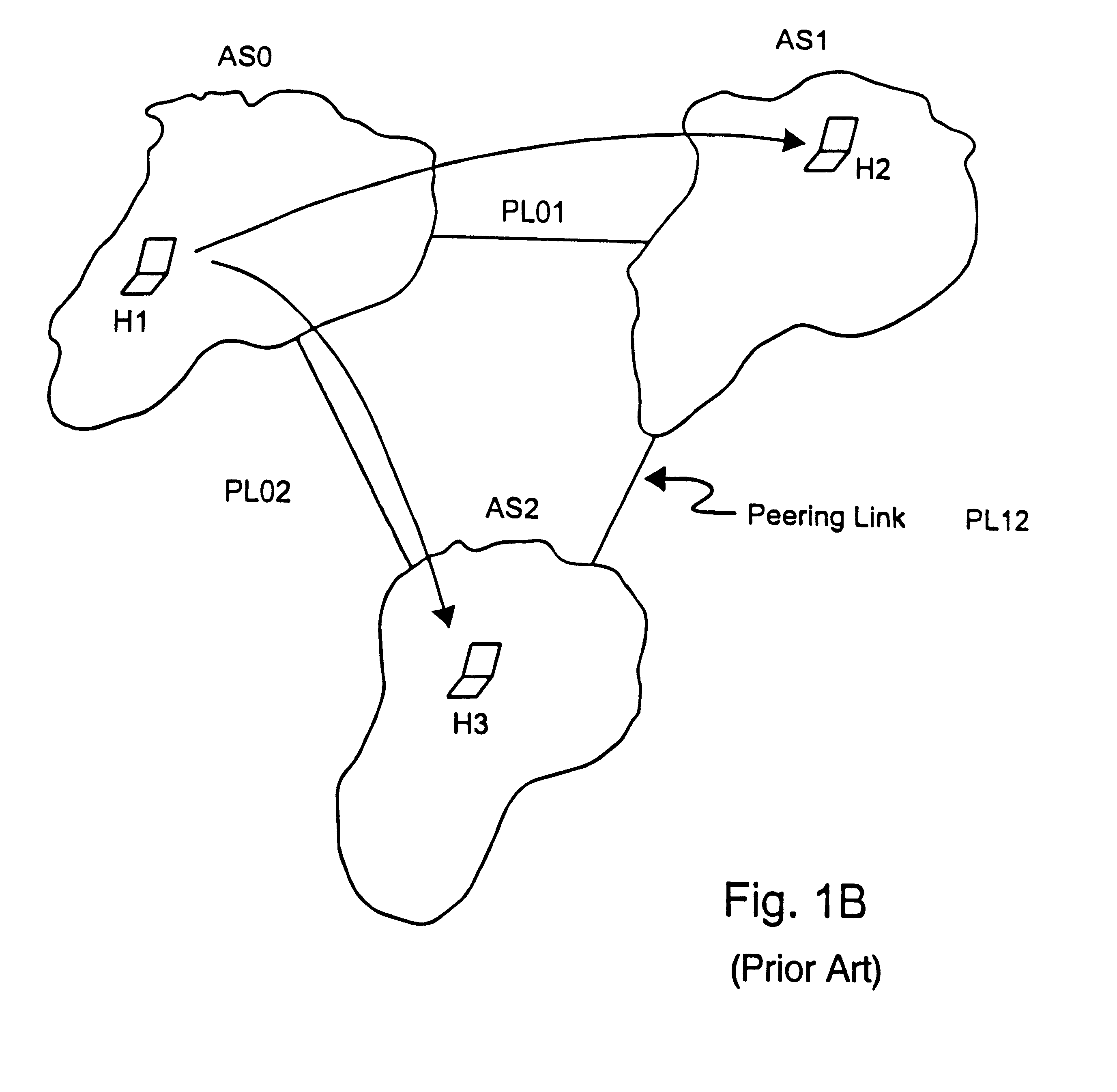
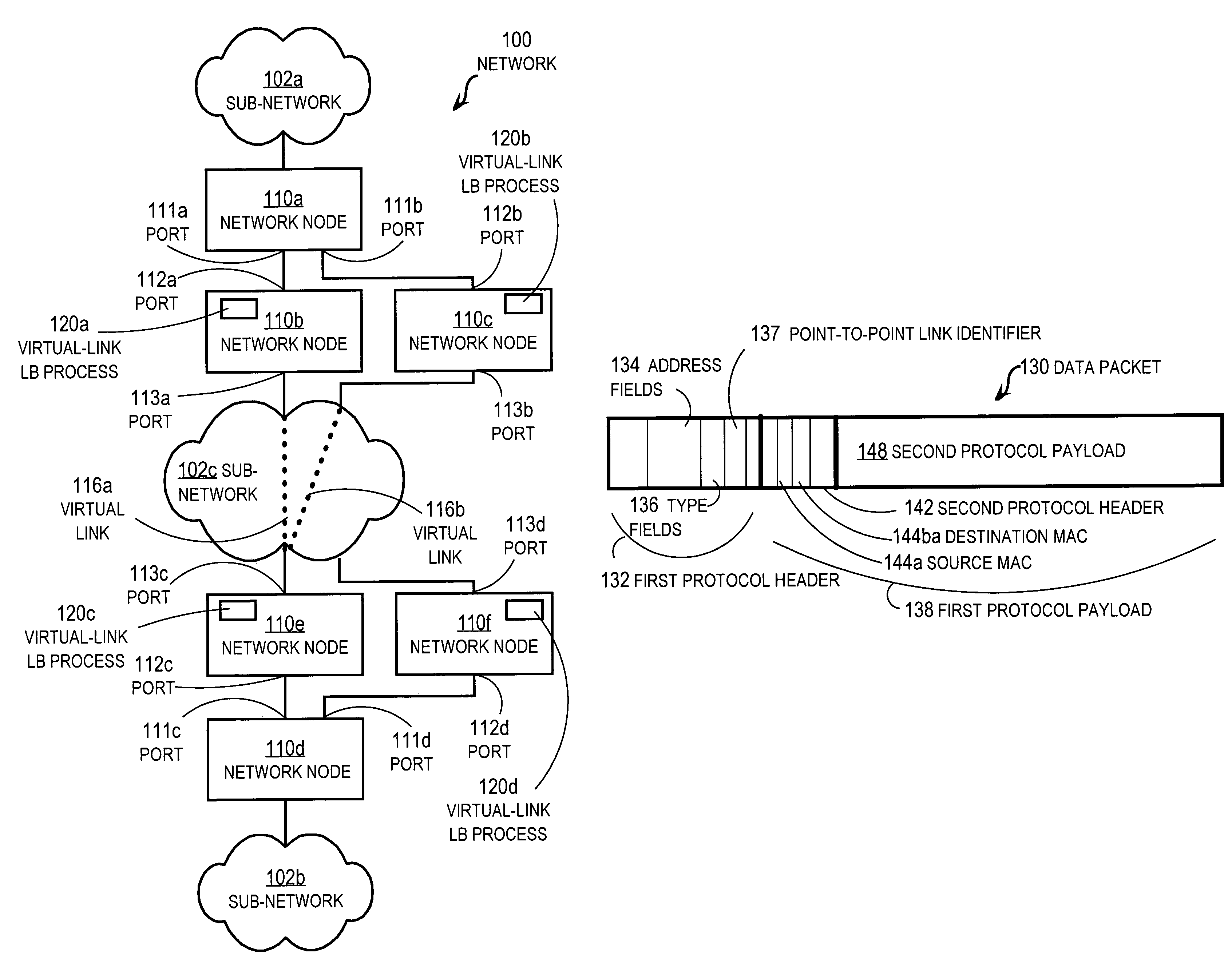
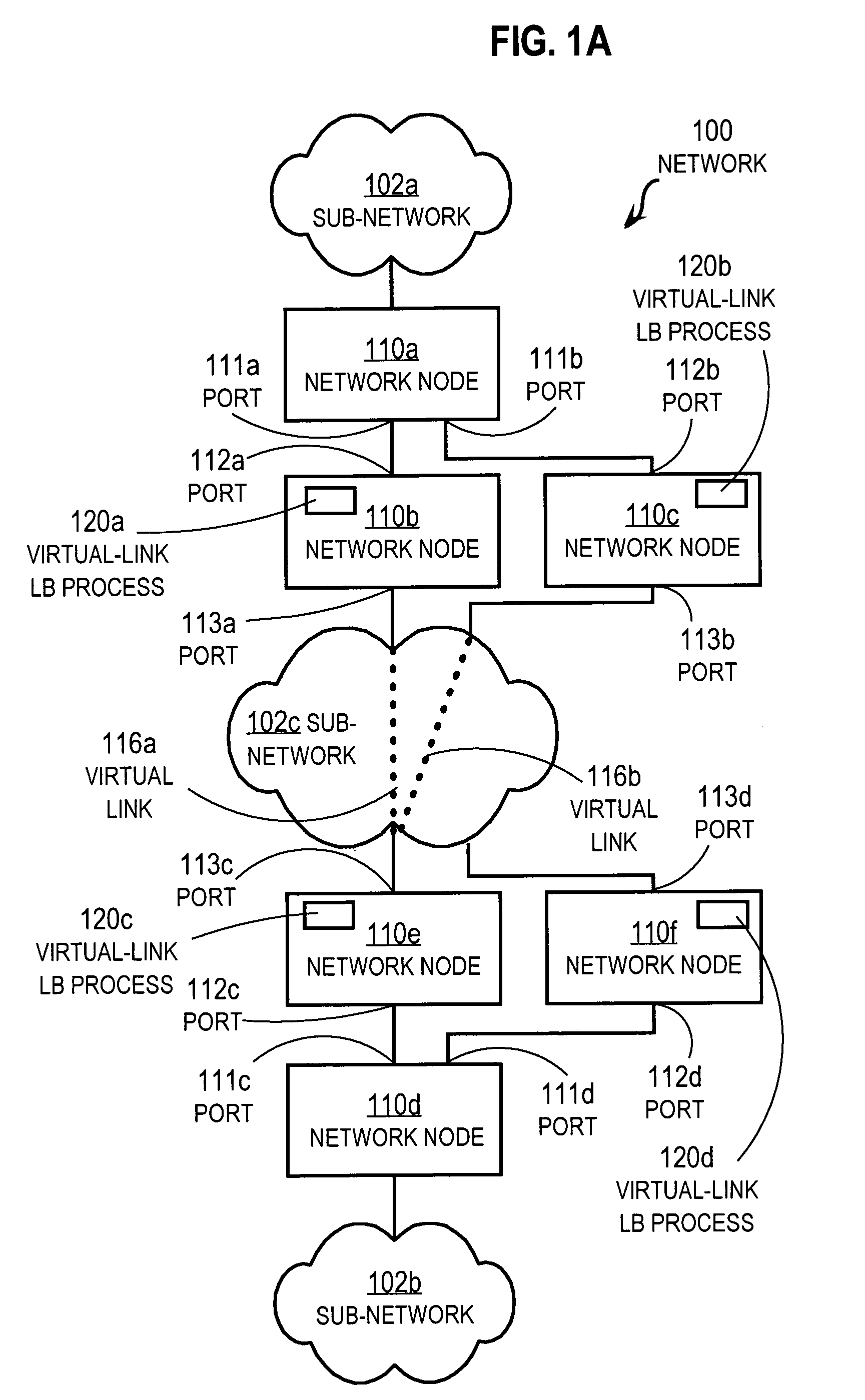
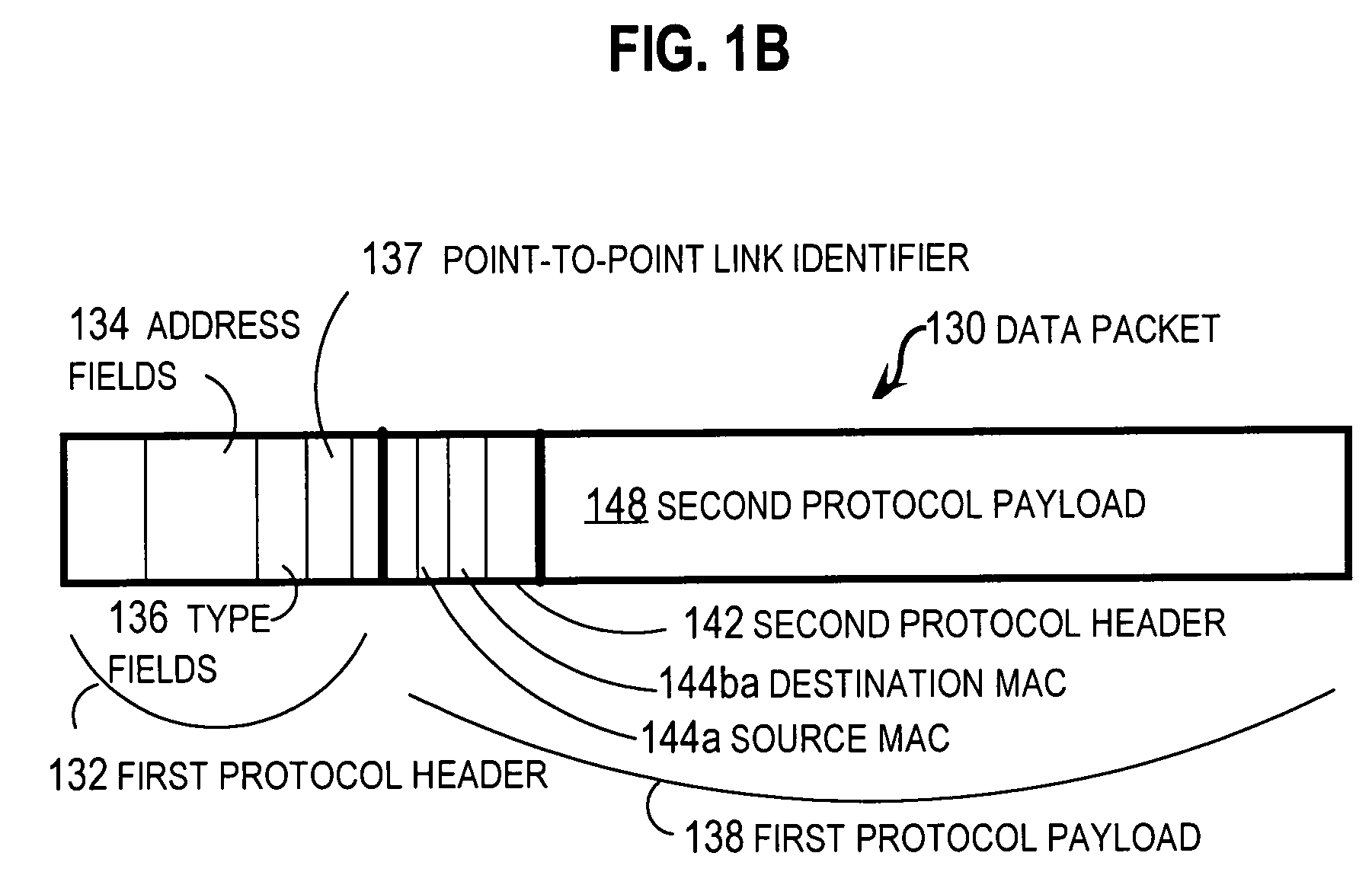
Method and apparatus for load balancing over virtual network links
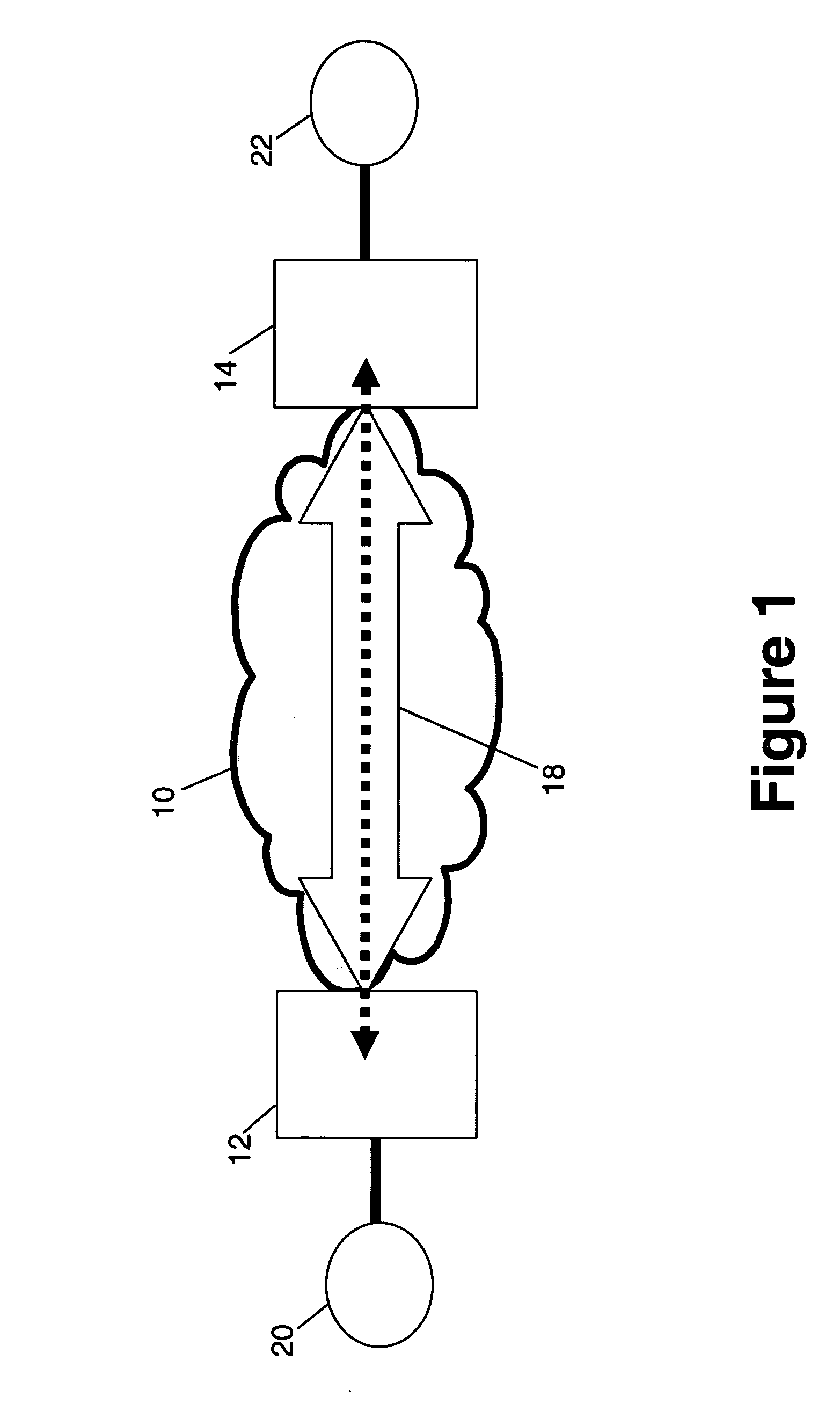
Techniques for load balancing network traffic over virtual point-to-point data links at a data-link layer include determining a particular group of virtual point-to-point data links that reach a particular local area network of one or more network nodes. A particular data-link address for a particular node of the particular local area network is associated with each virtual point-to-point data link of the particular group. When a data packet is received that includes data that indicates the particular data-link address as a destination; one virtual point-to-point data link of the group is determined to balance traffic among the group. The data packet is sent only over the one virtual point-to-point data link. These techniques enable virtual point-to-point data links through two or more intermediate network nodes, such as a pair of provider edge nodes, to be bundled for load balancing purposes.
Owner:CISCO TECH INC
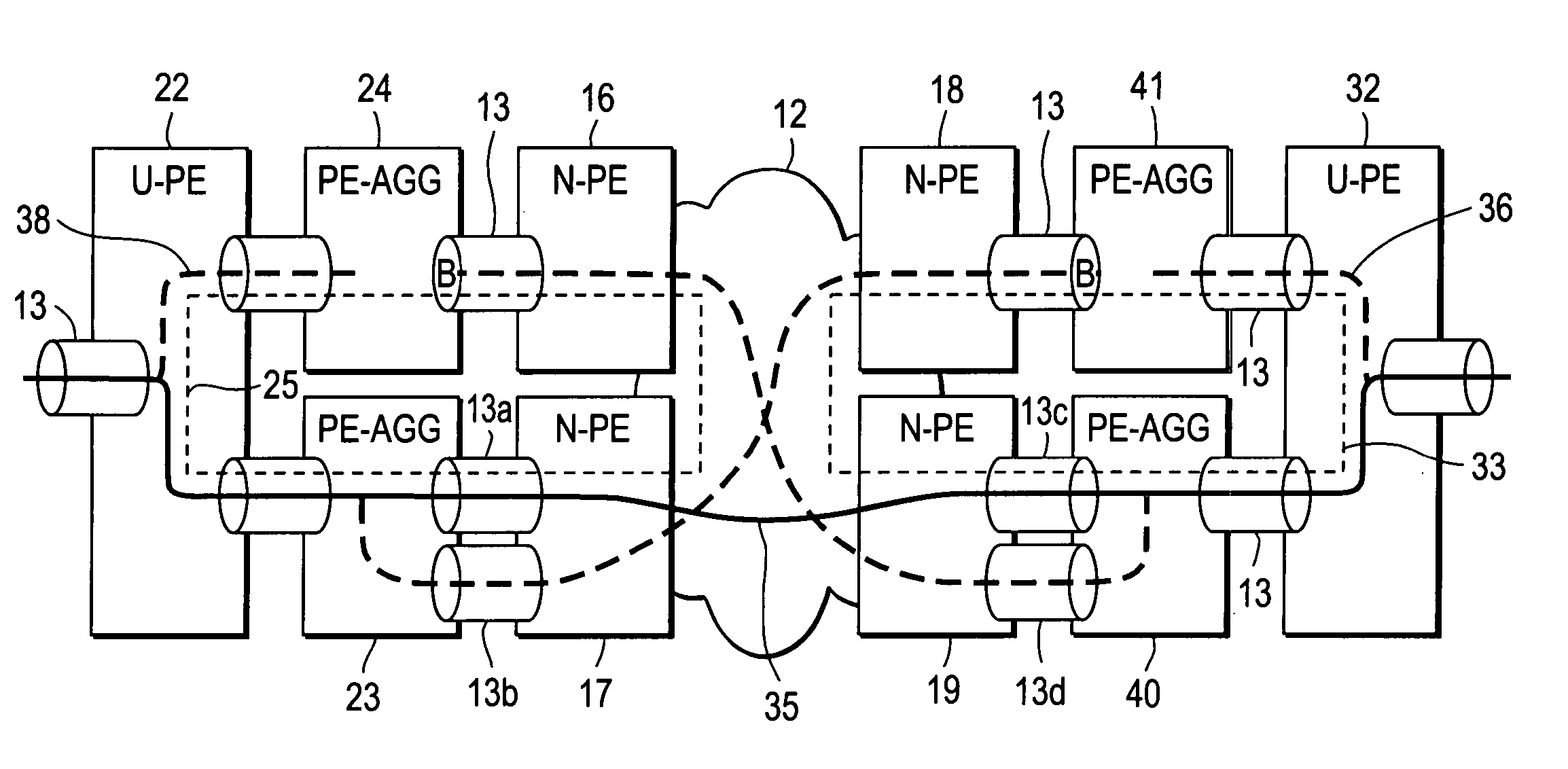
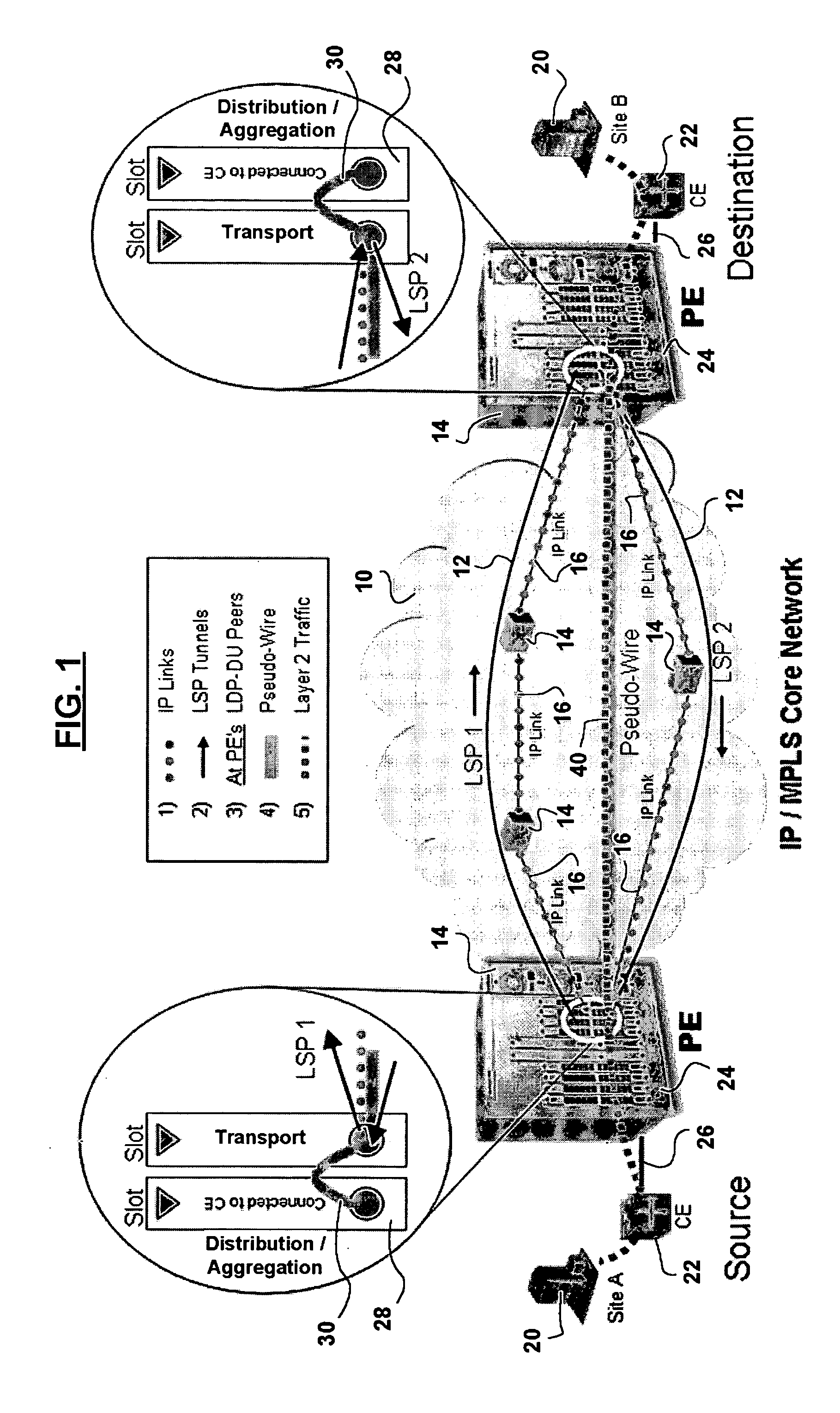
Computer network with point-to-point pseudowire redundancy
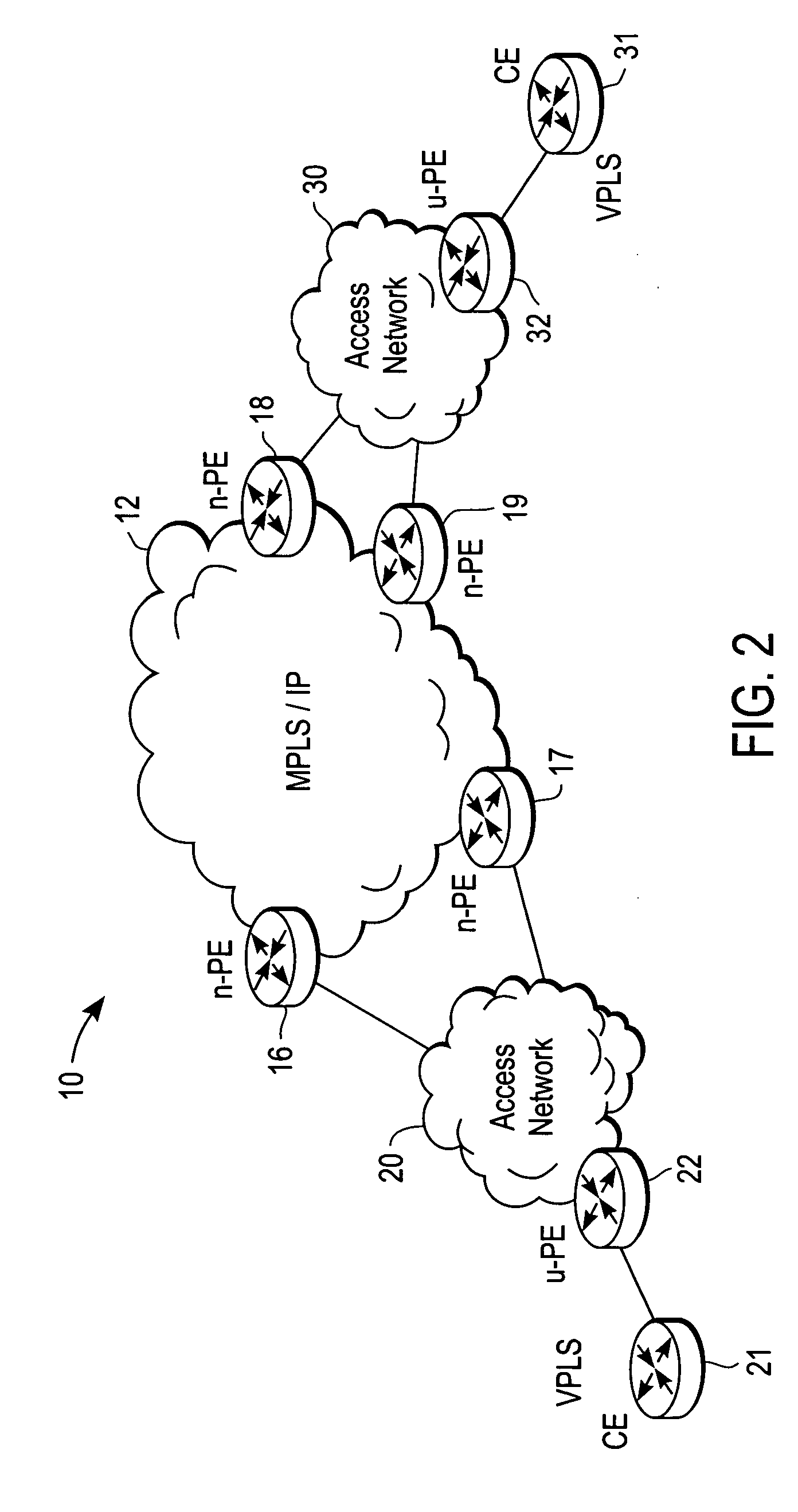
A computer network includes a core network connected with first and second Ethernet access domain networks, each of Ethernet access domain networks including a user-facing provider edge (u-PE) device, a primary network-facing provider edge (n-PE) device, a redundant n-PE device, and a plurality of aggregation provider edge (Agg-PE) devices providing connectivity between to the u-PE device and the primary and redundant n-PE devices, the Agg-PE devices running a spanning-tree protocol (STP) algorithm. A primary data path is provided along with first and second redundant data paths that include first and second redundant pseudowires (PWs), respectively, connected across the core network, the first and second redundant data paths being blocked by the STP algorithm when the primary data path is available, the STP algorithm unblocking either the first or second redundant data path in response to a failure of the primary data path. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
Enabling virtual private local area network services
InactiveUS20080159301A1Well formedNetworks interconnectionNetwork connectionsEdge nodeComputer science
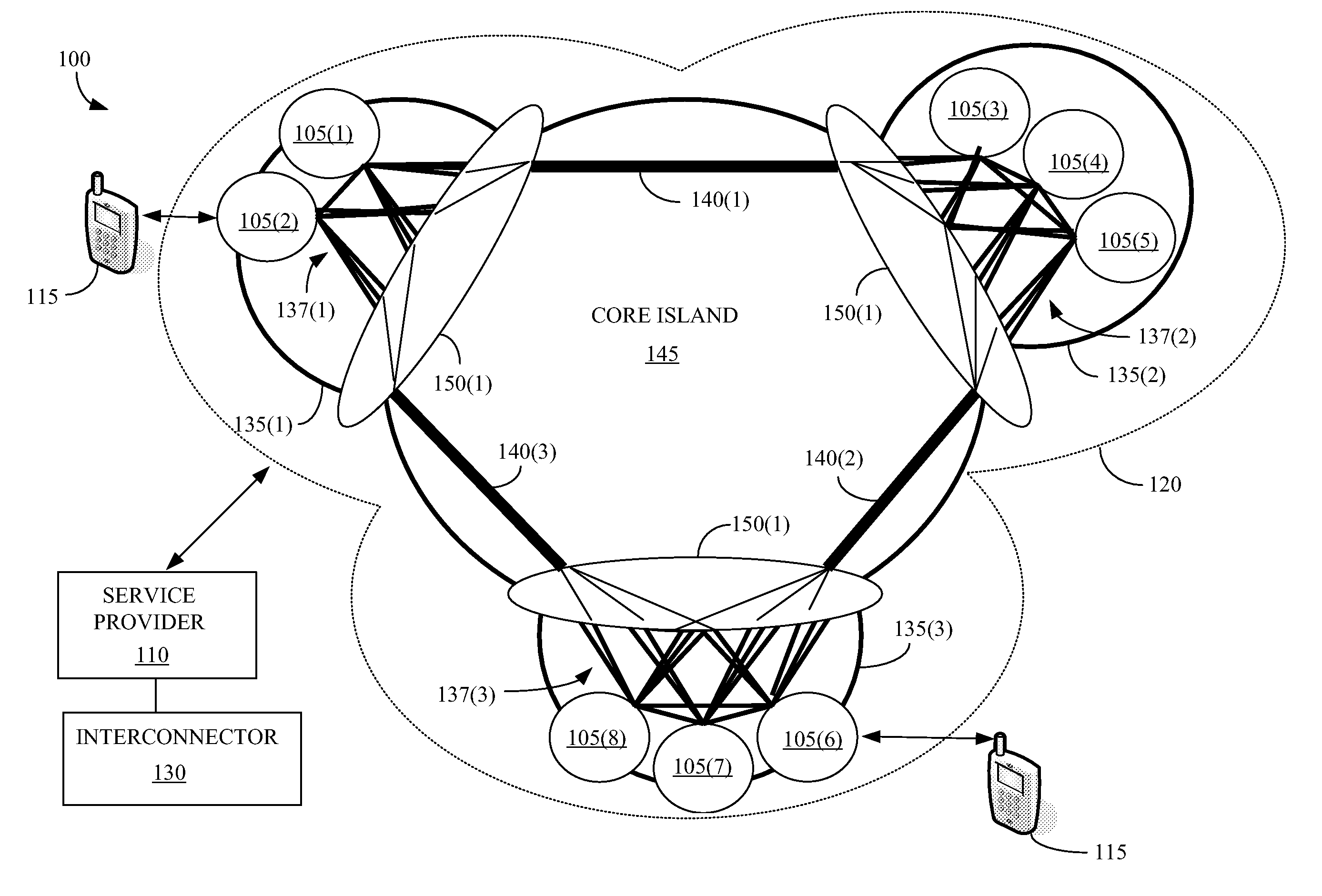
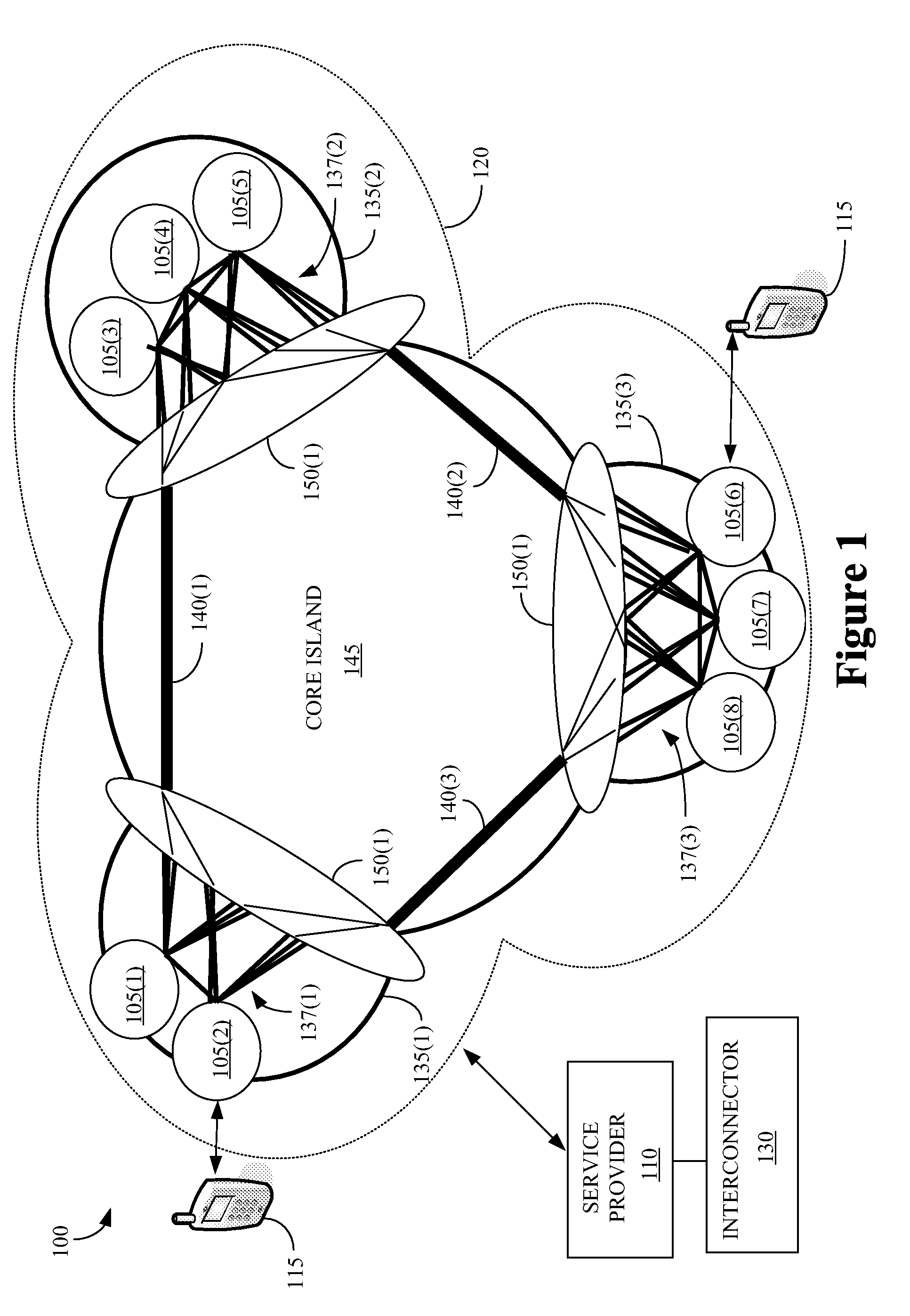
The present invention provides a method for interconnecting a plurality of local area networks that are each communicatively coupled to one of a plurality of provider edge nodes. The method includes forming a plurality of tunnels to communicatively connect each of the plurality of provider edge nodes with each of the other nodes in the plurality of provider edge nodes. The method also includes grouping provider nodes to form at least one first island and at least one second island. The first and second pluralities of provider nodes each include at least one of the provider edge nodes and at least one of the provider nodes is configured to function as a first island edge node. At least one inter-island tunnel is formed from the tunnels to communicatively connect each first island edge node with each second island edge node.
Owner:LUCENT TECH INC
Full mesh LSP and full mesh T-LDP provisioning between provider edge routers in support of Layer-2 and Layer-3 Virtual Private Network services
ActiveUS20050213513A1Increased operation management personnel productivityReduce probabilityError preventionTransmission systemsQuality of serviceService provision
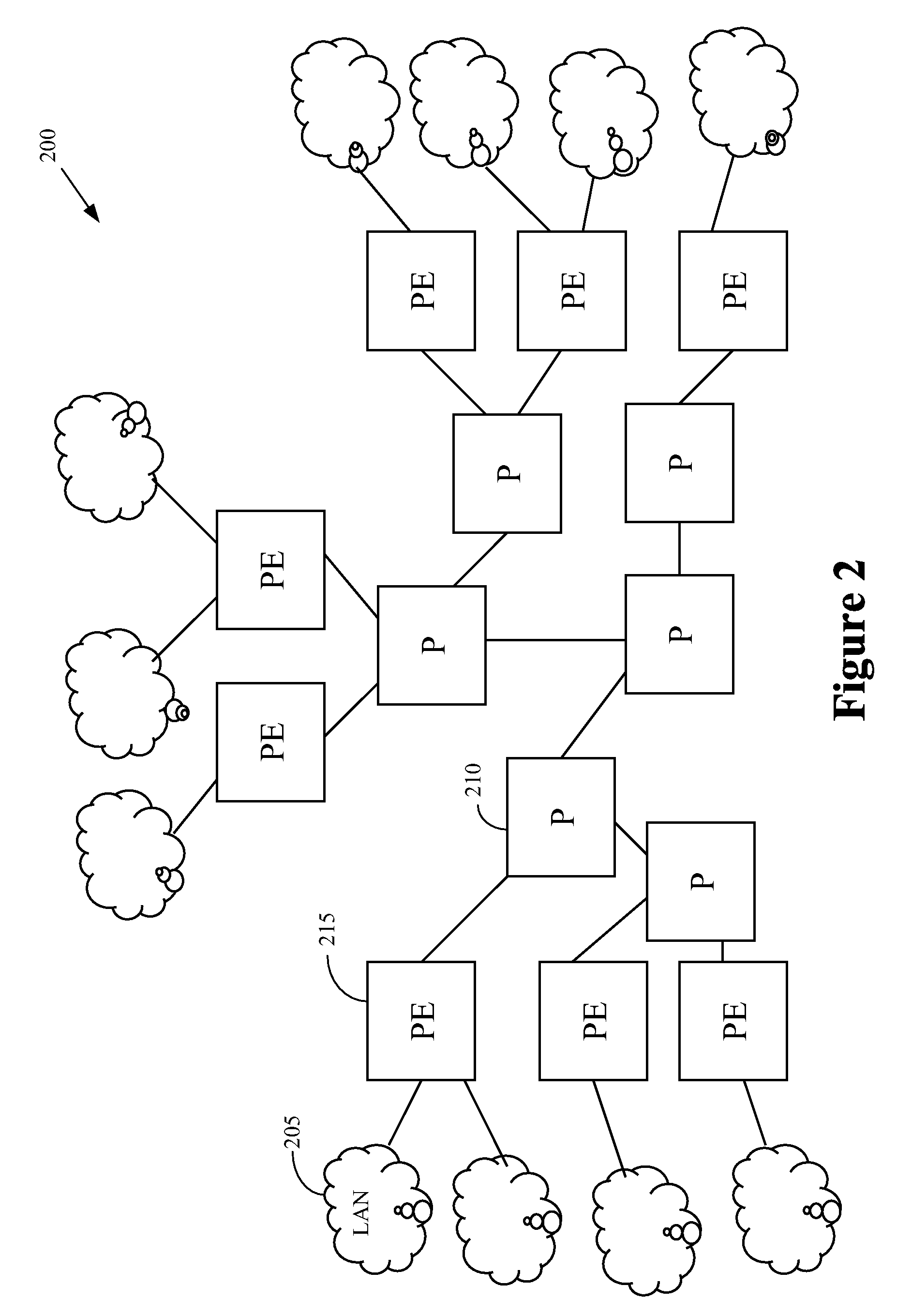
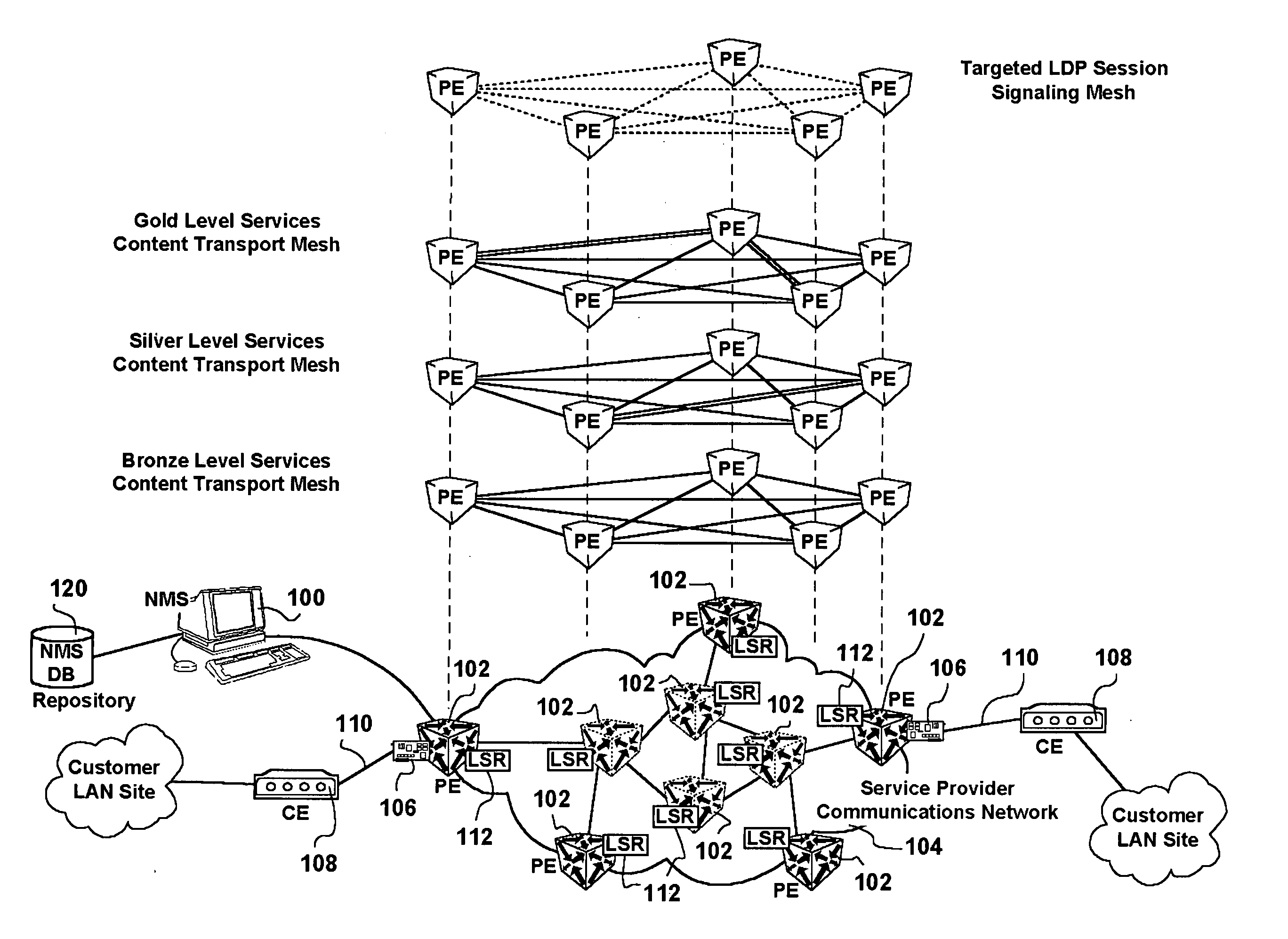
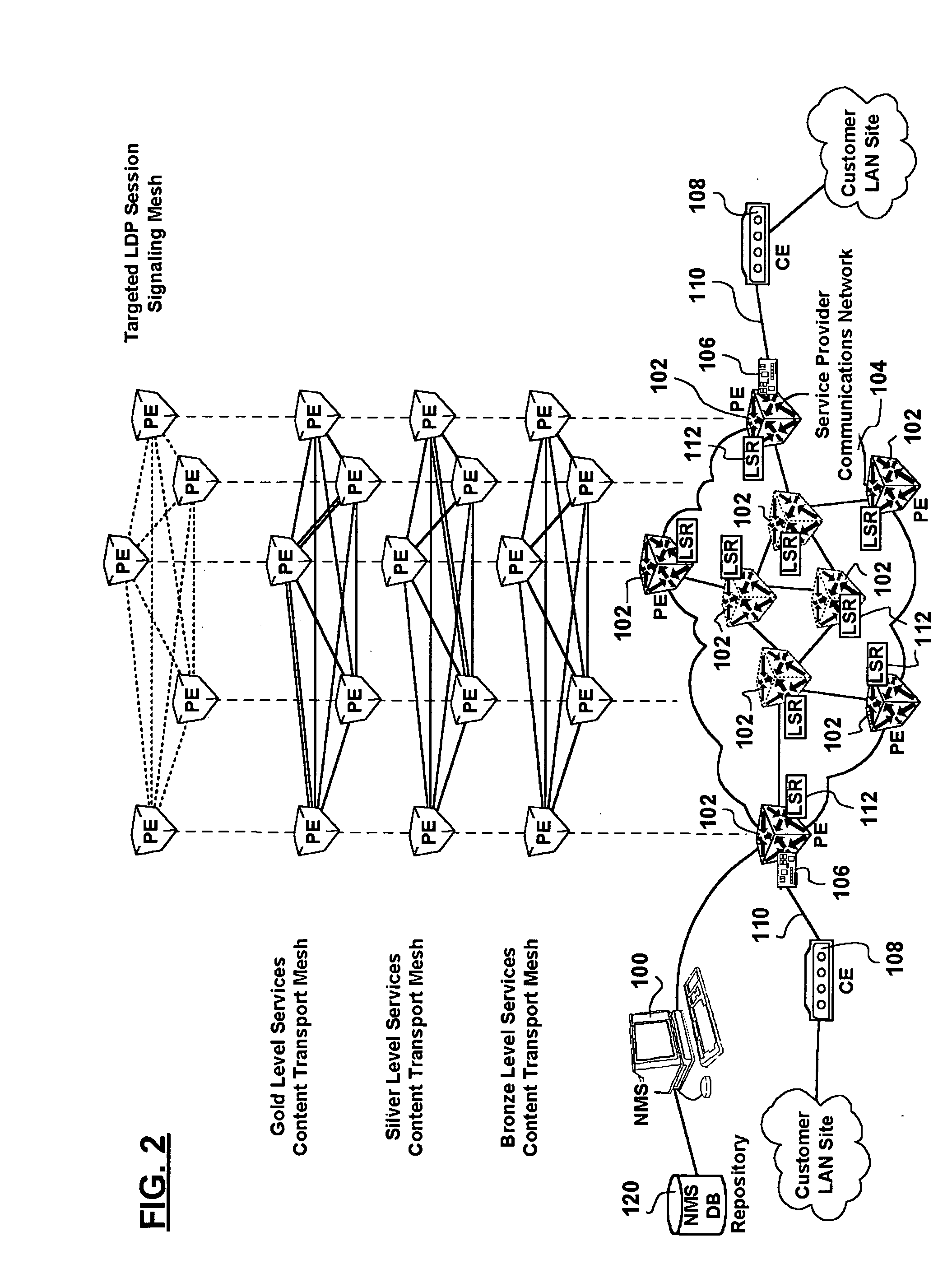
A network management system, and a method of, centrally provisioning a full transport LSP mesh and a full targeted LDP signaling session mesh in support of VPN services provisioning are provided. A network management system repository tracks Provider Edge nodes (PE) having label switch router functionality, transport LSP meshes and targeted LDP session meshes. The method includes selecting PE nodes for inclusion in a node group, identifying PE node pairs, and issuing commands to paired PE nodes to commission managed transport LSPs and targeted LDP signaling sessions. The advantages are derived from the full mesh LSP content transport provisioning and targeted LDP signaling session provisioning effected in a centralized network management context enabling service providers to: assure network resiliency, assure service quality, and provide accounting, in respect of Layer-2 and Layer-3 VPN services irrespective of client side deployed infrastructure while leveraging installed infrastructure in the service provider communications network core. Additional advantages are derived from increased operations management personnel productivity while reducing the probability of human error compared to manual provisioning thereof enabling wide availability of VPN services.
Owner:WSOU INVESTMENTS LLC
Label control method and apparatus for virtual private LAN segment networks
InactiveUS7260097B2Improved label control methodNetworks interconnectionTraffic capacityDistributed computing
A network can be organized for providing virtual private LAN segment (VPLS) services to customers into a network core and an associated number of logical provider edges. Each logical provider edge is partitioned into a plurality of Edge-PEs and a Core-PE. Customers connect to the Edge-PE. The Edge-PE maintains a context (a virtual bridge) for each customer VPLS it serves, VPLS service is realized by a full mesh of so called virtual circuit (VC) tunnels between virtual bridge ports. Each VC tunnel is identified by 3 VC labels in each direction, the first label is used in the encapsulation of customer traffic from the ingress Edge-PE to the ingress Core-PE, the second from ingress Core-PE to egress Core-PE and the third from egress Core-PE to Egress Edge-PE. The mechanisms for the allocation of the label values to and how the label values are used provide a realization of VPLS service that is scalable and easy to administer.
Owner:RPX CLEARINGHOUSE
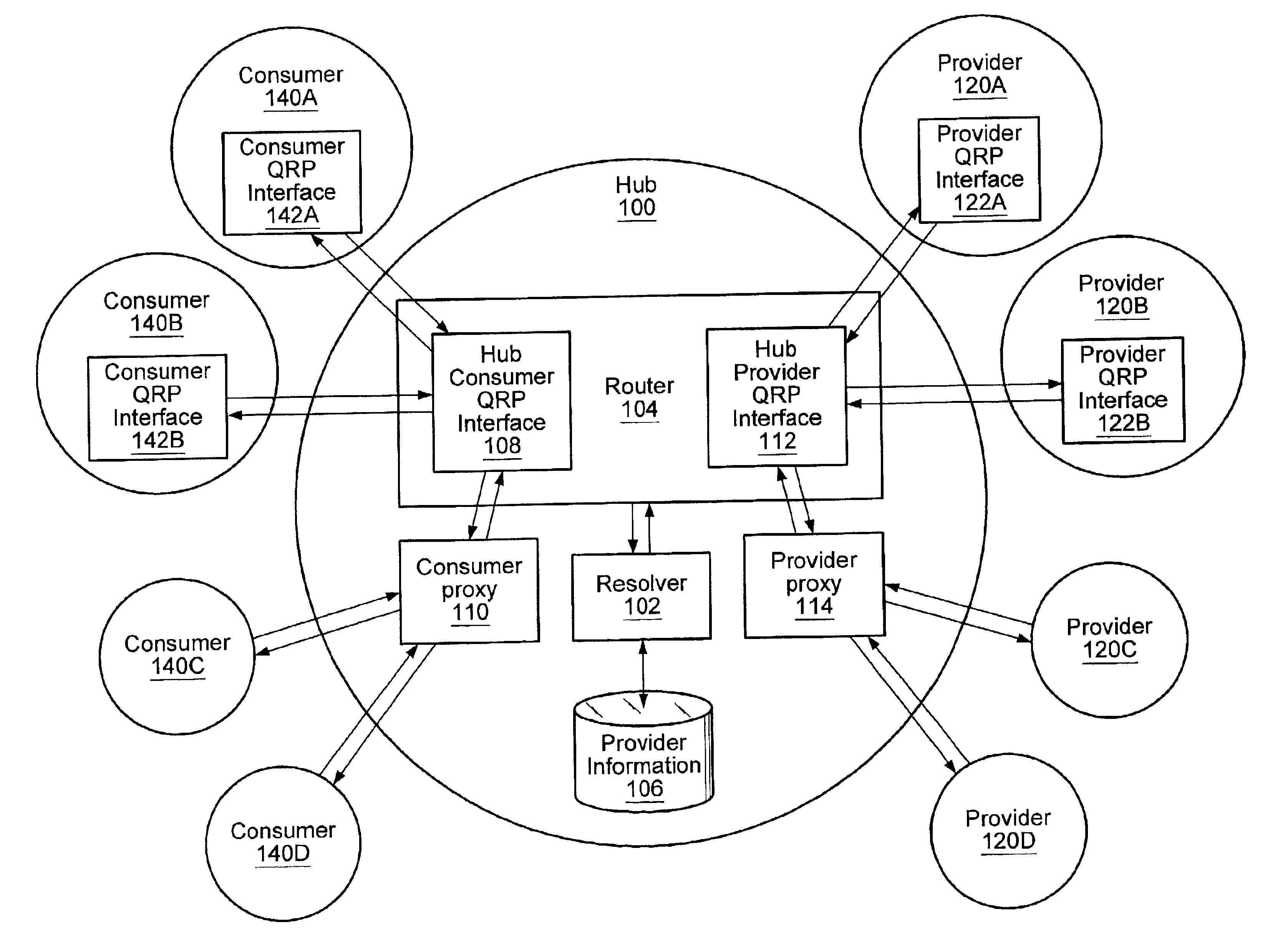
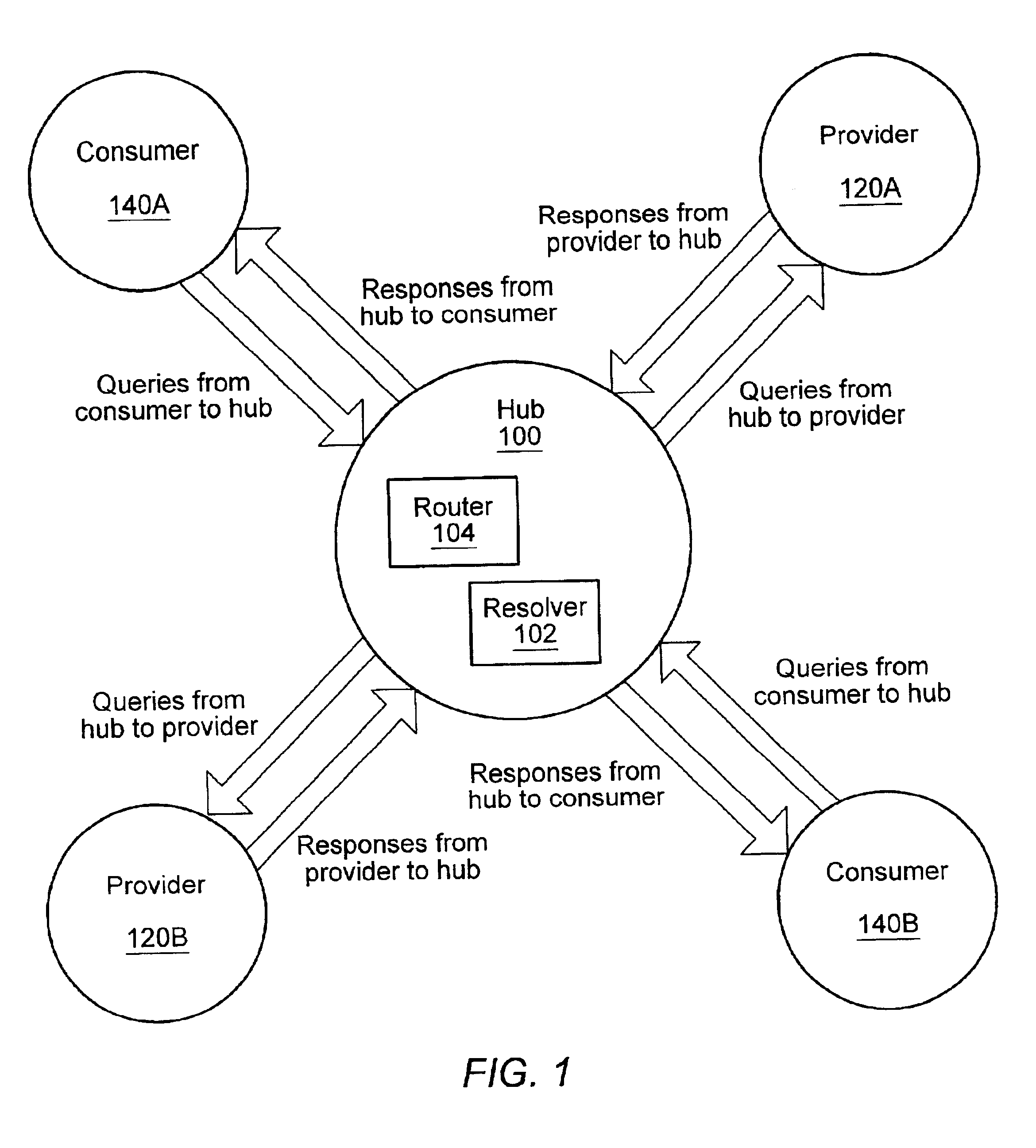
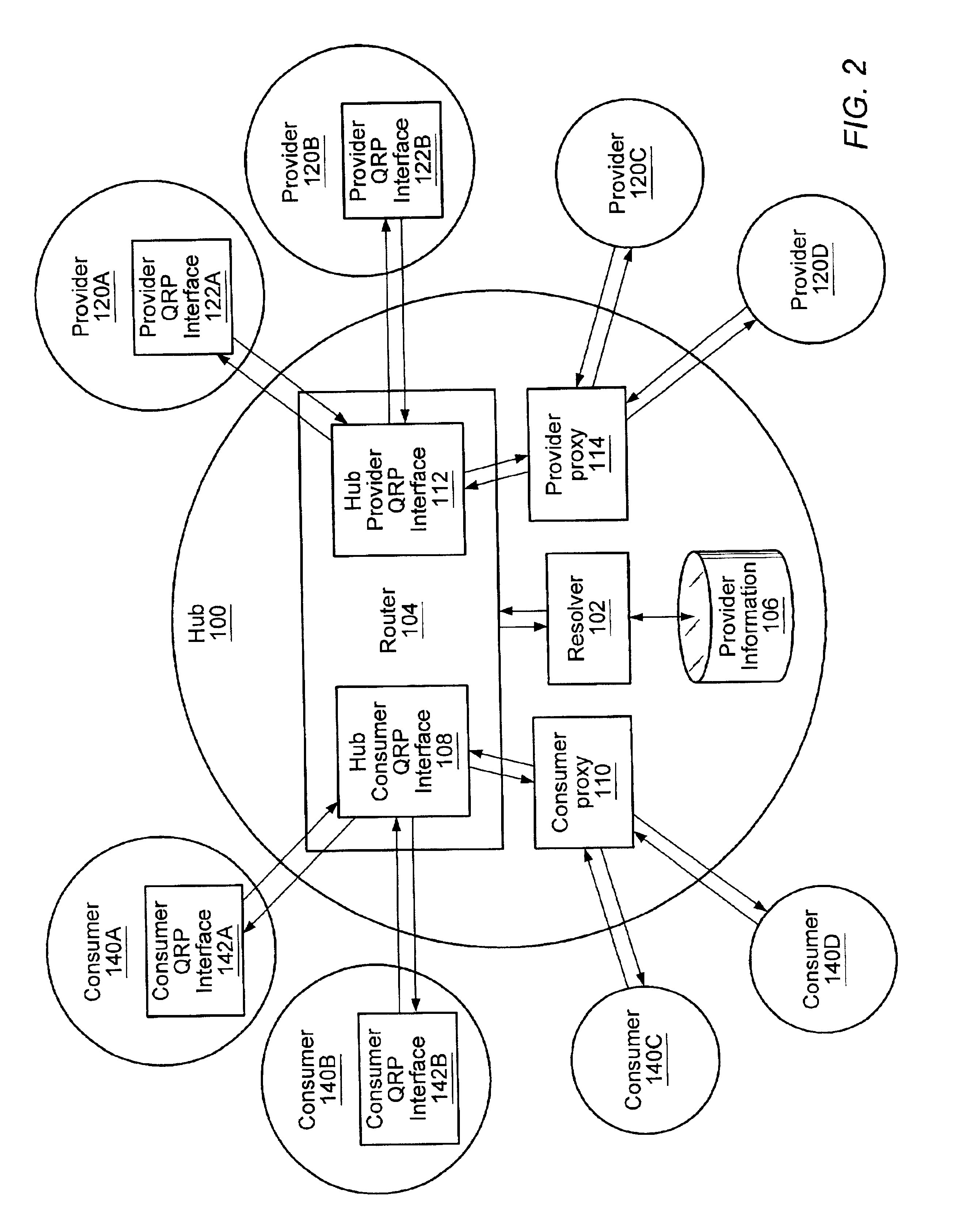
System and method for resolving distributed network search queries to information providers
InactiveUS6950821B2Data processing applicationsDigital data information retrievalRoute searchData mining
Owner:ORACLE INT CORP
Metro ethernet network with scaled broadcast and service instance domains
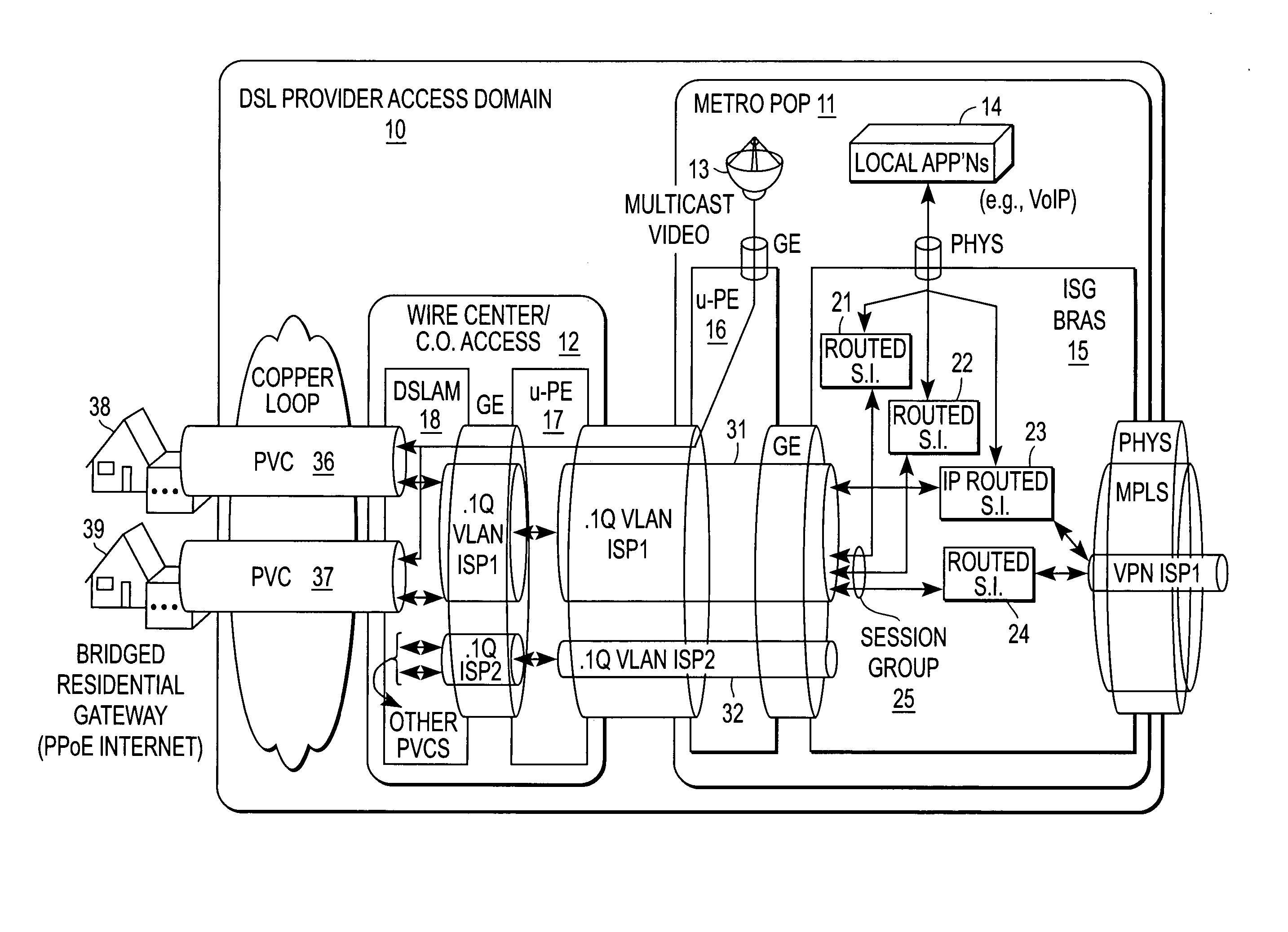
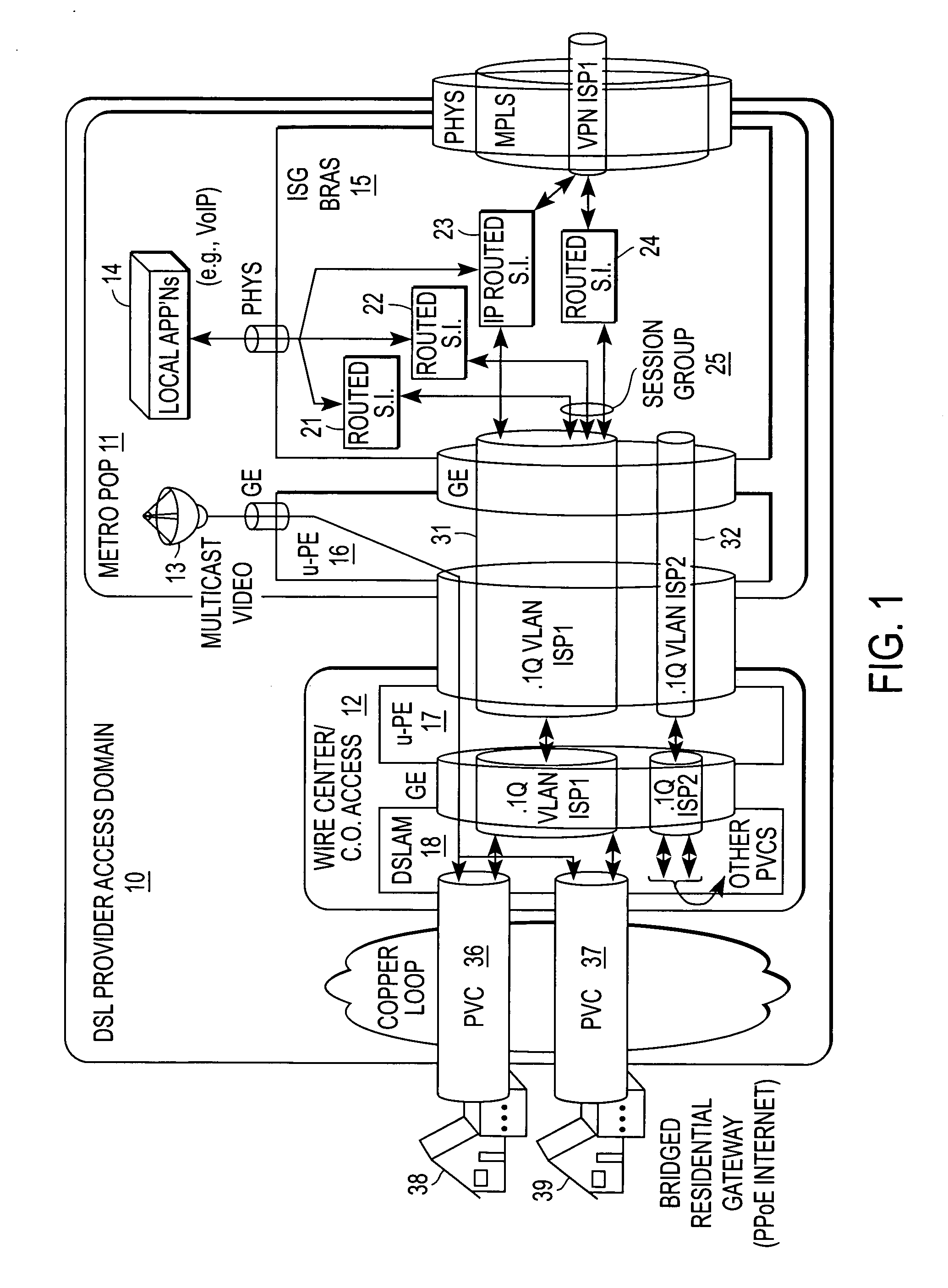
ActiveUS20060245438A1Special service provision for substationMetropolitian area networksAccess networkVirtual LAN
A method of operation for a provider edge device of a core network includes receiving a customer frame from an access network; the customer frame having a first Virtual Local Area Network (VLAN) tag of a first predetermined bit length. The first VLAN tag including a service instance identifier. The service instance identifier of the first VLAN tag is then mapped into a second VLAN tag of a second predetermined bit length greater than the first predetermined bit length. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
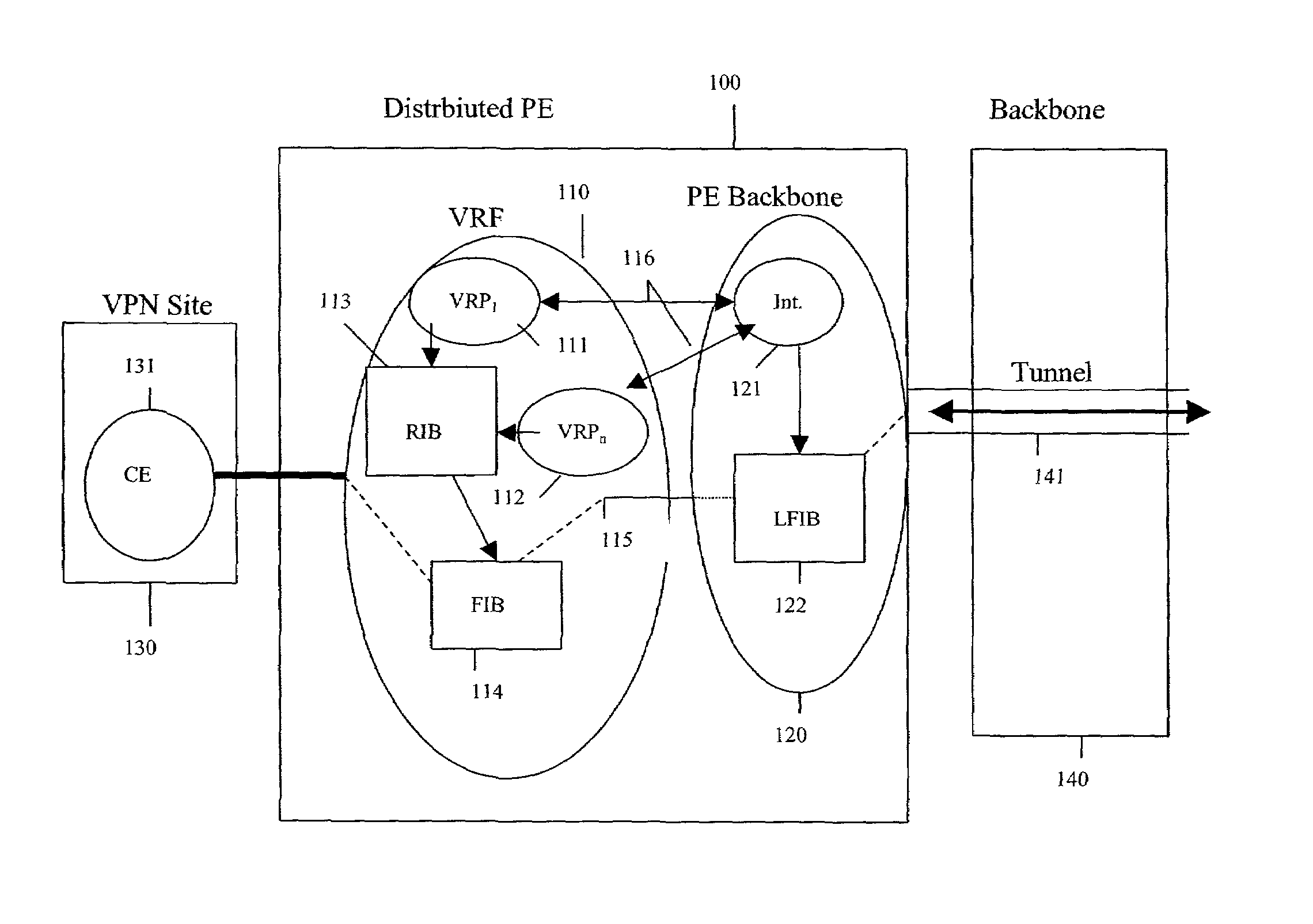
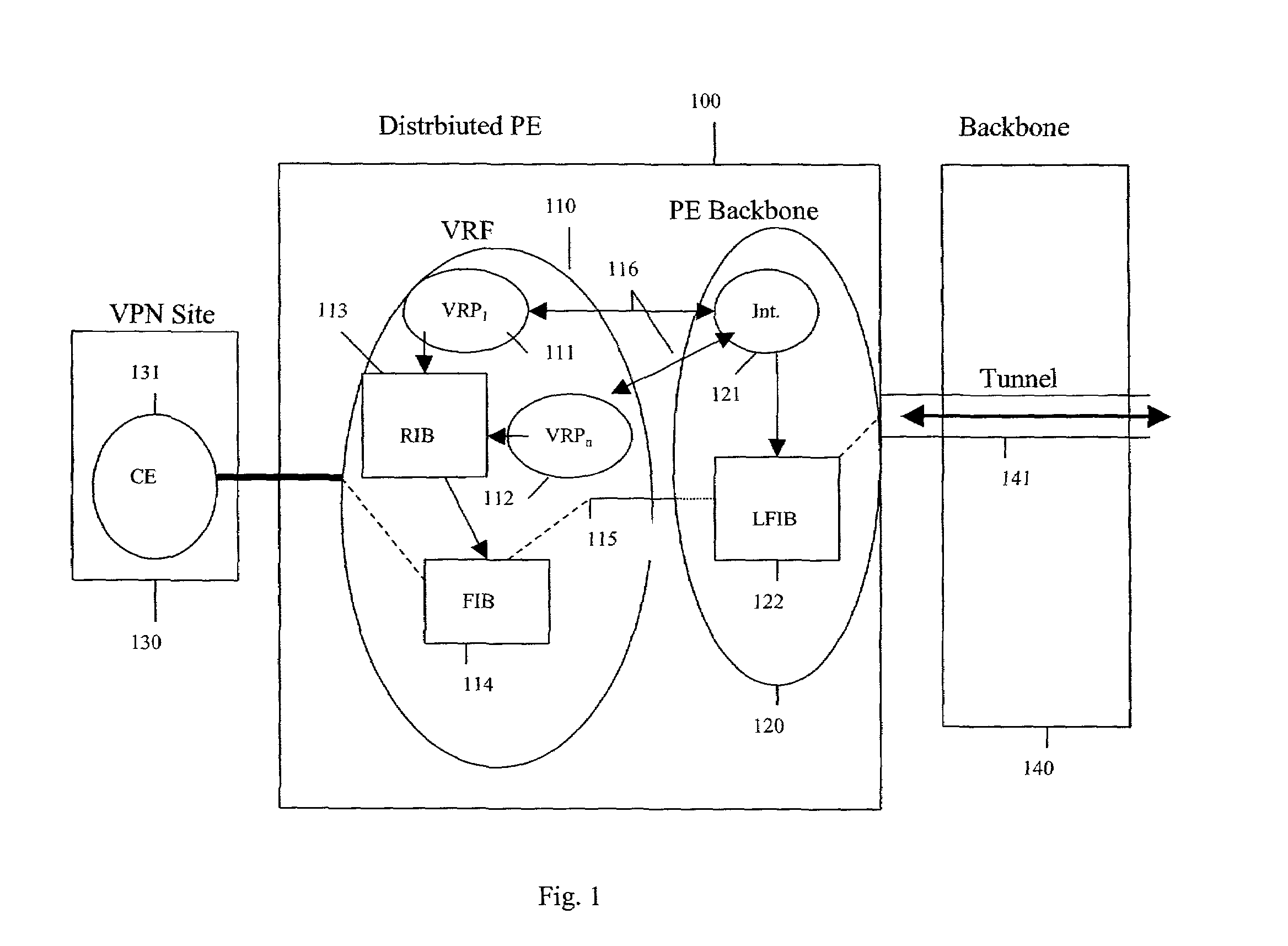
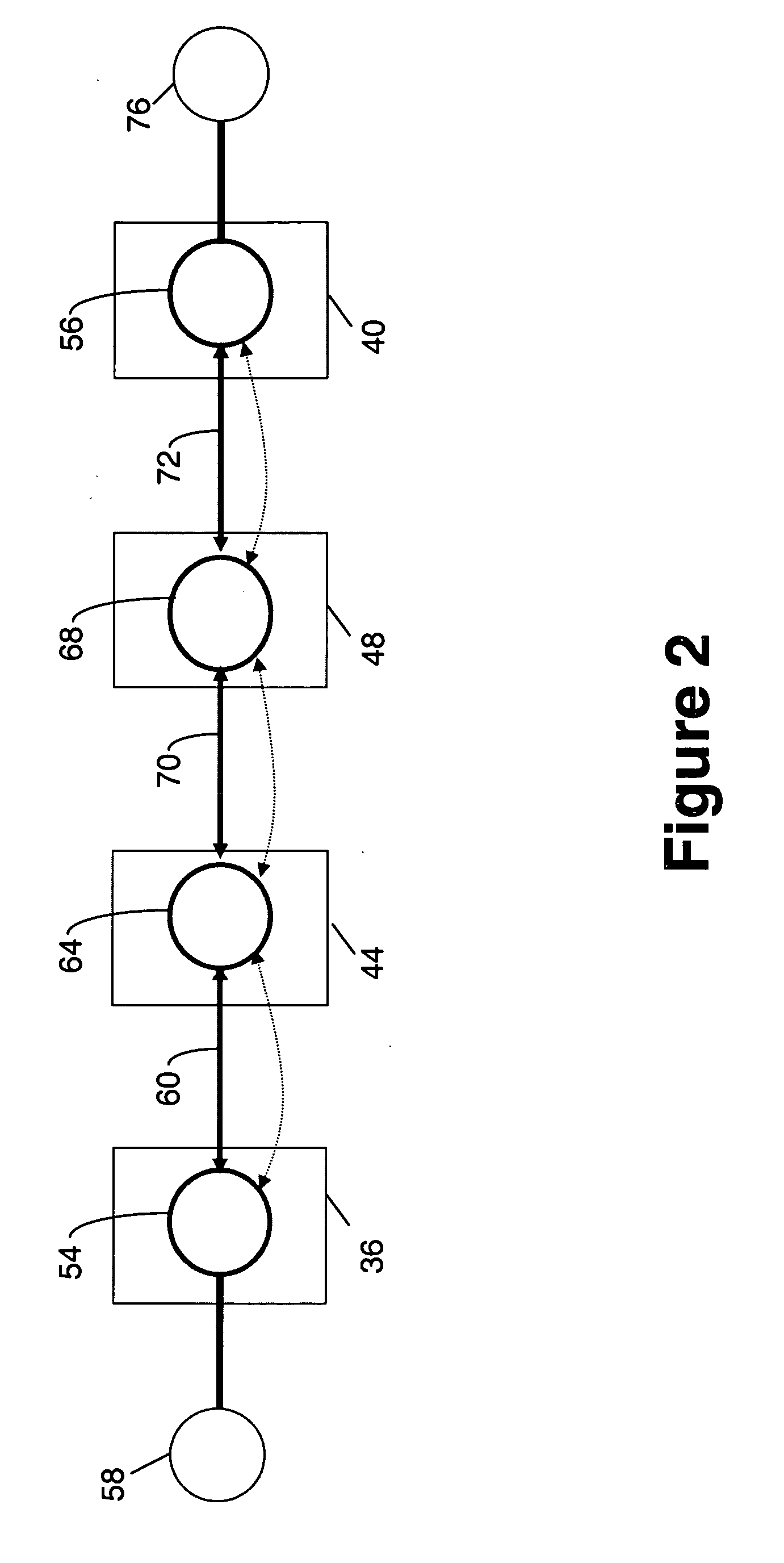
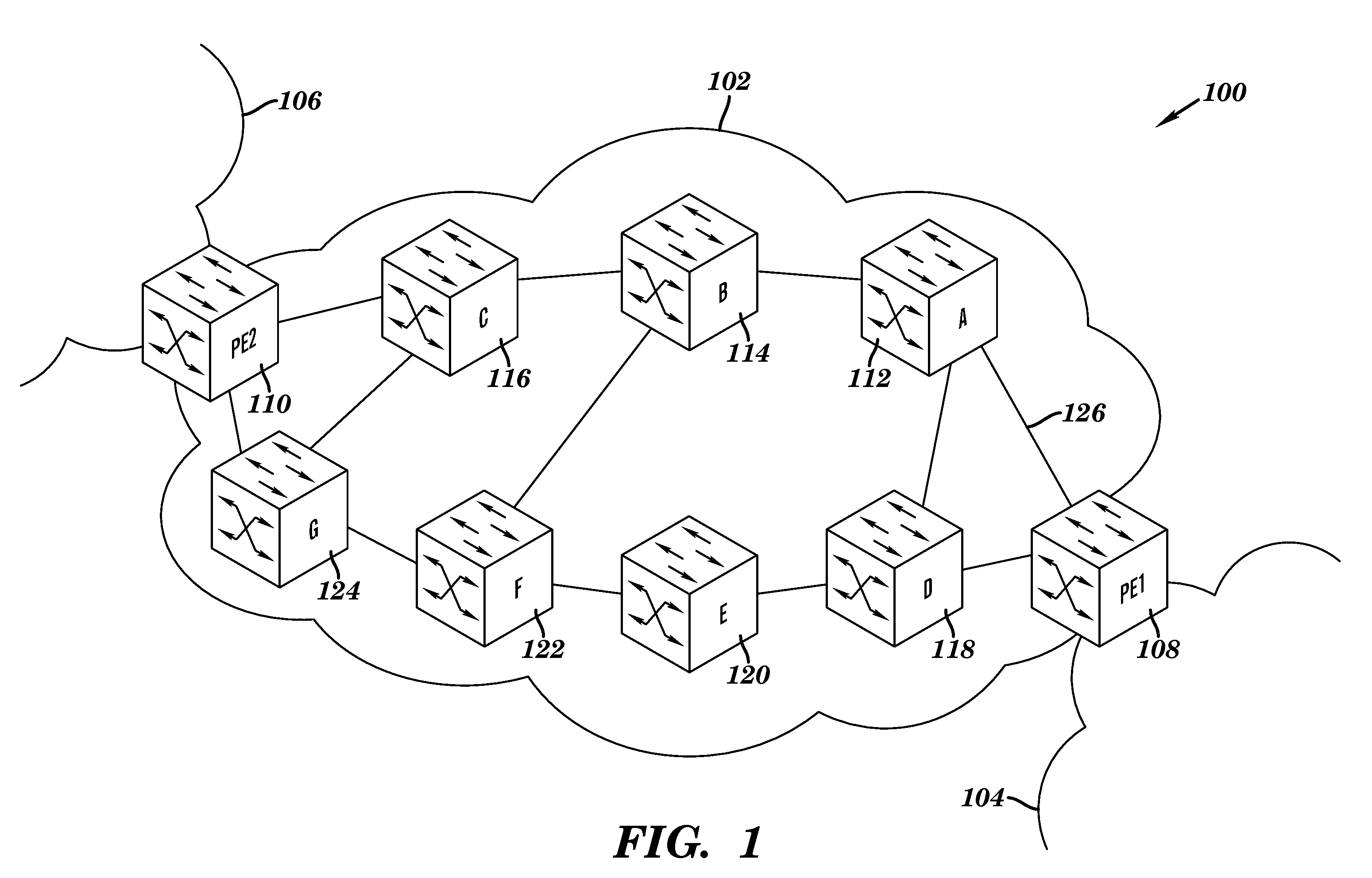
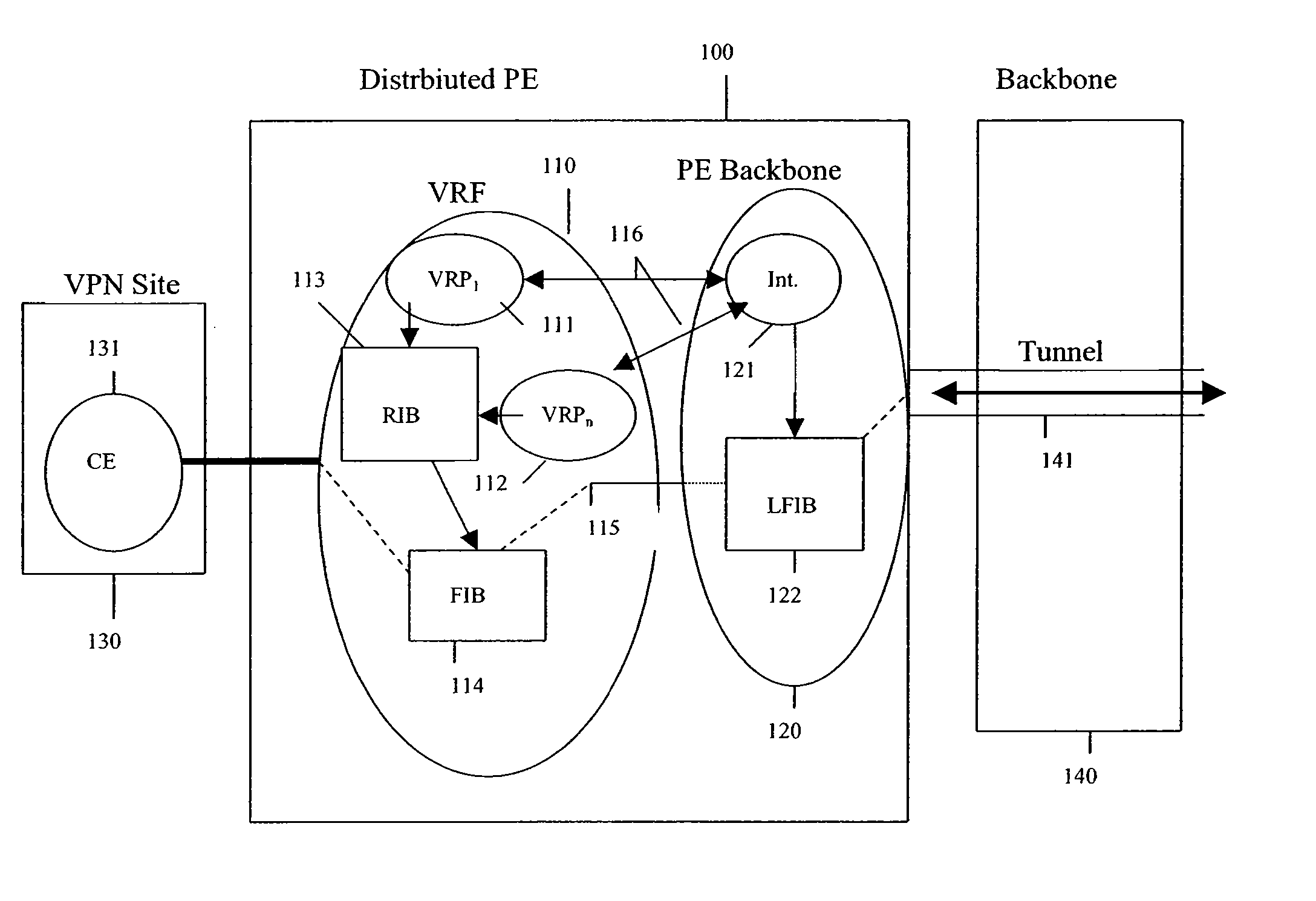
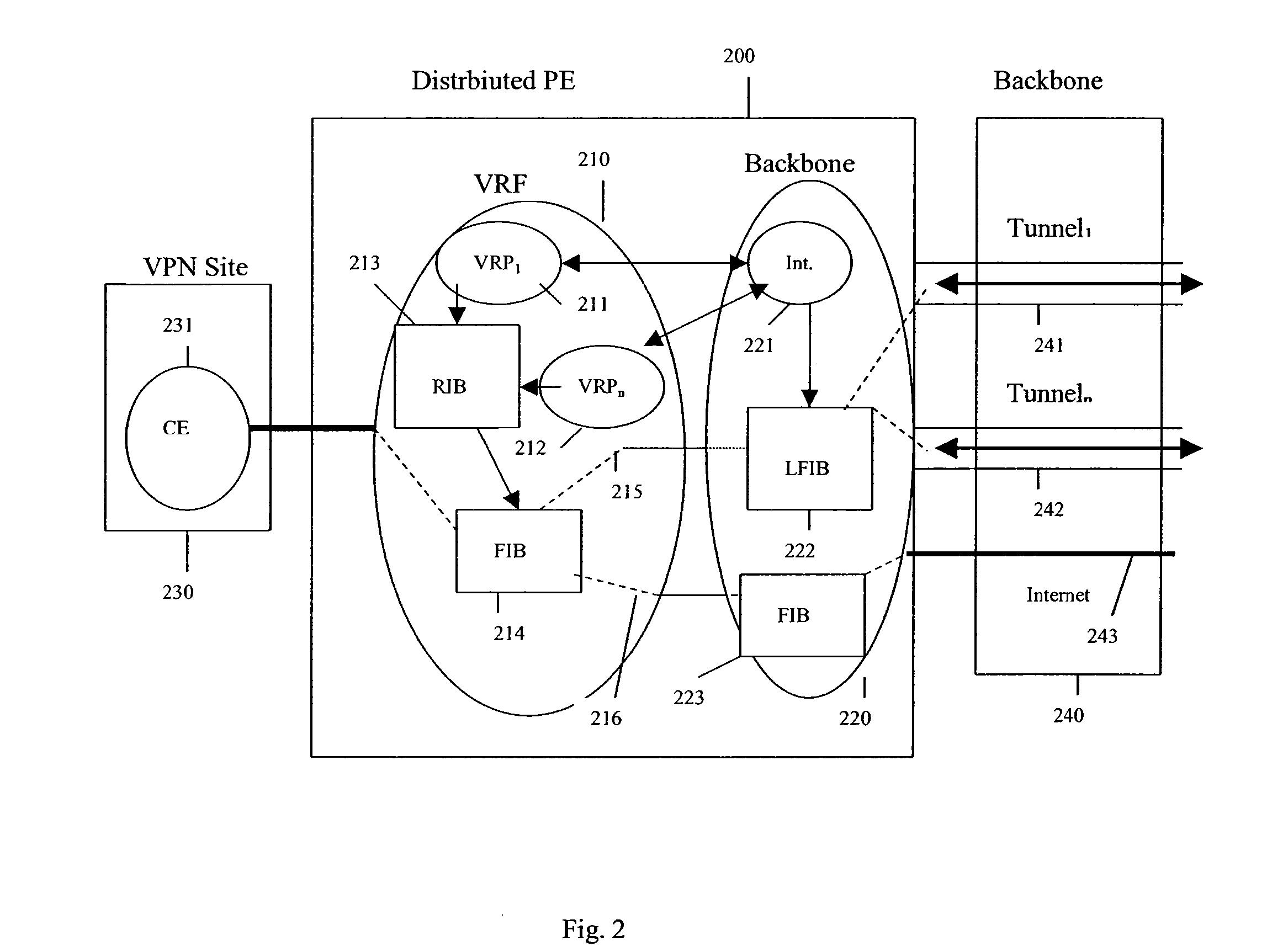
Methods and systems for a distributed provider edge
Methods and Systems are provided for a distributed Provider Edge (PE). A single Virtual Routing and Forwarding device (VRF) is associated with a single customer site. The VRF includes a single routing table (RIB) and a single forwarding table (FIB). The VRF also includes a plurality of Virtual Private Network (VPN) Protocol Instance Modules (VRP), where each VRP is associated with a different VPN from the customer site. Each VRP accesses the RIB directly and the FIB indirectly to acquiring addressing / routing information for a received data packet. Moreover, each VRP uses a data plane of the VRP to communicate the data packets to a PE backbone device. In turn, the PE backbone device uses the data plane to communicate with each of the VRPs, and the PE backbone device communicates with one or more tunnels.
Owner:FORTINET
Redundant pseudowires between Ethernet access domains
A computer network includes first and second Ethernet access domain networks, each of Ethernet access domain networks including a user-facing provider edge (u-PE) device, and a stack group of network-facing provider edge (n-PE) devices coupled with the u-PE device, the n-PE devices running a bidding protocol to select one of the n-PE devices as a primary n-PE device for a single pseudowire connection path between the first and second Ethernet access domain networks. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
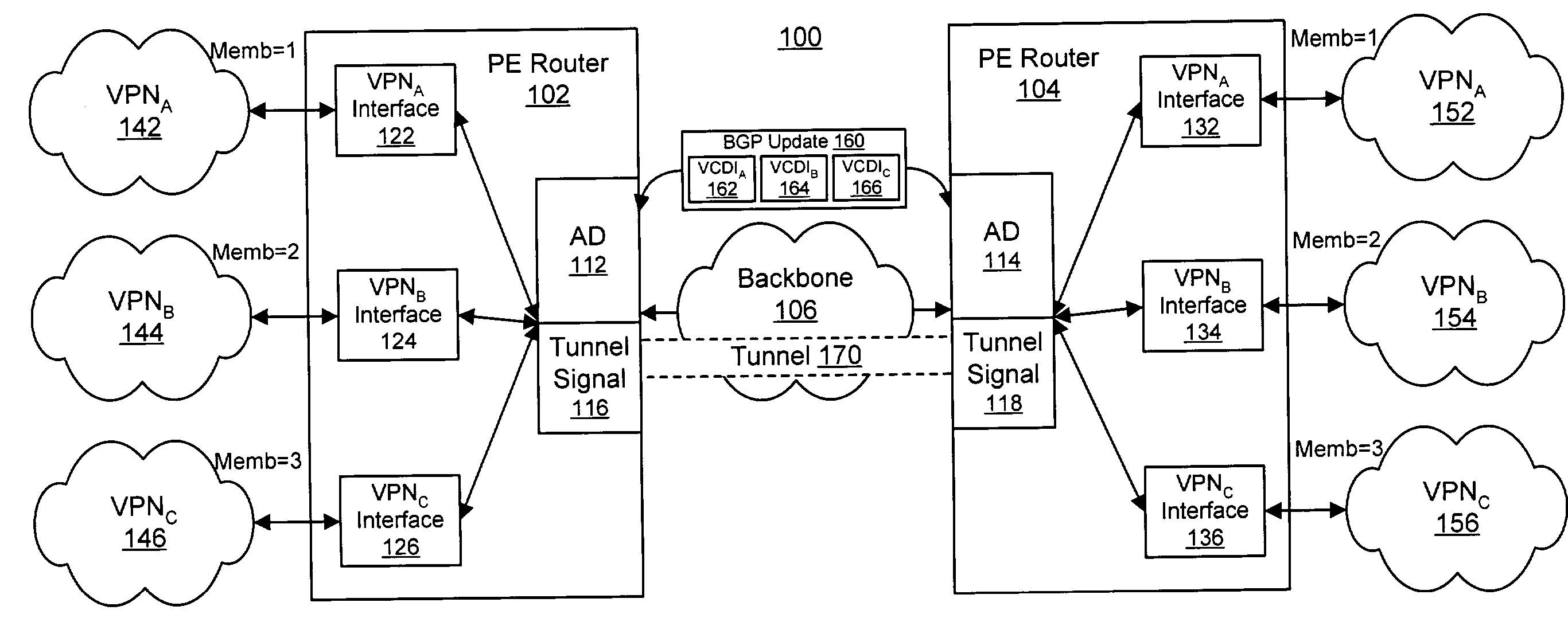
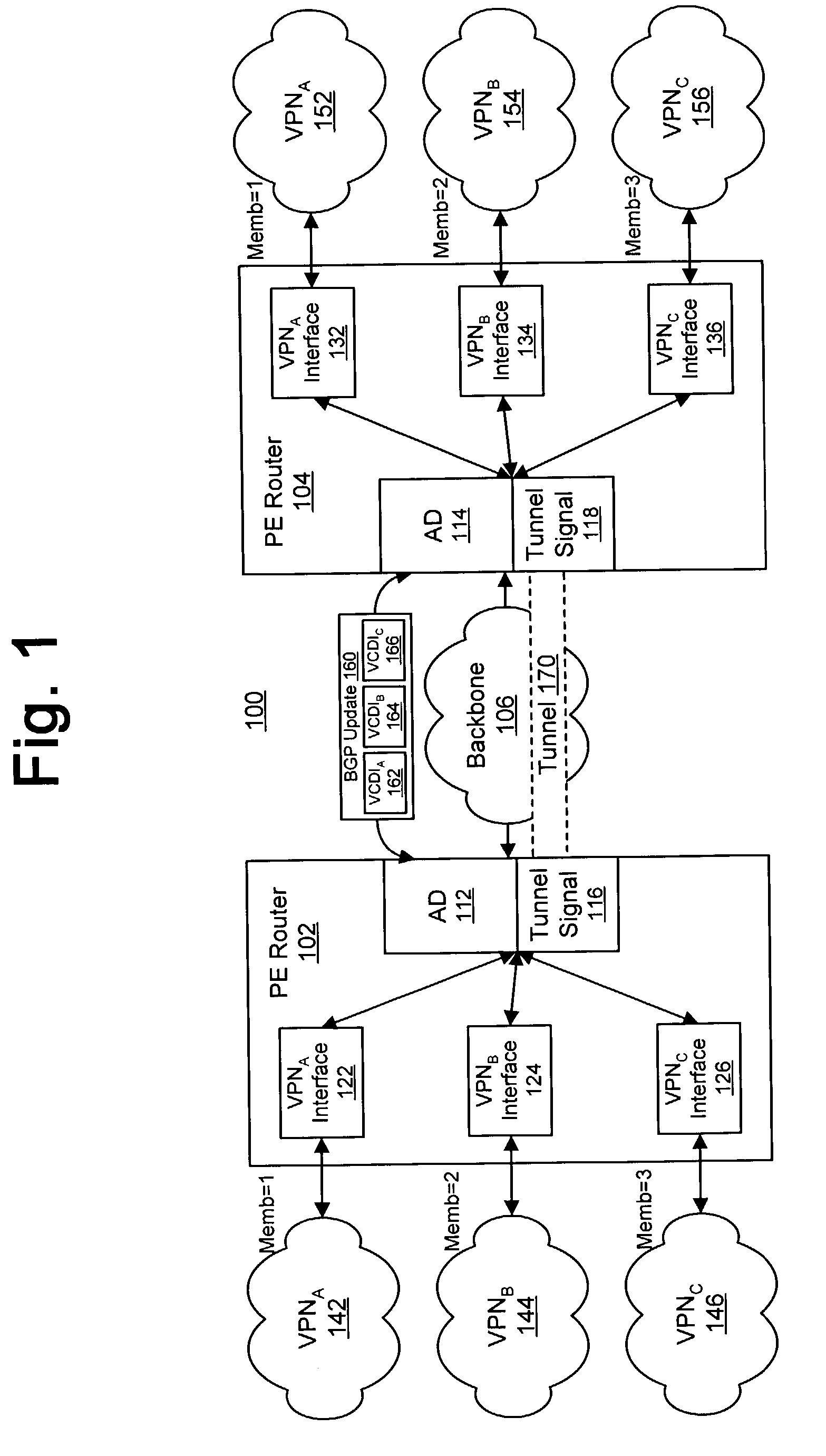
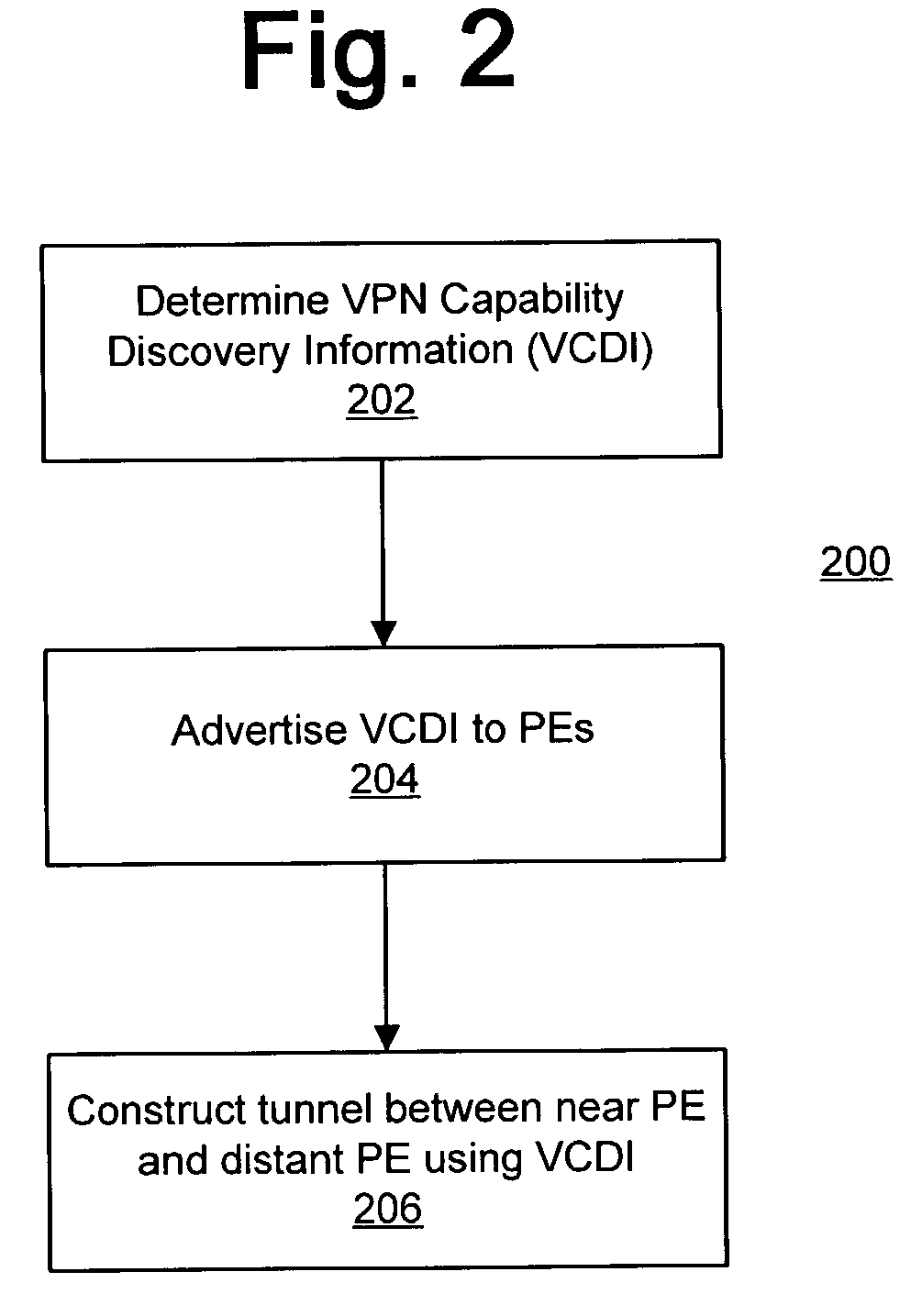
Autodiscovery for virtual networks
InactiveUS20050097203A1Facilitates automatic discoveryFacilitate signaling over LDP sessionsMultiplex system selection arrangementsDigital computer detailsBorder Gateway ProtocolProtocol for Carrying Authentication for Network Access
The present invention facilitates automatic discovery of VPN-related information, which relates to the existence or association of VPNs as supported by provider edge devices in a core network. In particular, the Border Gateway Protocol (BGP) is used to facilitate the automatic discovery, and the provider edge devices are capable of subsequently and automatically triggering Label Distribution Protocol (LDP) processes to facilitate signaling over LDP sessions within the core network.
Owner:RPX CLEARINGHOUSE
Method for building MAC (Media Access Control) address table and provider edge device
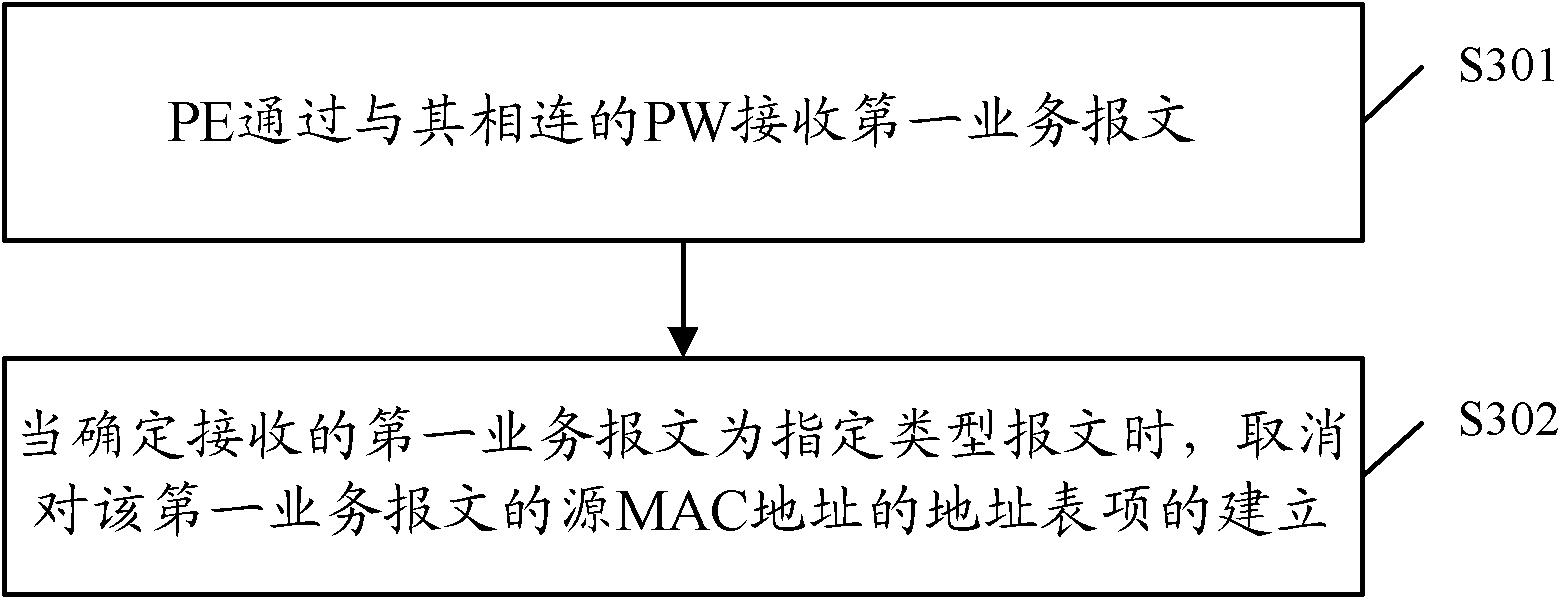
ActiveCN102164091AReduce in quantityReduce capacityData switching networksAddress Resolution ProtocolMedia access control
The invention discloses a method for building an MAC (Media Access Control) address table and a provider edge device. In the method, a PE (Provider Edge Device) receives a first service message by a PW (Pseudo Wire) connected with the PE; when the first received service message is confirmed to be a specific-type message, the building of the address table entry of the source MAC address of the first service message is cancelled, wherein the specific-type message is an unknown unicast message, a multicast message or the broadcasting message of a non-free ARP (Address Resolution Protocol) message. According to the scheme provided by the embodiment of the invention, the amount of the address table entries built by the PE is reduced so as to reduce the volume of the MAC address table.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Managing L3 VPN virtual routing tables
InactiveUS20050188106A1Efficiently setupEffective maintenanceDigital computer detailsNetworks interconnectionRouting tablePrivate network
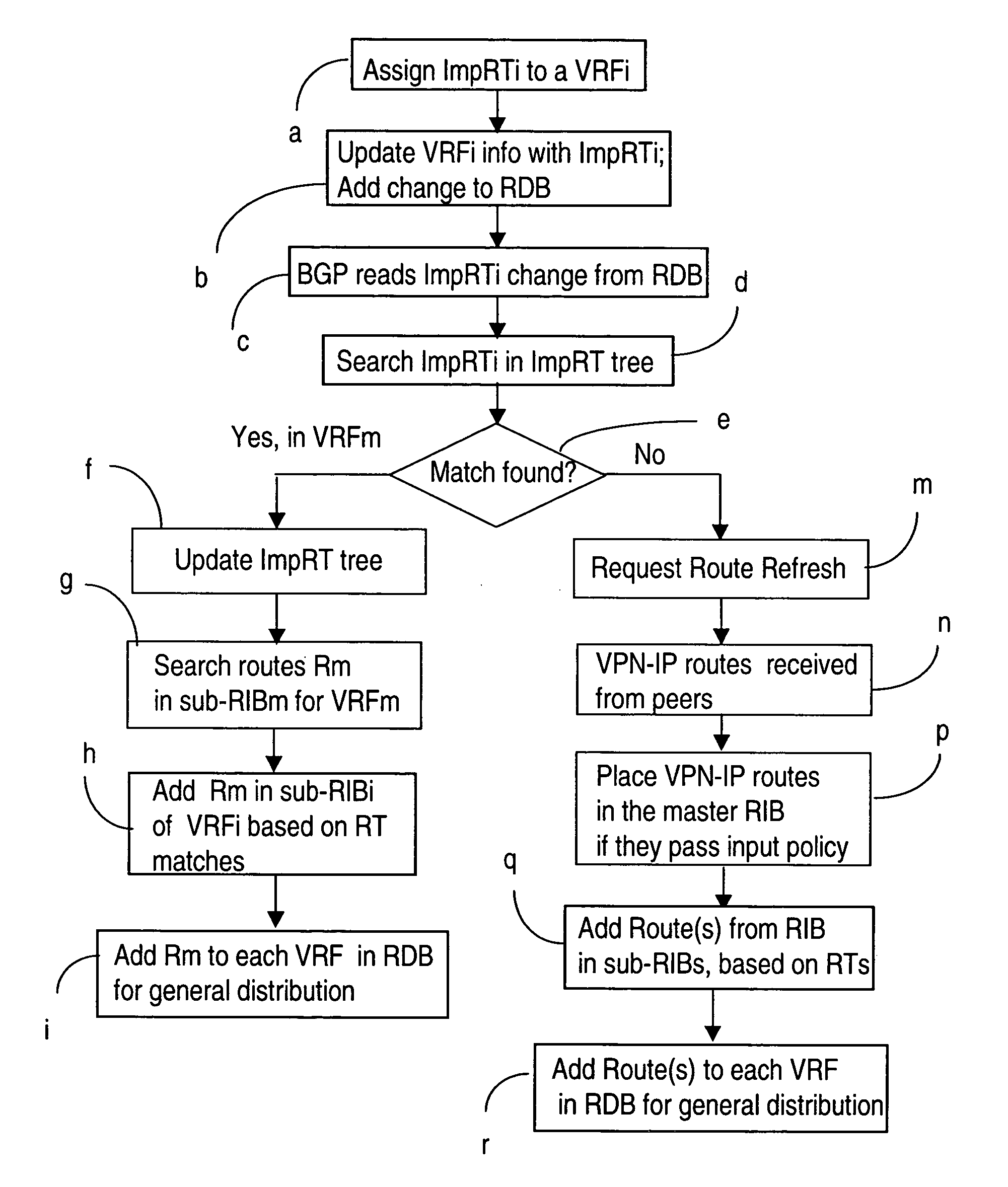
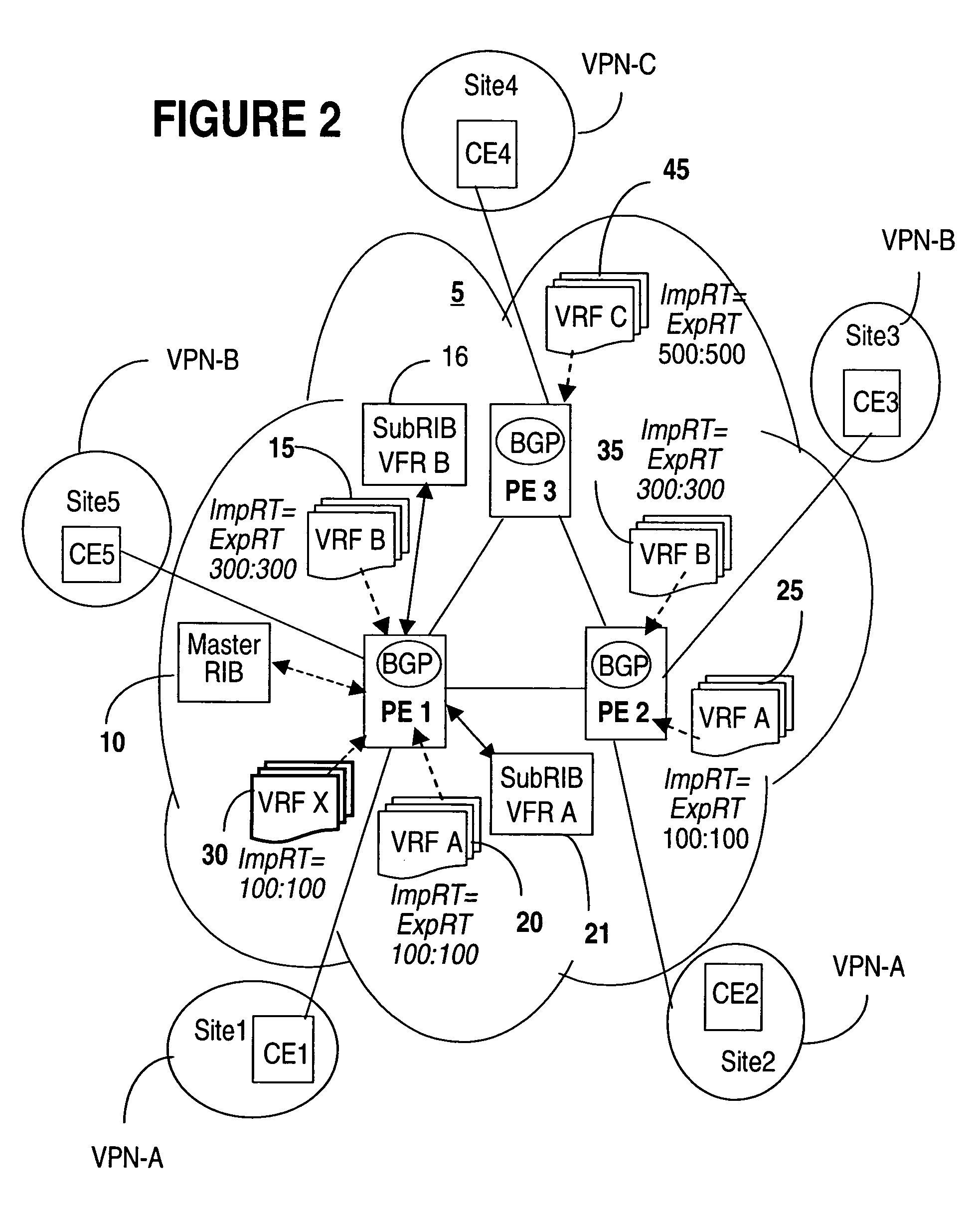
A method of managing virtual routing forwarding (VRF) tables at a provider edge PE router of a L3 virtual private network (VPN) is provided. An import route target (ImpRT) tree is maintained at the PE router, which keeps the association between all ImpRT attributes currently configured on said PE router and the virtual routing table VRF at that router. When an ImpRT attribute is configured on a VRF table, the PE router first searches the tree to identify a local VRF table that contains a route(s) with that ImpRT attribute. If this information is available locally, the VRF is updated by copying the route information, and there is no need to do a route refresh. When an ImpRT is deleted from a VRF, a route refresh is avoided by parsing all the routes in the VRF and removing the routes that no longer have a matching route target. In an alternative implementation, the local source is the master RIB (routing information base) which includes all routes in all VRFs at the router, and optionally even rejected routes that were filtered out using ImpRTs. In this variant, even routes associated with ImpRTs that are new to the router would be available to update the VRF without requiring a route refresh.
Owner:WSOU INVESTMENTS LLC
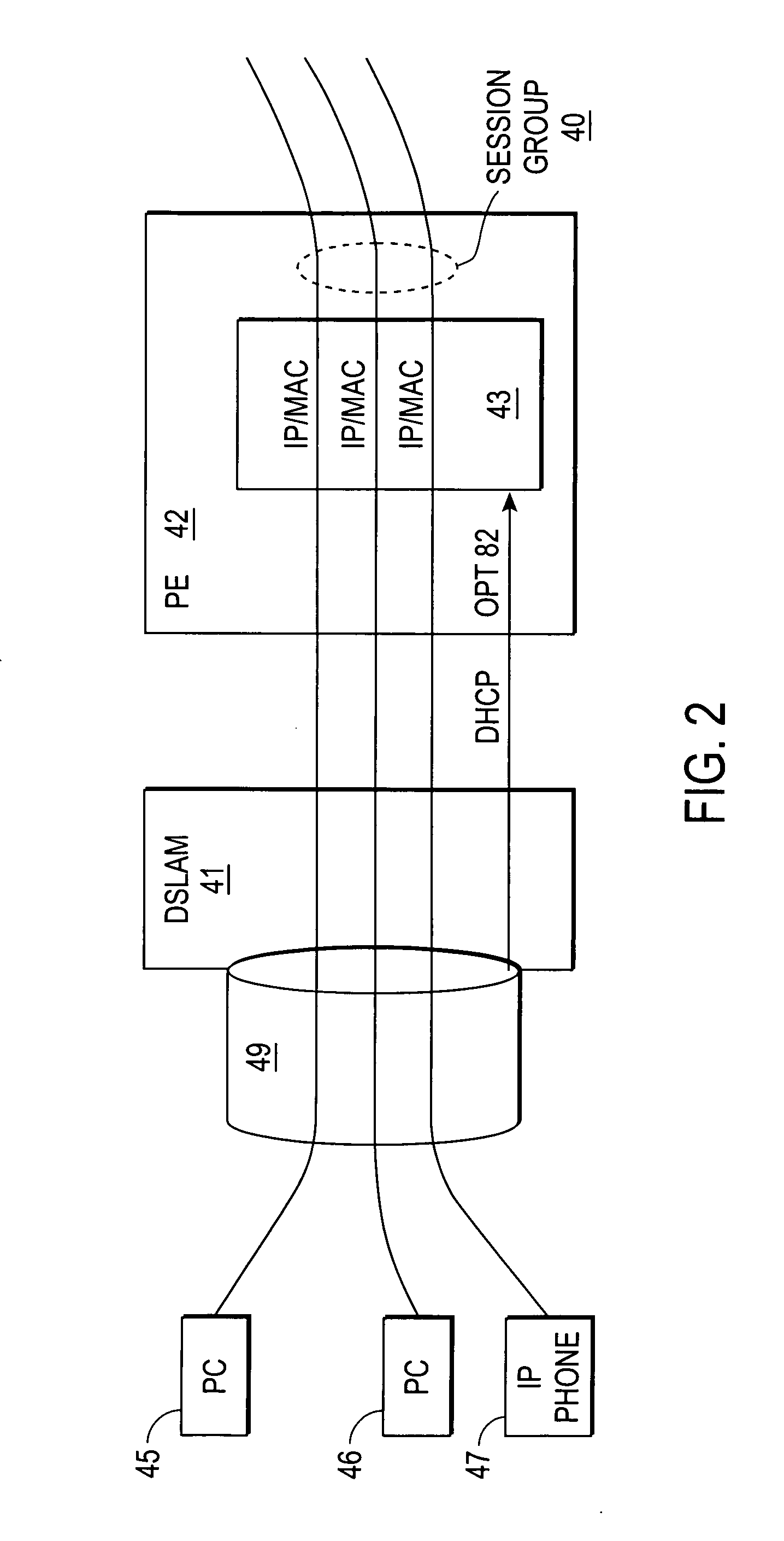
Quality of service based on logical port identifier for broadband aggregation networks
A provider edge (PE) device provides subscribers with access to an Internet Service Provider (ISP) network. The subscribers are connected to the PE device via a broadband aggregation device. The PE device includes a processor operable to snoop control plane traffic for a logical identifier that allows subscriber traffic having varying data plane information to be treated as a session group. The processor is further operable to instantiate the session group based on the logical identifier. A unit of the PE device applies a QOS policy to traffic flow associated with the session group. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
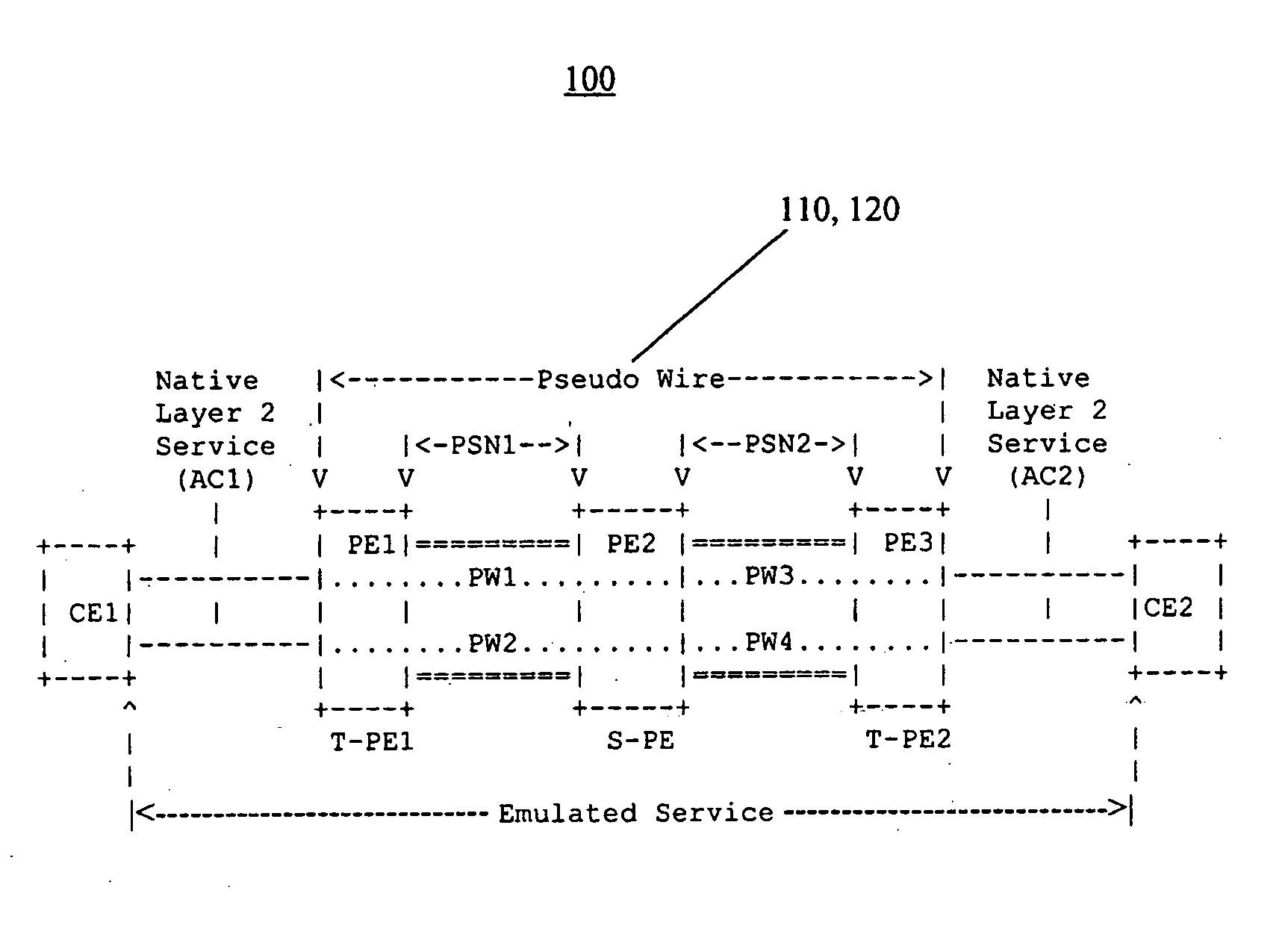
Apparatus and method for multihop MPLS/IP/ATM/frame relay/ethernet pseudo-wire
InactiveUS20050147104A1Eliminates end to end signallingEliminates end to end encapsulation negotiationNetworks interconnectionFrame RelayPseudo-wire
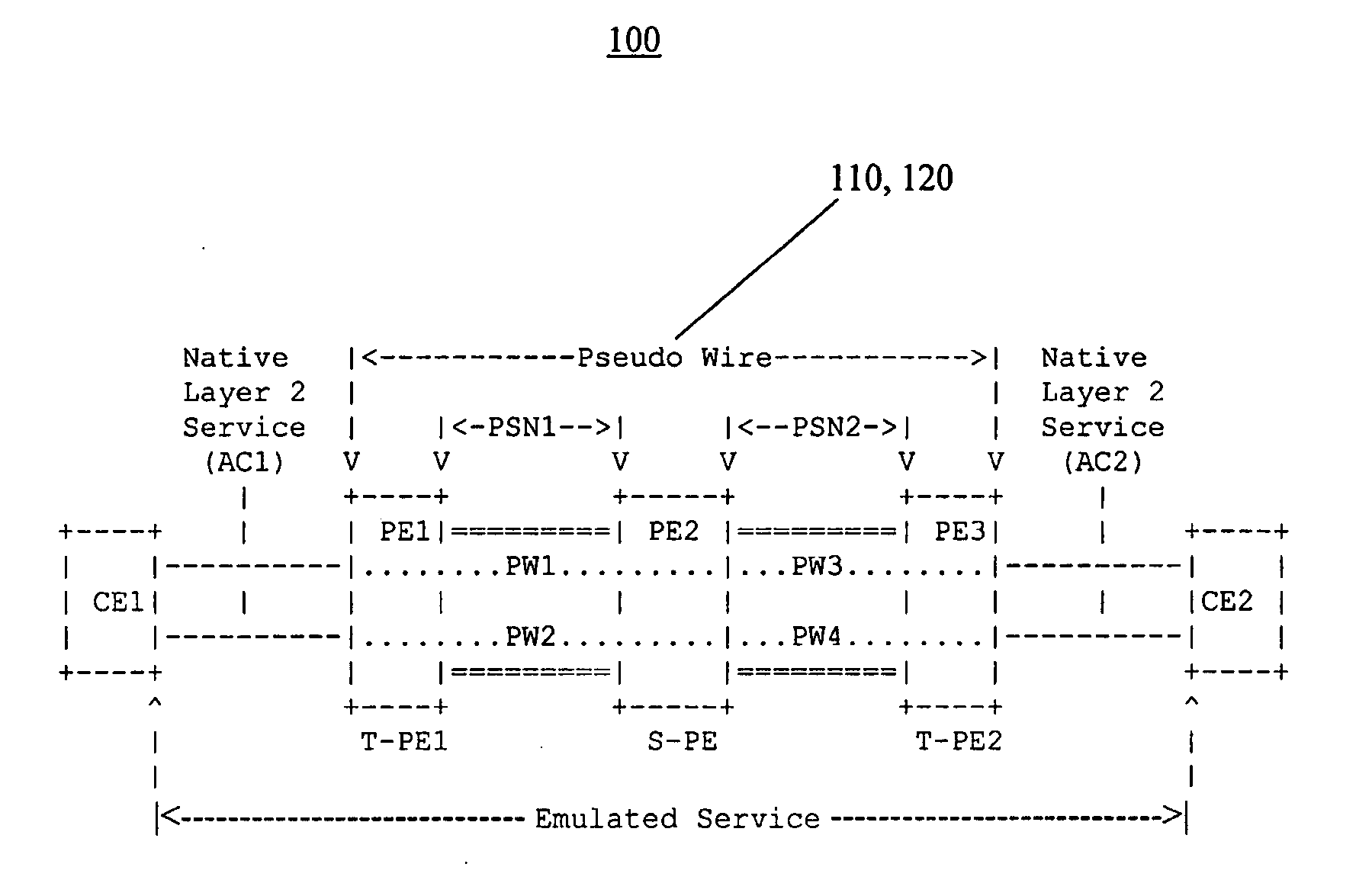
An apparatus for emulating a layer-2 service over at least one network is disclosed. The apparatus includes a signal transmission path. Two provider edge devices are located at opposite ends of the signal transmission path. A provider device is located along the signal transmission path, and this provider device divides the signal transmission path into segments. One of the provider edge devices includes code for adding a demultiplexing header onto data units prior to the data units being transmitted along the signal transmission path.
Owner:RPX CLEARINGHOUSE
Techniques configuring customer equipment for network operations from provider edge
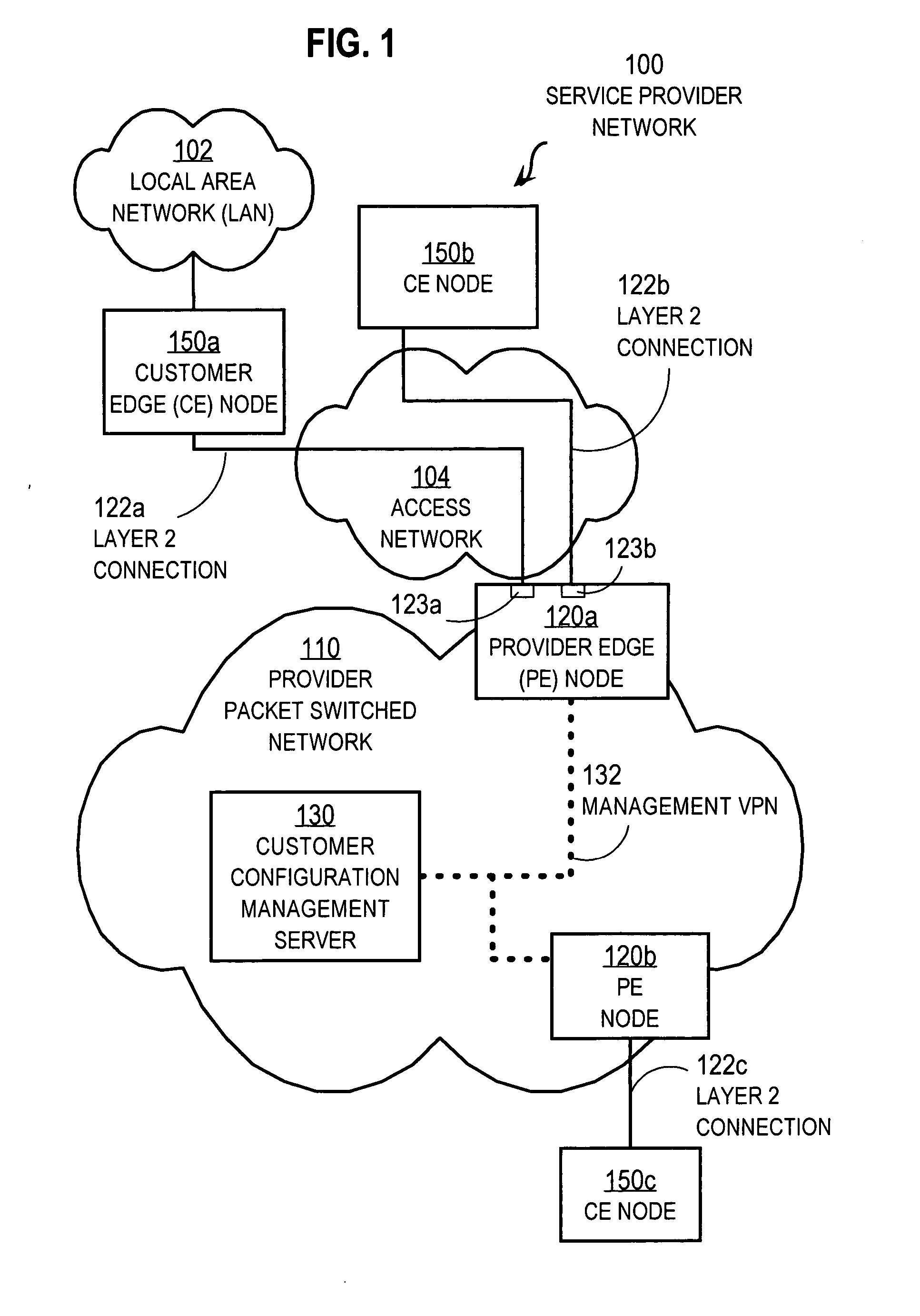
Techniques for configuring customer premises equipment for communication with a provider network include establishing a physical layer network connection between a particular customer node and a first provider node. The particular customer node is an intermediate network node on a customer premises. The first provider node is an intermediate network node on a first provider network of a first service provider different from the customer. Configuration data for one or more network interfaces on the particular customer node are automatically received through the physical layer network connection. The particular customer node is automatically configured based on that configuration data. The automatic provisioning of the customer node allows equipment to be more economically shipped and installed at customer premises and allows upgraded or replacement equipment to be more economically swapped in place of equipment previously installed. Traffic management data can also be automatically received and used at the particular customer node.
Owner:CISCO TECH INC
System and method for load balancing traffic in a mpls network
InactiveUS20110063986A1Error preventionFrequency-division multiplex detailsTraffic capacityPacket loss
A method and system for managing traffic between a first provider edge and a second provider edge in a network. The network includes logical paths between the first provider edge and the second provider edge. For each logical path, jitter, packet delay, and packet loss are identified. For each logical path, a path usage is calculated as a function of the identified jitter, packet delay, and packet loss. Most recent data received by the first provider edge is transmitted to the second provider edge via a selected logical path that has a highest path usage for which transmitting the received most recent data does not result in the selected logical path managing a higher percentage of network traffic than is dictated by the highest usage value for the selected logical path.
Owner:KYNDRYL INC
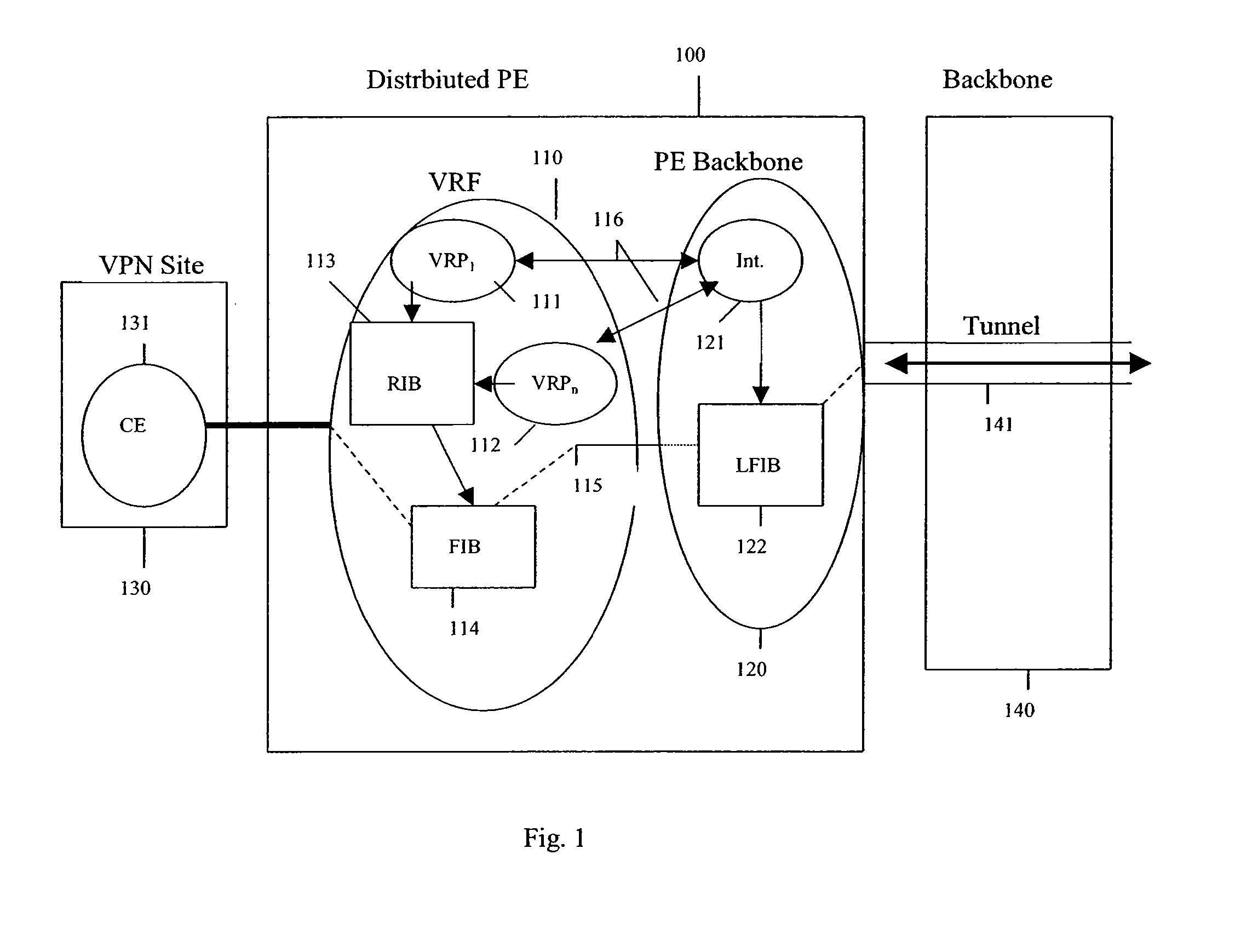
Methods and systems for a distributed provider edge
Methods and Systems are provided for a distributed Provider Edge (PE). A single Virtual Routing and Forwarding device (VRF) is associated with a single customer site. The VRF includes a single routing table (RIB) and a single forwarding table (FIB). The VRF also includes a plurality of Virtual Private Network (VPN) Protocol Instance Modules (VRP), where each VRP is associated with a different VPN from the customer site. Each VRP accesses the RIB directly and the FIB indirectly to acquiring addressing / routing information for a received data packet. Moreover, each VRP uses a data plane of the VRP to communicate the data packets to a PE backbone device. In turn, the PE backbone device uses the data plane to communicate with each of the VRPs, and the PE backbone device communicates with one or more tunnels.
Owner:FORTINET
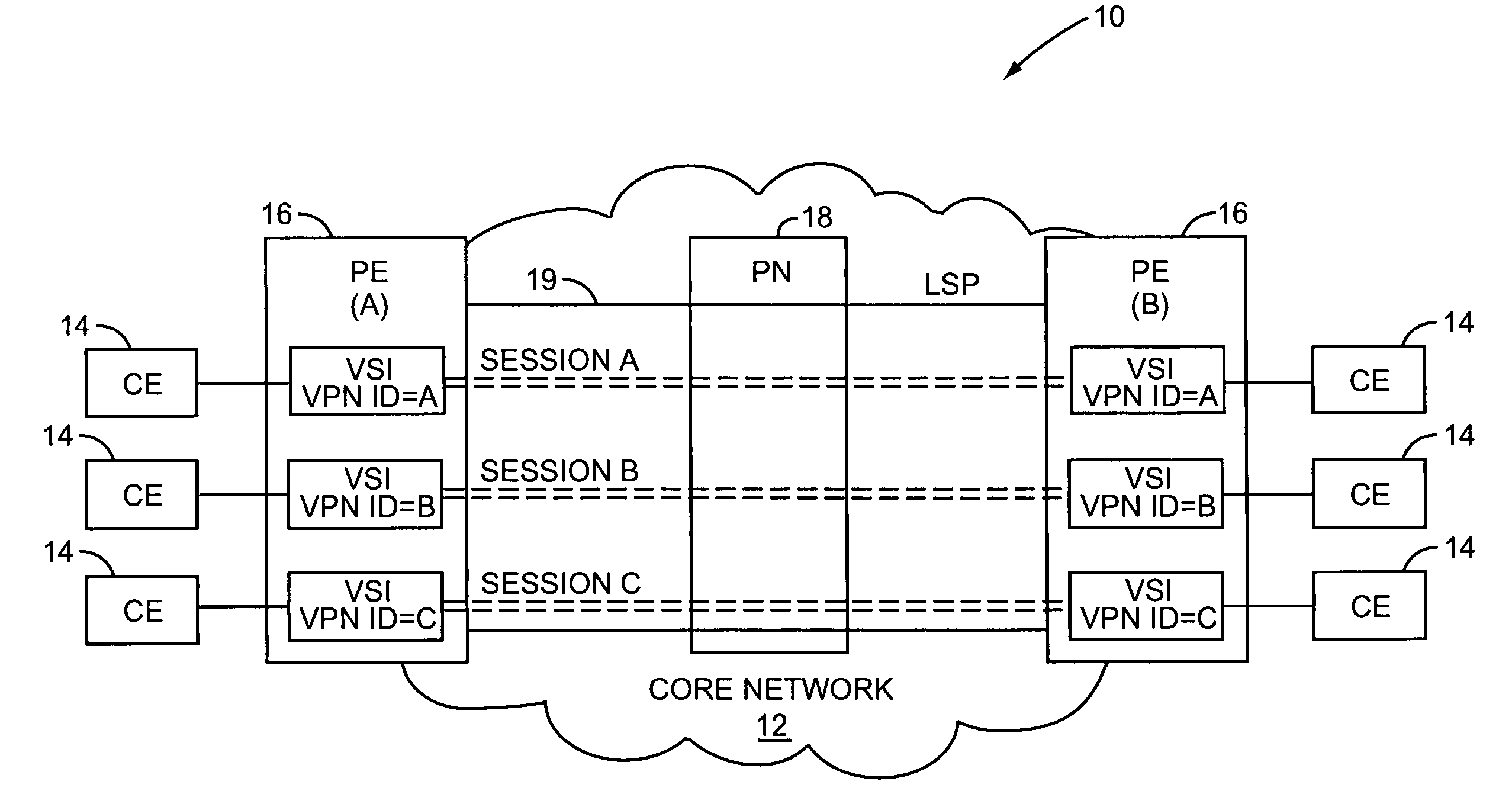
Resource allocation using an auto-discovery mechanism for provider-provisioned layer-2 and layer-3 virtual private networks
InactiveUS7478167B2Guaranteed maximum utilizationDigital computer detailsNetworks interconnectionPrivate networkSelf adaptive
A technique for resource distribution using an auto-discovery mechanism for Provider-Provisioned Layer-2 and Layer-3 Virtual Private Networks. In one particular exemplary embodiment, the technique may be realized by a method for establishing a Virtual Private Network (VPN) tunnel between a first provider edge (PE) device and a second (PE) device of a provider-provisioned VPN. The method may comprise advertising at least one tunnel-based parameter to one or more PE devices over a network backbone using an auto-discovery mechanism, the one or more PE devices including at least one of the first and second PE devices. The method further may comprise configuring a VPN tunnel between the first and second PE devices based at least in part on the at least one tunnel-based parameter.
Owner:INT LICENSE EXCHANGE OF AMERICA LLC
Optimal bridging over MPLS / IP through alignment of multicast and unicast paths
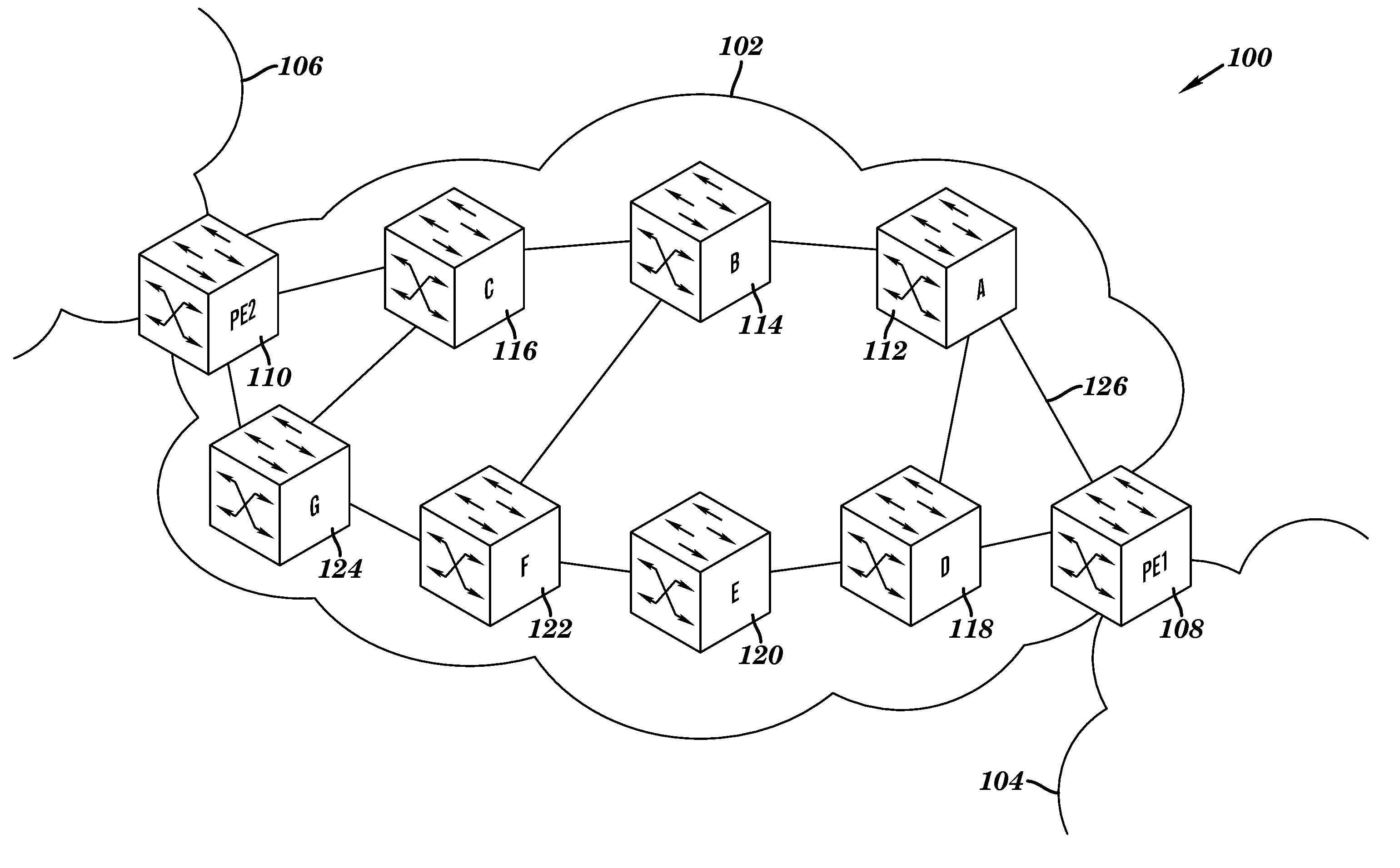
A provider edge (PE) node of a network operates to send a trace path message over the network to a receiver PE node, the trace path message recording a list of intermediate nodes of a unicast path from the PE node to the receiver PE node; and receive a join message initiated from the receiver PE node, the join message using the list to propagate to the source PE node through the intermediate nodes such that a branch of a multicast tree is aligned with the unicast path. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
Method and system for verifying connectivity of multi-segment pseudo-wires
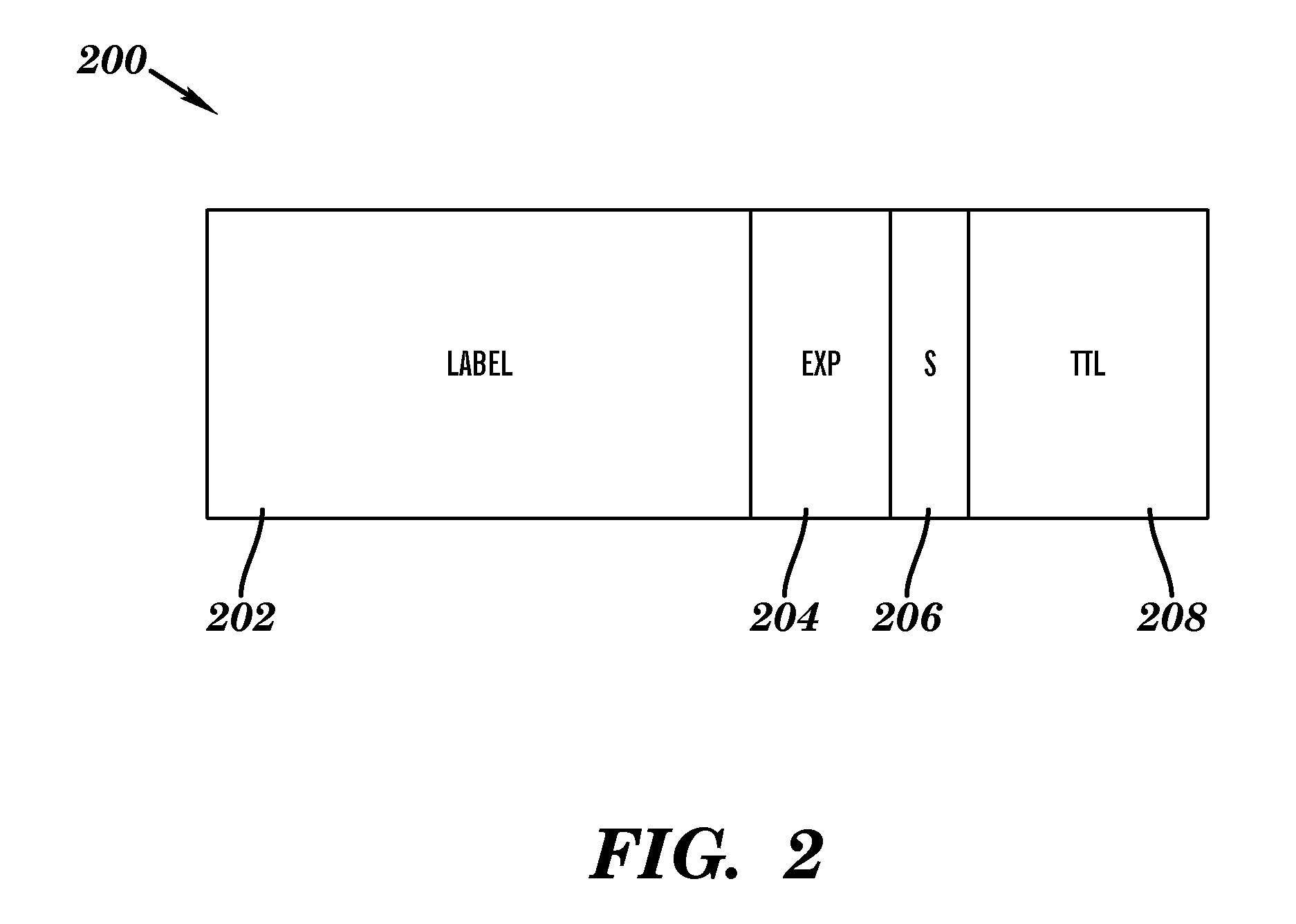
ActiveUS20080279110A1Confirming connectivityError preventionTransmission systemsTime to liveProvider Edge
A method for testing connectivity of a multi-segment pseudo-wire (“MS-PW”) in a network, the method comprising: sending an echo request message from a first provider edge (“PE”) device to a second provider edge (“PE”) device for a section of the multi-segment pseudo-wire (“MS-PW”) between the first provider edge (“PE”) device and the second provider edge (“PE”) device; the echo request message being identified as such by a control word contained therein; an inner label of the echo request message having a time-to-live (“TTL”) value set to a number of segments in the section; the time-to-live (“TTL”) value for determining whether the control word is to be inspected as it traverses the section; upon the echo request message arriving at the second provider edge (“PE”) device, the second provider edge (“PE”) device recognizing the echo request message as such by inspecting the control word contained therein; and, receiving an echo reply message from the second provider edge (“PE”) device in response to the echo request message, the echo reply message confirming connectivity of the section.
Owner:ALCATEL LUCENT SAS
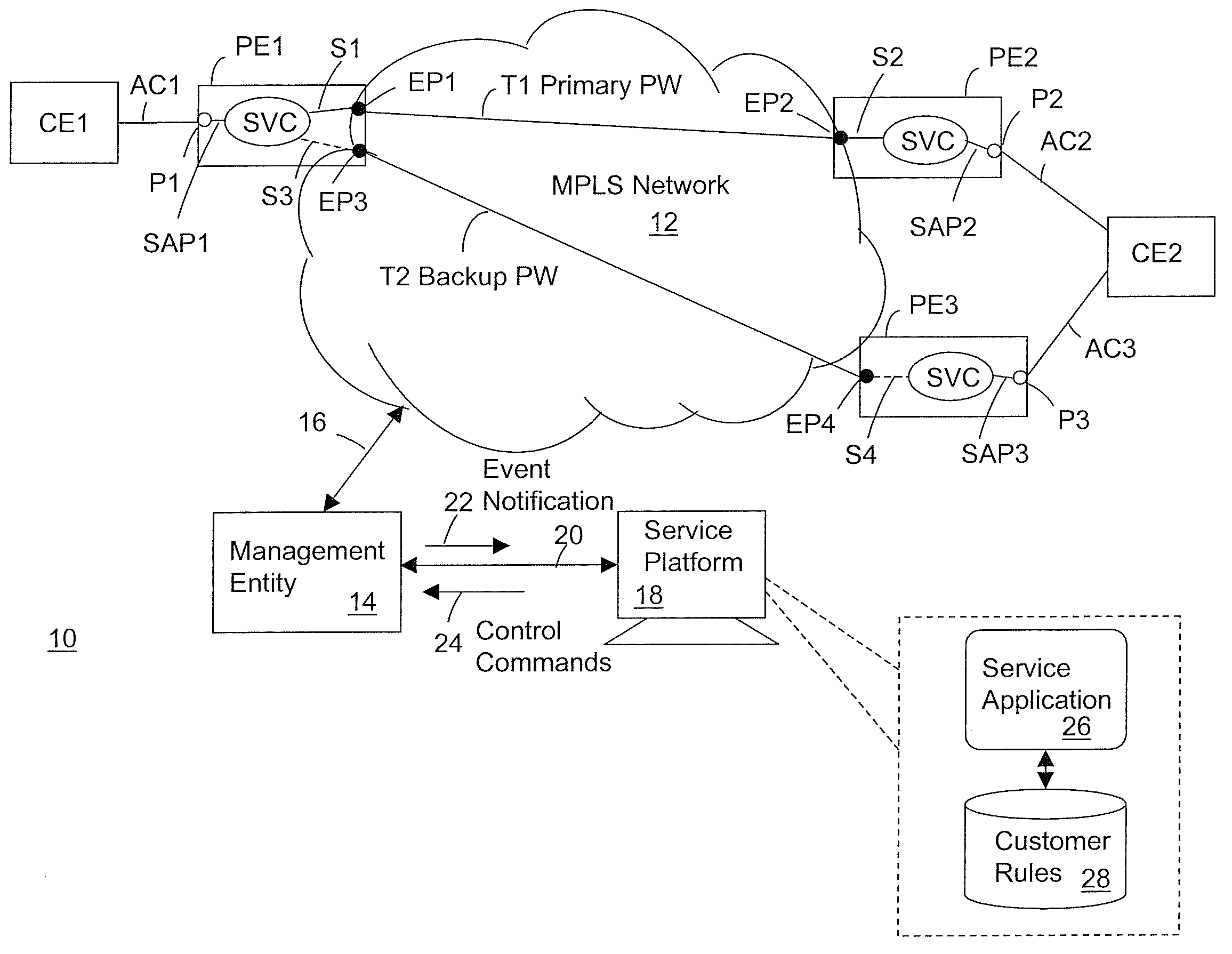
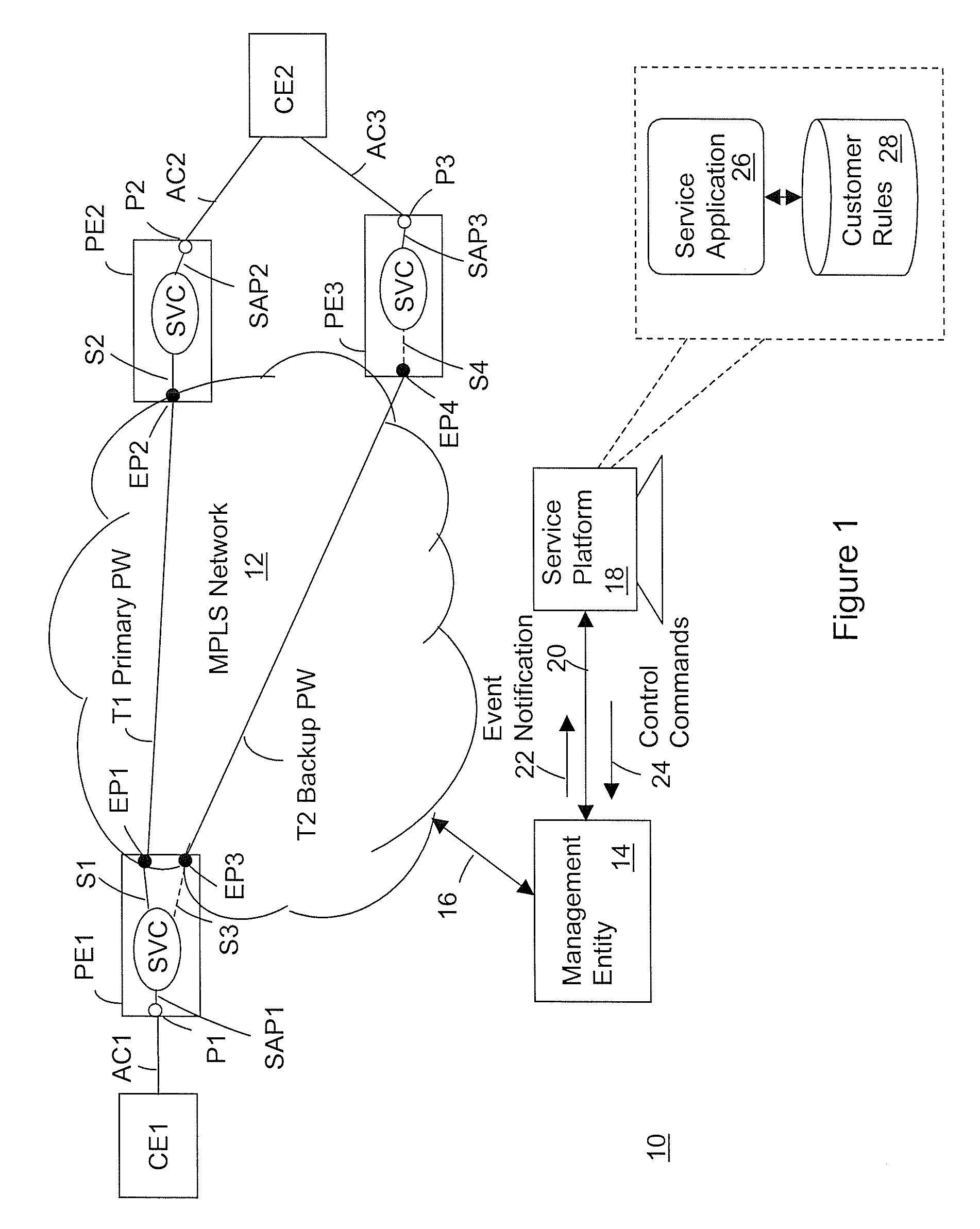
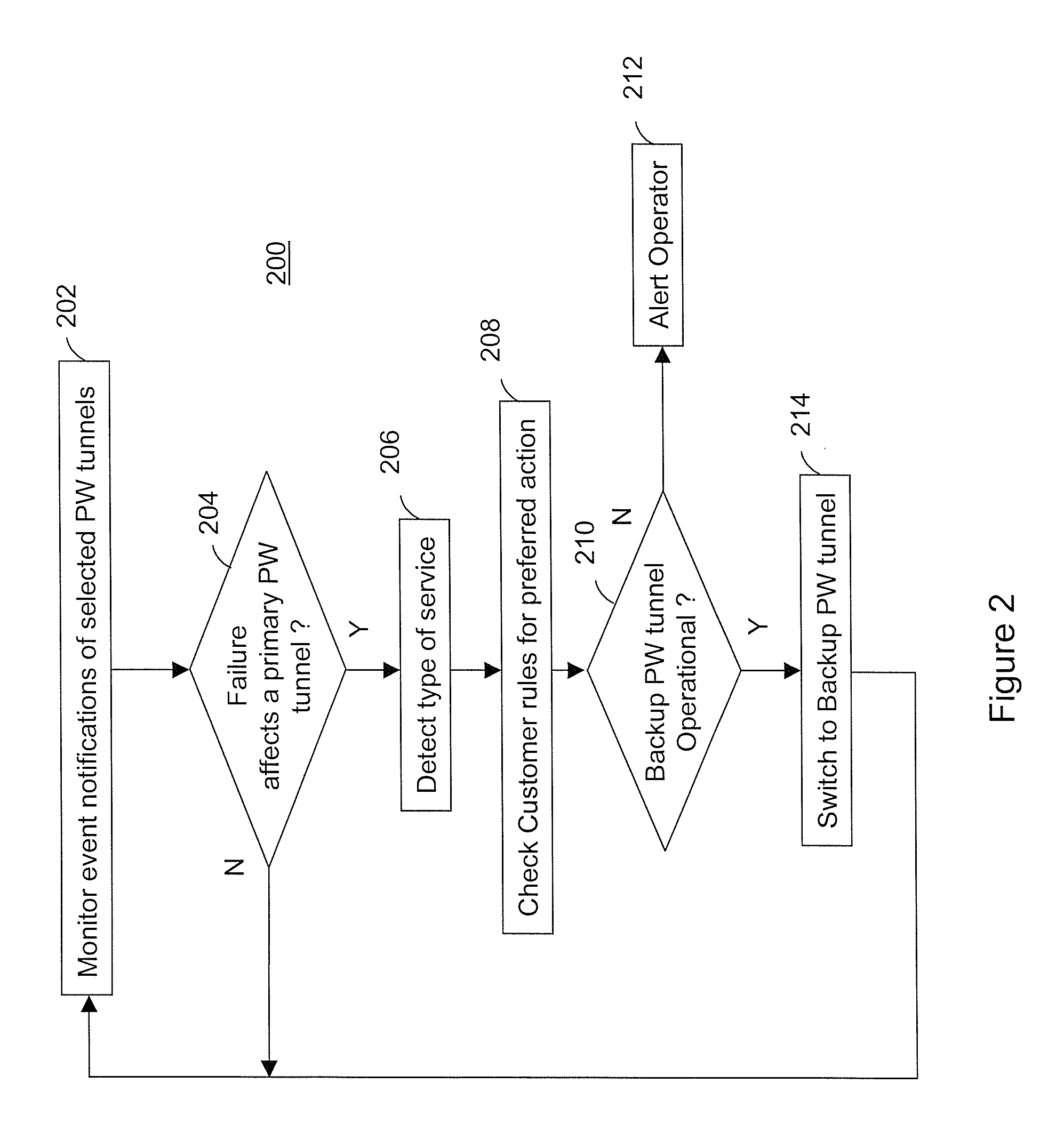
Pseudowire tunnel redundancy
ActiveUS20100226246A1Error preventionTransmission systemsAutomatic protection switchingNetwork management
The invention is directed to providing pseudowire tunnel redundancy for VPLS and VLL services in the form of automatic protection switching of the service from a primary pseudowire tunnel to a backup pseudowire tunnel upon detection of a failure affecting the primary pseudowire tunnel. Embodiments of the invention monitor event notifications reported by a network management entity for an indication of a failure affecting the primary pseudowire tunnel; and responsive to detecting the indication, switch a service carried by the primary pseudowire tunnel to the backup pseudowire tunnel. Such event notifications include those corresponding to any of provider edge routers, interface ports, service access points, spokes, and tunnel endpoints that are related to operation of the primary pseudowire tunnel
Owner:ALCATEL LUCENT SAS
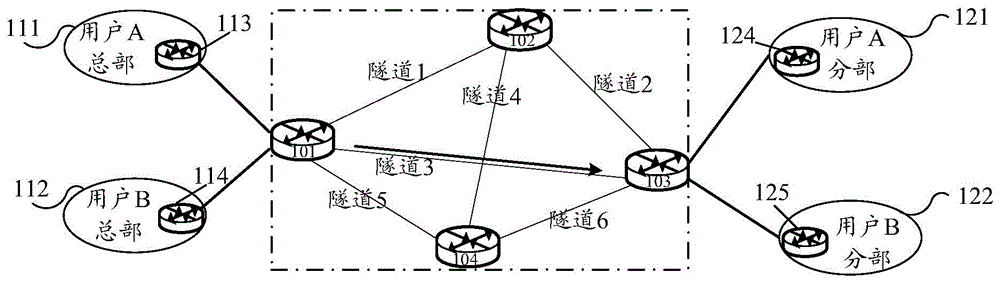
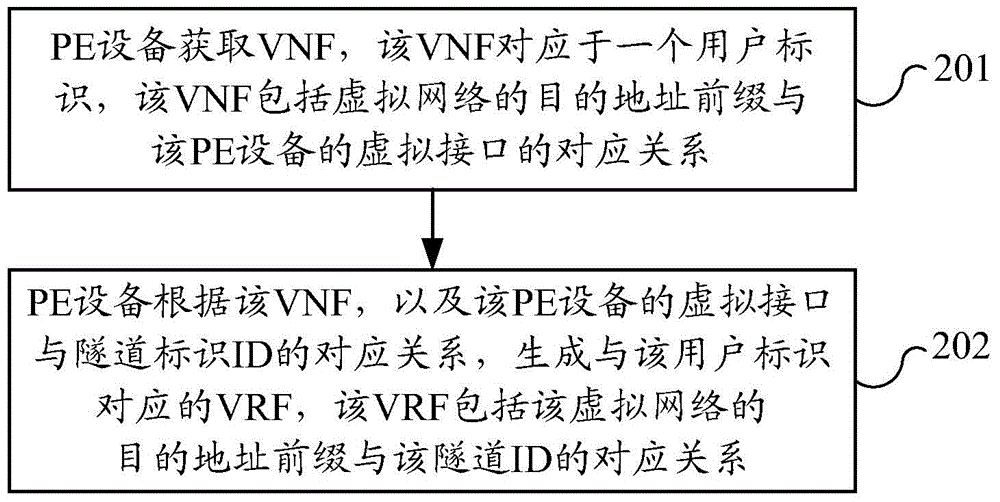
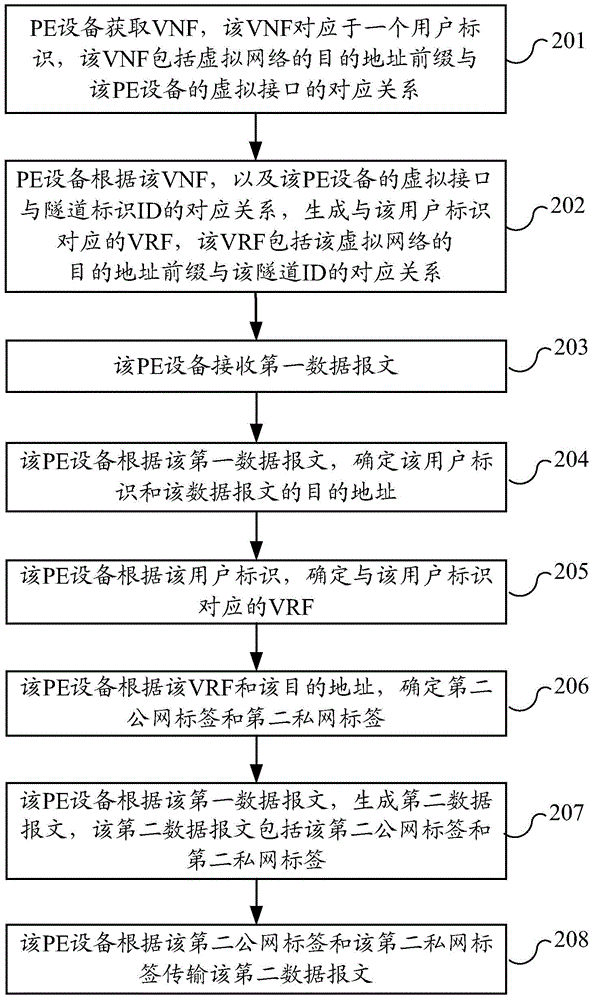
Method for determining route in virtual network and provider edge equipment
The embodiments of the invention provide a method for determining a route in a virtual network. The method comprises the following steps that: provider edge (PE) equipment obtains a virtual network forward (VNF) corresponding to one user identifier, wherein the VNF includes a corresponding relation between a destination address prefix of a virtual network and a virtual interface of the PE equipment; and according to the VNF and a corresponding relation between the virtual interface of the PE equipment and a channel identity (ID), the PE equipment generates a virtual route forward (VRF) corresponding to the user identifier, wherein the VRF includes a corresponding relation between the destination address prefix of the virtual network and the channel ID. According to the embodiments of the invention, the PE equipment obtains the VNF corresponding to the user identifier and then generates the VRF corresponding to the user identifier based on the VNF, so that a data packet corresponding to the user identifier can be forwarded according to a route designated by the VRF and thus the user can plan the route by himself.
Owner:HUAWEI TECH CO LTD
Refresh and filtering mechanisms for LDP based VPLS and L2VPN solutions
InactiveUS20050089047A1Limit BGP usageReduce usageTime-division multiplexNetworks interconnectionPrivate networkNetwork Communication Protocols
Refresh and filtering mechanisms for LDP based VPLS and L2VPN solutions are disclosed. A method for improving information communication in a network is achieved by these refresh and filtering mechanisms. The network includes provider edge devices which can communicate with each other. The provider edge devices run a communications protocol. The method includes a step of using the communications protocol in providing a first of the provider edge devices with a list of layer-2 virtual private network instances to which a second of the provider edge devices belongs. Another step in the method is filtering layer-2 virtual private network information to be communicated to the second provider edge device from the first provider edge device by reference to the layer-2 virtual private network instances to which the second provider edge device belongs.
Owner:RPX CLEARINGHOUSE
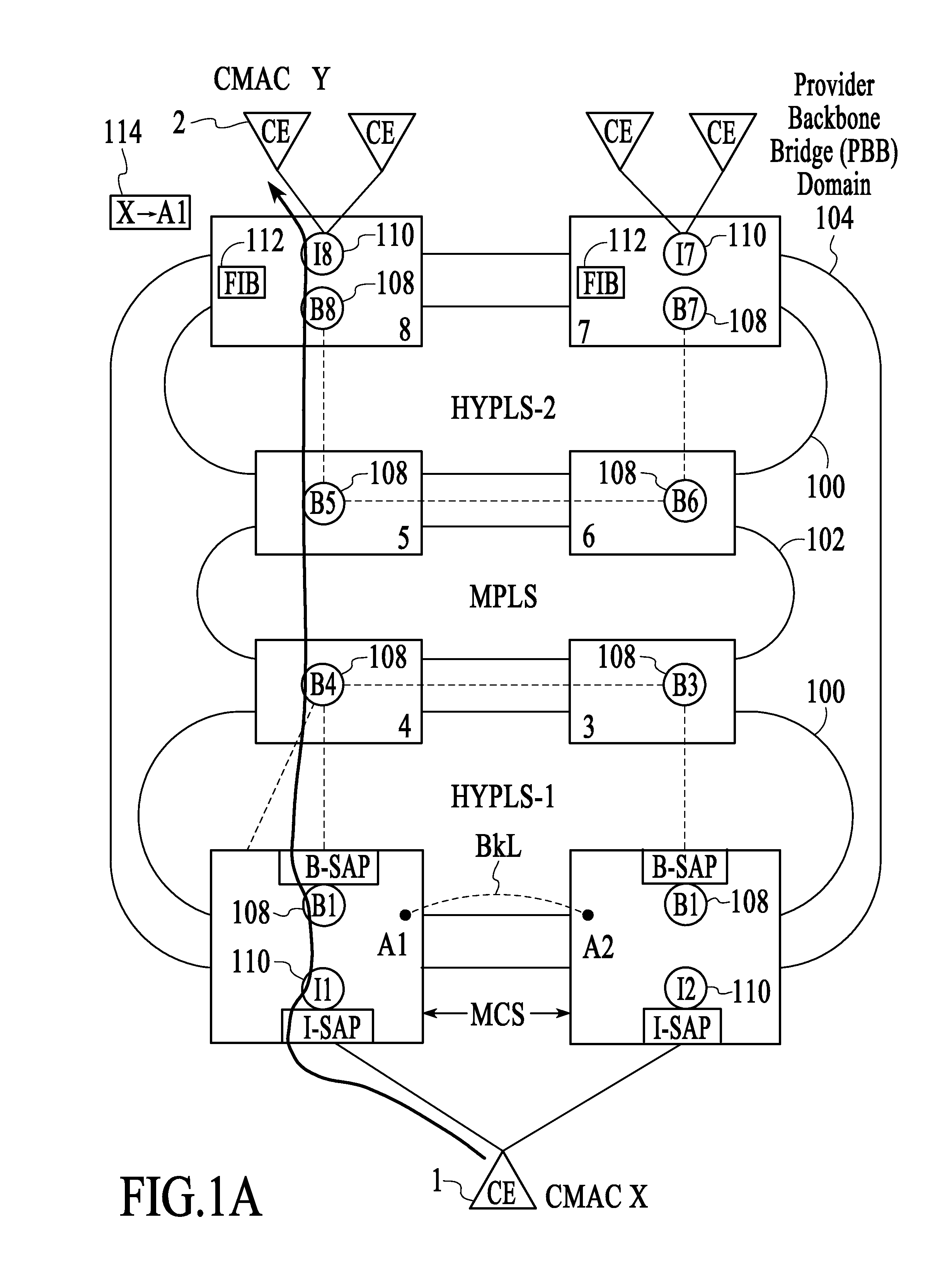
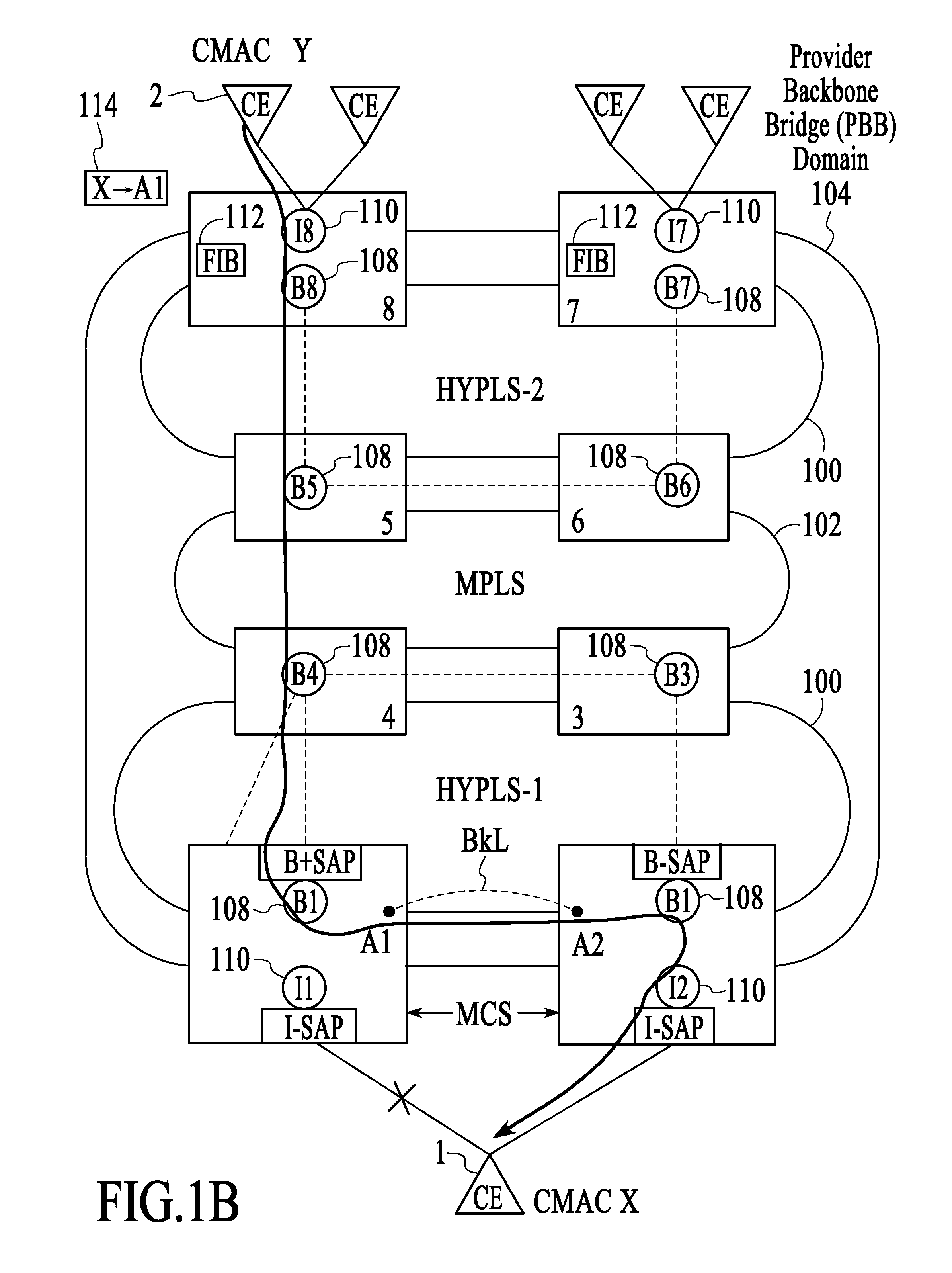
Failure protection in a provider backbone bridge network using selective redirection
ActiveUS20080228943A1Digital computer detailsData switching networksTraffic capacityComputer science
A technique for operating a network involves controlling the black-holing of traffic by selectively redirecting unicast traffic destined for a dual-homed customer equipment (CE) device from a first provider backbone bridge (PBB) provider edge (PE) device to a second PBB PE device in response to a service failure. Unicast traffic is selectively redirected from the first PBB PE device to the second PBB PE device for a time interval that is long enough to enable the customer source MAC address (CMAC)-to-backbone MAC address (BMAC) association of the second PBB PE device to be learned by other PBB PE devices.
Owner:WSOU INVESTMENTS LLC
High bandwidth broadcast system having localized multicast access to broadcast content
InactiveUS6965593B2Reduce severityBig advantageSpecial service provision for substationTelevision system detailsDigital dataCable Internet access
A method and arrangement is provided for the multicasting of streaming digital content to a plurality of Internet users. Streaming digital audio, video or other digital data content that is to be multicast to Internet users is formatted into IP protocol at a head-end content source transmission site. The streaming IP digital data is transmitted from the head-end transmission site to at least one distant / remote routing station of an Internet service provider (i.e., a provider-edge router or Internet point of presence) via a bandwidth portion of a digital communications data transport service or transmission medium that is substantially unaffected by conventional Internet communications traffic. The Internet service provider (ISP) maintains at least one access router for providing Internet access via its Internet domain for its customers accessing the Internet via conventional two-way IP connection. The streaming IP digital data received from the content source transmission site by the ISP routing station may then be multicast via the IPS's existing infrastructure to one or more of its Internet access customer.
Owner:HANGER SOLUTIONS LLC +1
Method and apparatus for load balancing over virtual network links
Techniques for load balancing network traffic over virtual point-to-point data links at a data-link layer include determining a particular group of virtual point-to-point data links that reach a particular local area network of one or more network nodes. A particular data-link address for a particular node of the particular local area network is associated with each virtual point-to-point data link of the particular group. When a data packet is received that includes data that indicates the particular data-link address as a destination; one virtual point-to-point data link of the group is determined to balance traffic among the group. The data packet is sent only over the one virtual point-to-point data link. These techniques enable virtual point-to-point data links through two or more intermediate network nodes, such as a pair of provider edge nodes, to be bundled for load balancing purposes.
Owner:CISCO TECH INC
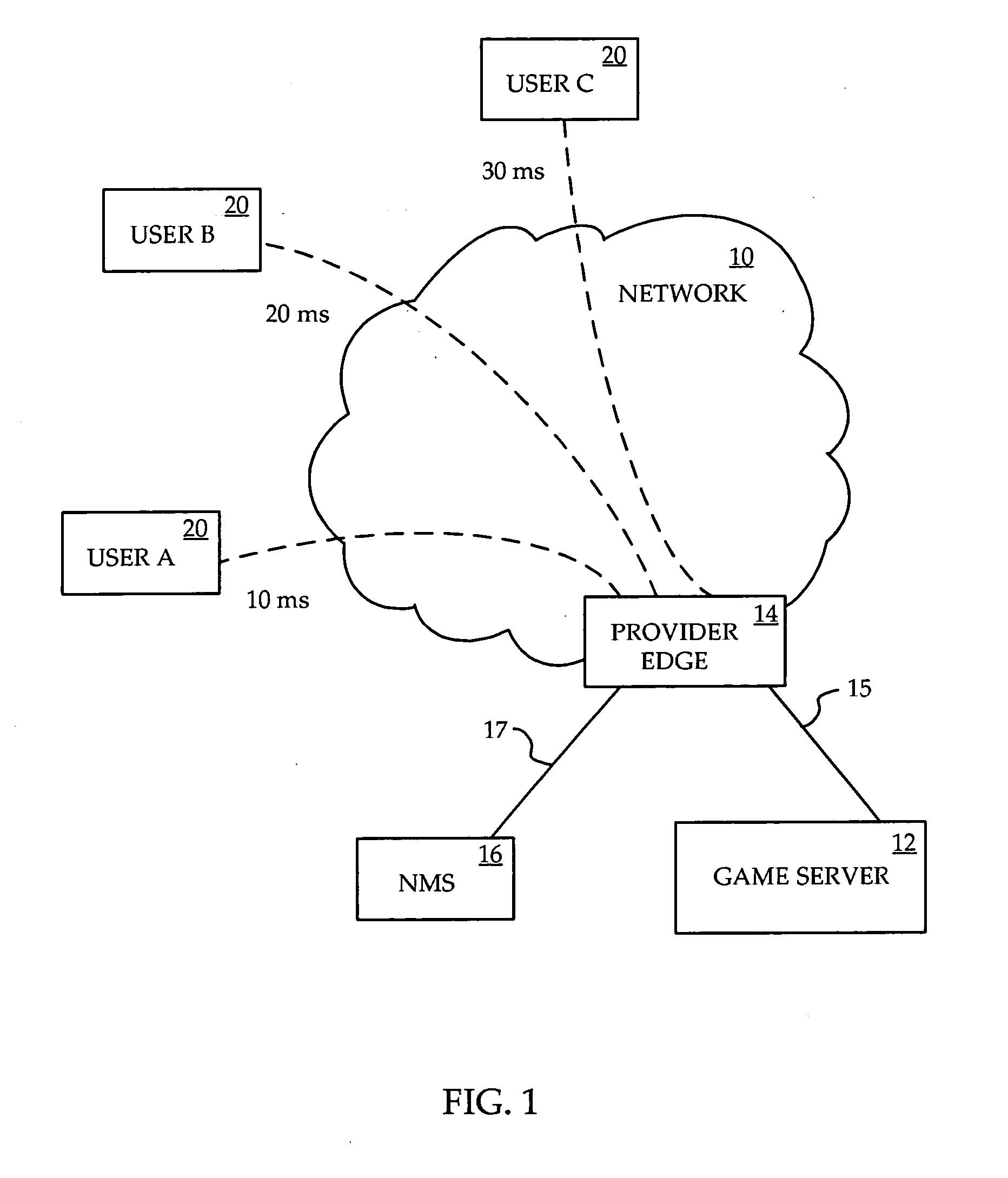
Equalized network latency for multi-player gaming
InactiveUS20070070914A1Reduce latency varianceLatency connectionError preventionFrequency-division multiplex detailsTraffic capacityApplication server
A method is provided for equalizing latency among a group of connections that are being used by the same latency-sensitive application, such as for multi-player network gaming. Delay is added to the packet flow in each connection as necessary at the provider edge router connecting the application server to the network. An NMS connected to the provider edge router continuously monitors the round-trip delay of each connection, determines the additional delay of each connection required to equalize the delays, and informs the provider edge router. The provider edge router buffers traffic on each connection for the respective duration as indicated by the NMS. The NMS may also reroute some of the connections over higher latency resources to reduce the amount of buffering required, which provides the additional advantage of using what might otherwise be less used or economically less valued resources.
Owner:RPX CORP
Stability Site for VPLS Multi-Homing
ActiveUS20140056125A1Reduce lossesError preventionFrequency-division multiplex detailsFailoverService provision
Novel tools and techniques are described for mitigating data loss during failover in a VPLS multi-homed network. In one aspect, a primary link might be established between a lowest numbered provider edge (“PE”) router in the service provider network and a lowest numbered physical site at customer premises outside the service provider network. A stability site might be established within the service provider network, communicatively coupled to at least the lowest numbered PE router via a primary virtual circuit. The stability site might be designated as the lowest numbered virtual site, which might have a site ID number lower than the lowest numbered physical site. In response to the primary link failing or becoming broken, one or more backup virtual circuits might be established between a plurality of ingress PE routers and a plurality of egress PE routers in the service provider network, without destroying the primary virtual circuit.
Owner:CENTURYLINK INTPROP
Method and system for verifying connectivity of multi-segment pseudo-wires by tracing
ActiveUS20080095061A1Error preventionFrequency-division multiplex detailsExchange networkPseudo-wire
A method for testing connectivity of a multi-segment pseudo-wire in a packet switched network, the method comprising: (a) sending an echo request message from a first provider edge device to a second provider edge device for a first segment of the multi-segment pseudo-wire between the first provider edge device and the second provider edge device; and, (b) receiving an echo reply message from the second provider edge device in response to the echo request message, the echo reply message: confirming connectivity of the first segment; indicating whether there is a second segment in the multi-segment pseudo-wire between the second provider edge device and a third provider edge device; and, if there is a second segment, including information pertaining to the second segment.
Owner:ALCATEL LUCENT SAS
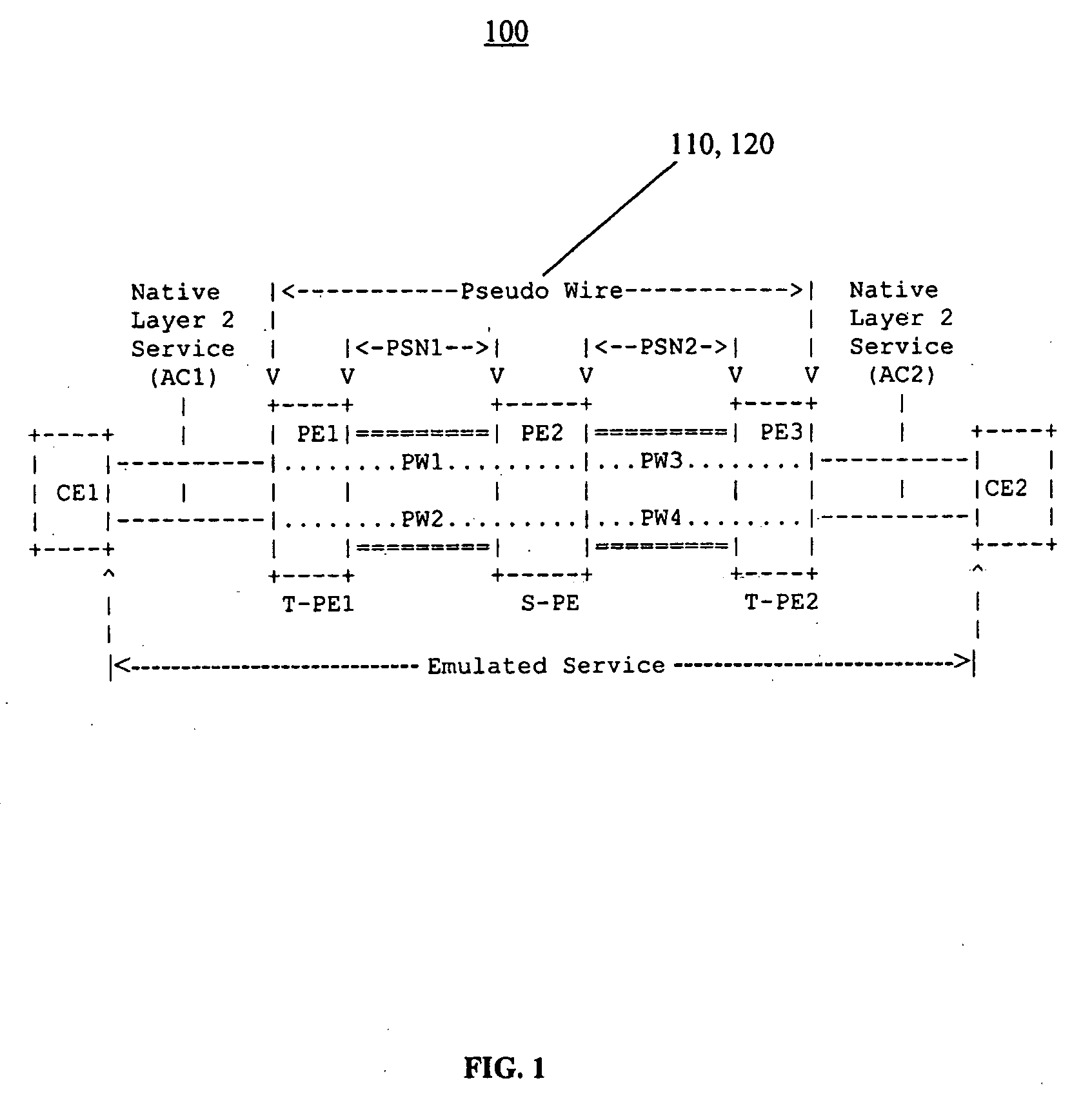
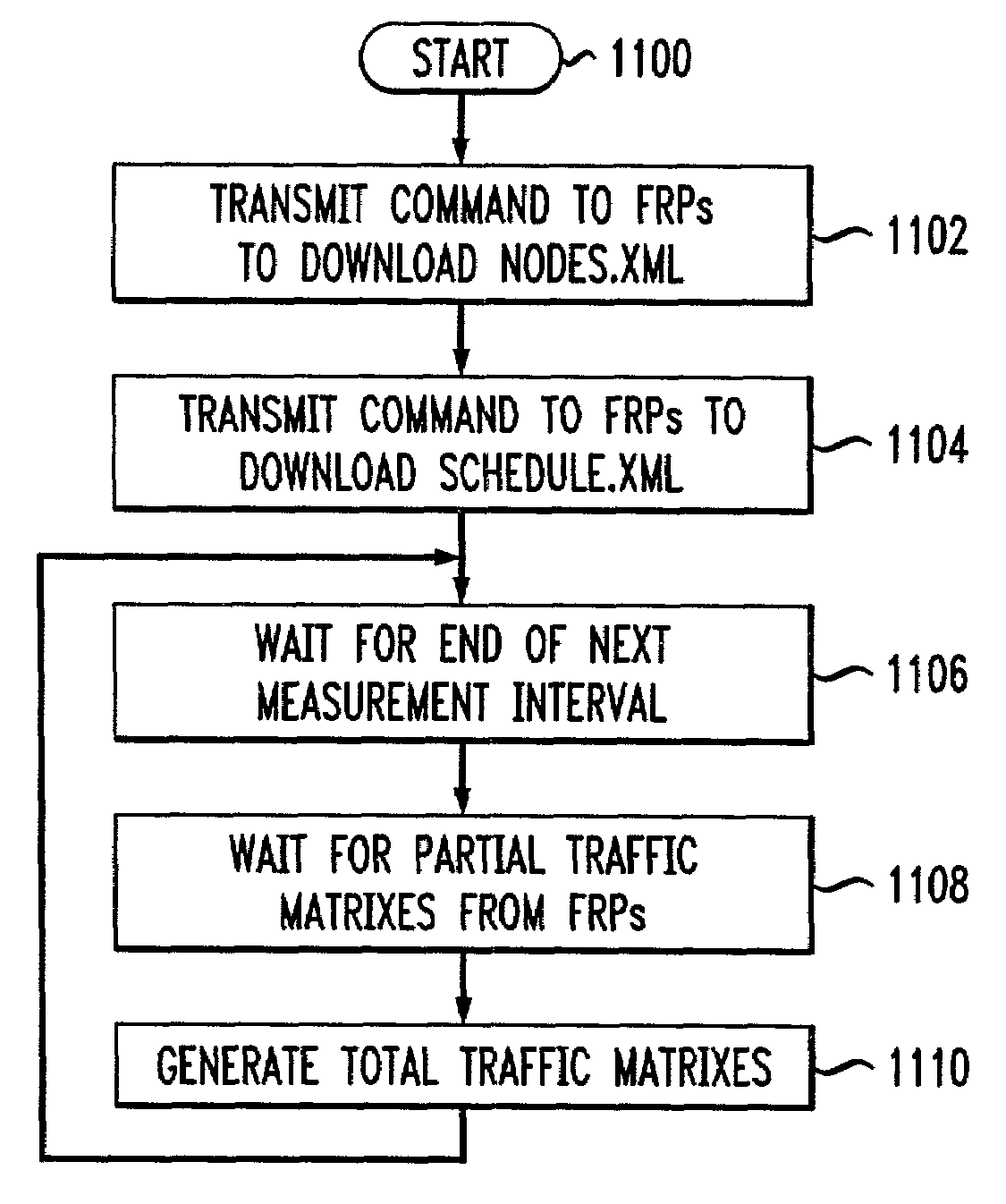
Traffic matrix computation for a backbone network supporting virtual private networks
InactiveUS7027396B1Shorten the timeView accuratelyError preventionTransmission systemsTraffic capacityInternet traffic engineering
This invention provides a more effective method for capacity planning and traffic engineering of packet networks that connect Virtual Private Network (VPN) sites. A distributed architecture efficiently computes traffic matrixes that show the number of bytes and / or packets exchanged among provider edge (PE) routers and / or service nodes. Each PE router in a service node is exports flow records to a Flow Record Processor (FRP) in the same location. The FRPs use these records in conjunction with configuration data extracted from the PE routers to compute partial traffic matrixes. The partial traffic matrixes are uploaded to a Matrix Generator to create a total traffic matrix. The total traffic matrix is essential input for capacity planning or traffic engineering tools.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com