Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
7139 results about "Private network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
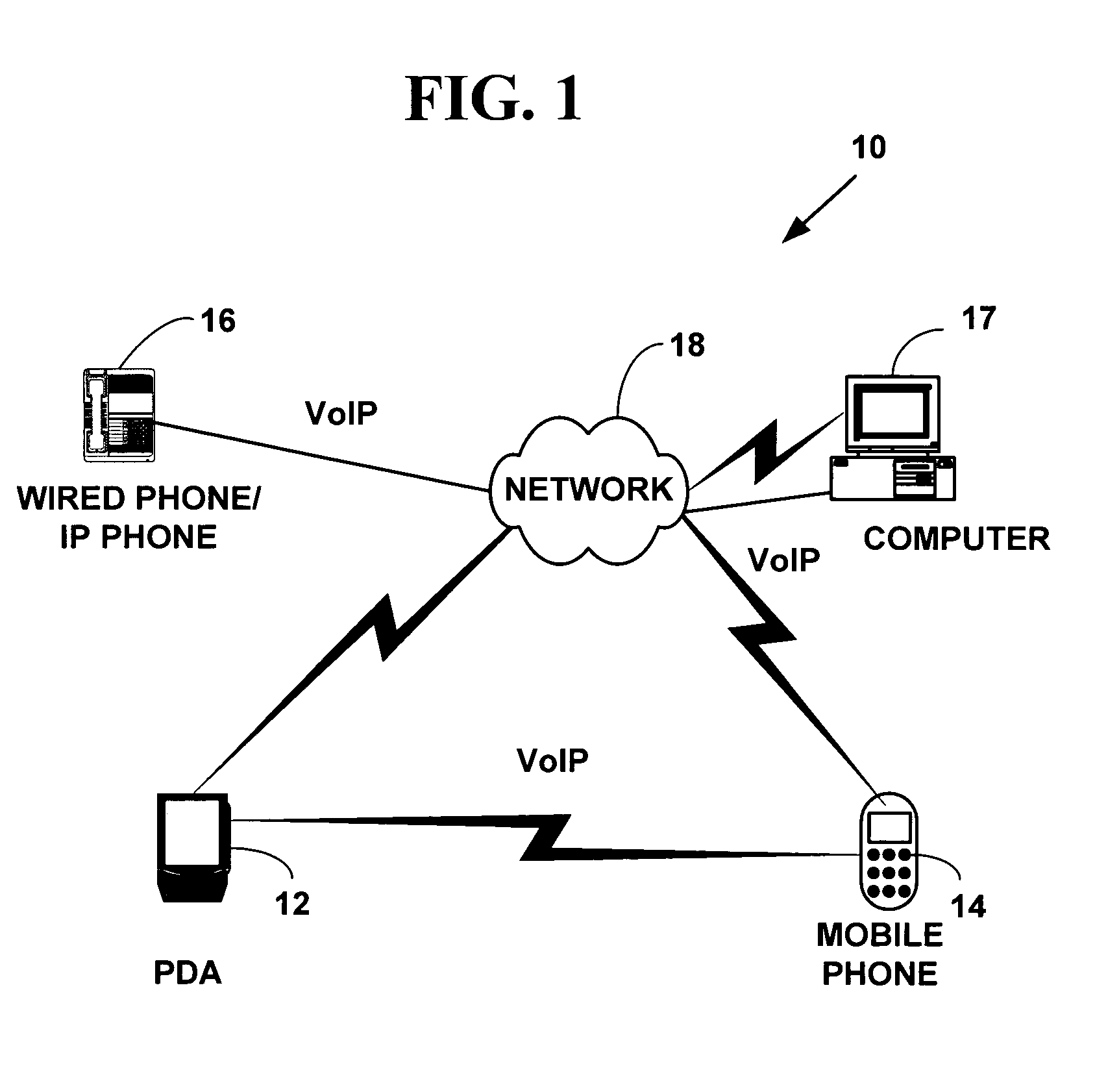
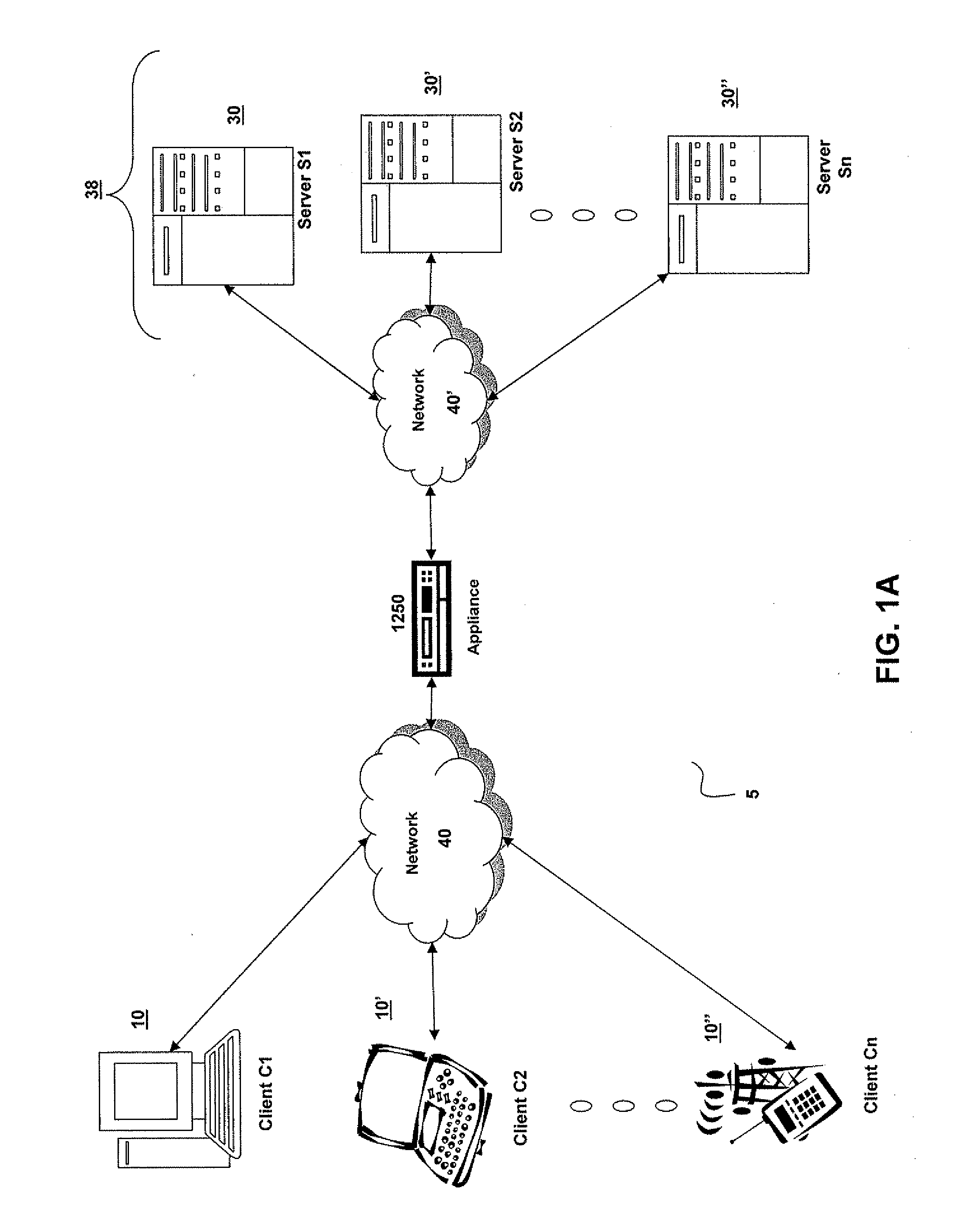
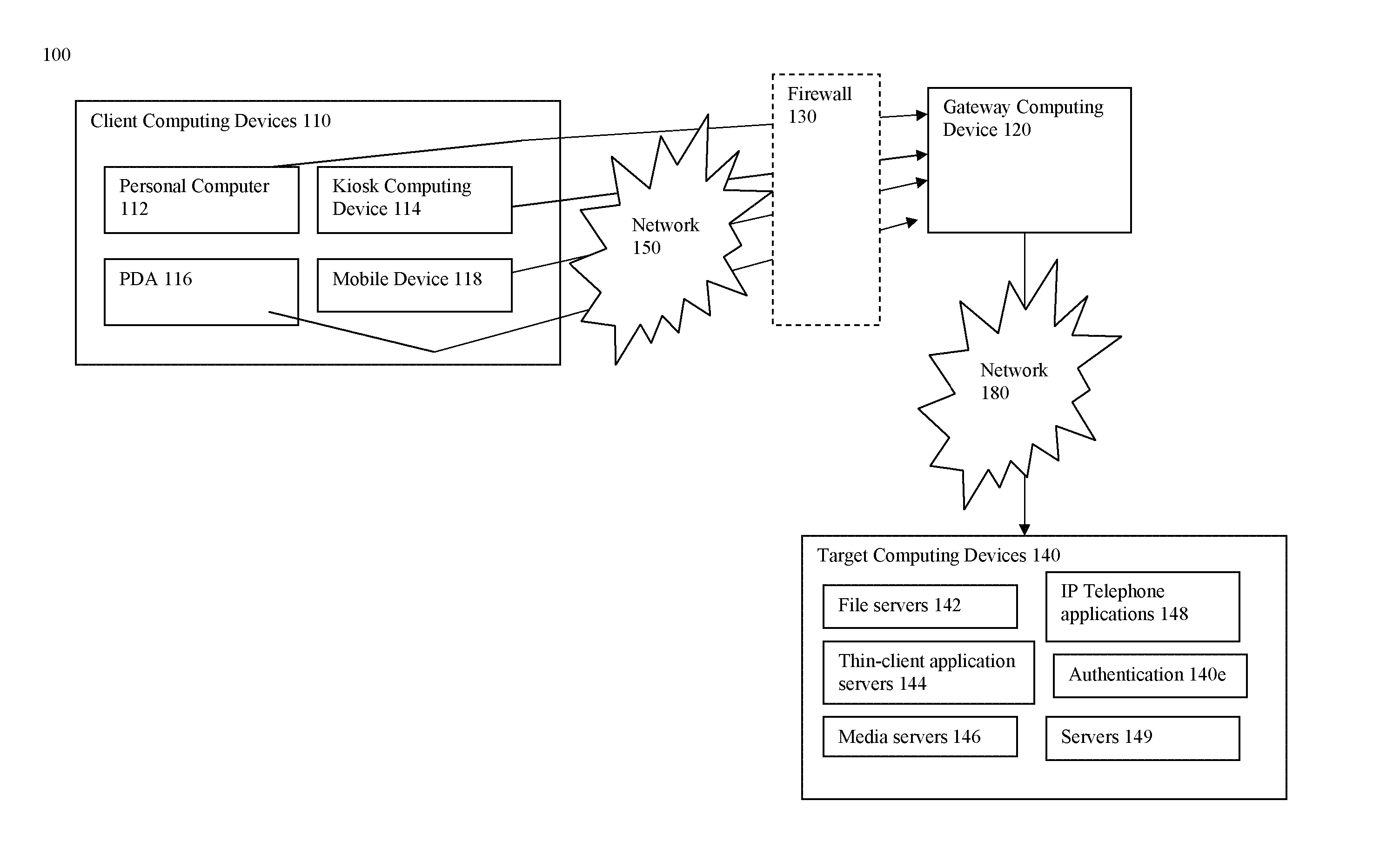
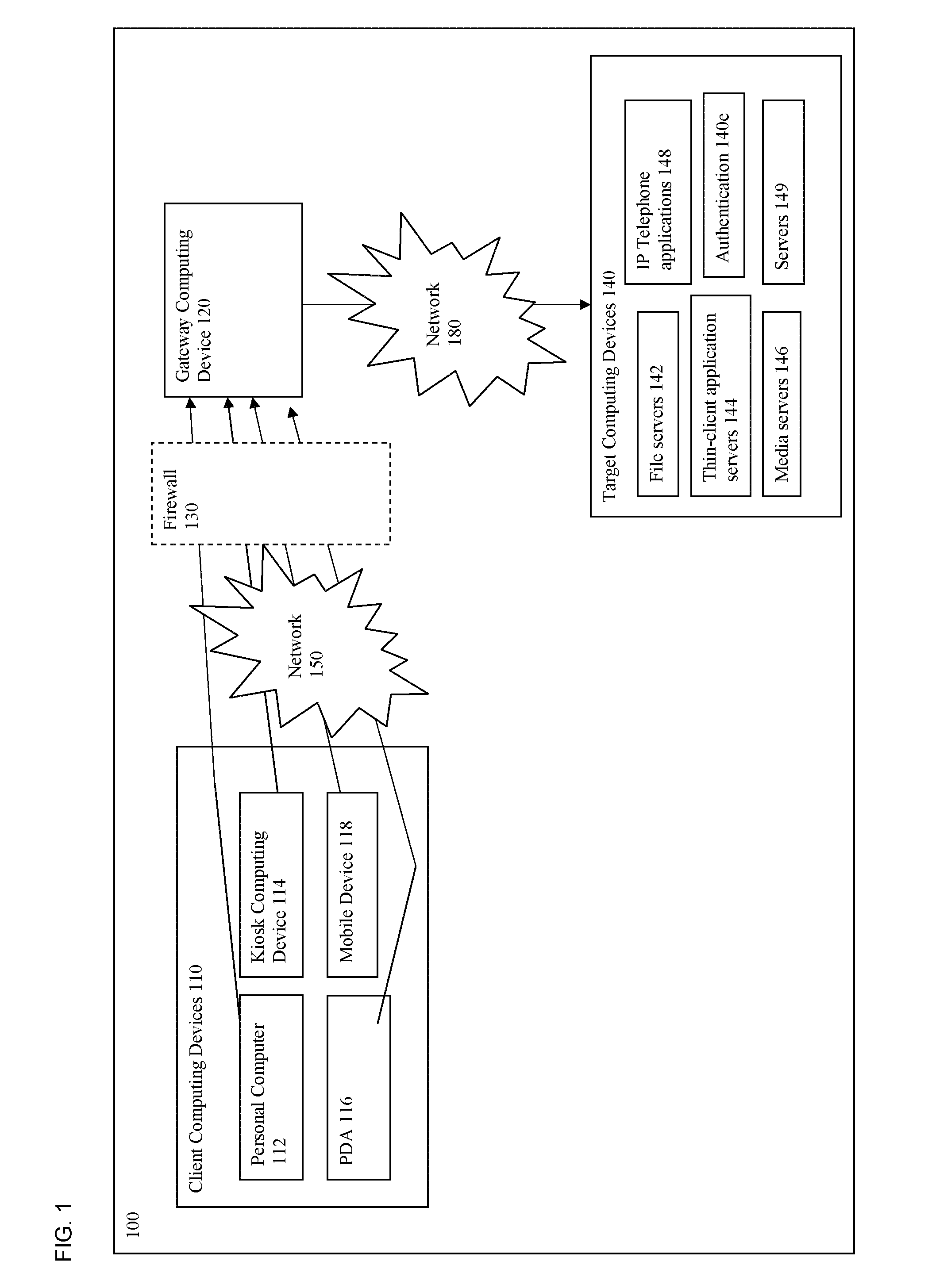
In the Internet addressing architecture, a private network is a network that uses private IP address space. Both, the IPv4 and the IPv6 specifications define private IP address ranges. These addresses are commonly used for local area networks (LANs) in residential, office, and enterprise environments.
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
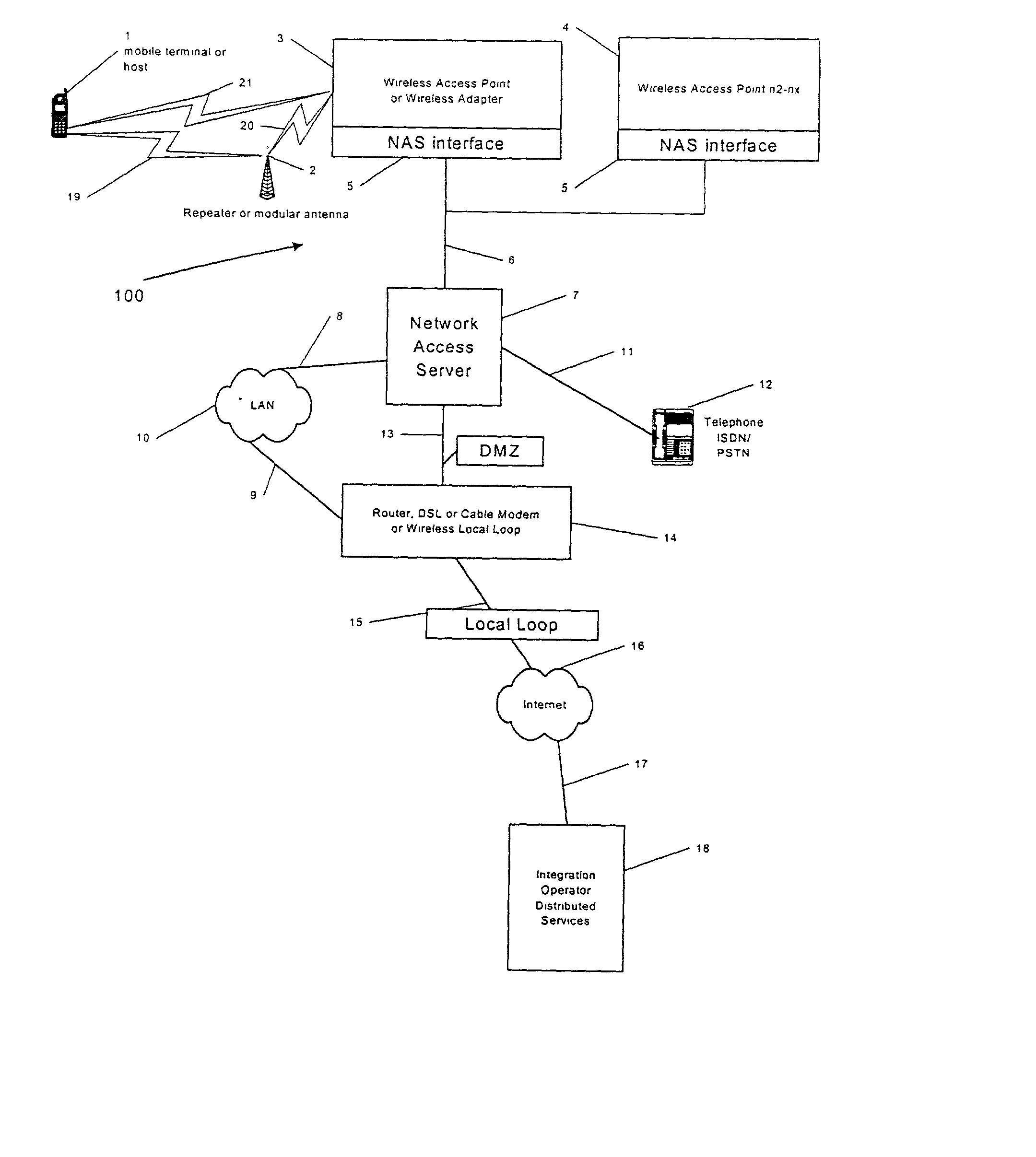
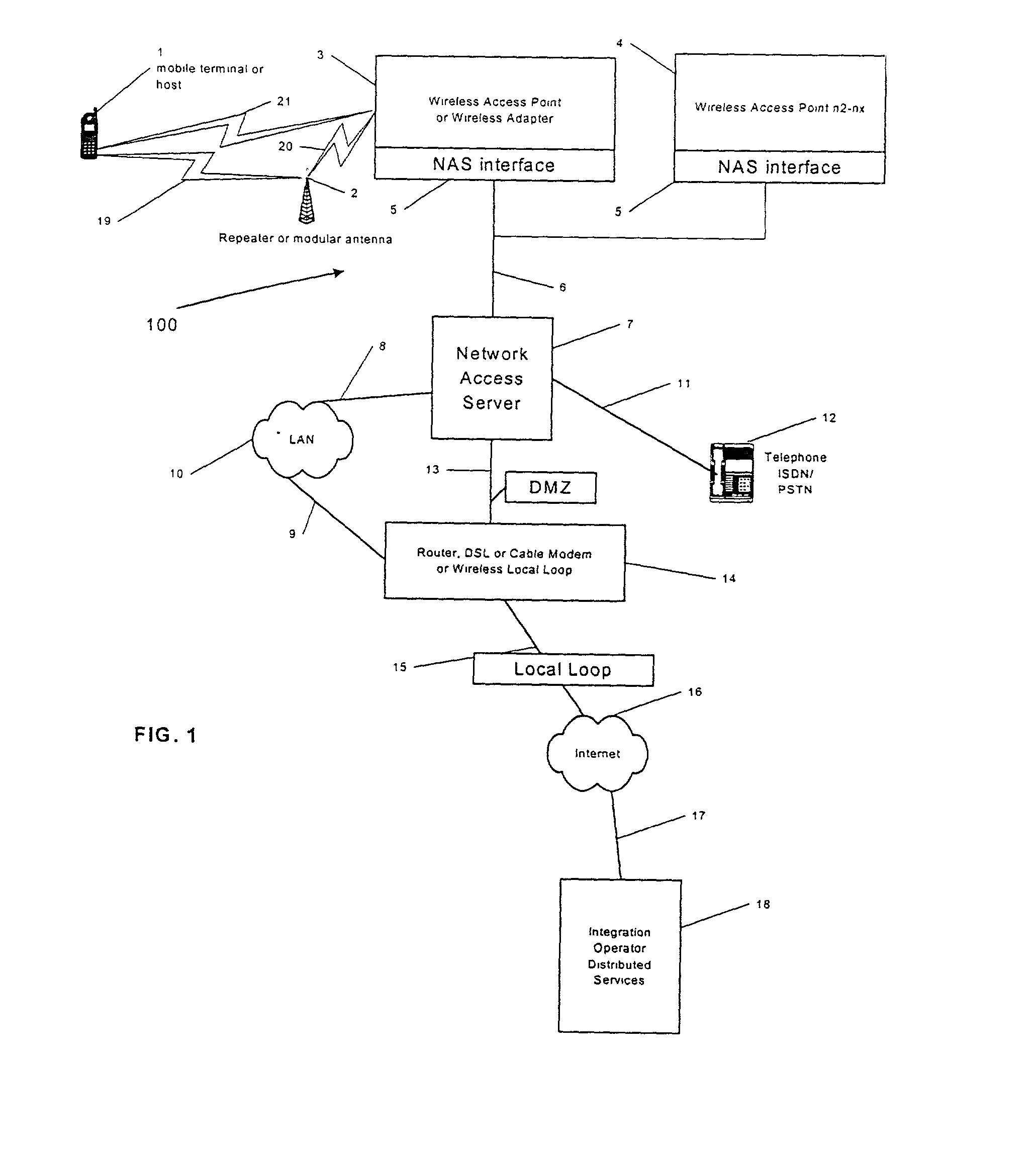
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
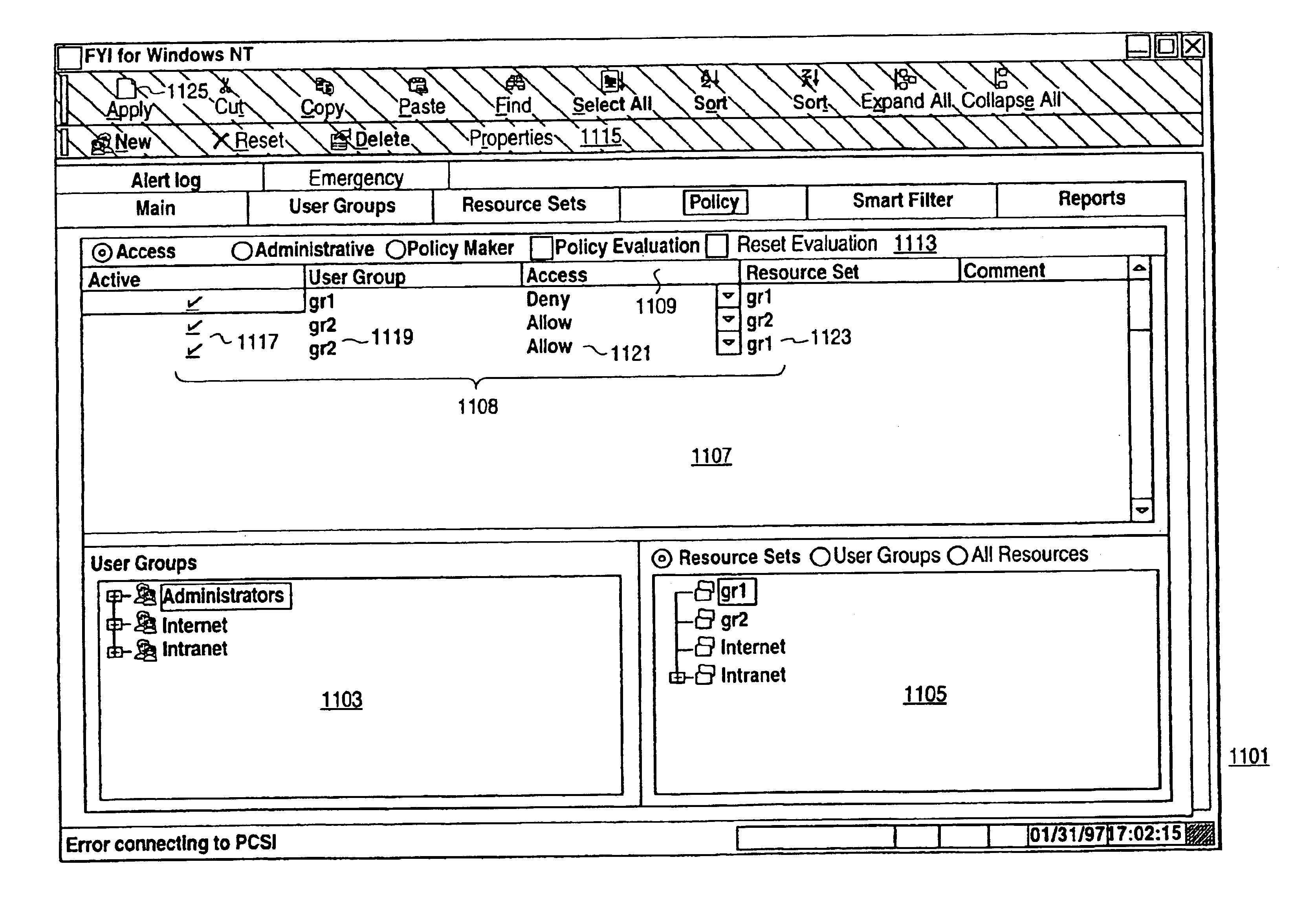
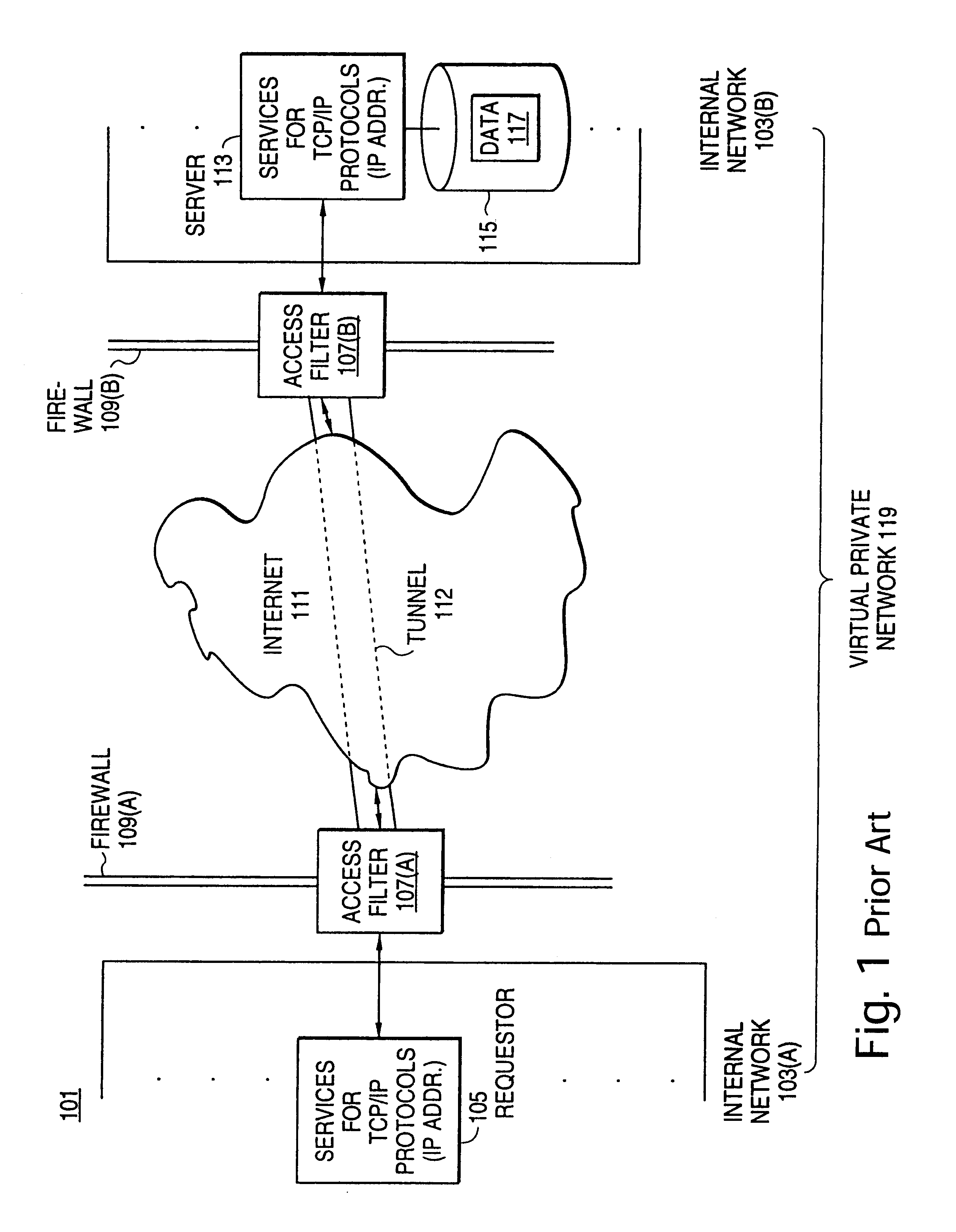
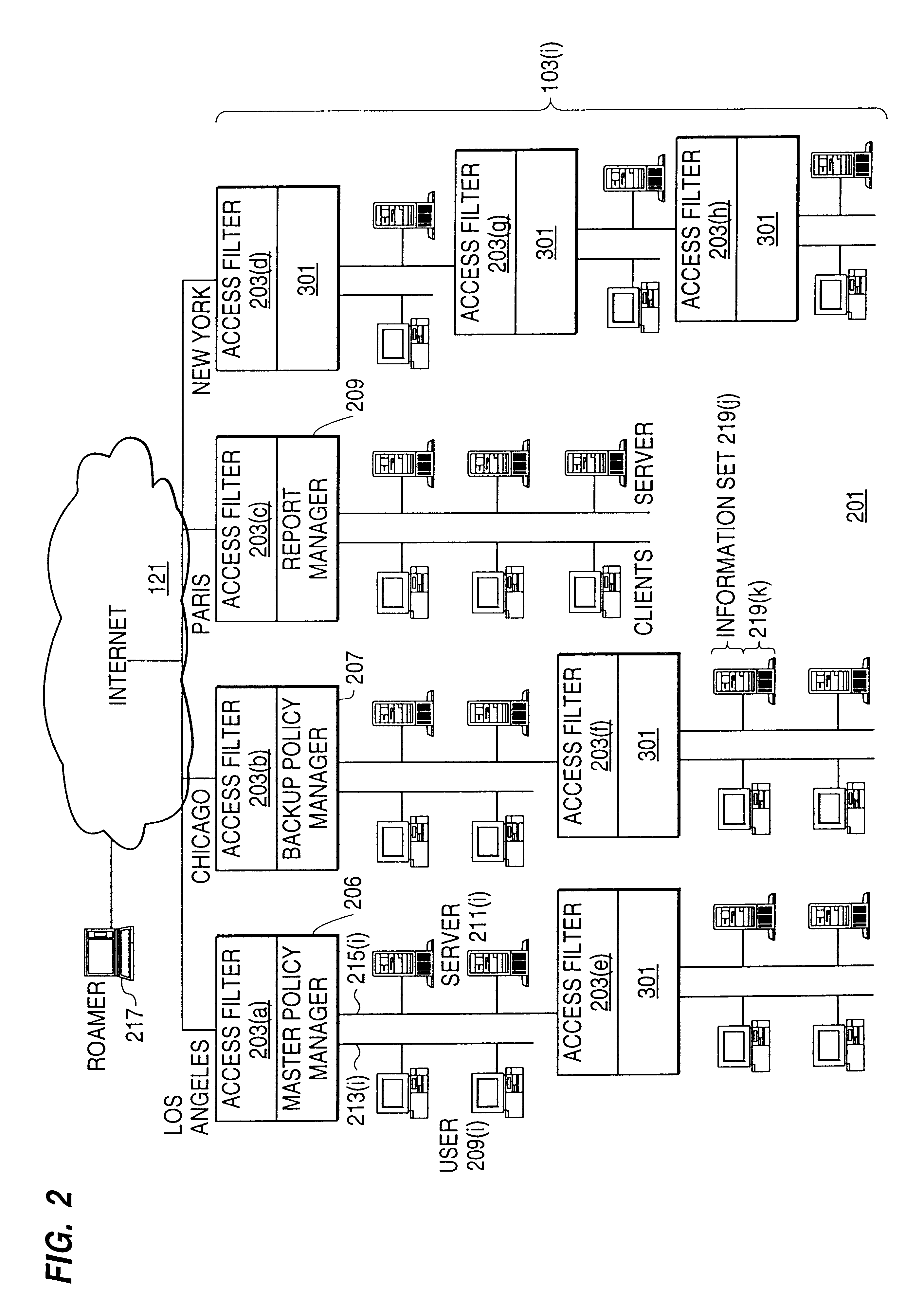
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
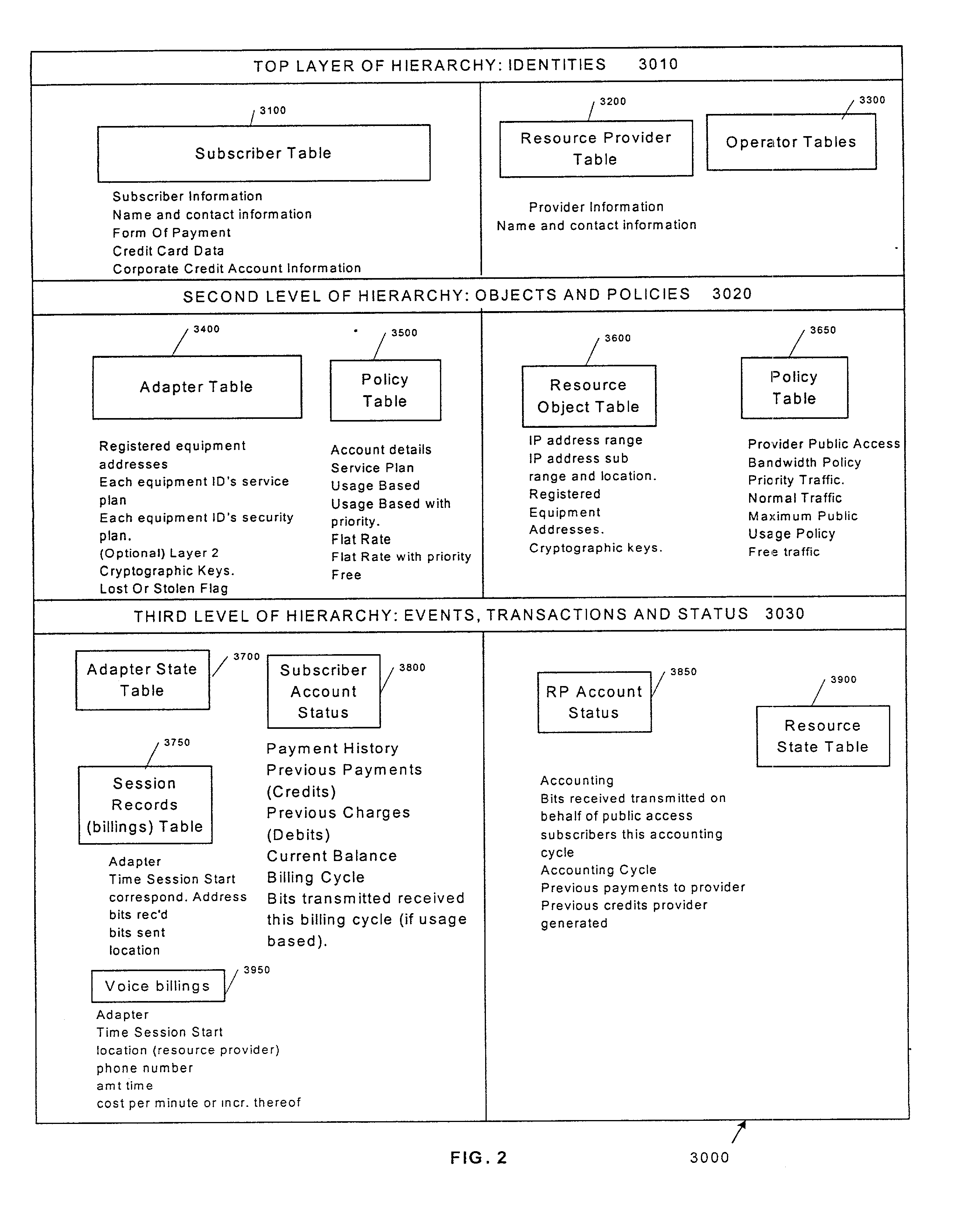
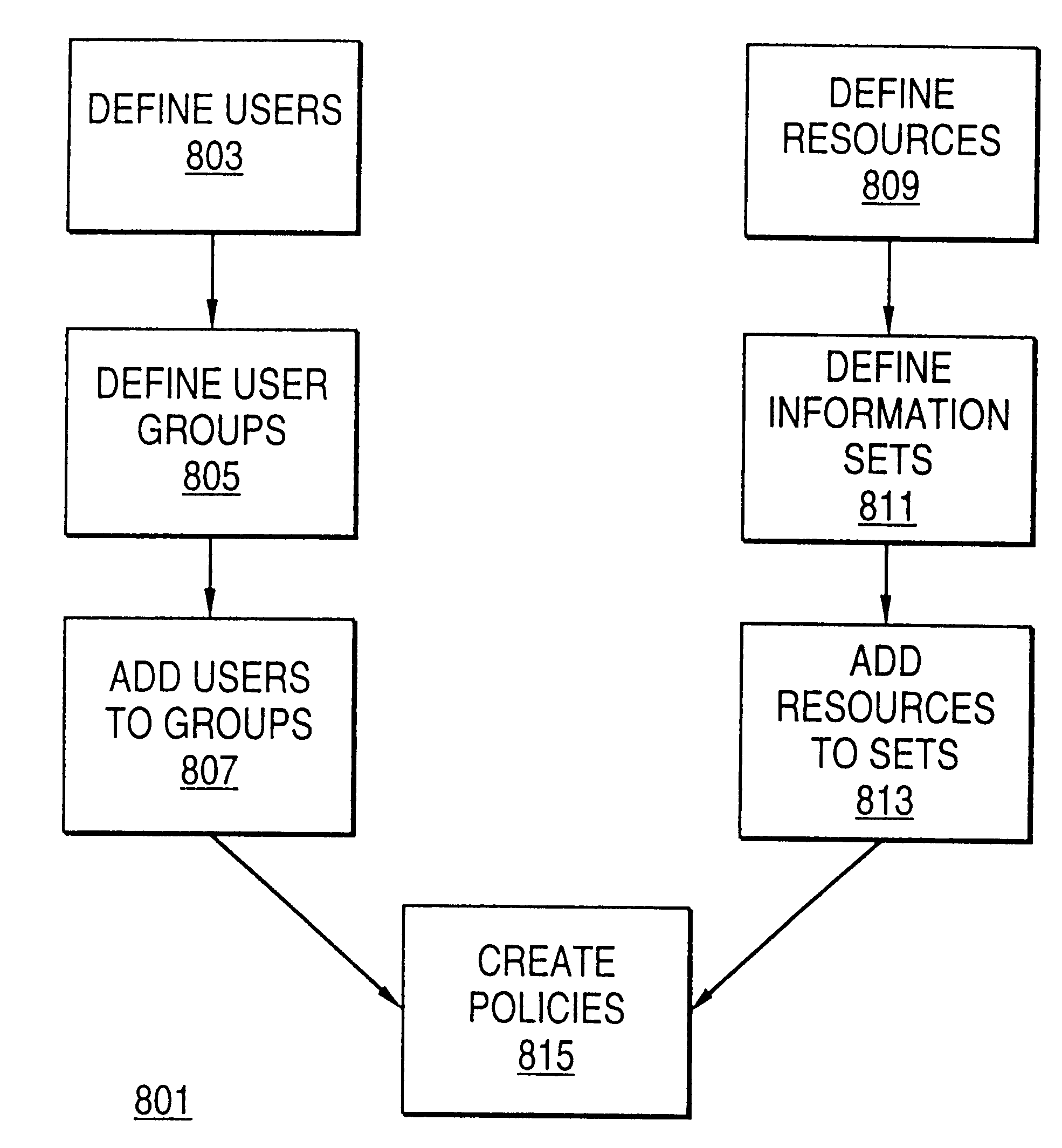
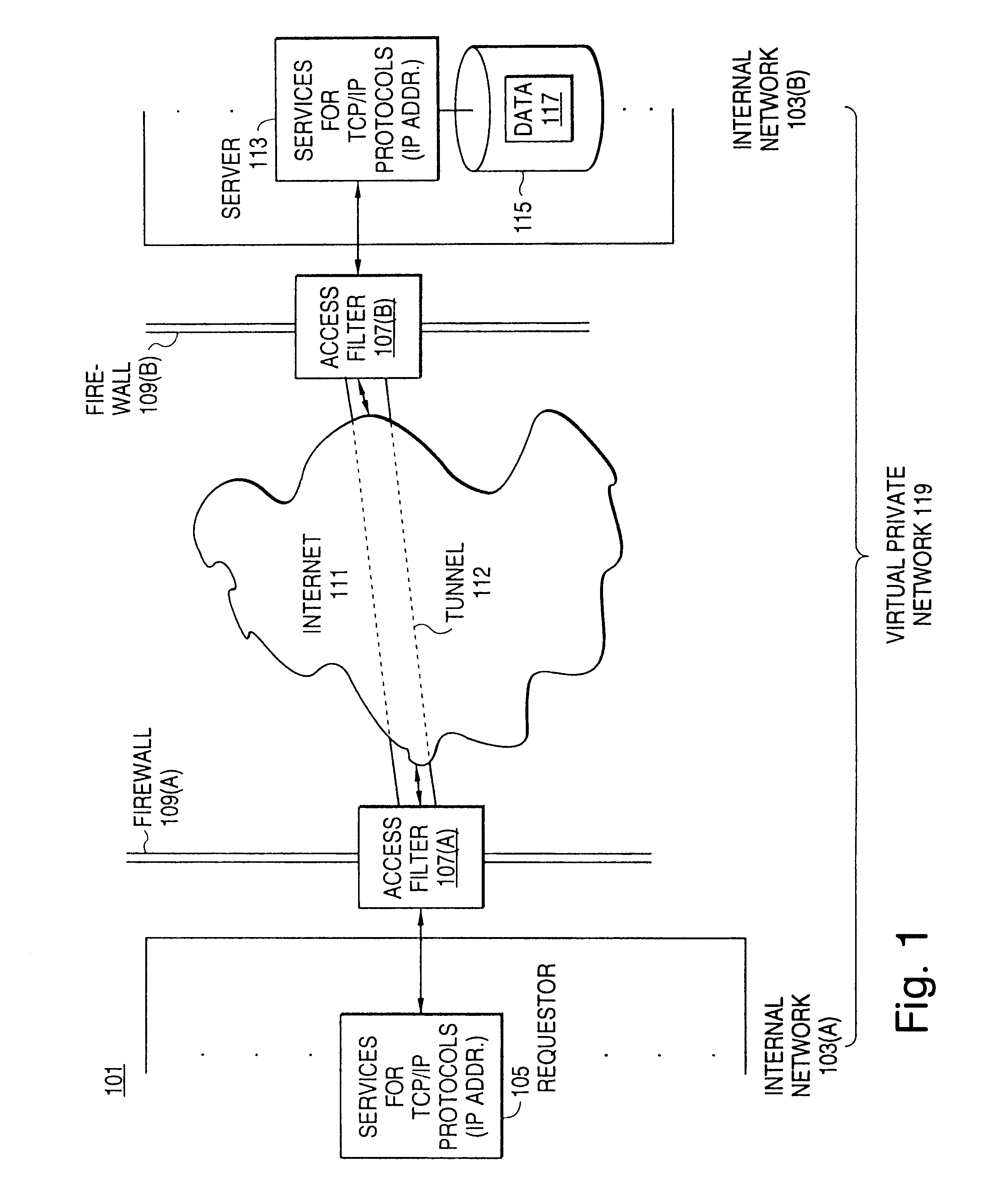
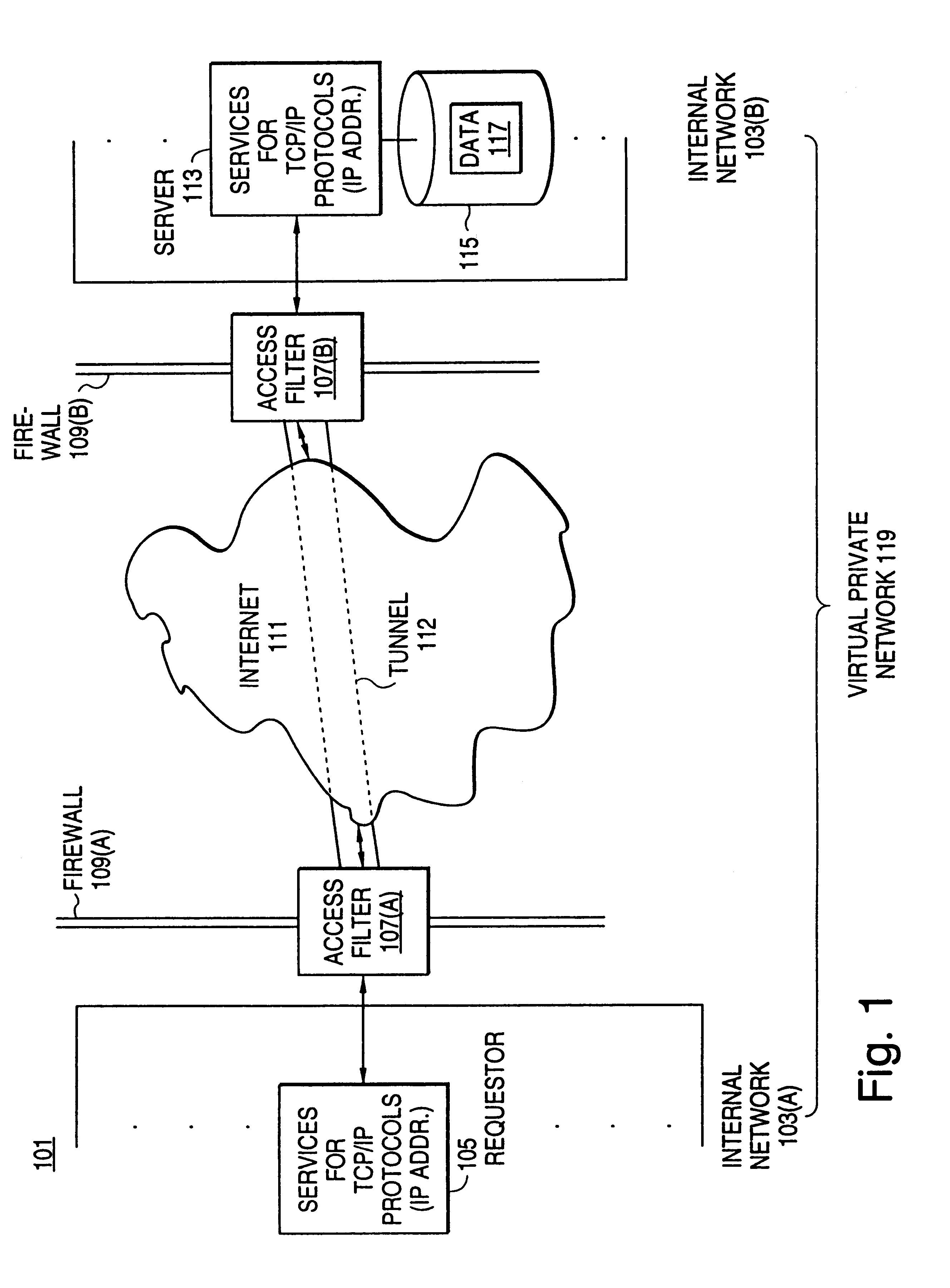
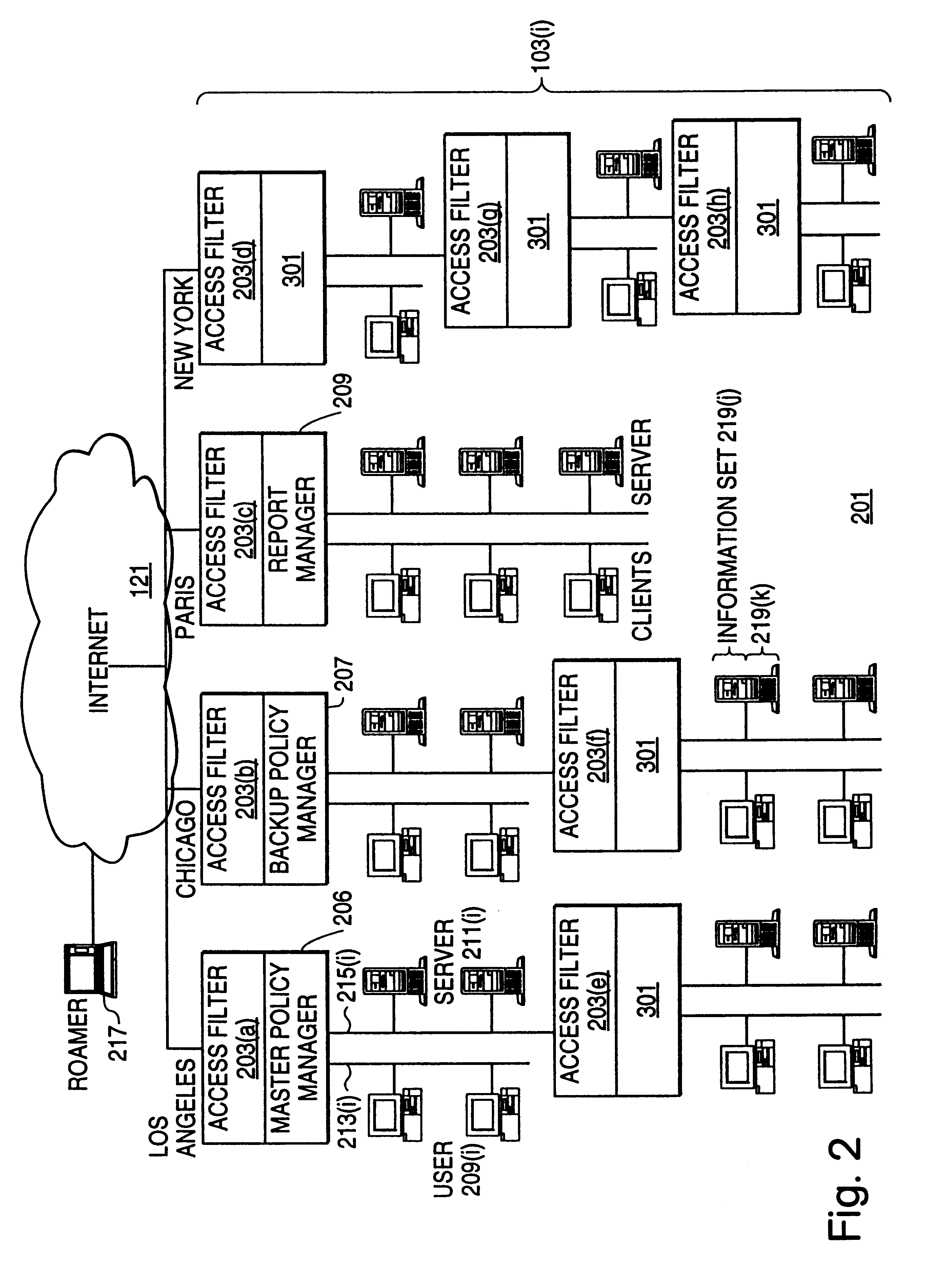
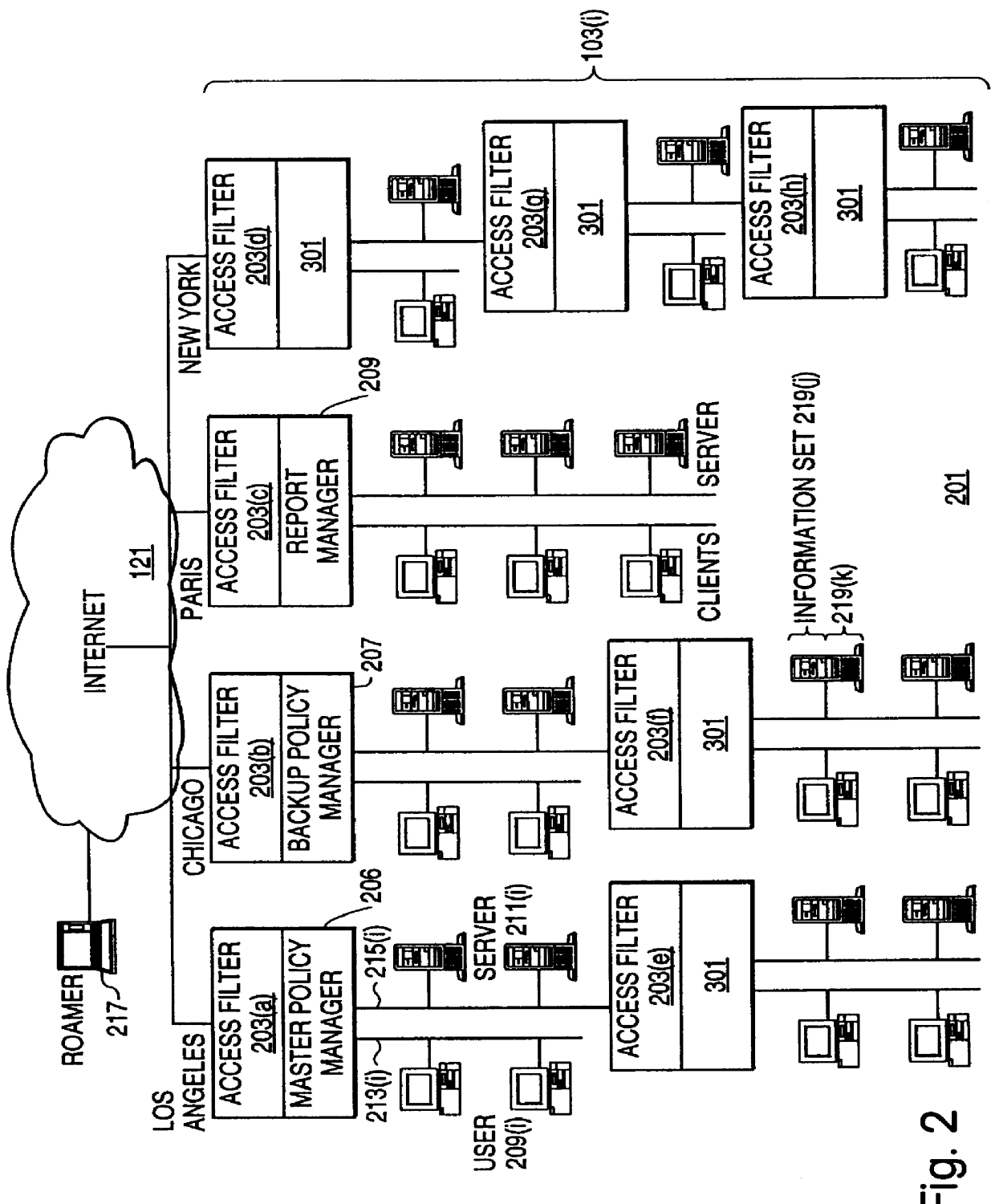
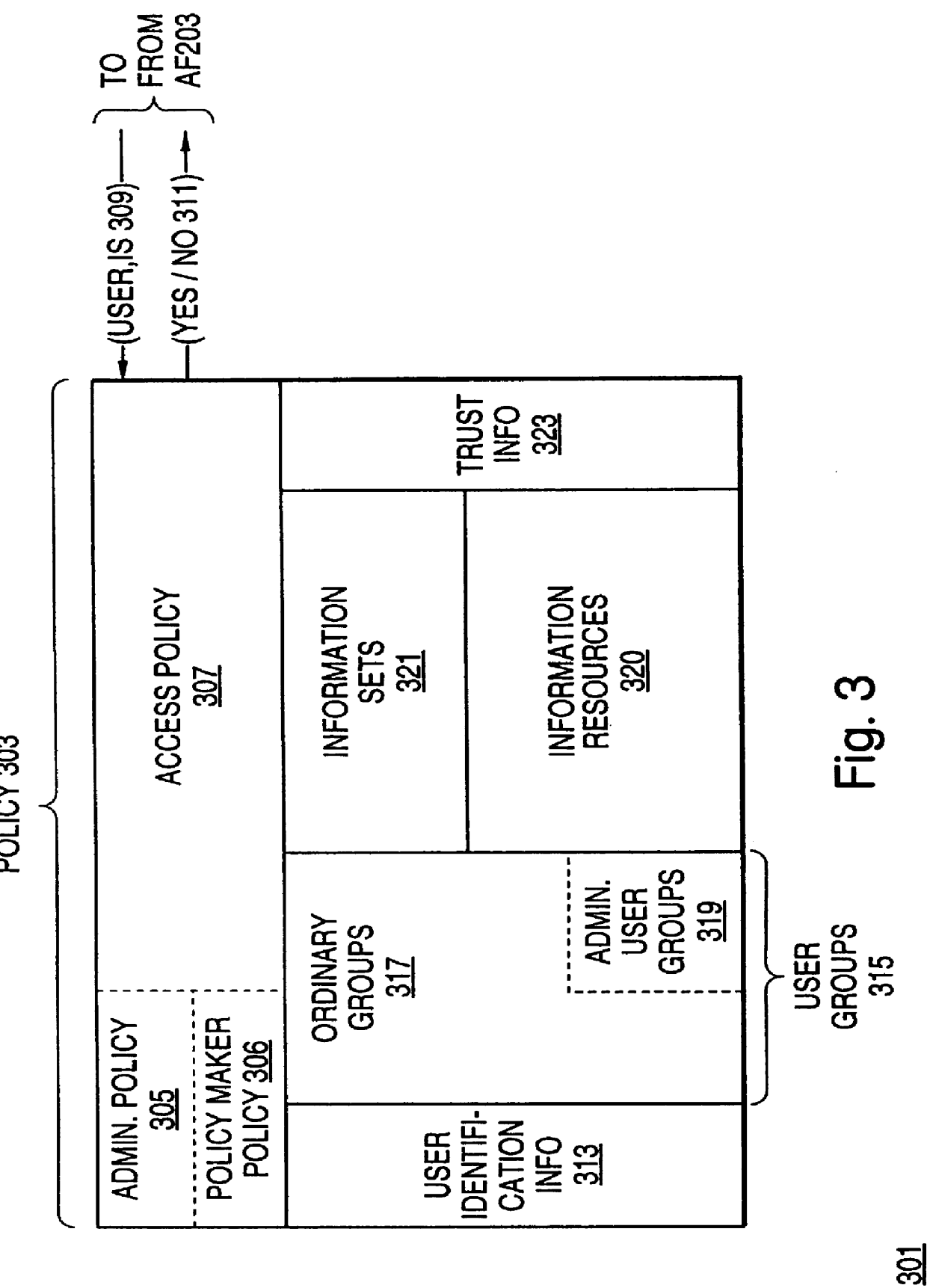
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Secure delivery of information in a network
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Techniques for eliminating redundant access checking by access filters
InactiveUS6105027AData processing applicationsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter uses a local copy of an access control data base to determine whether an access request is made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
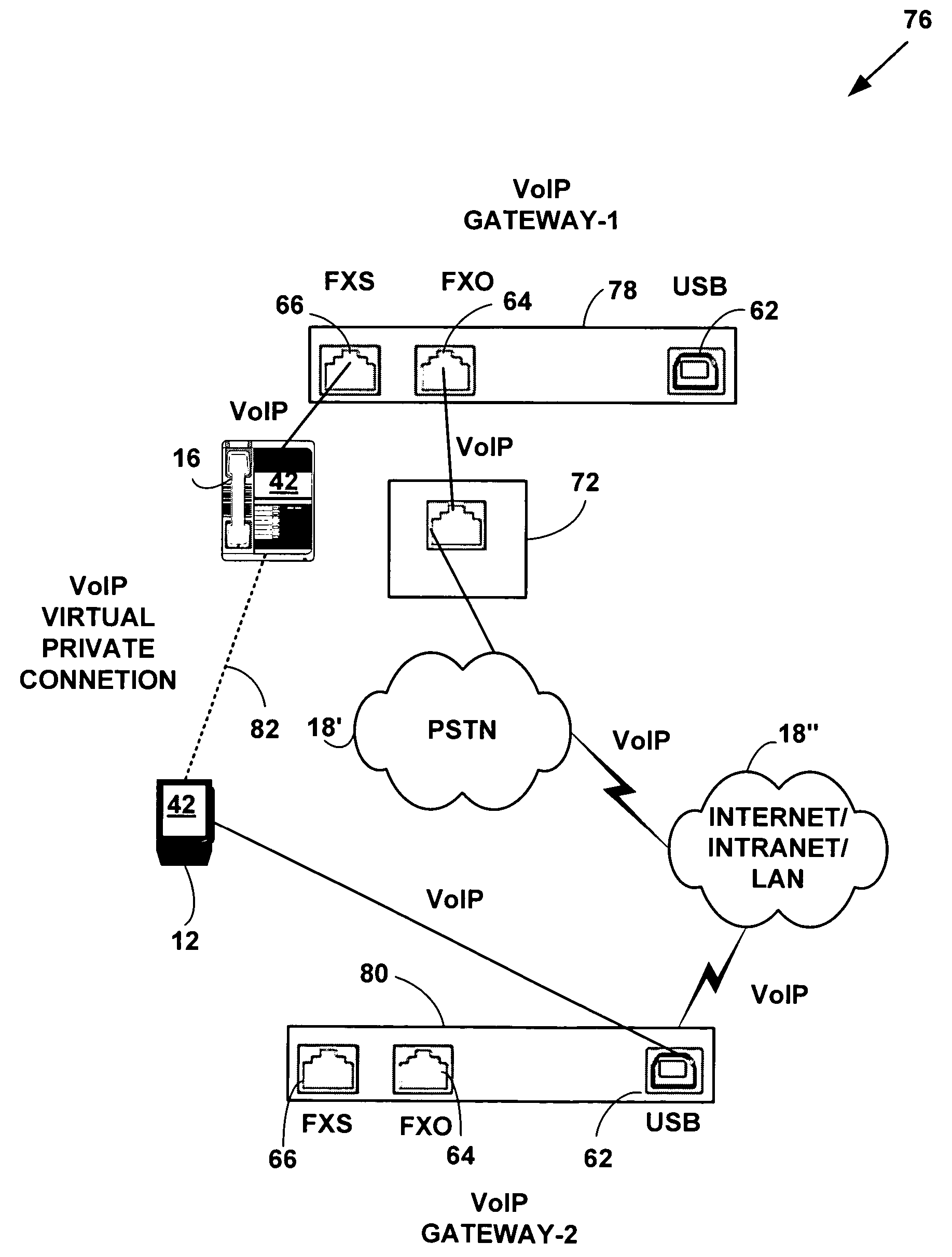
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
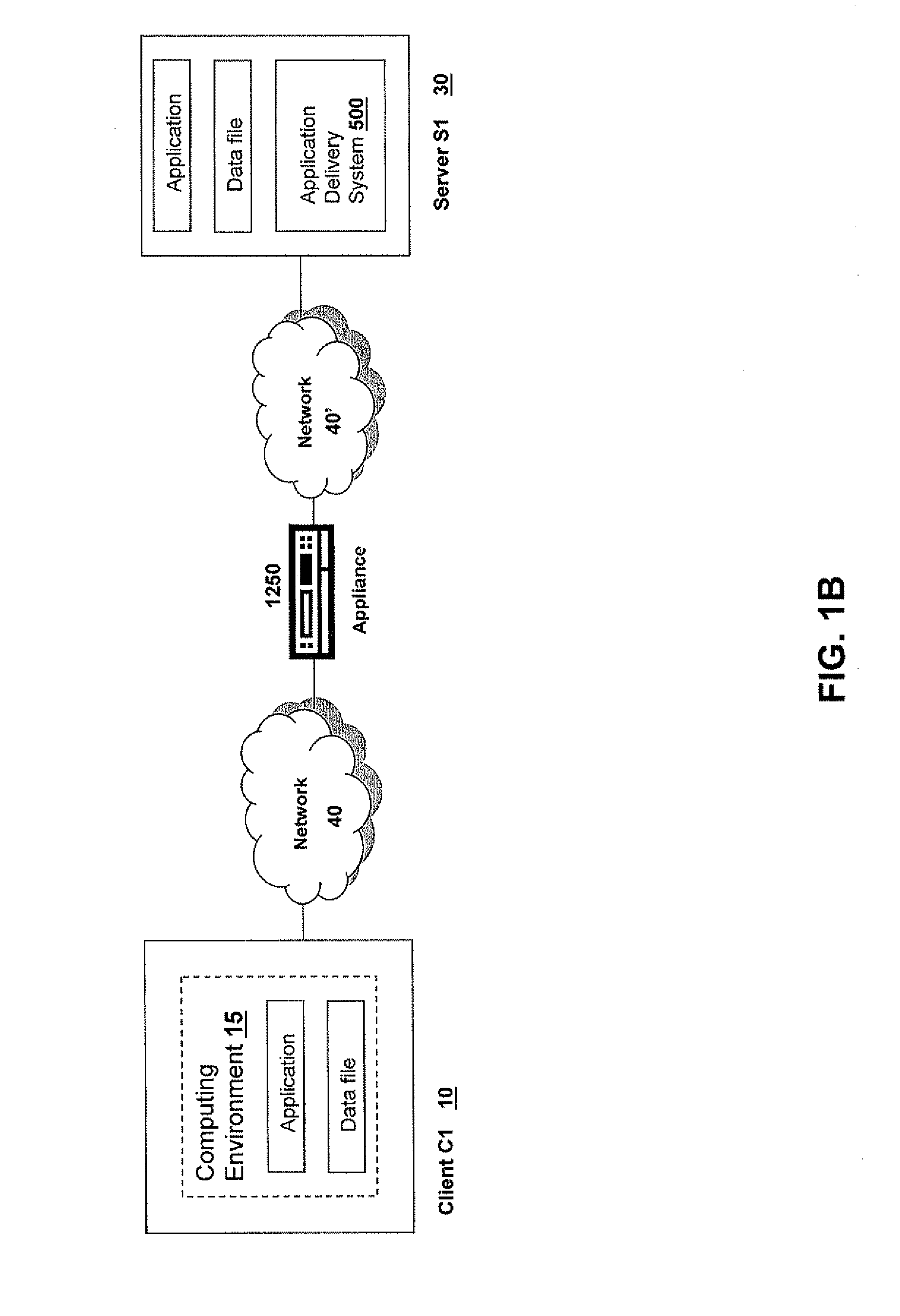
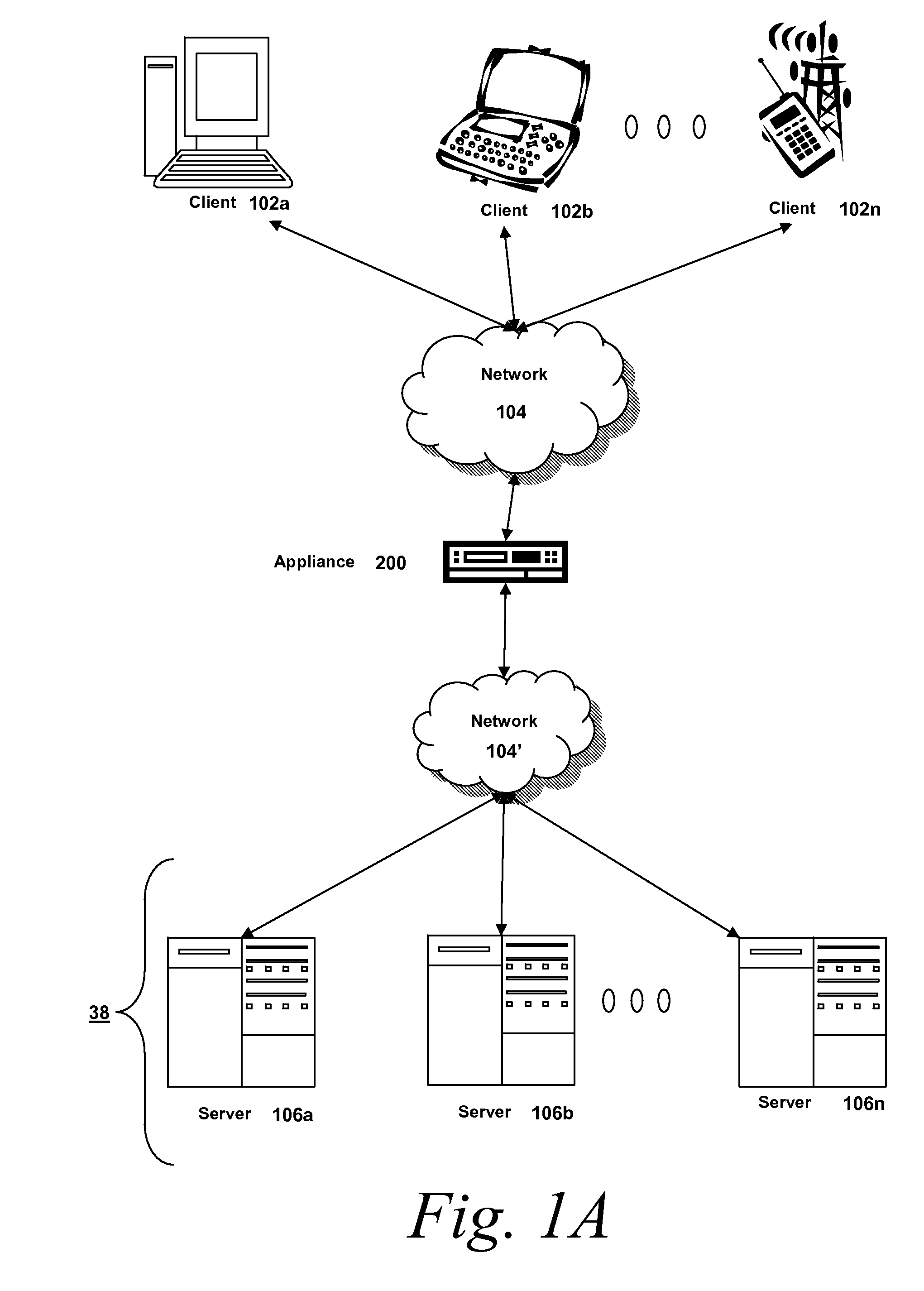
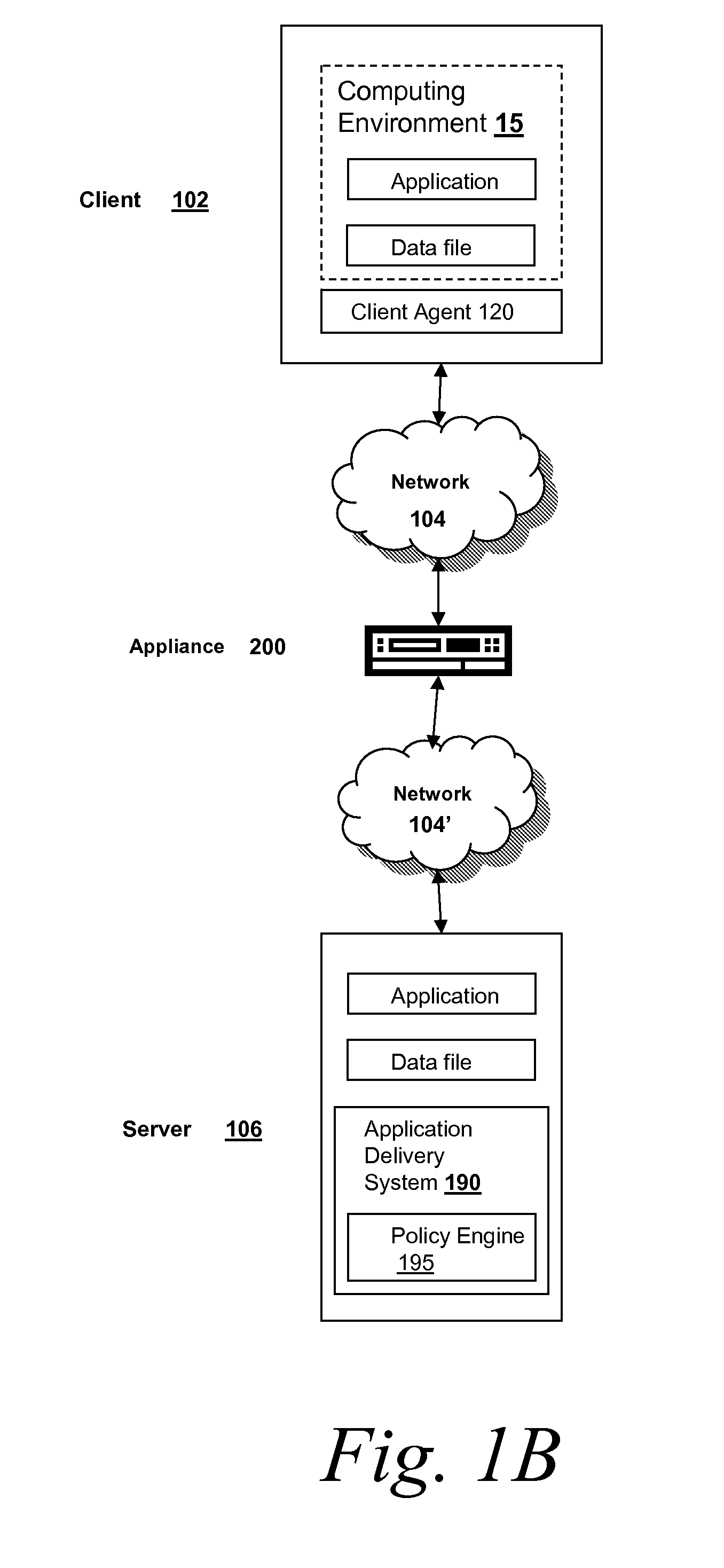
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
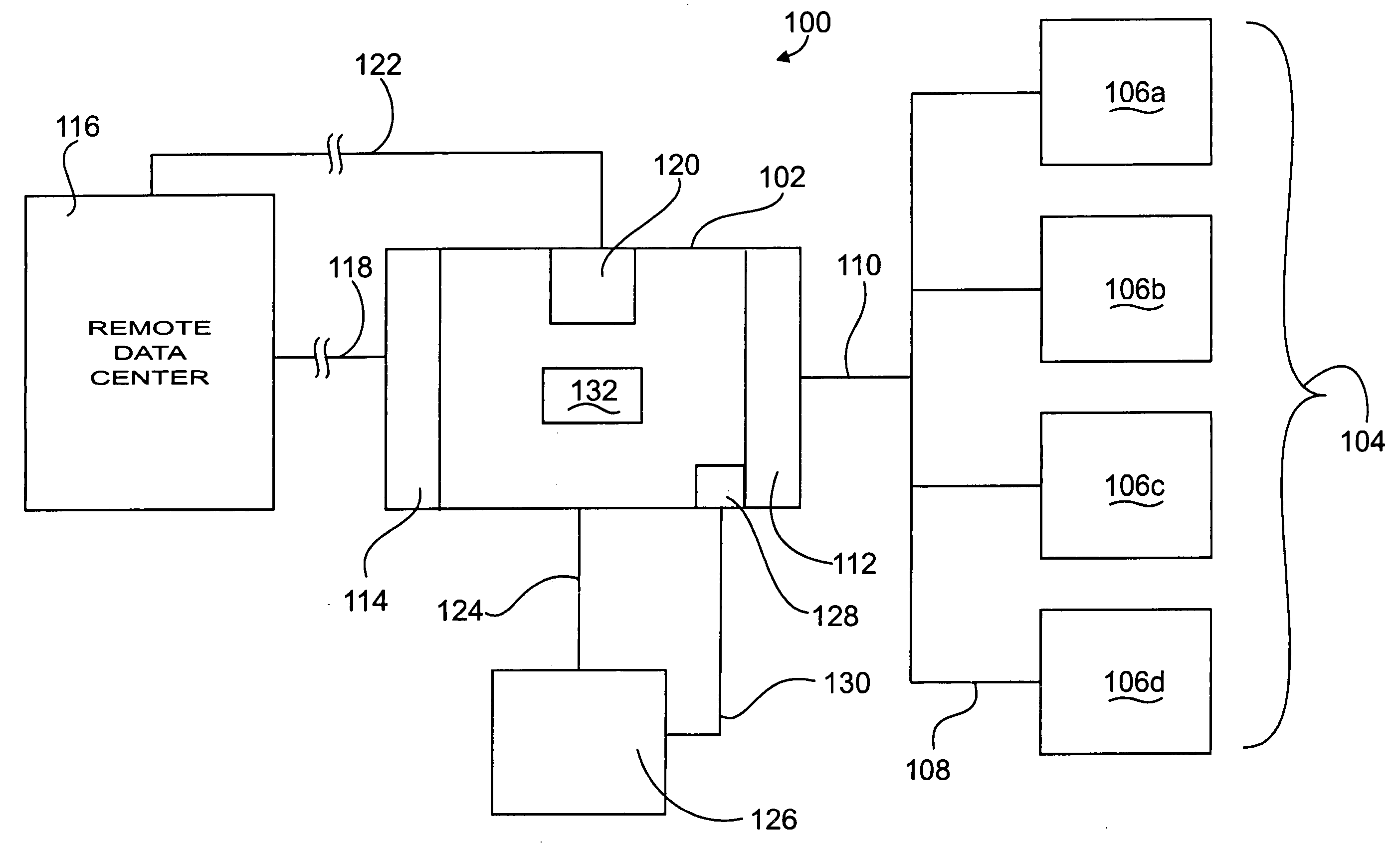
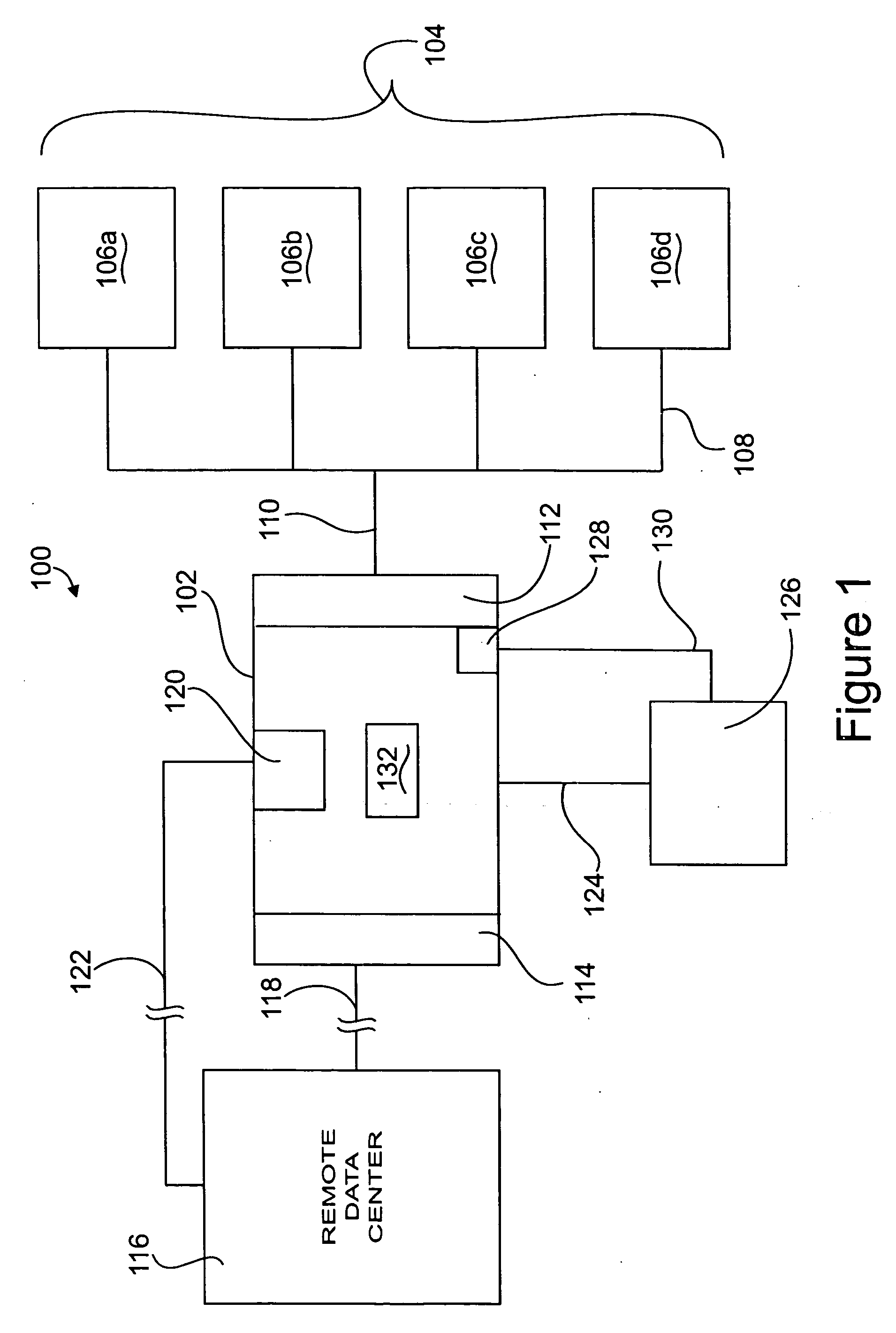
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
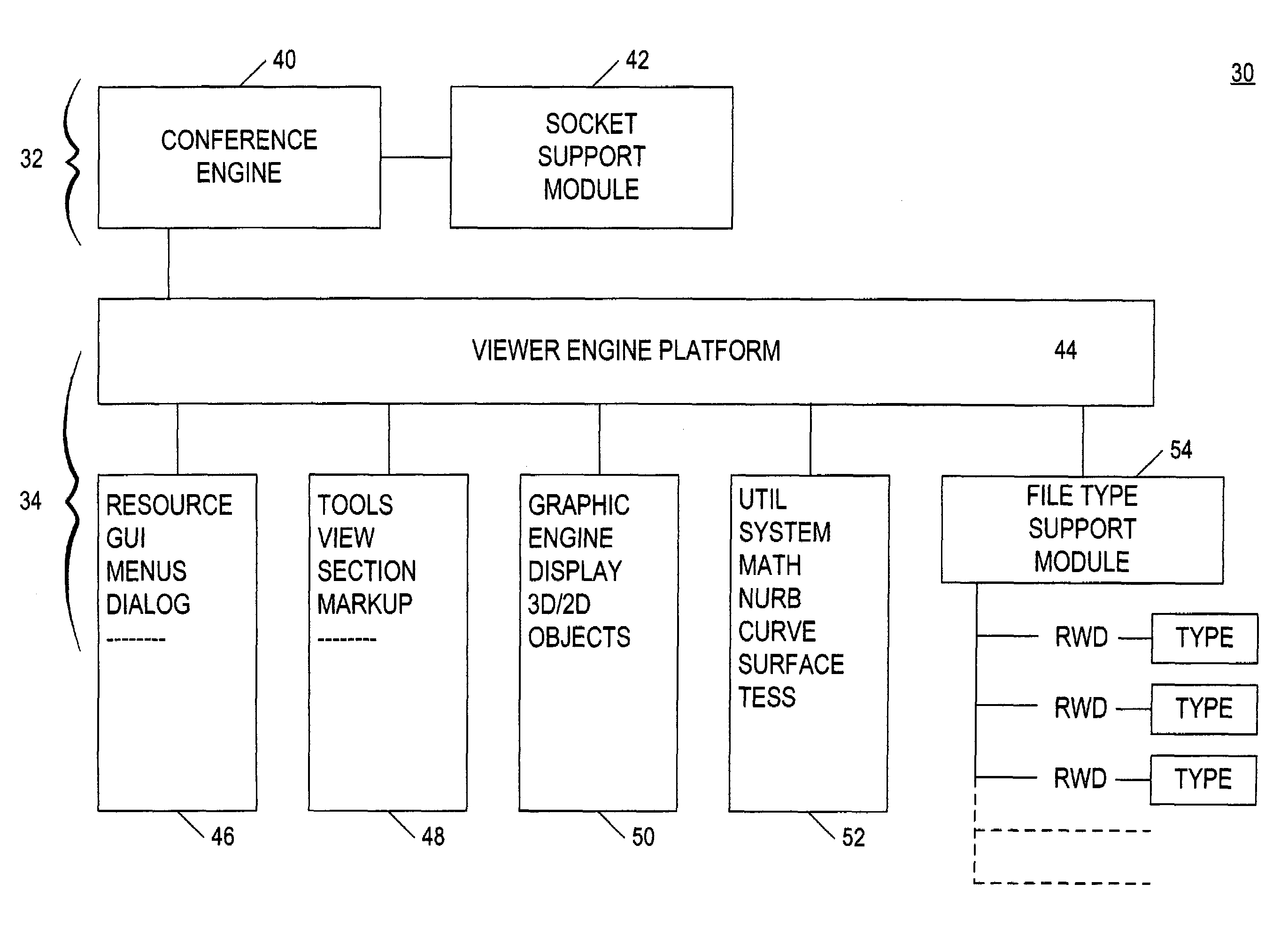
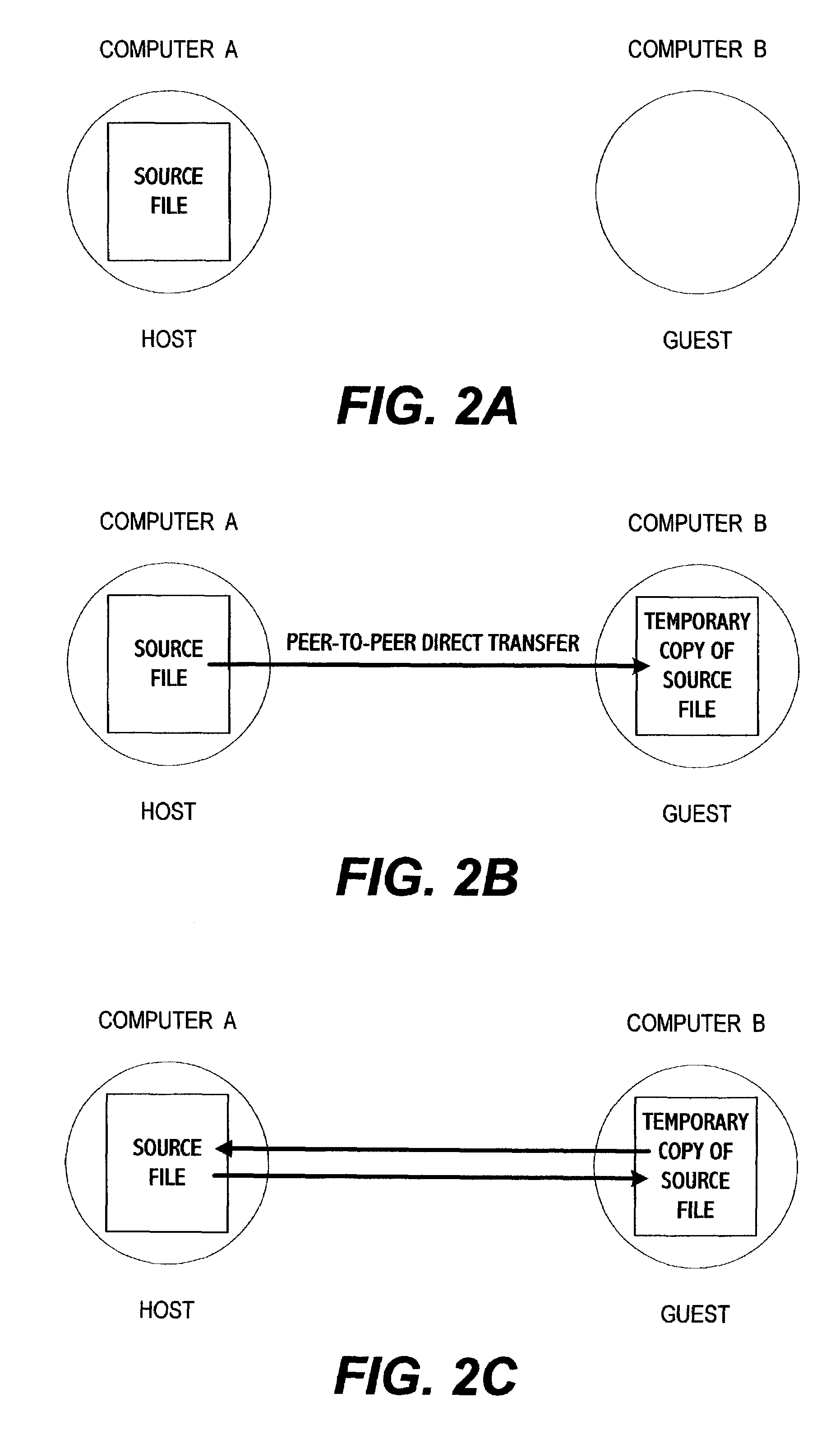
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
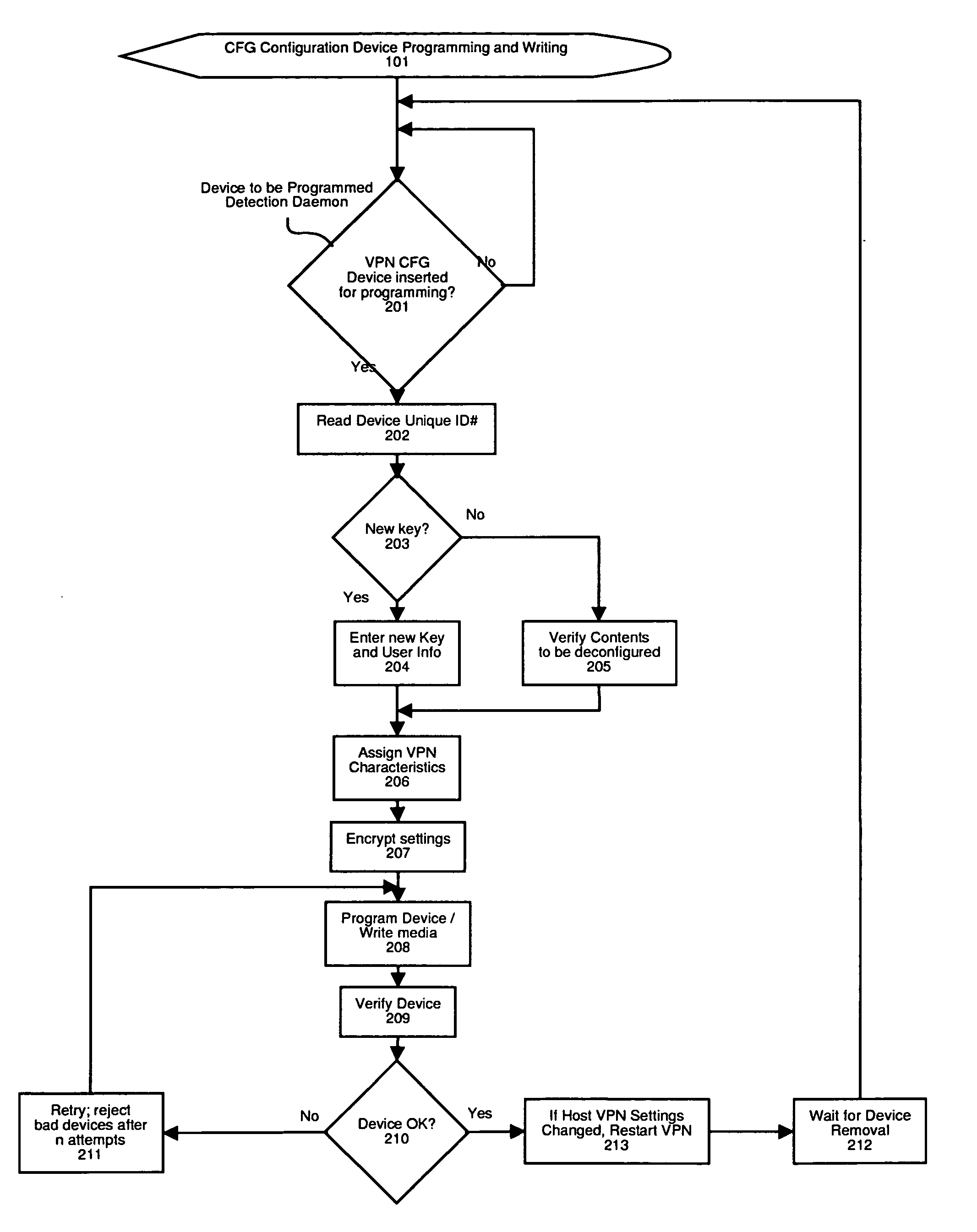
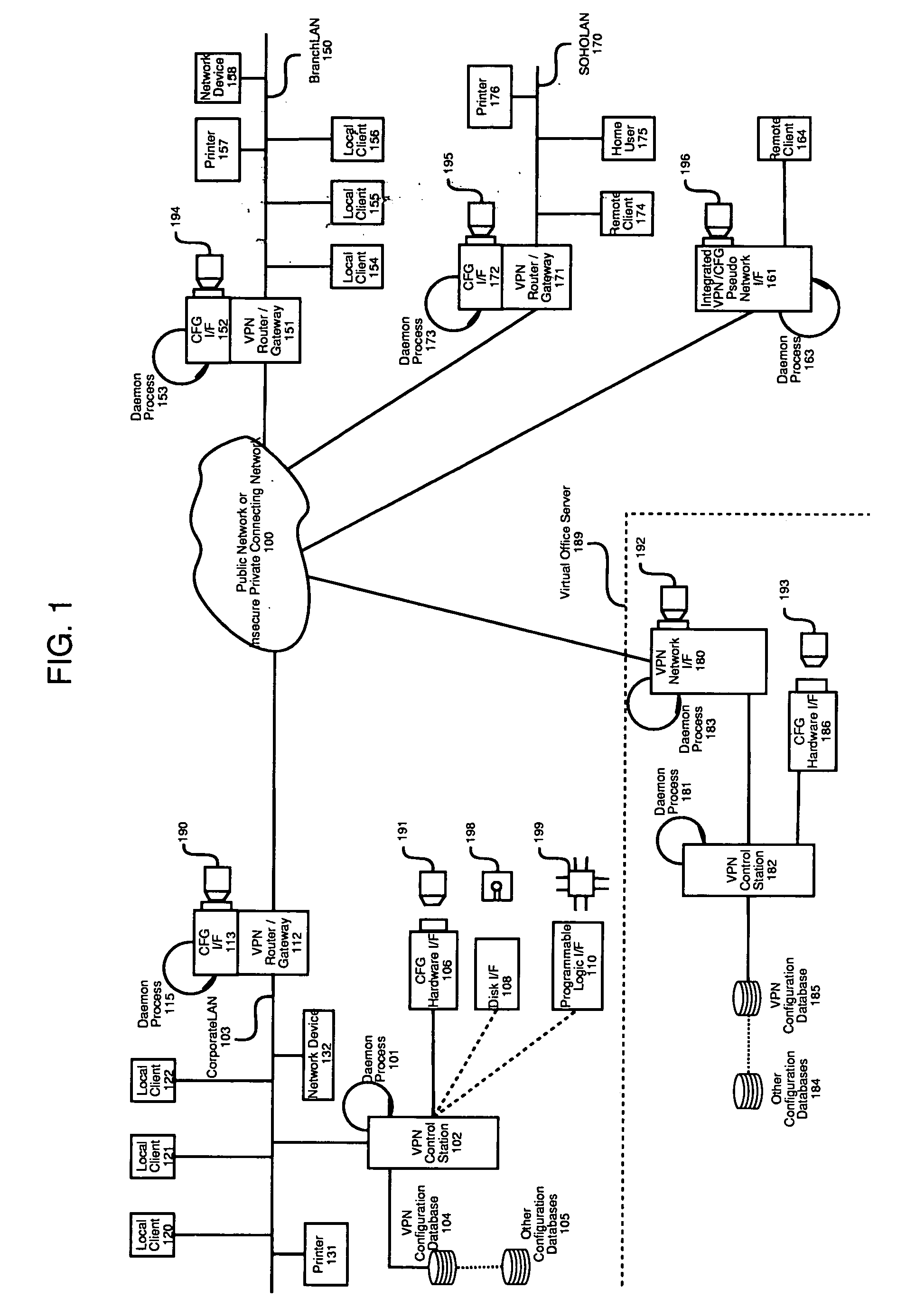
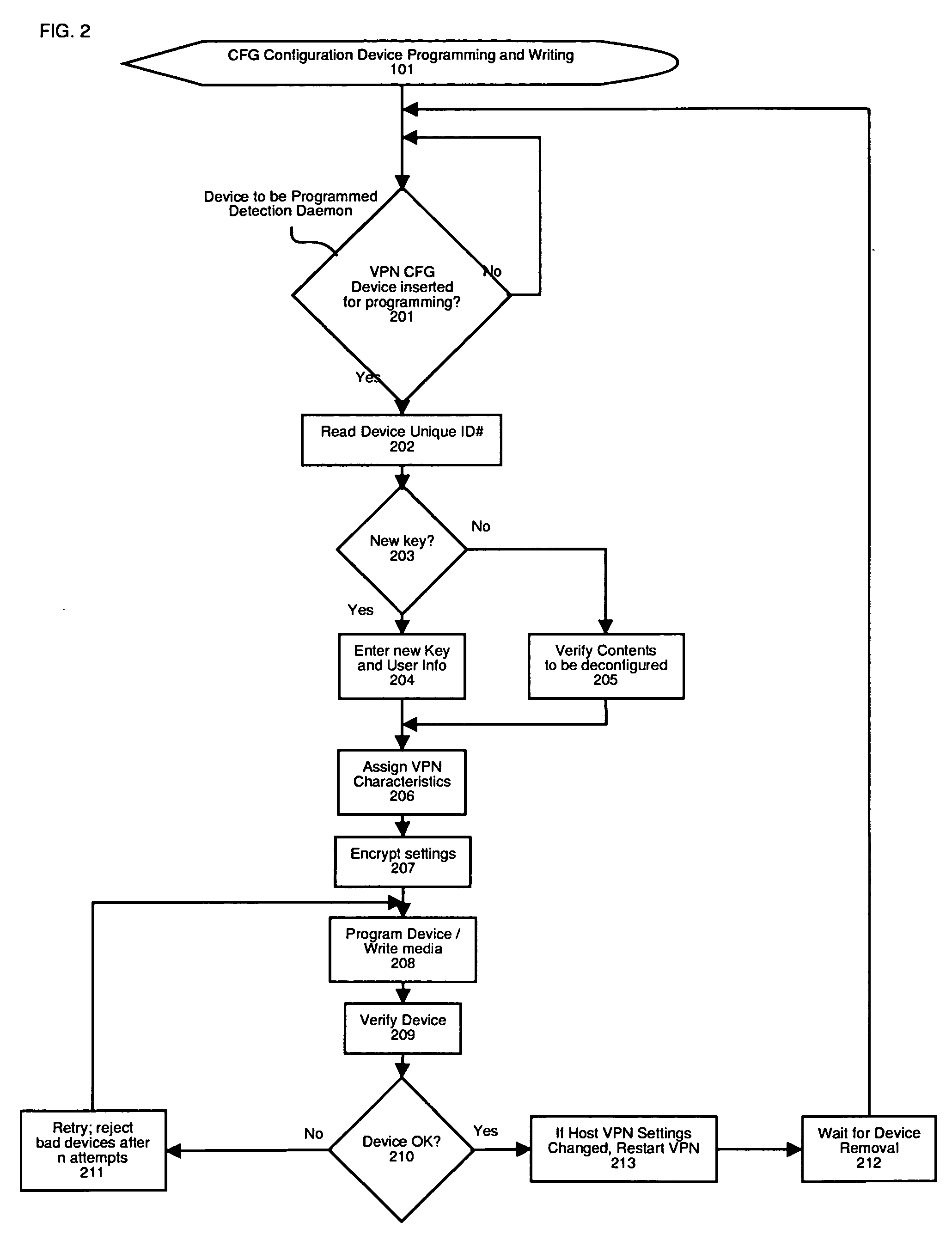
Method and apparatus for automatic configuration and management of a virtual private network
InactiveUS20050193103A1Reduce chanceDigital computer detailsTransmissionAuto-configurationPrivate network
The present invention provides a method and apparatus for automatic configuration and management of a virtual private network operating over a public data network, and a method and apparatus for delivery of the configuration parameters to client interface equipment participating in the virtual private network. The system defines allowed connections between client and server gateway devices, and the parameters associated with the virtual private network. The system defines methods and apparatus for automatic startup, configuration, and shutdown of nodes of the resulting virtual private network based on factors such as the presence of a configuration carrier device. The present invention also describes a class of pseudo-interface mechanism that can hide the complexity of the underlying system from client devices incorporating the present invention, via a conventional network device interface.
Owner:DRABIK JOHN
Business card and contact management system
InactiveUS6883000B1More cost-effectivelyMore accurateAdvertisementsOffice automationBusiness cardWeb browser
An Internet (or World-Wide-Web or other such public or private network) based business card and contact management system capable of conveying and managing advertising as well as traditional and other non-traditional business contact information. The invention is a system that: (1) accepts a Universal Contact Locator (UCL) as encoded on a business card in man and / or machine readable format and, when the Universal Contact Locator (UCL) is entered into a client program running on a client computer, (2) causes a web browser (or like program) and associated communications software to establish a communications session with a remote server computer which (3) accesses the stored contact and advertisement and news information of the card issuer associated with the Universal Contact Locator and (4) downloads the business contact and / or personal contact information and targeted advertisements and news items associated with the Universal Contact Locator to a client program running on a client computer which (5) loads the contact data into the Contact Management or Personal Information Management (PIM) system of the users choosing running on the users client computer and (6) stores the advertisements and news items downloaded from the server computer on the client computer's secondary storage device (i.e. hard disk) and (7) causes the advertisements and news items stored on the client computer's secondary storage device to be displayed to the user on a predetermined schedule in a portion of the client computer's output device (i.e. CRT or LCD panel).
Owner:MICROSOFT TECH LICENSING LLC
Headset-Based Telecommunications Platform
ActiveUS20100245585A1Extend battery lifeTelevision system detailsOptical rangefindersData streamPeer-to-peer
A hands-free wireless wearable GPS enabled video camera and audio-video communications headset, mobile phone and personal media player, capable of real-time two-way and multi-feed wireless voice, data and audio-video streaming, telecommunications, and teleconferencing, coordinated applications, and shared functionality between one or more wirelessly networked headsets or other paired or networked wired or wireless devices and optimized device and data management over multiple wired and wireless network connections. The headset can operate in concert with one or more wired or wireless devices as a paired accessory, as an autonomous hands-free wide area, metro or local area and personal area wireless audio-video communications and multimedia device and / or as a wearable docking station, hot spot and wireless router supporting direct connect multi-device ad-hoc virtual private networking (VPN). The headset has built-in intelligence to choose amongst available network protocols while supporting a variety of onboard, and remote operational controls including a retractable monocular viewfinder display for real time hands-free viewing of captured or received video feed and a duplex data-streaming platform supporting multi-channel communications and optimized data management within the device, within a managed or autonomous federation of devices or other peer-to-peer network configuration.
Owner:EYECAM INC
Secure virtual community network system
ActiveUS20040249911A1Convenient introductionMultiple digital computer combinationsOffice automationPrivate networkPublic network
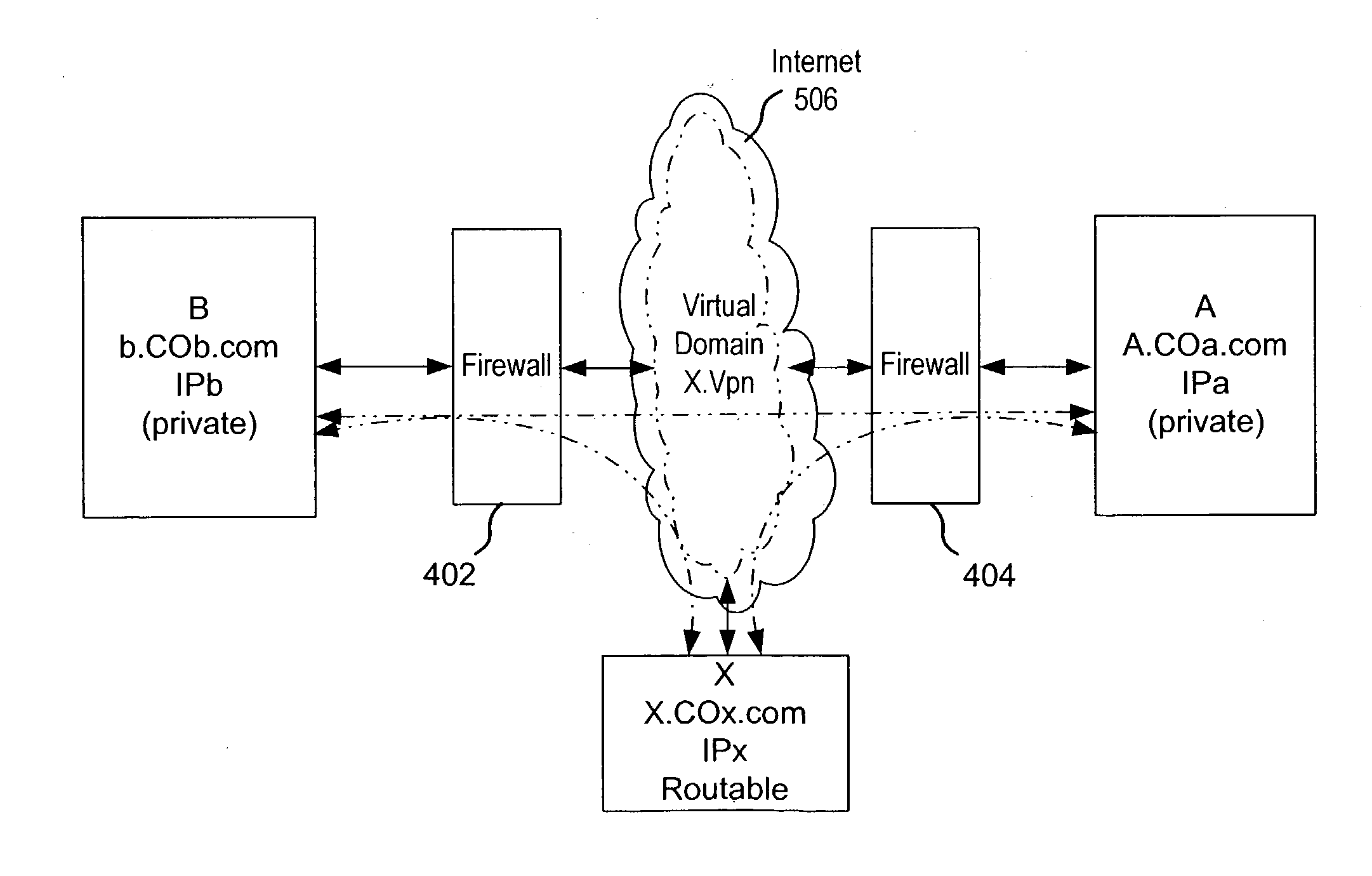
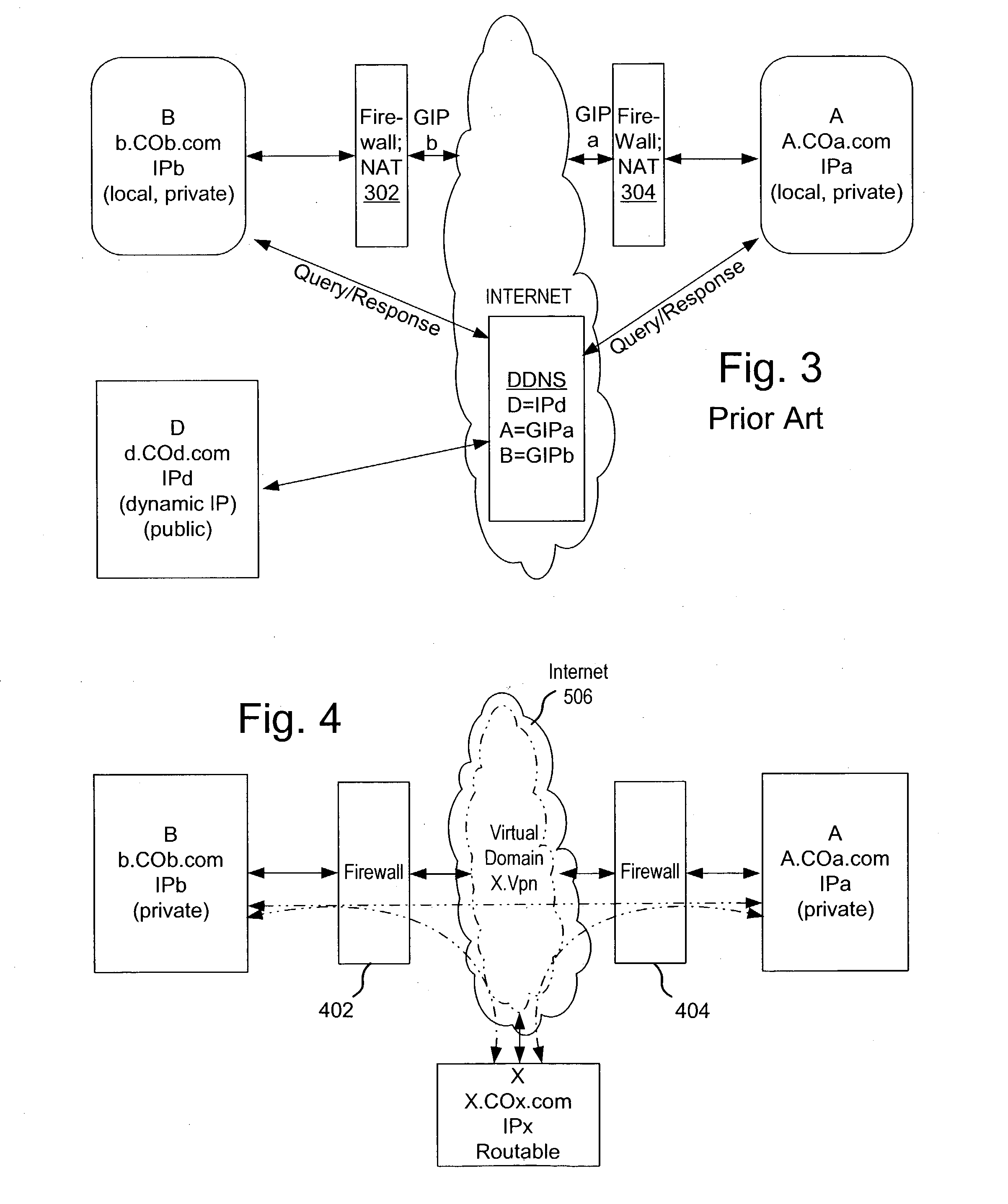
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:F POSZAT HU
A method and systems for securing remote access to private networks
ActiveUS20060037071A1Reduce the burden onImprove experienceMultiple digital computer combinationsProgram controlPrivate networkNetwork address translation
A method for securing remote access to private networks includes a receiver intercepting from a data link layer a packet in a first plurality of packets destined for a first system on a private network. A filter intercepts from the data link layer a packet in a second plurality of packets transmitted from a second system on the private network, destined for an system on a second network. A transmitter in communication with the receiver and the filter performing a network address translation on at least one intercepted packet and transmitting the at least one intercepted packet to a destination.
Owner:CITRIX SYST INC
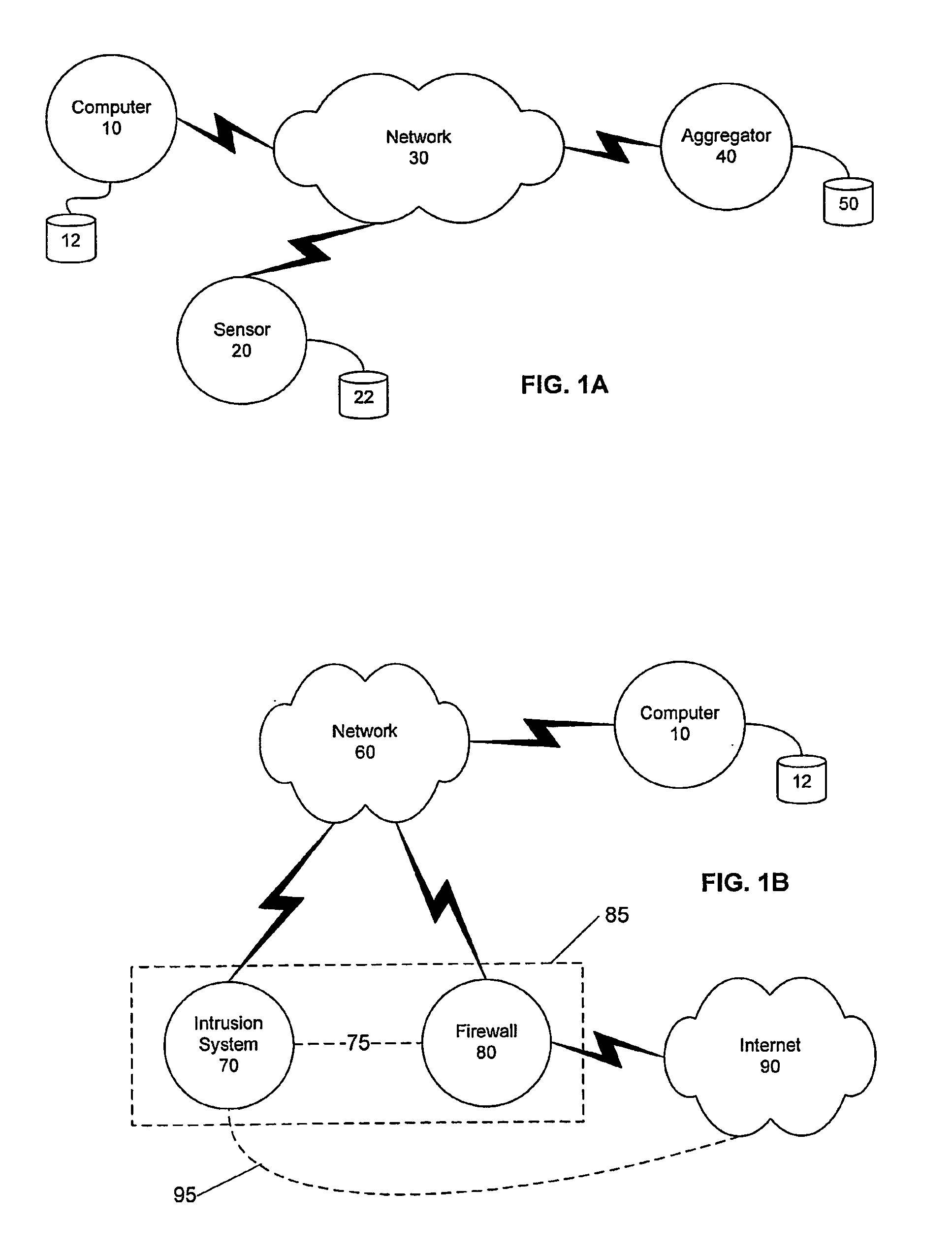
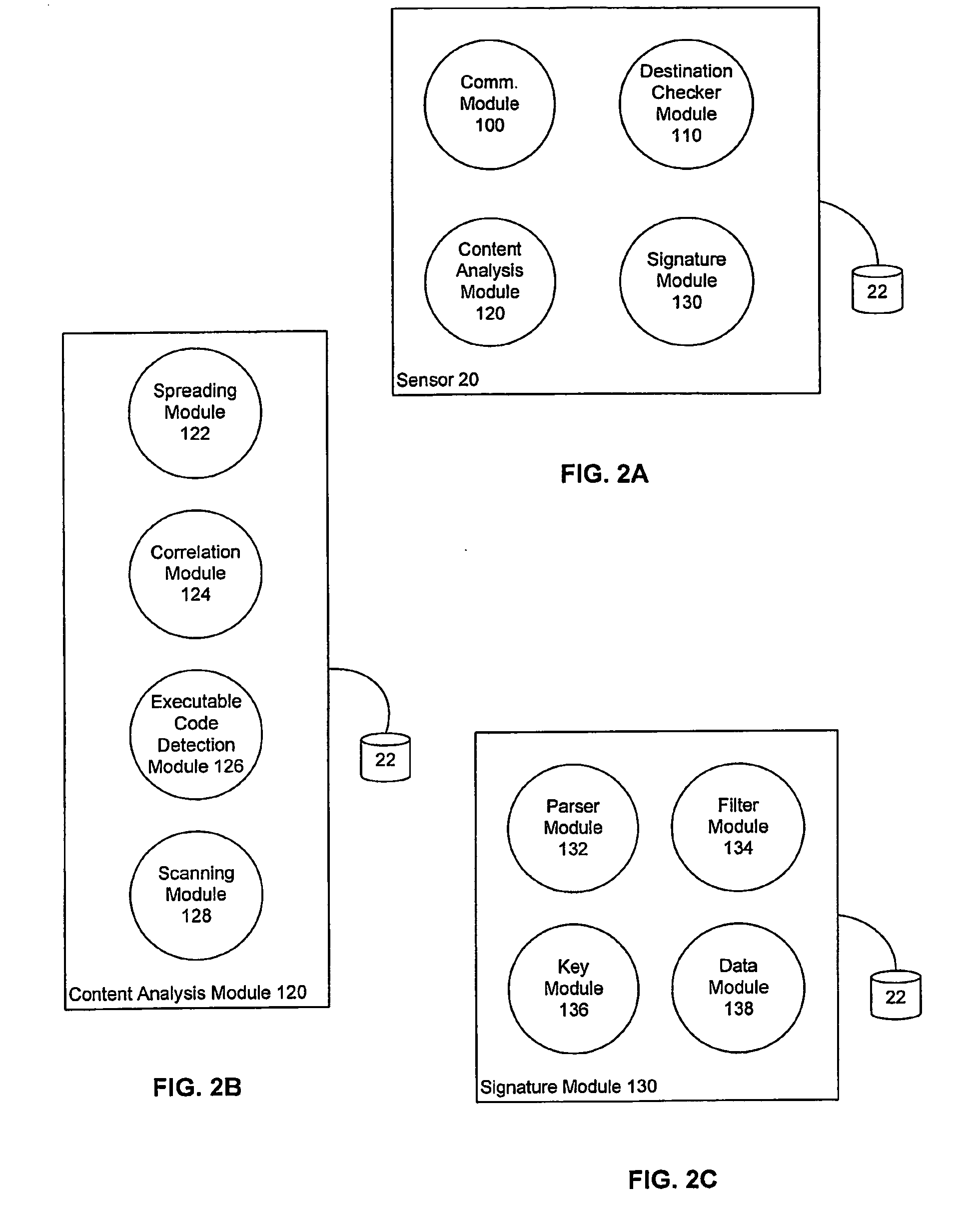
Detecting Public Network Attacks Using Signatures and Fast Content Analysis
ActiveUS20080307524A1Memory loss protectionUser identity/authority verificationComputer hardwarePrivate network
Network worms or viruses are a growing threat to the security of public and private networks and the individual computers that make up those networks. A content sifting method if provided that automatically generates a precise signature for a worm or virus that can then be used to significantly reduce the propagation of the worm elsewhere in the network or eradicate the worm altogether. The content sifting method is complemented by a value sampling method that increases the throughput of network traffic that can be monitored. Together, the methods track the number of times invariant strings appear in packets and the network address dispersion of those packets including variant strings. When an invariant string reaches a particular threshold of appearances and address dispersion, the string is reported as a signature for suspected worm.
Owner:RGT UNIV OF CALIFORNIA
Distributed administration of access to information
InactiveUS6785728B1Cathode-ray tube indicatorsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
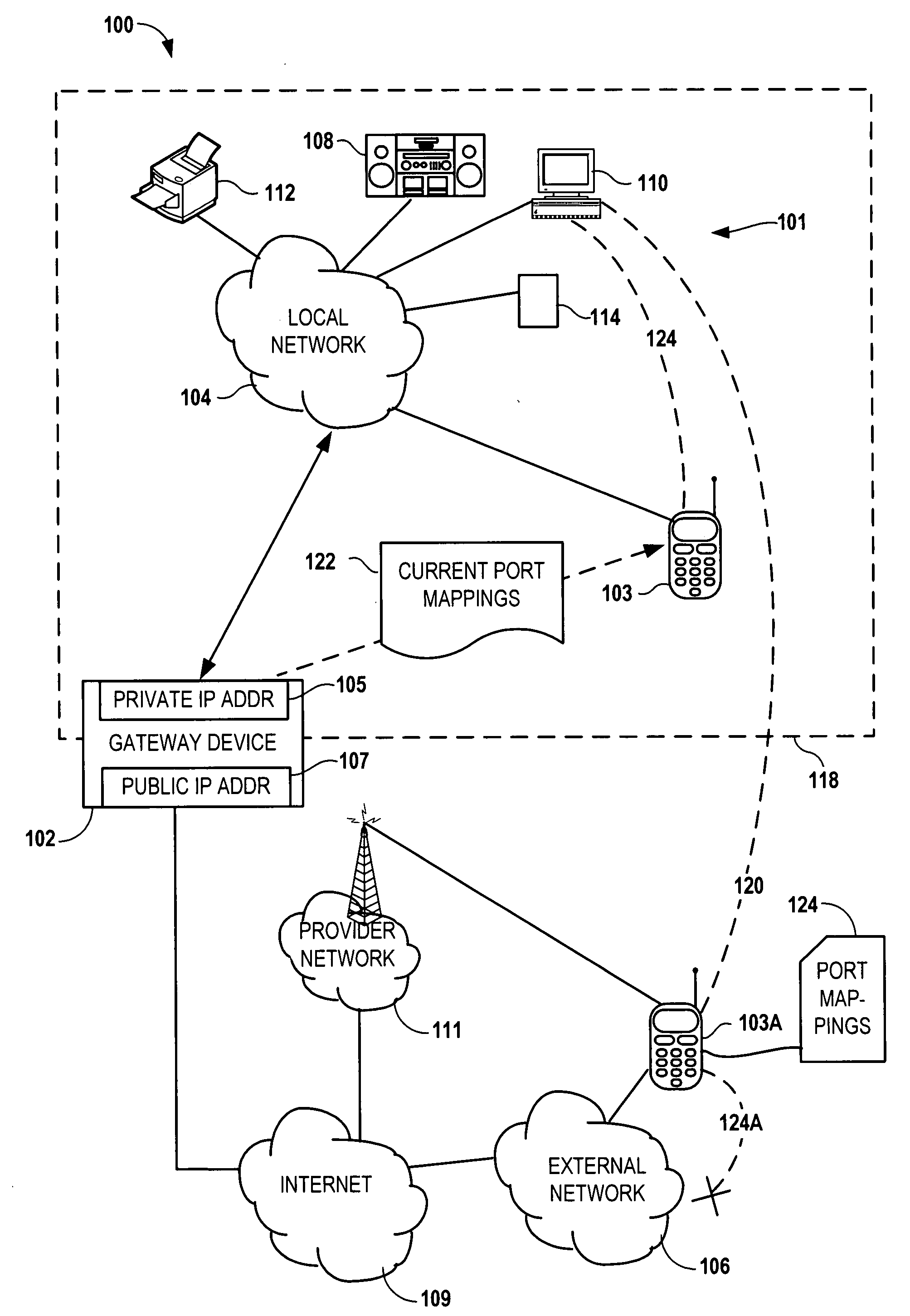
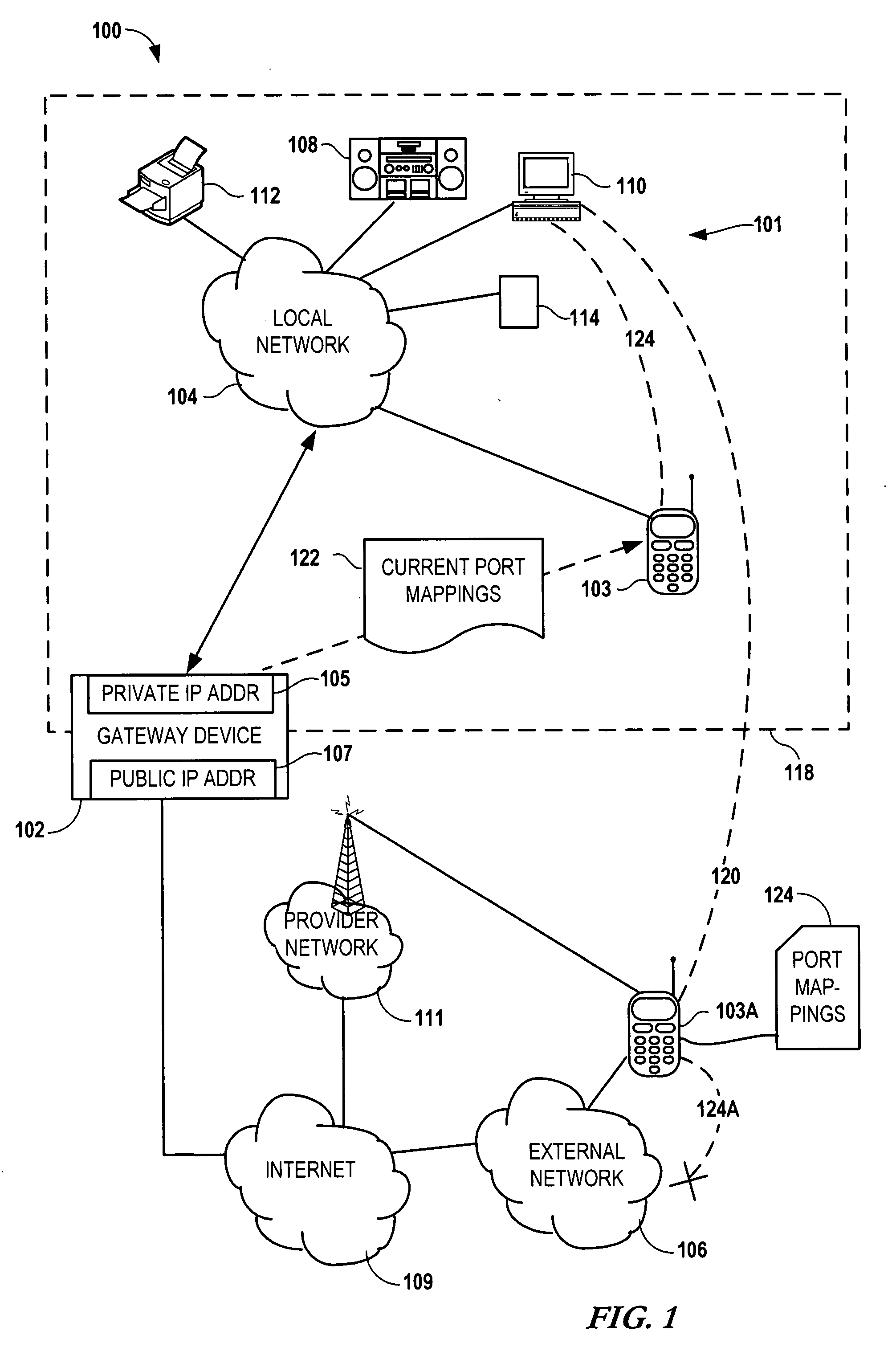
Configuring a user device to remotely access a private network
InactiveUS20090129301A1Network traffic/resource managementRadio transmissionPrivate networkPublic network
Configuring a mobile device to remotely access a private network involves determining, via the private network, first network parameters that enable the mobile device utilize to a computing service of the private network. The device also determines, via a gateway coupled to the private network, second network parameters that allow the mobile to utilize the computing service via a public network. The first and second network parameters are stored on the mobile device. A request is received from a user of the mobile device to access the computing service. It is determined that the mobile device is not on the private network. In response to determining that the mobile device is not on the private network, the second network parameters are utilized to access the computing service via the gateway in response to the request.
Owner:NOKIA CORP
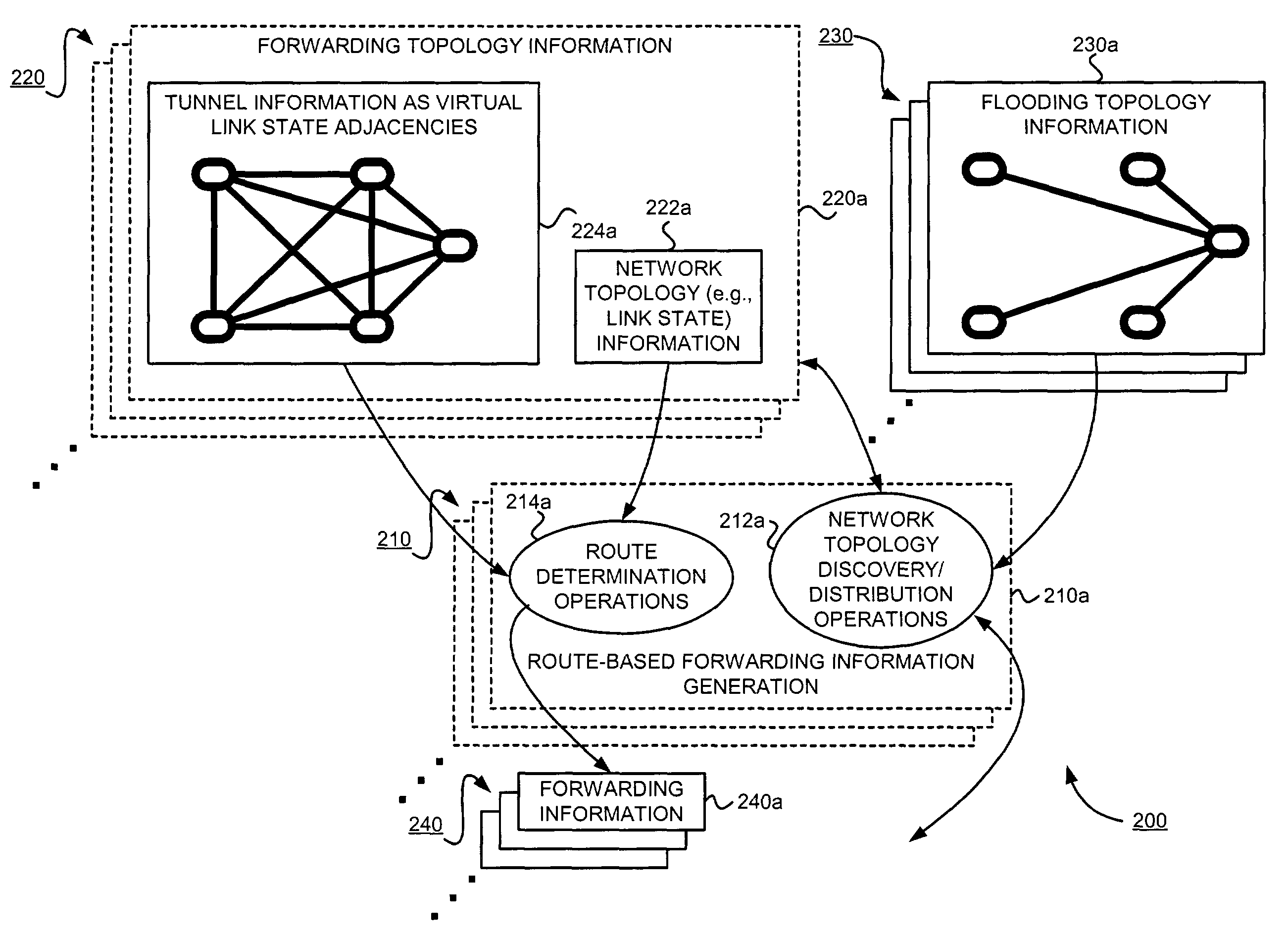
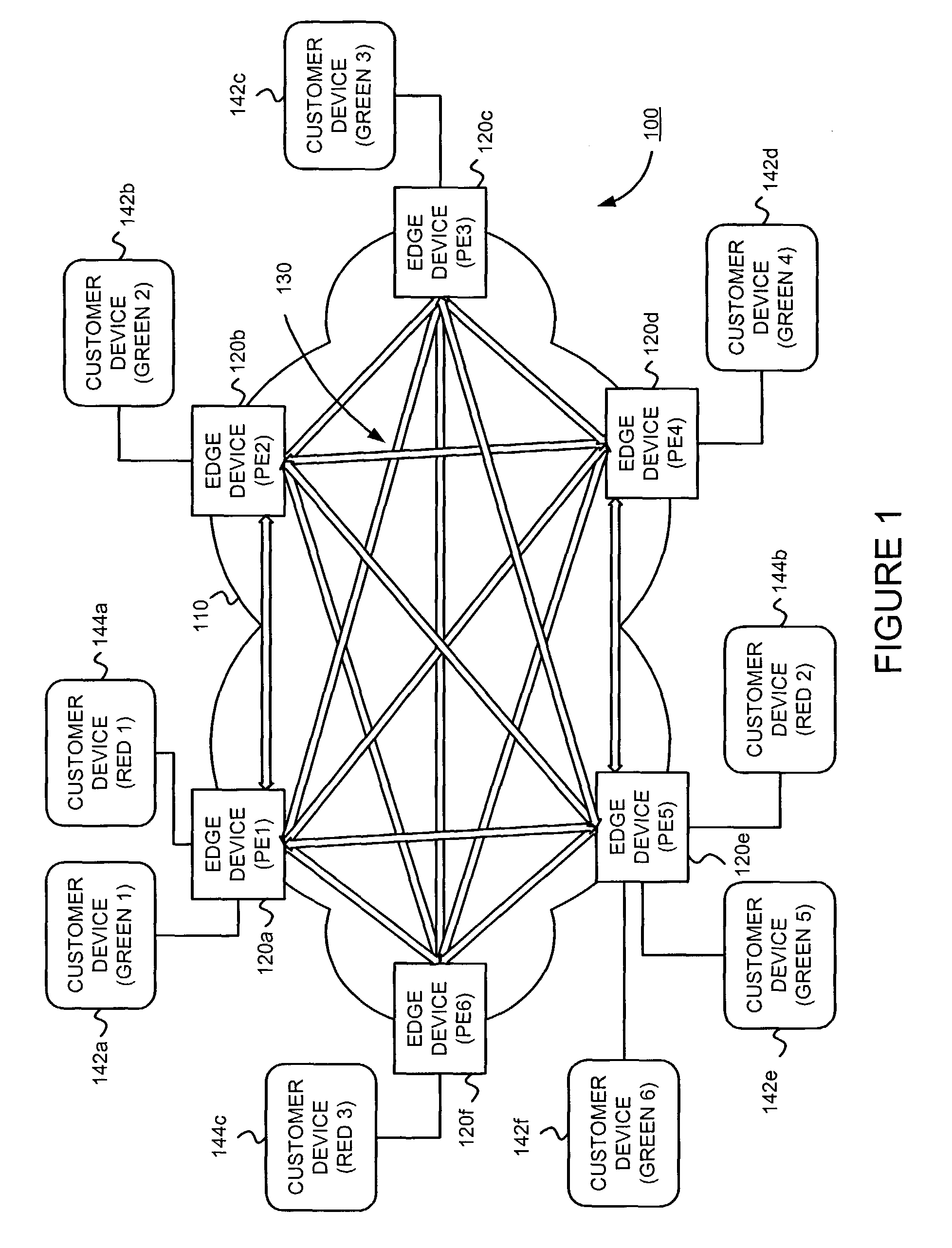
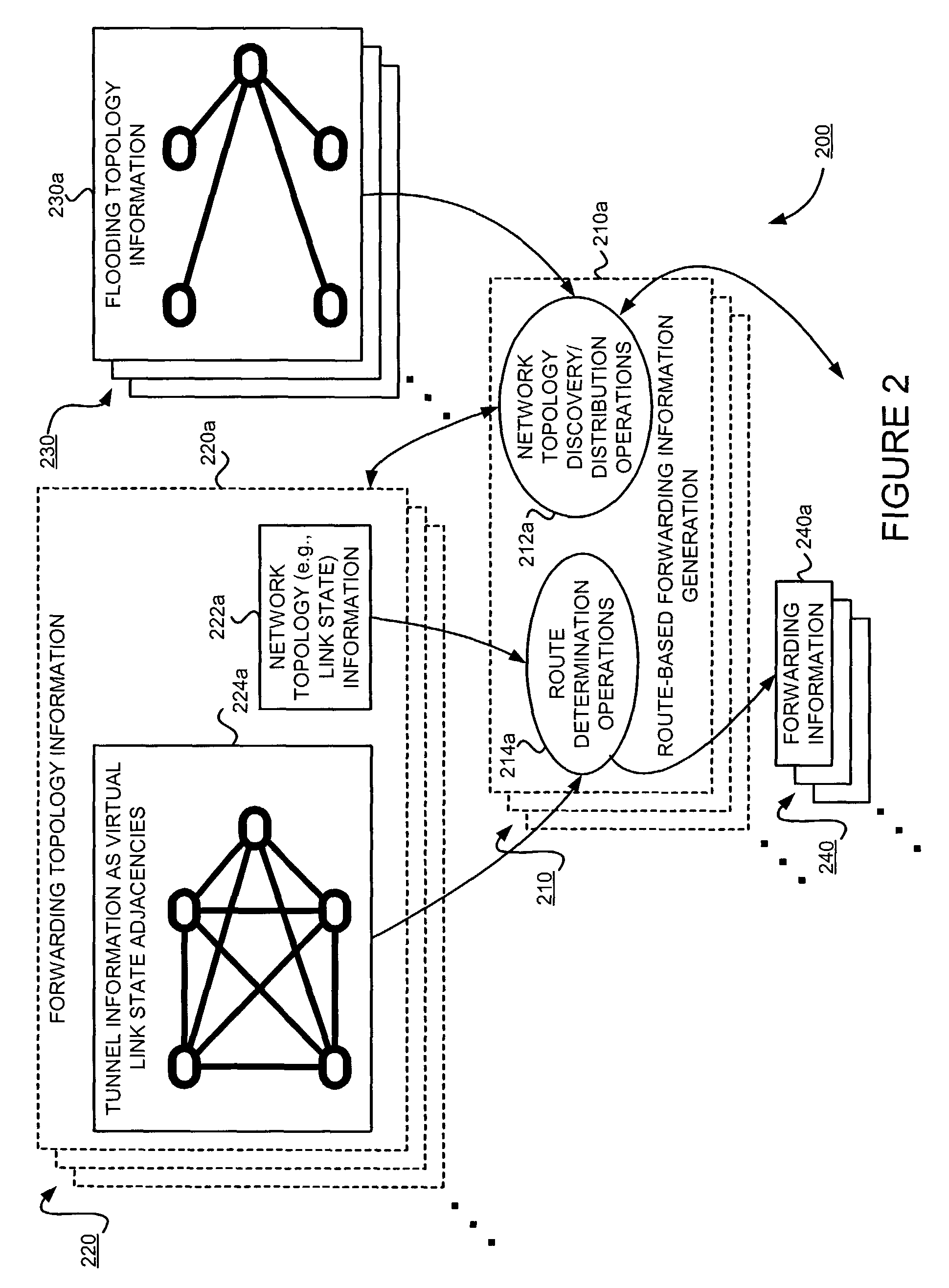
Supporting virtual private networks using a first network topology for forwarding and a subset of the first network topology or a smaller topology for signaling
InactiveUS7792987B1Avoid problemsError preventionTransmission systemsBorder Gateway ProtocolTTEthernet
Virtual Private Networks (VPNs) are supported in which customers may use popular internet gateway protocol (IGPs) without the need to convert such IGPs, running on customer devices to a single protocol, such as the border gateway protocol (BGP). Scaling problems, which might otherwise occur when multiple instances of an IGP flood link state information, are avoided by using a flooding topology which is smaller than a forwarding topology. The flooding topology may be a fully connected sub-set of the forwarding topology.
Owner:JUMIPER NETWORKS INC
Systems and methods for automatically configuring and managing network devices and virtual private networks
ActiveUS20060236095A1Multiple digital computer combinationsSpecial data processing applicationsComputer hardwareGraphics
Systems and methods are disclosed for automatically configuring, managing, and maintaining a network device or VPN using a public network such as the Internet. Initial configuration of a network device or VPN occurs upon a user entering minimal information via a simple HTML page. After receipt of this minimal information, the present invention automatically configures the network device or VPN without user intervention. Thereafter, a user may modify the network device or VPN configuration via an easy-to-use and easy-to-understand graphical user interface. Parameters are presented such that a user simply checks and unchecks boxes, or clicks on radio buttons, to configure network device parameters. Upon completion of the selection, the user clicks on save, and the configuration is automatically modified. In addition, upon a significant change to any network device, the changed network device automatically initiates reconfiguration of the network device or VPN with zero input from a user.
Owner:ANXEBUSINESS
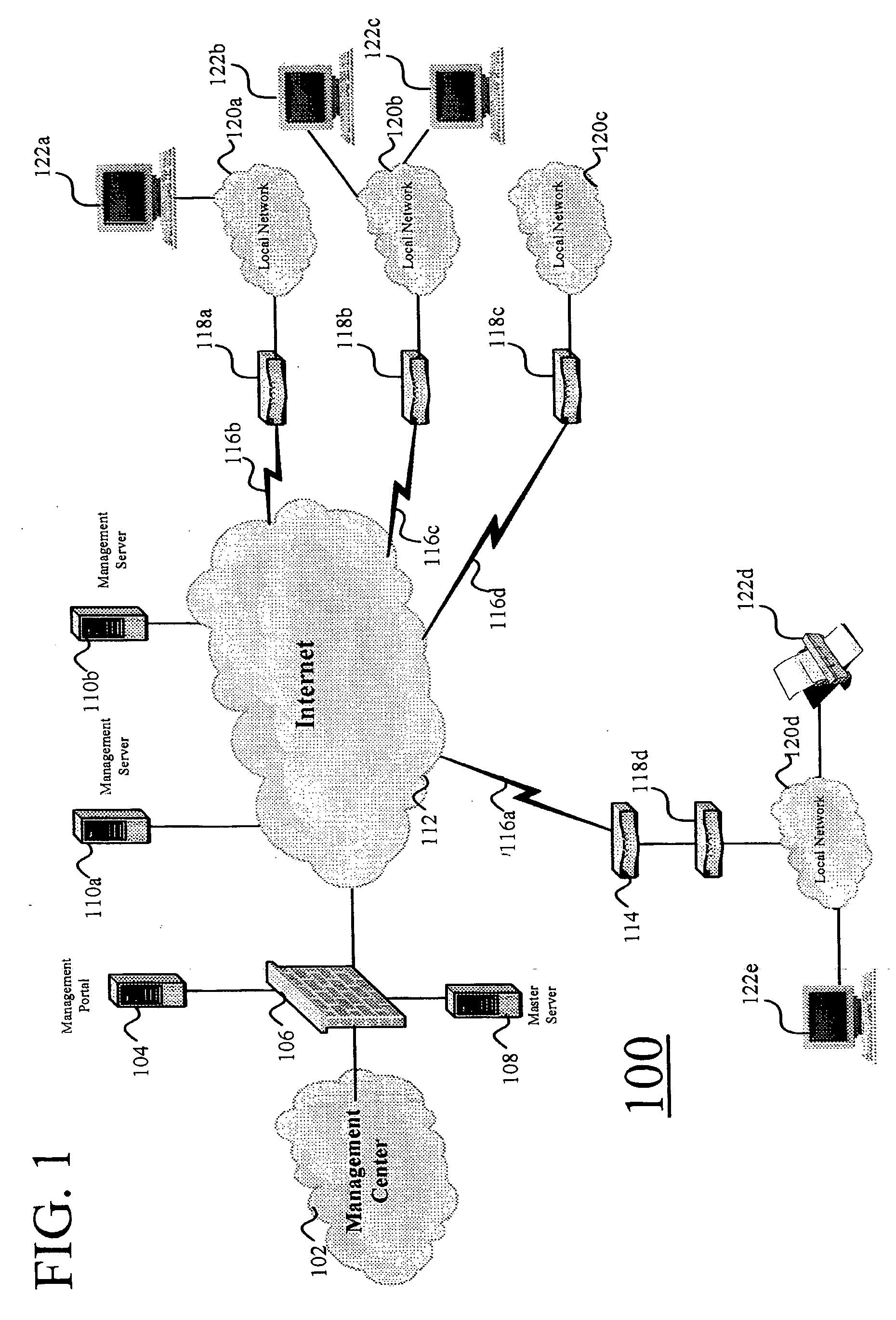
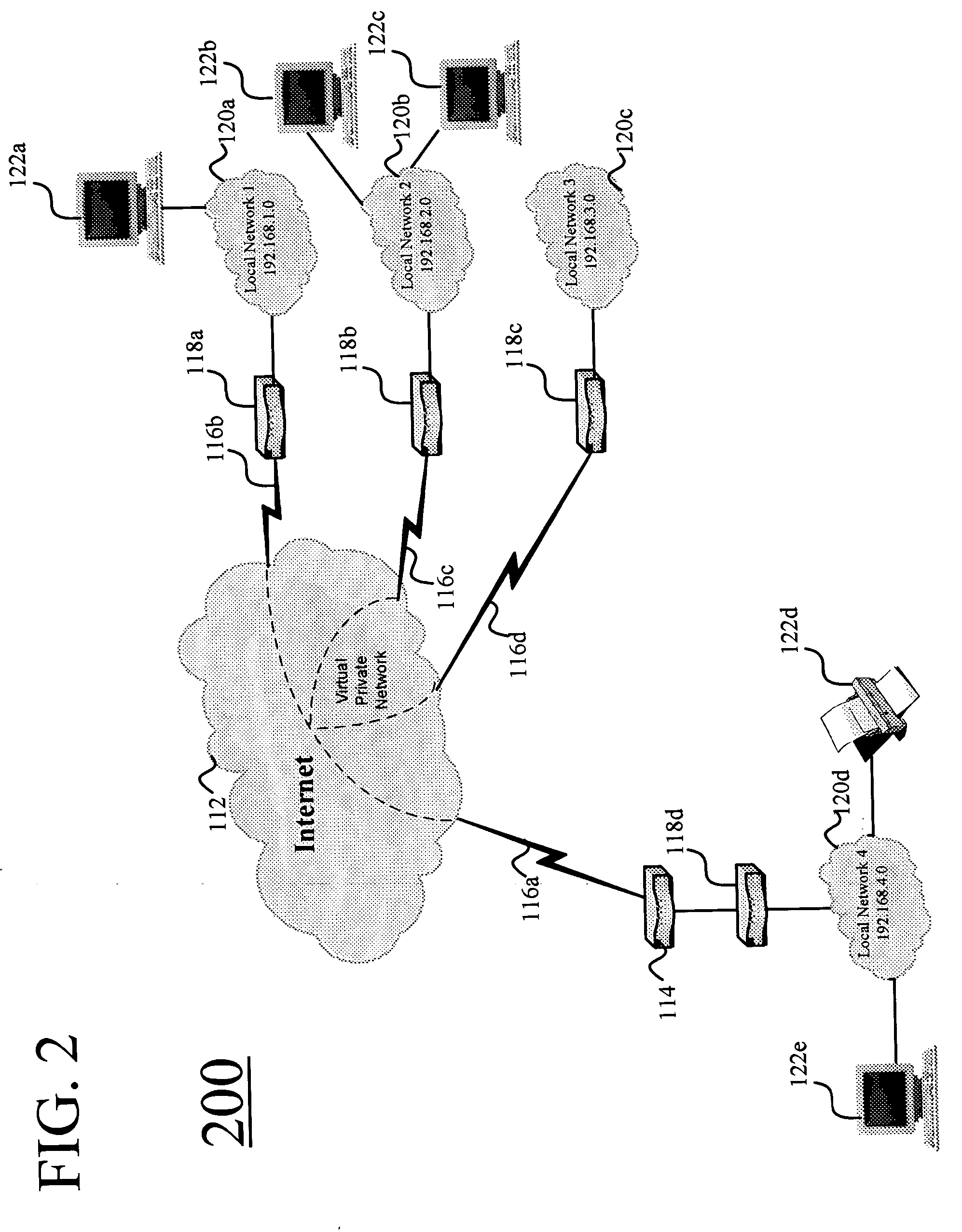
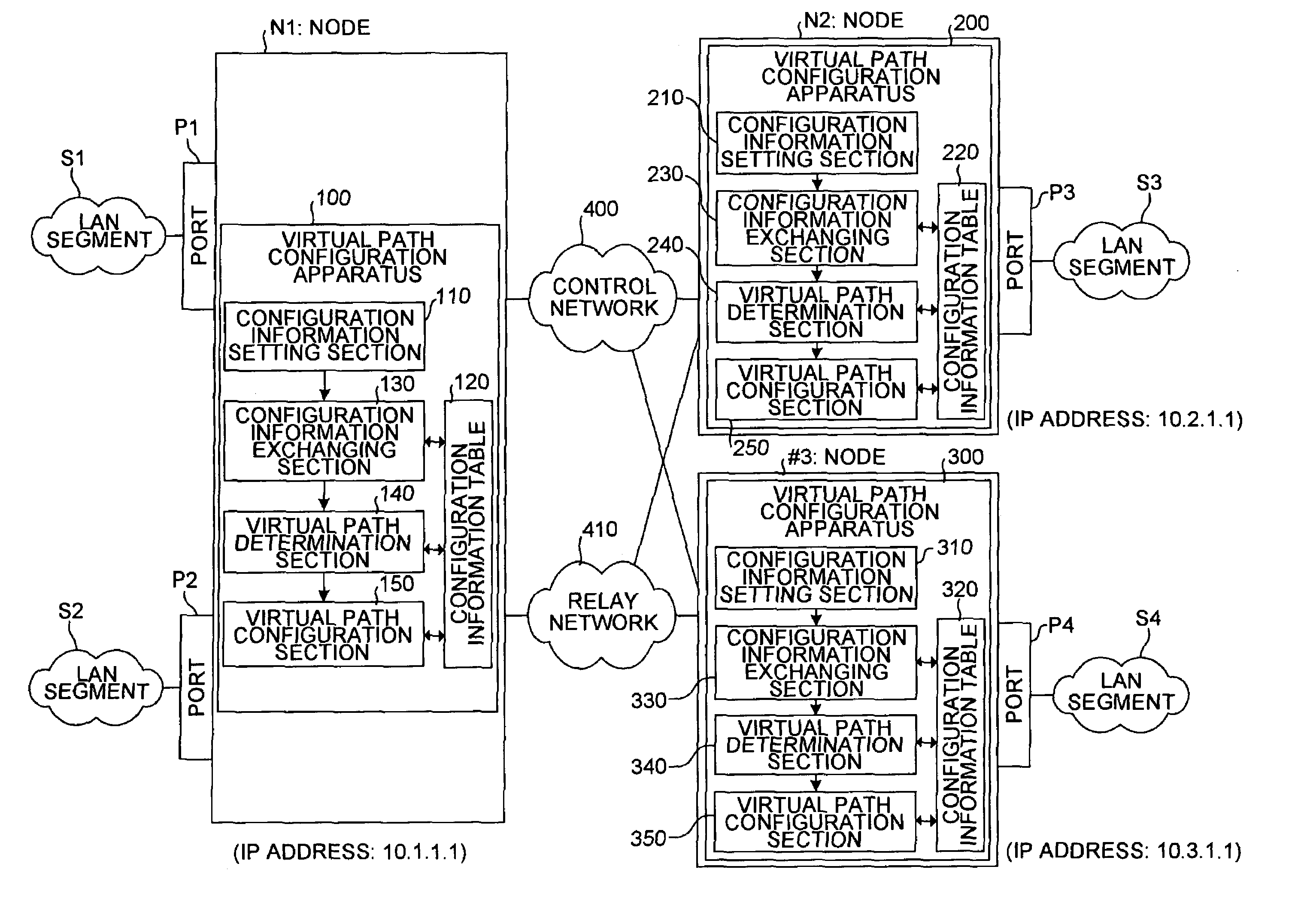
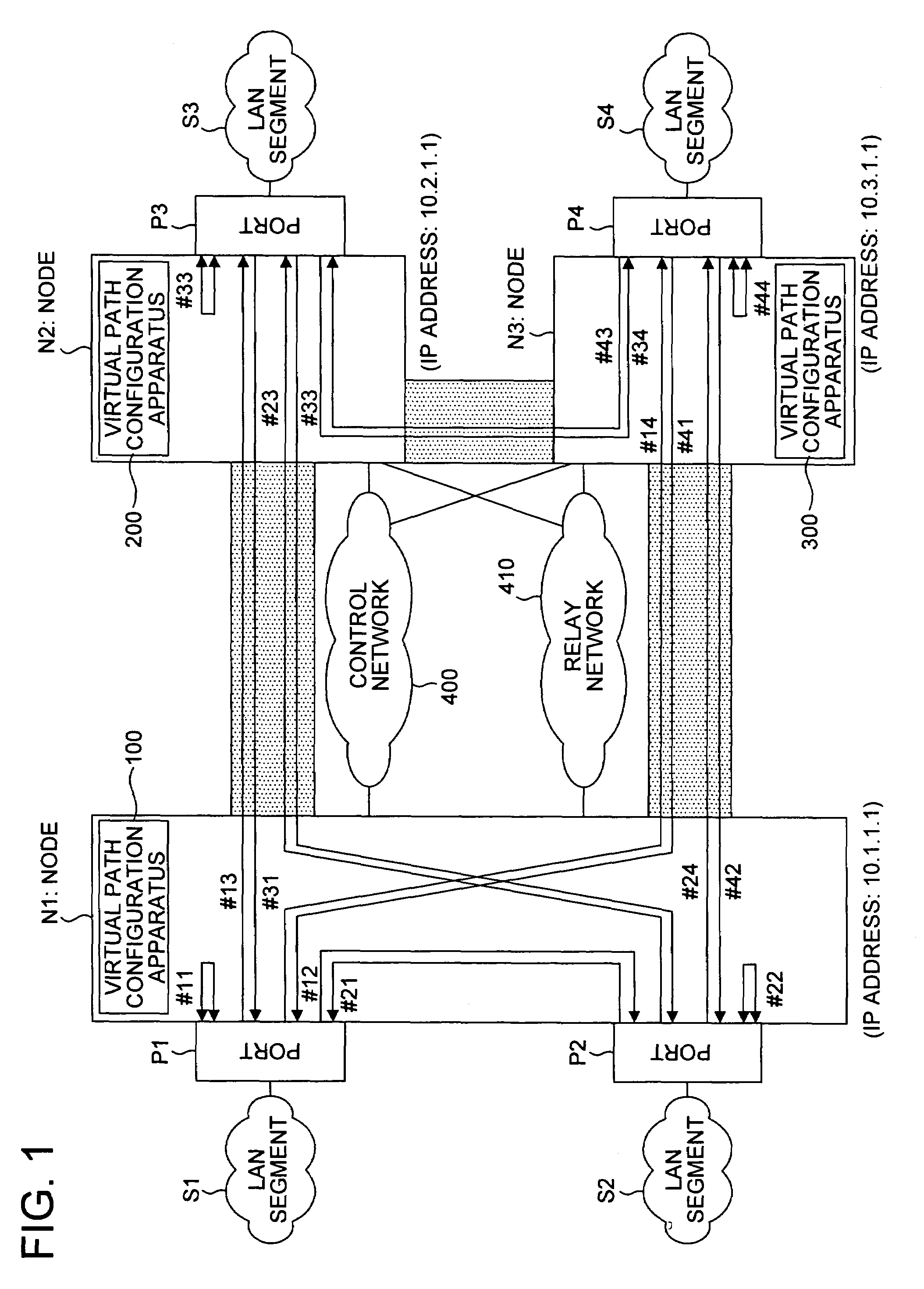
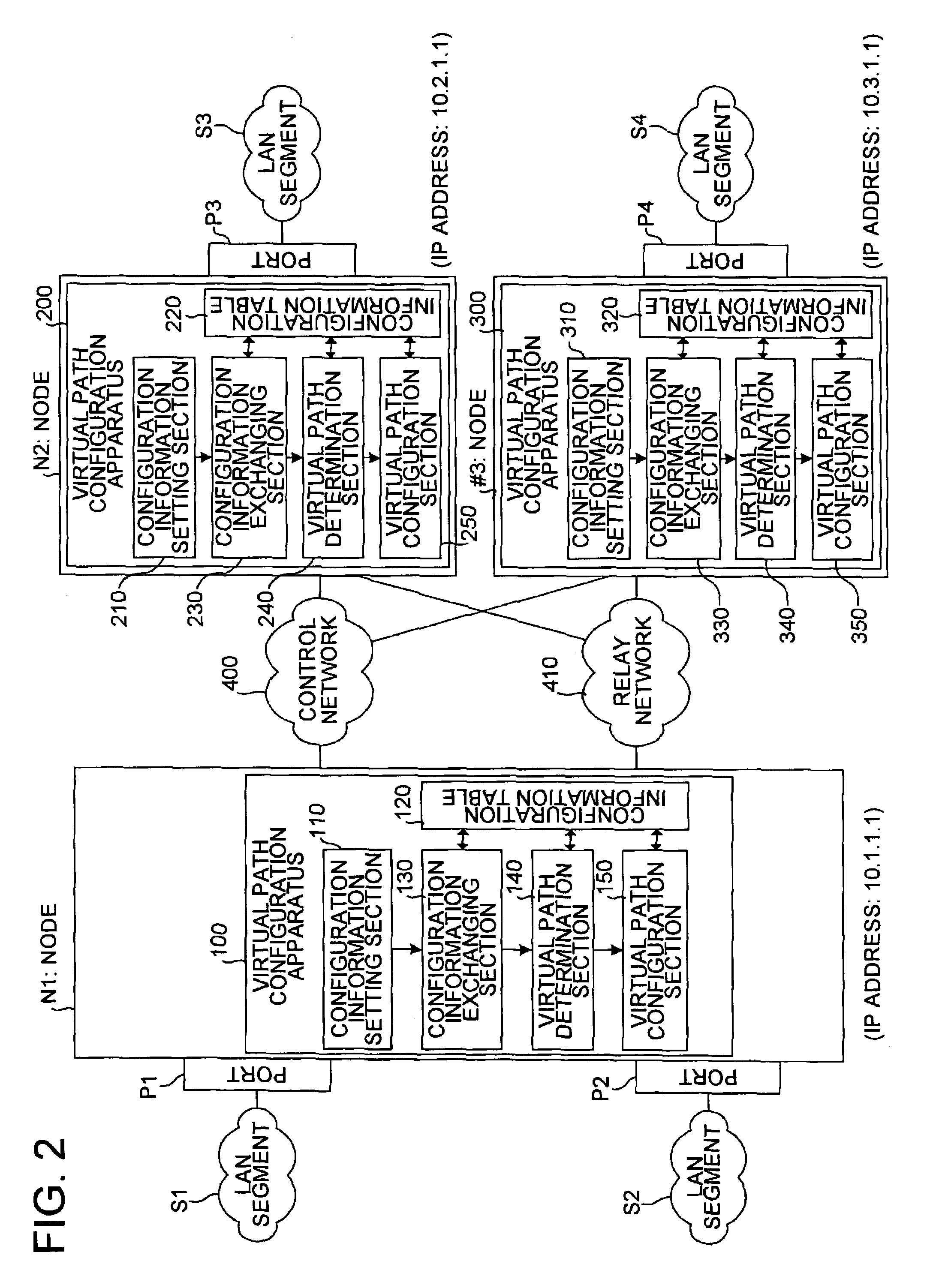
Virtual path configuration apparatus, virtual path configuration method, and computer product
InactiveUS7606260B2Solve problemsError preventionFrequency-division multiplex detailsComputer hardwarePrivate network
Configuration information set in one virtual path configuration apparatus is shared with all the virtual path configuration apparatuses in the virtual private network. The configuration information may be shared by transmitting the configuration information to other virtual path configuration apparatuses or receiving configuration information from the other virtual path configuration apparatuses.
Owner:FUJITSU LTD
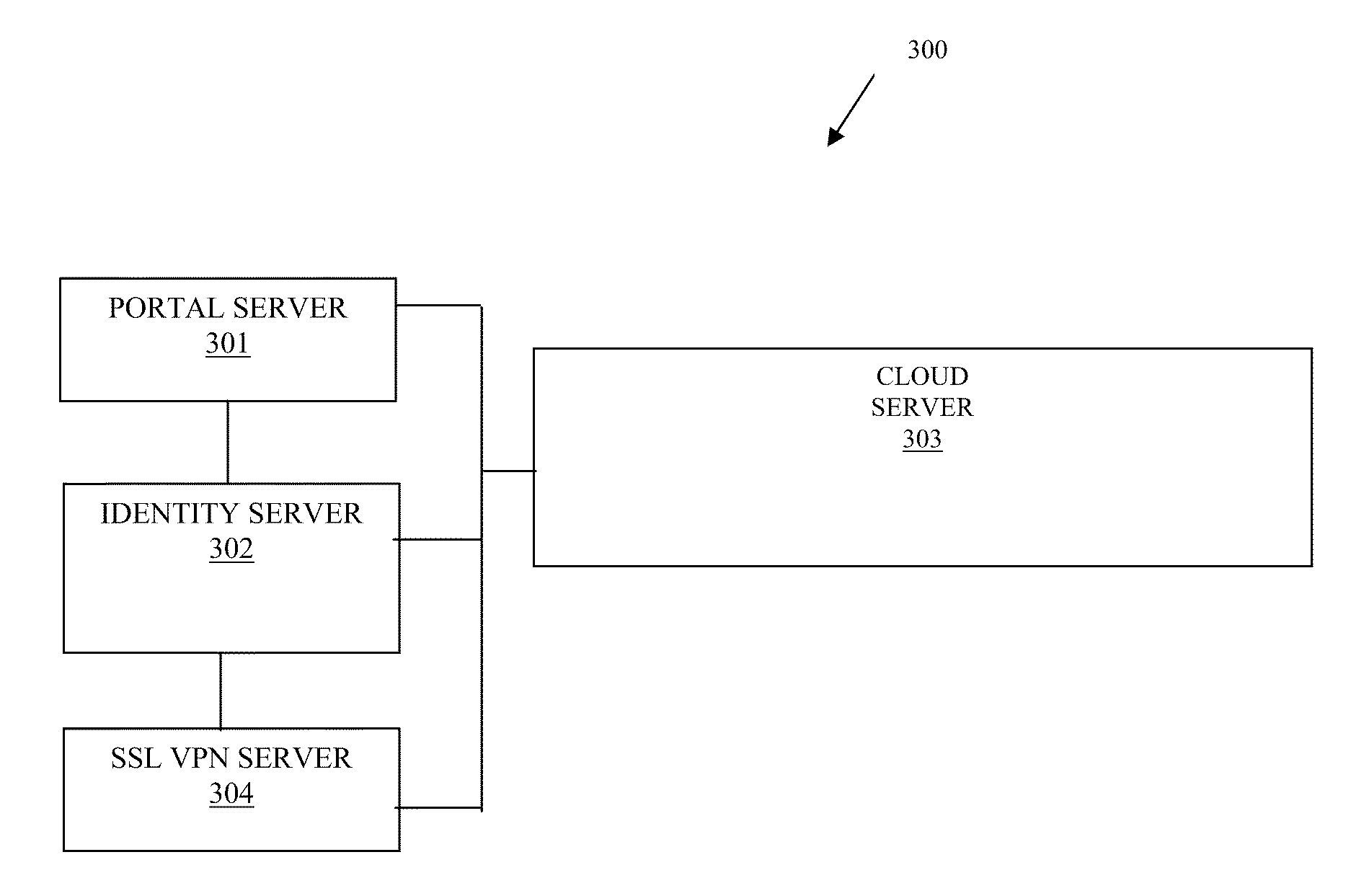
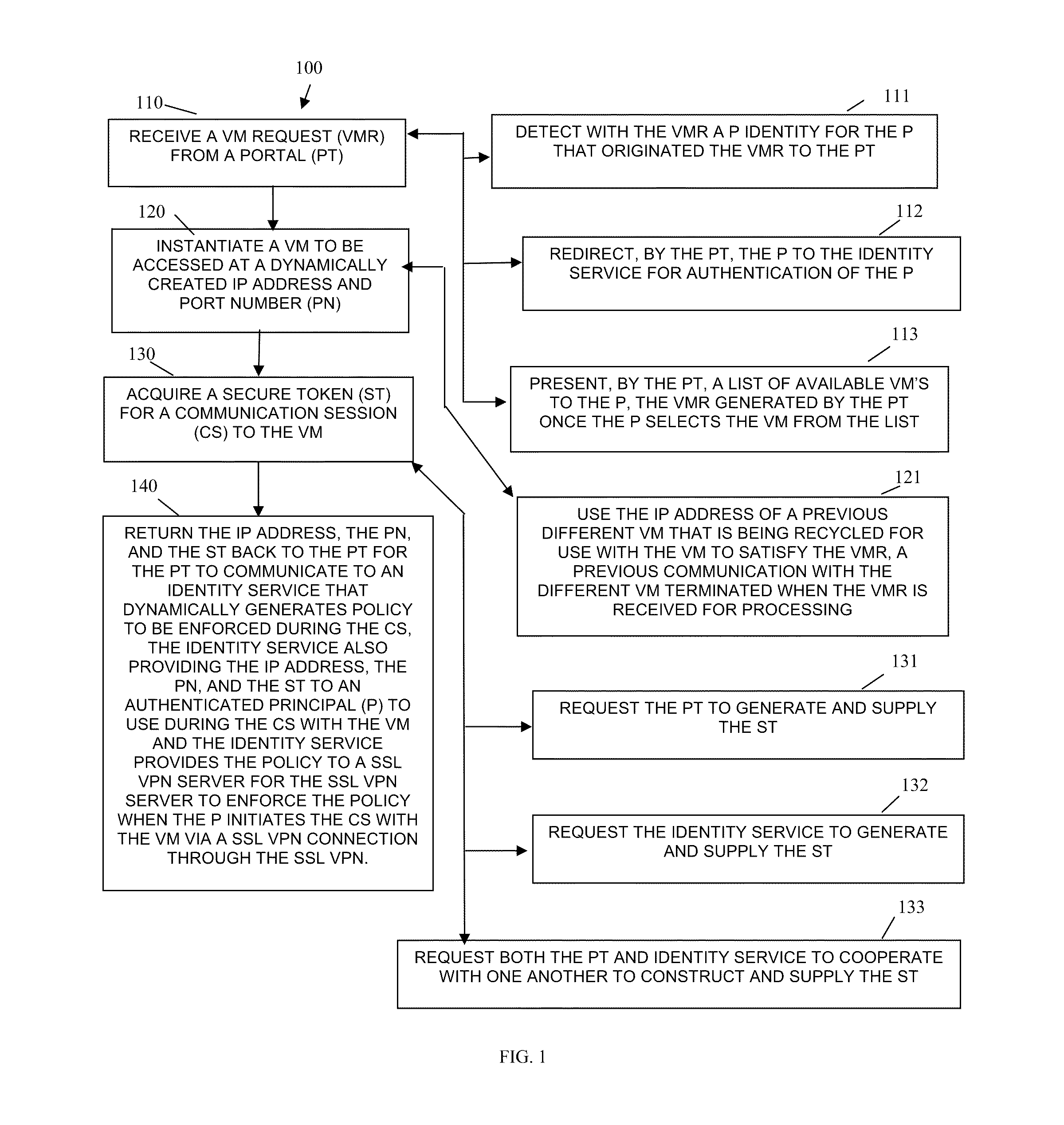
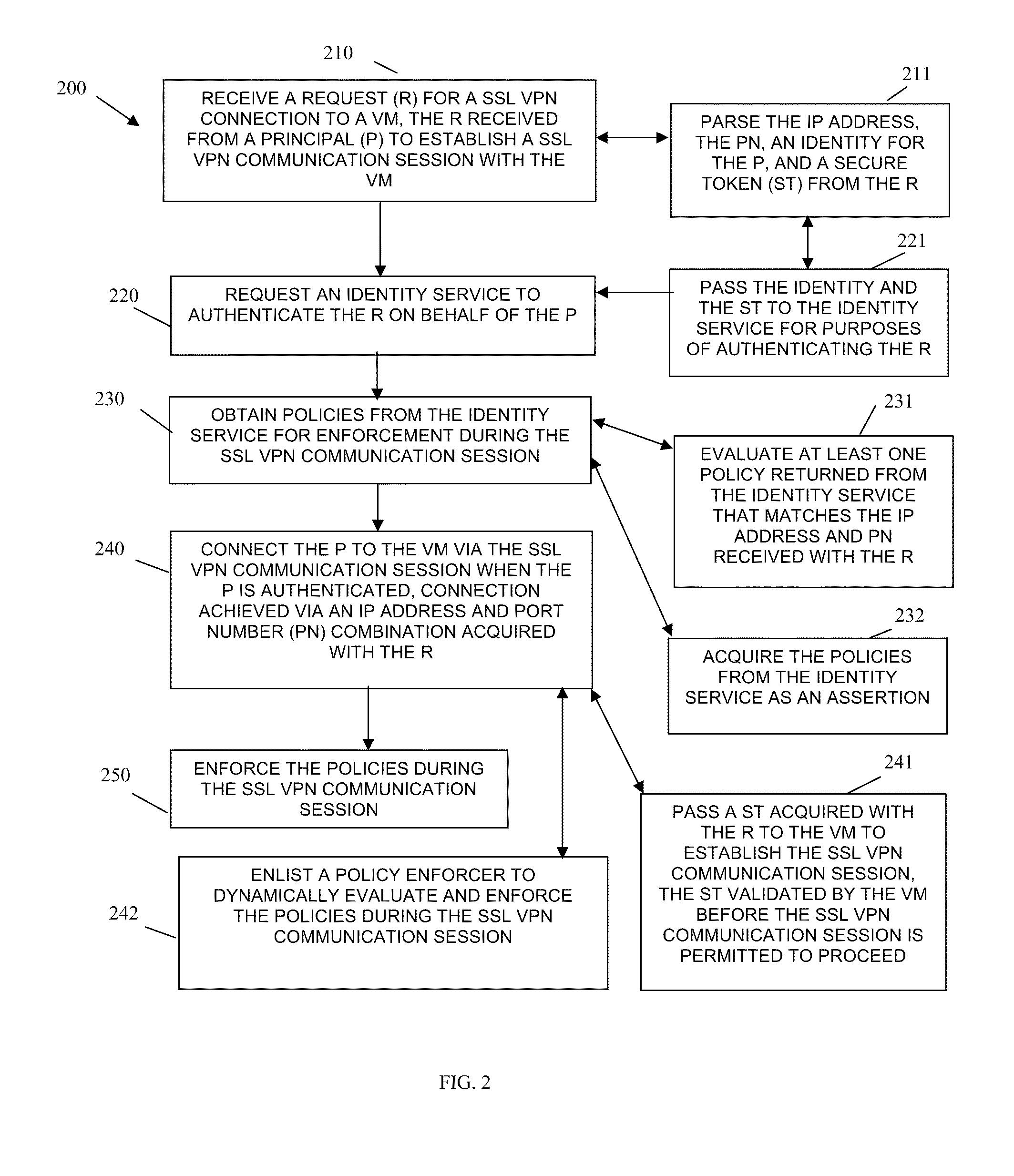
Techniques for secure access management in virtual environments
ActiveUS20110214176A1Multiple digital computer combinationsDigital data authenticationPrivate networkAccess management
Techniques for secure access management to virtual environments are provided. A user authenticates to a portal for purposes of establishing a virtual machine (VM). The portal interacts with a cloud server and an identity server to authenticate the user, to acquire an Internet Protocol (IP) address and port number for the VM, and to obtain a secure token. The user then interacts with a secure socket layer virtual private network (SSL VPN) server to establish a SSL VPN session with the VM. The SSL VPN server also authenticates the token through the identity server and acquires dynamic policies to enforce during the SSL VPN session between the user and the VM (the VM managed by the cloud server).
Owner:MICRO FOCUS SOFTWARE INC
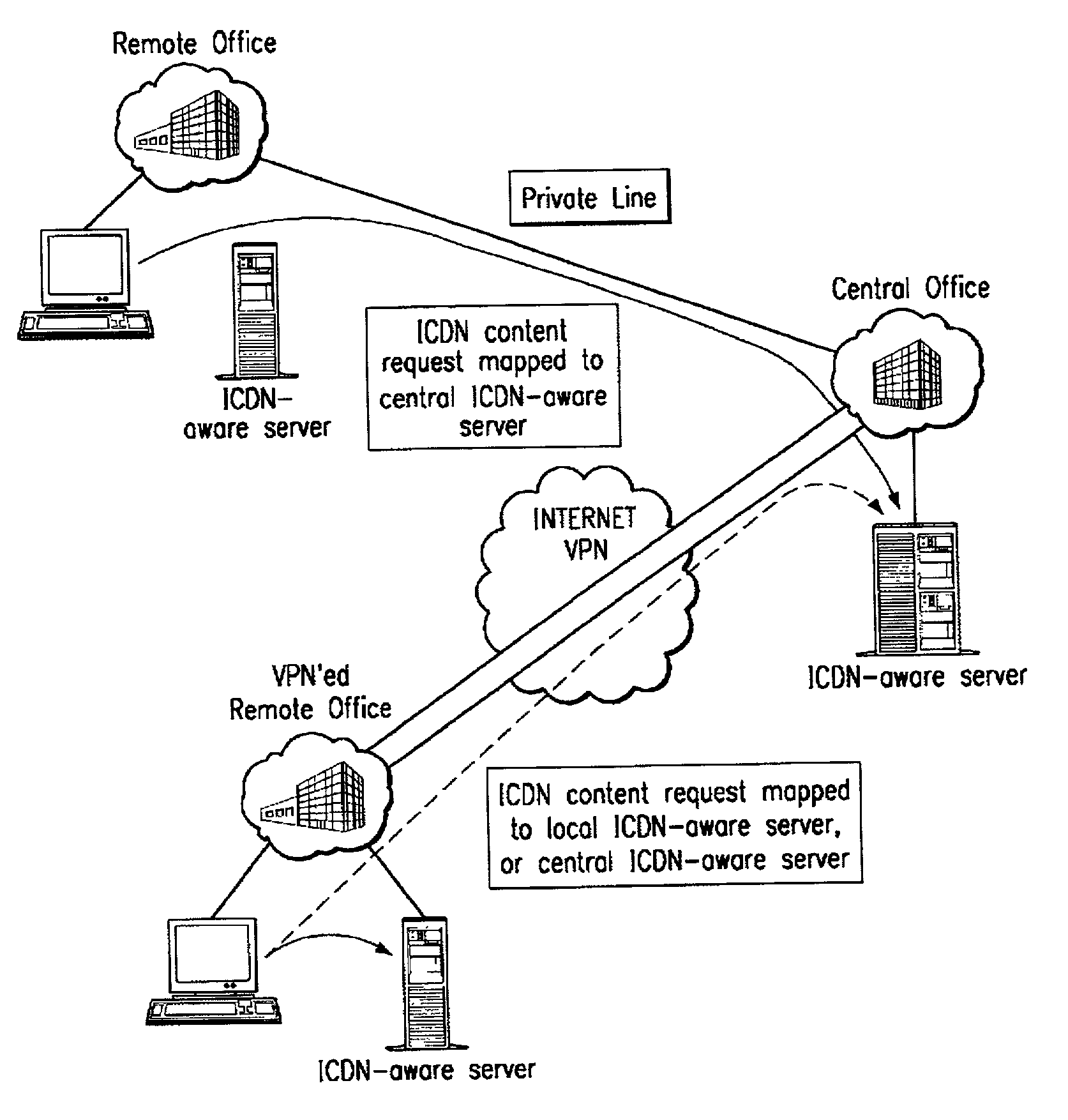
Extending an Internet content delivery network into an enterprise
ActiveUS7096266B2Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsSecuring communicationInternet contentPrivate network
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
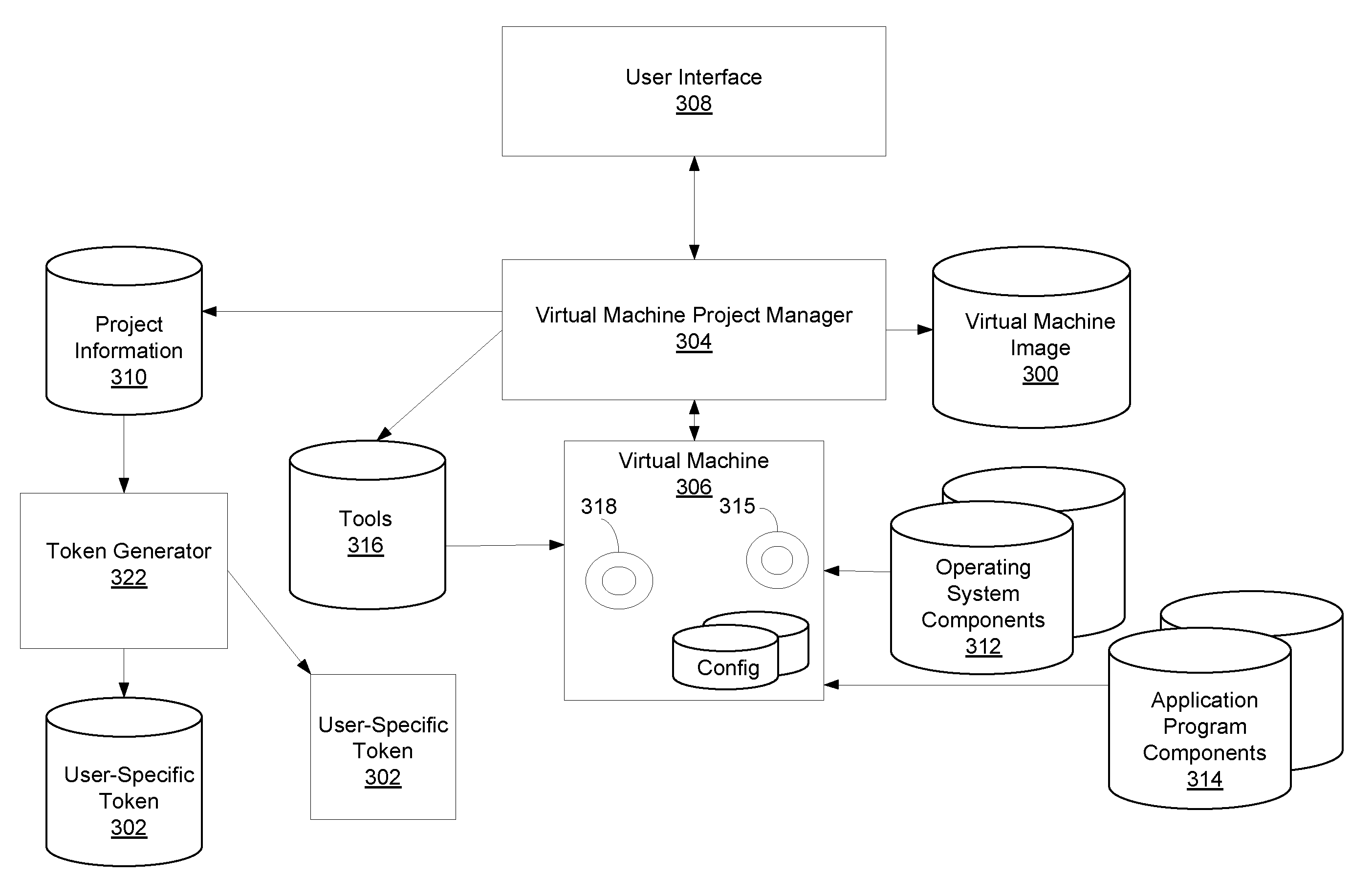
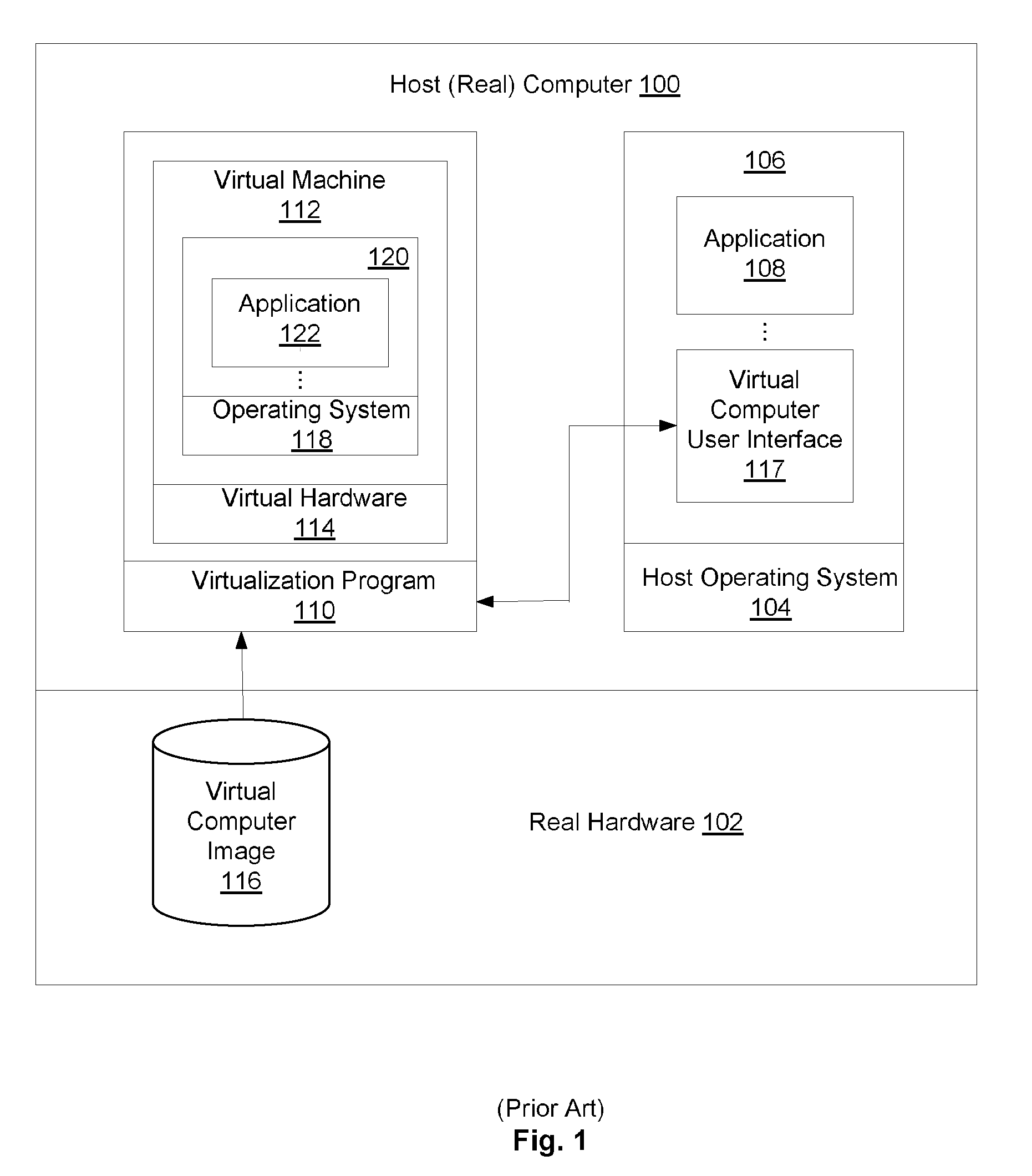
Remote Network Access Via Virtual Machine
ActiveUS20070300220A1User identity/authority verificationMultiple digital computer combinationsPrivate networkSoftware engineering
A virtual machine project manager creates a generic, i.e., not user-specific, virtual machine image file. Copies of this image file may be distributed to one or more users, each of whom may then use an automated procedure to generate a user-specific virtual machine image file and, thus, a user-specific virtual machine on his / her remote host computer. The generic virtual machine image file may be distributed on computer-readable media, such as a DVD disks, or the file may be stored on a server and downloaded (such as via the Internet) by the users. Each user also receives or downloads a token, which contains a small amount of user-specific information that is used by the automated procedure to provision the generic virtual machine image file for the particular user. A virtual machine accesses a security token connected to a host computer to automatically authenticate or re-authenticate a user, such as when a virtual private network connection is restarted. Substantially identical session identifiers are used by a host computer and a virtual machine, or by two or more virtual machines and, when communicating with an integrated access server. A file server stores virtual machine images that are accessed by a plurality of host computers.
Owner:MICROSOFT TECH LICENSING LLC
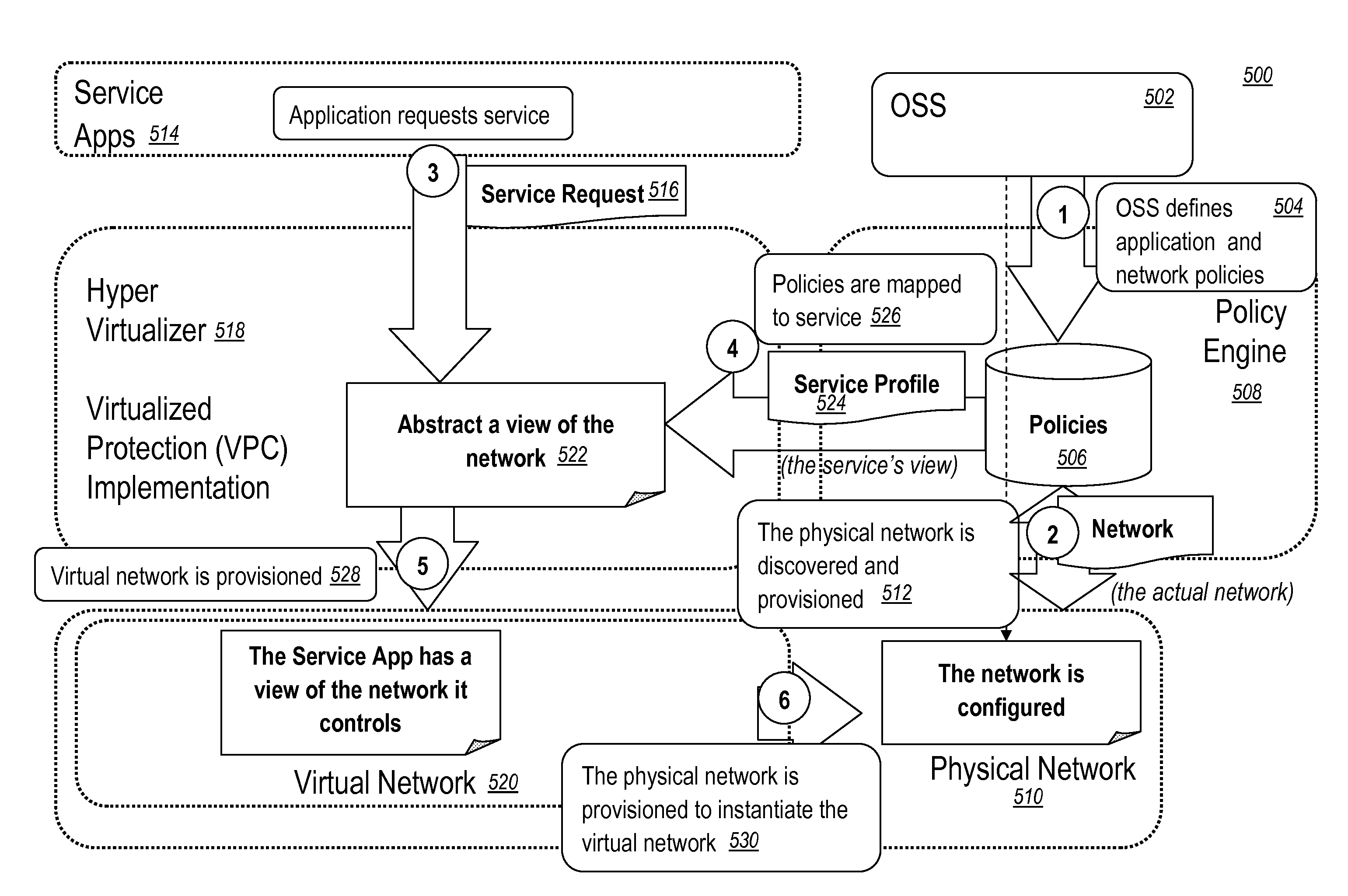
Virtualized shared protection capacity
The present disclosure relates a network, a network element, a system, and a method providing an efficient allocation of protection capacity for network connections and / or services. These may be for services within a given Virtual Private Network (VPN) or Virtual Machine (VM) instance flow. Network ingress / egress ports are designed to be VM instance aware while transit ports may or may not be depending on network element capability or configuration. A centralized policy management and a distributed control plane are used to discover and allocate resources to and among the VPNs or VM instances. Algorithms for efficient allocation and release of protection capacity may be coordinated between the centralized policy management and the distributed control plane. Additional coupling of attributes such as latency may provide more sophisticated path selection algorithms including efficient sharing of protection capacity.
Owner:CIENA
Virtual private network having automatic reachability updating
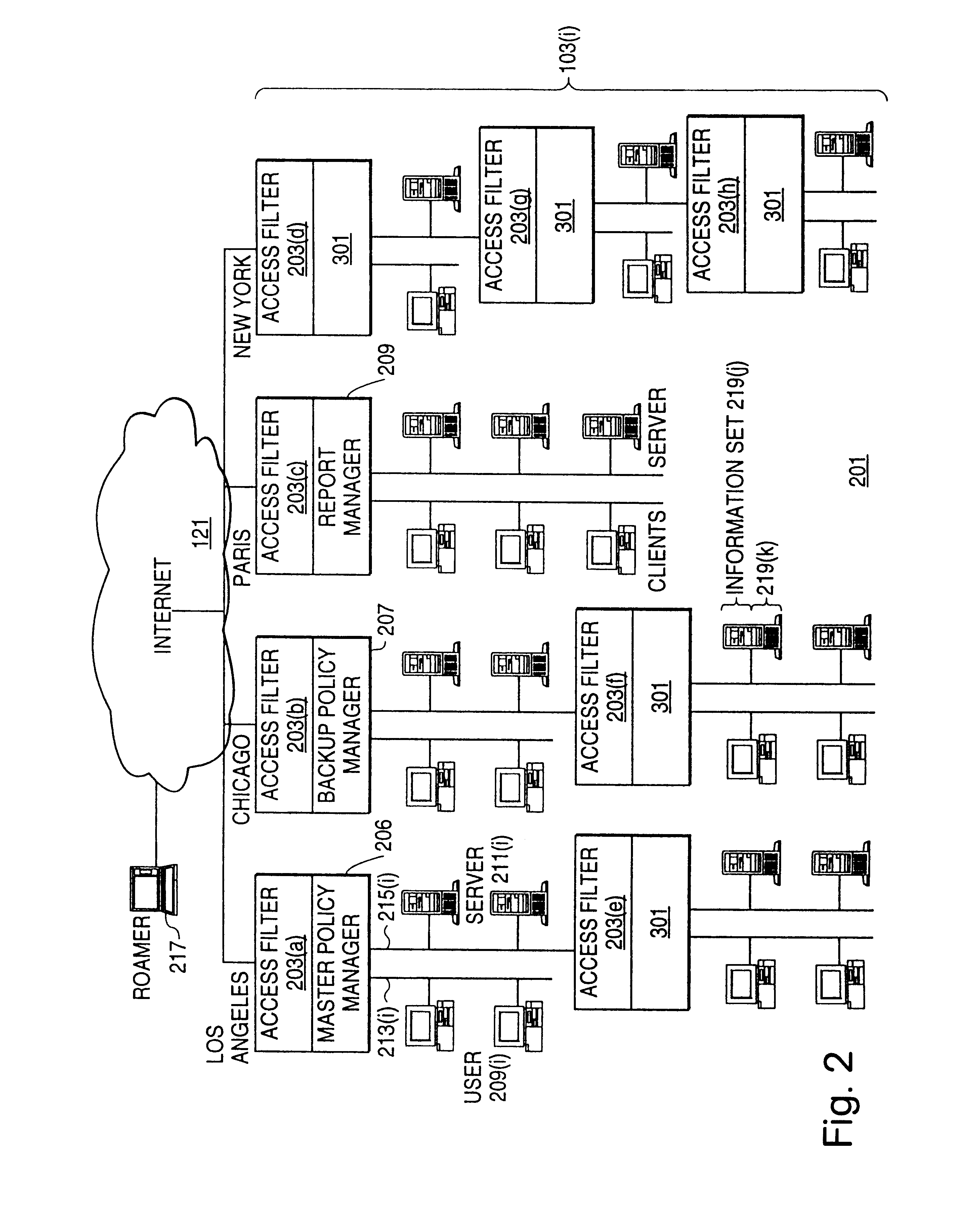
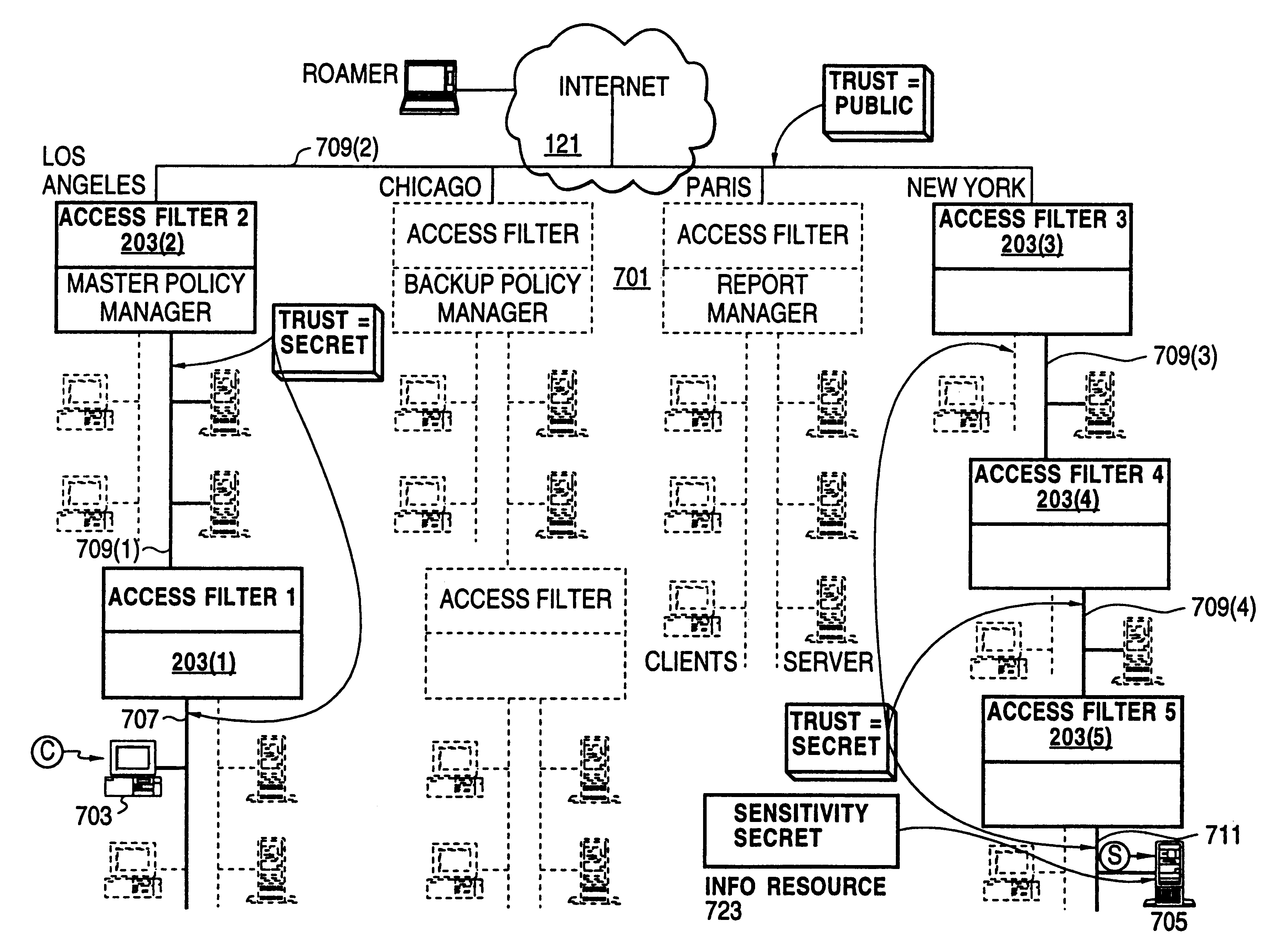
InactiveUS20050138204A1Easy to createCommunication securityEnergy efficient ICTDigital data protectionPrivate networkReachability
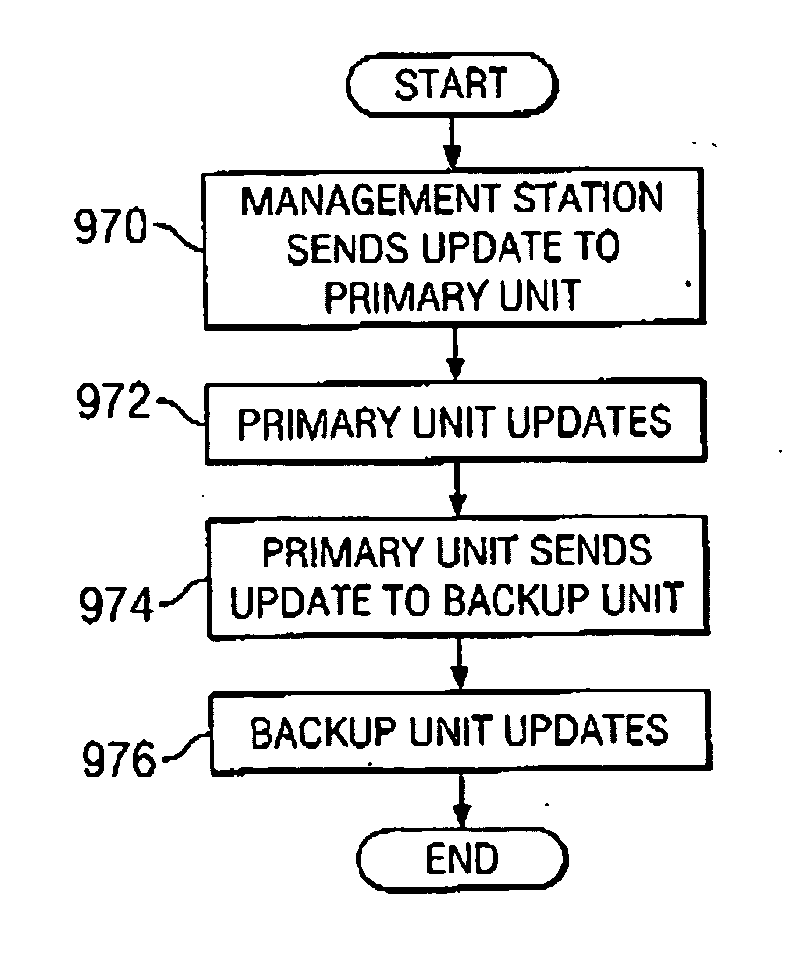
A unified policy management system for an organization including a central policy server and remotely situated policy enforcers. A central database and policy enforcer databases storing policy settings are configured as LDAP databases adhering to a hierarchical object oriented structure. Such structure allows the policy settings to be defined in an intuitive and extensible fashion. Changes in the policy settings made at the central policy server are automatically transferred to the policy enforcers for updating their respective databases. Each policy enforcer collects and transmits health and status information in a predefined log format and transmits it to the policy server for efficient monitoring by the policy server. For further efficiencies, the policy enforcement functionalities of the policy enforcers are effectively partitioned so as to be readily implemented in hardware. The system also provides for dynamically routed VPNs where VPN membership lists are automatically created and shared with the member policy enforcers. Updates to such membership lists are also automatically transferred to remote VPN clients. The system further provides for fine grain access control of the traffic in the VPN by allowing definition of firewall rules within the VPN. In addition, policy server and policy enforcers may be configured for high availability by maintaining a backup unit in addition to a primary unit. The backup unit become active upon failure of the primary unit.
Owner:IYER SHANKER V +3
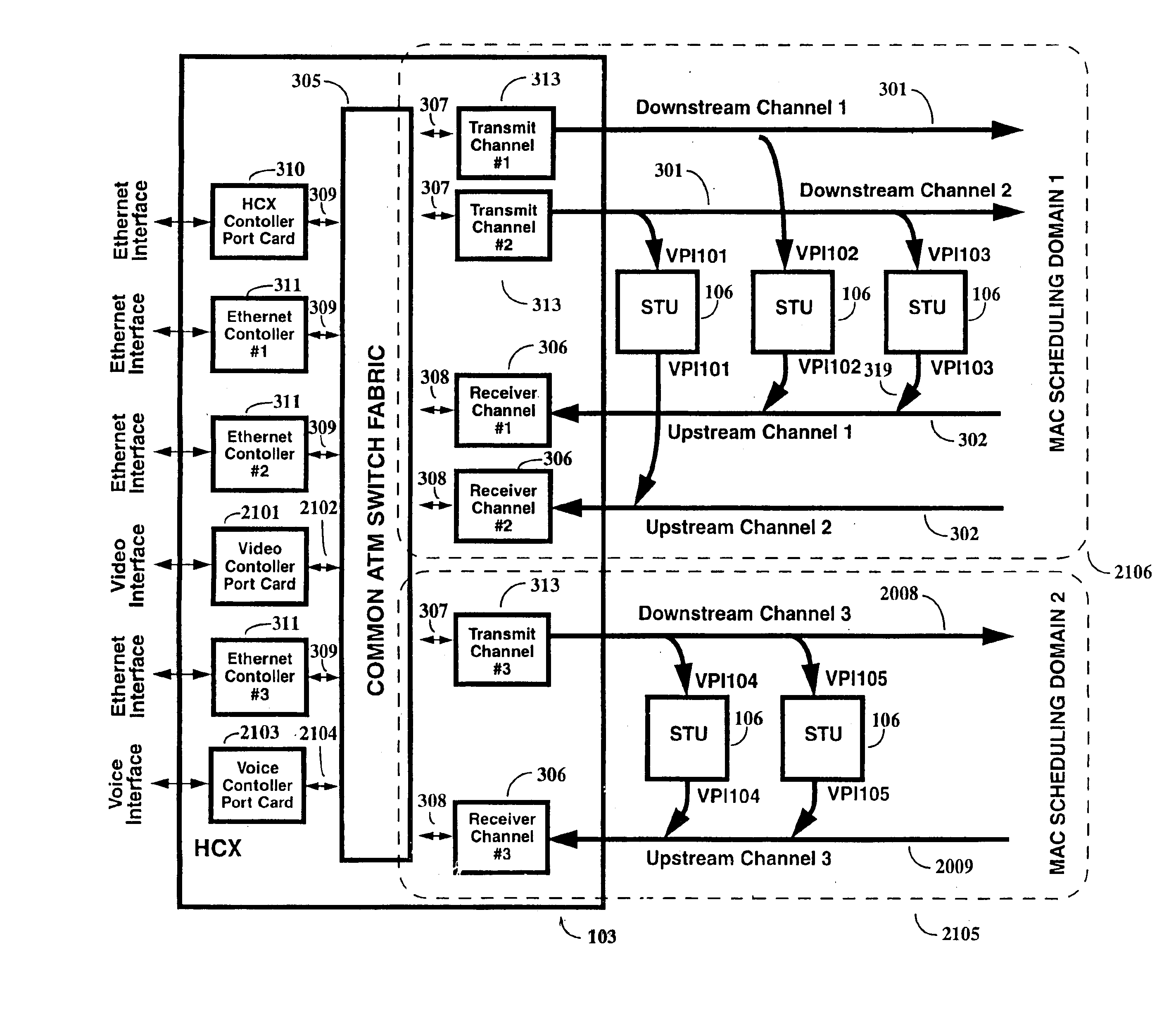
Multi-channel support for virtual private networks in a packet to ATM cell cable system
InactiveUS6917614B1Avoid compromiseExtension of timeBroadband local area networksFrequency-division multiplexQuality of serviceScheduling function
A two-way cable network offering high-speed broadband communications delivered via virtual private networks over a multi-channel shared media system. Bi-directional transmission of packet to ATM cell based communications is established between a head end communication controller and a number of subscriber terminal units, whereby individual cells are prioritized and routed according to a virtual connection. Virtual connections are organized to support multiple virtual private networks in a shared media CATV system. The virtual private network to which a particular STU belongs is user selectable and has the flexibility of handling multi up / downstream channels with different MAC domains. The present invention can also handle non-ATM MAC domains via the same common ATM switch. To overcome the limited number of addresses inherent to common ATM switches, a mapping / remapping function is implemented in the port cards. Furthermore, downstream as well as upstream traffic are filtered at each STU. In one embodiment, information pertaining to downstream traffic is used to implement predictive scheduling in order to improve the timing associated with the request / grant cycle. In another embodiment, a user has the ability to select a quality of service that best suits the needs of the current application. In a further embodiment, the scheduling function is associated with each of the receivers in order to provide improved scalability.
Owner:ARRIS ENTERPRISES LLC
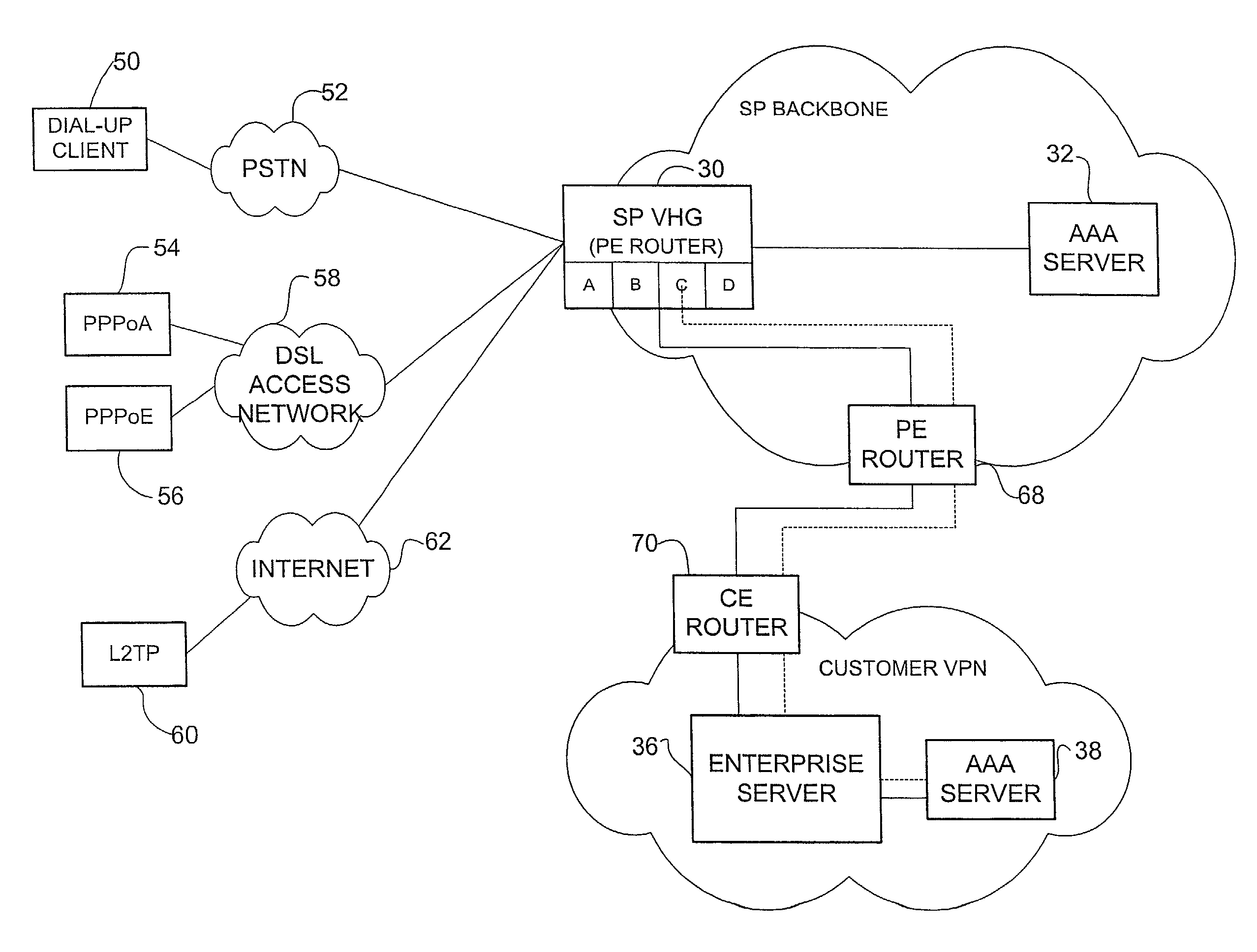
Method and system for providing authorization, authentication, and accounting for a virtual private network
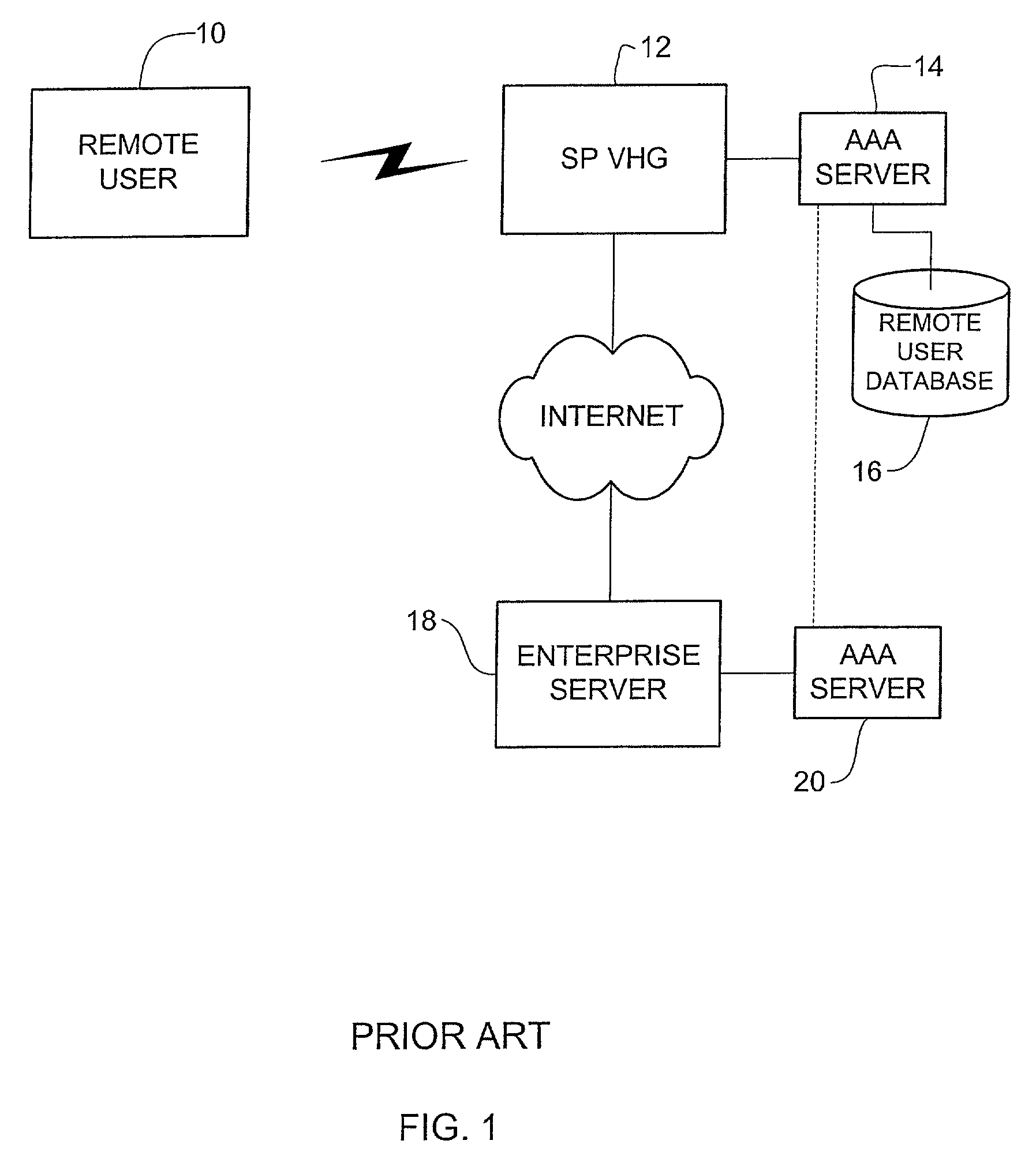
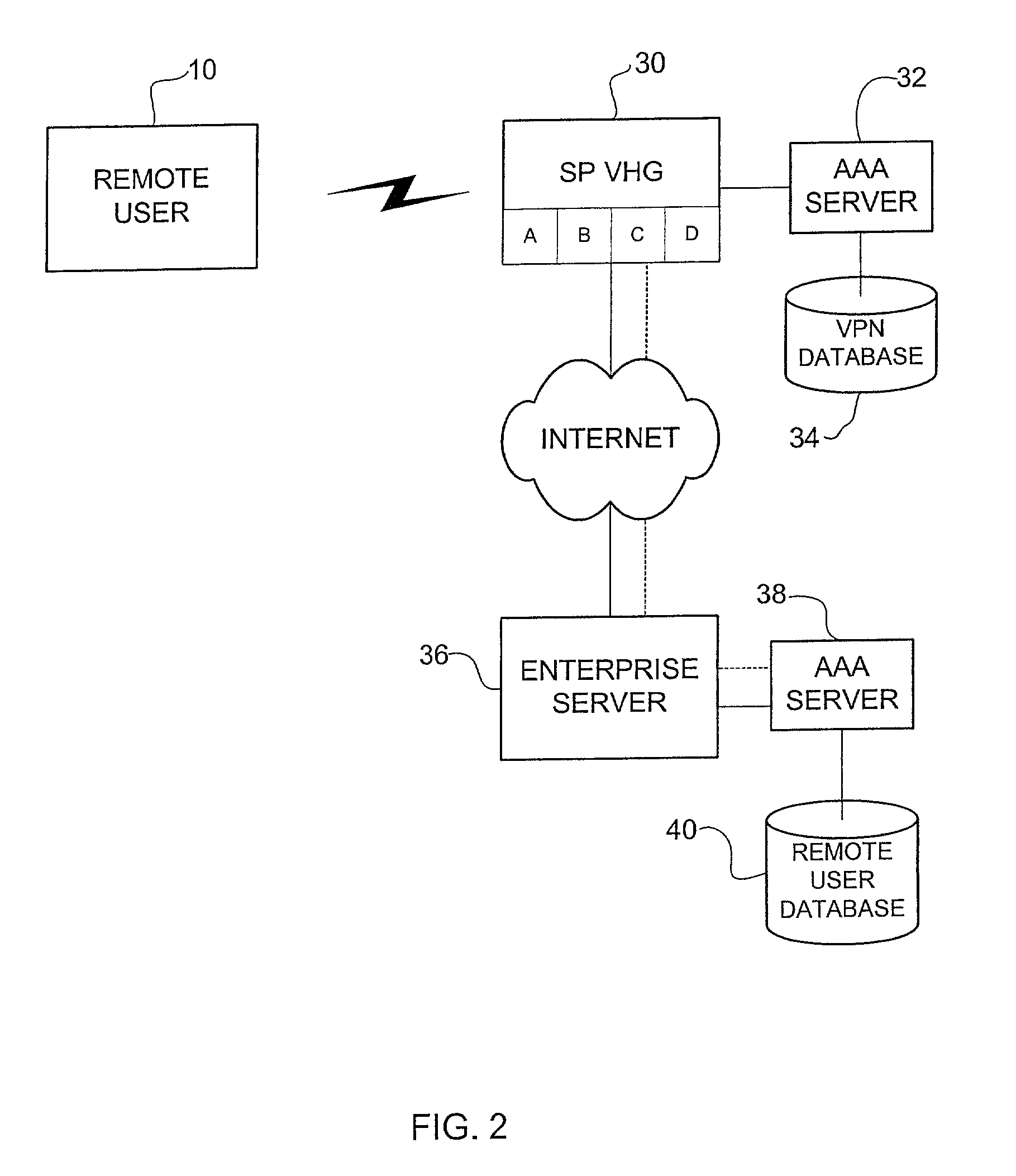
InactiveUS7469294B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivate networkAuthorization
A method and system for providing authentication in a virtual private network having a private AAA server is disclosed. The method generally includes receiving a request from a remote user for connection with a virtual private network at a virtual home gateway and associating the remote user with the virtual private network The virtual home gateway sends a request to authenticate the remote user to the AAA server. The remote user is then connected to the virtual private network if the AAA server authenticates the user.
Owner:CISCO TECH INC
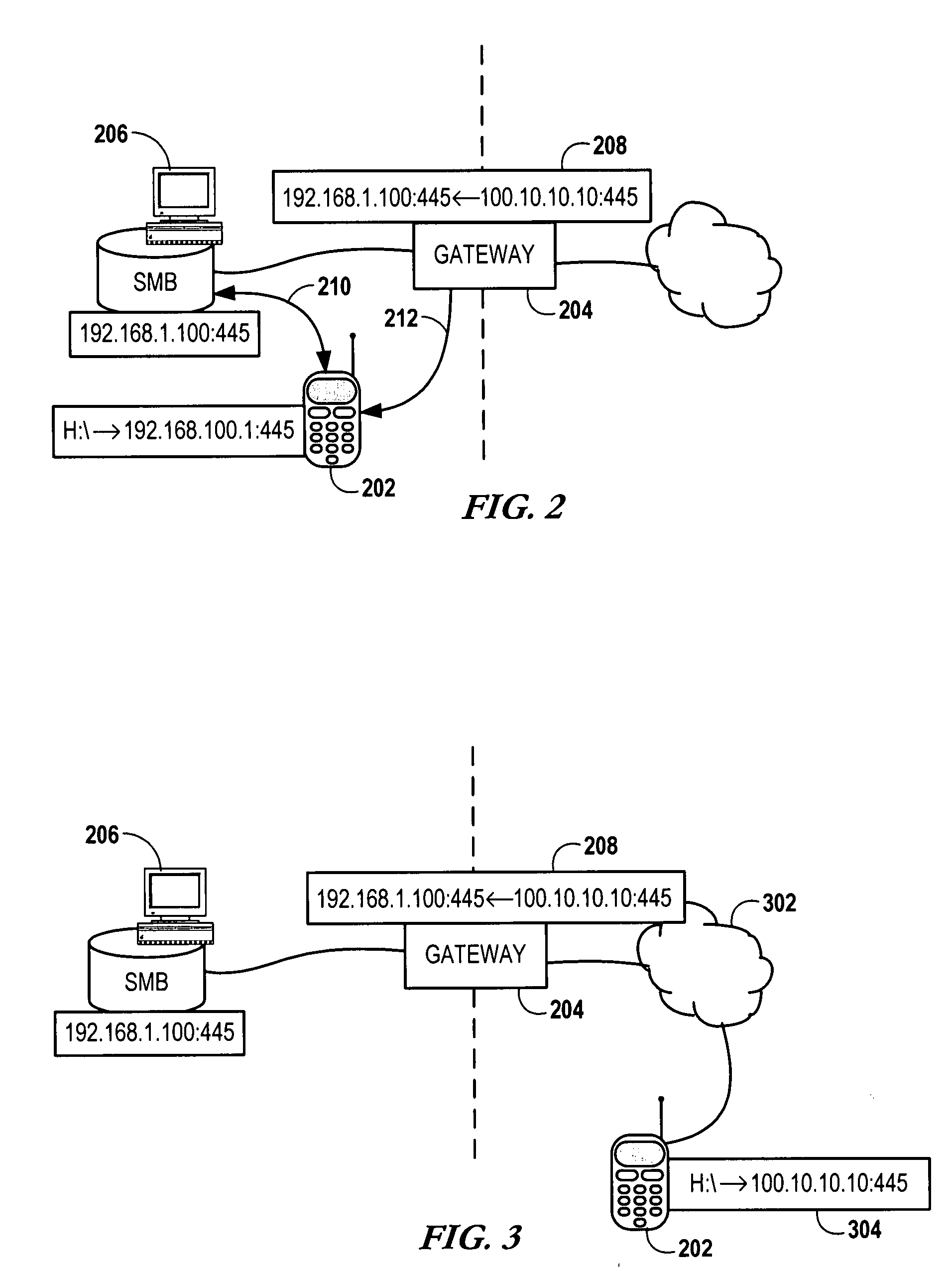
Methods and systems for securing access to private networks using encryption and authentication technology built in to peripheral devices
A method for routing packets from a peripheral device to a Virtual Private Network (VPN) gateway includes the step of implementing, by a peripheral device, a change to a routing table. The peripheral device receives an outbound packet. The peripheral device transmits information about the outbound packet to a VPN client application. The peripheral device modifies address information on the outbound packet with address information associated with the VPN client application. The peripheral device transmits the modified outbound packet to the VPN client application.
Owner:CITRIX SYST INC
Extending an internet content delivery network into an enterprise
InactiveUS20060282522A1Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsElectric digital data processingInternet contentPrivate network
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
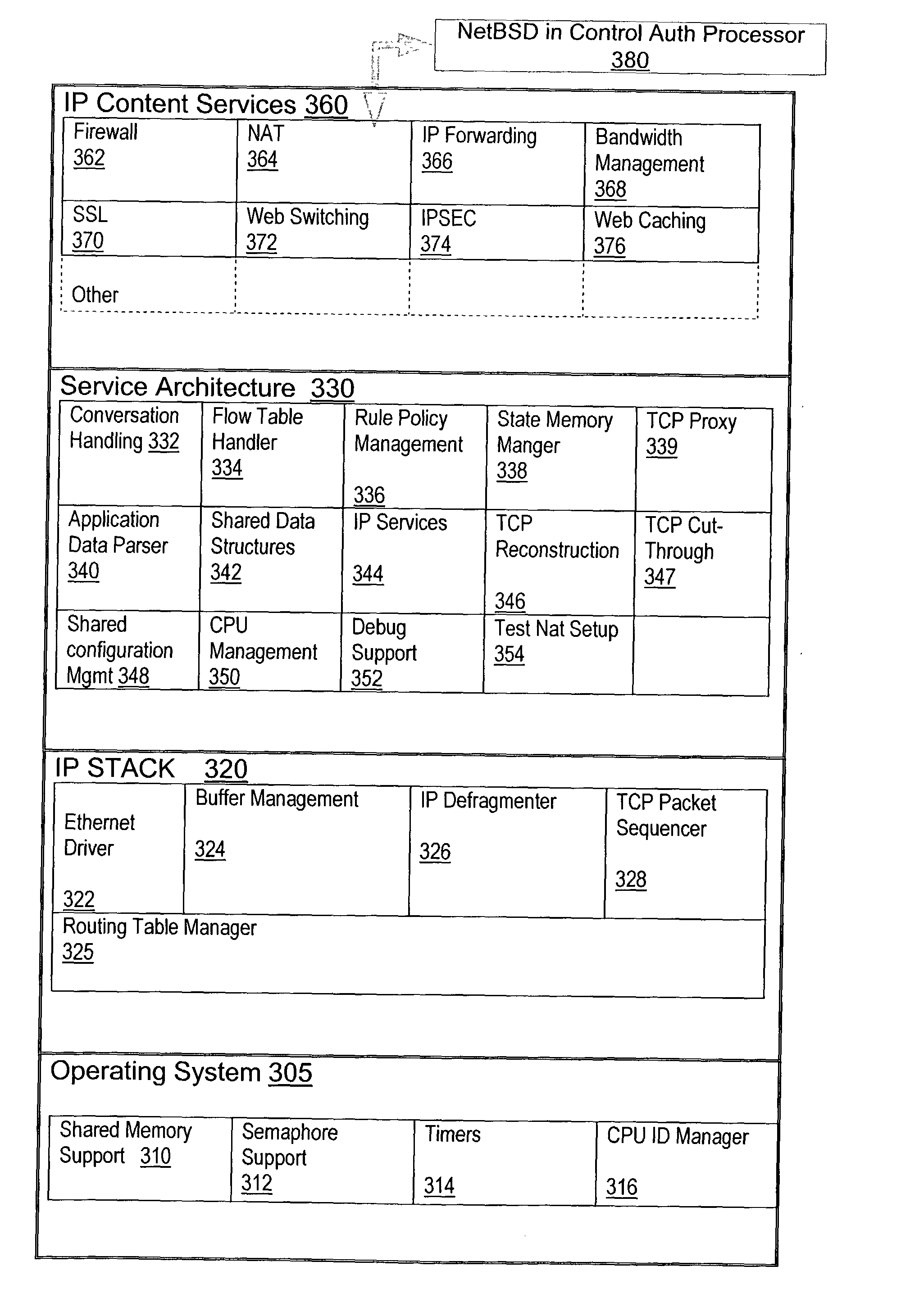
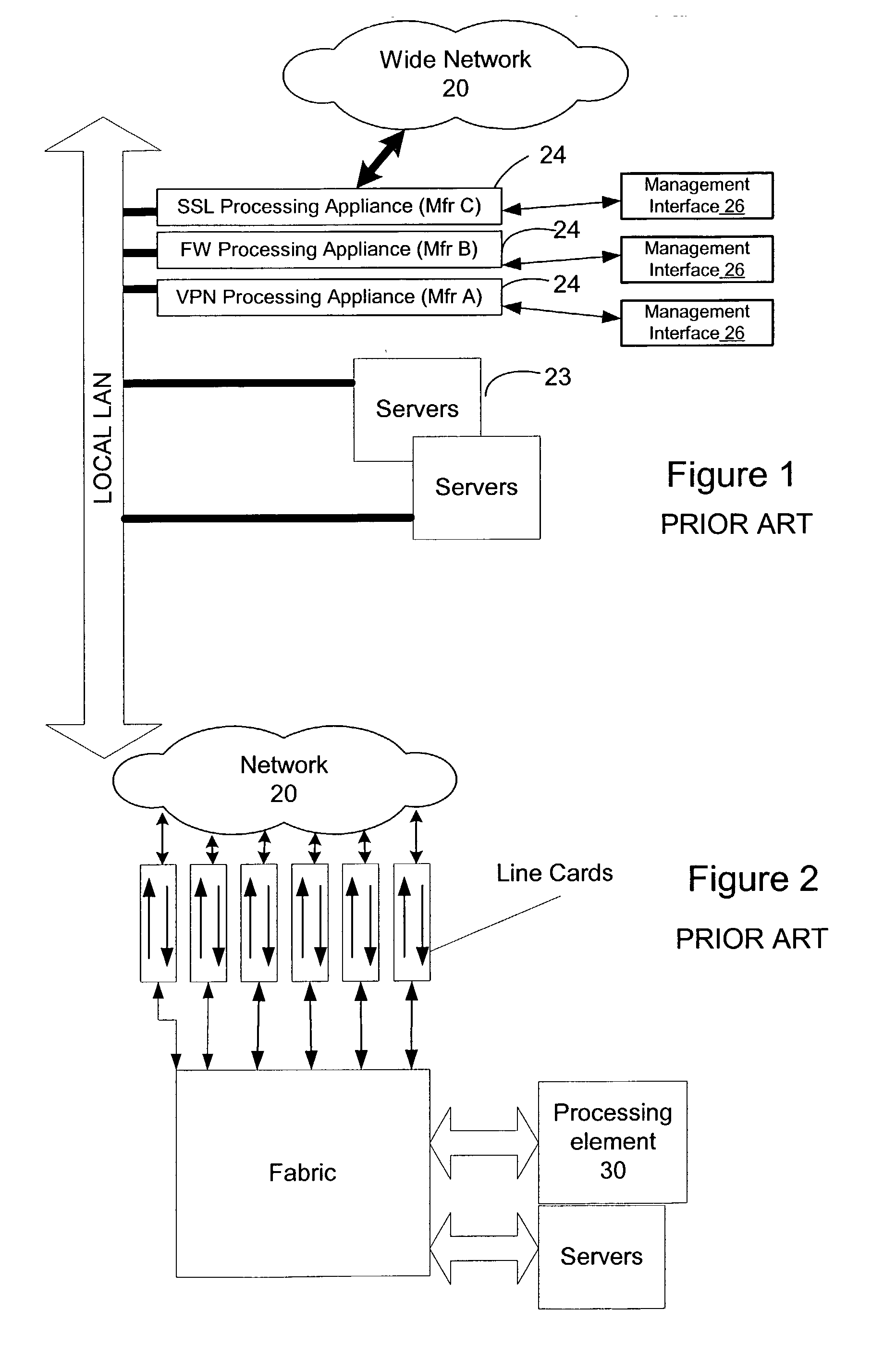
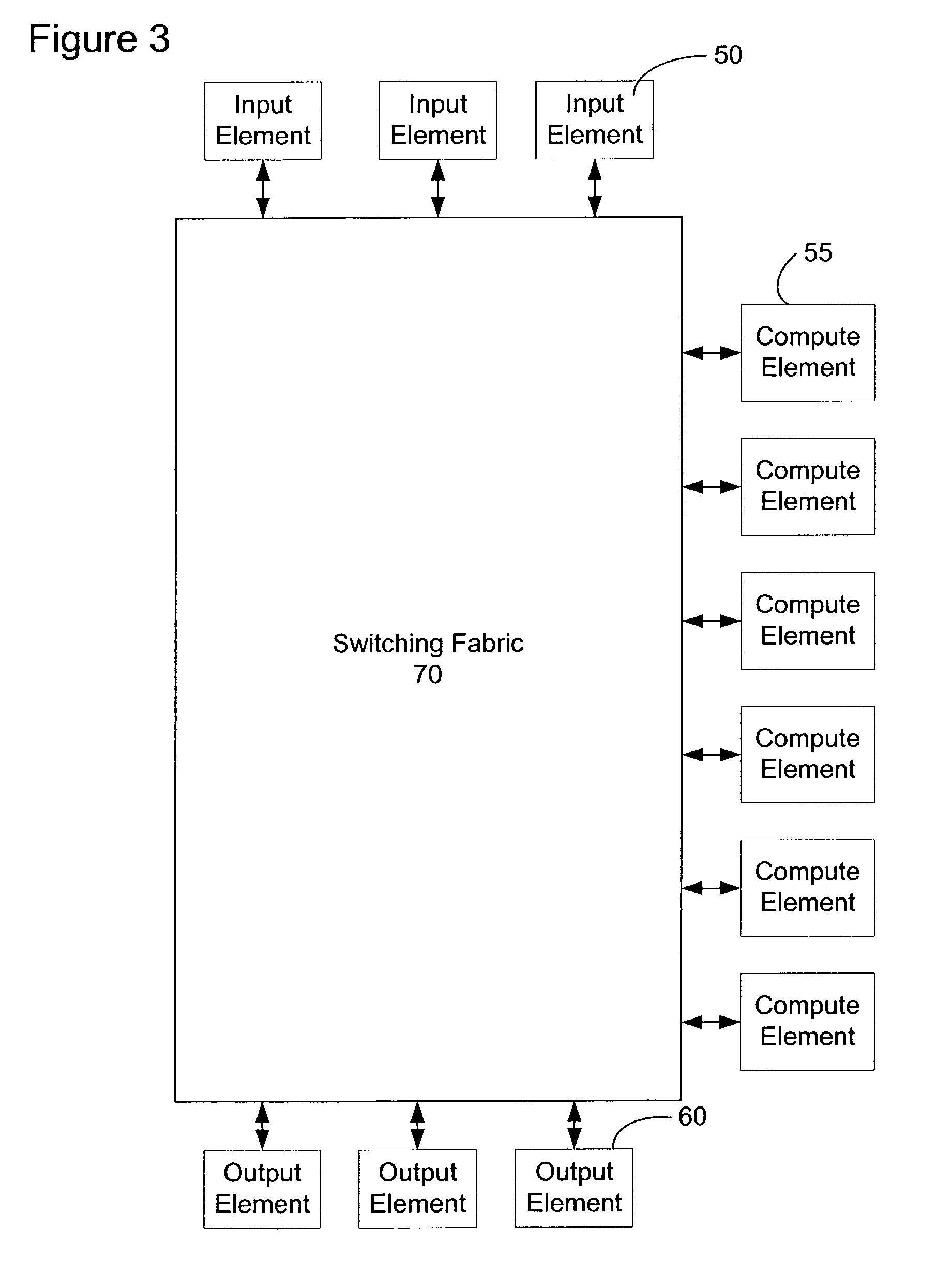
Content service aggregation system
ActiveUS20030126233A1Easy to processMultiple digital computer combinationsElectric digital data processingPrivate networkStructure of Management Information
A network content service apparatus includes a set of compute elements adapted to perform a set of network services; and a switching fabric coupling compute elements in said set of compute elements. The set of network services includes firewall protection, Network Address Translation, Internet Protocol forwarding, bandwidth management, Secure Sockets Layer operations, Web caching, Web switching, and virtual private networking. Code operable on the compute elements enables the network services, and the compute elements are provided on blades which further include at least one input / output port.
Owner:NEXSI SYST +1
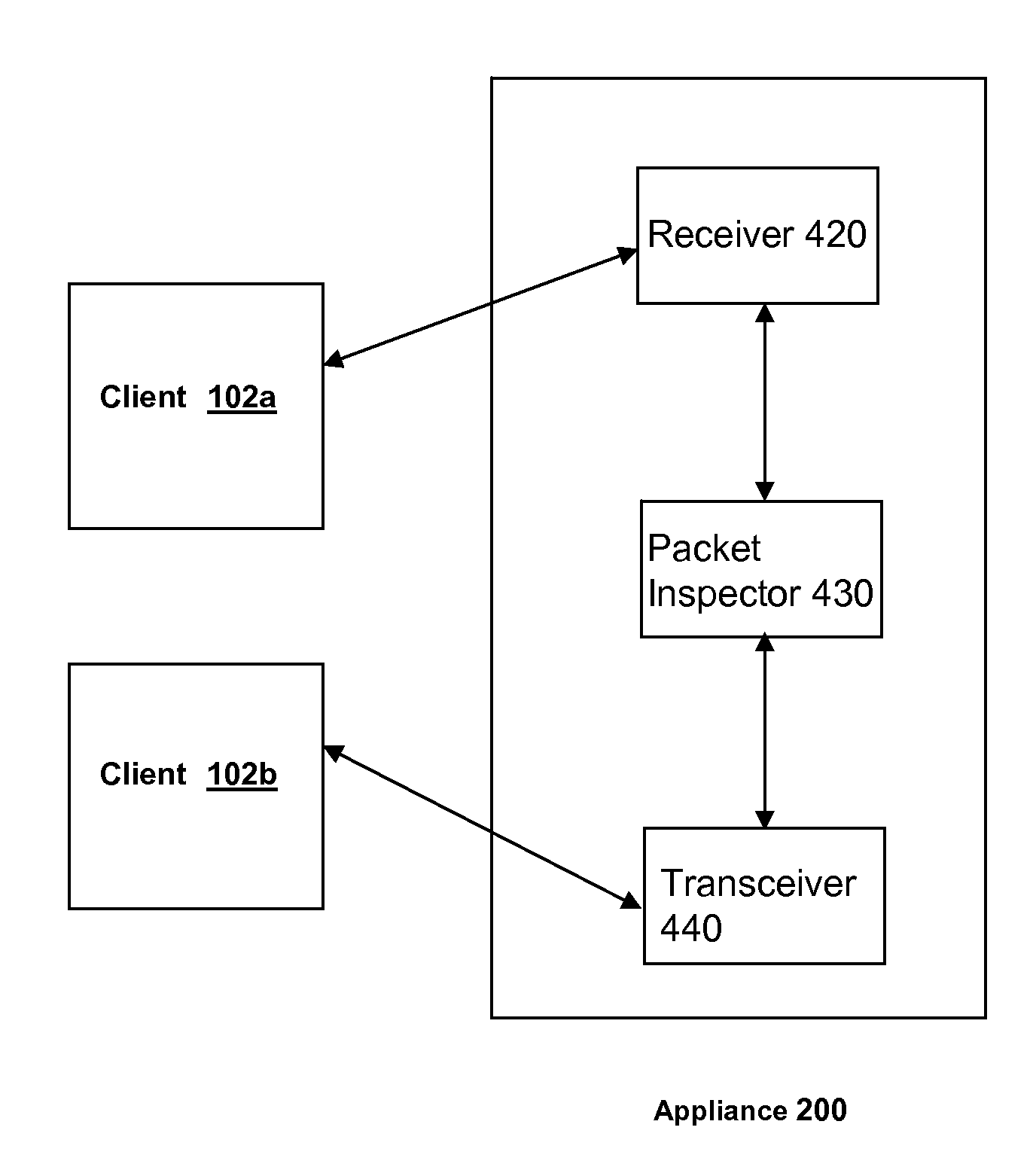
Methods and systems for routing packets in a vpn-client-to-vpn-client connection via an ssl/vpn network appliance
ActiveUS20080034416A1Digital data processing detailsMultiple digital computer combinationsConnection typePrivate network
In a method and system for routing packets between clients, a packet is received from a first client connected to a secure sockets layer virtual private network (an SSL / VPN) network appliance. An identification is made, responsive to an inspection of the received packet, of i) a type of connection required for transmission of the received packet to a destination address identified by the received packet and ii) a second client connected via an SSL / VPN connection to the SSL / VPN network appliance and associated with the identified destination address. A request is made for establishment by the second client of a connection of the identified type within the SSL / VPN connection. The received packet is transmitted to the second client via the established connection of the identified type.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com