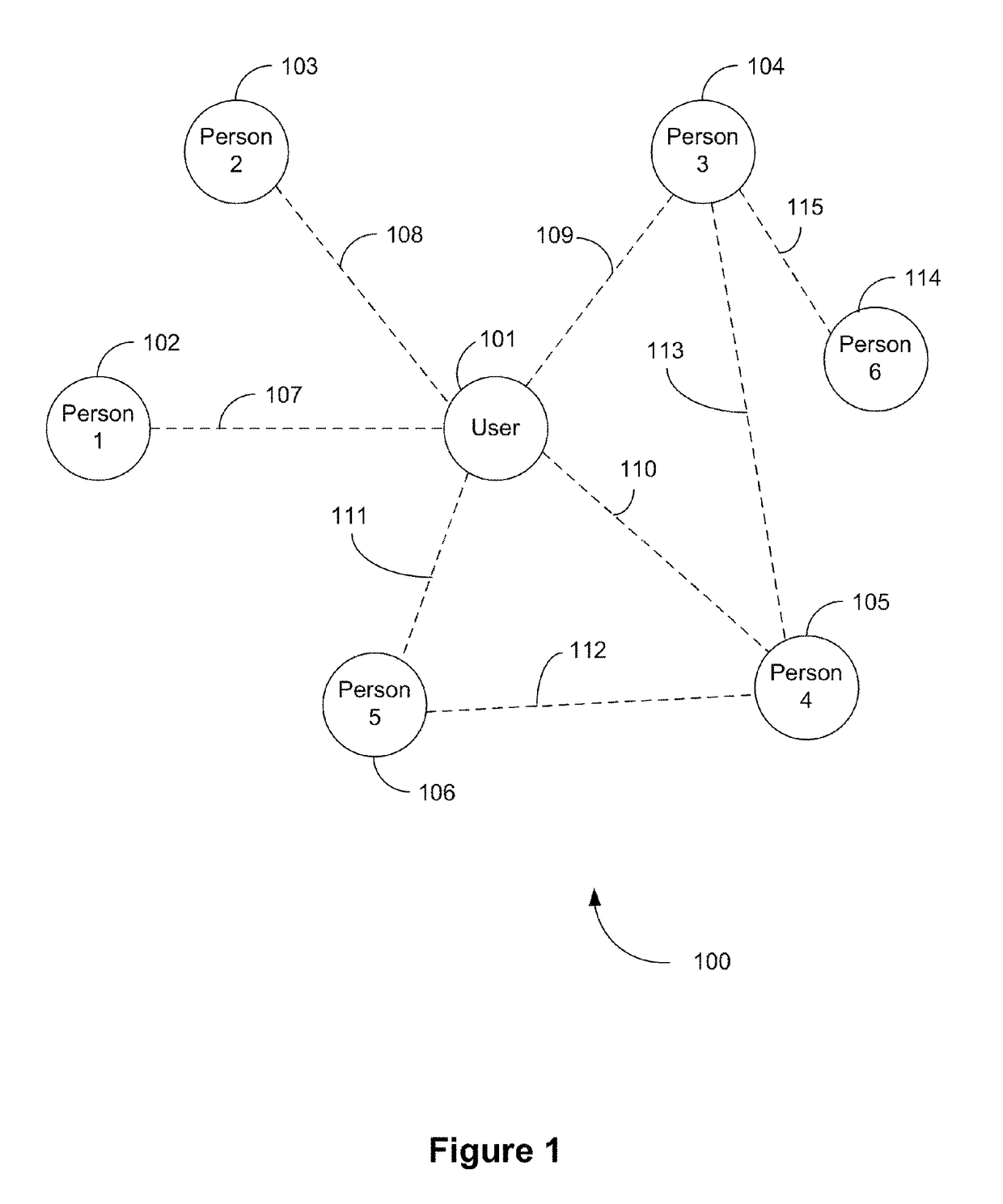
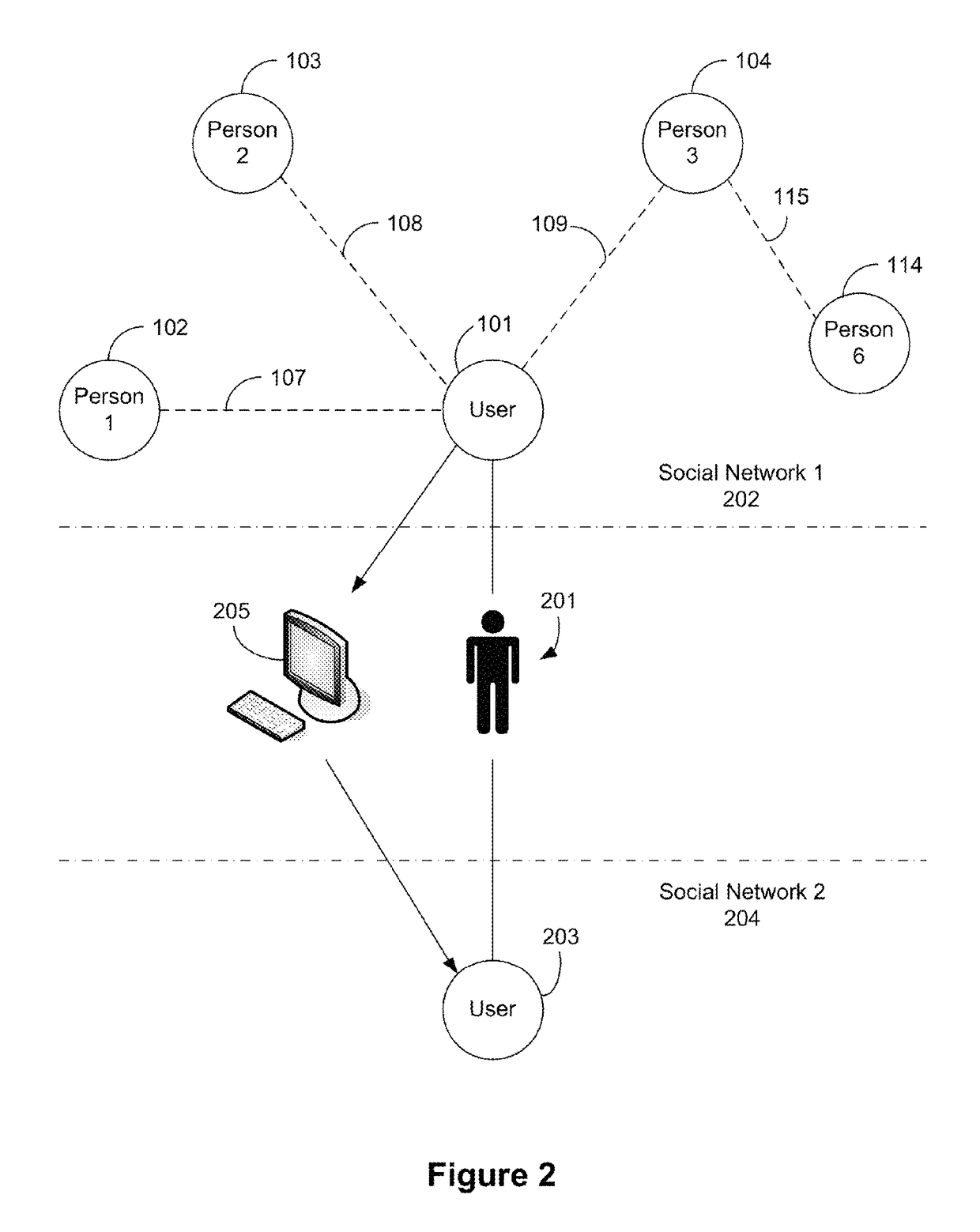
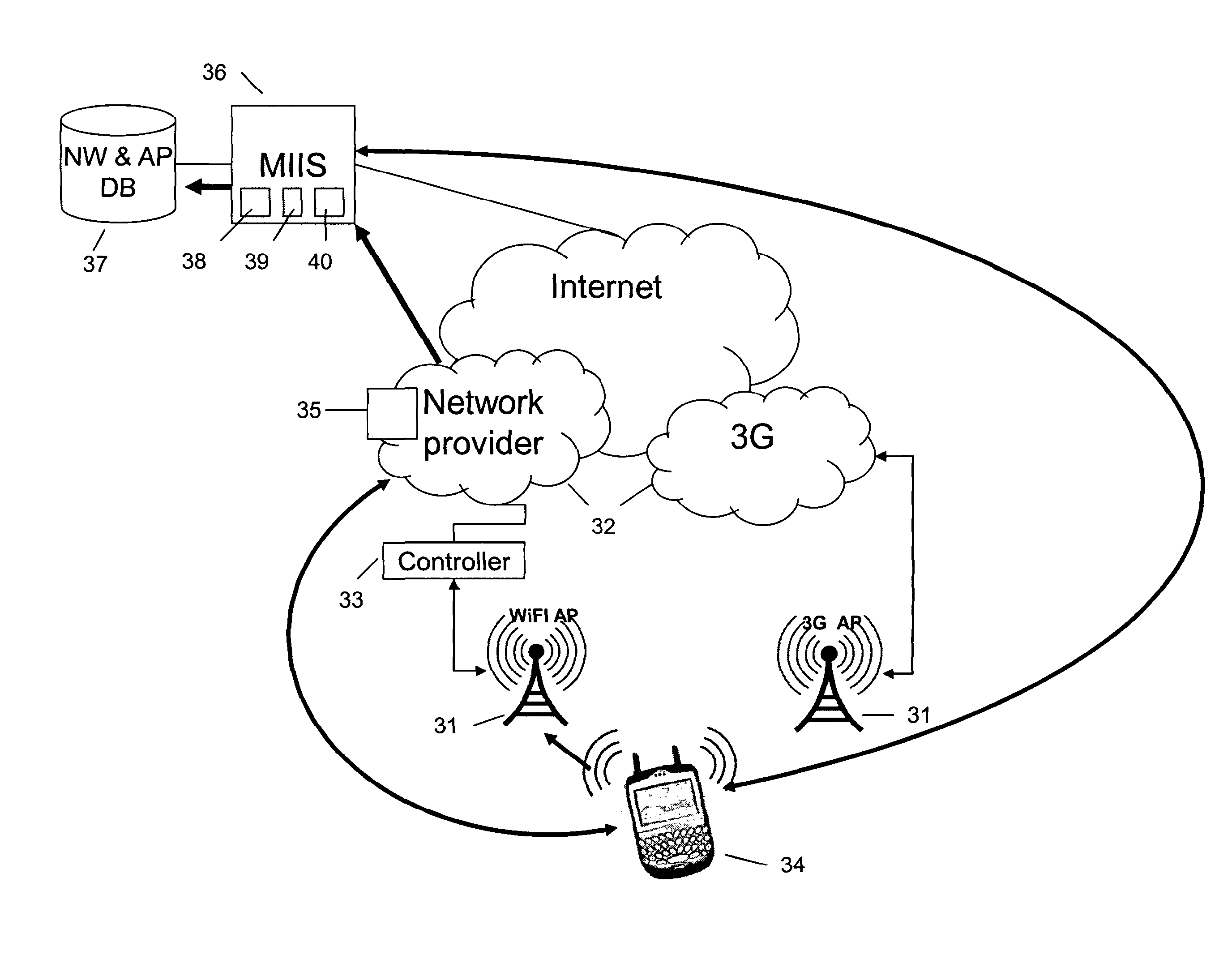
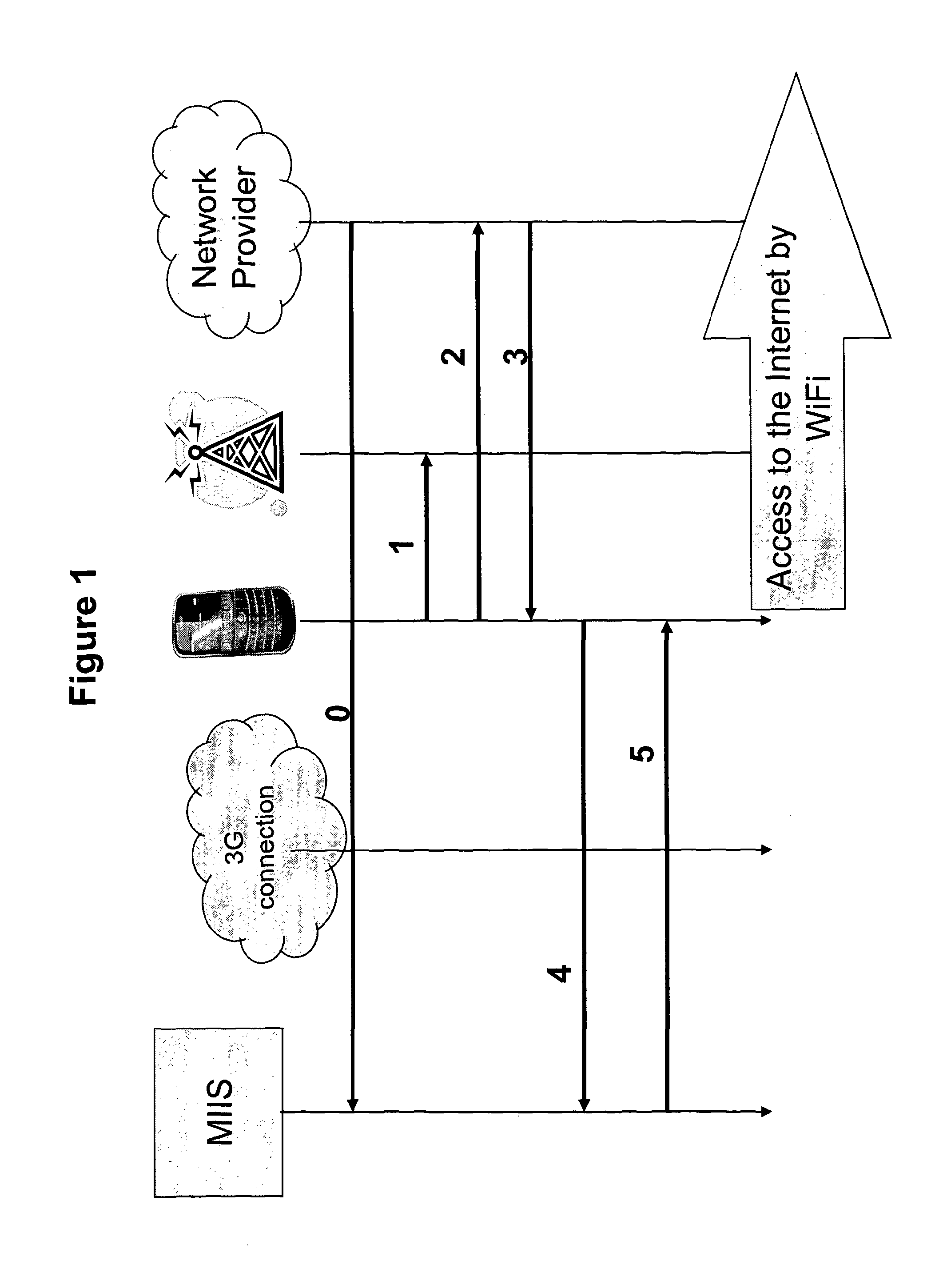
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1832 results about "Cable network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Broadly speaking, a network cable is a type of cable wiring used in telecommunications that relays data from individual computers to a larger network mainframe. Sometimes these cables are external, and can be used to do things like plug computers into Internet modems or grounded ports.
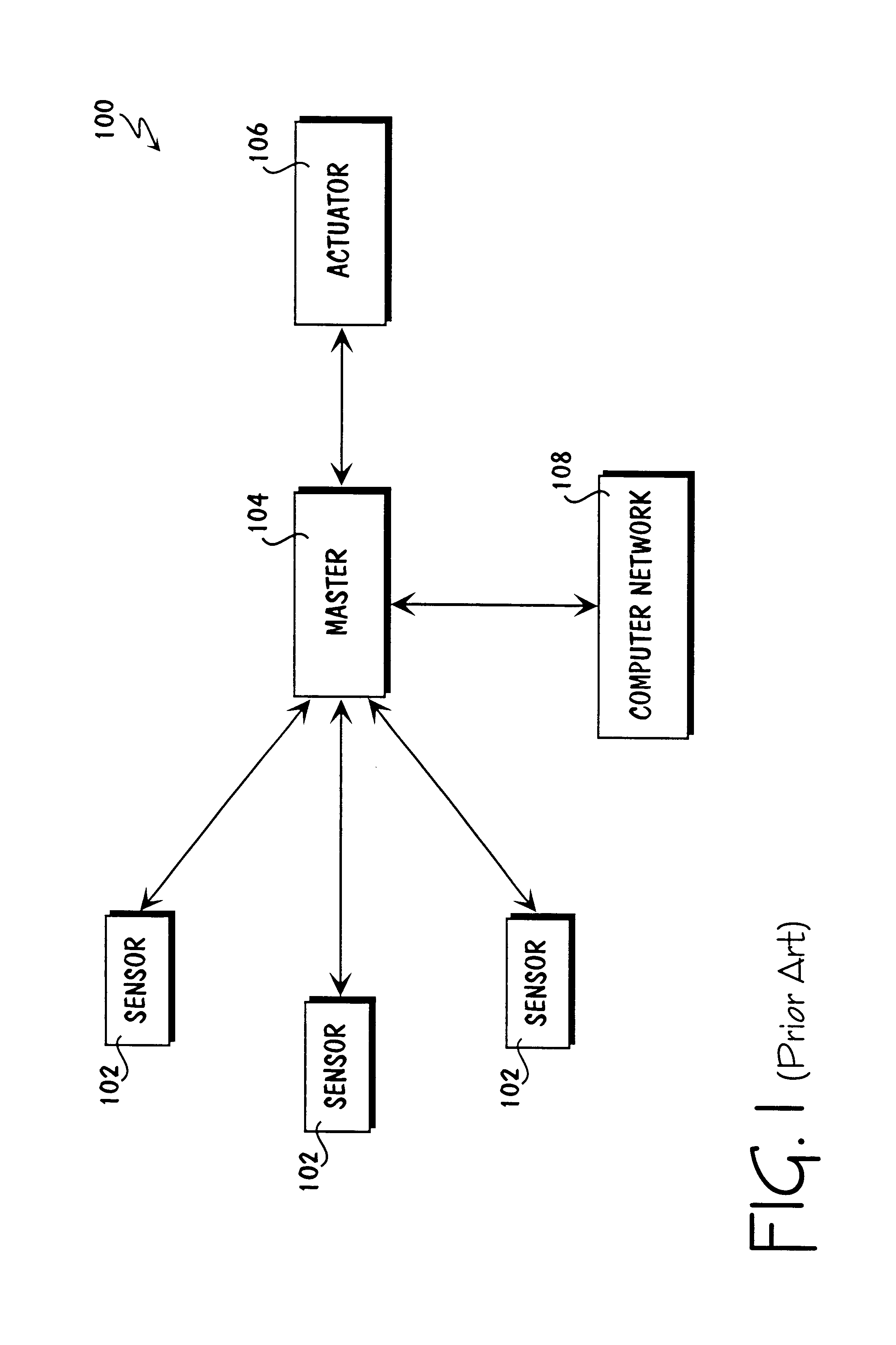
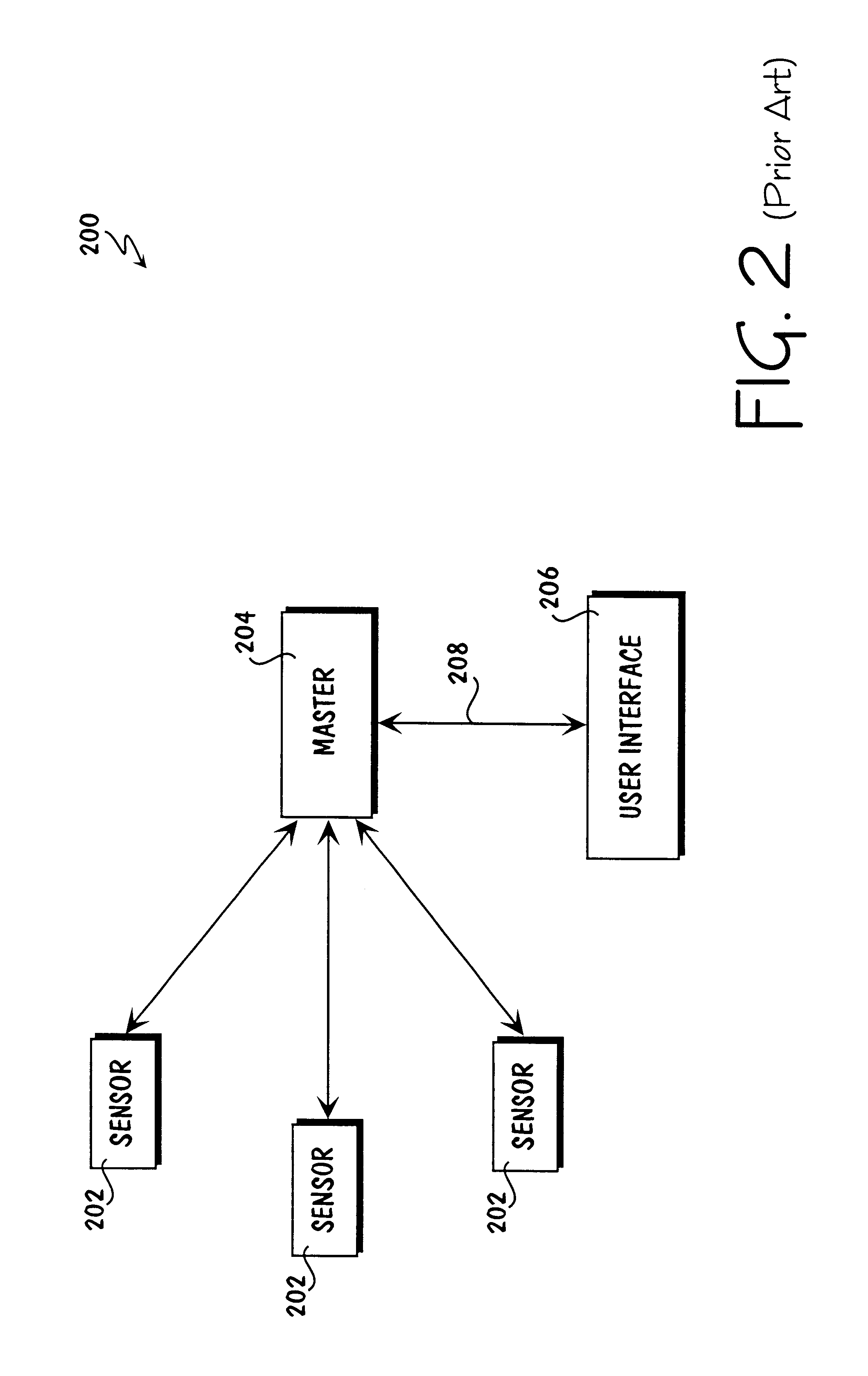
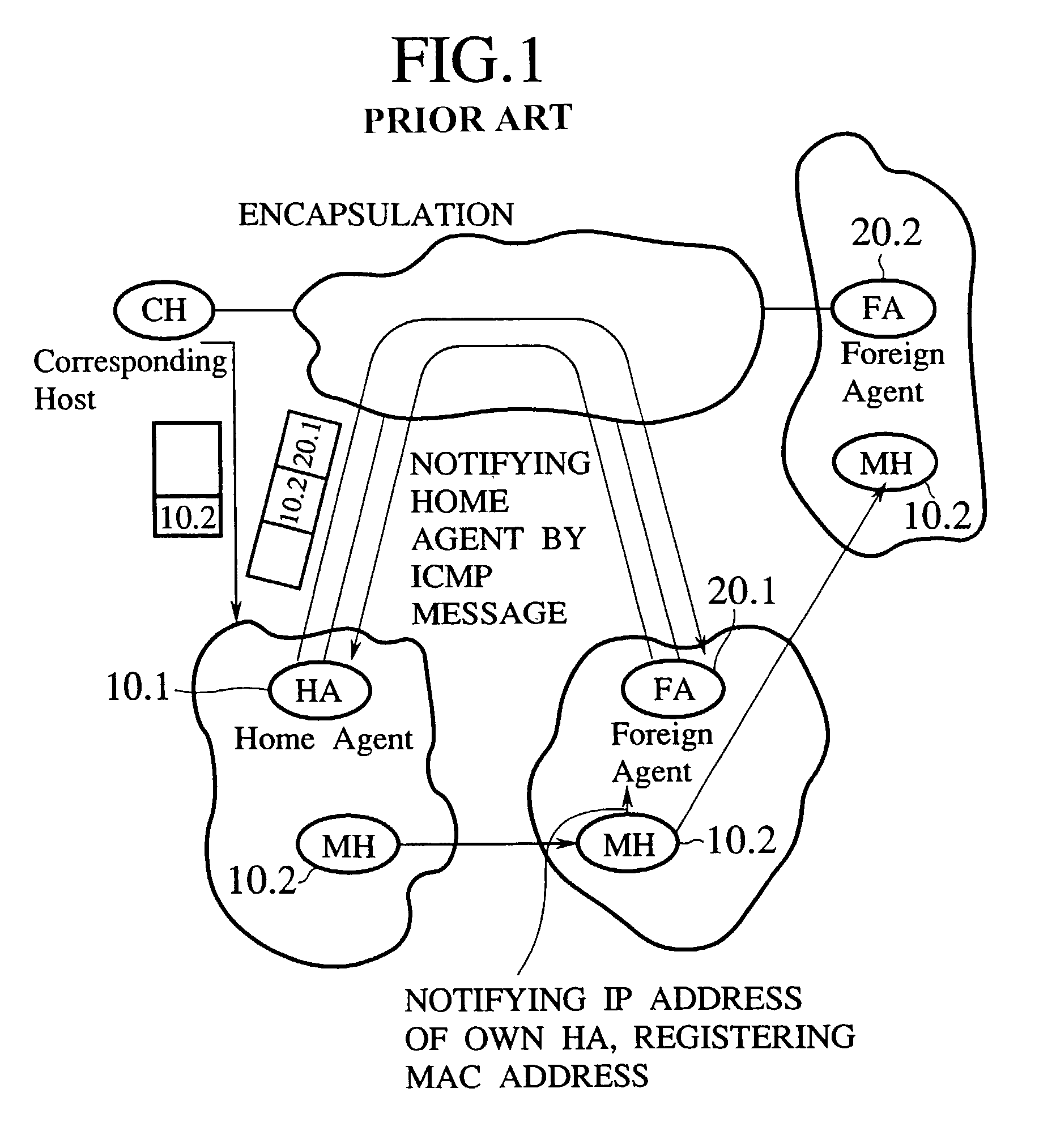
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
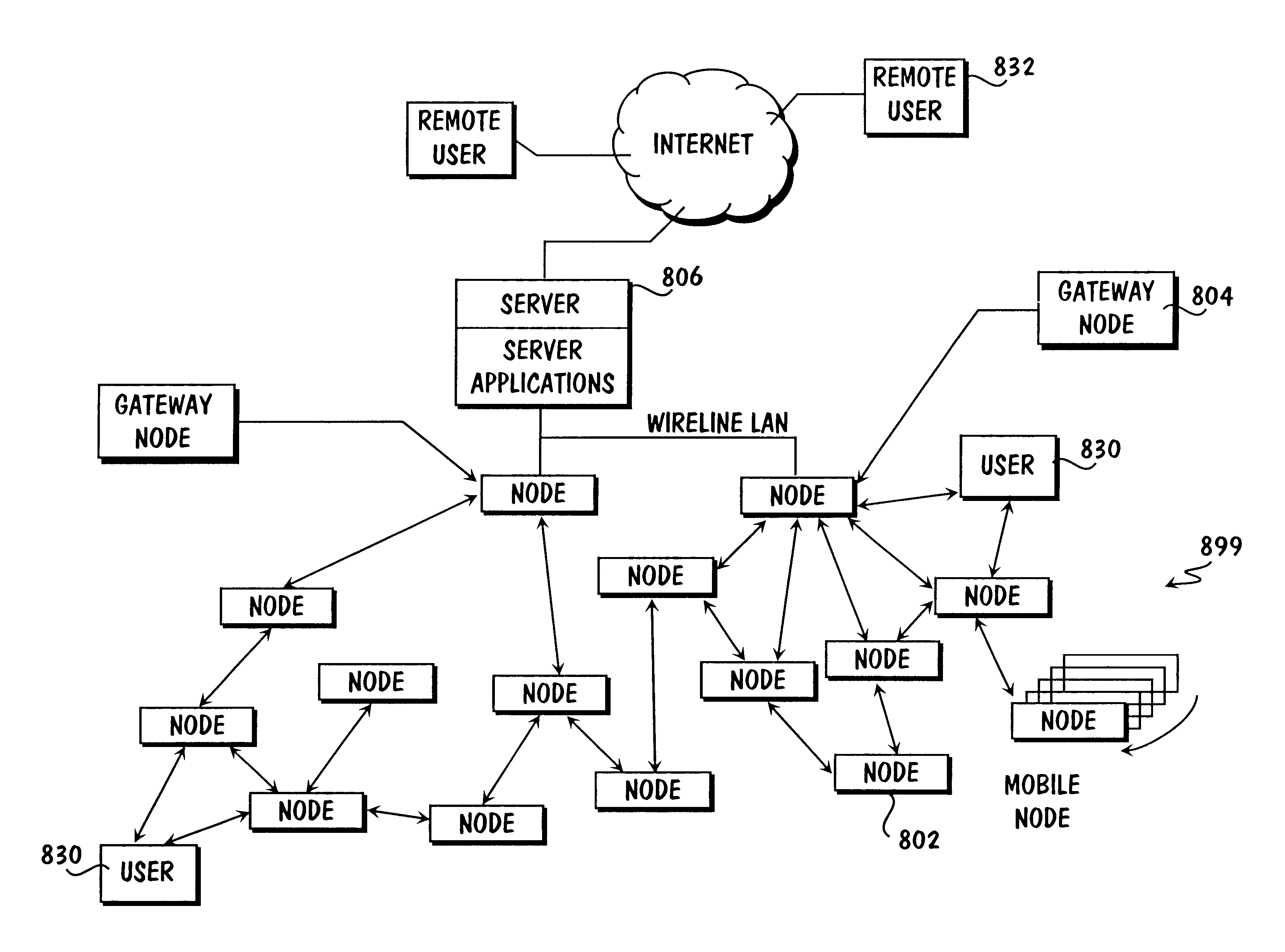
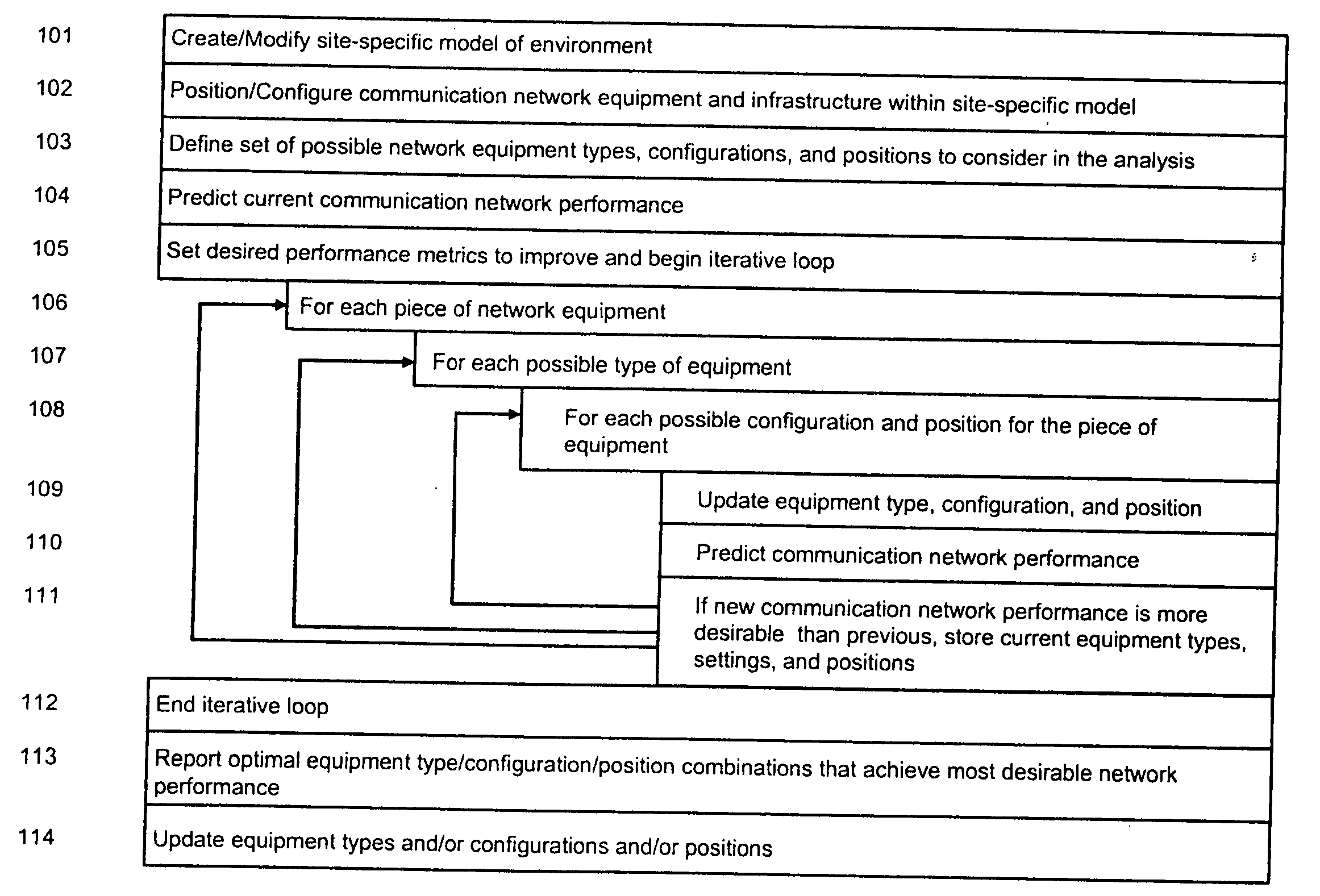
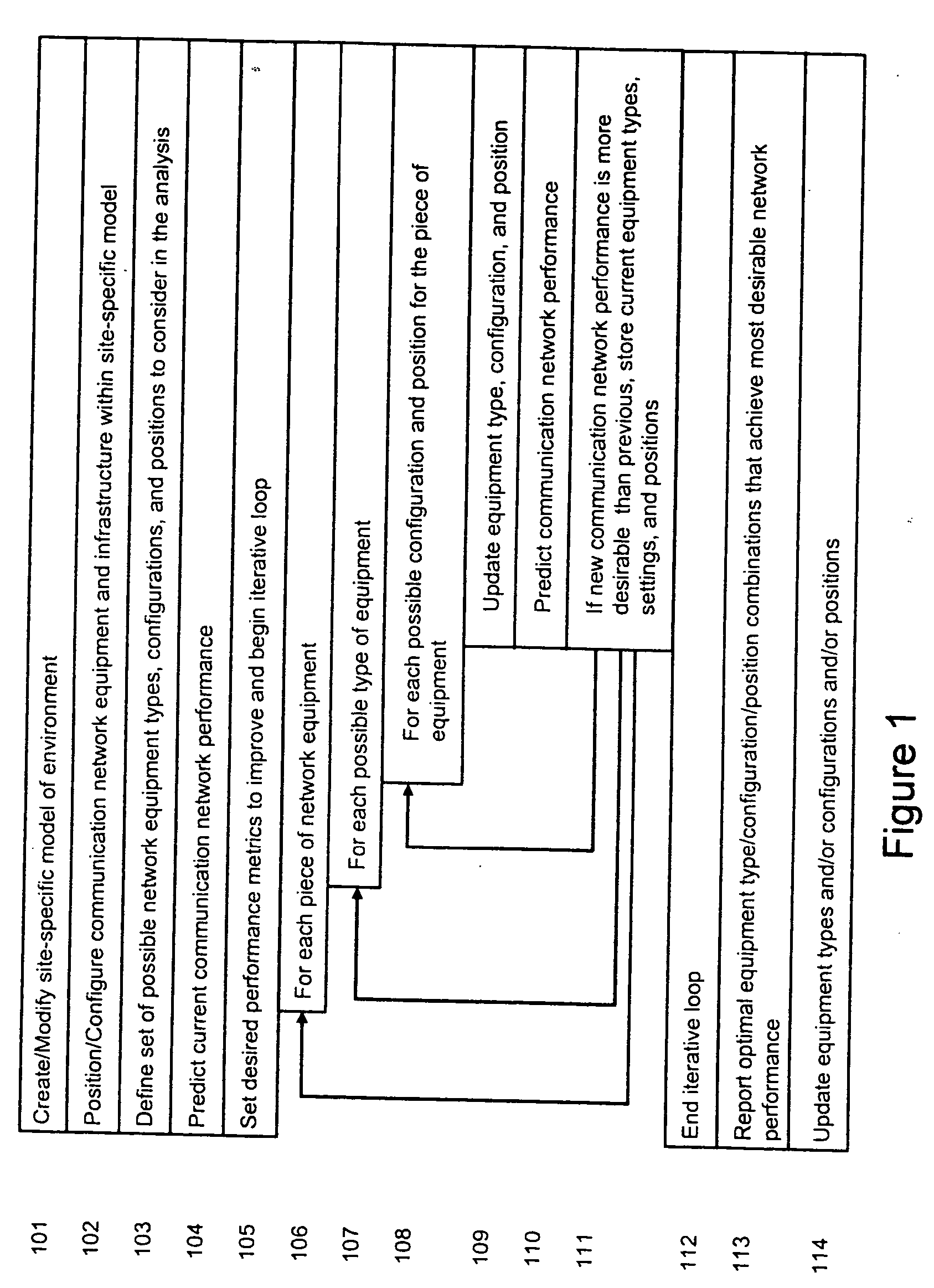
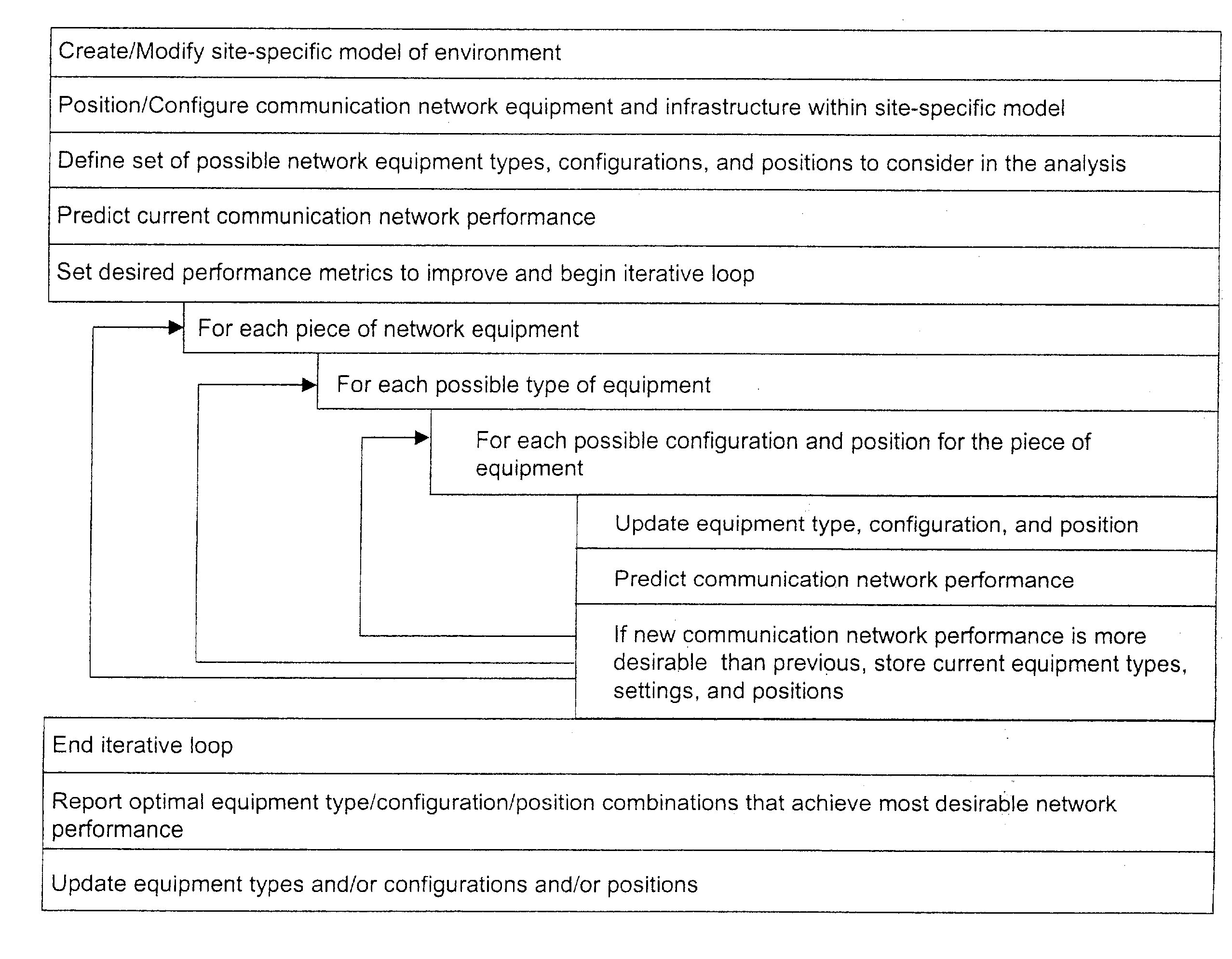
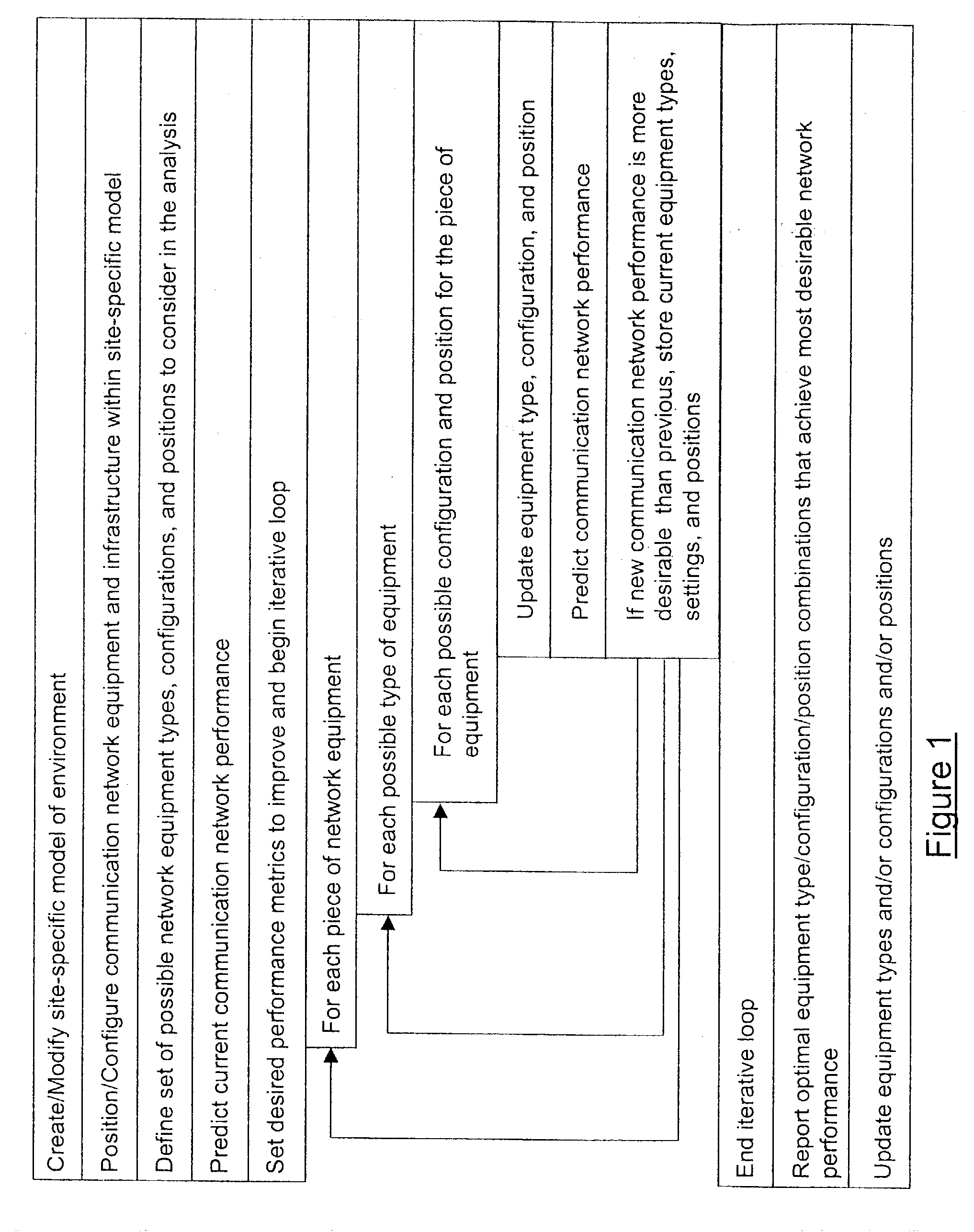
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
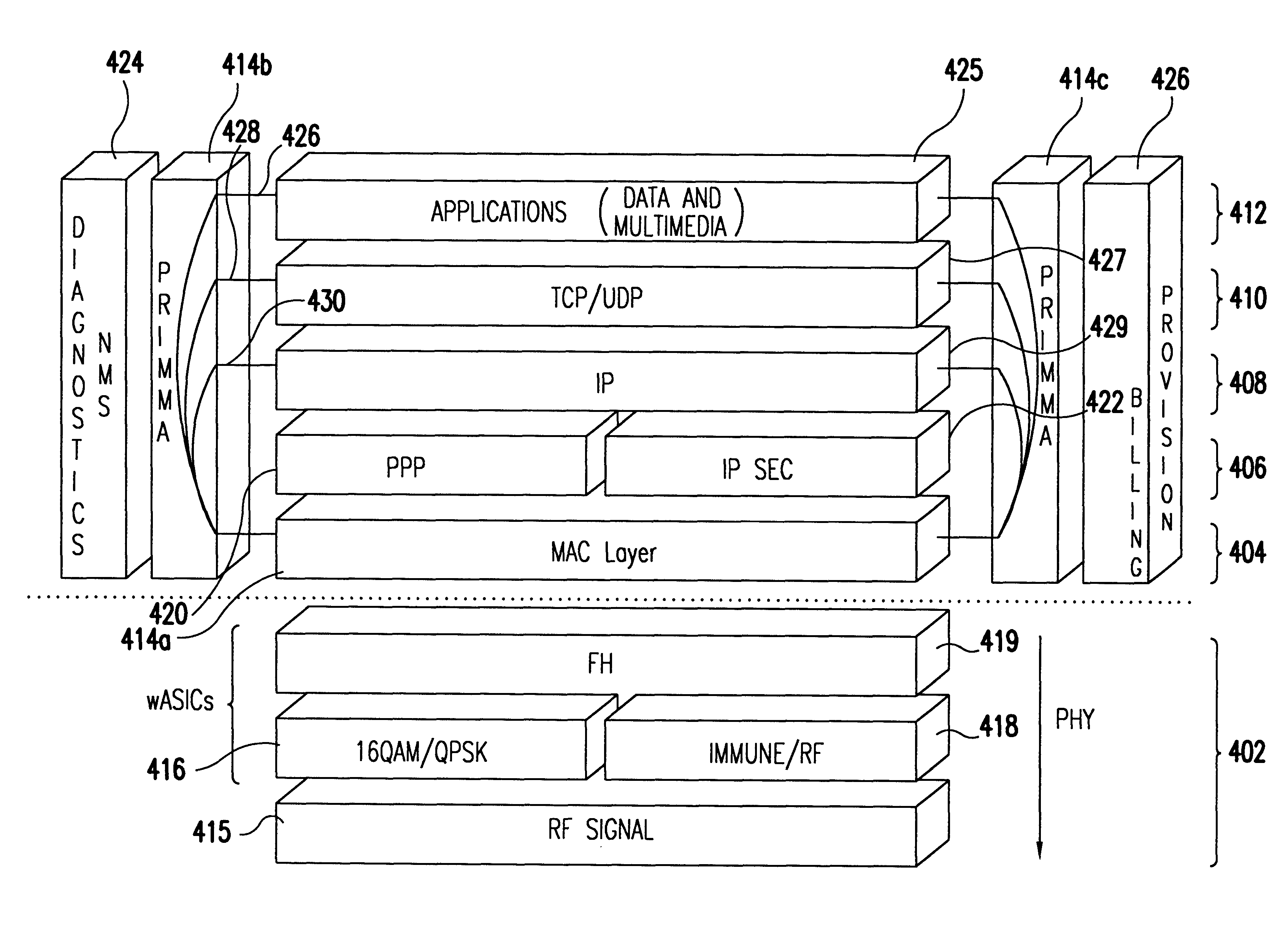
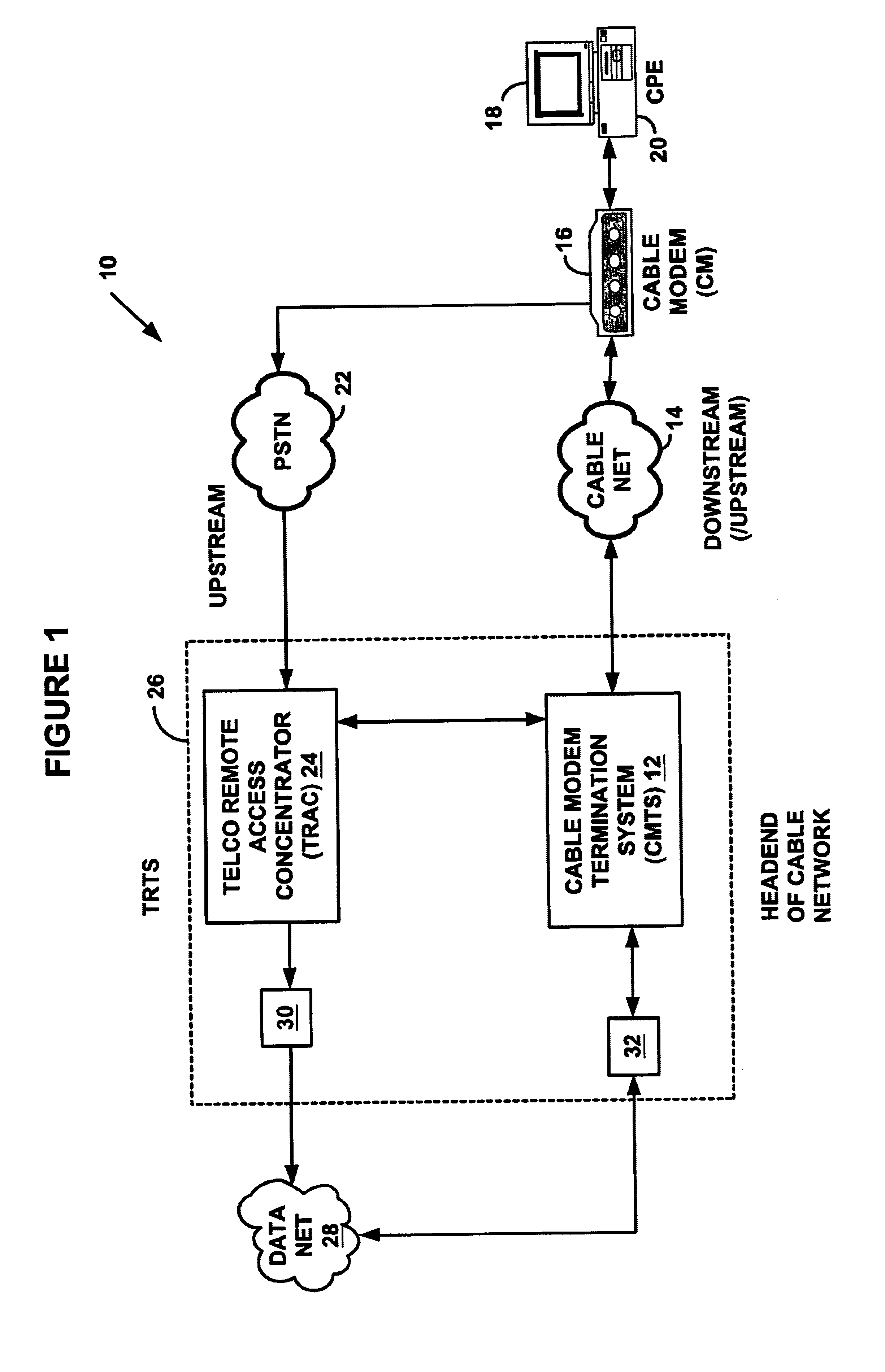
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
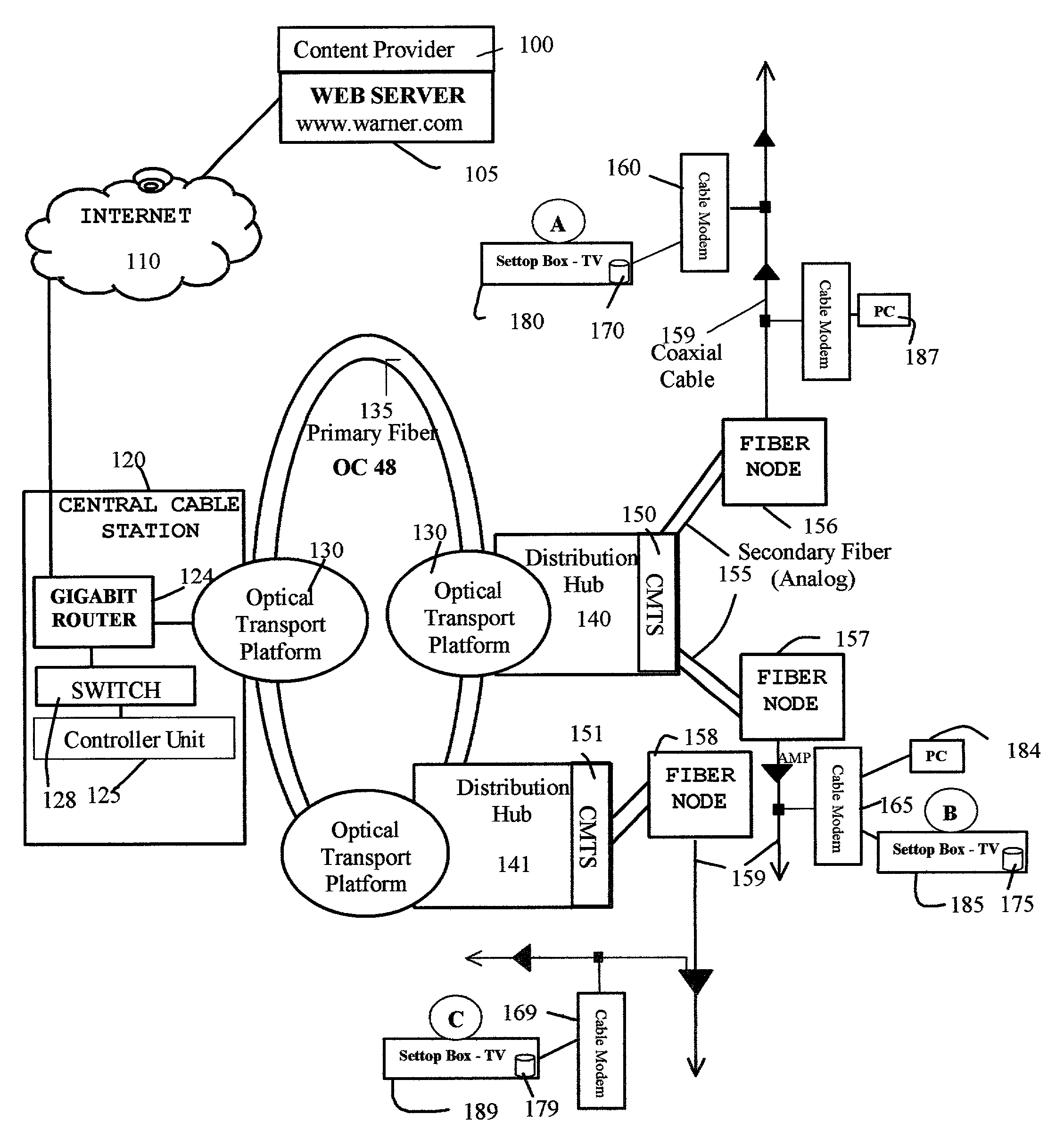
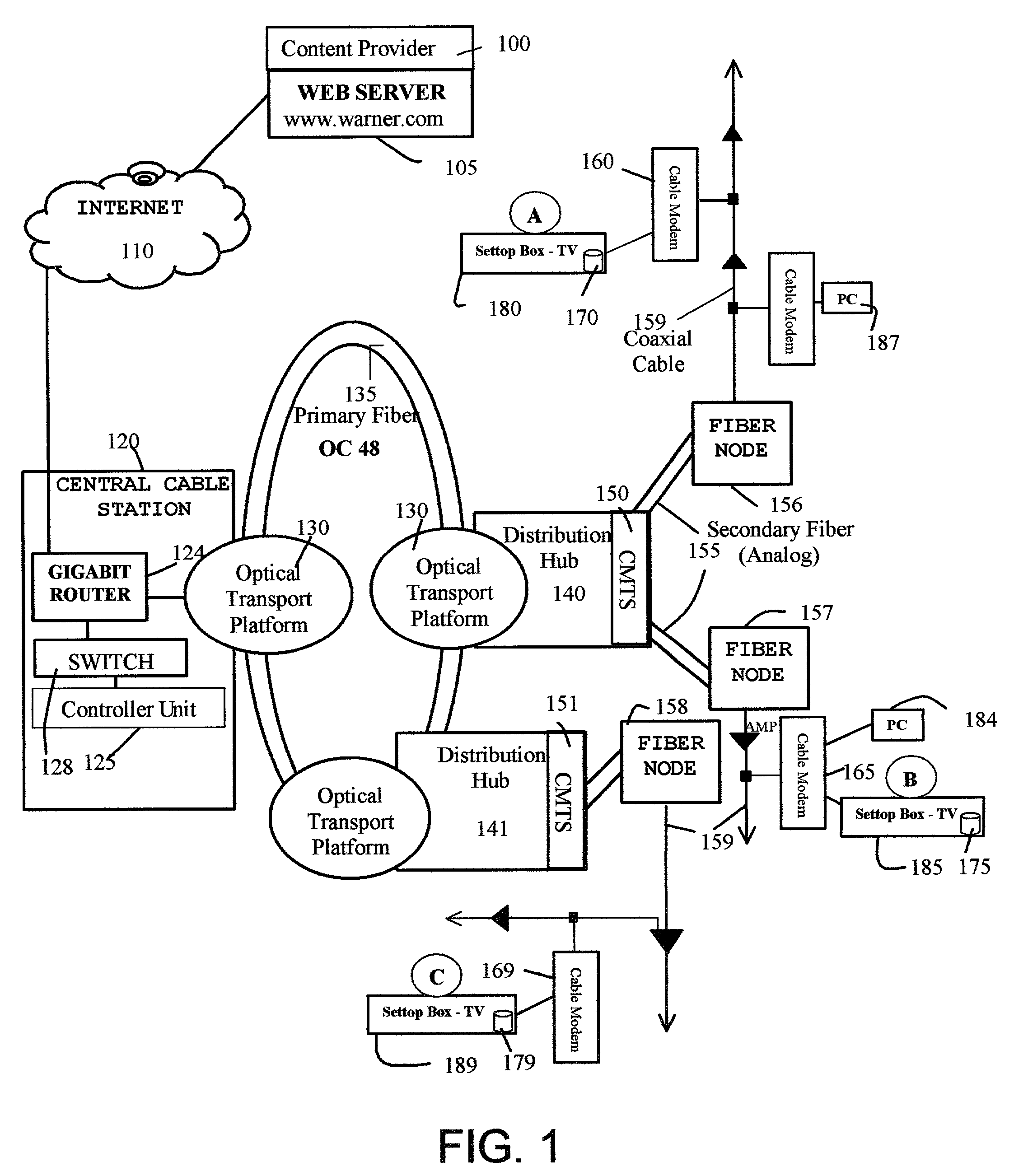
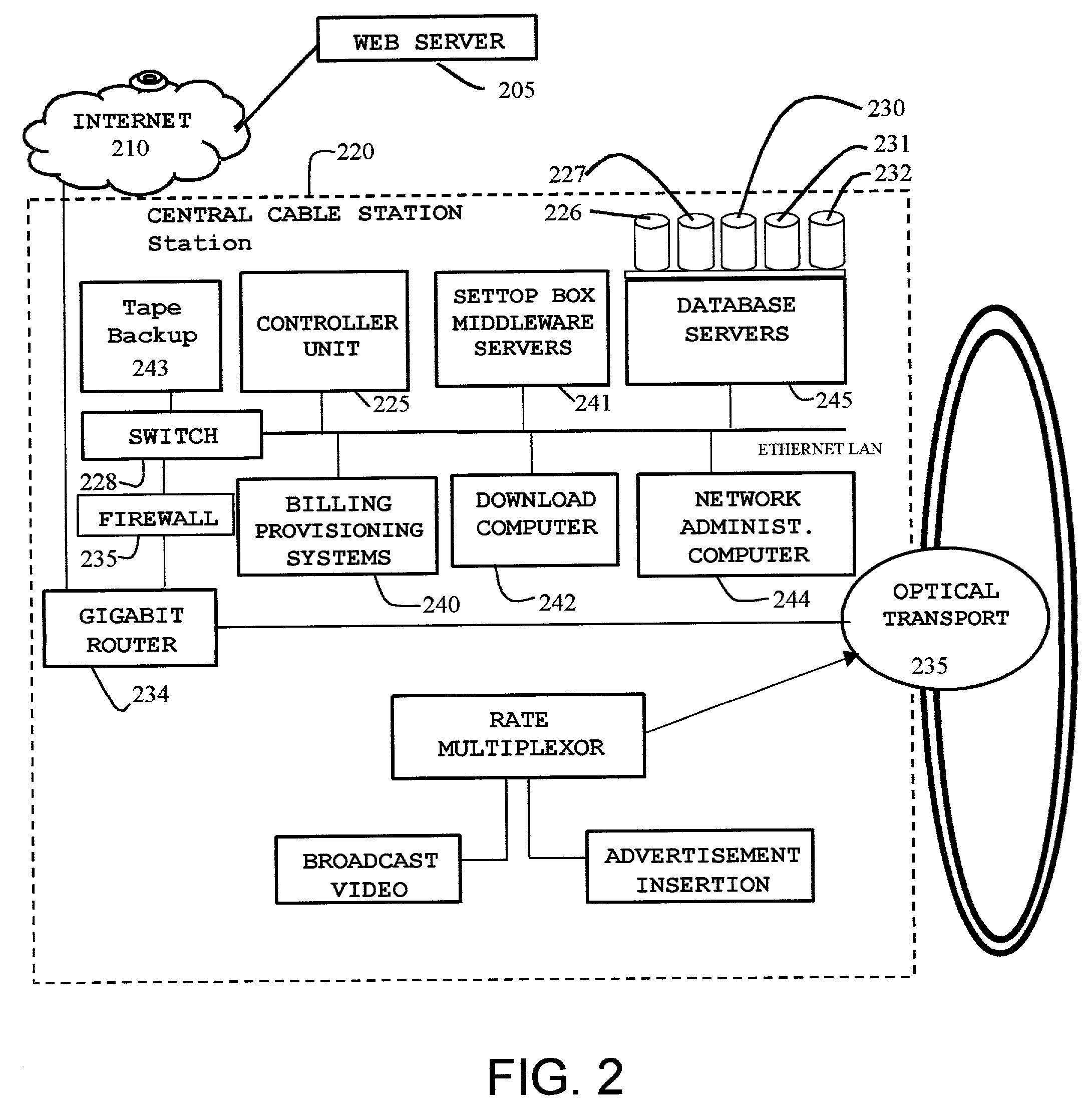
System and method for distributed storage and presentation of multimedia in a cable network environment
InactiveUS7080400B1Overcome disadvantagesSuitable for storageAnalogue secracy/subscription systemsMultiple digital computer combinationsThe InternetPersonal computer
A method and apparatus for distributing multimedia content (such as video, games, music, pictures), where the multimedia content is stored in a plurality of set-top boxes that are connected to a cable network. A controller unit located at a central cable station manages the multimedia content. The multimedia content stored in the set-top boxes is made available to any set-top box on request to the controller in the central cable station. The controller unit also interfaces with a plurality of multimedia owners, many situated on the Internet, to source the multimedia content and to source service properties associated with the multimedia content. The controller unit informs the content owners and appropriate billing systems when a multimedia content has been delivered to a remote set-top box and has been consumed by an end user. The end user accesses the multimedia content through a television, a personal computer, or other multimedia appliance.
Owner:NAVAR MURGESH S
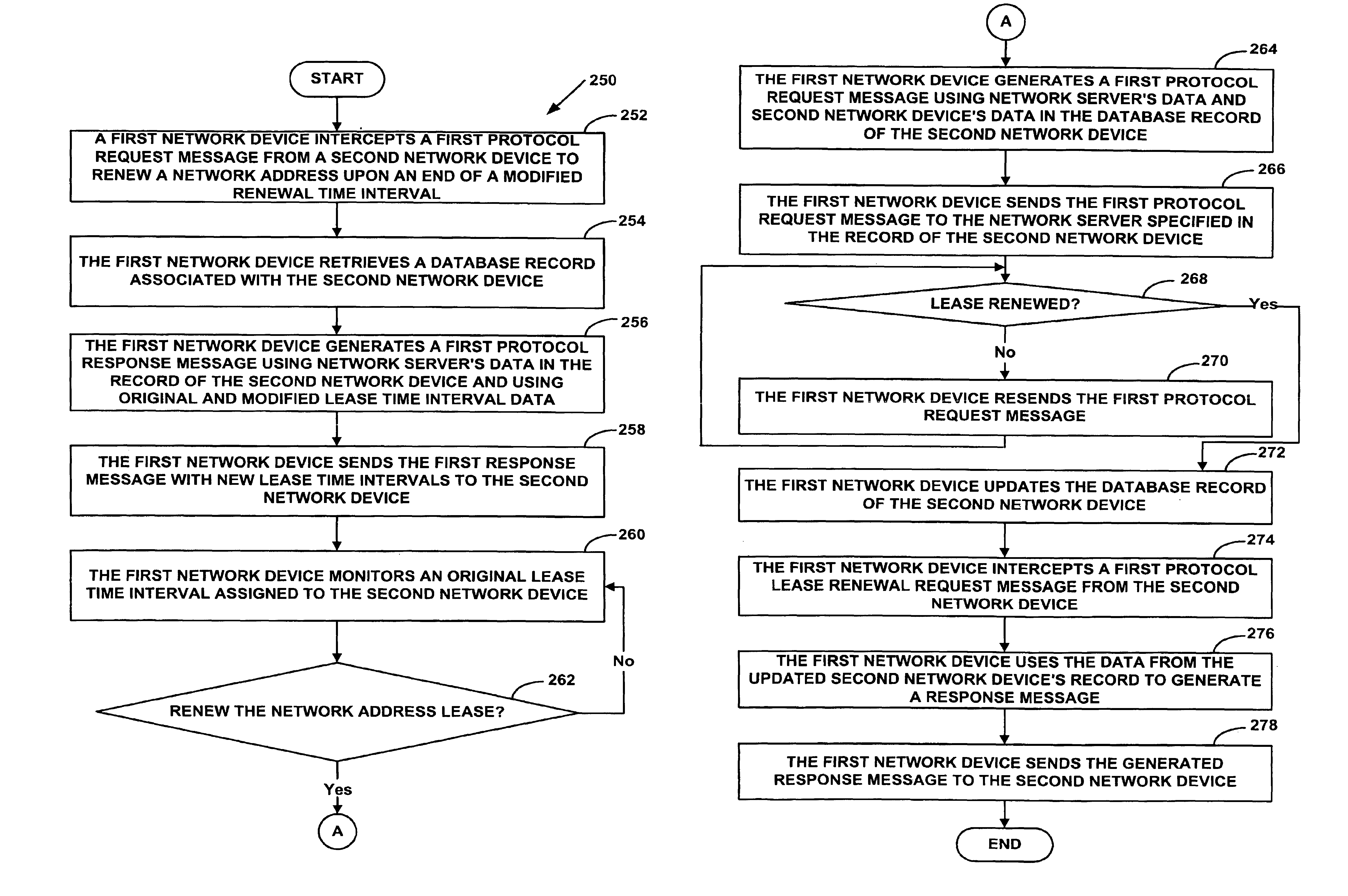
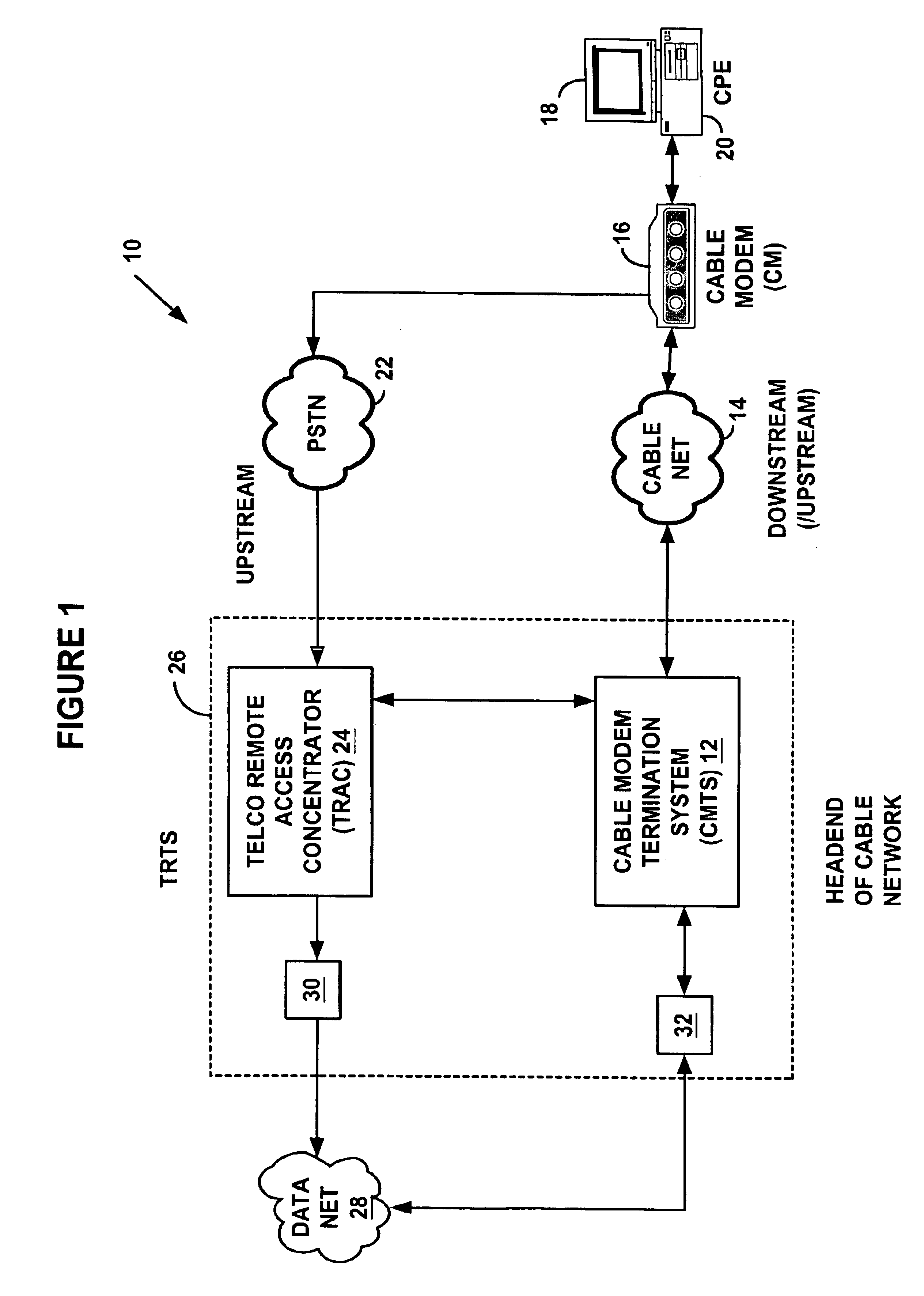
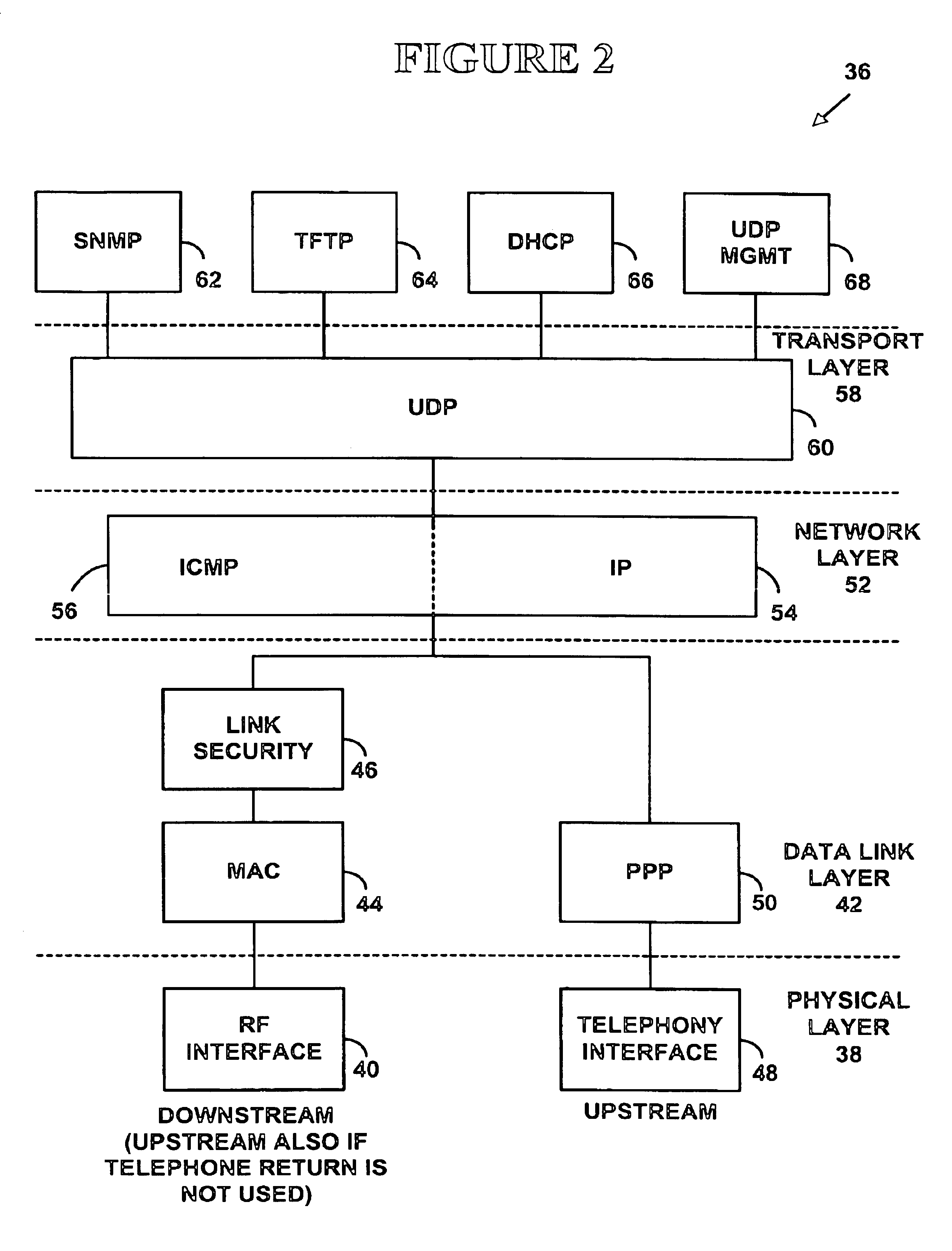
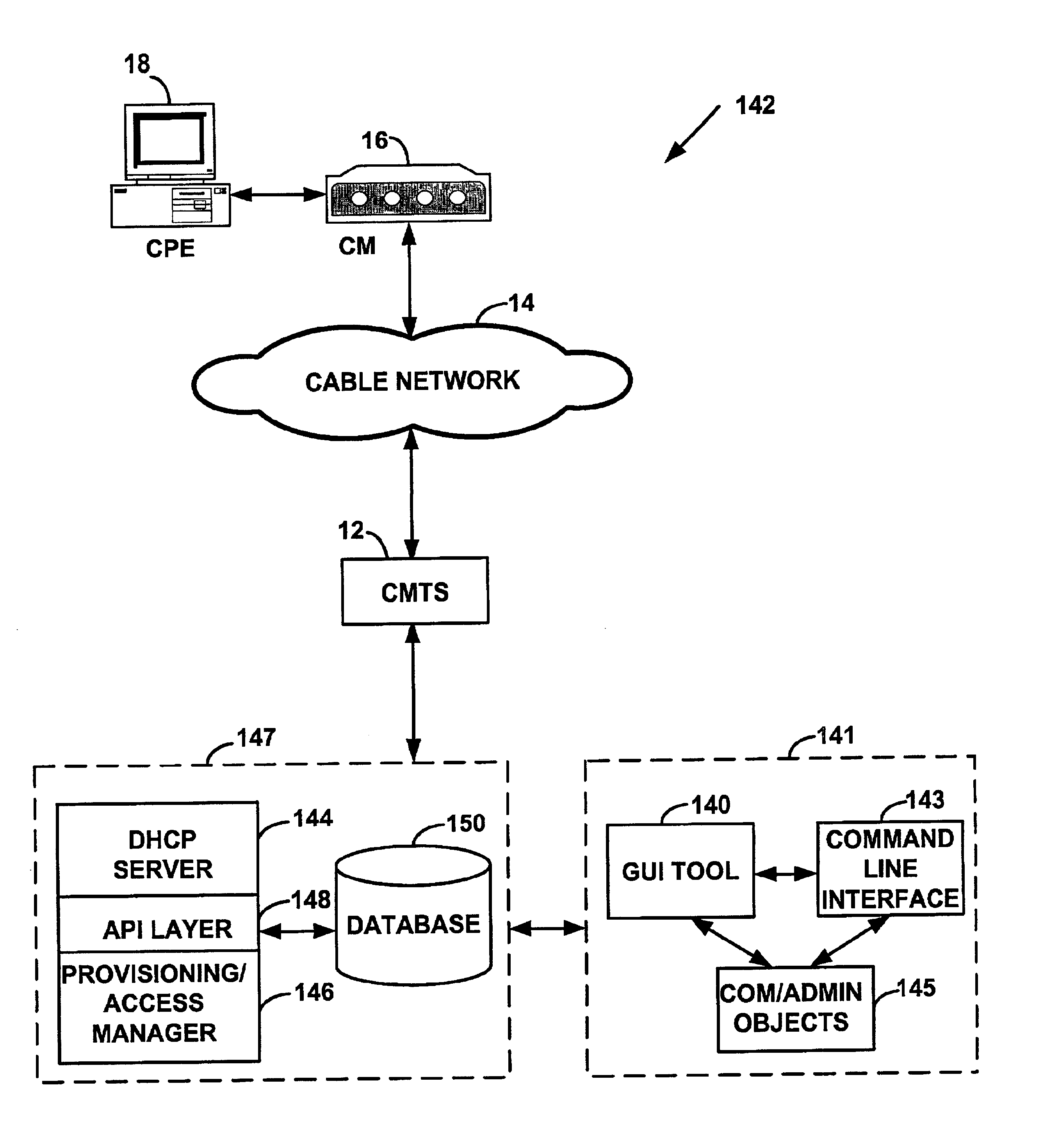
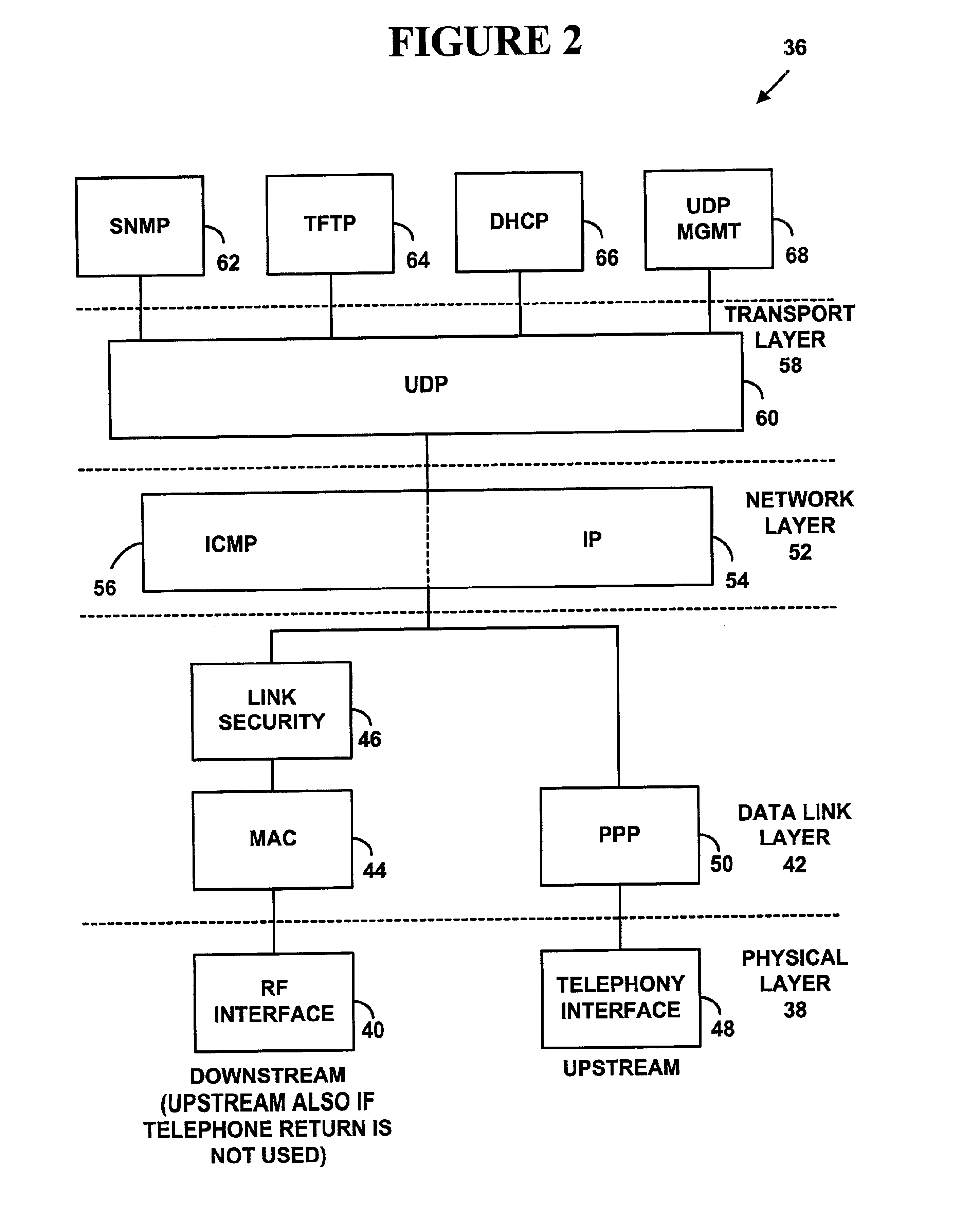
System and method for a specialized dynamic host configuration protocol proxy in a data-over-cable network
A system and method for proxying Dynamic Host Configuration Protocol (“DHCP”) network services for a network device, such as, a customer premise equipment entity, on a network device, such as, a cable modem, include creating a specialized proxy task for the customer premise equipment entity on the cable modem. One method of the present invention includes intercepting DHCP message flow between a customer premise equipment having a specialized proxy task created on the cable modem and a DHCP server selected by the customer premise equipment entity. The methods further include modifying lease time intervals prior to providing a routable network address lease to a customer premise equipment entity and renewing an initial lease for the customer premise equipment entity by a cable modem prior to expiration of the lease time interval provided by a DHCP server. The methods include using known protocols, such as, for example, the Dynamic Host Configuration Protocol.
Owner:VALTRUS INNOVATIONS LTD
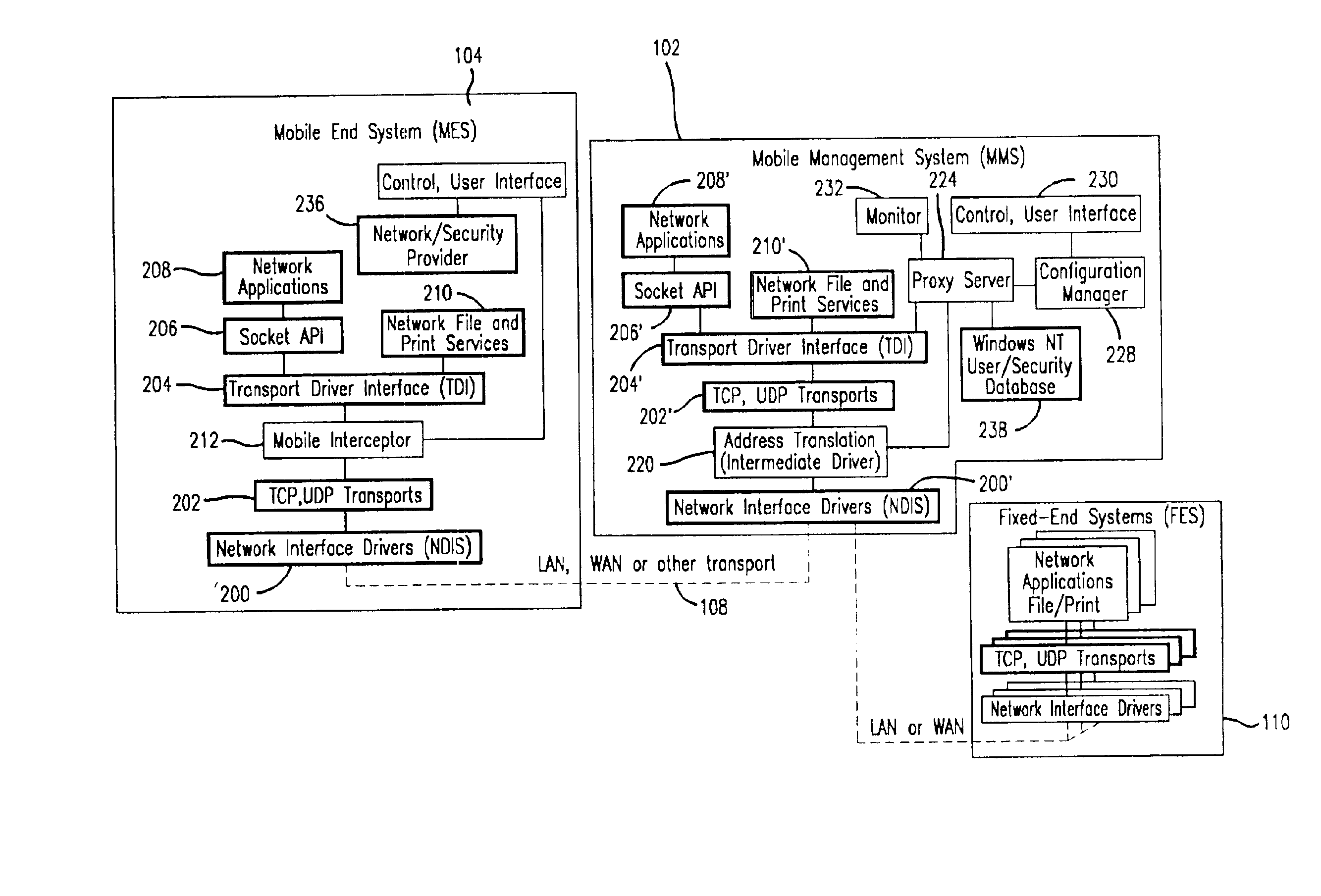
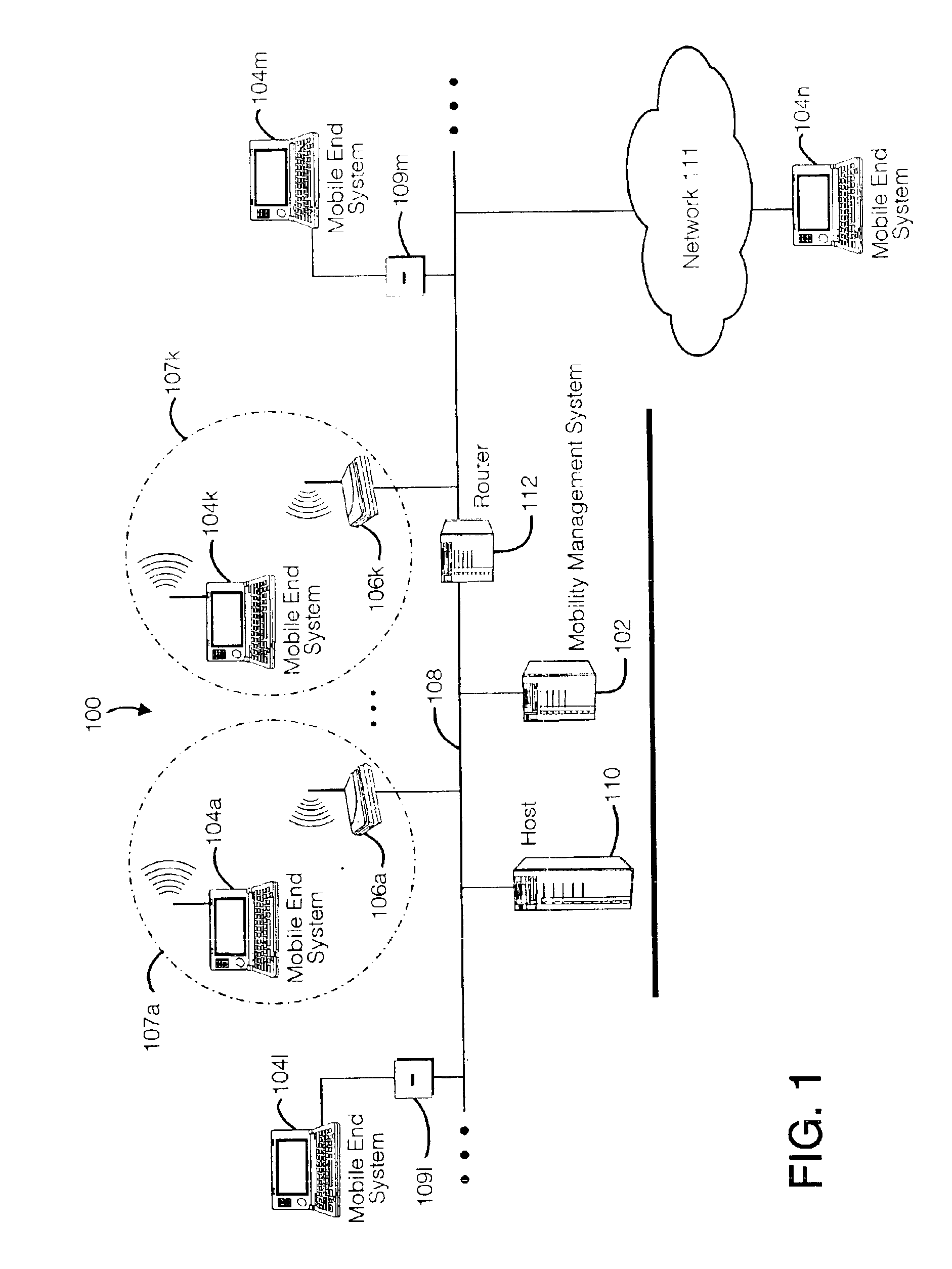
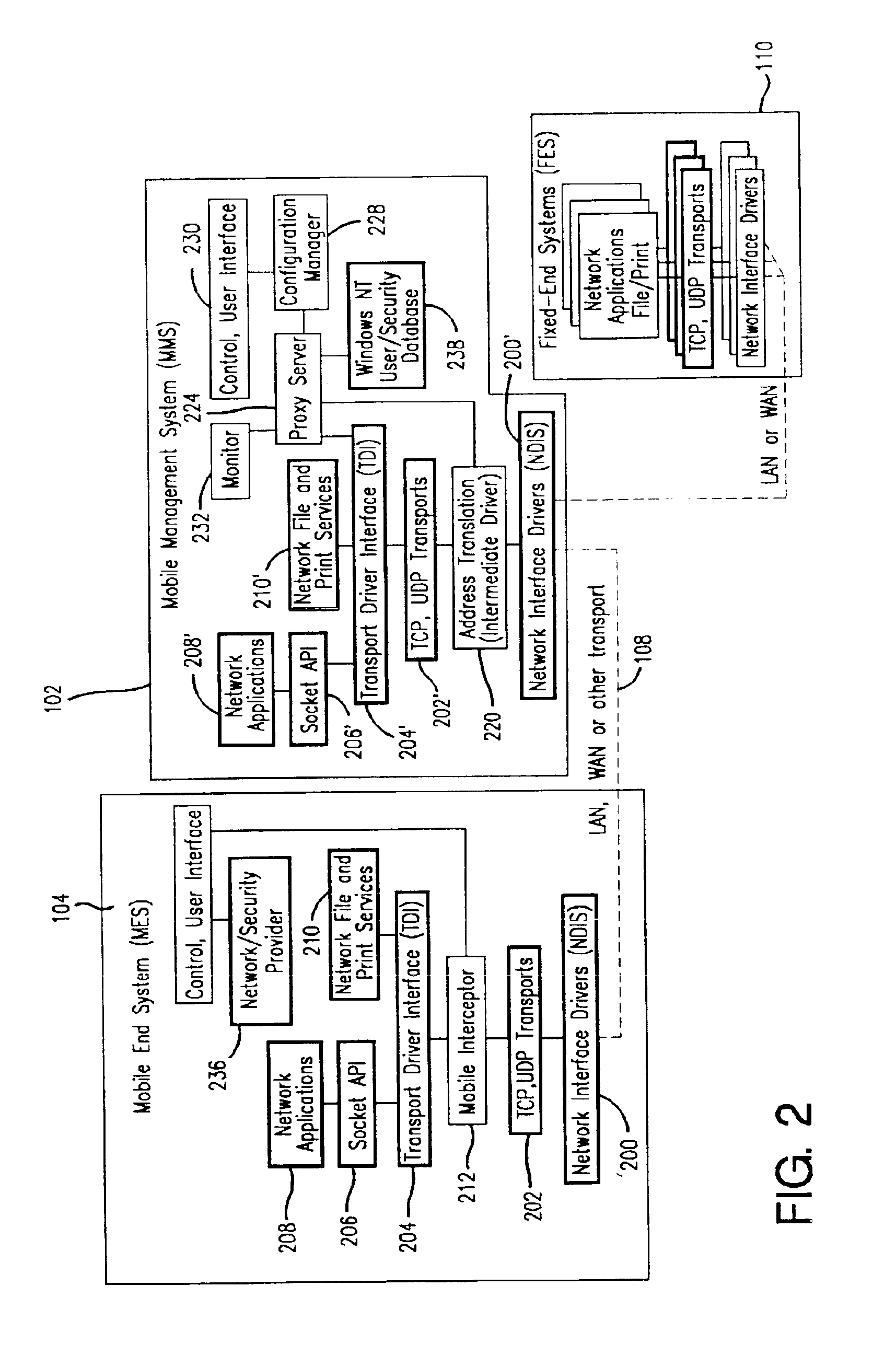
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
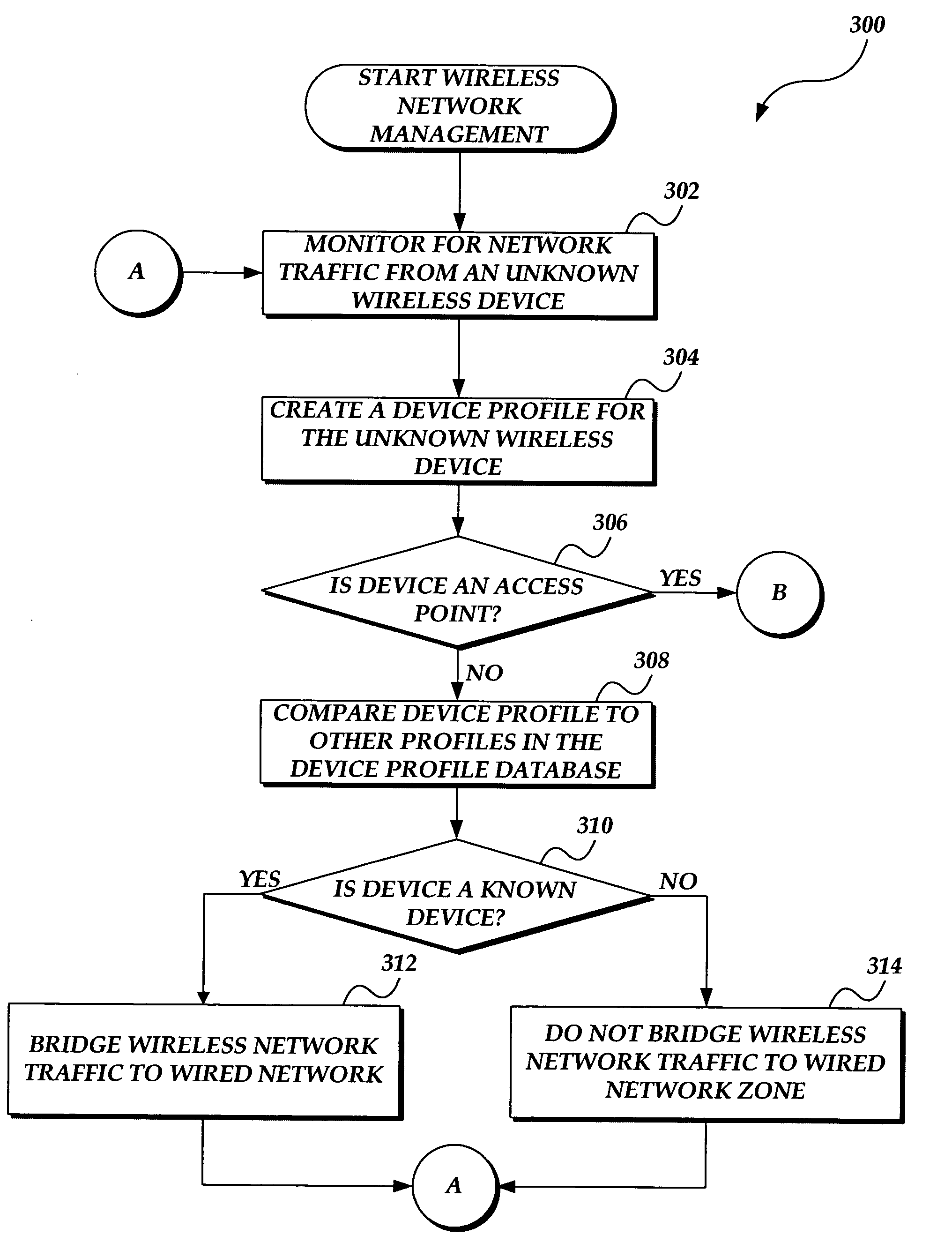
System and method for wireless local area network monitoring and intrusion detection
InactiveUS7340768B2Memory loss protectionDigital data processing detailsThreat levelNotification system
The present invention provides a system and method for providing real-time wireless network monitoring and intrusion detection. The present invention profiles wireless devices and maintains a database of known / authorized wireless device profiles. Wireless devices are analyzed to determine the threat level they pose to the network, and if the threat level exceeds a predetermined threshold, the invention refuses to bridge the network traffic from the wireless devices to the wired network. The present invention provides reporting of the wireless network activity, the known and unknown wireless devices, and the threat levels posed by the wireless devices. If an unknown wireless device is determined to be, or may be, a wireless access point, an alert is generated, such as notifying a system administrator to take appropriate action.
Owner:WIMETRICS CORP
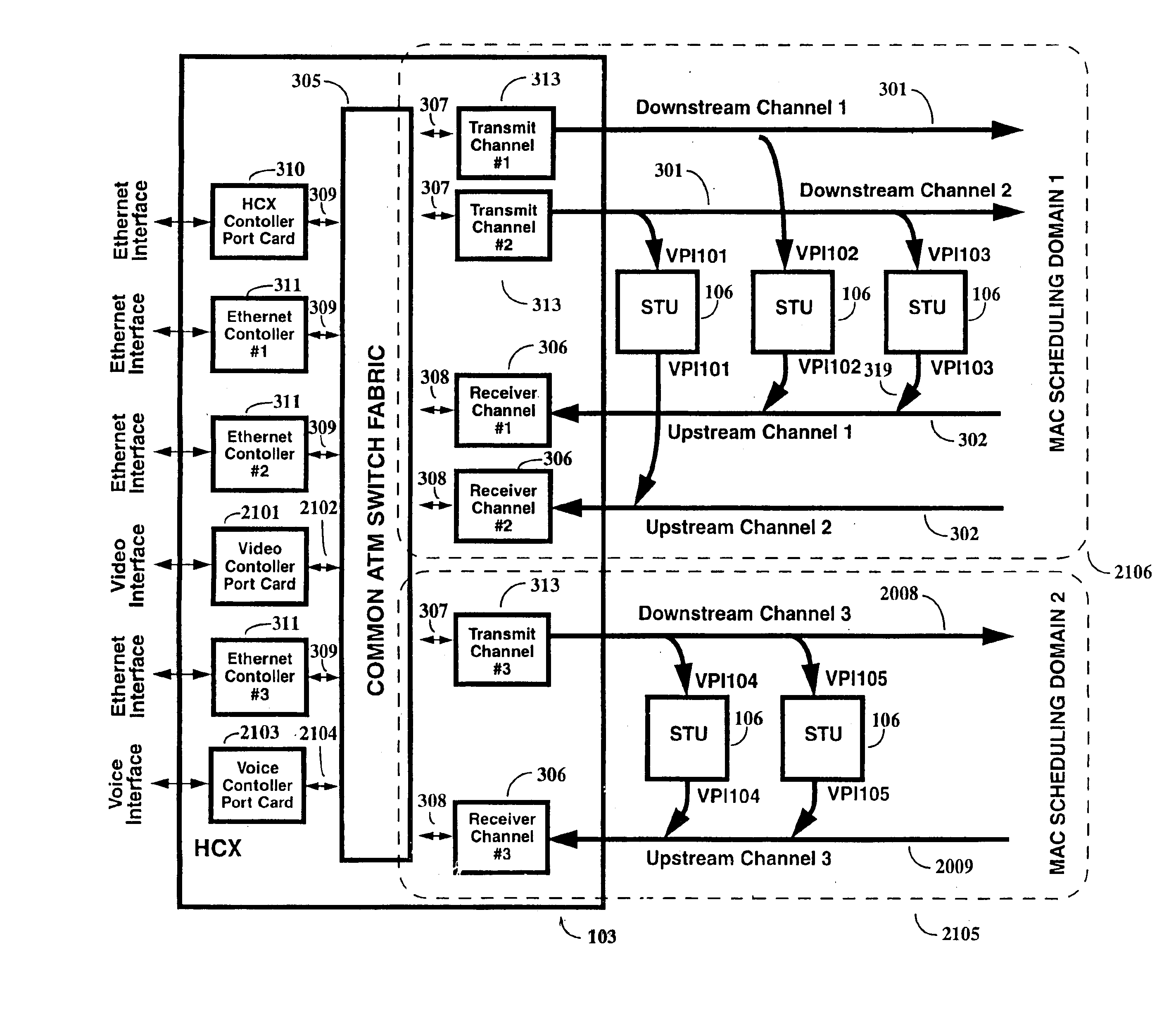
Multi-channel support for virtual private networks in a packet to ATM cell cable system
InactiveUS6917614B1Avoid compromiseExtension of timeBroadband local area networksFrequency-division multiplexQuality of serviceScheduling function
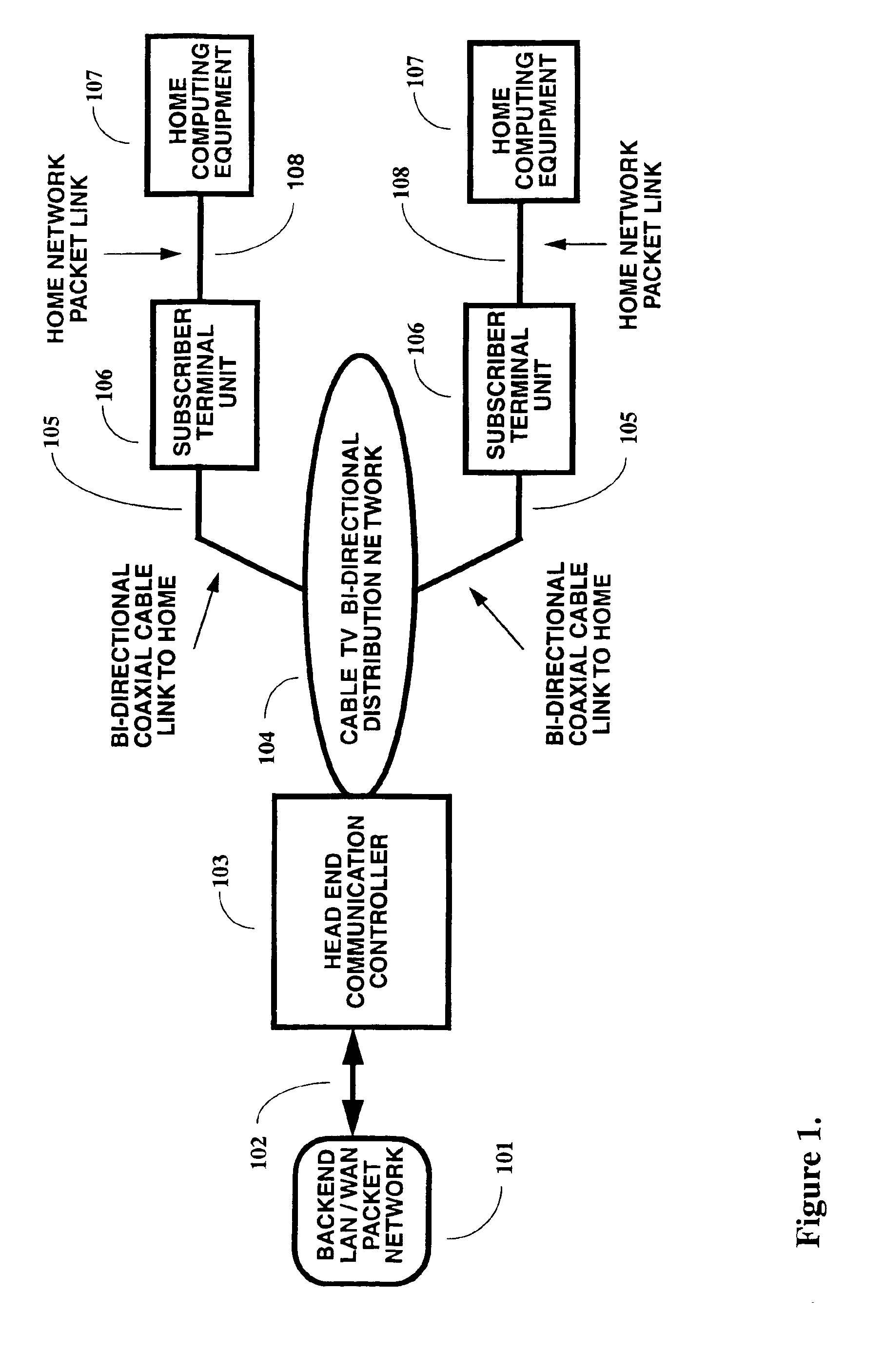
A two-way cable network offering high-speed broadband communications delivered via virtual private networks over a multi-channel shared media system. Bi-directional transmission of packet to ATM cell based communications is established between a head end communication controller and a number of subscriber terminal units, whereby individual cells are prioritized and routed according to a virtual connection. Virtual connections are organized to support multiple virtual private networks in a shared media CATV system. The virtual private network to which a particular STU belongs is user selectable and has the flexibility of handling multi up / downstream channels with different MAC domains. The present invention can also handle non-ATM MAC domains via the same common ATM switch. To overcome the limited number of addresses inherent to common ATM switches, a mapping / remapping function is implemented in the port cards. Furthermore, downstream as well as upstream traffic are filtered at each STU. In one embodiment, information pertaining to downstream traffic is used to implement predictive scheduling in order to improve the timing associated with the request / grant cycle. In another embodiment, a user has the ability to select a quality of service that best suits the needs of the current application. In a further embodiment, the scheduling function is associated with each of the receivers in order to provide improved scalability.
Owner:ARRIS ENTERPRISES LLC
Secure wireless local area network
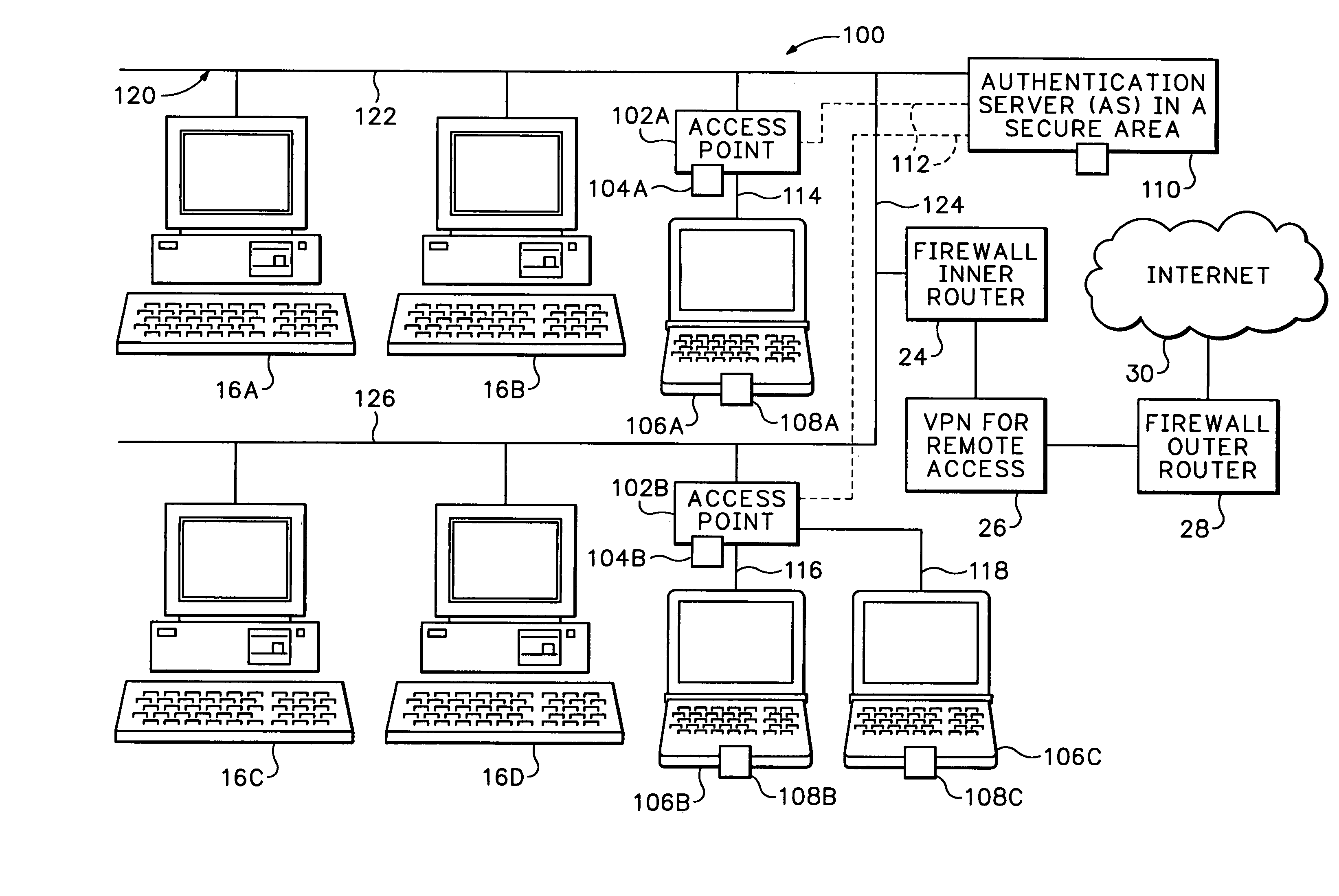
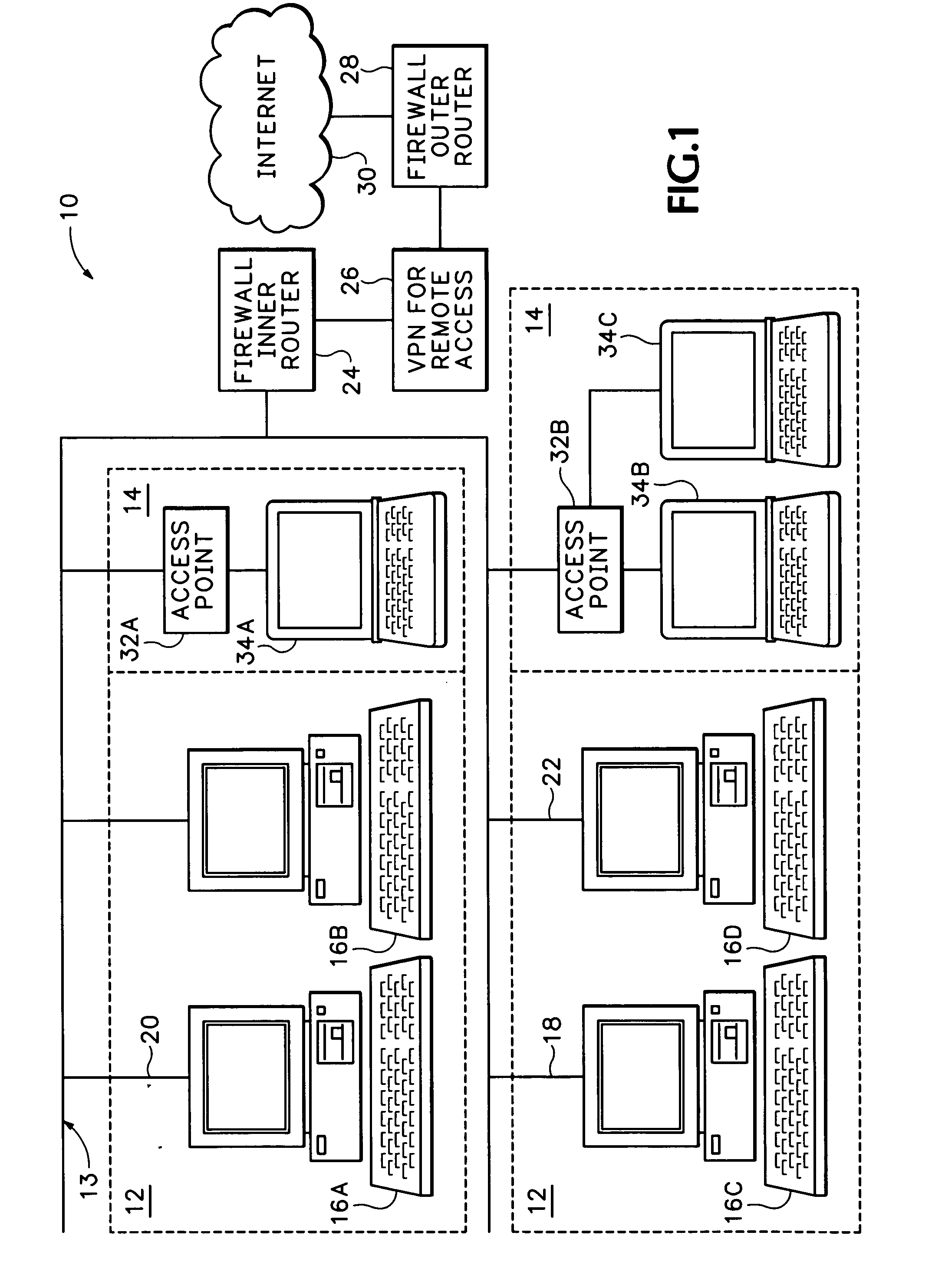
InactiveUS7174564B1Digital data processing detailsUser identity/authority verificationPasswordNetwork addressing
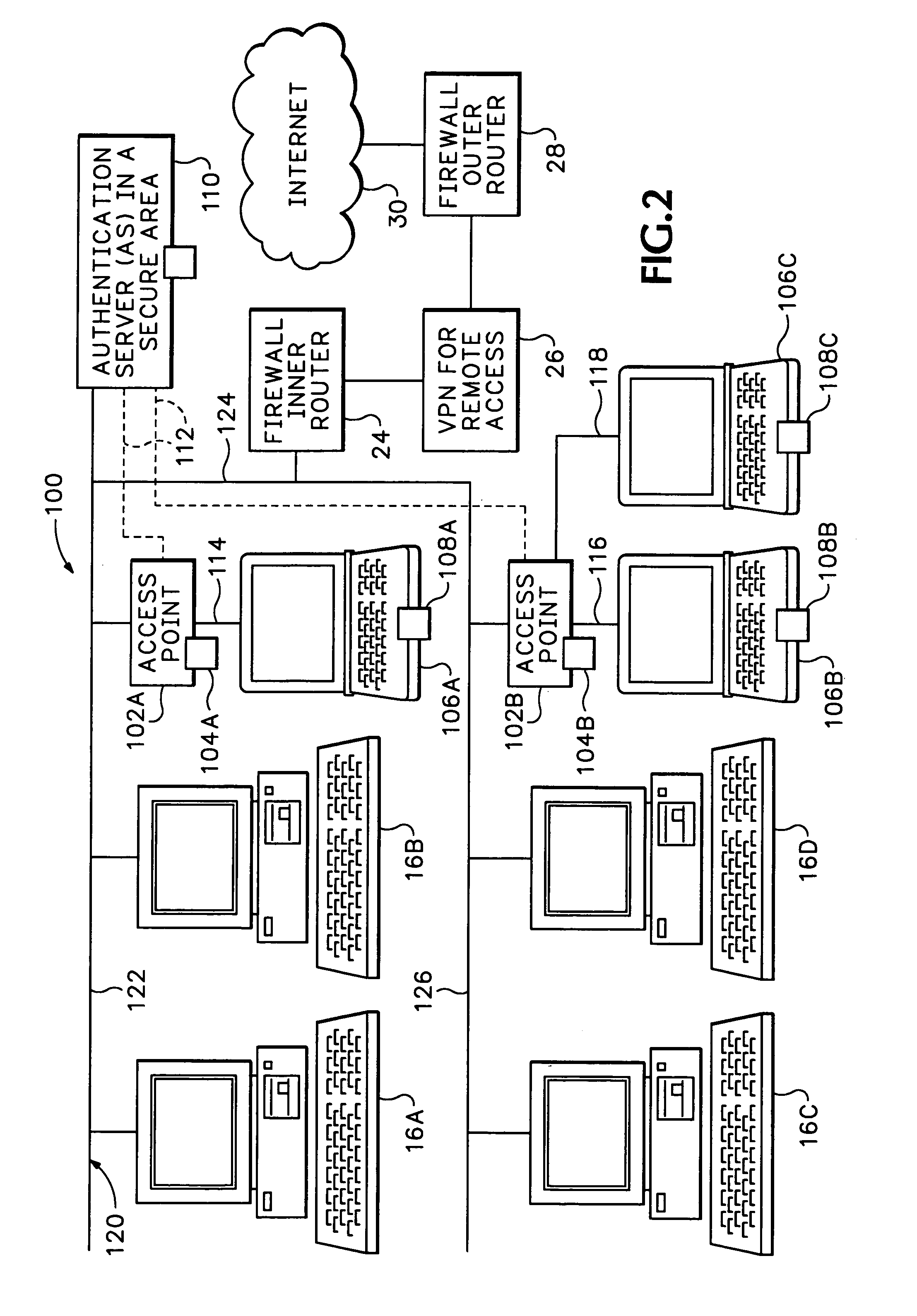
The secure wireless local area network of the present invention includes a single wired network that supports both wired and wireless devices. The network addresses security concerns by including an authentication server that services a plurality of access points. Each access point includes a first authentication device that generates and transmits a first authentication message to the corresponding wireless device over an air channel. The first authentication message includes encrypted validating information about the access point including an access point key that uniquely identifies the access point. Each wireless device includes a second authentication device. The wireless device receives the first authentication message and determines whether the access point is authorized to connect to the wired network. If the access point is valid, the second authentication device responds to the first authentication message by generating and transmitting a second authentication message to the access point. The second authentication message includes encrypted validating information about the wireless device and operator, e.g., a device key and the operator's logon name and password. The access point determines the authenticity of the wireless device by decrypting the portion of the second authentication message that includes the device key. If the wireless device is valid, the AP opens a control channel with the authentication server. The AP transmits the first and second authentication messages to the authentication server. If the authentication server validates the access point and the operator's logon name and password, it will authorize access to the wired network.
Owner:INTEL CORP
Cable network repair control system
InactiveUS6671824B1Shorten the timeSupervisory/monitoring/testing arrangementsSubstation equipmentControl systemEngineering
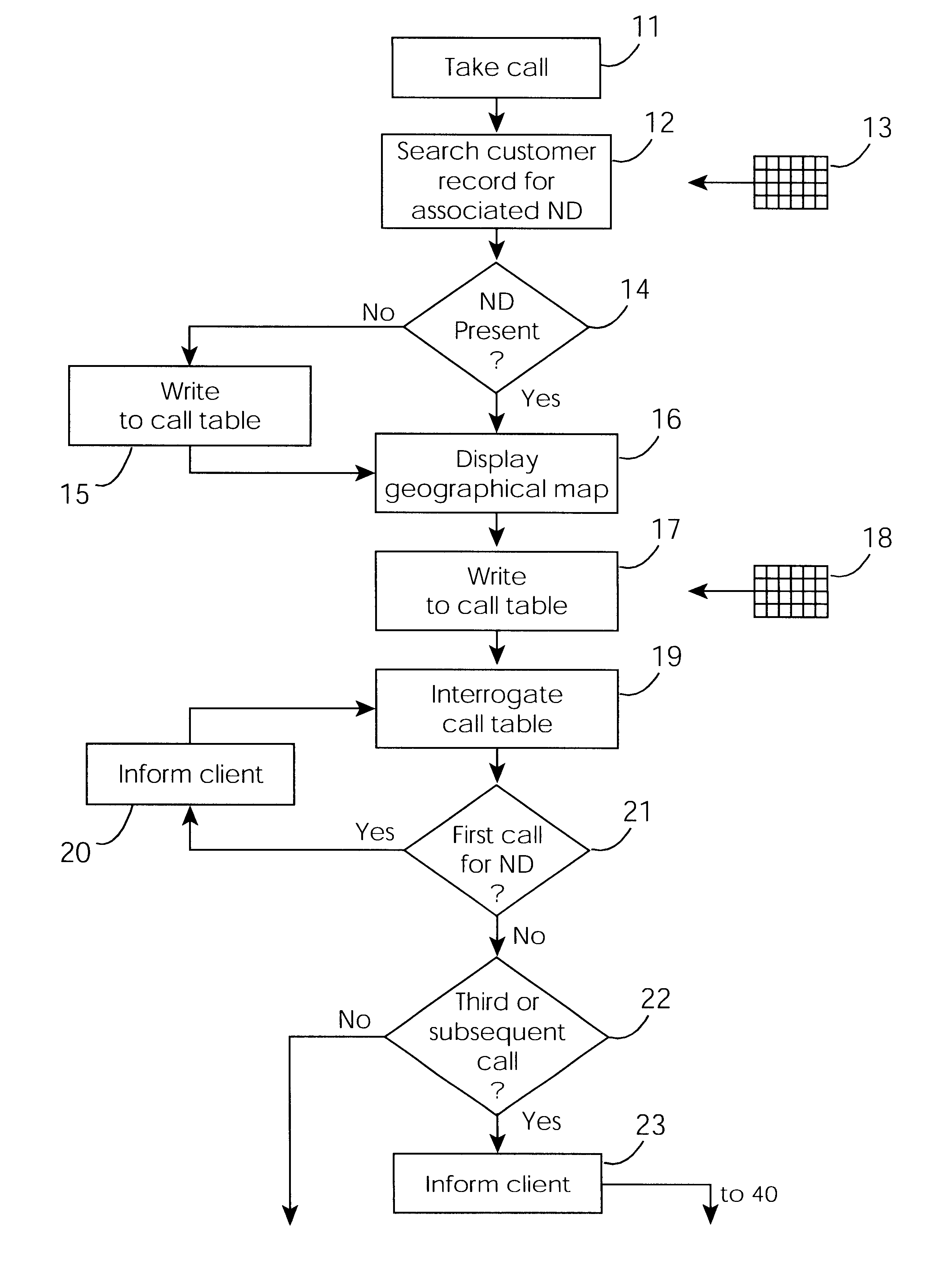
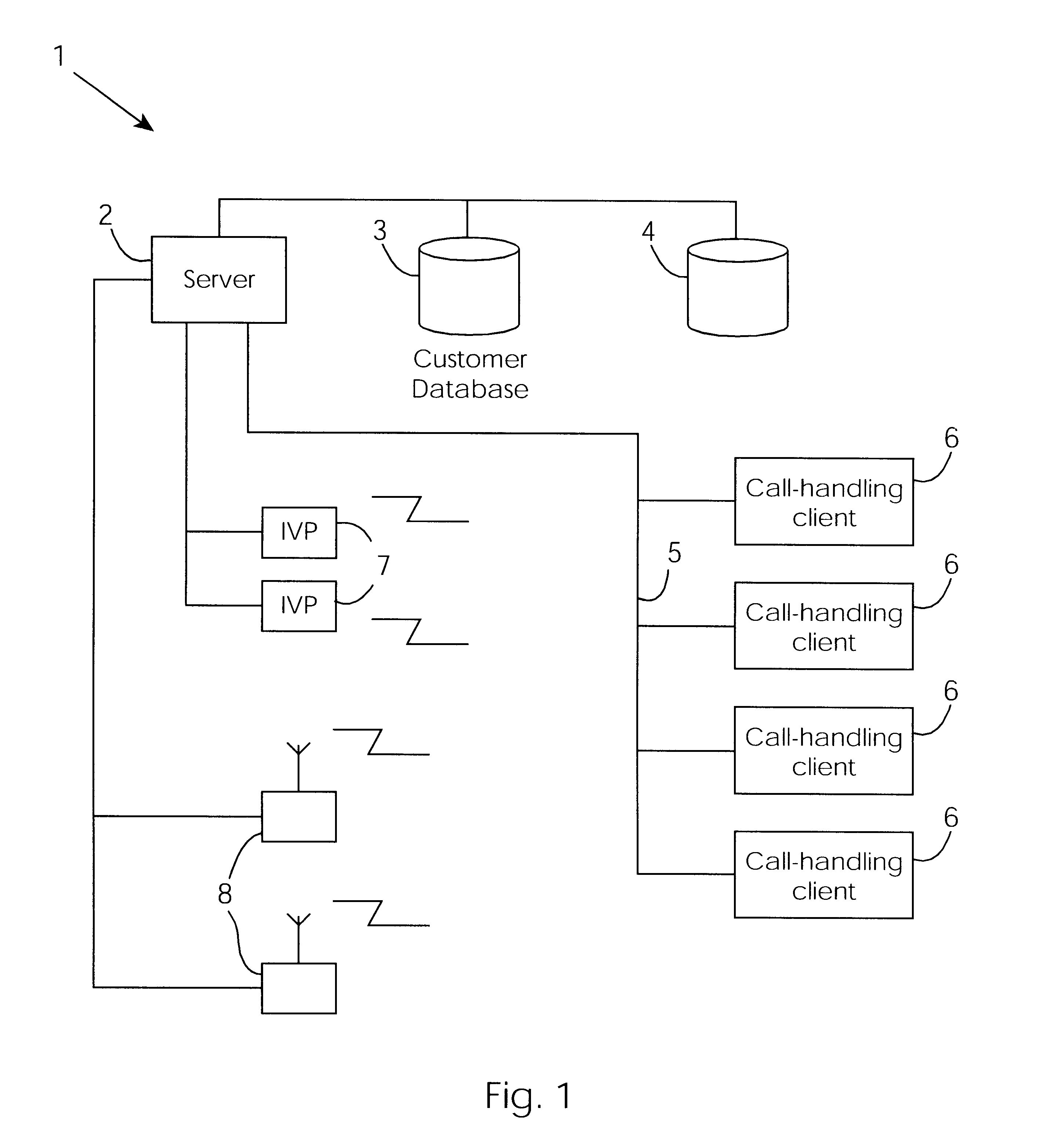
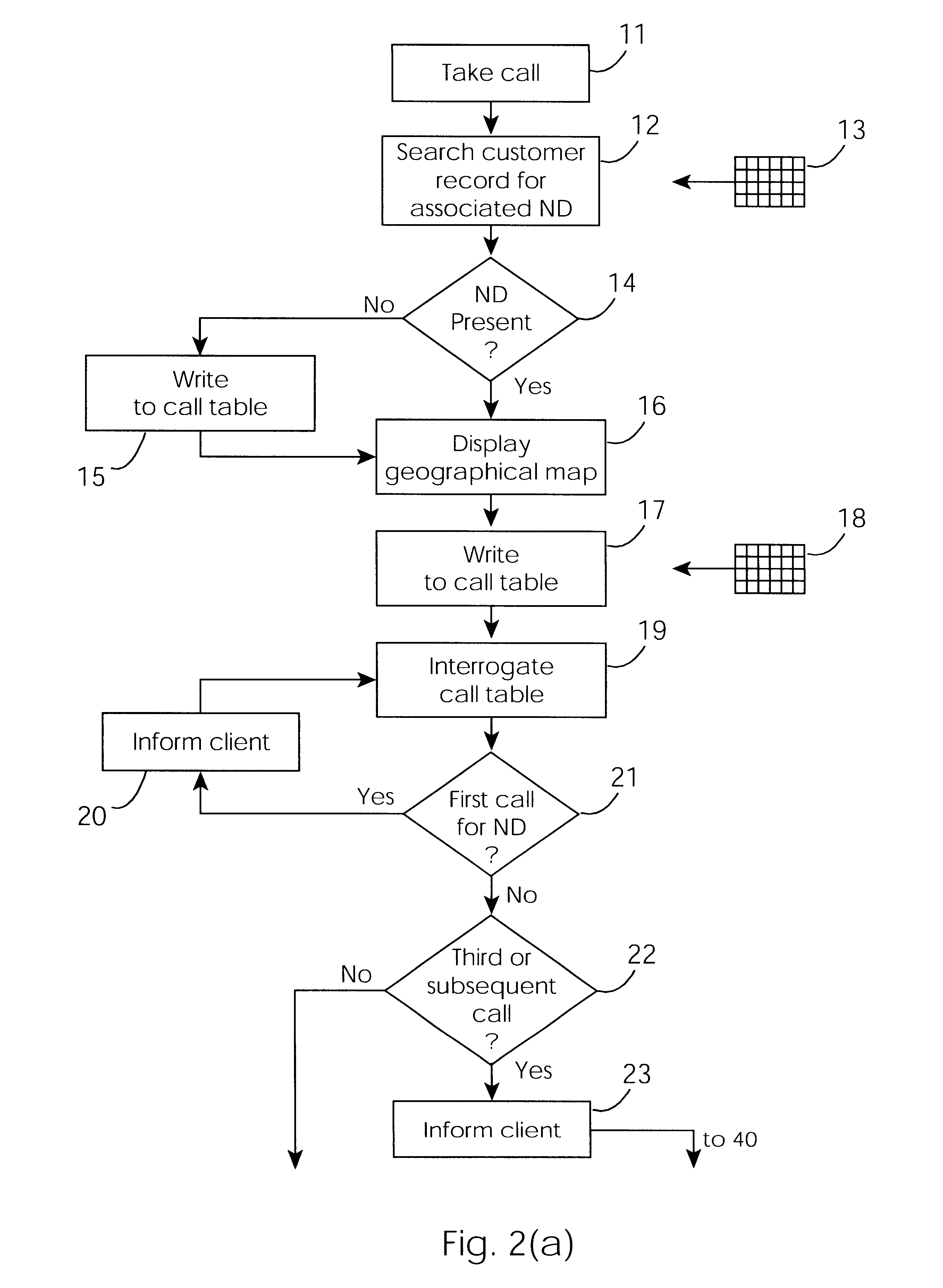
A cable network repair control system including a server communicating with multiple call-handling clients in a trouble call center. The databases are used to automatically determine an associated network device for the customer who makes a trouble call. When a second call is received for a particular network device, an inferencing engine automatically operates to identify potential repairs crews and to control communication with them to ensure that optimum use of the repair crew time and quick repair. Various tables are generated dynamically and are used to update management status tables for reviewing of network repair status.
Owner:LAKEFIELD ETECH GROUP
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Method and system for authenticating a point of access
ActiveUS8893246B2Raise the possibilityEasy to implementUnauthorised/fraudulent call preventionDigital data processing detailsAuthentication serverComparator
Rogue or malicious access points pose a threat to wireless networks (32) and the users of these networks. In order to prevent or reduce this threat a method and system is proposed that verifies that an access point (31) is genuine and not rogue before setting up a connection between the access point and a wireless device (34). The authentication is based on comparing an identifier of the wireless device (34) obtained from an authentication server (33, 35) in the wired network to an identifier of a wireless device obtained directly from the wireless device. A comparator (39) in an information server (36) receives the two sets of data and compares the two identifiers and if they match the access point is verified as genuine.
Owner:BRITISH TELECOMM PLC
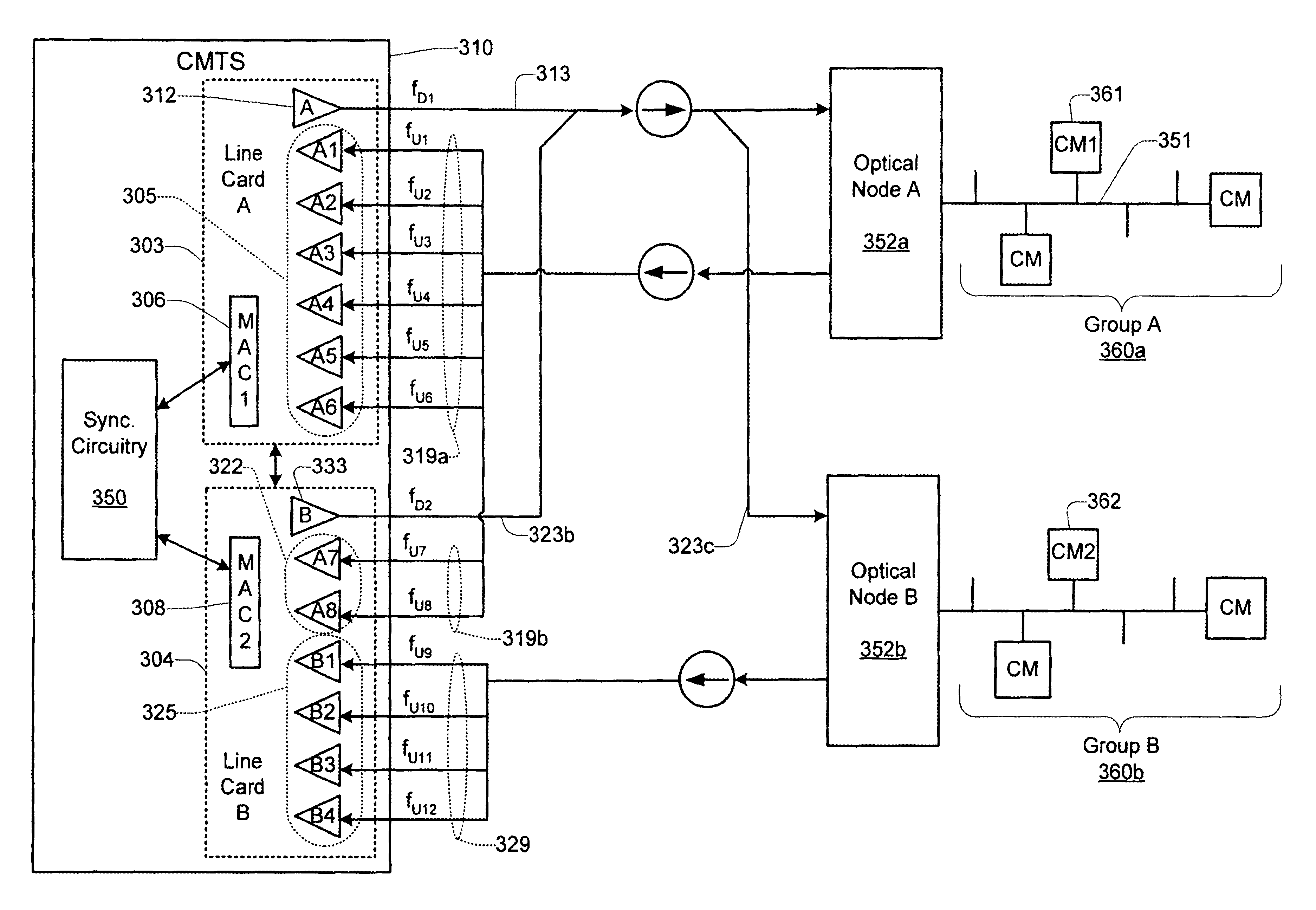
Technique for synchronizing multiple access controllers at the head end of an access network
InactiveUS7065779B1Broadband local area networksAnalogue secracy/subscription systemsAccess networkTimestamp
A technique is described which may be used to synchronize a plurality of different access controllers which control a plurality of distinct ports at the Head End of an access network. In the context of a cable network, the technique of the present invention may be used to synchronize desired upstream and / or downstream channels across different line cards within a Cable Modem Termination System (CMTS). The technique involves utilizing a master time reference device which maintains and updates a current time reference, and periodically distributes synchronization signals to desired line cards in the system in order to synchronize these line cards. In a specific embodiment, the synchronization signals include current timestamp data generated from the master time reference device and distributed to all (or selected) line cards in the system. A slave time reference device on each of the line cards receives the periodic synchronization updates and uses the synchronization data to remain synchronized with the master time reference device. There are also provisions in this protocol to allow for hot insertion and removal of line cards, software reset or loading of the master and / or slave time reference devices, and redundant master time reference devices, including master time reference device fault detection and automatic fail over.
Owner:CISCO TECH INC
System and method for automatic load balancing in a data-over-cable network
A method and system for load balancing in a network system such as a data-over-cable system. One method includes receiving a first message on a first network device such as a cable modem termination system (“CMTS”) from a second network device and marking the first message with an identifier of a network access device. The method further includes intercepting the first message on a third network device such as a provisioning / access manager prior to any first protocol server such a Dynamic Host Configuration Protocol server receives the first message. When the third network device intercepts the first message, the third network device determines capabilities of the second network device and applies a set of rules to load balance any requests between a plurality of channel pairs. Each charmel pair is associated with at least one capability of a network device and also has a load factor parameter and a threshold value defining a capacity of a channel pair. The third network device assigns the second network device to a predetermined channel pair based on the capabilities of the second network device, a load factor of the channel pair and a capacity of the channel pair.
Owner:VALTRUS INNOVATIONS LTD
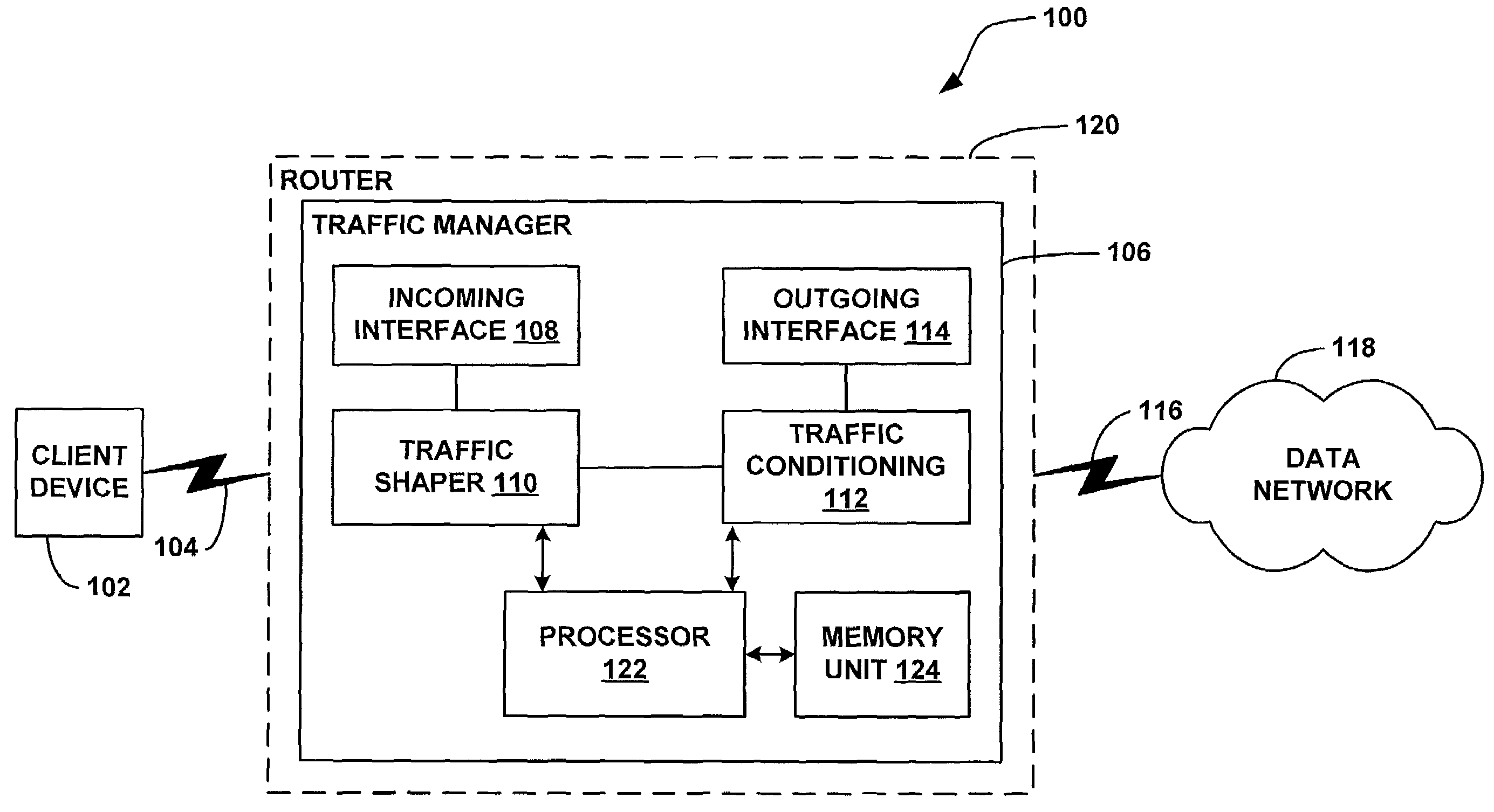
System and method for traffic shaping based on generalized congestion and flow control
ActiveUS7088678B1Overcome problemsError preventionFrequency-division multiplex detailsPacket arrivalModem device
A system and methods are shown for traffic shaping and congestion avoidance in a computer network such as a data-over-cable network. A headend of the data-over-cable system includes a traffic shaper configured to calculate a packet arrival rate from a cable modem and a traffic conditioner configured to calculate an average queue size on an output interface to an external network. For example, the traffic shaper compares the packet arrival rate to three packet arrival thresholds including a committed rate threshold, a control rate threshold and a peak rate threshold. If the calculated packet arrival rate falls between the committed threshold and control rate threshold, the traffic shaper applies a link layer mechanism, such as a MAP bandwidth allocation mechanism, to lower the transmission rate from the cable modem.
Owner:VL COLLECTIVE IP LLC
Method and system for location-aware wireless mobile devices including mobile user network message interfaces and protocol
InactiveUS6909903B2Improve usabilityEmergency connection handlingSpecial service for subscribersUsabilityWireless mobile devices
A method and system for location-aware wireless mobile devices including a mobile user network interfaces and protocol. A network-independent location-aware network protocol provides communication with location-aware wireless mobile devices. The protocol is network-independent to support and deliver location-aware services over virtually any wireless or wired network transparently regardless of the protocols being used on a transport network. The protocol is location-aware of current geographic locations of plural wireless mobile devices. Alert information is provided to a location-aware wireless mobile device with the network-independent location-aware network protocol and interfaces. Location-aware wireless mobile devices are located and provided with alert information with the network-independent location-aware network protocol and interfaces. The method, system, interfaces and protocol may help improve usability of mobile devices by allowing the mobile devices to be location-aware.
Owner:3E TECH INT
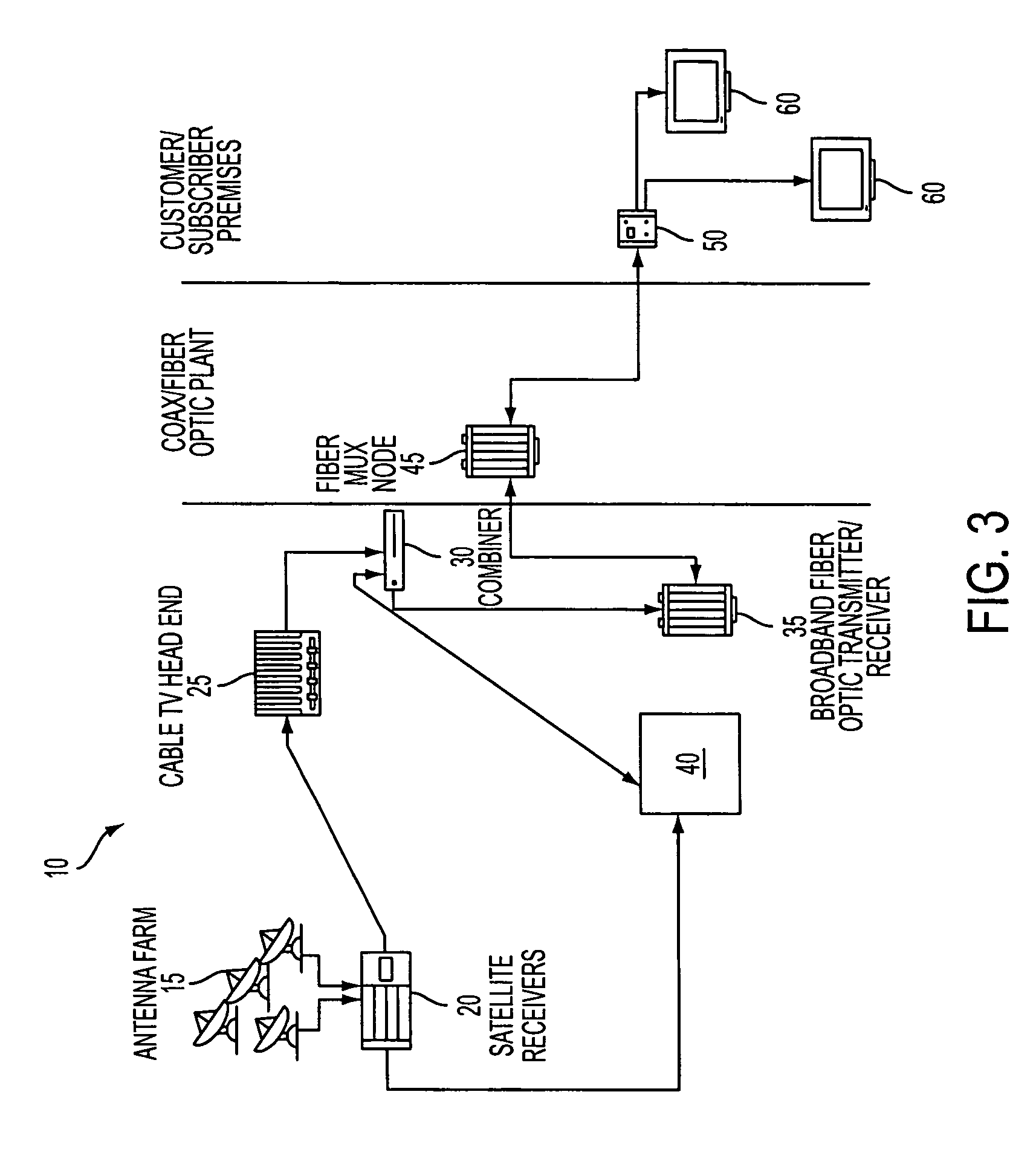
Network based digital information and entertainment storage and delivery system
InactiveUS7908626B2Transcending traditional program schedule limitationEffectiveTelevision system detailsBroadcast-related systemsDelivery systemVideo on demand
Live television broadcast and other information and entertainment programs, e.g., videos-on-demand (VOD), are provided to a user through a communications network, e.g., a cable network. A processing unit is employed at an headend of the communications network to respond to user requests for PVR-like functions, e.g., pausing, rewinding and fast-forwarding, to be performed on the program content being viewed. The processing unit in accordance with the invention causes a delivery of an appropriate version of the program content to meet such user requests.
Owner:TIME WARNER CABLE ENTERPRISES LLC +1
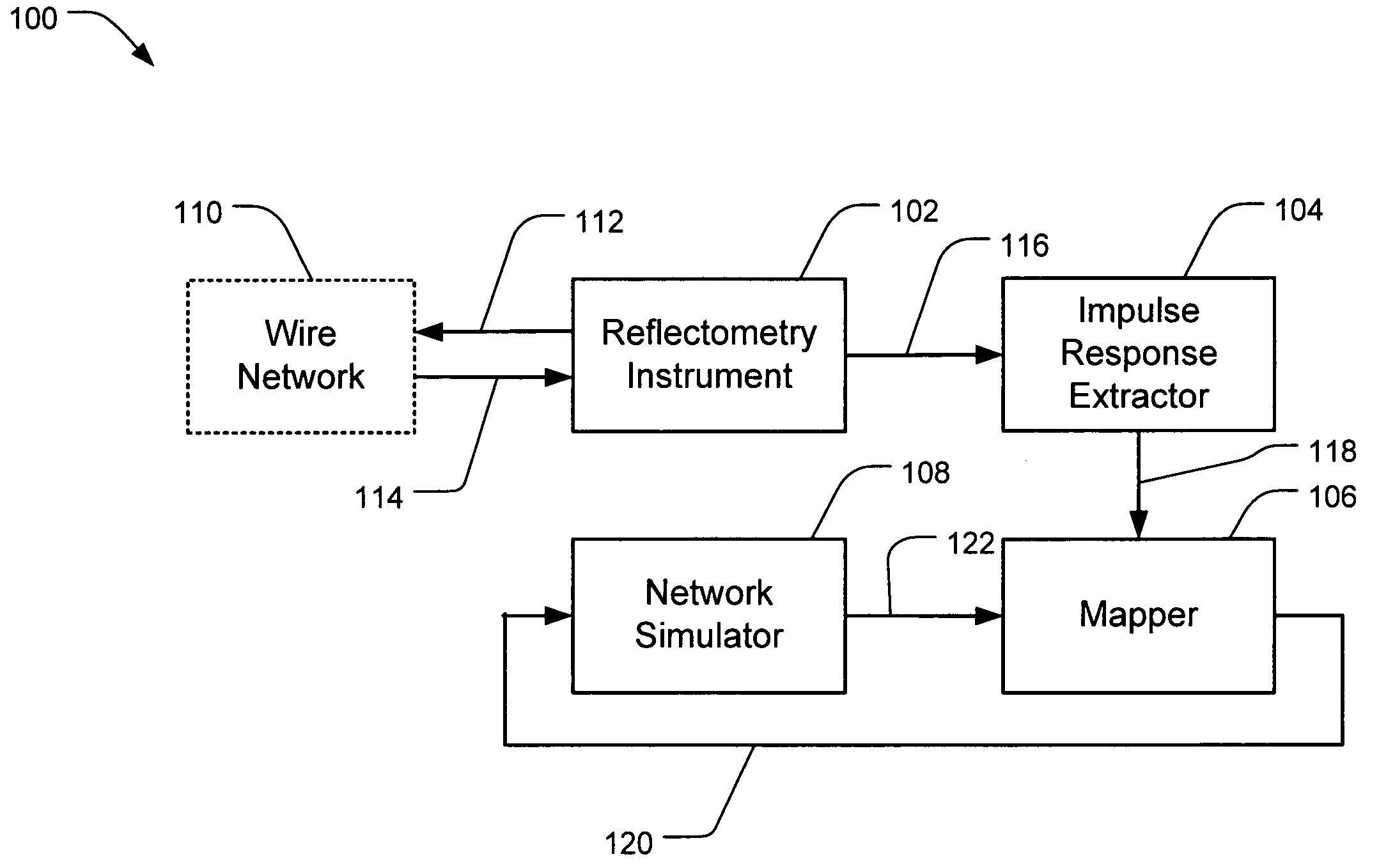
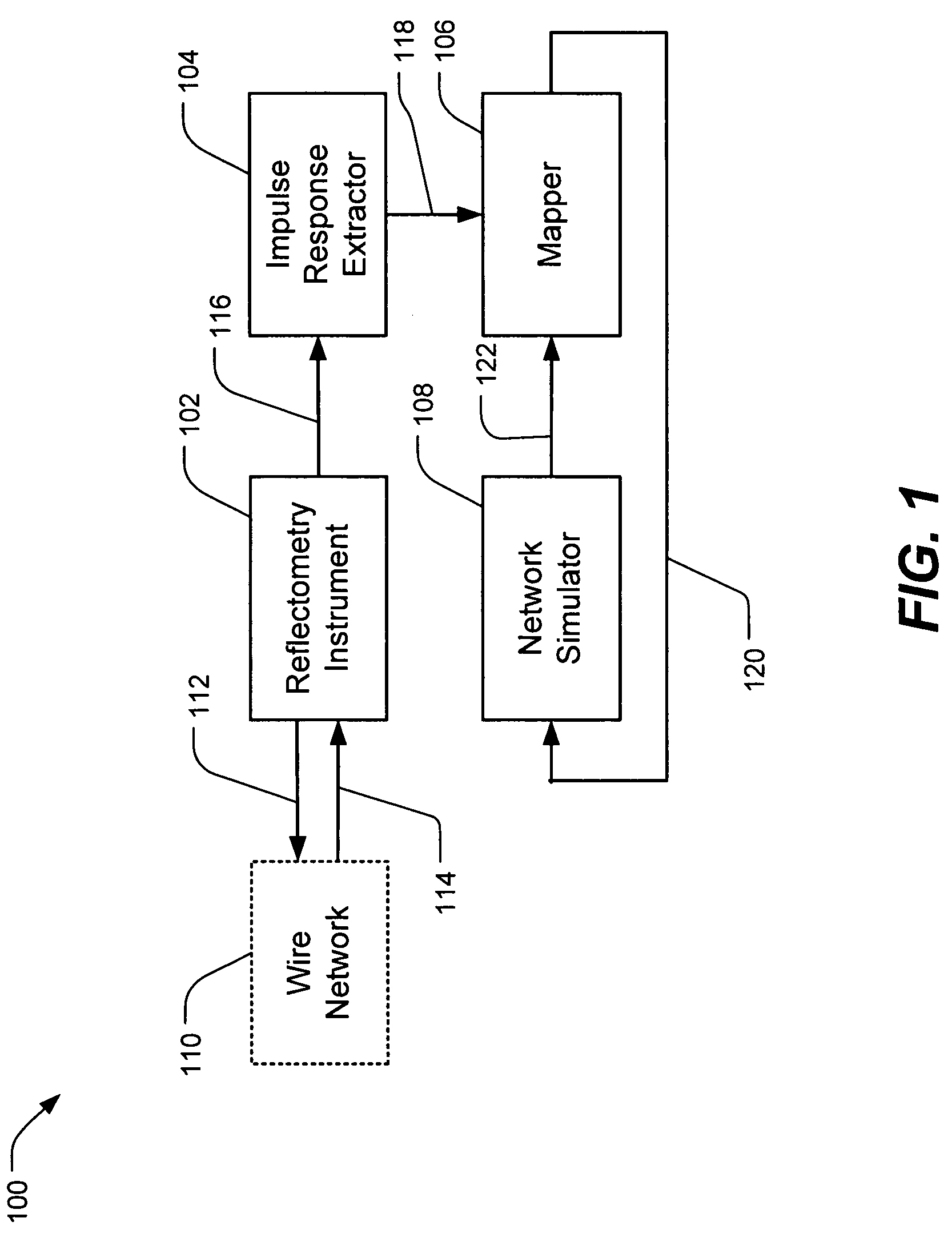
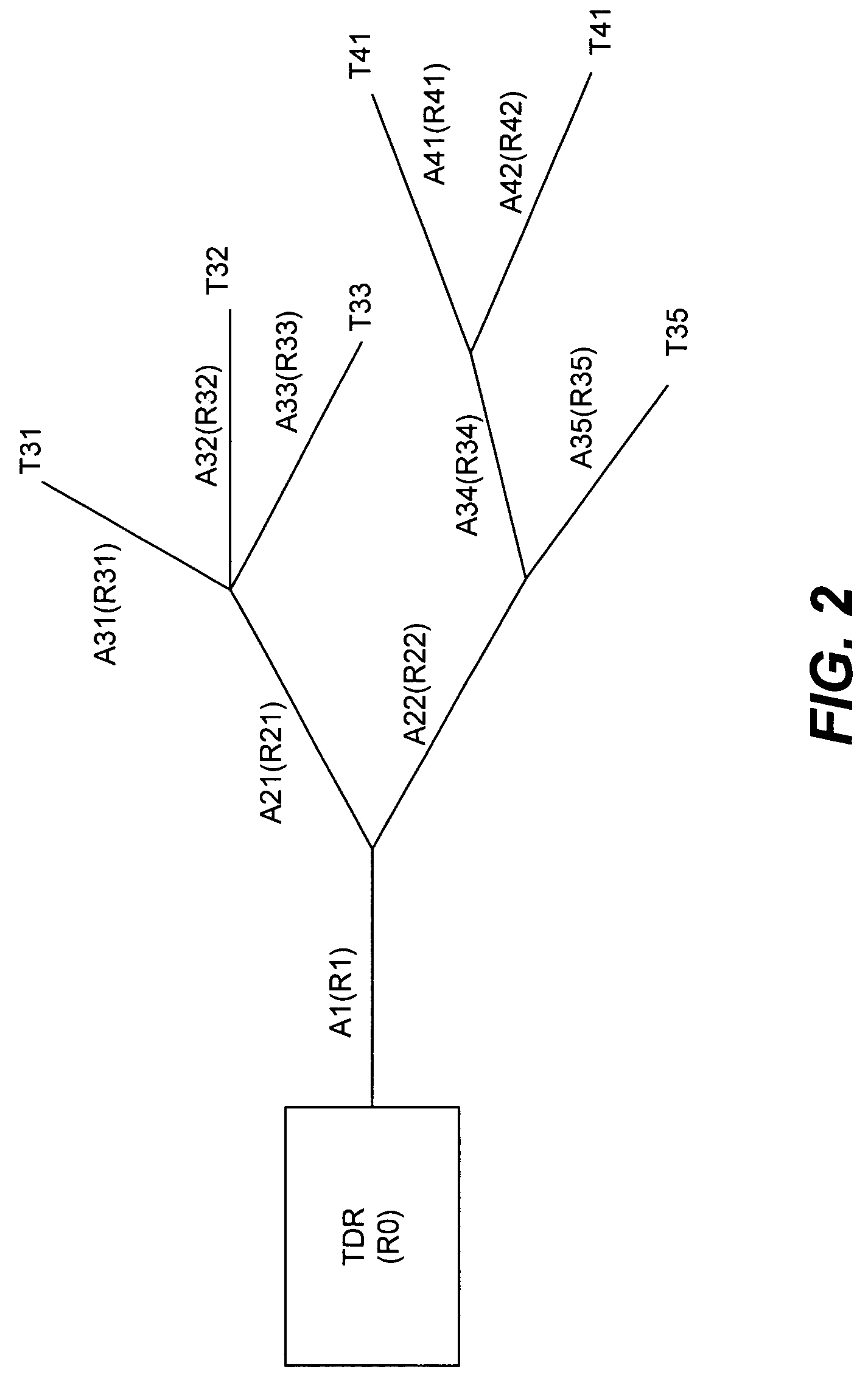
Wire network mapping method and apparatus using impulse responses
ActiveUS7282922B2Reduce the differenceFault location by pulse reflection methodsFinite impulse responseNetwork model
A method and apparatus for mapping a wire network is disclosed. The method includes obtaining a reflectometry test signal of the wire network. An estimated network impulse response is estimated from the reflectometry response. A wire network model is then initialized, and iteratively improved by simulating an impulse response of the wire network model and adjusting the wire network model to reduce differences between the simulated impulse response and estimated network impulse response.
Owner:UNIV OF UTAH RES FOUND
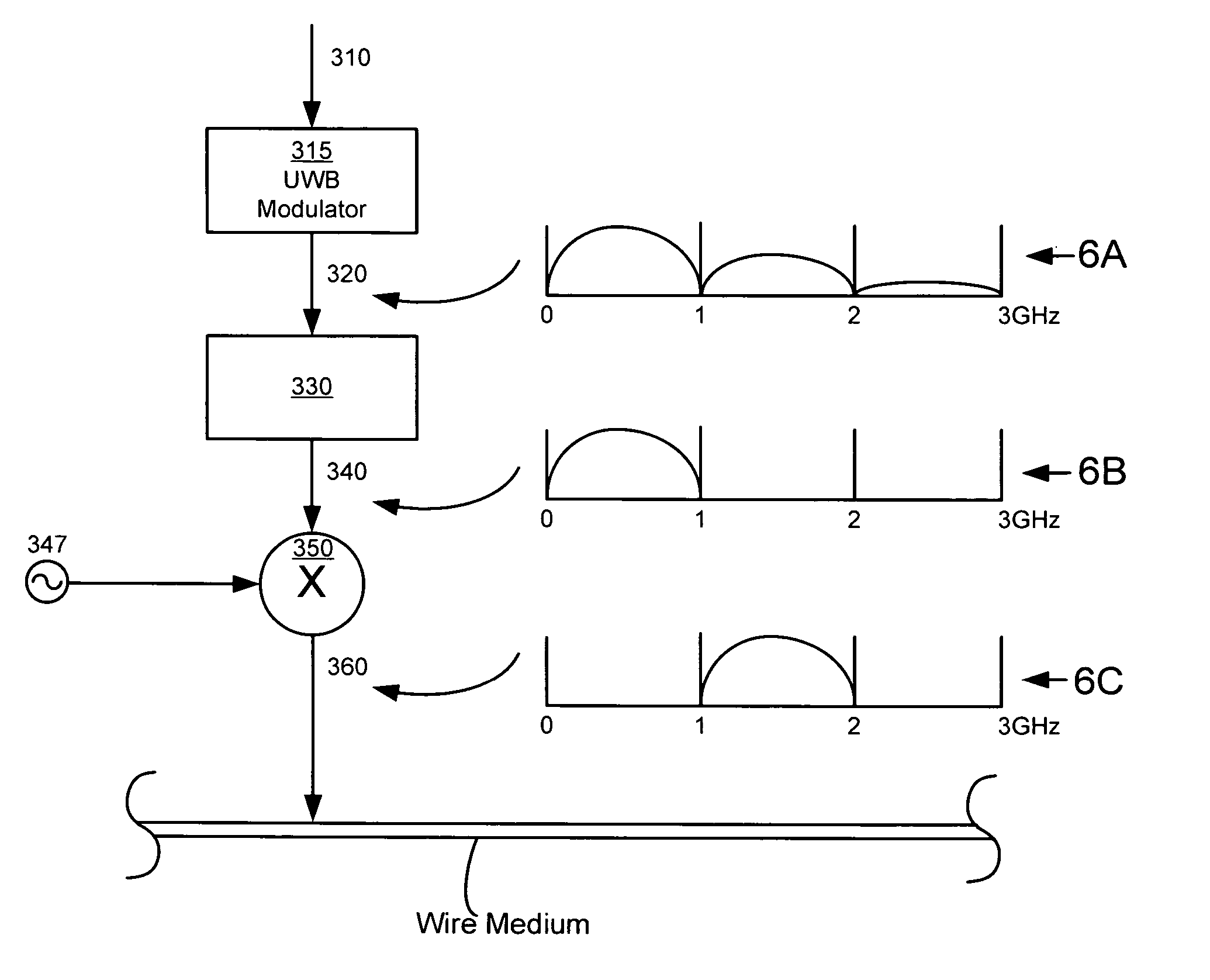
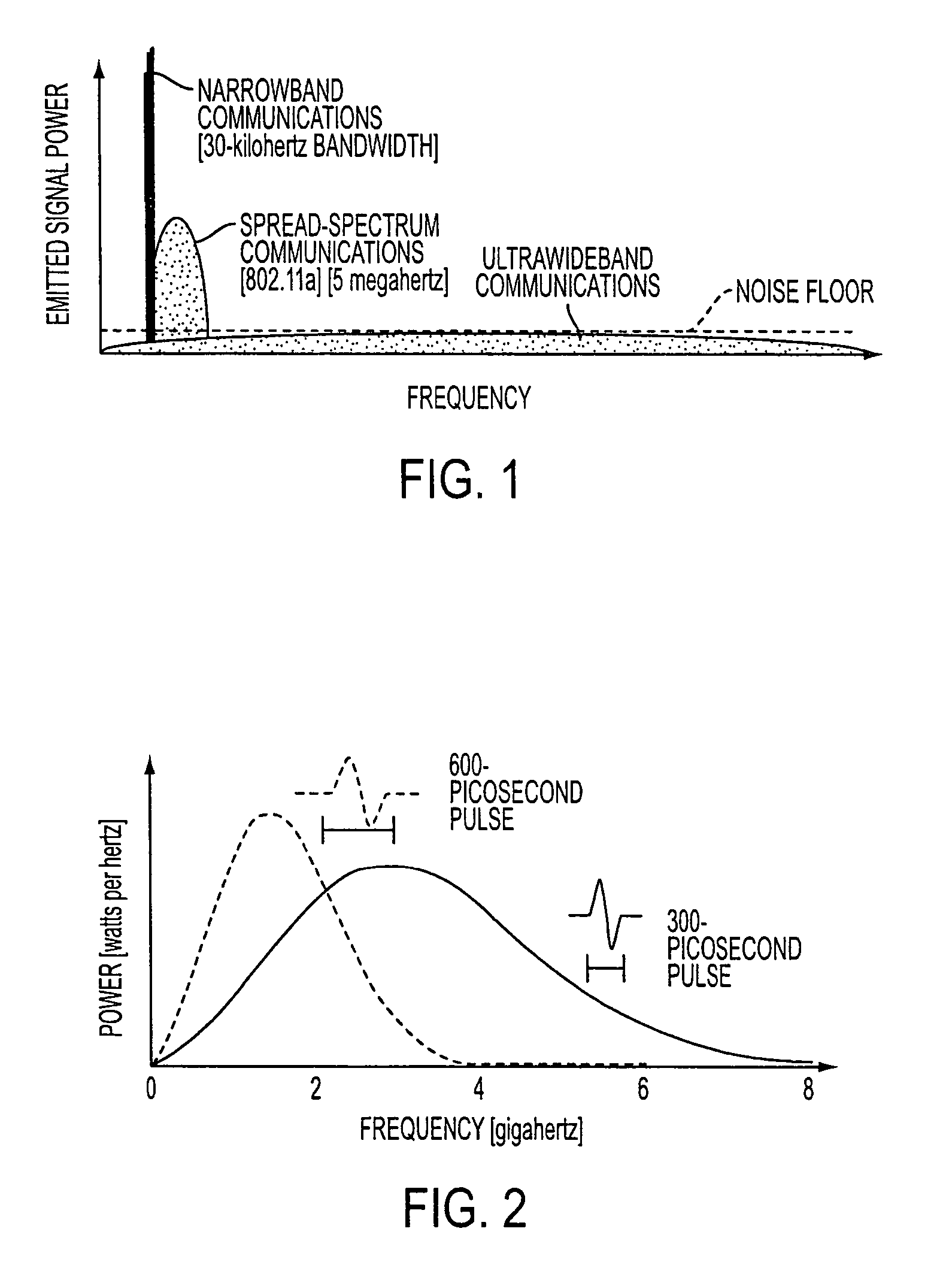
Ultra-wideband communication through a wire medium
InactiveUS7099368B2High bandwidthImprove rendering capabilitiesTransmission/receiving by adding signal to wavePolarisation multiplex systemsUltra-widebandSubject matter
Methods and apparatus for creating, transmitting and receiving ultra-wideband pulses through wire media are presented. One embodiment of the present invention transmits ultra-wideband pulses that occupy radio frequencies that are not used by other electromagnetic signals present in a wire medium of interest. Other embodiments of the invention may create, transmit, and receive ultra-wideband pulses that use radio frequency(s) that are not used by other signals present on wire media within a wire network of interest. This Abstract is provided for the sole purpose of complying with the Abstract requirement rules that allow a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the explicit understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:INTELLECTUAL VENTURES HLDG 73
Broadband communications access device
InactiveUS7257106B2Network traffic/resource managementTime-division multiplexCable telephonyShared resource
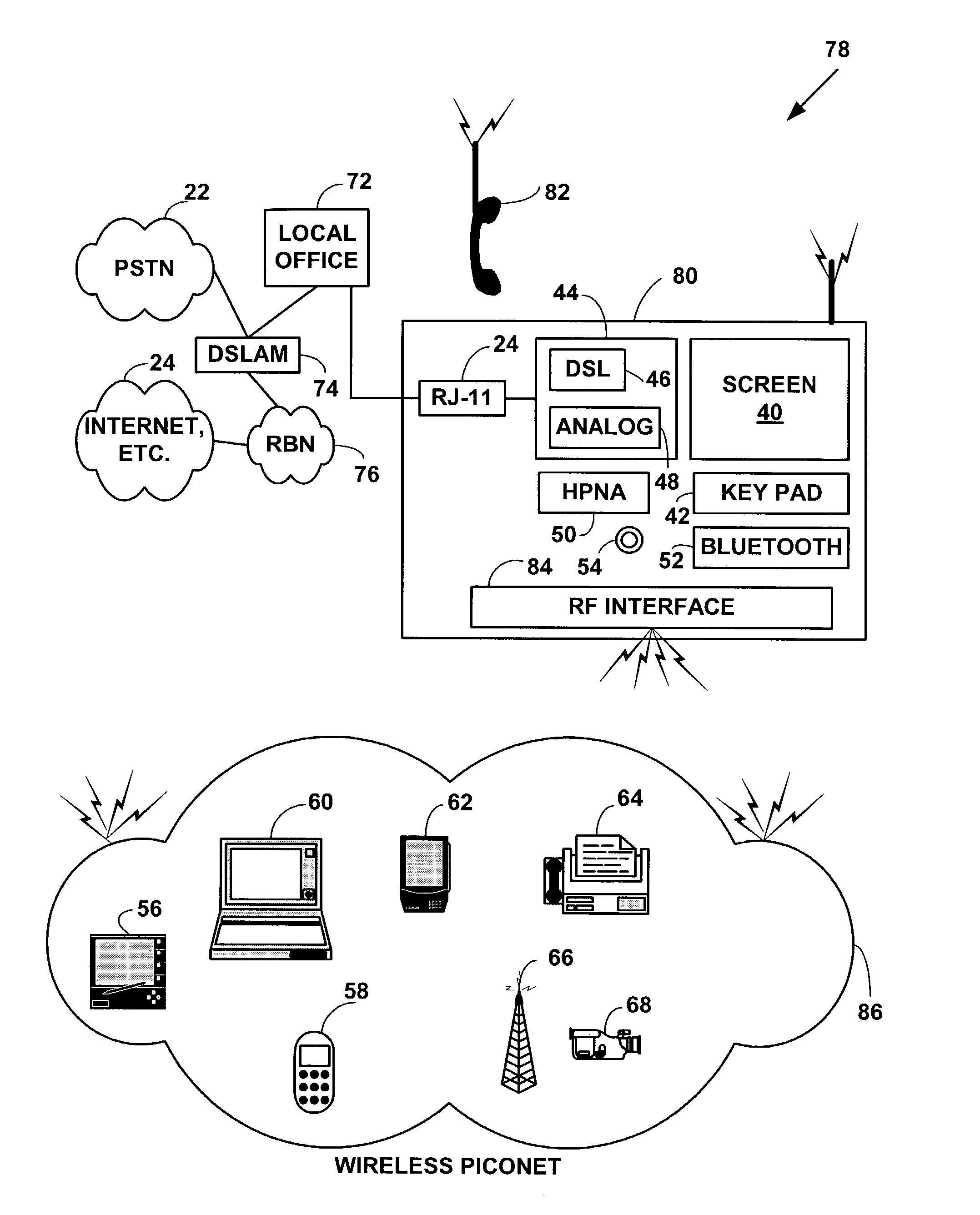
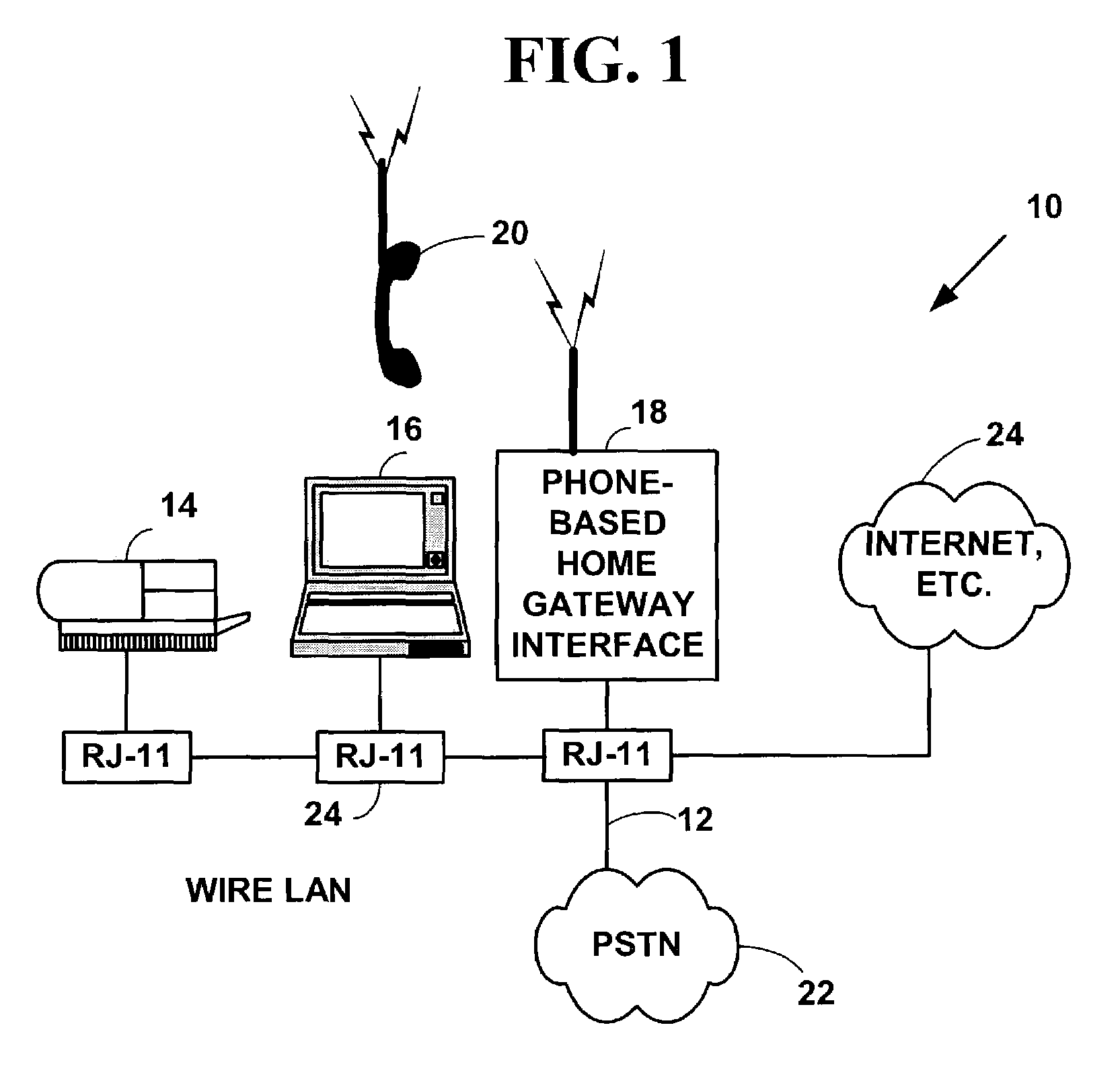
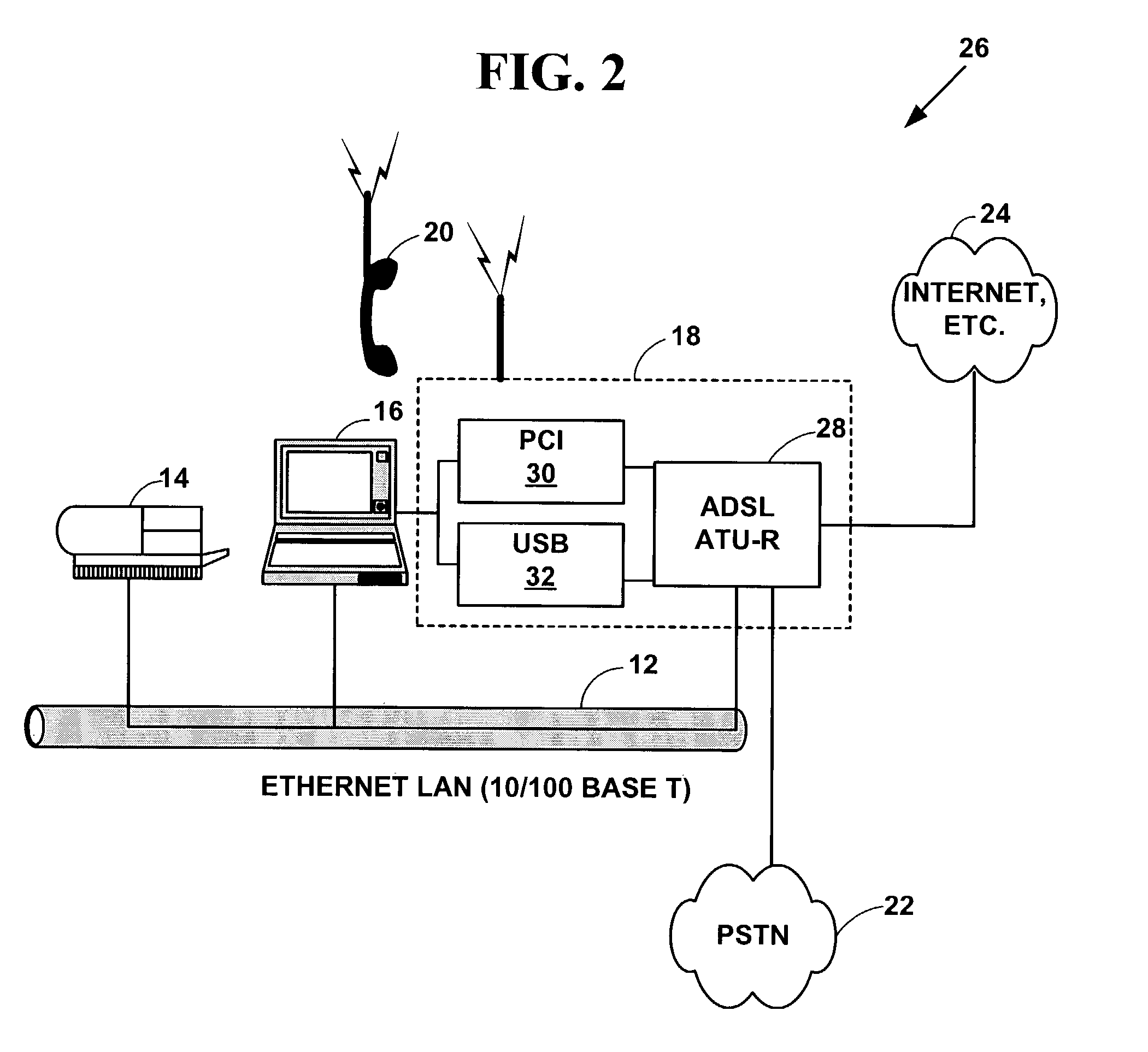
An integrated phone-based home gateway system. The integrated phone-based home gateway system is a multi-function wireless and wired networking, wireless and wired telephony, broadband, gateway device. It provides automatic wireless and wired broadband initialization, configuration and service provisioning, gateway, routing and bridging functionality, wireless and wired data and telephony functionality and allows resource sharing among multiple wireless and wired devices.
Owner:ZHIGU HLDG
WiFi phone system
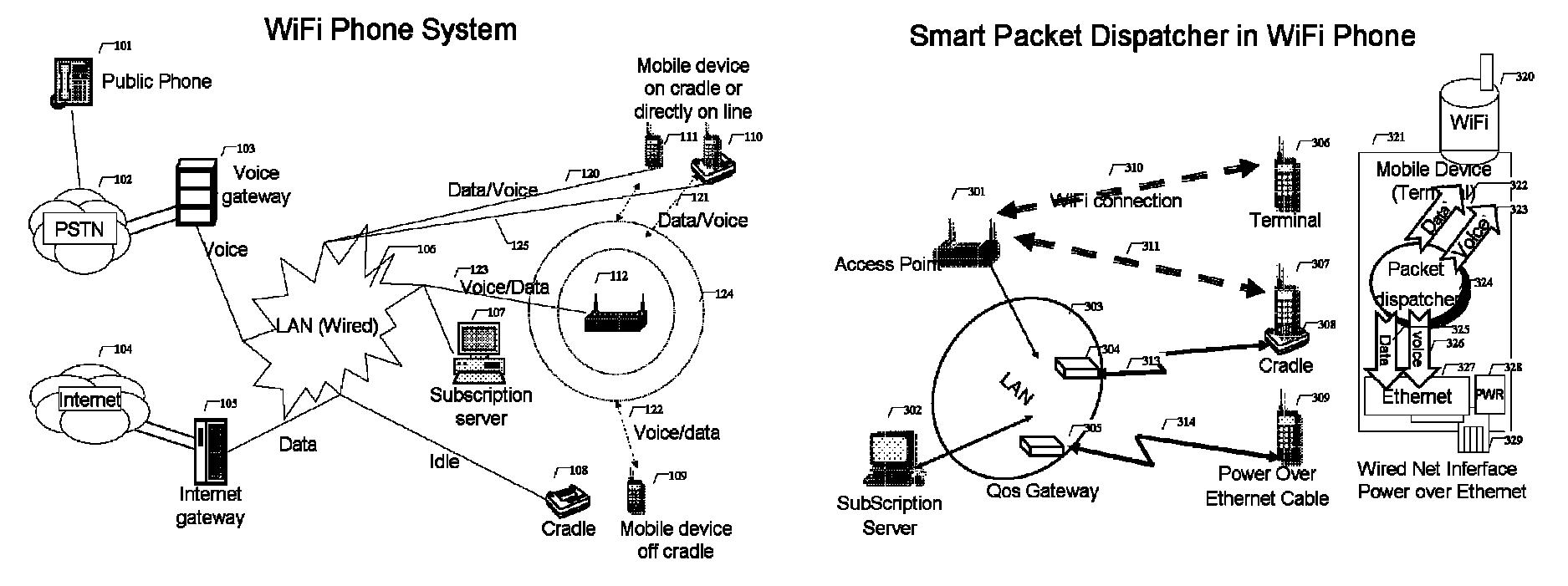
ActiveUS8503340B1Small rangeFast transferNetwork topologiesSubstation equipmentQuality of serviceData stream
A voice communication system over WiFi 802.11 network includes: WiFi phone devices, subscription servers and wireless access points. Through voice and data gateways the system can transfer both voice and data streams through WiFi; Phone devices with both wired and WiFi wireless interfaces can automatically switches between wired network and wireless network through WiFi access points. Subscription server maintains the current status of each device every time it changes location. Voice packets are prioritized over regular data packets and dispatched to different network interface by smart packet dispatcher. Quality of service for voice conversation over WiFi is achieved by various methods: piggy-tail method and ACK enhancements and other improvements to reduce delay and latency of real time voice packets.
Owner:XU YONGYONG
Location-based testing for wireless data communication networks
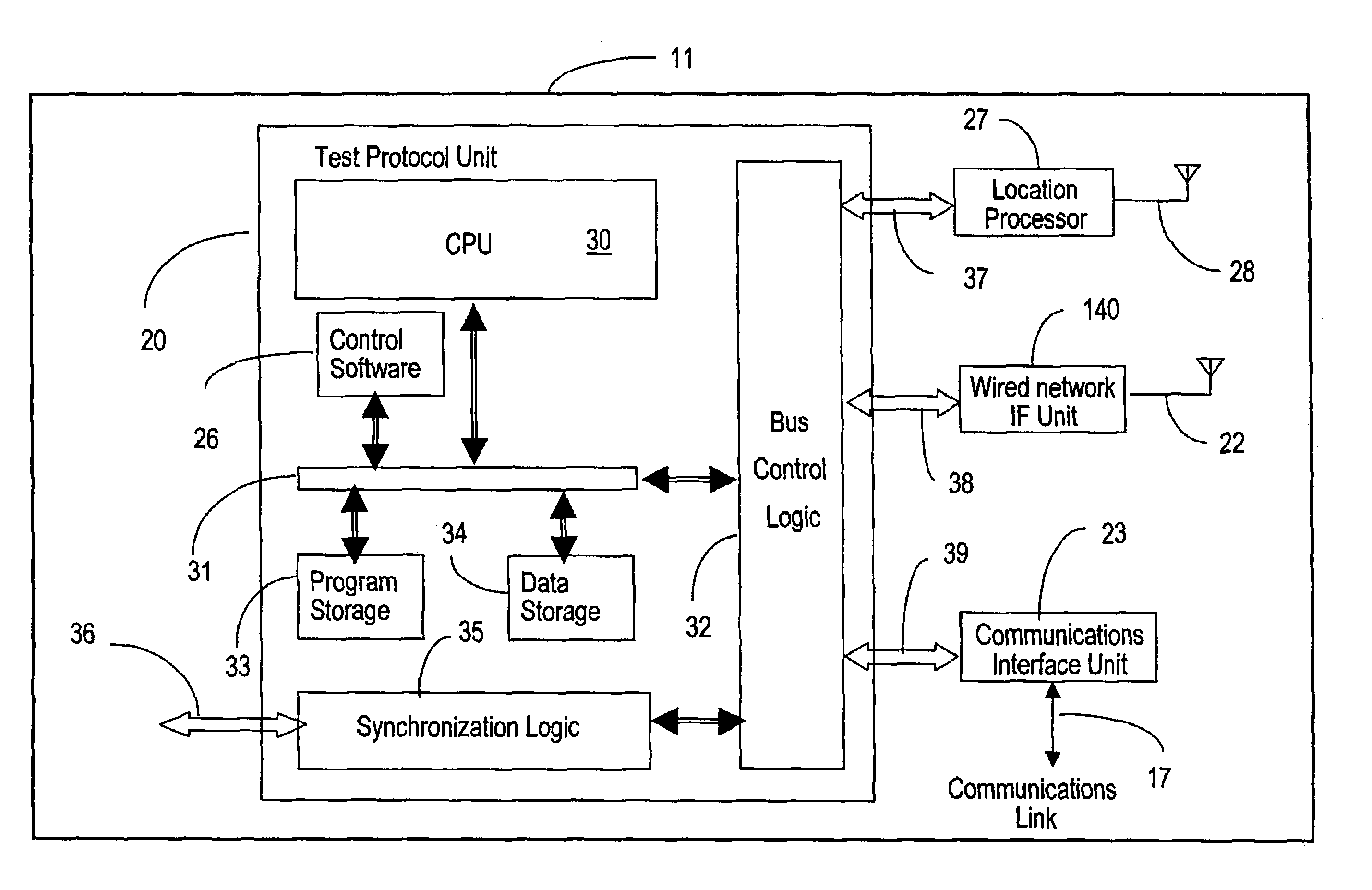
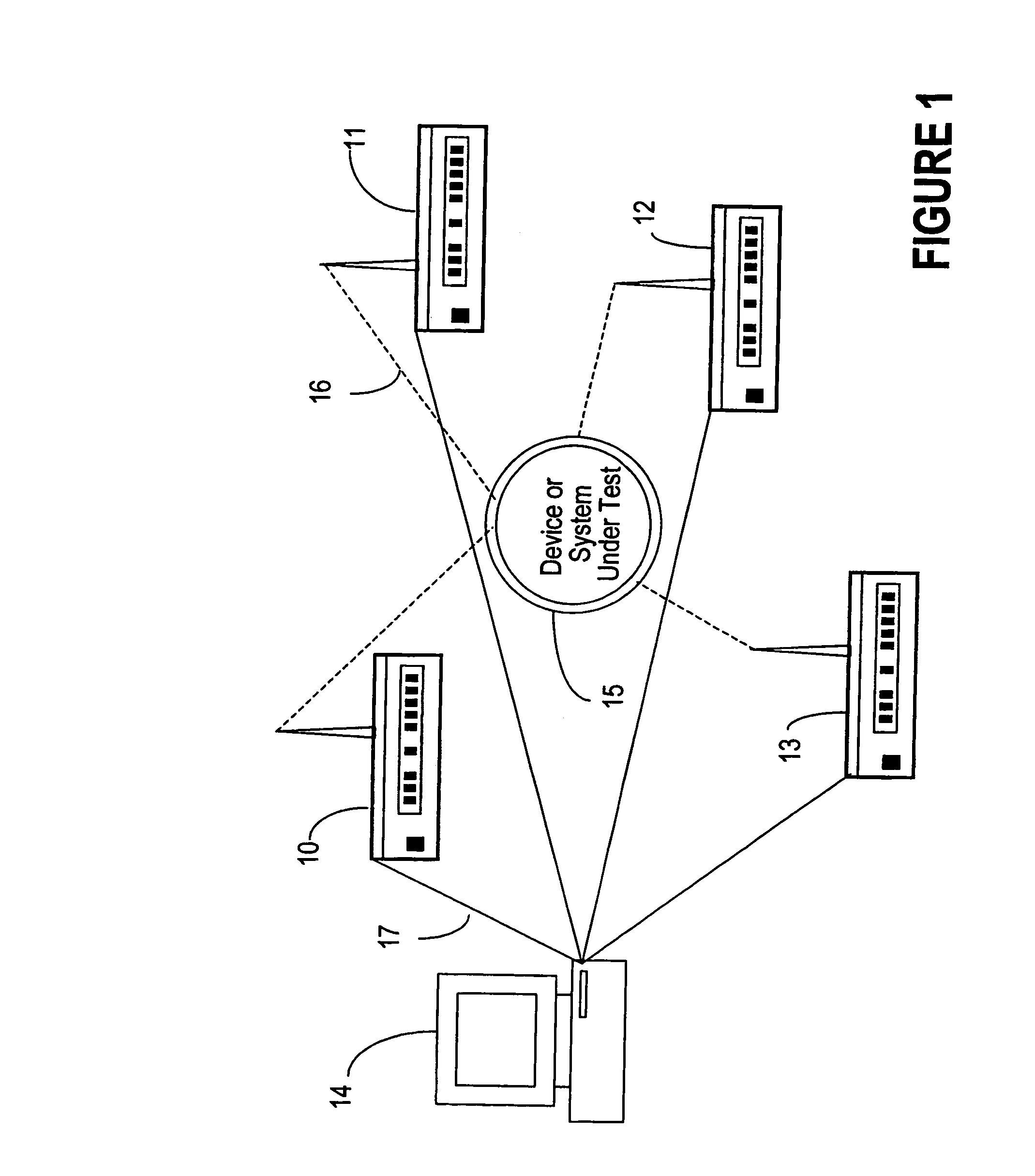
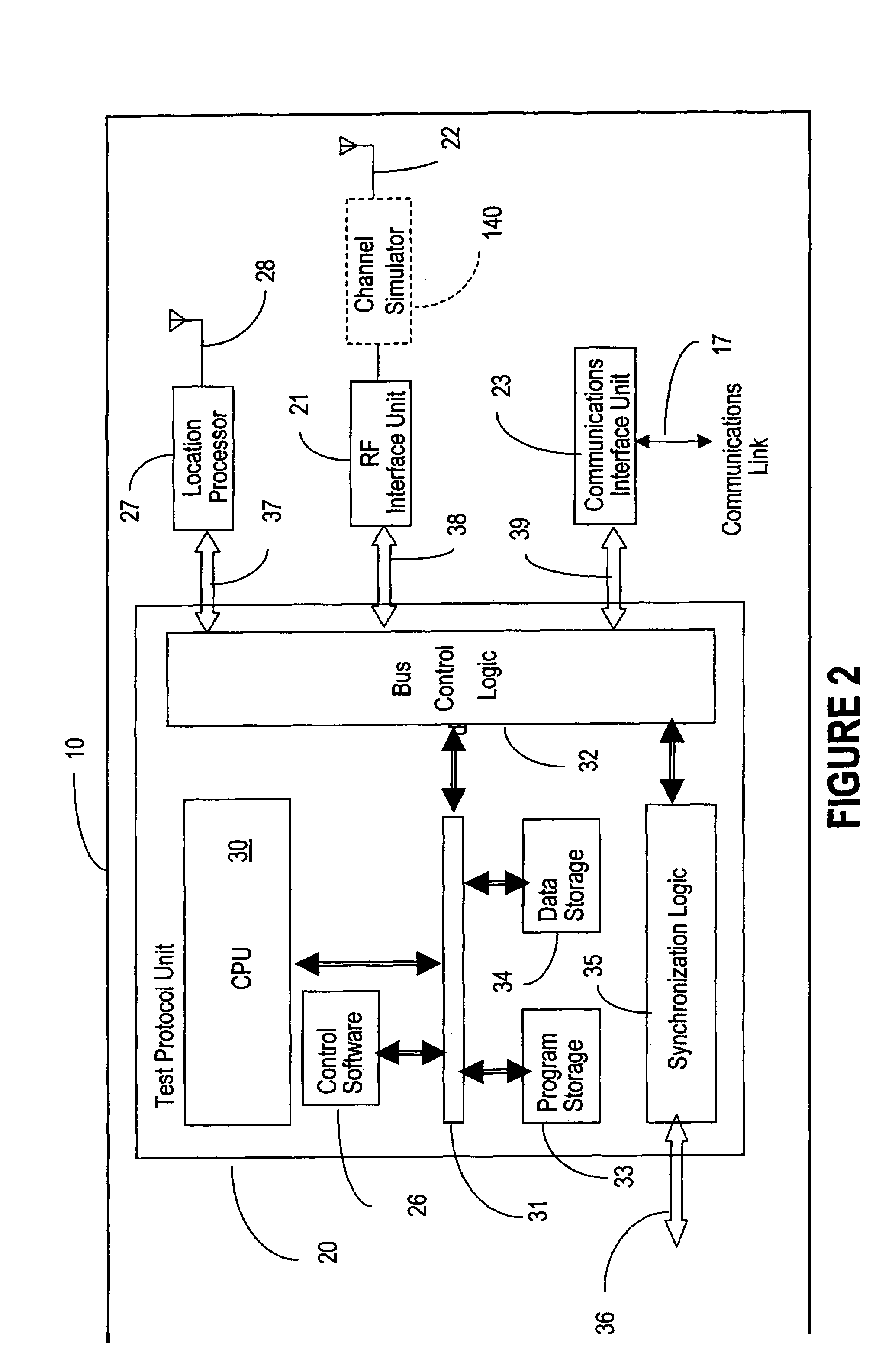
ActiveUS7539489B1Easy to optimizeFacilitate data communicationError preventionFrequency-division multiplex detailsTest stimulusSystem under test
Apparatus and methods facilitating a distributed approach to performance and functionality testing of location-sensitive wireless data communication systems and equipment are described. A plurality of test units, geographically distributed at arbitrary points in a three-dimensional volume surround the system or equipment under test. Each test unit generates test stimuli and records responses from the device under test, and emulates the effects of changes in spatial location within an actual wireless network environment. A central controller co-ordinates the set of test units to ensure that they act as a logical whole, and enables testing to be performed in a repeatable manner in spite of the variations introduced by the location sensitive characteristics of wireless data communication networks. The central controller also maintains a user interface that provides a unified view of the complete test system, and a unified view of the behavior of the system or equipment under test. For diagnostic purposes, the recorded responses may be regenerated to view any defects as many times as necessary to correct them. Alternatively, each test unit may have either wired network interface units, instead of a wireless interface unit to test systems or equipment forming part of a wired network portion in the wireless data communication system.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
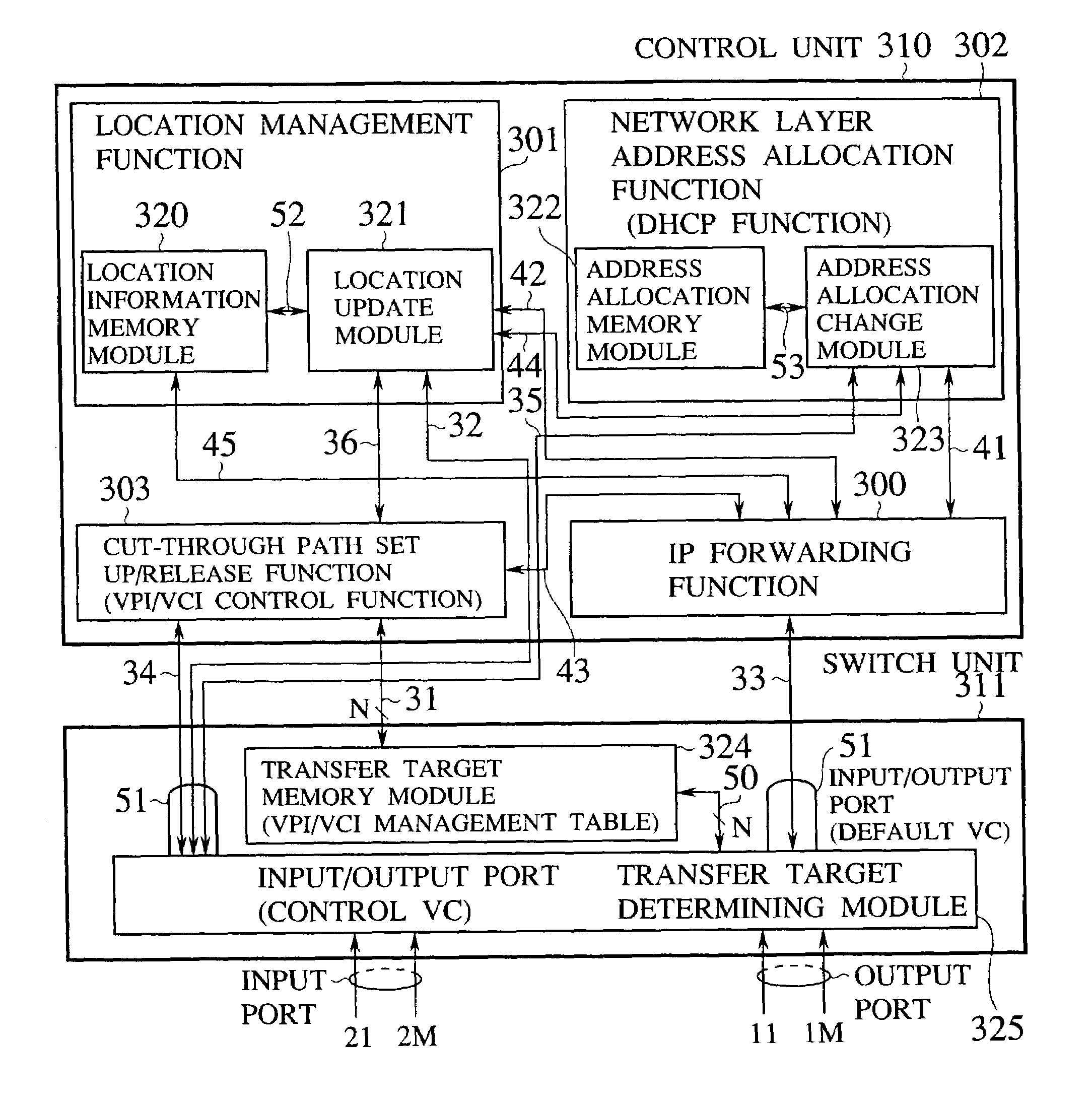
Router device, datagram transfer method and communication system realizing handoff control for mobile terminals
InactiveUS7151758B2Increase speedEasy to controlData switching by path configurationWireless network protocolsCommunications systemHandoff control
A mobile supporting router device for realizing the handoff control associated with the moving in high speed is forms by at least one first interface connected with radio base stations, each capable of accommodating at least one mobile terminal; at least one second interface connected with a wire network; an information exchanging unit for exchanging a routing protocol on a network layer, through the second interface; a memory unit for storing information regarding a routing on the network layer based on the routing protocol exchanged by the information exchanging unit; a transfer unit for transferring datagram through the first interface according to the information regarding the routing on the network layer stored in the memory unit; a moving detection unit for detecting a moving of the mobile terminal among the radio base stations; and an information updating unit for updating the information regarding the routing on the network layer stored in the memory unit when the moving of the mobile terminal is detected by the moving detection unit.
Owner:KK TOSHIBA
Wireless network having real-time channel allocation
ActiveUS20060104232A1Network traffic/resource managementNetwork topologiesTime conditionNetwork architecture
A wireless network having a real-time channel allocation is described herein. In one embodiment, an exemplary network architecture includes, but is not limited to, multiple access points coupled to a wired network, where each of the access points is capable of communicating with one or more mobile nodes over a wireless network. The exemplary network architecture further includes a controller coupled to the access points over the wired network. The controller maintains one or more parameters that control one or more characteristics of each access points. The controller adjusts and communicates the one or more parameters to each of the access points in response to a detection of real-time conditions changed. Other methods and apparatuses are also described.
Owner:GIDWANI SANJAY M
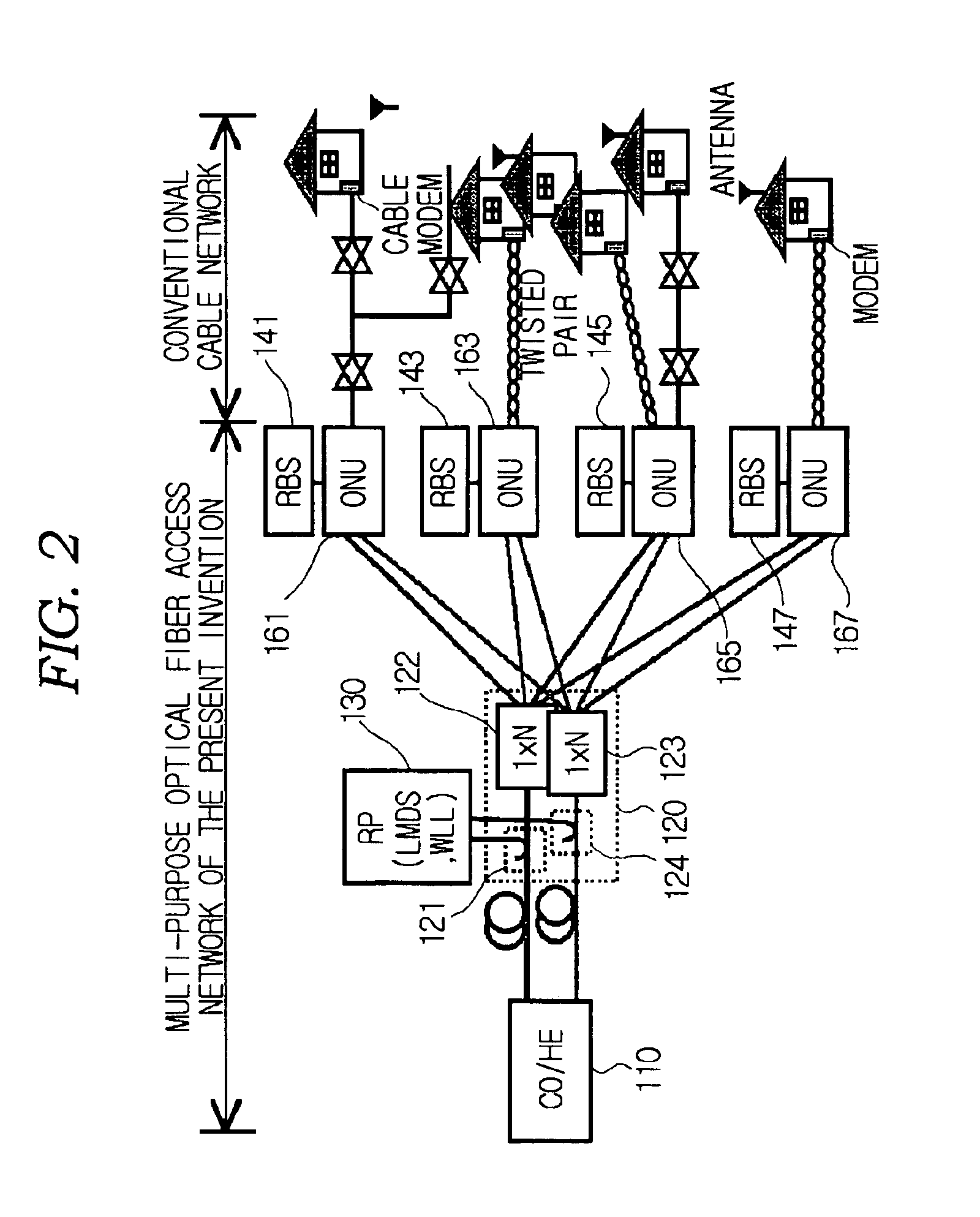
Multi-purpose optical fiber access network
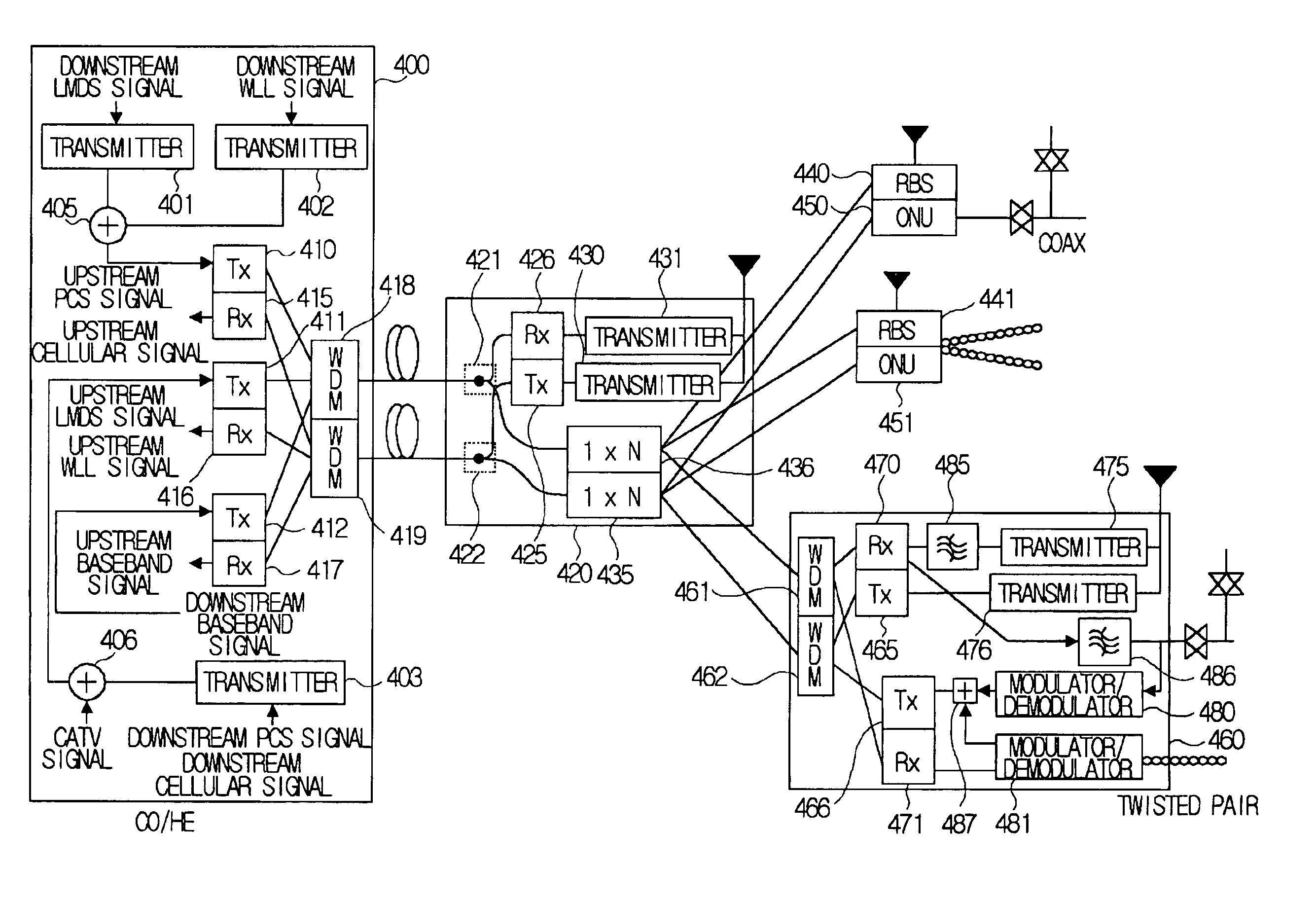
InactiveUS6895185B1Wavelength-division multiplex systemsWireless communicationAccess networkCoaxial cable
The present invention relates to an optical fiber access network, and more particularly, to a multi-purpose optical fiber access network capable of accepting all services provided by hybrid wireline / wireless access network.According to the present invention, in an optical fiber access network of double star structure where a central office / headend and several optical network units are connected through a splitting / combining device, a multi-purpose optical fiber access network capable of accepting not only wired telephone service, wired CATV and wired data service but also various kinds of wireless services including LMDS, WLL, PCS and so forth, in which LMDS local wireless base station is located in a place adjacent to the splitting / combining device, WLL local wireless base station is located in a place adjacent to the splitting / combining device, optical network unit connects the conventional wired network composed of said optical fiber access network, twisted pair and coaxial cable, telephone service, data service and CATV service are provided through the optical network unit and PCS local wireless base station is located in a place adjacent to the optical network unit, is provided.
Owner:KOREA ADVANCED INST OF SCI & TECH
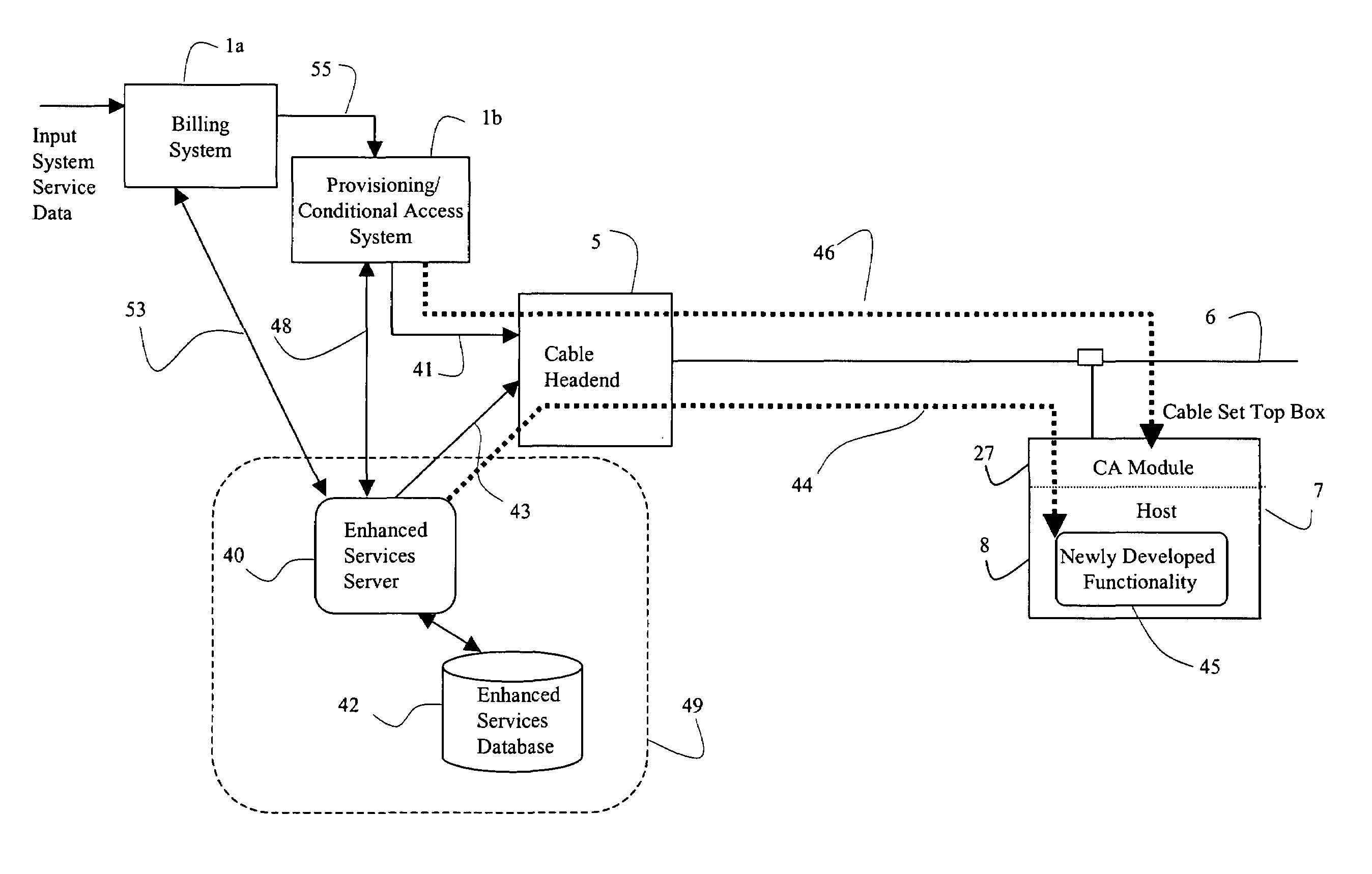
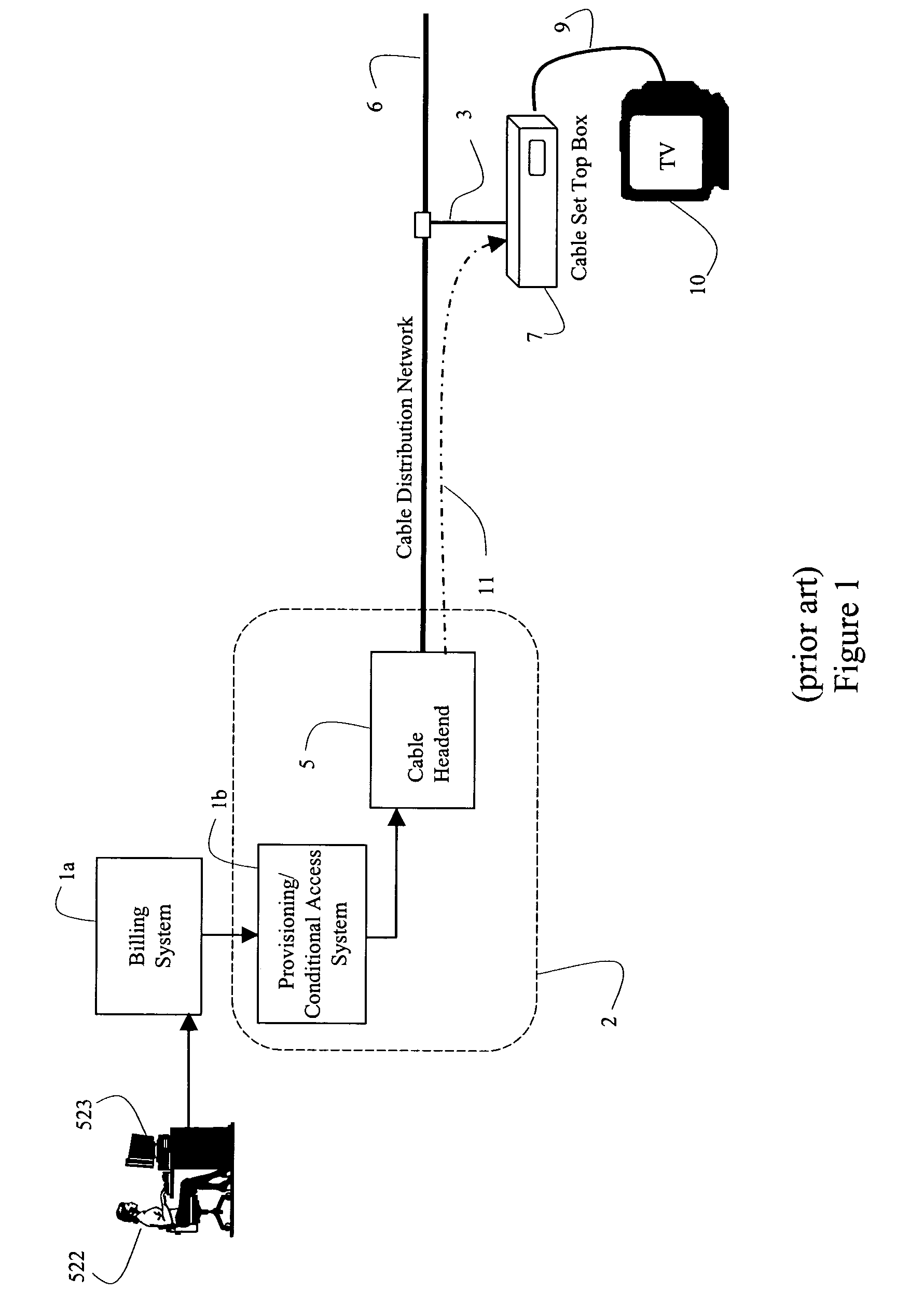
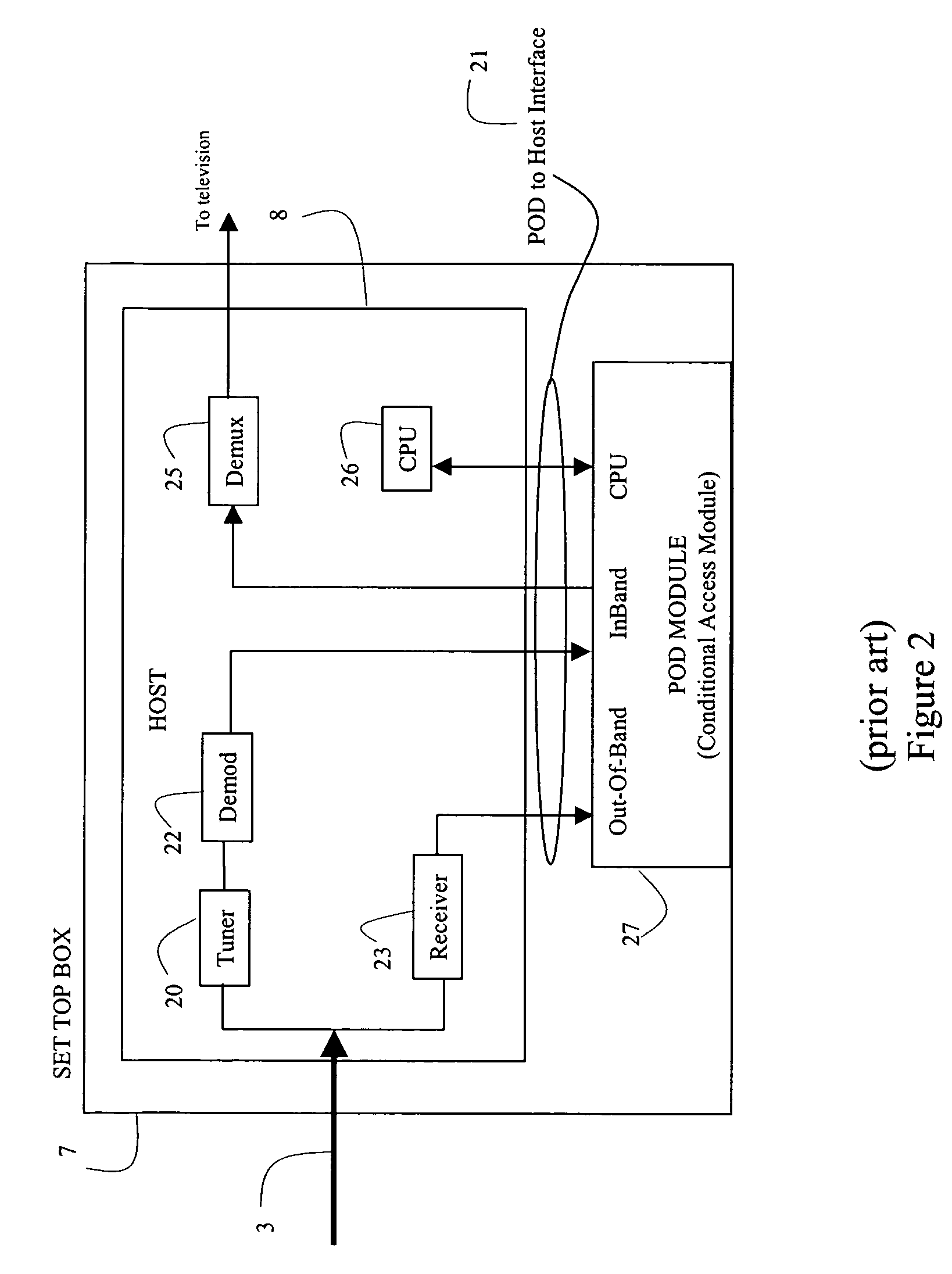
Systems and methods for provisioning a host device for enhanced services in a cable system
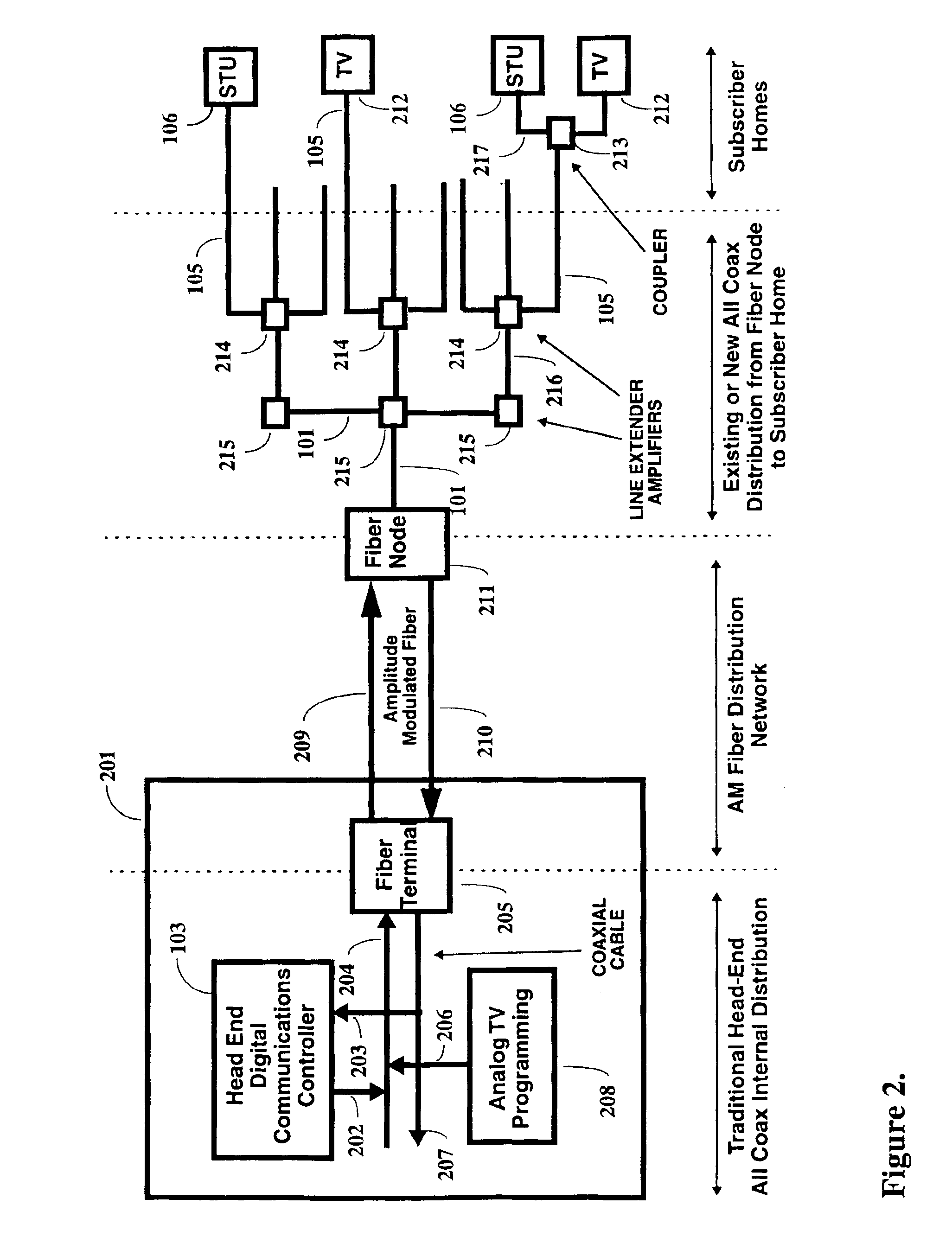
ActiveUS7194756B2Good flexibilityAnalogue secracy/subscription systemsMultiple digital computer combinationsComputer scienceEnhanced service
Flexible systems and methods are disclosed that may be used for provisioning, configuring, and controlling a host embodied in a cable set top box or other digital device attached to a digital communication network, such as cable distribution network. An enhanced services system maintains various host files for various types of hosts that a cable subscriber may purchase and connect to the cable network. The Enhanced Services Server interacts with the host using the host files. The host files may be downloaded from the host manufacturer into a database that distributes the modules as required to the various enhanced services systems. The host may be purchased by the cable subscriber and provisioning may be initiated by the retailer at the time of purchase using a provisioning network interacting with the appropriate cable system serving the subscriber. This abstract is not intended to limit or construe the scope of the claims.
Owner:ERICSSON TELEVISION
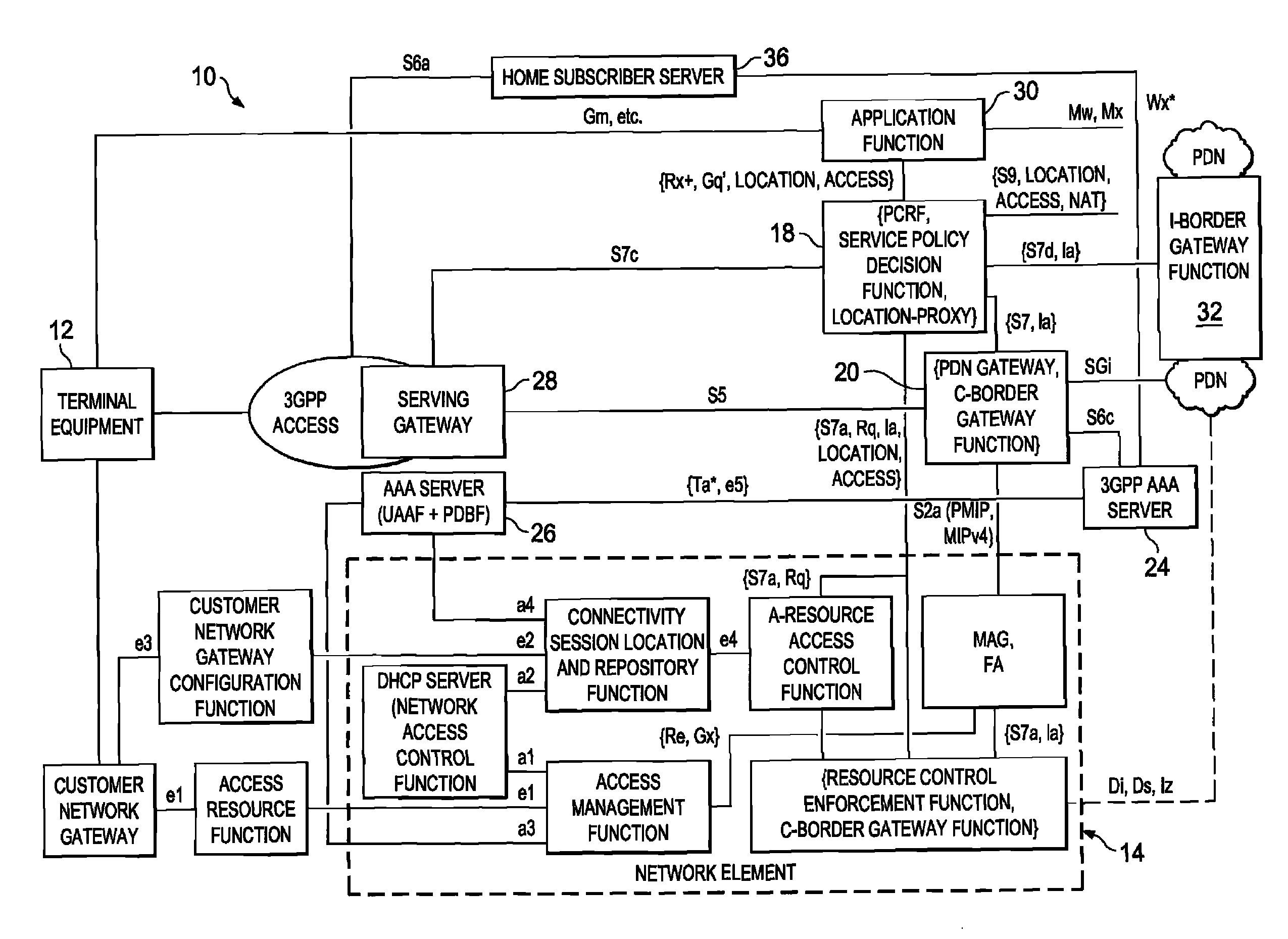
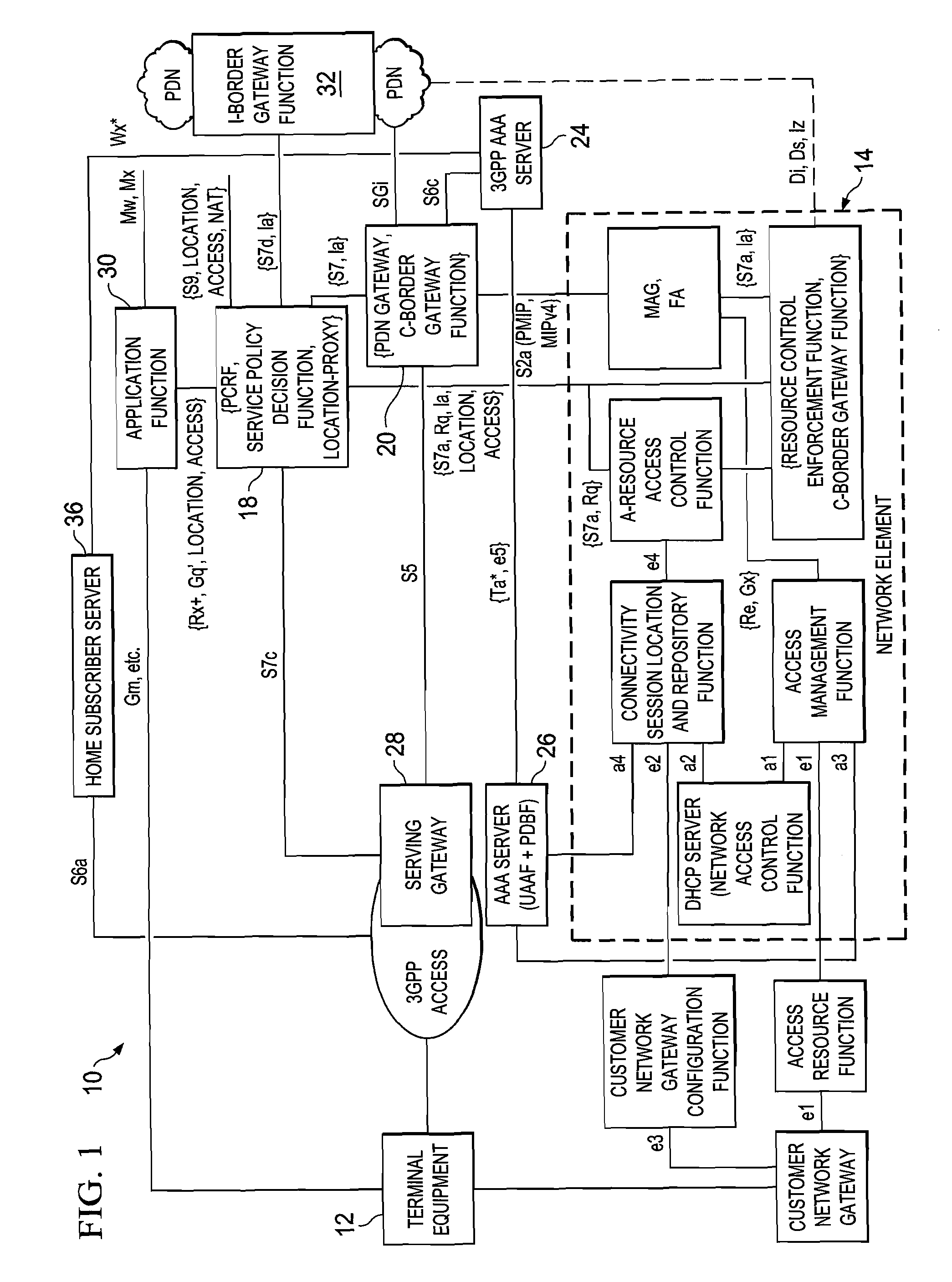
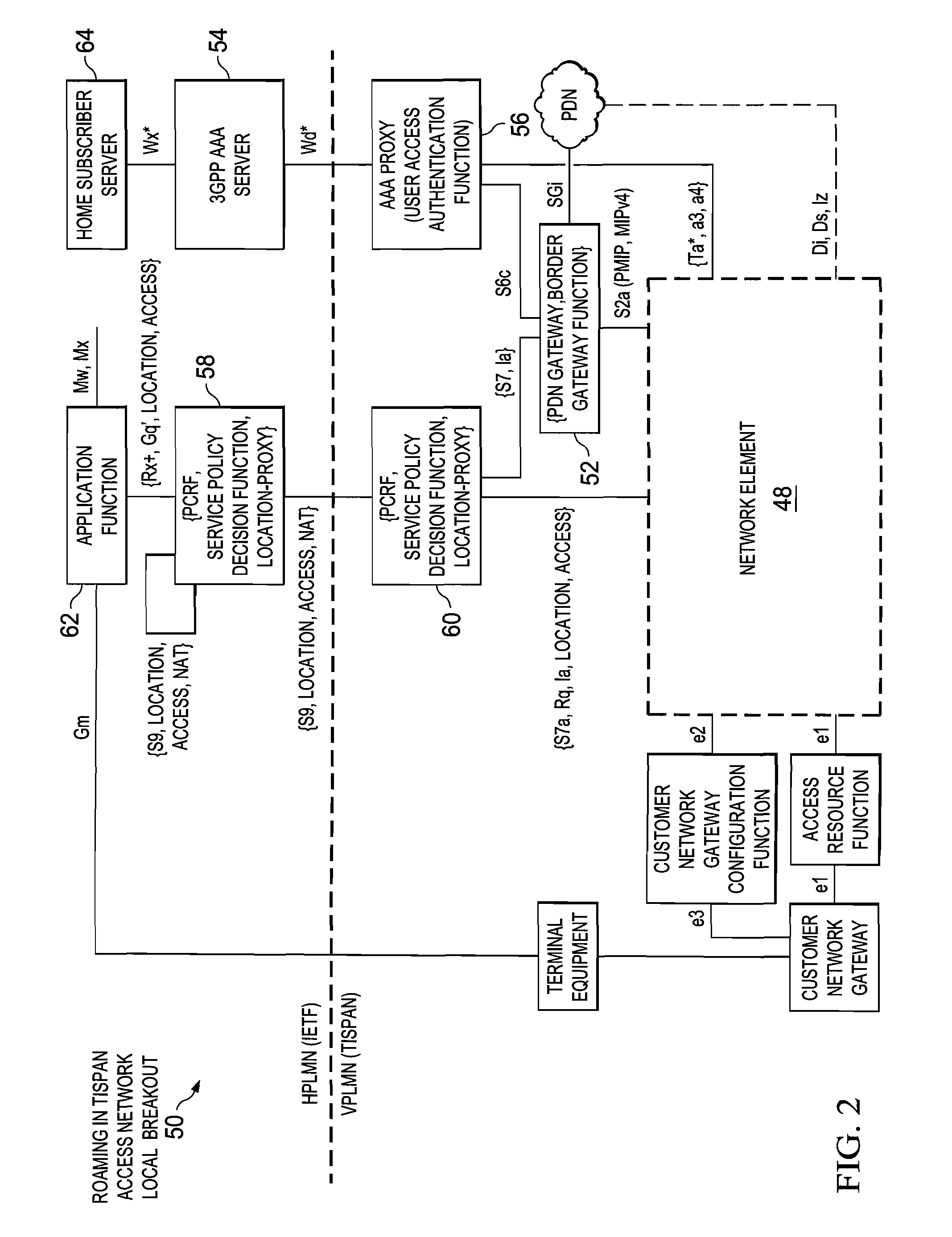
System and method for providing location and access network information support in a network environment
ActiveUS7899039B2Accounting/billing servicesNetwork traffic/resource managementAccess networkApplication software
A method is provided in one example embodiment and includes communicating location and access network information for an end user to a policy and charging rules function (PCRF) element that is coupled to a network element. The network element receives packets for a communications flow from the end user if the flow is initiated through a wireless network and through a wireline network. In more specific embodiments, the location and access network information is used to initiate one or more applications for the end user. The method could also include communicating to an application function that the end user has attached to one of the networks, has been assigned an Internet Protocol (IP) address, and the location and access network information for the end user.
Owner:CISCO TECH INC
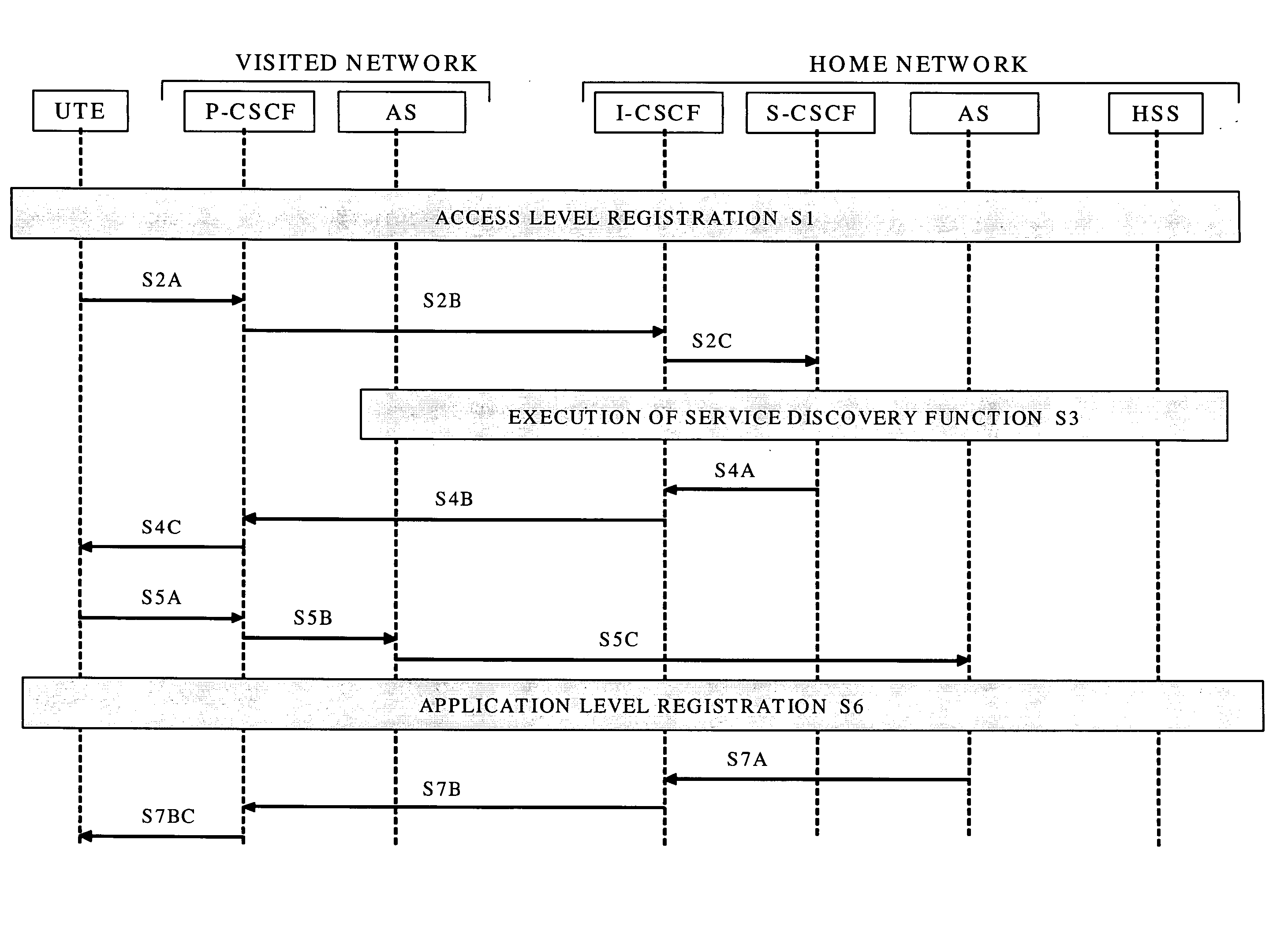
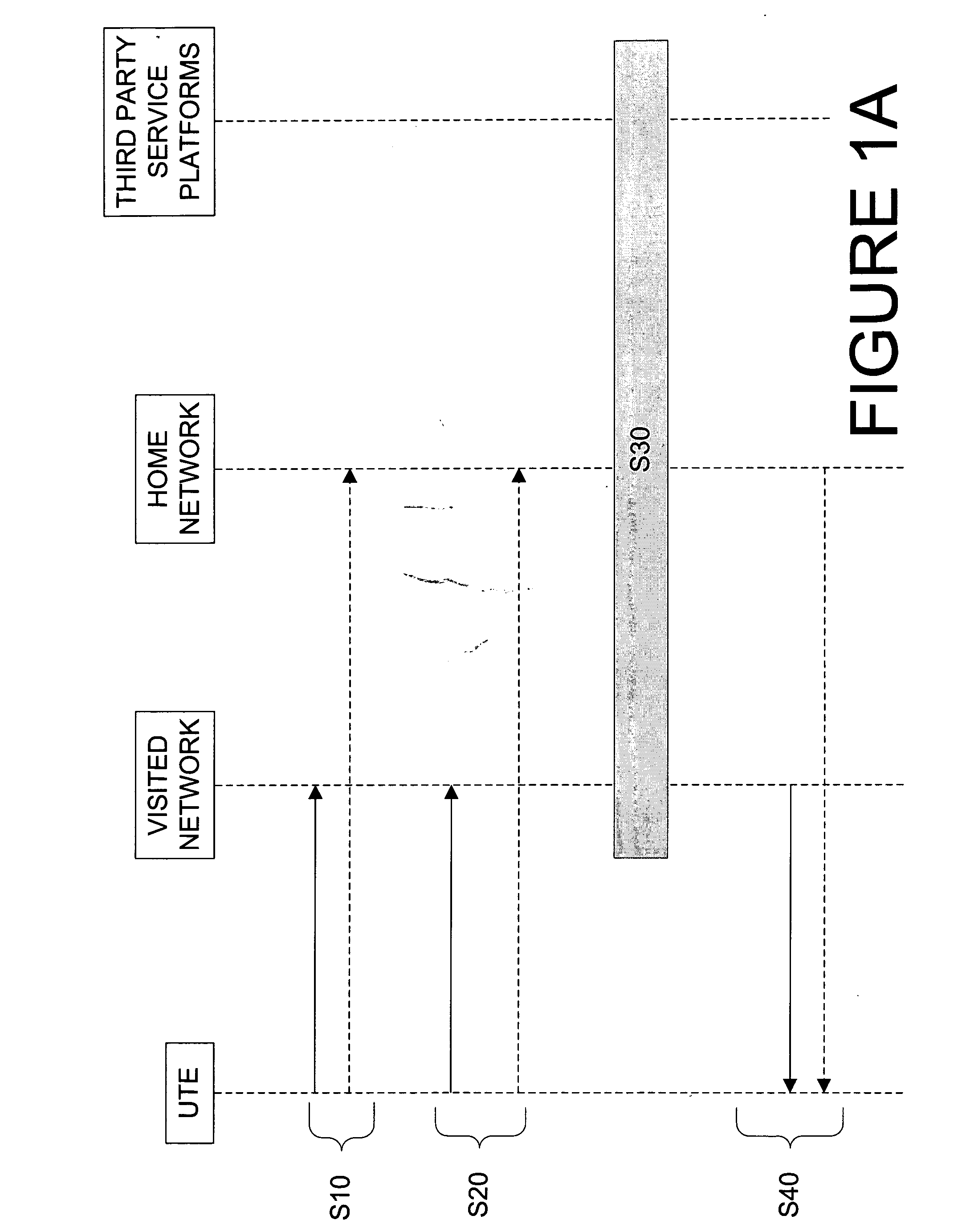
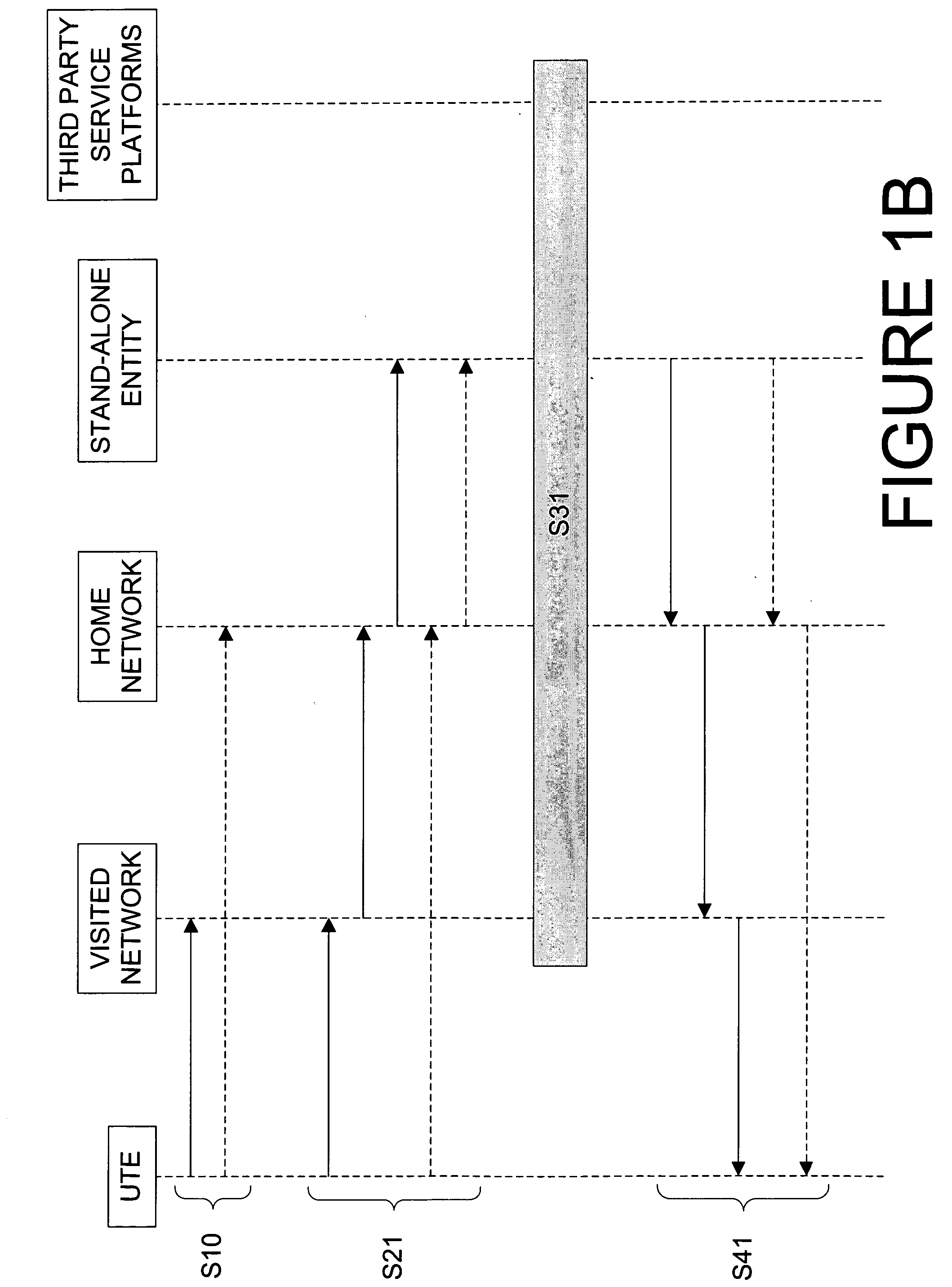
Service discovery method in a network
A centralized service discovery process performed in a data or telecommunications network collects a list of services available to user terminal equipment connected to a network based on user-specific data (e.g., the user's identification and preferences, the location and capabilities of the user terminal equipment). The list of services is then communicated to the user. The list of services may include home environment (HE) services the user is authorized to receive by a home network, and value-added services being offered to the user by the home network, a visited network, or third party service platforms. Both application and bearer services may further be collected in the list of available services. The service discovery process can be integrated in wireless and wireline networks, or implemented in a stand-alone service enabler.
Owner:LUCENT TECH INC
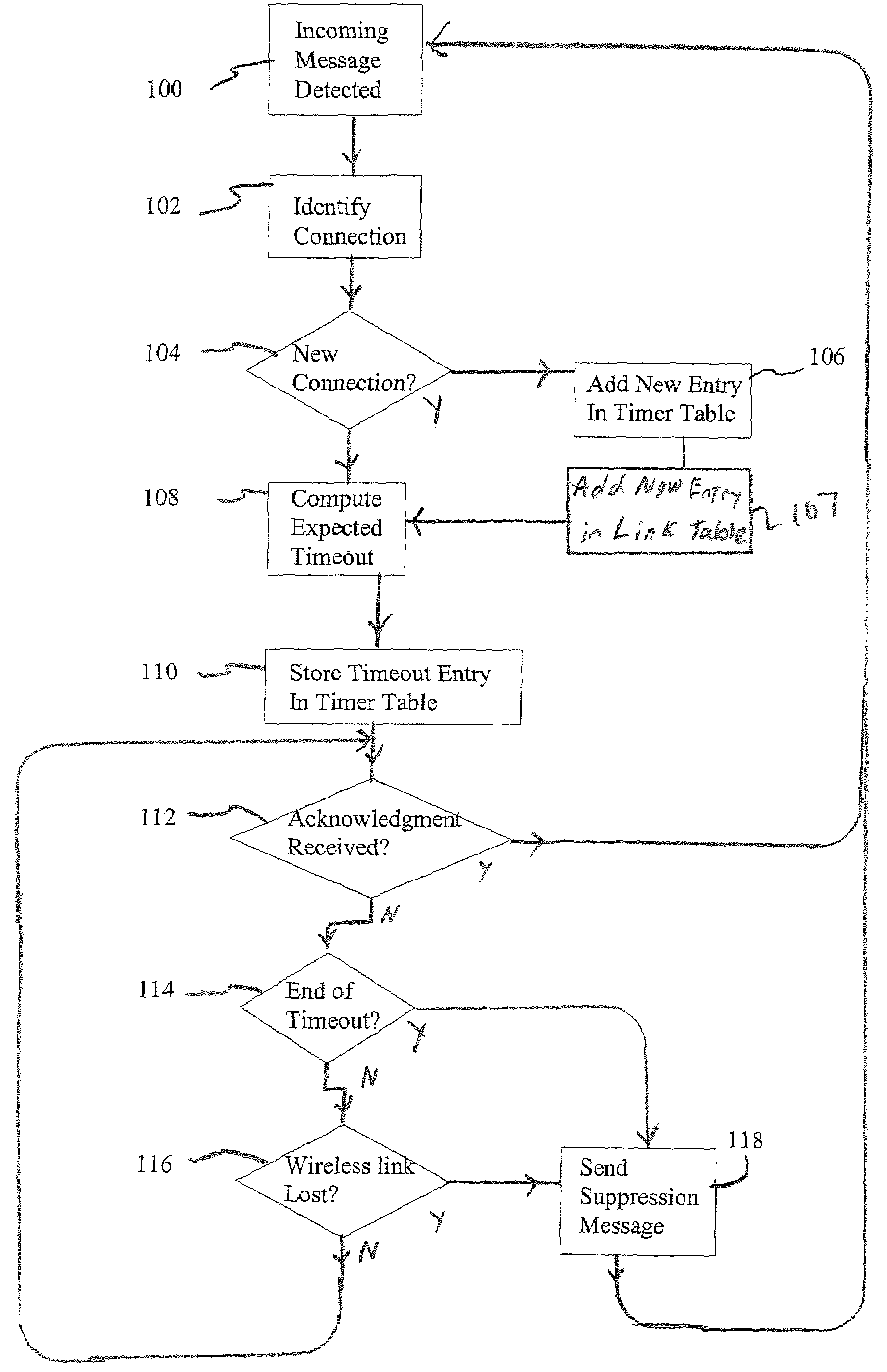
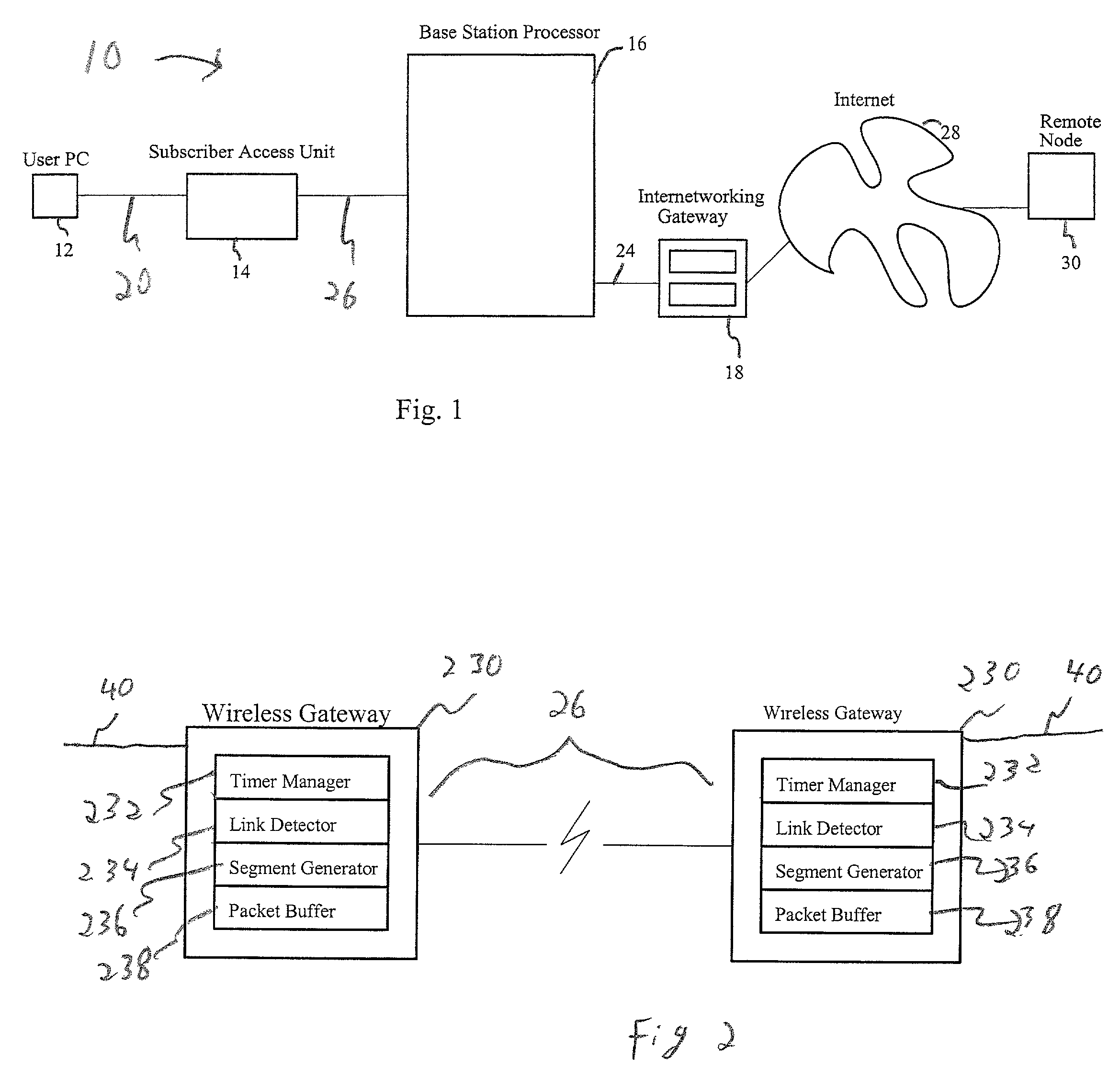
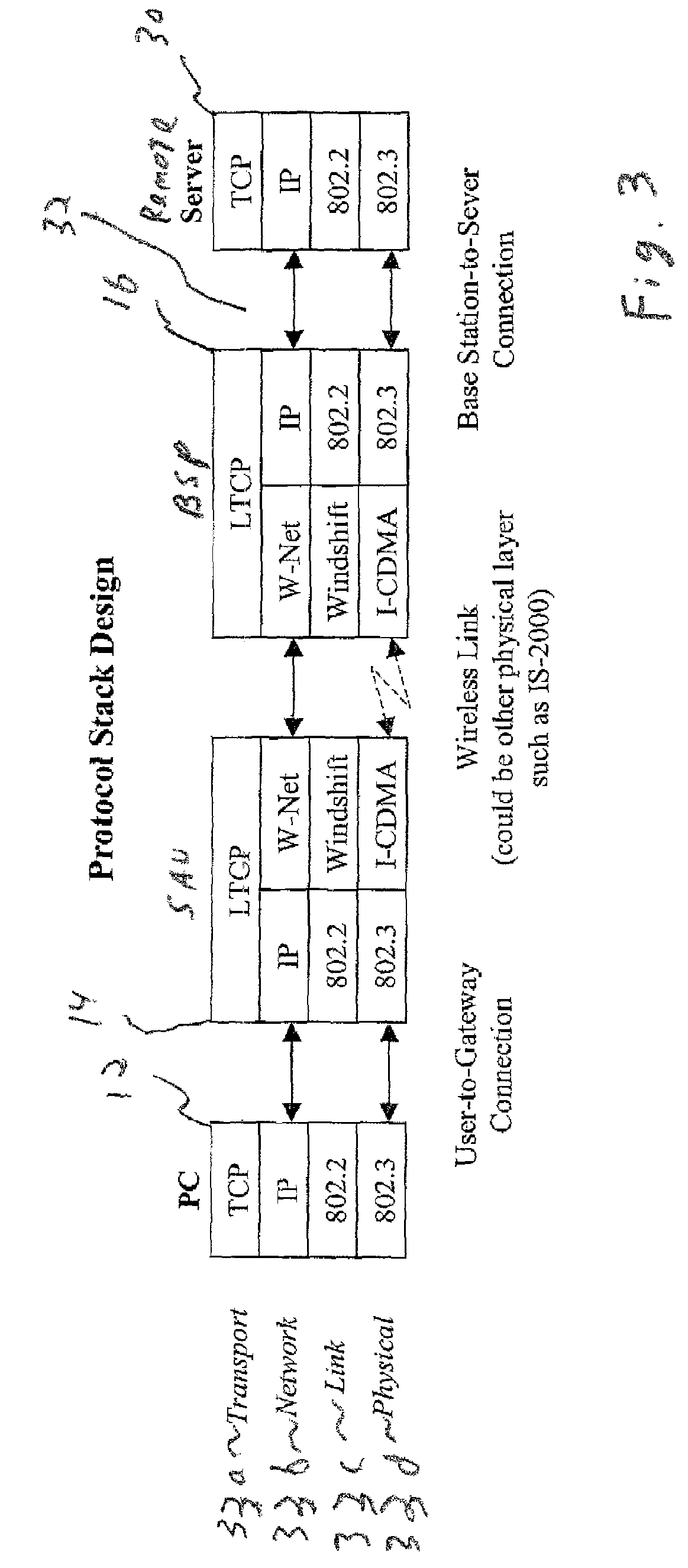
Link-aware transmission control protocol
InactiveUS7184401B2Reduction in message throughput caused by congestion control mechanisms is avoidedAvoid controlError prevention/detection by using return channelFrequency-division multiplex detailsSlow-startBiological activation
In a TCP / IP network, congestion control techniques such as slow start and congestion avoidance are employed. Such networks include wired and wireless links. However, normal operation of the wireless links exhibit different latencies than those exhibited over the wired link. The protocols employed in the wired network do not lend themselves well to efficient communication over wireless connections, and can cause slow start to be triggered. Determining when a sender will timeout due to non-receipt of an ACK, and intervening with a suppression message having an advertised window of zero to pause the user, are employed to prevent congestion control mechanisms such as slow start and congestion avoidance from activation
Owner:IPR LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com