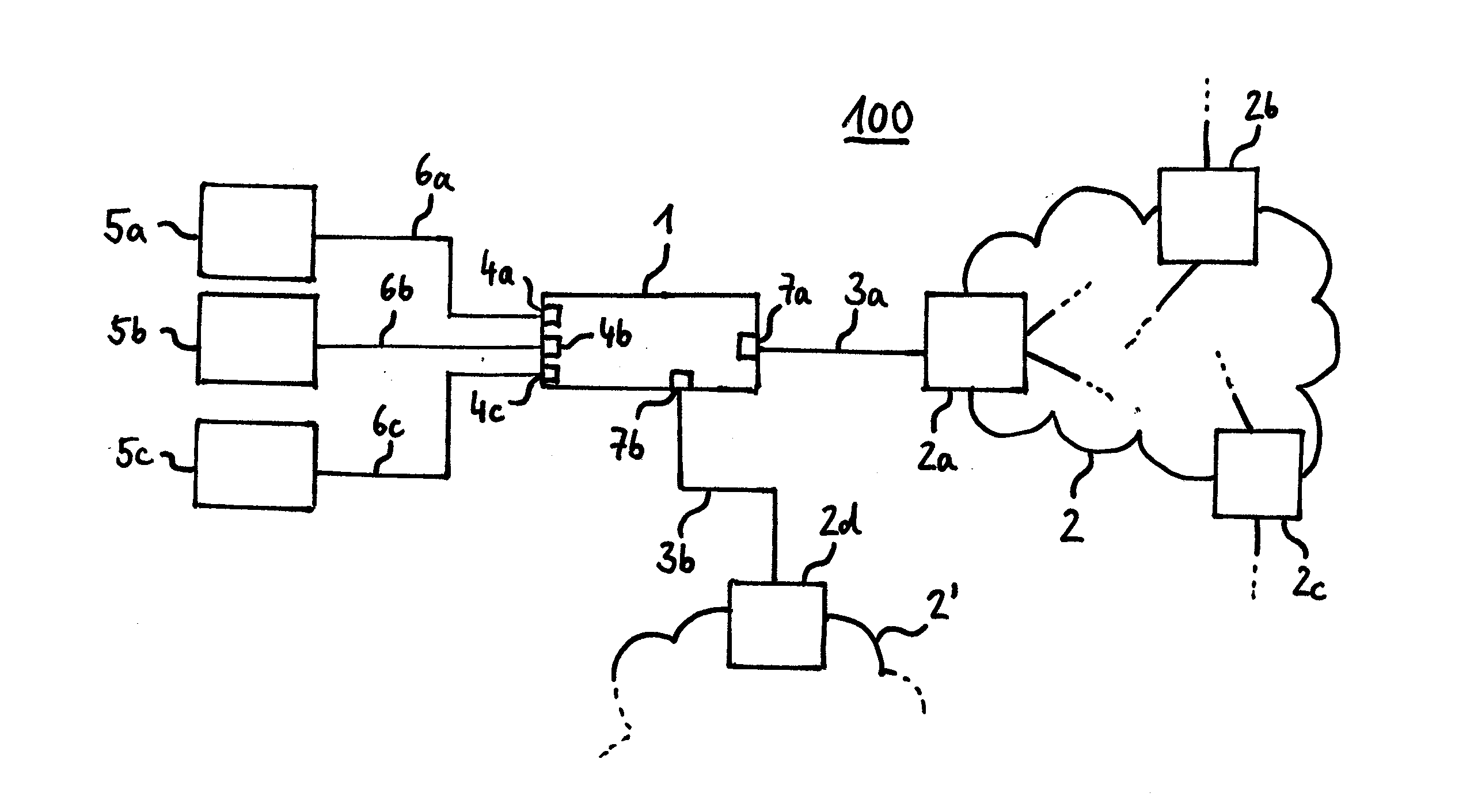
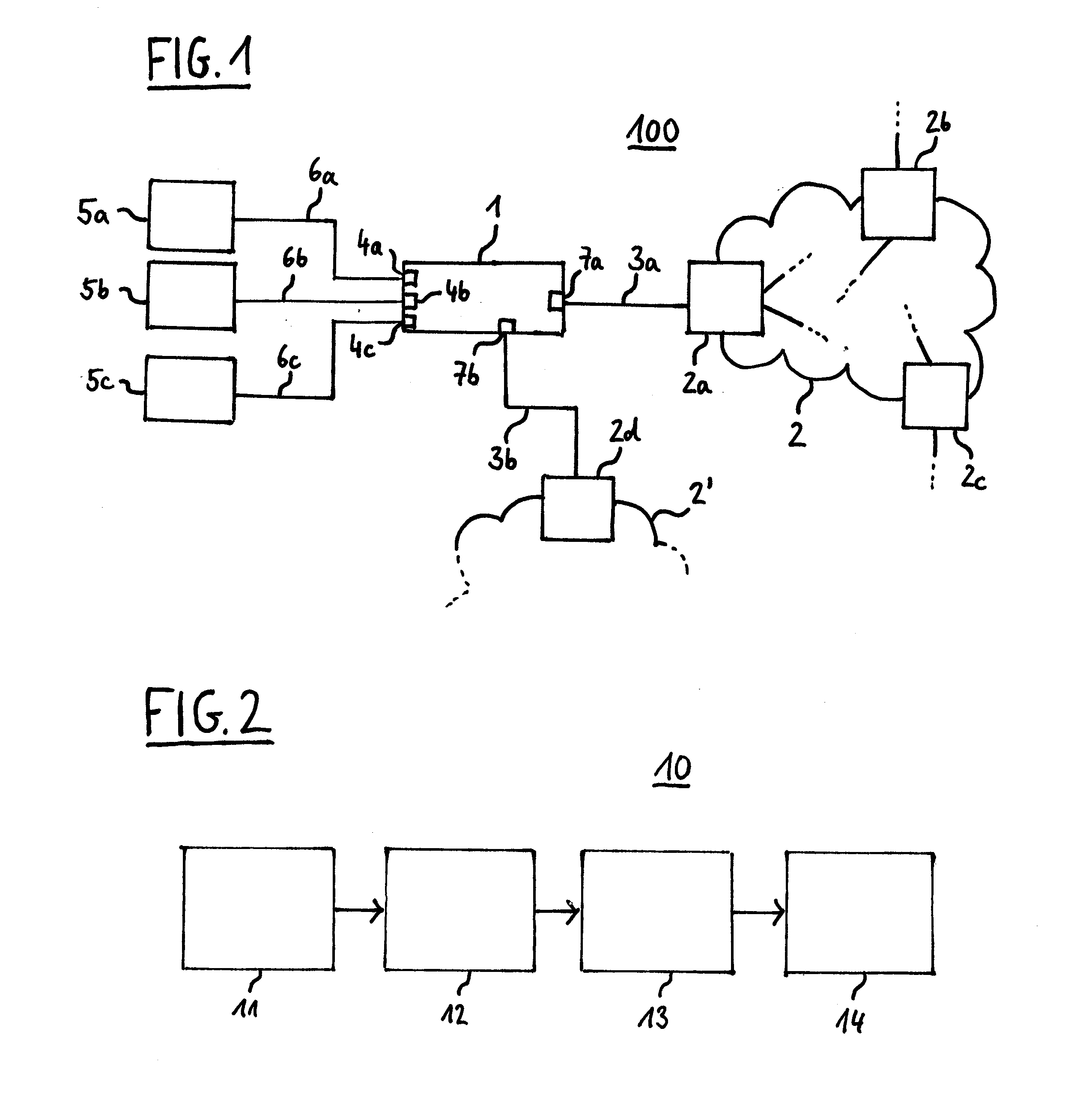
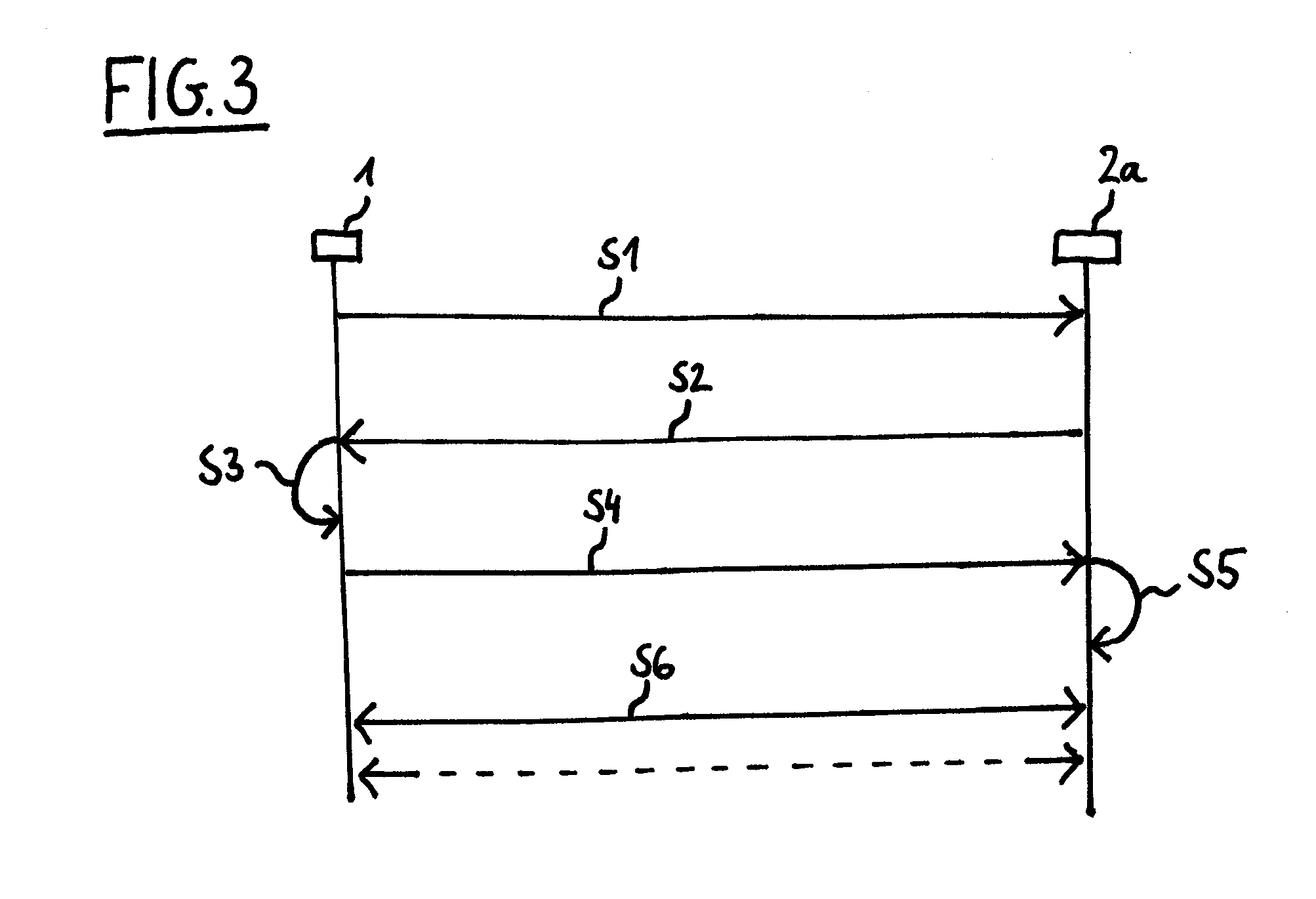
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2389 results about "Link layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
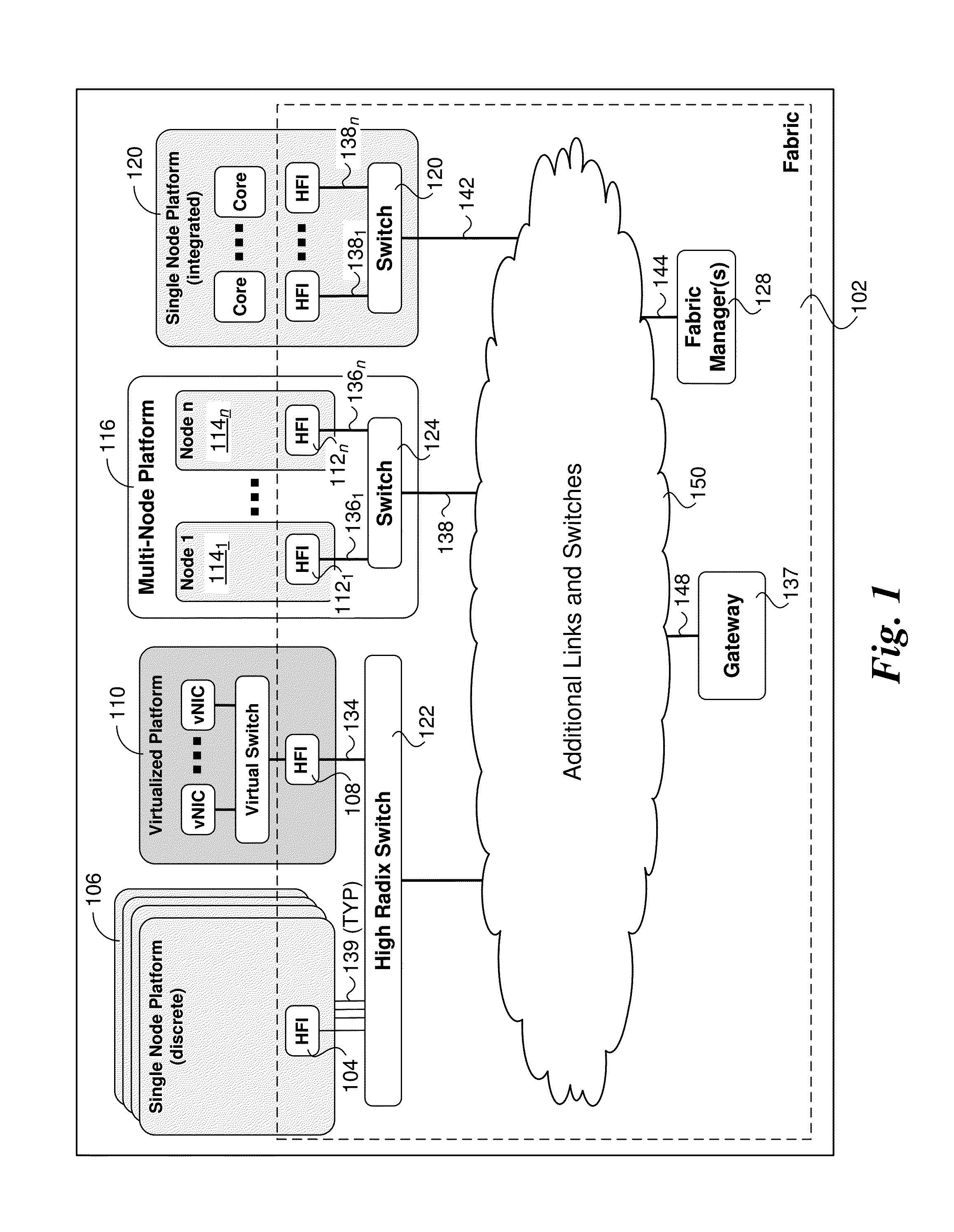
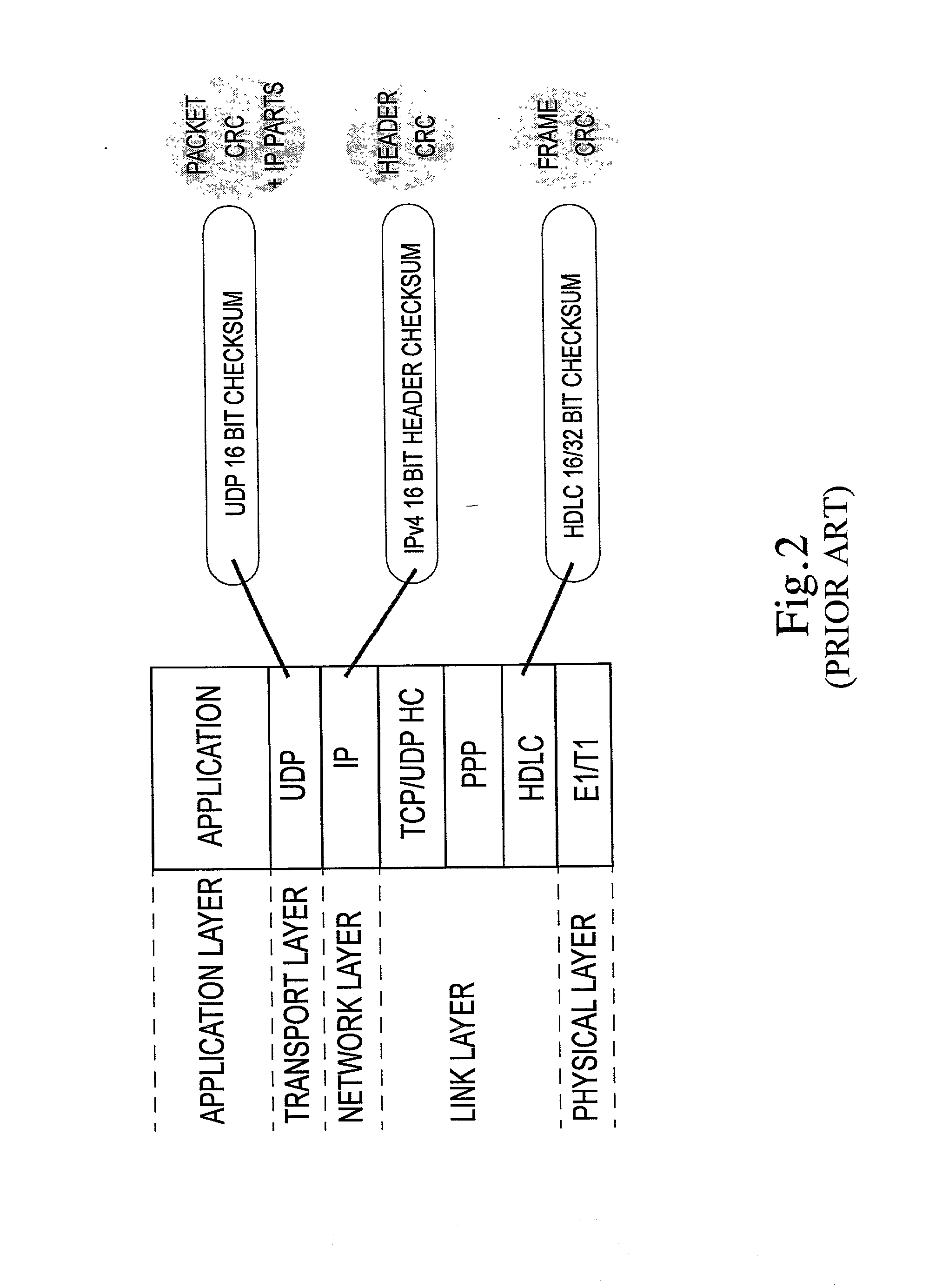
In computer networking, the link layer is the lowest layer in the Internet Protocol Suite, the networking architecture of the Internet. It is described in RFC 1122 and RFC 1123. The link layer is the group of methods and communications protocols that only operate on the link that a host is physically connected to. The link is the physical and logical network component used to interconnect hosts or nodes in the network and a link protocol is a suite of methods and standards that operate only between adjacent network nodes of a local area network segment or a wide area network connection.
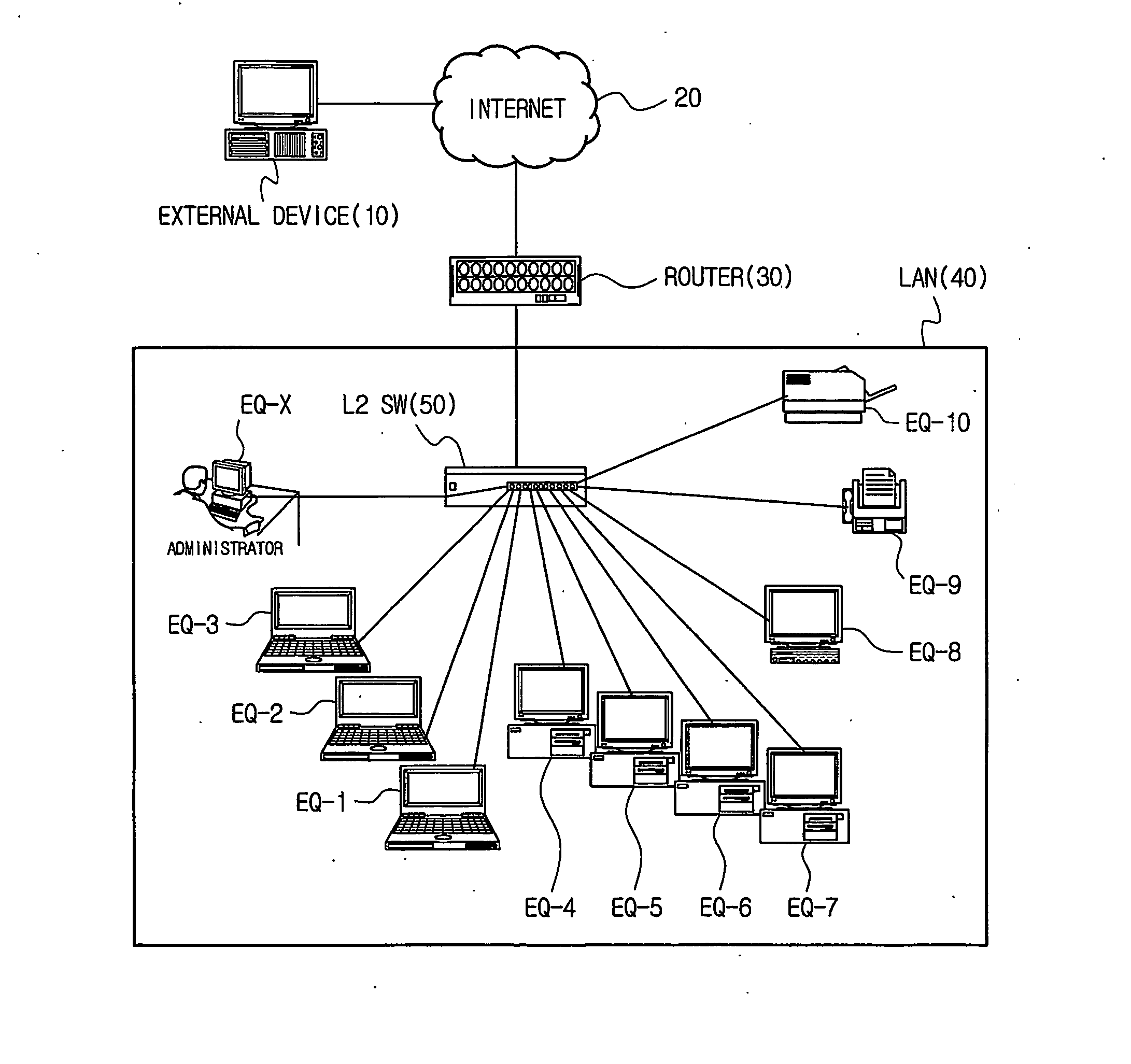
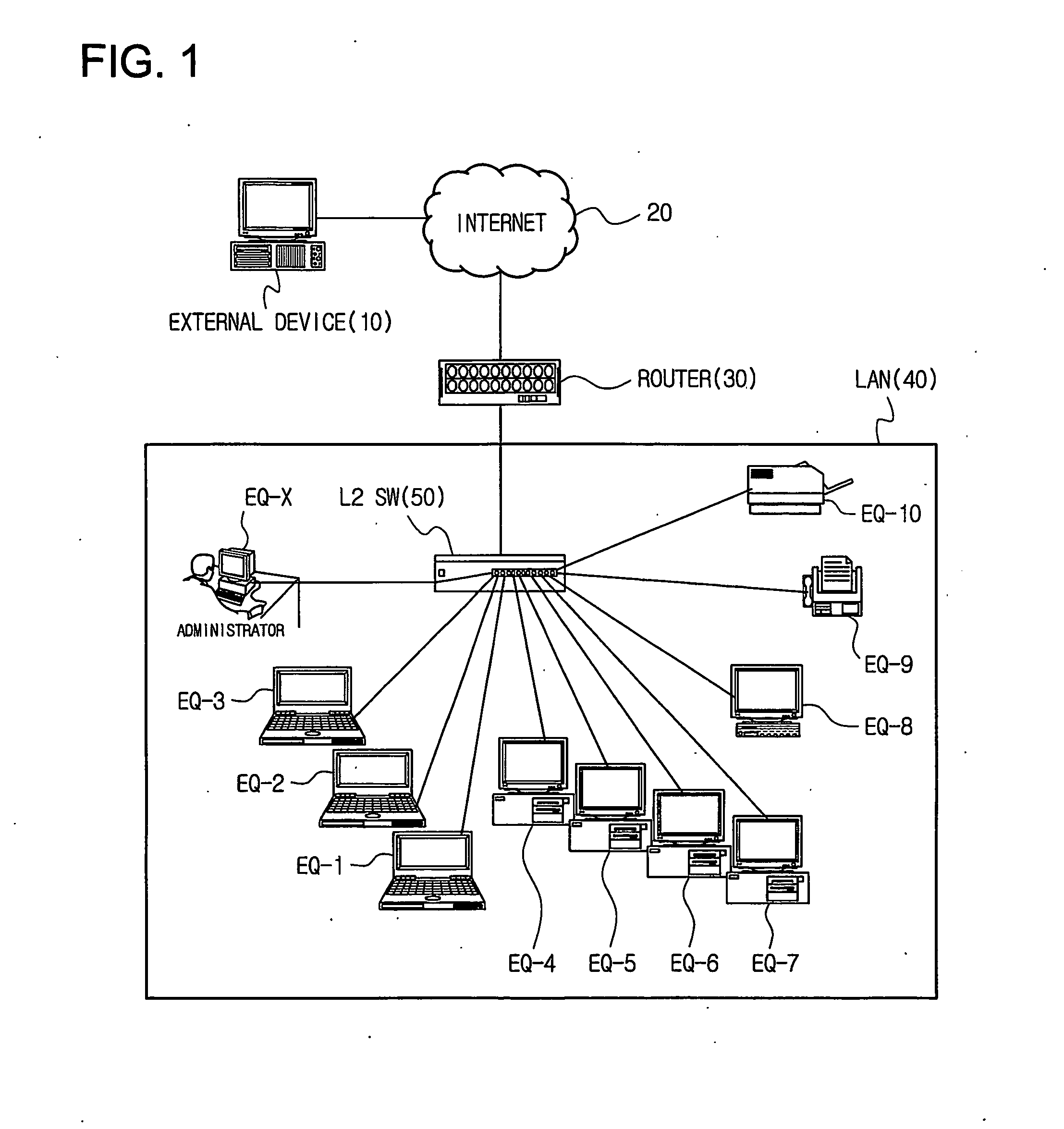
Method of controlling communication between devices in a network and apparatus for the same
InactiveUS20070064689A1Avoid collisionReduce communicationSpecial service provision for substationNetworks interconnectionAddress Resolution ProtocolVirtual firewall
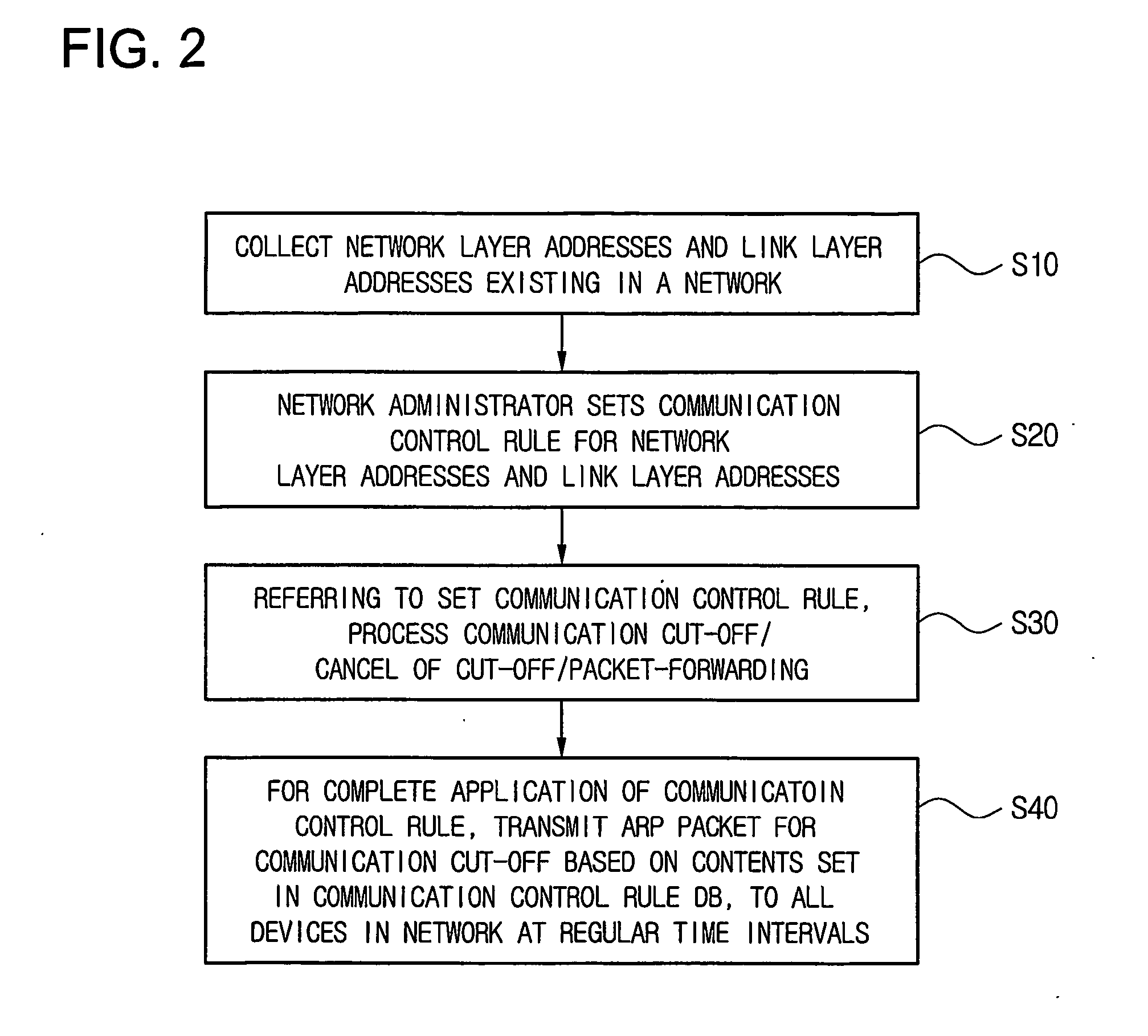
Disclosed is a technology by which rules on communication permission or control are enforced to network internal devices such that an environment which looks as if to have a virtual firewall existing between network internal devices can be established. A communication control apparatus for this is located on the same level in the network as other devices are located. By using this communication control apparatus, an address resolution protocol (ARP) packet in which a data link layer address is manipulated is provided to devices that are the objects of communication cut-off, such that data packets transmitted by the communication cut-off object devices are transmitted to manipulated abnormal addresses. By doing so, communication with the communication cut-off object devices is cut off. For a device which is in a communication cut-off state although the device is not an object of communication cut-off any more, the communication control apparatus transmits an ARP packet including normal address information to the device such that the communication cut-off state is canceled.
Owner:INIMAX
Method and apparatus for operating the internet protocol over a high-speed serial bus
InactiveUS6219697B1Efficiently and correctly determineDigital computer detailsTransmissionInternet protocol suiteTransport layer
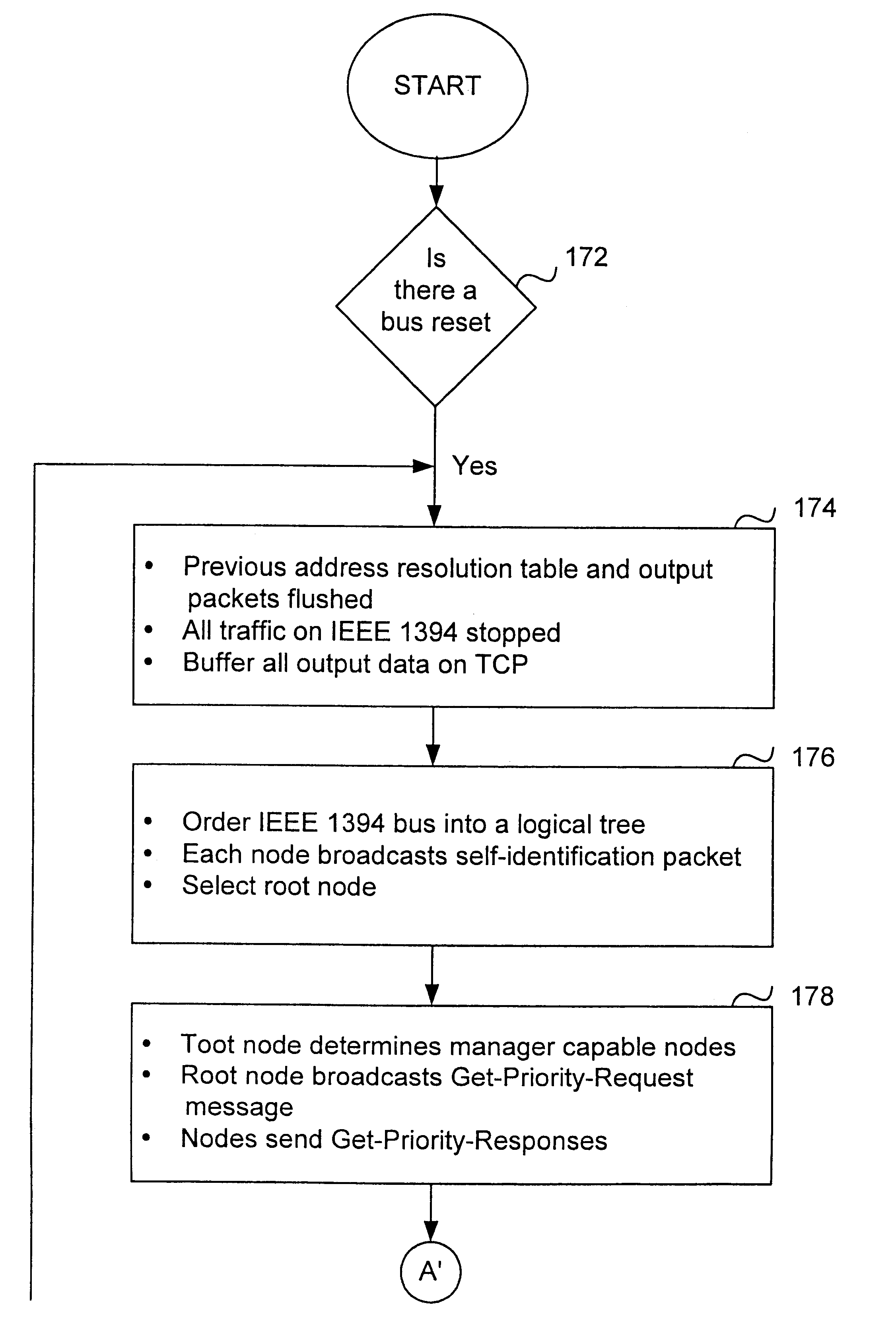
A method and apparatus of integrating the IEEE 1394 protocol with the IP protocol in which the IEEE 1394 high speed serial bus operates as the physical and link layer medium and the IP operates as the transport layer. There are differences in the protocols which require special consideration when integrating the two protocols. The IEEE 1394 configures packets with memory information and the IP operates under channel based I / O thereby necessitating a modification of the data transfer scheme to accomplish IP transfers over the IEEE 1394. Further, due to differences in packet headers, the IEEE 1394 packet header is modified to encapsulate IP packets. Moreover, in order to determine network packets quickly and efficiently, an identifier is inserted in each network packet header indicating that the packet should be processed by the network. Finally, in order to support the ability to insert or remove nodes on the network without a loss of data, the IP interface must not be disturbed. This is accomplished by maintaining constant IP addresses across bus resets which are caused by insertion or removal of nodes from the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
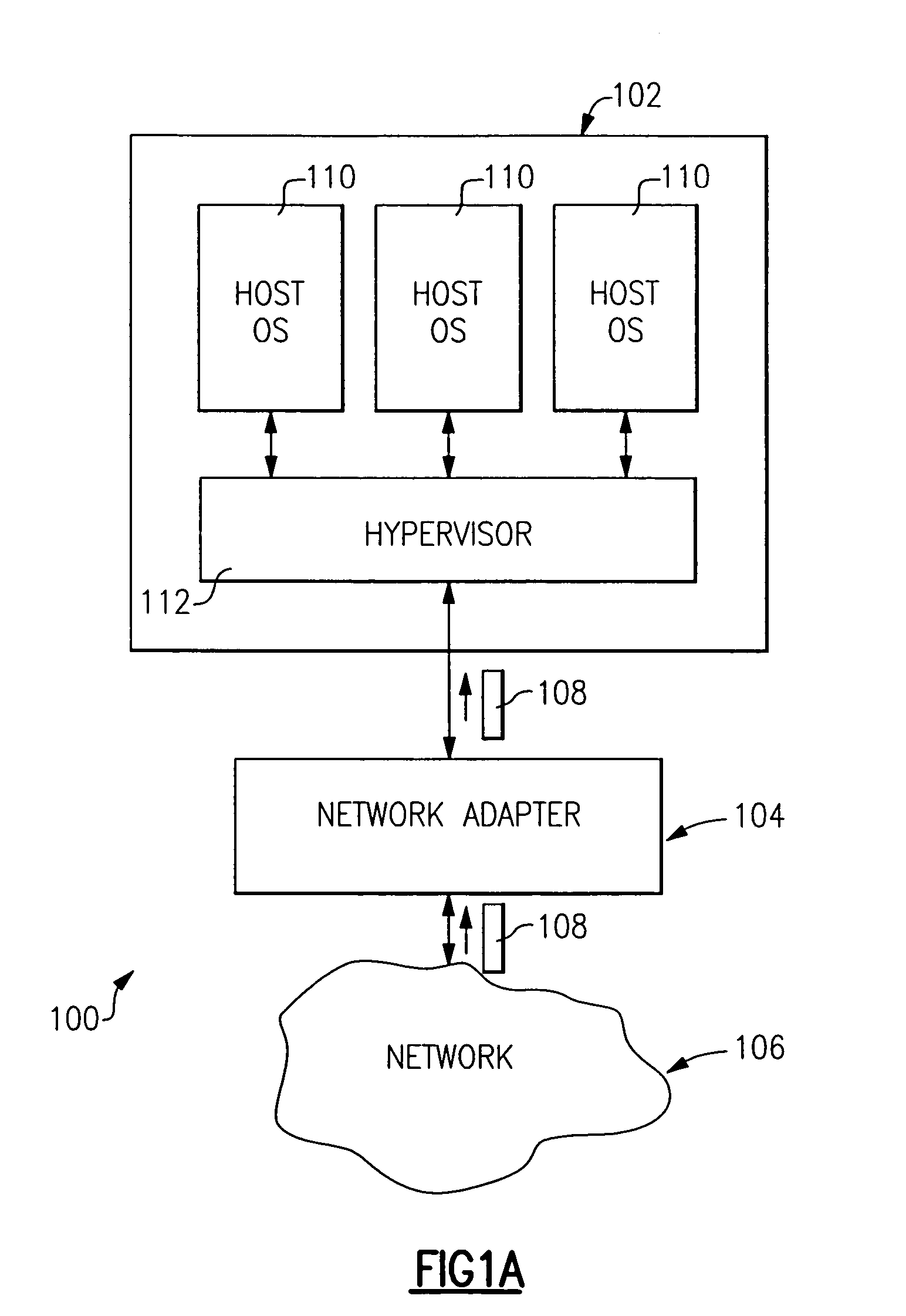
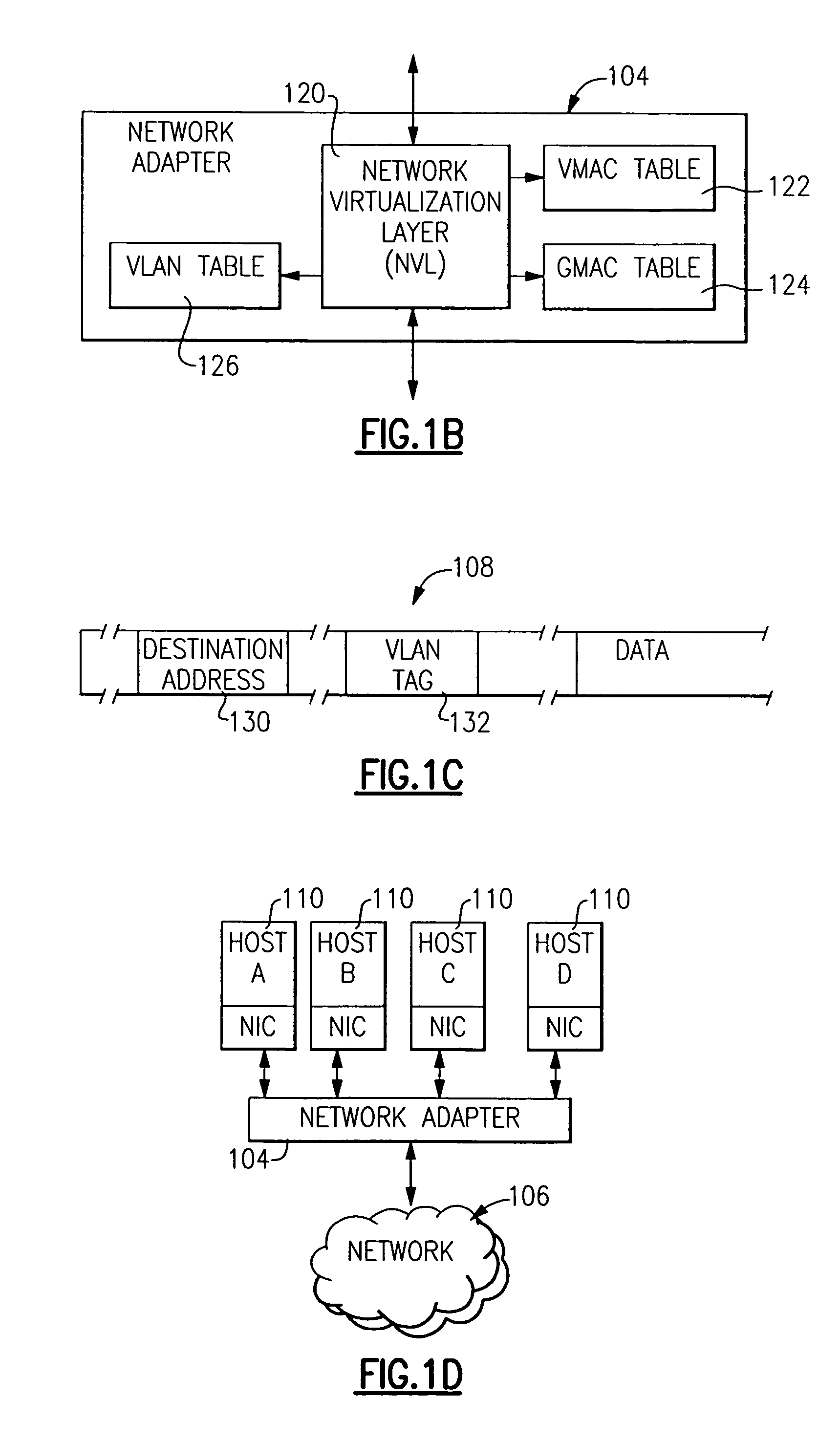
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
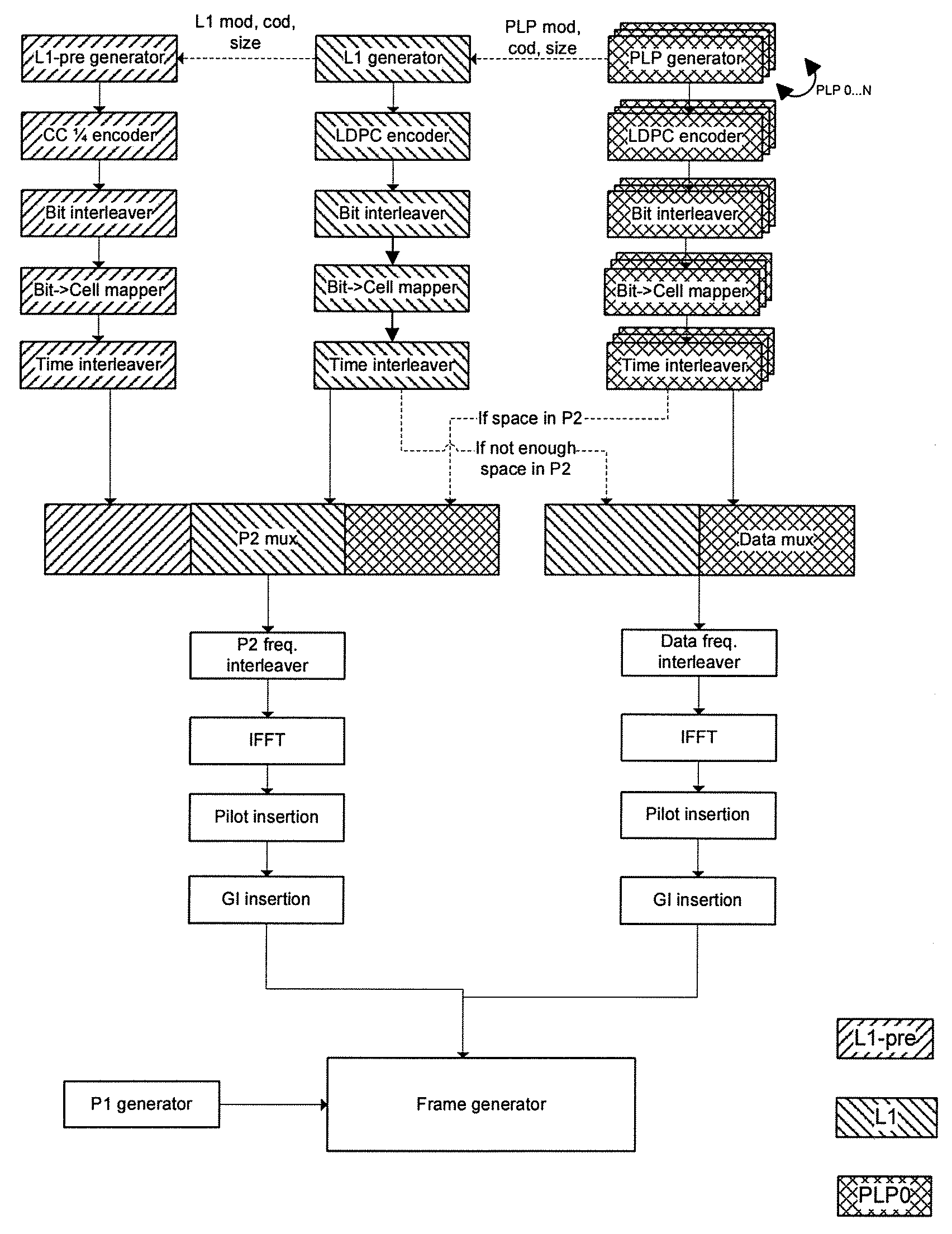
Digital Broadcast Signaling Metadata
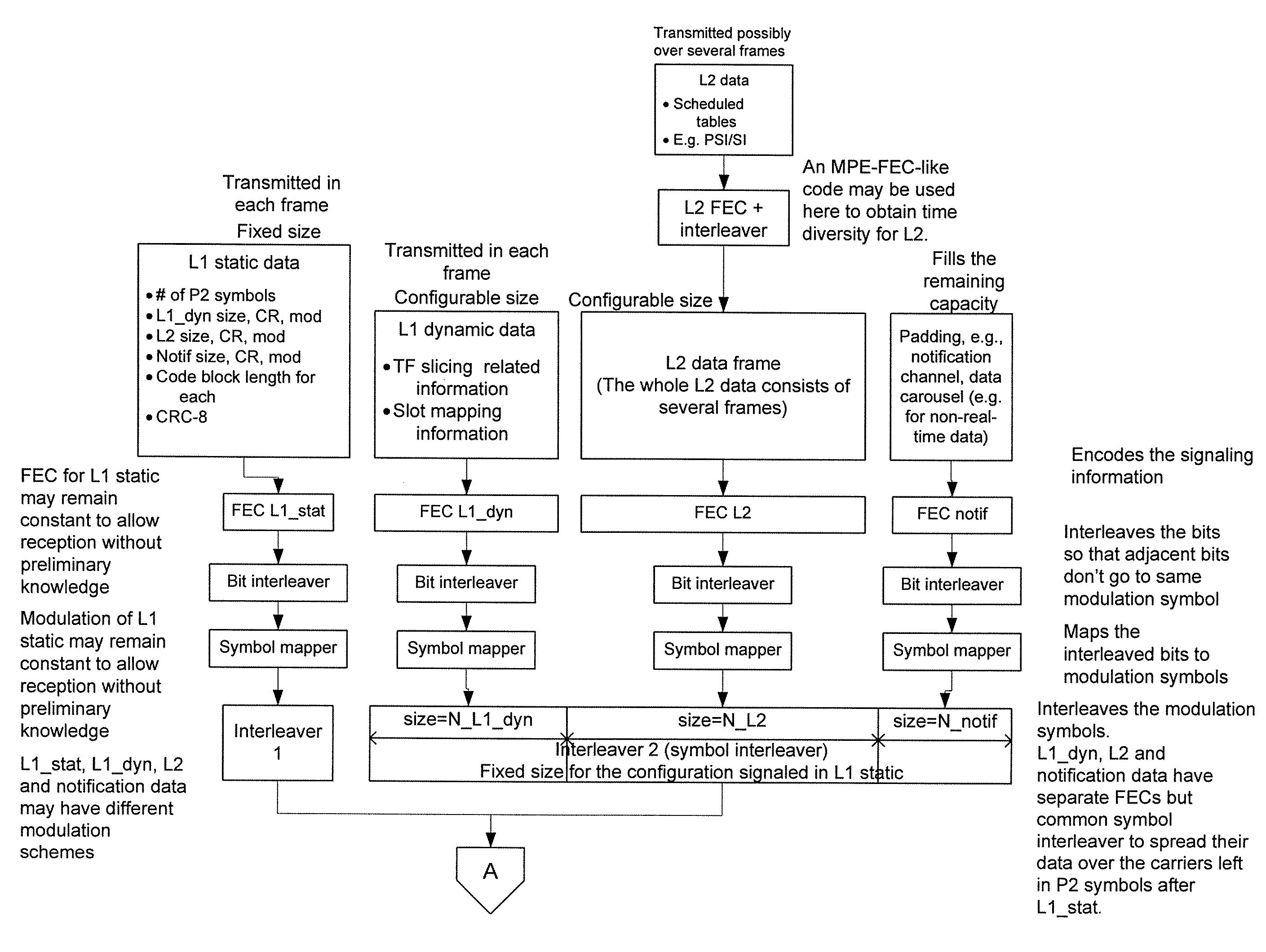
ActiveUS20090103649A1Error correction/detection using convolutional codesError preventionDigital broadcastingData link layer
Embodiments are directed to transmitting L1 pre-signaling information with predetermined modulation and code rate such that L1 pre-signaling information can be received without preliminary knowledge on the network. L1 pre-signaling information makes it possible to receive the L1 signaling information, data link layer information, and notification data that may have configurable code rates and modulation. Therefore, L1 pre-signaling information can be thought of as signaling metadata (i.e., information about other signaling information). L1 signaling is divided into pre-signaling and signaling parts. The pre-signaling part includes parameters used for receiving the L1 signaling information. L1 pre-signaling signaling enables the receiver to receive the signaling itself (L1 signaling and data link layer information) by informing the receiver about the type of modulation, coding, and the like, used to transmit the L1 signaling, data link layer, and notification information.
Owner:SAMSUNG ELECTRONICS CO LTD
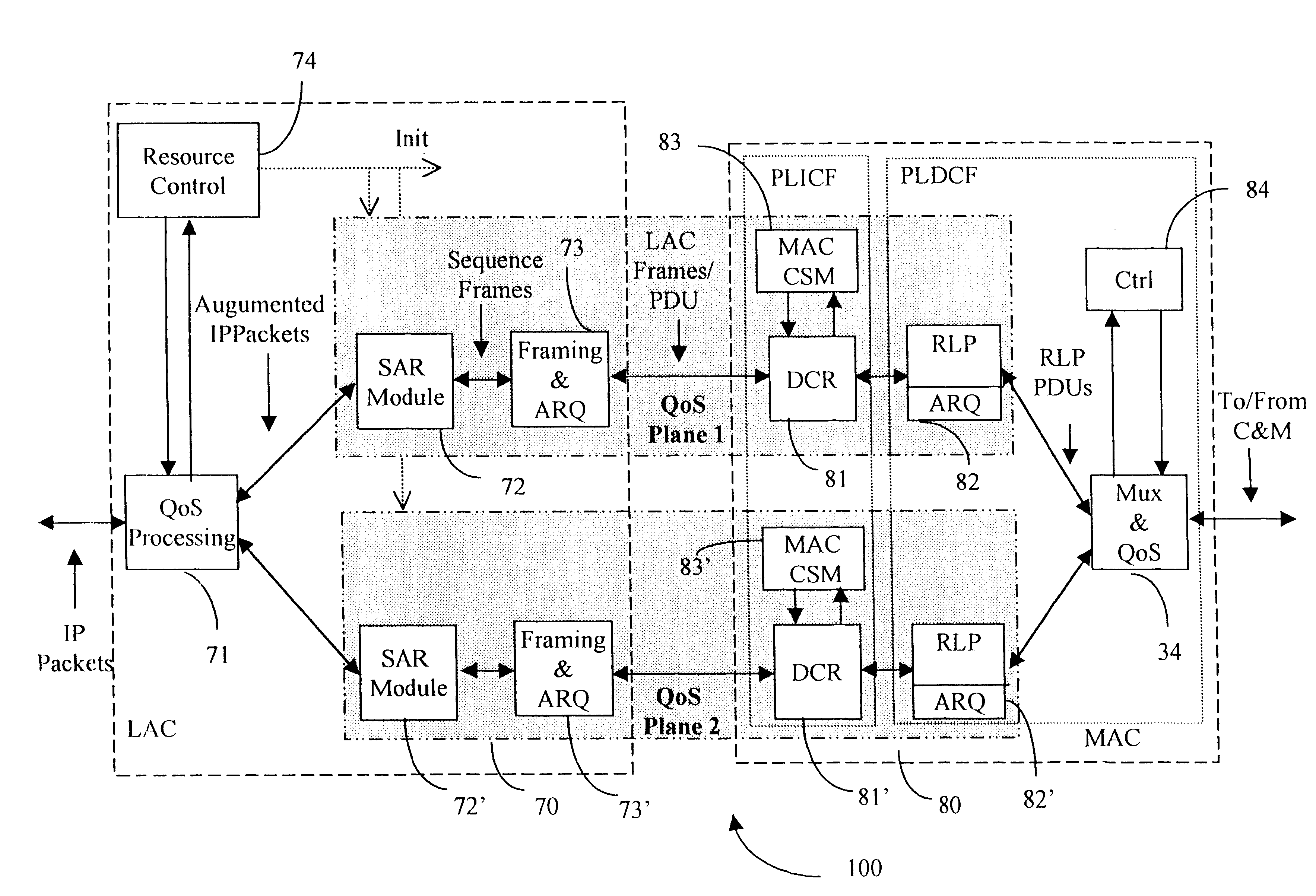
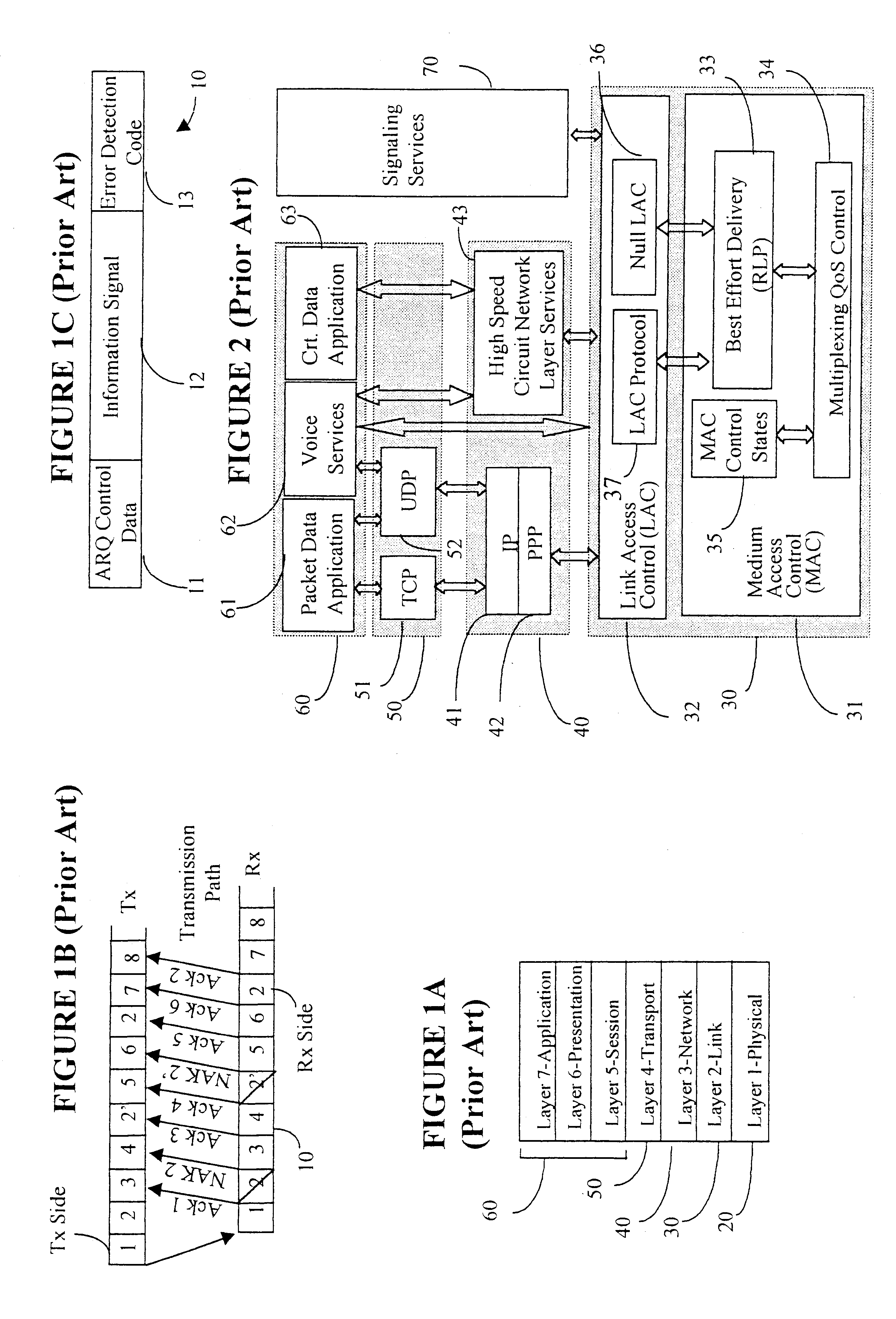
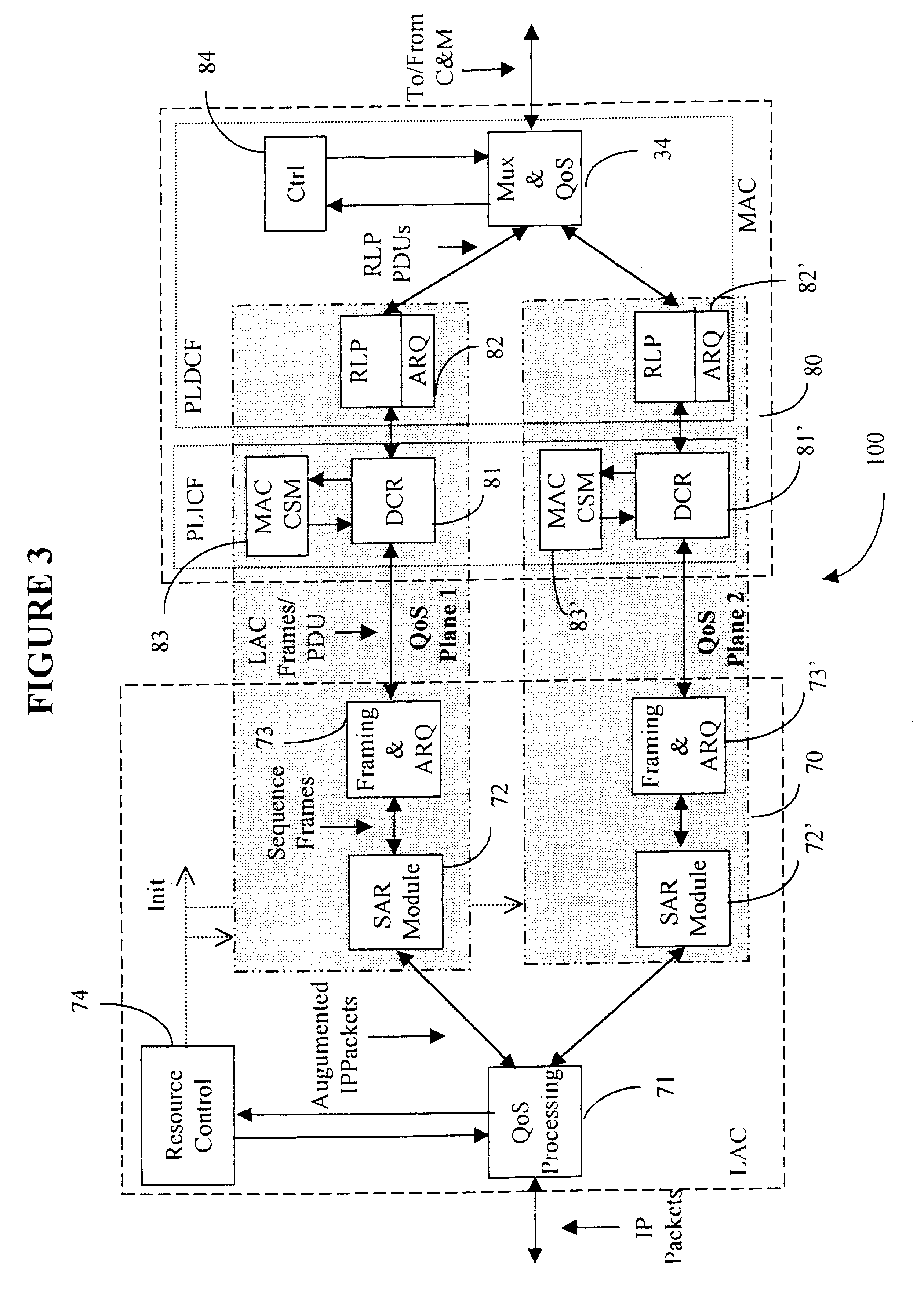
Data link control proctocol for 3G wireless system
InactiveUS6542490B1Error prevention/detection by using return channelElectronic circuit testingTelecommunications linkDual mode
A Data Link Control protocol for 3G wireless communication system for direct support for network layer protocols, e.g. the Internet Protocol (IP), is provided. The Link Layer disclosed comprises a Link Access Control (LAC) sublayer and a Medium Access Control (MAC) sublayer. At a transmit end of the wireless system, a plurality of Quality of Service (QoS) data planes are created to directly support the IP QoS. Each QoS data plane is optimized to handle QoS requirements for a corresponding Class of Service (CoS). Data packets received at the LAC sublayer are directed to a QoS data plane according to the particular QoS information they contain and processed according to the particular QoS requirement to generate variable size LAC frames. The variable size LAC frames are transmitted to the MAC sublayer for generating radio link protocol data units (RLP PDUs) to be transmitted to a receiving end. A new level of error correction is provided at the LAC sublayer as the size of the LAC PDUs can be dynamically adjusted in response to the conditions of the communication link. A dual mode ARQ is provided at the MAC sublayer to improve the quality of the air transmission for bursty as well as non-bursty traffic conditions.
Owner:ALCATEL LUCENT SAS
Physical Layer and Data Link Layer Signalling in Digital Video Broadcast Preamble Symbols
Aspects of the invention are directed to physical layer and data link layer signaling in digital video broadcast preamble symbols. Embodiments are directed to distributing physical layer pre-signalling data among preamble symbols. If physical layer data is larger than a predetermined number of preamble symbols, then excess physical layer data is written to data symbols immediately following the preamble symbols in top-down order symbol by symbol or the predetermined number of preamble symbols is increased. If physical layer data is not larger than the predetermined number of preamble symbols such that there is excess preamble symbol space, physical layer pipe 0 data comprising link layer signaling and notification data is carried in the excess preamble symbols or the excess preamble symbols are left empty. Different permutation rules may be used to frequency interleave odd-numbered versus even-numbered orthogonal frequency division multiplexing symbols.
Owner:SAMSUNG ELECTRONICS CO LTD
Frame aggregation in wireless communications networks
InactiveUS20060056443A1Improve throughputReduce complexityError preventionNetwork traffic/resource managementTelecommunicationsMedia access control
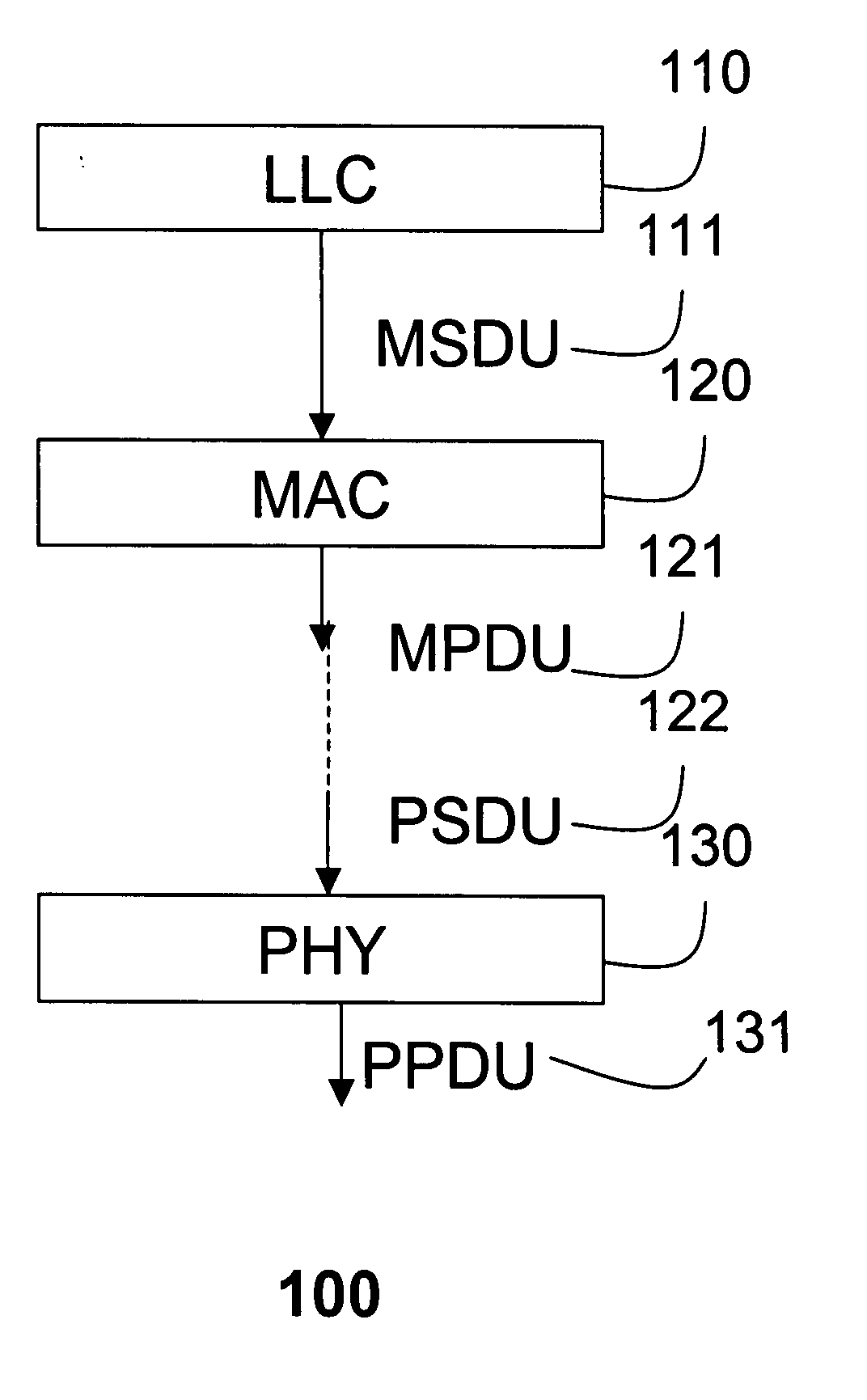
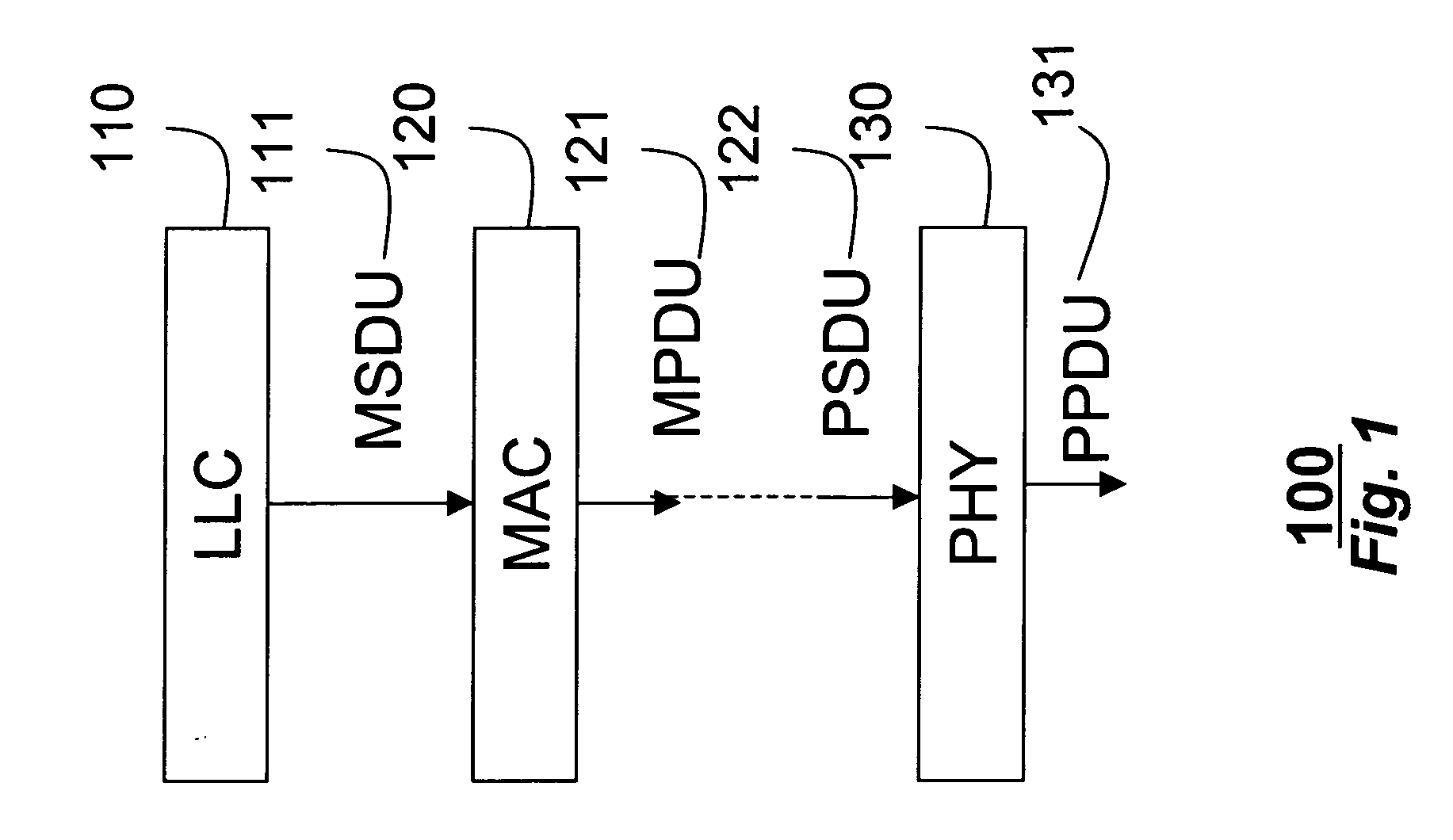
A method aggregates frames to be transmitted over a channel in a wireless network into a single frame. Multiple MSDU frames having identical destination addresses and identical traffic classes, received in the media access control layer from the logical link layer in a transmitting station are aggregated into a single aggregate MPDU frame, which can be transmitted on the channel to a receiving station. In addition, aggregate MSDU frames with different destination addresses and different traffic classes received from the media access control layer can be further aggregated into a single aggregate PPDU frame before transmission.
Owner:MITSUBISHI ELECTRIC RES LAB INC
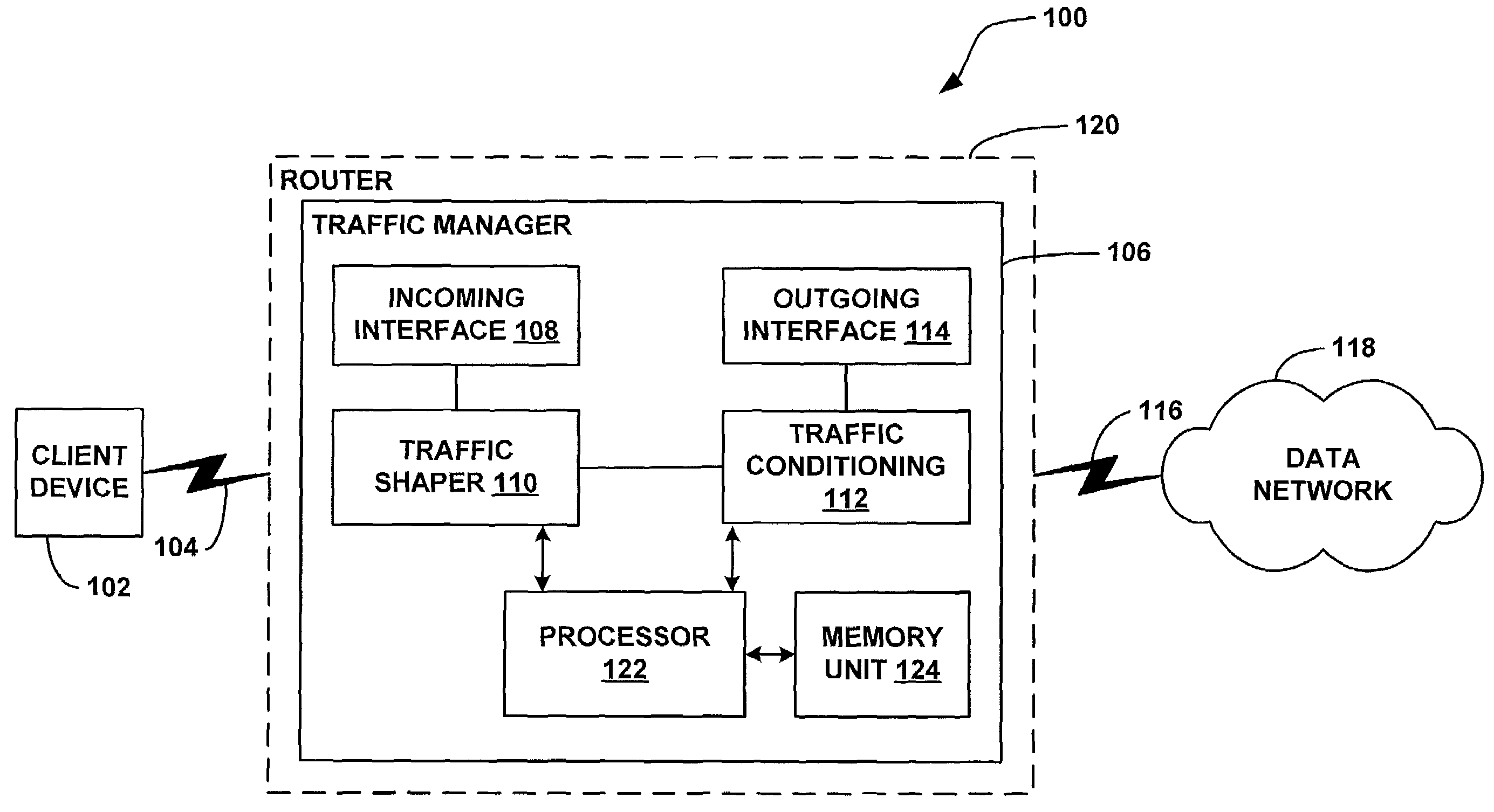
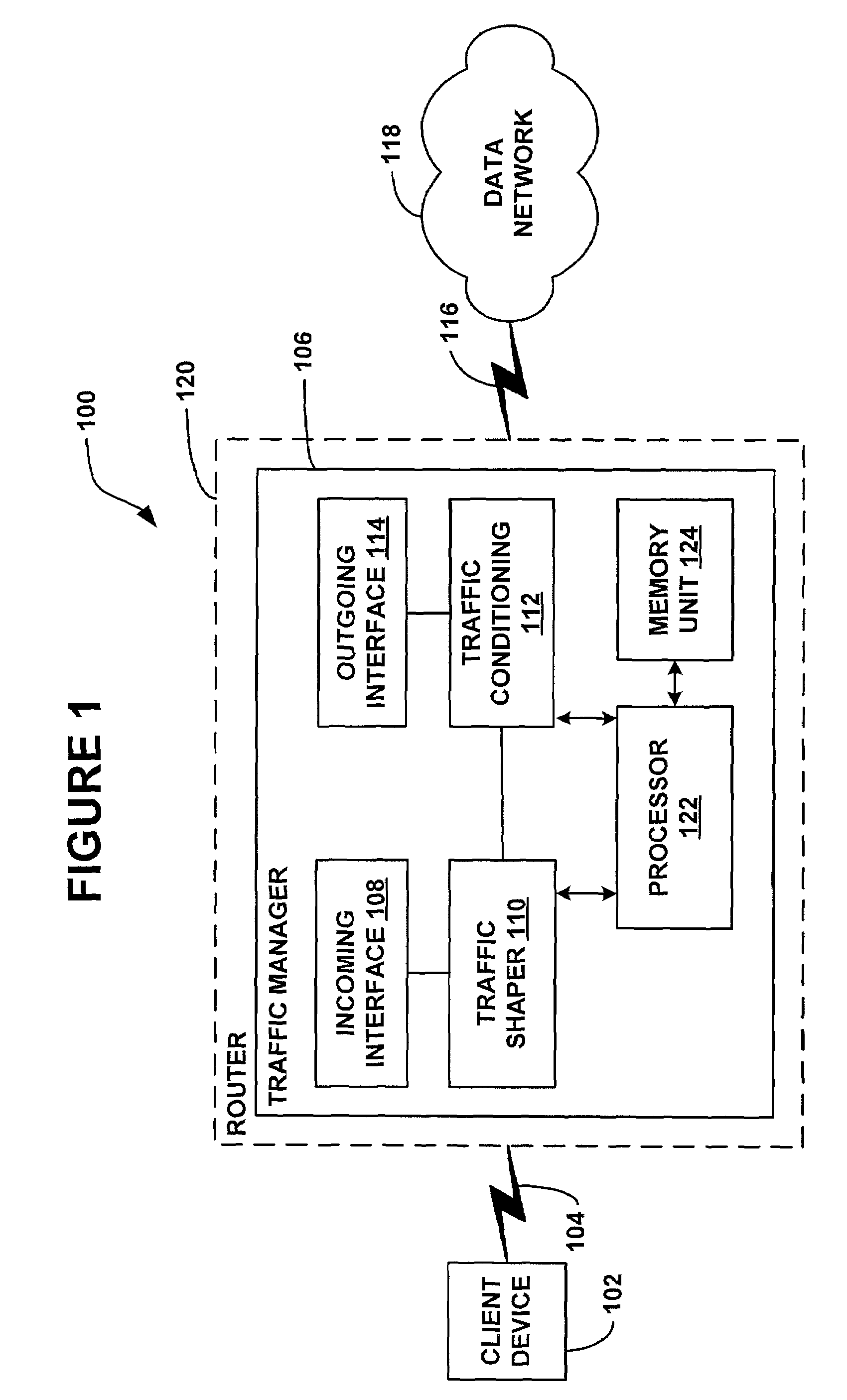
System and method for traffic shaping based on generalized congestion and flow control
ActiveUS7088678B1Overcome problemsError preventionFrequency-division multiplex detailsPacket arrivalModem device
A system and methods are shown for traffic shaping and congestion avoidance in a computer network such as a data-over-cable network. A headend of the data-over-cable system includes a traffic shaper configured to calculate a packet arrival rate from a cable modem and a traffic conditioner configured to calculate an average queue size on an output interface to an external network. For example, the traffic shaper compares the packet arrival rate to three packet arrival thresholds including a committed rate threshold, a control rate threshold and a peak rate threshold. If the calculated packet arrival rate falls between the committed threshold and control rate threshold, the traffic shaper applies a link layer mechanism, such as a MAP bandwidth allocation mechanism, to lower the transmission rate from the cable modem.
Owner:VL COLLECTIVE IP LLC
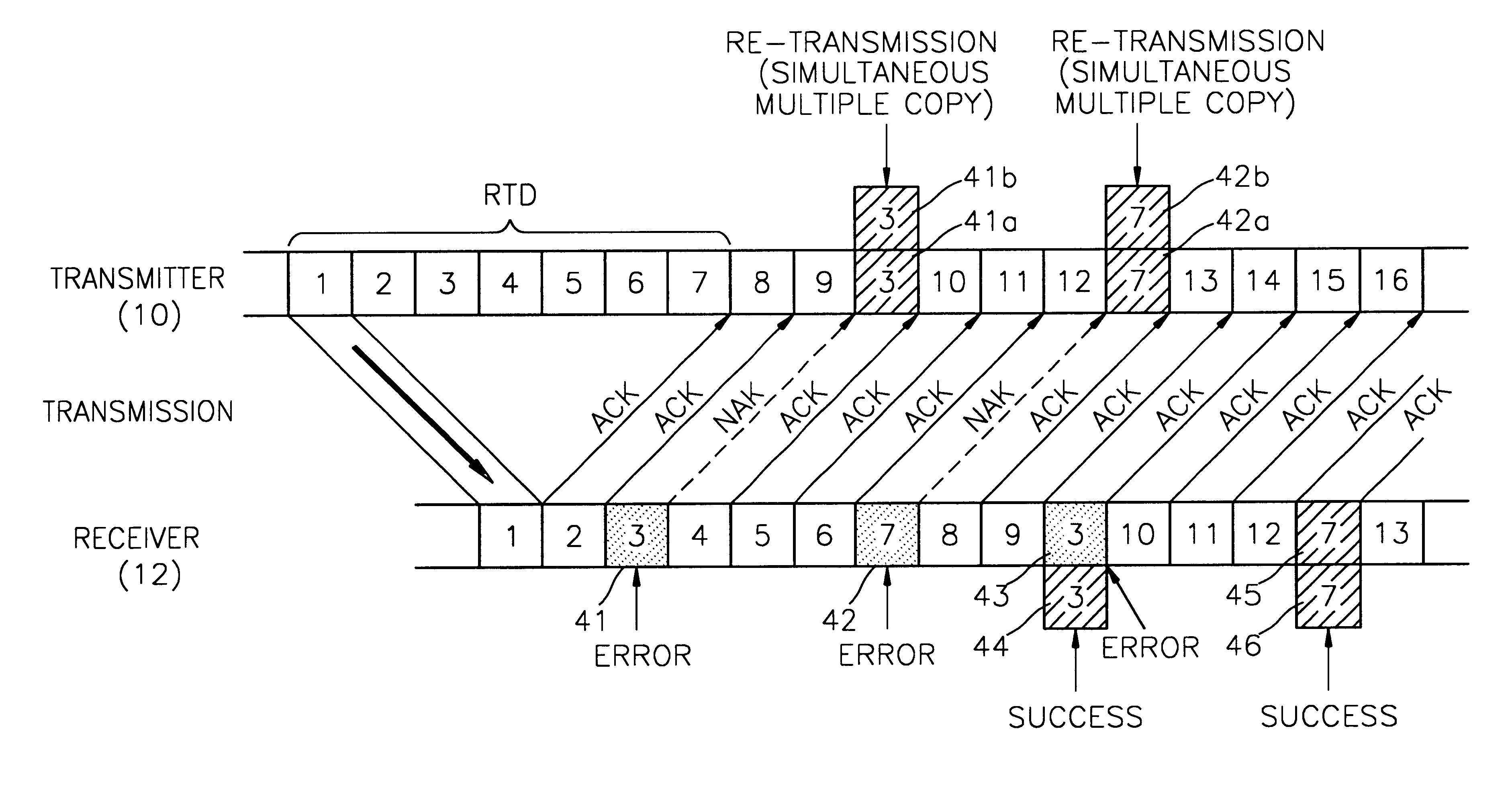
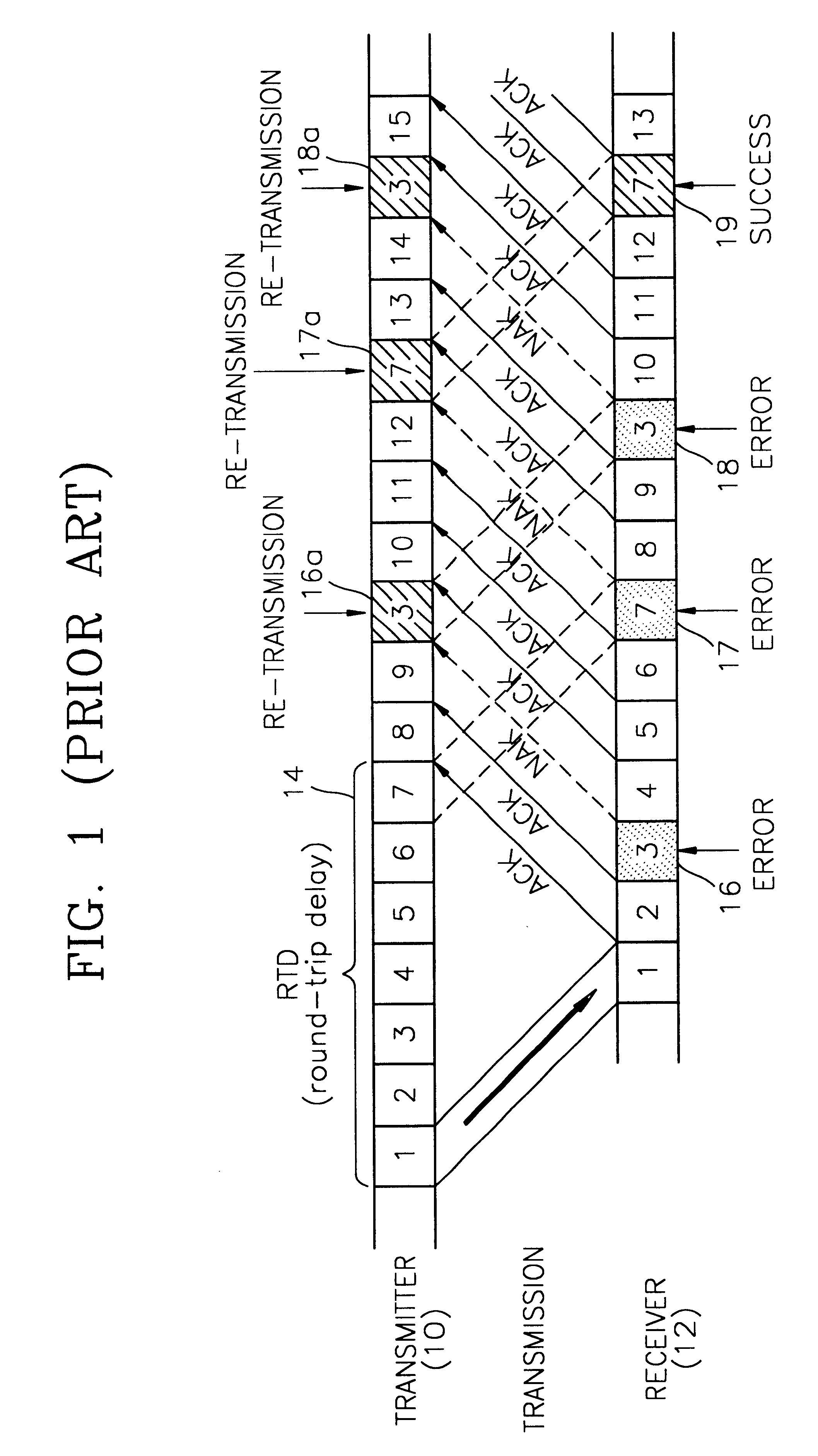
Method for controlling errors in link layer in wideband wireless communication and computer readable media therefor
InactiveUS6615382B1Error prevention/detection by using return channelTransmission systemsDelayed timeData link layer
A method for controlling errors in a wireless link layer using a simultaneous multiple copy scheme and an adaptive forward error correction (FEC) scheme in a wideband wireless communication is provided. The method for controlling errors in a link layer in wideband wireless communication using an automatic repeat request (ARQ) scheme, in which a wideband wireless channel is used for communication between a first node and a second node, includes the steps of (a) estimating the error ratio of a forward (a direction in which a cell is transmitted from the first node to the second node) channel using the state of a backward (a direction in which a cell is transmitted from the second node to the first node) channel, and transmitting a cell, in which a forward error correction (FEC) code having an encoding ratio that varies depending on the estimated error ratio is included in a protocol data unit (PDU) of a wireless link layer, through the forward channel and (b) re-transmitting the copy of a cell transmitted in the step (a), when feedback information that indicates that an error exists in the cell transmitted in the step (a) is received through the backward channel. It is possible to reduce the number of times of re-transmission by improving the probability of correcting forward errors using more error controlling bits as the state of the channel is worse and to minimize the waste of resources using less error controlling bits as the state of the channel is better, to thus obtain the optimal performance and guarantee the minimum delay time.
Owner:SAMSUNG ELECTRONICS CO LTD
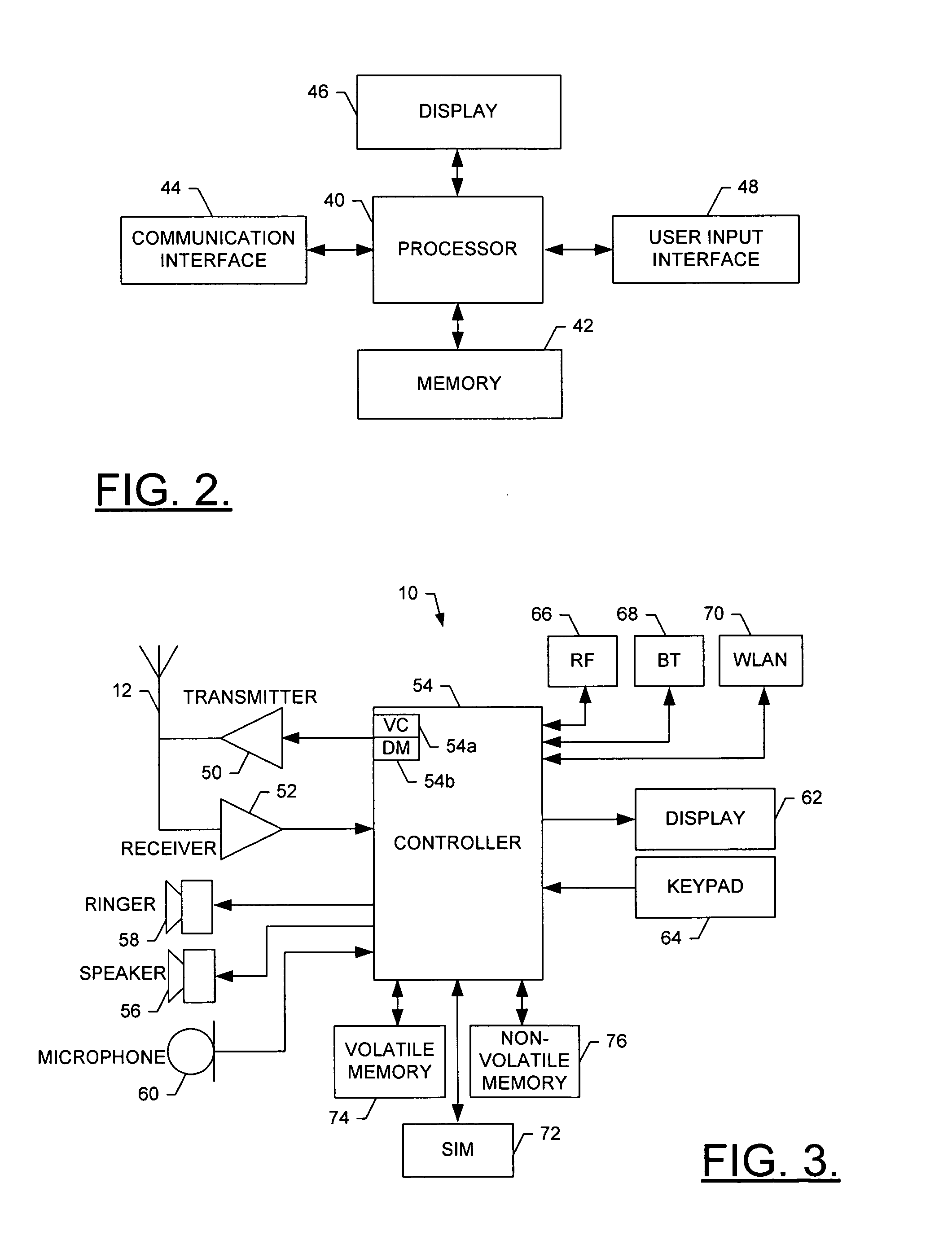
Secure networking using a resource-constrained device
ActiveUS20050108571A1Easy to adaptCommunication securityDigital data processing detailsHardware monitoringSecure communicationClient-side
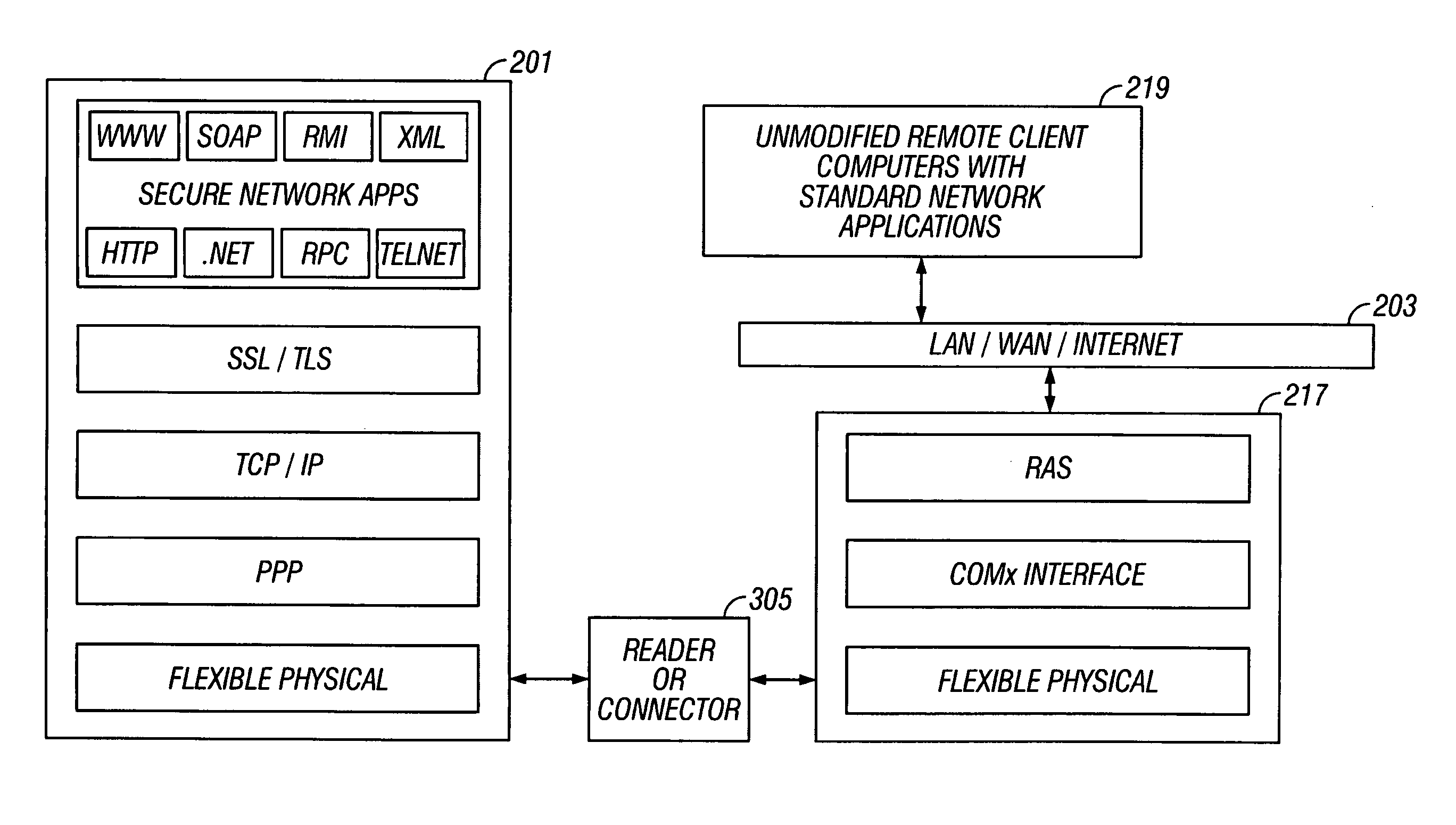
Secure communication between a resource-constrained device and remote network nodes over a network with the resource-constrained acting as a network node. The remote network nodes communicate with the resource-constrained device using un-modified network clients and servers. Executing on the resource-constrained device, a communications module implements one or more link layer communication protocols, operable to communicate with a host computer, operable to communicate with remote network nodes and operable to implement network security protocols thereby setting a security boundary inside the resource-constrained device.
Owner:GEMPLU
Transport of ethernet packet data with wire-speed and packet data rate match
ActiveUS20150222533A1Multiplex system selection arrangementsSignal allocationReliable transmissionWire speed
Method, apparatus, and systems for reliably transferring Ethernet packet data over a link layer and facilitating fabric-to-Ethernet and Ethernet-to-fabric gateway operations at matching wire speed and packet data rate. Ethernet header and payload data is extracted from Ethernet frames received at the gateway and encapsulated in fabric packets to be forwarded to a fabric endpoint hosting an entity to which the Ethernet packet is addressed. The fabric packets are divided into flits, which are bundled in groups to form link packets that are transferred over the fabric at the Link layer using a reliable transmission scheme employing implicit ACKnowledgements. At the endpoint, the fabric packet is regenerated, and the Ethernet packet data is de-encapsulated. The Ethernet frames received from and transmitted to an Ethernet network are encoded using 64b / 66b encoding, having an overhead-to-data bit ratio of 1:32. Meanwhile, the link packets have the same ratio, including one overhead bit per flit and a 14-bit CRC plus a 2-bit credit return field or sideband used for credit-based flow control.
Owner:INTEL CORP
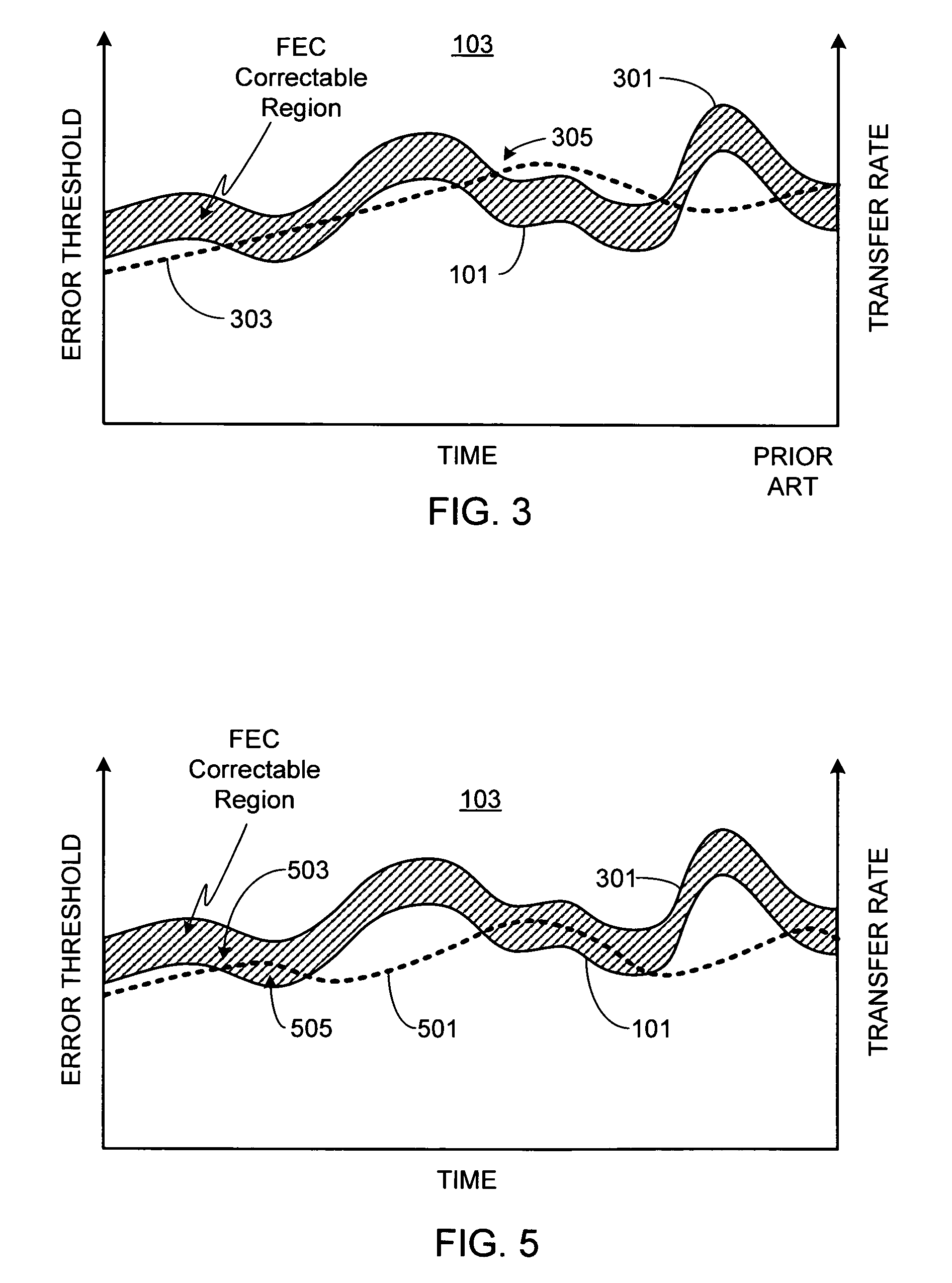
Adaptive information delivery system using FEC feedback
InactiveUS20060150055A1Useful resultError detection/prevention using signal quality detectorReceiver specific arrangementsTelecommunications linkThe Internet
A method and apparatus for optimizing the data transfer rate over a transport layer (i.e., communication link) such as the Internet is provided. Initially the data is prepared for transmission by a transfer rate controller, then the data is encoded by a Forward Error Correction (FEC) encoder. After the data has been transferred over the transport layer, the quality of the data transfer link is assessed by an FEC decoder that determines if any errors occurred during data transfer and if errors are detected, the magnitude of the errors (i.e., FEC-correctable packets, FEC-uncorrectable packets). This information is used to generate a feedback message which is used by the transfer rate controller to adjust and optimize the data transfer rate for the link quality as determined at that point in time. By continually monitoring and assessing link quality and providing feedback to the transfer rate controller, the transfer rate can be continually adapted to the varying link quality. In addition to generating feedback used by the transfer rate controller to optimize data transfer rate, the FEC decoder can generate feedback that is used by the FEC encoder to optimize the FEC algorithm. If desired, feedback from the FEC decoders within the link layer demodulator and / or feedback from the receiver can be used to augment the feedback generated by the FEC decoder.
Owner:TERAYON COMM SYST
Serving network selection and multihoming using IP access network
InactiveUS20050165953A1Simple methodAssess restrictionMultiple digital computer combinationsAccess networkClient-side
In some illustrative embodiments, an IP-layer based network selection and multihoming method is provided that enables a flexible and secure dynamic selection of one or more serving networks for use by a client node. The method is independent of any link-layer technology. A serving network can be an ISP network, a NAP network exchange facility, a VLAN, or the like. Network information is advertised to a client node, the client node is authenticated and authorized for use of an access router, and a secure tunnel is established between the client node and the access router. The method can be implemented by using standard protocols, and can work over any existing or future link-layer technologies that are able to carry IP datagrams, without any modification.
Owner:TELCORDIA TECHNOLOGIES INC +2
Fibre channel over ethernet
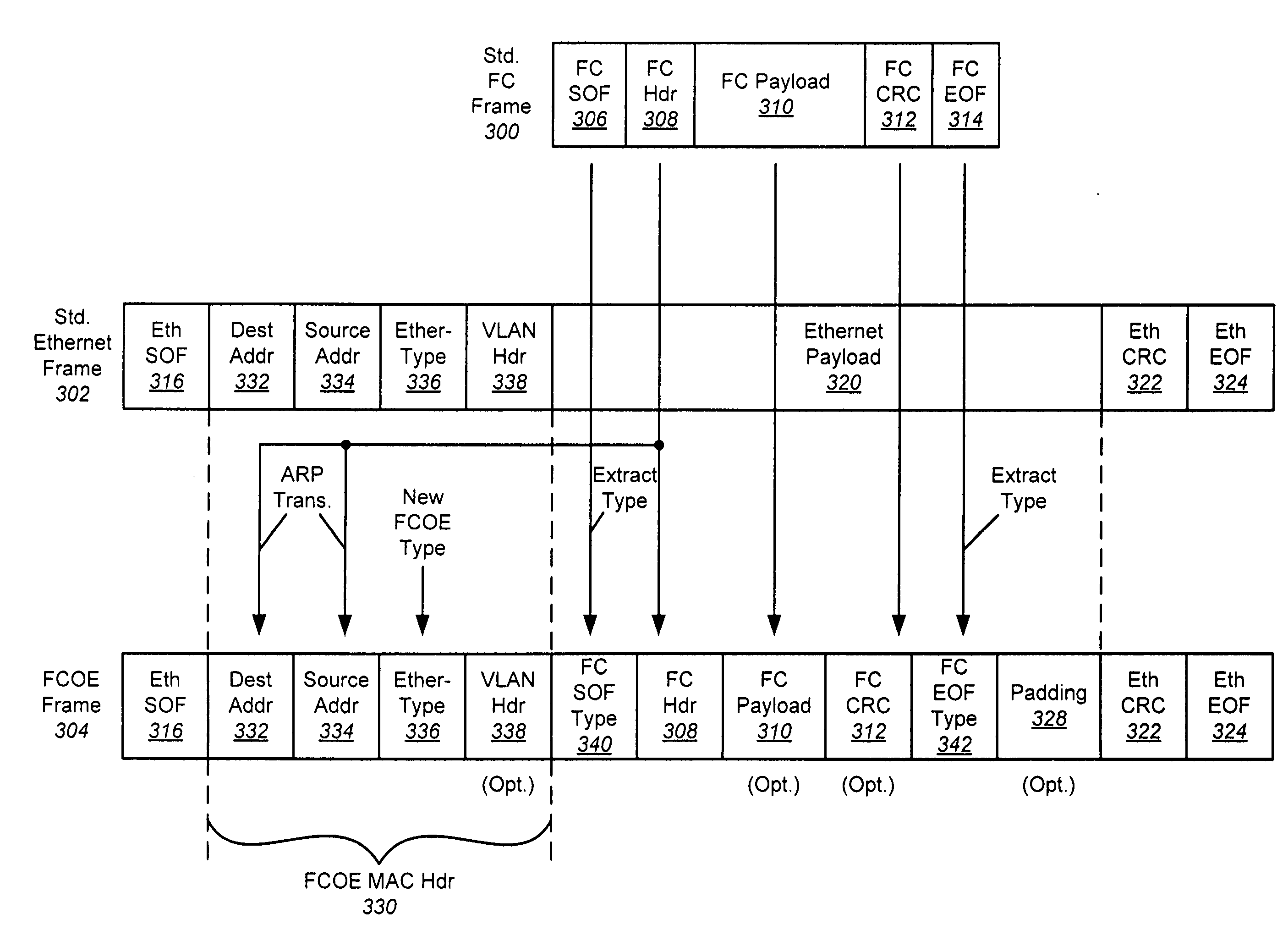
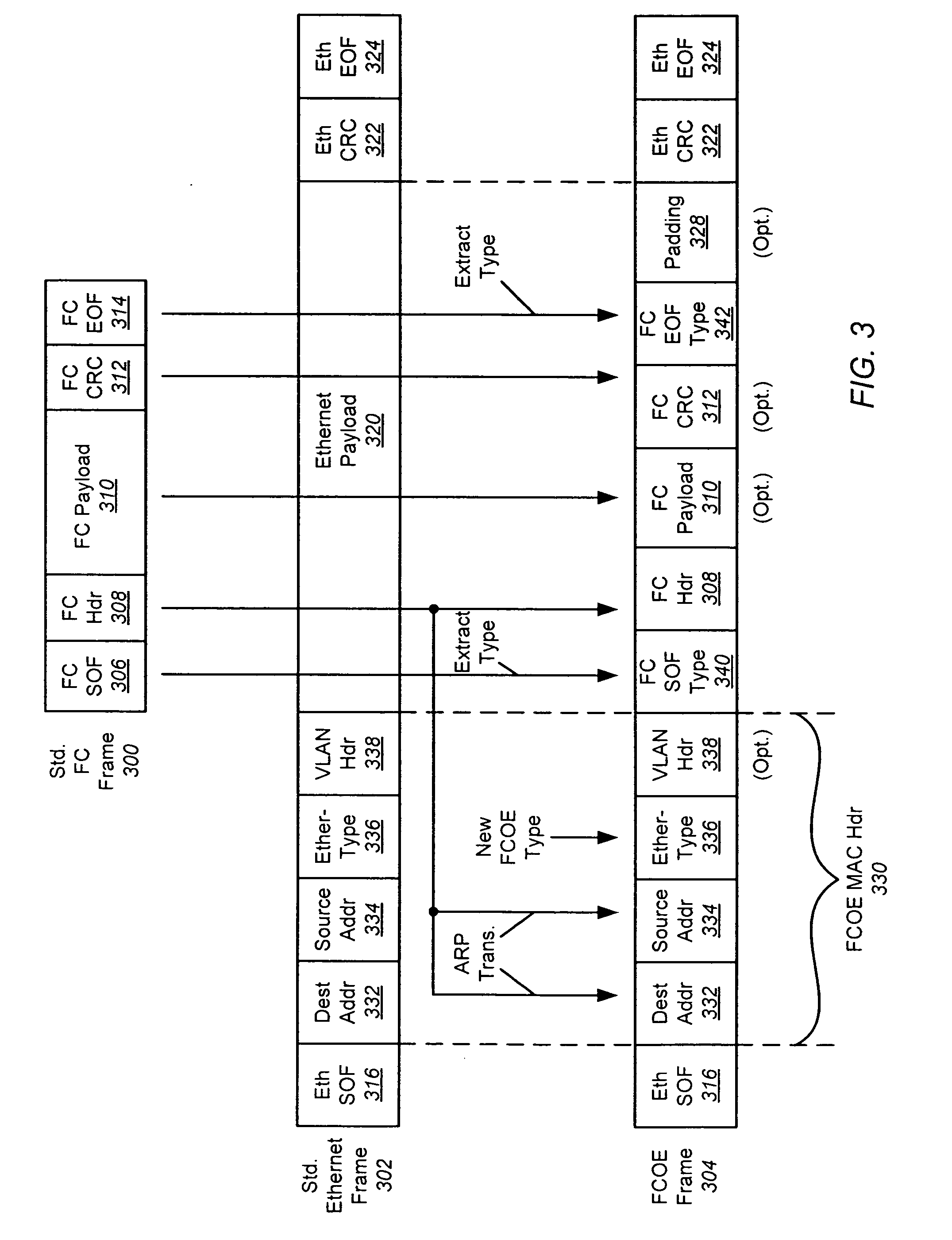
The use of Ethernet as an underlying transport for Fibre Channel (FC) frames is disclosed in the Fibre Channel Over Ethernet (FCOE) protocol. In FCOE, the FC physical layer and part of the FC-2 link layer are replaced with the Ethernet physical and link layers. Each FC frame is encapsulated within an Ethernet Frame. The payload of the FCOE frame contains type information from the FC Start Of Frame (SOF) indicator, the FC header, an optional FC payload, and type information from the FC End Of Frame (EOF) indicator. In one embodiment, an Ethernet network carrying FCOE replaces a standard FC network. In another embodiment, devices implementing FCOE may be implemented in a blade server. The entire backplane is Ethernet, over which both storage and networking traffic can be run. The Ethernet links are connected to an Ethernet switch, a FCOE / FC converter, and a FC switch.
Owner:AVAGO TECH INT SALES PTE LTD
Method and system for media synchronization in QoS-enabled wireless networks
ActiveUS7486658B2Improve performanceGood synchronizationSynchronisation arrangementError preventionData synchronizationWireless mesh network
Owner:CISCO TECH INC
Method and a system for enabling data to be stored in a computer network; a method and a system for storing data in a computer network
InactiveUS20050010685A1Increasing optical bandwidthDigital computer detailsData switching by path configurationDistributed computingLink layer
A method for enabling storage of data in a computer network comprising a plurality of computer nodes, wherein each computer node comprises at least one connection oriented link layer unit, the method comprising the steps of defining a looping path in the computer network, wherein the looping path comprises a plurality of computer nodes and connections between the computer nodes and configuring a connection unit at each node along the looping path, the connection unit being supported by the connection oriented link layer unit, such that the connection oriented link layer unit at each computer node is able to send incoming data which is to be stored in the computer network to a next computer node along the looping path based on the connection unit, thereby providing the looping path for data to be circulated therein, and thereby enabling the storage of data in the computer network.
Owner:AGENCY FOR SCI TECH & RES
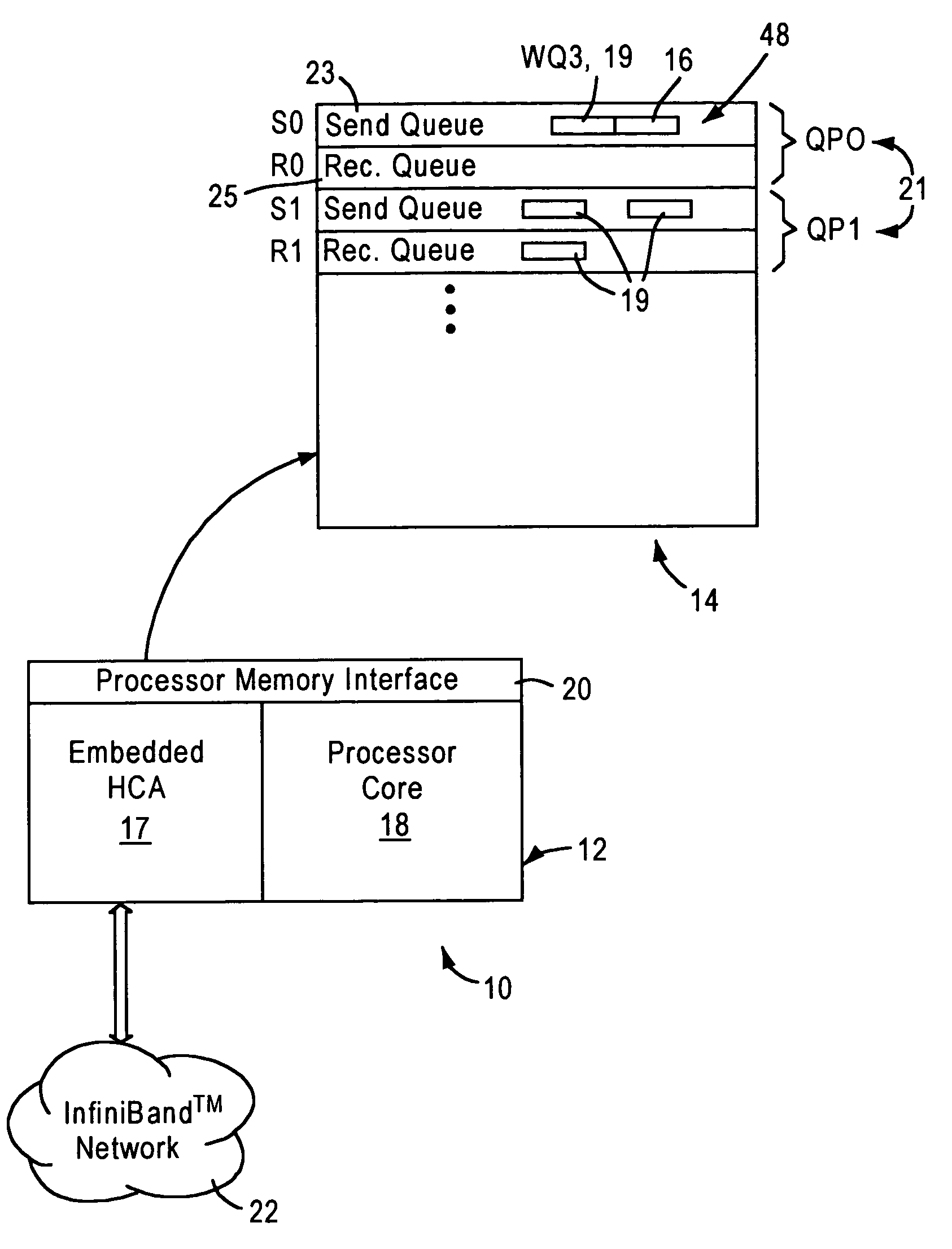
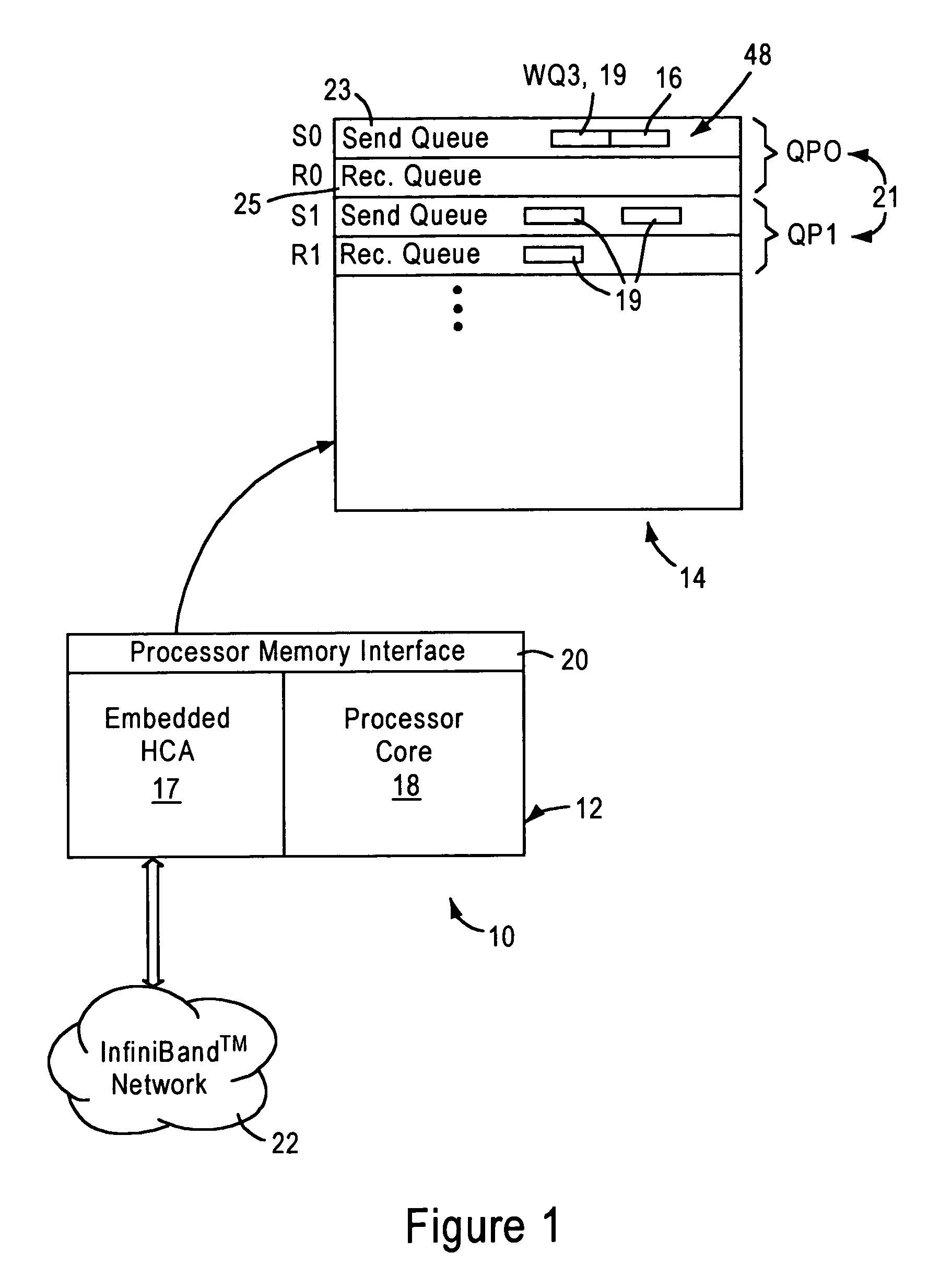
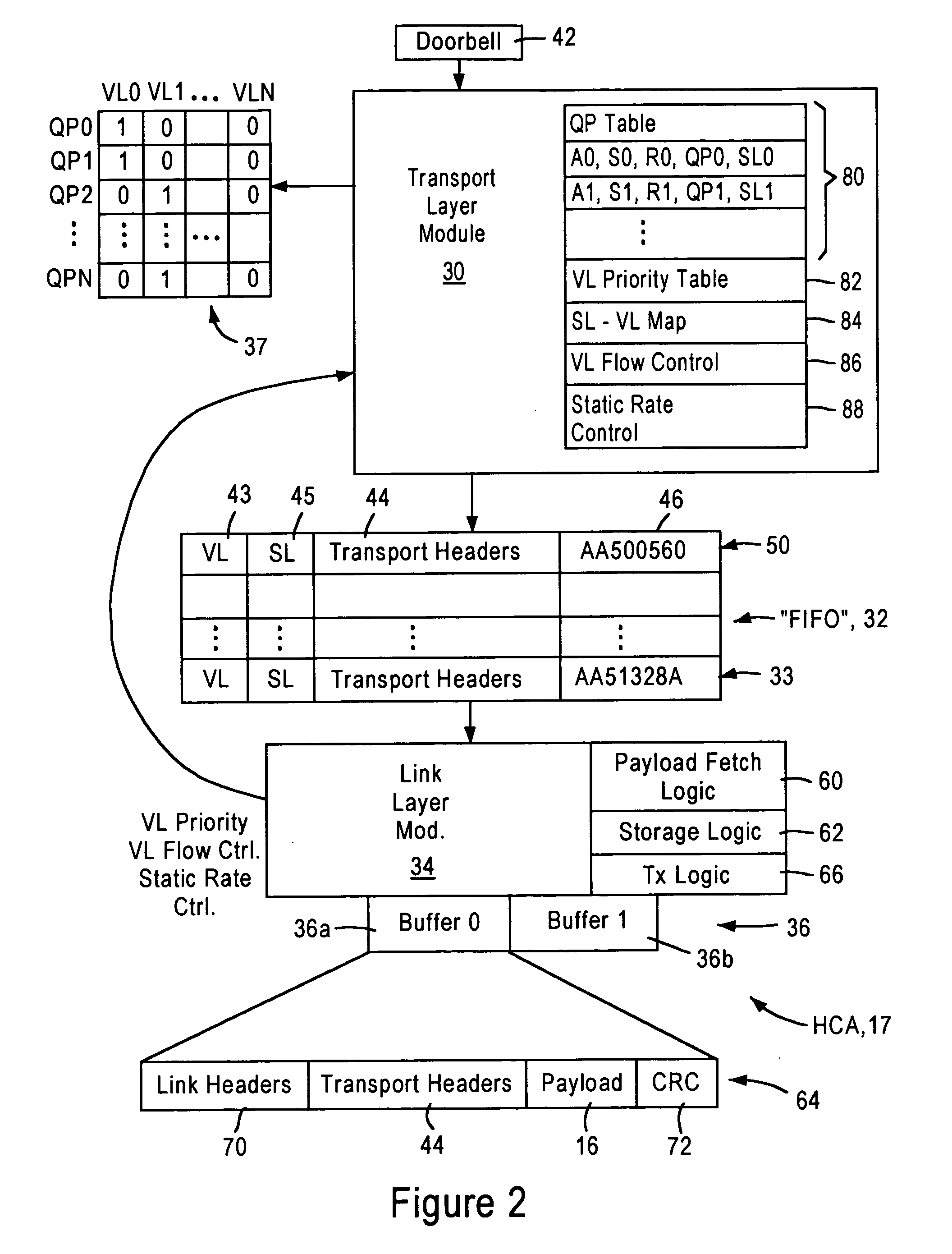
Embedded channel adapter having transport layer configured for prioritizing selection of work descriptors based on respective virtual lane priorities
ActiveUS7076569B1Efficient and economicalMinimize the numberMultiple digital computer combinationsTransmissionData packTransport layer
An embedded host channel adapter includes a transport layer module, a transport layer buffer, and a link layer module. The transport layer buffer is configured for storing transmit packet entries for virtual lanes serviced by the embedded host channel adapter. The link layer module is configured for supplying virtual lane priority information and virtual lane flow control information, for each virtual lane, to the transport layer module. The link layer module also configured for constructing transmit packets to be transmitted based on retrieval thereof from the transport layer buffer. The transport layer module is configured for selecting one of the virtual lanes for servicing based on the supplied virtual lane priority information and virtual lane flow control information for each of the virtual lanes, enabling the transport layer module to prioritize received work notifications, for generation of respective transmit packet entries.
Owner:ADVANCED MICRO DEVICES INC
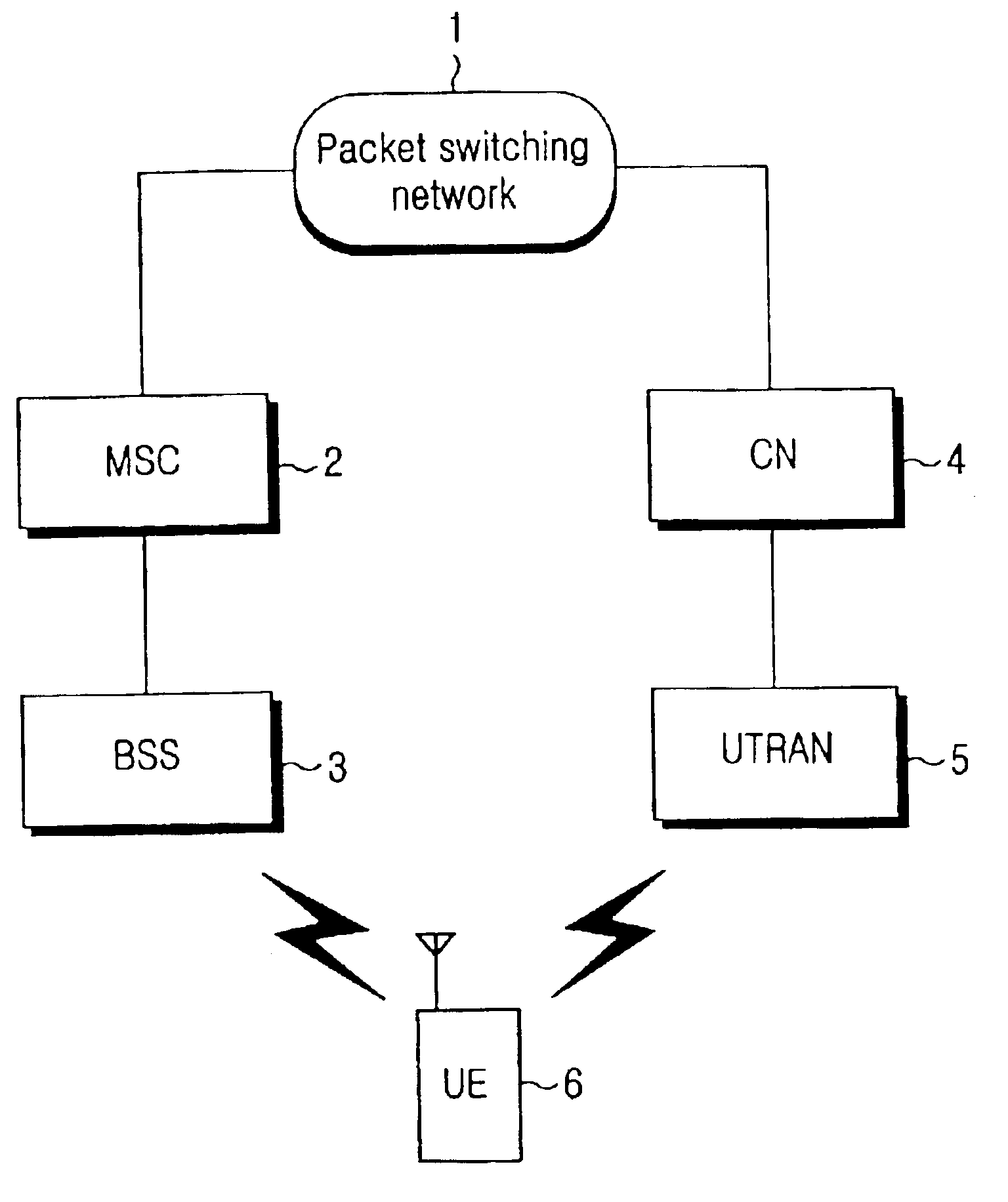
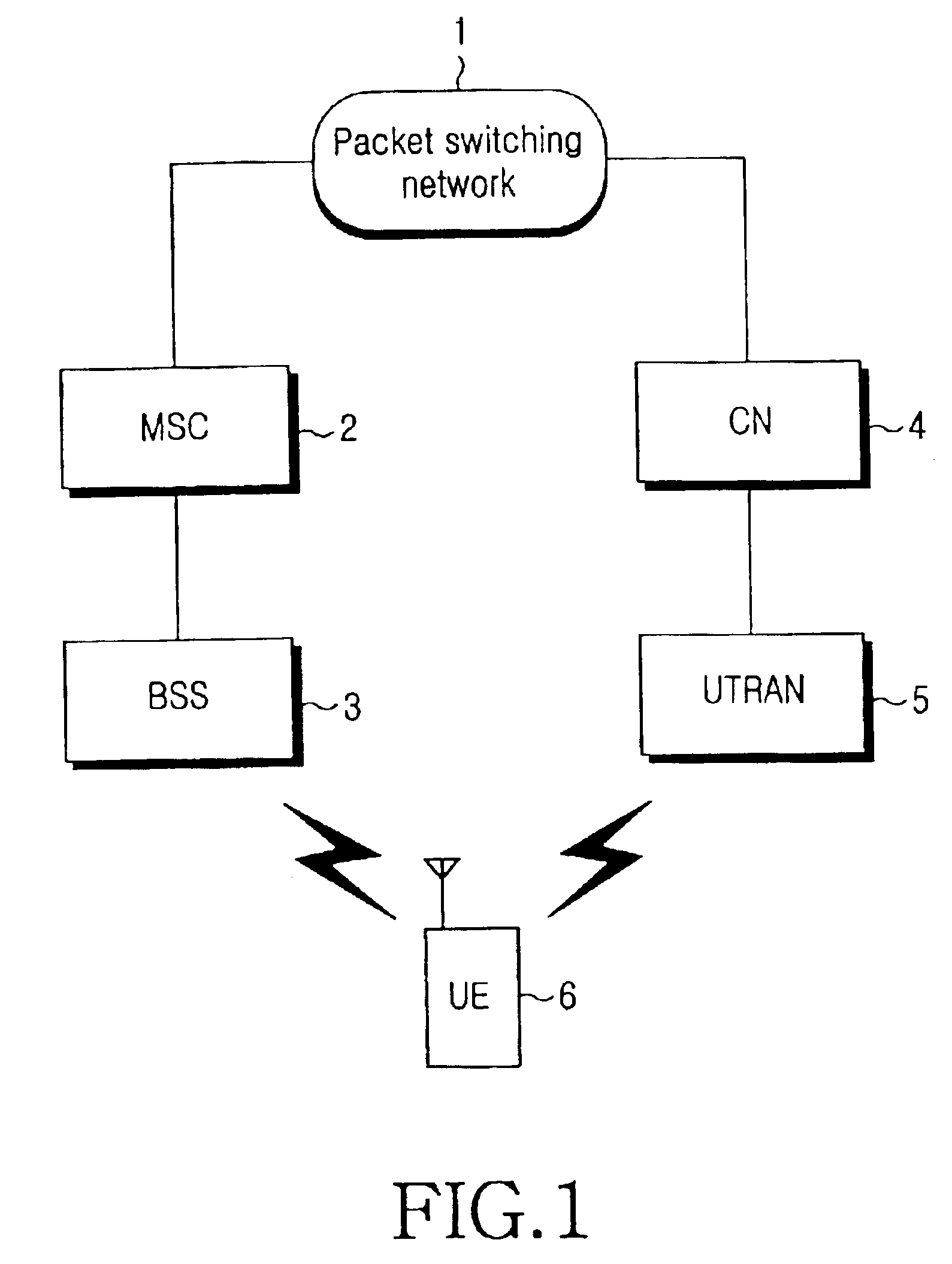
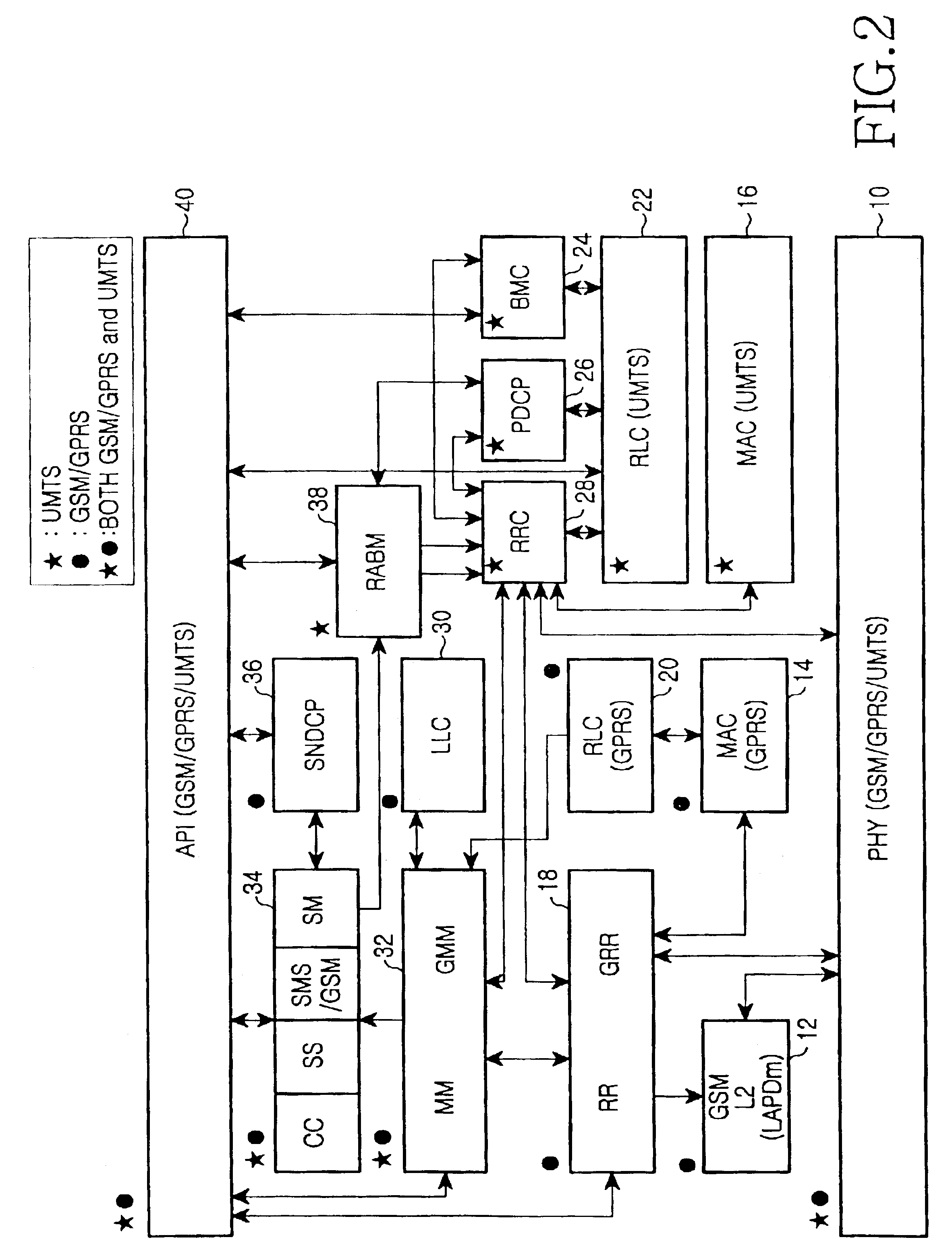
Method for performing inter system handovers in mobile telecommunication system
ActiveUS6963745B2Radio/inductive link selection arrangementsWireless communicationDual modeData link layer
An inter system handovers in a mobile telecommunication system is performed when a dual mode user equipment (UE) covered by both GSM / GPRS network and UMTS network connects a dedicated channel and sets up a call in a BSS region where the GSM / GPRS provides coverage, and then moves to a UTRAN (UMTS Terrestrial Radio Access Network) where the UMTS provides coverage, wherein the method includes the steps of: if the dual mode UE receives an inter system handover command, i.e. from the BSS to the UTRAN, requesting GSM / GPRS data link layer to suspend a GSM / GPRS data link by a sublayer RR of GSM / GPRS network layer in the UE, requesting a GSM / GPRS physical layer to release a physical channel of the GSM / GPRS, and sending the inter system handover command to the UTRAN for authorizing a sublayer RRC of UMTS network layer in the UE to continue a call; requesting, at the RRC in the UE, a UMTS physical channel to be configured as a UMTS physical channel, and monitoring if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel as requested; if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel, requesting, at the RRC in the UE, a UMTS data link layer to configure a UMTS data link, and conveying information to the UTRAN through a UMTS channel that the handover between systems from the BSS to the UTRAN has been successfully performed; and sending, at the RRC, a GSM / GPRS resource release message to RR / GRR, thereby resetting the GSM / GPRS physical layer and the GSM / GPRS data link layer.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for configuring security in a plug-and-play architecture
InactiveUS20070208948A1Security configurationConfiguring security in a PnP architectureDigital data processing detailsUnauthorized memory use protectionDocumentationProtocol Application
A plug-and-play (PnP) for configuring security in a PnP architecture includes a security manager and a PnP device. The PnP device is adapted to send a device description document to a user entity. The device description document includes an address pointing to the security manager, and as such, the user entity is capable of accessing the security manager based upon the address. The security manager is adapted to authenticate the user entity, and it authenticated, to communicate with the user entity to configure application-layer security of the PnP device, whereby configuring the application-layer security includes creating an access control list (ACL) document for restricting access to a service of the PnP device. In a further aspect, the PnP device may bootstrap establishing its link-layer security with configuring its application-layer security.
Owner:CORE WIRELESS LICENSING R L
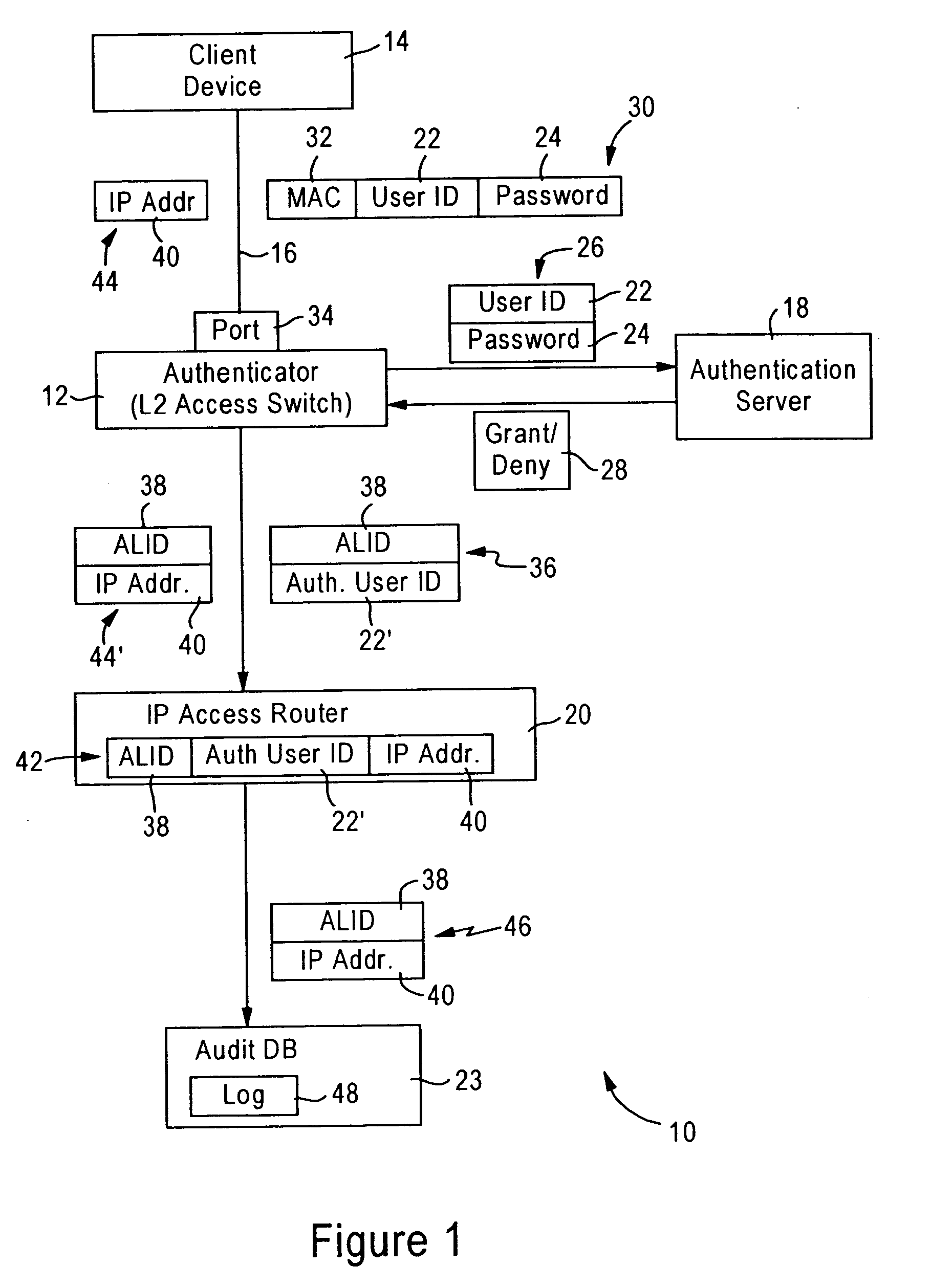
Arrangement for tracking IP address usage based on authenticated link identifier
ActiveUS20060028996A1Reliable trackingError preventionFrequency-division multiplex detailsIp addressClient-side
Link layer authentication information is supplied by a link layer authentication device to an access router for tracking IP address usage by a client device. The authentication information supplied to the access router includes an authenticated client identifier and a corresponding authenticated link identifier for the client device that attached to the network based on the authenticated link identifier. The access router, in response to receiving a message that specifies the authenticated link identifier and a source IP address, adds the source IP address to a cache entry that specifies the authenticated client identifier and the corresponding authenticated link identifier, and outputs to an audit resource a record that specifies the source IP address and the authenticated link identifier.
Owner:CISCO TECH INC
Method for accessing a network and network access device
ActiveUS20130188634A1Inhibit functioningOptimizationEnergy efficient ICTData switching by path configurationNetwork access serverPrivate network
The invention provides for a method for accessing a virtual private network over a packet switched network, the method comprising sending, by a provider edge router, network labelling information about data packet labels to a network access device using a layer 2 network protocol. The method may be performed for accessing a hierarchical Virtual Private LAN Service network using a link layer distribution protocol as signalling protocol for Multi-Protocol Label Switching labels attached to data packets of the packet switched network.
Owner:ADVA OPTICAL NETWORKING SE
Dynamic packet buffering system for mobile handoff
InactiveUS20070014259A1Reducing resource allocation needTime-division multiplexWireless network protocolsComputer networkMobile device
The present invention relates to the use of buffering packets for the mobile node at an access router or network node near the edge of the network that the mobile is moving away from or towards. The buffered packets are then forwarded to the mobile node once the handoff process is completed. This invention also relates to the use of buffering packets originating from the mobile node during the handoff process. The buffered packets are then forwarded to their intended destinations once the handoff process is completed. The buffering system is used in conjunction with existing mobility protocols, access protocols, or as an independent network or link layer mechanism.
Owner:TELCORDIA TECHNOLOGIES INC
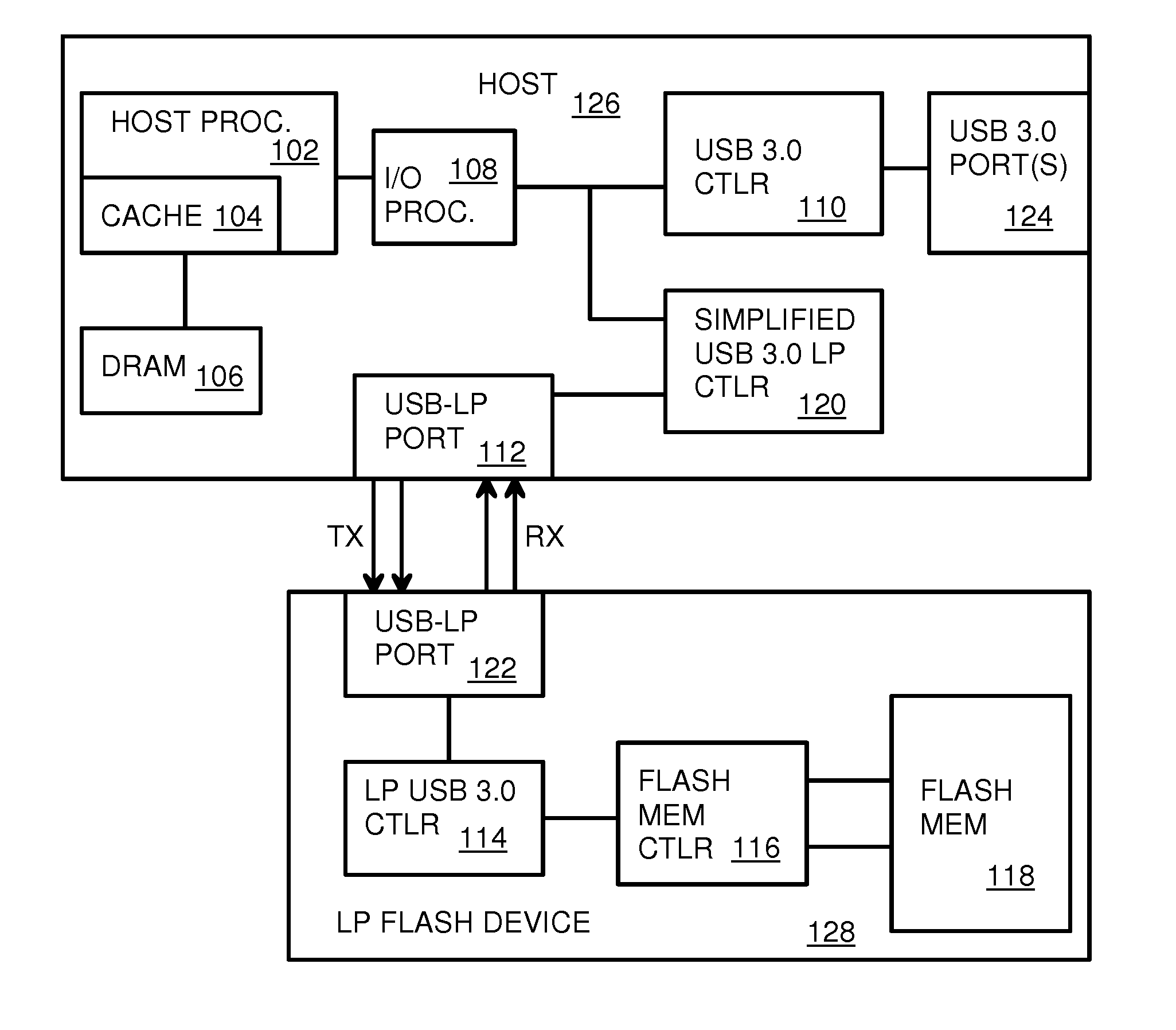
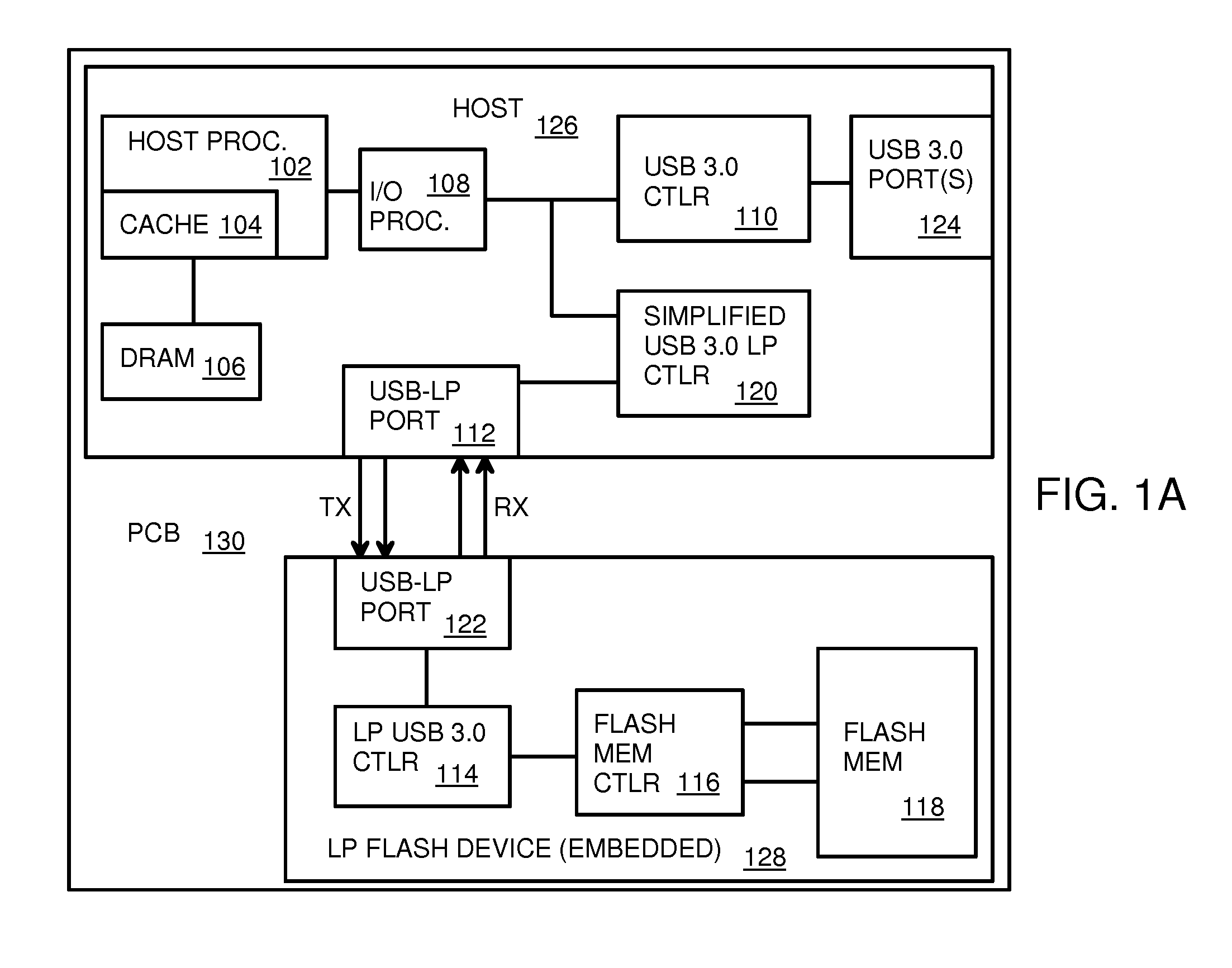
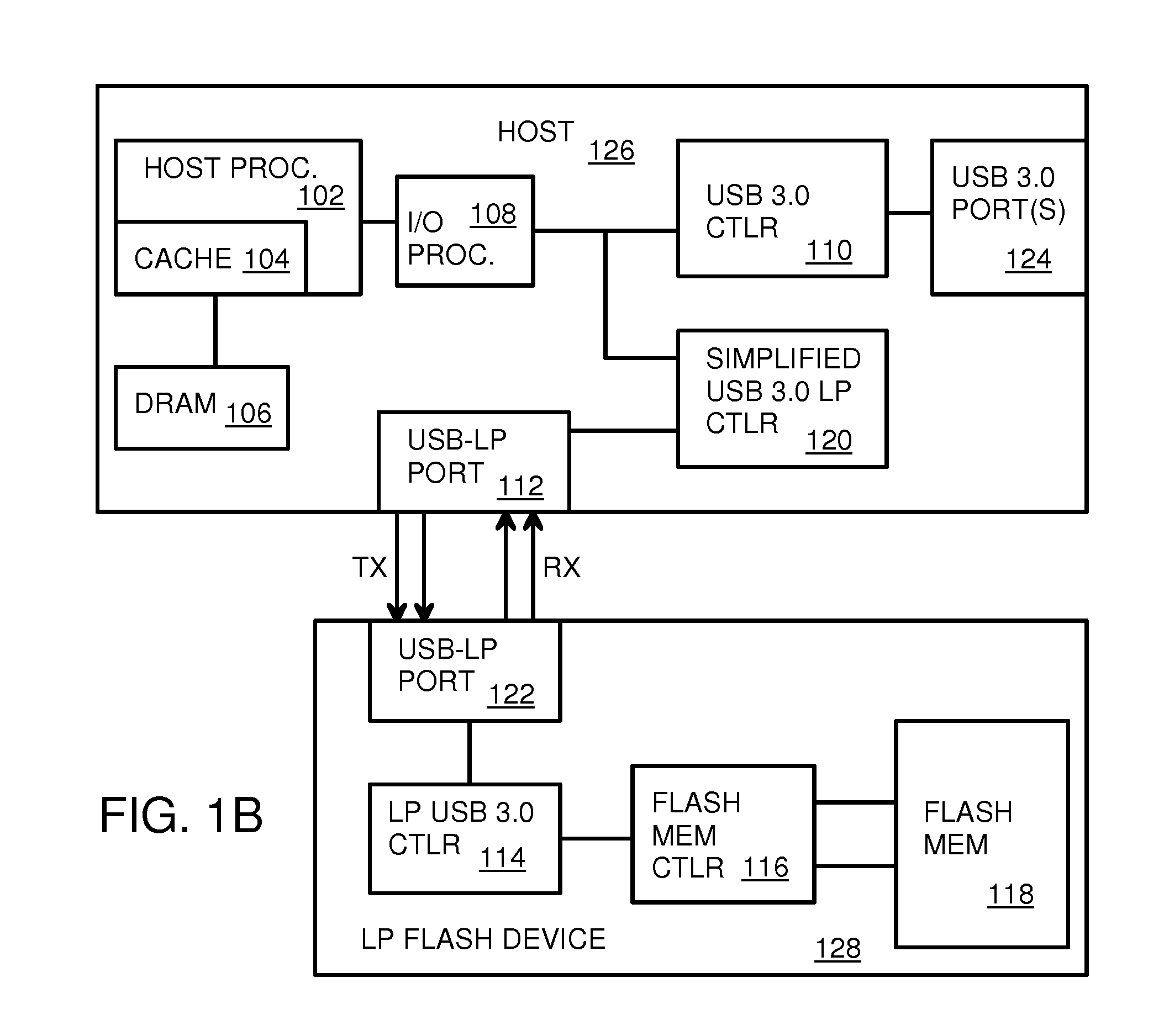
Low-Power USB SuperSpeed Device with 8-bit Payload and 9-bit Frame NRZI Encoding for Replacing 8/10-bit Encoding
A Low-power flash-memory device uses a modified Universal-Serial-Bus (USB) 3.0 Protocol to reduce power consumption. The bit clock is slowed to reduce power and the need for pre-emphasis when USB cable lengths are short in applications. Data efficiency is improved by eliminating the 8 / 10-bit encoder and instead encoding sync and framing bytes as 9-bit symbols. Data bytes are expanded by bit stuffing only when a series of six ones occurs in the data. Header and payload data is transmitted as nearly 8-bits per data byte while framing is 9-bits per symbol, much less than the standard 10 bits per byte. Low-power link layers, physical layers, and scaled-down protocol layers are used. A card reader converter hub allows USB hosts to access low-power USB devices. Only one flash device is accessed, reducing power compared with standard USB broadcasting to multiple devices.
Owner:SUPER TALENT TECH CORP
Method, apparatus and system for QOS within high performance fabrics
ActiveUS20150180782A1Error preventionFrequency-division multiplex detailsQuality of serviceTransport layer
Method, apparatus, and systems for implementing Quality of Service (QoS) within high performance fabrics. A multi-level QoS scheme is implemented including virtual fabrics, Traffic Classes, Service Levels (SLs), Service Channels (SCs) and Virtual Lanes (VLs). SLs are implemented for Layer 4 (Transport Layer) end-to-end transfer of fabric packets, while SCs are used to differentiate fabric packets at the Link Layer. Fabric packets are divided into flits, with fabric packet data transmitted via fabric links as flits streams. Fabric switch input ports and device receive ports detect SC IDs for received fabric packets and implement SC-to-VL mappings to determine VL buffers to buffer fabric packet flits in. An SL may have multiple SCs, and SC-to-SC mapping may be implemented to change the SC for a fabric packet as it is forwarded through the fabric, while maintaining its SL. A Traffic Class may include multiple SLs, enabling request and response traffic for an application to employ separate SLs.
Owner:INTEL CORP
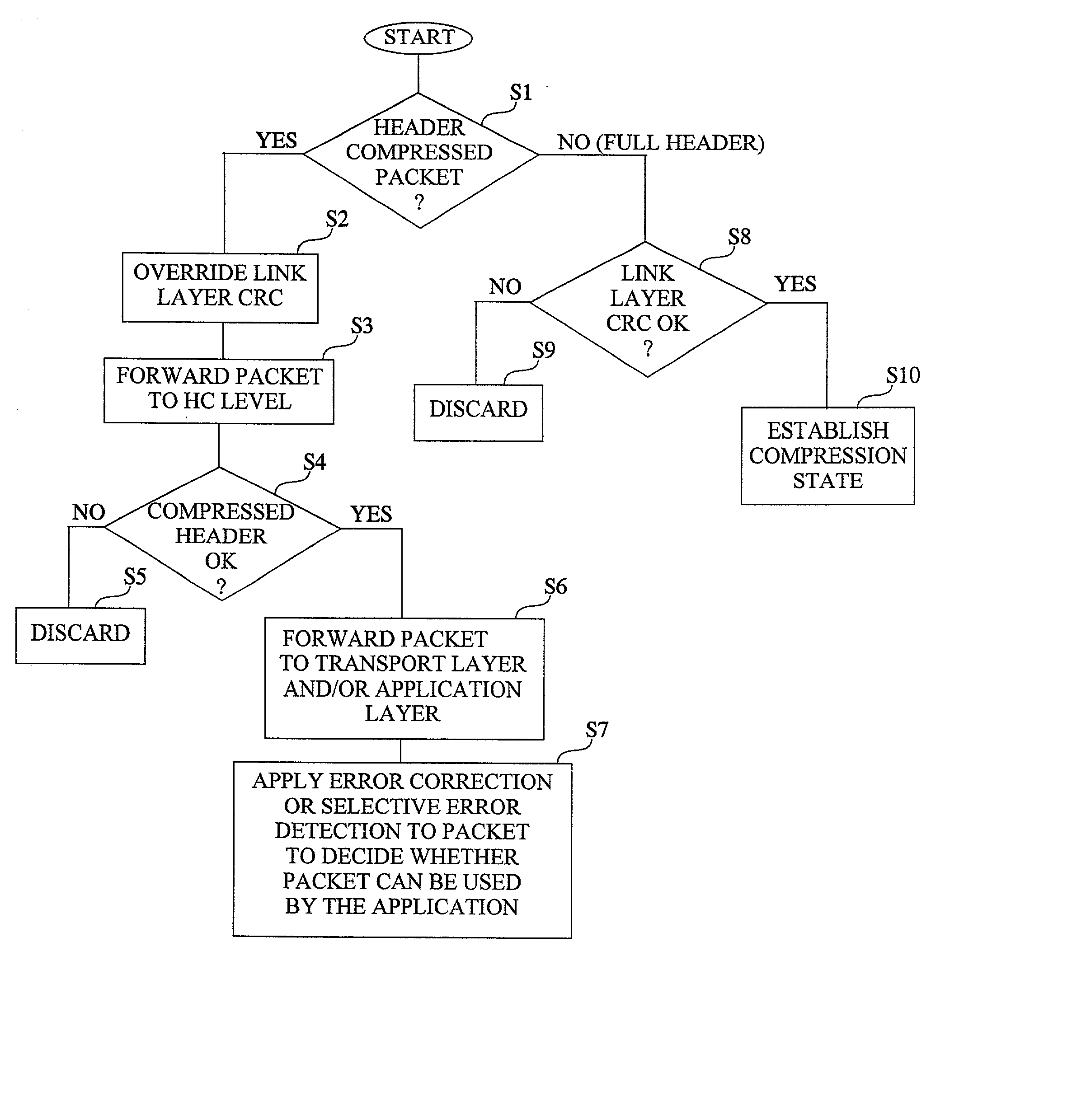
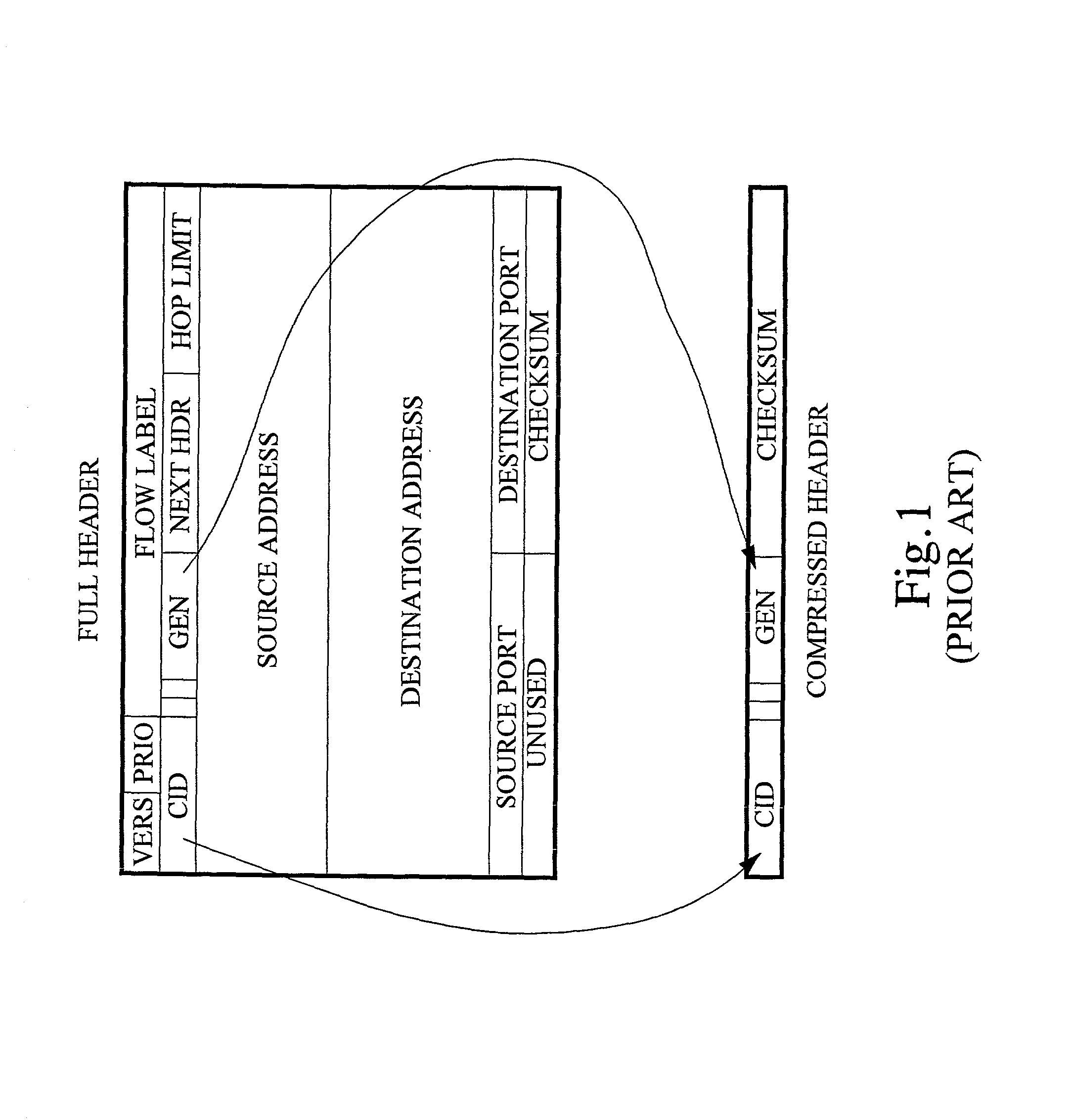
Bit error resilience for an internet protocol stack
ActiveUS20020071432A1Accurate protectionWithout seriously degrading application qualityError preventionTransmission systemsInternet protocol suitePacket loss
The invention concerns the bit error resilience of an IP protocol stack based on a secure link layer, in which packet flows are header compressed according to a suitable header compression standard. According to the invention, by analyzing each packet at the link layer it can be determined whether the packet is a full header packet, in which case the link layer checksum evaluation is used as normal for discarding faulty full header packets, or a header compressed packet in which case the link layer checksum evaluation is ignored and the packet is propagated upwards in the protocol stack. This solution not only opens up for more intelligent higher-level handling of faulty header compressed packets, but also solves the problem of properly protecting full header packets at the link layer. In order to compensate for ignoring the link layer checksum evaluation for header compressed packets, header protection is introduced at the header compression level of the link layer by using one or more local checksums. The invention is particularly applicable to delay-sensitive real-time data such as compressed voice or video.
Owner:TELEFON AB LM ERICSSON (PUBL)
Framework of Media-Independent Pre-Authentication
ActiveUS20070204155A1Minimize and eliminate packet lossAvoid lostUser identity/authority verificationWireless network protocolsMediaFLOEngineering
This application describes, among other things, a framework of Media-independent Pre-Authentication (MPA), a new handover optimization mechanism that has a potential to address issues on existing mobility management protocols and mobility optimization mechanisms. MPA is a mobile-assisted, secure handover optimization scheme that works over any link-layer and with any mobility management protocol. This application also shows, among other things, an initial implementation of MPA in our testbed and some performance results to show how existing protocols could be leveraged to realize the functionalities of MPA.
Owner:TELCORDIA TECHNOLOGIES INC
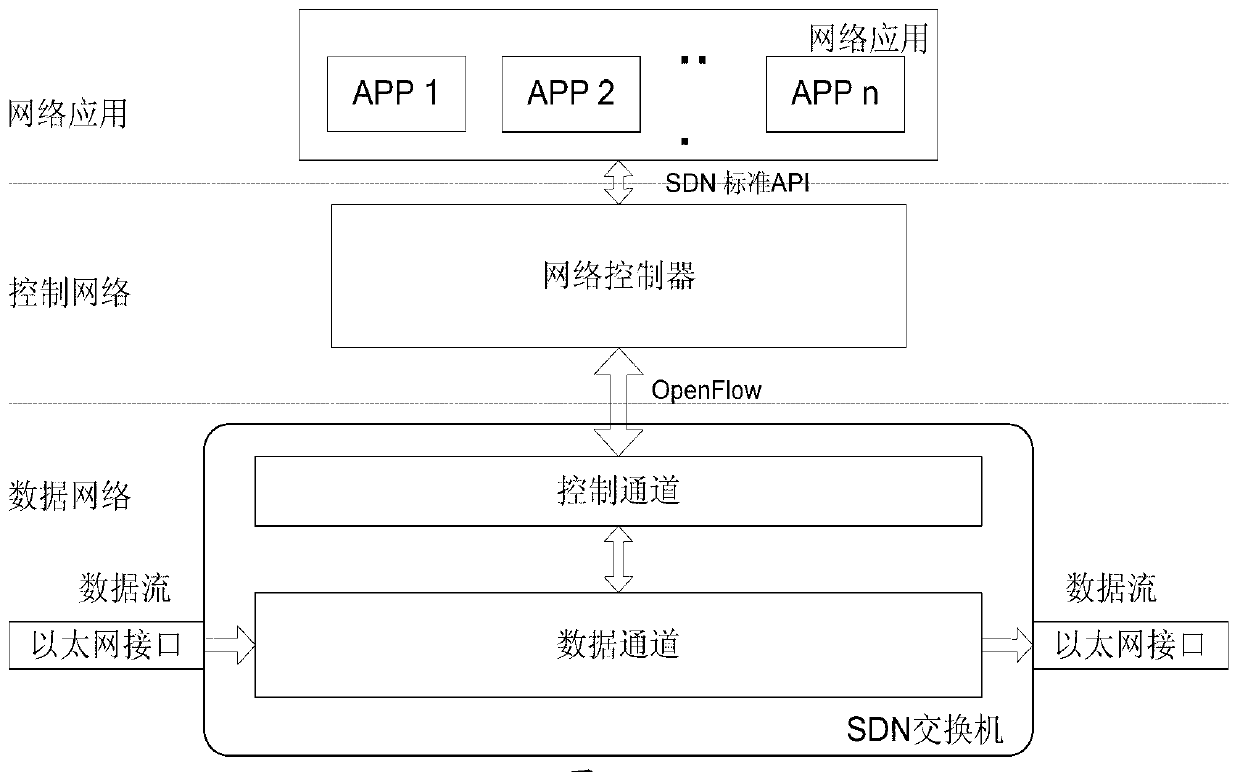
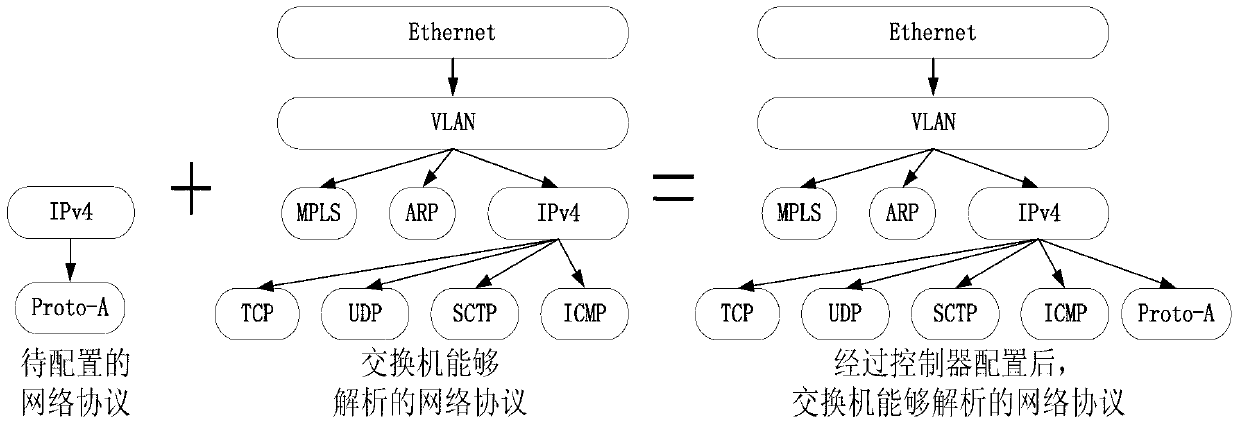
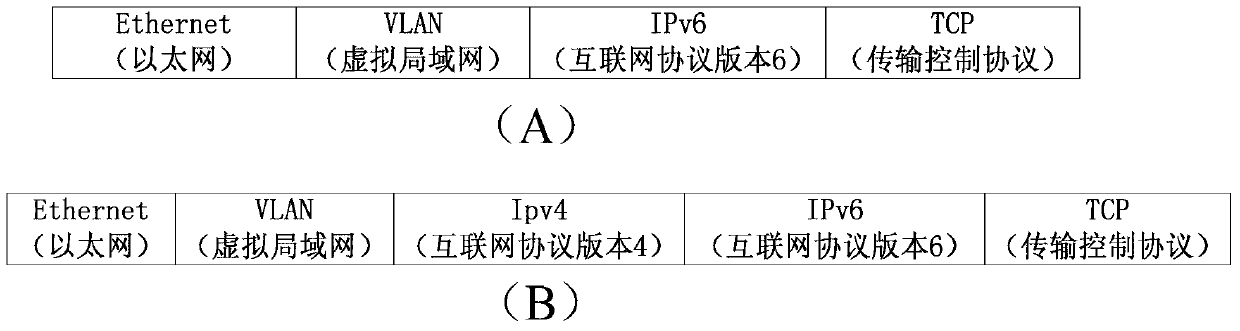
OpenFlow network system and method for enhancing programmable capability
InactiveCN103347013AExtension moduleFunction increaseData switching networksNetworking protocolNetwork control
The invention provides an OpenFlow network system and method for enhancing programmable capability. Two assembling devices of the system are expanded respectively, for a network controller, a protocol analysis and configuration module, a data packet processing and programming module, a queue resource allocating module and a link-layer protocol allocating module are added, and an interchanger is additionally provided with four modules which are a protocol analysis module, a data packet processing assembly line module, an output queue module and a link-layer protocol analysis module and respectively correspond to the four modules additionally arranged for the network controller. Through cooperation of the four sets of corresponding modules, the OpenFlow network system can deploy a plurality of heterogeneous networks to achieve data forwarding independent to protocols, and network programmability is enhanced. According to the OpenFlow network system and method, different heterogeneous networks which are of different systematic structures, have an independent addressing function, routes, and related network protocol execution functions are deployed in the OpenFlow network system, software defining capacity and software defining category in an existing SDN are substantially improved, and programmability of the whole SDN is obviously improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Network direct memory access
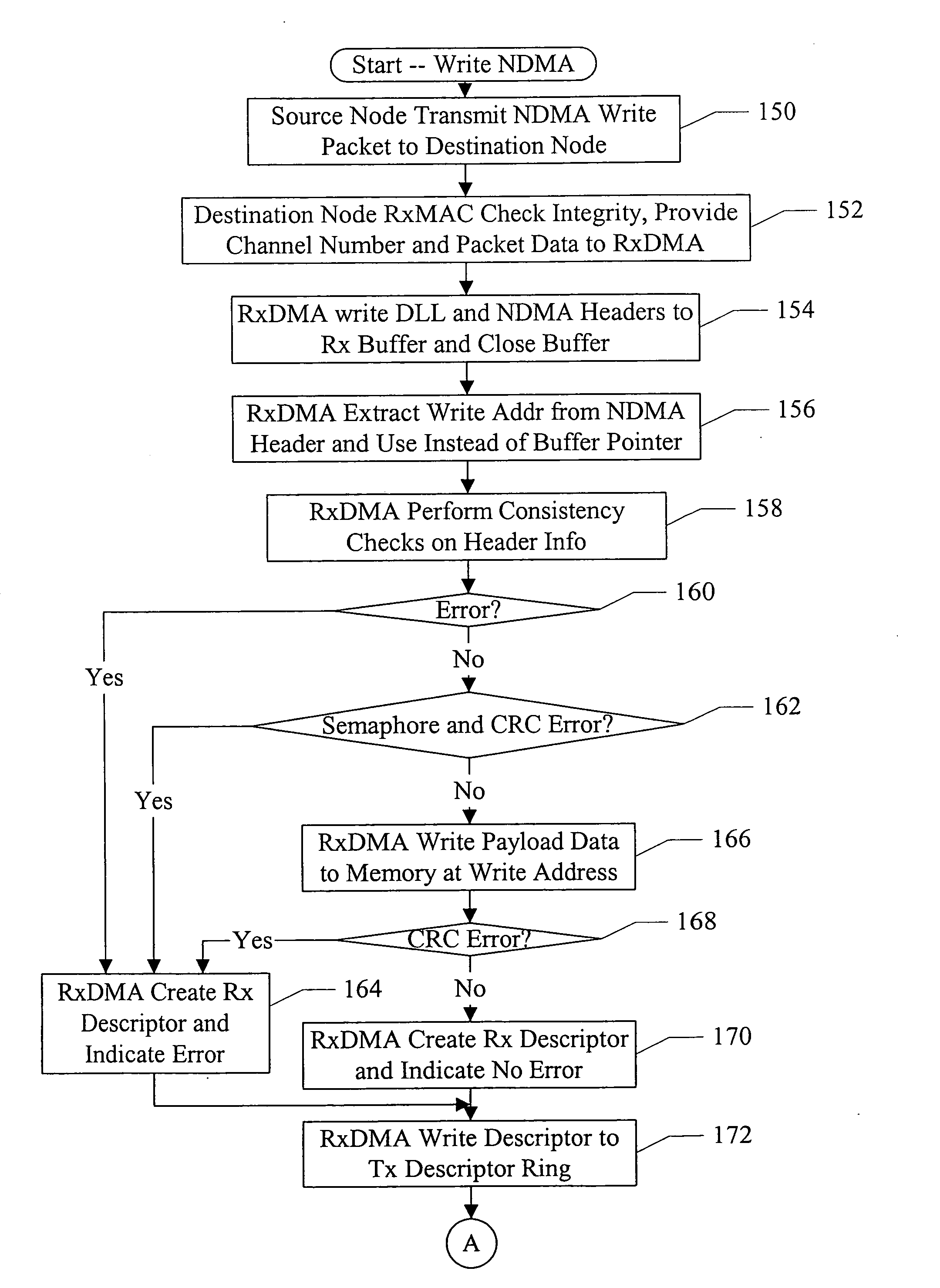
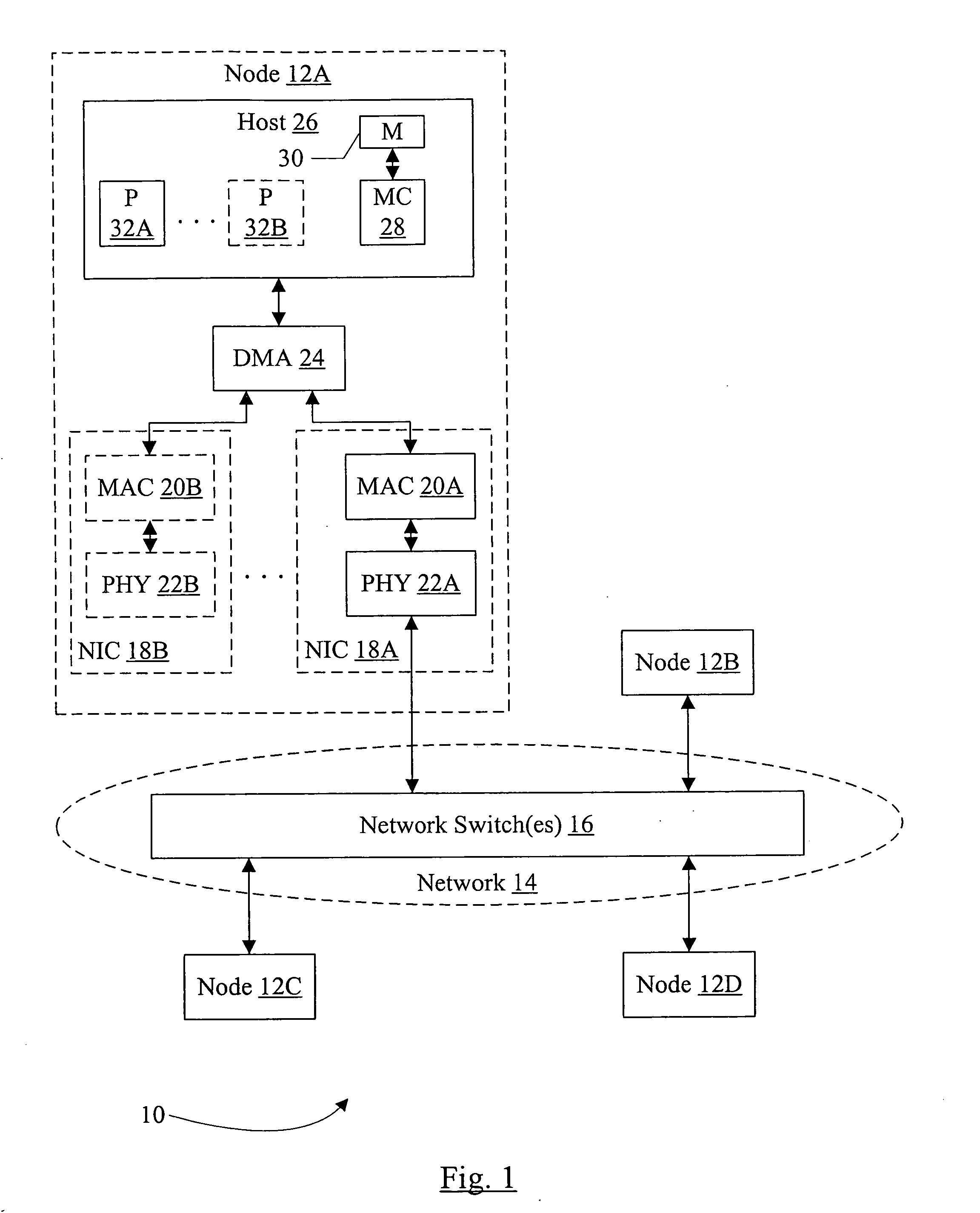
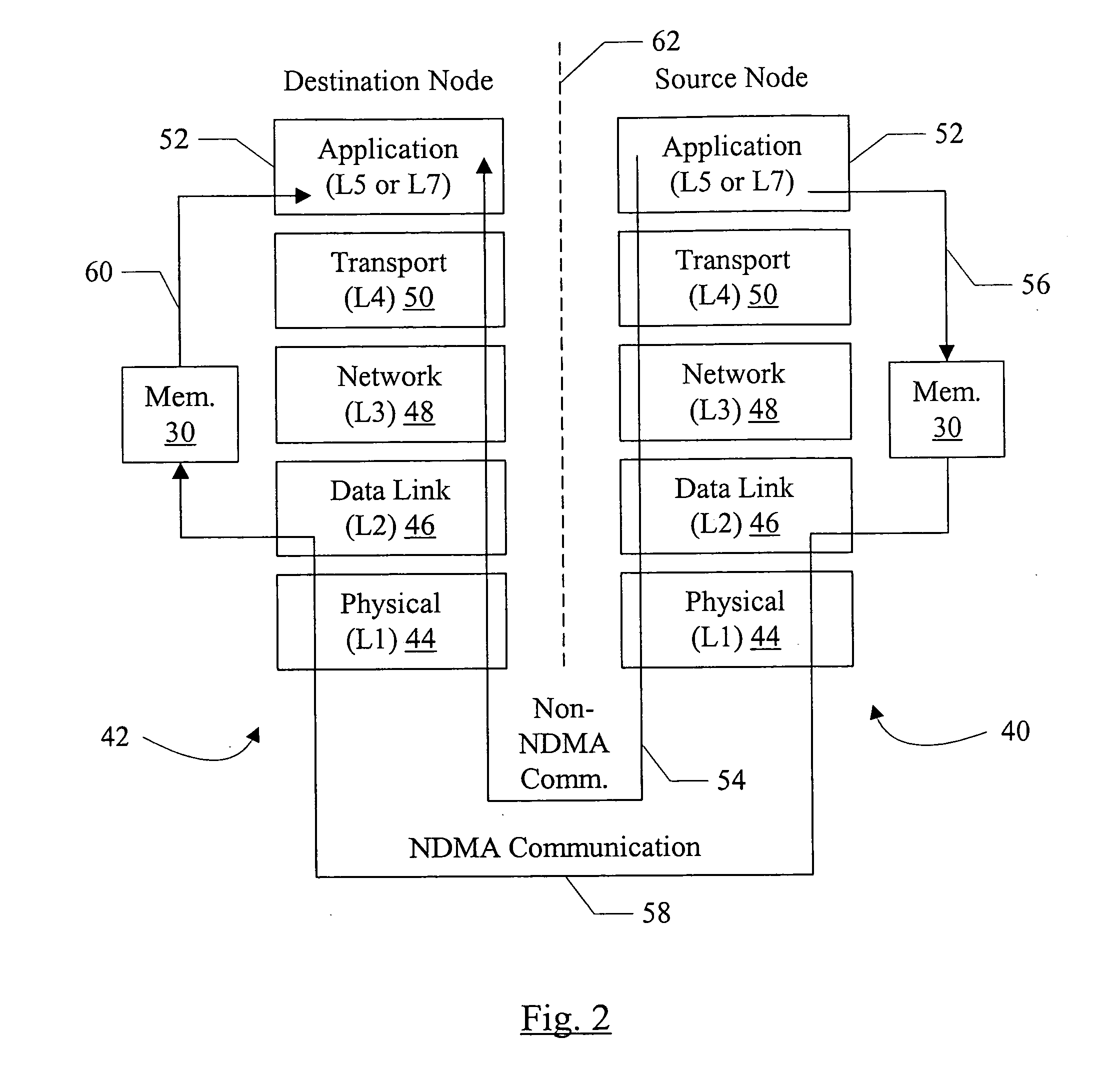
InactiveUS20080043732A1Data switching by path configurationMultiple digital computer combinationsDirect memory accessRemote direct memory access
In one embodiment, a system comprises at least a first node and a second node coupled to a network. The second node comprises a local memory and a direct memory access (DMA) controller coupled to the local memory. The first node is configured to transmit at least a first packet to the second node to access data in the local memory and at least one other packet that is not coded to access the local memory. The second node is configured to capture the packet from a data link layer of a protocol stack, and wherein the DMA controller is configured to perform one more transfers with the local memory to access the data specified by the first packet responsive to the first packet received from the data link layer. The second node is configured to process the other packet to a top of the protocol stack.
Owner:APPLE INC
Bit Indexed Explicit Replication For Layer 2 Networking
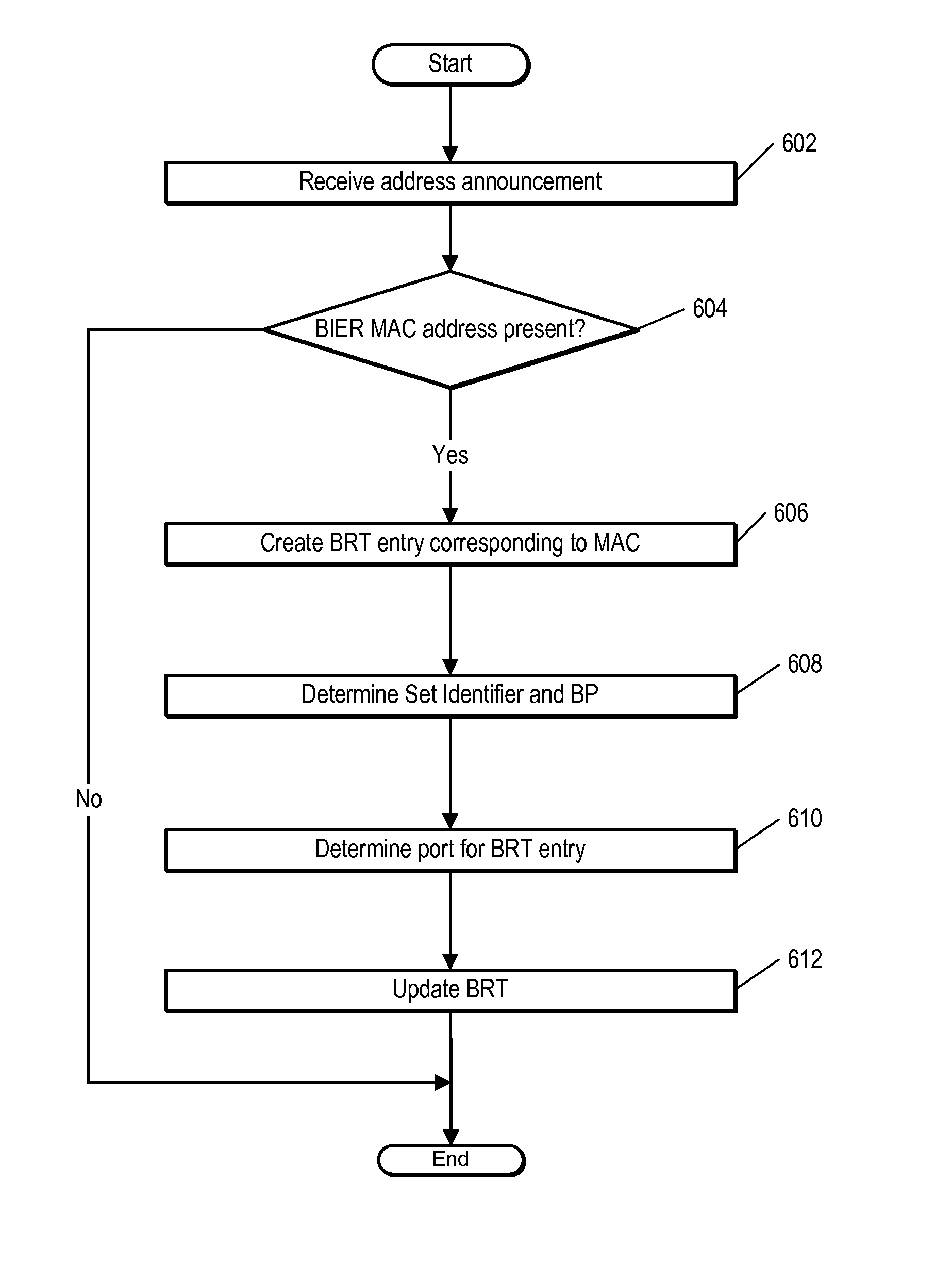
InactiveUS20150078380A1Special service provision for substationData switching by path configurationComputer scienceLink layer
Various systems and methods for performing bit indexed explicit replication (BIER). For example, one method involves receiving a link layer protocol frame at a network device. The link layer protocol frame includes a MAC address that identifies the link layer protocol frame as a being a multicast frame. The method then involves selecting a subset of ports included on the network device and forwarding the link layer protocol frame to only the selected subset of ports.
Owner:CISCO TECH INC
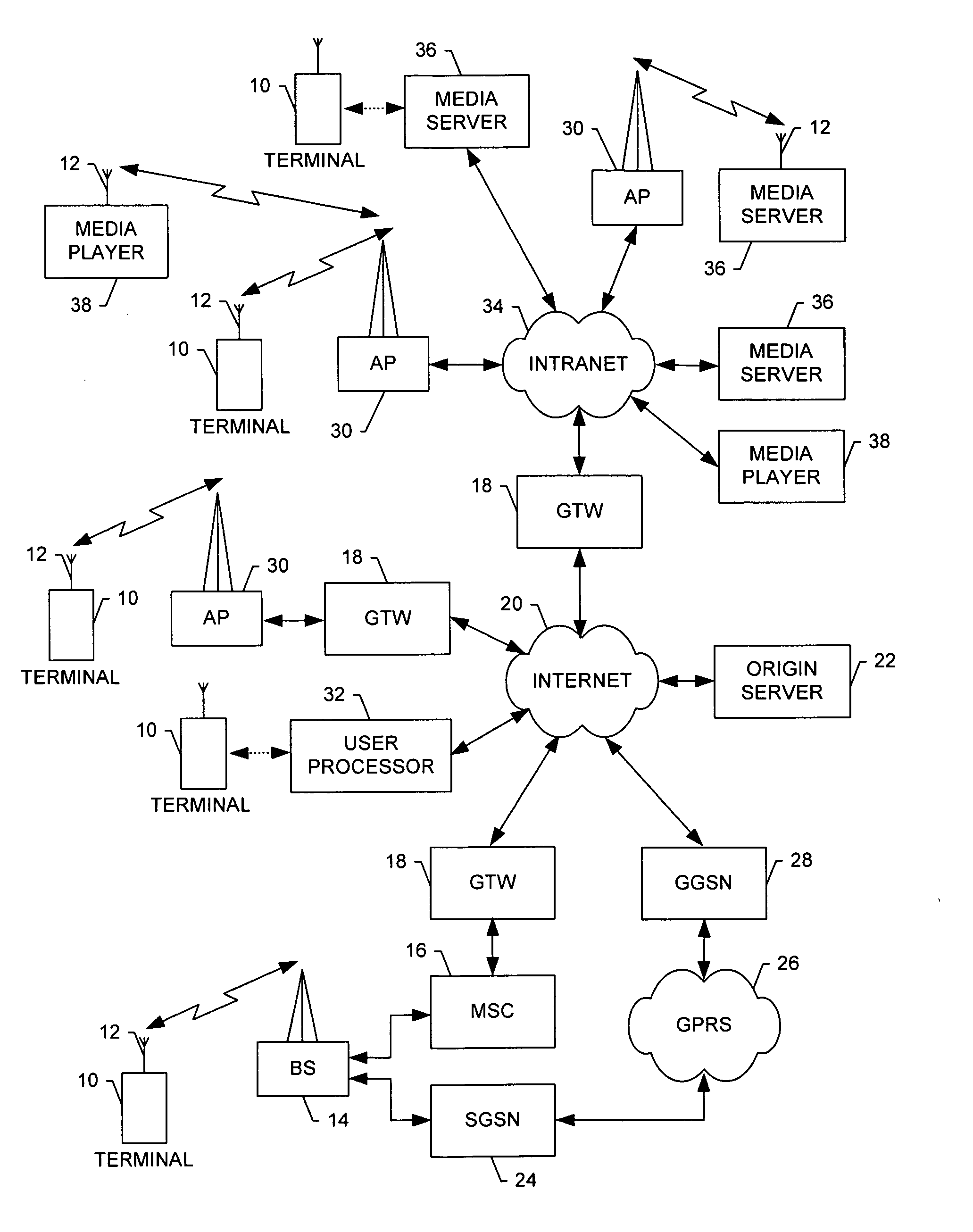
System and method for effectuating a connection to a network
InactiveUS20060274695A1Reducing sequenceReduce exchangeRadio/inductive link selection arrangementsWireless commuication servicesPhysical layerTrust relationship
A system for connecting a mobile node includes a target network, and may include an anchor network. The anchor network can generate token information based upon a trust relationship between the mobile node and the anchor network, and a trust relationship between the target network and the anchor network. The anchor network can then transmit the token information to the mobile node. Thereafter, during connection of the mobile node, the target network is capable of establishing a link-layer connection with the mobile node over a previously established physical-layer connection. The target network is also capable receiving of a handoff attach message including the token information, and thereafter authenticating the mobile node based upon the handoff attach message. And if the mobile node is authenticated, the target network is capable of establishing a network-layer connection with the mobile node over the link-layer connection.
Owner:NOKIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com