Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6430 results about "Network on" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
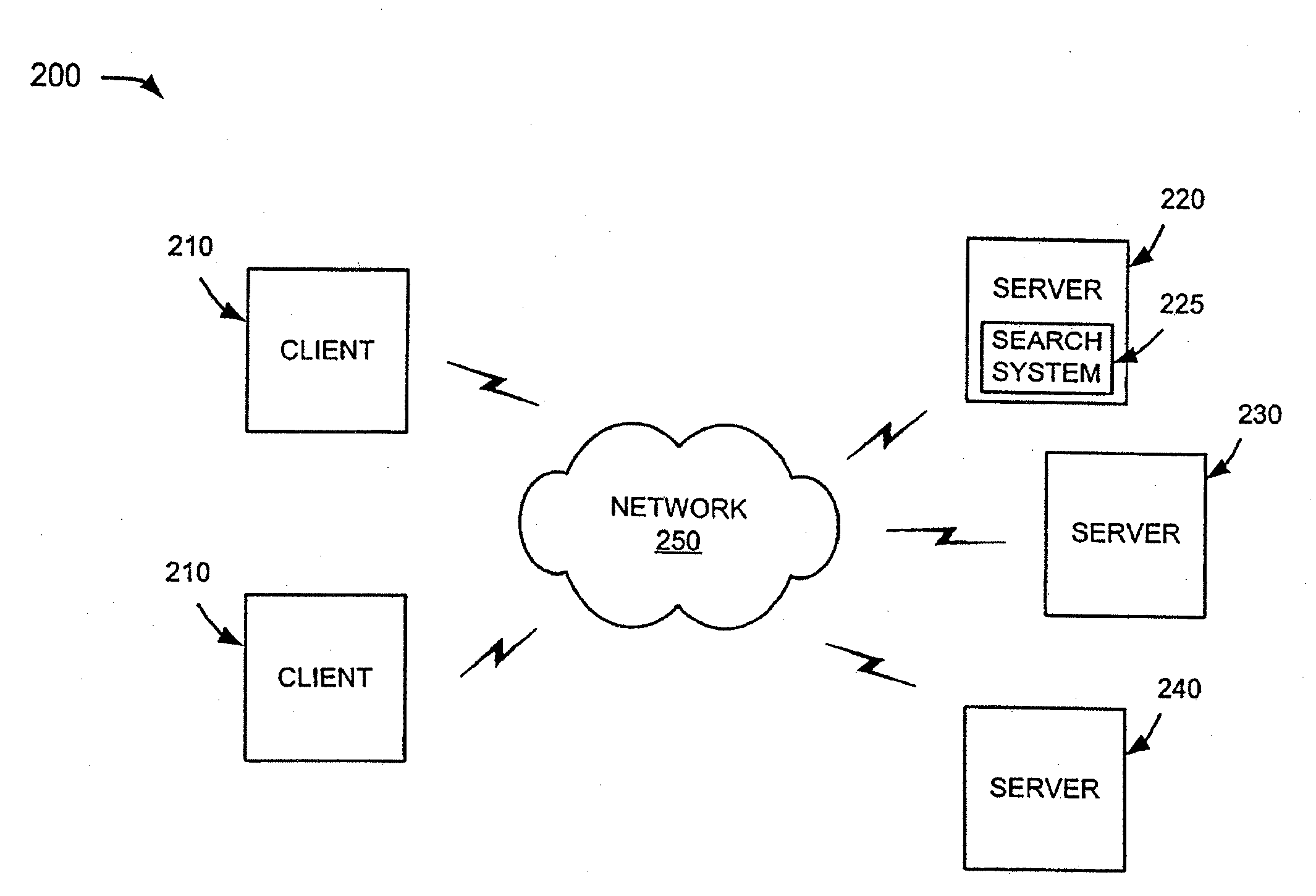
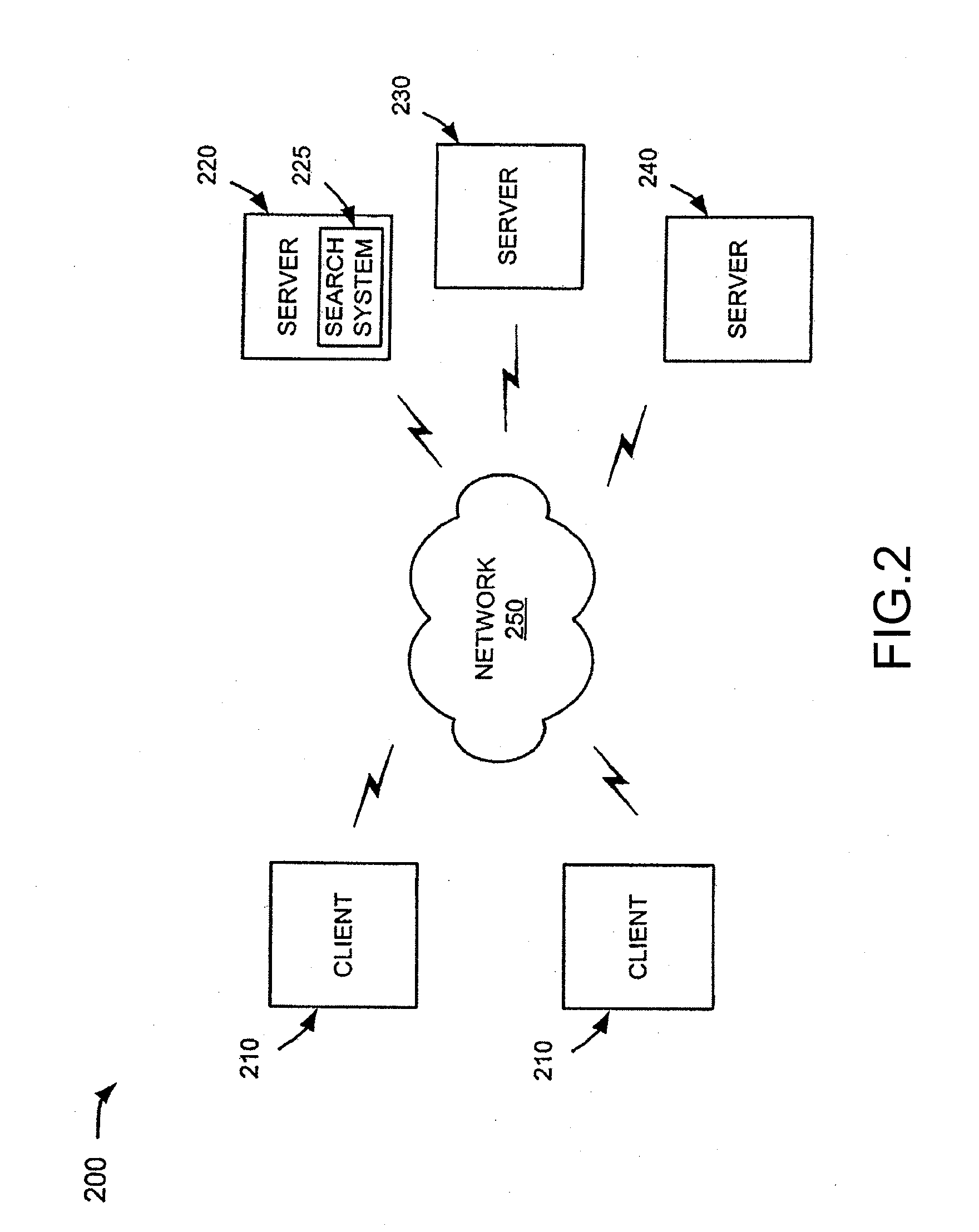
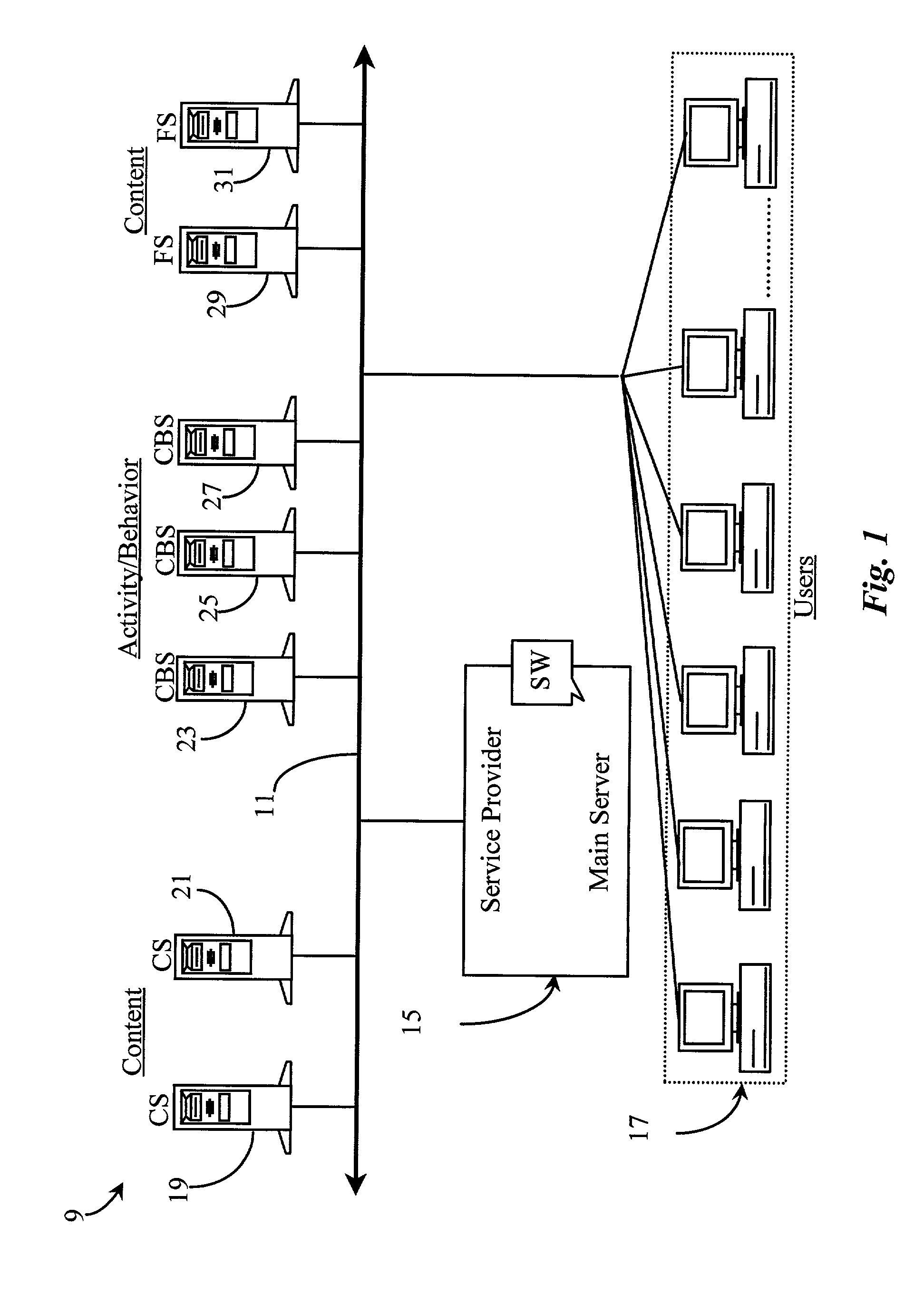
Social network systems and methods
InactiveUS20100306249A1Digital data processing detailsSpecial data processing applicationsInternet privacySocial web
Embodiments of computer-implemented methods and systems are described, including: in a computer network system, providing a user page region viewable by a user; providing to the user, in the user page region, indicators of each of three categories, the categories consisting essentially of: (i) what the user has, (ii) what the user wants, and (c) what the user has thought or is thinking; wherein the user page region accepts a post by the user; after the post by the user, displaying the post in a group page region, viewable by a set of one of more persons other than the user, the set of persons being separated from the user at locations on a network; before the displaying, requiring the user to select one of the three categories to be associated with the post; and displaying the category selected by the user, with the post, in the group page region.
Owner:FOSTER JOHN C
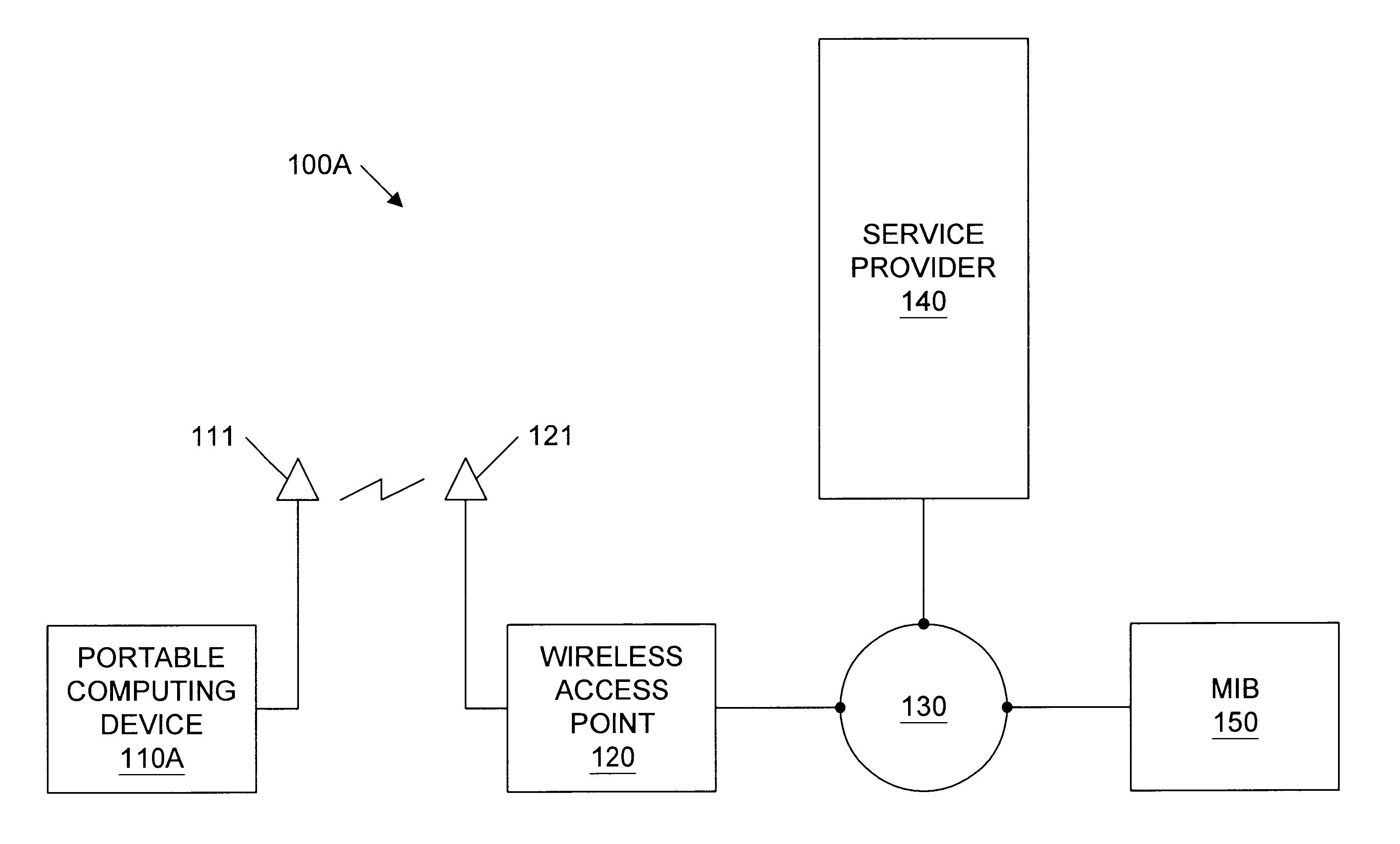
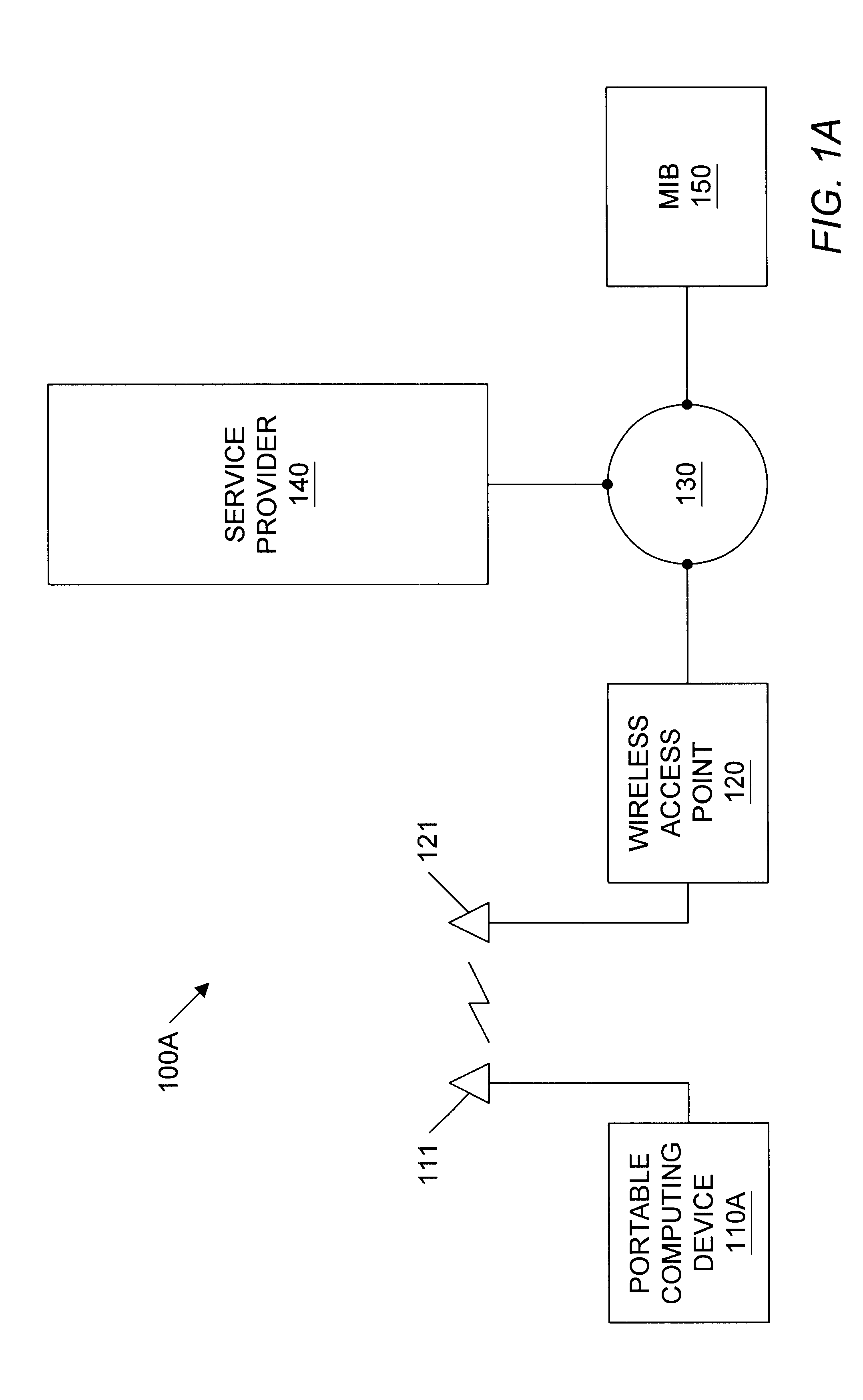
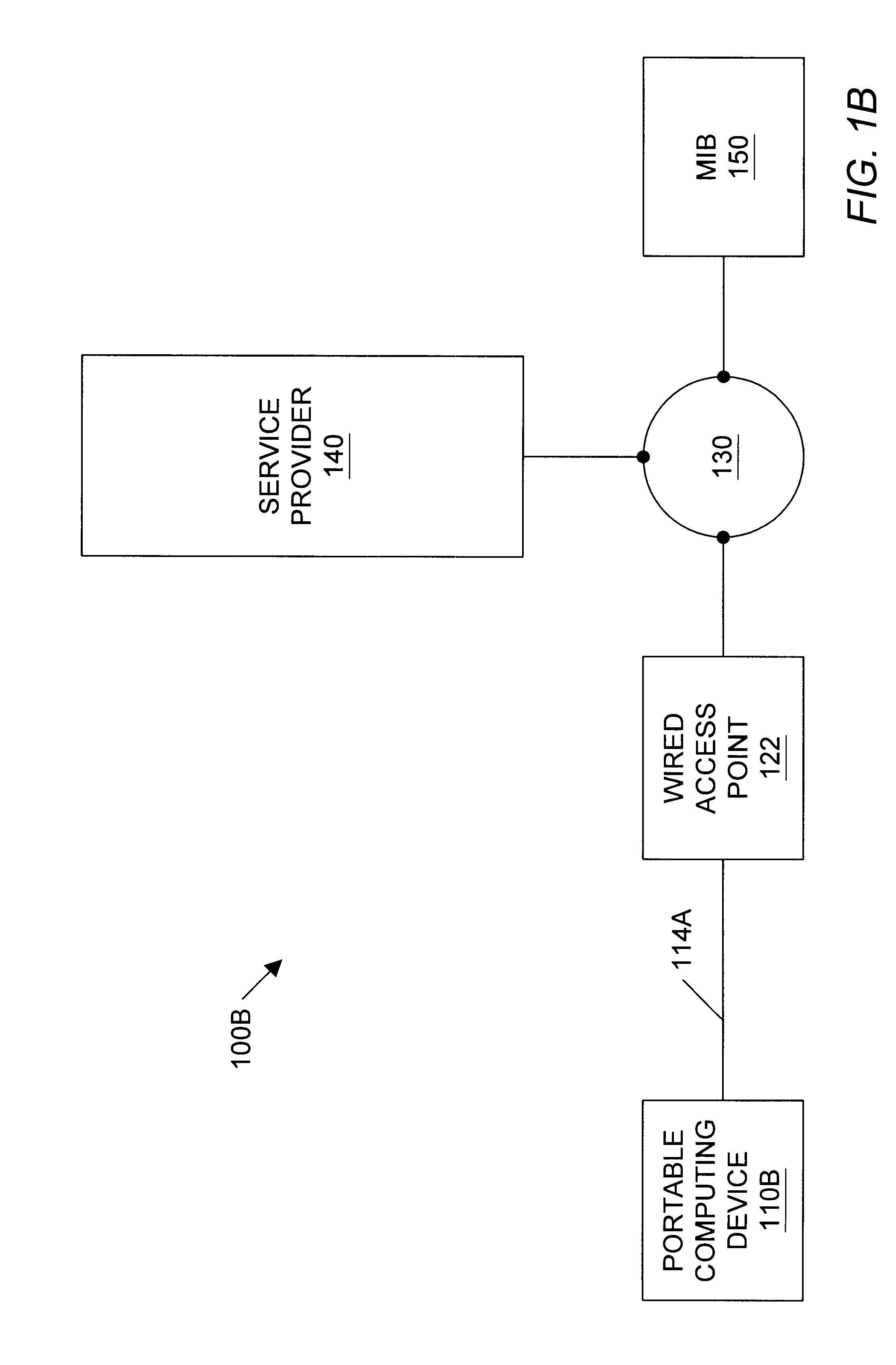
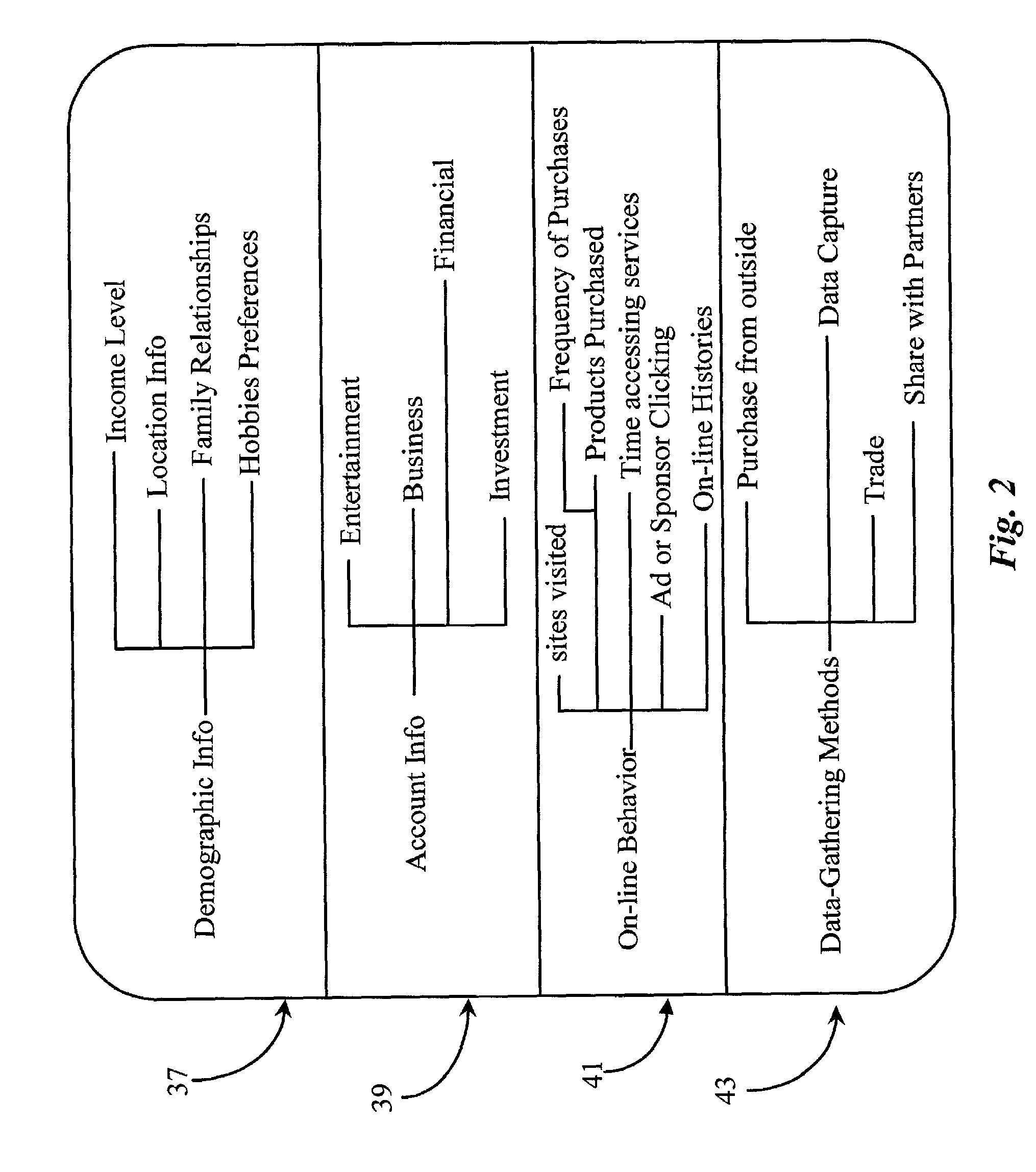
Geographic based communications service
InactiveUS6259405B1Direction finders using radio wavesBeacon systems using radio wavesGeographic regionsGeolocation
A geographic based communications service system that includes a network and a plurality of access points connected to the network and arranged at known locations in a geographic region. One or more service providers or information providers may be connected to the network to provide services or information on the network. A mobile user (MU) may use a portable computing device (PCD) to connect to the network and access information or services from the network. The PCD may be configured to transmit a signal indicating a presence of the PCD as well as identification information indicating the mobile user. Upon detection of the wireless signal by a first access point in proximity to the PCD, and upon receipt of the identification information indicating the user of the PCD, the first access point may transmit the identification information, as well as the known geographic location of the first access point, to one or more providers on the network. The known geographic location of the first access point indicates the approximate location of the PCD of the mobile user. A first information provider may receive this information and provide content information or services to the mobile user. For example, the first information provider may select content information dependent upon the known geographic location of the first access point and demographic information or past activities of the mobile user of the PCD. The first information provider may then provide the selected content information through the network and through the first access point to the PCD of the mobile user.
Owner:WAYPORT
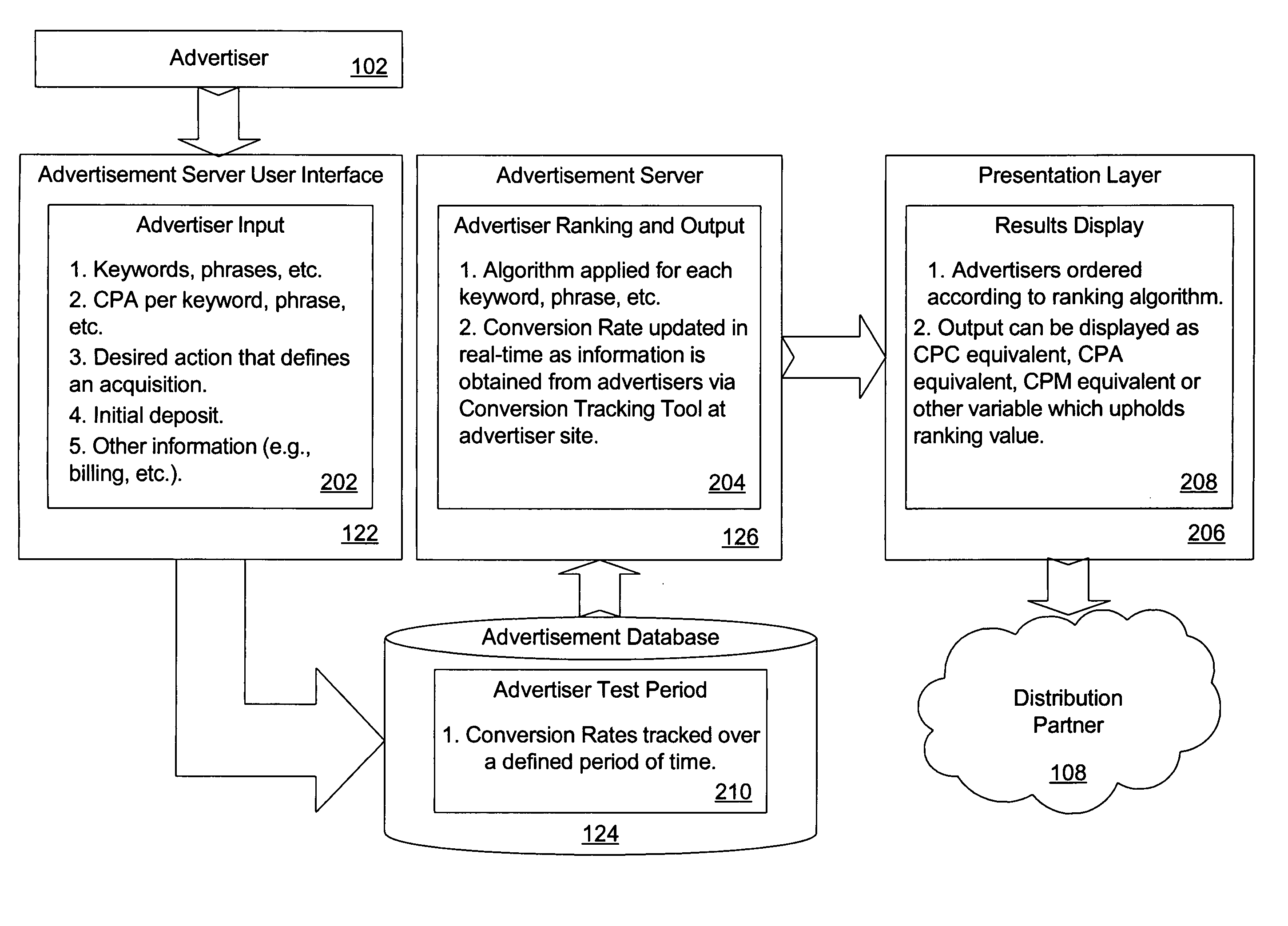
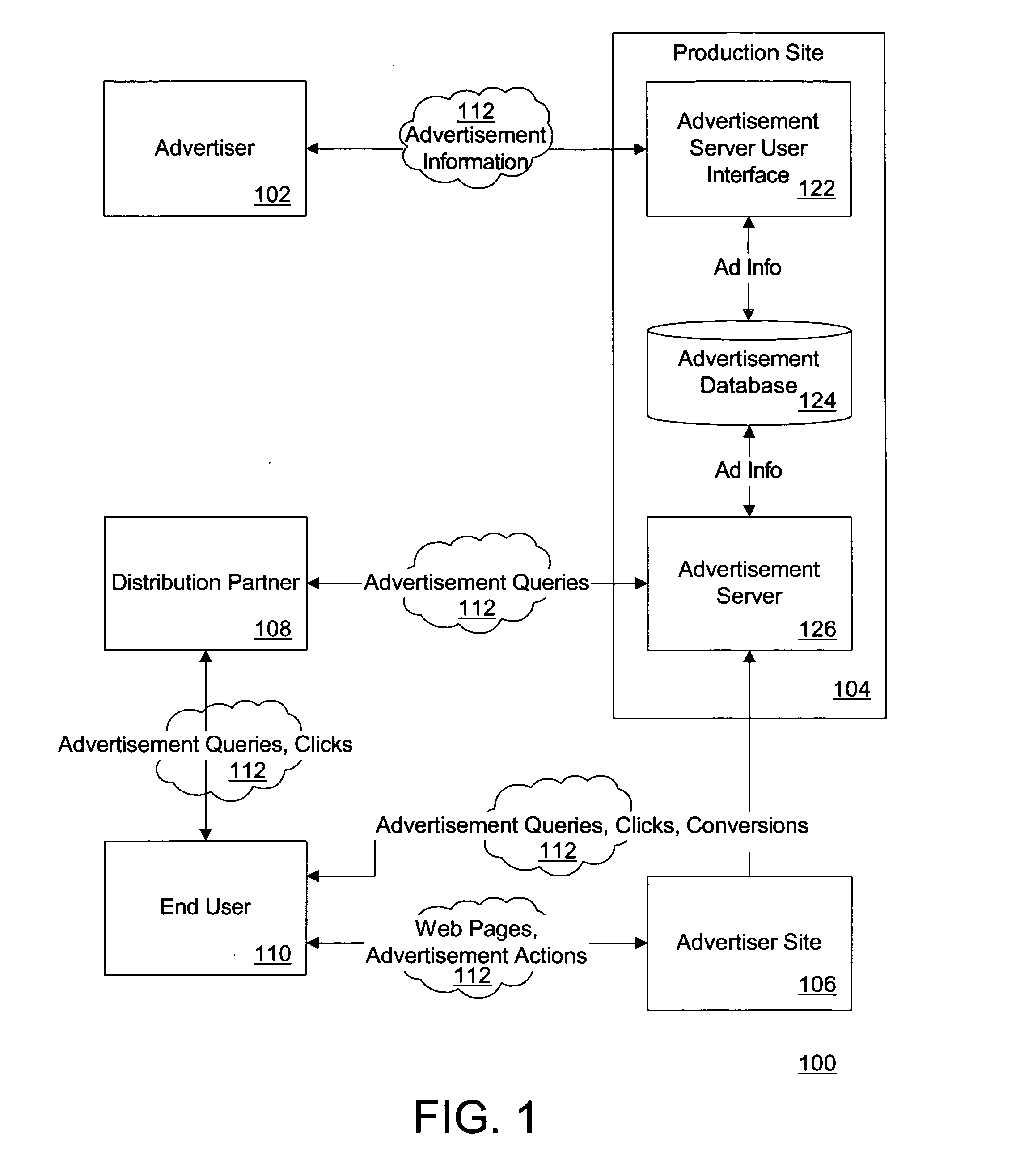
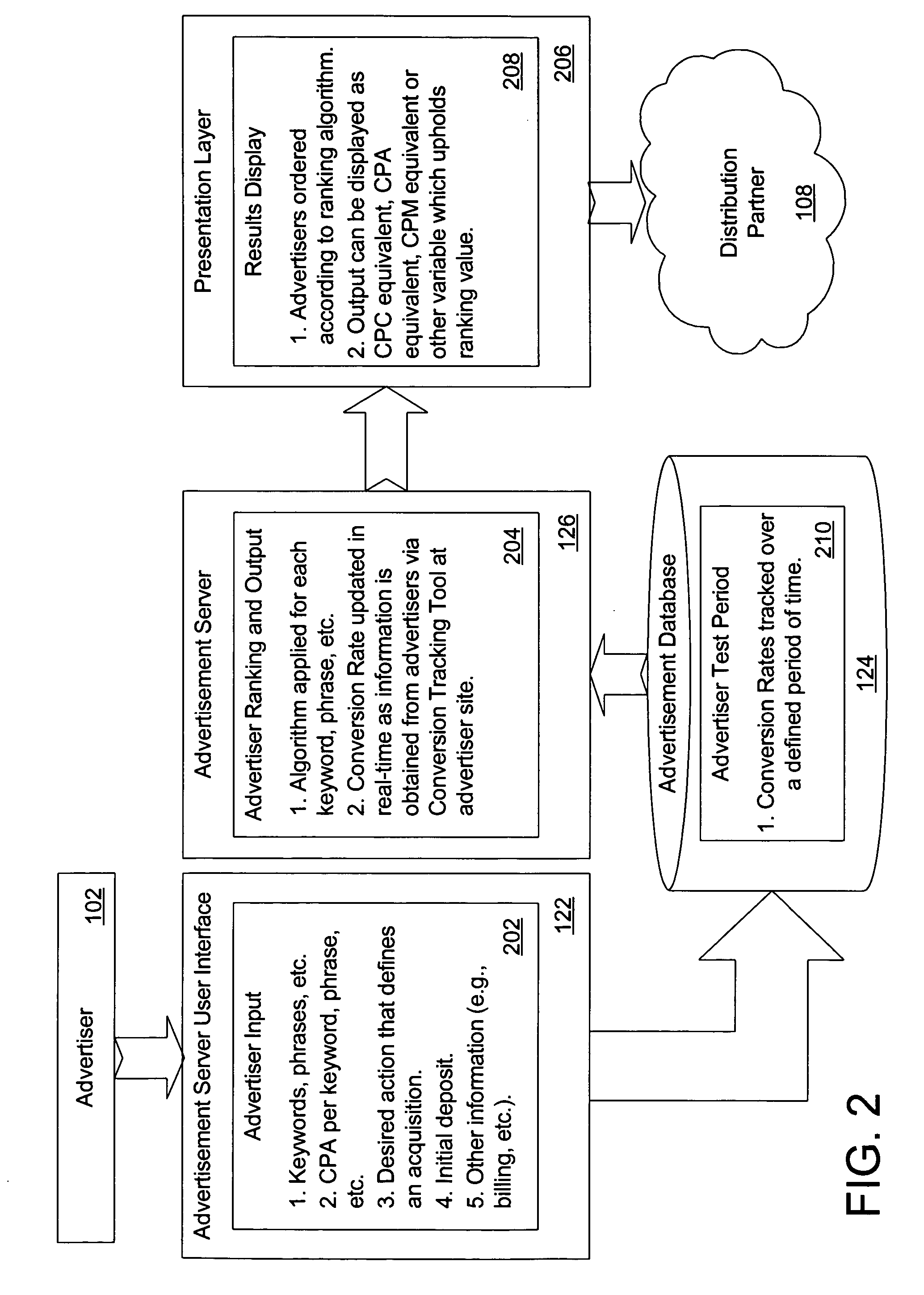
Performance-based online advertising system and method
ActiveUS20050097204A1AdvertisementsDigital data processing detailsOnline advertisingCost per acquisition
A system, method, and computer program product for online advertising, including computing and dynamically updating a cost-per-click (CPC) value of an advertisement for an advertisement traffic source based on a variable; and automatically uploading and distributing the advertisement to the traffic source. The variable includes price, advertisement traffic source, and / or advertiser variableS. Further embodiments include dynamically updating an advertisement listing that has a cost-per-acquisition (CPA)-based value with associated CPC or cost-per-1000 (CPM) values; and distributing the advertisement listing to an advertisement distribution network that serves the listing based on the CPC or CPM values. The distribution network includes CPC-based, CPA-based, and / or CPM-based distribution networks. Further embodiments include determining a CPC value for a CPA-based advertisement; and placing the advertisement on an advertising network at the determined CPC based on a ratio of an expected number of conversions at a CPA value divided by a number of clicks at the CPC.
Owner:MARCHEX
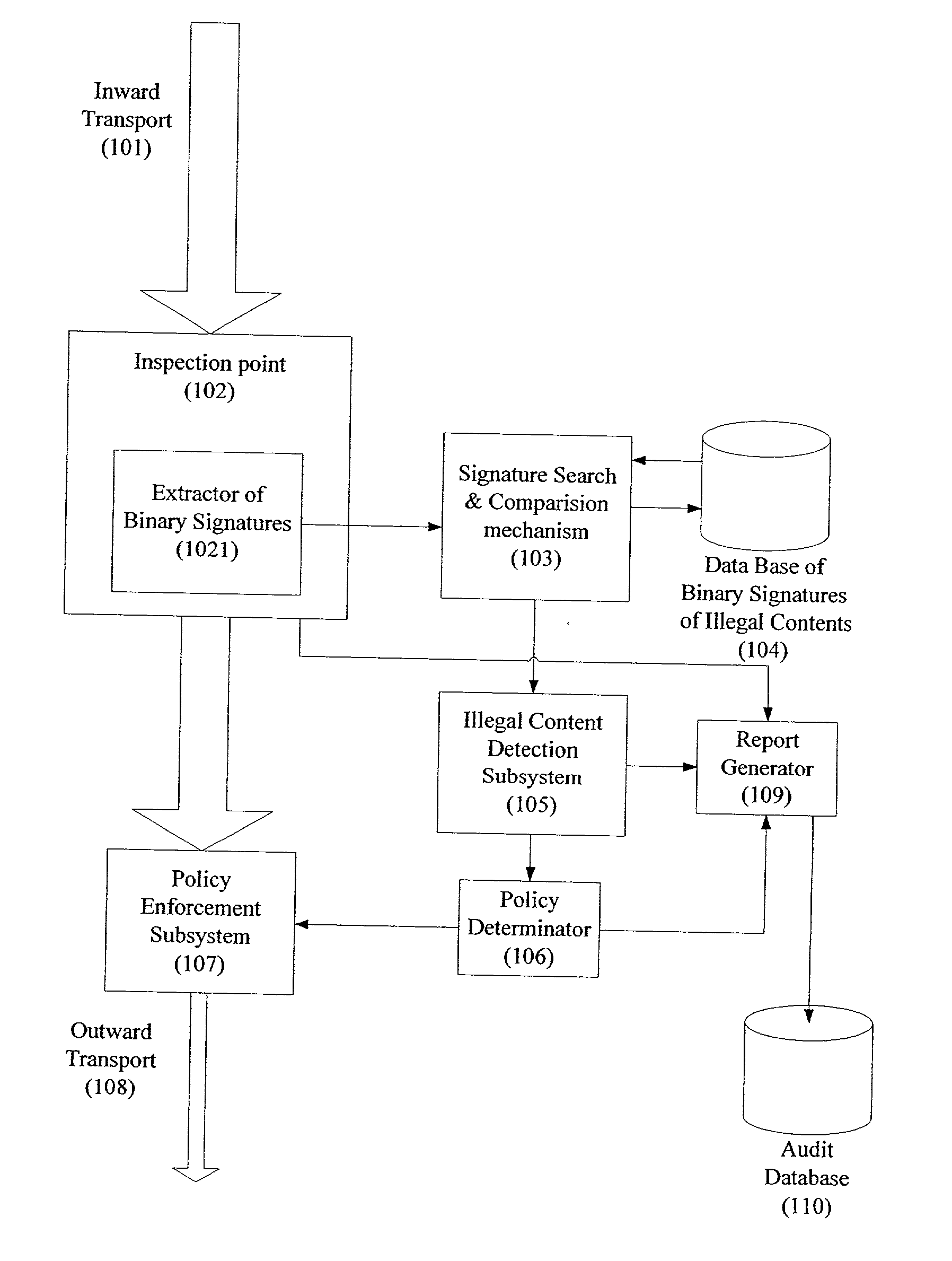
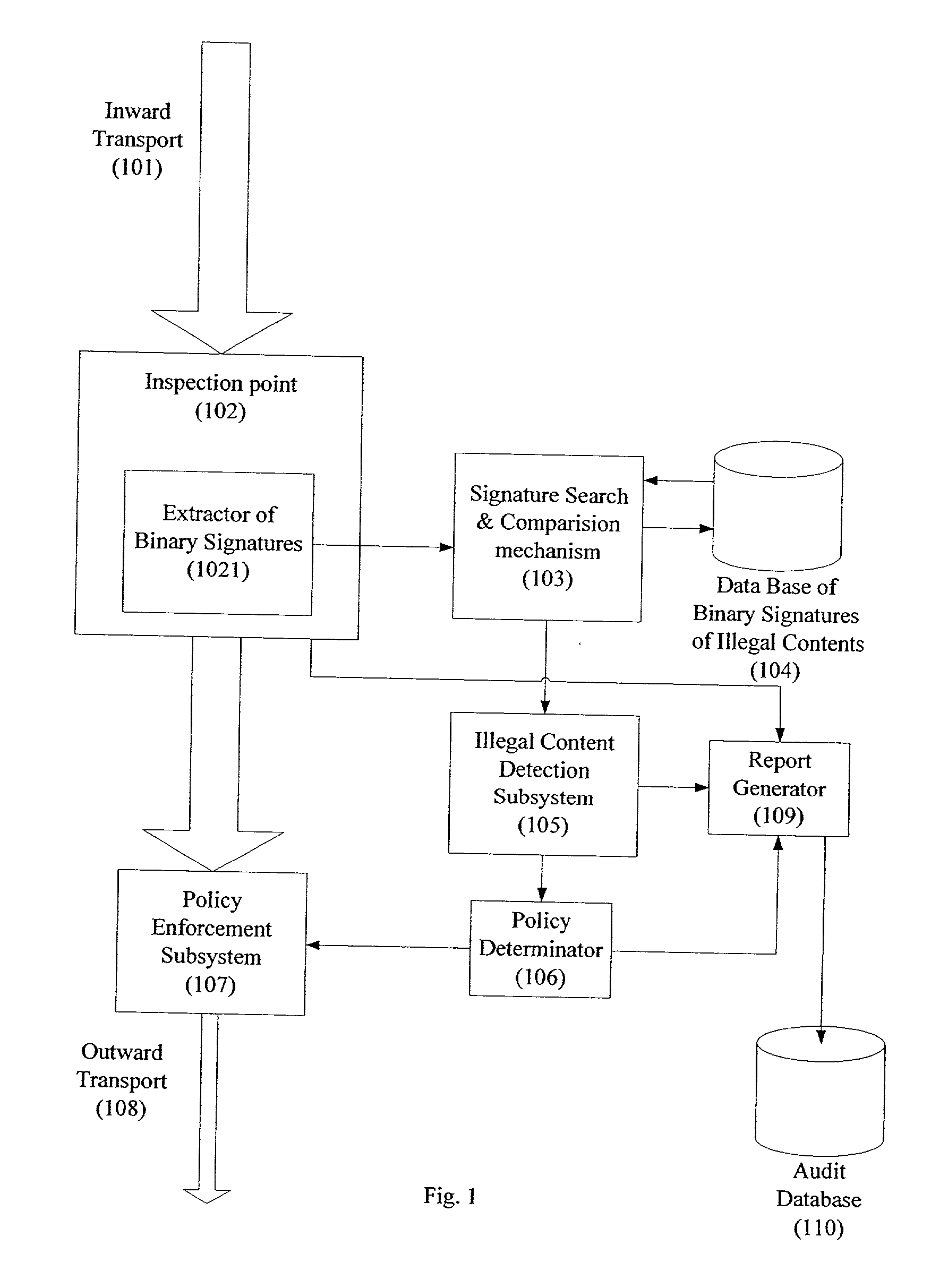
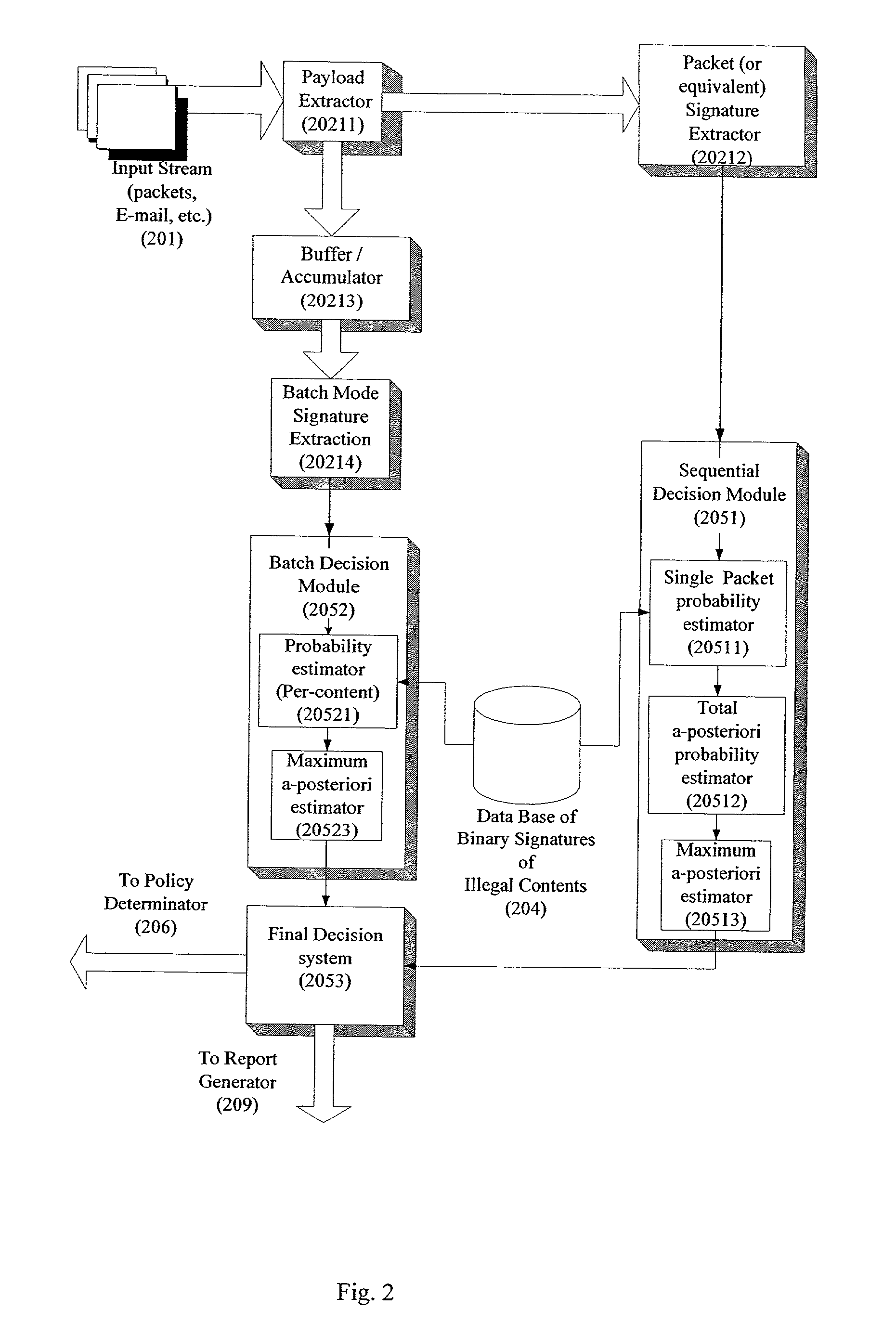
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
System and method for searching, finding and contacting dates on the Internet in instant messaging networks and/or in other methods that enable immediate finding and creating immediate contact
InactiveUS20050086211A1Highly integratedIncrease motivationWeb data indexingDigital data processing detailsWeb siteNetwork on
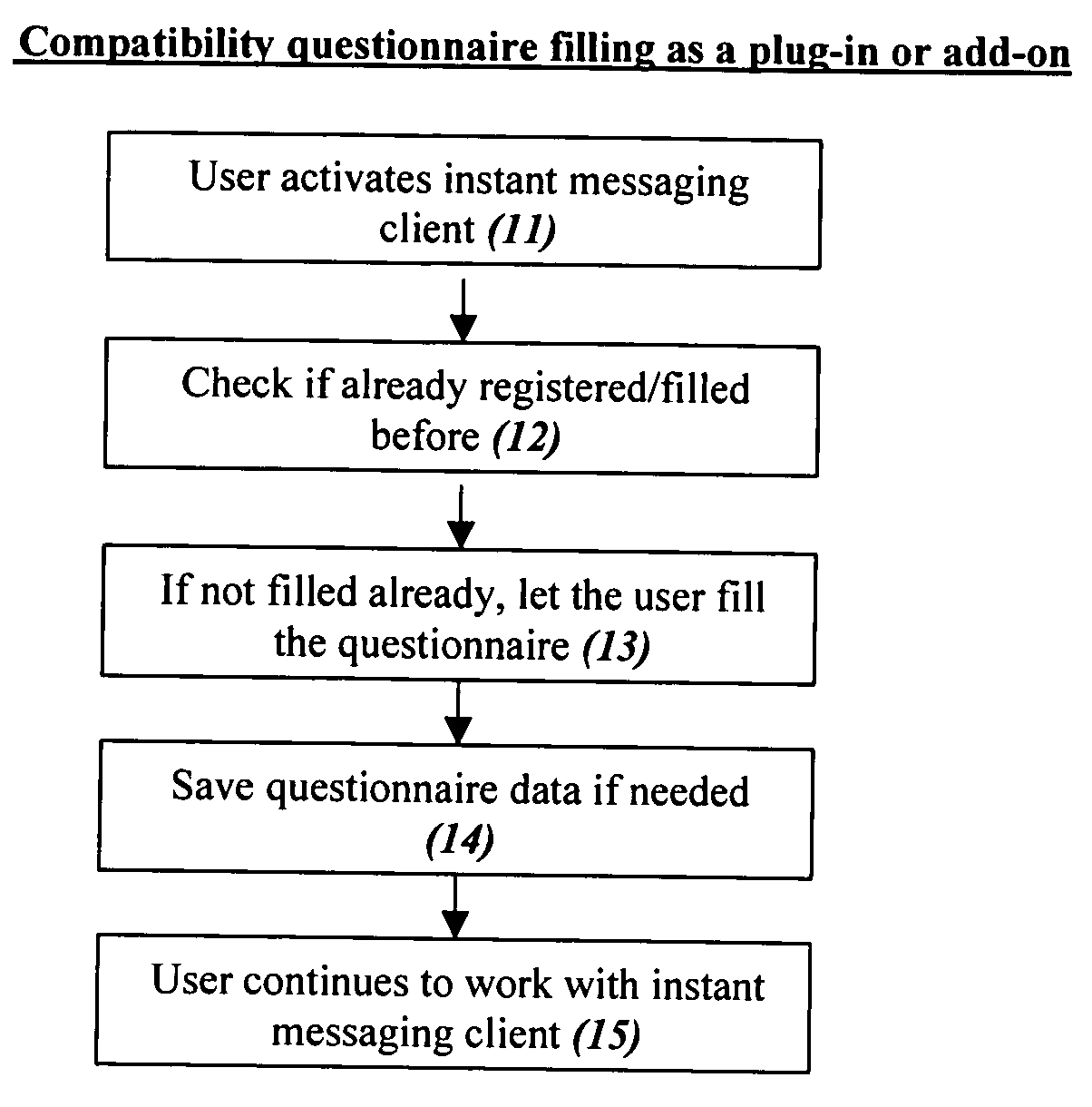
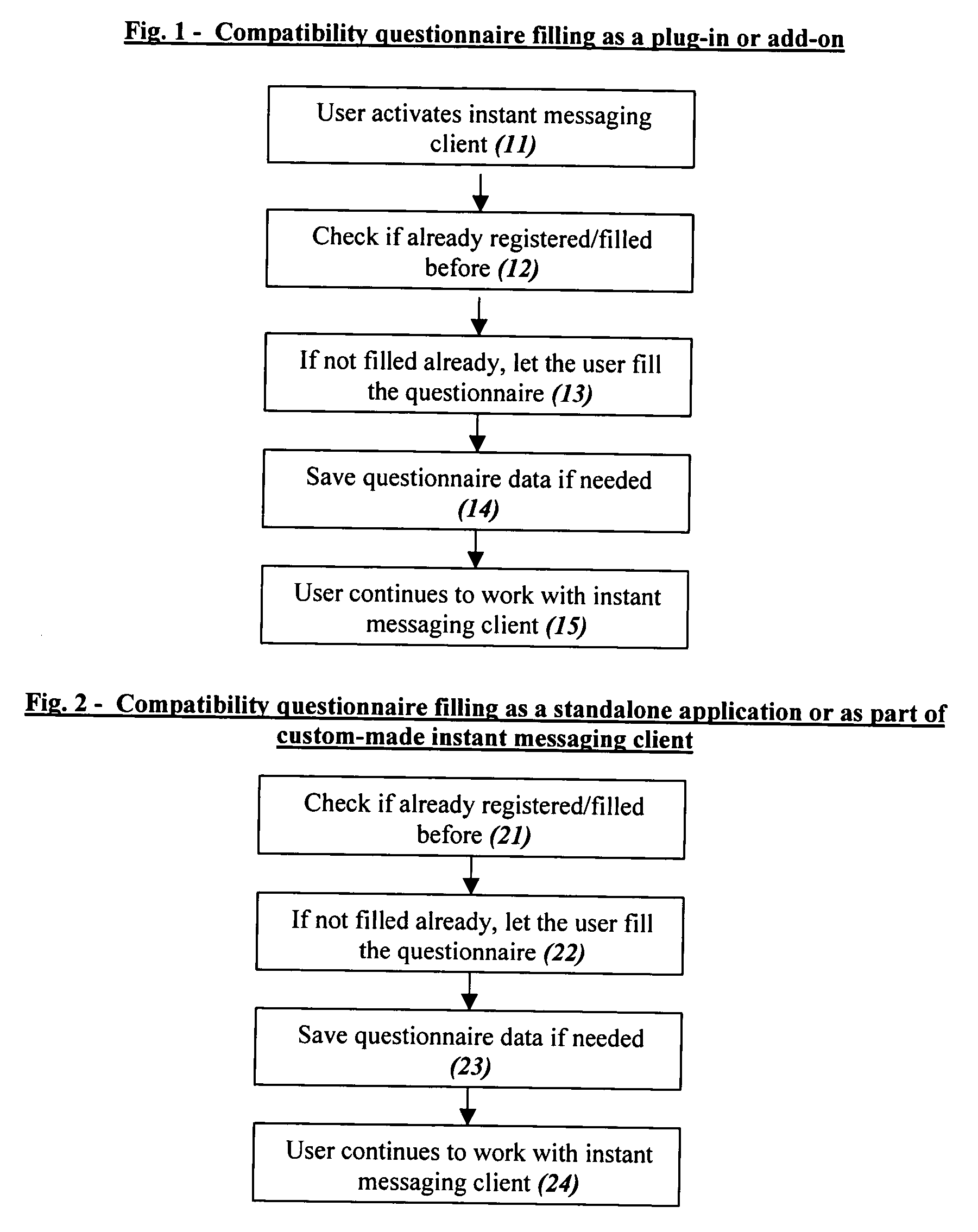
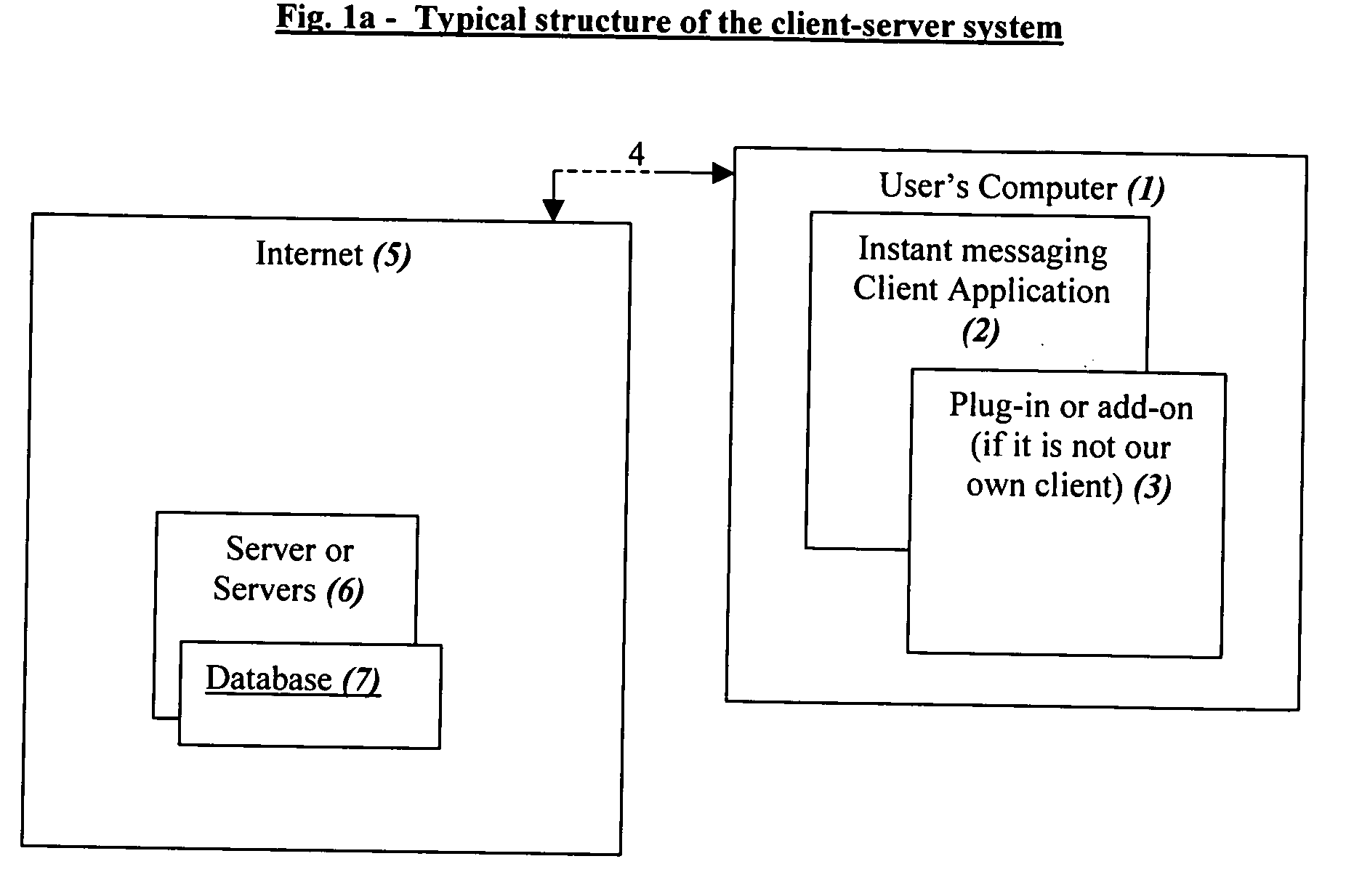
Computer dating is applied to instant messaging, in a novel, systematic and flexible way. This system and method enable the user to search and find instantly compatible dates in instant messaging networks on the basis of attribute search or 1-way compatibility search or 2-way compatibility search, and to search either for potential dates that are currently Online or also for dates that are currently Offline. Many additional features are described, and especially for example features that are based on improved integration between computer dating and instant messaging. Important features include for example: a. Integration of the dating environment with the contactee list (buddy list). b. Generating a list of compatible dates with different markings for people that are online or offline or a list divided into sub-lists or separate lists according to this. c. Applying a reverse variation by adding Instant messaging features to an Online dating site. d. Automatic instant notification when a new highly compatible date is available, instead of only periodical reports. e. Using a database of systematic pictures to which the users relate in defining their own appearance and the appearance of the desired date. f. Automatic finding of duplicate records. g. Addition of “OR” and / or “IF” relationships between questions instead of only the usual “AND”.
Owner:MAYER YARON
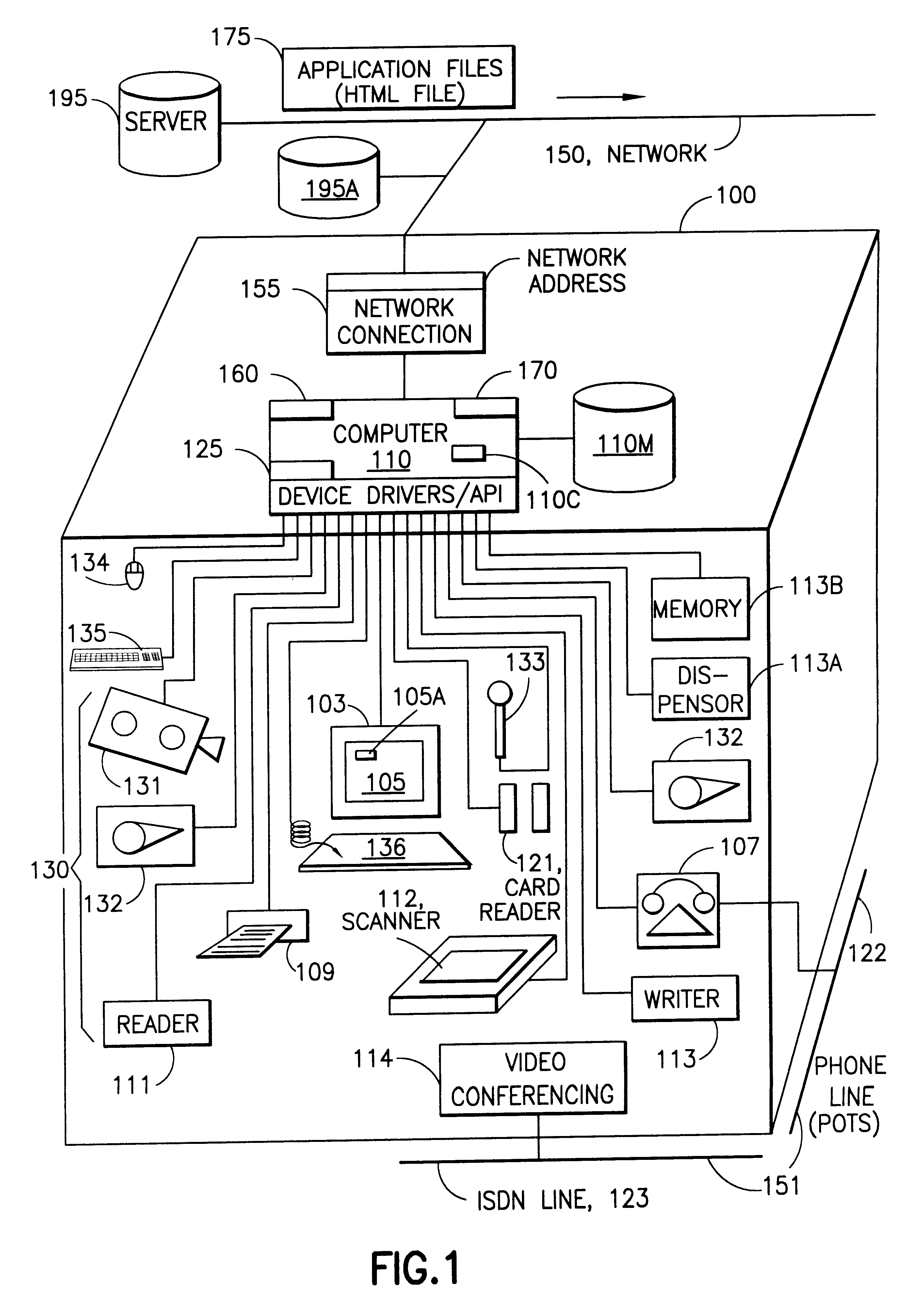
Server for reconfiguring control of a subset of devices on one or more kiosks
InactiveUS6195694B1Faster and reliable accessLow costAcutation objectsData switching by path configurationM-governmentComputer terminal
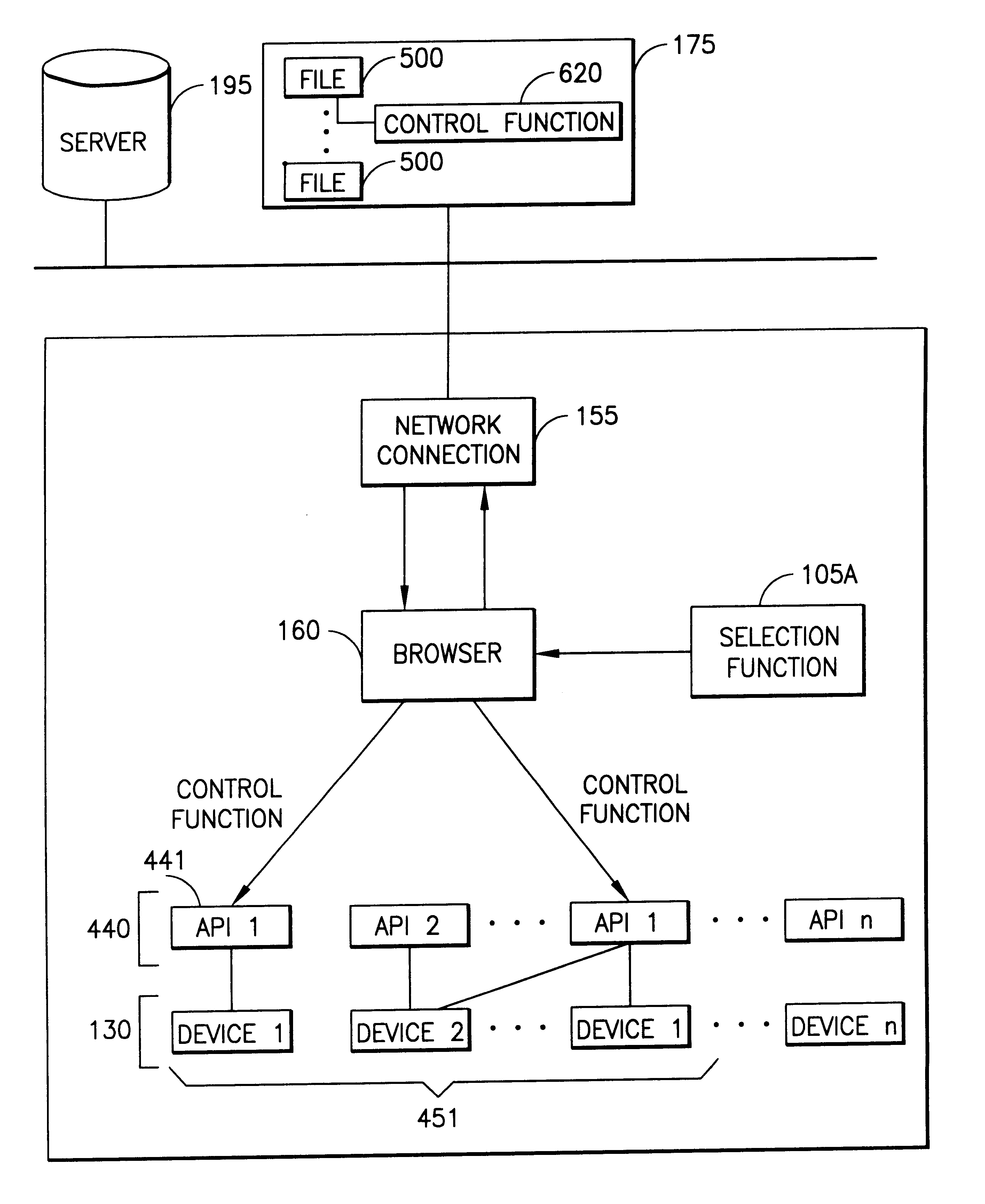
A server system that is connected to one or more networks, e.g., the Internet, corporate or government intranets, extranets, etc. The server has one or more application files or configuration sets that the server serves to from one or more kiosks on the network. The configuration sets are application specific. (An application is a use for which the kiosks are configured or reconfigured.) One or more of the files in the configuration sets include one or more embedded (control) programs that are used to control the local APIs of one or more of the devices on the kiosk. In this way, the devices are controlled to configure the kiosk to perform the application.
Owner:IBM CORP
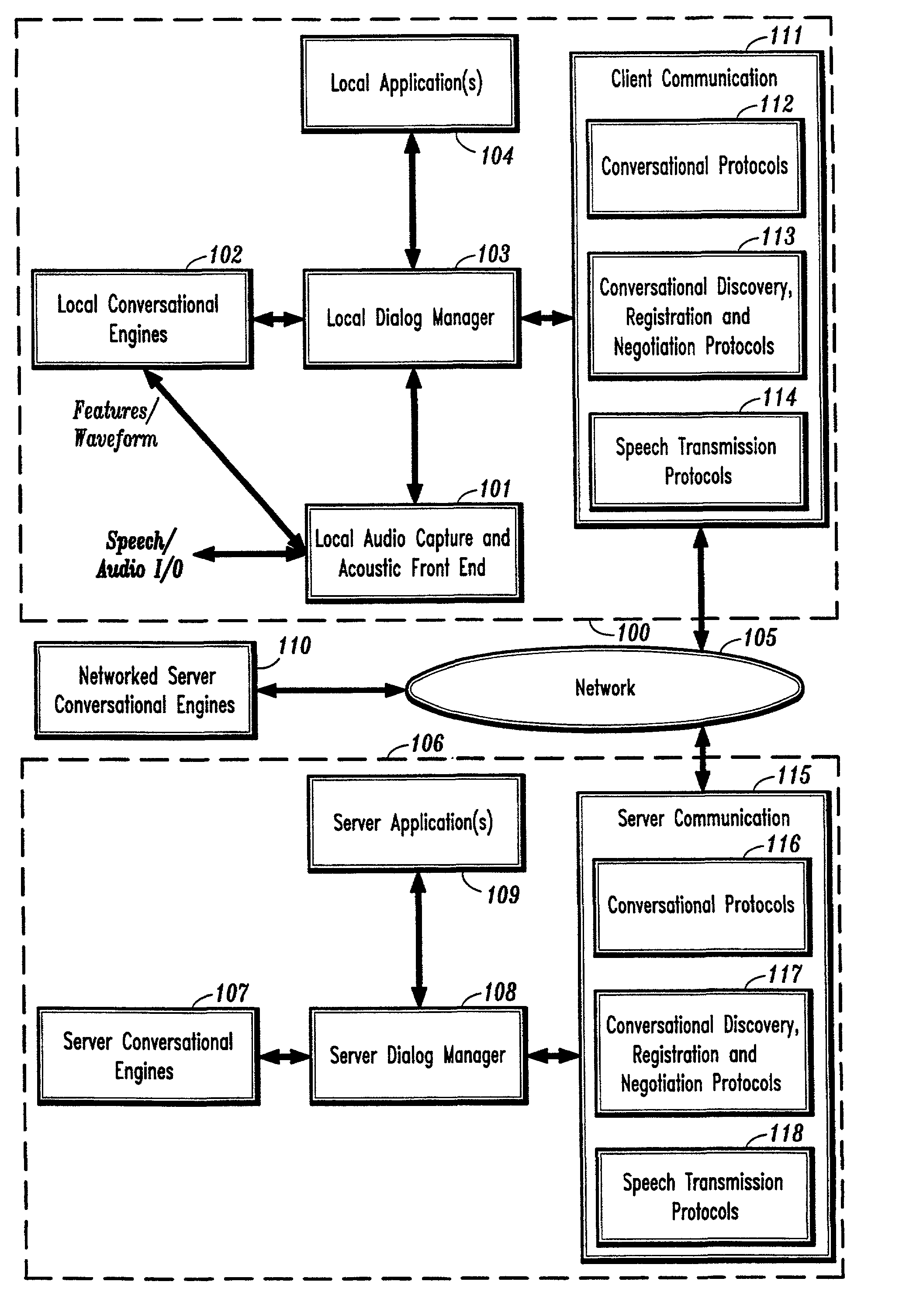
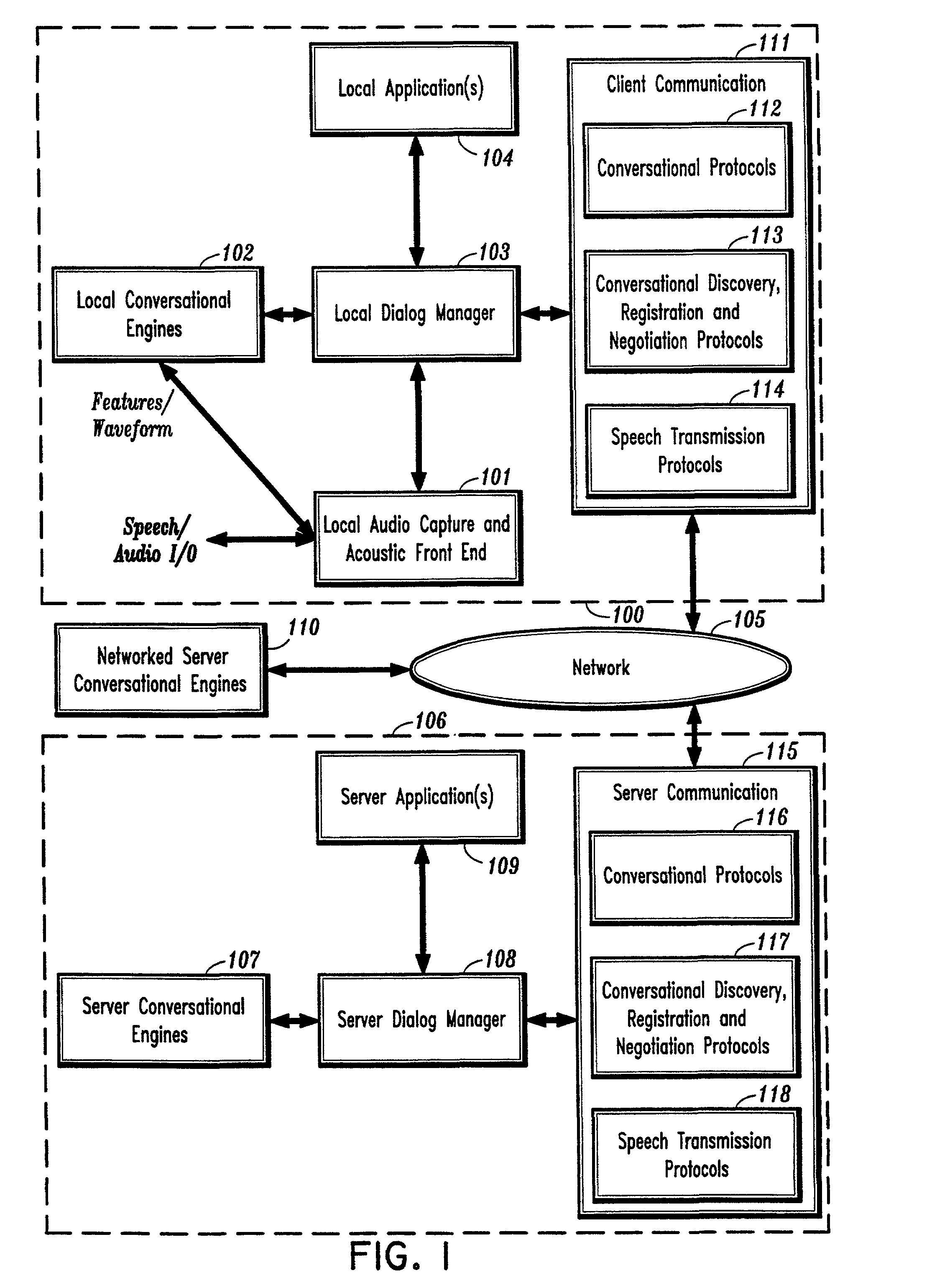
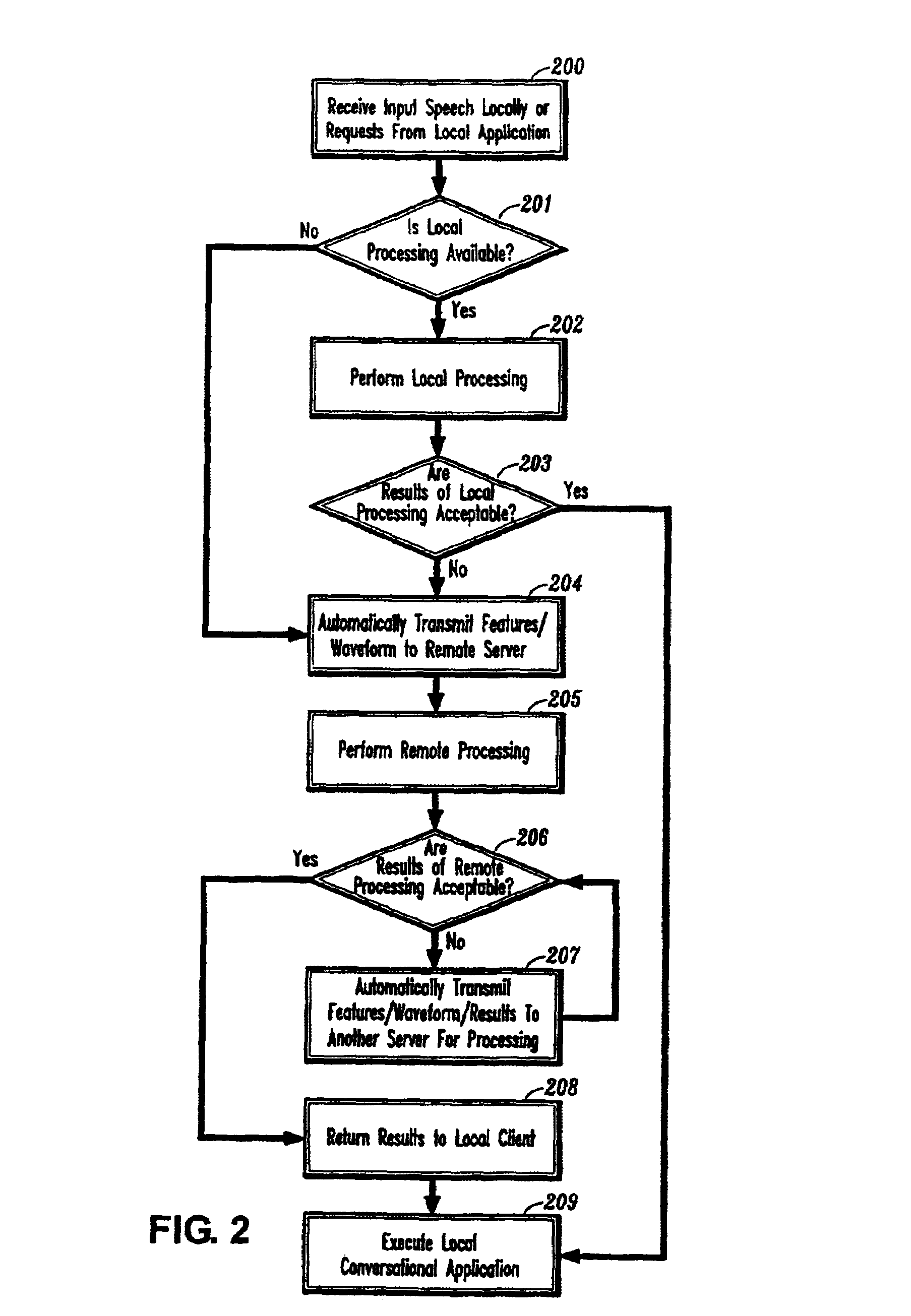
System and method for providing network coordinated conversational services
InactiveUS7003463B1Complex capabilitySimplifies taskMultiple digital computer combinationsSpeech recognitionApplication softwareDistributed computing
A system and method for providing automatic and coordinated sharing of conversational resources, e.g., functions and arguments, between network-connected servers and devices and their corresponding applications. In one aspect, a system for providing automatic and coordinated sharing of conversational resources inlcudes a network having a first and second network device, the first and second network device each comprising a set of conversational resources, a dialog manager for managing a conversation and executing calls requesting a conversational service, and a communication stack for communicating messages over the network using conversational protocols, wherein the conversational protocols establish coordinated network communication between the dialog managers of the first and second network device to automatically share the set of conversational resources of the first and second network device, when necessary, to perform their respective requested conversational service.
Owner:NUANCE COMM INC
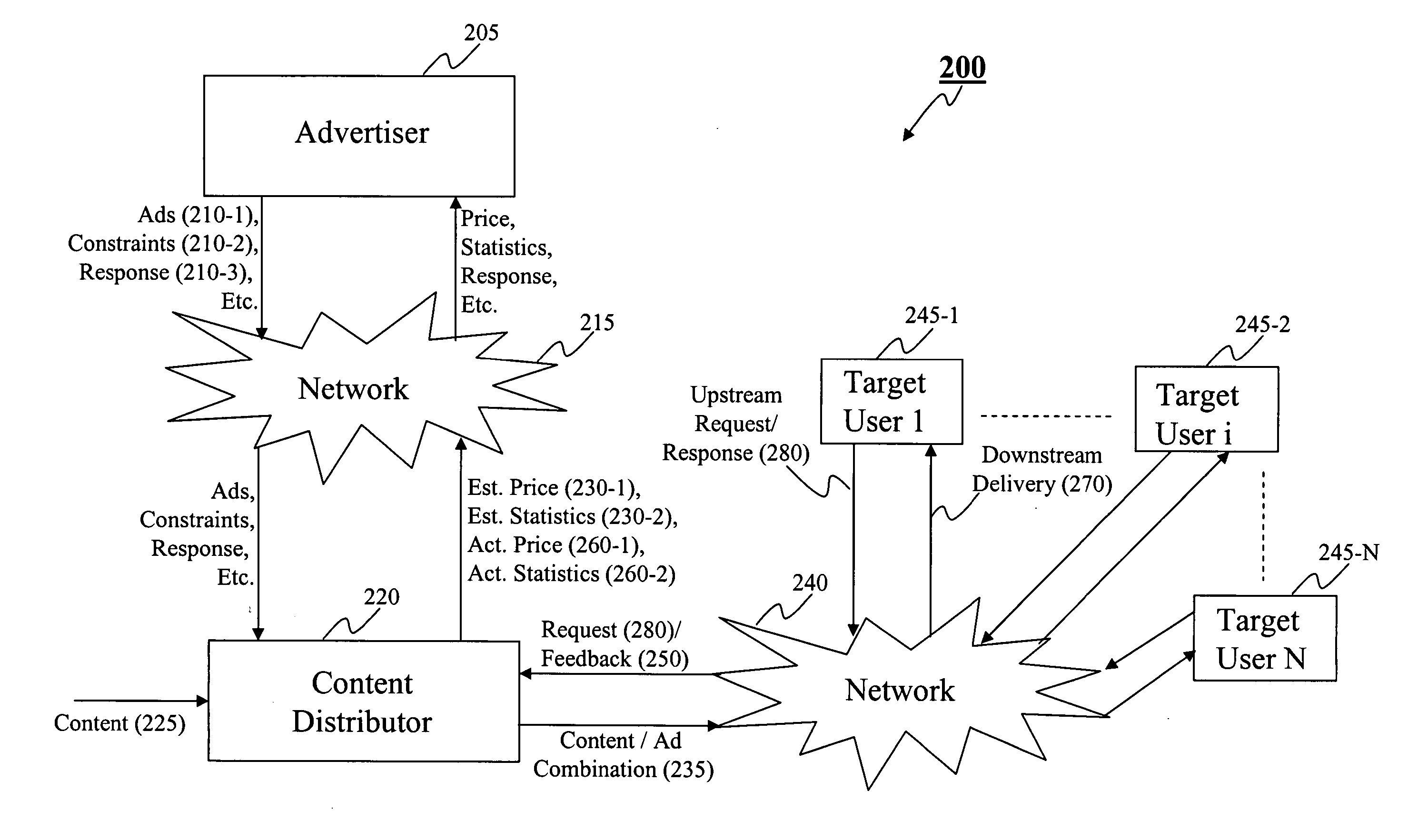
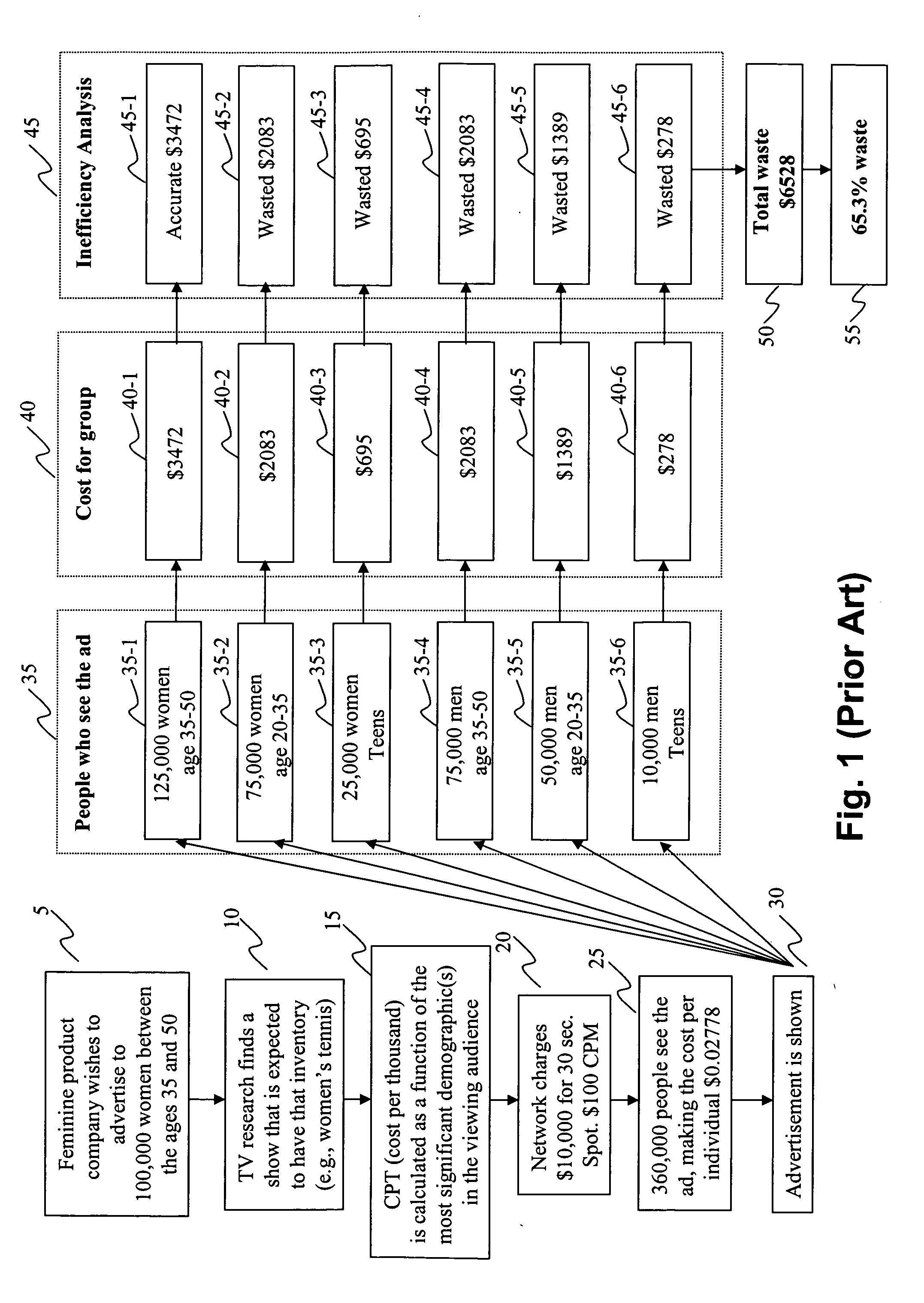
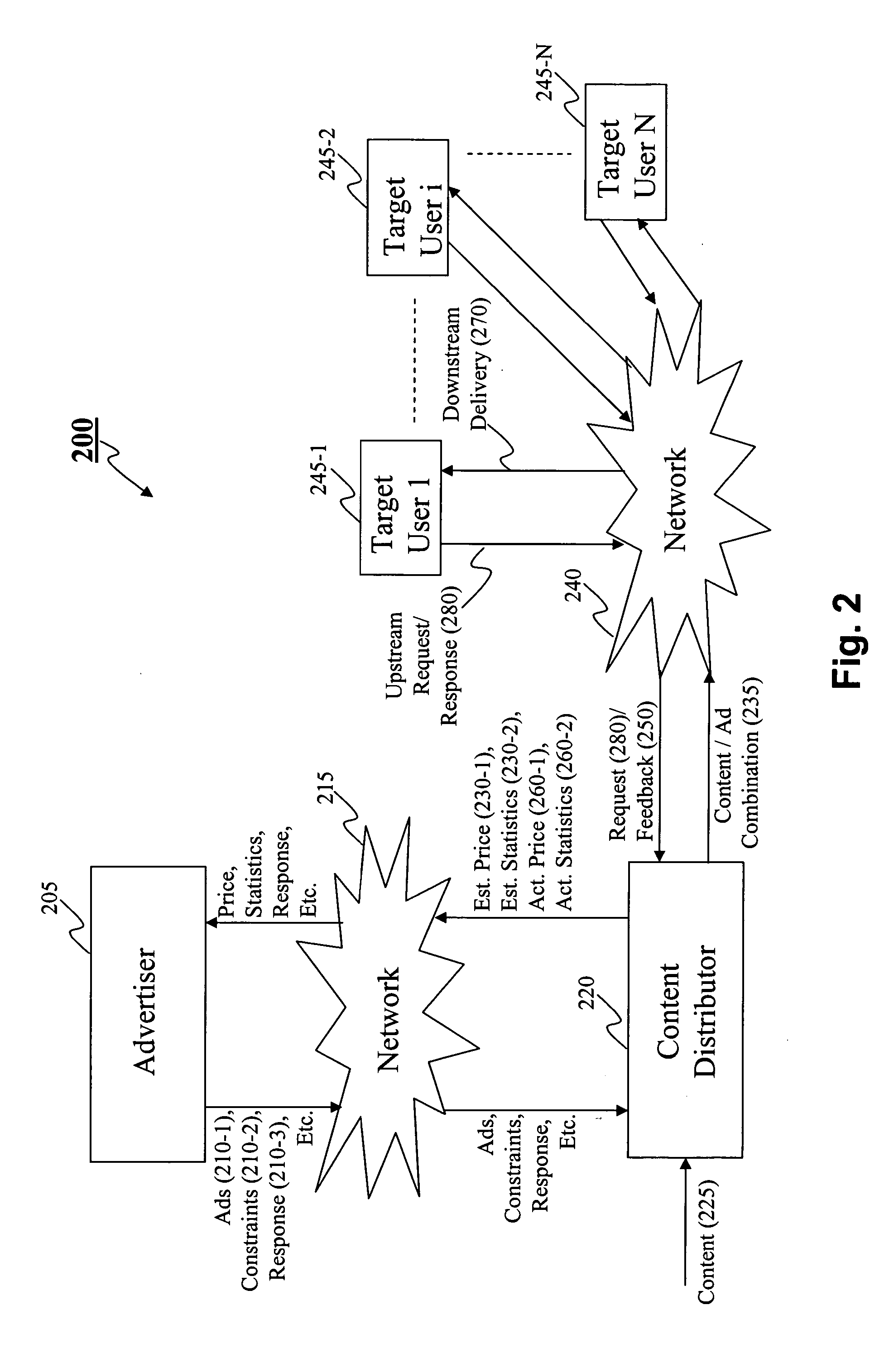
Method and system for advertising over a data network
A method and system for statistics-based individualized advertising over a network in which an advertiser provides to a content distributor one or more constraints defining the characteristics of desired target users and the manner by which the advertisement is to be delivered. The content distributor determines an estimated price based on statistics computed based on target users selected and the advertising periods allocated based on the constraints and individualized content delivery.
Owner:INDIVIDUAL NETWORK INC
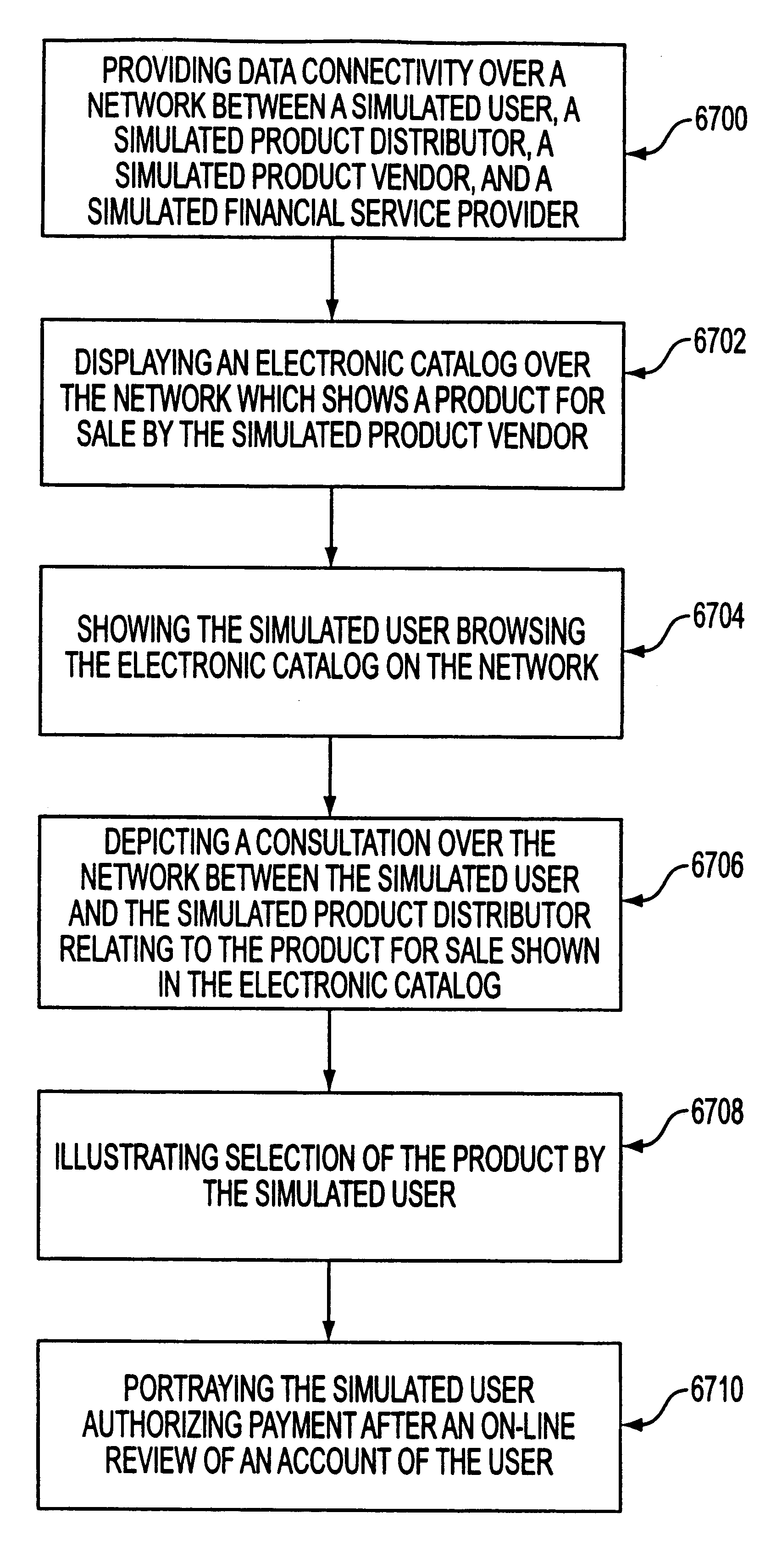
System, method and article of manufacture for demonstrating E-commerce capabilities via a simulation on a network
A system, method and article of manufacture are provided for demonstrating e-commerce capabilities on a network via a simulation. Data connectivity is provided over a network between a simulated user, a simulated product distributor, a simulated product vendor, and a simulated financial service provider. An electronic catalog is displayed over a network that shows a product for sale by the simulated product vendor. The simulated user is shown browsing the electronic catalog on the network. Further, a consultation over the network, relating to the product for sale shown in the electronic catalog, is depicted between the simulated user and the simulated product distributor. Selection of the product by the simulated user is illustrated. The simulated user is portrayed to authorize payment alter an on-line review of an account of the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
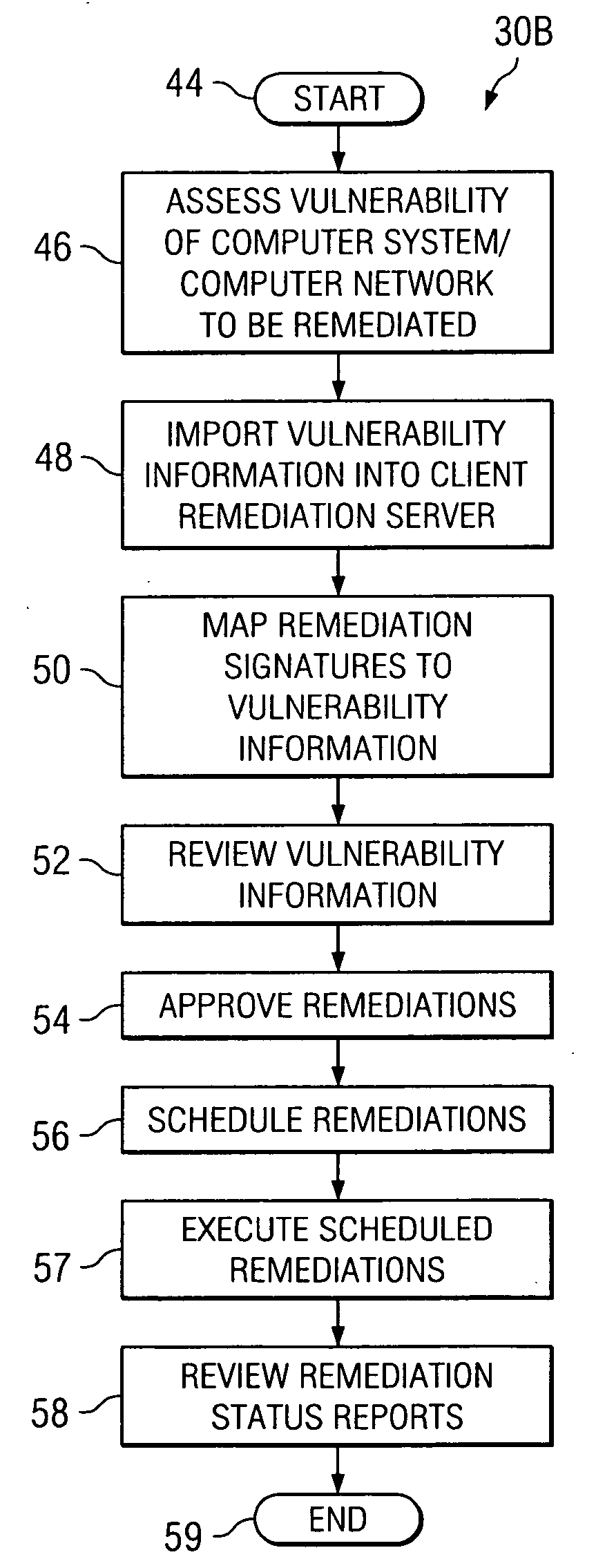
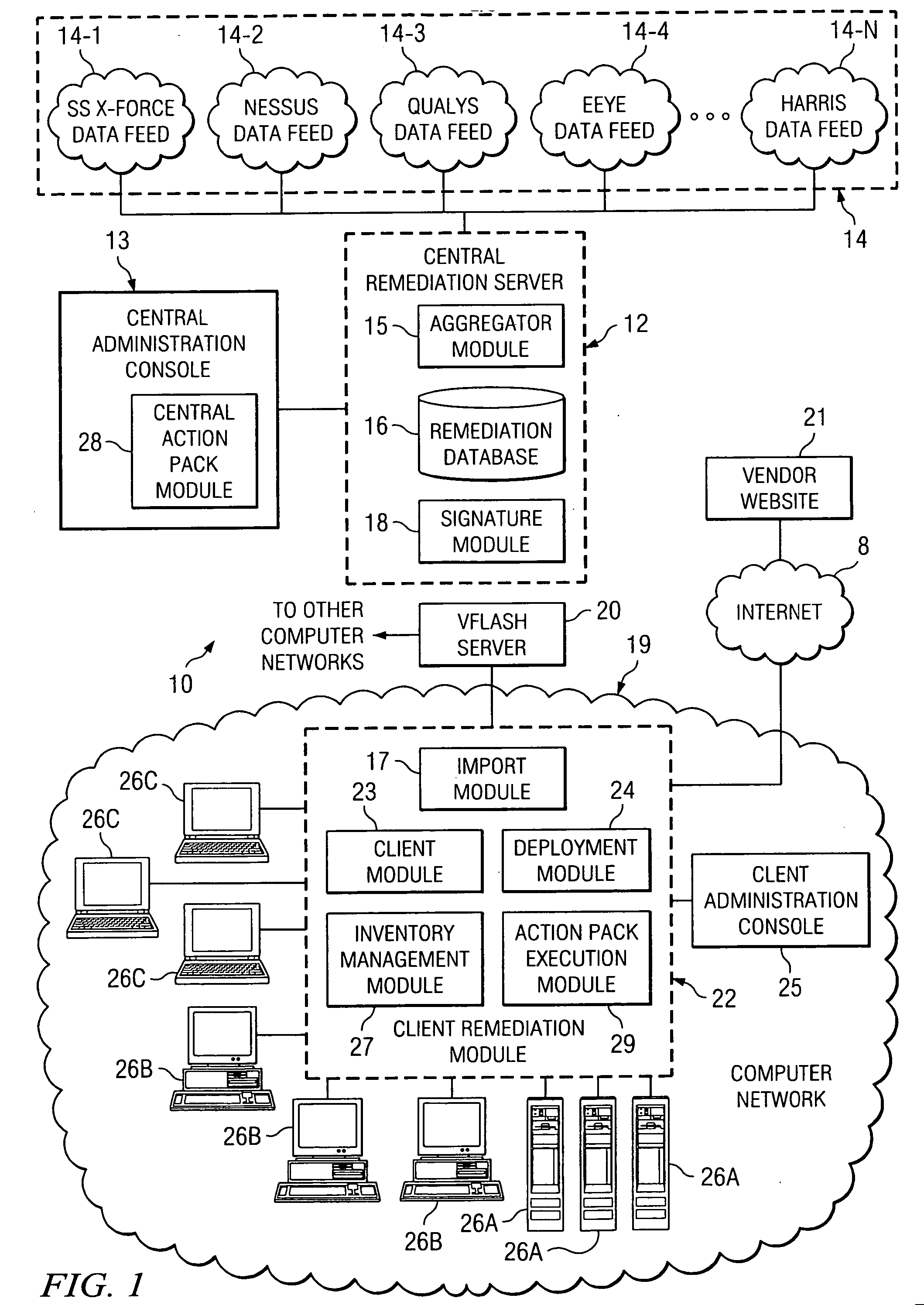
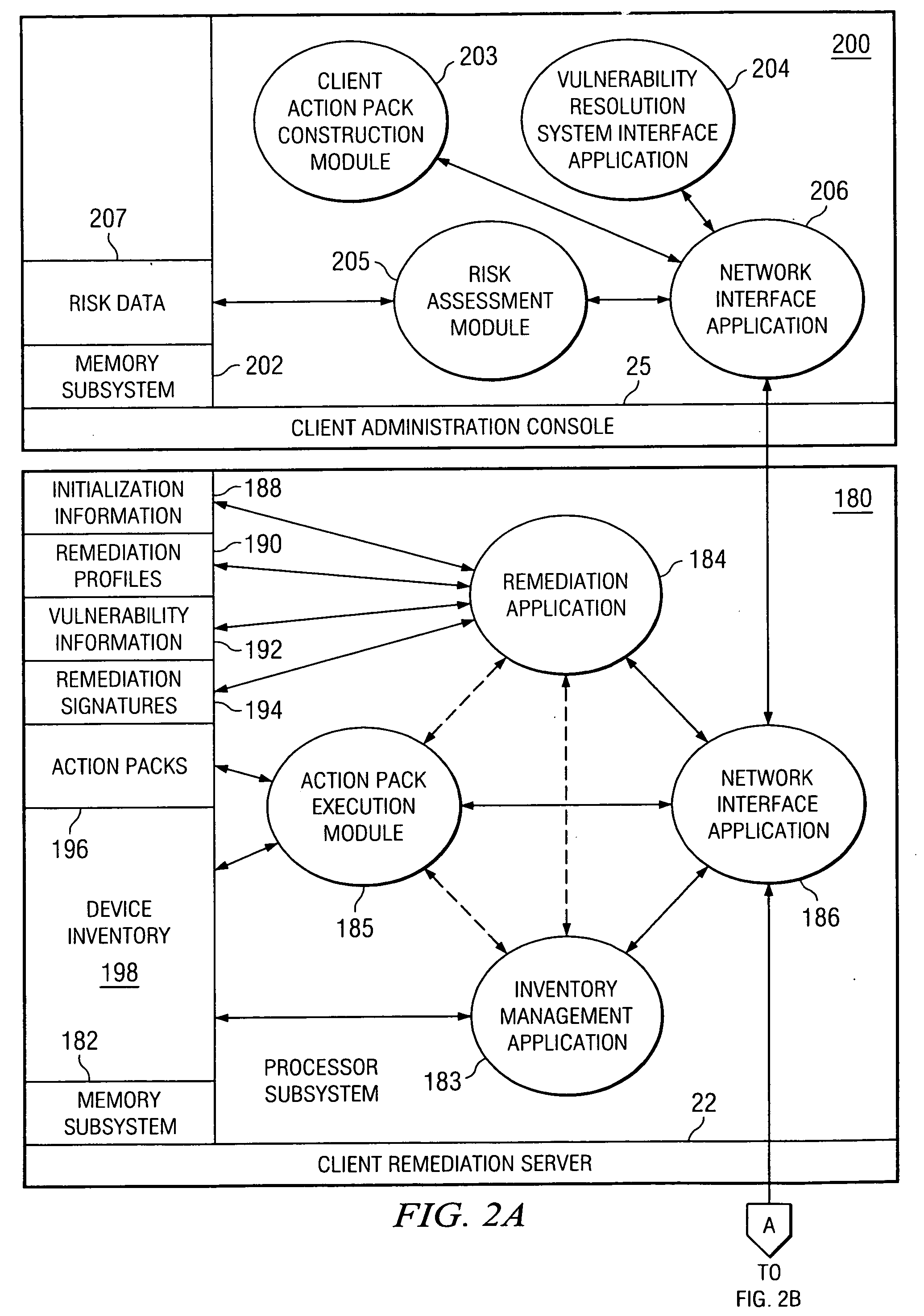
Inventory management-based computer vulnerability resolution system
A remediation server, downloadable software and an associated method for protecting a computer network from vulnerabilities. Software in the form of at least one network protection module is downloaded to the remediation server for the computer network and executed to protect the computer network from vulnerabilities. Upon execution thereof, the network protection module queries a device inventory for the computer network which is maintained at the remediation server to determine if any devices of a specified device type reside on the computer network. For each such device determined to reside on the computer network, the network protection module subsequently resolves vulnerabilities for the device using a remediation signature associated with the device query.
Owner:MCAFEE INC
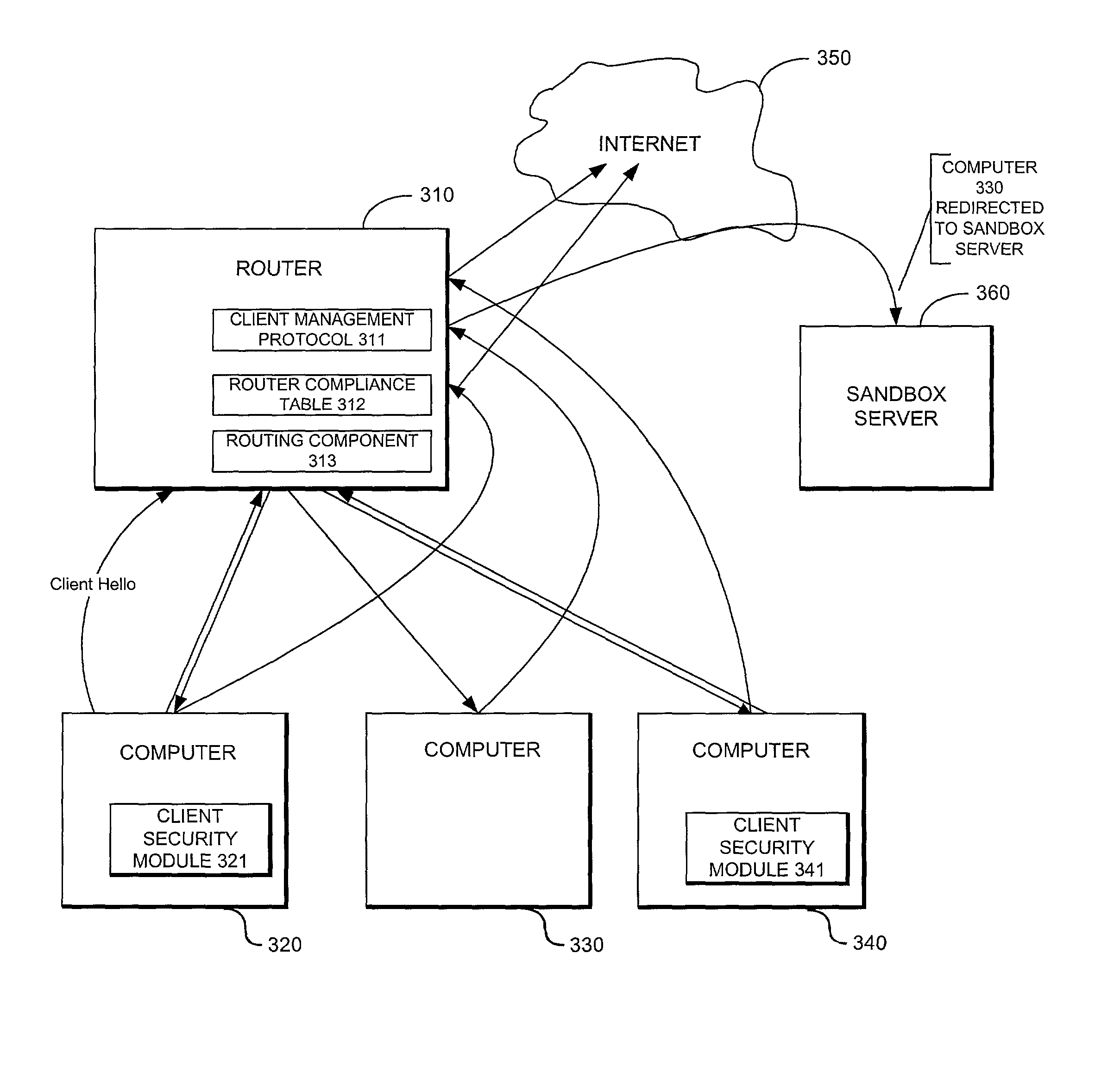
System providing internet access management with router-based policy enforcement
ActiveUS20030055962A1Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
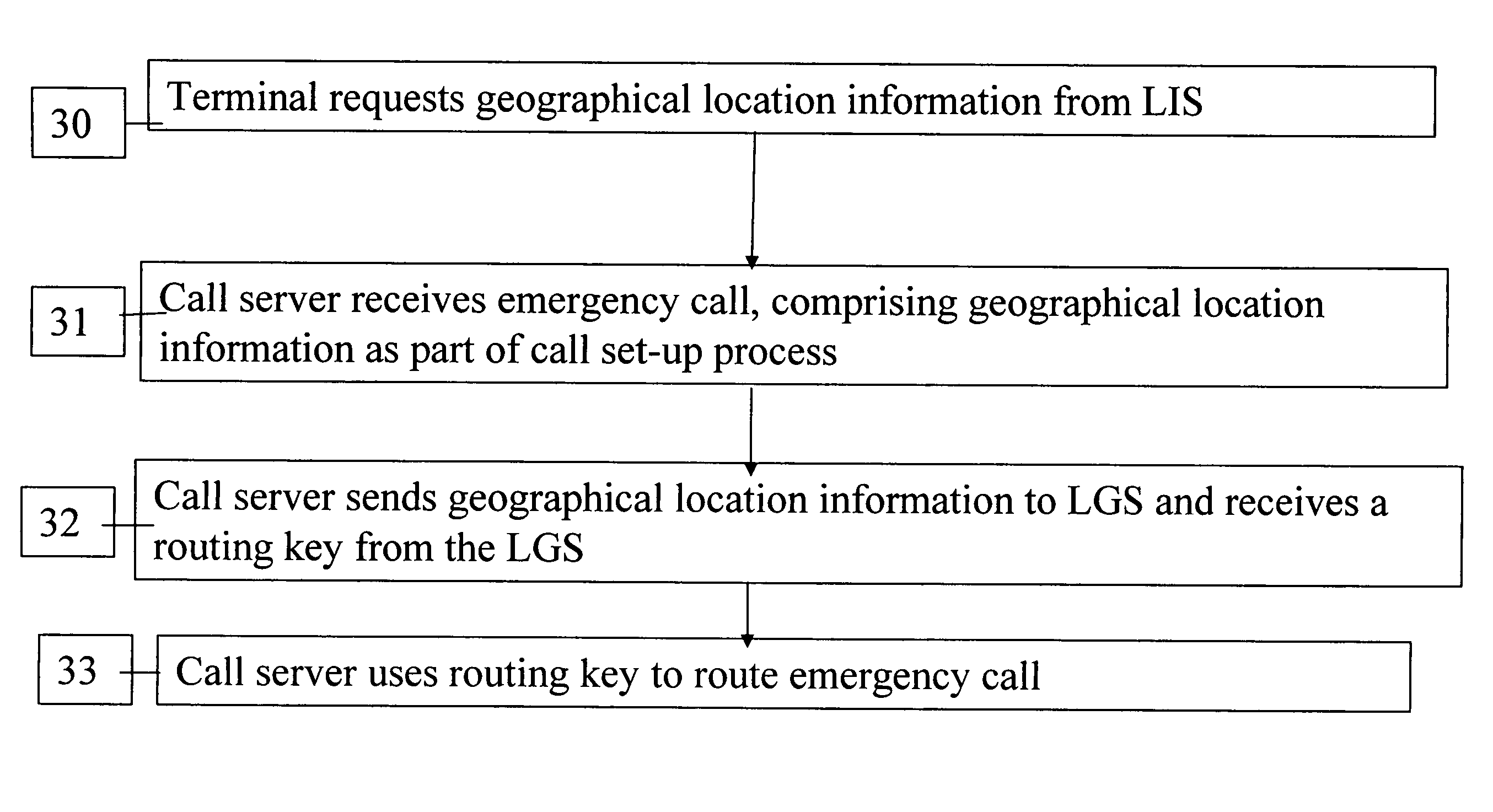
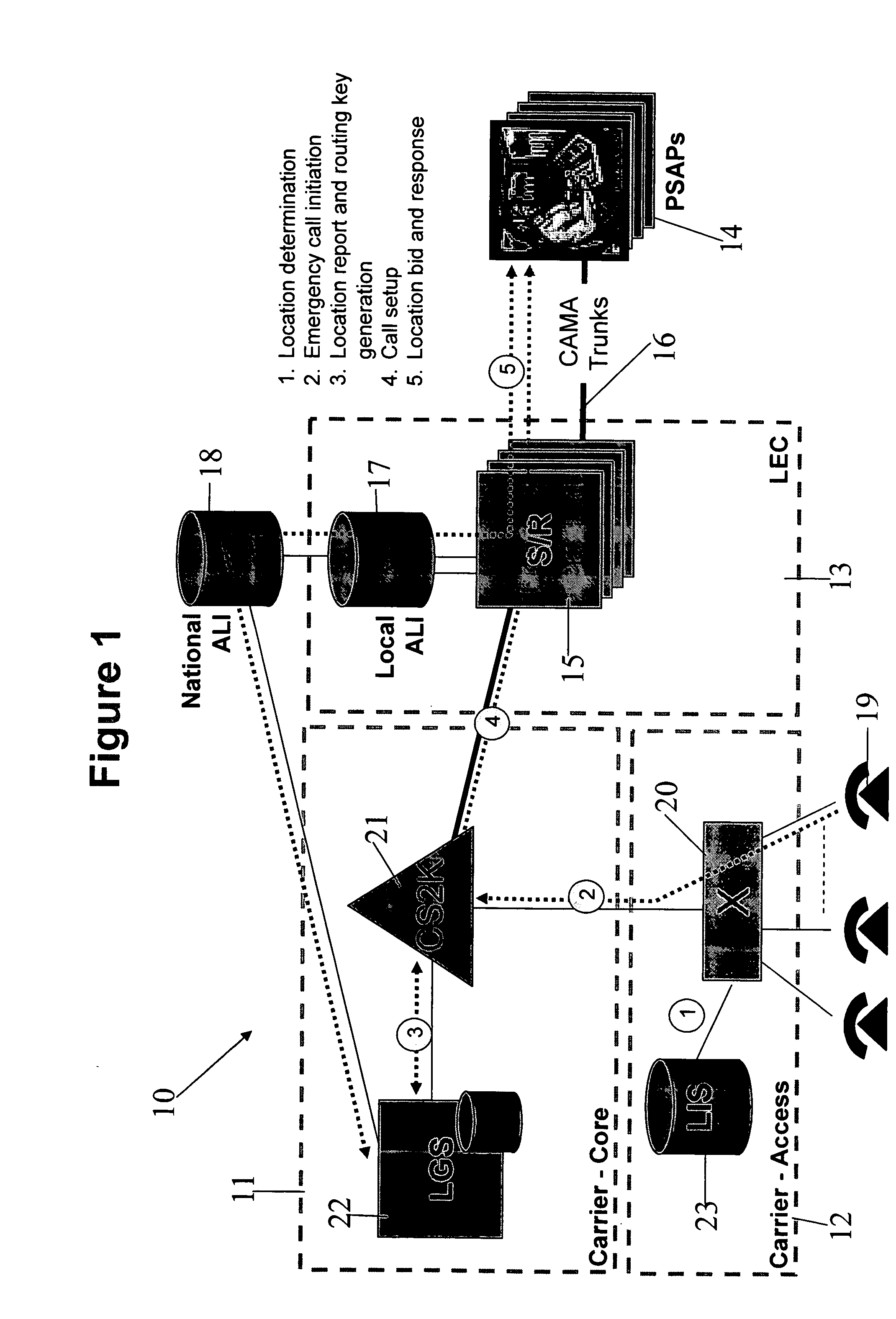
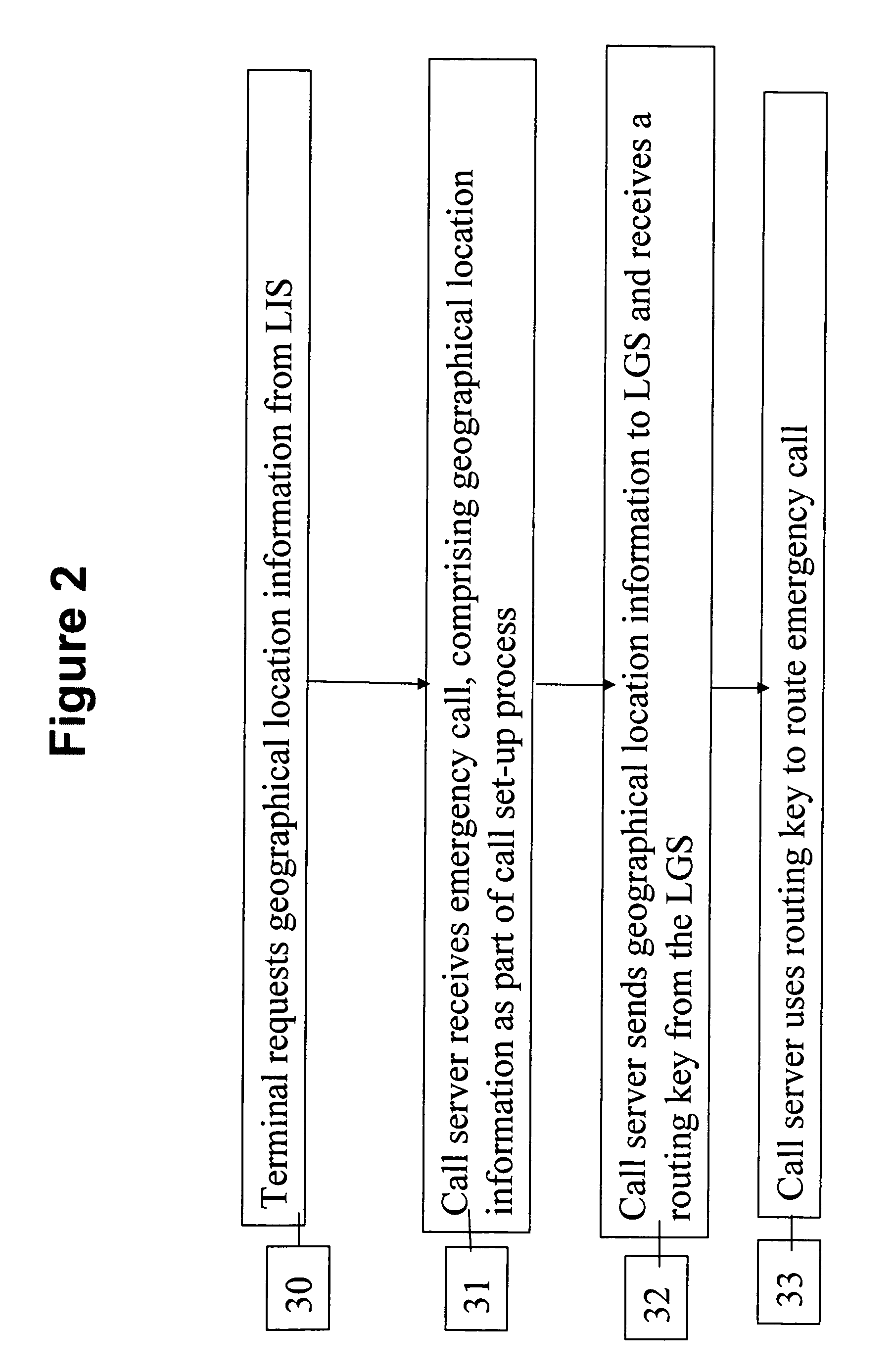
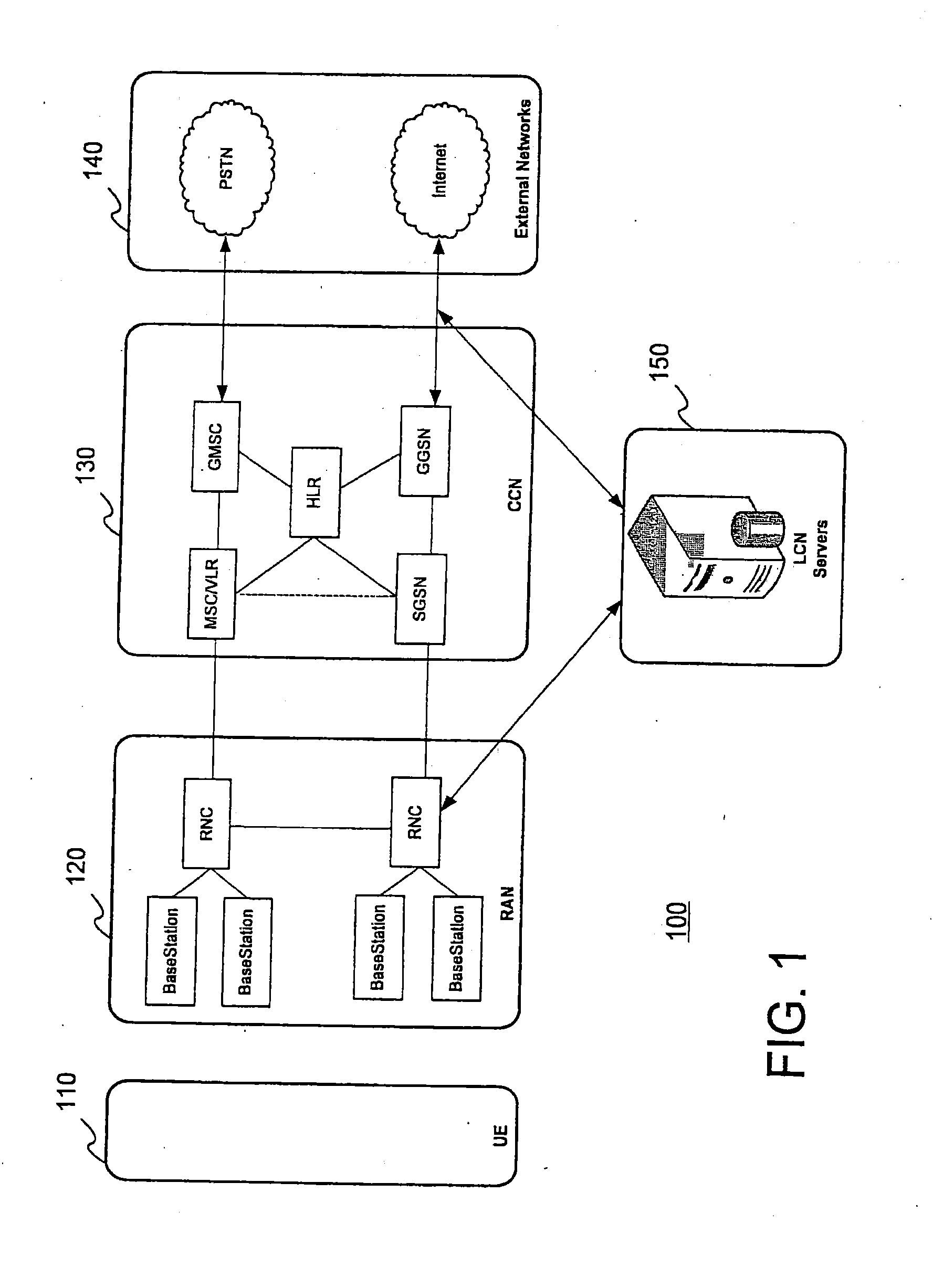
Determining the geographical location from which an emergency call originates in a packet-based communications network
ActiveUS20050190892A1Reduce needLow costSpecial service for subscribersNetwork connectionsCommunications systemSpeech sound
In order that emergency service vehicles can be dispatched to the correct destination promptly, accurate information about the location of the caller is needed. Another problem concerns routing emergency calls to the correct destination. For emergency calls a universal code is used such as 911 in North America and 112 in Europe. This universal code cannot be used to identify the destination of the call. These problems are particularly acute for nomadic communications systems such as voice over internet protocol communications networks. That is because user terminals change network location. These problems are solved by enabling the geographical location of the emergency caller to be determined by entities within a packet-based network without the need for modification of existing emergency services network infrastructure.
Owner:AVAYA INC
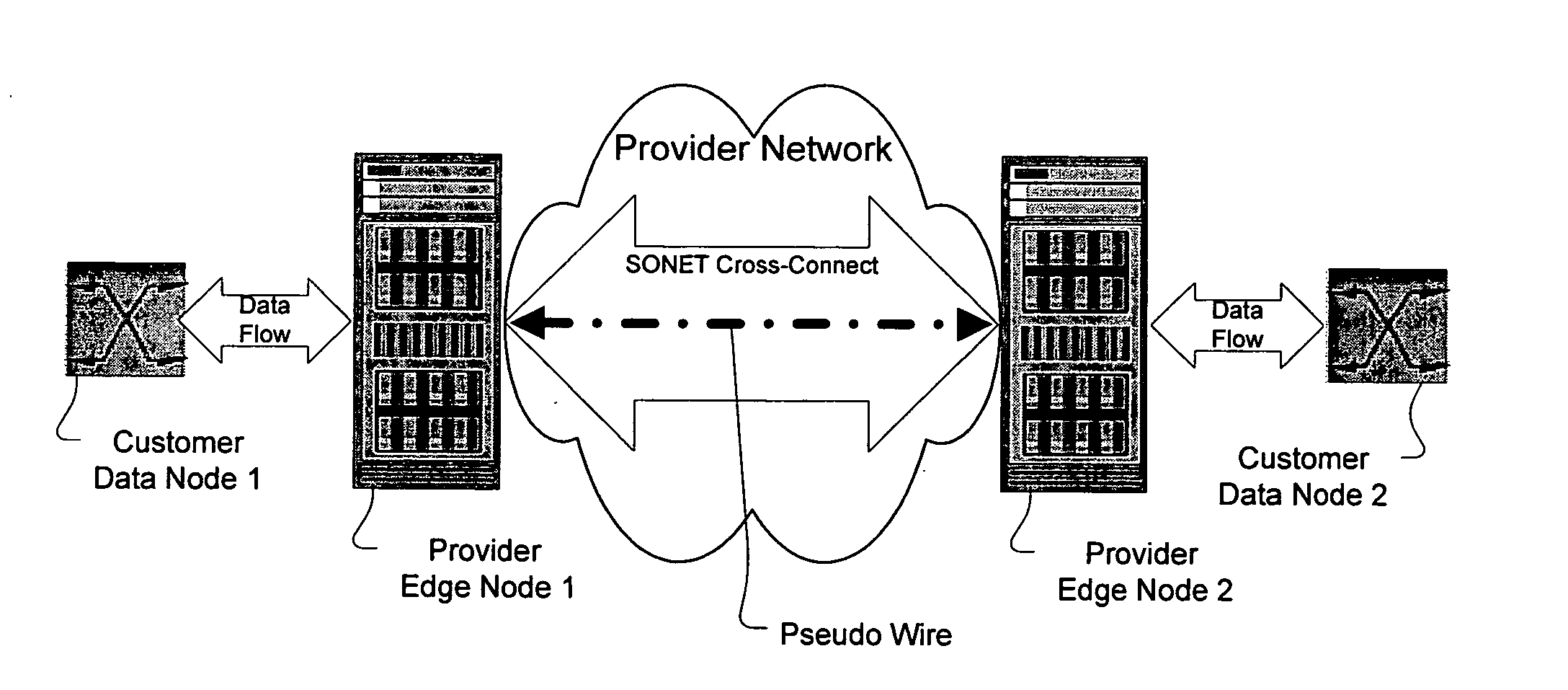
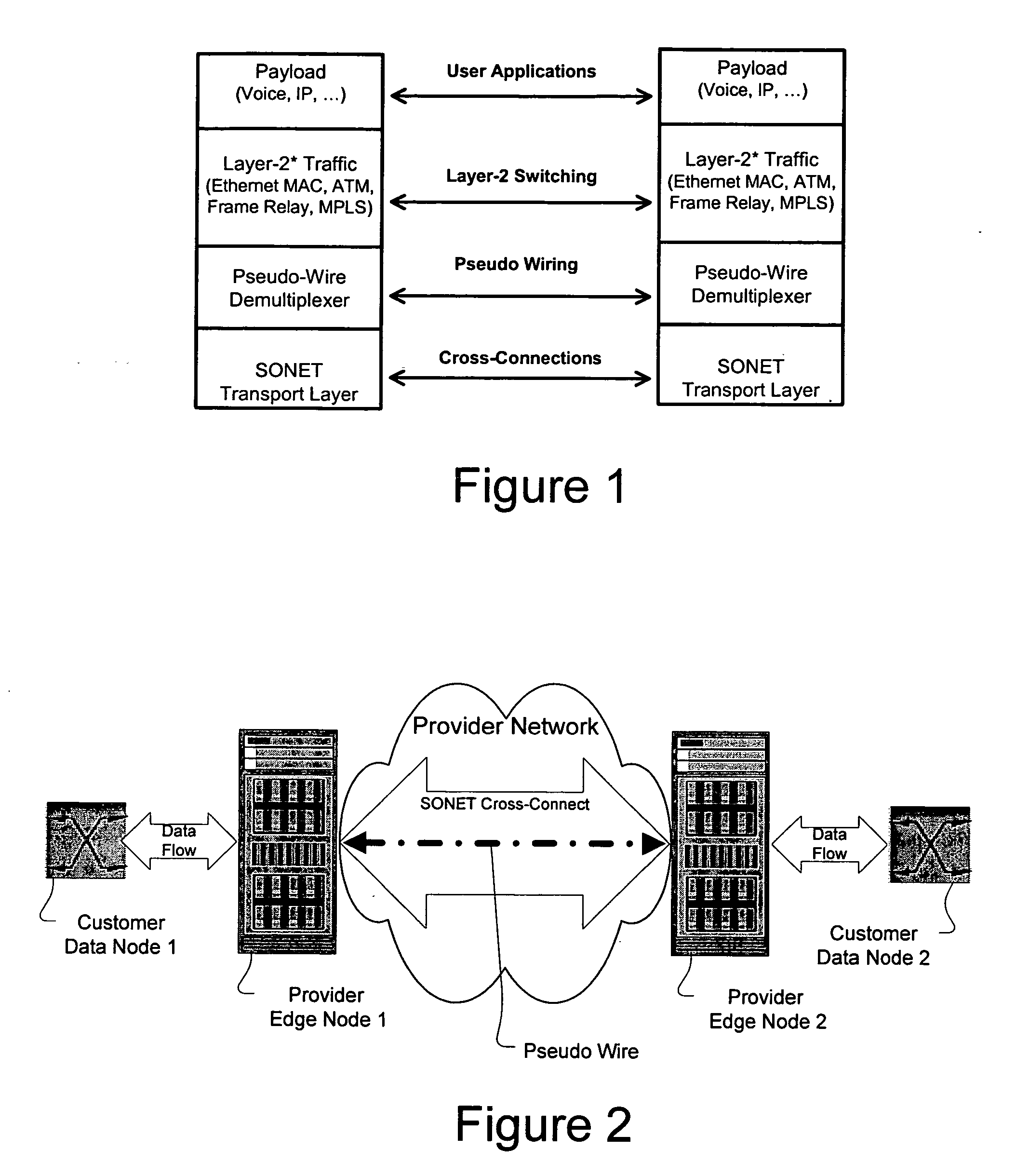
Method and apparatus for performing data flow ingress/egress admission control in a provider network
A method, apparatus and network for transporting layer-2 frames, such as Ethernet MAC, ATM AAL5, and Frame Relay, over MPLS, SONET / SDH, or OTN optical transport networks as well as electrical transport networks is disclosed. The method establishes "pseudo-wires" between, for example, routers, Layer-2 packet switches, or SONET / SDH switches. Inter-related ingress and egress resource tables may be used by provider edge nodes to negotiate consistently managed data tunnels across a provider network on behalf of data flowing from / to a diverse base of customer edge nodes. Detailed network resource information particular to each of the data flows is exchanged between provider edge nodes during the creation of pseudo-wires. Admission control algorithms are applied at the ingress and egress points in order to manage the data flows into a provider network and exiting from a provider network to customer equipment. By applying pseudo-wire shuffling and preemption techniques, the providers can make better use of their network resources by admitting more pseudo-wires.
Owner:CIENA
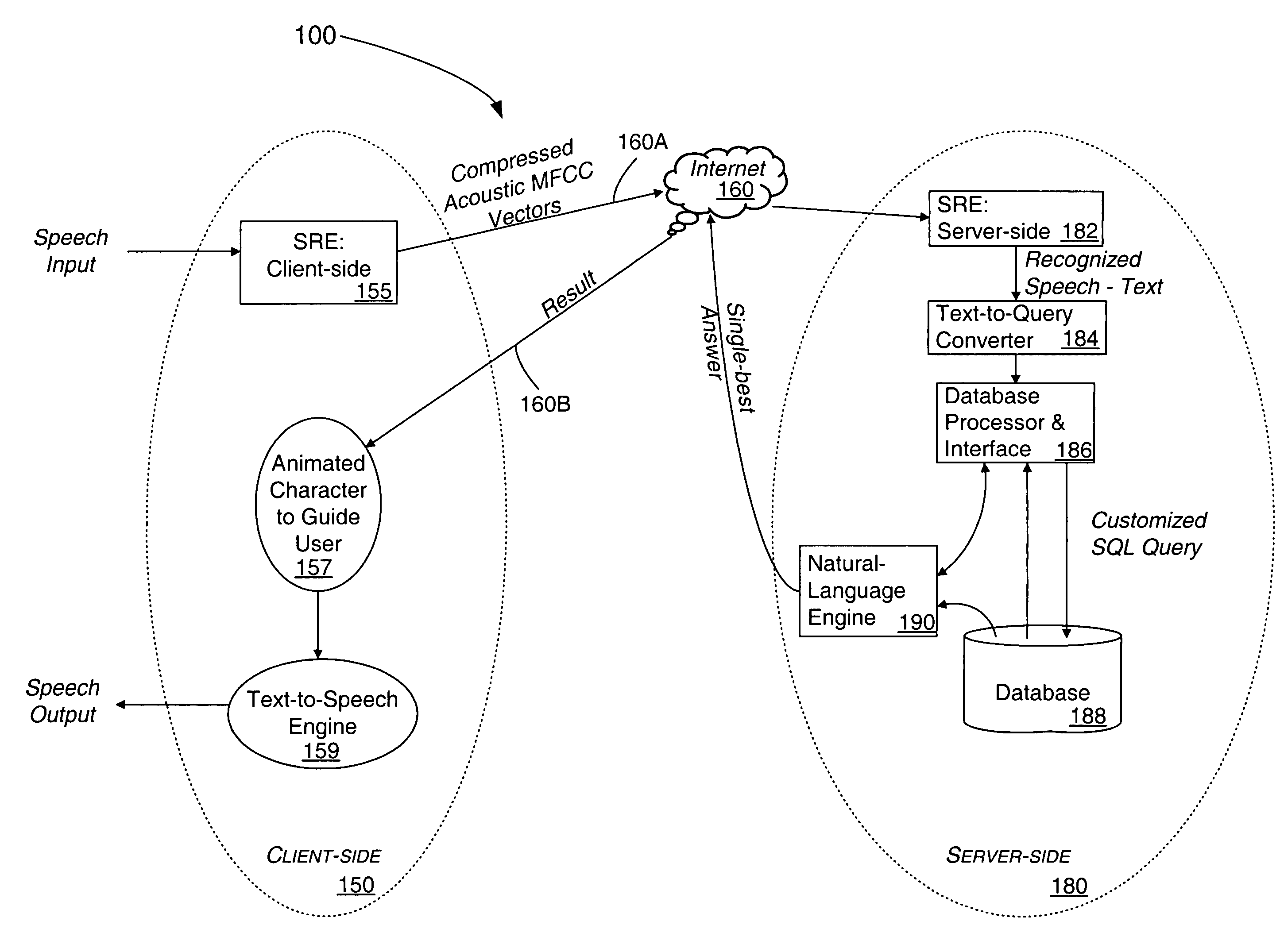
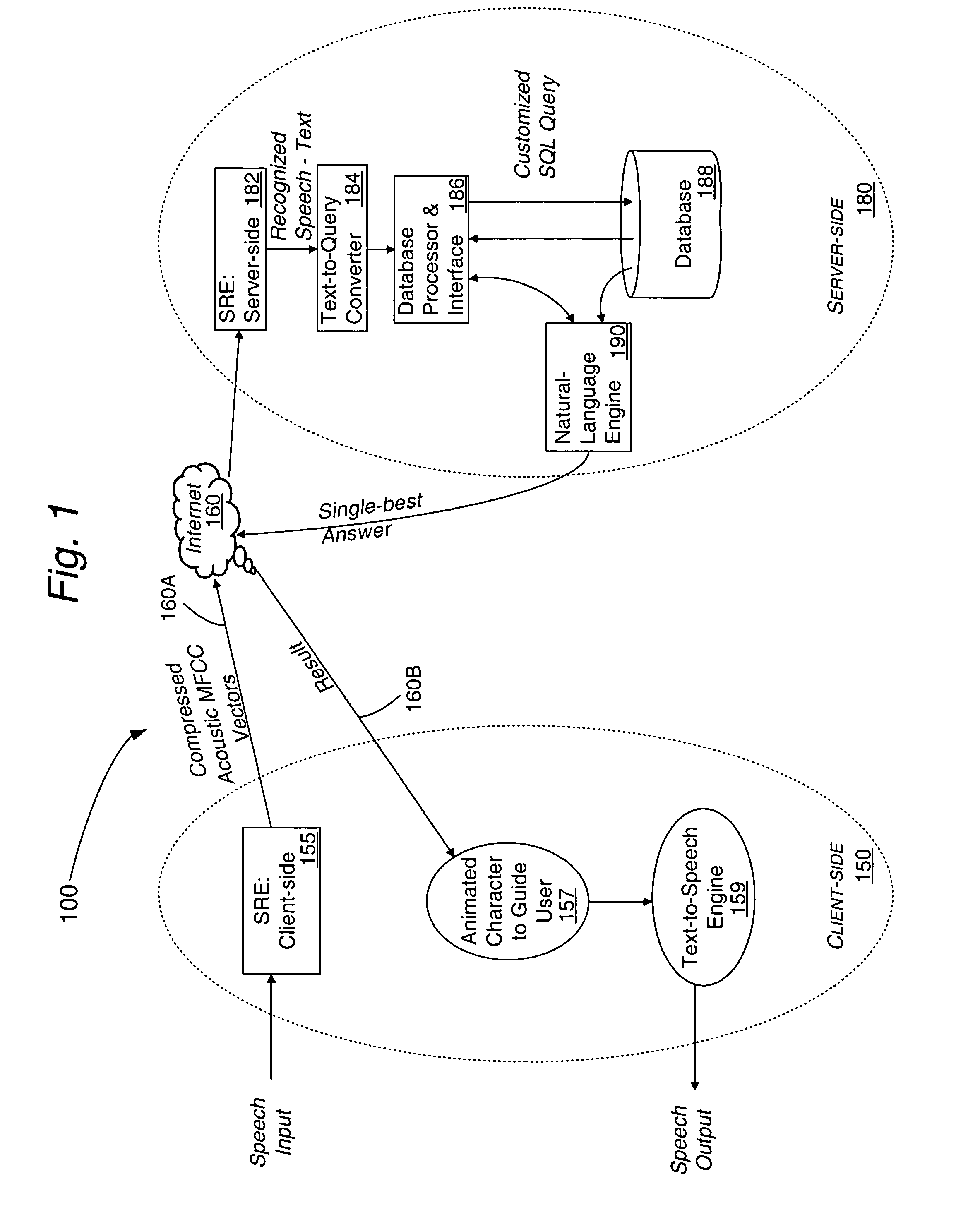
Method for processing speech signal features for streaming transport
InactiveUS7376556B2Flexibly and optimally distributedImprove accuracyNatural language translationData processing applicationsNetwork onClient server systems
Speech signal information is formatted, processed and transported in accordance with a format adapted for TCP / IP protocols used on the Internet and other communications networks. NULL characters are used for indicating the end of a voice segment. The method is useful for distributed speech recognition systems such as a client-server system, typically implemented on an intranet or over the Internet based on user queries at his / her computer, a PDA, or a workstation using a speech input interface.
Owner:NUANCE COMM INC
System and method of identifying the source of an attack on a computer network
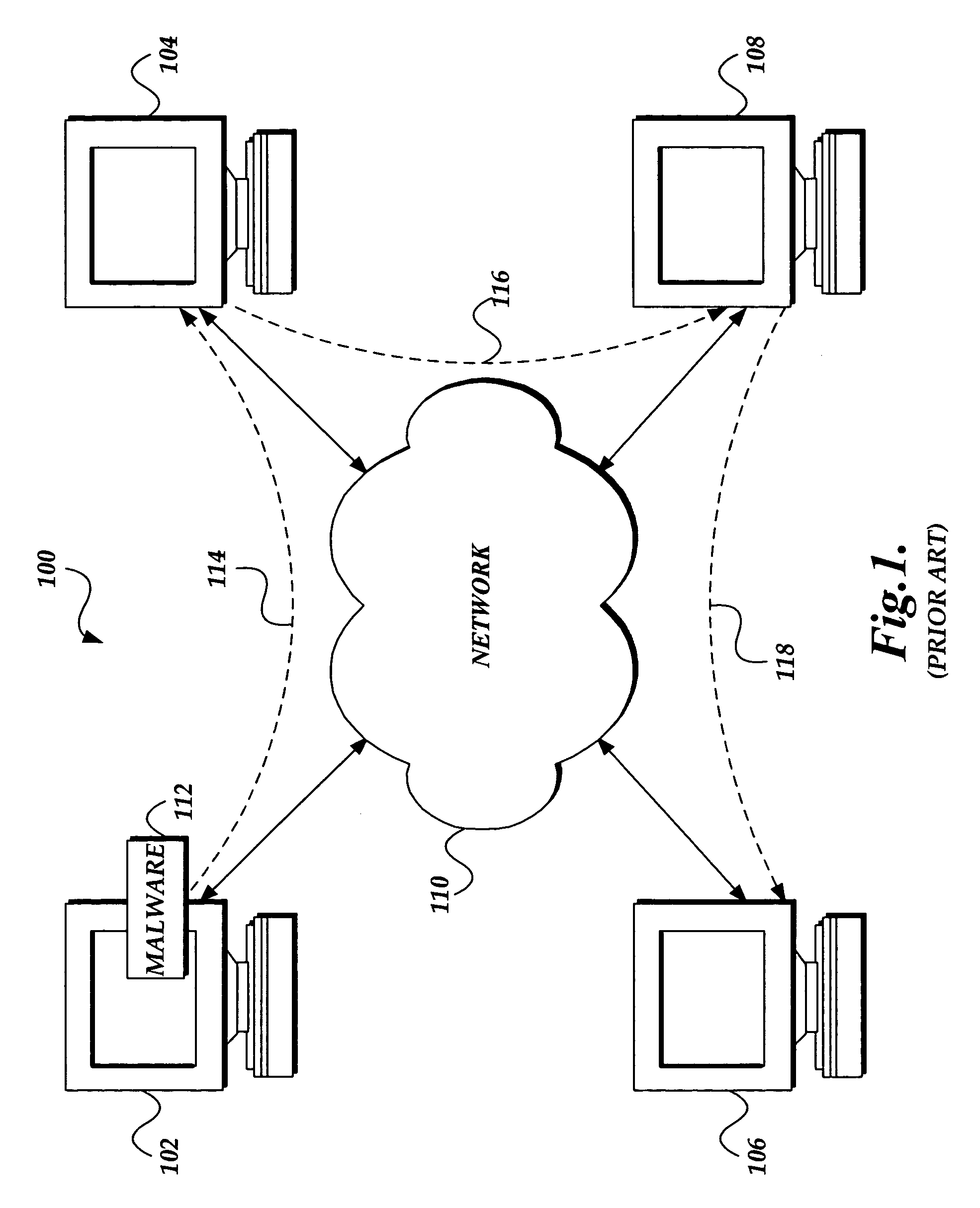
The present invention provides a system and method of tracing the spread of computer malware in a communication network. One aspect of the present invention is a method that traces the spread of computer malware in a communication network. When suspicious data characteristic of malware is identified in a computing device connected to the communication network, the method causes data that describes the state of the computing device to be stored in a database. After a specific attack against the communication network is confirmed, computing devices that are infected with the malware are identified. Then, the spread of the malware between computing devices in the communication network is traced back to a source.
Owner:MICROSOFT TECH LICENSING LLC
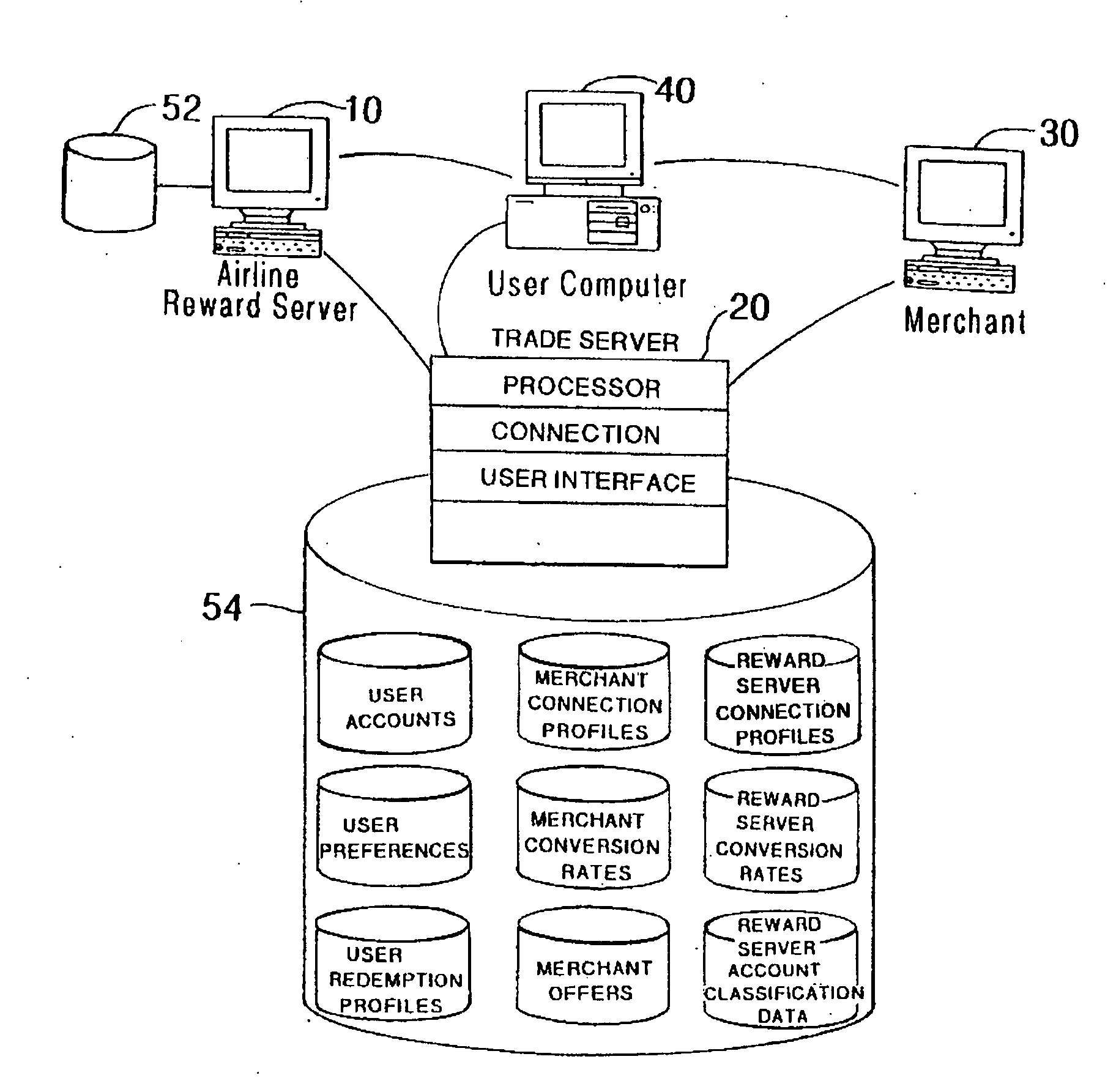
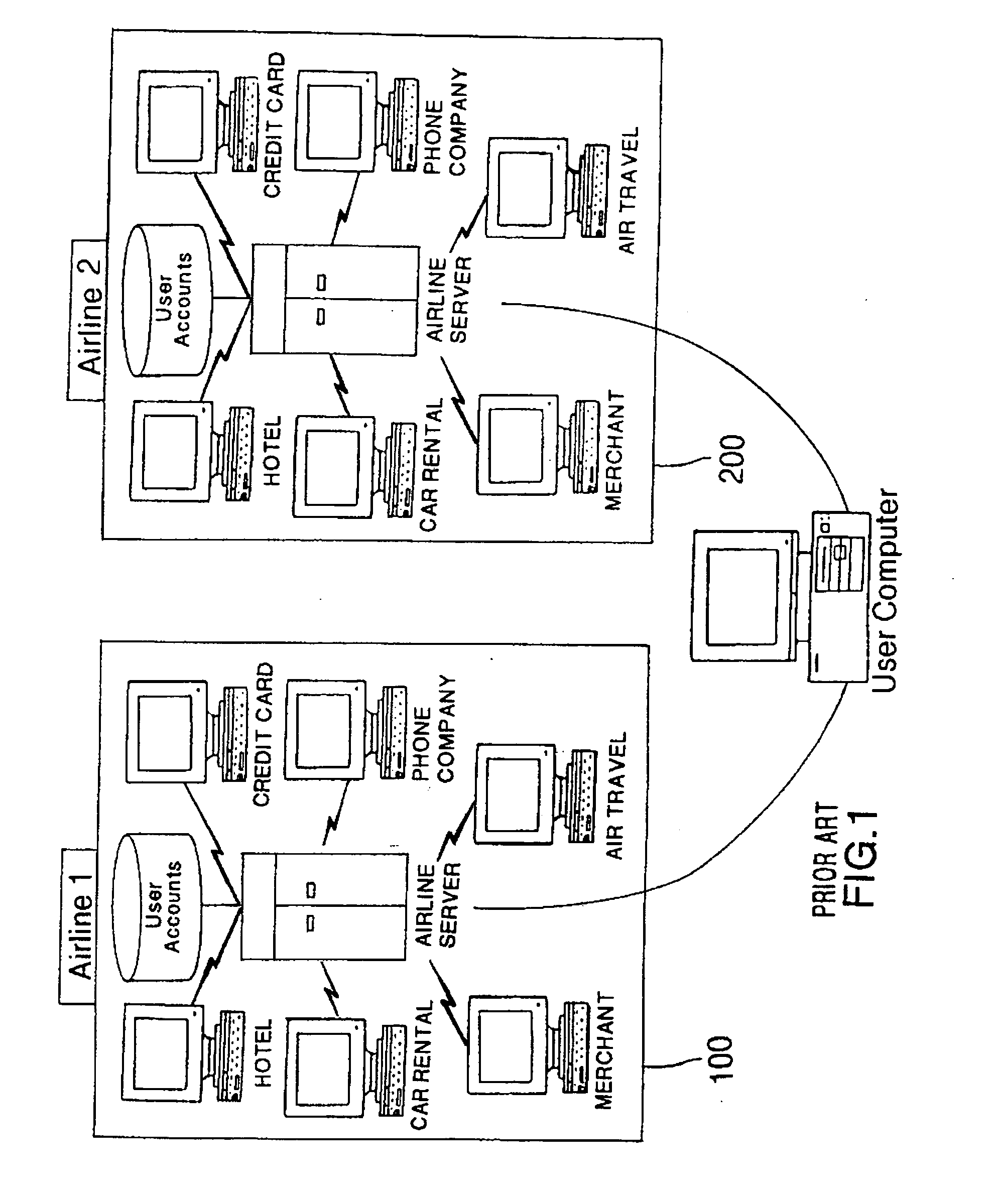
Method and system for issuing, aggregating and redeeming merchant loyalty points with an acquiring bank
InactiveUS20050021401A1High cost of administrationHigh cost of setupPayment architectureMarketingCredit cardComputer science
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by the acquiring bank. The reward account is maintained on the acquiring bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
Systems, methods and computer program products for facilitating the sale of commodity-like goods/services
InactiveUS6965872B1Facilitating the sale of goods/servicesPrice fluctuationAdvertisementsBuying/selling/leasing transactionsComputer scienceEnd user
The invention provides systems and methods for facilitating the sale of commodity-like goods / services. The commodity-like goods / services at which the invention is directed, are of a type that are relatively indistinguishable from one brand, identity and / or outlet to another in end-use functionality and features. These types of goods / services are many times sold at retail under various brands or identities at multiple locations, to the final end user. Such goods / services may also or separately be of a type that are repeatedly purchased at intervals, and / or for which the price varies between purchases, from outlet to outlet or brand to brand. The goods / services may also be of a character such that they are not deliverable to the consumer, but require the consumer to travel to the retailer outlet. The system and methods also provide information relating to the consumers and competitors of a retailer of such goods / services. The invention establishes methods and procedures to define, organize, collect, distribute, and maintain information that can be used by the owner of a business selling commodity-like goods / services as well as by its customers. This information may include, but is not limited to, name brand of the product, location of the retailer, price of the product, other related goods / services available and their prices, and promotions. These processes may be performed and implemented on a computer network that is accessible in real time via a suitable communication device, such as a computer, wireless communication device, telephone or the like. A database of such information is created, allowing the consumer and other retailers to query the database using various search criteria. The consumer has the opportunity to obtain information about retailers of commodity-like goods / services that meet the consumer's requirements, and pricing may be guaranteed by the retailer.
Owner:GRDINA JEROME M
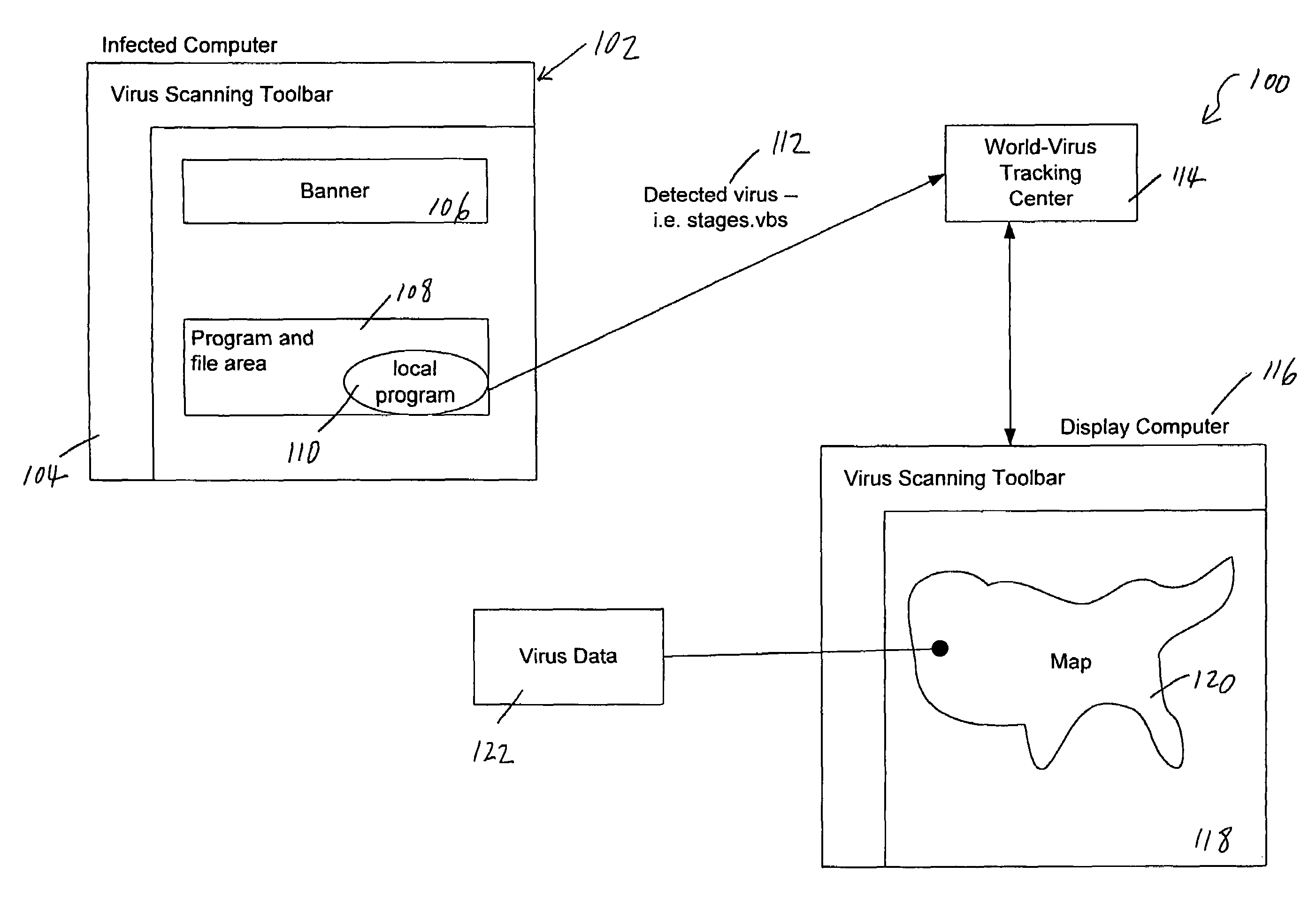
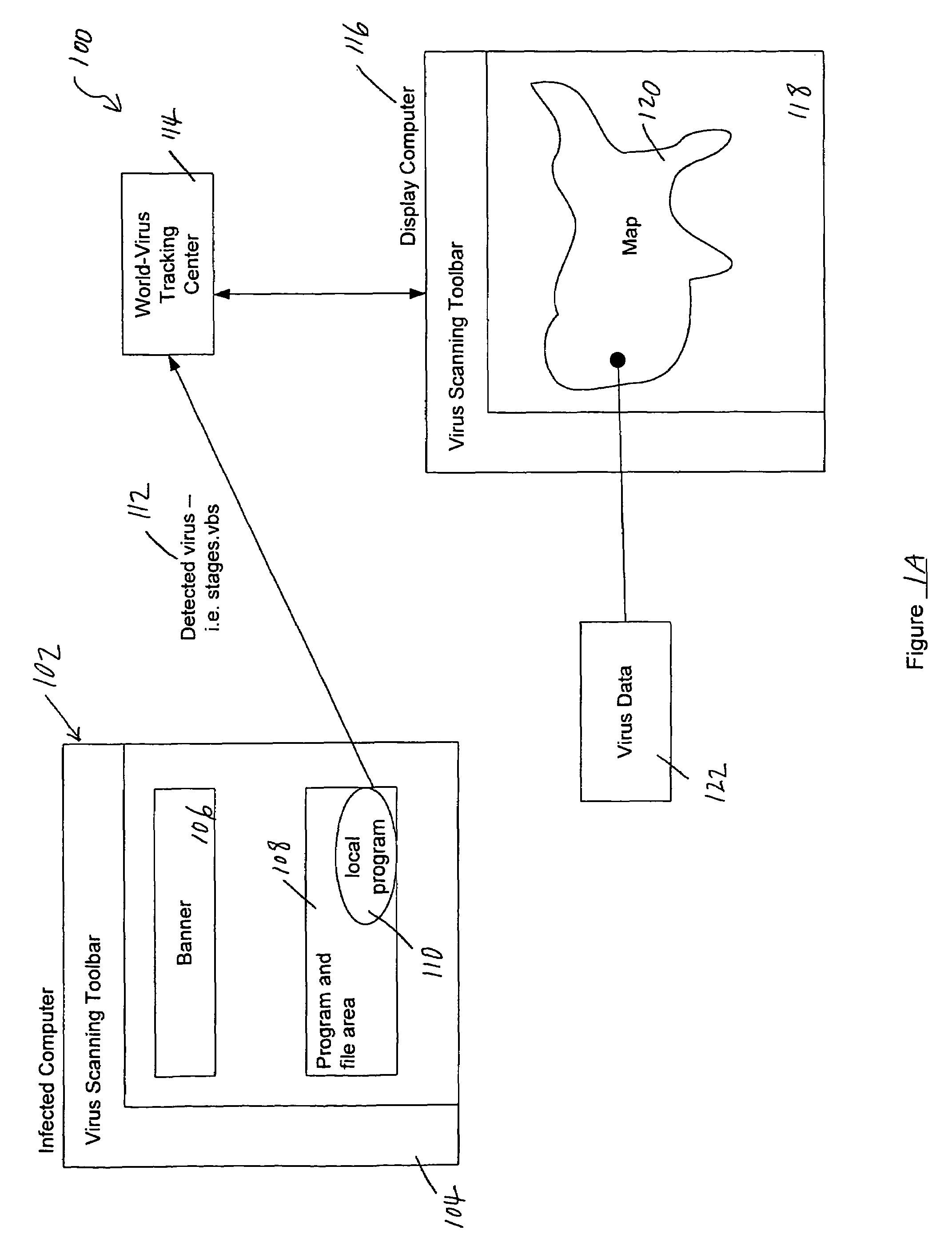
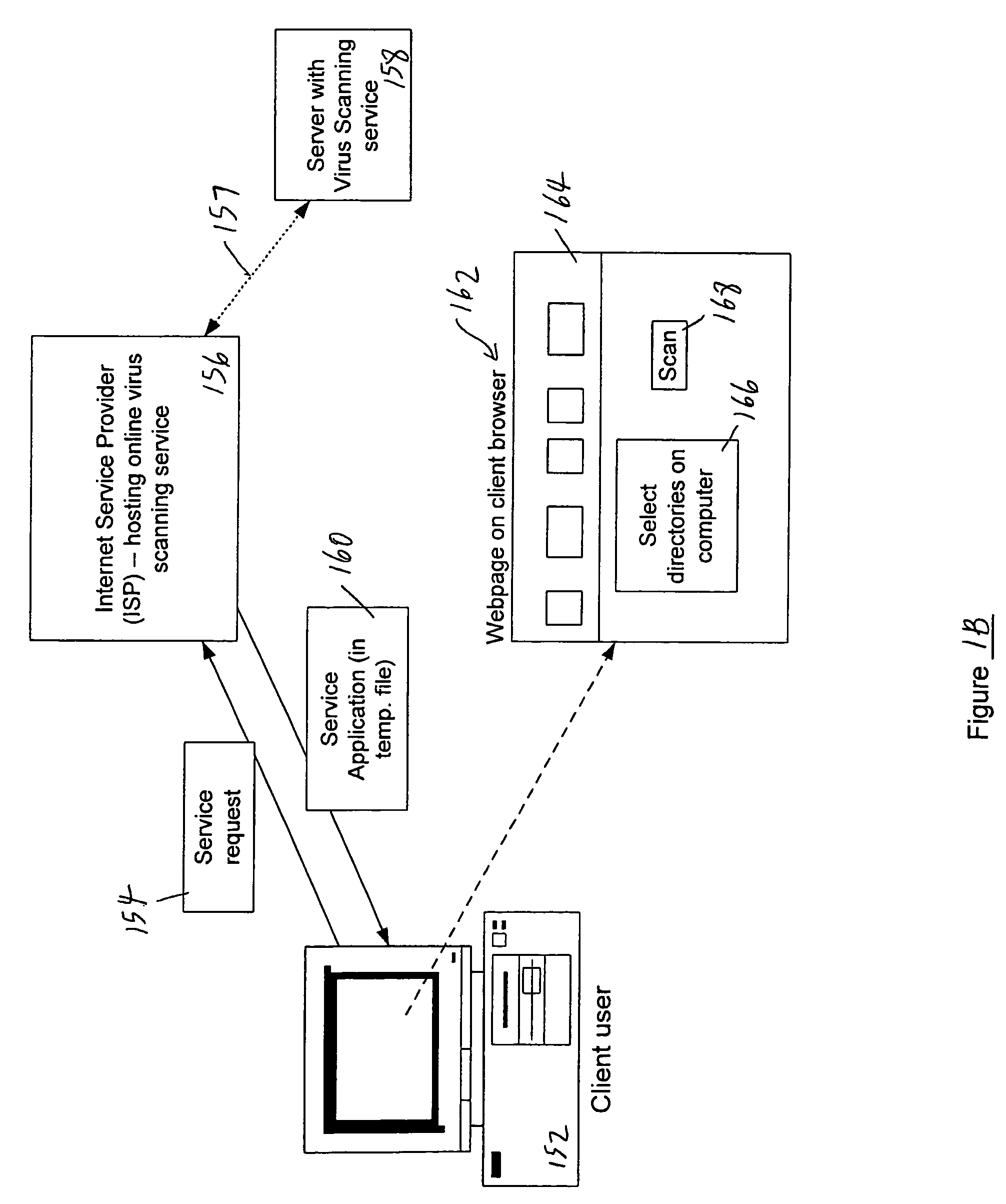
Tracking and reporting of computer virus information
An apparatus and method for providing real-time tracking of virus information as reported from various computers on a distributed computer network. Each client computer on the distributed network contacts an anti-virus scanning site. The site provides a small program or applet that resides in temporary memory of the client computer. The client-user invokes the scan with supplied pattern updates for detecting recent viruses. When the scan has been completed, the user is prompted to supply a country of origin. The name of the virus, its frequency of occurrence, and the country are forwarded as a virus scan log to a virus tracking server, which receives the virus information and thereafter stores it in a database server, which is used to further calculate virus trace display information. A tracking user contacts the virus tracking server and receives map information, which traces the virus activity. The maps show, according to user preference, the names of the viruses encountered in each country, and their frequencies of occurrence.
Owner:TREND MICRO INC
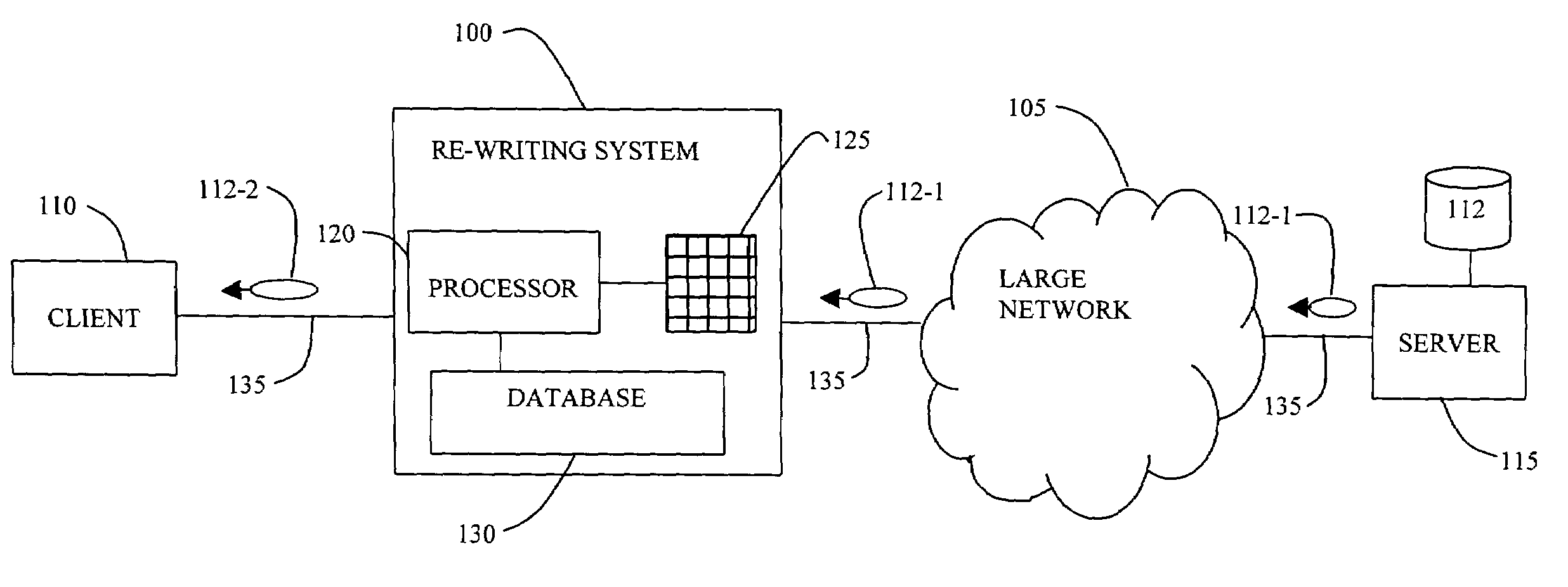
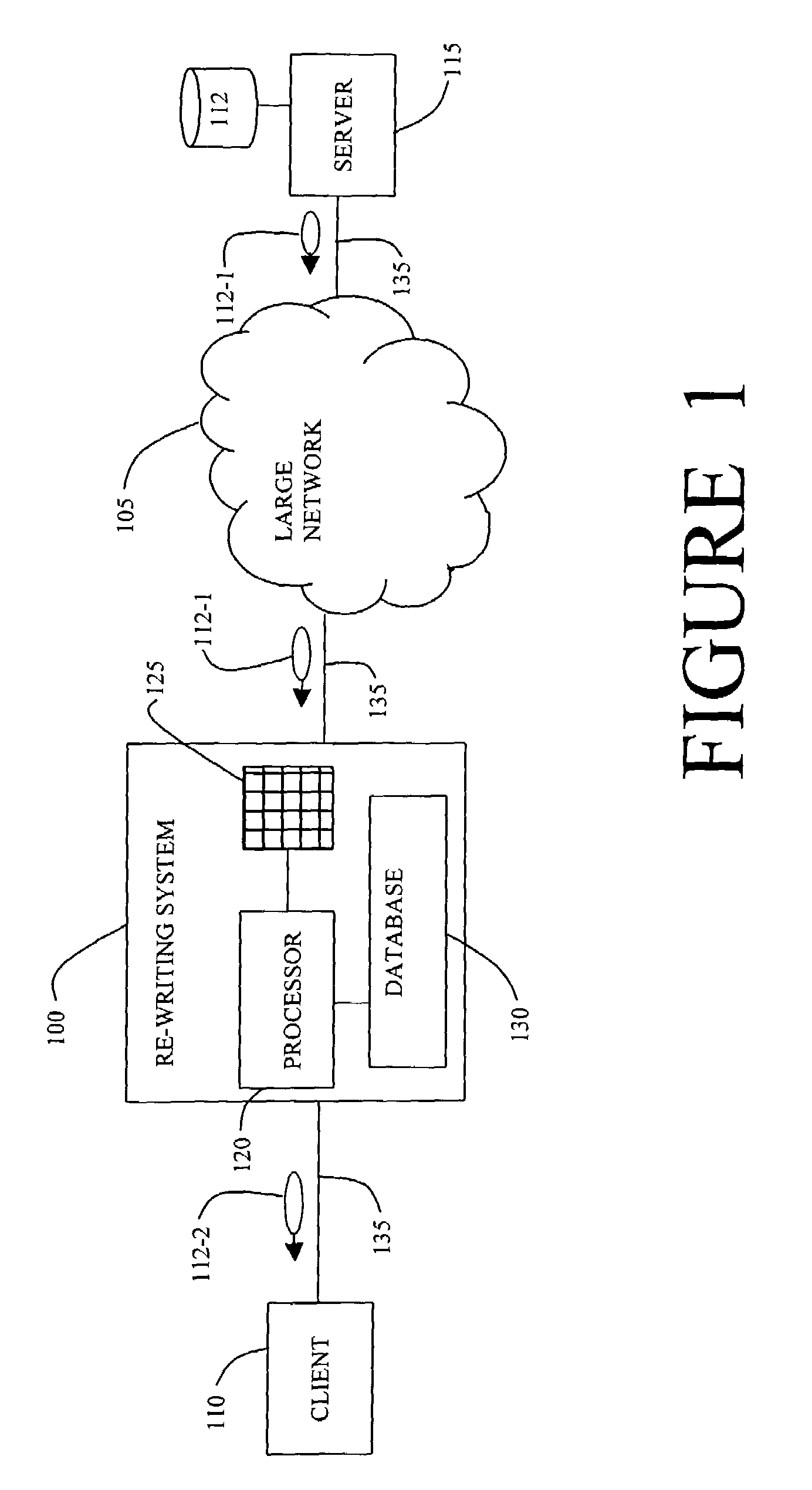
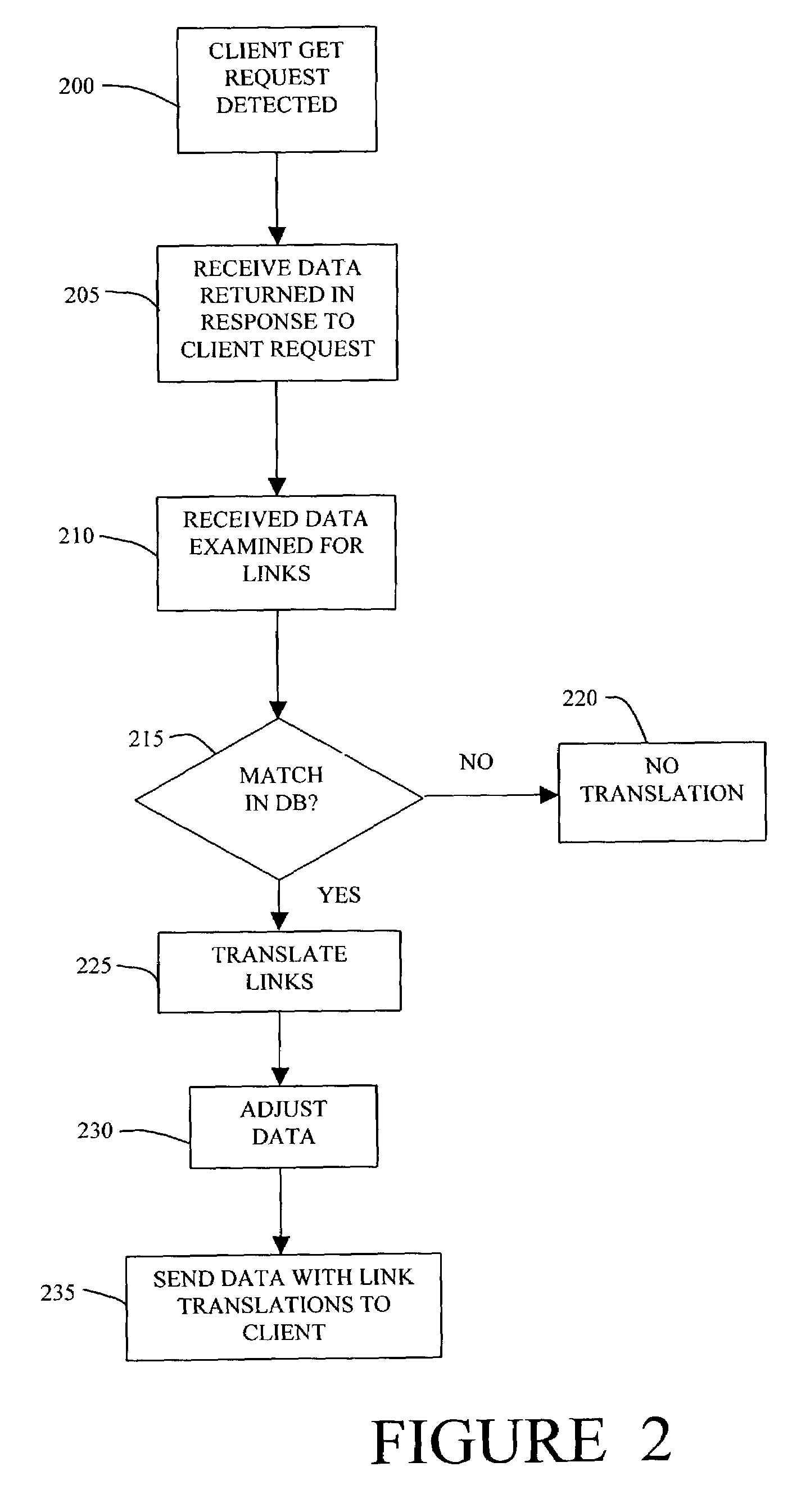
System and method for generalized URL-rewriting
ActiveUS7058633B1Efficient content routingReduces DNS request/reply overheadData processing applicationsDigital data information retrievalRewrite engineUniform resource locator
A URL re-writing system and method in a network examines and modifies HTML data and its embedded URLs. The re-writing system can be implemented in a router and can replace URLs found in the HTML data in order to accomplish more efficient routing for example to a close mirror site or for content routing. The re-writing system can also use URL replacement to insert important or emergency information to data received by users on a Web-based network.
Owner:CISCO TECH INC
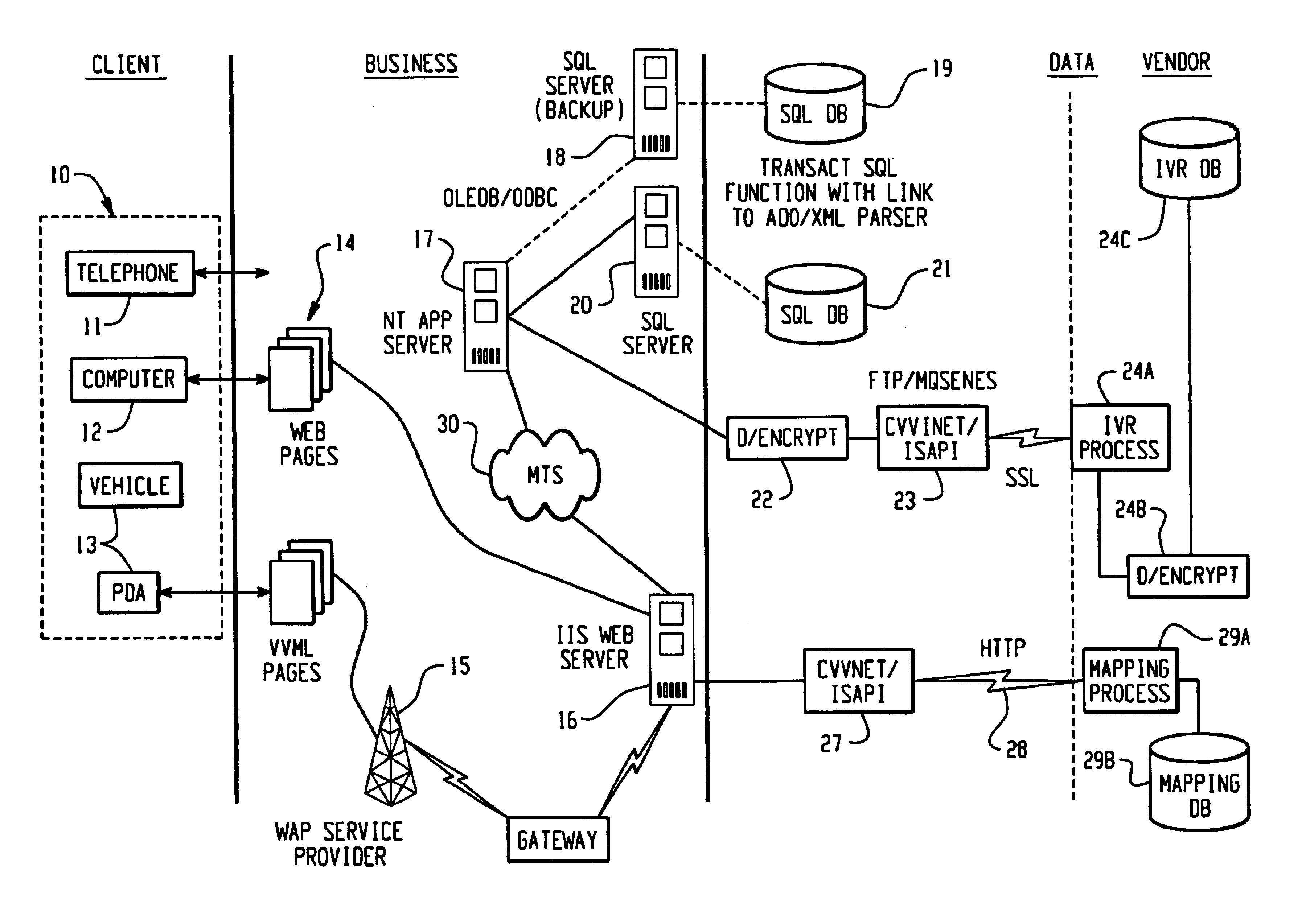
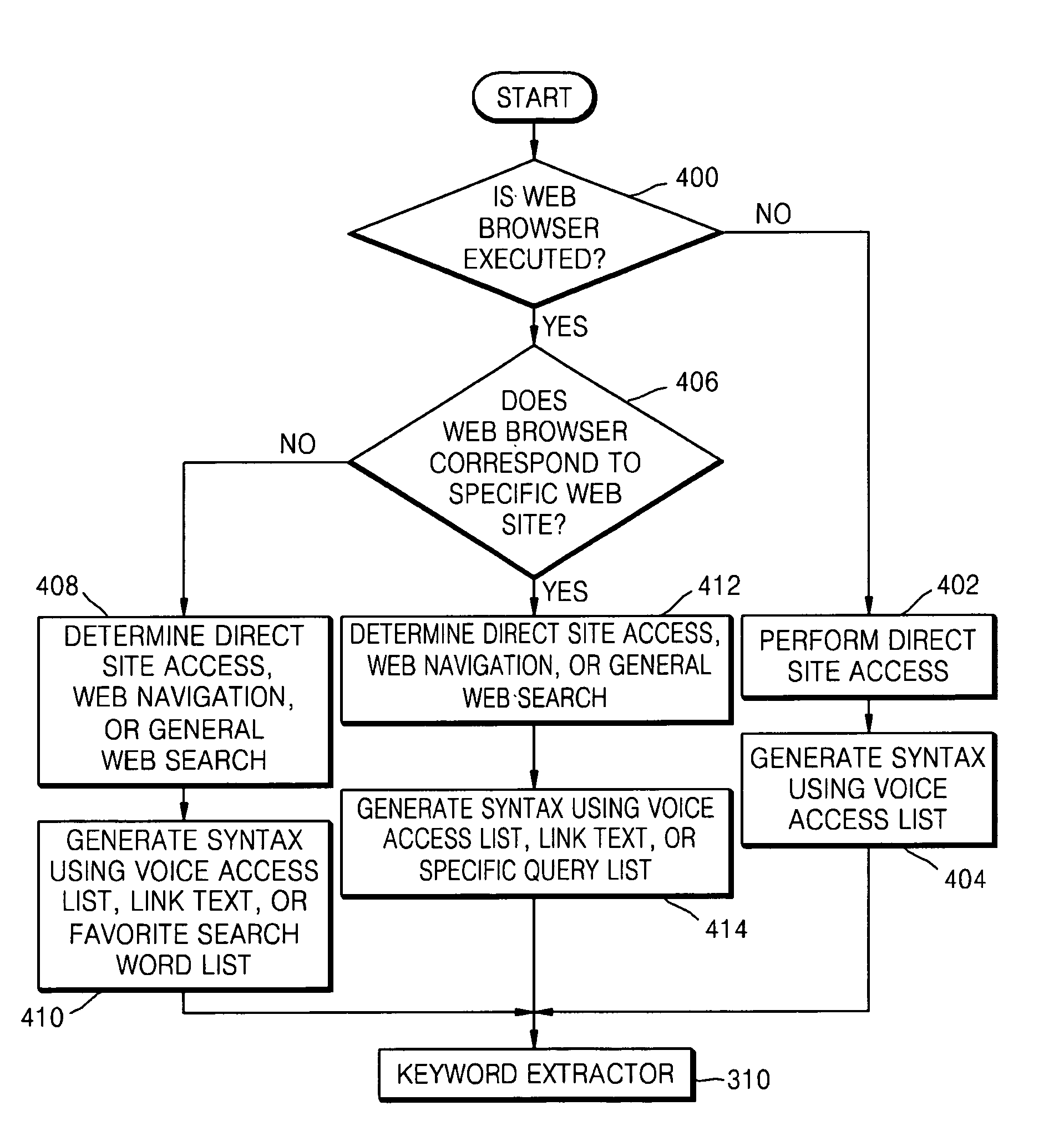
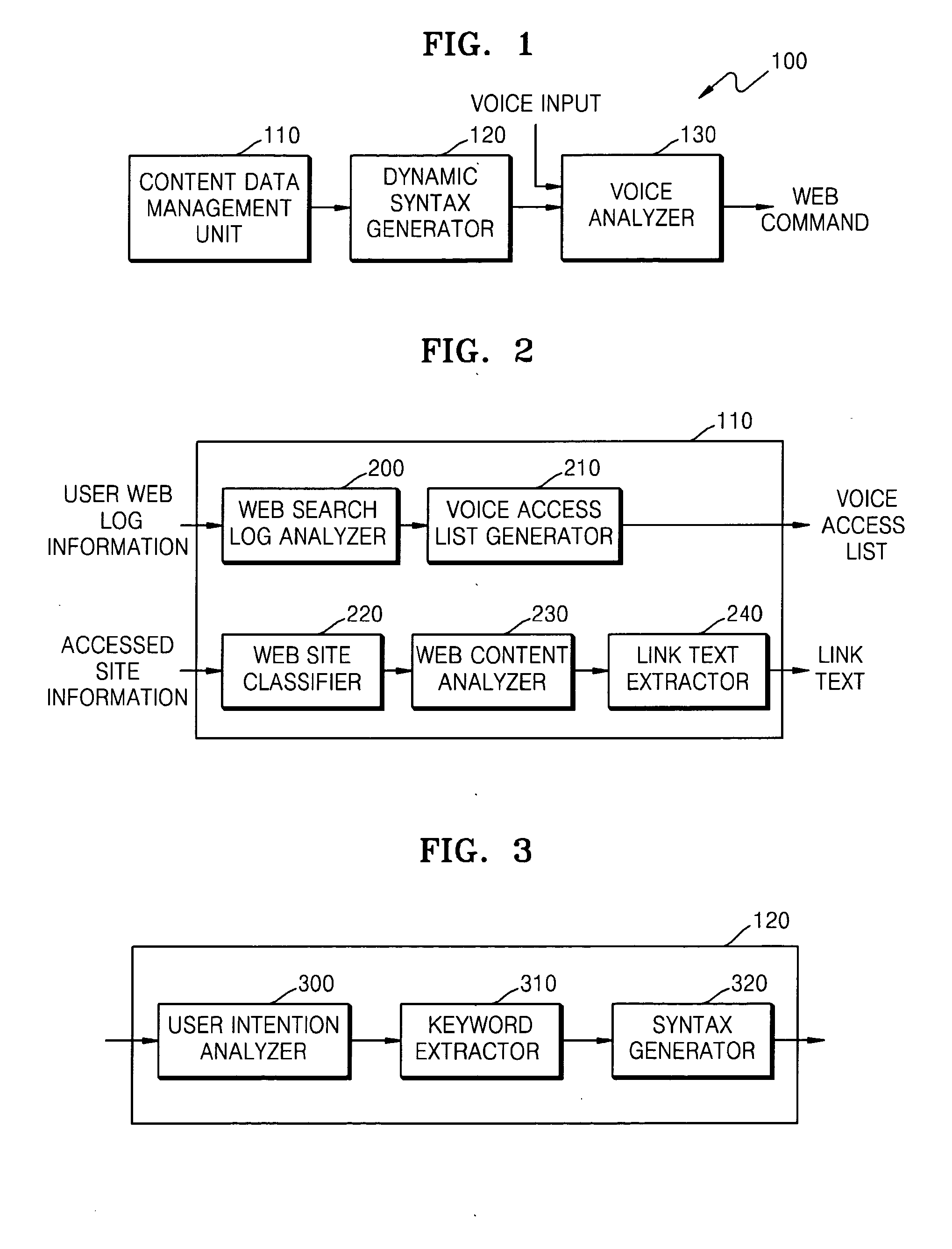
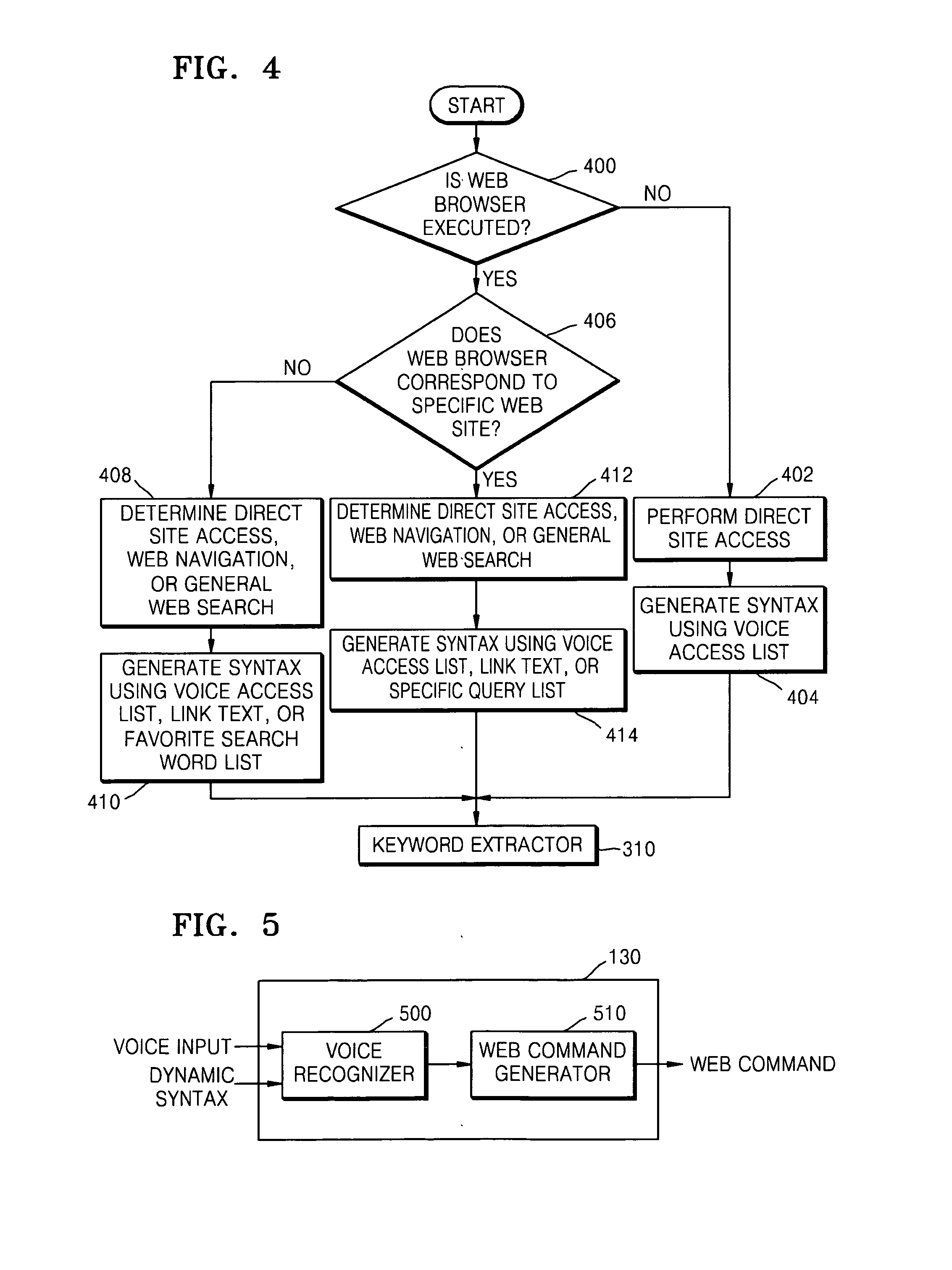
Method, medium and apparatus for providing mobile voice web service
Provided are a method and apparatus for providing a mobile voice web service in a mobile terminal. The method includes analyzing a web history of a user from web search logs of the user and generating a voice access list based on the analysis results, and performing voice recognition by dynamically generating a voice recognition syntax according to the generated voice access list. Accordingly, by limiting syntax required for voice recognition by generating a syntax suitable for a web context of the user, efficient voice recognition, which can be performed in a terminal not a server, can be implemented.
Owner:SAMSUNG ELECTRONICS CO LTD
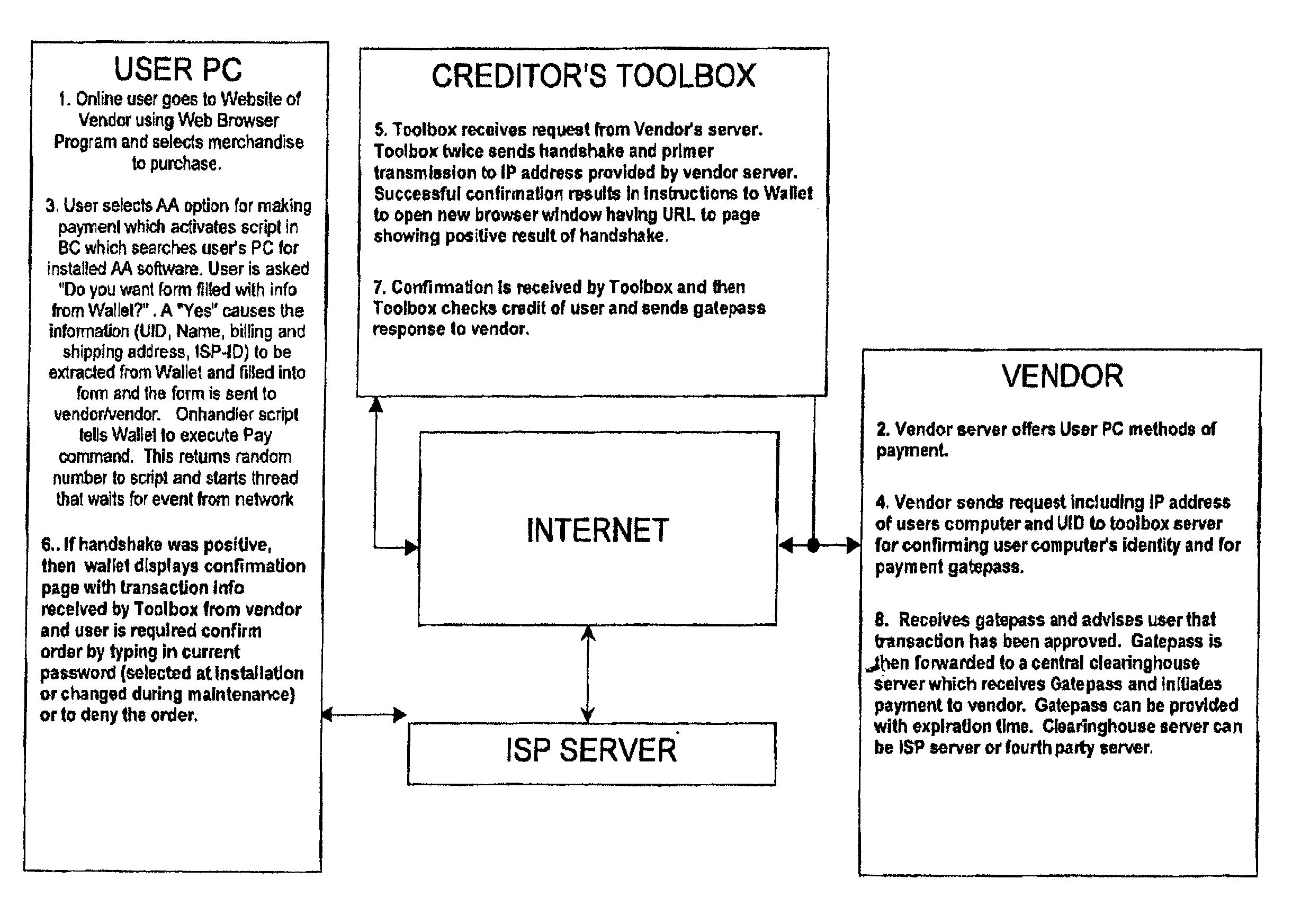
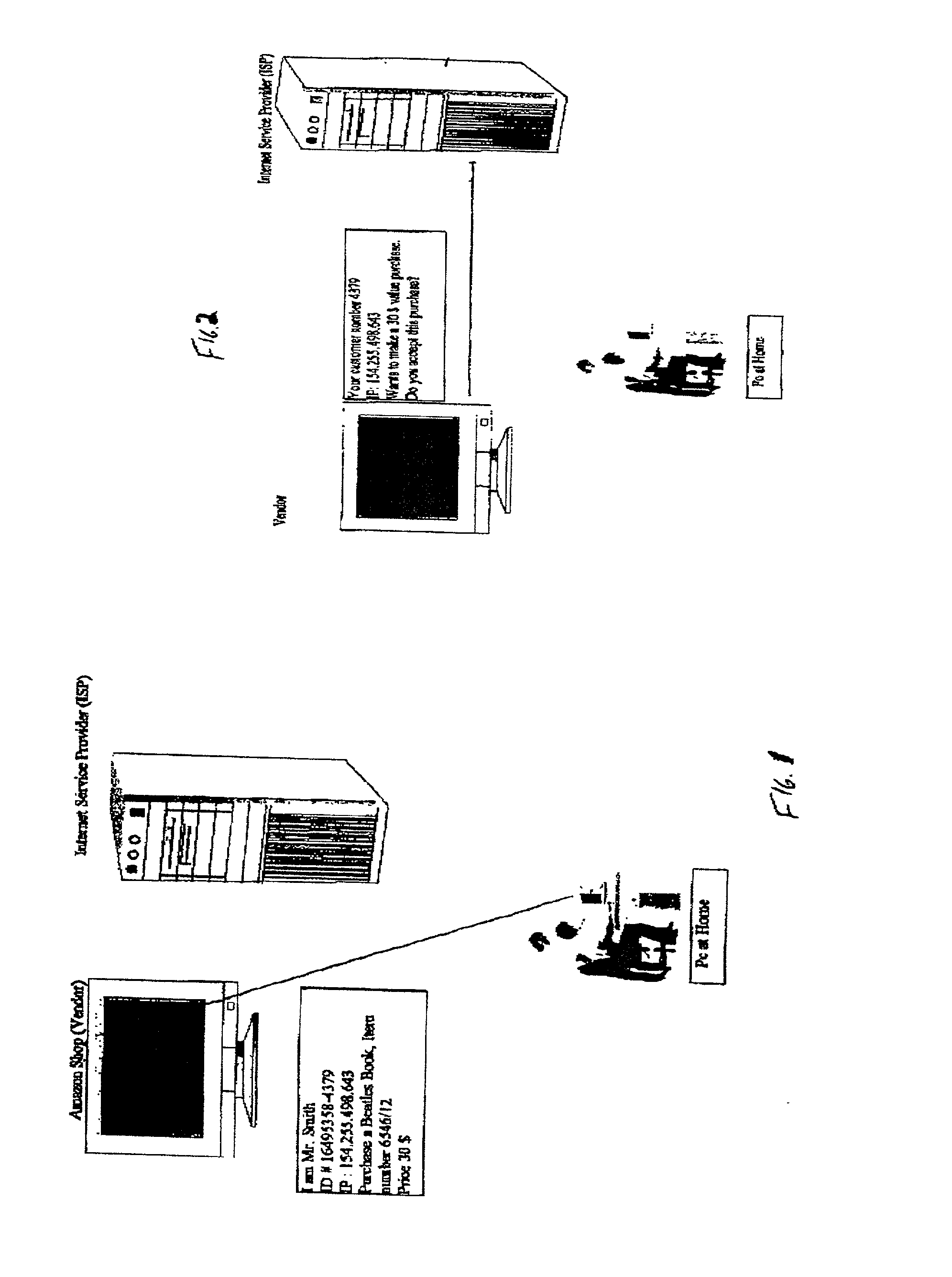
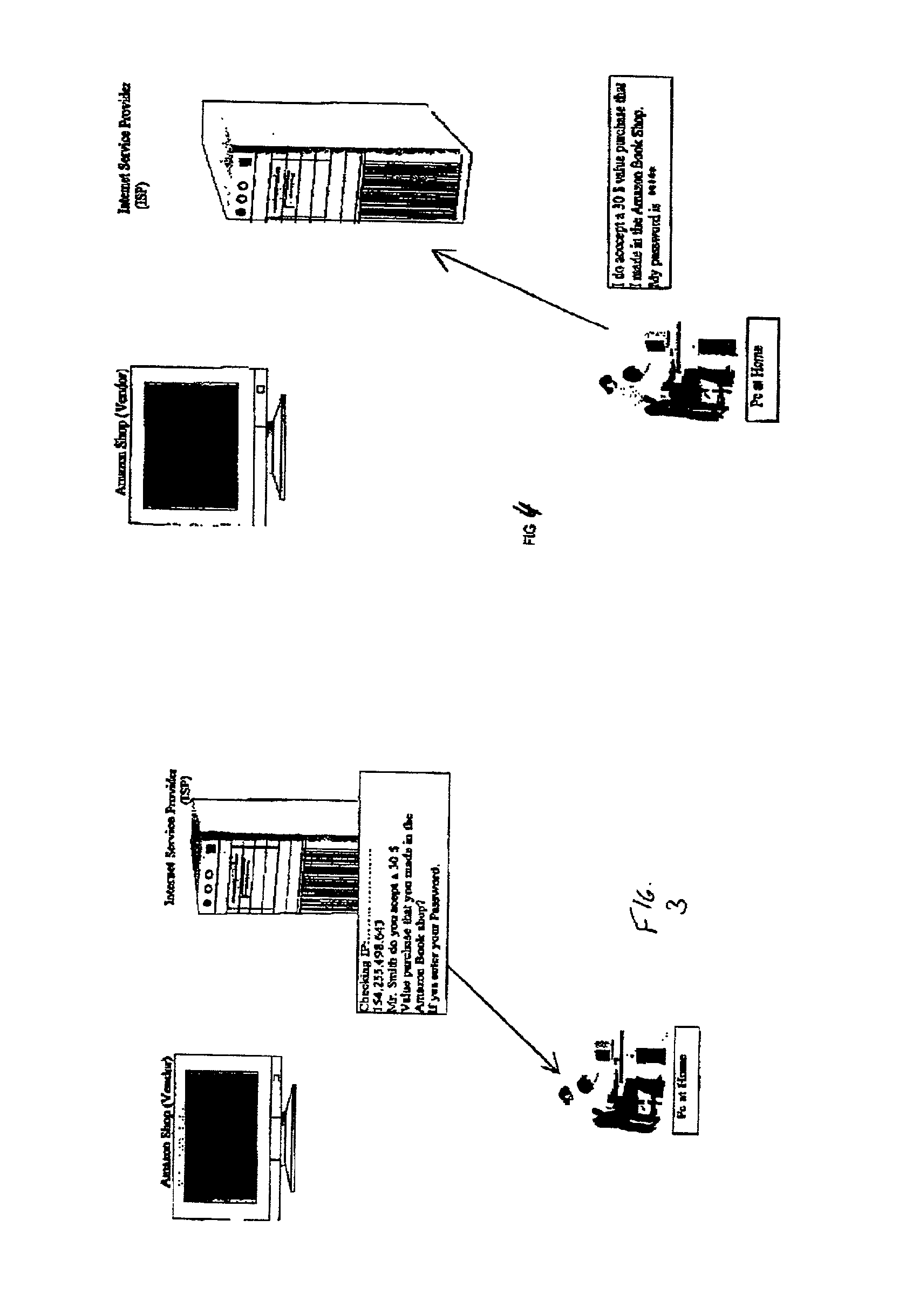
System and method for secure network purchasing
InactiveUS20020073046A1Improve securityCharacter and pattern recognitionDigital data authenticationSecure Electronic TransactionInternet privacy
A system for permitting a secure electronic transaction on a network is disclosed. The network has a user device having a fingerprint, a provider's server and a means for providing verification of user's identity. In response to a request by the provider's server the means for providing verification positively identifies the fingerprint of the user device. It thereupon requests a confirmation from the user device of the transaction and upon receiving the confirmation completes the transaction.
Owner:CHANNEL IP BV
Method and system for efficient communication
InactiveUS20140071818A1Error preventionFrequency-division multiplex detailsTelecommunicationsNetwork on
Owner:INNOVATION SCI LLC
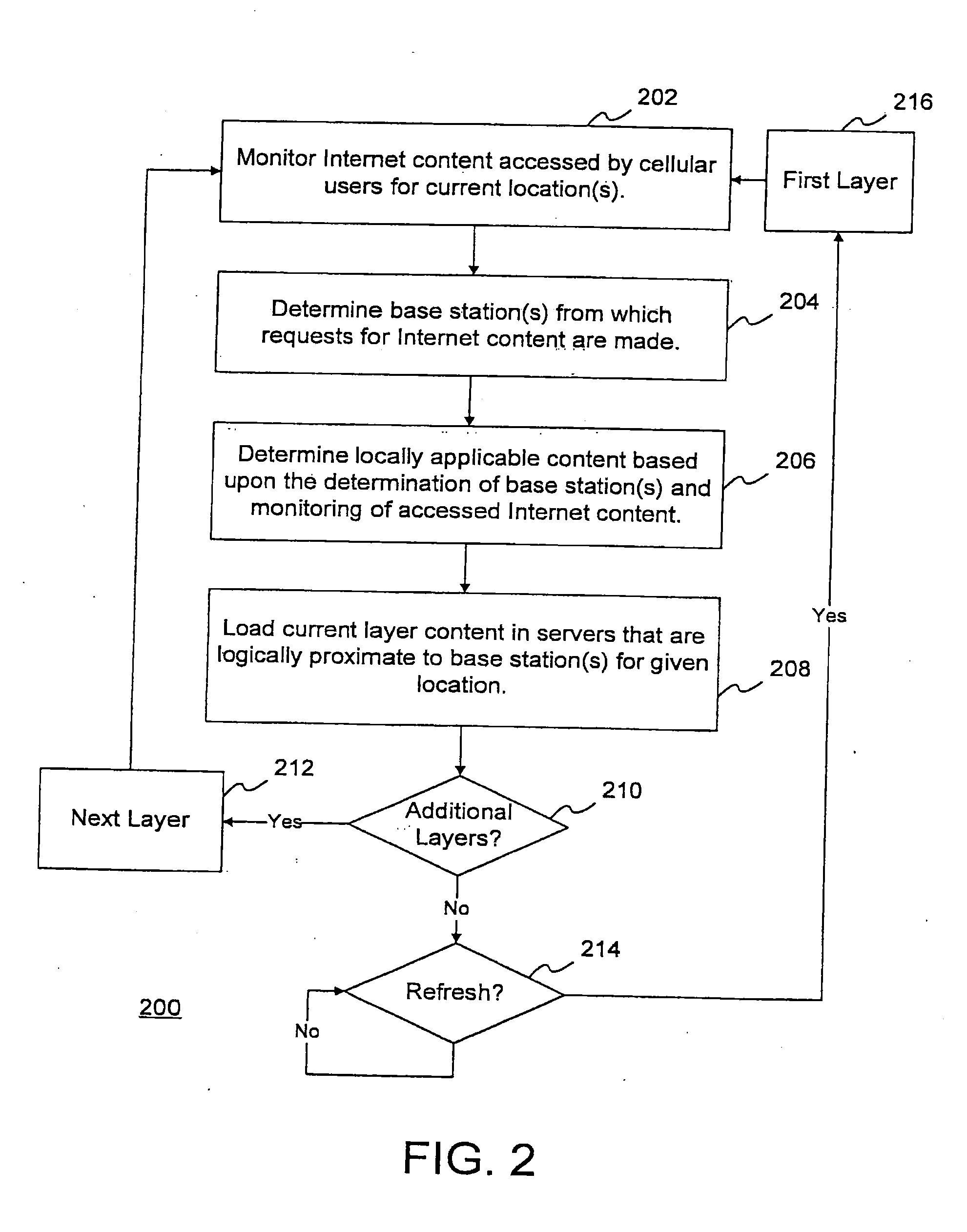
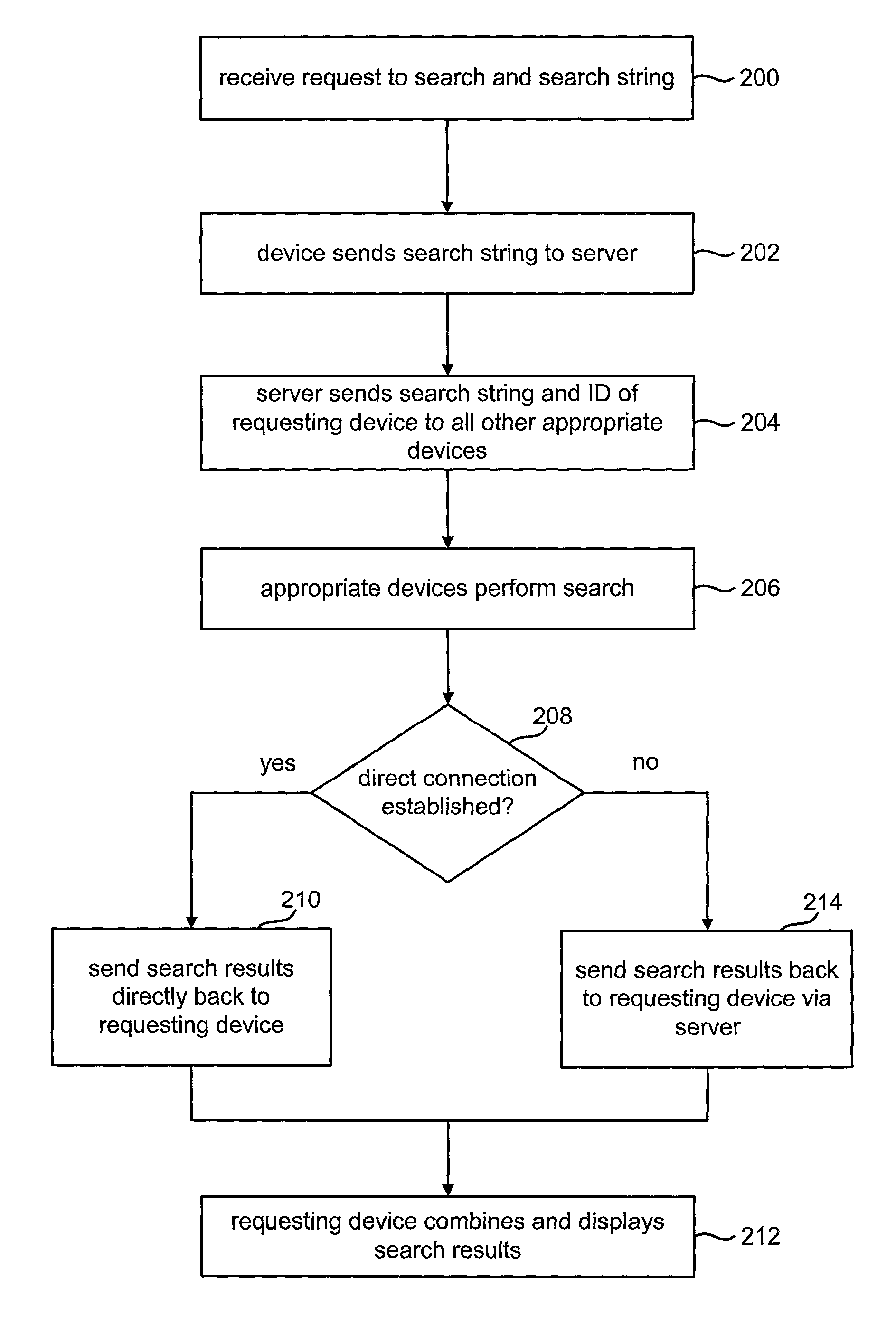
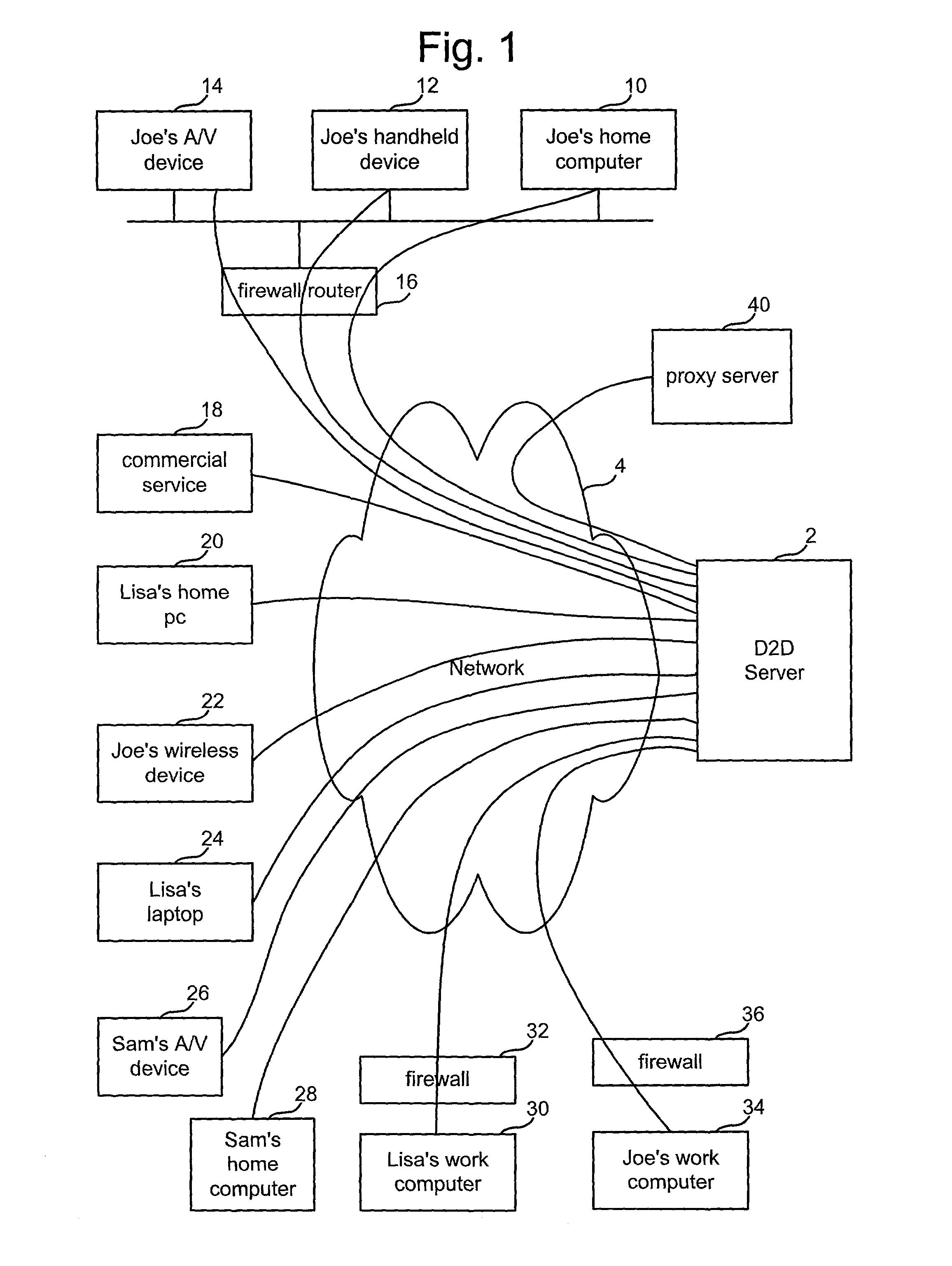
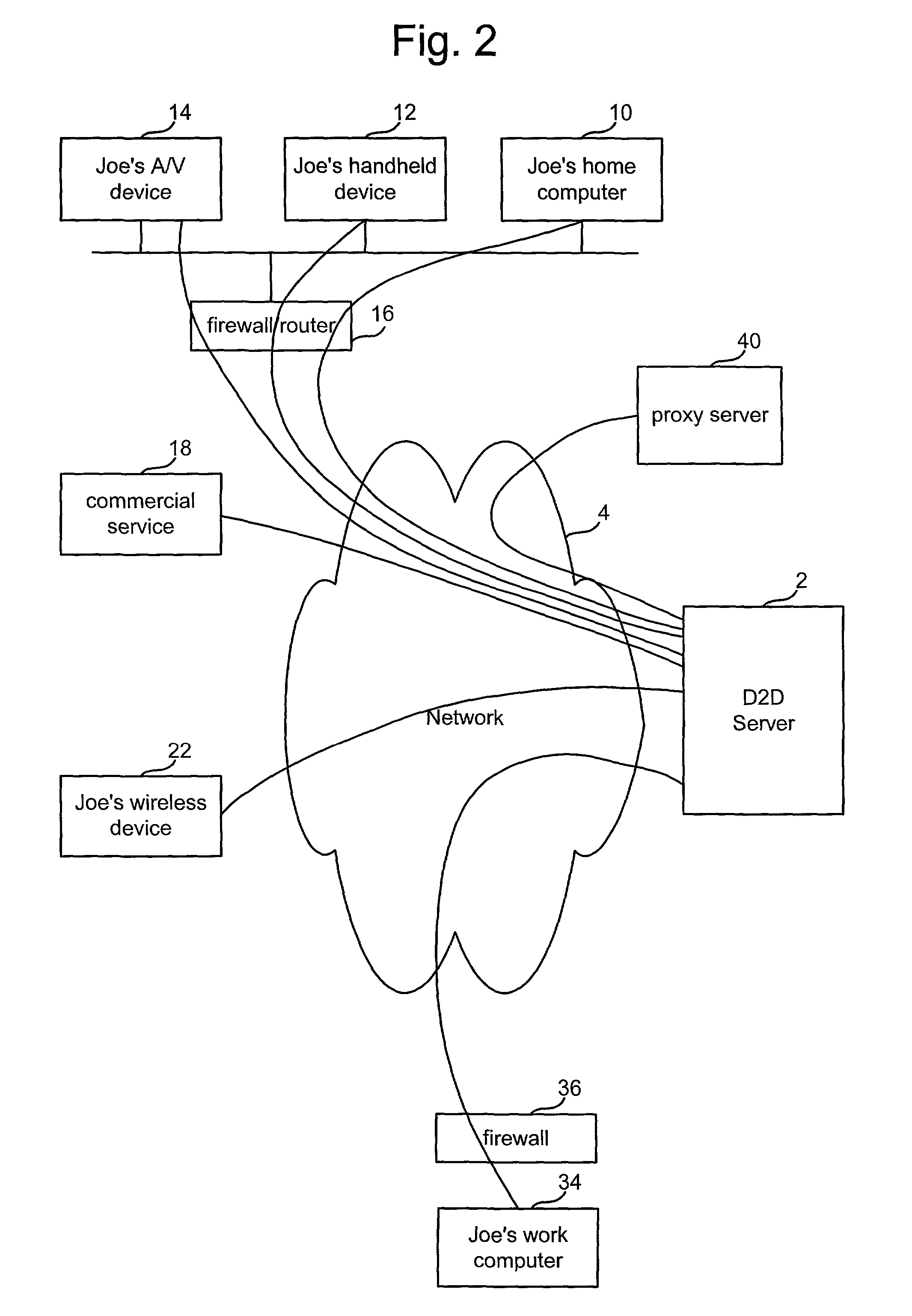
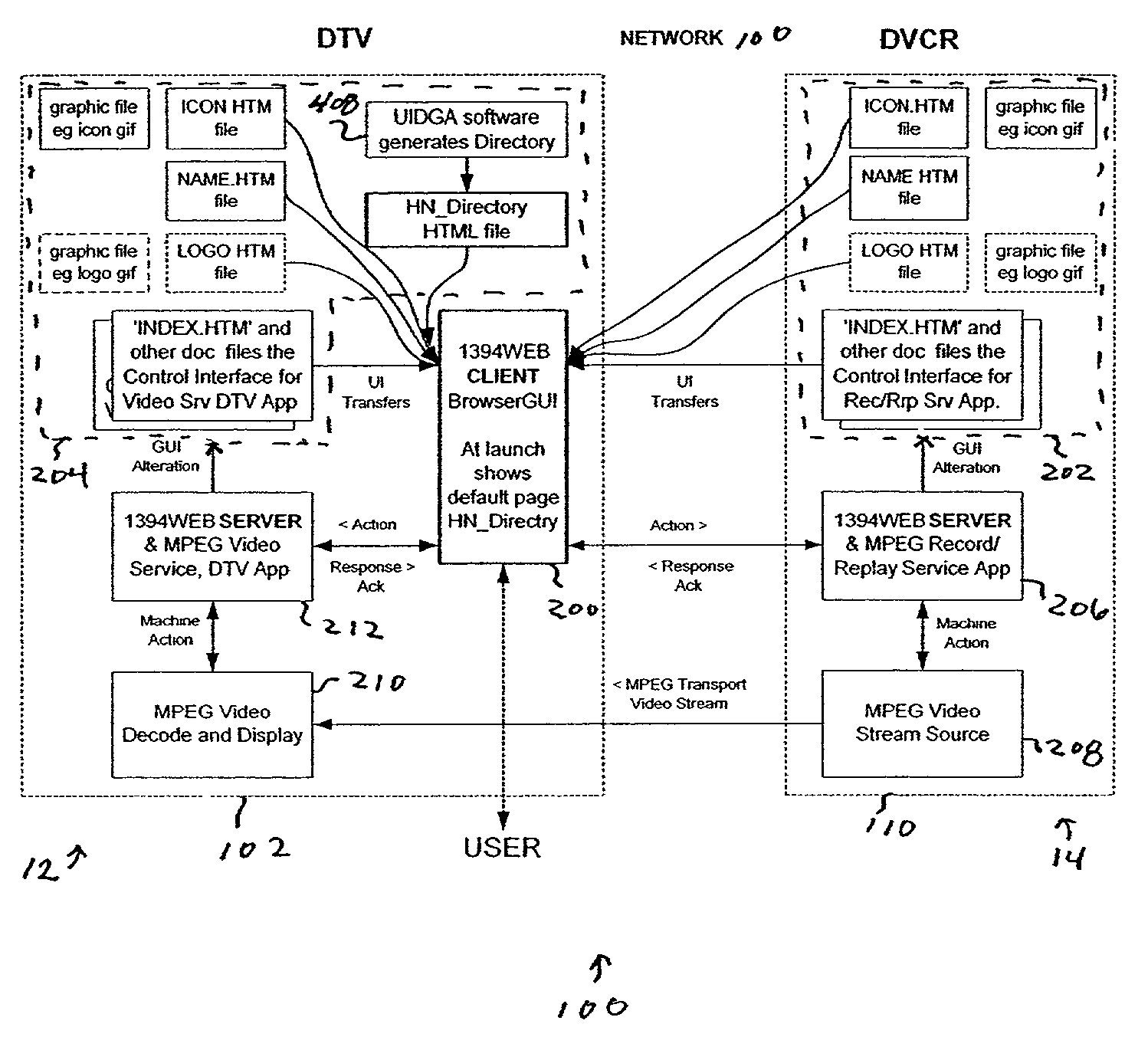
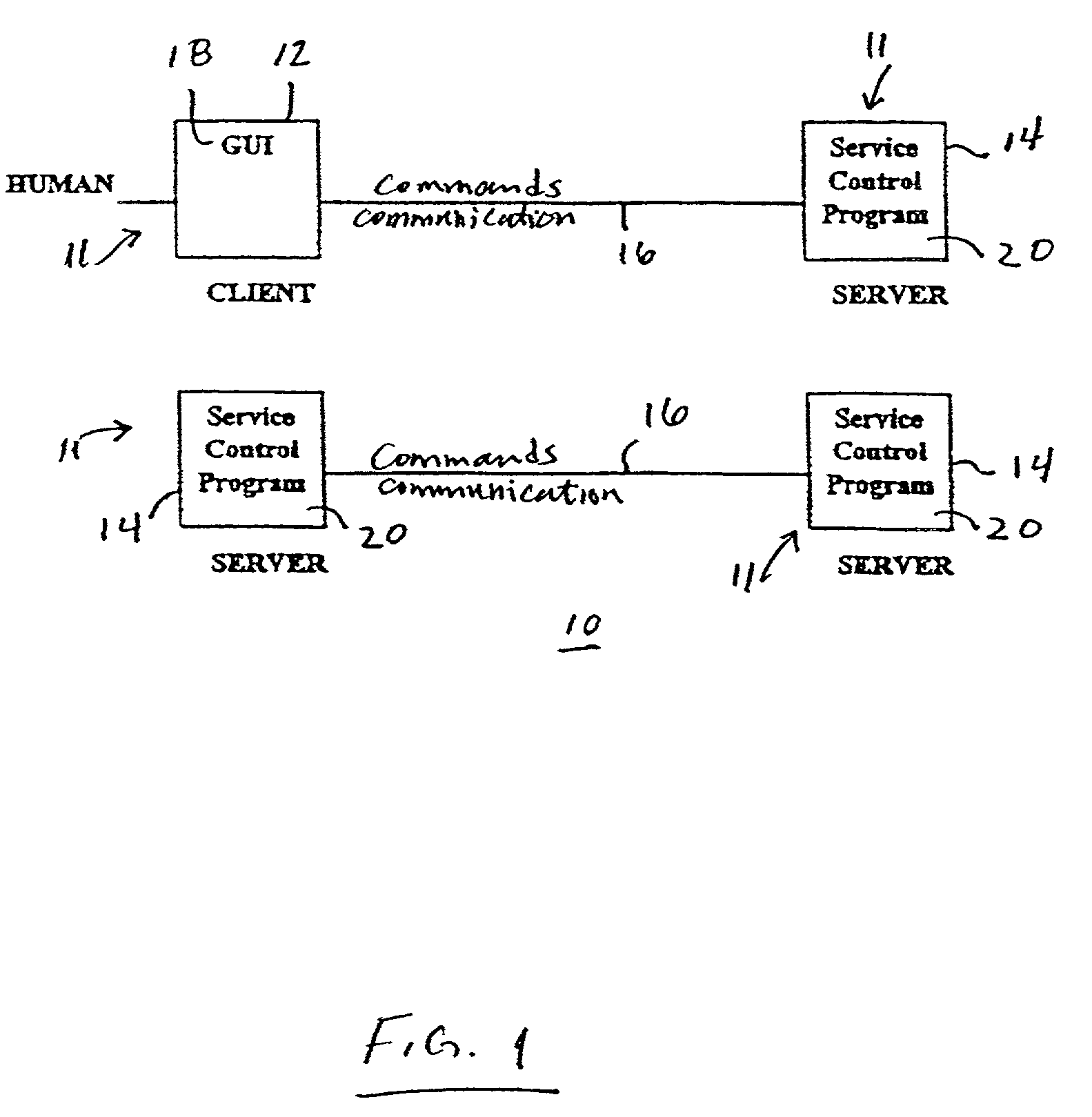
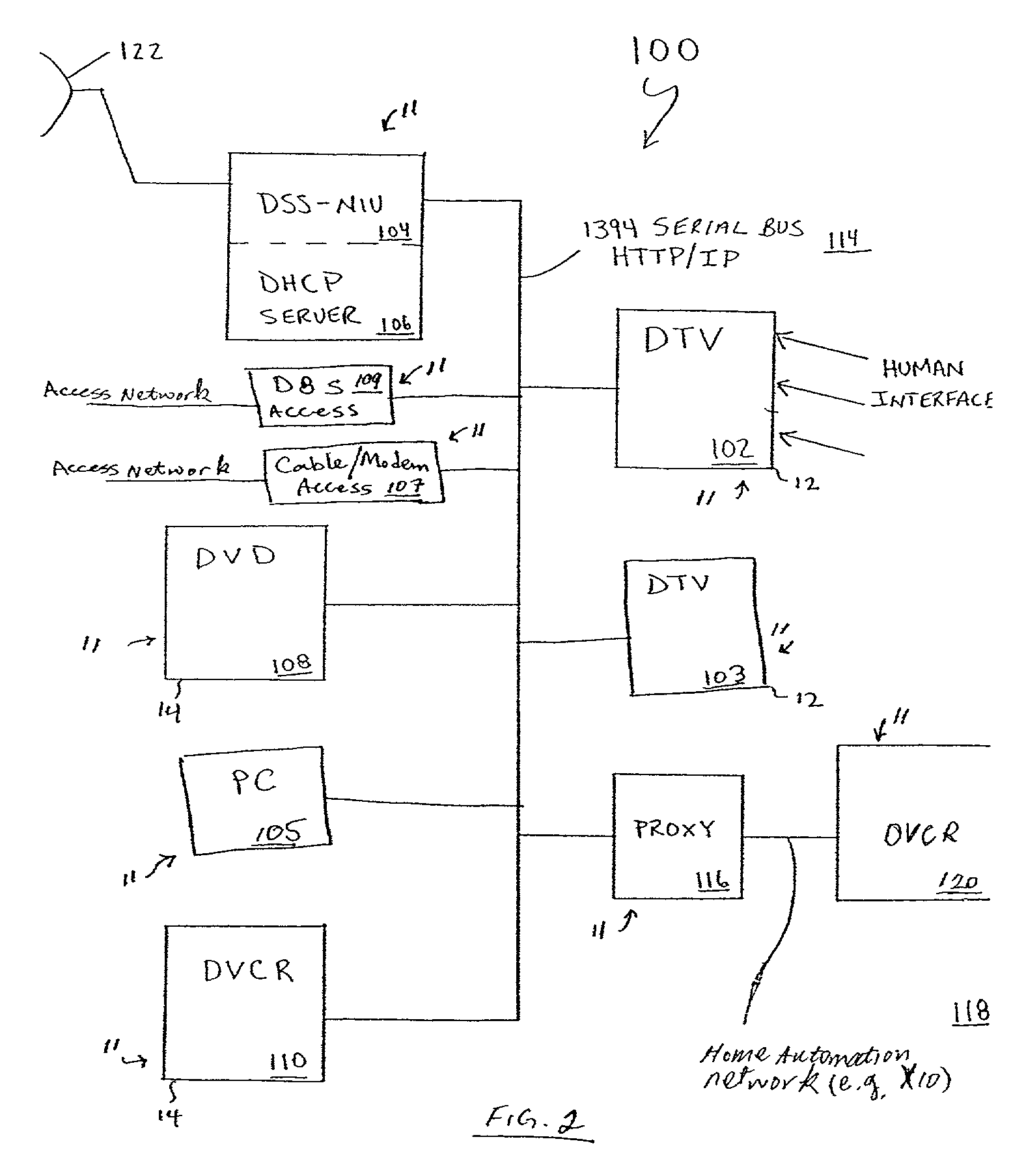
Architecture for home network on world wide web with private-public IP address/URL mapping
InactiveUS7349967B2Special service provision for substationTelevision system detailsIp addressNetwork on
A method for providing user interfaces in a first network to a remote access device, the first network including interconnected first devices and at least one interface device for connecting the first network to a second network. The remote access device establishes communication with the second network and sends a request to the interface device for accessing the first network; at least one of the first devices obtains information from one or more of the first devices, and generates a user interface description including at least one reference associated with the device information, the reference including an external address such that the device is accessible from the remote access device; the interface device sends the user interface description to the remote access device; and the remote access device displays a user interface based on the user interface description.
Owner:SAMSUNG ELECTRONICS CO LTD
Target information generation and ad server
InactiveUS7155508B2Increase ratingsGreater profit margin for ad companiesDigital computer detailsTransmissionMass storageApplication software
An advertisement selection and delivery system for selecting advertisements based on profile information and rendering the advertisements as accessible to a user operating a network-capable appliance connected to a data-packet-network is provided. The system comprises, a first server node connected to the network, the first server node functioning as a user access point on the network, a mass storage repository accessible to the first server node, the repository for storing and serving user profile data, a second server node connected to the network, the second server node for generating user preference data, at least one advertisement server connected to the network, the advertisement server for serving advertisement data, a software application for generating user preference lists and performing advertisement selection and at least one network-capable appliance connected to the network the network-capable appliance for receiving the advertisement data. A user operating the network-capable appliance accesses the first server node and receives the advertisement data, the advertisement data selected for service by matching the user preference data to stored advertisements and rendered accessible to the user during the time of user access to the system from the network-capable appliance.
Owner:YODLEE COM INC
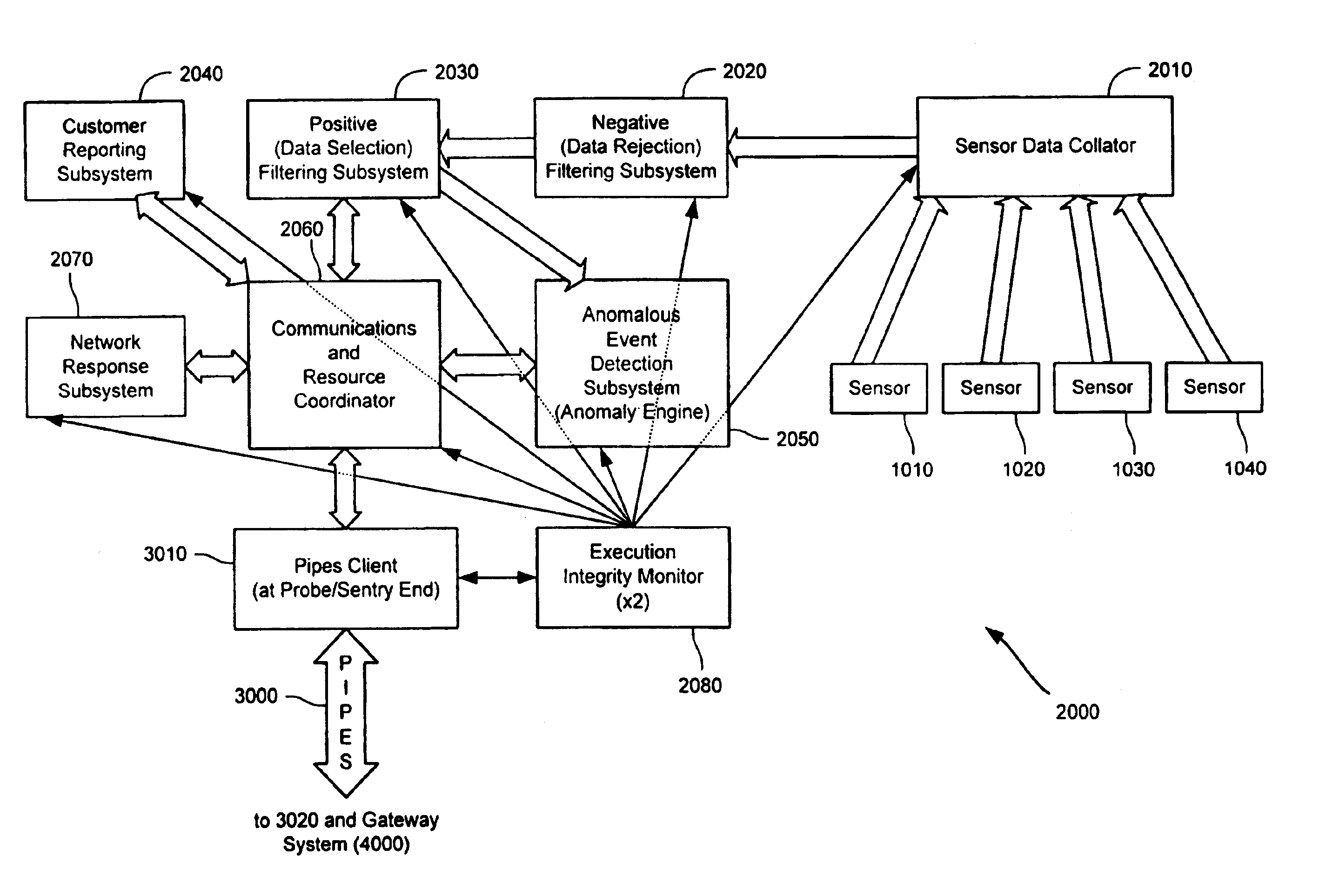
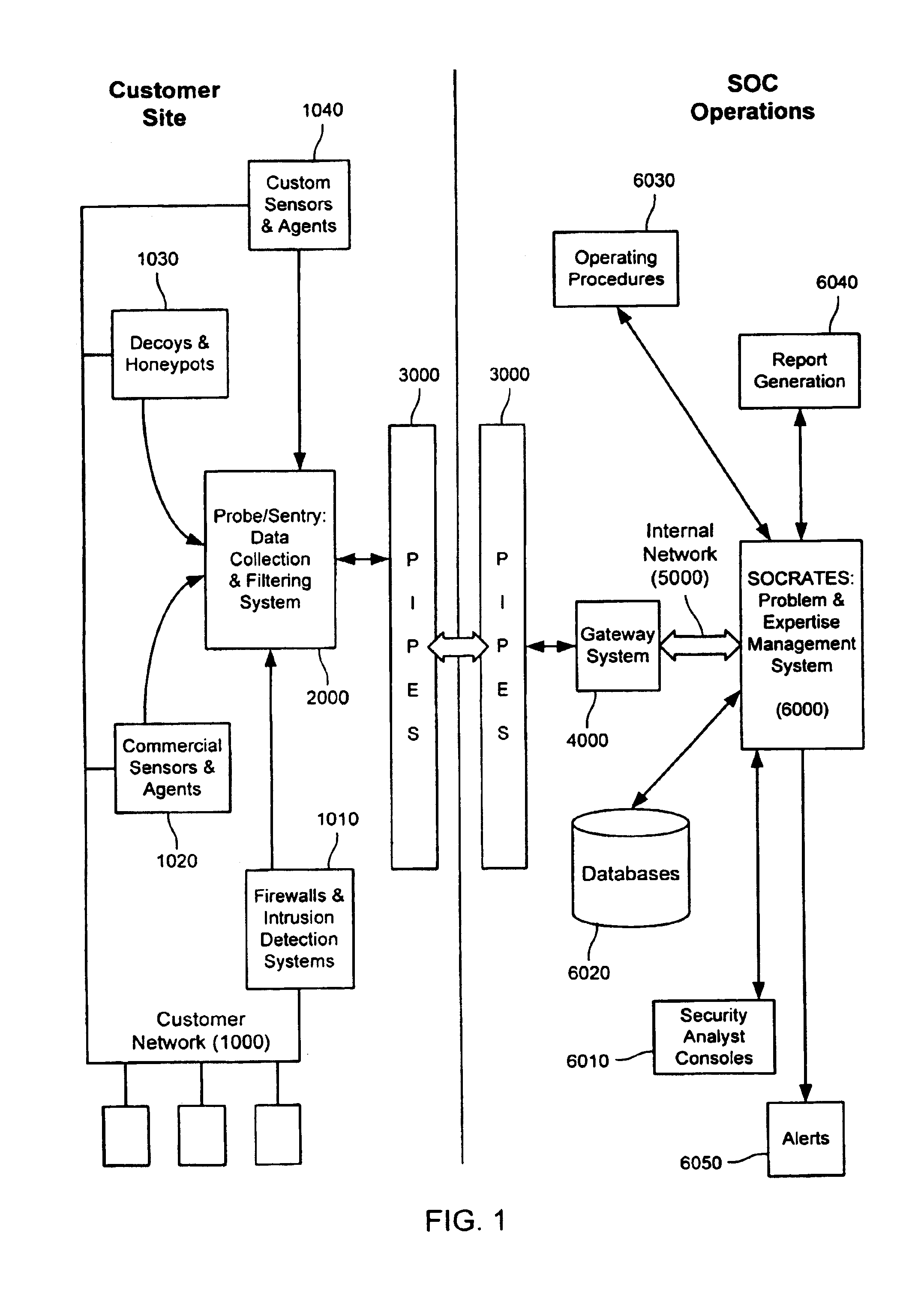
Method and system for dynamic network intrusion monitoring, detection and response
InactiveUS7159237B2Eliminate false positivesIncrease in sizeMemory loss protectionDigital data processing detailsProblem resolutionVulnerability
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
Method and system for voice messaging
InactiveUS6907112B1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersVoice communicationInterconnection
This invention discloses a voice communication system including a telephone network including a multiplicity of telephones interconnected by telephone network interconnections, a computer network having a multiplicity of nodes and enabling e-mail communication between said nodes, a multiplicity of voice response computers, each voice response computer being connected to a node of the computer network and being actuable by an input received from one of the multiplicity of telephones via the telephone network for communicating voice received via said one of the multiplicity of telephones via e-mail over the computer network.A method of voice communication including a telephone network including a multiplicity of telephones interconnected by telephone network interconnections is also disclosed.
Owner:ONMOBILE LIVE
Device-to-device network
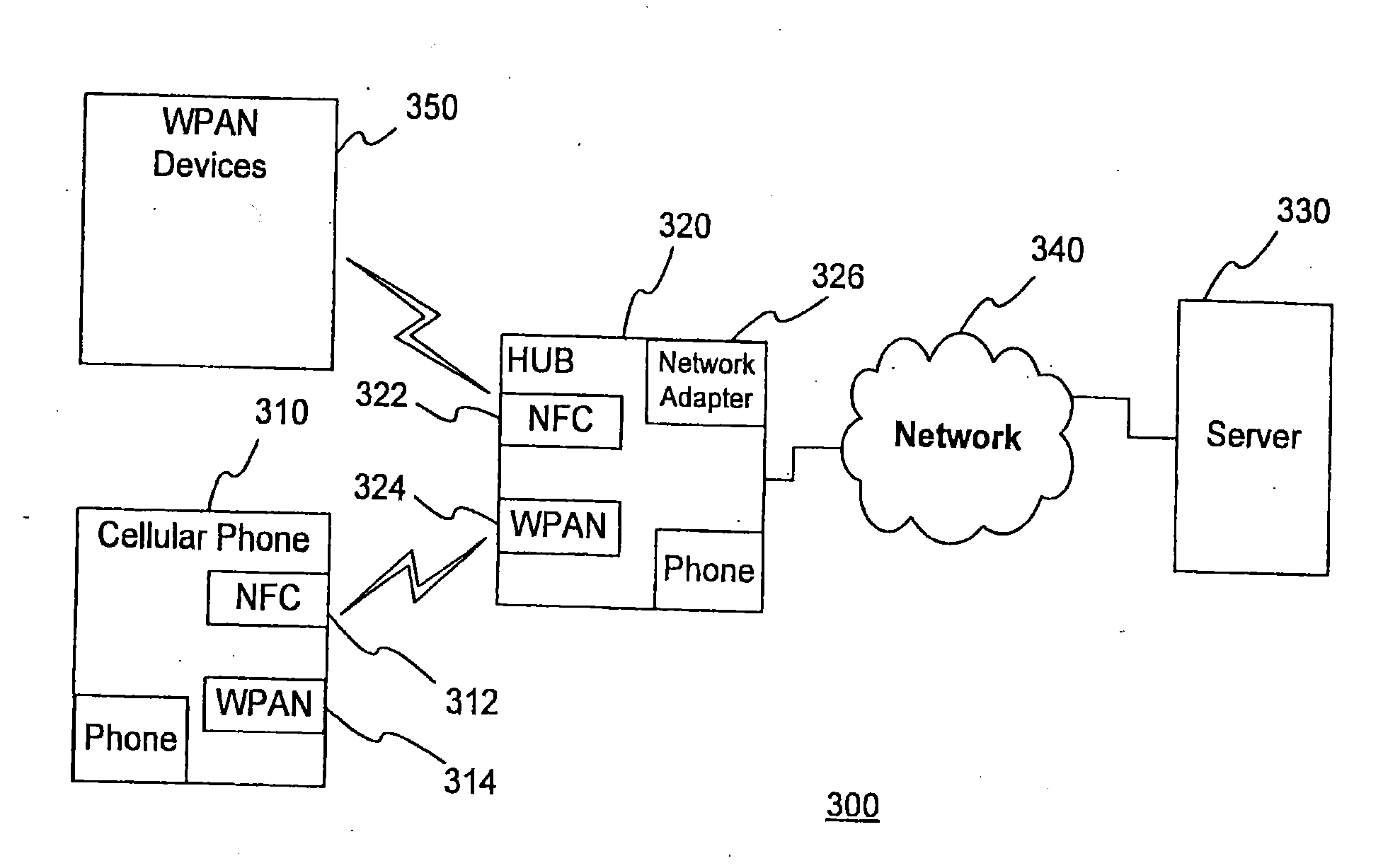
ActiveUS8281001B2Digital data processing detailsMultiple digital computer combinationsDevice to deviceNetwork on
A device to device network allows an entity to seamlessly access content stored on various devices. Many devices can be registered on a network; however, an entity will only have access to devices for which the entity is authorized to access. In one embodiment, the entity can only access devices that have been authenticated with the same username. While using the device-to device network, an entity can transfer files, stream files, create and use play lists, send commands to various devices and explore the contents of various devices.
Owner:HARMAN INT IND INC
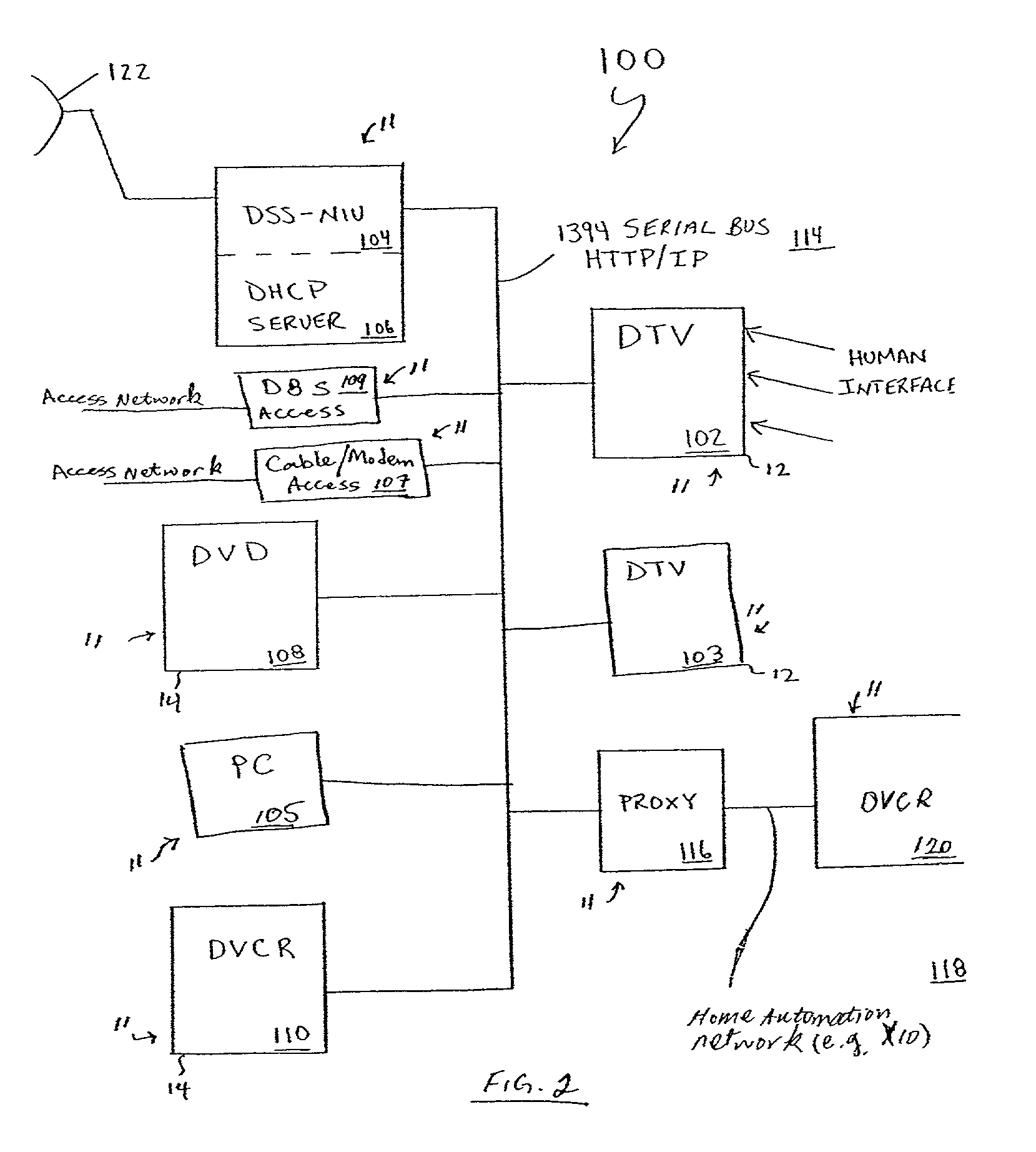
Architecture for home network on world wide web
InactiveUS7337217B2Special service provision for substationTelevision system detailsComputer networkNetwork on
A method for providing user interfaces in a first network to a remote access device, the first network including first devices and at least one interface device for communication with the remote access device, the user interfaces for controlling the devices currently connected to the first network. The remote access device establishes communication with the first network via the interface device; the remote access device sends a request to the interface device for accessing the first network; at least one of the first devices in the first network obtains information from one or more of the first devices, the information including device information, and generating a user interface description including at least one reference associated with the device information of each of the one or more first devices; the interface device sends the user interface description to the remote access device; and the remote access device displays a user interface based on the user interface description.
Owner:SAMSUNG ELECTRONICS CO LTD
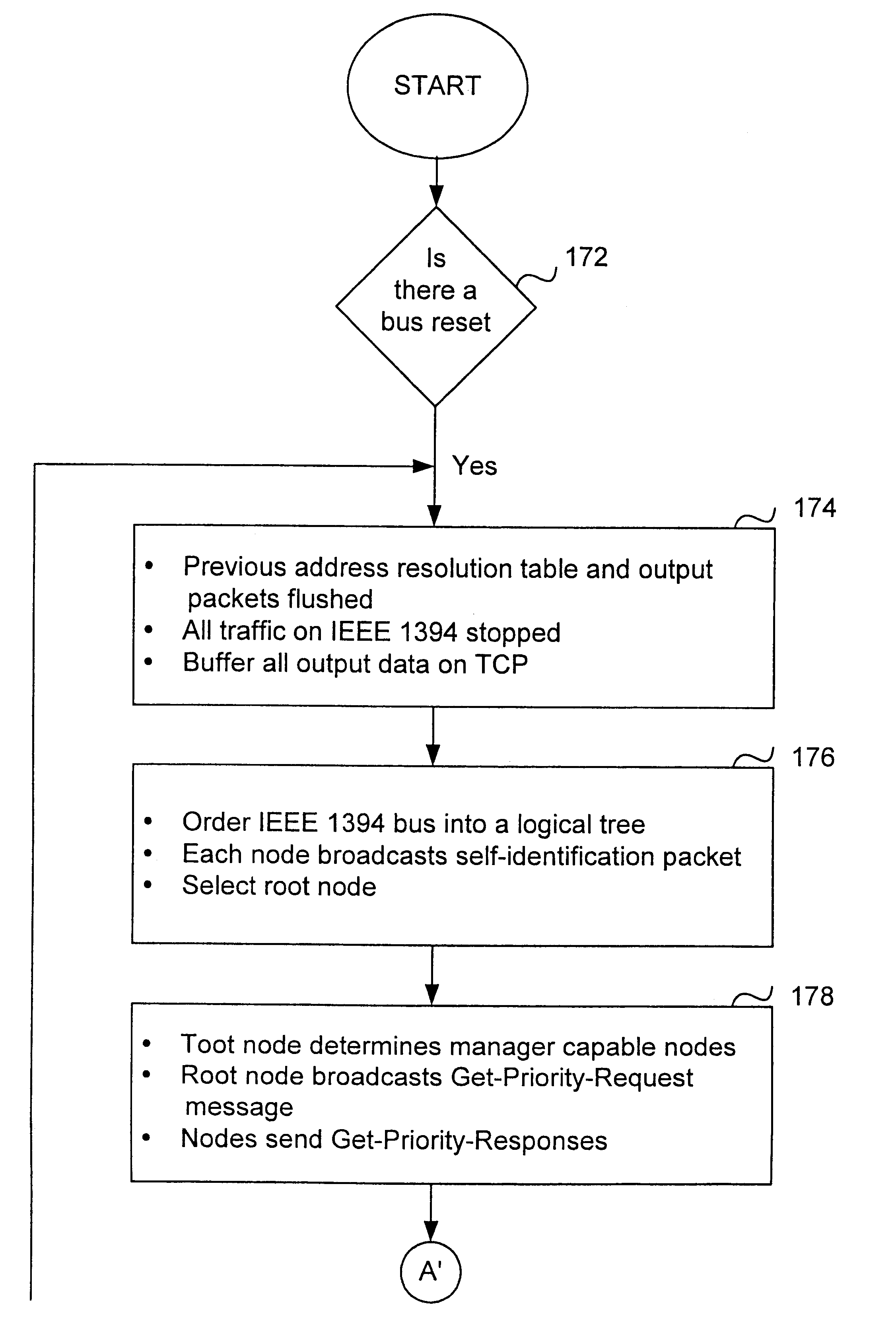
Method and apparatus for operating the internet protocol over a high-speed serial bus
InactiveUS6219697B1Efficiently and correctly determineDigital computer detailsTransmissionInternet protocol suiteTransport layer
A method and apparatus of integrating the IEEE 1394 protocol with the IP protocol in which the IEEE 1394 high speed serial bus operates as the physical and link layer medium and the IP operates as the transport layer. There are differences in the protocols which require special consideration when integrating the two protocols. The IEEE 1394 configures packets with memory information and the IP operates under channel based I / O thereby necessitating a modification of the data transfer scheme to accomplish IP transfers over the IEEE 1394. Further, due to differences in packet headers, the IEEE 1394 packet header is modified to encapsulate IP packets. Moreover, in order to determine network packets quickly and efficiently, an identifier is inserted in each network packet header indicating that the packet should be processed by the network. Finally, in order to support the ability to insert or remove nodes on the network without a loss of data, the IP interface must not be disturbed. This is accomplished by maintaining constant IP addresses across bus resets which are caused by insertion or removal of nodes from the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com