Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1297 results about "Web access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
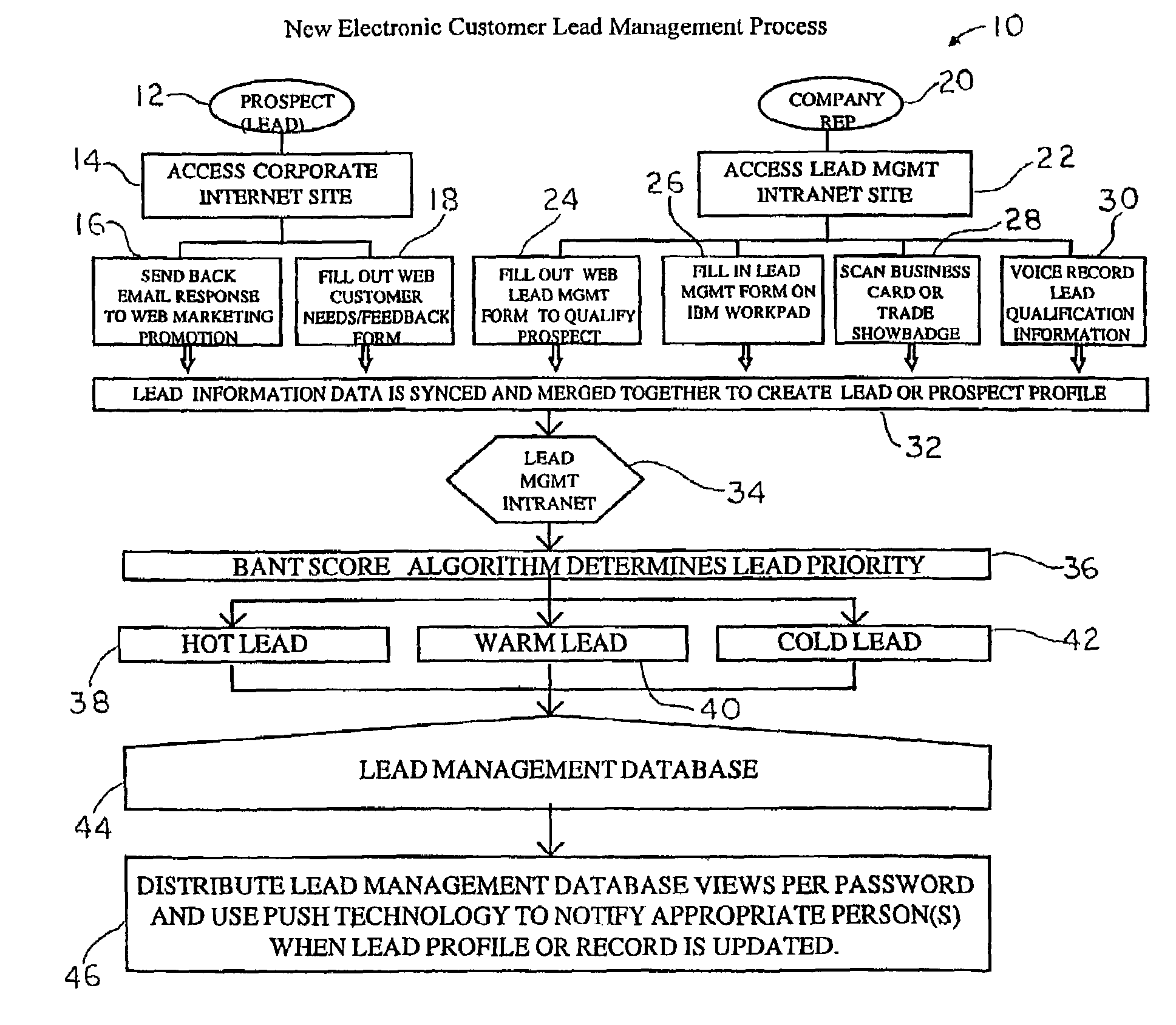
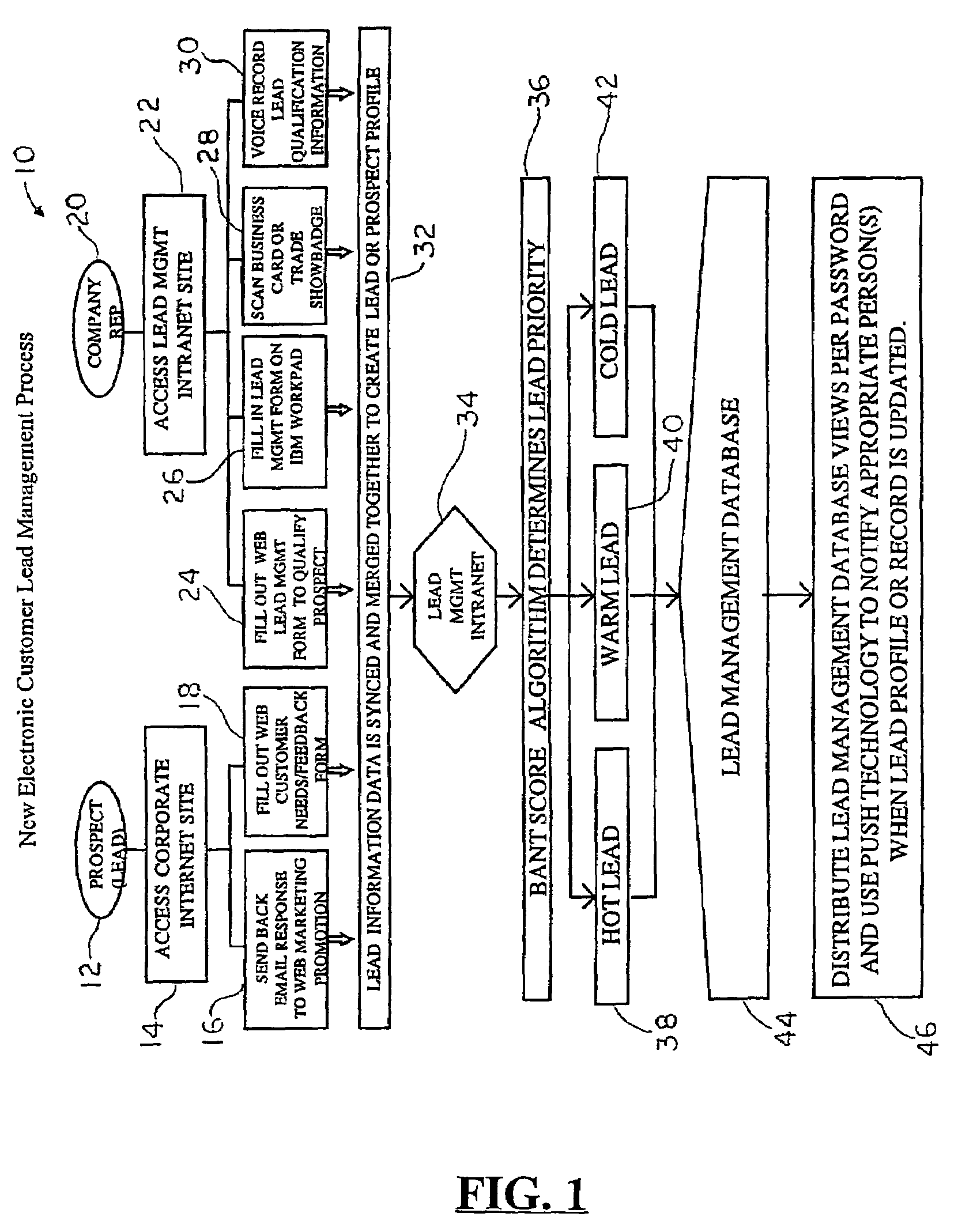
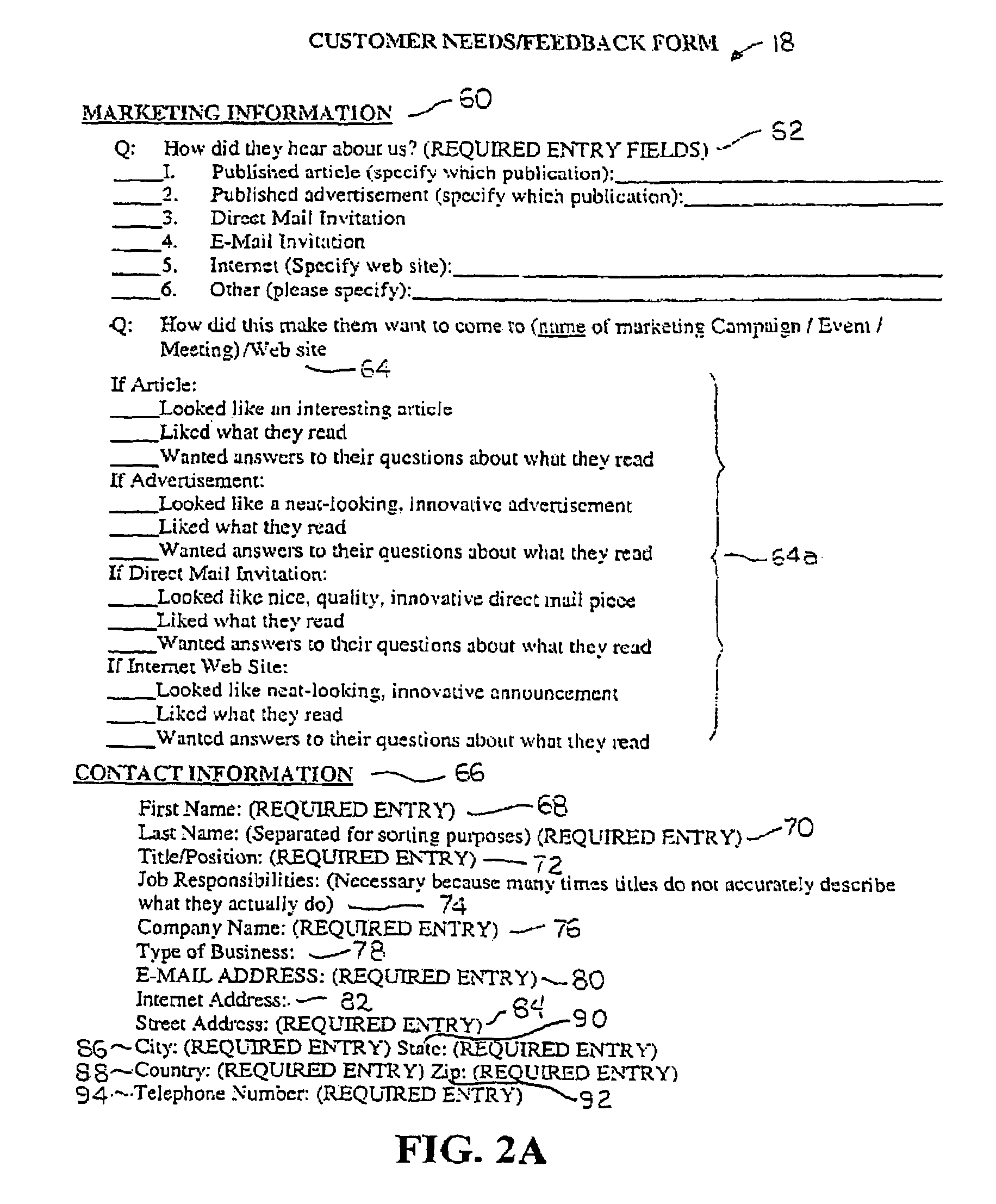
System and method for generating, capturing, and managing customer lead information over a computer network
A customer lead management system that relates to a system and method for collecting and organizing customer-marketing data, which is then made available to business representatives to assess. Specifically, using a computer network, and data on a potential customer's Budget, Authority, Needs, Timeframe, and other related customer data is collected. While this data is being collected, the customer lead management system stores the customer lead data in real-time instantly, automatically ranking the viability of the customer lead on the interest level of the customer lead and other variable criteria used in the web-based algorithm calculation, and automatically electronically notifies the appropriate company and / or company representative about the customer lead. The resulting customer lead profile record is located in a web server database, and can be accessed and undated in real-time by a portable computer or electronic device that has been web-enabled. The customer lead data is then capable of being accessed via a computer network by various companies that have goods / services that satisfy the needs and requirements of the customer lead. A company representative can be automatically notified when a customer lead profile has been updated.
Owner:CXT SYST INC
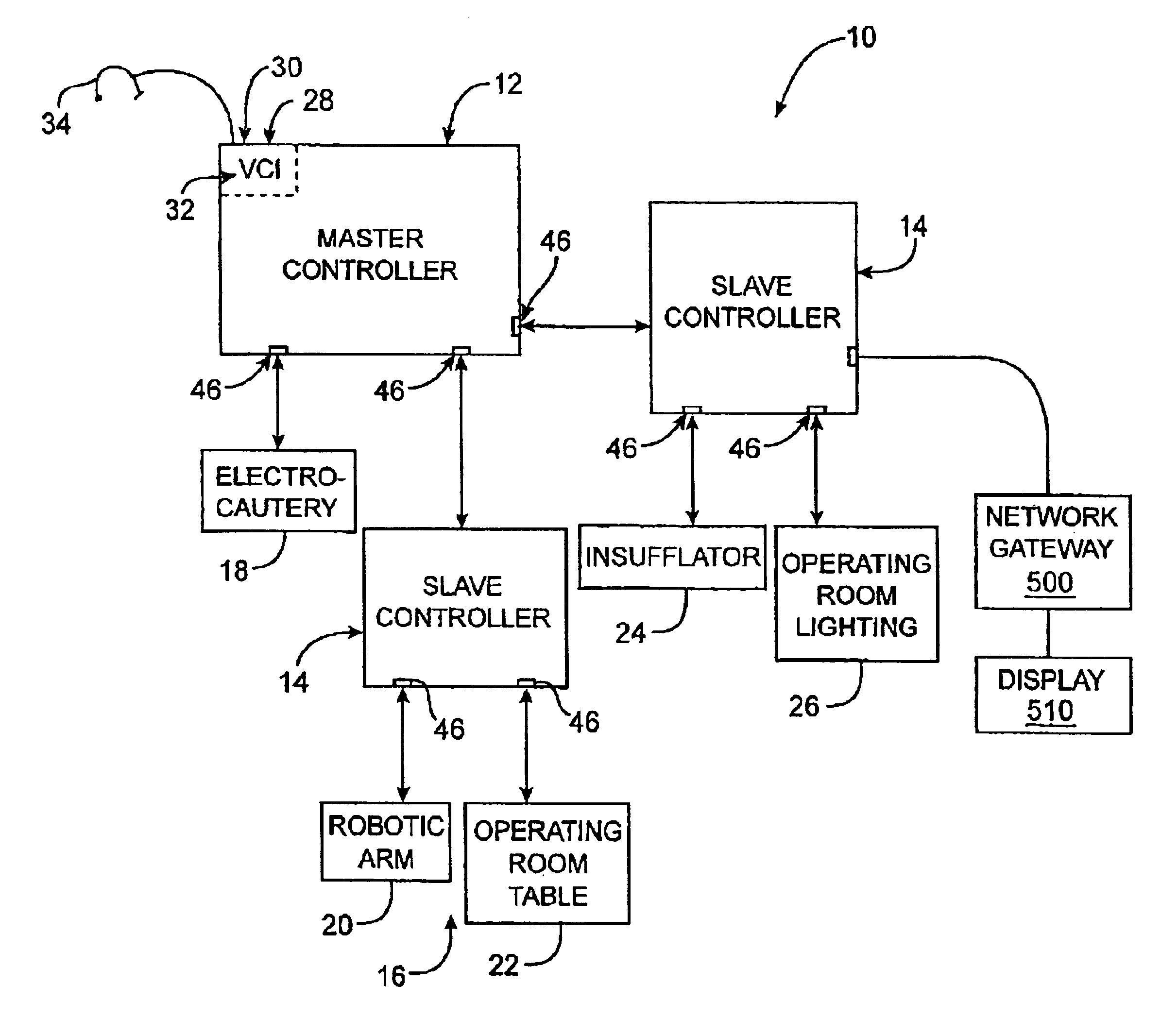
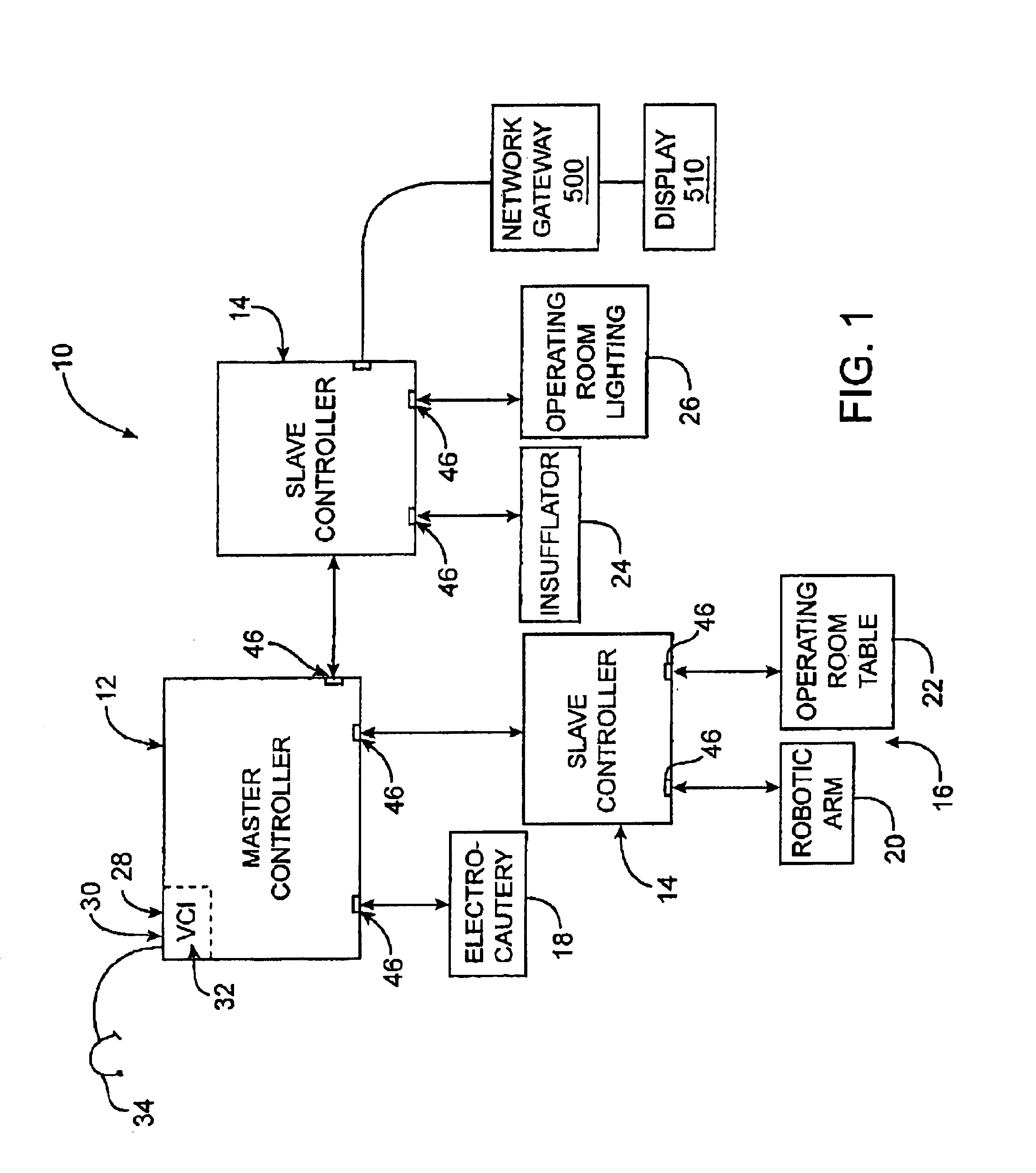
Method and apparatus for accessing medical data over a network
A method and apparatus for retrieving, accessing, and storing medical data relating to a patient during a medical procedure. The invention provides a single interface to many disparate forms of medical data, which is accessible over a local area network, wide area network, direct connection, or combinations thereof. In one embodiment, an operating room control system for use during a medical procedure on a patient includes an input device, a display device, and a controller that is coupled to the input device and the display device. The controller receives one or more user inputs, transmits a command to a server located outside of the operating room to retrieve medical data, receives the medical data from the server, and displays the medical data on the display device.
Owner:INTUITIVE SURGICAL OPERATIONS INC +1
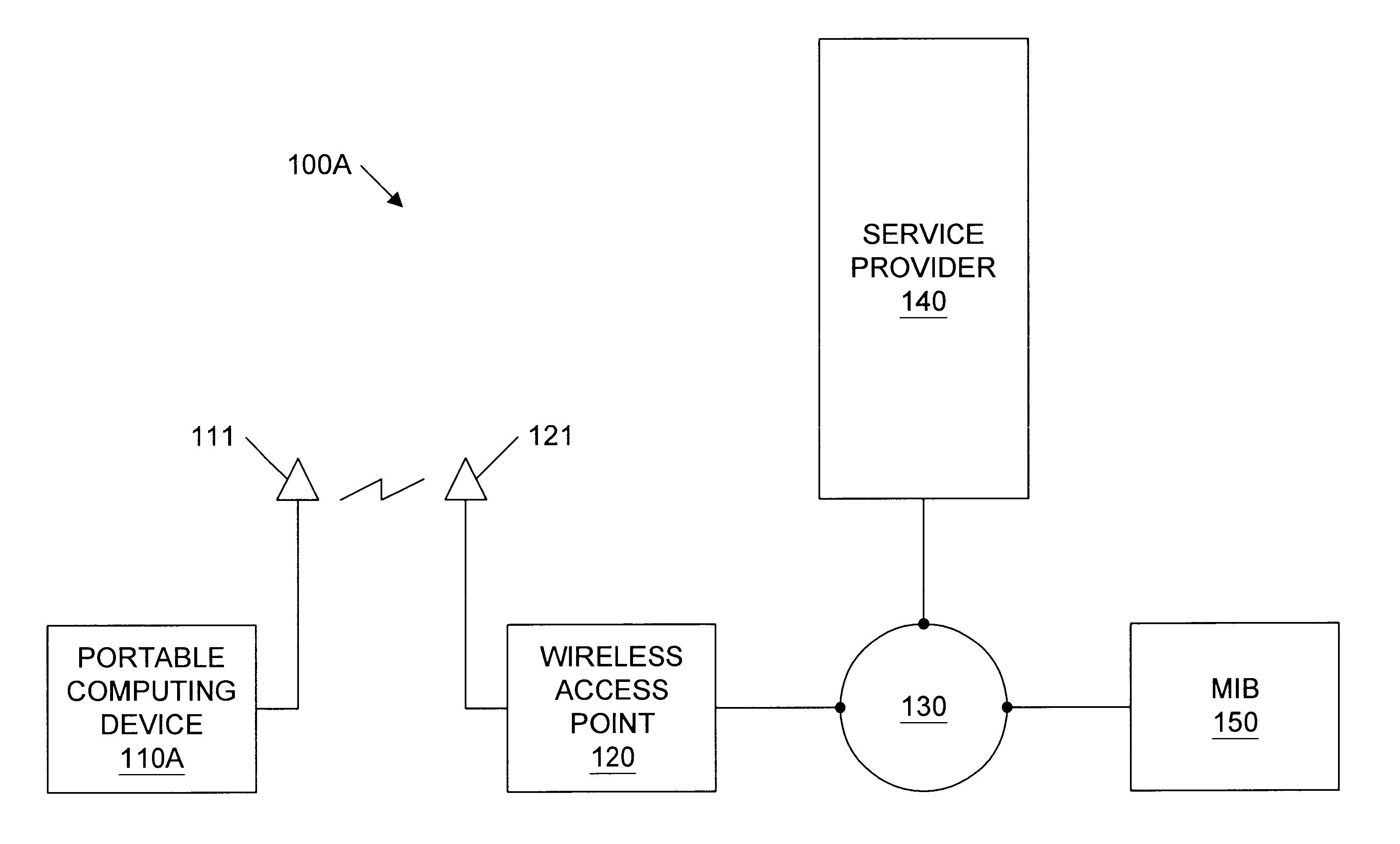
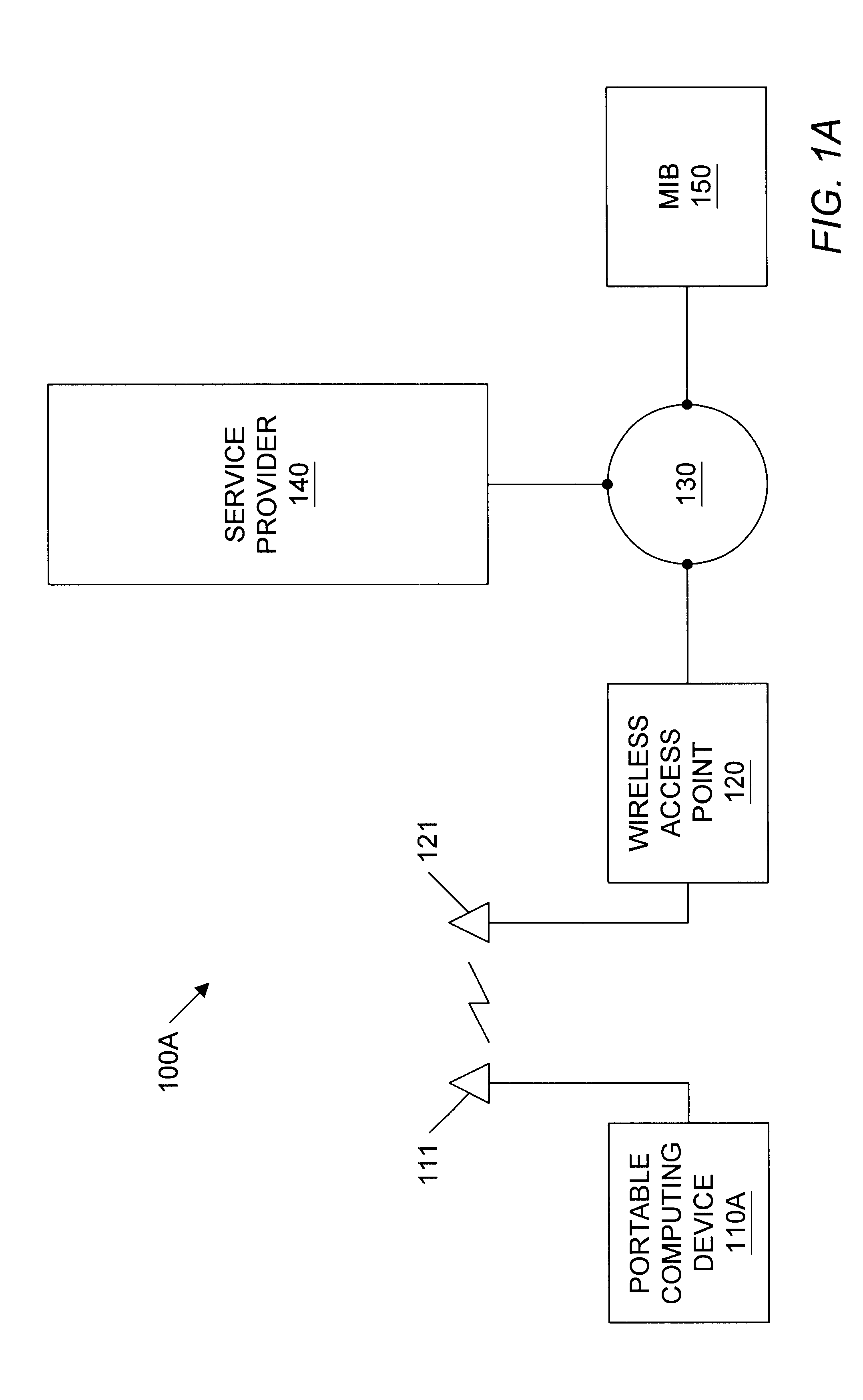
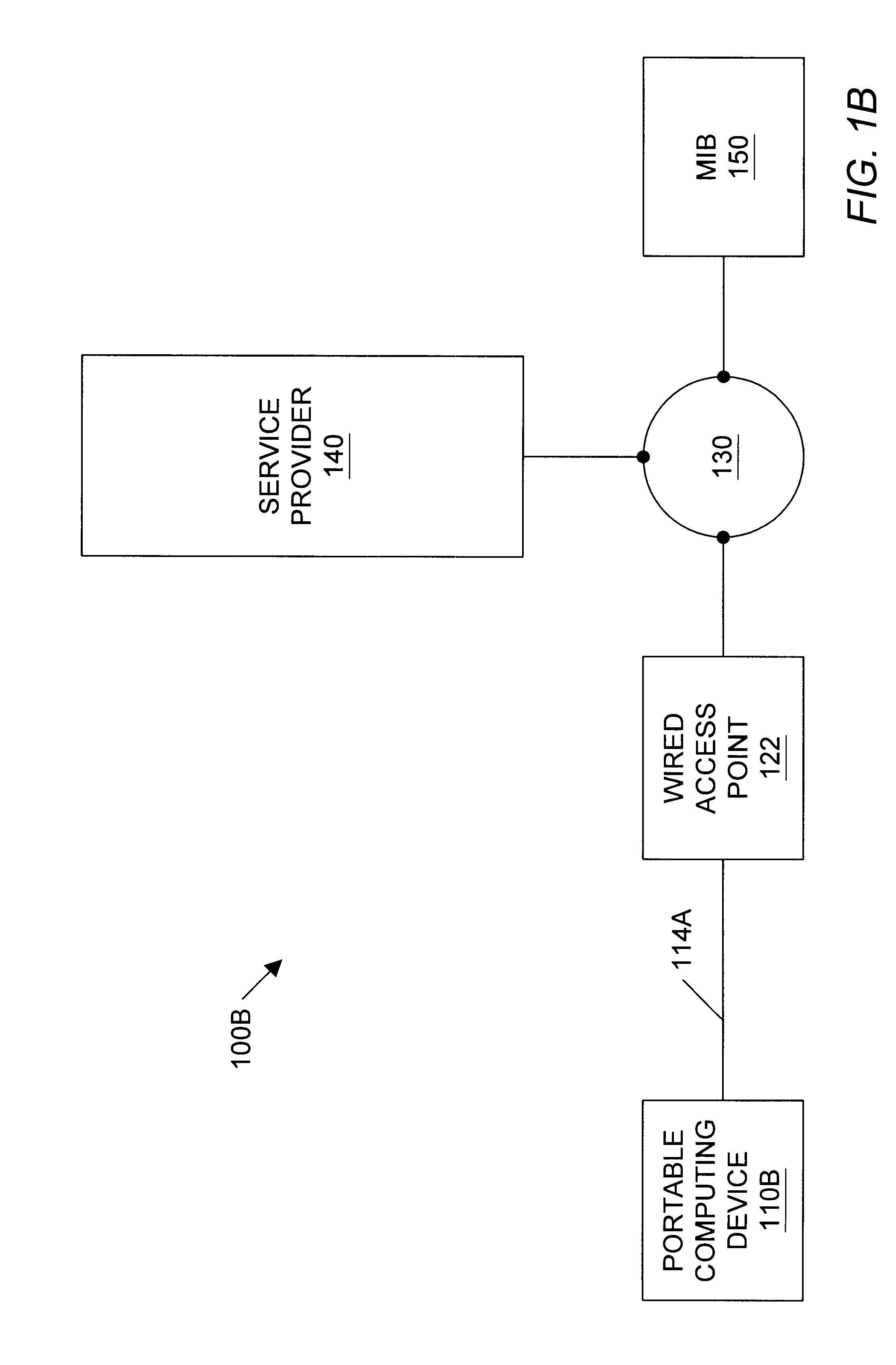
Geographic based communications service
InactiveUS6259405B1Direction finders using radio wavesBeacon systems using radio wavesGeographic regionsGeolocation
A geographic based communications service system that includes a network and a plurality of access points connected to the network and arranged at known locations in a geographic region. One or more service providers or information providers may be connected to the network to provide services or information on the network. A mobile user (MU) may use a portable computing device (PCD) to connect to the network and access information or services from the network. The PCD may be configured to transmit a signal indicating a presence of the PCD as well as identification information indicating the mobile user. Upon detection of the wireless signal by a first access point in proximity to the PCD, and upon receipt of the identification information indicating the user of the PCD, the first access point may transmit the identification information, as well as the known geographic location of the first access point, to one or more providers on the network. The known geographic location of the first access point indicates the approximate location of the PCD of the mobile user. A first information provider may receive this information and provide content information or services to the mobile user. For example, the first information provider may select content information dependent upon the known geographic location of the first access point and demographic information or past activities of the mobile user of the PCD. The first information provider may then provide the selected content information through the network and through the first access point to the PCD of the mobile user.
Owner:WAYPORT
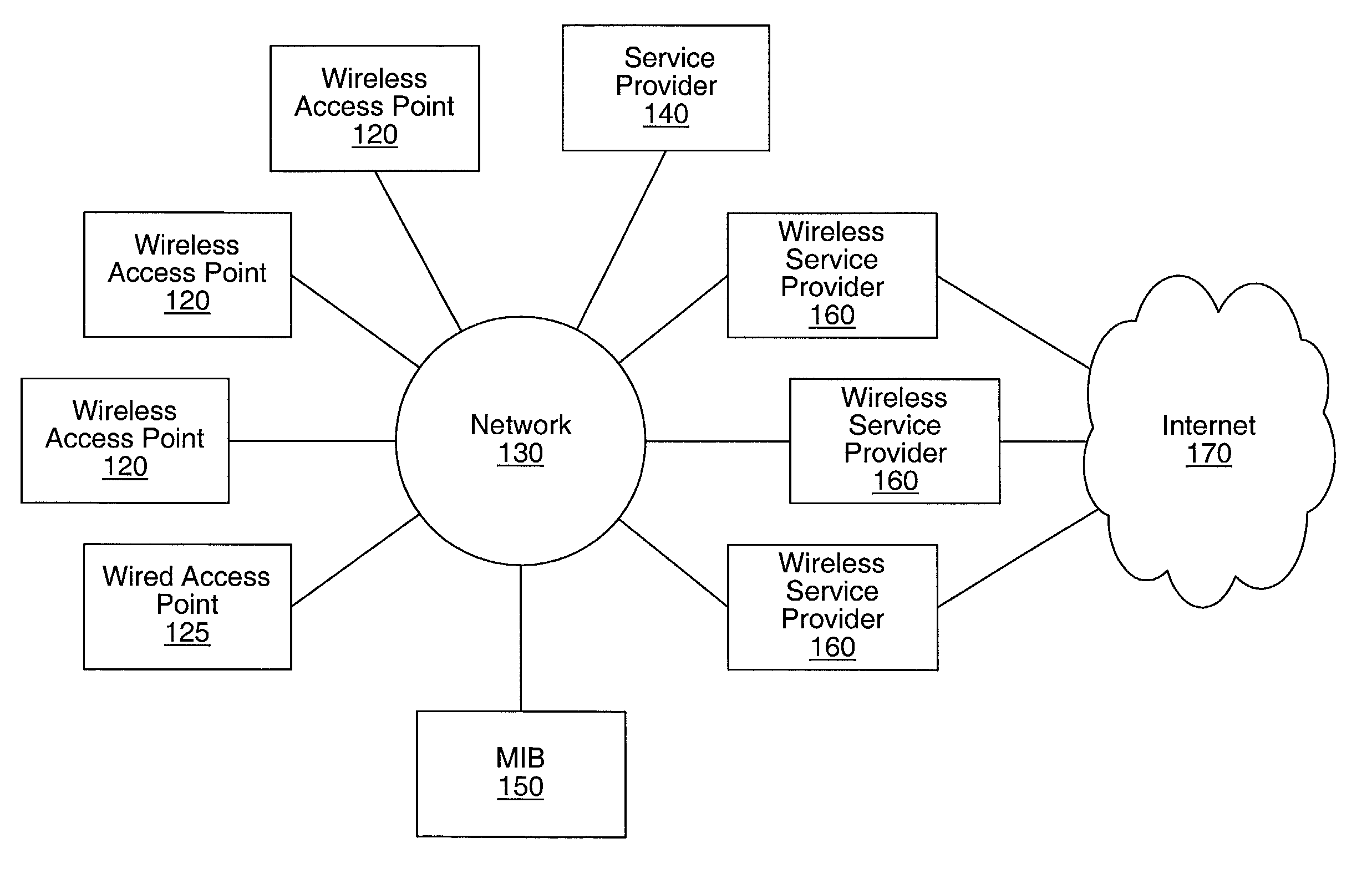
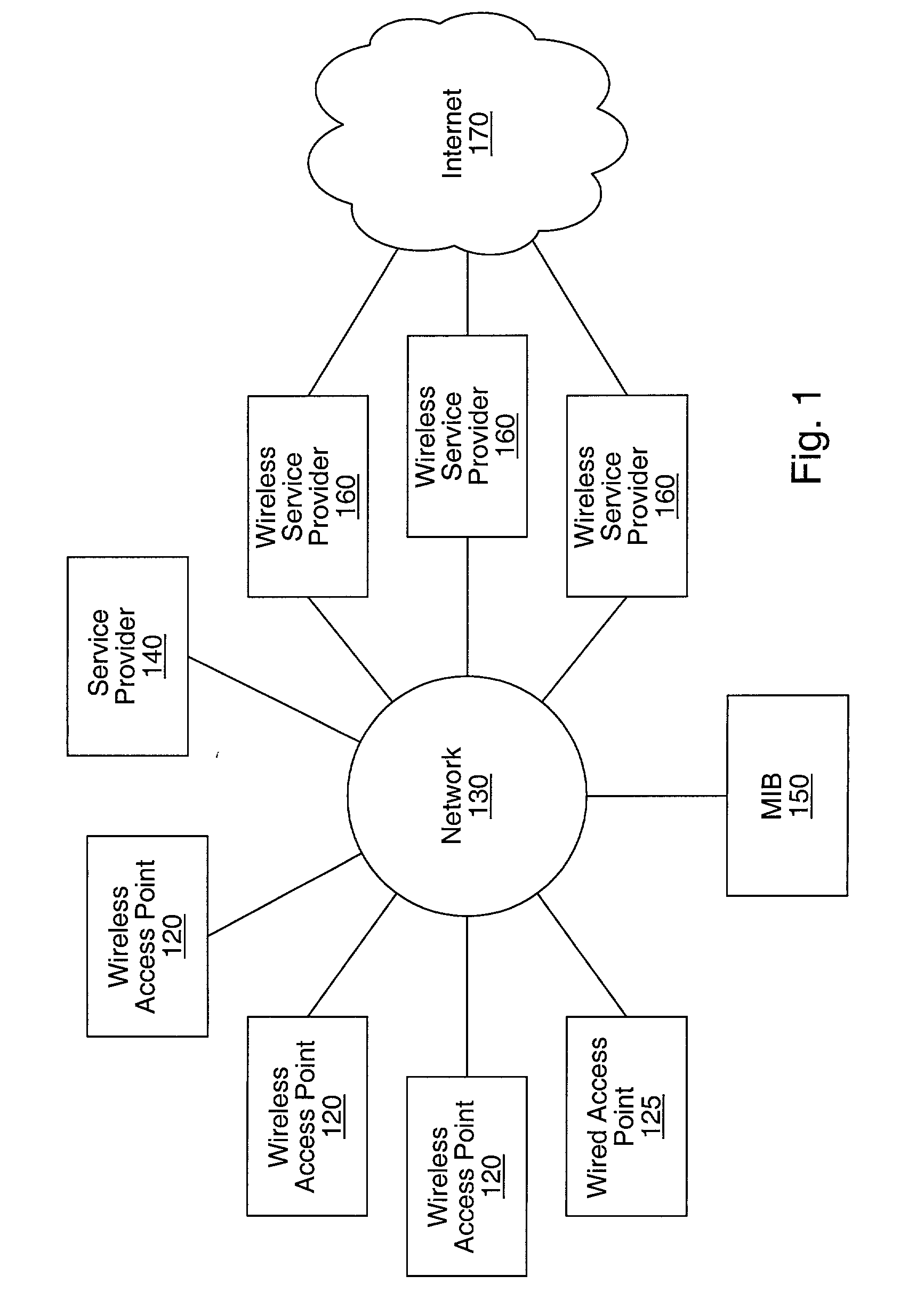
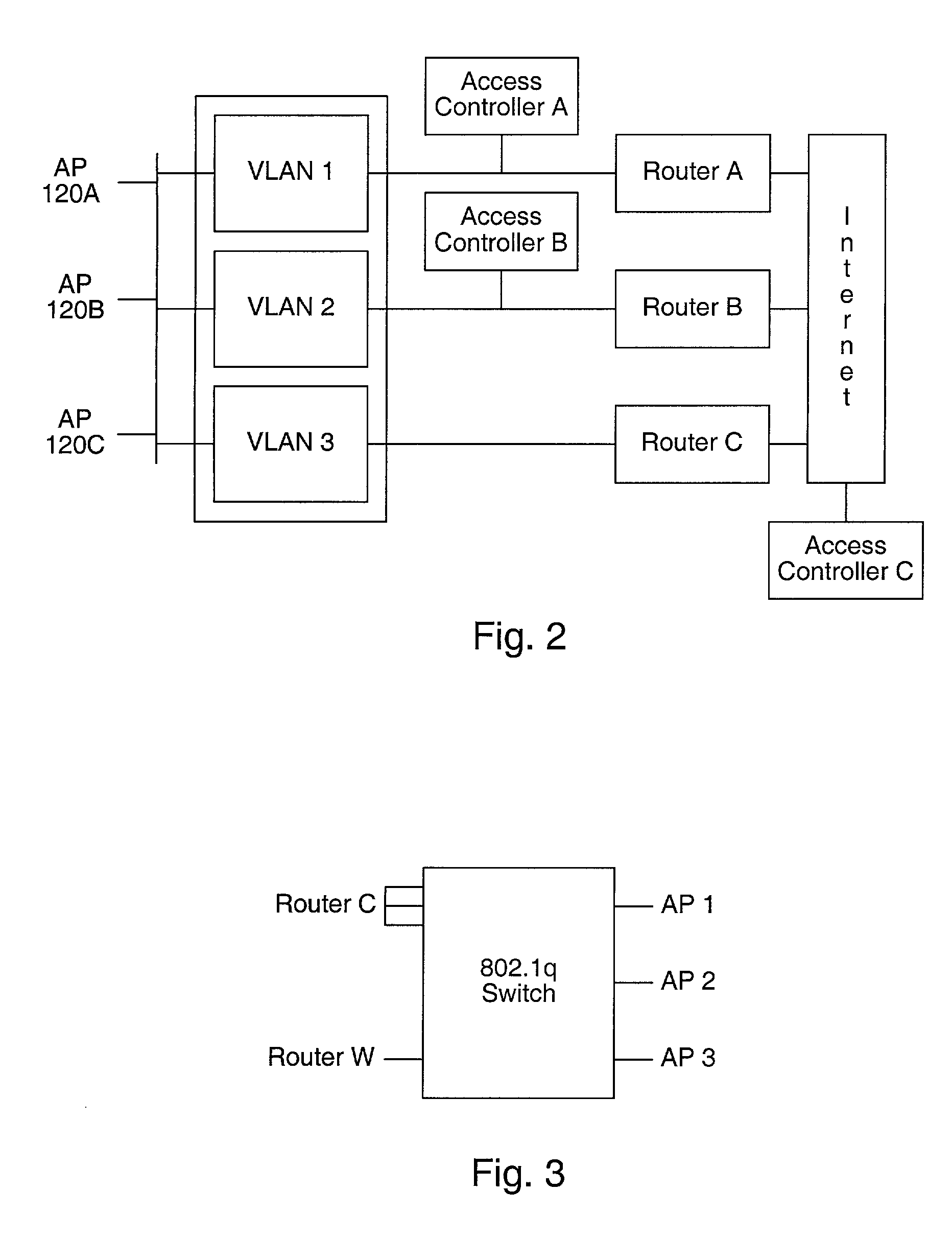
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
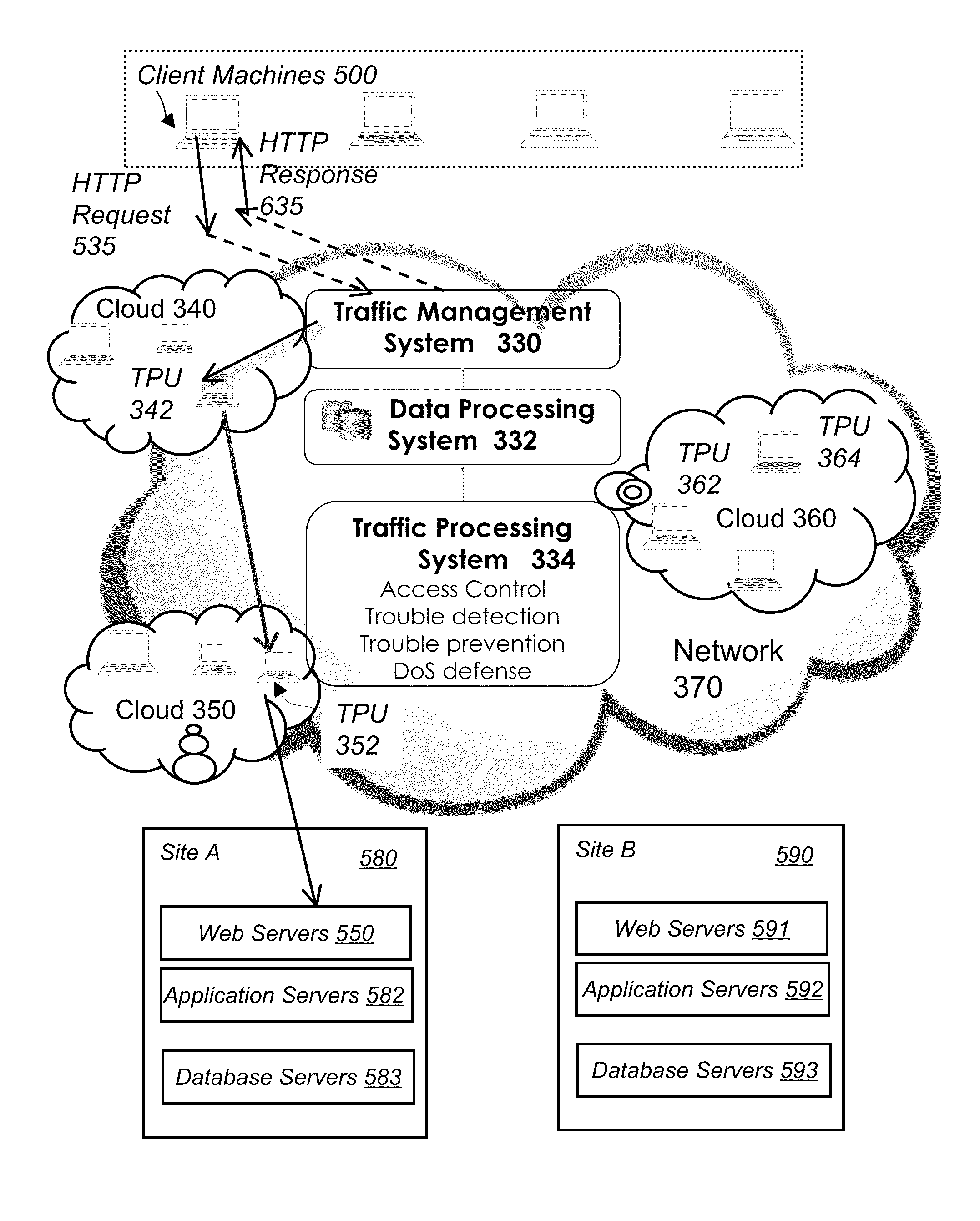
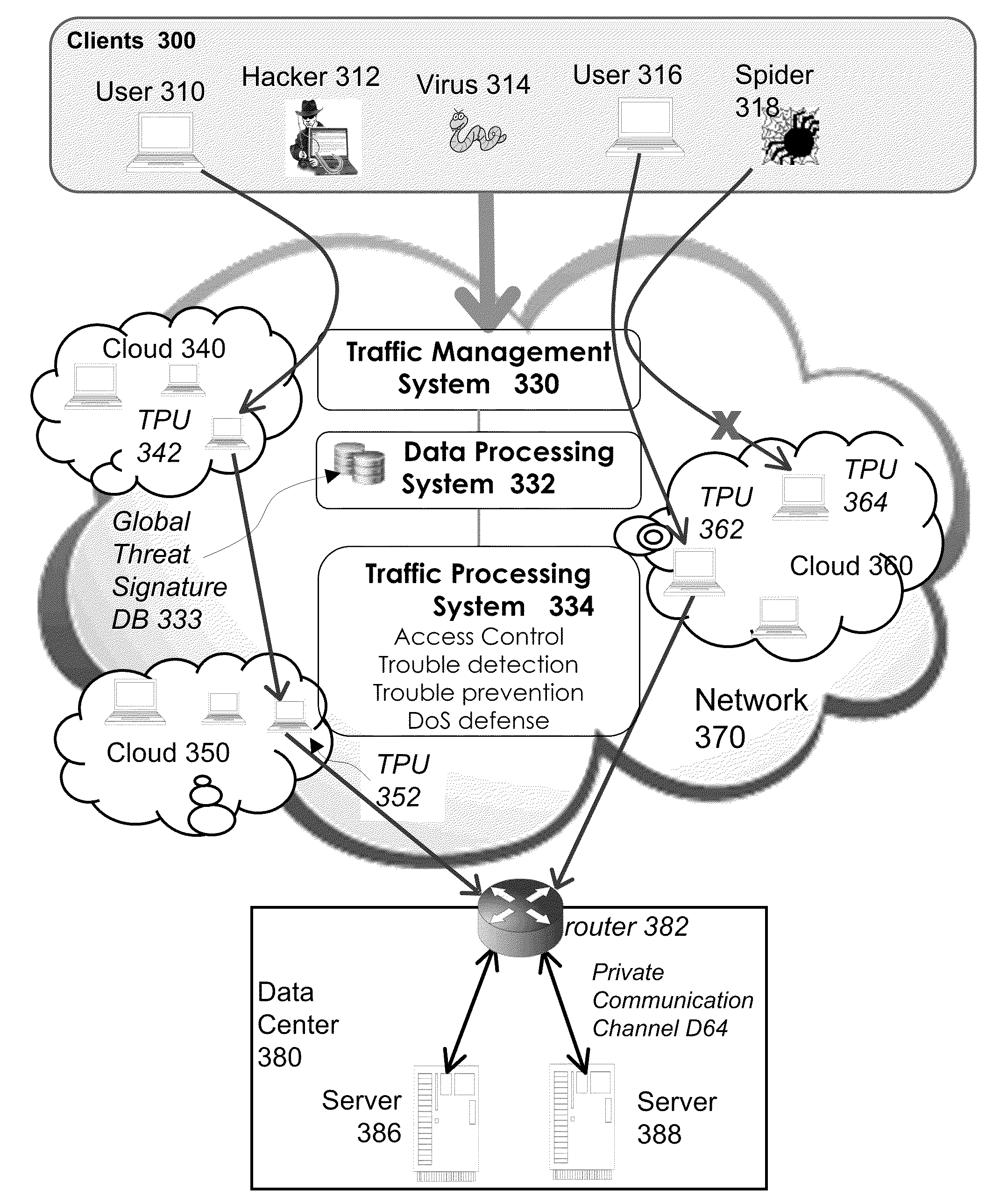
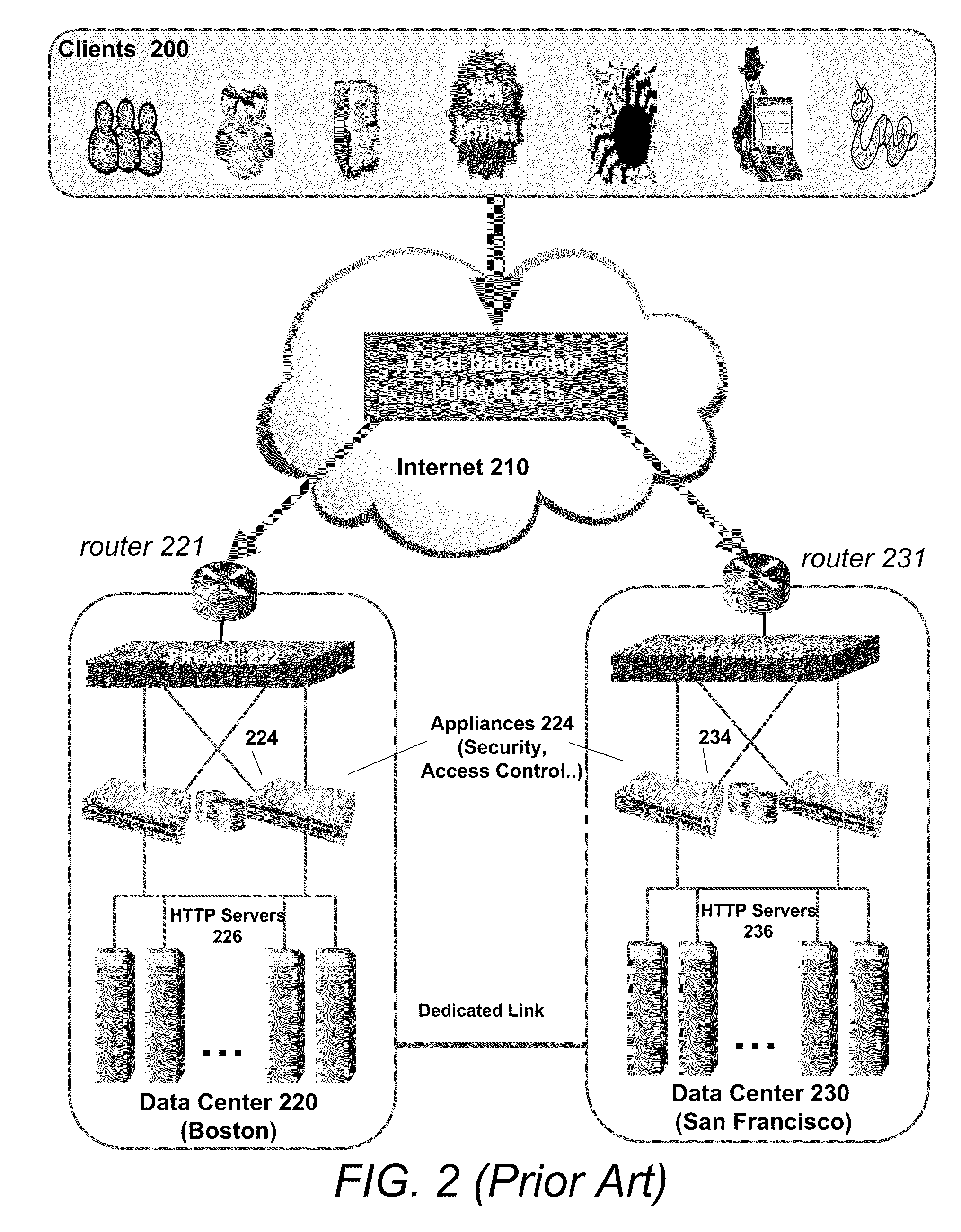
System and method for network traffic management and load balancing
InactiveUS20100223364A1Improve application performanceImprove availabilityMultiple digital computer combinationsLocation information based serviceTraffic capacityFailover
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network. Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
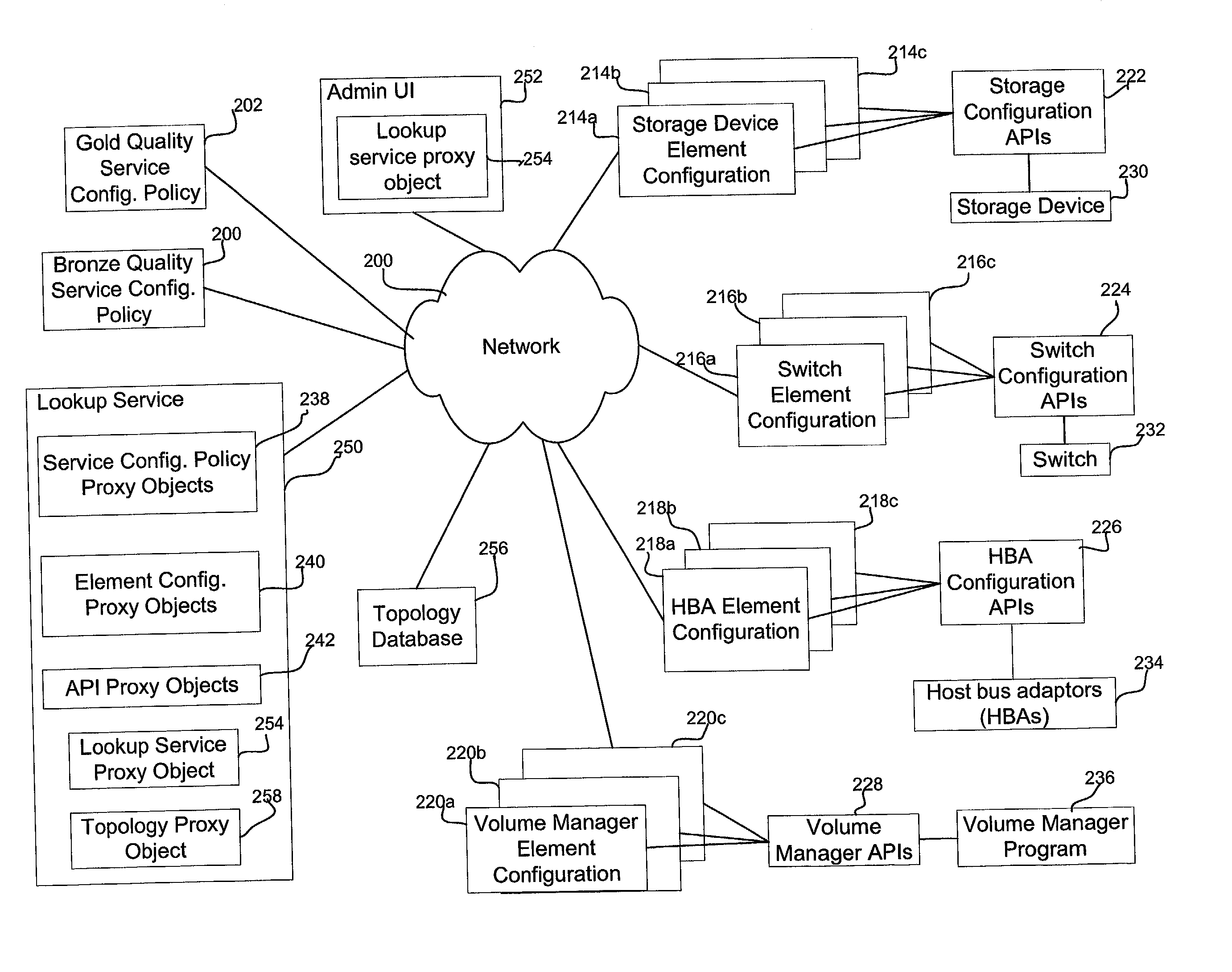
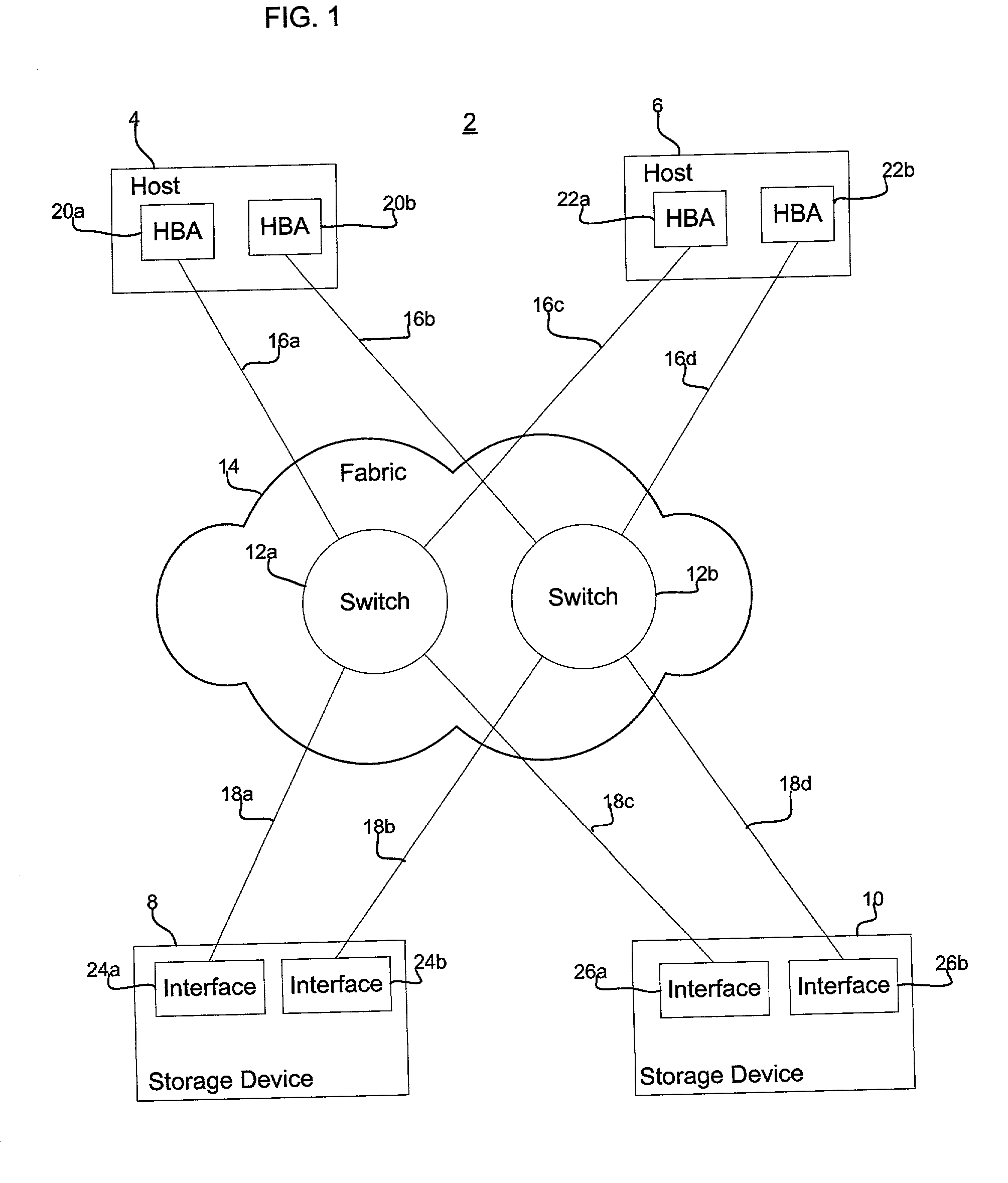
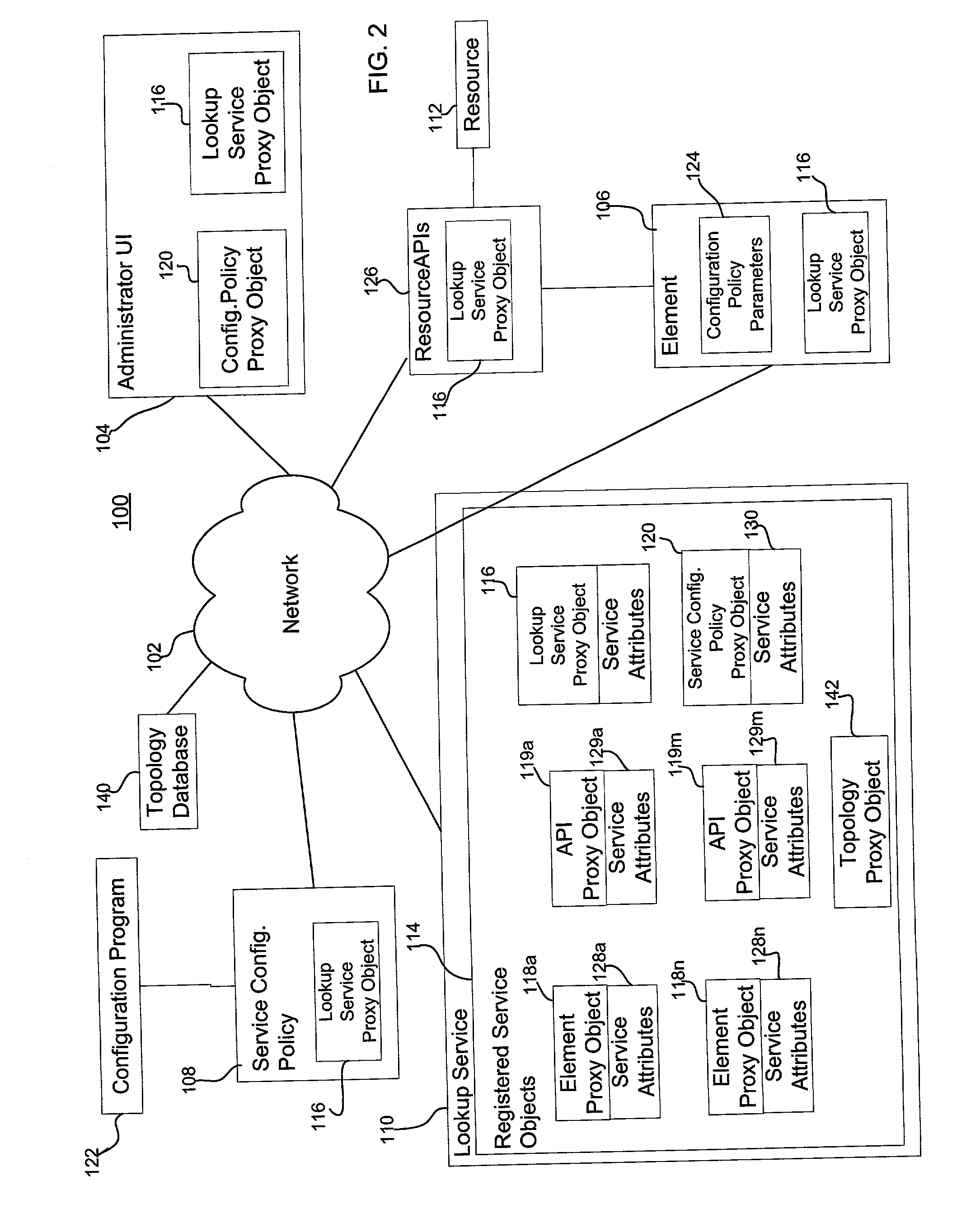
Method, system, and program for determining a modification of a system resource configuration
InactiveUS20030135609A1Resource allocationMultiple digital computer combinationsManagement systemReal-time computing
Provided are a method, system, and program for managing multiple resources in a system at a service level, including at least one host, network, and a storage space comprised of at least one storage system that each host is capable of accessing over the network. A plurality of service level parameters are measured and monitored indicating a state of the resources in the system. A determination is made of values for the service level parameters and whether the service level parameter values satisfy predetermined service level thresholds. Indication is made as to whether the service level parameter values satisfy the predetermined service thresholds. A determination is made of a modification to one or more resource deployments or configurations if the value for the service level parameter for the resource does not satisfy the predetermined service level thresholds.
Owner:SUN MICROSYSTEMS INC
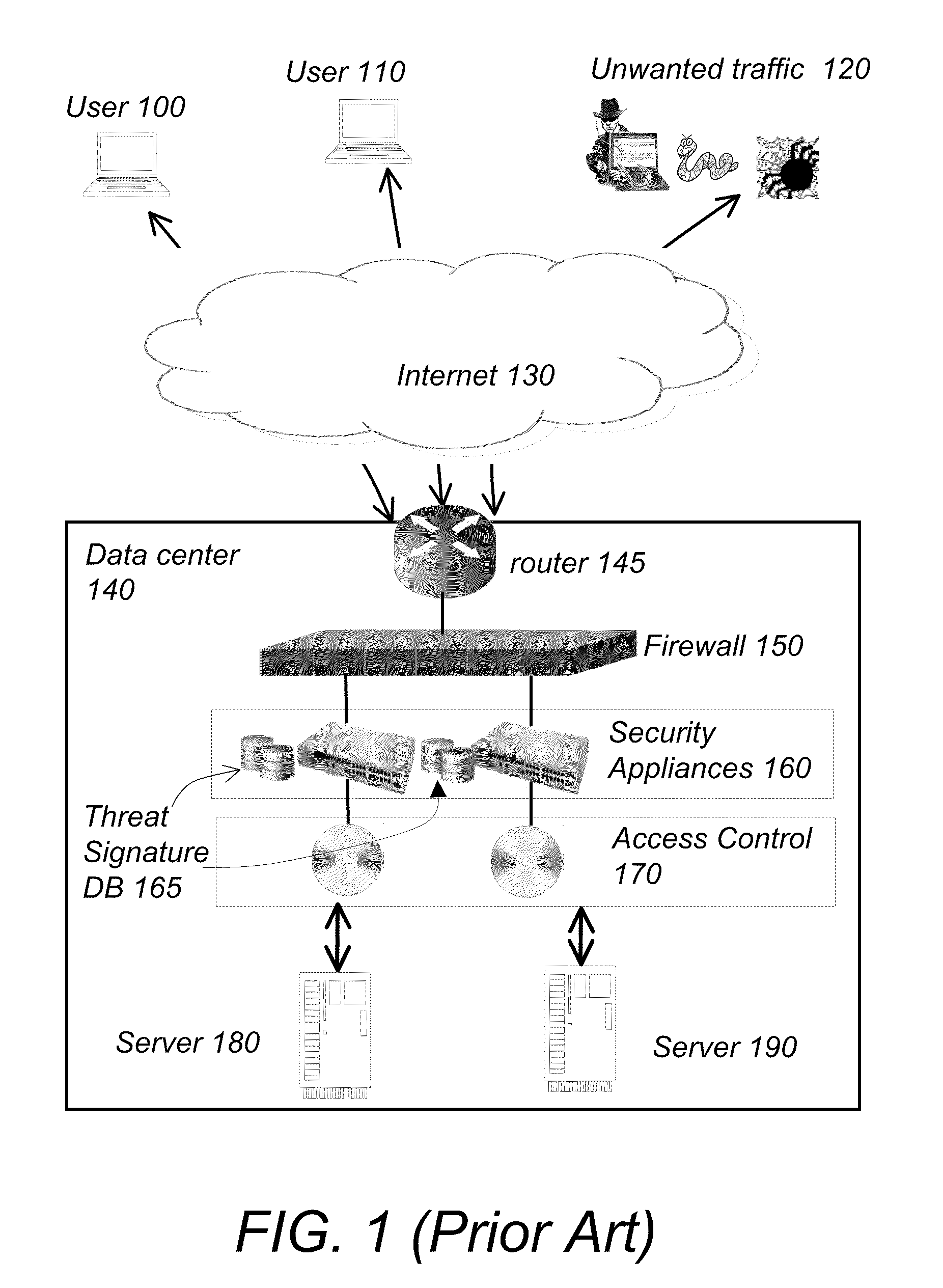
System and method for access management and security protection for network accessible computer services
InactiveUS20100251329A1Detection problemGrows and shrinks capacity and bandwidth capacityMemory loss protectionError detection/correctionTraffic capacityService provision
A method for providing access management and security protection to a computer service includes providing a computer service that is hosted at one or more servers and is accessible to clients via a first network, providing a second network that includes a plurality of traffic processing nodes and providing means for redirecting network traffic from the first network to the second network. Next, redirecting network traffic targeted to access the computer service via the first network to a traffic processing node of the second network via the means for redirecting network traffic. Next, inspecting and processing the redirected network traffic by the traffic processing node and then routing only redirected network traffic that has been inspected, processed and approved by the traffic processing node to access the computer service via the second network.
Owner:YOTTAA
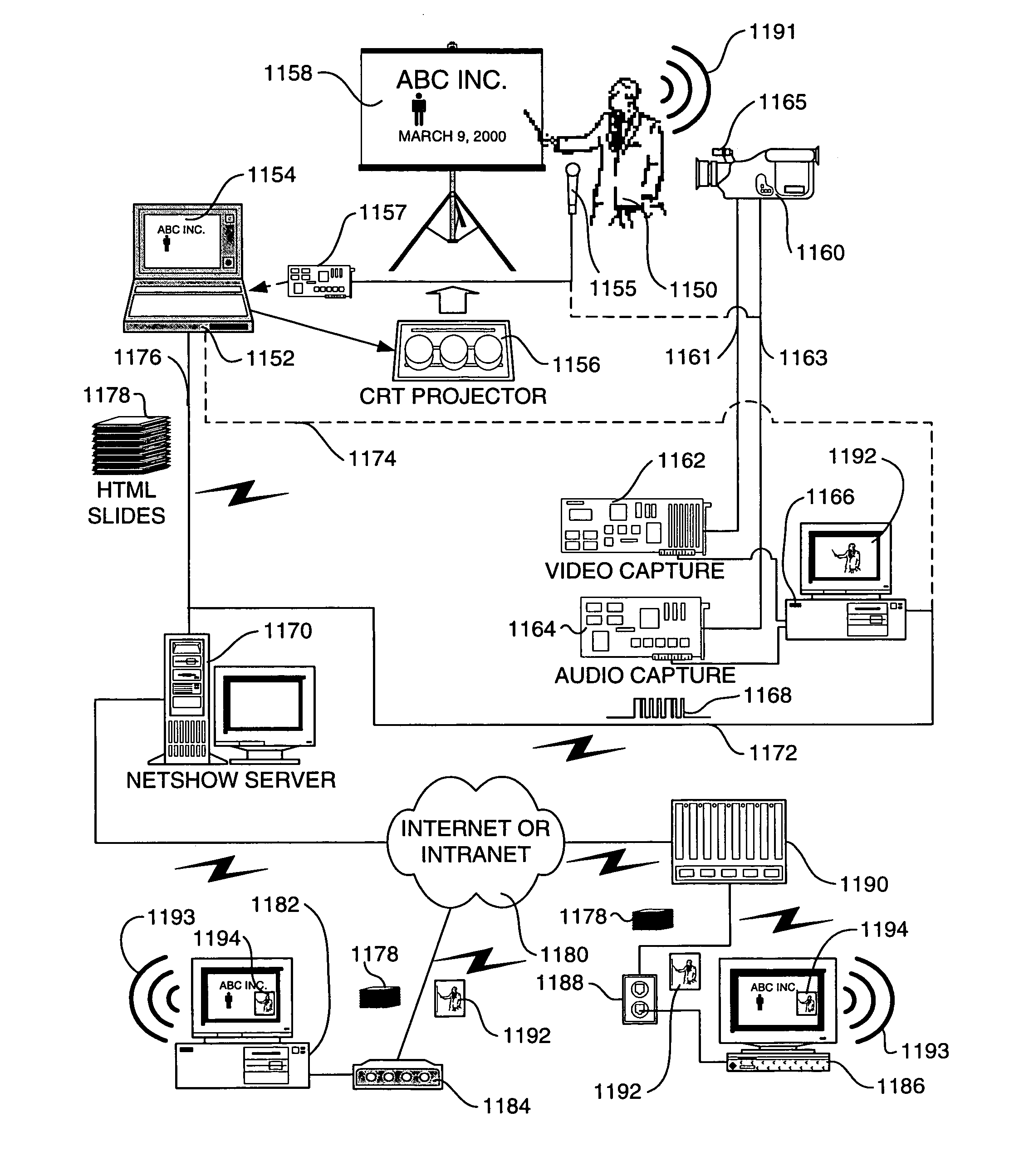
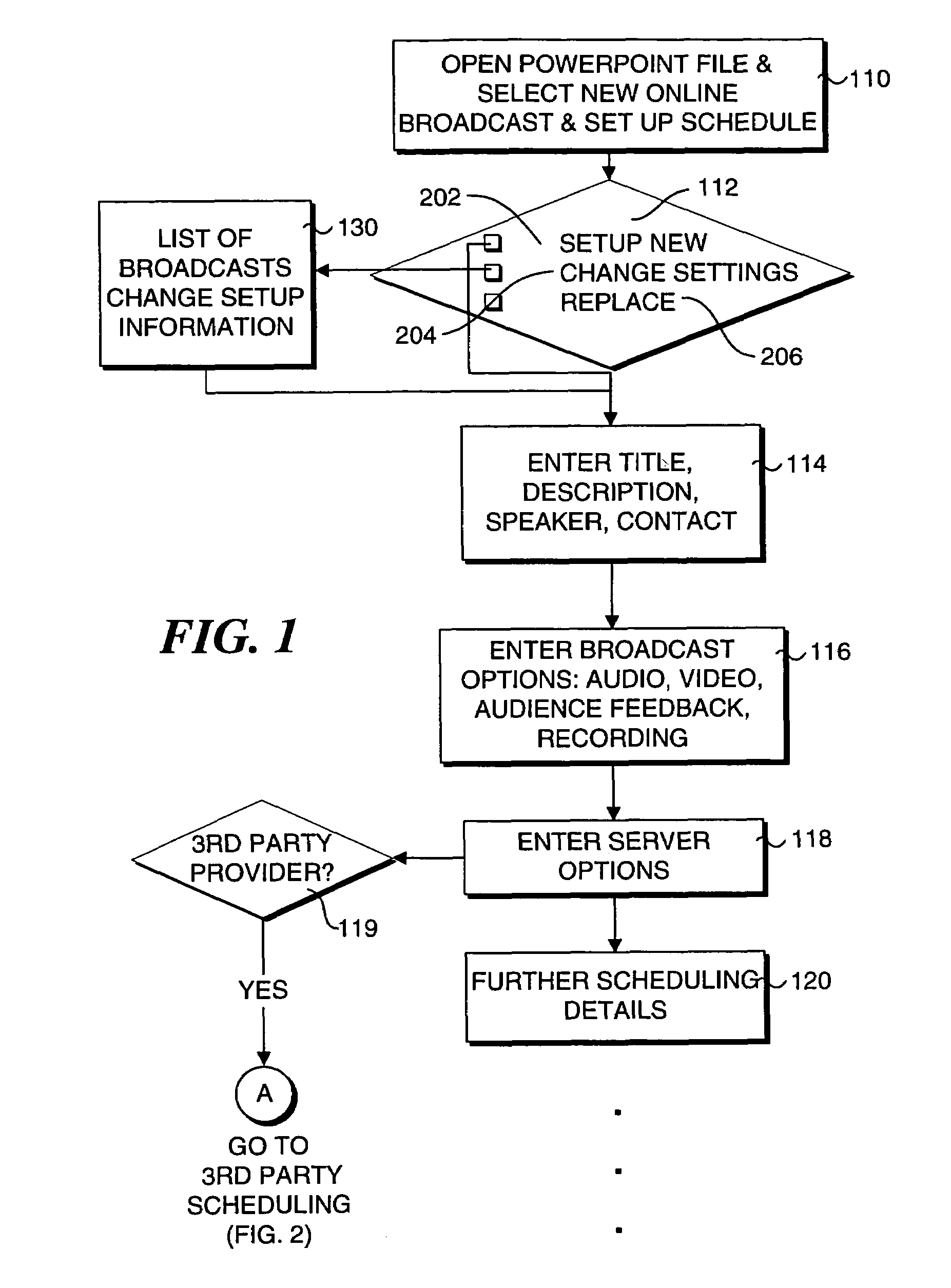
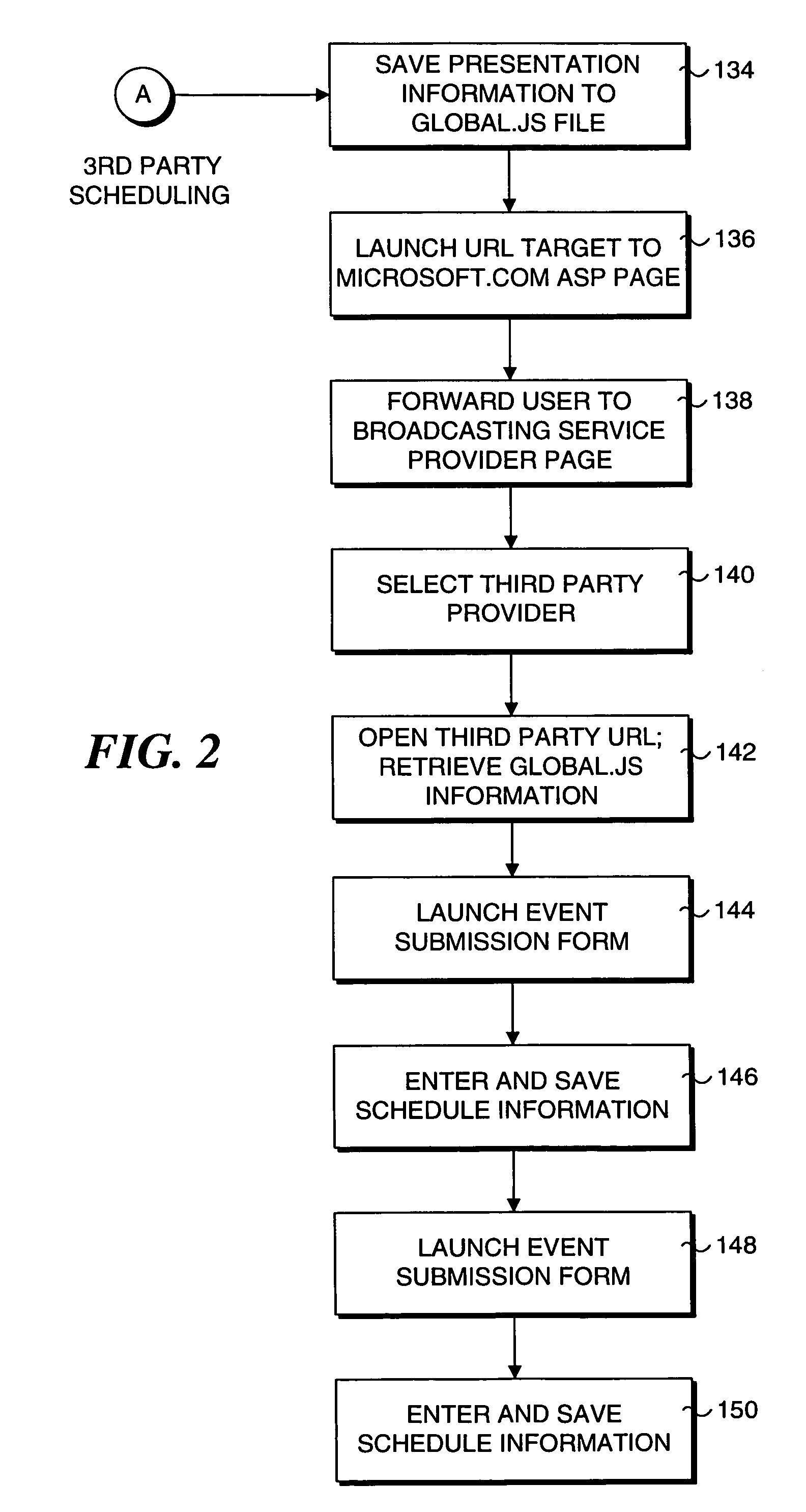
System and method for recording a presentation for on-demand viewing over a computer network
InactiveUS7330875B1Improve viewing experienceMultiple digital computer combinationsOffice automationData streamOn demand
A system and method for recording and playback of a live presentation that enables a reproduction of audio and visual aspects of the live presentation and enables on-demand viewing of the presentation at a later time. A live presentation comprising a plurality of presentation slides, audio content, and optionally, visual content are recorded as a data stream, so that when the recording of the data stream is played, the presentation slides are displayed in substantial synchrony with reproduced audio and visual content on a viewer's computer, thereby reproducing the live presentation. The plurality of presentation slides are saved as HTML files to a predetermined location that is accessible by the viewer's computer over a computer network, such as the Internet. During the presentation, the live audio and visual content is captured and encoded into the data stream, which is in an active streaming format (ASF), and the data stream is saved to a file. Also, slide display commands produced in conjunction with the display of the presentation slides during the presentation are interleaved into the data stream. In response to a viewer's request to view the presentation at a later time, the data stream file is downloaded to the viewer's computer and played back using a media player, which decodes the data stream file to replicate the live audio and visual content of the presentation. As the slide display commands are encountered during playback of the data stream file, corresponding HTML slide files are downloaded over the computer network to the viewer's computer and displayed so that they are substantially synchronized with the reproduced audio and visual content of the presentation.
Owner:MICROSOFT TECH LICENSING LLC
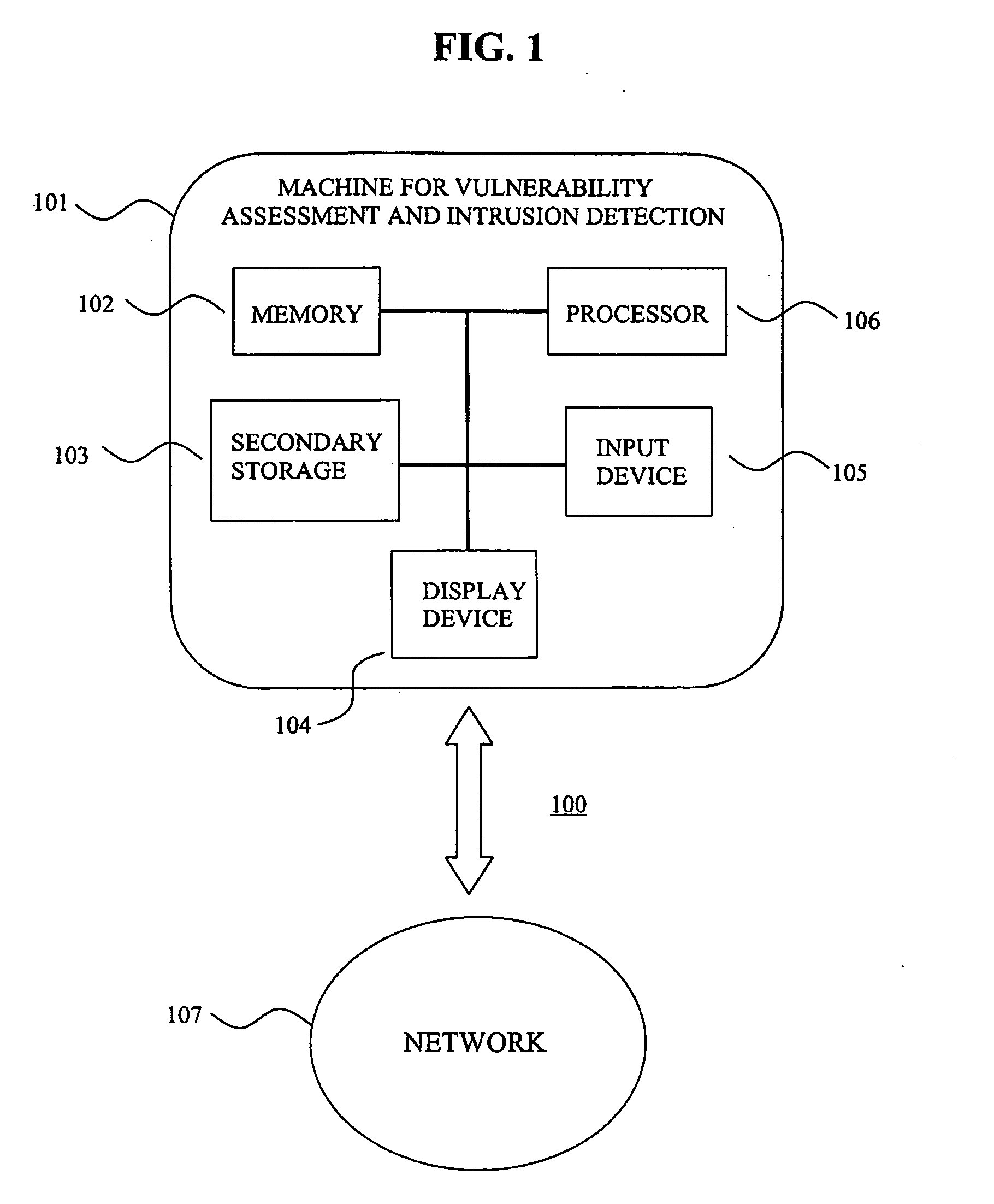
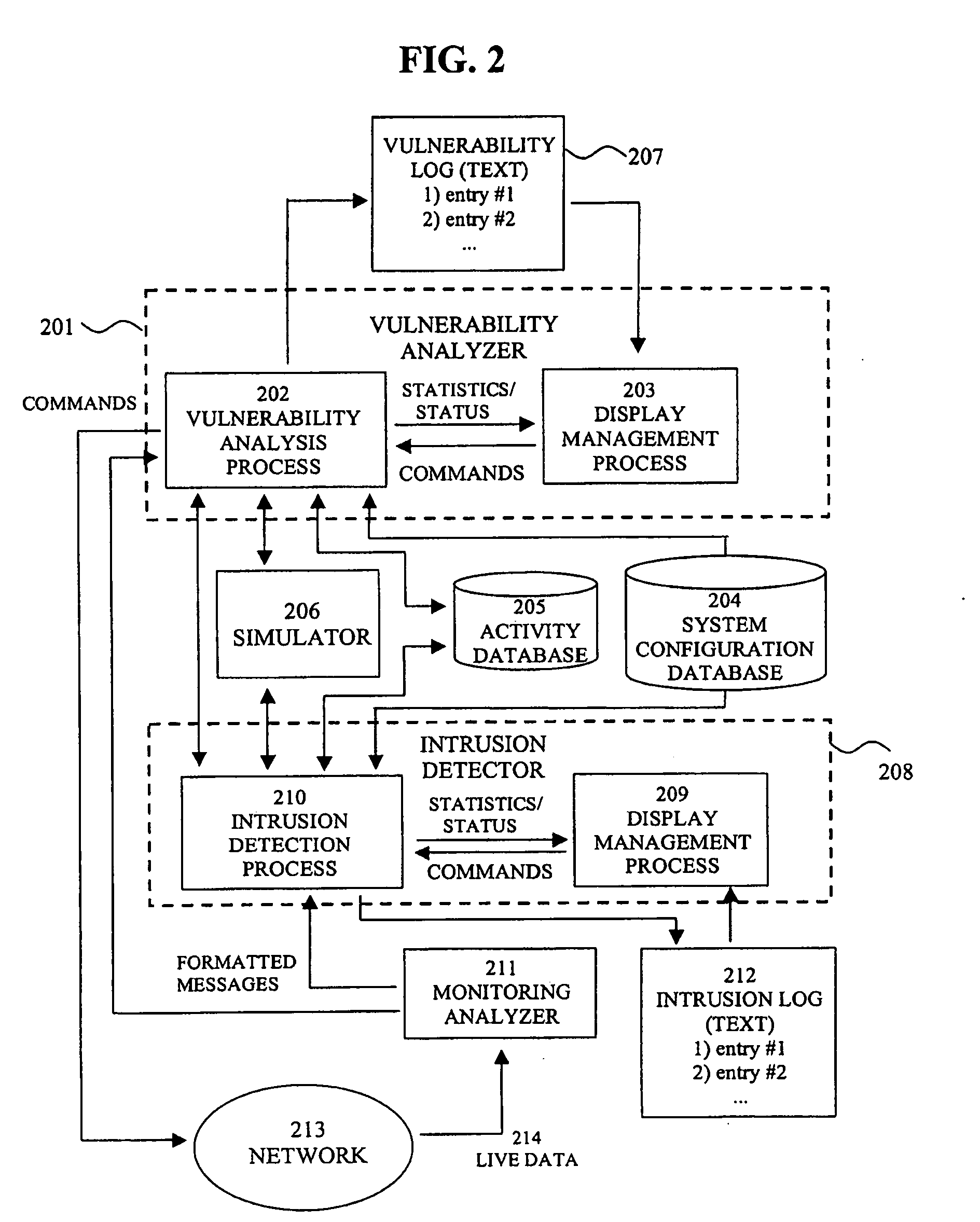
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
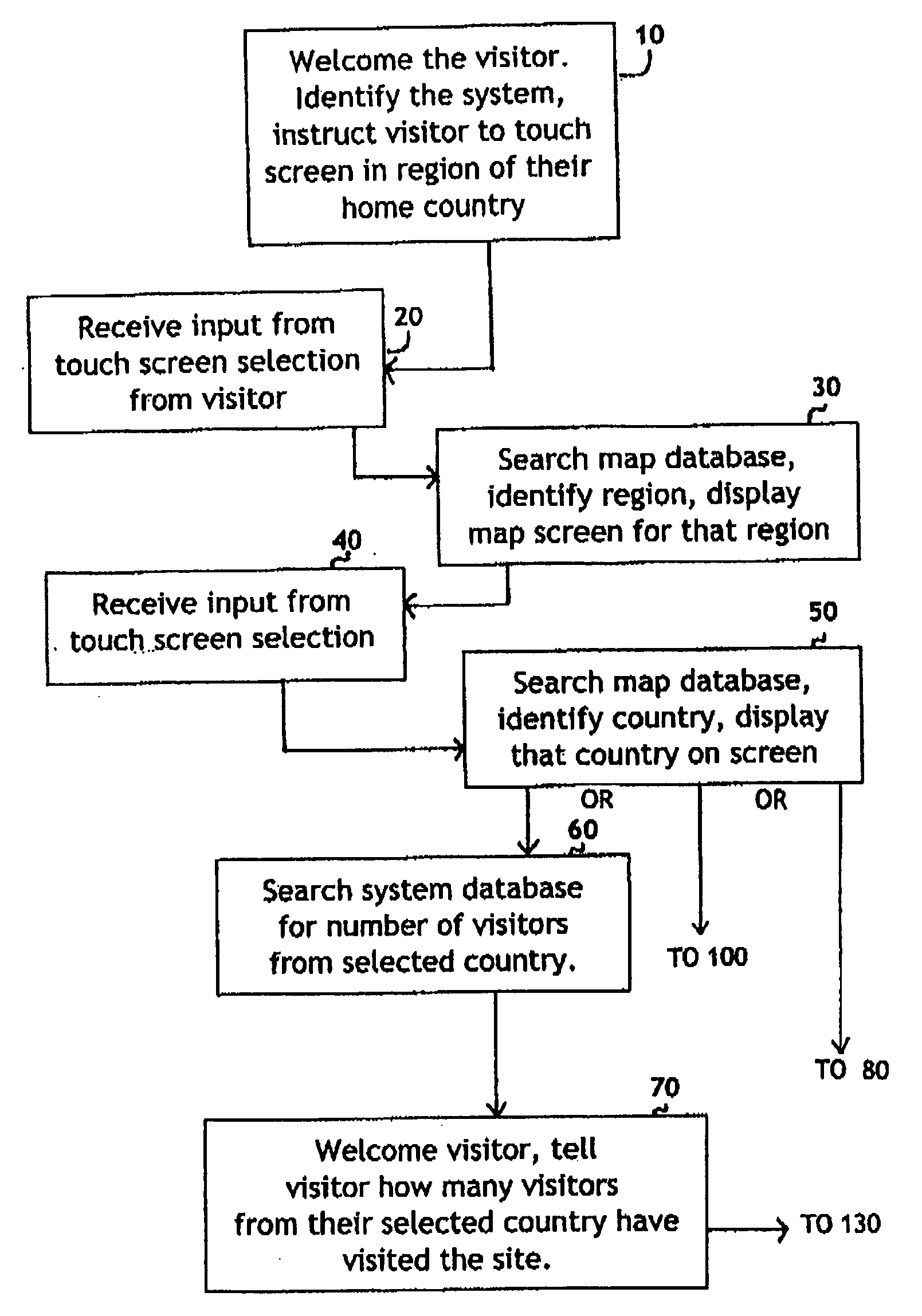
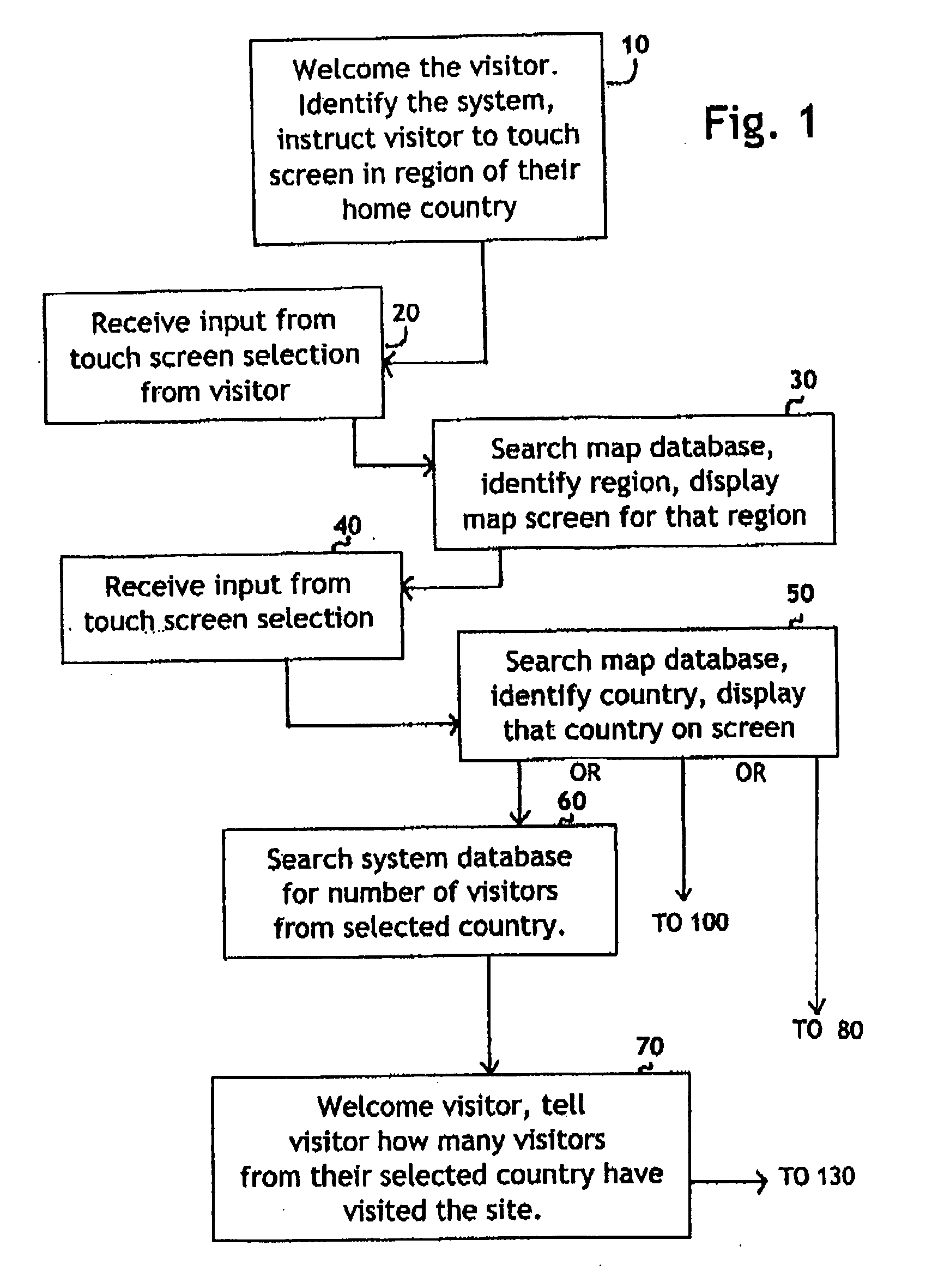
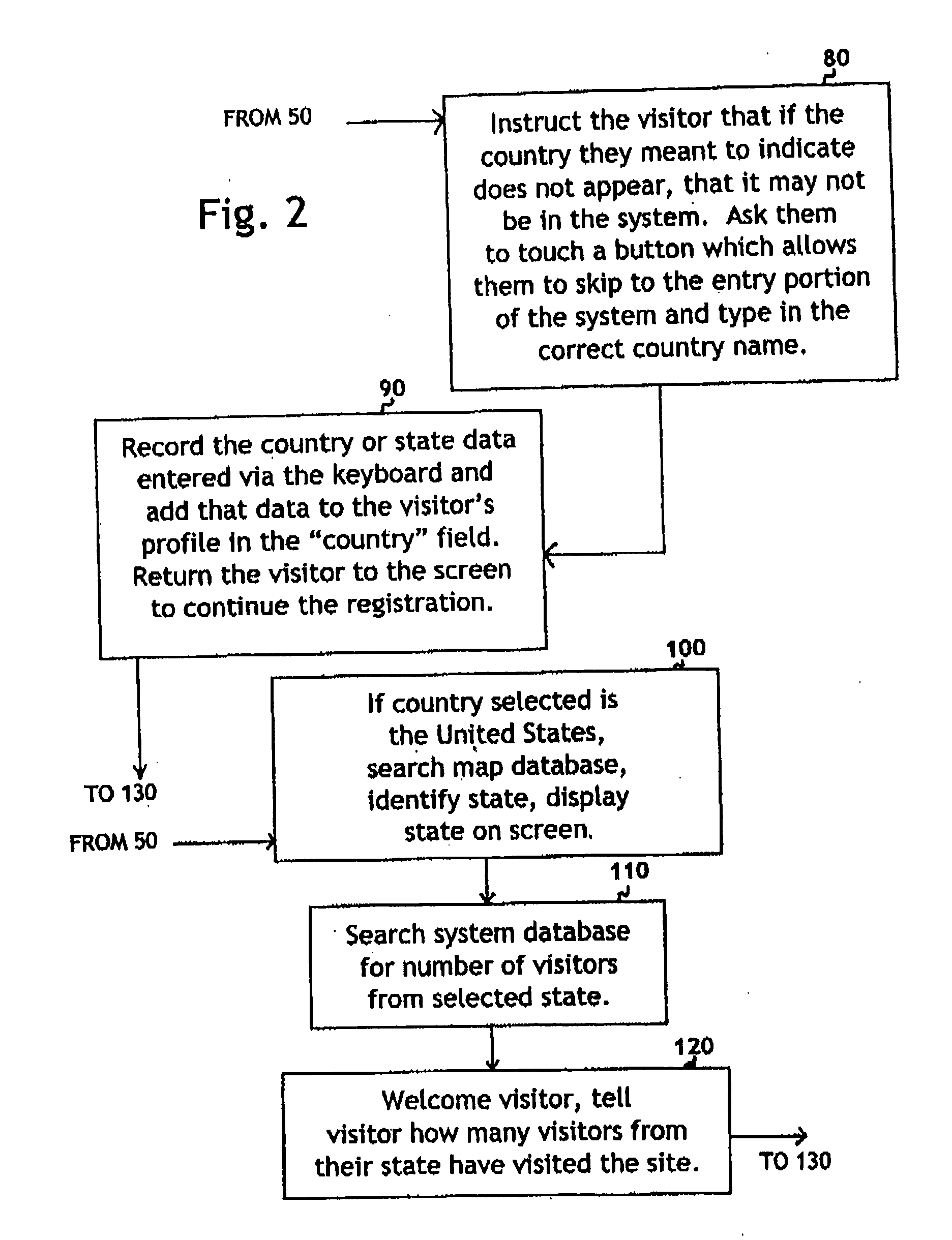
System for self-registering visitor information with geographic specificity and searchable fields
InactiveUS20080270938A1Easy retrievalBetter servedOffice automationGeographical information databasesEmail addressGeographic feature
An interactive visitor self-registration system for visitors to museums or other public sites using a digital computer or internet appliance device and a touchscreen monitor, which accesses a dedicated website, through a global computer network such as the Internet. It focuses on gathering information regarding residence of visitors as well as the information gathered by a traditional paper guest book. The system is searchable by visitors and by site staff. The information gathered by the system is stored on a dedicated website. A second, administration website, also password protected with an unpublished web address can be used by Site Administrators to customize the looks and options of their specific visitor self-registration system. Additionally, there is a public website which is accessible via the Internet which stores travel information for every signer to the system who logs on with his or her email address. These visitors can track their own travel via a map displayed on the website and be linked to the website for the sites they visit.
Owner:CARLSON ELIZABETH MARIE
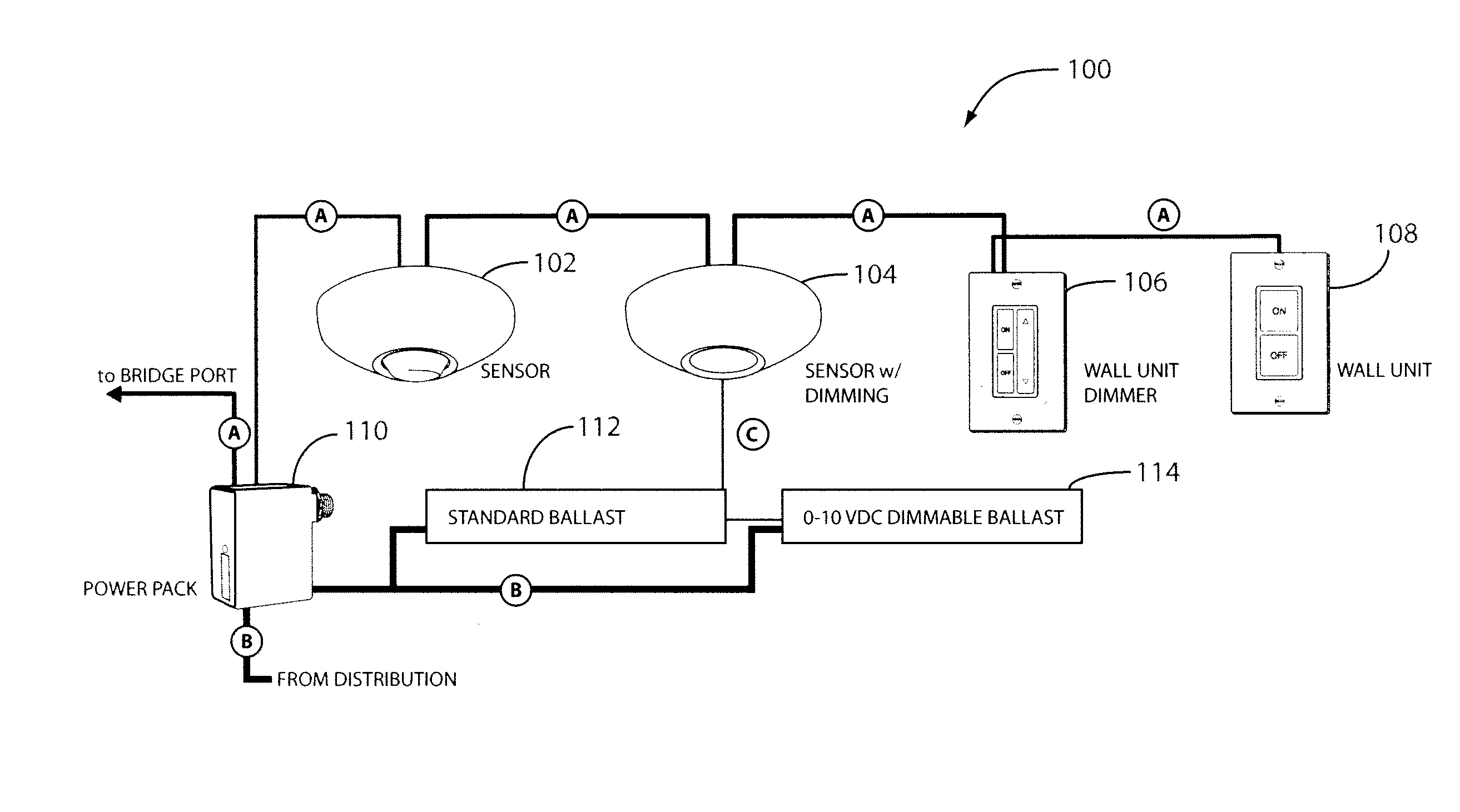
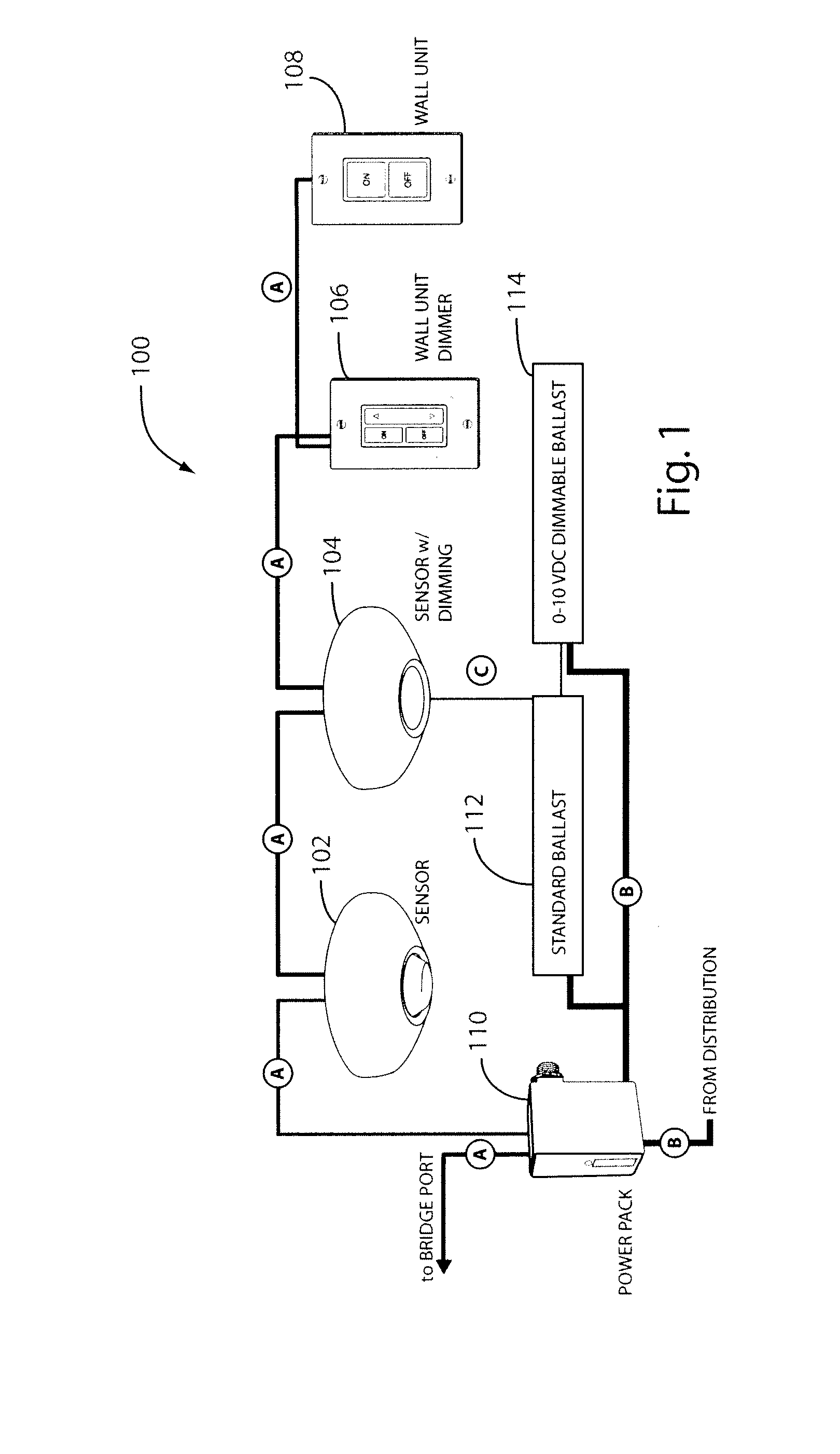
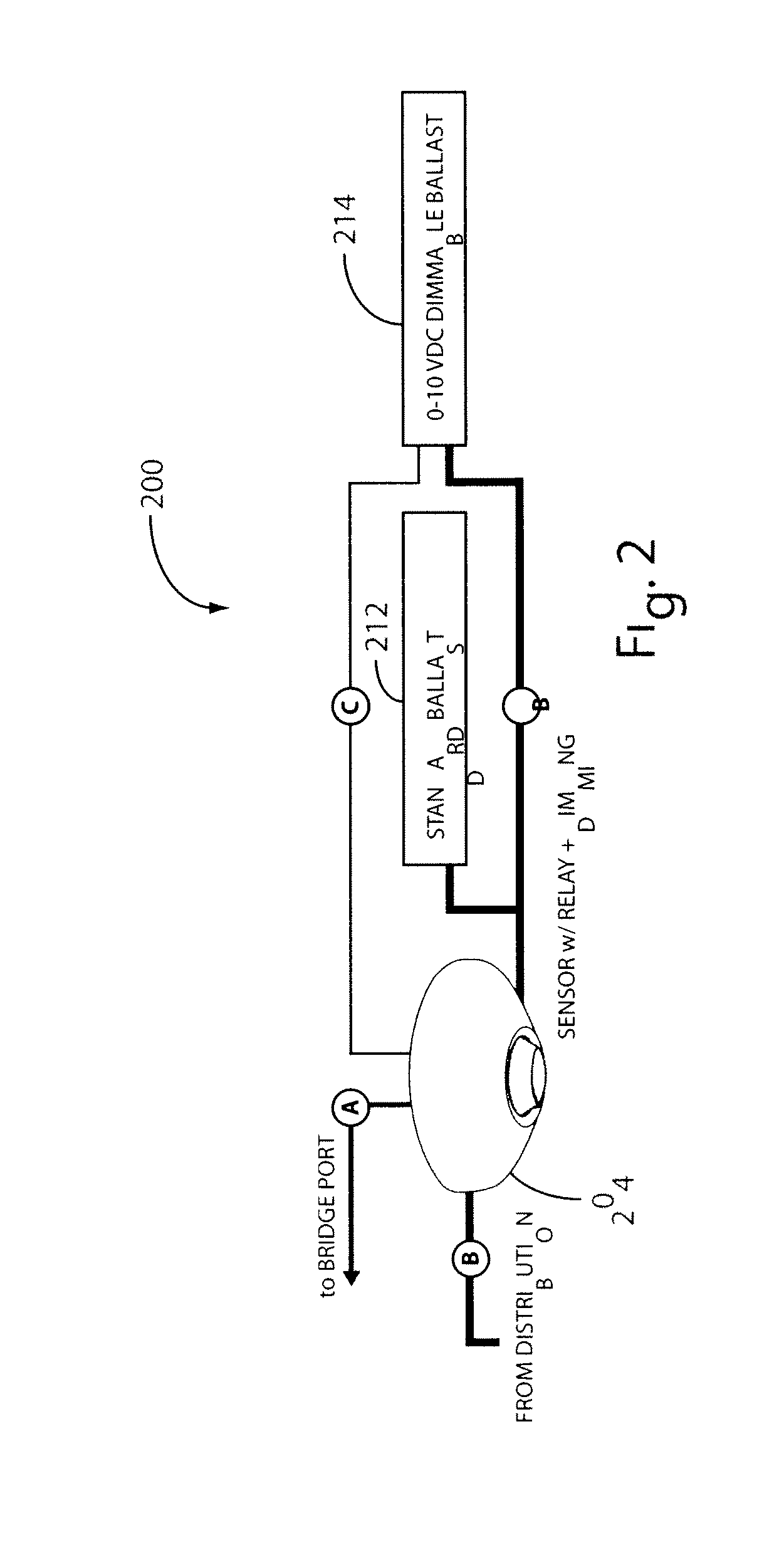
Networked, wireless lighting control system with distributed intelligence
ActiveUS20090278479A1Eliminating tediousEliminating time-consume taskElectrical apparatusSignalling system detailsDistributed intelligenceDaylight
A programmable lighting control system integrates time-based, sensor-based, and manual control of lighting and other loads. The system includes one or more groups of controlled lighting areas, which may be, for example, floors of a building. Each group may have one or more lighting zones, which may be, for example, individual rooms or offices on a building floor. Each lighting zone includes occupancy and / or daylight sensors that may be wirelessly coupled to a gateway of the group. Each gateway is coupled to a network, such as, for example, a local area network (LAN). Control software, residing on a computer (e.g., a personal computer or a server) coupled to the network and accessible via the network, remotely communicates with and controls the lighting zones either individually, groupwise, or globally. Each lighting zone can also be locally controlled at the gateway and can function independently of the control software and the gateway.
Owner:ABL IP HLDG
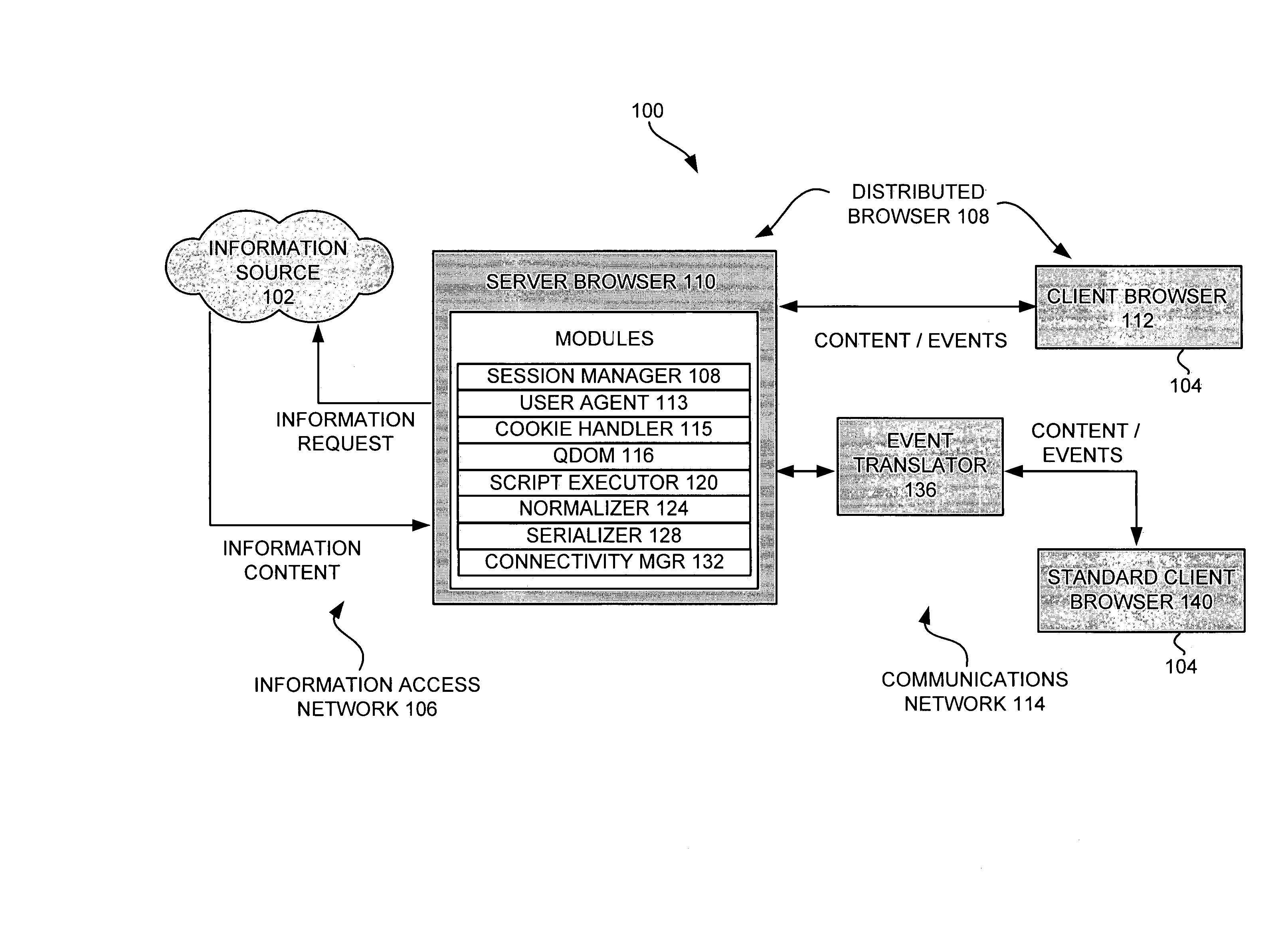
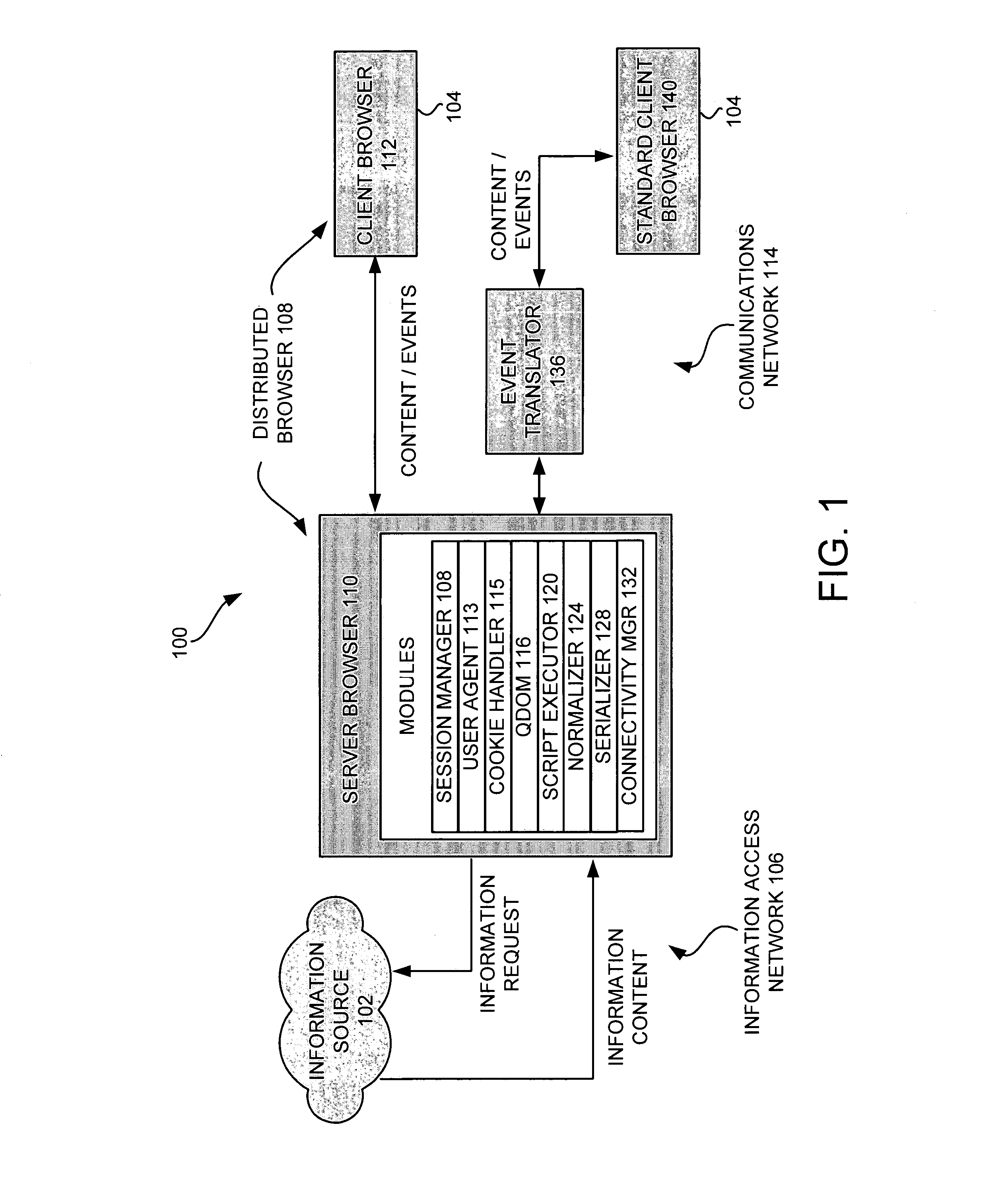
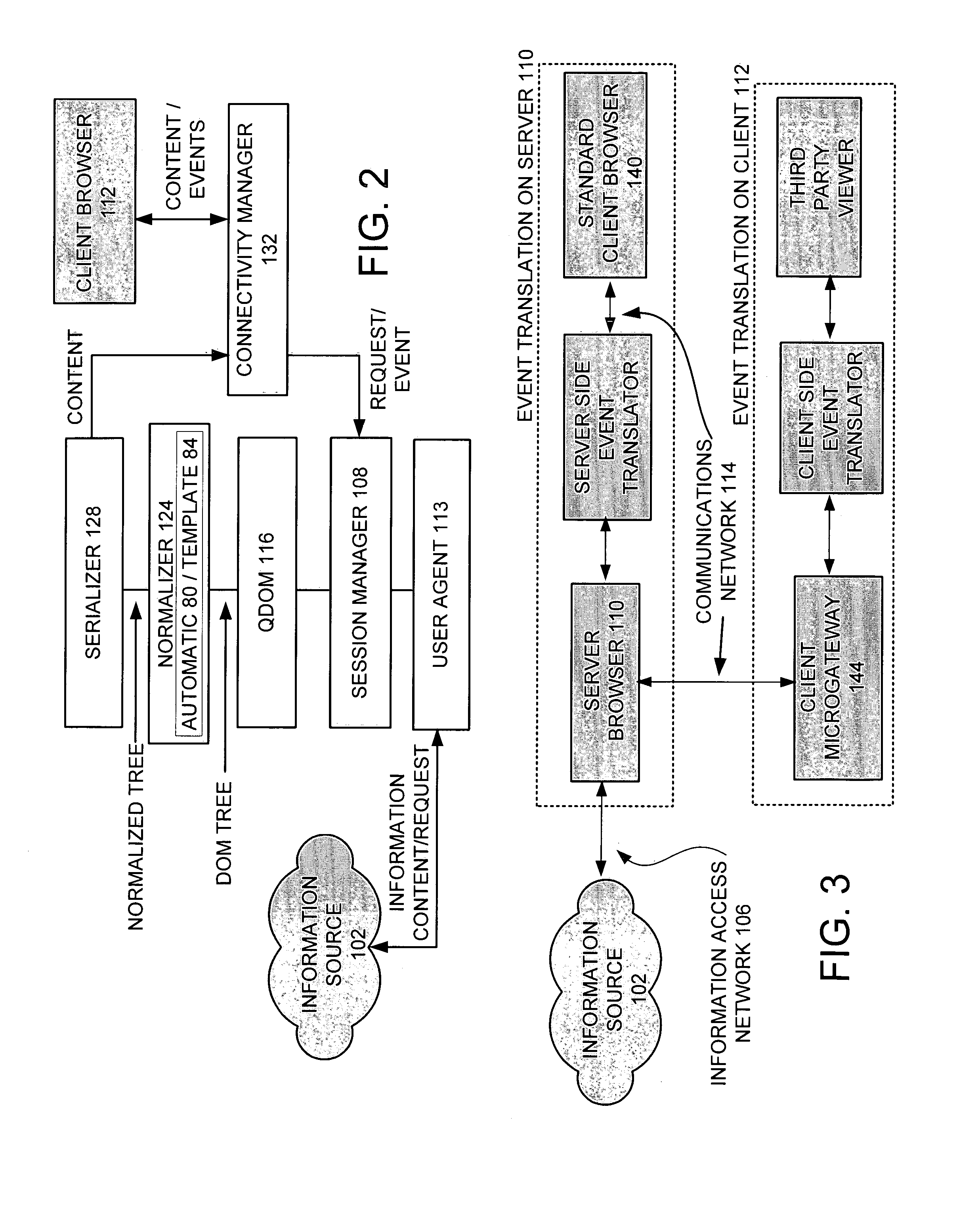
System and method for accessing customized information over the internet using a browser for a plurality of electronic devices
InactiveUS7072984B1High CPU powerLarge displayDigital data information retrievalMultiple digital computer combinationsComputer compatibilityClient-side
A system and method is provided for enabling an electronic device to efficiently access information content. A server browser accesses the information content over a network. The accessed information content is retrieved and adapted for presentation for the electronic device. A serializer dynamically formats the adapted information content according to a client browser. The client browser receives and presents the information content on the electronic device. An event translator is included to provide additional compatibility with commercially available client browsers.
Owner:RPX CORP
Intelligent personalization system and method
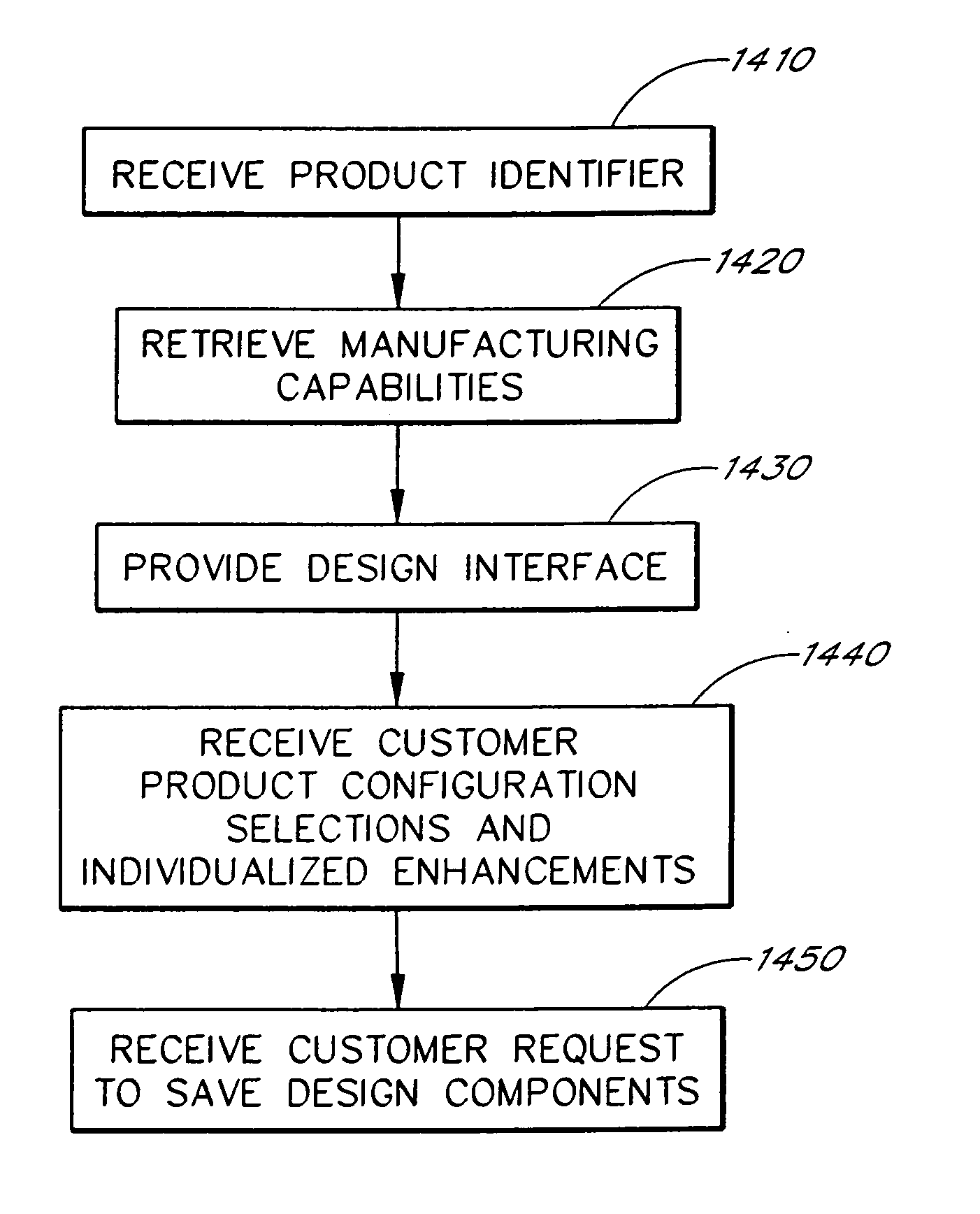
A system and method for facilitating the creation of personalized products is disclosed, wherein a user on a user computer can access a host merchant computer via a communication network, such as the Internet. The host merchant computer communicates with a products database containing information on products available for personalization and further contains manufacturing capabilities for the products. The method includes providing to the user via the communication network an assortment of product selections available in the products database, receiving a message from the user via the communication network indicating a selection of a product from the assortment, retrieving a set of manufacturing capabilities for the selected product from the products database, and providing to the user via the communication network a design interface including design tools which allow the user to select product configuration options and to create individualized enhancements, wherein the design tool is conformed to only allow configuration options and enhancements that satisfy the manufacturing capabilities.
Owner:DELUXE CORPORATION
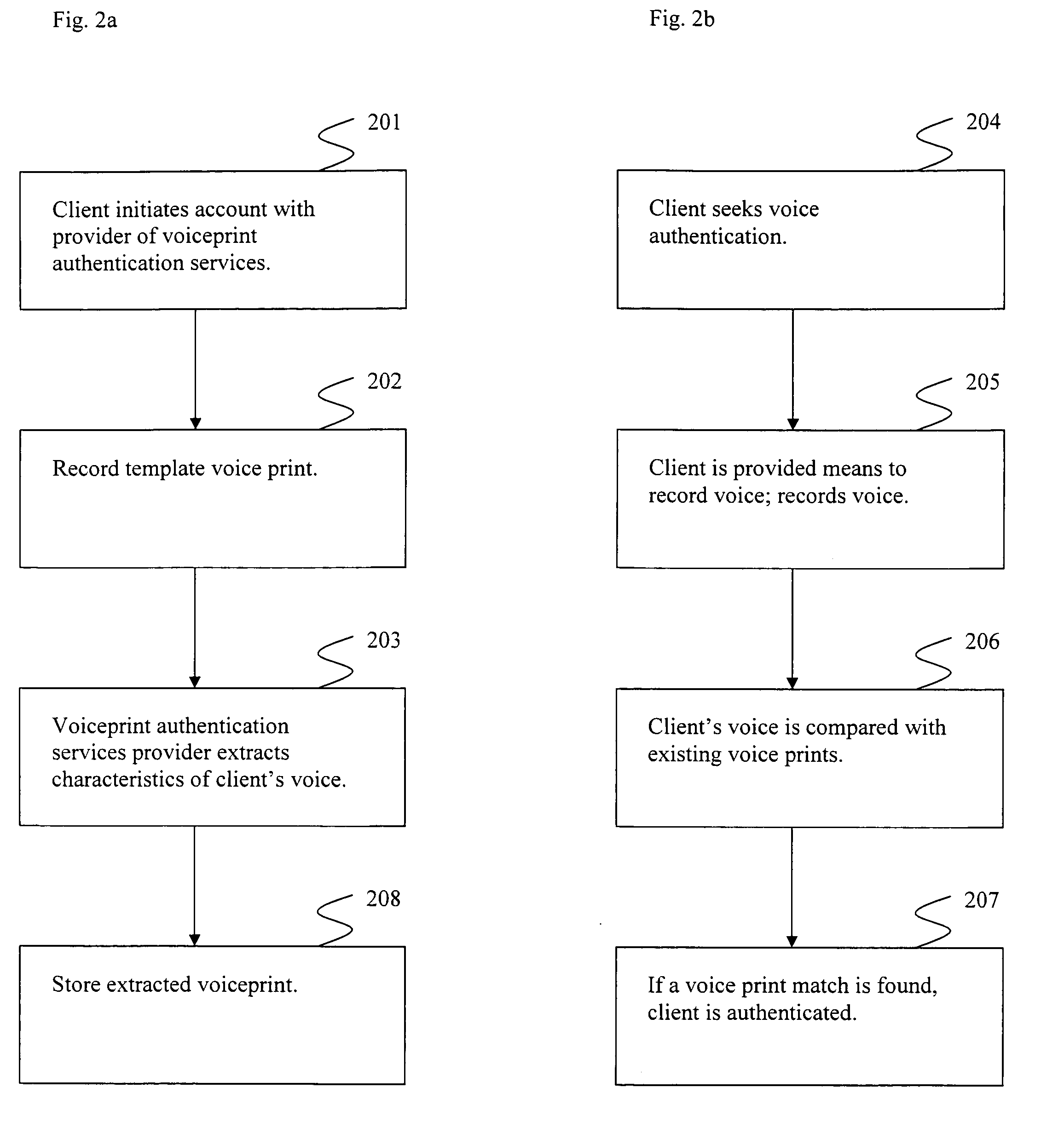
Voice print identification portal
InactiveUS20080256613A1Digital data processing detailsMultiple digital computer combinationsSecure voiceSpeech identification
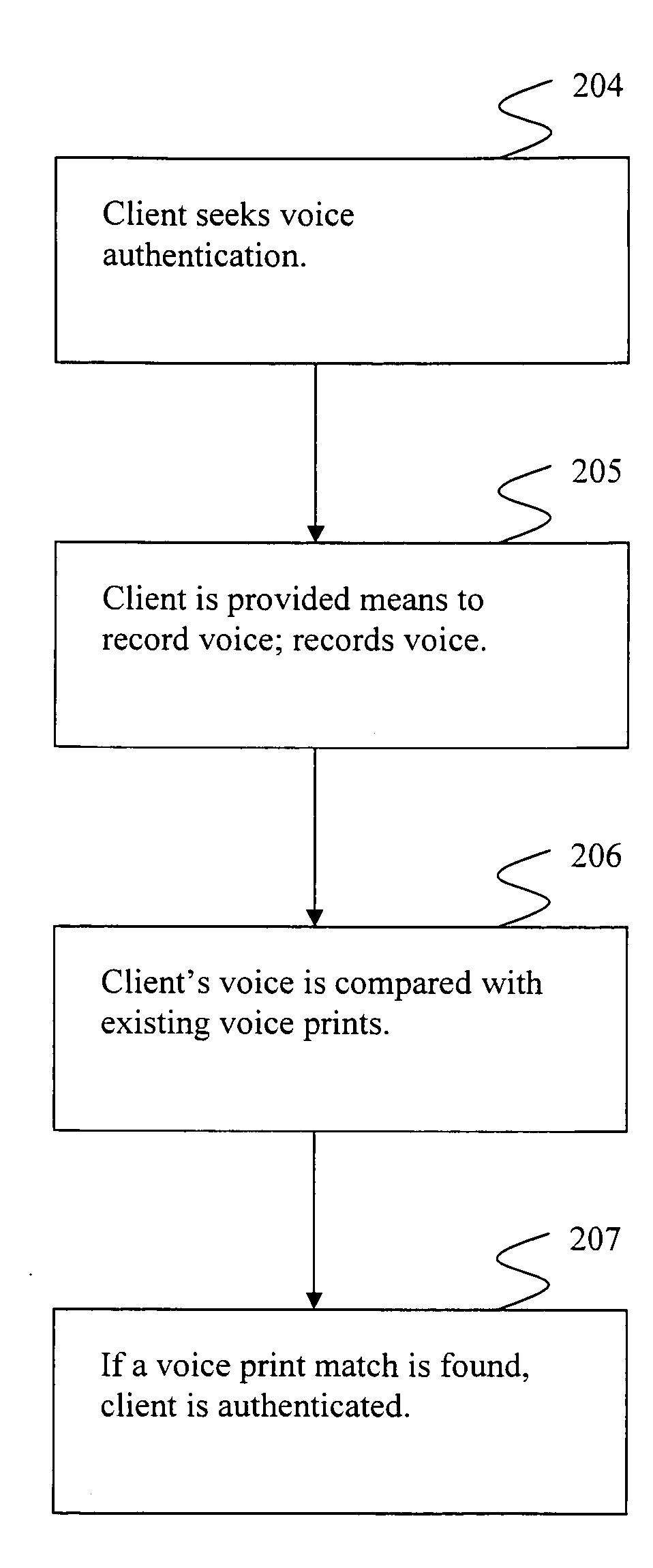
Systems and methods providing for secure voice print authentication over a network are disclosed herein. During an enrollment stage, a client's voice is recorded and characteristics of the recording are used to create and store a voice print. When an enrolled client seeks access to secure information over a network, a sample voice recording is created. The sample voice recording is compared to at least one voice print. If a match is found, the client is authenticated and granted access to secure information.Systems and methods providing for a dual use voice analysis system are disclosed herein. Speech recognition is achieved by comparing characteristics of words spoken by a speaker to one or more templates of human language words. Speaker identification is achieved by comparing characteristics of a speaker's speech to one or more templates, or voice prints. The system is adapted to increase or decrease matching constraints depending on whether speaker identification or speaker recognition is desired.
Owner:VOICEIT TECH
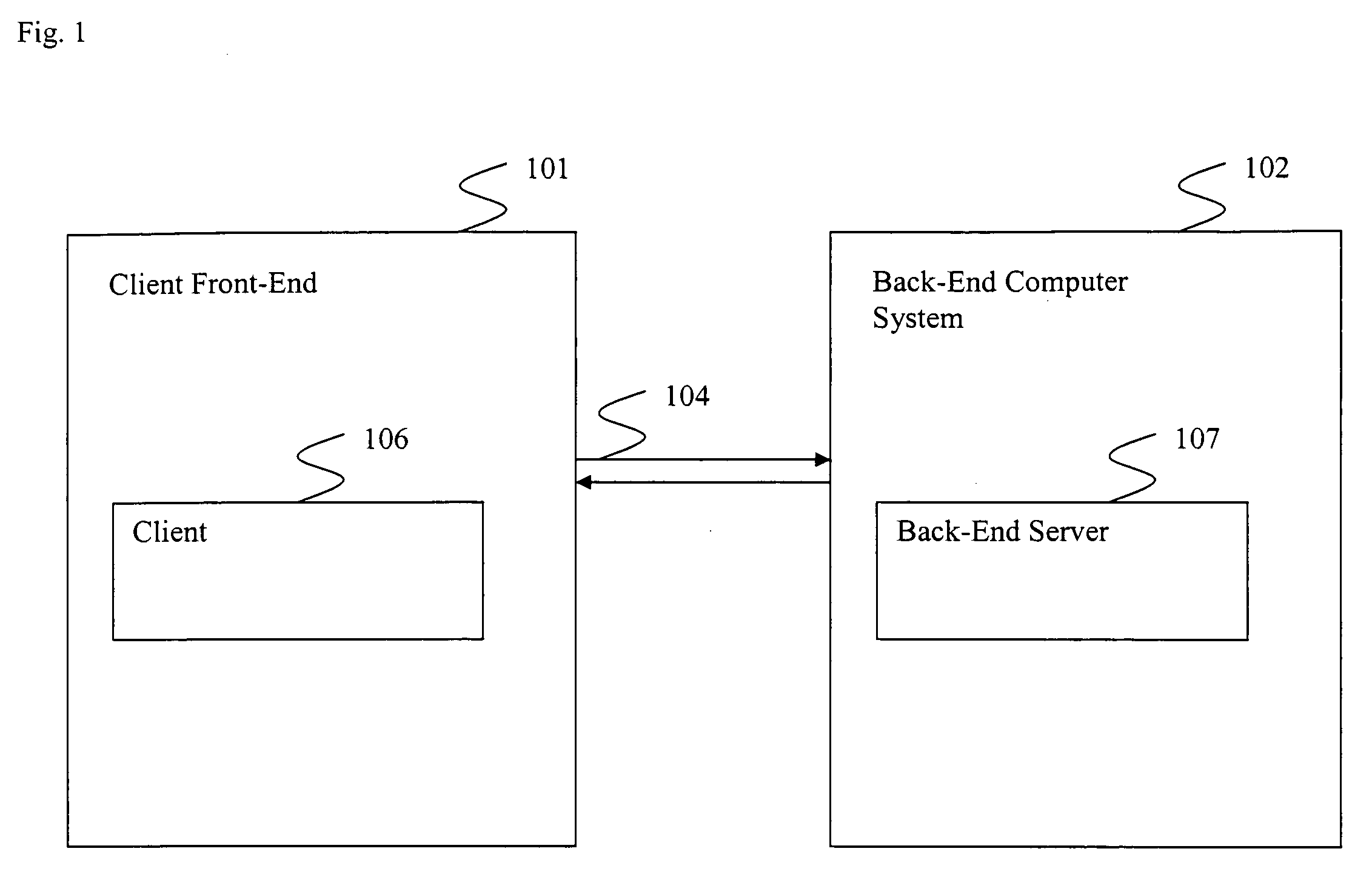
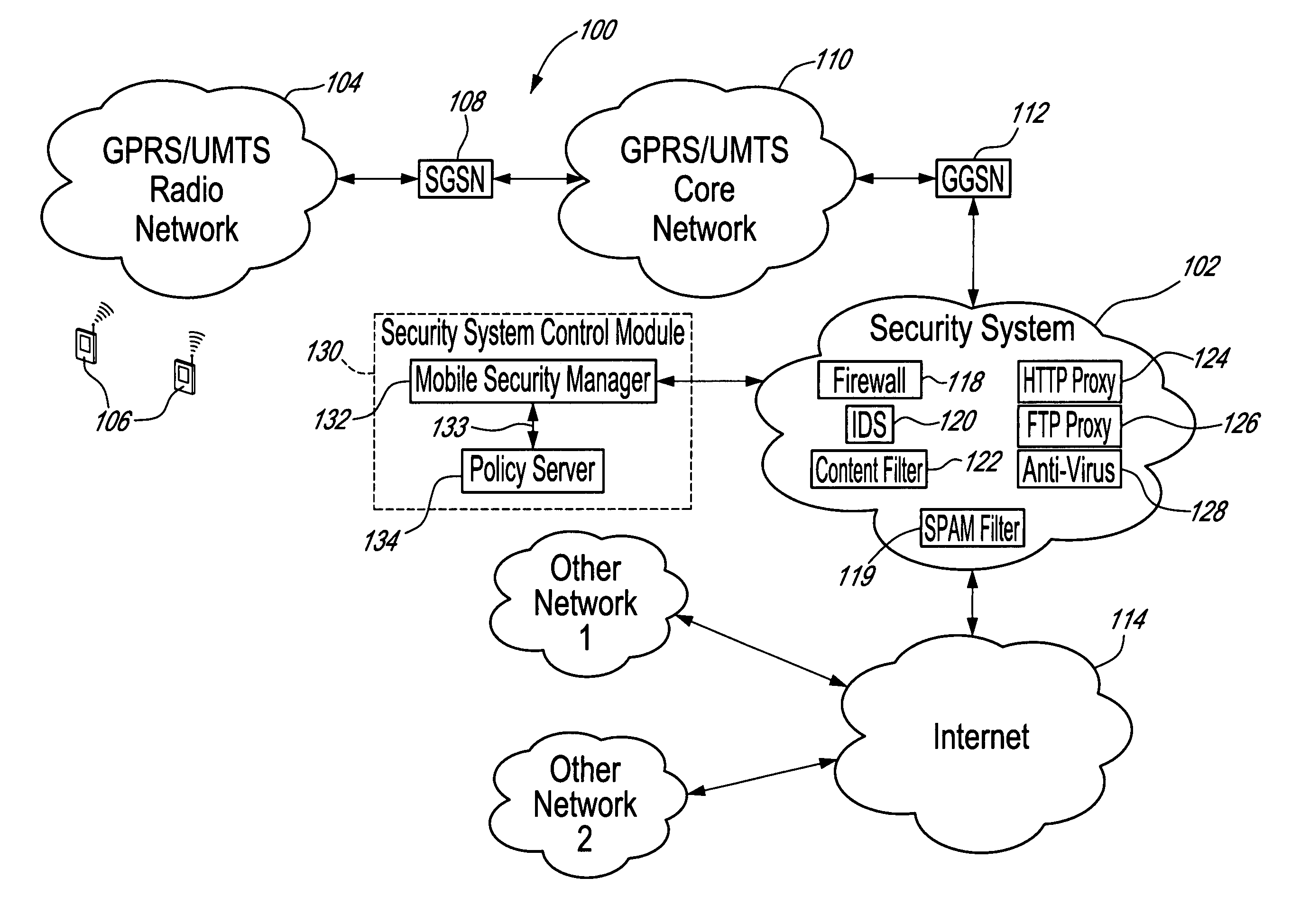
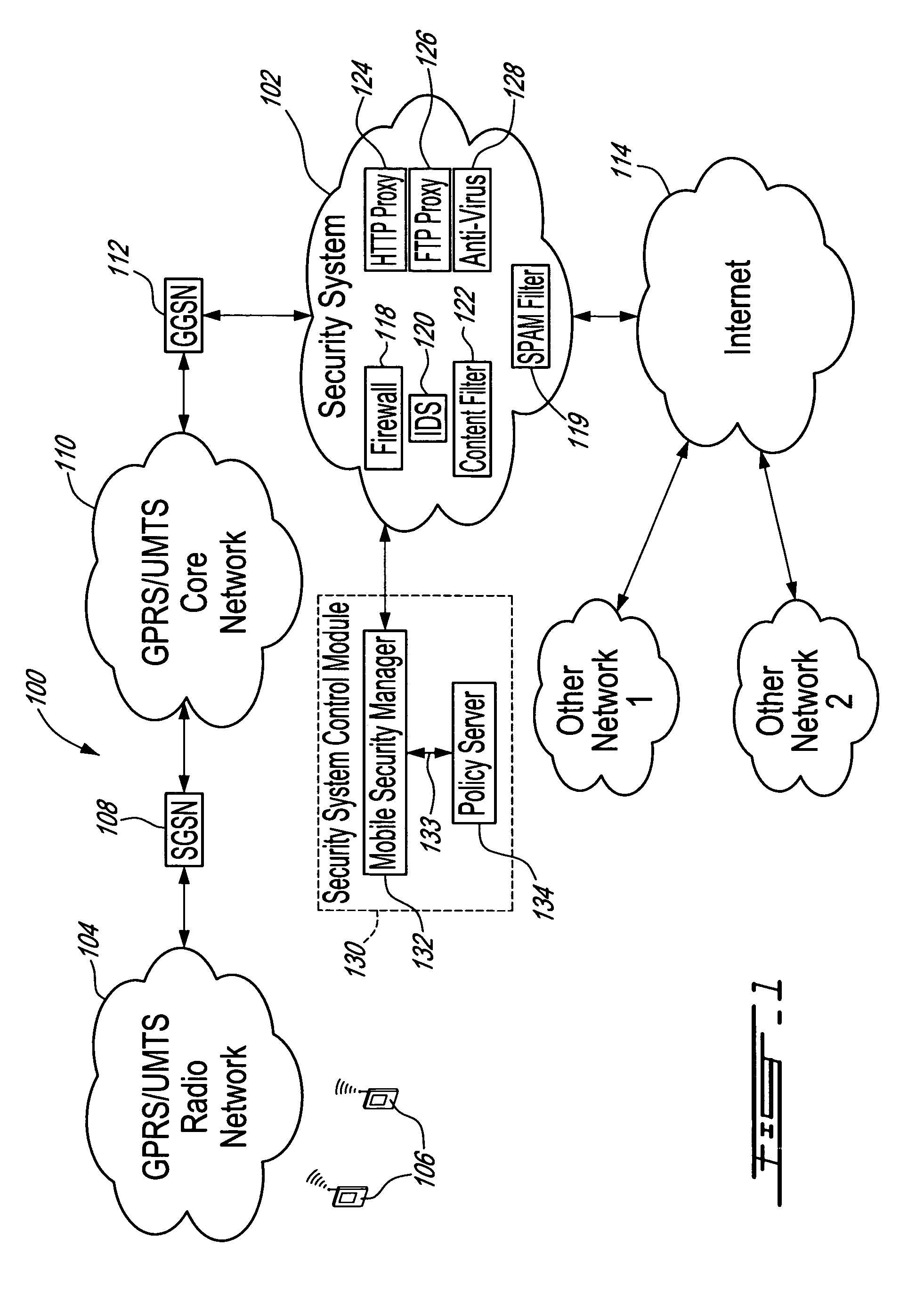
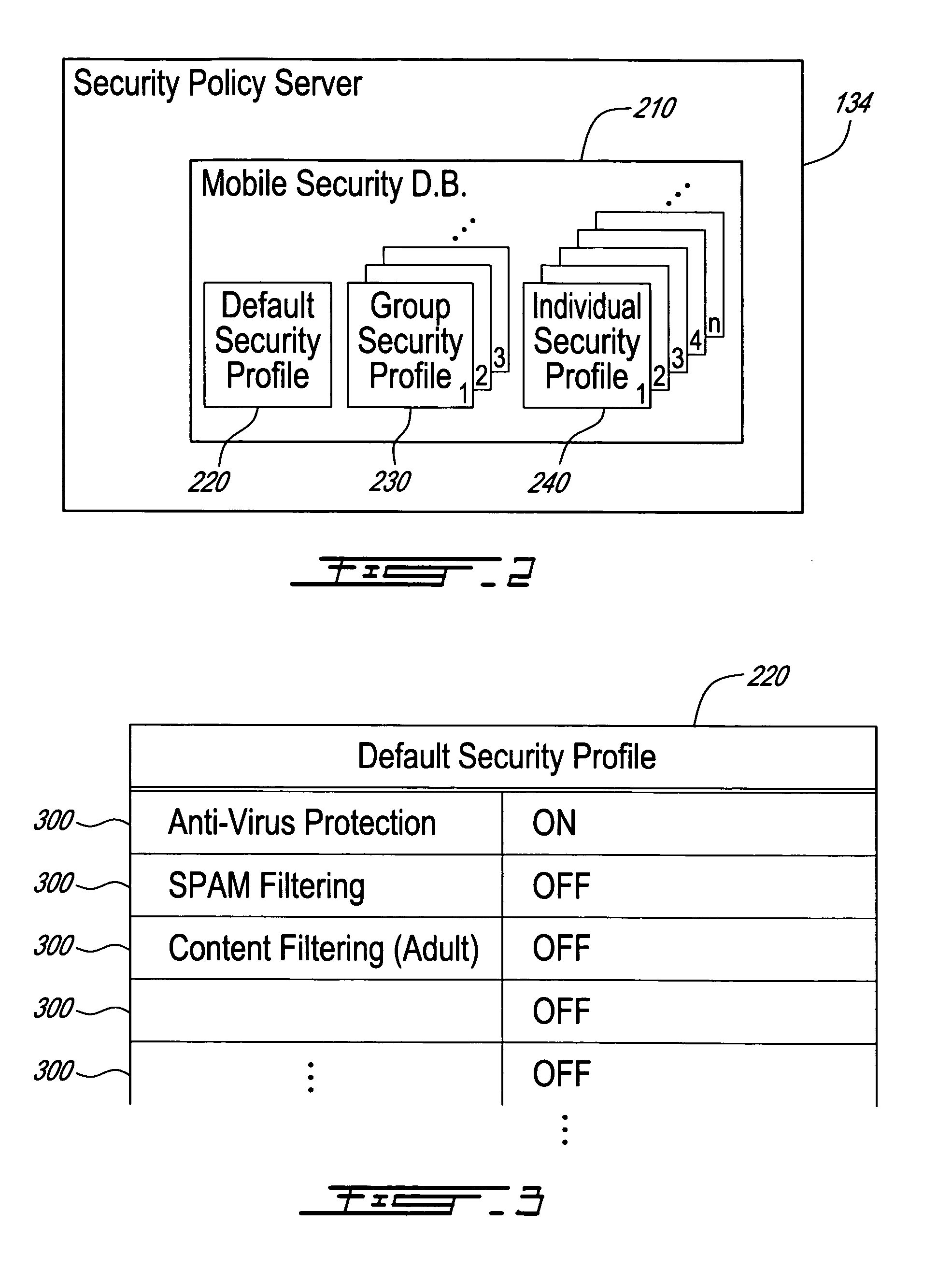
Method, security system control module and policy server for providing security in a packet-switched telecommunications system
ActiveUS7418253B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile station
A method, security system control module and policy server for providing security for Mobile Stations (MSs) in a Packet-Switched Telecommunications System. When an MS accesses the system, its identity is sent to a security system control module that retrieves a security profile associated with the MS. A policy server of the security system control module stores individual security profiles, default security profiles and group security profiles for registered subscribers. Security settings associated with the MS security profile are returned from the policy server to a mobile security manager of the control module, which then determines if they should be propagated in the system. When no previous network access was made in a given time period by an MS having similar security settings, i.e. belongs to the same group security profile, the settings are propagated in the system in order to be enforced, for providing security protection for the MS.
Owner:TELEFON AB LM ERICSSON (PUBL)
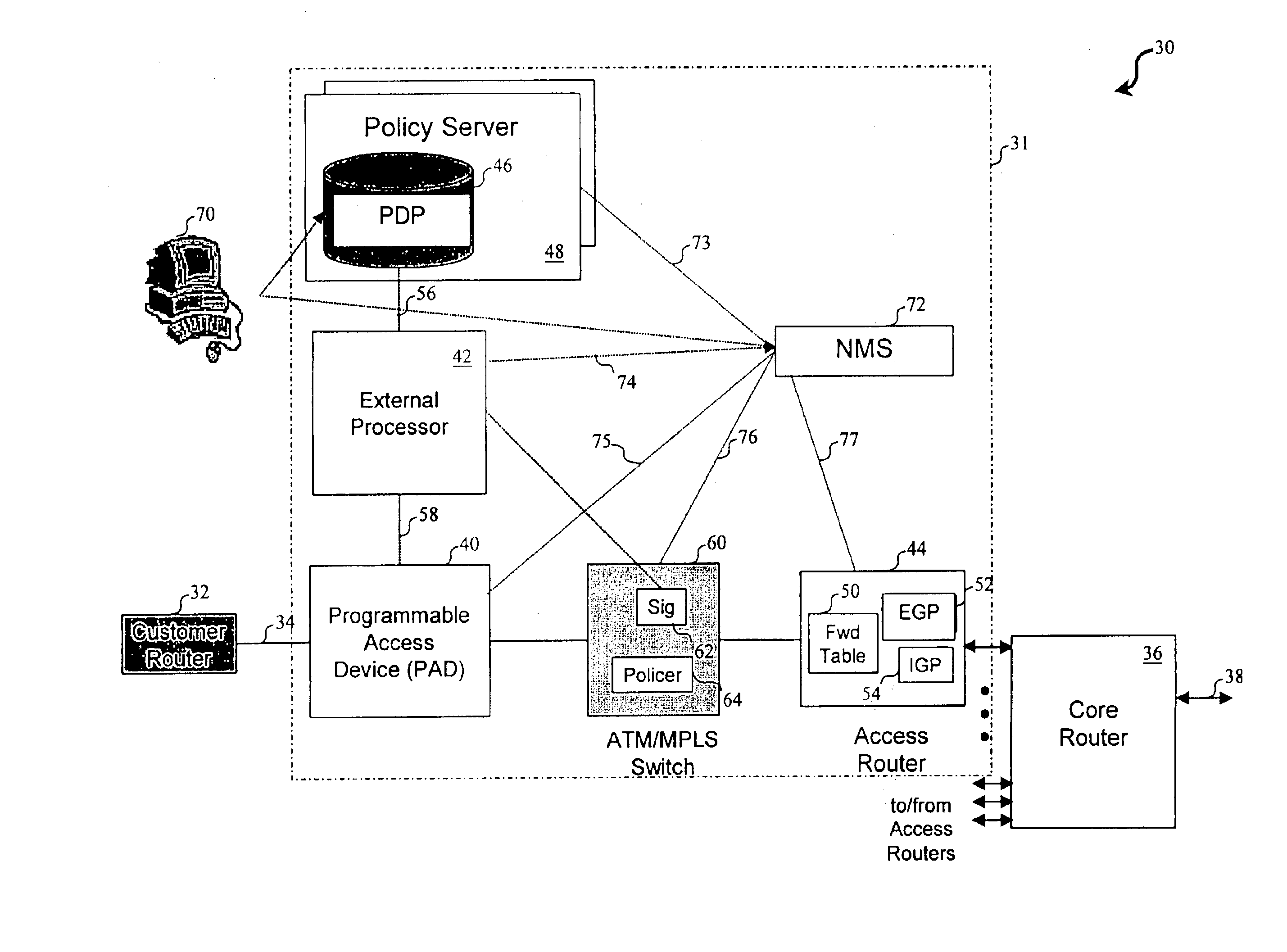
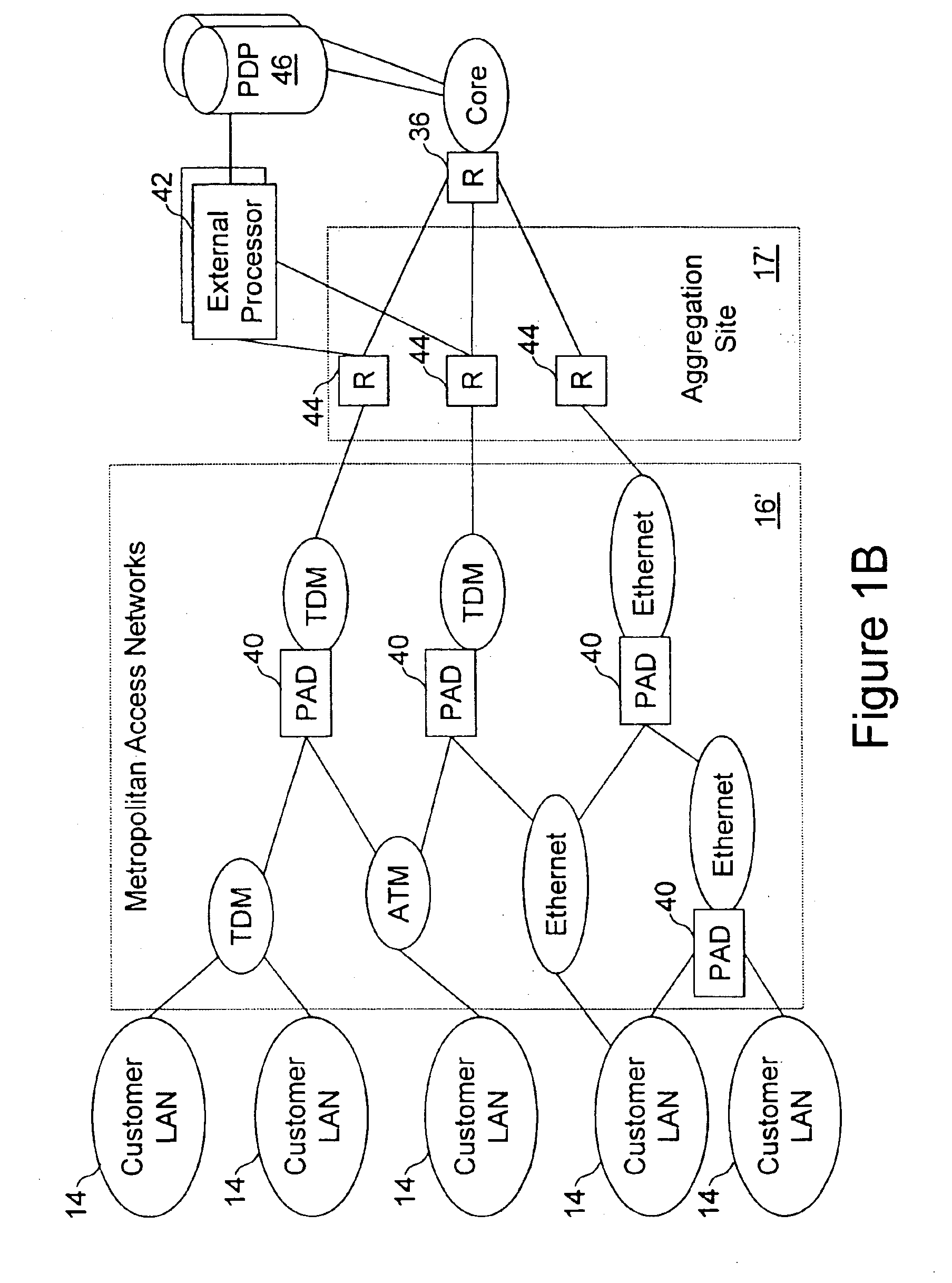
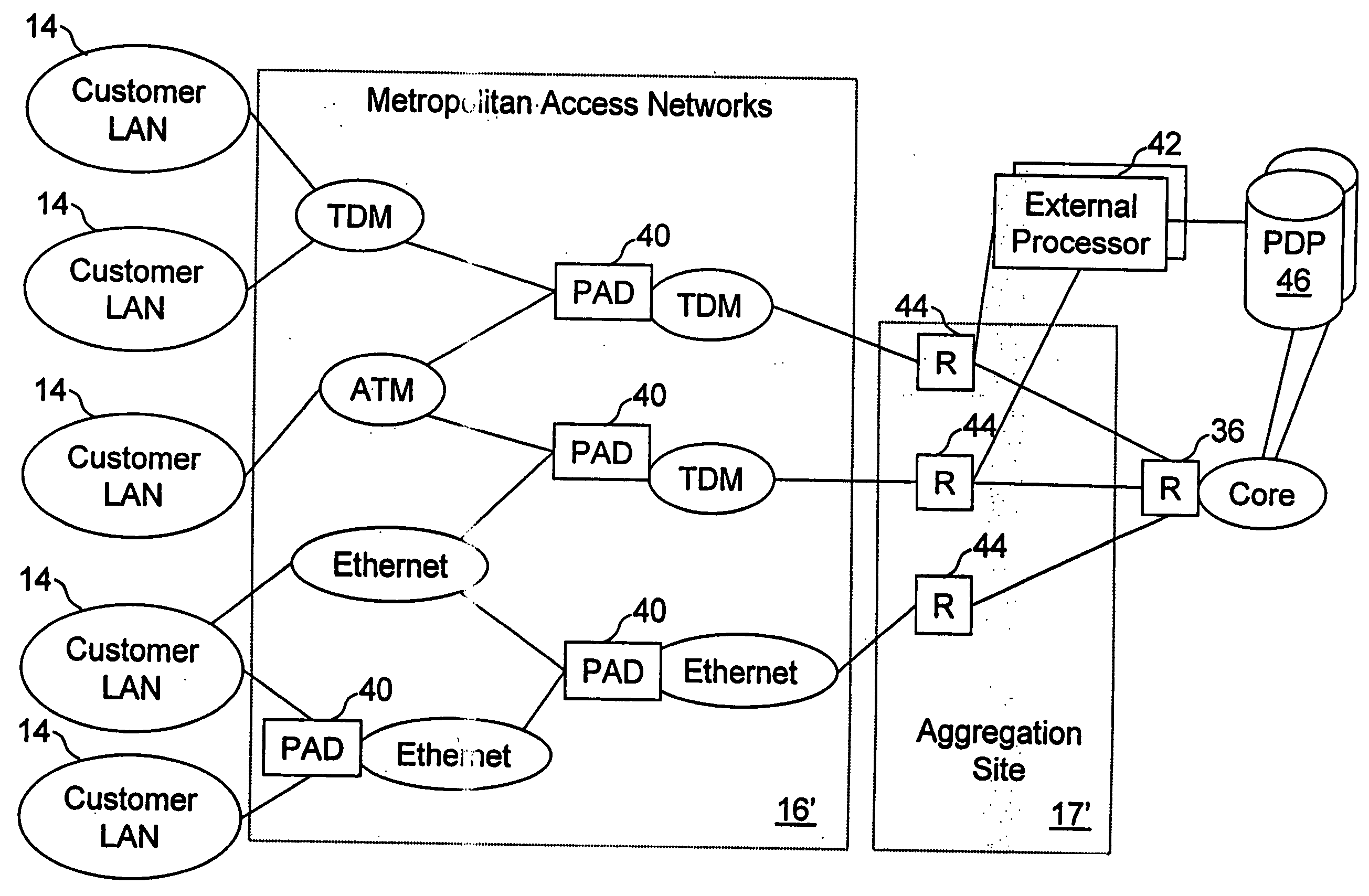
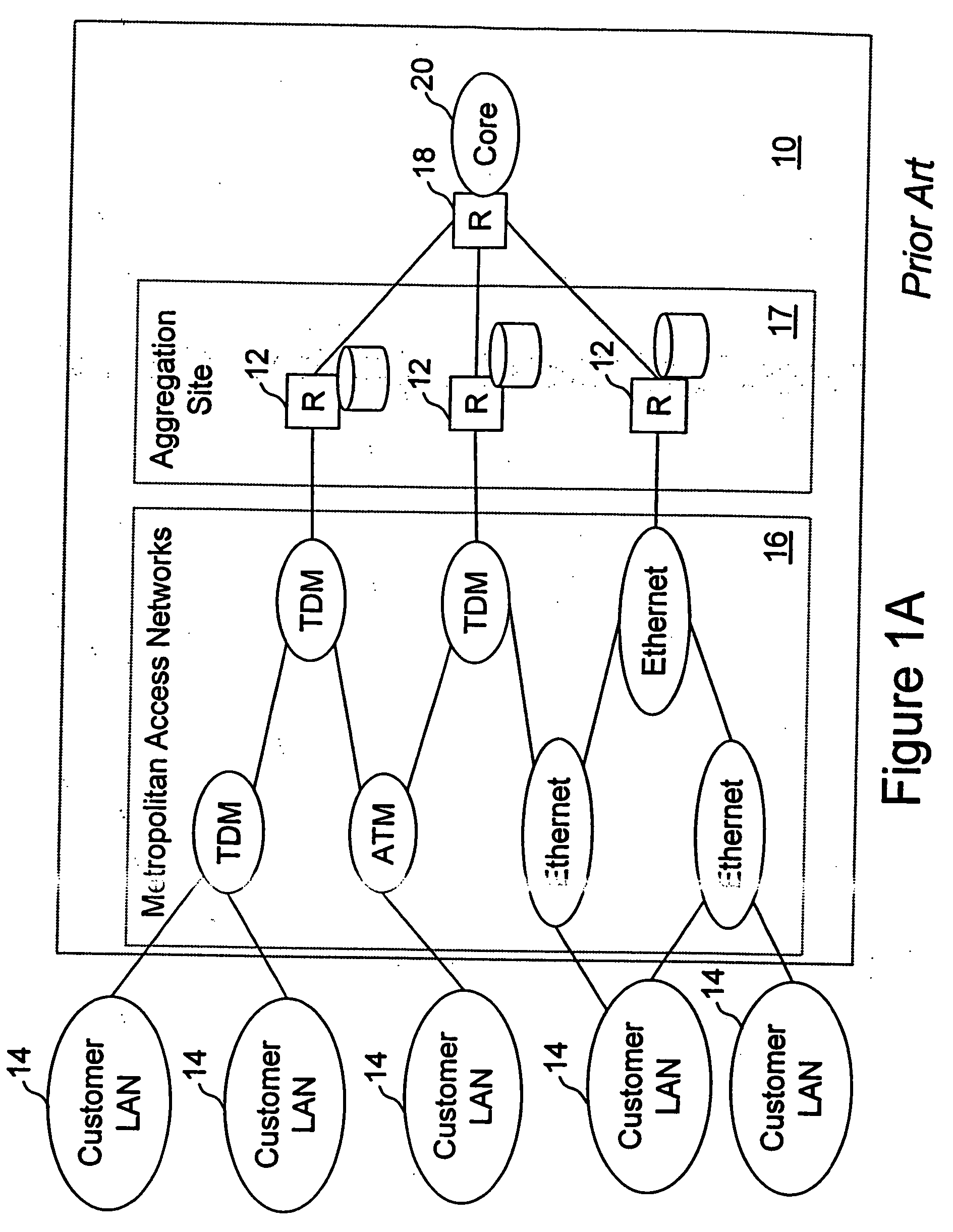
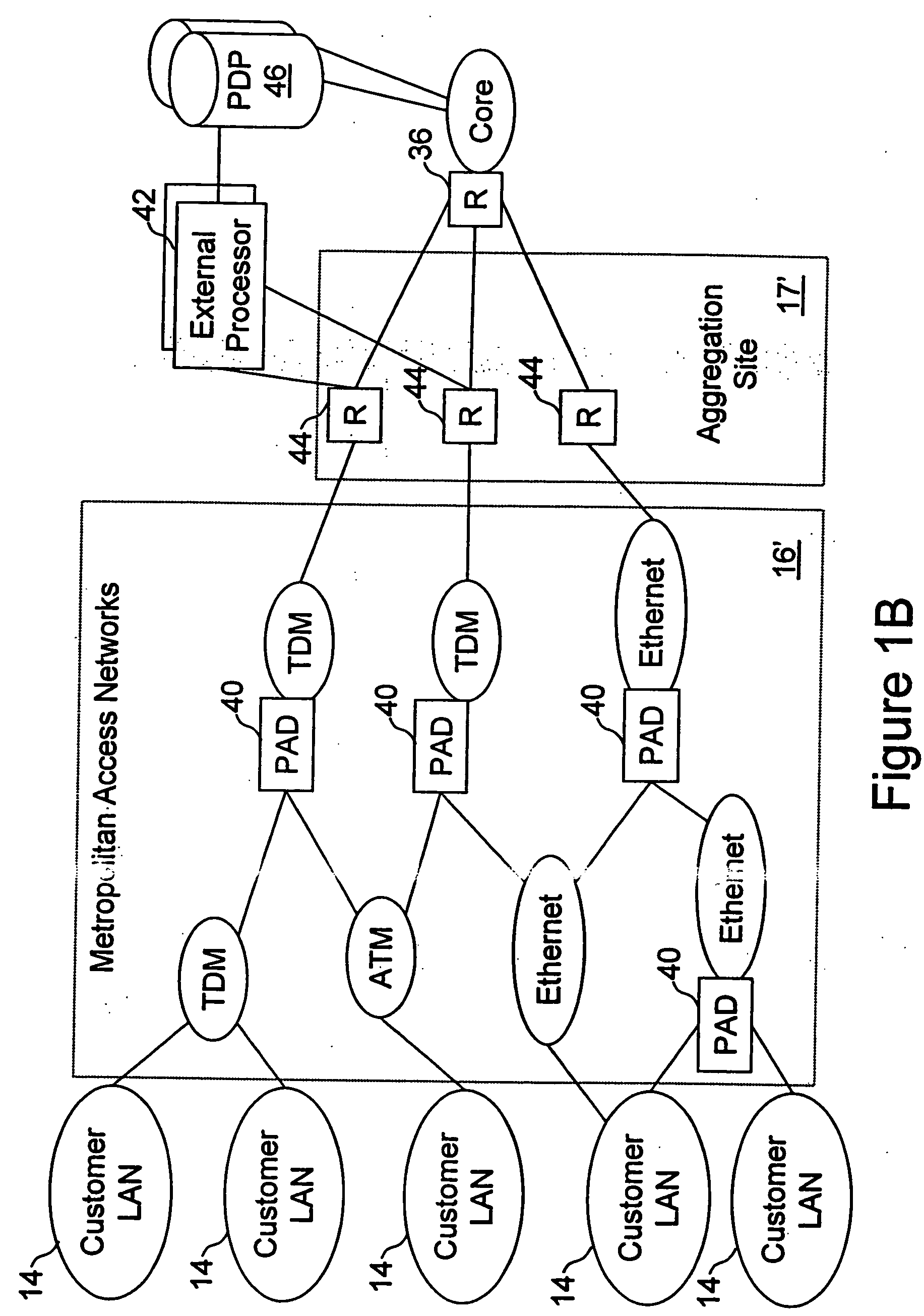
Network access system including a programmable access device having distributed service control
InactiveUS7046680B1Good extensibilityIncrease flexibilityData switching by path configurationMultiple digital computer combinationsProgrammable logic deviceMessage Passing Interface
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network. The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communicated between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
Intelligent network providing network access services (INP-NAS)
InactiveUS7496652B2Efficient use ofConsiderable timeBroadband local area networksMultiple digital computer combinationsIntelligent NetworkSmart network
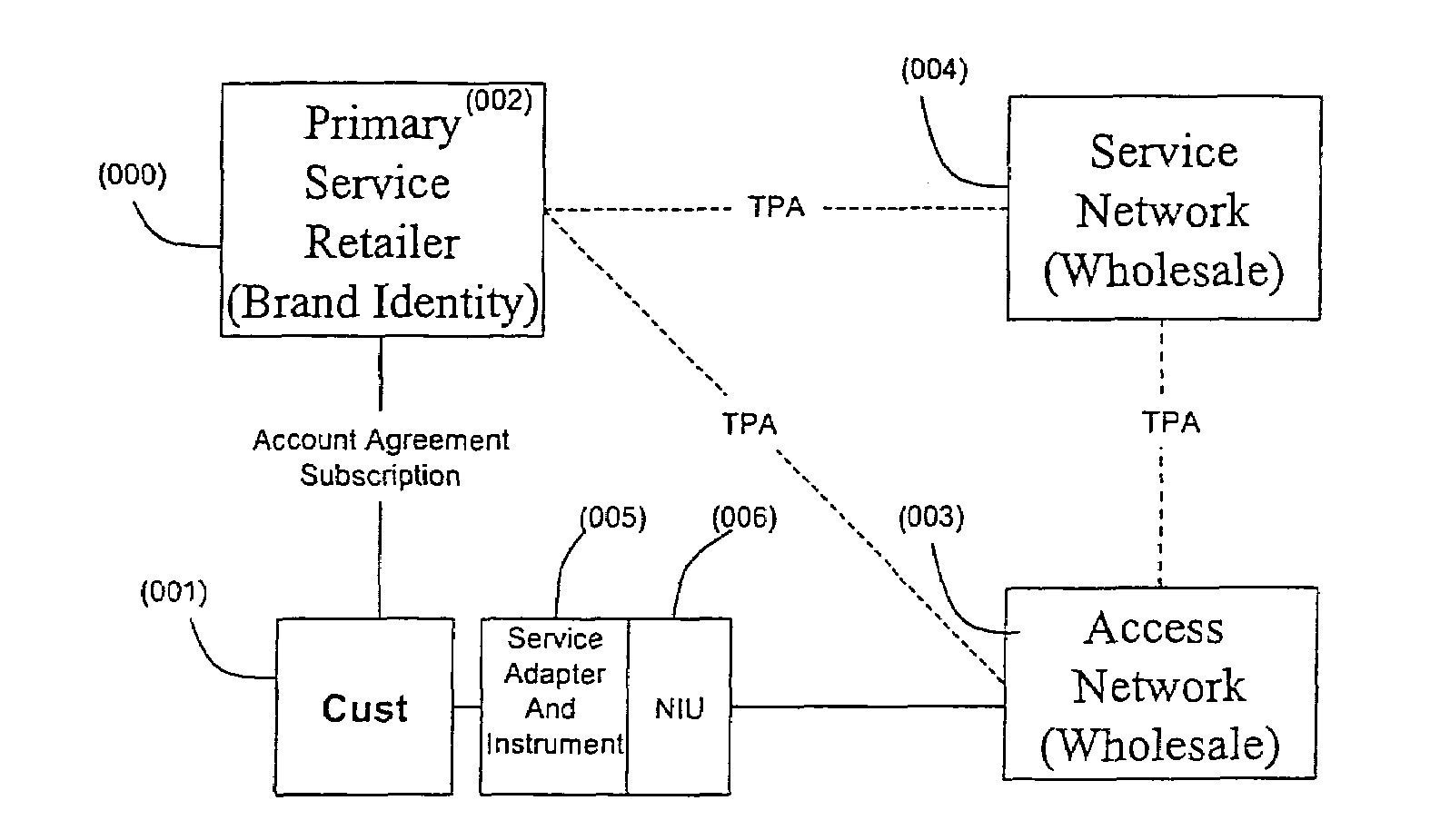
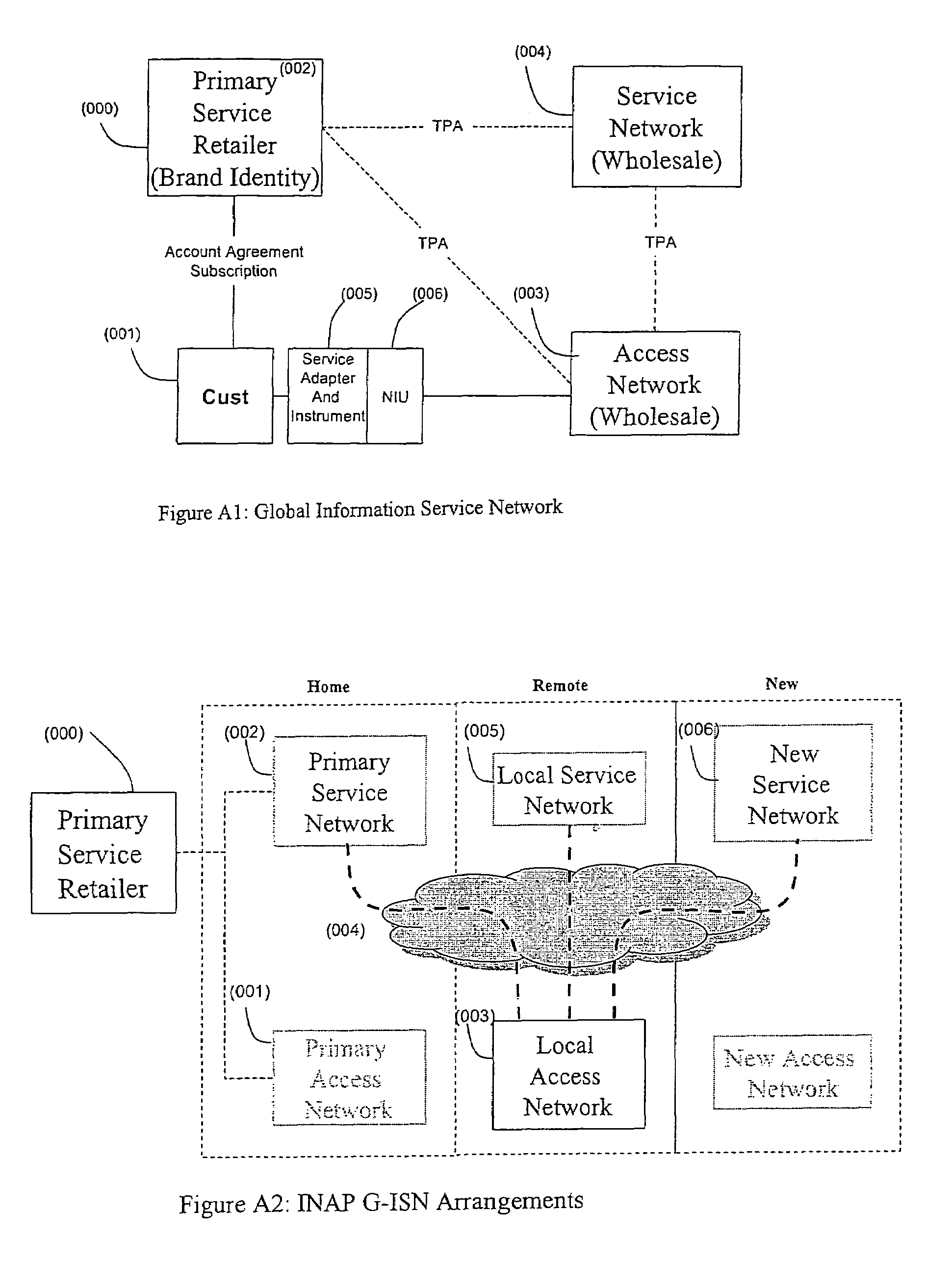
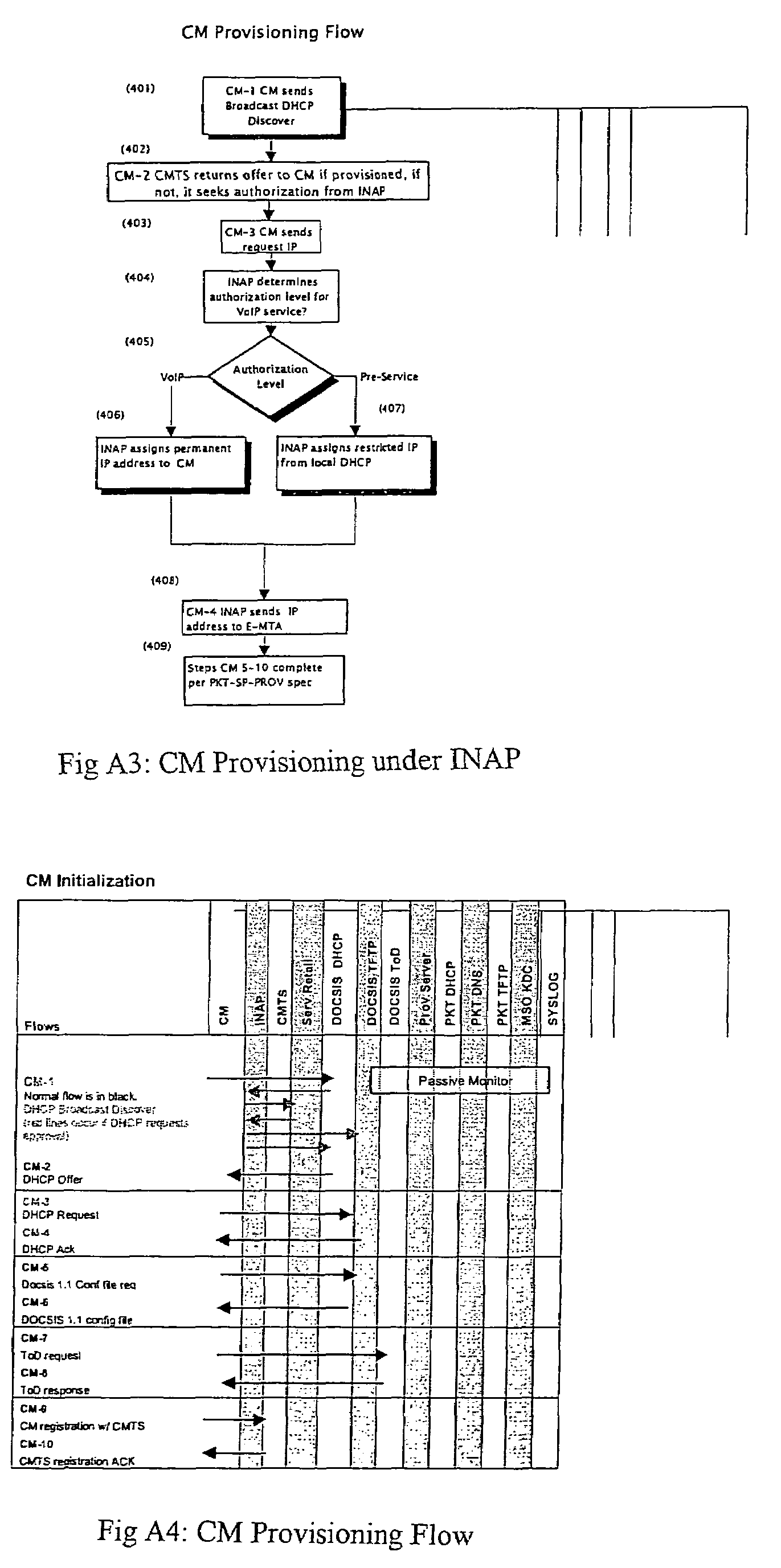
An open Information Services network architecture is disclosed which enables multiple business entities to assume specialized roles of access provider, service provider, and service retailer. The disclosed technology provides instant plug-and-play service, decouples access and service networks and provides seamless (single step) access enabling customers to maintain a service account regardless of location. The benefits of the disclosed technology, among others, include: Multi-level and multi-service registration; Broker Services providing customers with a choice of provider; Security Services relating to distribution; Revenue Assurance services, Gentle Reminder / Gentle Touch; Revenue Assurance services pertaining to usage integrity verification upon registration; mobile services derived from G-ISN; and claim benefits pertaining to LNP services derived from G-ISN.
Owner:AI-CORE TECH LLC +1
Network access system including a programmable access device having distributed service control
InactiveUS20050117576A1Good extensibilityIncrease flexibilityData switching by path configurationPacket communicationService control
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communication between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
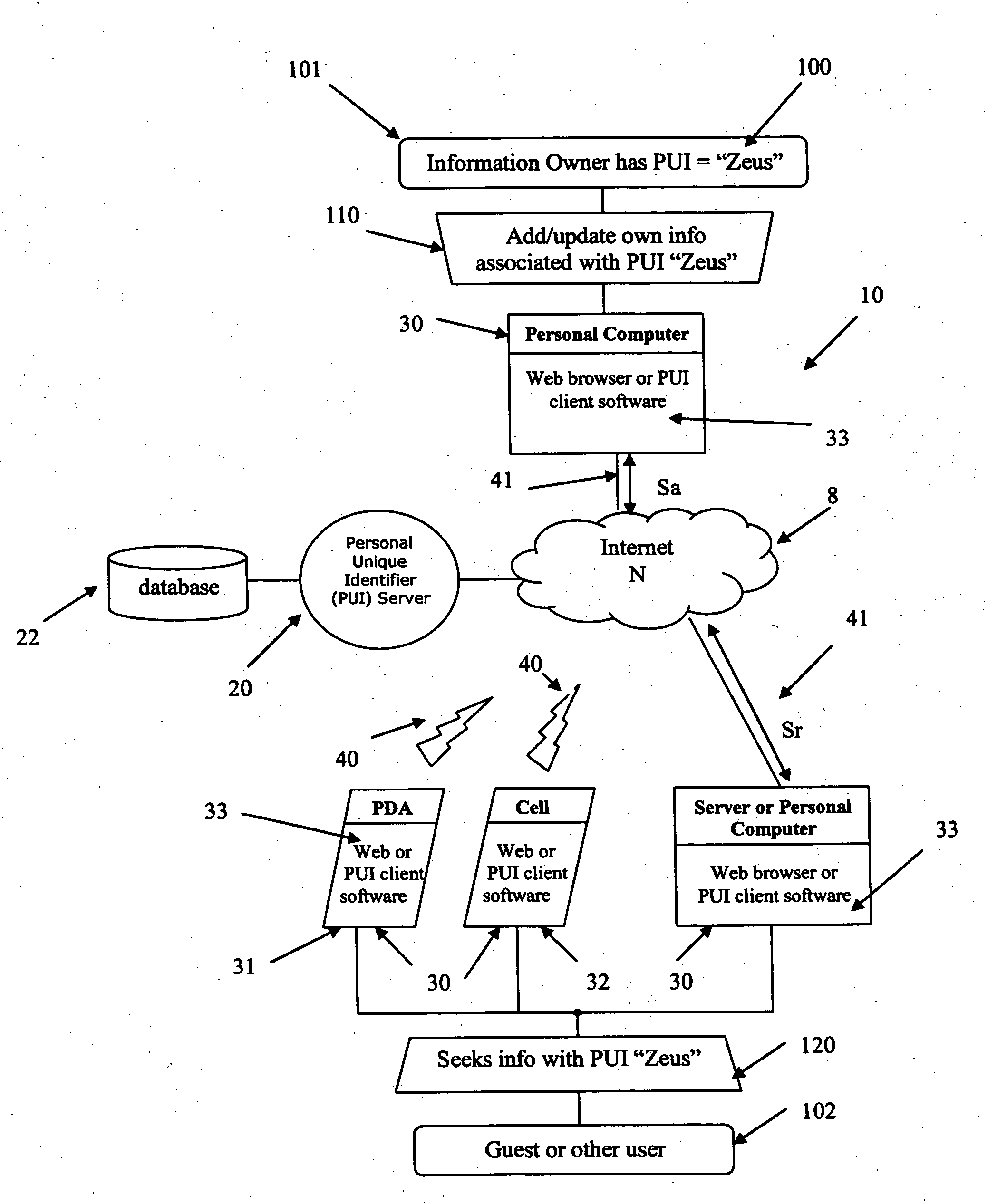
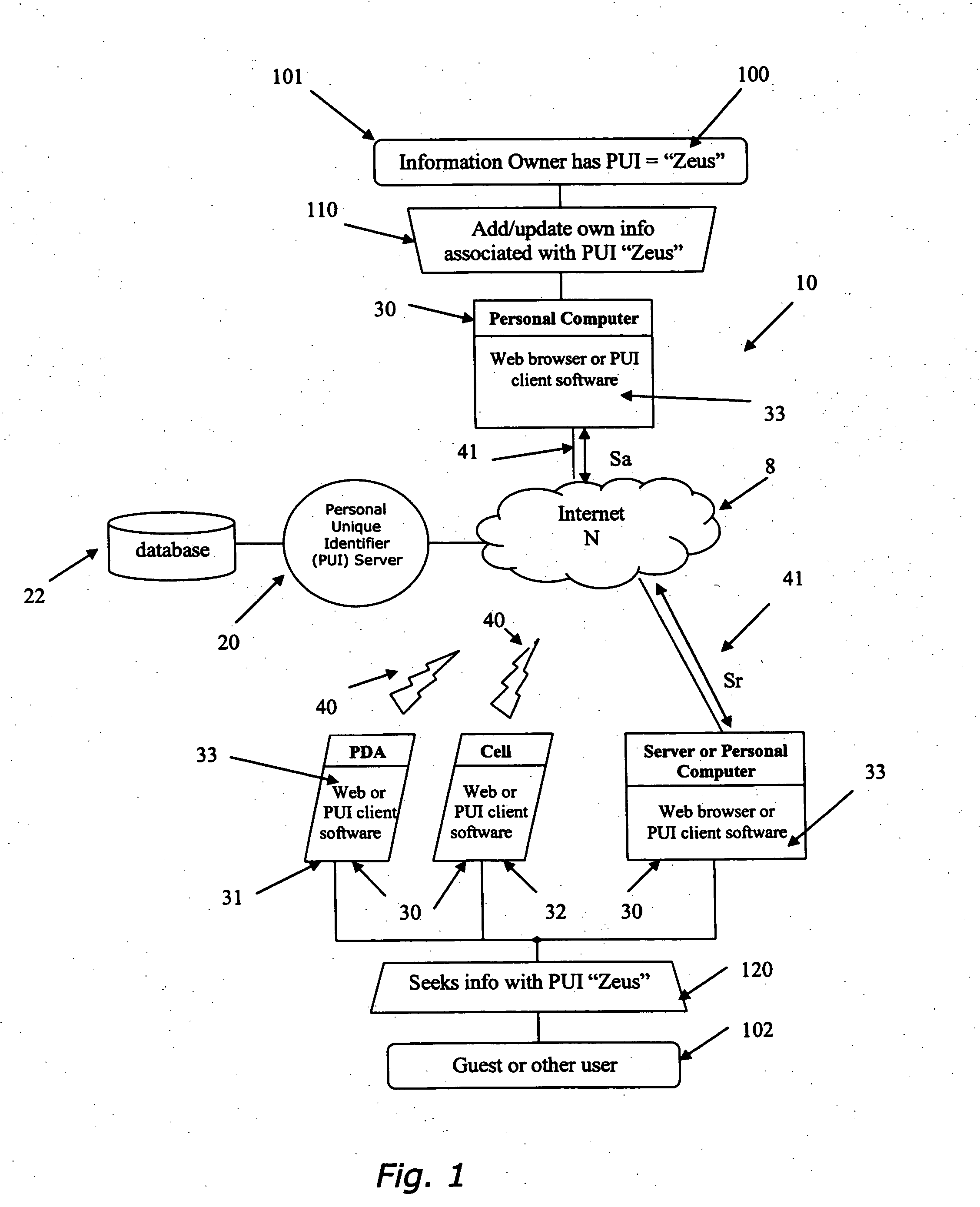
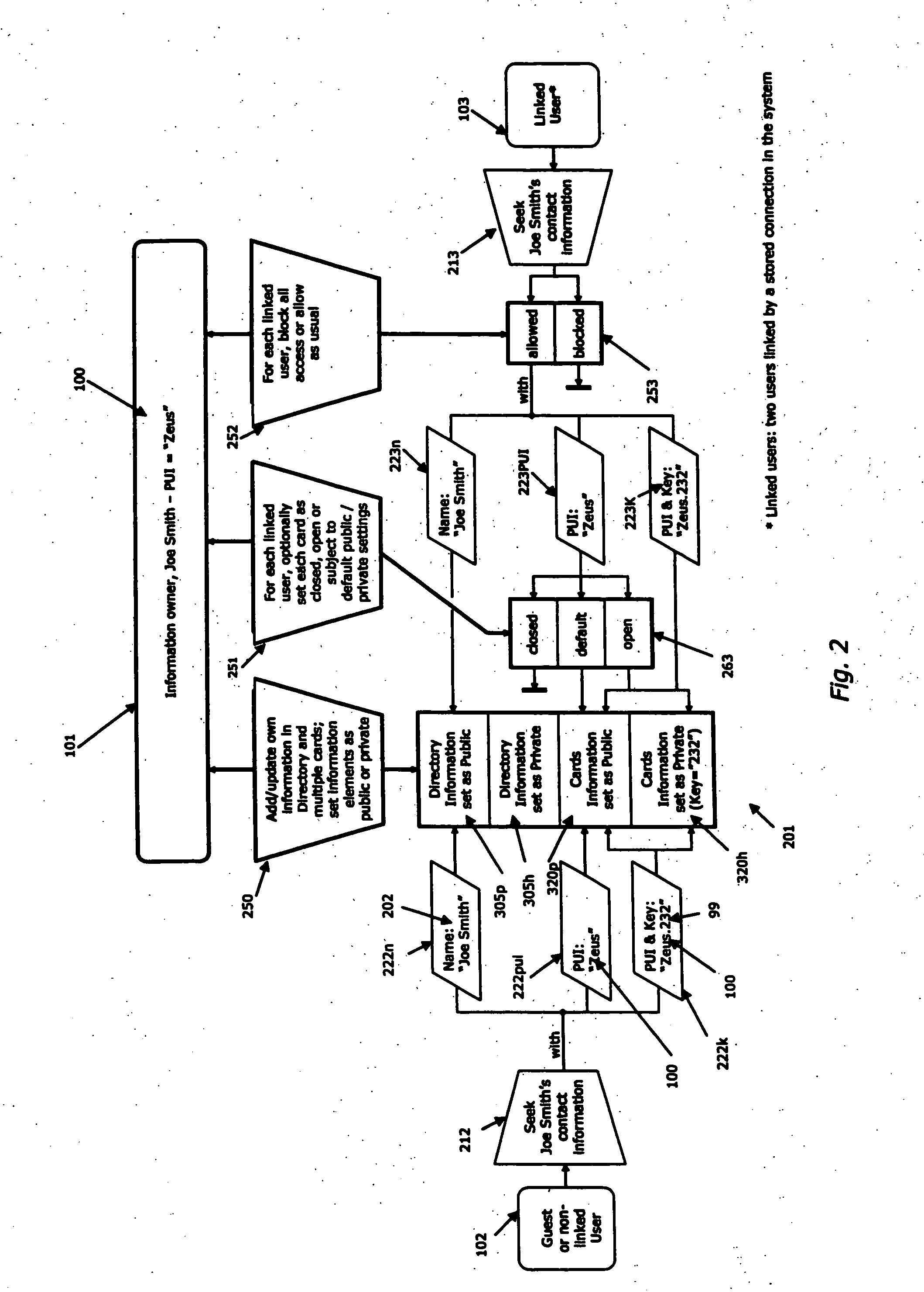
Method and system for granting access to personal information
InactiveUS20070130101A1Modified easily and seamlesslyOvercome disadvantagesDigital data processing detailsSpecial data processing applicationsWeb siteThird party
A system and method to permit users to have personal unique identifiers associated with personal information stored on a database accessed by an identity server is disclosed. The identity server is connected to one or more networks including the Internet. Users can distribute the personal unique identifier to third parties who can then obtain the personal information by accessing the server through the network. The users may modify the information stored in the database, which can then assist third parties in obtaining the modified information by inputting the personal unique identifier, or permitting client software to do so automatically on their behalf, in turn making updates to that information for the third party. This can be done over a large period of time such that third parties can easily access personal information of the user even if that information changes. The third parties may also be organizations or corporations with extensive customer lists that wish to update their client contact information with minimum interference to the customers and at minimal costs to the organization. Furthermore, users can use the personal unique identifier to populate electronic forms, such as web forms, provided on web sites hosted by organization or corporation, for the convenience of the organization or corporation and the use. The personal information of the user may also be organized in different cards having a variety of reveal and hidden status levels permitting access to additional information if a key, comprising an alphanumeric code, is entered together with the unique identifier.
Owner:ANDERSON TERRY PAUL +1
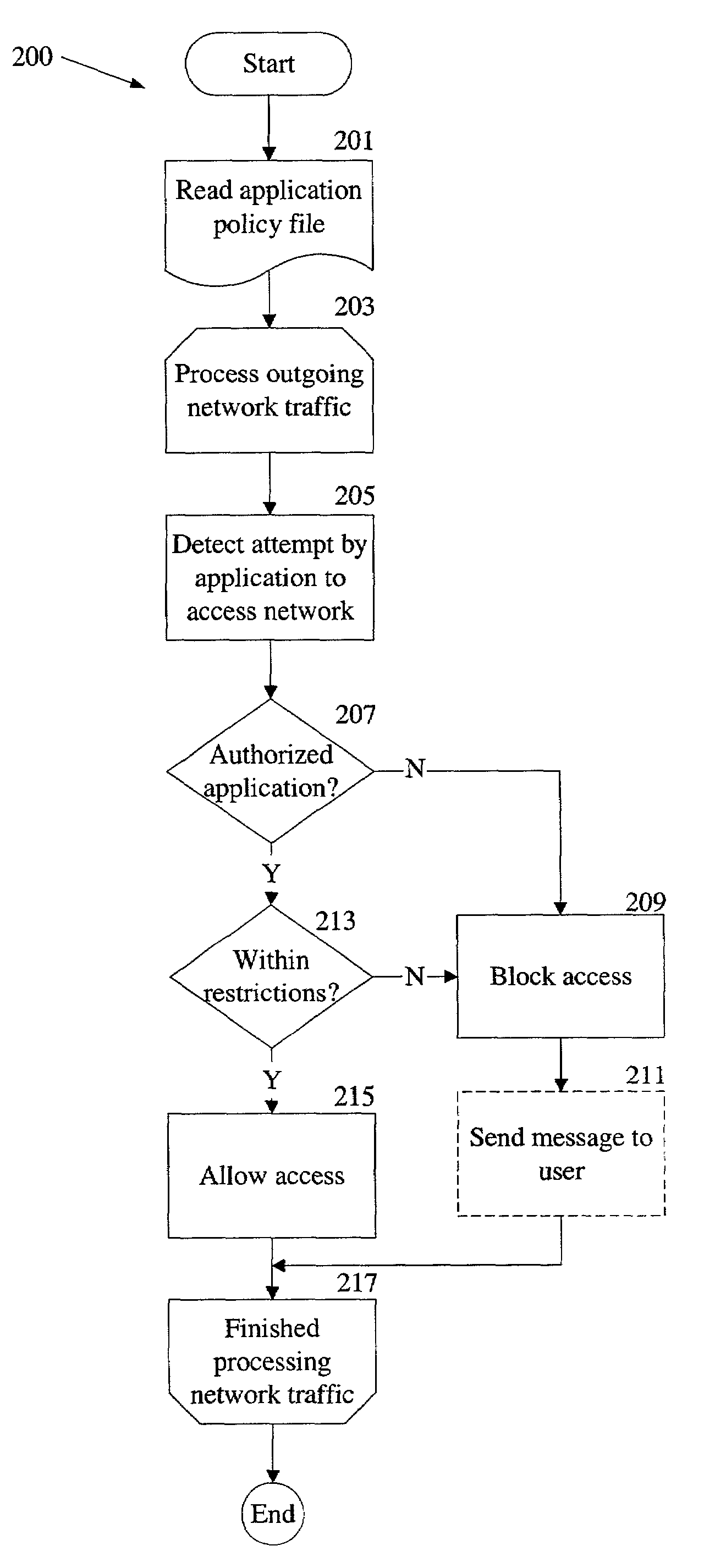
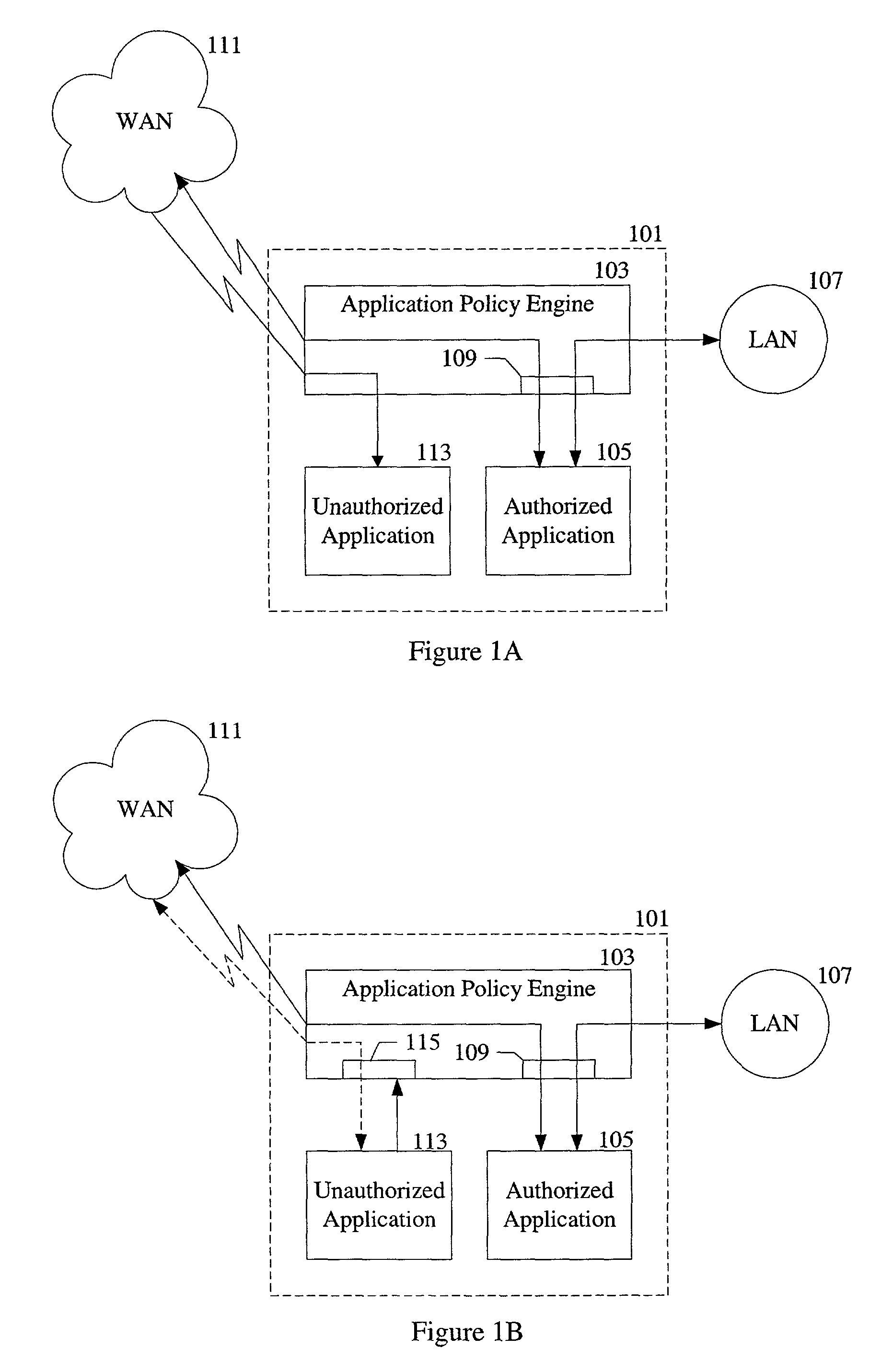
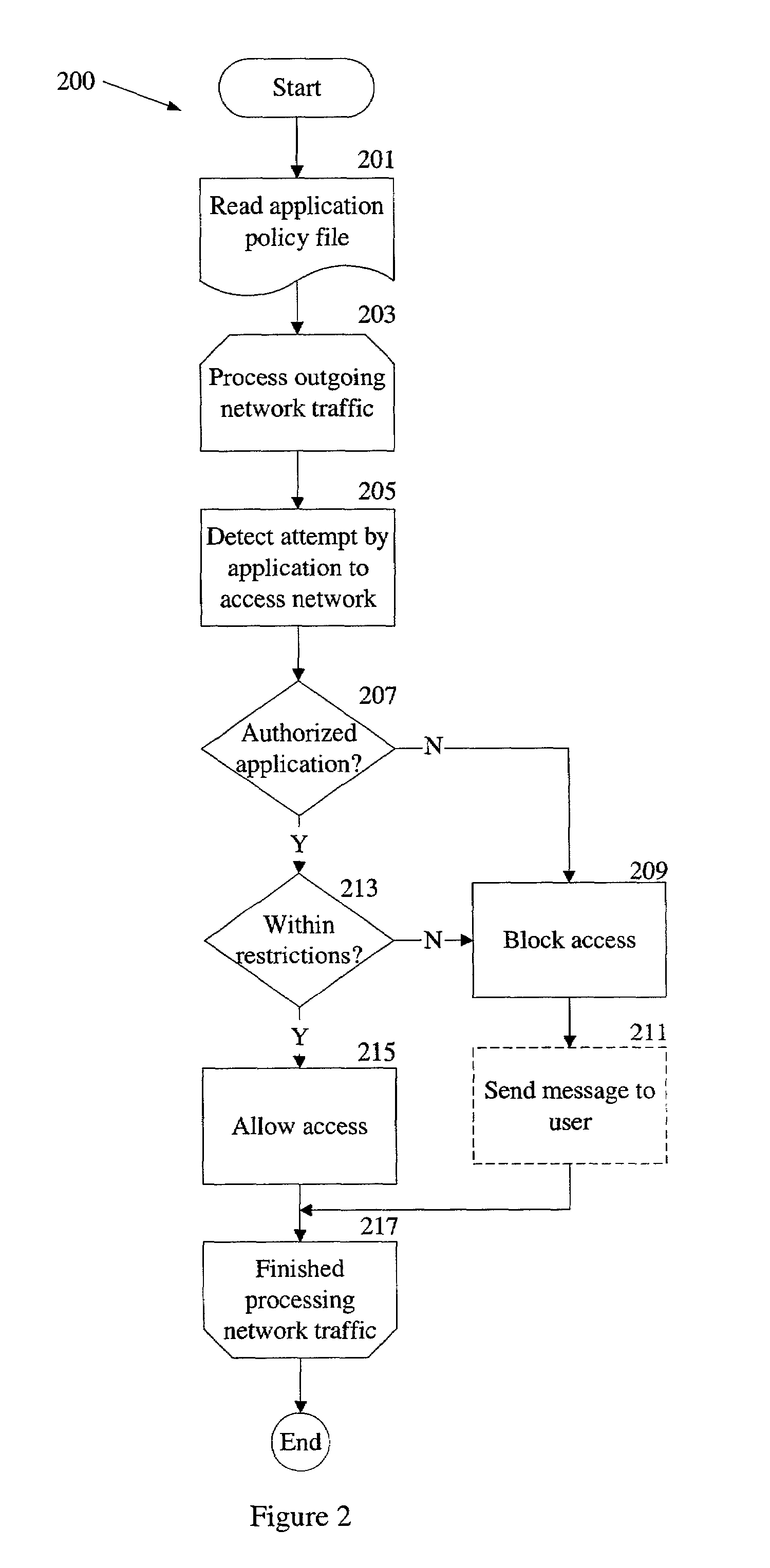
Control of interaction between client computer applications and network resources
An application policy engine for a computer blocks access to network resources by applications executing on the computer that are not authorized for such access by an application policy file. The application policy engine monitors outgoing network traffic from the computer and compares an identifier for the application contained in a network access request with application identifiers stored in the application policy file. If the application identifier is associated with an unauthorized application, access to the network is blocked by the application policy engine. In another aspect, an unauthorized application is allowed access to certain resources on a network while being blocked from other resources on the same network. In still a further aspect, an authorized application may be permitted only certain types of access to a network or network resource.
Owner:MCAFEE LLC
System and device for facilitating a transaction through use of a proxy account code
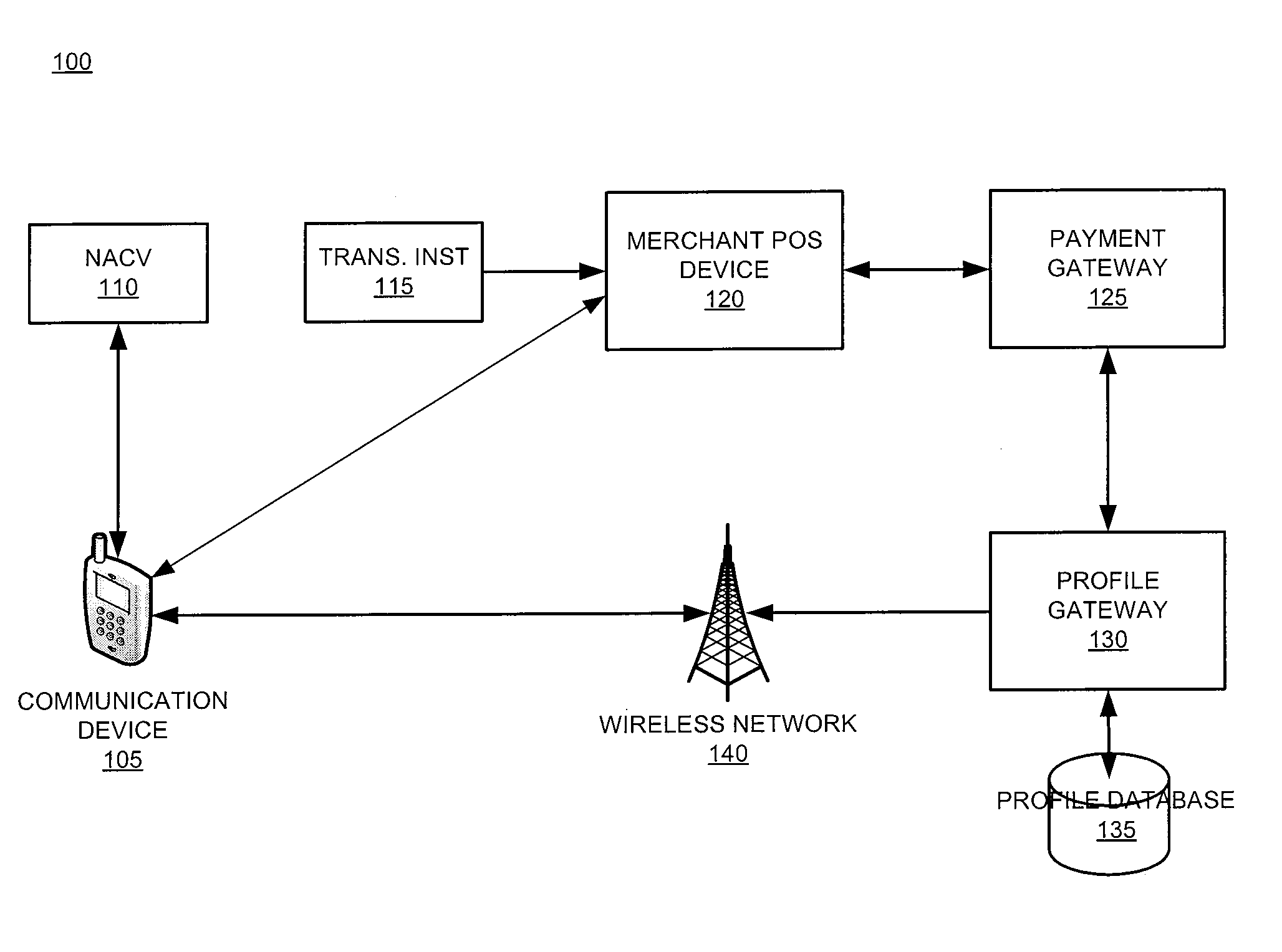
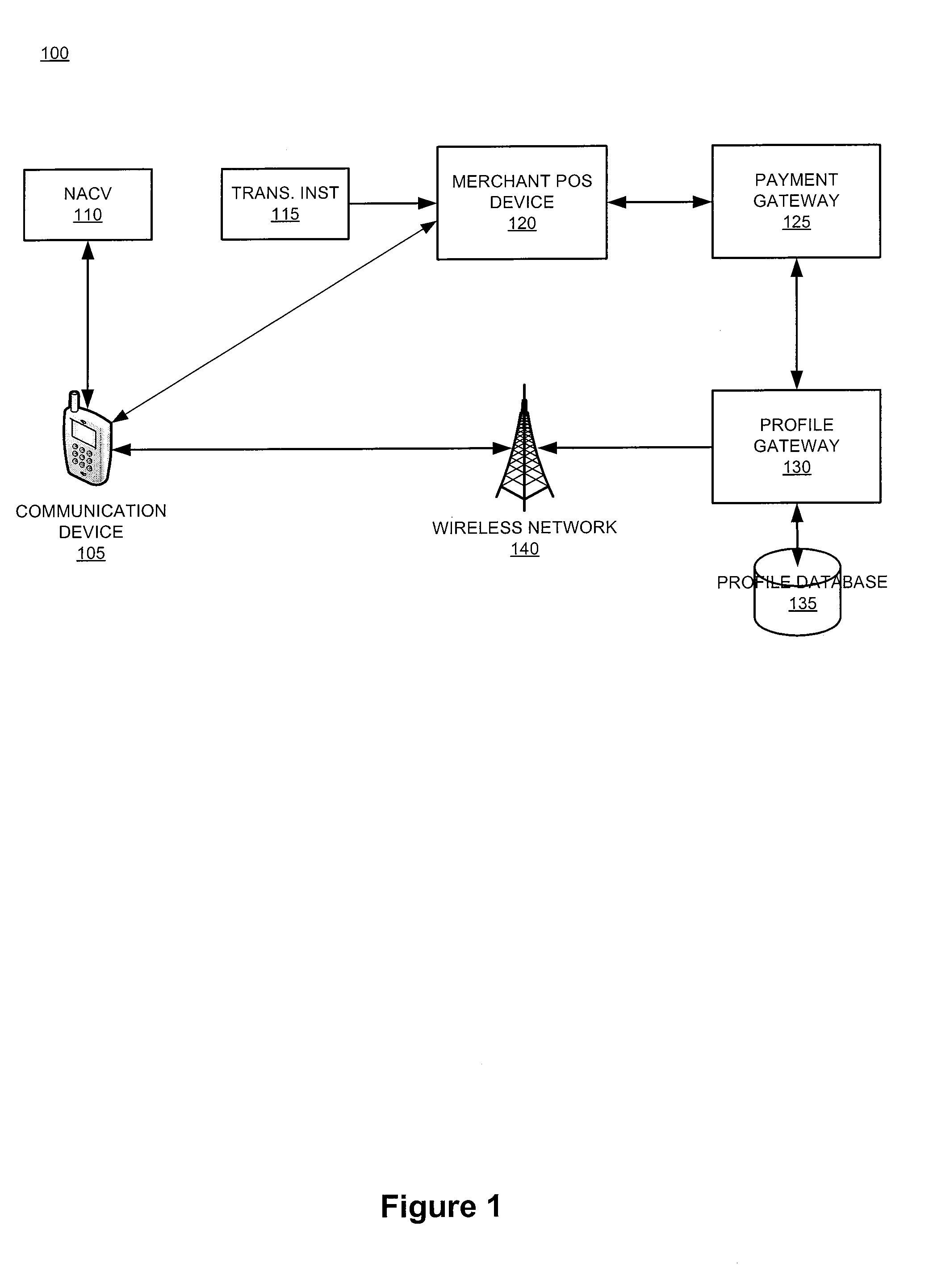
InactiveUS20110246317A1Increase dependenceFacilitating secure and convenient electronic transactionsFinancePoint-of-sale network systemsPayment transactionSmart card
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
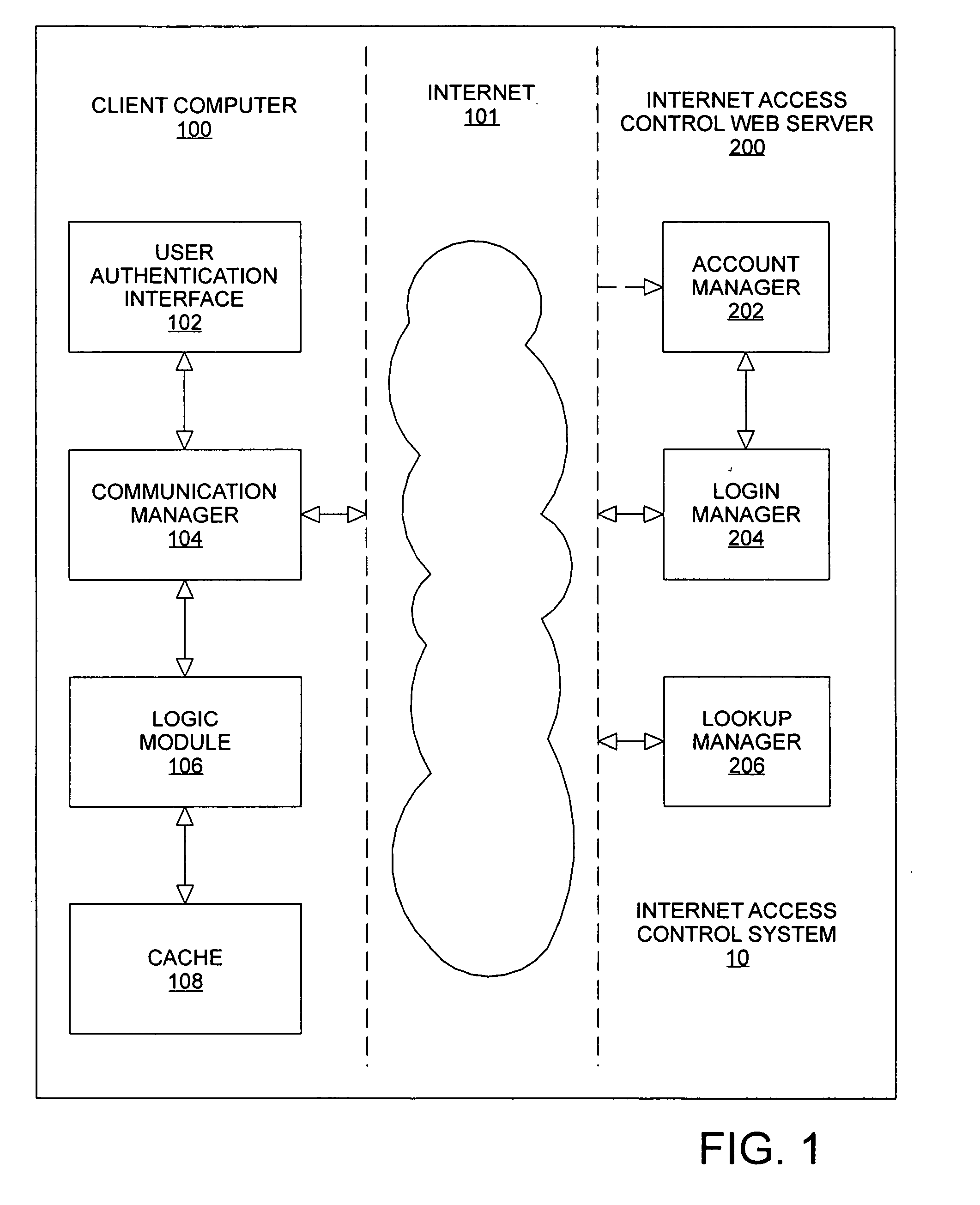
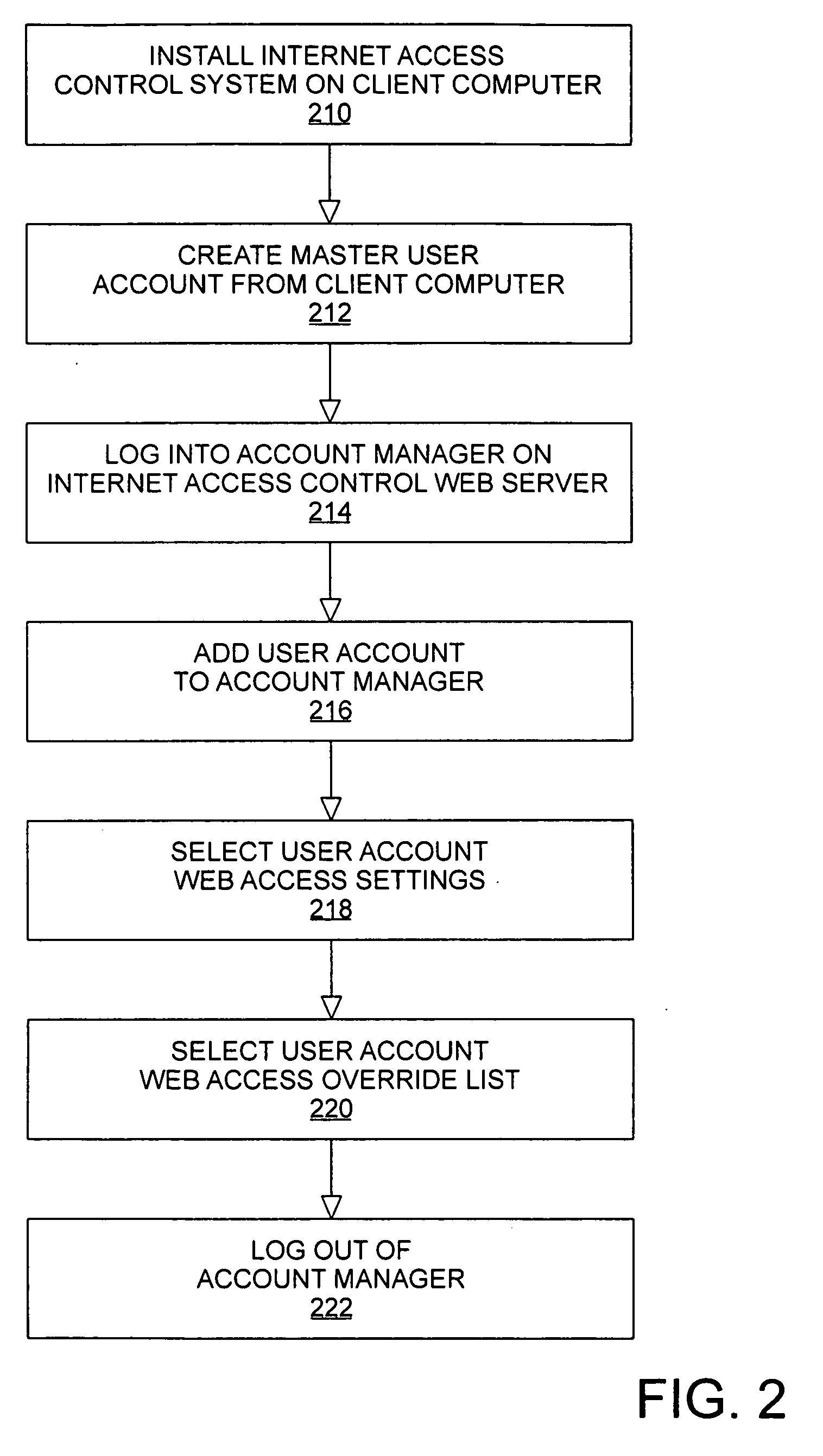
Method and apparatus for providing content access controls to access the internet
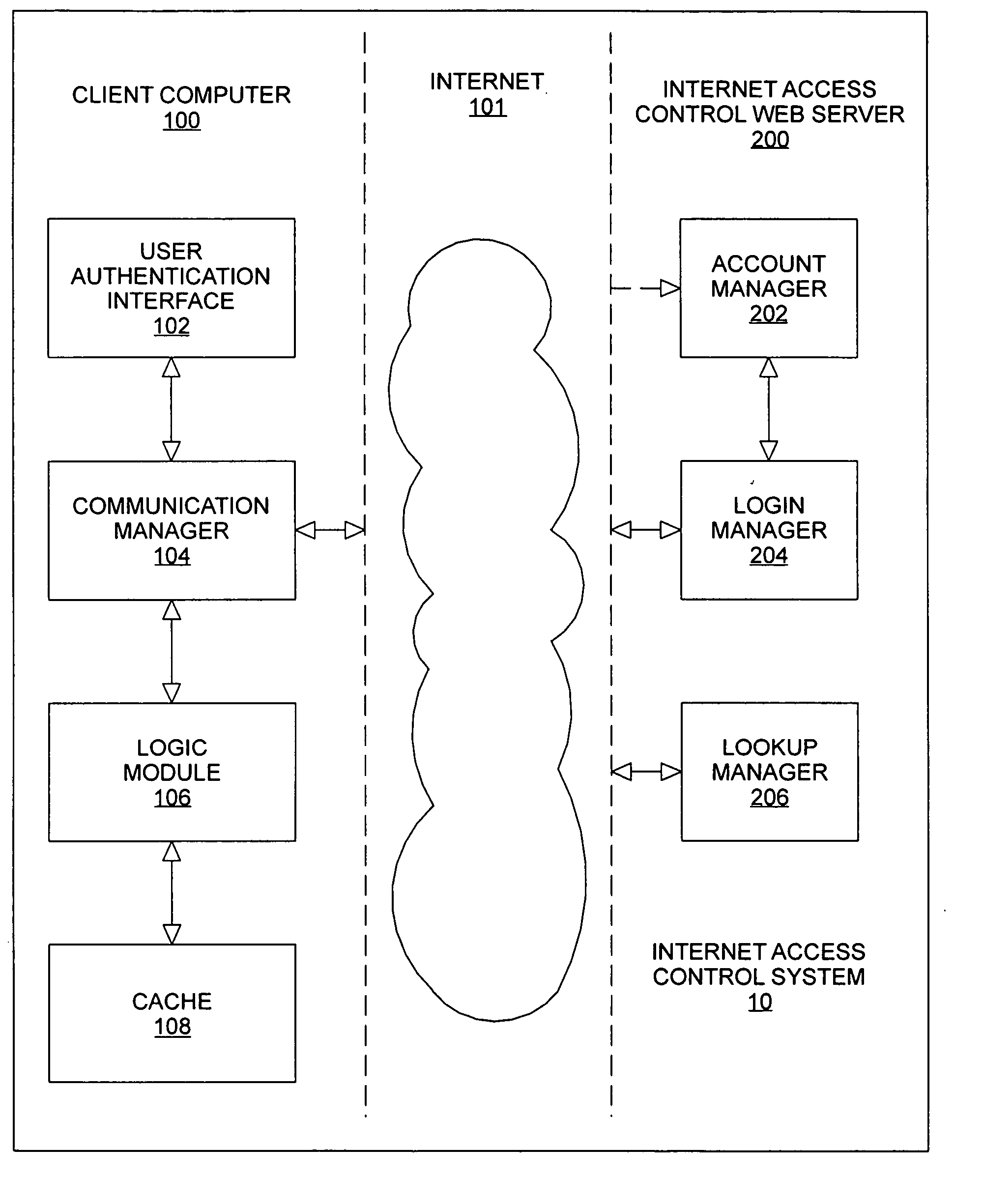
InactiveUS20050144297A1Multiple digital computer combinationsTransmissionInformation transmissionControl system
An Internet access control system is defined using a client-server architecture. The computer program installed on the client computer validates / identifies the user and user specific information is passed to the client computer. All user requests to access the Internet are intercepted by an application executing on the client computer. The URL extracted from the internet access request is sent to the Internet access control web server to determine if the URL is in a master list of previously evaluated websites. If the URL is found, the website ratings and subject matter categories are sent to the client computer for determination of whether or not the website contains information appropriate for the user attempting to access the Internet using web access settings defined by, for example, a parent or employer. If the URL is determined to be appropriate, the Internet access request is sent to the computer networking layer to which the request was originally routed; otherwise, the Internet access request is edited and is sent to the computer networking layer to which the request was originally routed for redirection of the transmission request.
Owner:KIDSNET
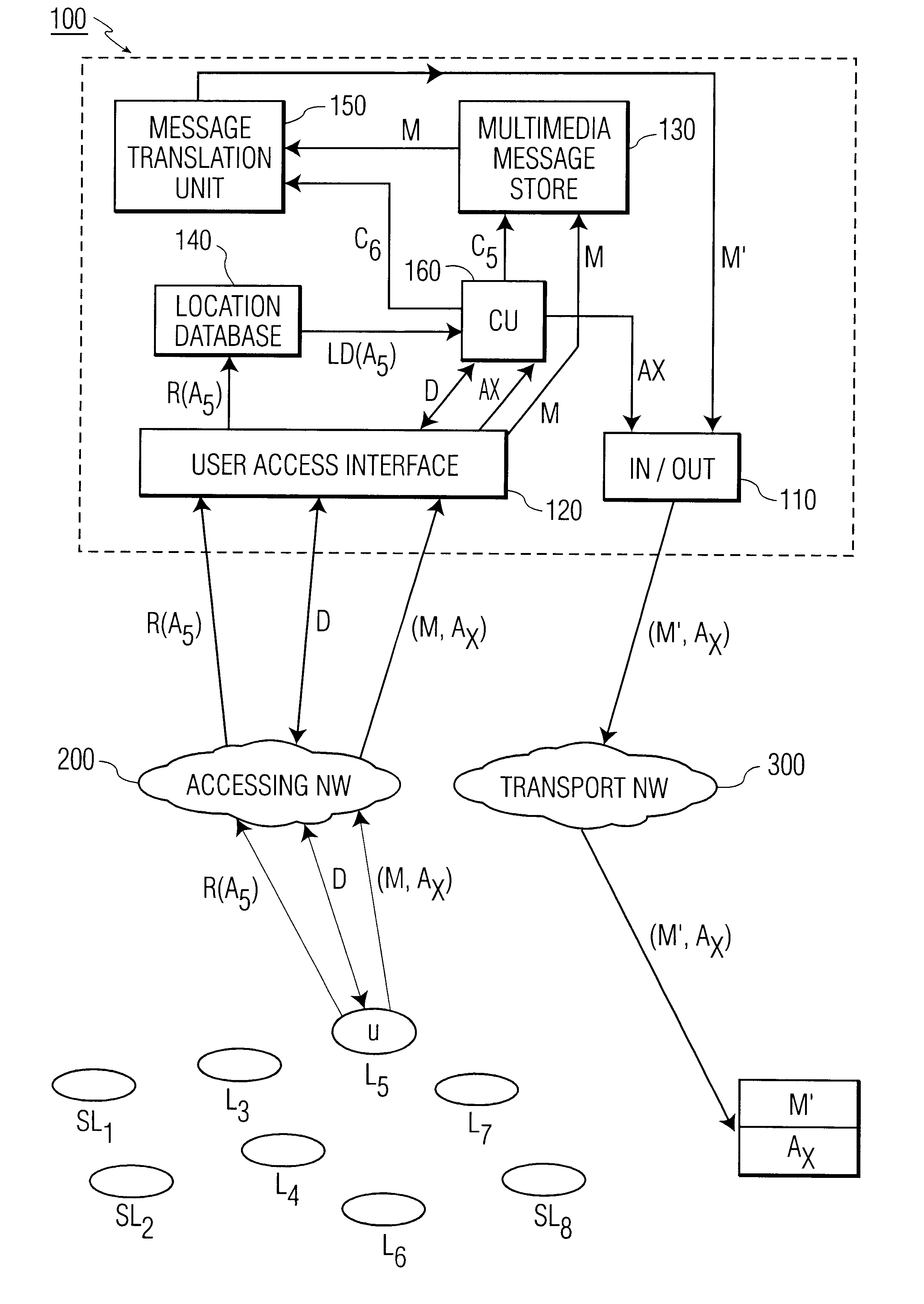
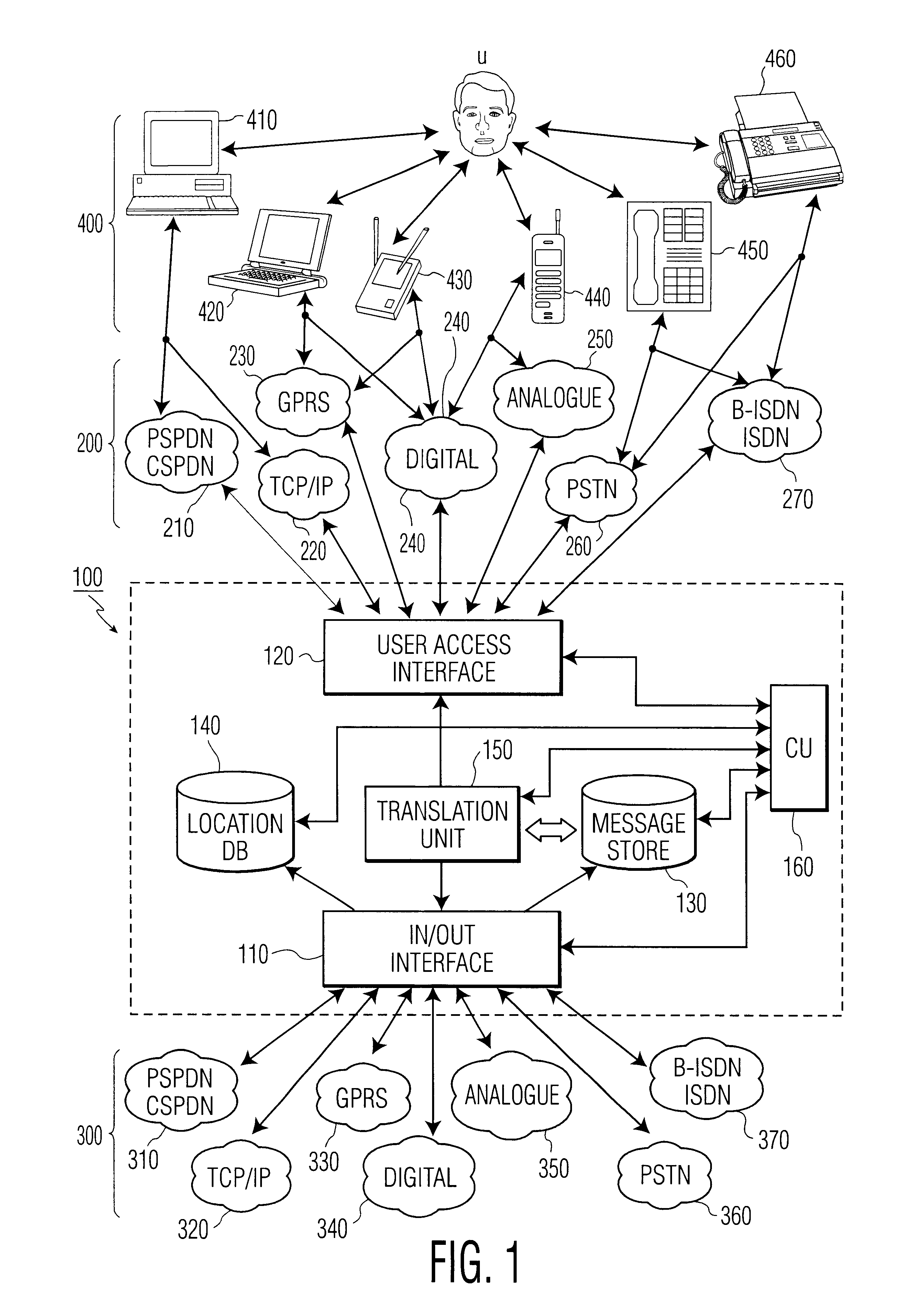
Methods and arrangement in a communication system
InactiveUS6333919B2Minimization requirementsMultiplex system selection arrangementsSpecial service provision for substationAccess networkCommunications system
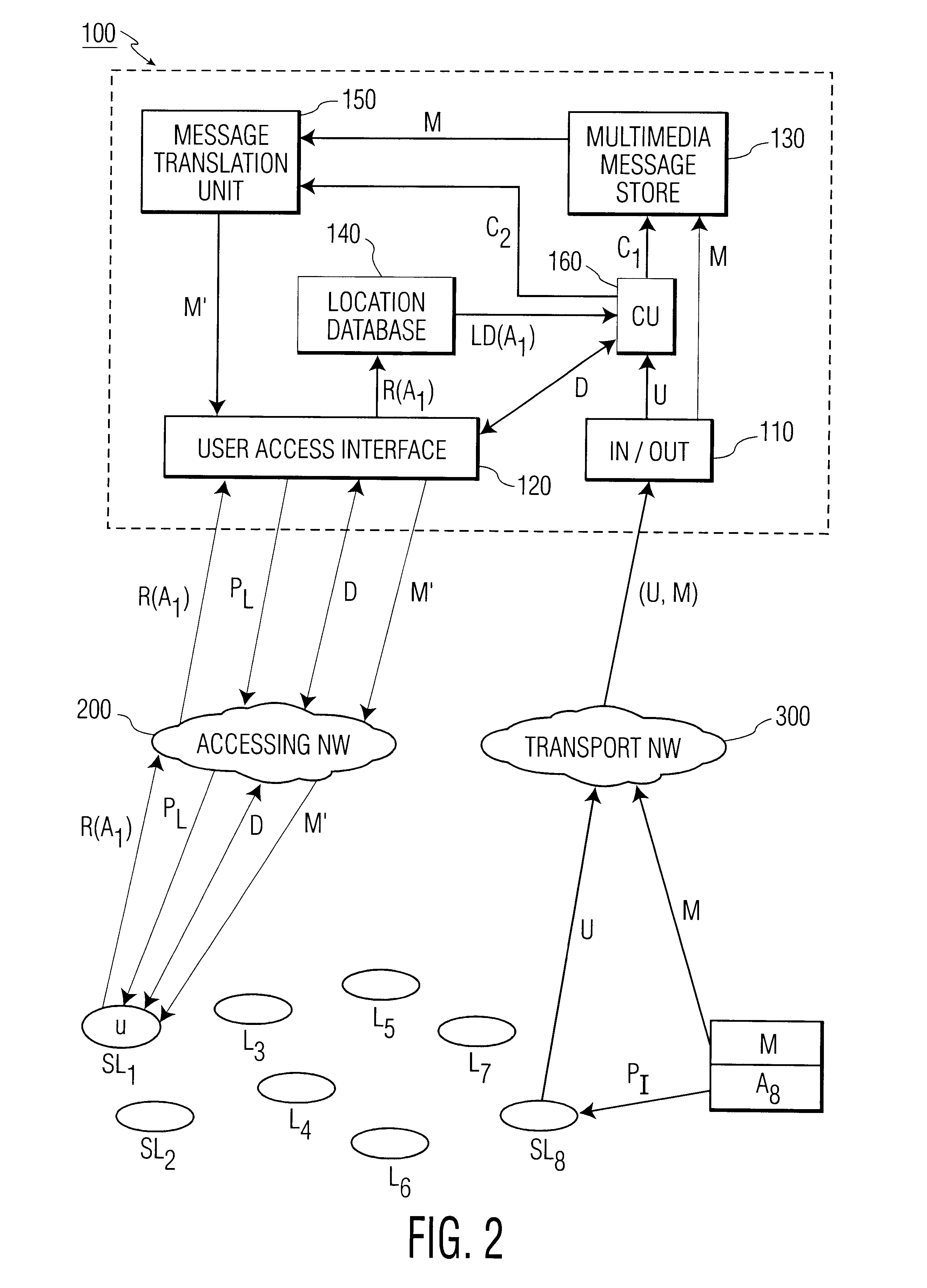
The present invention relates to methods and an arrangement for receiving, storing, and originating multimedia messages. An incoming message is transmitted to an in / out interface via a transport network. The message is stored in a message store, translated in a translation unit into a format adapted to the presentation capabilities of receiver's current terminal and delivered to the receiver over a user access interface and an access network with guidance from a location database. Earlier received messages, which are kept in the message store, can be accessed and edited via any standardized access network using media translation in the translation unit. A multimedia message is originated by a user in the system via any access network and the user access interface. The message is then stored in the message store, translated in the translation unit, and delivered to the destination through the in / out interface and an appropriate transport network.
Owner:IDTP HLDG
Integrated security and communications system with secure communications link
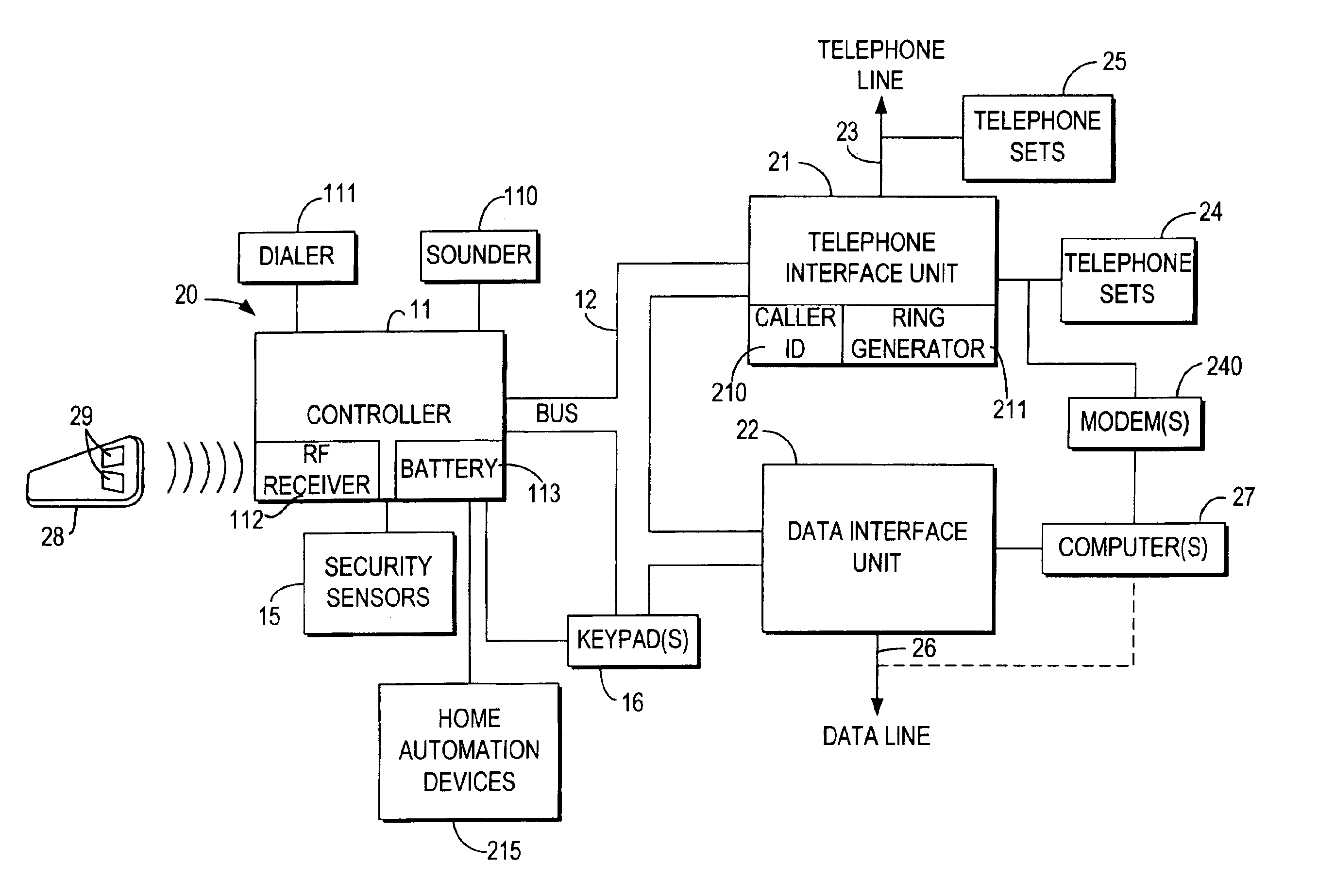
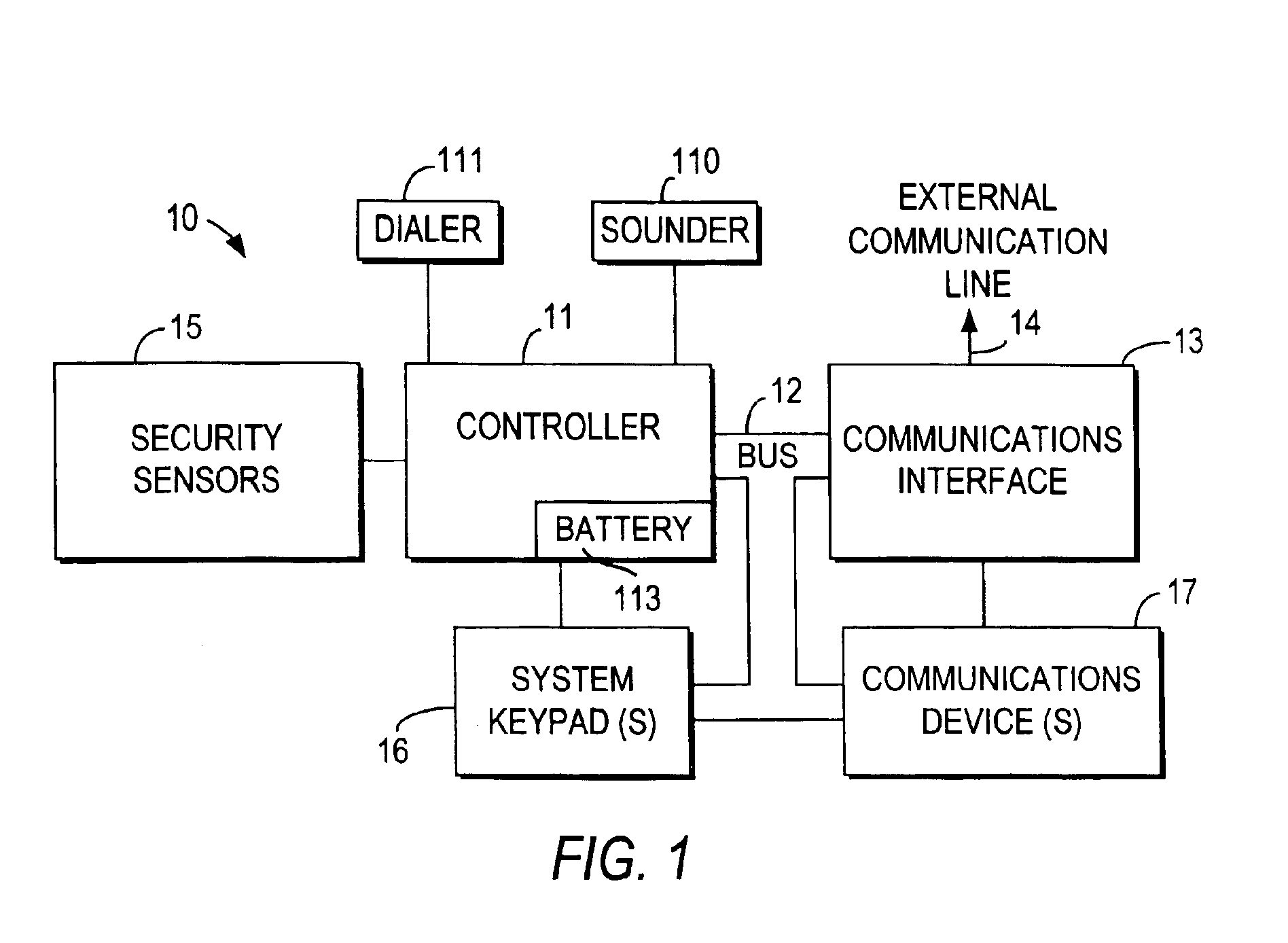
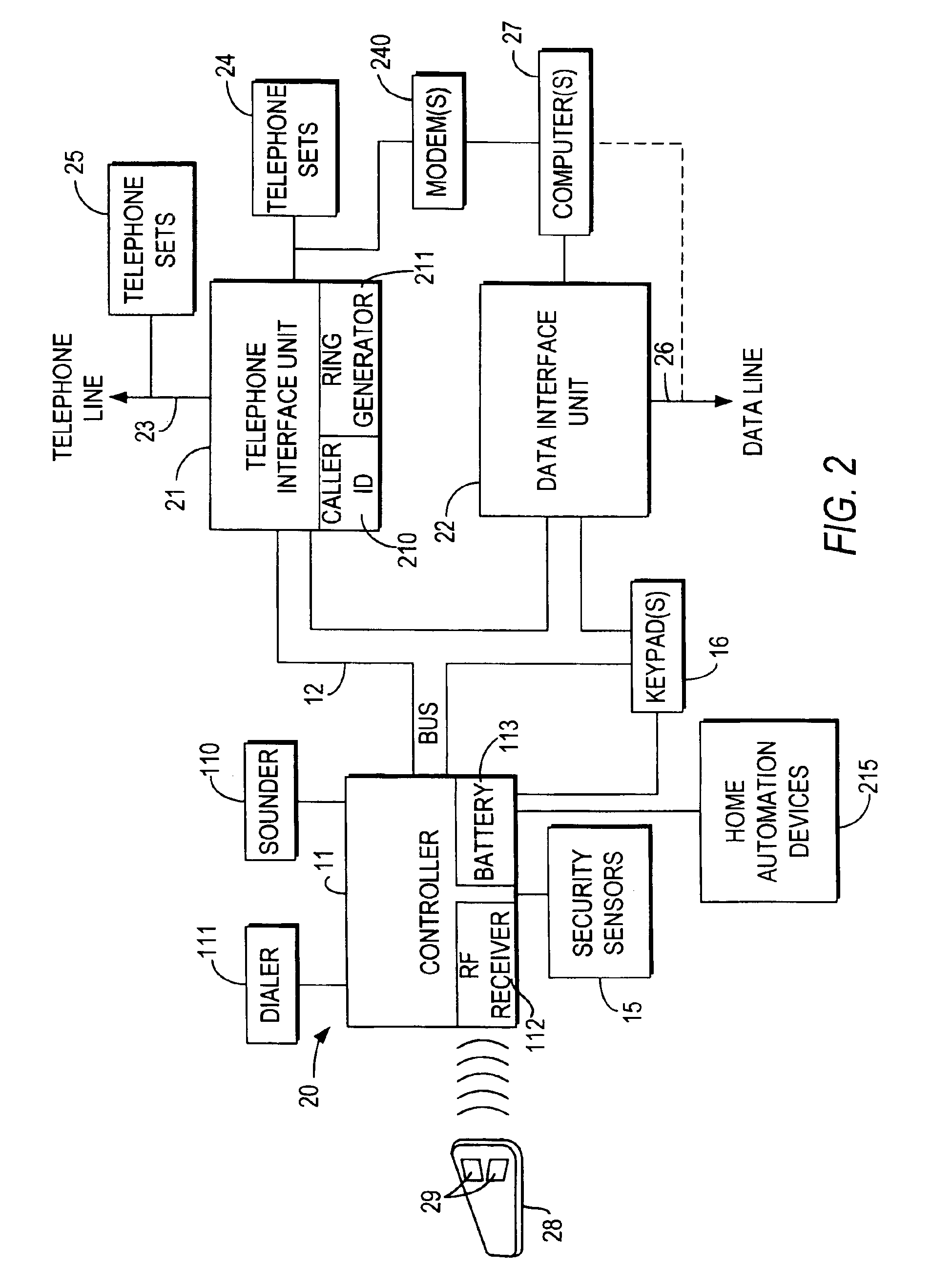
InactiveUS6928148B2Minimize the numberImprove securitySpecial service for subscribersCalled number recording/indicationData interfaceSecurity system
An integrated security and communications system combines a security system to either or both of a telephone system interface and a data interface. Users have access to voice-mail or other PBX-type telephone functions, many or all of which can be accessed not only at telephone sets, but also at keypads of the security system. Data functions such as electronic mail and possible partial or full World Wide Web access may also be provided at the keypads, as well as at connected personal computers or computer terminals. The system keypads may be enhanced to better accommodate some of the added functions. A central communications station could be used to maintain secure, shared private key encrypted communications with each premises system, using a redirector arrangement or relay to allow each premises system to communicate securely with a central monitoring station and with other systems. The secure communications system could be used without a security system to allow secure computer-to-computer communications.
Owner:ADEMCO INC
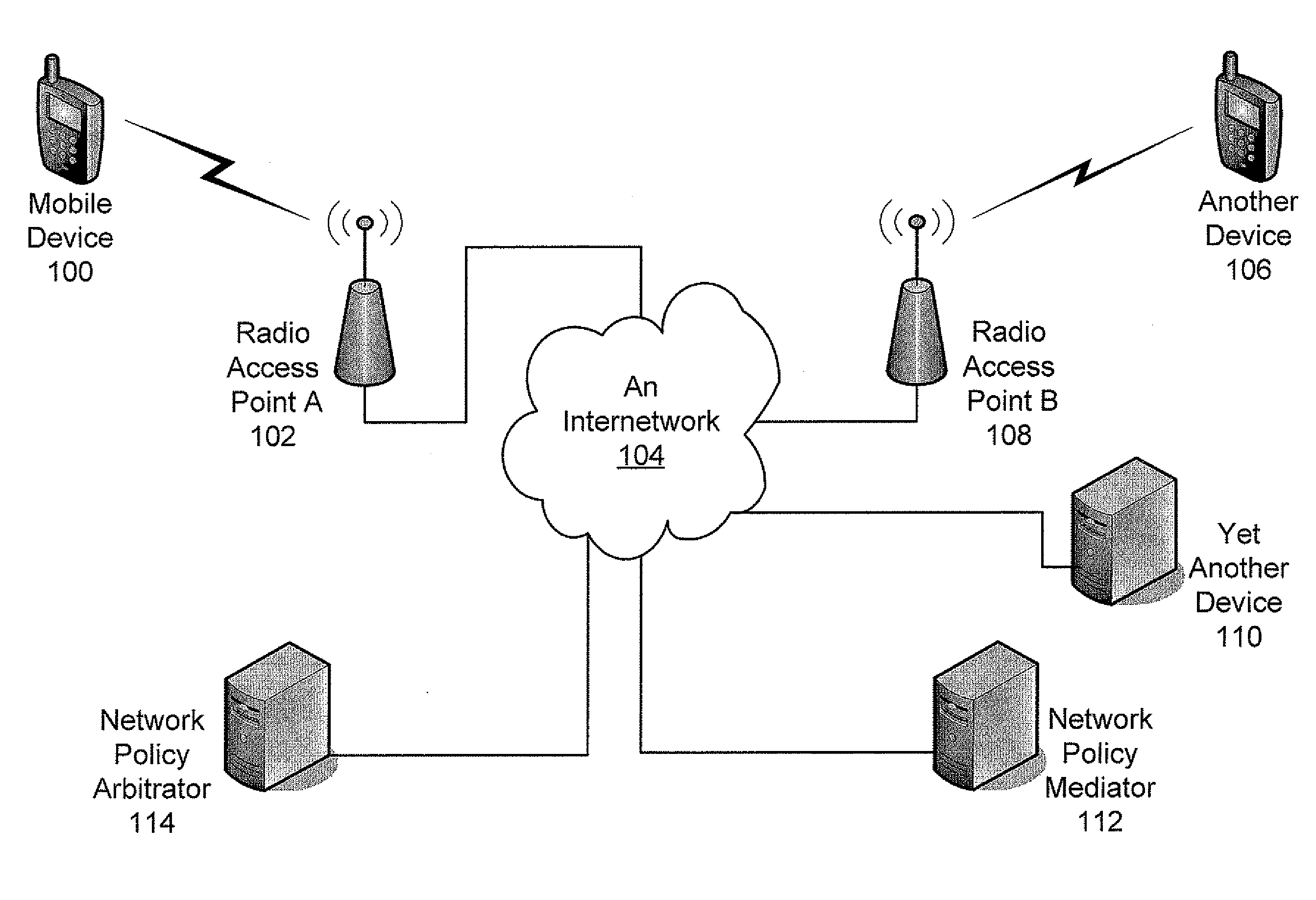
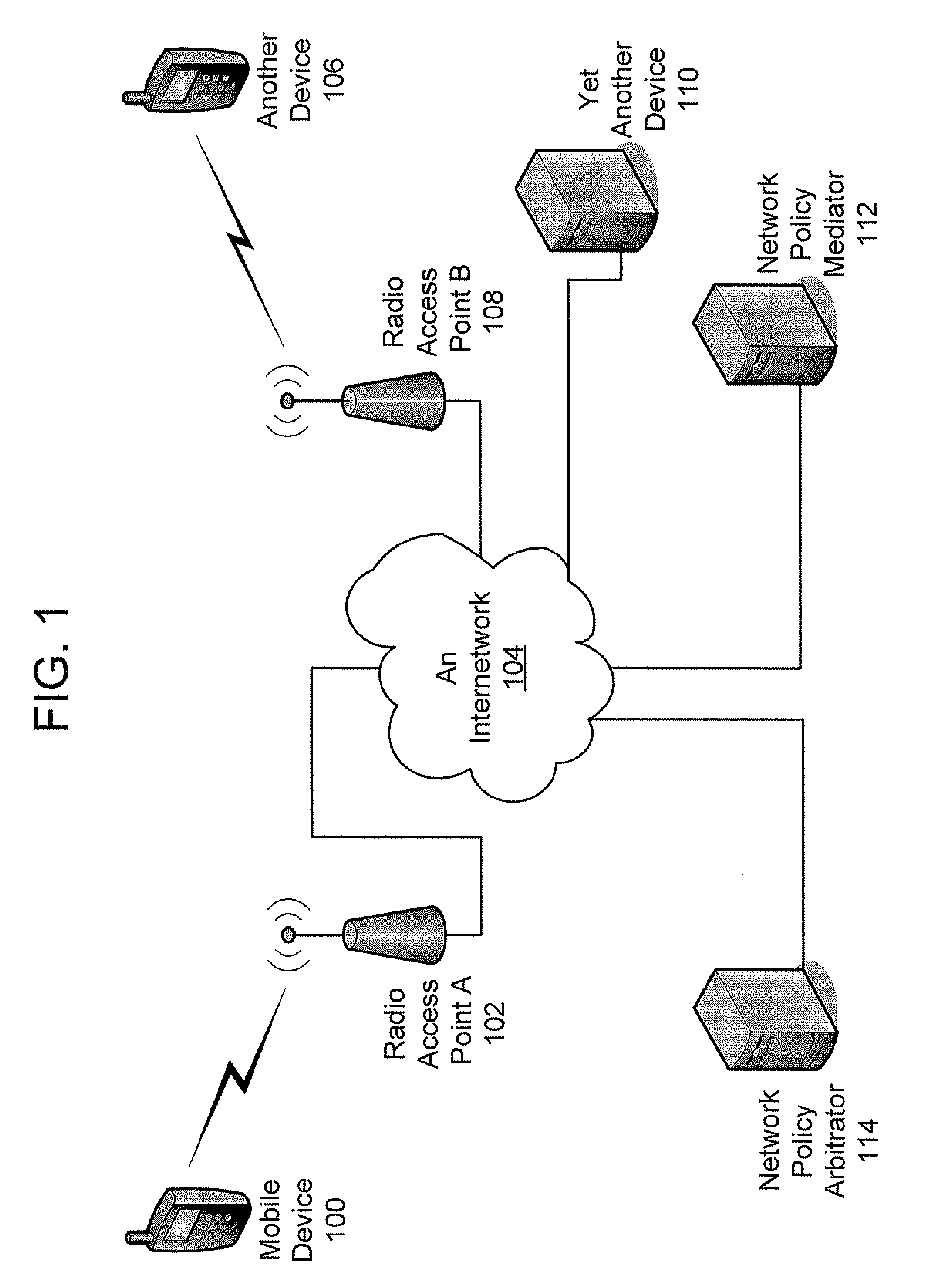
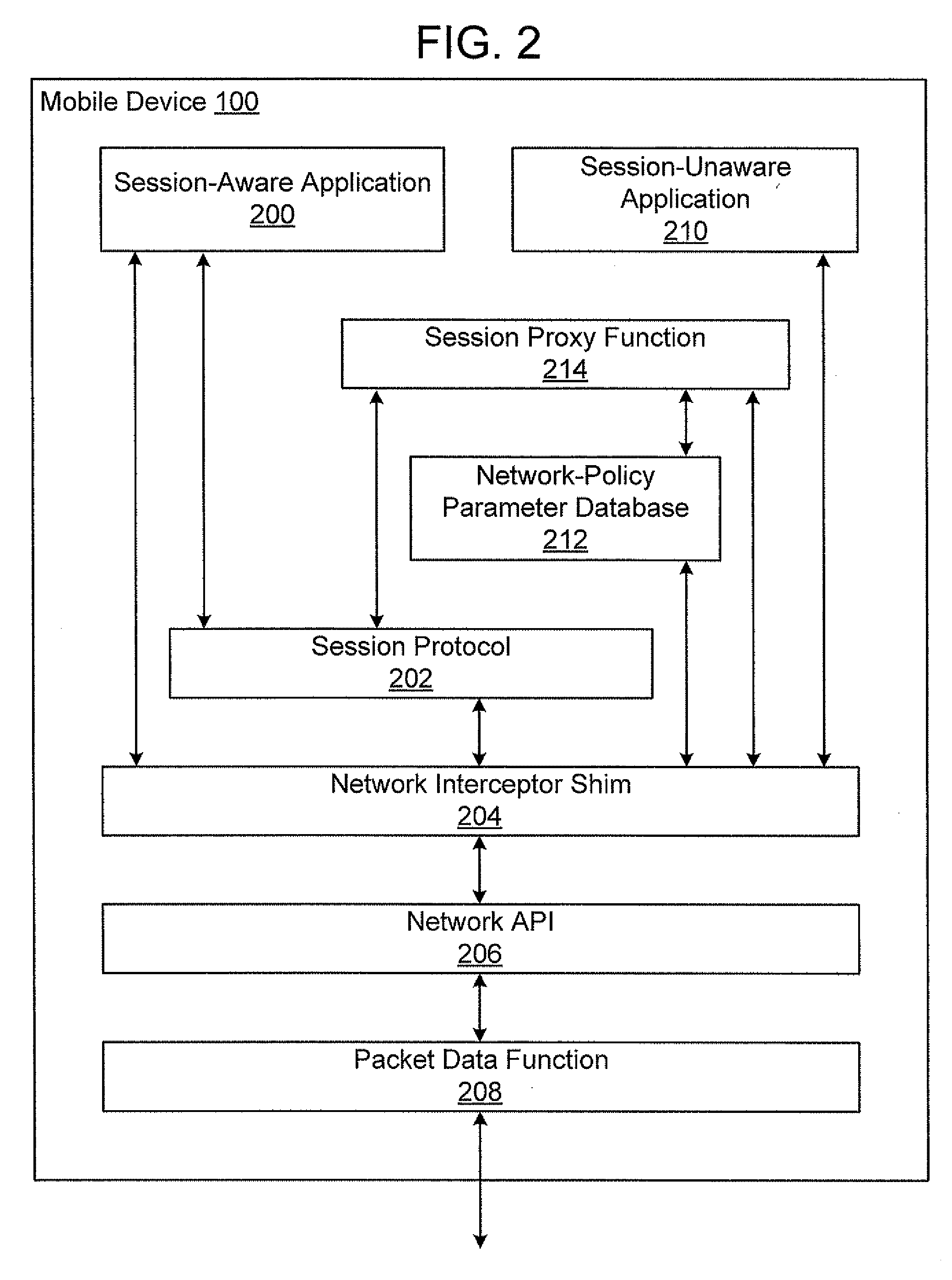
Establishing Network Policy For Session-Unaware Mobile-Device Applications
ActiveUS20080162704A1Network traffic/resource managementAssess restrictionNetworking protocolApplication software
The present invention provides the benefits of negotiated network resources to session-unaware applications. When a session-unaware application runs on a mobile device, the device, knowing that the application is session-unaware, negotiates appropriate network-policy parameters for the application. The application remains unaware, but it receives the benefits of the network-policy parameter negotiation. The network-policy parameter negotiation is carried on between the mobile device and a “network policy mediator” in the network. Together, they reserve the appropriate network resources and secure the appropriate guarantees. In some embodiments, a software “shim” runs in the network-protocol stack on the mobile device. By intercepting network-access attempts sent by the session-unaware application, the shim knows to begin the network-policy parameter negotiation. In some embodiments, the mobile device downloads information about session-unaware applications from the network. This information includes a list of which network-policy parameter guarantees would be most beneficial to each application.
Owner:U S CELLULAR
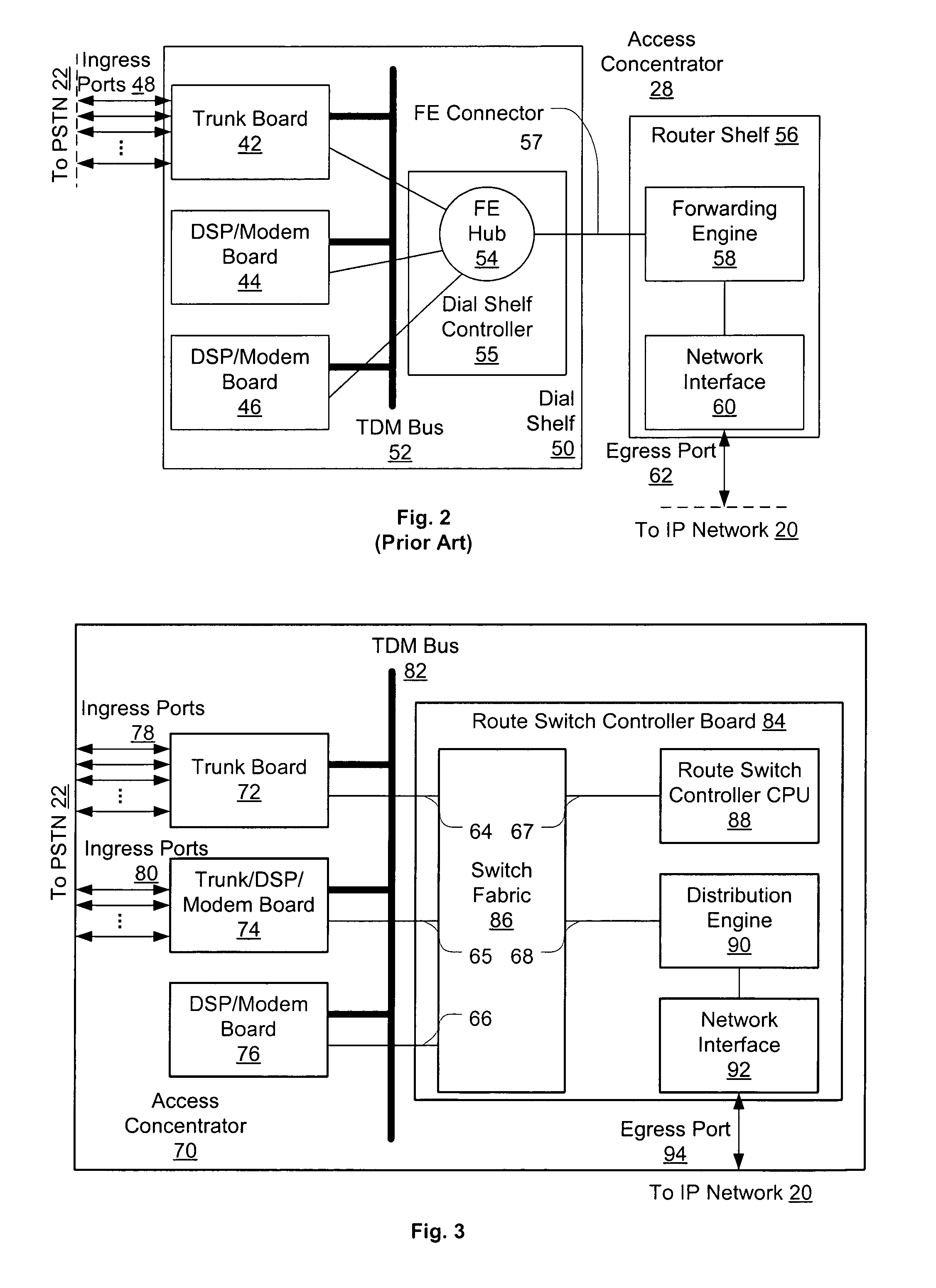
Distributed packet processing architecture for network access servers
InactiveUS6954463B1Increase the number ofRaise countData switching by path configurationNetwork access serverComputer hardware
An access server architecture, and methods for use of the architecture, are disclosed. The architecture and methods are designed to increase the scalability of and balance processor load for a network access server. In this architecture, packet forwarding and packet processing are distributed amongst the cards serving the low-speed access lines, such that each line card is responsible for performing forwarding and packet processing for packets associated with the low-speed ports that line card serves. As the number of line cards expands, forwarding resources are expanded in at least rough proportion. The NAS route switch controller, and the high-speed ports, are largely relieved of packet processing tasks because the egress port uses a distribution engine that performs a cursory examination on one or more header fields on packets received—comprehending only enough information to allow each packet to be distributed to the appropriate line card for full processing.
Owner:CISCO TECH INC
User fraud detection and prevention of access to a distributed network communication system
ActiveUS20040236702A1Digital data processing detailsMultiple digital computer combinationsCommunications systemGeolocation
A system and method are disclosed for user fraud protection and prevention of access to a distributed network communication system. A first set of identification data associated with a first network access are stored. A second set of identification data associated with a second network access are stored. The first and second sets of identification data comprise a first computing device identification and a second computing device identification, respectively. If one or more fraud indicators are determined in the two sets of identification data, then the first and / or second network access may be revoked. The fraud indicators may include, e.g., use of the same username with different computing device identifications, use of the same computing device identification at different geographical locations, violation of a threshold for computing device identifications, violation of a threshold for authentication failures, and violation of a threshold for rate of network propagation by a user account.
Owner:WAYPORT
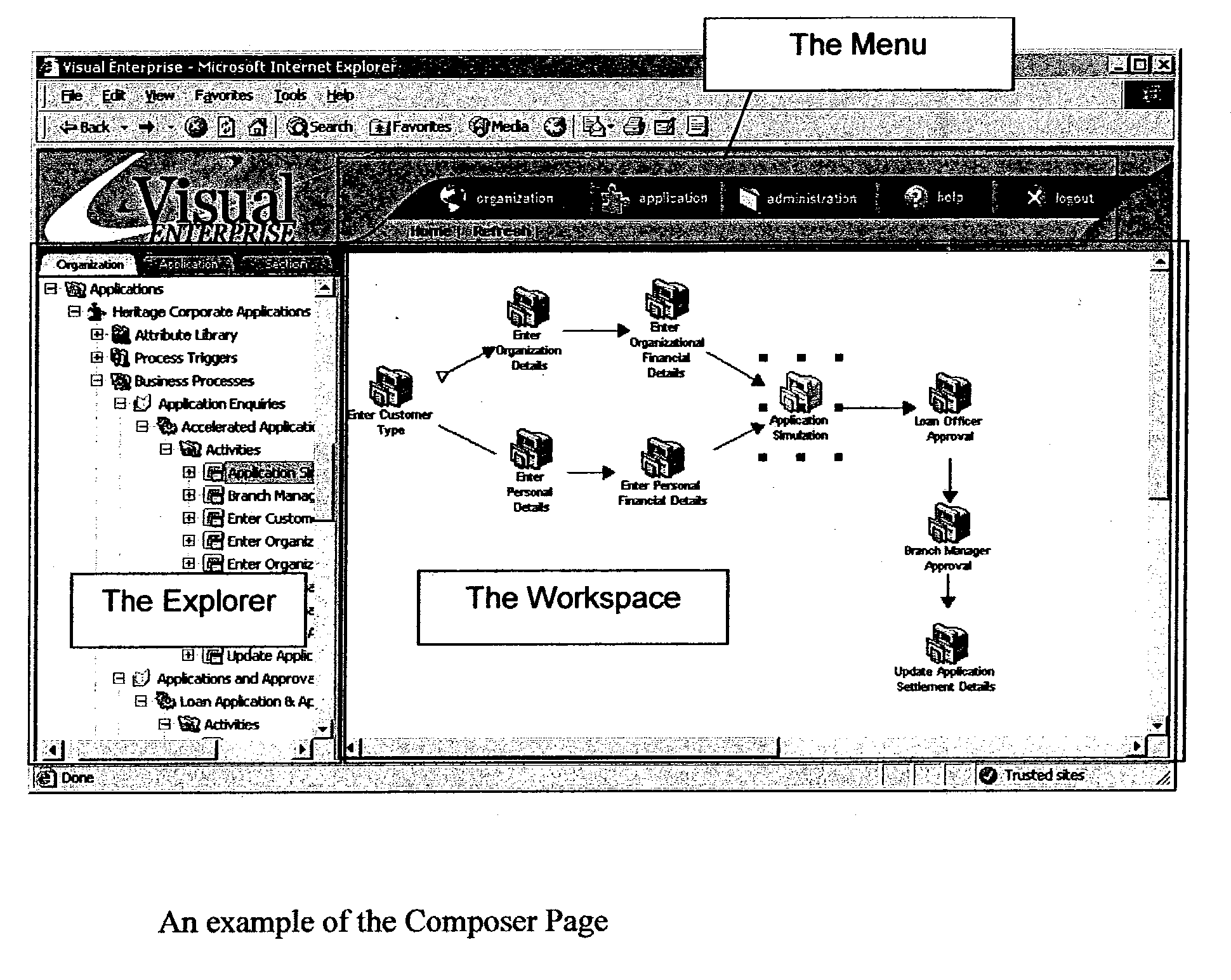
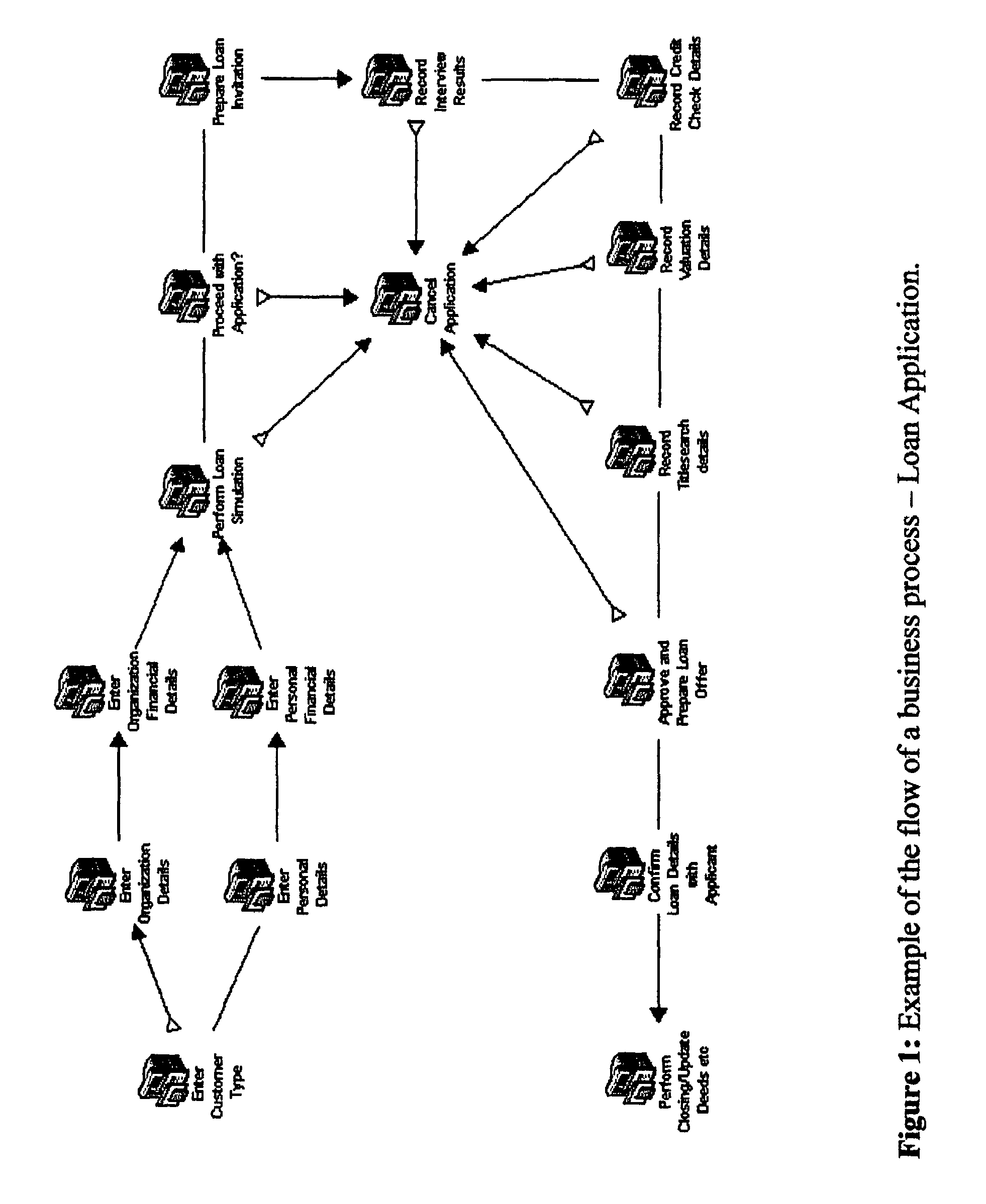
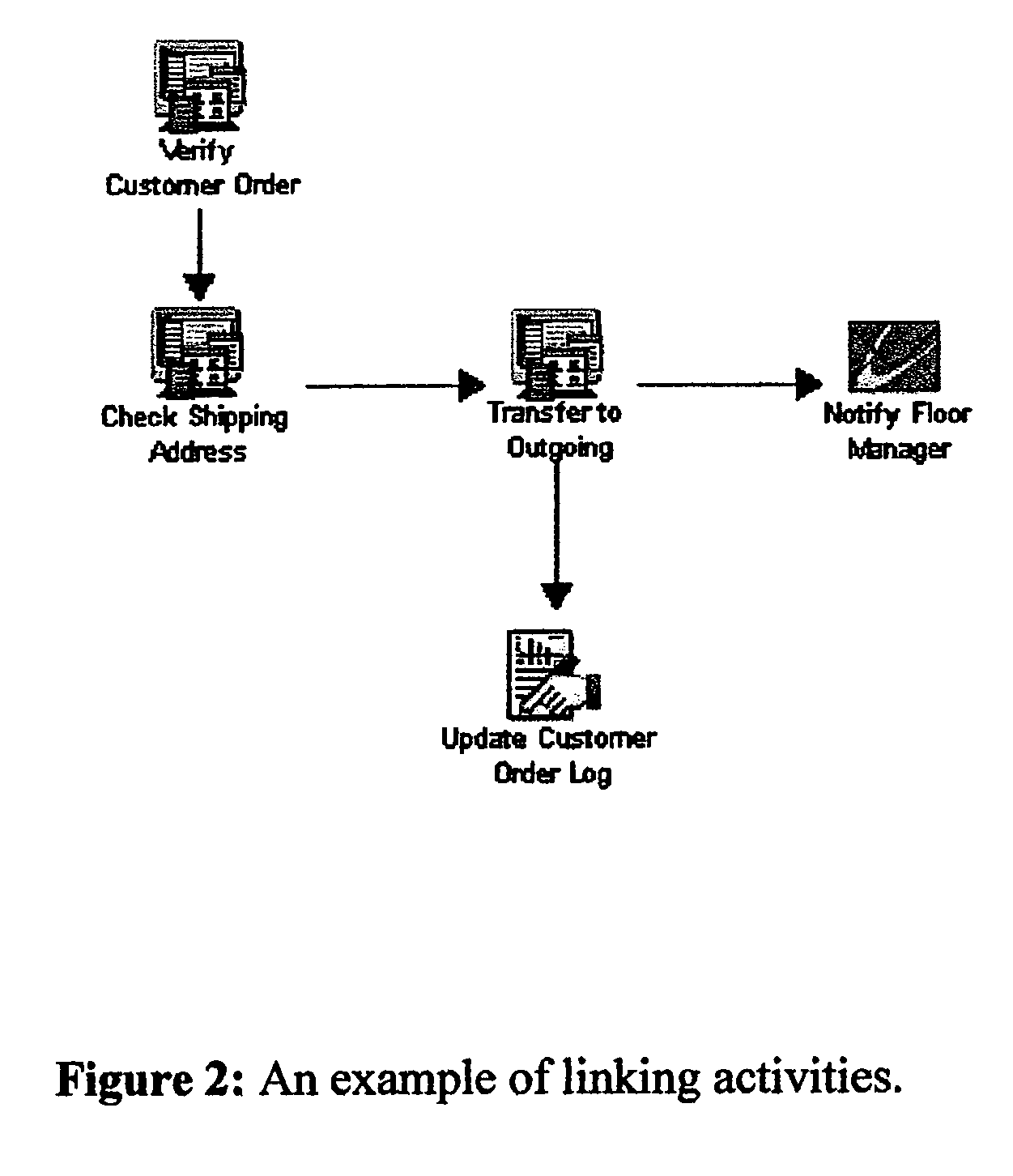
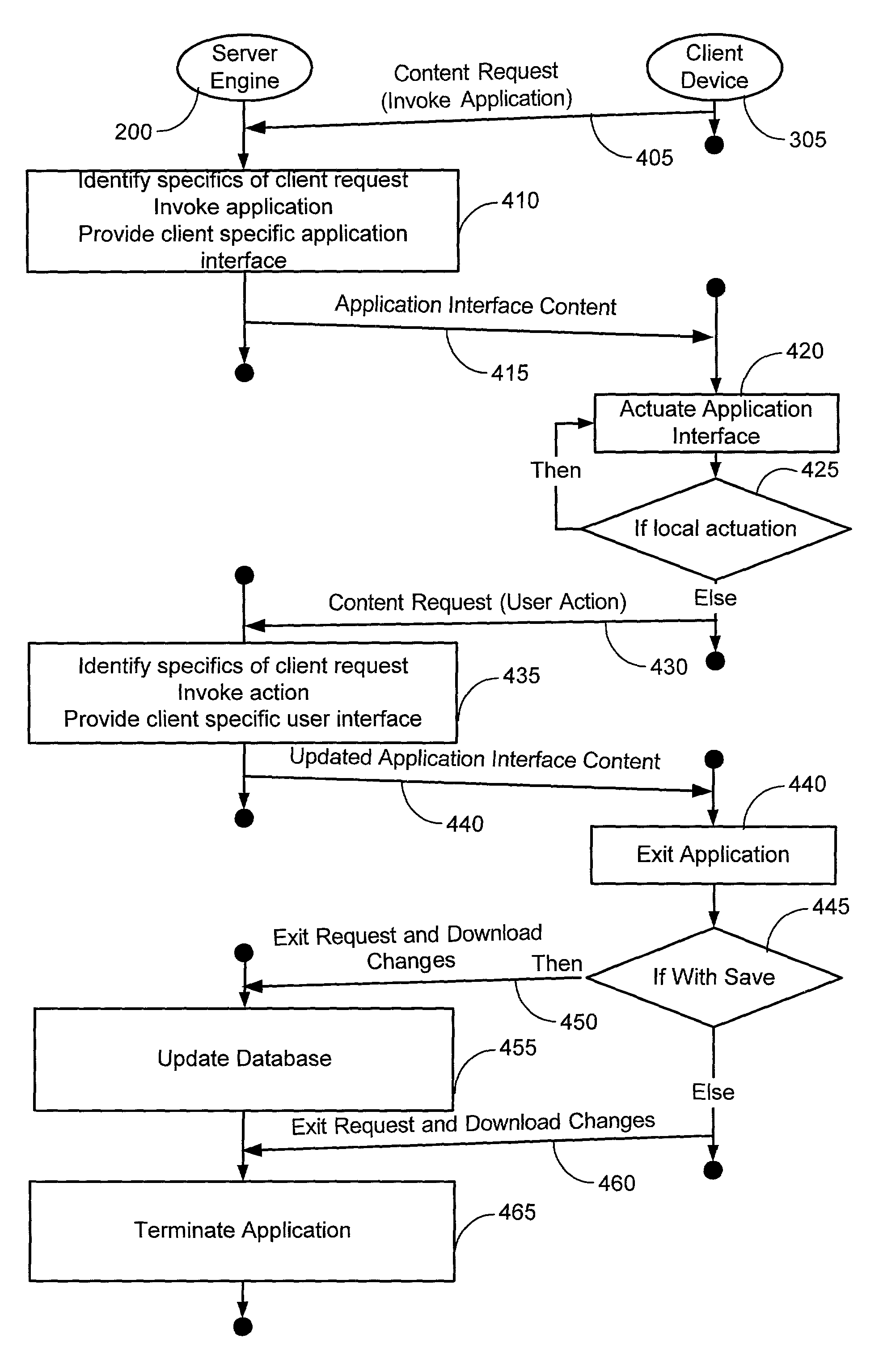
System and method for the composition, generation, integration and execution of business processes over a network
ActiveUS7610575B2Multiprogramming arrangementsOffice automationBusiness practiceSoftware engineering
A system and method providing an environment for the composition, generation, integration and execution of business processes and / or transactions over a distributed computing-based network. In a preferred embodiment, a business process expert develops a business model by using a network browser to access the composition environment via the network. The preferred embodiment includes a Composer and a Player. The Composer allows a business process engineer to model the processes, process rules and data structures of an entity upon the basis of a plurality of software resources. The Player executes the modeled processes and access relevant data in real-time, according to rules and resources as related within a software structure generated by the business process engineer. The preferred embodiment dynamically constructs web pages based on the process, rule and data definitions prepared by a business process engineer / expert and does so through a Process Interpreter and Grammar Engine so as to encapsulate all the software resources necessary to complete the desired business process without the need of people programming, scripting or coding. Pages are constructed only when required, ensuring that the solutions are flexible, error free and based upon the most current business practices, providing agile, integrated, error free and real-time software solutions capabilities.
Owner:AVOLIN LLC
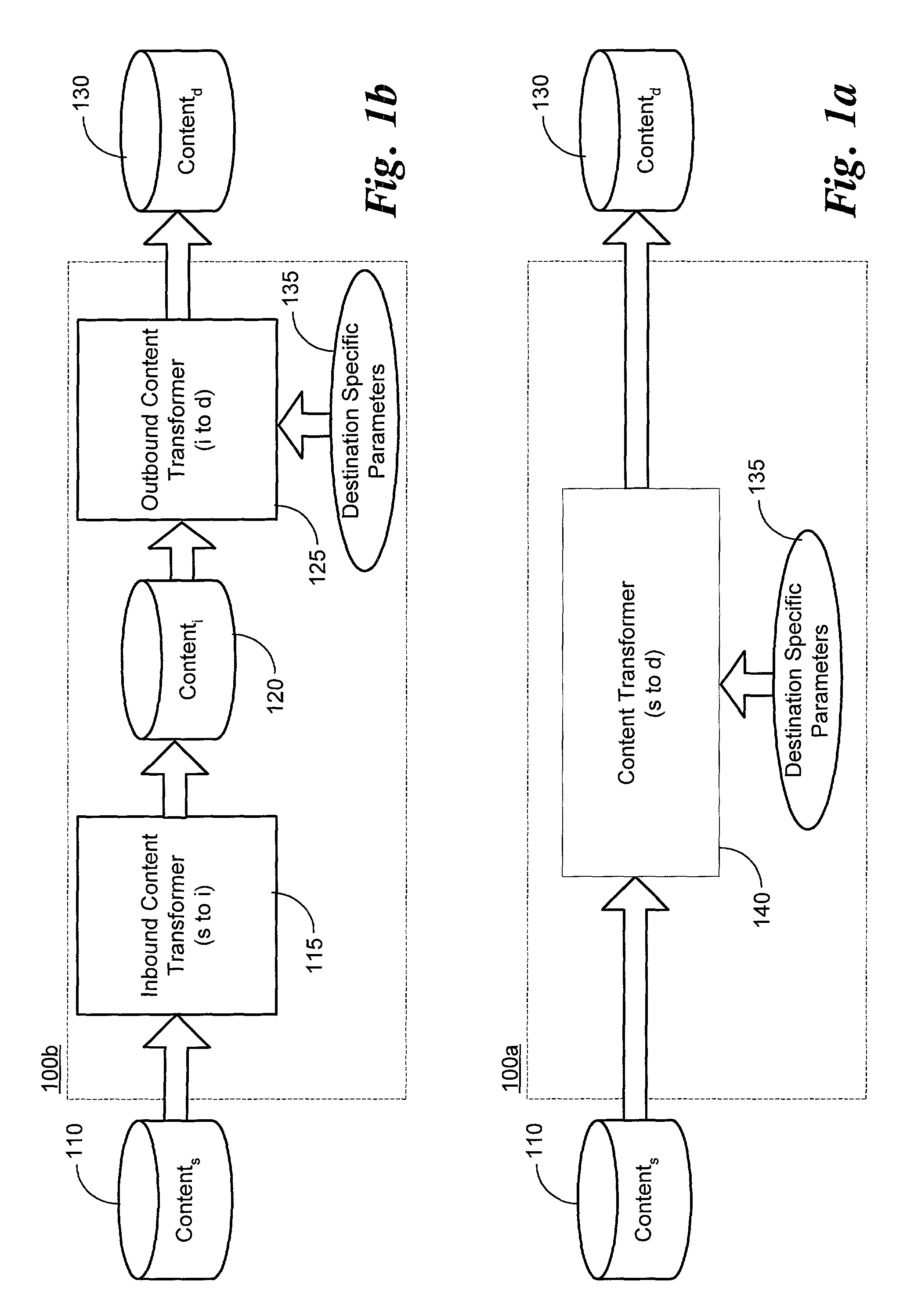
Content management and transformation system for digital content
InactiveUS7016963B1Improve practicalityImprove performanceWeb data indexingText processingDevice typeDigital content
A transformation engine that enables content and information to be transformed from one format, a source format, to a format that is compatible with the requesting device, a destination format. Advantageously, various device types can access and share content via a network without concern as to the original format of the content. When a client device provides a request for content, the transformation engine identifies delivery characteristics of the client device, and identifies a source for the requested content. The transformation engine then transforms the source formatted content into a format identified through a best fit analysis of the delivery characteristics of the device.
Owner:INTELLECTUAL VENTURES II
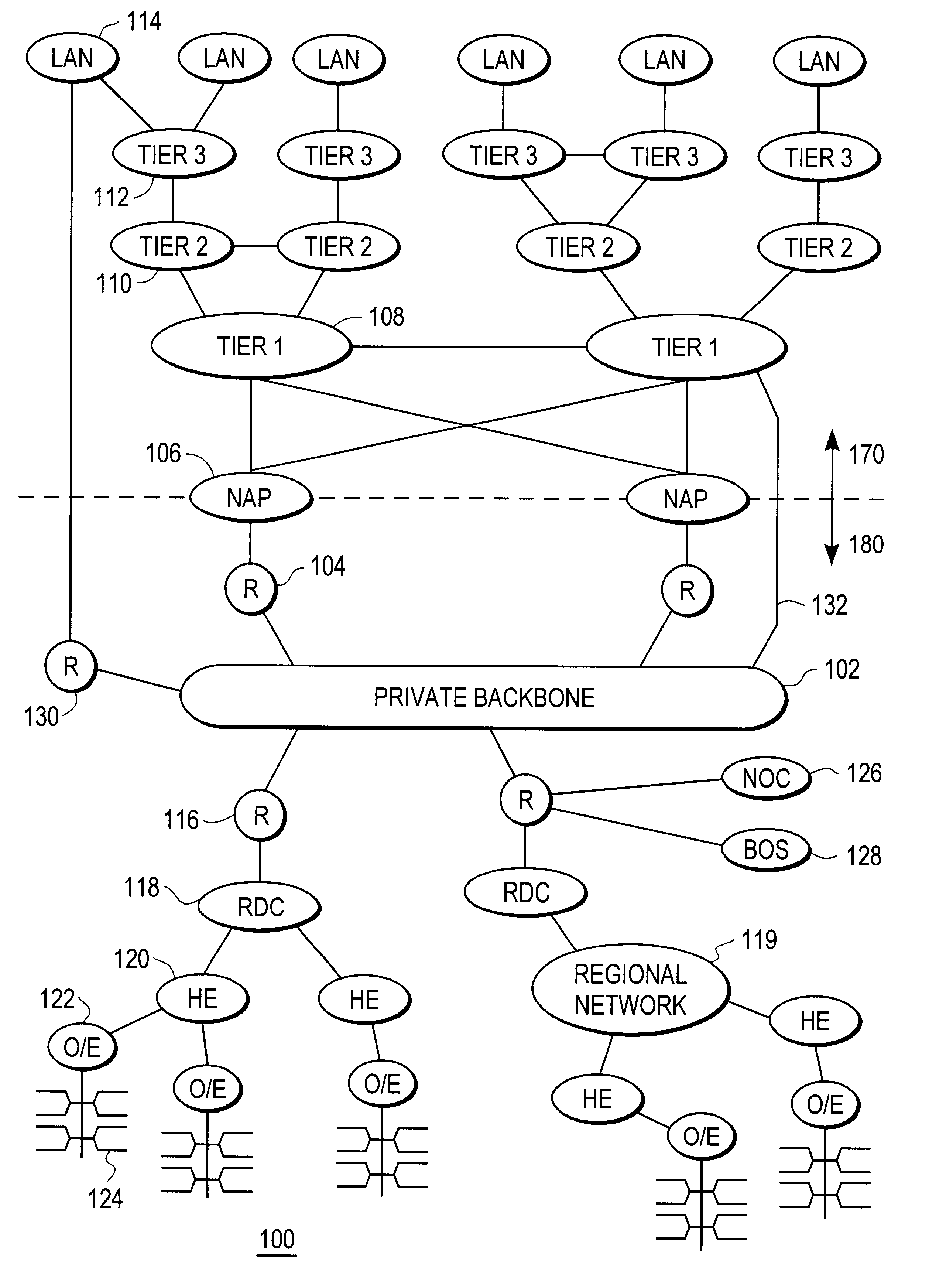
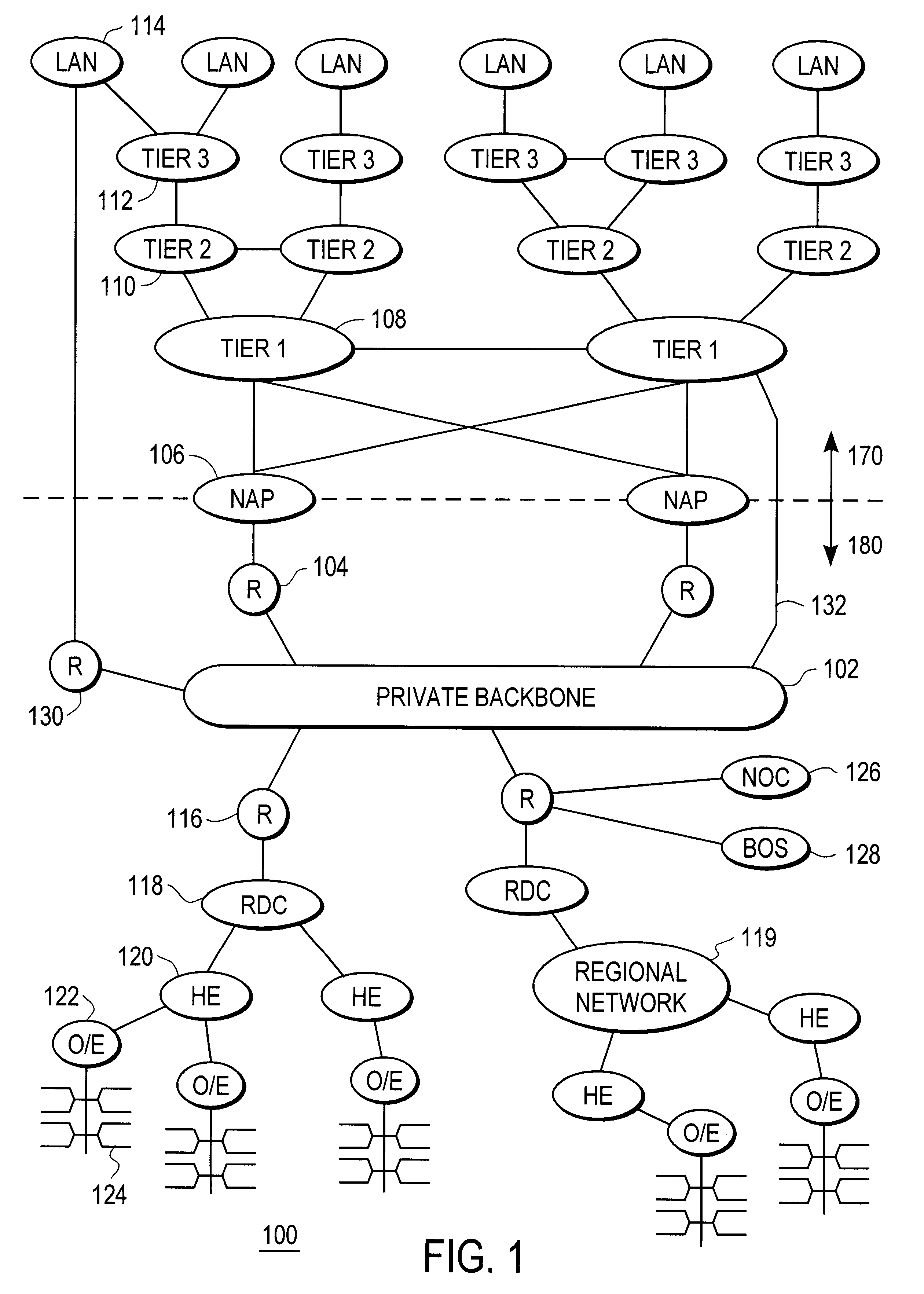
System and method for delivering high-performance online multimedia services
InactiveUS6370571B1Easy to scaleIncrease speedSpecial service provision for substationResource allocationFiberCoaxial cable
Disclosed is a scalable, hierarchical, distributed network architecture and processes for the delivery of high-performance, end-to-end online multimedia services, including Internet services such as World Wide Web access. The network architecture connects a high-speed private backbone to multiple network access points of the Internet, to a network operation center, to a back office system, and to multiple regional servers in regional data centers. Each of the regional servers connects to several caching servers in modified head-ends, which in turn connect via fiber optics to many neighborhood nodes. Finally, each node connects via coaxial cable to multiple end-user systems. The processes include those for replicating and caching frequently-accessed content, and multicasting content customized per region or locality.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com