Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1502results about How to "Minimization requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
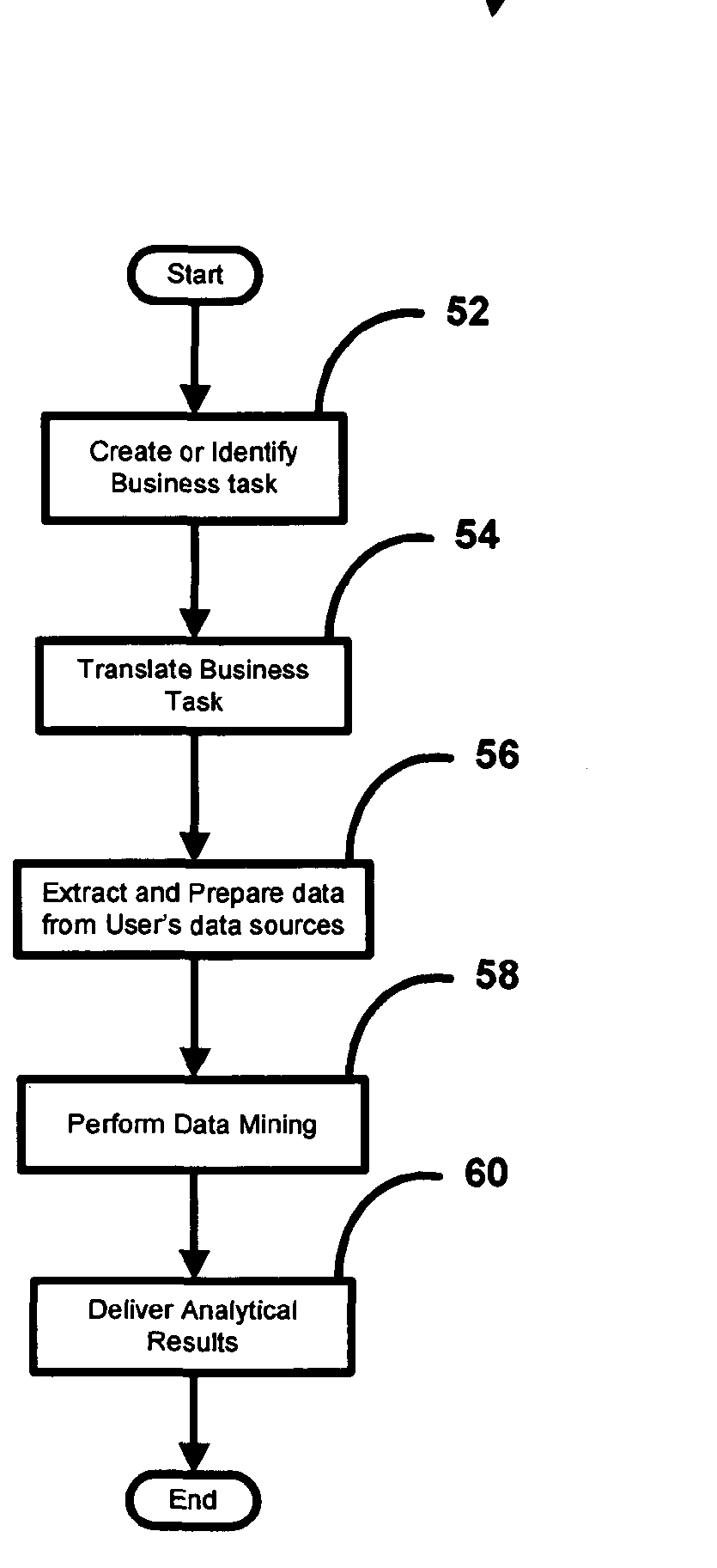
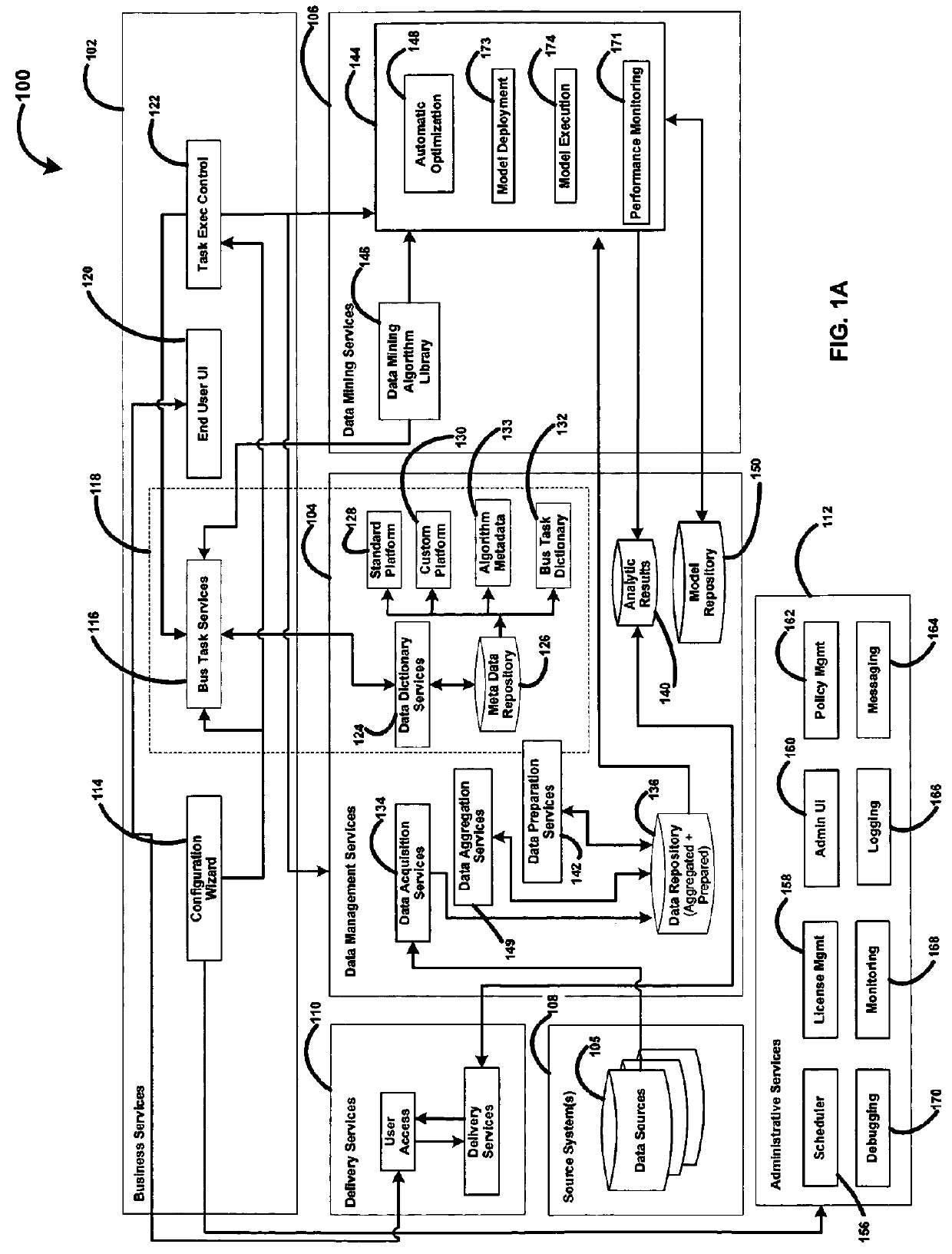
Platform independent plug-in methods and systems for data mining and analytics
ActiveUS8417715B1Lower barrierShorten cycle timeFinanceDigital data processing detailsData conversionSoftware
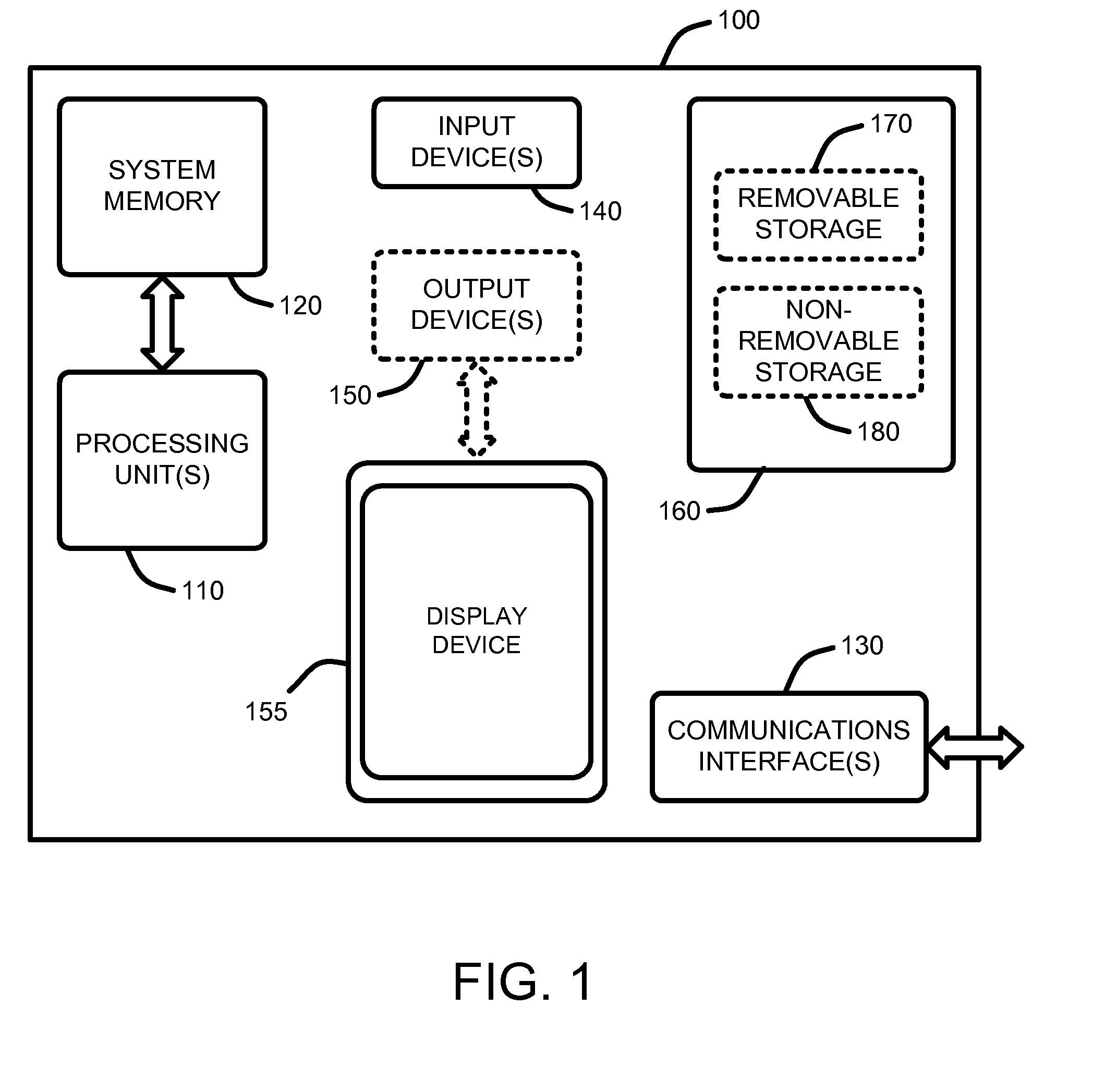
The present invention comprises methods, system, and apparatuses for generating and delivering analytic results for any simple or highly complex problem for which data exists that software or similar automated means can analyze. The present invention thus contemplates methods, systems, apparatuses, software, software processes, computer-readable medium, and / or data structures to enable performance of these and other features. In one embodiment, a method of the present invention comprises extracting and converting data using a data management component into a form usable by a data mining component, performing data mining to develop a model in response to a question or problem posed by a user.
Owner:BRUCKHAUS TILMANN +1
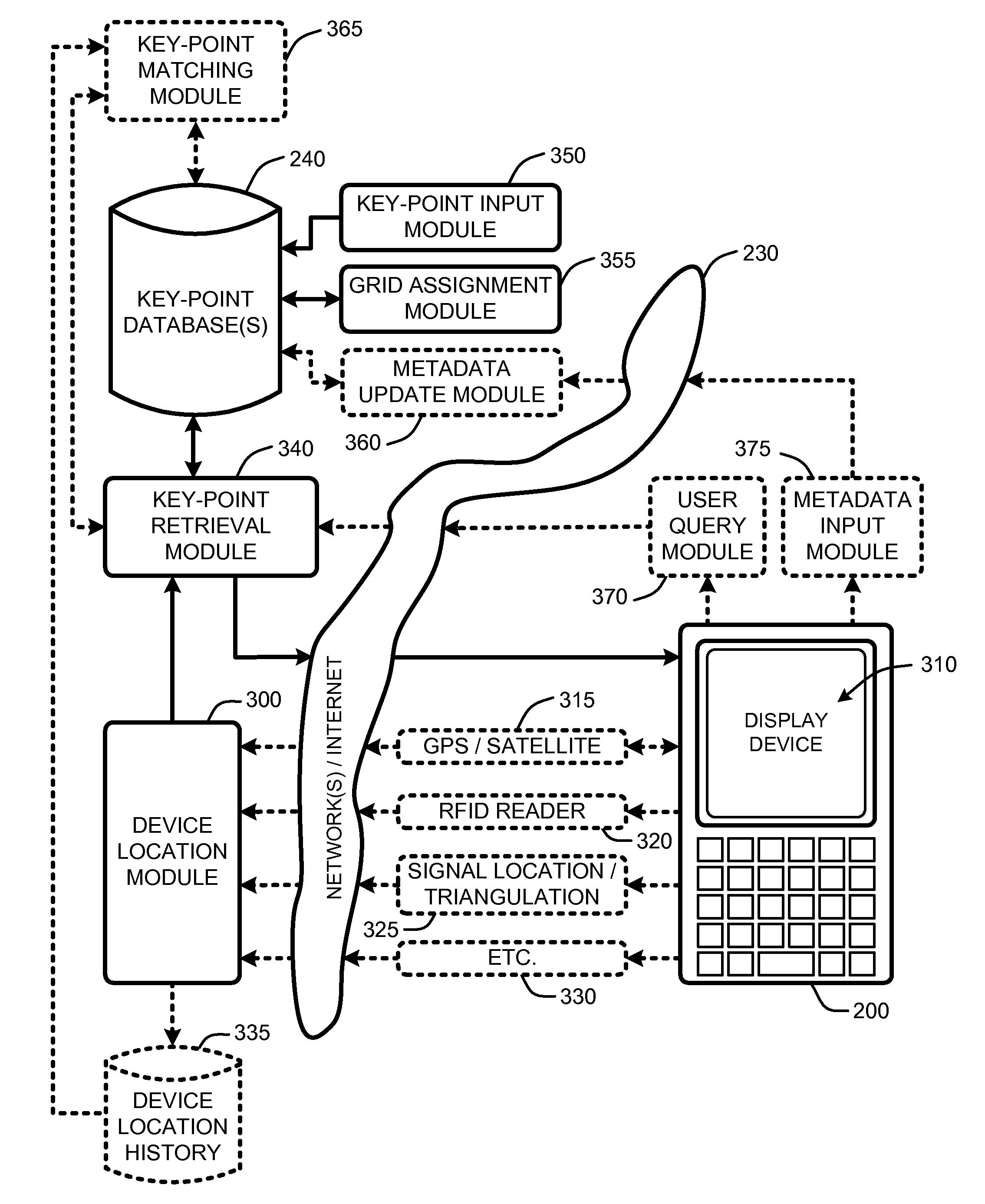
Location mapping for key-point based services
ActiveUS20080172173A1Minimizes bandwidth requirementMaximize user experienceInstruments for road network navigationRoad vehicles traffic controlCrucial pointUser device
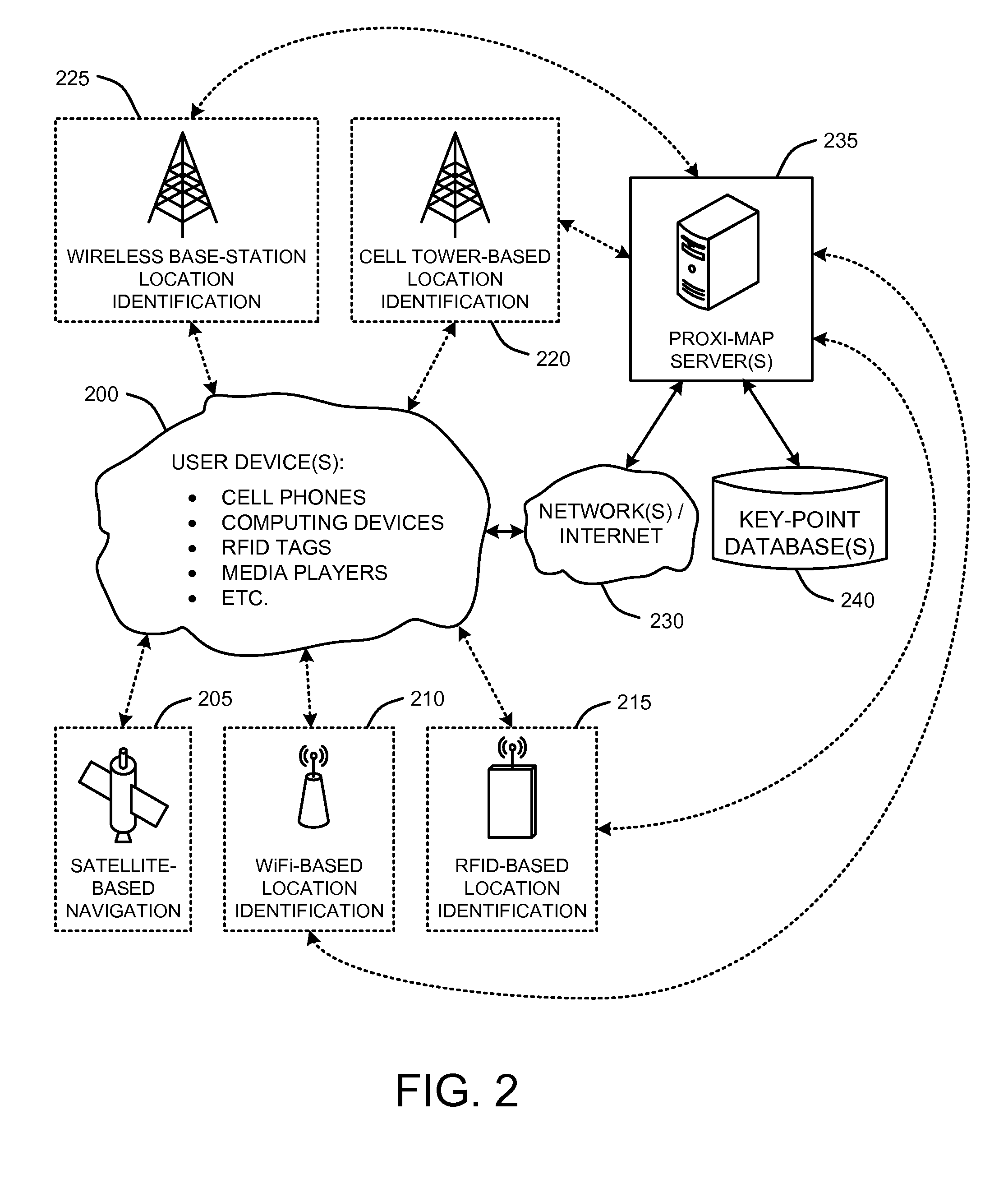
A “Proxi-Mapper” combines location based services (LBS), local searching capabilities, and relative mapping in a way that minimizes bandwidth requirements and maximizes user experience. The Proxi-Mapper automatically determines approximate locations of one or more local user devices (cell phones, PDA's, media players, portable computing devices, etc.) and returns a lightweight model of local entities (“key-points”) representing businesses, services or people to those devices. Key-points are maintained in one or more remote databases in which key-points are assigned to predetermined grid sections based on the locations of the corresponding entities. Metadata associated with the key-points provides the user with additional information relating to the corresponding entities. In various embodiments, user query options allow the Proxi-Mapper to pull or push relevant local key-point based information to user devices via one or more wired or wireless networks.
Owner:UBER TECH INC
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
Malicious mobile code runtime monitoring system and methods
InactiveUS7058822B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Owner:FINJAN LLC
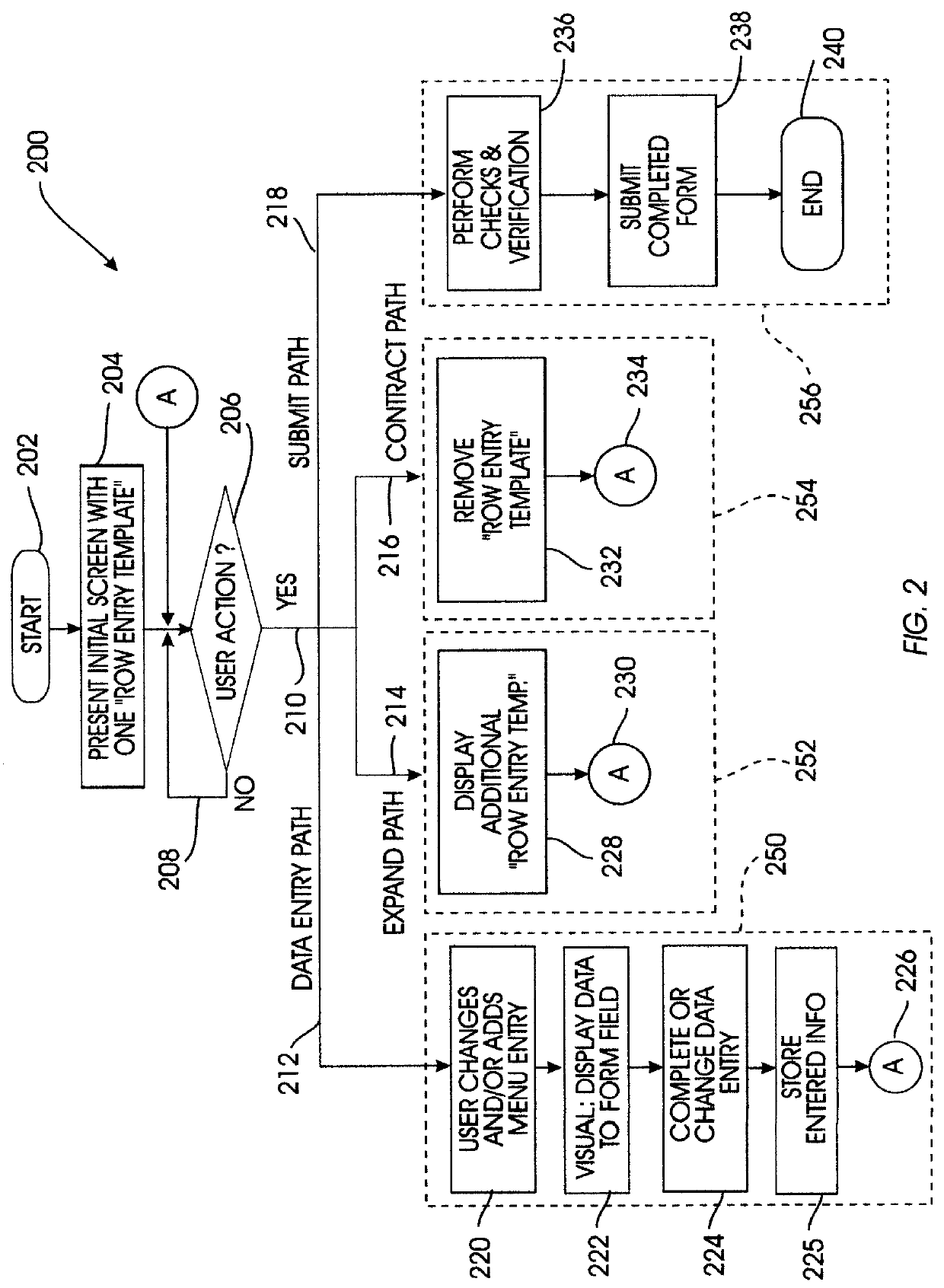
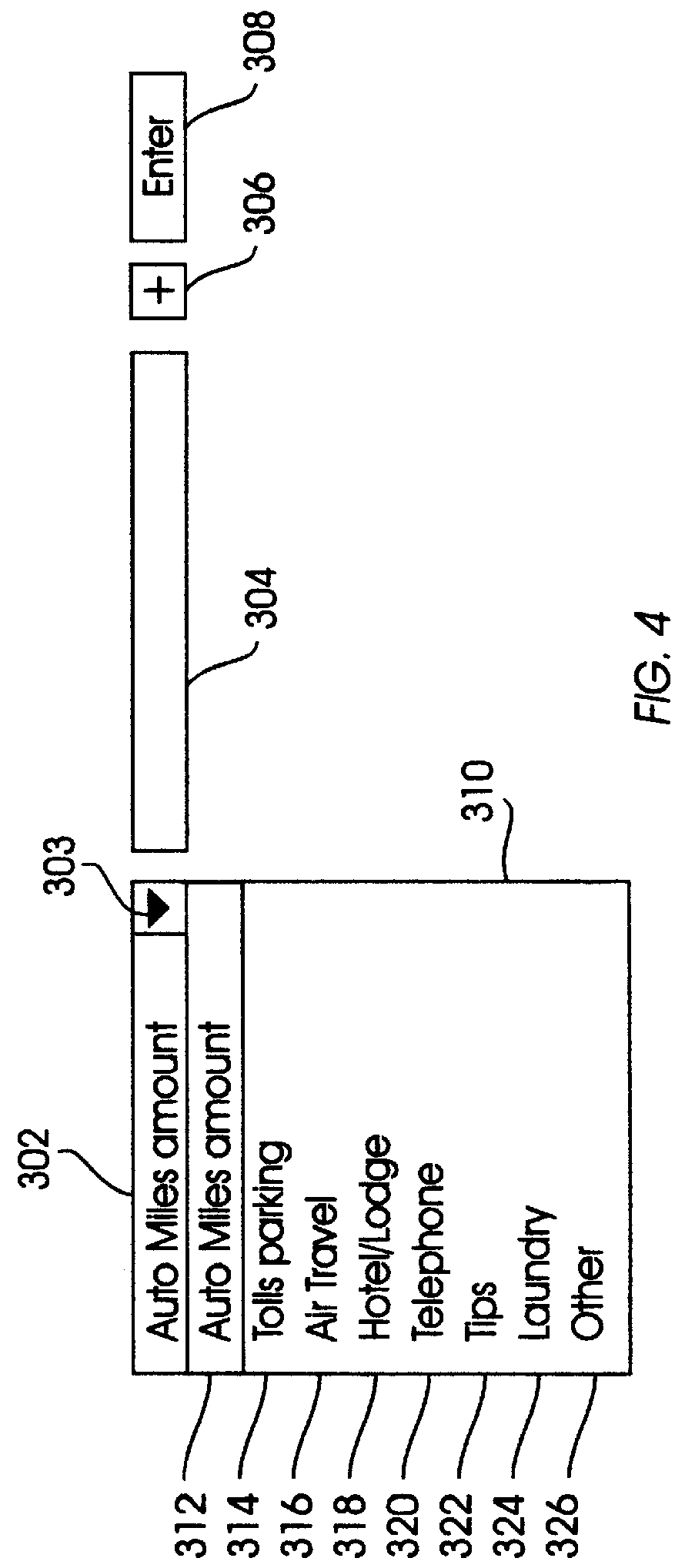
System for directly accessing fields on electronic forms
InactiveUS6084585AQuickly and efficiently completeMinimization requirementsNatural language data processingSpecial data processing applicationsGraphical user interfaceLinked list
A computer system provides a graphical user interface (GUI) to assist a user in completing electronic forms. The computer includes components such as a processor, user interface, and video display. Using the video display, the processor presents a row entry template including a menu field and an associated data field. The user completes the menu field by selecting a desired menu entry from a list of predefined menu entries. The user completes the data field by entering data into the data field. This format is especially useful when the data entry provides data categorized by the menu entry, explains the menu entry, or otherwise pertains to the menu entry. Each time the GUI detects activation of a form expand key, it presents an additional row entry template for completion by the user. Upon selection of a submit key, data of the completed form is sent to a predefined destination, such as a linked list, table, database, or another computer. Thus, by planned selection of menu entries, the user can limit his / her completion of an electronic form to blanks applicable to that user, avoiding the others. Nonetheless, the form can be easily expanded row by row to accommodate as many different blanks as the user wishes to complete. The invention may be implemented by a host sending a remote computer machine-executable instructions which the remote computer executes to provide the GUI, where the remote computer ultimately returns the completed form data to the host.
Owner:IBM CORP
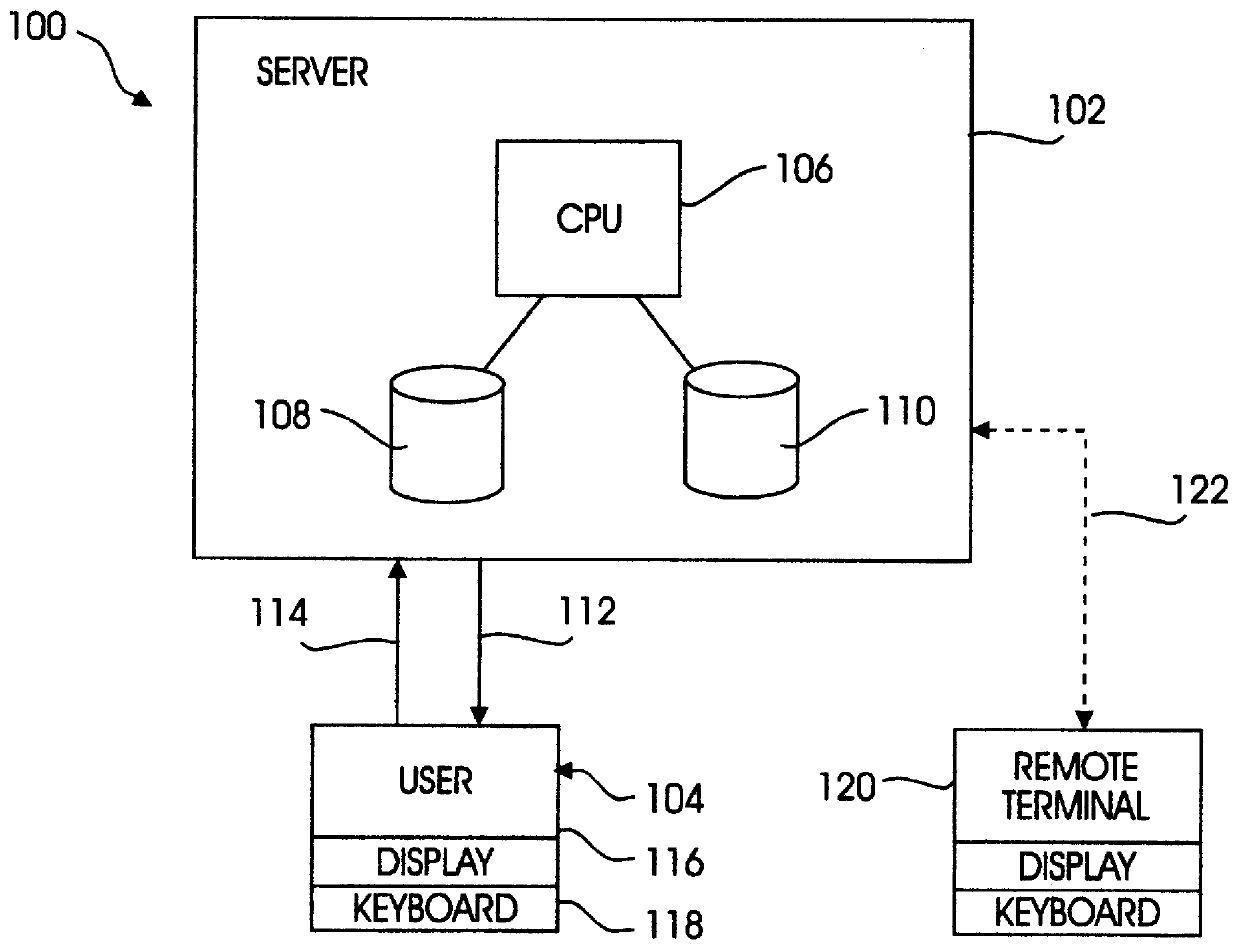
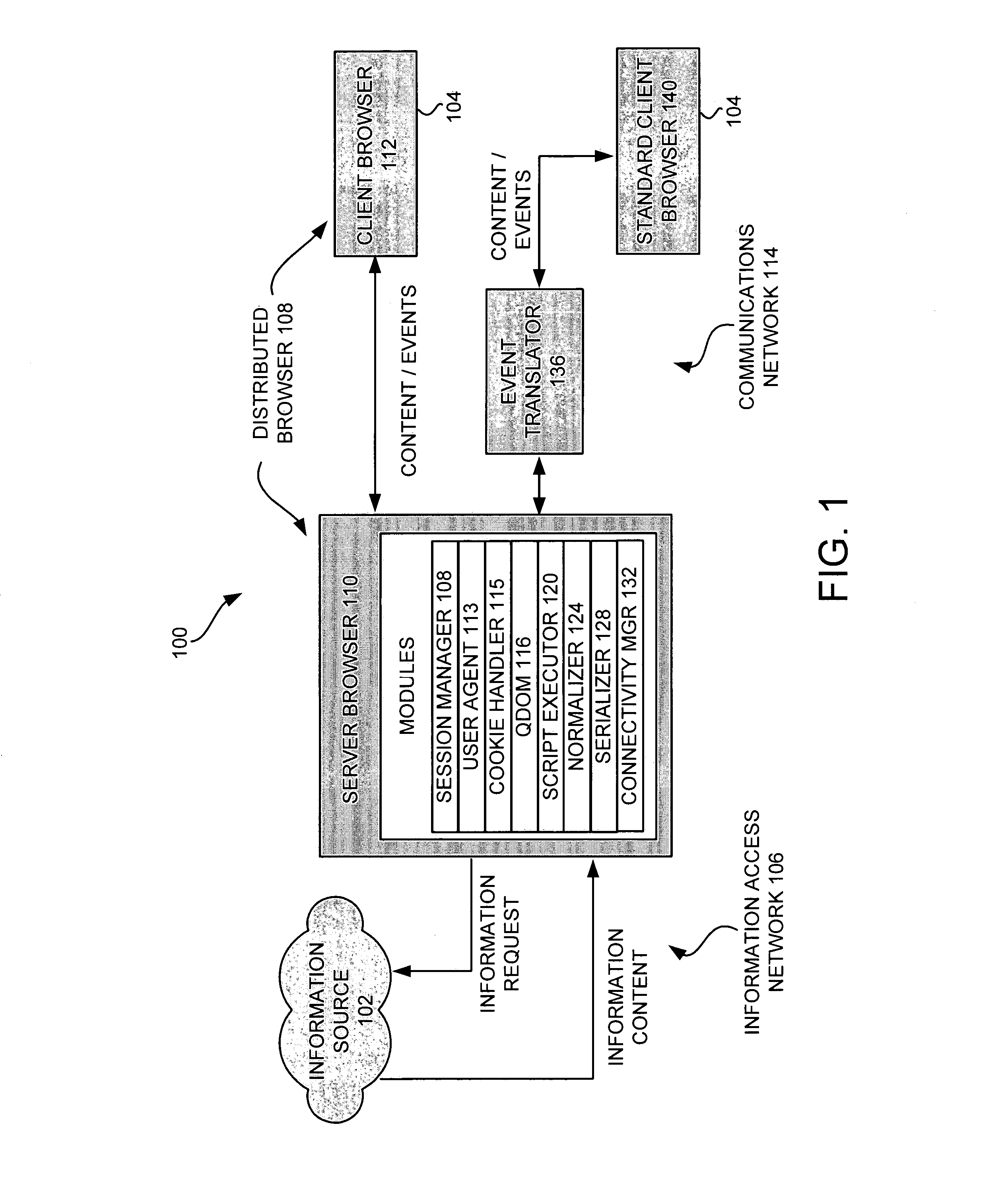
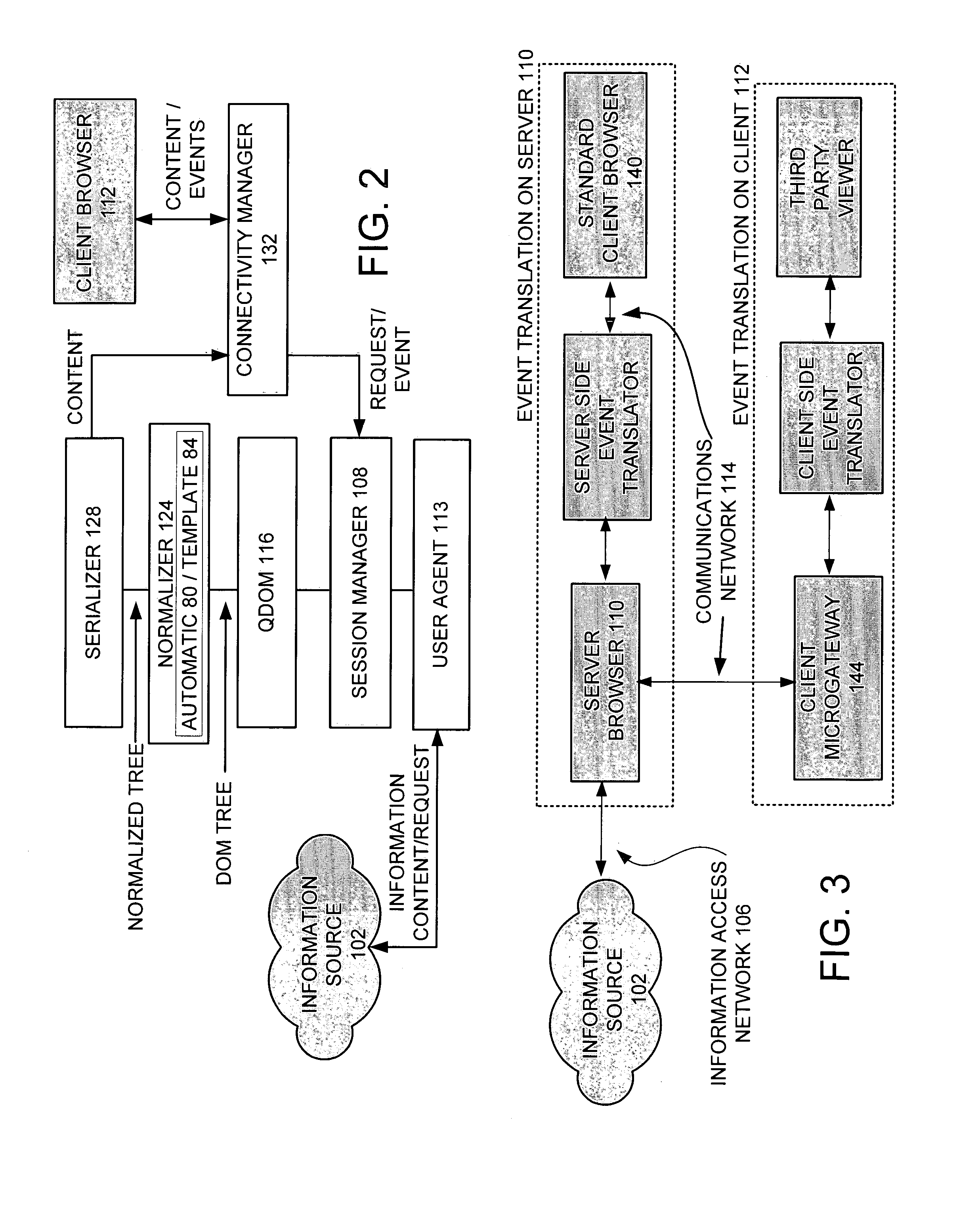
System and method for accessing customized information over the internet using a browser for a plurality of electronic devices
InactiveUS7072984B1High CPU powerLarge displayDigital data information retrievalMultiple digital computer combinationsComputer compatibilityClient-side
A system and method is provided for enabling an electronic device to efficiently access information content. A server browser accesses the information content over a network. The accessed information content is retrieved and adapted for presentation for the electronic device. A serializer dynamically formats the adapted information content according to a client browser. The client browser receives and presents the information content on the electronic device. An event translator is included to provide additional compatibility with commercially available client browsers.
Owner:RPX CORP
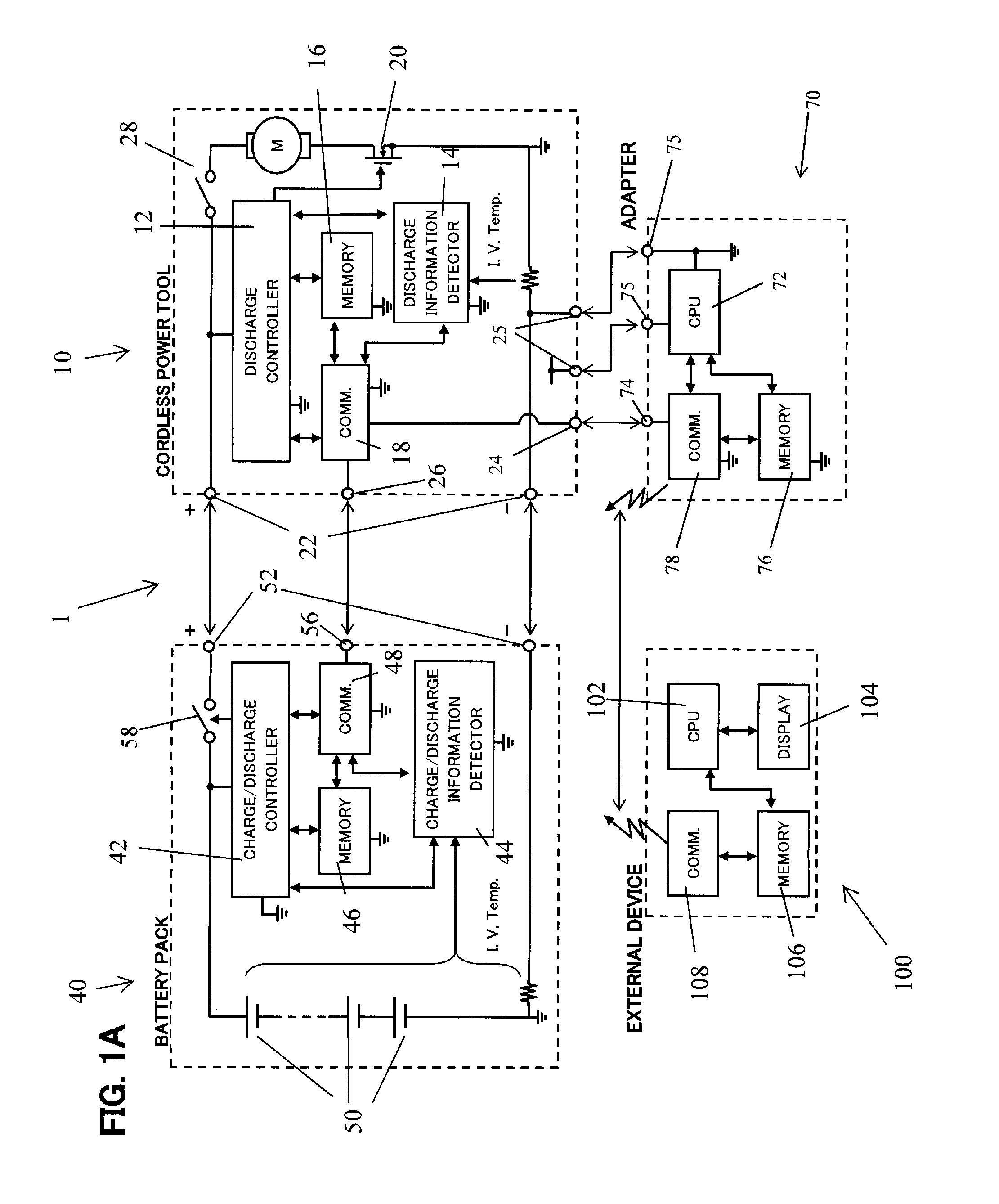
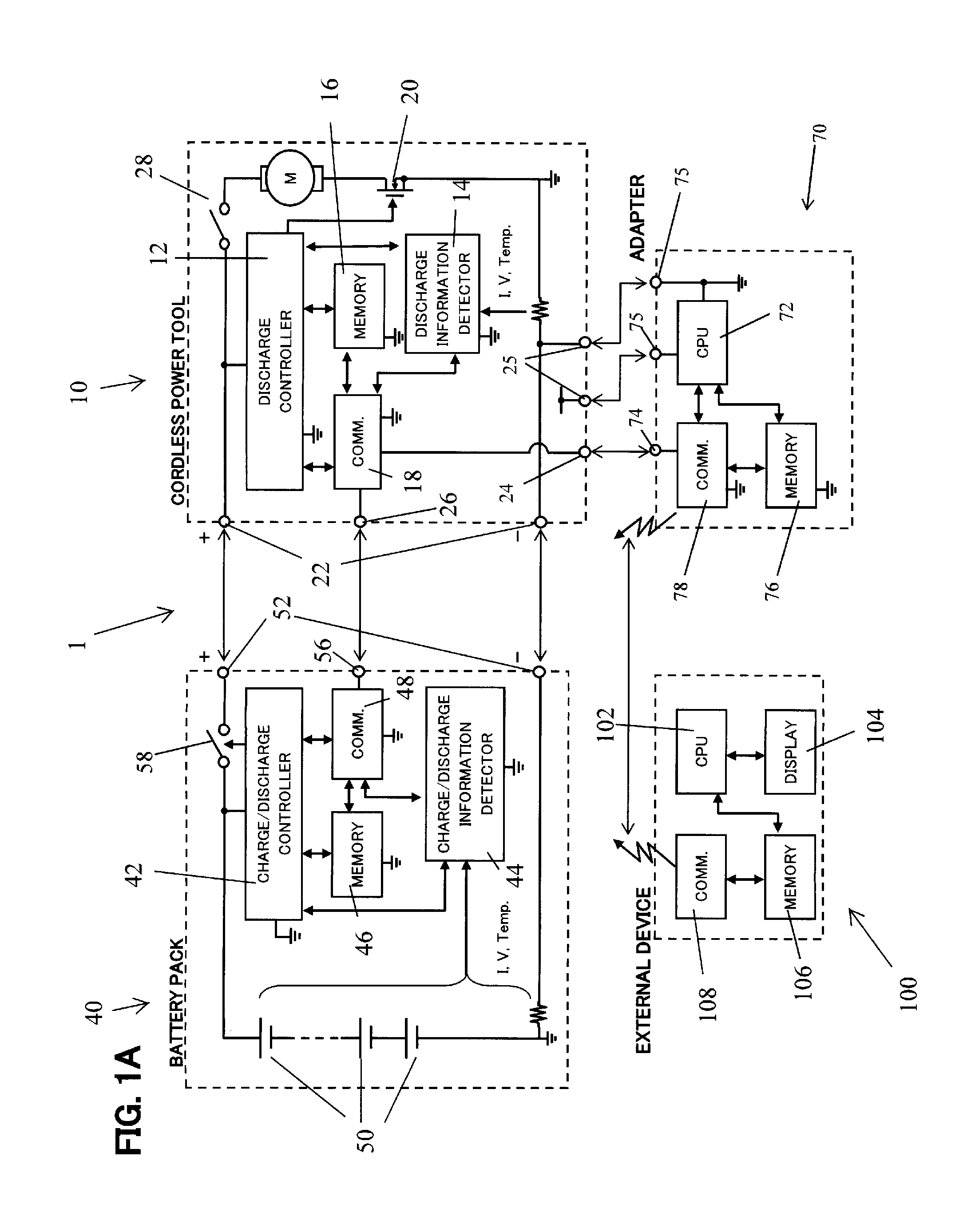
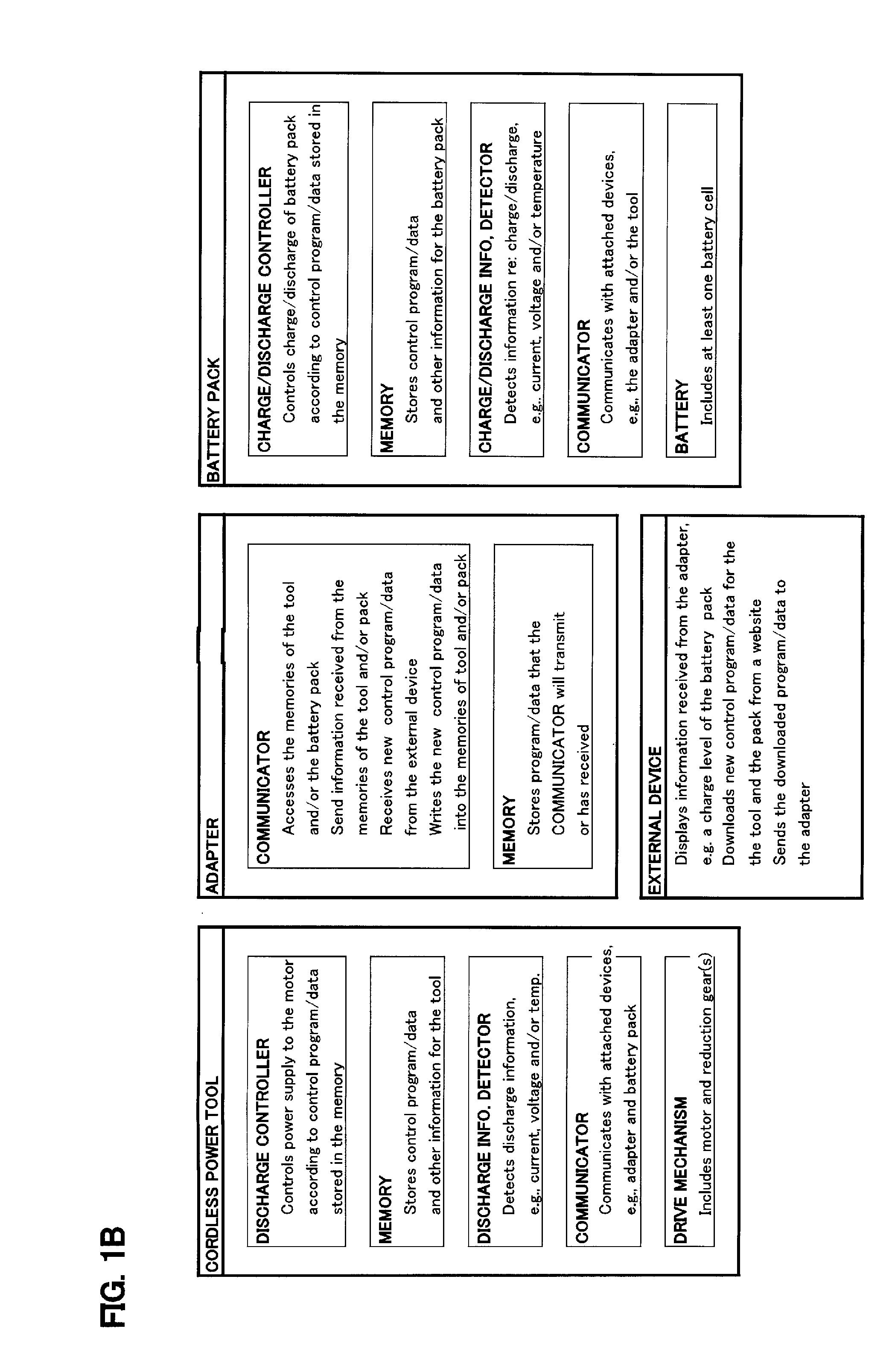
Portable battery pack charging system, method for recharging a battery pack, and adapter therefor
ActiveUS20140159662A1Readily dislodged from the power tool during operationMinimization requirementsBatteries circuit arrangementsTransmission systemsElectric power transmissionElectricity
Owner:MAKITA CORP
Surgical device for endoscopic vein harvesting
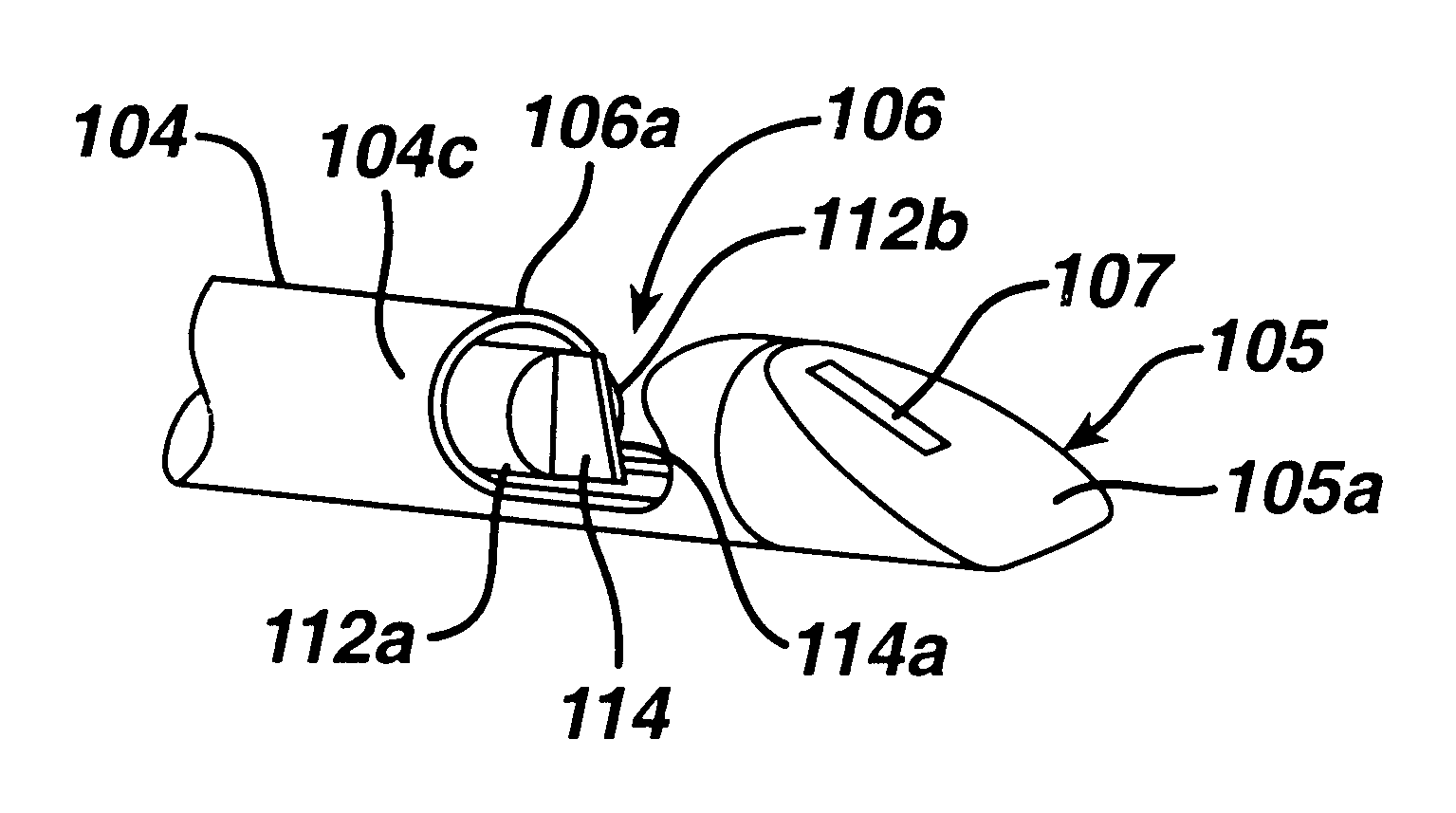
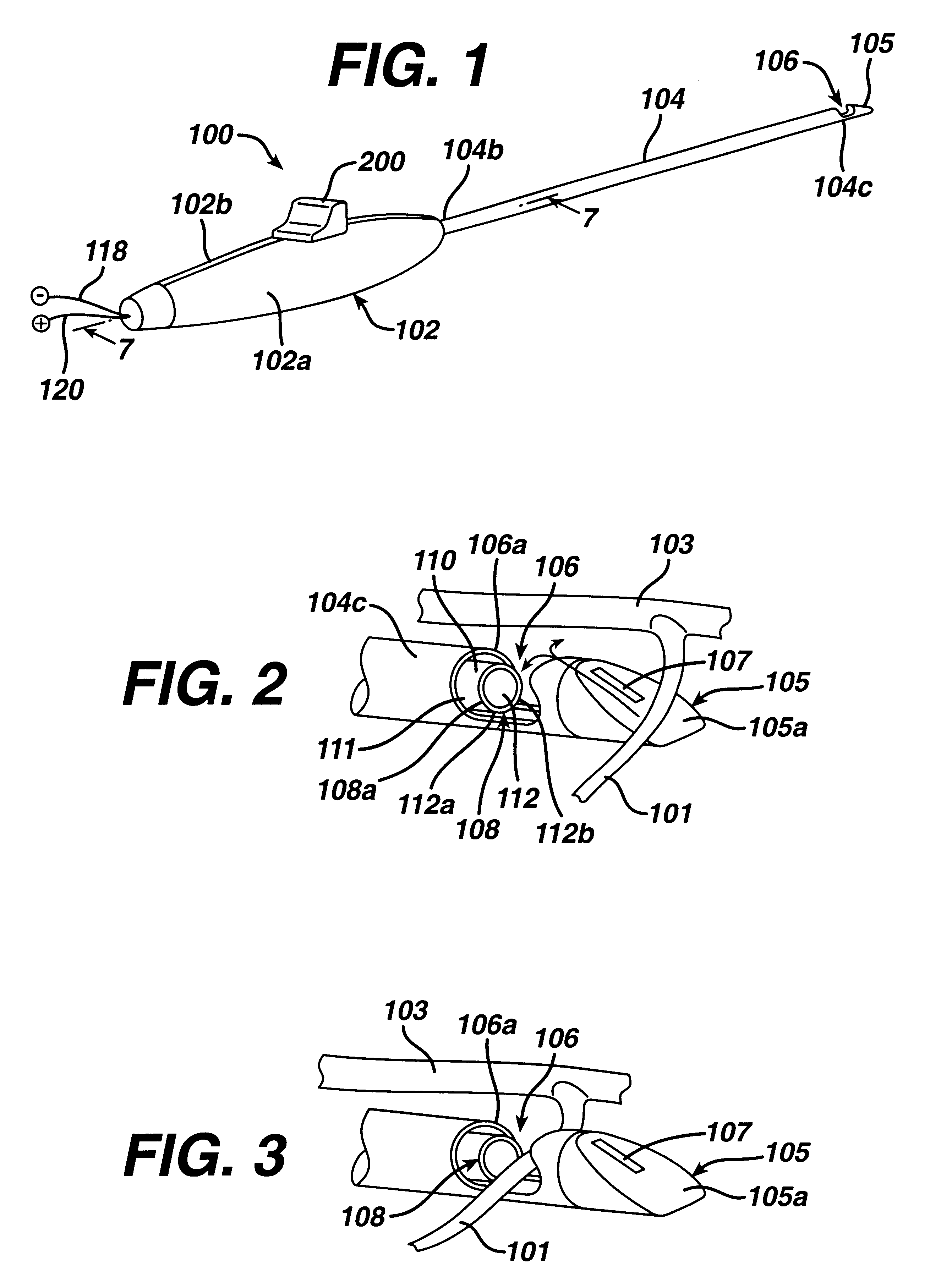
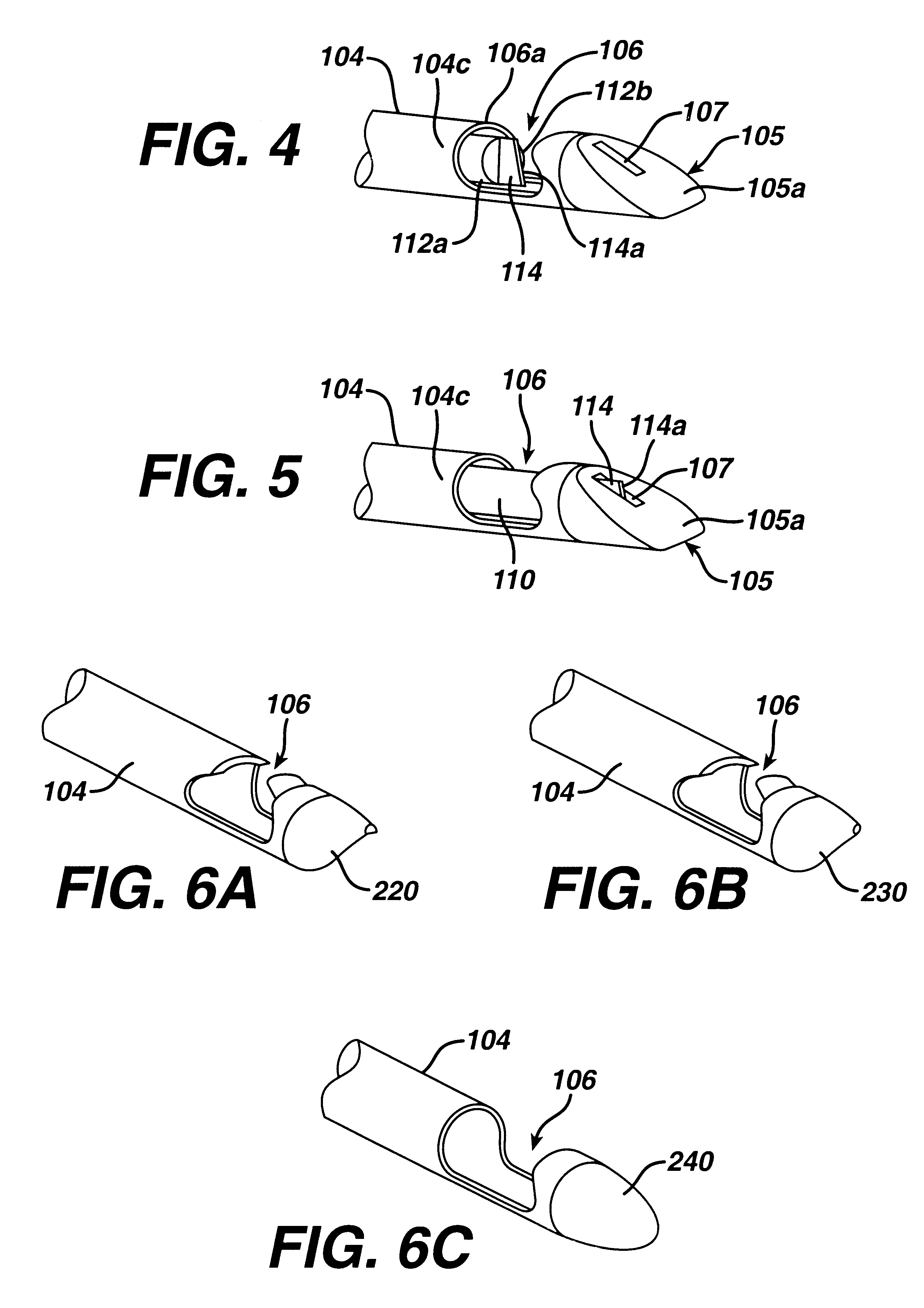
InactiveUS6527771B1Eliminate needControl spreadSurgical instruments for heatingSurgical forcepsVeinVein harvesting
A surgical device including: a first shaft having a first projection radially offset from an axial direction of the first shaft, the first projection having a first clamping surface; a second shaft slidably disposed relative to the first shaft, the second shaft having a second projection radially offset from the axial direction, the second projection having a second clamping surface; a dissector for dissecting tissue from a blood vessel to be harvested; a first actuator for sliding the second projection relative to the first projection to capture a side branch of the vessel between the first and second clamping surfaces; at least one electrode for applying cauterizing energy to cauterize the captured side branch; a cutting blade movably disposed on one of the first or second projections; and a second actuator for moving the cutting blade to sever the side branch captured between the first and second projections.
Owner:SORIN GRP USA INC
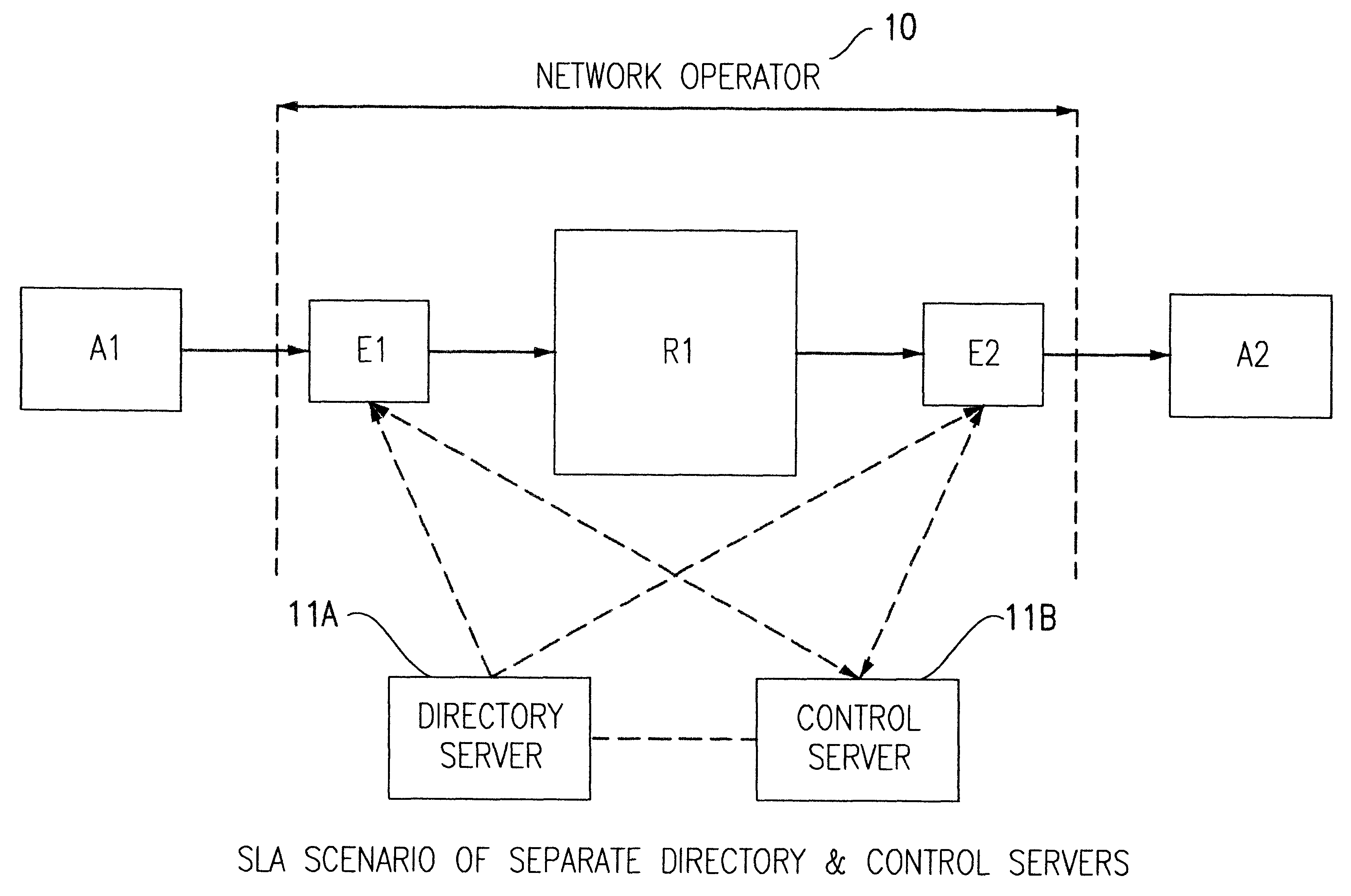
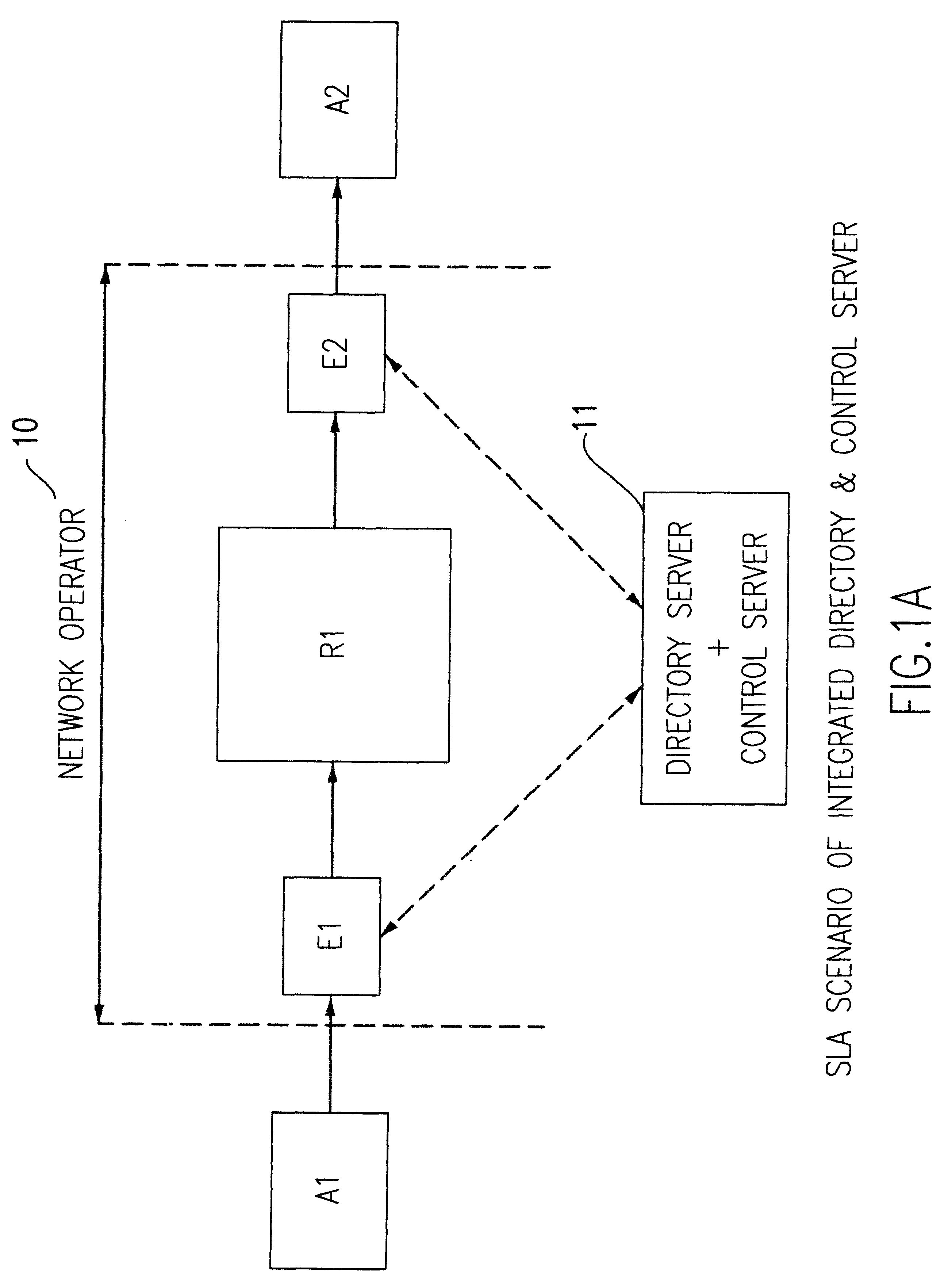
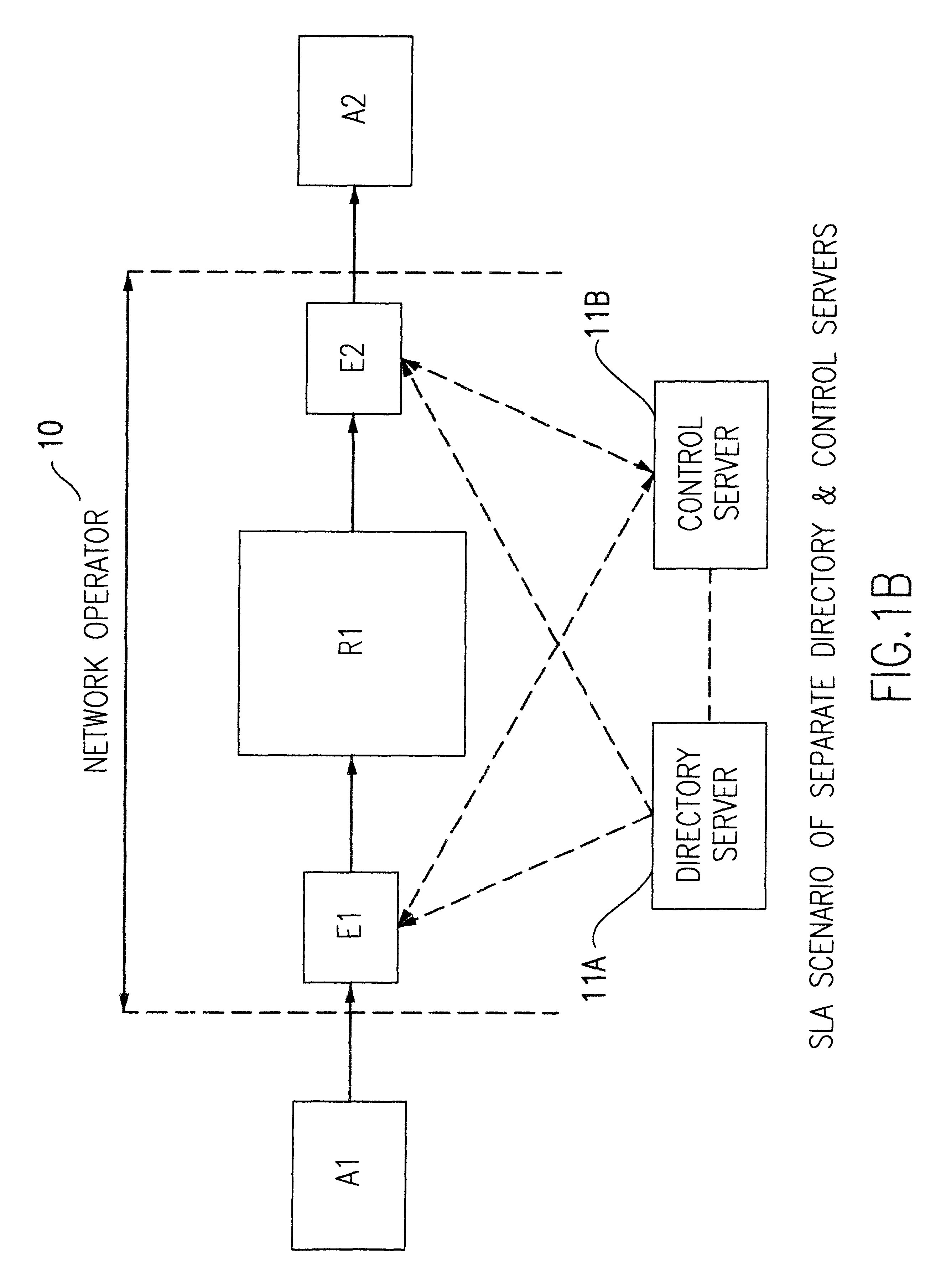
Architecture for supporting service level agreements in an IP network
InactiveUS6459682B1Effective controlOptimizationError preventionFrequency-division multiplex detailsLoss rateTraffic capacity
A method of controlling packet traffic in an IP network of originating, receiving and intermediate nodes to meet performance objectives established by service level agreements. Traffic statistics and performance data such as delay and loss rates relating to traffic flows are collected at intermediate nodes. A control server processes the collected data to determines data flow rates for different priorities of traffic. A static directory node is used to look up inter-node connections and determine initial traffic classes corresponding to those connections. The rates are combined with the initial traffic classes to define codes for encoding the headers of packets to determine their network priority.
Owner:IBM CORP
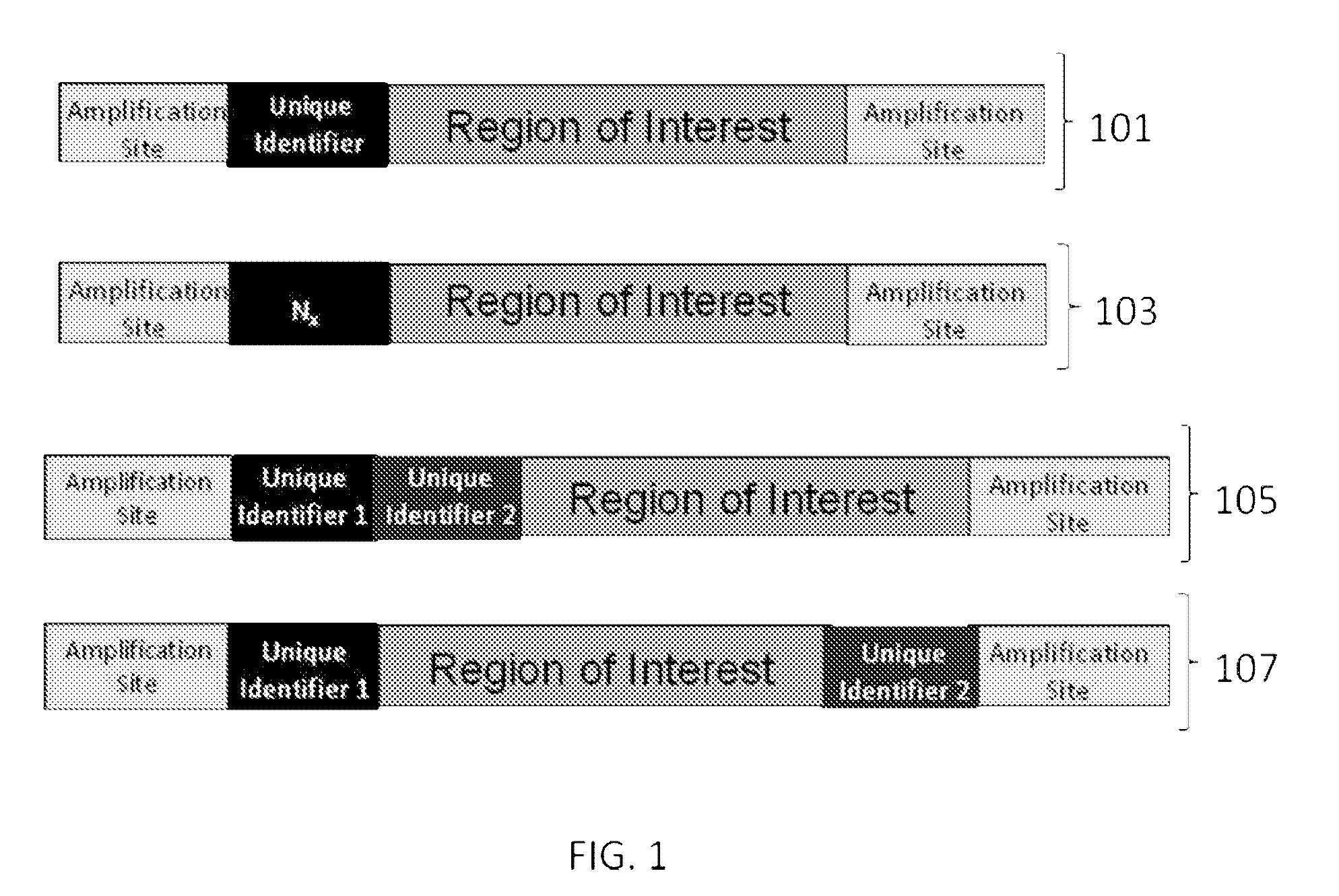
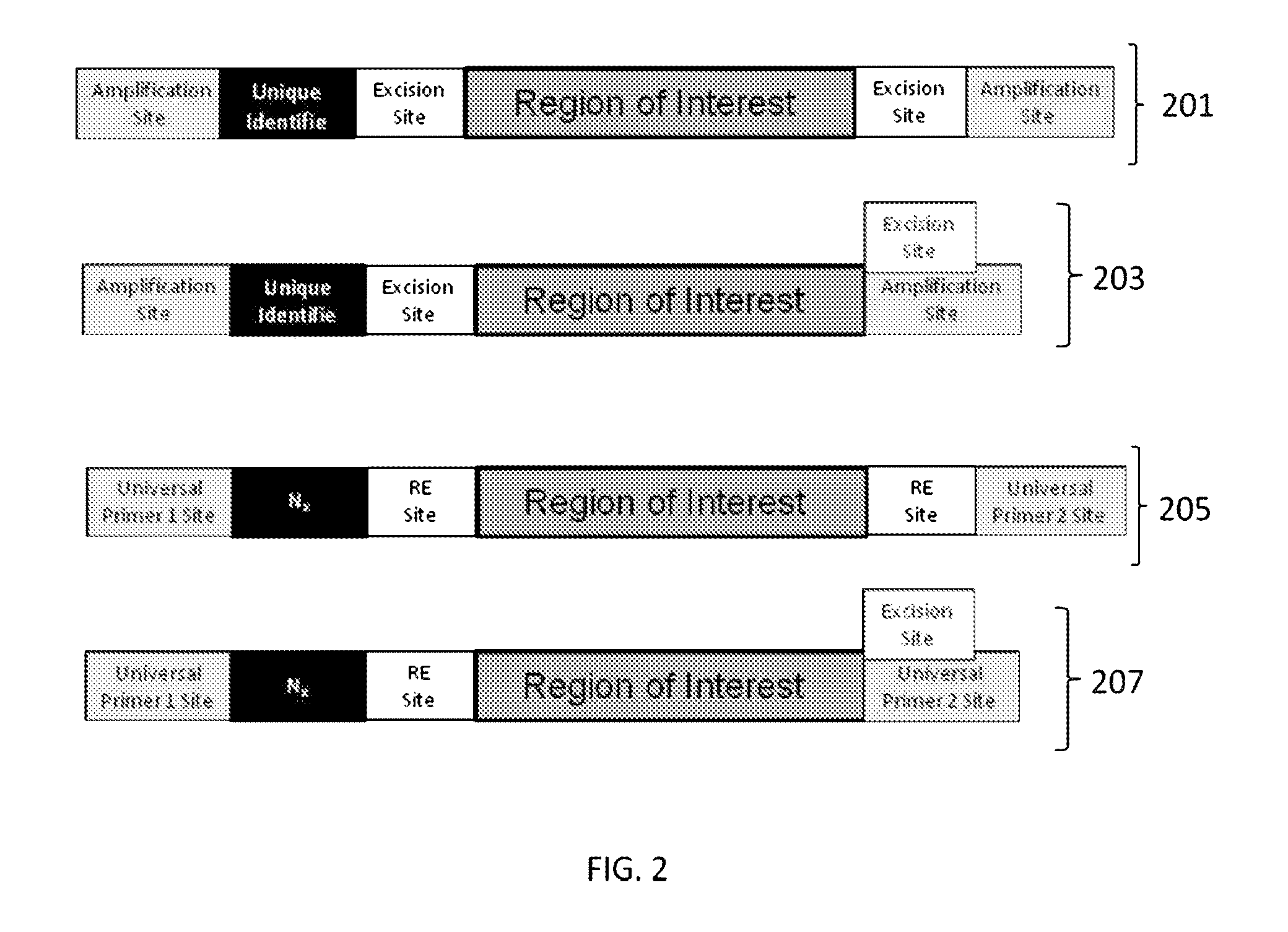
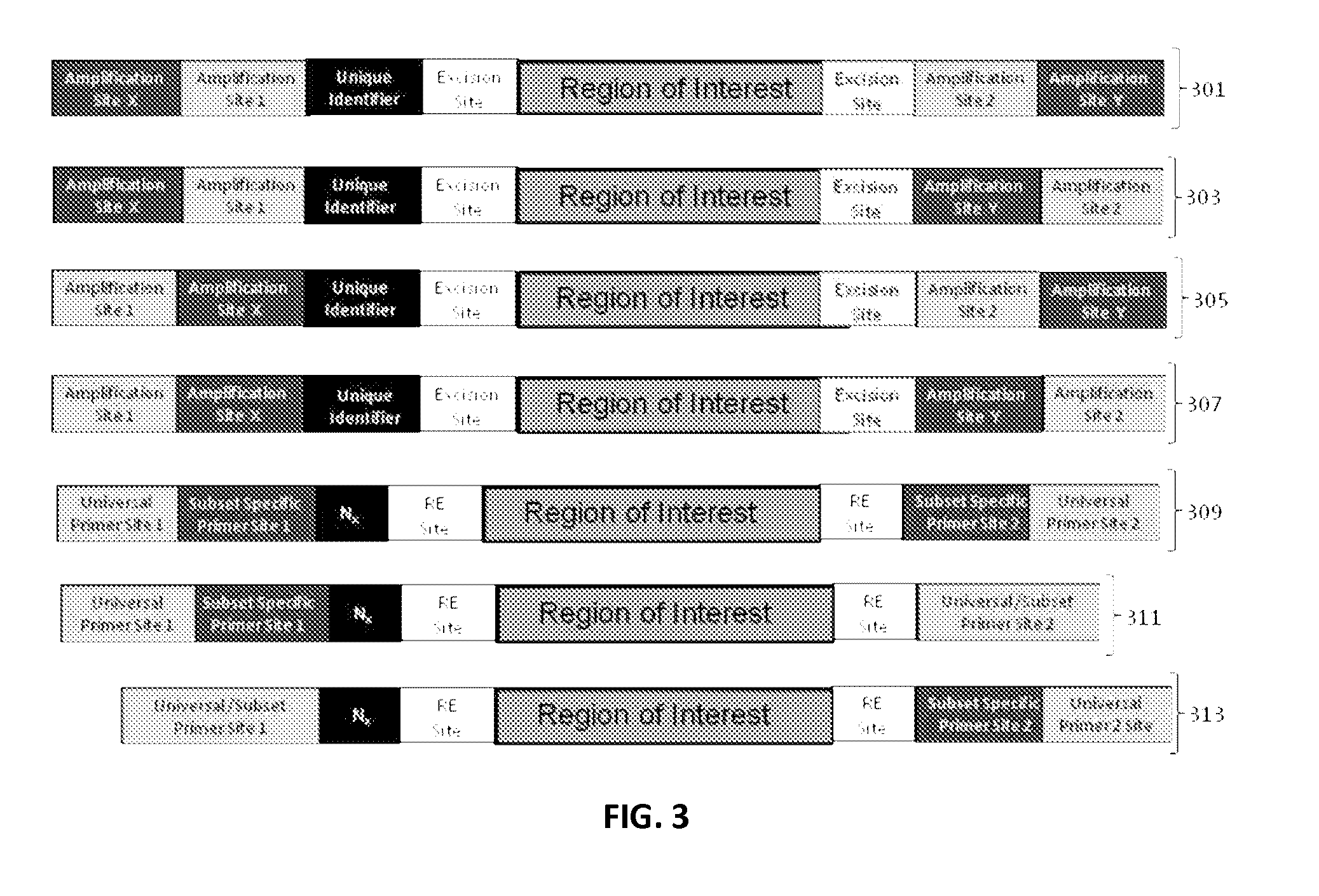
Nucleic acid constructs and methods of use
ActiveUS9085798B2Minimization requirementsSugar derivativesMicrobiological testing/measurementSynthetic biologyMutation screening
The present invention provides oligonucleotide constructs, sets of such oligonucleotide constructs, and methods of using such oligonucleotide constructs to provide validated sequences or sets of validated sequences corresponding to desired ROIs. Such validated ROIs and constructs containing these have a wide variety of uses, including in synthetic biology, quantitative nucleic acid analysis, polymorphism and / or mutation screening, and the like.
Owner:PROGNOSYS BIOSCI
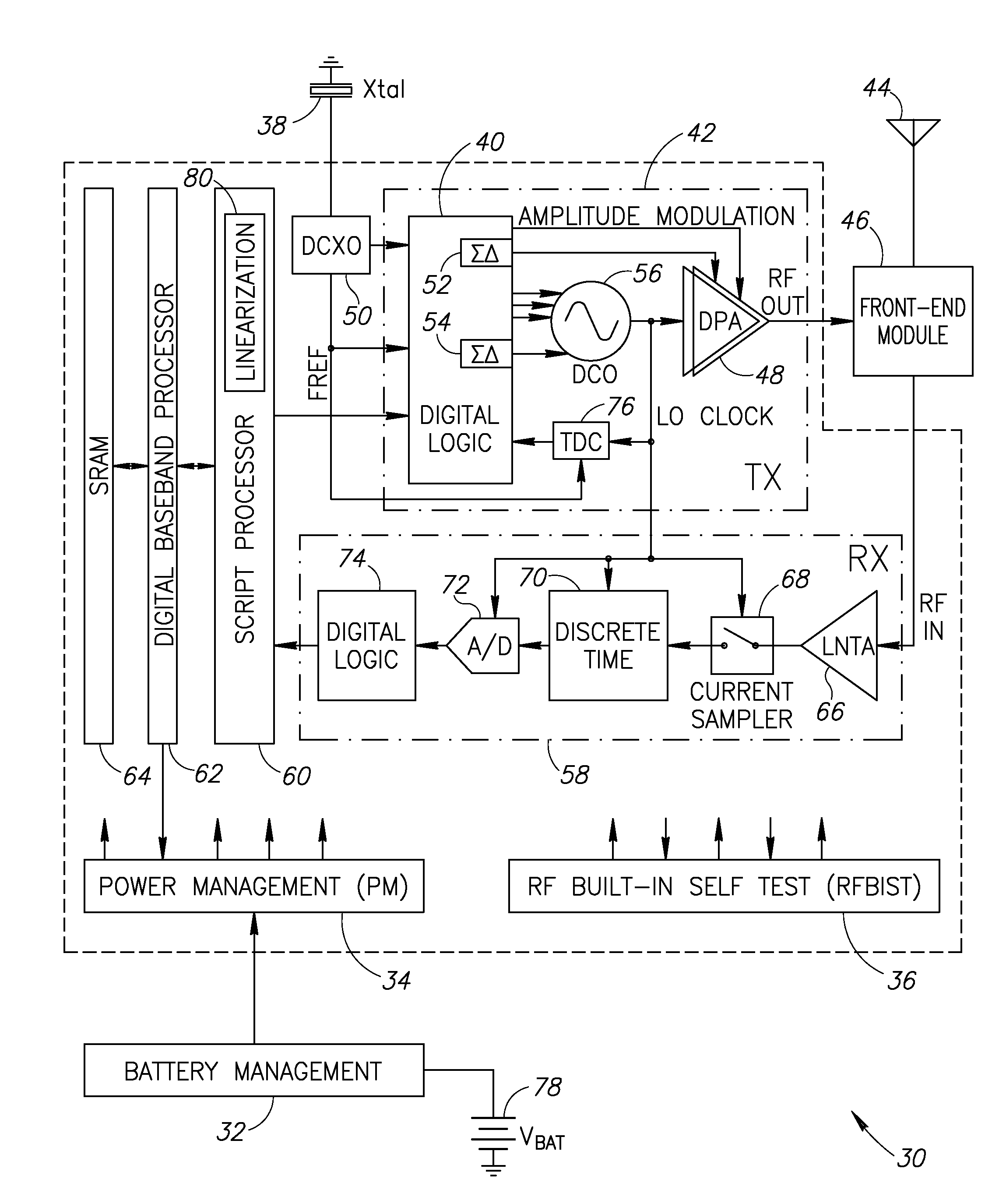
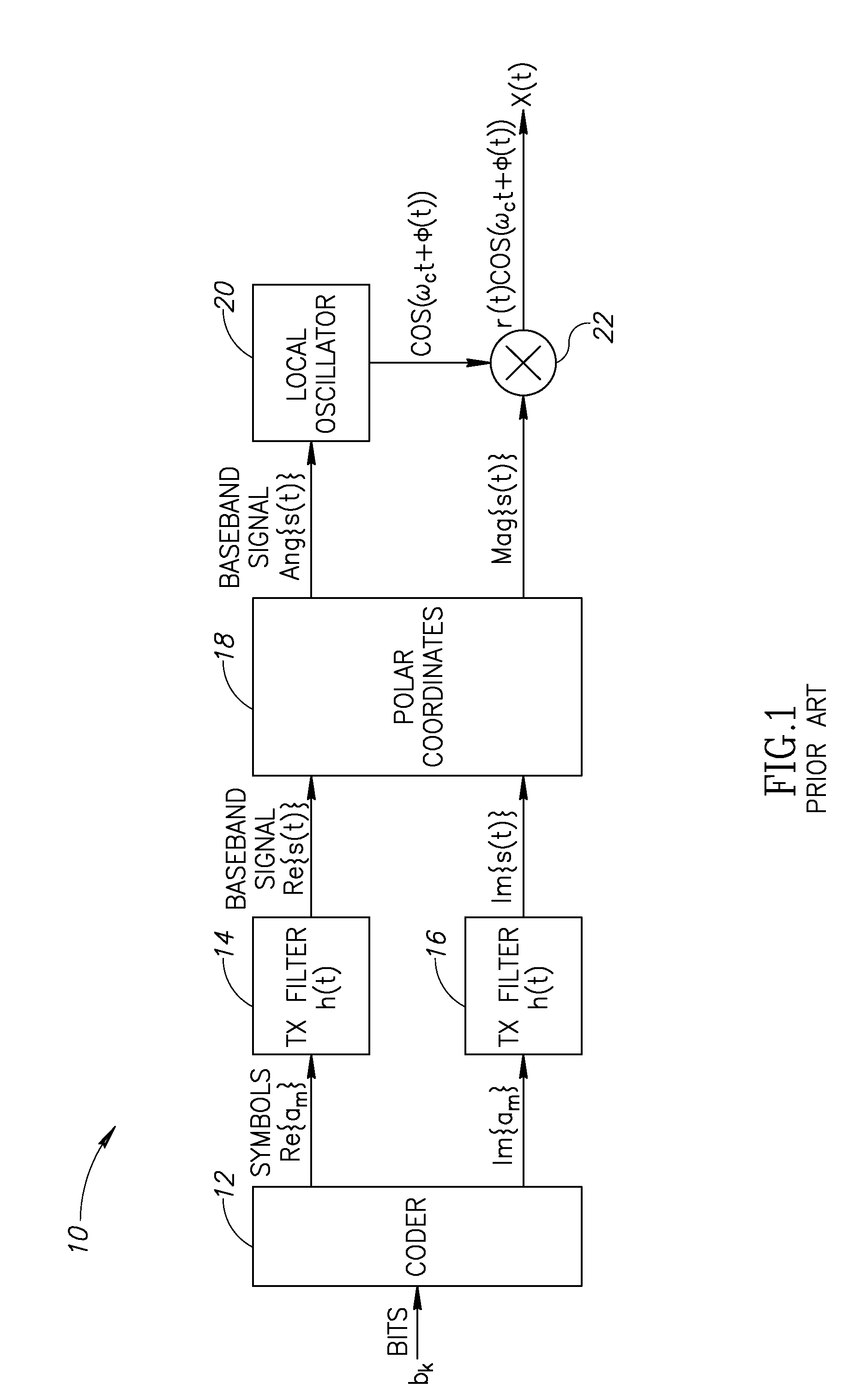
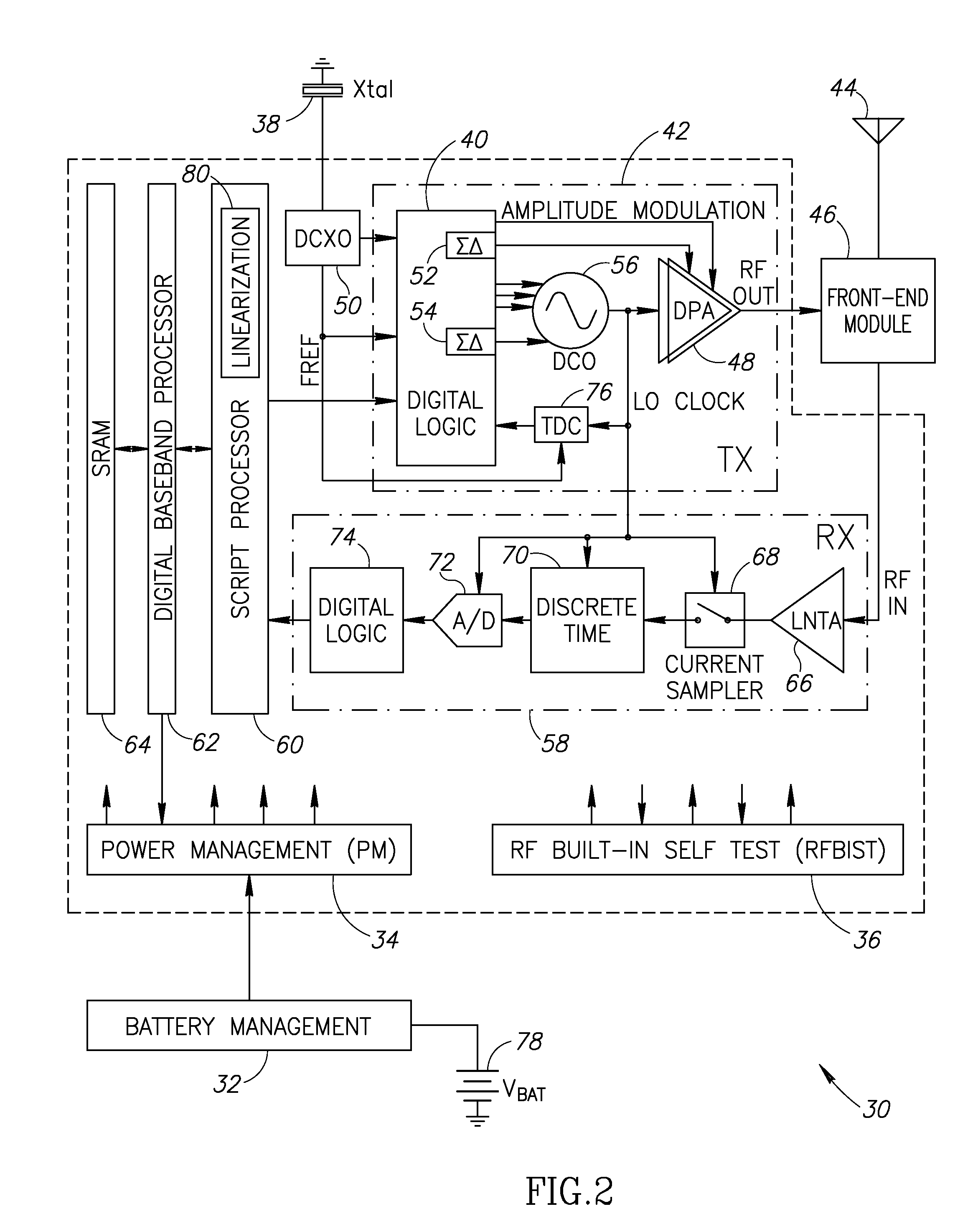
Linearization of a transmit amplifier
ActiveUS20070190952A1Reduce sensitivitySimple calculationResonant long antennasTransmission monitoringLinearizationEngineering
A novel apparatus and method of linearization of a digitally controlled pre-power amplifier (DPA) and RF power amplifier (PA). The mechanism is operative to perform predistortion calibration to compensate for nonlinearities in the DPA and PA circuits. A predistortion look up table (LUT) stores measured distortion compensation data that is applied to the TX data before being input to the digital to frequency converter (DFC), DPA and PA. The mechanism of the invention takes advantage of the on-chip receiver, which is normally inactive during the TX burst in a half-duplex operation, to demodulate the RF PA output and use the digital I / Q RX outputs to perform calibration of the TX pre-distortion tables. Controlled RF coupling is used to provide a sample of the RF output signal that to the receiver chain. The contents of the predistortion LUT are typically updated during the PA power up or down ramp. While the digitally-controlled PA (DPA) code is increasing (or decreasing), the amplitude and phase of the recovered I / Q samples are used to determine the instantaneous value of the AM / AM and AM / PM pre-distortion from which an update to the predistortion tables may be computed.
Owner:TEXAS INSTR INC
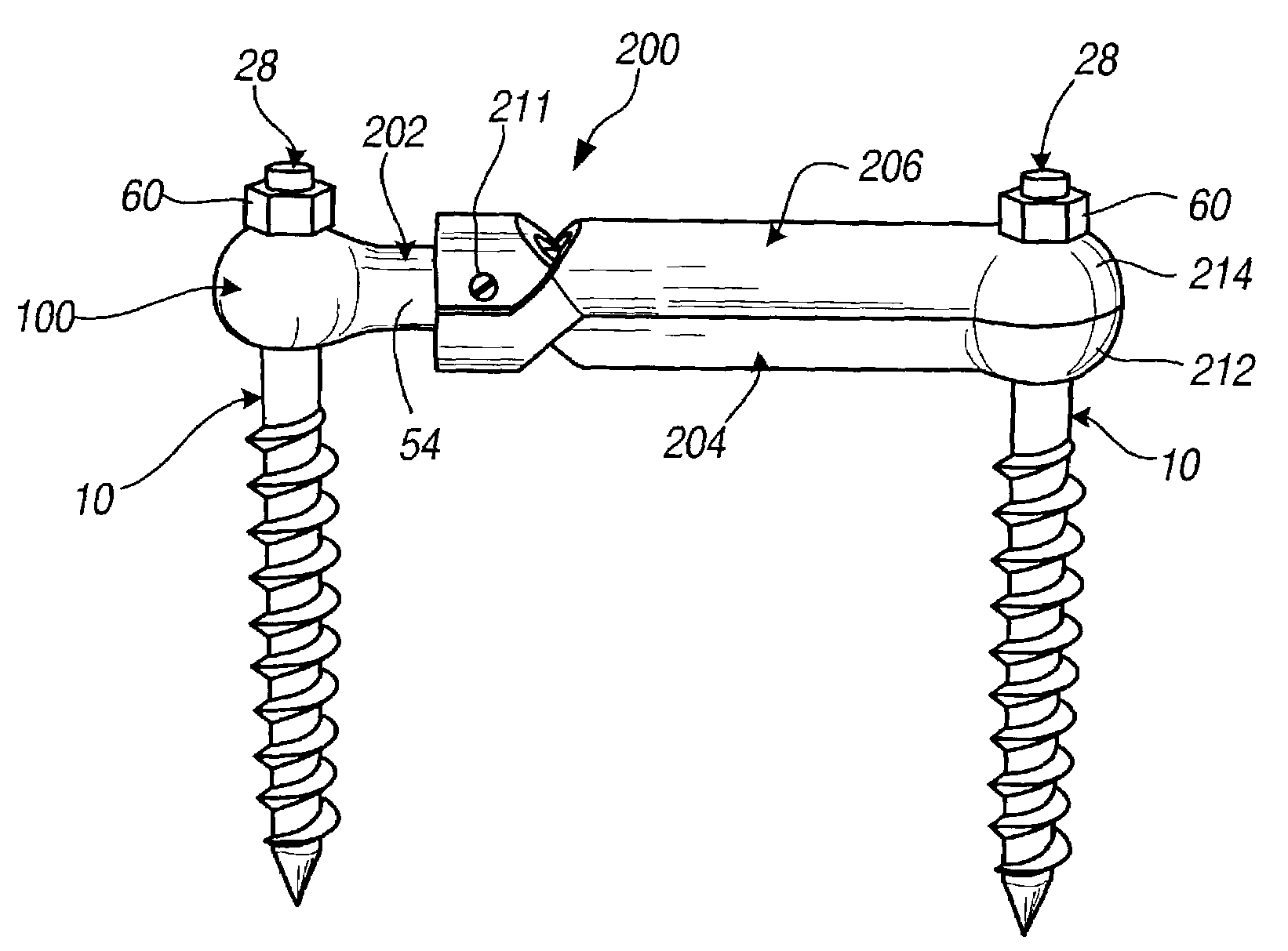
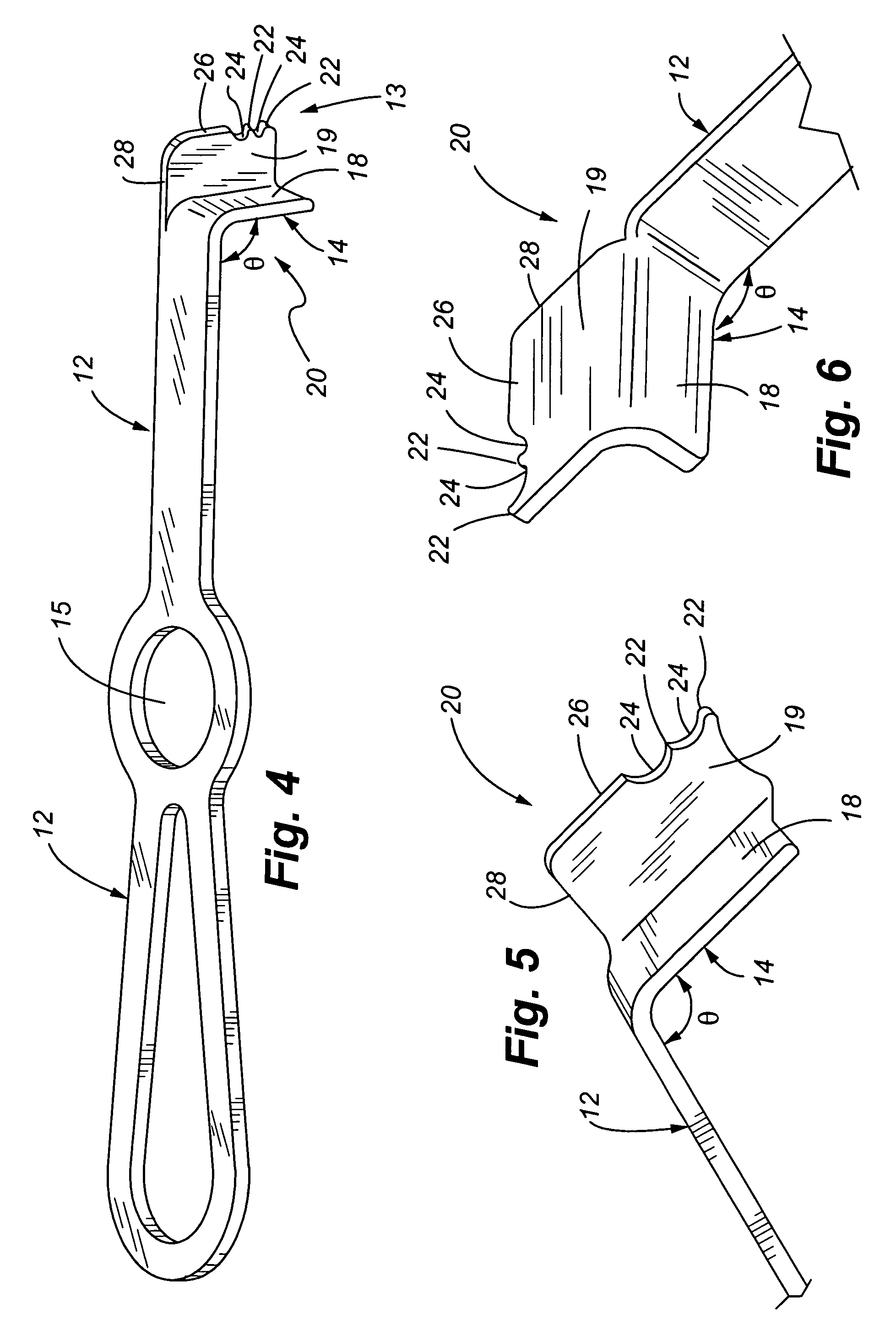
Connection rod for screw or hook polyaxial system and method of use
InactiveUS7207992B2Increase the areaPrevent rotationInternal osteosythesisJoint implantsCouplingPedicle screw
A low-profile surgical implant assembly is provided that includes a connector device that is an integral part of a rod, the connector device allowing the rod to be attached directly to a bone screw, such as a pedicle screw. Another aspect of the invention is a clamp device that allows the length of a rod spanning to attachment devices to be adjusted at the time of implantation, and further allows the clamp device to be secured by tightening a securing end of the clamp at the attachment device. The assemblies are useful for insertion into bone and connecting a foreign object to bone via a polyaxial coupling mechanism. A method for implanting the assembly is also provided.
Owner:RITLAND STEPHEN
Surgical device for clamping, ligating, and severing tissue
InactiveUS6616661B2Eliminate needControl spreadSurgical instruments for heatingSurgical forcepsSurgical device
A surgical device for severing tissue, the surgical device comprising; a first shaft having a first internal lumen and a first slot disposed at a distal end; a clamp slidingly disposed in the first slot between open and closed positions to capture tissue in the first slot, the clamp having a clamping surface disposed at a distal end; at least one electrode for applying RF energy to the tissue captured in the first slot; a cutting blade slidingly disposed in the first slot between open and closed positions, the cutting blade having a cutting edge to sever the tissue; first actuation means for actuating the clamp between the open and closed positions; and second actuation means for actuating the cutting blade between the open and closed positions.
Owner:SORIN GRP USA INC
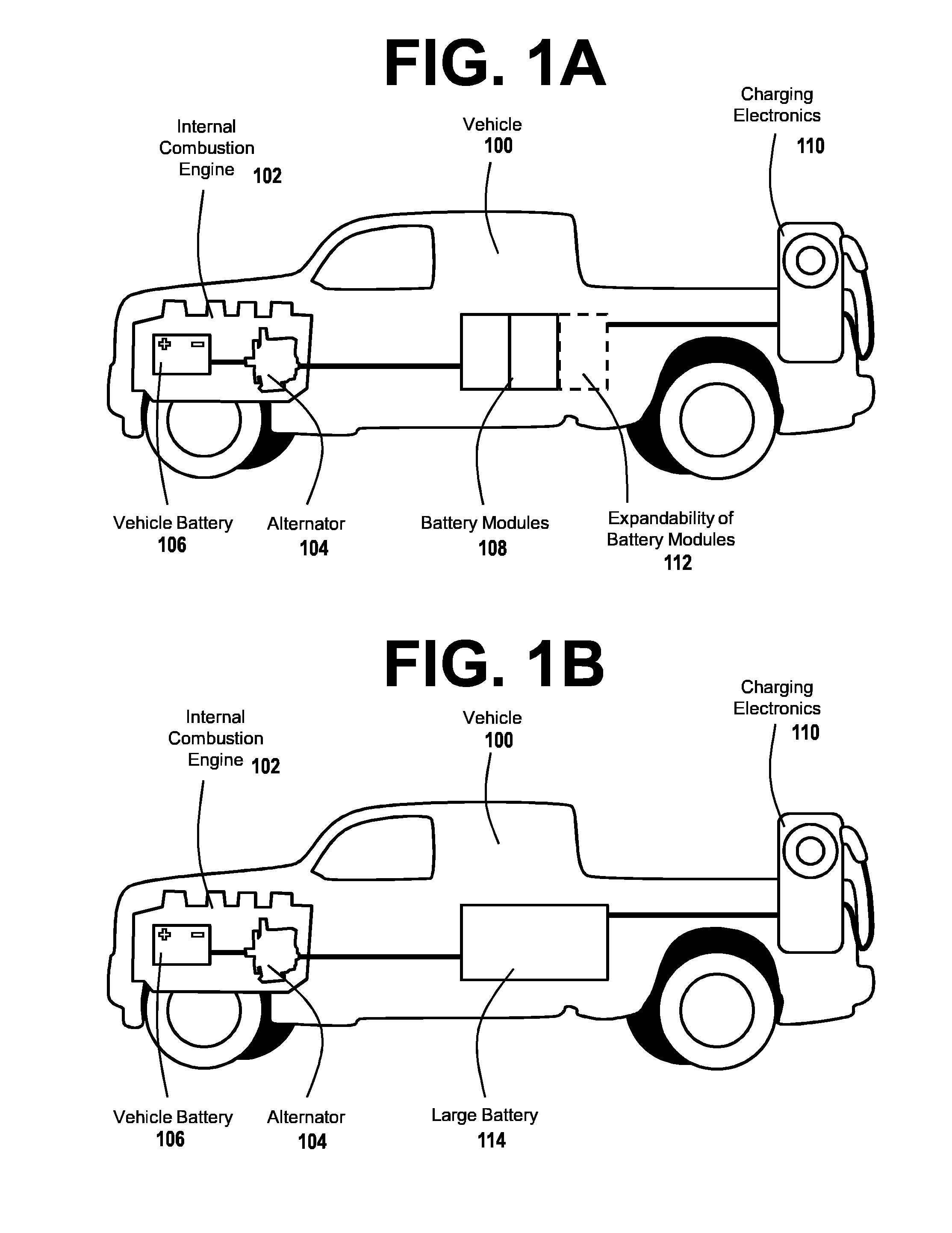
Charging Service Vehicle Network
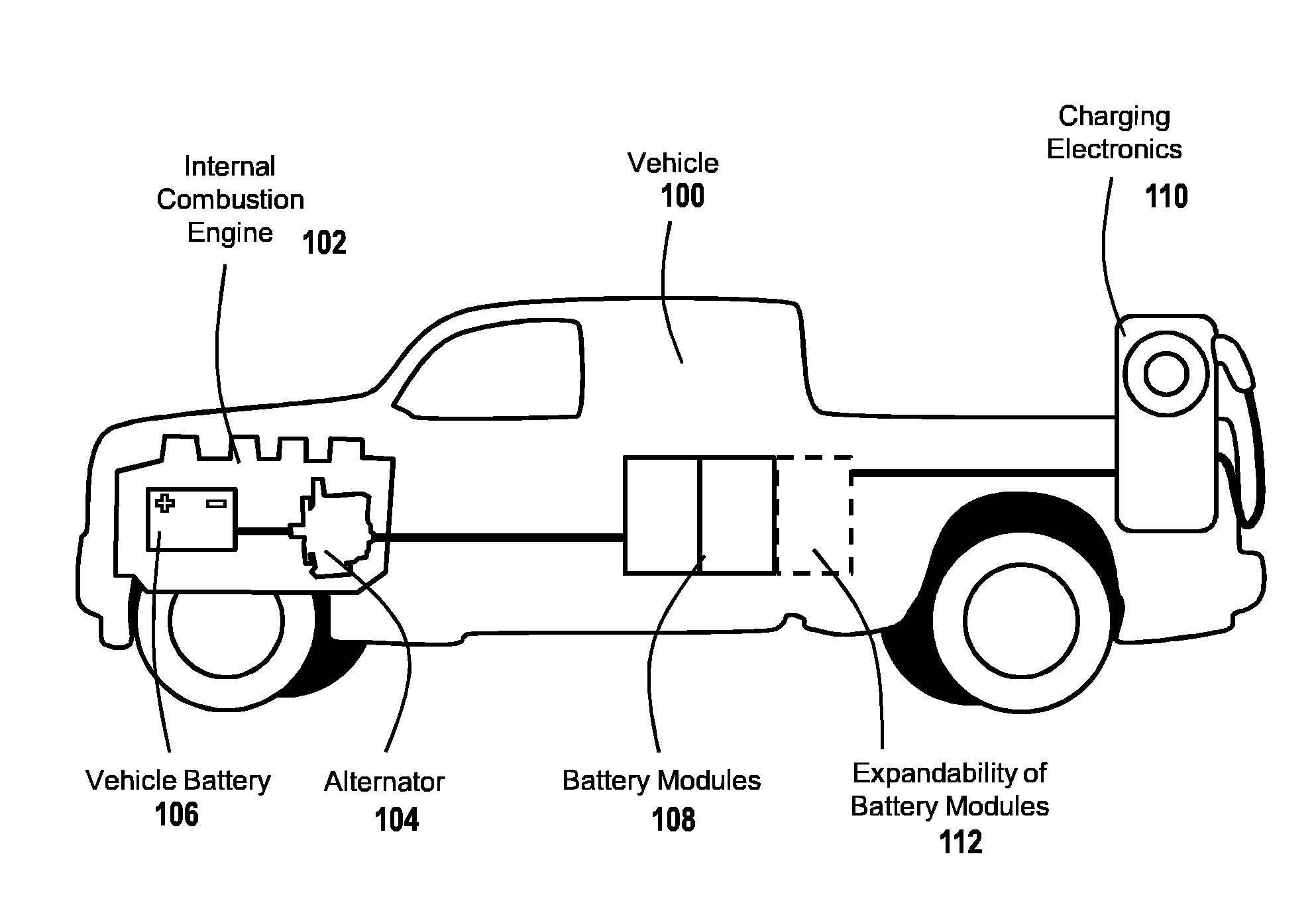
InactiveUS20120303397A1Increase capacityEfficient redeploymentBatteries circuit arrangementsCharging stationsEngineeringSystem controller
Charging service vehicle networks are among the embodiments disclosed herein, including battery module-powered EV charging roadside service vehicles. Battery modules are removably mounted to the service vehicles and manually exchanged within a system of battery module storage locations. Some embodiments provide resupply vehicles for delivering battery modules between storage locations and / or service vehicles, and may be used to exchange battery modules. Controllers are used to reserve battery modules at the storage locations to ensure availability for high priority activities. Some storage locations have charging apparatus to recharge battery modules stored there, and some storage locations are repositionable mobile units. Multiple tiers or levels of system controllers used by service vehicles to control centers are implemented to manage operations and optimize usage of battery modules and charging services across wide areas, including providing additional service vehicles to supply temporary needs for charging services.
Owner:GREEN CHARGE NETWORKS
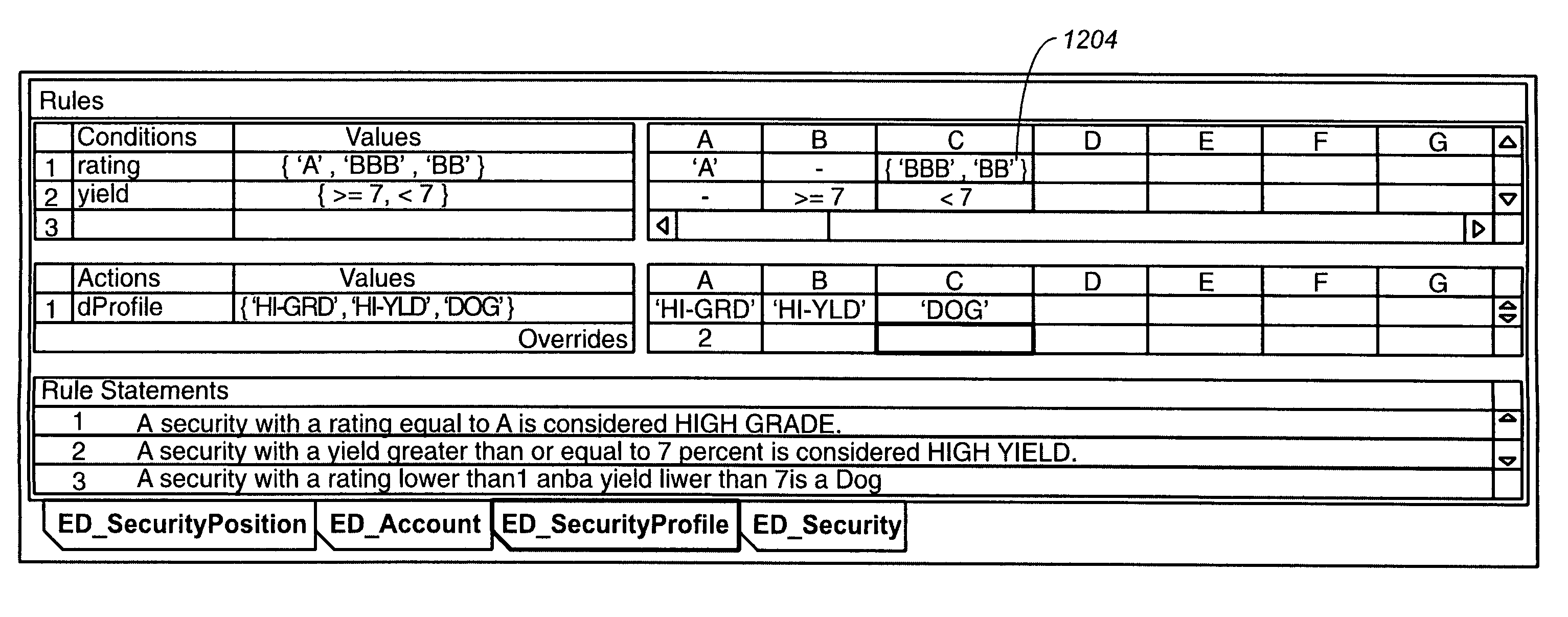
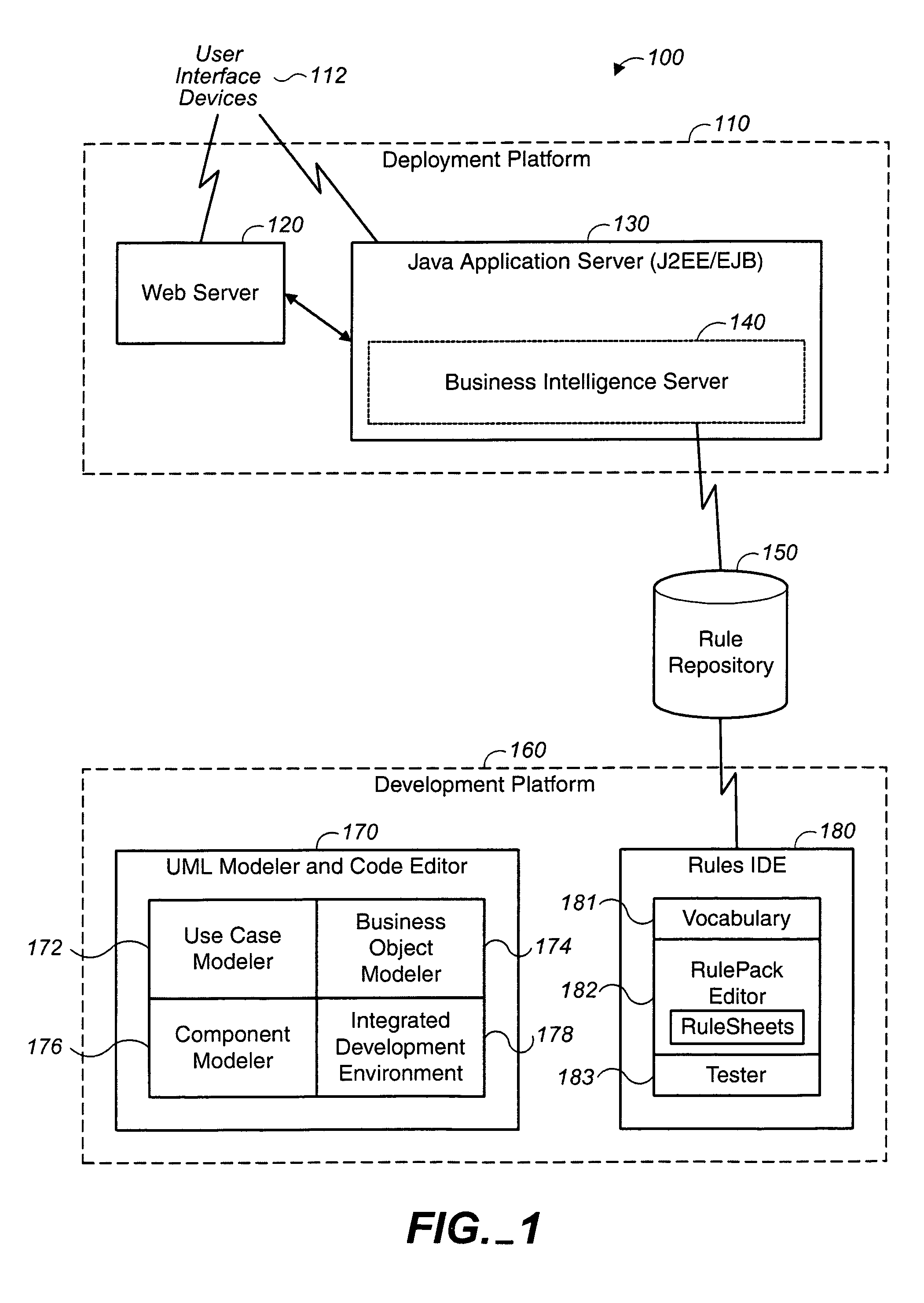
Business rules user interface for development of adaptable enterprise applications
ActiveUS7020869B2Reduce complexityMinimization requirementsTechnology managementVisual/graphical programmingApplication softwareDisplay list
Methods and apparatus, including computer program products, for interacting with a user to define business rules in a declarative manner. The invention operates to display a rule set as an editable list of conditions and an editable list of actions, the conditions and actions being linked to each other by the combination of an editable list of if-values and an editable list of then-values, wherein if-values and then-values are explicitly linked to each other, conditions and if-values are explicitly linked to each other, and then-values and actions are explicitly linked to each other in the displayed lists.
Owner:PROGRESS SOFTWARE
Virtual display apparatus for mobile activities
InactiveUS20030030597A1Prevent slippagePrevent dislodgingCathode-ray tube indicatorsOptical elementsComputer scienceField of view
The present invention teaches a method of constructing head-mounted virtual display apparatuses for mobile activities based on a non-cross-cavity optical configuration, which simultaneously provides the user with "look toward" access to an inset virtual image and an unobstructed forward field of view of at least 35 degrees. In one embodiment, a pair of light deflecting elements and associated adjustment means project a light path from the normal peripheral field of view towards the eye without geometric distortion of the virtual image associated image plane tilt.
Owner:GEIST RICHARD EDWIN
Delivery of oral drugs
InactiveUS20010020147A1Comfortable and convenient motionComfortable and convenient feelPowder deliveryLiquid surface applicatorsMean diameterHuman patient
Disclosed is a system for delivery of a drug comprising a multiple unit dosing device comprising a housing and an actuator, said device containing multiple doses of multiparticulates comprising drug particles, said device upon actuation delivering a unit dose of said multiparticulates, said drug particles having a mean diameter of greater than 10 mum to about 1 mm such that an effective dose of said drug cannot be delivered into the lower lung of a human patient. Also disclosed are novel methods, devices and dosage forms for delivering a drug.
Owner:PHARMAKODEX LTD
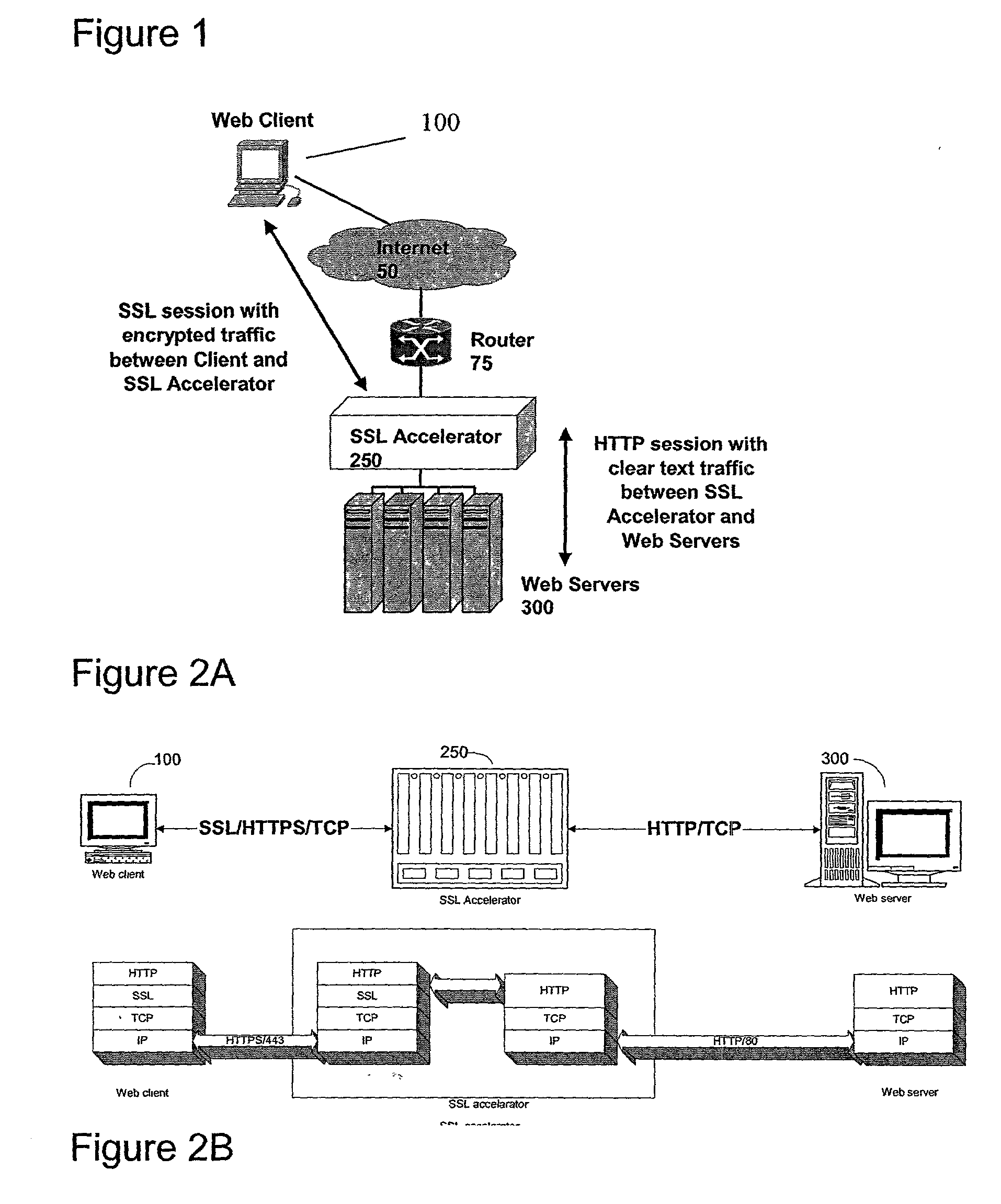
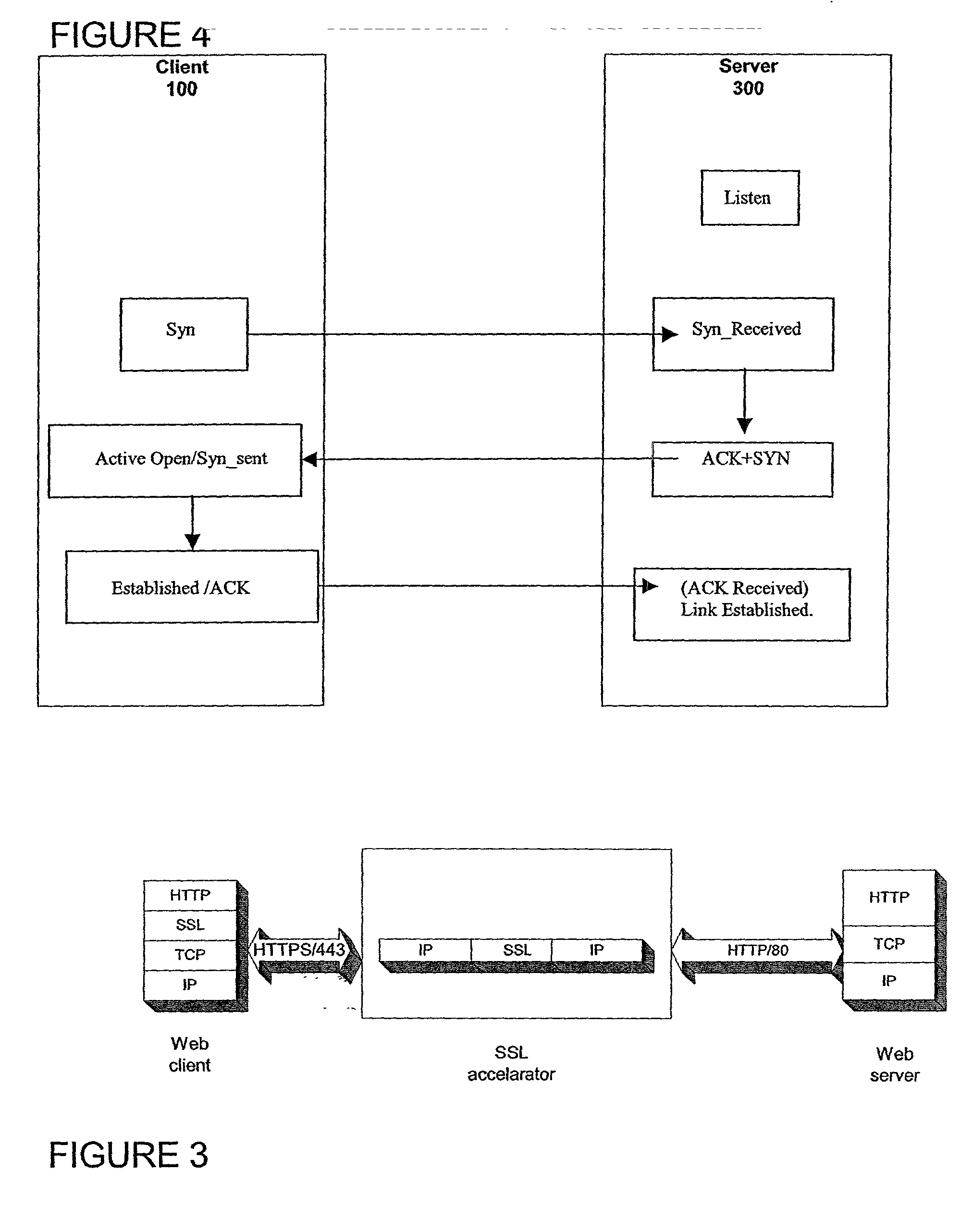
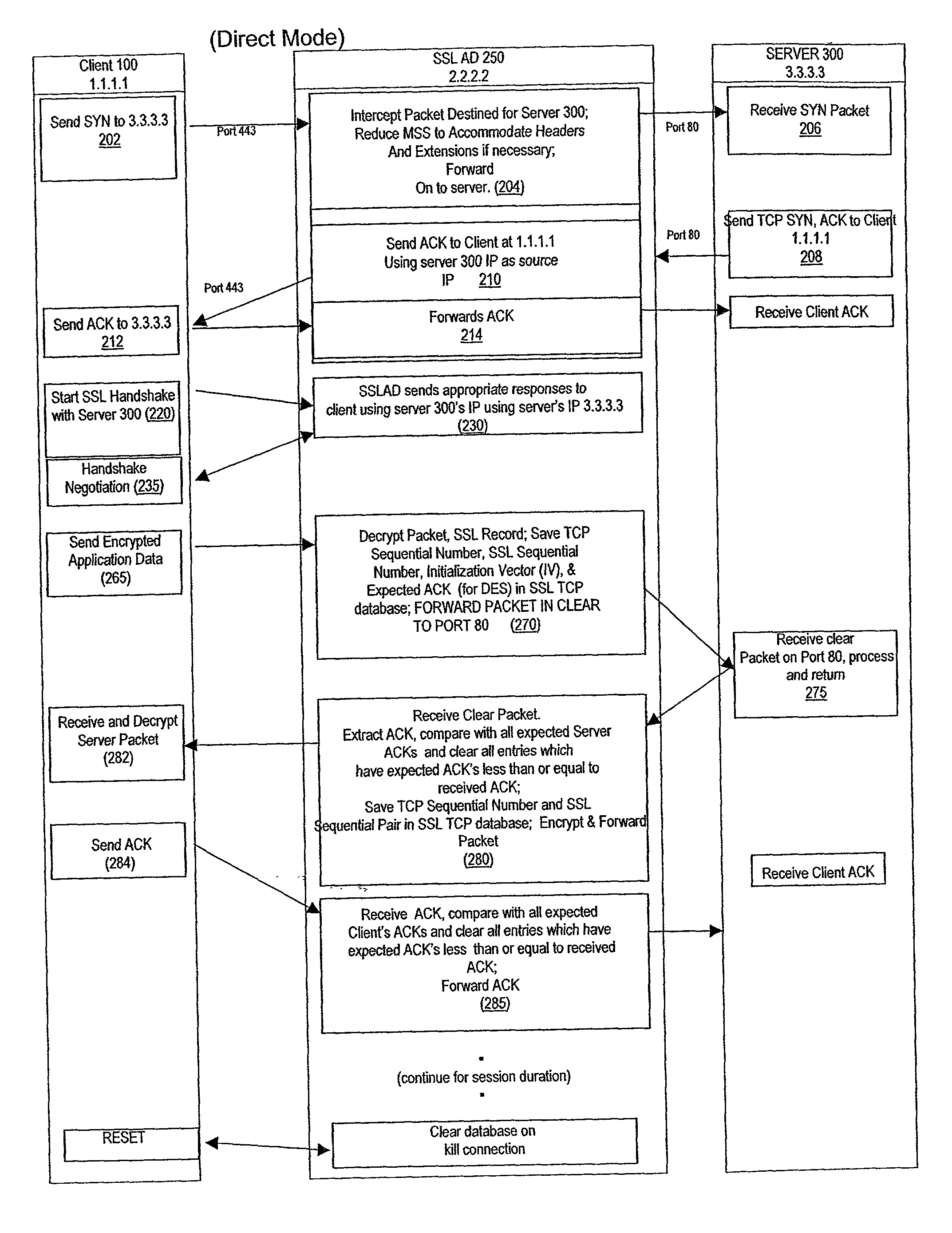
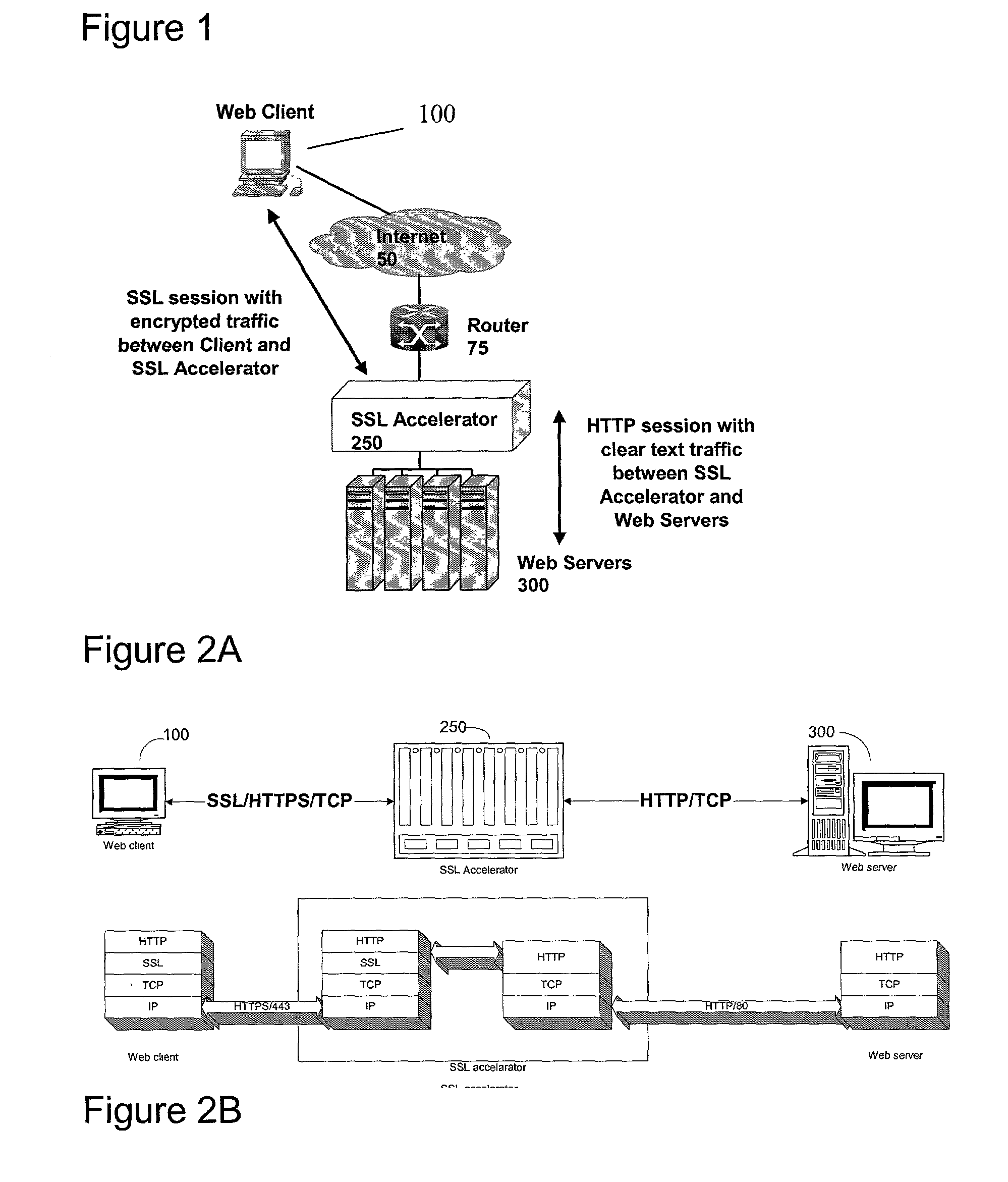
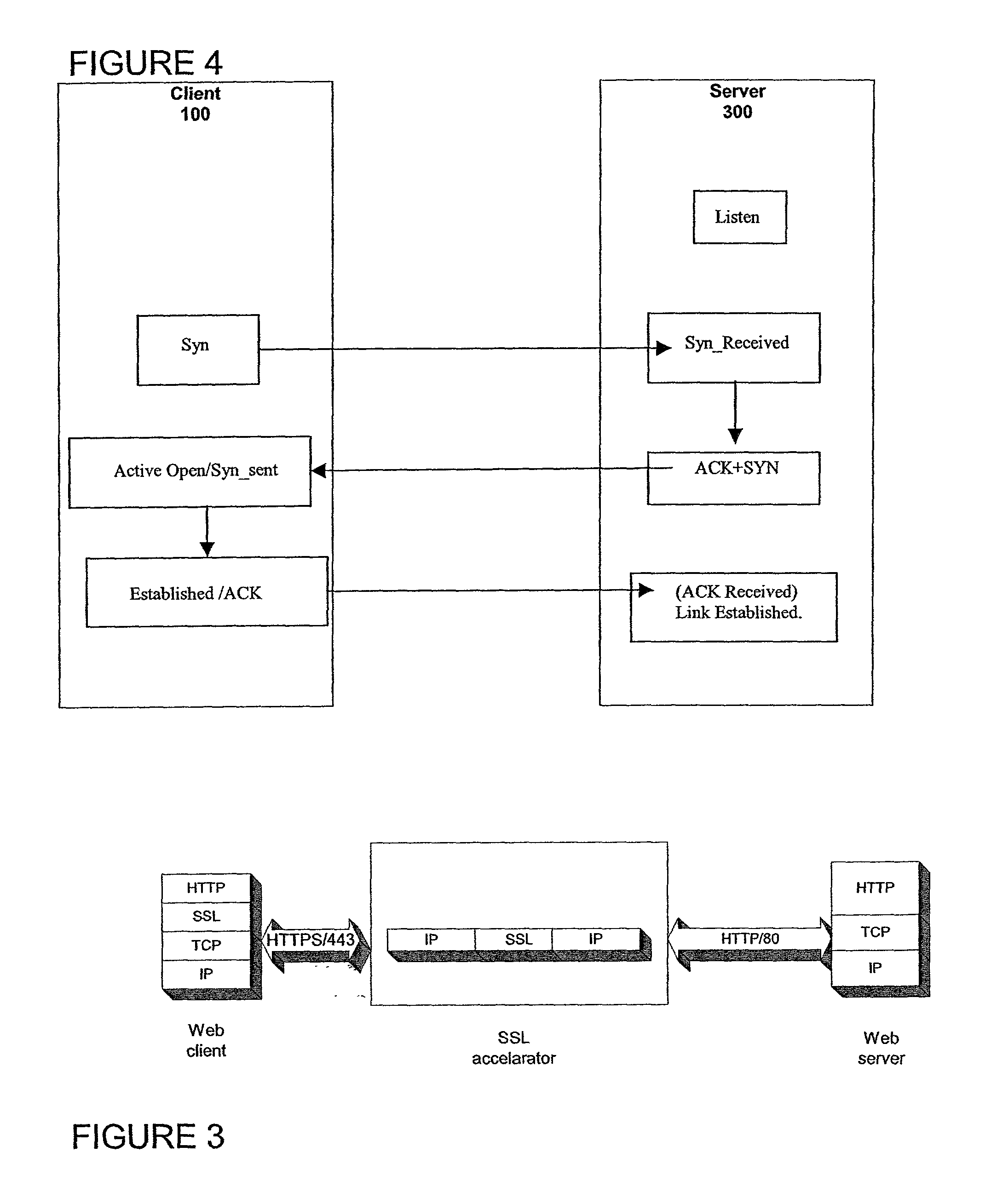
Secure sockets layer proxy architecture
ActiveUS20030014628A1Low hardware requirementsLower latencyError detection/correctionMultiple digital computer combinationsSecure communicationChannel coupling
A method for secure communications between a client and one of a plurality of servers performed on an intermediary device coupled to the client and said plurality of servers. In one aspect, the method comprises: establishing an open communications session between the intermediary device and the client via an open network; negotiating a secure communications session with the client; establishing an open communications session with said one of said plurality of servers via a secure network; receiving encrypted data from the client via the secure communications session; decrypting encrypted application data; forwarding decrypted application data to the server via the secure network; receiving application data from the server via the secure network; encrypting the application data; and sending encrypted application data to the client. In a further aspect, an apparatus including a network interface communicating with the public network and the secure network at least one processor, programmable dynamic memory addressable by the processor, and a communications channel coupling the processor, memory and the network communications interface is provided. The apparatus further includes a proxy TCP communications engine, a proxy SSL communications engine, a server TCP communications engine; and a packet data encryption and decryption engine.
Owner:NEXSI SYST
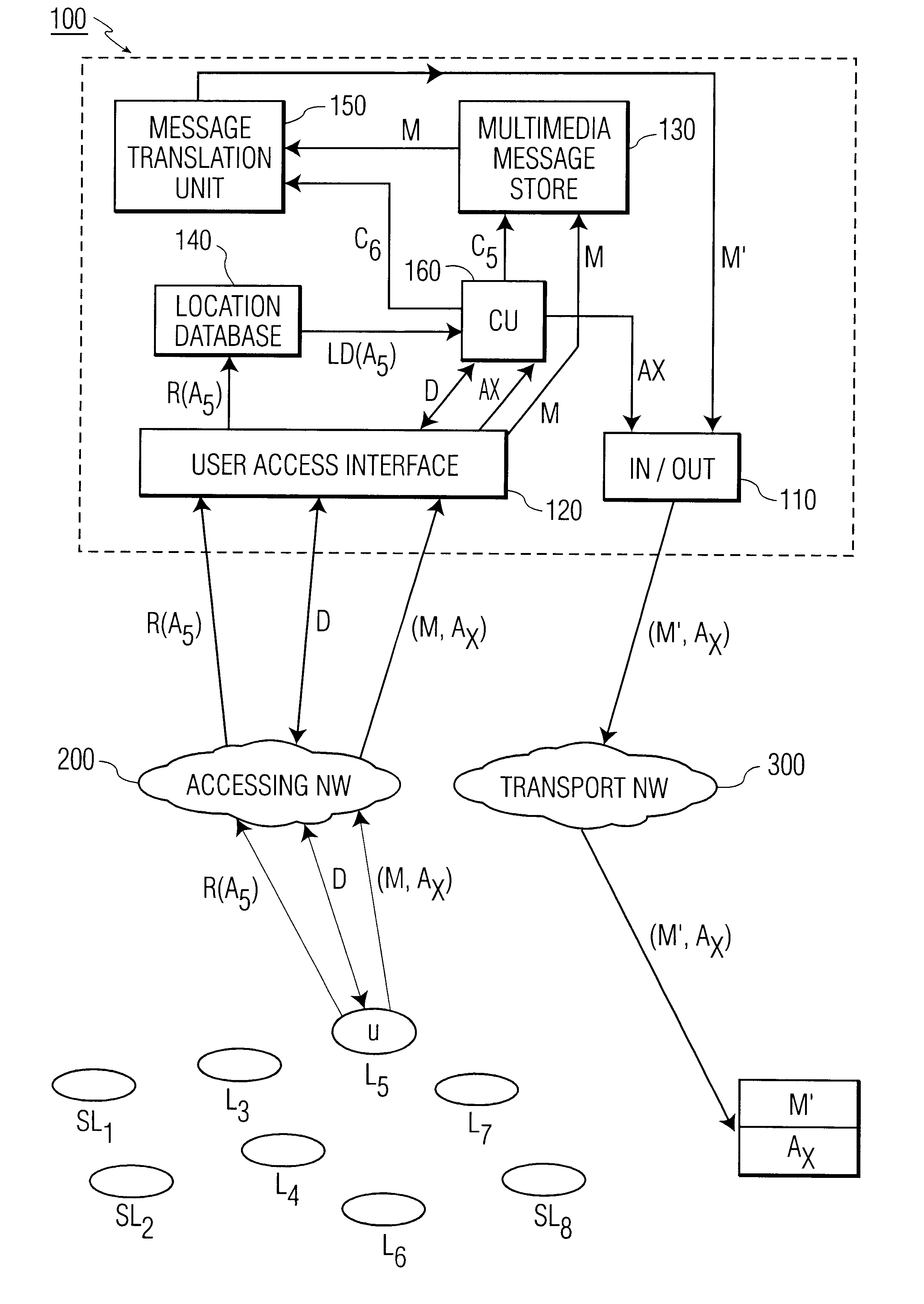
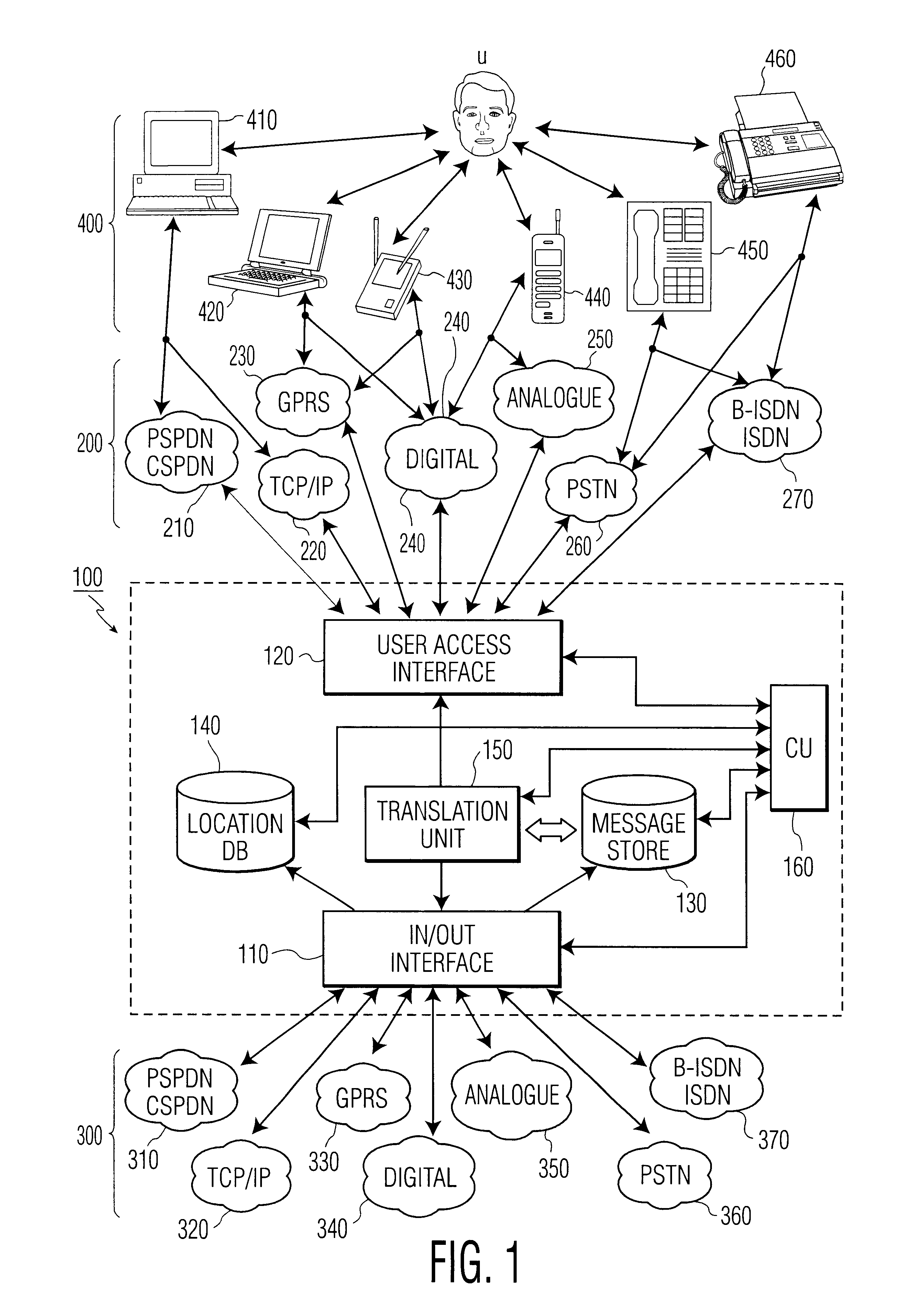
Methods and arrangement in a communication system
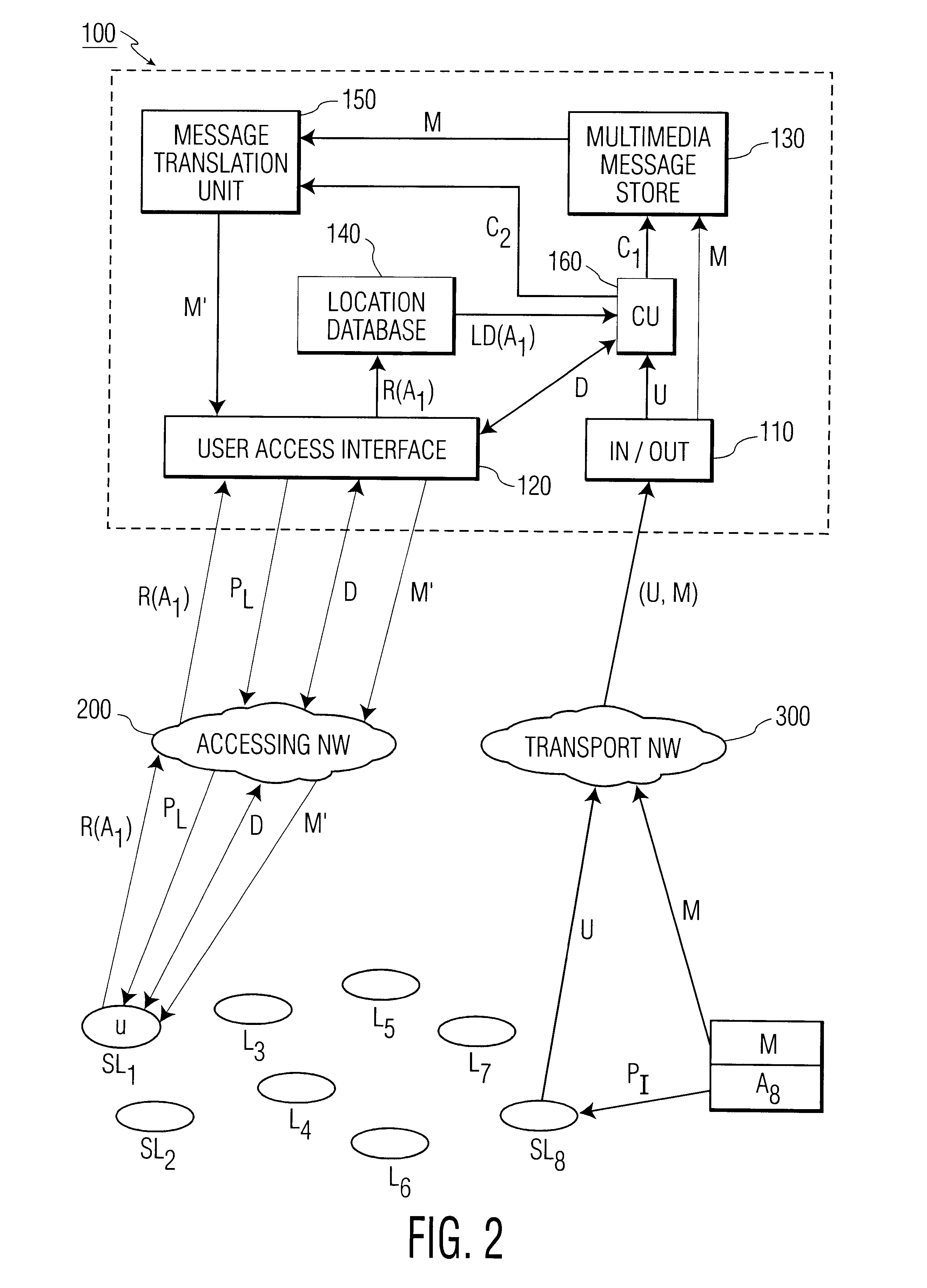
InactiveUS6333919B2Minimization requirementsMultiplex system selection arrangementsSpecial service provision for substationAccess networkCommunications system
The present invention relates to methods and an arrangement for receiving, storing, and originating multimedia messages. An incoming message is transmitted to an in / out interface via a transport network. The message is stored in a message store, translated in a translation unit into a format adapted to the presentation capabilities of receiver's current terminal and delivered to the receiver over a user access interface and an access network with guidance from a location database. Earlier received messages, which are kept in the message store, can be accessed and edited via any standardized access network using media translation in the translation unit. A multimedia message is originated by a user in the system via any access network and the user access interface. The message is then stored in the message store, translated in the translation unit, and delivered to the destination through the in / out interface and an appropriate transport network.
Owner:IDTP HLDG
Extended release formulations of opioids and method of use thereof
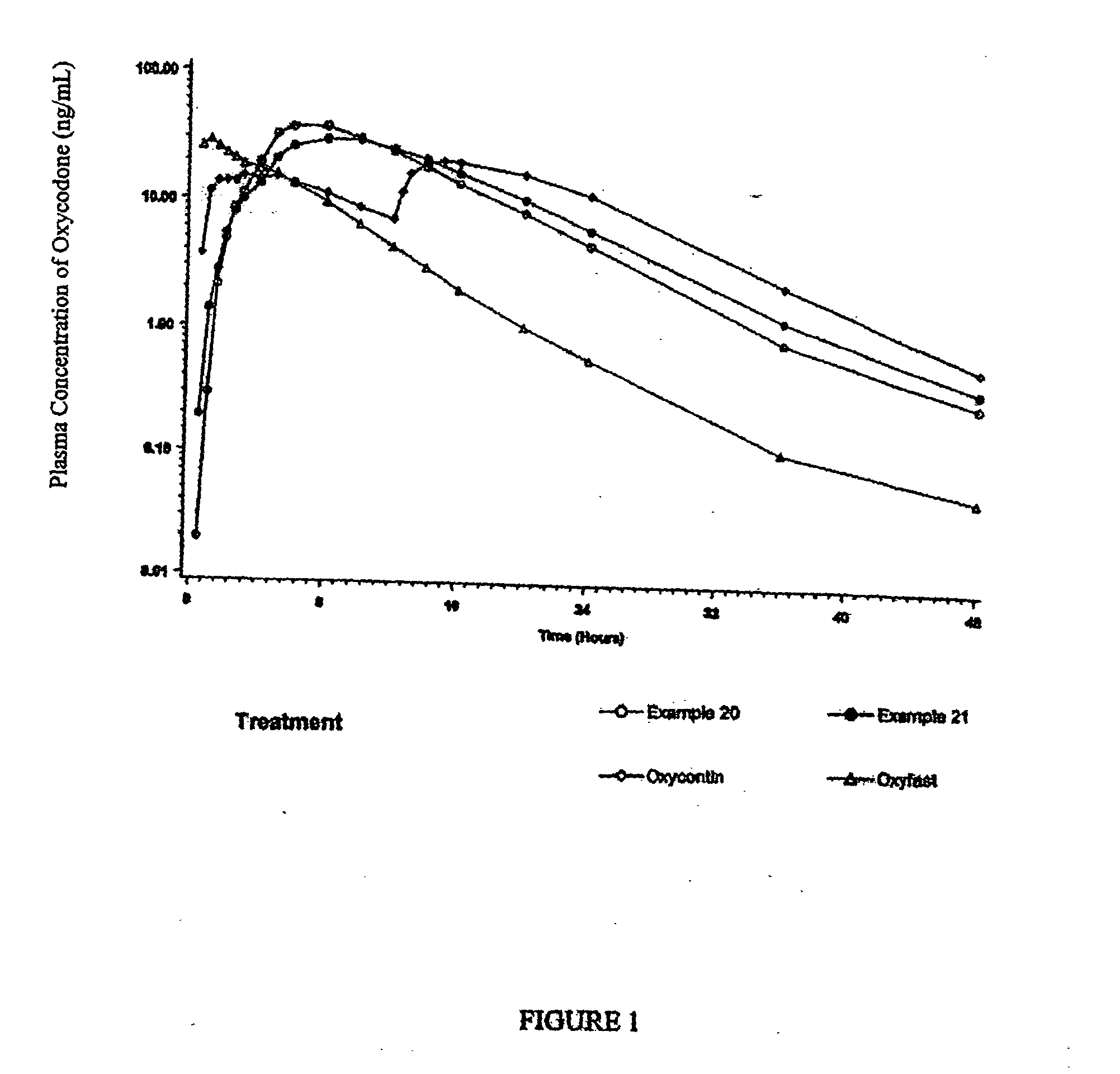
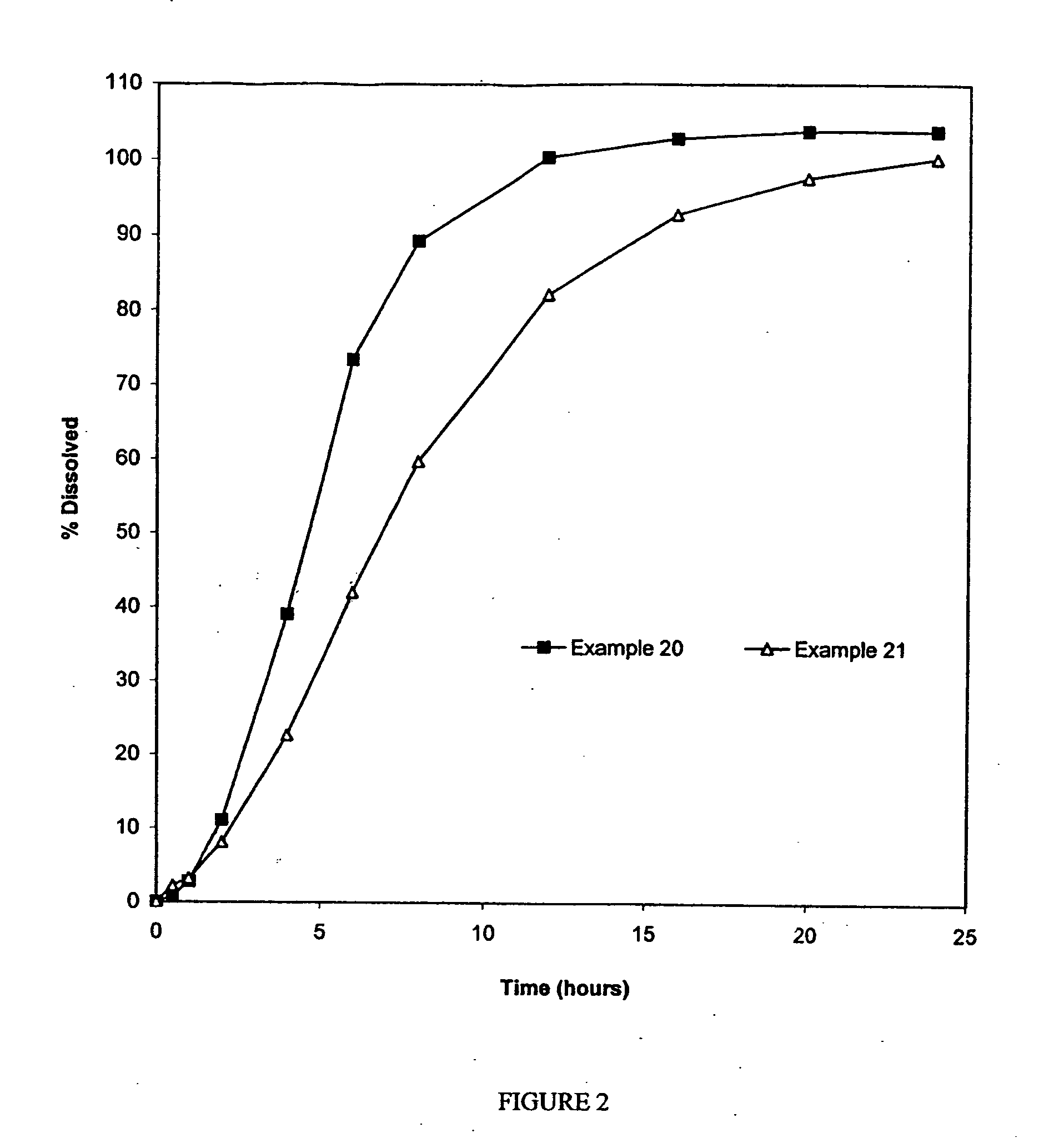
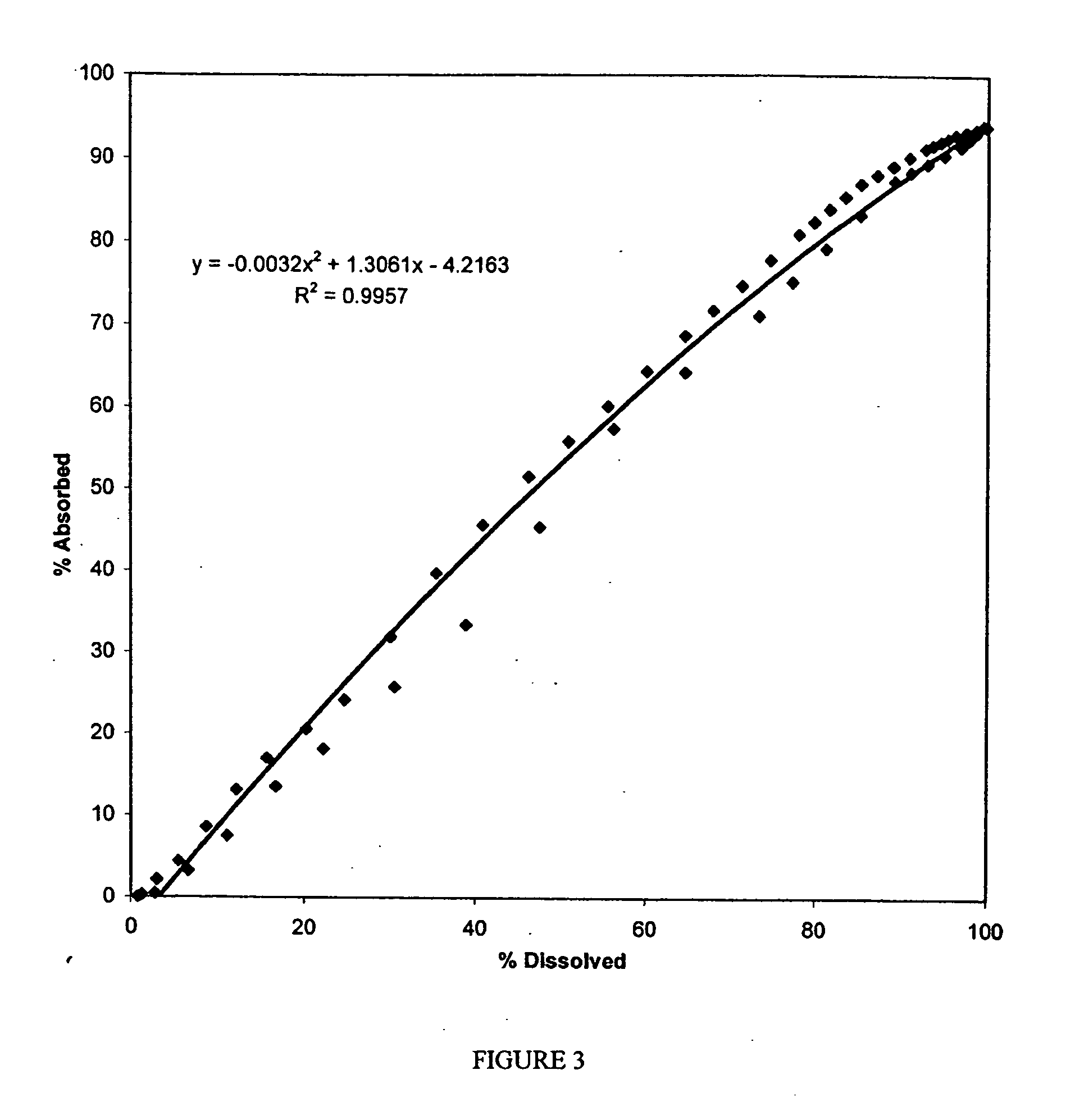
InactiveUS20050074493A1Reduce plasma concentrationReduce incidenceBiocideNervous disorderOpioid antagonistDrug
Extended release formulations for the delivery of opioid agonists, including oxycodone, are provided which exhibit low peak to trough plasma concentration fluctuations and sufficiently high plasma concentrations over an extended period of time to provide a once a day dosage administration, wherein the formulations provide pain relief for up to 24 hours The extended release formulations may be customized to achieve the desired plasma concentration profile, e.g. two or more different extended release drug-loaded pellets or granules may be combined in a formulation. Additional formulations include combinations of drug loaded and extended release opioid agonists-loaded pellets or granules. Other formulations include a combination of an opioid agonist and an opioid antagonist, as well as a combination of an opioid agonist and a NSAID.
Owner:MEHTA ATUL M +1
Secure sockets layer cut through architecture
ActiveUS20030014623A1Low hardware requirementsLower latencyDigital data processing detailsUser identity/authority verificationSecure communicationSession management
A method for secure communications between a client and a server. The method includes the steps of managing a communications negotiation between the client and the server; receiving encrypted data packets from the client; decrypting each encrypted packet data; forwarding unencrypted data packets to the server; receiving data packets from the server; encrypting the data packets from the server; and forwarding encrypted data packets to the client. In a further embodiment, an apparatus communicating with a client via a public network and communicating with one of a plurality of servers via a secure network is disclosed. The apparatus includes a network communications interface, at least one processor, programmable dynamic memory, and a communications channel coupling the processor, memory and network communications interface. In addition, the apparatus includes a client / server open communications session manager, a client secure communication session manager, a client / server secure communications session tracking database; and a data packet encryption and decryption engine.
Owner:NEXSI SYST
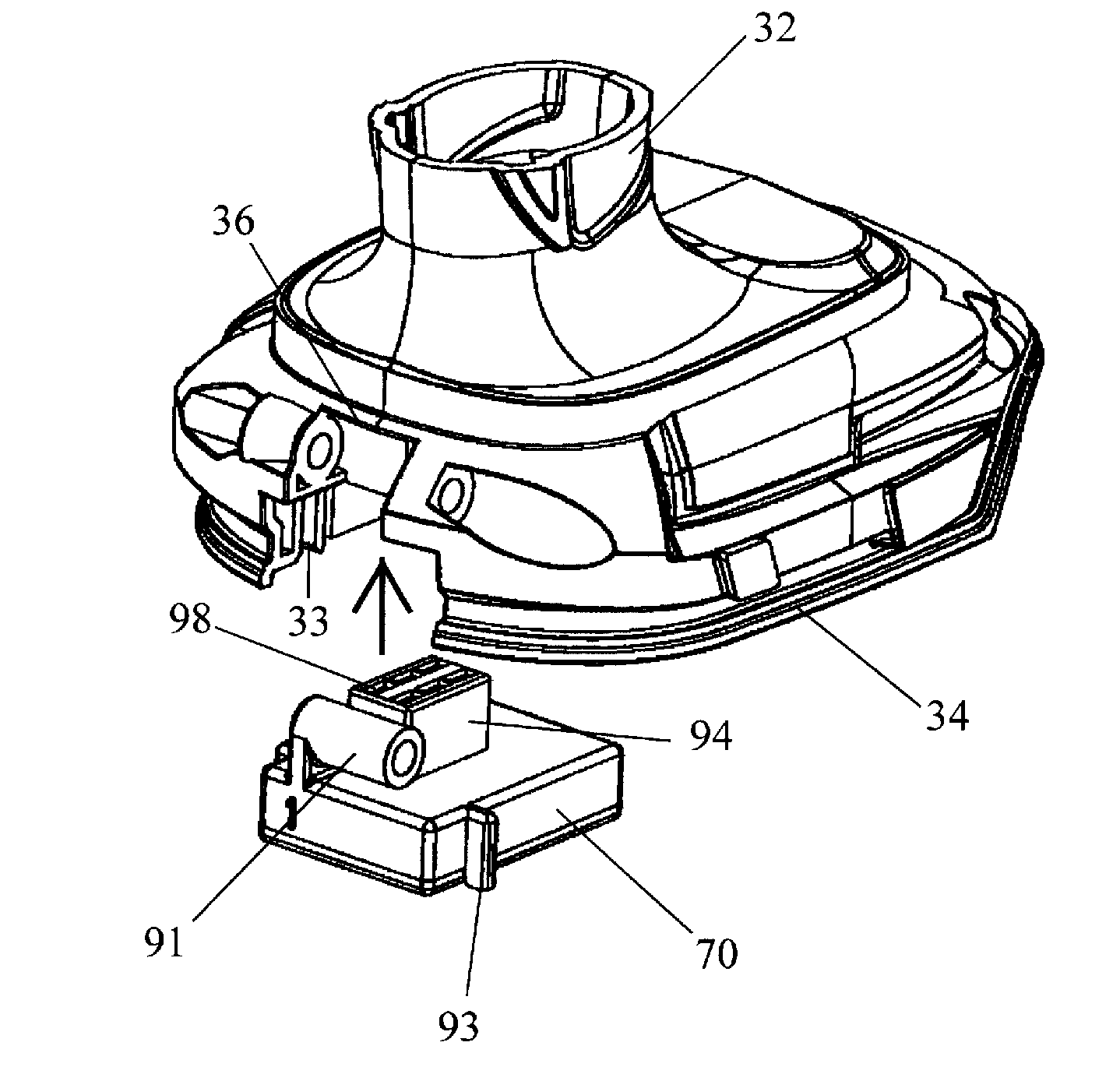
Power tool system and adapter therefor
InactiveUS20140151079A1Stable structureReadily dislodged from the power tool during operationBatteries circuit arrangementsTransmission systemsElectricityEngineering
A power tool system includes a hand-held power tool having a housing with a battery pack interface, an electrically-driven device and a first connector. A battery pack is detachably attached to the battery pack interface and supplies current to the electrically-driven device. An adapter has a second connector physically and electrically connected with the first connector in a detachable manner. The adapter receives power from the battery pack via the hand-held power tool and provides at least one additional electrical function to the hand-held power tool or performs at least one additional electrical function that the hand-held power tool is not otherwise capable of performing. Further, the adapter is at least partially disposed in a space defined in part by the housing and in part by the battery pack when the housing and battery pack are attached to each other.
Owner:MAKITA CORP
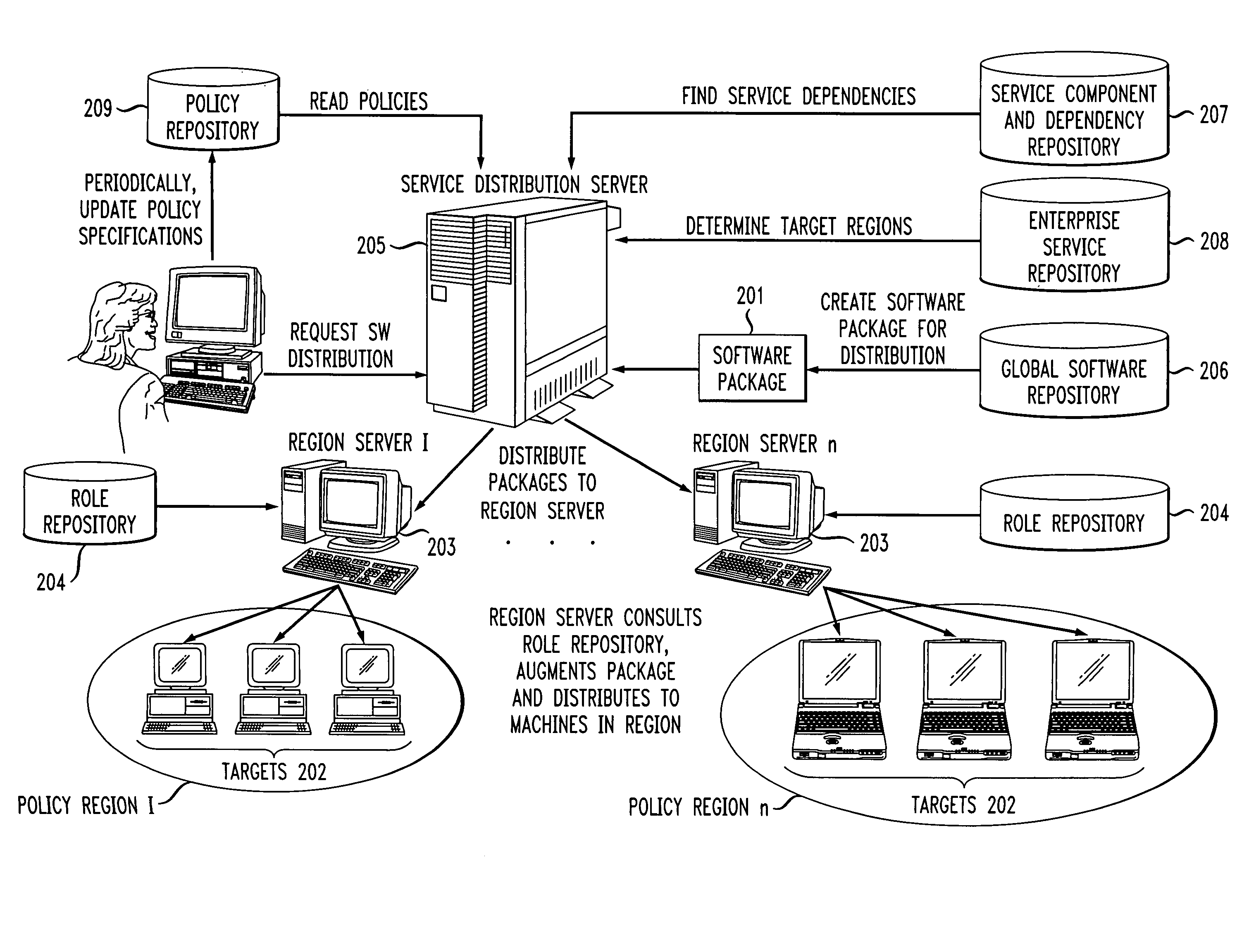
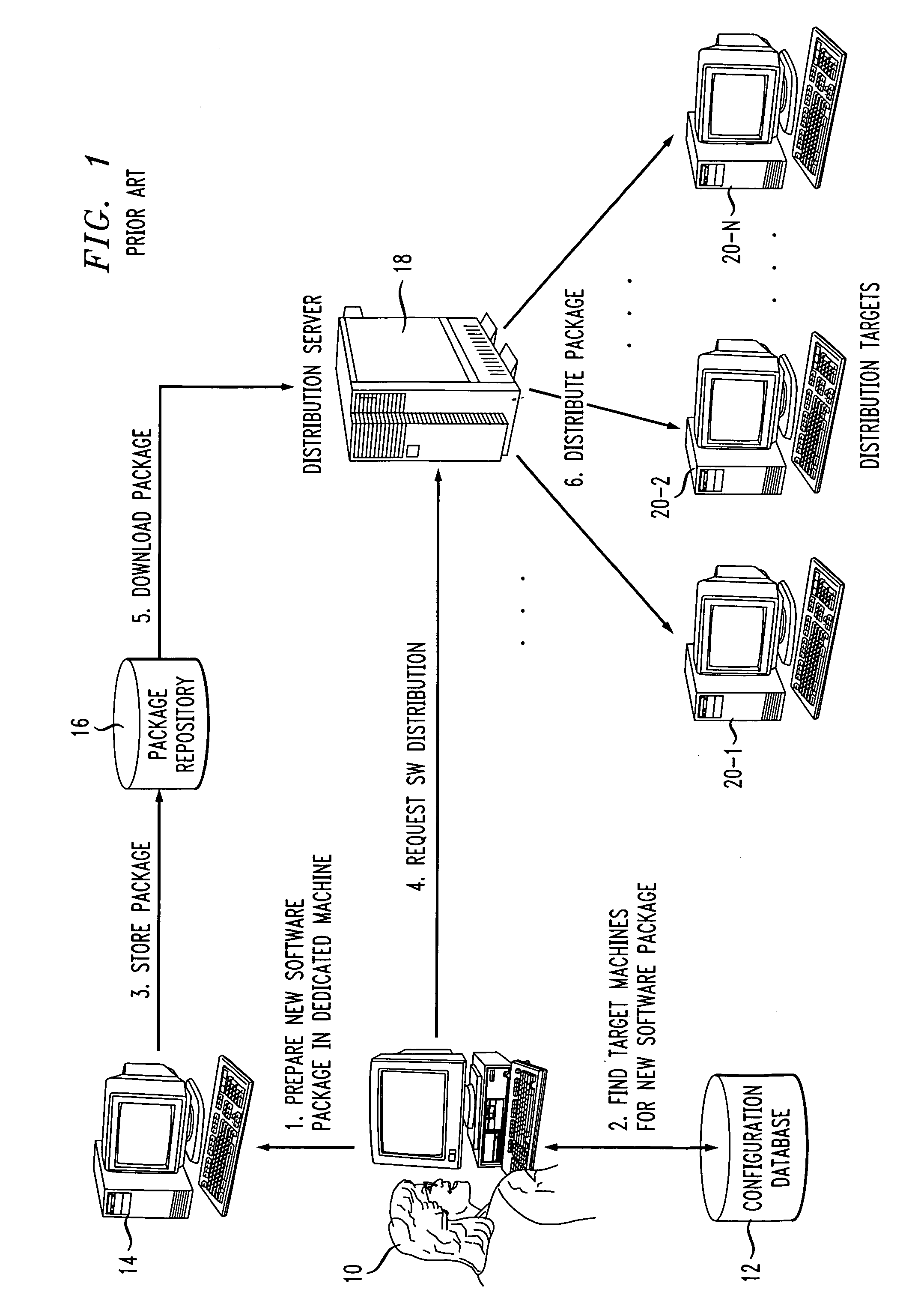
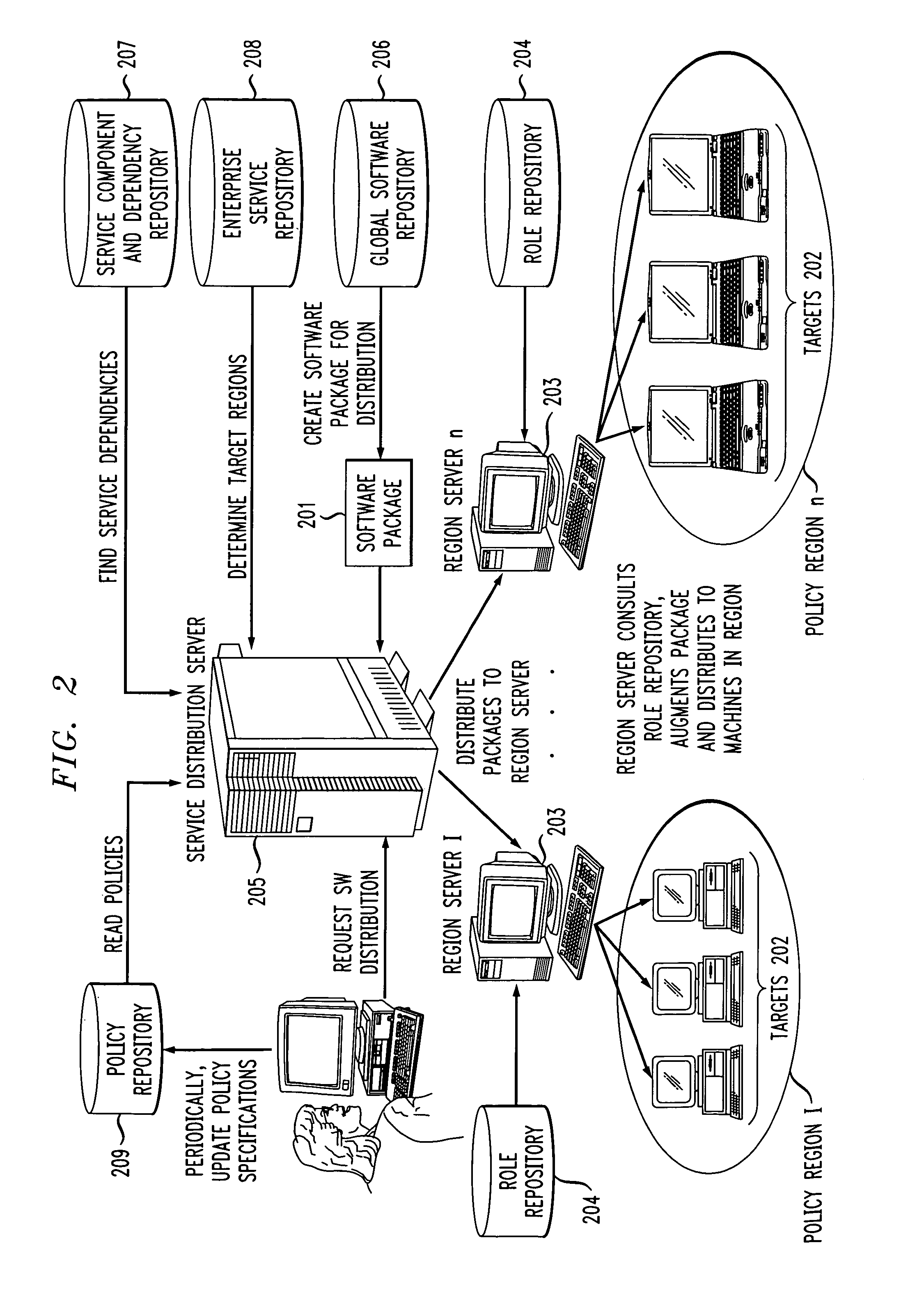
Systems and methods for service and role-based software distribution
InactiveUS7013461B2Good and more scaleable distributionMinimization requirementsProgram control using stored programsDigital computer detailsSoftware distributionSoftware package
Computer-based methods and systems for performing automated distribution of a software package to one or more target machines in one or more regions of a distributed network of target machines, comprises the following steps. First, a base software package is prepared for each of the one or more regions based on at least one of: (i) policy data indicating which of the one or more regions are candidates for receiving the software package, (ii) dependency information indicating requisites for a service provided by the software package, and (iii) configuration information for each of the candidate regions. The base software package is then distributed to each of the candidate regions of the distributed network. The base software package received at each of the candidate regions is then customized based on at least one of: (i) regional distribution policies, (ii) dependency information specific to one or more roles performed by the target machines in that region, and (iii) individual target machine configuration information. Lastly, the software package customized in each of the candidate regions is distributed to at least one of the target machines in the candidate regions of the distributed network.
Owner:INT BUSINESS MASCH CORP
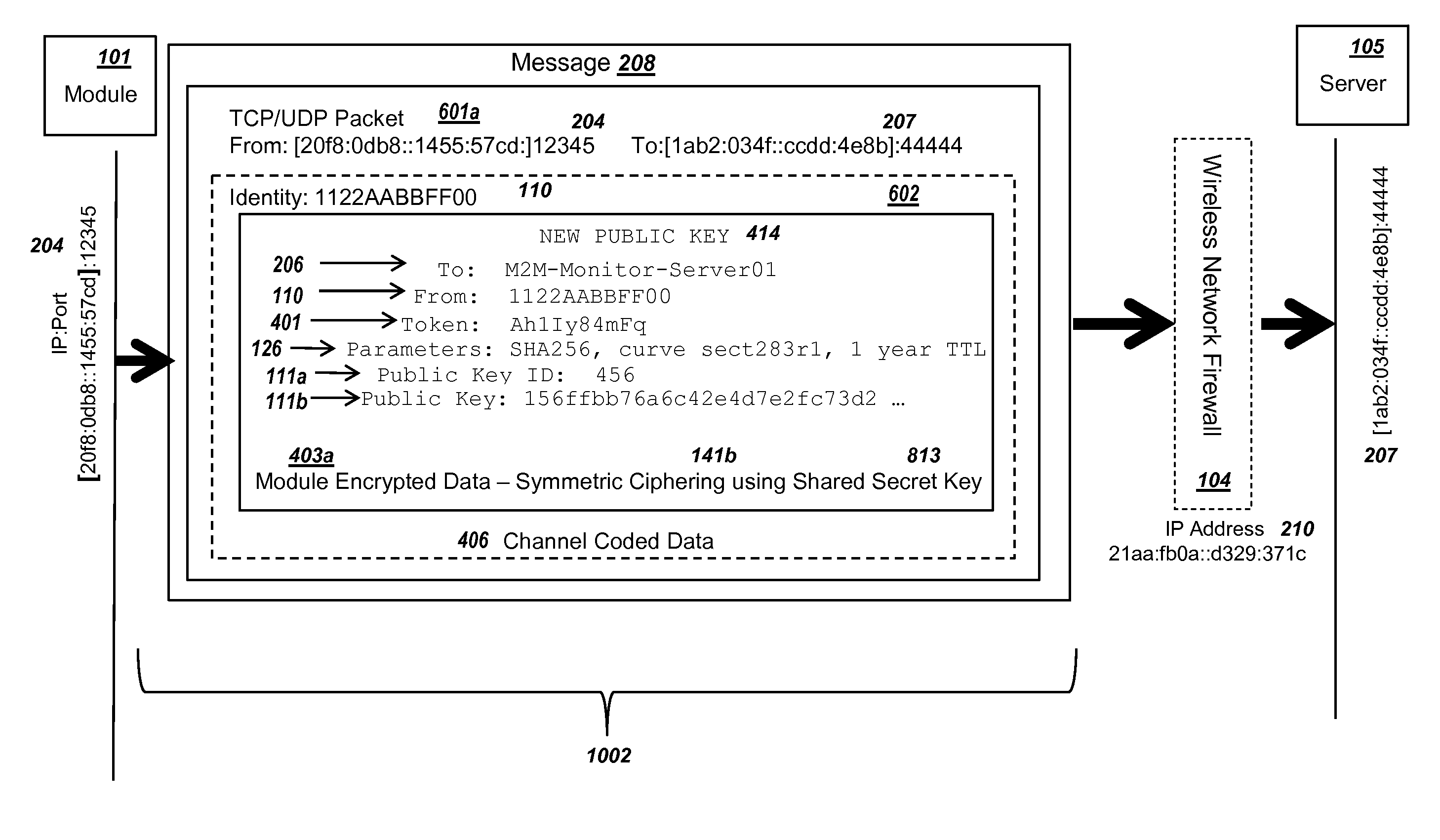
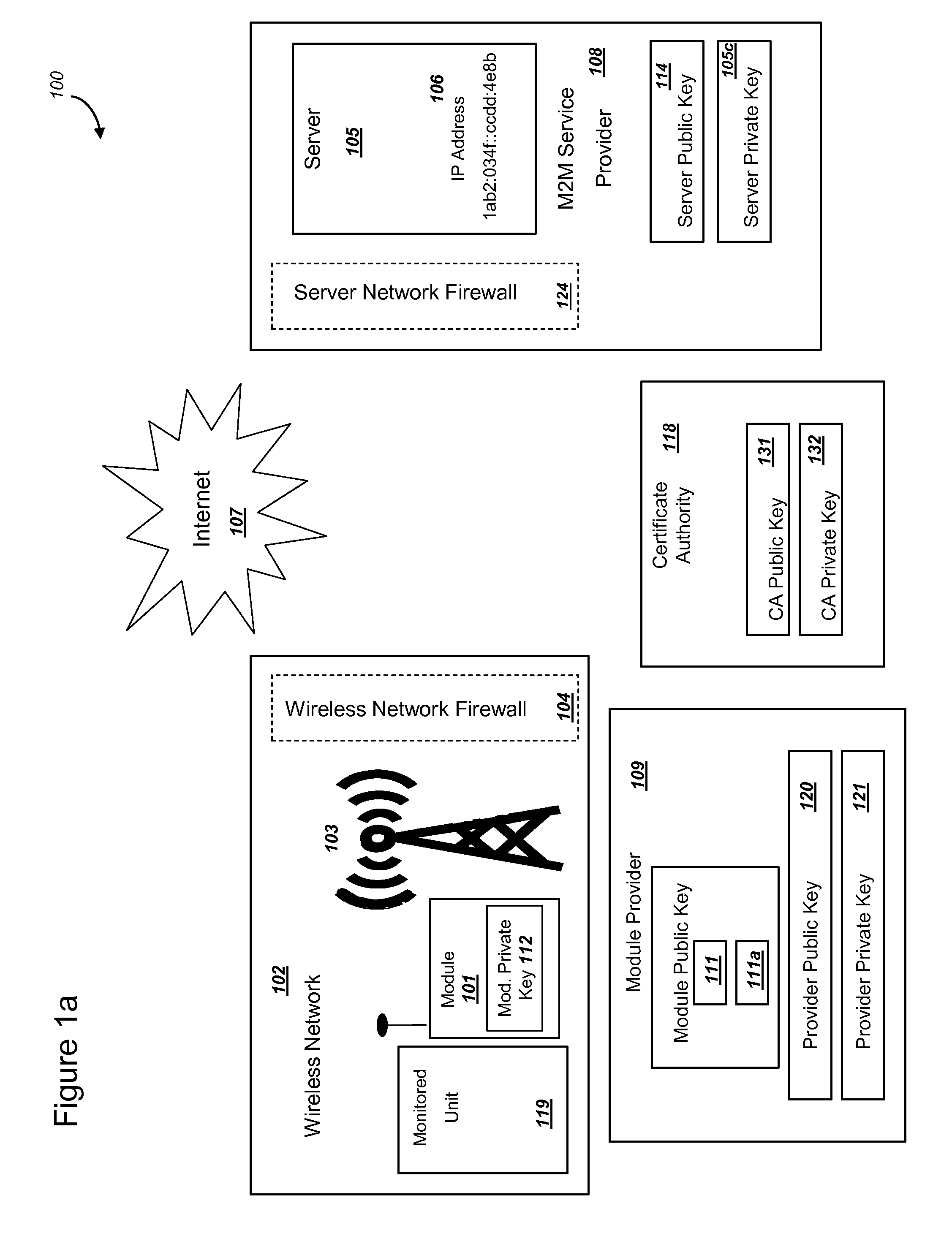
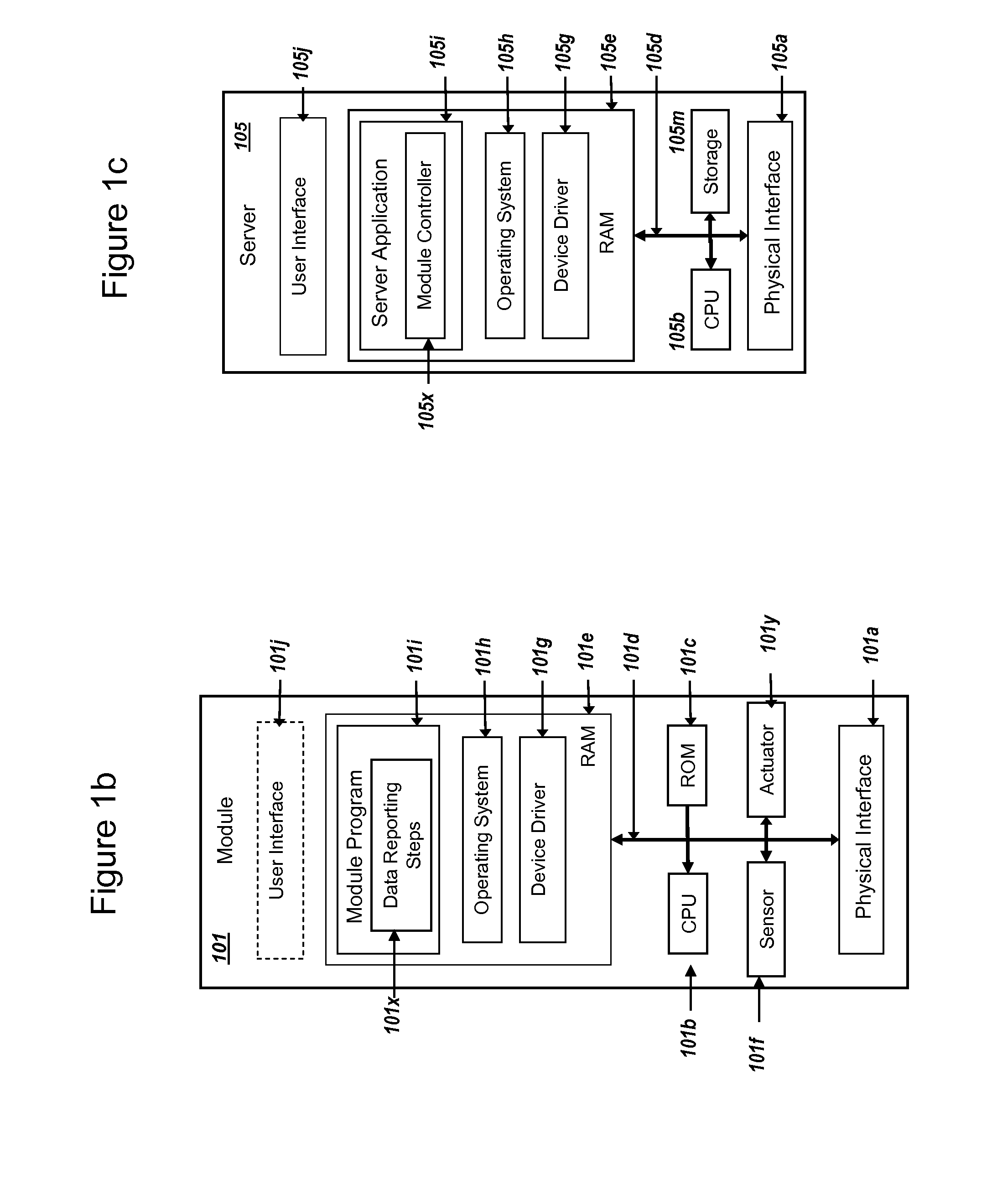
Secure PKI Communications for "Machine-to-Machine" Modules, including Key Derivation by Modules and Authenticating Public Keys
ActiveUS20150095648A1Extend battery lifeImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareDigital signature
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
Surgical navigation planning system and method for placement of percutaneous instrumentation and implants
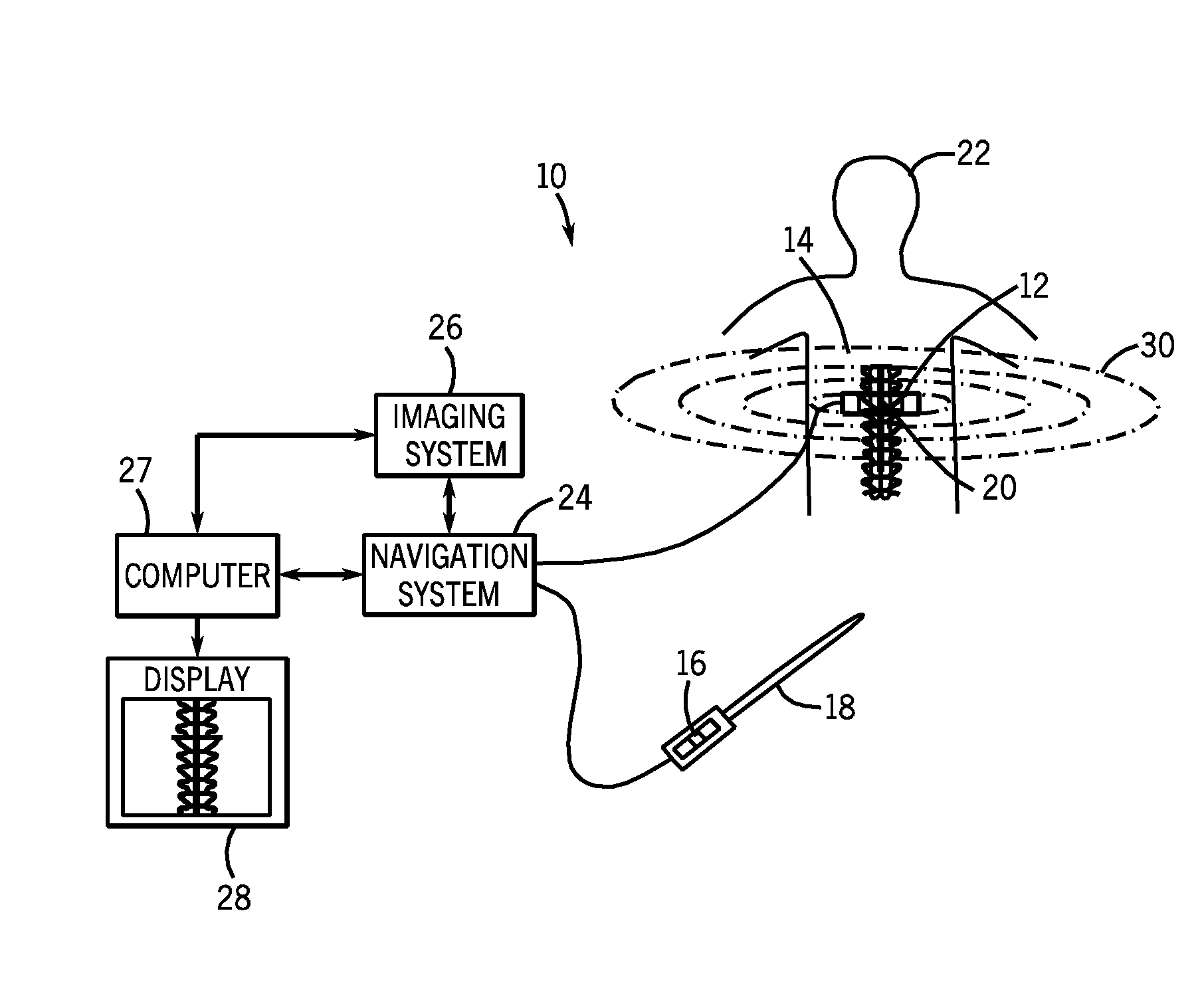
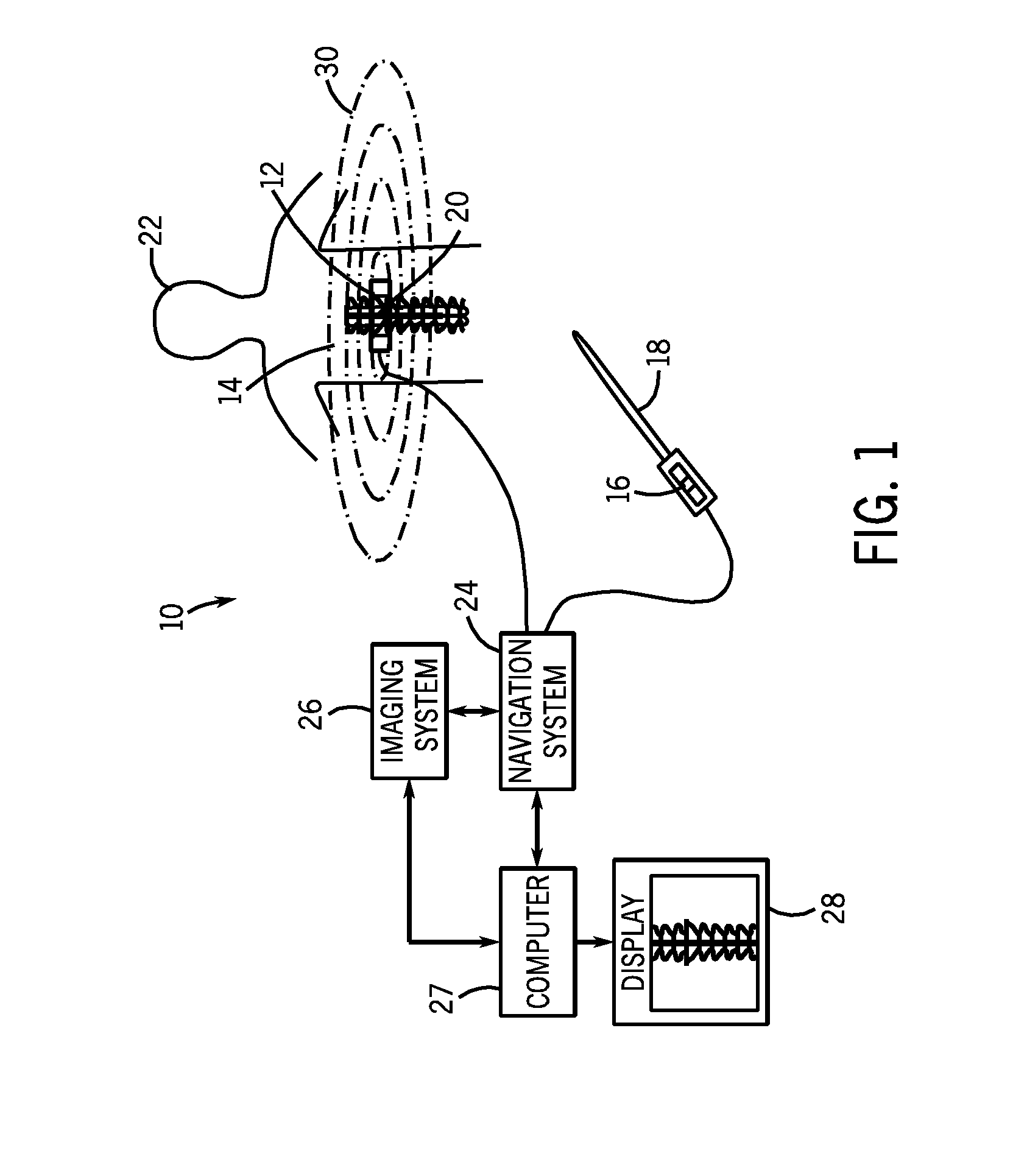
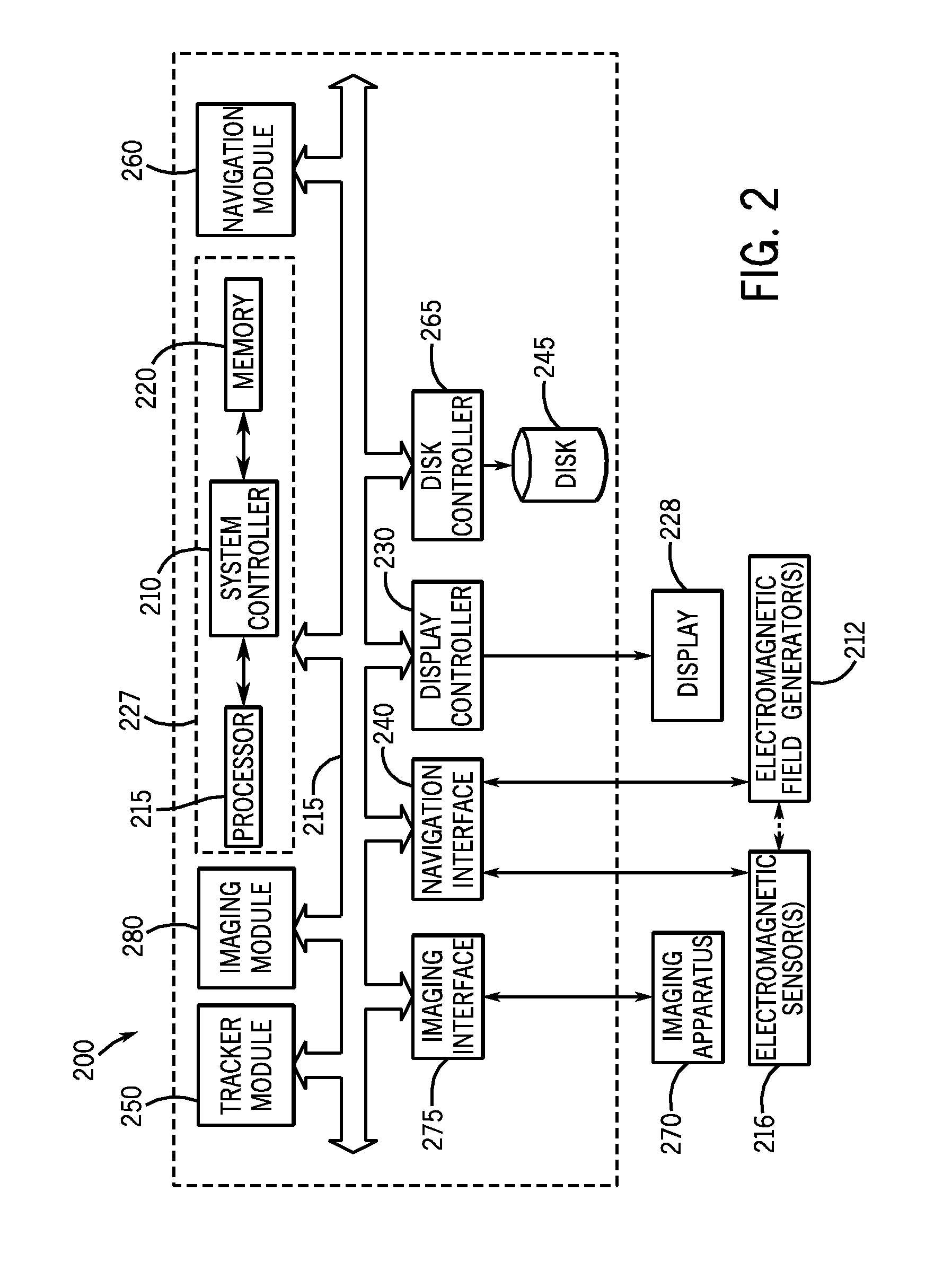
InactiveUS20080177203A1Minimization requirementsSurgical navigation systemsPerson identificationDisplay deviceNavigation system
A system and method for placement of at least one implant comprising an imaging system configured for taking at least one image of a patient; a navigation system configured for tracking position and orientation of at least one implant; a computer configured to measure and calculate the position and orientation of the at least one implant; and a display configured to display the at least one image of the patient and superimpose a graphical representation of the at least one implant with position and orientation information of the at least one implant on the at least one image of the patient.
Owner:GENERAL ELECTRIC CO
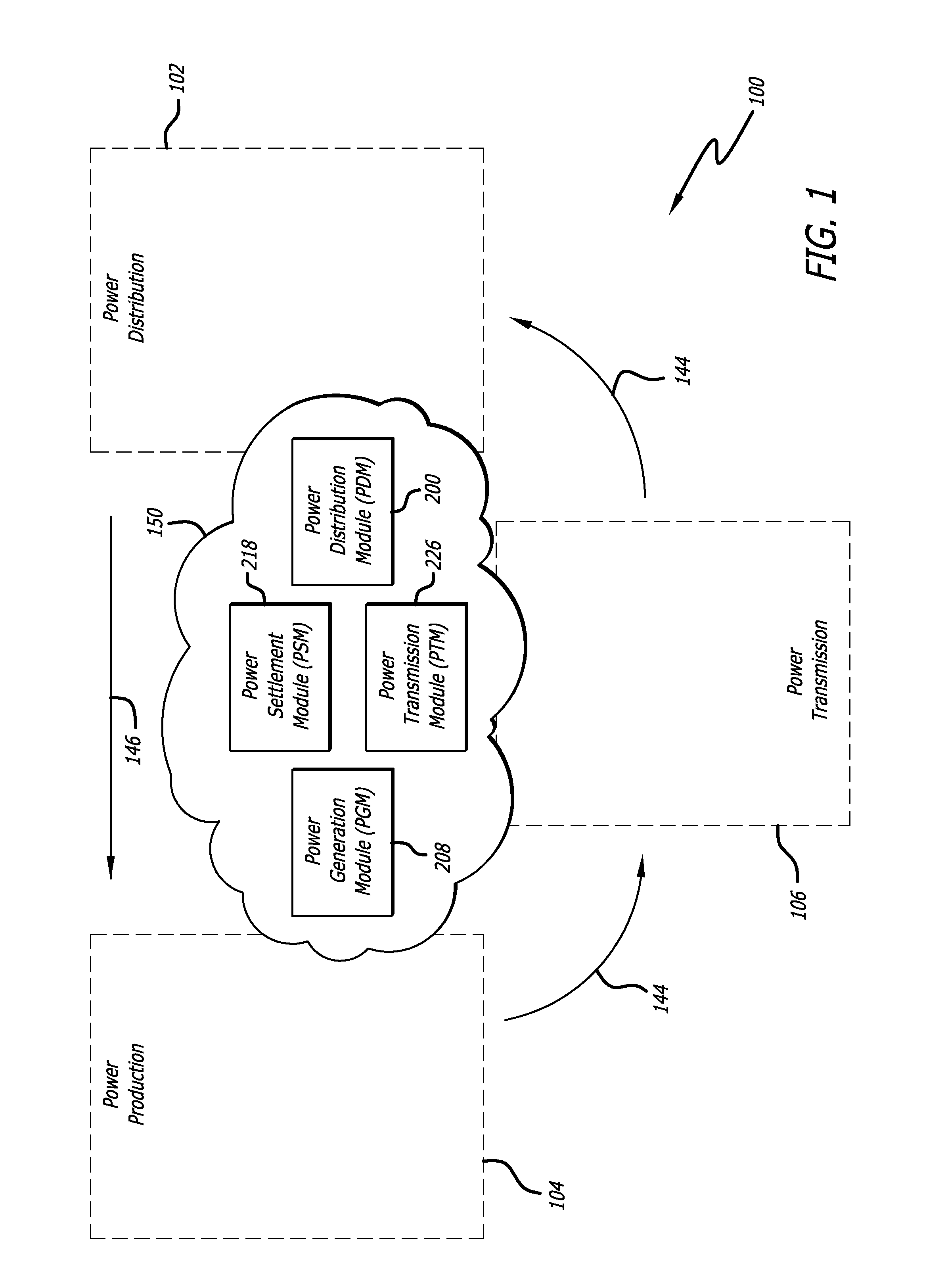
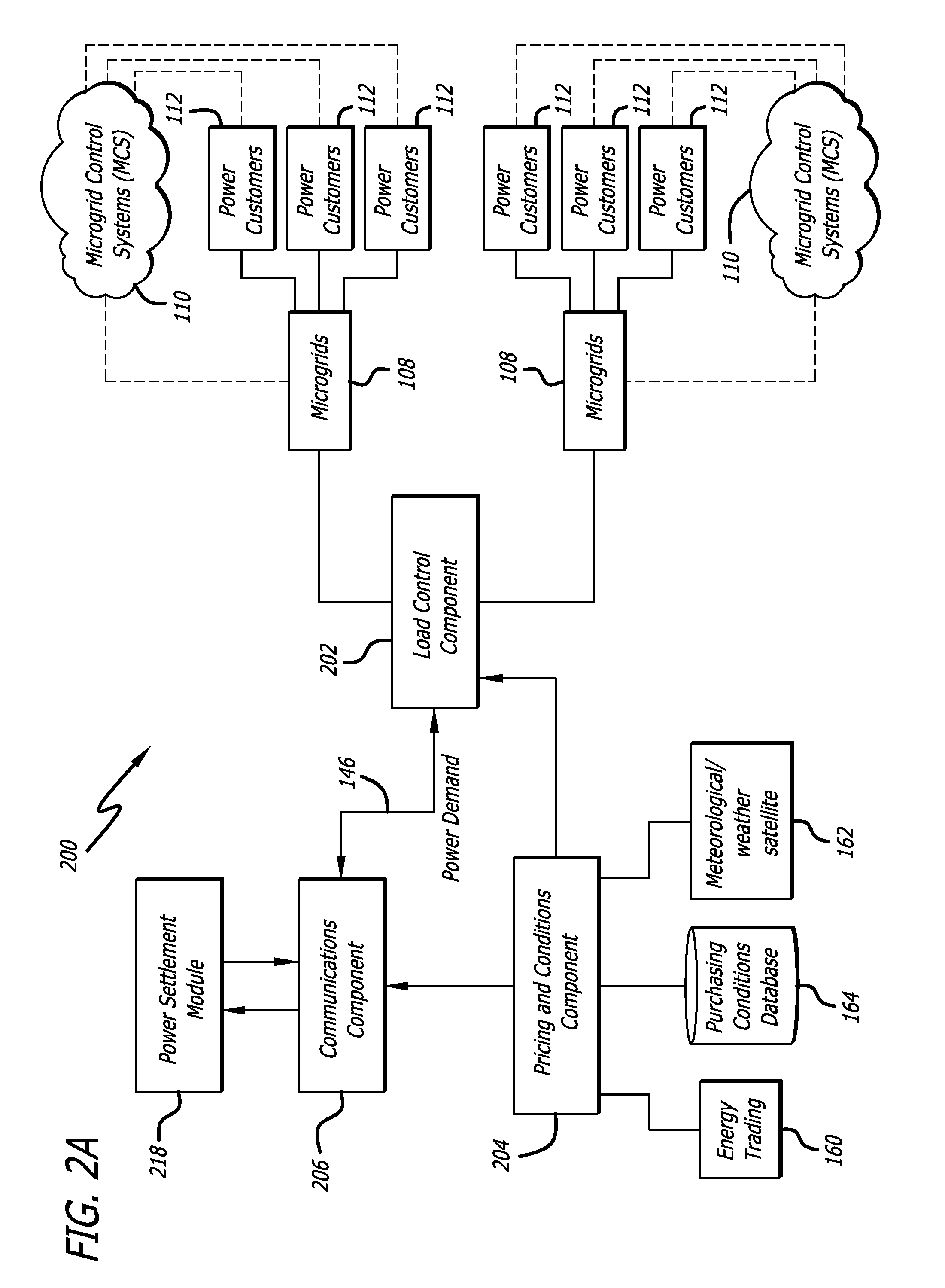
Energy management system for power transmission to an intelligent electricity grid from a multi-resource renewable energy installation
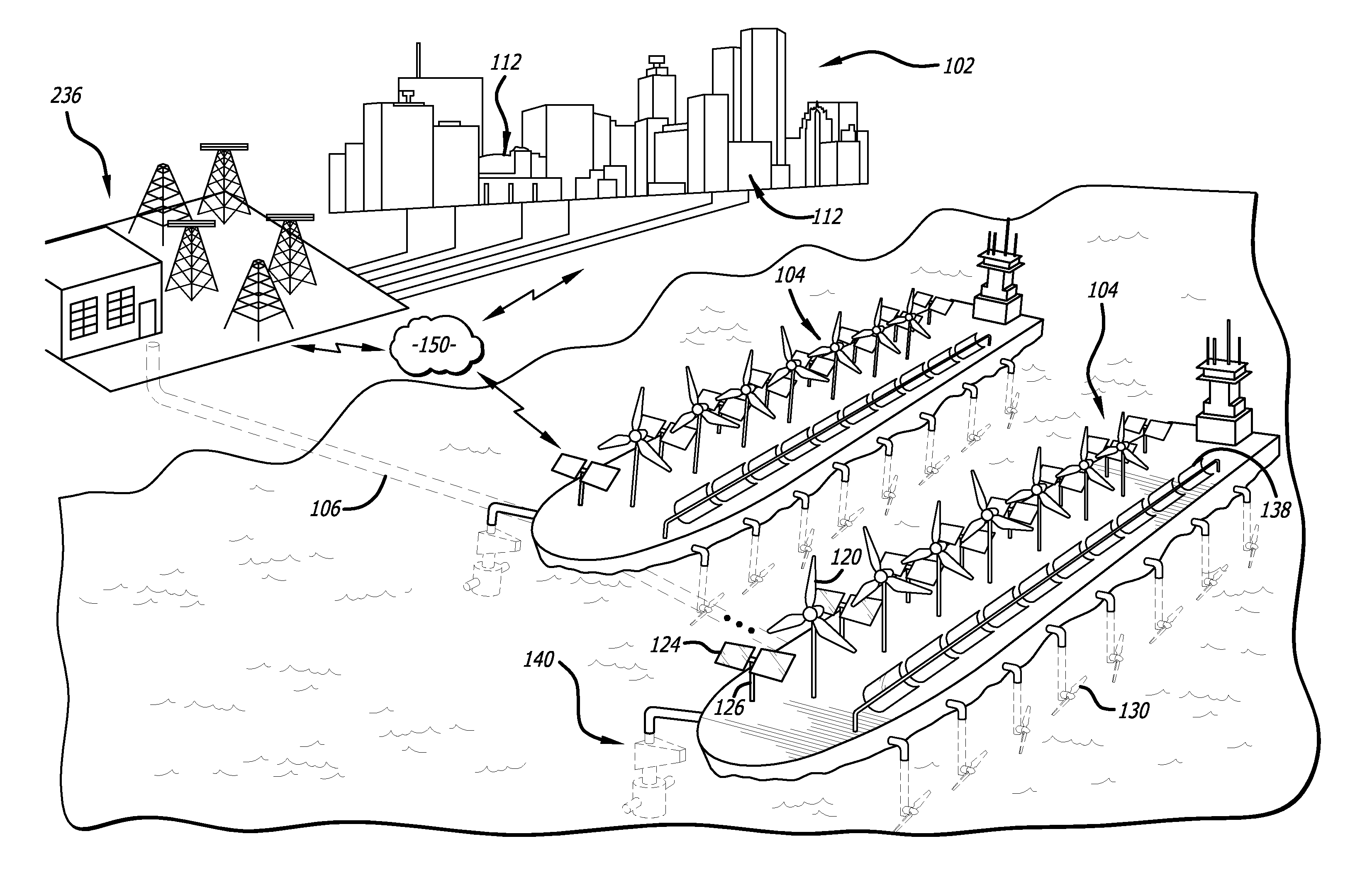
InactiveUS20120150679A1Balance power productionEfficiently and effectively respondGeneration forecast in ac networkMachines/enginesElectric power transmissionMicrogrid
A renewable energy resource management system manages a delivery of a power requirement from a multi-resource offshore renewable energy installation to an intelligent power distribution network. The installation includes multiple renewable energy resource components and is capable of variably and independently generating power from each to microgrids comprising the intelligent power distribution network so that the entire power requirement is satisfied from renewable energy resources. An electricity grid infrastructure is also disclosed in which power production is balanced with power consumption so that power storage requirements are minimized.
Owner:LAZARIS SPYROS J
Method and device for microsurgical intermuscular spinal surgery
InactiveUS7166073B2Minimization requirementsMinimizing retractionIncision instrumentsSpinal columnArticular processes
A retractor is provided for performing spinal surgery with a minimal approach, and which spares the lumbar muscles from surgical disruption. A preferred embodiment includes a blade having first and second faces wherein the faces are positioned substantially transverse to one another, and wherein at least one of the faces has a tapered width. Alternatively, both the first and second faces are tapered. Additionally, a third face positioned transverse to the first face and substantially parallel to the third face may be incorporated into the retractor. The second face also preferably includes at least one tooth, and more preferably, a plurality of teeth at its distal end for laterally engaging an articular process of a vertebra of the spine.
Owner:RITLAND STEPHEN
Robotic surgical system and method for surface modeling
ActiveUS7974674B2Reduce exposureMinimization requirementsElectrotherapySurgical navigation systemsCardiac surfaceEngineering
Owner:ST JUDE MEDICAL ATRIAL FIBRILLATION DIV
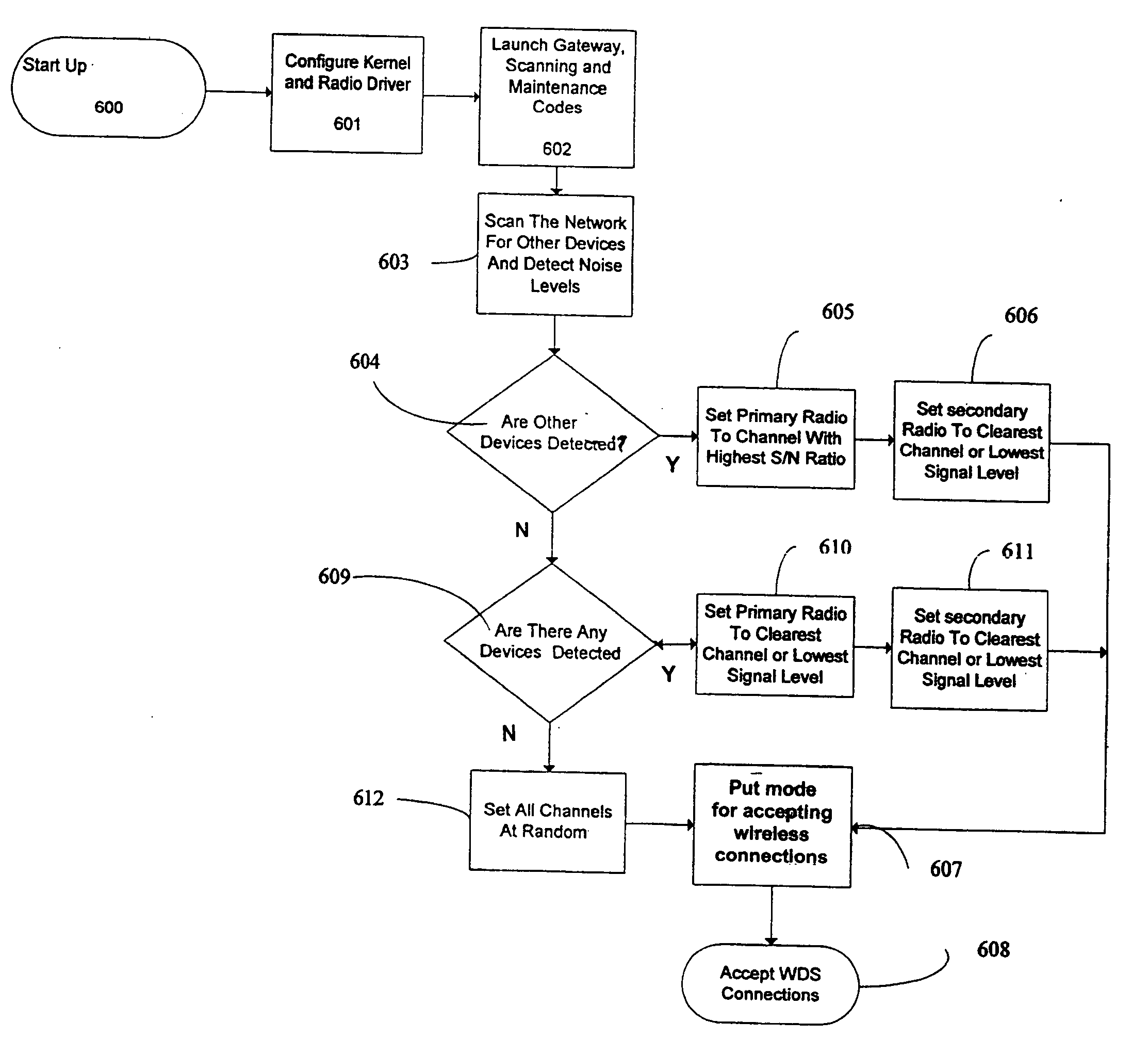
System and method for communication in a wireless mobile ad-hoc network
ActiveUS20070038743A1Reduce buildMinimal protocol overheadNetwork traffic/resource managementNetwork topologiesTransceiverWireless transceiver
A system and method for improving digital communication in a wireless mobile ad-hoc network. More specifically, the system includes one or more portable network devices operable to support the seamless operation of a self-initializing, self-healing, adaptive portable network. The portable network devices implement protocols that provide bandwidth management capabilities for use with radios, routers and other wireless network devices. Each portable network device includes at least one wireless transceiver, a processor and control software. The processor and control software are logically coupled to the wireless transceiver to facilitate digital communication via a plurality of communication channels with other network devices.
Owner:RAJANT CORP
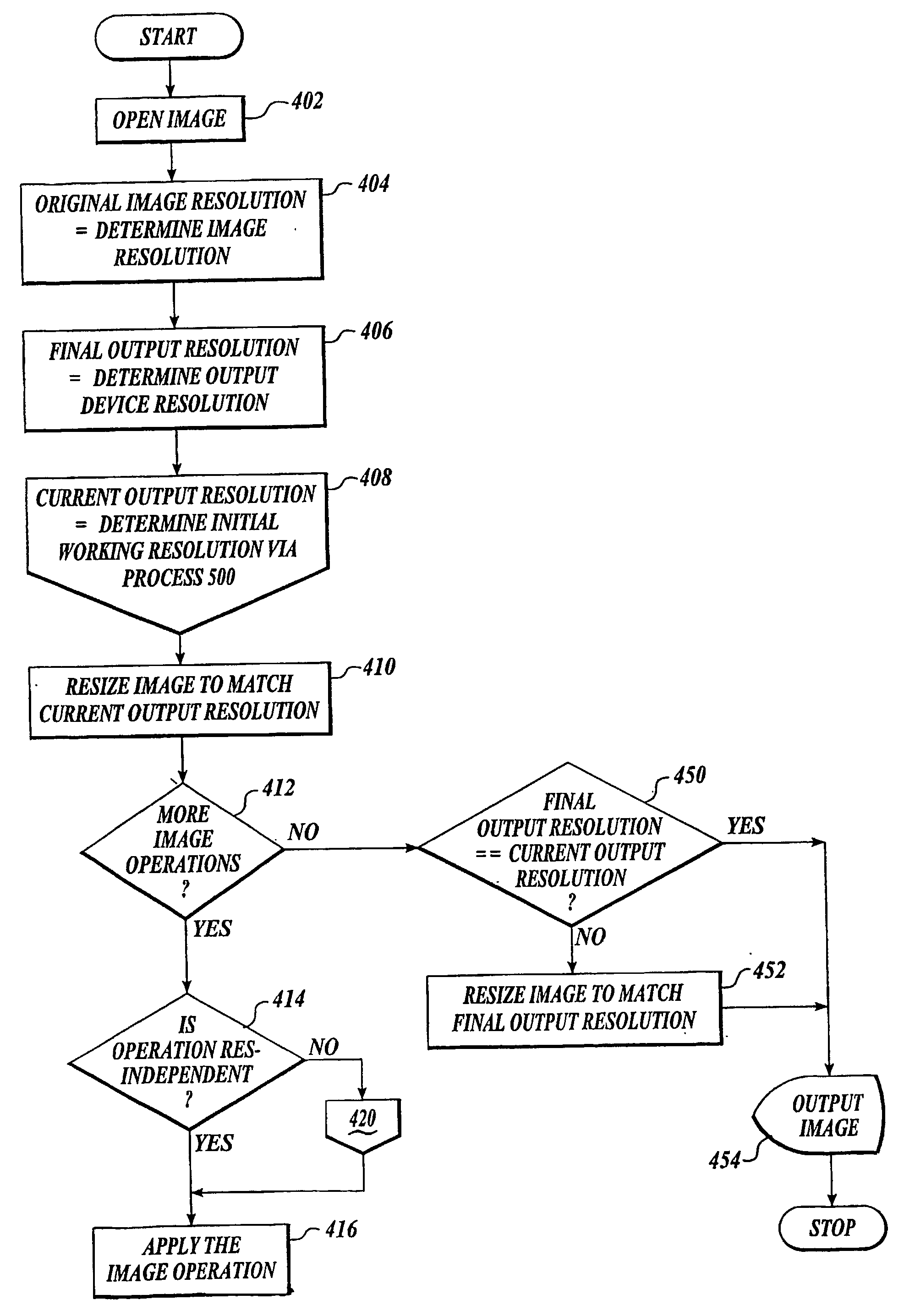
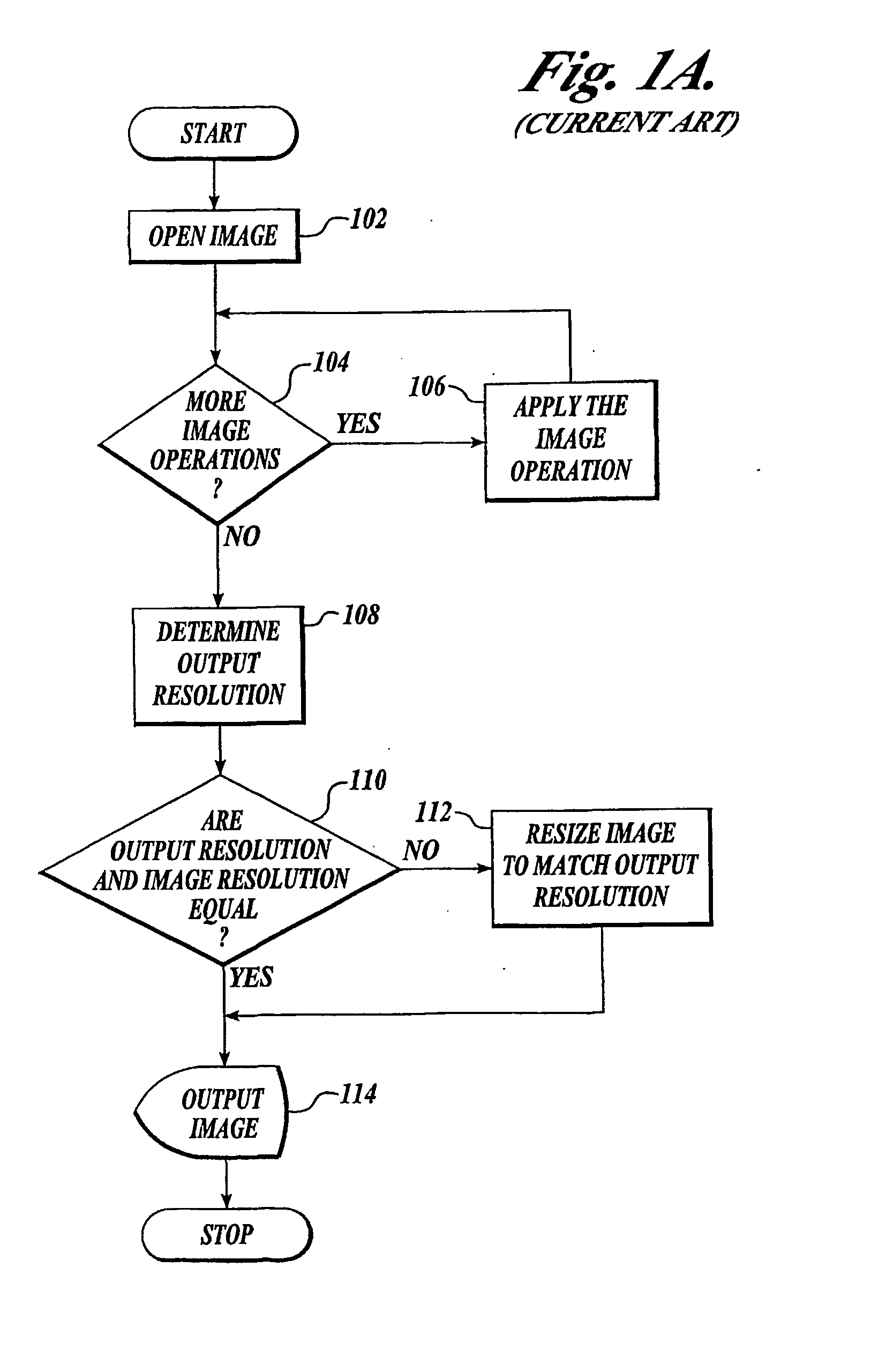
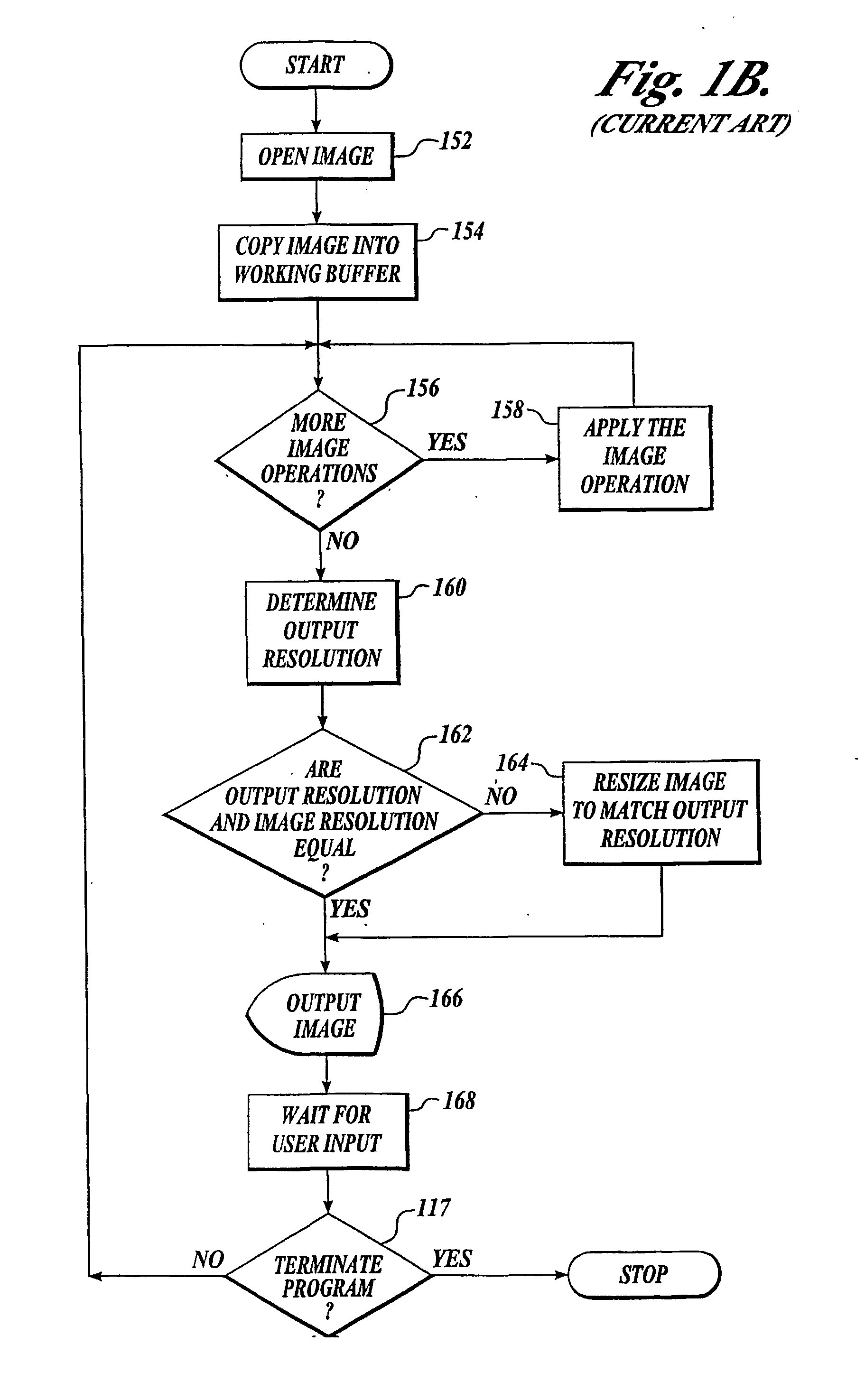
Techniques for resolution independent rendering of images
InactiveUS20040027593A1Low-processing powerSmall memoryDigitally marking record carriersGeometric image transformationPerformance improvementImage resolution
A method to improve the performance of rendering image data (402) by converting what would normally be considered resolution-dependent image behavior into behavior that is substantially resolution-independent. This allows significant performance improvement since the rendering (454) can be performed on the lower-resolution image data used, for example, for on-screen viewing and when the image effect is applied to a higher resolution rendering, the effect, as viewed, is substantially the same as the effect viewed at a lower resolution. This conversion of normally resolution-dependent behaviors into pseudo-resolution-independent behaviors also allows the image effects to be applied to be carried out on a lower resolution image with confidence that when the image is rendered at a higher resolution that the image effects applied will substantially have the same appearance that the effect had at the lower resolution.
Owner:EASTMAN KODAK CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com