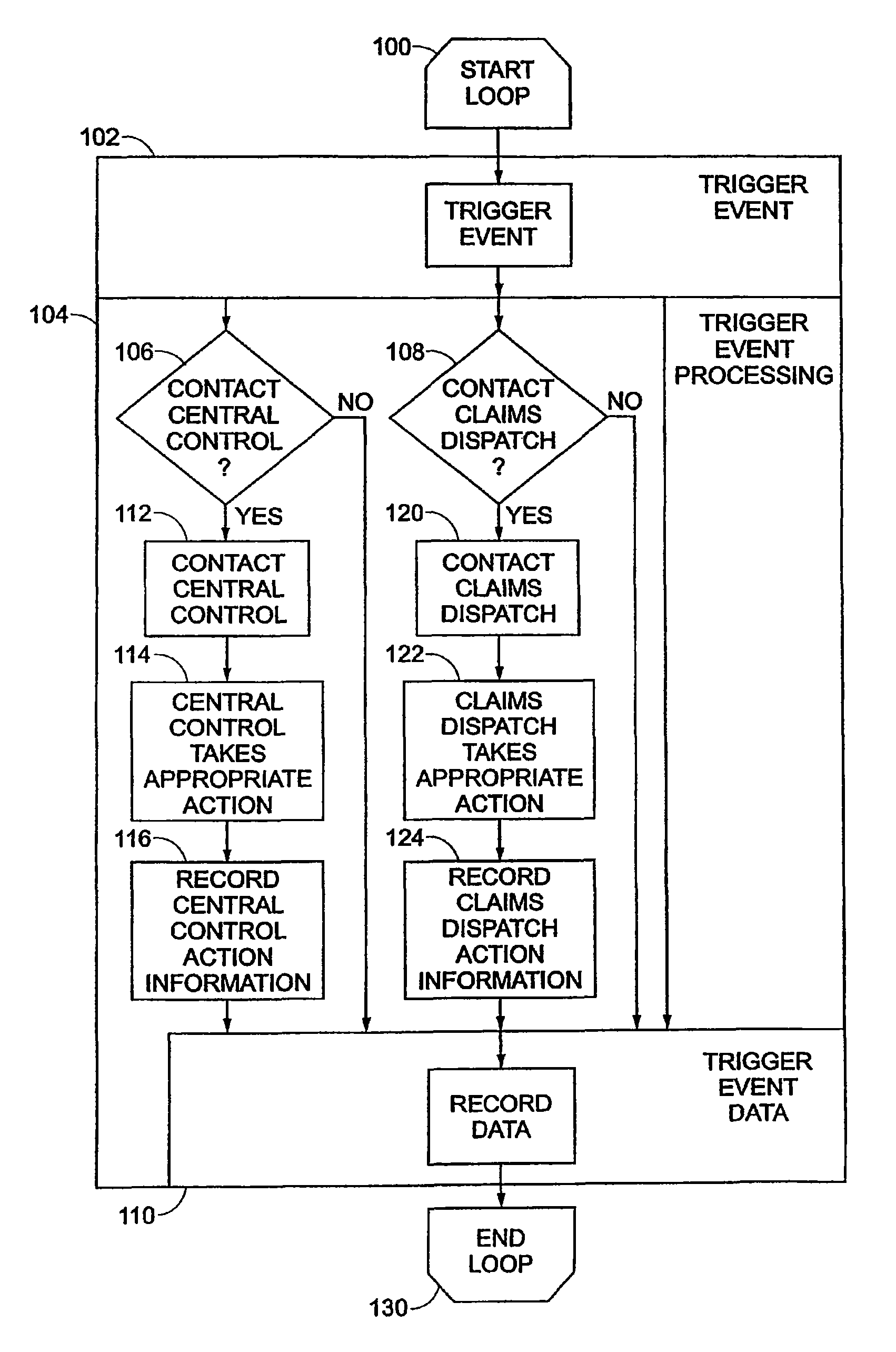
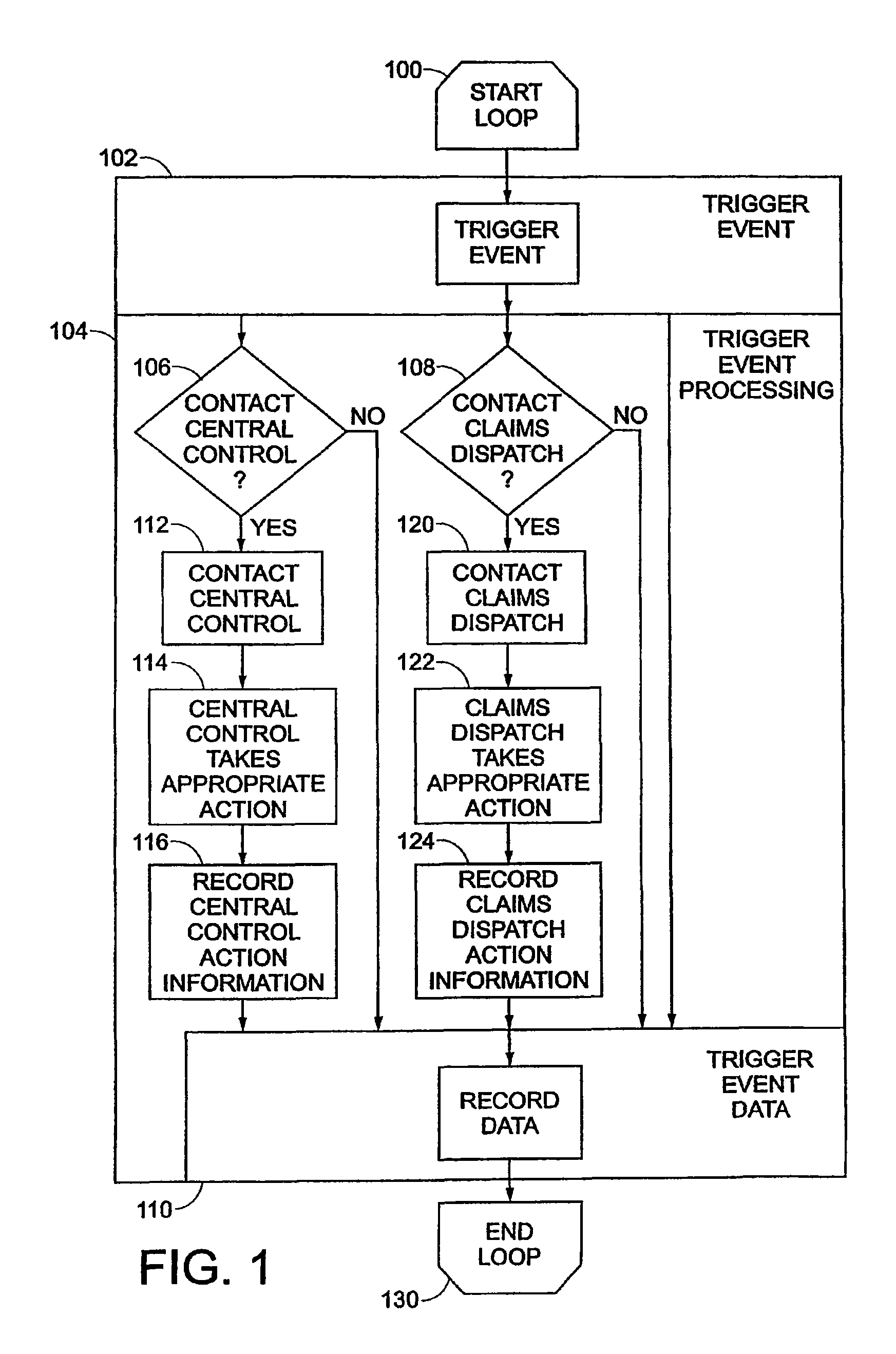
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71595results about "Error detection/correction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
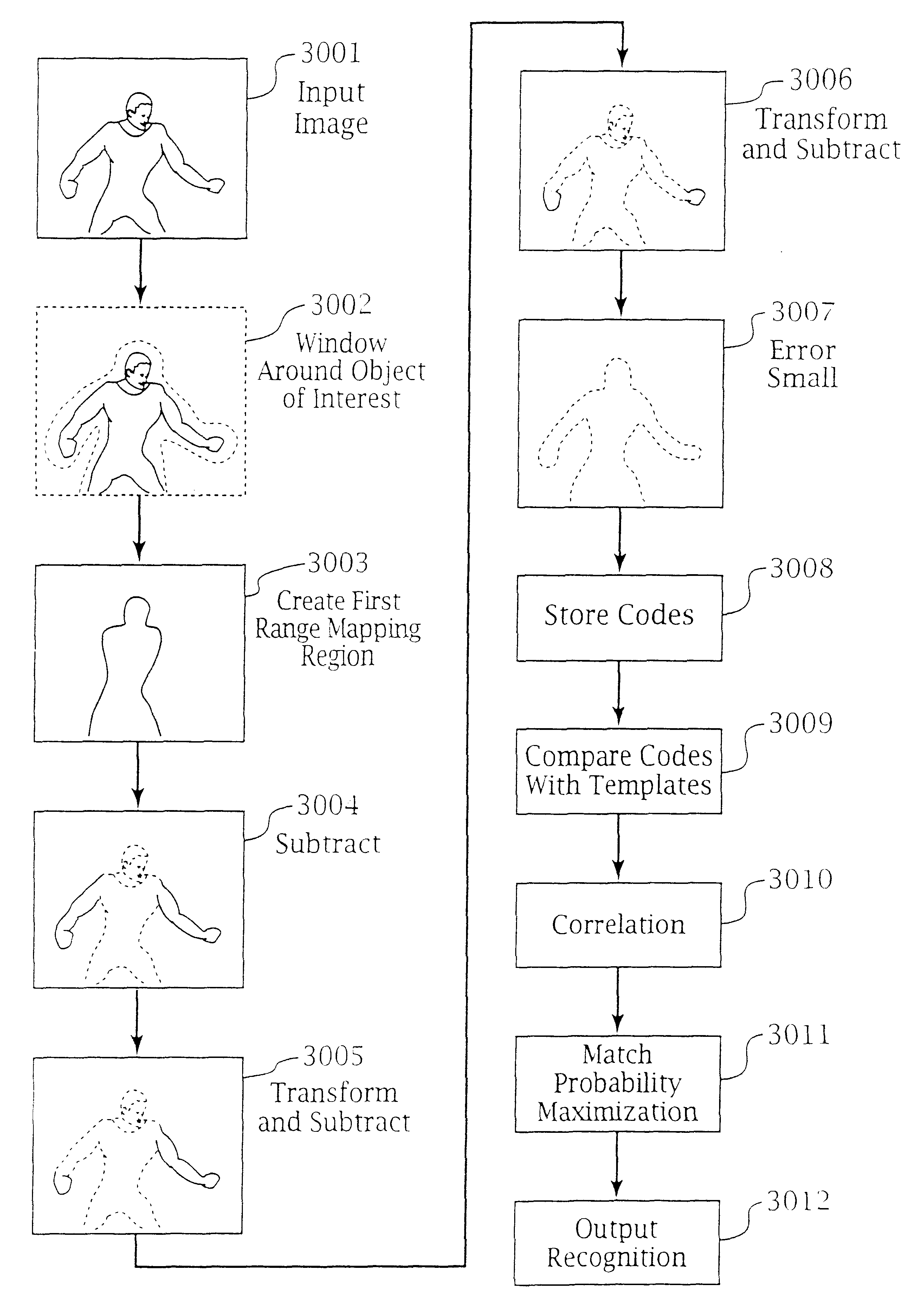
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
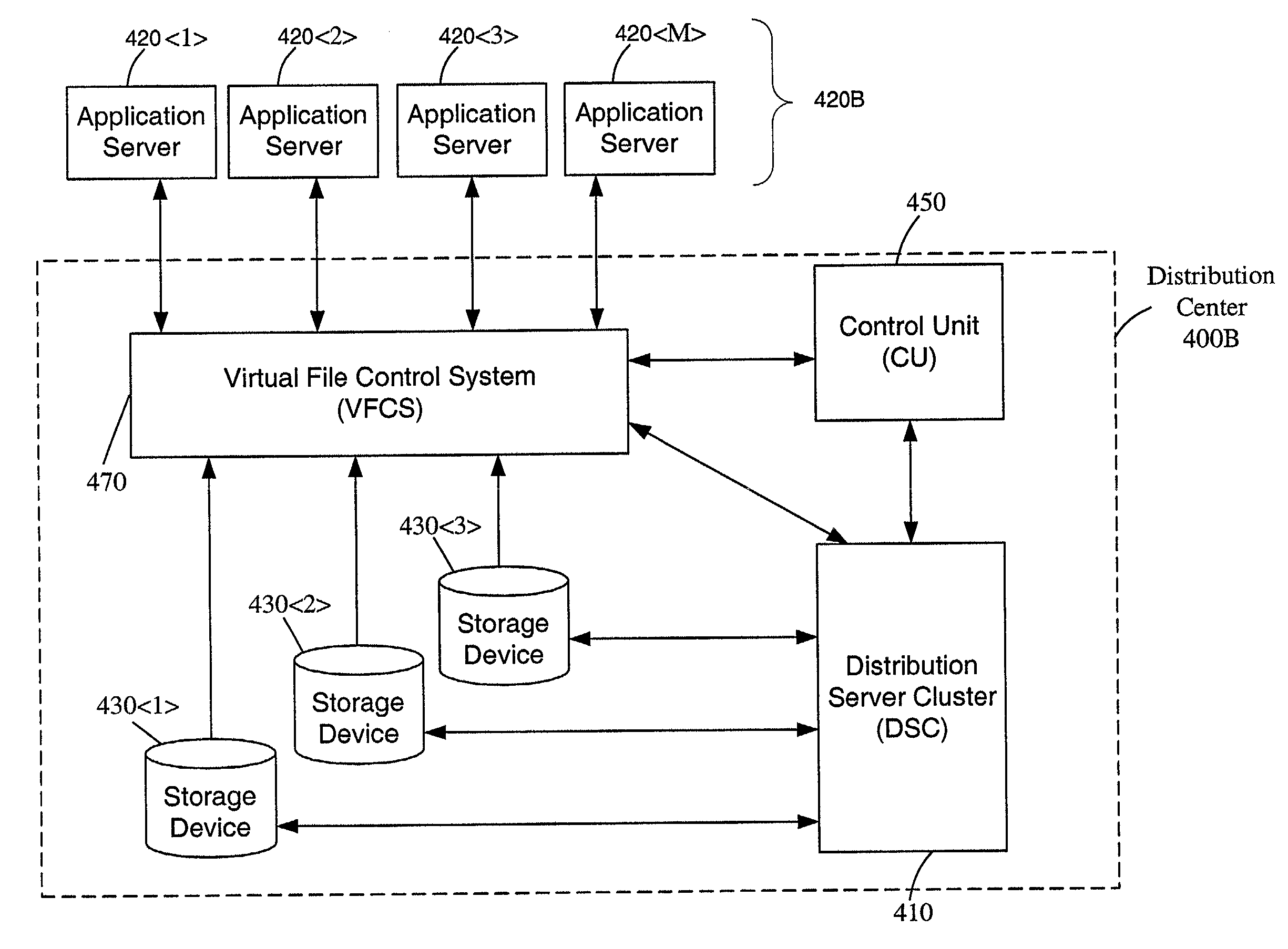
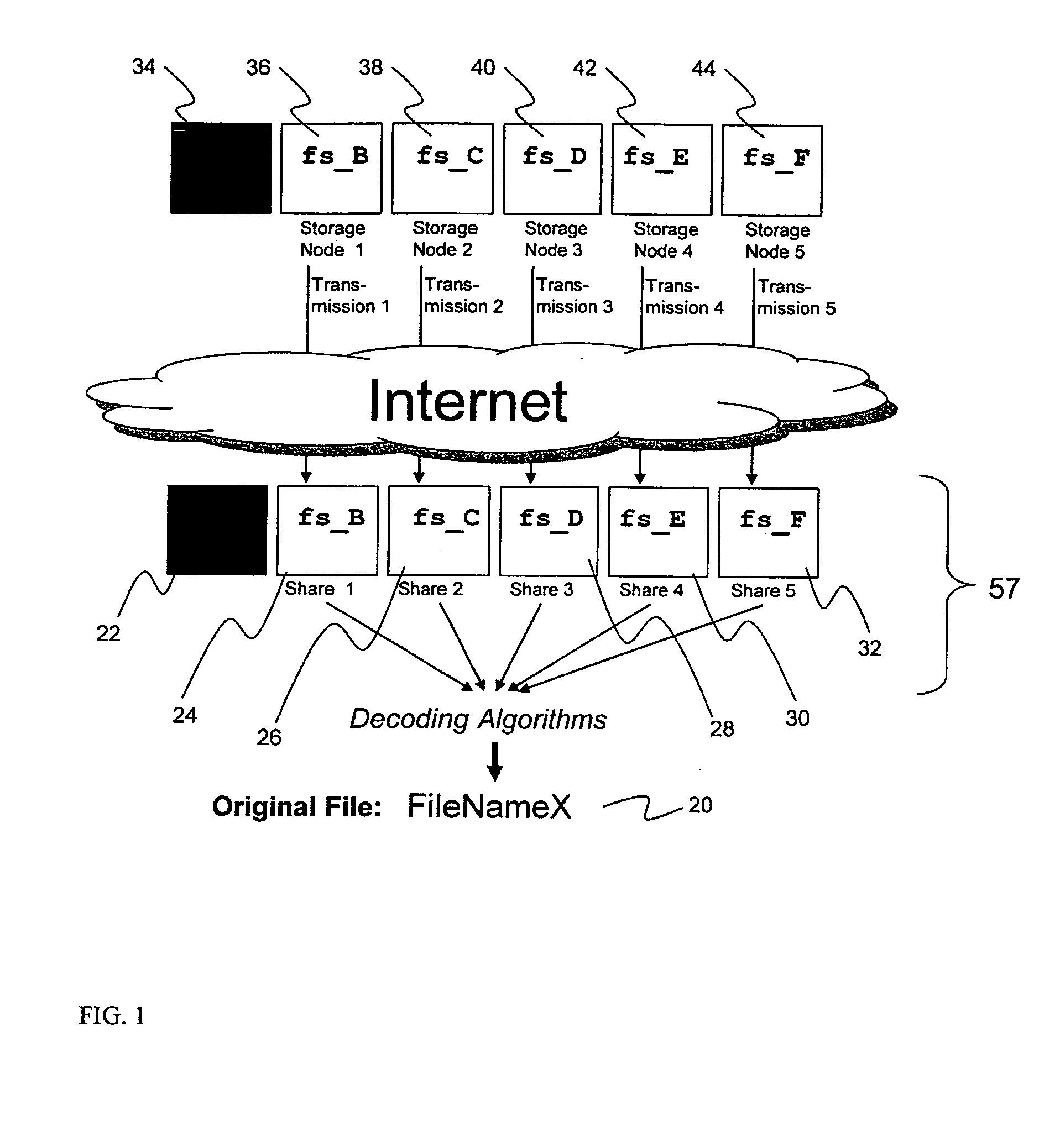
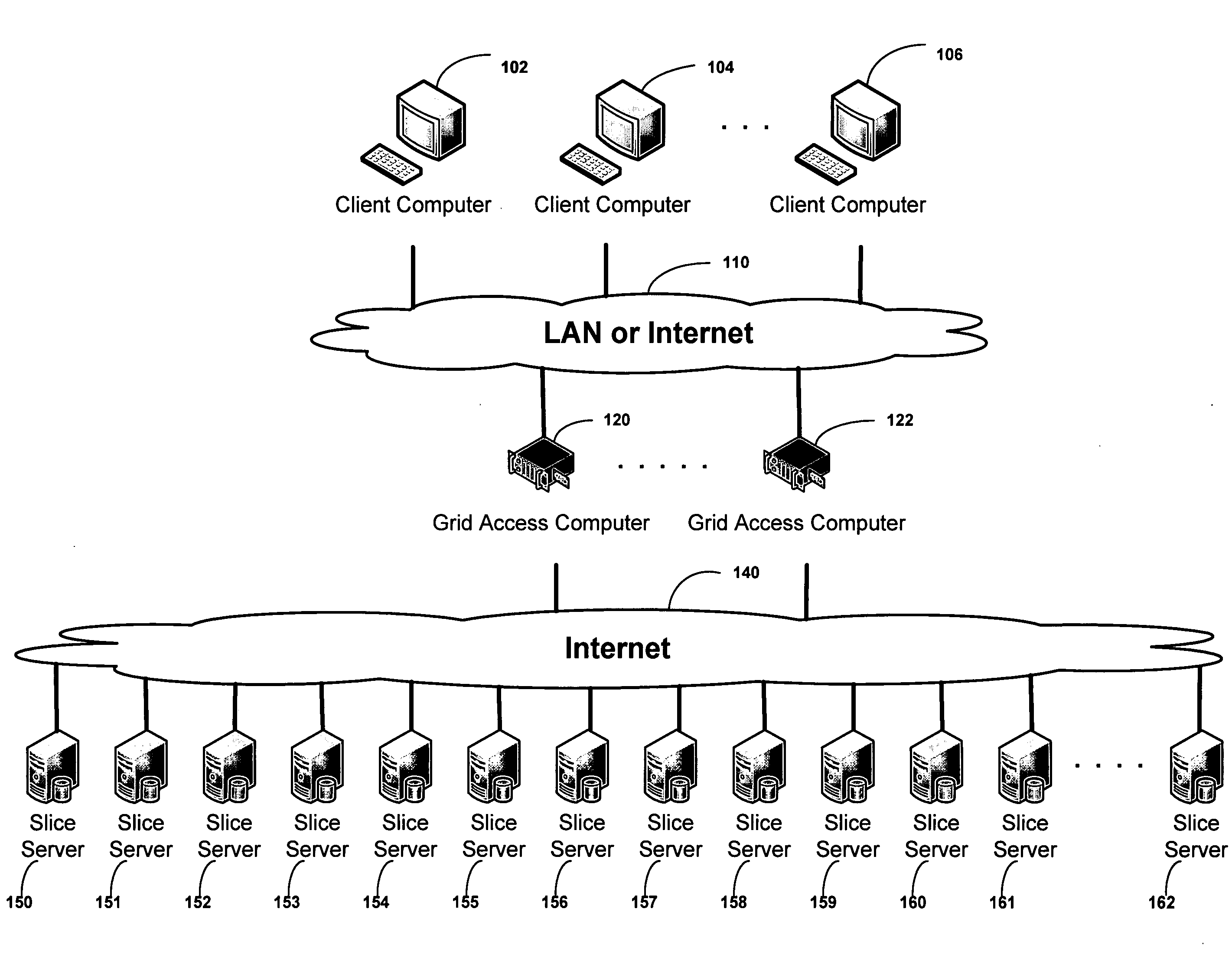
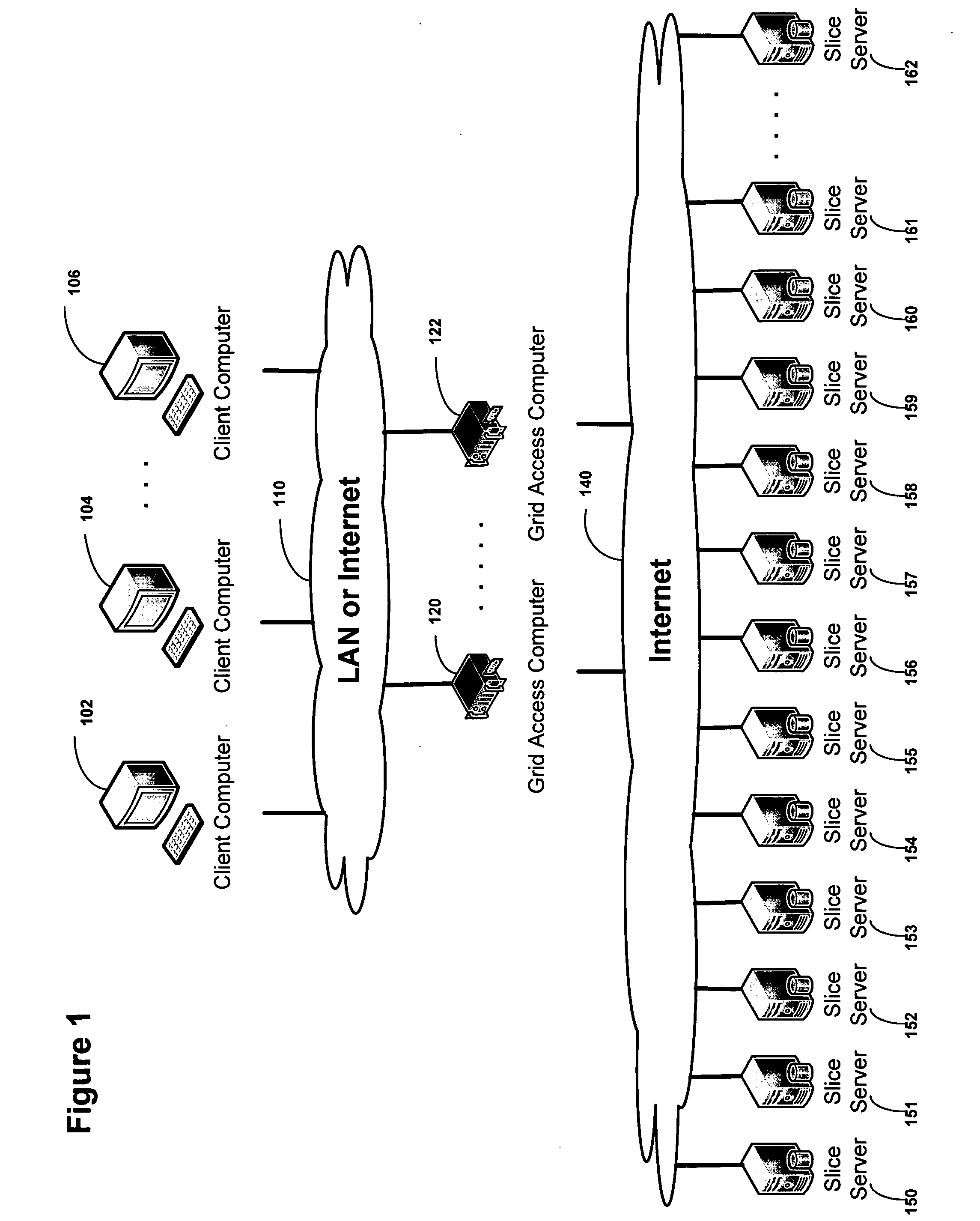
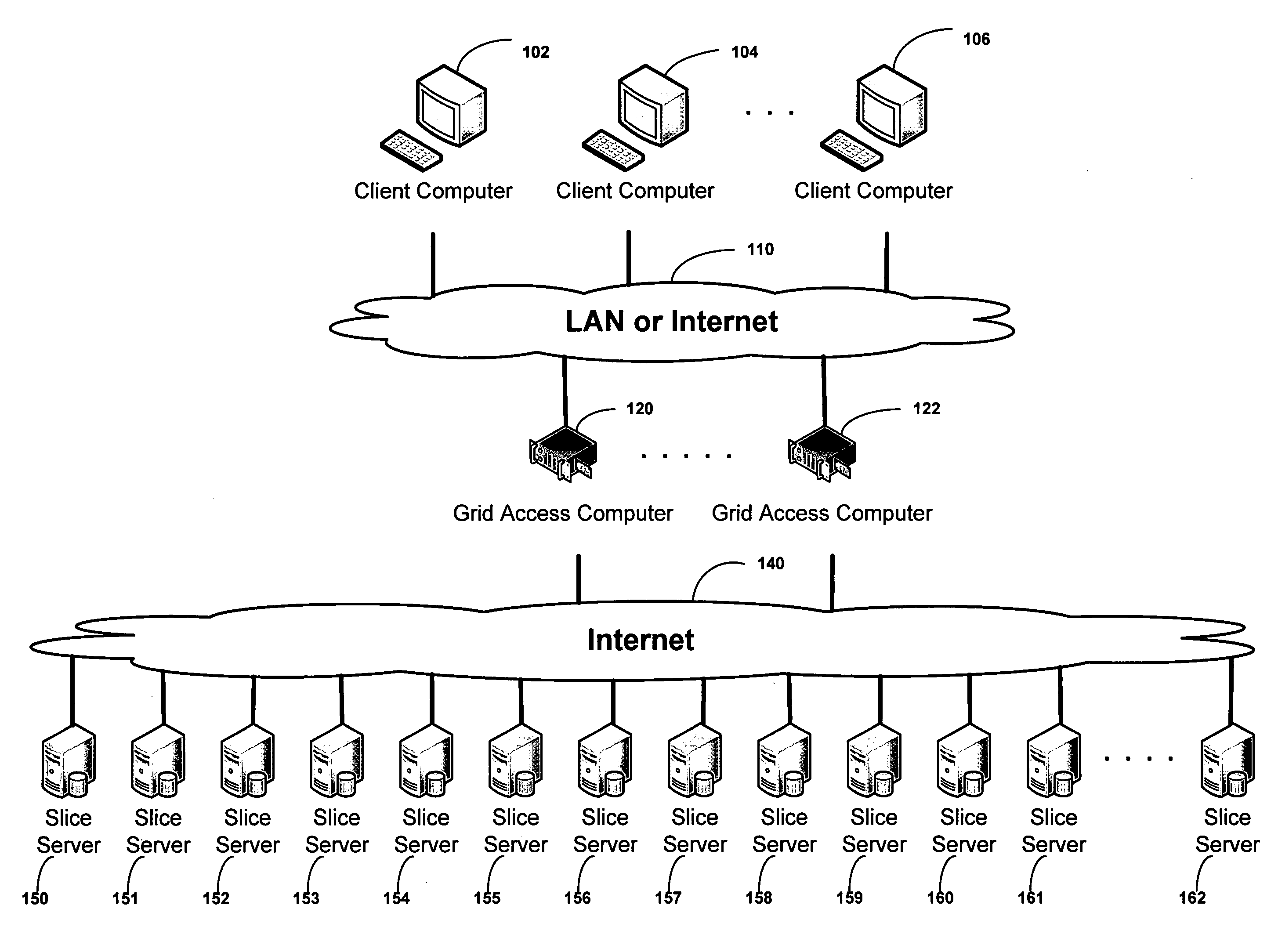
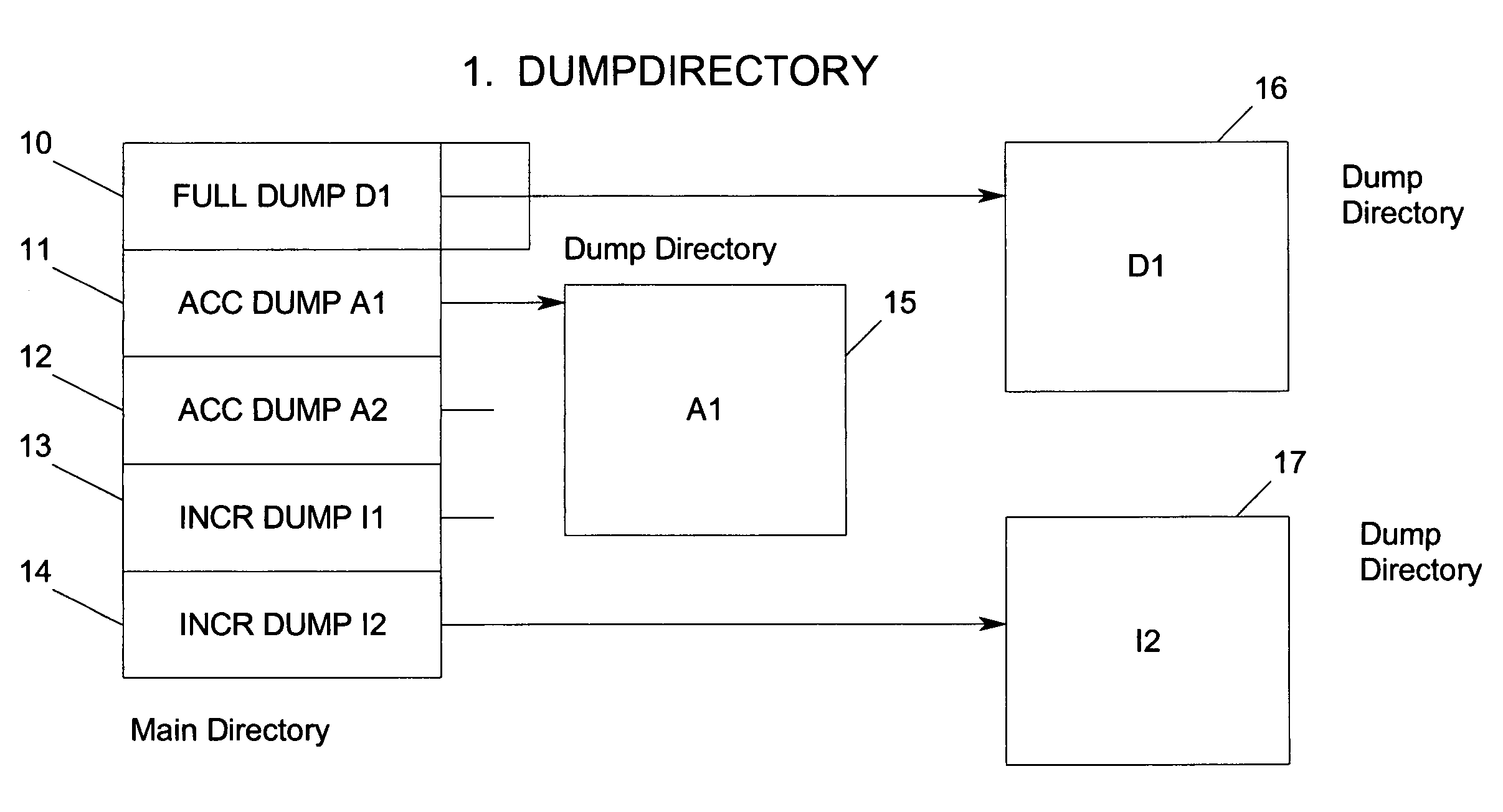
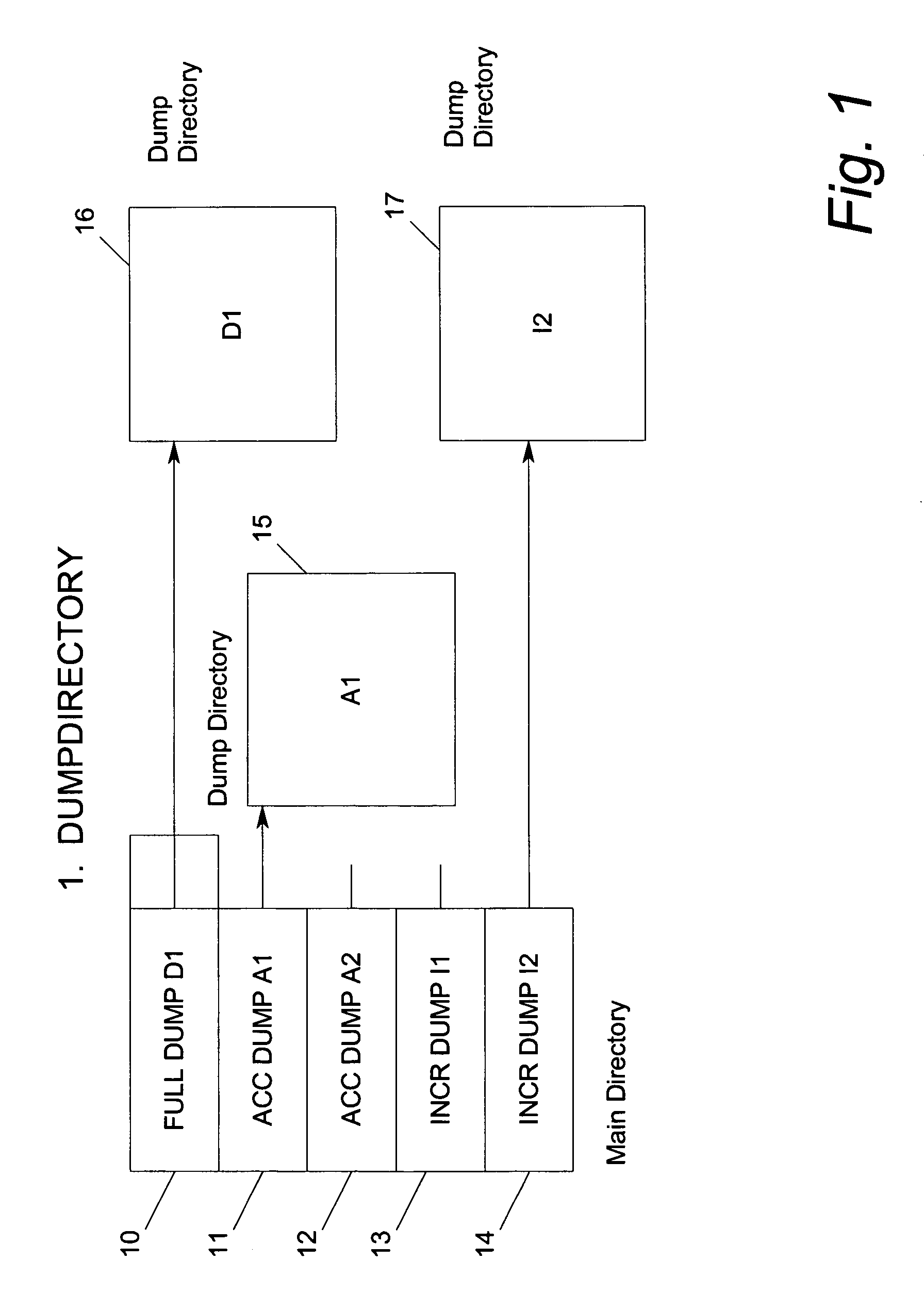
Method and system for managing distributed content and related metadata
InactiveUS7272613B2Reduce storage requirementsReduce amountData processing applicationsError detection/correctionControl systemFile system
The invention provides a method and system for creating an innovative file system that separates its directory presentation from its data store. The method and system include processing, division, distribution, managing, synchronizing, and reassembling of file system objects that does not delay the presentation of the content to the user, but also uses a reduced amount of storage space. The invention includes the ability to manage and control the integrity of the files distributed across the network, and the ability to serve and reconstruct files in real time using a Virtual File Control System.
Owner:PRISMEDIA NETWORK +1
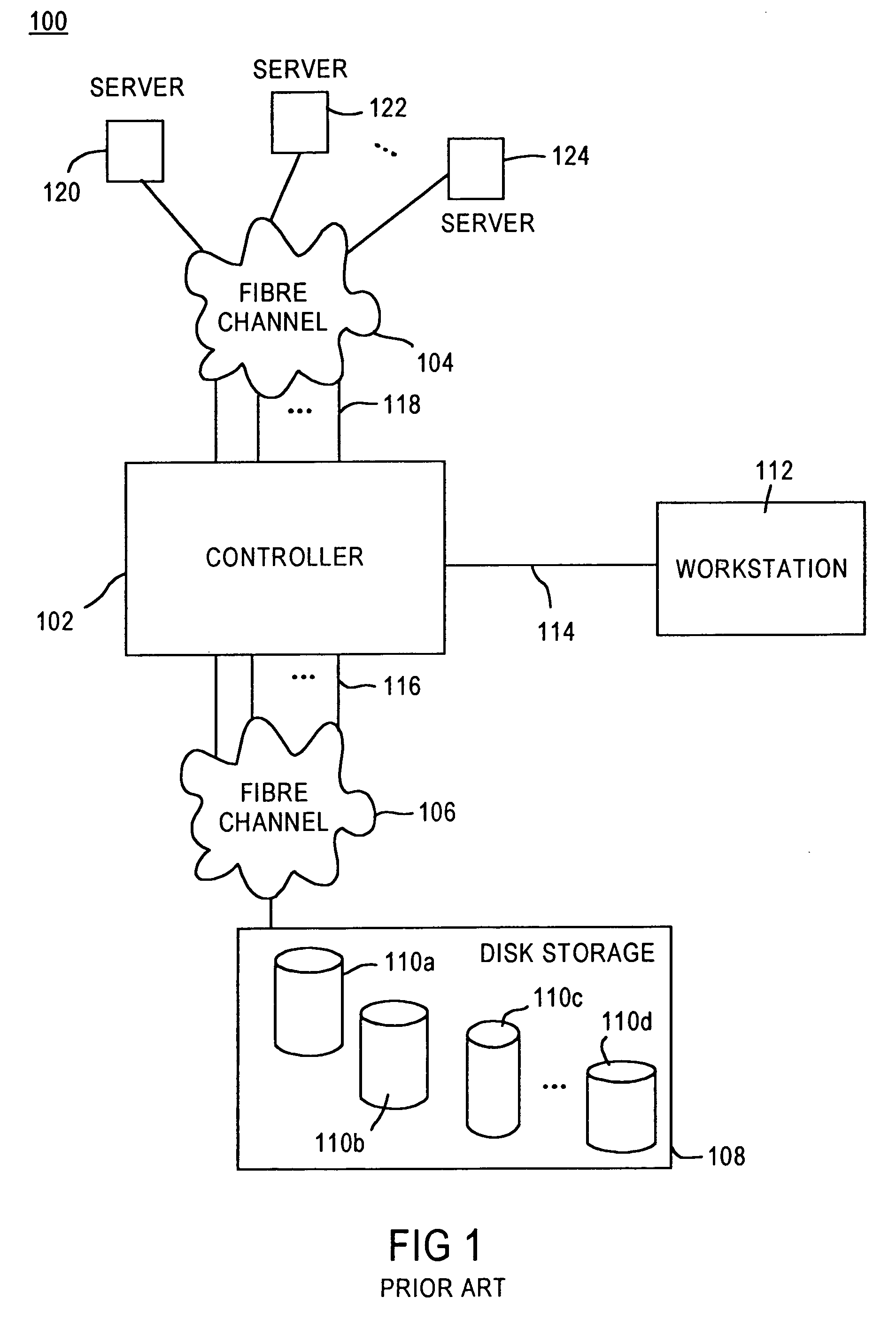
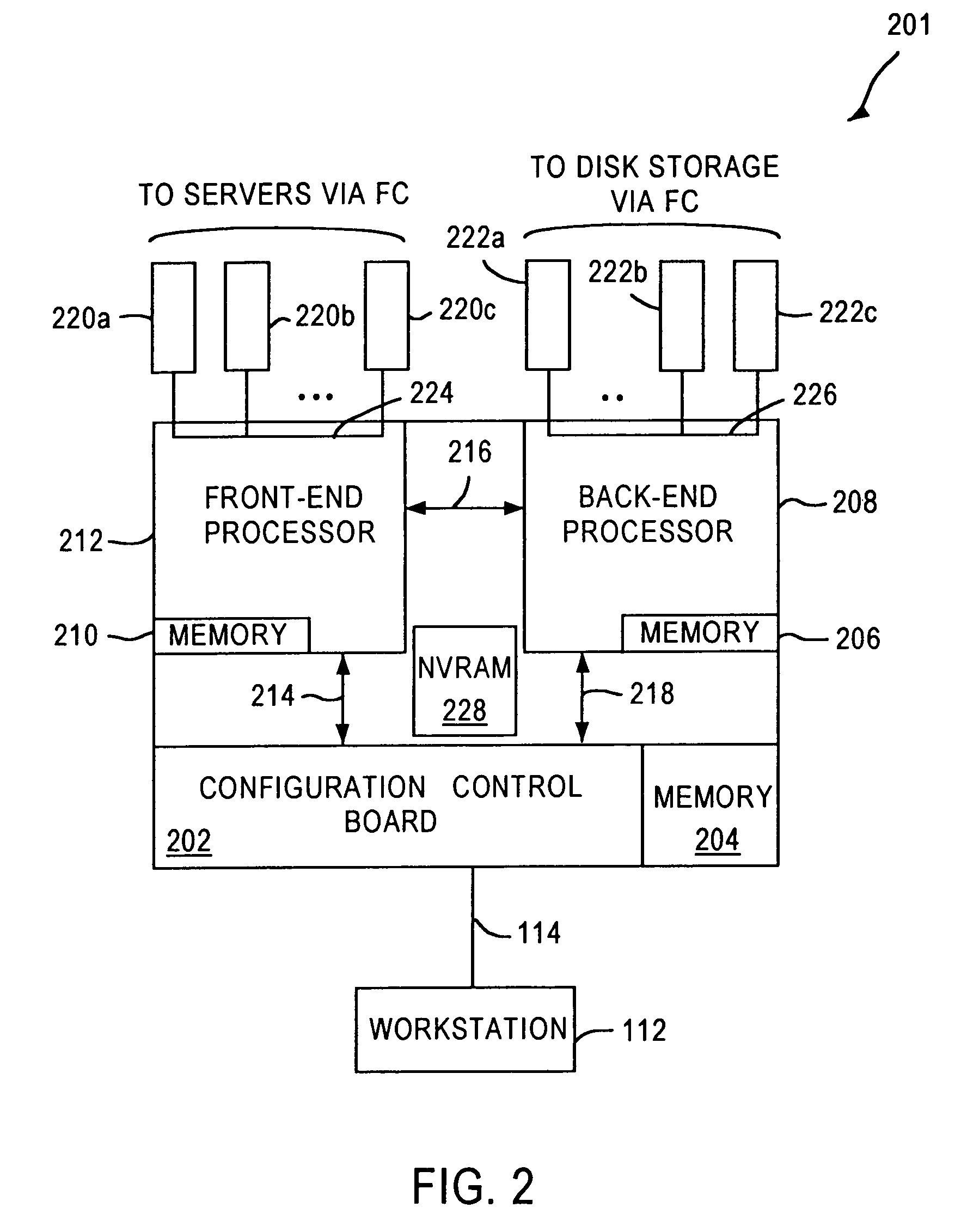
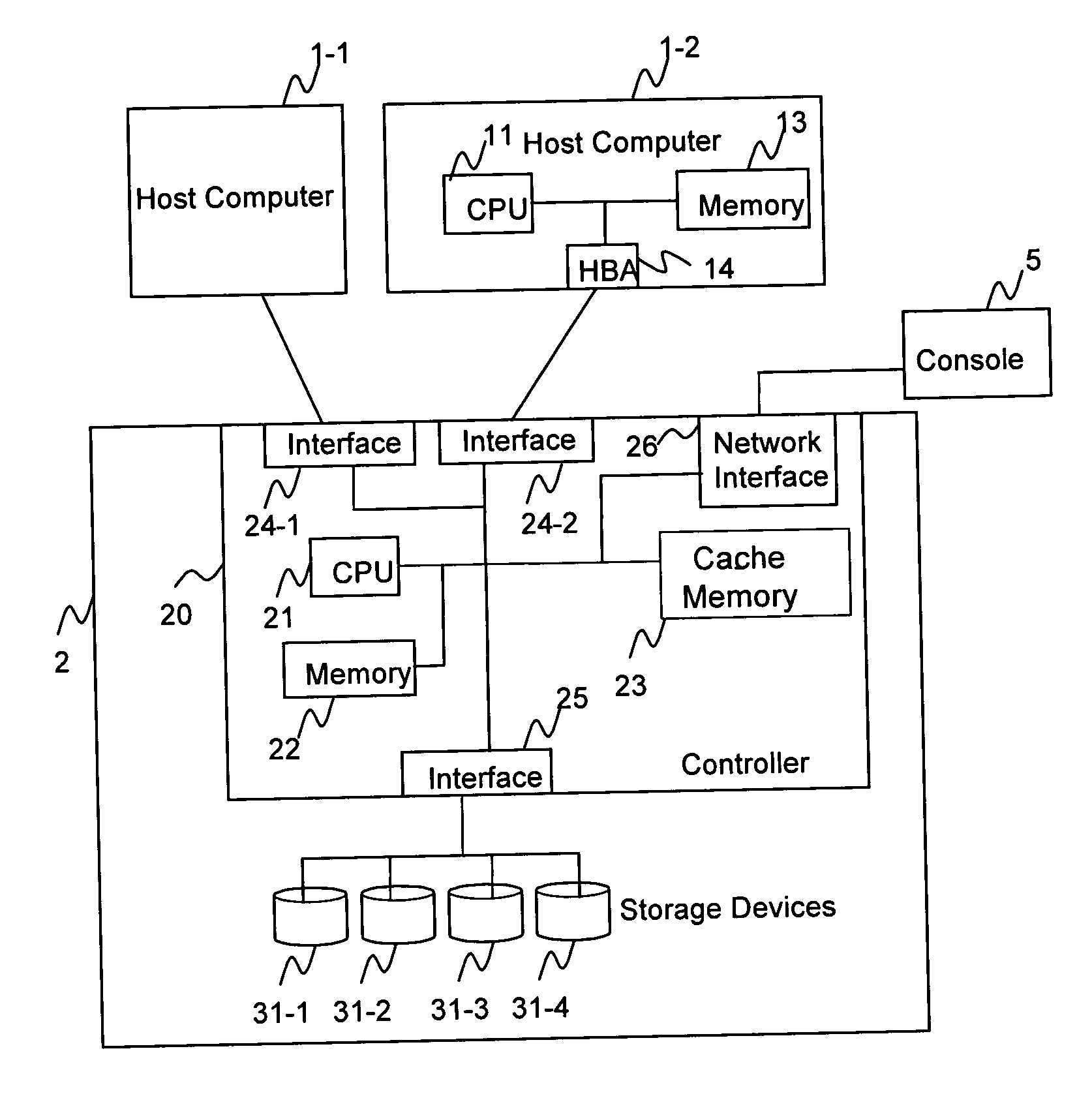
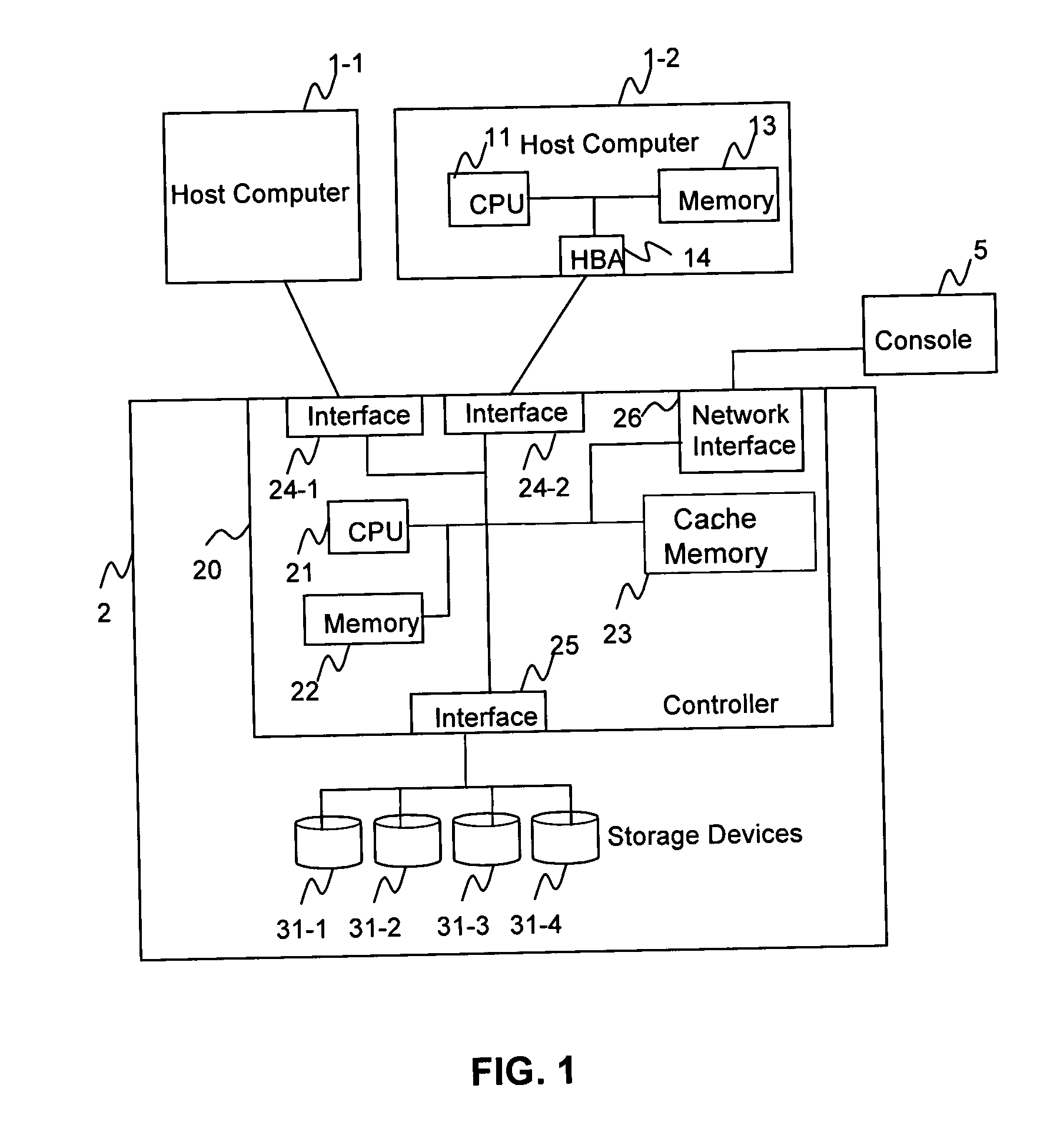
System and method for a reserved memory area shared by all redundant storage controllers
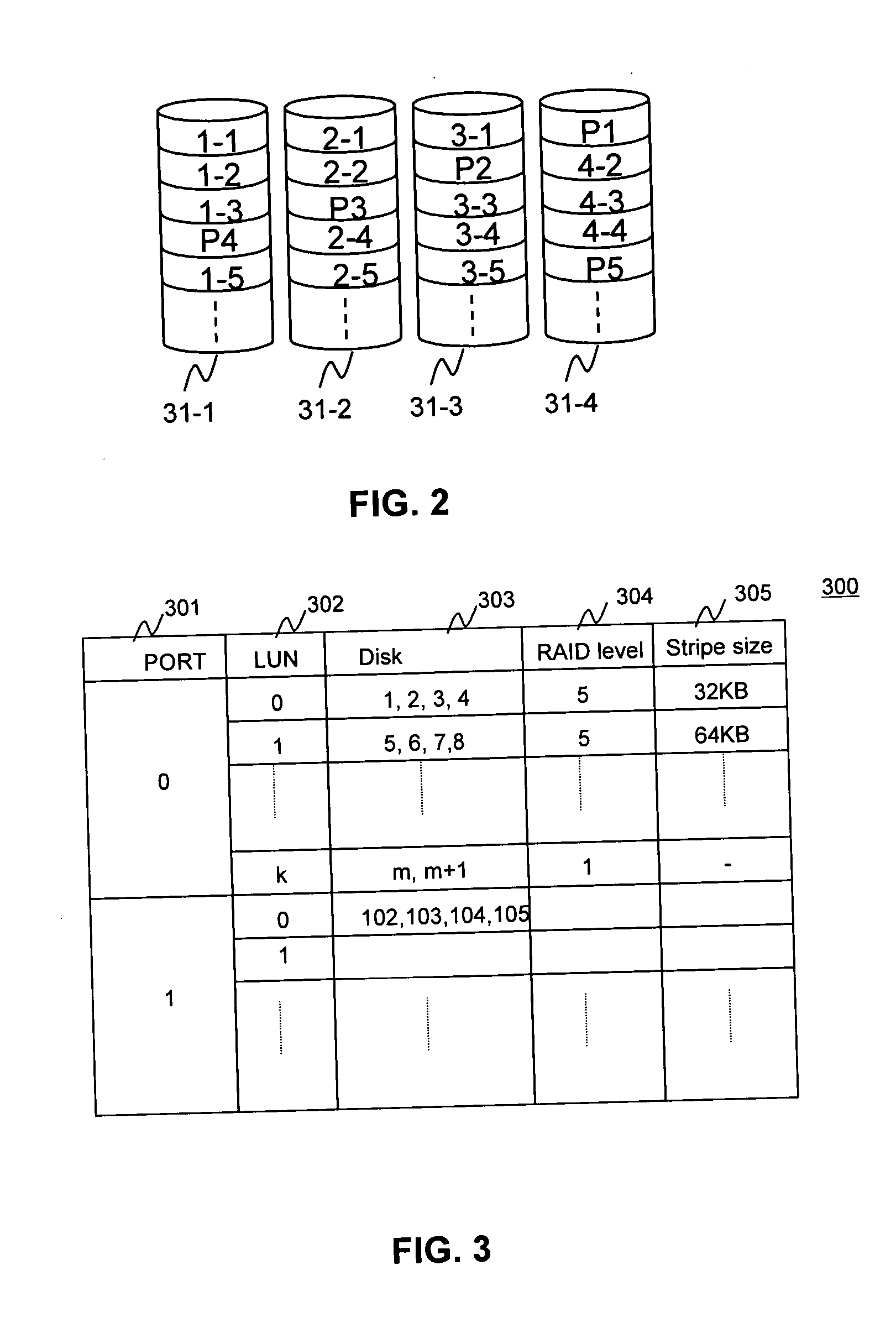
A fibre channel storage area network (SAN) provides virtualized storage space for a number of servers to a number of virtual disks implemented on various virtual redundant array of inexpensive disks (RAID) devices striped across a plurality of physical disk drives. The SAN includes plural controllers and communication paths to allow for fail-safe and fail-over operation. The plural controllers can be loosely-coupled to provide n-way redundancy and have more than one independent channel for communicating with one another. In the event of a failure involving a controller or controller interface, the virtual disks that are accessed via the affected interfaces are re-mapped to another interface in order to continue to provide high data availability. In particular, a common memory storage device is connected to the back-ends of every controller to provide a storage area. In this manner, the common memory storage device can be accessed via operations similar to those a controller already uses to presently access the physical disks which are connected to the back-end of the controllers.
Owner:VSIP HLDG LLC
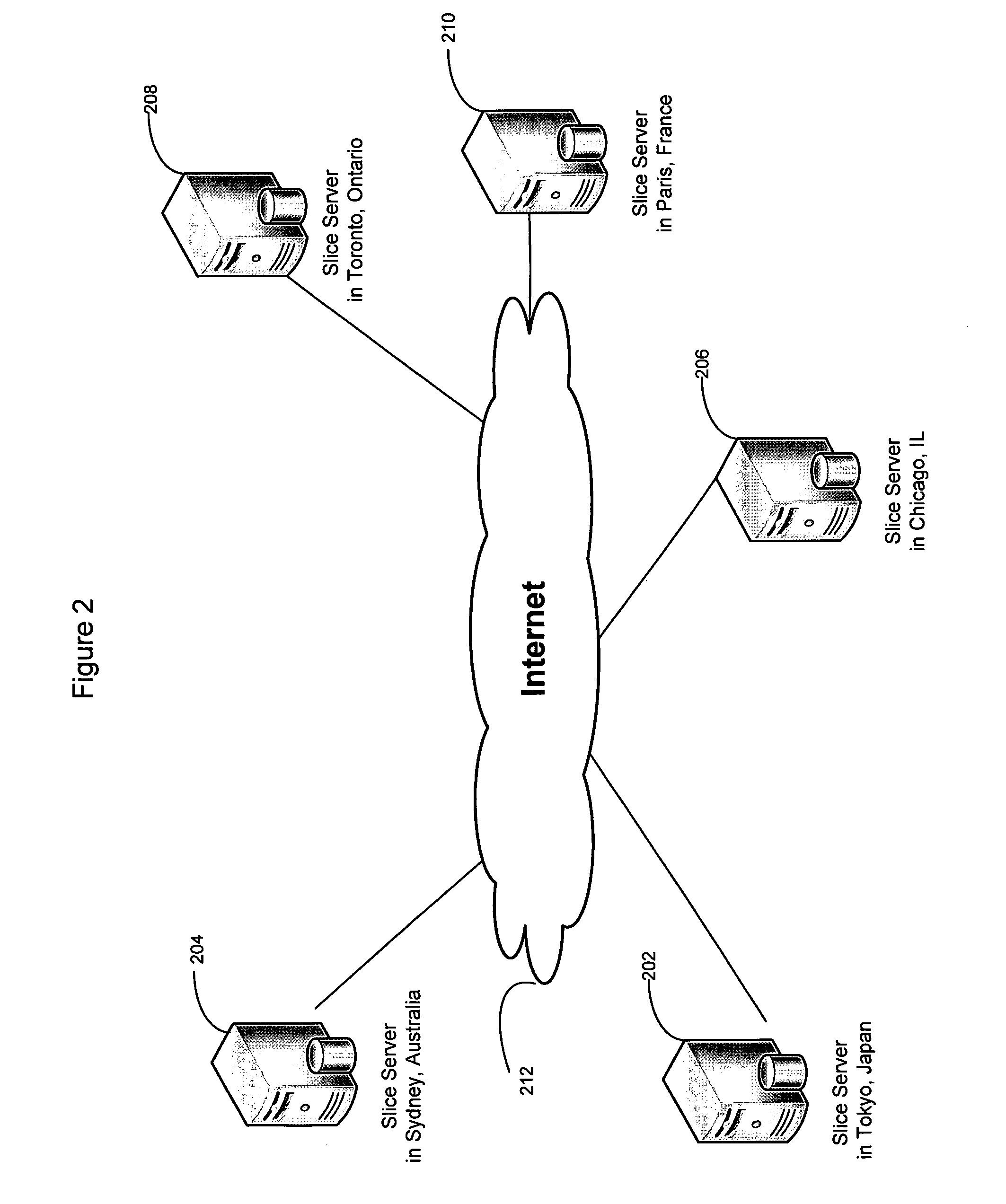
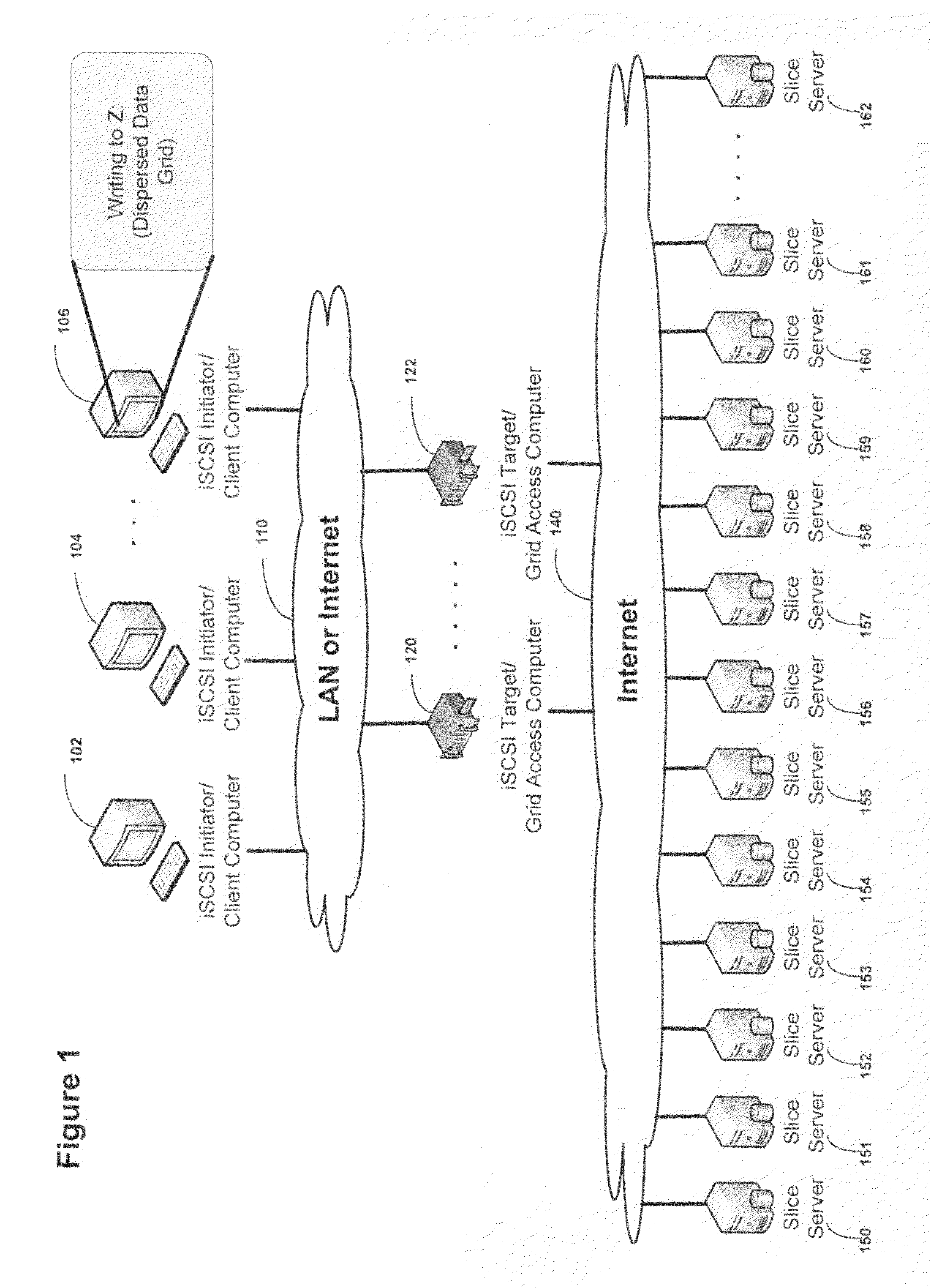
System for rebuilding dispersed data
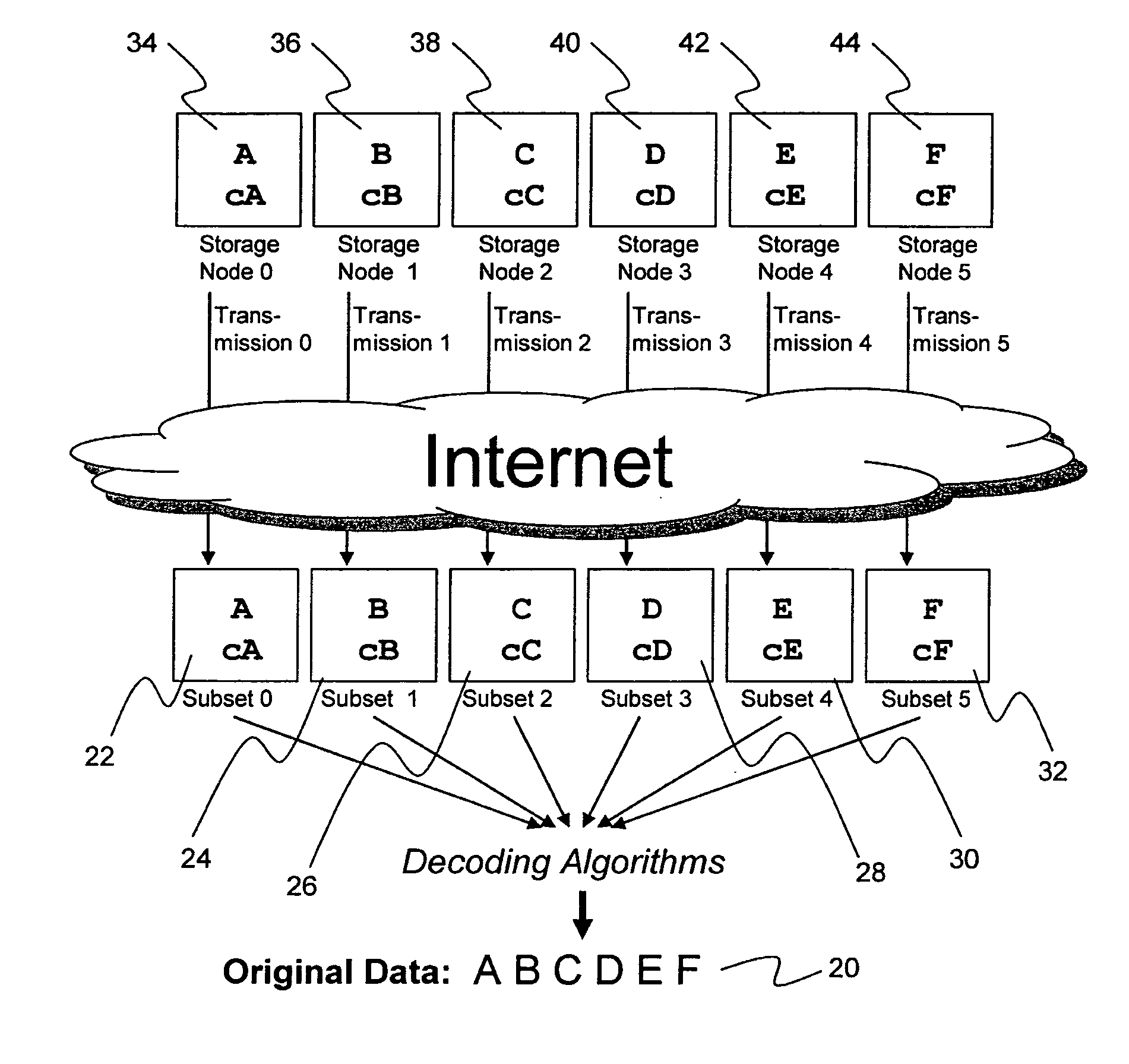
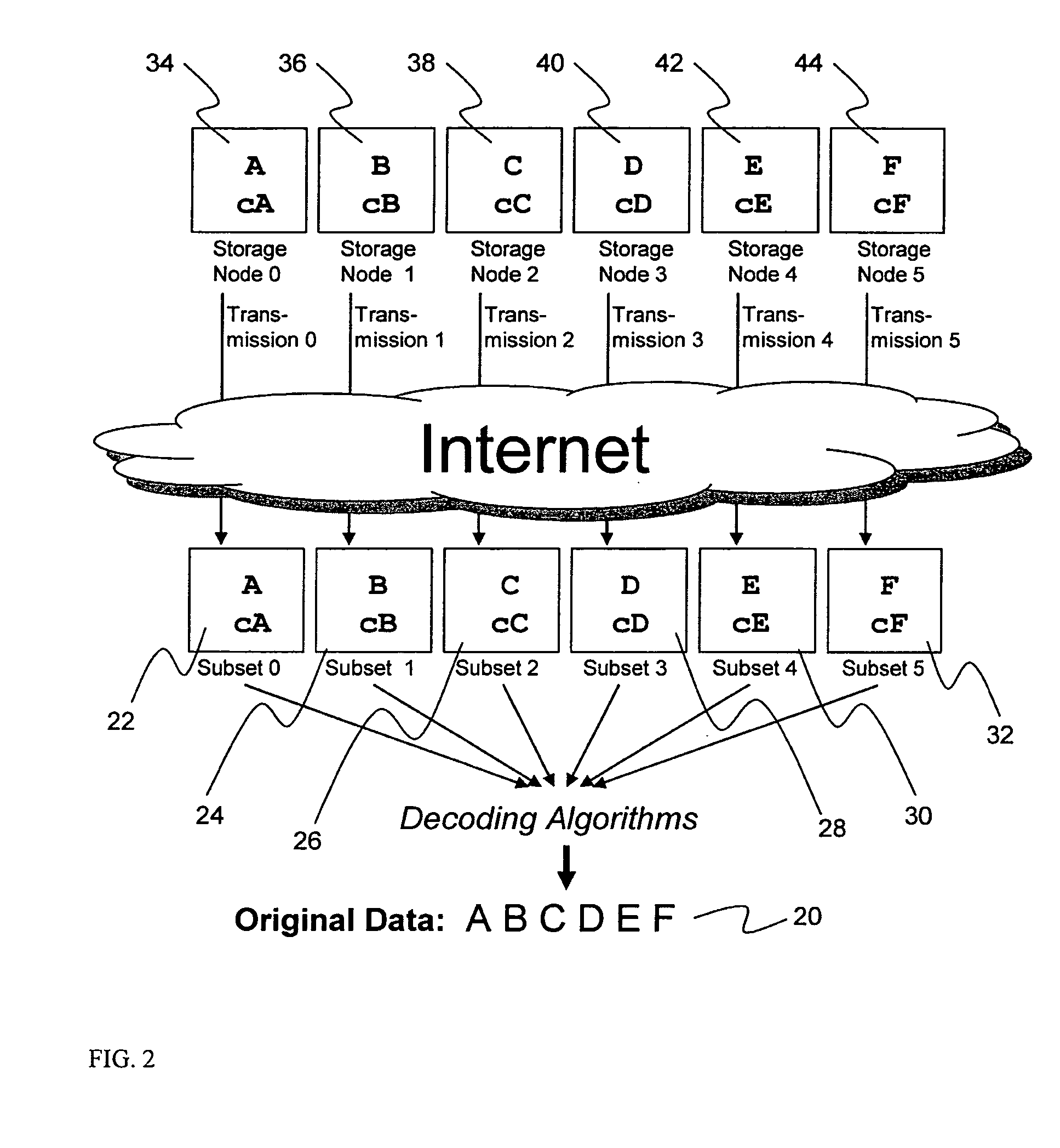
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
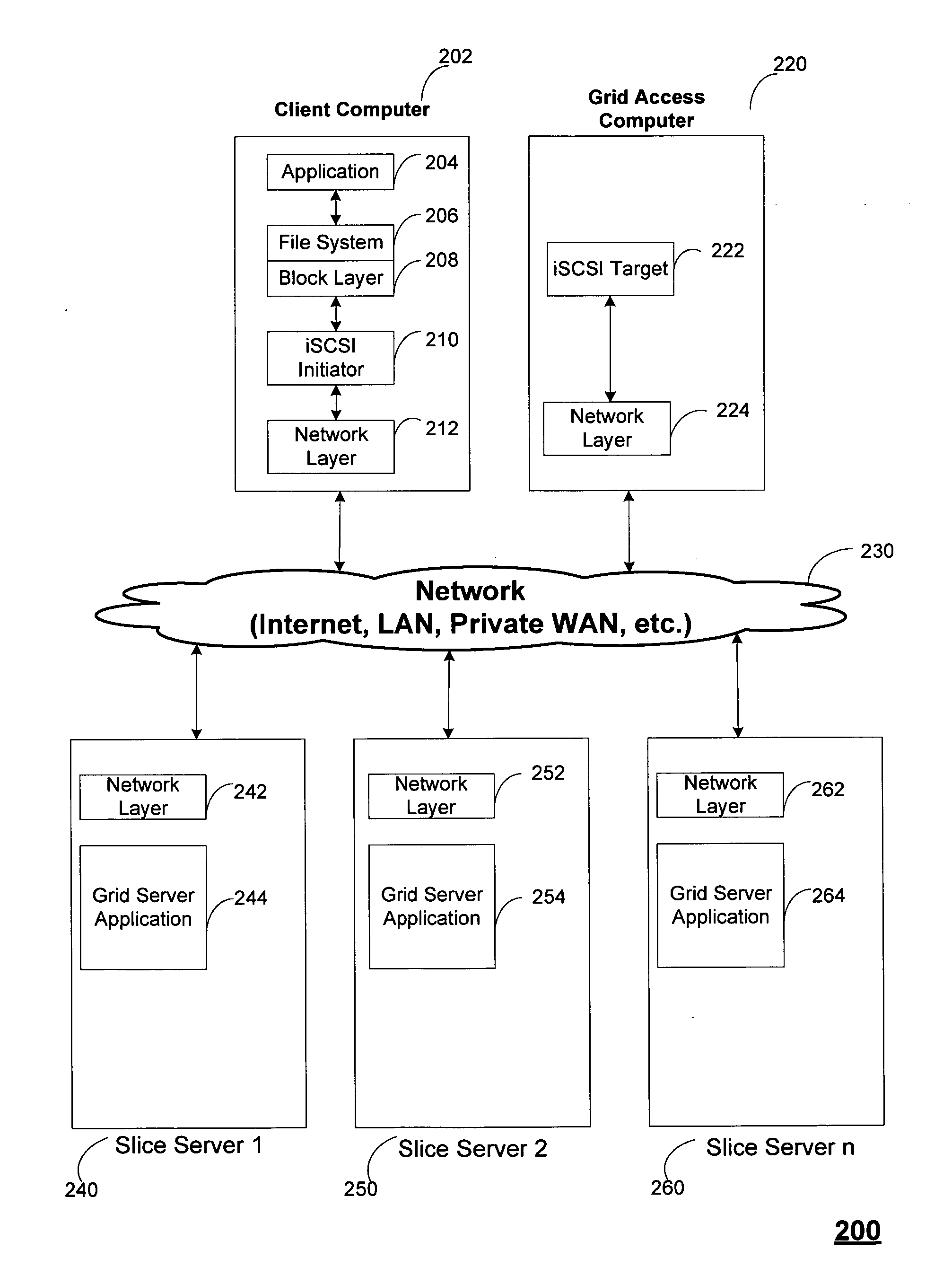
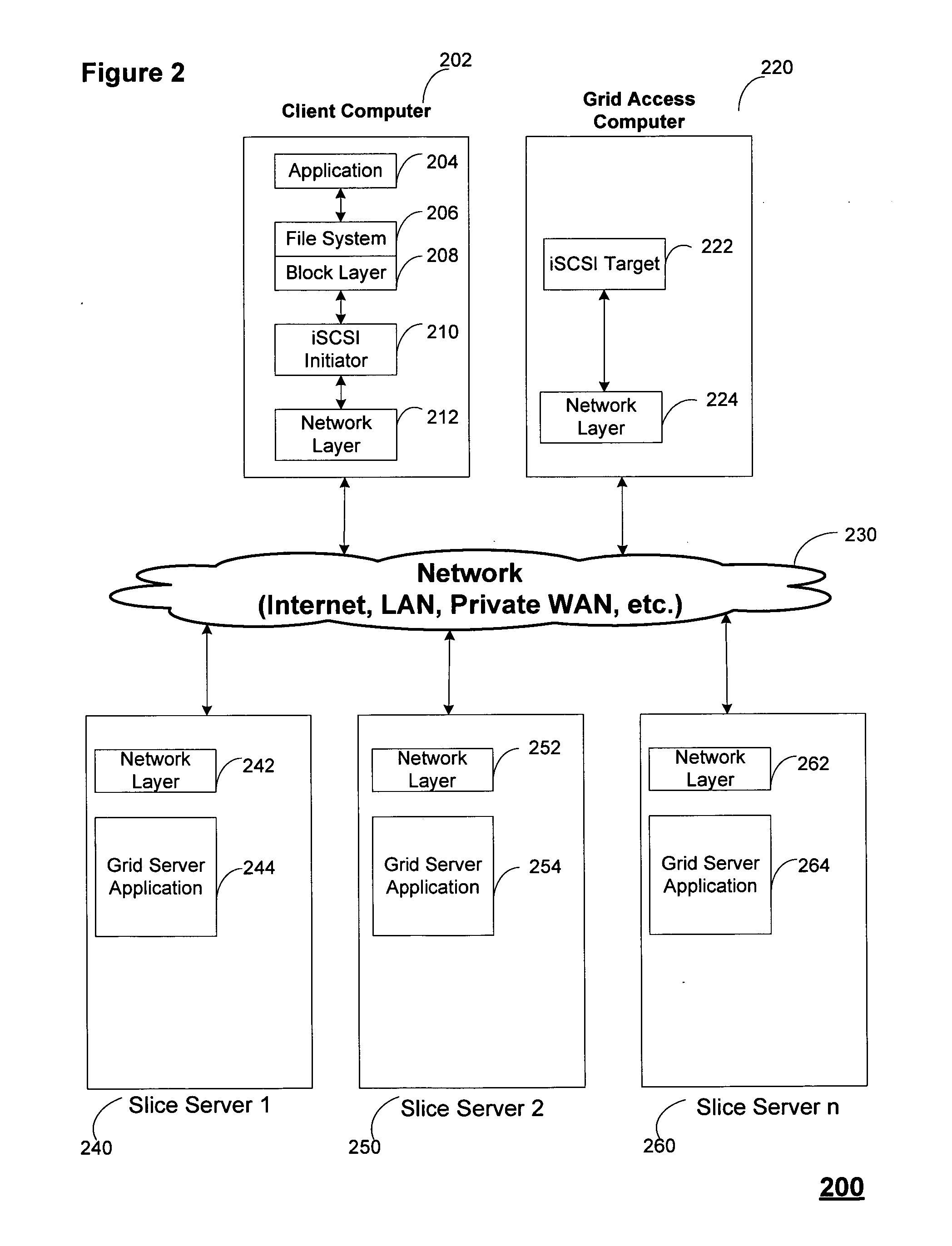
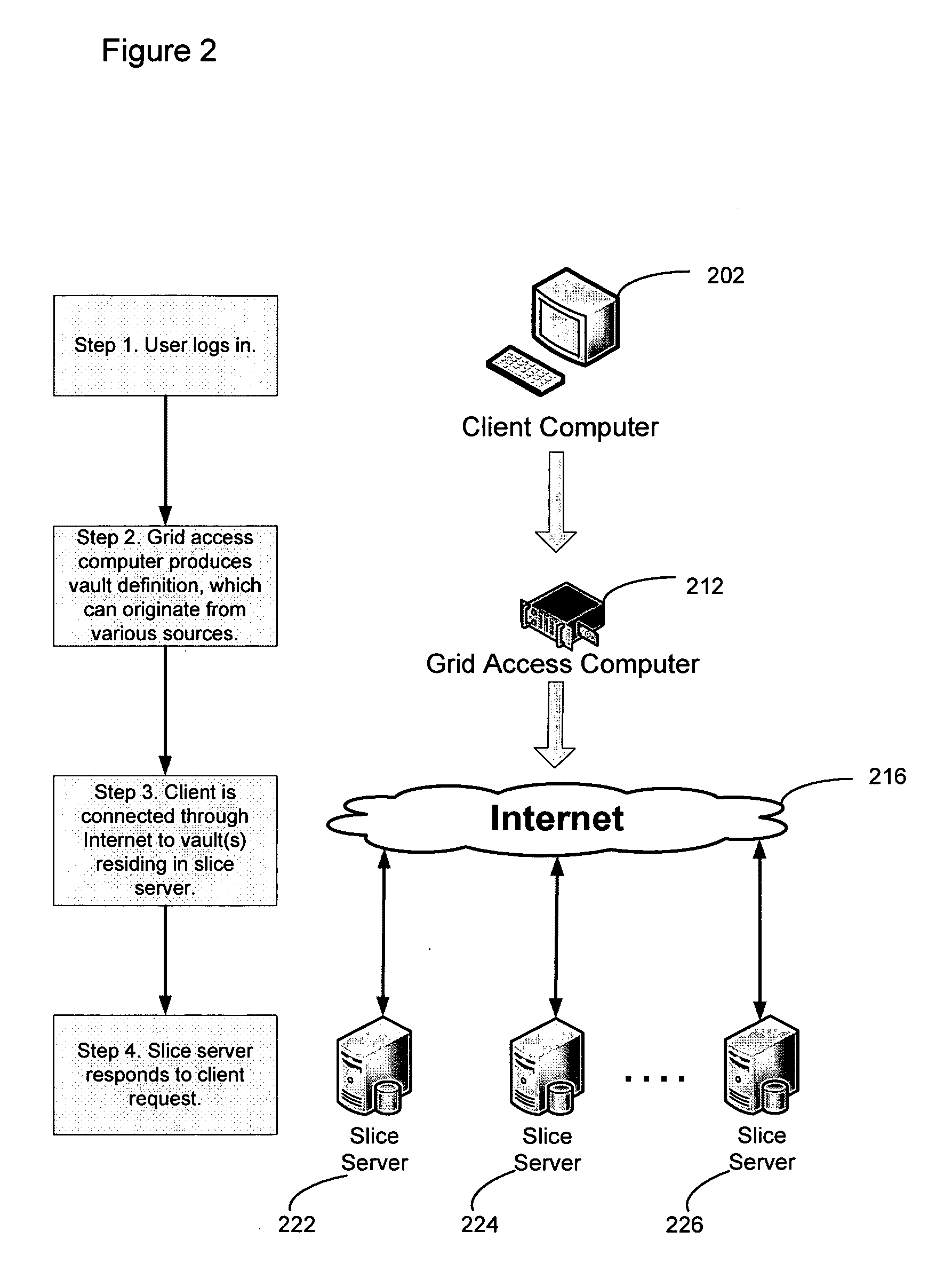
Smart access to a dispersed data storage network
ActiveUS20090094318A1Efficient accessImprove network performanceError preventionFrequency-division multiplex detailsData segmentRanking
An improved system for accessing data within a distributed data storage network (“DDSN”) is disclosed. In a system implementing the disclosed invention, traffic is routed to individual slice servers within the DDSN in accordance with objective criteria as well as user-defined policies. In accordance with one aspect of the disclosed invention, when a data segment is written to a DDSN, the segment is divided into multiple data slices, which are simultaneously transmitted to different slice servers. In accordance with another aspect of the disclosed invention, when a data segment is read from a DDSN, a list of slice servers, each containing a data slice that could be used to reconstruct the requested data segment, is assembled, and sorted in accordance with a preference rating assigned to each of the slice servers. Sufficient data slices to reconstruct the data segment are then read in accordance with the preference ranking of the slice servers.
Owner:PURE STORAGE
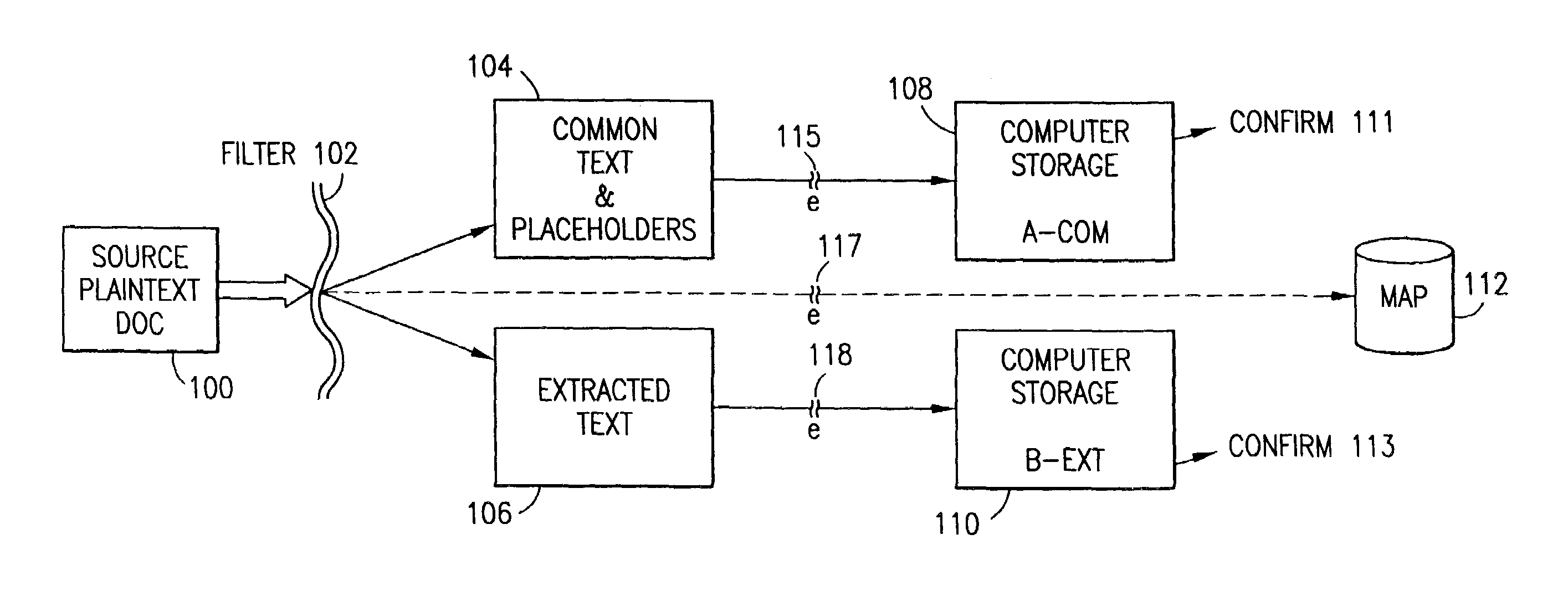
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
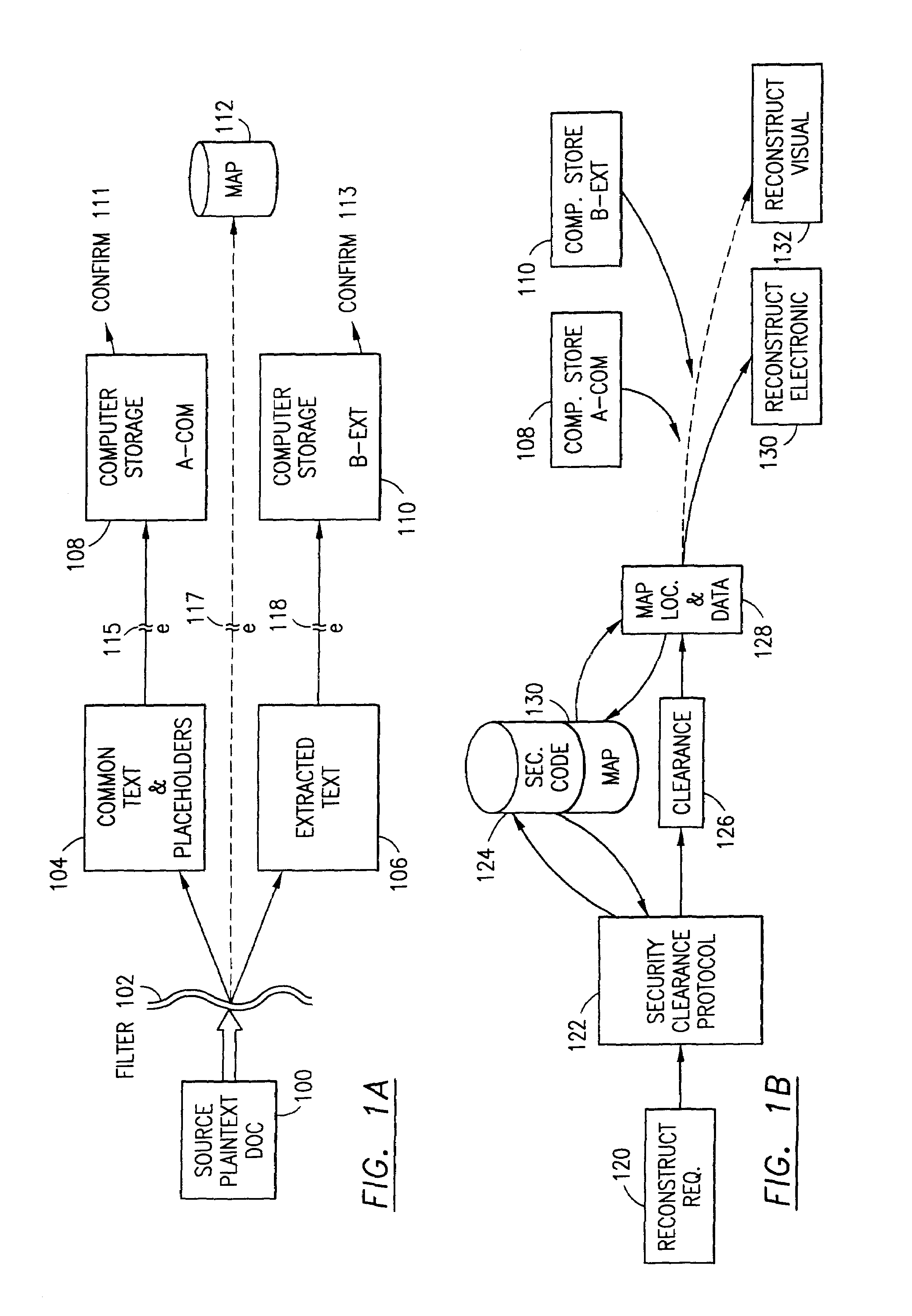
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
Method and apparatus for reconstructing data in object-based storage arrays
A method and apparatus for placing objects on a storage device of a storage system and reconstructing data of objects in the storage device. The storage system stores data as objects and implements a RAID architecture including a plurality of the storage devices, and a disk controller for processing Object-based Storage Device (OSD) commands. Each object includes data and attribute. Parity data is calculated for reconstructing an object upon occurrence of a storage device failure. Each storage device includes plural stripes each having a predetermined length. Each object is stored in a stripe wherein an attribute is stored in the head of the stripe and data is stored after the attribute. When the object size exceeds the stripe length, the remainder of the object is stored in the next stripe, and when another object is to be stored, an attribute is stored at a head of a further next stripe and data is stored just after the attribute.
Owner:GOOGLE LLC
Block based access to a dispersed data storage network
ActiveUS20100023524A1Simple methodDigital data processing detailsError detection/correctionFile systemData store
A block-based interface to a dispersed data storage network is disclosed. The disclosed interface accepts read and write commands from a file system resident on a user's computer and generates network commands that are forwarded to slice servers that form the storage component of the dispersed data storage network. The slice servers then fulfill the read and write commands.
Owner:PURE STORAGE
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
Method for reducing database recovery time
ActiveUS7222133B1Reduce database recovery timeShorten recovery timeData processing applicationsError detection/correctionComplete dataComputer science
Owner:UNISYS CORP
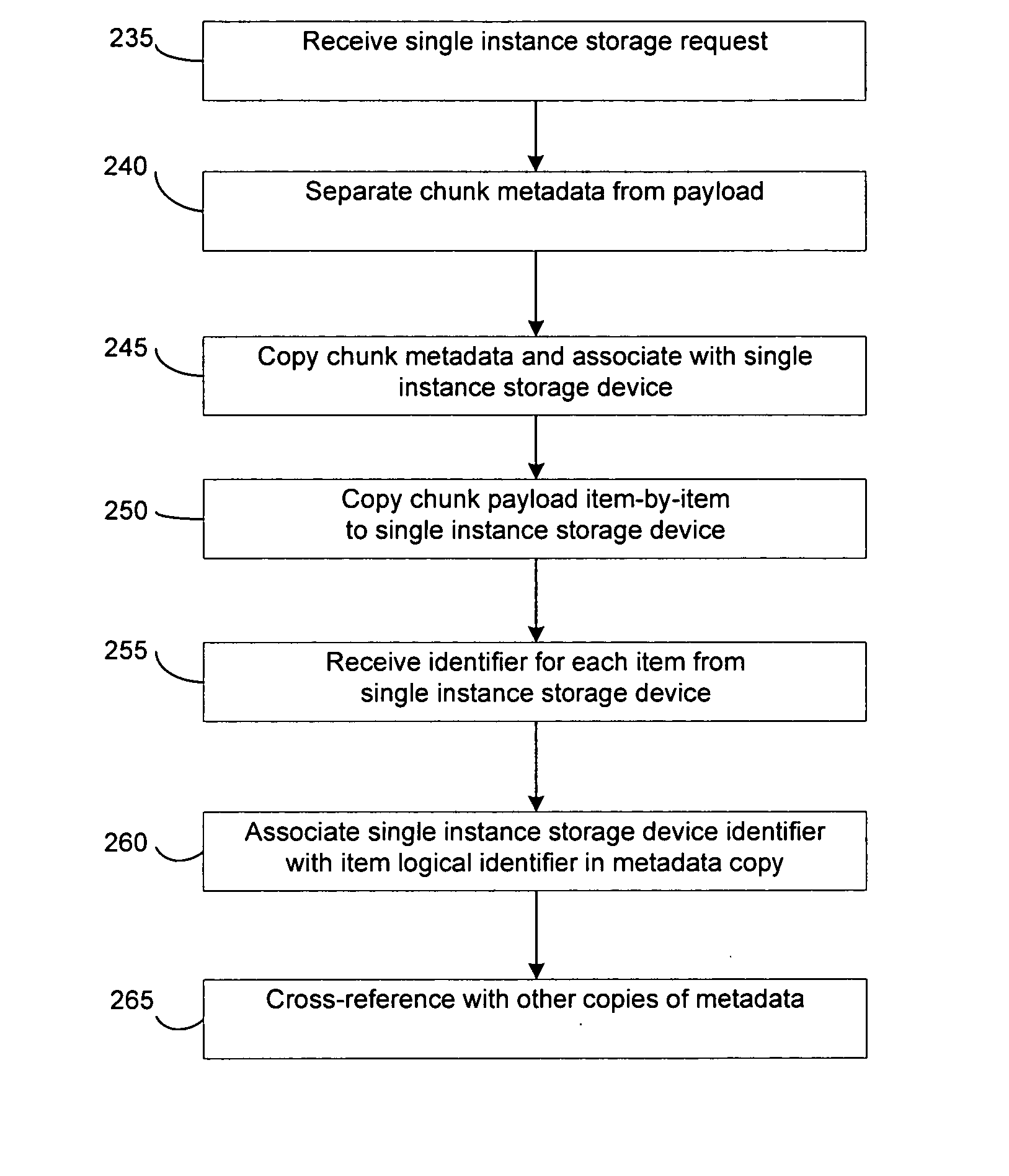
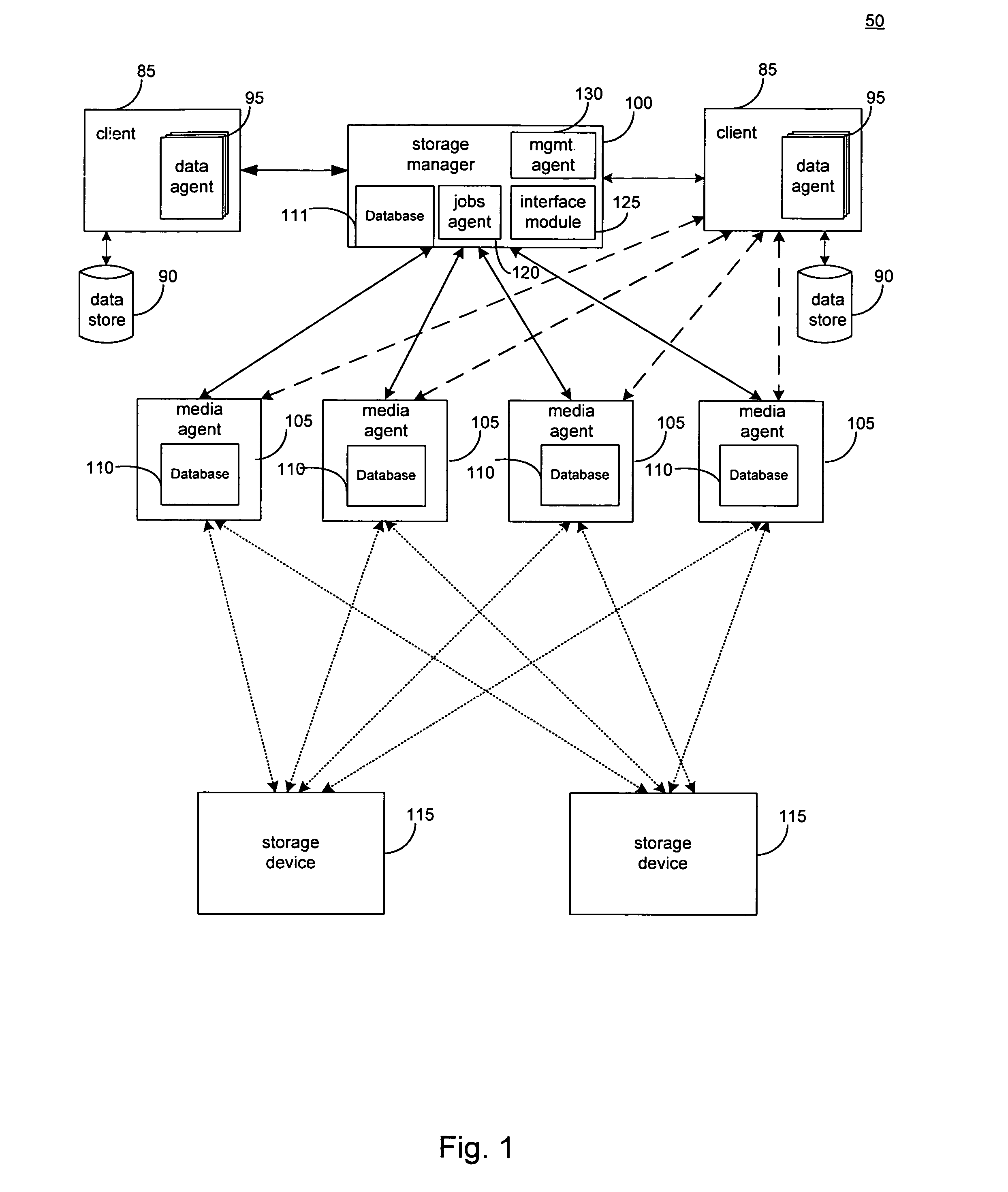
System and method to support single instance storage operations
Systems and methods for single instance storage operations are provided. Systems constructed in accordance with the principals of the present invention may process data containing a payload and associated metadata. Often, chunks of data are copied to traditional archive storage wherein some or all of the chunk, including the payload and associated metadata are copied to the physical archive storage medium. In some embodiments, chunks of data are designated for storage in single instance storage devices. The system may remove the encapsulation from the chunk and may copy the chunk payload to a single instance storage device. The single instance storage device may return a signature or other identifier for items copied from the chunk payload. The metadata associated with the chunk may be maintained in separate storage and may track the association between the logical identifiers and the signatures for the individual items of the chunk payload which may be generated by the single instance storage device.
Owner:COMMVAULT SYST INC
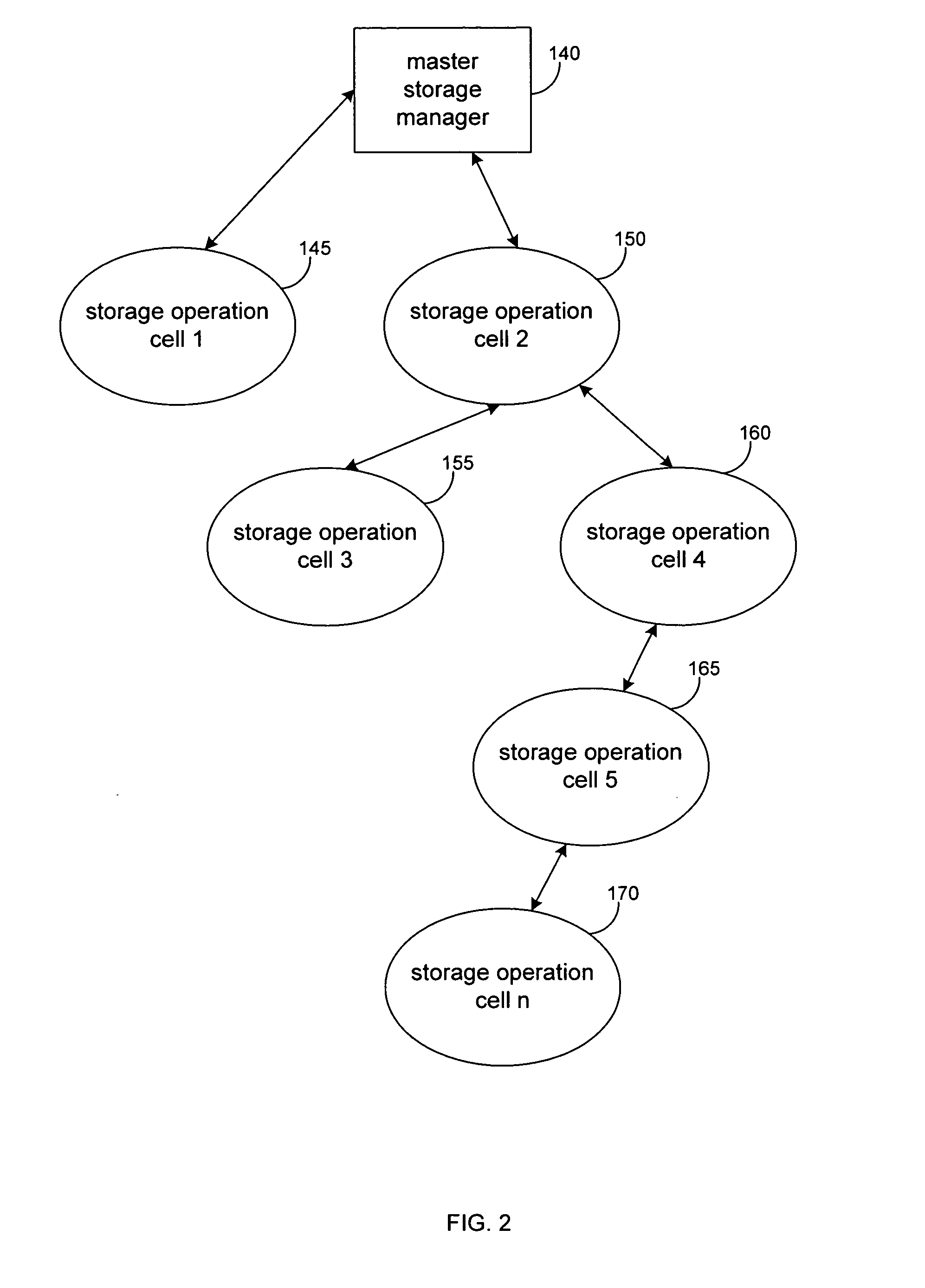
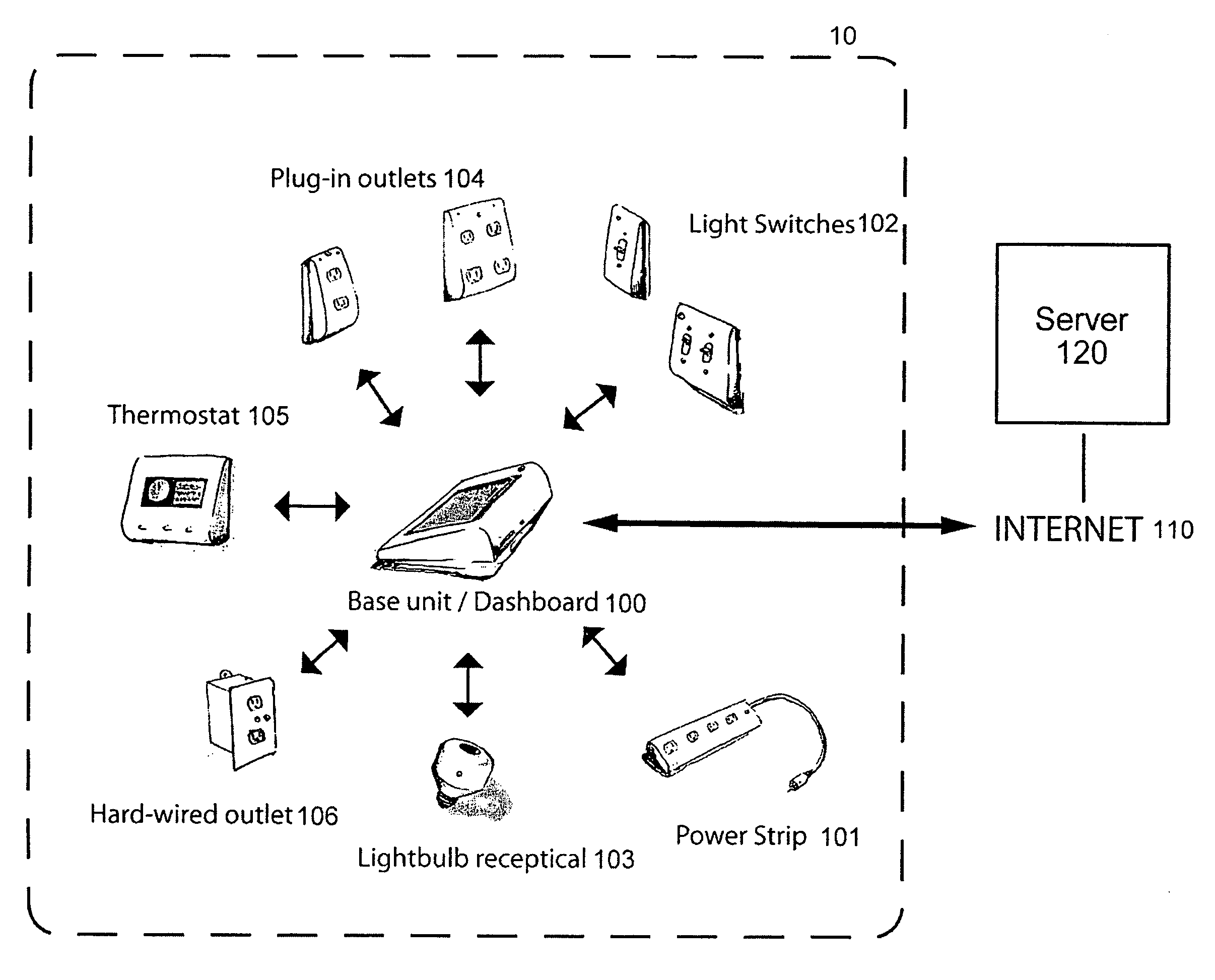
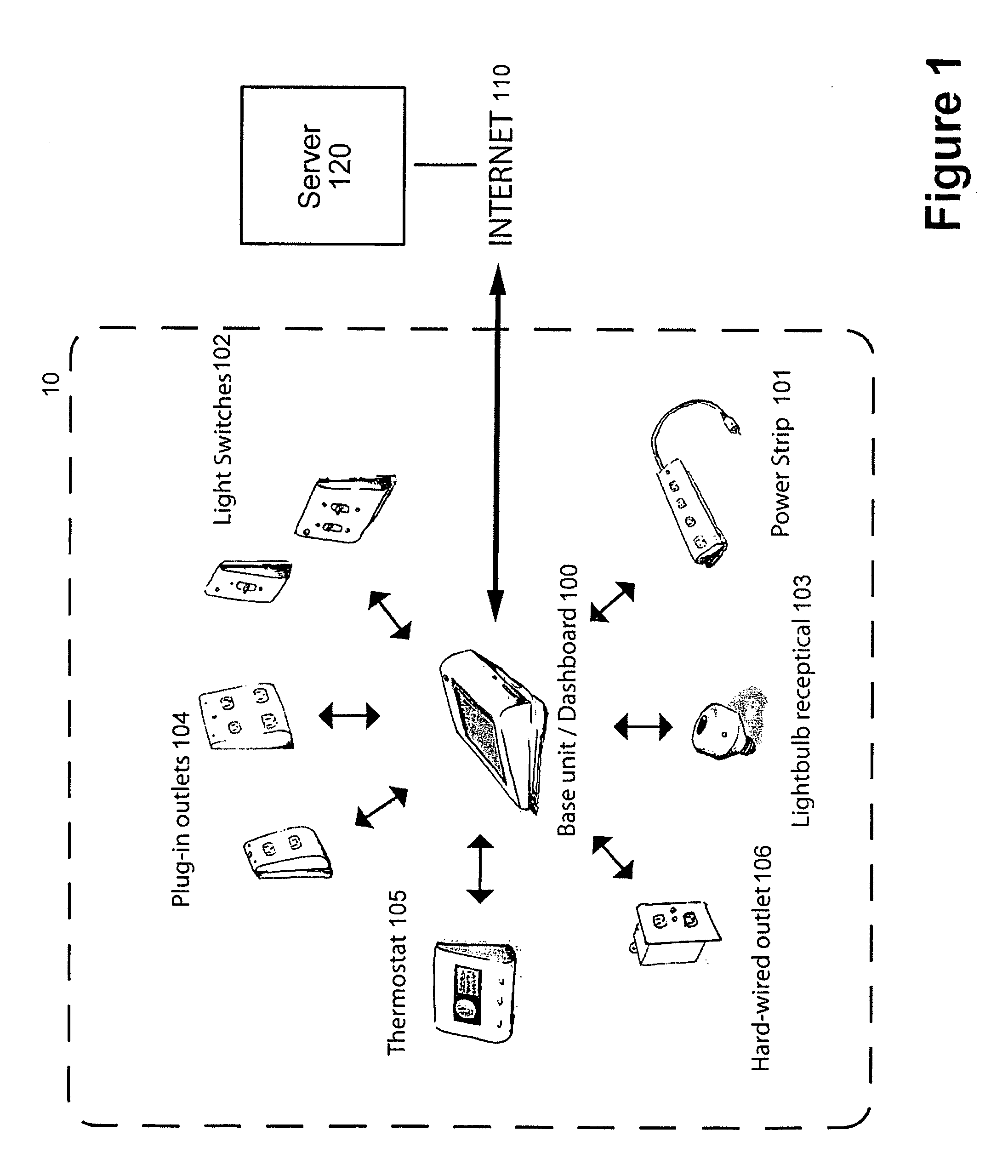
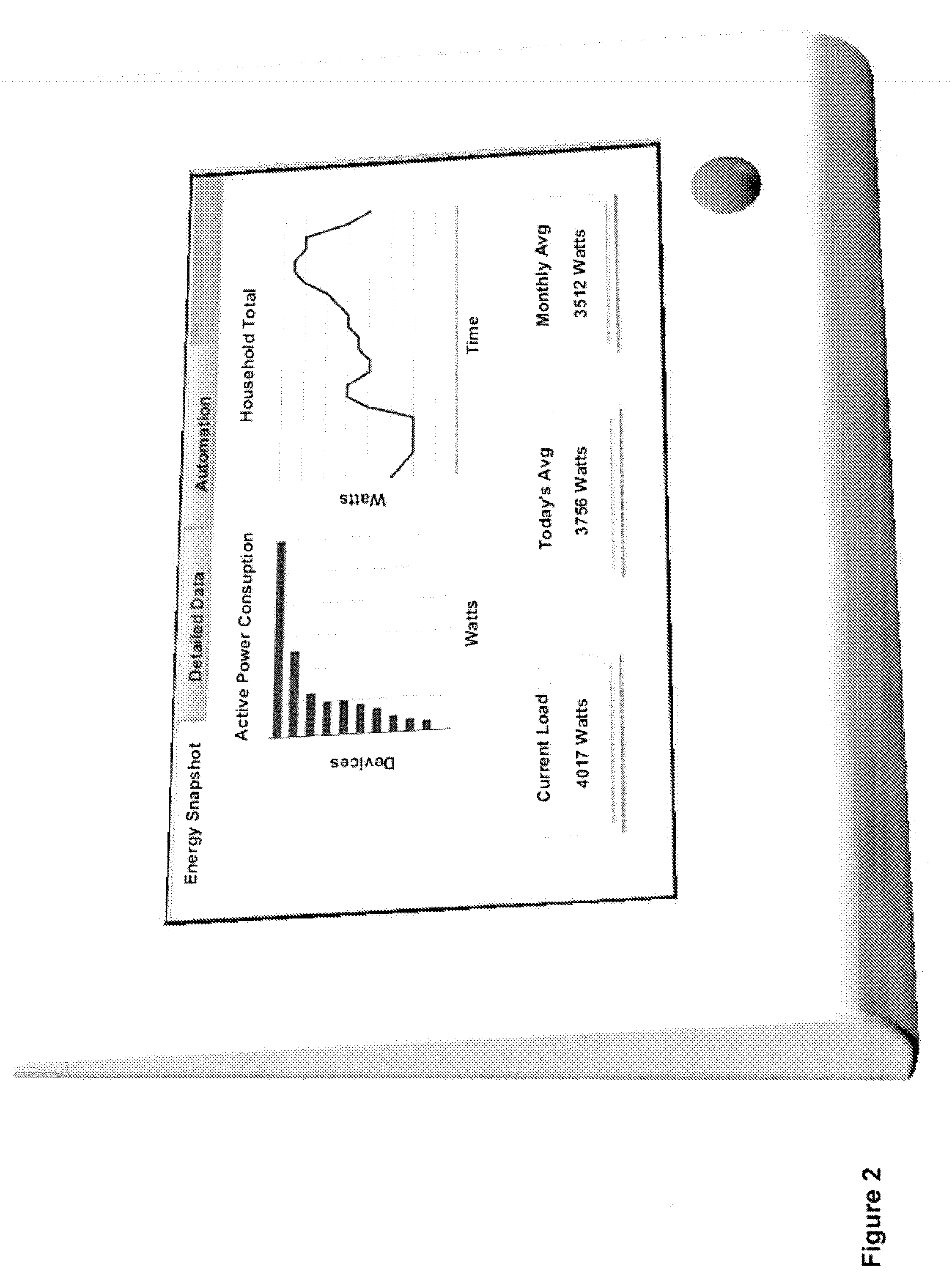
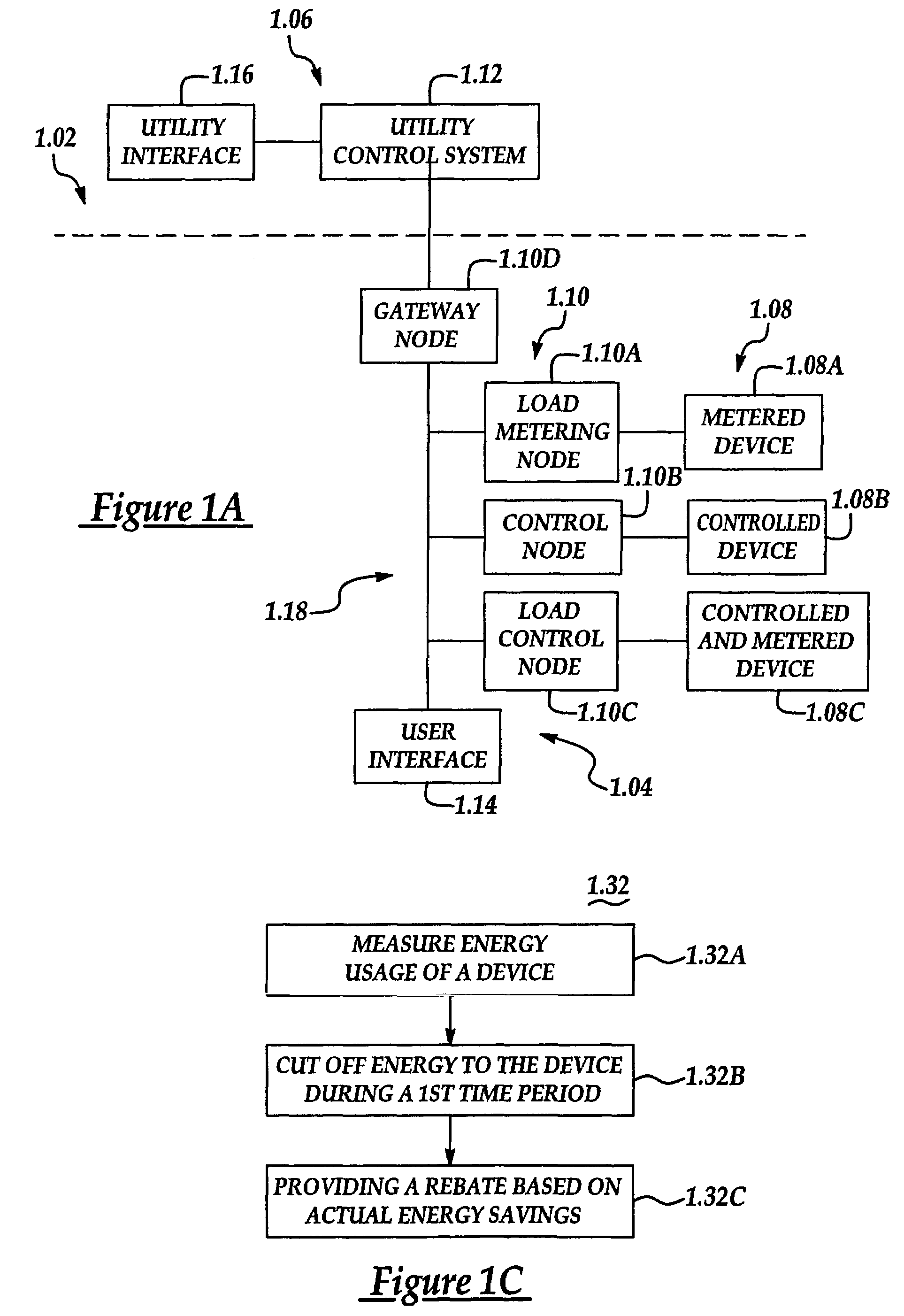
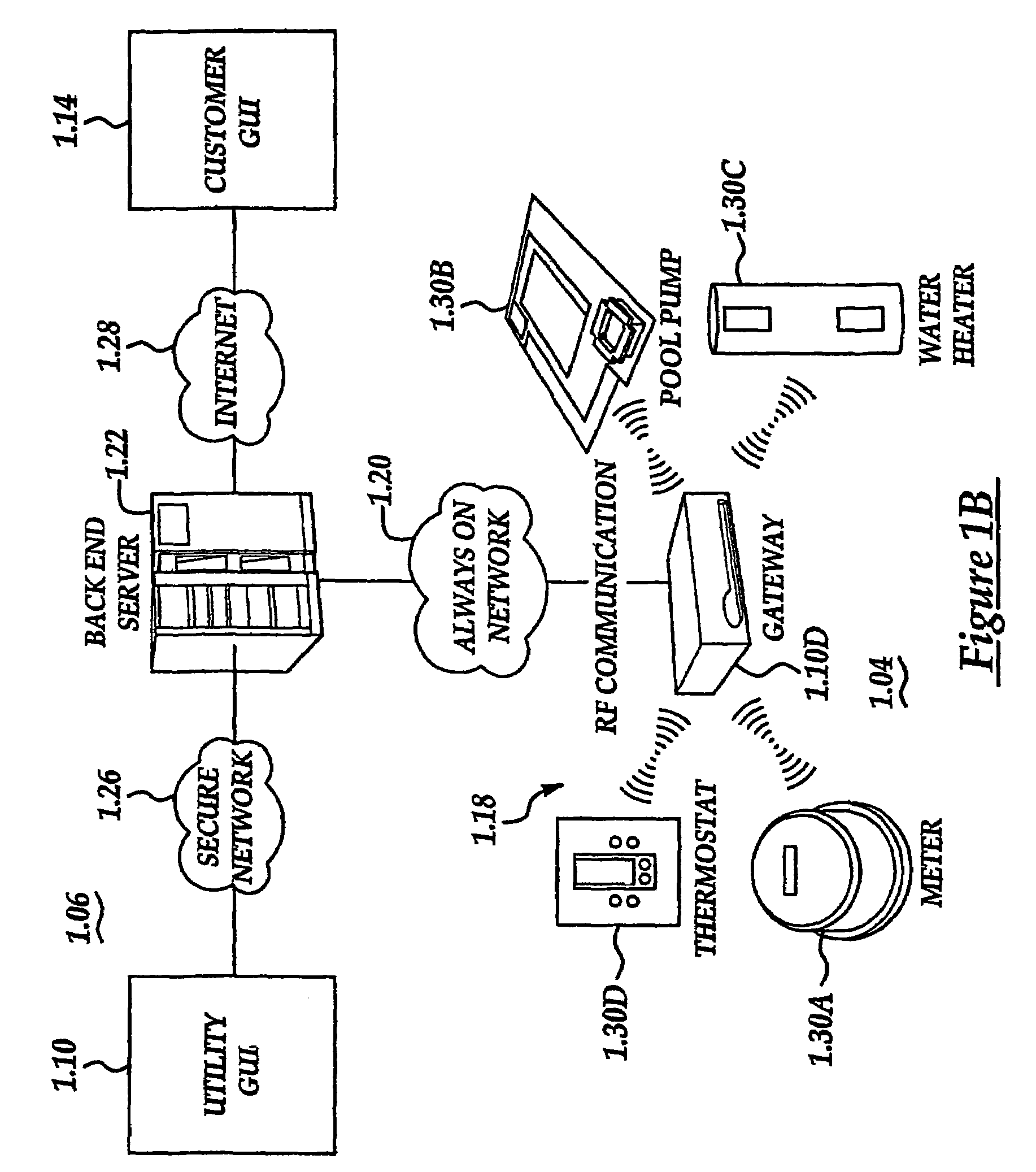
System and method for home energy monitor and control
ActiveUS20090195349A1Increase powerEfficient managementLevel controlPayment architectureCommunity basedMonitoring system
The invention generally concerns systems and methods for monitoring and controlling the power consumption of a power-consuming device. The system and method may connect to a power source and a power-consuming device, connecting the power-consuming device to the power source. The power usage of the power-consuming device may then be measured and monitored. This monitoring data may then be stored and optionally sent to a controlling device on a data network. The location of the power-consuming device may also be determined, recorded, and sent to a controlling device. The system may also control the power usage of the power-consuming device. In some cases, a remote server may connect multiple energy monitoring systems in order to gain additional efficiencies and foster a community-based social network.
Owner:ENERGYHUB
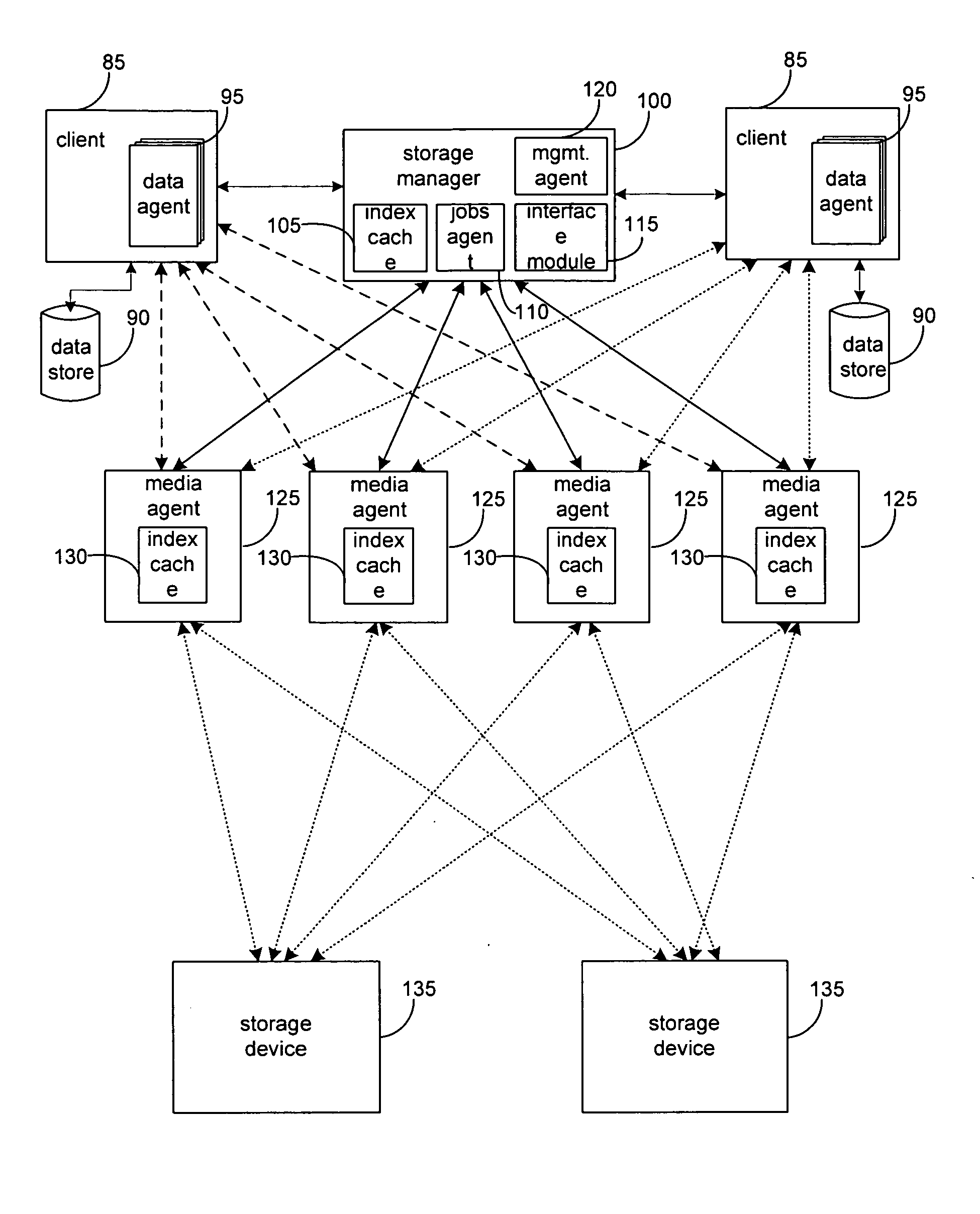
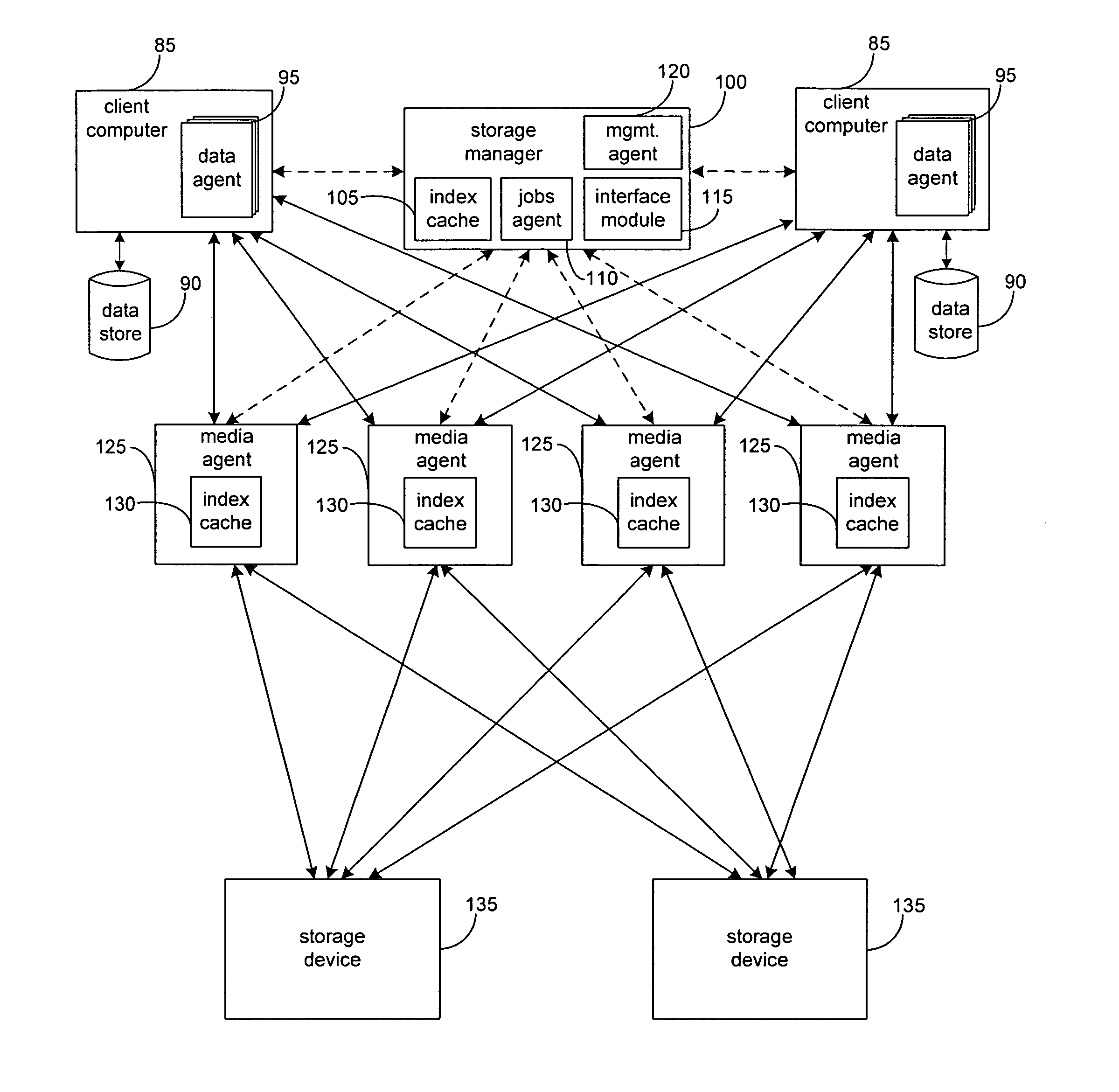
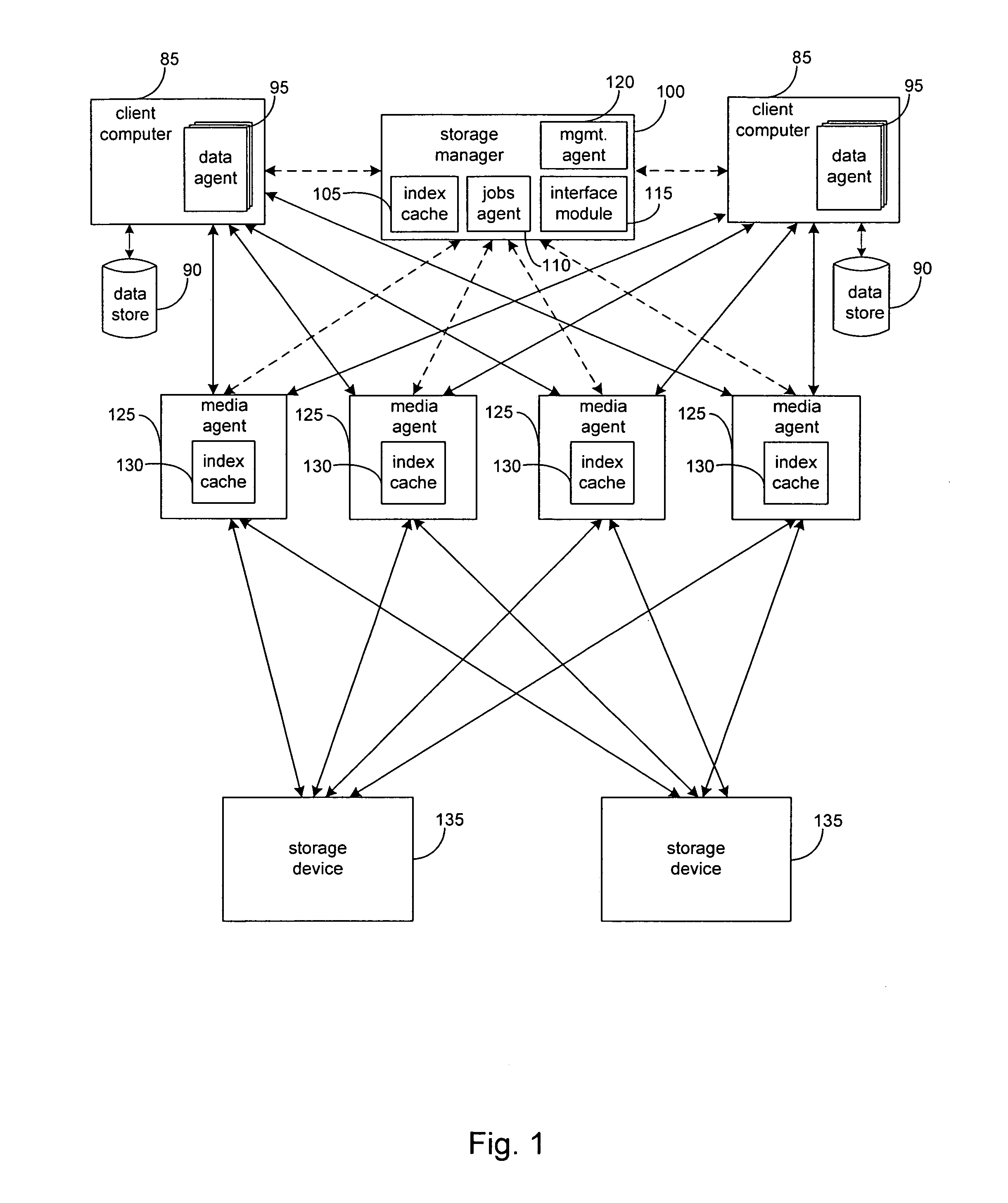
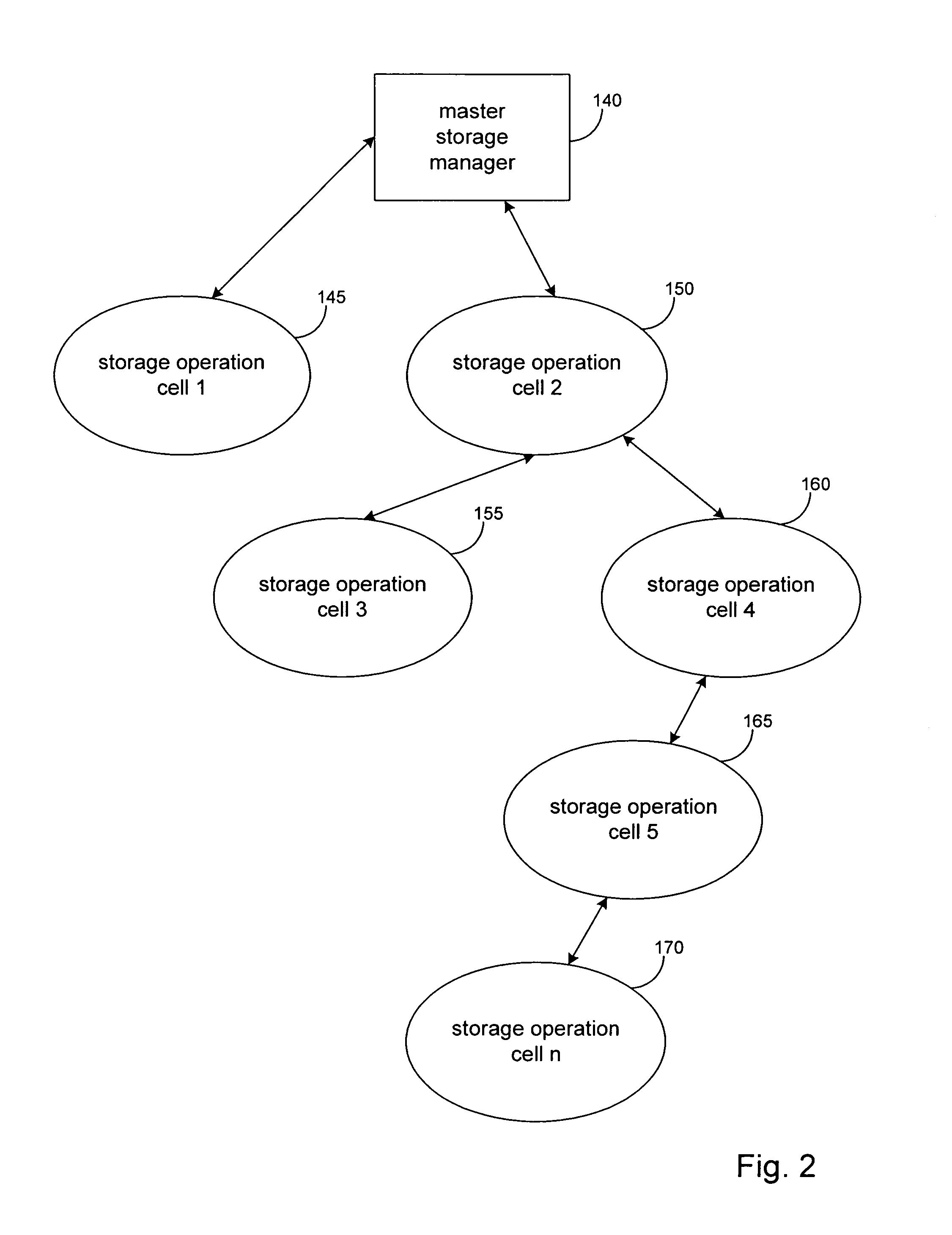
Hierarchical systems and methods for providing a unified view of storage information
The present invention provides systems and methods for data storage. A hierarchical storage management architecture is presented to facilitate data management. The disclosed system provides methods for evaluating the state of stored data relative to enterprise needs by using weighted parameters that may be user defined. Also disclosed are systems and methods evaluating costing and risk management associated with stored data.
Owner:COMMVAULT SYST INC
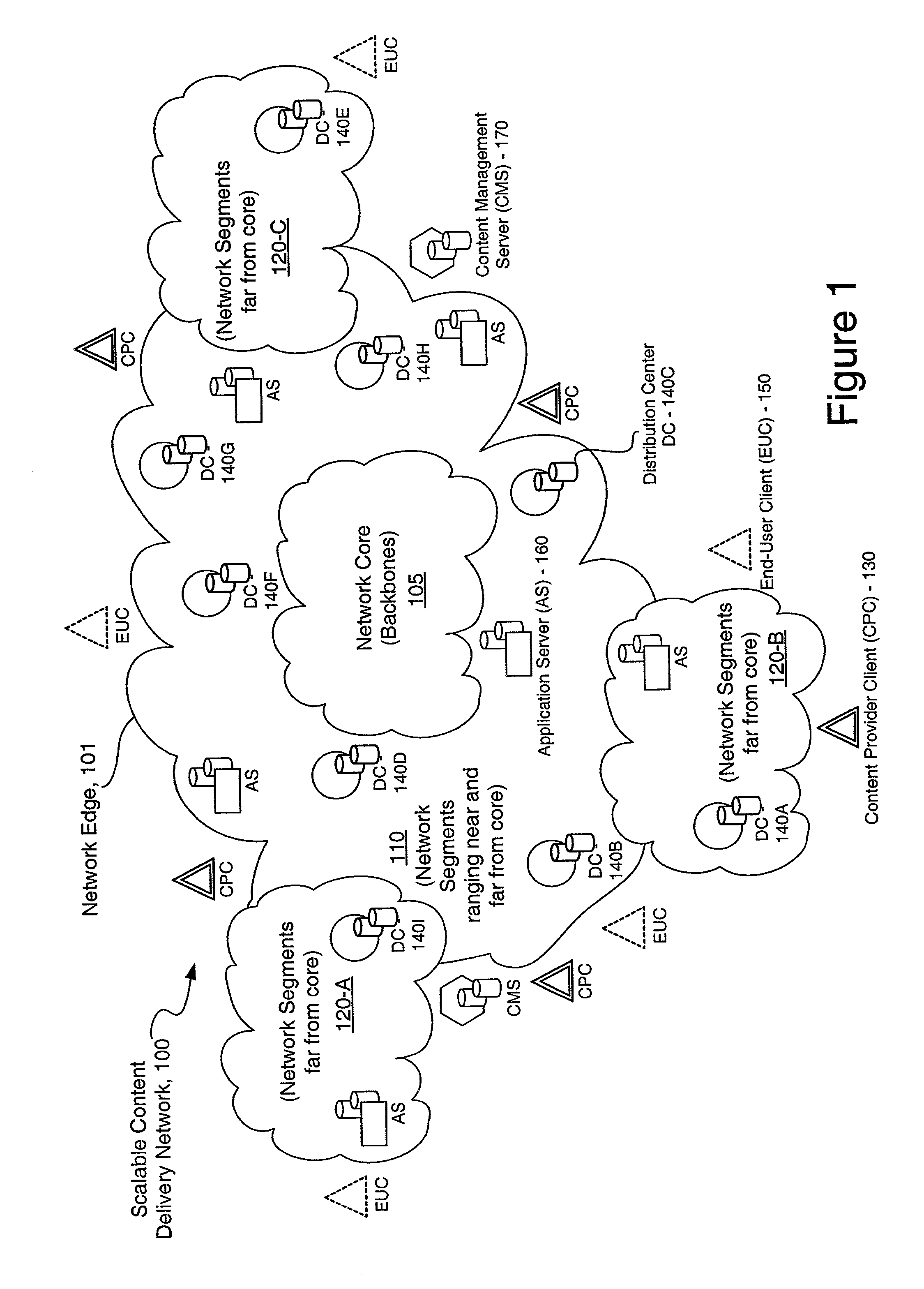
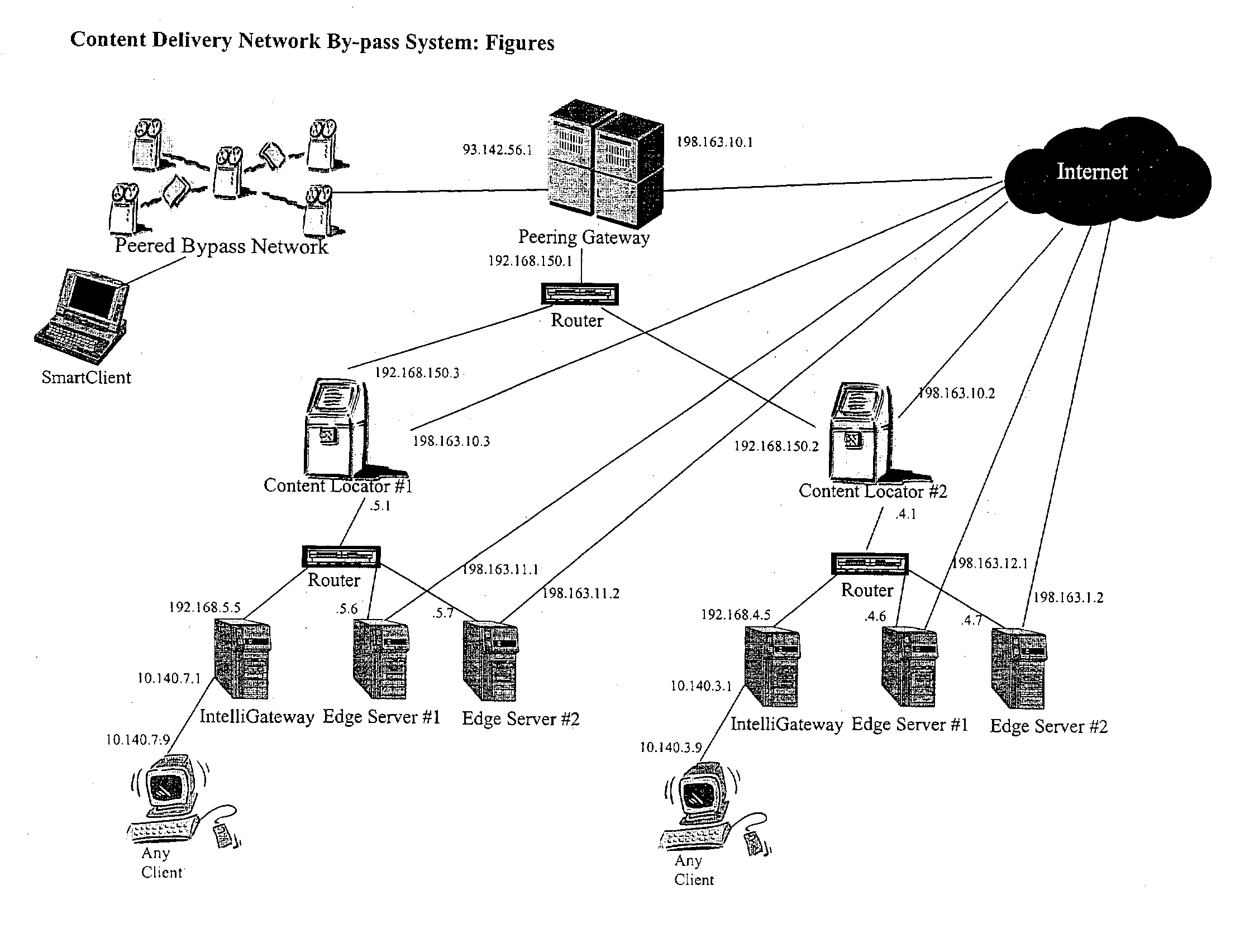
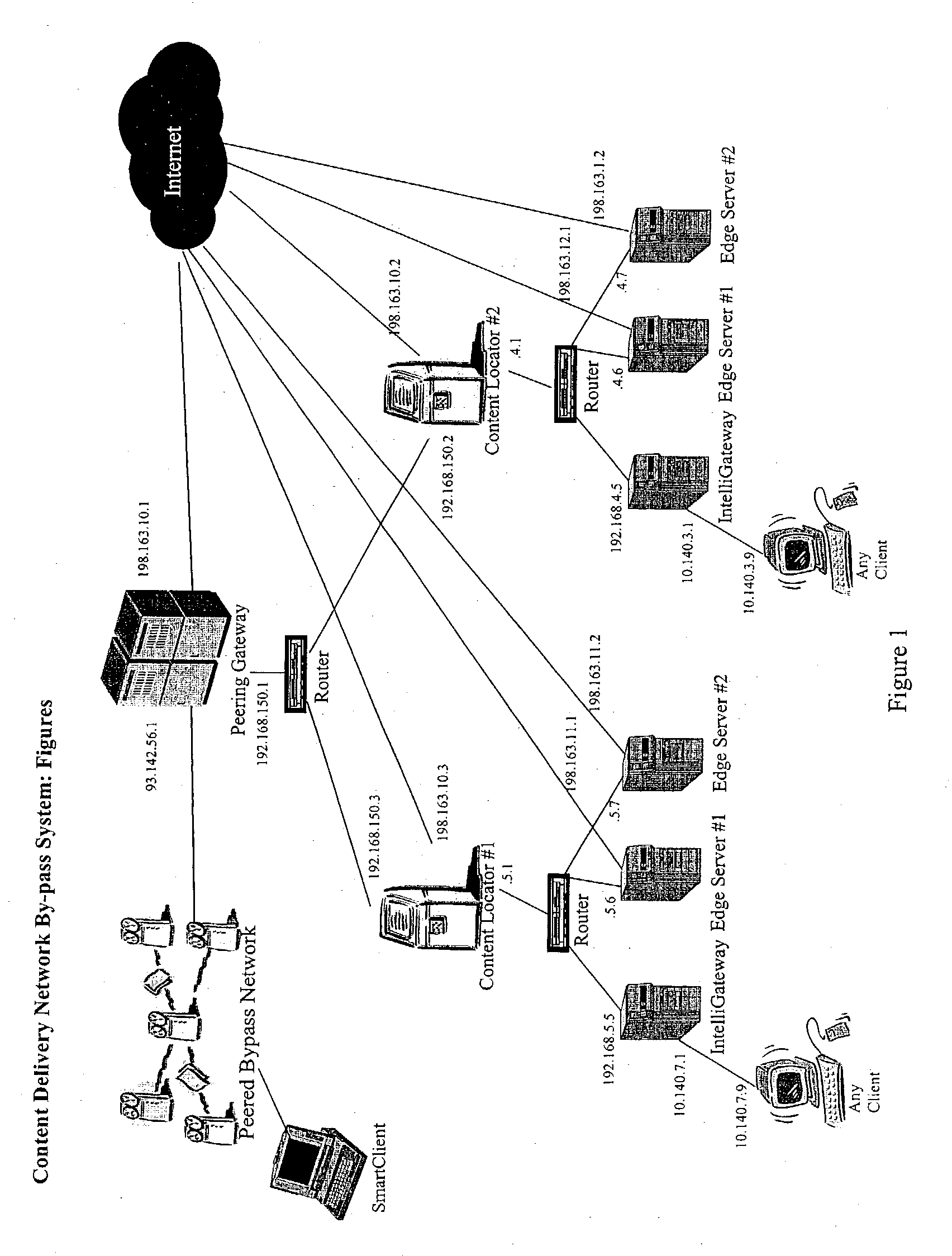
Content delivery network by-pass system
InactiveUS20030174648A1Increase capacityIncrease in sizeError preventionTransmission systemsWeb sitePeering
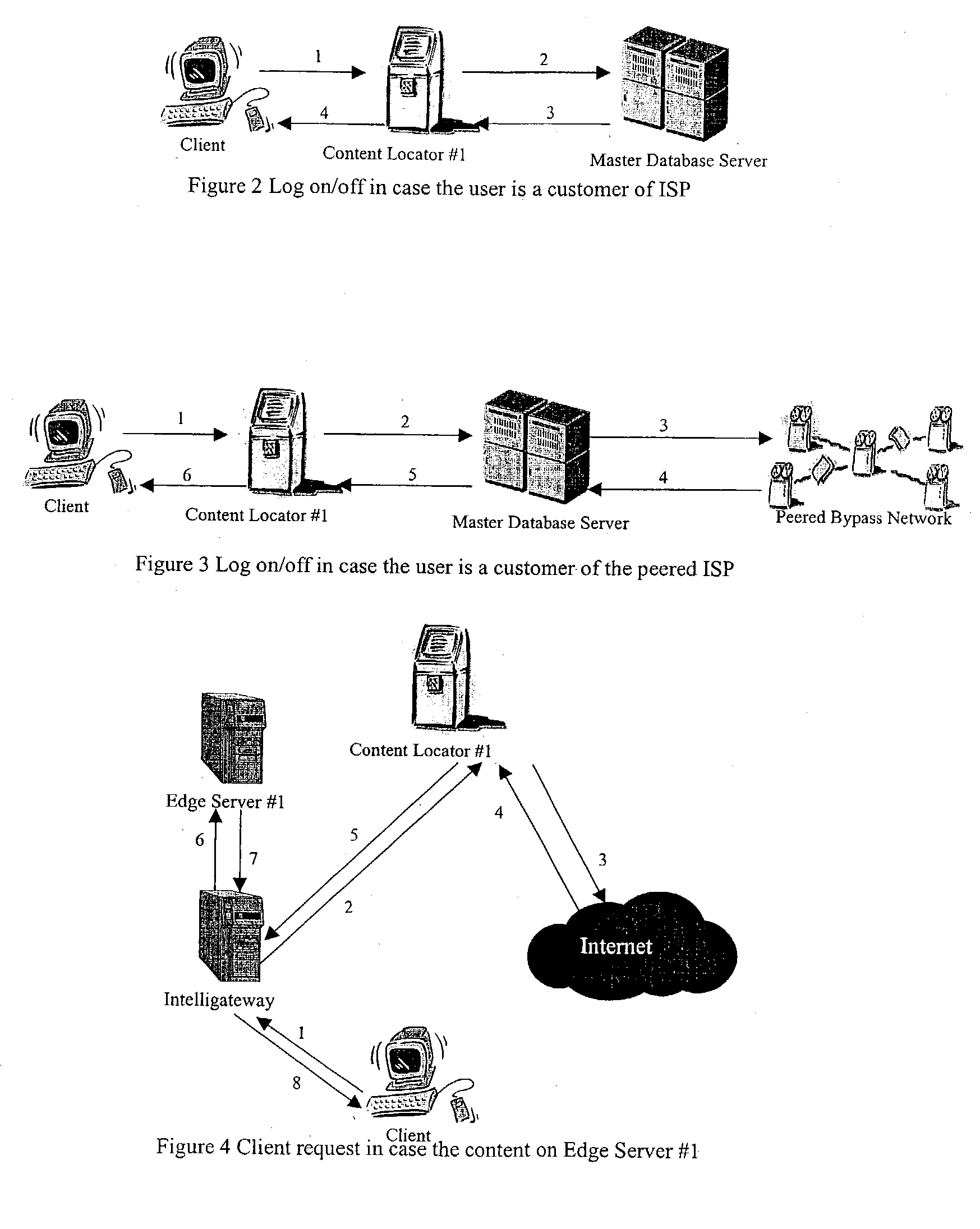
The bypass network is designed to provide fast access and high quality streaming media services anywhere anytime. There are five major components including Peering Gateway, Content Locator, Edge Server, Gateway and Client. The whole bypass network is divided into number of self-managed sub-networks, which are referred as local networks in this document. Each local network contains Edge Servers, gateways, and a Content Locator. The Edge Servers serve as cache storage and streaming servers for the local network. The gateways provide a connection point for the client computers. Each local network is managed by a Content Locator. The Content Locator handles all client requests by communicating with the Peering Gateway and actual web sites, and makes the content available on local Edge Servers. The Content Locator also balances the load on each Edge Server by monitoring the workload on them. One embodiment is designed for home users whose home machine does not move around frequently. A second embodiment is designed for business users who travel around very often where the laptops would self-configure as a client of the network.
Owner:TELECOMM RES LAB
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
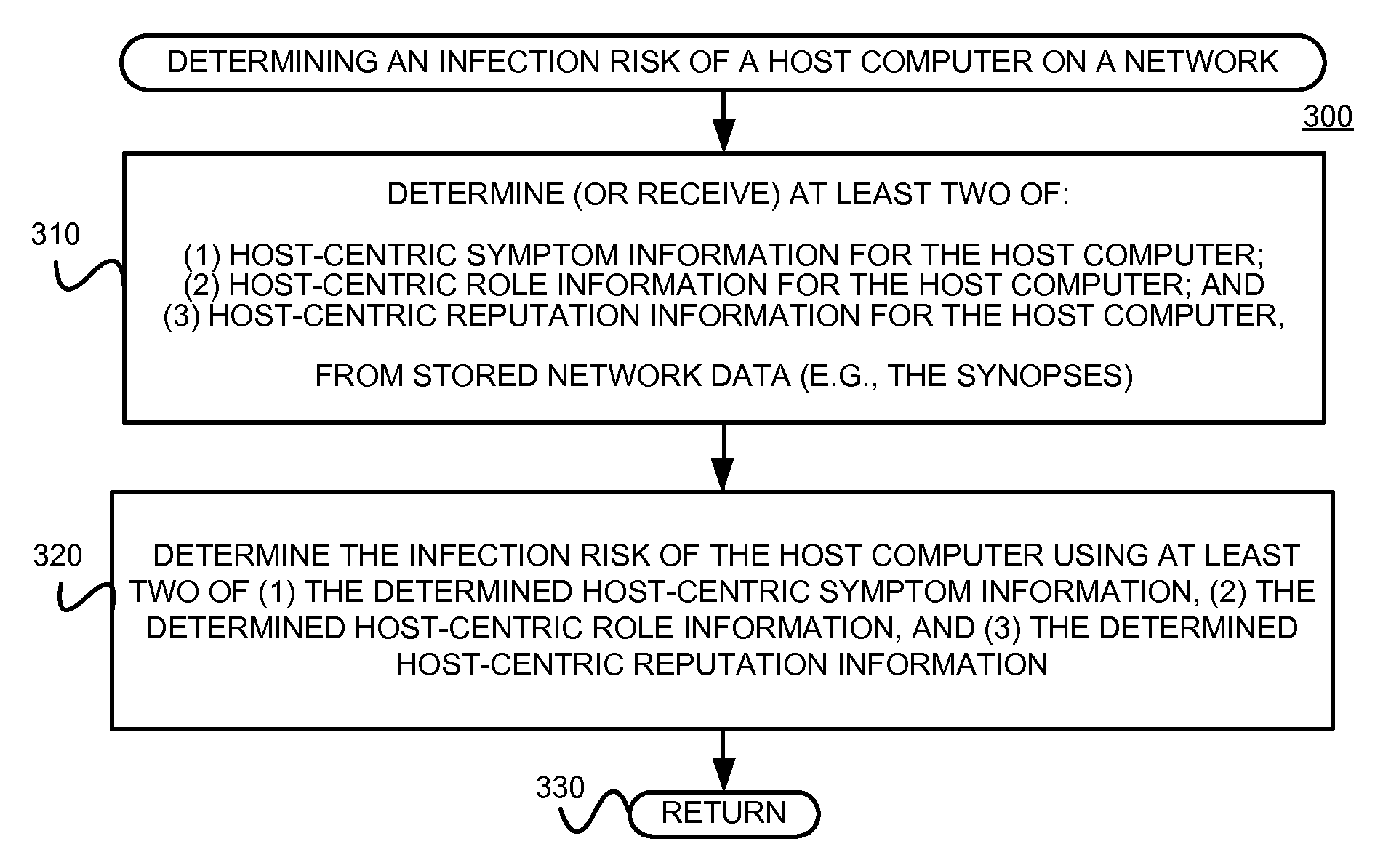
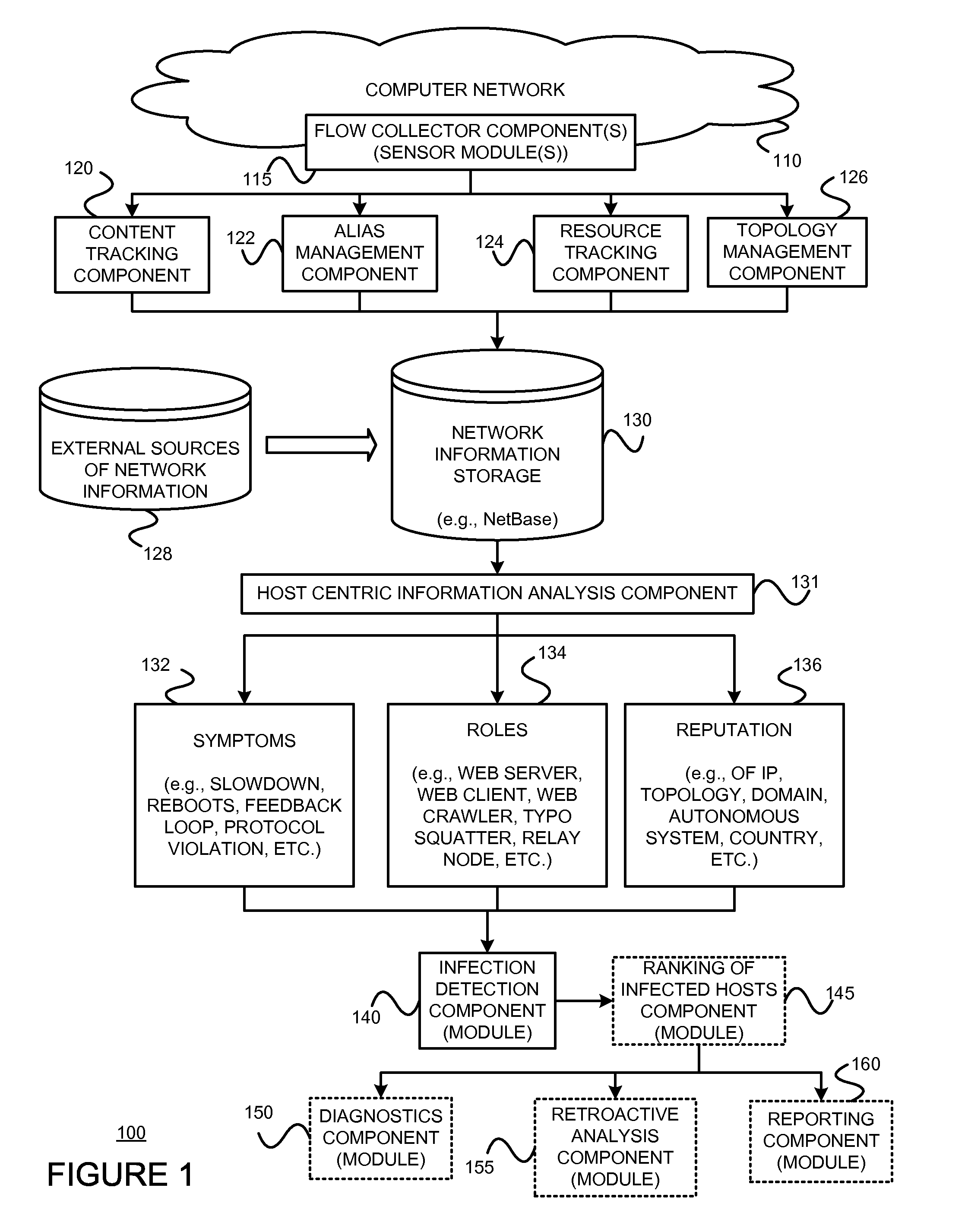
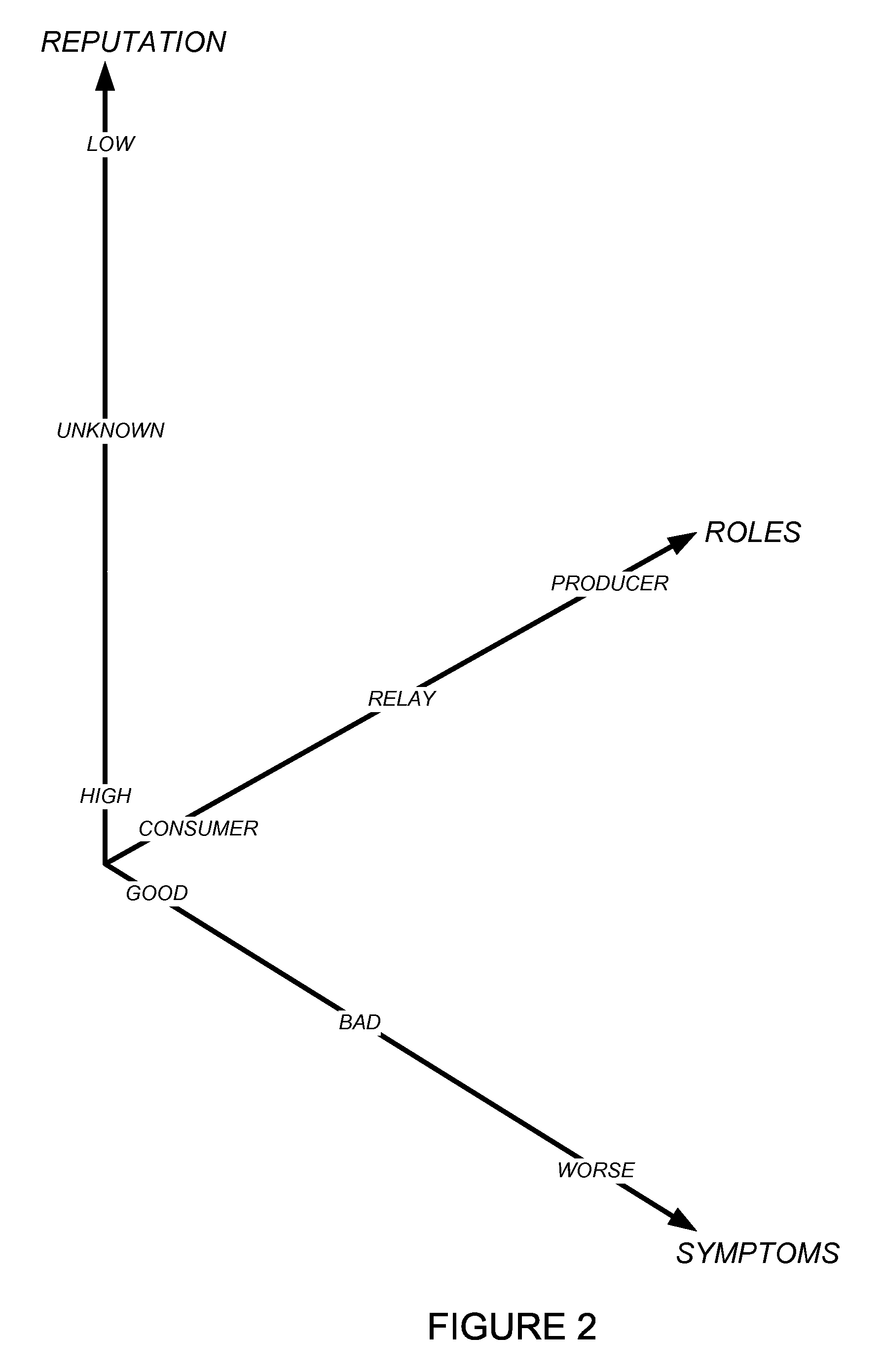
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Vehicle monitoring system
InactiveUS8140358B1FinanceRegistering/indicating working of vehiclesDriver/operatorMonitoring system
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files related to a level of risk or safety and other software that may be related to those files.
Owner:PROGRESSIVE CASUALTY INSURANCE
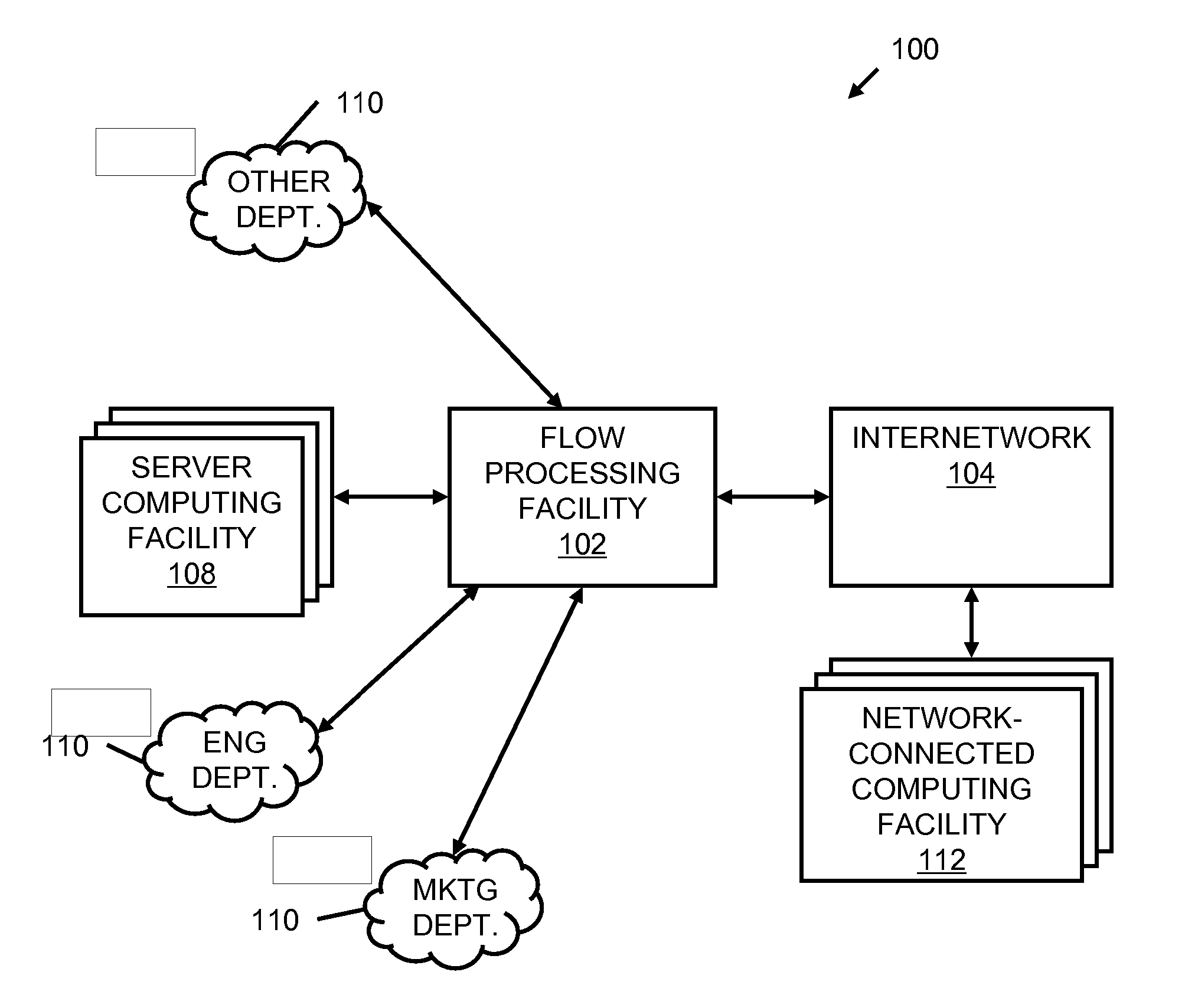
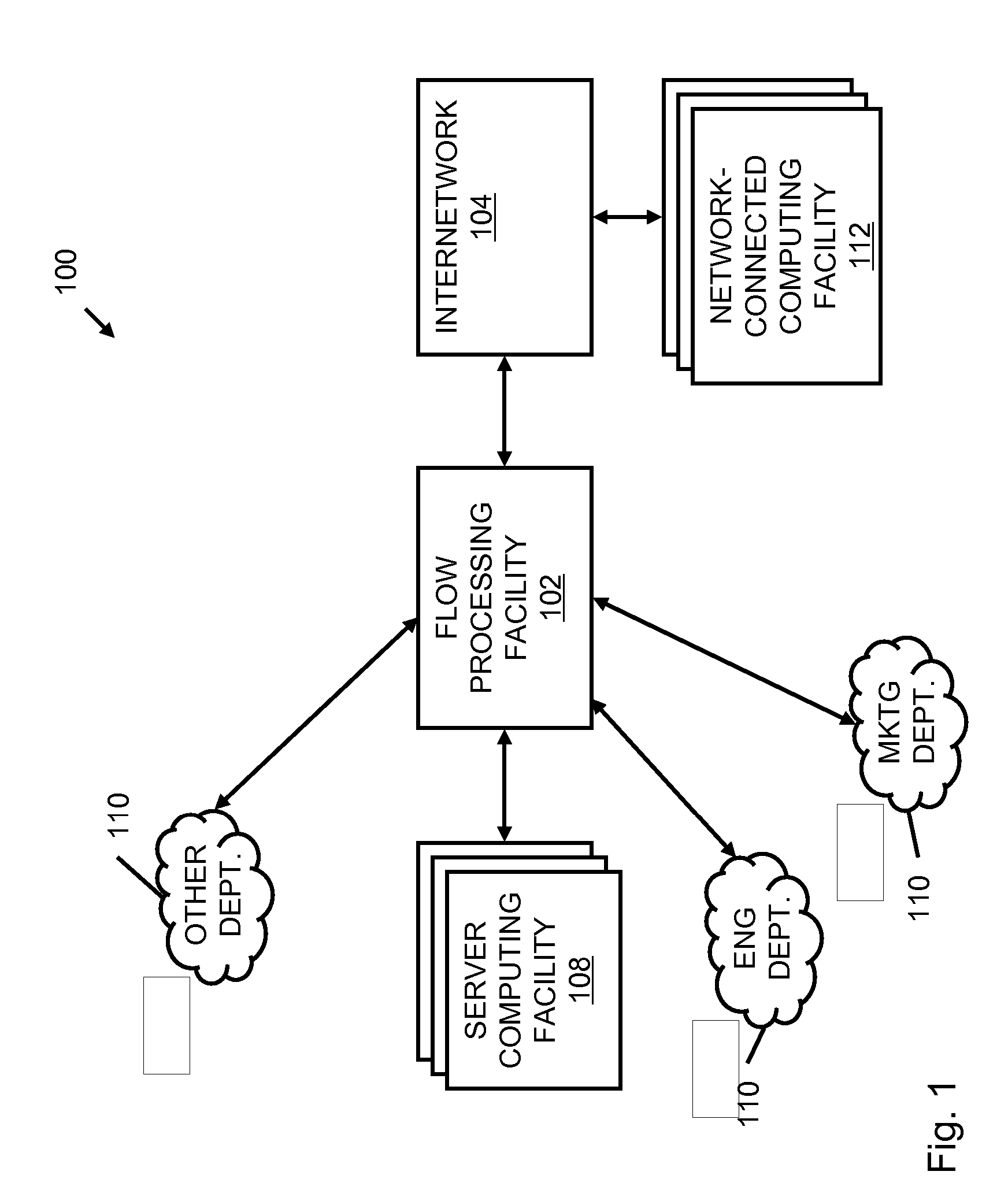
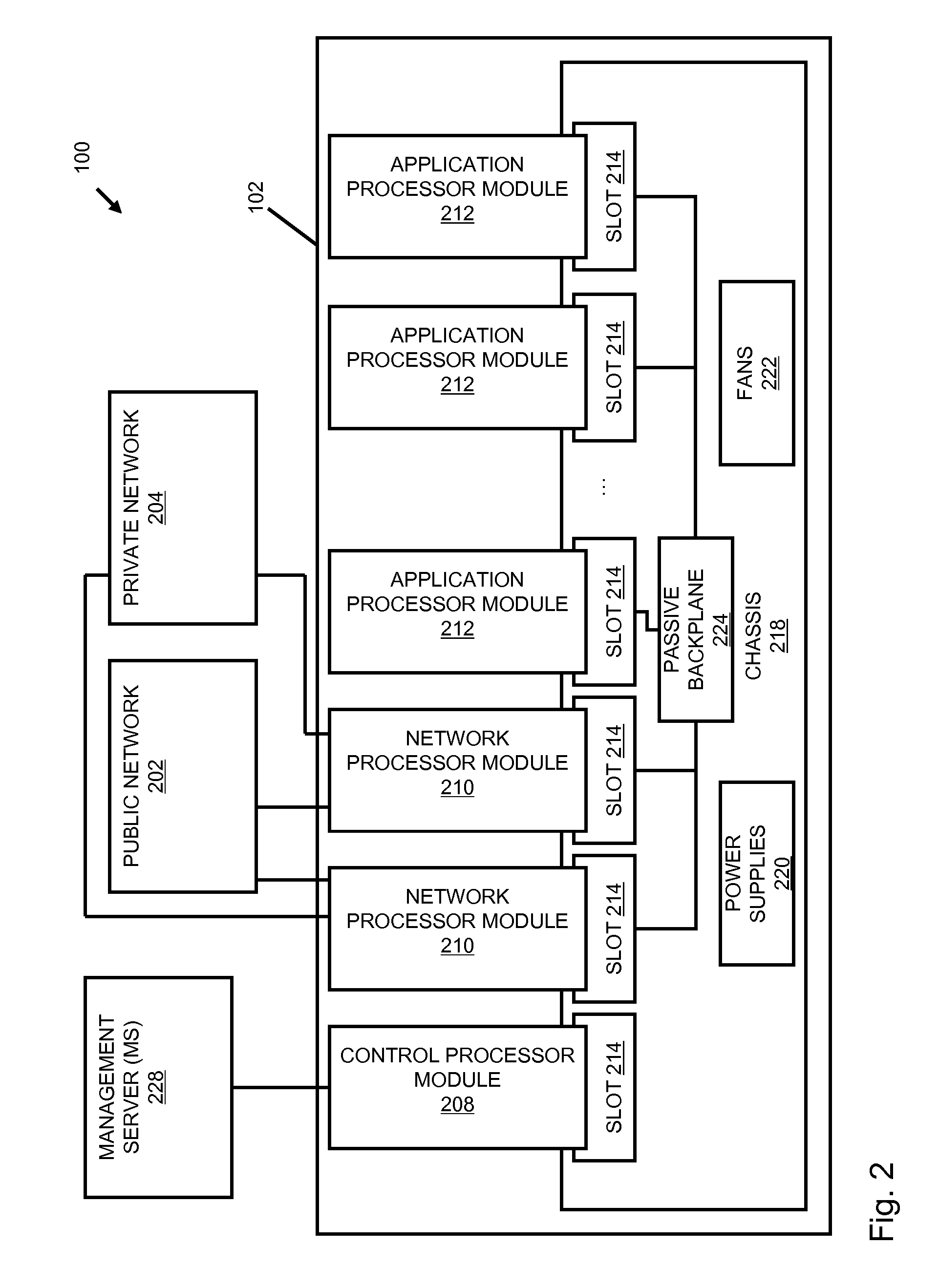
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
Systems and methods using cryptography to protect secure computing environments
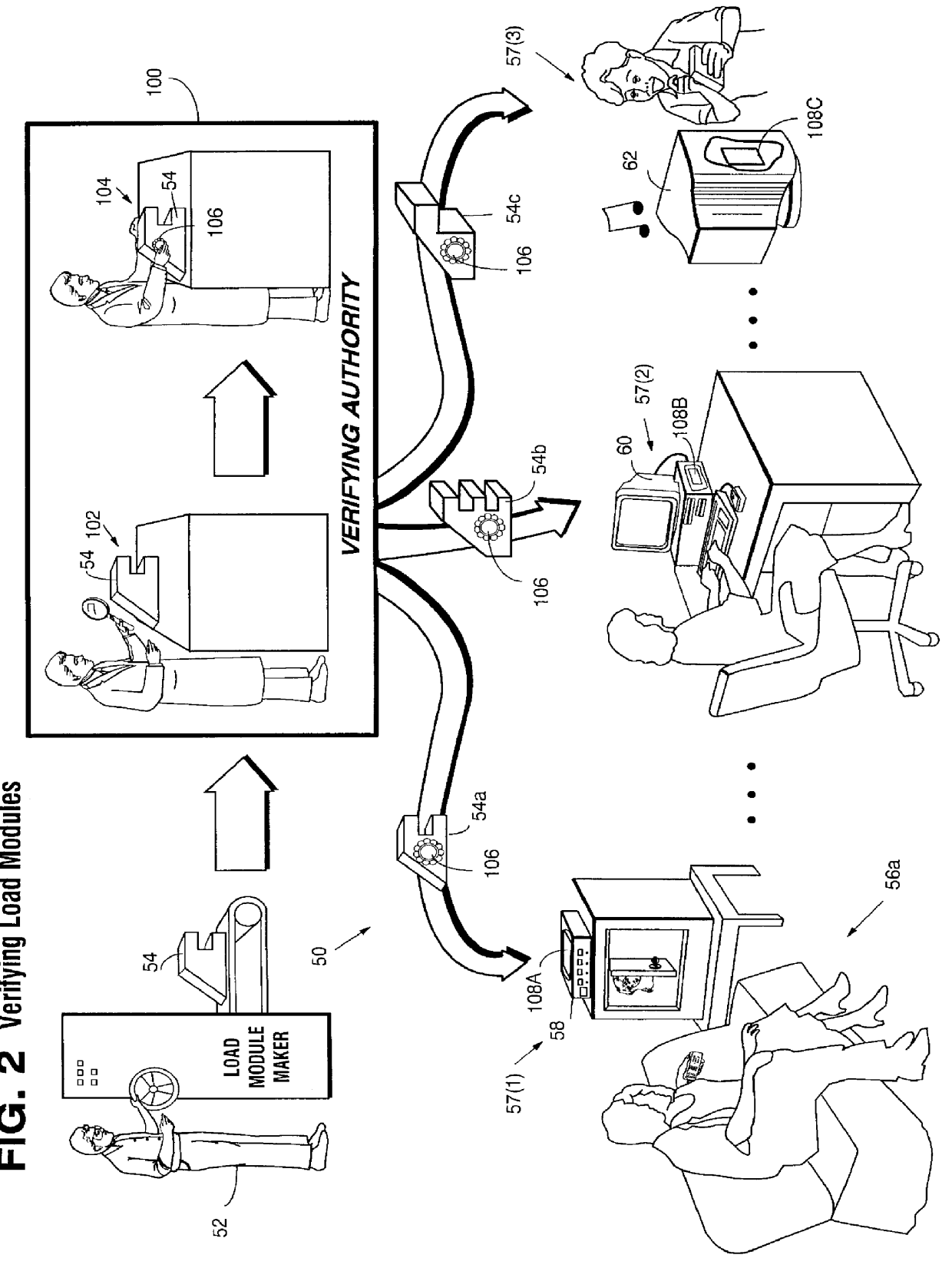
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
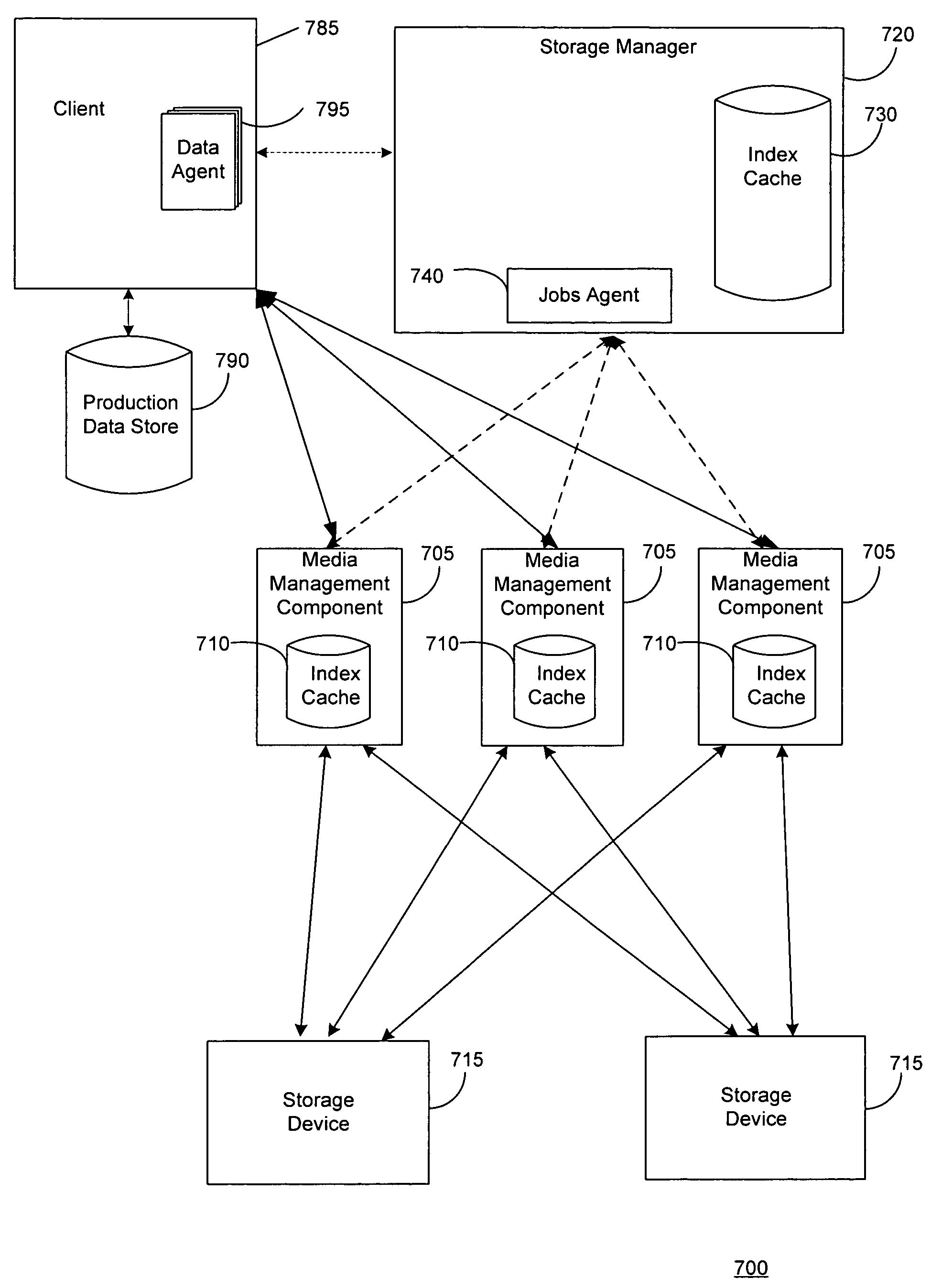
System and method for performing auxiliary storage operations
Systems and methods for protecting data in a tiered storage system are provided. The storage system comprises a management server, a media management component connected to the management server, a plurality of storage media connected to the media management component, and a data source connected to the media management component. Source data is copied from a source to a buffer to produce intermediate data. The intermediate data is copied to both a first and second medium to produce a primary and auxiliary copy, respectively. An auxiliary copy may be made from another auxiliary copy. An auxiliary copy may also be made from a primary copy right before the primary copy is pruned.
Owner:COMMVAULT SYST INC
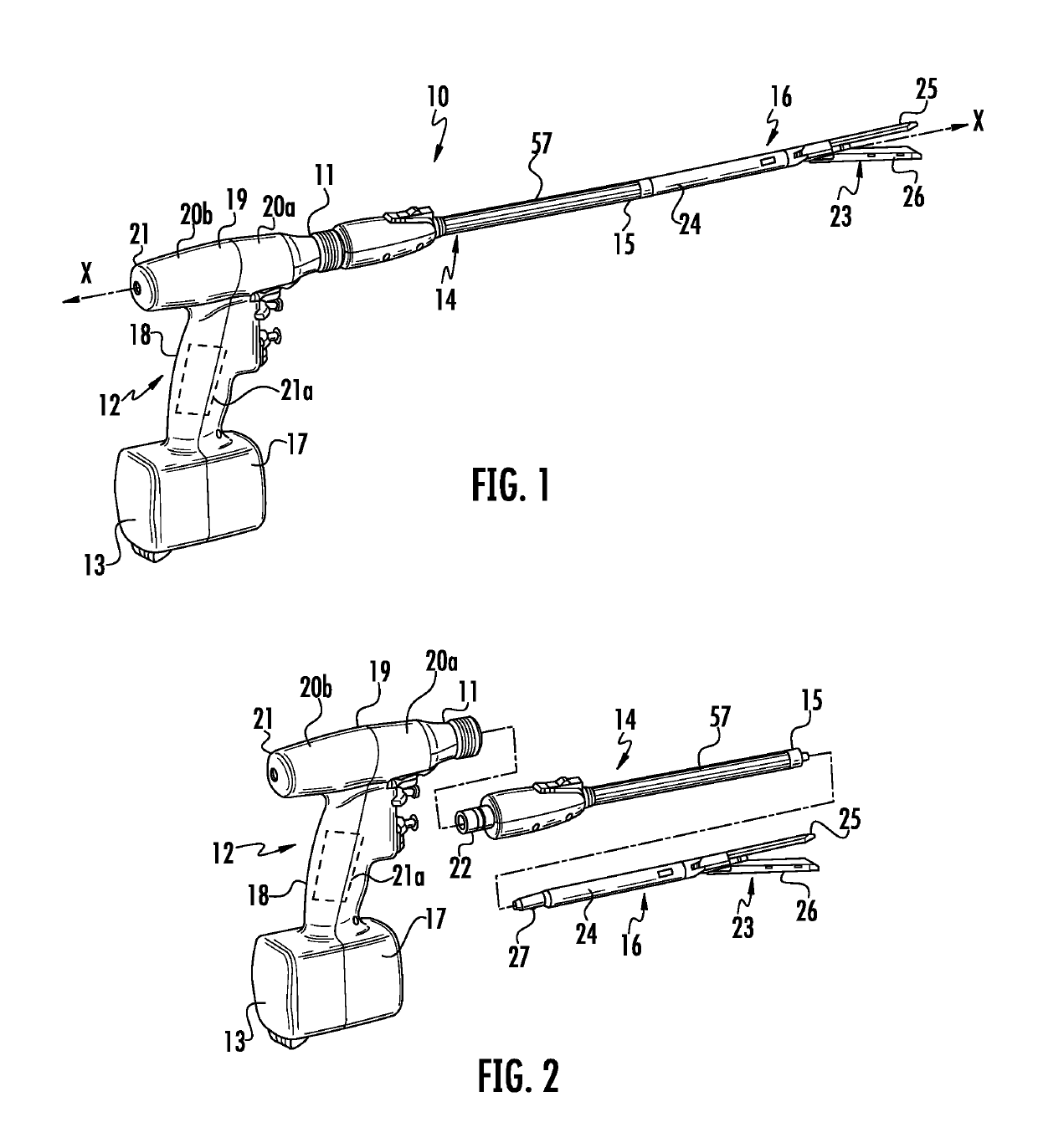
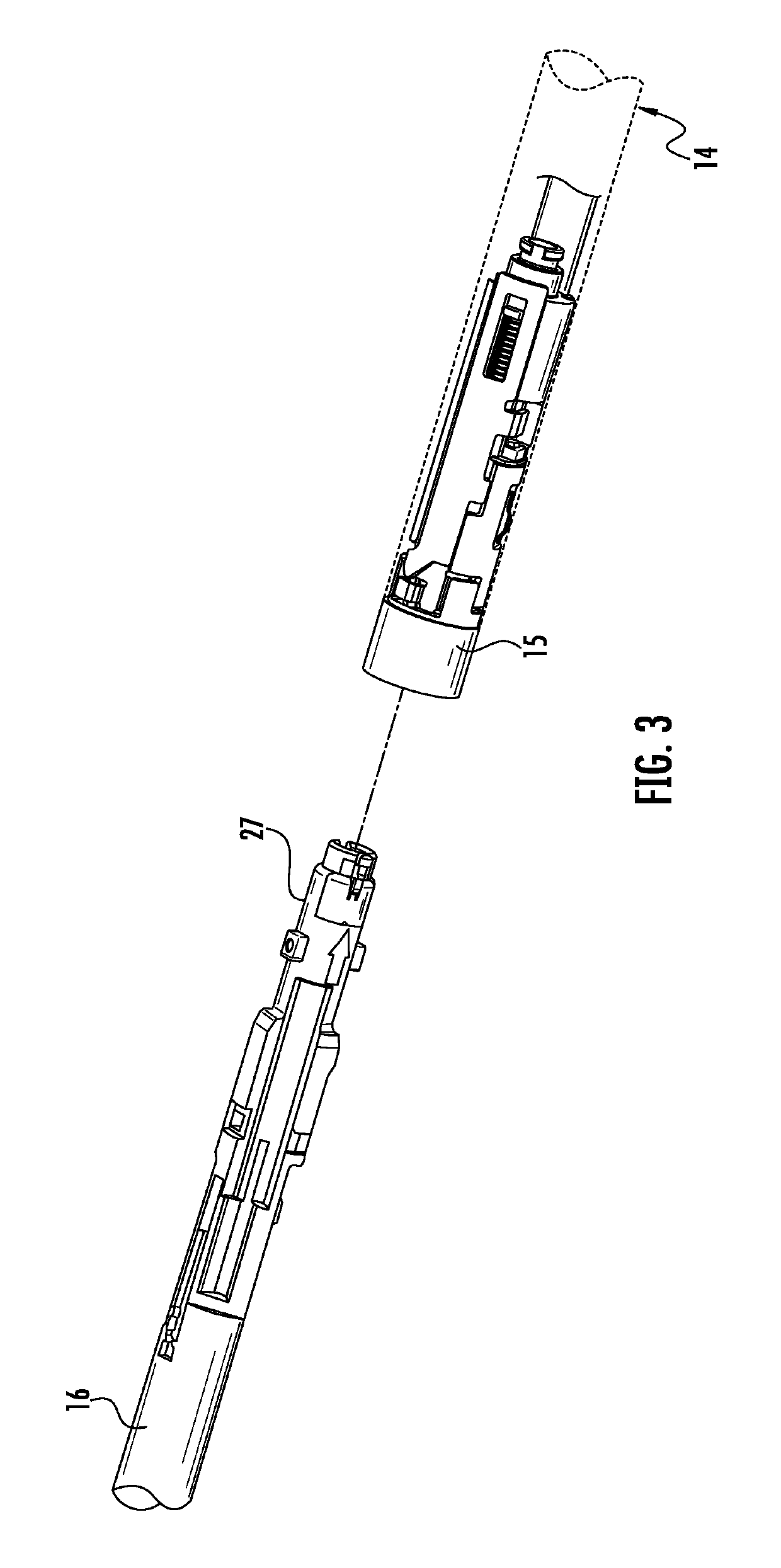
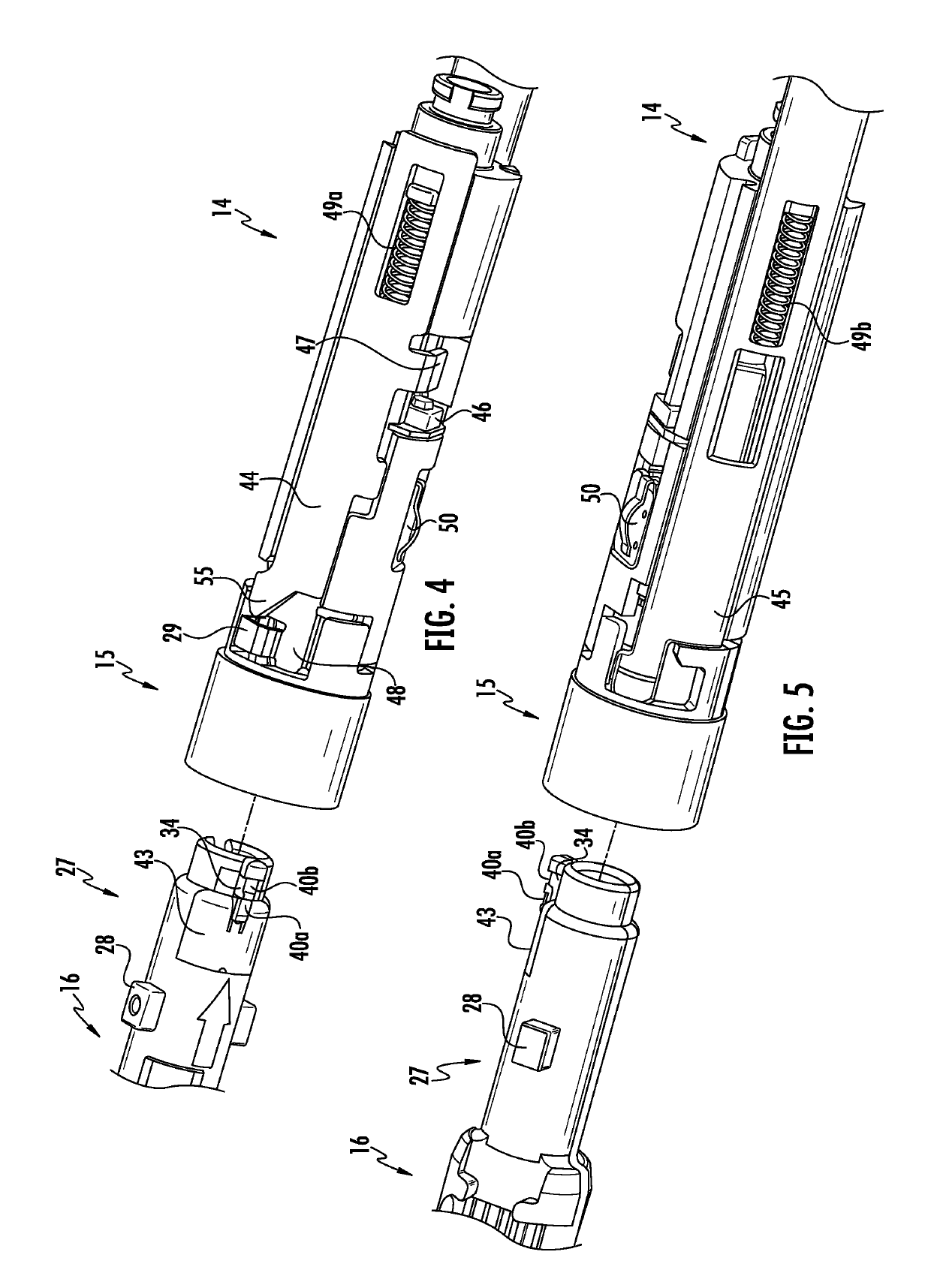
Authentication and information system for reusable surgical instruments
An authentication and information system for use in a surgical stapling device includes a handle assembly having a controller, the controller having at least one program and a memory, an adapter assembly, and a loading unit having a tool assembly mounted for articulation and a member for actuating articulation of the tool assembly, the loading unit having at least one chip assembly having a chip storing data indicating a position of the member when the tool assembly is in a fully articulated position.
Owner:TYCO HEALTHCARE GRP LP
System and method to support simulated storage operations
ActiveUS7536291B1Error detection/correctionMultiple digital computer combinationsOperating systemSimulated data
The present invention includes a system for simulating the performing of data storage operations. The system may include a storage manager component, at least one media management component directed by the storage manager component to manage storage operations to at least one storage device, and a storage emulation module adapted to simulate the characteristics of the at least one storage device. Under the direction of the storage manager, the emulation module may be adapted to simulate storage operations to one or more storage devices performed by one or more of the media management components.
Owner:COMMVAULT SYST INC
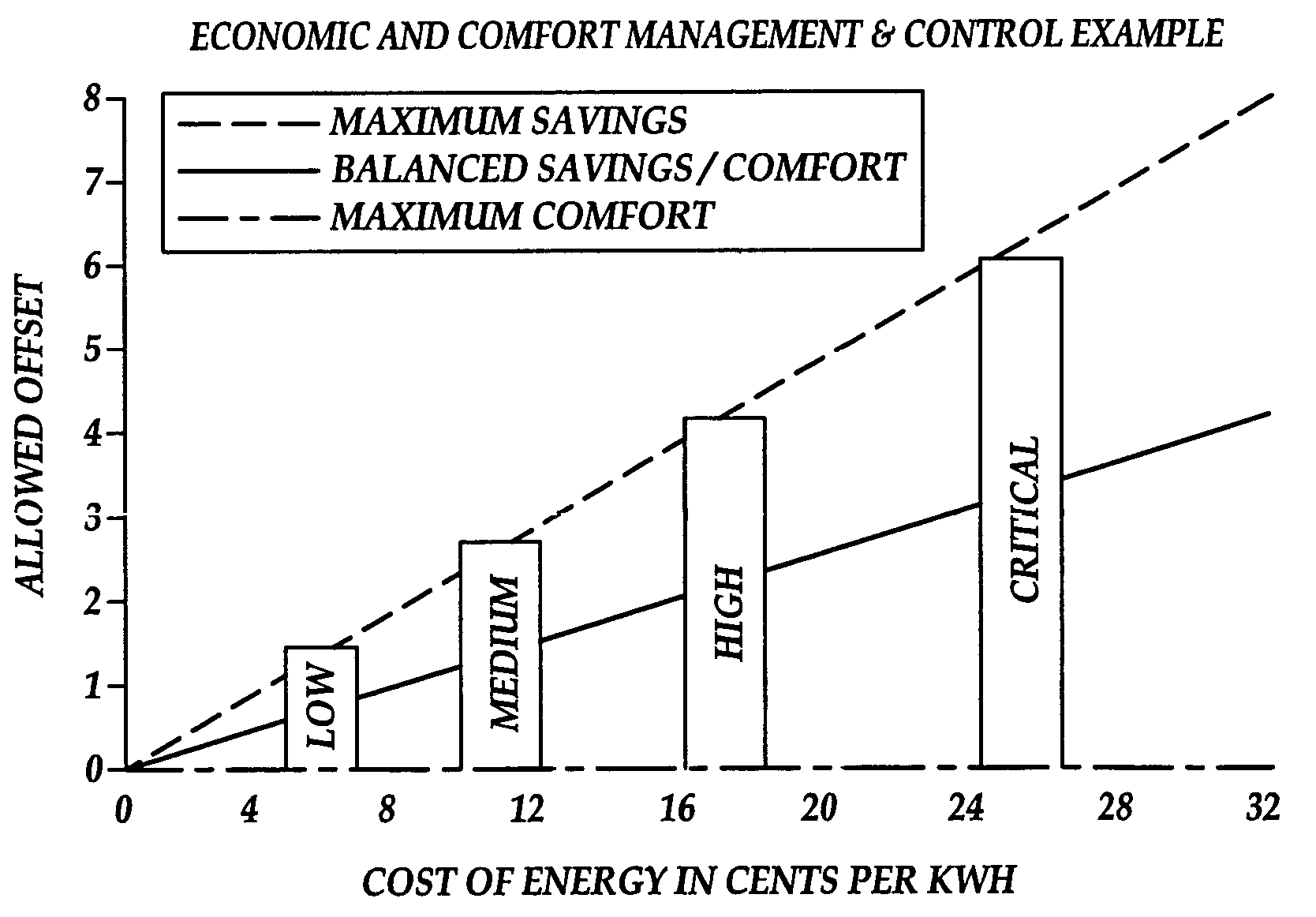
System and method of controlling an HVAC system
A system and method manage delivery of energy from a distribution network to one or more sites. Each site has at least one device coupled to the distribution network. The at least one device controllably consumes energy. The system includes a node and a control system. The node is coupled to the at least one device for sensing and controlling energy delivered to the device. A control system is coupled to the node and distribution network for delivery to the node at least one characteristic of the distribution network. The node controls the supply of energy to the device as a function of the at least one characteristic.
Owner:INVENSYS SYST INC
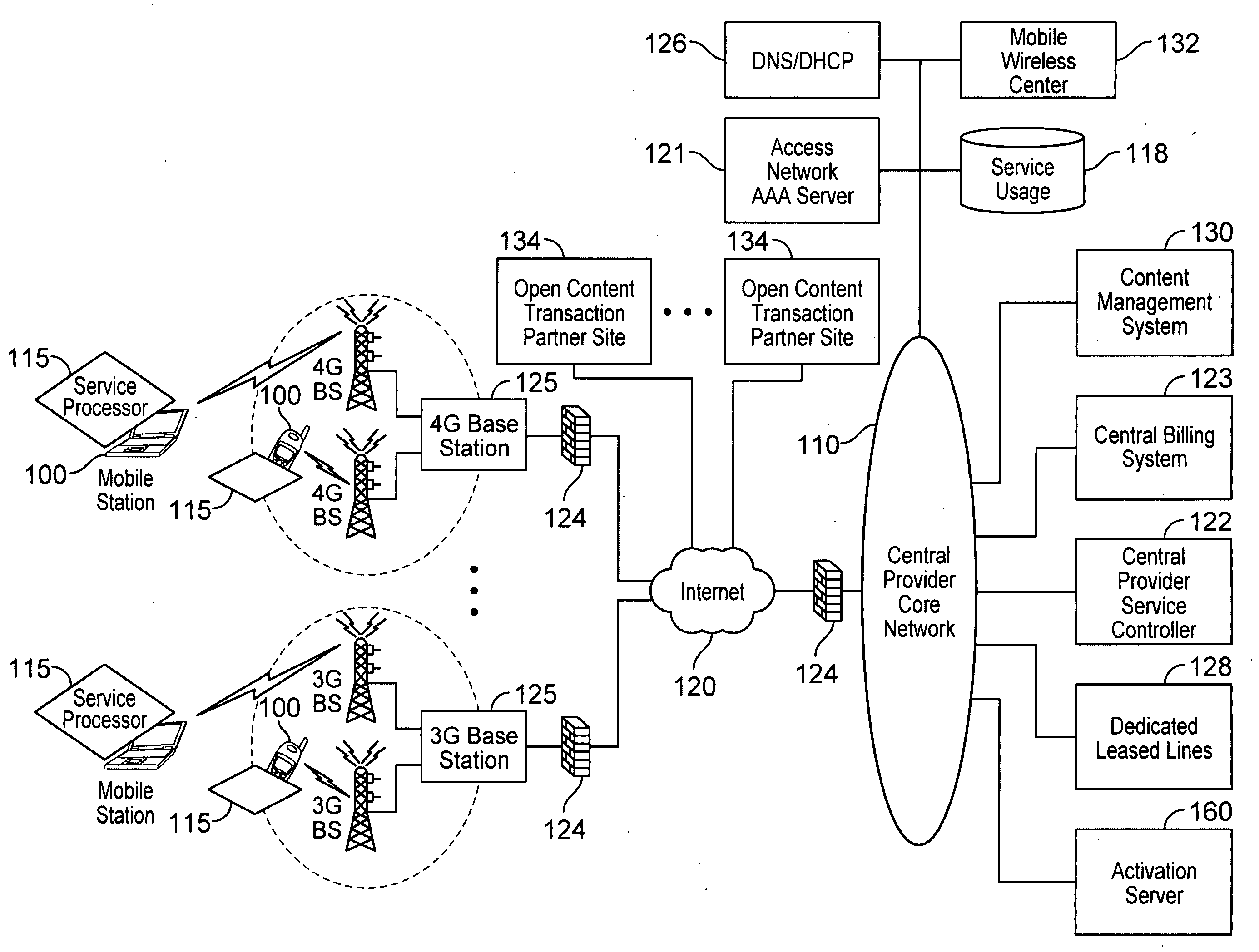
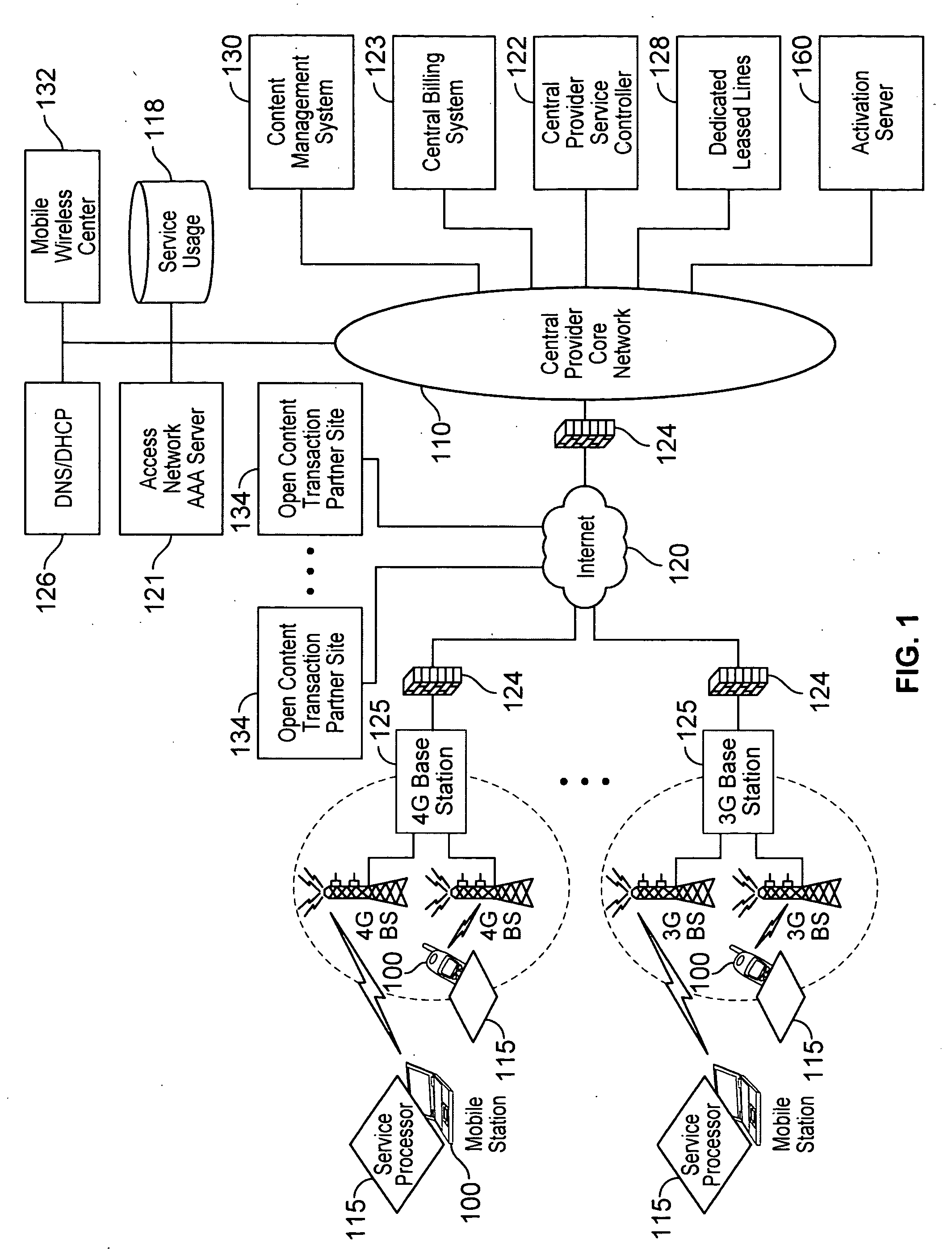
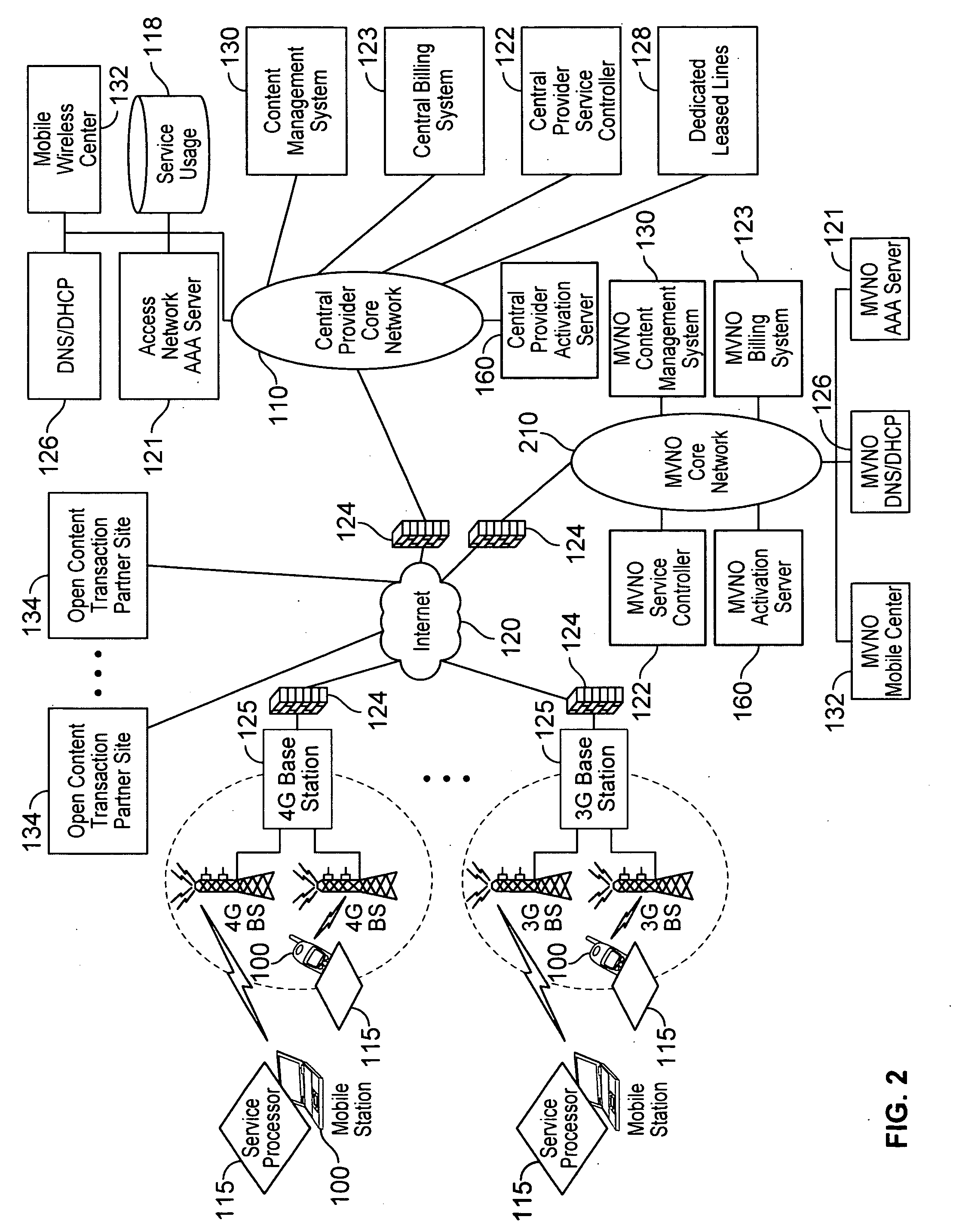
Verifiable device assisted service policy implementation
ActiveUS20100188975A1Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which the implementation of the service policy is verified.
Owner:HEADWATER RES LLC
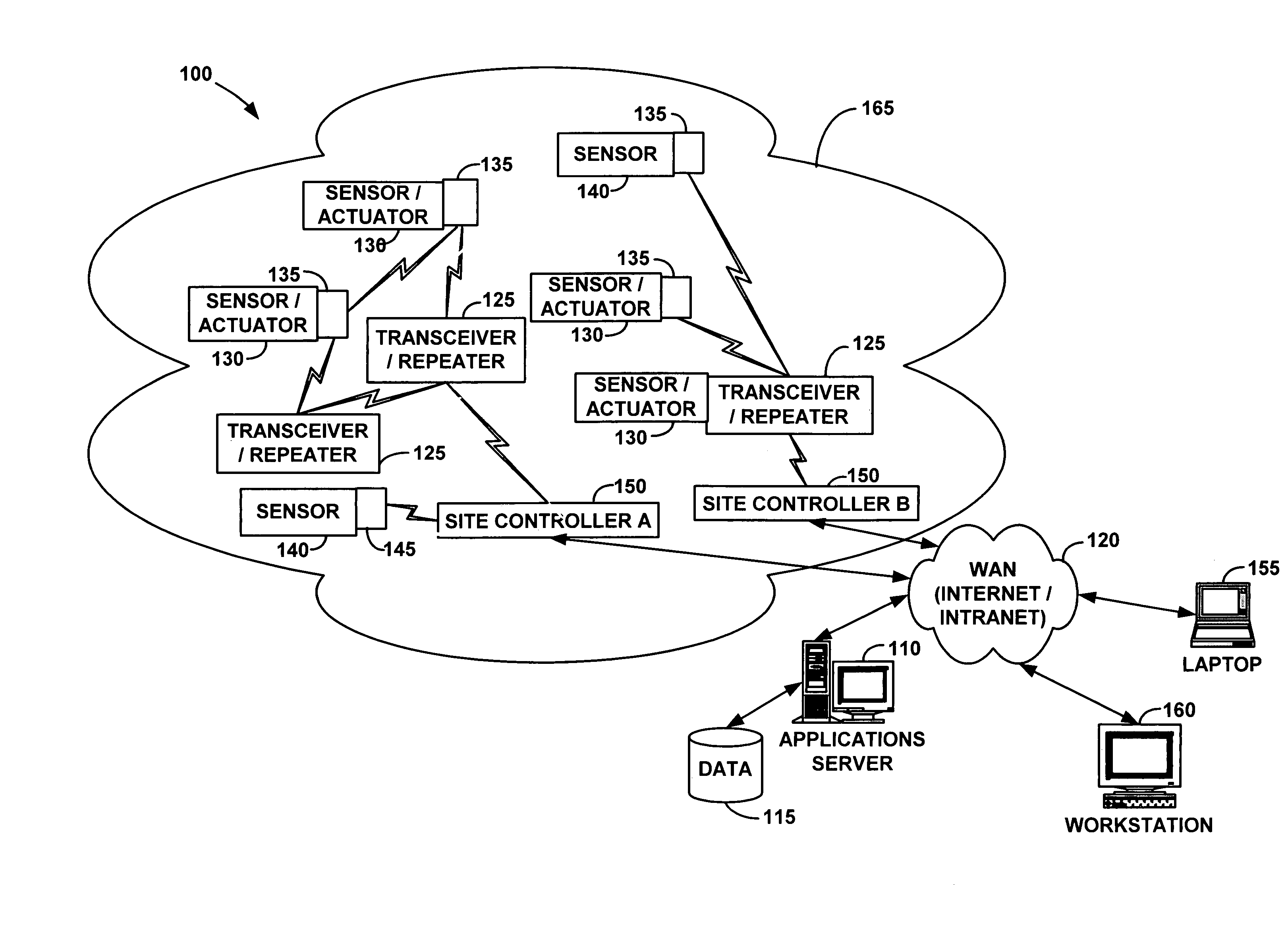
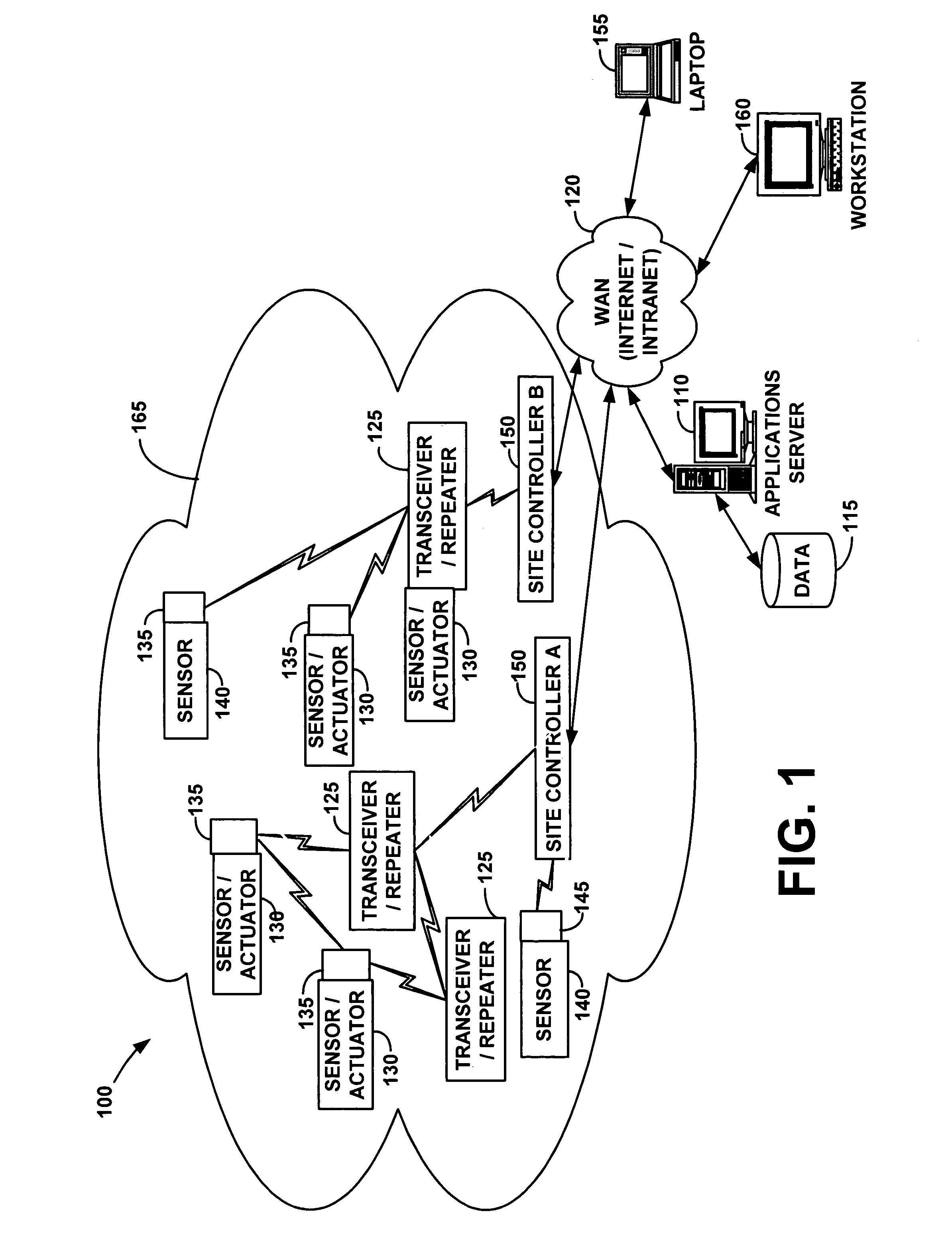
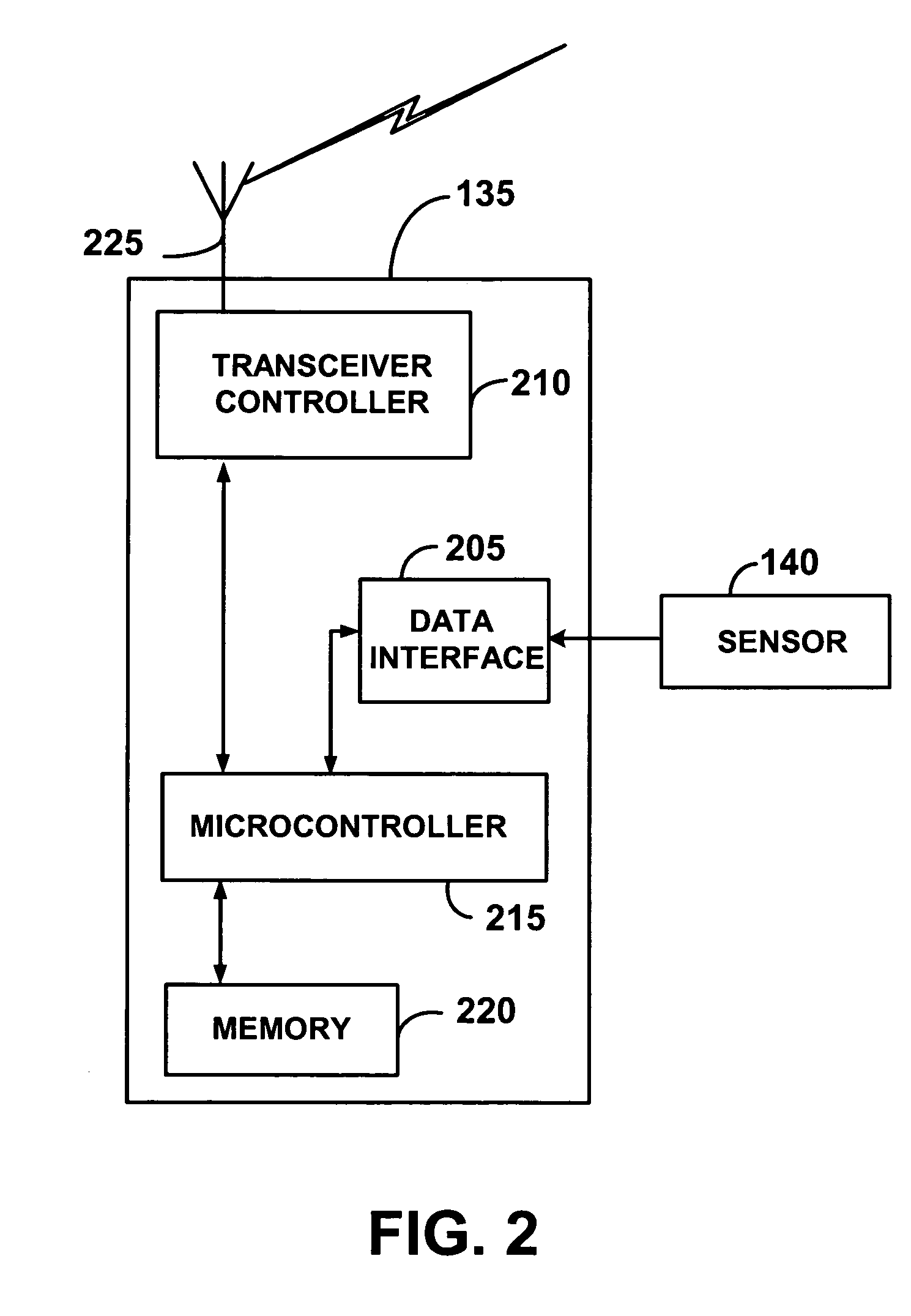
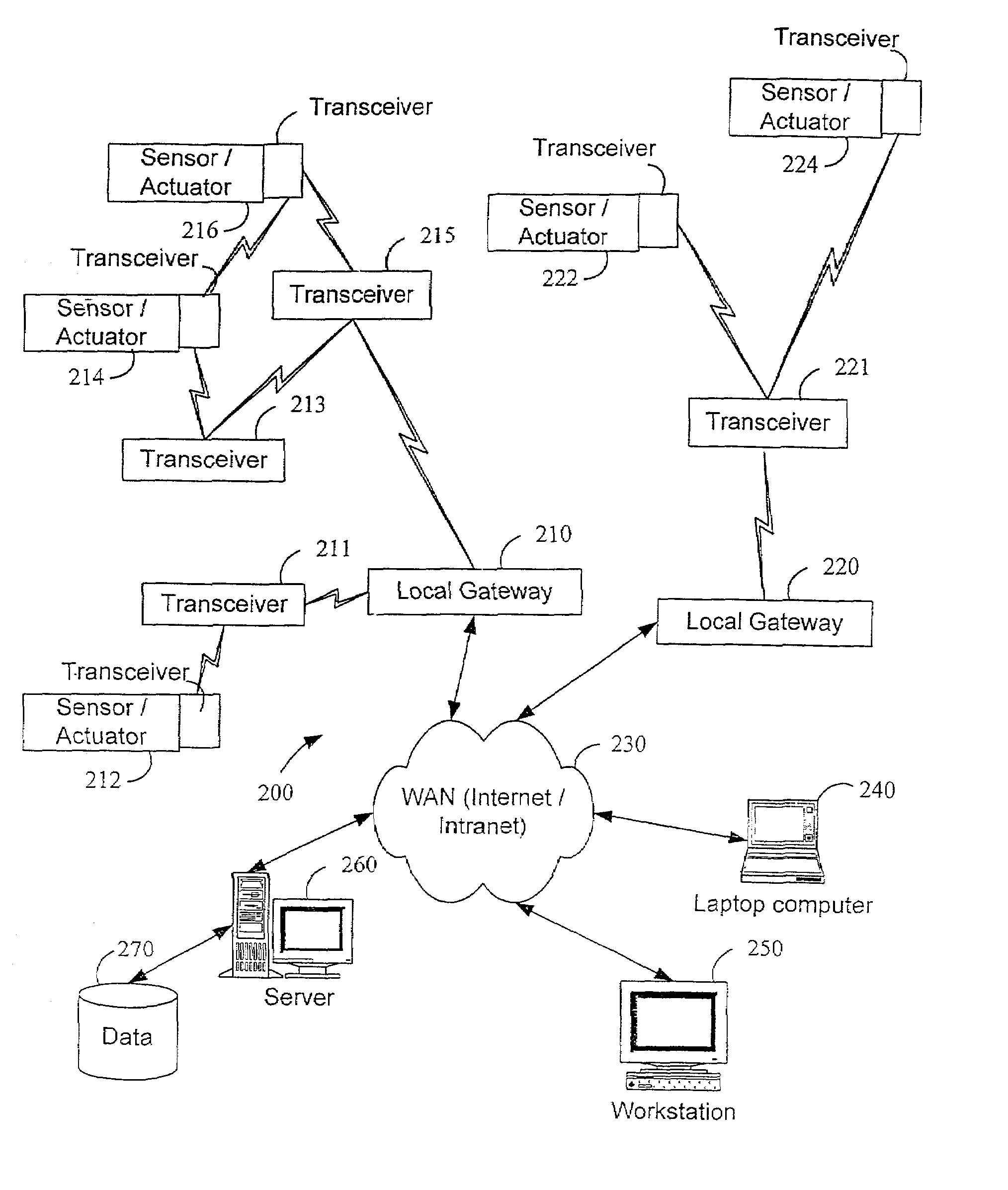
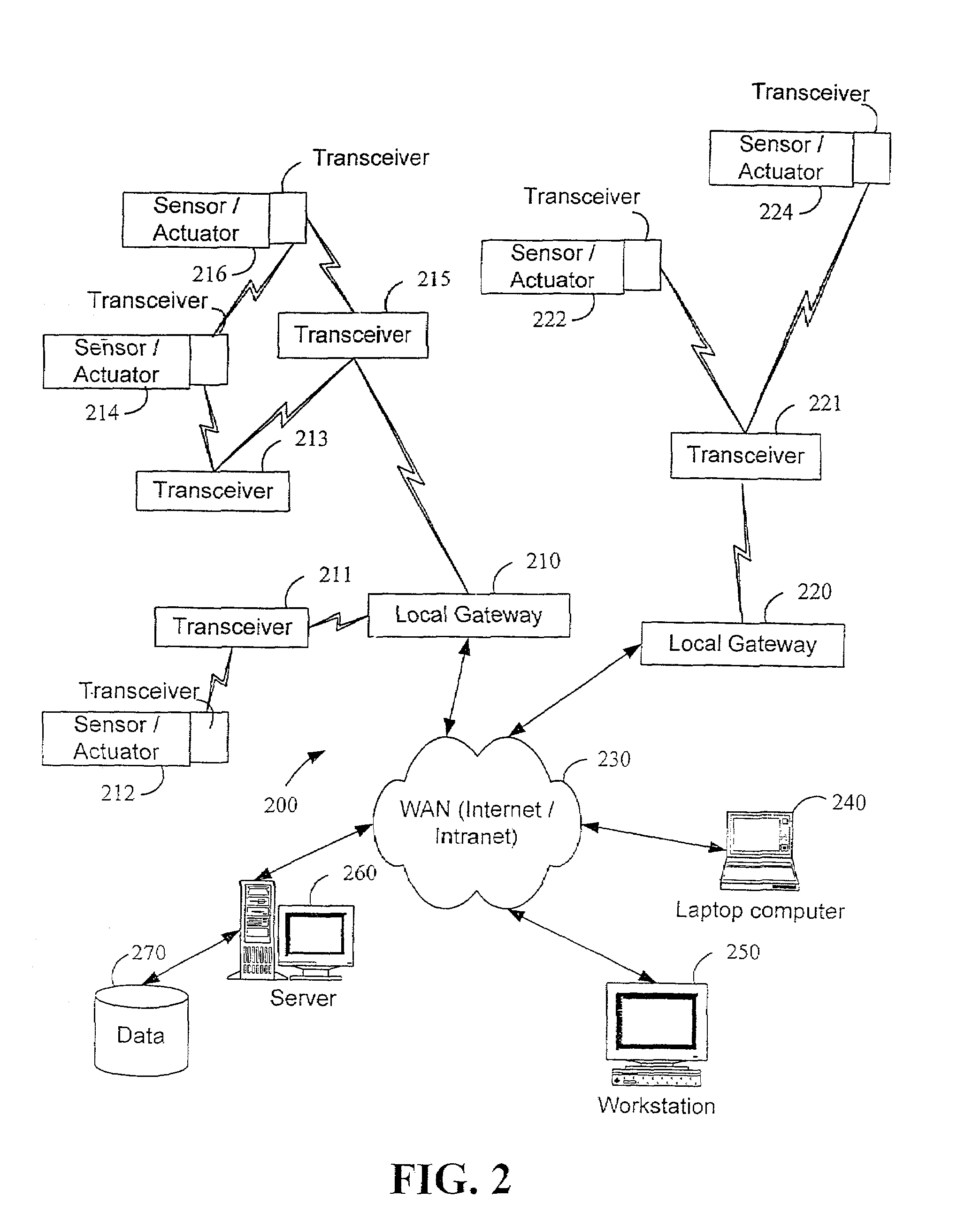
Wireless communication networks for providing remote monitoring of devices
InactiveUS7103511B2Cost-effectiveElectric signal transmission systemsError detection/correctionWireless communication protocolTransceiver
Wireless communication networks for monitoring and controlling a plurality of remote devices are provided. Briefly, one embodiment of a wireless communication network may comprise a plurality of wireless transceivers having unique identifiers. Each of the plurality of wireless transceivers may be configured to receive a sensor data signal from one of the plurality of remote devices and transmit an original data message using a predefined wireless communication protocol. The original data message may comprise the corresponding unique identifier and sensor data signal. Each of the plurality of wireless transceivers may be configured to receive the original data message transmitted by one of the other wireless transceivers and transmit a repeated data message using the predefined communication protocol. The repeated data message may include the sensor data signal and the corresponding unique identifier. Furthermore, at least one of the plurality of wireless transceivers may be further configured to provide the original data messages and the repeated data messages to a site controller connected to a wide area network. The site controller may be configured to manage communications between the wireless communication network and a host computer connected to the wide area network.
Owner:SIPCO
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
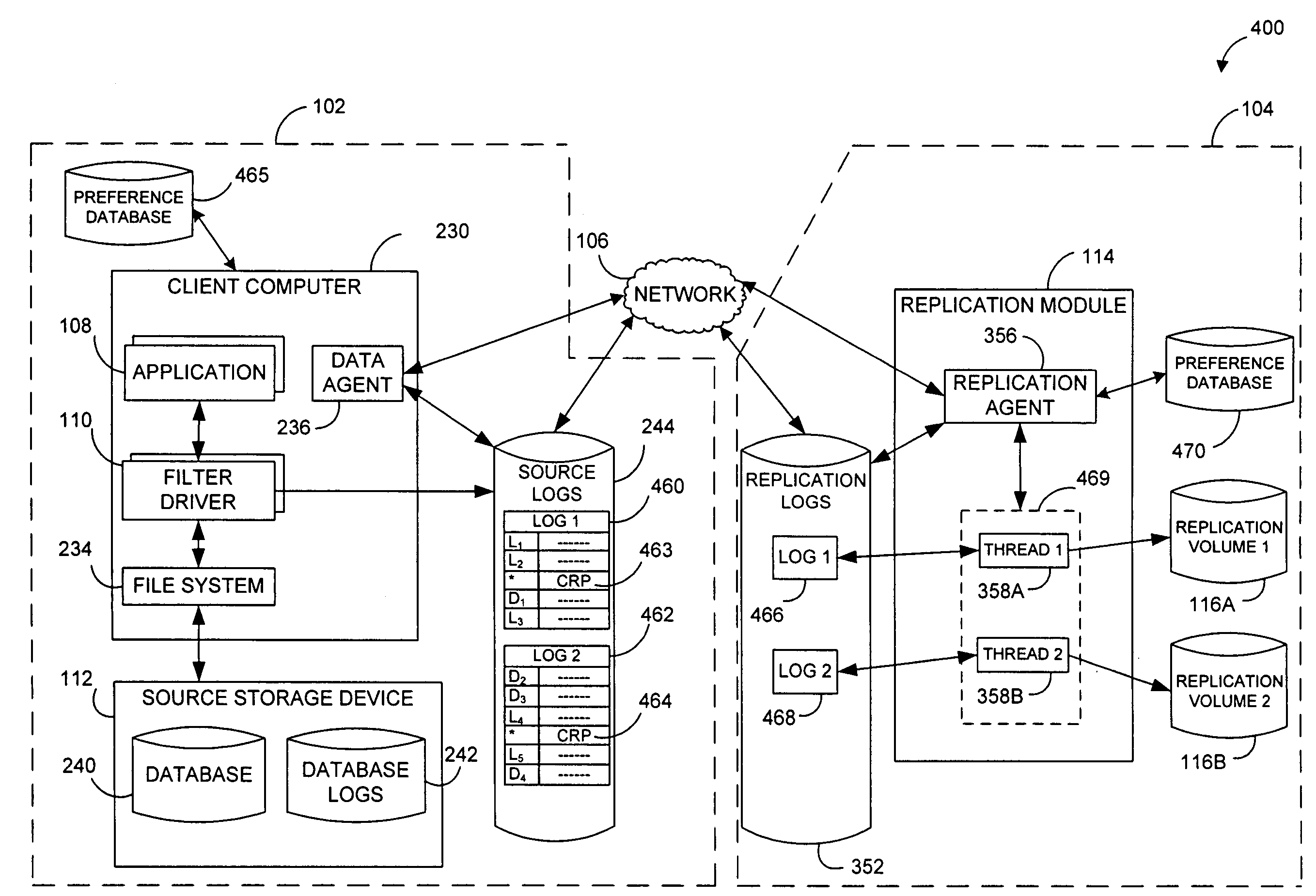
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
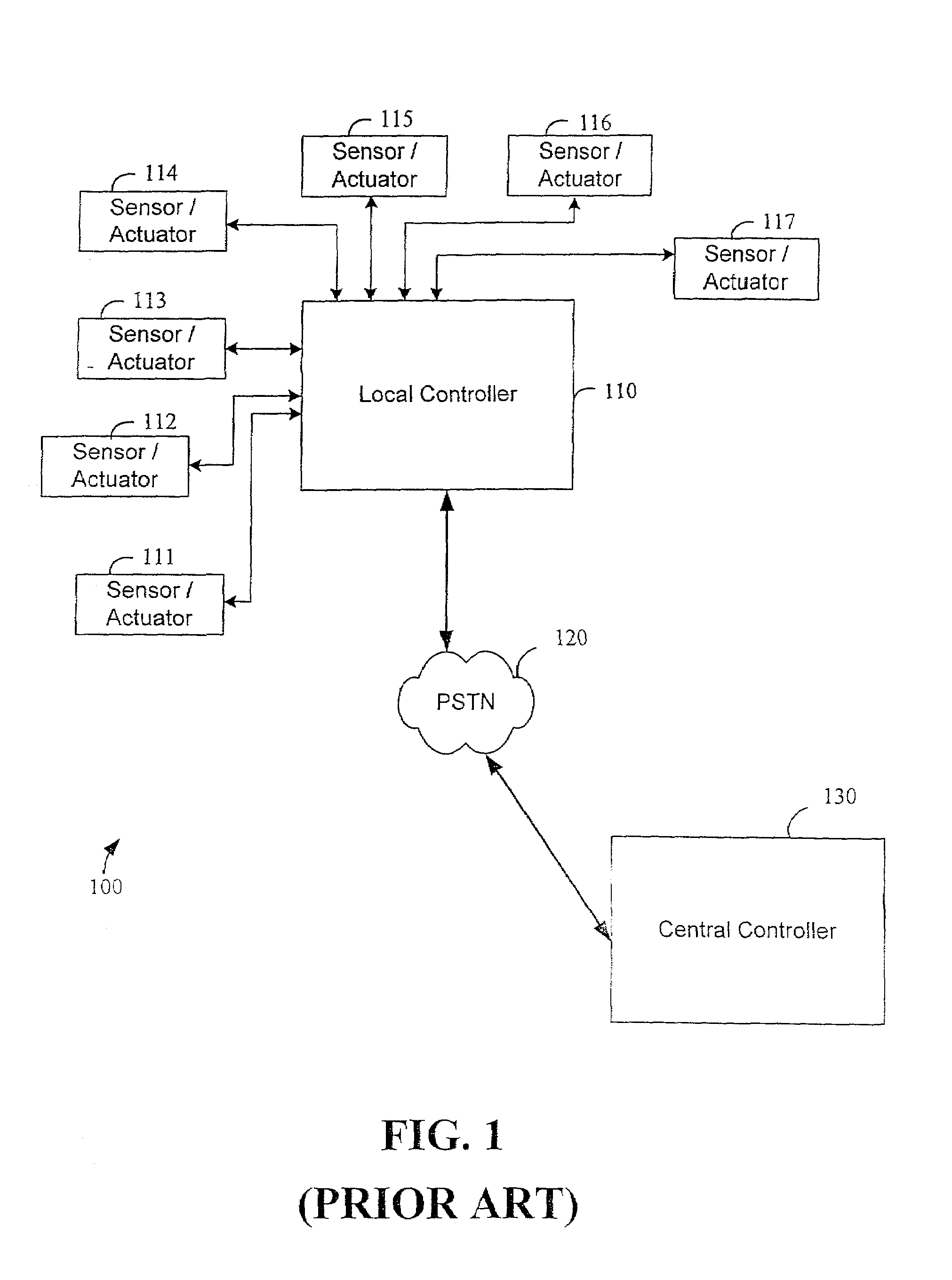
System and method for monitoring and controlling remote devices
InactiveUS7053767B2Closed feedback loopIntegrated inexpensivelyError preventionFrequency-division multiplex detailsTransceiverControl signal
The present invention is generally directed to a system for monitoring a variety of environmental and / or other conditions within a defined remotely located region. In accordance with one aspect of the invention, a system is configured to monitor utility meters in a defined area. The system is implemented by using a plurality of wireless transmitters, wherein each wireless transmitter is integrated into a sensor adapted to monitor a particular data input. The system also includes a plurality of transceivers that are dispersed throughout the region at defined locations. The system uses a local gateway to translate and transfer information from the transmitters to a dedicated computer on a network. The dedicated computer, collects, compiles, and stores the data for retrieval upon client demand across the network. The computer further includes means for evaluating the received information and identifying an appropriate control signal, the system further including means for applying the control signal at a designated actuator.
Owner:SIPCO
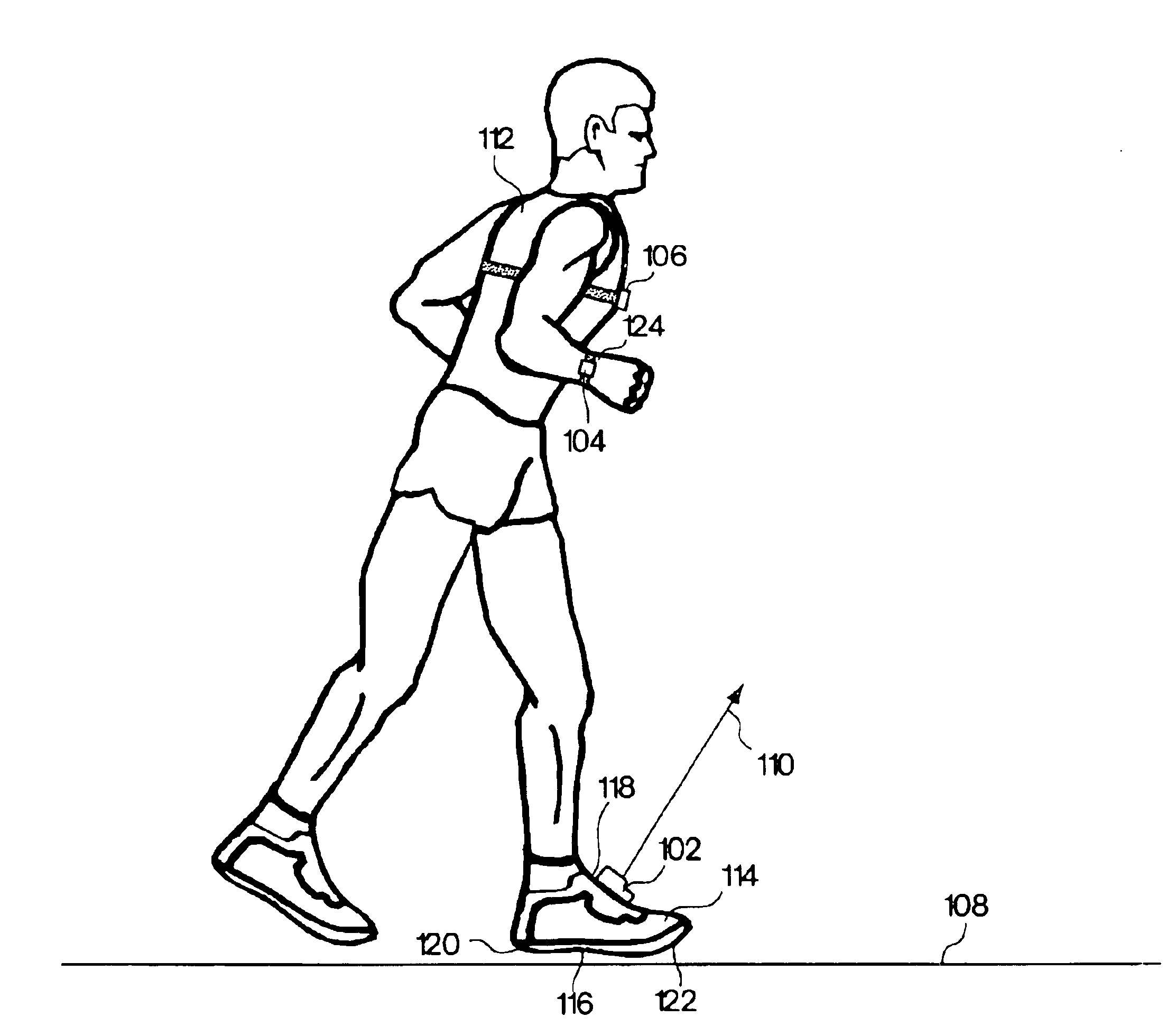
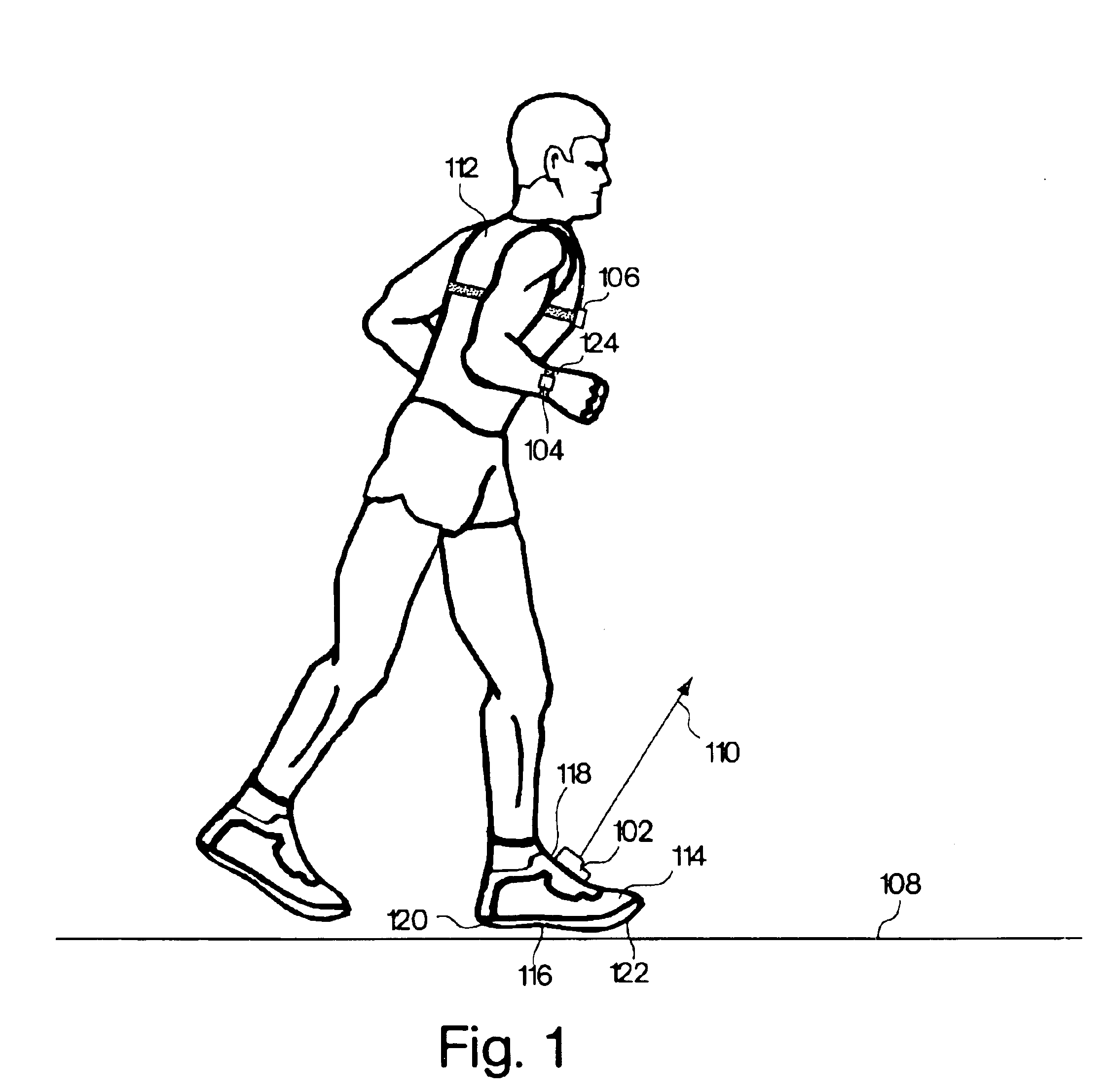
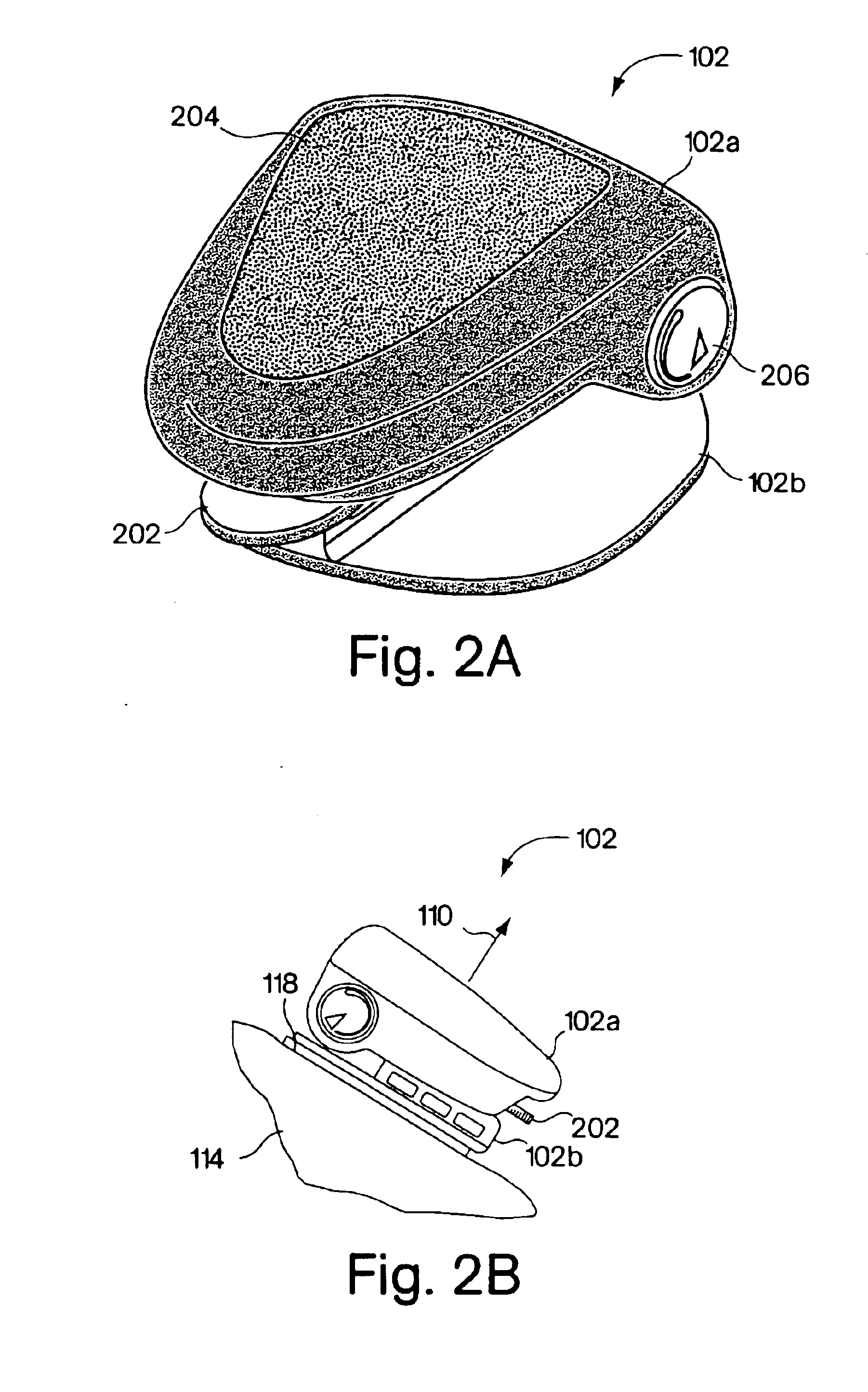
Monitoring activity of a user in locomotion on foot
InactiveUS6898550B1Physical therapies and activitiesTime indicationPhysical medicine and rehabilitationSimulation
Owner:NIKE INC +1
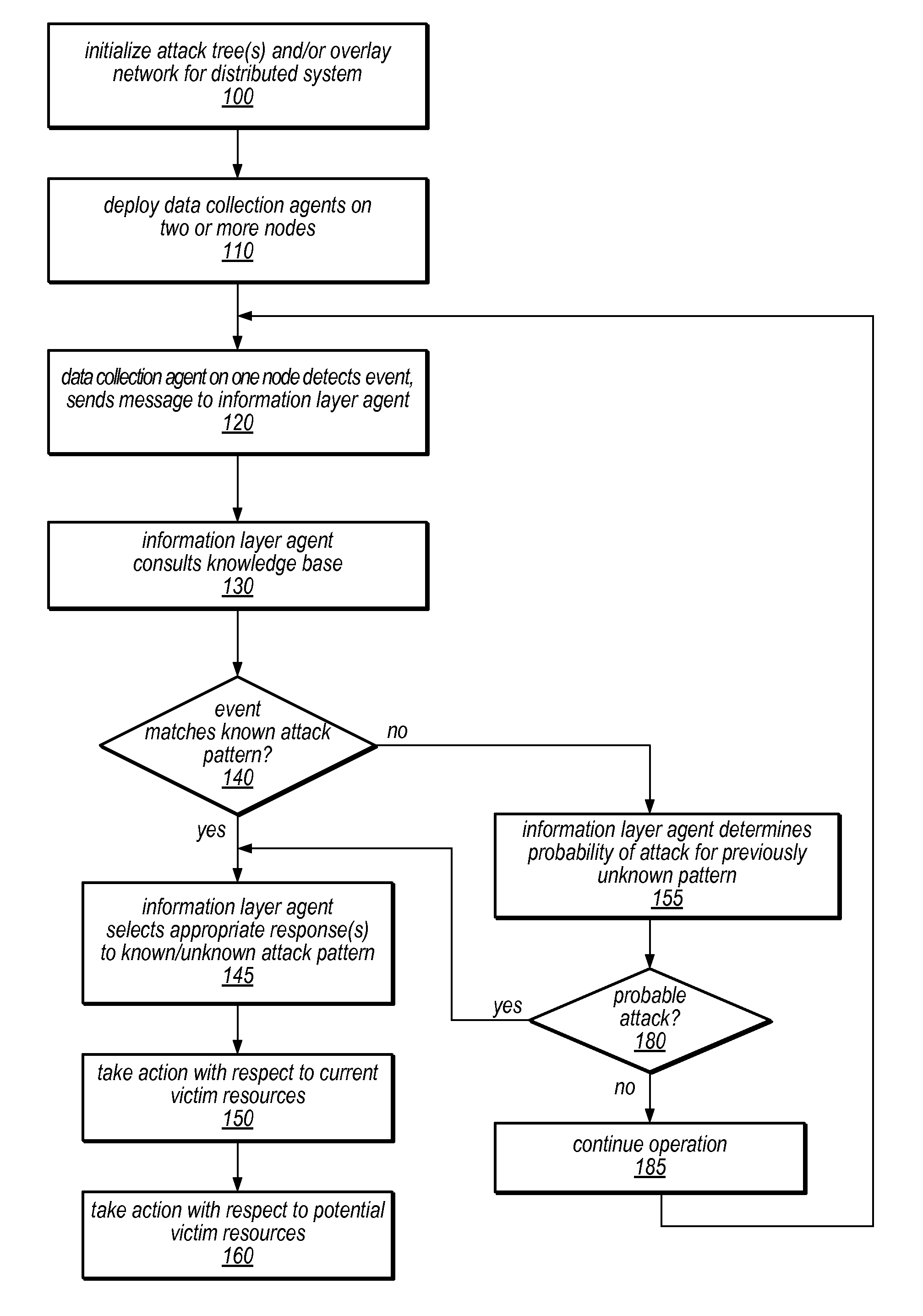
System and Method for Distributed Denial of Service Identification and Prevention
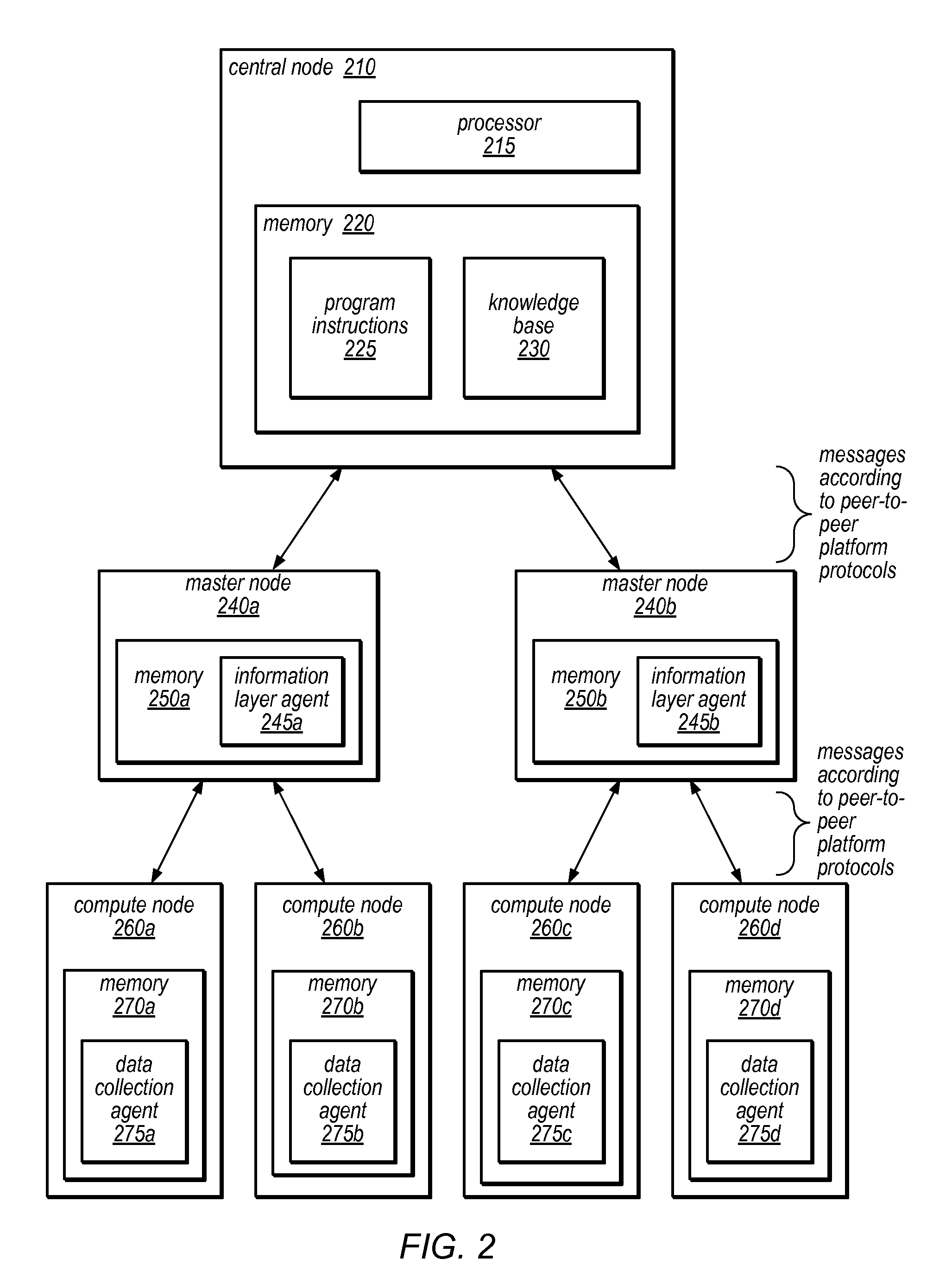
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com