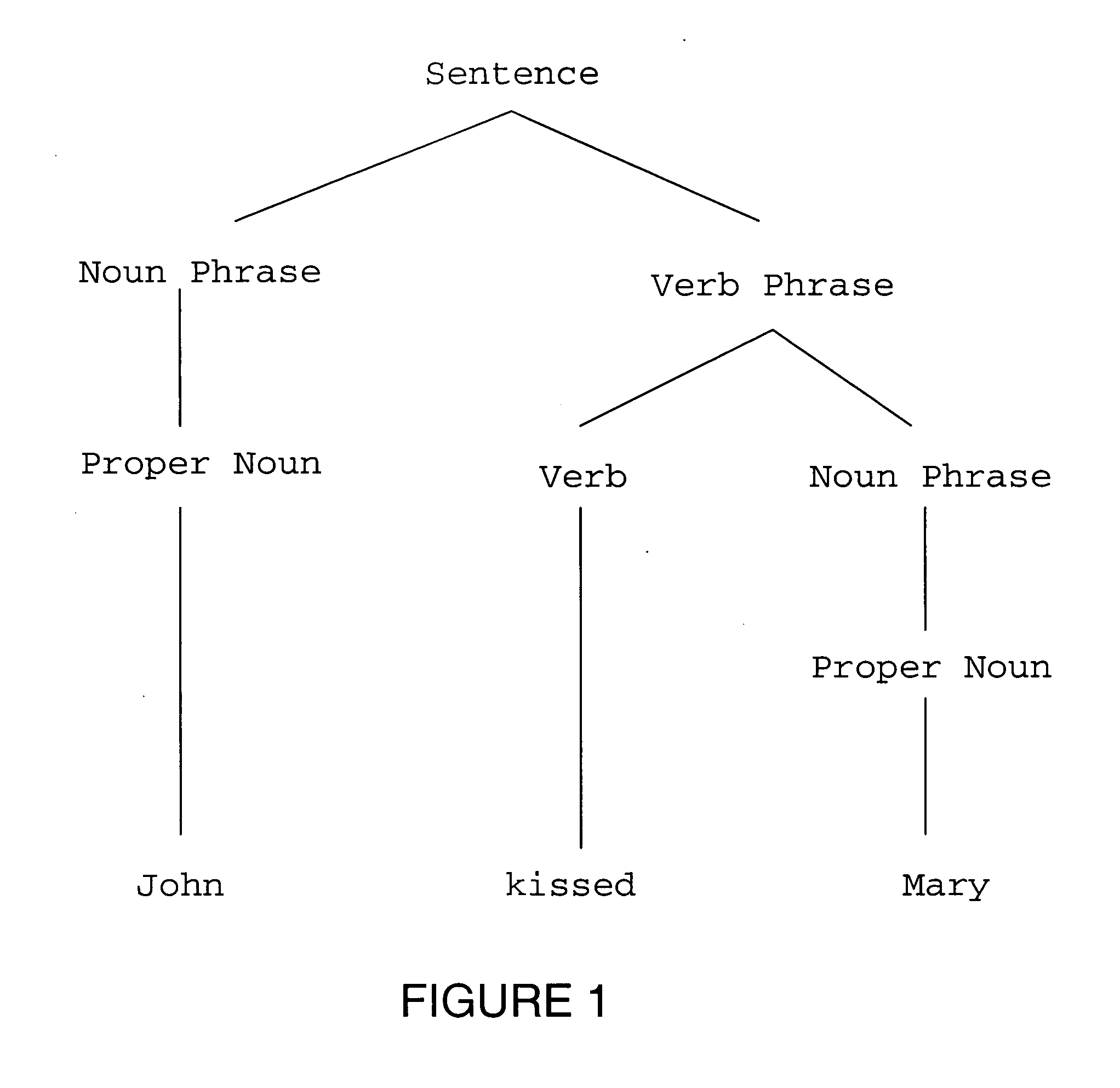
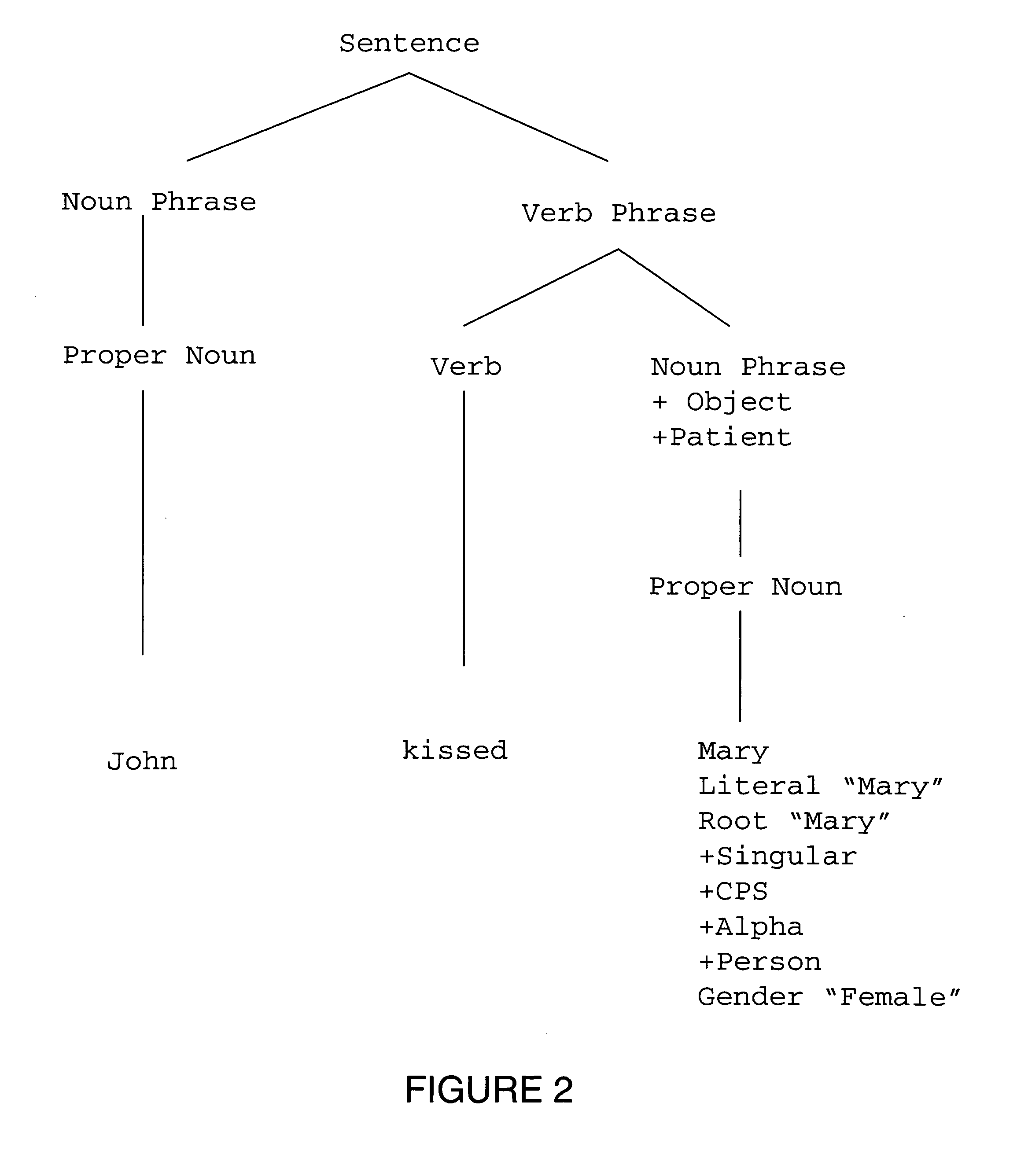
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6714 results about "User defined" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
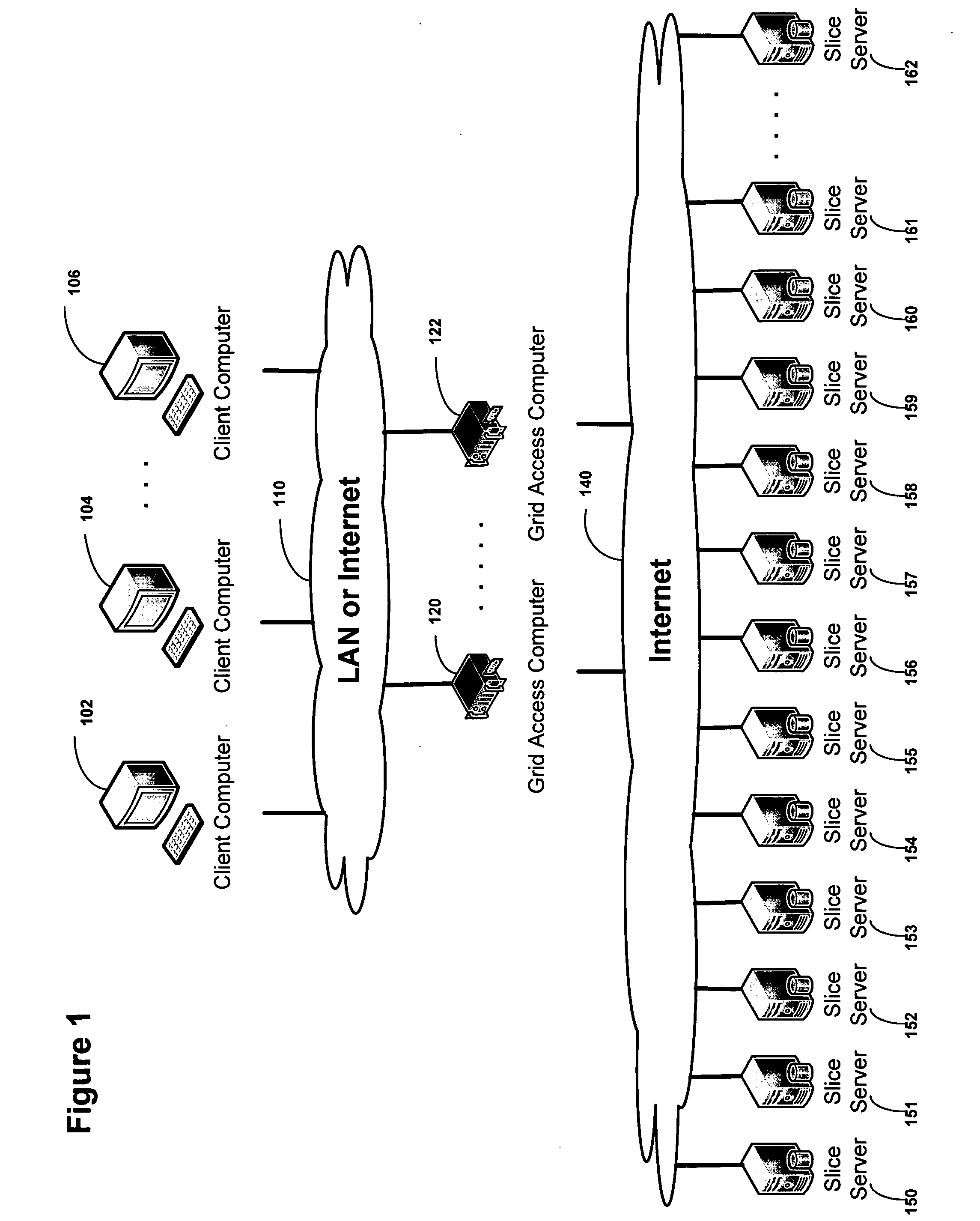
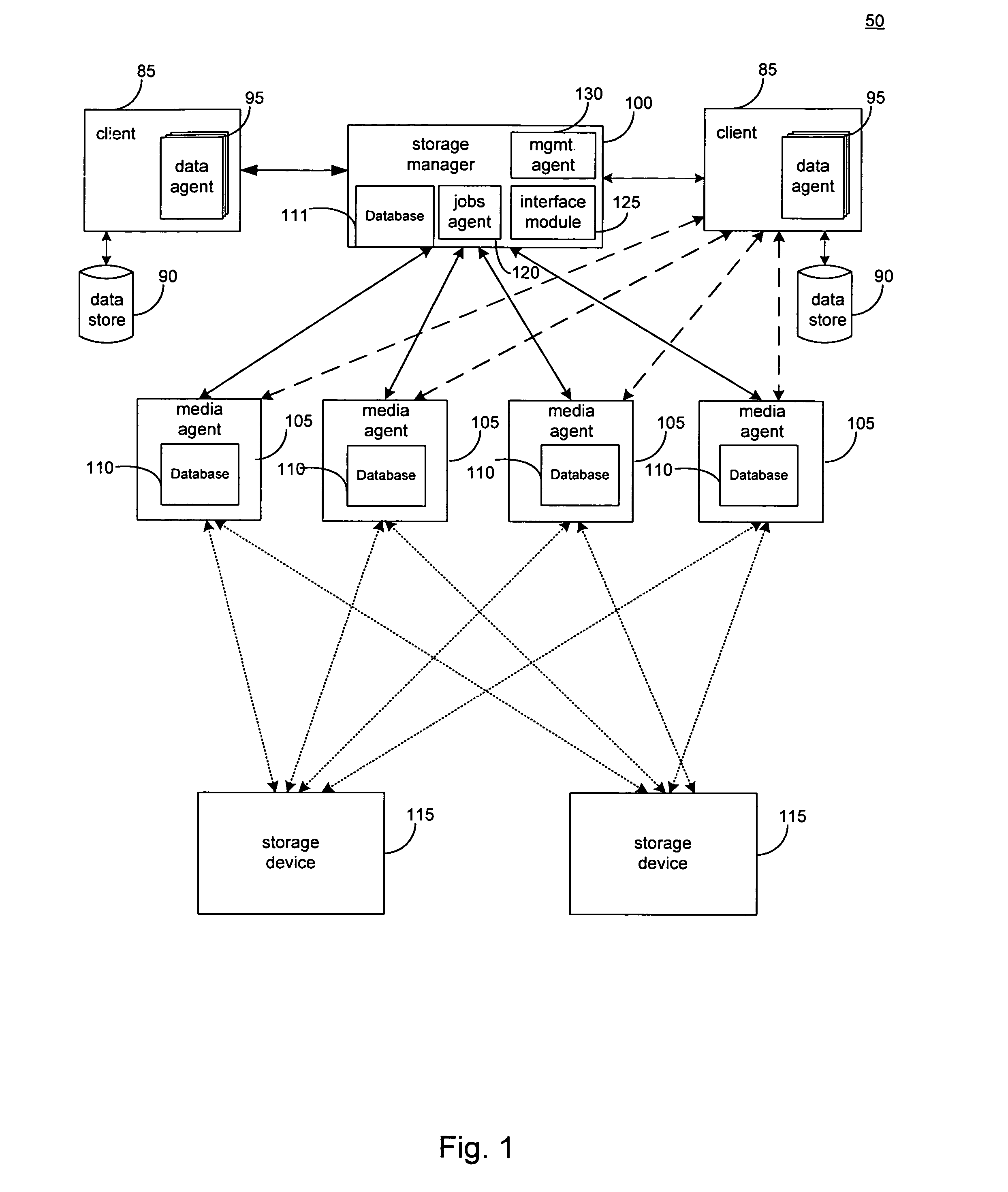
Database access system
ActiveUS7181438B1Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Smart access to a dispersed data storage network
ActiveUS20090094318A1Efficient accessImprove network performanceError preventionFrequency-division multiplex detailsData segmentRanking
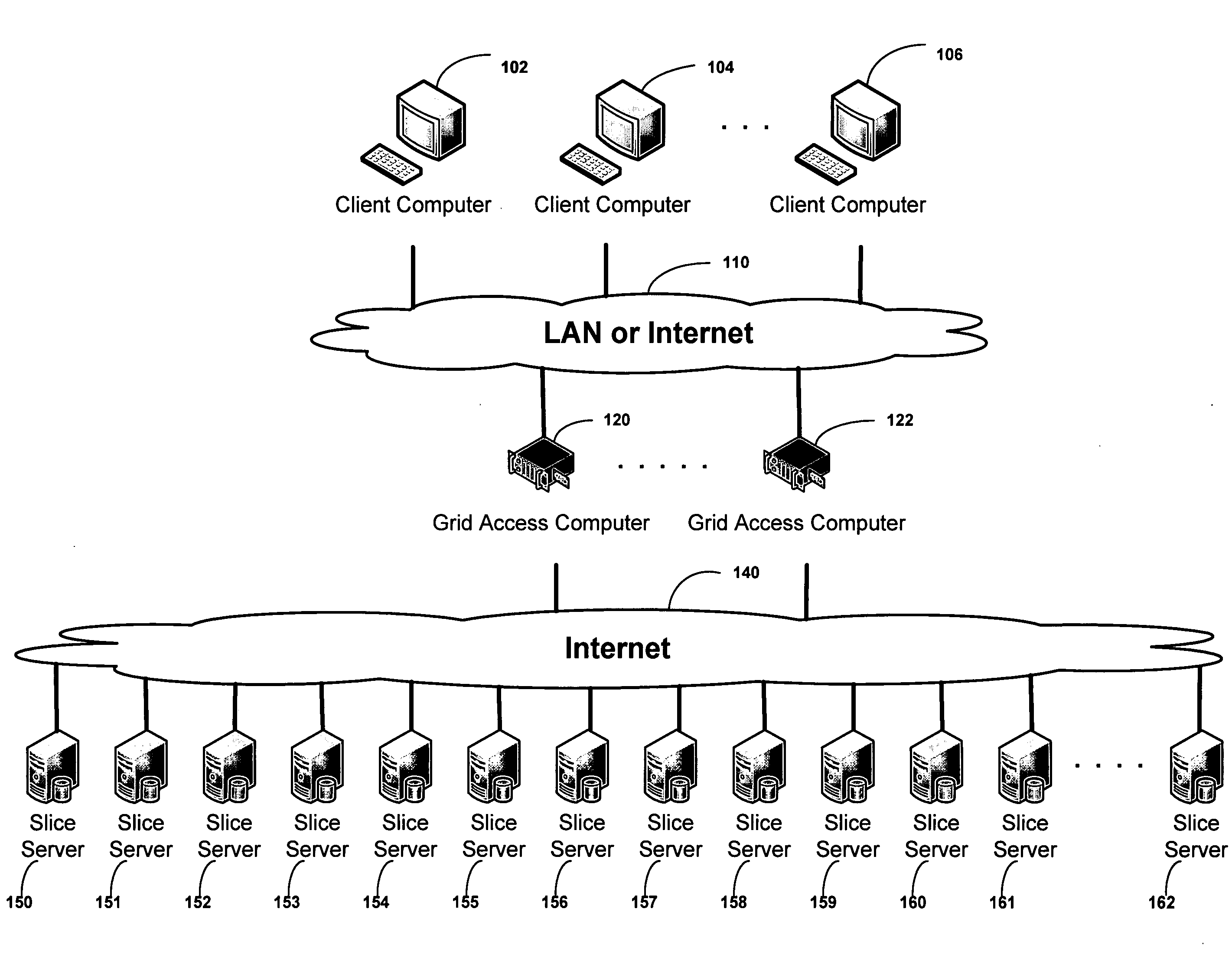
An improved system for accessing data within a distributed data storage network (“DDSN”) is disclosed. In a system implementing the disclosed invention, traffic is routed to individual slice servers within the DDSN in accordance with objective criteria as well as user-defined policies. In accordance with one aspect of the disclosed invention, when a data segment is written to a DDSN, the segment is divided into multiple data slices, which are simultaneously transmitted to different slice servers. In accordance with another aspect of the disclosed invention, when a data segment is read from a DDSN, a list of slice servers, each containing a data slice that could be used to reconstruct the requested data segment, is assembled, and sorted in accordance with a preference rating assigned to each of the slice servers. Sufficient data slices to reconstruct the data segment are then read in accordance with the preference ranking of the slice servers.
Owner:PURE STORAGE
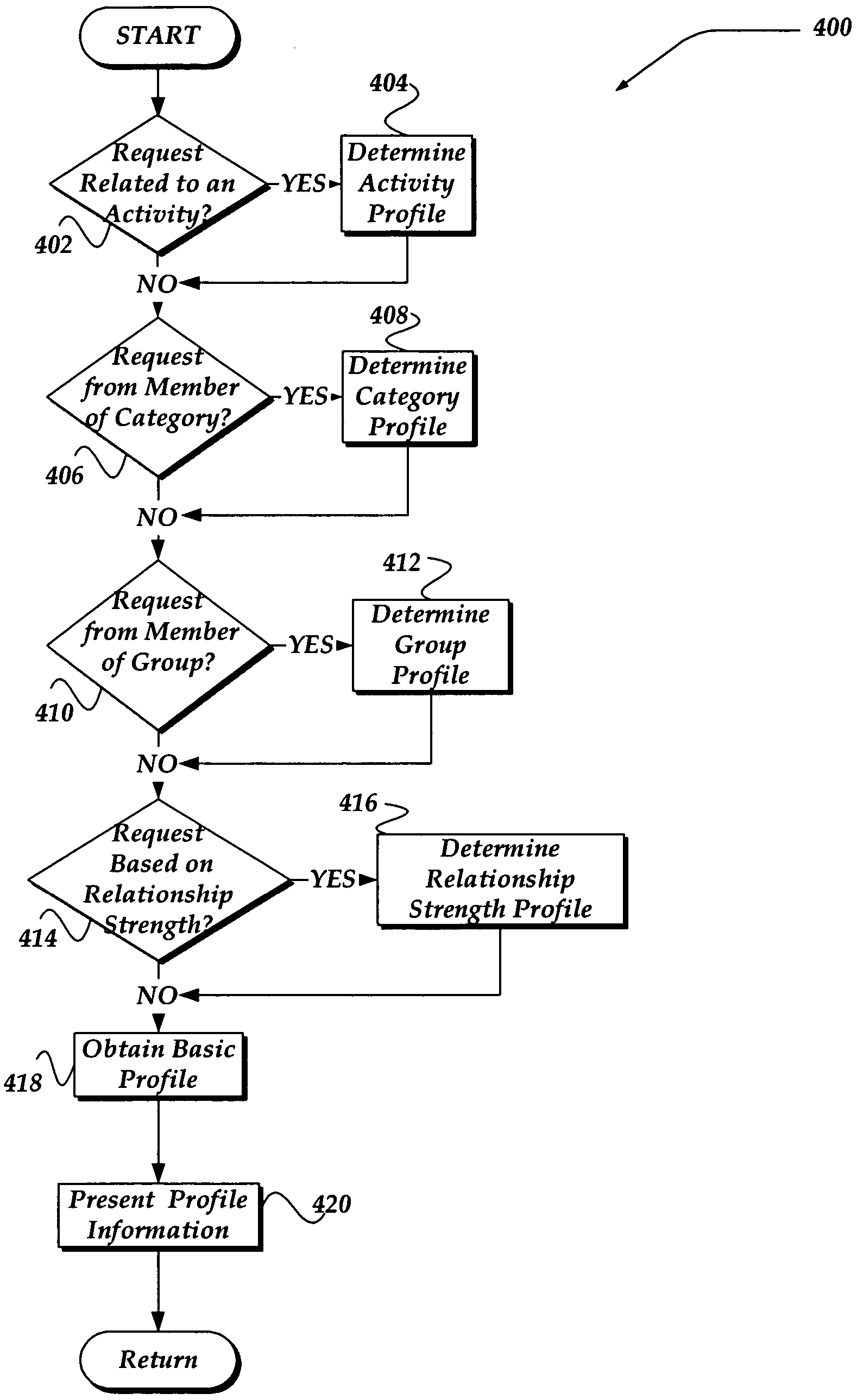
Method and system for customizing views of information associated with a social network user
A method, apparatus, and system are directed towards managing a view of a social network user's personal information based, in part, on user-defined criteria. The user-defined criteria may be applied towards a user's relationship with each prospective viewer. The user-defined criteria may include degrees of separation between members of the social network, a relationship to the prospective viewer, as well as criteria based, in part, on activities, such as dating, employment, hobbies, and the like. The user-defined criteria may also be based on a group membership, a strength of a relationship, and the like. Such user-defined relationship criteria may then be mapped against various categories of information associated with social network user to provide customized views of the social network user.
Owner:SLACK TECH LLC
Database access system
InactiveUS20070156677A1Increased formationGood user interfaceDigital data information retrievalAdvertisementsPersonal detailsAnonymity
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Hierarchical systems and methods for providing a unified view of storage information
The present invention provides systems and methods for data storage. A hierarchical storage management architecture is presented to facilitate data management. The disclosed system provides methods for evaluating the state of stored data relative to enterprise needs by using weighted parameters that may be user defined. Also disclosed are systems and methods evaluating costing and risk management associated with stored data.
Owner:COMMVAULT SYST INC
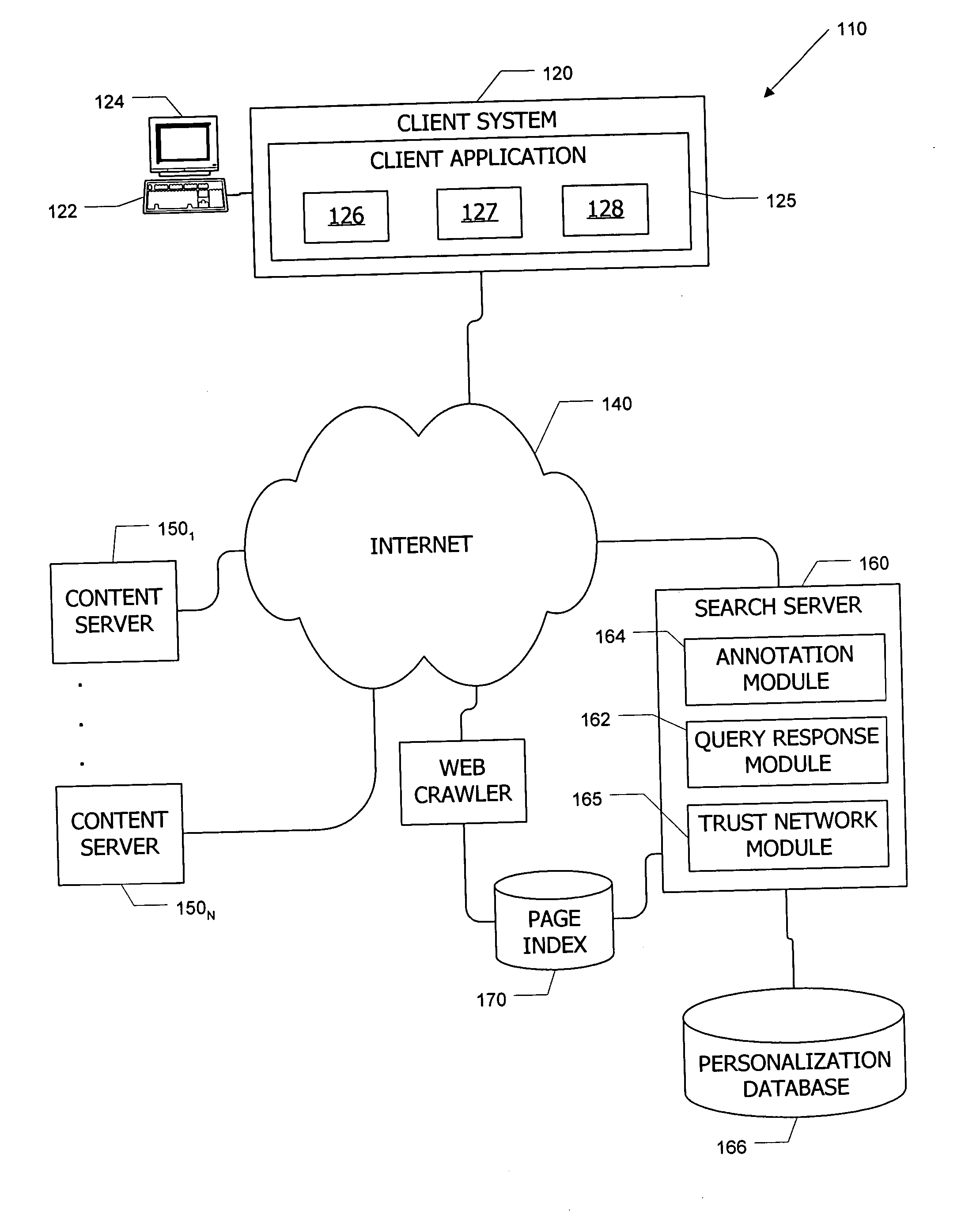
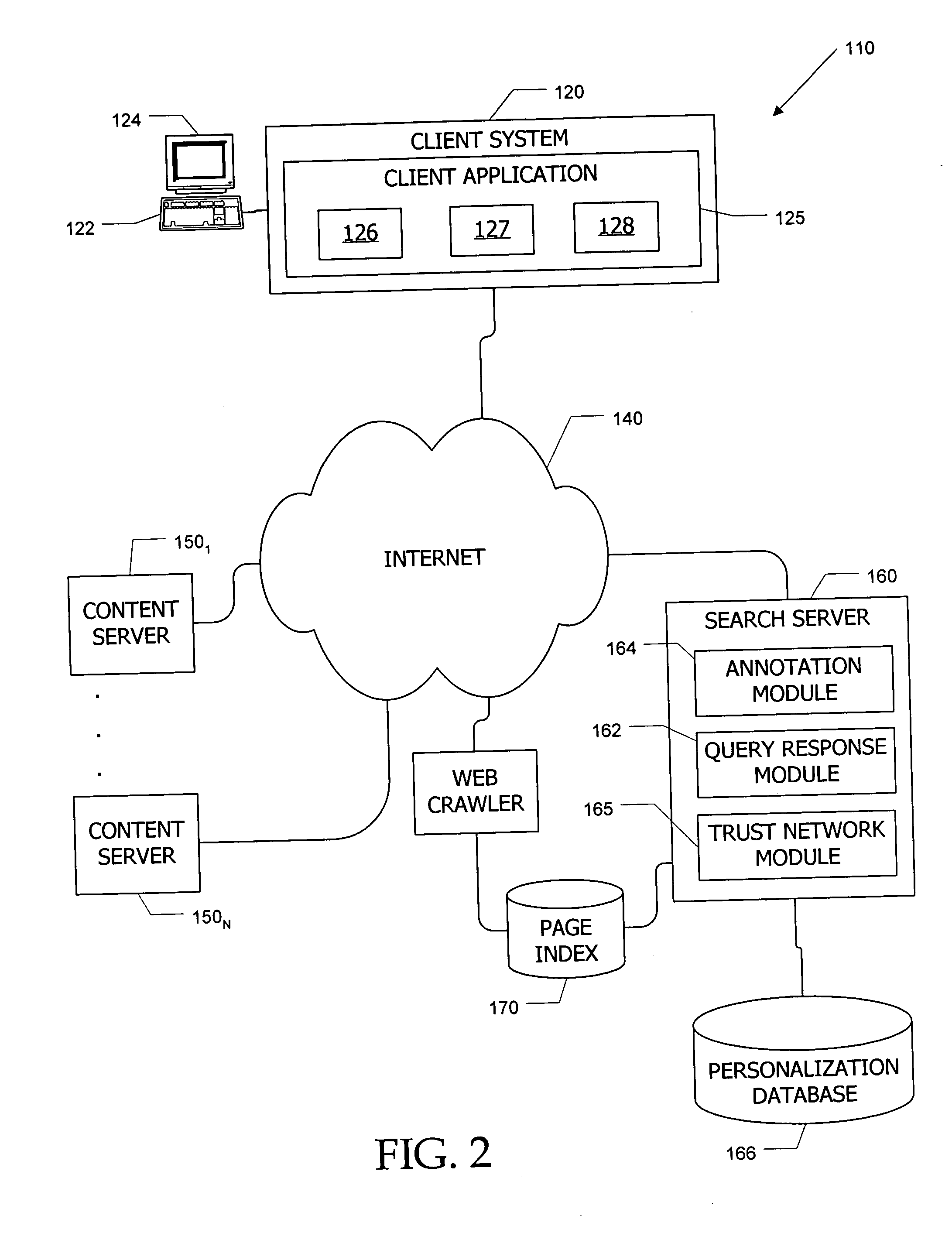
Search system and methods with integration of user annotations from a trust network
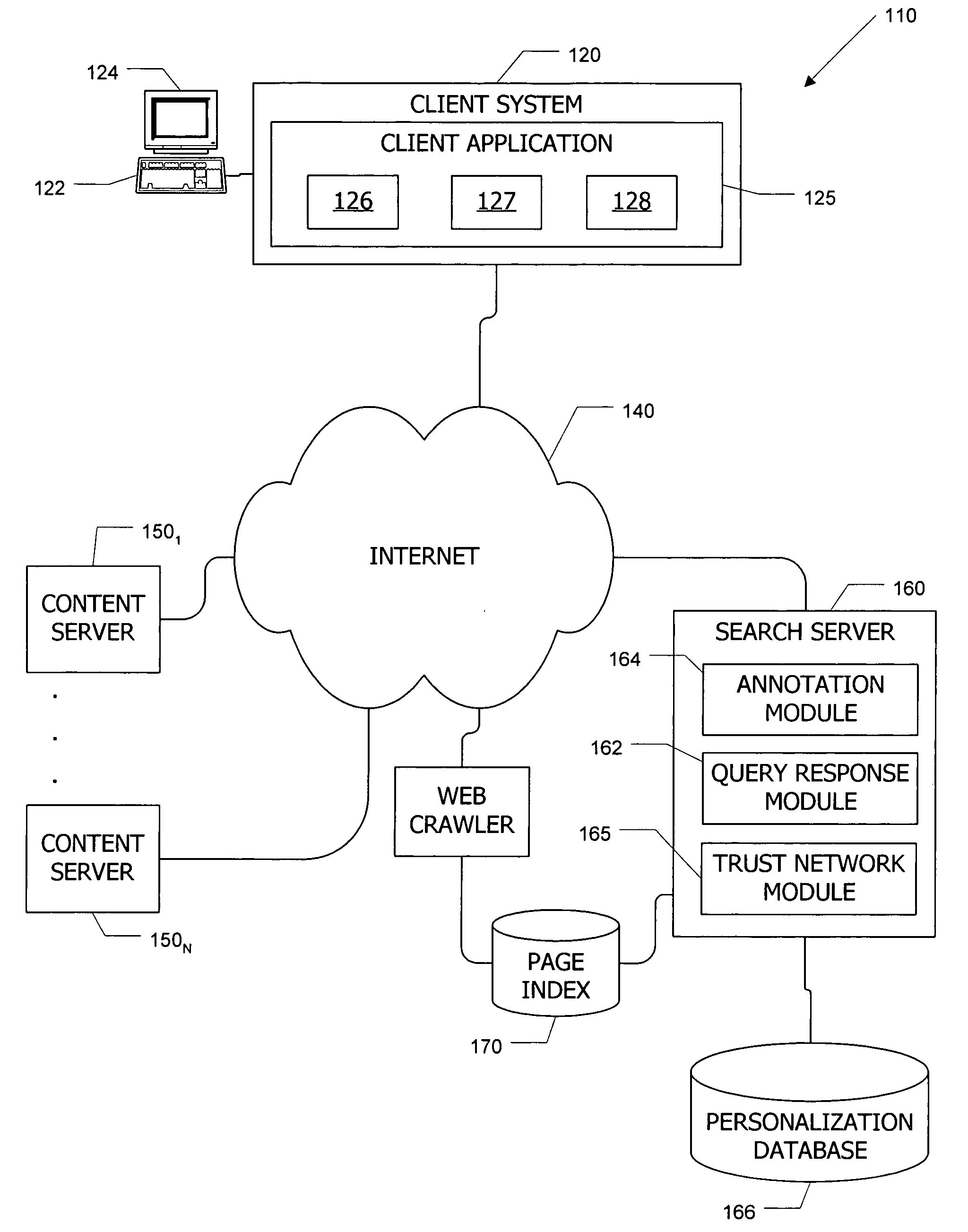
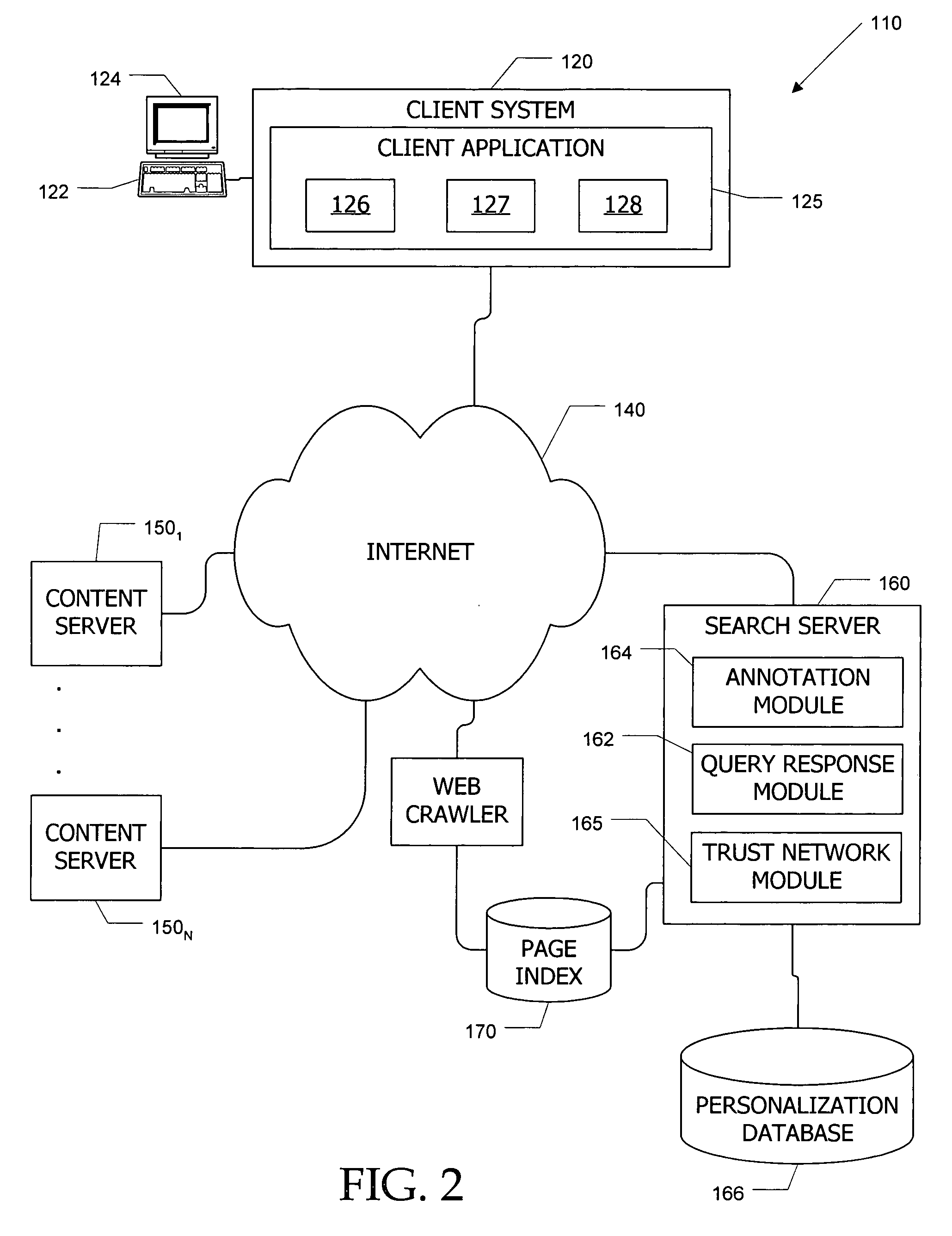
ActiveUS20050256866A1Enhance querying user 's experienceImprove browsing experienceData switching networksSpecial data processing applicationsTrust networkUser defined
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of a first user's trust network are made visible to the first user during search and / or browsing of the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:SALESFORCE COM INC
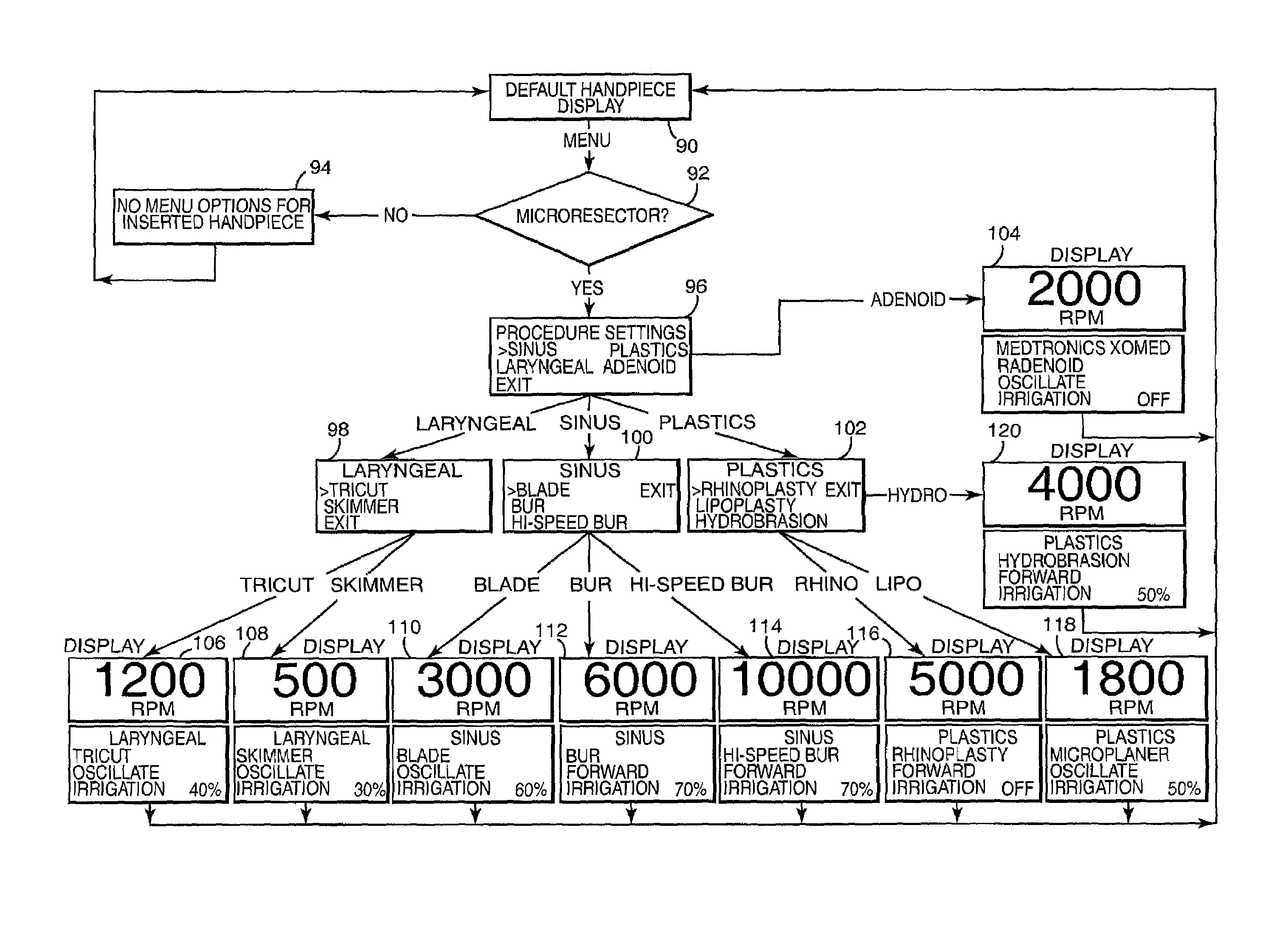
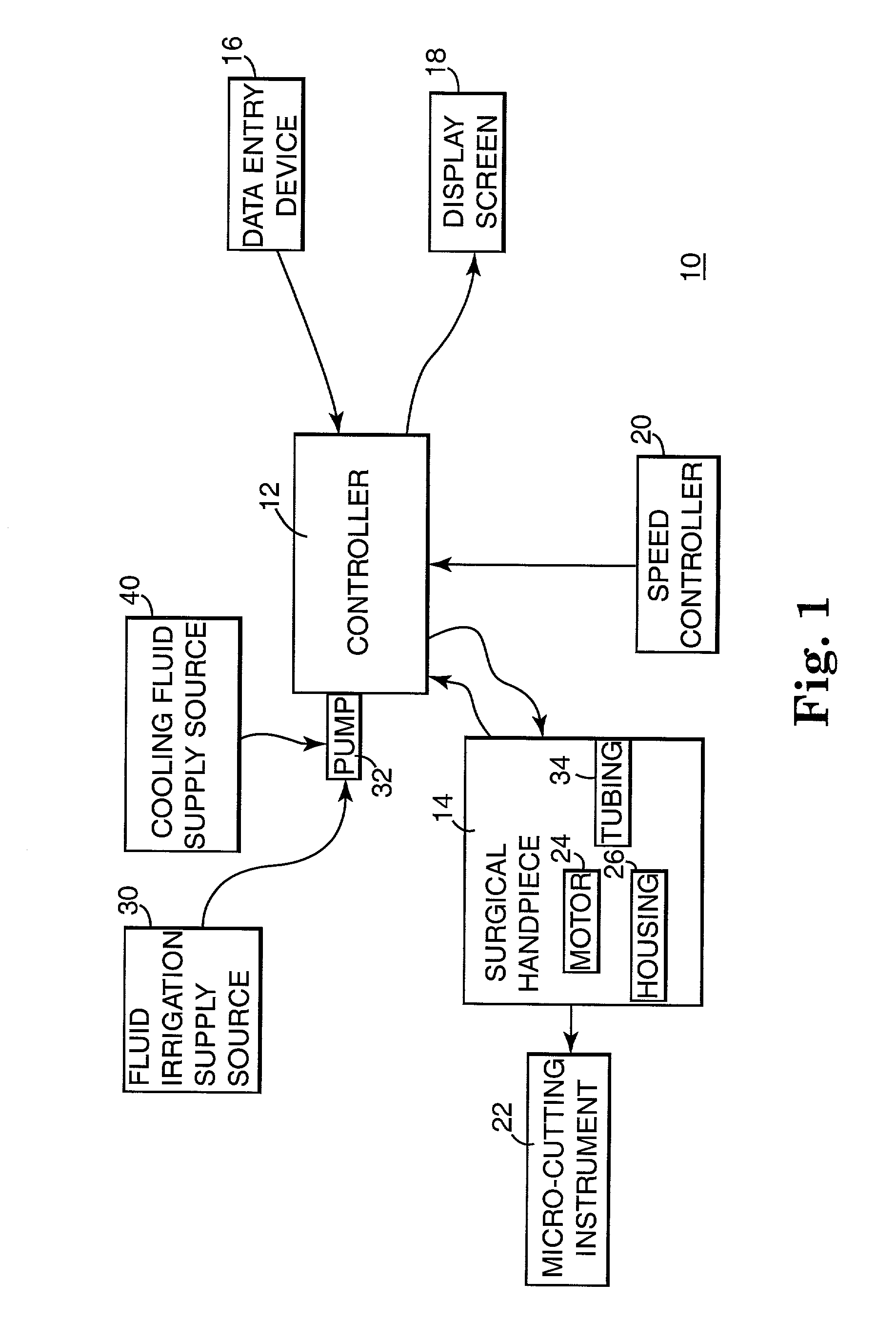
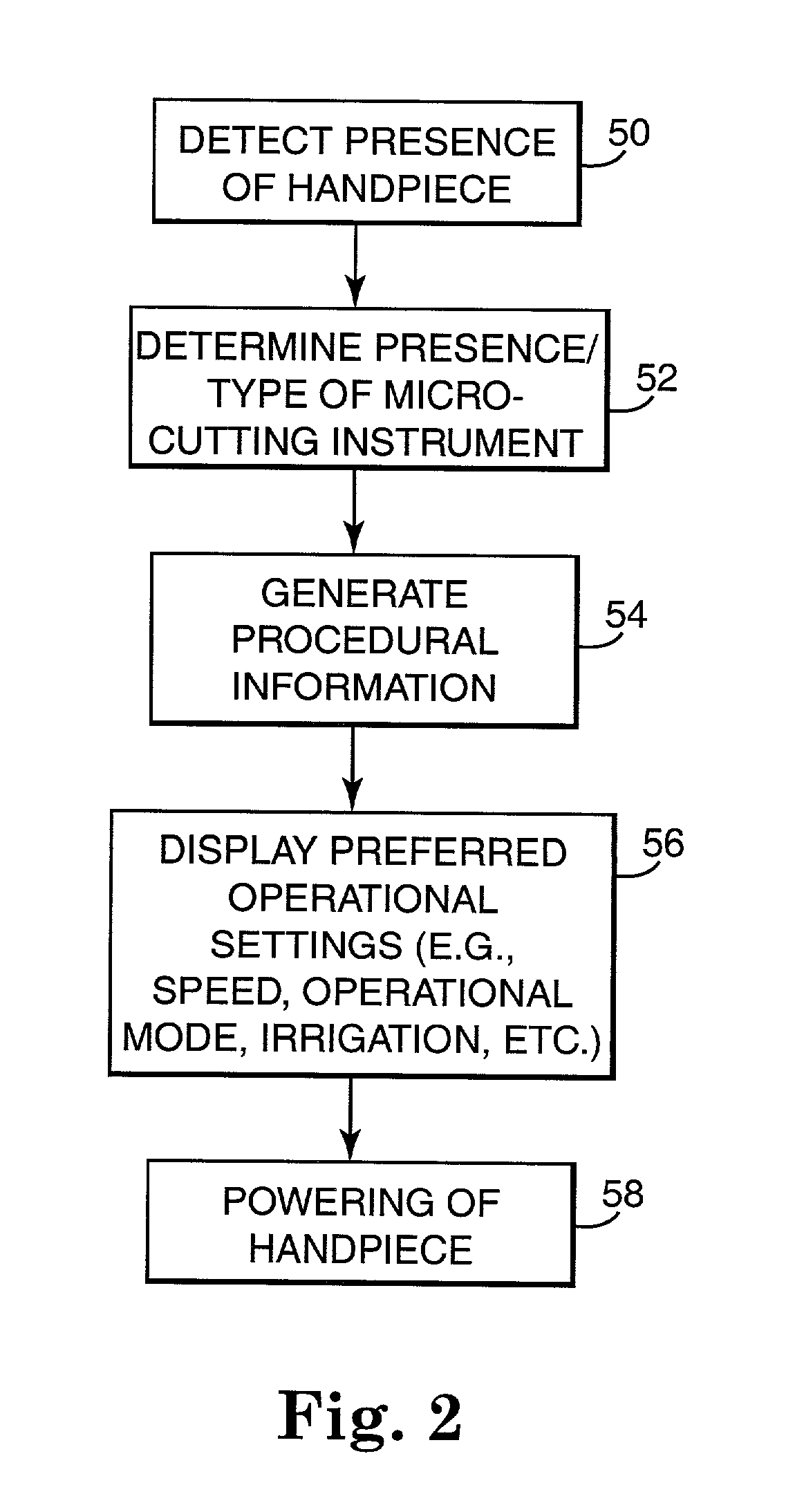
Motor control system for a surgical handpiece
A system and method for powered surgical handpiece capable of powering various micro-cutting instruments is described. The system is comprised of a controller adapted for controlling / interfacing with a powered surgical handpiece based upon user-defined procedural information. A data entry device is used for entering the user-defined procedural information used by the controller for configuring and operating the motor control system.
Owner:MEDTRONIC INC
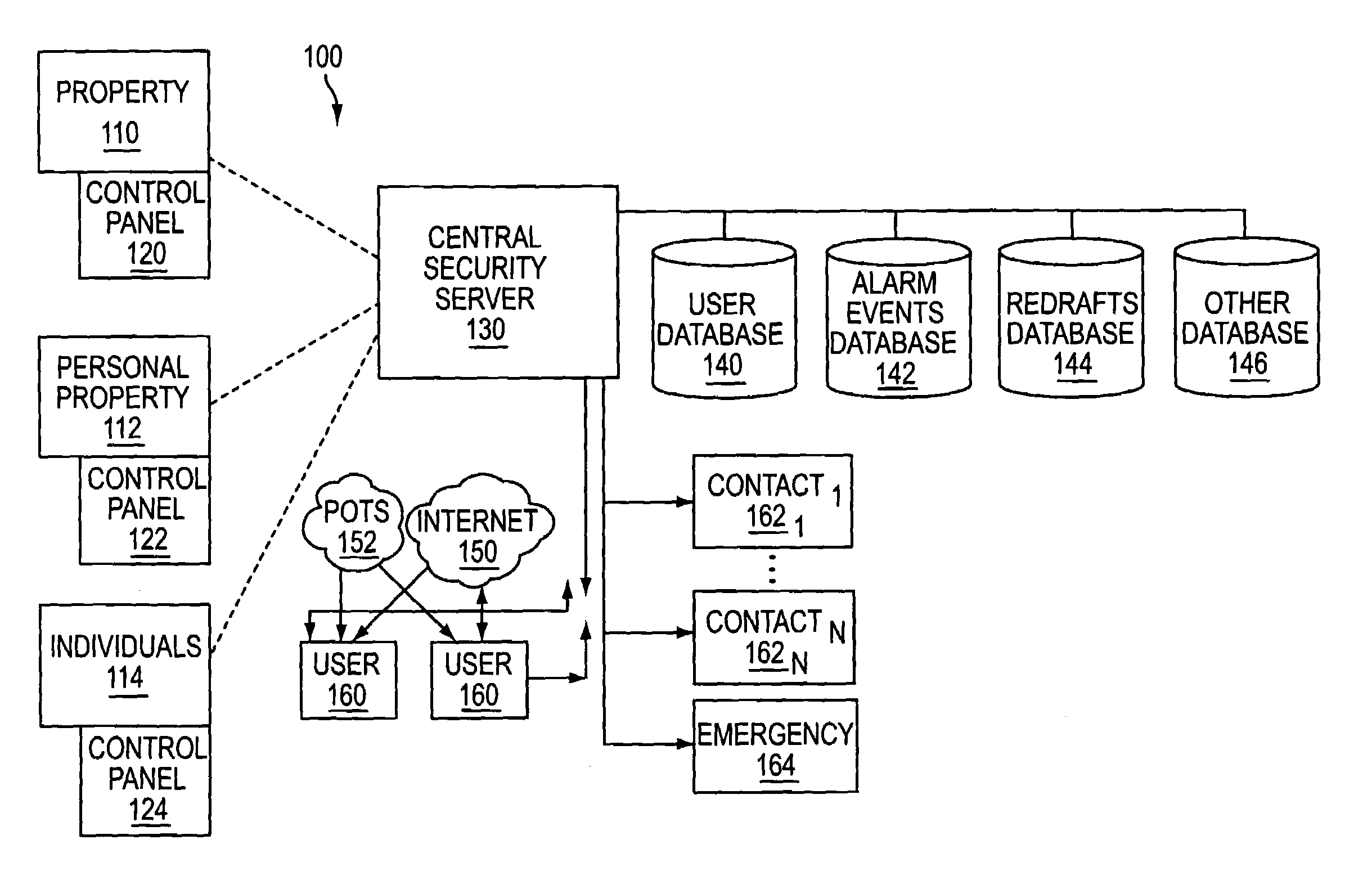
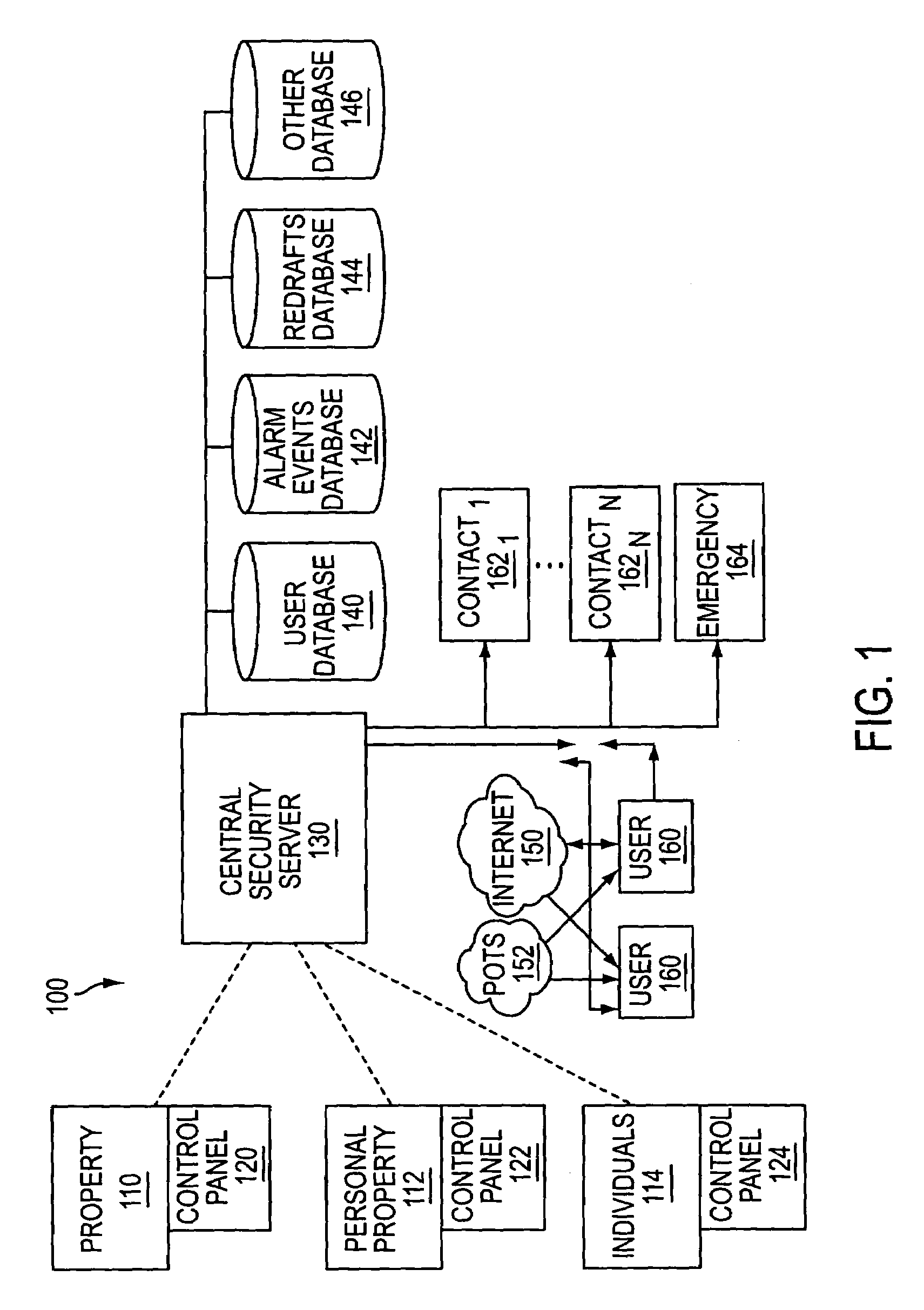
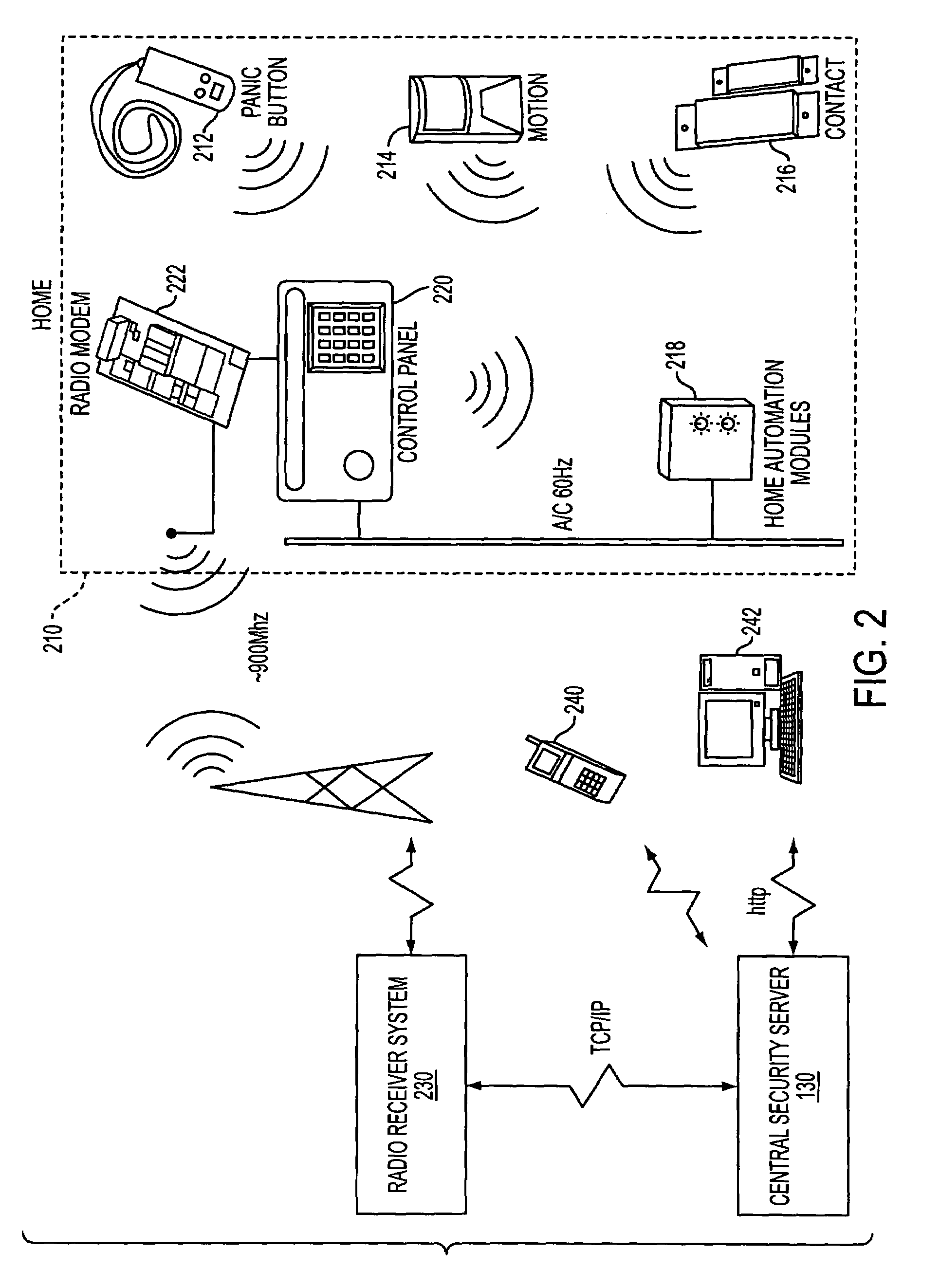
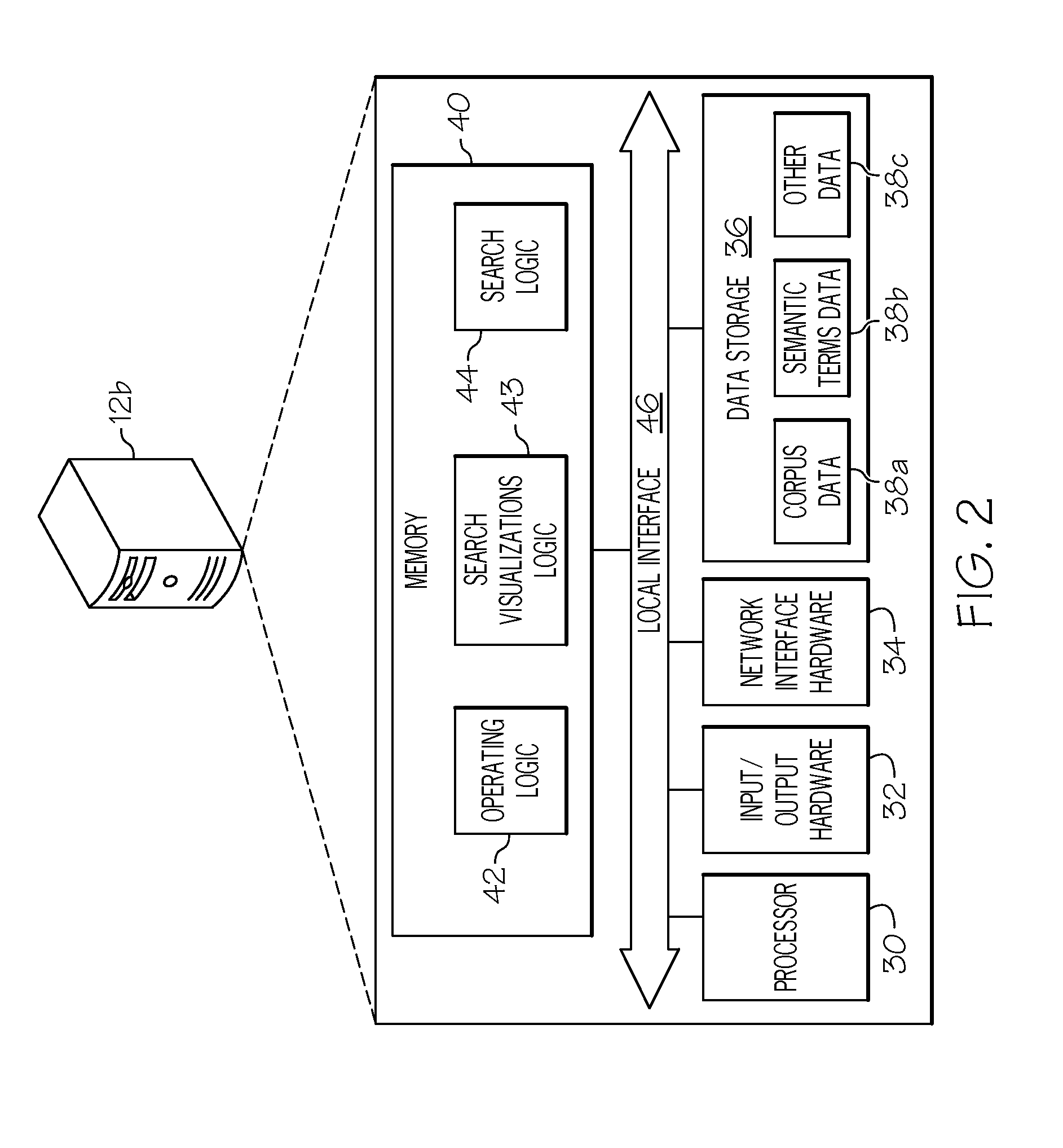
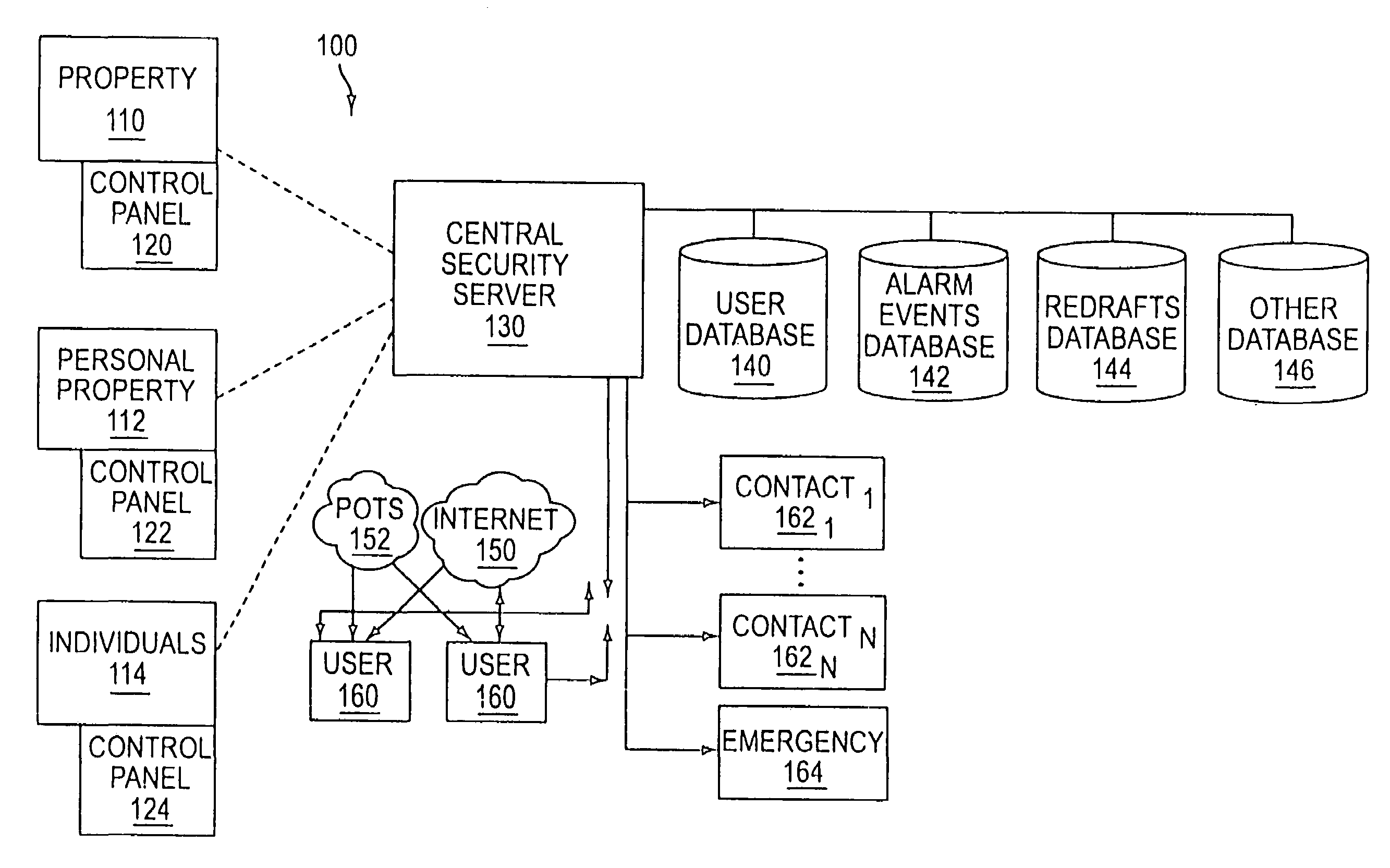
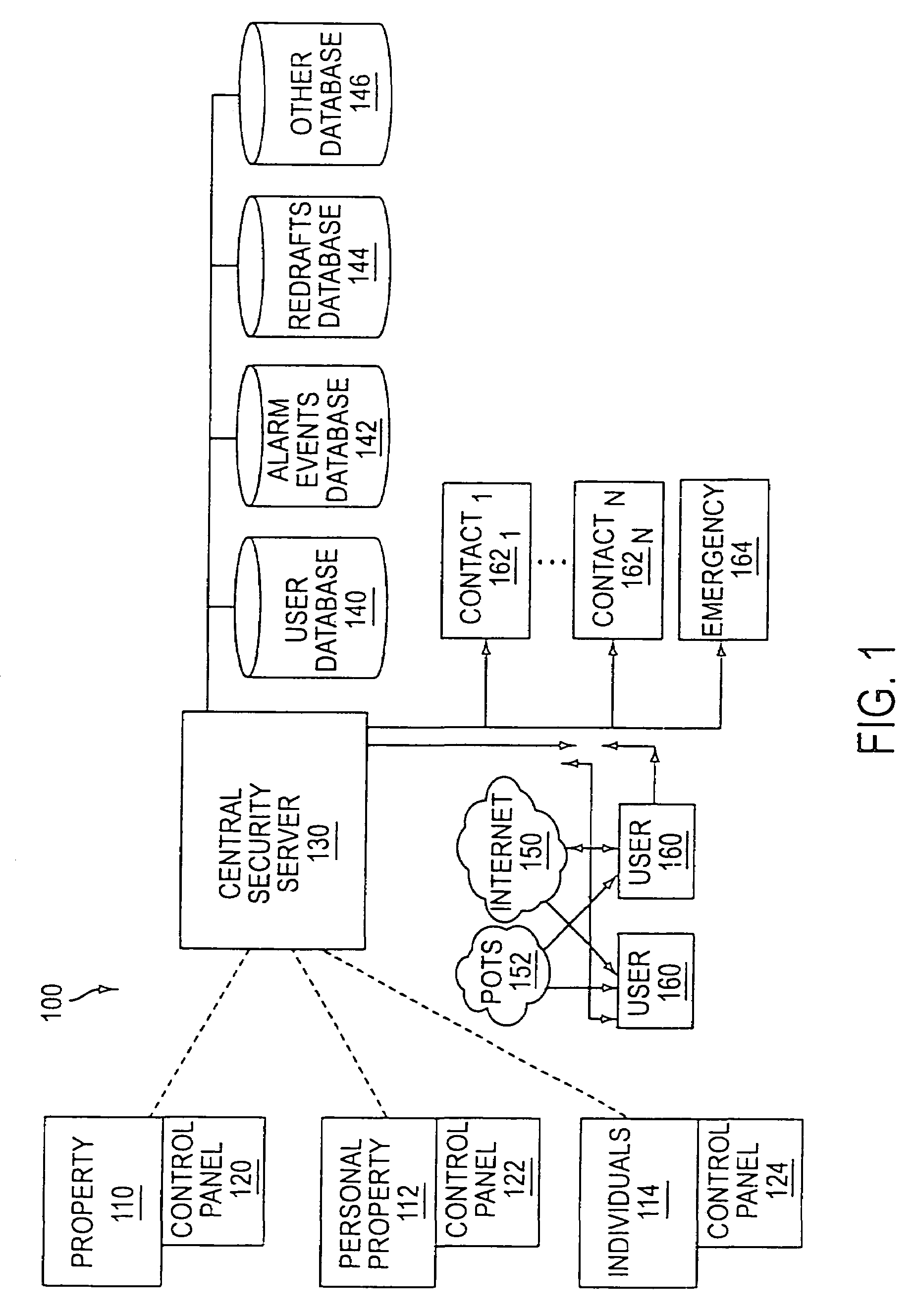
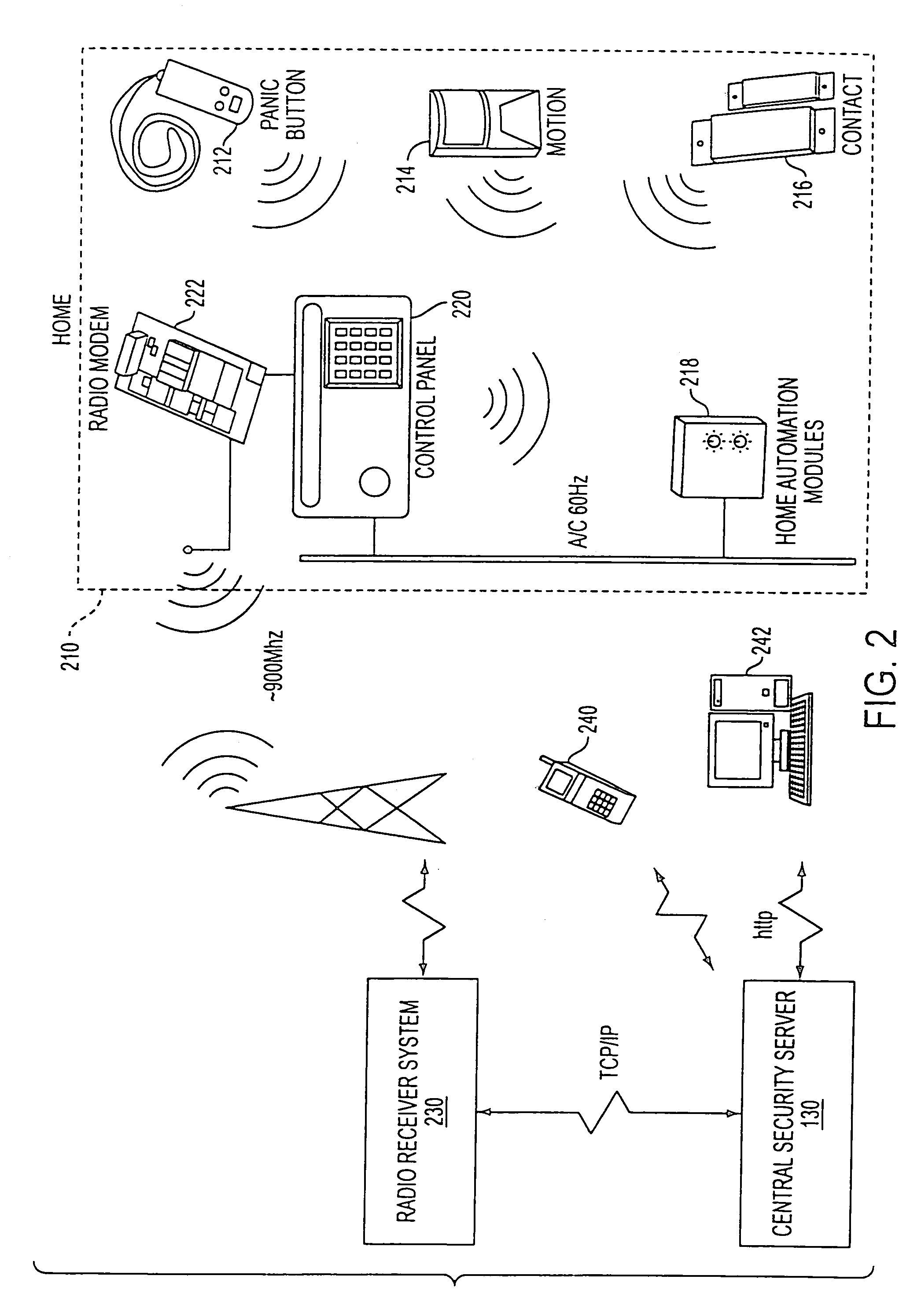
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
Method and system for gesture category recognition and training using a feature vector
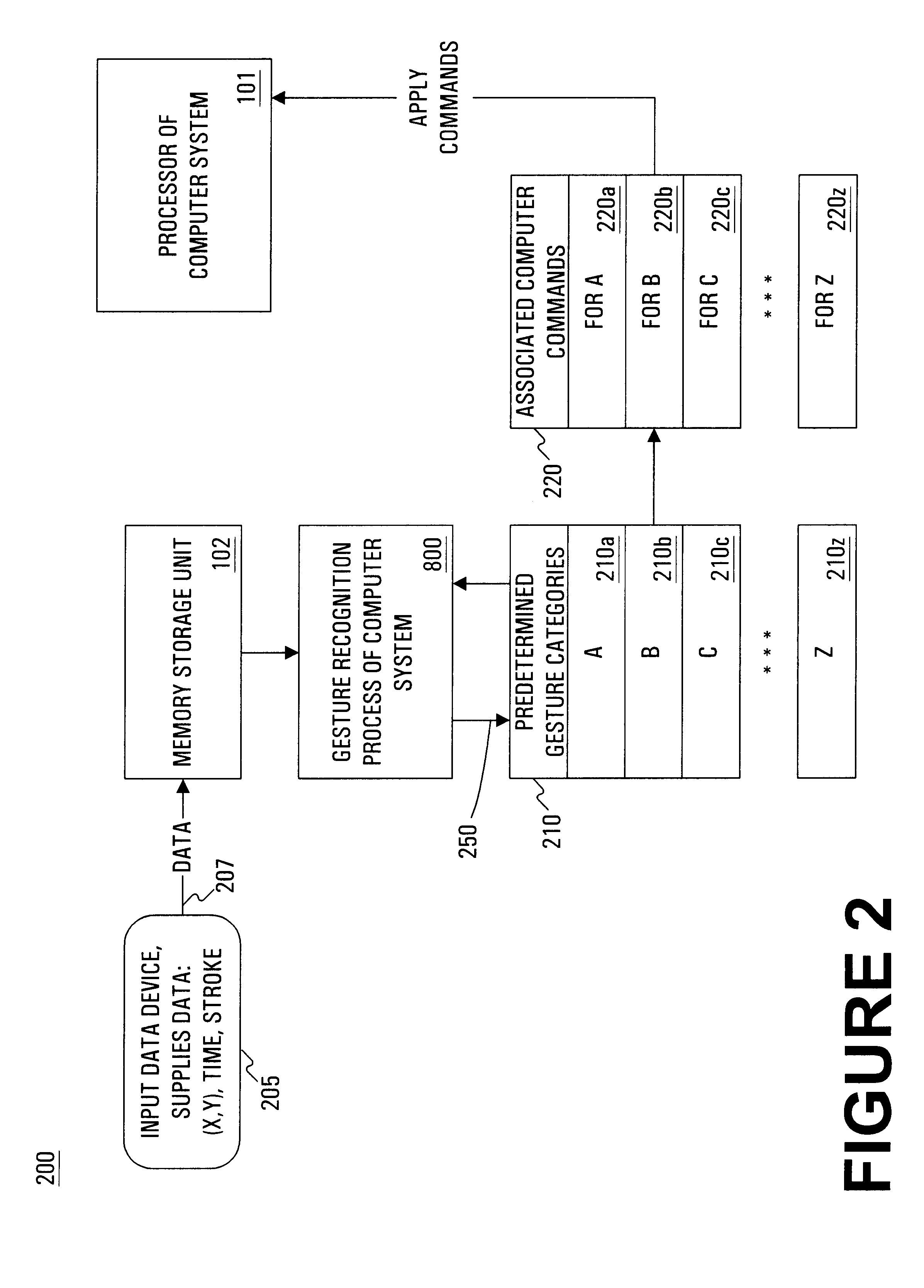
InactiveUS6249606B1Image analysisCathode-ray tube indicatorsCategory recognitionApplication software
A computer implemented method and system for gesture category recognition and training. Generally, a gesture is a hand or body initiated movement of a cursor directing device to outline a particular pattern in particular directions done in particular periods of time. The present invention allows a computer system to accept input data, originating from a user, in the form gesture data that are made using the cursor directing device. In one embodiment, a mouse device is used, but the present invention is equally well suited for use with other cursor directing devices (e.g., a track ball, a finger pad, an electronic stylus, etc.). In one embodiment, gesture data is accepted by pressing a key on the keyboard and then moving the mouse (with mouse button pressed) to trace out the gesture. Mouse position information and time stamps are recorded. The present invention then determines a multi-dimensional feature vector based on the gesture data. The feature vector is then passed through a gesture category recognition engine that, in one implementation, uses a radial basis function neural network to associate the feature vector to a pre-existing gesture category. Once identified, a set of user commands that are associated with the gesture category are applied to the computer system. The user commands can originate from an automatic process that extracts commands that are associated with the menu items of a particular application program. The present invention also allows user training so that user-defined gestures, and the computer commands associated therewith, can be programmed into the computer system.
Owner:ASSOCIATIVE COMPUTING +1
Systems and Methods for Modifying Power Usage
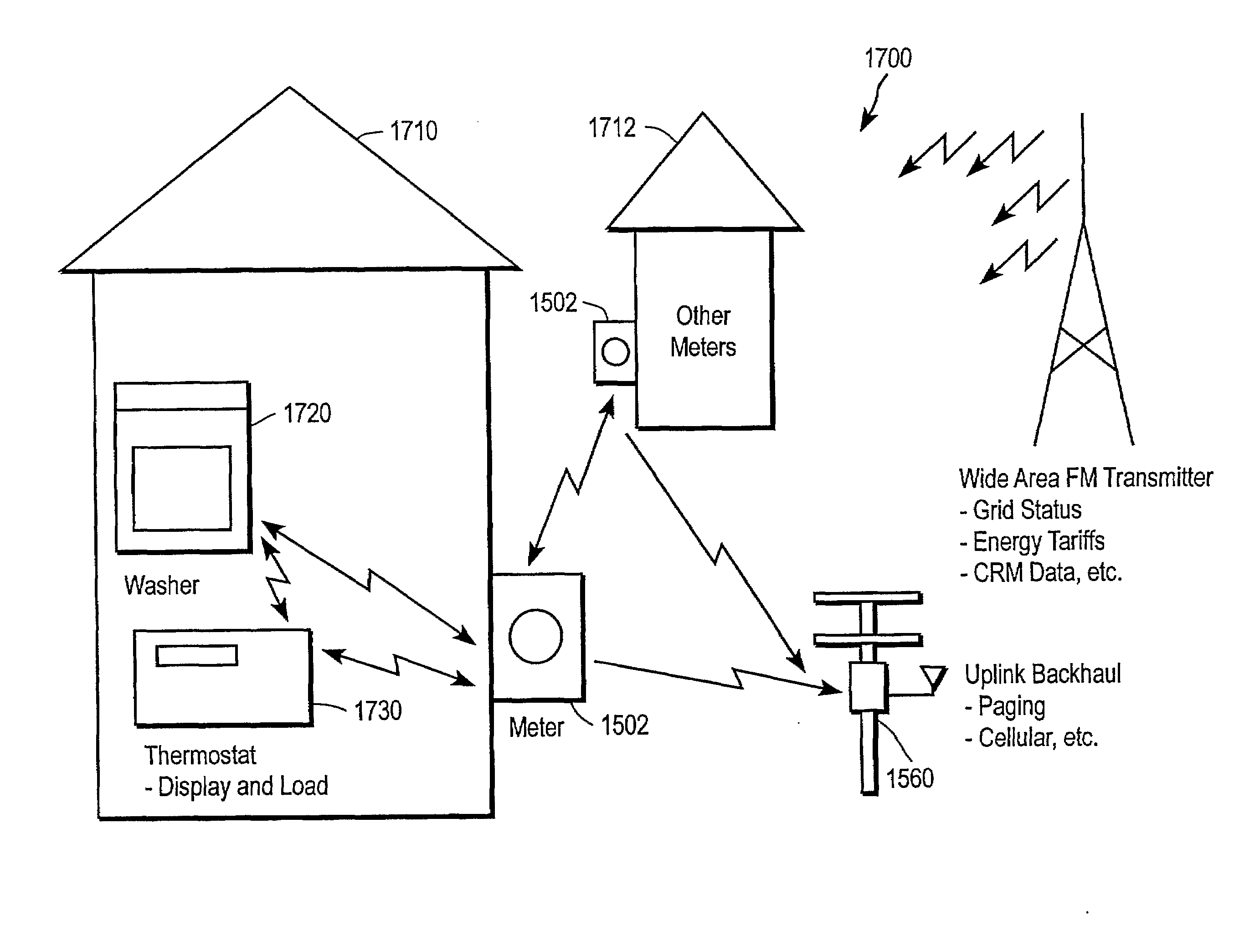
ActiveUS20080272934A1Increase coverageInformed choiceElectric signal transmission systemsLevel controlTransceiverPower usage
Systems and methods for providing energy management utilize wireless wide-area network broadcast signals and a decentralized receiver architecture to allow customers to make informed choices with regard to energy consumption and load shedding for particular appliances. A receiver assembly embedded within an appliance receives a broadcast signal, e.g., an FM subcarrier signal, including tariff data and other electrical grid data. A processor coupled with the receiver controls the appliance in accordance with the received data and in accordance with user-defined preferences. In some embodiments, a transceiver assembly is embedded in one or more appliances in a household. Each transceiver is configured to receive broadcast signals regarding grid data, and to communicate with other appliances and / or a usage meter over a wireless personal area network. Meter data from one or more households may be aggregated and uplinked back to the energy provider or other entities.
Owner:E RADIO USA
Personalized content control
InactiveUS20070208751A1Improve customizationOffice automationSpecial data processing applicationsPersonalizationThe Internet
A content modification platform facilitates personalized presentation and interaction associated with content such as web content, document content, transactional content, multimedia content, and the like. The platform provides sharing of personalization features to facilitate developing a community view of content, such as the internet Menu features are configured to modify source content through simple commands such as add, delete, replace targeted toward content and links to content. The content modification platform is beneficially and effectively used in a variety of on-line content types, environments, transactions, business activity, e-commerce, stock trading, education, human resources and many others. By facilitating a user defining what relationships between and among content is important to them, a customized view of the internet can be presented to the user.
Owner:GROUPON INC
Apparatus and method for content annotation and conditional annotation retrieval in a search context
InactiveUS20080005064A1Natural language data processingSpecial data processing applicationsDocumentationTrust network
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of the querying user's trust network are made visible to the querying user during search and / or browsing of the corpus if the querying user and trust network members use similar queries to identify documents in the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:OATH INC
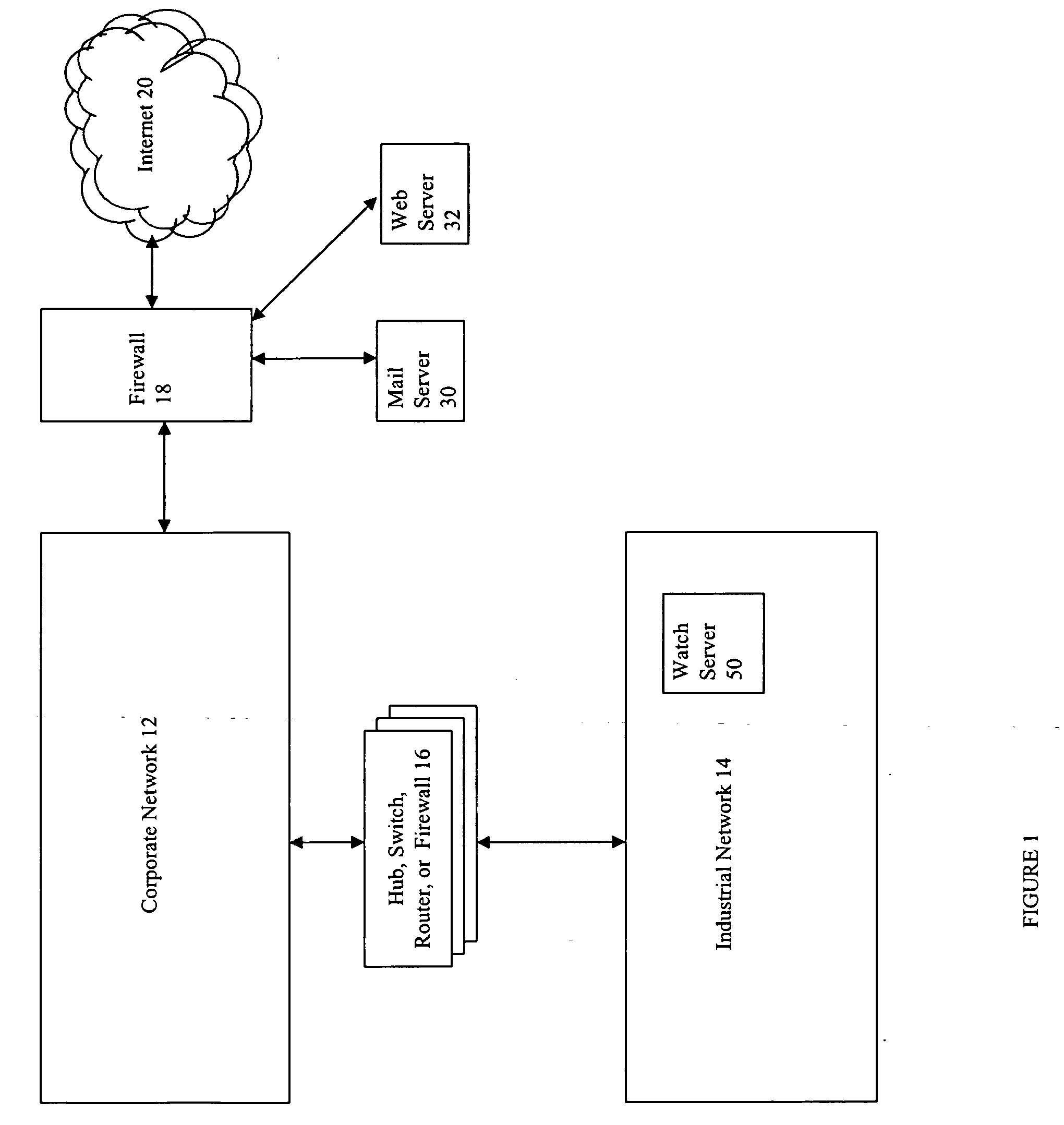
Event monitoring and management
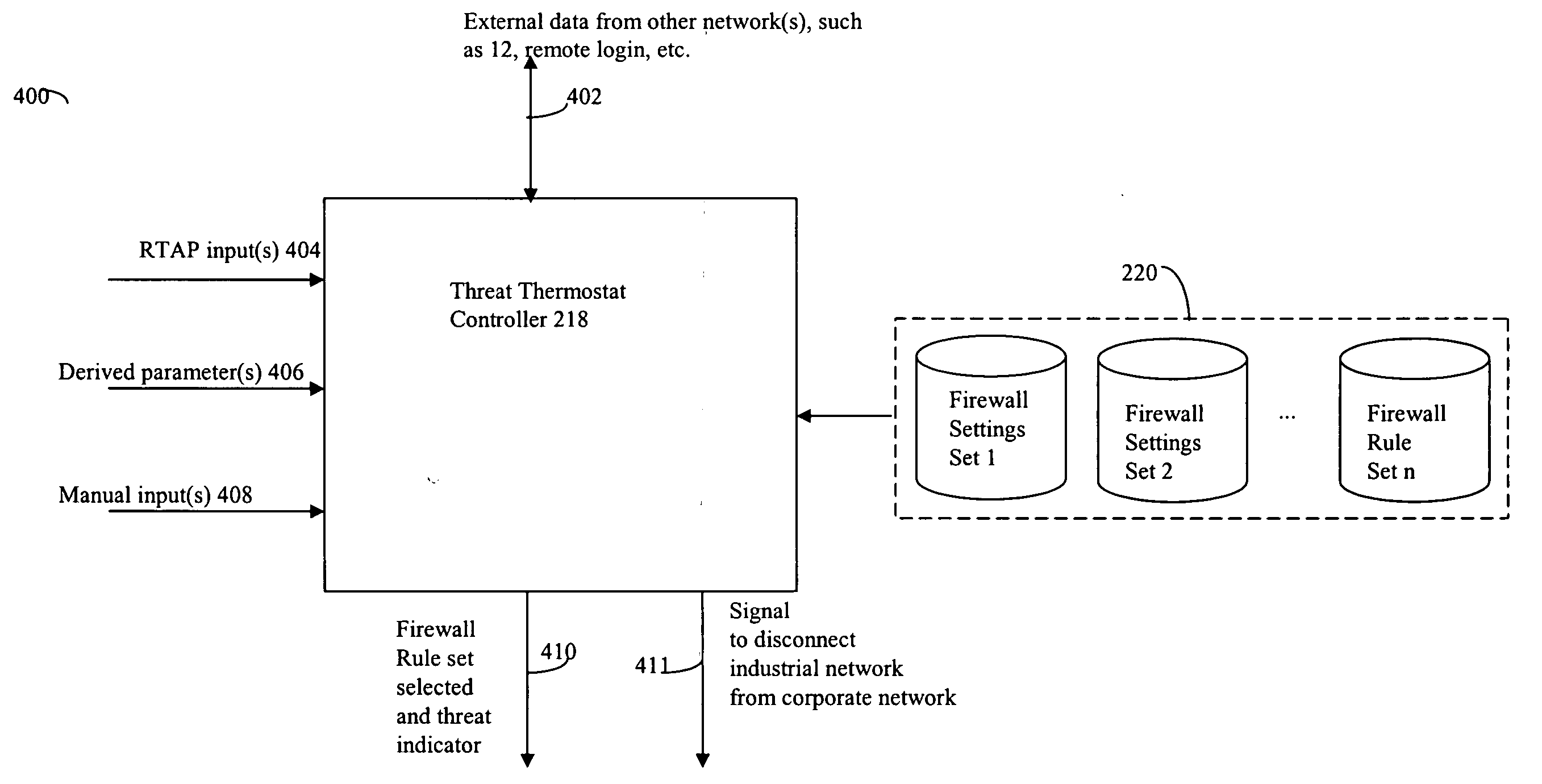
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
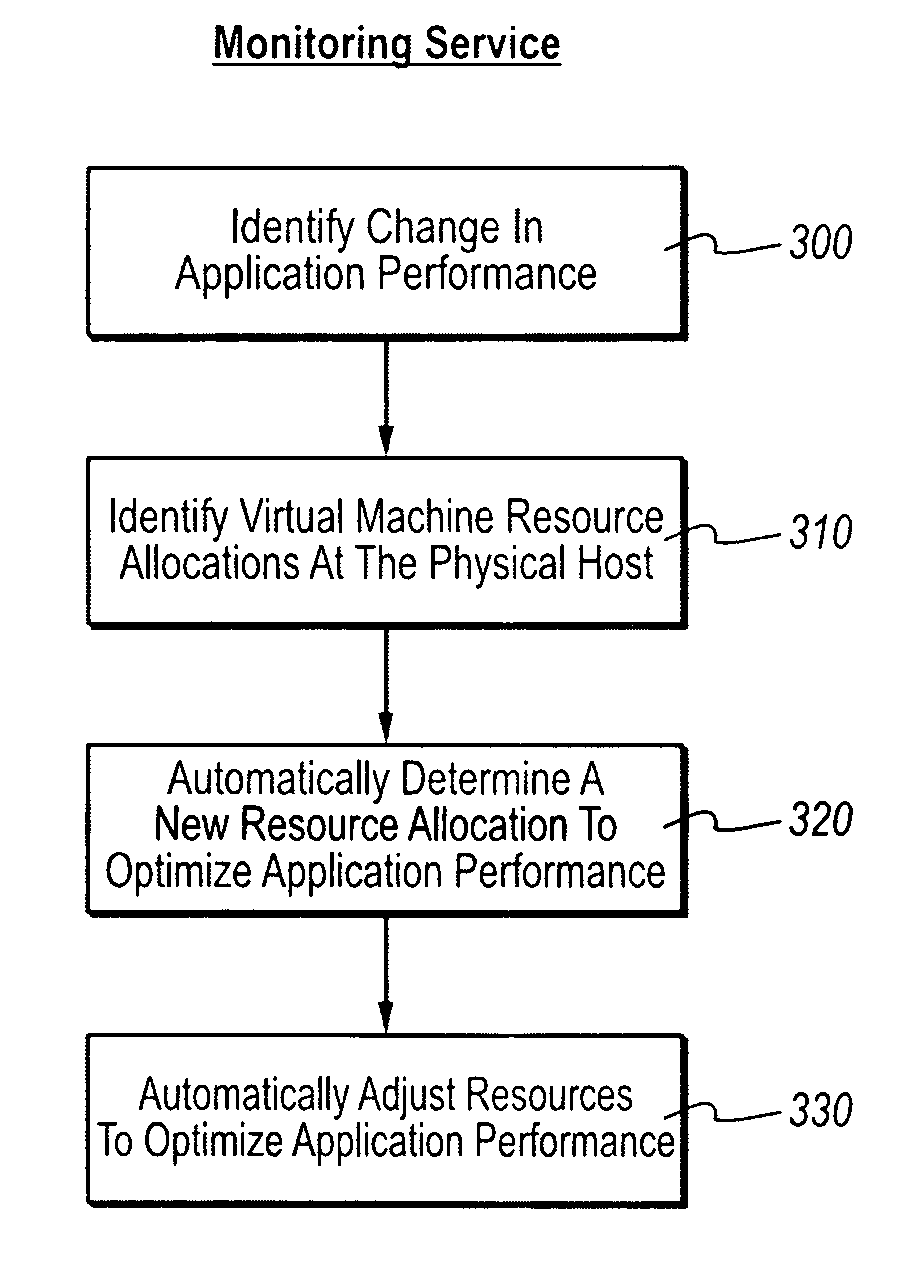
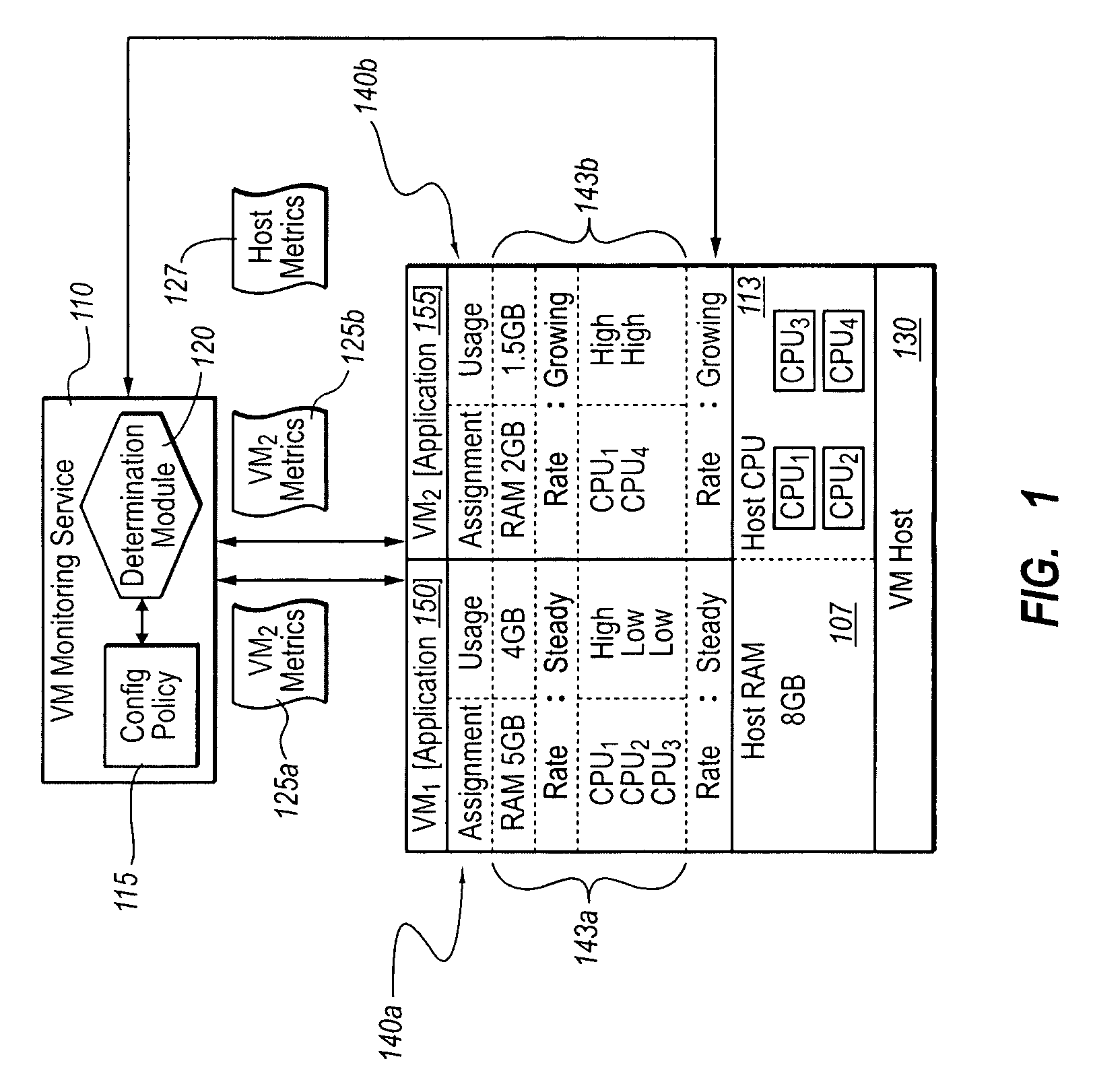
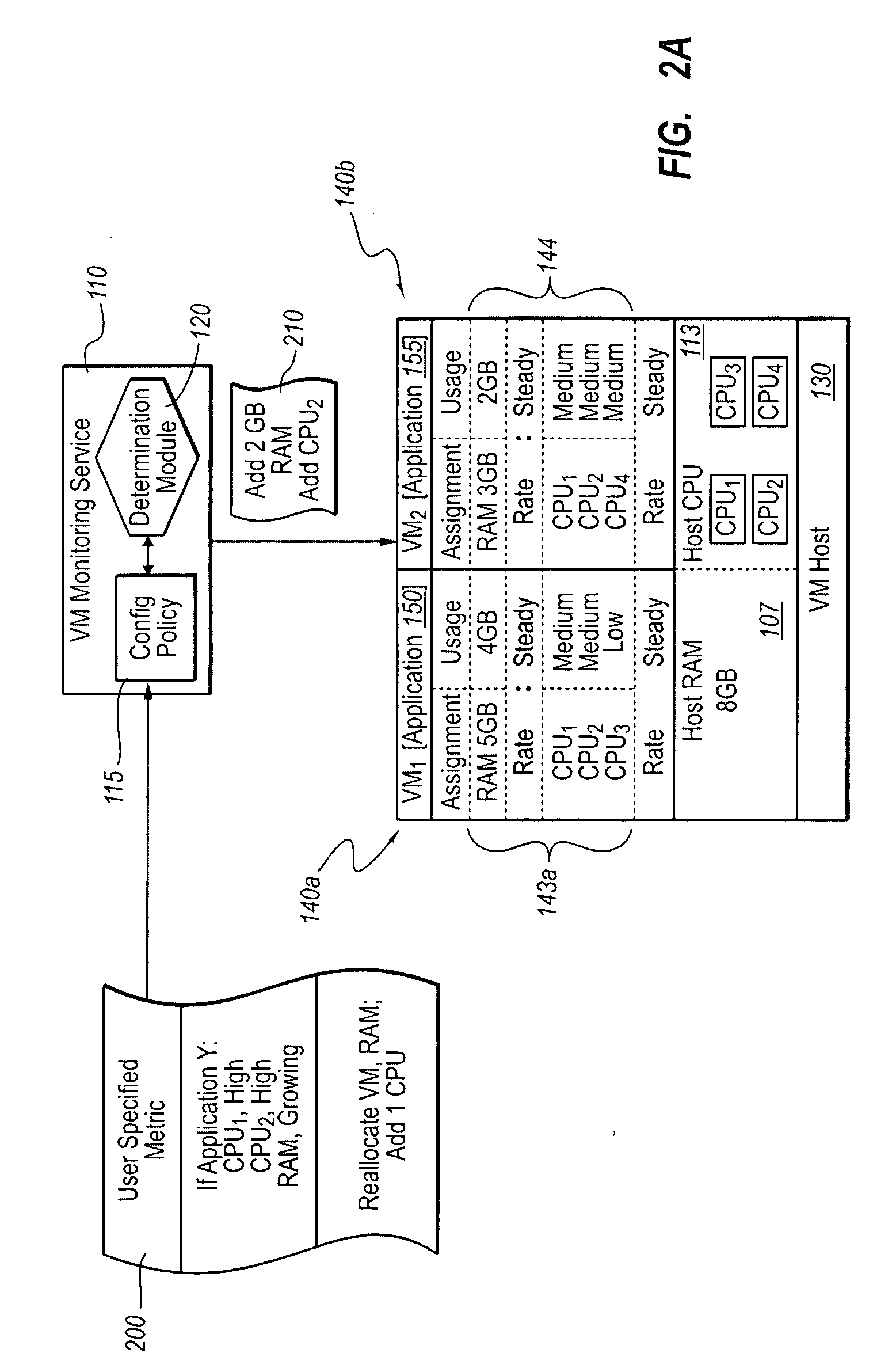
Optimizing application performance on virtual machines automatically with end-user preferences
InactiveUS20090265707A1Improve performanceError detection/correctionMultiprogramming arrangementsUser inputResource utilization
A virtual machine management / monitoring service can be configured to automatically monitor and implement user-defined (e.g., administrator-defined) configuration policies with respect to virtual machine and application resource utilization. In one implementation, the monitoring service can be extended to provide user-customized alerts based on various particularly defined events that occur (e.g., some memory or processing threshold) during operation of the virtual machines and / or application execution. The user can also specify particularly tailored solutions, which can include automatically reallocating physical host resources without additional user input on a given physical host, or moving / adding virtual machines on other physical hosts. For example, the monitoring service can be configured so that, upon identifying that a virtual machine's memory and processing resources are maxed out and / or growing, the monitoring service adds memory or processing resources for the virtual machine, or adds a new virtual machine to handle the load for the application program.
Owner:MICROSOFT TECH LICENSING LLC
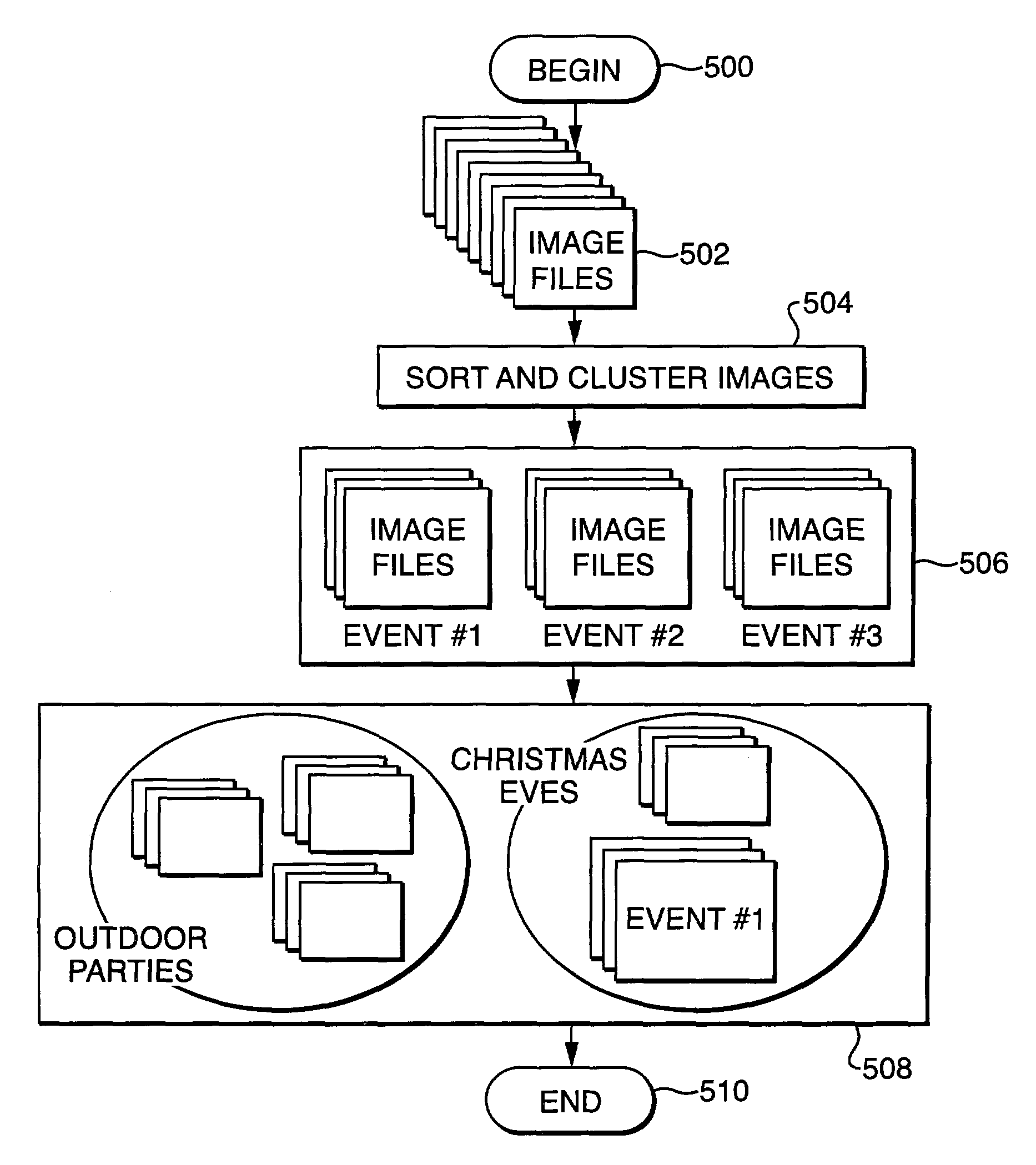
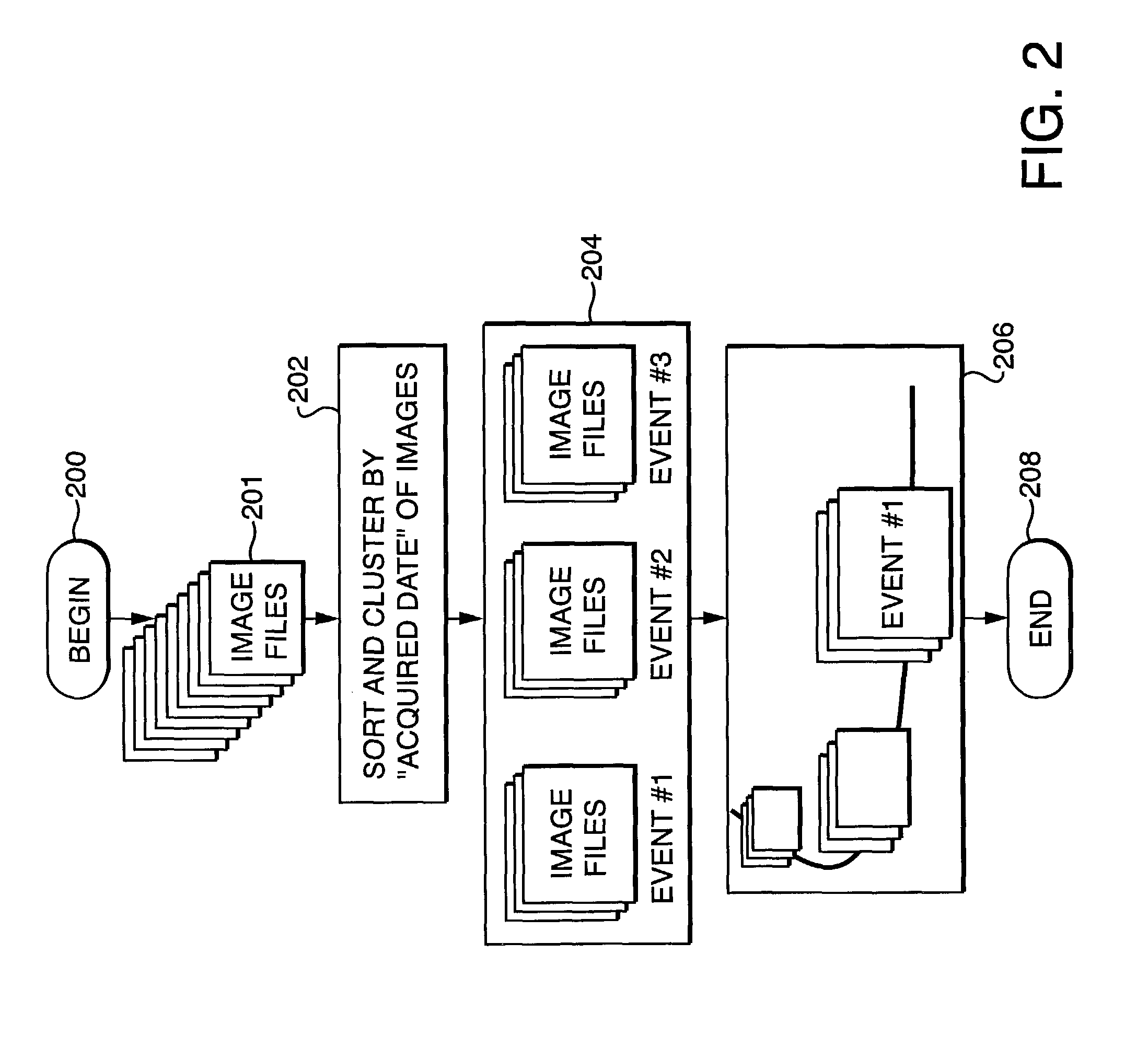
Method and apparatus for archiving and visualizing digital images
ActiveUS7970240B1SuperbEasy to findCharacter and pattern recognitionStill image data indexingGraphicsGraphical user interface
A computer based, digital image management system that visually presents an entire archive in a manner that facilitates easy, non-textual, searching for specific images. The system consists of two main elements; a file management methodology, and a graphical user interface. The file management method utilizes reference files that contain multiple properties (metadata) relating to each image file. Image files are grouped into a multiplicity of collections based on user-defined associations of the properties. The graphical user interface visually represents the groups of image files on 2-dimensional or 3-dimensional graphic metaphors. In addition, the graphical interface uses multiple display variables such as icons, mnemonics, size, movement, color, and luminance to signify relationships between groups, and / or communicate key properties of individual or groups of images.
Owner:GOOGLE LLC
Relevancy of advertising material through user-defined preference filters, location and permission information
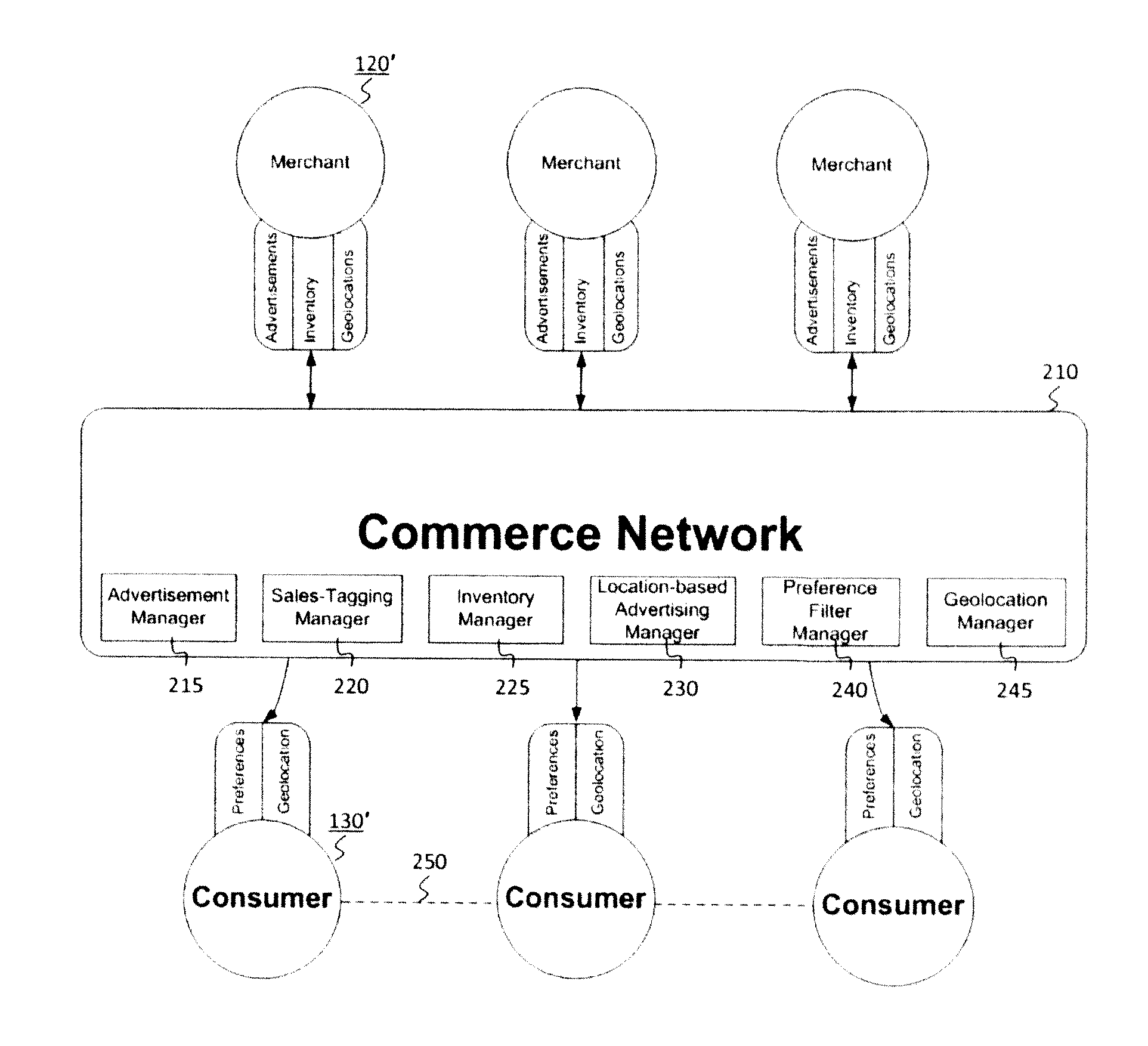
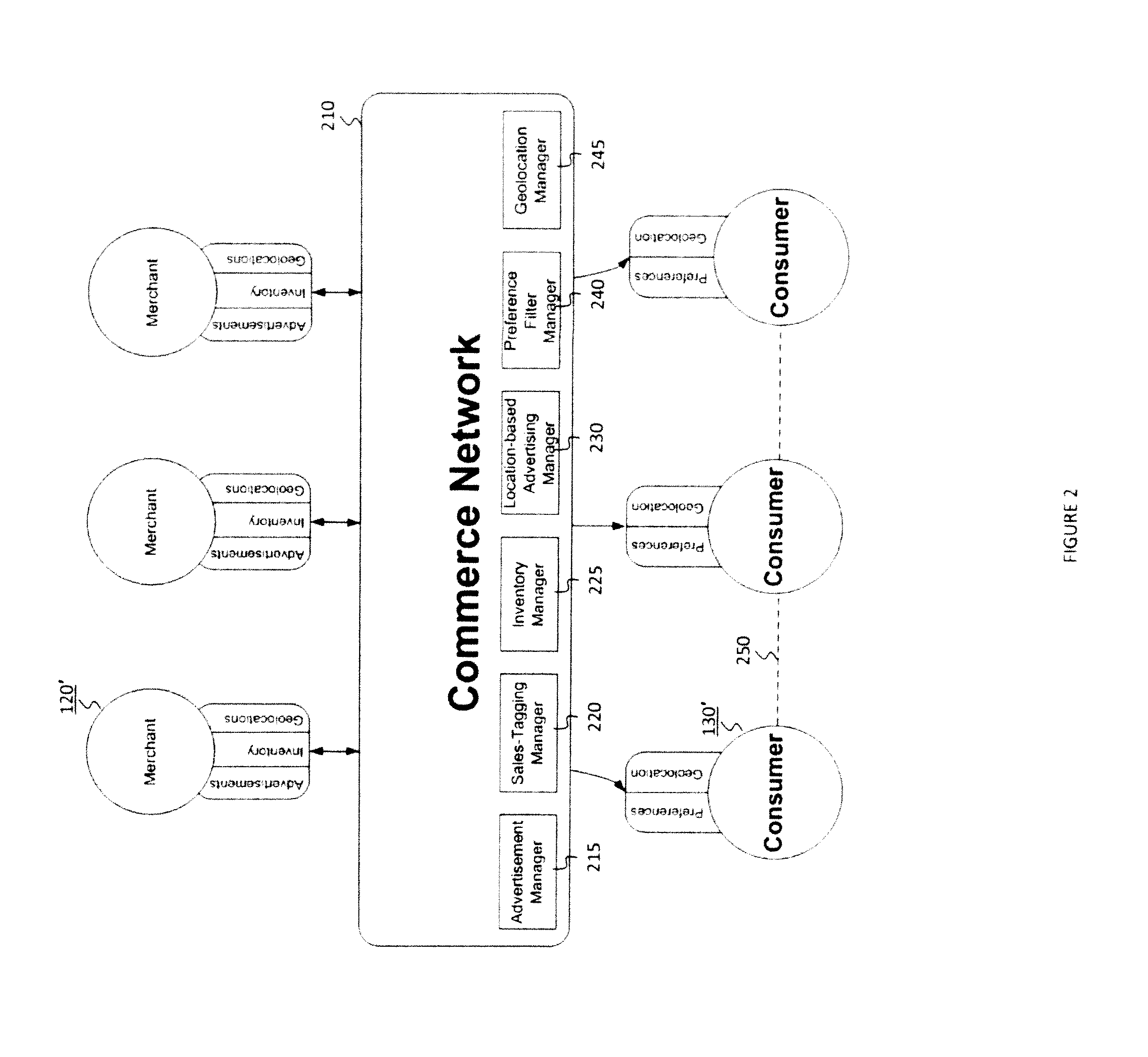
The present invention provides methods to improve the relevancy of rendered advertising material to one or more consumers based on user-defined preferences, geolocation, and user-granted permission. The present invention achieves this through the presentation of exemplary methods for: i) the consolidation of advertisement information to include description, inventory, price, quantity and geolocation information of one or more merchants in a commerce network; ii) the delivery of relevant advertising material to one or more consumers using preference filters that can specify one or more merchants, merchant locations, products and services, and / or regions of interest at any time; and, iii) the presentation of location-based advertisements that are based on consumer-based permission and preference filters. These methods improve the user-targeting, geographic and time relevancy of advertisements by connecting merchants with relevant consumers who are looking to purchase items at that point in time.
Owner:SHEIKH OMAR M
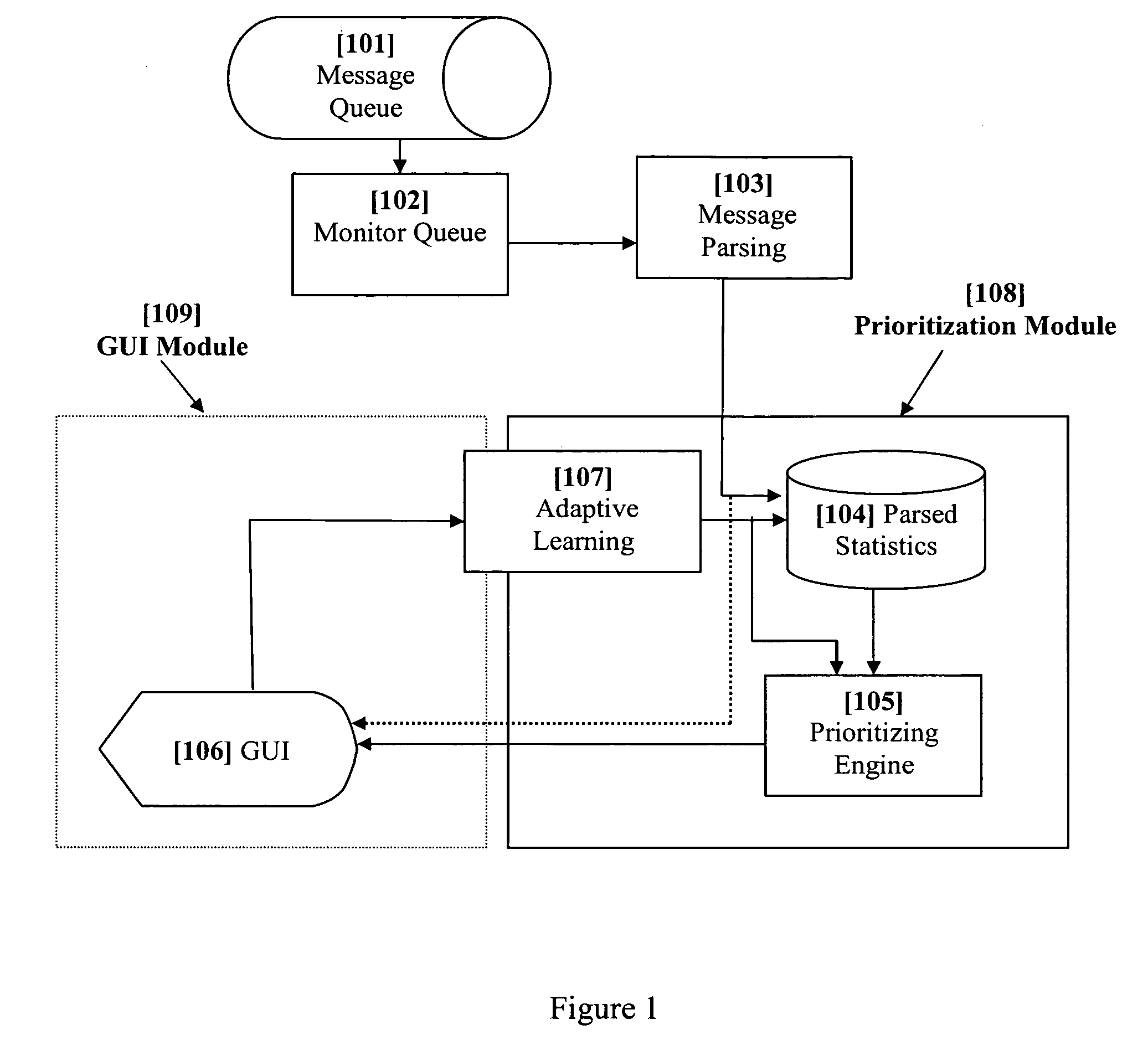
System and method for dynamic adaptive user-based prioritization and display of electronic messages
InactiveUS20060010217A1Improve response efficiencyReduce effortMultiple digital computer combinationsTransmissionAdaptive learningStructured content
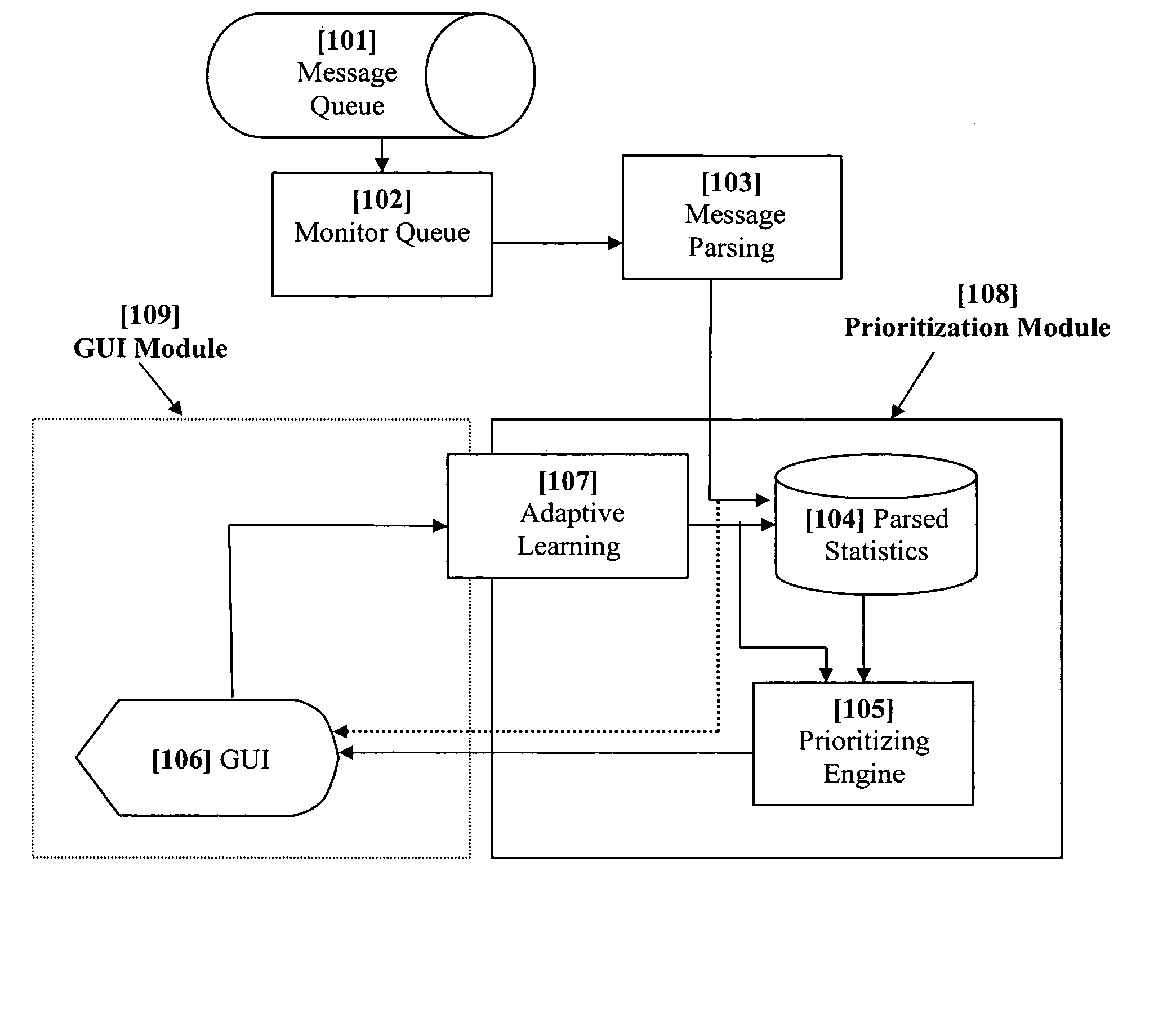
A method and system that dynamically ranks electronic messages based on their situational and inherent dimensions, which are judged by a set of filters. These filters evaluate the different elemental metadata constituting a message and produce a priority value based on filters relevance and importance. The system iterates through queued messages, examine the structured content for expected attributes, statistically analyze unstructured content, apply dynamically weighted rules and policies to deliver a priority ranking, and then display the message and its vital attributes in accordance with the priority ranking. The system also adaptive learns and adjusts its weighted rules and policies to permit priority ranking to change on real-time or interval-based (may be user-defined) schedule. The system includes a GUI for increasing reading and processing efficiency. The GUI performs supervised and unsupervised learning from the user's behaviors, and displays messages in accordance with their priority classification.
Owner:MESSAGEMIND LLC
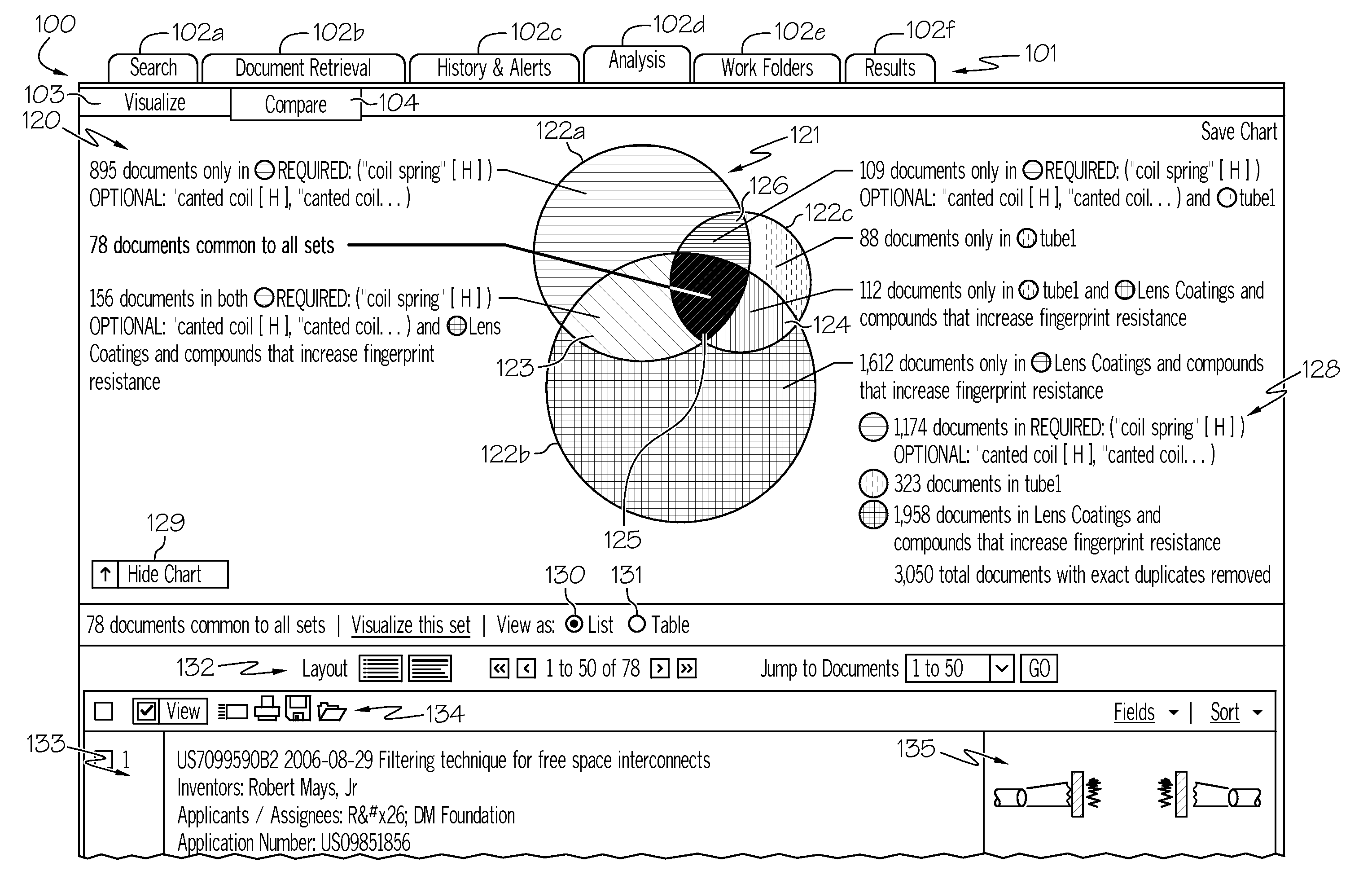
Methods for electronic document searching and graphically representing electronic document searches
Methods for electronic document searching and graphically representing an electronic document search are disclosed. In one embodiment, a method of graphically representing electronic document searches includes generating a Venn diagram for display on a graphic display device including a first circle that represents a first document set and a second circle that represents a second document set. The first circle overlaps the second circle in an overlap region depicting common electronic documents that are within the first document set and the second document set. The method further includes generating a first visualization chart from the first circle and a second visualization chart from the second circle. The first visualization chart and the second visualization chart depict proportions of the first document set and the second document set according to a user-defined parameter. Additional search queries may be suggested based on similar topics within electronic documents within the Venn diagram.
Owner:RELX INC
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
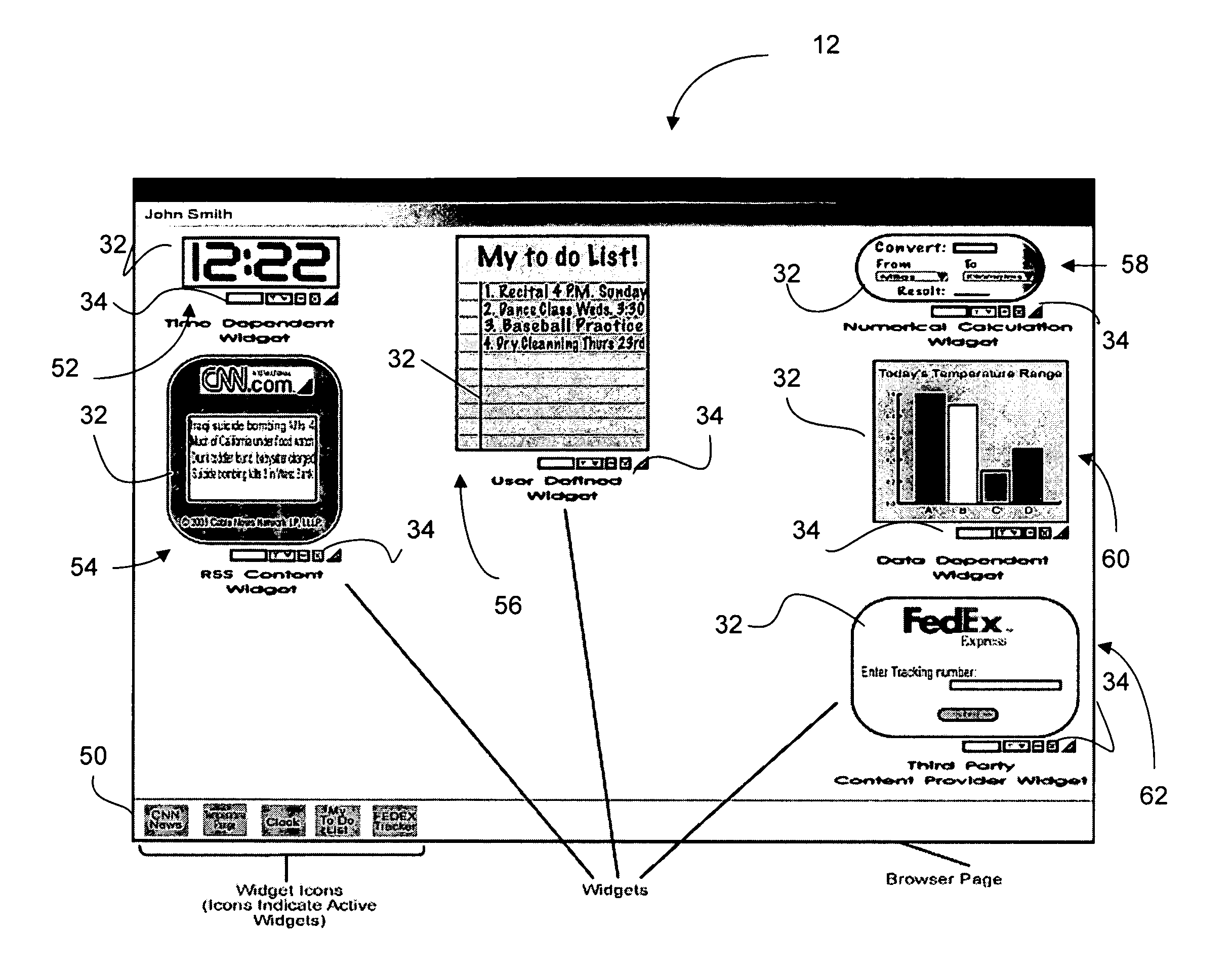
Service for generation of customizable display widgets
A system for presenting dynamically generated images in a computing environment is provided. The system generates visual elements, such as widgets, for example, by combining image data, user-defined data which may include alphanumeric data, and real-time data indicative of current conditions. The widgets may be implemented in a purely server-side application environment which alleviates the need for any installation of client software on the client computing device.
Owner:FELLMAN BARRY
Extraction of facts from text
InactiveUS20050108630A1Digital data information retrievalDigital computer detailsPattern matchingText annotation
A fact extraction tool set (“FEX”) finds and extracts targeted pieces of information from text using linguistic and pattern matching technologies, and in particular, text annotation and fact extraction. Text annotation tools break a text, such as a document, into its base tokens and annotate those tokens or patterns of tokens with orthographic, syntactic, semantic, pragmatic and other attributes. A user-defined “Annotation Configuration” controls which annotation tools are used in a given application. XML is used as the basis for representing the annotated text. A tag uncrossing tool resolves conflicting (crossed) annotation boundaries in an annotated text to produce well-formed XML from the results of the individual annotators. The fact extraction tool is a pattern matching language which is used to write scripts that find and match patterns of attributes that correspond to targeted pieces of information in the text, and extract that information.
Owner:LEXISNEXIS GROUP
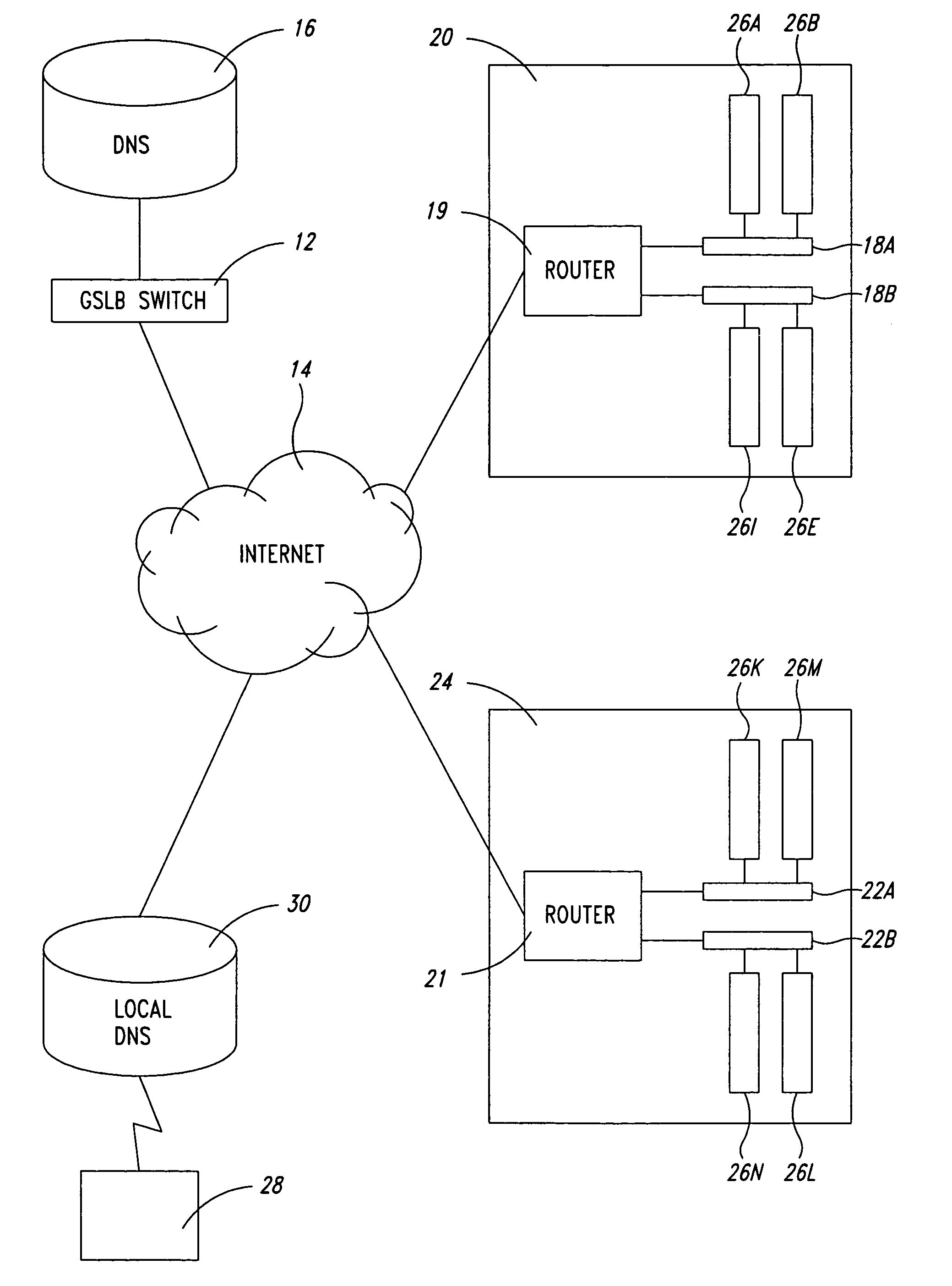
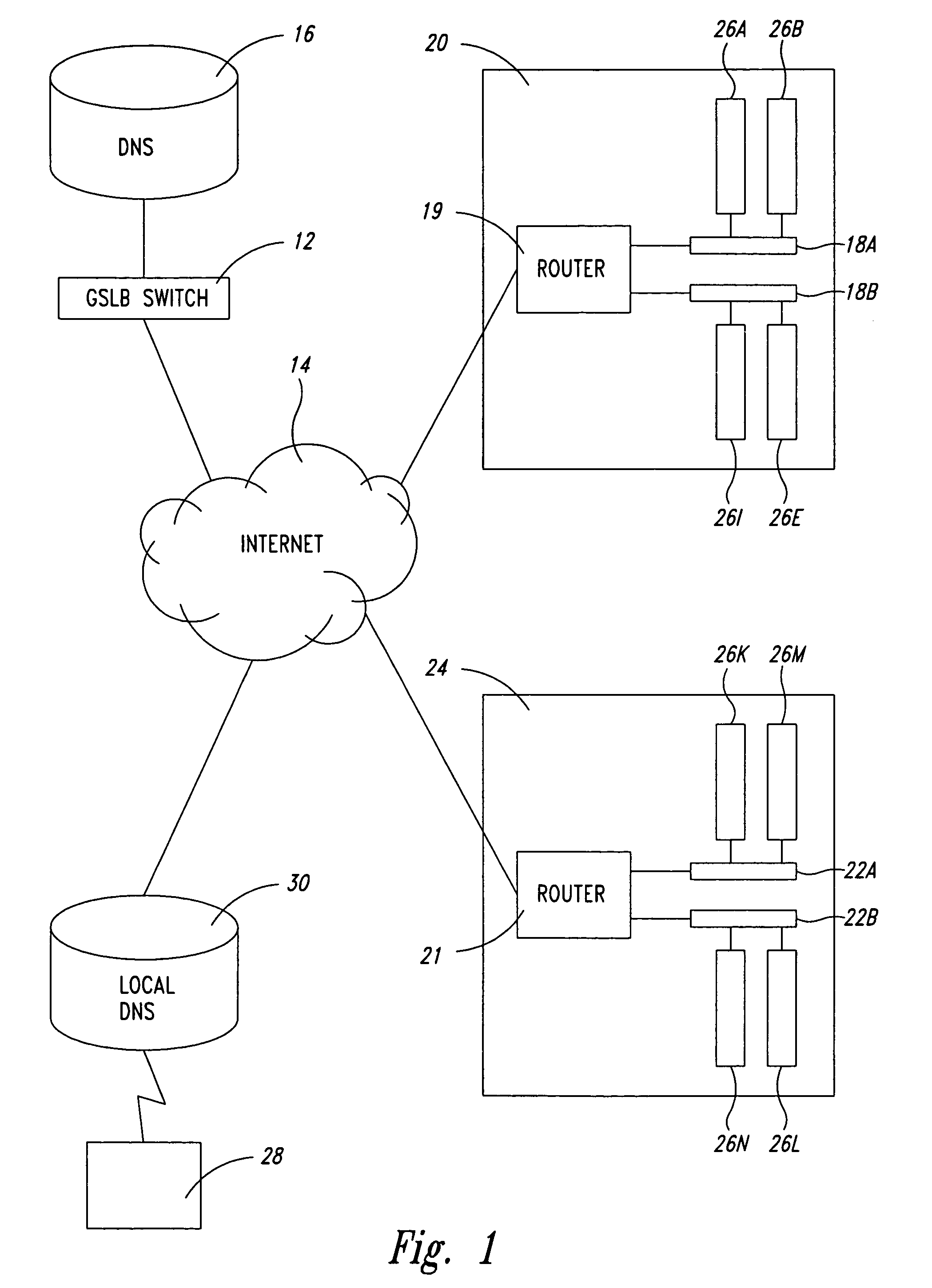
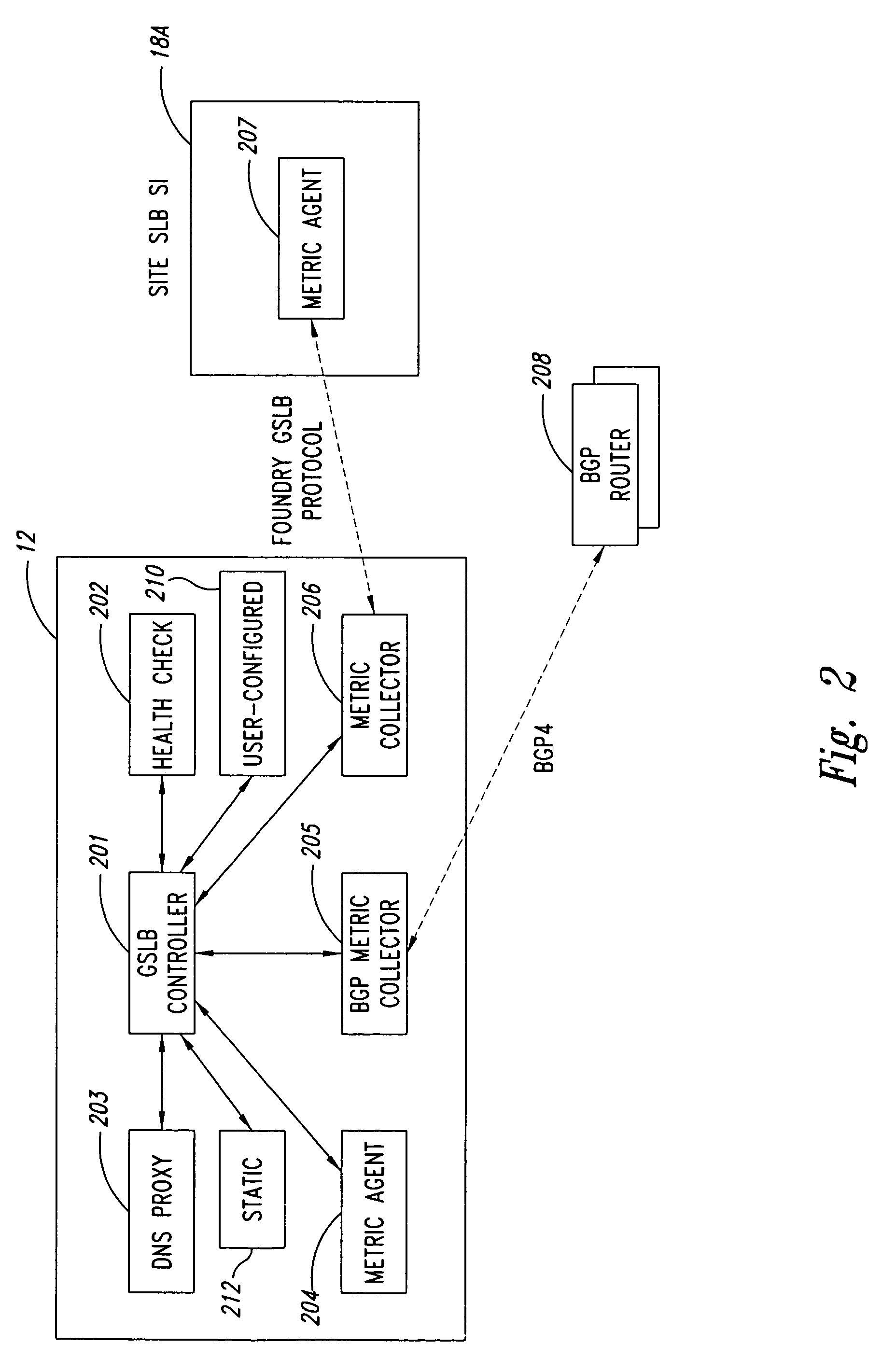
Configurable geographic prefixes for global server load balancing
ActiveUS7496651B1Traffic loadMultiprogramming arrangementsMultiple digital computer combinationsGeographic regionsIp address
In a load balancing system, user-configurable geographic prefixes are provided. IP address prefix allocations provided by the Internet Assigned Numbers Authority (IANA) and associated geographic locations are stored in a first, static database in a load balancing switch, along with other possible default geographic location settings. A second, non-static database stores user-configured geographic settings. In particular, the second database stores Internet Protocol (IP) address prefixes and user-specified geographic regions for those prefixes. The specified geographic region can be continent, country, state, city, or other user-defined region. The geographic settings in the second database can override the information in the first database. These geographic entries help determine the geographic location of a client and host IP addresses, and aid in directing the client to a host server that is geographically the closest to that client.
Owner:AVAGO TECH INT SALES PTE LTD
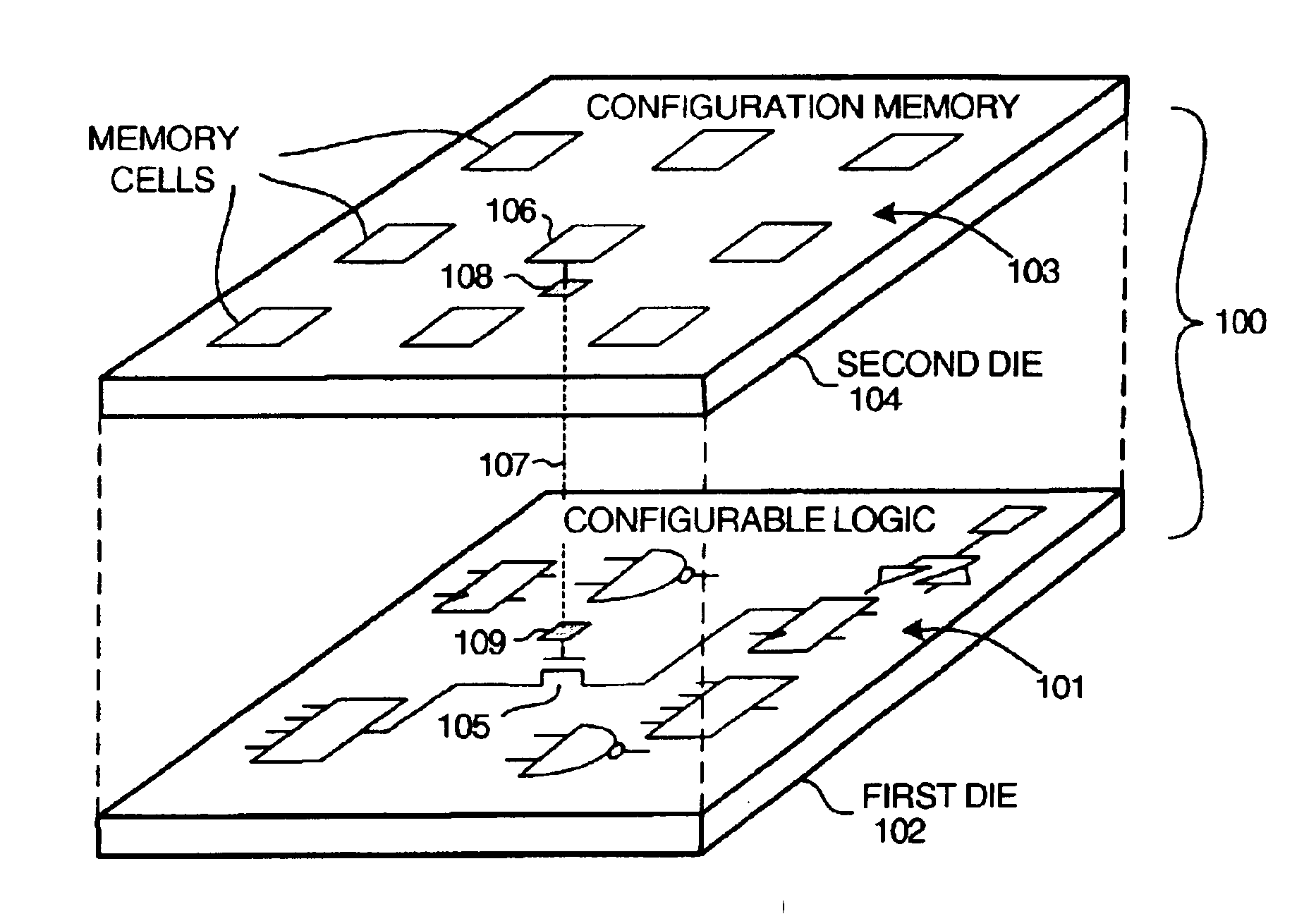
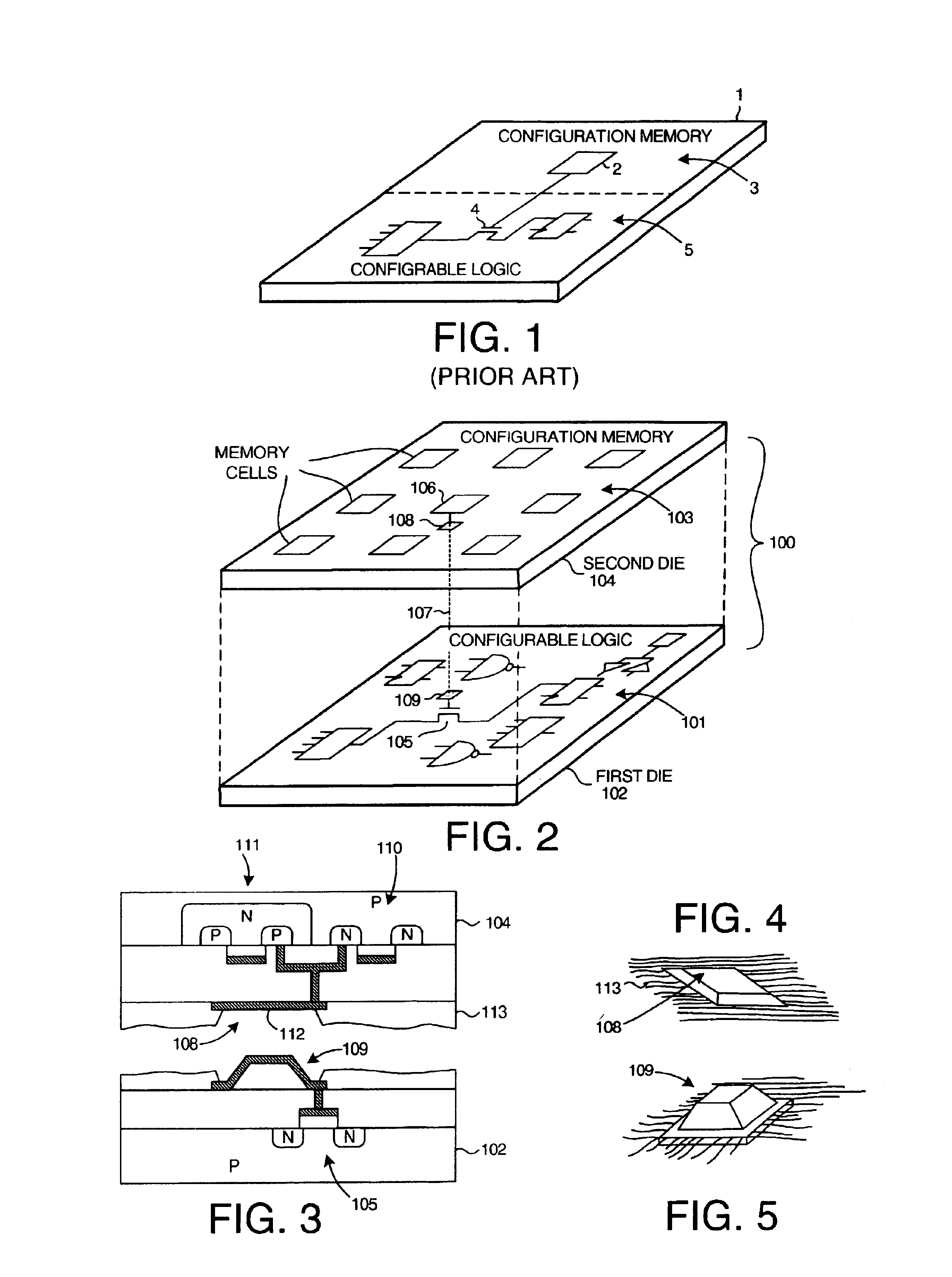
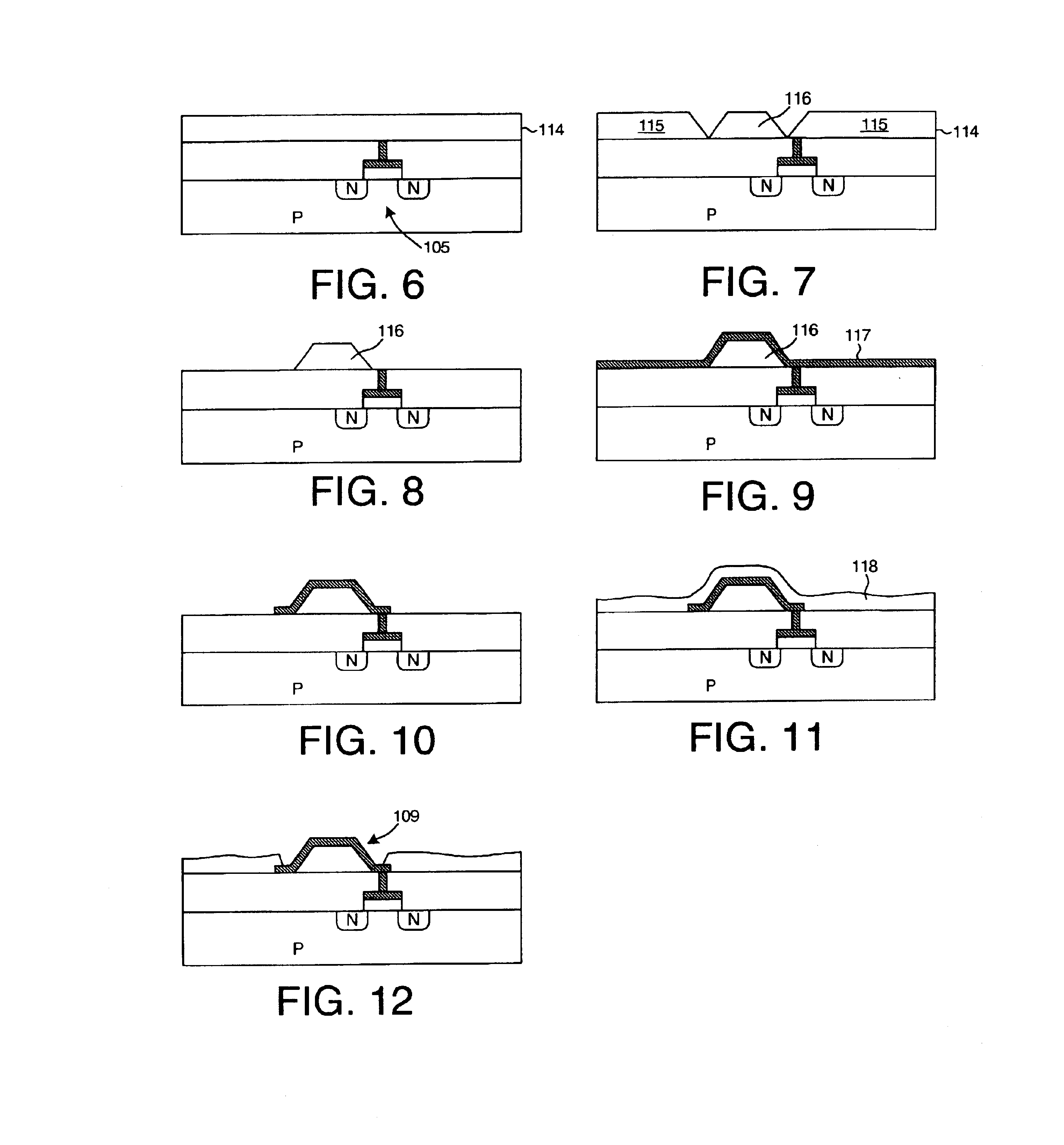
Multi-chip programmable logic device having configurable logic circuitry and configuration data storage on different dice
InactiveUS6917219B2Increase volumeIncrease productionSemiconductor/solid-state device detailsSolid-state devicesProgrammable logic deviceLogical part
The circuitry of a programmable logic device (for example, an FPGA) includes a configurable logic portion and a configuration memory. The configuration memory stores configuration data that configures the configurable logic portion to realize a user-defined circuit. The configurable logic portion is disposed on a first die whereas the configuration memory is disposed on a second die. The second die is bonded to the first die in stacked relation. Each bit of configuration data passes from the second die to the first die through a pair of micropads. One micropad of the pair is disposed on the first die and the other micropad of the pair is disposed on the second die. When the first die and second die are brought together in face-to-face relation, the two micropads form an electrical connection through which the configuration data bit passes from the second die to the first die.
Owner:XILINX INC
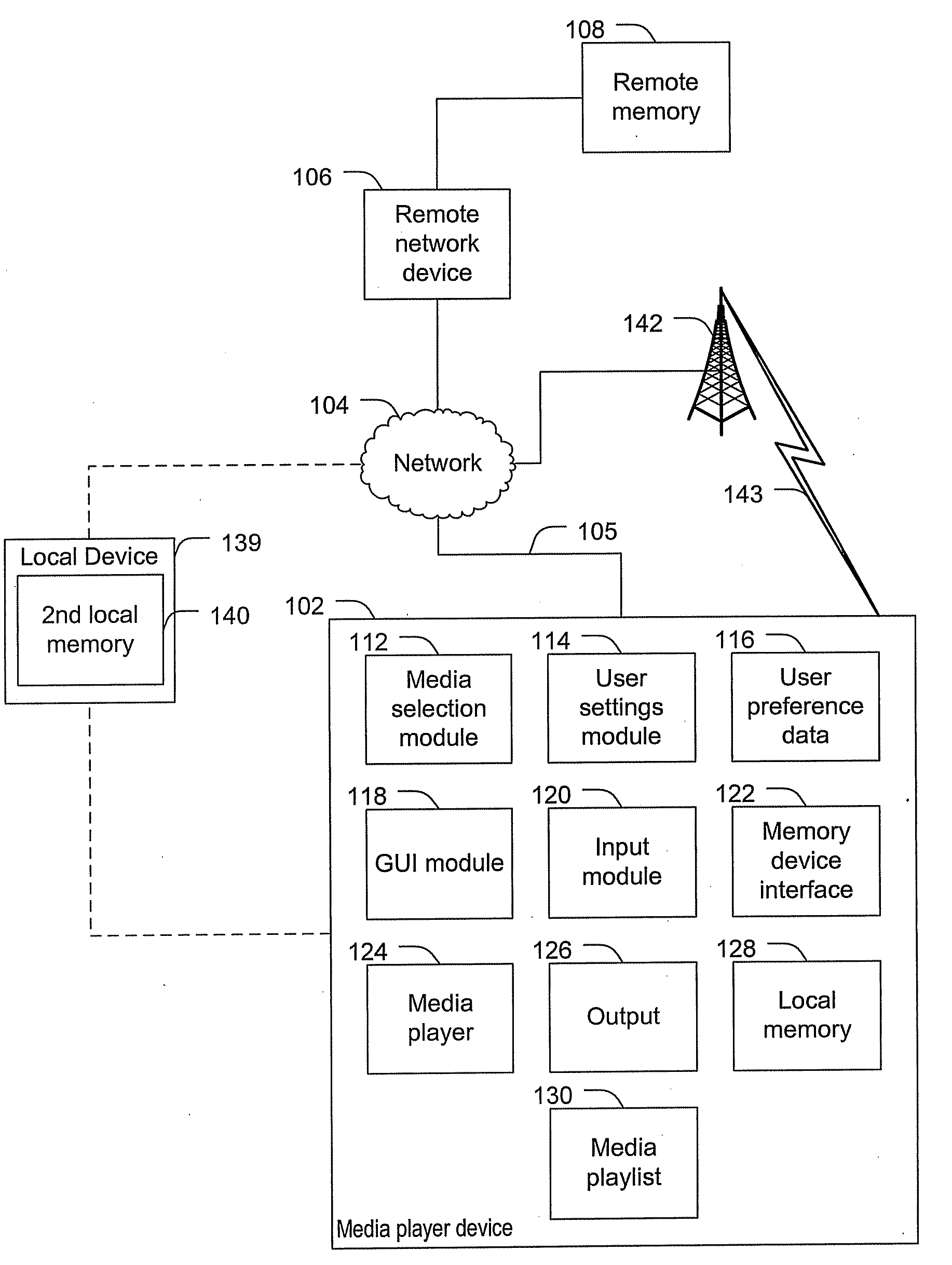
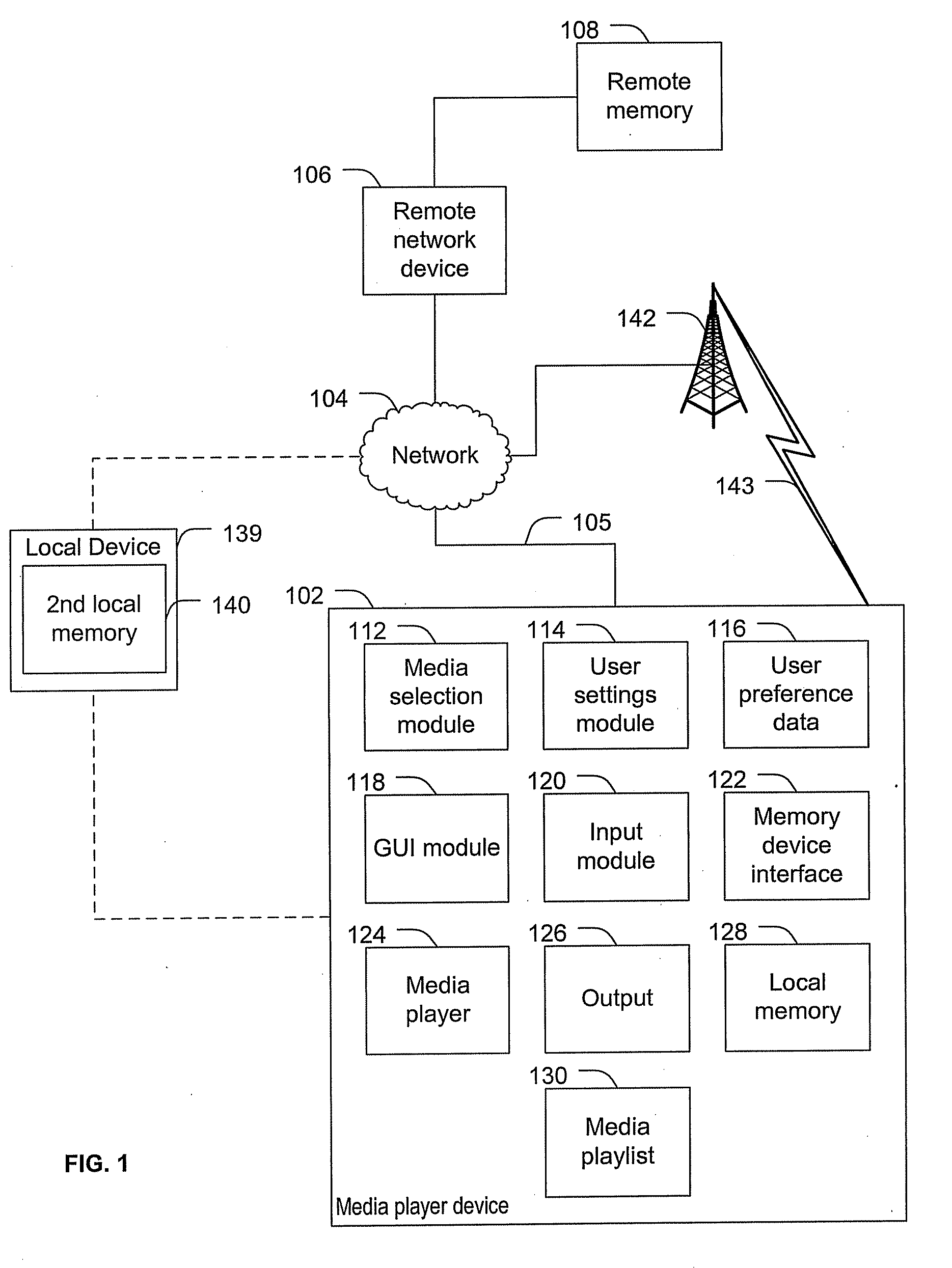
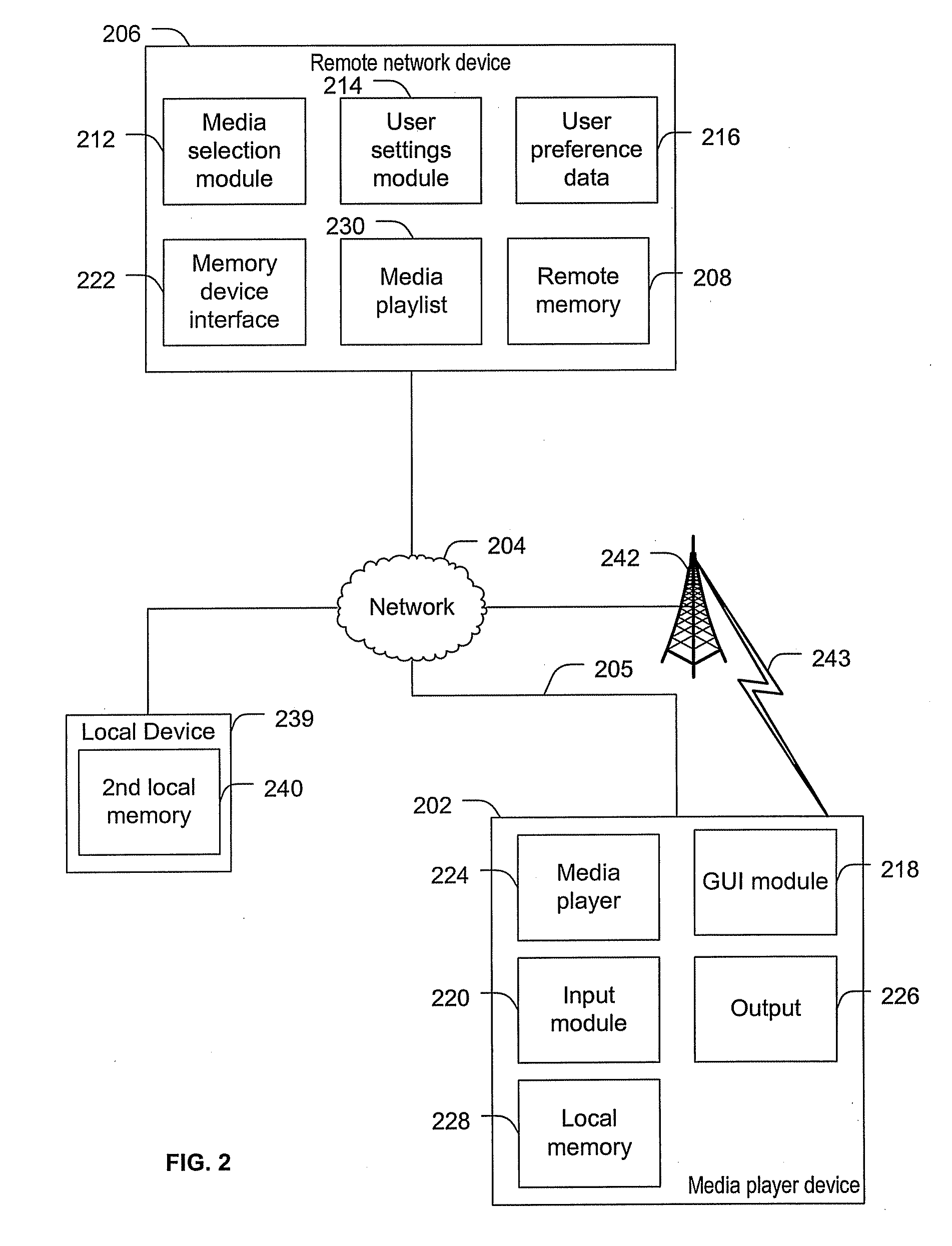
Systems and methods to select media content
ActiveUS20100131895A1Multiple digital computer combinationsSound input/outputUser definedDynamic choice
Systems and methods to select media content are provided. A method includes dynamically selecting content items for presentation via a media player based on user media selection settings. The user media selection settings specify a proportion of a first category of media content to be presented and a proportion of at least one second category of media content to be presented. The at least one second category includes a user defined category. First media content is associated with the first category based on an intrinsic property of the first media content and second media content is associated with the user defined category based on a property that is not intrinsic to the second media content. The method also includes generating an output stream presenting the dynamically selected content items.
Owner:AT&T INTPROP I L P
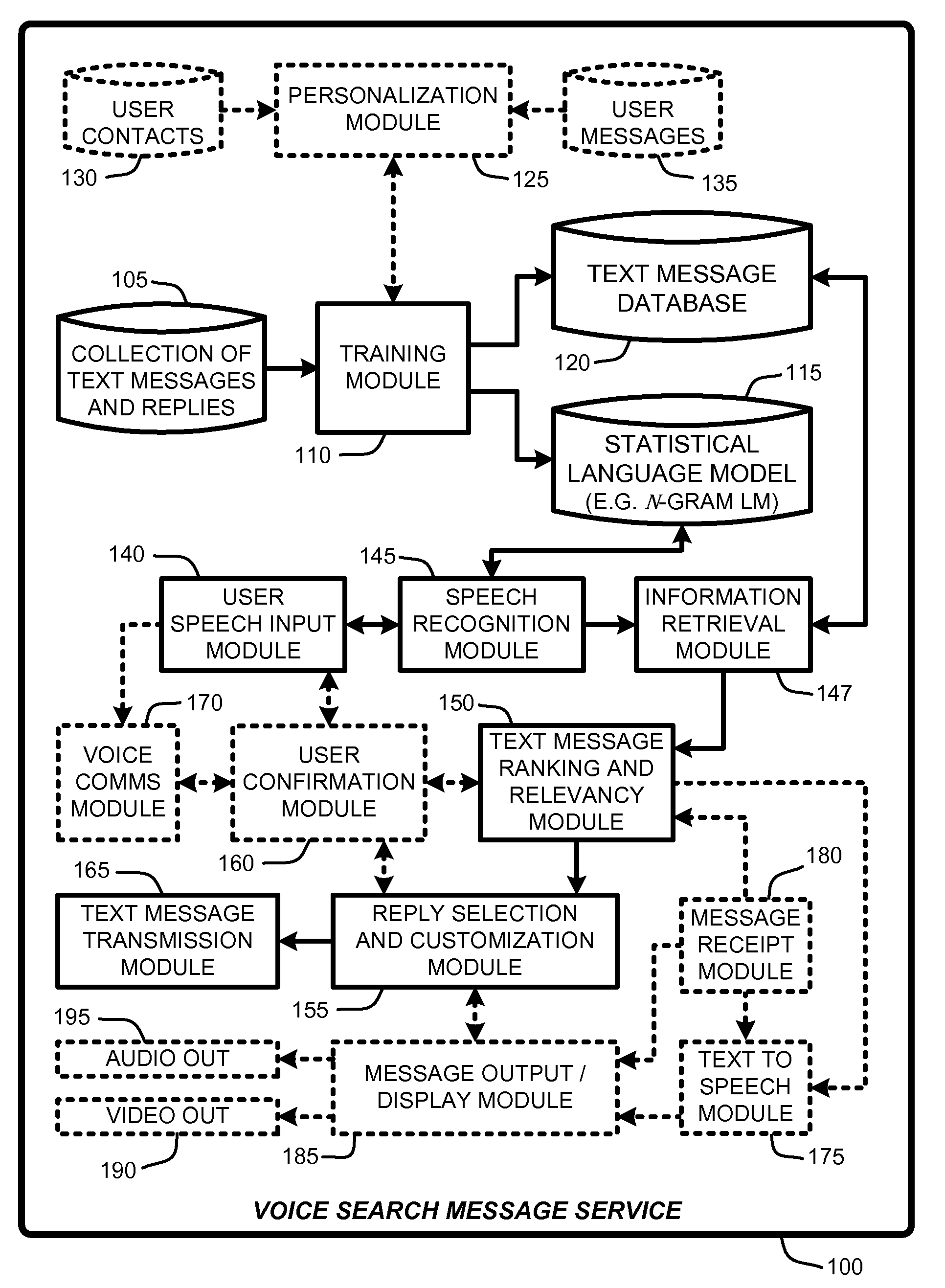
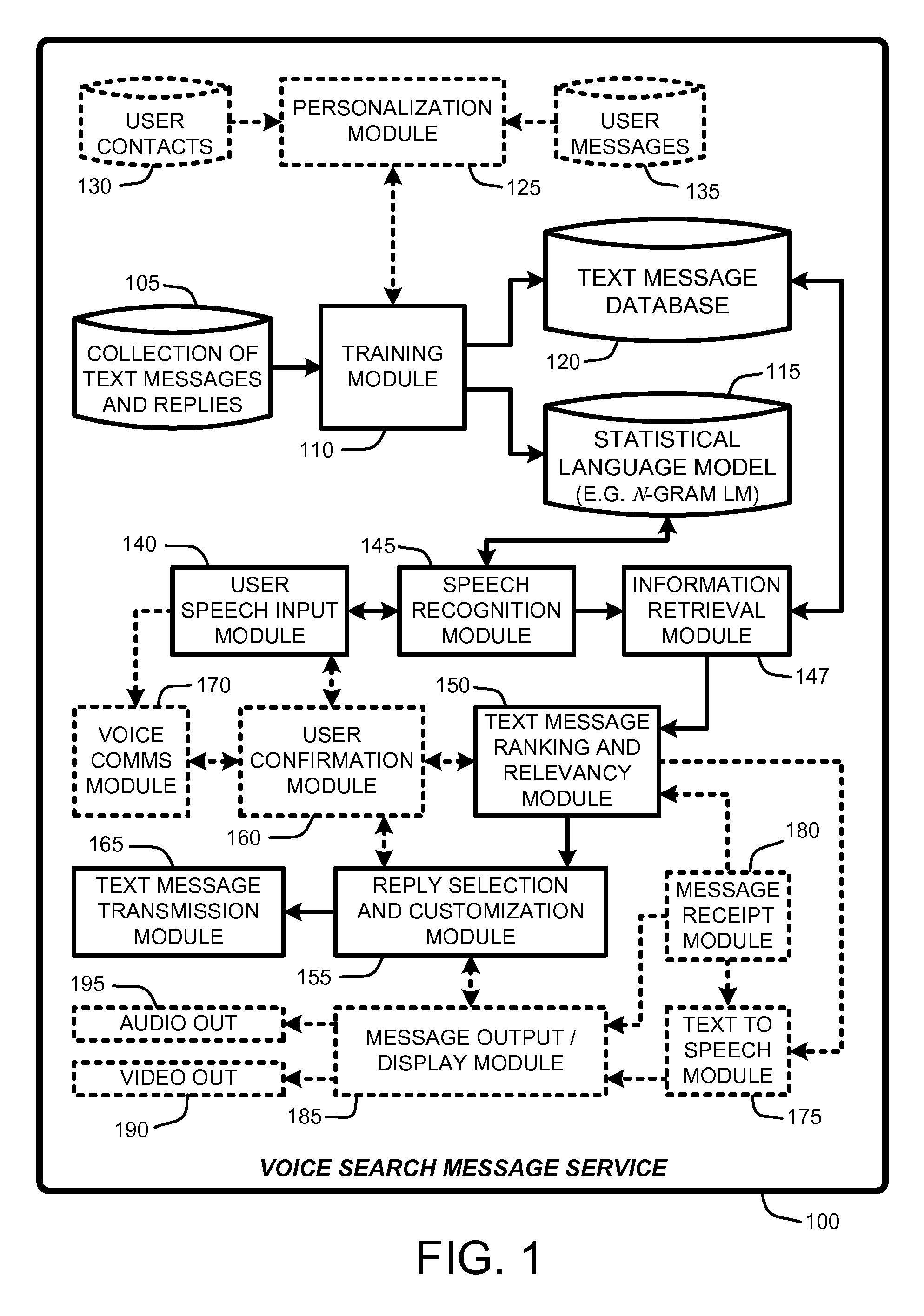
Replying to text messages via automated voice search techniques
Owner:MICROSOFT TECH LICENSING LLC
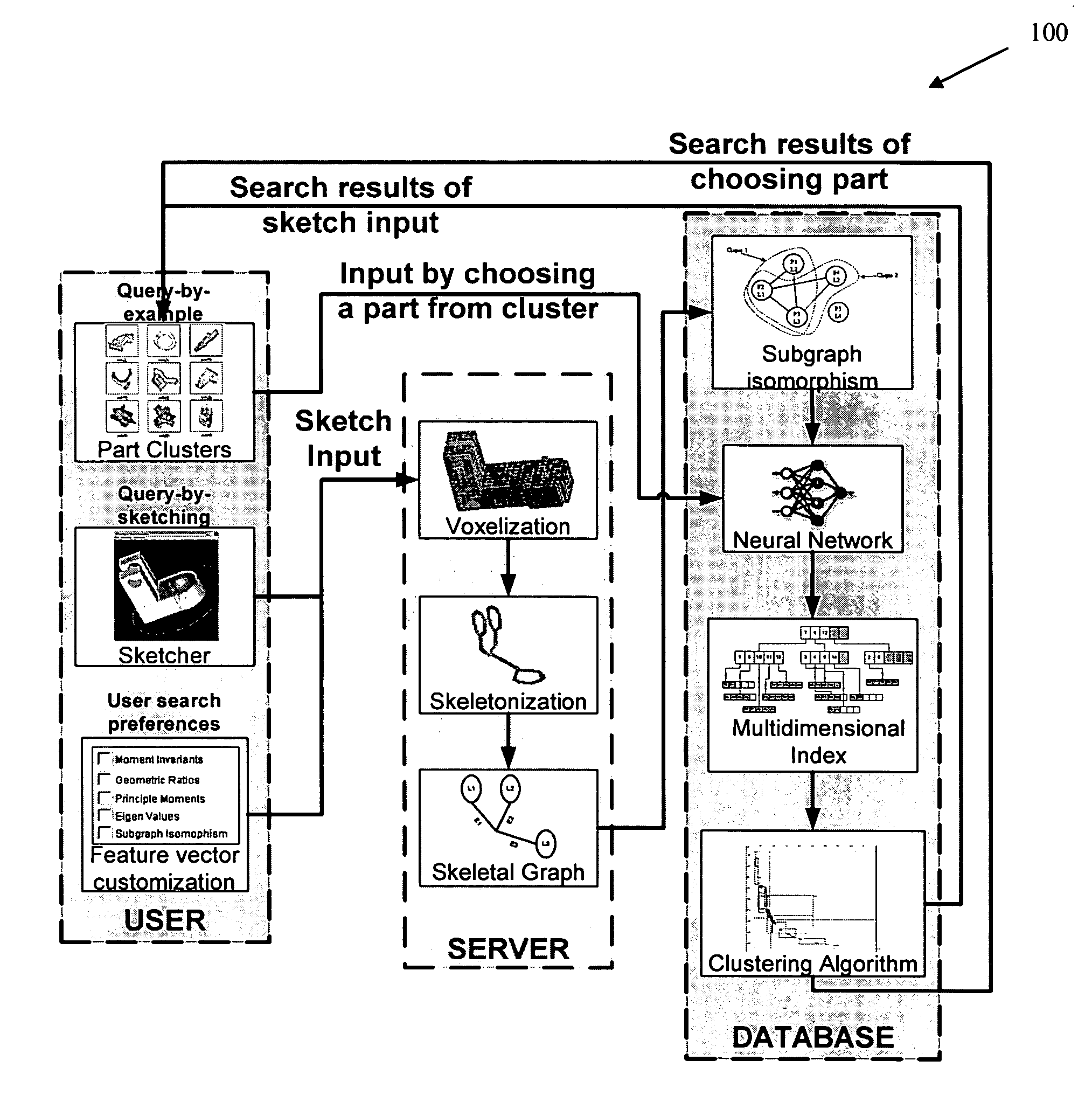
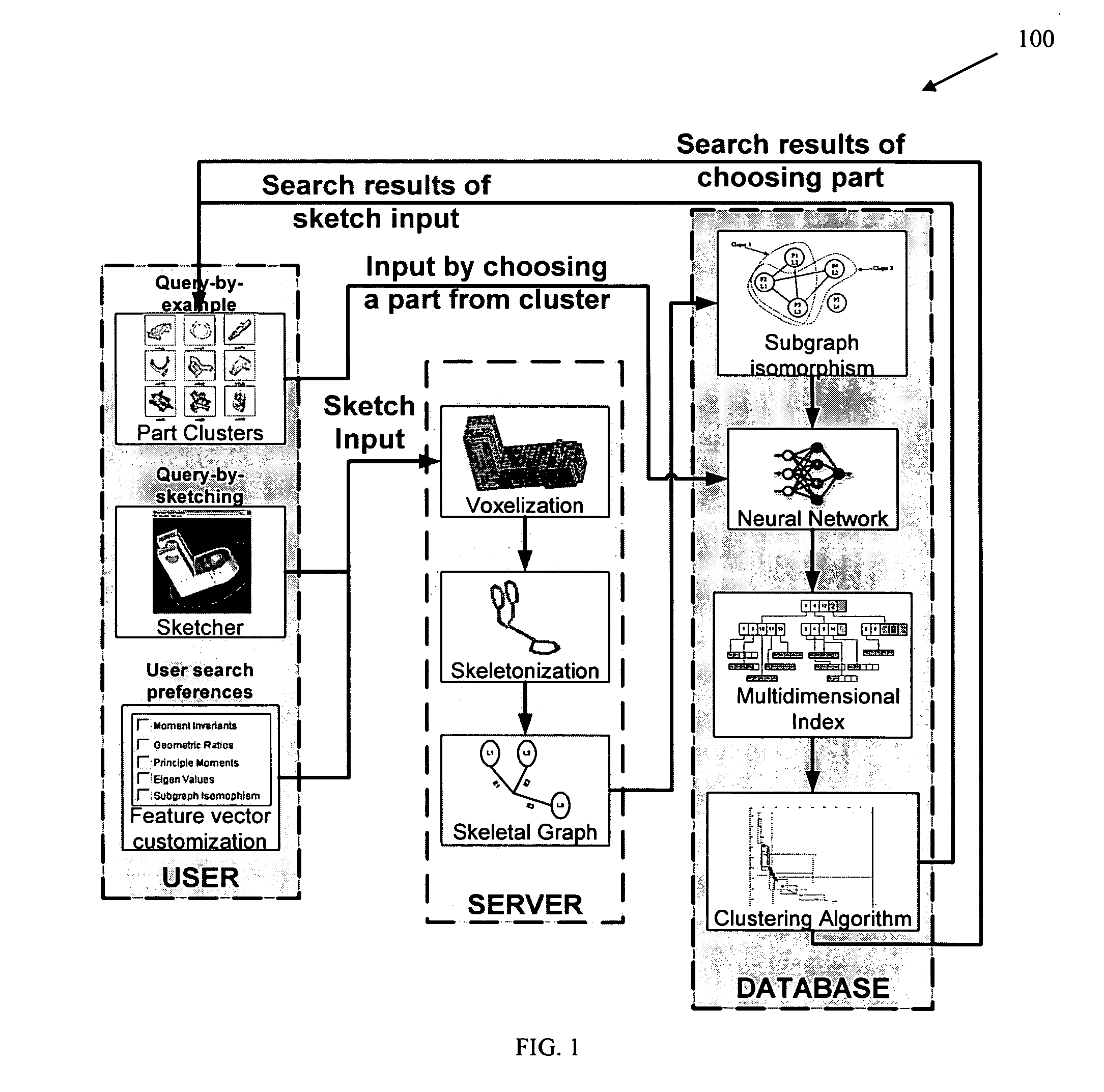
Methods, systems, and data structures for performing searches on three dimensional objects
Techniques are provided for searching on three dimensional (3D) objects across large, distributed repositories of 3D models. 3D shapes are created for input to a search system; optionally user-defined similarity criterion is used, and search results are interactively navigated and feedback received for modifying the accuracy of the search results. Search input can also be given by picking 3D models from a cluster map or by providing the orthographic views for the 3D model. Feedback can be given by a searcher as to which models are similar and which are not. Various techniques adjust the search results according to the feedback given by the searcher and present the new search results to the searcher.
Owner:PURDUE RES FOUND INC
System and methods providing automatic distributed data retrieval, analysis and reporting services
InactiveUS6944662B2Increasing computationalIncreasing storage burdenMultiple digital computer combinationsWebsite content managementData processing systemPush and pull
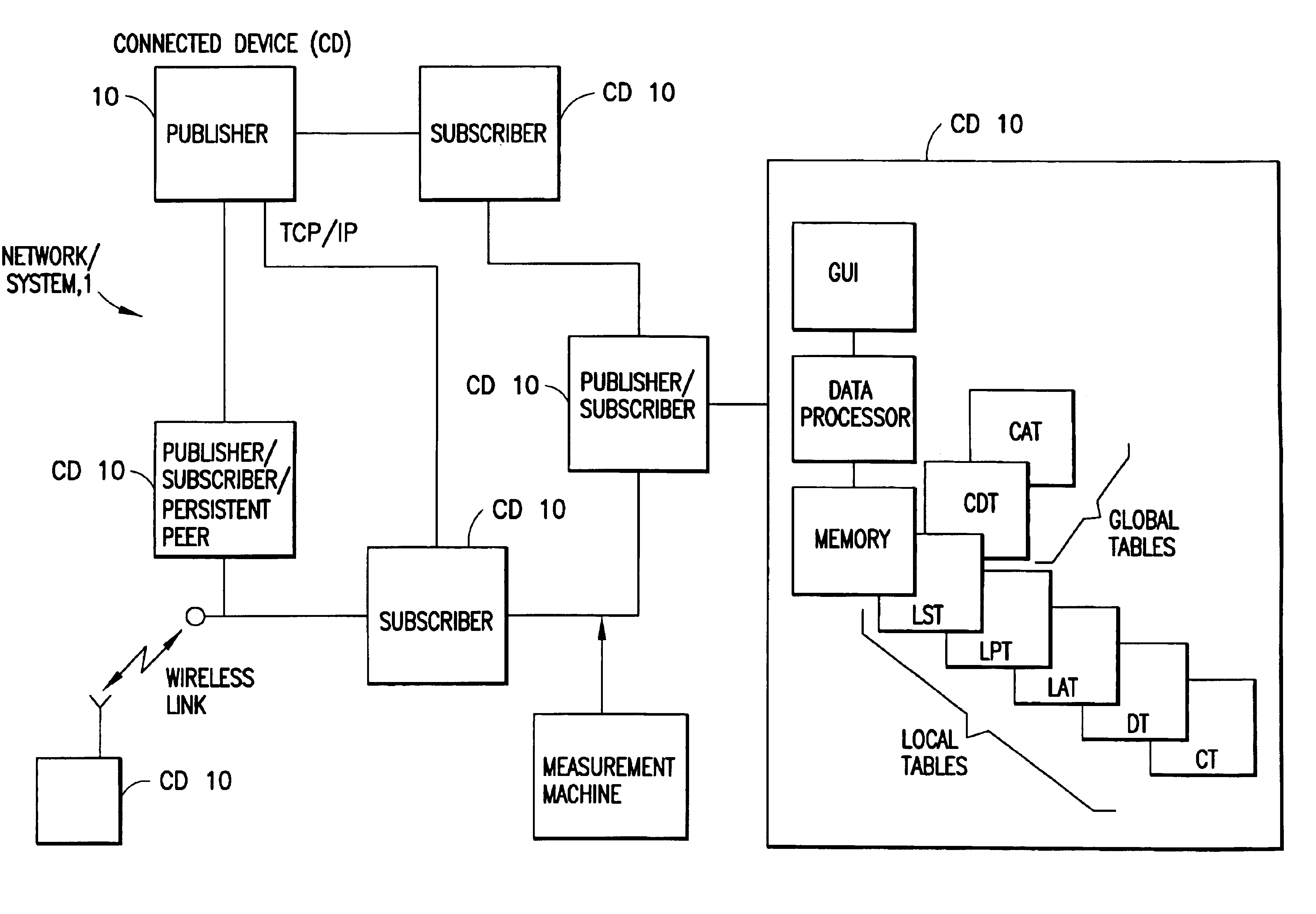
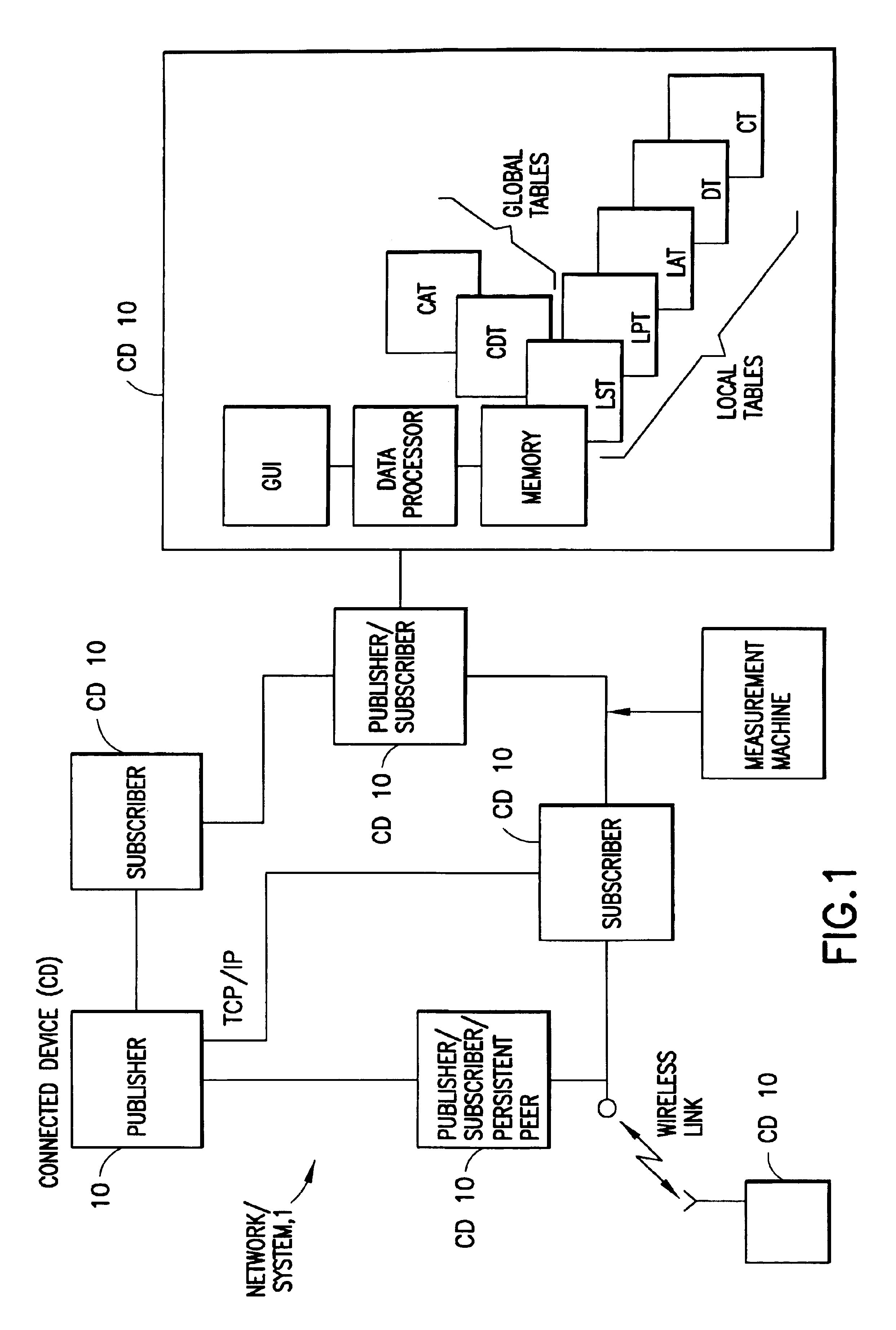
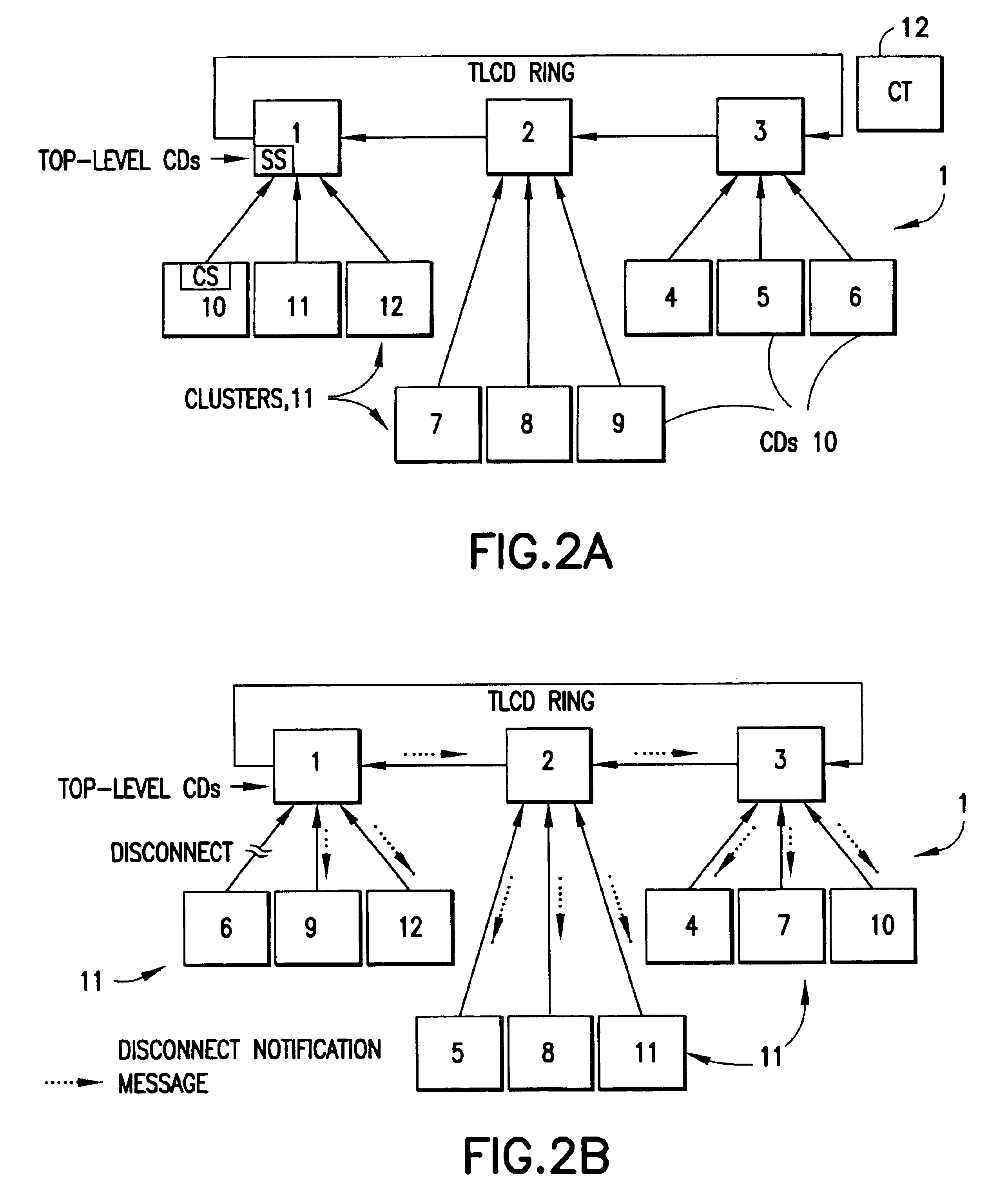
A data processing system includes a network containing of a set of connected devices, where individual ones of the connected devices include a data processor that executes a program for connecting to and disconnecting from the network and for maintaining a first list descriptive of other connected devices and a second list descriptive of at least some user-defined services published by individual ones of publisher connected devices that form a first sub-set of the connected devices. Individual ones of the publisher connected devices maintain a third list descriptive of an individual one or individual ones of registered service subscriber connected devices that form a second sub-set of connected devices. The publisher connected devices provide a service output to registered service subscriber connected devices upon an occurrence of at least one predetermined triggering event, which may be a push trigger, a pull trigger, or a combination of push and pull triggers. A given one of the connected devices may be a member of only the first sub-set of connected devices, or may be a member of only the second sub-set of connected devices, or may be a member of both the first sub-set of connected devices and the second sub-set of connected devices. The set of connected devices are logically organized into a plurality of clusters each having a top level connected device (TLCD), where the plurality of TLCDs are coupled together in a ring for propagating system administration information between the plurality of clusters. Services remain operative even after the connected device on which they initially reside becomes inoperative. This is accomplished by migrating the publication function to at least one other connected device when a current publisher's connected device becomes inoperative for any reason. A backup of last resort is referred to as a persistent connected device.
Owner:TAIWAN SEMICON MFG CO LTD
Automatic protection of partial document content
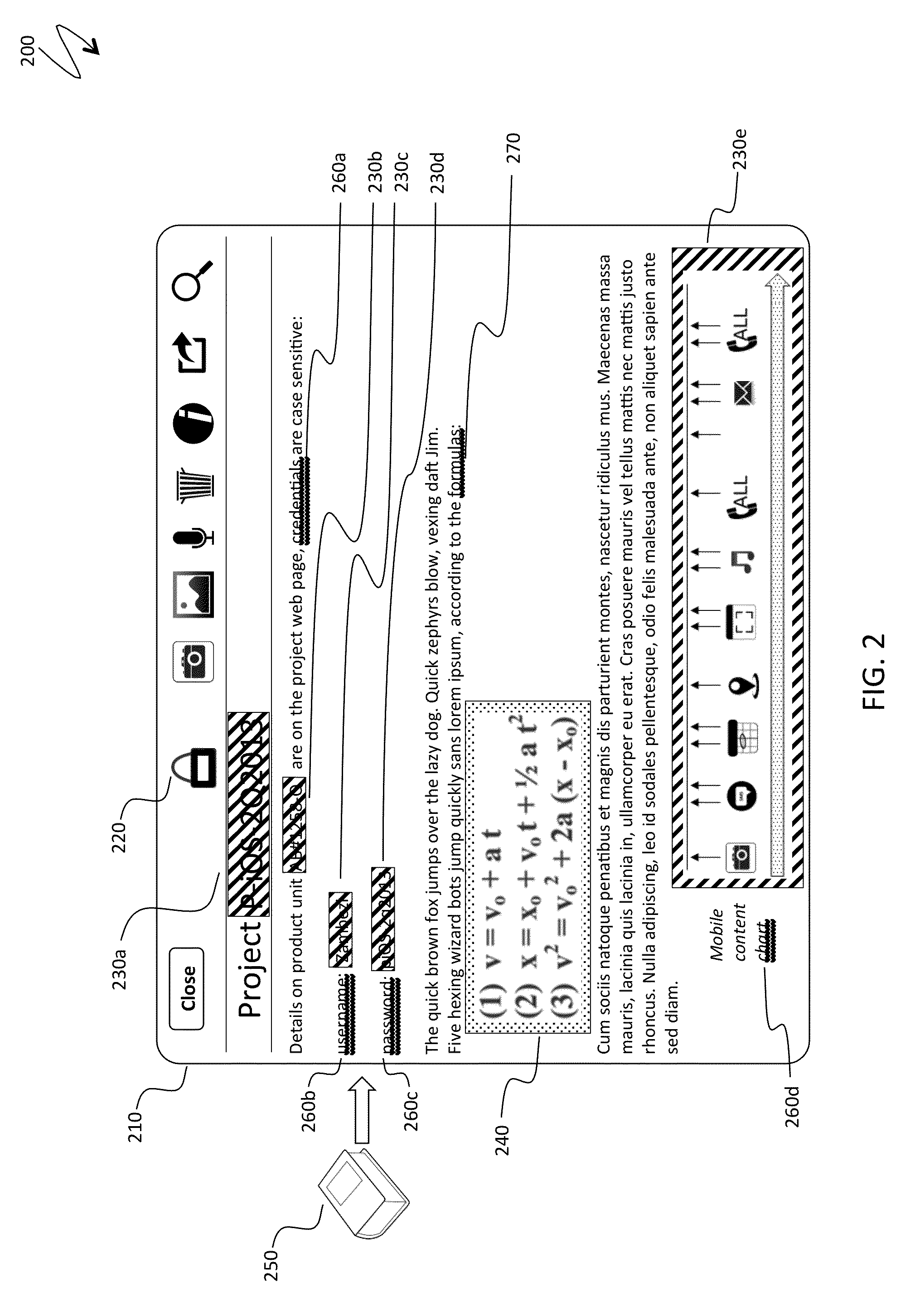
ActiveUS20140208418A1Reduce the amount requiredDigital data processing detailsUnauthorized memory use protectionPasswordDocumentation
Protecting a fragment of a document includes automatically detecting the fragment without user intervention based on the content of the fragment and / or the context of the fragment within a set of documents, selectively encrypting the fragment to prevent unauthorized access, and providing an alternative view of the fragment that prevents viewing and access of content corresponding to the fragment unless a decryption password is provided. Automatically detecting the fragment may include detecting numbers and alphanumeric sequences of sufficient length that do not represent commonly known abbreviations, detecting generic terms, detecting proper names, detecting terms signifying a type of content, detecting mutual location of terms and sensitive content, and / or detecting user defined terms. The generic terms may correspond to password, passcode, credentials, user name, account, ID, login, confidential, and / or sensitive. The proper names may be names of financial organizations and security organizations.
Owner:EVERNOTE
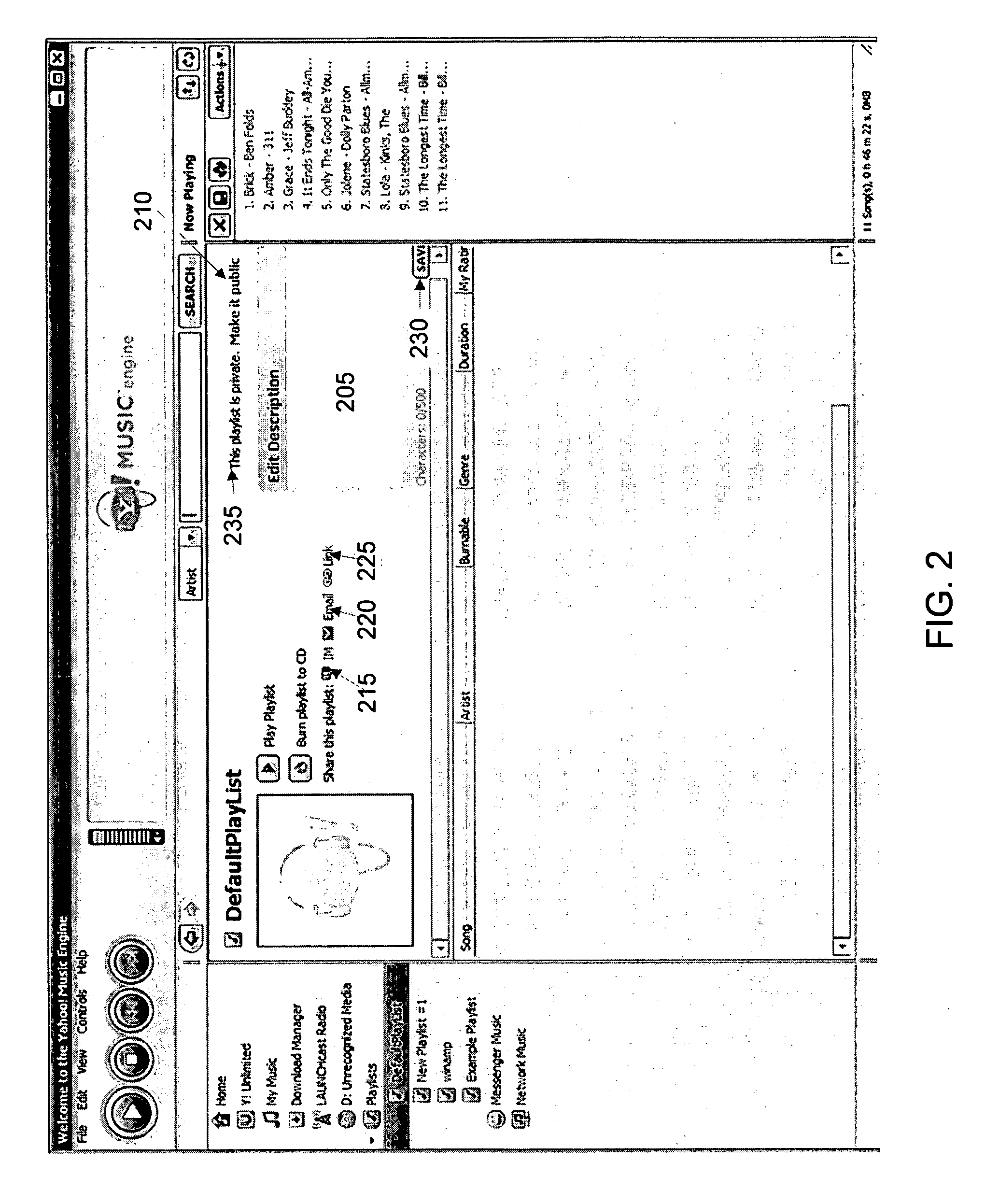
User interface for sharing and searching playlists
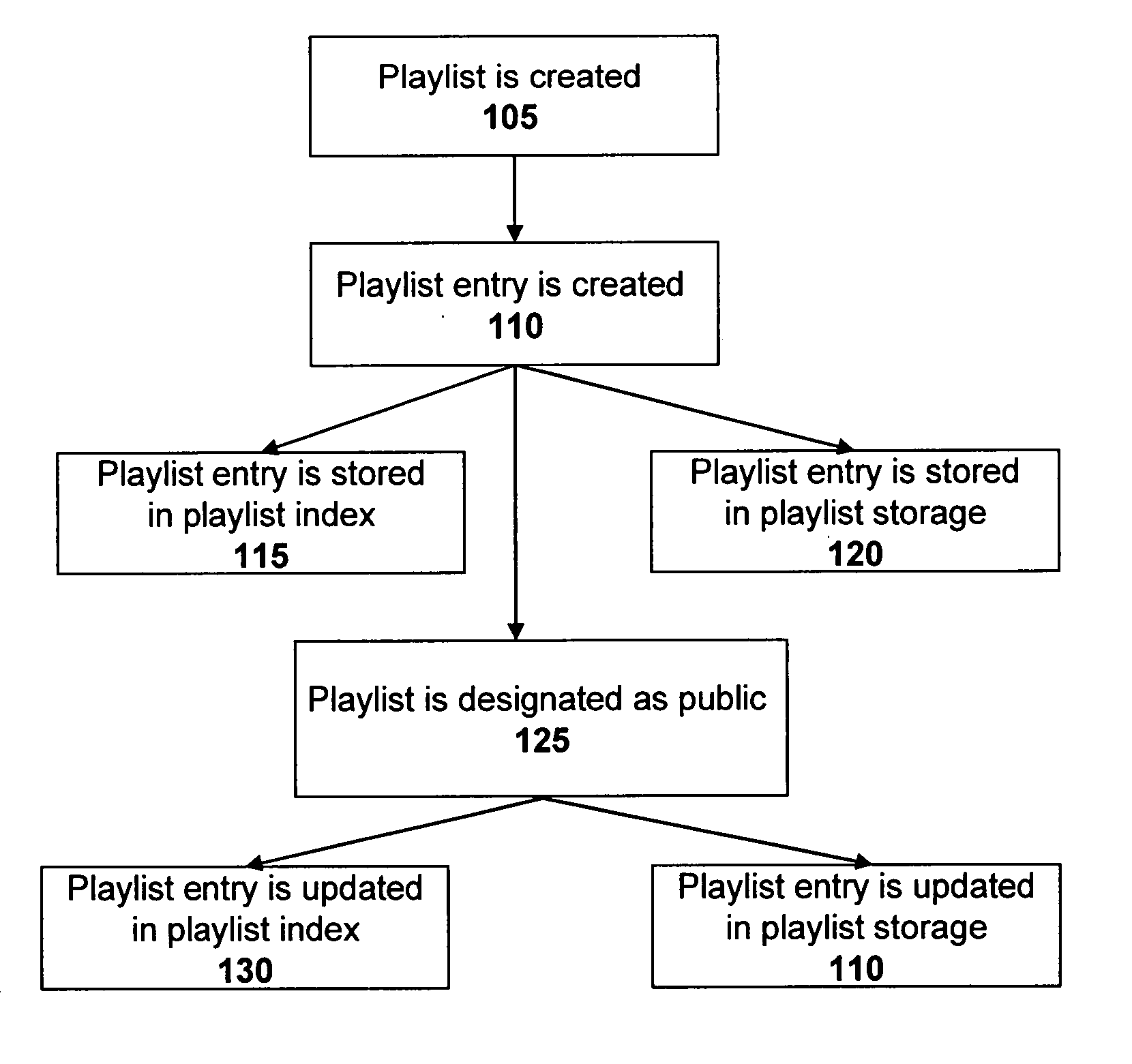
InactiveUS20060195480A1Record information storageData switching by path configurationUser interfaceUser defined
The present disclosure provides a user interface for making a playlist available to the public. In another embodiment, the present disclosure provides a user interface for creating a playlist comprising user-defined descriptor information. In another embodiment, the present disclosure provides a user interface for searching for such public playlists.
Owner:HUAWEI TECH CO LTD +1
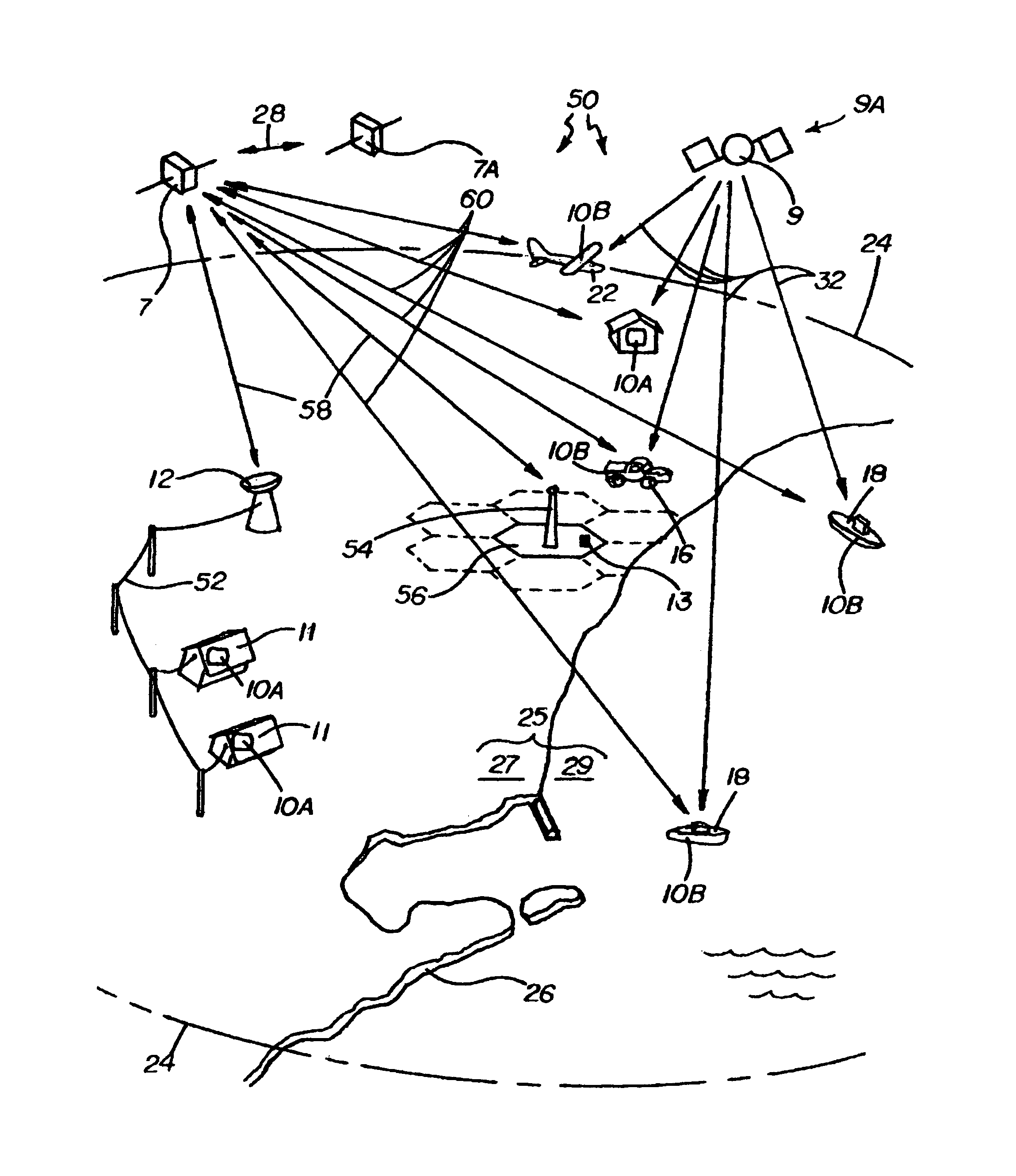
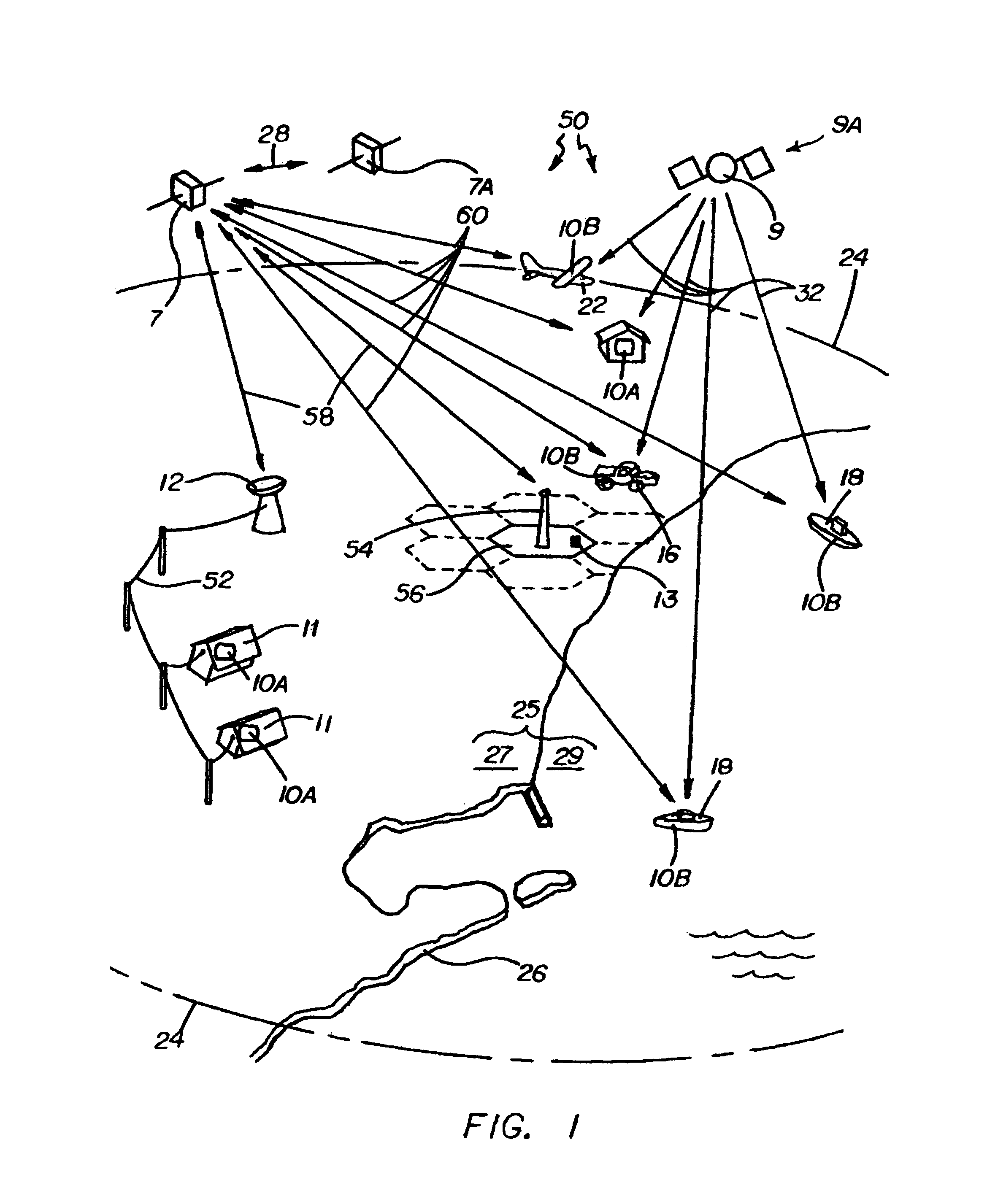
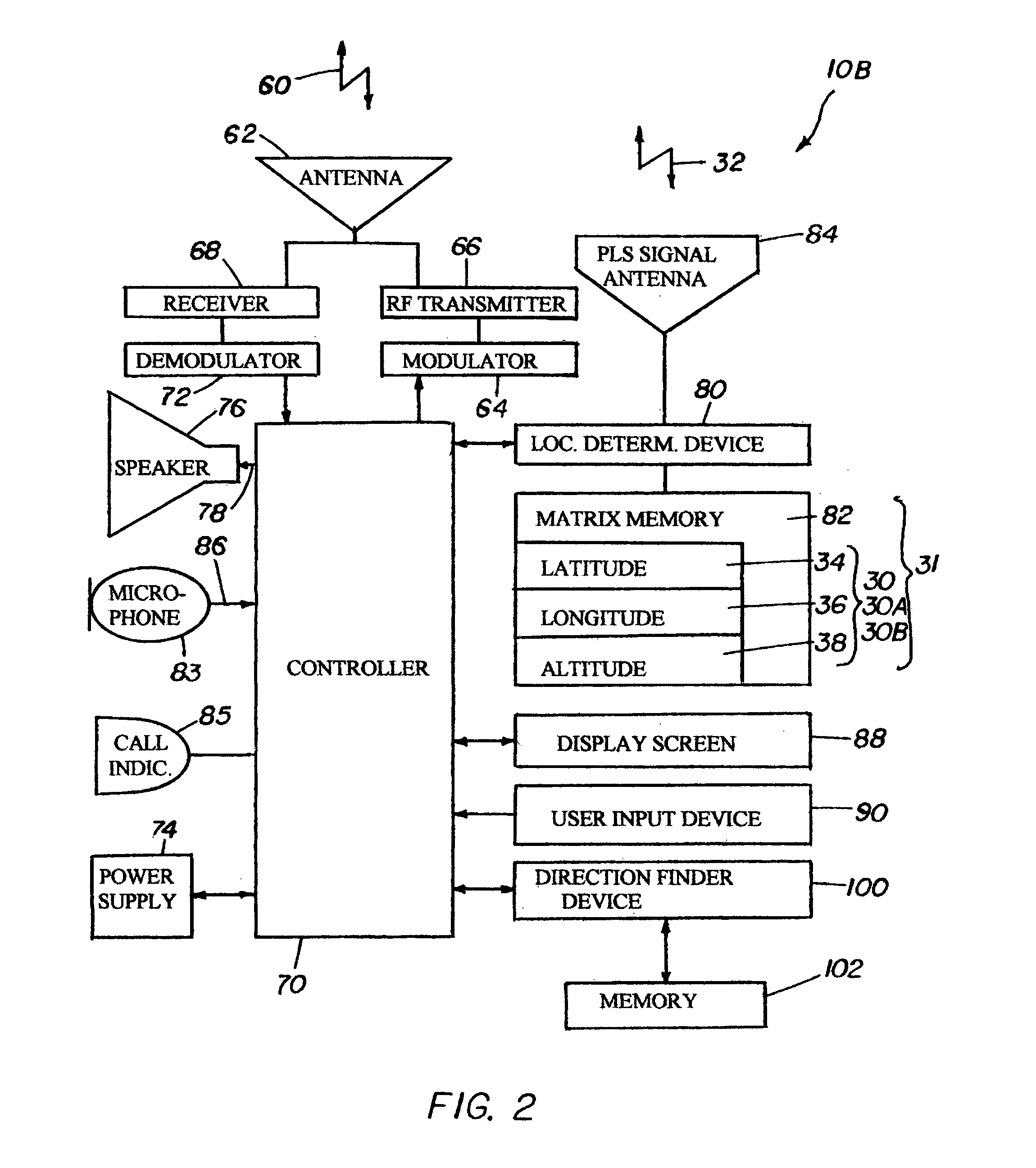
Location based communications system
InactiveUS7233795B1Position fixationRadio/inductive link selection arrangementsCommunications systemSTI Outpatient
A location based communications system uses a physical location system (PLS) or relative position system to determine a communication unit's location in two or three dimensions, and is configured for radiotelephonic calls through intermediary communications satellite systems, cellular systems or other mobile systems and land line systems, based on the location G# of the called telephone or on a caller-defined estimated area or space termed a G zone number GZ# surrounding the desired callee. The system is particularly advantageous for mobile communications, and may be interfaced with conventional stationary telephones, cellular phones and other communications devices. Multiple telephone units may be simultaneously contacted with messages in user-defined languages. Emergency features enable the location based communication system to locate and notify the nearest and / or best equipped party for assistance in the event of an emergency, issue warnings to all phones in a specific area of any size, calculate vehicle velocities and control traffic.
Owner:SAFE SECURE COMM LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com