Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3852 results about "Stream" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
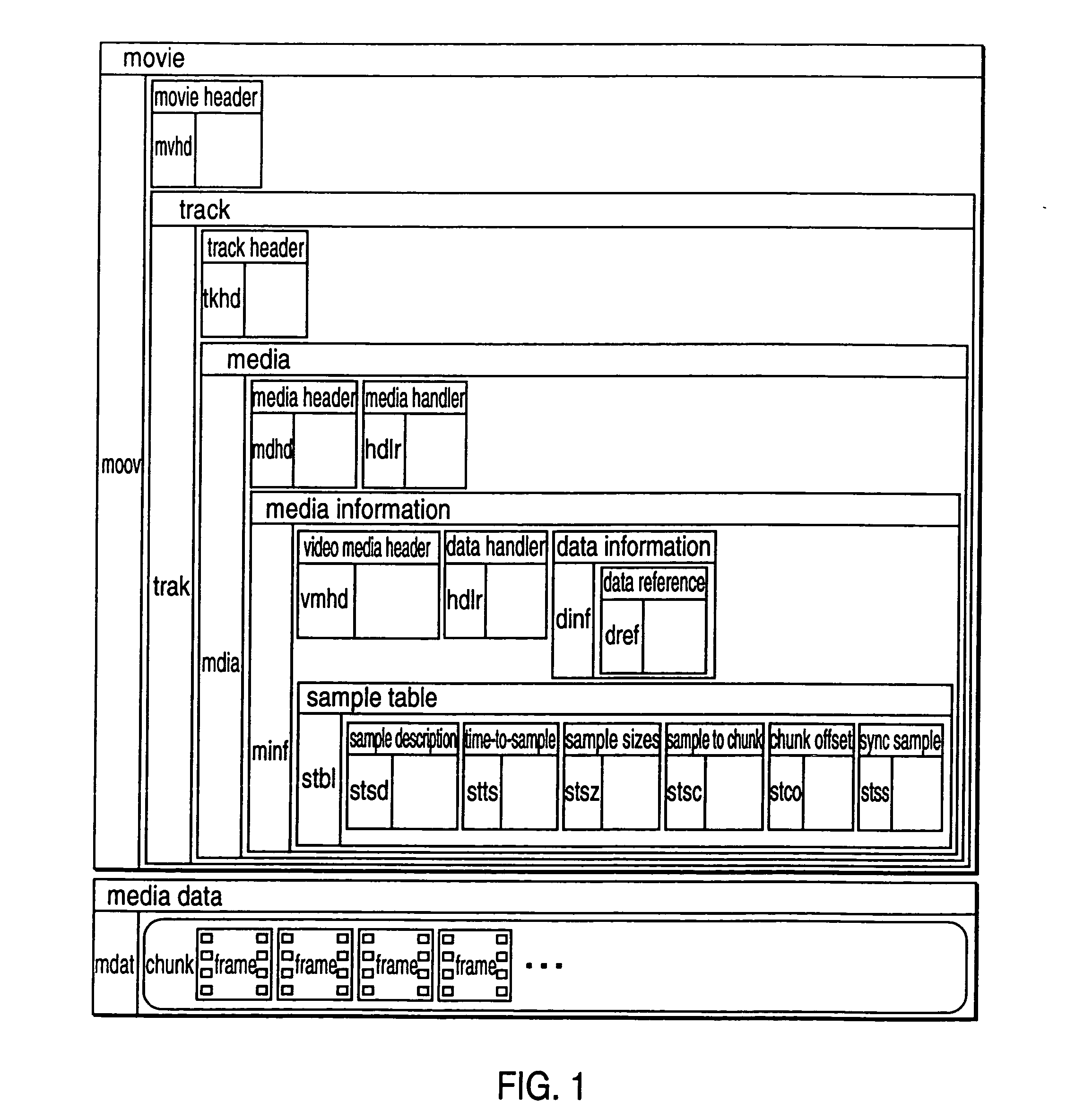
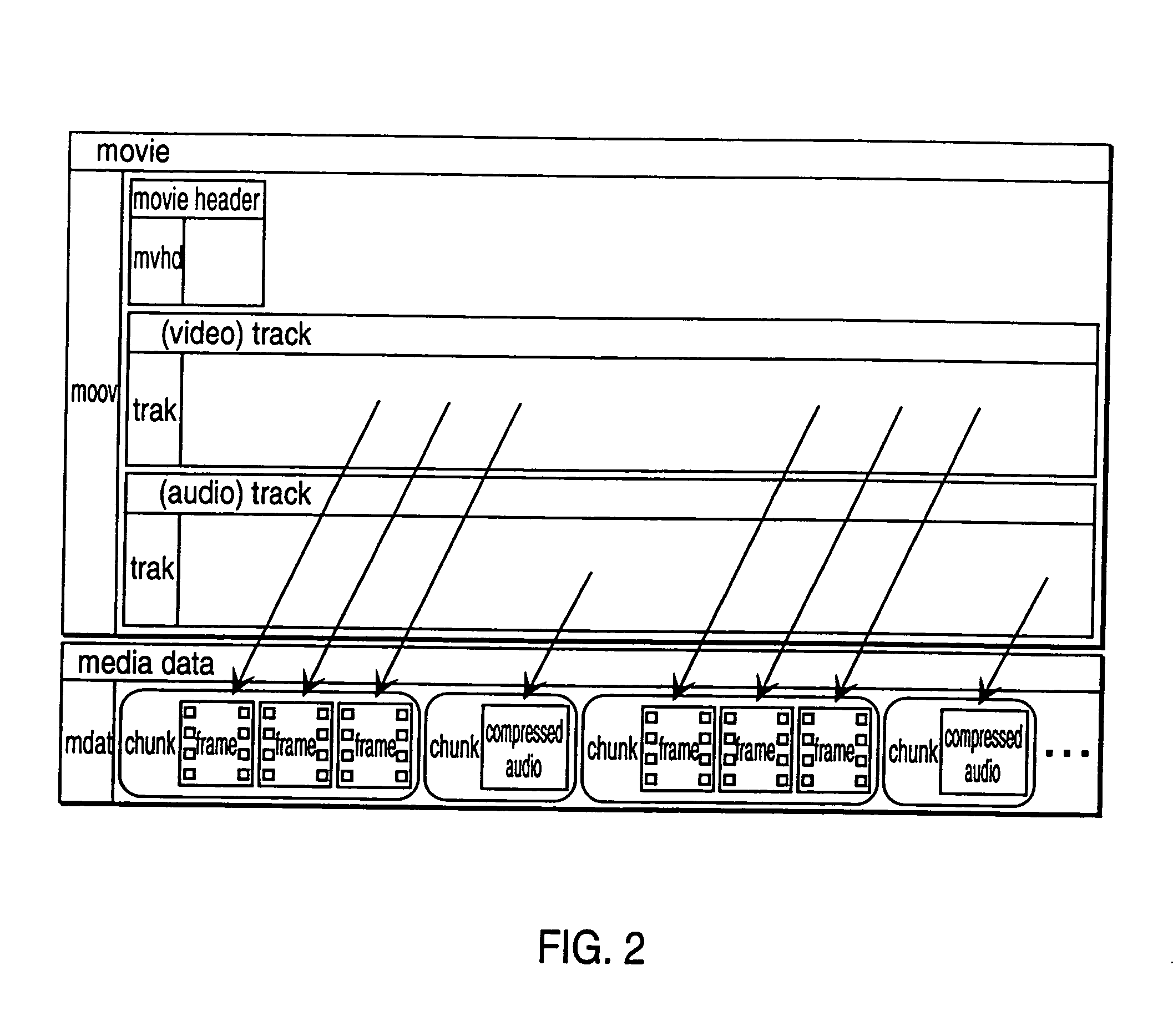
In computer science, a stream is a sequence of data elements made available over time. A stream can be thought of as items on a conveyor belt being processed one at a time rather than in large batches.
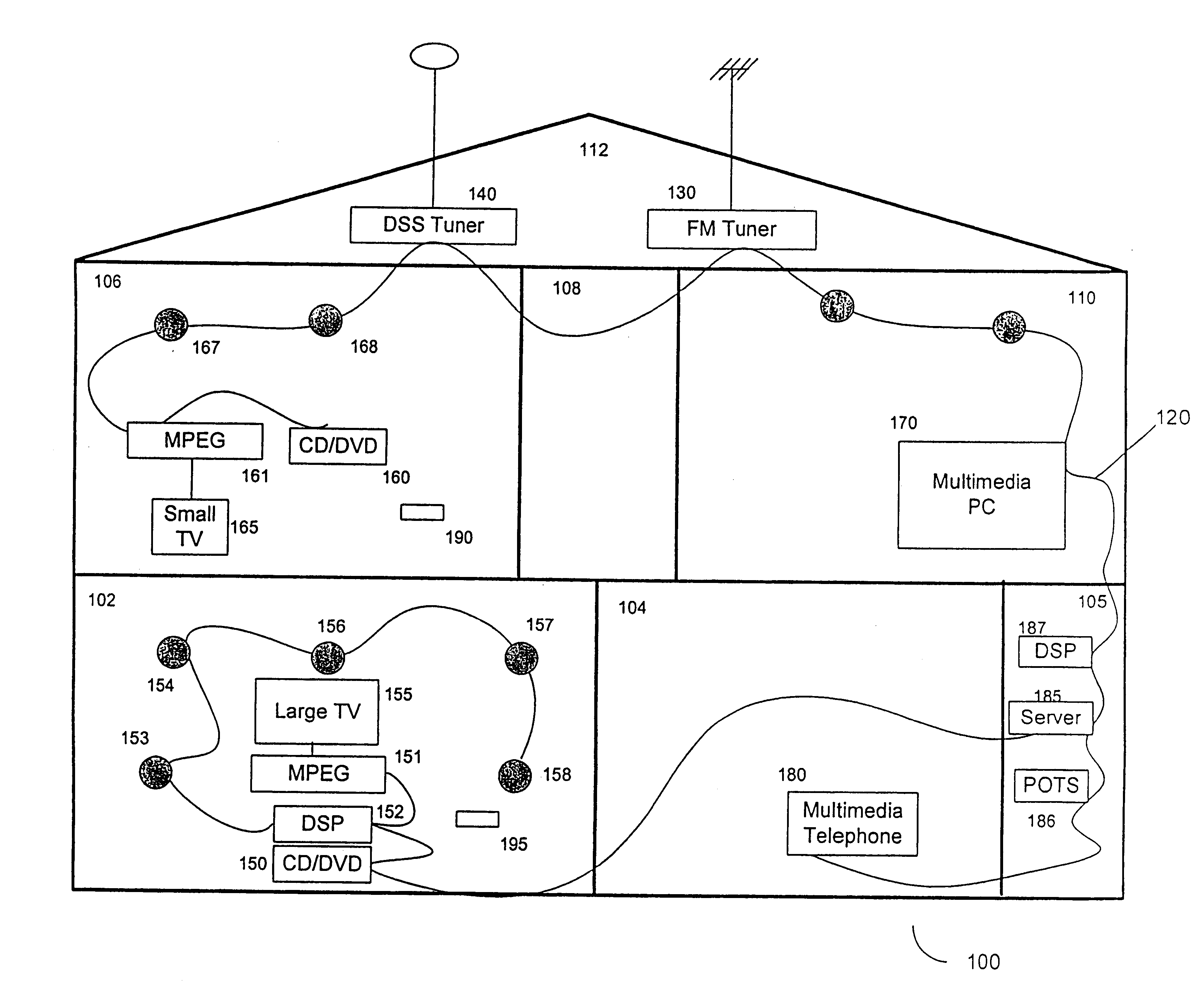
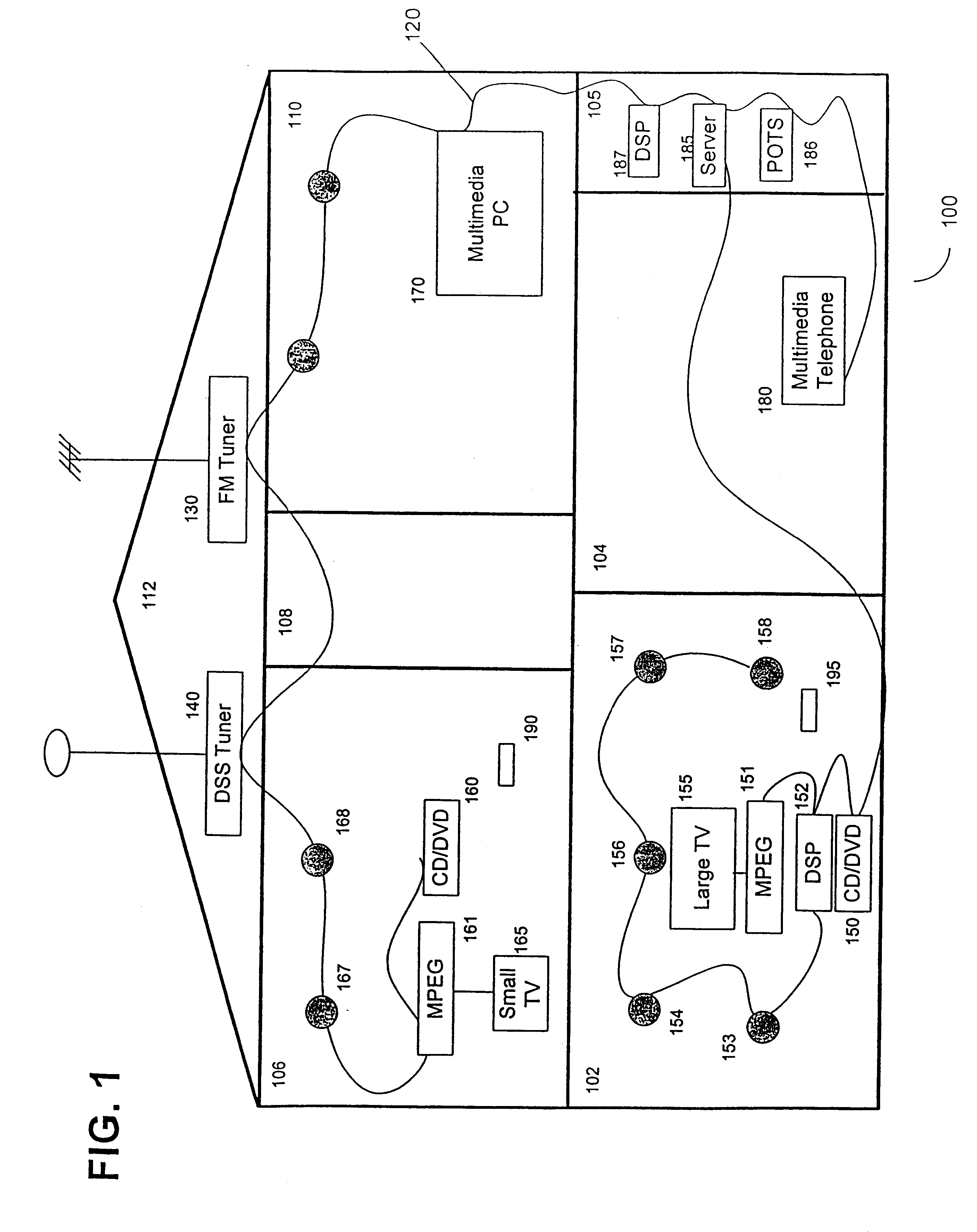
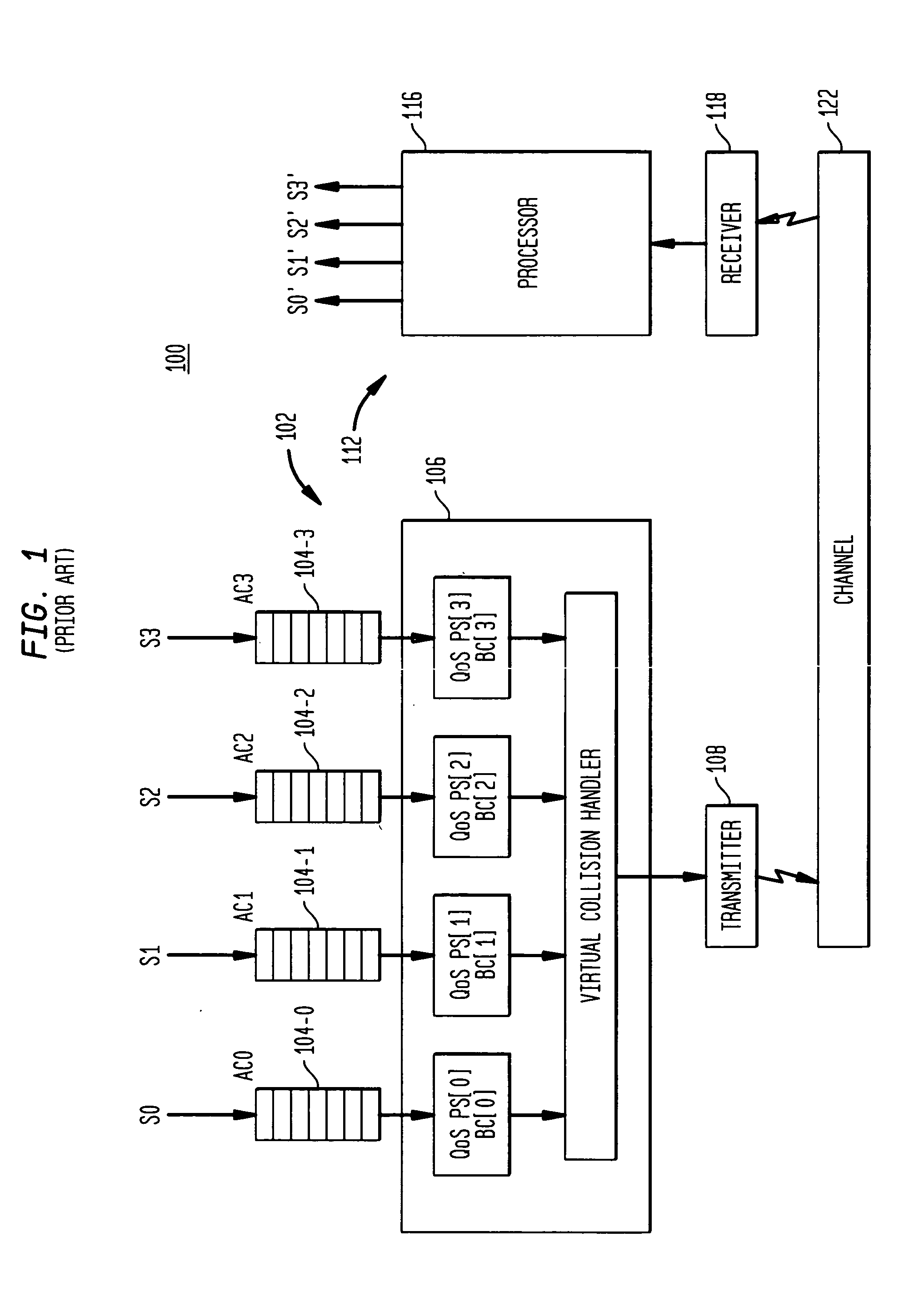
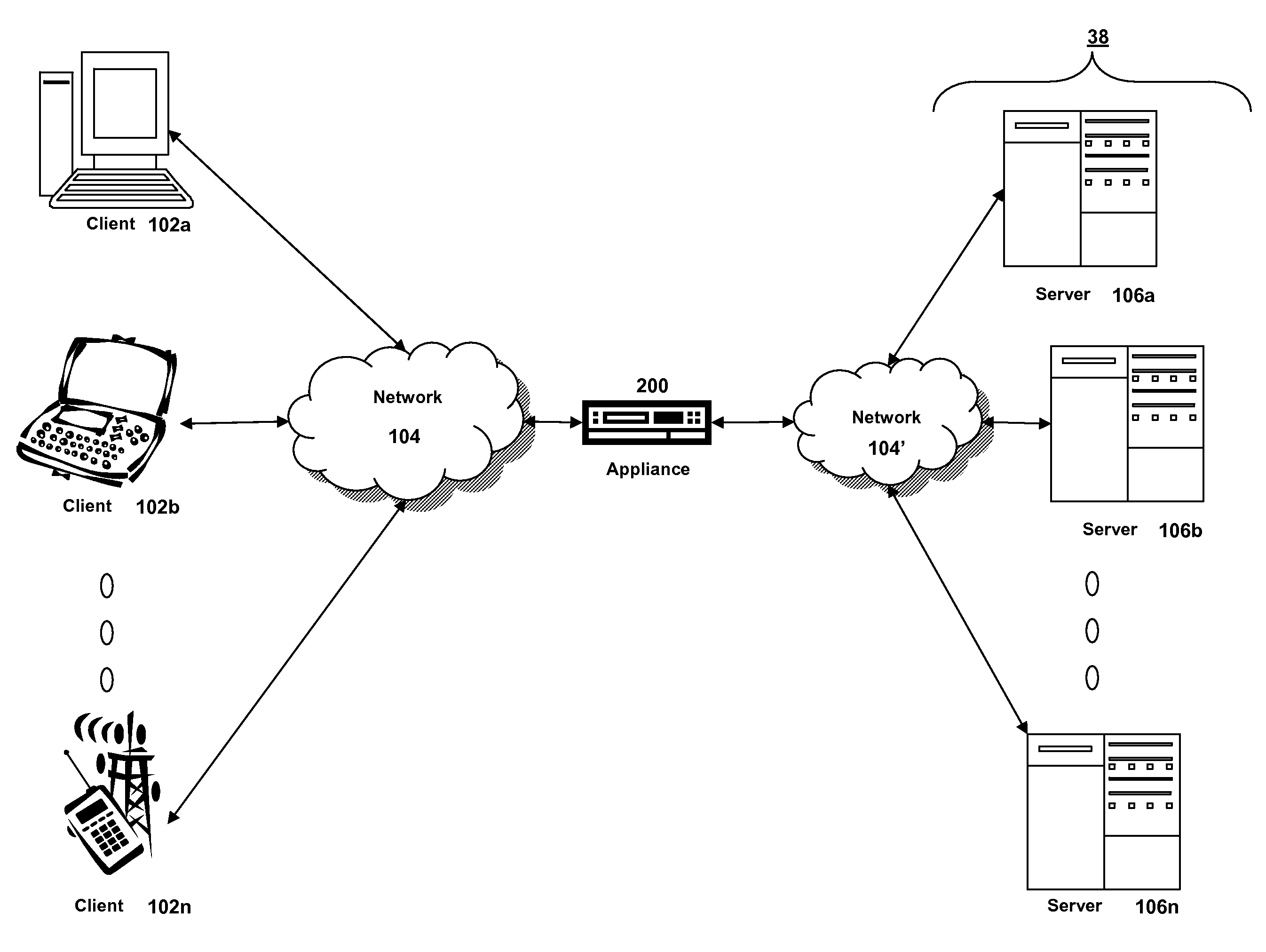
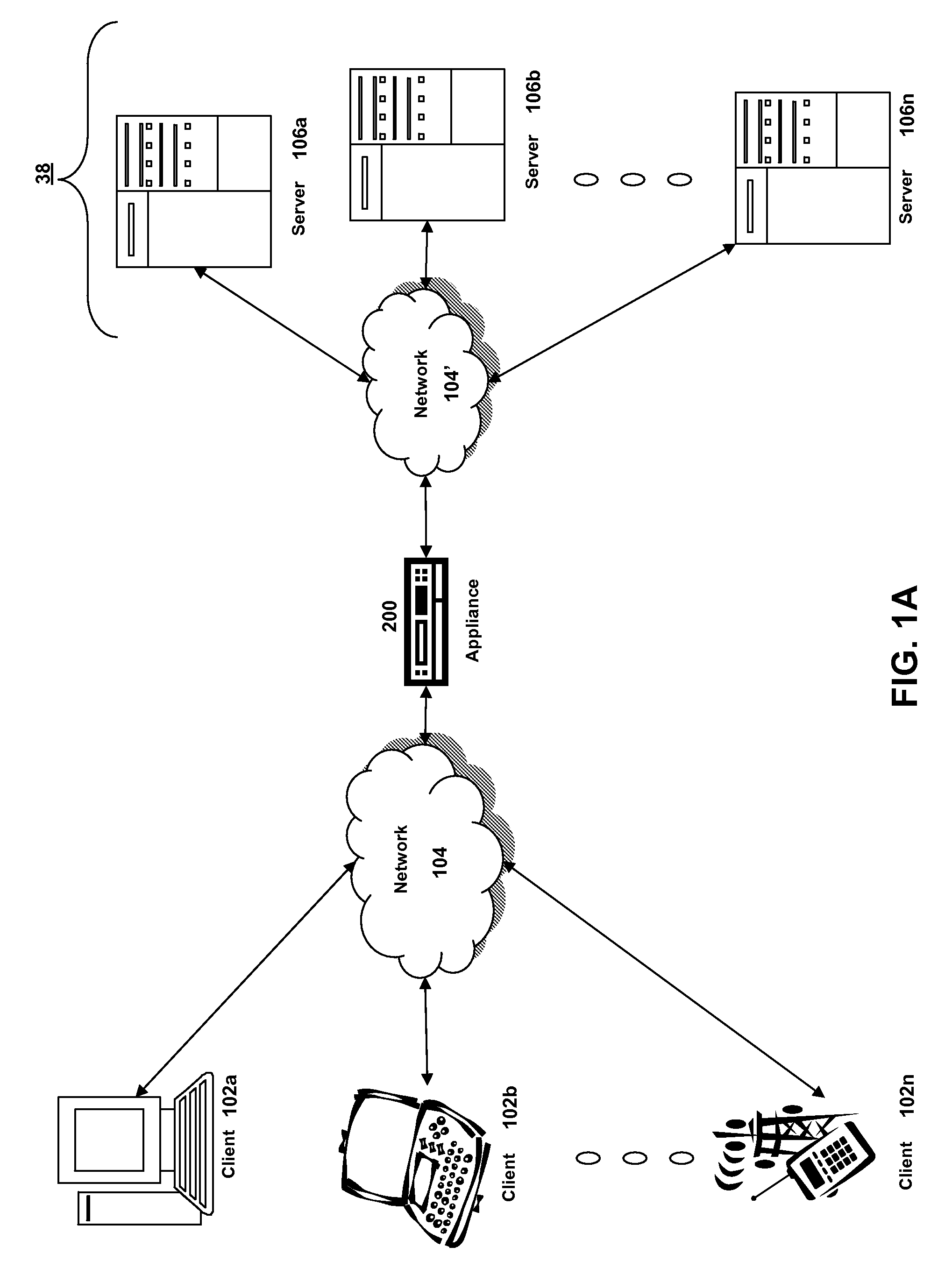
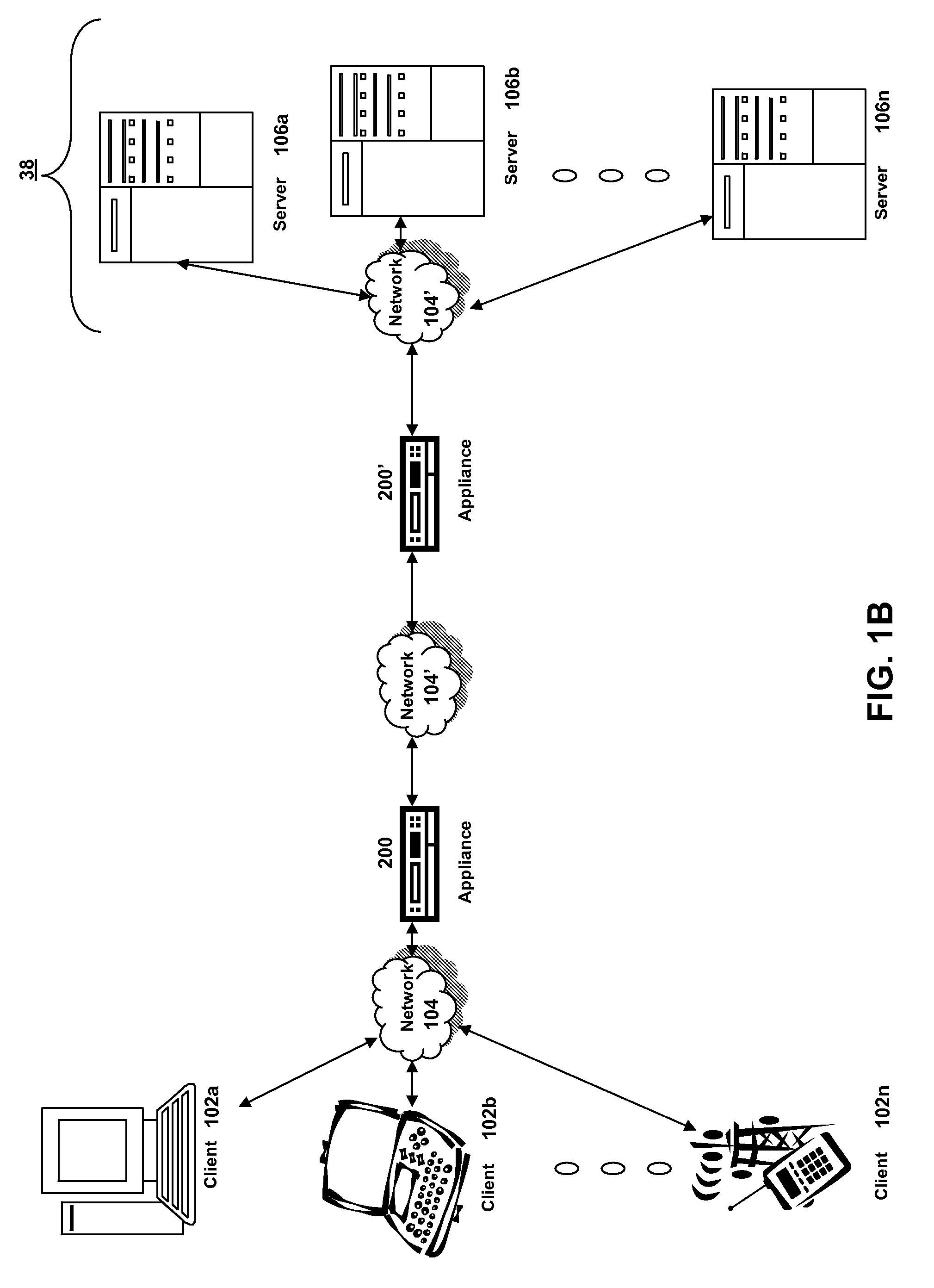
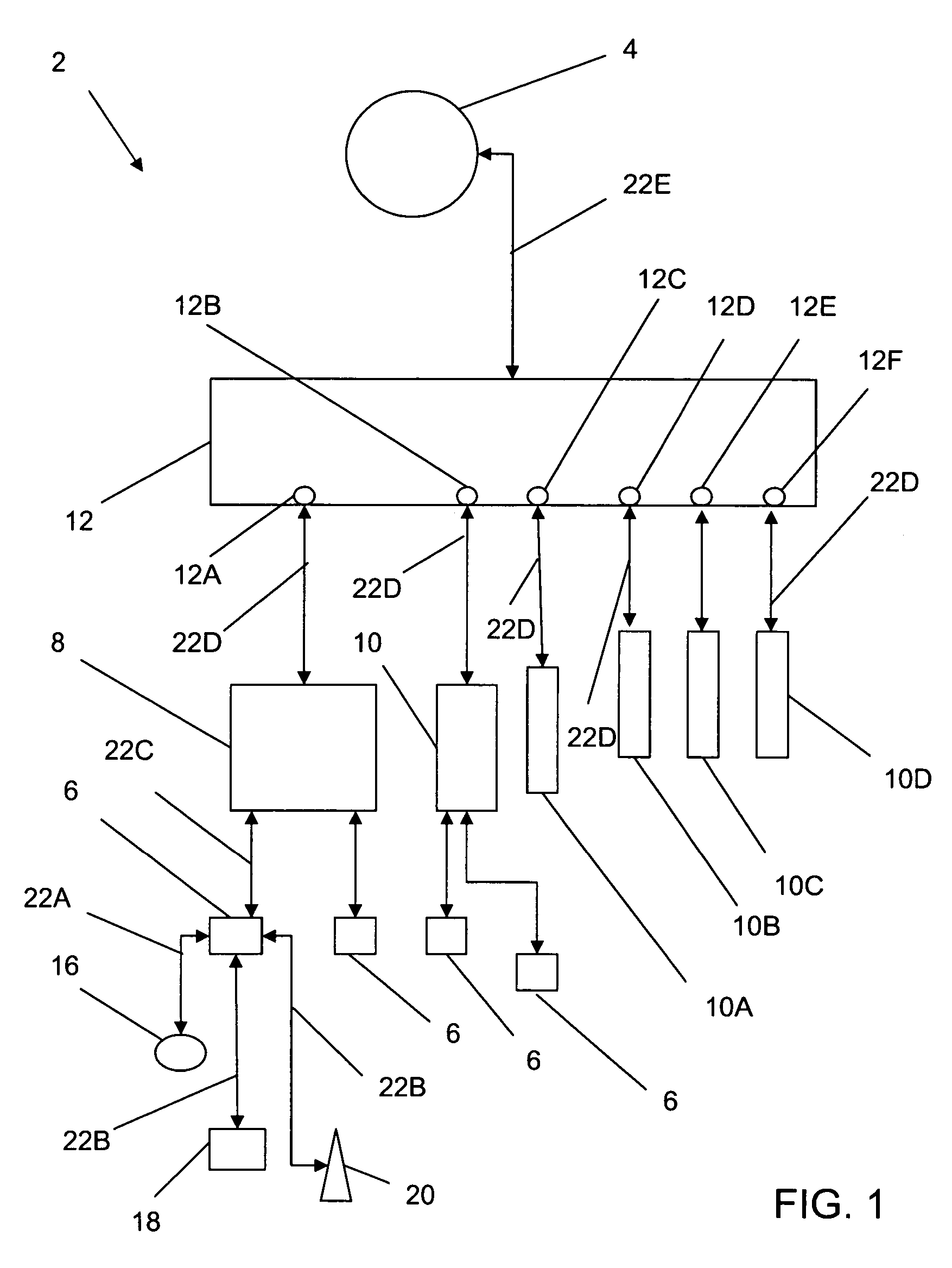
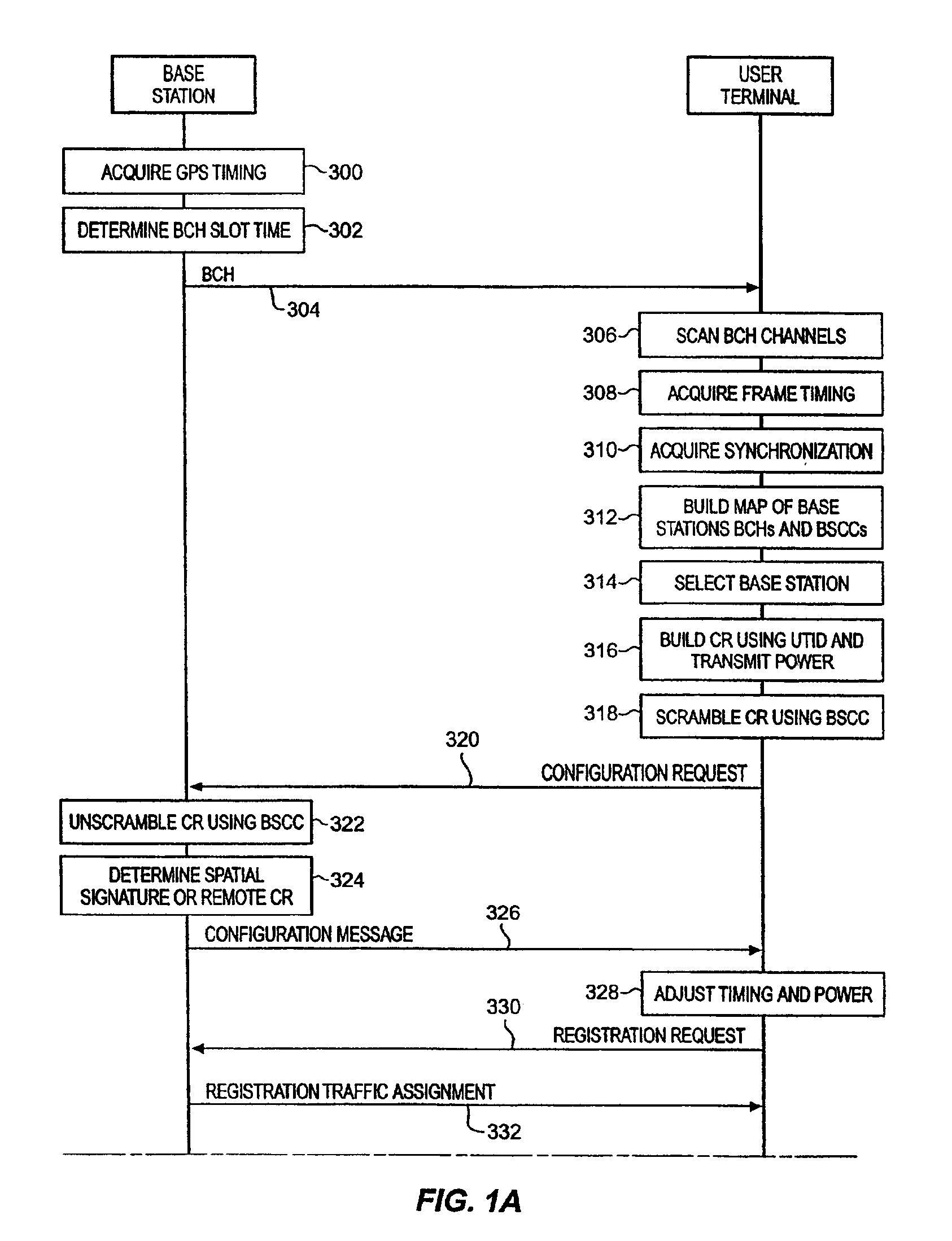
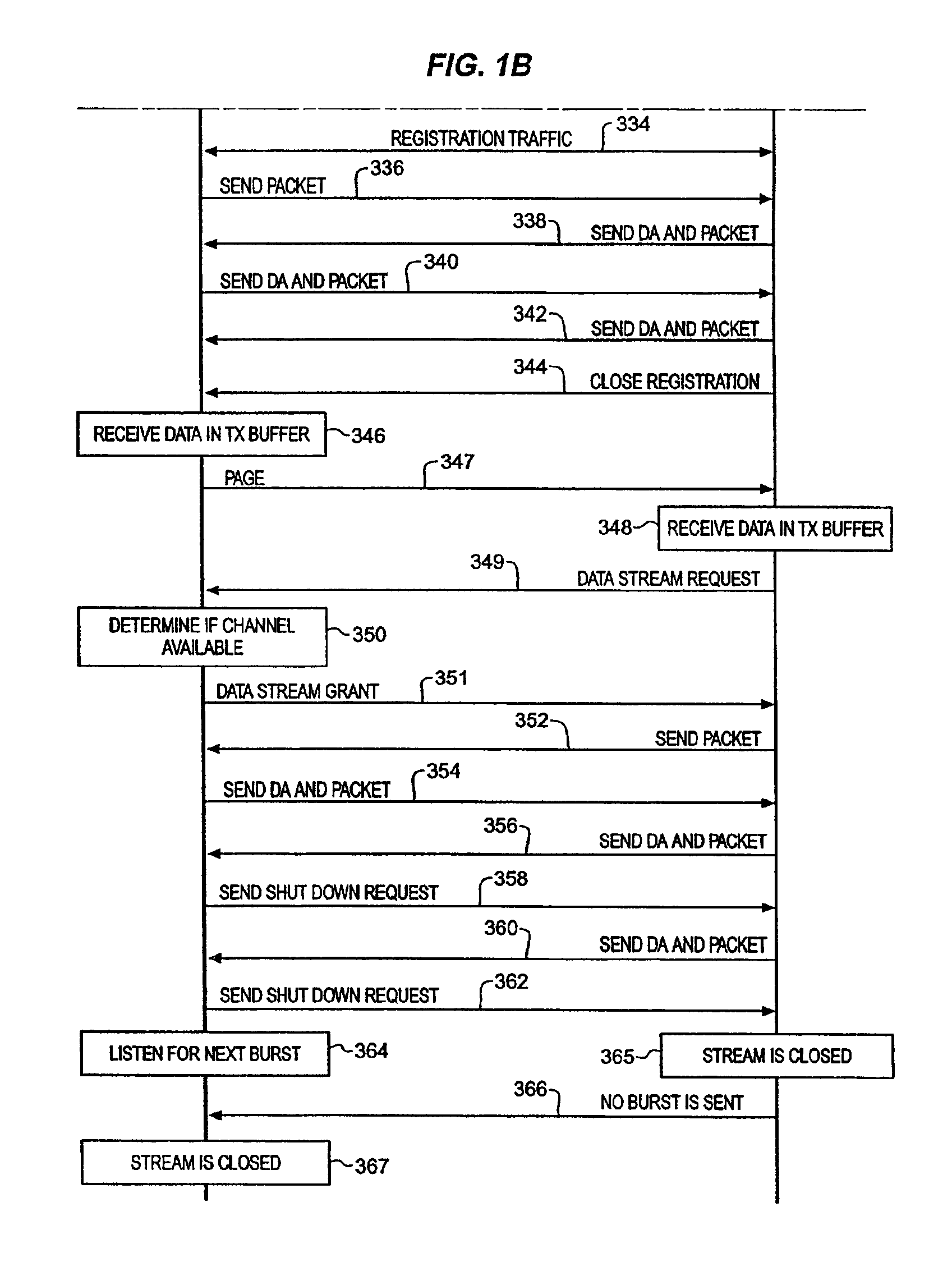
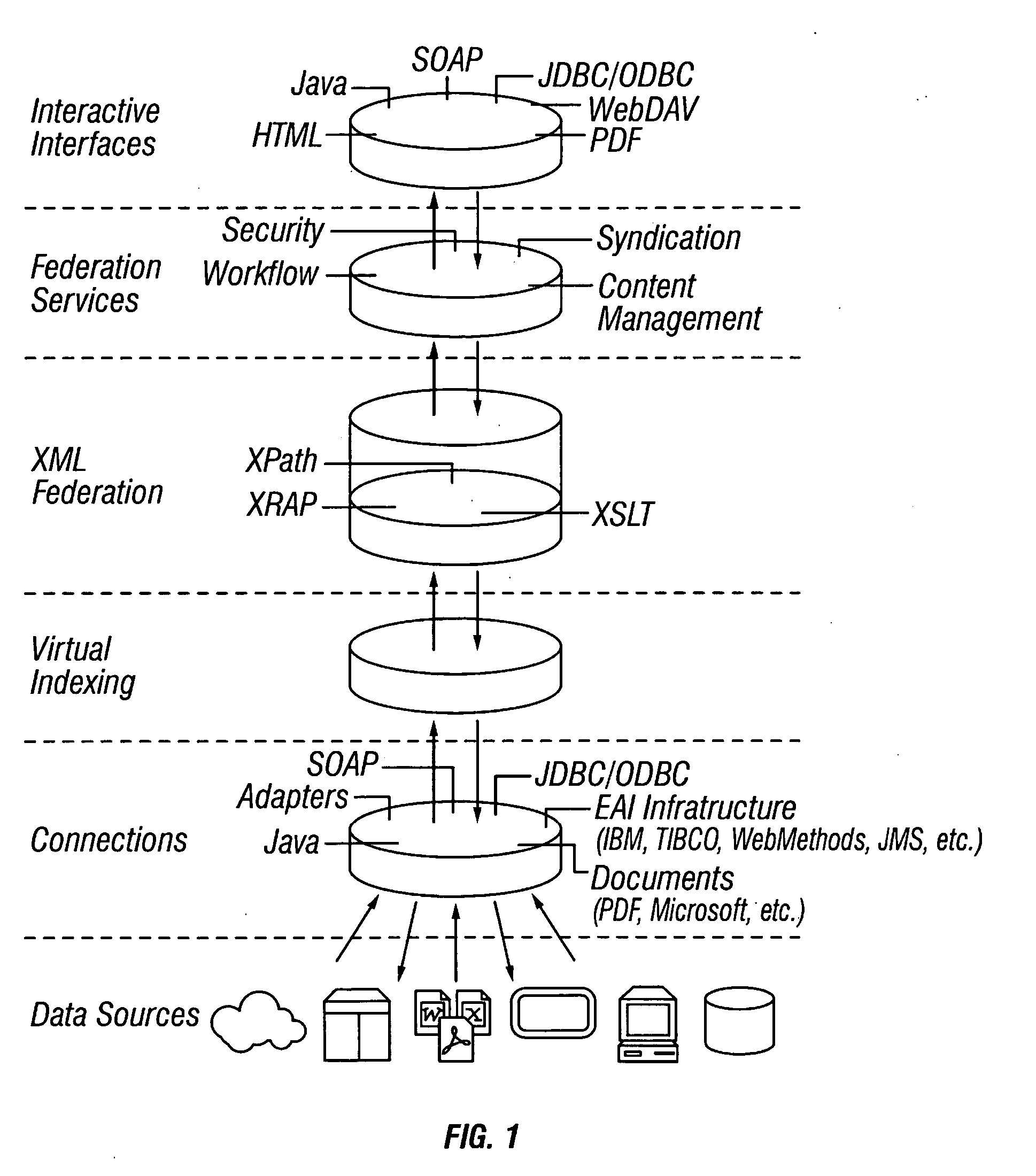
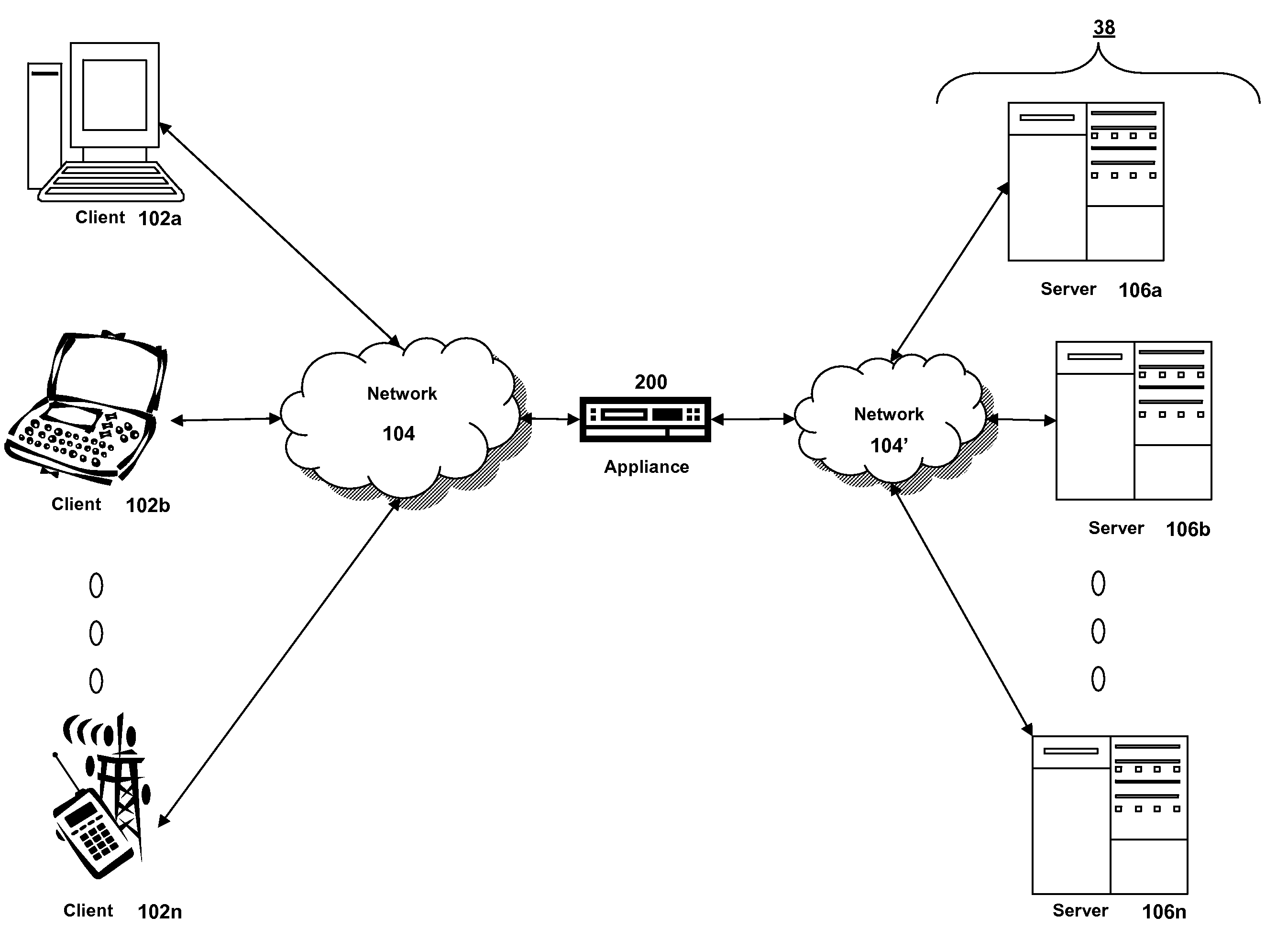
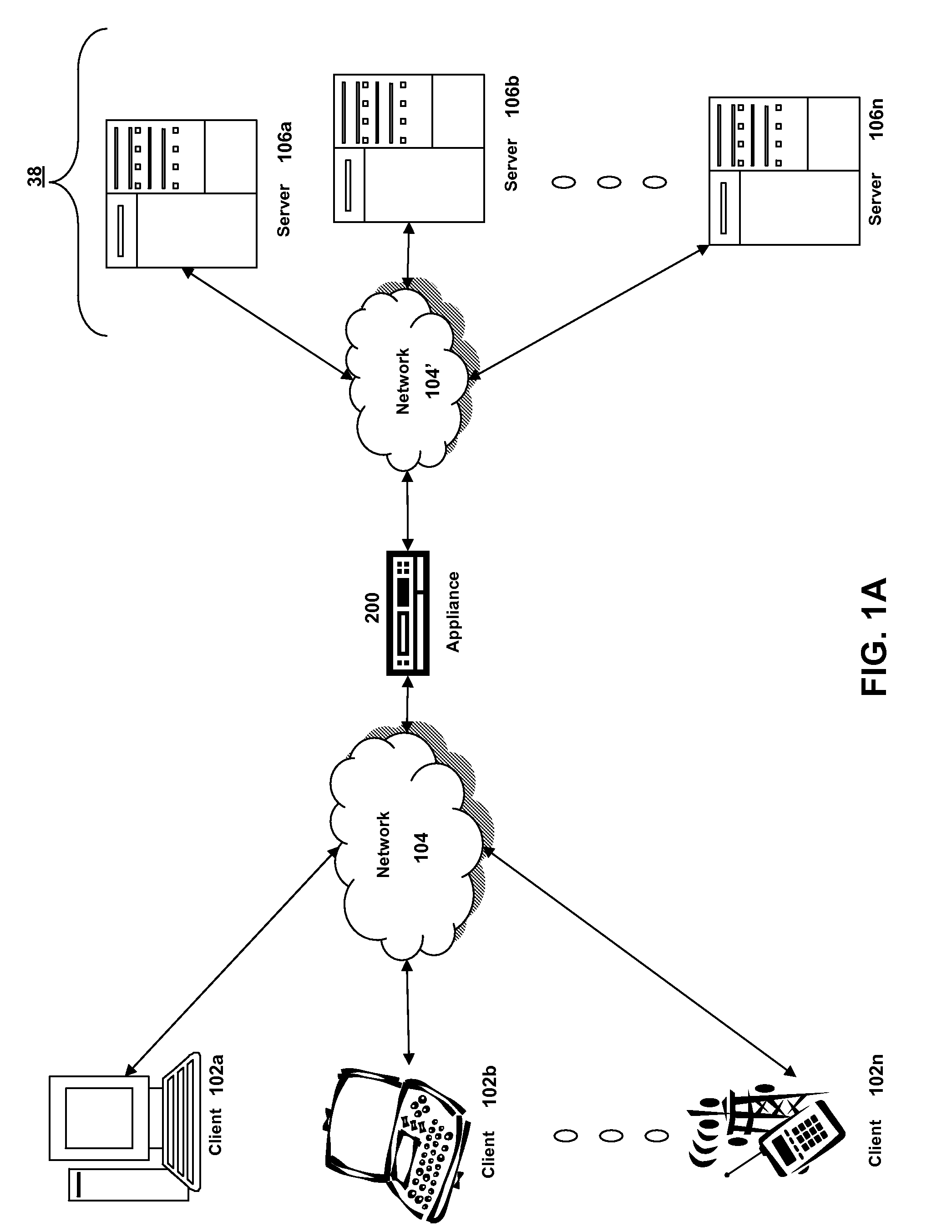
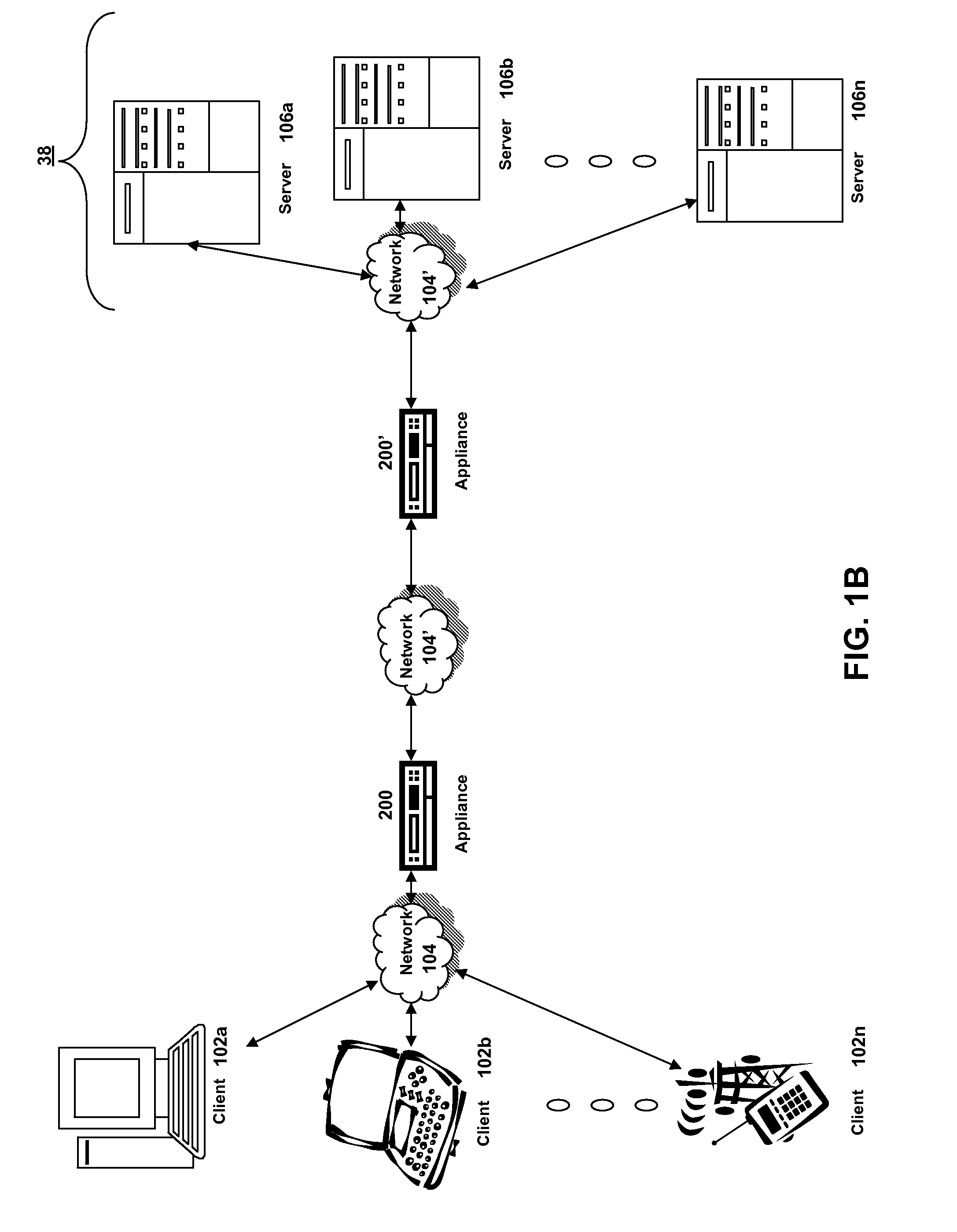
Synchronous network for digital media streams
InactiveUS6611537B1Avoid collisionPulse modulation television signal transmissionTime-division multiplexData streamNetwork clock
A network adapter for a synchronous logical ring network operates on existing physical twisted-pair telephone topologies. Information propagates around the logical ring, reaching every device on each revolution around the network. Network devices are full-duplex, transmitting and receiving information on every clock cycle. Network devices arbitrate to be elected the network clock device. By synchronizing all network devices to a single reference clock, and providing fixed frames of information propagating around the network at consistent time intervals, the logical ring network ensures that information propagates from one device to another at consistent time intervals. The fixed-length frames are divided into two independent streams: a data stream for the distribution of real-time continuous digital media streams; and a system command stream for the distribution of system commands.
Owner:CENTILLIUM COMM
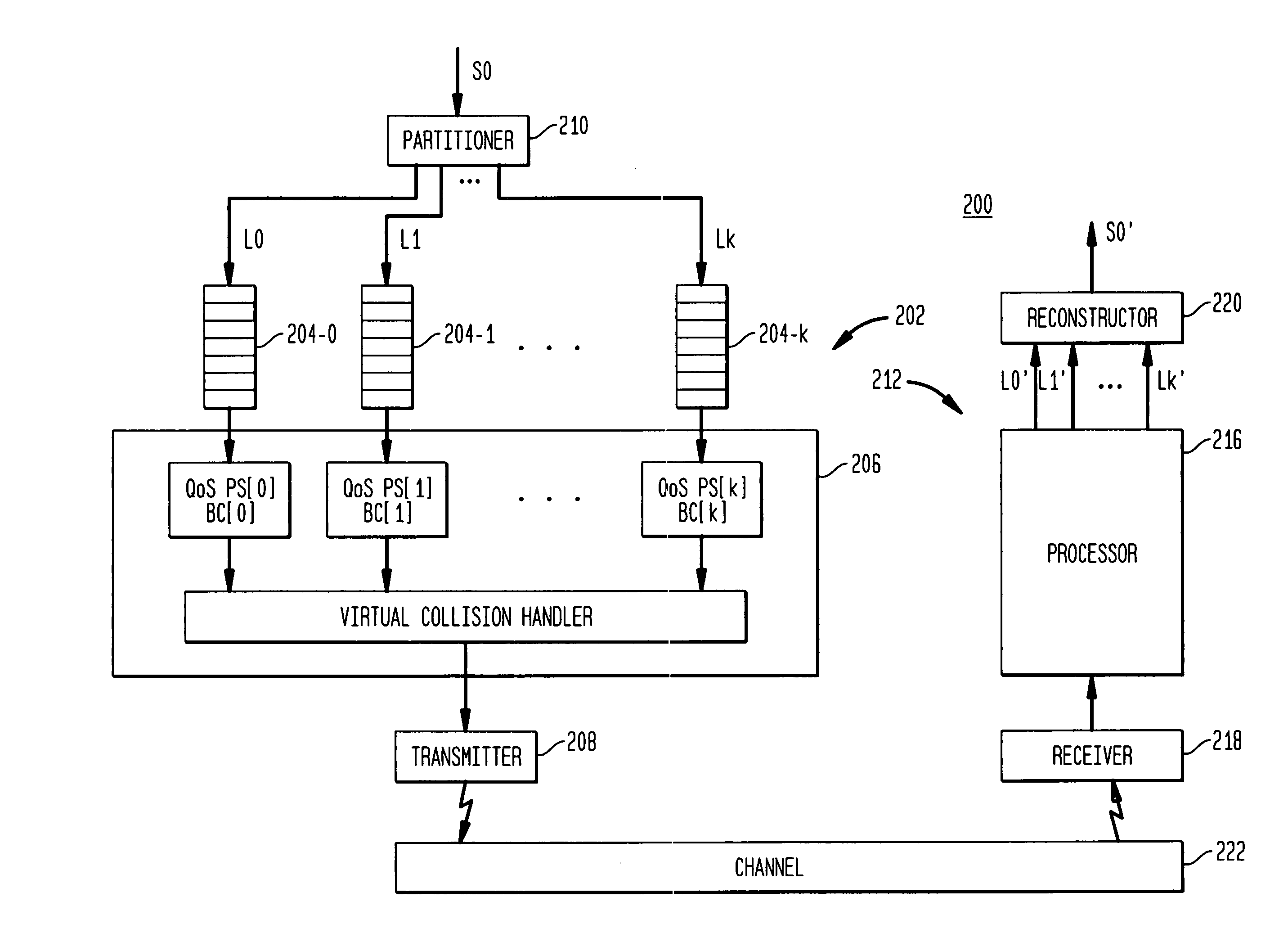
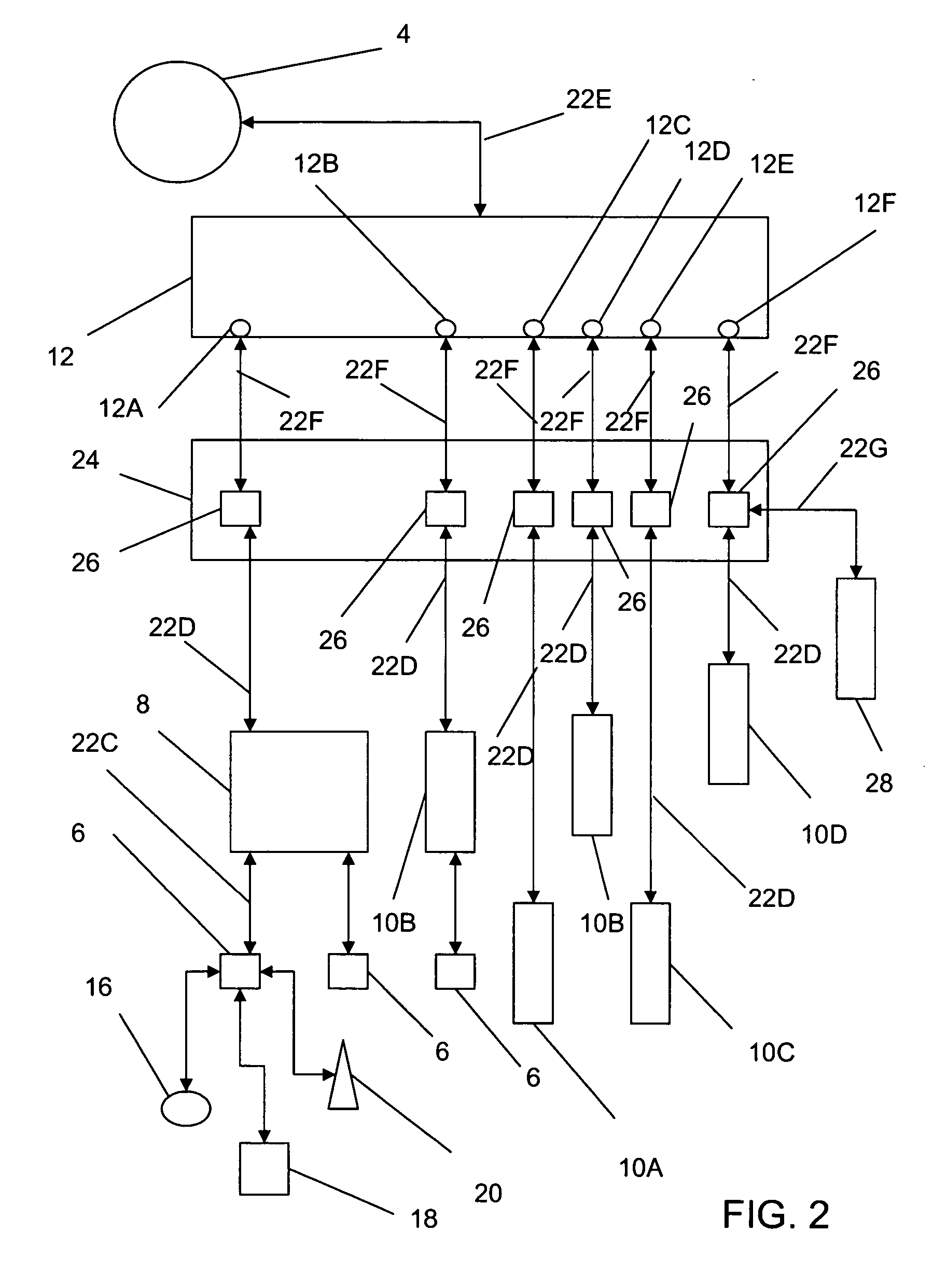
Media delivery using quality of service differentiation within a media stream
ActiveUS20050100022A1Equal qualityError preventionNetwork traffic/resource managementQos quality of serviceStation
A WLAN system adapted to apply QoS differentiation to a media stream to be transmitted from a transmitting station (STA) to a receiving STA of that system. The transmitting STA processes the media stream to generate a base sub-stream and one or more enhancement sub-streams for subsequent transmission over a wireless communication channel and assigns different priorities to different sub-streams. Depending on the channel conditions, the transmitting STA may select to discard, without transmission, portions of data from enhancement sub-streams. The selection process is based on the assigned priority and operates to preserve as much of relatively high-priority data as possible. The receiving STA then processes the received data to generate a reconstructed media stream, which provides signal quality equal to or better than the signal quality supported by the base sub-stream. Advantageously, a WLAN system of the invention is adapted to change signal quality dynamically and incrementally in a manner commensurate with current channel conditions without the need for communication between the higher and lower network layers. In addition, it provides gradual and graceful degradation of signal quality when channel conditions deteriorate as opposed to abrupt degradation inherent in analogous prior art systems.
Owner:AVAGO TECH INT SALES PTE LTD
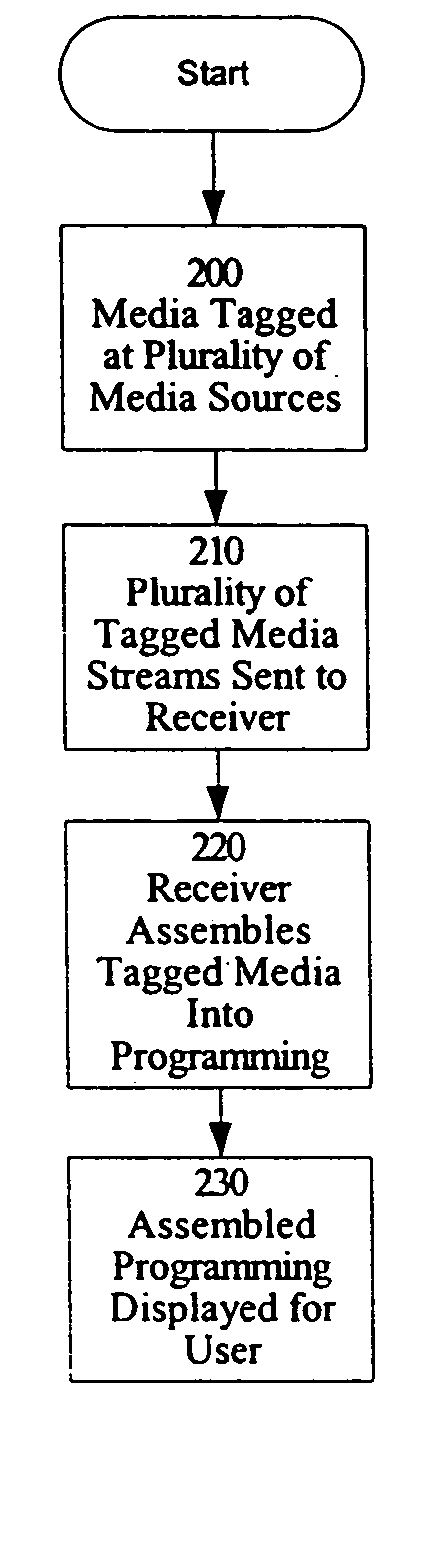
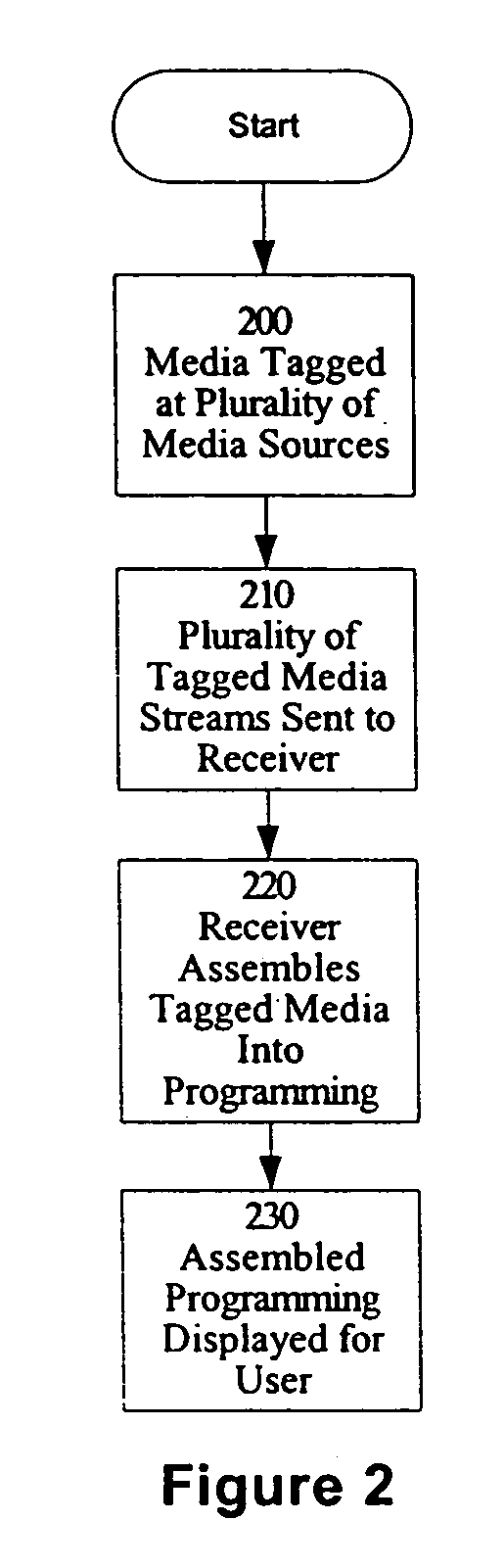
Method and apparatus for creation, distribution, assembly and verification of media
InactiveUS20060015904A1Television system detailsElectronic editing digitised analogue information signalsLook and feelWorld Wide Web
A method and apparatus for creation, distribution, assembly and verification of media, including one embodiment, media is transmitted to a receiver where the receiver assembles the media into programming. In another embodiment, media is transmitted to the receiver from a plurality of sources. In a further embodiment, a source of media performs a tagging operation to associate sets of tags with elements of the stream of media. In various embodiments, different combinations of look-and-feel, content and other tags are associated with the media stream. In an additional embodiment, tagging of the media stream is performed at the receiver. A user at the receiver may also provide data about the user to the receiver. In yet another embodiment, the receiver uses the tags to assemble the media into a program. In still further embodiments of the invention, various Royalty Only Aggregate Revenues or “ROAR” models and apparatus are disclosed.
Owner:NTECH PROPERTIES
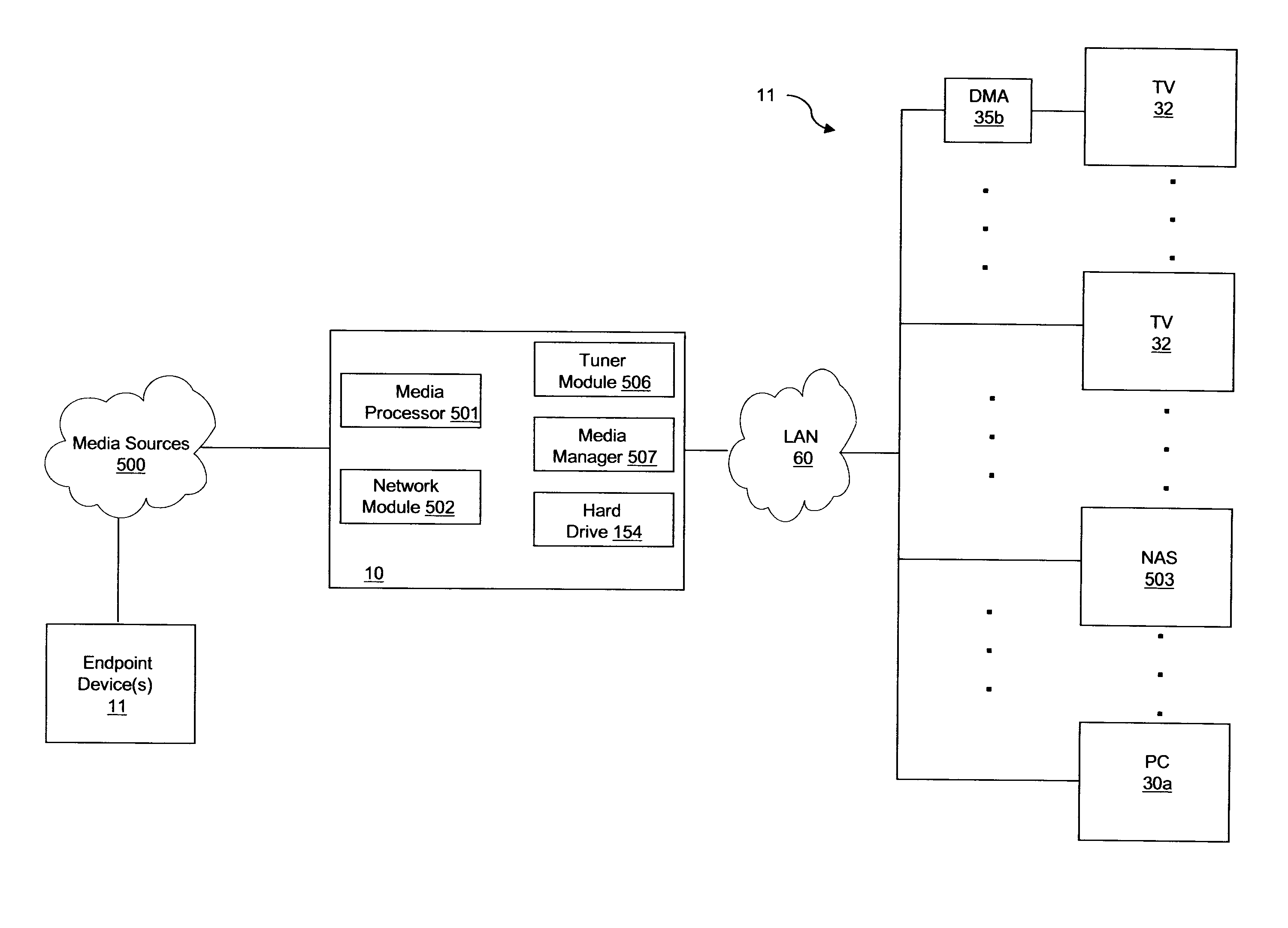
System And Method To Acquire, Aggregate, Manage, And Distribute Media
ActiveUS20080168523A1Simplify overall management of serviceReduce complexityMultiplex communicationBilling/invoicingComputer networkData format
A media content manager residing at a user premises having a tuner coupled to at least one media source operable to selectively receive at least one media stream of at least one type of media content. The media content manager also including a media processor coupled to the tuner and operable to receive the at least one media stream and convert the media stream to a predetermined data format, the at least one media stream comprising metadata. Additionally, the media content manages has a media manager coupled to the media processor and operable to receive the at least one media stream in the predetermined data format and direct the media stream to a selected media player device coupled to the media processor. Furthermore, the media content manager includes a storage device coupled to the media manager and operable to receive and store the at least one media stream in the predetermined data format.
Owner:KIP PROD P1 LP
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
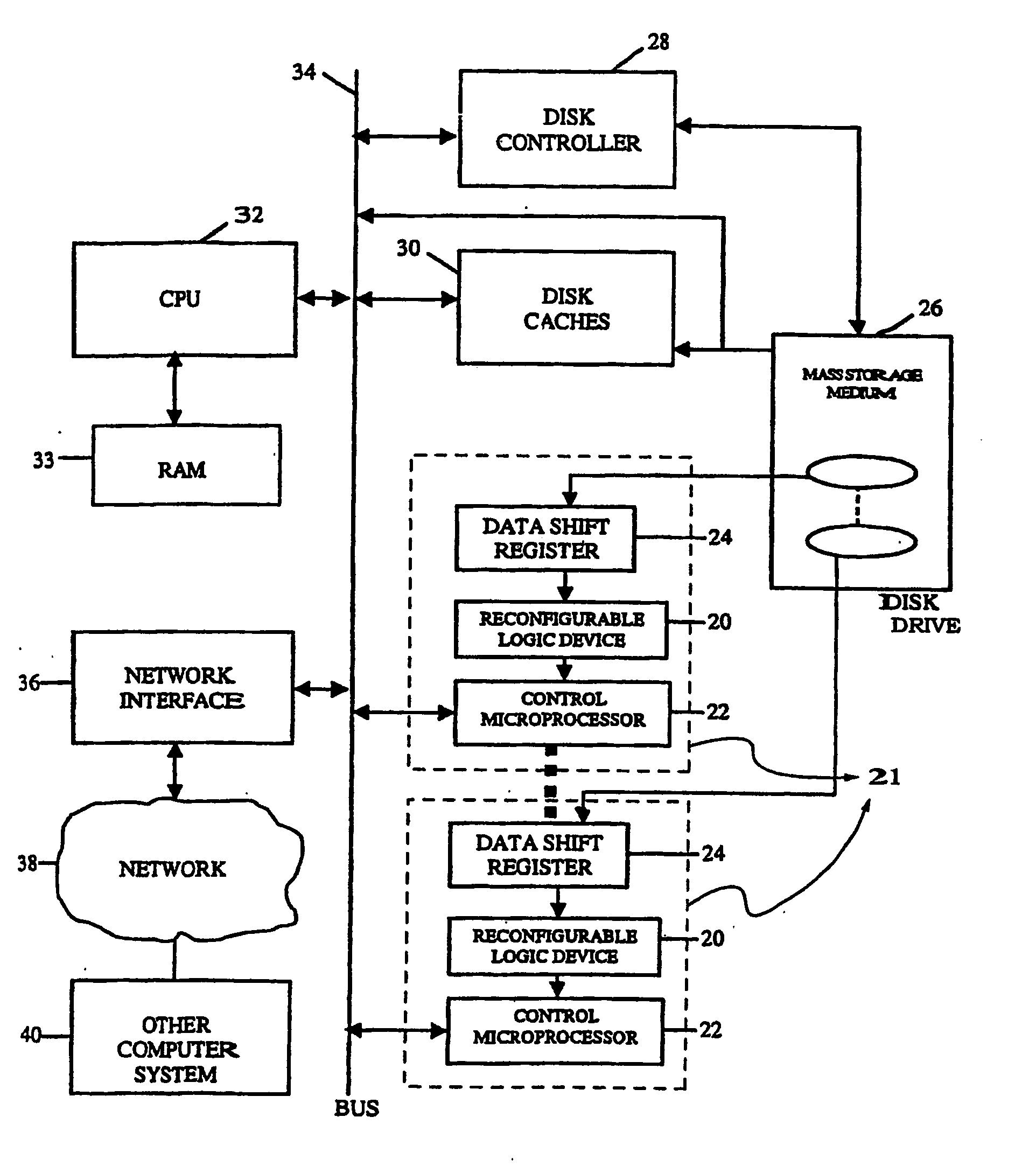
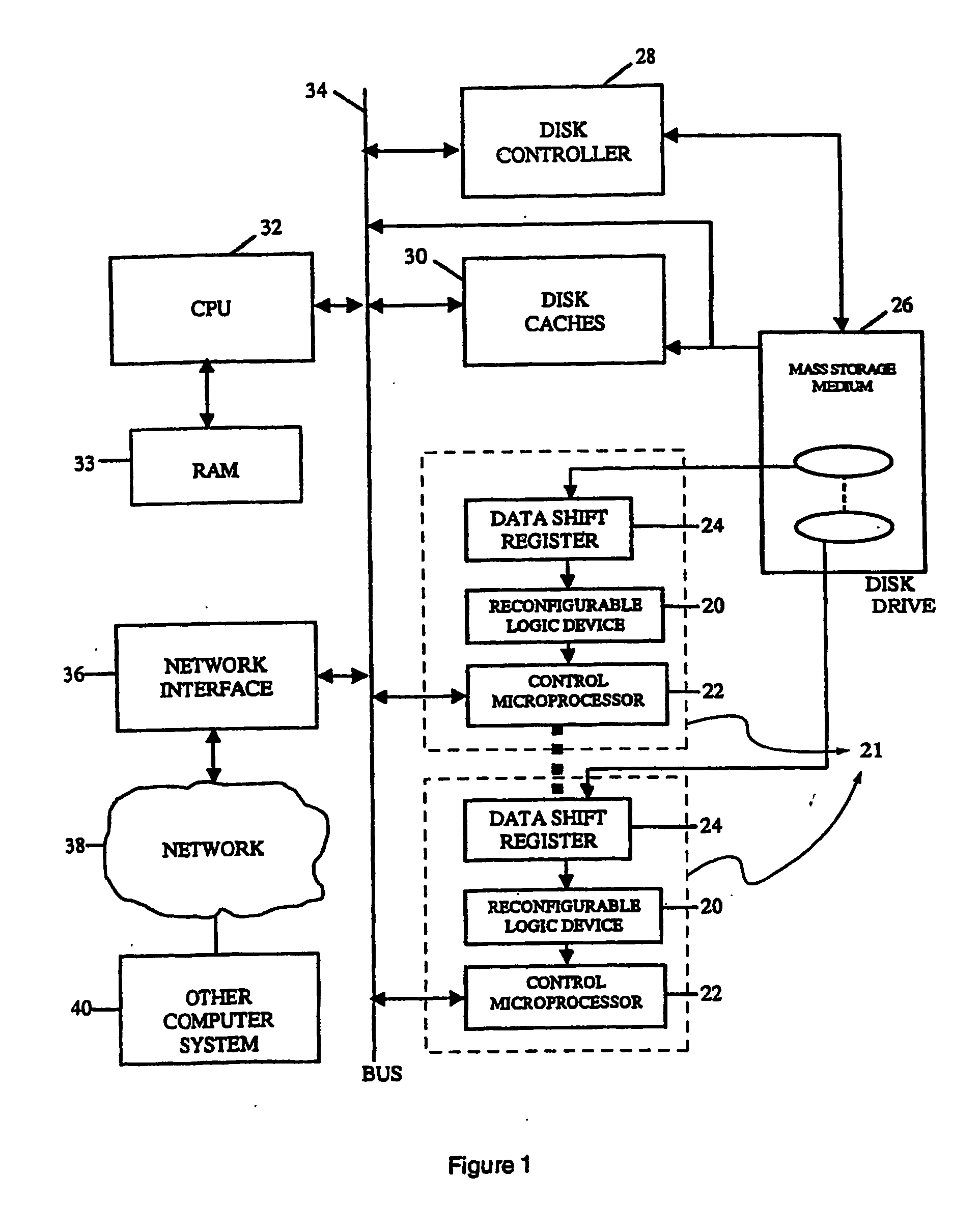
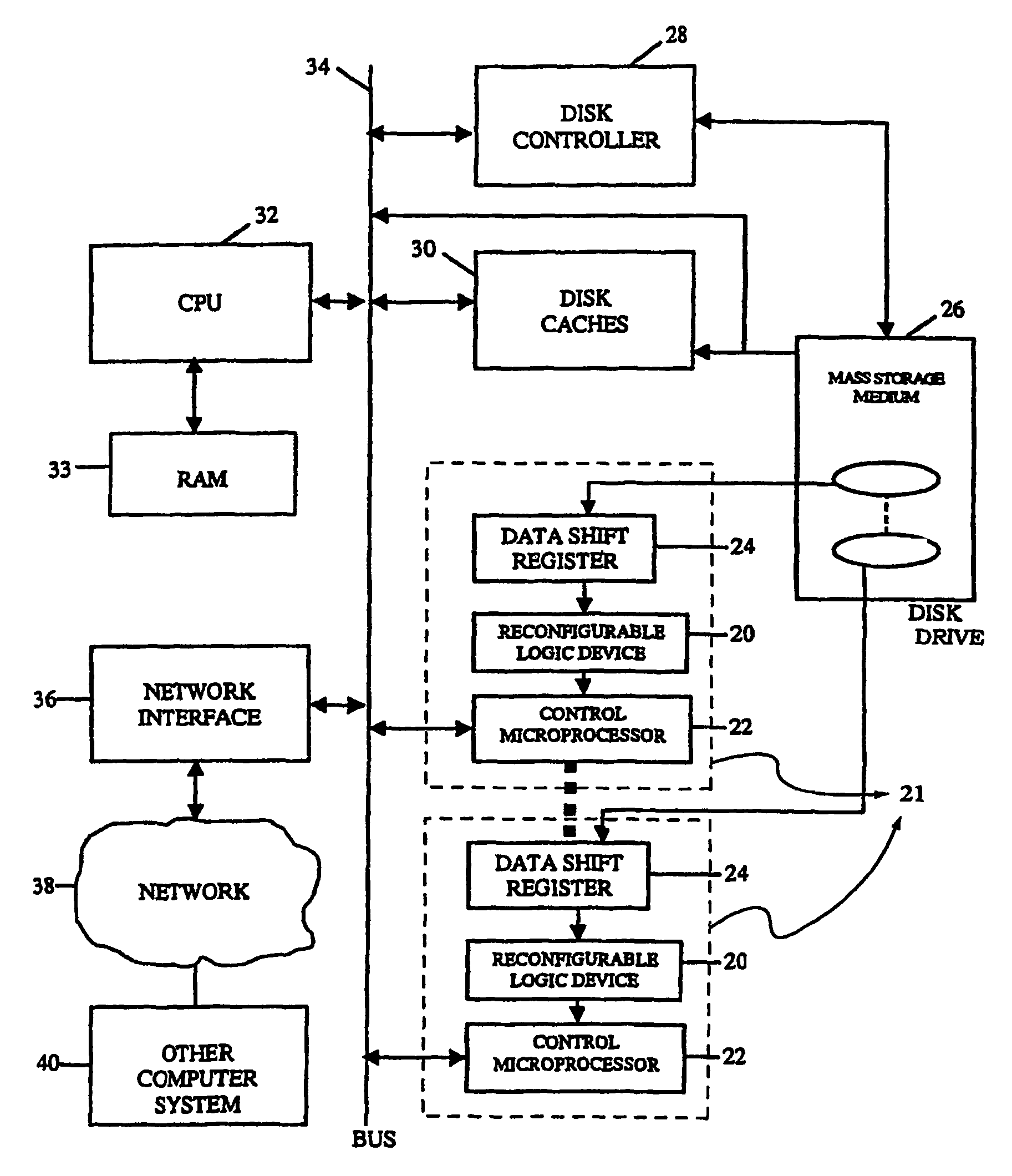
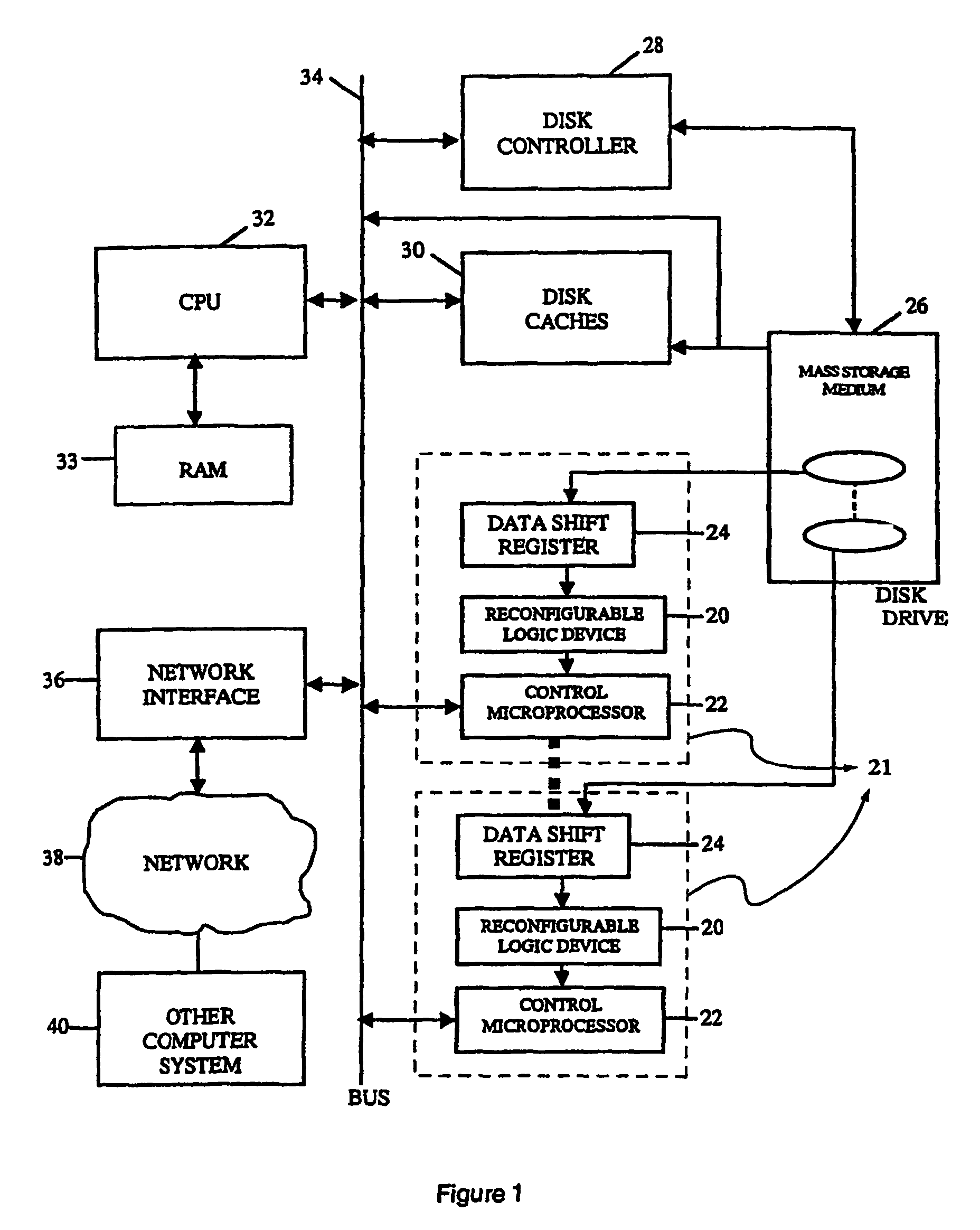
Intelligent data storage and processing using fpga devices
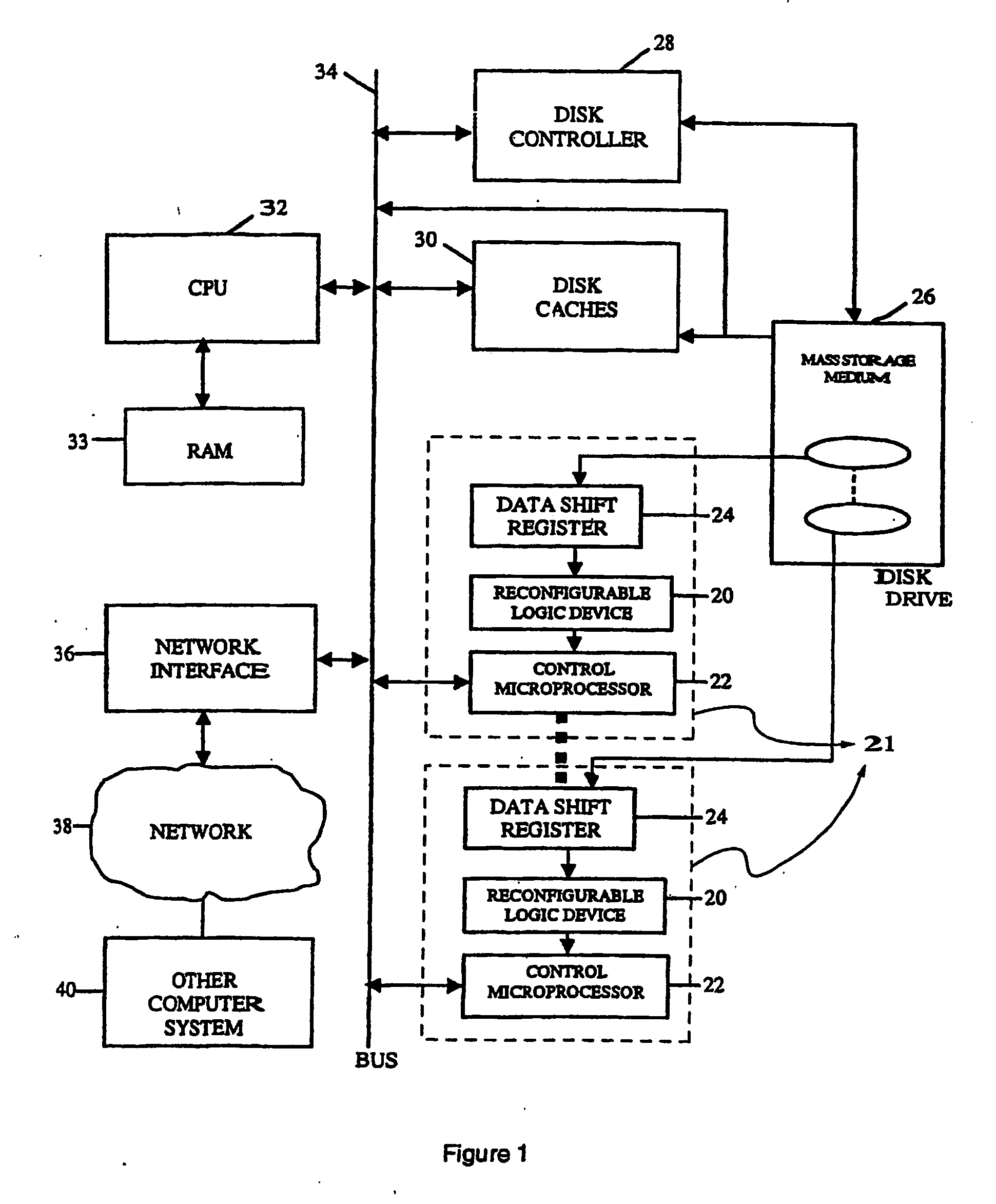
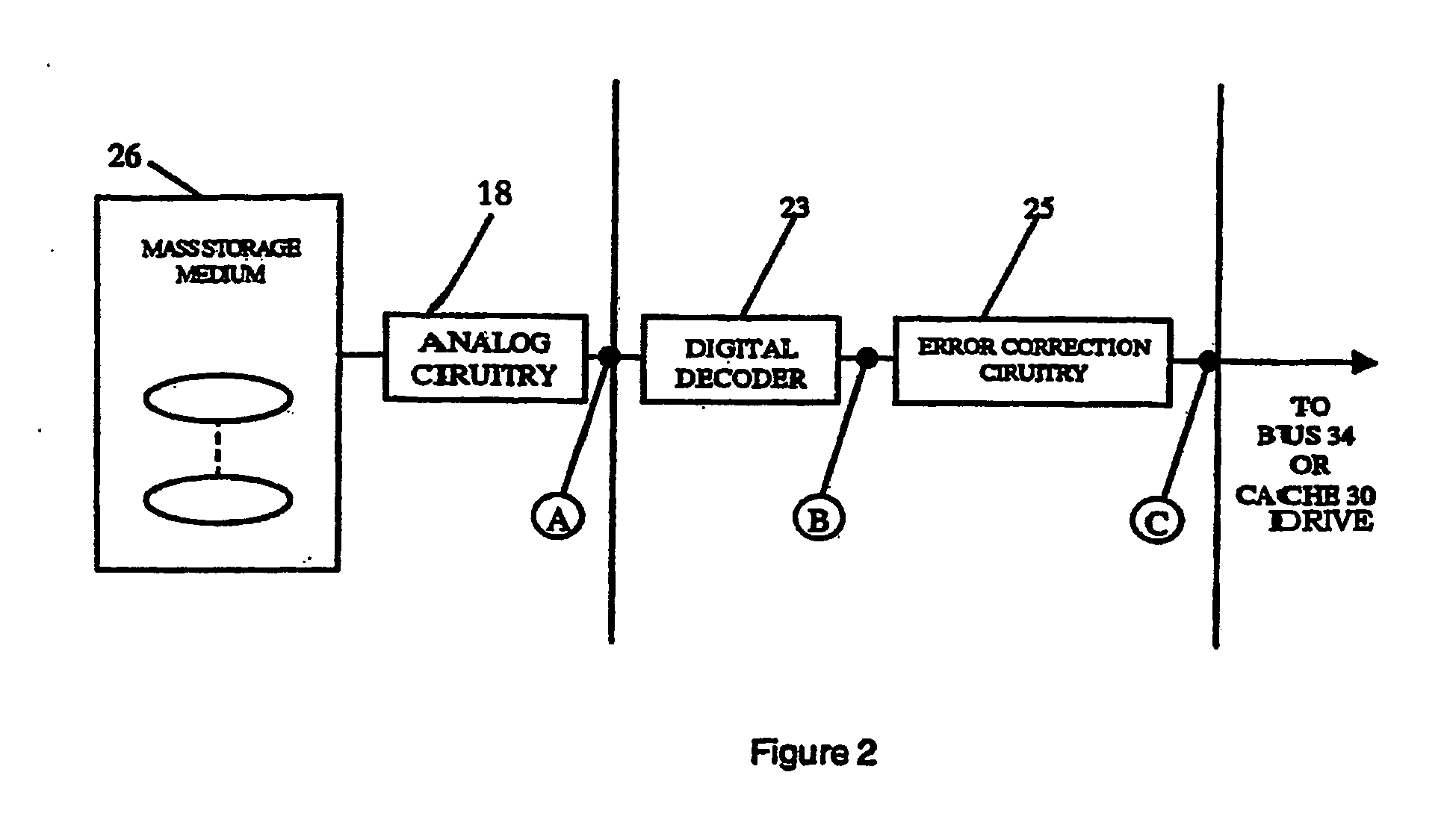
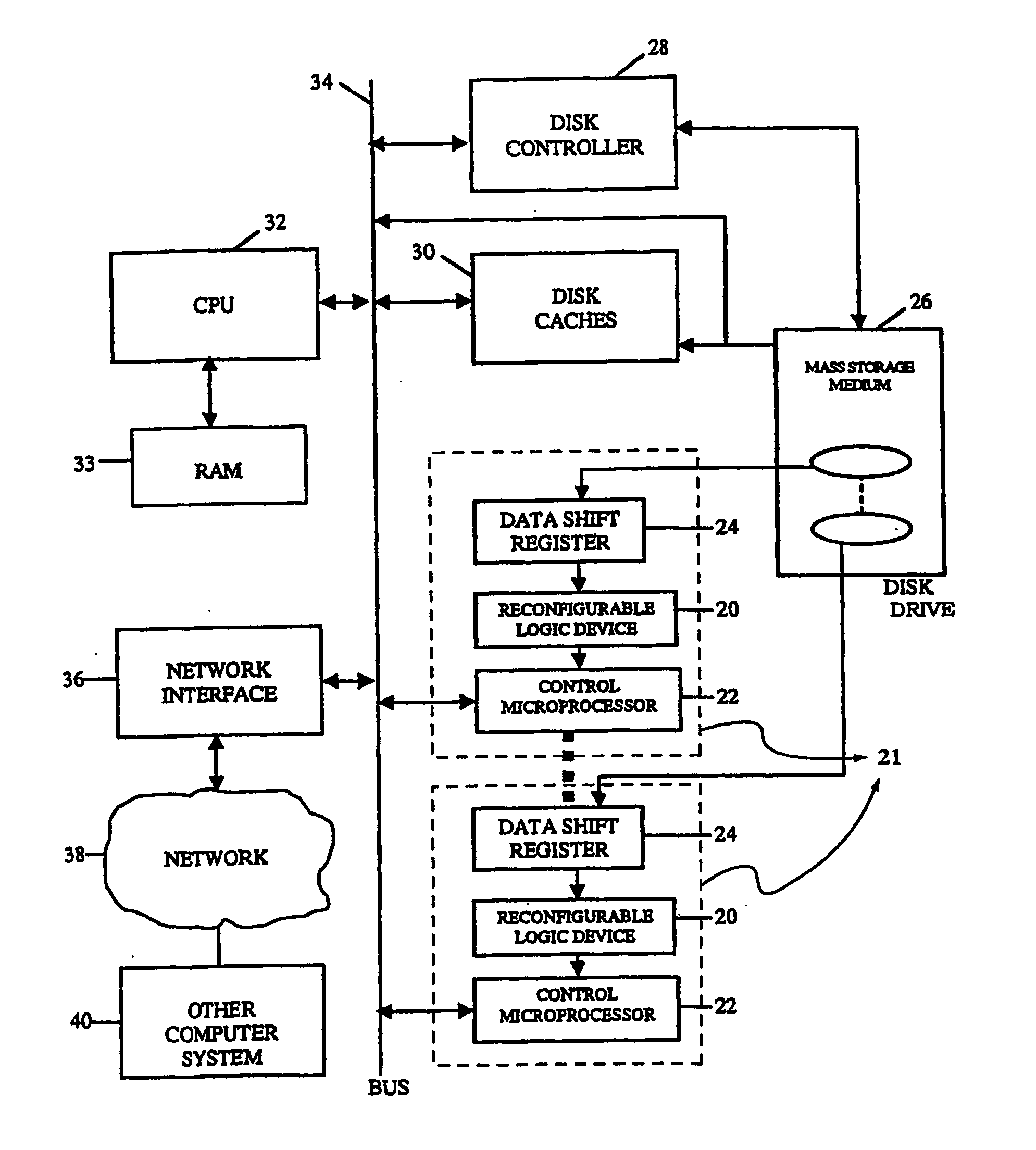
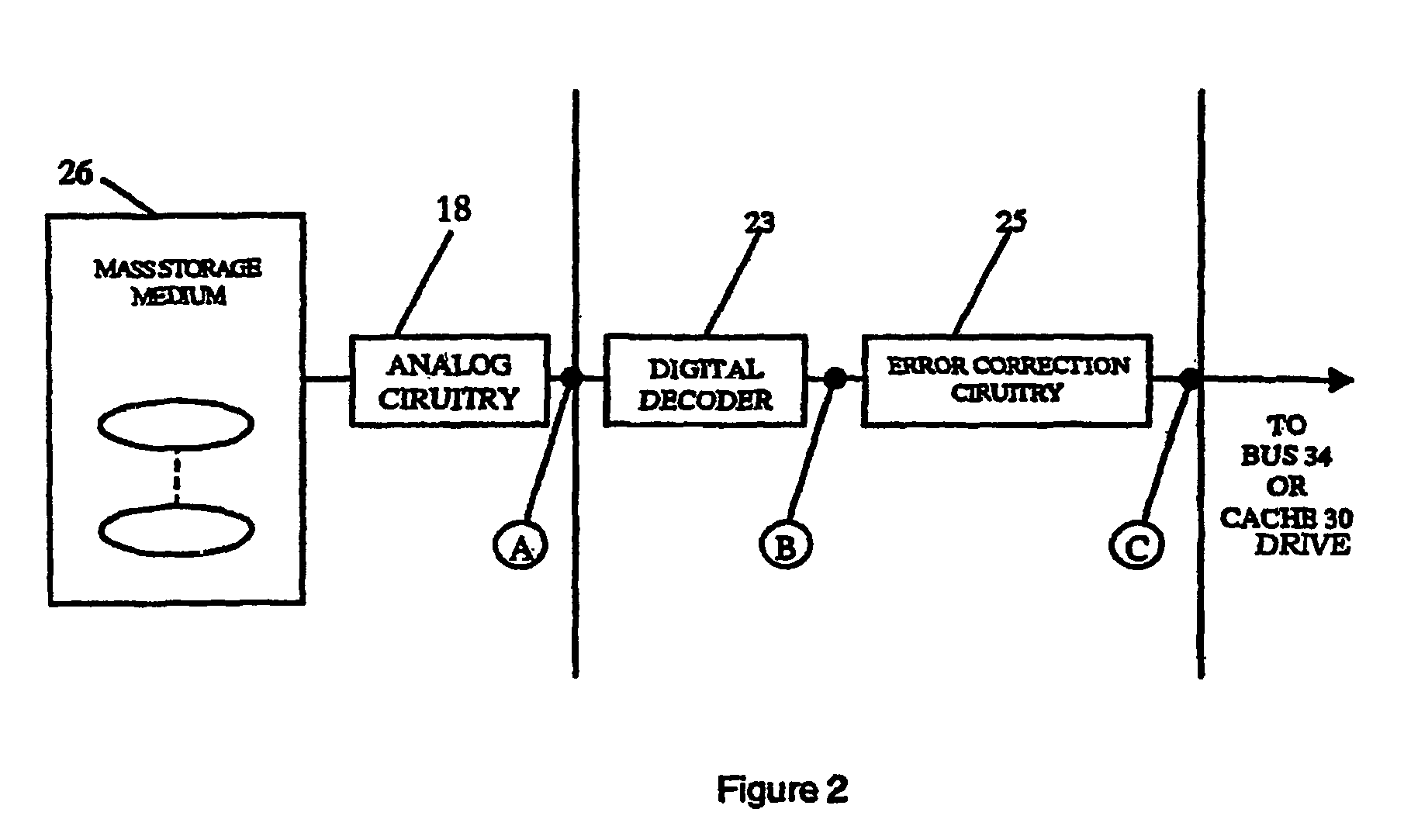
InactiveUS20070277036A1Improve data securityIncrease speedInput/output to record carriersDigital data information retrievalMagnetic storageComputerized system
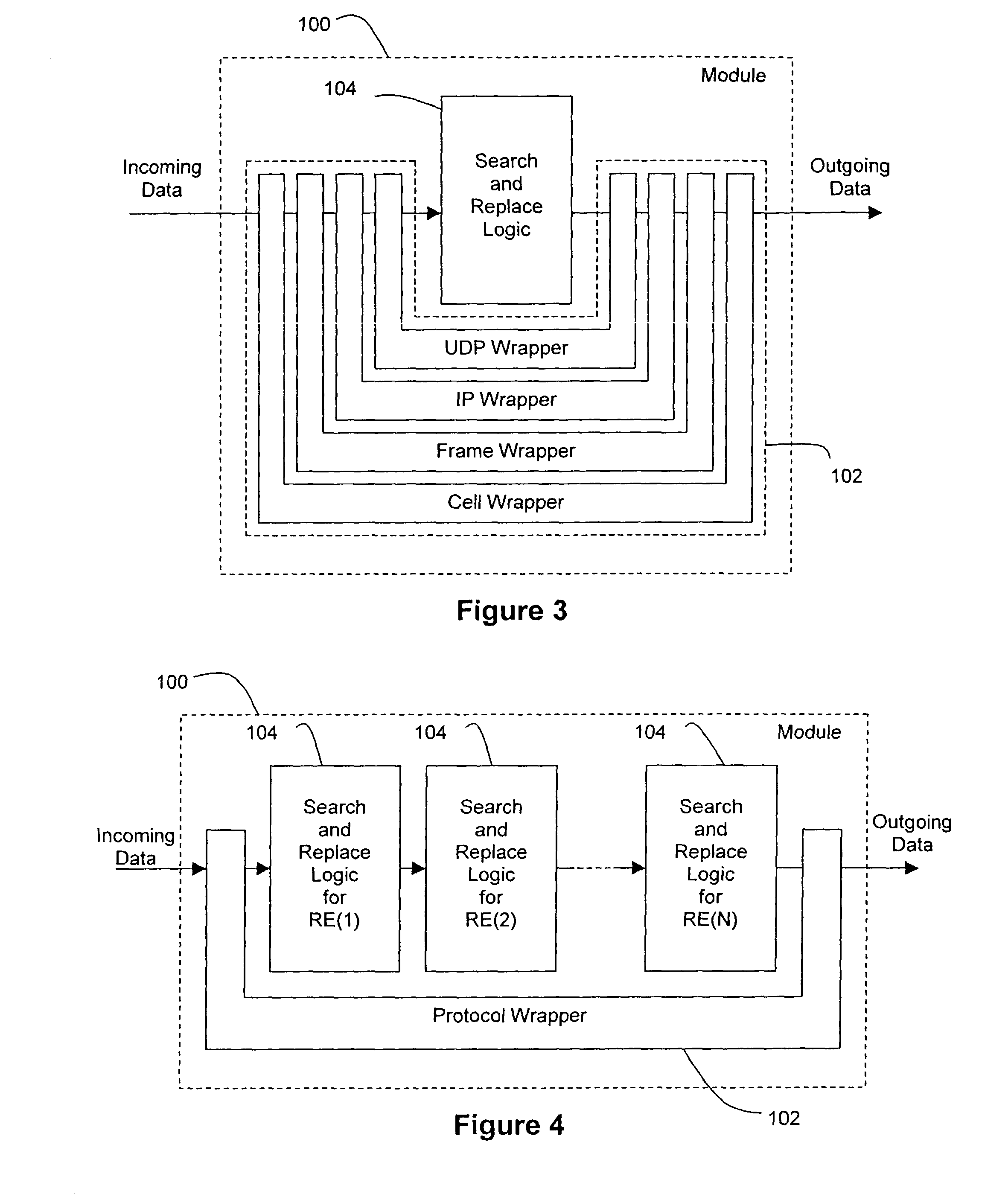
A data storage and retrieval device and method is disclosed. The device includes at least one magnetic storage medium configured to store target data and at least one re-configurable logic device comprising an FPGA coupled to the at least one magnetic storage medium and configured to read a continuous stream of target data therefrom, having been configured with a template or as otherwise desired to fit the type of search and data being searched. The re-configurable logic device is configured to receive at least one search inquiry in the form of a data key and to determine a match between the data key and the target data as it is being read from the at least one magnetic storage medium. This device and method can perform a variety of searches on the target data including without limitation exact and approximate match searches, sequence match searches, image match searches and data reduction searches. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN. In addition to performing search and data reduction operations, this device may also be used to perform a variety of other processing operations including encryption, decryption, compression, decompression, and combinations thereof.
Owner:IP RESERVOIR
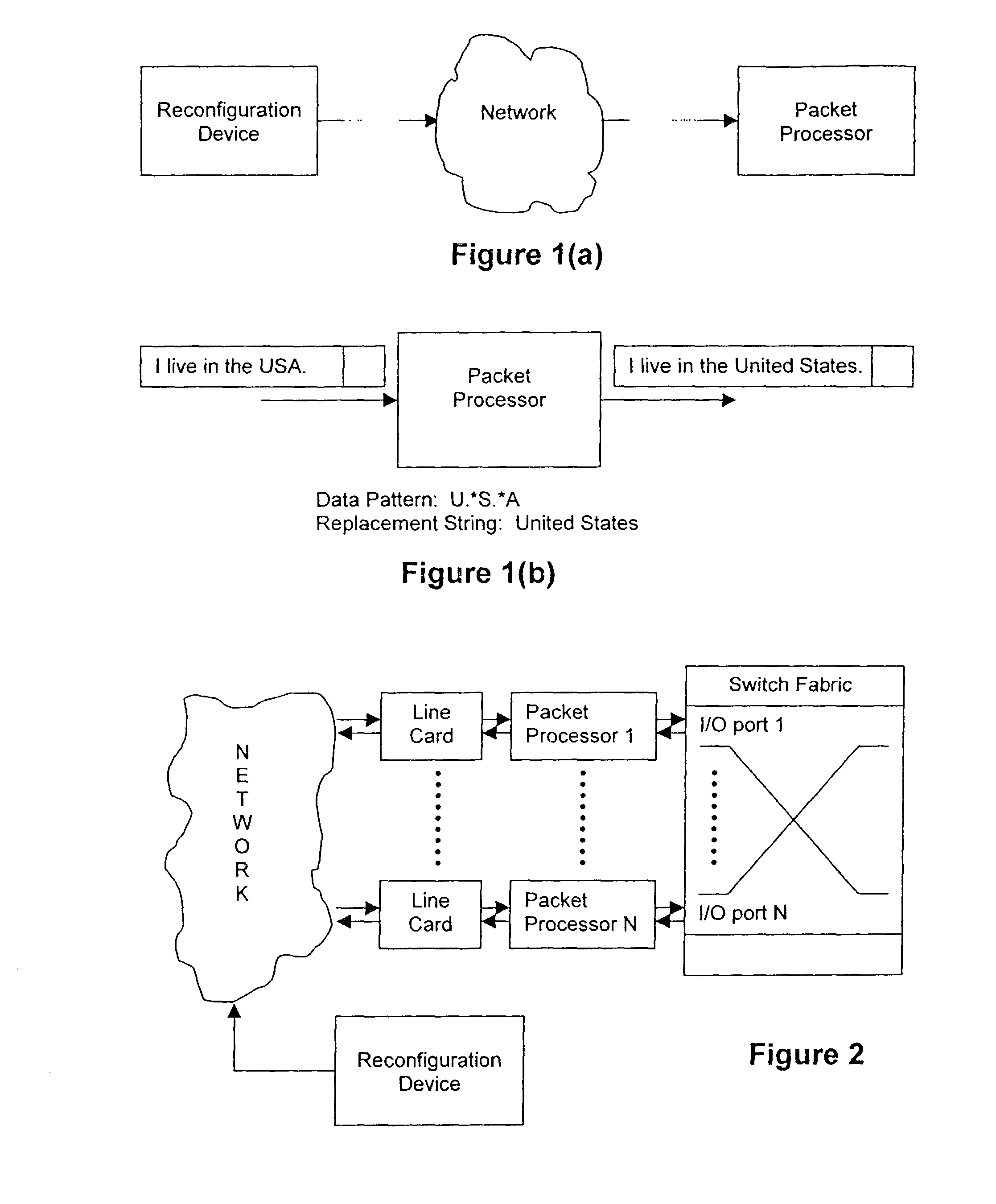
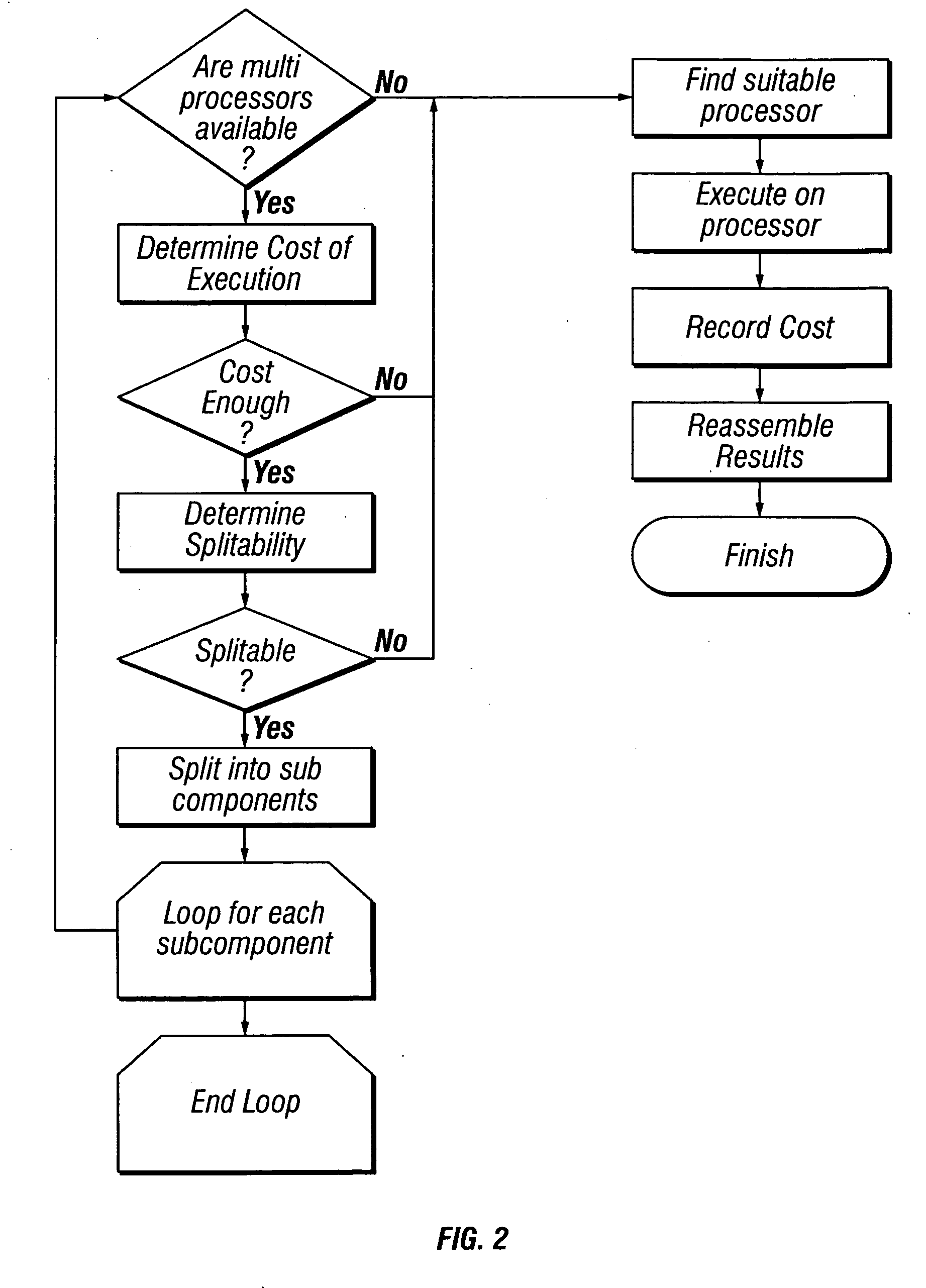
Methods, systems, and devices using reprogrammable hardware for high-speed processing of streaming data to find a redefinable pattern and respond thereto
InactiveUS7093023B2Prevent materialPrevented from reachingError detection/correctionMultiple digital computer combinationsProgrammable logic devicePacket processing
A reprogrammable packet processing system for processing a stream of data is disclosed herein. A reprogrammable data processor is implemented with a programmable logic device (PLD), such as a field programmable gate array (FPGA), that is programmed to determine whether a stream of data applied thereto includes a string that matches a redefinable data pattern. If a matching string is found, the data processor performs a specified action in response thereto. The data processor is reprogrammable to search packets for the presence of different data patterns and / or perform different actions when a matching string is detected. A reconfiguration device receives input from a user specifying the data pattern and action, processes the input to generate the configuration information necessary to reprogram the PLD, and transmits the configuration information to the packet processor for reprogramming thereof.
Owner:WASHINGTON UNIV IN SAINT LOUIS
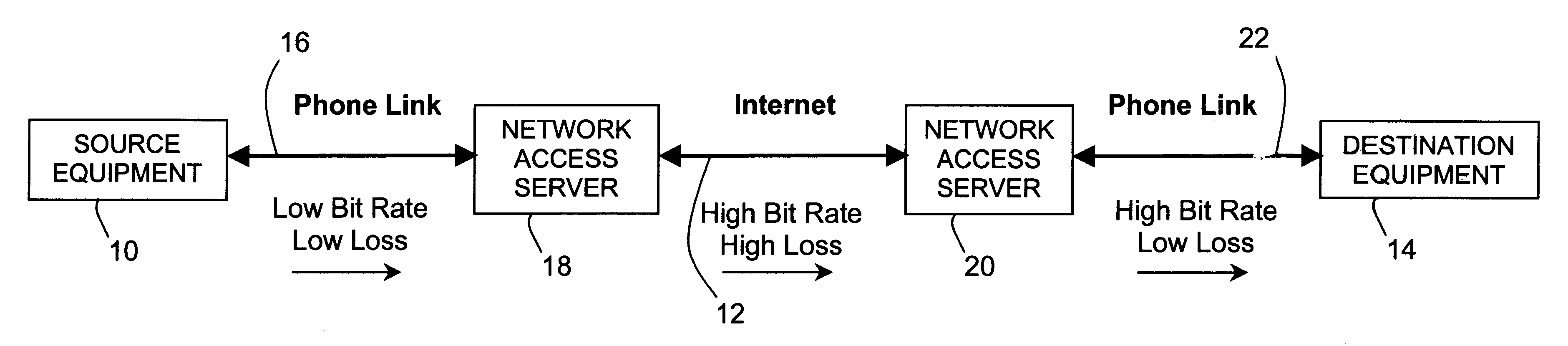
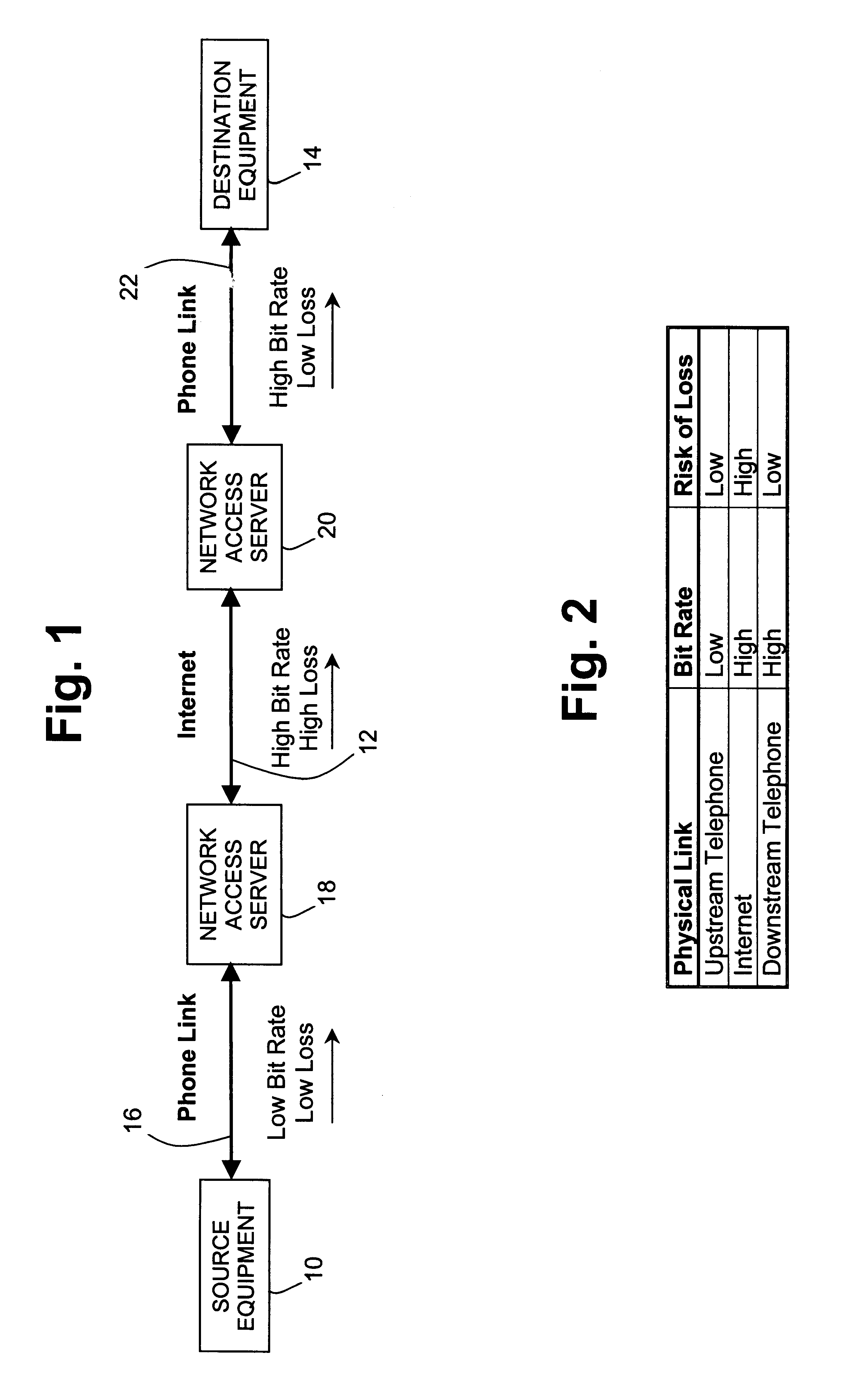
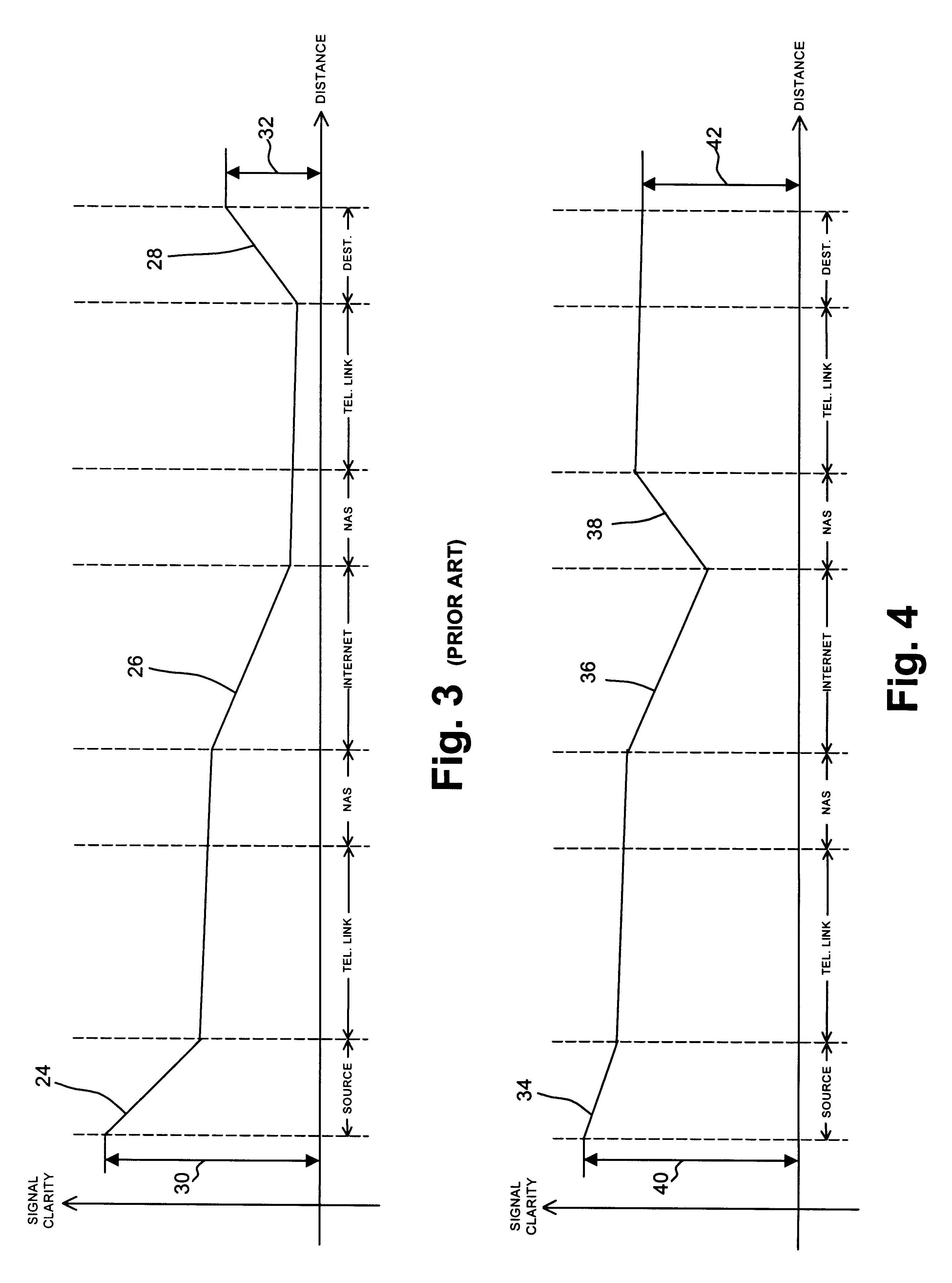
Data and real-time media communication over a lossy network
A method and apparatus for improving the speed and quality of end-to-end data or real-time media transmissions over an internet is disclosed. A media stream being transmitted to the internet is channel coded at the edge of the internet in order to free upstream bit rate for use in source coding the media. The channel coded media stream may then be decoded at a remote edge of the internet to recover lost packets.
Owner:UTSTARCOM INC
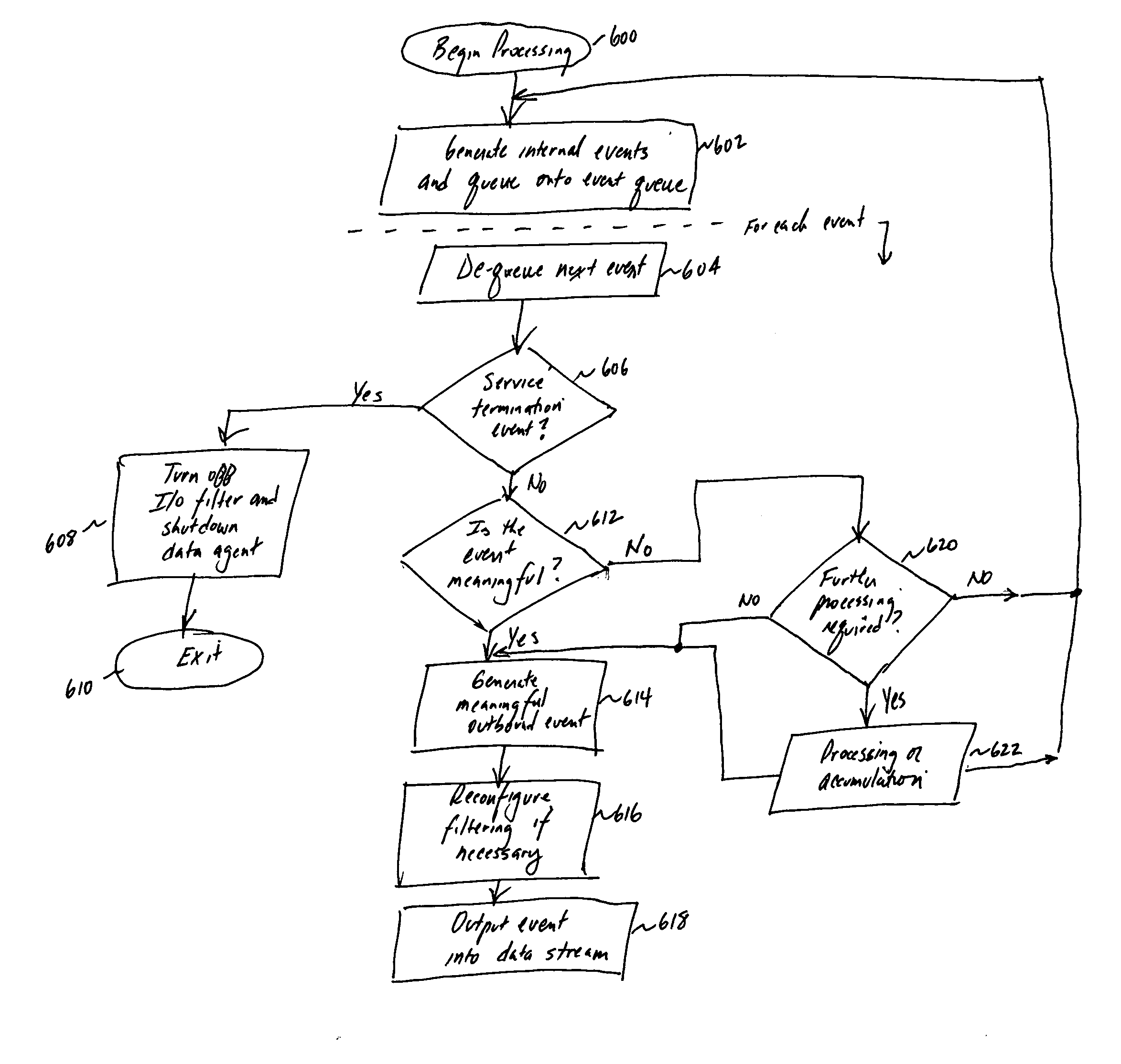
Method and system for real-time event journaling to provide enterprise data services
ActiveUS20050251540A1Good data serviceDigital data information retrievalError detection/correctionData connectionData stream
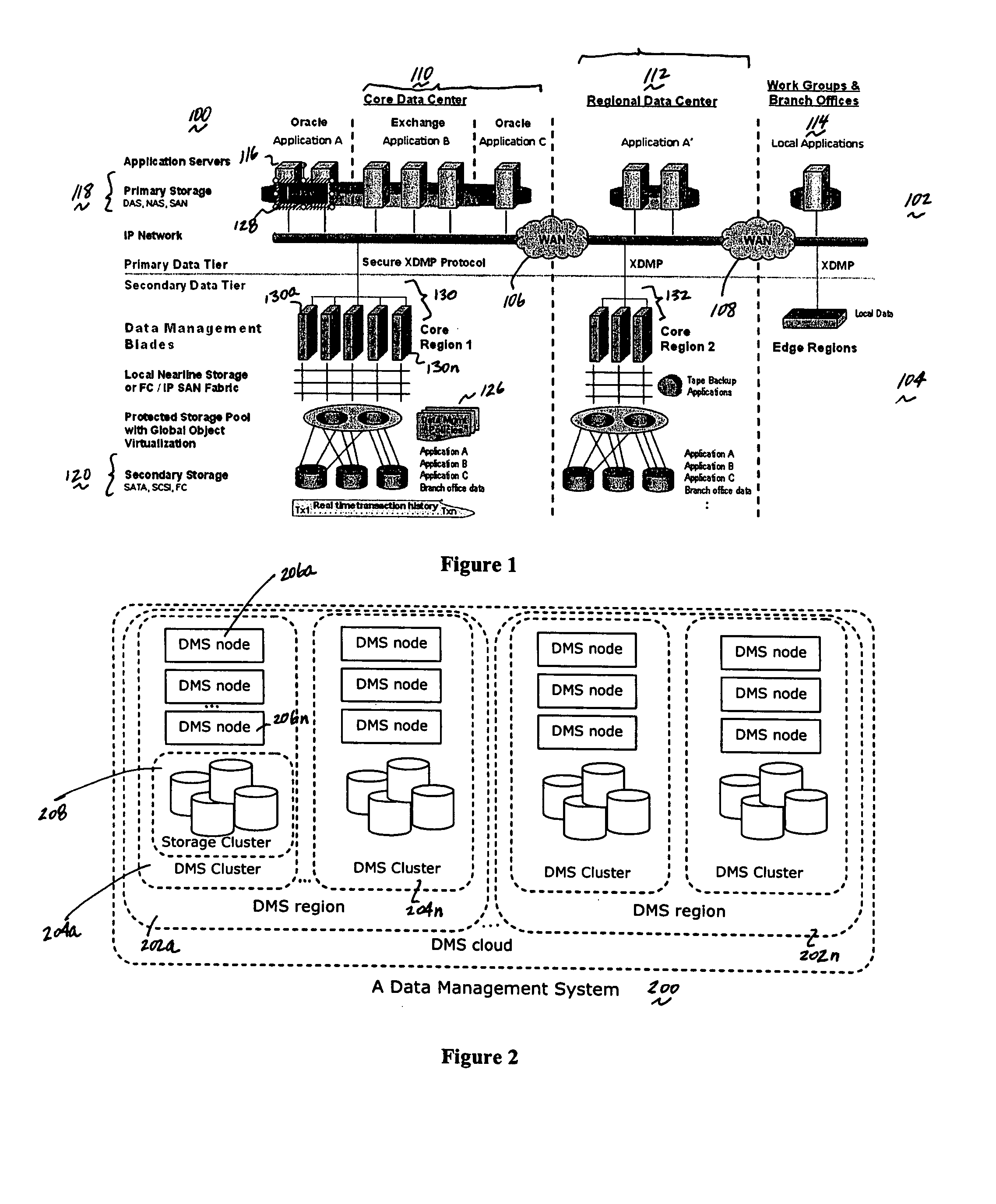
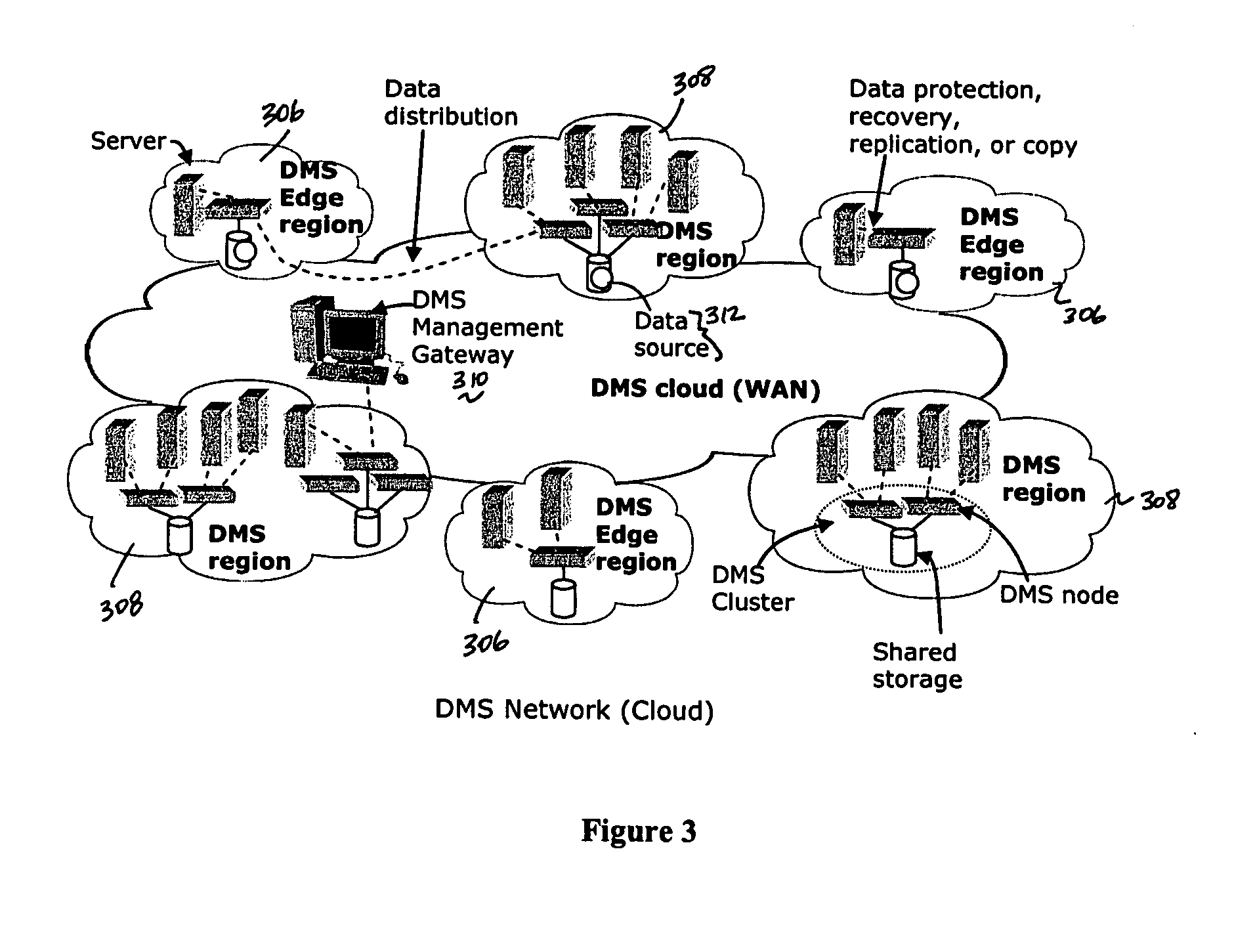
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data modifications and application state notifications and, in response, generating data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), and disaster recovery (data distribution and data replication).
Owner:QUEST SOFTWARE INC
Intelligent data storage and processing using fpga devices
InactiveUS20060294059A1Improve performanceDigital data information retrievalDigital data processing detailsComputer hardwareMagnetic storage
A data storage and retrieval device and method is disclosed. The device includes at least one magnetic storage medium configured to store target data and at least one re-configurable logic device comprising an FPGA coupled to the at least one magnetic storage medium and configured to read a continuous stream of target data therefrom, having been configured with a template or as otherwise desired to fit the type of search and data being searched. The re-configurable logic device is configured to receive at least one search inquiry in the form of a data key and to determine a match between the data key and the target data as it is being read from the at least one magnetic storage medium. This device and method can perform a variety of searches on the target data including without limitation exact and approximate match searches, sequence match searches, image match searches and data reduction searches. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN. In addition to performing search and data reduction operations, this device may also be used to perform a variety of other processing operations including encryption, decryption, compression, decompression, and combinations thereof.
Owner:IP RESERVOIR
Systems and methods for managing application security profiles
ActiveUS20080229381A1Efficient configurationEfficient processingMemory loss protectionError detection/correctionTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Method and apparatus for media data transmission
InactiveUS20070022215A1Reduce overheadAbility to presentPulse modulation television signal transmissionStill image data indexingData processing systemOperating point
Methods and apparatuses for processing media data for transmission in a data communication medium and for use with data processing systems. One exemplary method processes readable content stored in a stream or set of data which contains samples for presenting a presentation (e.g. video only or audio only or video and audio together) at a plurality of scales of scalable content. A second stream is derived from a first stream, where the second stream contains references to the first stream for use in selecting data, for an operating point within the scalable content, from the first stream. In one aspect of this method, references contained in the second stream are accessed to transmit or store the data from the first stream.
Owner:APPLE INC
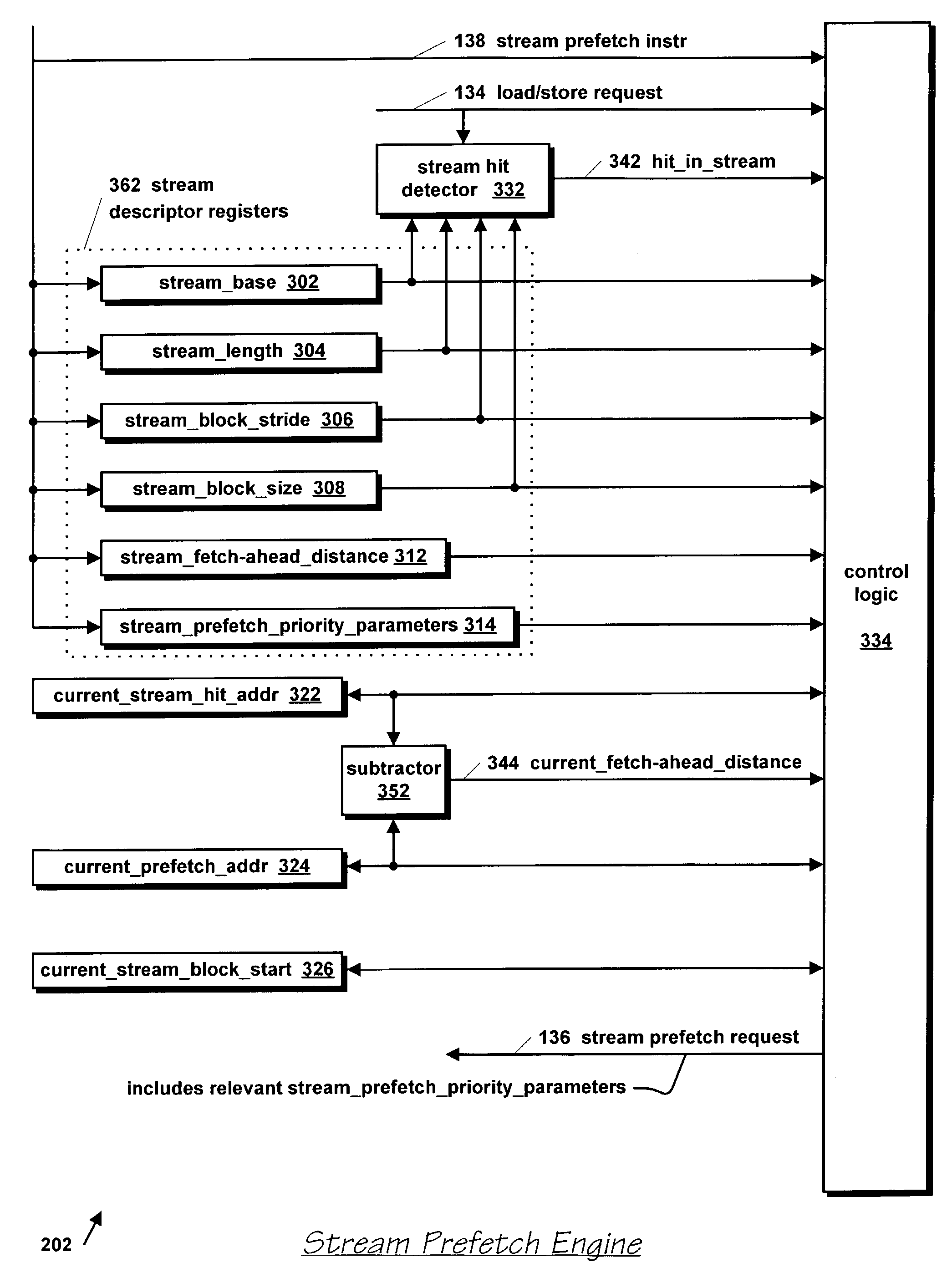
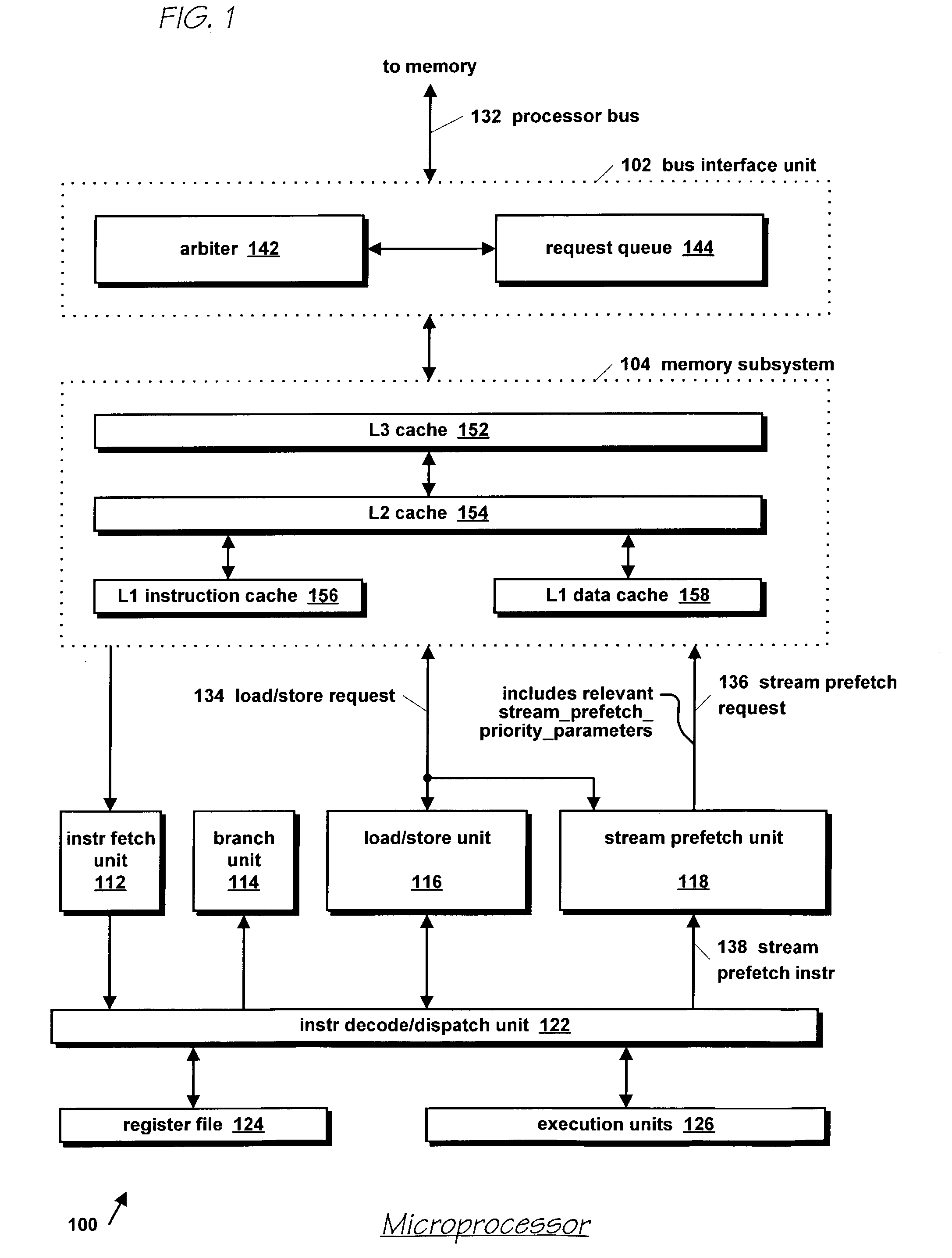
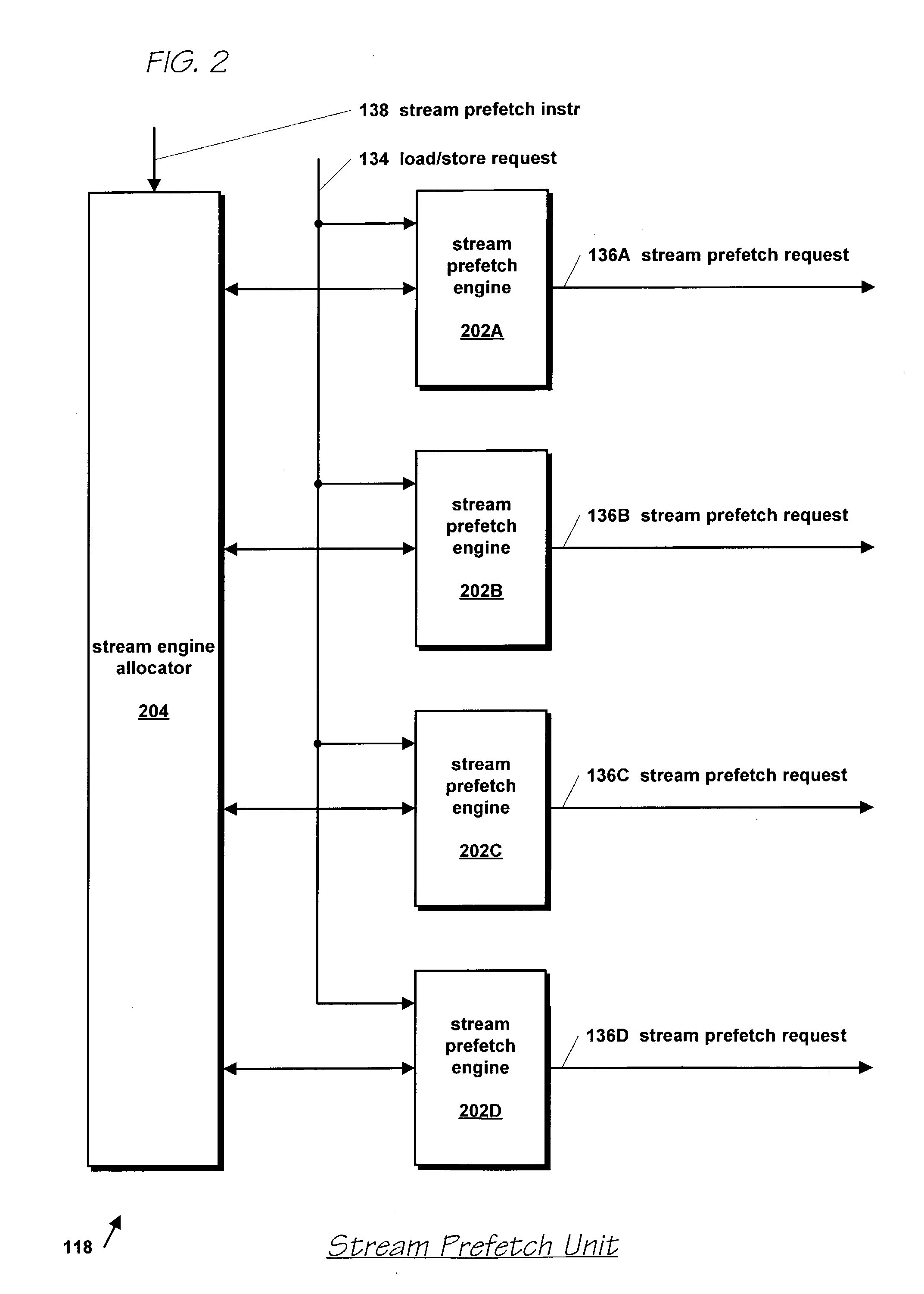
Microprocessor with improved data stream prefetching
ActiveUS7177985B1Improving data stream prefetchingMemory architecture accessing/allocationDigital computer detailsCache hierarchyPage fault
A microprocessor with multiple stream prefetch engines each executing a stream prefetch instruction to prefetch a complex data stream specified by the instruction in a manner synchronized with program execution of loads from the stream is provided. The stream prefetch engine stays at least a fetch-ahead distance (specified in the instruction) ahead of the program loads, which may randomly access the stream. The instruction specifies a level in the cache hierarchy to prefetch into, a locality indicator to specify the urgency and ephemerality of the stream, a stream prefetch priority, a TLB miss policy, a page fault miss policy, a protection violation policy, and a hysteresis value, specifying a minimum number of bytes to prefetch when the stream prefetch engine resumes prefetching. The memory subsystem includes a separate TLB for stream prefetches; or a joint TLB backing the stream prefetch TLB and load / store TLB; or a separate TLB for each prefetch engine.
Owner:ARM FINANCE OVERSEAS LTD
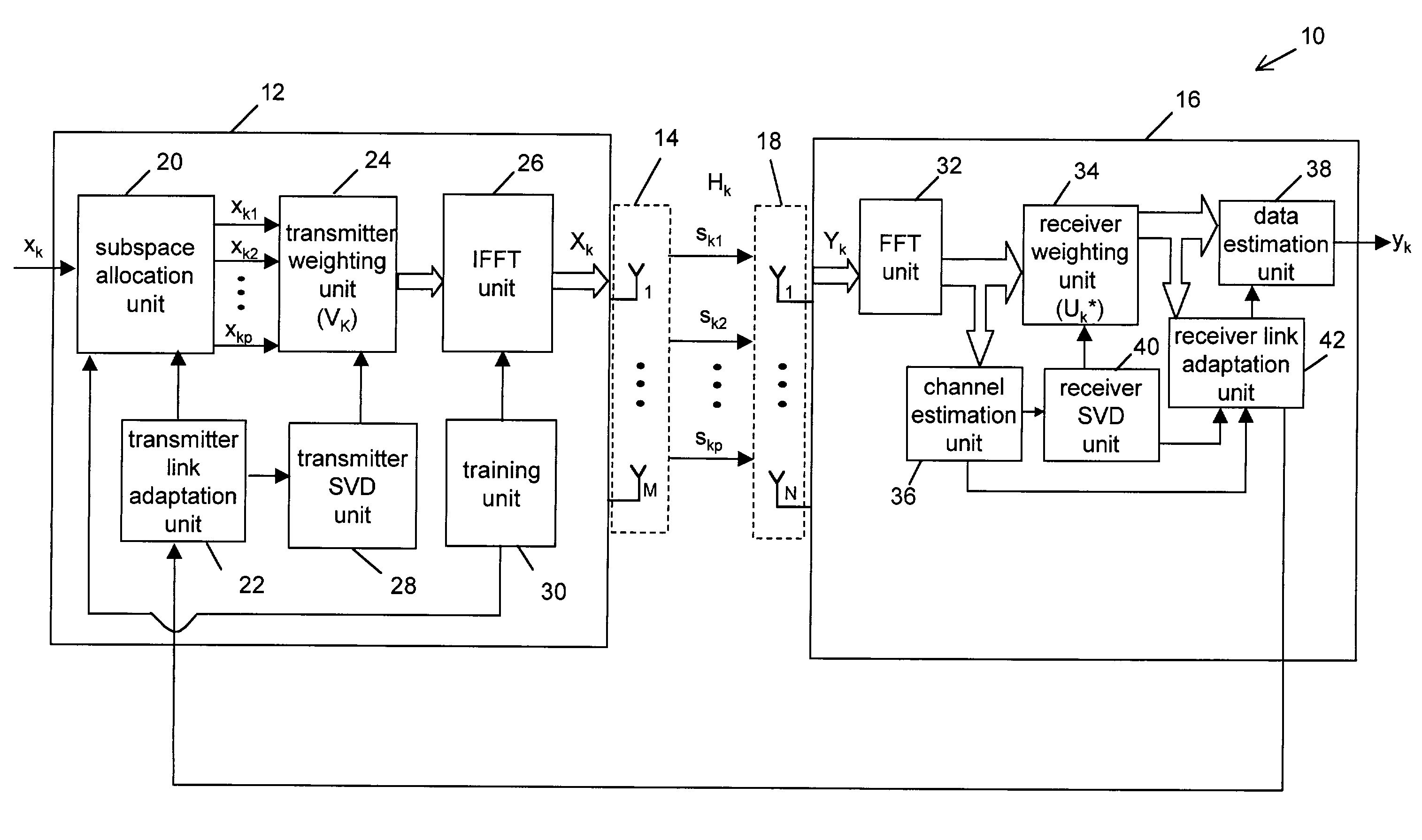
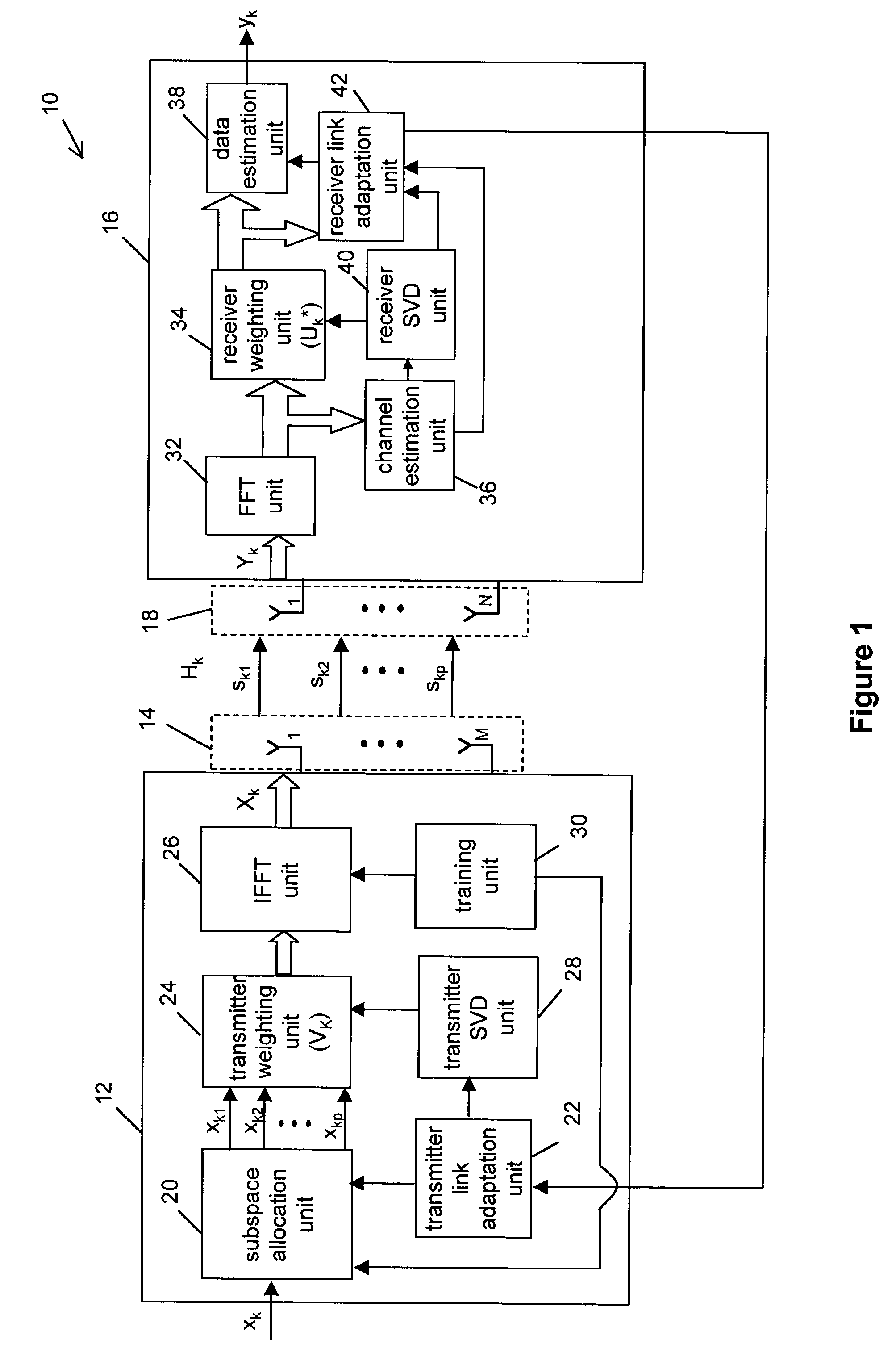
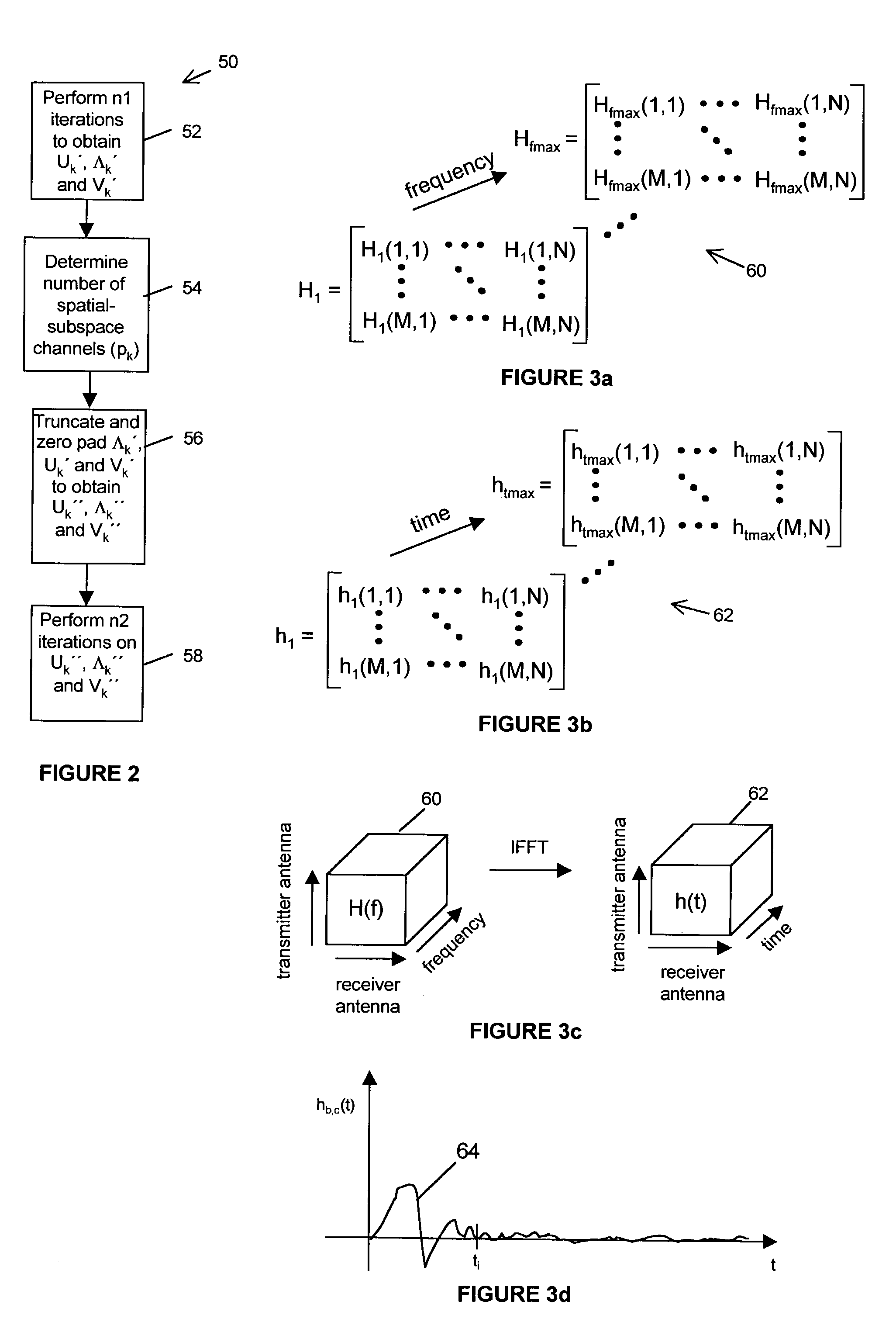
System and method for data detection in wireless communication systems
ActiveUS7327800B2Polarisation/directional diversityChannel estimationCommunications systemData detection
A system and method for data detection in a wireless communication system wherein the system comprises a receiver for receiving spatial-subspace data transmitted over a plurality of spatial-subspace channels of a sub-carrier which may comprise at least one of coded and uncoded spatial-subspace channels. The receiver comprises a receiver weighting unit for providing receive-weighed spatial-subspace data and a data estimation unit for performing an iterative processing method on the receive-weighted spatial-subspace data to estimate output data related to the input data symbol stream. The-iterative processing method comprises successively processing data on each of the plurality of spatial-subspace channels in the receive-weighted spatial-subspace data.
Owner:VECIMA NETWORKS
Multi-output packet server with independent streams
A method of serving content to multiple clients via a network is provided. Independent sessions with each of a plurality of clients are maintained, wherein the number of clients in the plurality of clients can vary over time, and wherein the start of each session and the end of each session can be independent of the start and end of other sessions. A stream of packet payloads is received, each packet payload of the stream of packet payloads including data generated from the content, wherein each packet payload in at least a subset of the stream of packet payloads includes a different set of data. Each packet payload in the stream of packet payloads is transmitted to each client of the plurality of clients in corresponding packets, wherein the packet payload transmitted to a client at any particular time is independent of the state of the corresponding session.
Owner:QUALCOMM INC
Method and system for transparent in-line protection of an electronic communications network
InactiveUS20060190997A1Improve performanceDigital data processing detailsUser identity/authority verificationComputing systemsAggregate data
The invention provides a method and system for enabling in-line communications channels between a plurality of computational systems and a switch, and / or a plurality of switches and a router. In a first version of the invention an in-line system receives uplinks of aggregated data from a plurality of switches and applies policies to the each aggregated data stream prior to transmission of the aggregated data streams from the in-line system to the router. At least one computational system provides a user identification associated with a user profile to the in-line system. The user profile informs indicates to the in-line system of the constraints imposed upon and activities permitted to the computational system originating the user identification. The constraints may include (a) one or more customized policies, (b) policies applicable to a group associated with the user identification, (c) virus / worm detection & protection, (d) a firewall, (e) virtual private network rules, and / or (f) encryption / decryption. In a second version the in-line system is configured to communicate directly with one or more computational systems as well as one or more switches.
Owner:NEVIS NETWORKS INC
Intelligent data storage and processing using FPGA devices
InactiveUS8095508B2Improve performanceDigital data information retrievalDigital data processing detailsComputer hardwareMagnetic storage
Owner:IP RESERVOIR
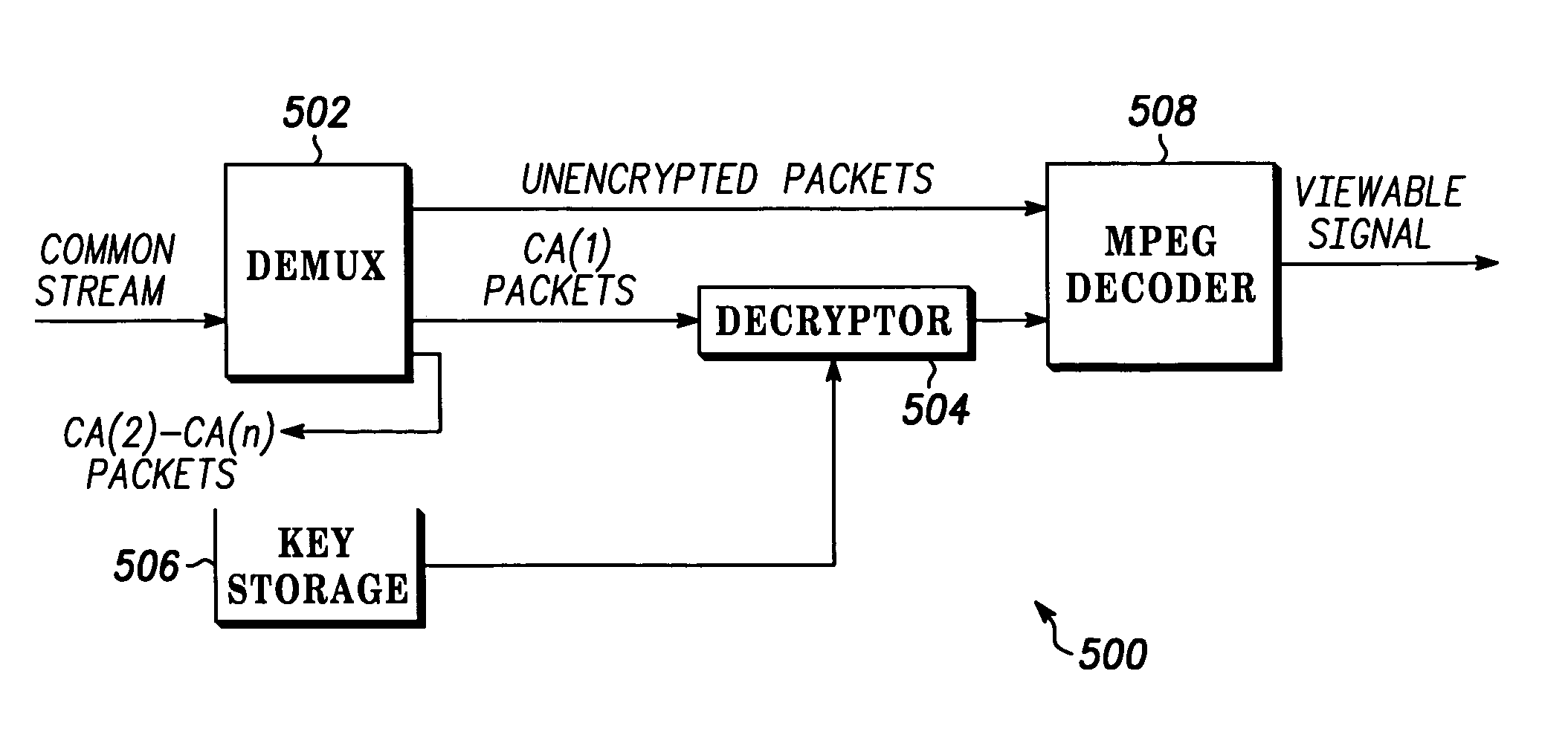
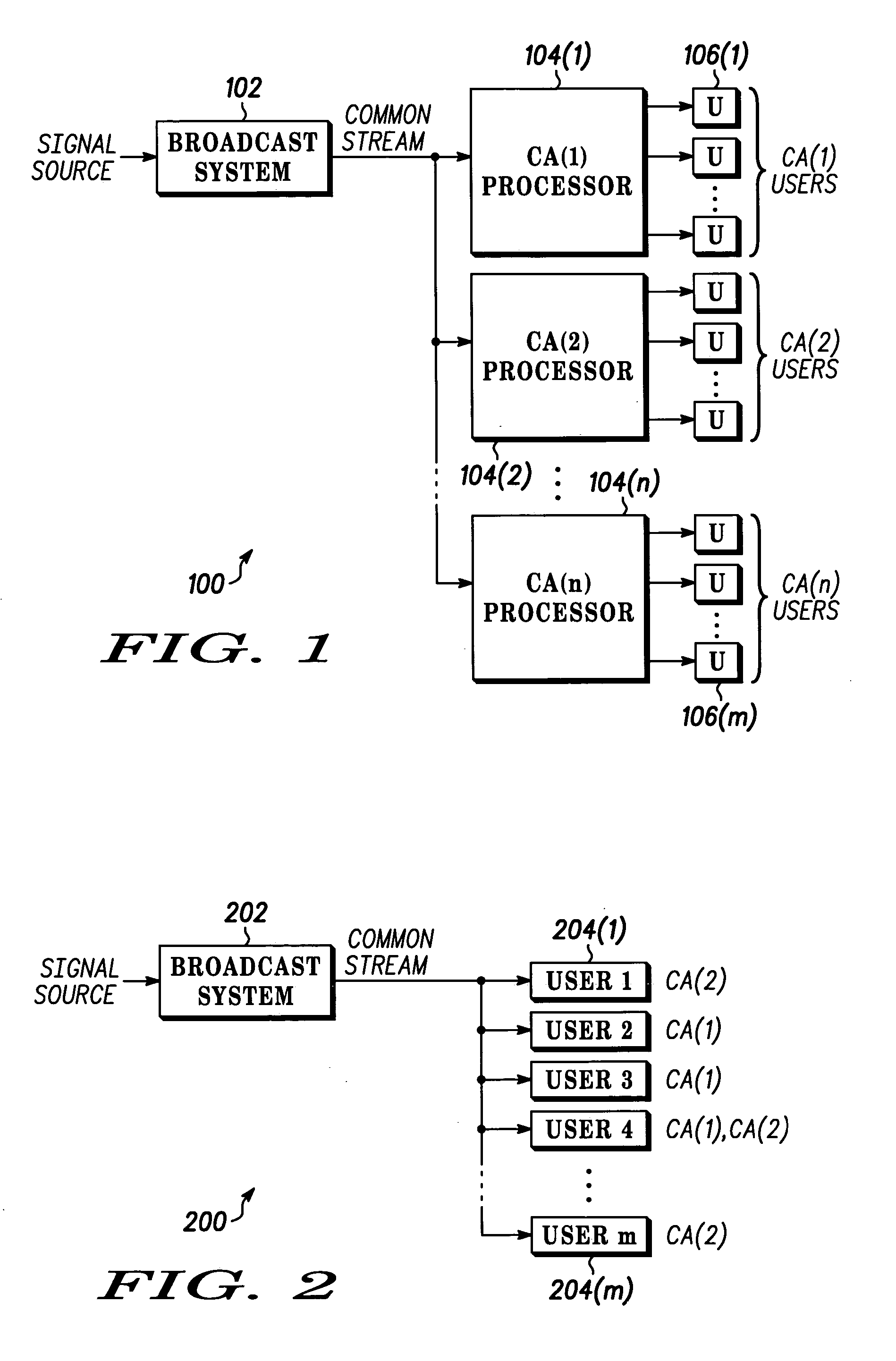
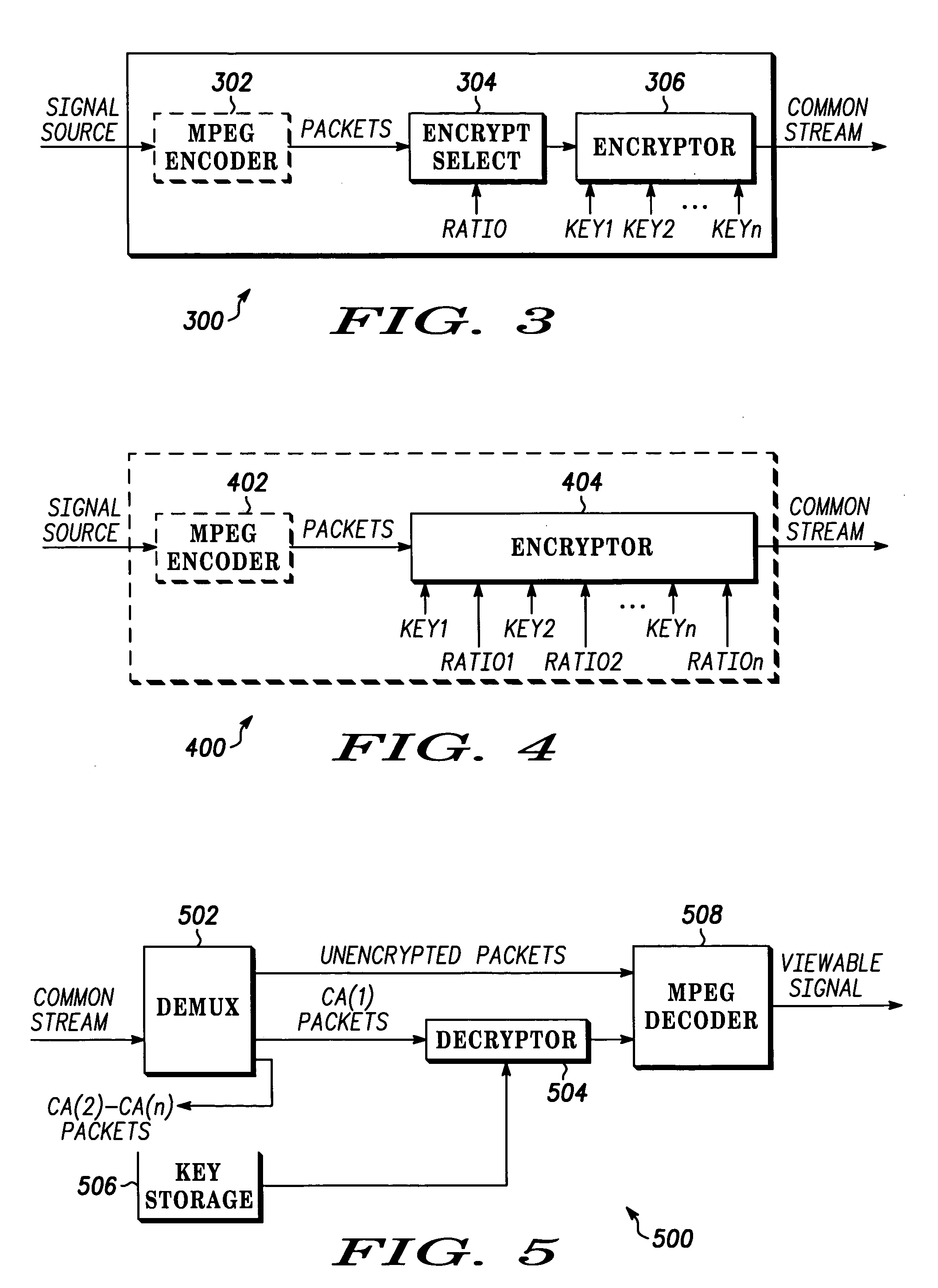
Efficient distribution of encrypted content for multiple content access systems
InactiveUS20040123094A1Television system detailsUnauthorized memory use protectionDigital dataEncryption
A system and method for digital data distribution is disclosed. The system and method provides a set of one or more source streams encoded by an encoder to form a common data stream for distribution to a plurality of destination systems, each authorized to access at least a portion of the common data stream. Encryption comprises obtaining the source stream, identifying some blocks of the source stream as secure blocks, identifying some other blocks of the source stream as unsecured blocks, encrypting the secure blocks for each of a plurality of destination system classes wherein each of the plurality of destination systems is a member of one or more destination system classes, and each of the blocks of an encrypted secure block set is decryptable by destination systems in the class associated with that encrypted secure block set.
Owner:GOOGLE TECH HLDG LLC
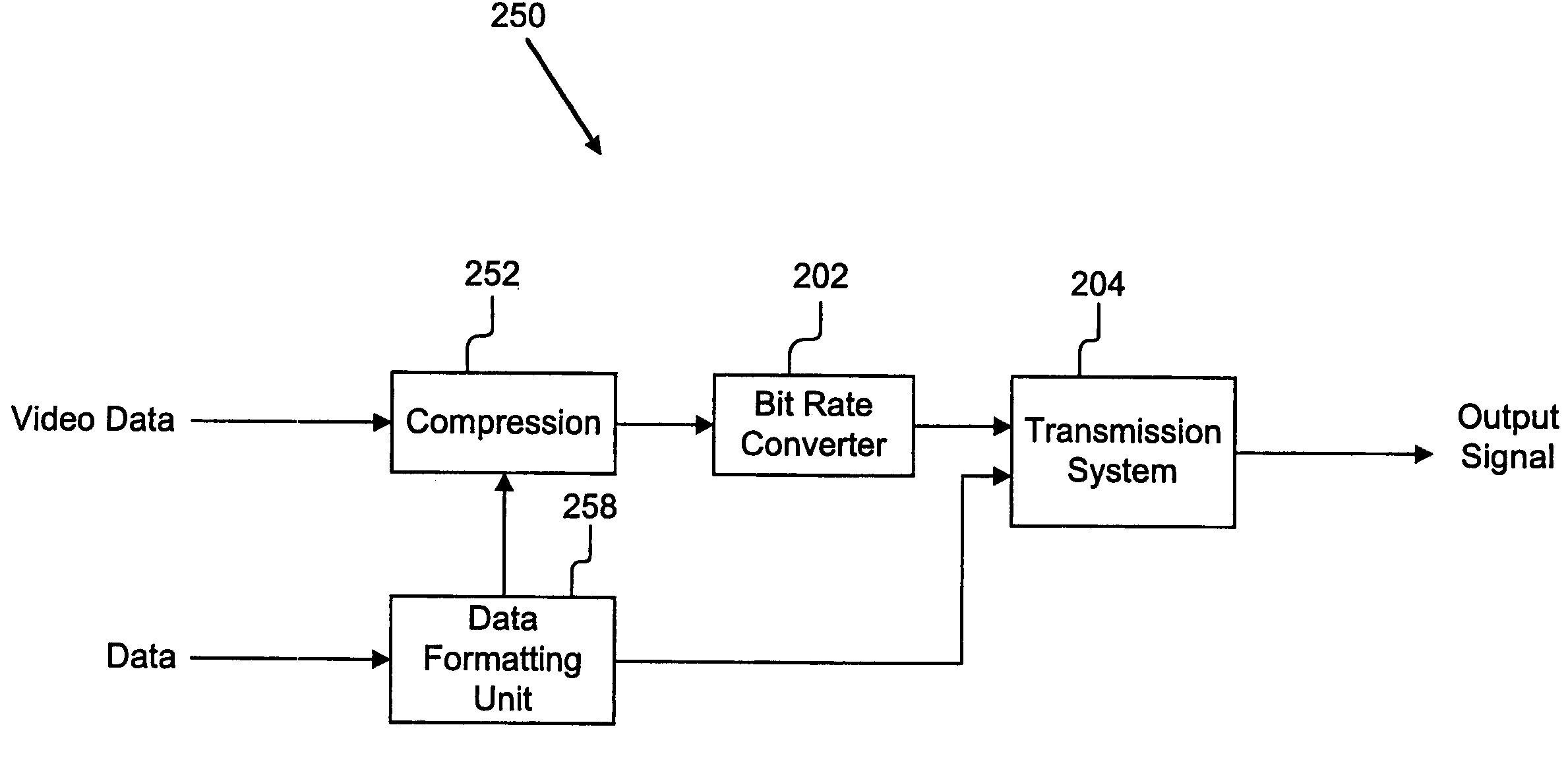
System and method for transporting a compressed video and data bit stream over a communication channel
InactiveUS7505480B1Eliminate needError preventionFrequency-division multiplex detailsAccess networkComputer science
Digitally compressed video / audio bit streams, when transmitted over digital communication channels such as digital subscriber loop (DSL) access networks, ATM networks, satellite, or wireless digital transmission facilities, can be corrupted due to lack of sufficient channel bandwidth. This invention describes schemes to ensure lossless transmission of bit streams containing pre-compressed video signals within the communication channels. The schemes herein comprises a rate conversion system that converts the bit rate of a pre-compressed video bit stream from one bit rate to another, and that is integrated with a digital communication channel, and a means to convey the maximum channel transmission rate to the rate conversion system to allow satisfactory transmission of the bit stream from the input of the rate converter through the transmission facility.
Owner:V BITS +1
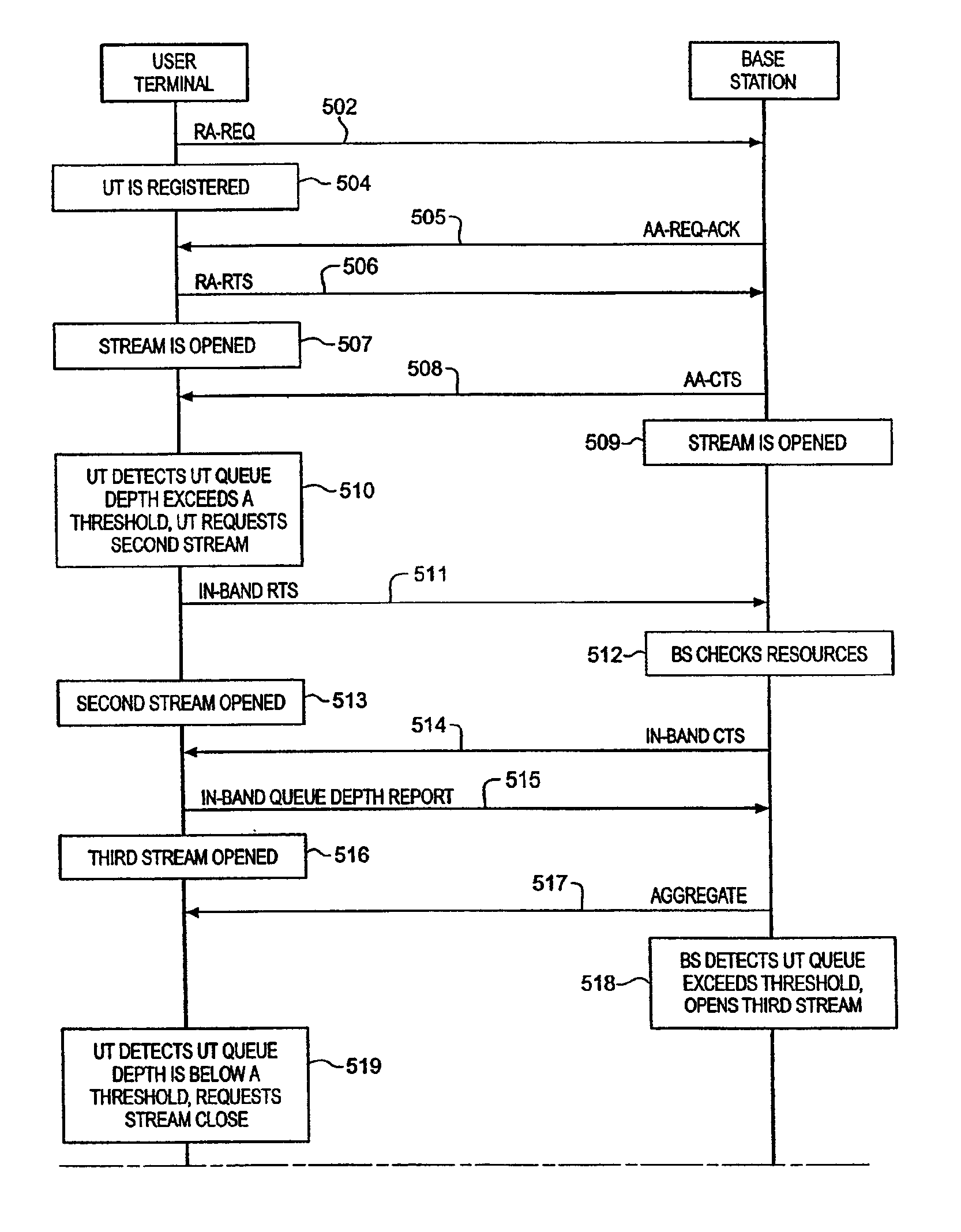
Dynamic allocation and de-allocation of multiple communication channels for bandwidth on-demand
InactiveUS7027415B1Network traffic/resource managementRadio transmissionTraffic capacityCommunications system
A method and apparatus are provided that dynamically allocates communication streams to provide flexible bandwidth to terminals of a communications system. In one embodiment the invention includes identifying a first terminal and a second terminal to each other for the communication of traffic over at least one of multiple streams; and dynamically allocating and de-allocating further streams based on the traffic to be carried and the traffic capacity of opened streams between the first and the second terminals. The invention may further include comparing traffic to be carried between the first terminal and the second terminal to the capacity of any open streams between the first terminal and the second terminal and allocating or de-allocating at least one stream based on the comparison. Alternatively, the invention may include comparing depths of transmit queues to the capacity of any open streams between the first terminal and the second terminal and allocating or de-allocating at least one stream based on the comparison.
Owner:INTEL CORP
Optimization methods for the insertion, protection, and detection of digital watermarks in digital data
Disclosed herein are methods and systems for encoding digital watermarks into content signals. Also disclosed are systems and methods for detecting and / or verifying digital watermarks in content signals.According to one embodiment, a system for encoding of digital watermark information includes: a window identifier for identifying a sample window in the signal; an interval calculator for determining a quantization interval of the sample window; and a sampler for normalizing the sample window to provide normalized samples.According to another embodiment, a system for pre-analyzing a digital signal for encoding at least one digital watermark using a digital filter is disclosed.According to another embodiment, a method for pre-analyzing a digital signal for encoding digital watermarks comprises: (1) providing a digital signal; (2) providing a digital filter to be applied to the digital signal; and (3) identifying an area of the digital signal that will be affected by the digital filter based on at least one measurable difference between the digital signal and a counterpart of the digital signal selected from the group consisting of the digital signal as transmitted, the digital signal as stored in a medium, and the digital signal as played backed.According to another embodiment, a method for encoding a watermark in a content signal includes the steps of (1) splitting a watermark bit stream; and (2) encoding at least half of the watermark bit stream in the content signal using inverted instances of the watermark bit stream.Other methods and systems for encoding / decoding digital watermarks are also disclosed.
Owner:WISTARIA TRADING INC
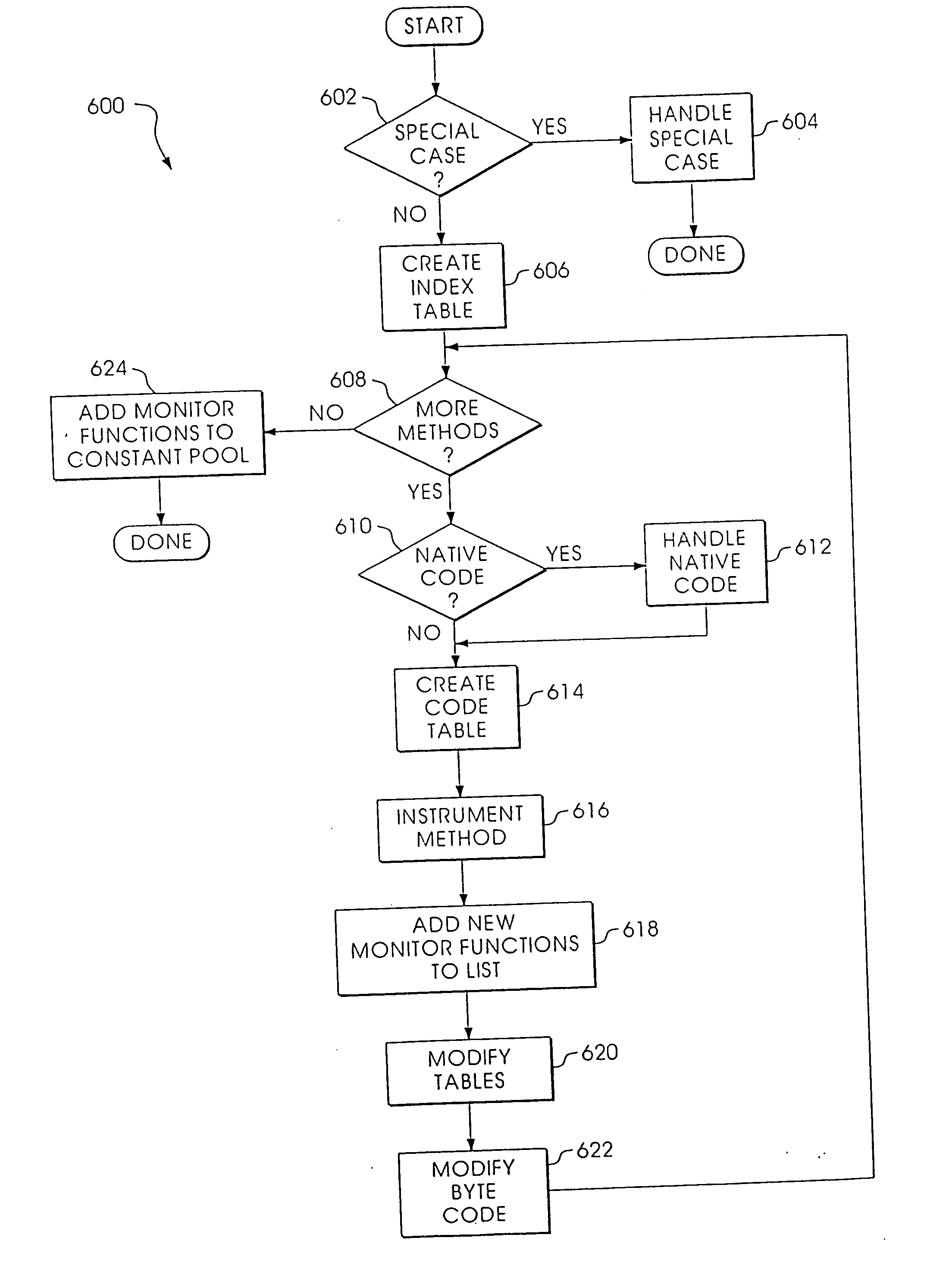
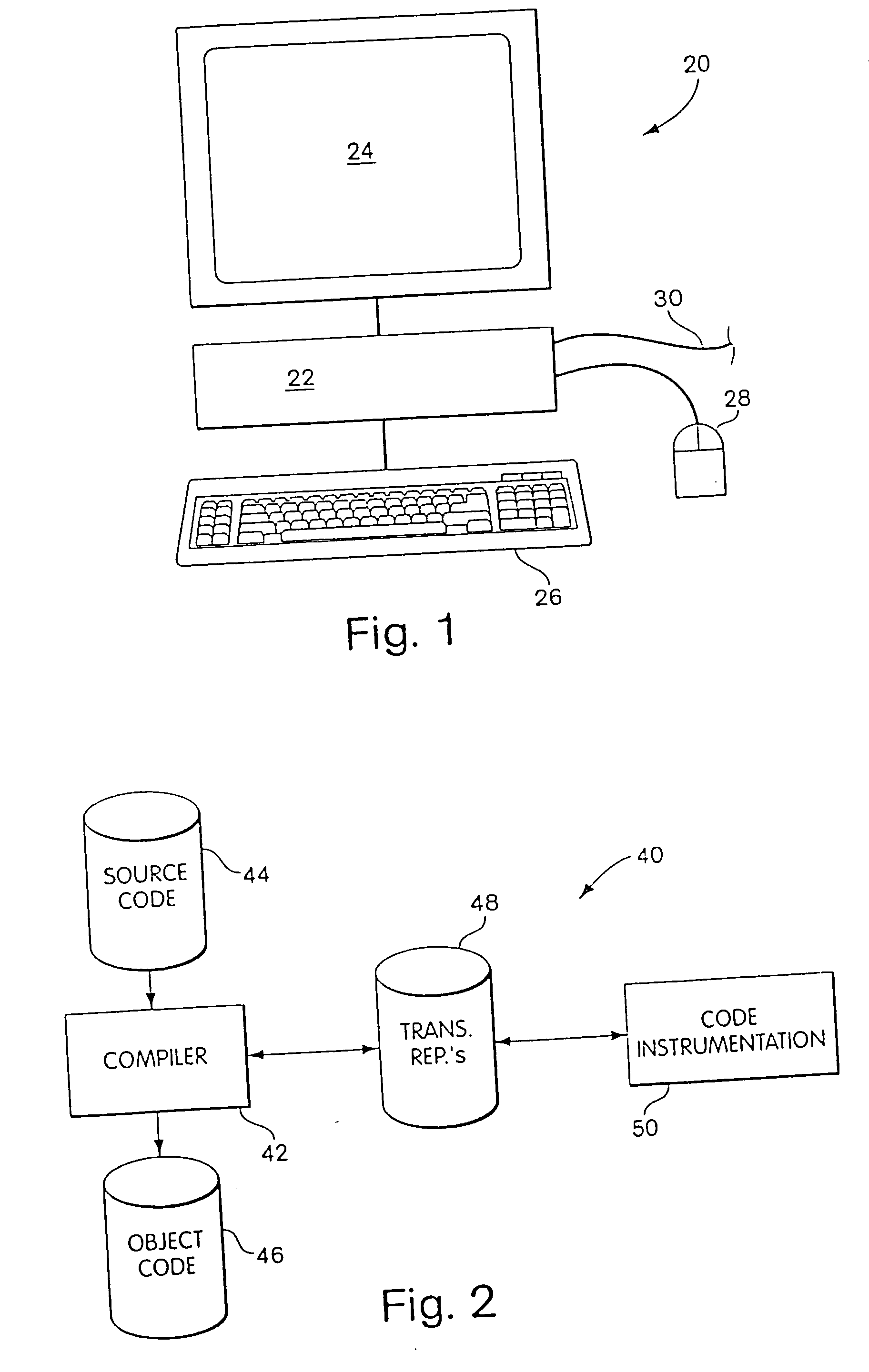
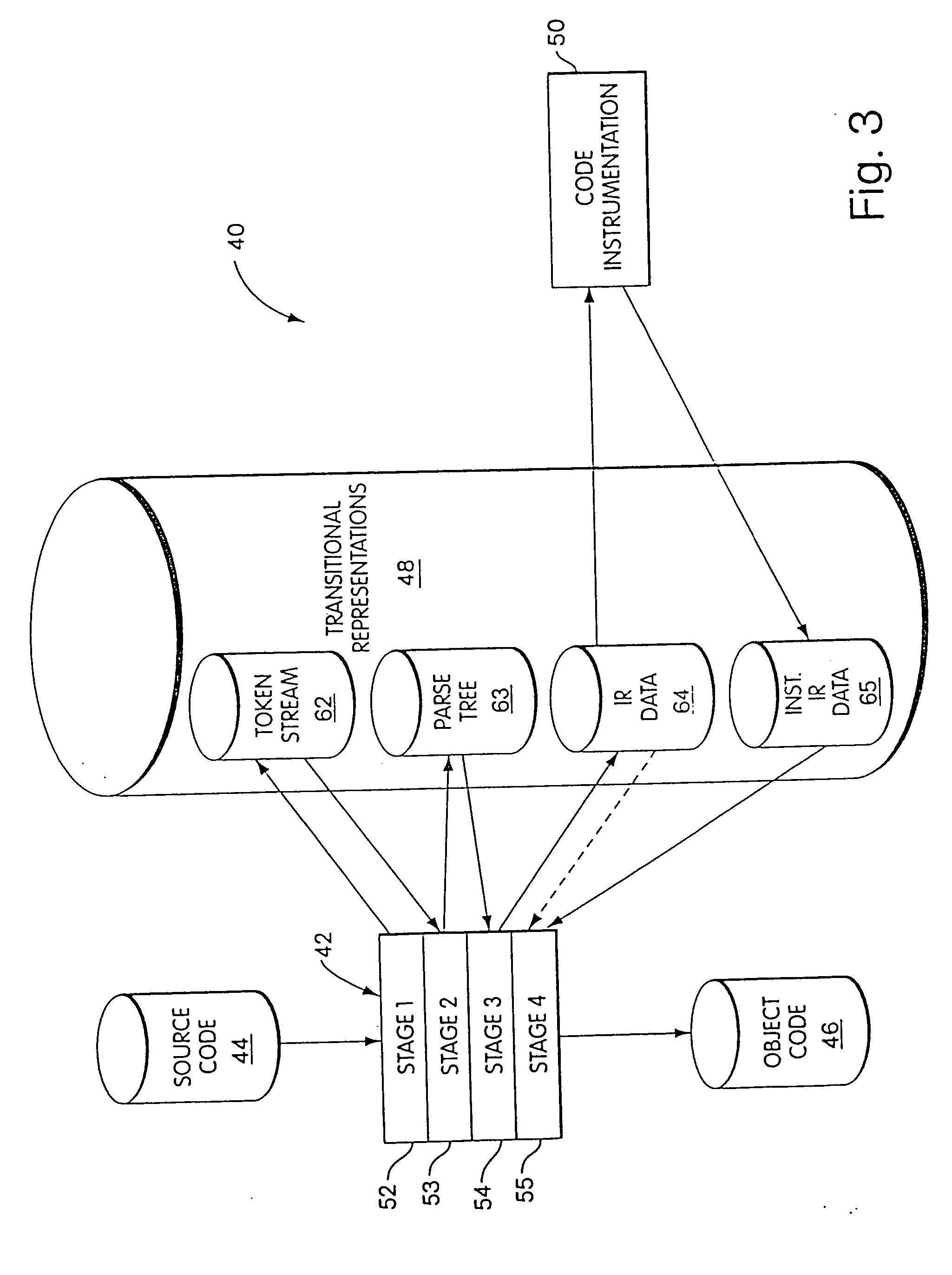
Byte code instrumentation
InactiveUS20040133882A1Reliability increasing modificationsSoftware testing/debuggingMessage flowParallel computing
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a thispointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
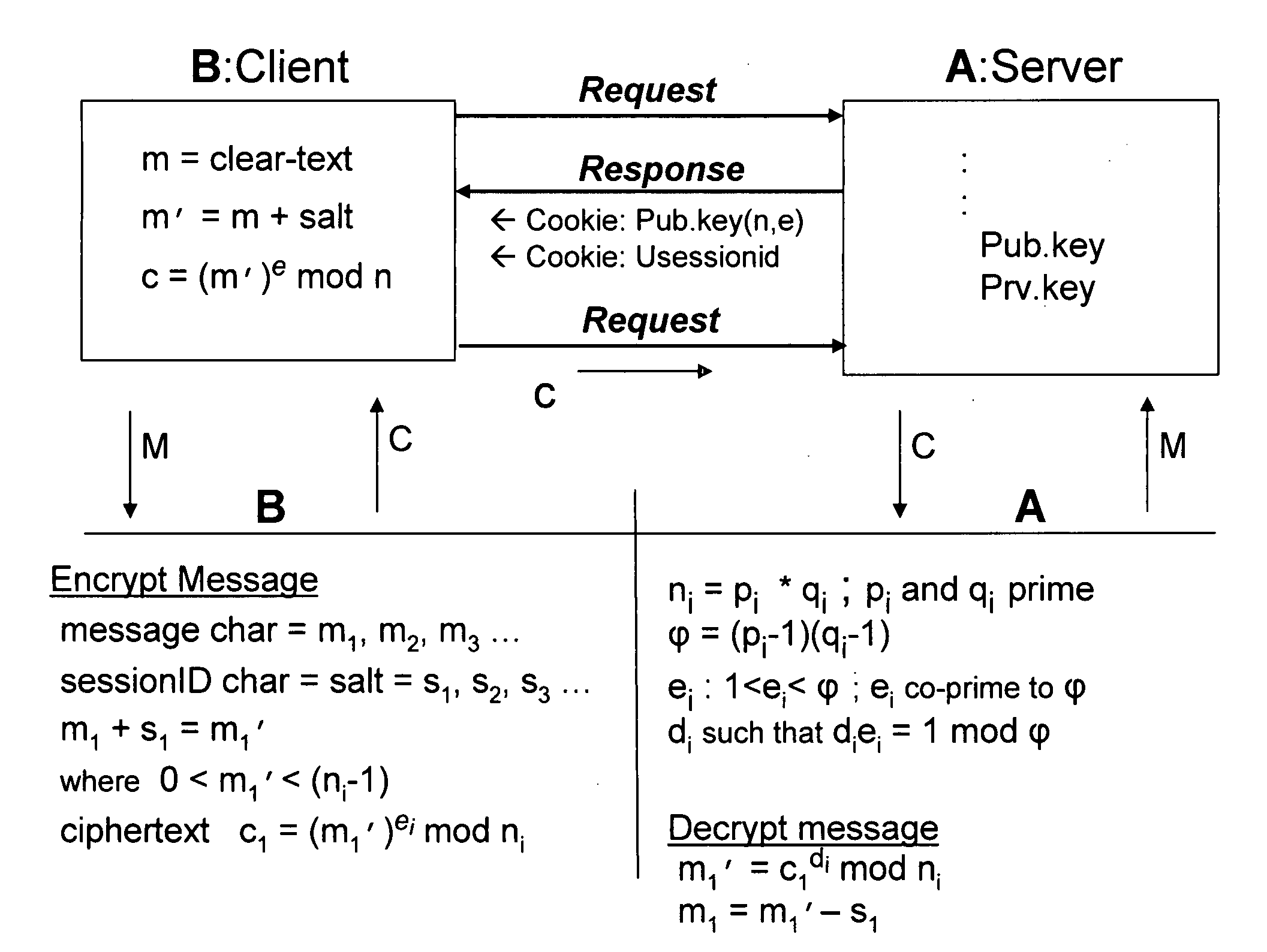
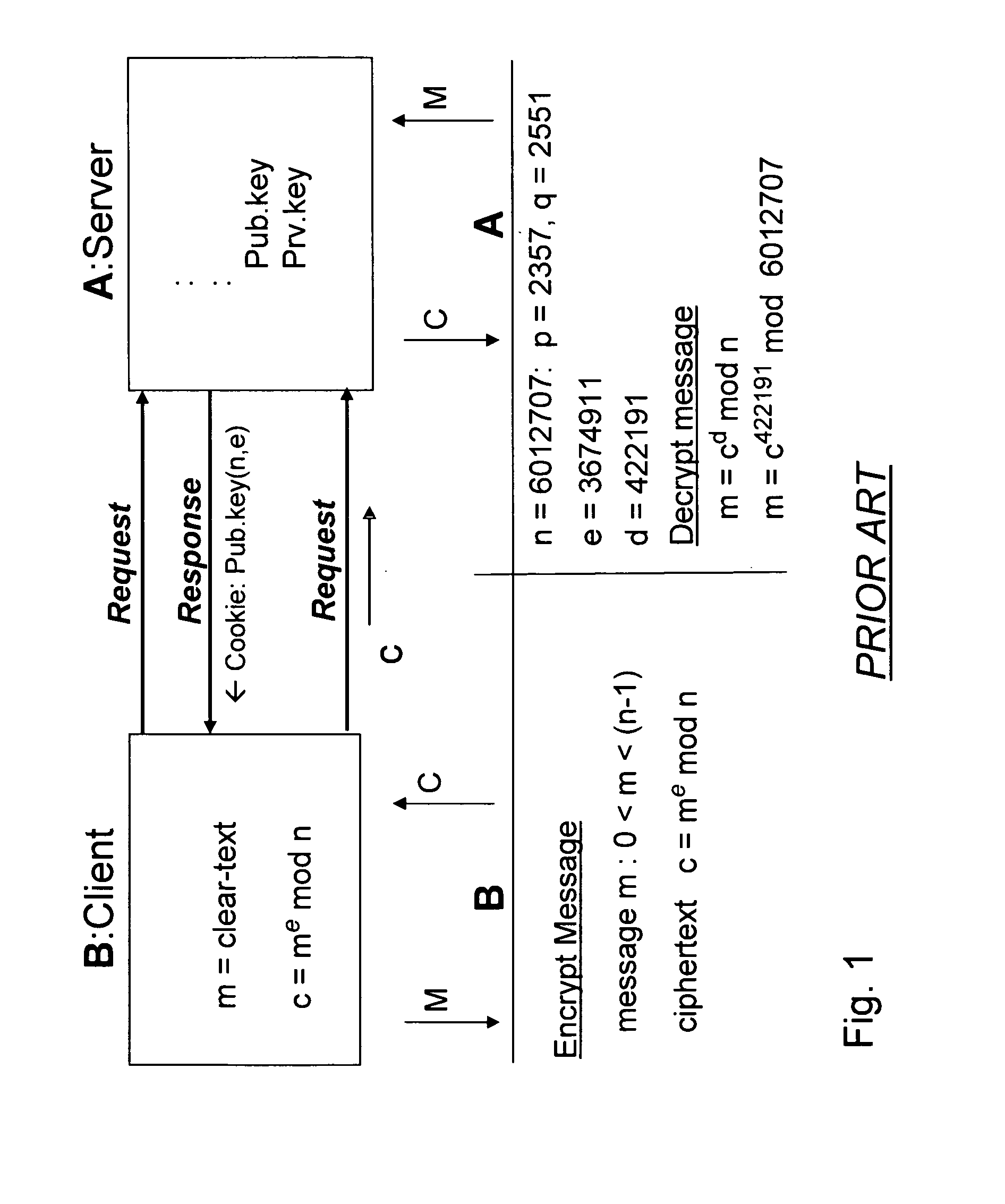
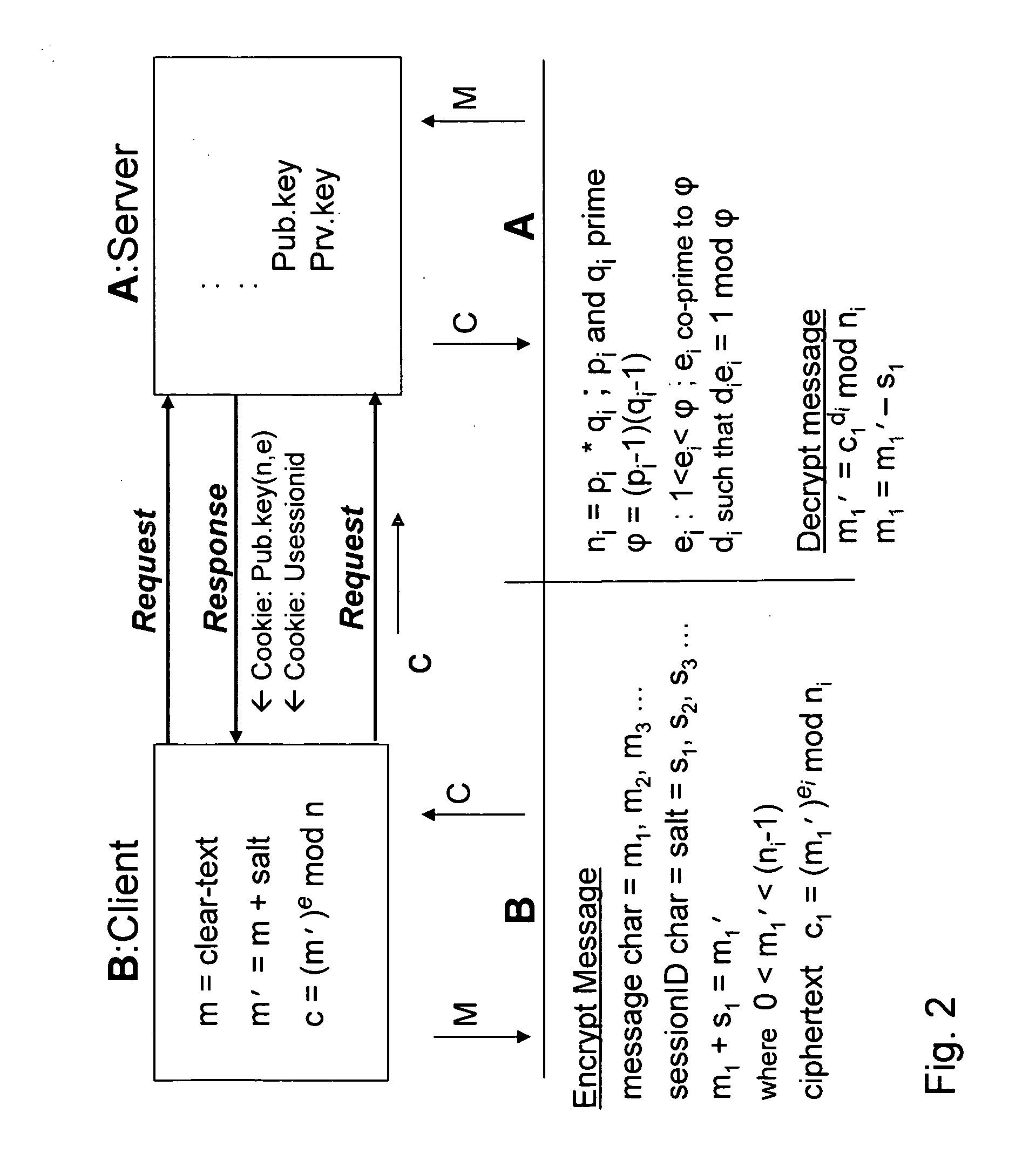
Bcencryption (BCE) - a public-key based method to encrypt a data stream
ActiveUS20070180230A1Increase safetyReduce loadData stream serial/continuous modificationUser identity/authority verificationClient-sideSession ID
A system and method for a web browser to convert an unencrypted character string into a cipher-text string combines a public-key encryption algorithm with a unique and constantly changing salt key. A private “server-key”, a public “client-key” and a server session ID are generated by the server, and the client-key and the session ID are sent to the browser with the code used to encrypt the message. The session-based string can be a randomly generated set of characters which changes between established user sessions and the salt key can be formed from the server session ID string. The server contains the matching code necessary to decrypt the stream using the private key.
Owner:KRONOS TECH SYST PARTNERSHIP
Transmission Quality Monitoring For Multimedia Streams
InactiveUS20070053303A1Loss of stateError detection/prevention using signal quality detectorTransmission systemsPacket lossTransmission quality
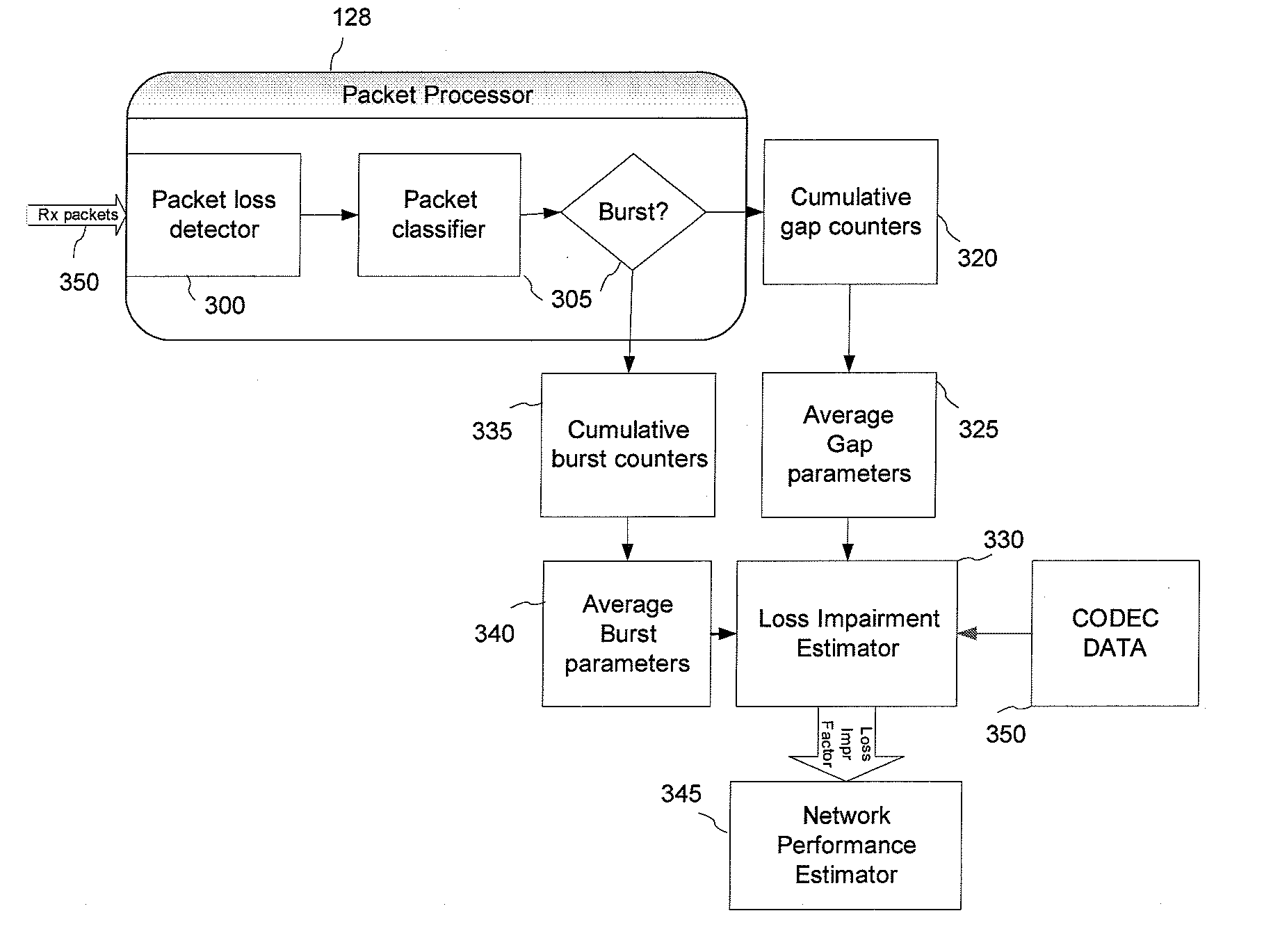
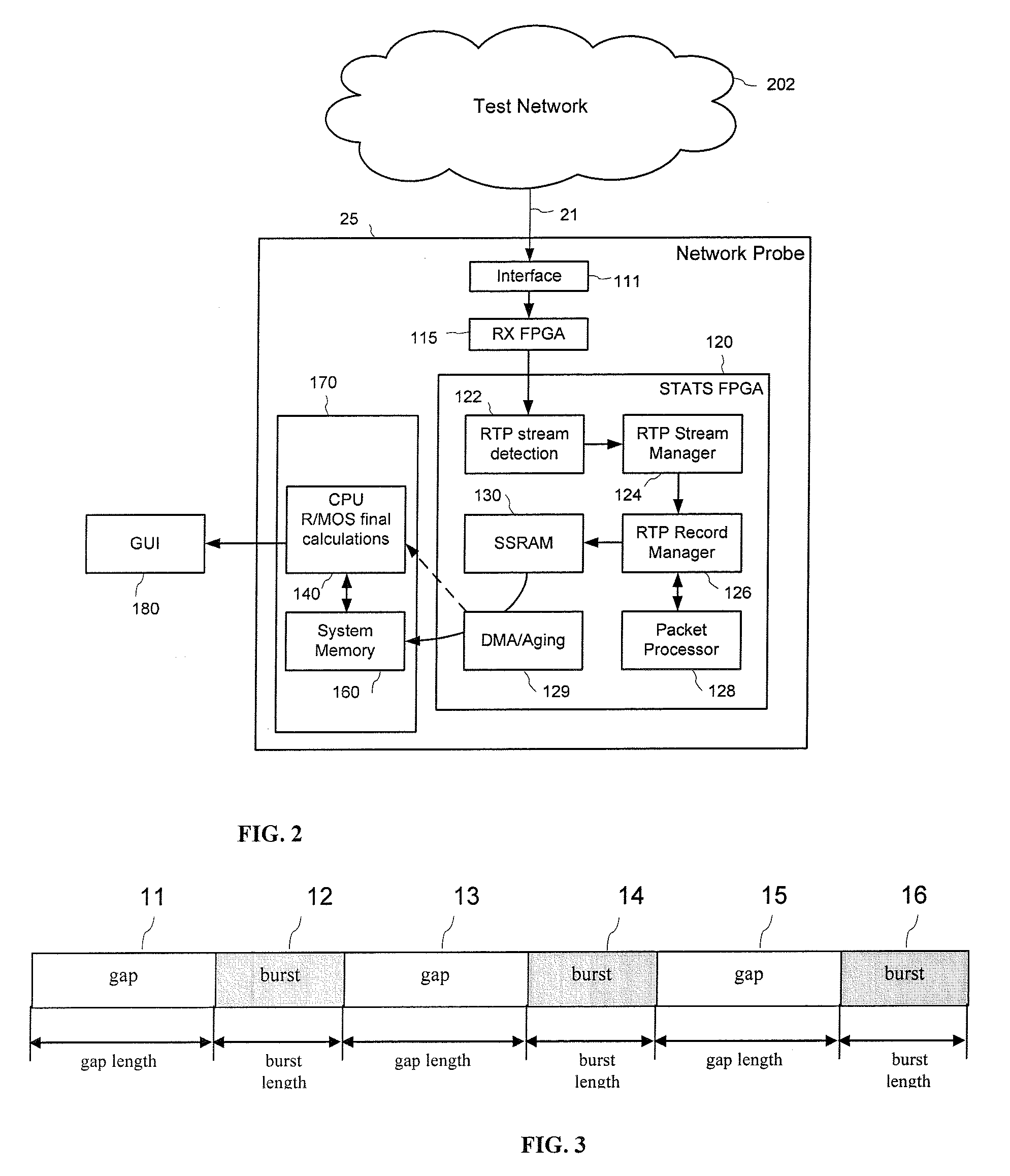
A network performance monitor and an associated method for monitoring the perceived transmission quality of a packetized multimedia signal encoded by a first codec are provided. The monitor includes a packet processor for performing real time direct counting of received and lost packets in the burst and gap states in the packet stream carrying the multimedia signal. A data processor is provided for determining packet loss distribution parameters using the burst and gap packet counters provided by the packet processor. In one aspect of the invention, the data processor is operative to compute an effective equipment impairment factor from the packet loss distribution parameters for a reference codec having known transmission impairments associated therewith, for assessing the network contribution to the perceived transmission quality of the multimedia signal.
Owner:ACTERNA LLC
Data federation methods and system
InactiveUS20050021502A1Simple methodProvide capabilityDigital data processing detailsSemi-structured data mapping/conversionFunction objectParse tree
A method is provided for processing tree like data structures in a streaming manner. An initial context of name / value bindings is set up. A tree of objects is constructed. Each element in the tree of objects is represented as a function object that accepts a context parameter and a target parameter that it can send a stream of start, content, and end events to represent tree output. The parse tree of objects is examined for element names that are recognized as commands. The commands are converted to special function objects that implement command's semantics. Other elements, that are not recognized as commands, are mapped to a default function object.
Owner:SNAPBRIDGE SOFTWARE
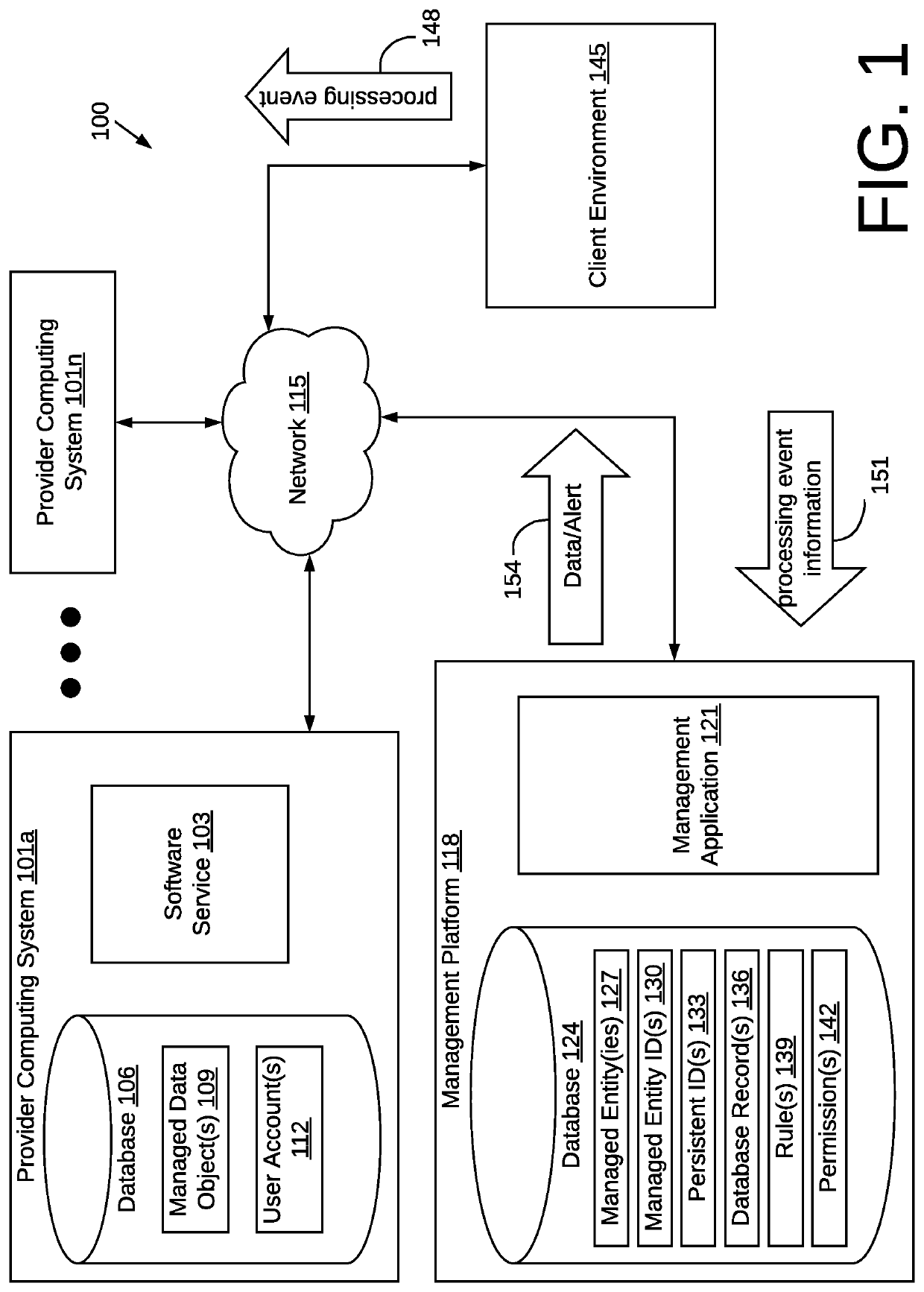
Methods and systems to manage data objects in a cloud computing environment
ActiveUS10965547B1Computer security arrangementsData switching networksData graphPersistent identifier
The present disclosure relates to managing activity taken with respect to cloud-based software services. A platform manages data objects processed by software services and / or those entities that initiate processing events. The platform uses identifiers such as, for example, a persistent identifier (PID) to track processing events. The platform implements rules and / or permissions related to the managed data objects and / or managed entities to determine whether processing events are in compliance. The platform may update database records, send alerts, send data graphs, or provide a real-time stream related to the managed data objects and / or managed entities. In addition, embodiments involve determining whether a PID-associated managed data object has been modified during processing to generate an additional version of the PID-associated managed data object and, if an object version is present, processing the additional version of the PID-associated managed data object to generate an integrated first PID-associated managed data object.
Owner:BETTERCLOUD INC
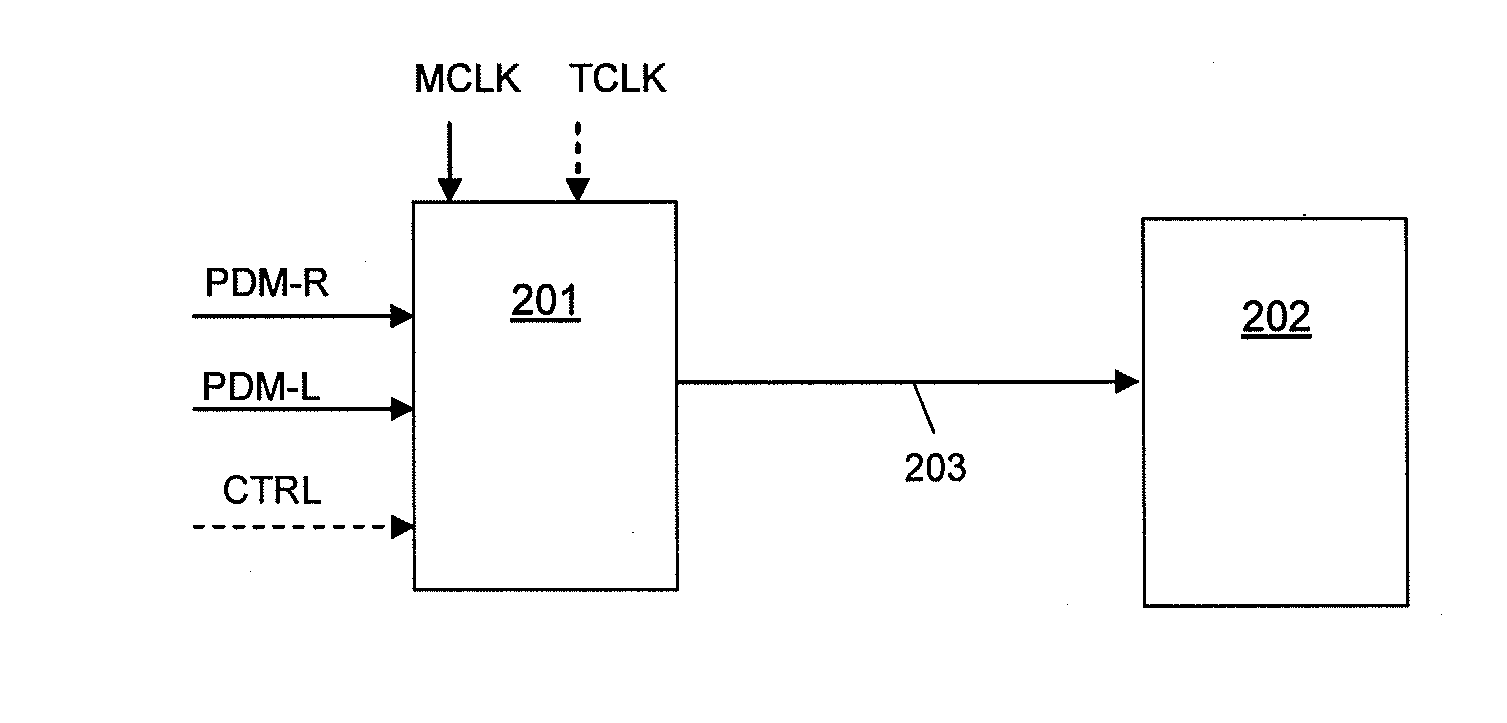
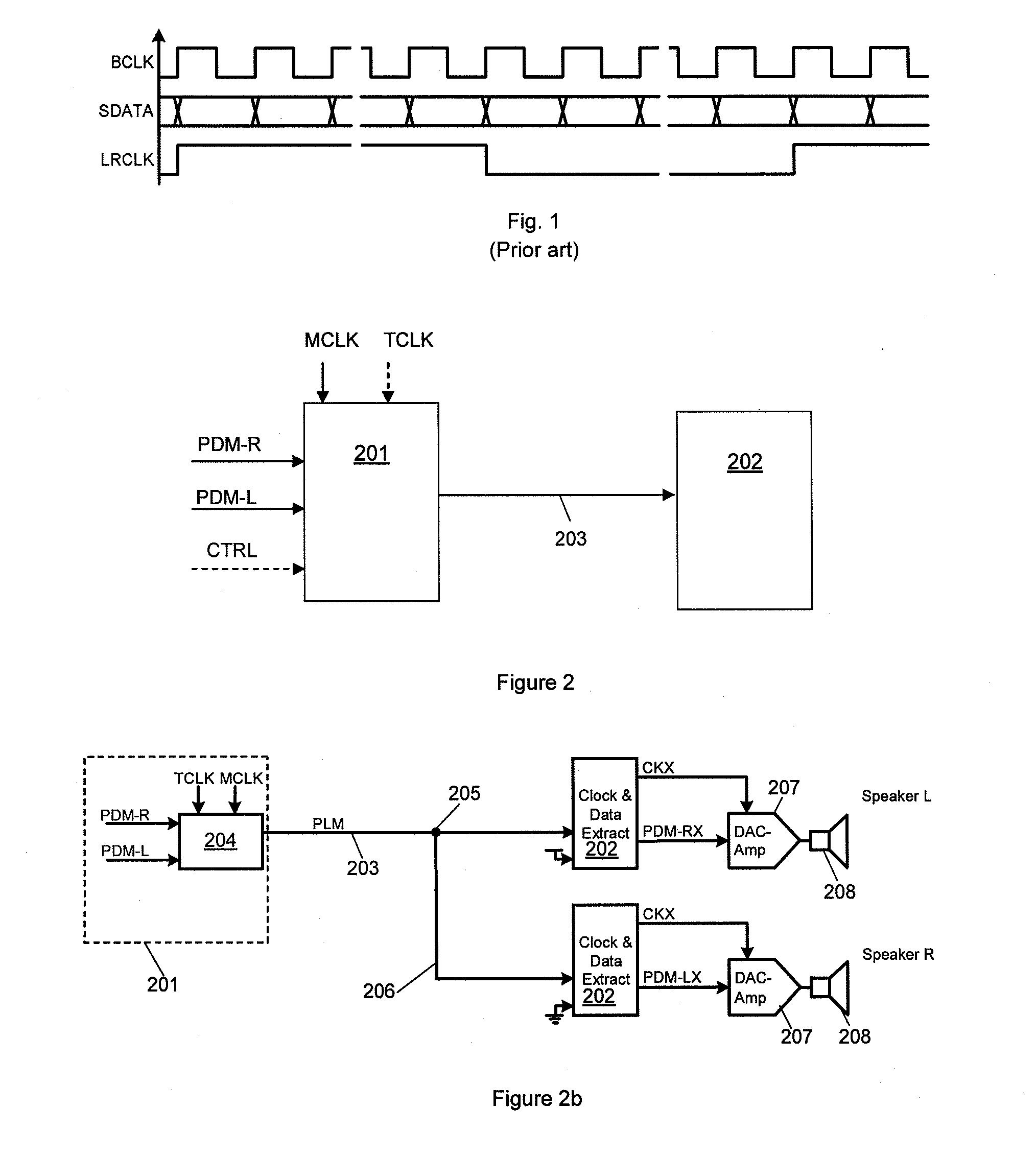
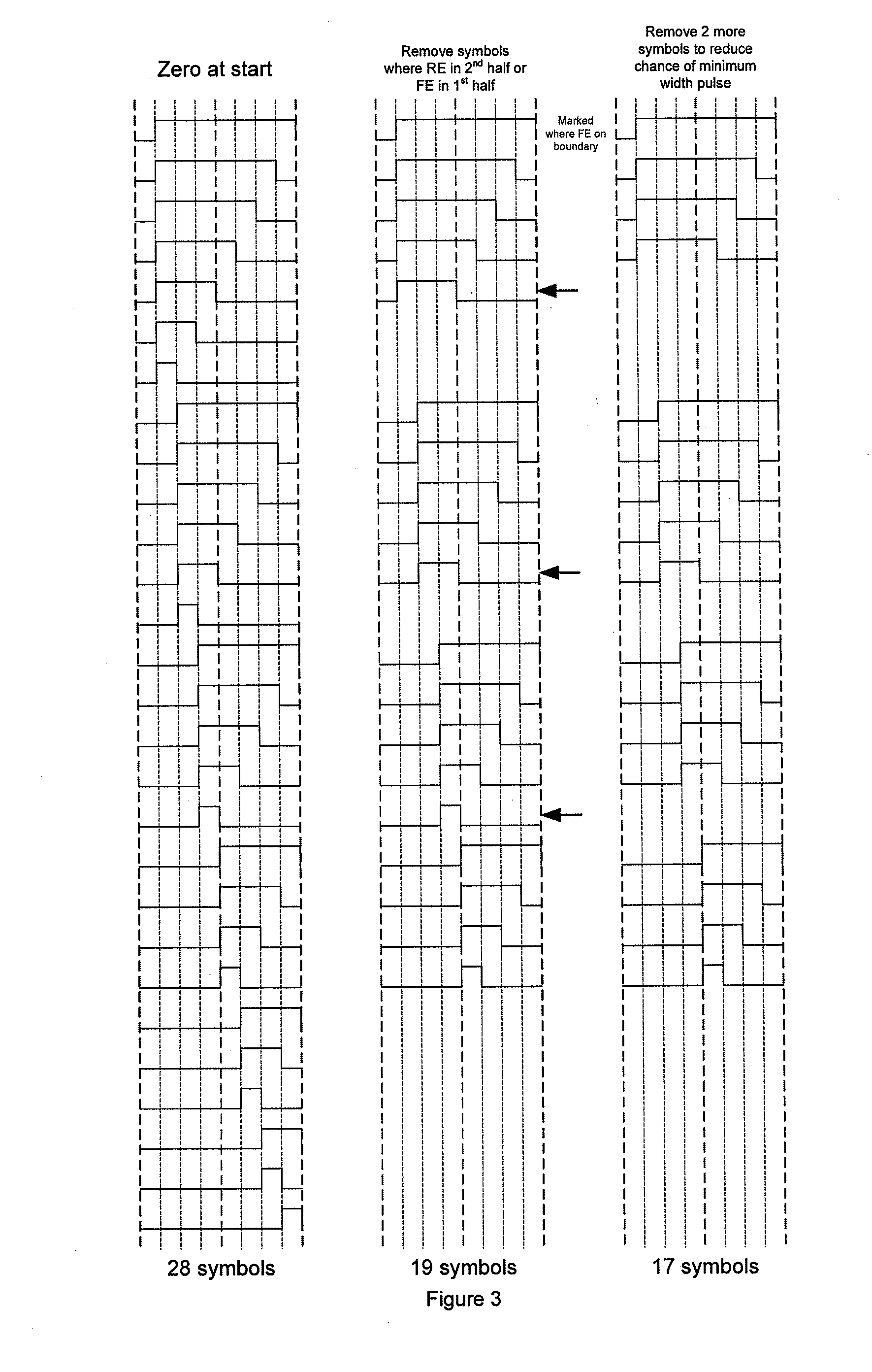
Data transfer
Circuitry for transferring multiple digital data streams, e.g. digital audio data, over a single communications link such as a single wire. A pulse-length-modulator is responsive to a plurality of data streams to generate a series of data pulses with a single data pulse having a rising and falling edge in each of a plurality of transfer periods defined by a first clock signal. The timing of the rising and falling edge of each data pulse is dependent on a combination of the then current data samples from the plurality of data streams. The duration and position of the data pulse in the transfer window in effect defines a data symbol encoding the data. An interface receives the stream of data pulses, and data extraction circuitry samples the data pulse to determine which of the possible data symbols the pulse represents and determines a data value for at least one received data stream.
Owner:CIRRUS LOGIC INC
Systems and methods for configuring flow control of policy expressions
ActiveUS20080225720A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
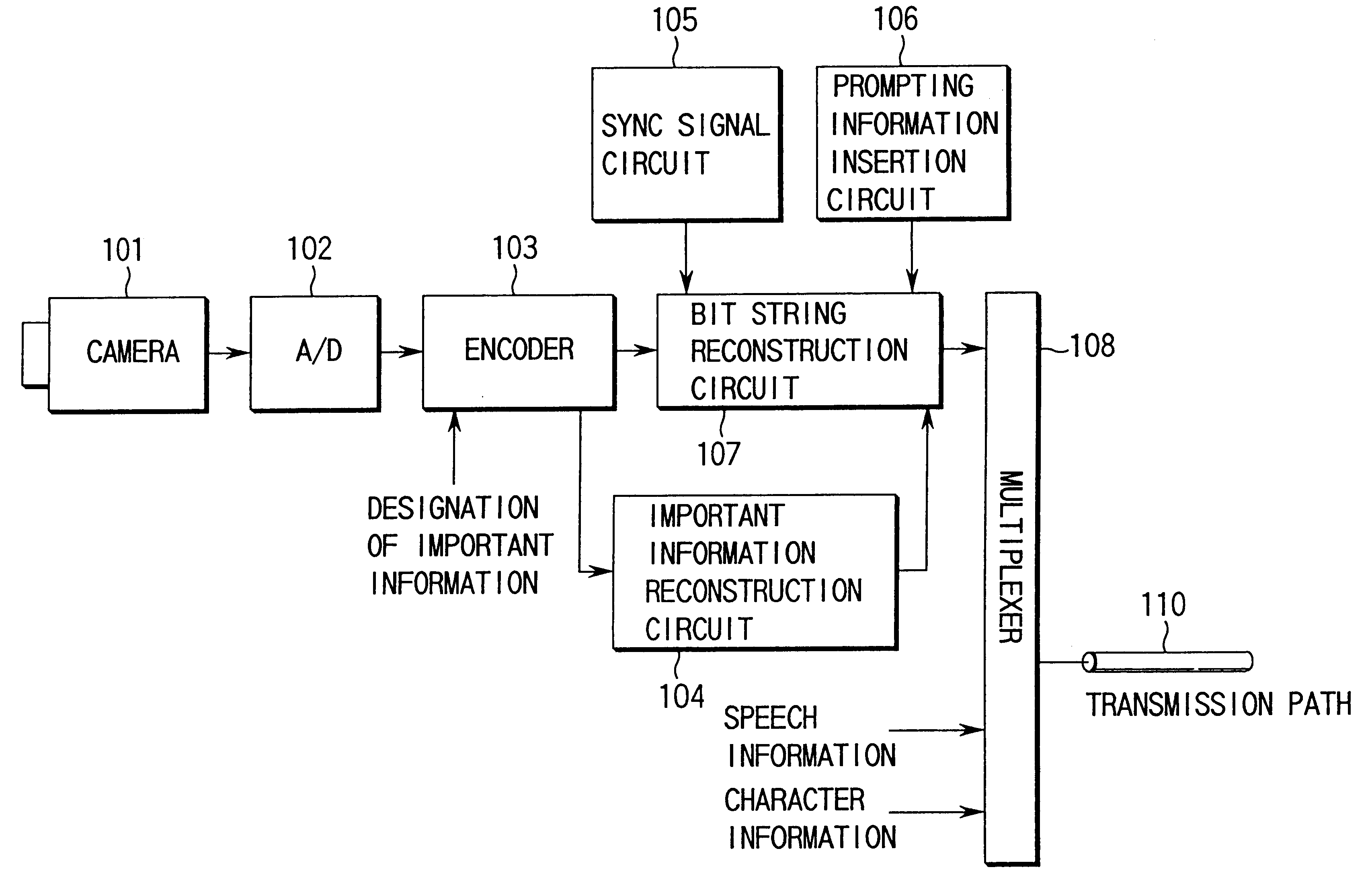
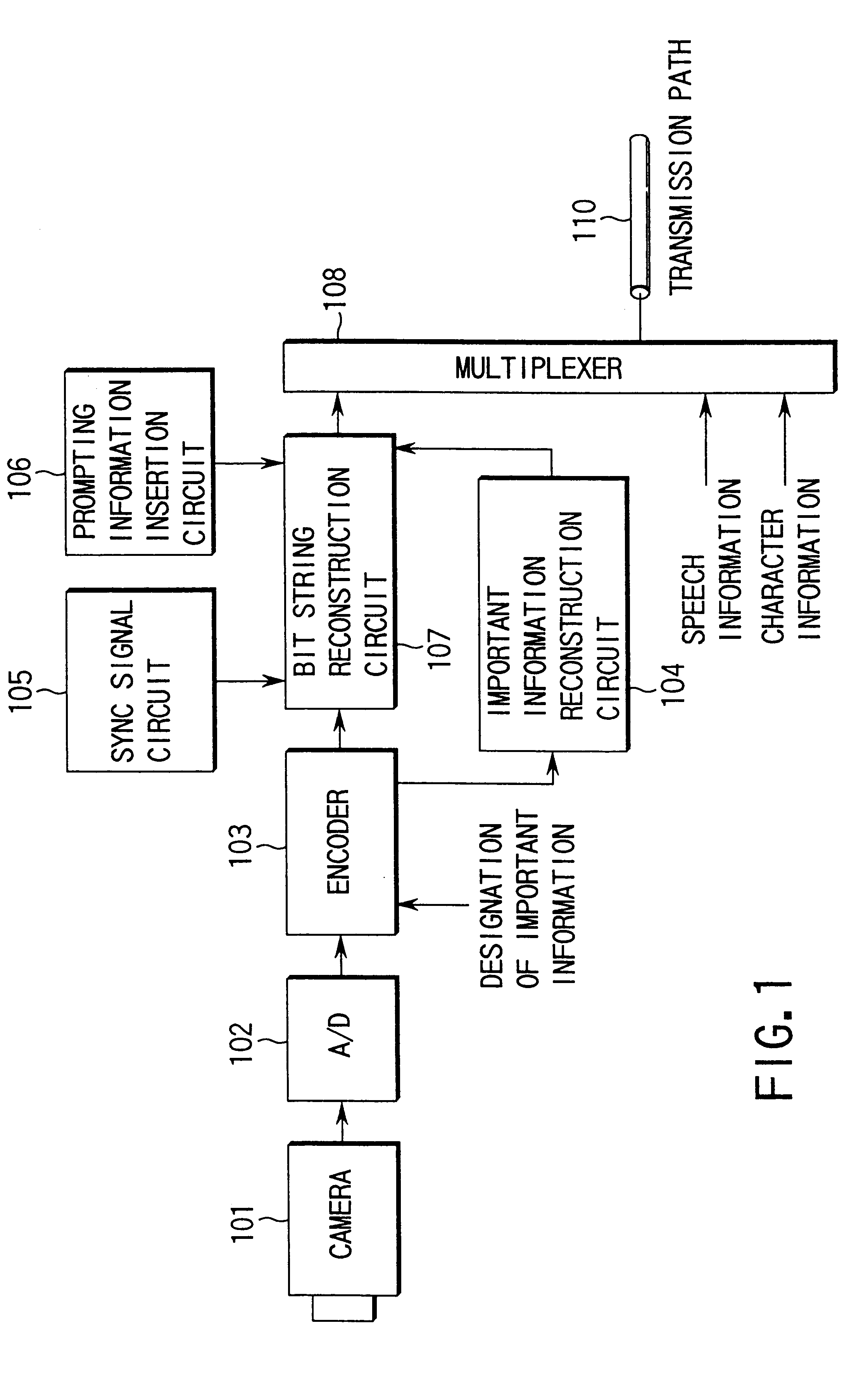
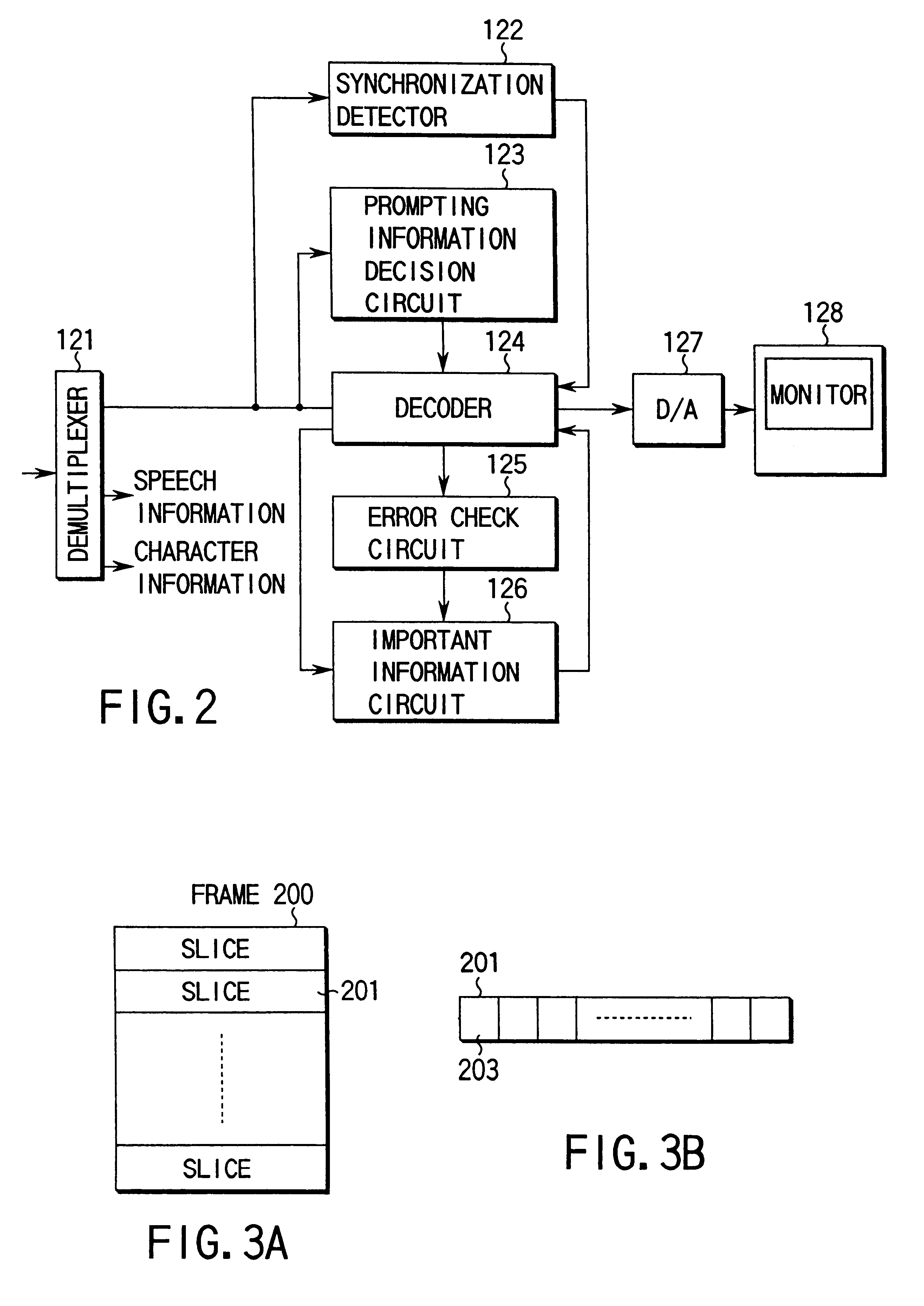
Information transmitting method, encoder/decoder of information transmitting system using the method, and encoding multiplexer/decoding inverse multiplexer
InactiveUS6310897B1Pulse modulation television signal transmissionCode conversionInformation transmissionData stream
An information transmission method when error robustness is provided for the bit stream itself so that decoding processing can be properly performed even in the event of an error in important information such as header information. A bit stream reconstruction circuit in an encoding apparatus adds sync signals to the heads of encoded data streams, which are encoded by an encoder, in certain bit stream units, and then inserts designation information in each bit stream by using a designation information insertion circuit. Each designation information indicates the addition of information for reconstructing important header information. By inserting the designation information in the bit stream obtained, reconstruction information can be added to the bit stream. Even if, therefore, an error is introduced into the header information, and the information cannot be used for decoding processing, the decoding processing can be properly continued by using the new reconstruction information designated by the designation information as a substitute.
Owner:KK TOSHIBA
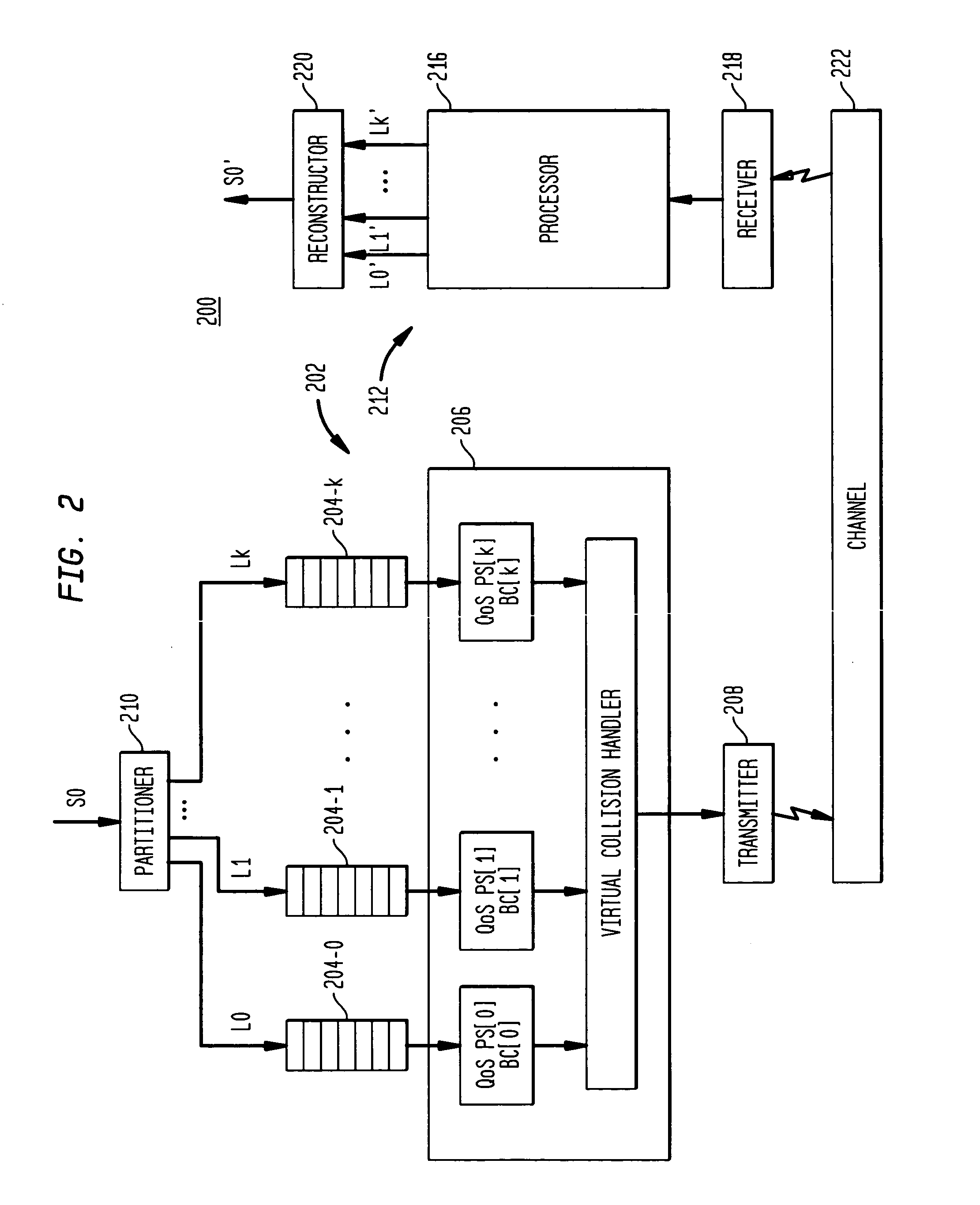
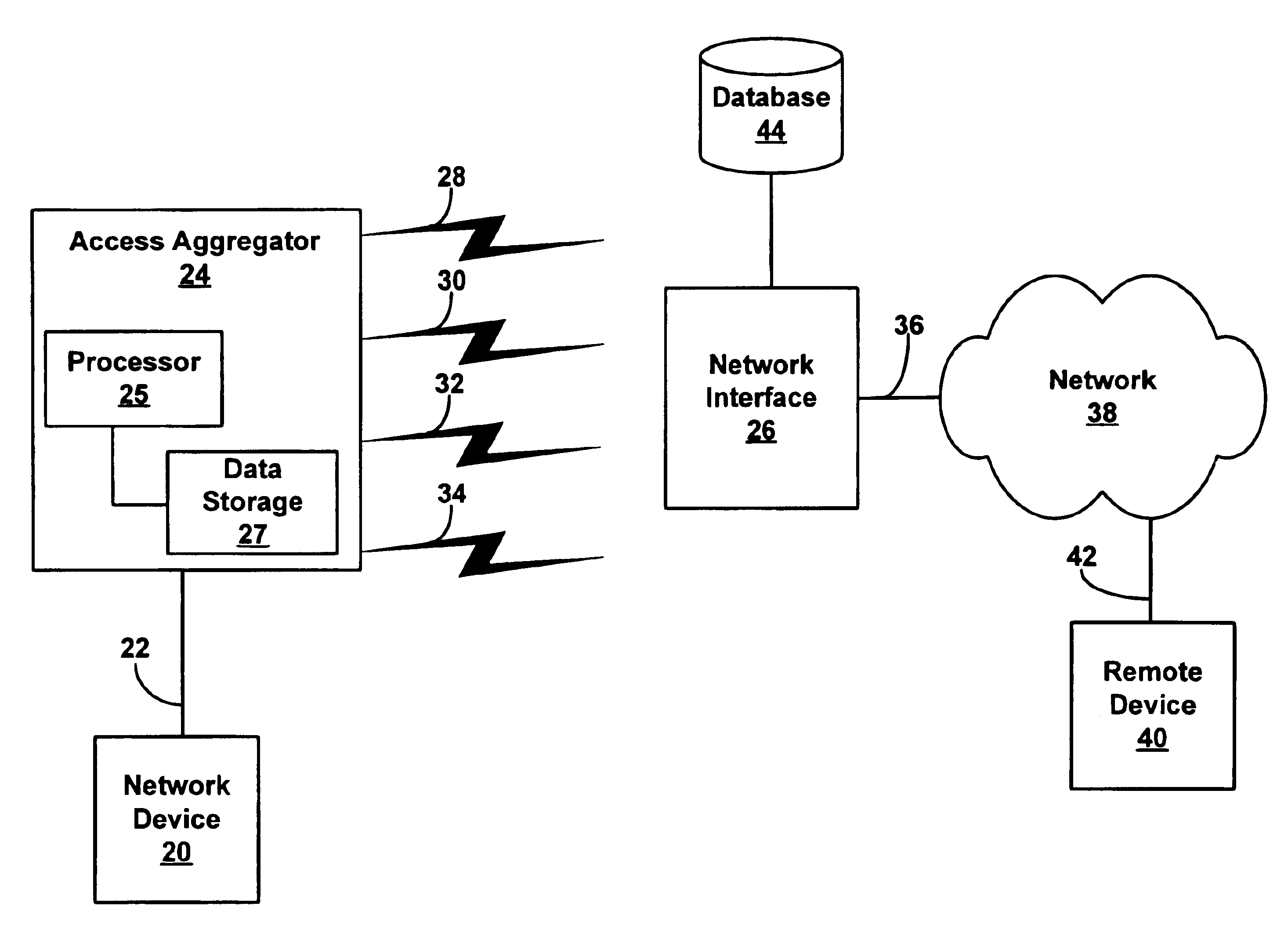
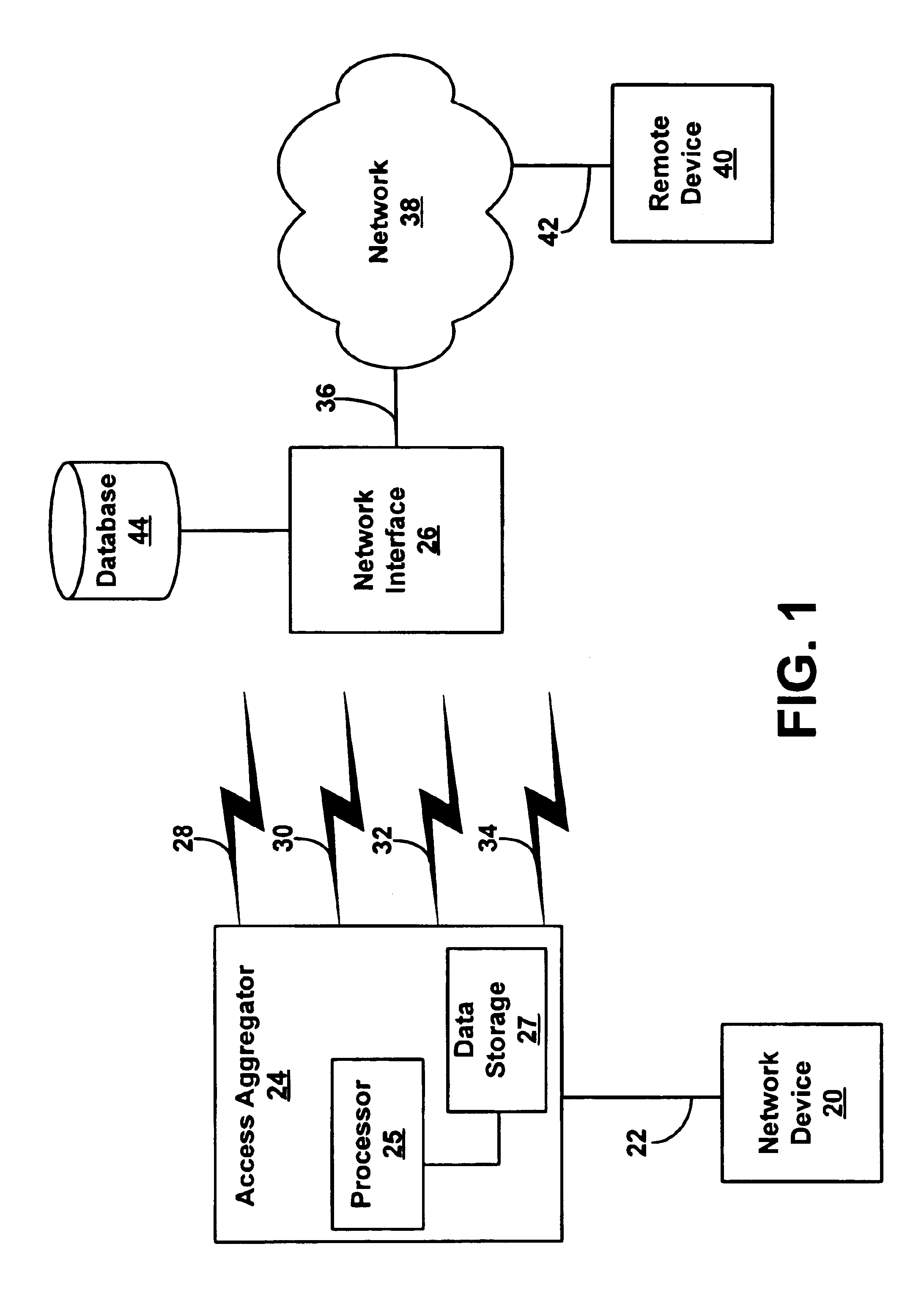
Method and system for increasing data rate in wireless communications through aggregation of data sessions
InactiveUS6842446B2Improve transfer rateNetwork traffic/resource managementHybrid switching systemsData streamData rate
An access aggregator may receive a data stream from a first computing device. The access aggregator may divide the data stream into a plurality of sub-streams. Then, the access aggregator may transmit the sub-streams over multiple wireless communication channels to a network interface. The network interface can then send the sub-streams to a second computing device. Similarly, the second computing device may send data to the network interface, where the data is divided into sub-streams. The sub-streams can be sent to the access aggregator over multiple wireless communication channels and then sent to the first computing device.
Owner:SPRING SPECTRUM LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com