Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6308 results about "Data value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
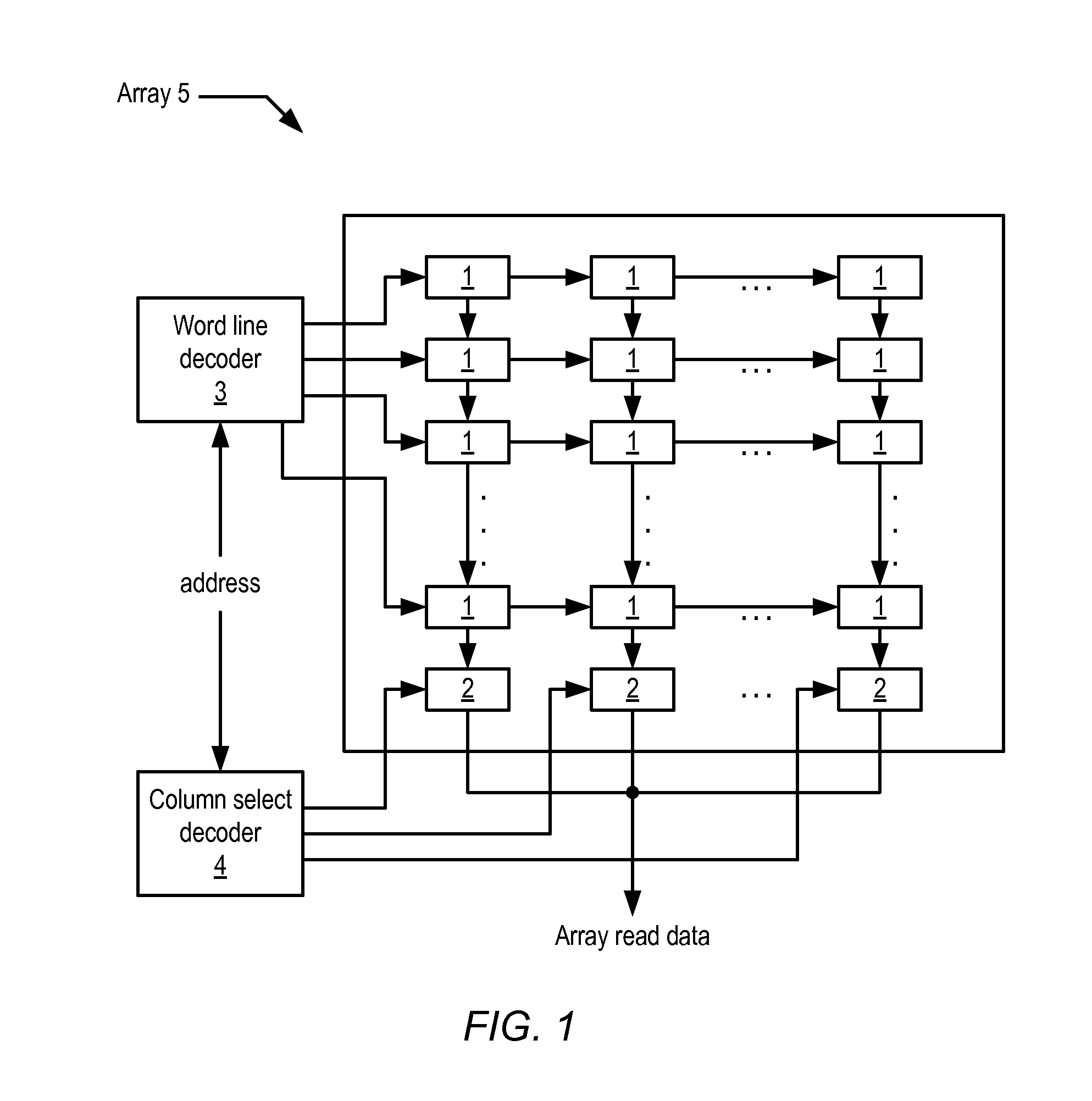
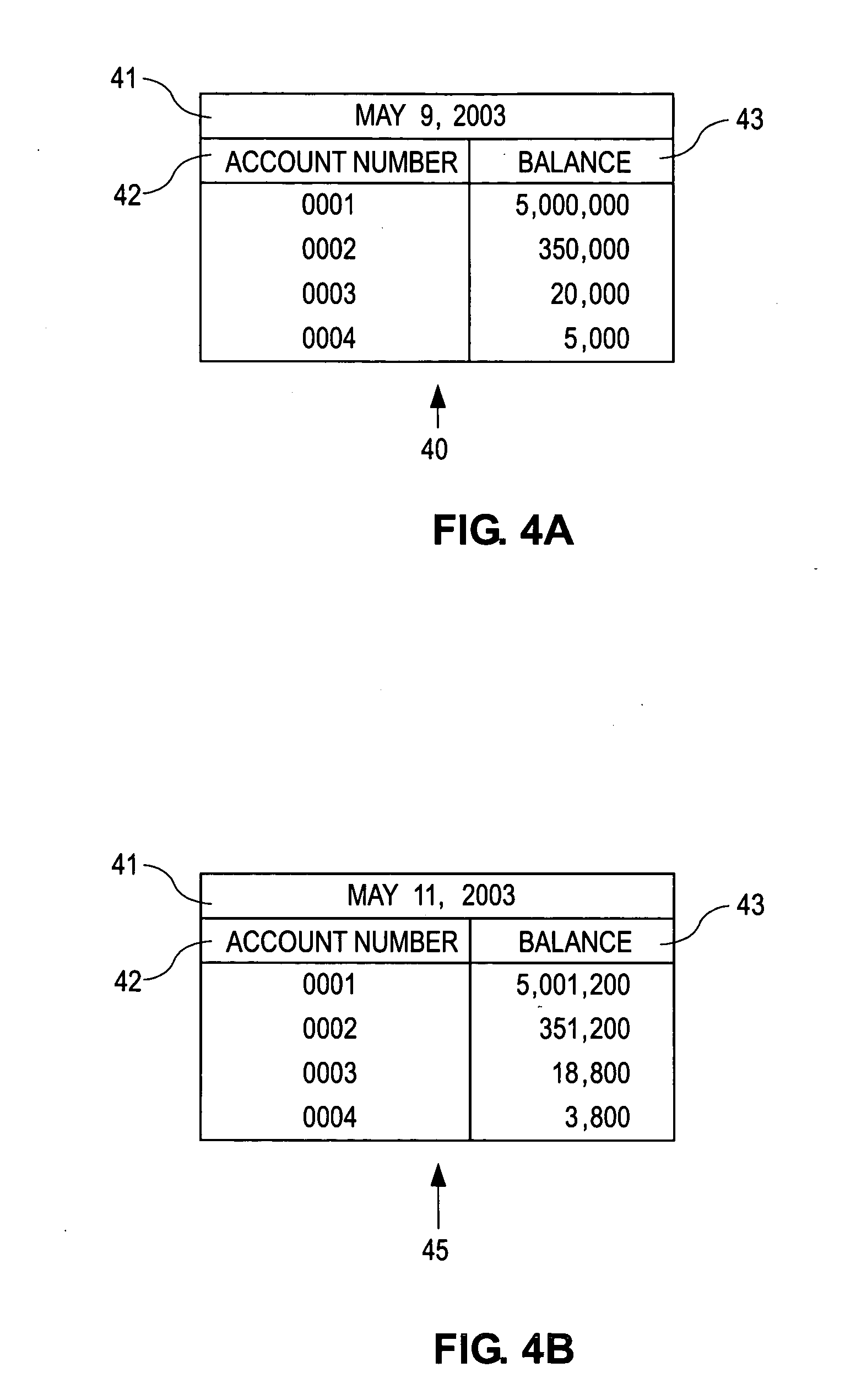
Data Values. Data values provide you with the ability to retrieve a list of possible values for input into the edit box of a qualification. They can be used to retrieve a list from the database of all available values or to display only a portion of the available values.
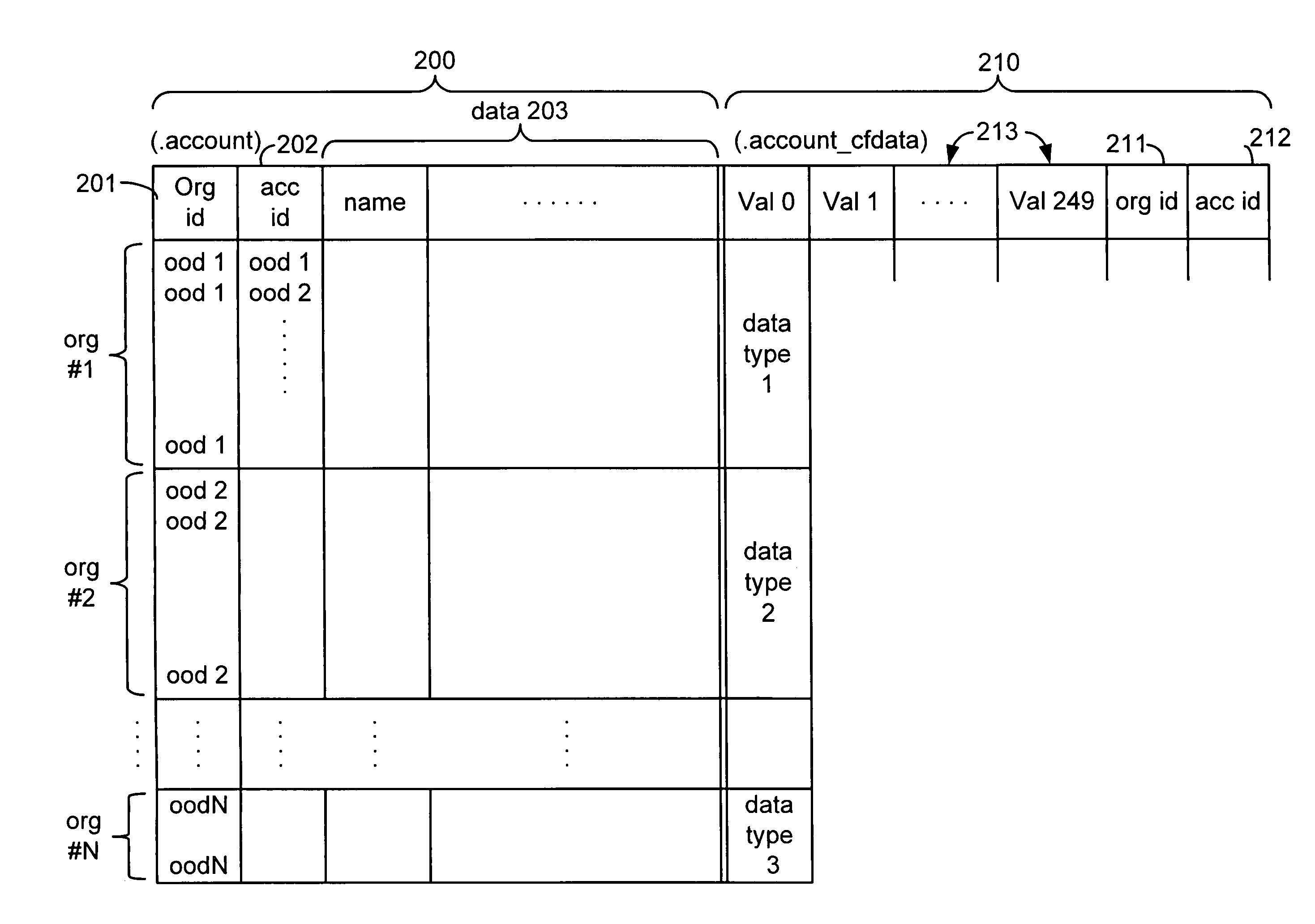
Custom entities and fields in a multi-tenant database system
Systems and methods for hosting variable schema data such as dynamic tables and columns in a fixed physical database schema. Standard objects, such as tables are provided for use by multiple tenants or organizations in a multi-tenant database system. Each organization may add or define custom fields for inclusion in a standard object. Custom fields for multiple tenants are stored in a single field within the object data structure, and this single field may contain different data types for each tenant. Indexing columns are also provided, wherein a tenant may designate a field for indexing. Data values for designated fields are copied to an index column, and each index column may include multiple data types. Each organization may also define custom objects including custom fields and indexing columns. Custom objects for multiple tenants are stored in a single custom object data structure. The primary key values for the single custom object table are globally unique, but also include an object-specific identifier which may be re-used among different entities.
Owner:SALESFORCE COM INC
System and method for tracking utilization data for an electronic device
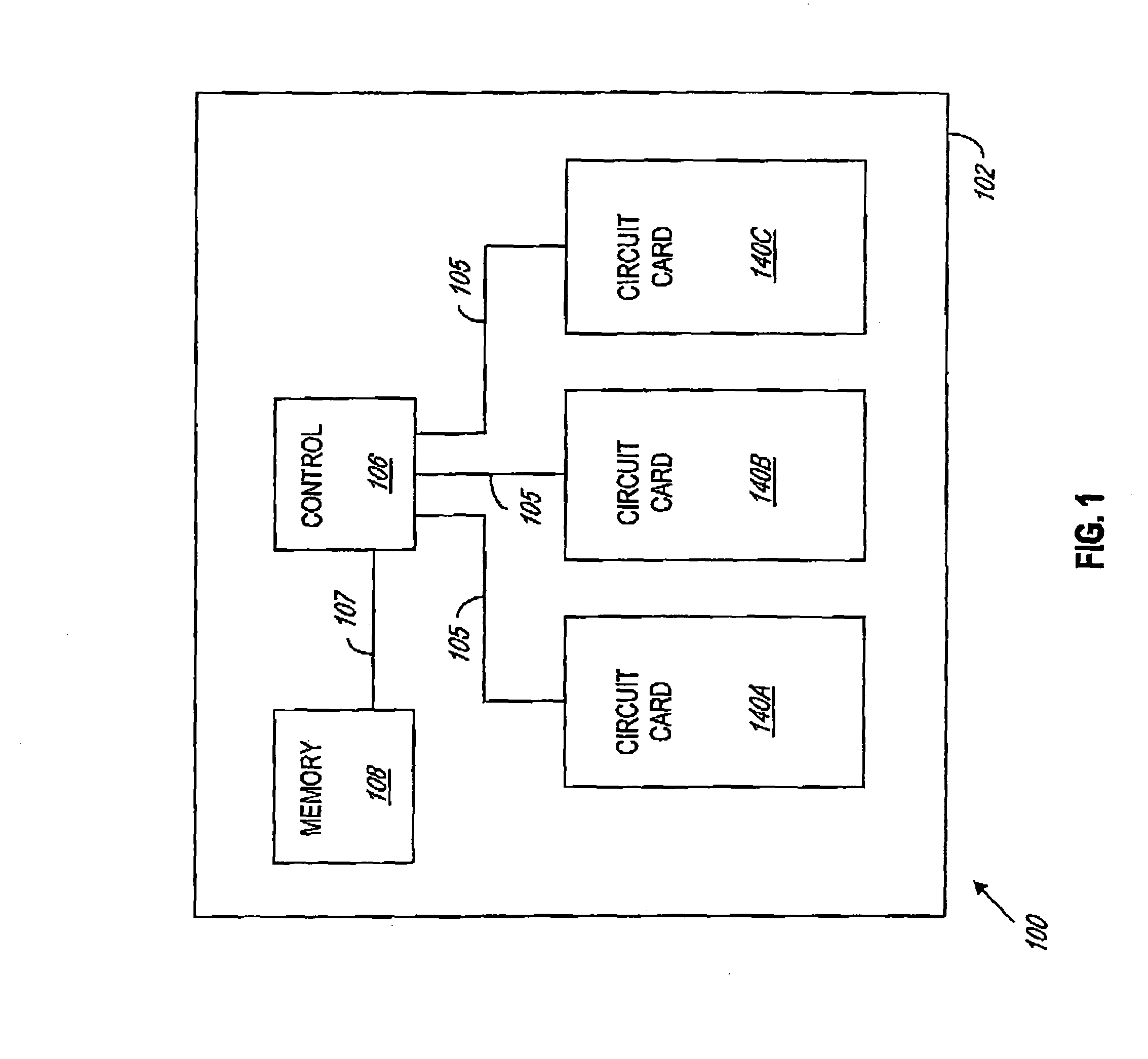
There is provided a system and method for tracking utilization data for an electronic device, the electronic device having a non-volatile data storage component associated therewith for retaining the utilization data. In an embodiment, the method includes the steps of: a) after passage of a utilization interval, reading a first utilization data value for the electronic device stored in the non-volatile data storage component; b) incrementing said read value; and c) storing said incremented value into the non-volatile data storage component. In an embodiment, the electronic device is a circuit card operating in a communication switch, and the utilization data value is a time value indicating cumulative time of operation of the circuit card in the communication switch.
Owner:ALCATEL CANADA
System and method for providing a real-time three-dimensional interactive environment
ActiveUS8072470B2Altering its appearanceAppearance of a physical object in the scene can be visually alteredCathode-ray tube indicatorsAnimationComputer graphics (images)Data value
Owner:SONY COMPUTER ENTERTAINMENT INC
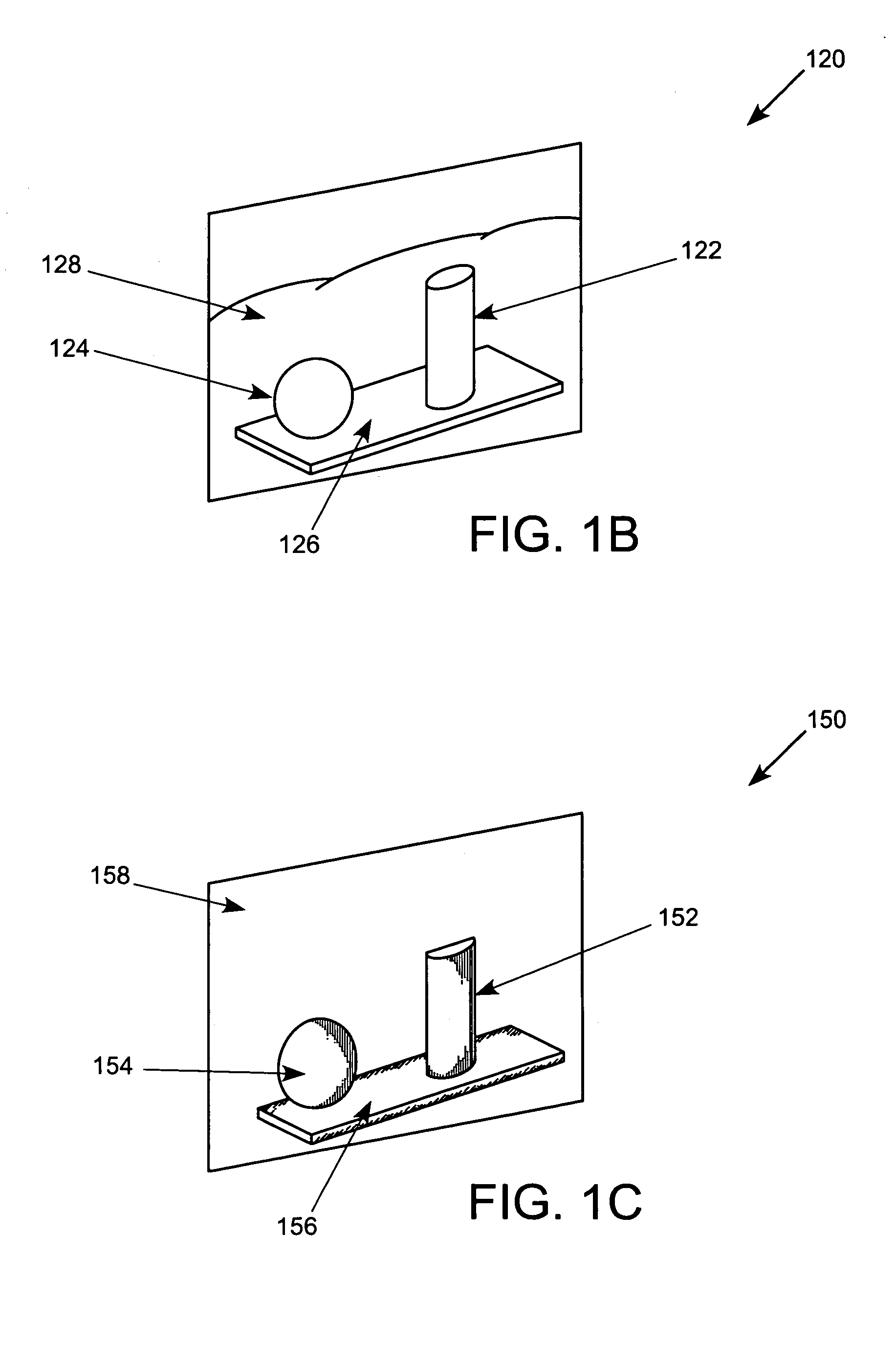
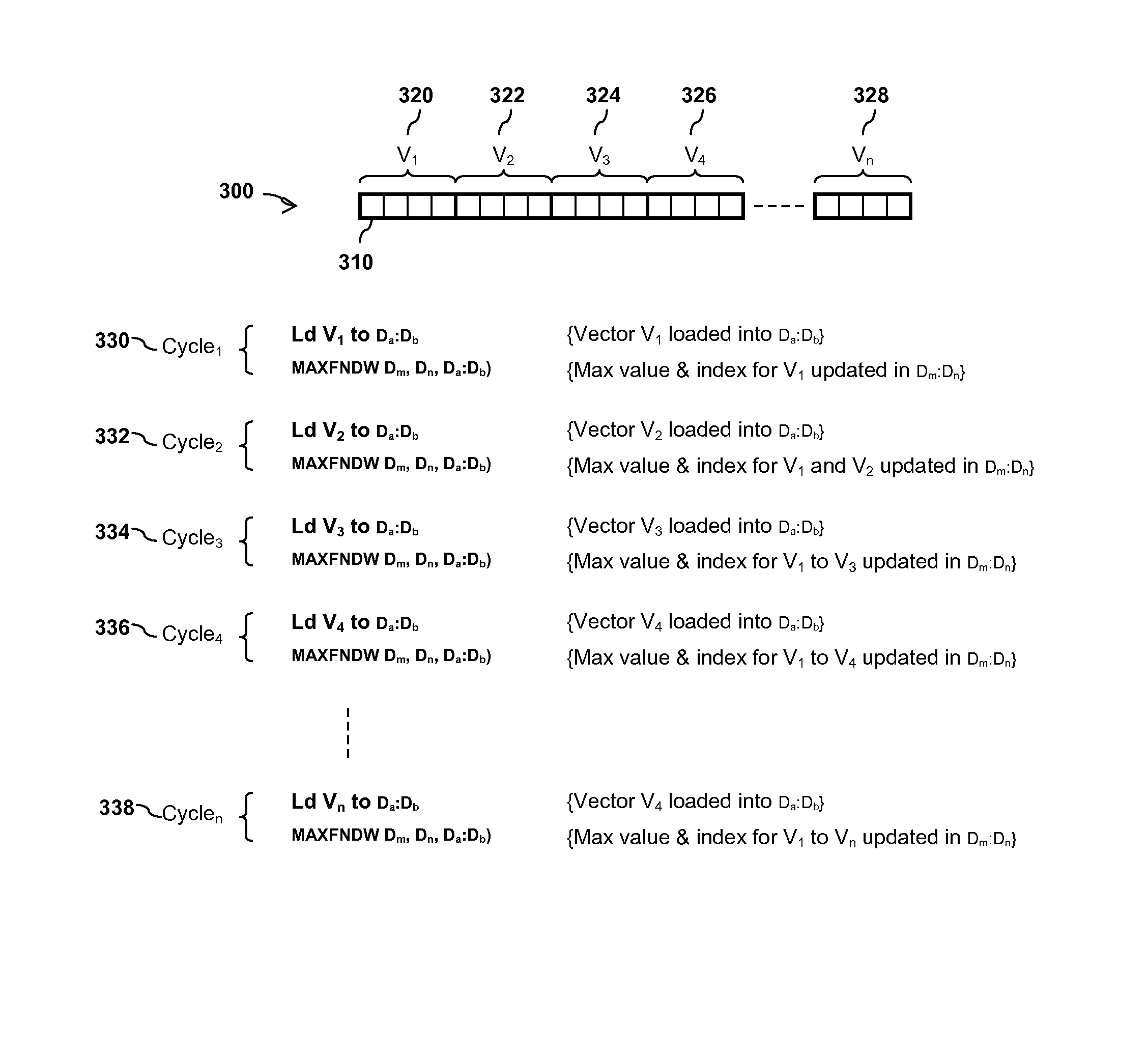
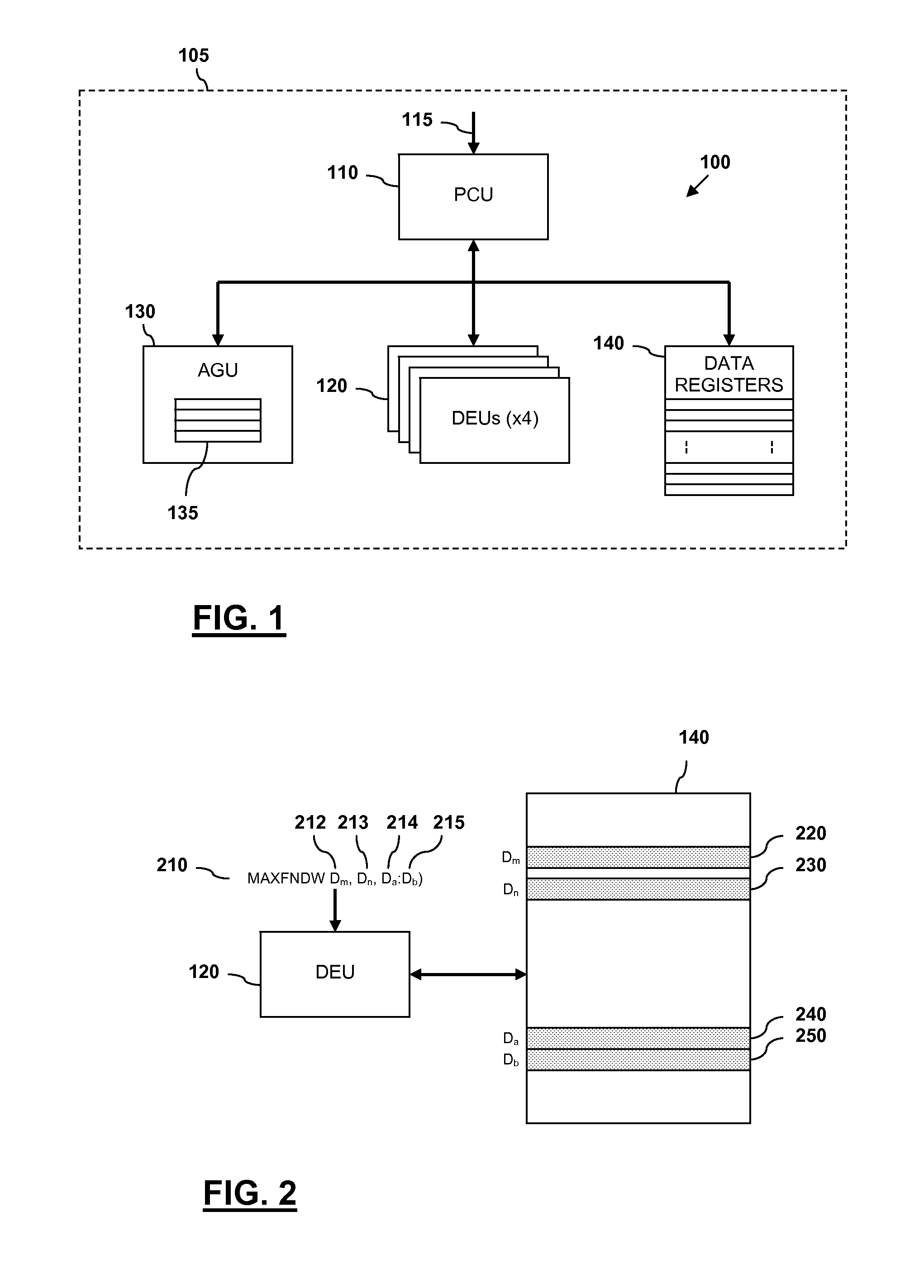
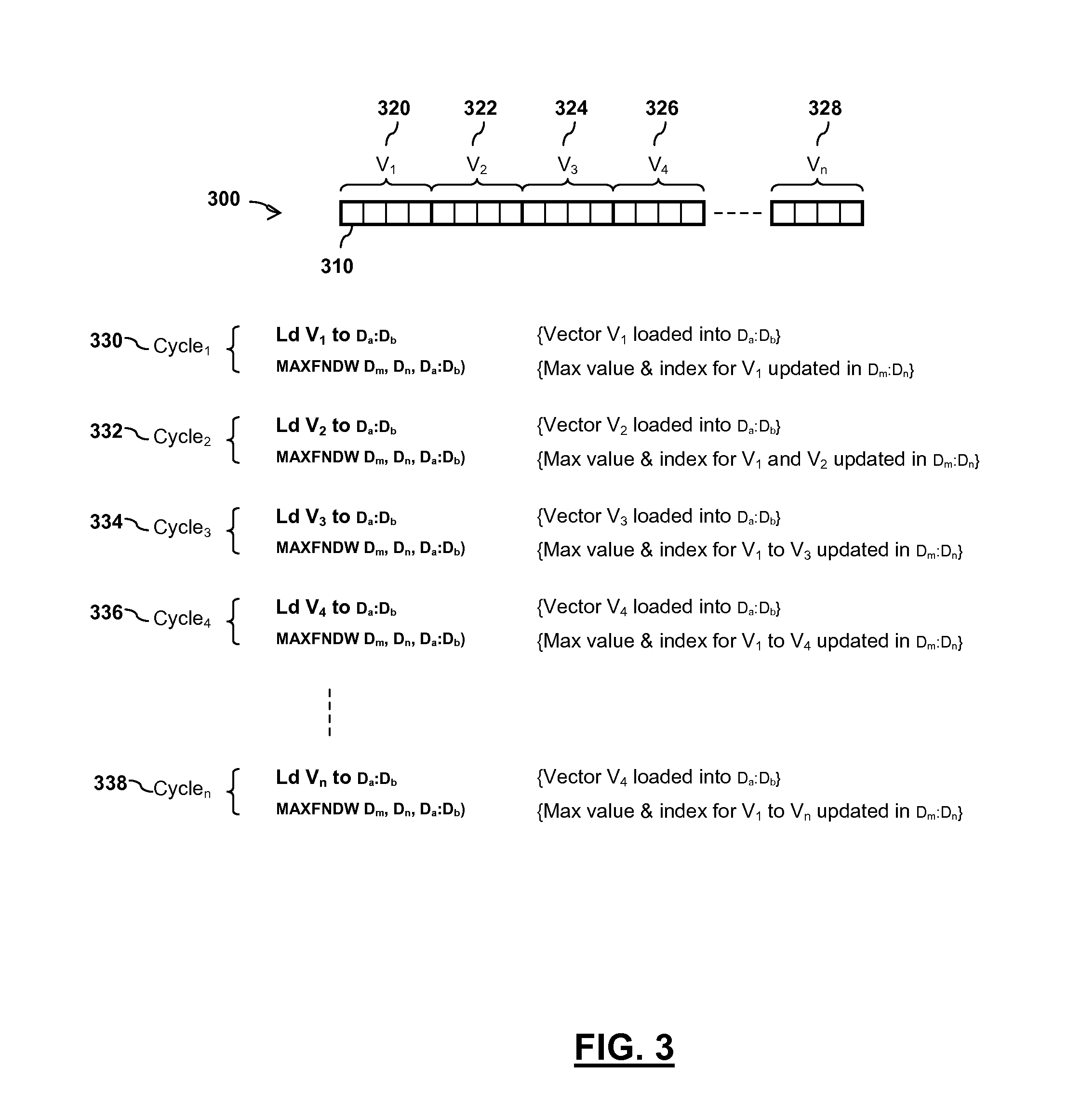
Integrated circuit device and method for determining an index of an extreme value within an array of values
InactiveUS9165023B2Digital data information retrievalDigital data processing detailsProcessor registerComputer module
An integrated circuit device comprises at least one digital signal processor, DSP, module, the at least one DSP module comprising a plurality of data registers and at least one data execution unit, DEU, module arranged to execute operations on data stored within the data registers. The at least one DEU module is arranged to, in response to receiving an extreme value index instruction, compare a previous extreme value located within a first data register set of the DSP module with at least one input vector data value located within a second data register set of the DSP module, and determine an extreme value thereof. The at least one DEU module is further arranged to, if the determined extreme value comprises an input vector data value located within the second data register set, store the determined extreme value in the first data register set, determine an index value for the determined extreme value, and store the determined index value in the first data register set.
Owner:NXP USA INC
Multidimensional structured data visualization method and apparatus, text visualization method and apparatus, method and apparatus for visualizing and graphically navigating the world wide web, method and apparatus for visualizing hierarchies
A method of displaying correlations among information objects comprises receiving a query against a database; obtaining a query result set; and generating a visualization representing the components of the result set, the visualization including one of a plane and line to represent a data field, nodes representing data values, and links showing correlations among fields and values. Other visualization methods and apparatus are disclosed.
Owner:BATTELLE MEMORIAL INST
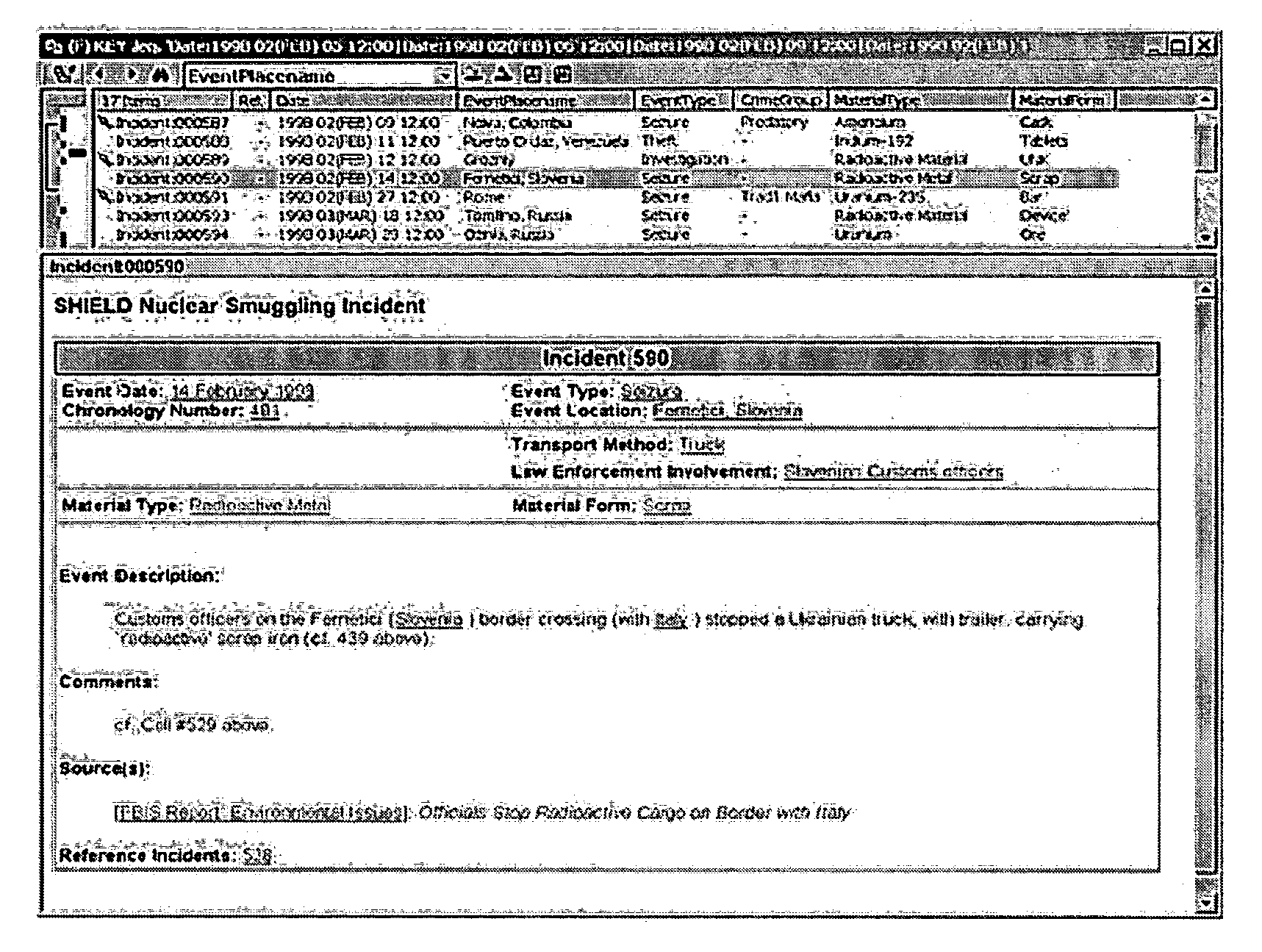
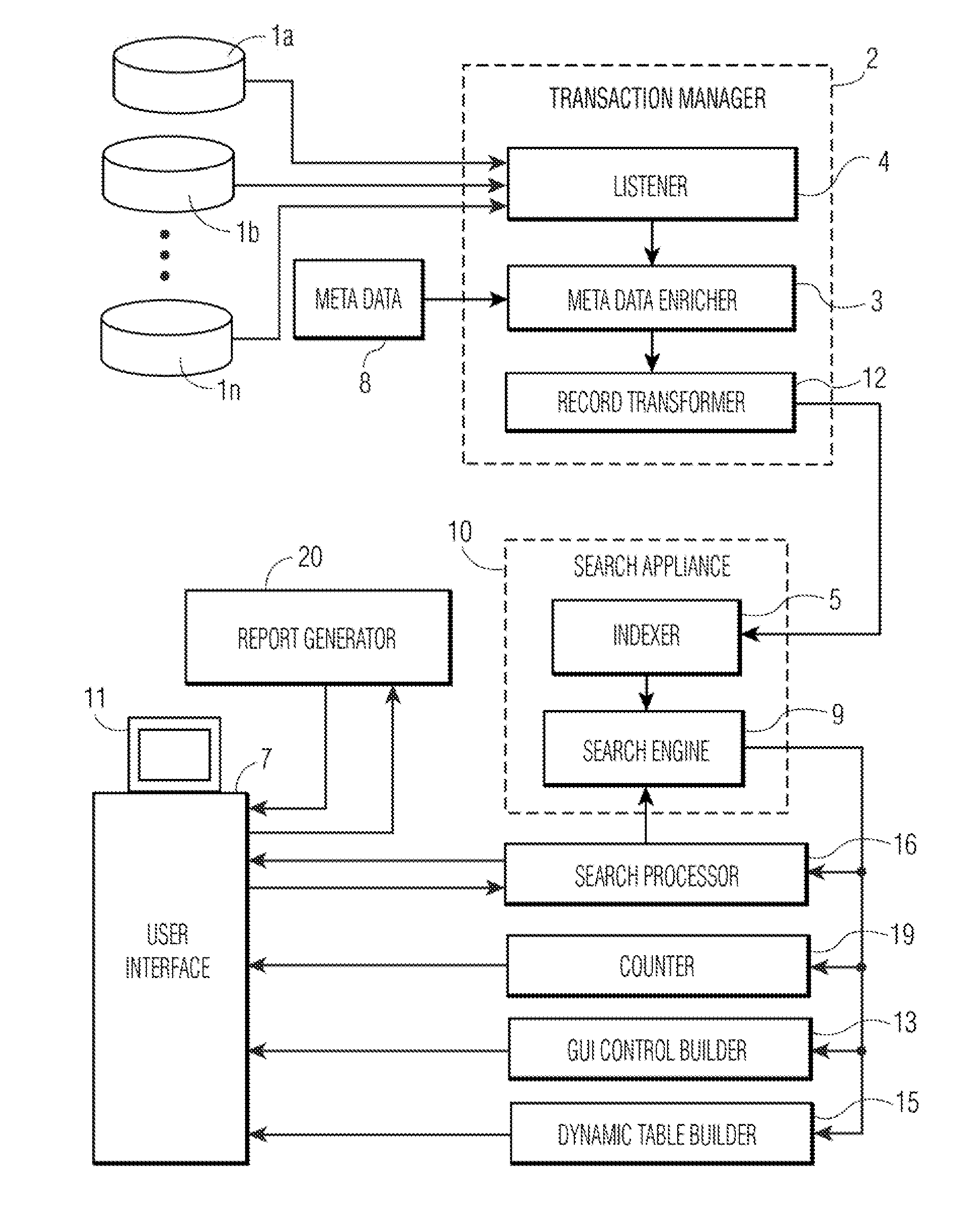
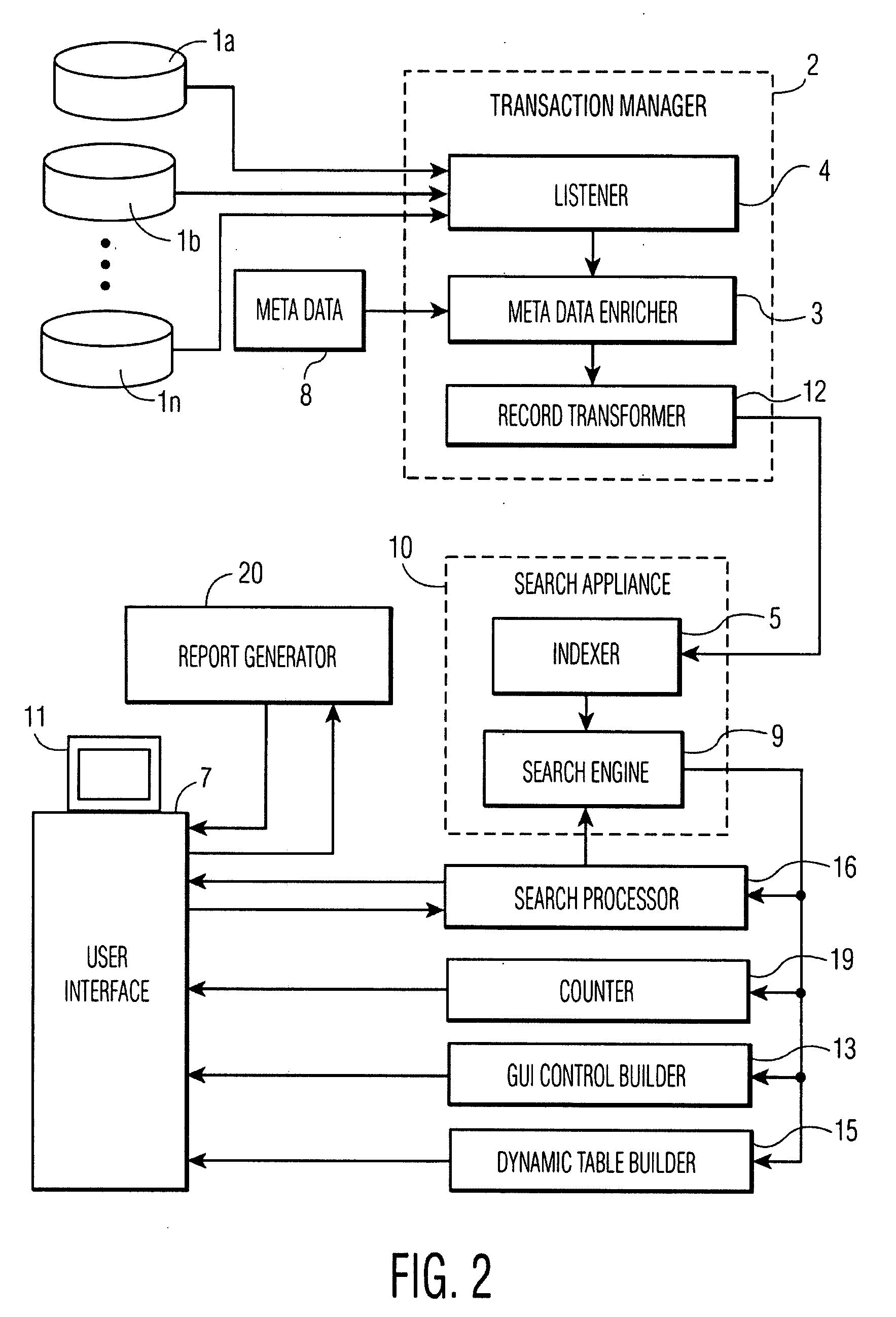
Apparatus and Method for Conducting Searches with a Search Engine for Unstructured Data to Retrieve Records Enriched with Structured Data and Generate Reports Based Thereon
InactiveUS20080104542A1Improve practicalityWeb data indexingSpecial data processing applicationsGraphicsRecordset
Records in databases or unstructured files are enriched with metadata and are indexed for retrieval by a search engine. In response to a search request, a graphical user interface (GUI) control based on the metadata associated with the search hits is constructed and displayed with the search results in a standard view. Selection of a metadata value via the GUI control filters the previously matched records down to those matching the value selected via the GUI control. The metadata in the search results is arranged in a tabular view which is embedded in the display of search results and rendered invisible until selected by the user. Reports can be constructed from an identifier each returned record set for presenting, analyzing and modifying the data, and for generating further reports.
Owner:INFORMATION BUILDERS INC
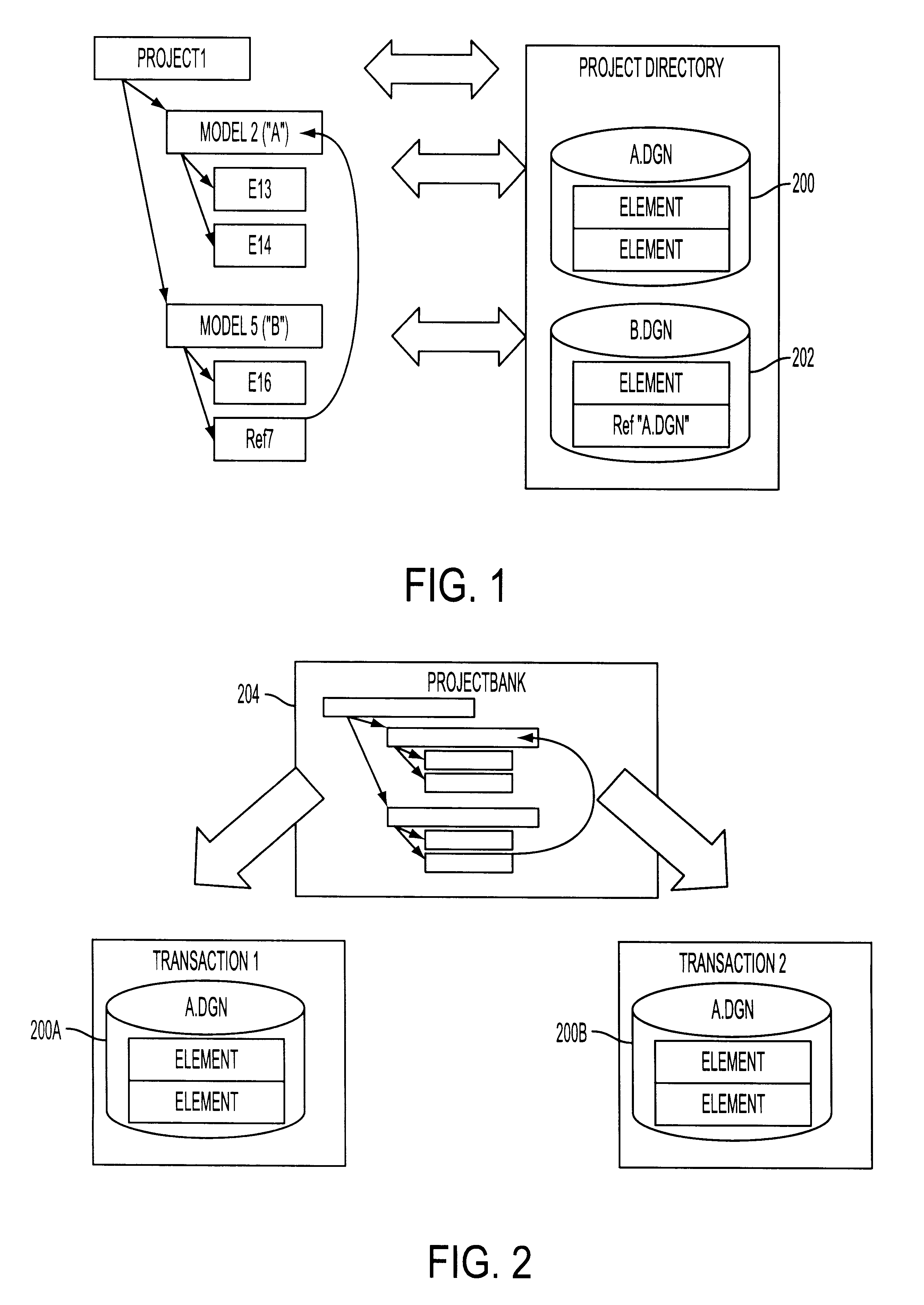
System for collaborative engineering using component and file-oriented tools
InactiveUS6341291B1Improve the level ofHigh currentData processing applicationsCAD network environmentSoftware engineeringIdenticon
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. Each component has a unique identifier, a set of fields, each field having a data type and a data value, and a program which interprets and modifies the fields. The plurality of components are stored in a repository of a server. The repository also stores a history of any changes made to the components. A plurality of client computers are bidirectionally connected to the server. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the server to replace the current versions in the repository. At the client computer, the user interacts with the components using conventional file-based software. Before locally edited versions of the components are committed to the server to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts therebetween. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
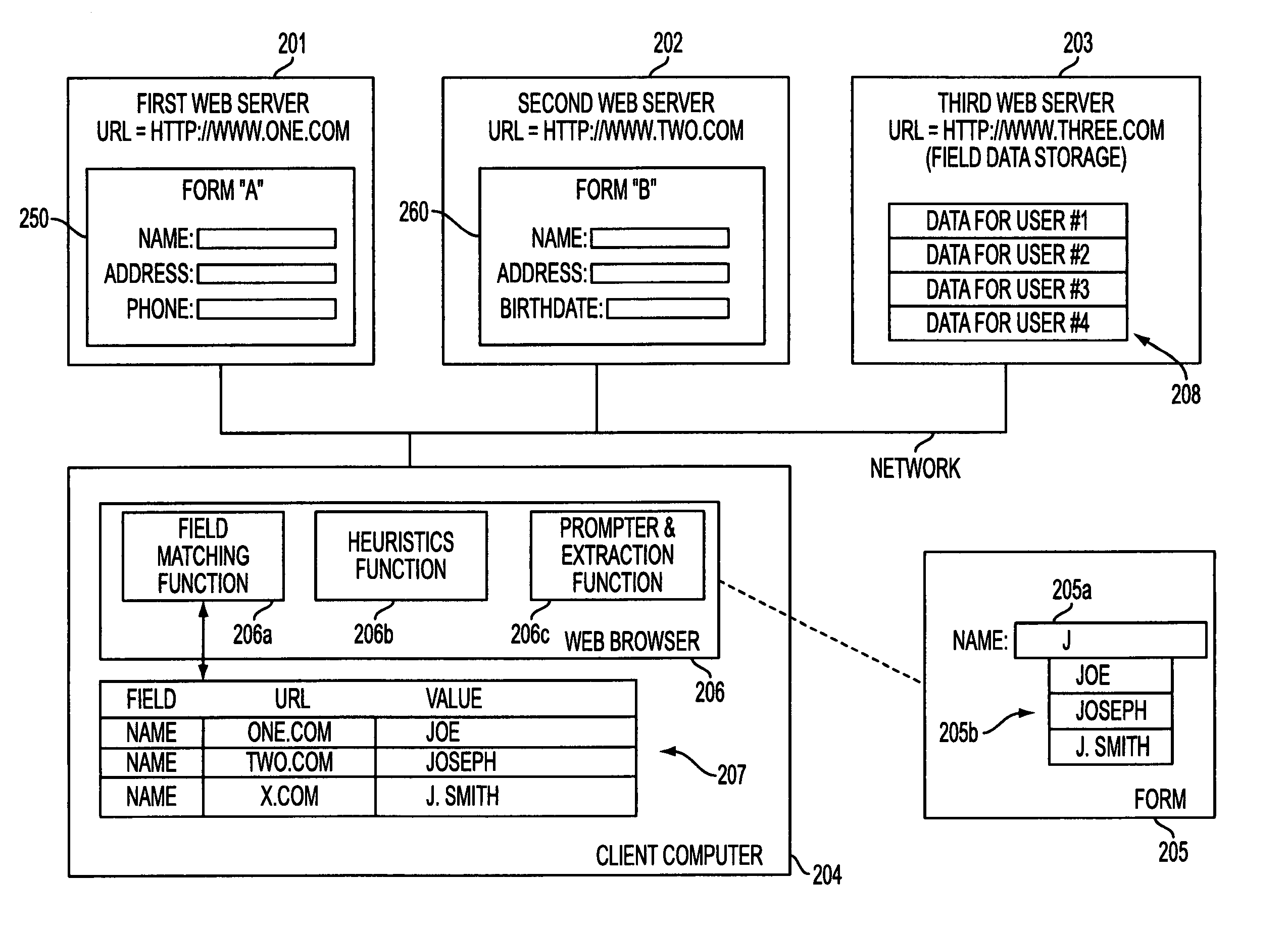
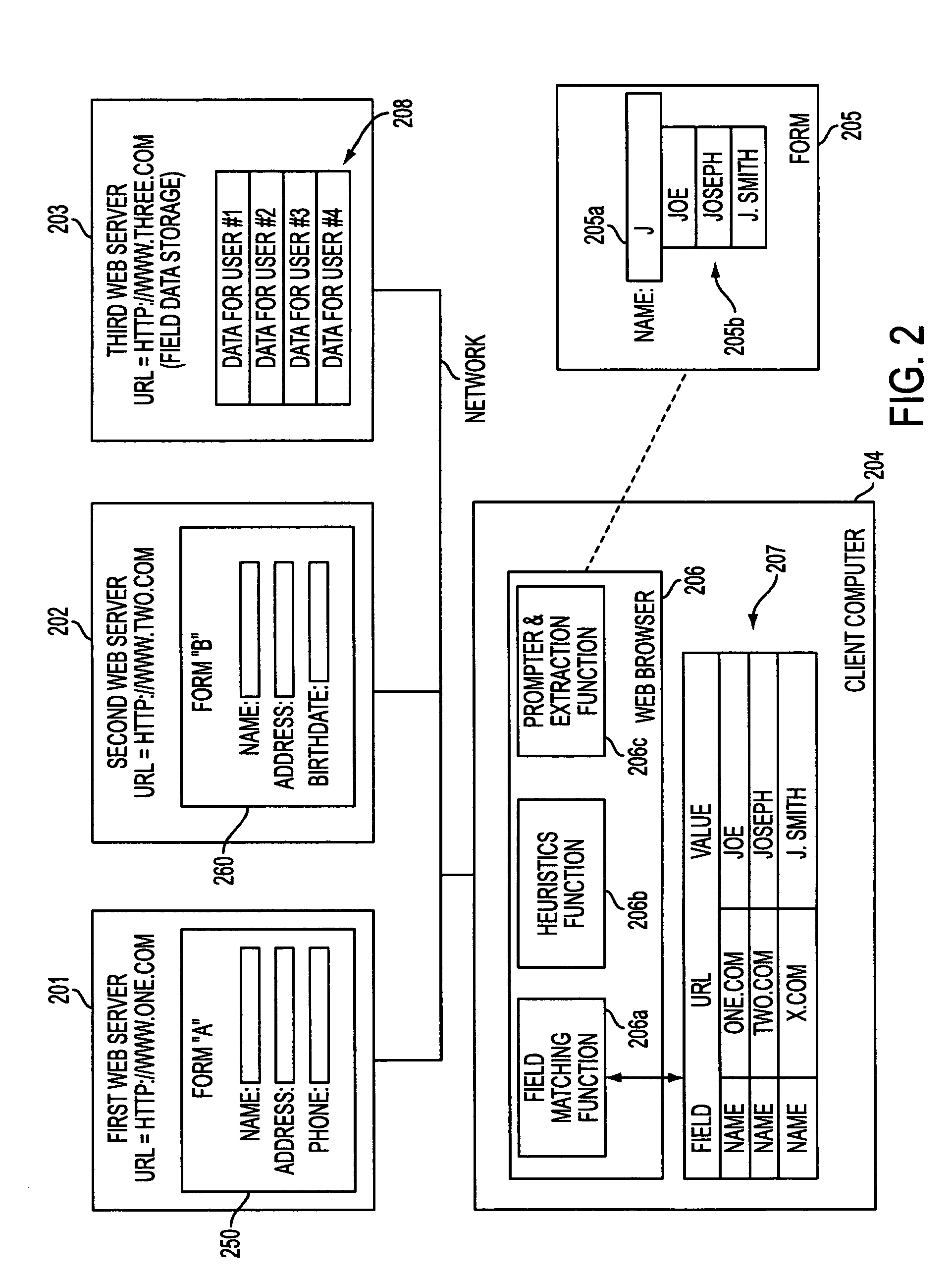
System and method for populating forms with previously used data values
InactiveUS7216292B1Compromising securityCompromising privacyDigital computer detailsNatural language data processingWeb siteWeb browser
A system and method is provided for learning data values over time as they are entered by a user on a form such as a web page form. An Internet web browser can be modified to suggest previously used data values for any form field that is the same as or similar to a previously used form field. Application programs that use the web browser can gain access to previously used form field values even if they have no knowledge of the field names. Software in a web browser associates field names across different Universal Resource Locators (URLs), so that when a user enters a value into a field (e.g., username) at a first web site, that same value can be automatically suggested when the user displays a different form on a different web site that uses the same field name.
Owner:MICROSOFT TECH LICENSING LLC
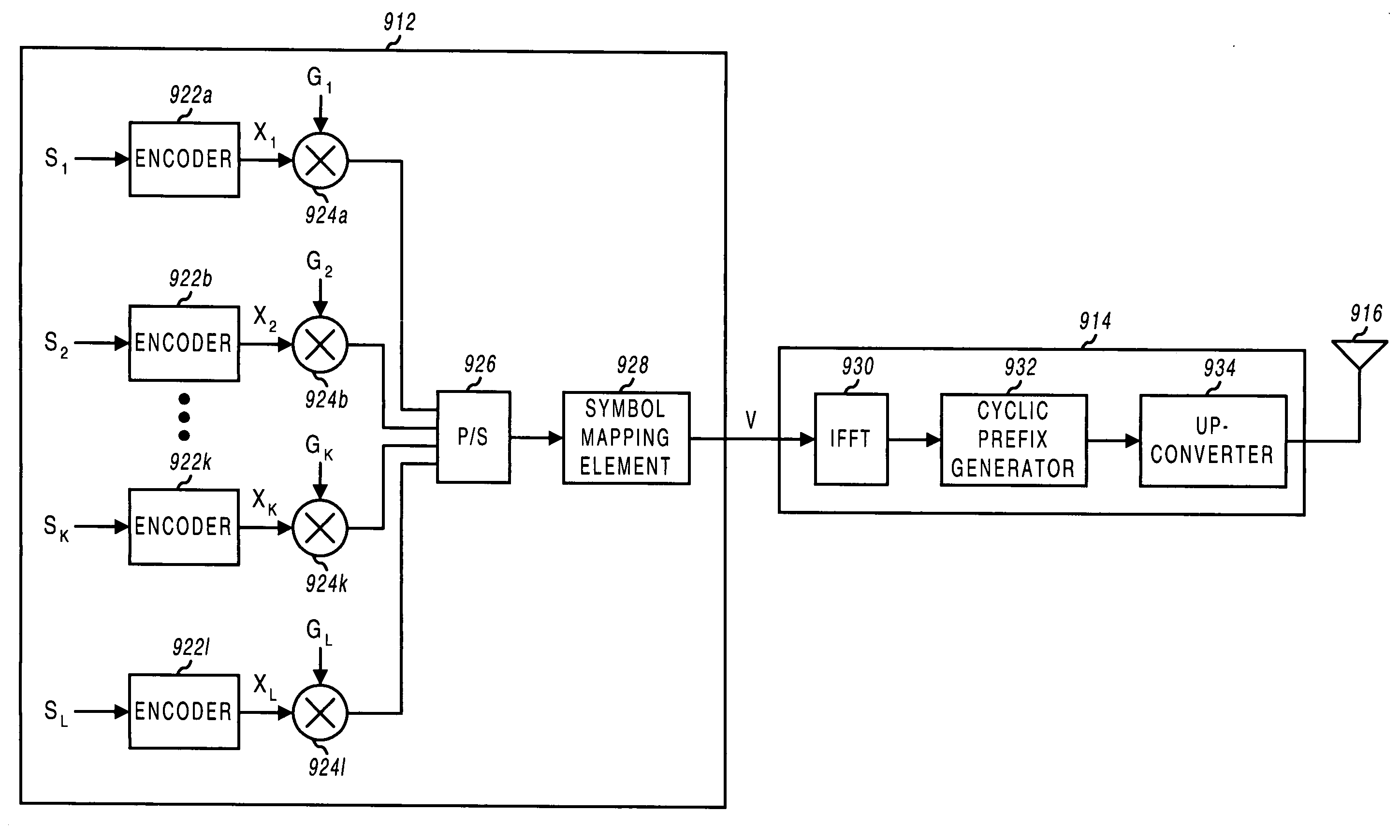
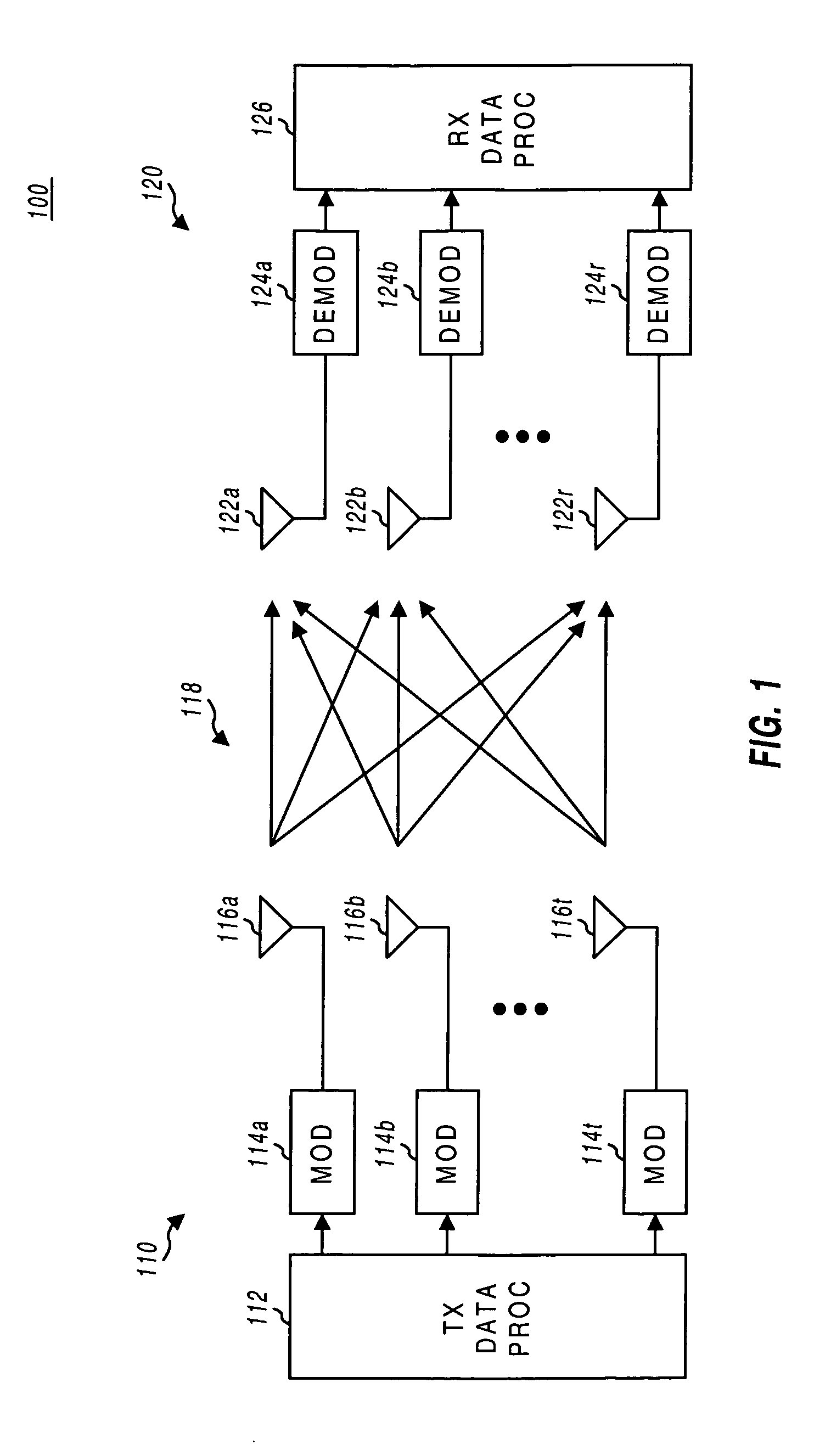
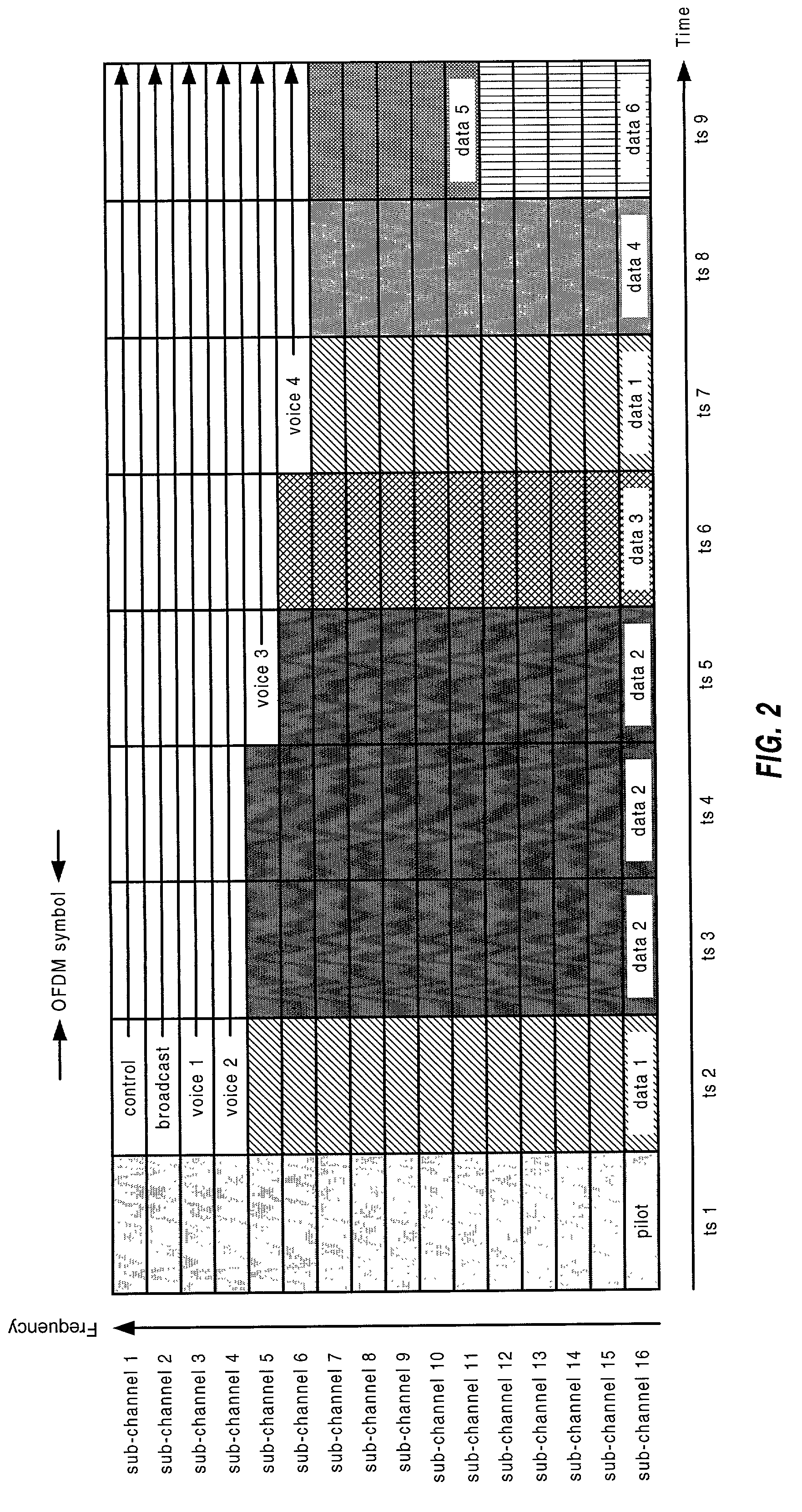
Multiplexing of real time services and non-real time services for OFDM systems
InactiveUS6952454B1Guaranteed normal transmissionImprove efficiencyFrequency-division multiplex detailsAmplitude-modulated carrier systemsData streamFull Rate
Transmitter and receiver units for use in an OFDM communications system and configurable to support multiple types of services. The transmitter unit includes one or more encoders, a symbol mapping element, and a modulator. Each encoder receives and codes a respective channel data stream to generate a corresponding coded data stream. The symbol mapping element receives and maps data from the coded data streams to generate modulation symbol vectors, with each modulation symbol vector including a set of data values used to modulate a set of tones to generate an OFDM symbol. The modulator modulates the modulation symbol vectors to provide a modulated signal suitable for transmission. The data from each coded data stream is mapped to a respective set of one or more “circuits”. Each circuit can be defined to include a number of tones from a number of OFDM symbols, a number of tones from a single OFDM symbol, all tones from one or more OFDM symbols, or some other combination of tones. The circuits can have equal size or different sizes. Different circuits can be used for full rate data (e.g., active speech) and low rate data (e.g., silence periods).
Owner:QUALCOMM INC
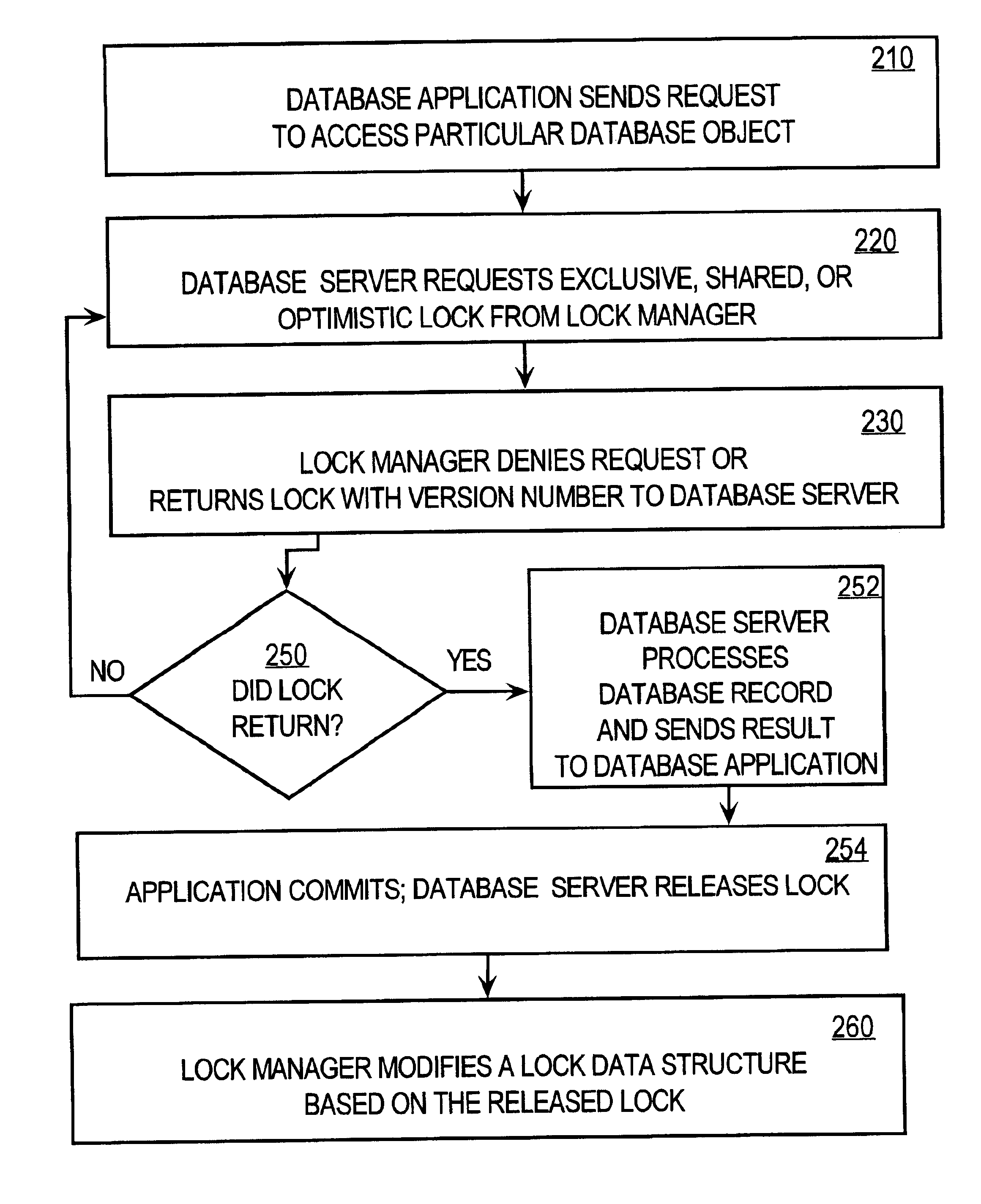
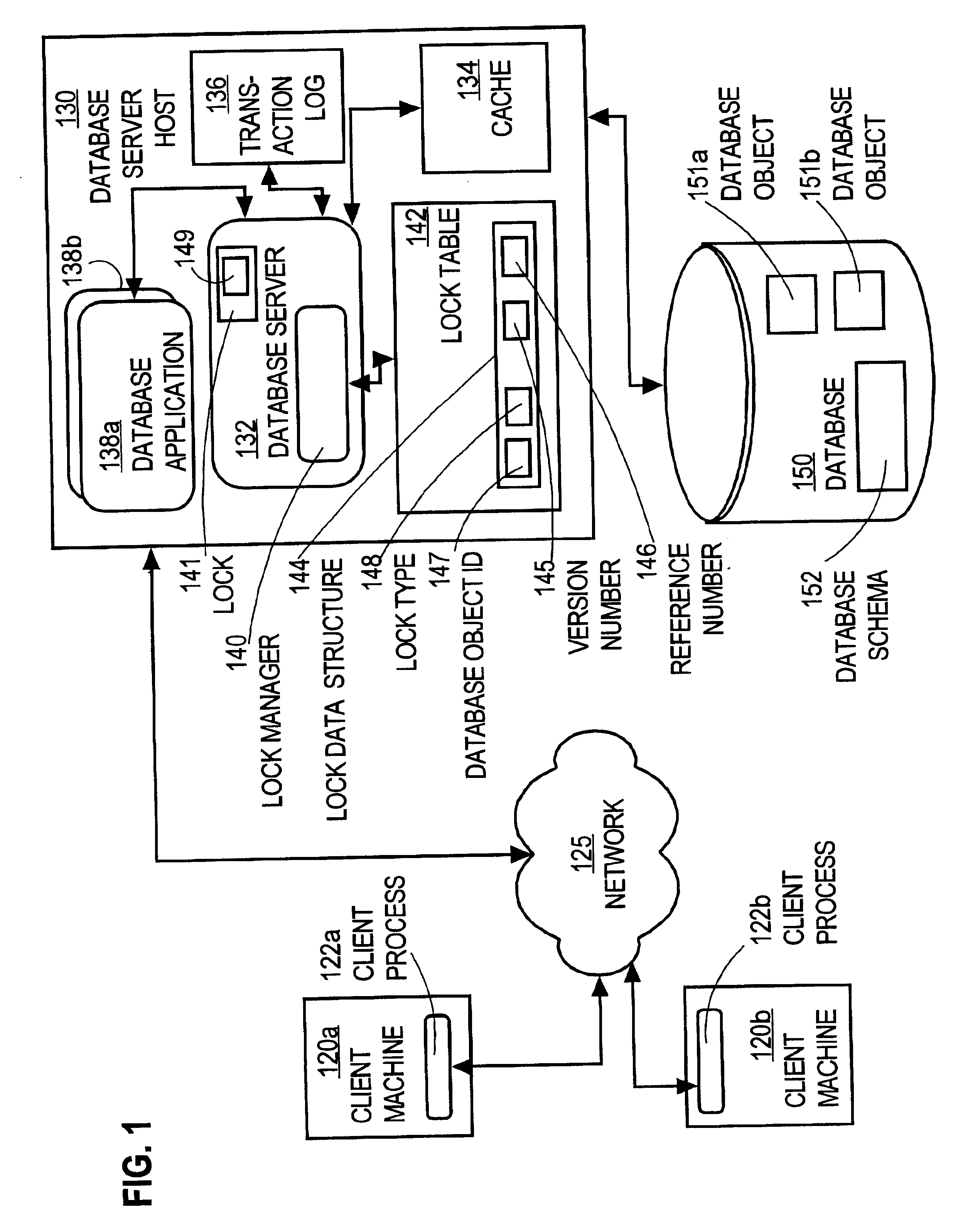
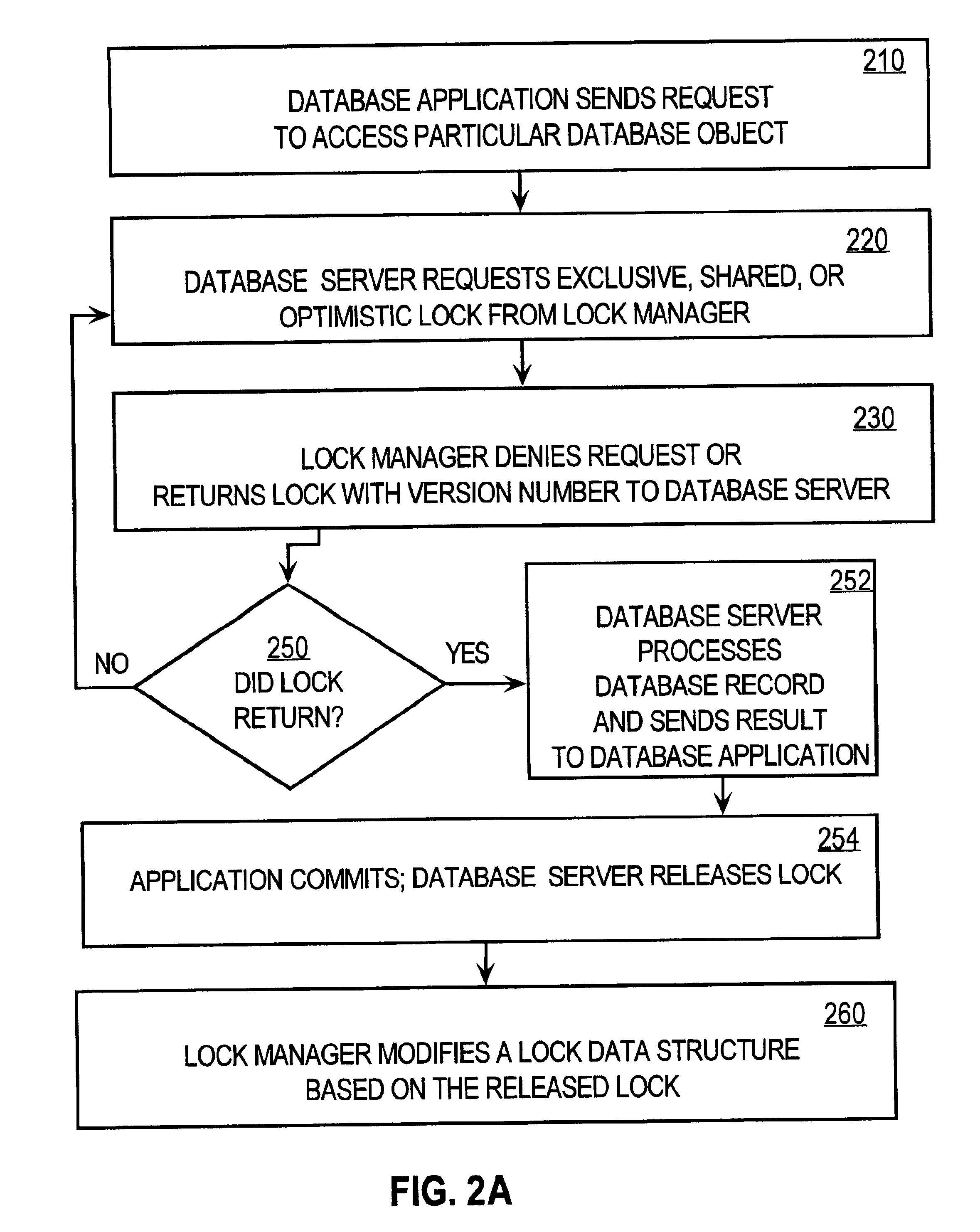
Method and apparatus providing optimistic locking of shared computer resources
InactiveUS6850938B1Digital data information retrievalData processing applicationsComputer resourcesLock manager
Techniques for concurrent access to a resource object, such as a database, include generating a lock data structure for a particular resource object. The lock data structure includes data values for a resource object identification, a lock type, and a version number. The version number is related to a number of changes to the resource object since the lock data structure was generated. A request is received from a requesting process. The request is for a requested lock type for access to the particular resource object. It is determined whether to grant the request based on the requested lock type and the lock type in the lock data structure. By carrying a lock version number in a lock data structure managed by a lock manager, improved optimistic locking is provided in a database. In particular, the approach enables introduction of optimistic locking to a legacy database without requiring burdensome changes to a database table schema.
Owner:CISCO TECH INC
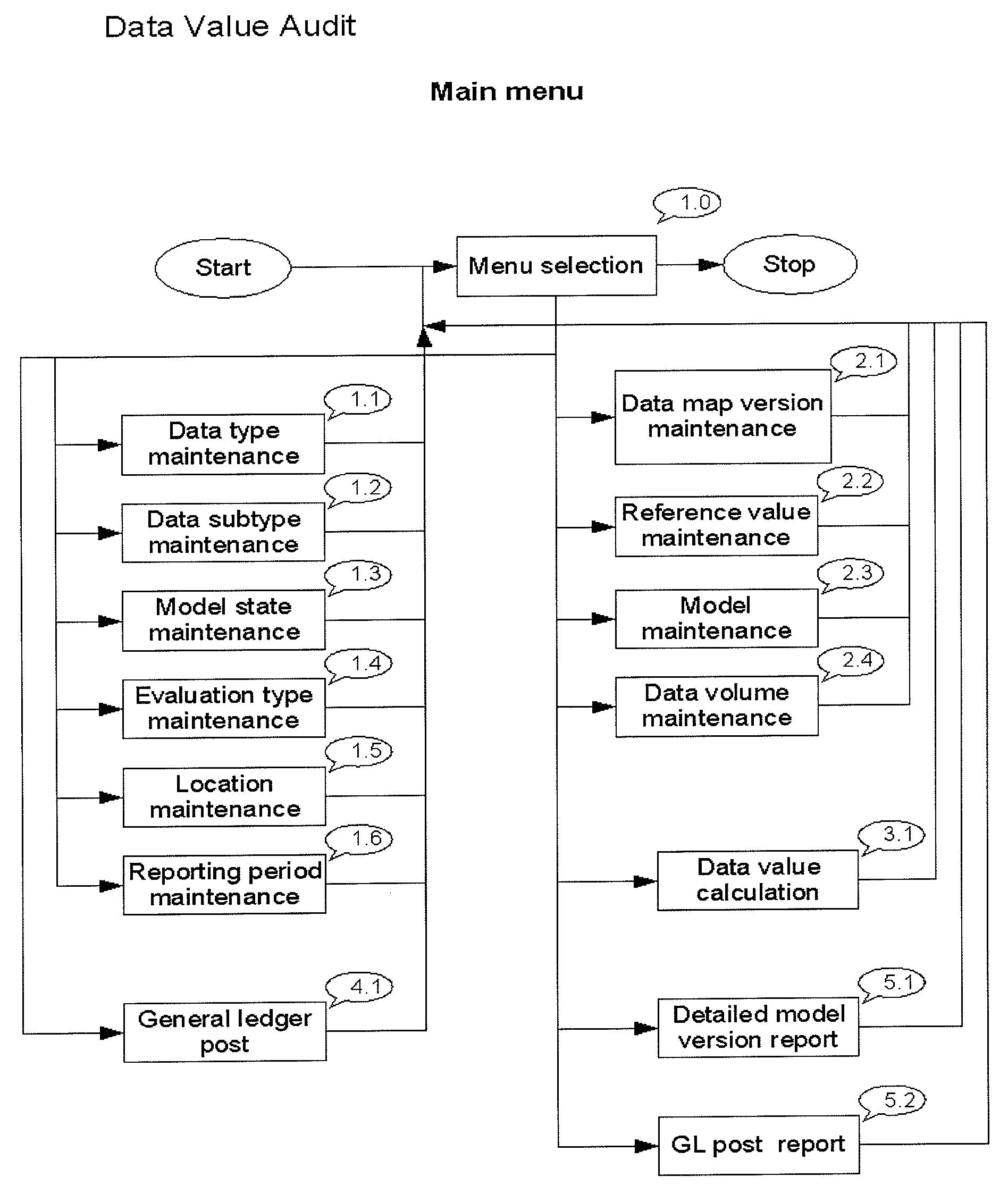
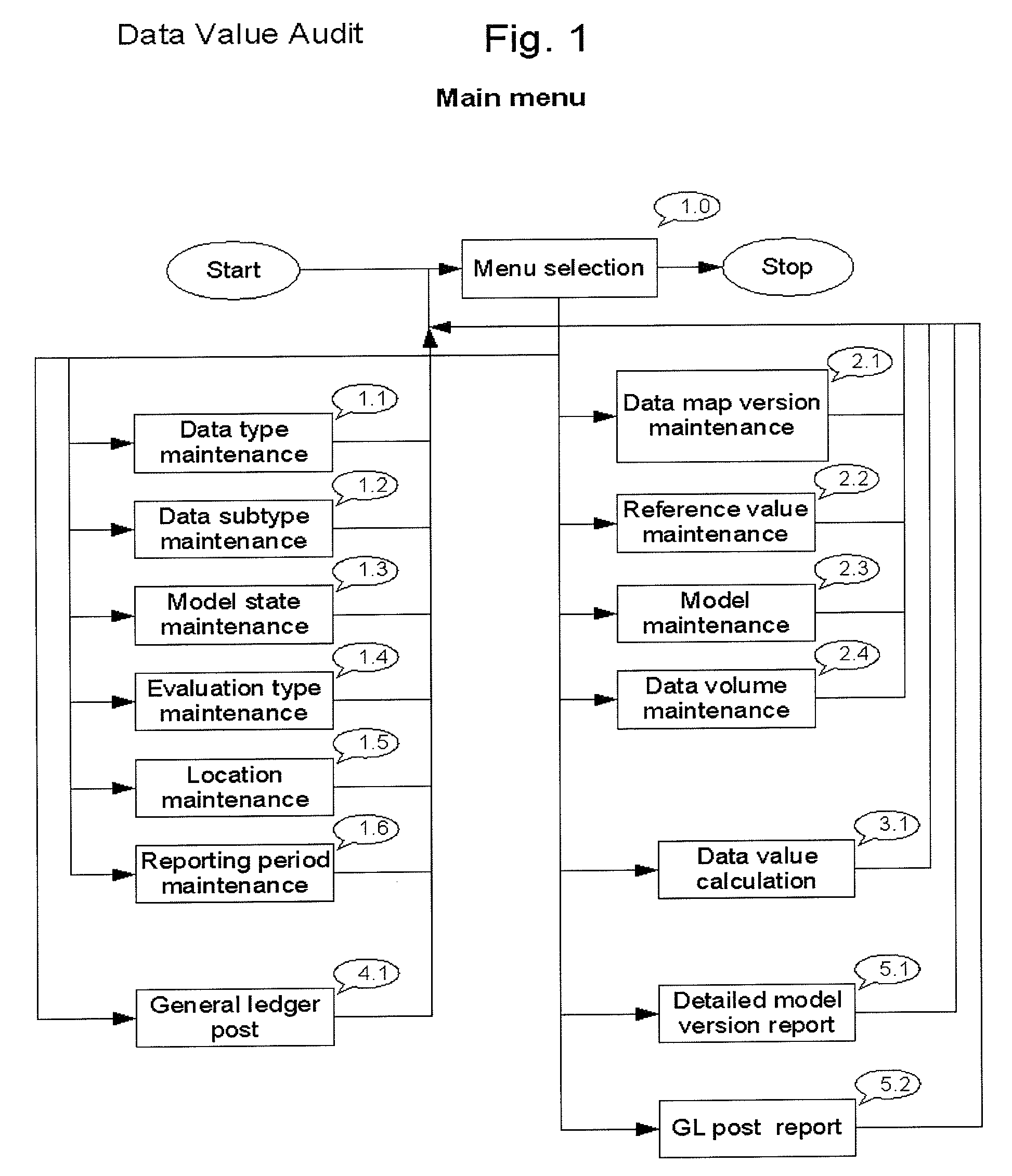
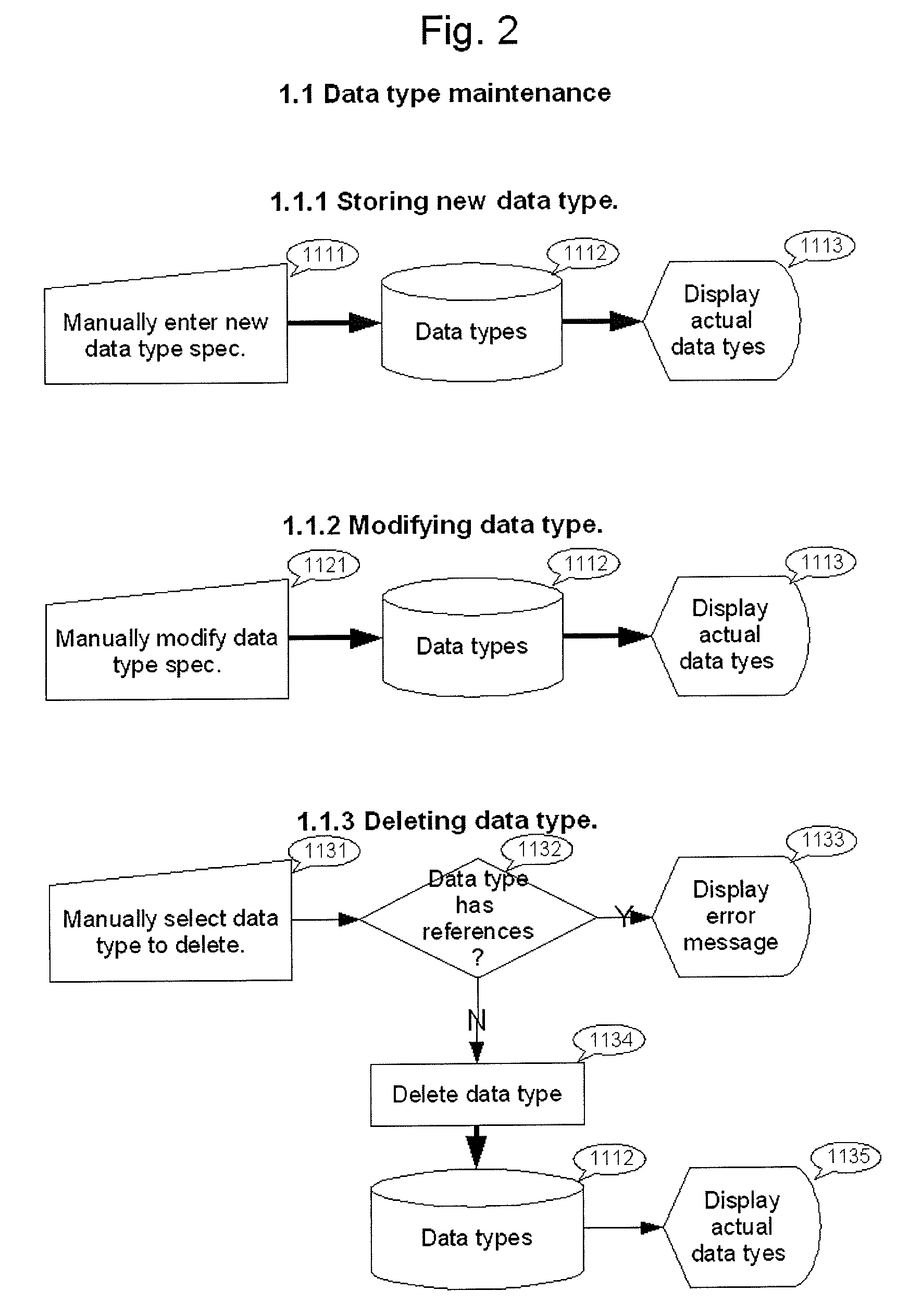
Assessment of corporate data assets
InactiveUS20100228786A1Improve corporate information technology managementEasy to manageDigital data processing detailsSpecial data processing applicationsData valueA-weighting
The present invention provides a data processing system and a method of assessing the data value of a data assets inventory which comprises:a) preparing a data map on a computer database comprising inputting data types and data subtypes into said database, connecting a data storing location to the data subtypes and recording the data subtype occurrences in said database;b) assigning a weighting to each data subtype occurrence in said database to provide a data assets inventory and recording the data assets inventory in said database;c) preparing evaluation types on said database wherein the evaluation type has a calculation type attribute and wherein the evaluation type is either quantity independent or quantity dependent;d) connecting at least one evaluation type to each data subtype with a reference value and recording the reference value in said database;e) determining the data value of the data assets inventory and recording the data value in said database wherein when the evaluation type is quantity dependent then the value is the product of the weighting, the reference value and the quantity at the data storing location for each data subtype occurrence or wherein when the evaluation type is quantity independent then the value is the product of the weighting and the reference value for each data subtype occurrence.
Owner:TOROK TIBOR
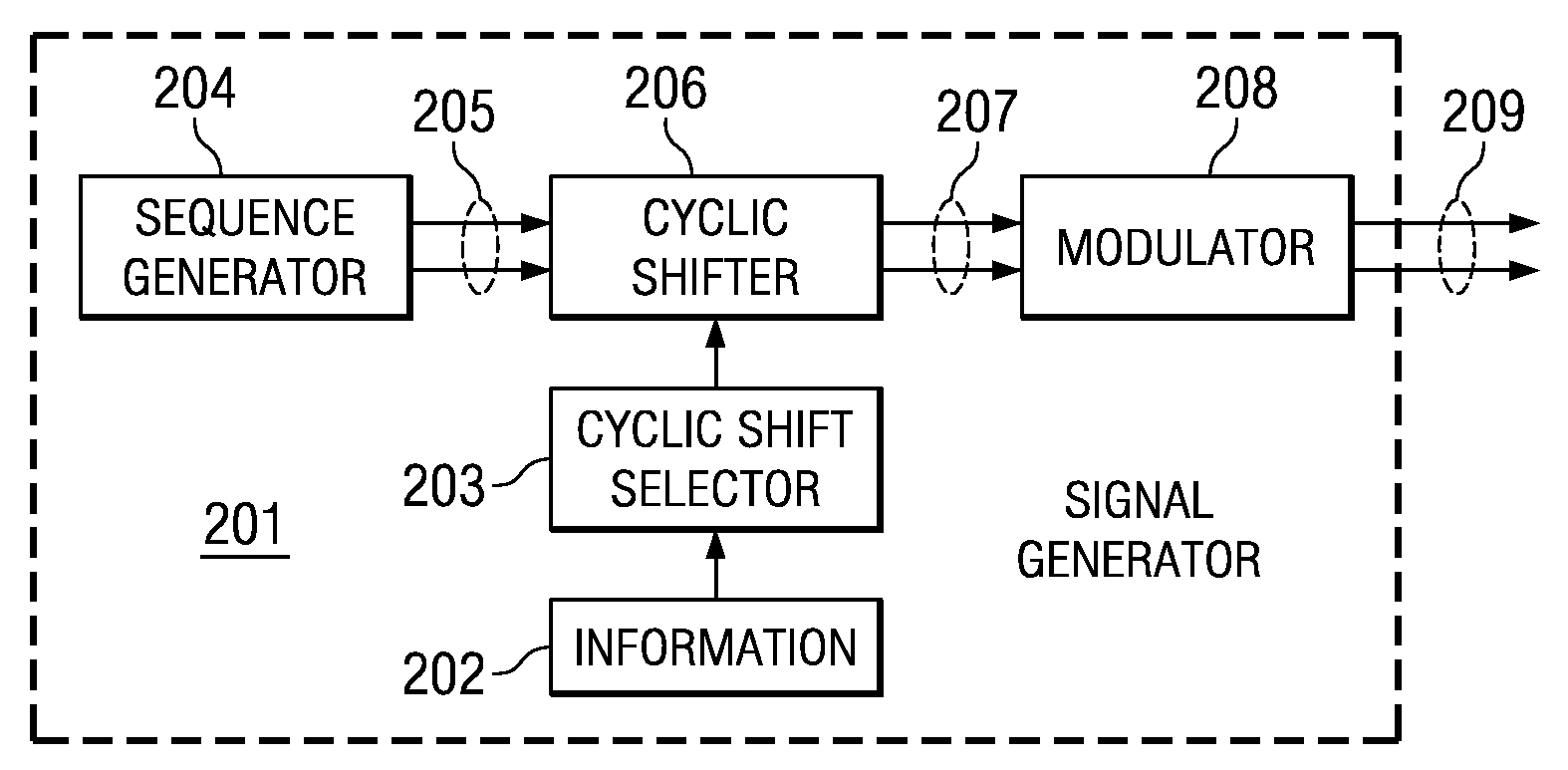
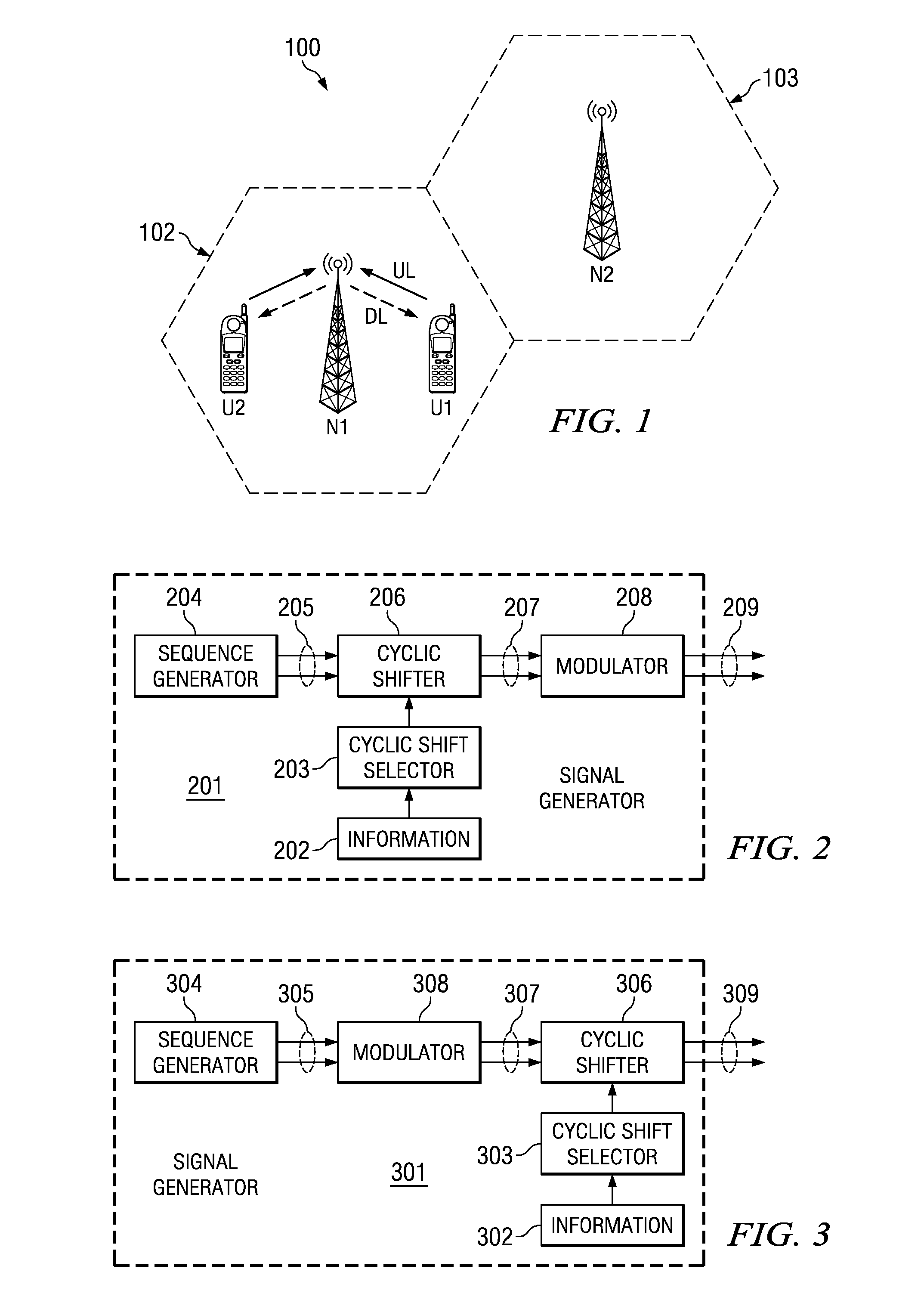
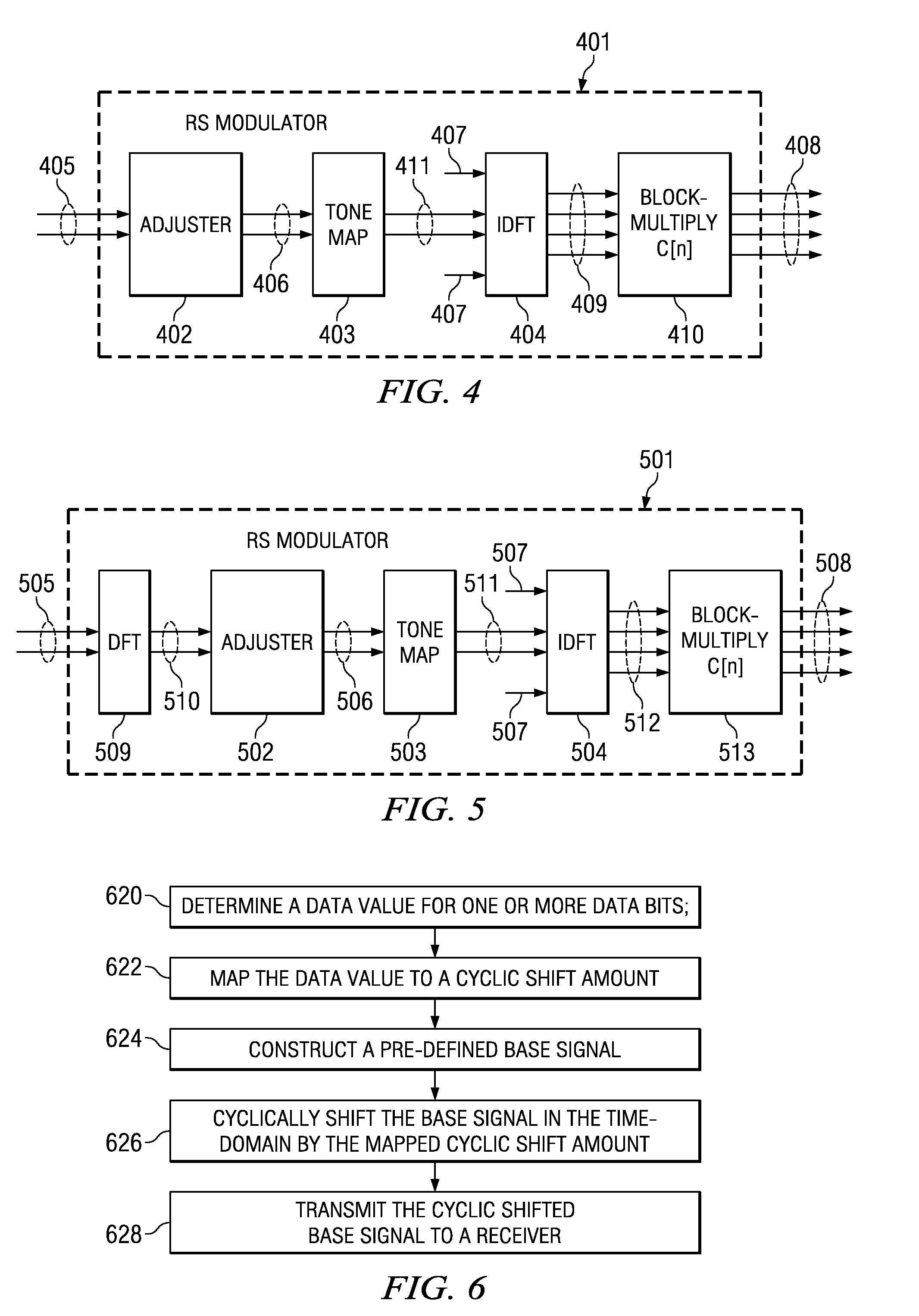
Transmission of ACK/NACK Bits and their Embedding in the Reference Signal
ActiveUS20080075184A1Error prevention/detection by using return channelTransmission path divisionWireless cellular networksData value
Transmitting a ACK / NACK response in a wireless cellular network by mapping the data value into a cyclic shifted version of a reference signal. A subframe is formed with a plurality of symbols with certain symbols designated as reference signal (RS) symbols. The receiver and transmitter both know when an ACK / NACK response is expected. If an ACK / NACK response is not expected, then an RS is inserted in the duration of symbols designated as RS symbols. If an ACK / NACK response is expected, then the ACK / NACK response is embedded in one or more of the symbols designated as RS symbols. The subframe is transmitted to a receiver, and the receiver can determine the ACK / NACK value in the RS symbol, if present, and also use the RS symbol for coherent demodulation of a CQI (channel quality indicator) or data.
Owner:TEXAS INSTR INC
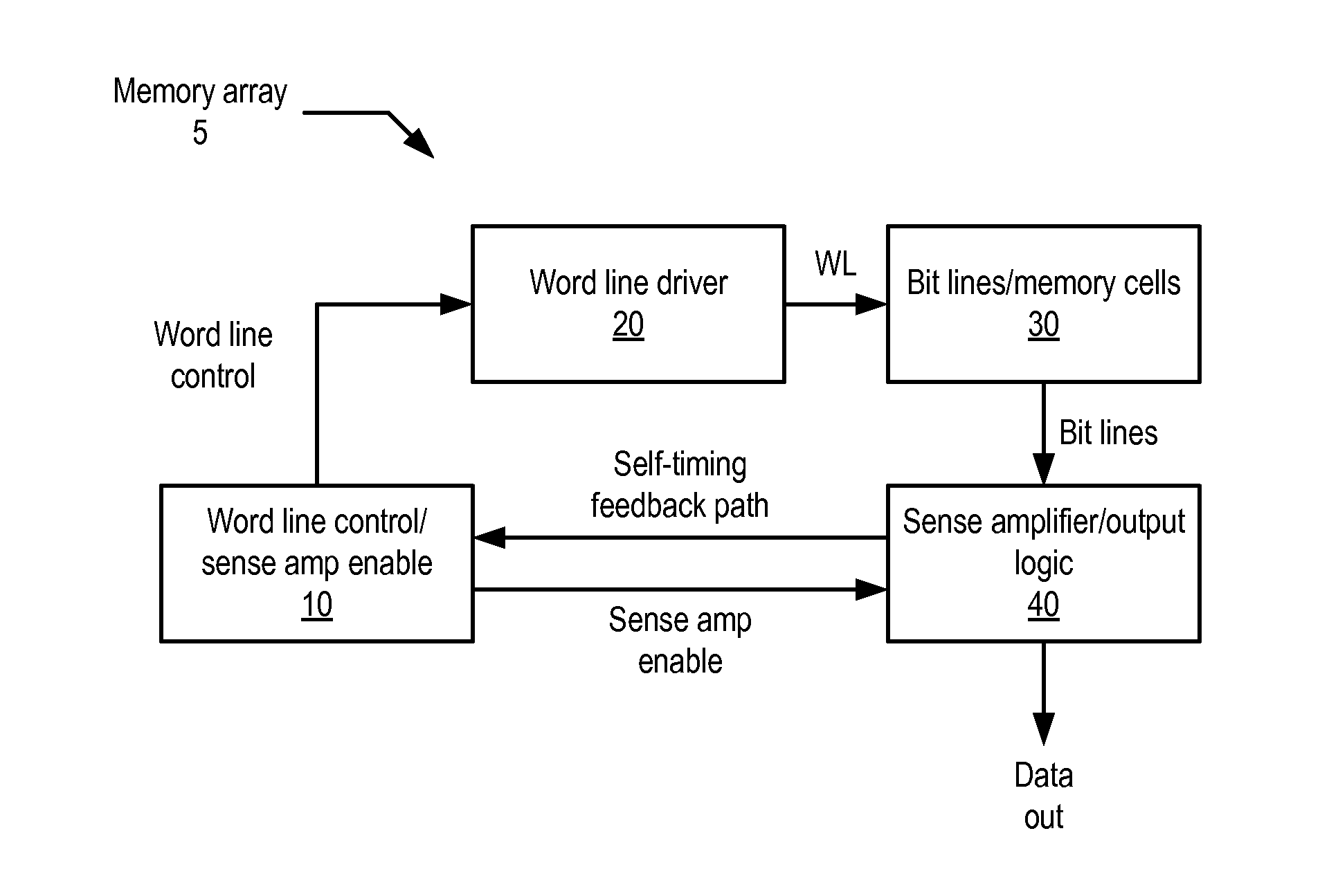
Sense amplifier latch with integrated test data multiplexer
A sense amplifier latch may be provided to controllably latch the output of a sense amplifier. The latch may open in response to assertion of a latch enable signal to receive data, and close in response to deassertion of the latch enable signal to capture and store the received data. Additionally, a multiplexer may be provided to select from among multiple sources of test data, such as scan data and bypass data. The multiplexer may produce a test data input to the sense amplifier latch that encodes a data value and a control value that causes the data value to be selected. Depending on the state of the test data input, the sense amplifier latch may output either a value received from the sense amplifier or a value encoded in the test data input.
Owner:ALLLE INC
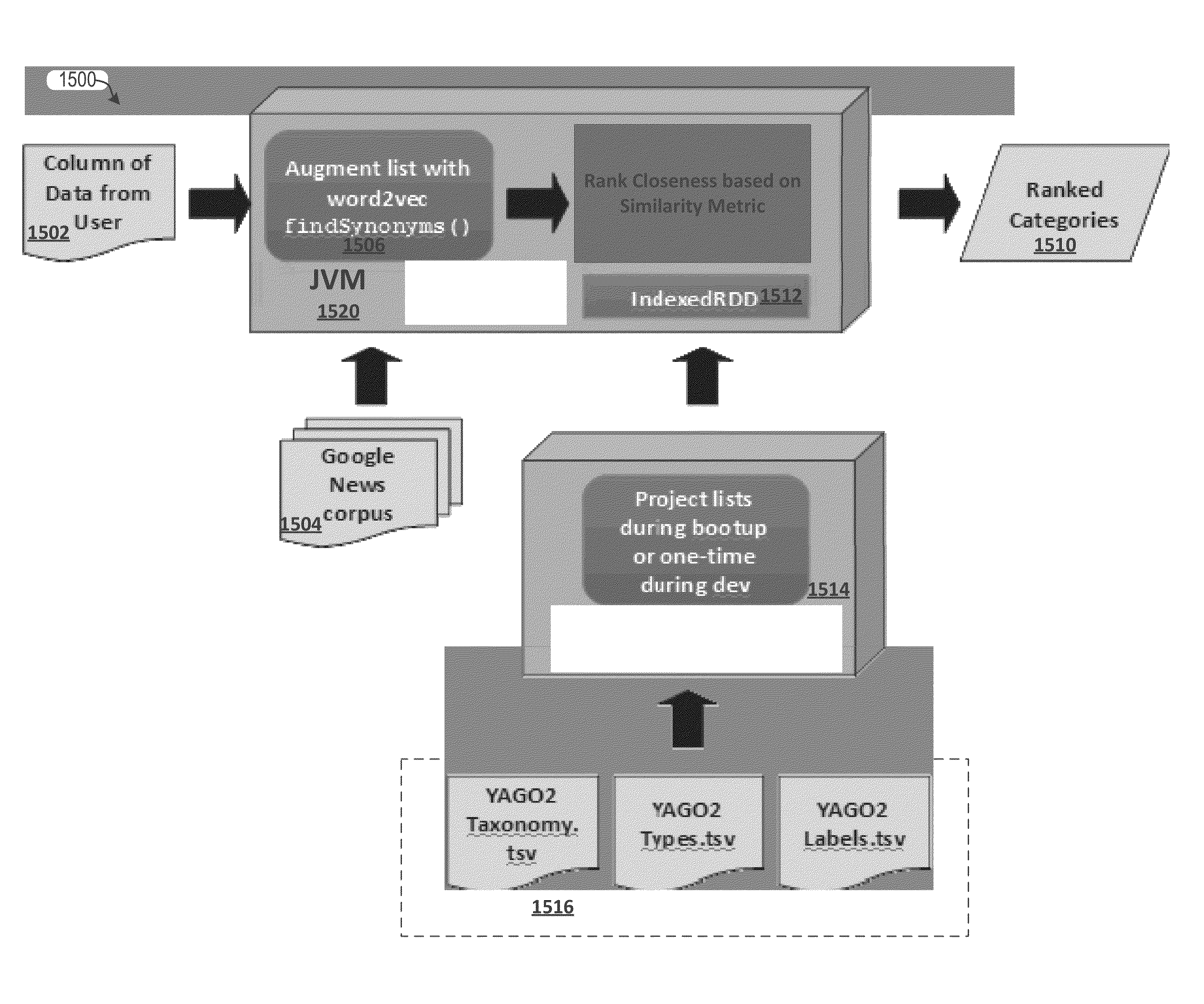
Techniques for similarity analysis and data enrichment using knowledge sources
ActiveUS20160092557A1Accurate resolutionAccurate labelingDigital data processing detailsRelational databasesKnowledge sourcesData set
The present disclosure relates to performing similarity metric analysis and data enrichment using knowledge sources. A data enrichment service can compare an input data set to reference data sets stored in a knowledge source to identify similarly related data. A similarity metric can be calculated corresponding to the semantic similarity of two or more datasets. The similarity metric can be used to identify datasets based on their metadata attributes and data values enabling easier indexing and high performance retrieval of data values. A input data set can labeled with a category based on the data set having the best match with the input data set. The similarity of an input data set with a data set provided by a knowledge source can be used to query a knowledge source to obtain additional information about the data set. The additional information can be used to provide recommendations to the user.
Owner:ORACLE INT CORP
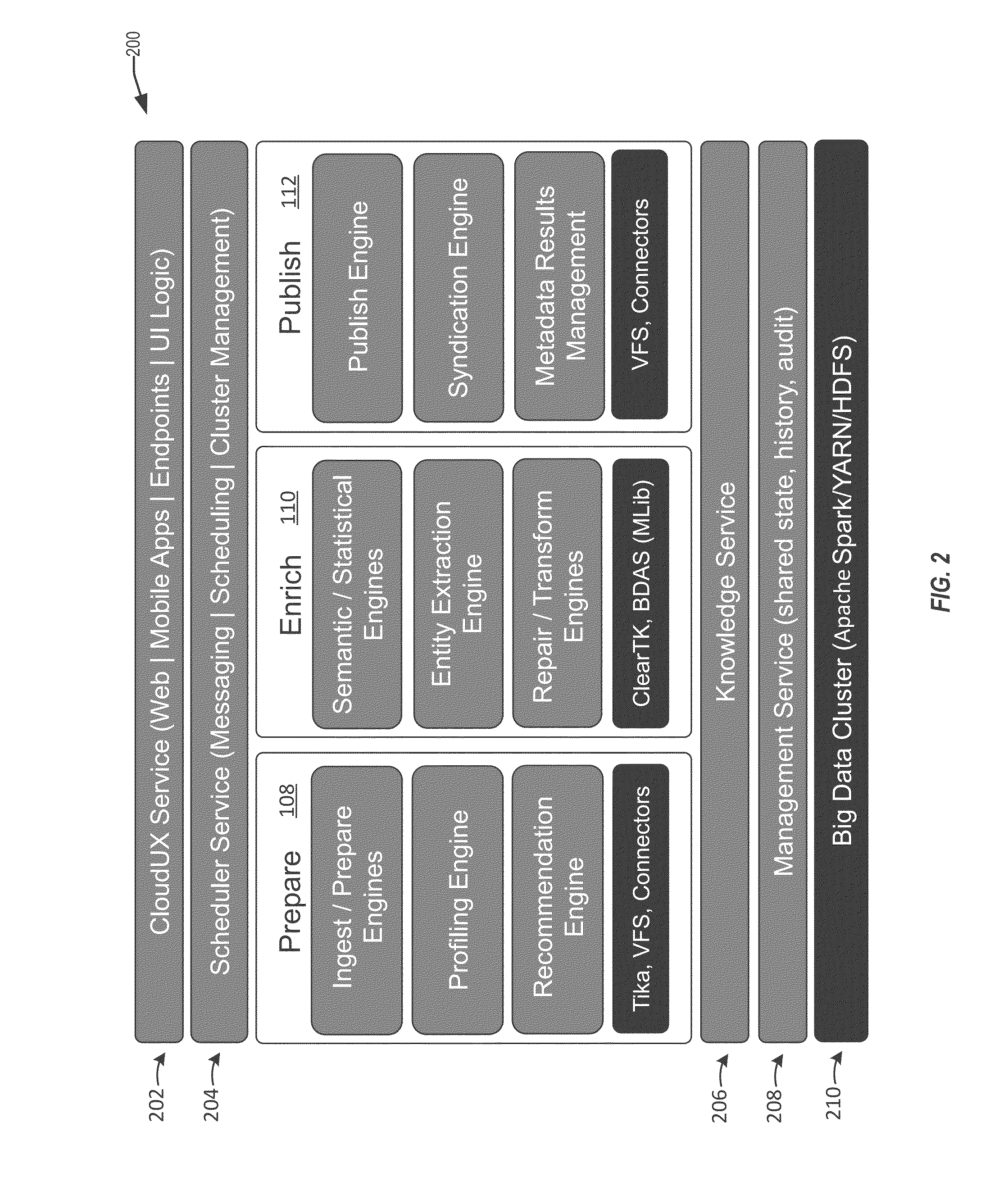
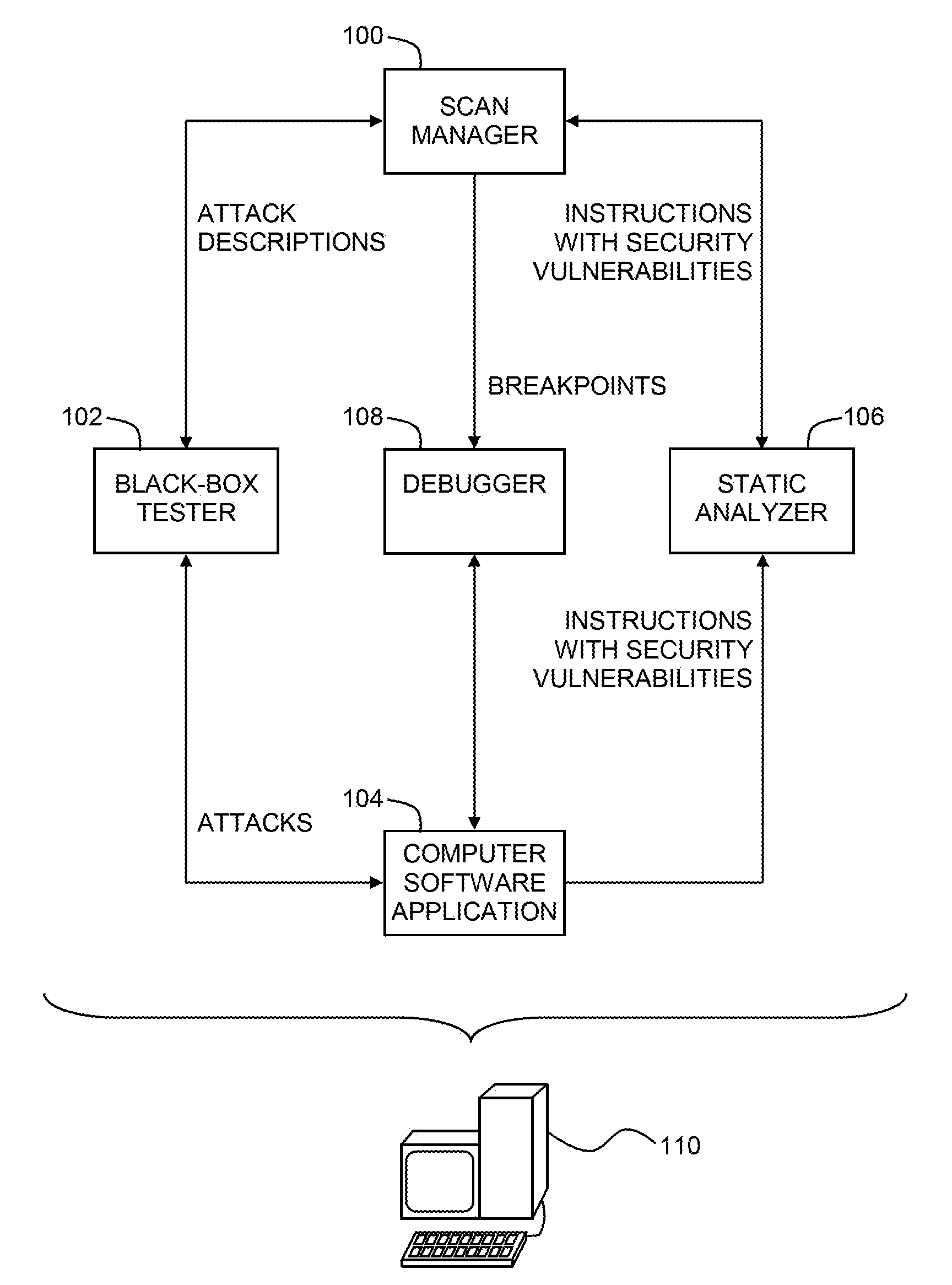
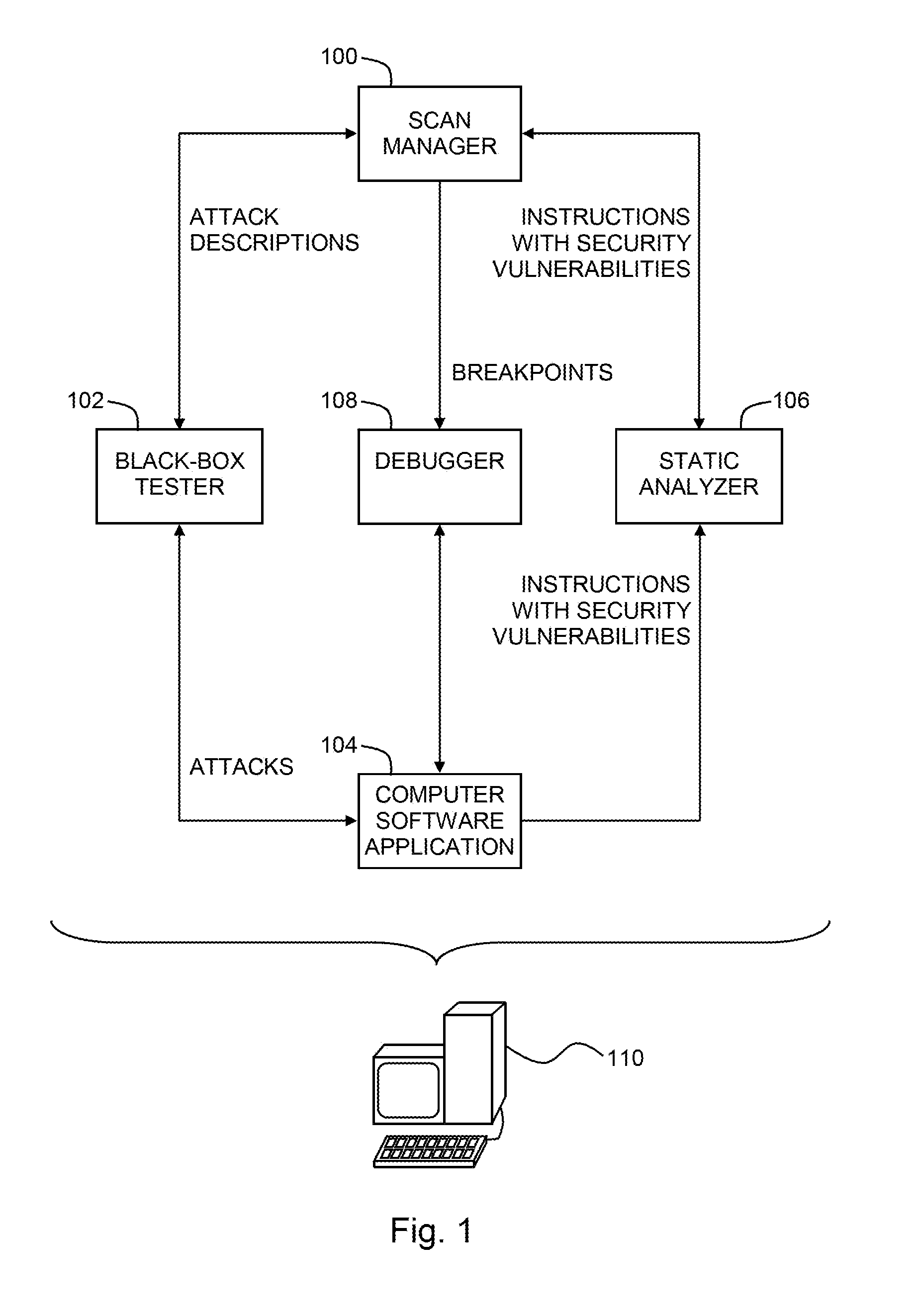
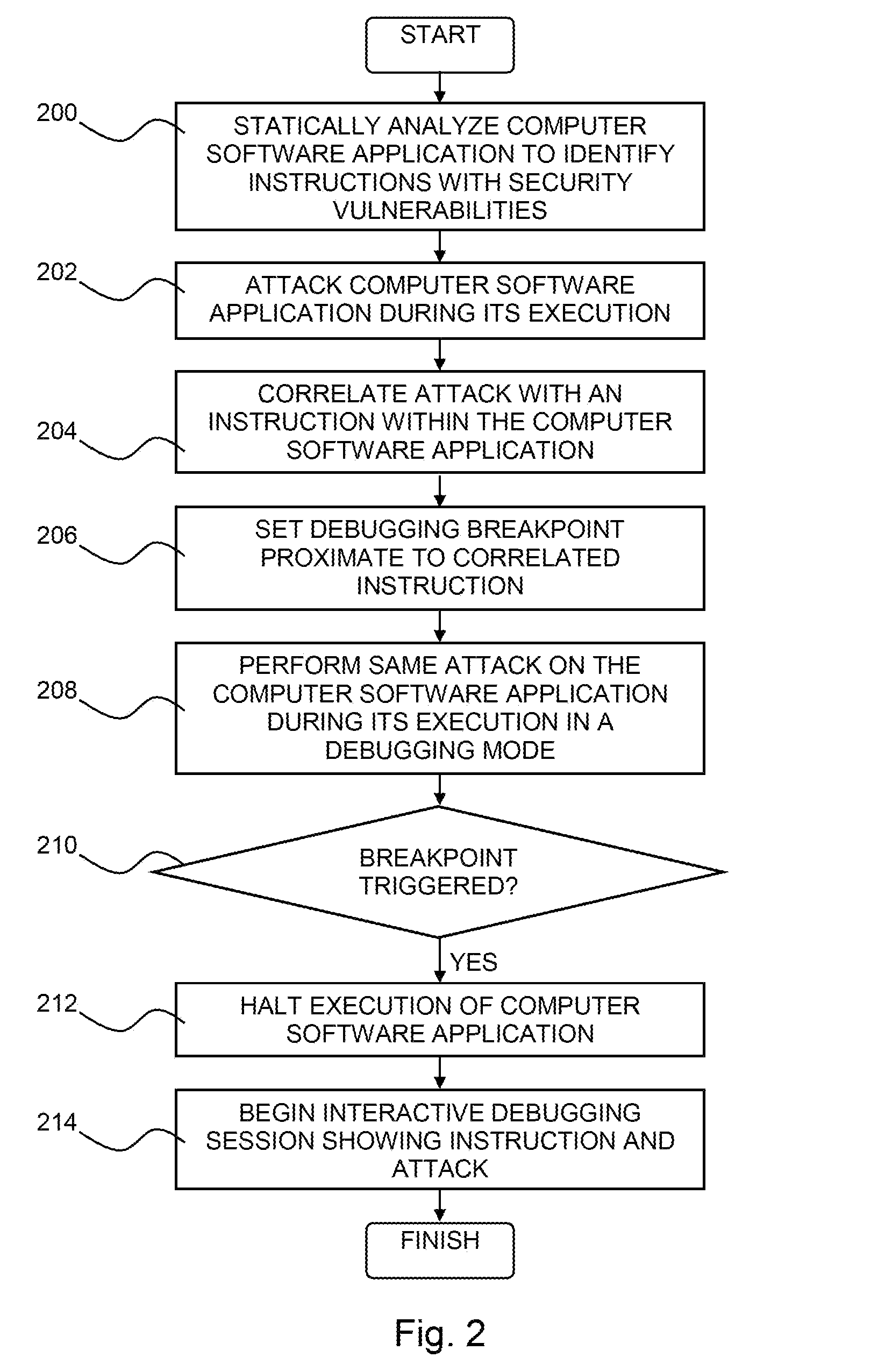
Pinpointing security vulnerabilities in computer software applications
ActiveUS8510842B2Memory loss protectionUnauthorized memory use protectionSoftware engineeringApplication software
Owner:FINJAN BLUE INC
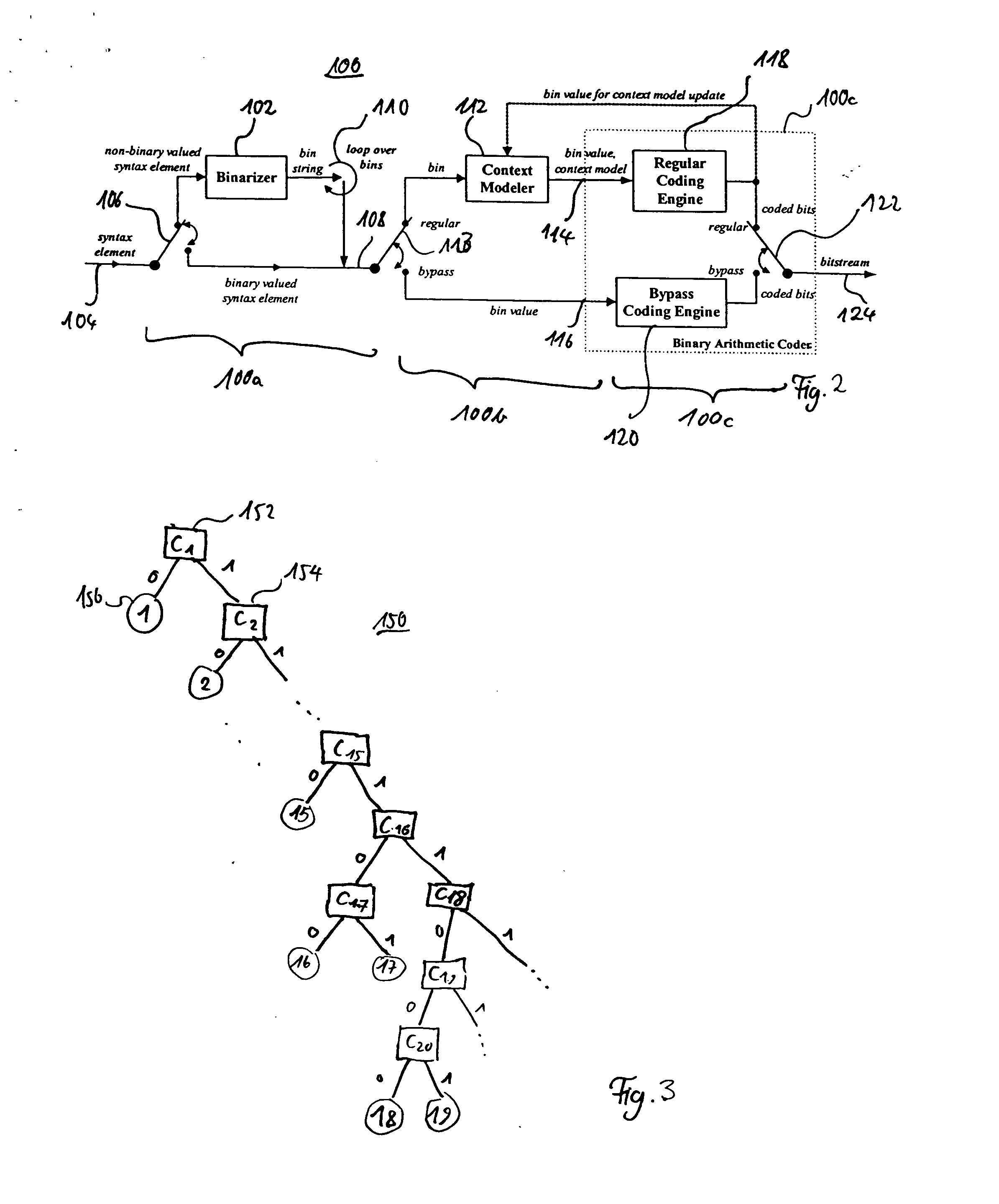
Method and apparatus for binarization and arithmetic coding of a data value
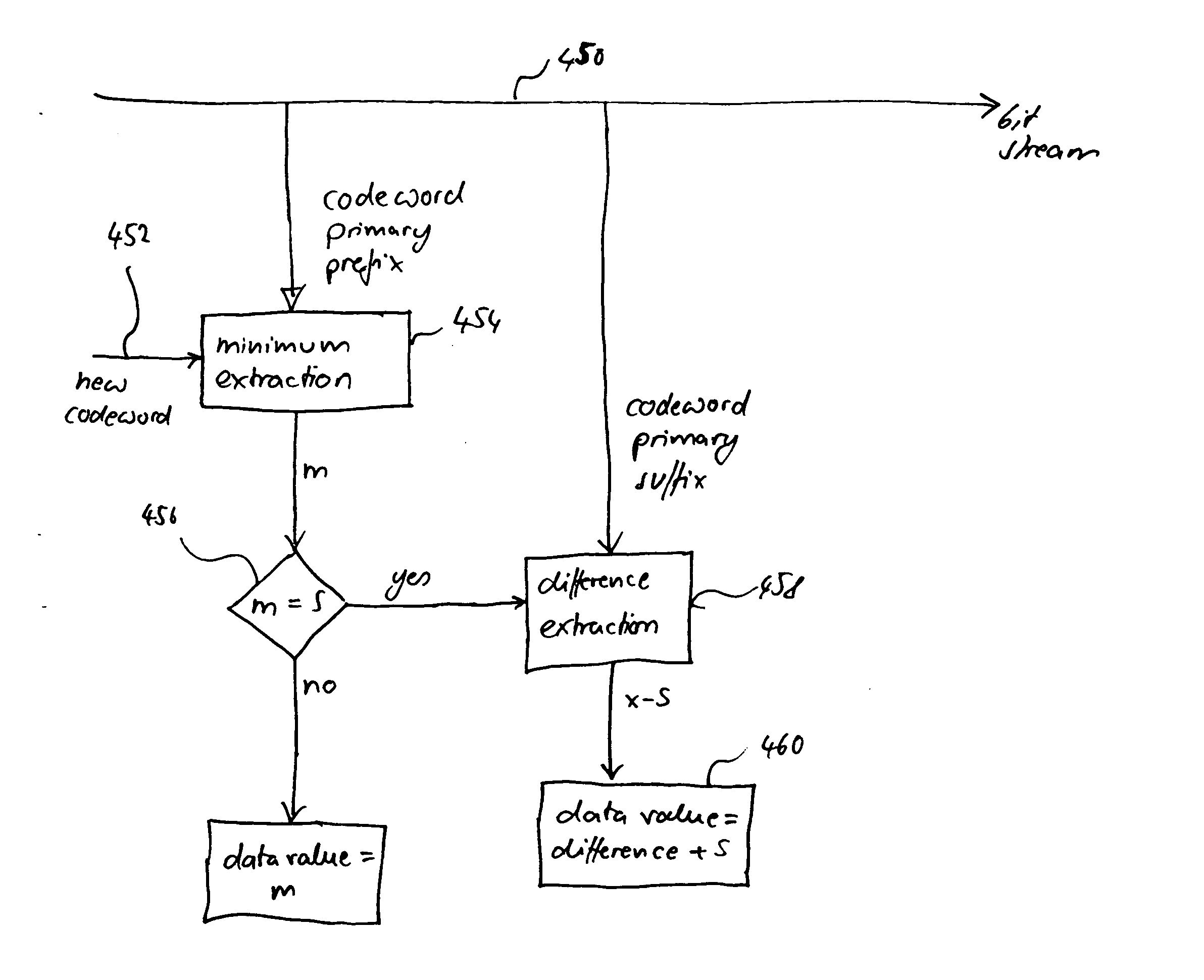
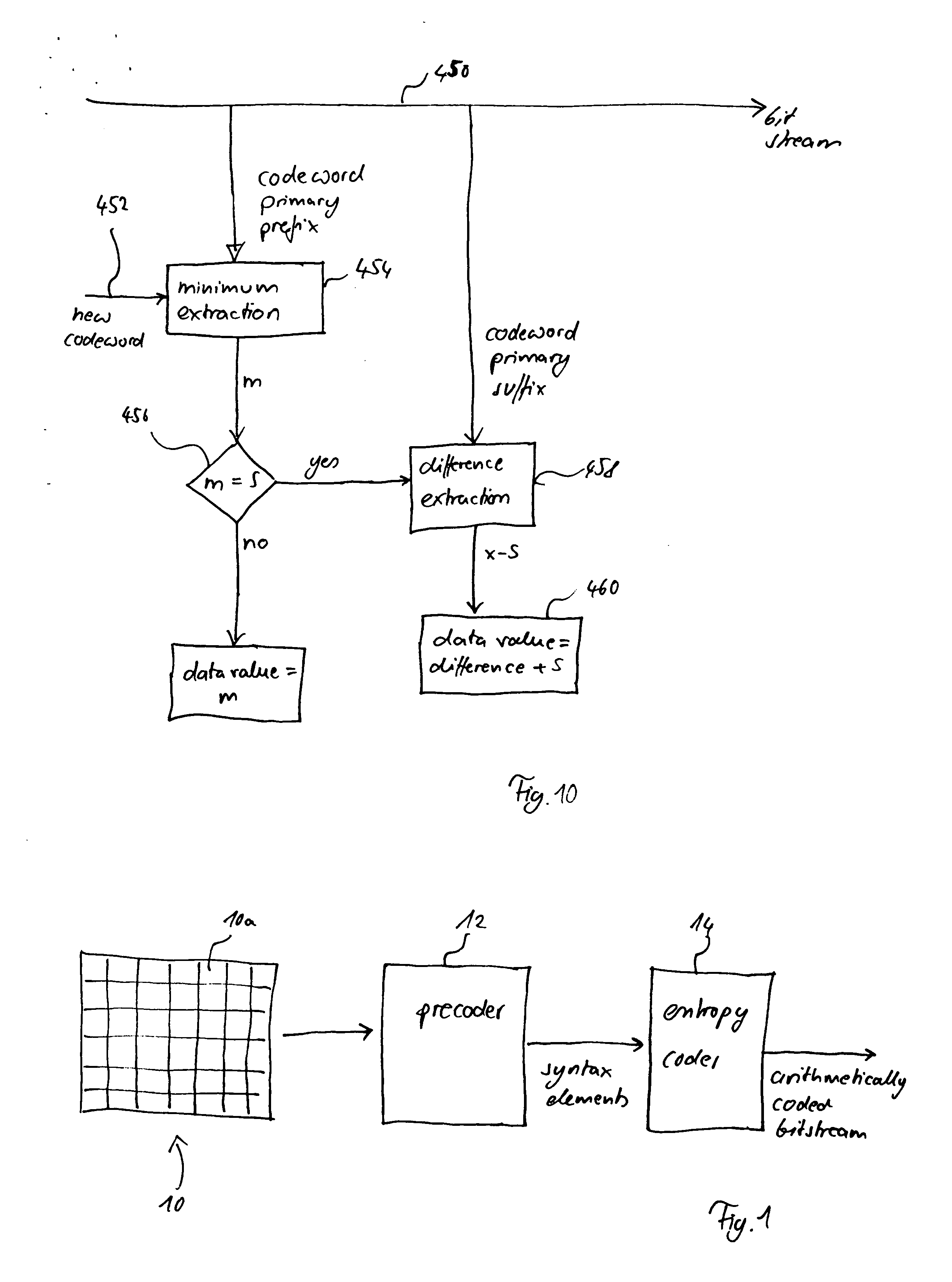
ActiveUS20050038837A1Moderate computational overheadEfficient compressionDigital data processing detailsDigital computer detailsComputer architectureCut off value
Binarization a data value comprises binarizing the minimum of the data value and a predetermined cut-off value in accordance with a first binarization scheme, in order to yield a primary prefix. If the data value is greater than the cut-off value, binarizing a difference of the data value minus the predetermined cut-off value in accordance with a second binarization scheme to obtain a binary suffix, the first binarization scheme being different from the second binarization scheme, and appending the primary suffix to the primary prefix is performed. A very effective compression of data values may be achiever by using the binarization scheme for preparing the syntax elements for the arithmetic coding, the binarization scheme substantially being a combination of two different binarization schemes, and by using binary arithmetic coding instead of m-ary arithmetic coding for coding the binarized syntax elements.
Owner:GE VIDEO COMPRESSION LLC
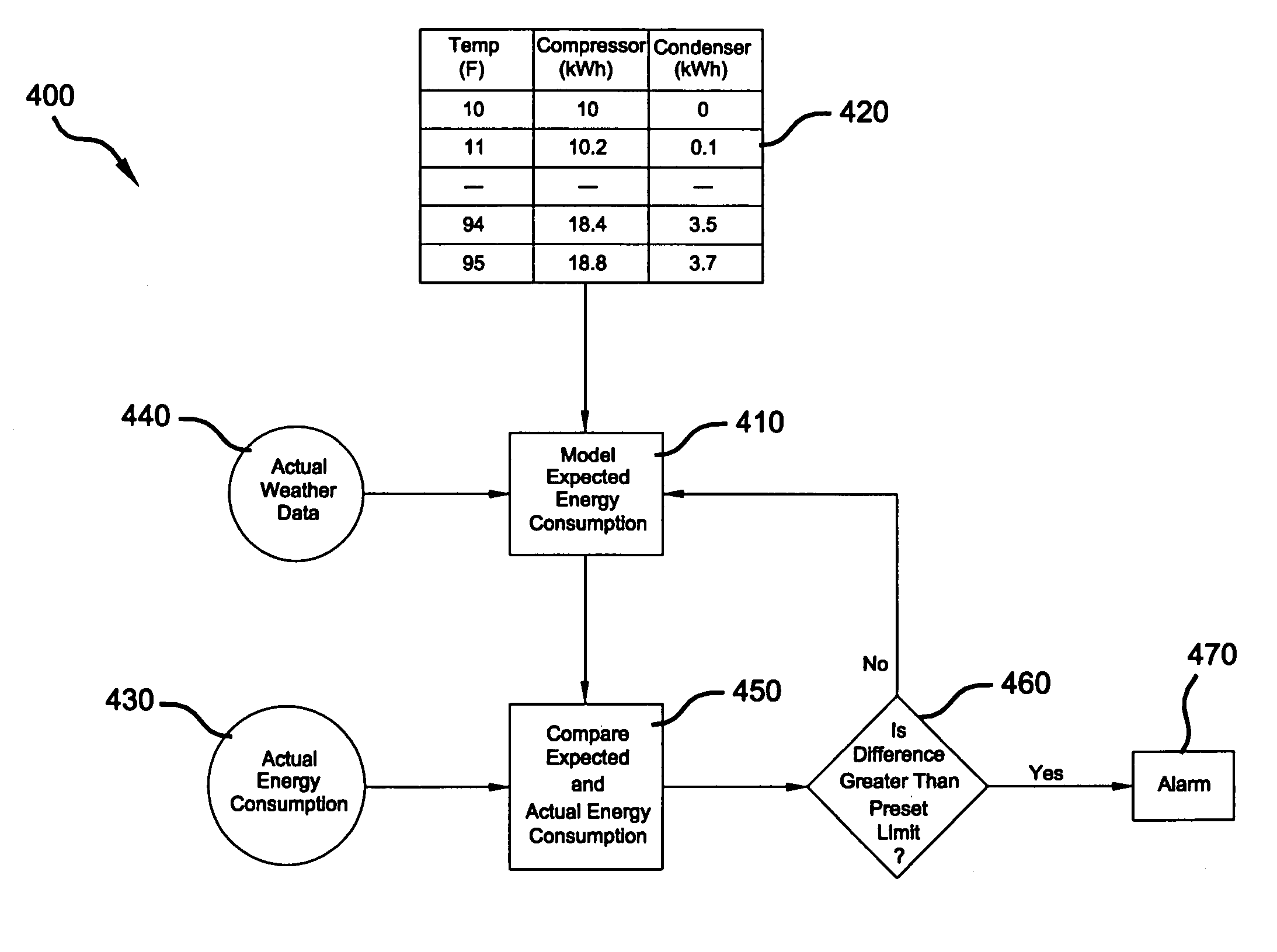
Model-based alarming
A system and method for managing energy consumption of a building system includes a source of actual energy consumption data, a source of actual weather data, and a database correlating discrete weather data values with expected energy consumption values for at least one component of the building system. A computer accesses the actual weather data, actual energy consumption data and database, wherein the computer compares the expected energy consumption values with actual energy consumption data and generates an output based on the comparison. The expected energy consumption values are generated for the discrete weather data values using an energy consumption model that functionally relates discrete weather data values and design information for the building system component.
Owner:EMERSON DIGITAL COLD CHAIN INC
Systems and methods for investigation of financial reporting information
InactiveUS20050222929A1FinanceSpecial data processing applicationsCluster algorithmStatistical analysis
Owner:PRICEWATERHOUSECOOPERS LLP
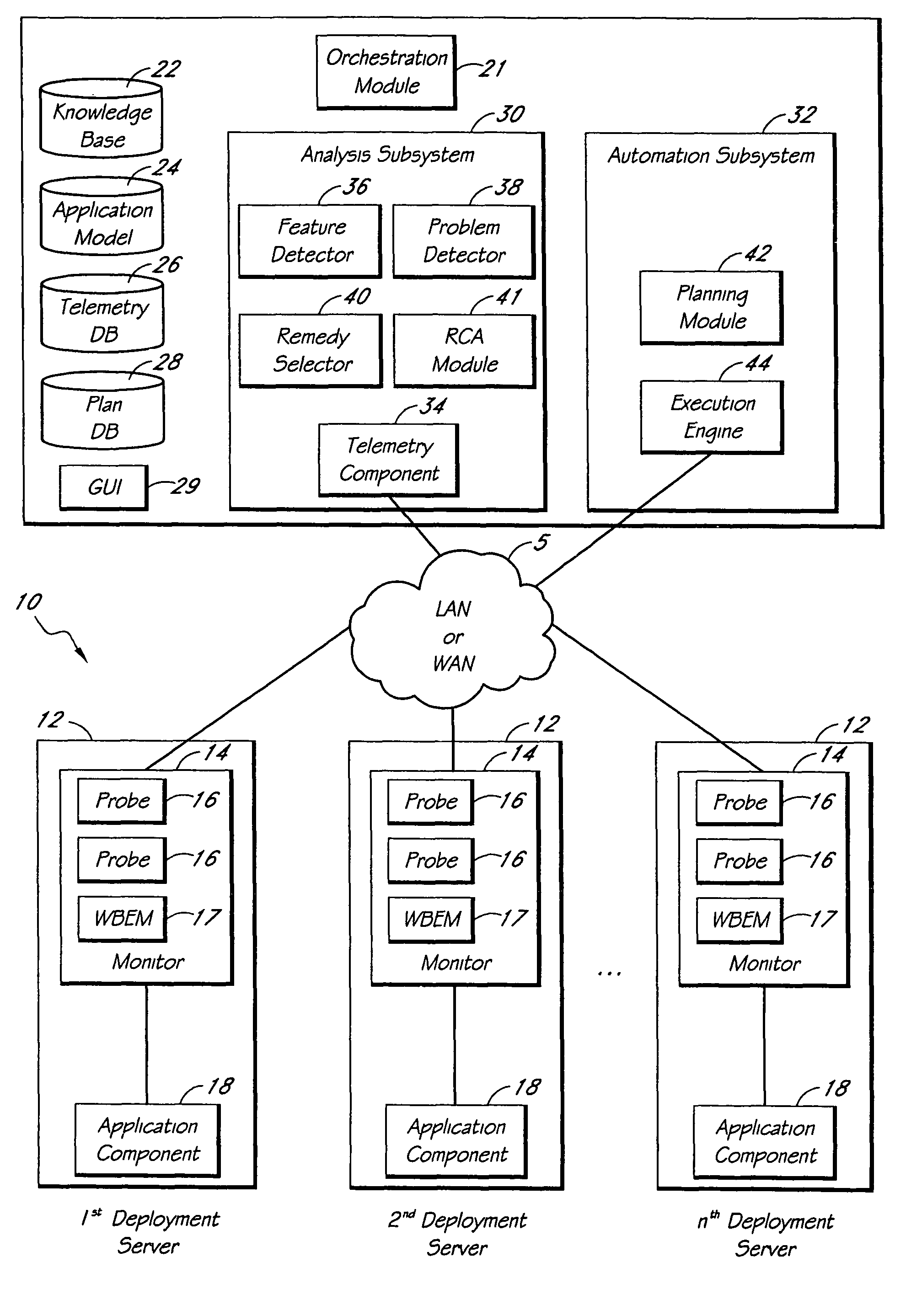
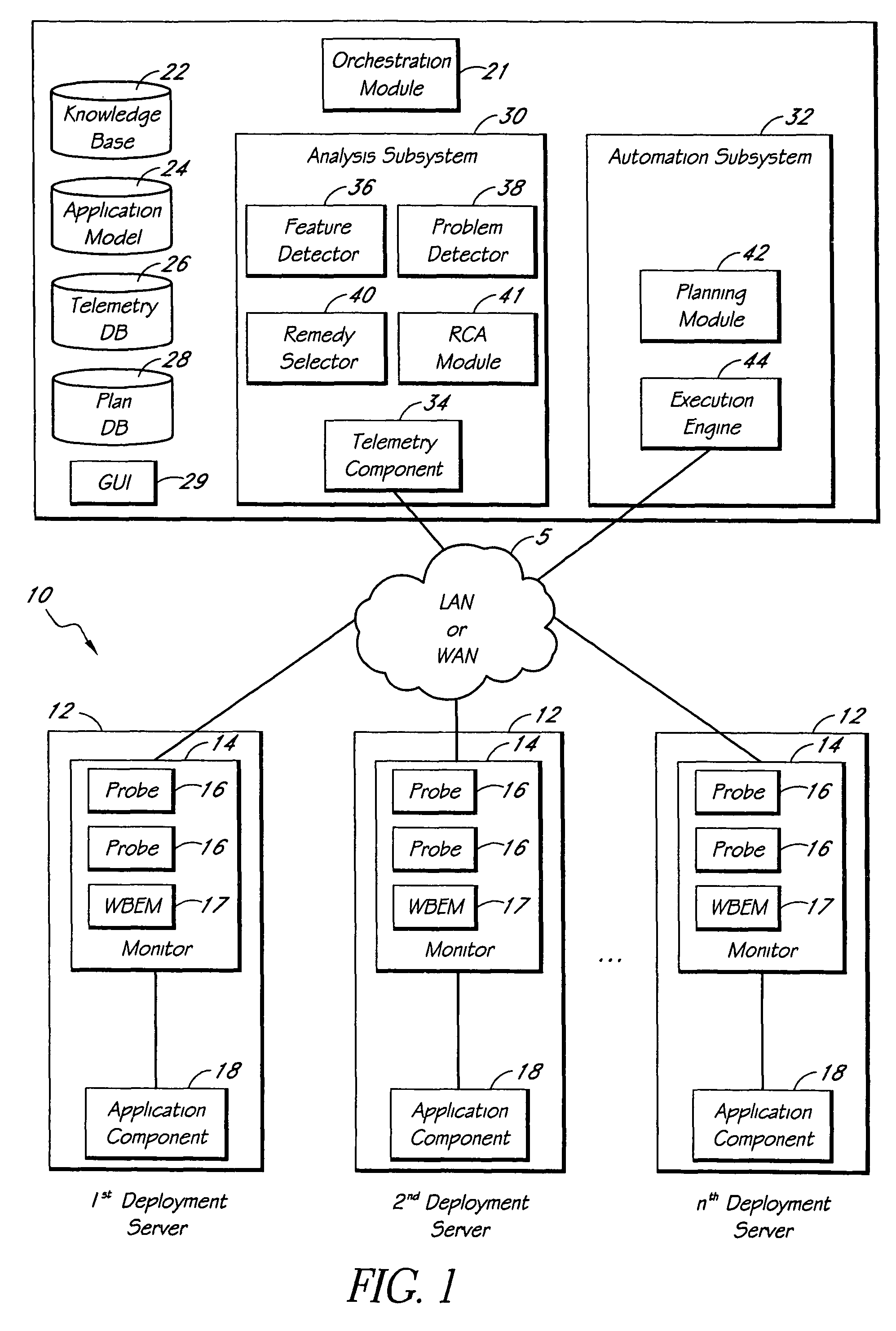
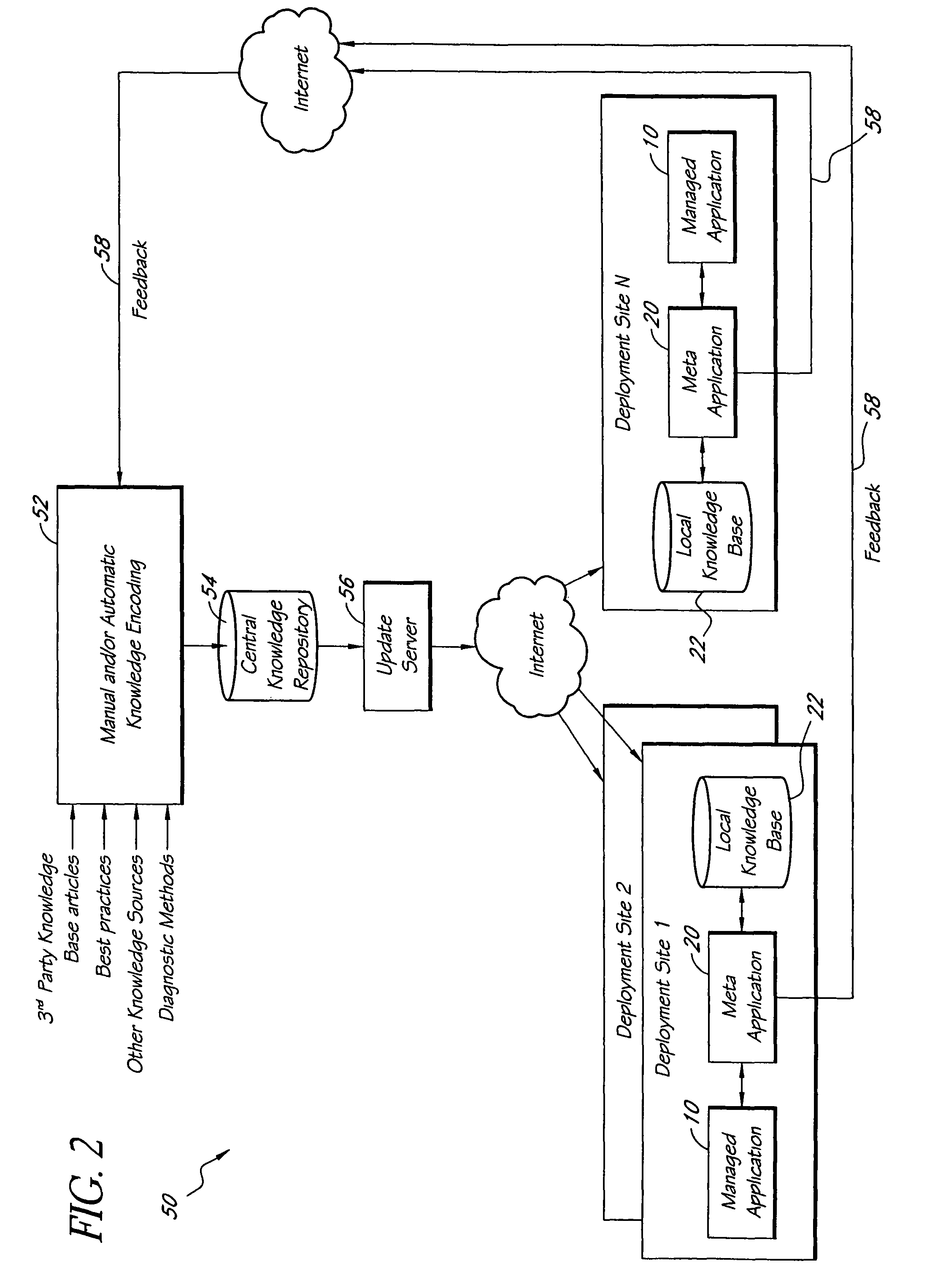
Automated detection of problems in software application deployments
ActiveUS7788536B1Efficient mappingGreat leverageError detection/correctionInference methodsData miningData value
A system for monitoring and analyzing the operation of a deployment of a software application is disclosed. The system includes a monitoring component, a repository that stores a plurality of rules, and an analysis engine. The monitoring component collects data values of each of a plurality of state metrics associated with the deployment of the software application. At least some of the rules in the repository map respective combinations of states associated with the state metrics to corresponding problems. The analysis engine programmatically detects instances of said problems, at least in-part, by using the rules to analyze the state metric data values collected by the monitoring component. The rules can also include remedies associated with the detected problems, and the system may include remedy selection and execution modules.
Owner:CITRIX SYST INC
Method and system for determining presence of probable error or fraud in a data set by linking common data values or elements
ActiveUS7373669B2Easy to operateEfficient and methodicalFinanceDigital data processing detailsFistData set
Owner:THE 41ST PARAMETER
System, method and technique for searching structured databases
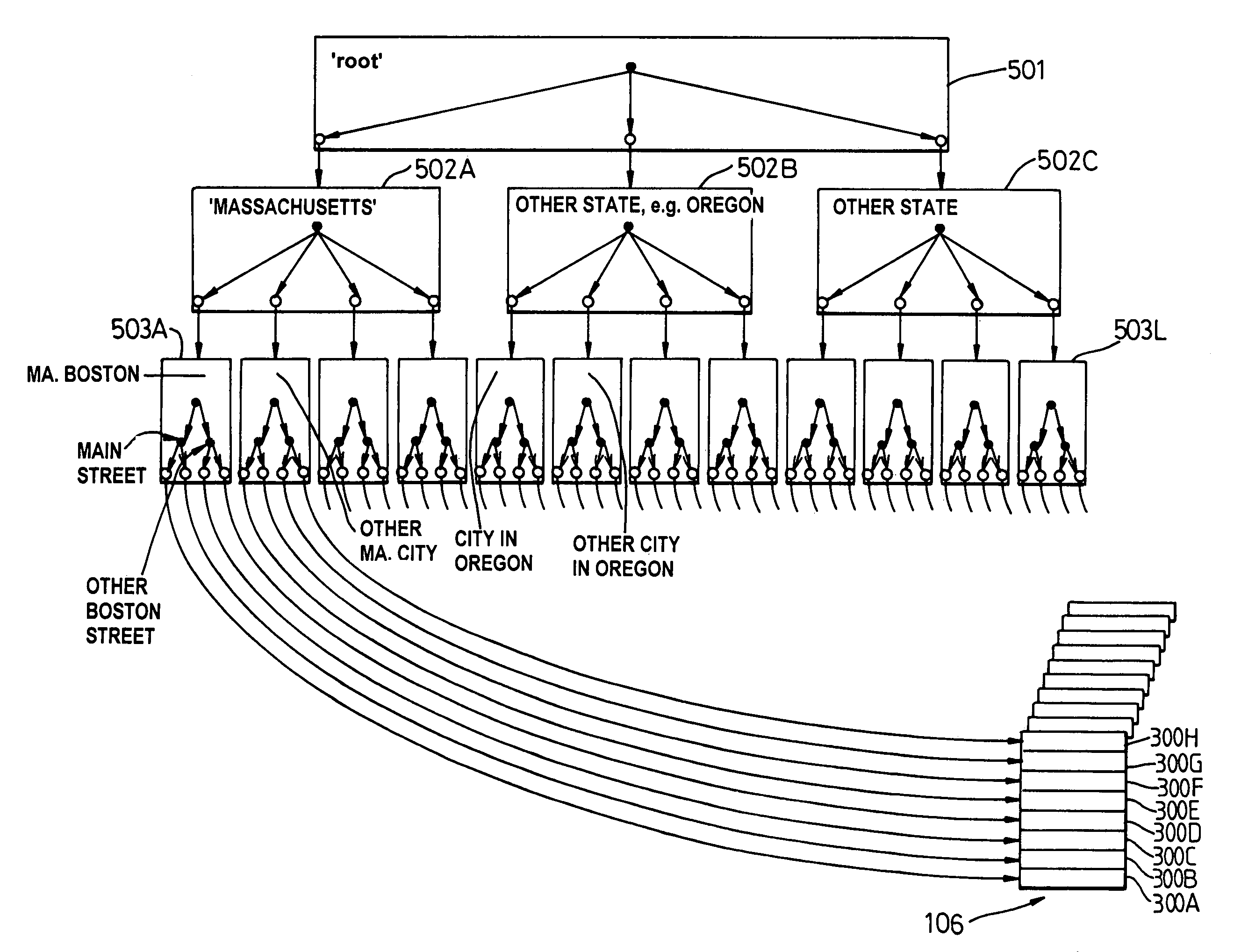
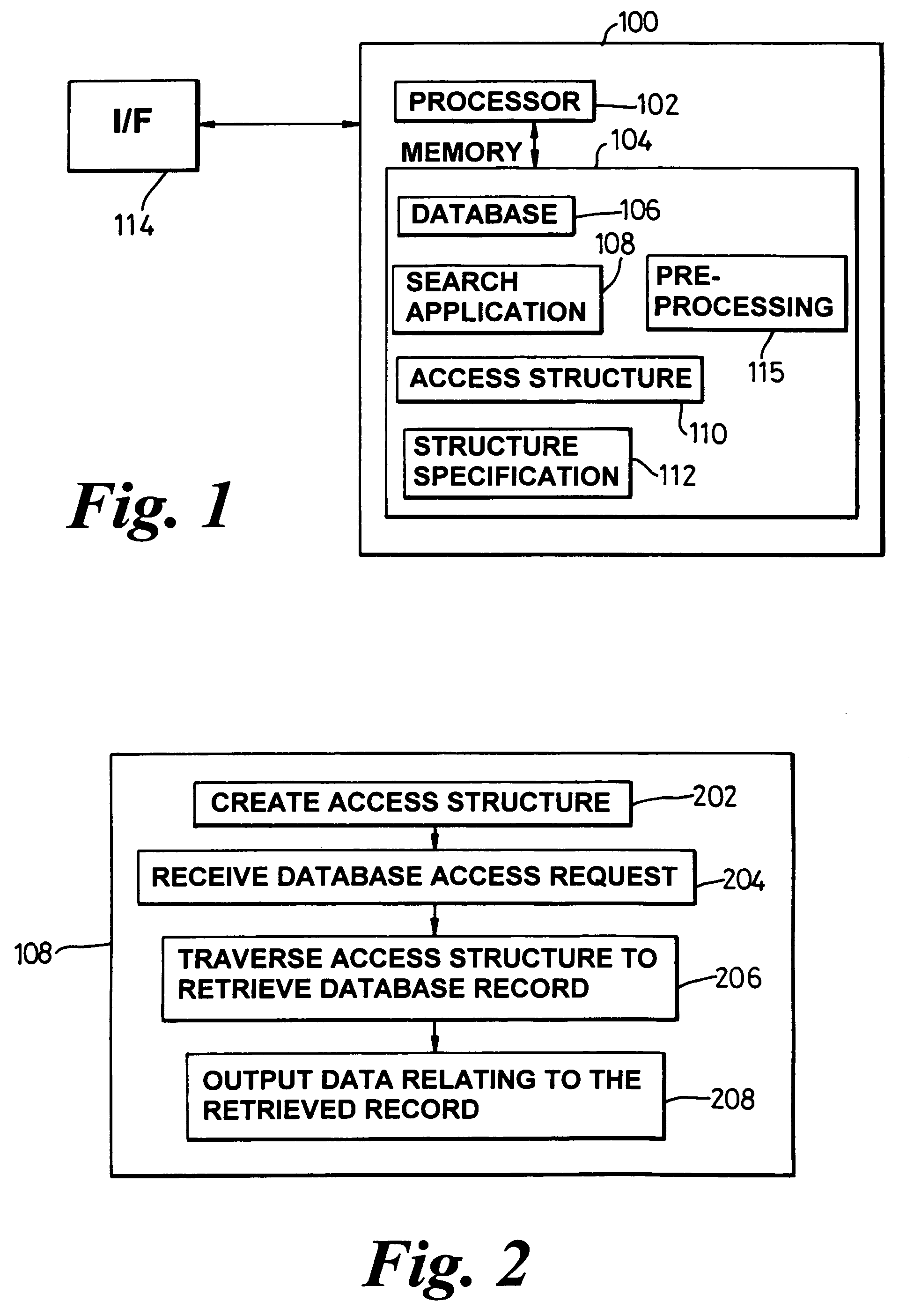
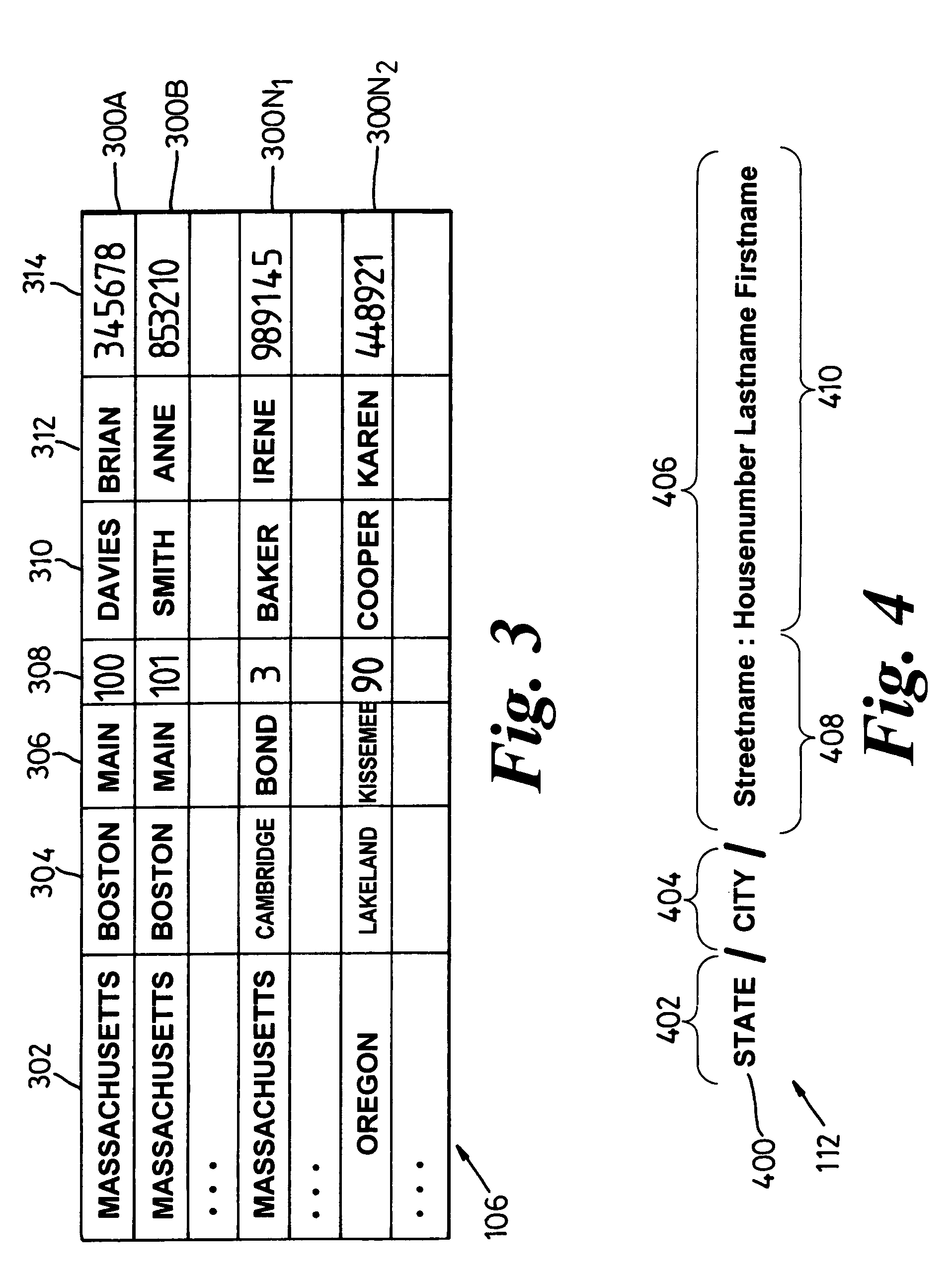
ActiveUS7403941B2Reliable resultsData processing applicationsDigital data information retrievalAccess structureTree (data structure)
Owner:APPLE INC
System and method for analyzing data in a report
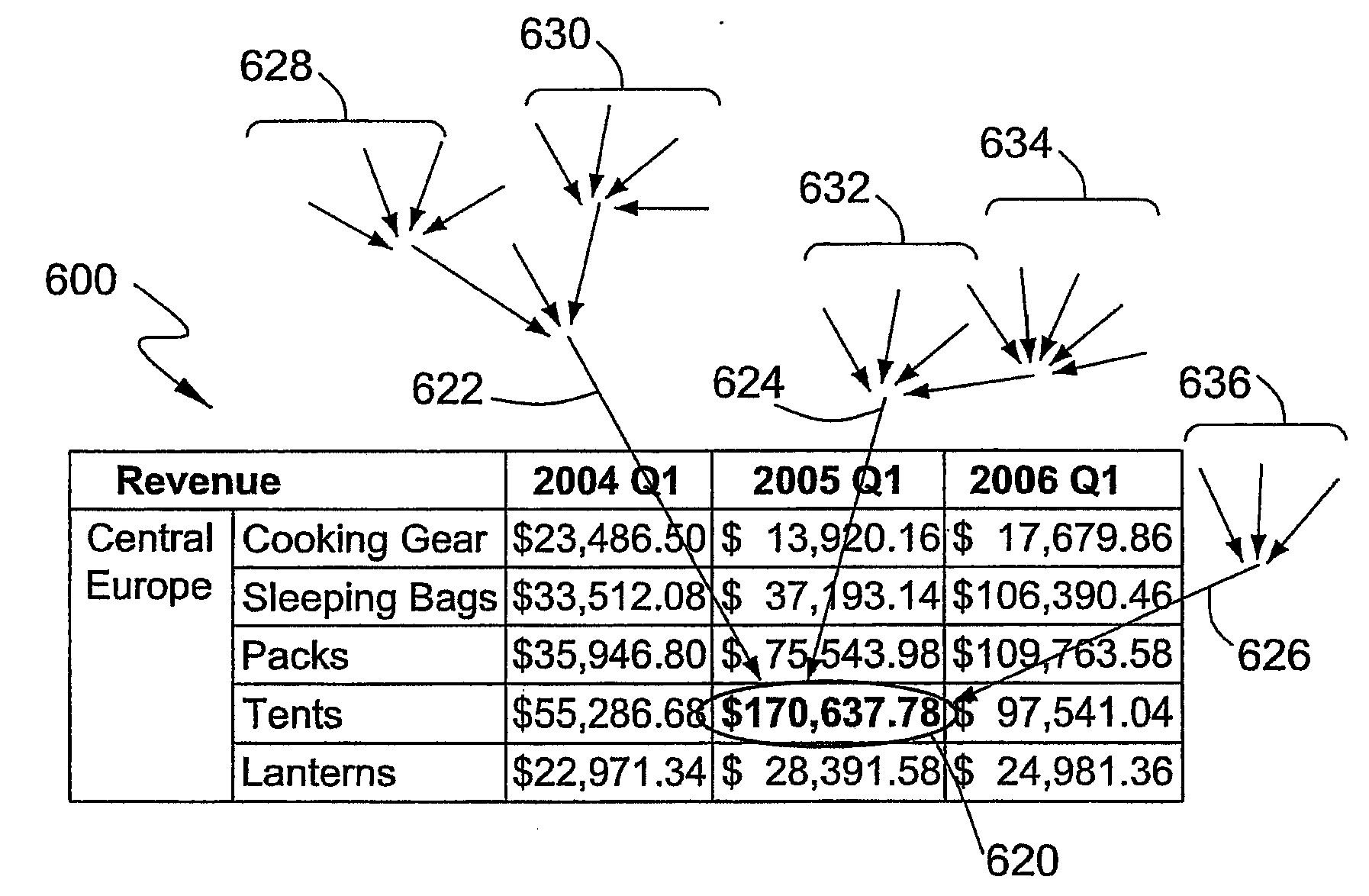
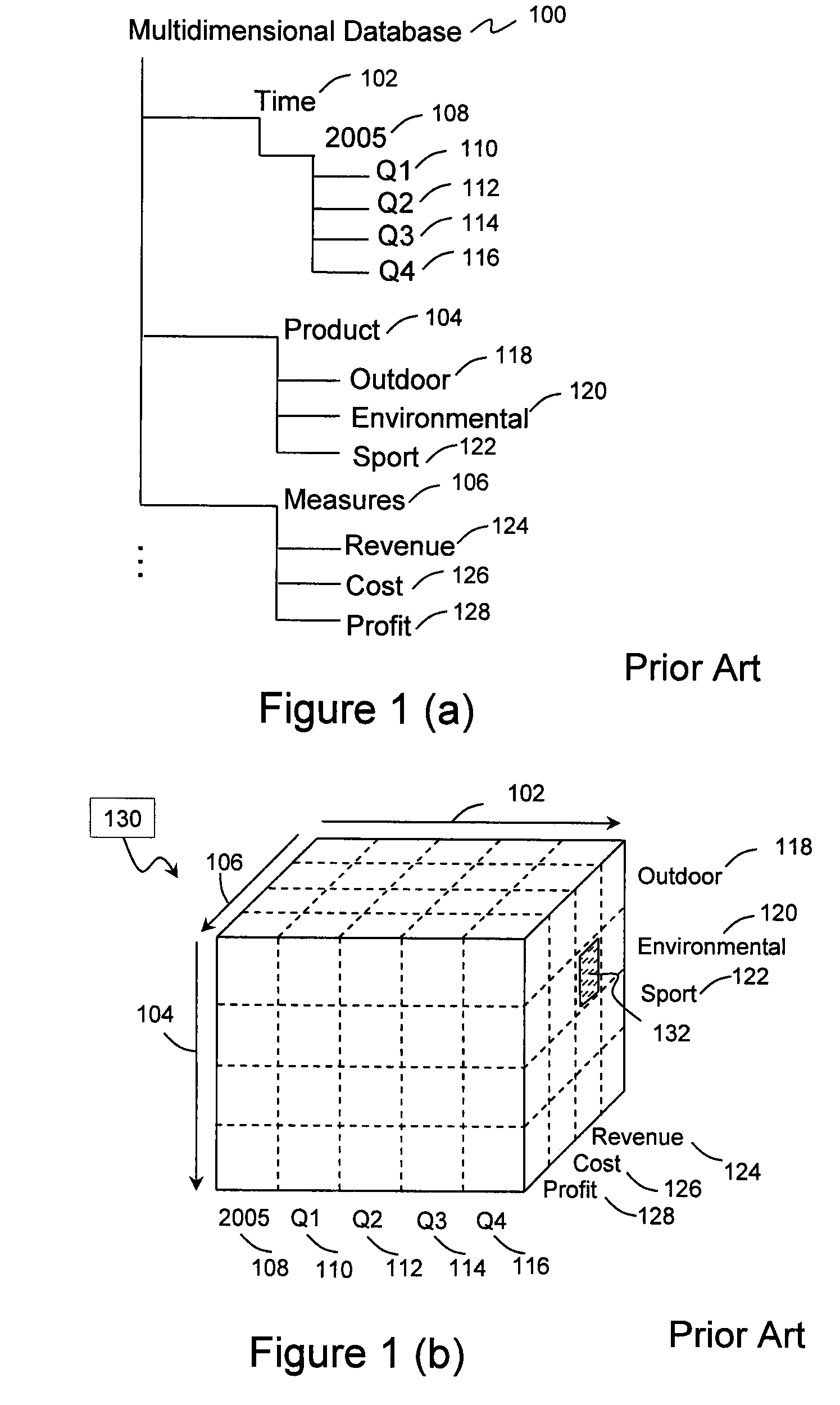
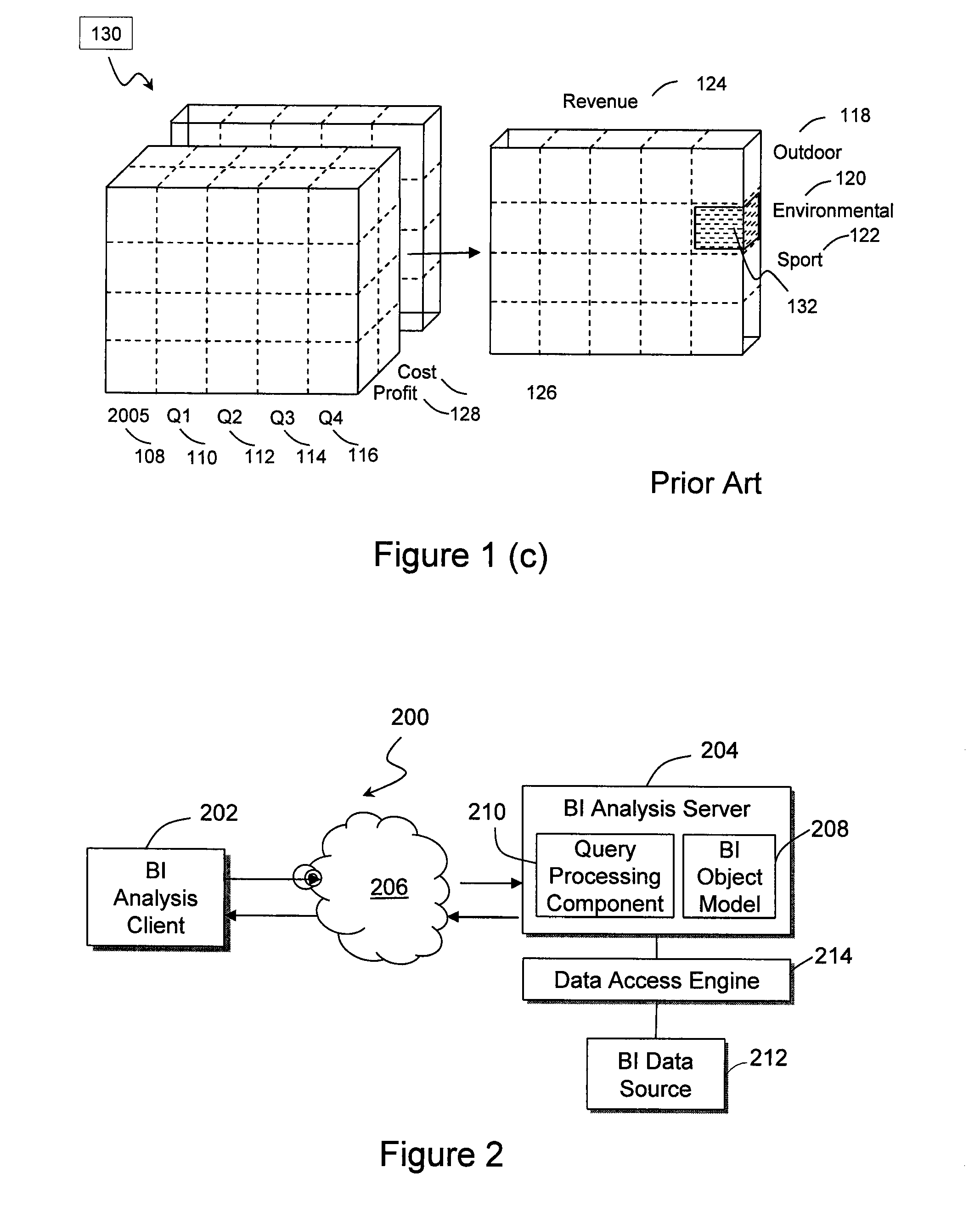
A method and a system for analyzing a data value of interest in a multidimensional database. The data value of interest is first identified in a structured report. The data source for the structured report is retrieved. A context for the data value of interest in the data source is collected, for example, by extracting a slicer from the structured report, by extracting members of master-detail pages, or by extracting a default measure from the structured report. An analysis specification based on the collected context is then built, and the data value of interest is analyzed using the analysis specification. The result from analyzing the data value of interest may be presented in an analysis view.
Owner:IBM CORP
Method for establishing secure communication link between computers of virtual private network
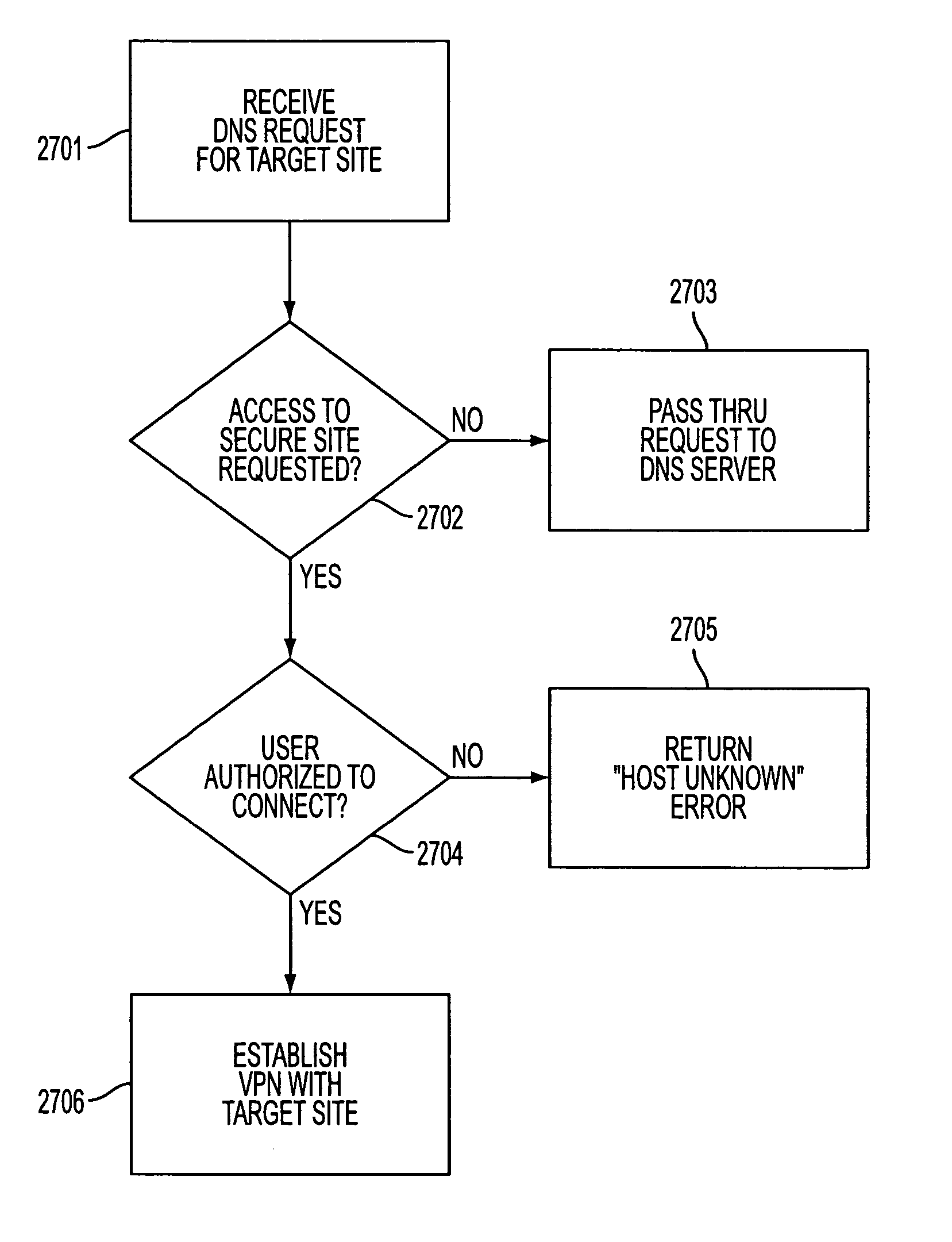
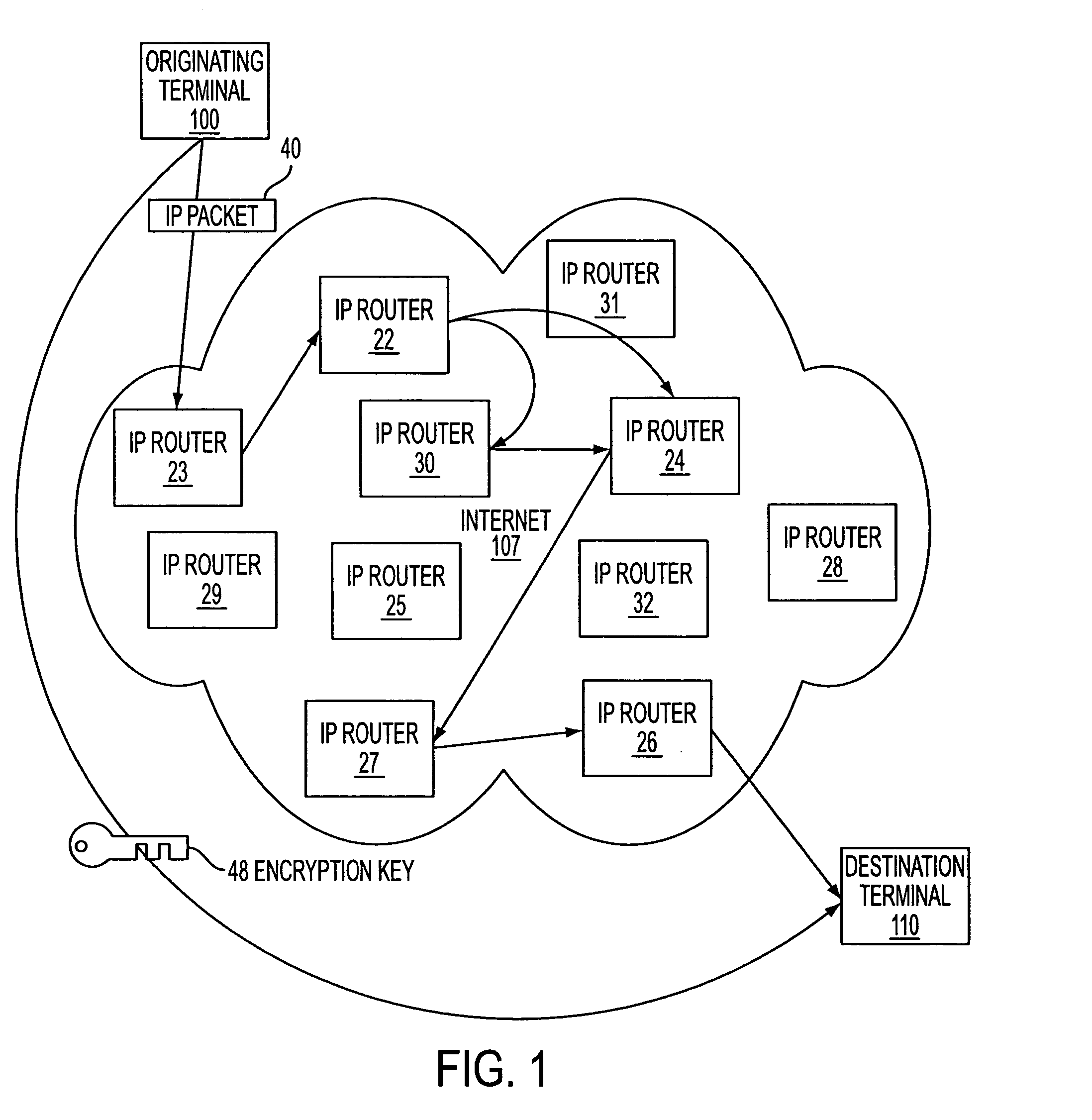
InactiveUS7188180B2Conveniently establishedMultiple digital computer combinationsData switching networksSecure communicationPrivate network
A technique is disclosed for establishing a secure communication link between a first computer and a second computer over a computer network. Initially, a secure communication mode of communication is enabled at a first computer without a user entering any cryptographic information for establishing the secure communication mode of communication. Then, a secure communication link is established between the first computer and a second computer over a computer network based on the enabled secure communication mode of communication. The secure communication link is a virtual private network communication link over the computer network in which one or more data values that vary according to a pseudo-random sequence are inserted into each data packet.
Owner:VIRNETX
Method for establishing secure communication link between computers of virtual private network without user entering any cryptographic information
InactiveUS6839759B2Conveniently establishedMultiple digital computer combinationsData switching networksSecure communicationUser input
A technique is disclosed for establishing a secure communication link between a first computer and a second computer over a computer network. Initially, a secure communication mode of communication is enabled at a first computer without a user entering any cryptographic information for establishing the secure communication mode of communication. Then, a secure communication link is established between the first computer and a second computer over a computer network based on the enabled secure communication mode of communication. The secure communication link is a virtual private network communication link over the computer network in which one or more data values that vary according to a pseudo-random sequence are inserted into each data packet.
Owner:VIRNETX
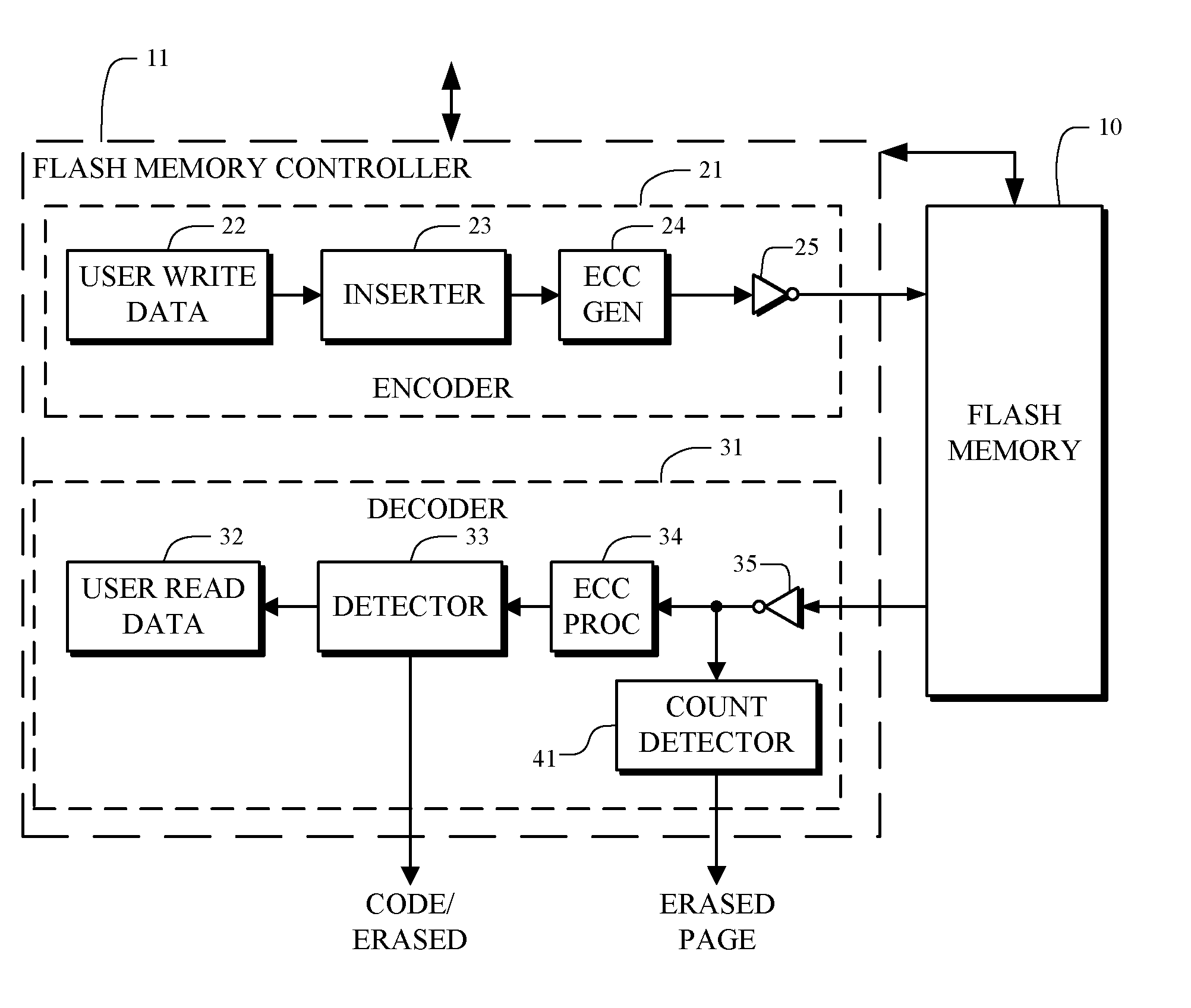
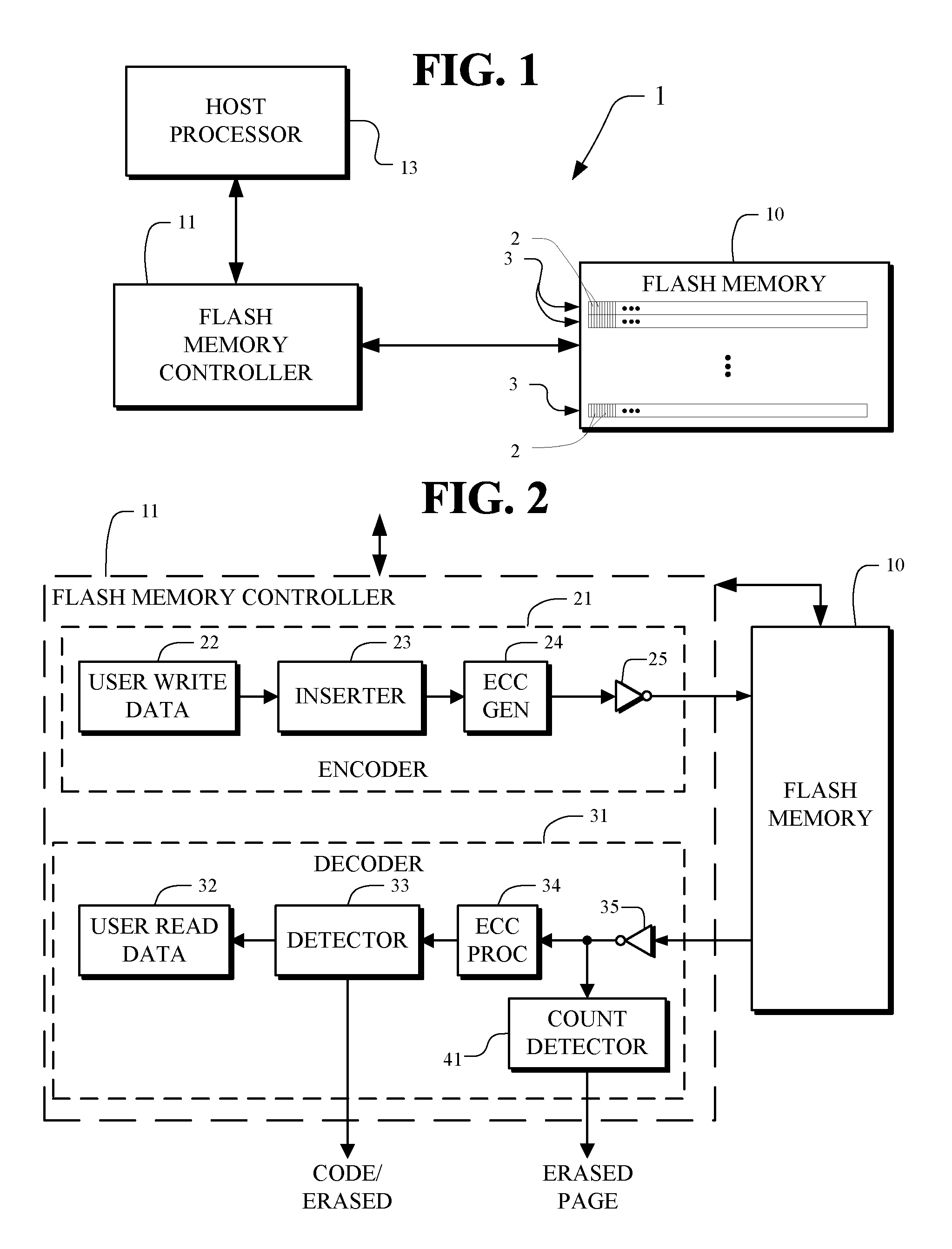
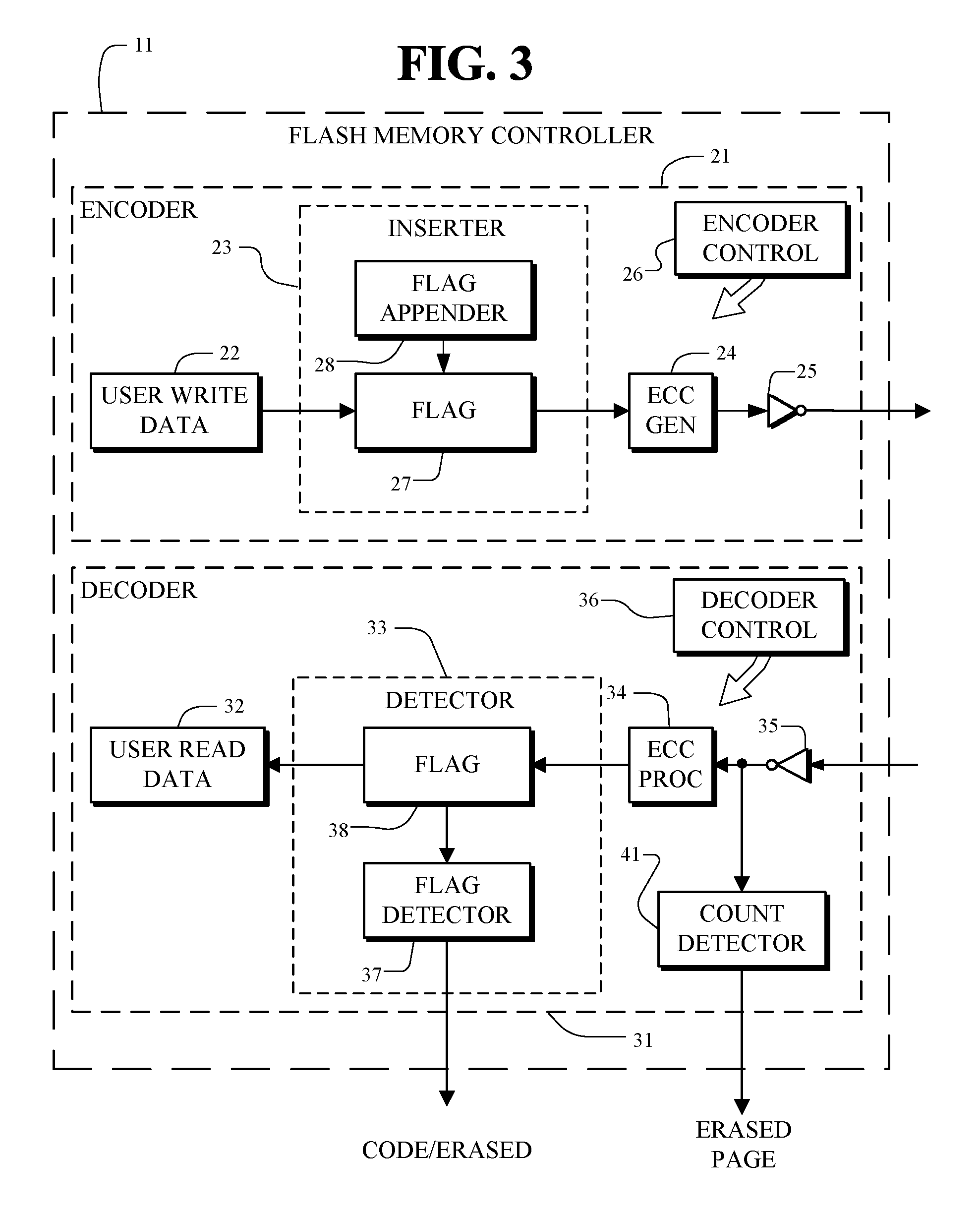
Erased page detection
A memory device and method, such as a flash memory device and method, includes a memory having a plurality of nonvolatile memory cells for storing stored values of user data. The memory device and method includes a memory controller for controlling the memory. The memory controller includes an encoder for encoding user write data for storage of code values as the stored values in the memory. The encoder includes an inserter for insertion of an indicator as part of the stored values for use in determining when the stored values are or are not in an erased state. The memory controller includes a decoder for reading the stored values from the memory to form user read data values when the stored values are not in the erased state.
Owner:MARVELL ASIA PTE LTD
Scalable system and method for an integrated digital media catalog, management and reproduction system
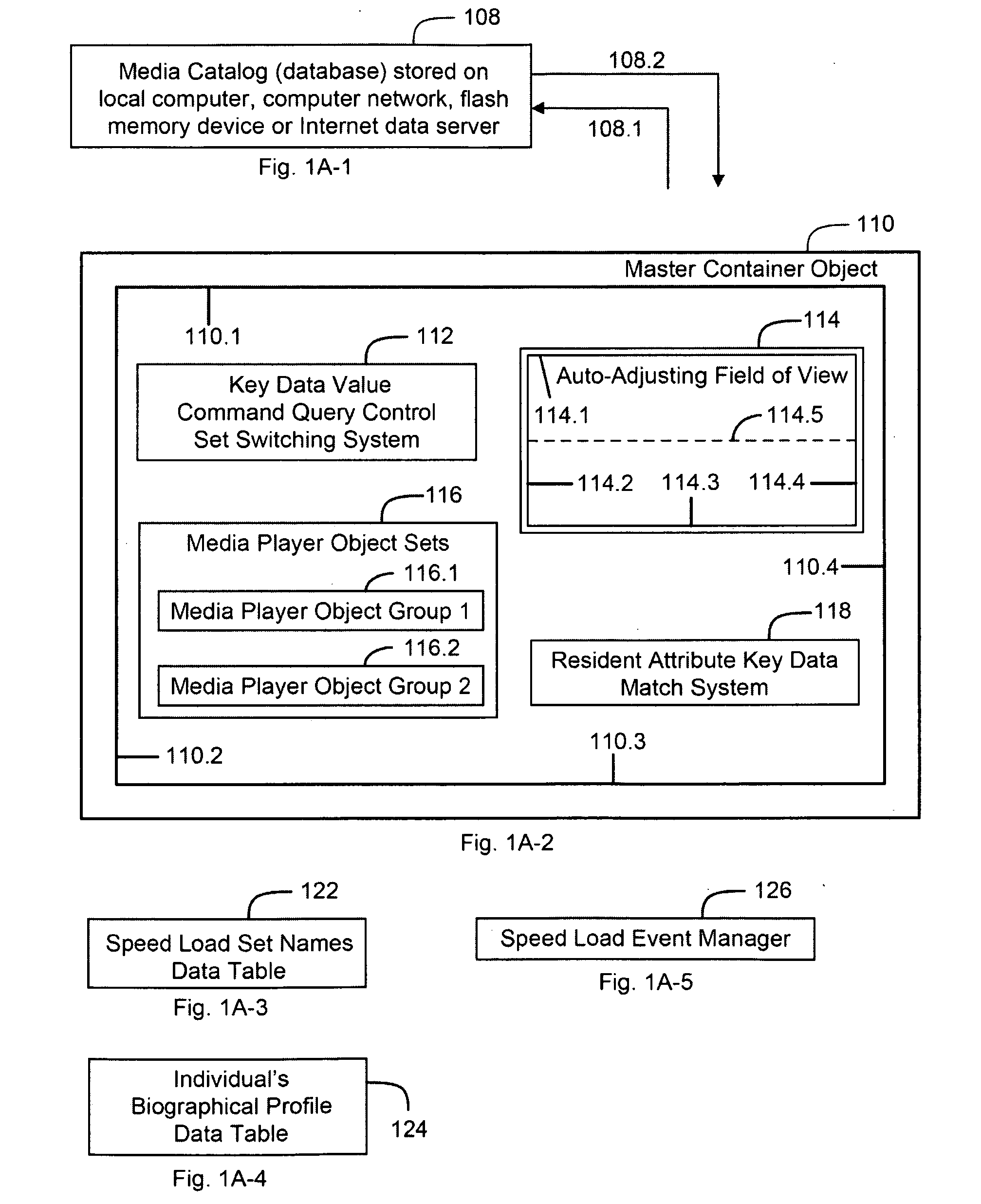
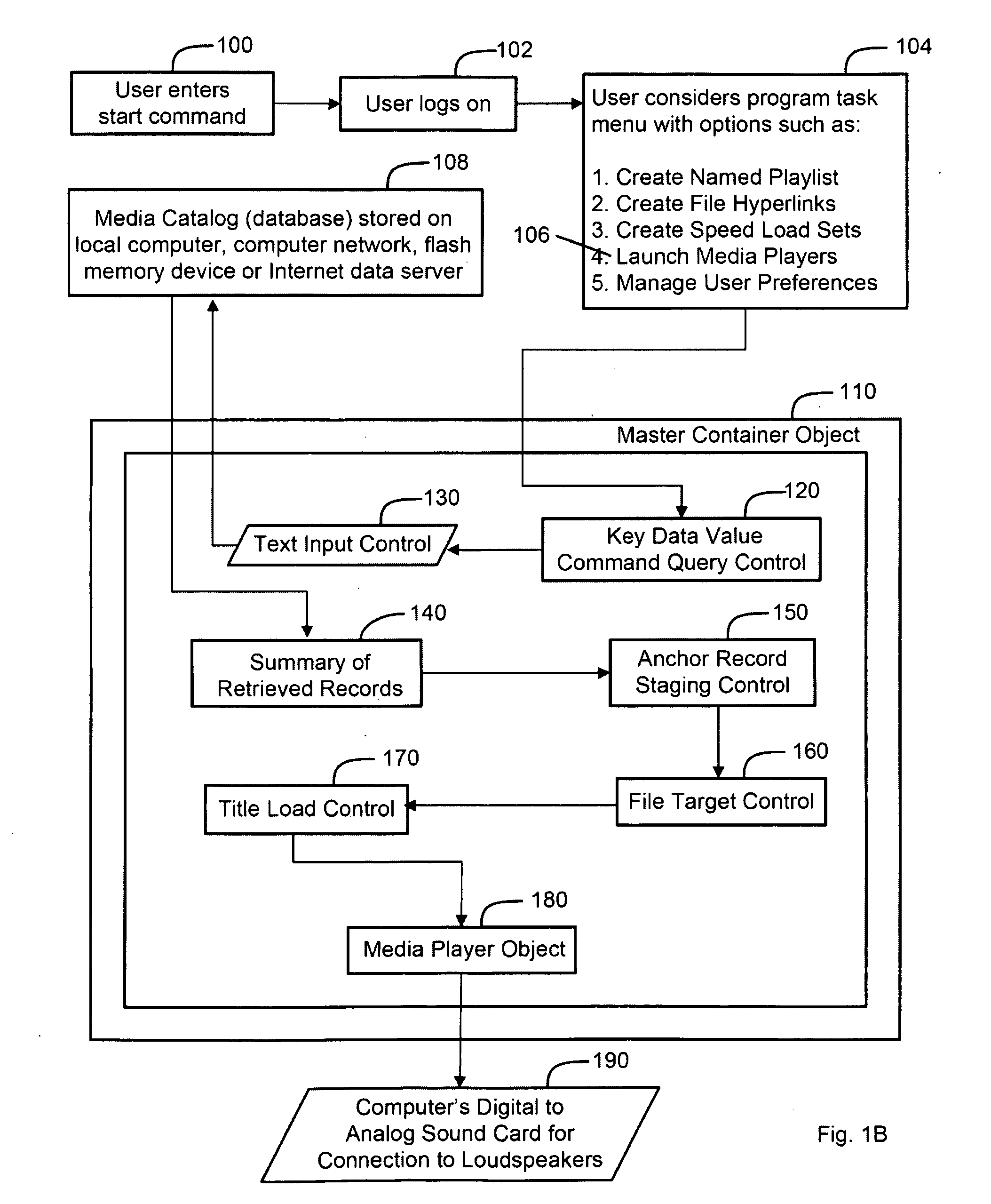
InactiveUS20090177301A1Reduce stepsEfficient managementRecord information storageSpecial data processing applicationsScalable systemVisually guided
A system and method for creating an integrated digital media management and reproduction device comprised of a database with key data values for a plurality of records, and a module with search controls that include sets of compound parallel attribute queries that can execute instructions for a data category, and concurrently retrieve and display records across a plurality of related categories—thereby revealing the associations between discrete records. The invention also has a plurality of software instantiated media players which, through instructions managed by a “master container” design, function as if they were dynamically aware of user actions and the quantifiable states of each other player object—and respond according to logic rules, visually guiding event workflow. The system has a memory module for storing query information, a processor configured to retrieve data, a display unit for retrieved data and a digital-to-analog converter for providing capability for connection to loudspeakers.
Owner:CODENTITY
Self-assembling wireless network, vehicle communications system, railroad wheel and bearing monitoring system and methods therefor
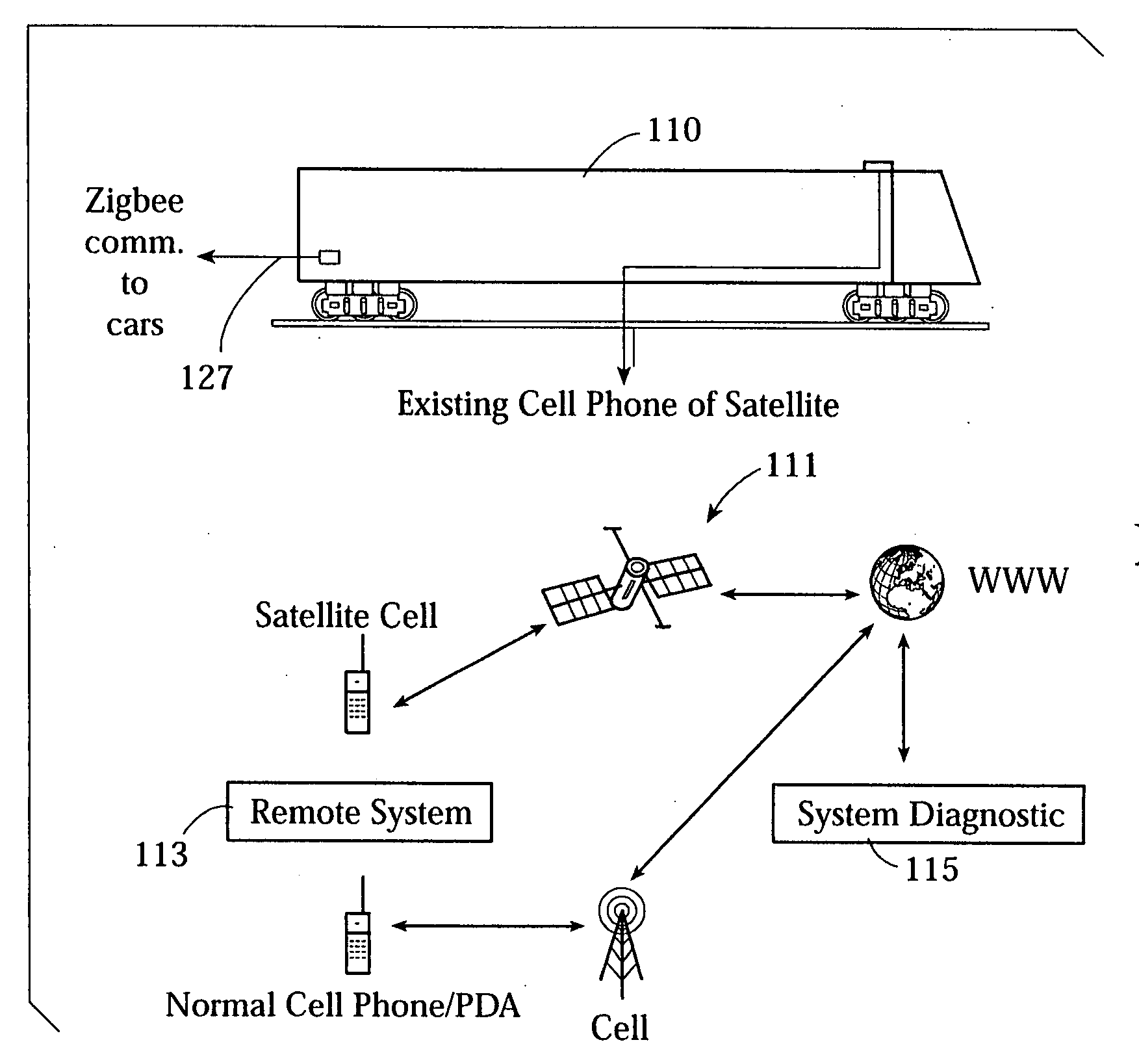
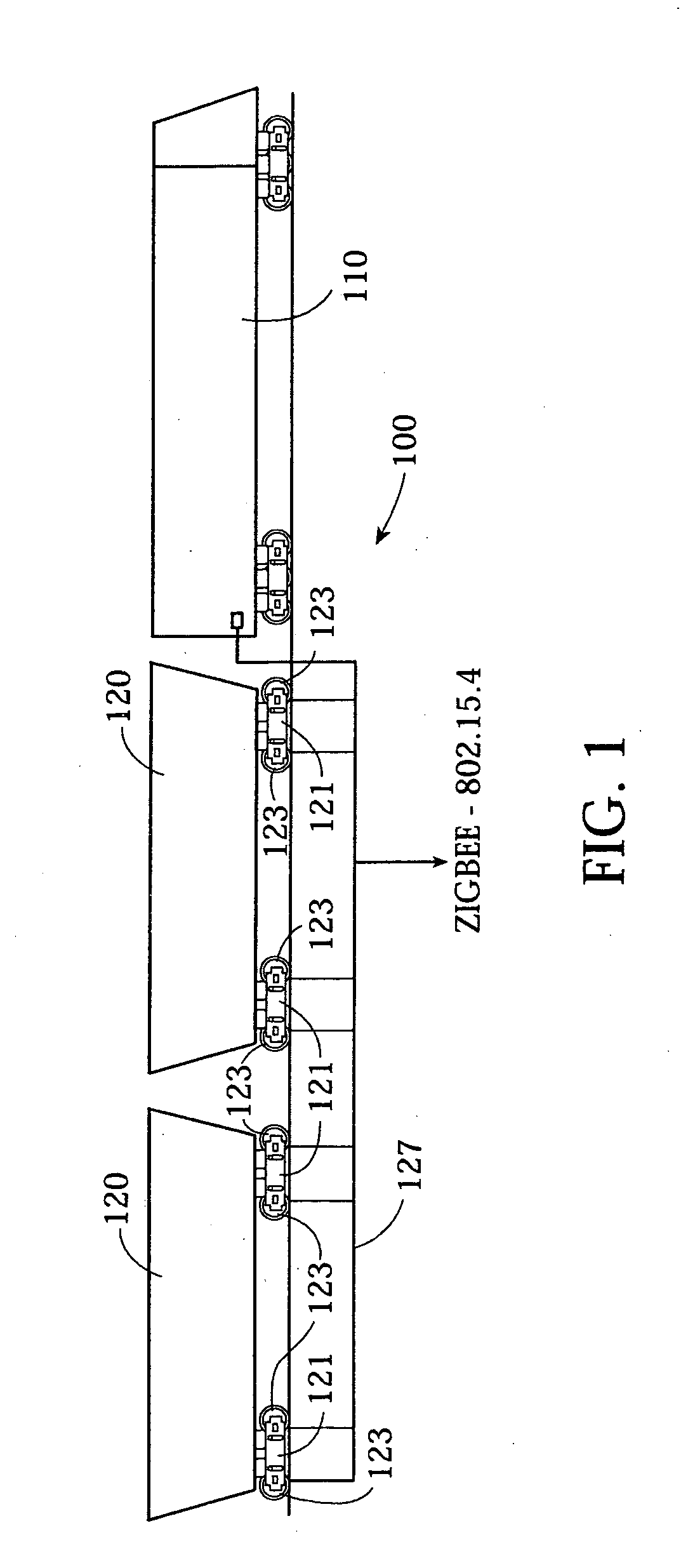
ActiveUS20070208841A1Continuous monitoringAccurate data analysisRolling contact bearingsMeasurement devicesWireless mesh networkCommunications system
A low power self-organizing network is made up of a plurality of wireless communication nodes communicating wirelessly with each other. The nodes each have a sensor providing a respective sensor data value indicative of a physical parameter in the environment of that node. The wireless network discontinues communication with any nodes in which the sensor data value is outside a range of network sensor data values. The network is preferably a group of vehicles moving together, especially a train in which each node is associated with a respective wheel of a railroad car. The nodes are low-power devices that communicate using wireless communications according to a Zigbee protocol. The nodes each have an additional sensor sensing a physical parameter the respective wheel thereof and determines from said electrical signal a degree of degradation of a bearing of the wheel, and transmits data of the degree of degradation to the main node. The main node communicates with another computer system using a higher power communication system and transmits thereto data indicative of degradation of said bearings.
Owner:CONVEY INC
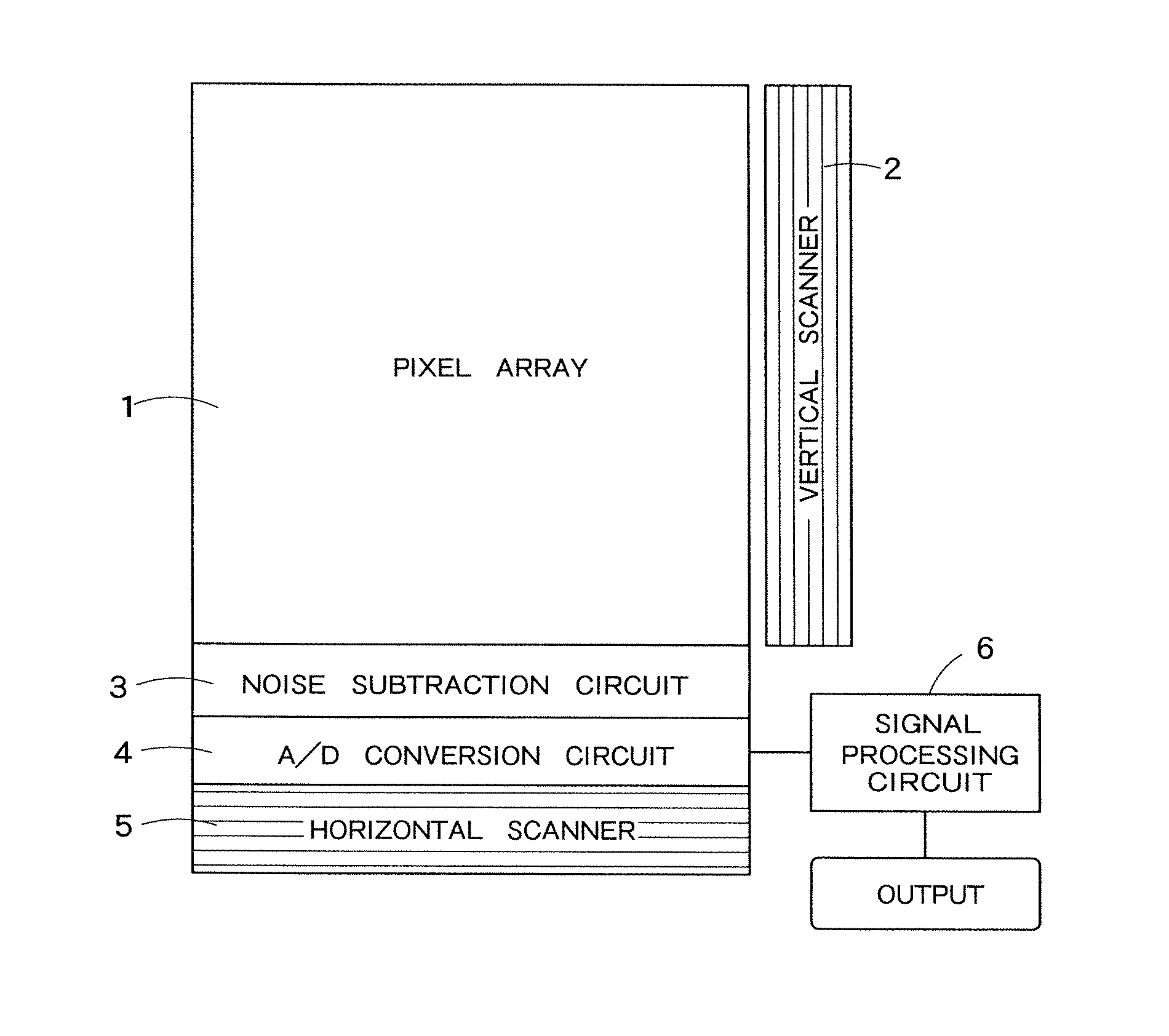
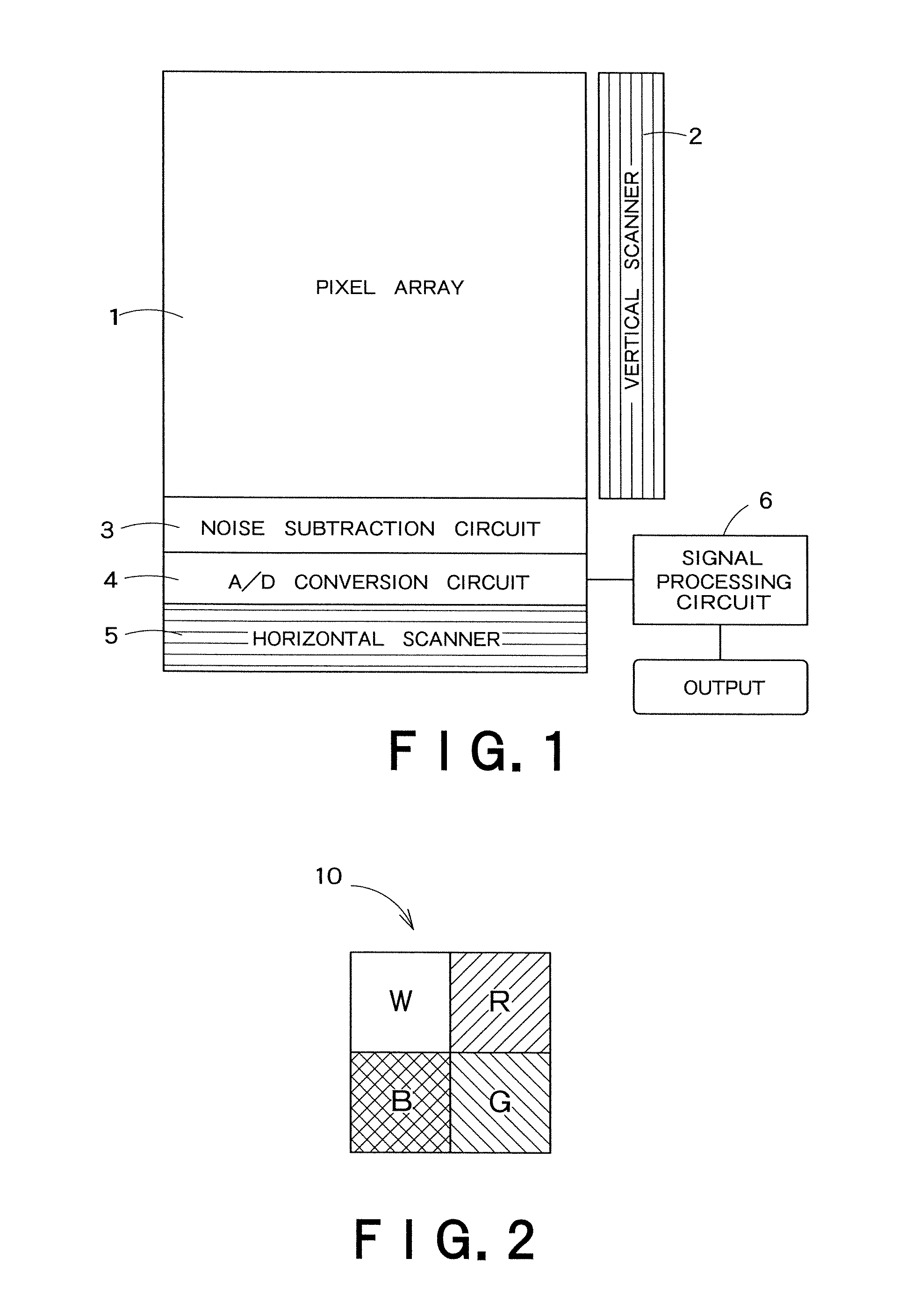
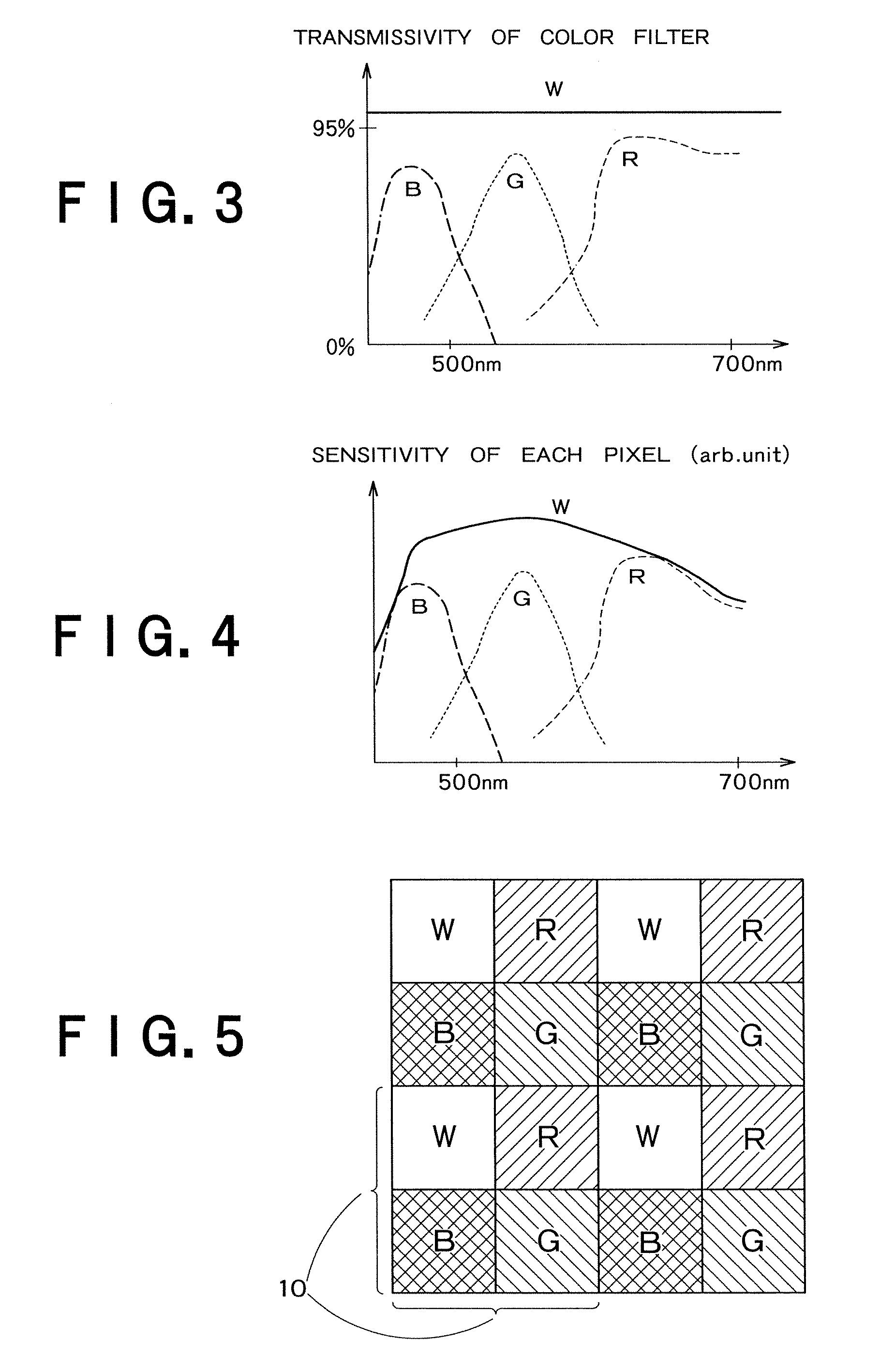
Solid-state image sensor
InactiveUS7990447B2High color reproductionTelevision system detailsTelevision system scanning detailsPattern recognitionColor correction
Owner:KK TOSHIBA
Data visualization techniques
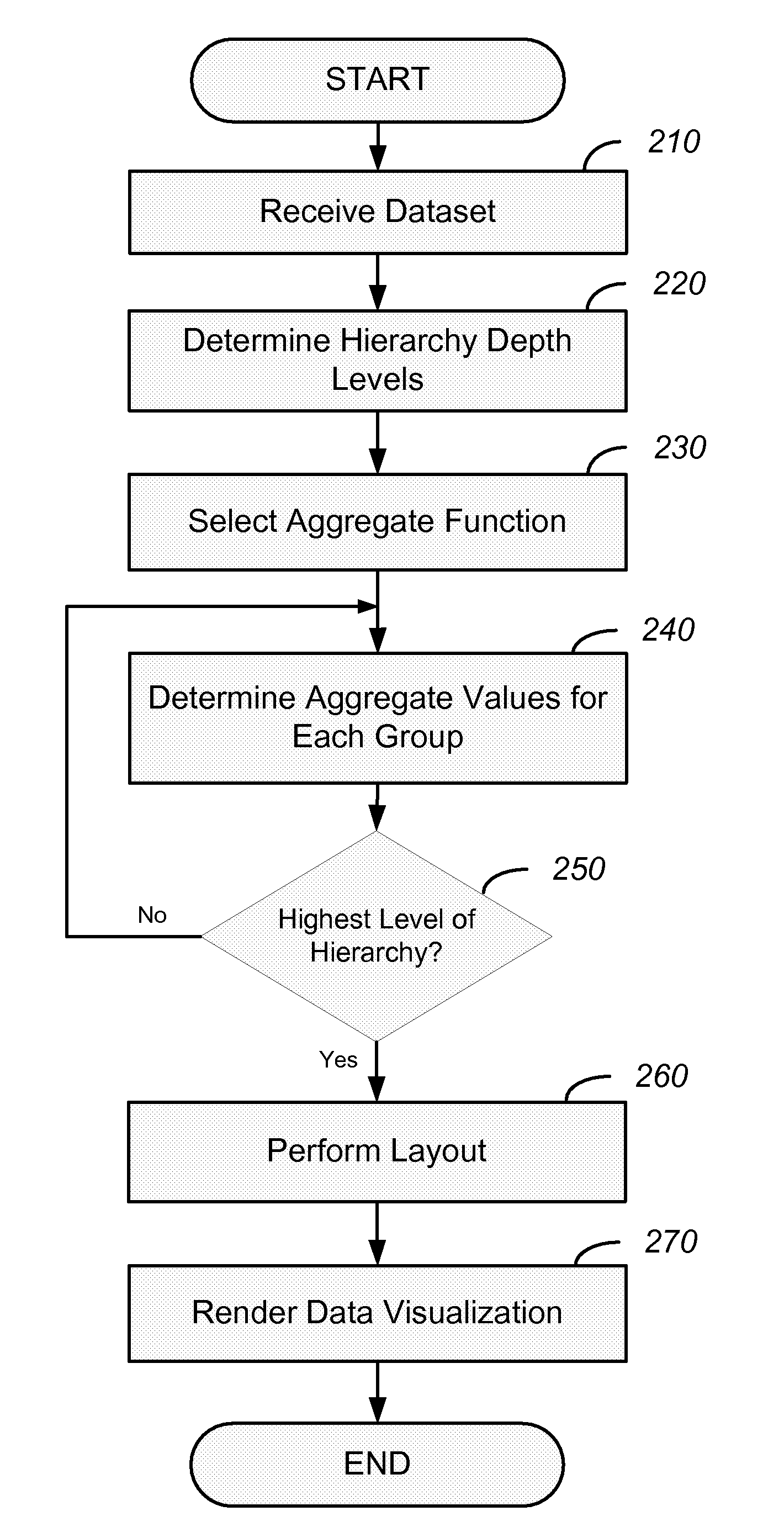
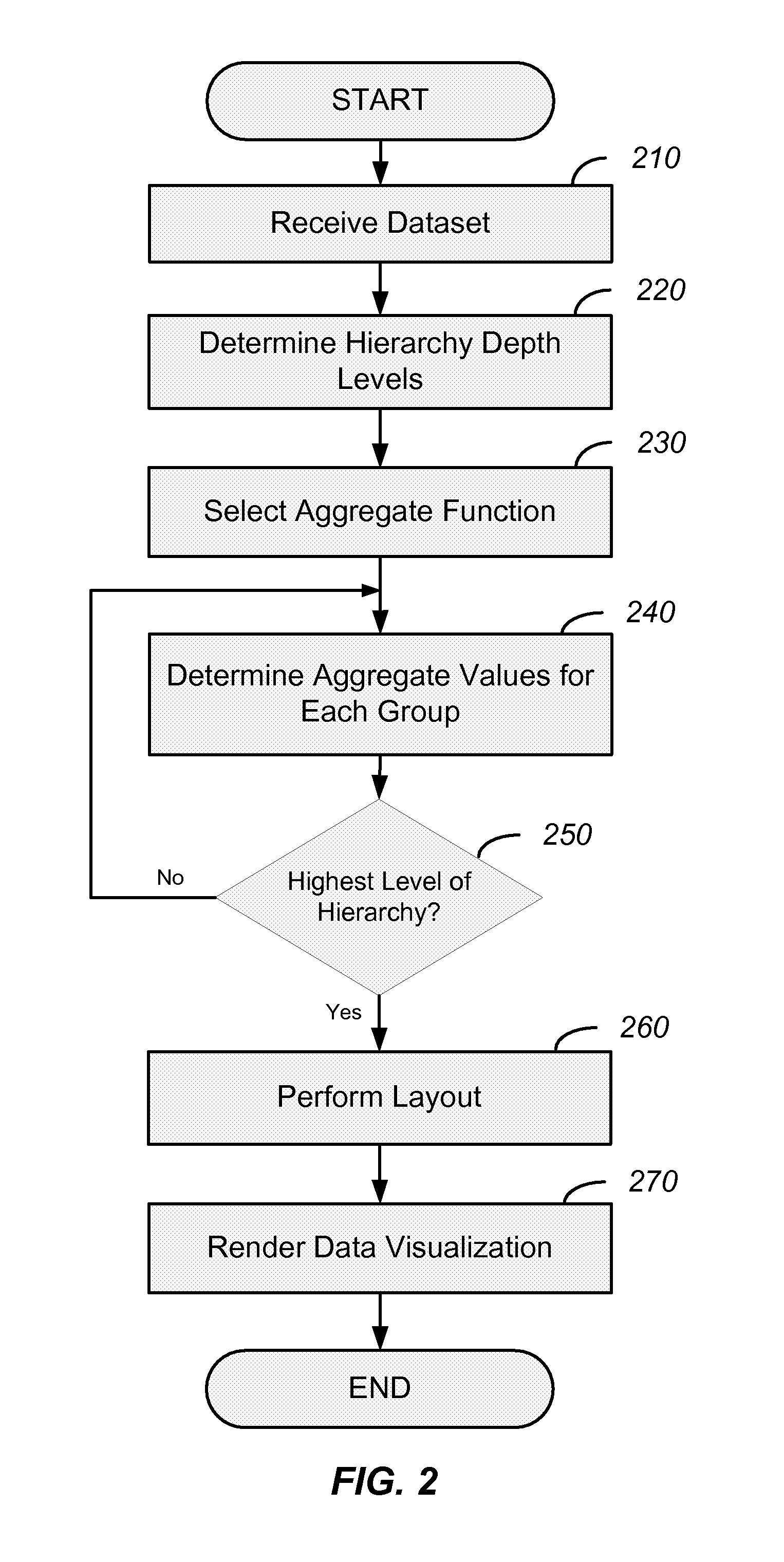
Systems and methods in accordance with various embodiments of the present invention provide for representing a plurality of data values of a hierarchical dataset as graphical elements in a configurable data visualization. A first data visualization may be displayed in a data visualization display page, along with a user interface. A selection of a rendered root node and rendered leaf nodes to be displayed in a second data visualization is received from the user interface. Based on the selection of the rendered root node and rendered leaf nodes, a number of depth levels to display is determined. Also, which of the depth levels to display are identified based on the selection of the rendered root node and rendered leaf nodes. The second data visualization is rendered based on the determined number of depth levels and the identified depth levels.
Owner:ORACLE INT CORP
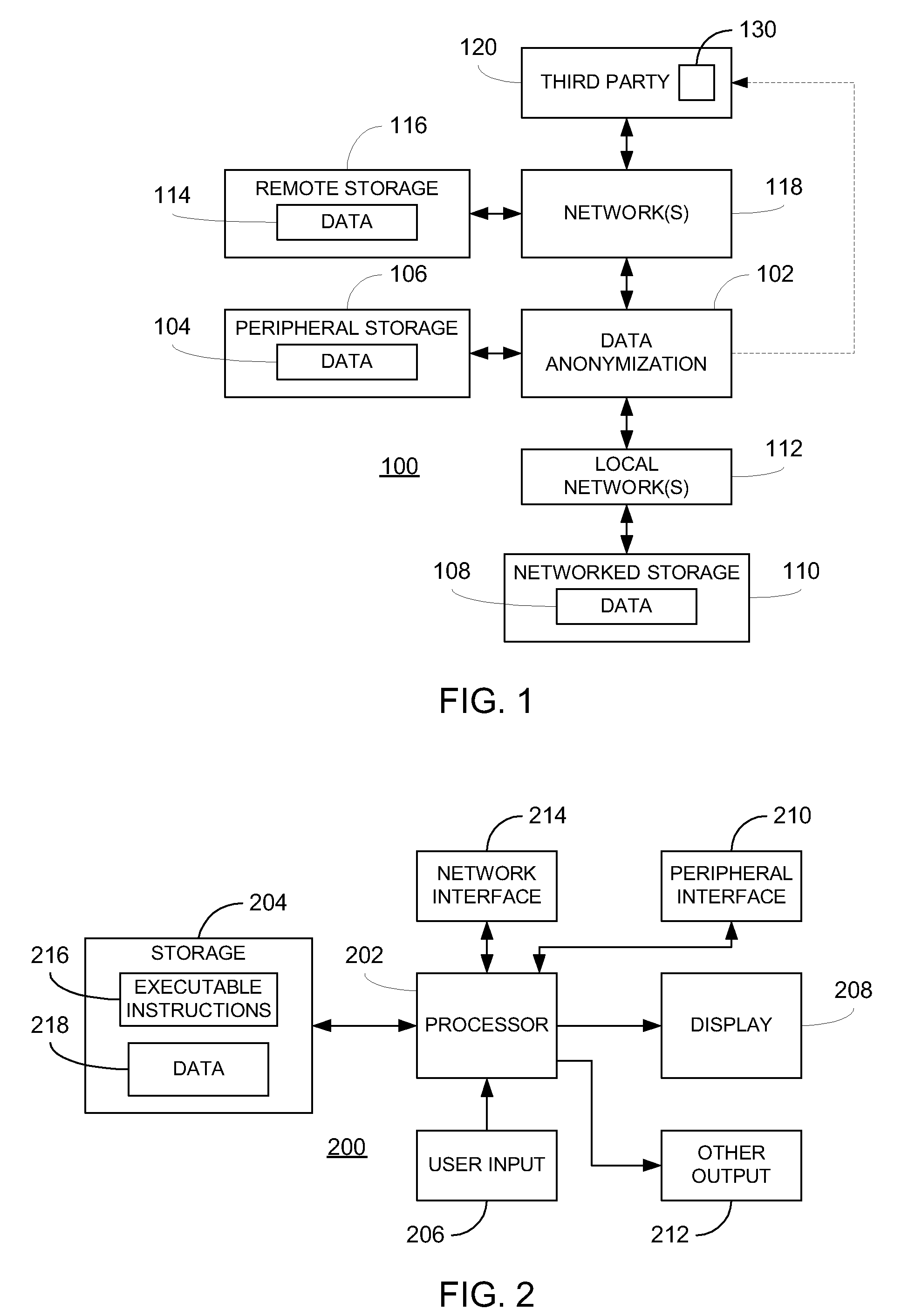
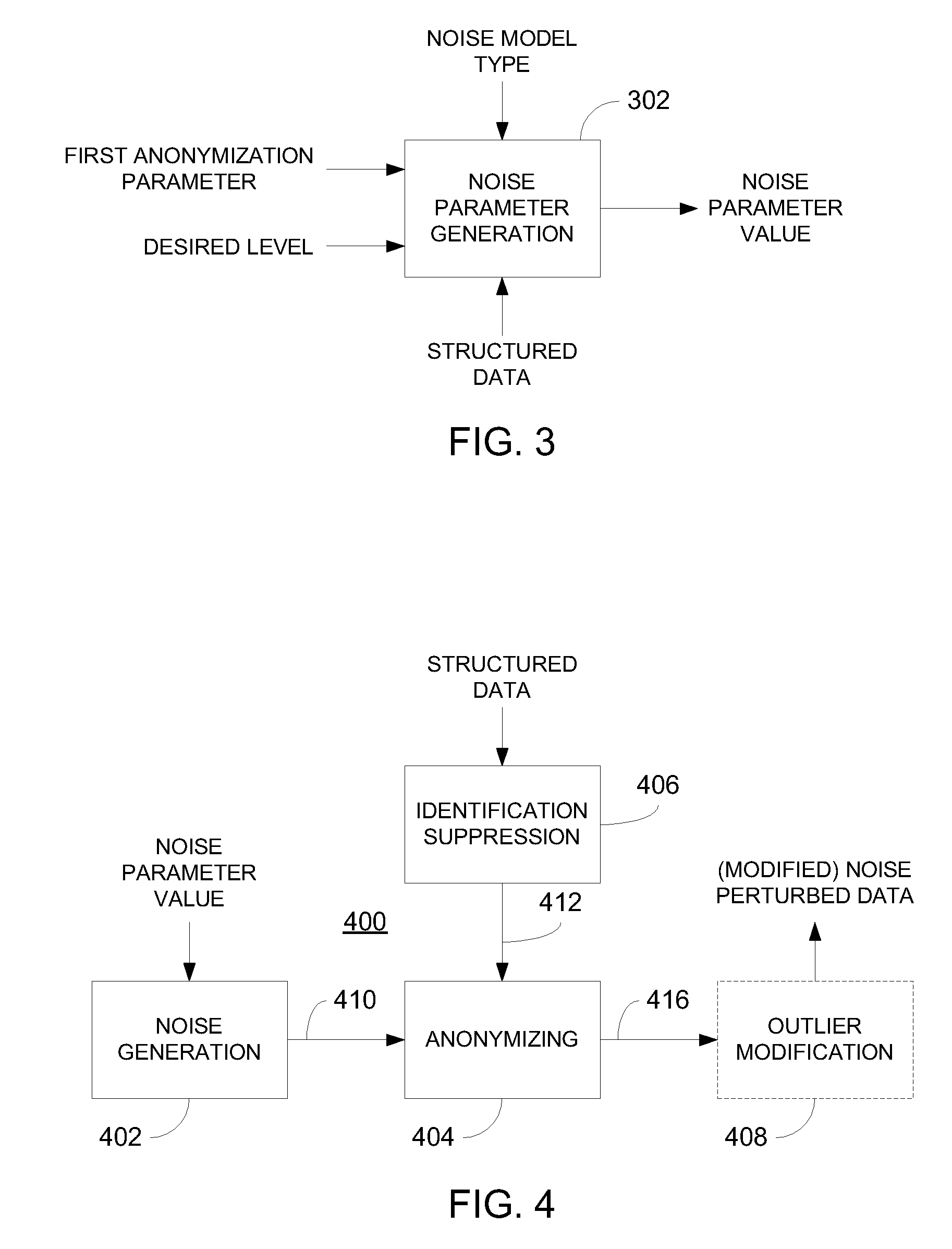
Data anonymization based on guessing anonymity
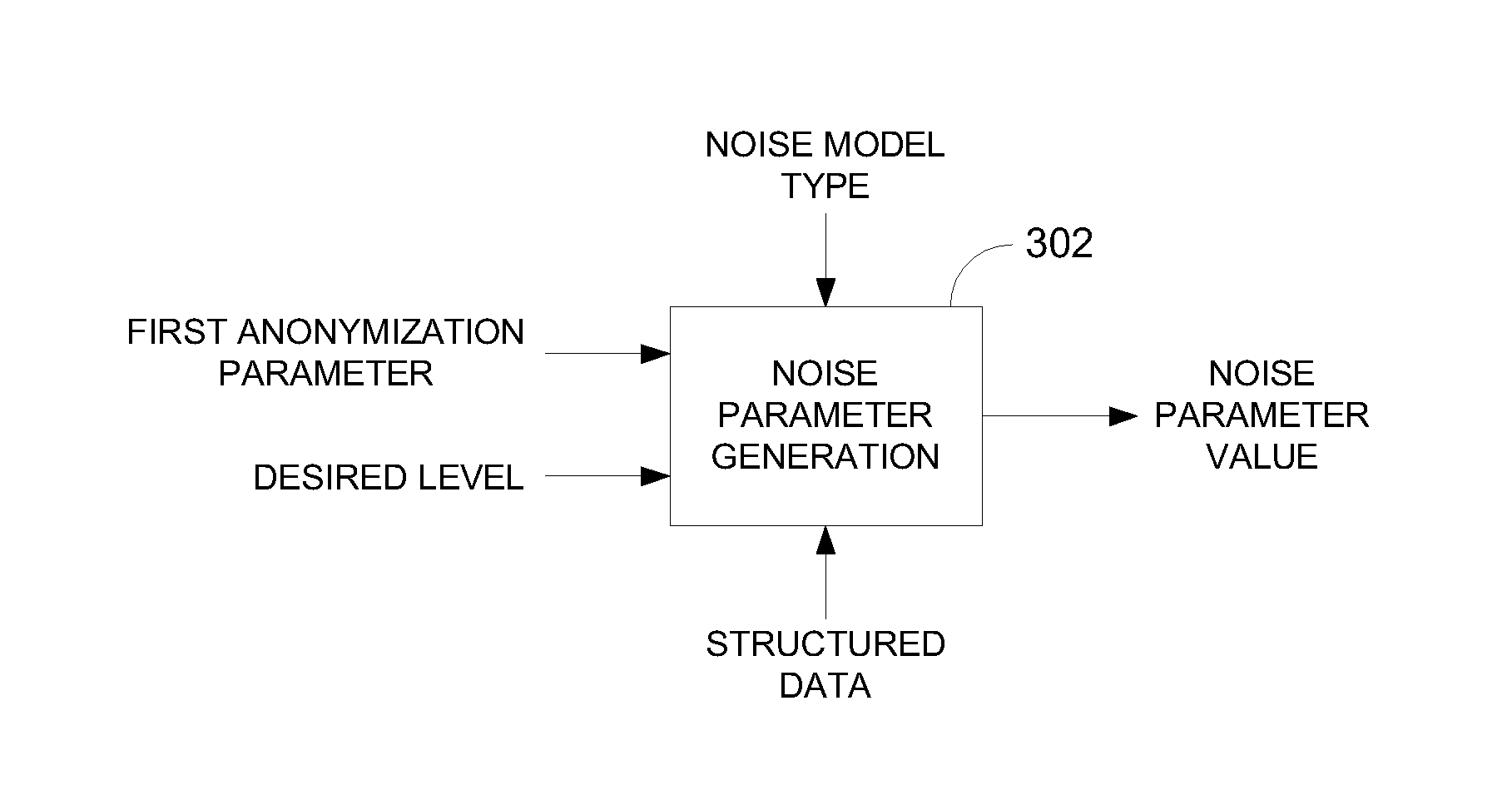
ActiveUS8627483B2Maximizes guessing anonymityMinimize distortionDigital data processing detailsPublic key for secure communicationGame basedOptimization problem
Privacy is defined in the context of a guessing game based on the so-called guessing inequality. The privacy of a sanitized record, i.e., guessing anonymity, is defined by the number of guesses an attacker needs to correctly guess an original record used to generate a sanitized record. Using this definition, optimization problems are formulated that optimize a second anonymization parameter (privacy or data distortion) given constraints on a first anonymization parameter (data distortion or privacy, respectively). Optimization is performed across a spectrum of possible values for at least one noise parameter within a noise model. Noise is then generated based on the noise parameter value(s) and applied to the data, which may comprise real and / or categorical data. Prior to anonymization, the data may have identifiers suppressed, whereas outlier data values in the noise perturbed data may be likewise modified to further ensure privacy.
Owner:ACCENTURE GLOBAL SERVICES LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com