Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
18587 results about "Data structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a data structure is a data organization, management, and storage format that enables efficient access and modification. More precisely, a data structure is a collection of data values, the relationships among them, and the functions or operations that can be applied to the data.
Easy-to-use data report specification
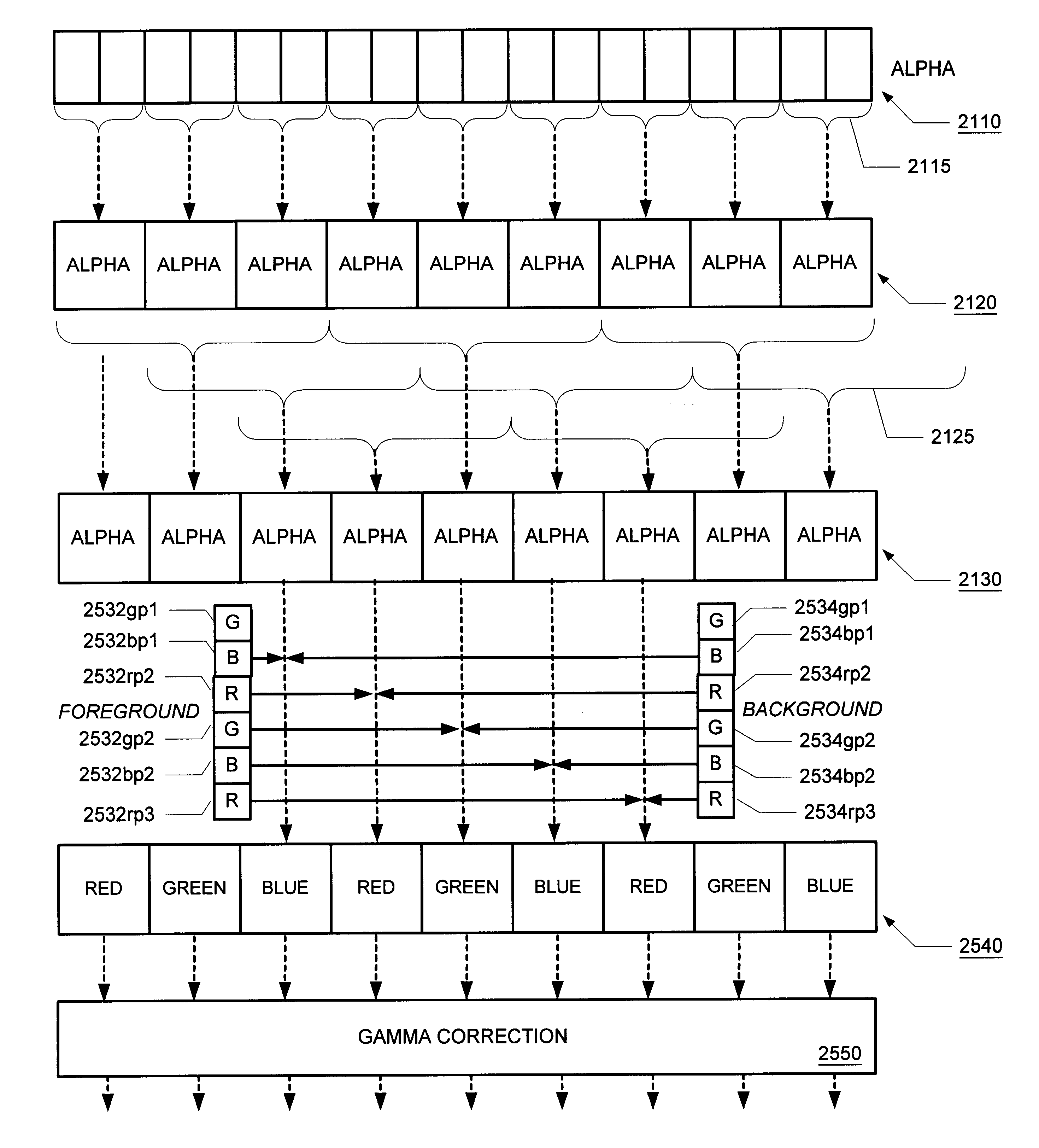
ActiveUS7289976B2Data processing applicationsDigital data information retrievalGraphicsGraphical specification
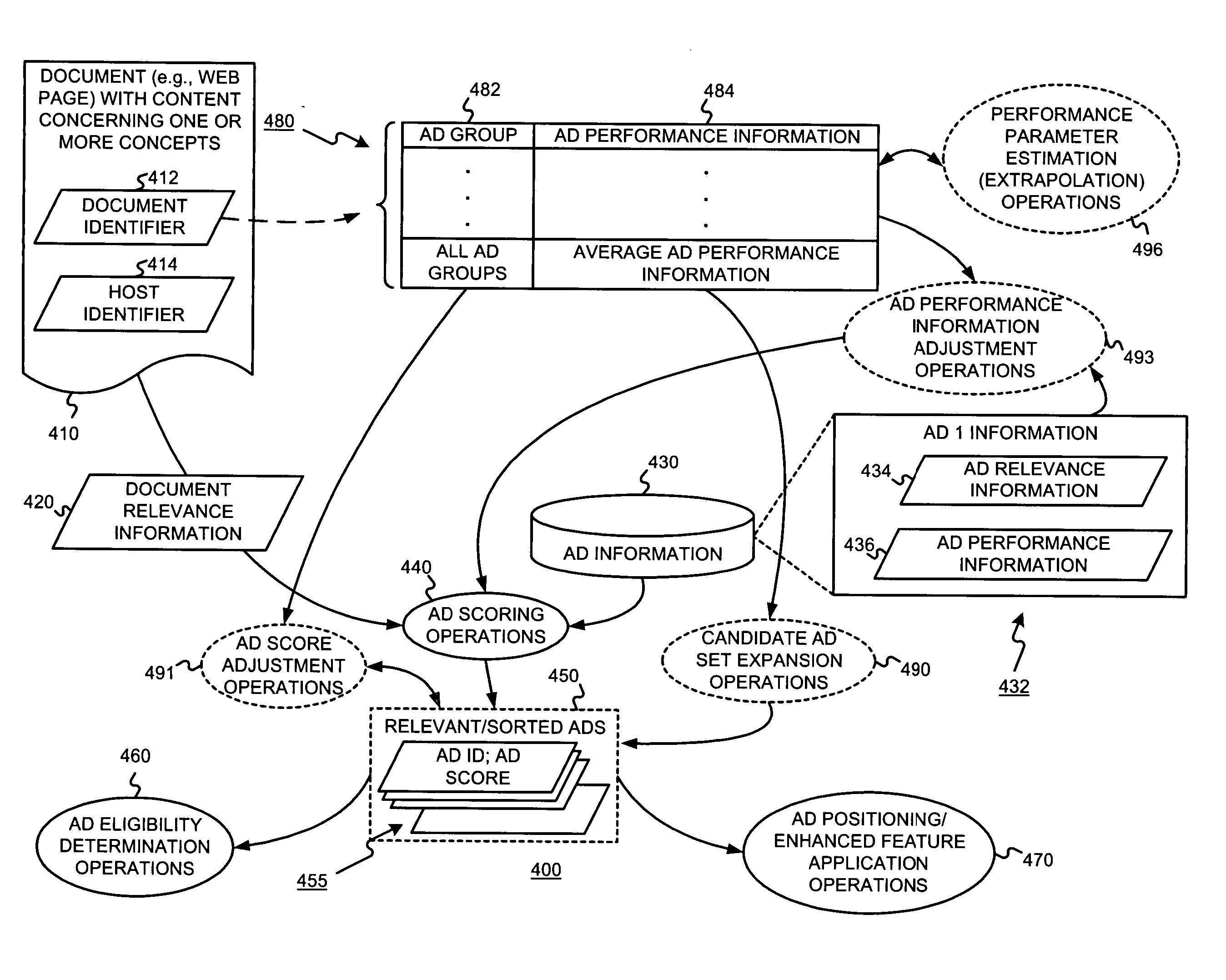
A method and system for the graphical specification and modification of reports is disclosed which enables data reports to be easily created via a report design dialogue. The report design dialogue includes a group-level outline panel containing controls for grouping, as well as other report controls such as those for sorting and aggregating. A method and system for creating a group-level outline panel using an existing database report is also disclosed. Finally, a computer-readable medium storing a computer-interpretable data structure that stores one or more report specifications is disclosed.
Owner:MICROSOFT TECH LICENSING LLC
Software framework that facilitates design and implementation of database applications
InactiveUS7412455B2Facilitates efficient design and implementationData processing applicationsDigital data information retrievalSoftware engineeringDatabase application
An intelligent framework is provided that is disposed between a high-level language environment and a database system environment. According to one embodiment, the framework programmatically receives information regarding definitions of data structures of objects participating in a software application and information regarding relationships among the objects. Based upon the particular request from the high-level language environment and upon the definitions and relationships, the framework programmatically and dynamically generates appropriate statements associated with the database system environment that accomplish the request. For example, the framework may issue statements to define the structure of a database, access information from the database, and / or manipulate information within the database.
Owner:RPX CORP
Custom entities and fields in a multi-tenant database system
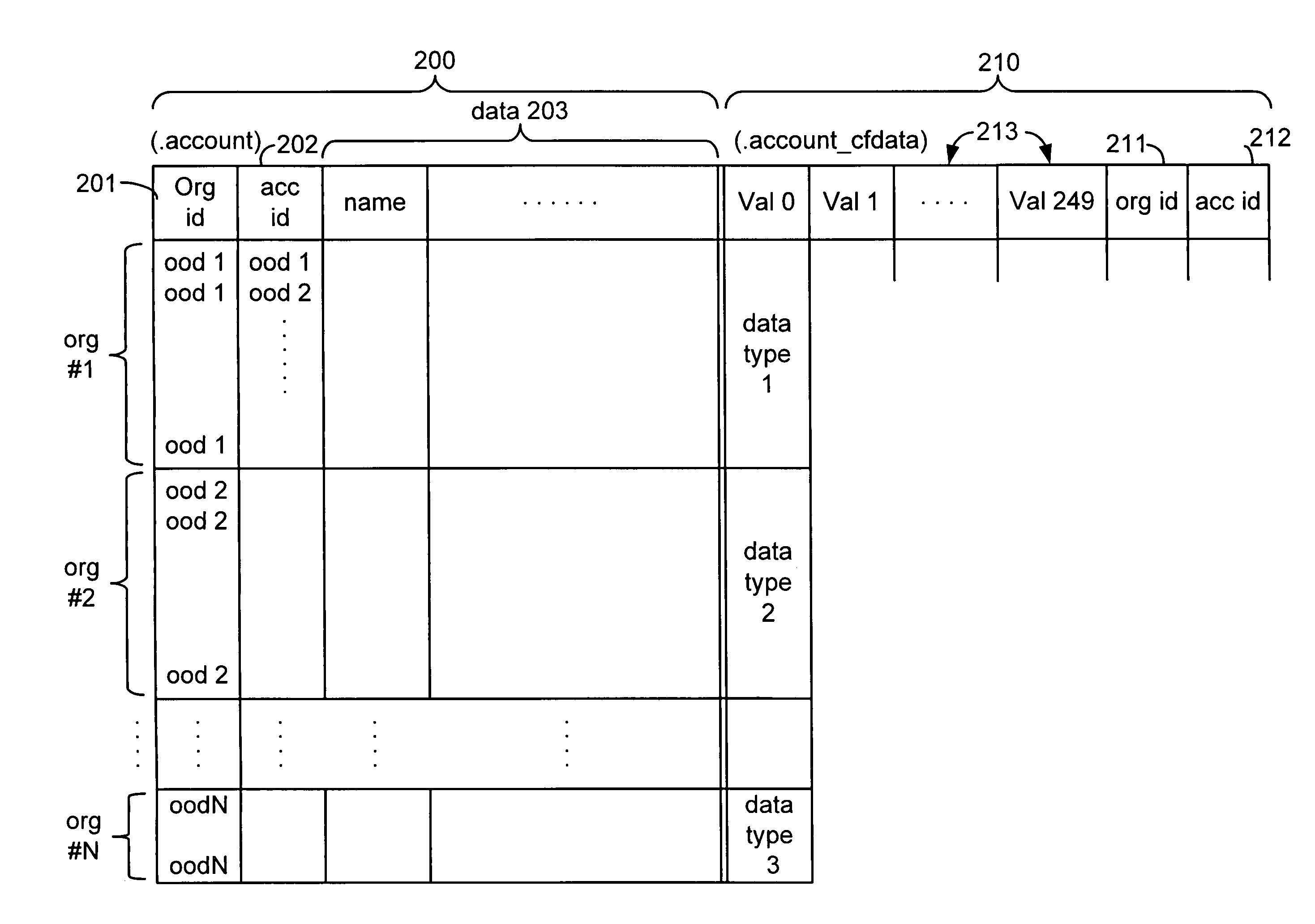
Systems and methods for hosting variable schema data such as dynamic tables and columns in a fixed physical database schema. Standard objects, such as tables are provided for use by multiple tenants or organizations in a multi-tenant database system. Each organization may add or define custom fields for inclusion in a standard object. Custom fields for multiple tenants are stored in a single field within the object data structure, and this single field may contain different data types for each tenant. Indexing columns are also provided, wherein a tenant may designate a field for indexing. Data values for designated fields are copied to an index column, and each index column may include multiple data types. Each organization may also define custom objects including custom fields and indexing columns. Custom objects for multiple tenants are stored in a single custom object data structure. The primary key values for the single custom object table are globally unique, but also include an object-specific identifier which may be re-used among different entities.
Owner:SALESFORCE COM INC
Content-targeted advertising using collected user behavior data
InactiveUS20050021397A1Quality improvementImprove user experienceSpecial data processing applicationsMarketingPaper documentDocument preparation
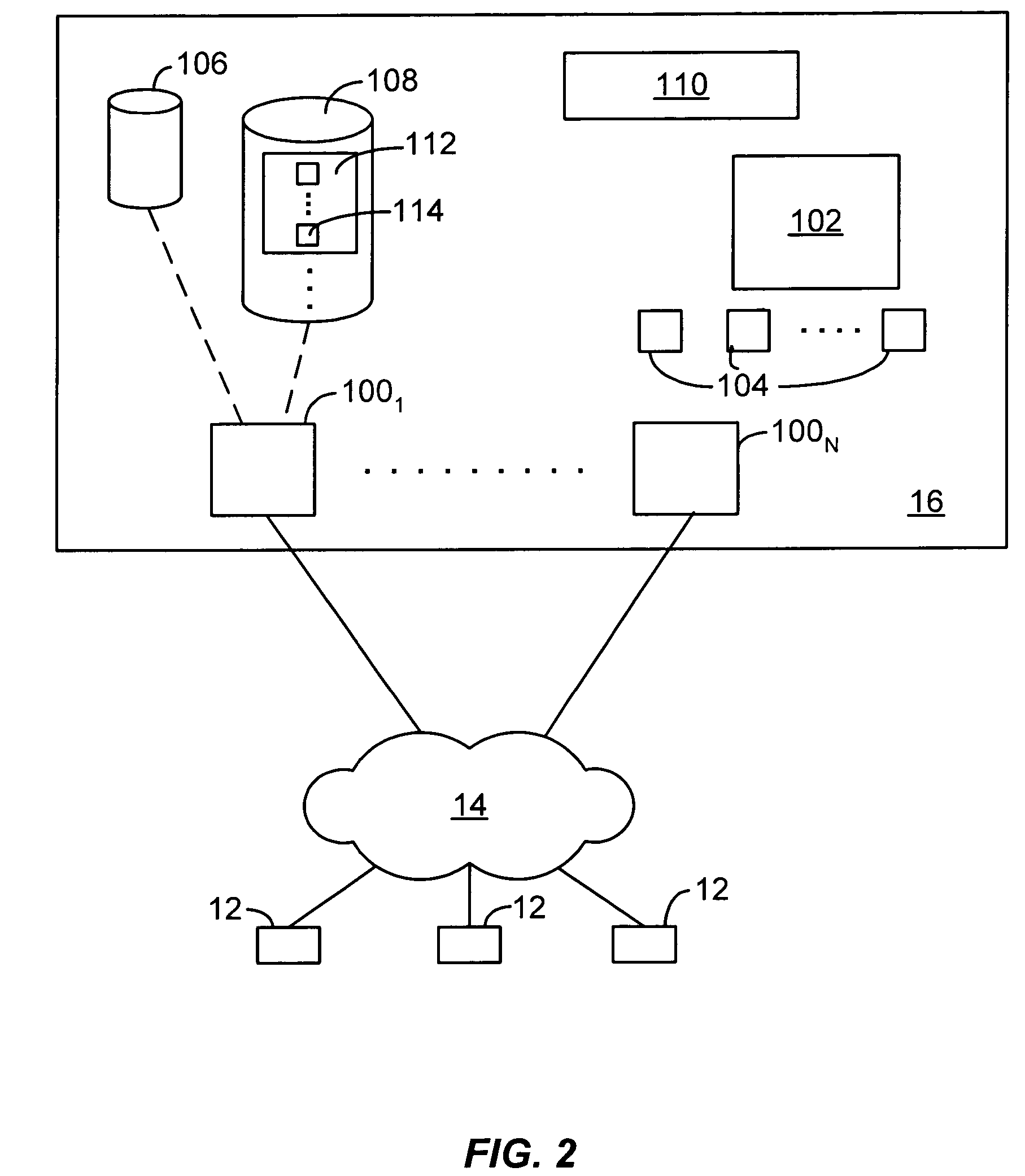
A content-targeting ad system is provided with a user behavior (e.g., selection (e.g., click), conversion, etc.) feedback mechanism. The performance of individual ads, or groups of ads, may be tracked on a per document (e.g. per URL) and / or on a per host (e.g. per Website) basis. The performance of ad targeting functions may also be tracked on a per document, and / or per host basis. Such user behavior feedback data may be processed (e.g., aggregated) into useful data structures. Such user behavior feedback data (raw or processed) may then be used in a content-targeting ad system to improve ad quality, improve user experience, and / or maximize revenue.
Owner:GOOGLE LLC
Voice-enabled documents for facilitating operational procedures
InactiveUS20140108010A1Increase productivityImprove efficiencyCharacter and pattern recognitionAutomatic exchangesClient-sideField service
A voice-enabled document system facilitates execution of service delivery operations by eliminating the need for manual or visual interaction during information retrieval by an operator. Access to voice-enabled documents can facilitate operations for mobile vendors, on-site or field-service repairs, medical service providers, food service providers, and the like. Service providers can access the voice-enabled documents by using a client device to retrieve the document, display it on a screen, and, via voice commands initiate playback of selected audio files containing information derived from text data objects selected from the document. Data structures that are components of a voice-enabled document include audio playback files and a logical association that links the audio playback files to user-selectable fields, and to a set of voice commands.
Owner:INTERMEC IP
System and method for autonomously generating heterogeneous data source interoperability bridges based on semantic modeling derived from self adapting ontology
InactiveUS20030172368A1Reduce dependenceImprove data securityVersion controlKnowledge representationTime errorData source
A system, including software components, that efficiently and dynamically analyzes changes to data sources, including application programs, within an integration environment and simultaneously re-codes dynamic adapters between the data sources is disclosed. The system also monitors at least two of said data sources to detect similarities within the data structures of said data sources and generates new dynamic adapters to integrate said at least two of said data sources. The system also provides real time error validation of dynamic adapters as well as performance optimization of newly created dynamic adapters that have been generated under changing environmental conditions.
Owner:COMPASS AL INC +1
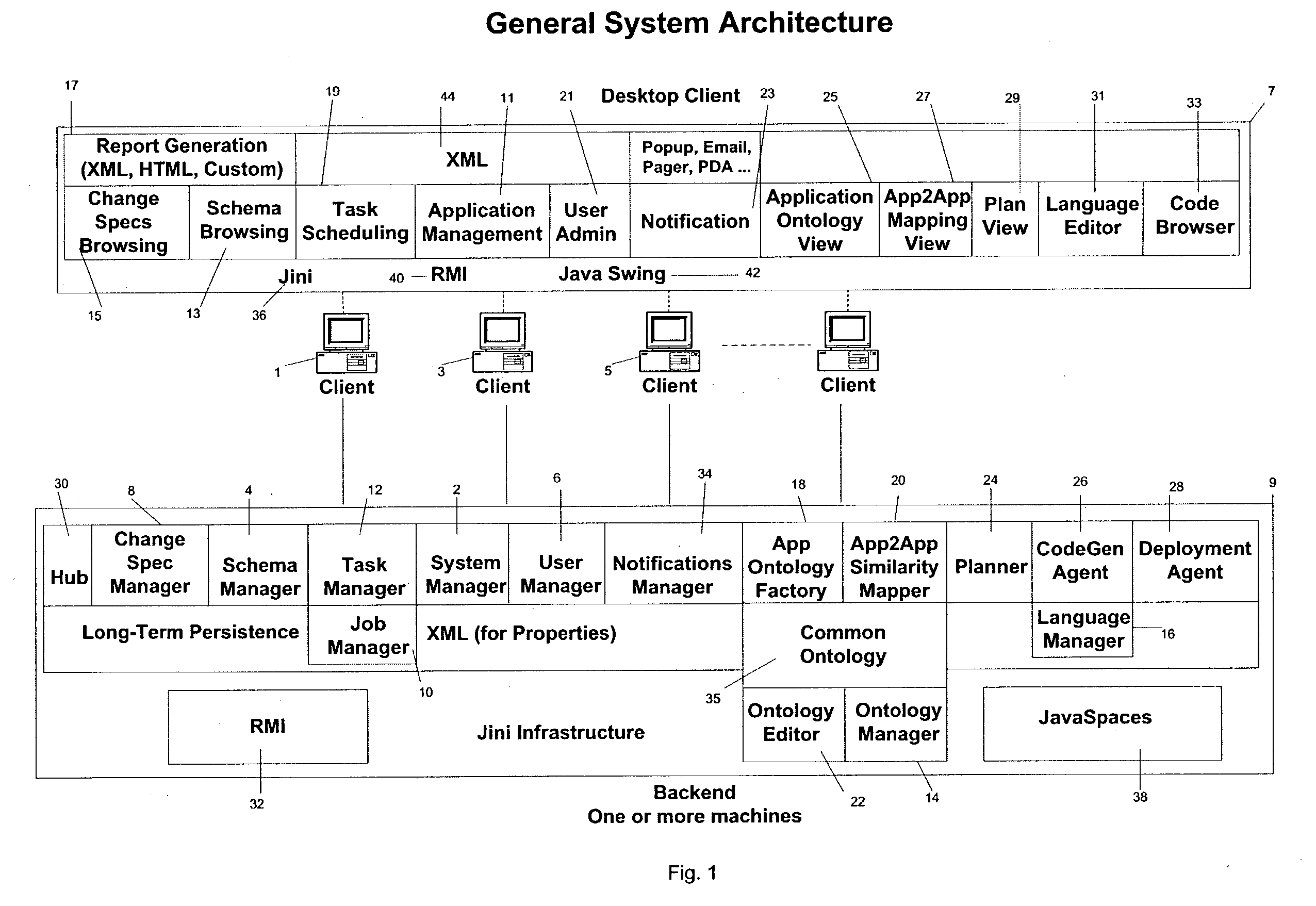
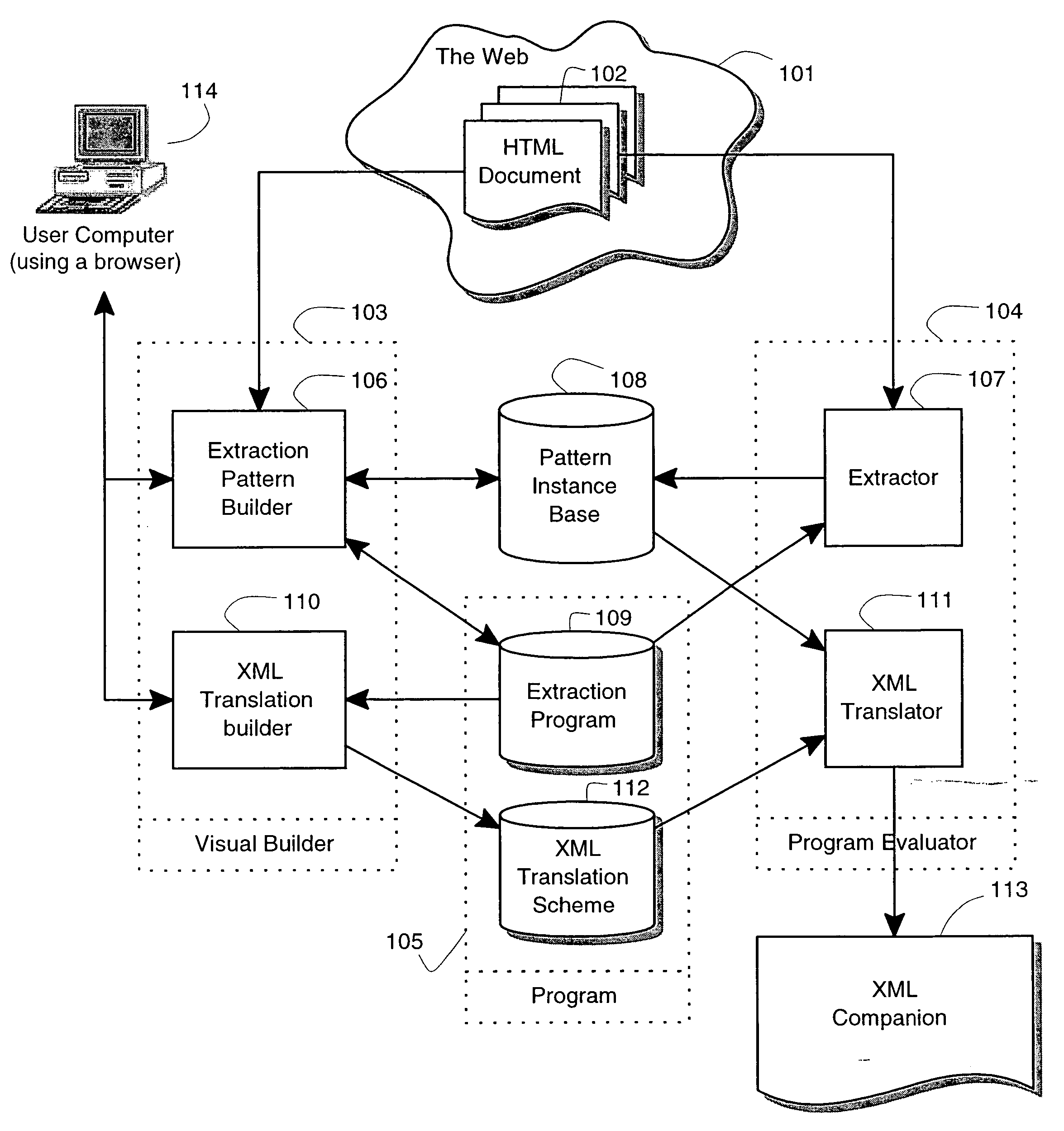
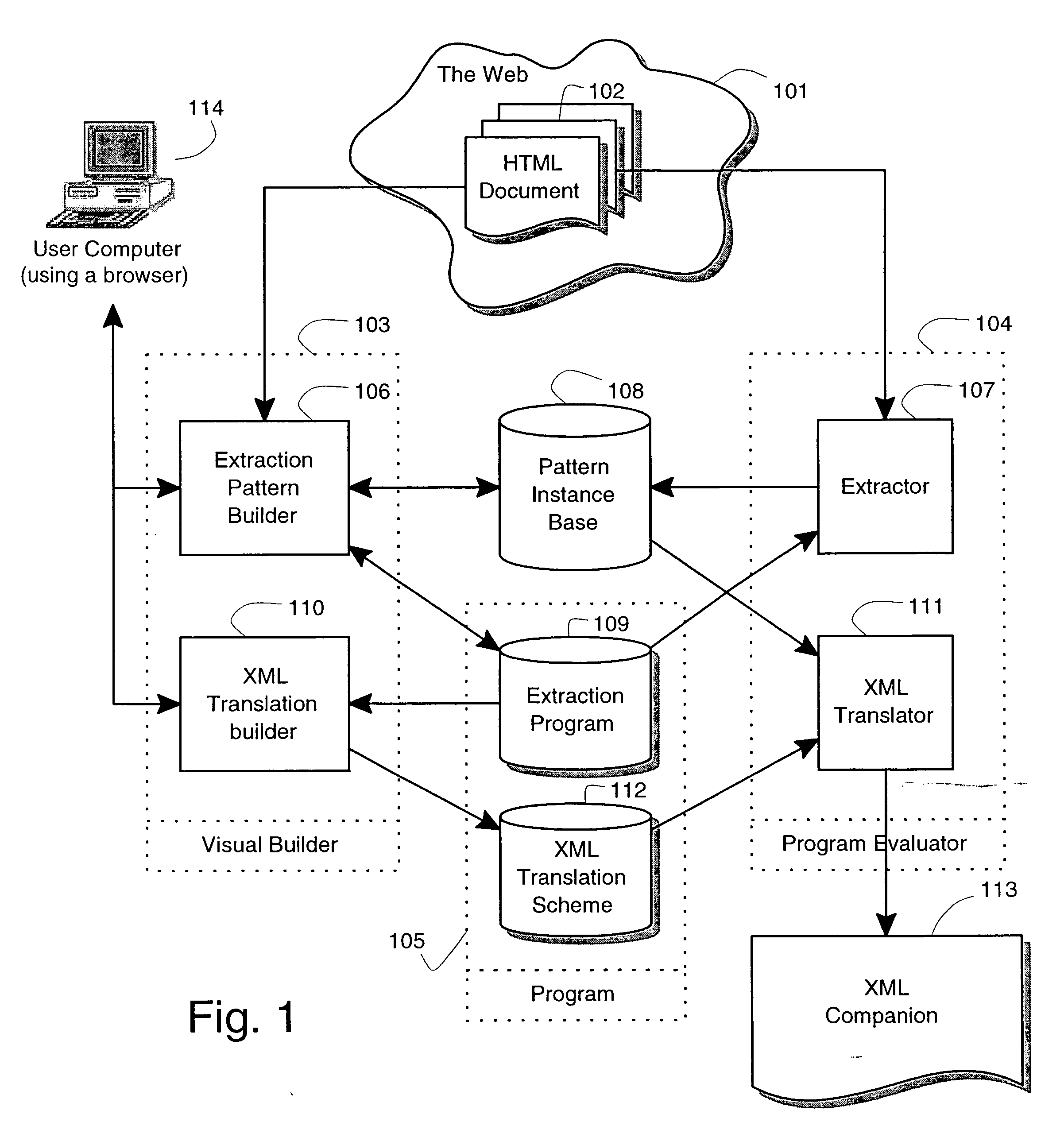
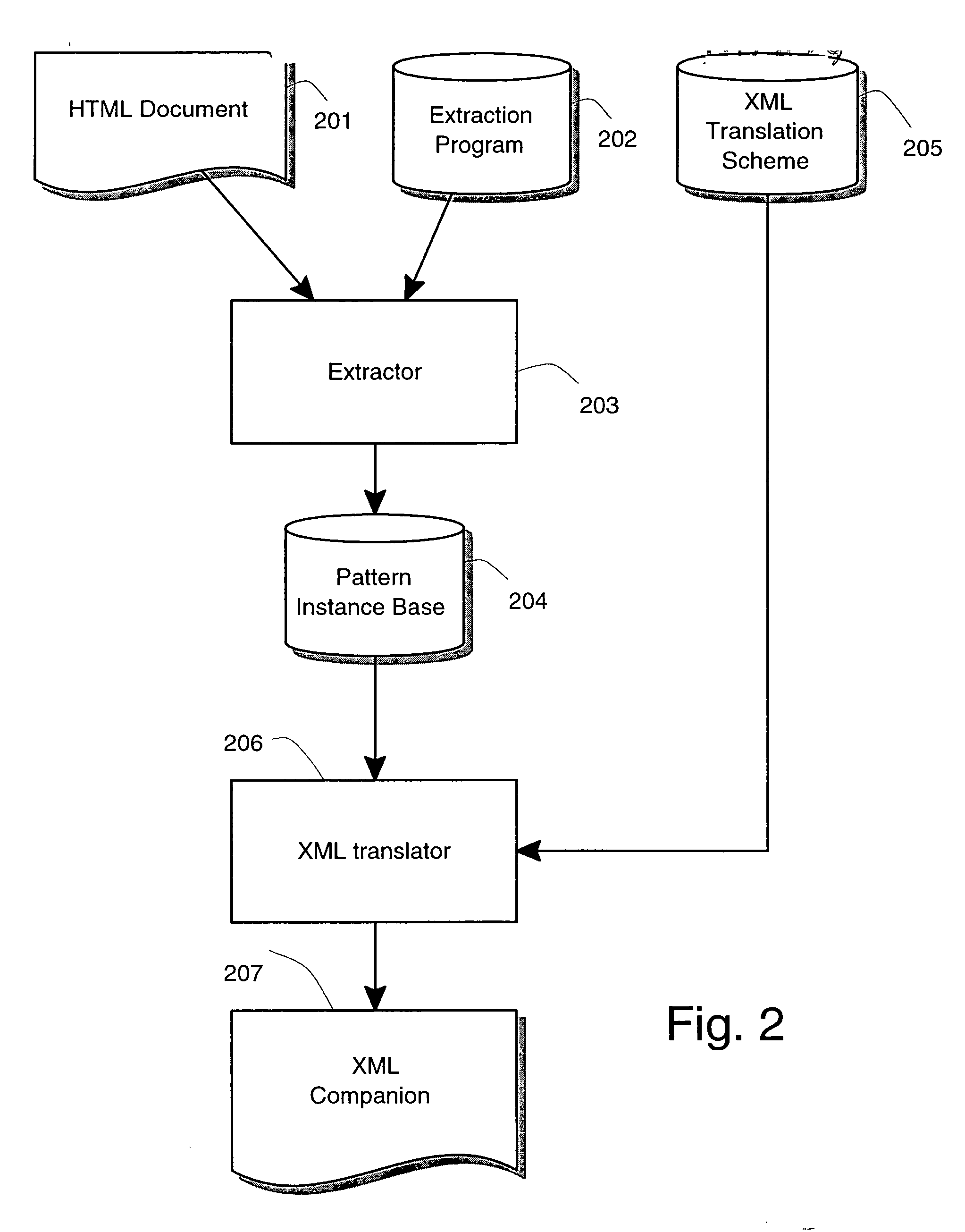
Visual and interactive wrapper generation, automated information extraction from web pages, and translation into xml
InactiveUS20050022115A1Data efficientEfficient codingDigital computer detailsSemi-structured data indexingData transformationEngineering
A method and a system for information extraction from Web pages formatted with markup languages such as HTML [8]. A method and system for interactively and visually describing information patterns of interest based on visualized sample Web pages [5,6,16-29]. A method and data structure for representing and storing these patterns [1]. A method and system for extracting information corresponding to a set of previously defined patterns from Web pages [2], and a method for transforming the extracted data into XML is described. Each pattern is defined via the (interactive) specification of one or more filters. Two or more filters for the same pattern contribute disjunctively to the pattern definition [3], that is, an actual pattern describes the set of all targets specified by any of its filters. A method and for extracting relevant elements from Web pages by interpreting and executing a previously defined wrapper program of the above form on an input Web page [9-14] and producing as output the extracted elements represented in a suitable data structure. A method and system for automatically translating said output into XML format by exploiting the hierarchical structure of the patterns and by using pattern names as XML tags is described.
Owner:LIXTO SOFTWARE
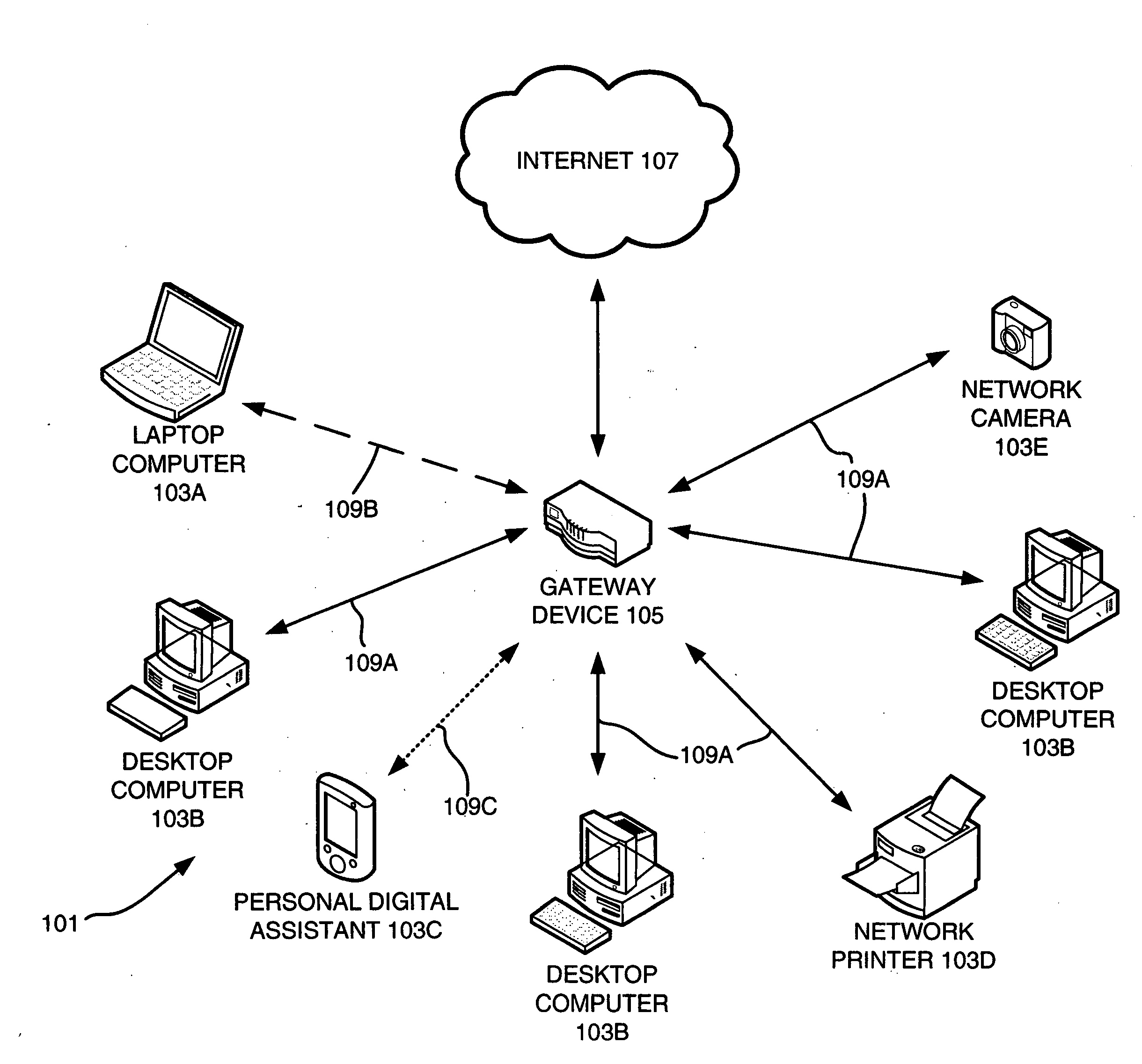
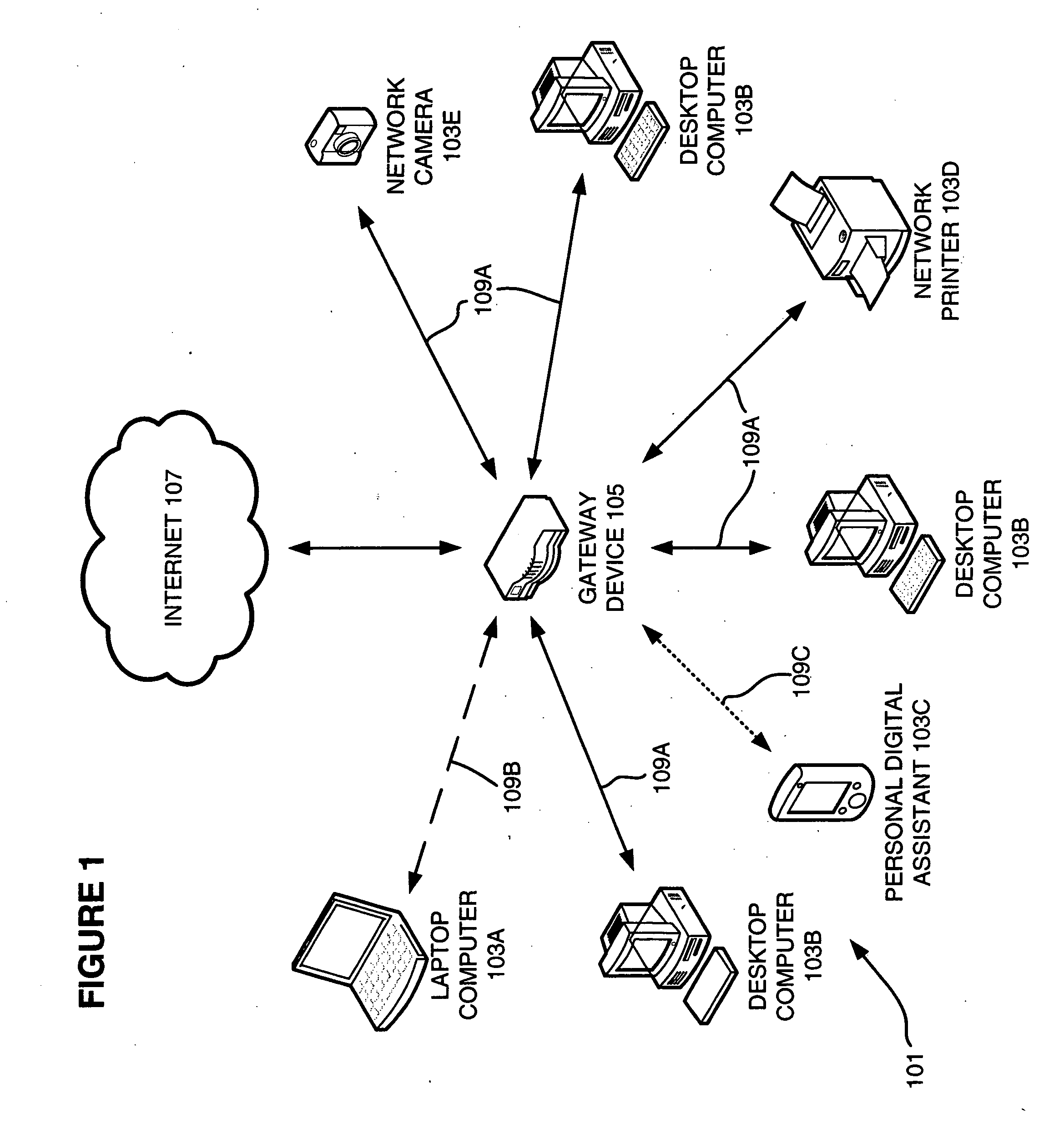
Network management
ActiveUS20090019141A1Digital computer detailsHome automation networksDevice PropertiesNetwork management
A tool for managing a computer network includes a gateway service module that identifies a gateway for a network and a network information service module. The network information service module identifies devices in the network, determines at least one property for each of the identified devices, and creates a network information data structure for storing device properties. A communication agent service module transmits at least one determined device property to other agent service modules associated with the network, receives at least one device property from another agent service module associated with the network, and provides the received at least one property device to the network information service module. A method of monitoring a computer network is also provided. The method includes identifying devices in a network, determining at least one property for each of the identified devices, receiving at least one determined device property from another device the network, and creating a network information data structure for storing the determined device properties.
Owner:CISCO TECH INC
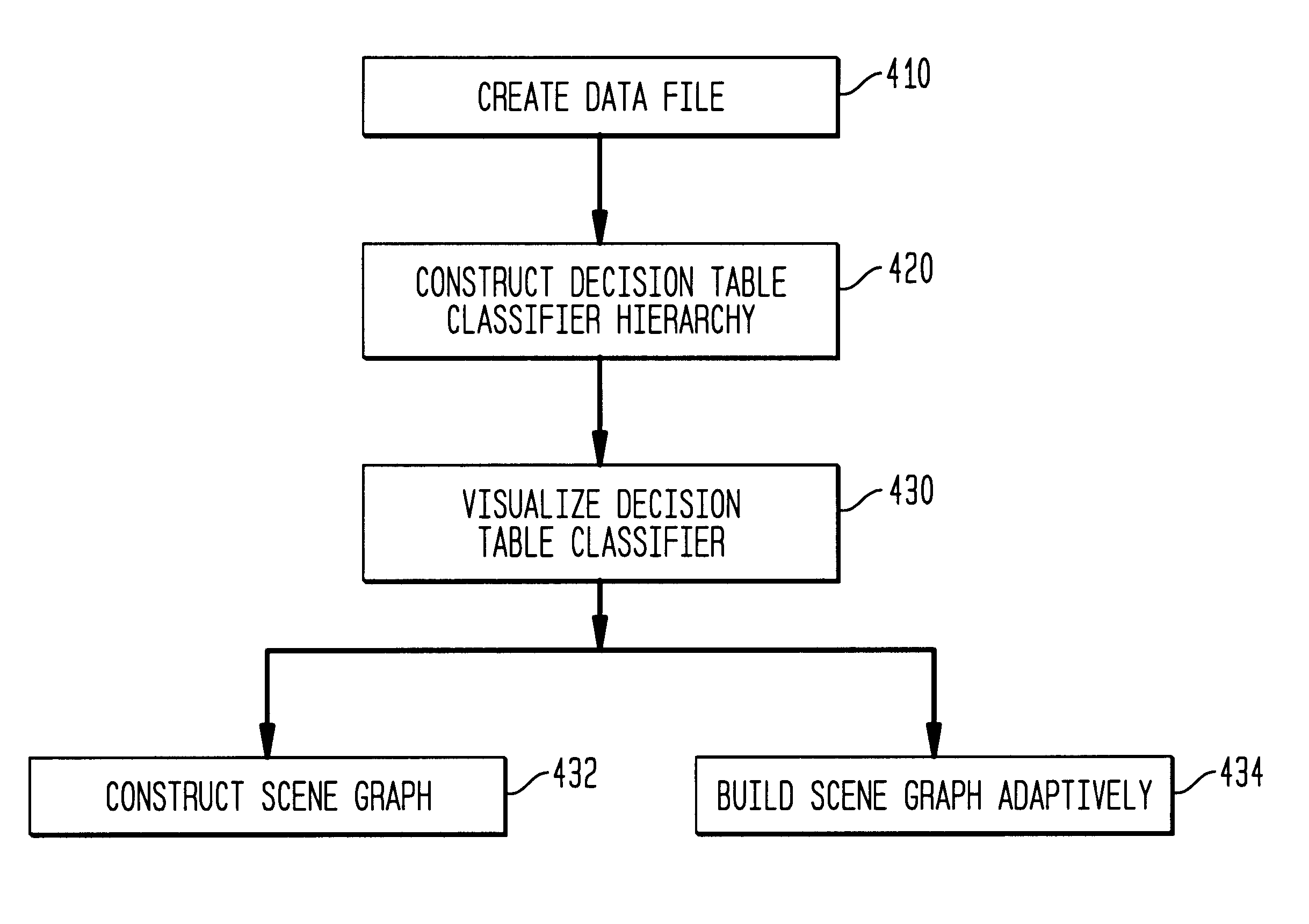
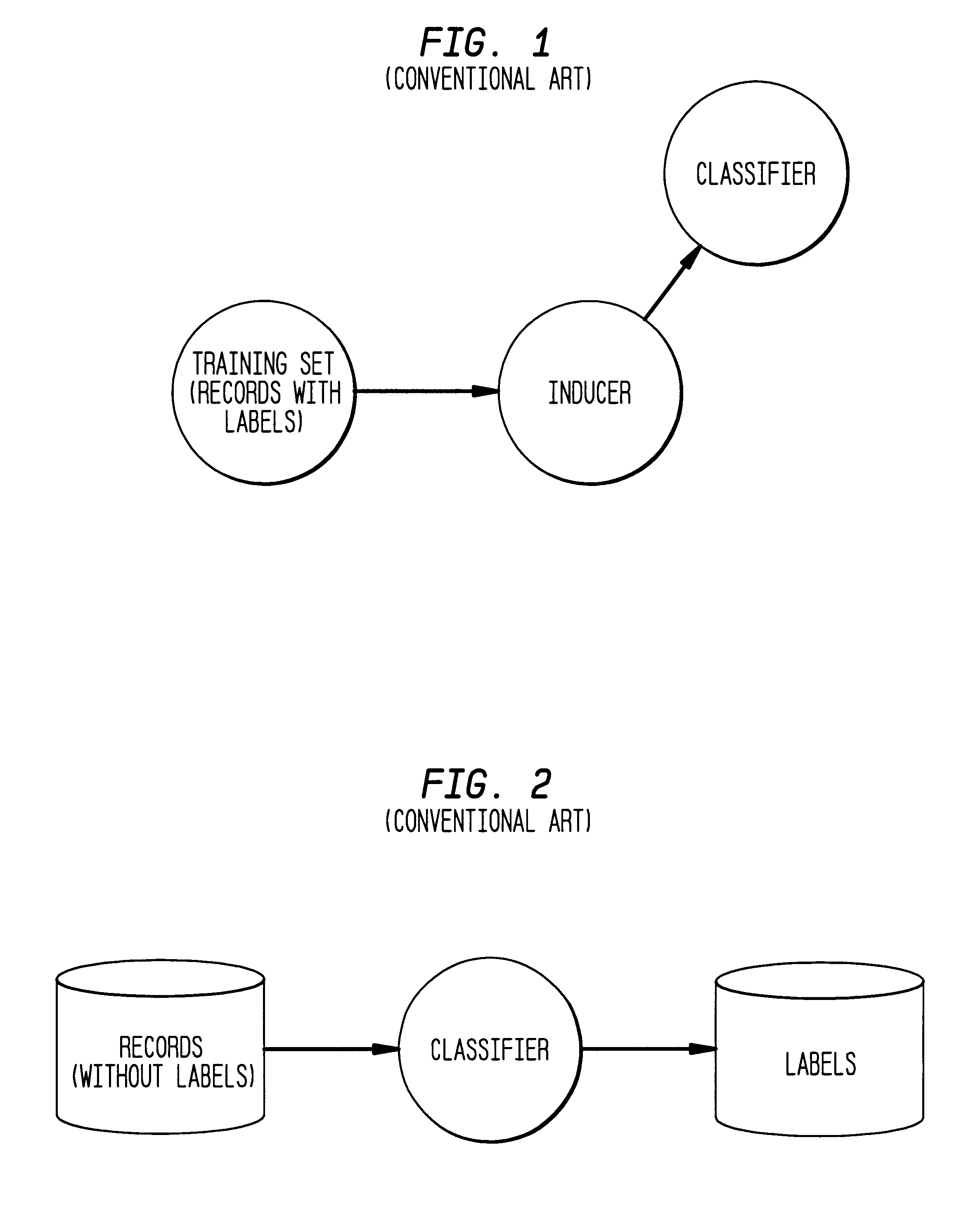
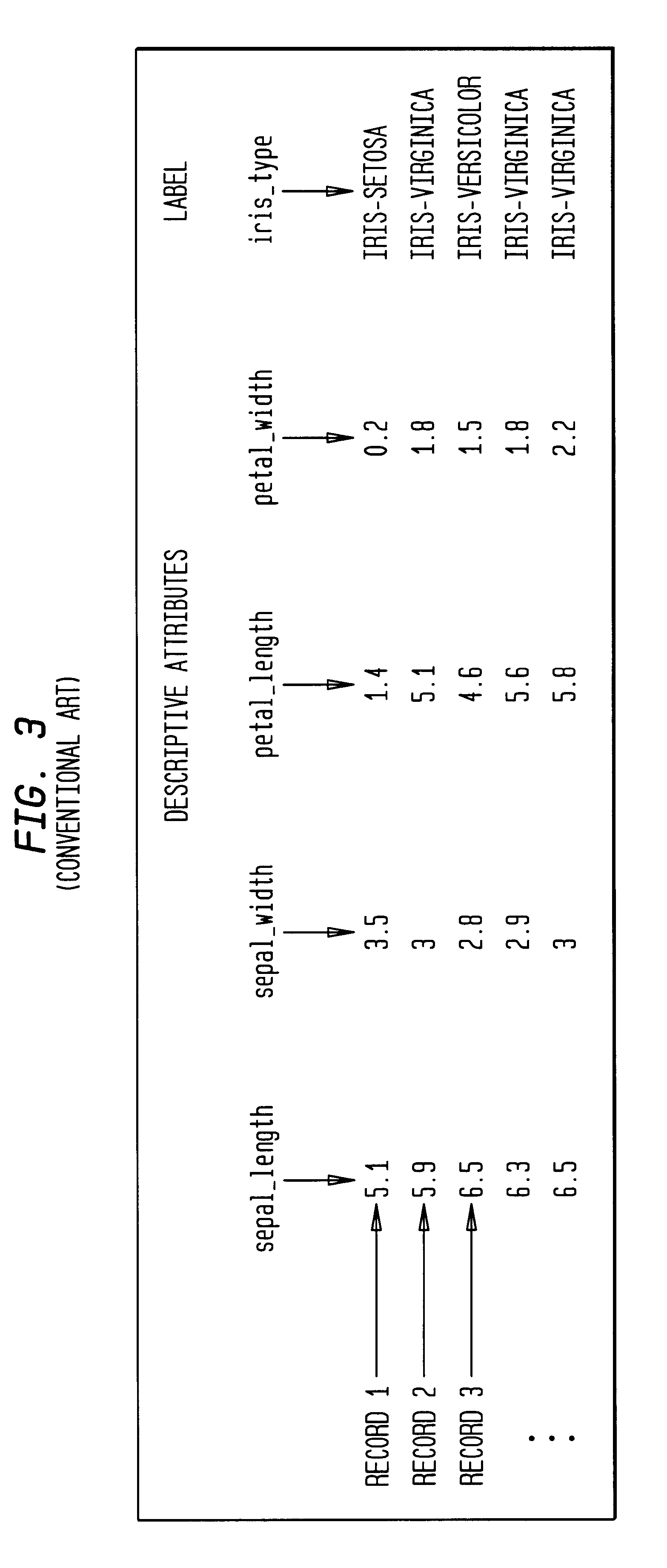
Method, system, and computer program product for visualizing a data structure
A data structure visualization tool visualizes a data structure such as a decision table classifier. A data file based on a data set of relational data is stored as a relational table, where each row represents an aggregate of all the records for each combination of values of the attributes used. Once loaded into memory, an inducer is used to construct a hierarchy of levels, called a decision table classifier, where each successive level in the hierarchy has two fewer attributes. Besides a column for each attribute, there is a column for the record count (or more generally, sum of record weights), and a column containing a vector of probabilities (each probability gives the proportion of records in each class). Finally, at the top-most level, a single row represents all the data. The decision table classifier is then passed to the visualization tool for display and the decision table classifier is visualized. By building a representative scene graph adaptively, the visualization application never loads the whole data set into memory. Interactive techniques, such as drill-down and drill-through are used view further levels of detail or to retrieve some subset of the original data. The decision table visualizer helps a user understand the importance of specific attribute values for classification.
Owner:RPX CORP +1
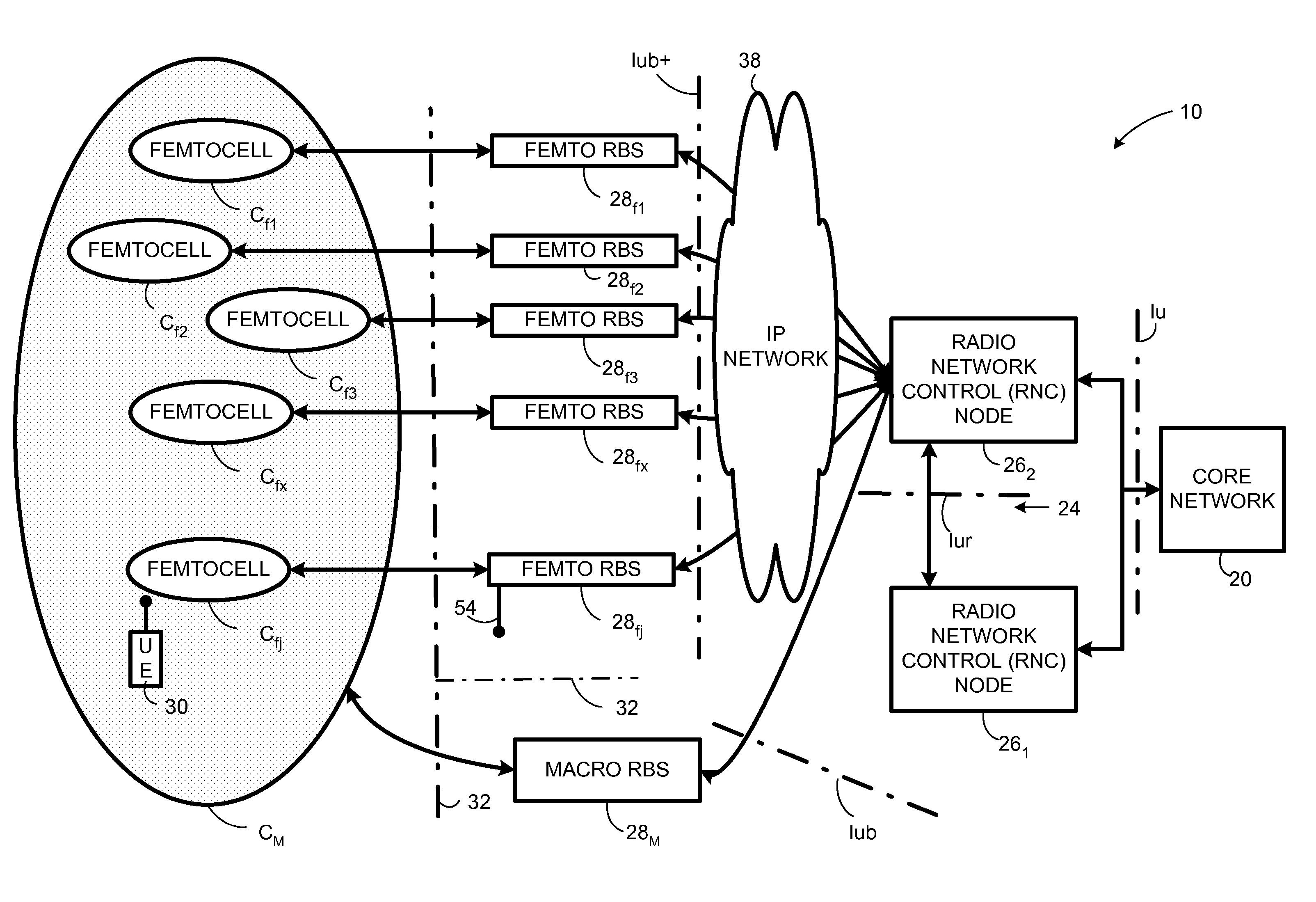
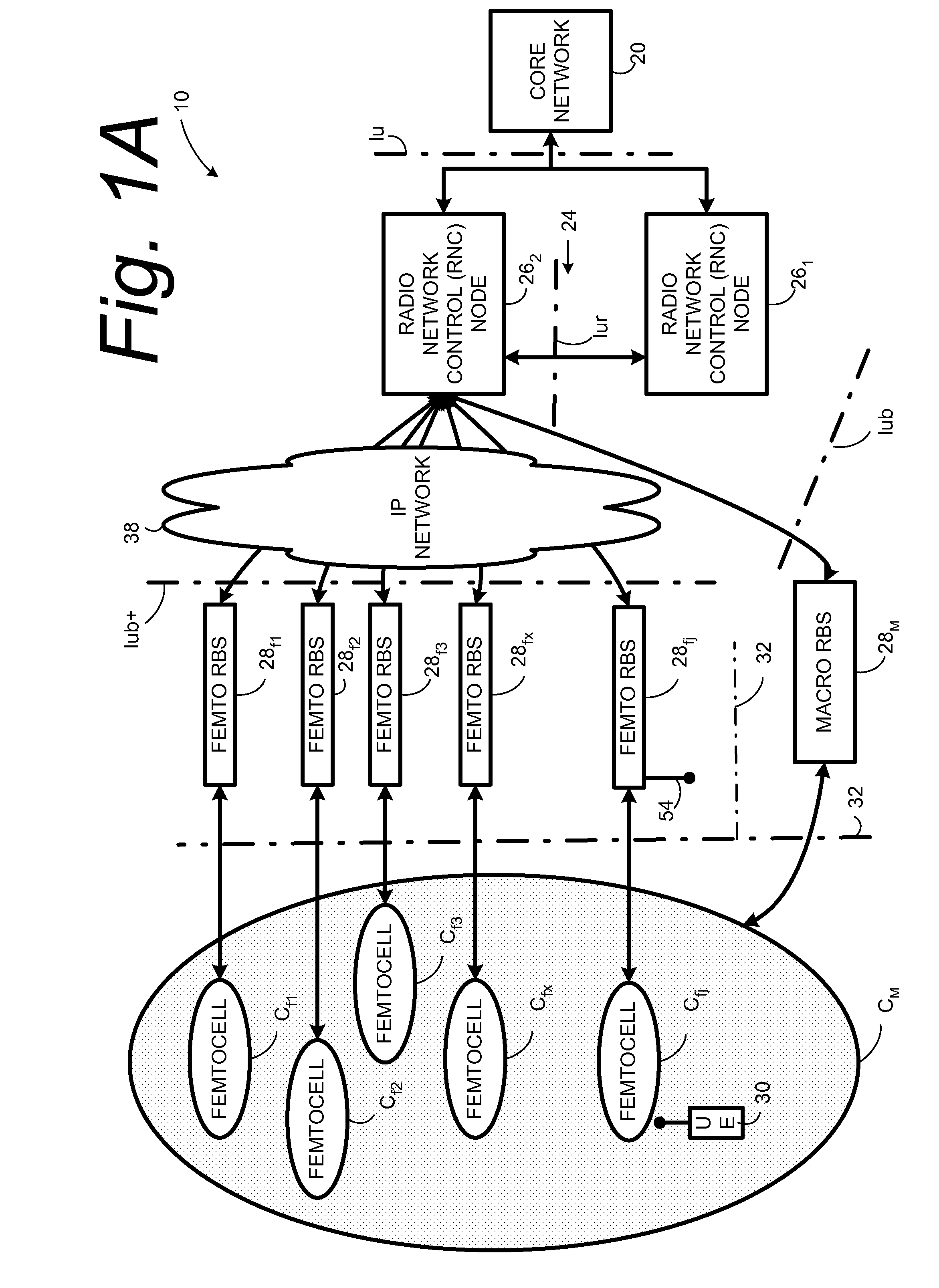
Automatic building of neighbor lists in mobile system
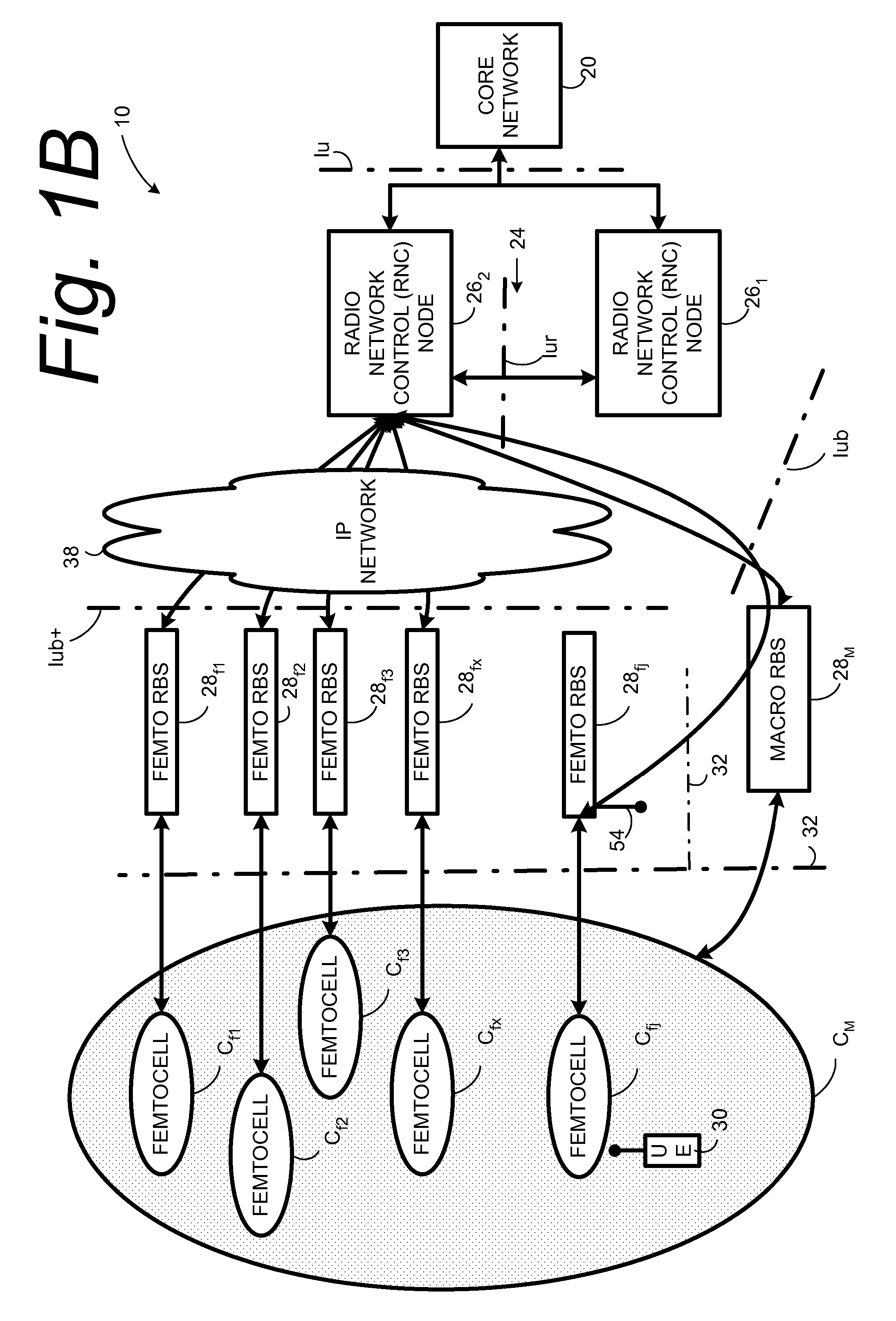
In a radio access network (24) a femto radio base station (28f) comprises a resident receiver (54) which acquires system information broadcast in a radio access network (24). At least part of the system information is used for building, at the femto radio base station (28f), a neighbor data structure (59) comprising information for neighboring cells. The neighbor data structure (59) is then used for building a neighbor list. The neighbor list is subsequently transmitted from the femto radio base station (28f) to a user equipment unit (30) served by the femto radio base station (28f). In some example embodiments and modes, the femto radio base station (28f) reports the neighbor data structure to a network node (26, 100) other than the femto radio base station. The other node (26, 100) uses the neighbor data structure for building the neighbor list at the other node. In some example embodiments and modes, acquisition of the system information comprises scanning a surrounding macro coverage area of the femto radio base station for obtaining cell identity information for detected cells. In other example embodiments and modes, the acquisition of the system information can additionally comprise camping on a macro cell and using / consulting at least one system information block in the camped-on macro cell is consulted / used for obtaining information about at least one neighboring cell.
Owner:TELEFON AB LM ERICSSON (PUBL)
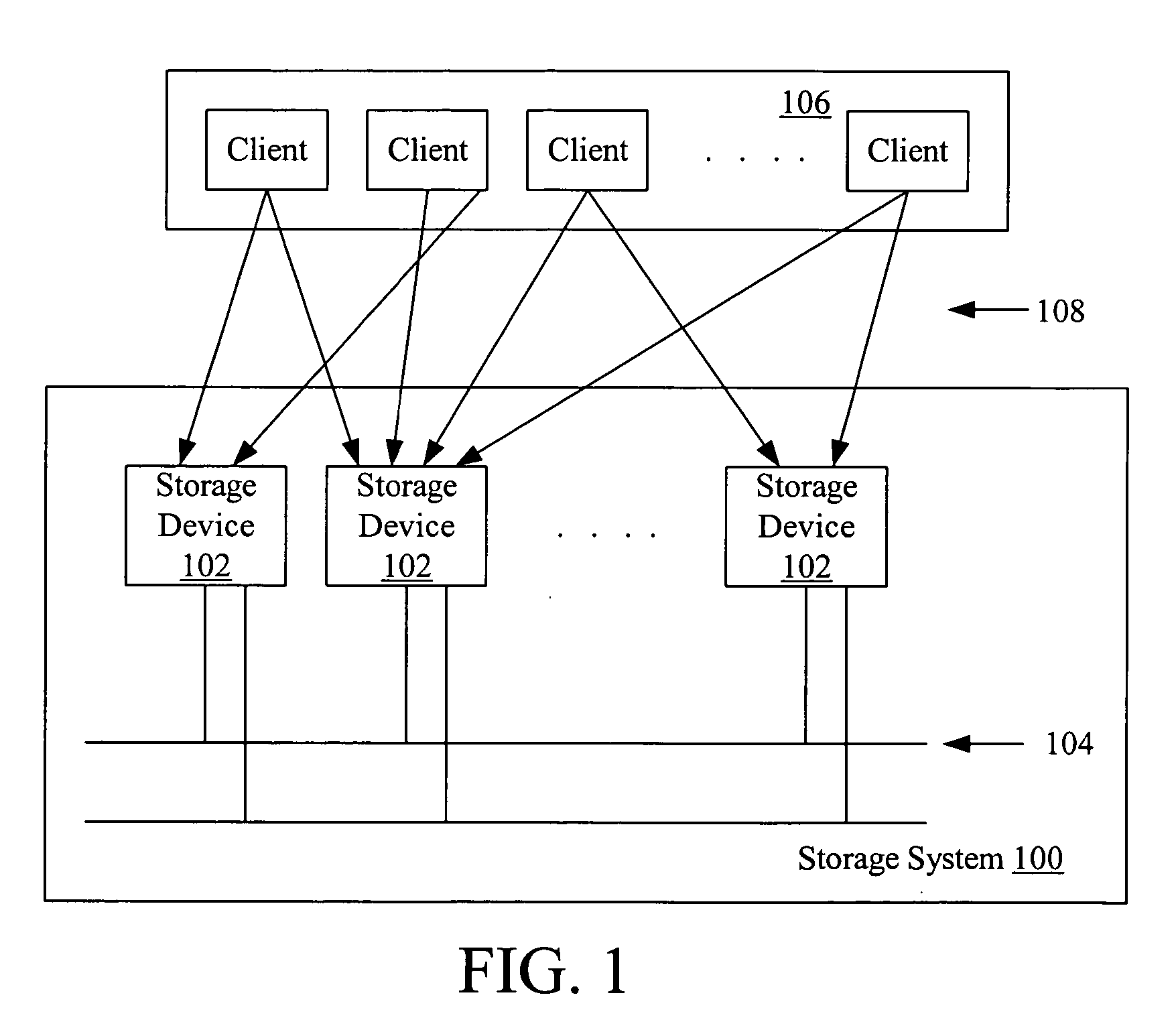
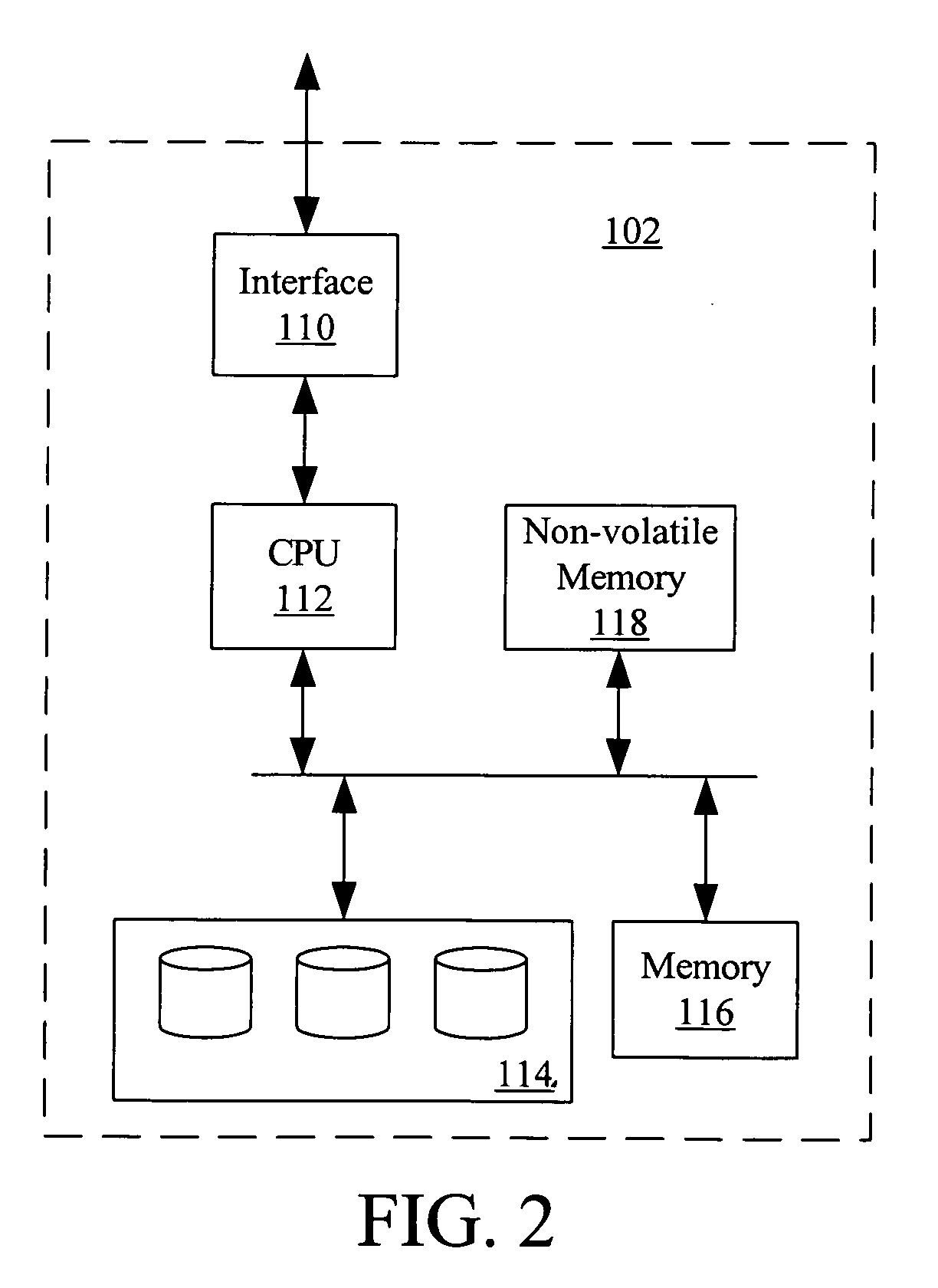
Maintaining erase counts in non-volatile storage systems
InactiveUS20040080985A1Memory architecture accessing/allocationMemory adressing/allocation/relocationData structureVolatile memory
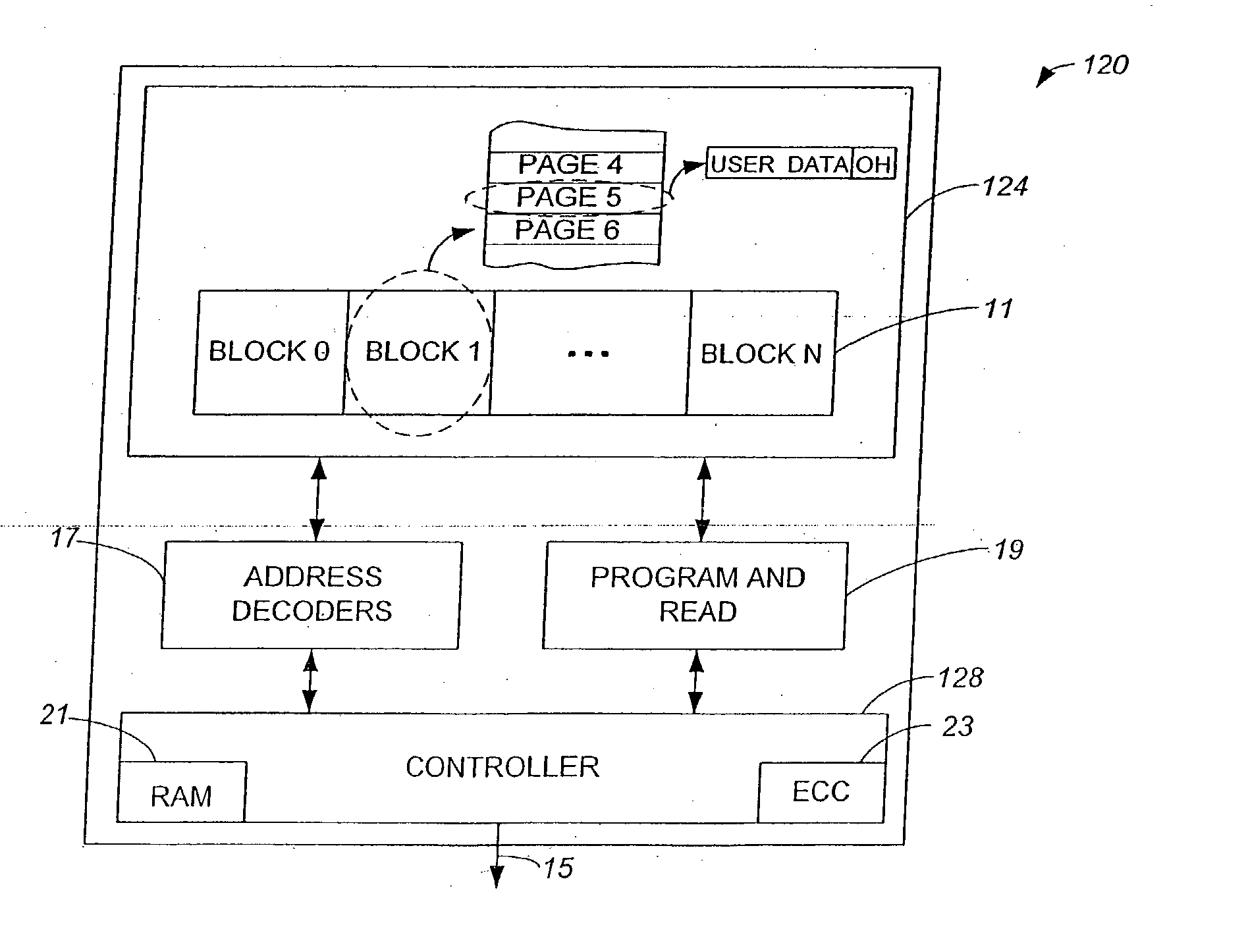
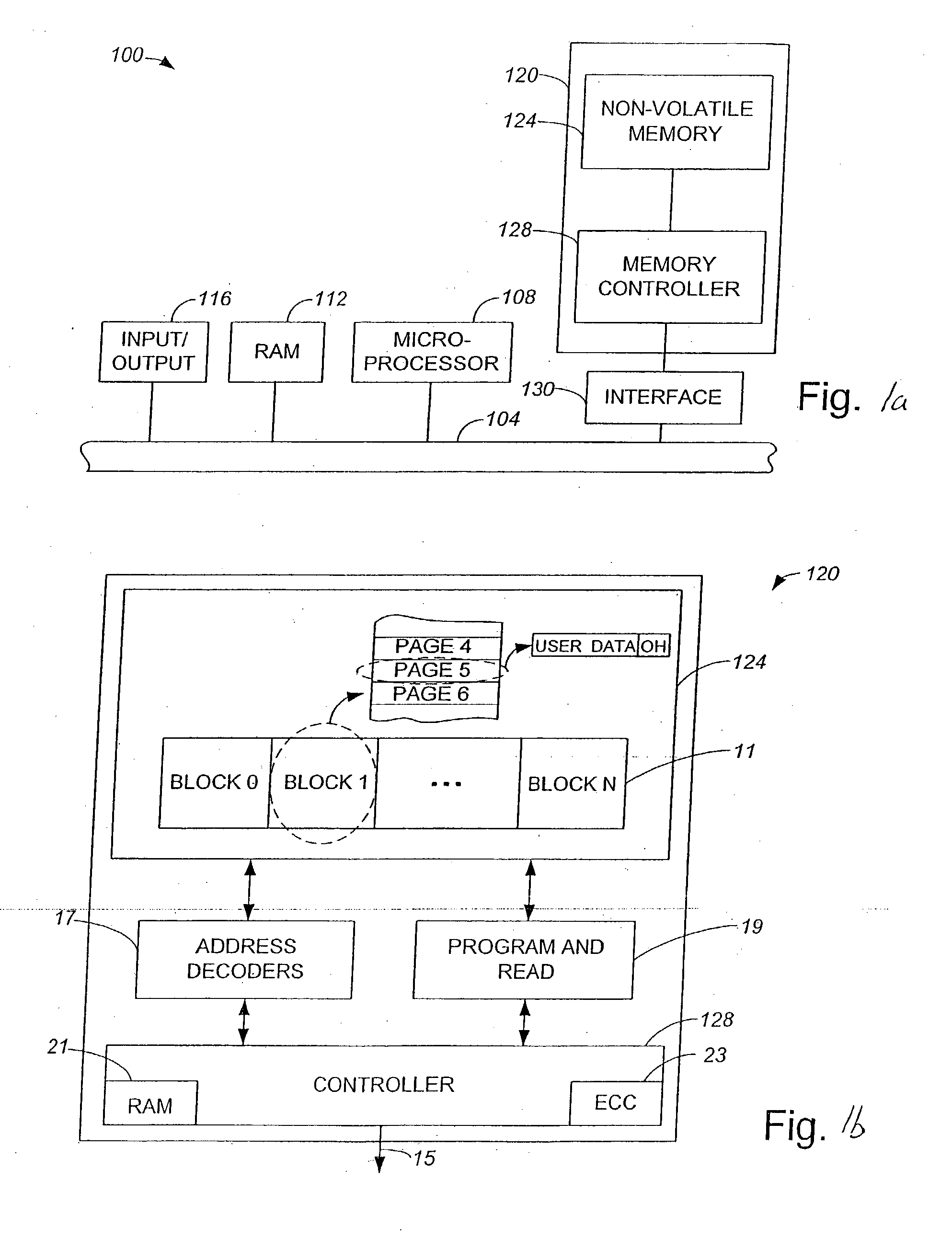
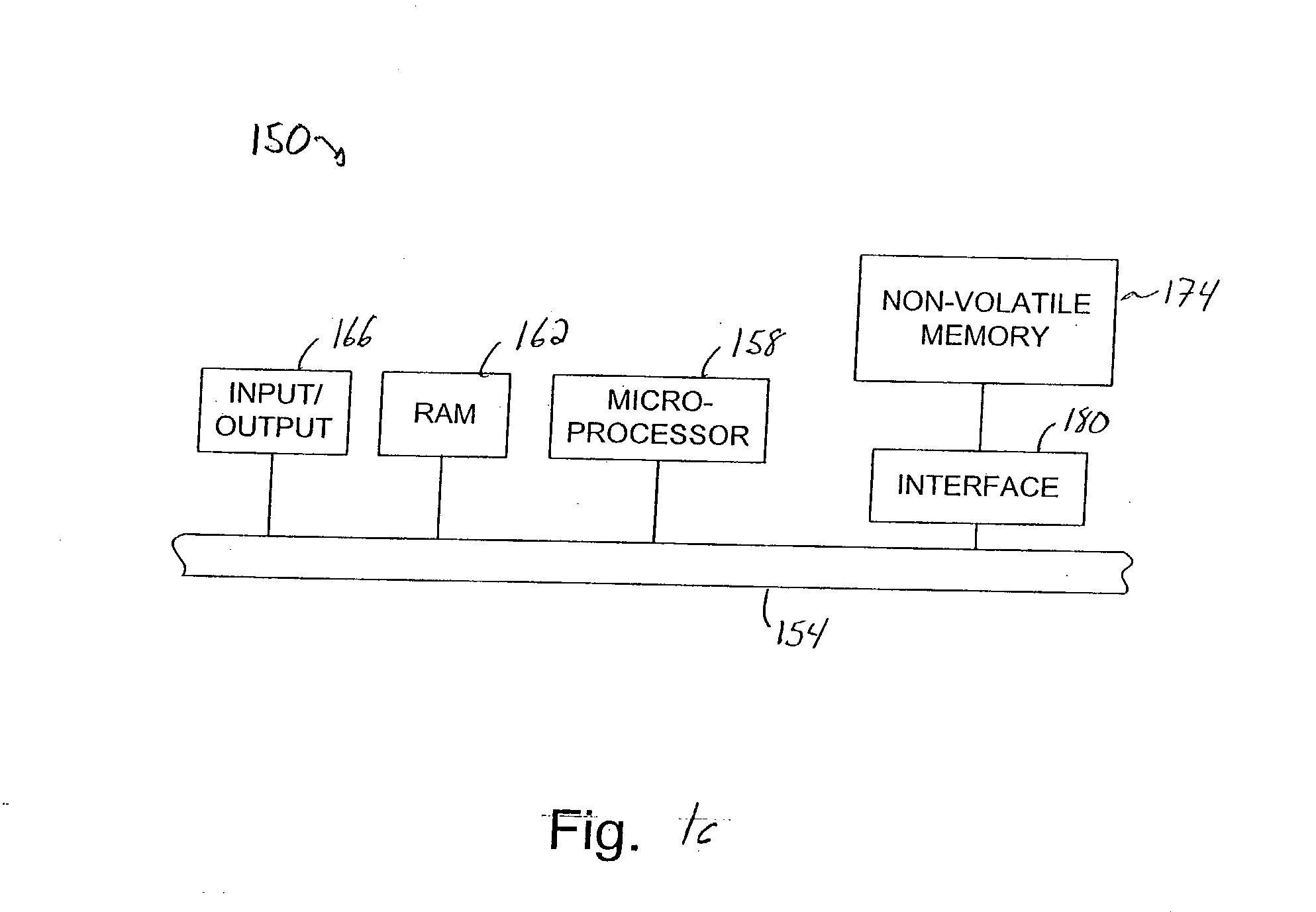
Methods and apparatus for storing erase counts in a non-volatile memory of a non-volatile memory system are disclosed. According to one aspect of the present invention, a data structure in a non-volatile memory includes a first indicator that provides an indication of a number of times a first block of a plurality of blocks in a non-volatile memory has been erased. The data structure also includes a header that is arranged to contain information relating to the blocks in the non-volatile memory.
Owner:SANDISK TECH LLC
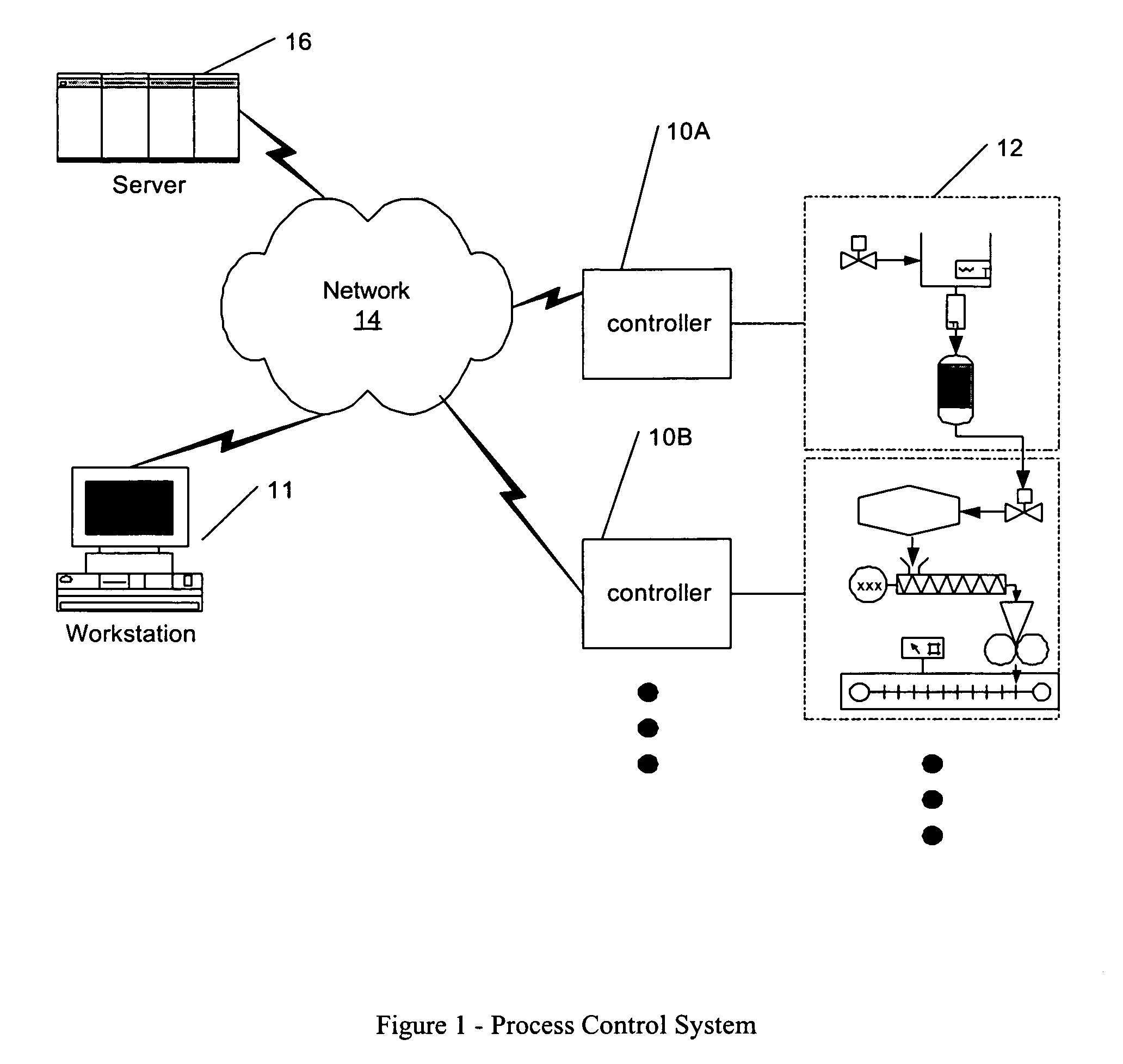
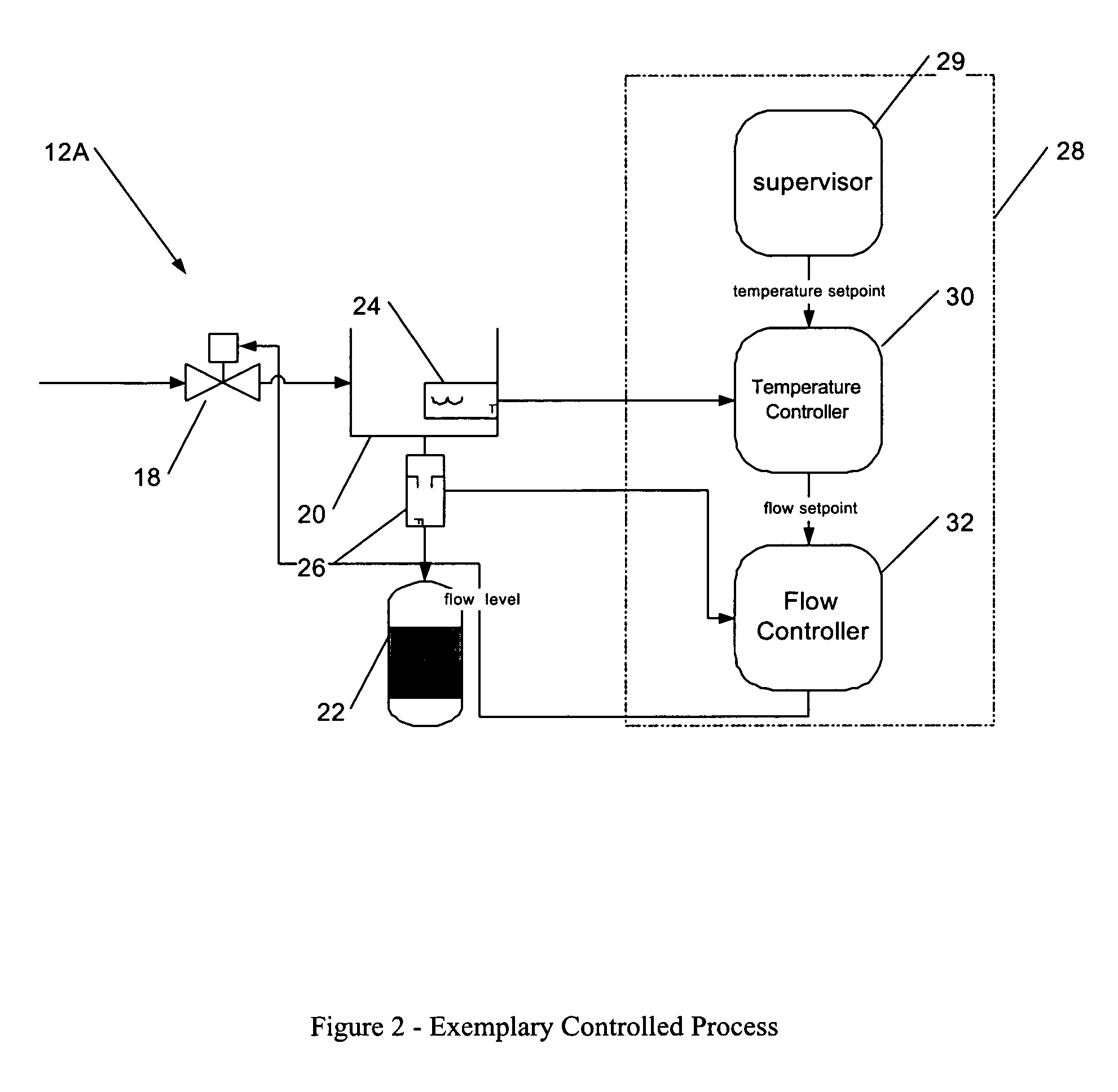
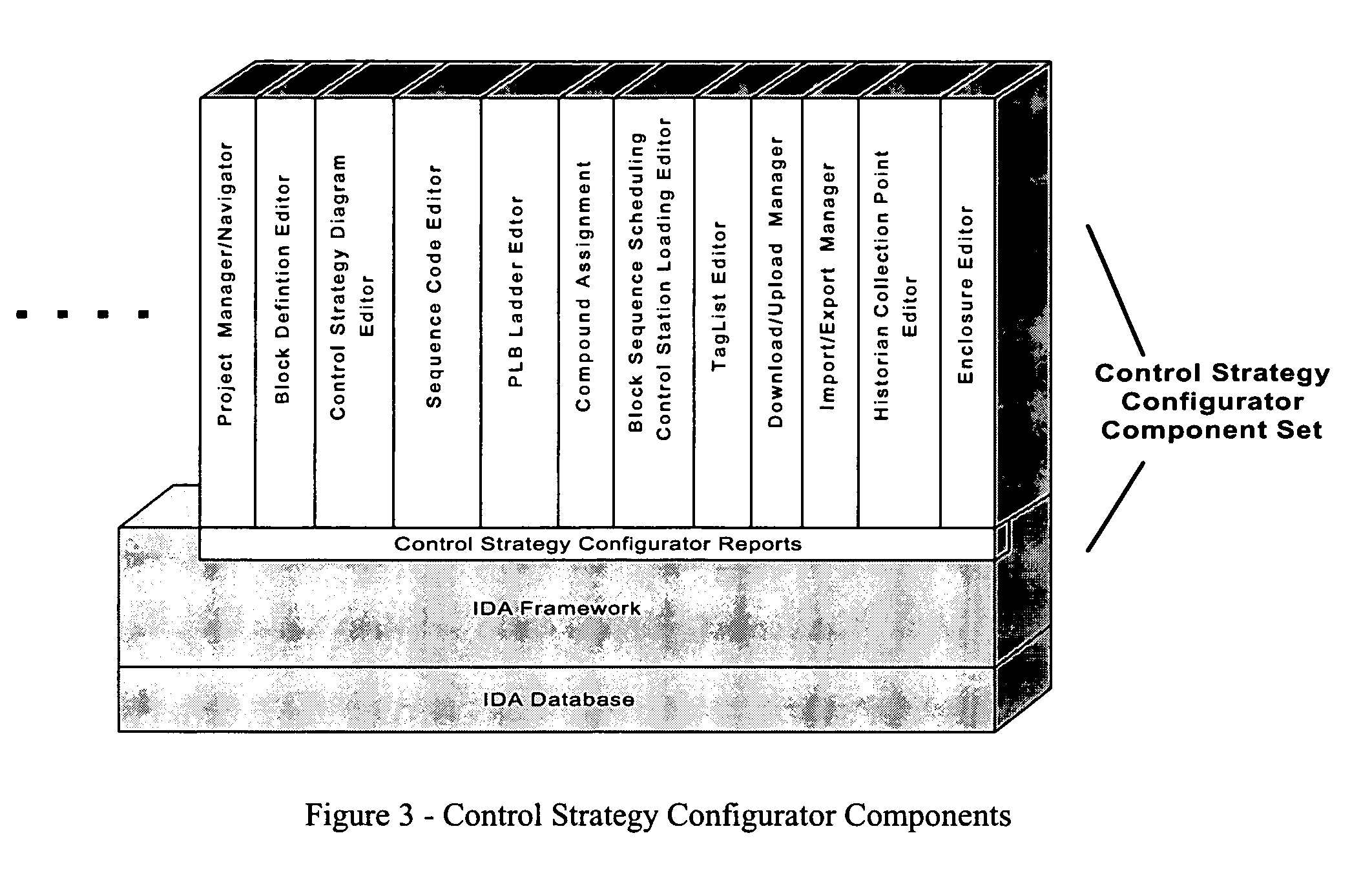
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
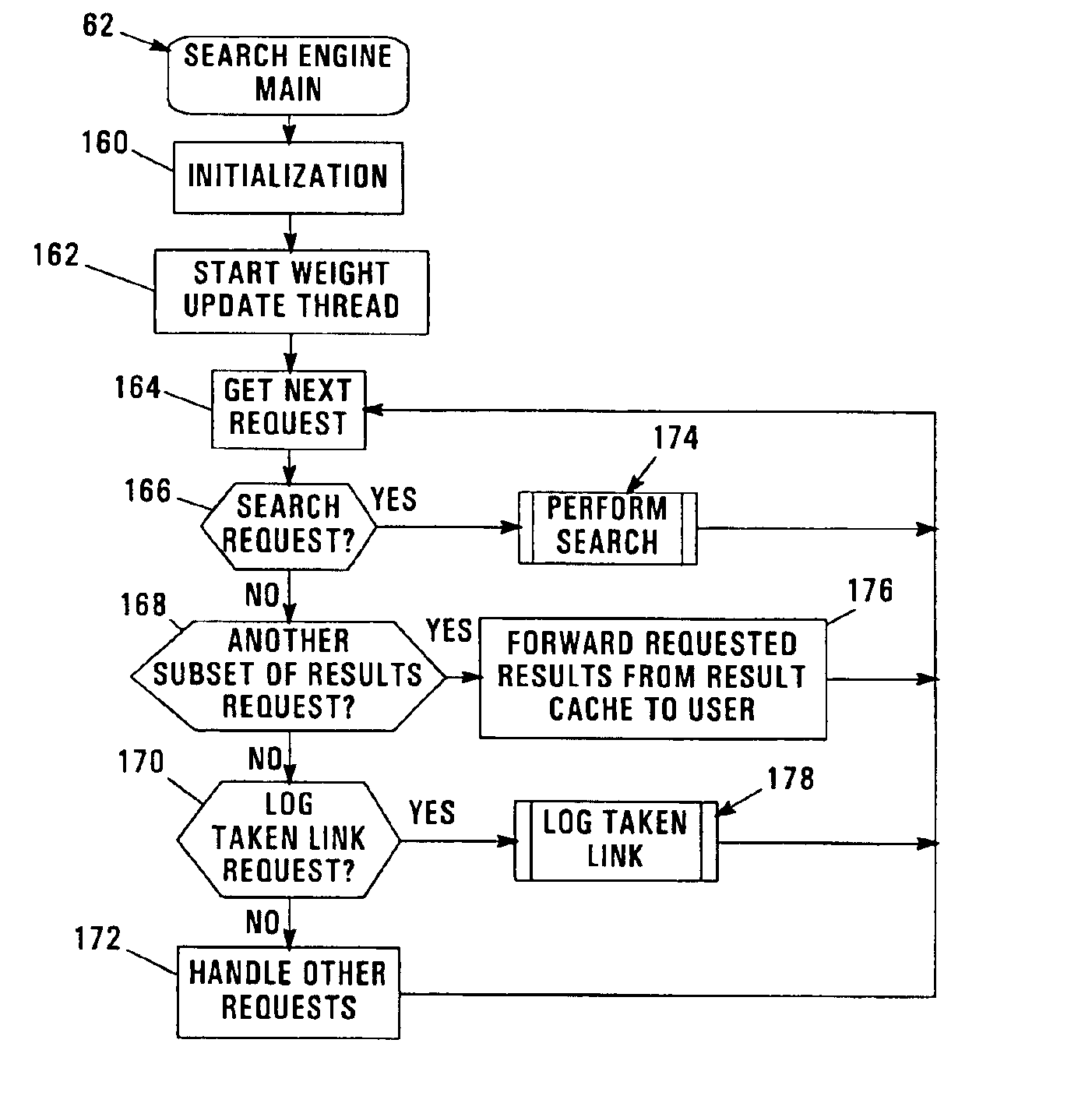
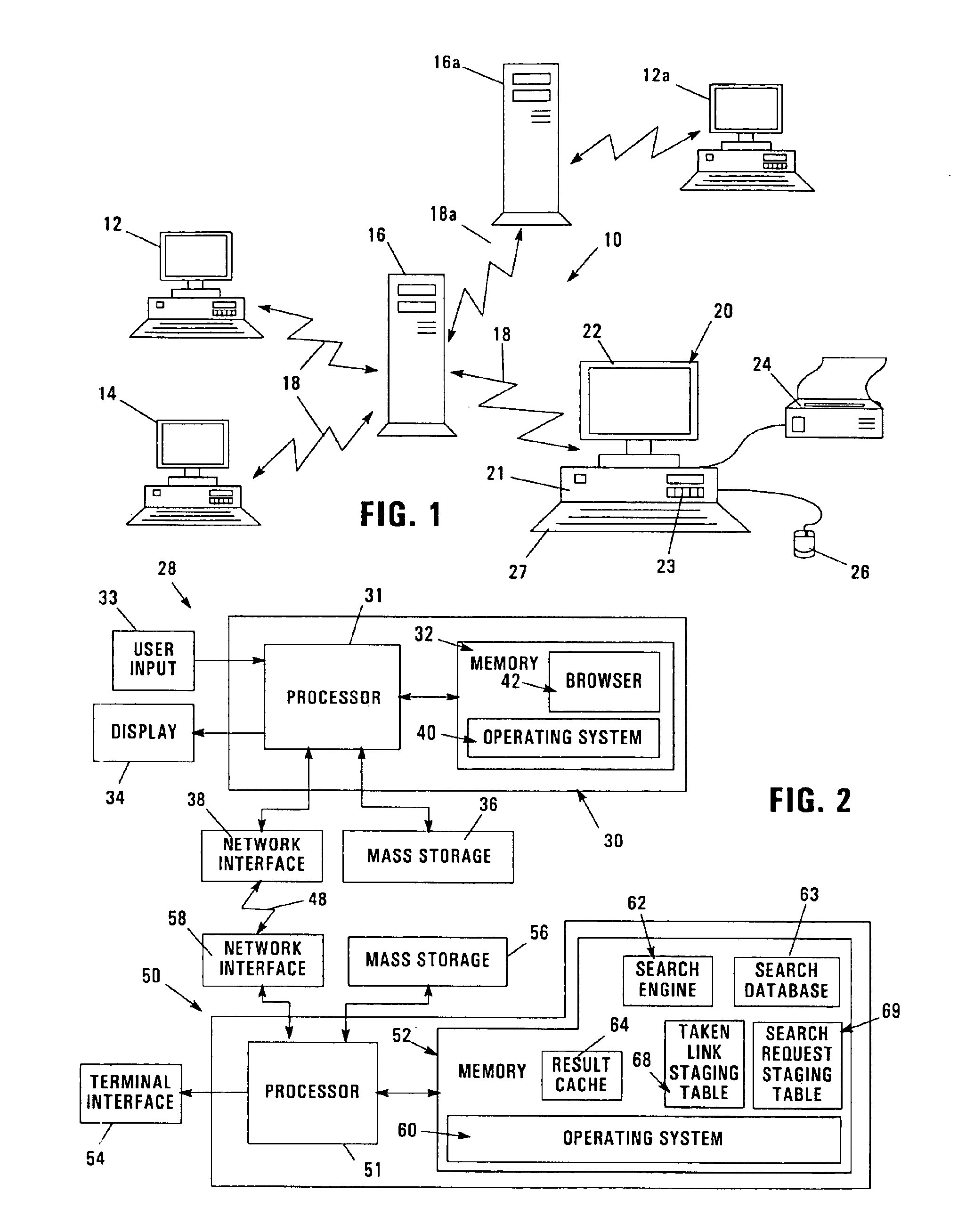
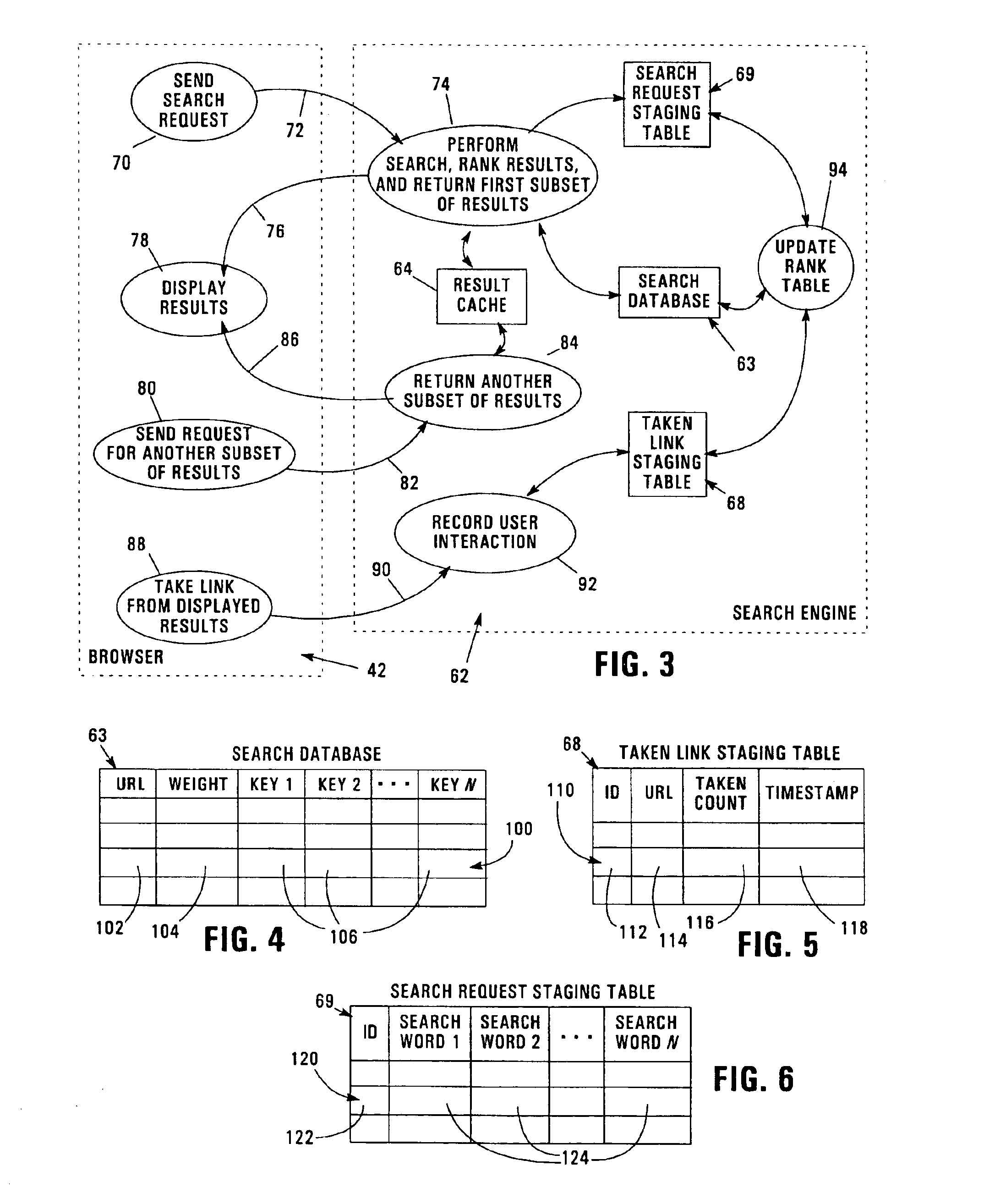
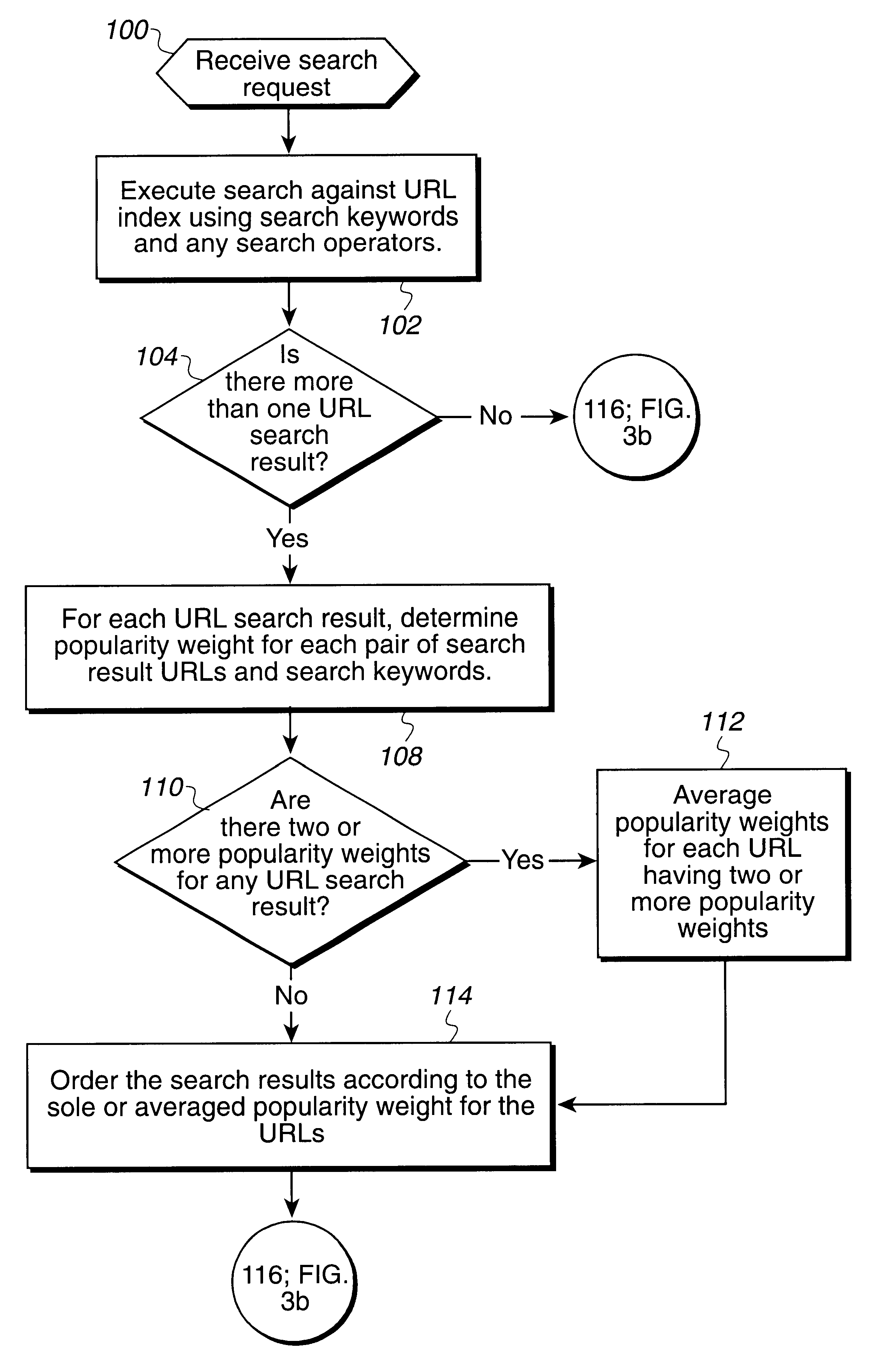
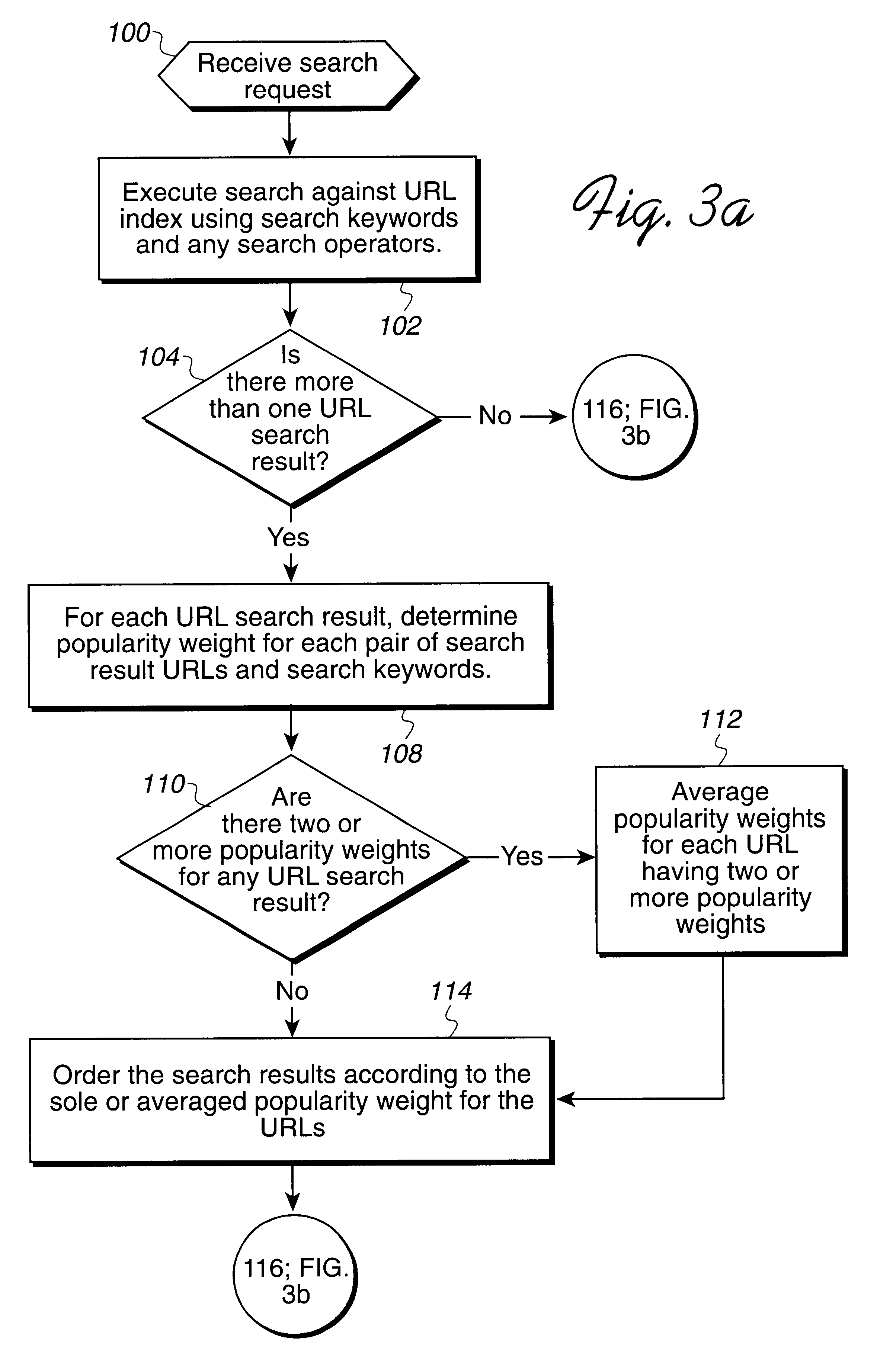
Ordering of database search results based on user feedback
An apparatus, program product, and method rely on user interaction in the ordering search results returned by a search engine. Each of a plurality of records in a database is associated with a user feedback parameter that is used in ordering the records identified in a result set generated in response to a search request. The user feedback parameter for a given record may be selectively updated in response to detecting multiple accesses thereto by a user and / or in response to detecting that the record is the most recently accessed record in the result set. In addition, the user feedback parameter for a given record may be configured with a plurality of weights that are respectively associated with particular keywords, such that ordering of the records in a result set can utilize only those weights that are associated with keywords that match a particular search request. Furthermore, a search request data structure may be utilized to store a plurality of search request records, each including a search request identifier identifying a unique combination of keywords, and a result set identifier identifying a subset of a plurality of records in a database that match the unique combination of keywords. The search request data structure may be accessed in response to a search request to locate a search request record including a search request identifier that matches the keywords provided in the search request, with a result set generated that identifies the subset of records identified in the result set identifier in the located search request record.
Owner:IBM CORP
Data collection and analysis system
ActiveUS20080228306A1Easy to useExcessive signalingTesting/monitoring control systemsDigital computer detailsDistributed memoryData harvesting
A sensor network collects time-series data from a process tool and supplies the data to an analysis system where pattern analysis techniques are used to identify structures and to monitor subsequent data based on analysis instructions or a composite model. Time-series data from multiple process runs are used to form a composite model of a data structure including variation. Comparison with the composite model gives an indication of tool health. A sensor network may have distributed memory for easy configuration.
Owner:KLA CORP
Optimizing media player memory during rendering
ActiveUS7054888B2Efficient identificationImprove playback experienceData processing applicationsElectronic editing digitised analogue information signalsPersonal computerSmall files
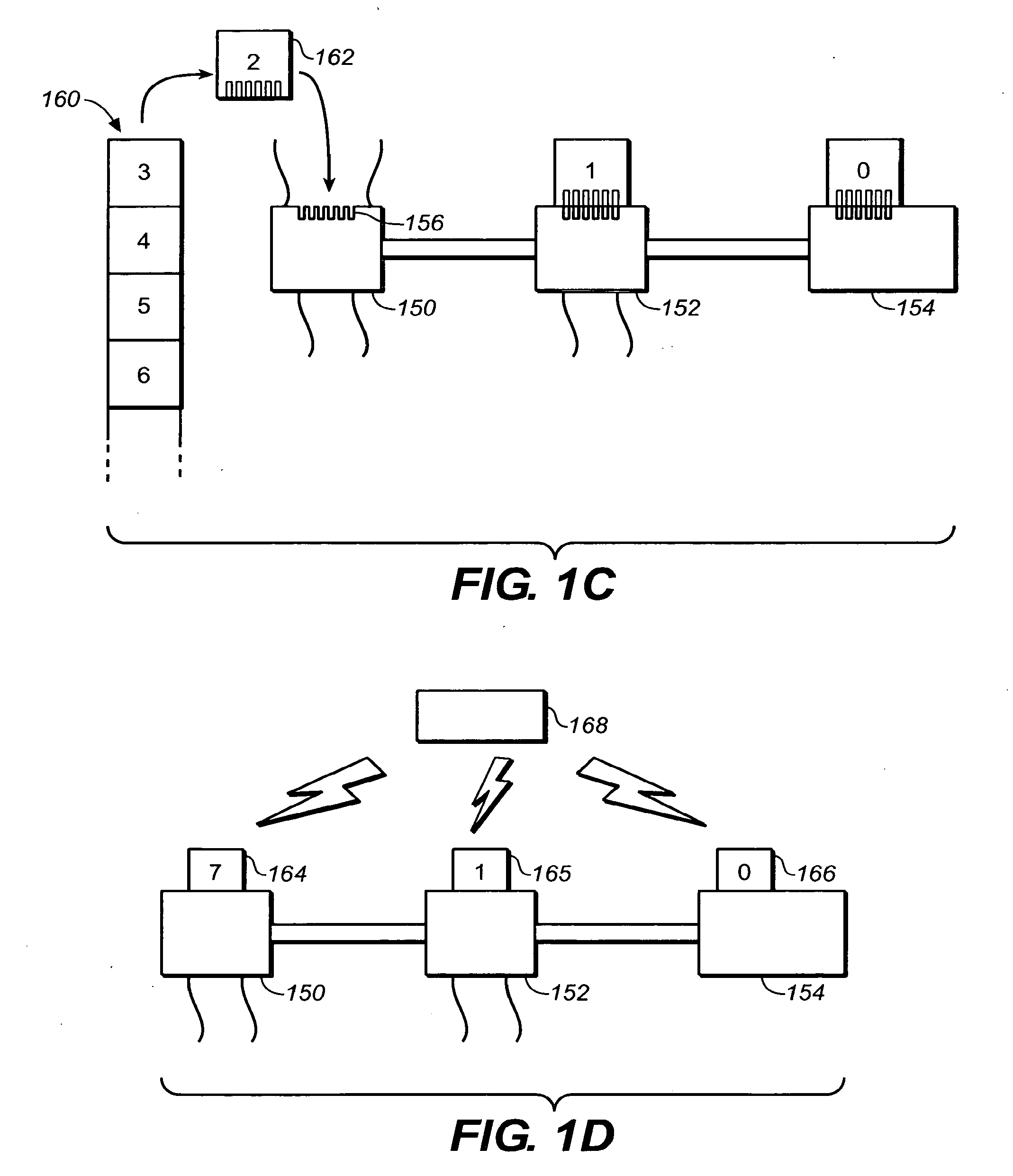
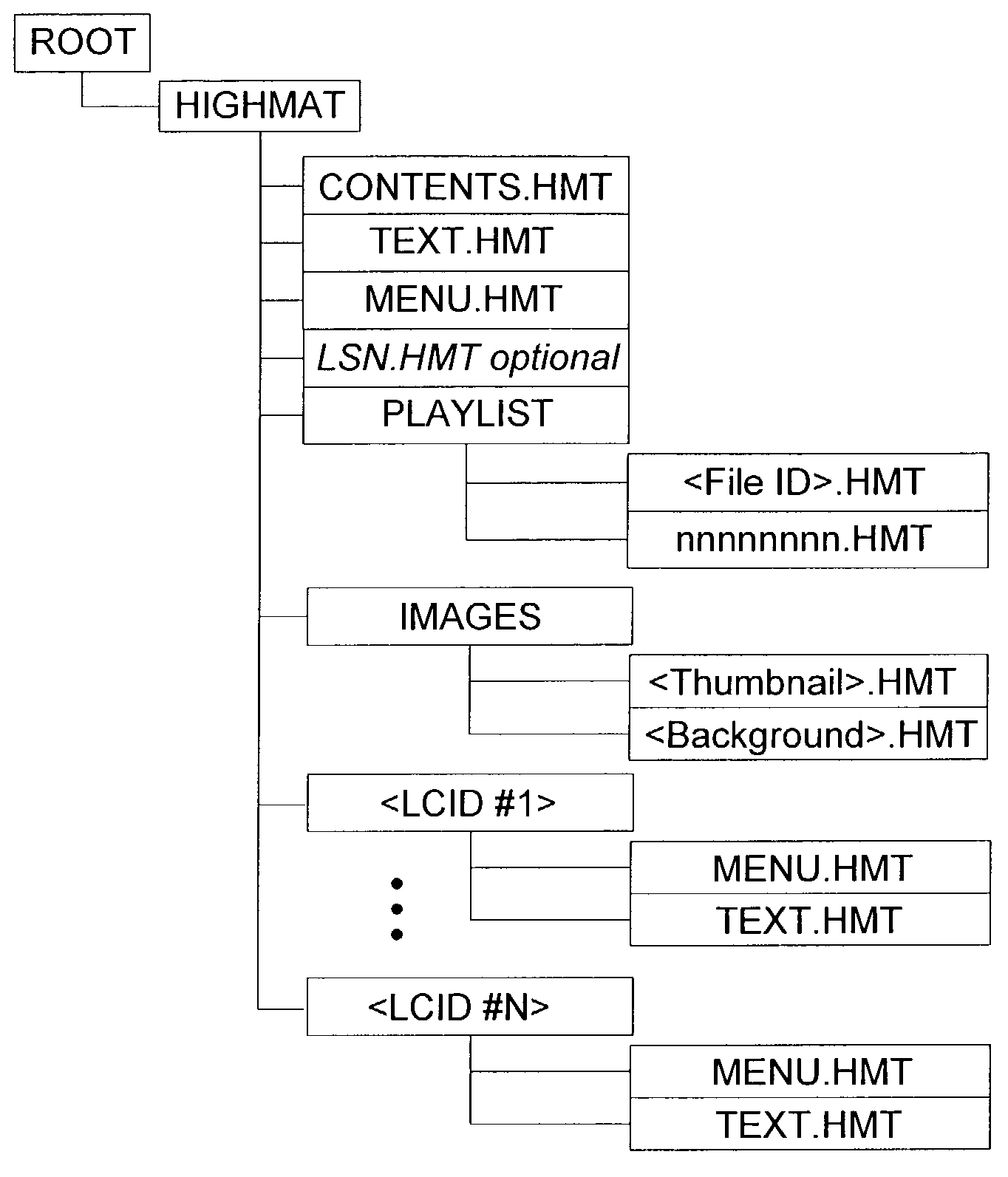
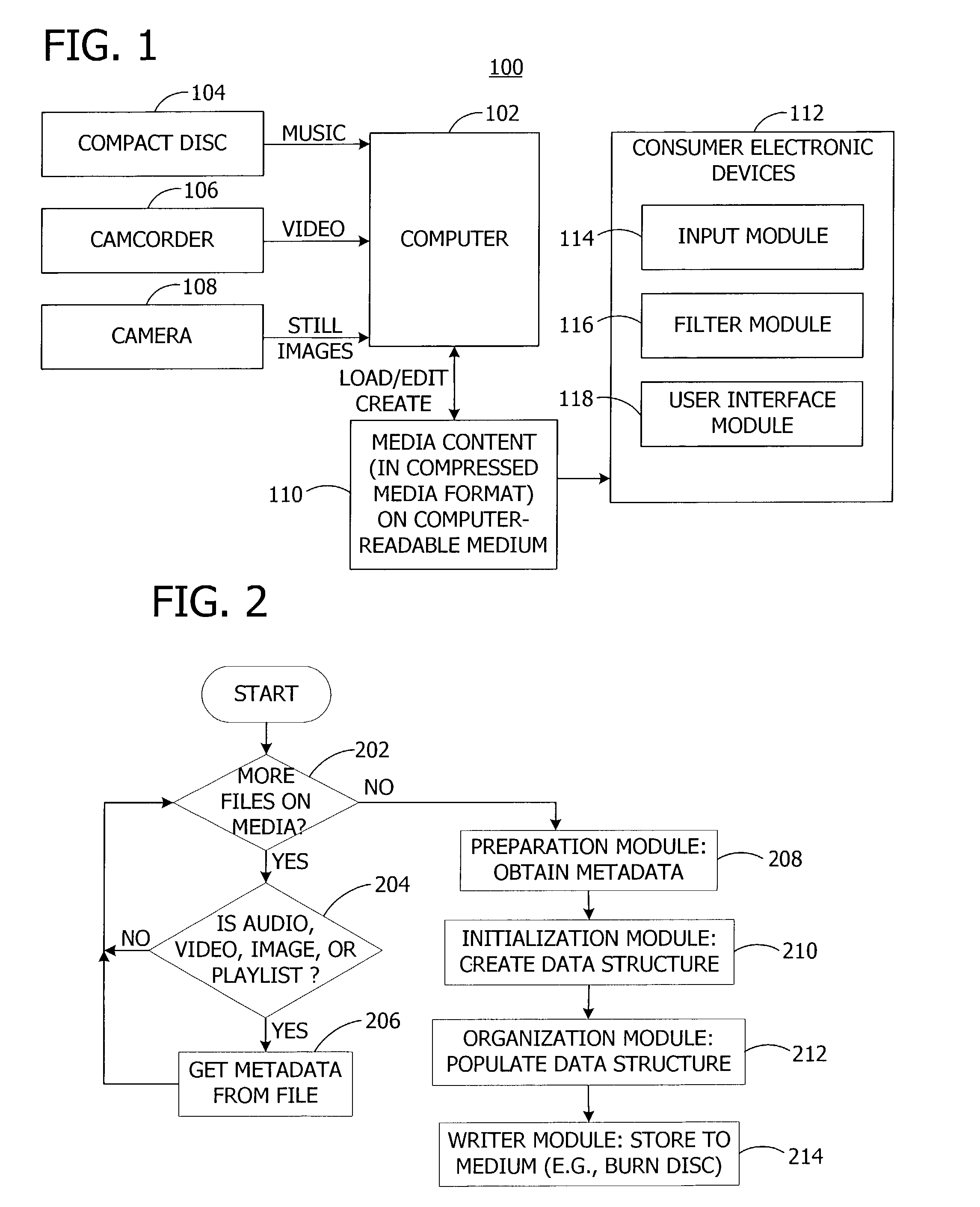
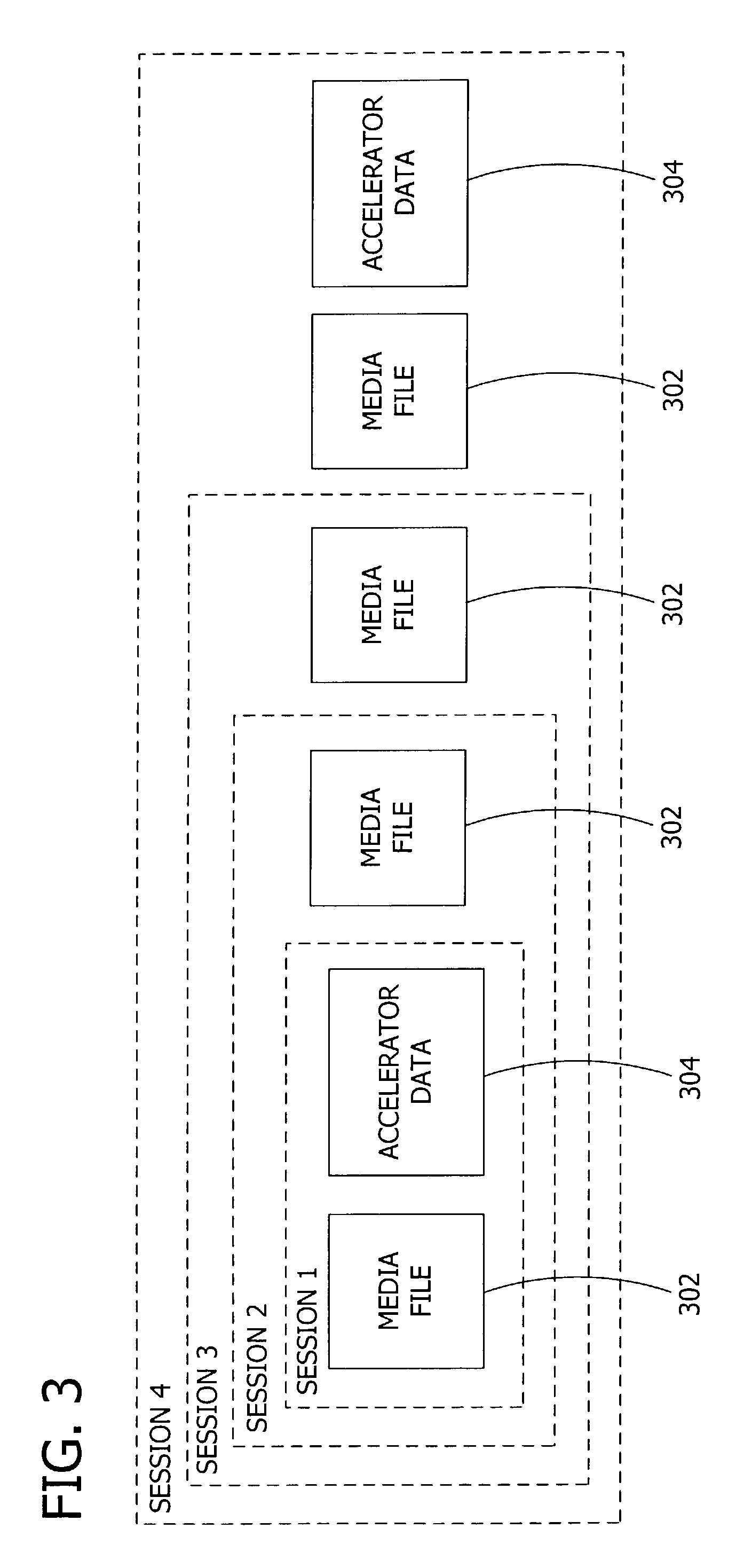
Optimizing operation of a media player during rendering of media files. The invention includes authoring software to create a data structure and to populate the created data structure with obtained metadata. The invention also includes rendering software to retrieve the metadata from the data structure and to identify media files to render. In one embodiment, the invention is operable as part of a compressed media format having a set of small files containing metadata, menus, and playlists in a compiled binary format designed for playback on feature-rich personal computer media players as well as low cost media players.
Owner:PANASONIC CORP +1
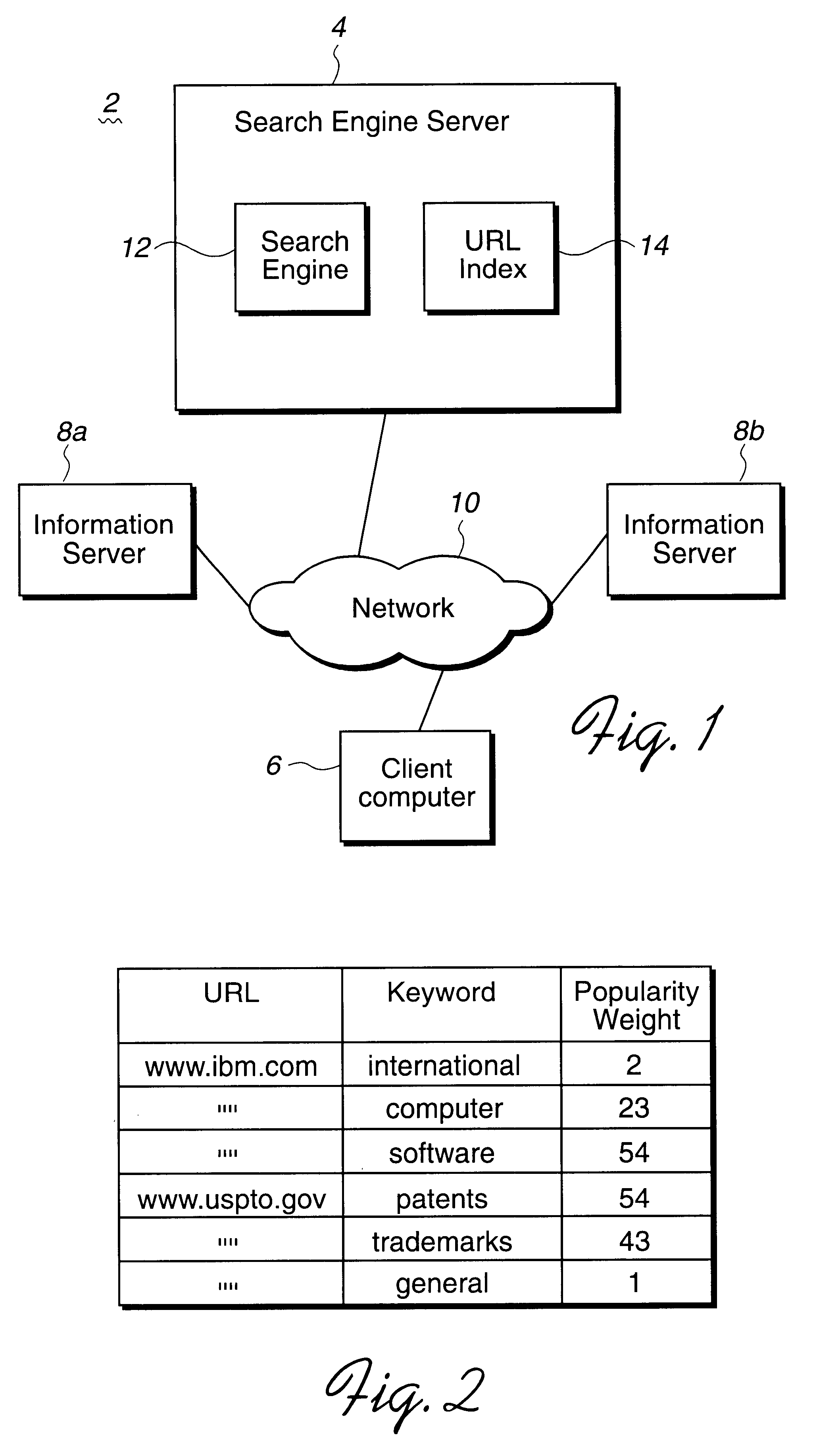
Method, system, and program for ordering search results using a popularity weighting
InactiveUS6480837B1Different popularityAccurately reflectData processing applicationsWeb data indexingDocument preparationUniform resource locator
Disclosed is a method, system, program, and data structures for ordering electronic files subject to searching. At least one keyword is associated with each file. A physical location of each file is identified by a file address, such as a URL. A popularity weight is associated with at least one file address and key word pair such that a file address is capable of having multiple associated keywords and one associated popularity weight for each file address and keyword pair. In response to executing a search query including search keywords, file address search results are received that have at least one associated keyword that matches at least one search keyword in response to executing the search query. The search results are ordered according to the popularity weight associated with each file address search result and keyword pair whose keyword matches the search keyword. A document is then coded to include the file address search results such that the document will display the file address search results according to the ordering.
Owner:LINKEDIN
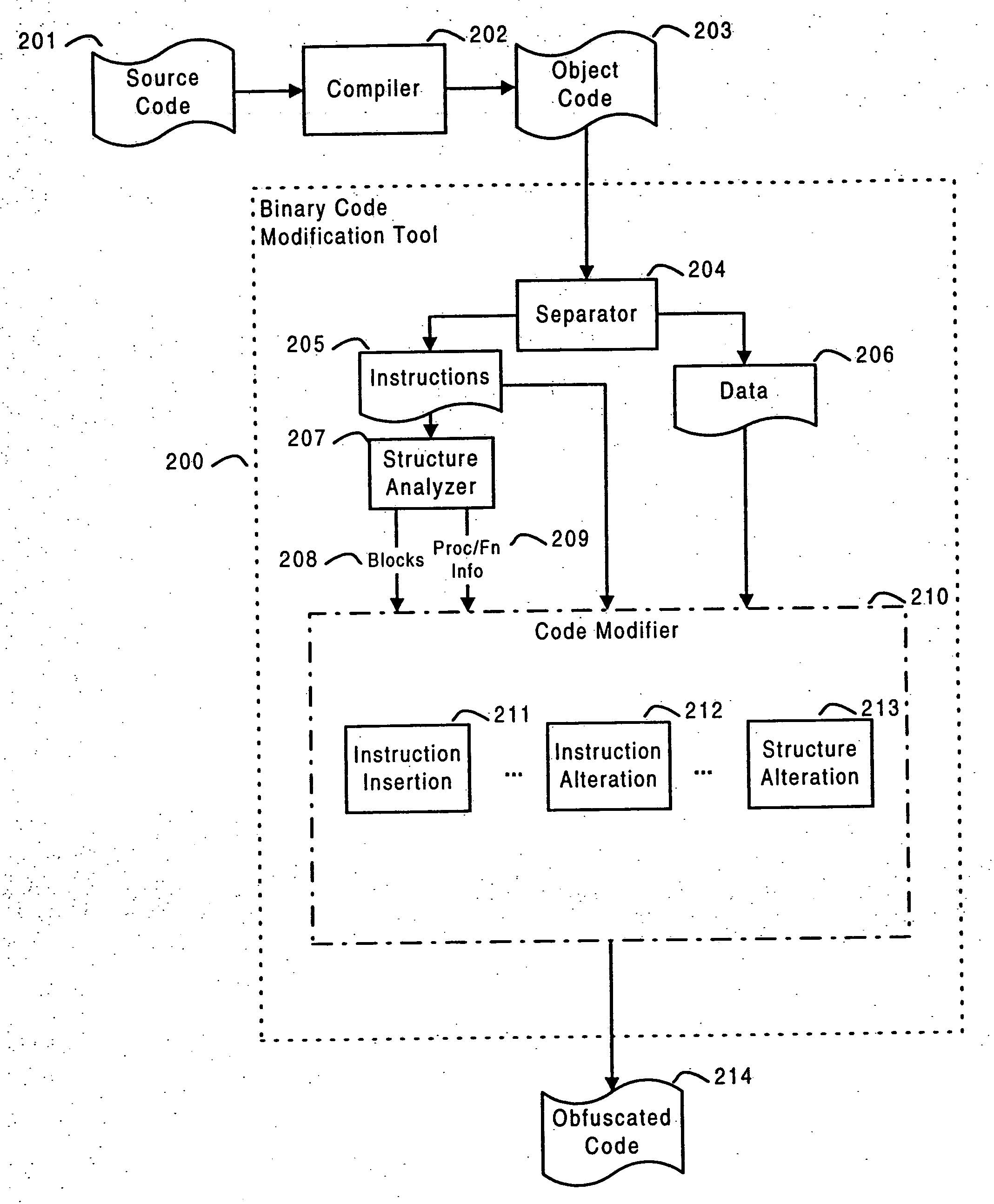
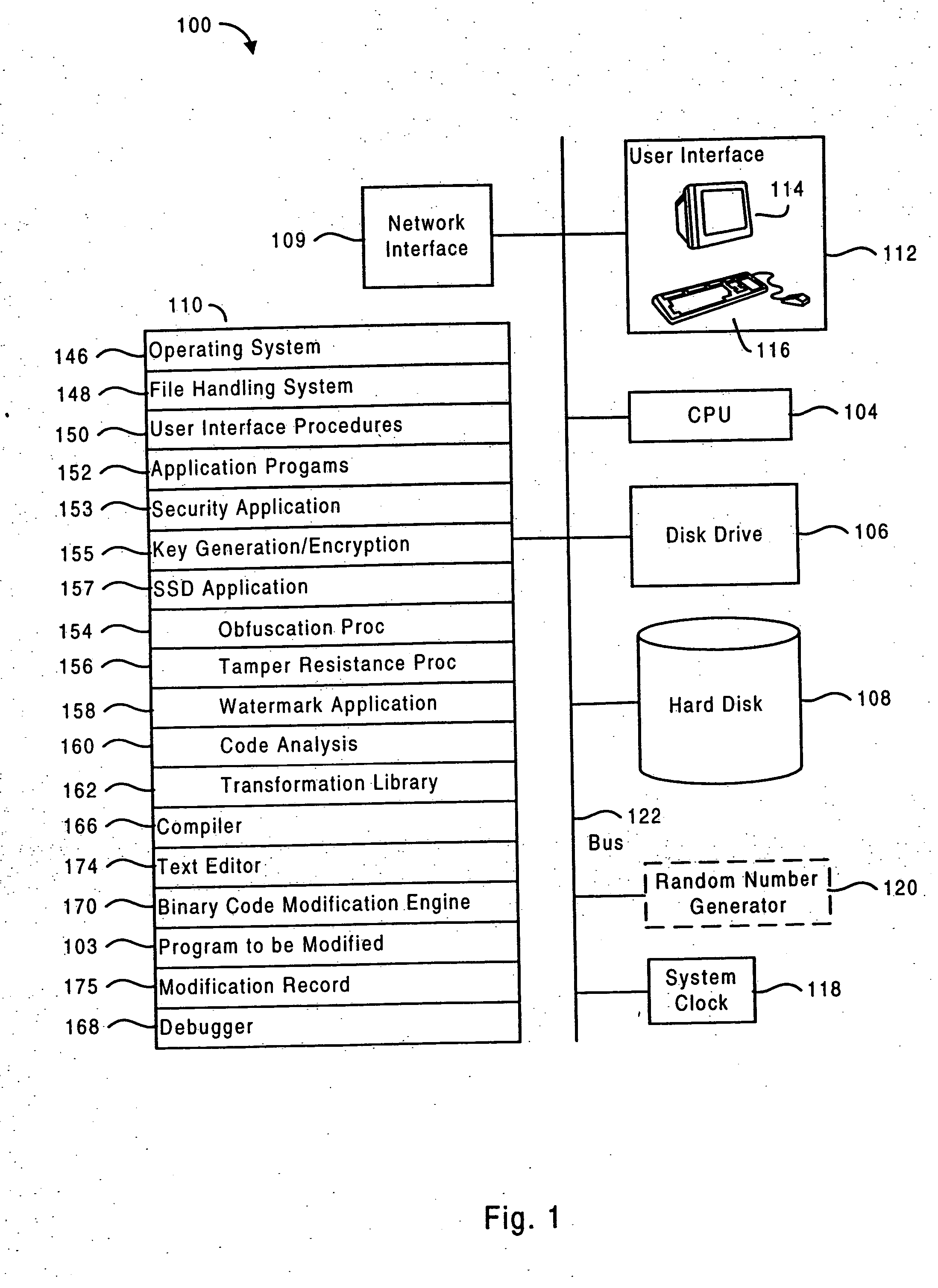
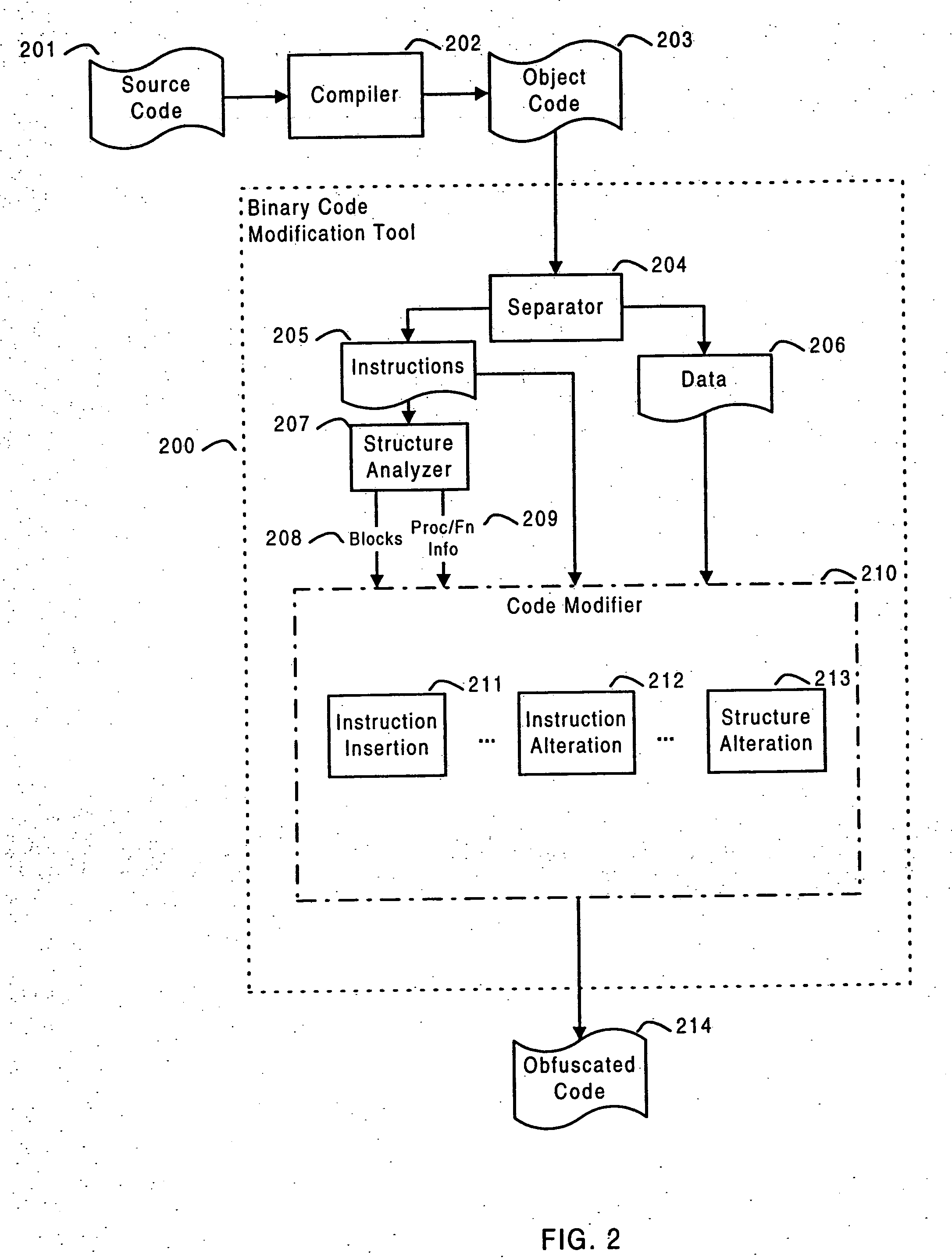
Software self-defense systems and methods
ActiveUS20050183072A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
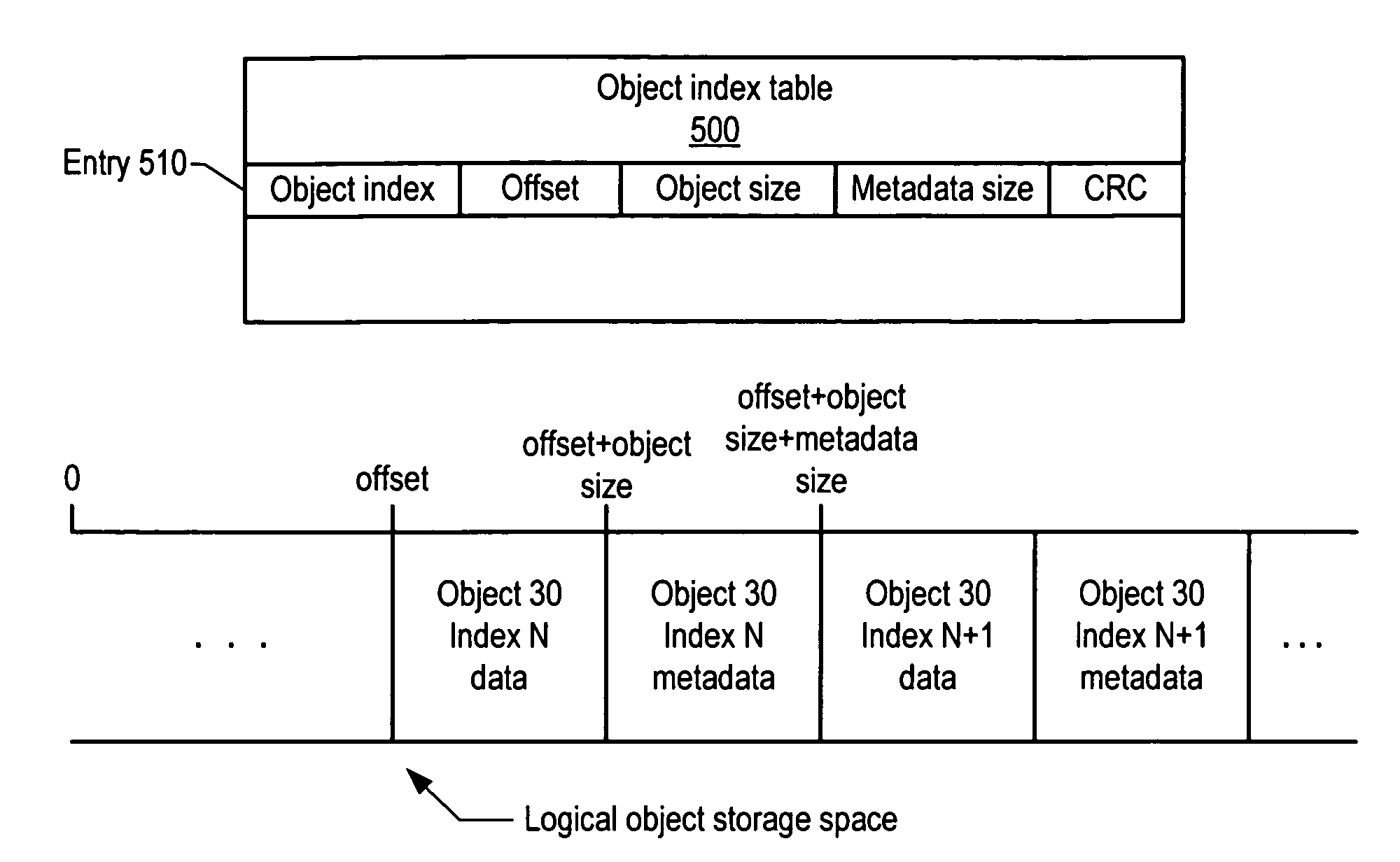
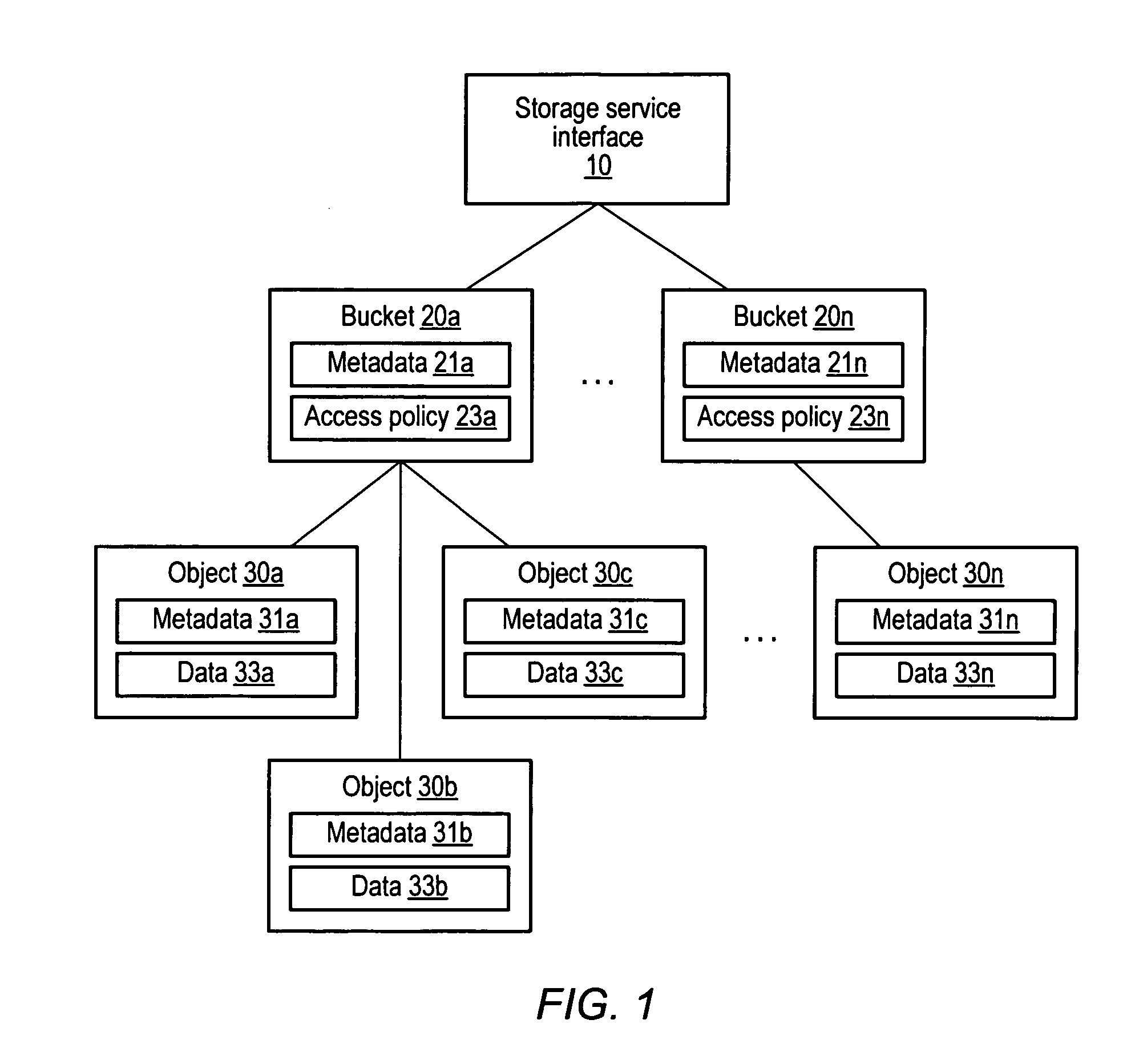
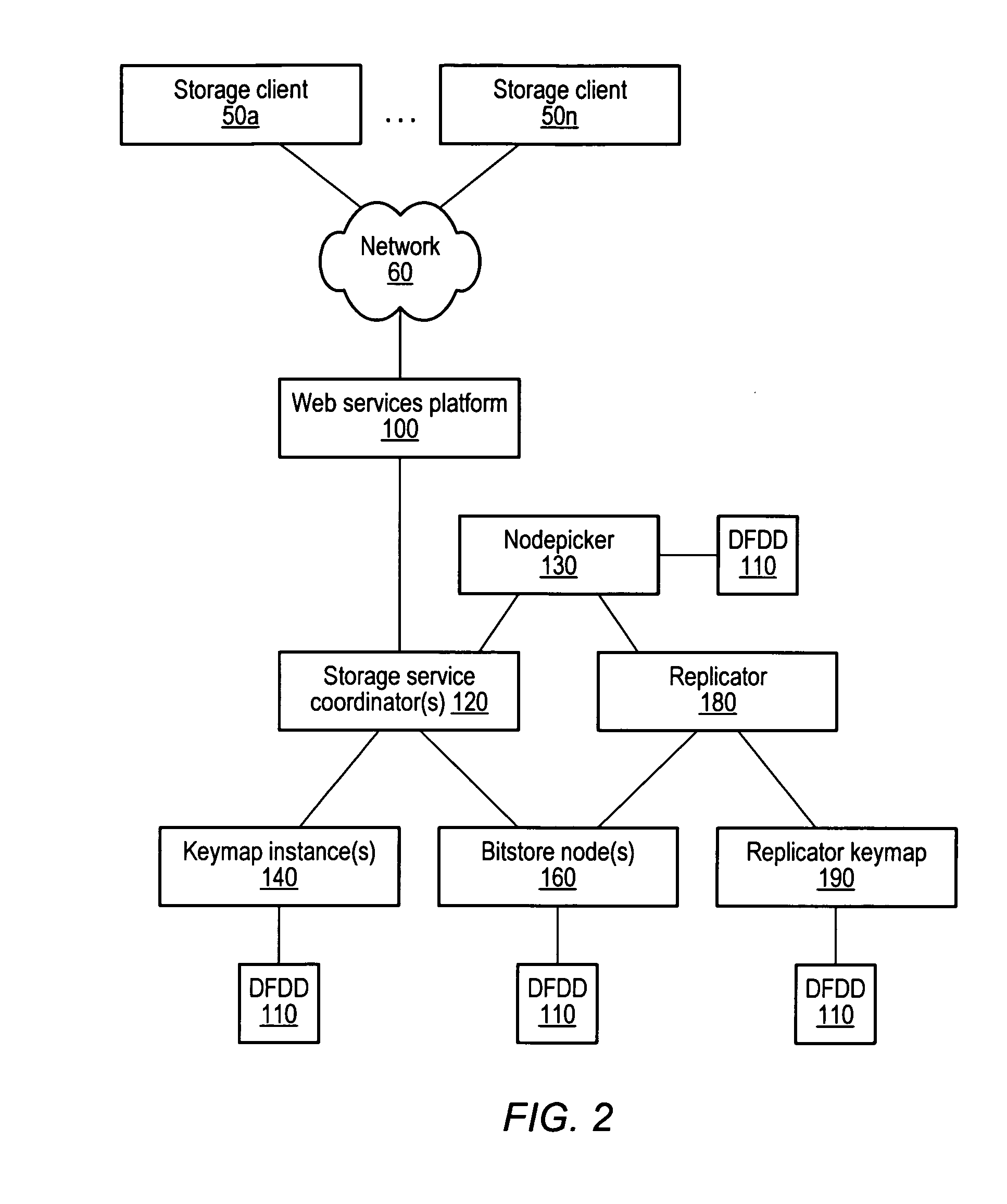
Keymap service architecture for a distributed storage system
A keymap service architecture for a distributed storage system. A system may implement storage nodes configured to store replicas of data objects, where each of the replicas is accessible via a respective locator value, and keymap instances each configured to store keymap entries corresponding respectively to the data objects. A given keymap entry may indicate a mapping from a given key value corresponding to a given data object to each respective locator value of its replicas. Each of the keymap instances may store a replica of the given keymap entry and may index its respective stored keymap entries within a respective index data structure including hierarchically arranged index nodes corresponding to keymap entries. For a given keymap entry having a given corresponding index node, each tag value associated with each ancestor of the given corresponding index node may be a prefix of the given key value.
Owner:AMAZON TECH INC
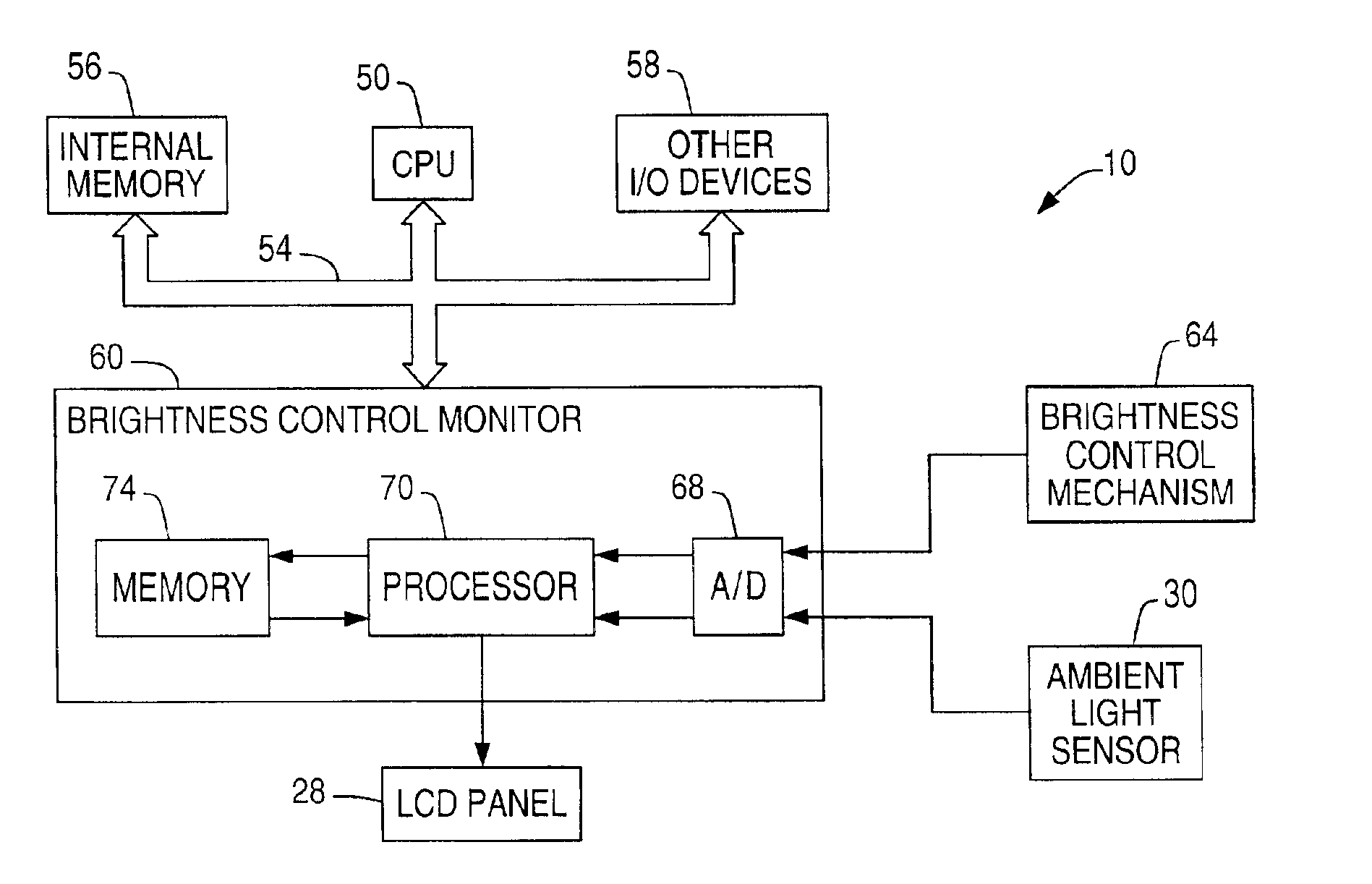
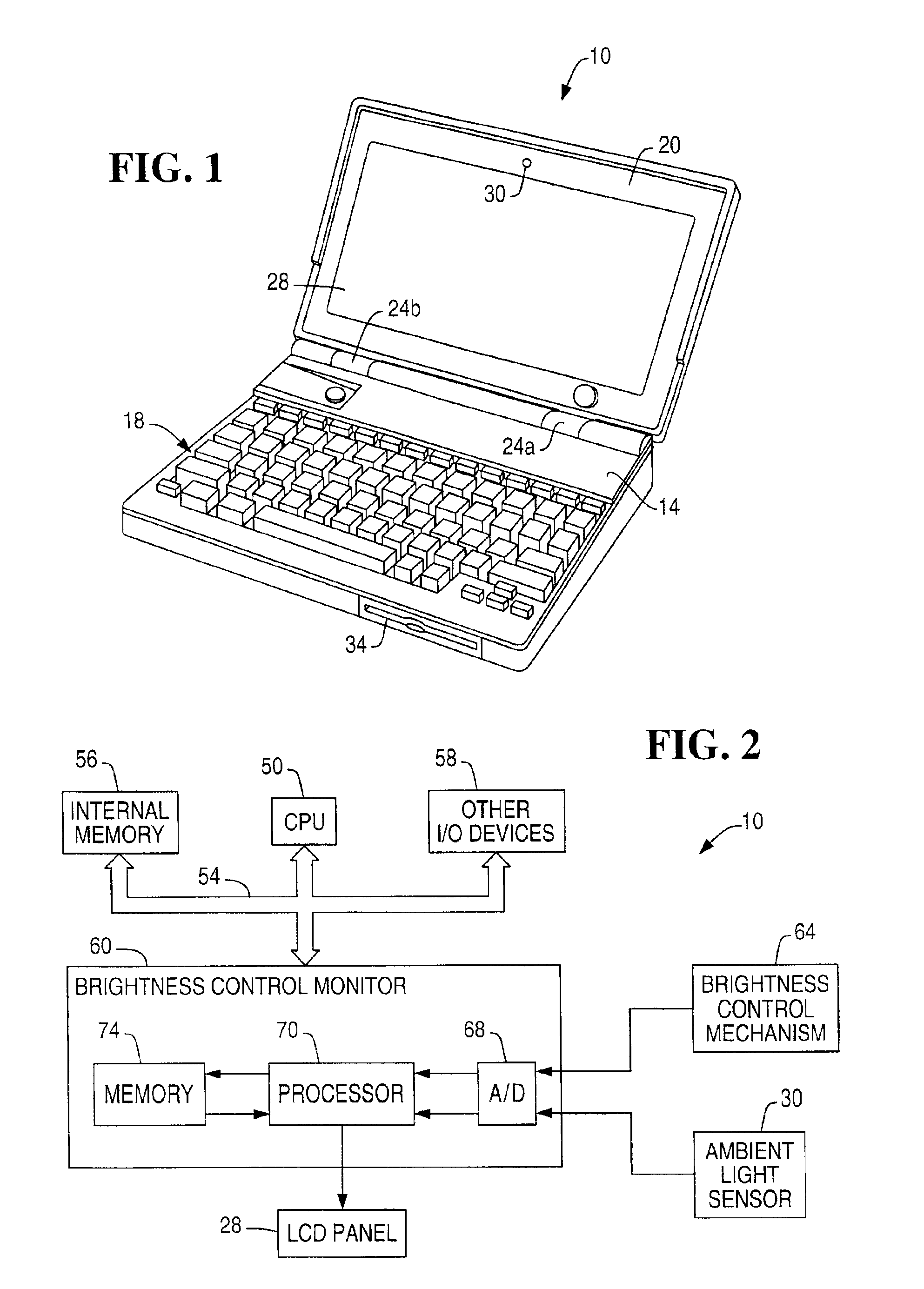
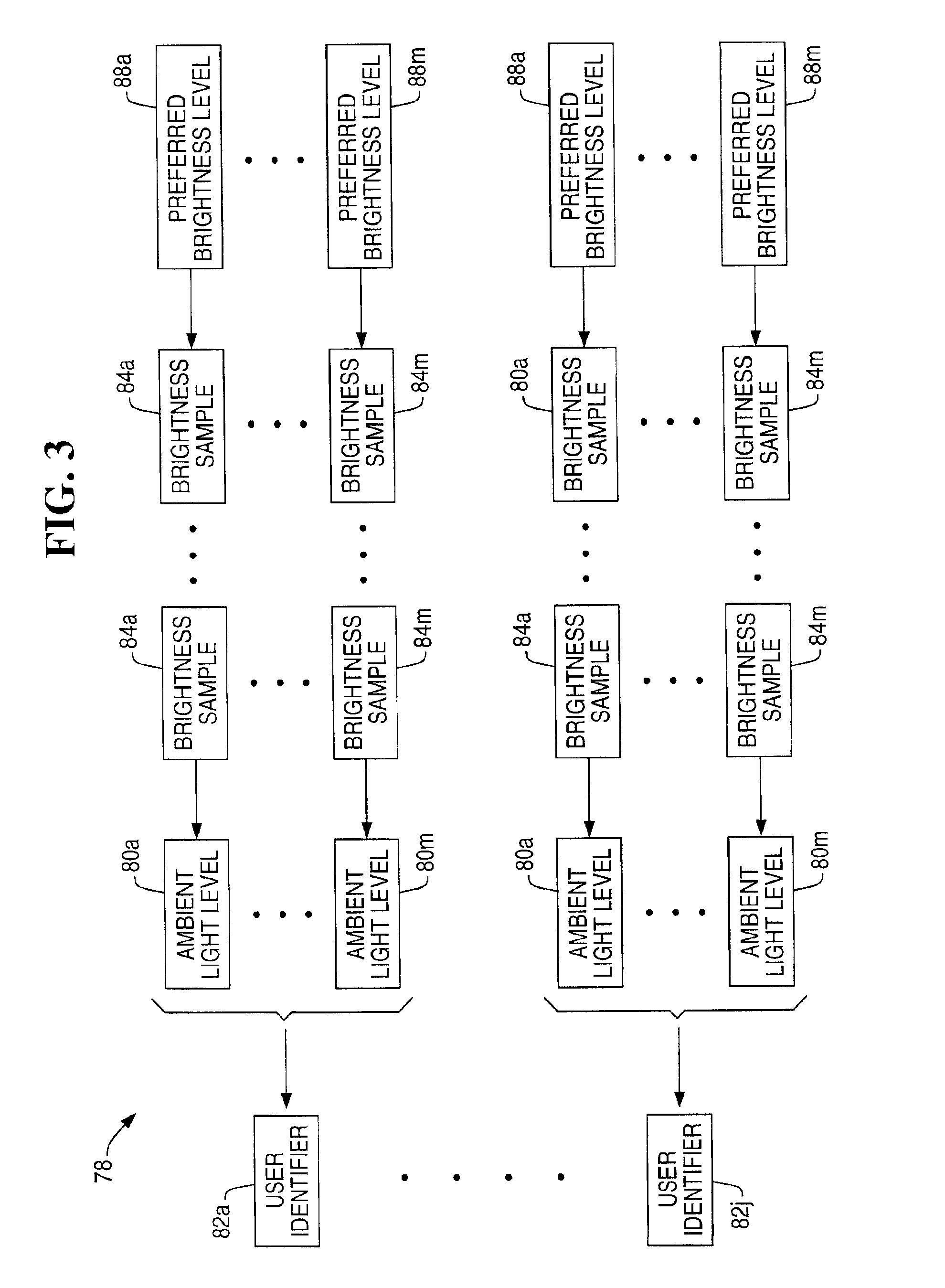
System and method for adjusting display brightness levels according to user preferences
InactiveUS6870529B1Television system detailsColor television detailsComputer graphics (images)Monitoring system
A display brightness monitoring system associates a brightness level and an ambient light level with a user identifier. Ambient light signals are received from an ambient light sensor mounted in proximity of an electronic display. Brightness levels are received from a brightness control mechanism for user selection of a display brightness. The monitoring system collects brightness levels and associates them with one of the ambient light levels associated with a user identifier. Preferably, a plurality of brightness levels are collected for each ambient light level and are used to compute a preferred brightness level indicative of a user's preferred display brightness for a given ambient light level. The brightness levels may be statistically averaged for computation of the brightness level. A data structure for associating brightness levels with ambient light levels and associating ambient light levels with a user identifier may be used to segregate one user's brightness levels from those of another. In this manner, the display may be driven using the preferred brightness levels for the user authorized to use a computer without altering the brightness levels stored for other users.
Owner:NCR CORP
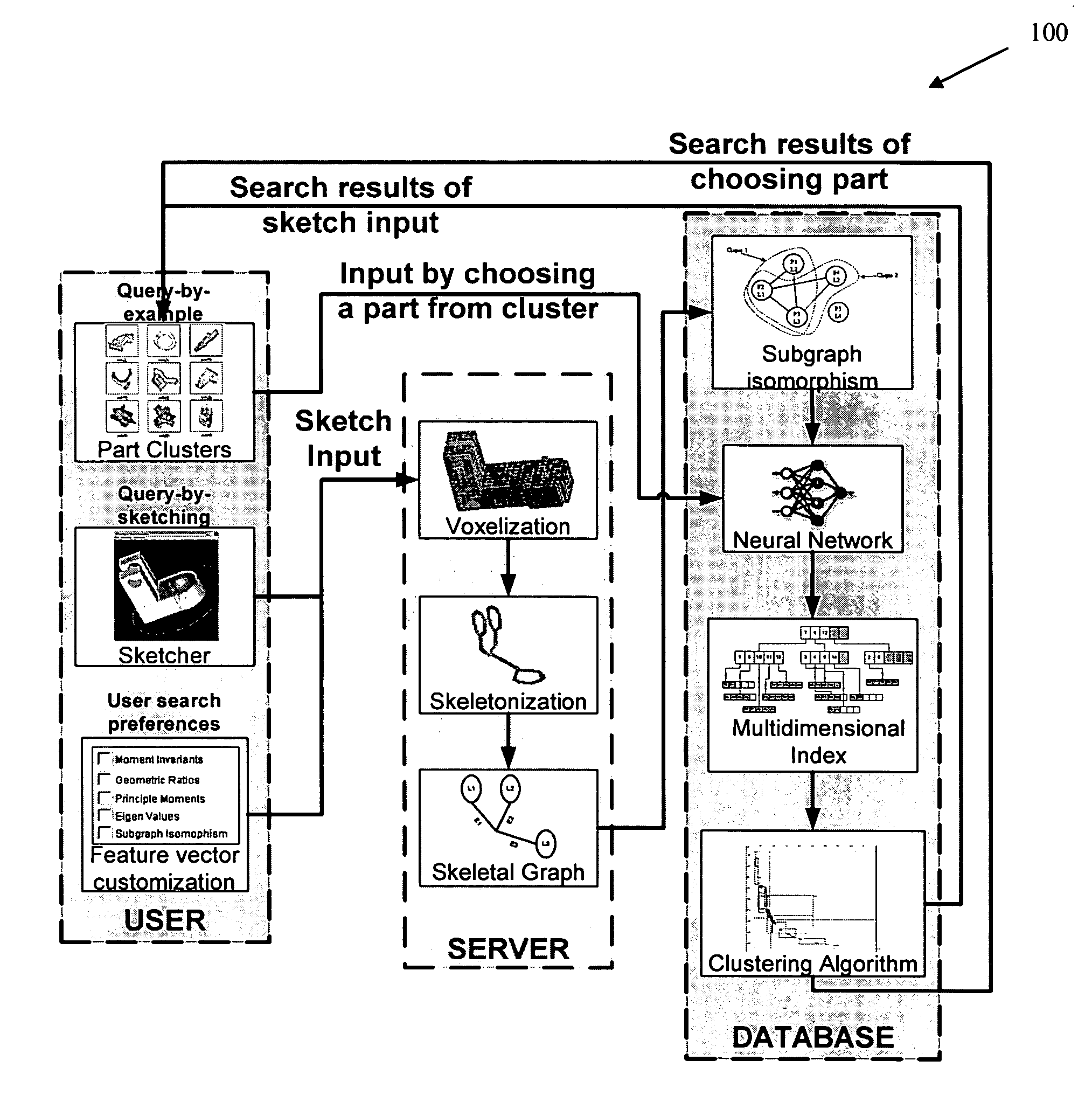
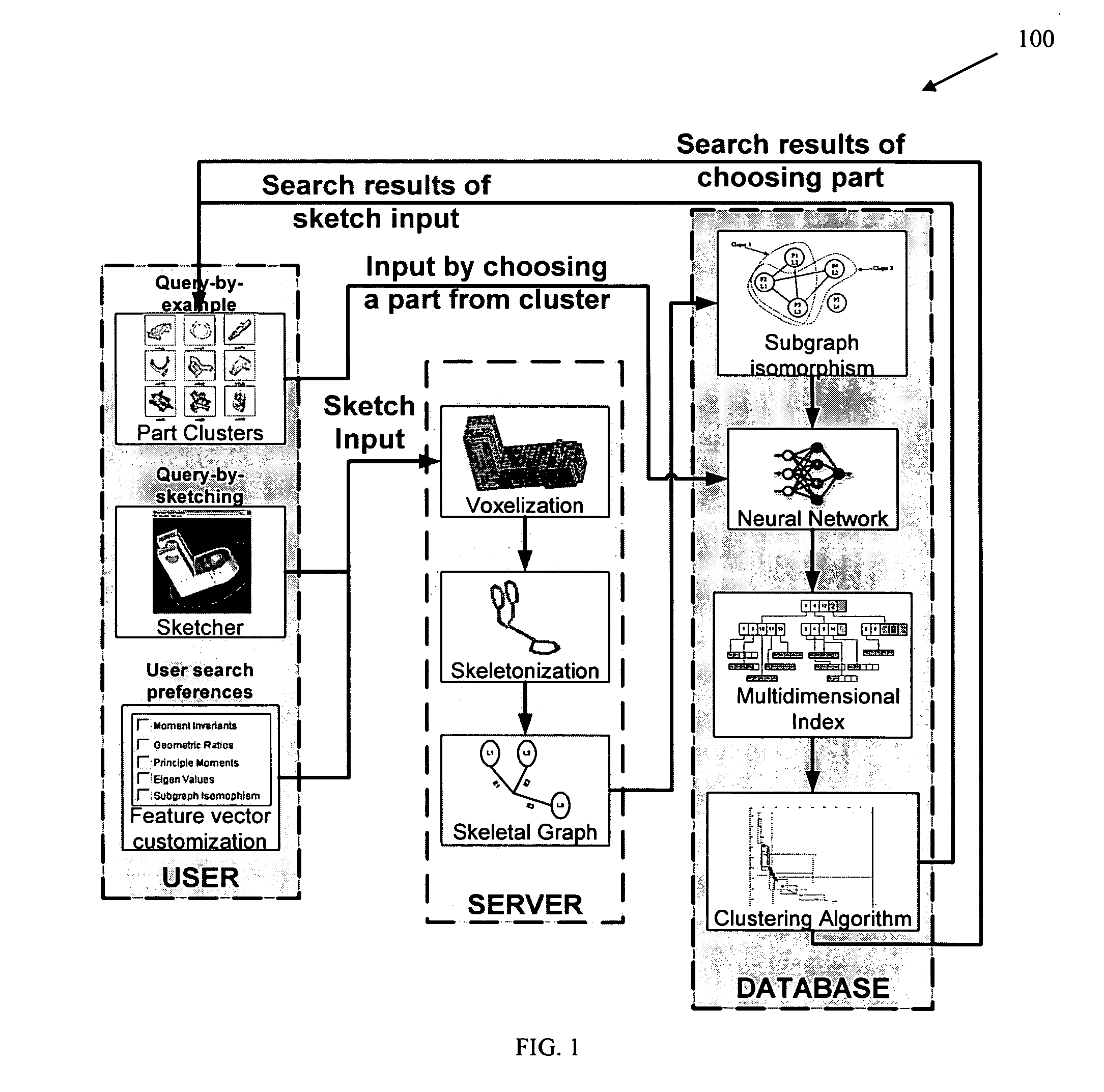
Methods, systems, and data structures for performing searches on three dimensional objects
Techniques are provided for searching on three dimensional (3D) objects across large, distributed repositories of 3D models. 3D shapes are created for input to a search system; optionally user-defined similarity criterion is used, and search results are interactively navigated and feedback received for modifying the accuracy of the search results. Search input can also be given by picking 3D models from a cluster map or by providing the orthographic views for the 3D model. Feedback can be given by a searcher as to which models are similar and which are not. Various techniques adjust the search results according to the feedback given by the searcher and present the new search results to the searcher.
Owner:PURDUE RES FOUND INC
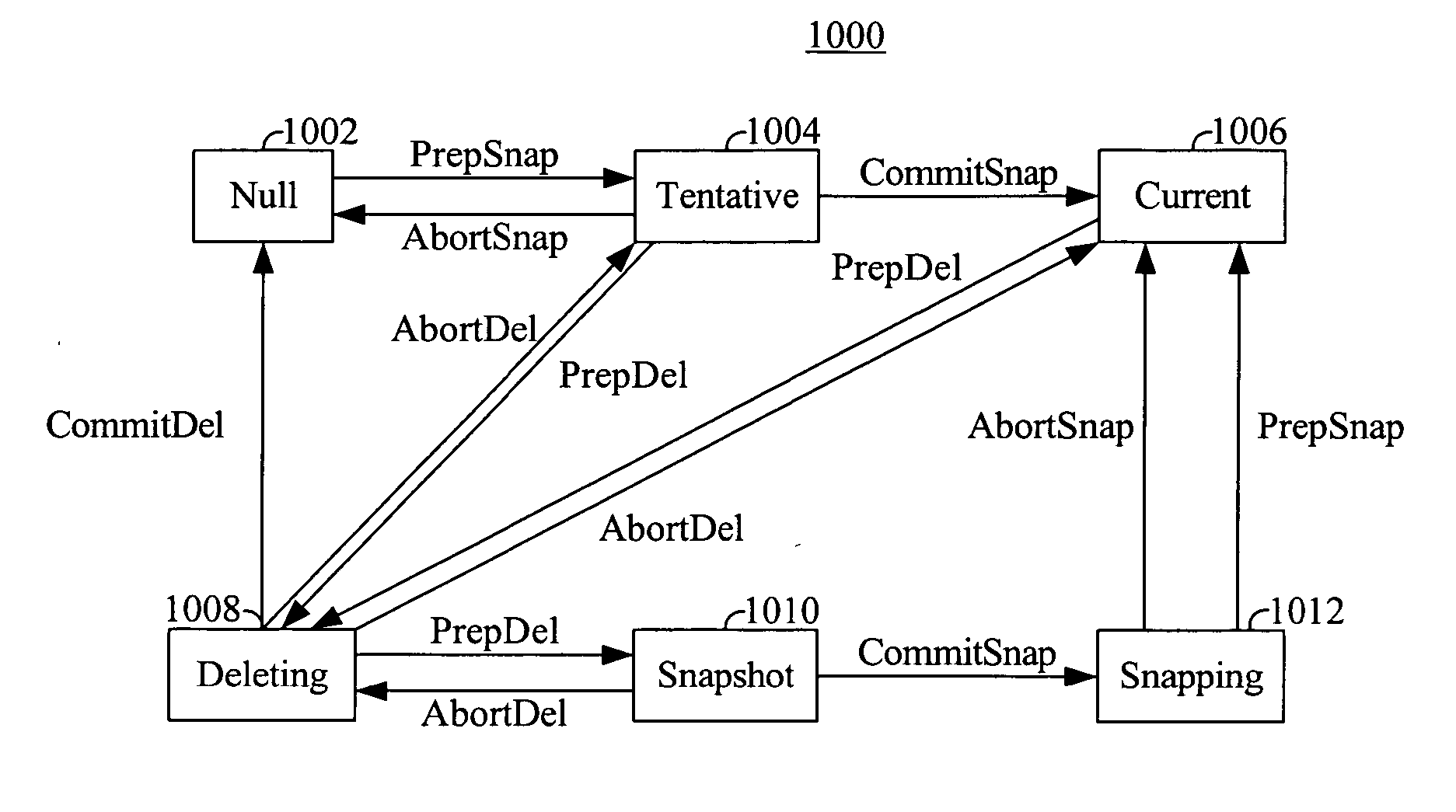
Method for taking snapshots of data
InactiveUS20060155946A1Memory loss protectionInput/output processes for data processingData miningData structure
A method for taking snapshots of data. In an embodiment, a first map data structure is obtained that records locations for a plurality of data blocks. A second map data structure is formed that is initially empty of locations, the second map data structure representing the snapshot after the snapshot is started. Writes on data that arrive before the snapshot starts are applied to the first map, and writes that arrive after the snapshot starts are applied to the second map.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
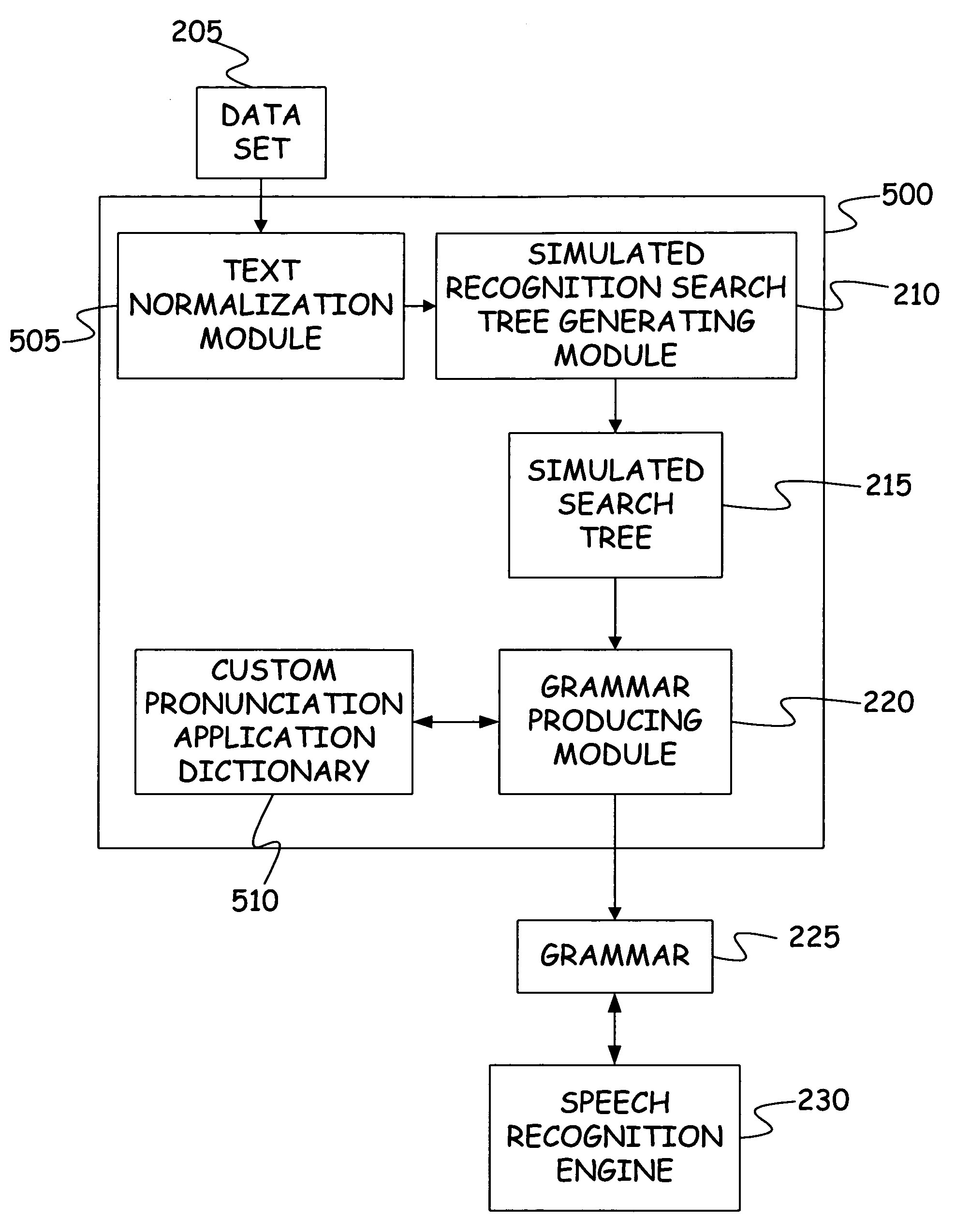
Method and apparatus for automatic grammar generation from data entries
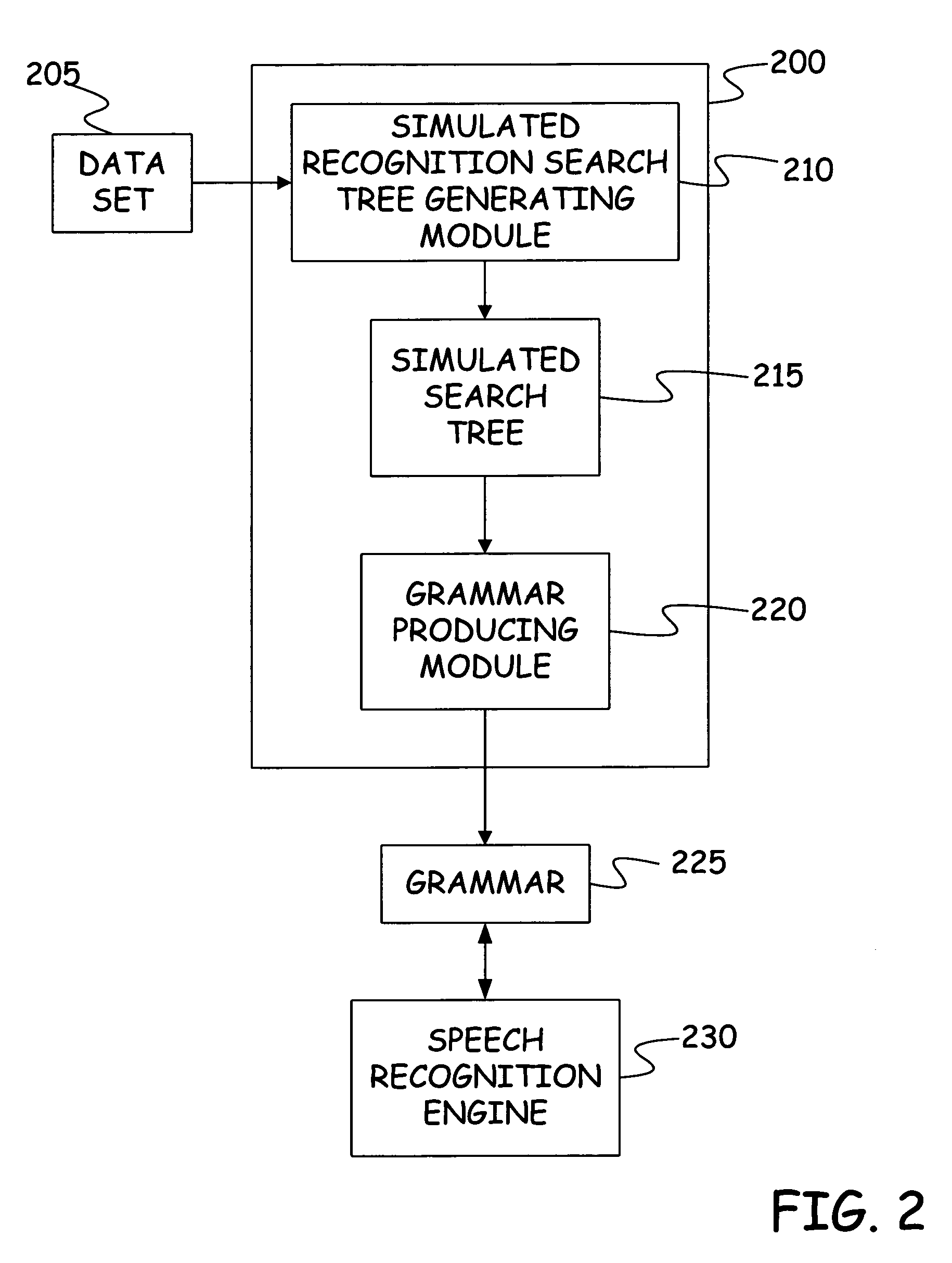
InactiveUS7636657B2Speech recognitionSpecial data processing applicationsData setTheoretical computer science
Owner:MICROSOFT TECH LICENSING LLC
Knowledge-based flexible natural speech dialogue system
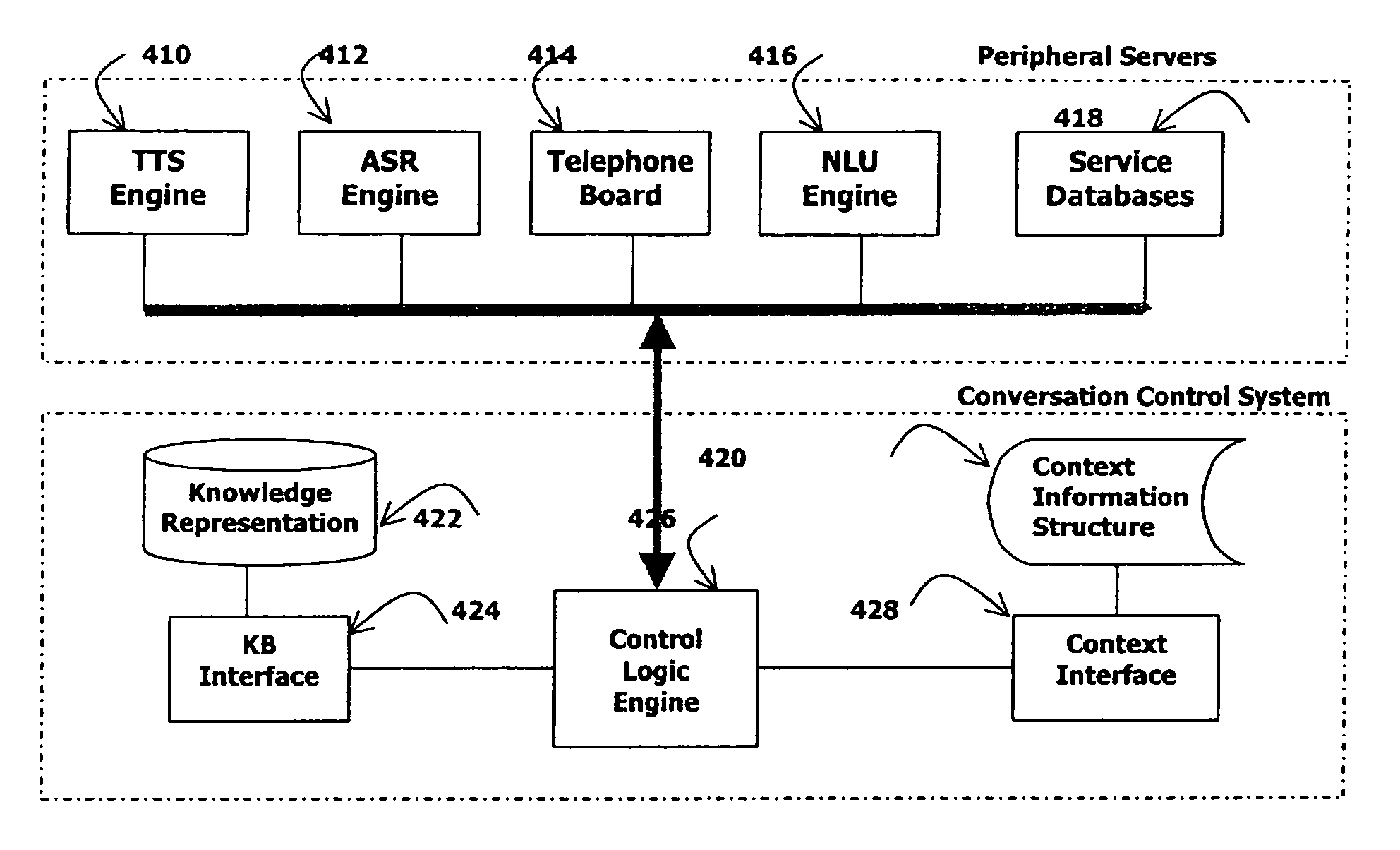
InactiveUS7386449B2Speech recognitionSpecial data processing applicationsHuman–computer interactionFixed position
A knowledge-based natural speech dialogue system includes: (i) a knowledge support system, (ii) a flexible dialogue control system, and (iii) a context information system. Flexibilities of the conversation structure, inherent in mixed-initiative mode for dealing with complex user request, are managed because the knowledge structures involved are represented by additional, powerful knowledge representation tools, and because the context information is retained by more specific data structures, which covers larger temporal scopes by the logic of the conversation, rather than by a fixed locality of the grammar flow. This system provides a simple yet reliable method to compensate for these factors to enable more powerful conversation engines with mixed-initiative capabilities.
Owner:VOICE ENABLING SYST TECH
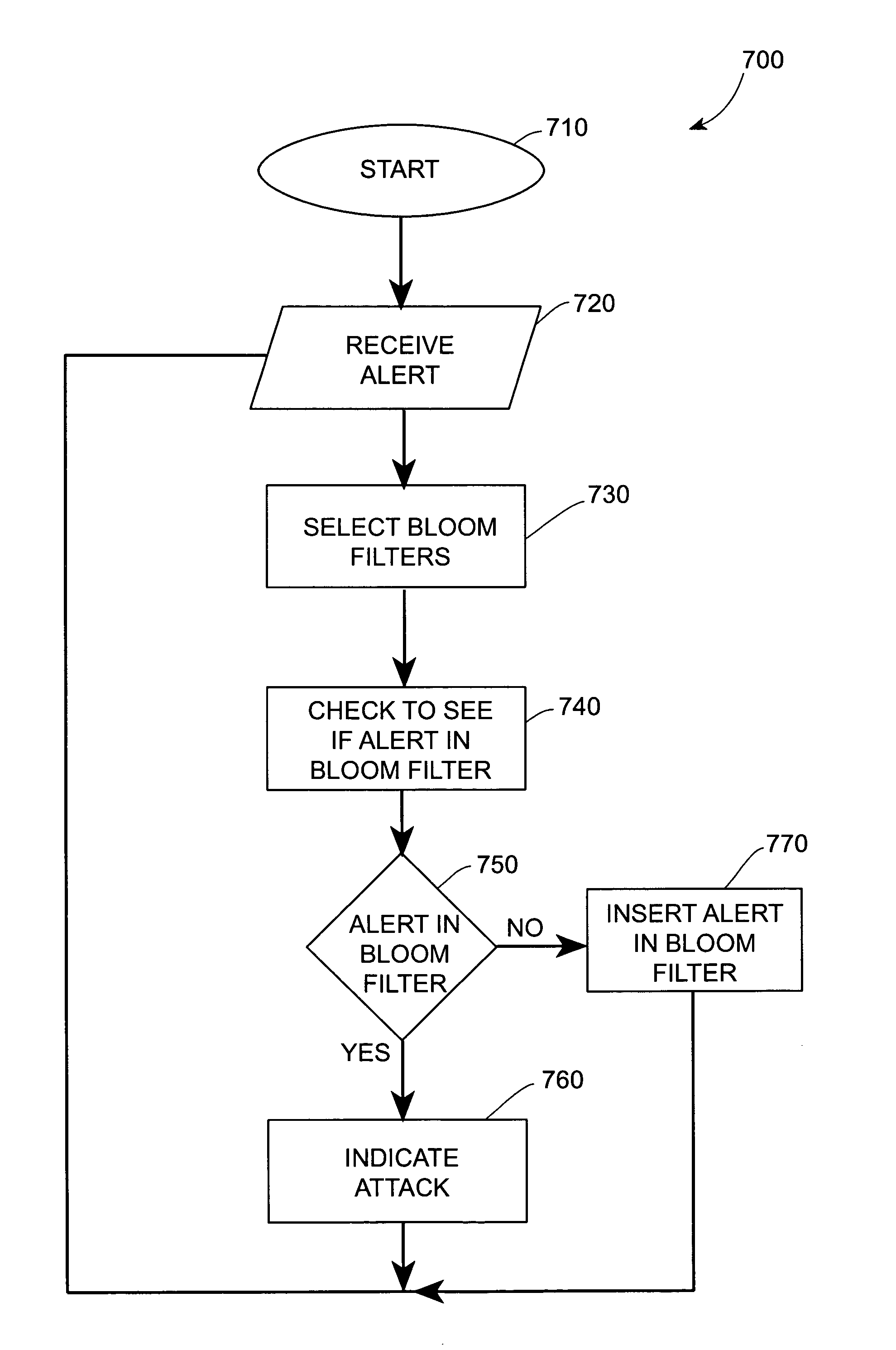
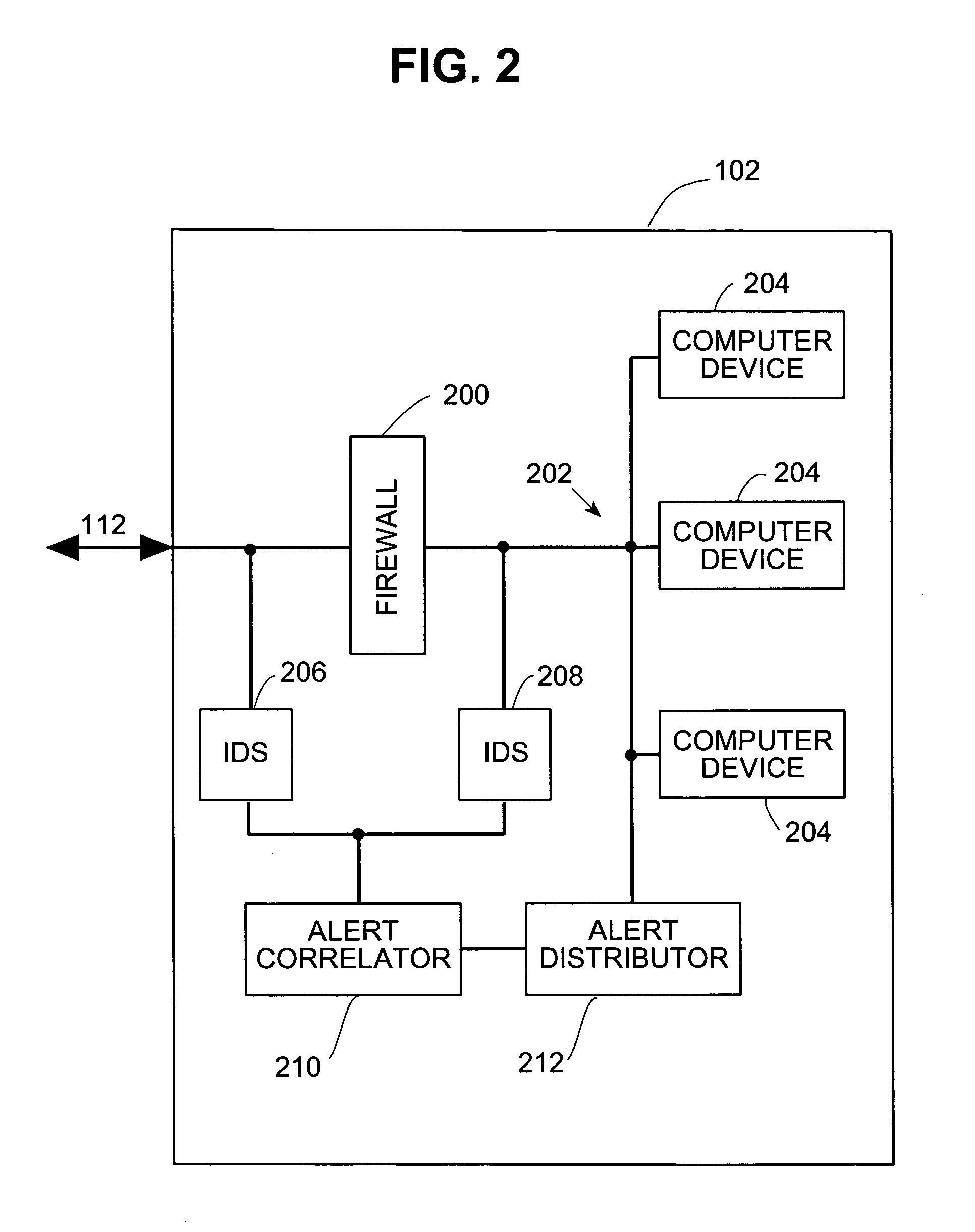
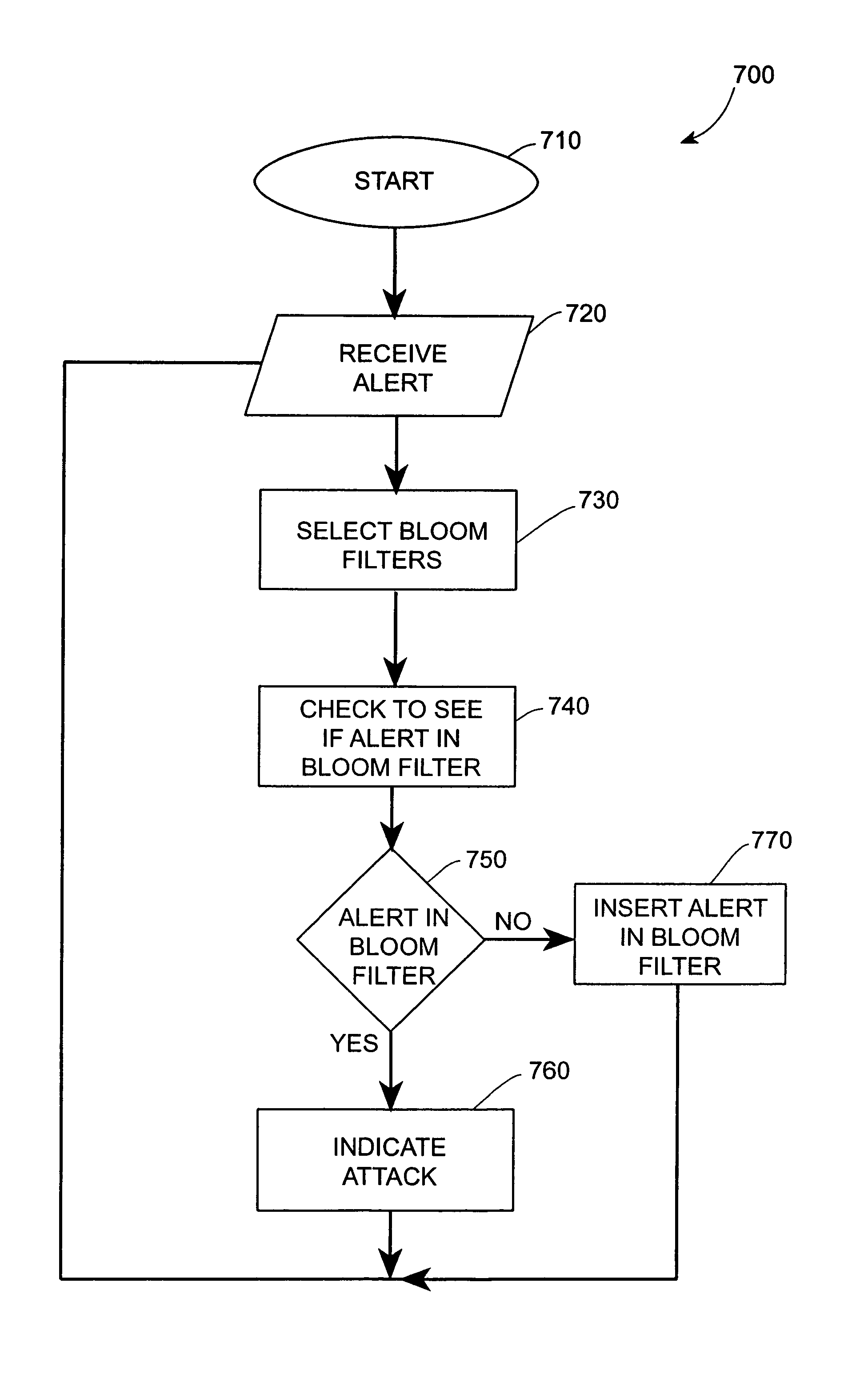
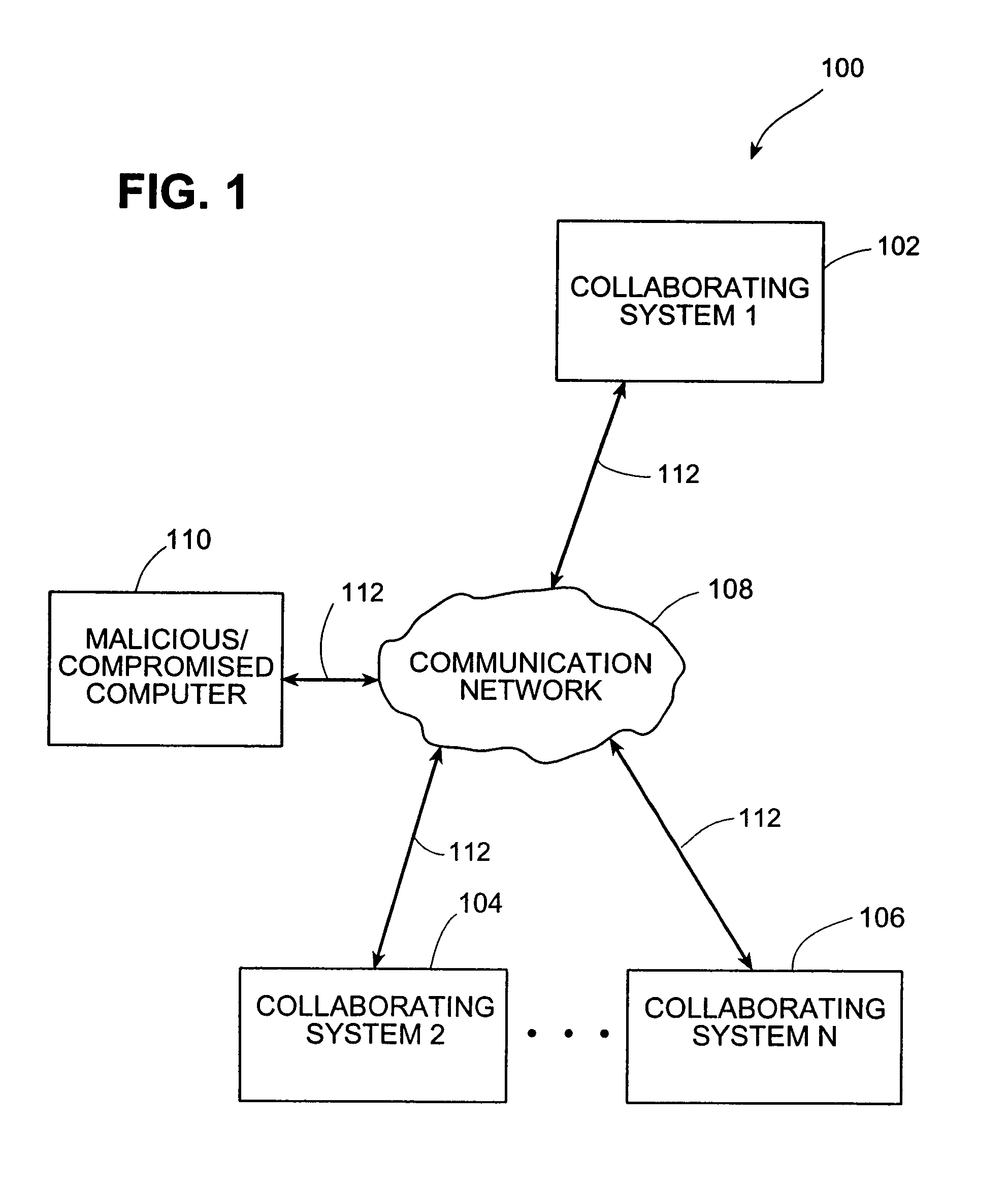
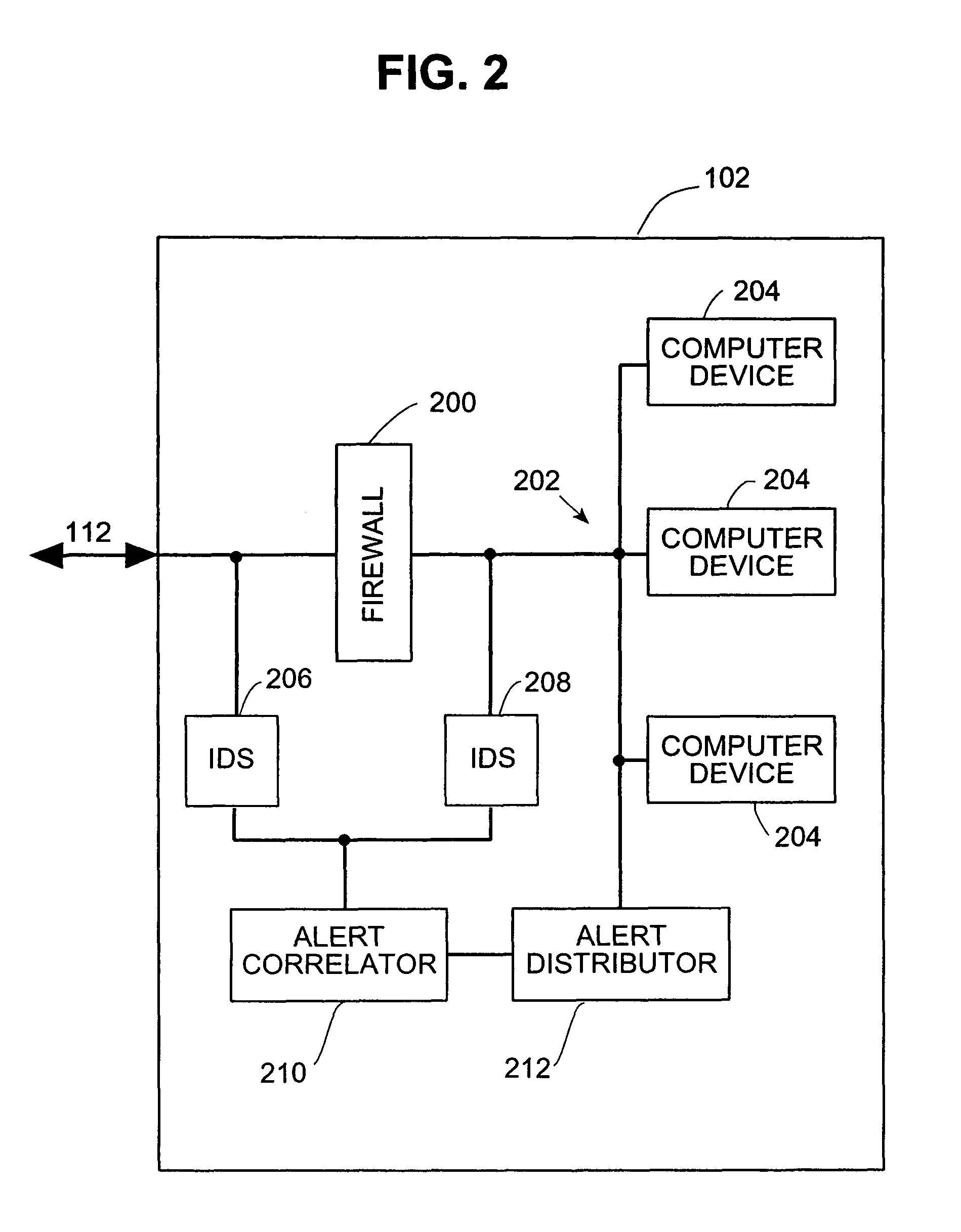
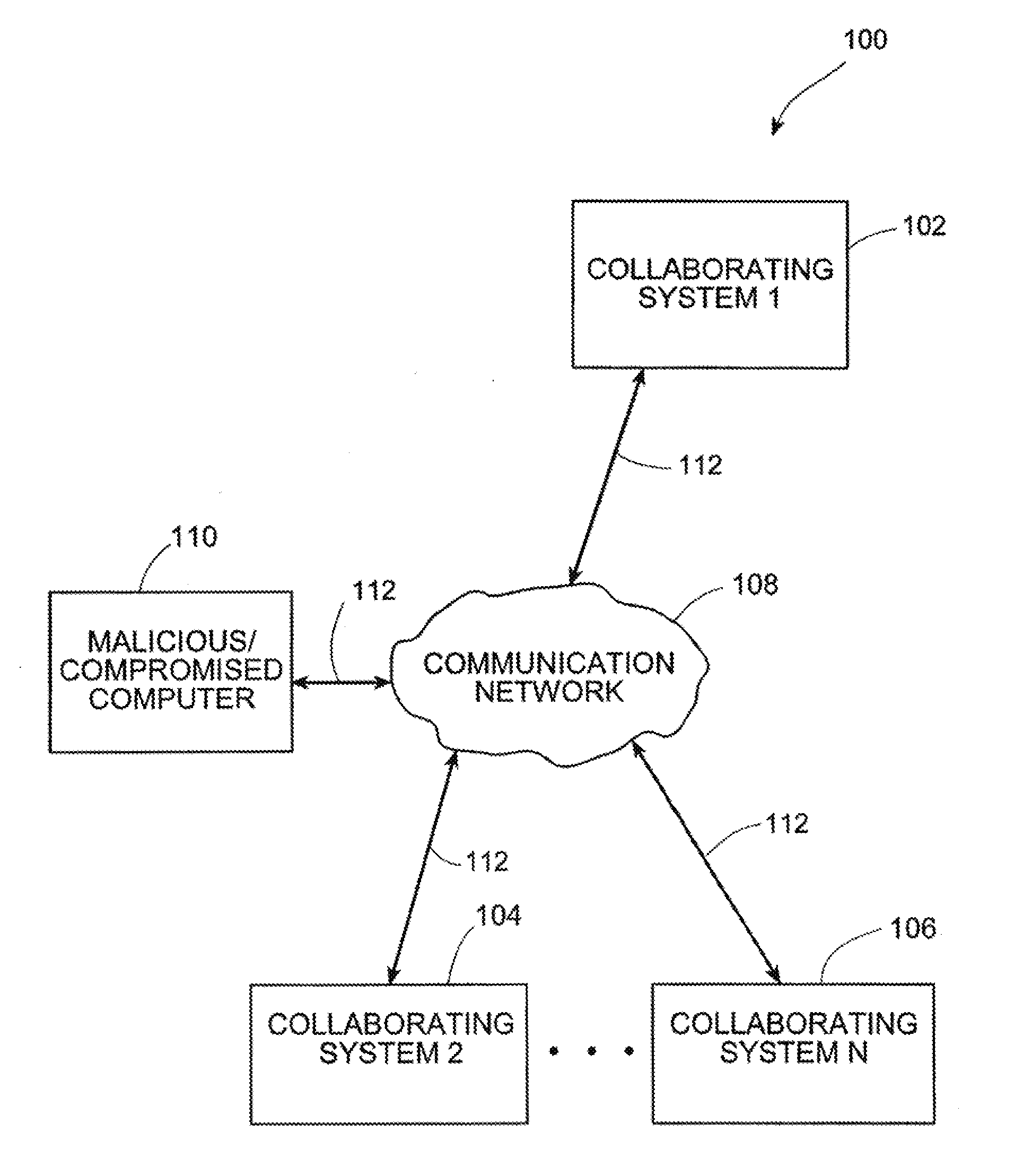
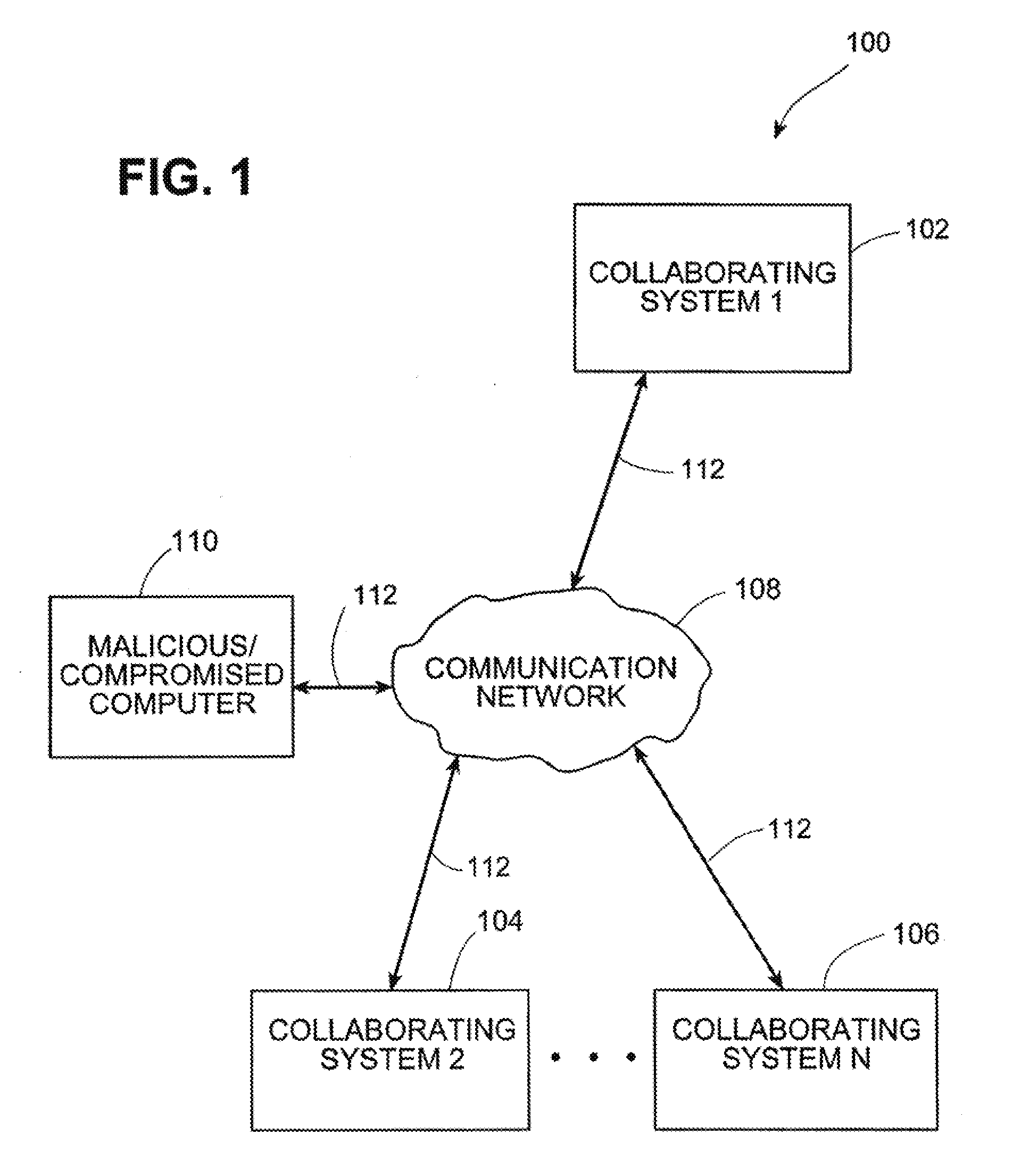
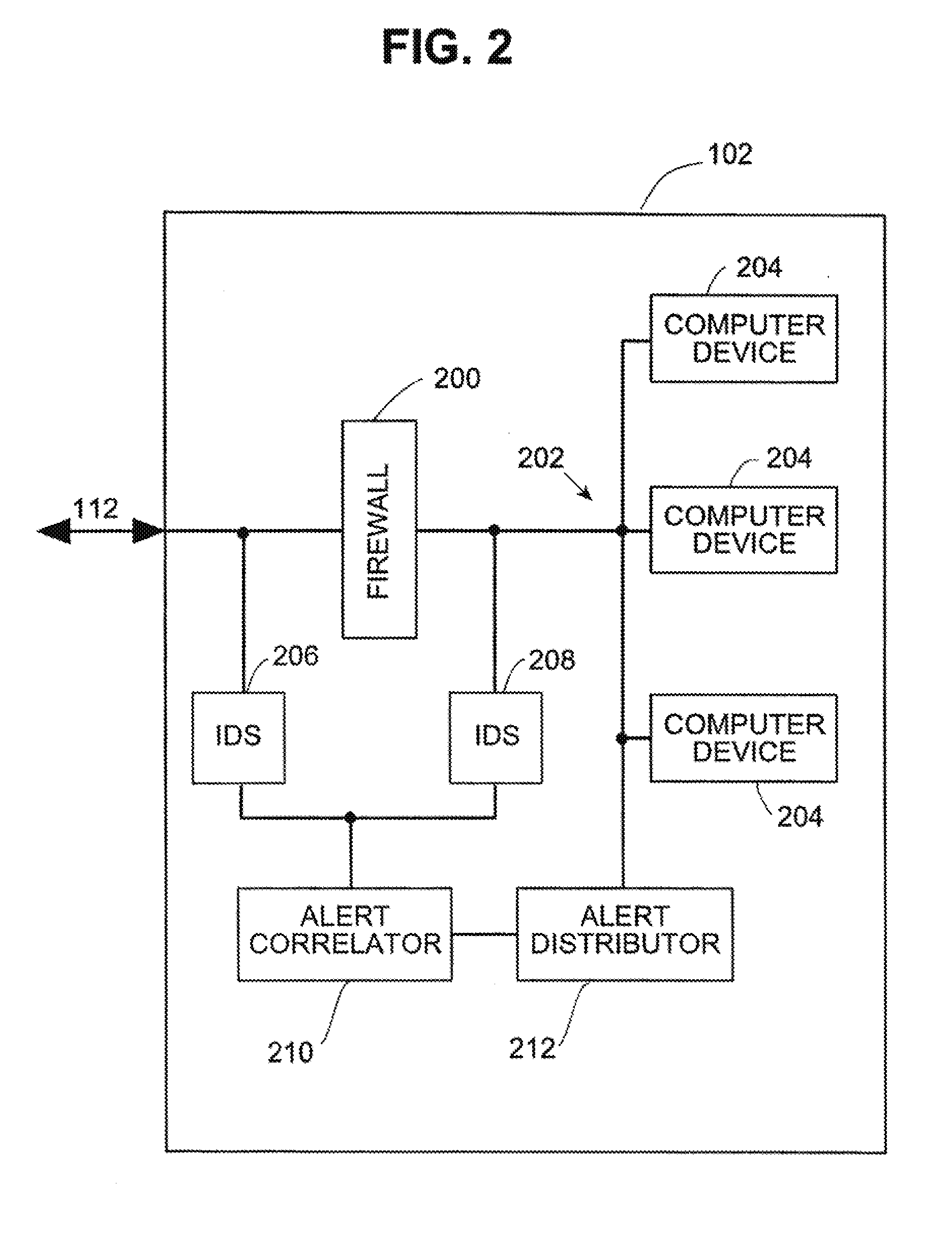
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7779463B2Technique is effectiveMemory loss protectionUser identity/authority verificationTraffic capacityEarly signs
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
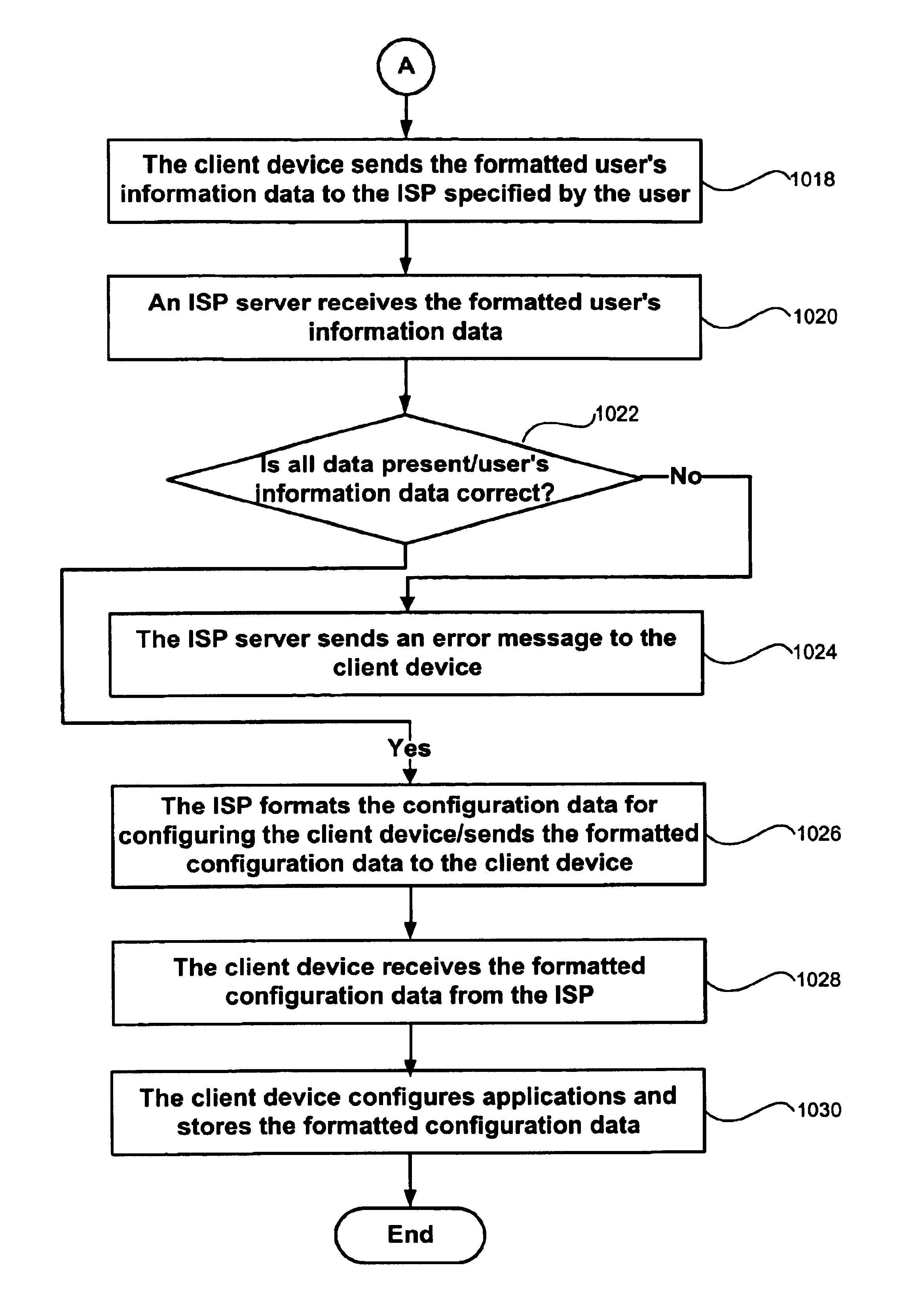
System and method for automatically configuring a client device
InactiveUS6938079B1Multiple digital computer combinationsProgram loading/initiatingAuto-configurationService provision
A user of a client device selects a service provider from a plurality of available service providers. The client device then queries the user for the user's information and formats the user's information into a predetermined data structure and format. The client device connects to the service provider and sends the formatted user's information to the service provider. The service provider responsively creates configuration data and provides it to the client device. The configuration data is used to configure a plurality of applications on the client device, allowing the user to establish future communication sessions with the service provider.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
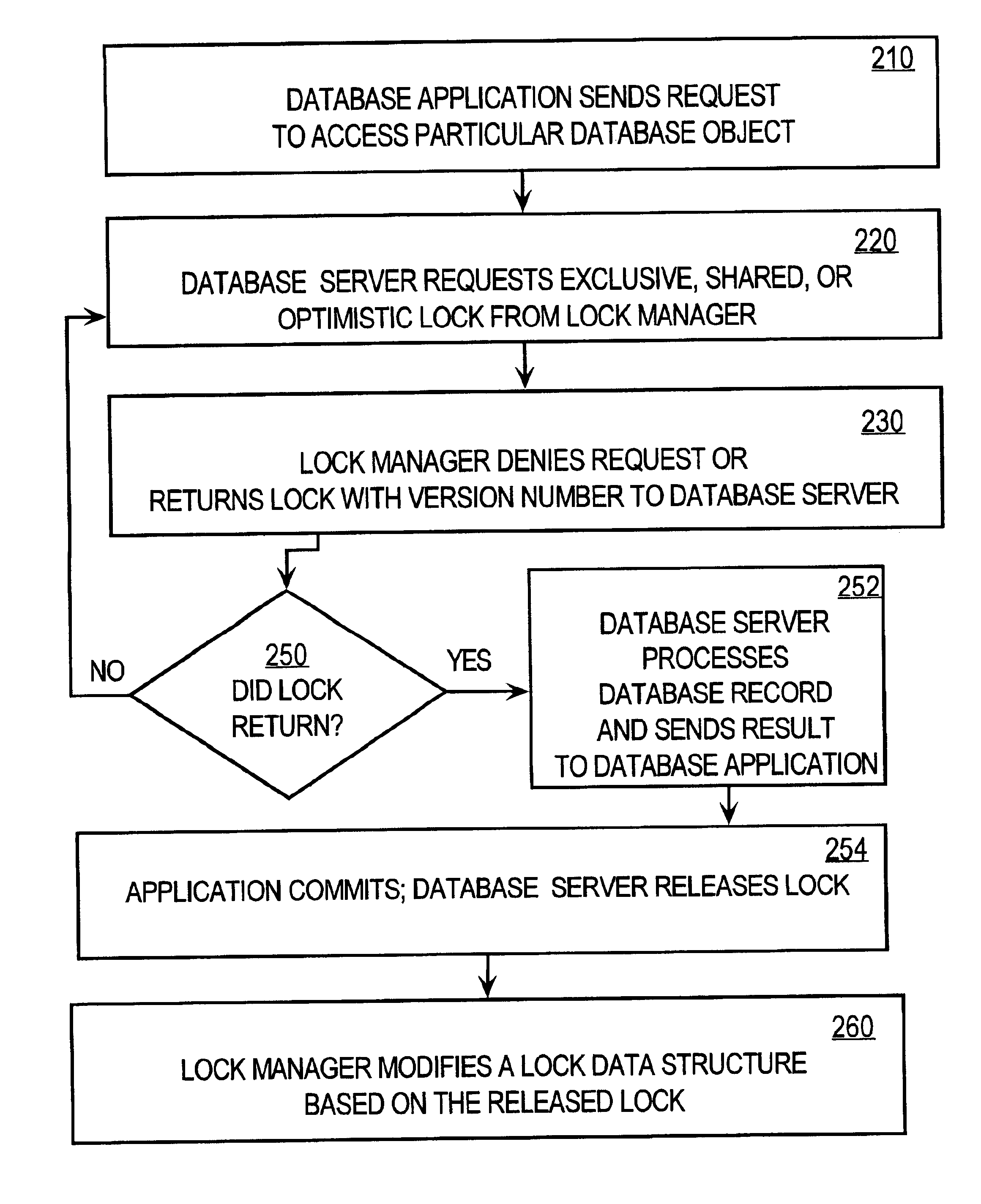
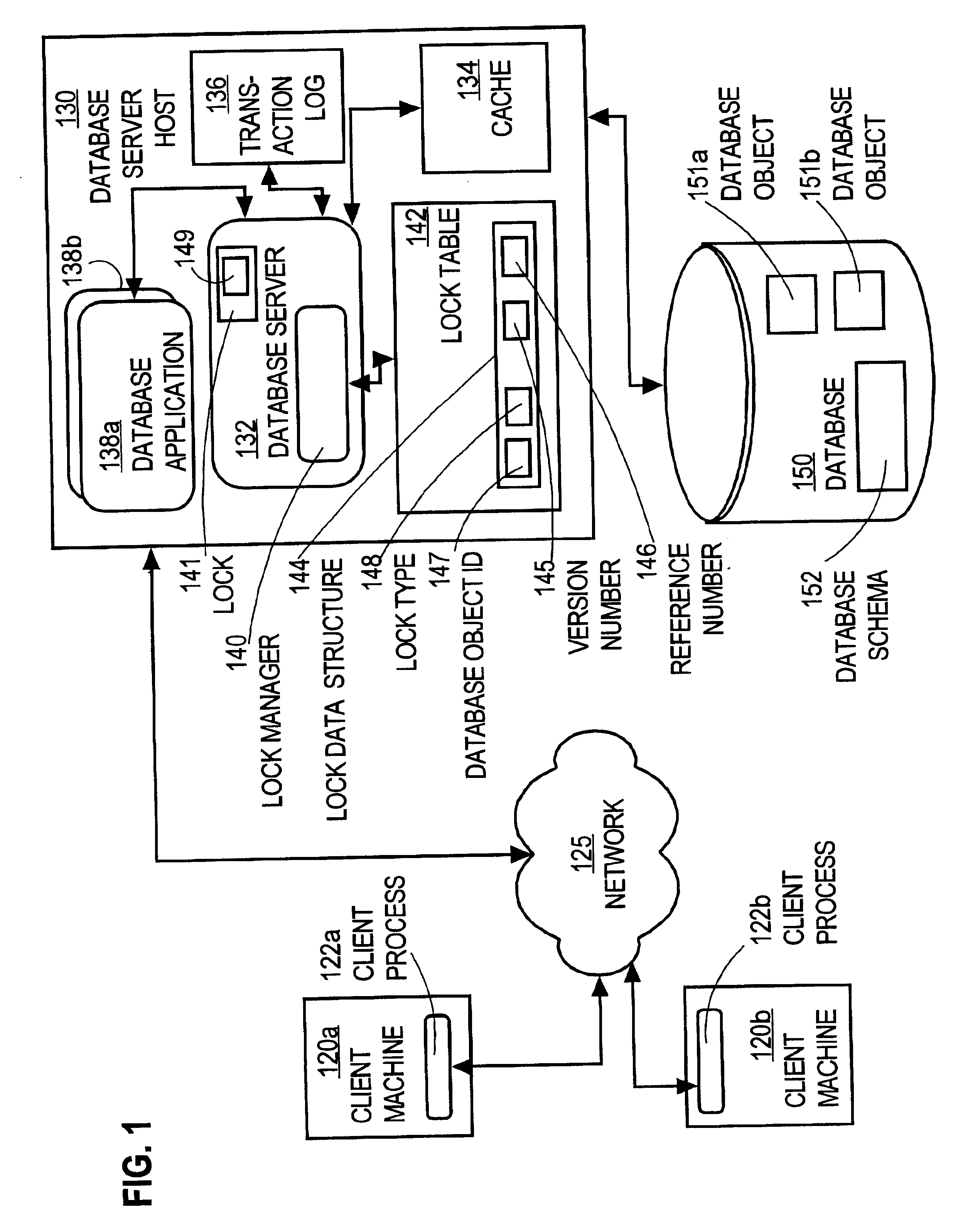
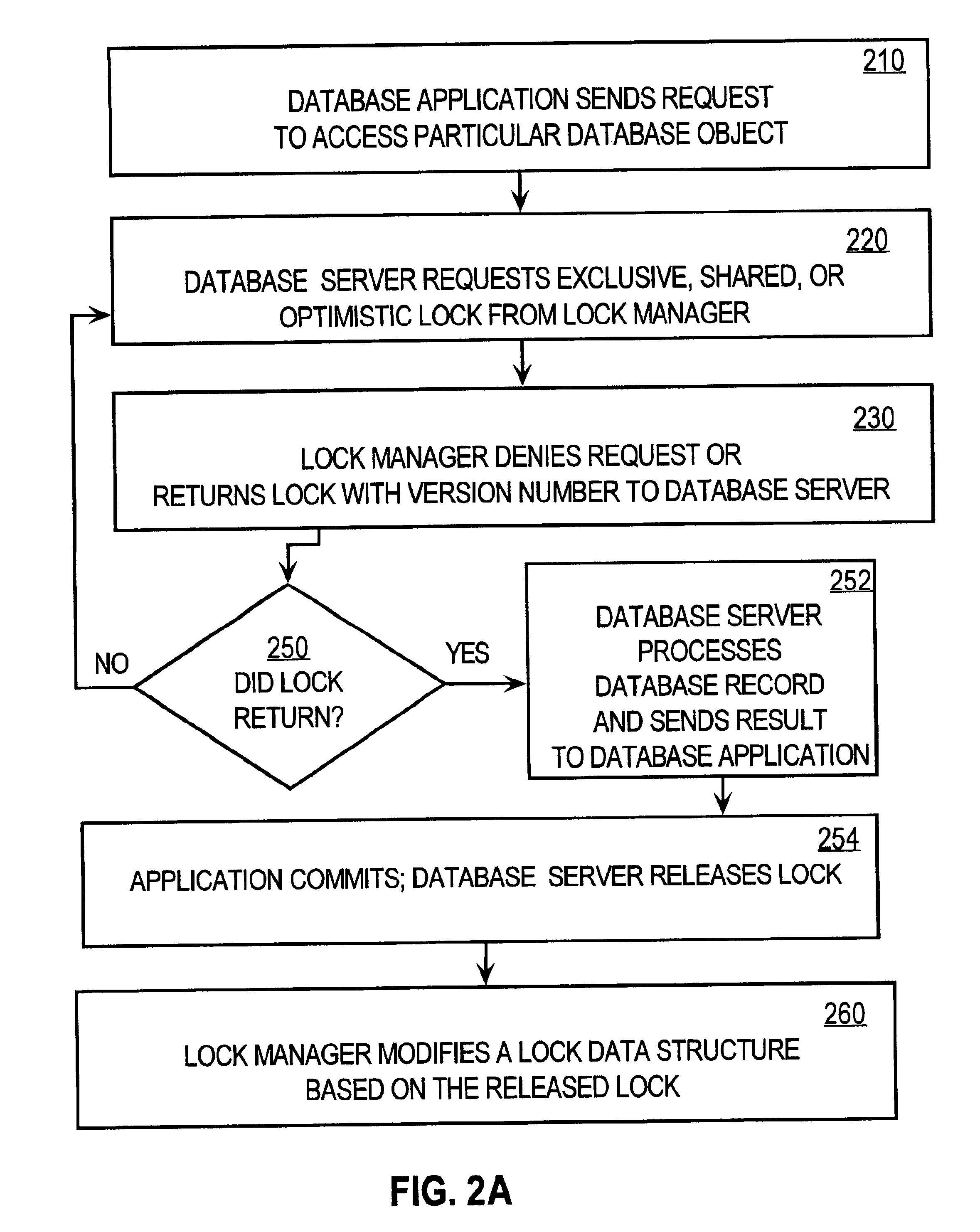
Method and apparatus providing optimistic locking of shared computer resources
InactiveUS6850938B1Digital data information retrievalData processing applicationsComputer resourcesLock manager
Techniques for concurrent access to a resource object, such as a database, include generating a lock data structure for a particular resource object. The lock data structure includes data values for a resource object identification, a lock type, and a version number. The version number is related to a number of changes to the resource object since the lock data structure was generated. A request is received from a requesting process. The request is for a requested lock type for access to the particular resource object. It is determined whether to grant the request based on the requested lock type and the lock type in the lock data structure. By carrying a lock version number in a lock data structure managed by a lock manager, improved optimistic locking is provided in a database. In particular, the approach enables introduction of optimistic locking to a legacy database without requiring burdensome changes to a database table schema.
Owner:CISCO TECH INC
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7784097B1Technique is effectiveMemory loss protectionUnauthorized memory use protectionTraffic capacityCollaborative computing
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems are provided. These systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Methods apparatus and data structures for enhancing the resolution of images to be rendered on patterned display devices
InactiveUS6393145B2Improve imaging resolutionHigh resolutionTelevision system detailsImage enhancementSub-pixel resolutionArray data structure
Techniques for improving the resolution of images (either analog images, analytic images, or images having a higher resolution than that of a display device) to be rendered on patterned displays. In one aspect of the present invention, an overscaling or oversampling process may accept analytic character information, such as contours for example, and a scale factor or grid and overscale or oversample the analytic character information to produce an overscaled or oversampled image. The overscaled or oversampled image generated has a higher resolution than the display upon which the character is to be rendered. Displaced samples of the overscaled or oversampled image are then combined (or filtered). An analytic image, such as a line drawing for example, may be applied to the oversampling / overscaling process as was the case with the character analytic image. However, since the analytic image may have different units than that of the character analytic image, the scale factor applied may be different. Since an ultra resolution image is already "digitized", that is, not merely mathematically expressed contours or lines between points, it may be applied directly to a process for combining displaced samples of the ultra-resolution image to generate another ultra-resolution image (or an image with sub-pixel information). The functionality of the overscaling / oversampling process and the processes for combining displaced samples may be combined into a single step analytic to digital sub-pixel resolution conversion process.
Owner:MICROSOFT TECH LICENSING LLC +1
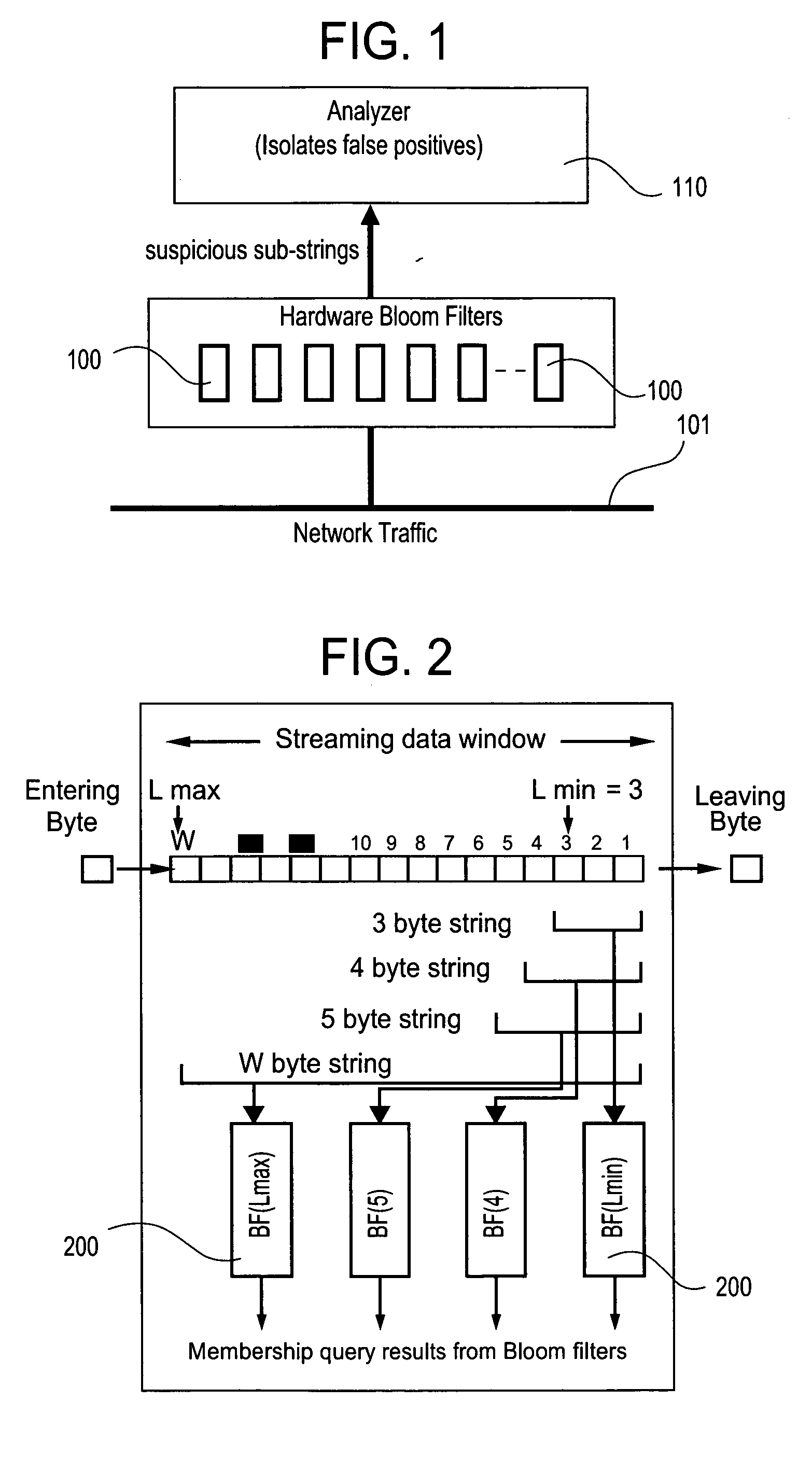
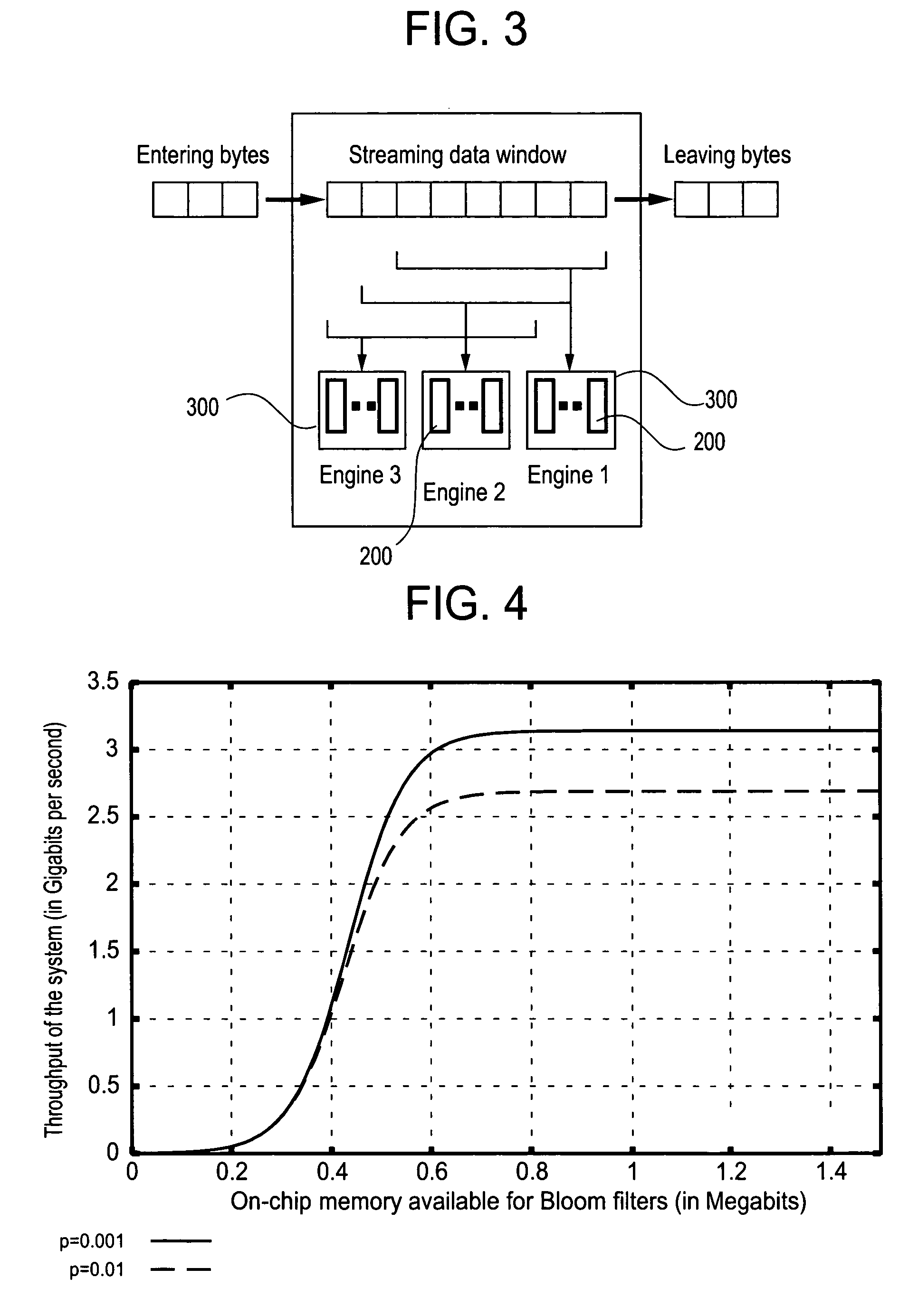
Method and apparatus for detecting predefined signatures in packet payload using bloom filters
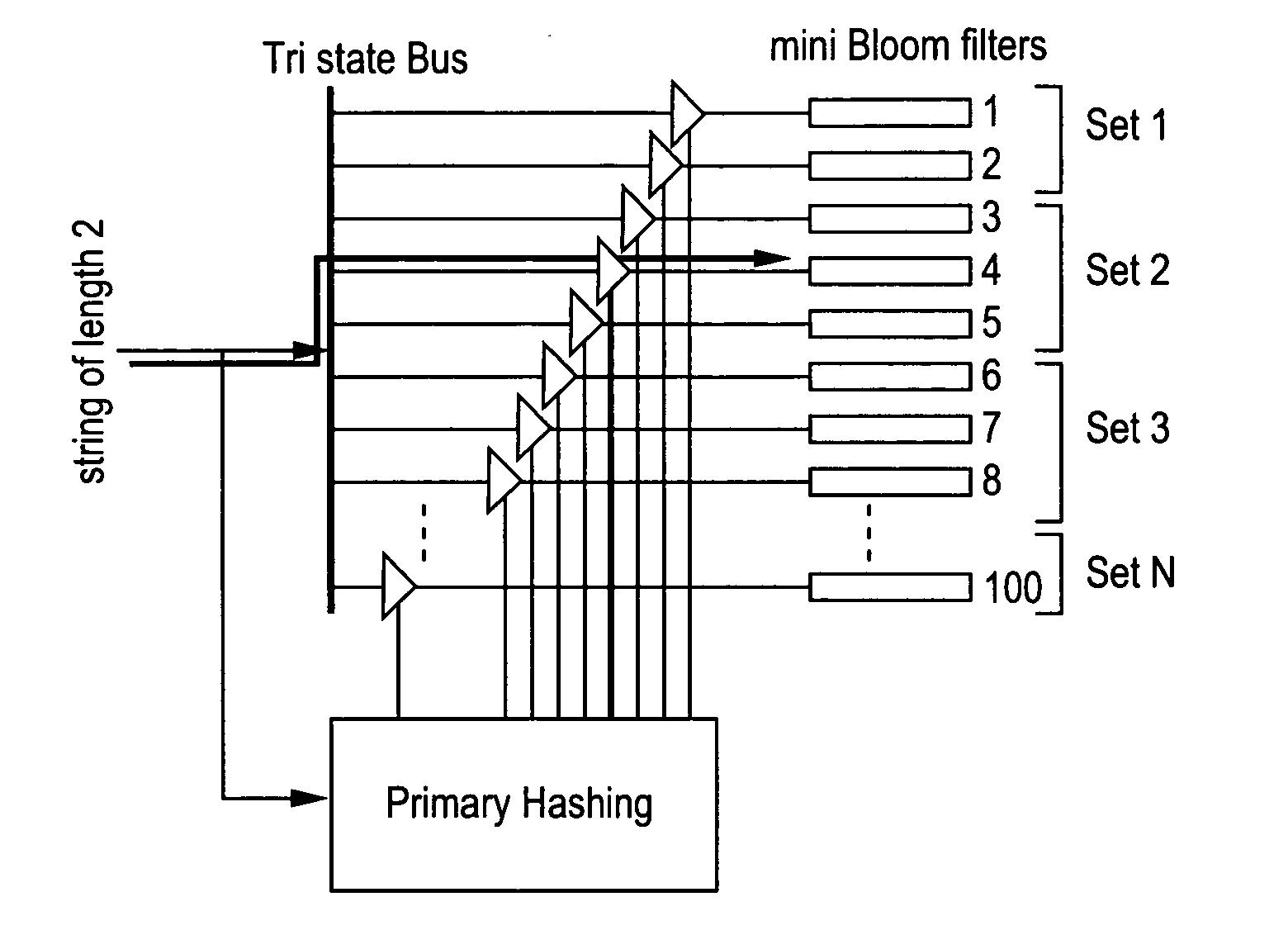
ActiveUS20050086520A1Digital data processing detailsUser identity/authority verificationBloom filterNetwork data
The present invention relates to a method and apparatus based on Bloom filters for detecting predefined signatures (a string of bytes) in a network packet payload. A Bloom filter is a data structure for representing a set of strings in order to support membership queries. Hardware Bloom filters isolate all packets that potentially contain predefined signatures. Another independent process eliminates false positives produced by the Bloom filters. The system is implemented on a FPGA platform, resulting in a set of 10,000 strings being scanned in the network data at the line speed of 2.4 Gbps.
Owner:WASHINGTON UNIV IN SAINT LOUIS
Systems and Methods for Correlating and Distributing Intrusion Alert Information Among Collaborating Computer Systems
ActiveUS20100281542A1Technique is effectiveMemory loss protectionError detection/correctionTraffic capacityCollaborative computing
Systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com